Software definition network safety enforcement method, system and controller thereof
A software-defined network and network security technology, applied in the field of systems and controllers, and software-defined network security implementation methods, to achieve the effect of solving security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0066] The inventor of the present application proposes that, according to the characteristics of software-defined networks, a security core module can be deployed in the control layer NOS, network security can be regarded as an independent aspect, and security interfaces can be abstracted and provided to upper-layer security applications, and security applications can analyze network security status and formulate security policies.
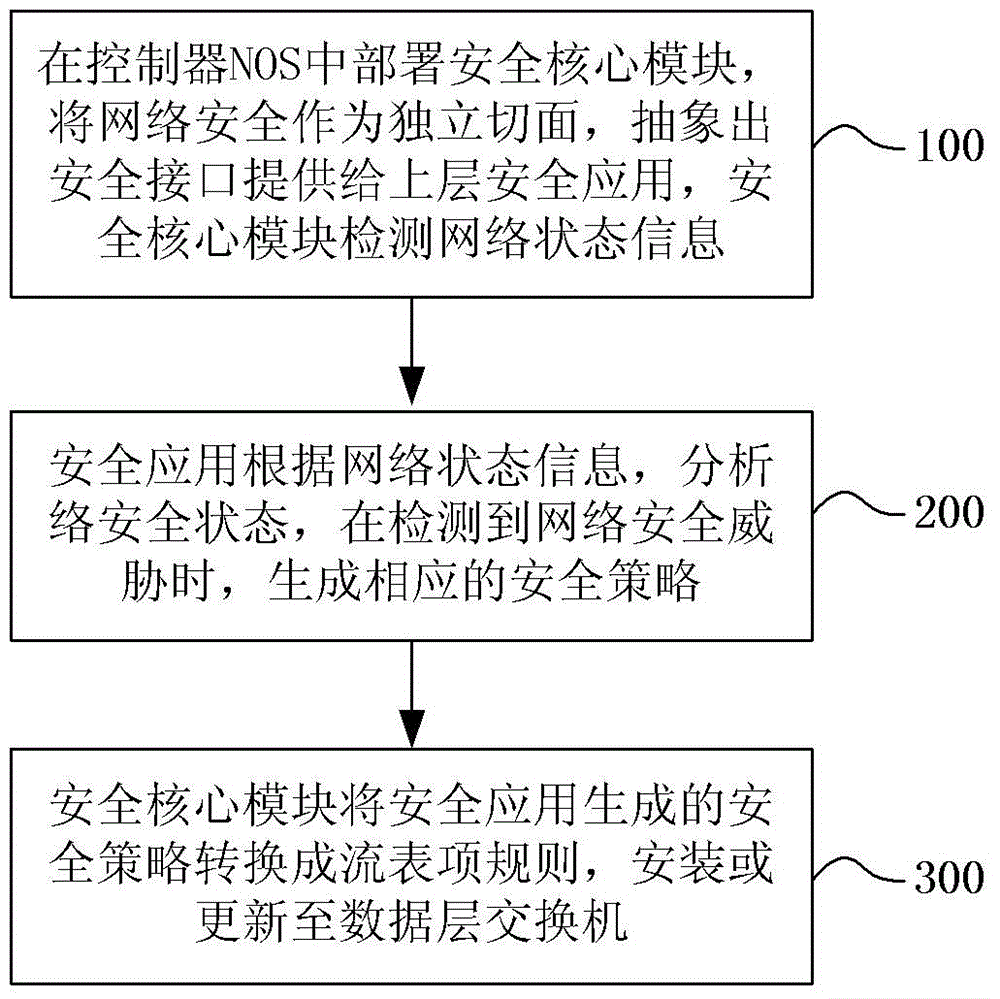
[0067] Based on the above idea, this embodiment provides a software-defined network security implementation method, such as figure 1 shown, including the following operations:
[0068] Step 100, deploying a security core module in the controller NOS, taking network security as an independent aspect, abstracting a security interface and providing it to an upper-layer security application, and the security core module detecting network state information;
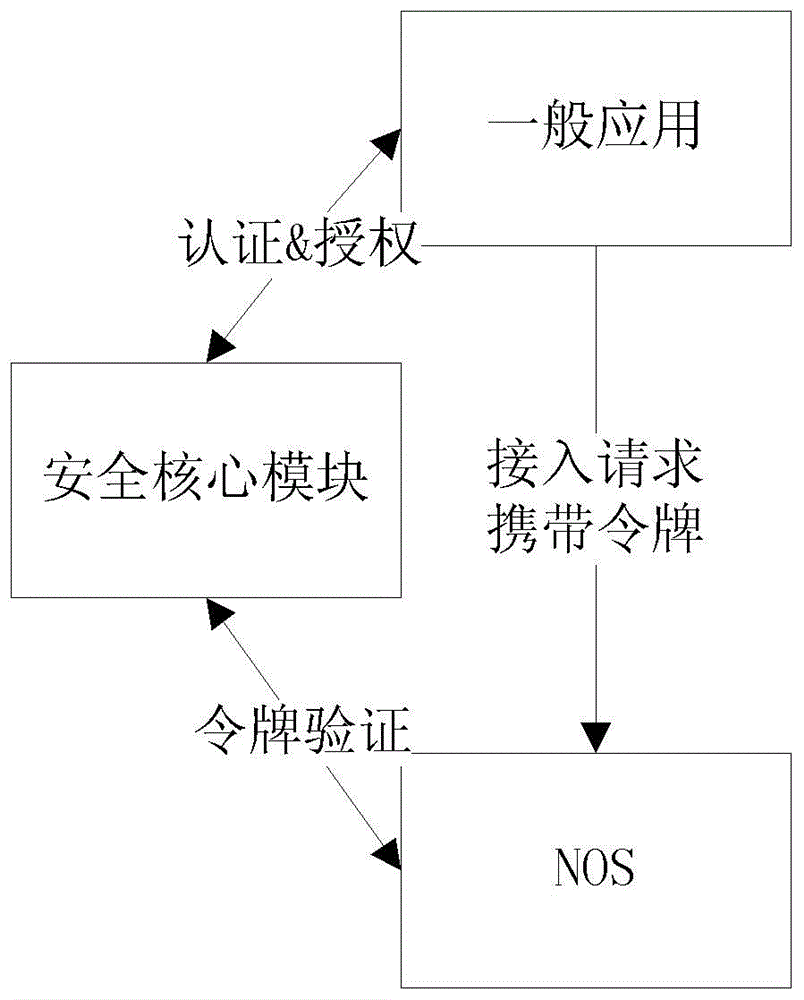
[0069] Optionally, general application access authentication and authorization services can a...
Embodiment 2
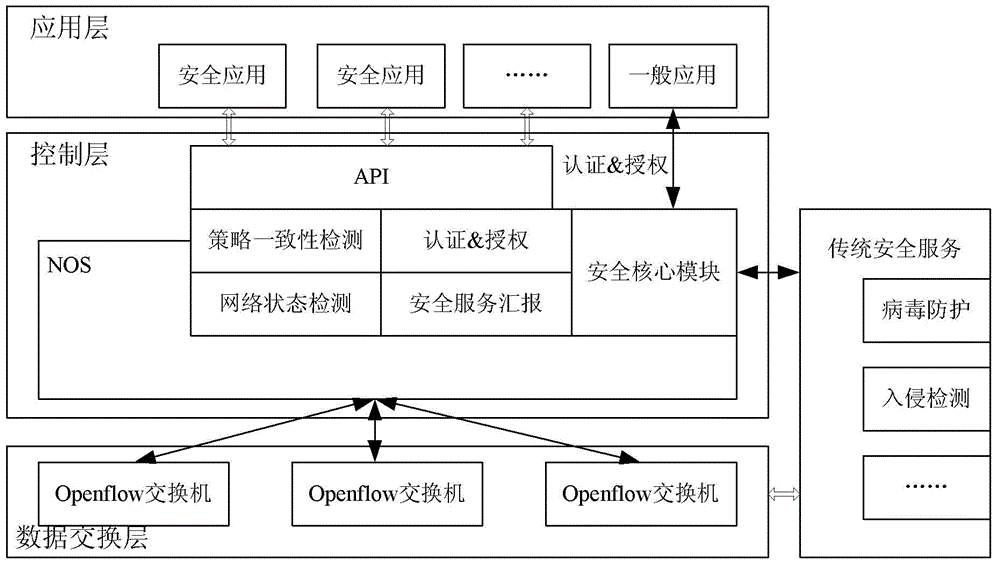
[0082] This embodiment provides a software-defined network security implementation system. By deploying a security core module in the control layer NOS, the software-defined network security aspect is independently presented, and a security interface is provided for the application layer security application program.
[0083] like figure 2 As shown, the software-defined network security implementation system includes a security core module deployed in the controller NOS. The security core module shields the data layer switch operation and the specific implementation of the control layer, and detects network status information (including network resources and equipment operating conditions) in real time. Provide exclusive security interfaces for security applications, convert security policies generated by security application sets into flow table entry rules, and install or update them on data layer switches.
[0084] And the security application set, according to the network...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com