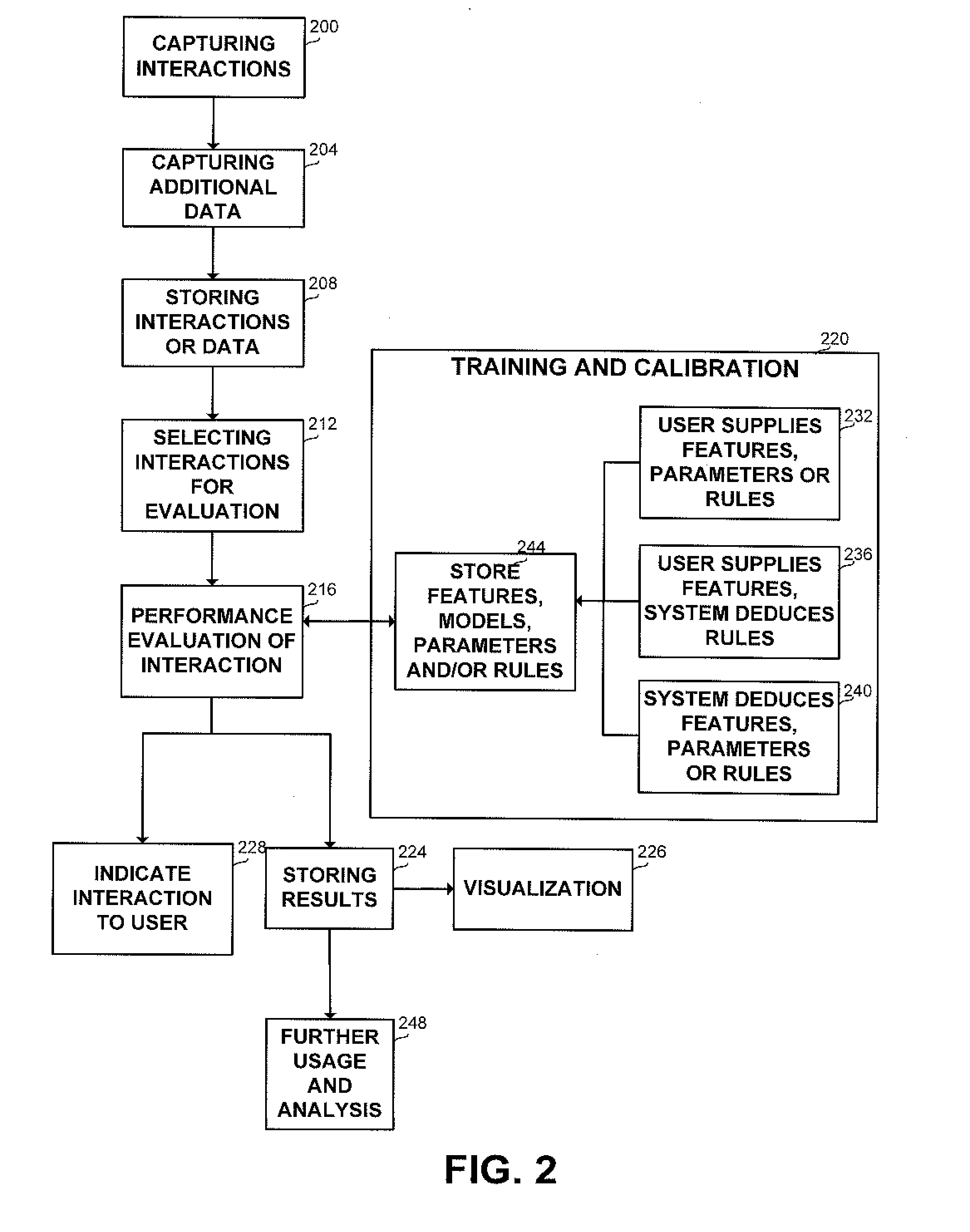
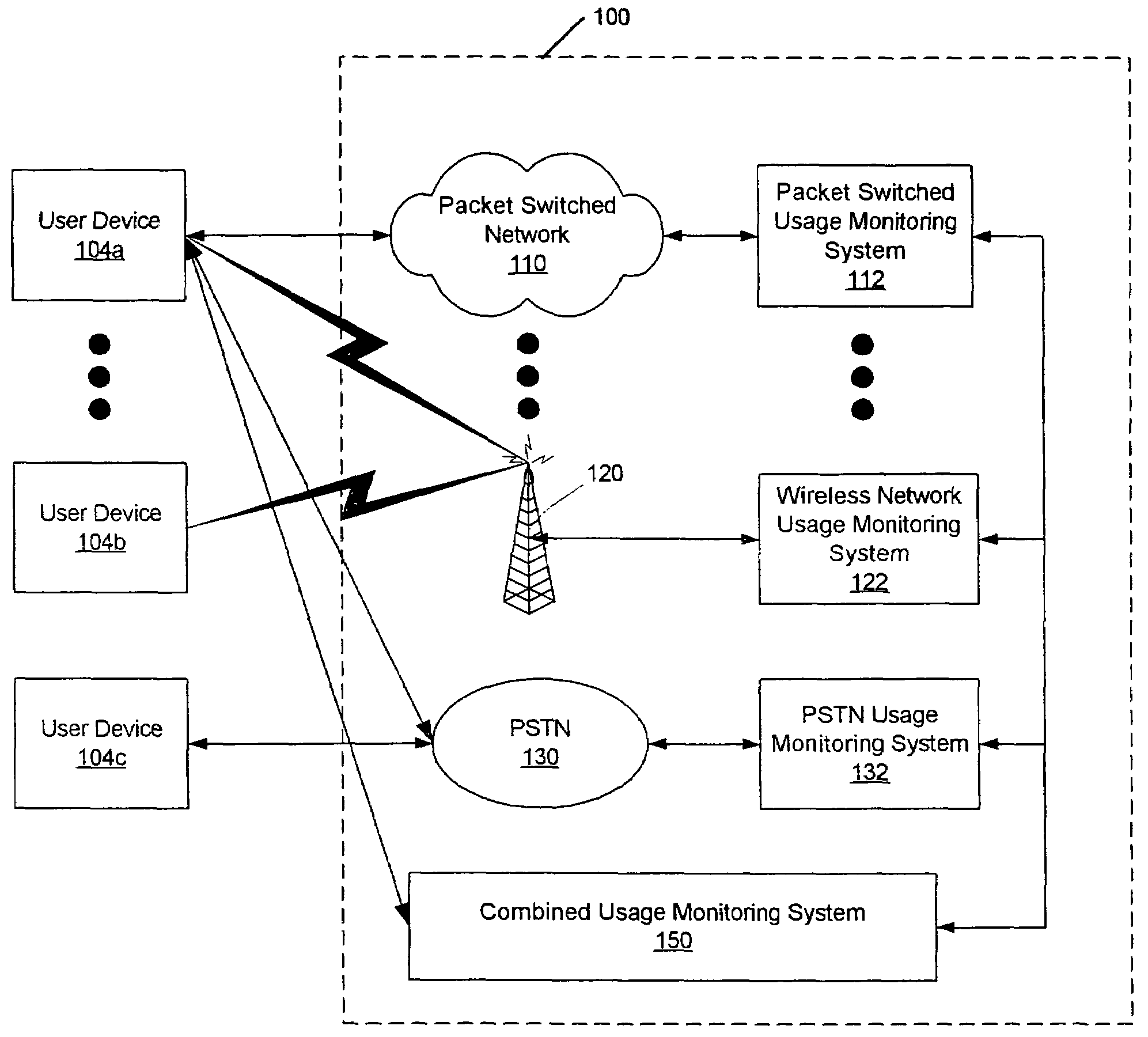
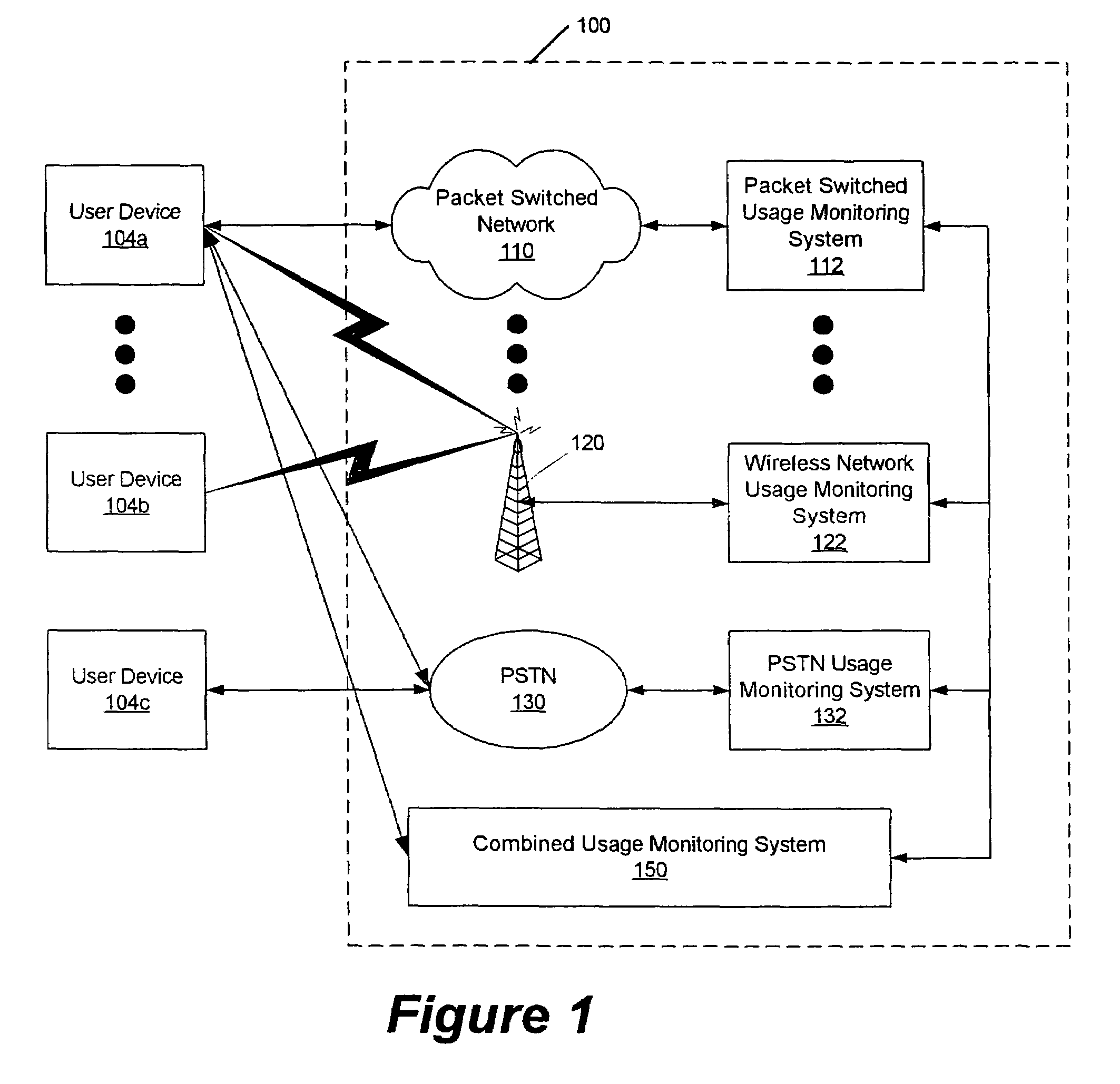
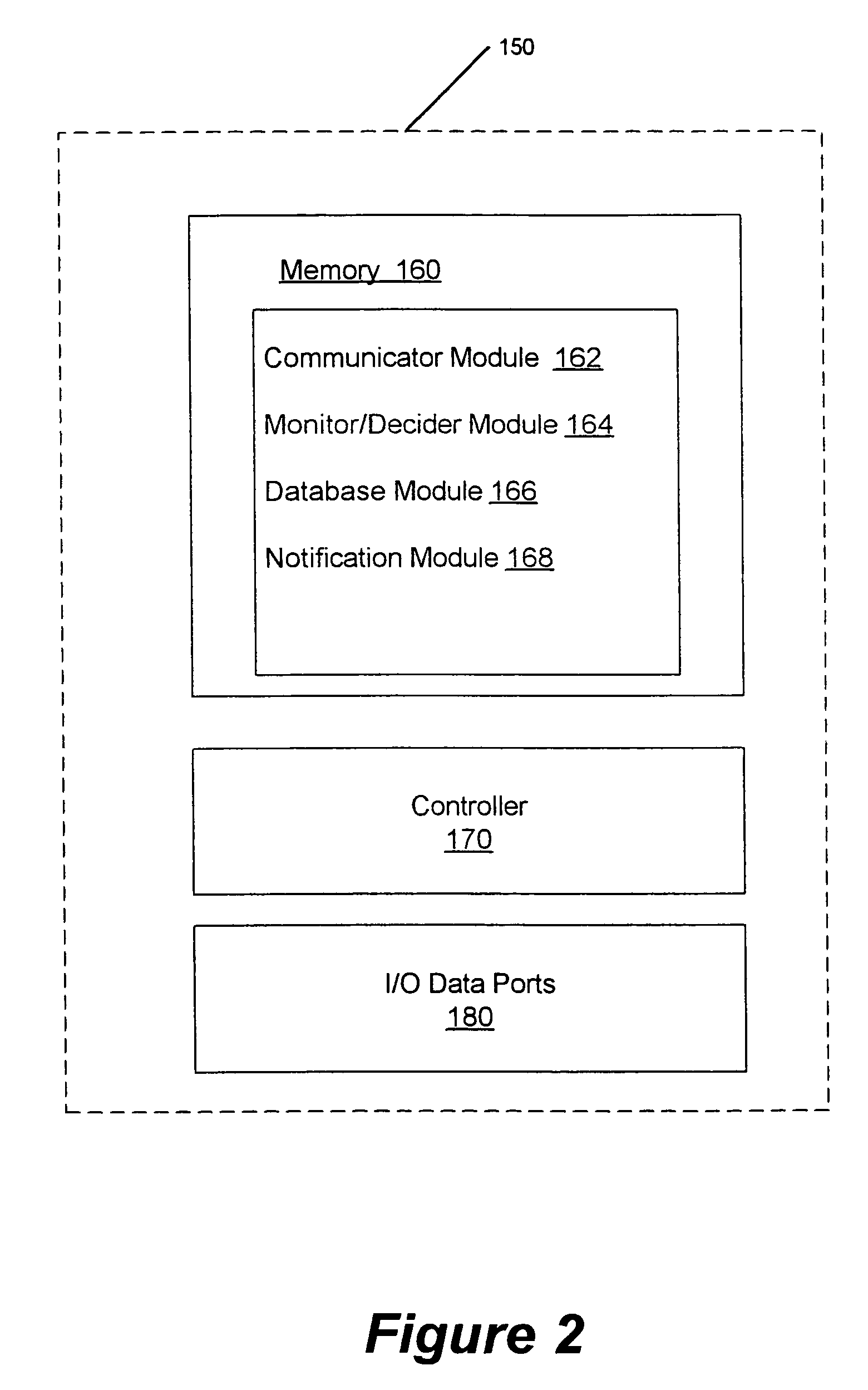
Patents
Literature
6585results about "Supervisory/monitoring/testing arrangements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for generating a dynamic interface via a communications network
InactiveUS6850949B2Prevent excessive inputIncrease administrative overheadData processing applicationsDigital data processing detailsSupporting systemNetwork generation
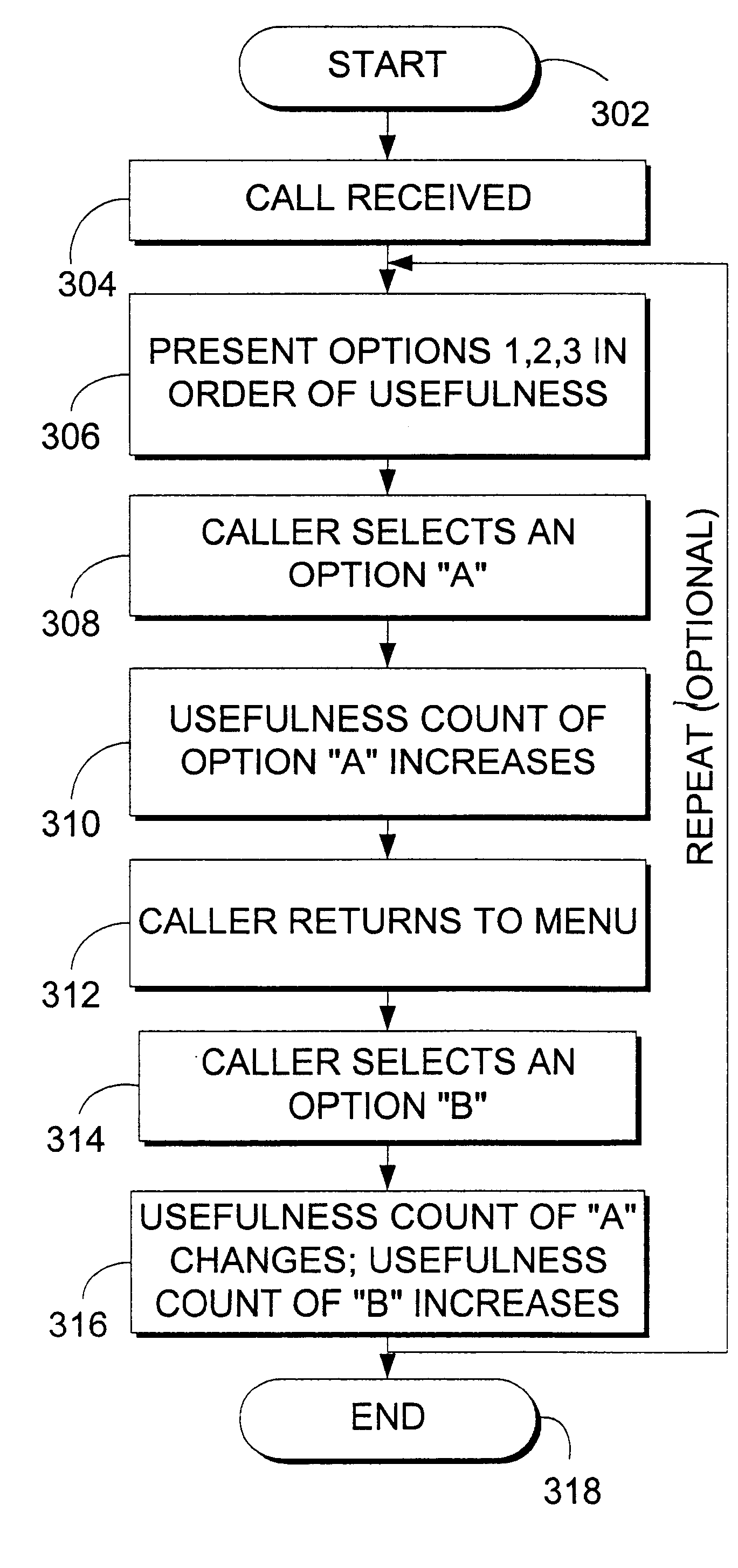
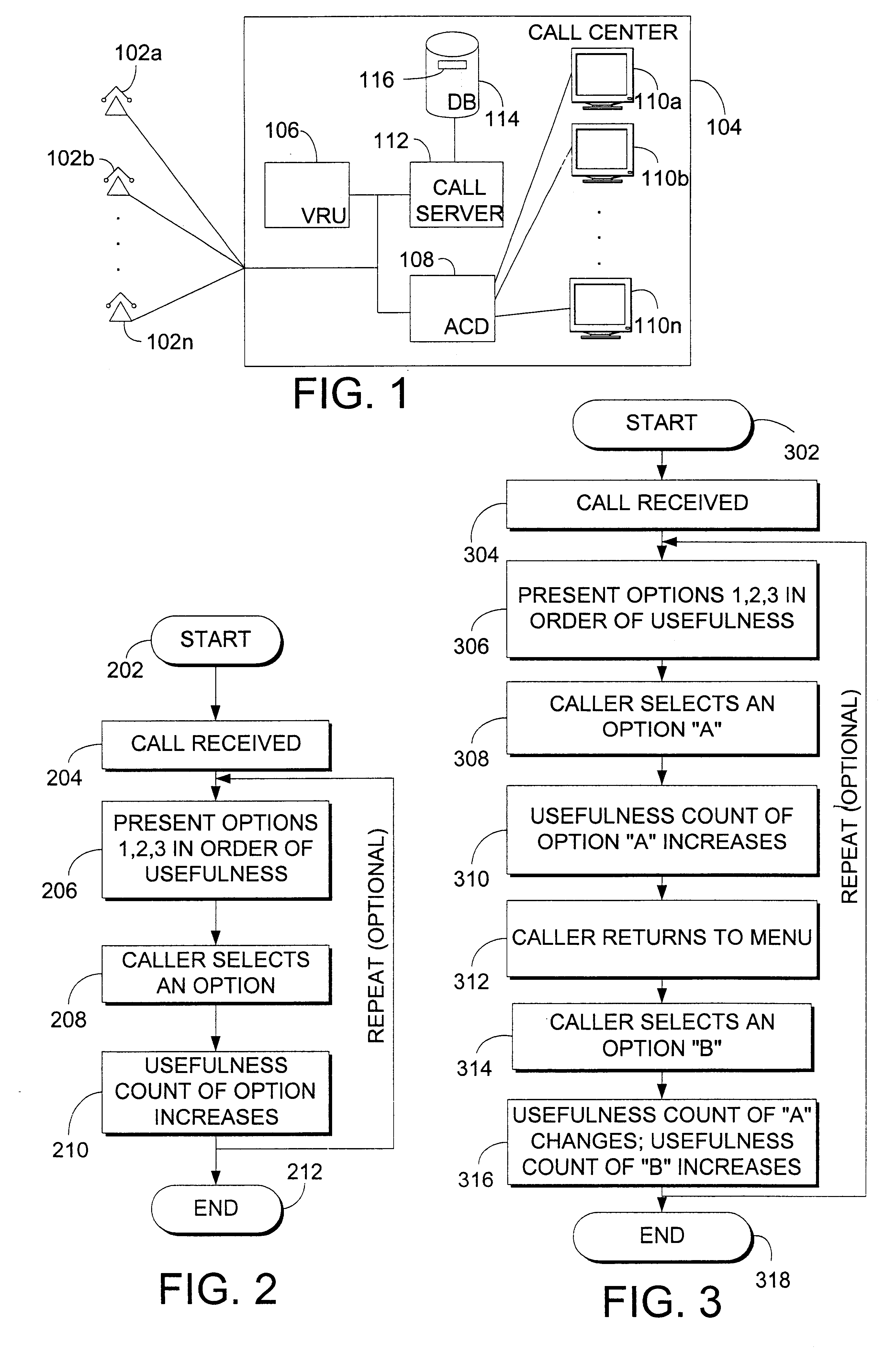
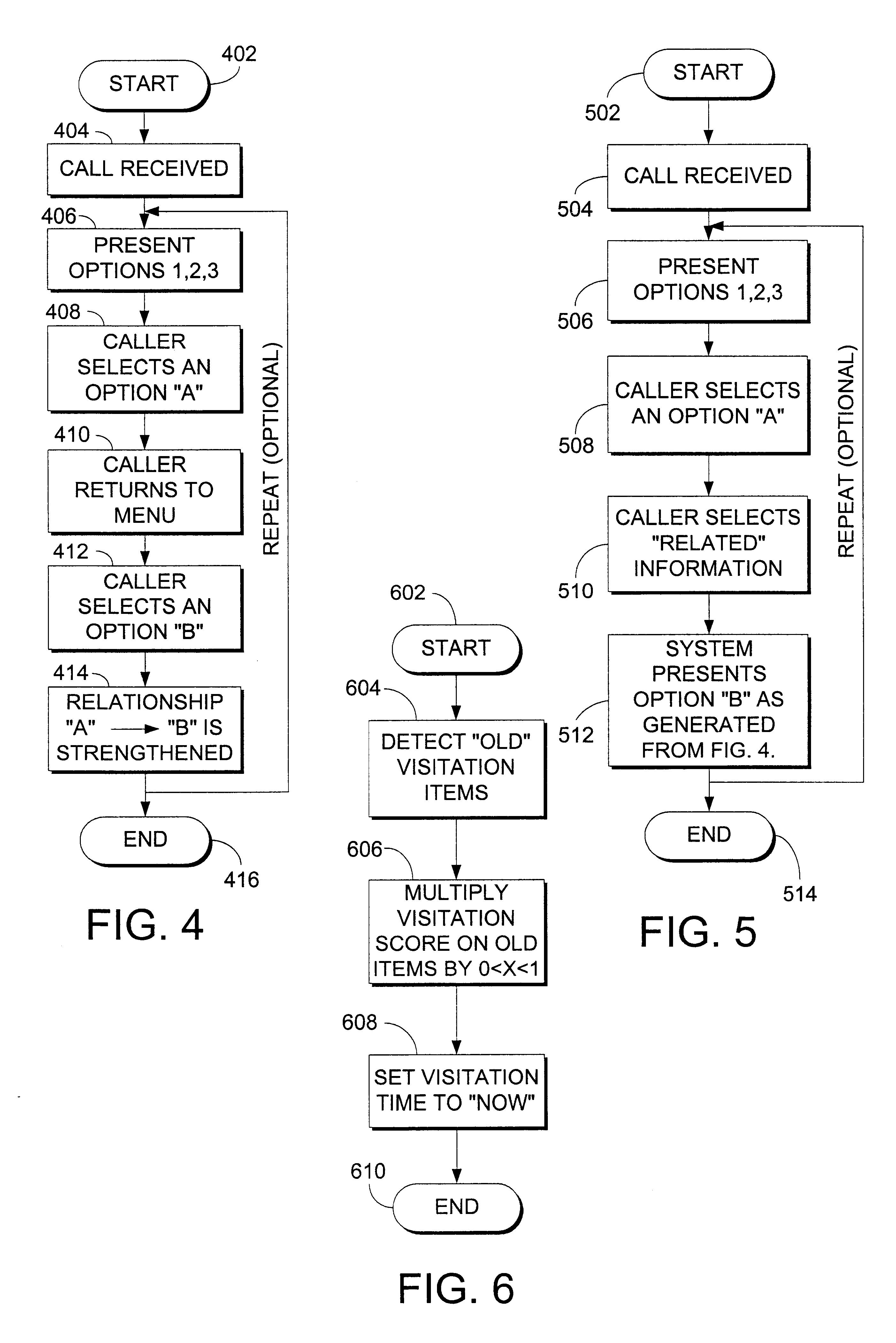
A system, method, and computer program product for dynamically adapting selections in an automatic phone support system is described. The invention may integrate a dynamic knowledge base of responses with the menu selections on an automated phone system or other response system to present the most frequently used items earlier in the option list, or otherwise order options and information. Call data may be captured from single callers or historical ensembles of callers. An automatically generated similarity relationship may be used to initialize the system without historical call data, based on textual similarity or other techniques. Prioritization of options provides a more enjoyable, efficient experience for callers without increasing administrative overhead.
Owner:ORACLE OTC SUBSIDIARY
Software fault management system
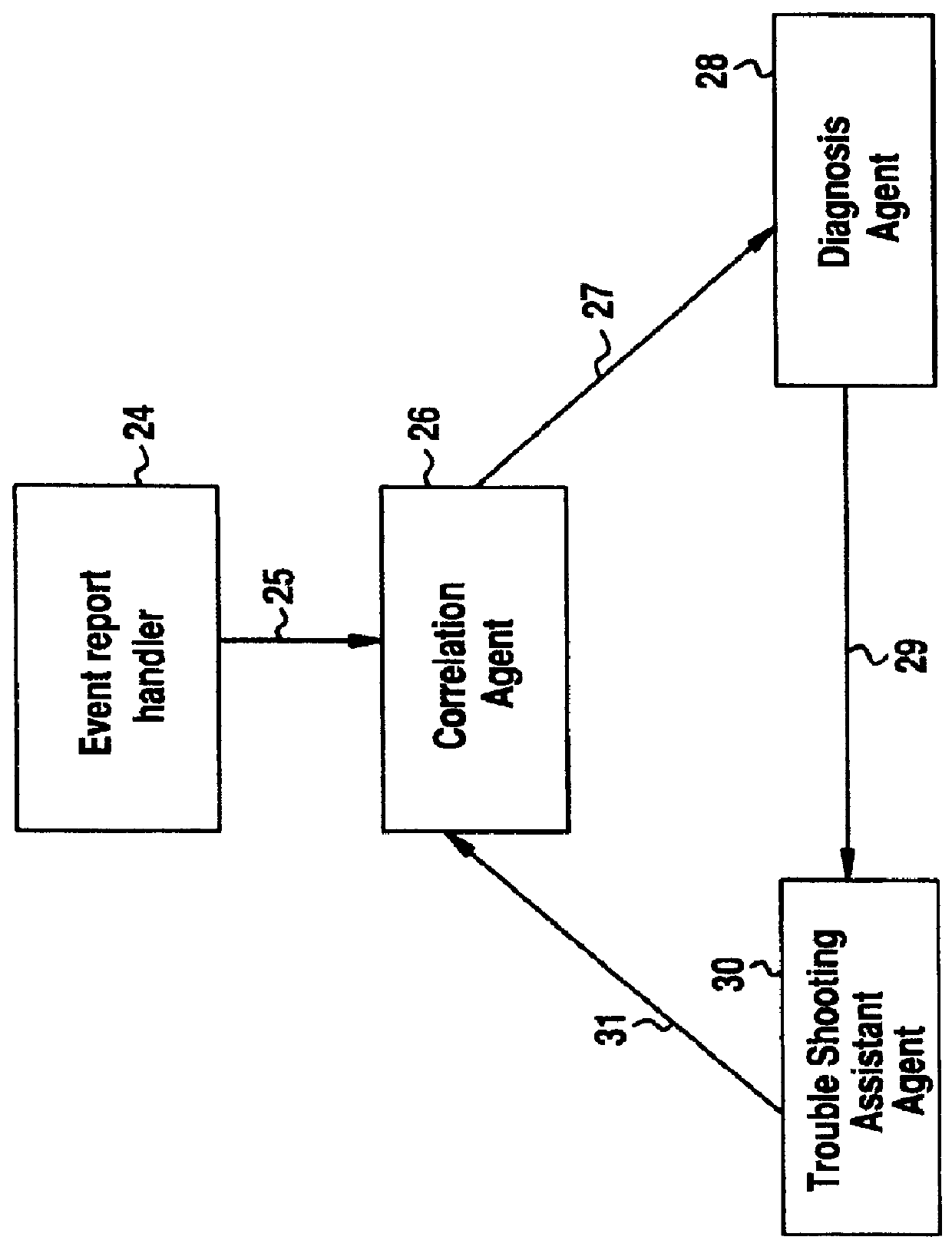
InactiveUS6012152ASupervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsInformation repositoryManagement information systems
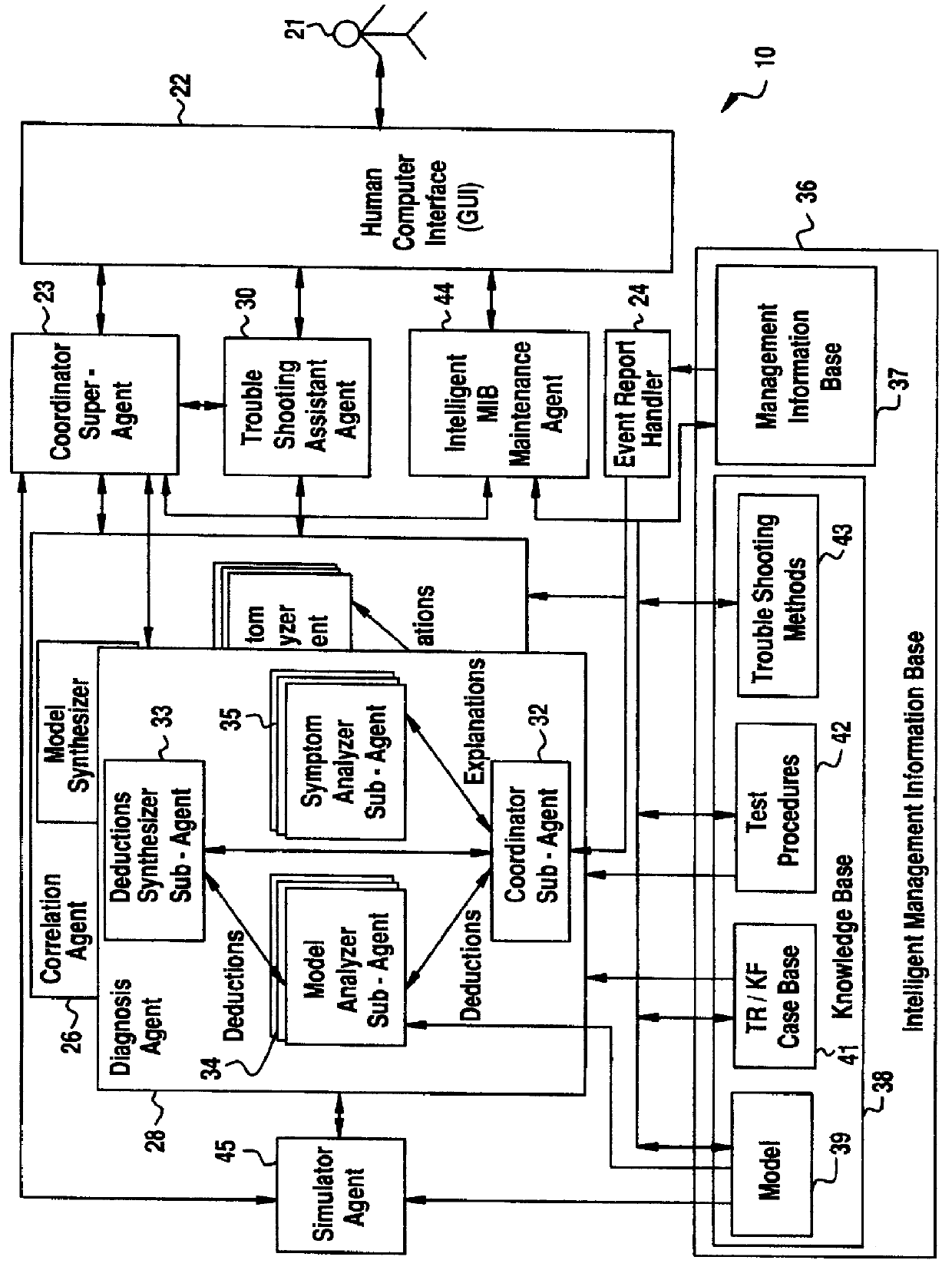
A Software Fault Management (SFM) system for managing software faults in a managed mobile telecommunications network. The SFM system includes an Intelligent Management Information Base (I-MIB) comprising a Management Information Base (MIB) and a Knowledge Base (KB) having a functional model of the managed network and a trouble report / known faults (TR / KF) case base. The SFM system also includes an intelligent multi-agent portion having a plurality of agents which process the software faults utilizing the functional model from the I-MIB, case-based information, and other management information. The I-MIB and the intelligent multi-agent portion are compliant with Telecomunications Management Network (TMN) principles and framework. Fault management is both proactive and reactive. The SFM system is made independent of technology-specific implementations by representing the underlying switch design knowledge in a modular and changeable form which is then interpreted by the intelligent multi-agent portion. A clear separation is maintained between the generic procedural inference mechanisms and agents, and the specific and explicit models of the different network elements of a mobile telecommunications network.
Owner:TELEFON AB LM ERICSSON (PUBL)
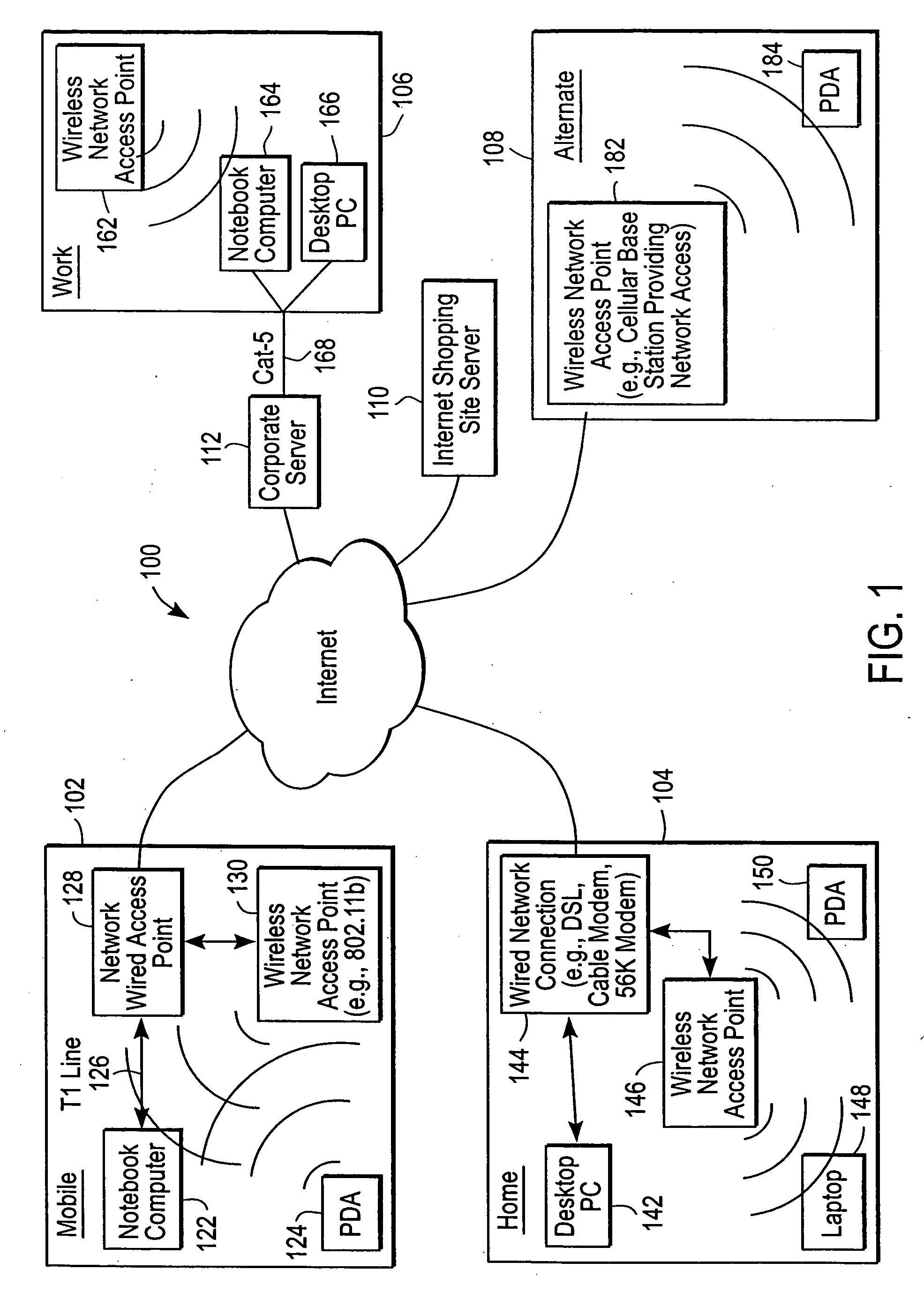
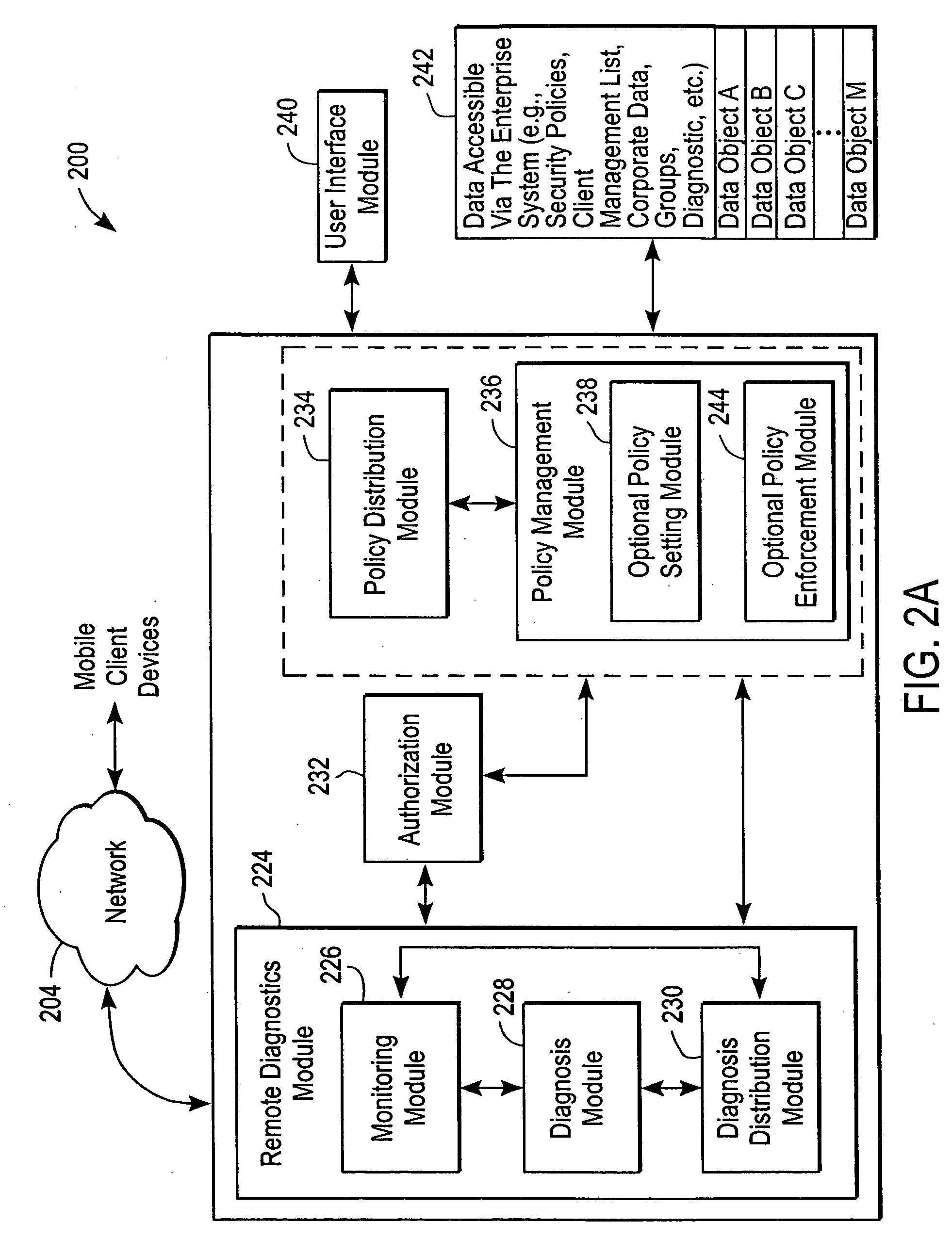
Administration of protection of data accessible by a mobile device
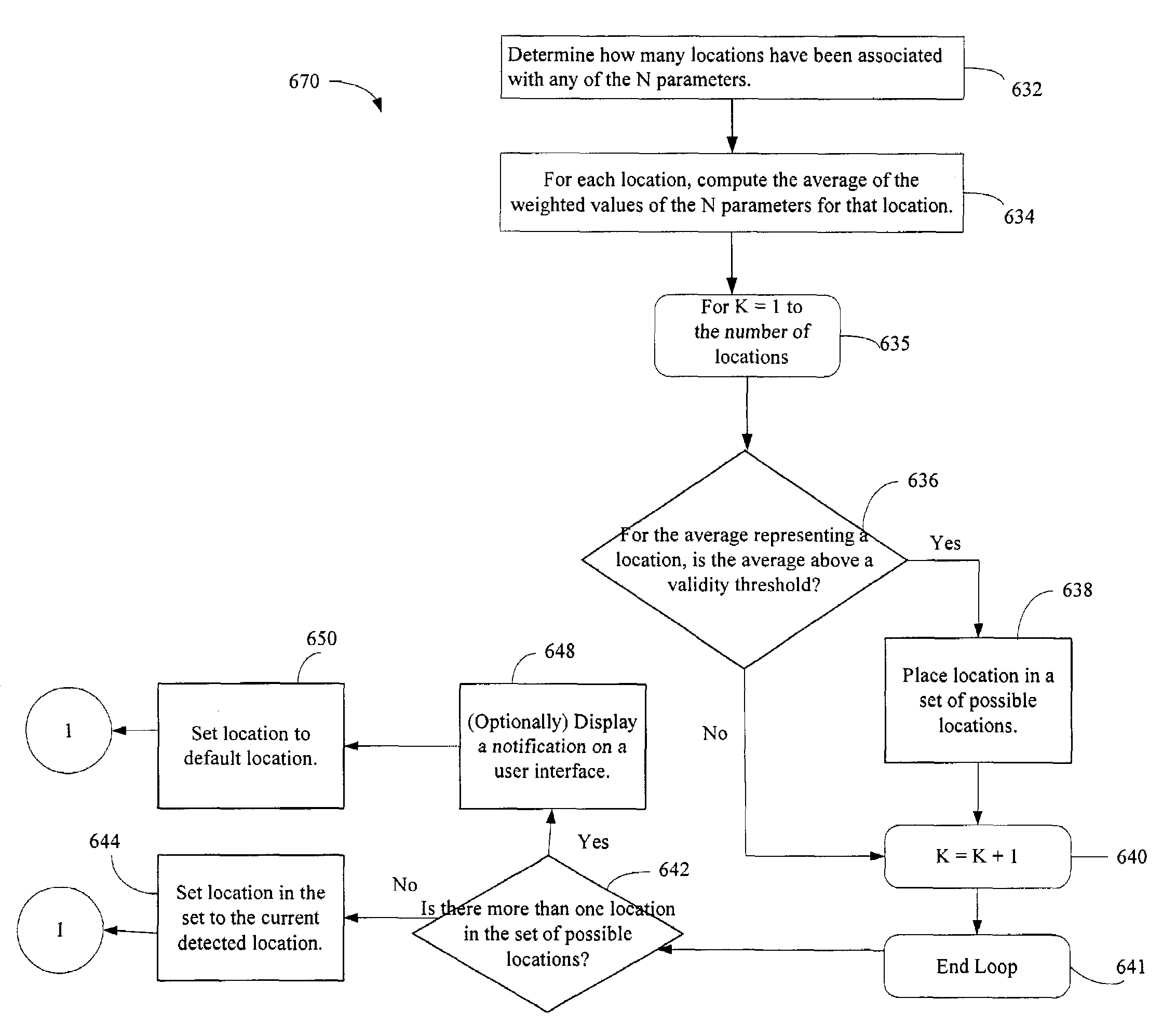
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Computer-based method and apparatus for controlling, monitoring, recording and reporting telephone access
InactiveUS7106843B1Improve securityLow costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsManagement unitCentralized management
A method and apparatus for managing institutional telephone activity utilizing a computer-based telephony management unit to connect institutional telephones with outside telephone lines. The unit provides institutional users with fully automated, direct dial and collect calling privileges for local, long distance, and international calls. The unit contains a database for storing the calling privileges and restrictions of institutional users, for recording calling transactions made by the users, and for managing user monetary accounts. The unit can record up to 400 hours of conversation in a digital format. The unit provides various administrative capabilities, including user account management, audit trails, transaction reports, centralized management and report capabilities, and detection of fraudulent calling.
Owner:AMERICAN CAPITAL FINANCIAL SERVICES +1
System and method for providing context sensitive recommendations to digital services
ActiveUS20040043758A1Reducing or minimizing the processing load and memoryReduces privacy concernInterconnection arrangementsDigital data information retrievalComputer networkRelevant information
A system and method is disclosed to provide recommendations to a wireless device, based on stored bookmark / short-cut data. When a wireless device accesses services, data pertaining to the service access, along with any context related information is transmitted within the wireless device, or to a remote server. The data is processed in conjunction with bookmarks / short-cuts specified within the device, and are organized and presented to the wireless device in accordance with preference instructions specified within the wireless device.
Owner:NOKIA TECHNOLOGLES OY
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
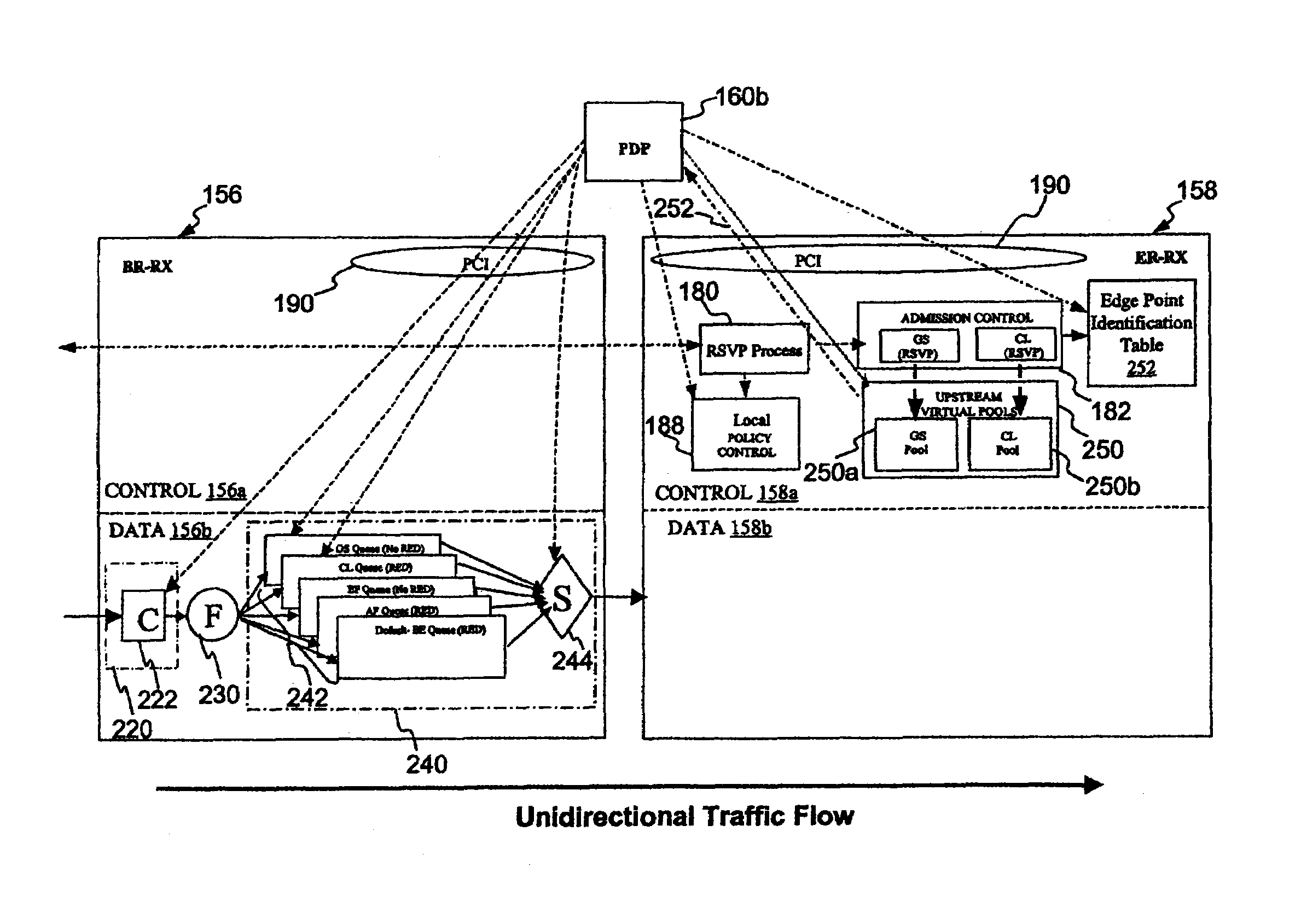
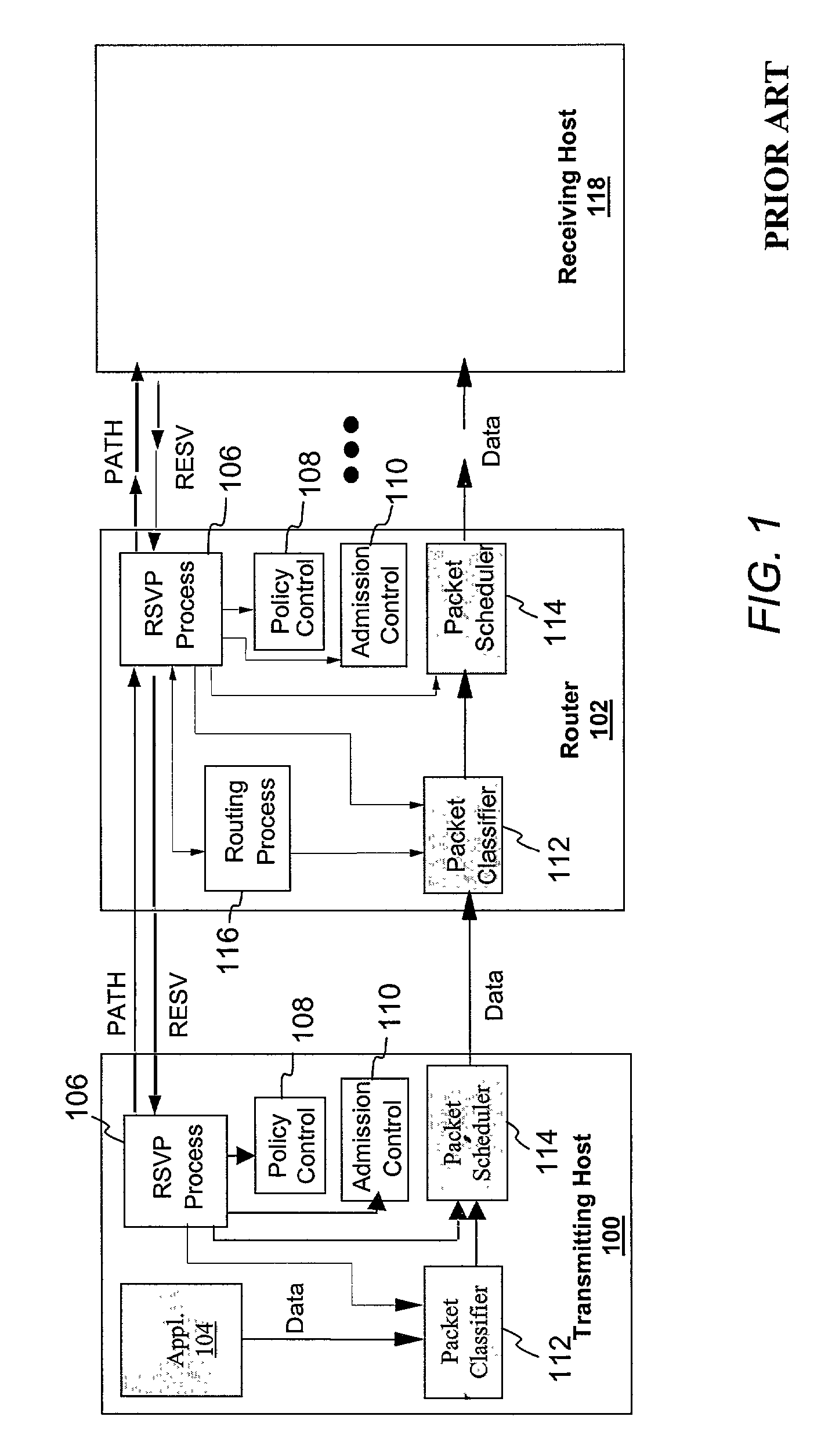
Pool-based resource management in a data network
ActiveUS7209439B2Metering/charging/biilling arrangementsInterconnection arrangementsNetworked systemResource management
In one embodiment, a network system of the present invention includes at least a first router and a second router coupled to an upstream link to permit data flow from the first router to the second router across the upstream link. The second router includes a control plane and a data plane having an input port coupled to the upstream link and an output port connectable to a downstream link. The control plane includes a virtual pool having a capacity corresponding to a resource capacity of the first router and an admission control function. In response to a request to reserve resources for a flow through the data plane from the input port to the output port, the admission control function performs admission control for the upstream link by reference to resource availability within the virtual pool. In one embodiment, the request is a request to reserve resources for an Integrated Services flow, and the capacity of the virtual pool corresponds to a resource capacity of a Integrated Services service class supported by the first router.
Owner:VERIZON PATENT & LICENSING INC
Femtocell Integration into the Macro Network
ActiveUS20080207170A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemNetwork control
Some embodiments of the invention provide a communication system that includes a first communication network, a second communication network, and a core network. The second communication network includes a network controller and a group of two or more access areas that are communicatively coupled to the core network by the network controller. Some embodiments service the second network access areas by providing access area identifiers to each access area while communicating with the first network or core network using a single are identifier assigned to the network controller. Some embodiments provide access control by sending a series of invalid messages to a user equipment (UE) that is not authorized to access services of the second network to reject the UE. Some embodiments reject the UE by sending a message to ban a UE from an access area with a particular access area identifier.
Owner:RIBBON COMM OPERATING CO INC
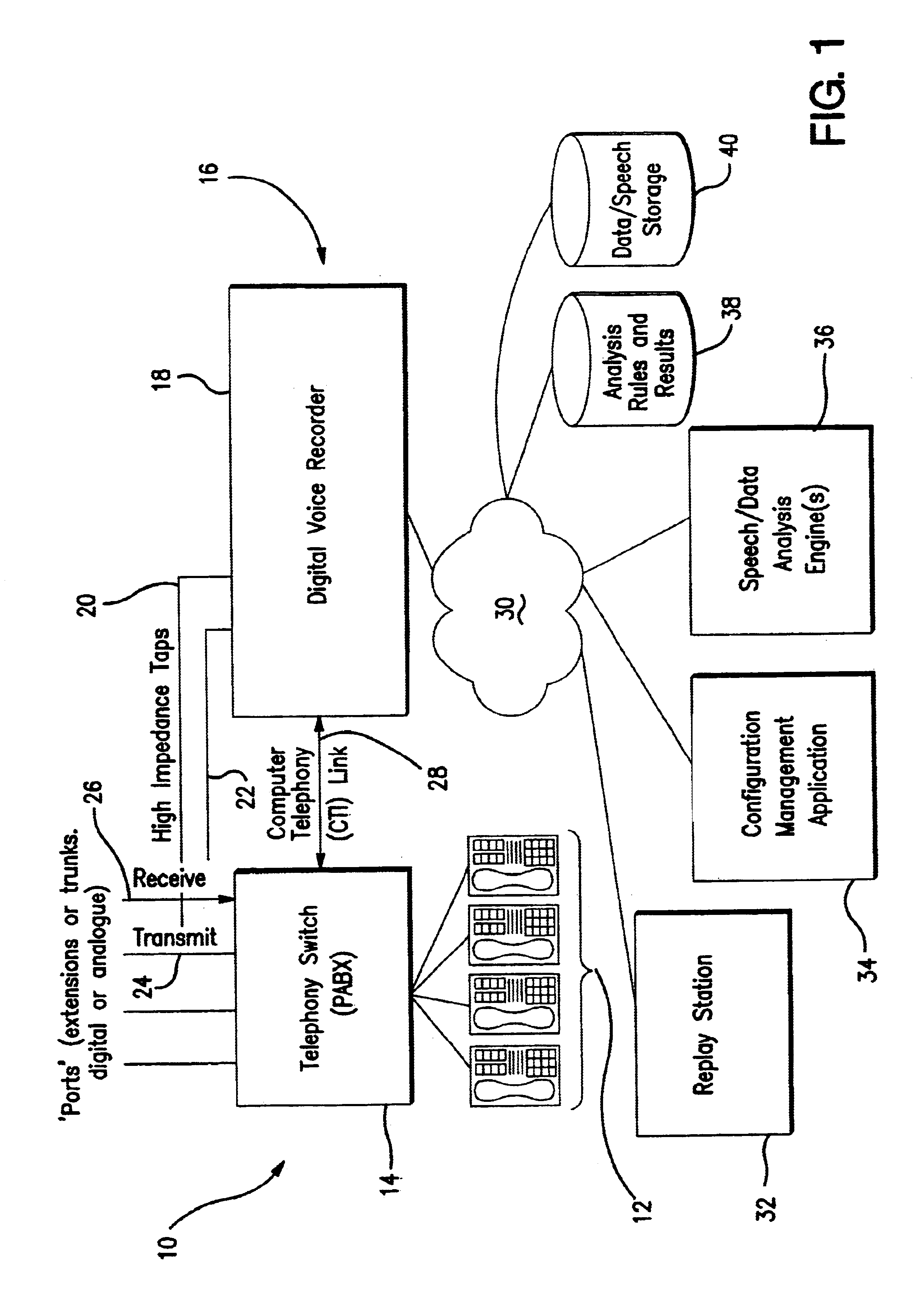
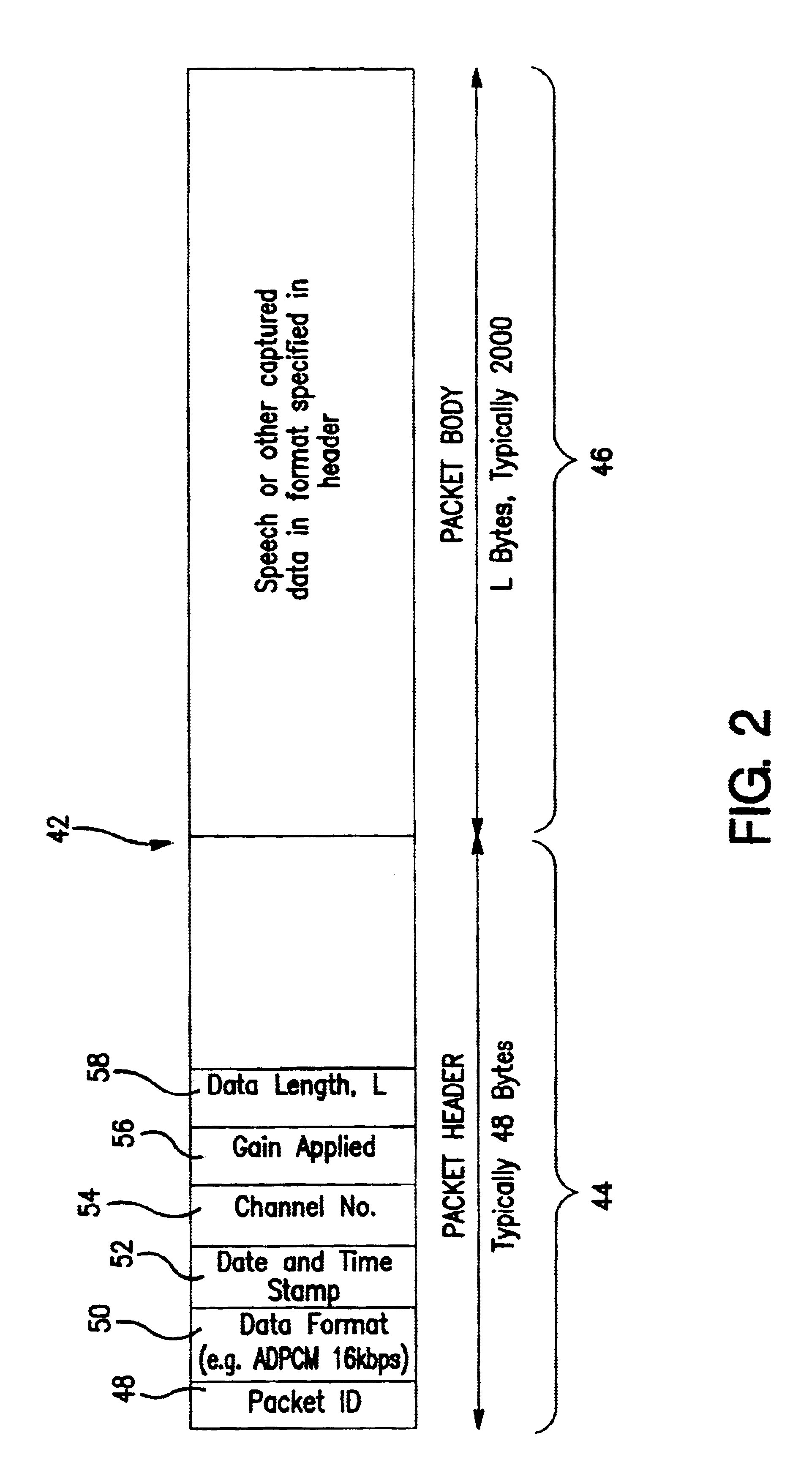
Signal monitoring apparatus analyzing voice communication content
InactiveUS6757361B2Easy to identifyInterconnection arrangementsSpecial service for subscribersVoice communicationSpeech sound
A signal monitoring apparatus and method involving devices for monitoring signals representing communications traffic, devices for identifying at least one predetermined parameter by analyzing the context of the at least one monitoring signal, a device for recording the occurrence of the identified parameter, a device for identifying the traffic stream associated with the identified parameter, a device for analyzing the recorded data relating to the occurrence, and a device, responsive to the analysis of the recorded data, for controlling the handling of communications traffic within the apparatus.
Owner:CREDIT SUISSE AS ADMINISTATIVE AGENT +1
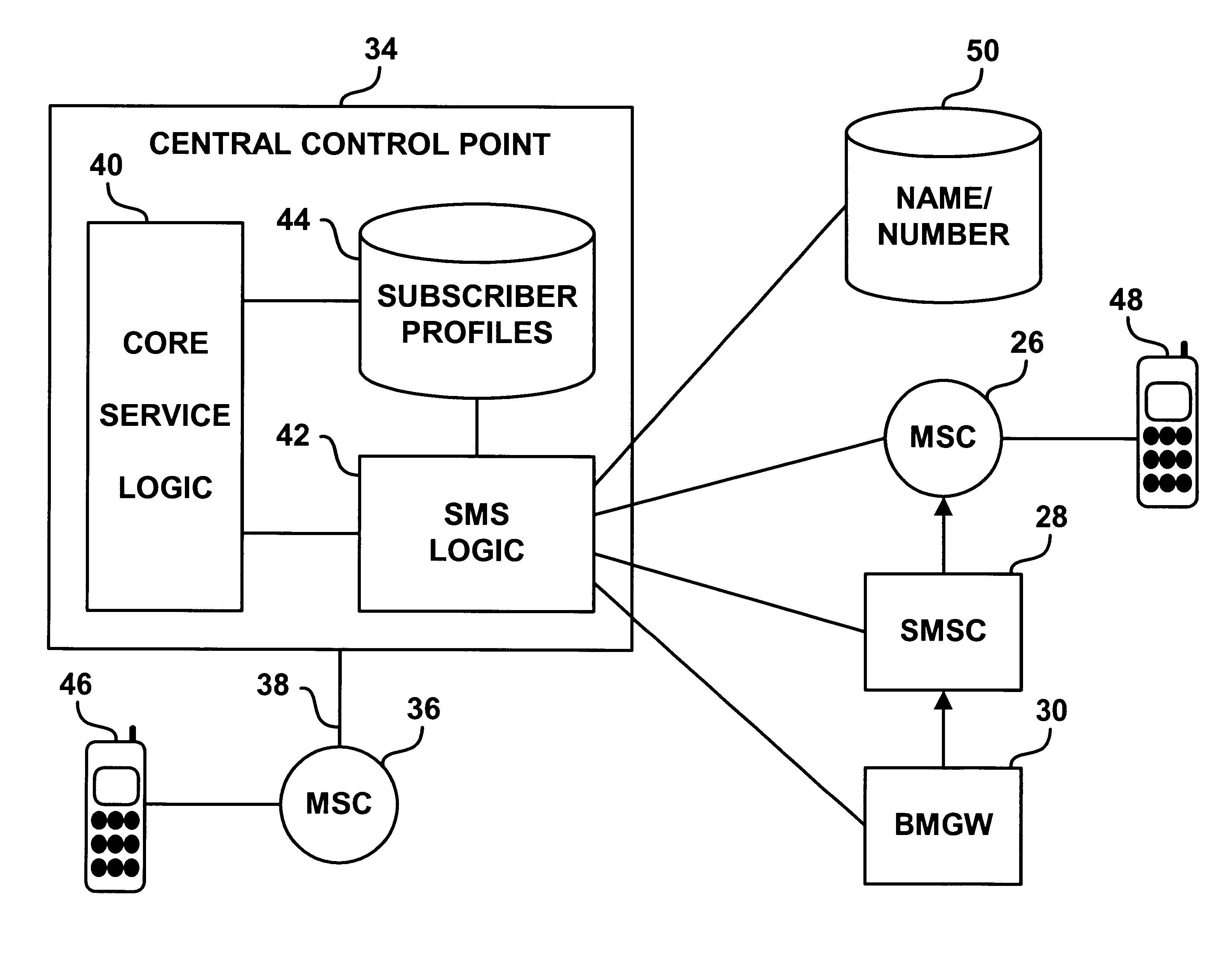
Automatic in-line messaging system
InactiveUS6718178B1Multiplex system selection arrangementsTelephone data network interconnectionsTelecommunications networkFacsimile
An automatic messaging system for a telecommunications network is disclosed. A call processing entity such as a switch or central control point recognizes a call-processing event and responsively generates and sends an informational message to a specified destination. The informational message may be a text description of the event, such as an indication that "calling party just placed a call to called party" or may take other forms, such as a video message, an audio message or a fax message.
Owner:SPRING SPECTRUM LP
Methods, systems and computer program products for monitoring service usage
InactiveUS20060045245A1Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemUse of services
Monitoring criteria is received that corresponds to a usage quantity for a plurality of services. Each of the plurality of services is provided over ones of a plurality of different communication systems. Actual service usage information is received for the plurality of services. The actual service usage information and the monitoring criteria are compared. An electronic notification message is sent when the monitoring criteria for one or more of the plurality of services is satisfied.
Owner:AT&T INTPROP I L P
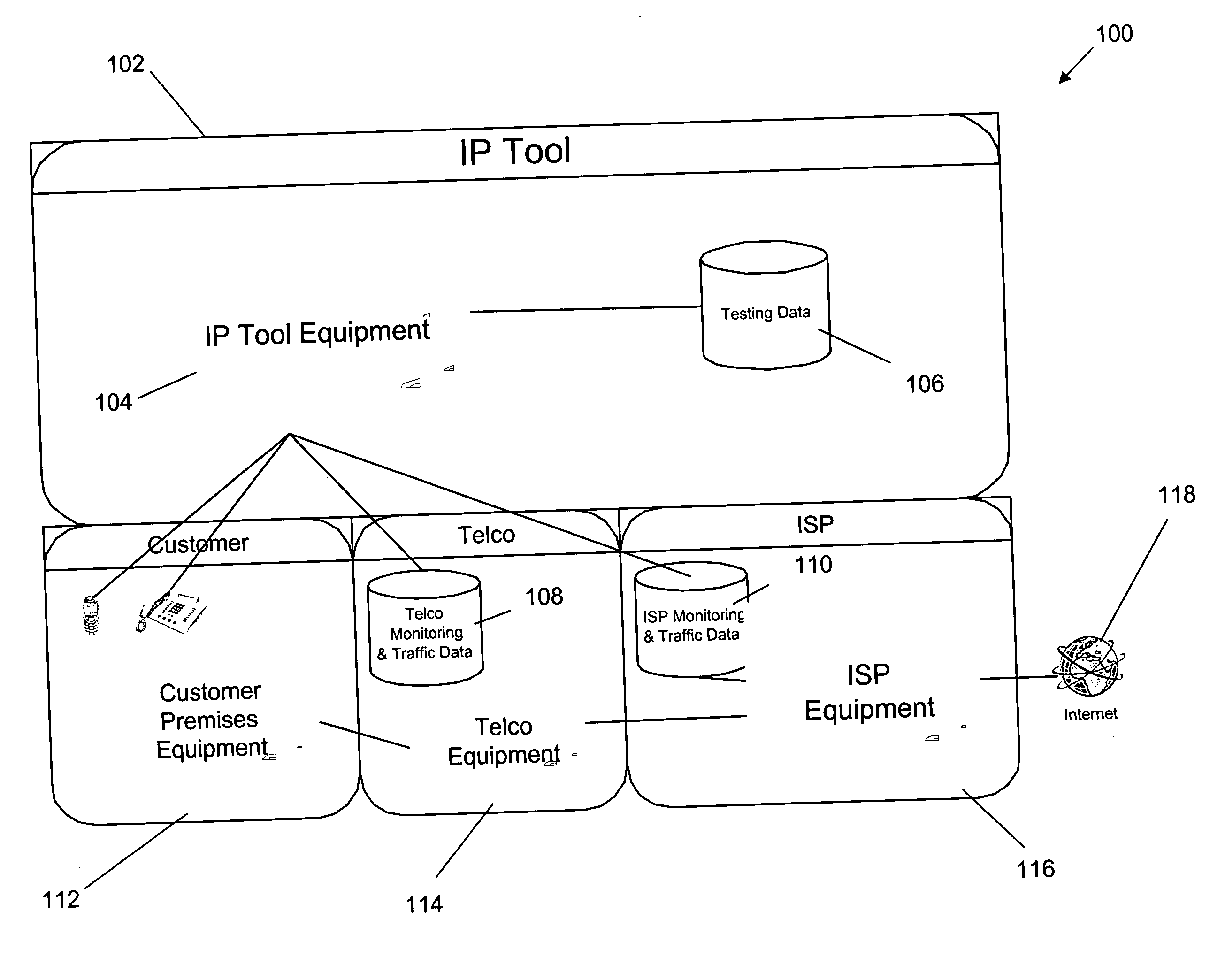
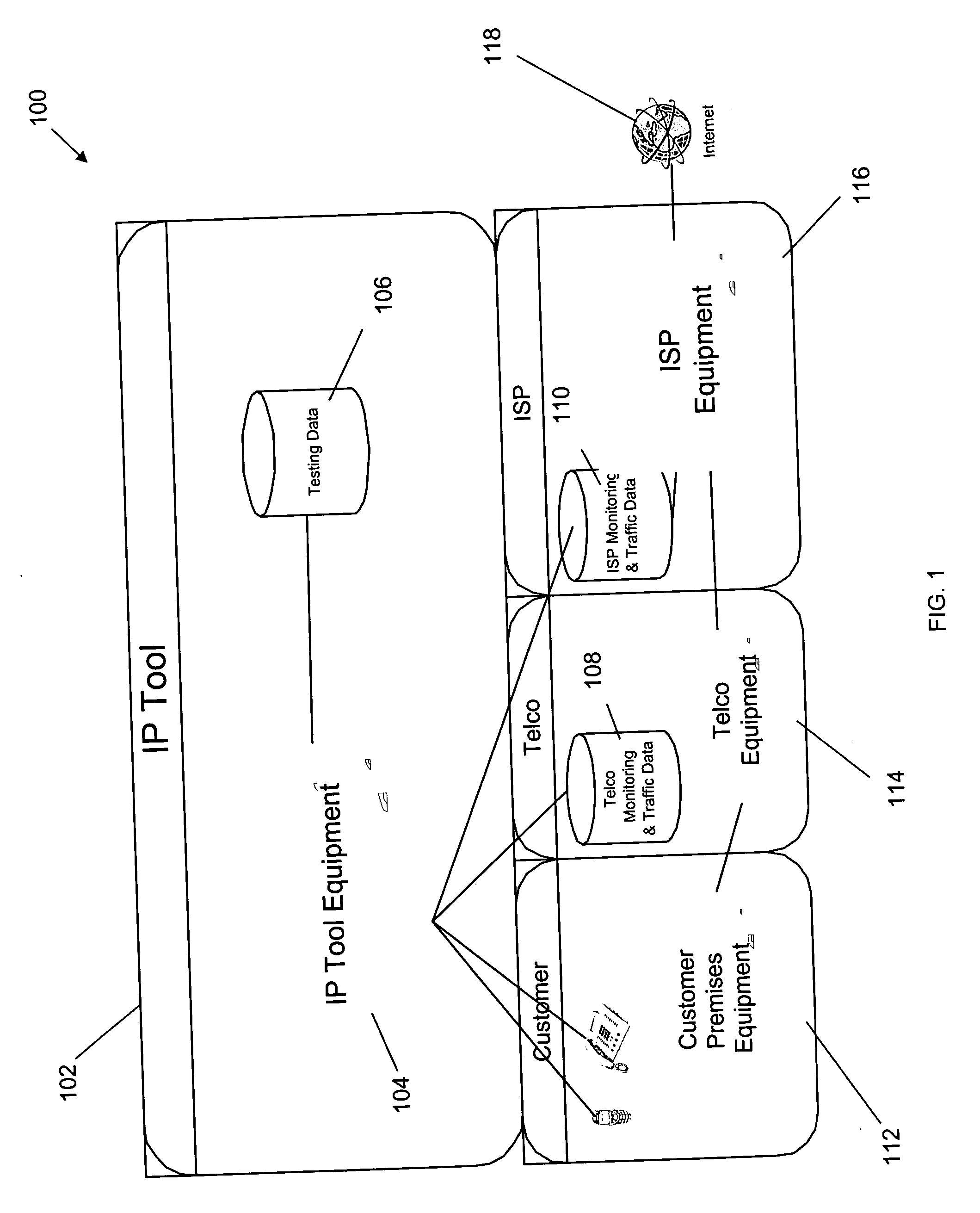
Method and system for comprehensive testing of network connections
InactiveUS20070041554A1Special service for subscribersSupervisory/monitoring/testing arrangementsData setNetwork connection
The present invention is an system and method for comprehensively testing a customer connection to a communications network. A customer is identified from information obtained at a customer interface. A test can be performed on the customer connection. A typical test compares two datasets related to the customer connection to determine a state of the customer connection. The first and second dataset can include historical data. A parameter in the first dataset obtained from a network element can be compared to a parameter in a second dataset obtained from a customer database. The comparison can be made in light of changes recorded in a provisioning database. Relevant network data can be obtained from customer premises equipment (CPE). The customer can be notified of a network issue proactively or upon customer inquiry.
Owner:SBC KNOWLEDGE VENTURES LP
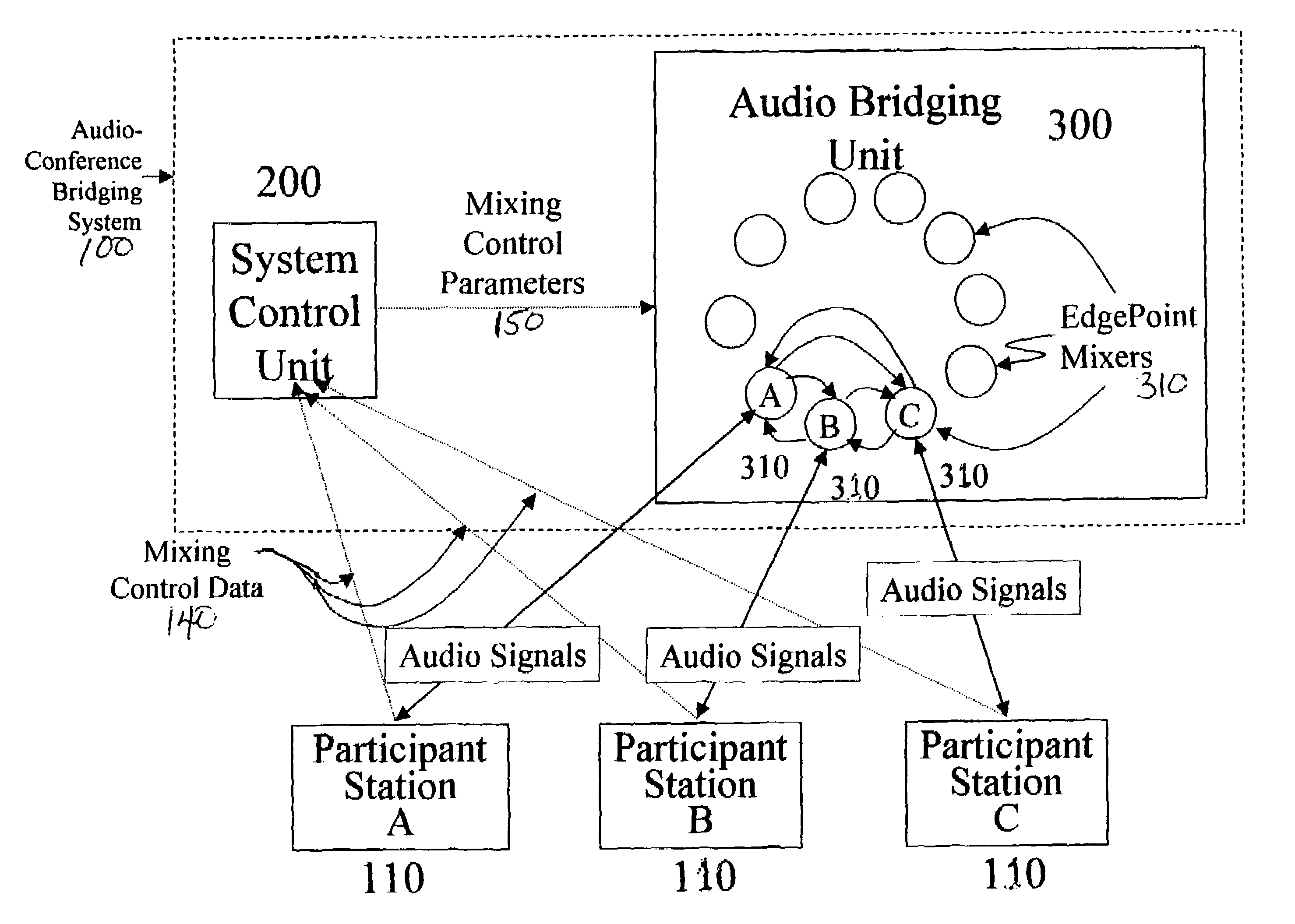
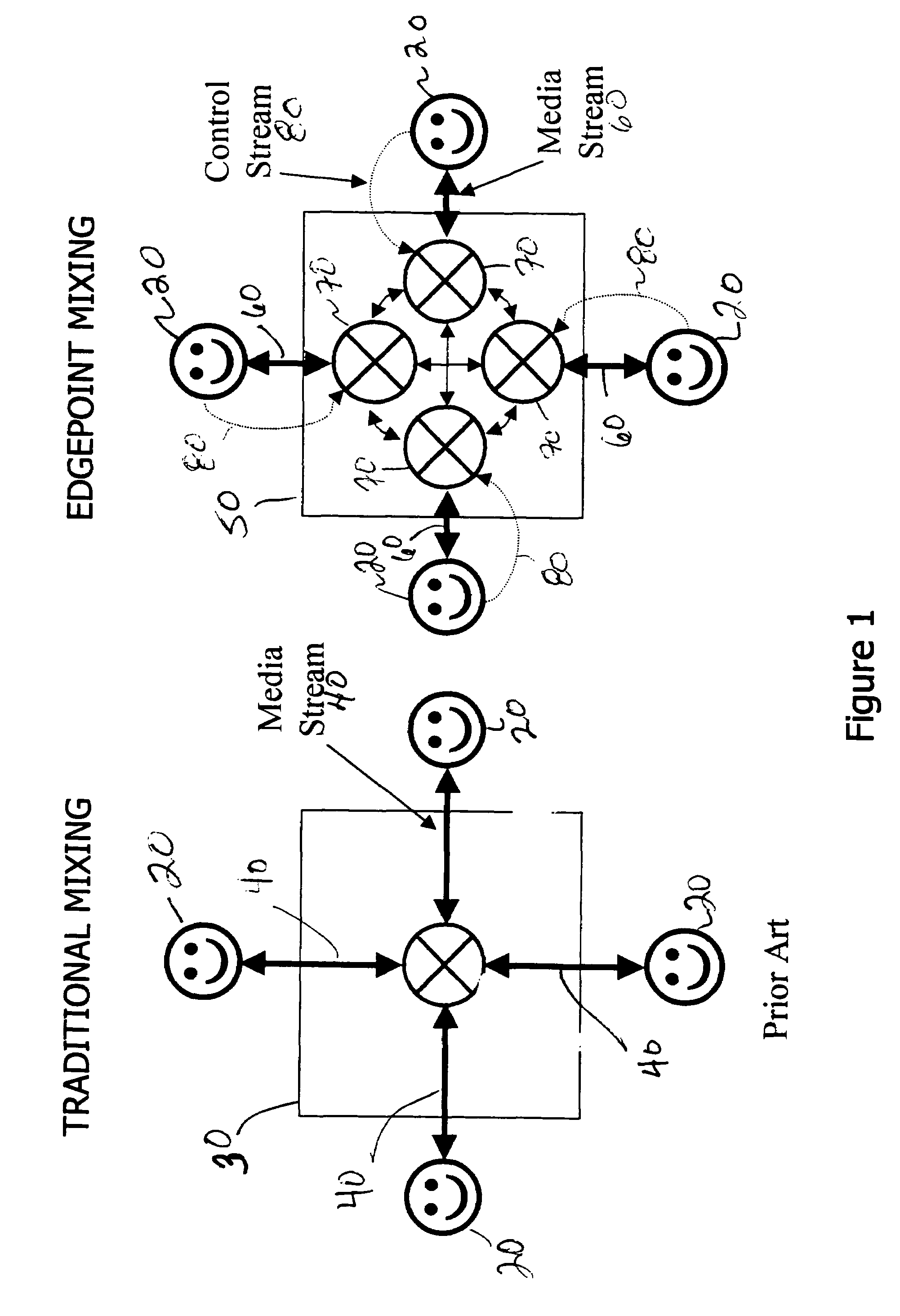
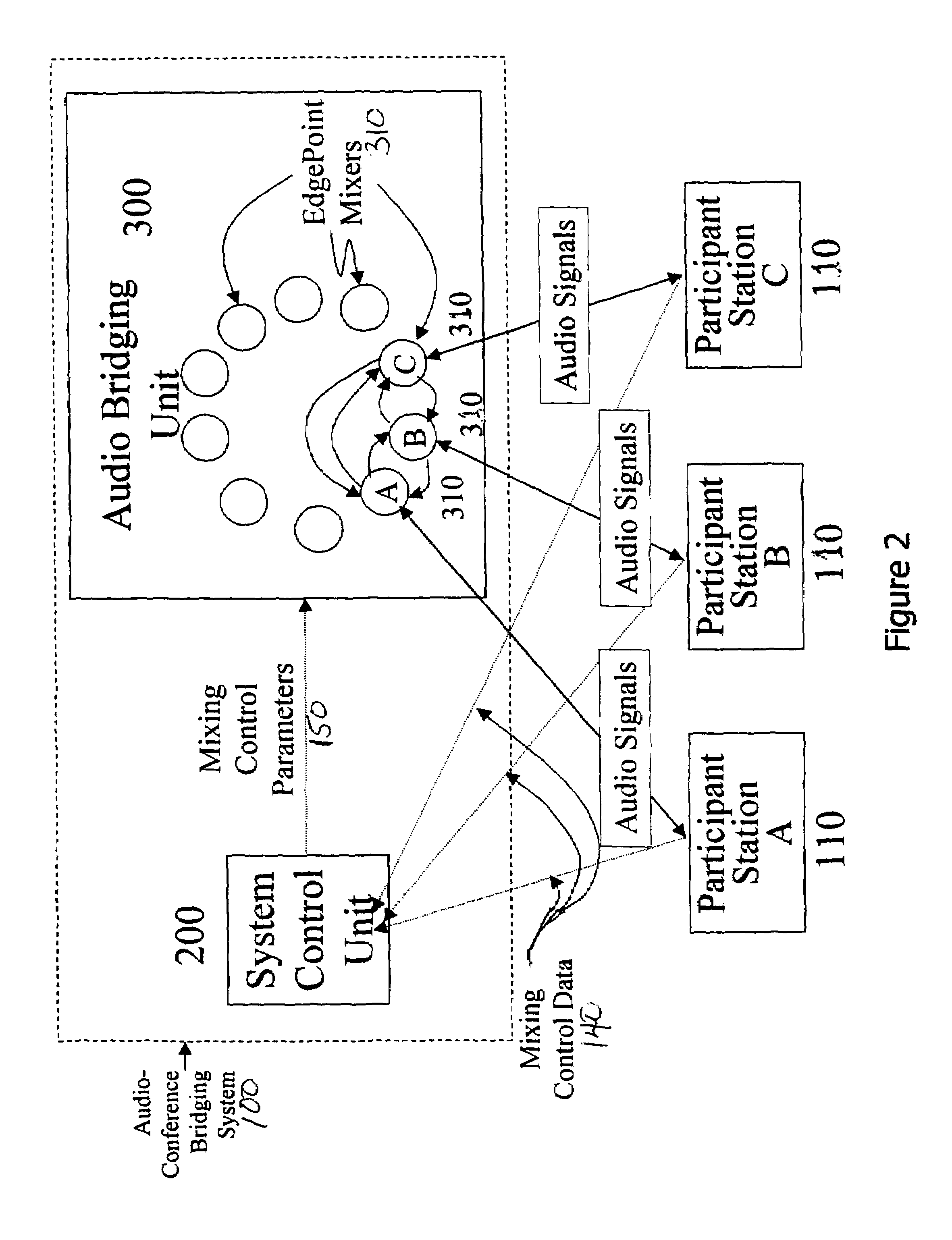
Teleconferencing bridge with EdgePoint mixing
InactiveUS7006616B1Overcome limitationsSpecial service provision for substationIndoor gamesQuality of serviceEngineering
In accordance with the principles of the present invention, an audio-conference bridging system and method are provided. The present invention discards the traditional notion of a single mixing function for a conference. Instead, the novel, flexible design of the present invention provides a separate mixing function for each participant in the conference. This new architecture is described generally herein as “EdgePoint mixing.” EdgePoint mixing overcomes limitations of traditional conferencing systems by providing each participant control over his / her conference experience. EdgePoint mixing also allows, when desired, the simulation of a “real-life” conference by permitting each participant to receive a distinctly mixed audio signal from the conference depending on the speaker's “position” within a virtual conference world. The present invention also preferably accommodates participants of different qualities of service. Each participant, thus, is able to enjoy the highest-level conferencing experience that his / her own connection and equipment will permit.
Owner:GOOGLE TECH HLDG LLC
Multi-party conversation analyzer & logger
InactiveUS20140247926A1Combat useAutomatic call-answering/message-recording/conversation-recordingSupervisory/monitoring/testing arrangementsSpeech soundData library
In one aspect, the present invention facilitates the investigation of networks of criminals, by gathering associations between phone numbers, the names of persons reached at those phone numbers, and voice print data. In another aspect the invention automatically detects phone calls from a prison where the voiceprint of the person called matches the voiceprint of a past inmate. In another aspect the invention detects identity scams in prisons, by monitoring for known voice characteristics of likely imposters on phone calls made by prisoners. In another aspect, the invention automatically does speech-to-text conversion of phone numbers spoken within a predetermined time of detecting data indicative of a three-way call event while monitoring a phone call from a prison inmate. In another aspect, the invention automatically thwarts attempts of prison inmates to use re-dialing services. In another aspect, the invention automatically tags audio data retrieved from a database, by steganographically encoding into the audio data the identity of the official retrieving the audio data.
Owner:SECURUS TECH LLC
Method and system for automatic quality evaluation
ActiveUS20080152122A1Overcome disadvantagesSupervisory/monitoring/testing arrangementsMultiple digital computer combinationsQuality assessmentKnowledge management
Owner:NICE LTD
Methods, systems and computer program products for monitoring service usage
InactiveUS7620162B2Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemUse of services
Monitoring criteria is received that corresponds to a usage quantity for a plurality of services. Each of the plurality of services is provided over ones of a plurality of different communication systems. Actual service usage information is received for the plurality of services. The actual service usage information and the monitoring criteria are compared. An electronic notification message is sent when the monitoring criteria for one or more of the plurality of services is satisfied.
Owner:AT&T INTPROP I LP
Cable network repair control system
InactiveUS6671824B1Shorten the timeSupervisory/monitoring/testing arrangementsSubstation equipmentControl systemEngineering
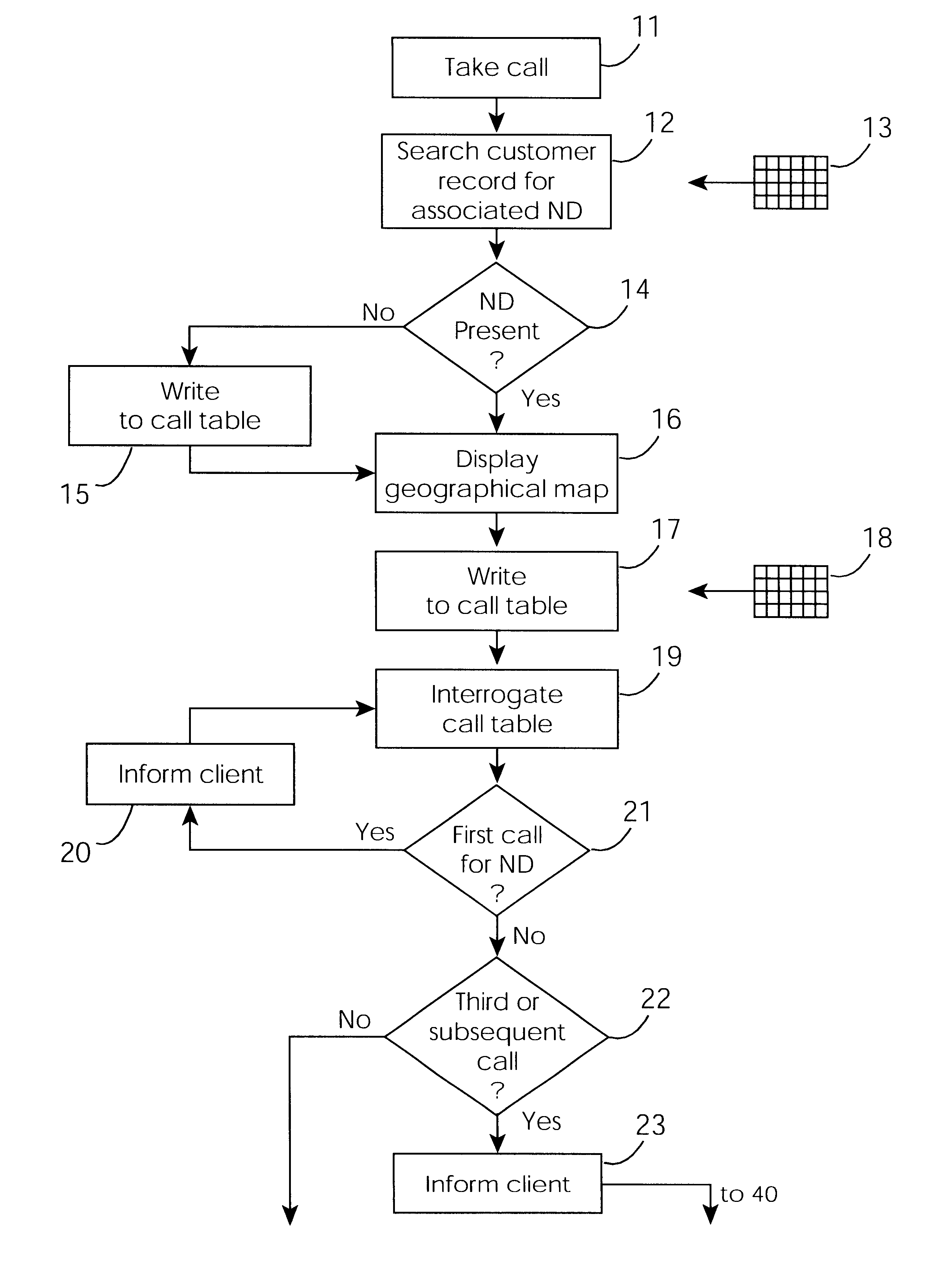
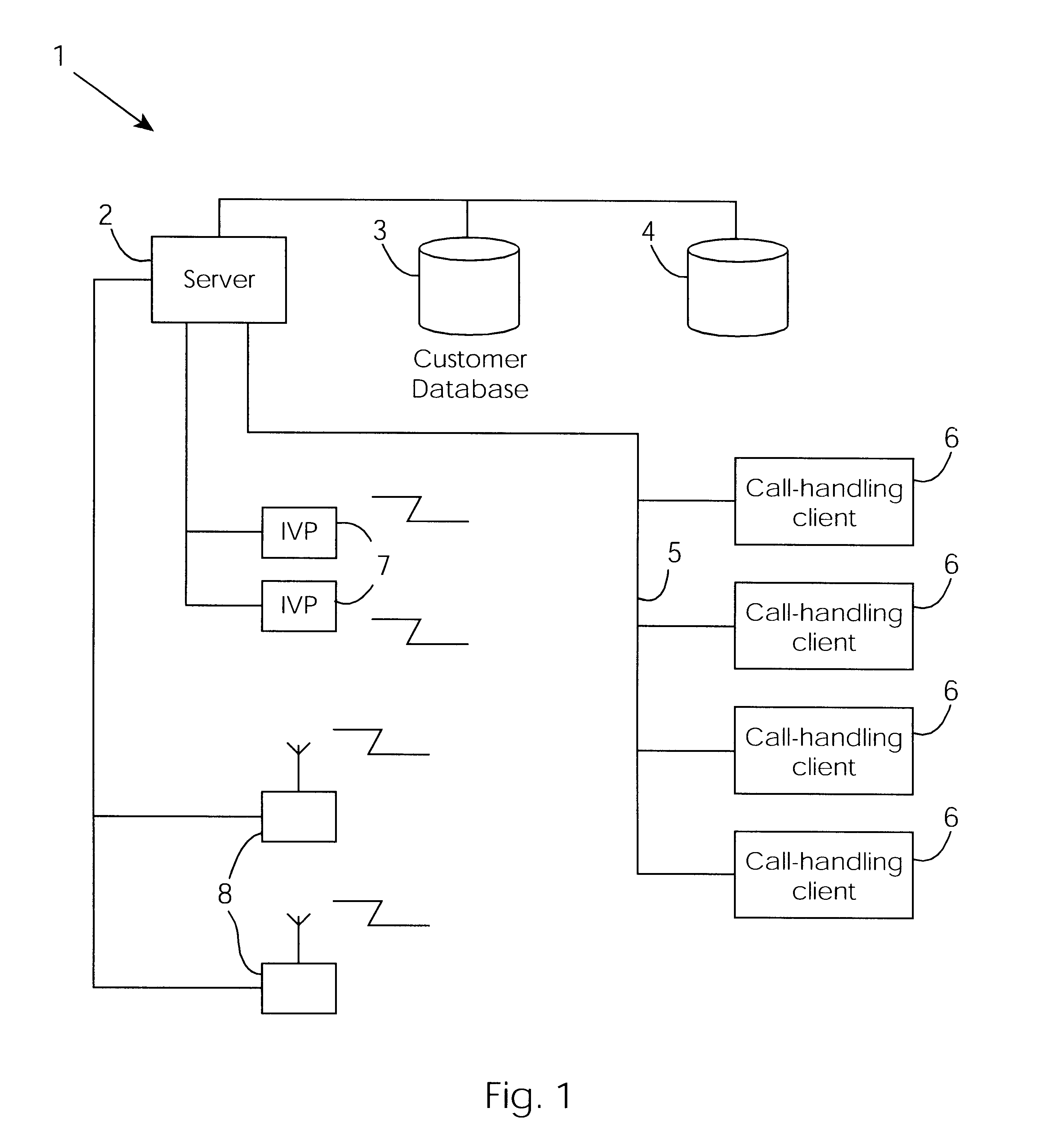
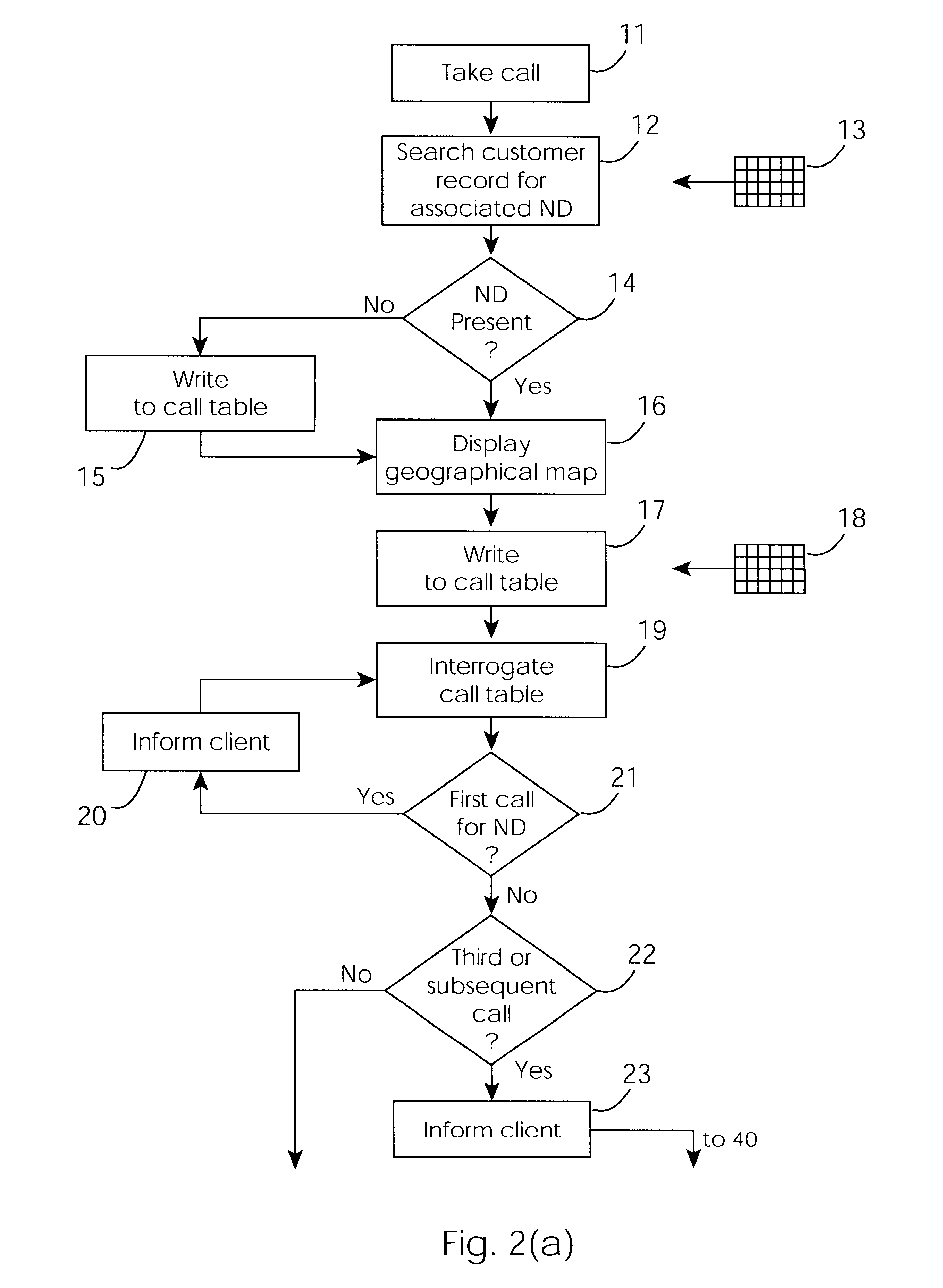
A cable network repair control system including a server communicating with multiple call-handling clients in a trouble call center. The databases are used to automatically determine an associated network device for the customer who makes a trouble call. When a second call is received for a particular network device, an inferencing engine automatically operates to identify potential repairs crews and to control communication with them to ensure that optimum use of the repair crew time and quick repair. Various tables are generated dynamically and are used to update management status tables for reviewing of network repair status.
Owner:LAKEFIELD ETECH GROUP
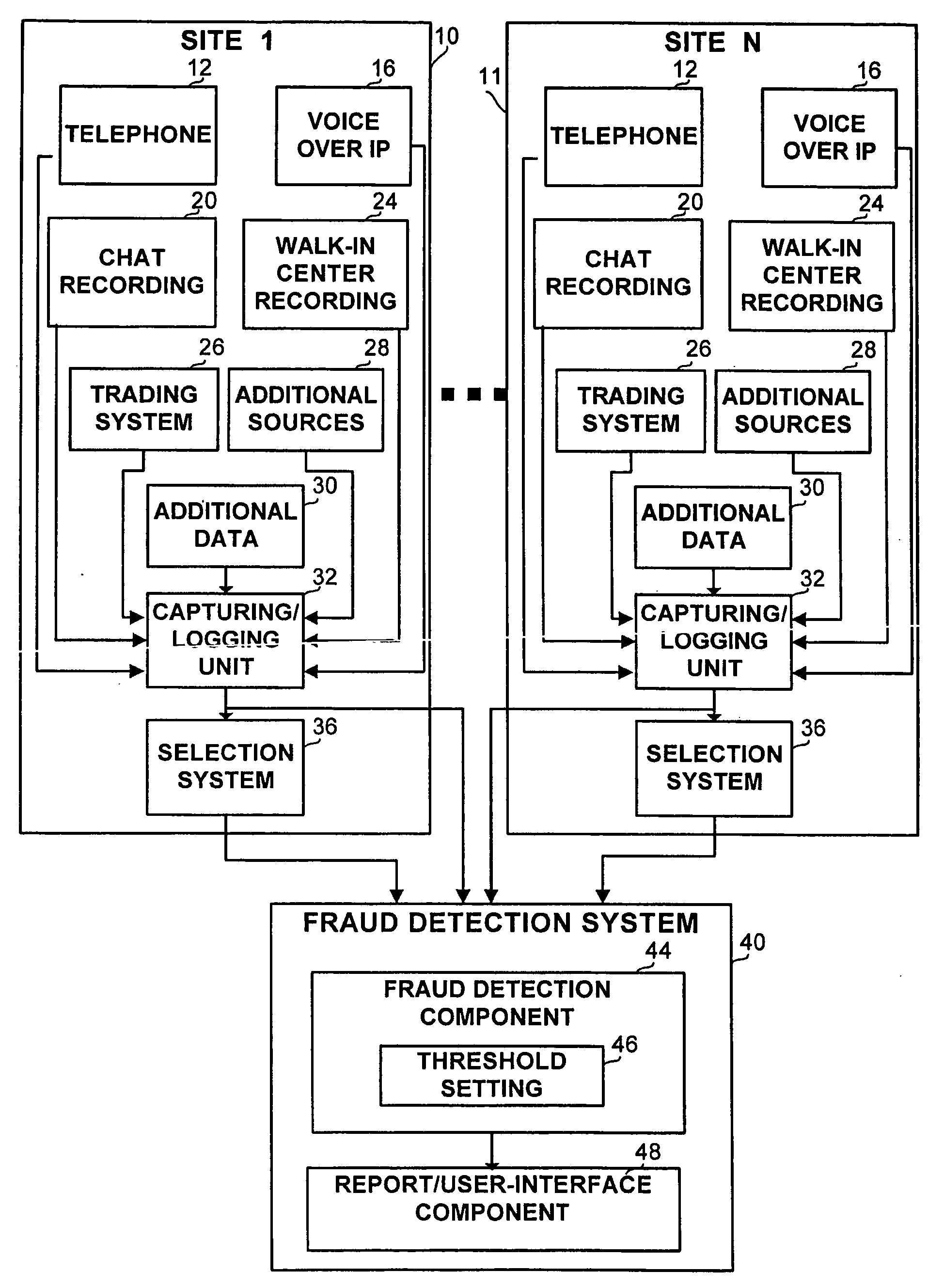
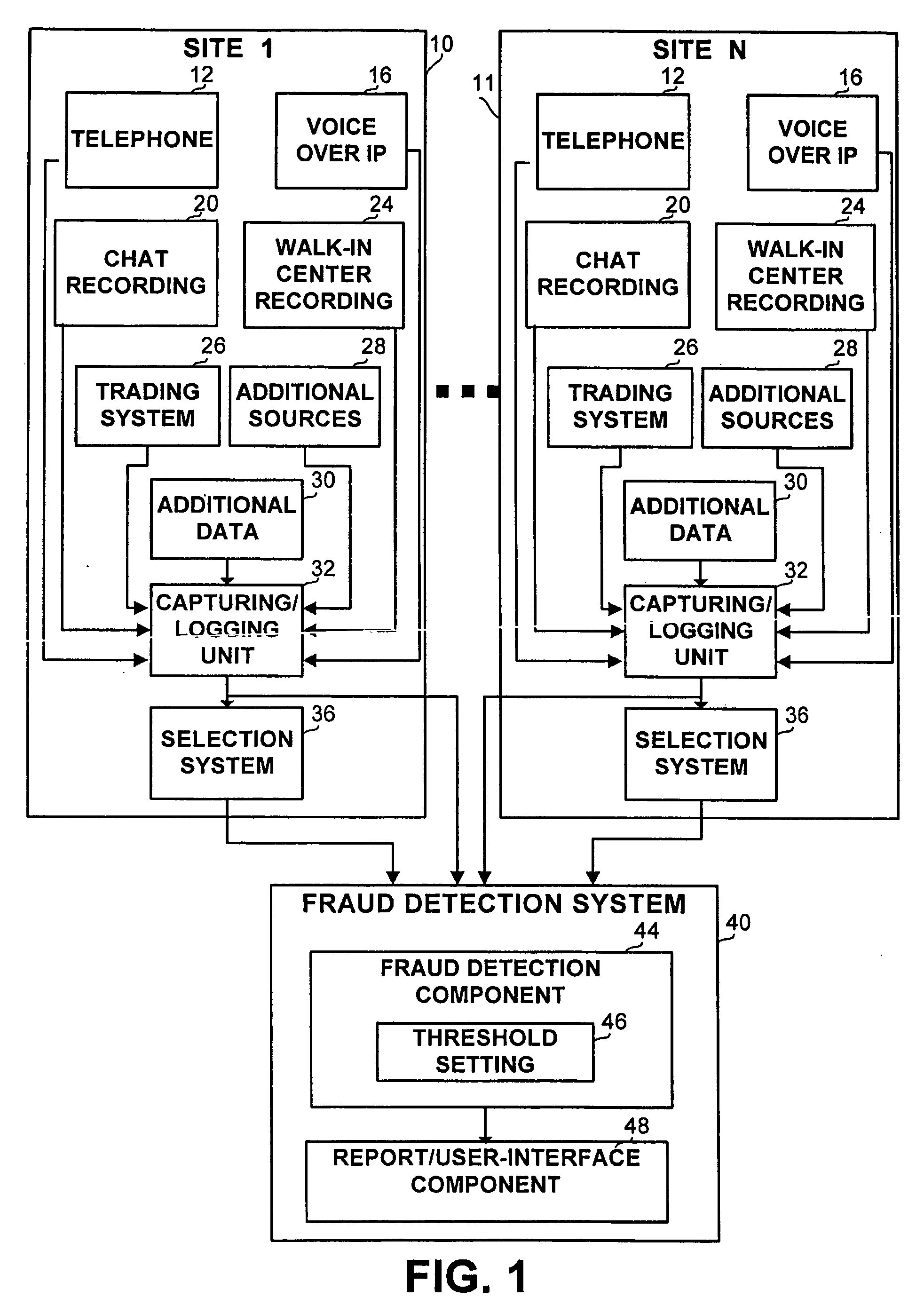
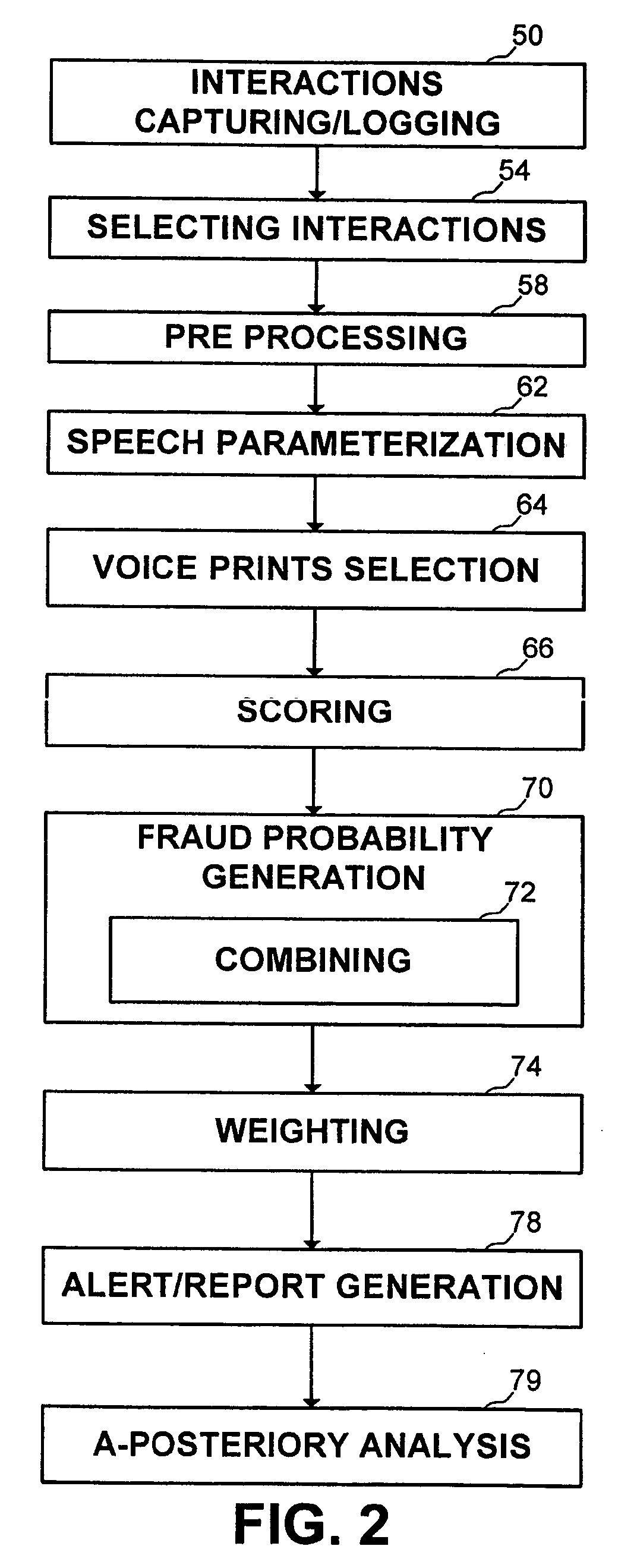
Method and apparatus for fraud detection
ActiveUS20060285665A1Overcome disadvantagesIncrease probabilitySpeech analysisSupervisory/monitoring/testing arrangementsInternet privacySpeech sound
Owner:NICE LTD
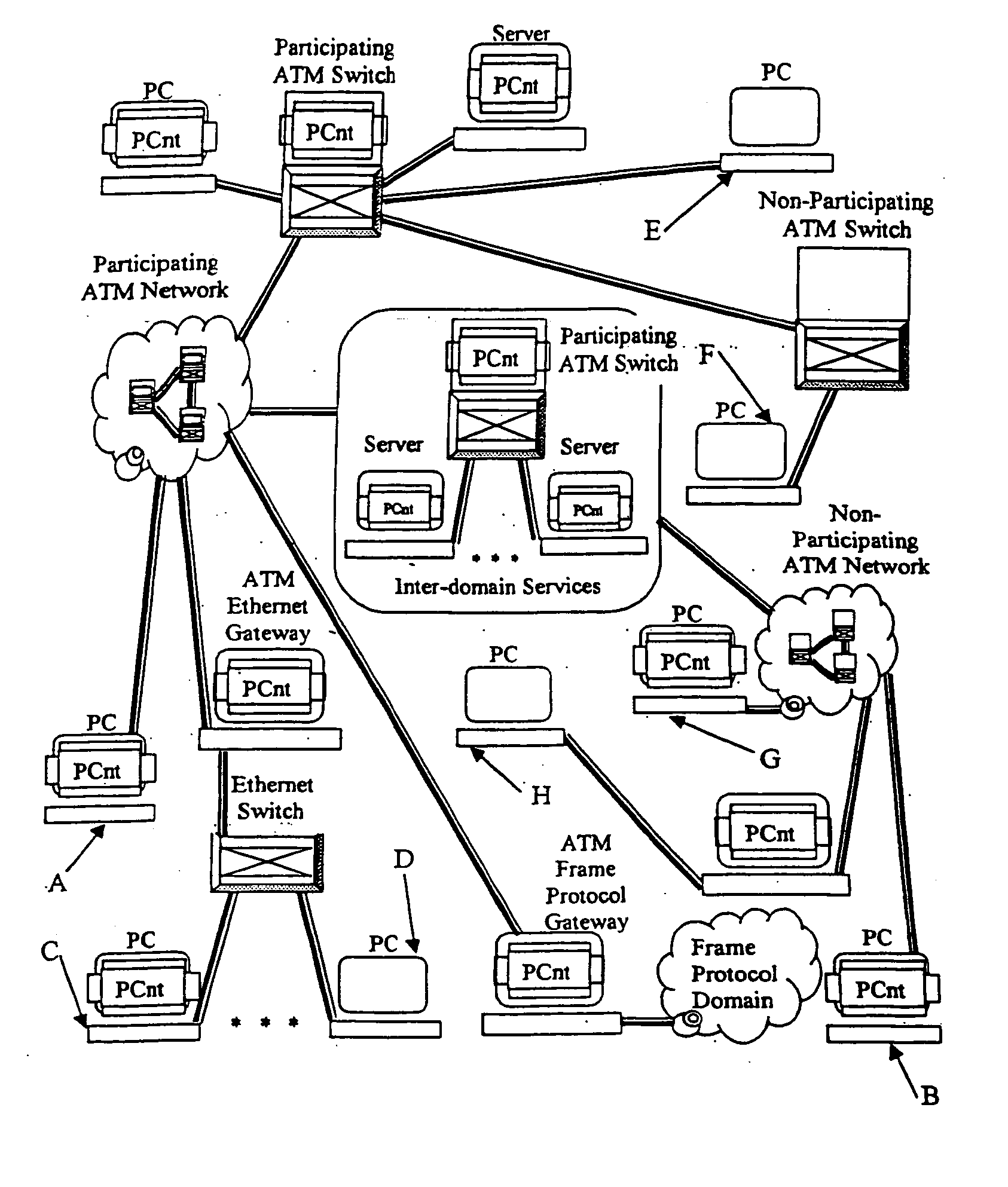
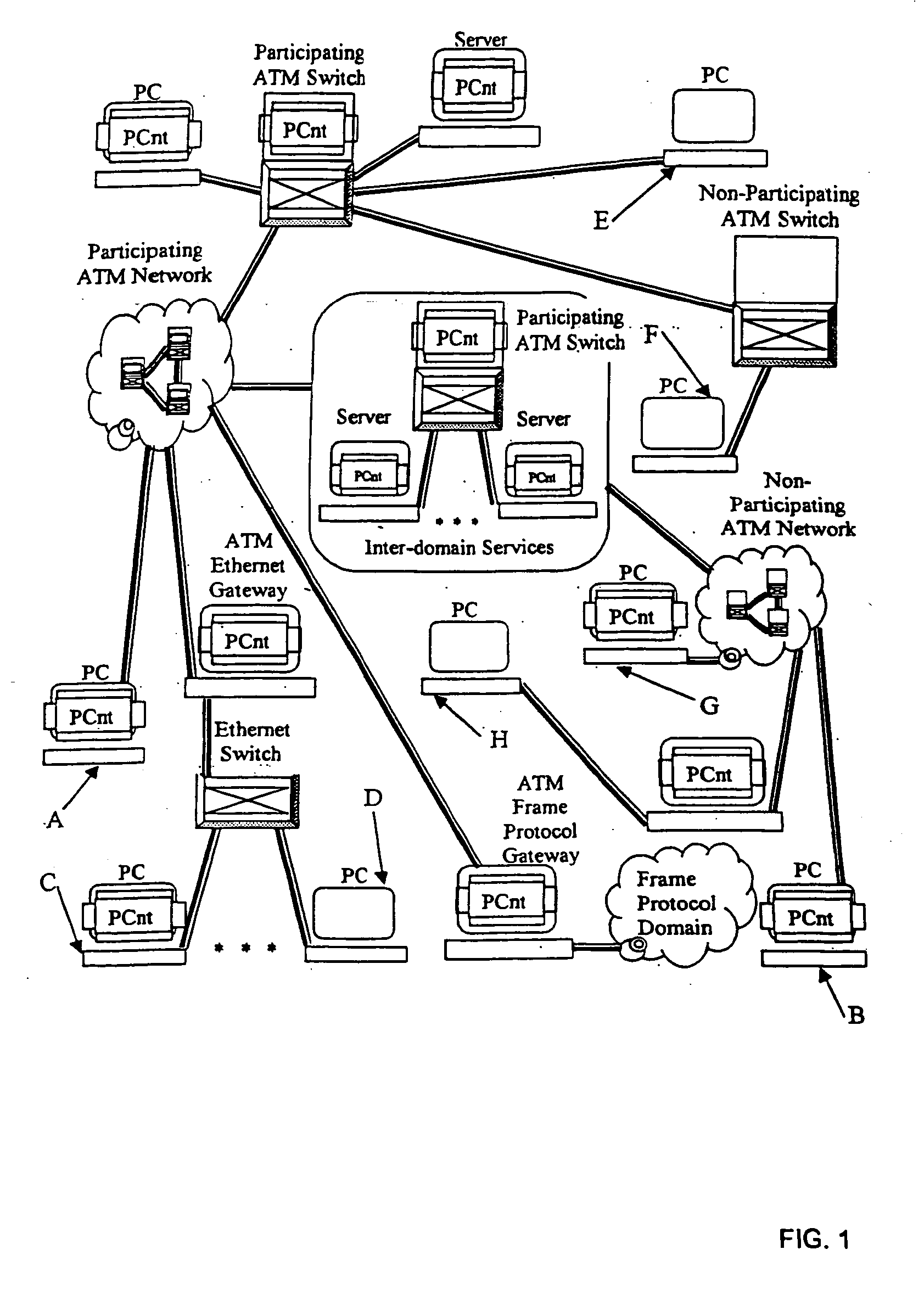
System and method for providing peer-oriented control of telecommunication services
InactiveUS20050027870A1Supporting development and deploymentHybrid switching systemsSupervisory/monitoring/testing arrangementsTelecommunications networkEngineering
In a telecommunications network environment including non-participating elements and participating elements, a method for providing a telecommunications service between a first peer element connected to the telecommunications network environment and a second peer element connected to the telecommunications network. At a first peer element, an indication of the type of telecommunications service to be provided between the first peer element and the second peer element is received. A telecommunications service template in association with the indicated telecommunications service is determined, the telecommunications service template including instructions for configuring the non-participating elements of the telecommunications network environment to provide the indicated telecommunications service and instructions for configuring the participating elements of the telecommunications network environment. Upon establishing a communication channel between the first peer element and the second peer element, the service template is transferred to the second peer element. The second peer element then executes the instructions to configure the participating elements and non-participating elements of the telecommunications network environment to provide the telecommunications service.
Owner:TREBES HAROLD HERMAN JR
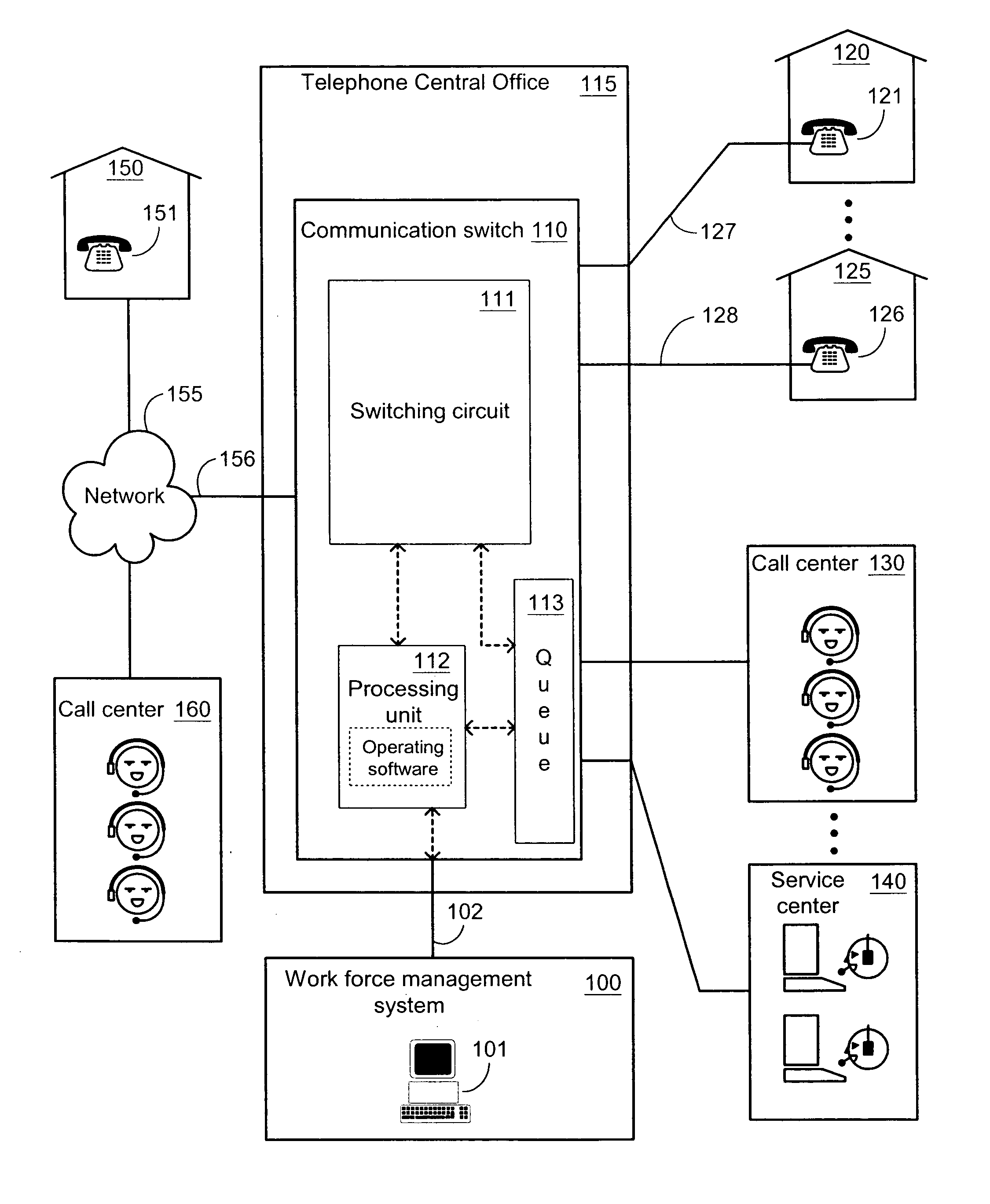
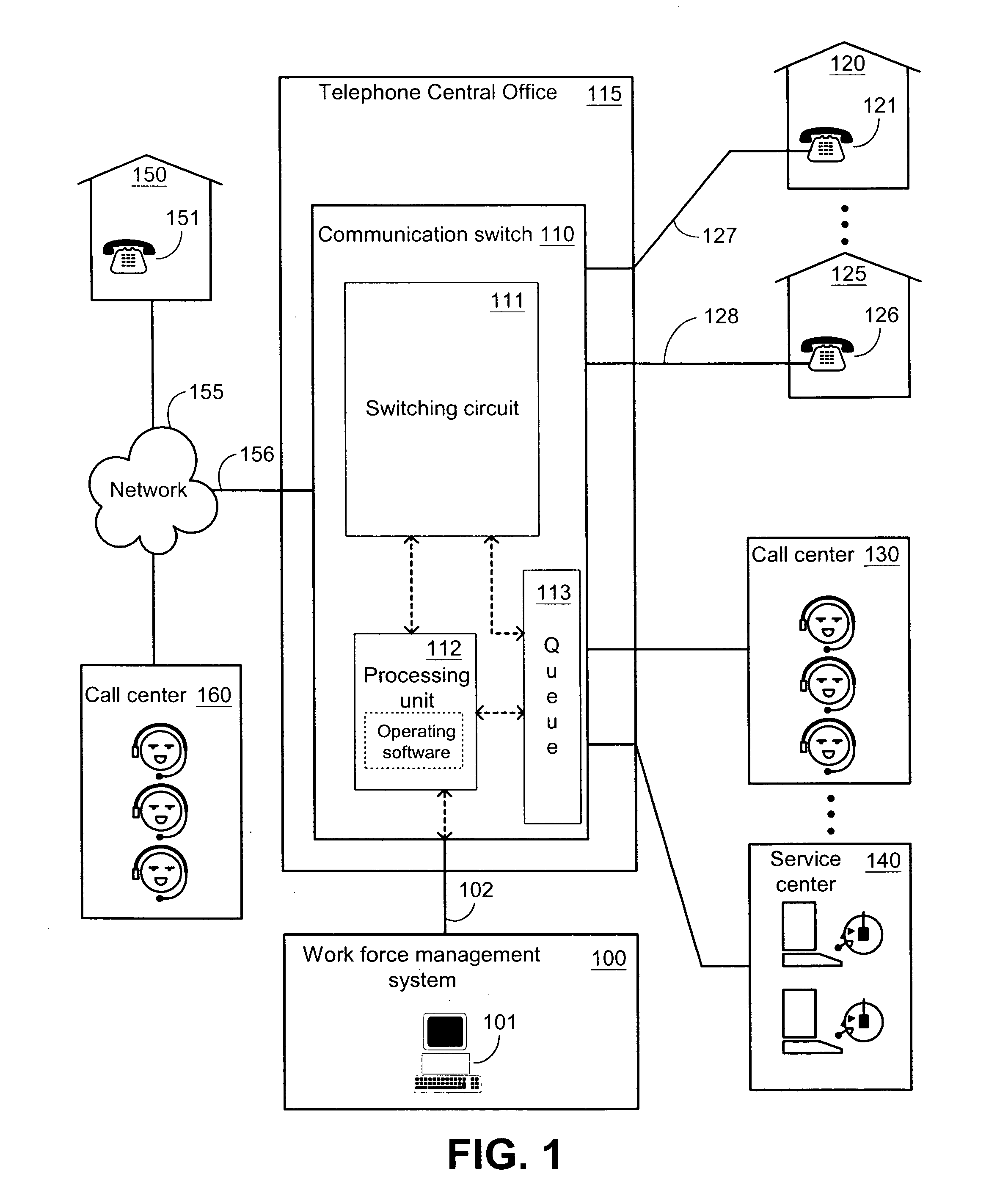
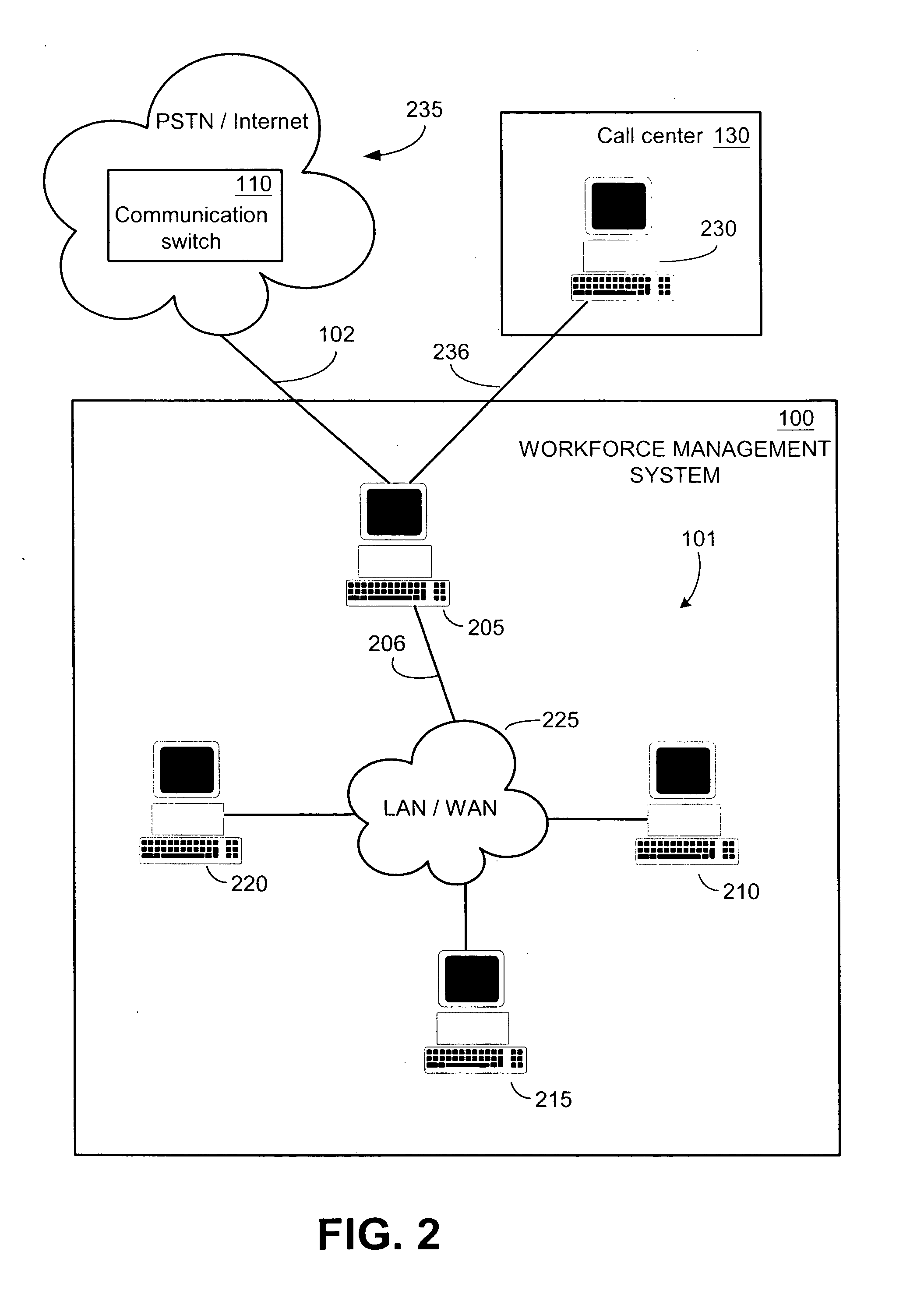
Workforce planning system incorporating historic call-center related data
InactiveUS20050129212A1Special service for subscribersSupervisory/monitoring/testing arrangementsProgram planningWork planning
Systems and methods for workforce planning, which in one embodiment among many, can be broadly summarized by a representative method of generating a forecast report by processing a work-planning input together with a performance report, the performance report having been generated by processing a call-history statistic obtained from a communication switch and / or a work-history statistic obtained from a call center. Another embodiment can be described as a workforce planning system that has logic configured to generate a forecast report by processing a work-planning input together with a performance report, the performance report having been generated by logic configured to process a call-history statistic obtained from a communication switch and / or a work-history statistic obtained from a call center.
Owner:AT&T INTPROP I L P
Voice integrated VOIP system
InactiveUS7095733B1Minimize delayImprove storage efficiencyInterconnection arrangementsTime-division multiplexExtensibilityTranscoding
An integrated VoIP unified message processing system includes a voice platform that processes data in native VoIP format. There is no use of hardware telephone interface cards (TICs) or software transcoding to transform data to PCM or other formats. Cost reductions are achieved by the elimination of expensive dedicated hardware and scalability is achieved by obviating the need for software transcoding.
Owner:R2 SOLUTIONS
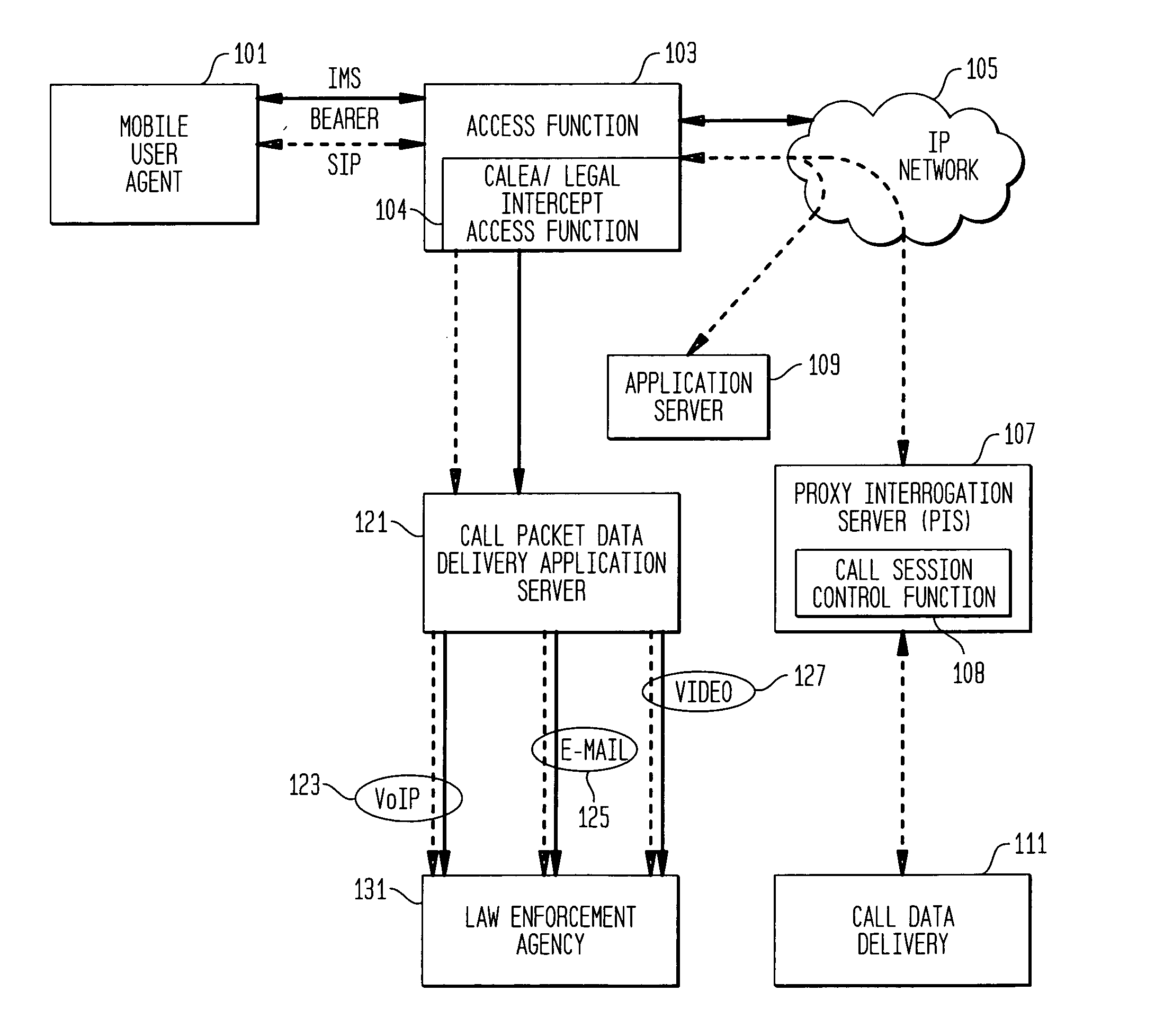
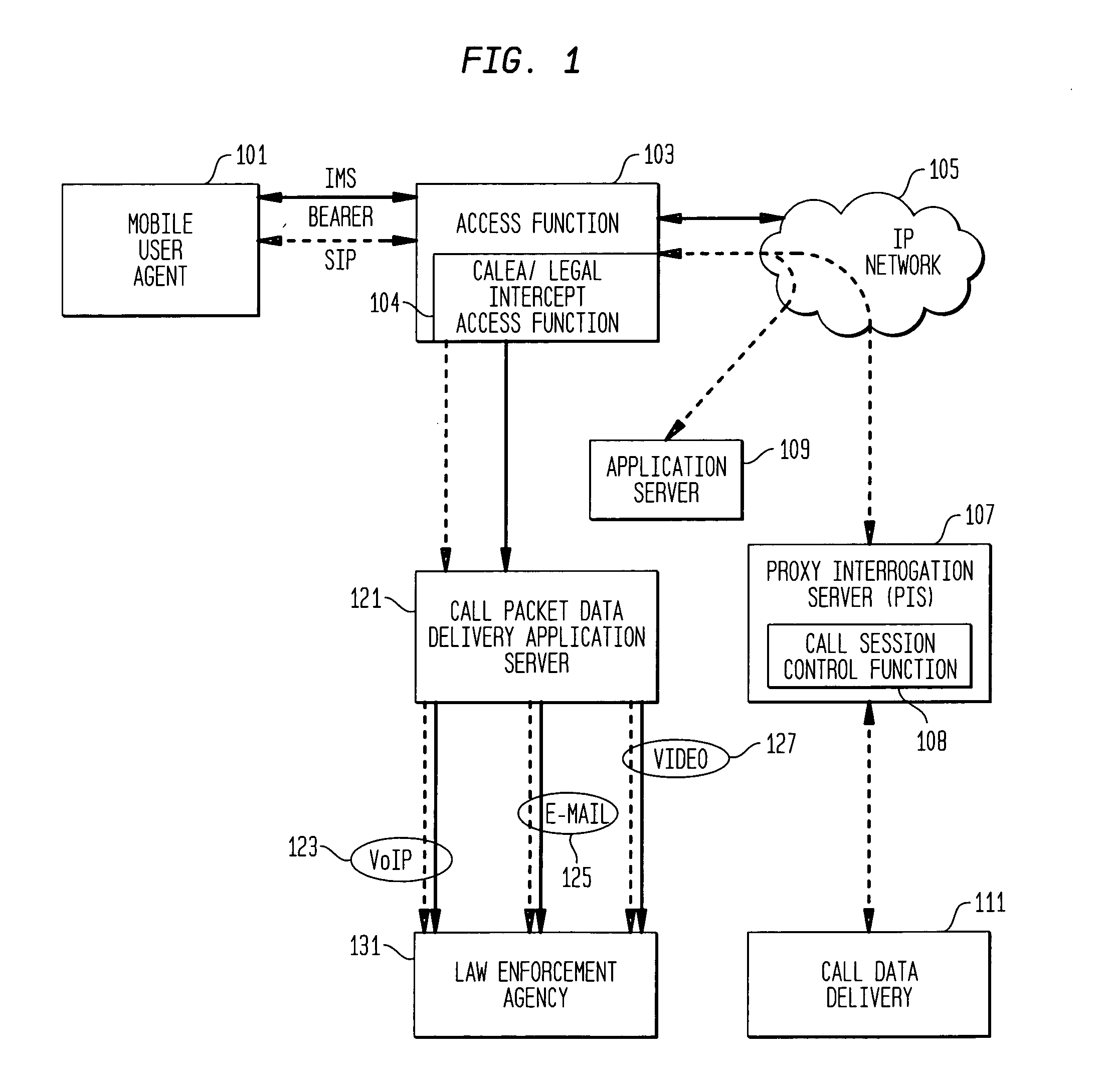
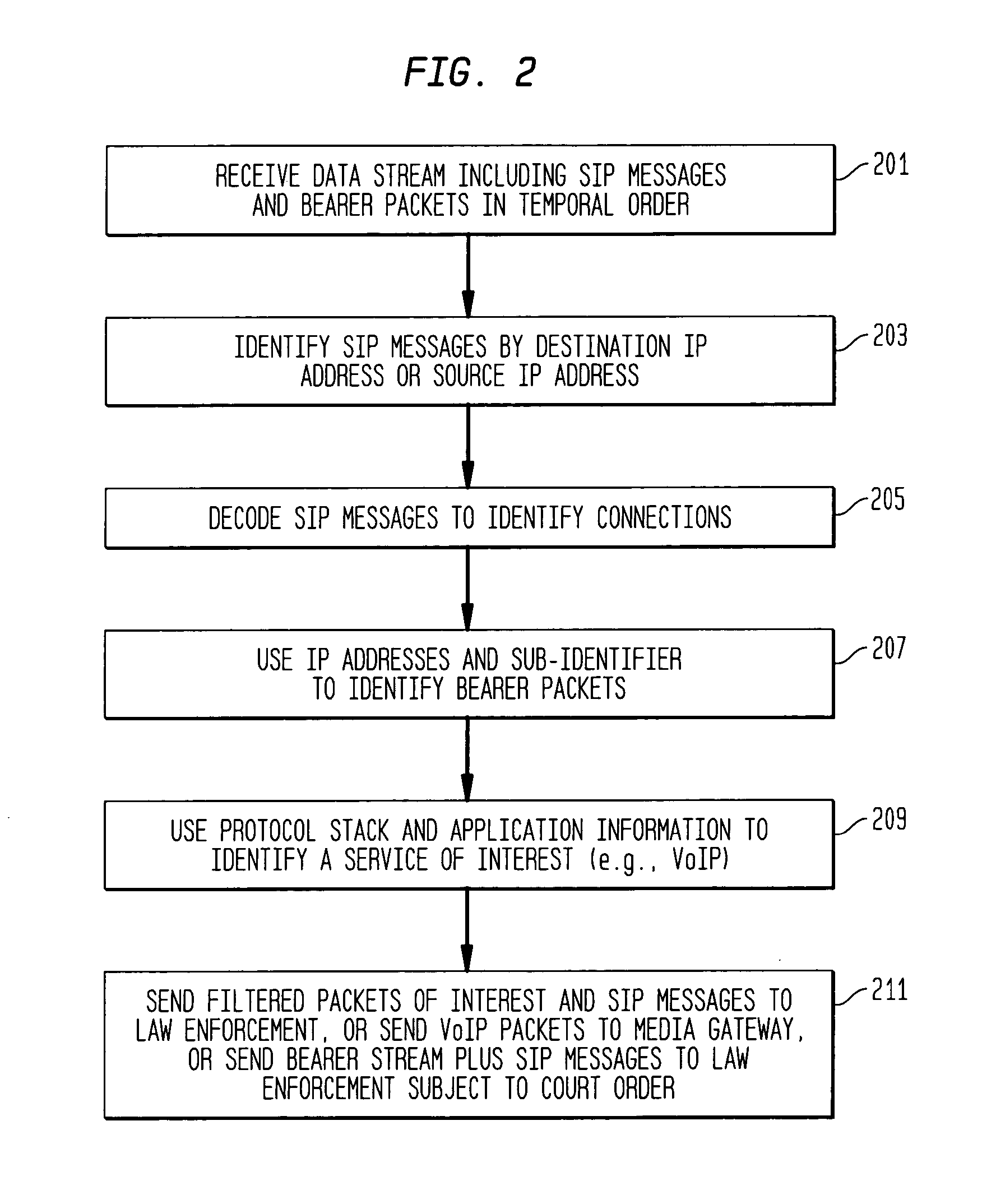
Providing CALEA/LegaI Intercept information to law enforcement agencies for internet protocol multimedia subsystems (IMS)
ActiveUS20060072550A1Supervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsData connectionApplication server
A method and apparatus for providing useful packet data to a CALEA / Legal Intercept collection function. At an access point to a network such as the Internet, sources and destinations of data connections are examined to determine whether any of the bearer messages should also be routed to a CALEA / Legal Intercept monitoring system. If this condition is recognized, the bearer messages and corresponding signaling control messages are correlated in a call packet delivery application server and then delivered to a CALEA / Legal Intercept monitoring system. Advantageously, the monitoring receives as a bundled message set the bearer message and the control messages used to route and otherwise process these bearer messages.
Owner:ALCATEL-LUCENT USA INC
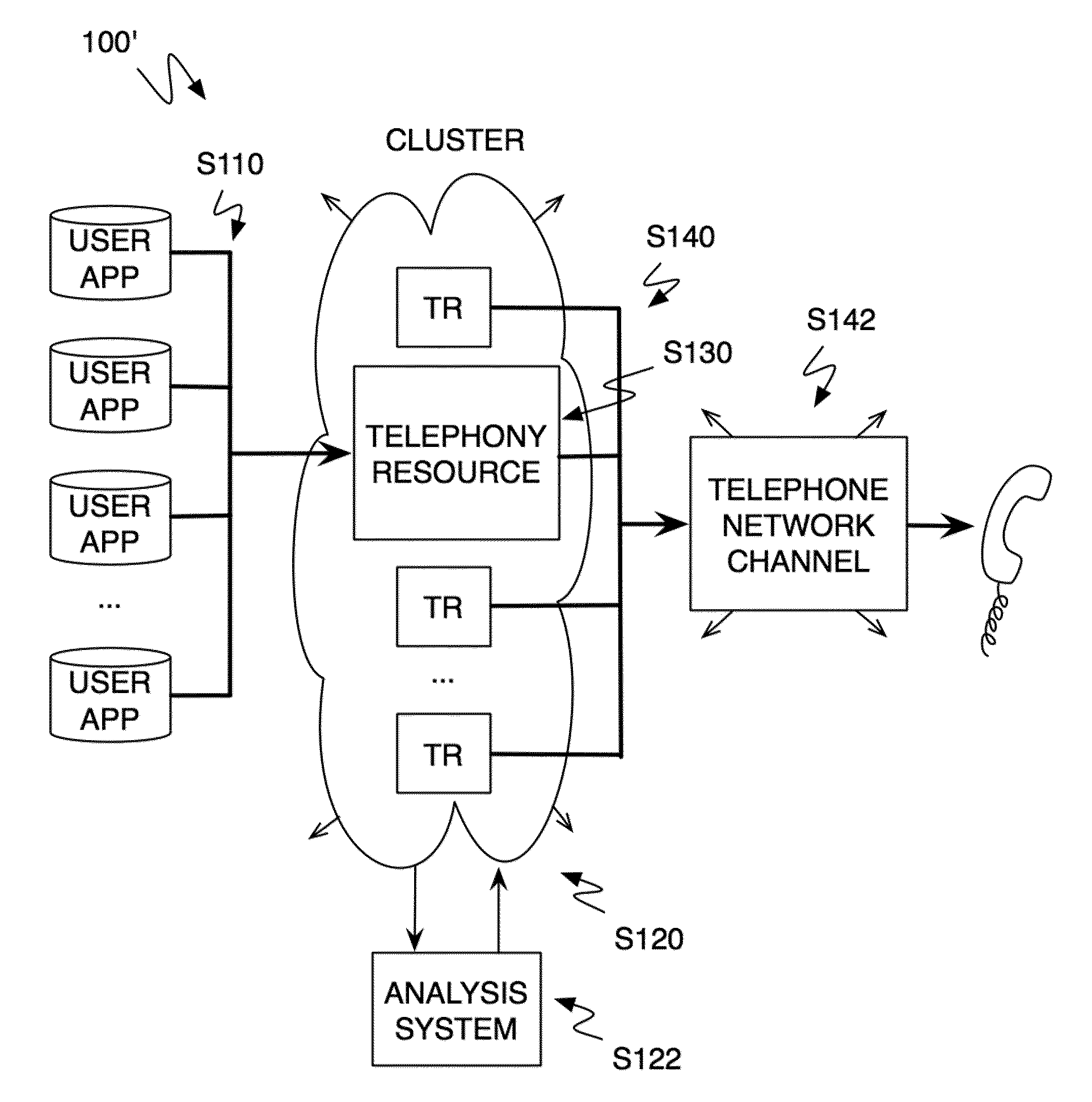
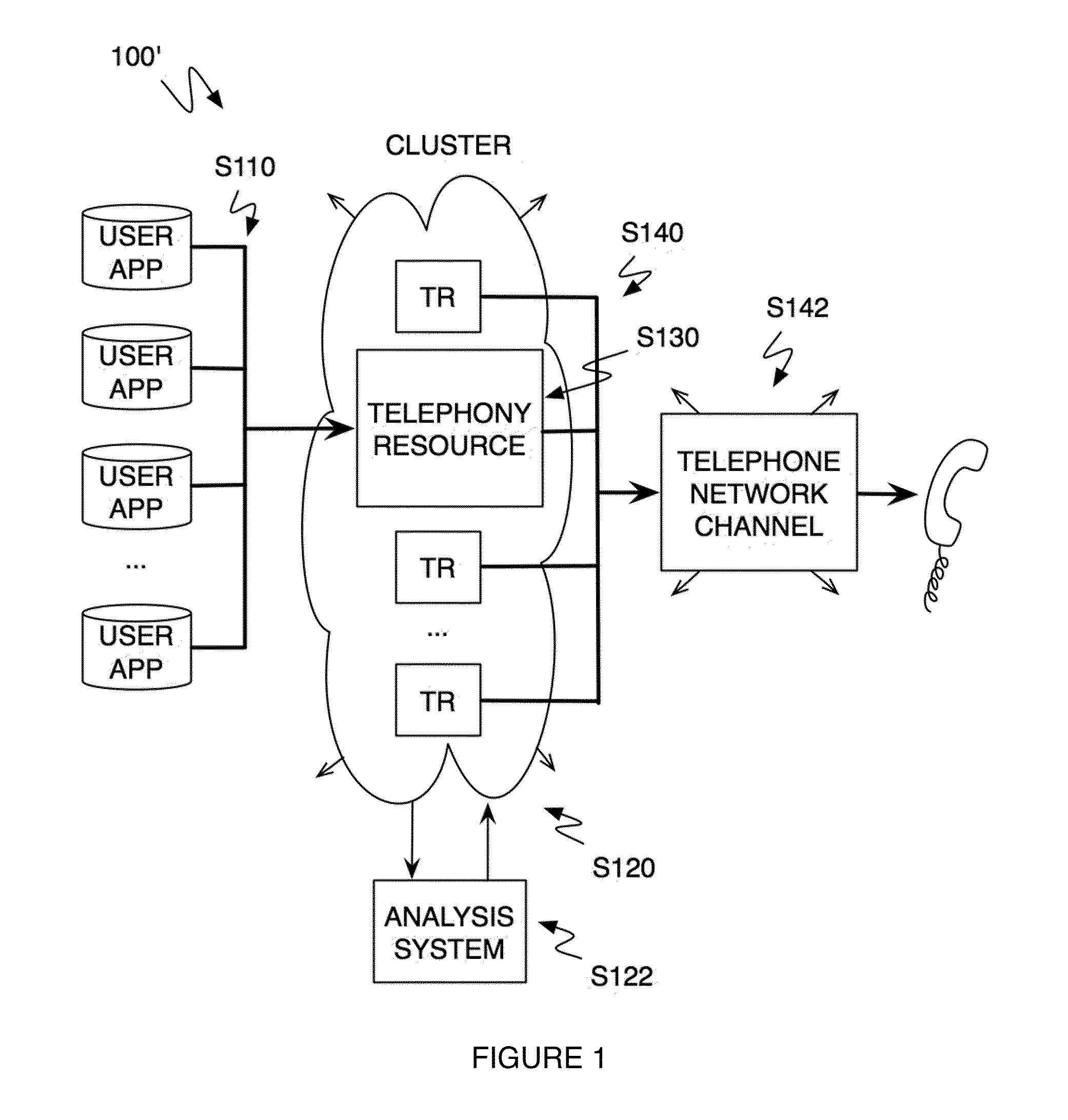
Method and system for a multitenancy telephone network
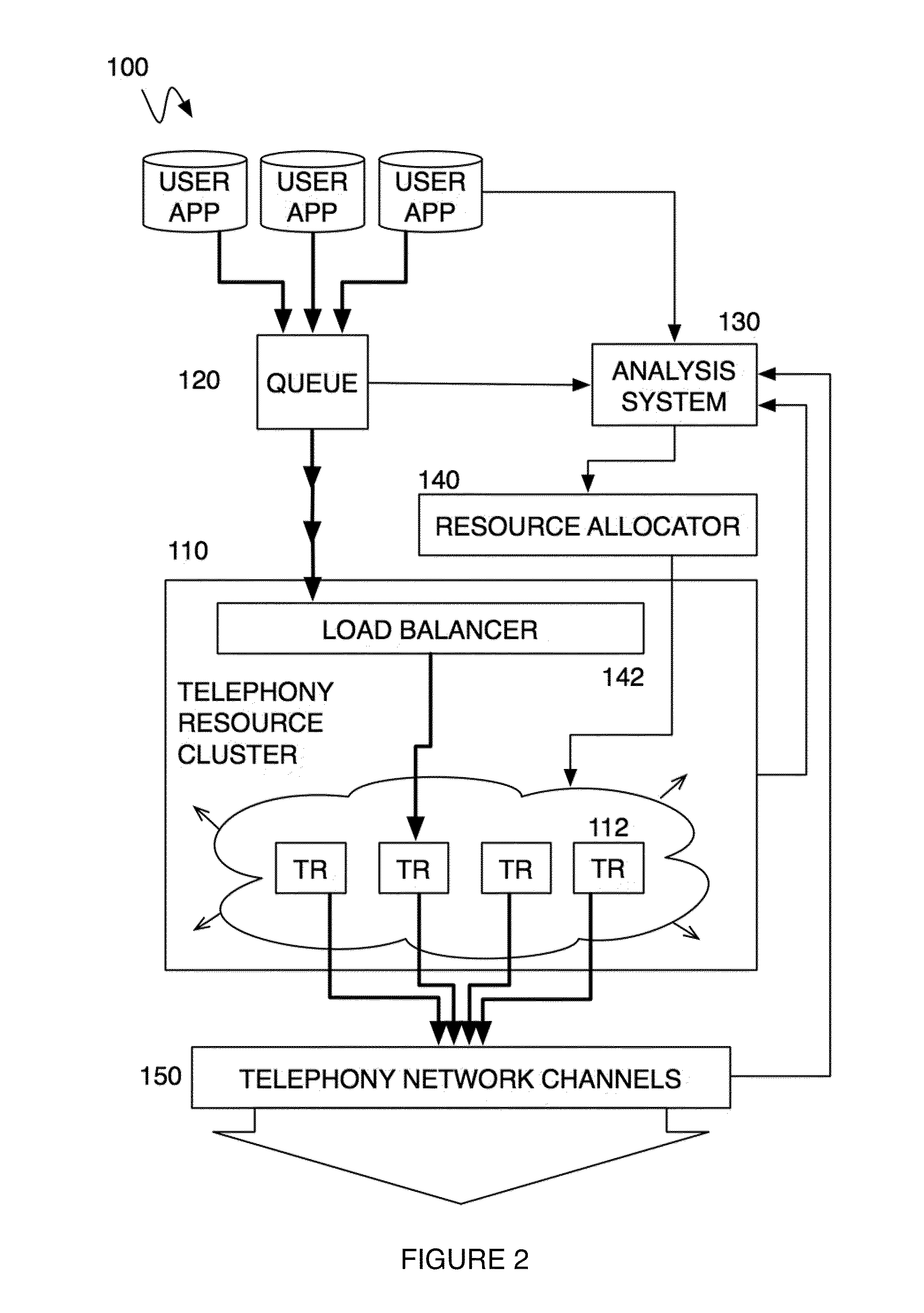
ActiveUS20100232594A1Energy efficient ICTSpecial service for subscribersTelephone networkMultitenancy
A method and system for operating a multitenancy telephony system including a call queue that stores call requests received from a plurality of users; an expandable and contractible telephony resource cluster that establishes call sessions for call requests; a analysis system that calculates capacity requirements of the system; a resource allocator that manages the scaling and operation of the telephony resource cluster; and a plurality of telephony network channels that are used as telephony communication channels for call sessions.
Owner:TWILO INC
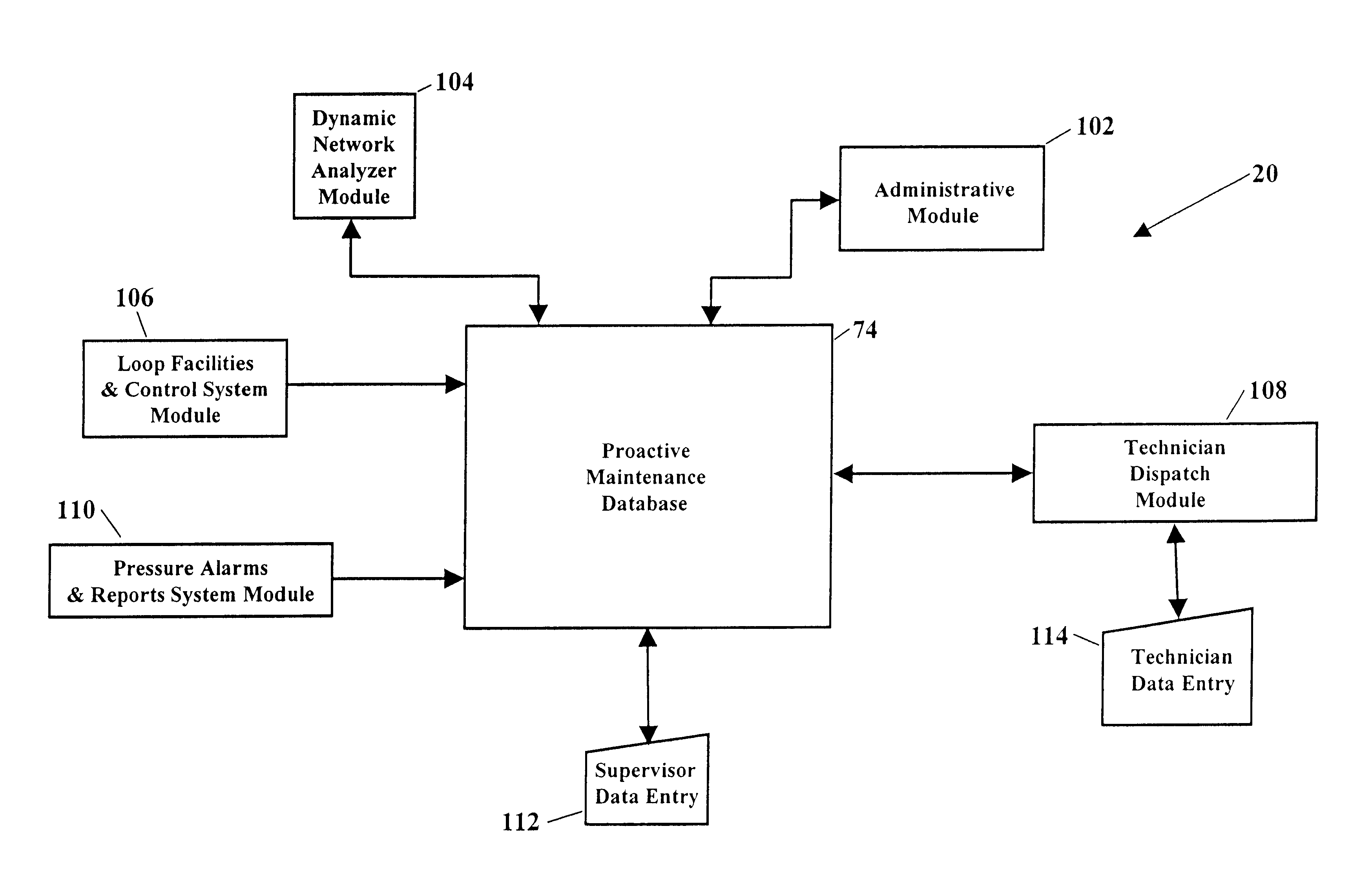
Pressure alarms and reports system module for proactive maintenance application
InactiveUS6771739B1Supervisory/monitoring/testing arrangementsSubstation equipmentFiberNetwork analytics
Methods and systems for proactively maintaining a telephone system local loop. One embodiment includes communicating with a communications network and acquiring information associated with pressure or flow sensors along fiber optic cables. Proactive maintenance of the fiber optic cables is predicted using the information associated with pressure or flow sensors. The embodiment may further include generating and dispatching work order information describing the predicted proactive maintenance. The embodiment may also include predicting proactive maintenance of telephone lines using information from a Dynamic Network Analyzer and using information from a Loop Facilities and Control System. Another embodiment includes a system for predicting proactive maintenance of a telephone system local loop. This embodiment includes a Pressure Alarms and Reports System Module, a database stored in memory, and a processor. The Pressure Alarms and Reports System Module communicates with a communications network and acquires at least one of i) pressure information associated with fiber optic cables and ii) flow information associated with fiber optic cables. The database stores the acquired information. The processor processes information stored in the database and generates predicted proactive maintenance.
Owner:BELLSOUTH INTPROP COR
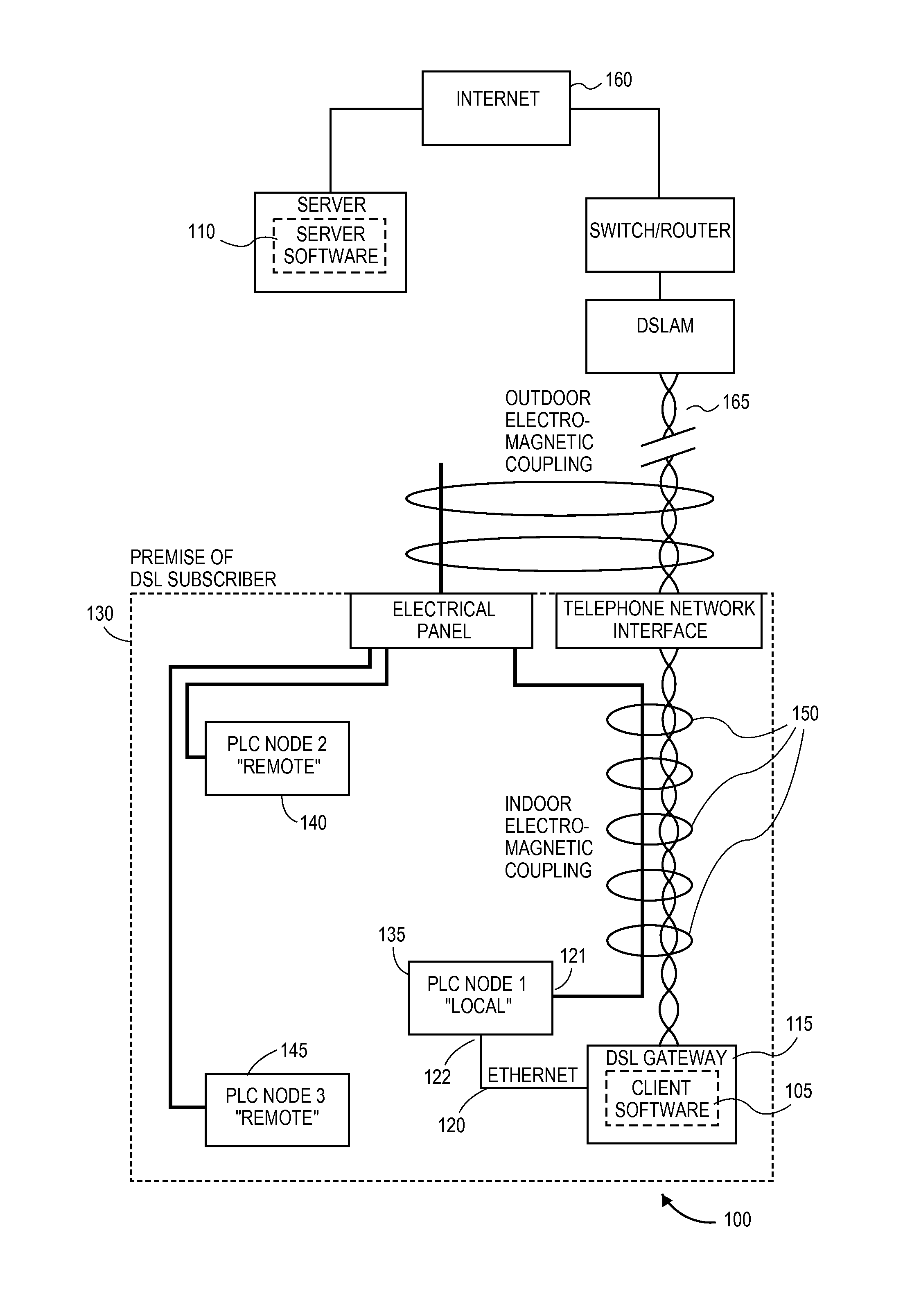
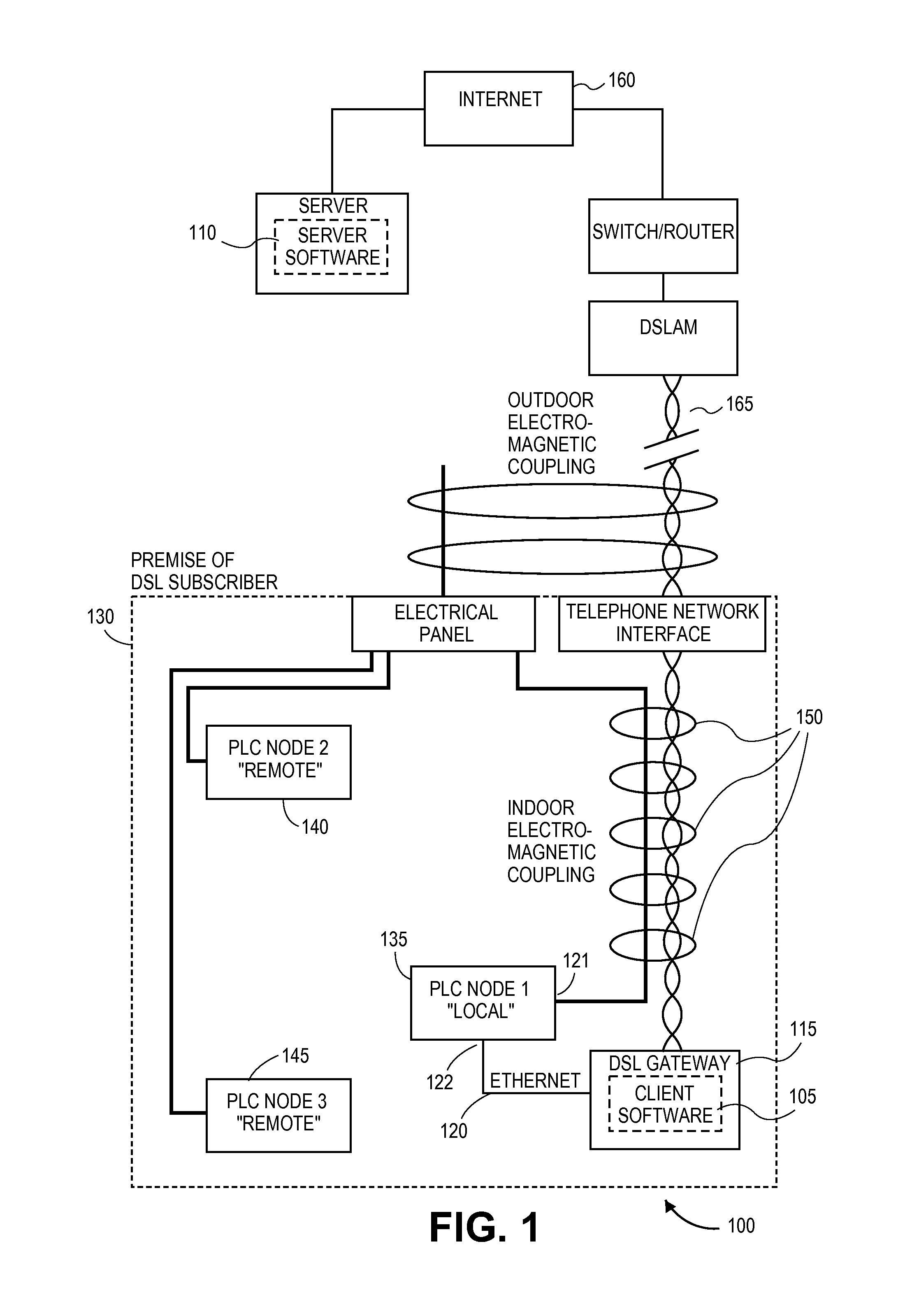
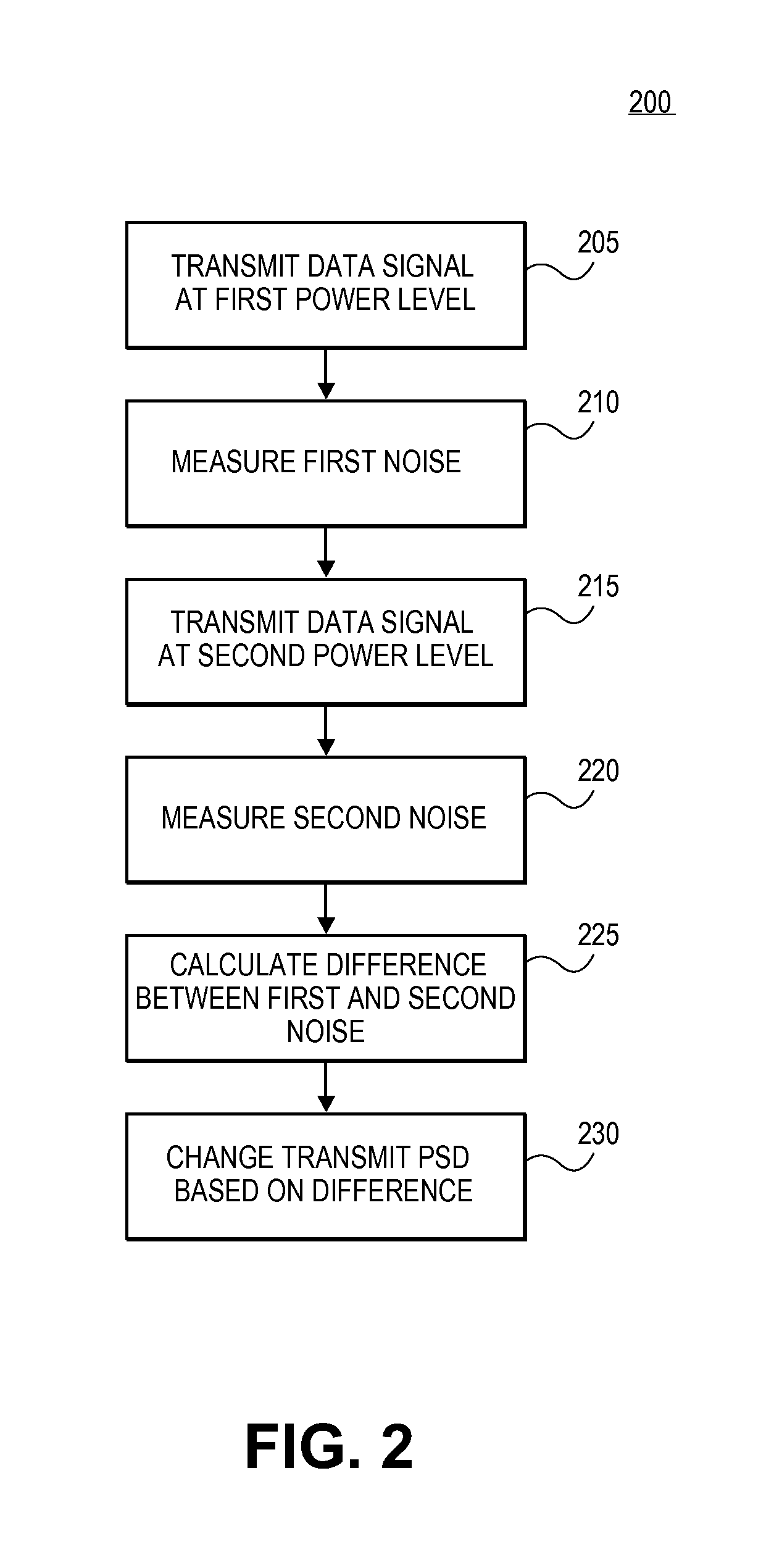
Method and apparatus for reducing the power of a signal electromagnetically coupled from a PLC medium to a DSL medium
ActiveUS20140369430A1Reduce impactDecrease phenomenonPower managementSystems with measurements/testing channelsDigital subscriber lineTransmitted power
Reducing a power of a signal electromagnetically coupled from a PLC medium to a digital subscriber line (DSL) medium. The method involves transmitting a data signal over the PLC medium at a first average power level from one of a plurality of PLC transmitters coupled to the PLC medium, then measuring first noise associated with a first signal received at a DSL receiver coupled to the DSL communication medium caused at least in part by the data signal transmitted over the PLC medium at a second average power level from the one PLC transmitter, the second average power level different than the first average power level, followed by measuring second noise associated with a second signal received at the DSL receiver coupled to the DSL communication medium caused at least in part by the data signal transmission over the PLC medium at the second average power level. A transmit power spectral density (PSD) for the data signal transmitted by the one PLC transmitter over the PLC medium is then changed, based on a difference between the first noise and the second noise, such that the changed transmit PSD for the data signal transmitted by the one PLC transmitter over the PLC medium reduces the power of the signal electromagnetically coupled from the PLC medium to the DSL medium caused by the data signal transmission from the one PLC transmitter over the PLC medium.
Owner:ASSIA SPE LLC CO THE CORP TRUST CO
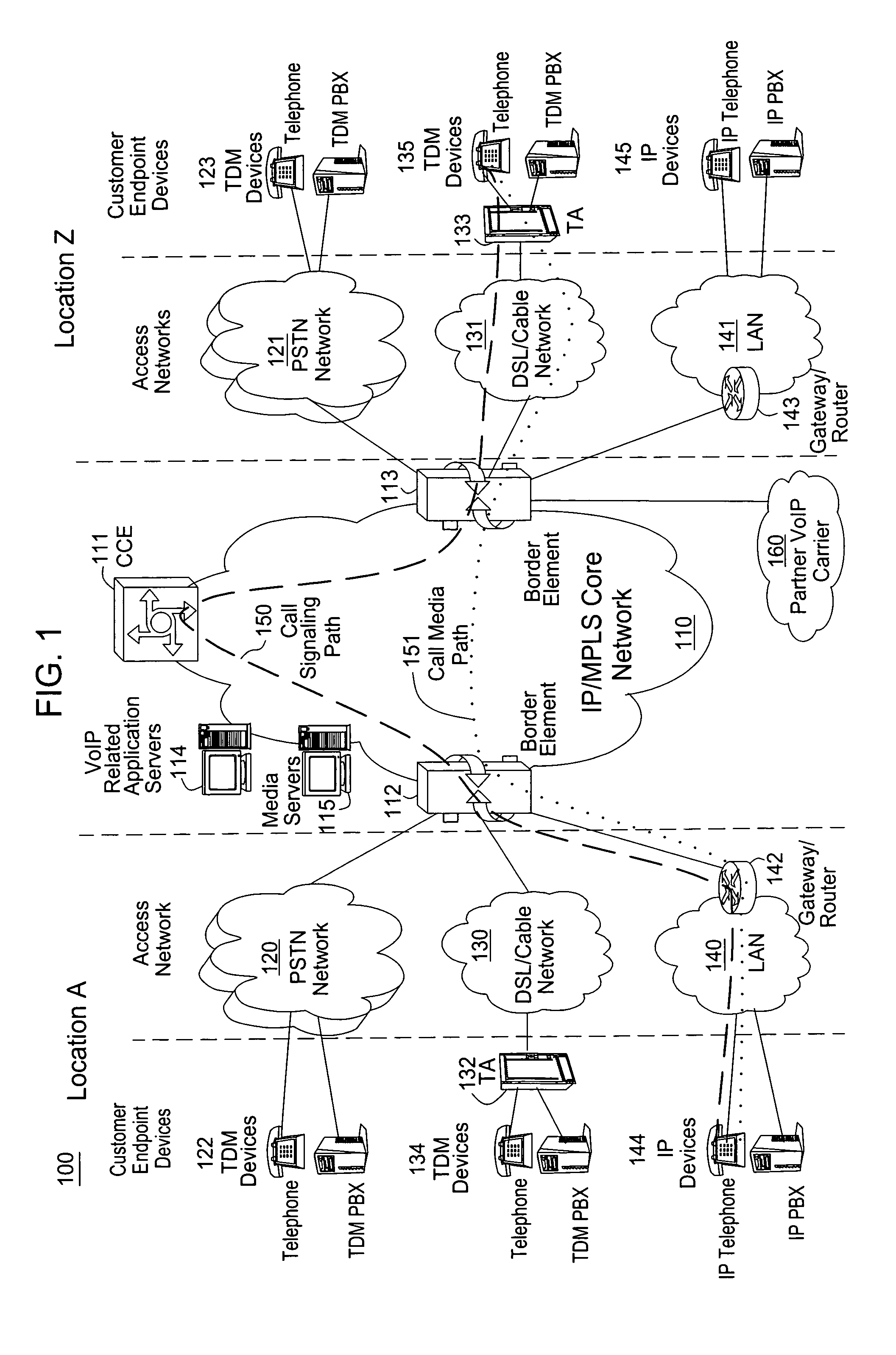
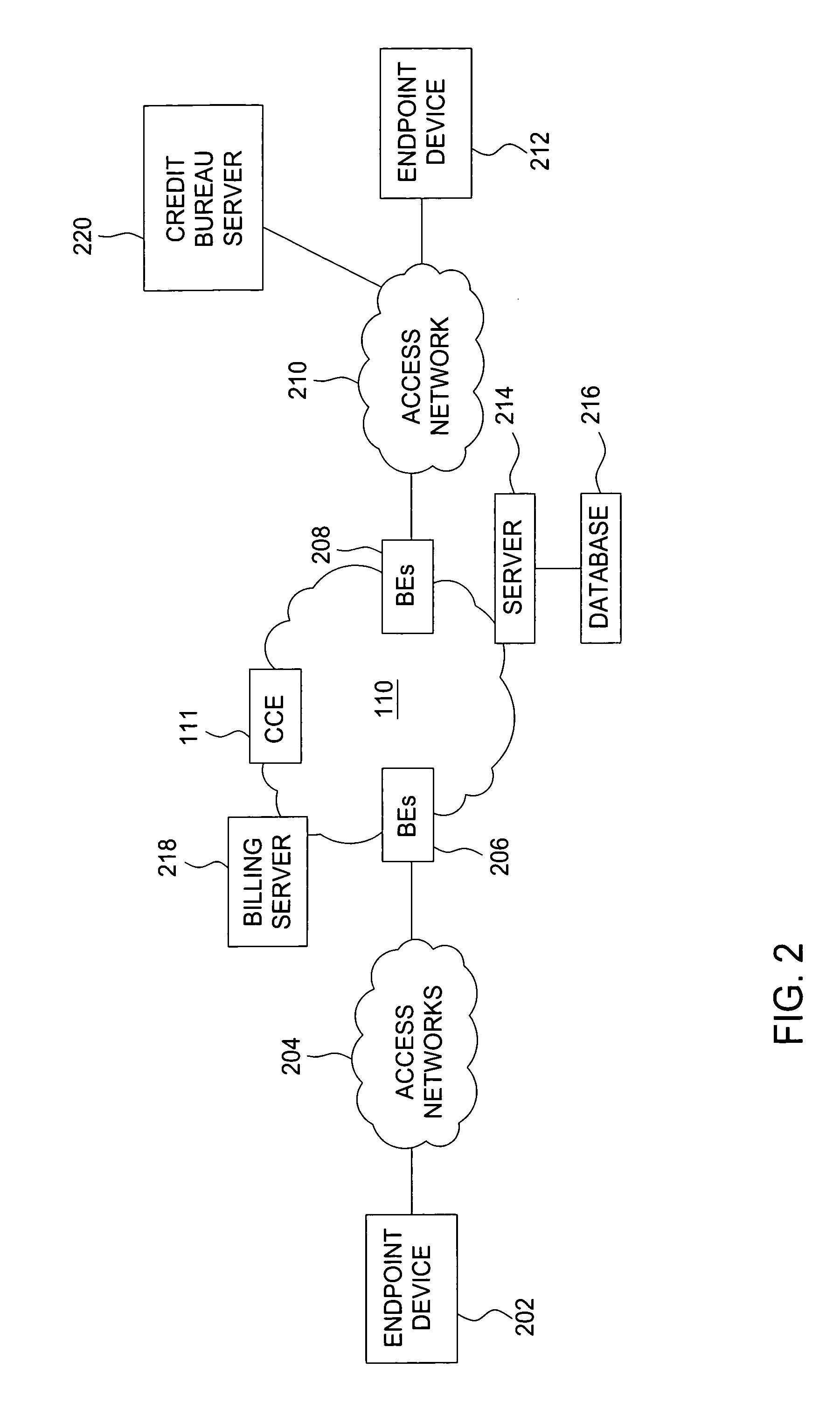
Method and apparatus for monitoring service usage in a communications network
InactiveUS7760861B1Accounting/billing servicesSupervisory/monitoring/testing arrangementsComputer hardwareService usage
A method and apparatus for detecting abnormal calling activity in a communications network is described. In one embodiment, usage data associated with at least one phone number is obtained from the communications network. The usage data is subsequently processed to determine if abnormal calling activity associated with the at least one phone number is exhibited.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
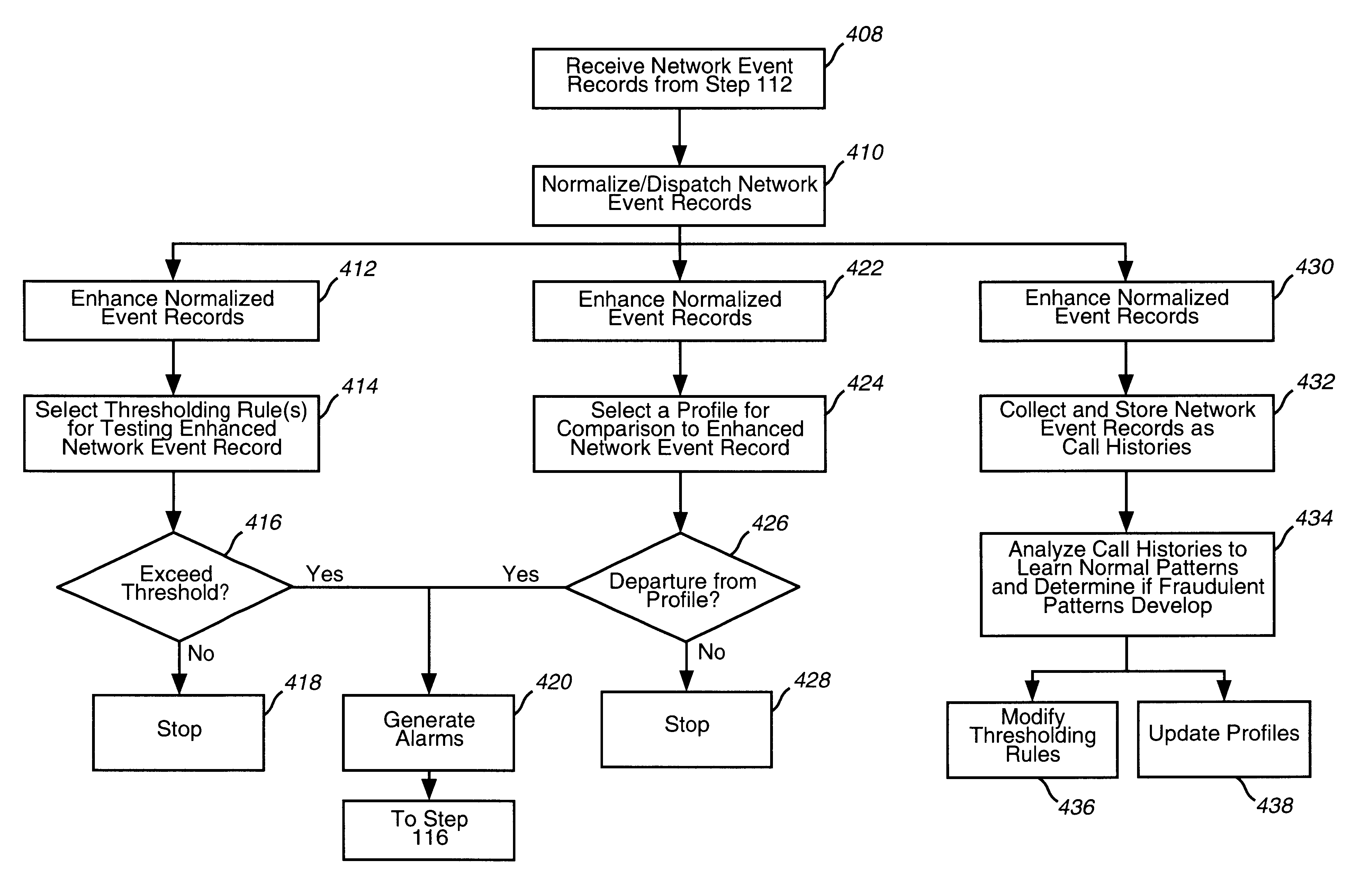
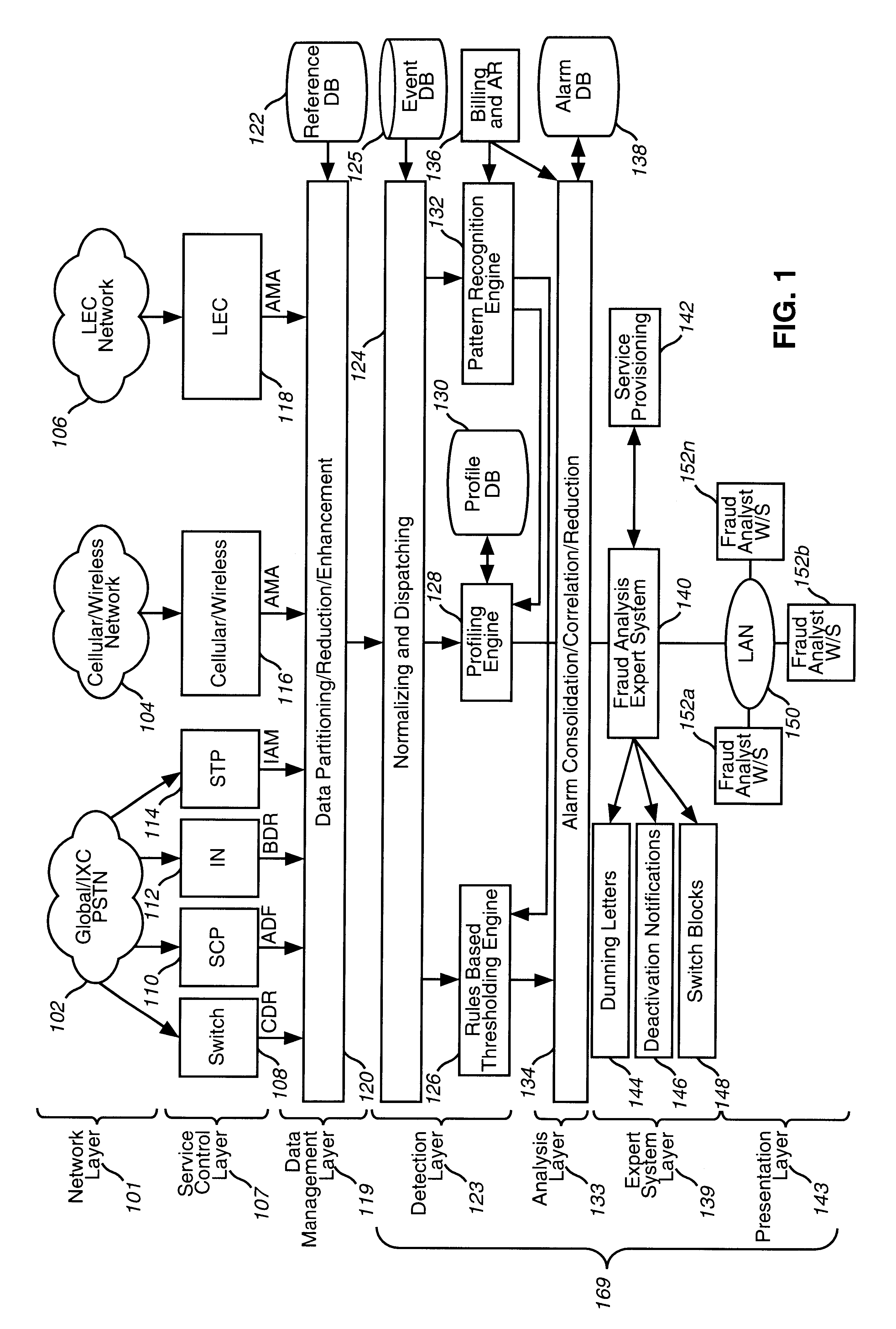
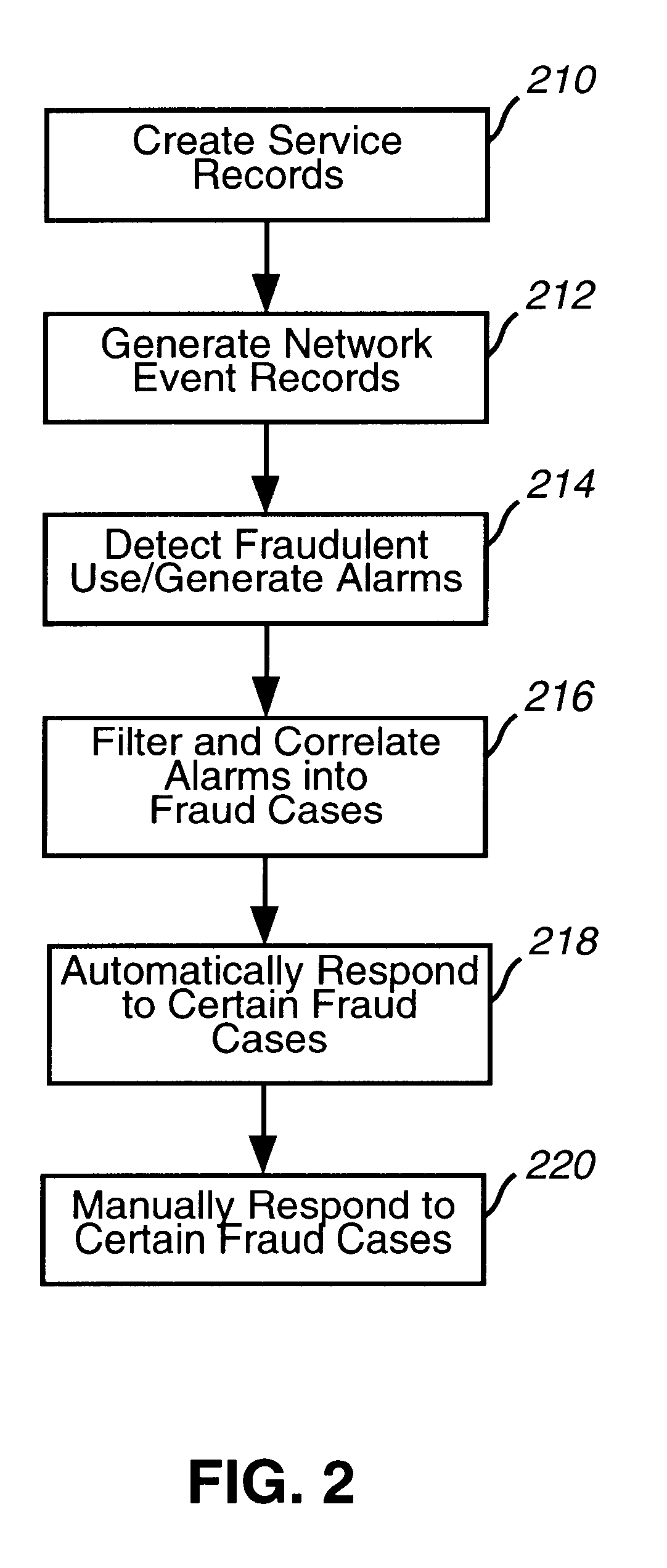
System and method for detecting and managing fraud
A system, method and computer program product for processing event records. The present invention includes a detection layer, an analysis layer, an expert systems layer and a presentation layer. The layered system includes a core infrastructure and a configurable, domain-specific implementation. The detection layer employs one or more detection engines, such as, for example, a rules-based thresholding engine and a profiling engine. The detection layer can include an AI-based pattern recognition engine for analyzing data records, for detecting new and interesting patterns and for updating the detection engines to insure that the detection engines can detect the new patterns. In one embodiment, the present invention is implemented as a telecommunications fraud detection system. When fraud is detected, the detection layer generates alarms which are sent to the analysis layer. The analysis layer filters and consolidates the alarms to generate fraud cases. The analysis layer preferably generates a probability of fraud for each fraud case. The expert systems layer receives fraud cases and automatically initiates actions for certain fraud cases. The presentation layer also receives fraud cases for presentation to human analysts. The presentation layer permits the human analysts to initiate additional actions.
Owner:VERIZON PATENT & LICENSING INC
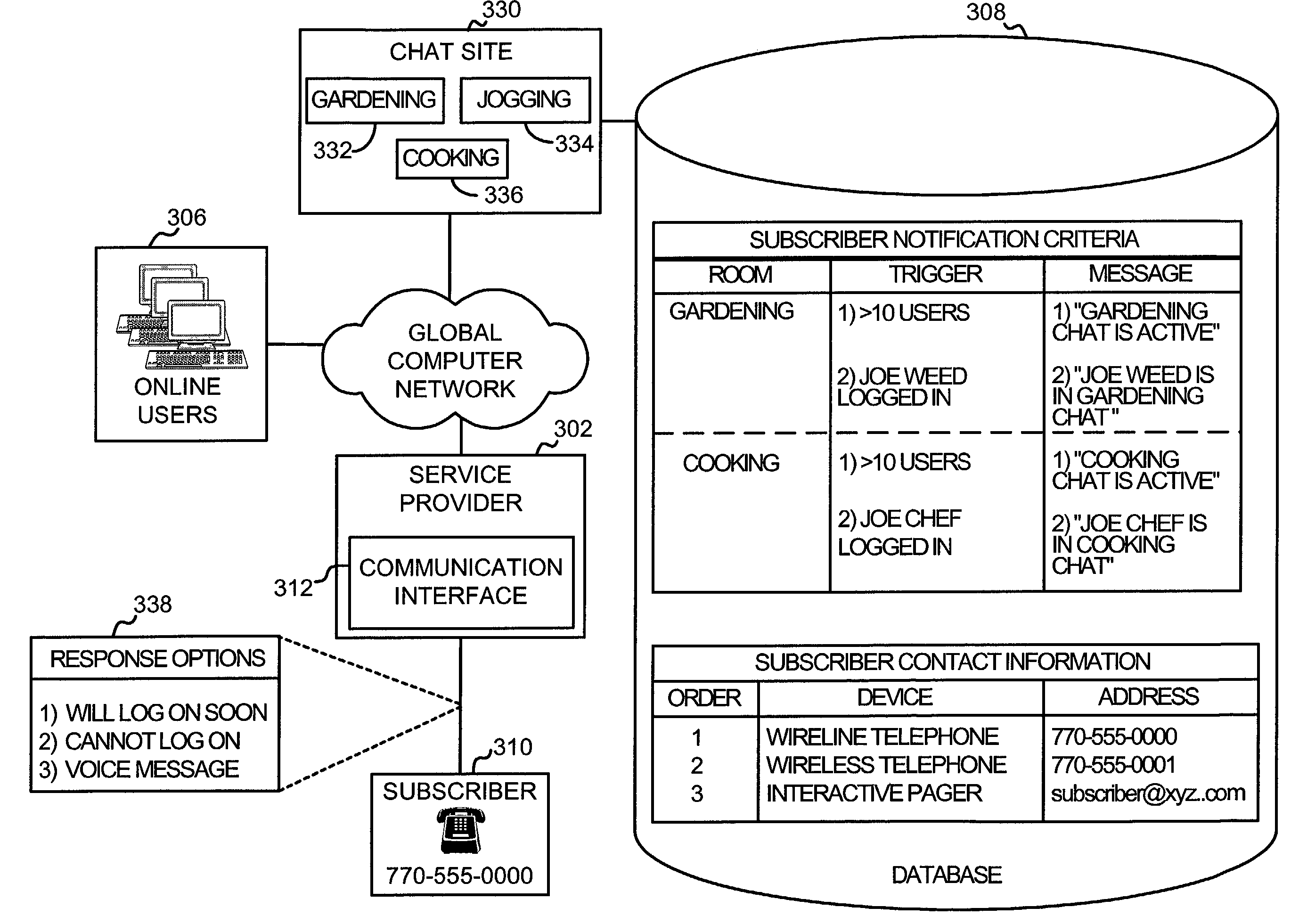
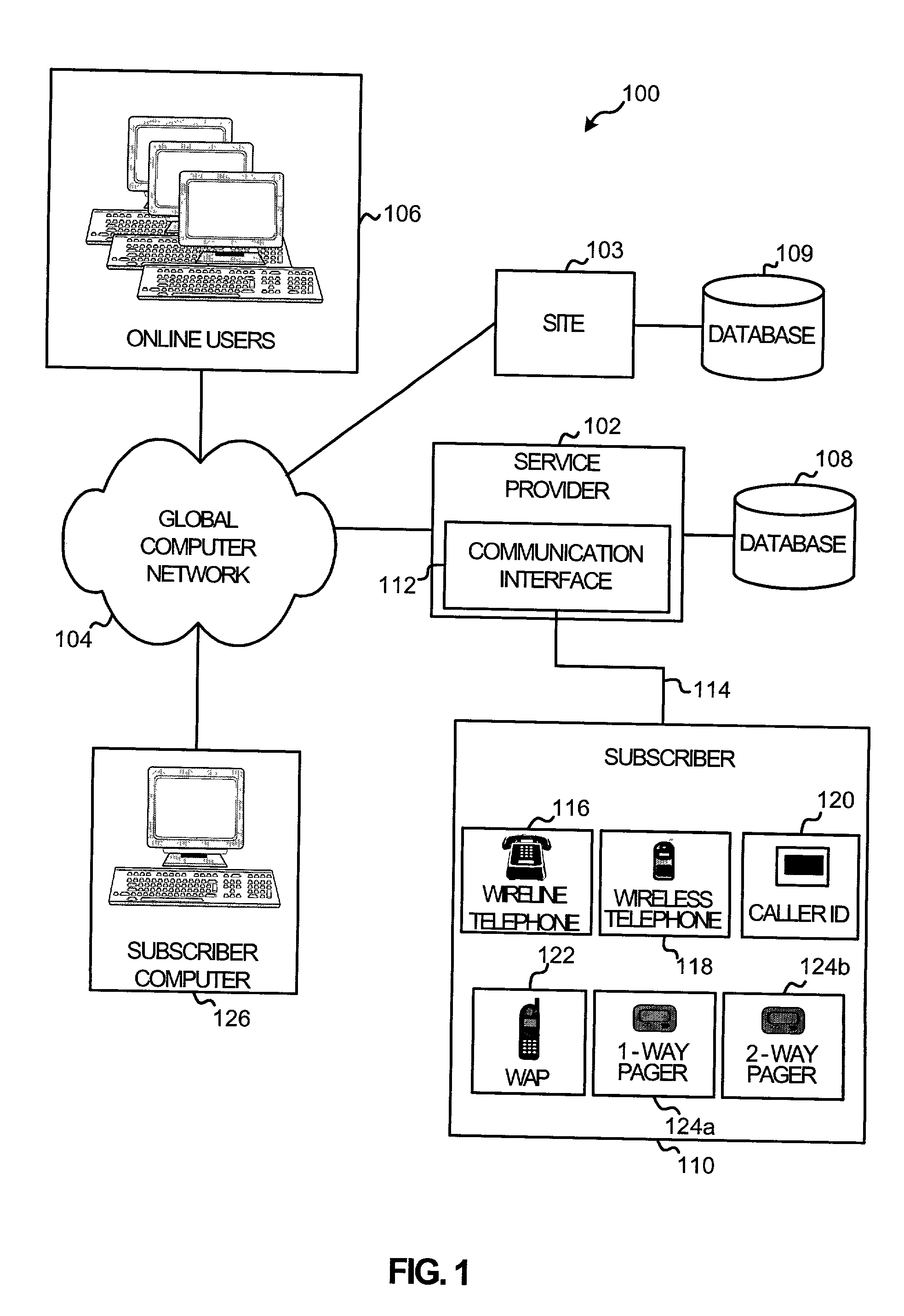
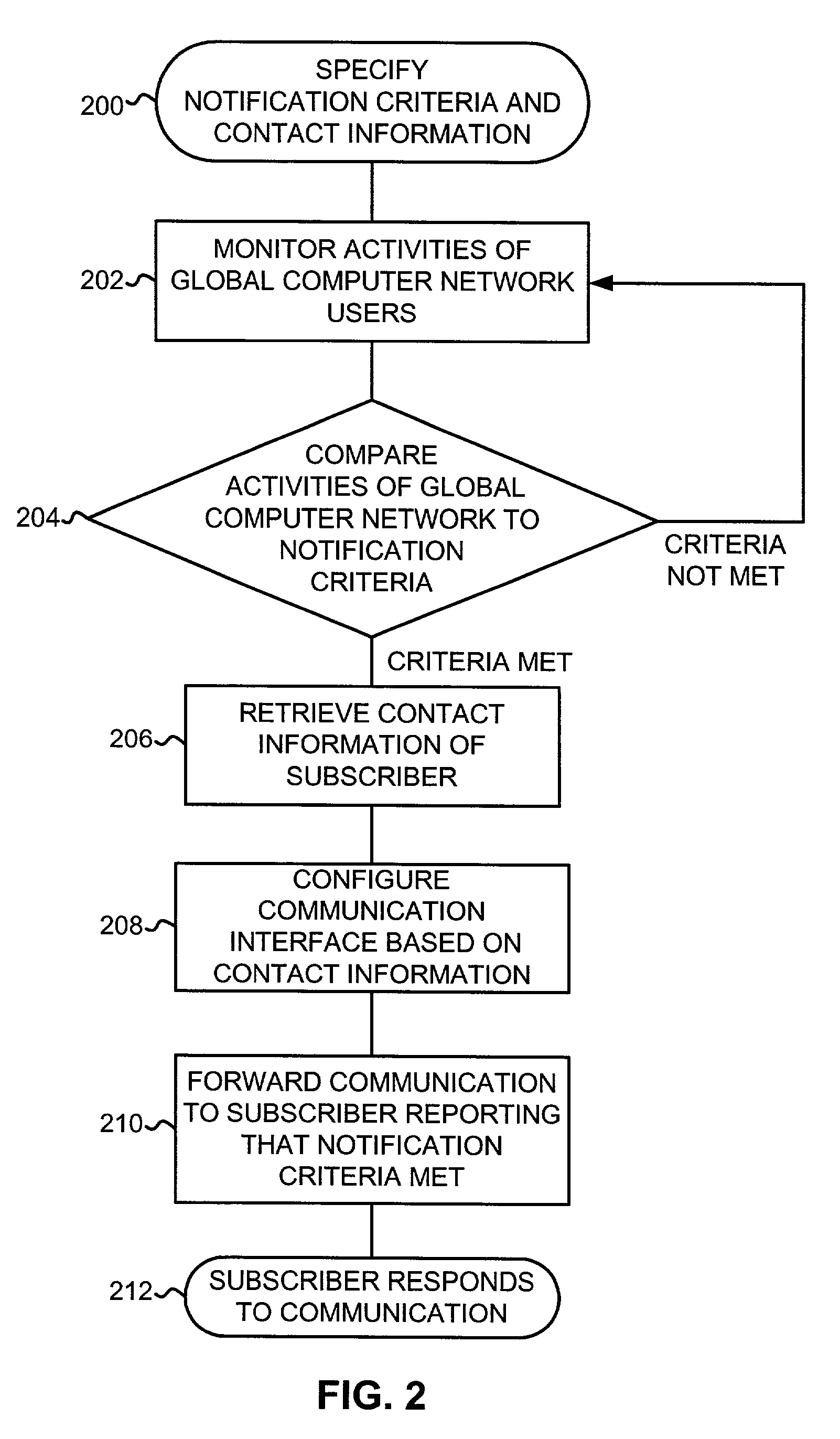
System and method for notifying an offline global computer network user of an online interaction
InactiveUS20050004984A1Easy to placeAvoid difficultySpecial service provision for substationFinanceChat roomPager
A system and method for notifying an offline global computer network user of an online interaction in which the offline user could participate. The system and method specify notification criteria of the offline user, monitor activities occurring on the global computer network, compare the activities to the notification criteria, and, if the activities satisfy the notification criteria, forward an offline communication to the offline user, which notifies the offline user of the online interaction. Examples of the online interactions include chat rooms, game sites, instant messaging services, auctions, and calls made over the global computer network. Examples of the offline communication include calls to a wireline telephone, calls to a wireless telephone, messages to a caller identification device, messages to a wireless access protocol device, messages to a one-way pager, and messages to an interactive pager.
Owner:BELLSOUTH INTPROP COR
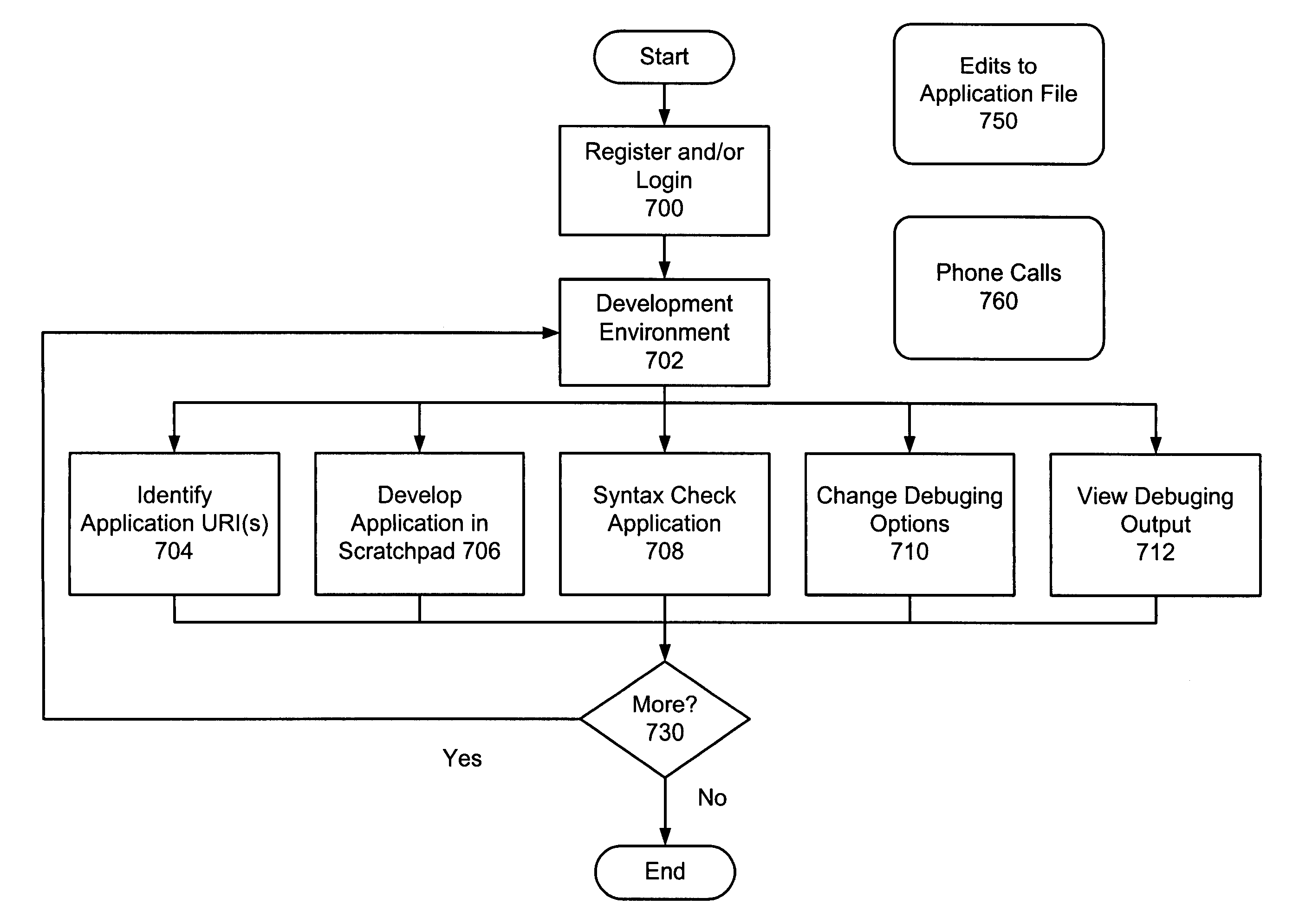
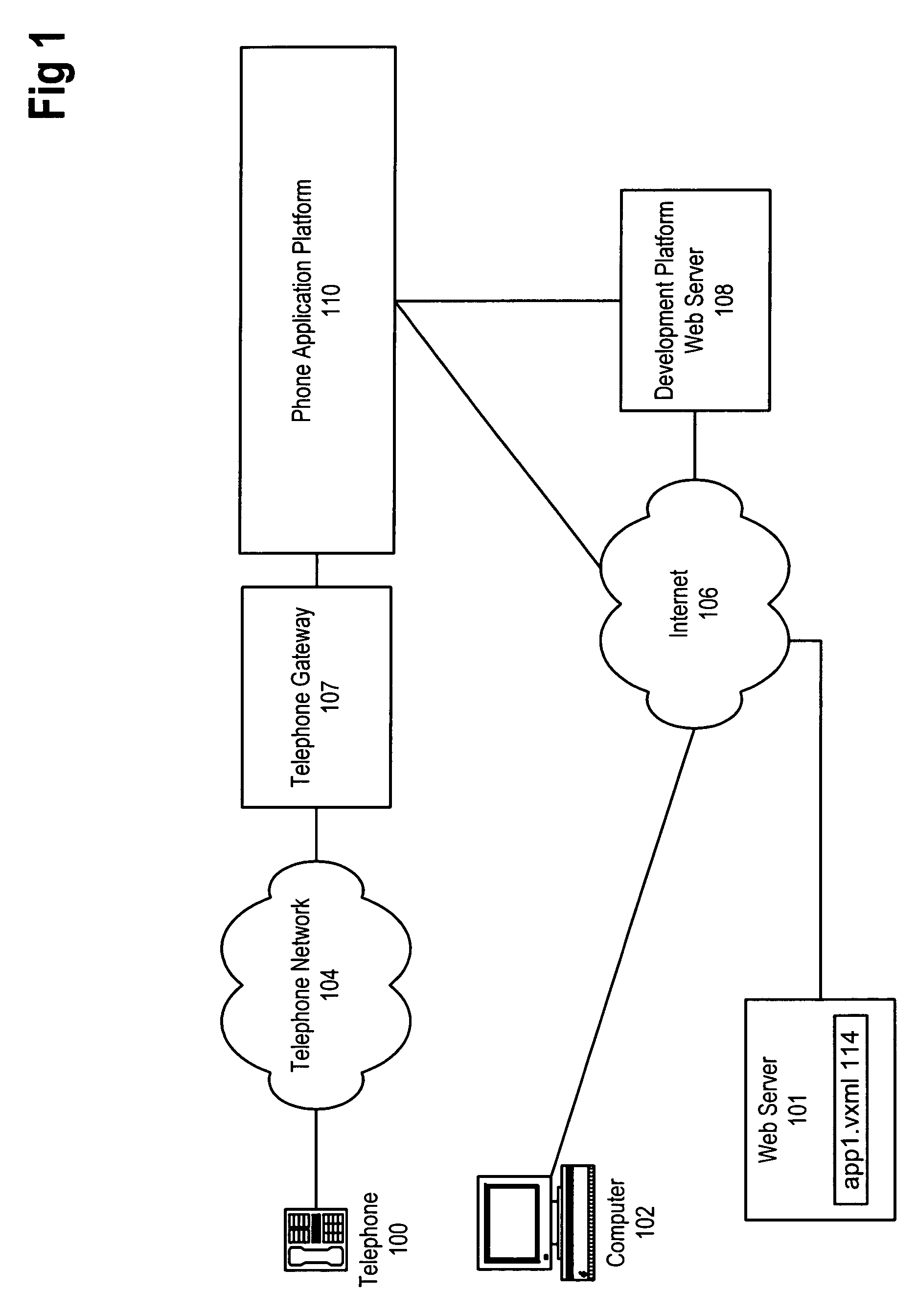
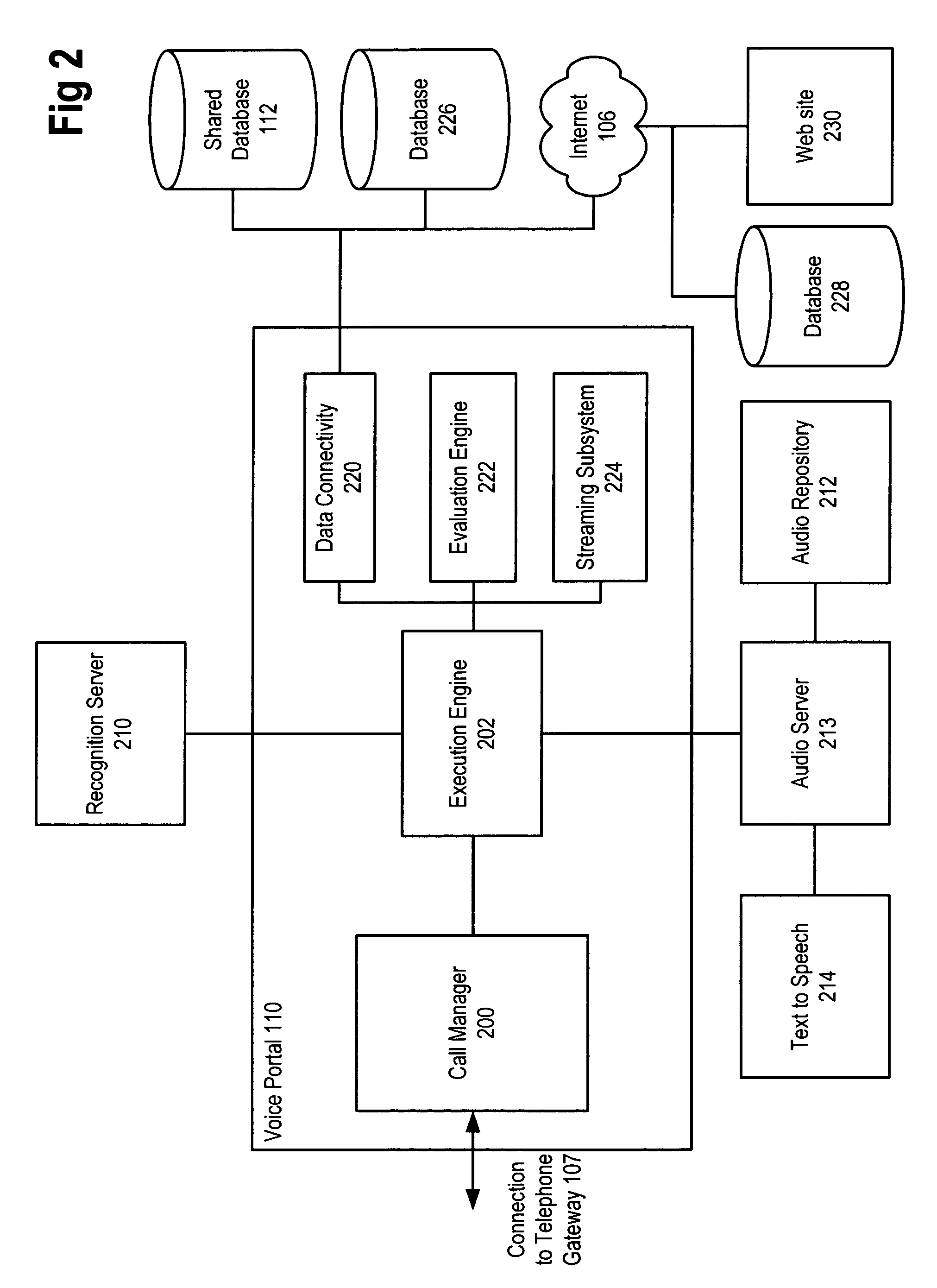
Method and apparatus for zero-footprint phone application development
InactiveUS7140004B1Avoid any surpriseTelephone data network interconnectionsError detection/correctionWeb browserApplication procedure
A zero-footprint remotely hosted phone application development environment is described. The environment allows a developer to use a standard computer without any specialized software (in some embodiments all that is necessary is a web browser and network access) together with a telephone to develop sophisticated phone applications that use speech recognition and / or touch tone inputs to perform tasks, access web-based information, and / or perform commercial transactions. Some embodiments support concurrent call flow tracking that allows a developer to observe, using a web browser, the execution of her / his application. A variety of reusable libraries are provided to enable the developer to leverage well-developed libraries for common playback, input, and computational tasks. Embodiments support rapid application deployment from the development environment to hosted application deployment to the intended audience.
Owner:MICROSOFT TECH LICENSING LLC
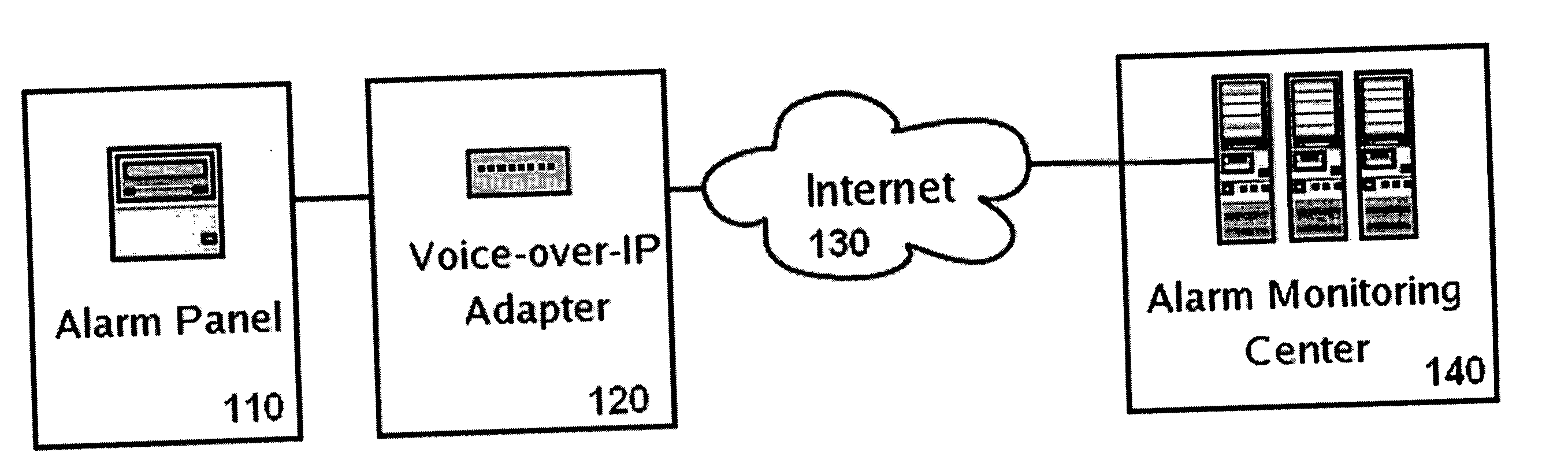
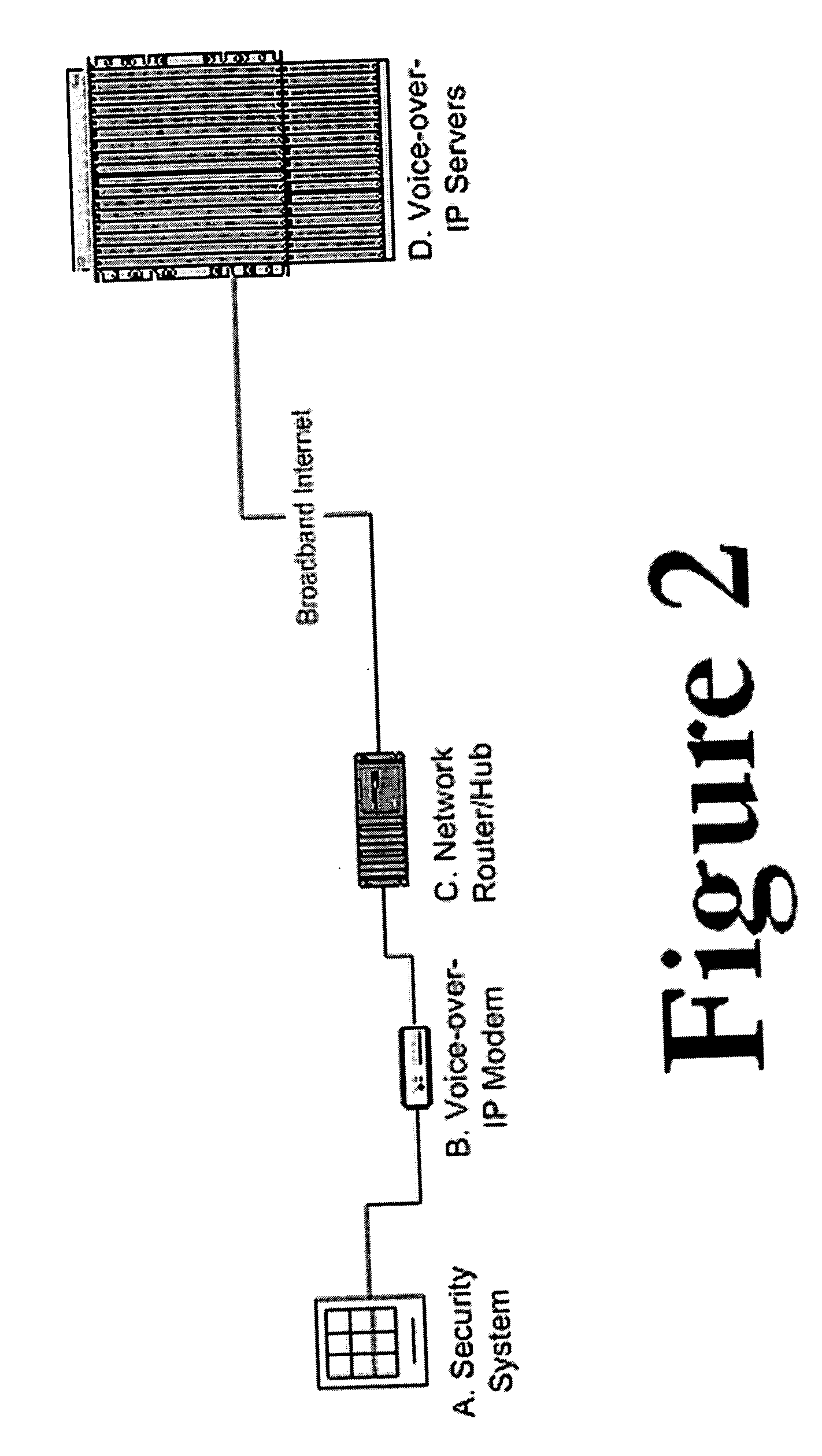
Private VoIP network for security system monitoring
InactiveUS20060067484A1Reduce errorsShort response timeInterconnection arrangementsFrequency-division multiplex detailsCommunications securityPrivate network
Security systems typically communicate with alarm monitoring centers using a telephone connection. Security systems will check in with the alarm monitoring center with a diagnostic signal at a predetermined interval—typically once per day. When a security system is connected to a Voice-over-IP service (using Broadband Internet), rather than a standard telephone line, the opportunity exists to poll in real-time the status of the connection, and alert the owner (or alert the alarm monitoring center) that the customer's connection has been broken. The present invention offers a system and technique for monitoring a security system connected using a Voice-over-IP connection, in real time, and alerting the owner of the security system, or the alarm-monitoring center, when the connection is broken. This alert can be used, for example, to issue a telephone call to the police, informing them of the breach of line integrity and possible compromise of the premise.
Owner:NUMEREX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com