Patents
Literature
12458 results about "Network data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
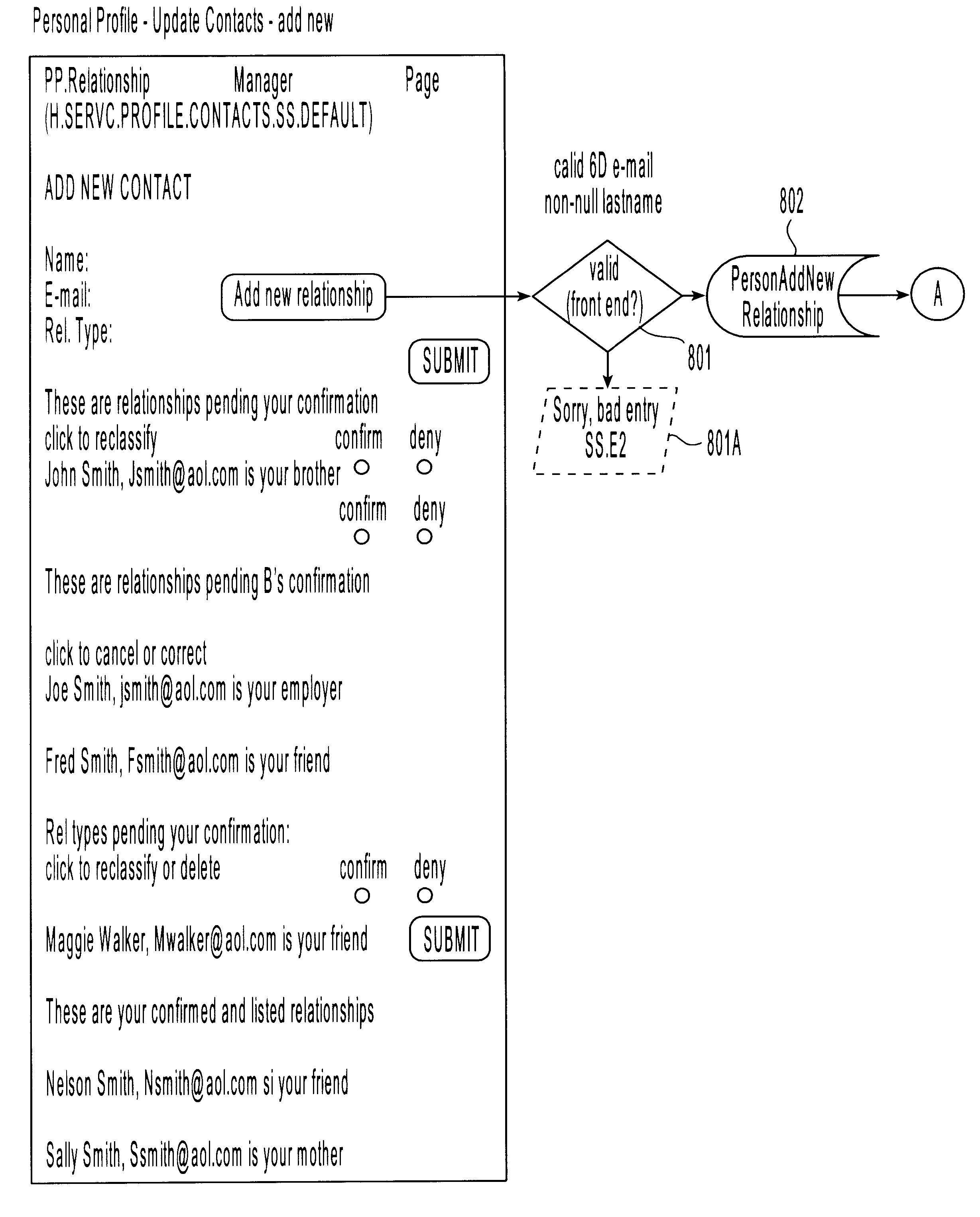
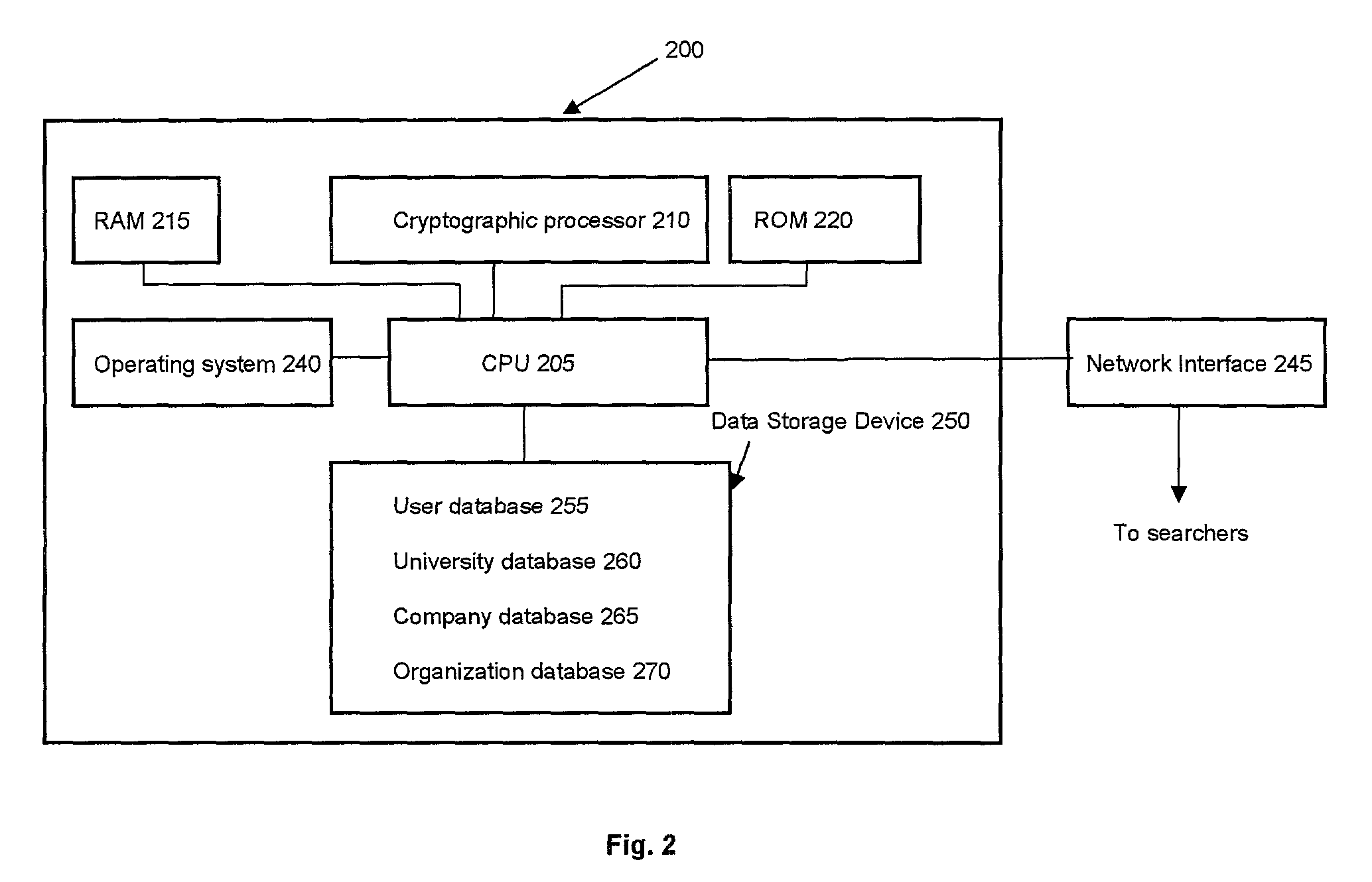
Method and apparatus for constructing a networking database and system
InactiveUS6175831B1Fast constructionGrowthOffice automationSpecial data processing applicationsMutually DefinedDatabase services
A networking database containing a plurality of records for different individuals in which individuals are connected to one another in the database by defined relationships. Each individual has the opportunity to define the relationship which may be confirmed or denied. E-mail messaging and interactive communication between individuals and a database service provider provide a method of constructing the database. The method includes having a registered individual identify further individuals and define therewith a relationship. The further individuals then, in turn, establish their own defined relationships with still other individuals. The defined relationships are mutually defined.
Owner:MACROVIEW COMM CORP +1
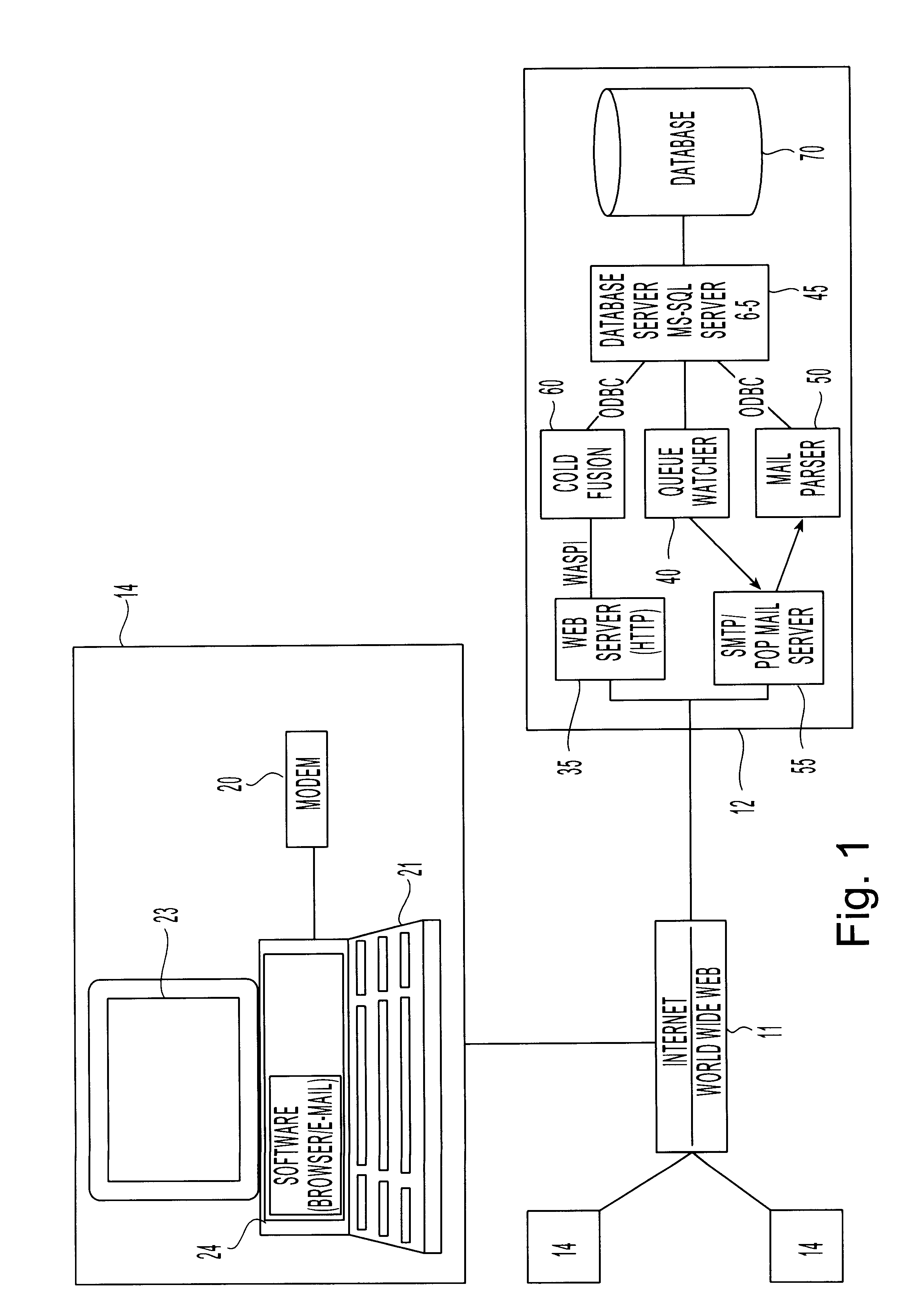
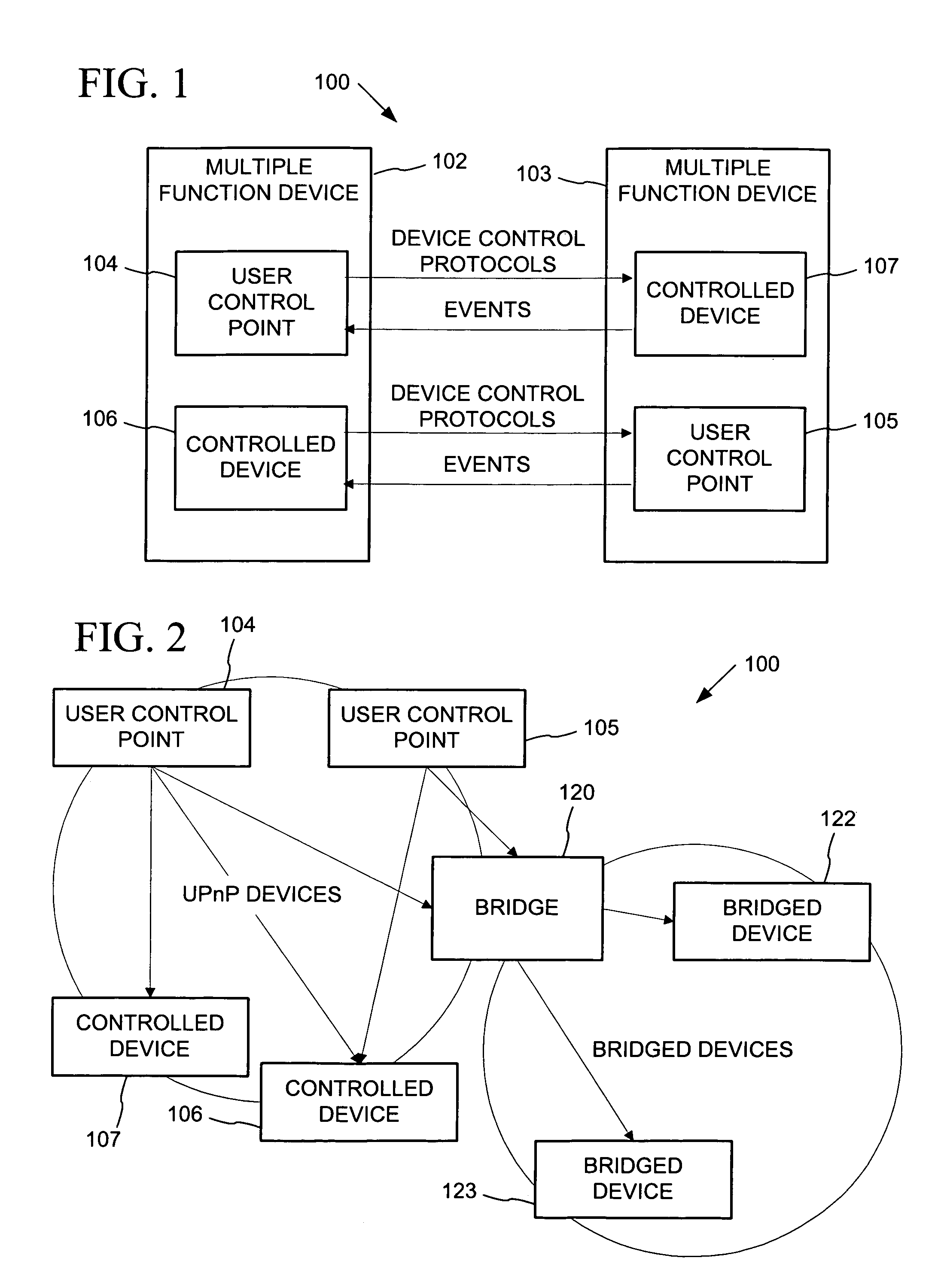
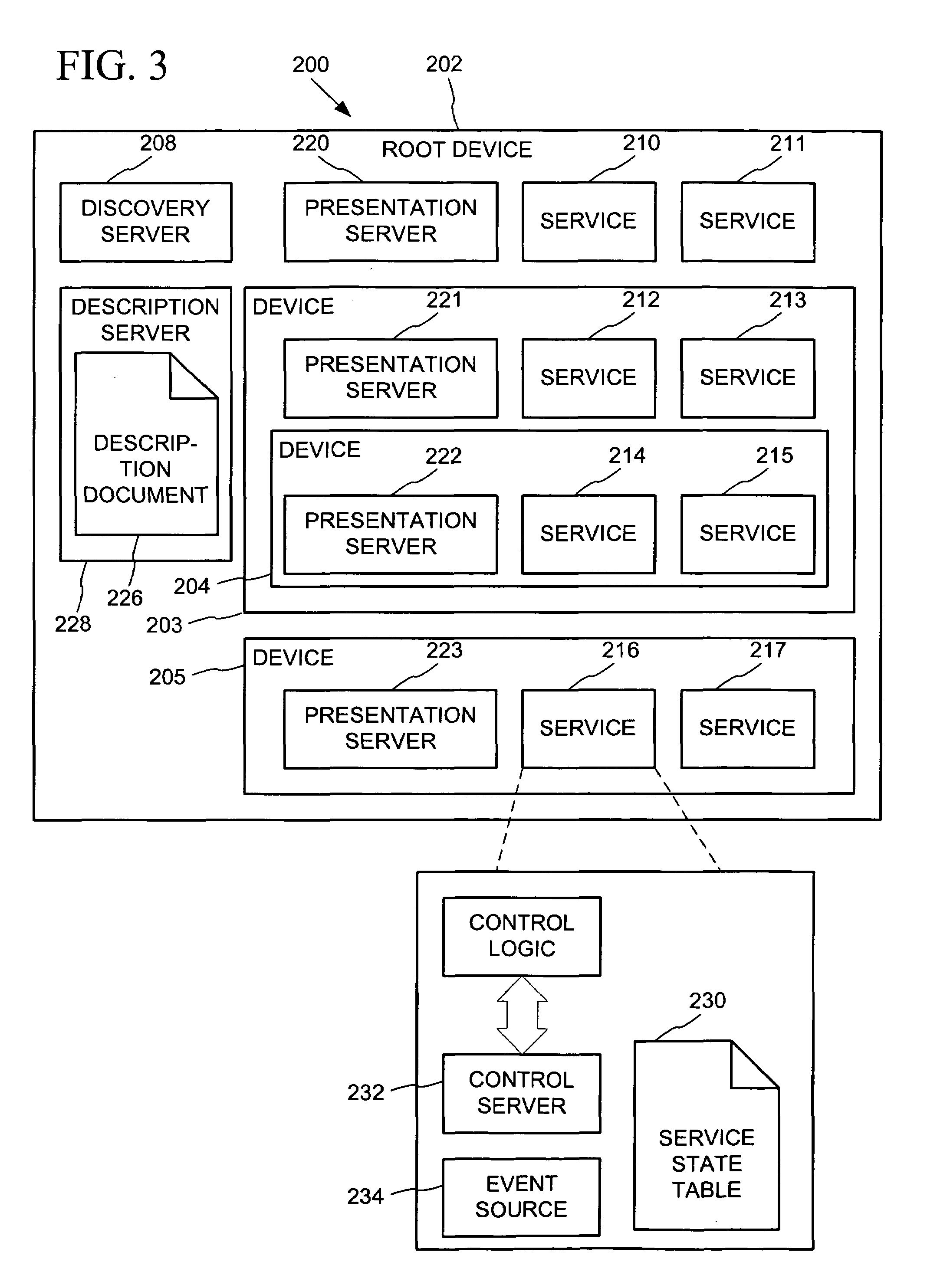
Data driven remote device control model with general programming interface-to-network messaging adapter
InactiveUS7085814B1CostConnectivity solutionMultiple digital computer combinationsNetworks interconnectionService protocolData description
A general programmatic interface-to-network messaging adapter exposes a suitable object integration interface or application programming interface to applications on a controller device and sends network data messages to invoke services or query status of a controlled device. The adapter maps application calls to the interface into network data messages according to service protocols of the controlled device. The general adapter provides the interface suitable to any specific service of a controlled device based on a data description of the interface, and converts the application calls to network data messages based on a data description of a protocol and format for network data messages to interact with the specific service. Once the interface / messaging description is obtained, applications on the controller device can programmatically interact with the adapter, and the adapter then handles appropriate message exchanges with the service of the controlled device. The general adapter allows controller device applications to be written using object-oriented programming, while avoiding code download.
Owner:ROVI TECH CORP
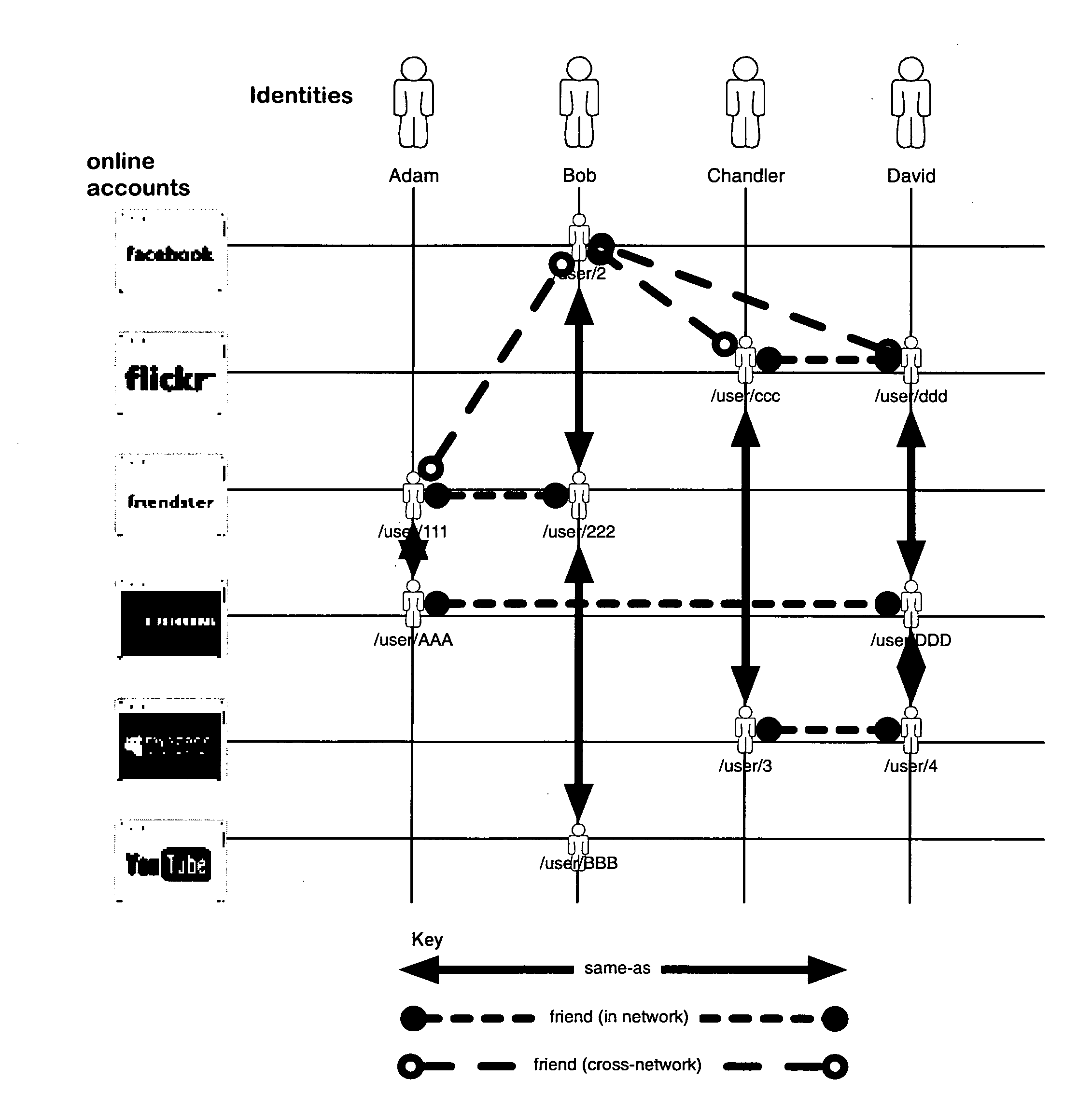
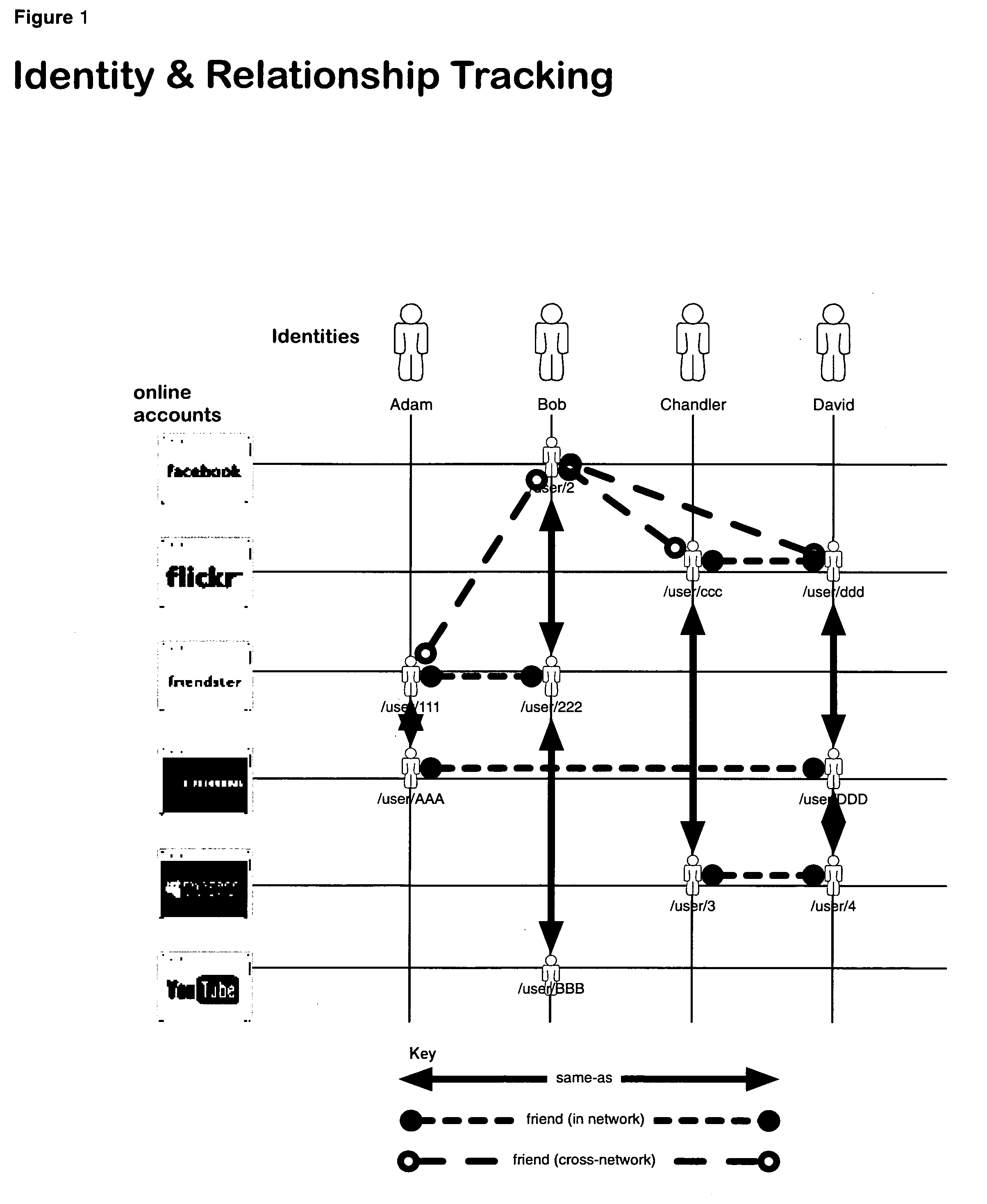
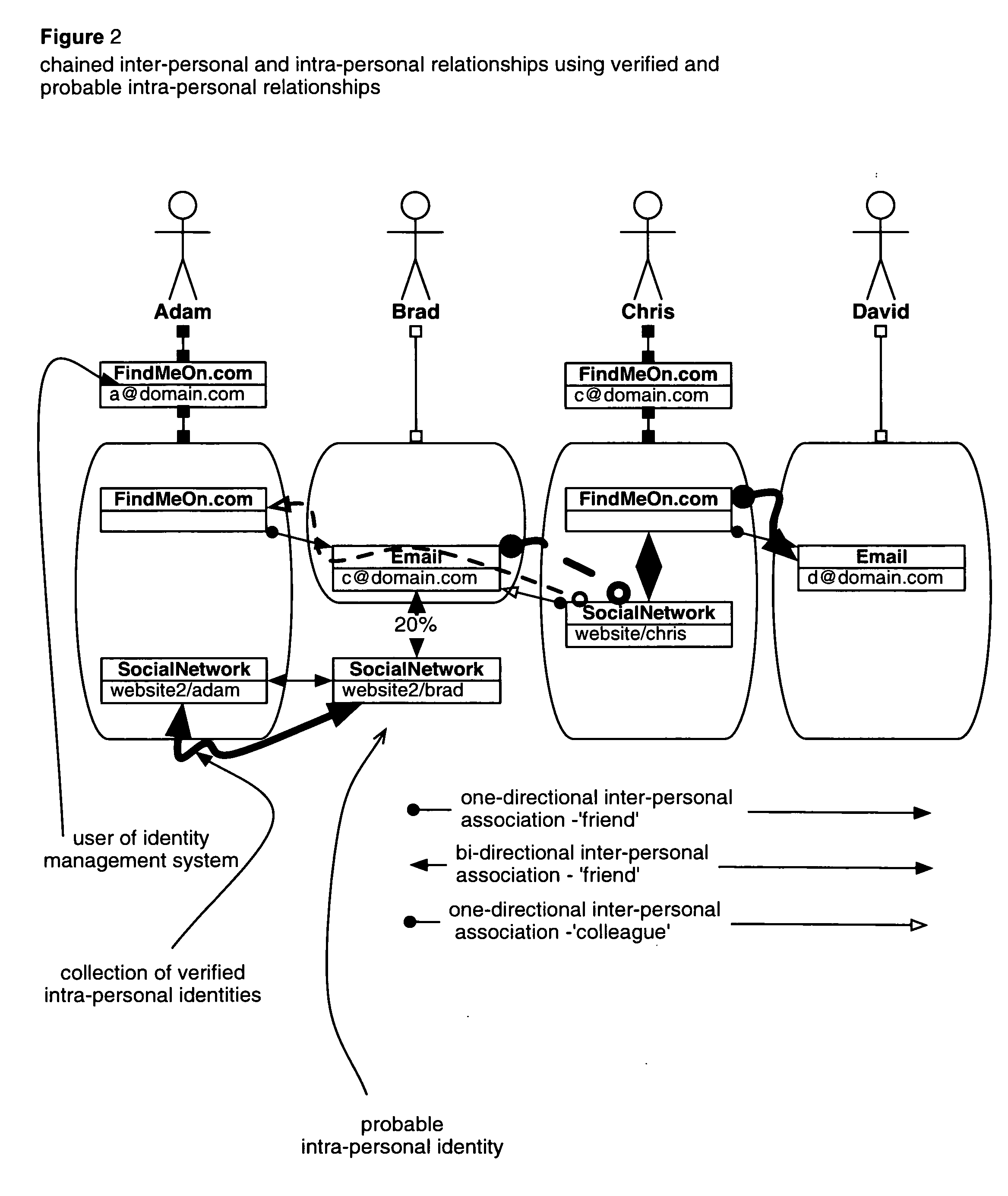
System and method for indexing, correlating, managing, referencing and syndicating identities and relationships across systems
ActiveUS20100274815A1Rich and more detailed and more completeRaise the possibilityDigital data information retrievalDigital data processing detailsThird partyFederated identity
A networking database containing a plurality of records for different identities in which identities are connected to one another by defined or interpreted Inter-Personal and Intra-Personal relationships. Individuals using the system may define, group and categorize specific identities and relationships; the system may also define, categorize and group both identities and relationships belonging to individuals registered with the system and unregistered users through computational analysis. Identities and relationships may be discovered by the system via an opt-in user-provided mechanism, via a third-party providing information, or through the system's own discovery. Identity and Relationship data can then be used to customize content.
Owner:VANASCO JONATHAN BRIAN
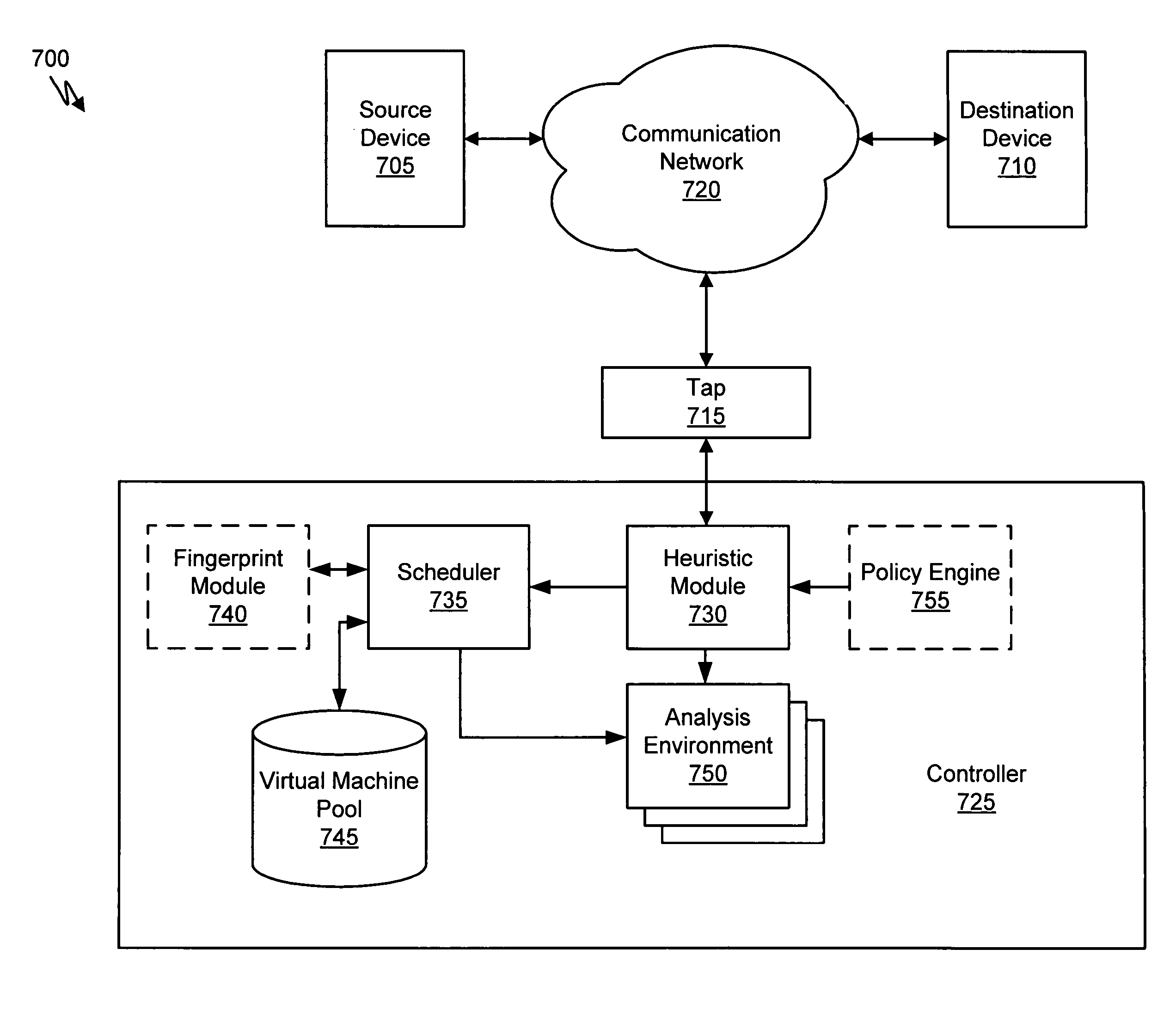
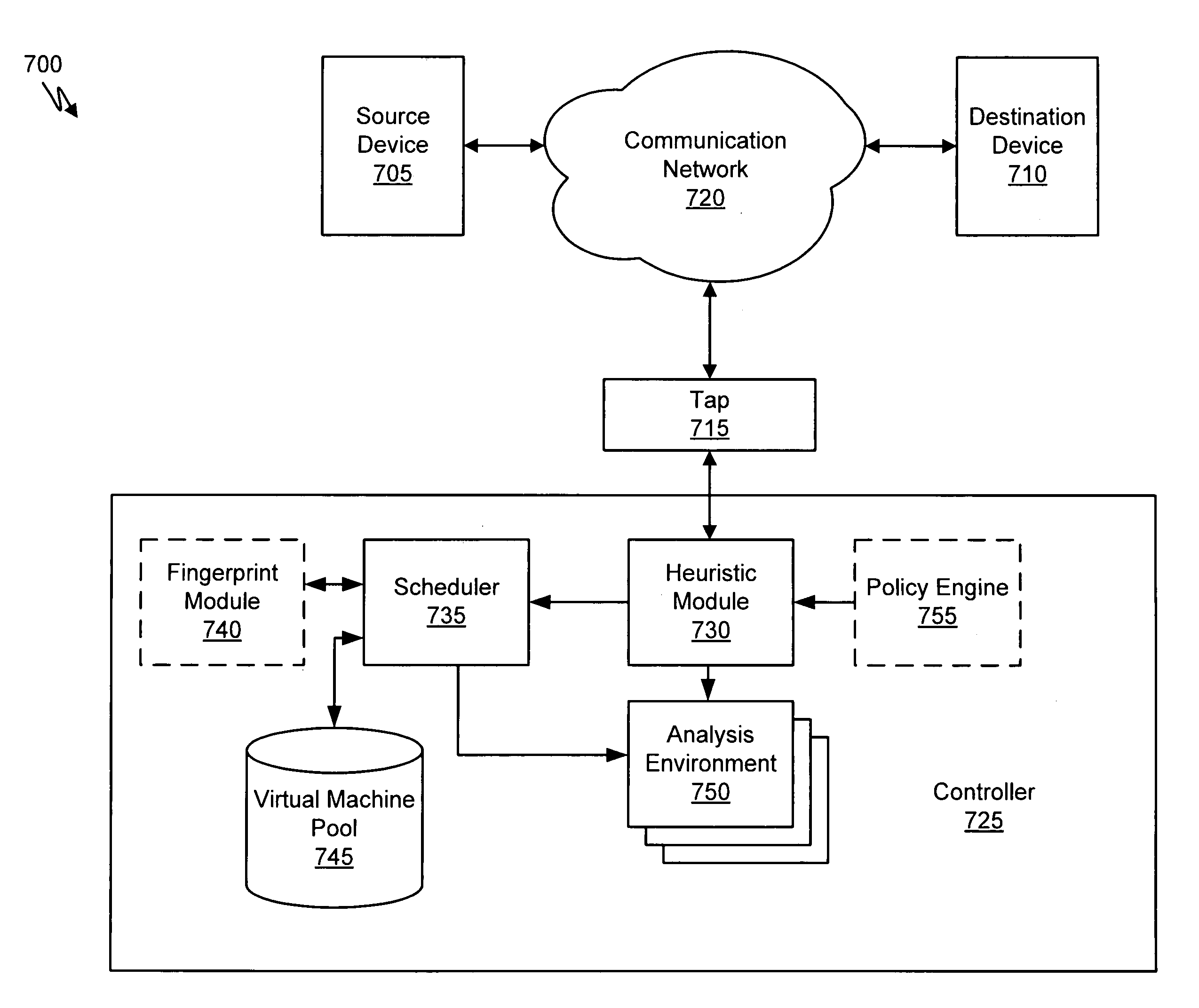
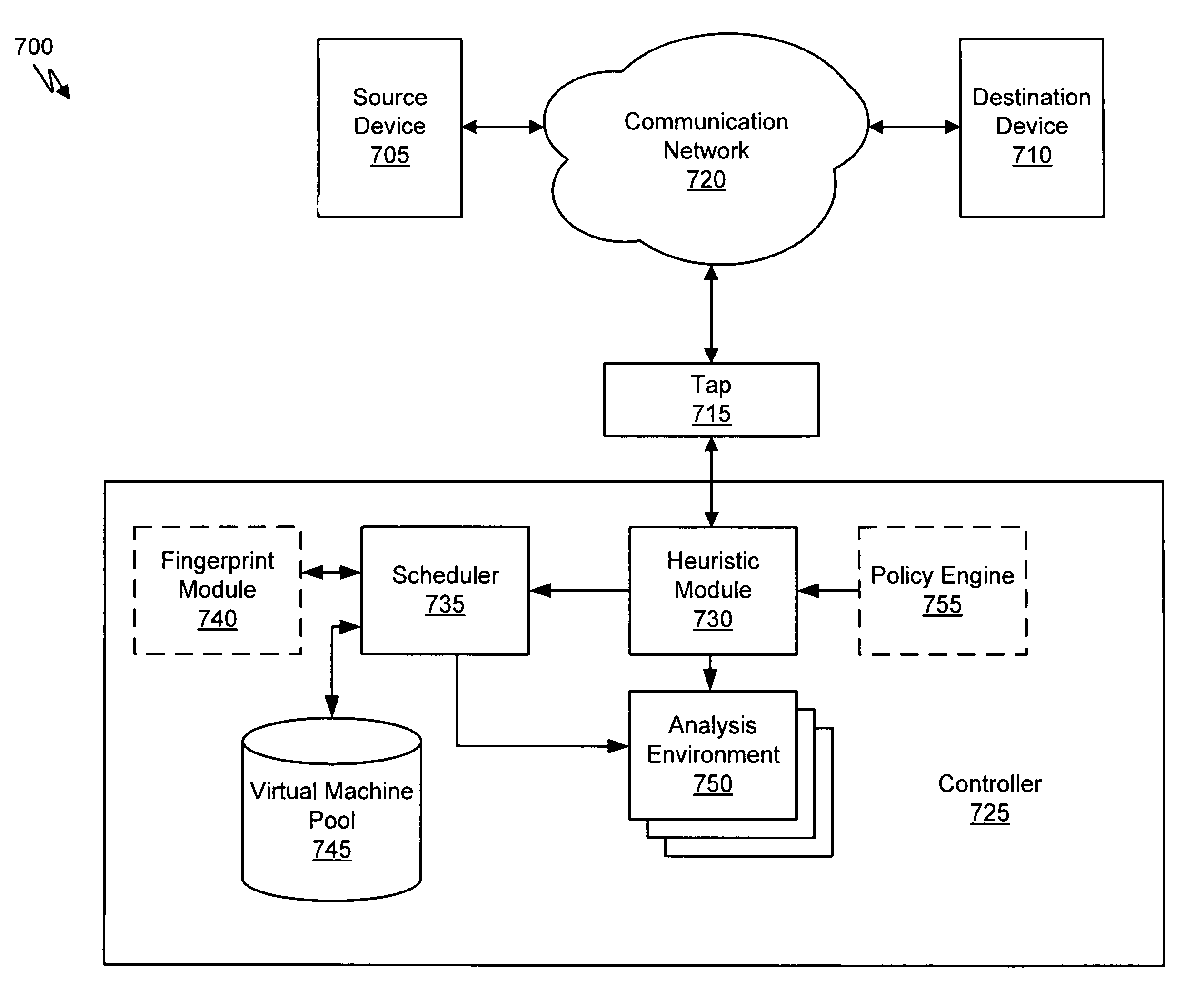
Virtual machine with dynamic data flow analysis
ActiveUS20070250930A1Memory loss protectionUnauthorized memory use protectionDynamic data flow analysisNetwork data
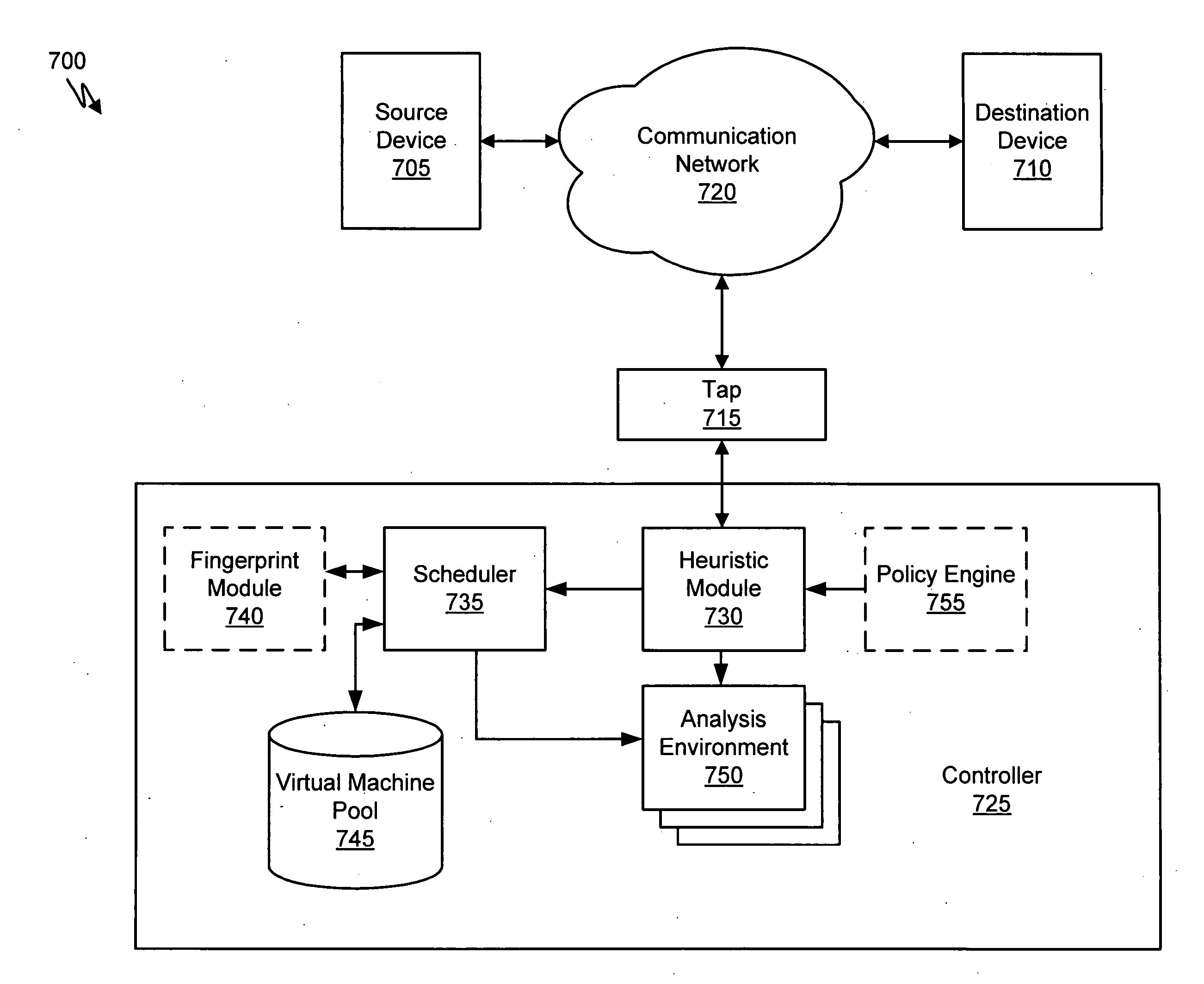
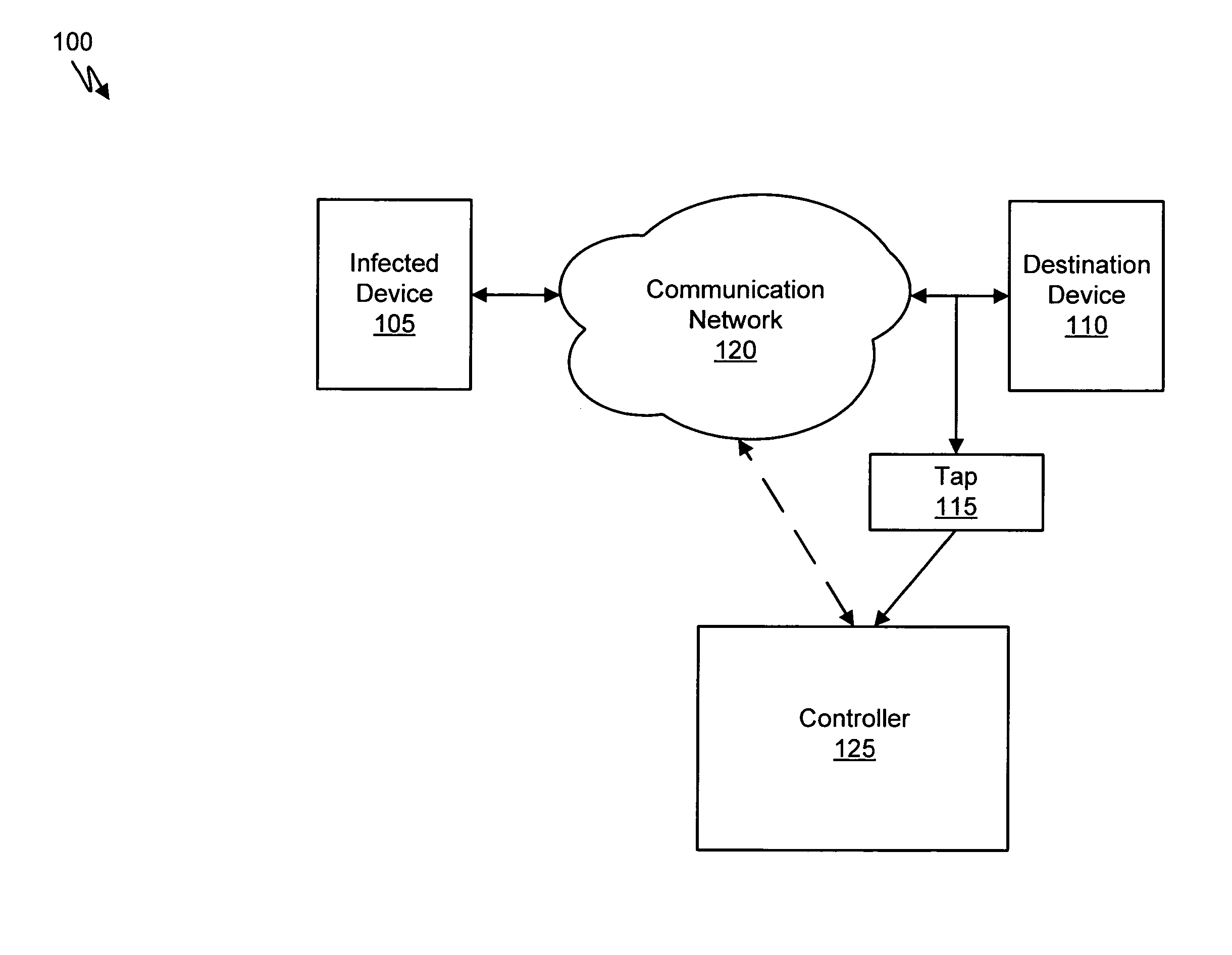
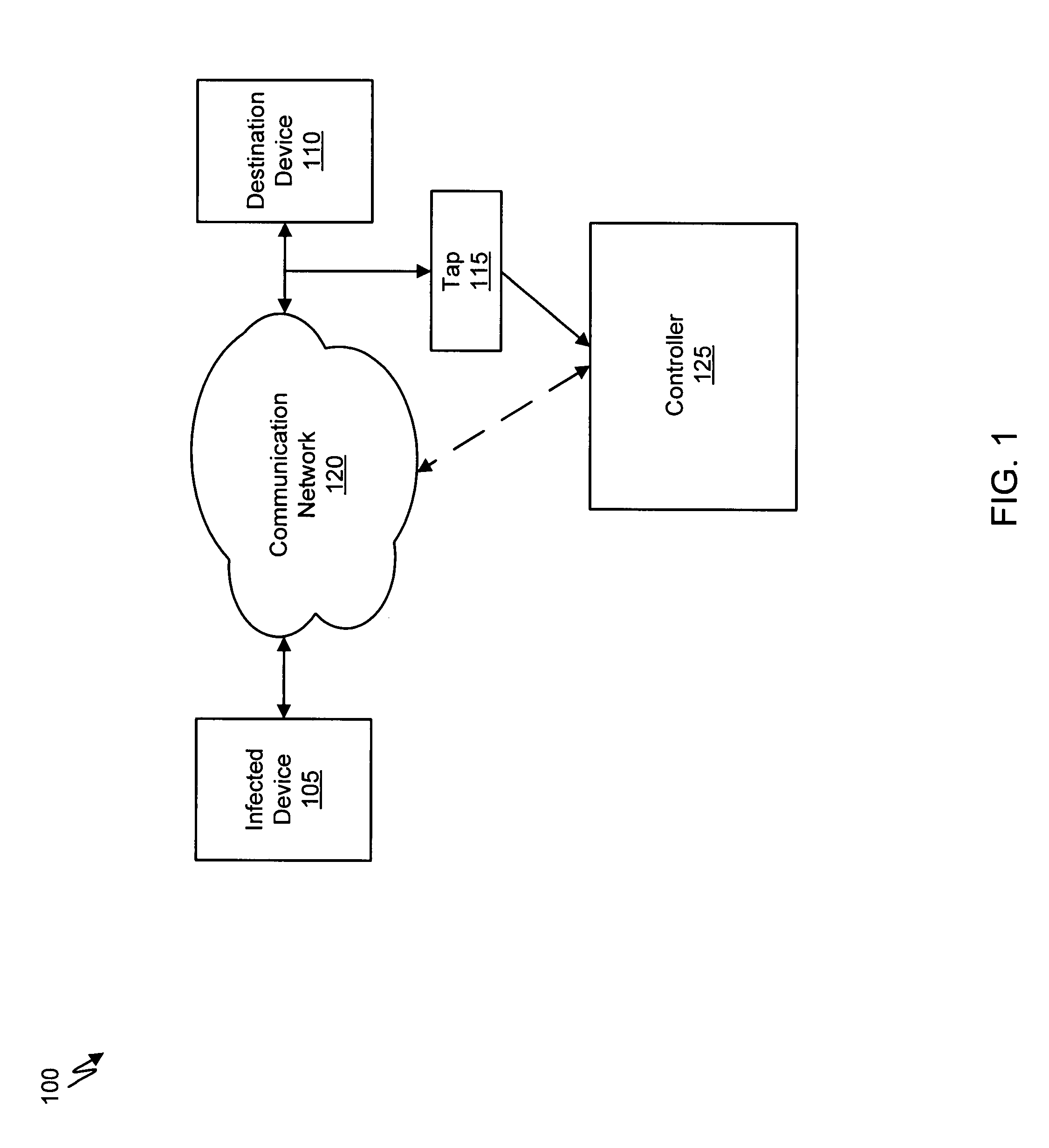
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, and concurrently simulate transmission of the network data to a plurality of destination devices.
Owner:FIREEYE SECURITY HLDG US LLC
Heuristic based capture with replay to virtual machine
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is coupled to the tap and is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to flag the network data as suspicious, and simulate transmission of the network data to a destination device.
Owner:FIREEYE SECURITY HLDG US LLC
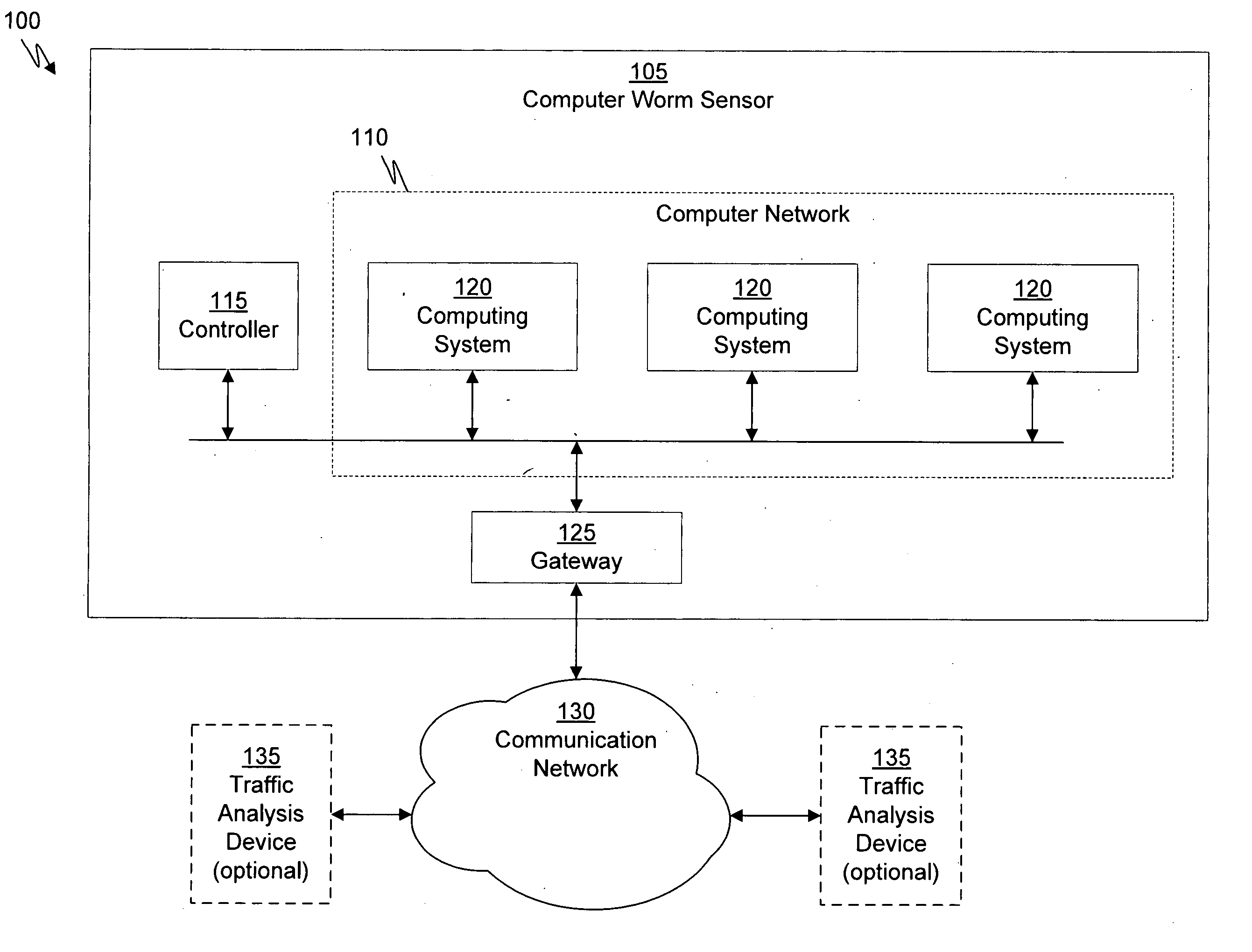
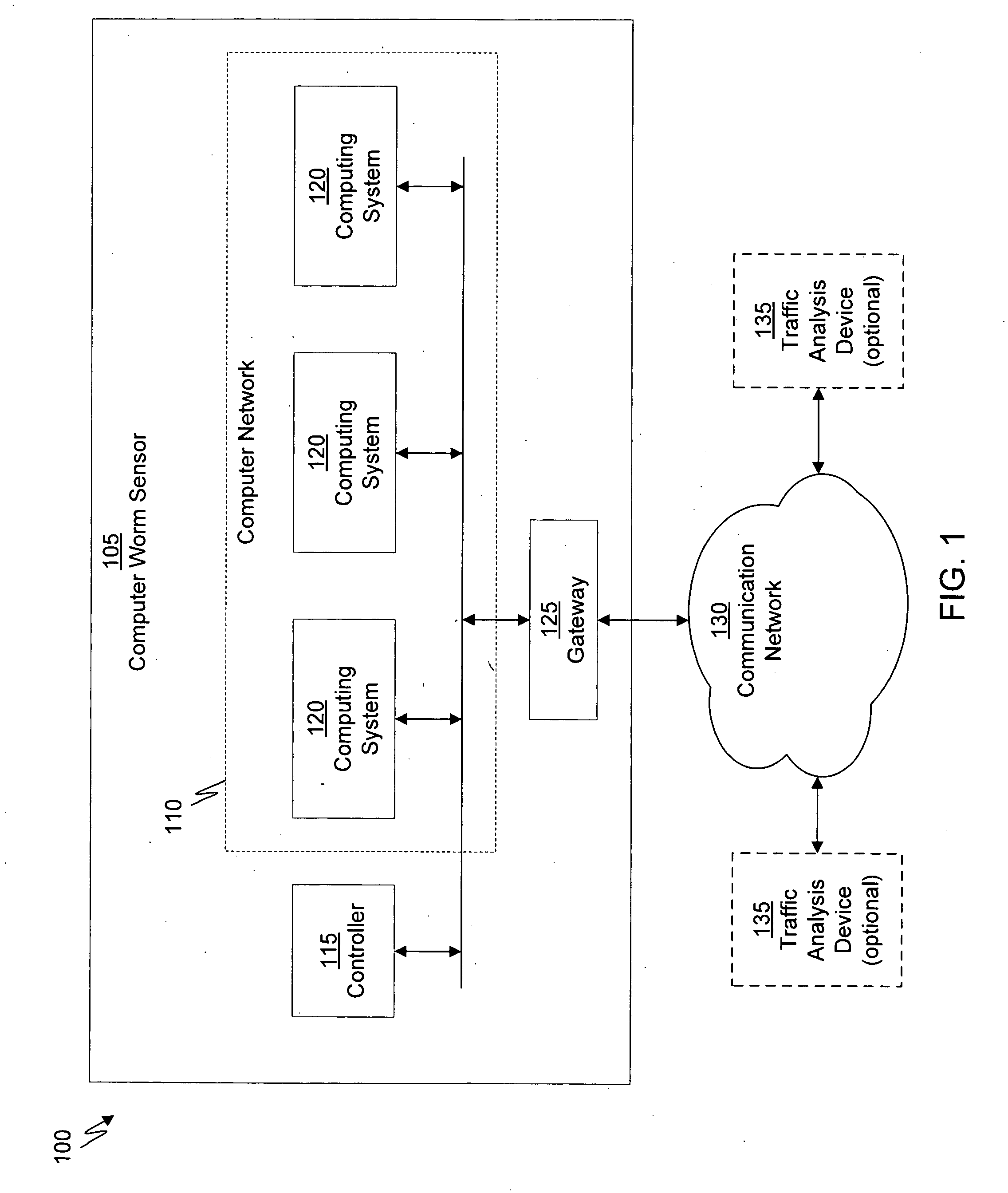
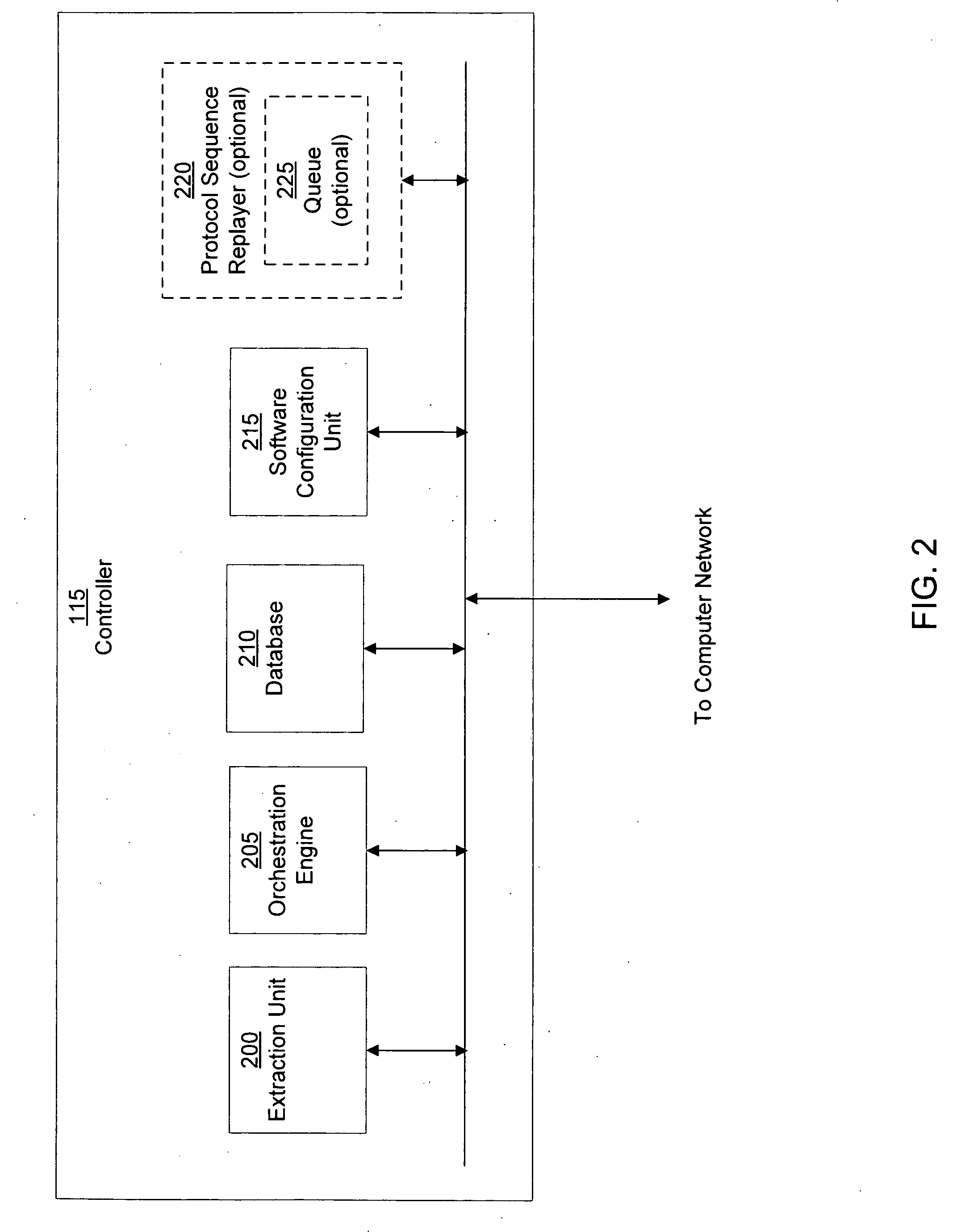
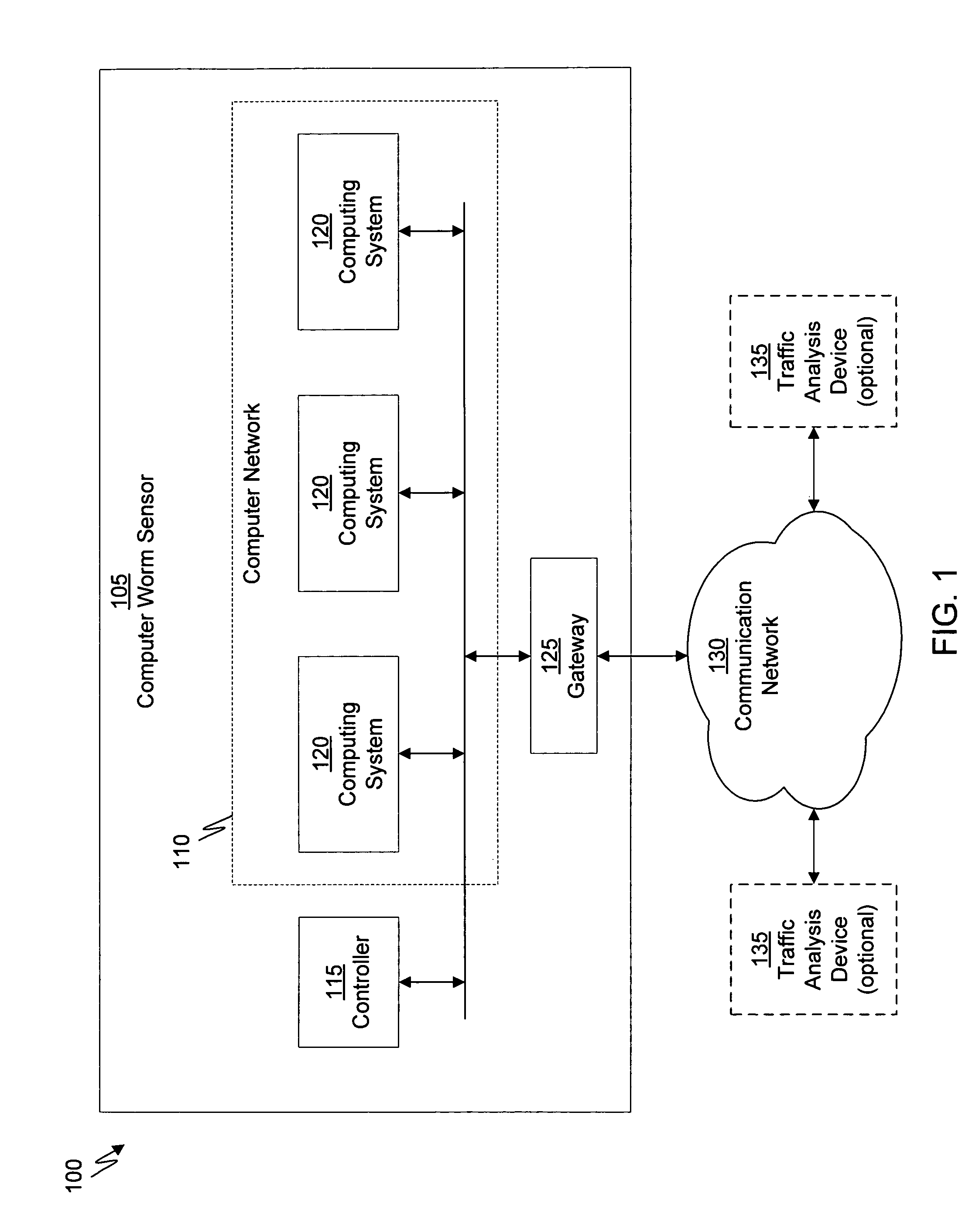
Apparatus and method for remotely monitoring a computer network
InactiveUS20060031476A1Easy to provideMinimize the possibilityDigital computer detailsTransmissionAnti virusPrivate network
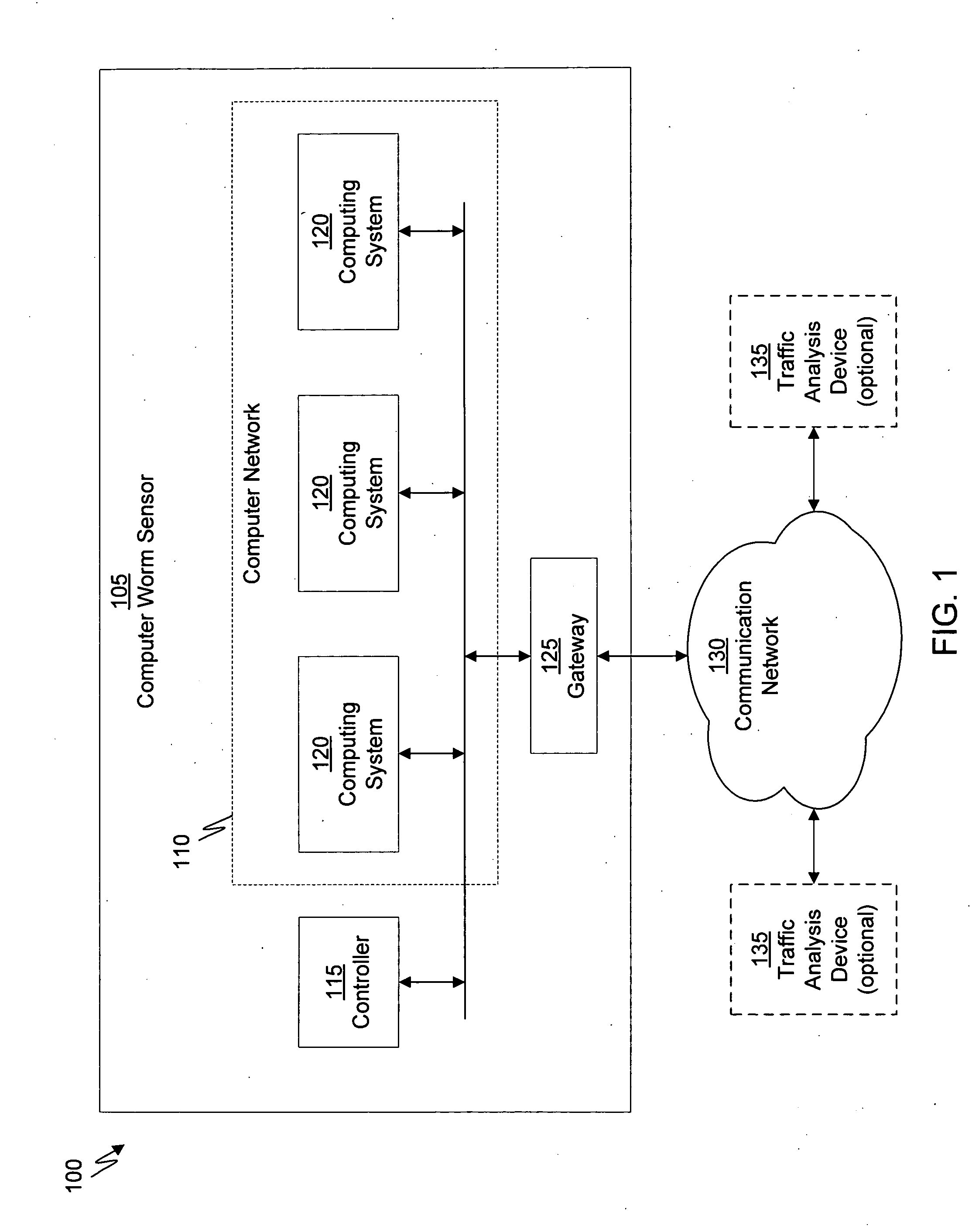
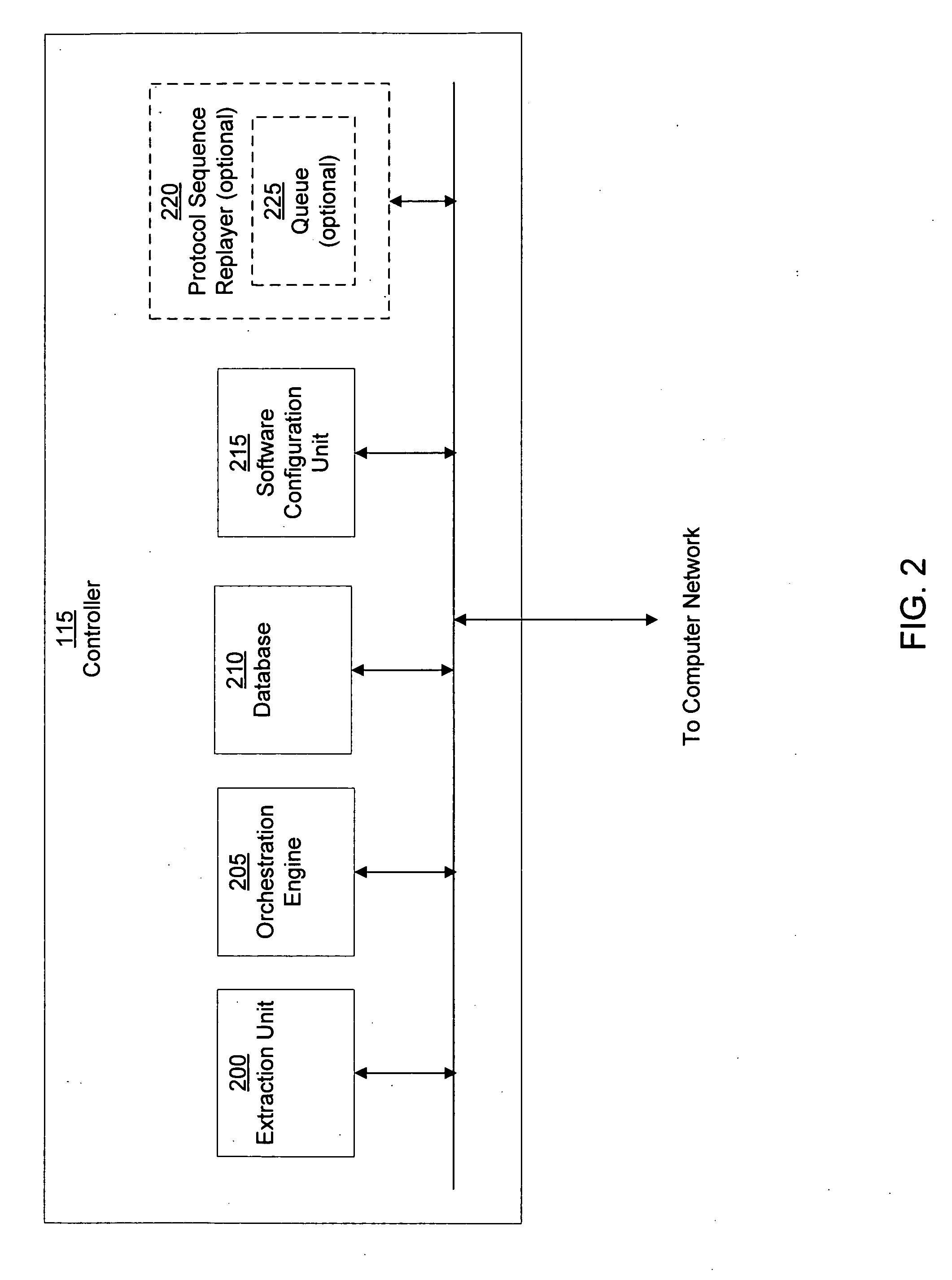
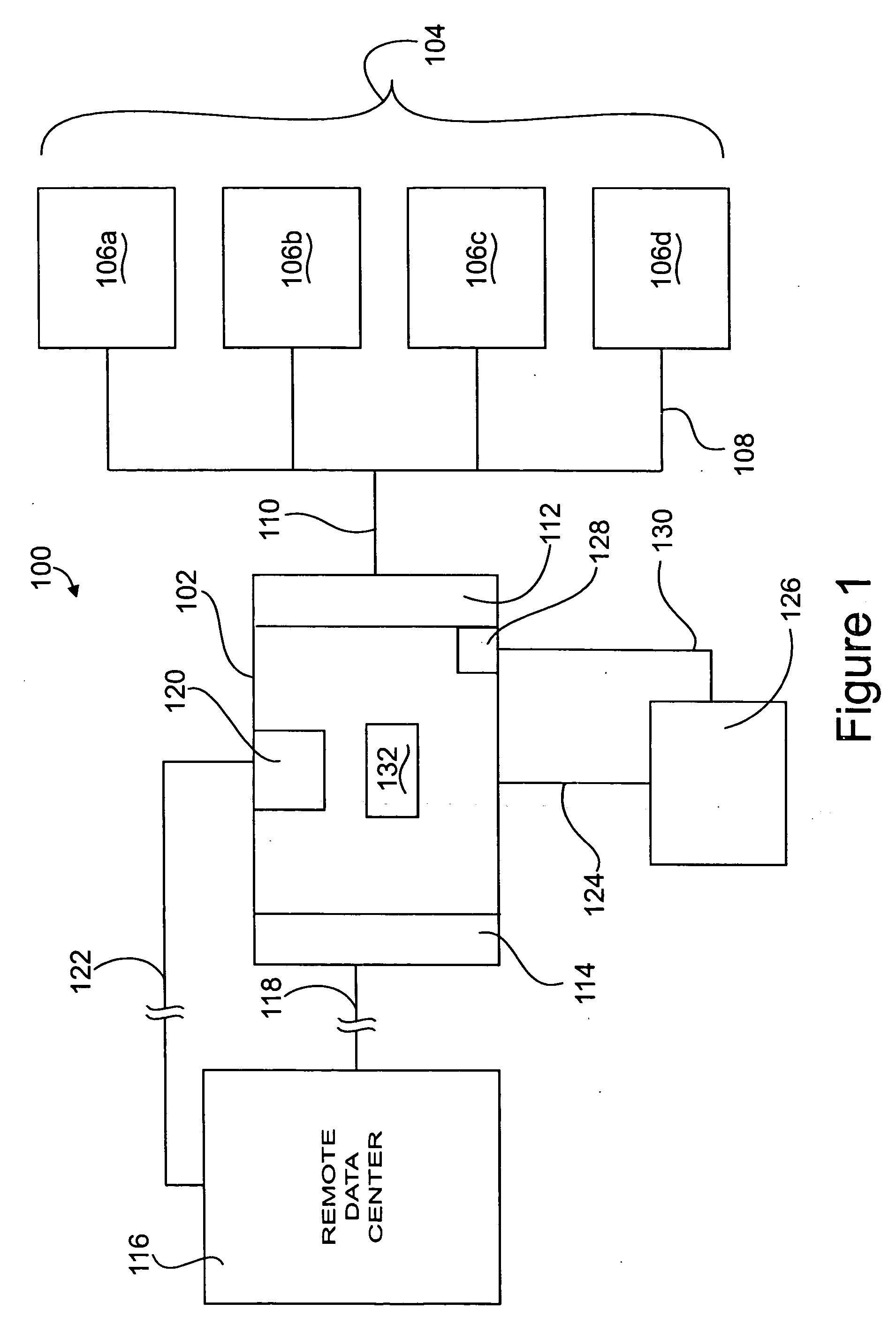
There is provided an apparatus for remotely monitoring a computer network. Monitoring is performed using an inside out approach from behind firewalls and other security devices. The monitoring appliance is shipped to a client site preconfigured and typically requires no technically trained person for installation. Collected network data is periodically transmitted to a remote monitoring facility where it is recorded and analyzed. Both the monitoring appliance and the remote center maintain the configuration data. Typically, no client data is transmitted to the remote monitoring site. If the monitoring appliance fails, a completely configured replacement may be shipped to the site and easily installed. The monitoring appliance is optionally equipped to provide network services. Services such as web hosting, file server, print server, virtual private network (VPN), shared Internet access, web content filtering, anti-virus, spam e-mail elimination, and IP telephony services as well as other such services may be easily provided.
Owner:MATHES MARVIN LEE +1
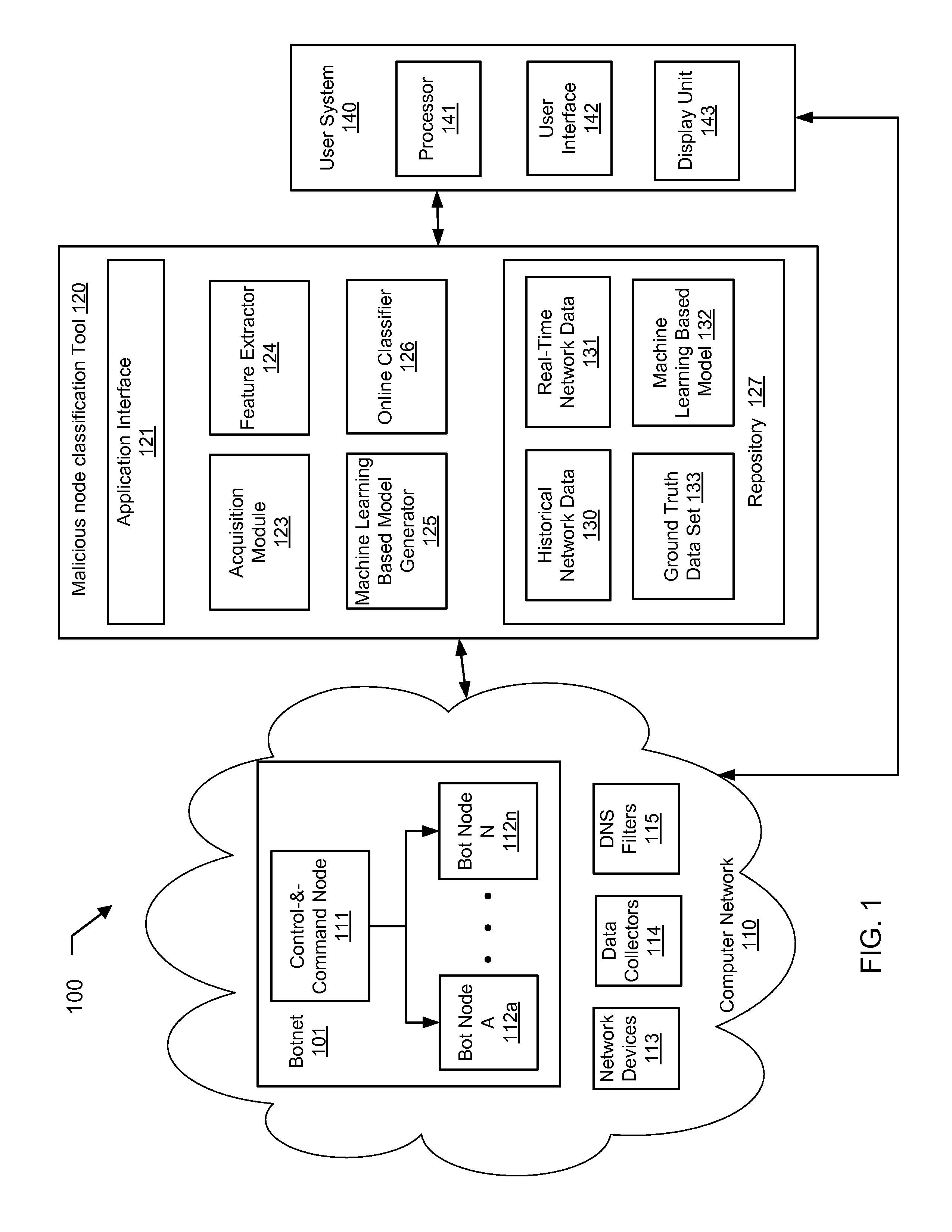
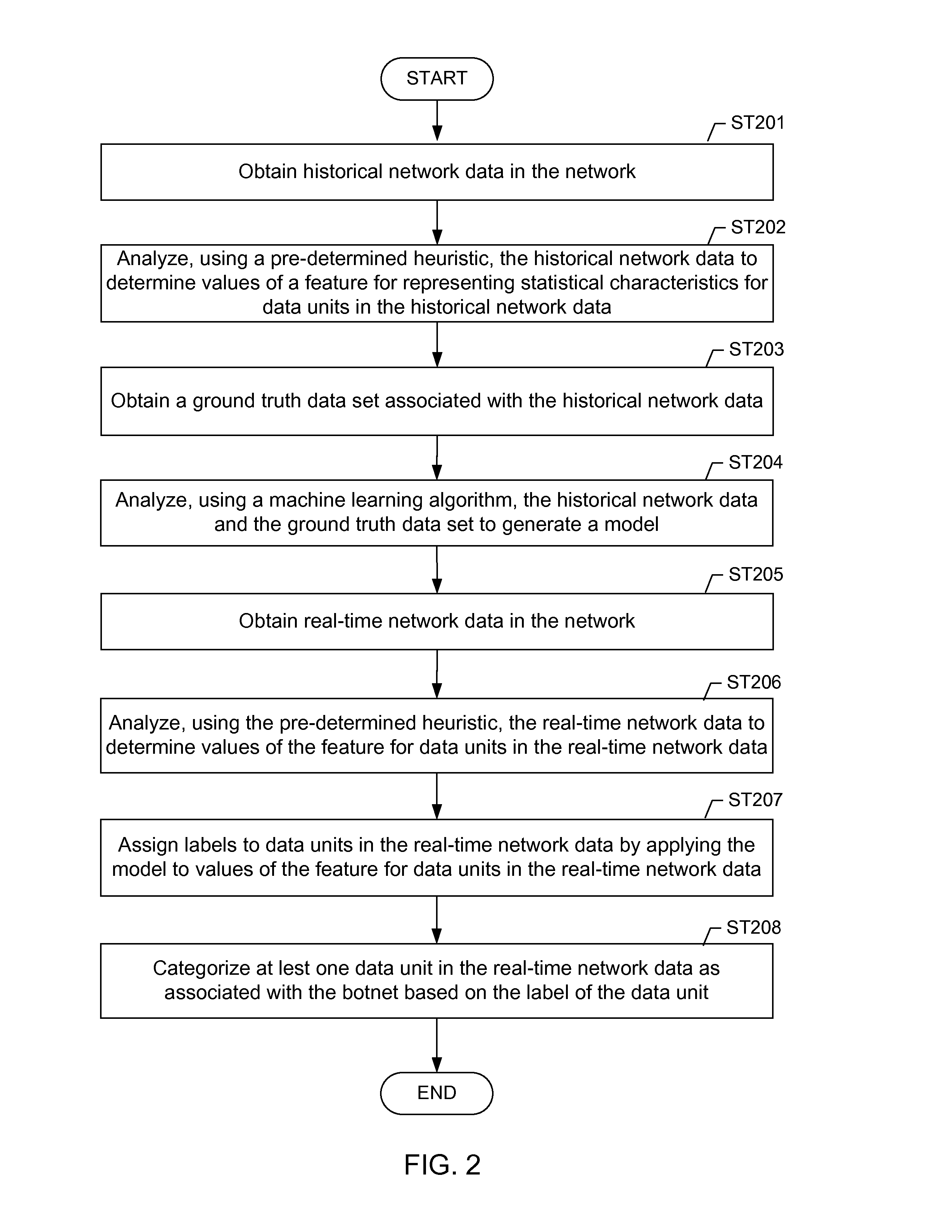
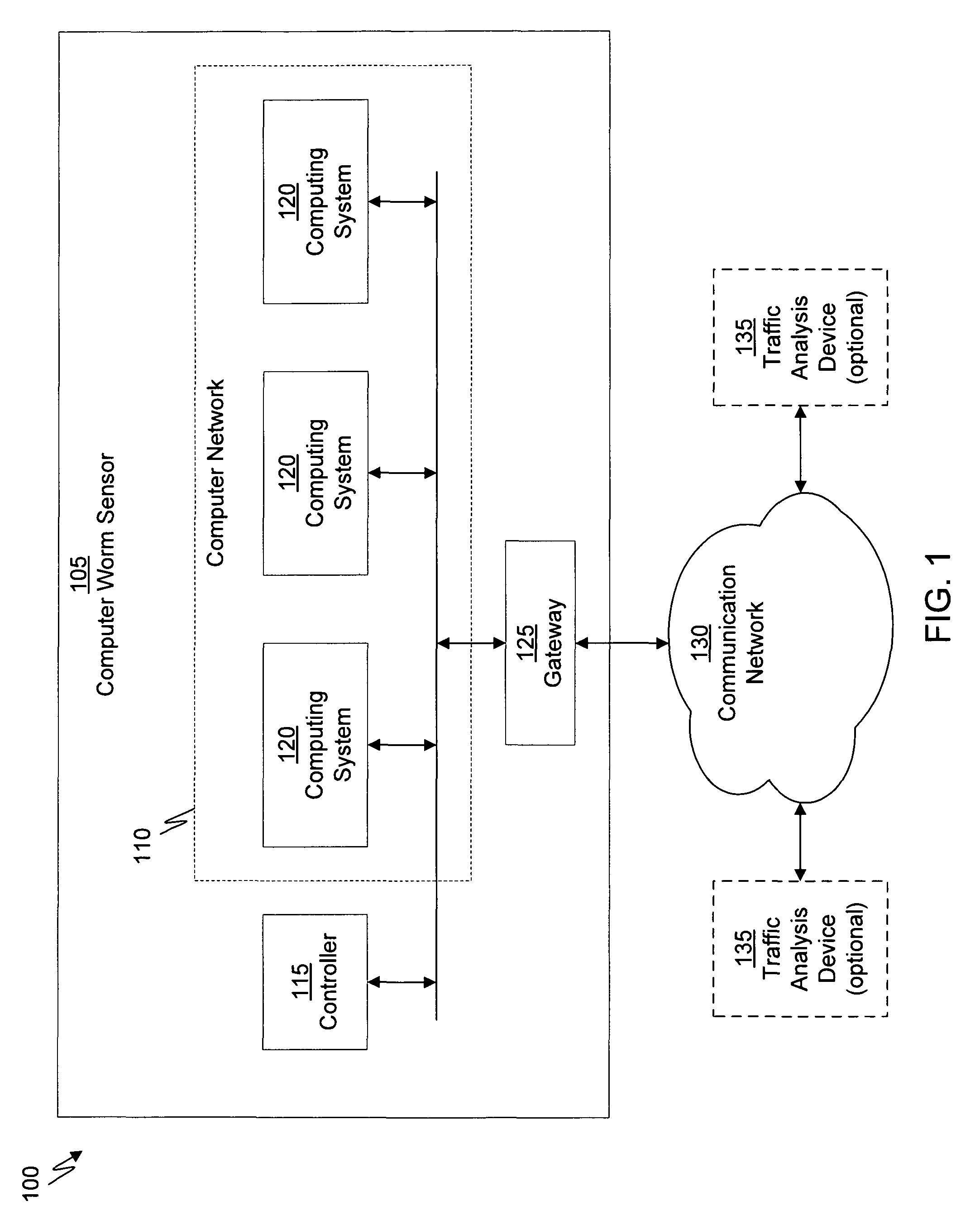
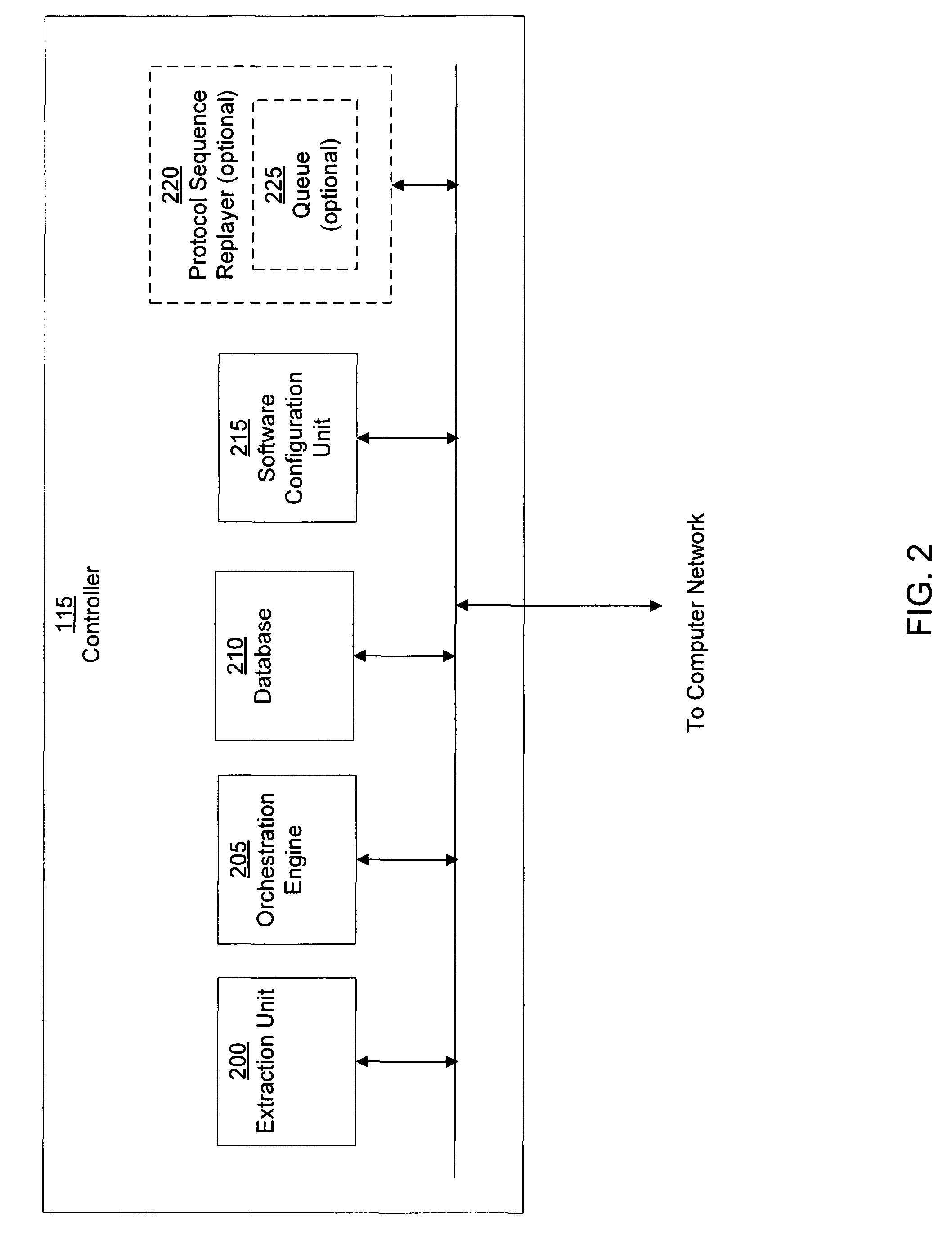
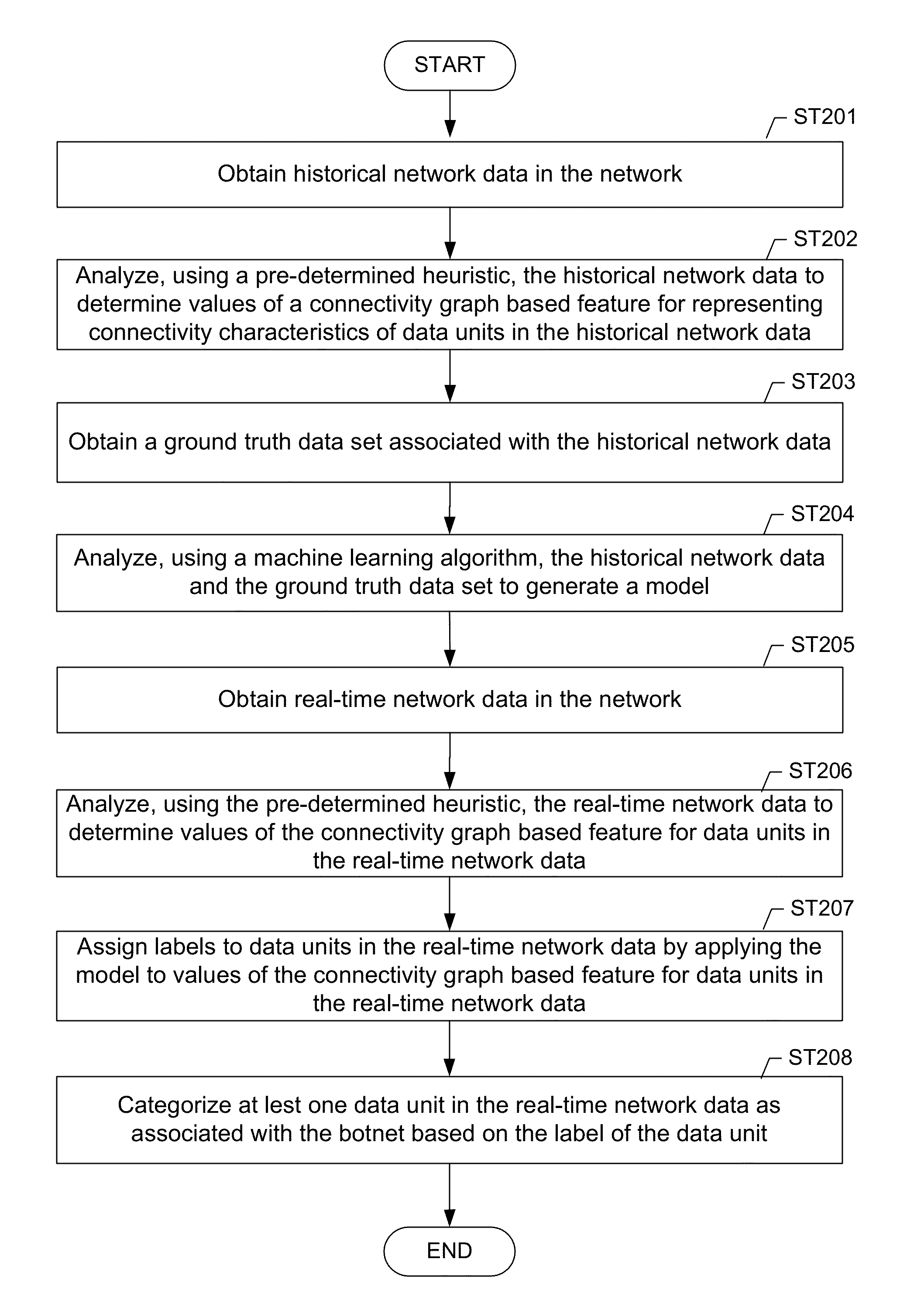
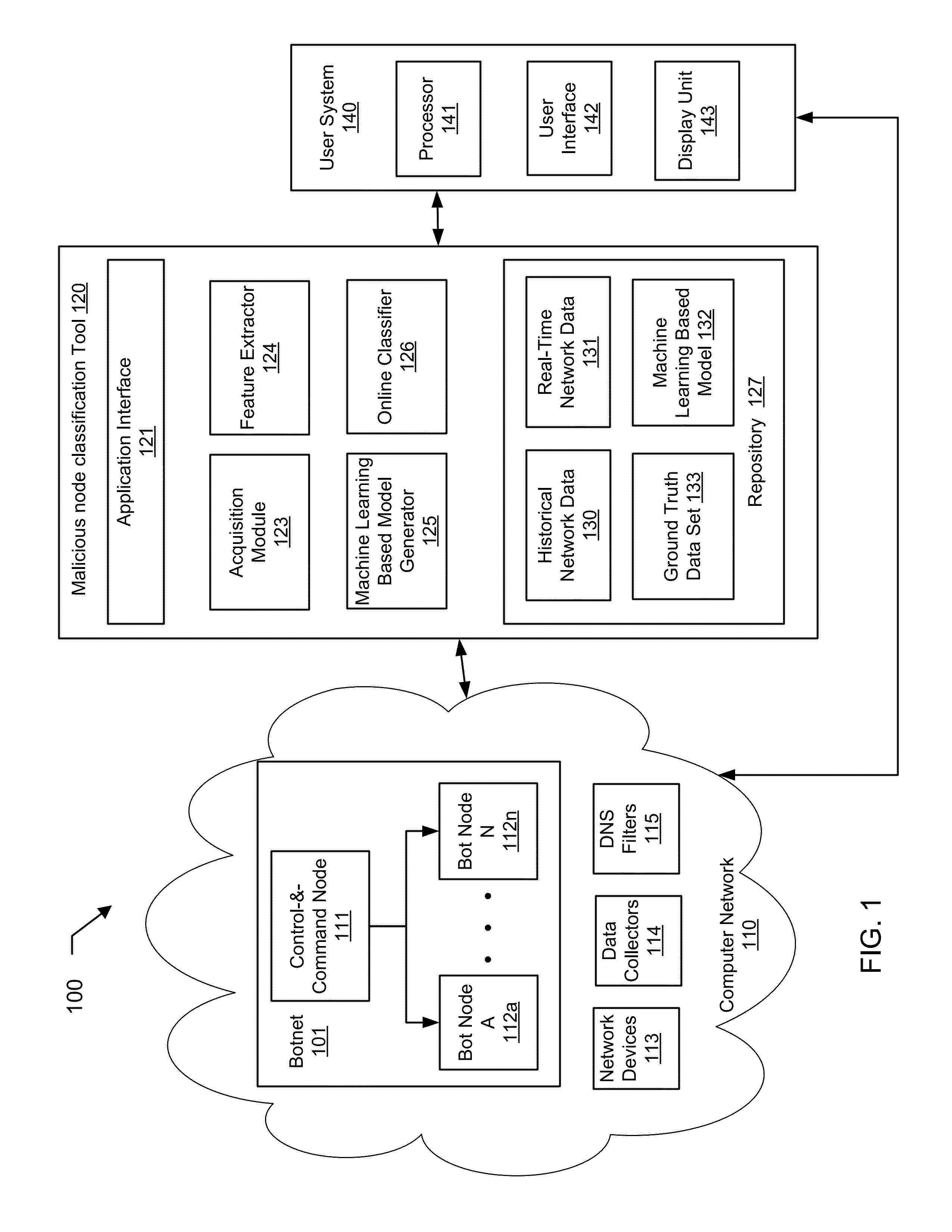
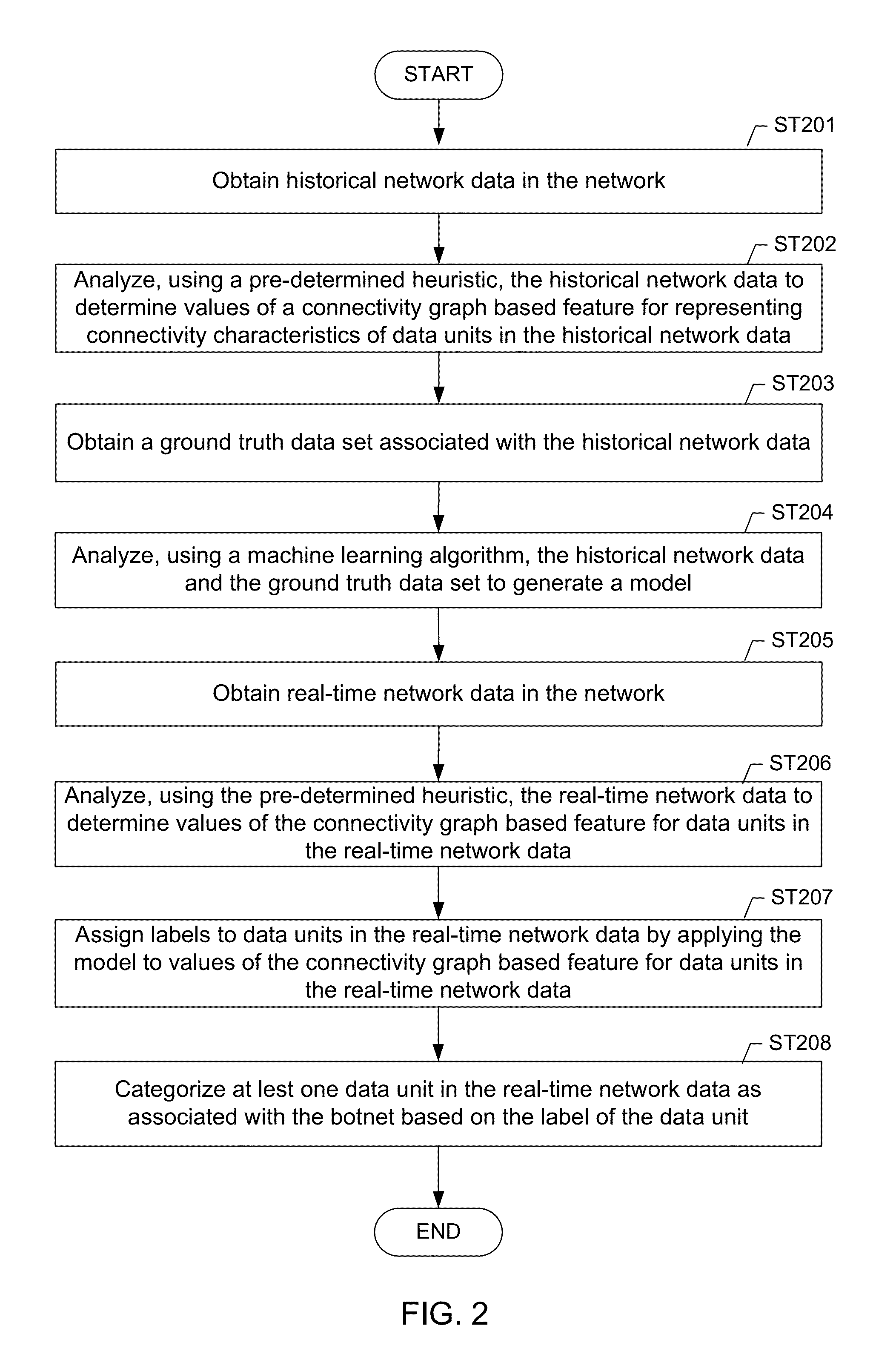
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
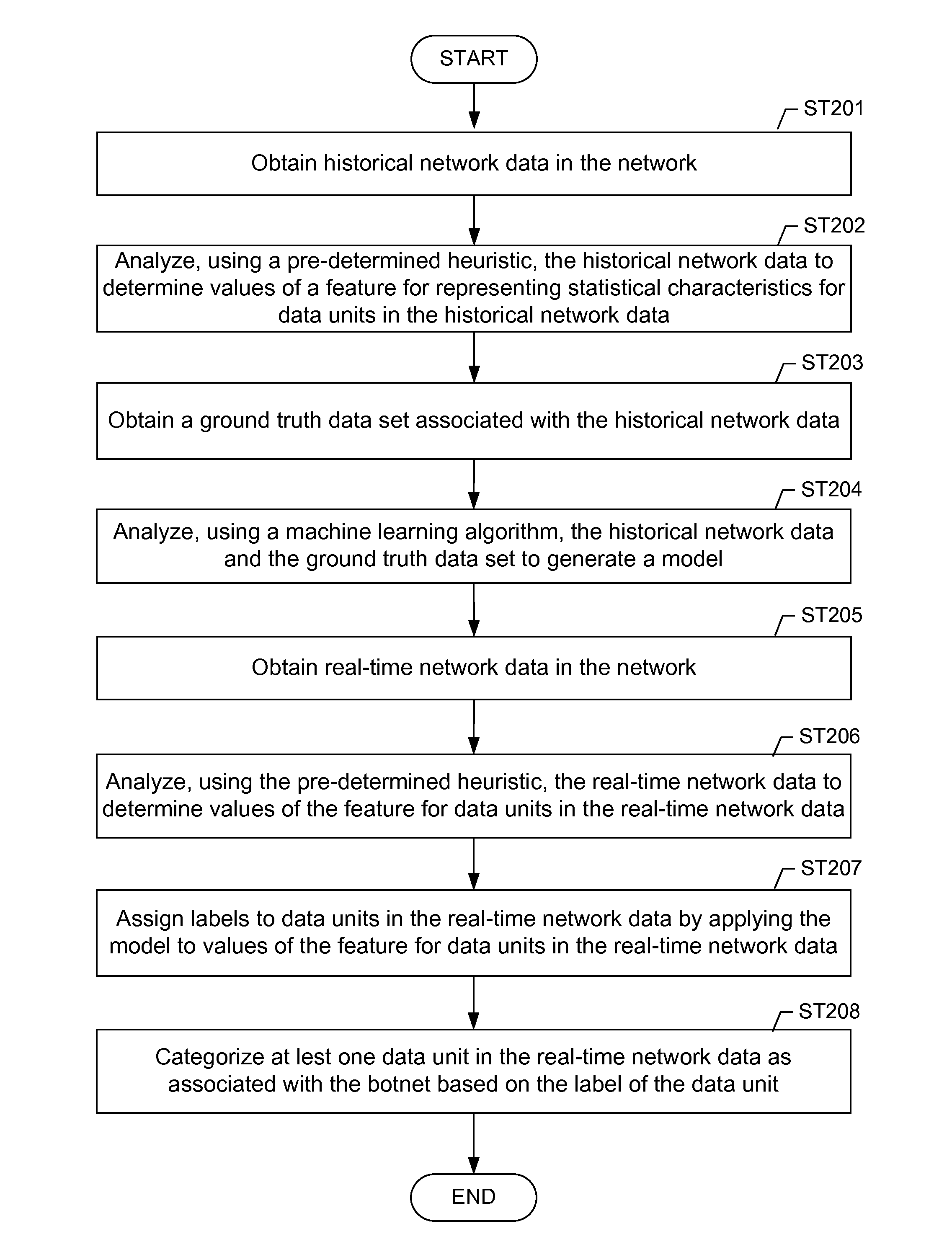
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
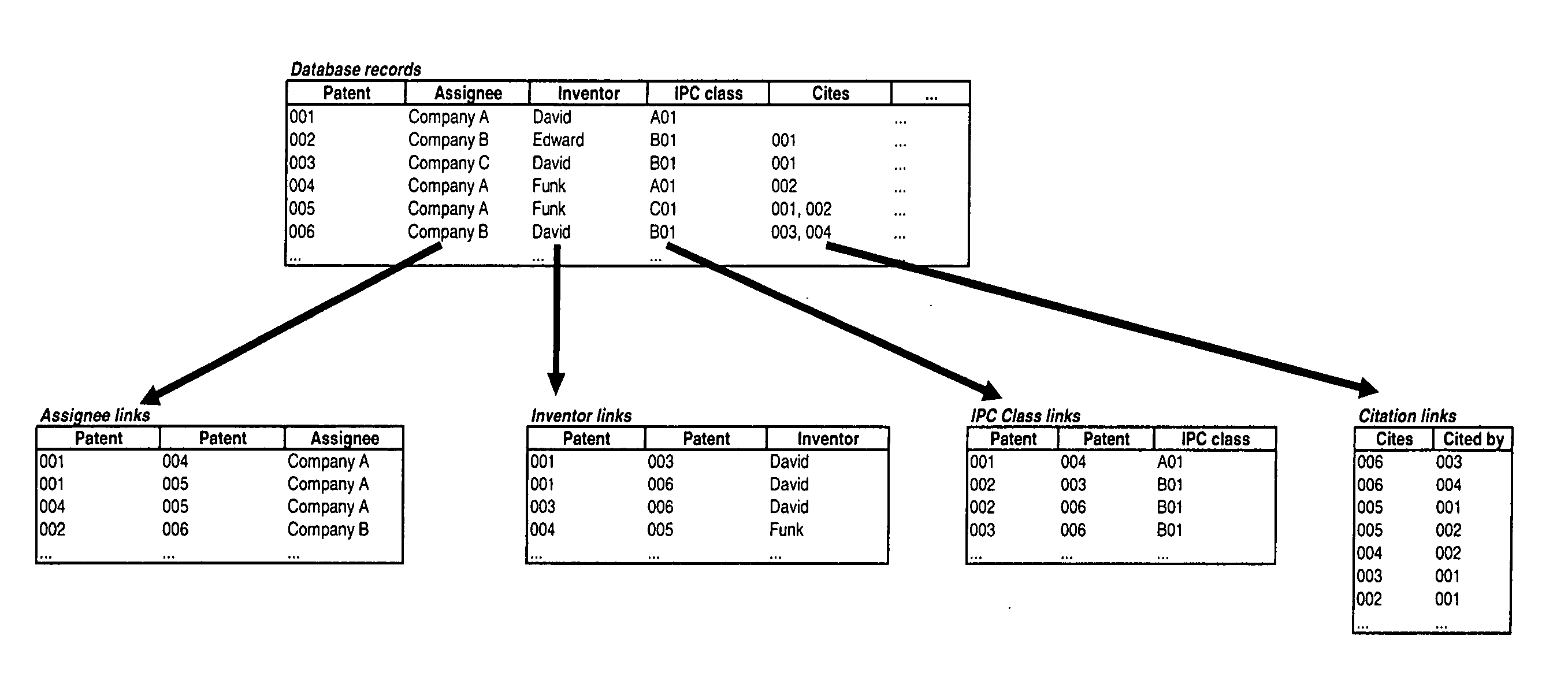
Method and apparatus for selecting, analyzing, and visualizing related database records as a network
A method and apparatus for selecting and converting database records or sets of related documents into network data and presenting that data in a network visualization system that enables users to select among, and move between various network displays by selecting one or more attributes of the data to be represented as the nodes and links of the network.
Owner:BOSTON CONSULTING GROUP
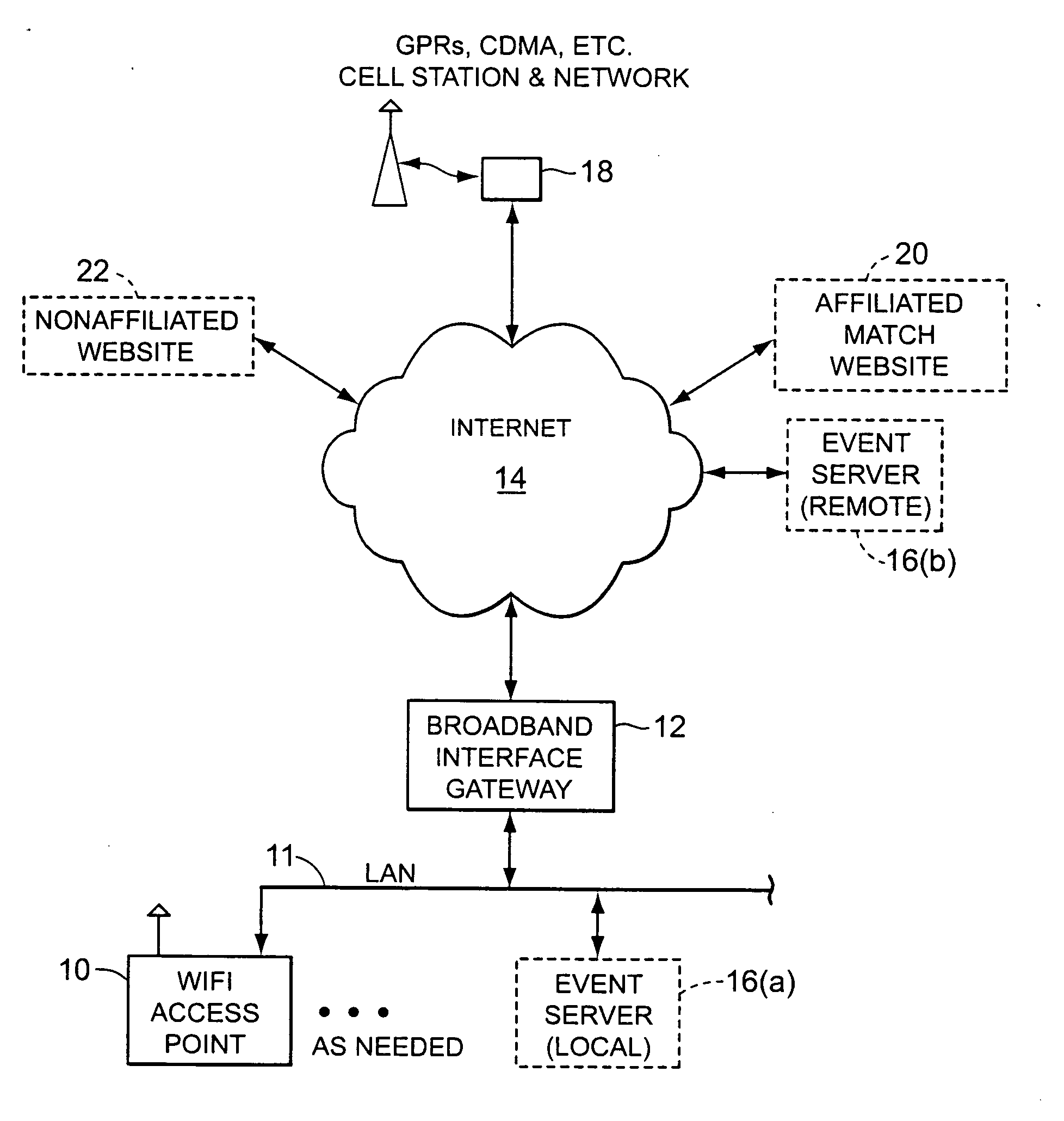
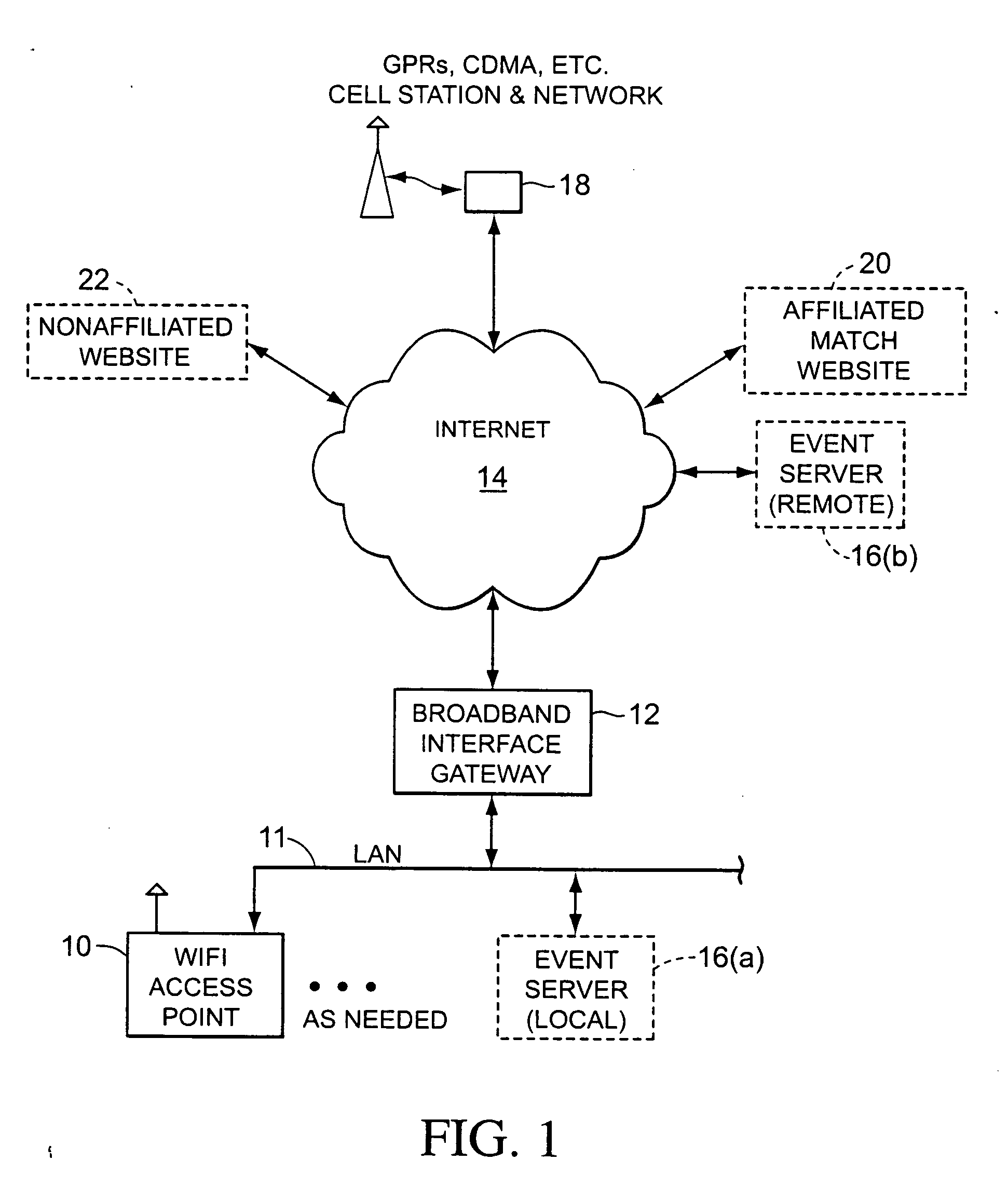
Realtime, interactive and geographically defined computerized personal matching systems and methods
ActiveUS20070032240A1Payment architectureRadio/inductive link selection arrangementsCommunications systemGeolocation
A system and method of interactive and live computerized matching in which a first user is provided with a personal data device including a wireless communication system. A secure network is configured to include a server programmed with a personal characteristic database and a database searching algorithm, and a wireless communication system at a specific geographic location that is capable of communicating with the user's personal data device. The first user is allowed to log on through the wireless communication system to the secure network using his or her personal data device, and communicates to and stores in the database personal data defining his or her characteristics and those for his or her ideal match. Either the secure network automatically identifies the first users precise geographic location, or the user himself otherwise indicates and stores in the database of the network an identifying address that indicates his current specific geographic location. The user then instructs the database searching algorithm to search for and identify other users similarly logged on to the network at the same specific geographic location. The user is able to initiate a search of the database for possible matches within the pool of other users also logged on to the network at the same specific geographic location. The secure network then indicates to the first user the results of the search.
Owner:RESIGHT LLC
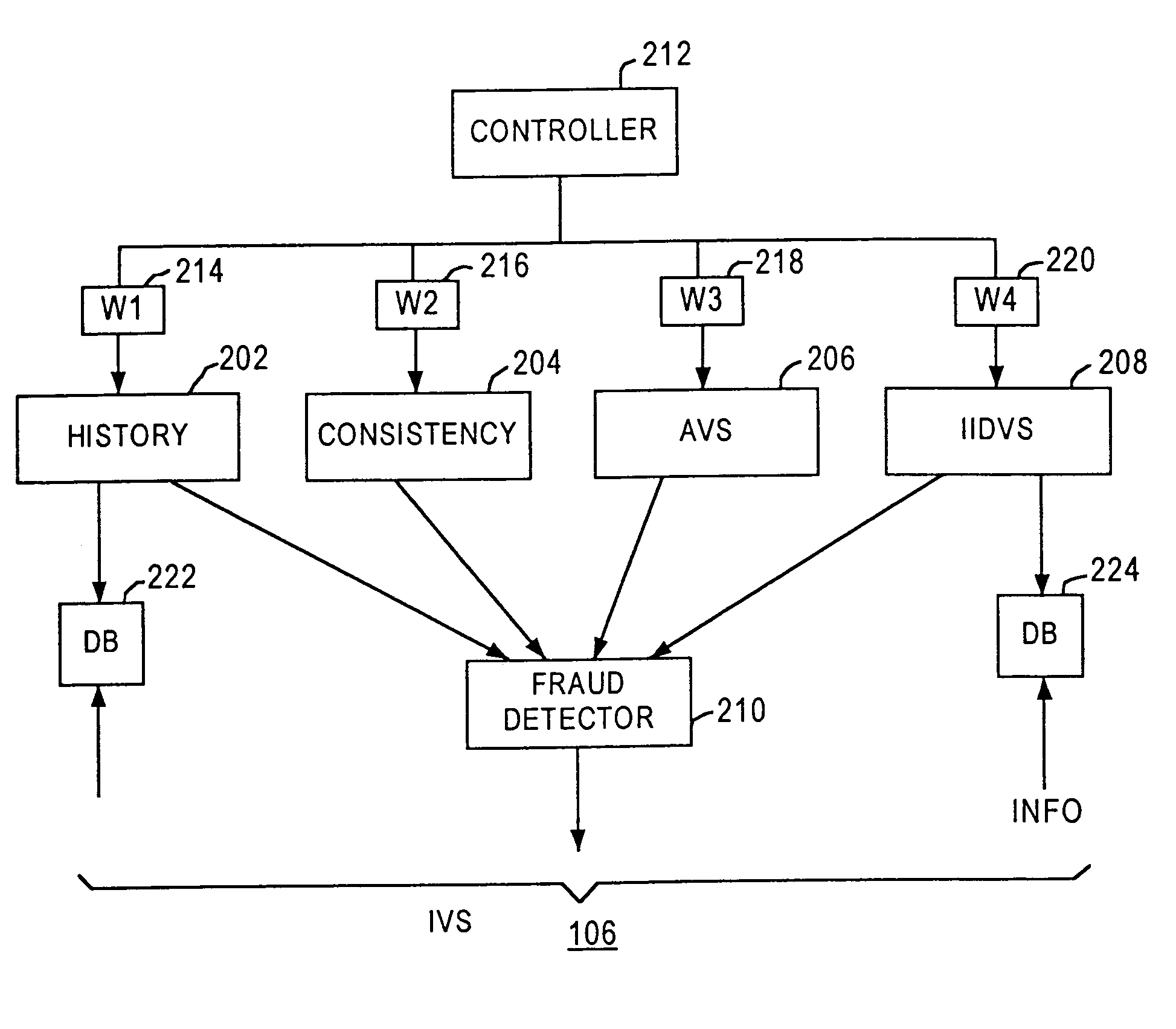
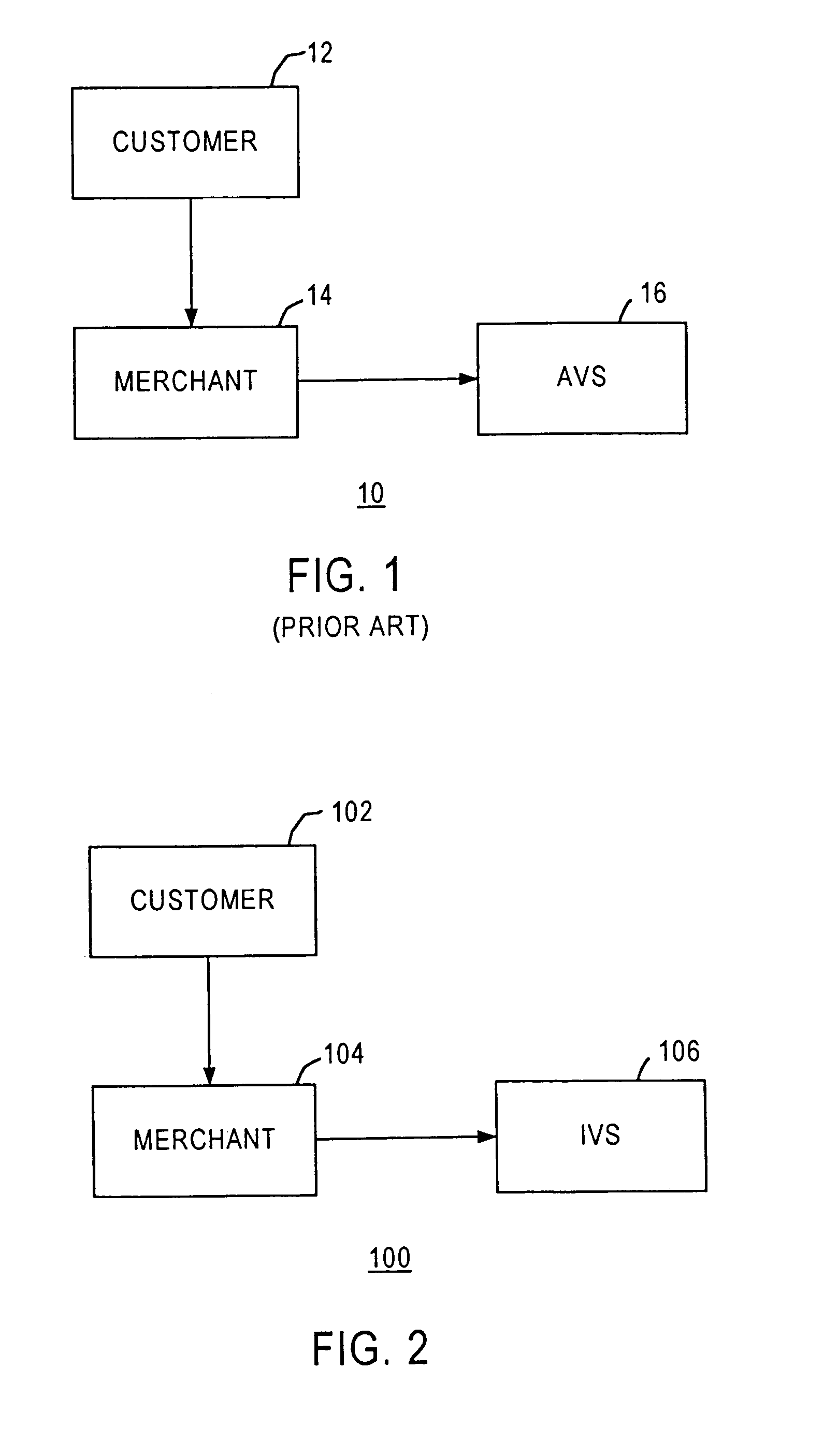
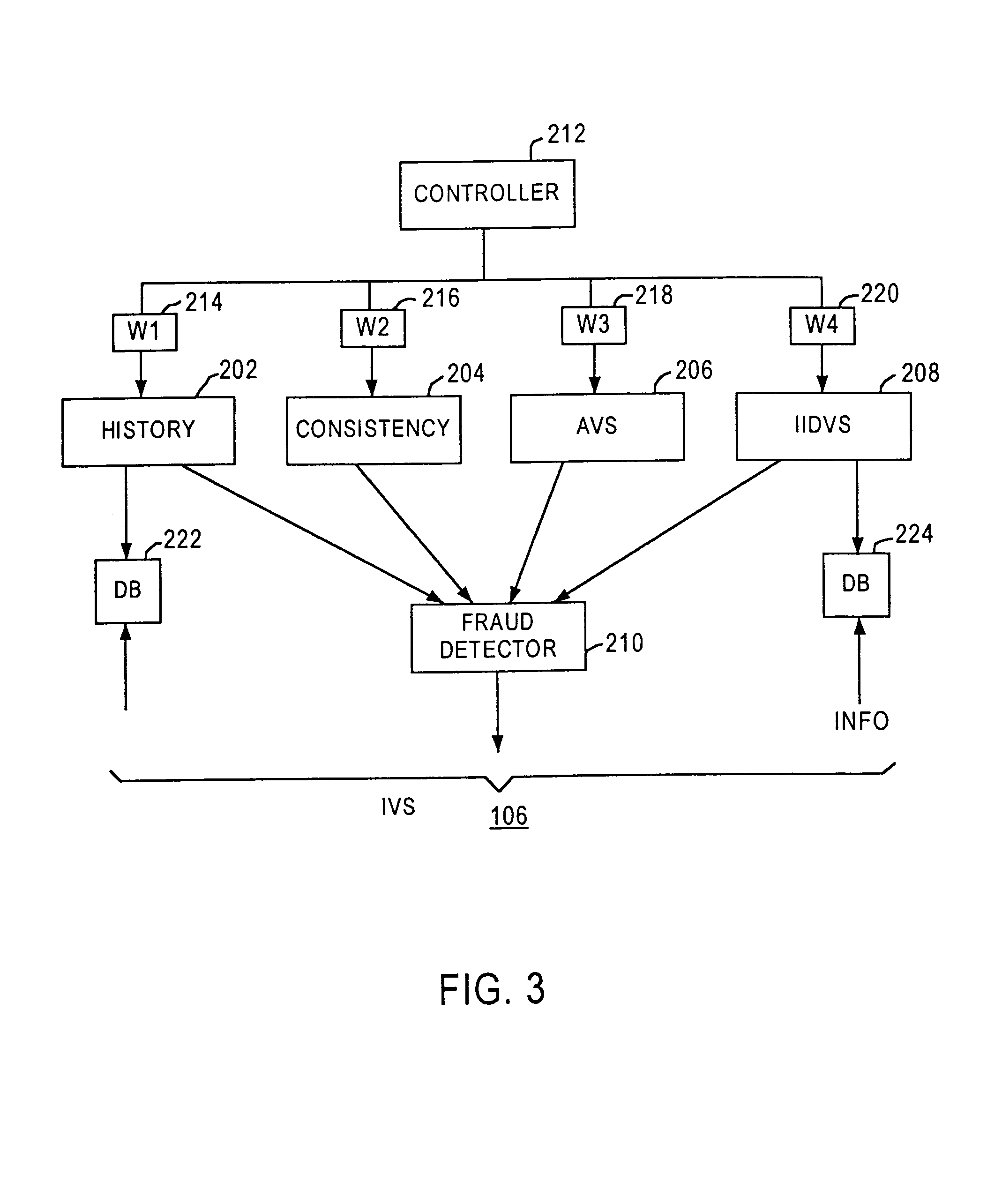
Method and apparatus for evaluating fraud risk in an electronic commerce transaction
A technique for evaluating fraud risk in e-commerce transactions between consumer and a merchant is disclosed. The merchant requests service from the system using a secure, open messaging protocol. An e-commerce transaction or electronic purchase order is received from the merchant, the level of risk associated with each order is measured, and a risk score is returned. In one embodiment, data validation, highly predictive artificial intelligence pattern matching, network data aggregation and negative file checks are used. The system performs analysis including data integrity checks and correlation analyses based on characteristics of the transaction. Other analysis includes comparison of the current transaction against known fraudulent transactions, and a search of a transaction history database to identify abnormal patterns, name and address changes, and defrauders. In one alternative, scoring algorithms are refined through use of a closed-loop risk modeling process enabling the service to adapt to new or changing fraud patterns.
Owner:CYBERSOURCE CORP
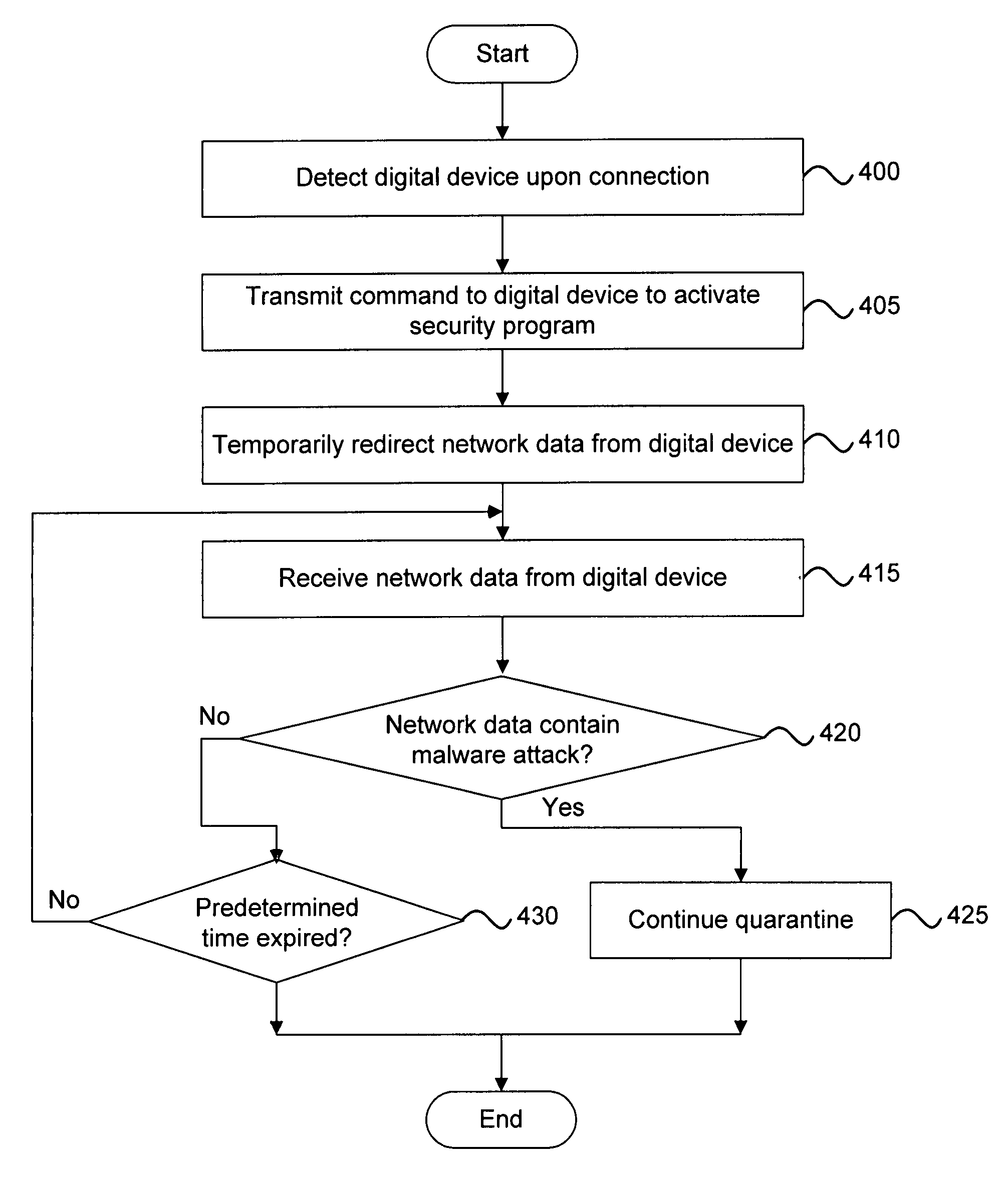
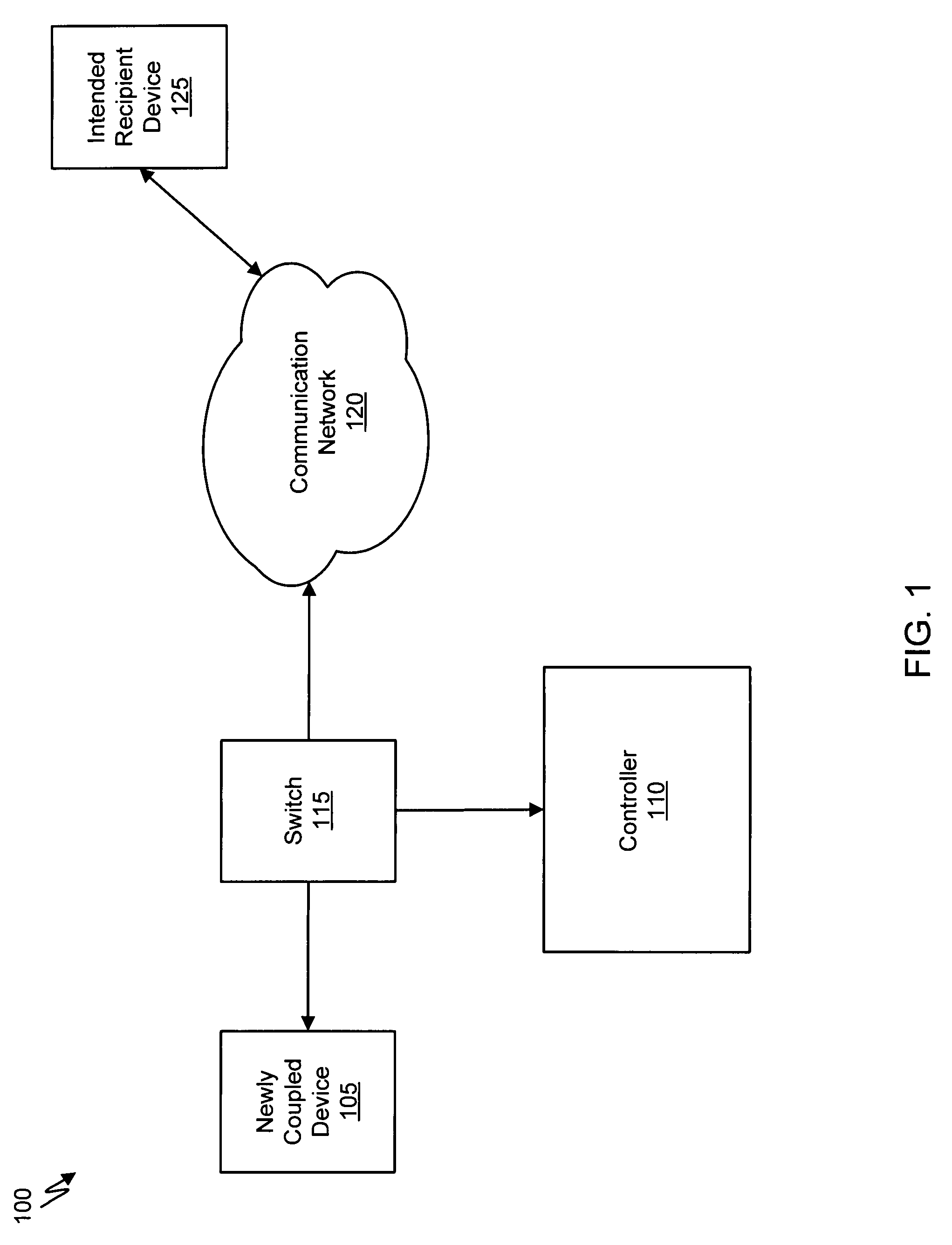
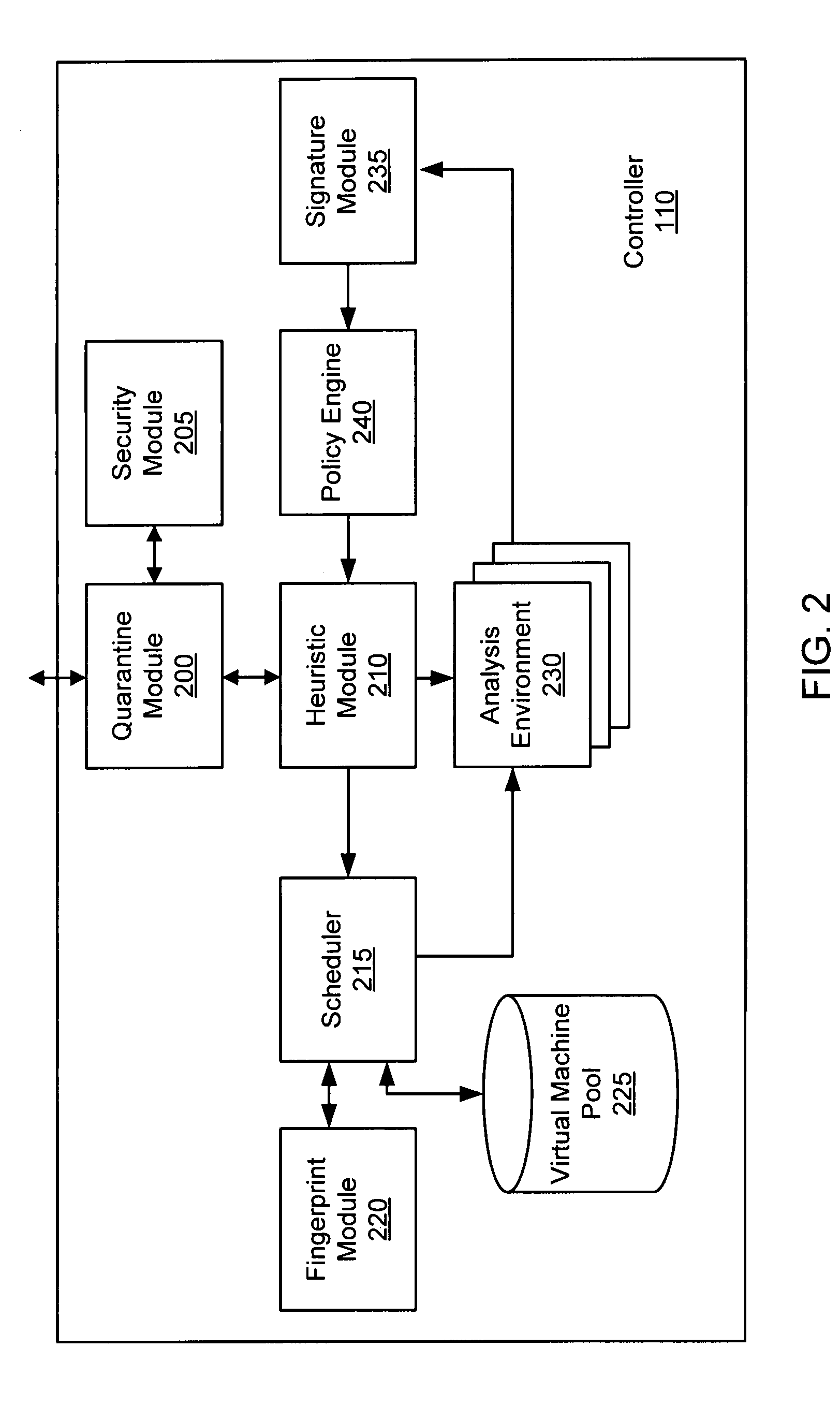
Malware containment and security analysis on connection
Systems and methods for malware containment and security analysis on connection are provided. Digital devices are quarantined for a predetermined period of time upon connection to the communication network. When a digital device is quarantined, all network data transmitted by the digital device is directed to a controller which then analyzes the network data to identify unauthorized activity and / or malware within the newly connected digital device. An exemplary method to contain malware includes detecting a digital device upon connection with a communication network, quarantining network data from the digital device for a predetermined period of time, transmitting a command to the digital device to activate a security program to identify security risks, and analyzing the network data to identify malware within the digital device.
Owner:FIREEYE SECURITY HLDG US LLC
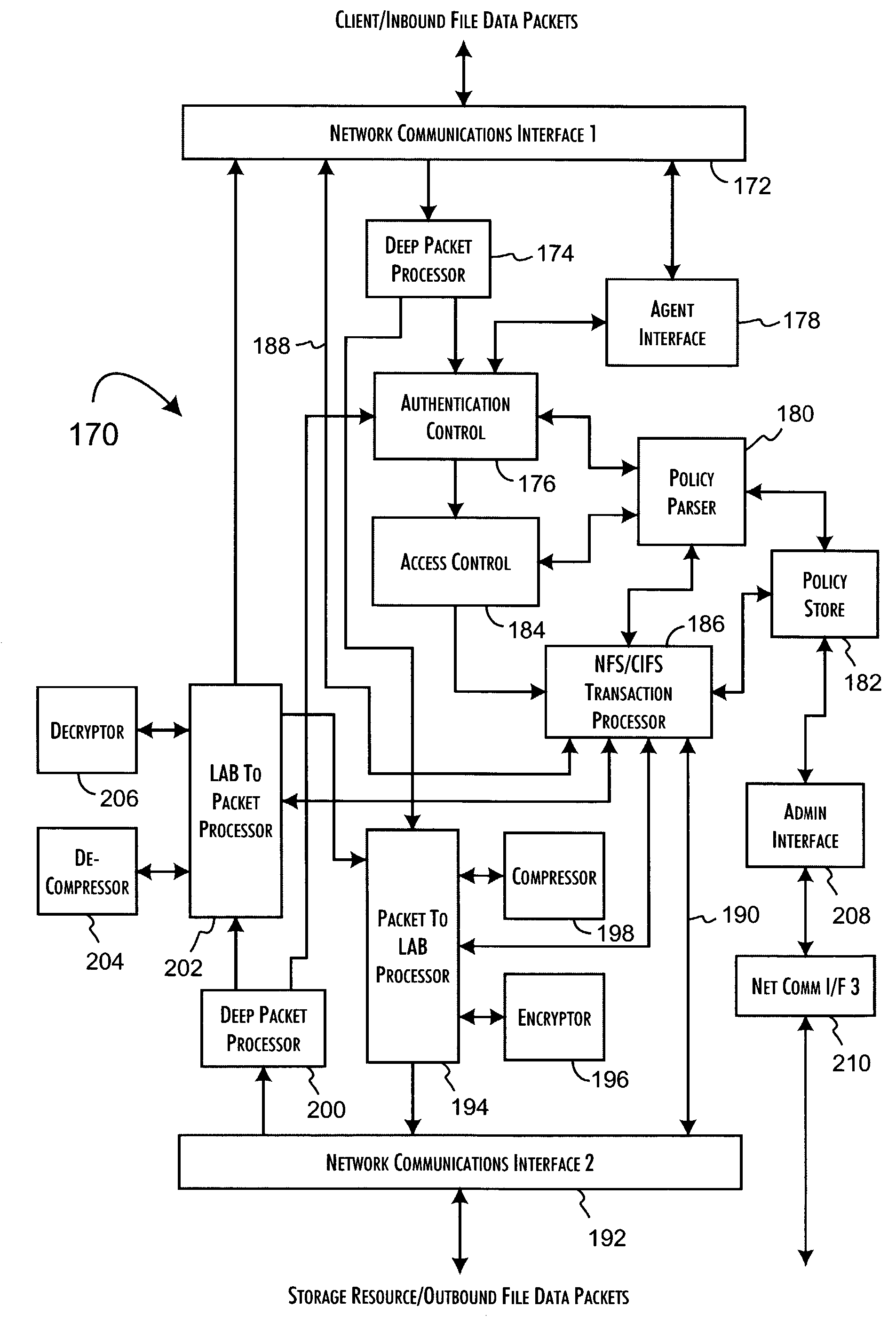
Logical access block processing protocol for transparent secure file storage
InactiveUS7334124B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationComputer hardwareDigital signature
Network data files are secure through the operation of an infrastructure gateway-based network file access appliance. Network file data, corresponding to network pocket payload data, are further reduced to a sequence of data blocks that are secured through any combination of block encryption, compression, and digital signatures. File meta-data, including encryption, compression and block-level digital signatures are persistently stored with the file data, either in-band in the file as stored or out-of-band key as a separately stored file or file policy record. File meta-data is recovered with accesses of the file data to support bidirectional encryption and compression and to detect tampering with the file data by comparison against block-level digital signatures.
Owner:THALES ESECURITY INC
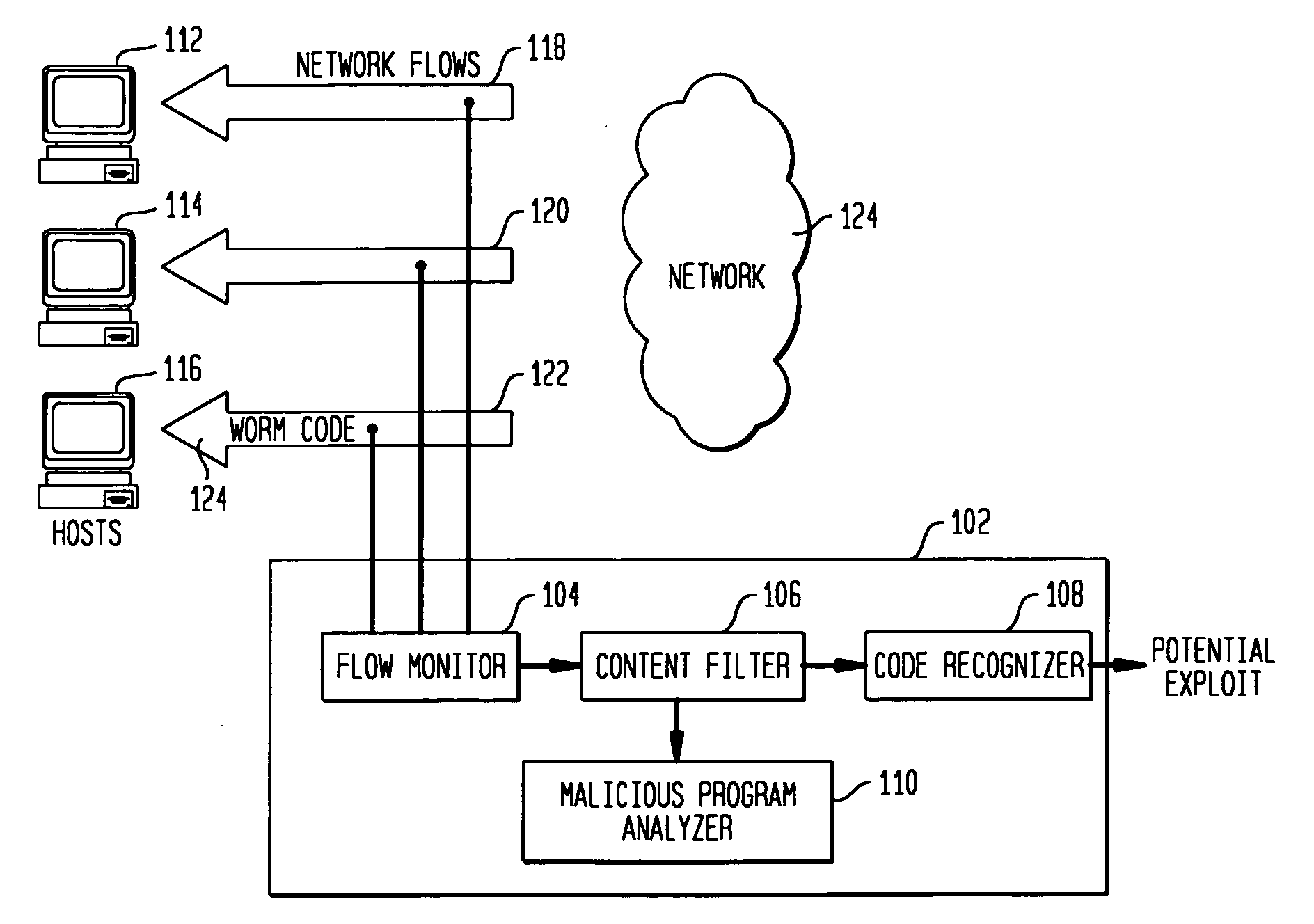
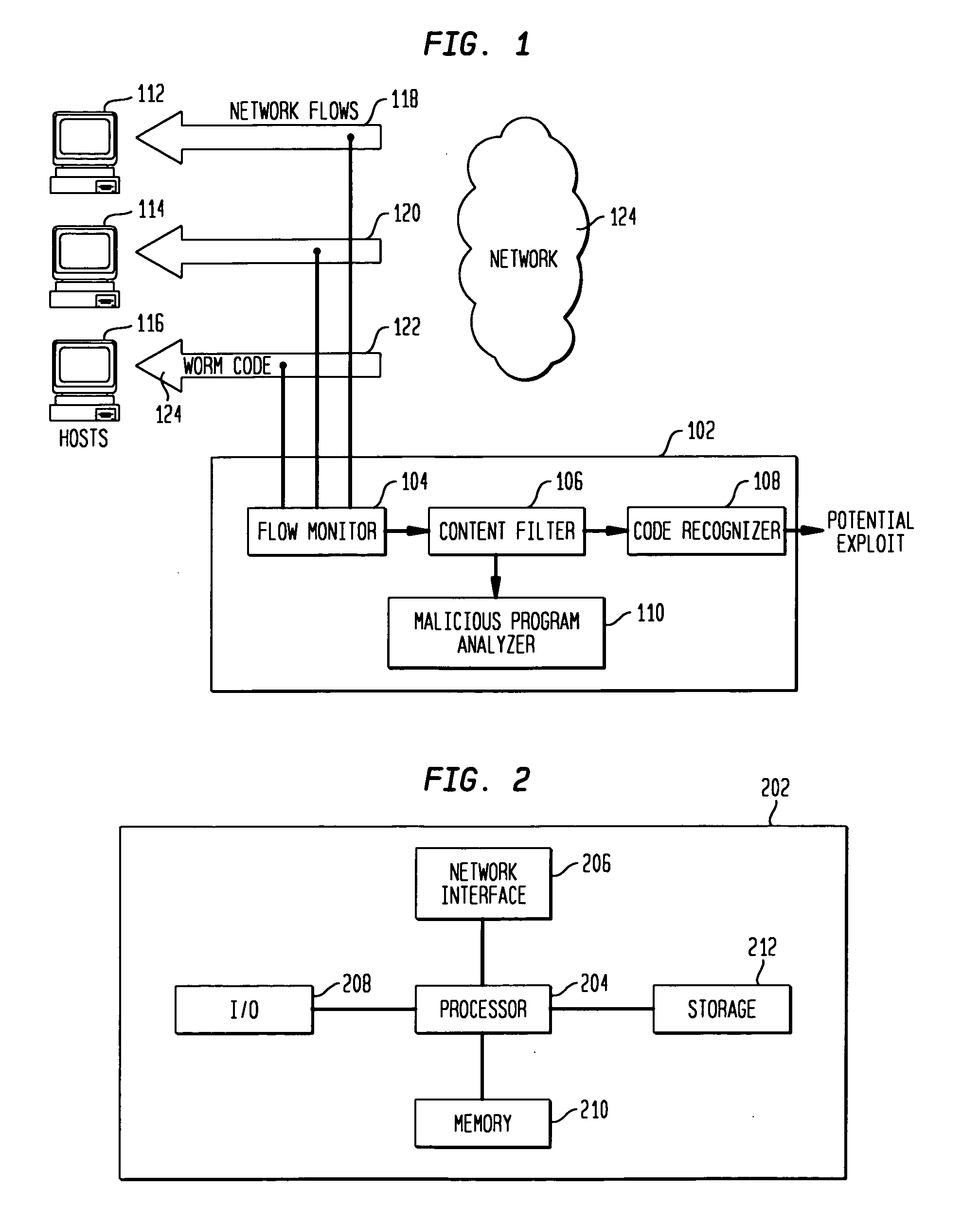
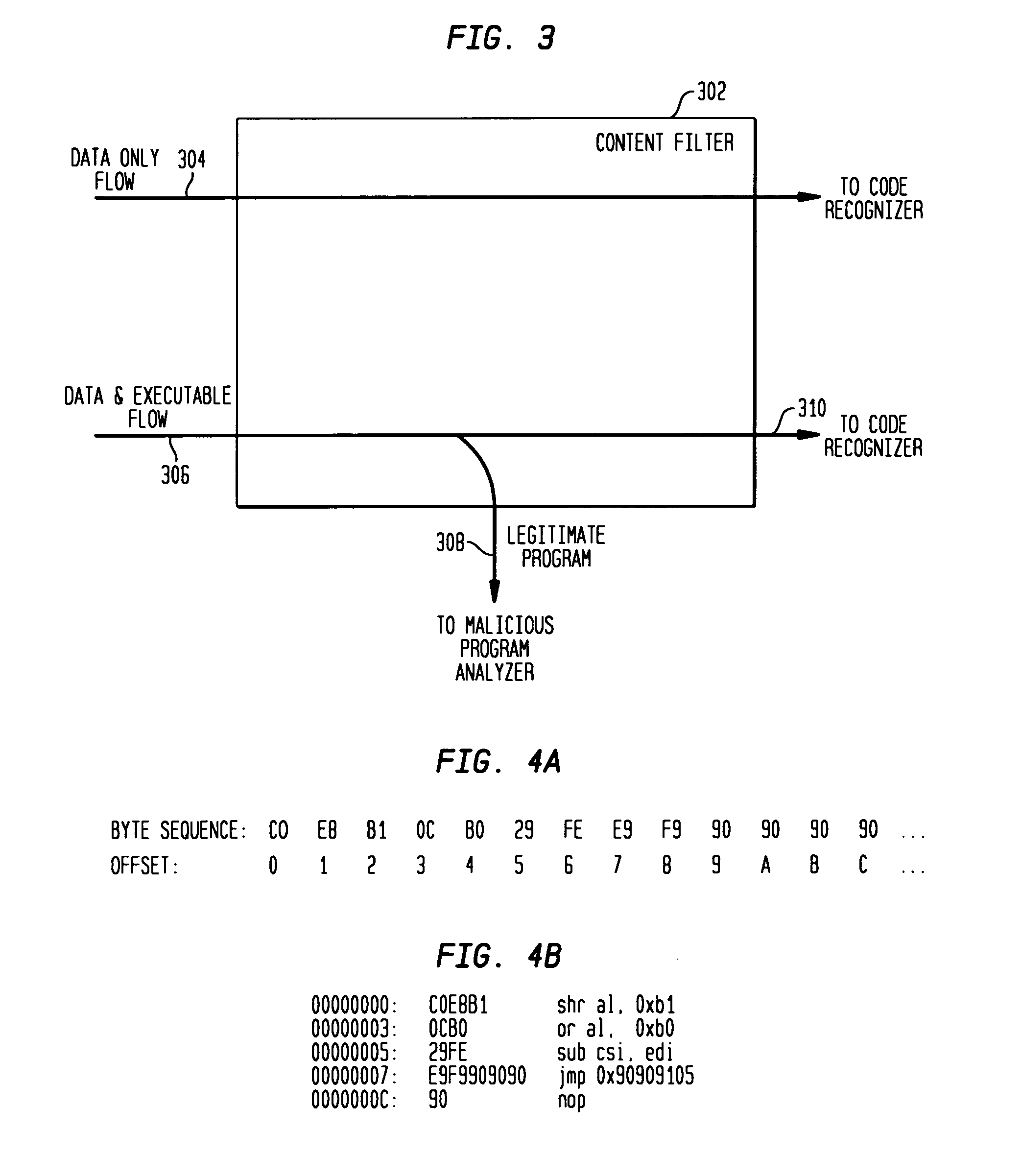
Detecting exploit code in network flows
InactiveUS20090328185A1Memory loss protectionUnauthorized memory use protectionData streamNetwork packet
Disclosed is a method and apparatus for detecting exploit code in network flows. Network data packets are intercepted by a flow monitor which generates data flows from the intercepted data packets. A content filter filters out legitimate programs from the data flows, and the unfiltered portions are provided to a code recognizer which detects executable code. Any embedded executable code in the unfiltered data flow portions is identified as a suspected exploit in the network flow. The executable code recognizer recognizes executable code by performing convergent binary disassembly on the unfiltered portions of the data flows. The executable code recognizer then constructs a control flow graph and performs control flow analysis, data flow analysis, and constraint enforcement in order to detect executable code. In addition to identifying detected executable code as a potential exploit, the detected executable code may then be used in order to generate a signature of the potential exploit, for use by other systems in detecting the exploit.
Owner:TELCORDIA TECHNOLOGIES INC
Heuristic based capture with replay to virtual machine
Owner:FIREEYE SECURITY HLDG US LLC
Systems and methods for malware attack prevention
Systems and methods for malware attack prevention are provided. Network data is copied from a communication network. It is then determined if a possible malware attack is within the copied network data. The network data is intercepted based on the determination. The network data is then analyzed to identify a malware attack.
Owner:FIREEYE SECURITY HLDG US LLC
Algorithms for identity anonymization on graphs
InactiveUS20090303237A1Preserving individual privacy and basic structure of networkDrawing from basic elementsTransmissionGraphicsRe identification
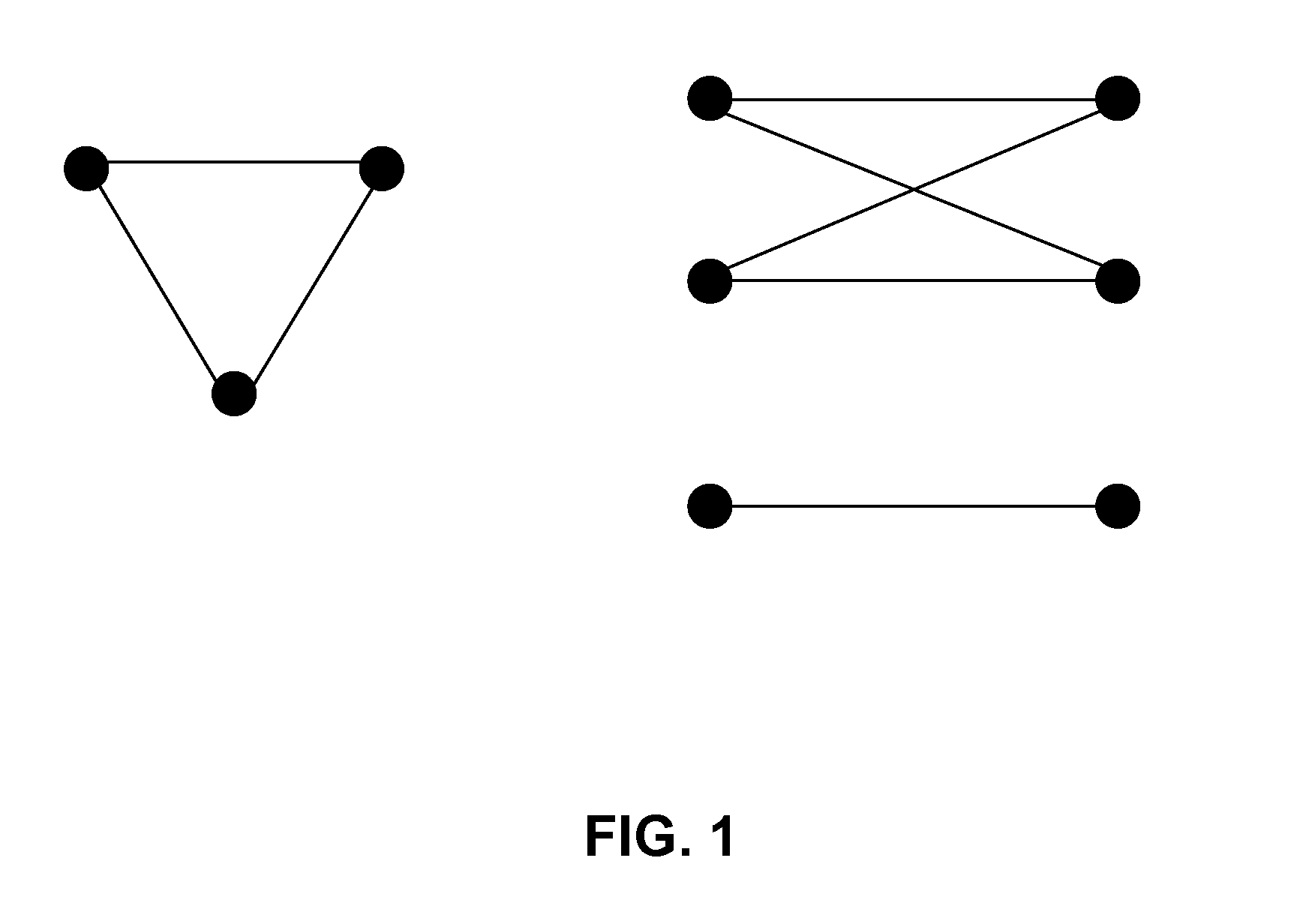
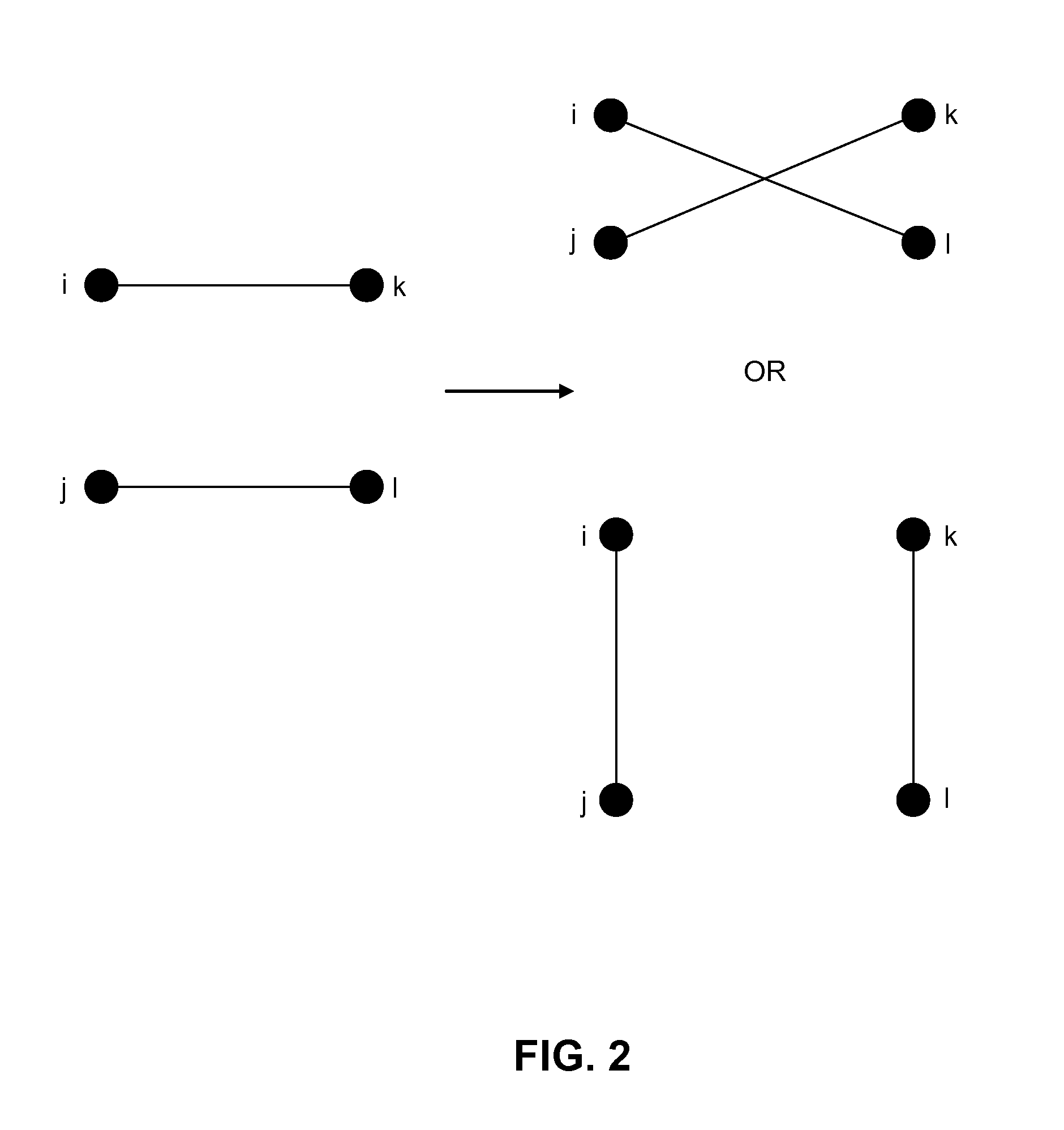
The proliferation of network data in various application domains has raised privacy concerns for the individuals involved. Recent studies show that simply removing the identities of the nodes before publishing the graph / social network data does not guarantee privacy. The structure of the graph itself, and in is basic form the degree of the nodes, can be revealing the identities of individuals. To address this issue, a specific graph-anonymization framework is proposed. A graph is called k-degree anonymous if for every node v, there exist at least k−1 other nodes in the graph with the same degree as v. This definition of anonymity prevents the re-identification of individuals by adversaries with a priori knowledge of the degree of certain nodes. Given a graph G, the proposed graph-anonymization problem asks for the k-degree anonymous graph that stems from G with the minimum number of graph-modification operations. Simple and efficient algorithms are devised for solving this problem, wherein these algorithms are based on principles related to the realizability of degree sequences.
Owner:IBM CORP
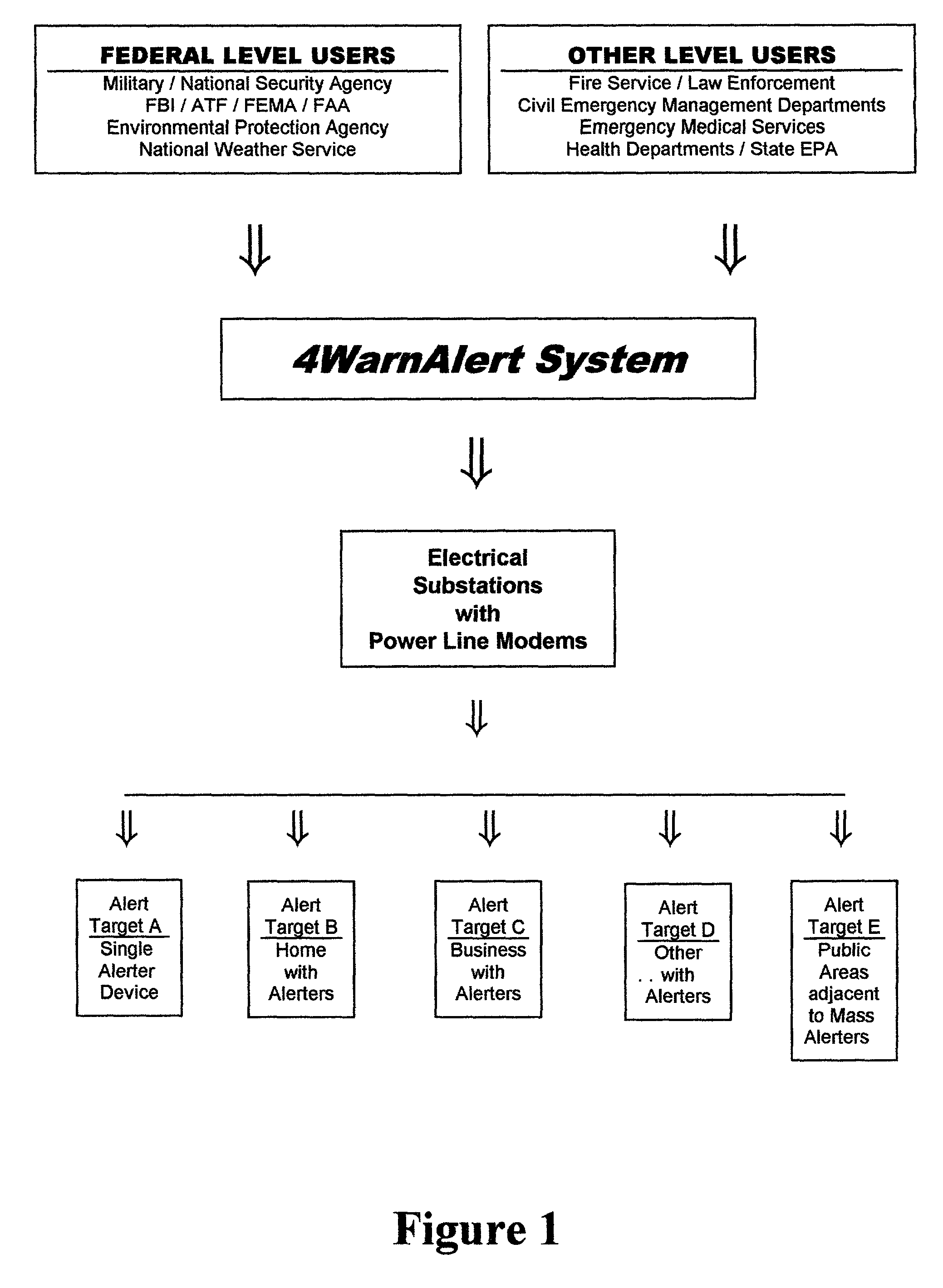
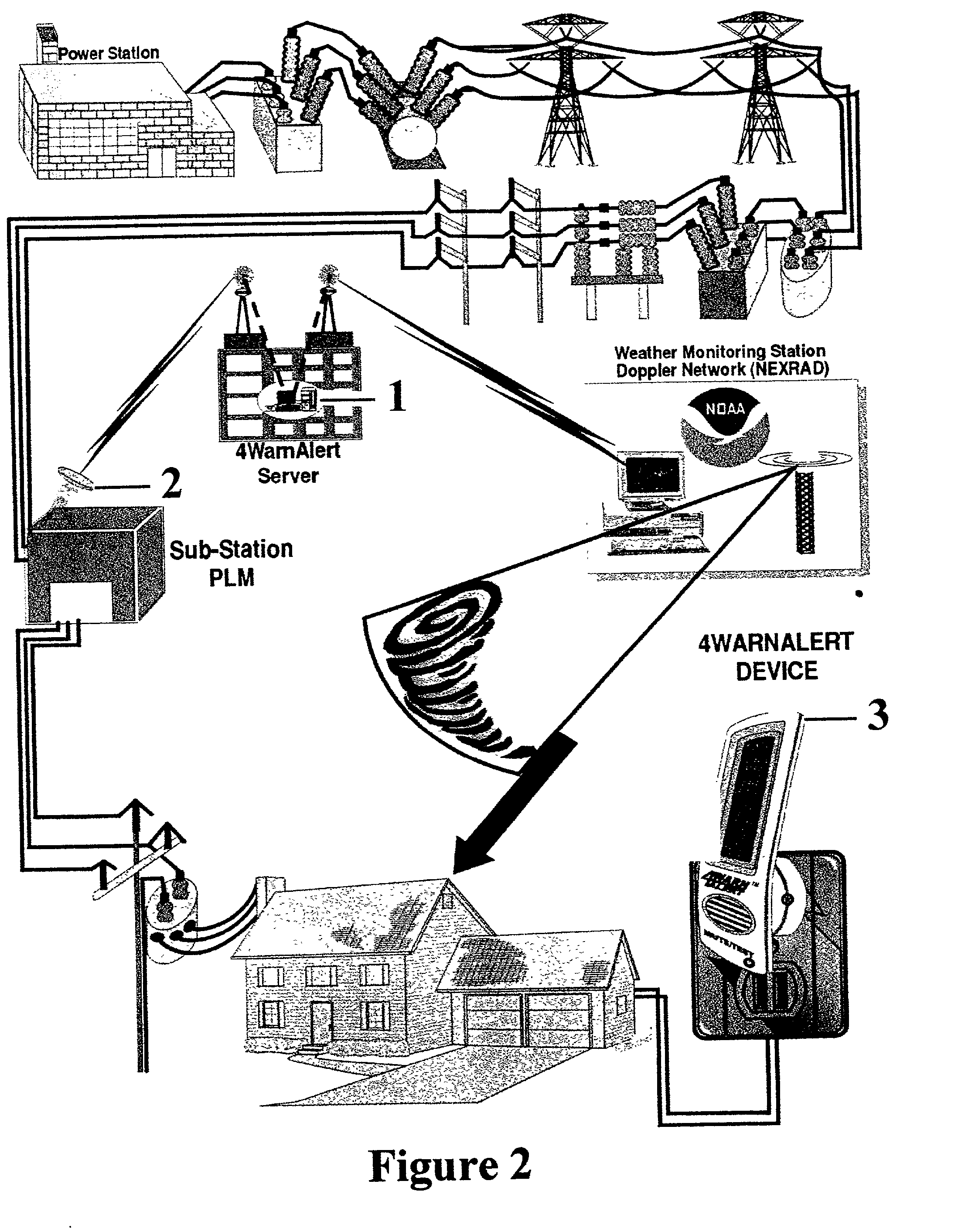
Civil defense alert system and method using power line communication
InactiveUS20020024424A1Special service provision for substationFrequency-division multiplex detailsModem deviceNetworked system
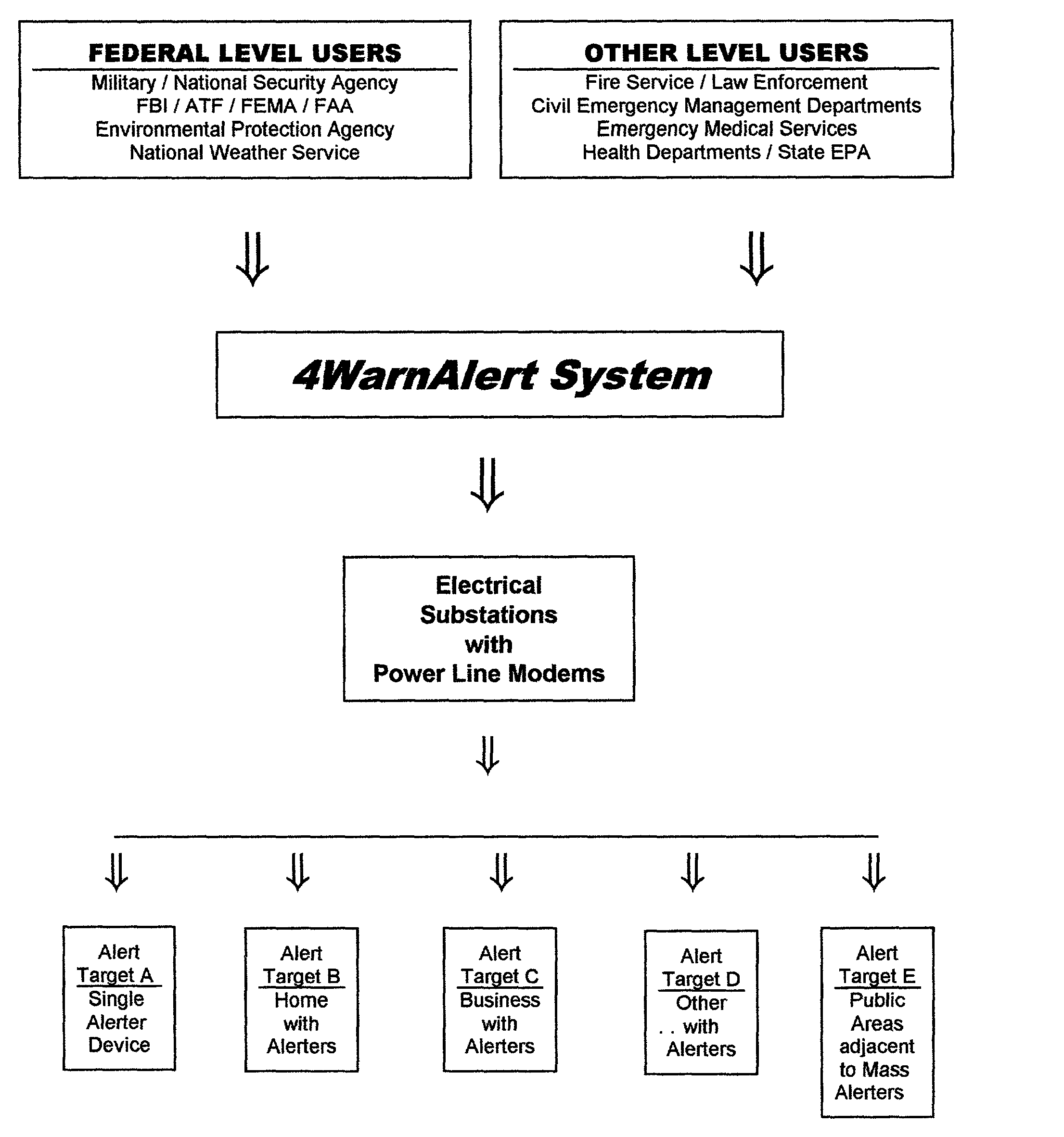
This invention pertains to the use of power line communication in a civil defense alerting system. The idea encapsulates the use of existing technology both in power line communication via a power line modem and network data transfer and applies it to an area to which it has never before been applied. Substantial improvement to both is developed through this invention as the prior art had never included or addressed the need for and ability to communicate over the power lines when no electrical power was flowing from the utility. The invention demonstrates that through a communications network it is possible for a system user to activate a single warning alerter device or a multitude of warning alerter devices that are connected to a standard power distribution network. Overall, this invention provides governmental users a more comprehensive and more fail-safe method and process f warning the public of risks, potentially hazardous situations, and safety instructions to minimize the loss of life and injury.
Owner:BURNS T D +1
Virtual machine with dynamic data flow analysis
ActiveUS8584239B2Memory loss protectionUnauthorized memory use protectionDynamic data flow analysisNetwork data
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, and concurrently simulate transmission of the network data to a plurality of destination devices.
Owner:FIREEYE SECURITY HLDG US LLC
Systems and methods for malware attack detection and identification
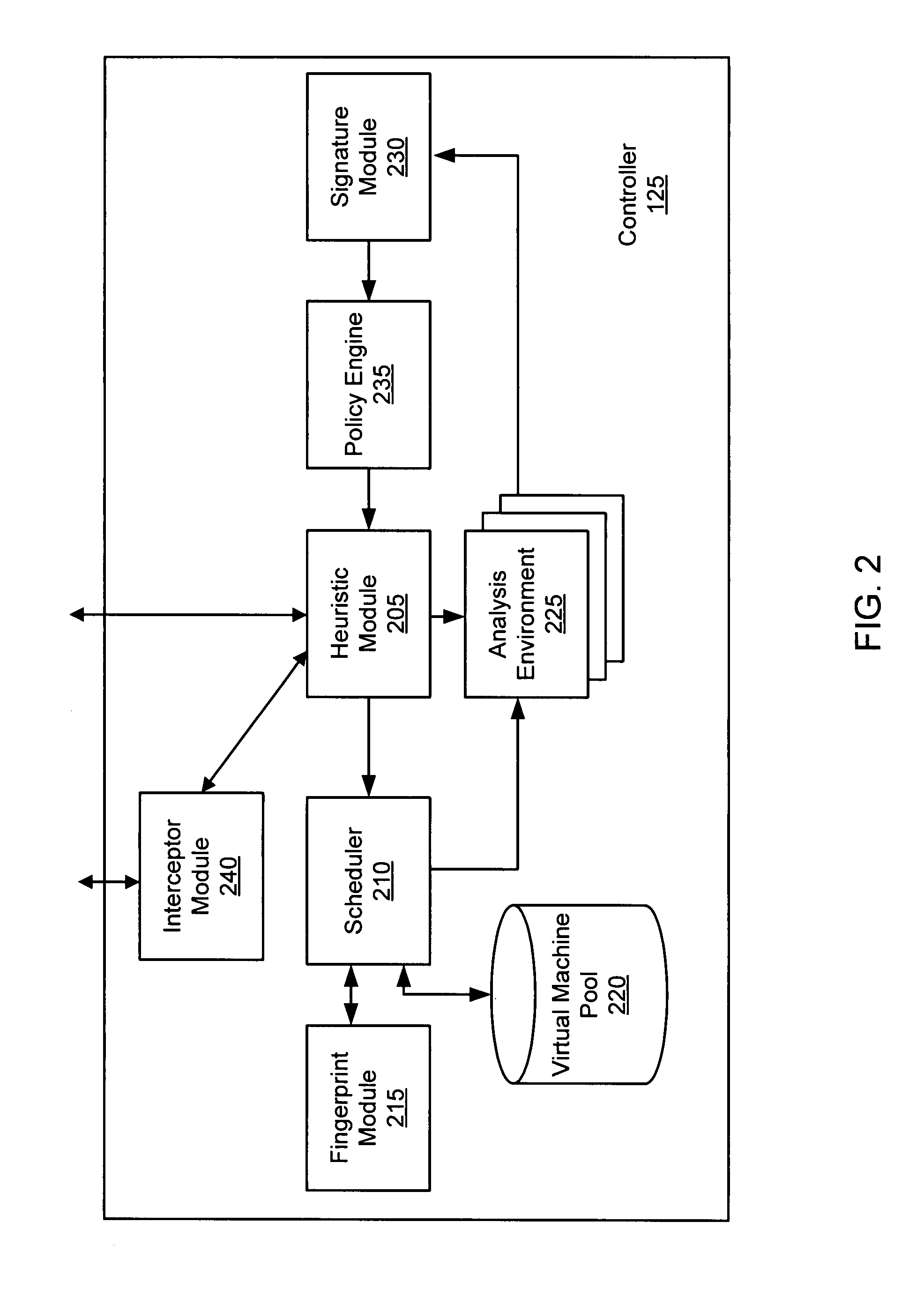
Exemplary systems and methods for malware attack detection and identification are provided. A malware detection and identification system can comprise a controller. The controller can comprise an analysis environment configured to transmit network data to a virtual machine, flag input values associated with the network data from untrusted sources, monitor the flagged input values within the virtual machine, identify an outcome of one or more instructions that manipulate the flagged input values, and determine if the outcome of the one or more instructions comprise an unauthorized activity.
Owner:FIREEYE SECURITY HLDG US LLC
Method and apparatus for detecting predefined signatures in packet payload using bloom filters
ActiveUS20050086520A1Digital data processing detailsUser identity/authority verificationBloom filterNetwork data
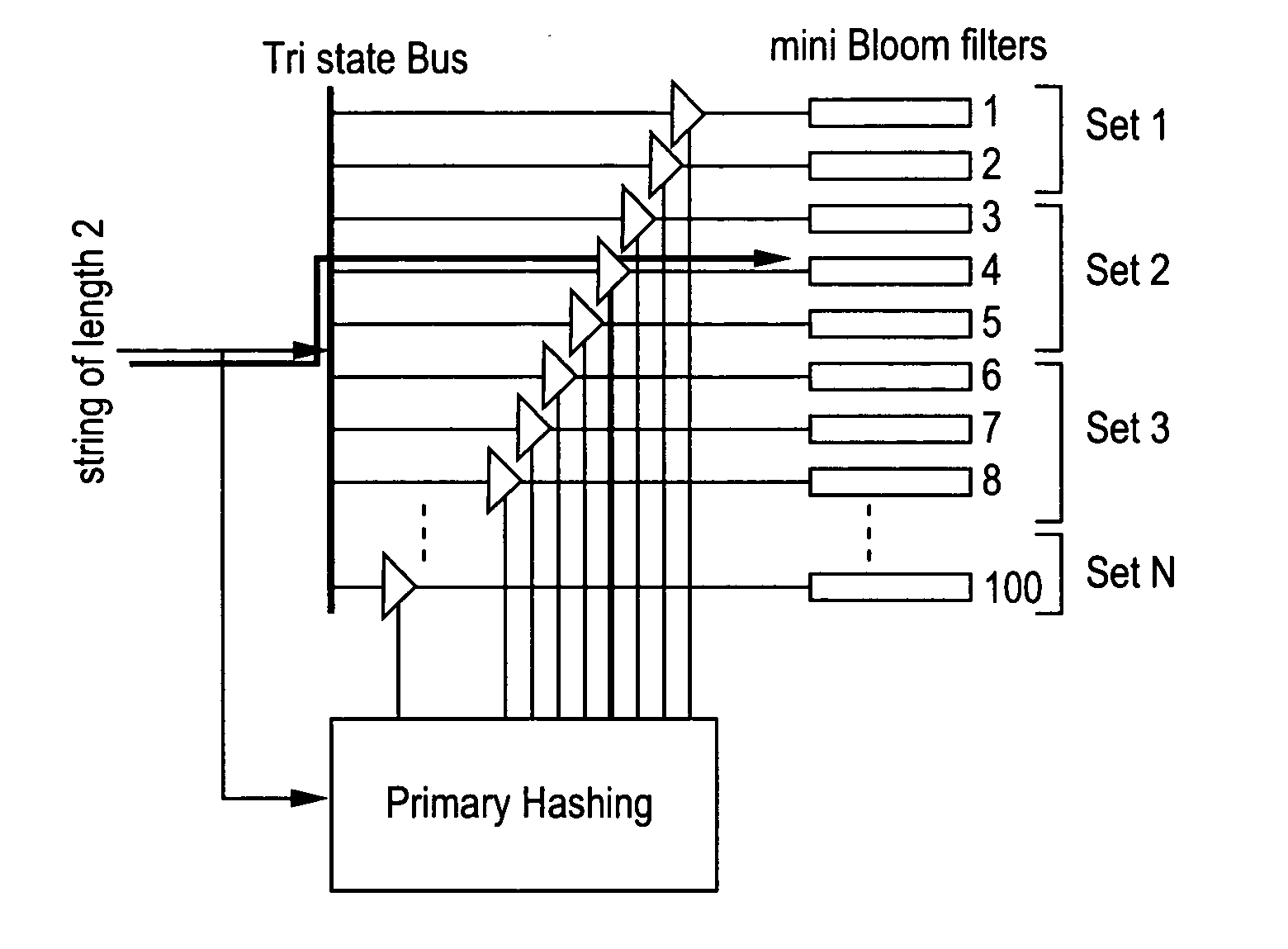
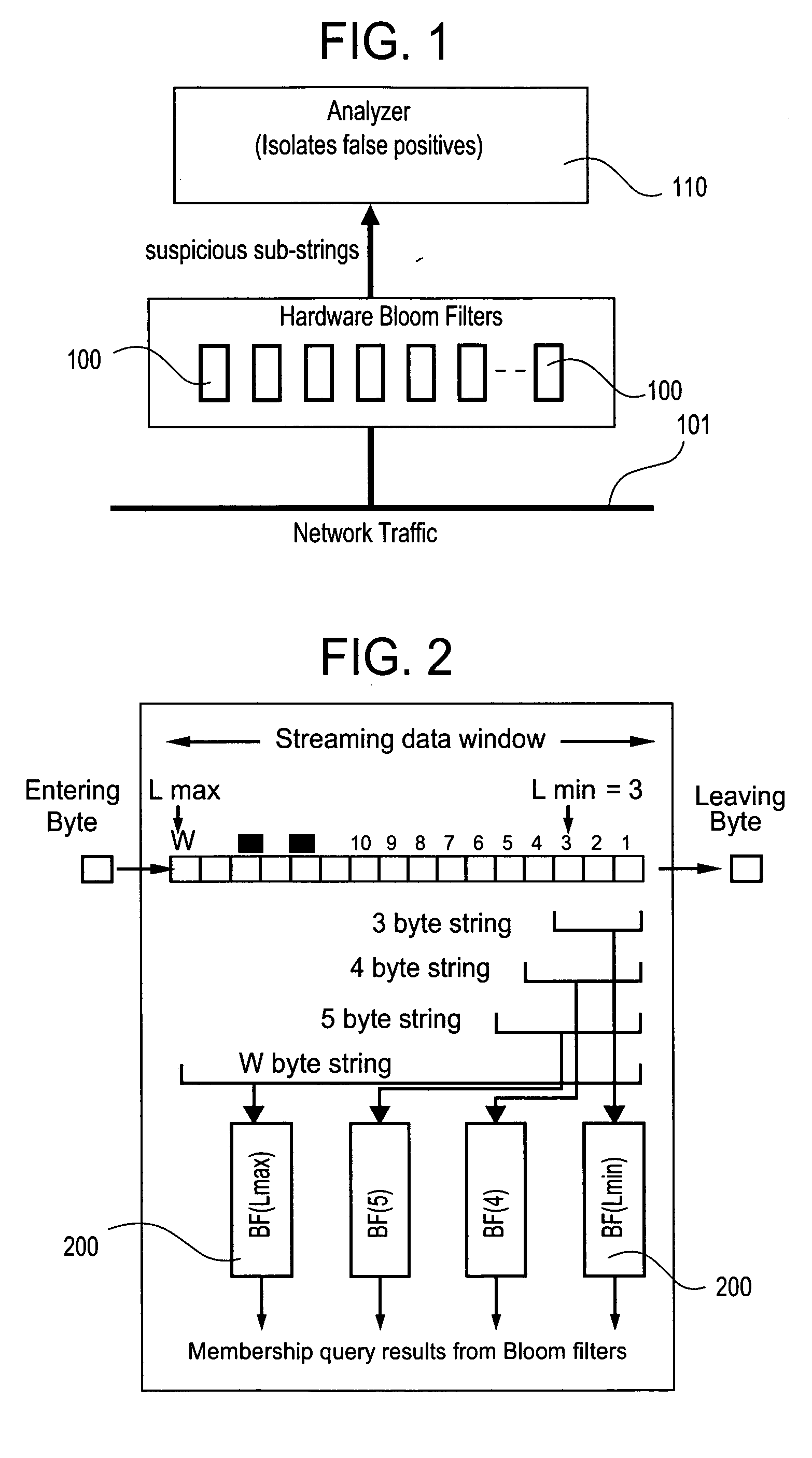
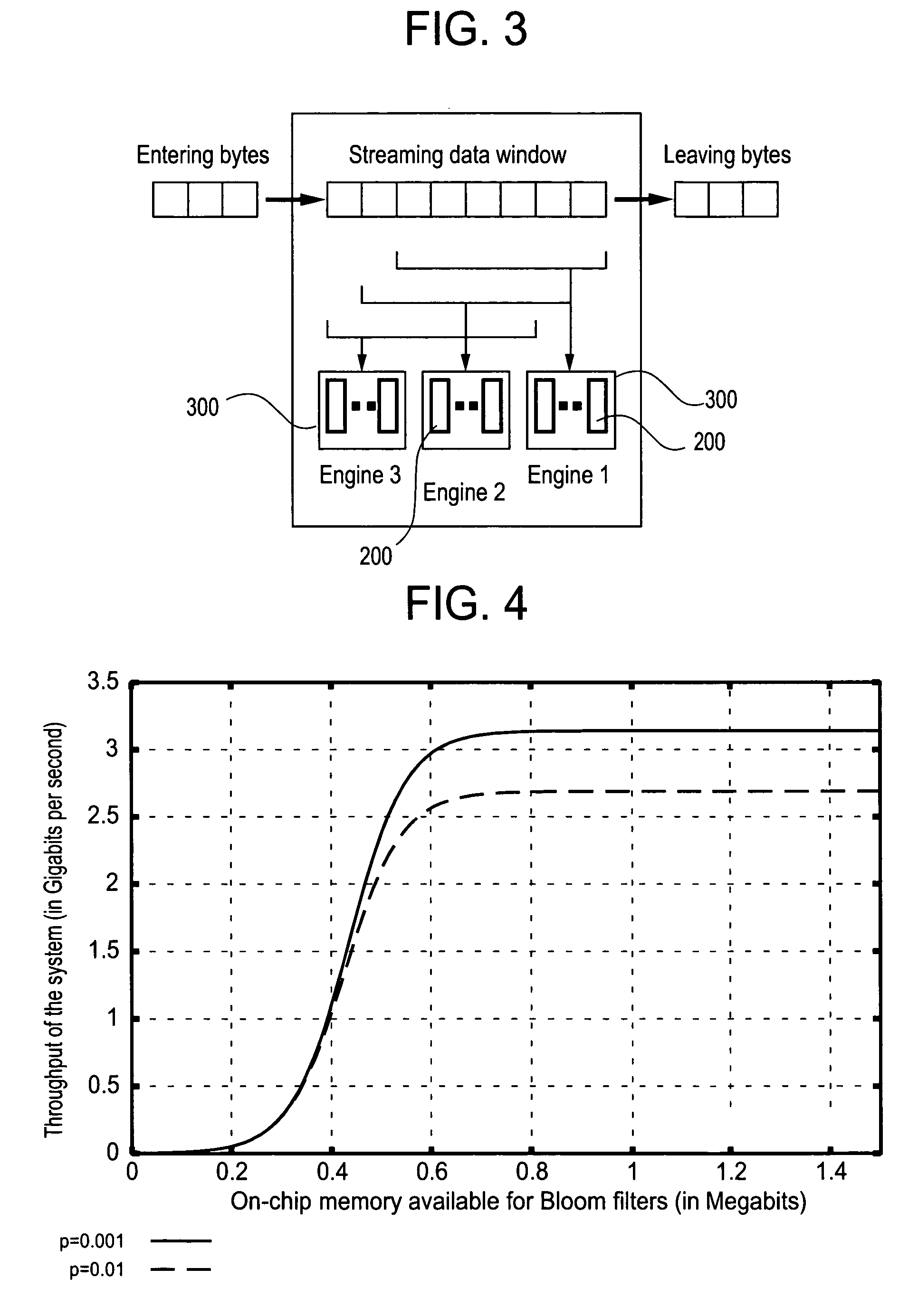
The present invention relates to a method and apparatus based on Bloom filters for detecting predefined signatures (a string of bytes) in a network packet payload. A Bloom filter is a data structure for representing a set of strings in order to support membership queries. Hardware Bloom filters isolate all packets that potentially contain predefined signatures. Another independent process eliminates false positives produced by the Bloom filters. The system is implemented on a FPGA platform, resulting in a set of 10,000 strings being scanned in the network data at the line speed of 2.4 Gbps.
Owner:WASHINGTON UNIV IN SAINT LOUIS
Dynamic signature creation and enforcement
Owner:FIREEYE SECURITY HLDG US LLC
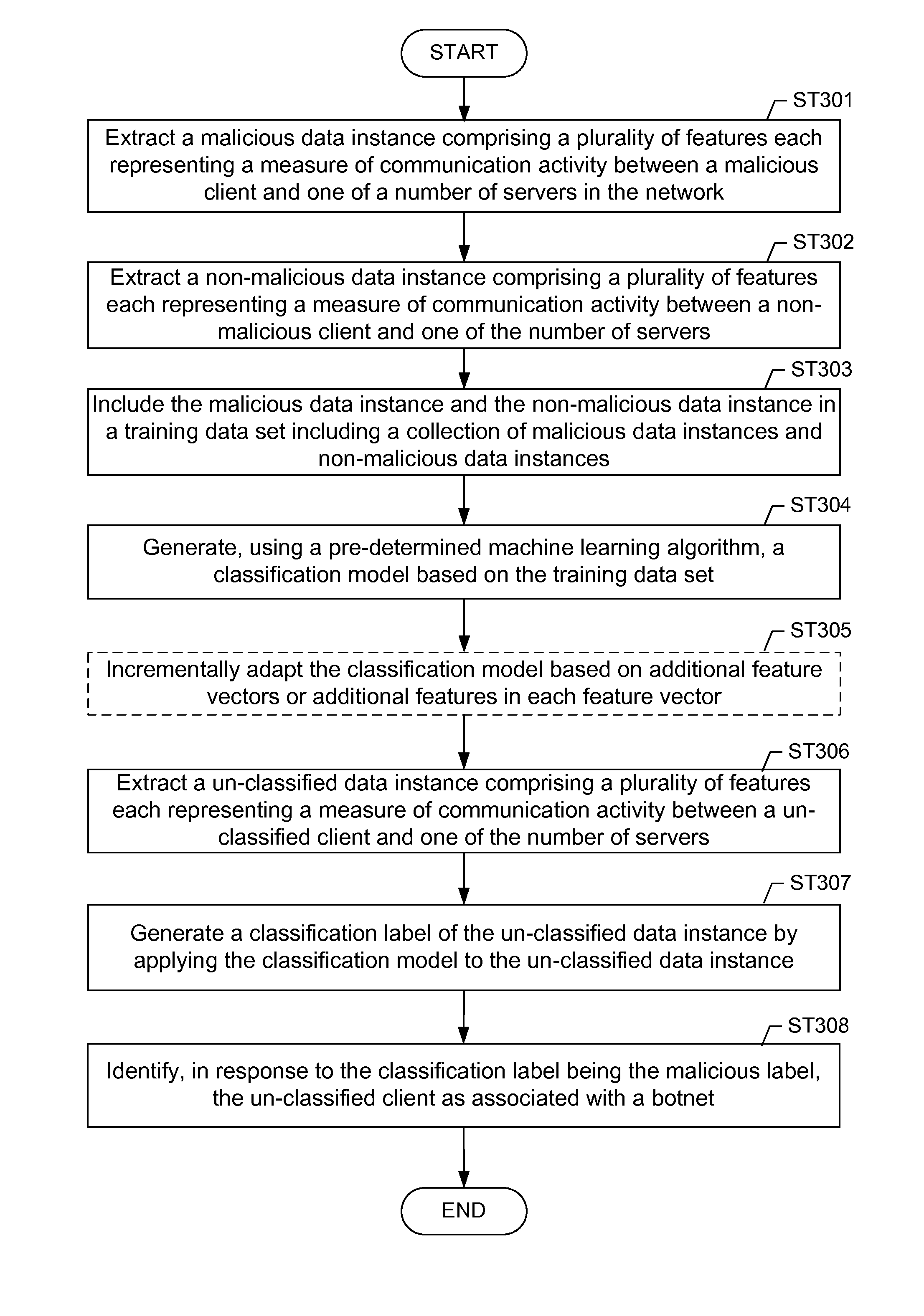
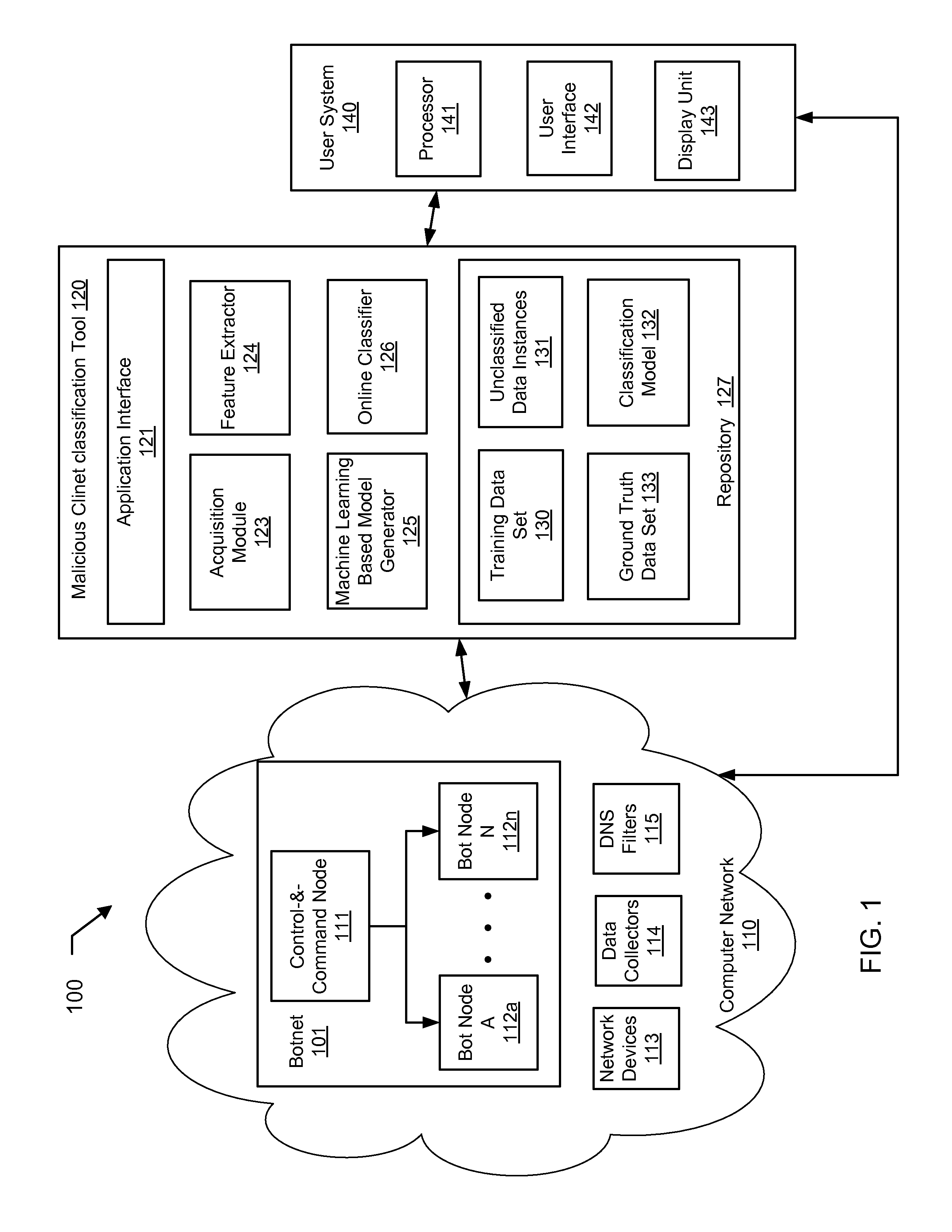
Machine learning based botnet detection with dynamic adaptation
Embodiments of the invention address the problem of detecting bots in network traffic based on a classification model learned during a training phase using machine learning algorithms based on features extracted from network data associated with either known malicious or known non-malicious client and applying the learned classification model to features extracted in real-time from current network data. The features represent communication activities between the known malicious or known non-malicious client and a number of servers in the network.
Owner:THE BOEING CO
Dynamic signature creation and enforcement
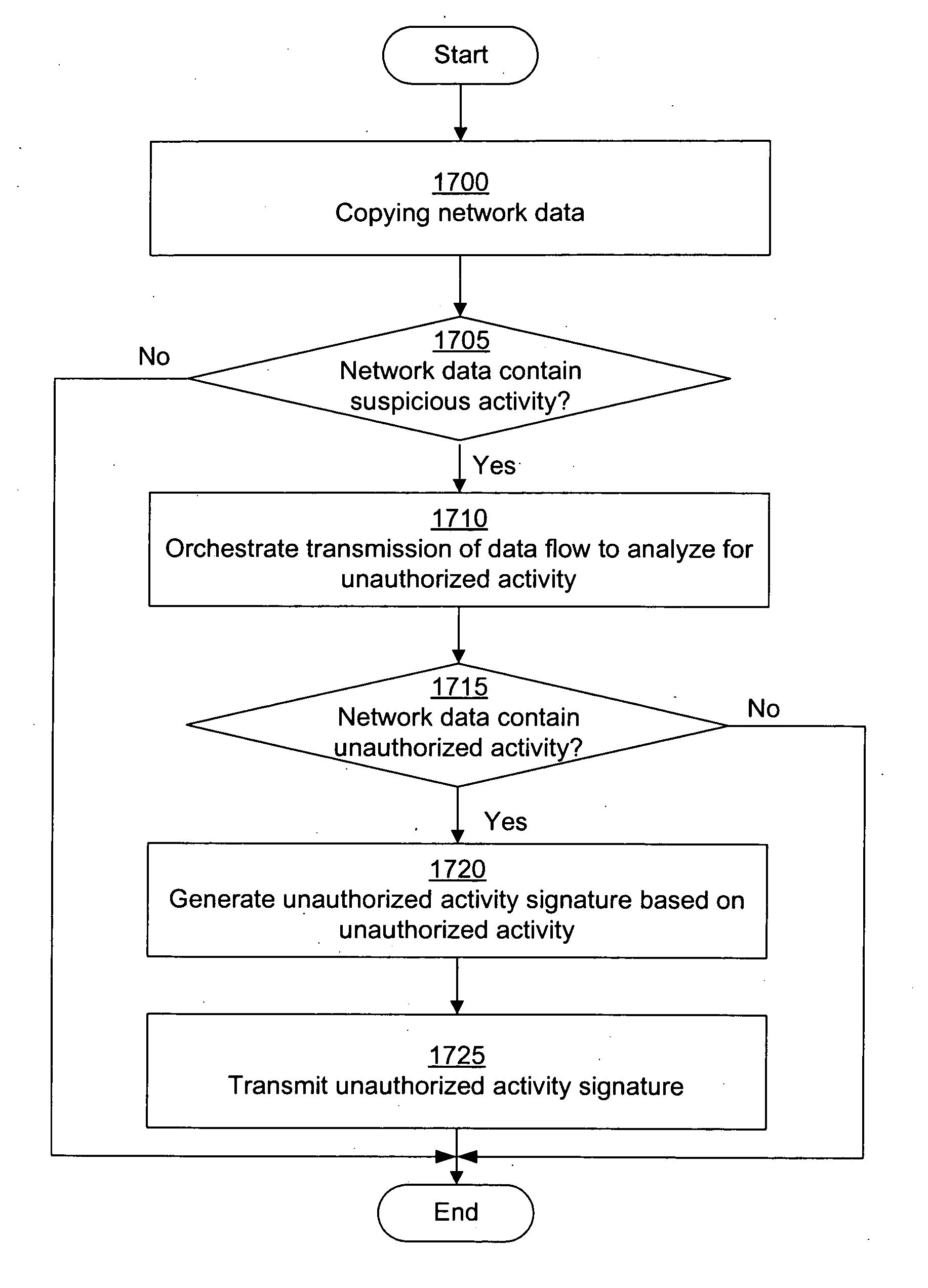
ActiveUS20120331553A1Memory loss protectionDigital data processing detailsNetwork dataDigital device
A dynamic signature creation and enforcement system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, simulate transmission of the network data to a destination device to identify unauthorized activity, generate an unauthorized activity signature based on the identification, and transmit the unauthorized activity signature to a digital device configured to enforce the unauthorized activity signature.
Owner:FIREEYE SECURITY HLDG US LLC
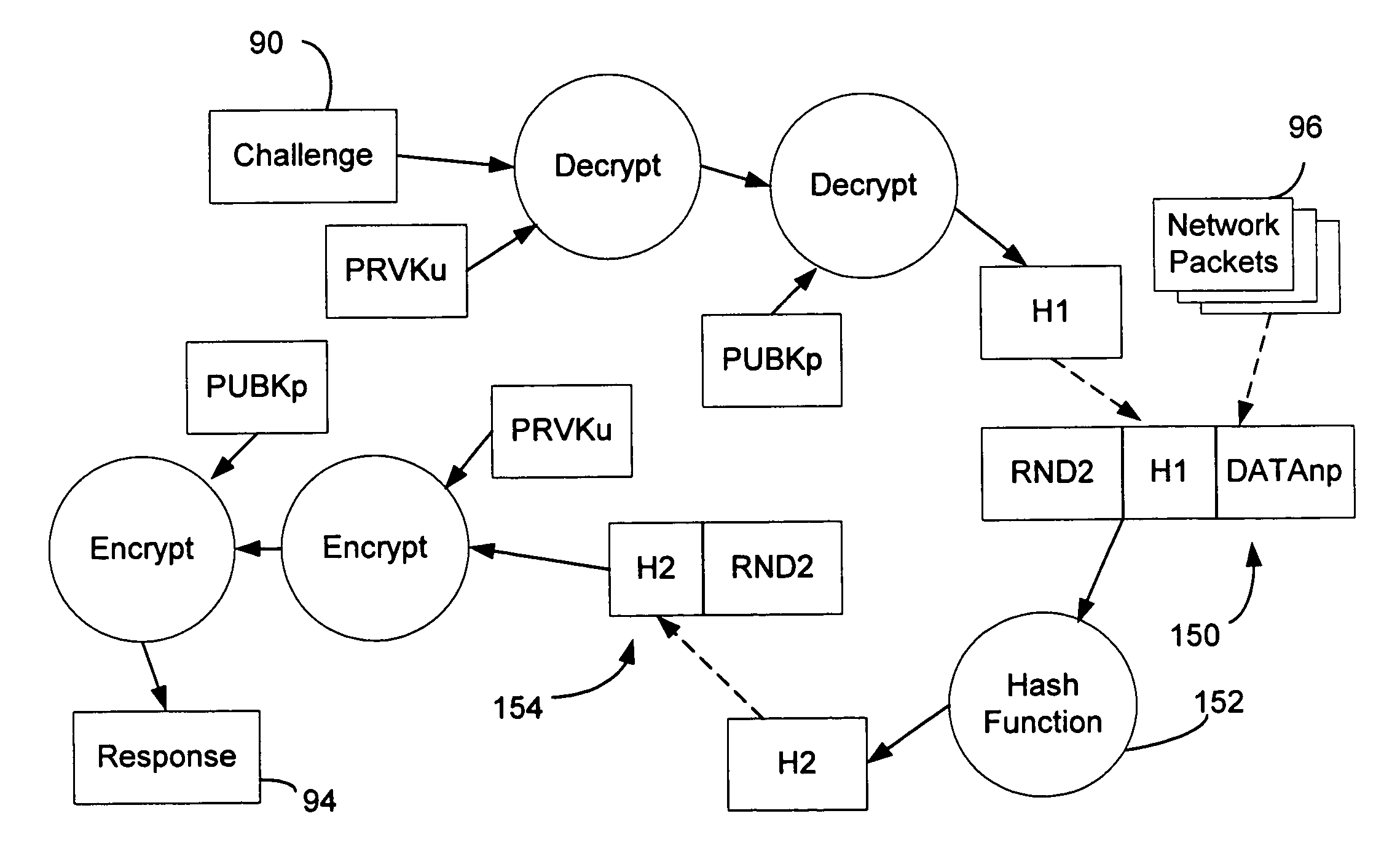
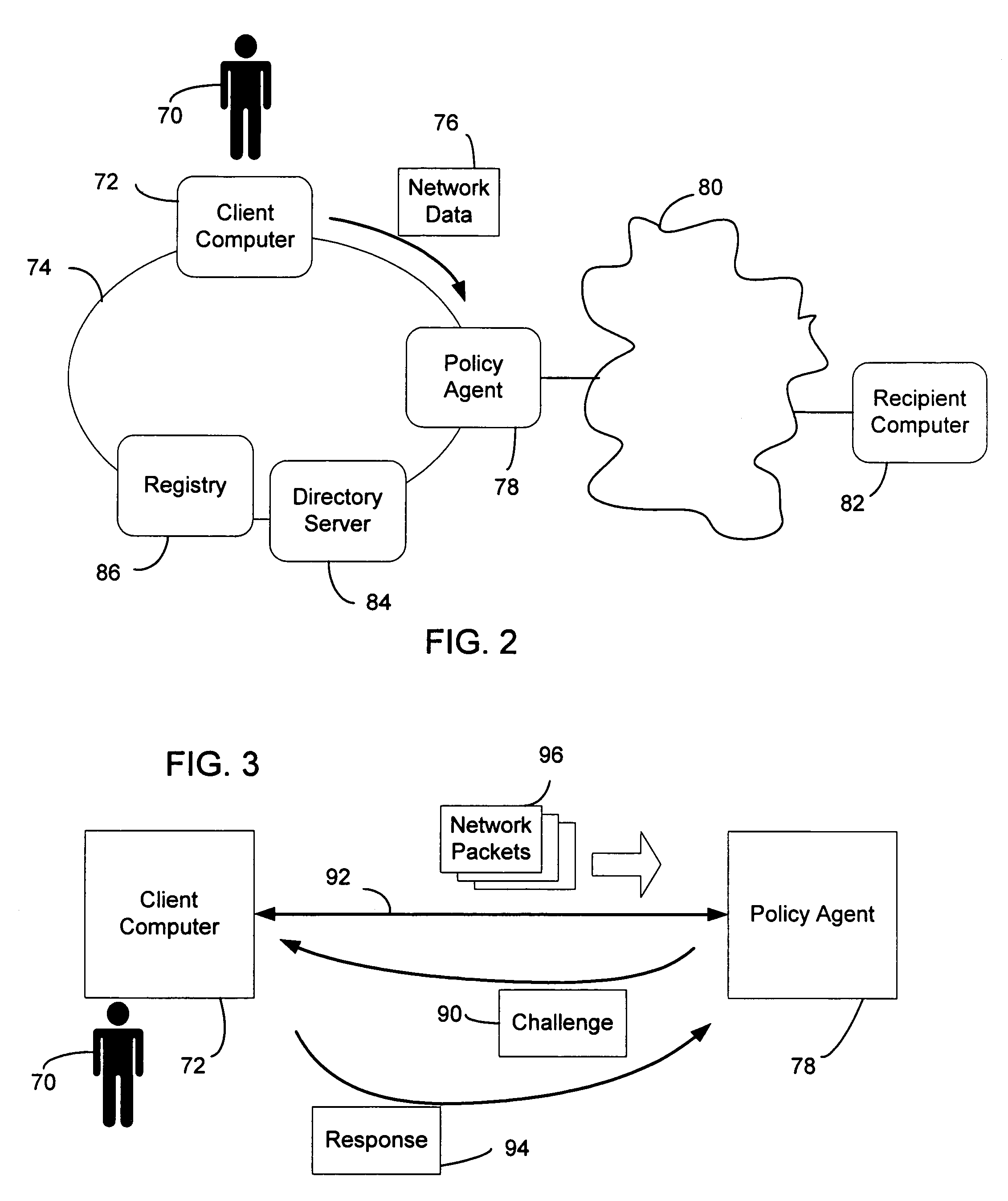
System and method of user authentication for network communication through a policy agent
InactiveUS7039713B1Digital data processing detailsComputer security arrangementsData connectionUser authentication
A policy agent of a network performs an out-of-band user authentication process to verify the identity of a user of a client computer and associates the network data received from the client computer with the user. When the client computer initiates a network data connection to or through the policy agent, the policy agent sends an encrypted challenge to the client computer. The challenge is encrypted with a private key of the policy agent. When the client computer receives the challenge, it decrypts the challenge and prepares a message digest value based on the challenge and the network data sent by the user. The message digest value is then encrypted with the private key of the user to form a response, and the response is sent to the policy agent. The policy agent decrypts the response with the public key of the user to obtain the message digest value and calculates a digest value based on the challenge and the received network data. The policy agent then compares the calculated digest value with the decrypted digest value. A match between the two digest values indicates that the user is successfully authenticated and that the received network data are associated with the user. The policy agent may then apply network policies based on the credentials of the authenticated user.
Owner:MICROSOFT TECH LICENSING LLC
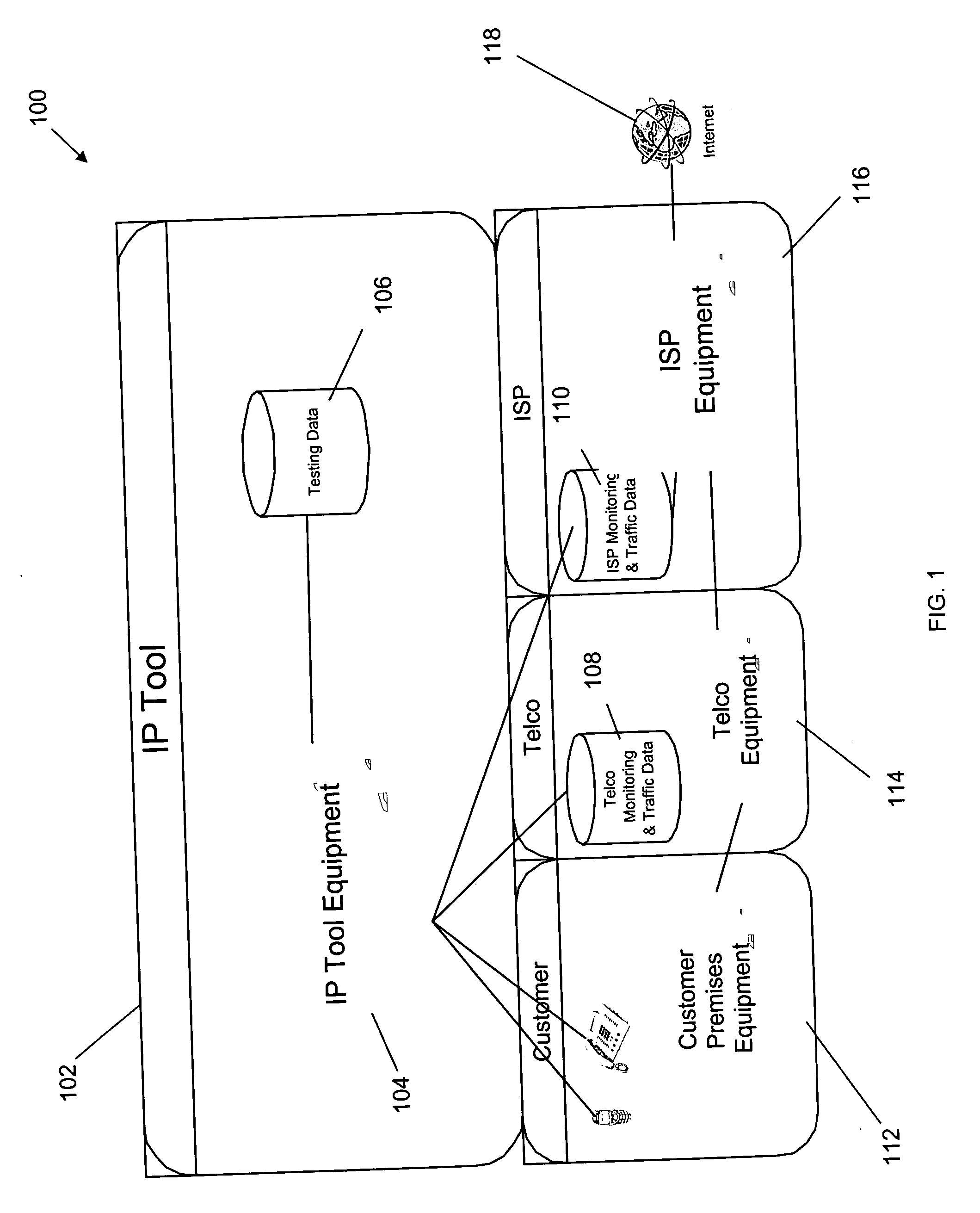
Method and system for comprehensive testing of network connections
InactiveUS20070041554A1Special service for subscribersSupervisory/monitoring/testing arrangementsData setNetwork connection
The present invention is an system and method for comprehensively testing a customer connection to a communications network. A customer is identified from information obtained at a customer interface. A test can be performed on the customer connection. A typical test compares two datasets related to the customer connection to determine a state of the customer connection. The first and second dataset can include historical data. A parameter in the first dataset obtained from a network element can be compared to a parameter in a second dataset obtained from a customer database. The comparison can be made in light of changes recorded in a provisioning database. Relevant network data can be obtained from customer premises equipment (CPE). The customer can be notified of a network issue proactively or upon customer inquiry.
Owner:SBC KNOWLEDGE VENTURES LP
Machine learning based botnet detection using real-time connectivity graph based traffic features
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a connectivity graph based feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the connectivity graph based feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the connectivity graph based feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the connectivity graph based feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
Cyber Behavior Analysis and Detection Method, System and Architecture
A scalable cyber-security system, method and architecture for the identification of malware and malicious behavior in a computer network. Host flow, host port usage, host information and network data at the application, transport and network layers are aggregated from within the network and correlated to identify a network behavior such as the presence of malicious code.
Owner:CYBER ADAPT INC
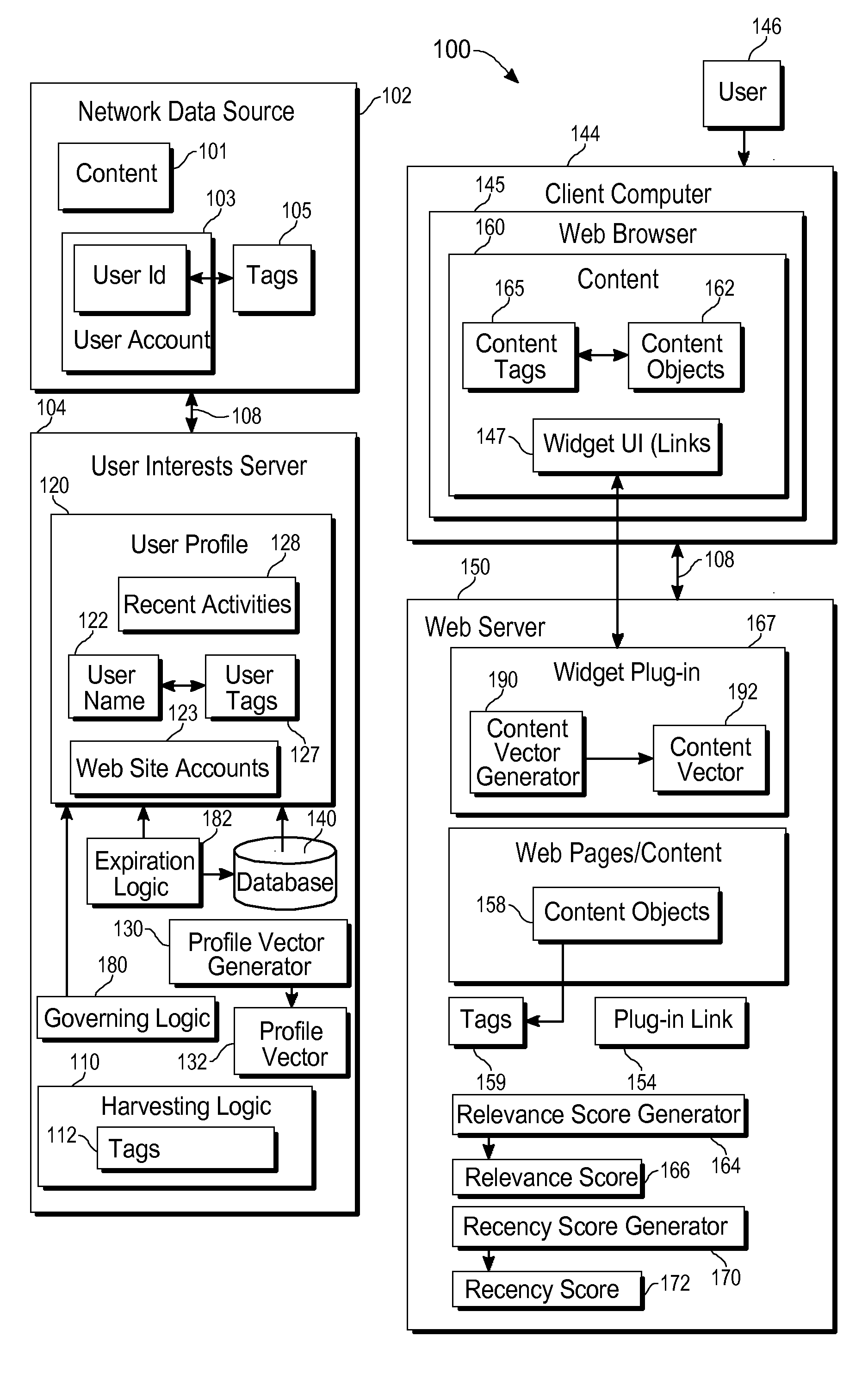
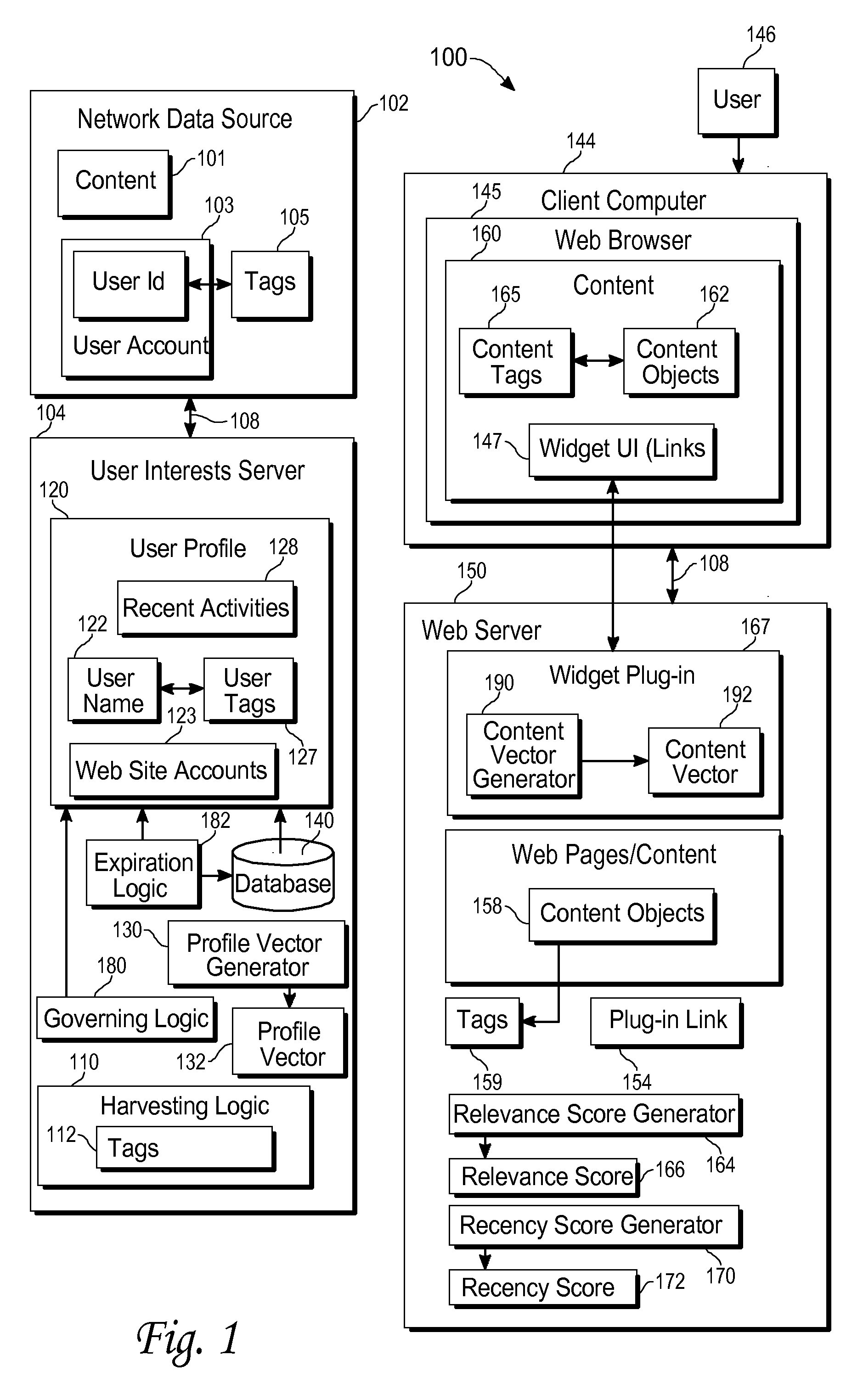
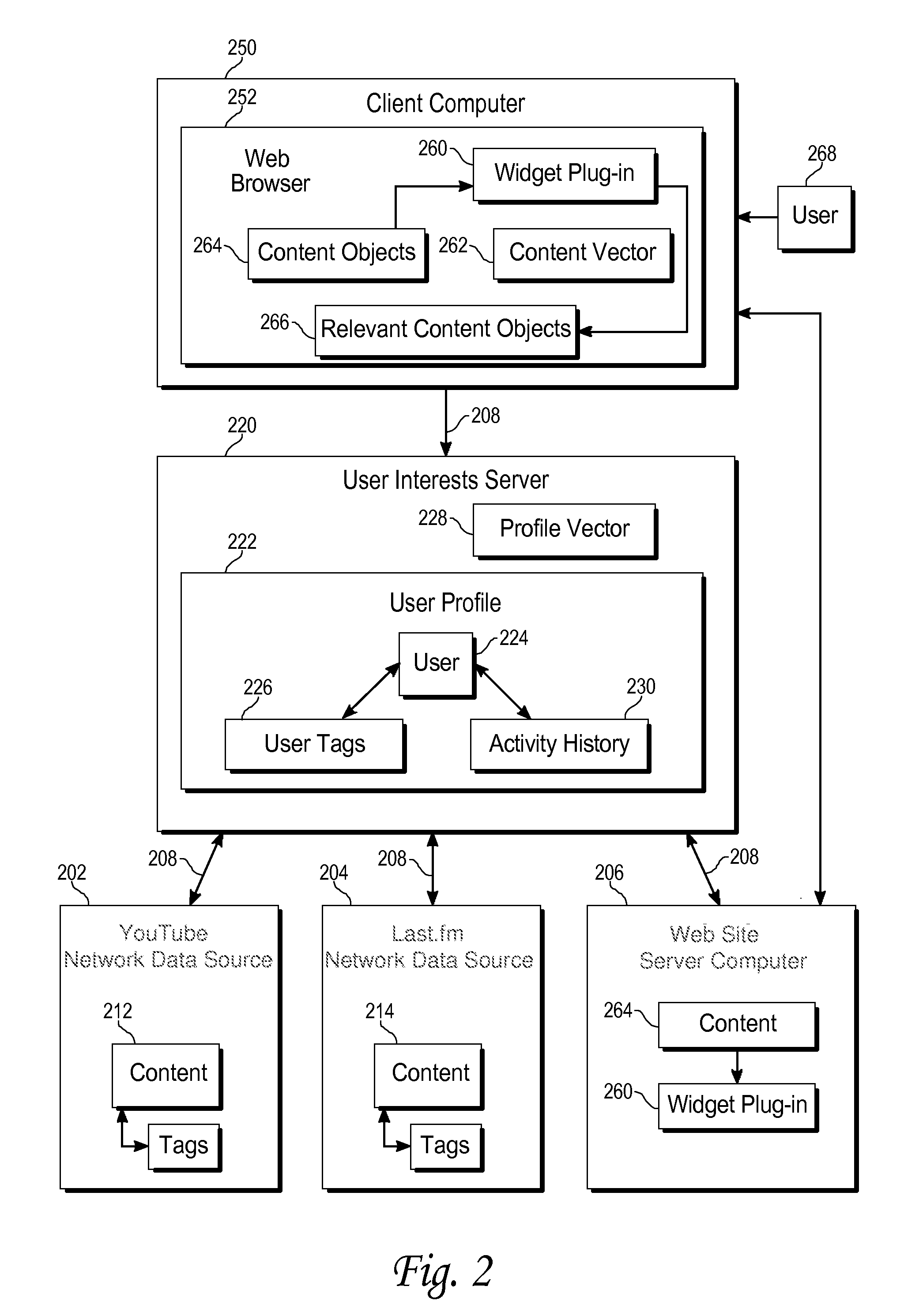
Augmenting online content with additional content relevant to user interests
ActiveUS20100023506A1Prolong lifeDigital data processing detailsSpecial data processing applicationsData sourceNetwork data
A method of gathering information relevant to the interests of a user includes receiving activity history associated with the user from a network data source, where the activity history includes a description of a user action initiated by the user, generating a first metadata item based upon the activity history; and storing the first metadata item as user profile information associated with the user in a user profile database. Generating the first metadata item may include extracting text from the activity history and generating the first metadata item based upon the text. The activity history may include a description of a user action. The method may further include providing a server plugin for performing a second method in response to access of web content on a server by the user, the second method comprising retrieving a content object from the server, determining if the first metadata item is relevant to the content object, adding a web link to the web content as a reference to the content object in response to the content object being relevant to the first metadata item; and providing the web content to the user.
Owner:R2 SOLUTIONS
Method and apparatus for optimizing networking potential using a secured system for an online community
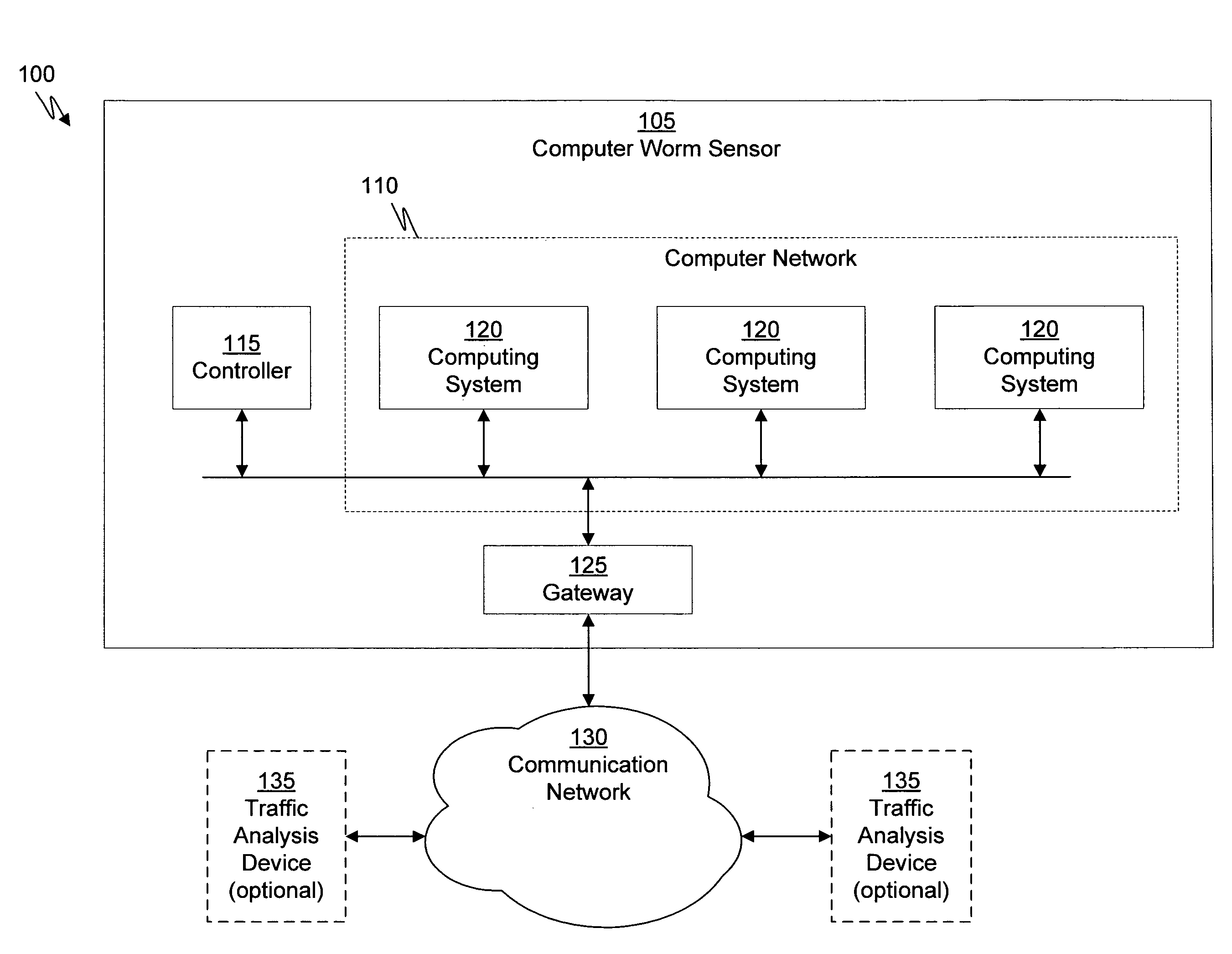
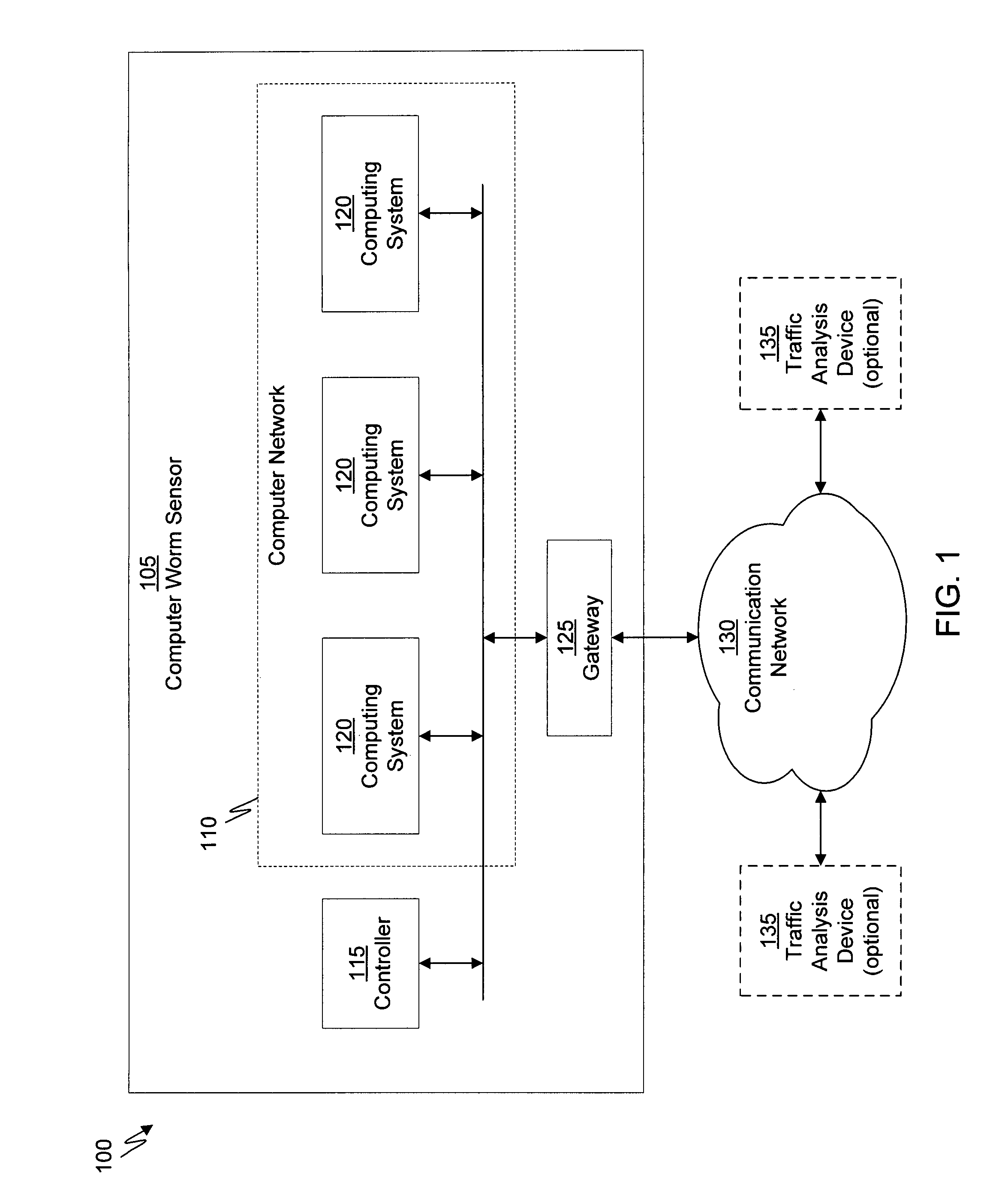
The present invention provides a method and apparatus for users to search networks, both their own network and their peers' networks, all under the umbrella of a “multiple level access” security system. The present invention has been designed to optimize networking capabilities among users in a comprehensive online community. Networking among such a secured environment will allow users an opportunity to enhance their networking potential by expanding their networks to their peers' and beyond. A user registers with the online community and personally adds individuals that they know to their personal networking database. While adding these peers to the networking database, the user grants a specific level of access to each individual. This security measure is devised to discourage solicitation from other unwanted online users. The levels of access give the user an opportunity to control the amount of personal information, including contacts that they make, available to their individual peers. Based on the level of access granted by the user, the peer may or may not be able to access the users information or the user's personal databases for potential networking. The level of access granted by two individuals need not be the same for each other.
Owner:MICROSOFT TECH LICENSING LLC
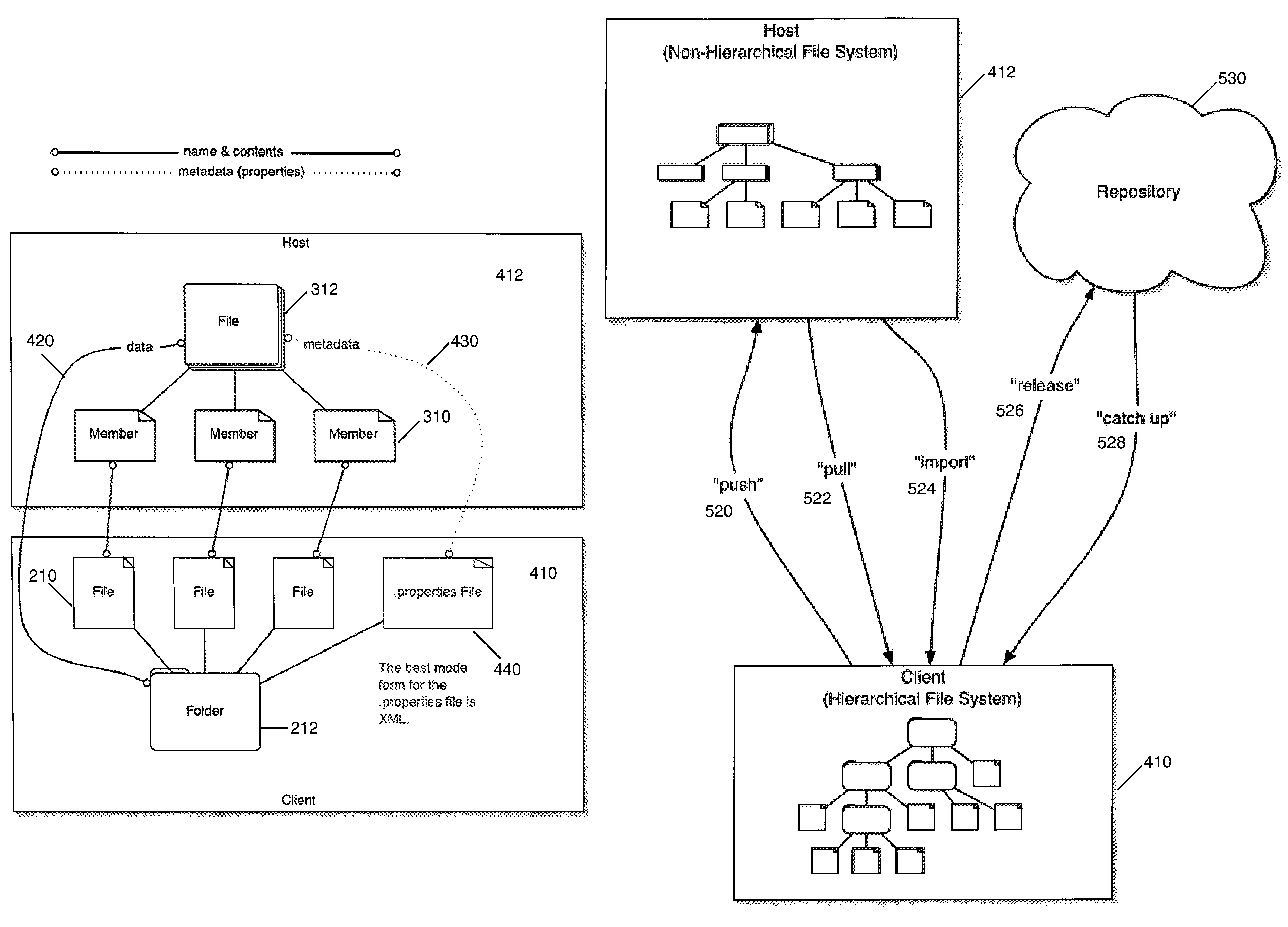
Transferring data and storing metadata across a network
InactiveUS7617222B2Improve flowData processing applicationsDigital data information retrievalFile systemThe Internet
Data is now able to be transferred back and forth between computer systems which have disparate file systems, e.g., between a computer having a hierarchical file system and a computer having a nonhierarchical file system. The differences, however, are not limited to the file storage system. Data may now be transferred across different platforms, different human and computer languages, different binary codes, etc. From one computer system the associated metadata is stored in a interpretable format on the second computer system so that when data and its associated metadata are transferred, the second computer system can interpret the transferred data. Data transfer can be accomplished in both directions. Thus, a tool writer or a software developer using a integrated development environment, such as Eclipse, on a Linux workstation with its hierarchical file system may download source files and other resources from an iSeries computer server with its OS / 400 nonhierarchical file system, modify the resources, and then put them back onto the iSeries machine for use on the iSeries. The metadata of the source file and other resources are stored in a .properties file which, if in XML format, supports the transfer of resources across the Internet.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com