Patents
Literature
2204 results about "Communications security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Communications security is the discipline of preventing unauthorized interceptors from accessing telecommunications in an intelligible form, while still delivering content to the intended recipients. In the North Atlantic Treaty Organization culture, including United States Department of Defense culture, it is often referred to by the abbreviation COMSEC. The field includes cryptographic security, transmission security, emissions security and physical security of COMSEC equipment and associated keying material.
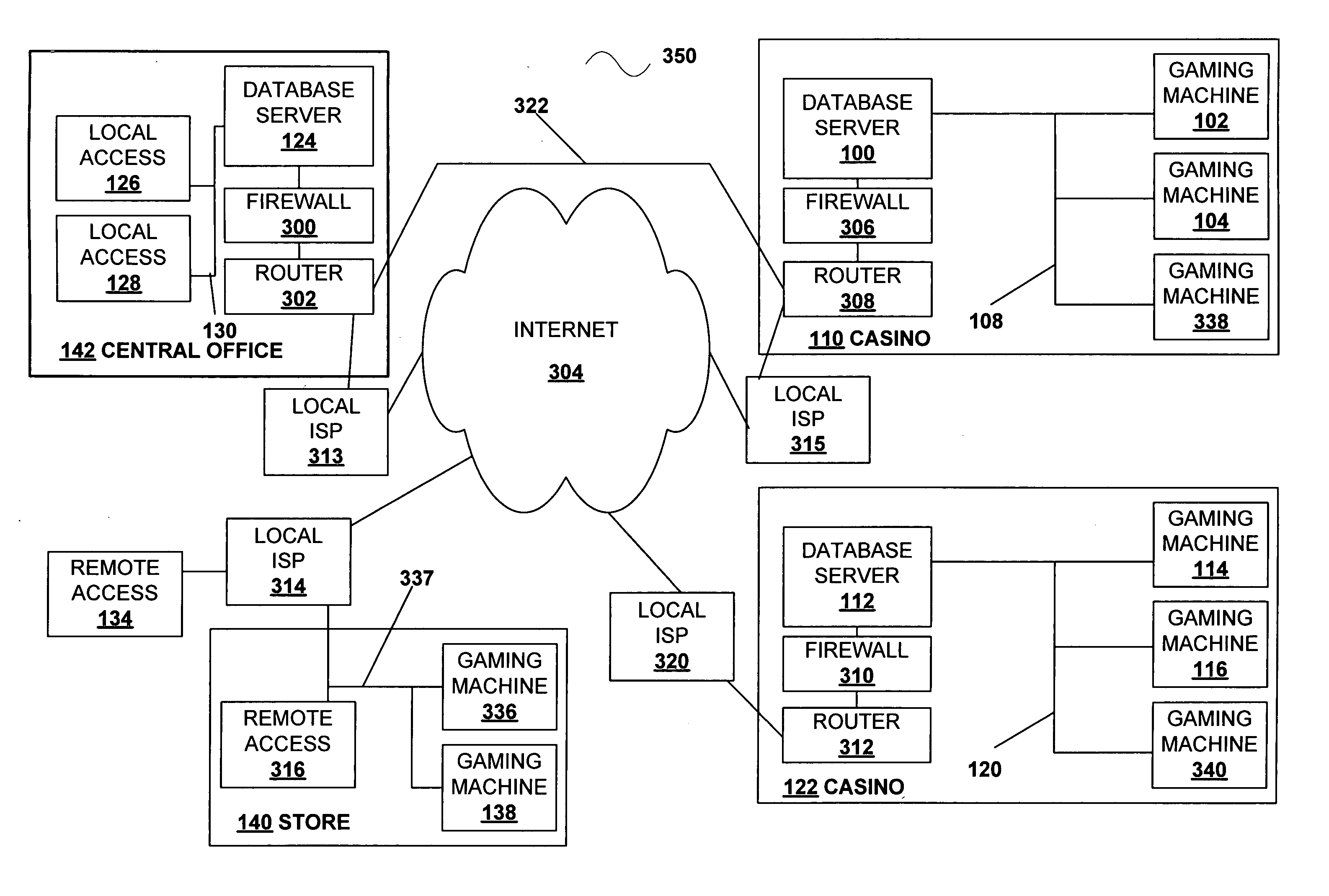
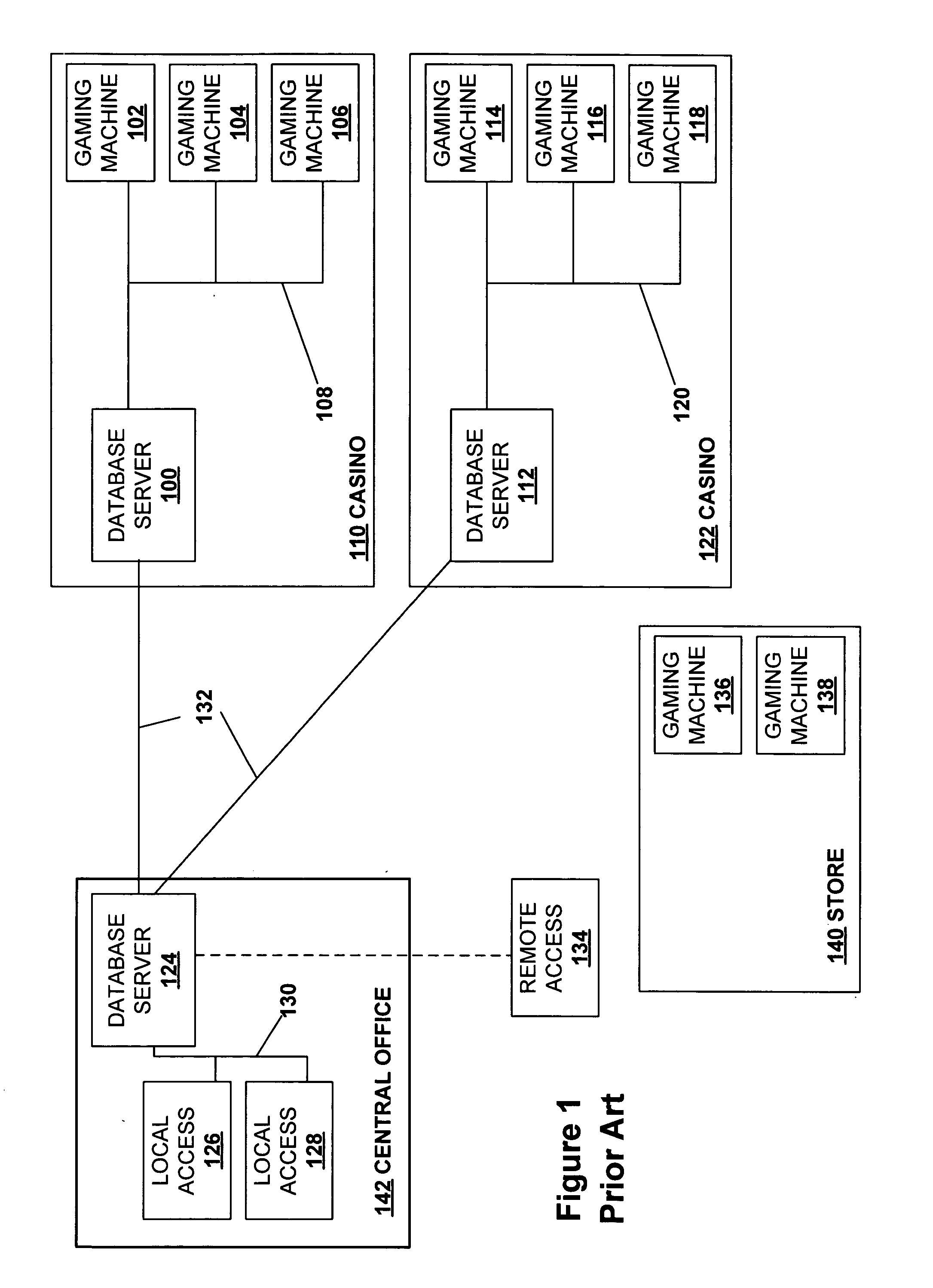
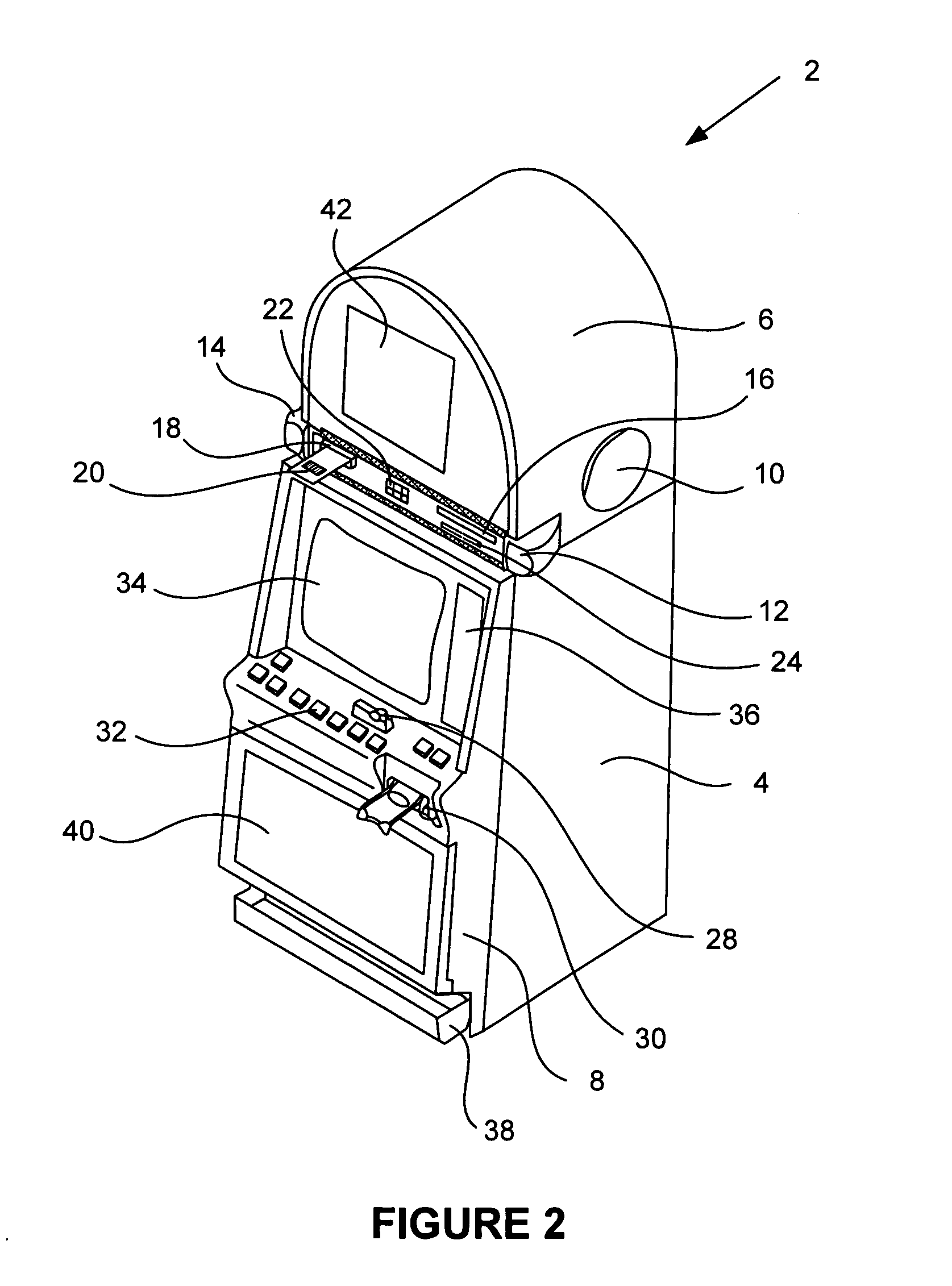
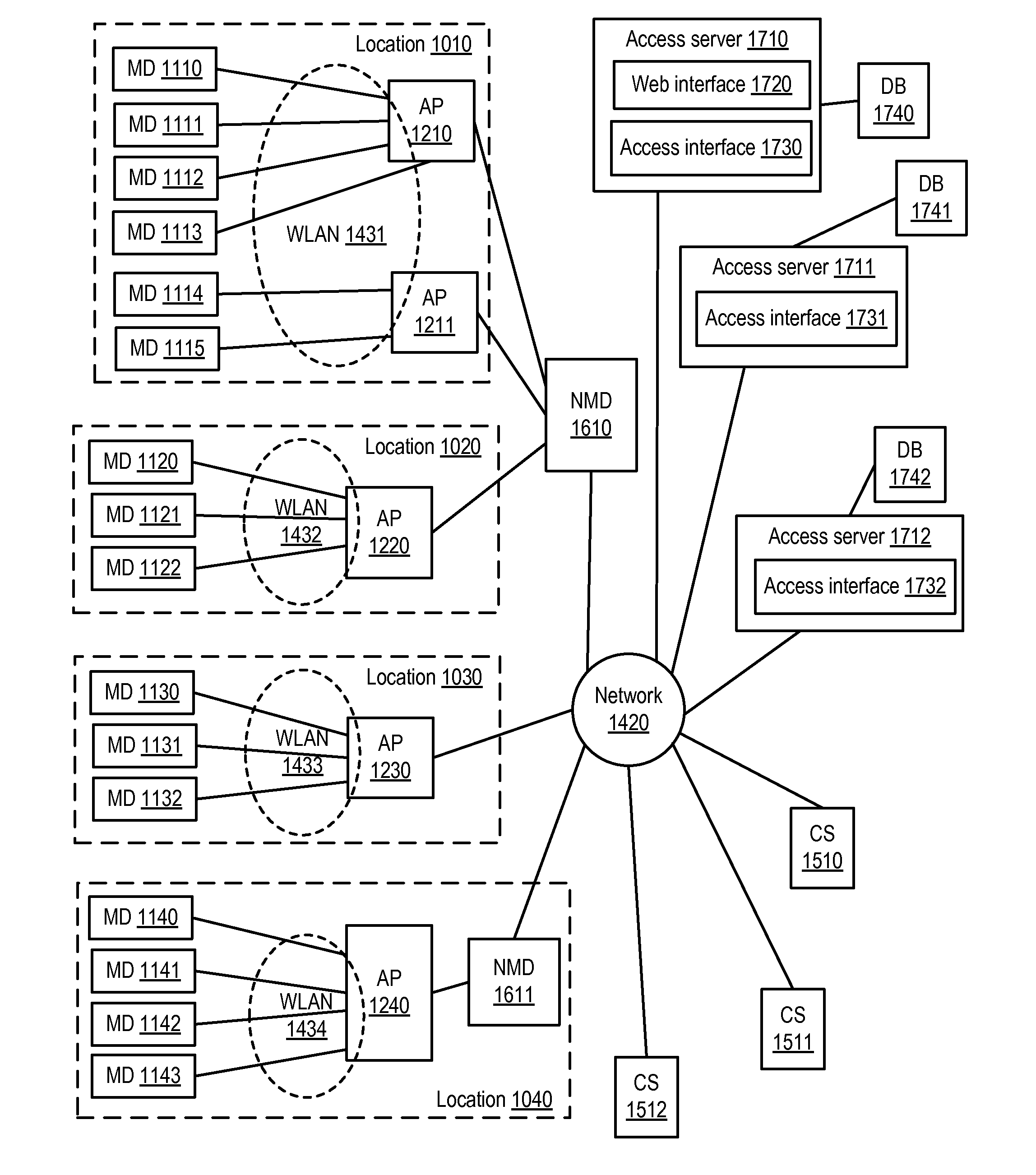
Secured virtual network in a gaming environment
InactiveUS20050192099A1Key distribution for secure communicationApparatus for meter-controlled dispensingSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
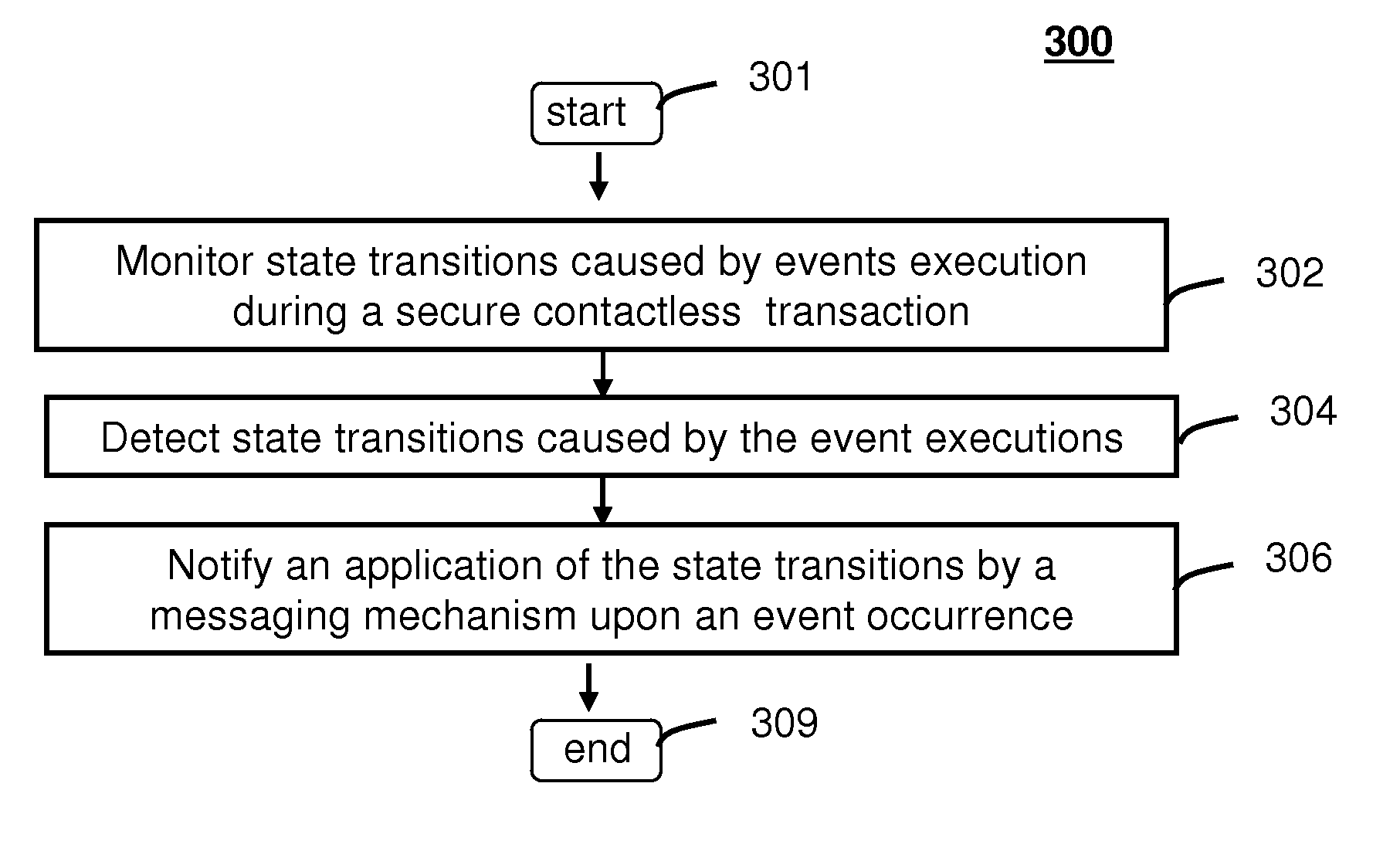
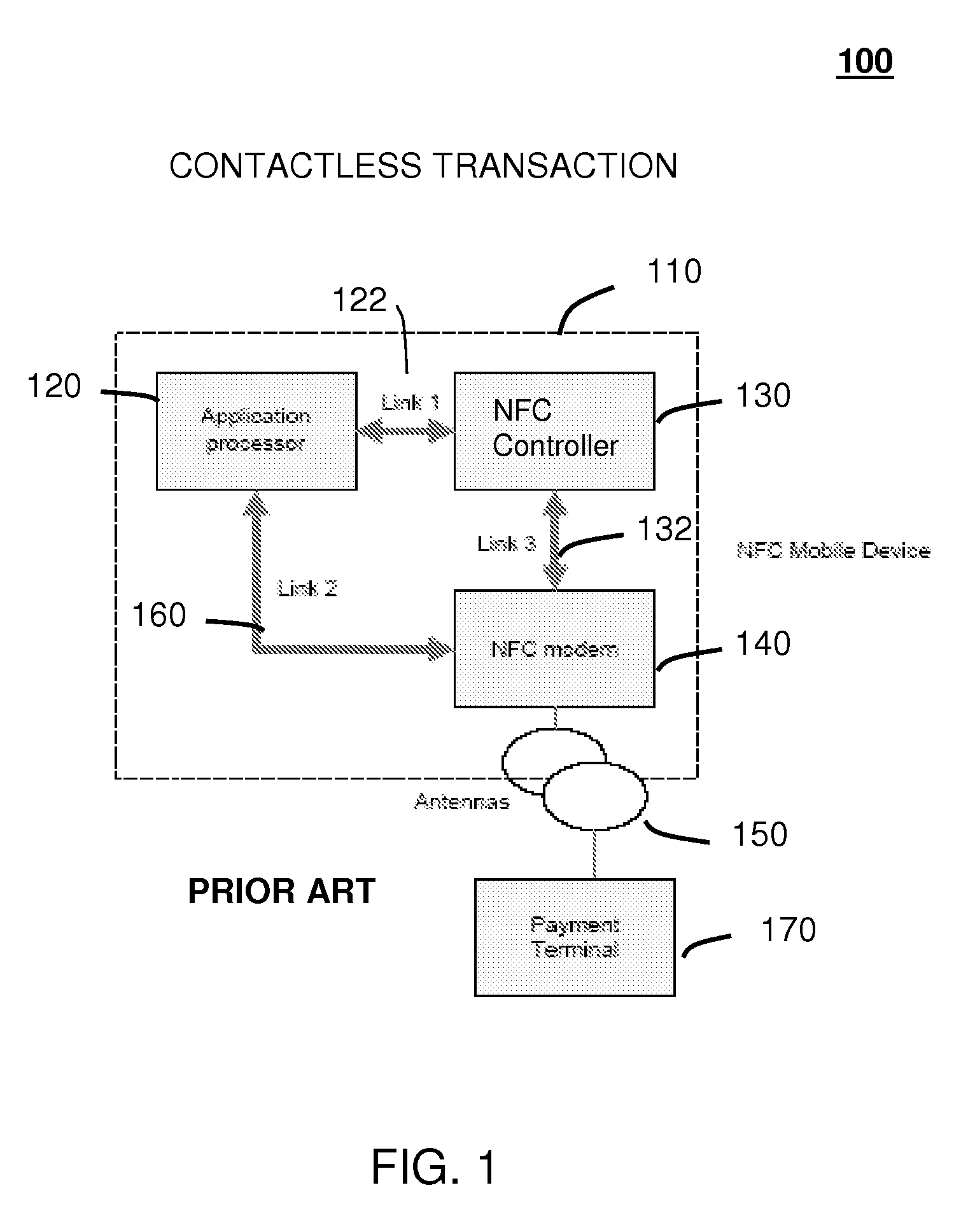
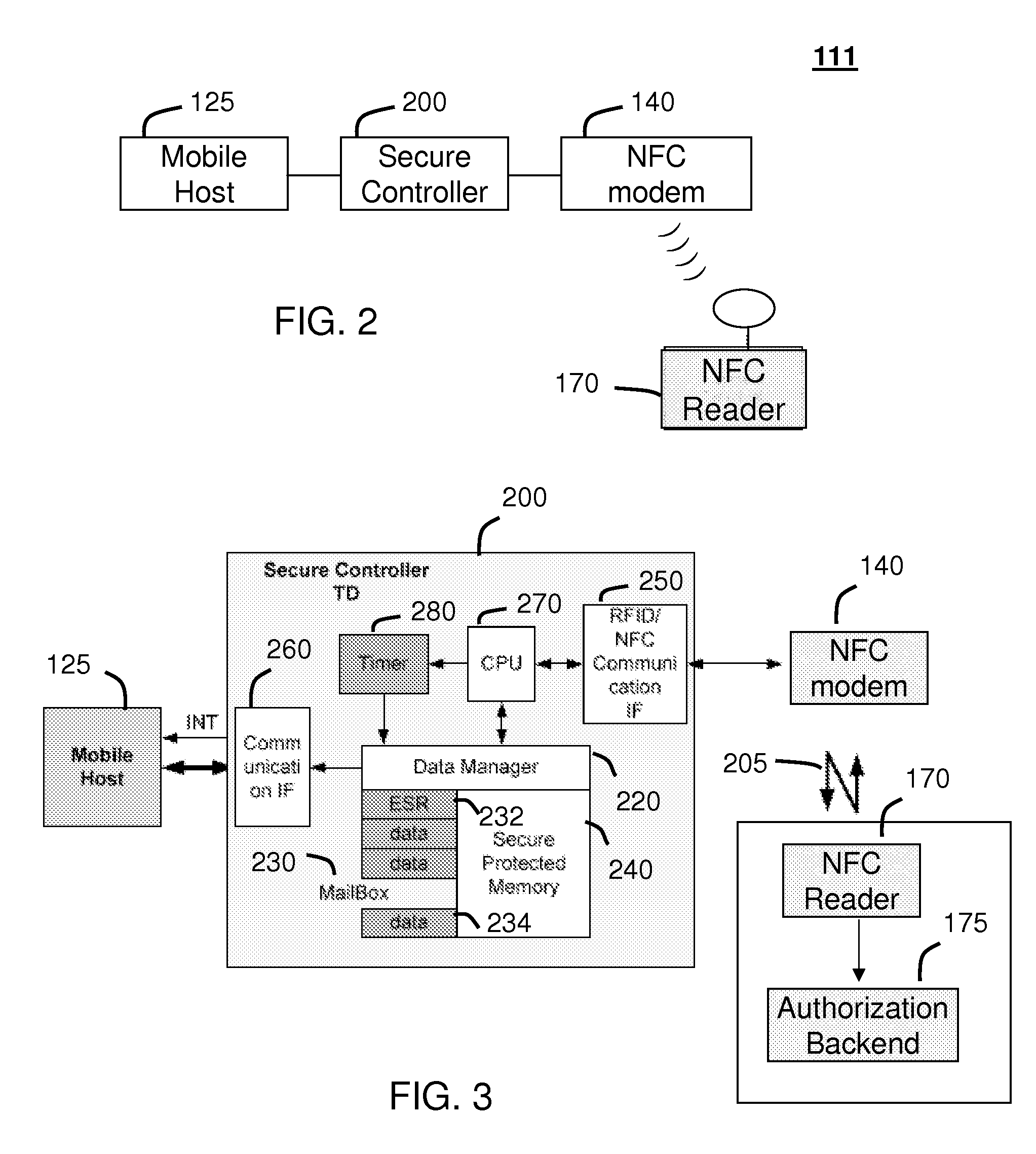
Method and system for monitoring secure application execution events during contactless rfid/nfc communication
ActiveUS20080162361A1Radio transmissionSecuring communicationCommunications securityTechnical communication
A system (211) and method (300) for reliable monitoring of secure application execution events is provided. The system can include a Near Field Communication (NFC) modem (140) for communicating transaction events of a secure contactless transaction (358) with a NFC reader (170), a secure controller (200) for monitoring state transitions caused by the transaction events, and a mobile host communicatively coupled to the secure controller for receiving hardware event notifications of the state transitions. The secure controller can generate message using a hardware interrupt to a mobile host based on secure applet state transition monitoring by setting up the events flag such as a Transaction Completion Flag (TCF) (372) into an Events Status Register (232) to identify a status of a secure contactless transactions
Owner:GOOGLE TECH HLDG LLC
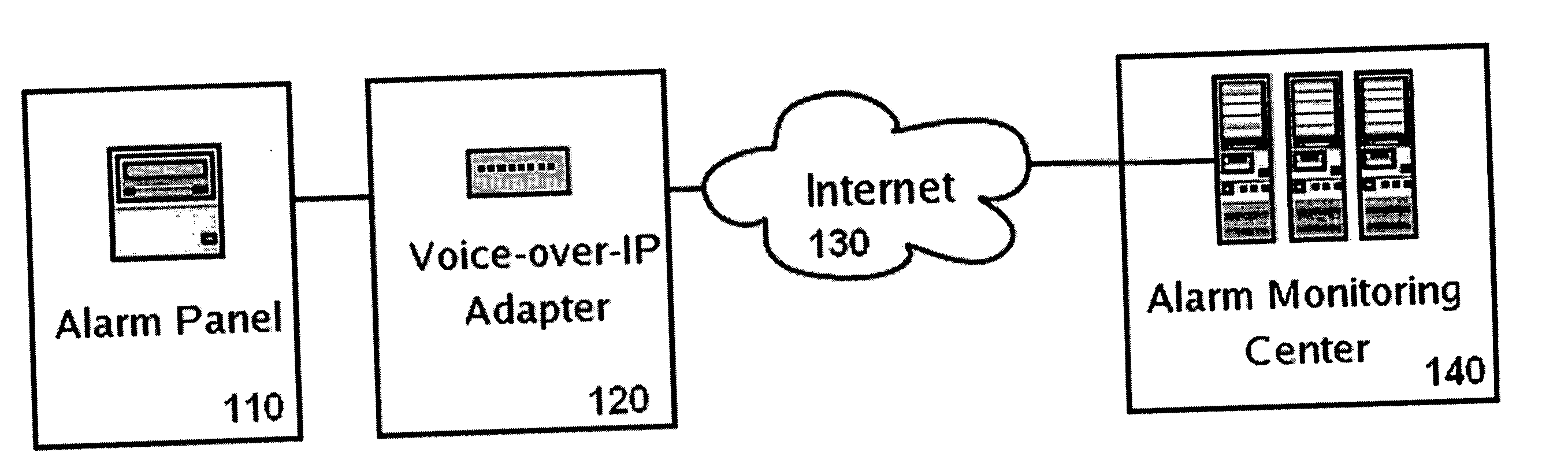
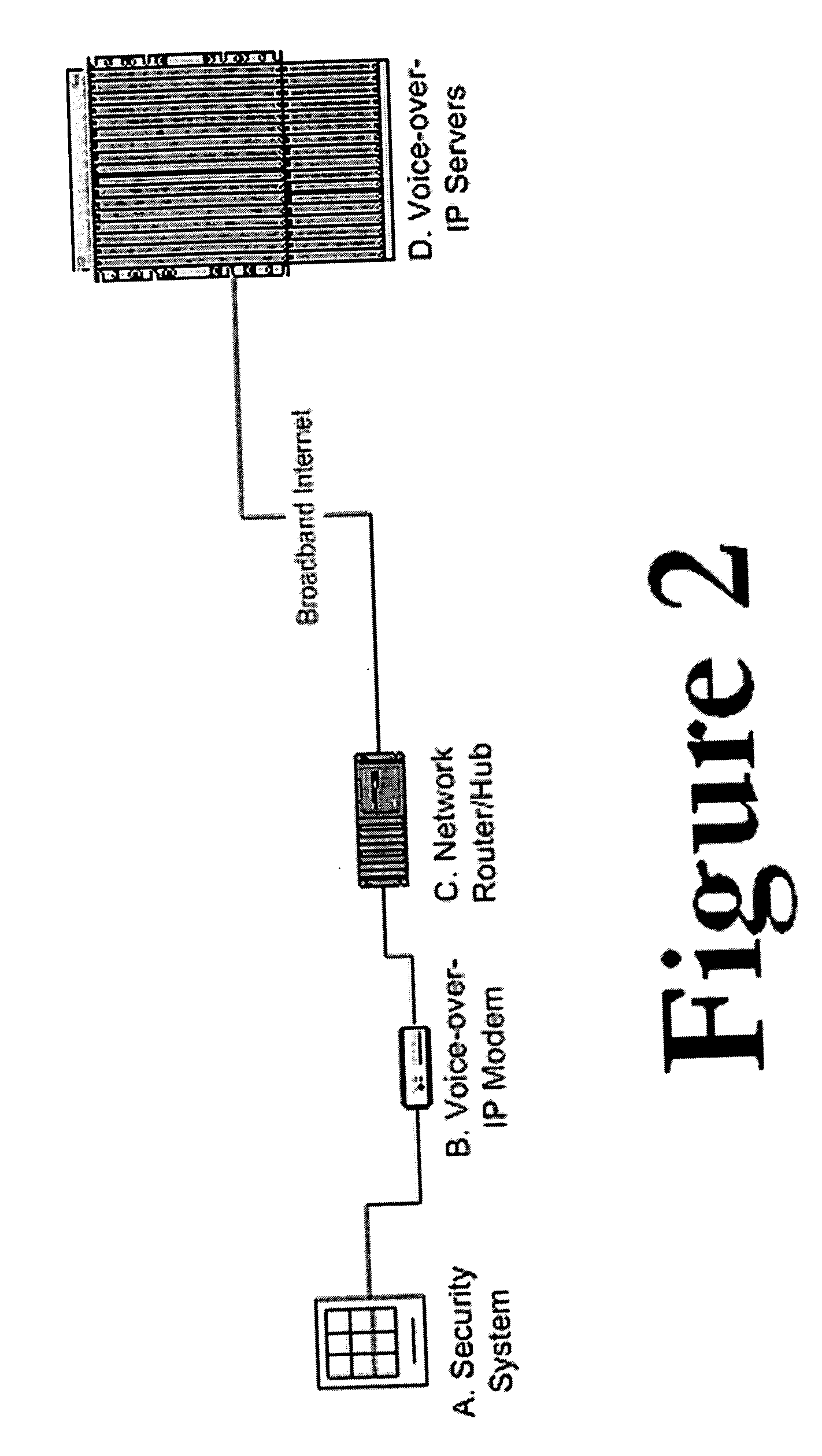
Private VoIP network for security system monitoring
InactiveUS20060067484A1Reduce errorsShort response timeInterconnection arrangementsFrequency-division multiplex detailsCommunications securityPrivate network
Security systems typically communicate with alarm monitoring centers using a telephone connection. Security systems will check in with the alarm monitoring center with a diagnostic signal at a predetermined interval—typically once per day. When a security system is connected to a Voice-over-IP service (using Broadband Internet), rather than a standard telephone line, the opportunity exists to poll in real-time the status of the connection, and alert the owner (or alert the alarm monitoring center) that the customer's connection has been broken. The present invention offers a system and technique for monitoring a security system connected using a Voice-over-IP connection, in real time, and alerting the owner of the security system, or the alarm-monitoring center, when the connection is broken. This alert can be used, for example, to issue a telephone call to the police, informing them of the breach of line integrity and possible compromise of the premise.
Owner:NUMEREX CORP
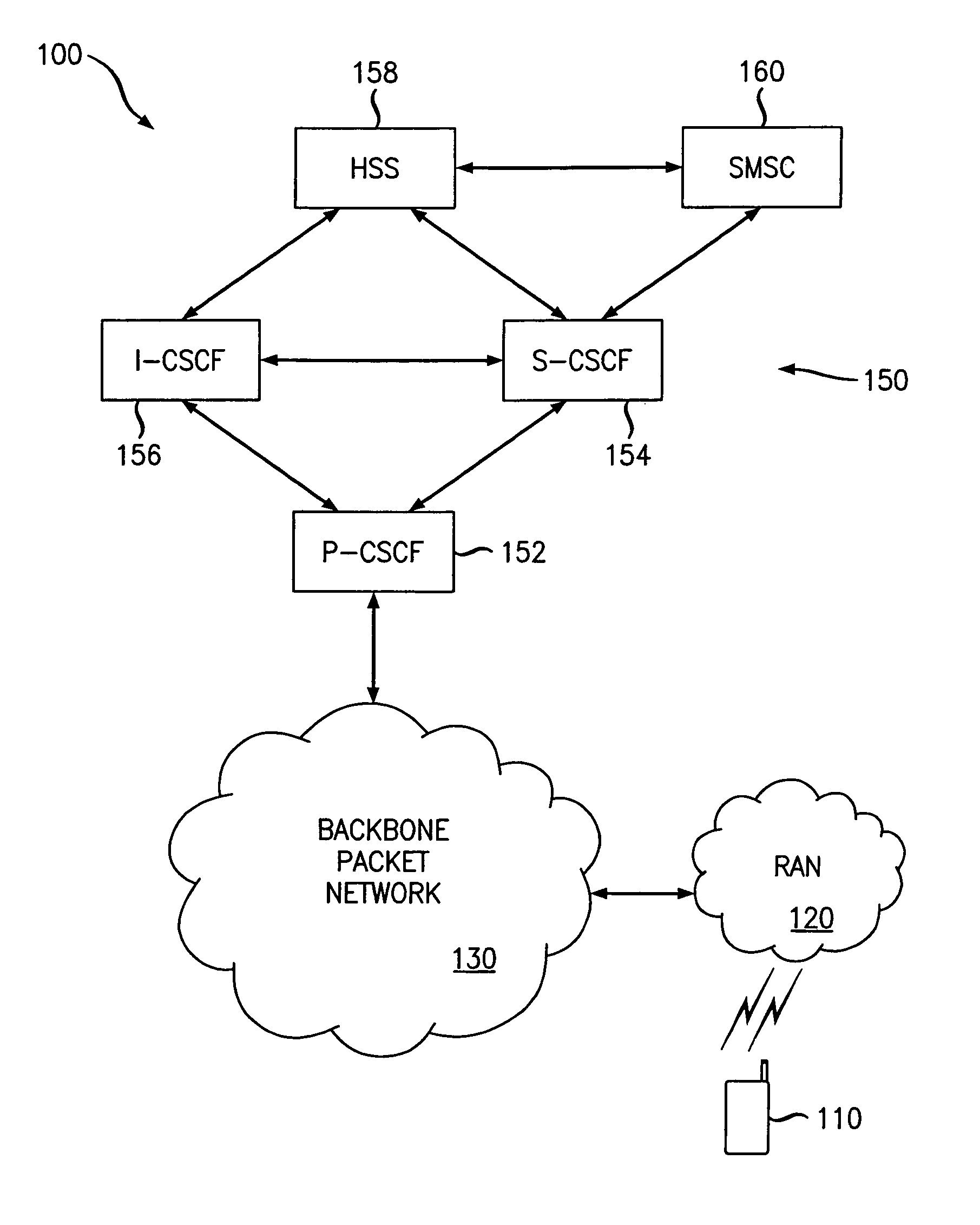
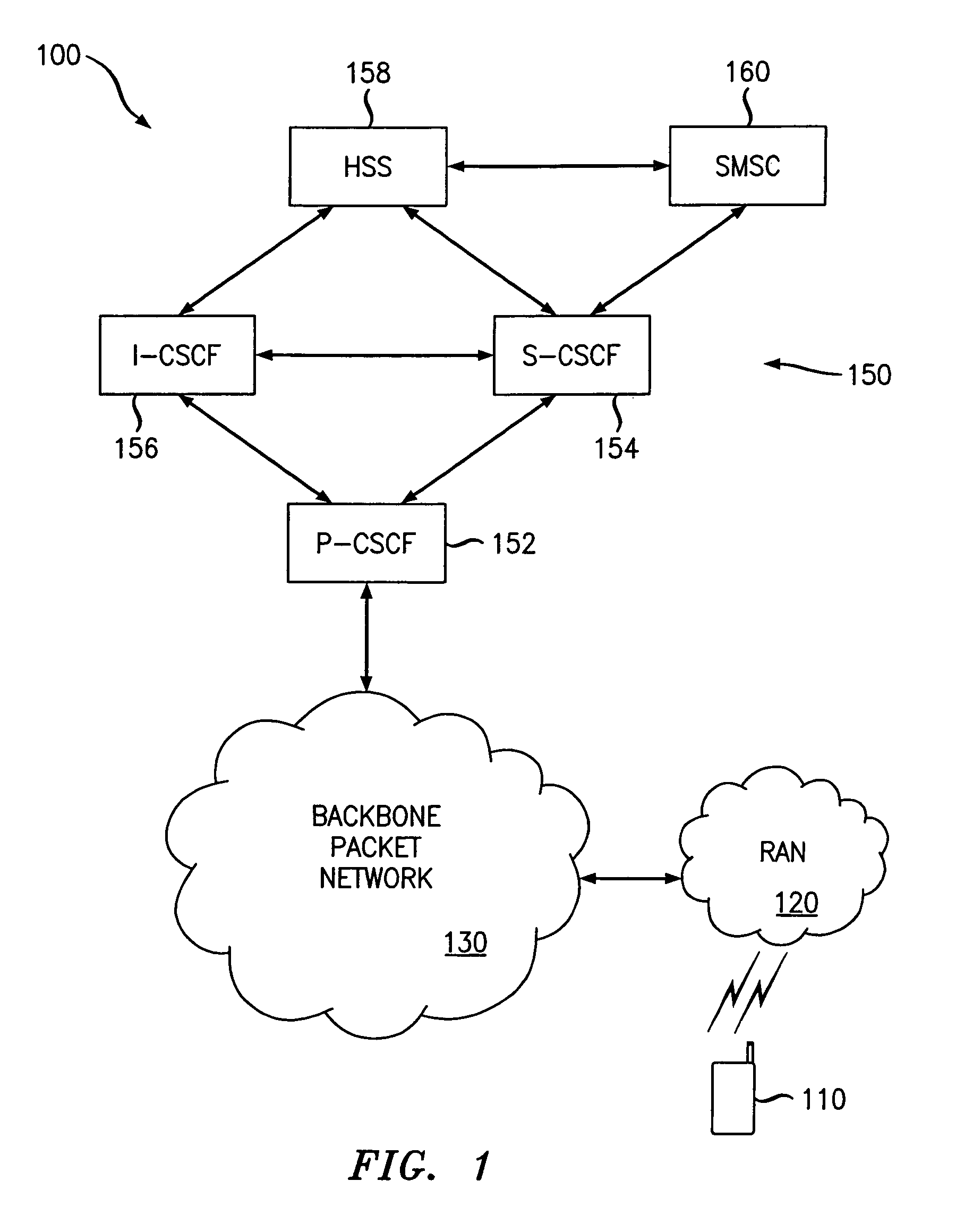
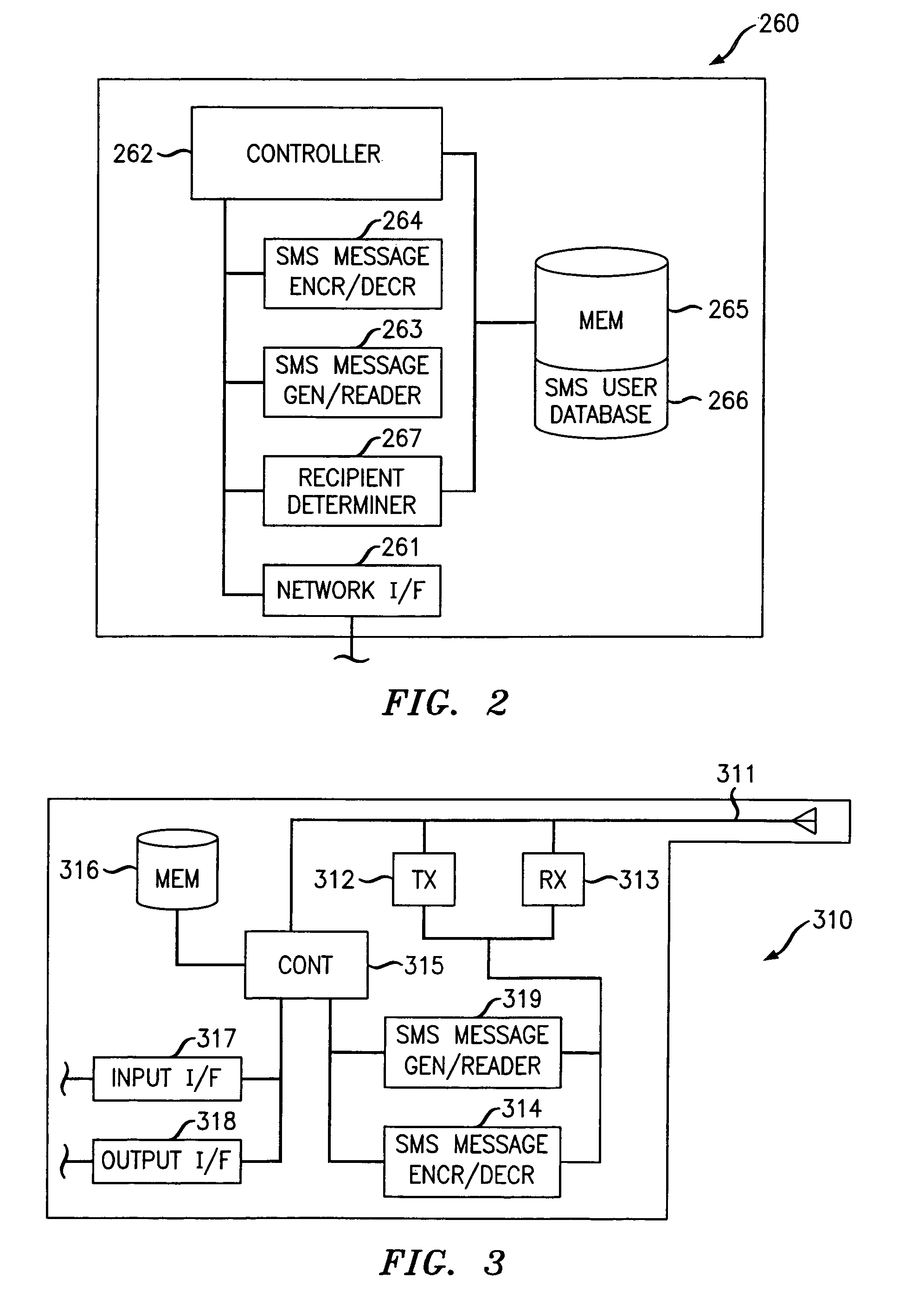
Short message service communication security
ActiveUS8131266B2Facilitate communicationImprove securityUser identity/authority verificationCathode-ray tube indicatorsCommunications securityAccess network
Owner:ALCATEL LUCENT SAS
V2v safety system using learned signal timing
ActiveUS20170243485A1More dataPower managementRoad vehicles traffic controlCommunications securityIp address
A vehicle-to-vehicle (V2V) communication transponder for use in V2V communication, safety, optimization and anti-collision systems wherein the transponder records and shares observed traffic signal timing and phasing, and uses this information to make recommendations or perform automatic operation to optimize parameters such as safety, gas mileage, travel time, and overall traffic flow. Methods for sharing and making recommendations are described. Embodiments include considerations of traffic and road history in recommendations. No central authority, road-side equipment, (RSU), or pre-determined lane maps are required. Embodiments include a hybrid protocol using both TDMA and CSMA. Some embodiments are free of MAC and IP addresses. Embodiments include equipped vehicles and V2V system using the transponder.
Owner:ZETTA RES & DEV - FORC SERIES
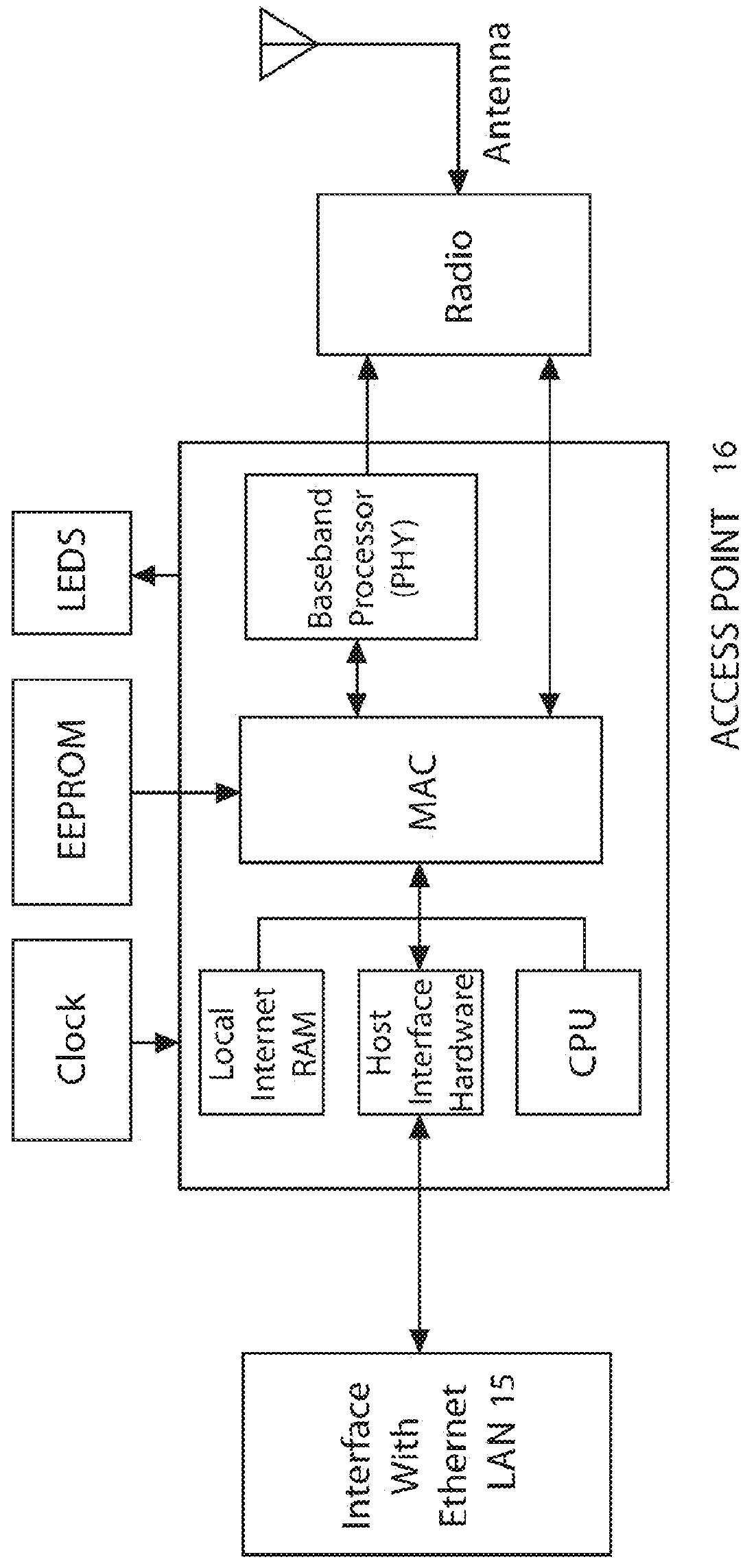
Communication network with secure access for portable users
InactiveUS8406427B2Multiple digital computer combinationsSecret communicationCommunications securityMedia access control
A communication network includes a local area network (LAN) and a wireless access point coupled to the LAN. In one embodiment, each access point includes a medium access control (MAC) stage, and a radio frequency (RF) transmitter / receiver for communicating unsecure message data via RF links with users of associated wireless devices. An optical transmitter / receiver in the access point enables the users to communicate secure message data over the LAN via free space optical (FSO) links with the users. The MAC stage operates (i) to direct unsecure data from the LAN to the wireless device users and to direct unsecure data from the users to the LAN, via the RF transmitter / receiver; and (ii) to direct secure data from the LAN to the wireless device users and to direct secure data from the users to the LAN, via the optical transmitter / receiver. An integrated VoIP / FSO portable handset is also disclosed.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
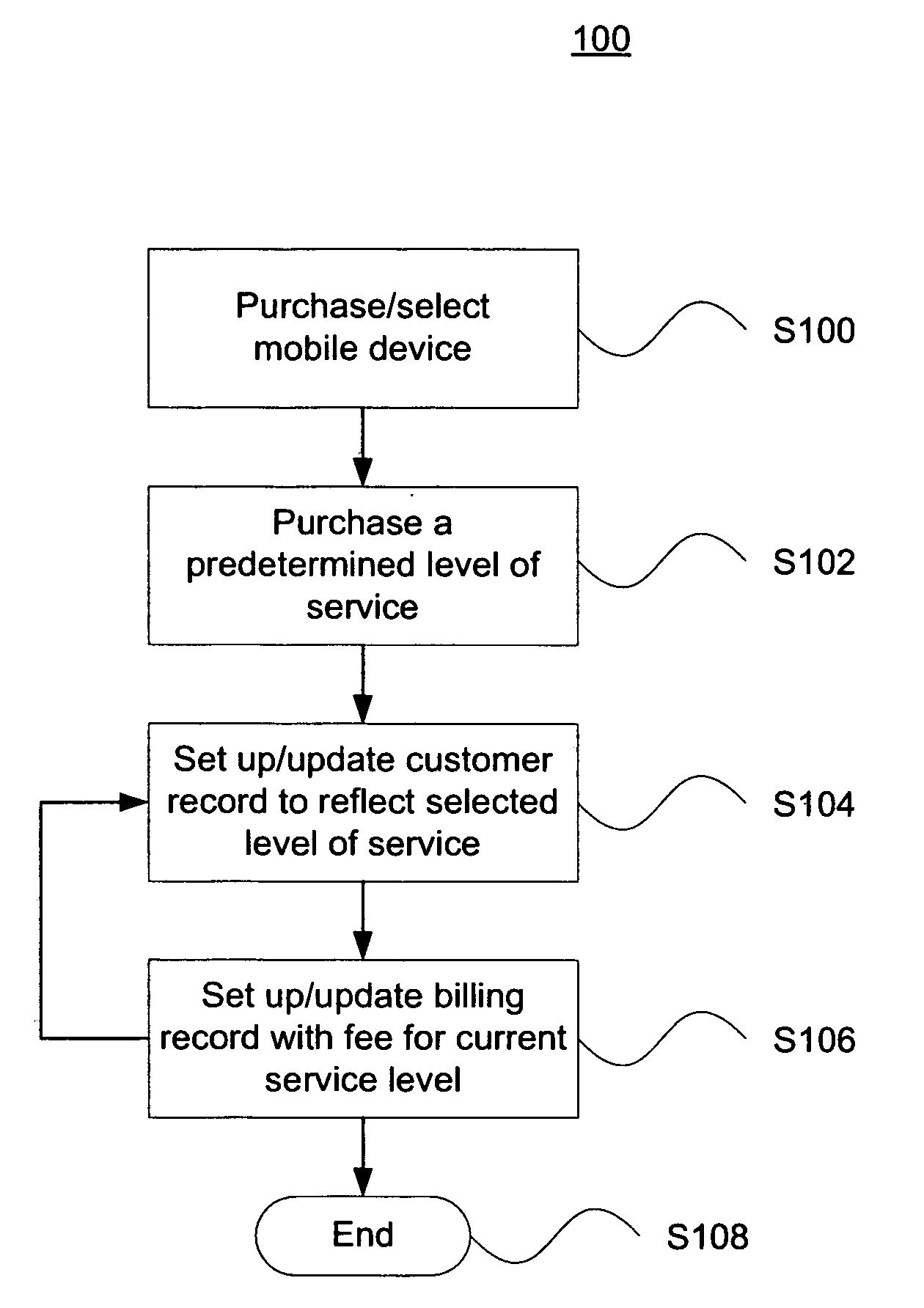
Multi-tier and secure service wireless communications networks
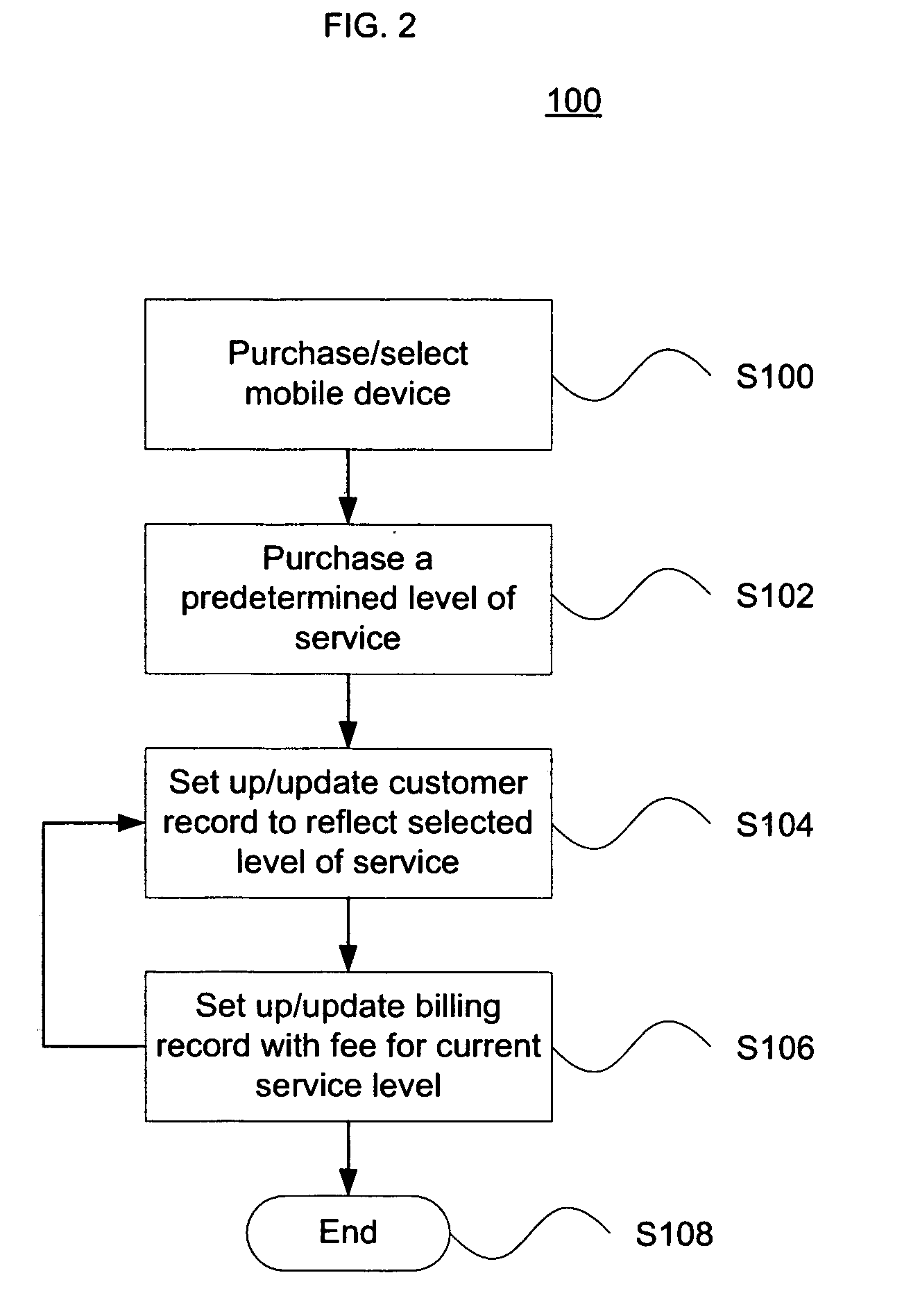
ActiveUS20100279653A1Power managementAccounting/billing servicesCommunications securitySecure communication
The present invention pertains to improved communication quality and security of transmission in cellular communication networks. A customer has the option to pay different fees for different tiers of service relating to voice quality, bandwidth access, and different tiers of service relating to communications security. Higher tiers may guarantee a specific vocoder or bit rate is used, or guarantee a specific encryption protocol is use to ensure secure communications. Different tiers may be associated with customers' records for billing purposes. The network may afford high end devices higher voice quality and / or security via a lookup table indicating what level of service is associated with a given device. Calling or receiving devices may negotiate with each other to change to a more robust vocoder or bit rate to ensure a higher quality and / or security. Furthermore, the user may opt to change the quality and / or security level before or during a call.
Owner:PRIVILEGE WIRELESS
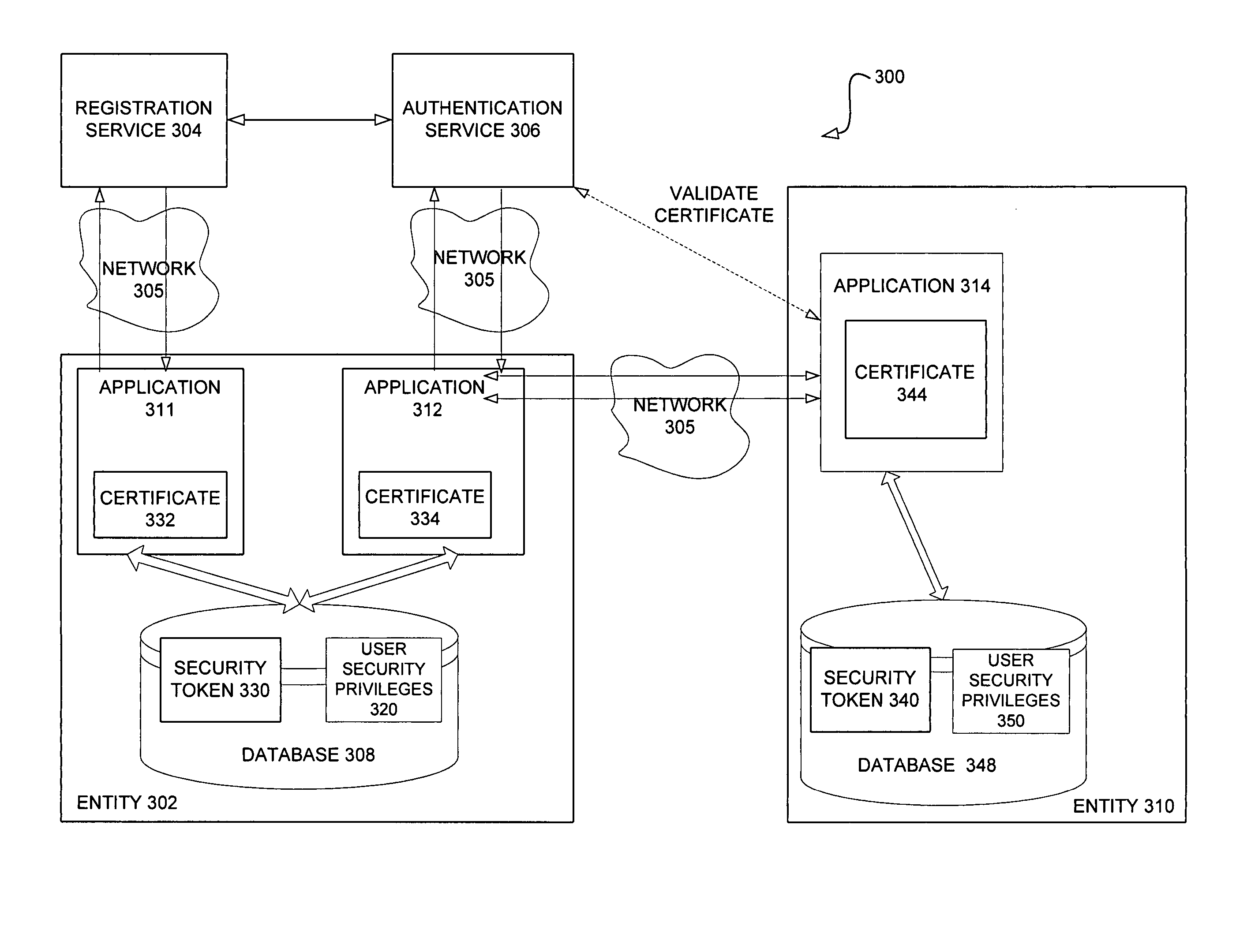
Systems and methods for enhancing security of communication over a public network
InactiveUS20050120214A1Improve securityDigital data processing detailsUser identity/authority verificationCommunications securityPublic network
An authentication protocol is disclosed for use in enhancing the security of communications between software applications and Internet-based service providers. The protocol incorporates a two level authentication model based on a distribution of authentication responsibilities, wherein the application authenticates users and the service provider authenticates the application. Embodiments of the protocol incorporate public key infrastructure and digital certificate technology. Other embodiments of the present invention pertain to applying a corresponding protocol to peer-to-peer communication scenarios.
Owner:MICROSOFT TECH LICENSING LLC
Systems and Methods for Enhanced Security in Wireless Communication
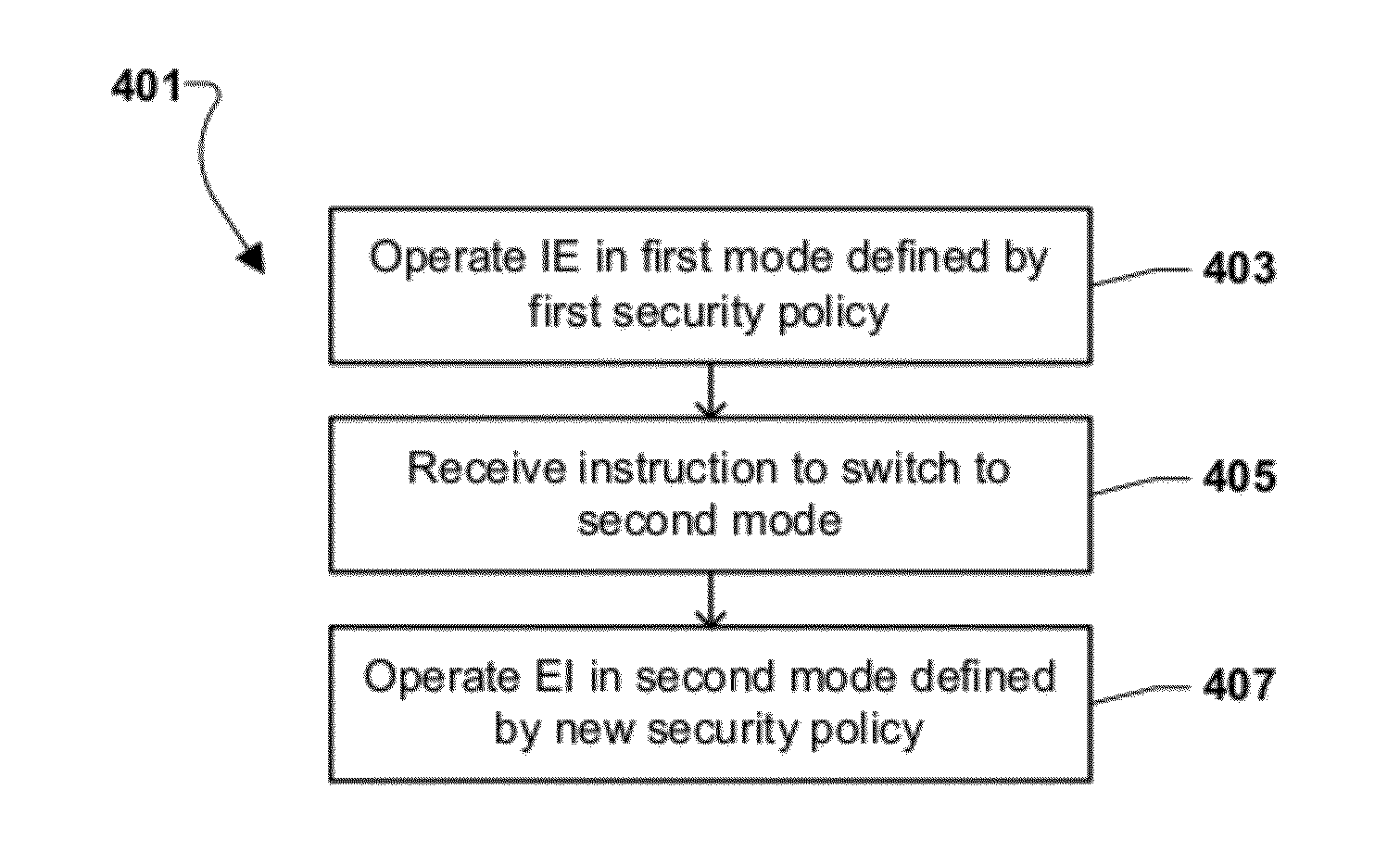
ActiveUS20120216242A1Error detection/correctionPlatform integrity maintainanceSecure communicationCommunications security
A communication system having a policy server coupled to a communications network for managing secure communication with and among end instruments (EI). The EI comprises a memory, and a processor coupled to the memory with processor-executable instructions, including instructions for an operating system kernel; and instructions for a protection core that monitors operations of the operating system kernel in accordance with a security policy for the EI. Security policies can intercept calls to an operating system kernel and for each call, determining whether the call is allowed under the security policy(ies). Policies are stored in a policy library and transmitted to an EI over a wireless communication network.
Owner:REDWALL TECH
Method for a public-key infrastructure for vehicular networks with limited number of infrastructure servers
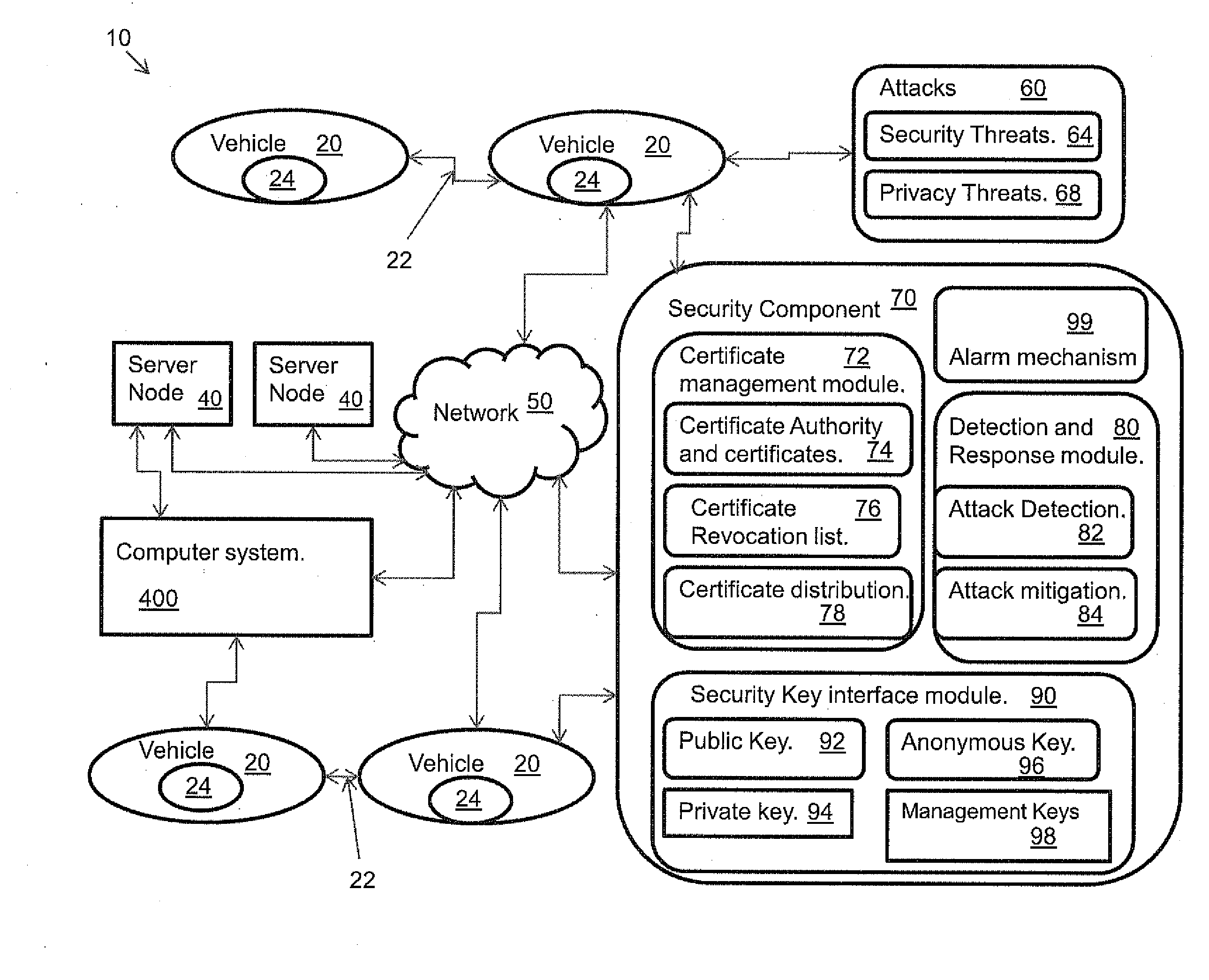
InactiveUS20110083011A1Provide securityCommunication securityDigital data processing detailsNetwork topologiesCommunications securitySecure communication
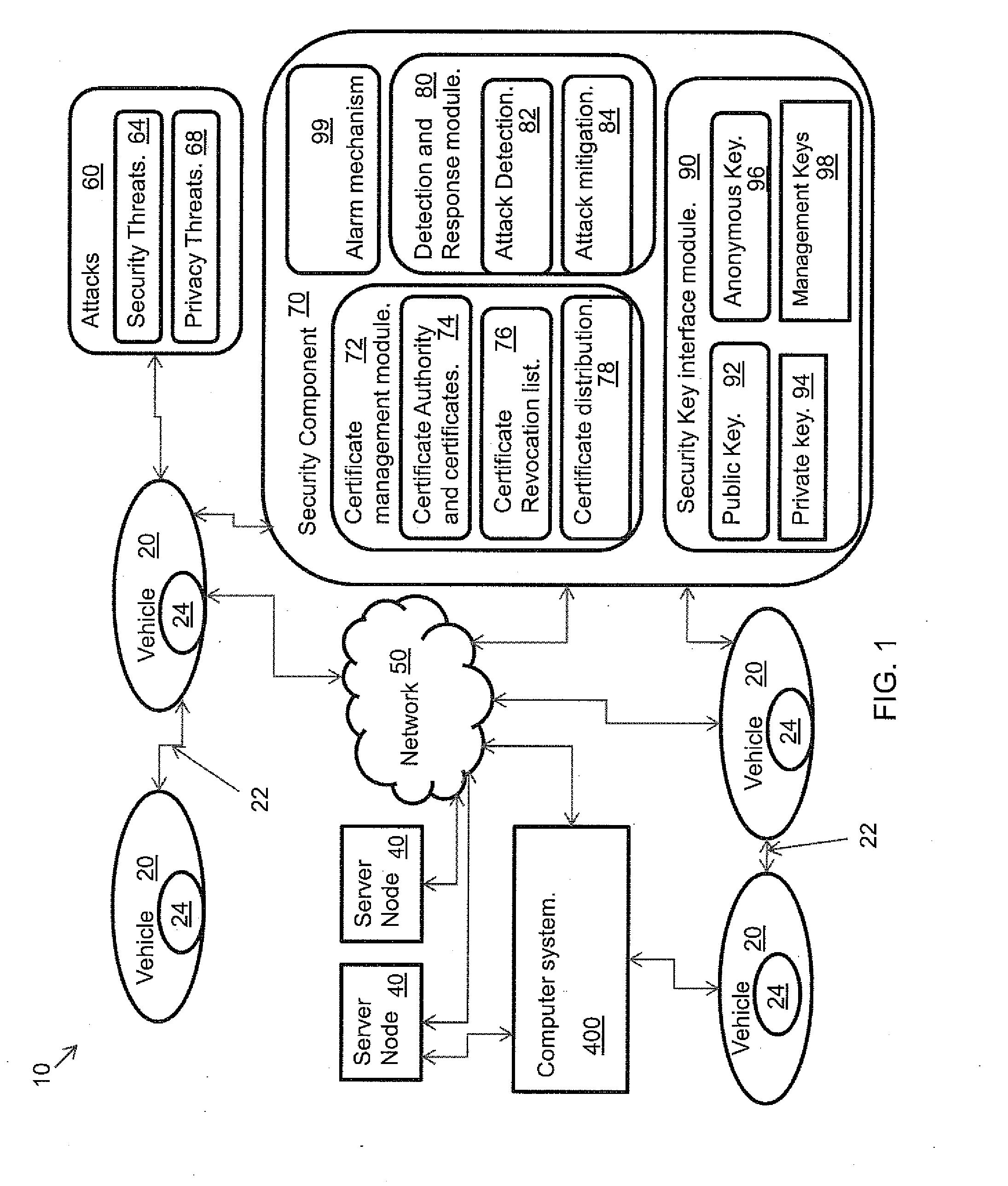
A system, and method related thereto, for providing a vehicular communications network public-key infrastructure. The system comprises a plurality of communications infrastructure nodes and a plurality of vehicles each having a communications component. The communications component provides vehicle to vehicle (V2V) communications, and communications via infrastructure nodes. A communications security component in each of the plurality of vehicles provides security for the communications between the plurality of vehicles using a plurality of security modules. The security modules include a certificate management module. A public key interface module may include a public key, a private key, an anonymous key and a management key. The system further includes a detection and response module for attack detection and attack mitigation. The communications security component assigns and installs at least one security key, a certificate of operation, and a current certificate revocation list. The communications component provides secure communications between the plurality of vehicles.
Owner:TELCORDIA TECHNOLOGIES INC
Method for communication security and apparatus therefor
InactiveUS7152240B1Preventing numberMemory loss protectionDigital data processing detailsCommunications securityRelevant information
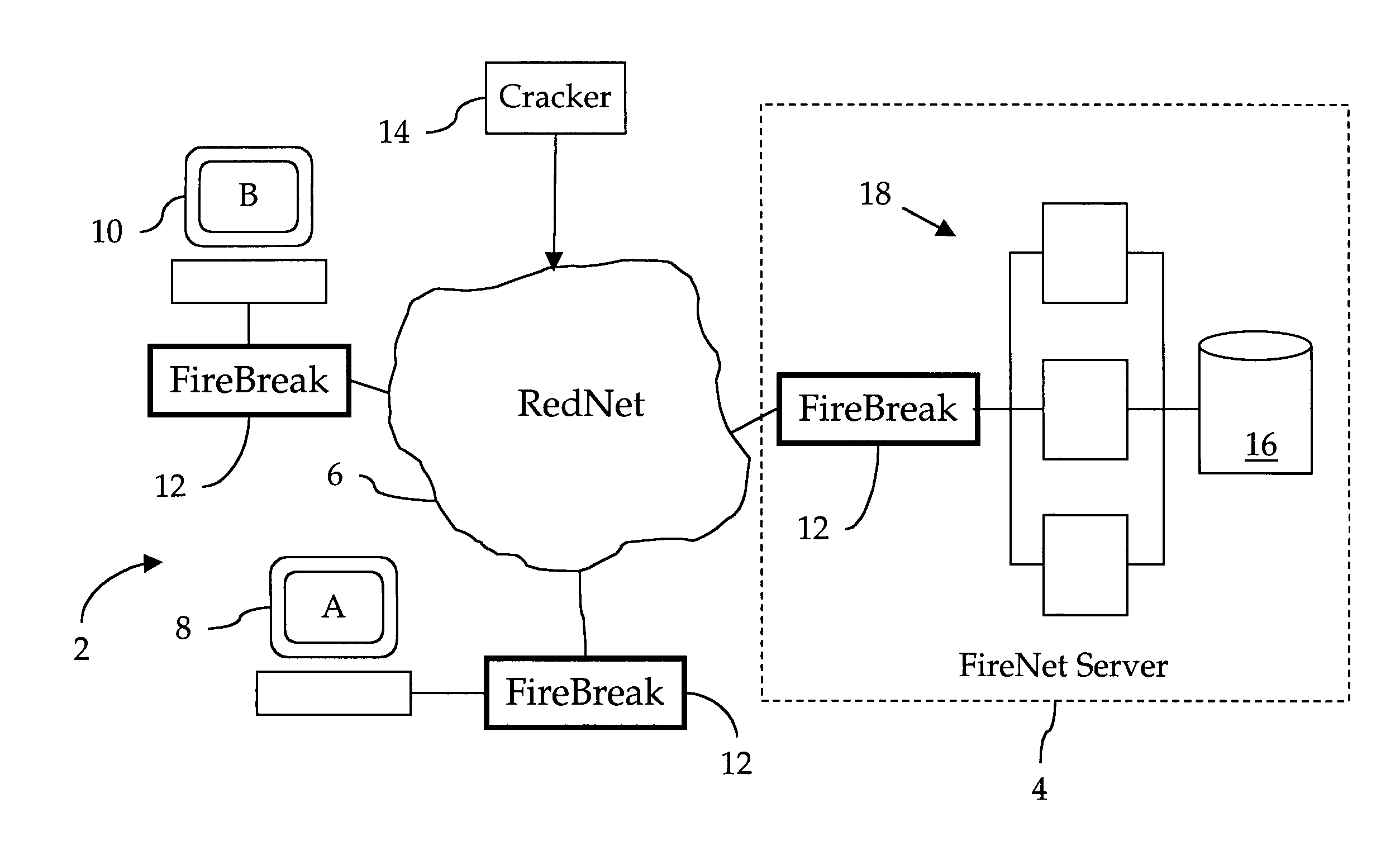
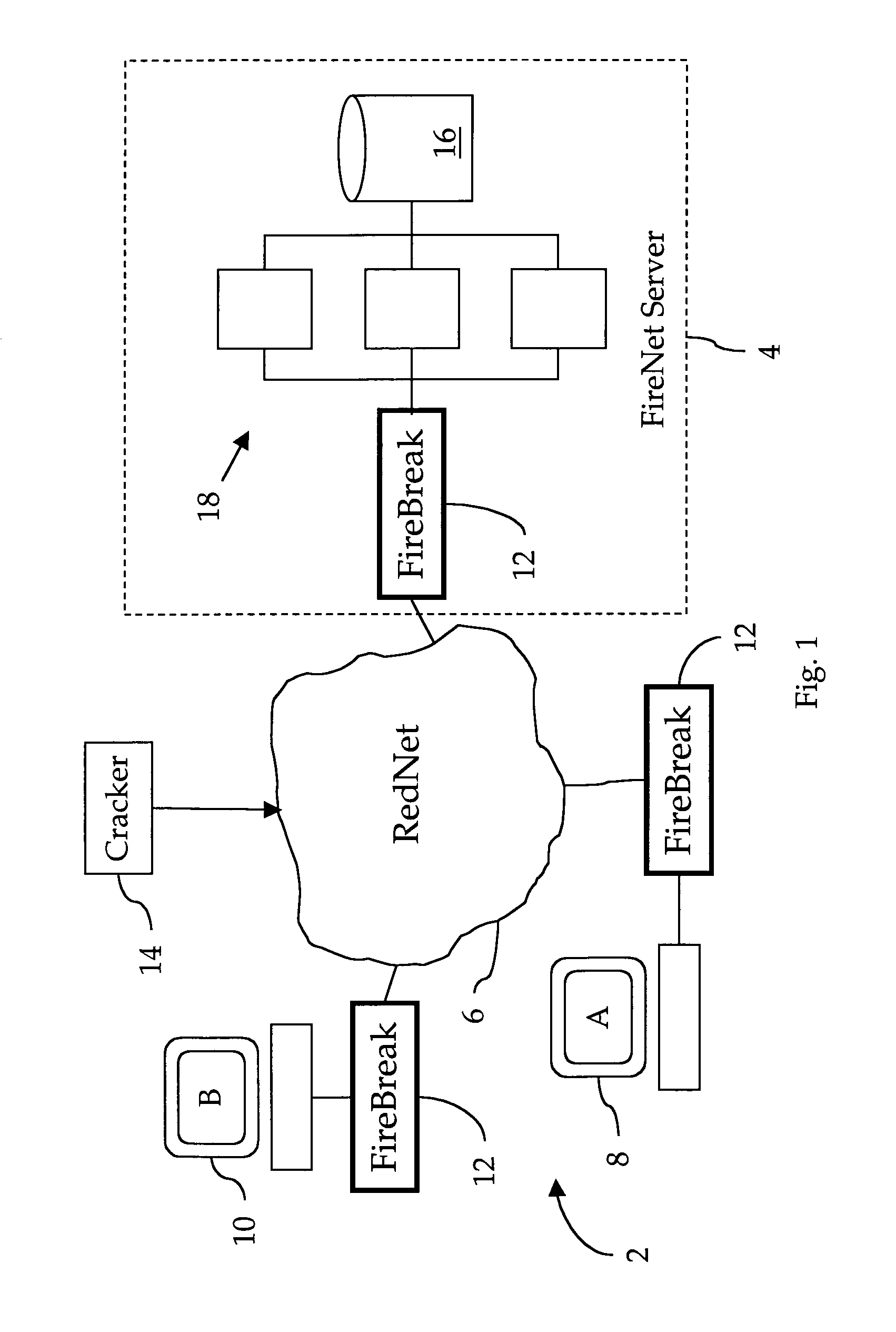
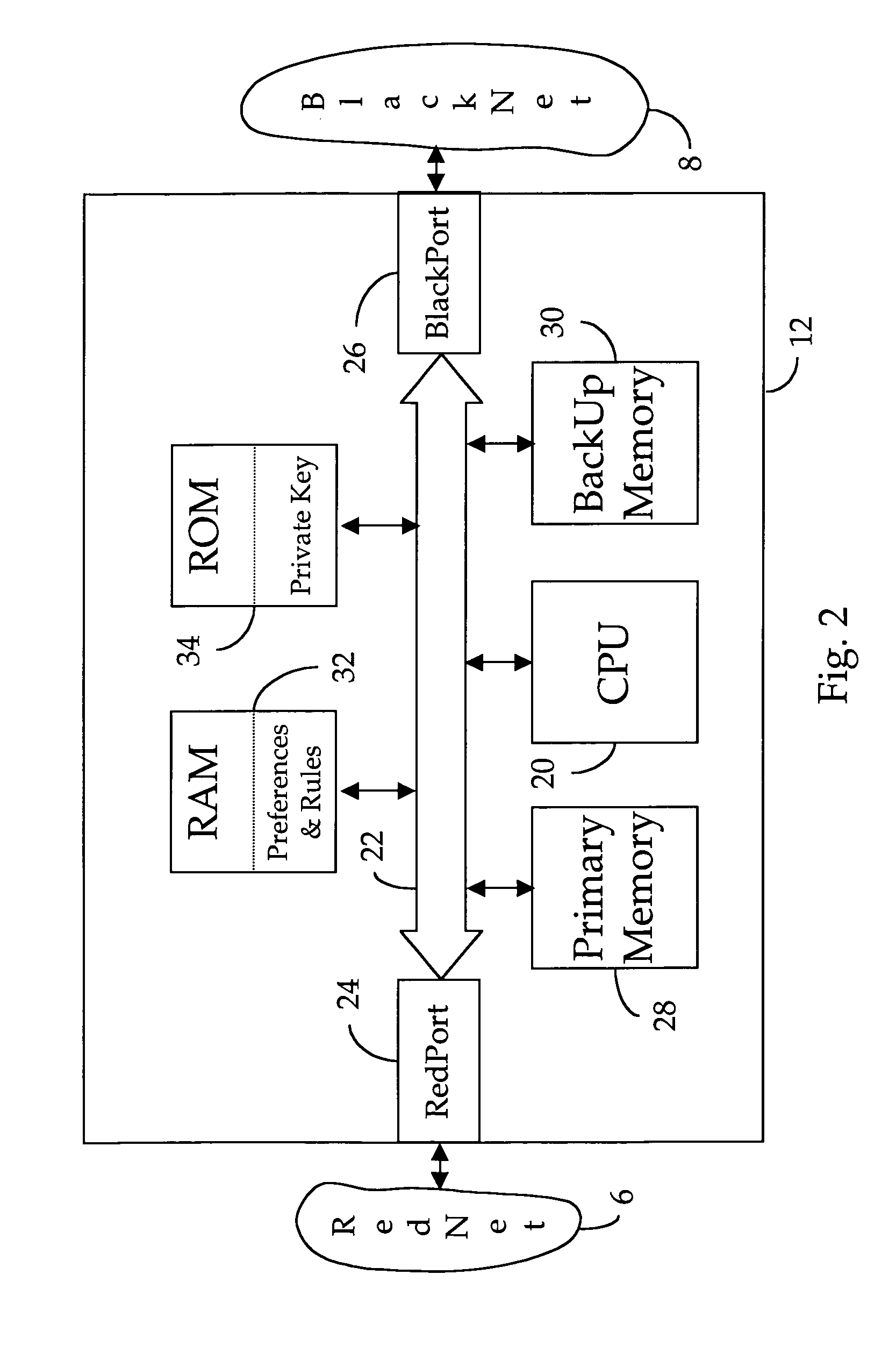
A FireNet security system in which trustworthy networks, called BlackNets, each comprising One (1) or more client computers, are protected by FireBreaks against attacks from untrustworthy networks, called RedNets. All incoming transactions from the RedNet are examined by the FireBreak to determine if they violate any of a plurality of protection rules stored in a local protection rules database. Any transaction found to be in violation is discarded. Valid transactions are forwarded to the BlackNet. If an otherwise valid transaction is found to be suspicious, the FireBreak will forward to a FireNet Server relevant information relating to that transaction. If the FireNet Server verifies that the transaction is indeed part of an attack, the FireNet Server will create new protection rules suitable to defend against the newly identified source or strategy of attack. Periodically, all FireBreaks in the FireNet system will transfer, directly or indirectly, all new rules.
Owner:CUFER ASSET LTD LLC
Communication secured between a medical device and its remote control device
InactiveUS20150207626A1Low production costImprove remote control performanceTransmission systemsPublic key for secure communicationRemote controlMedical device
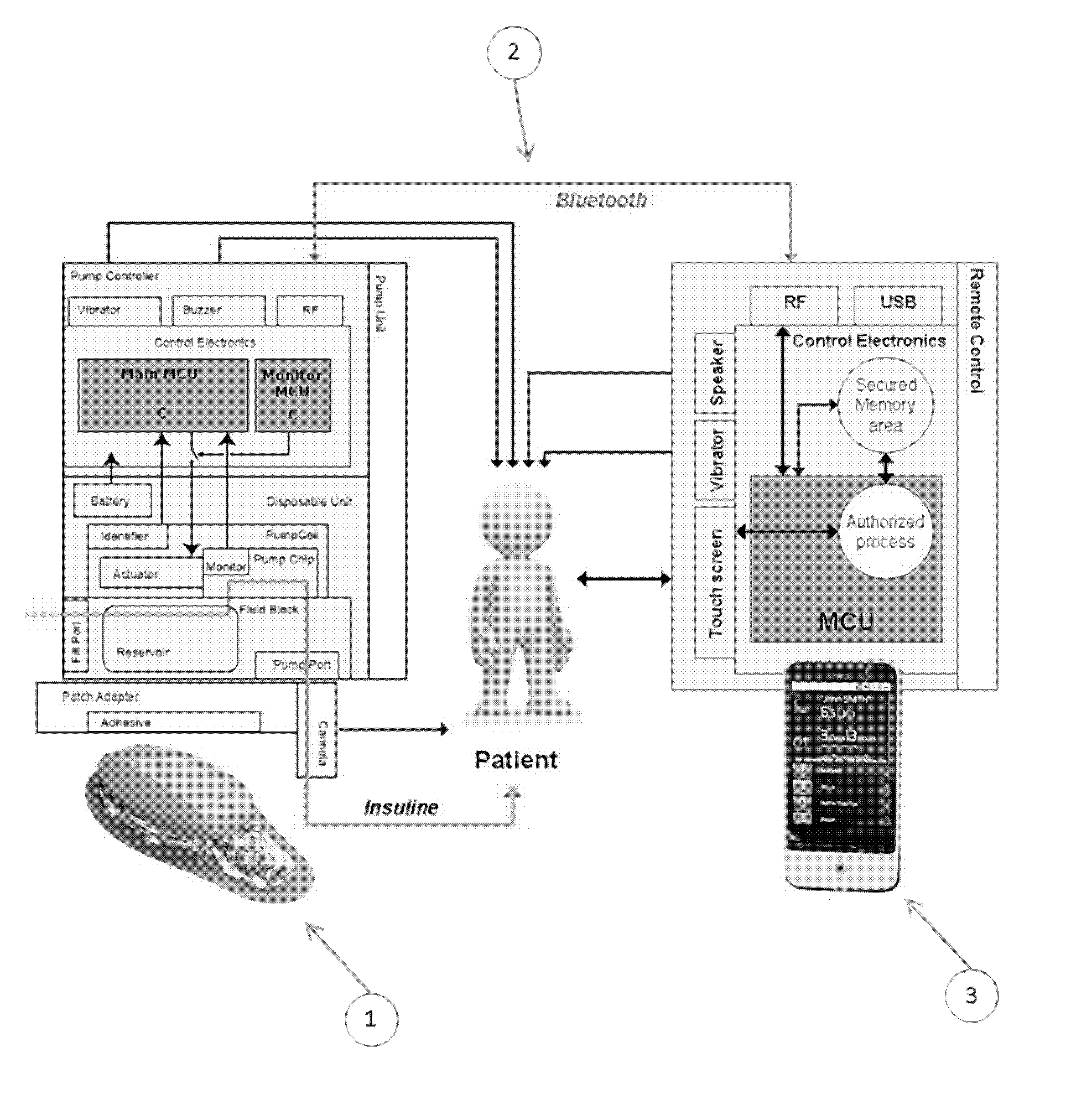
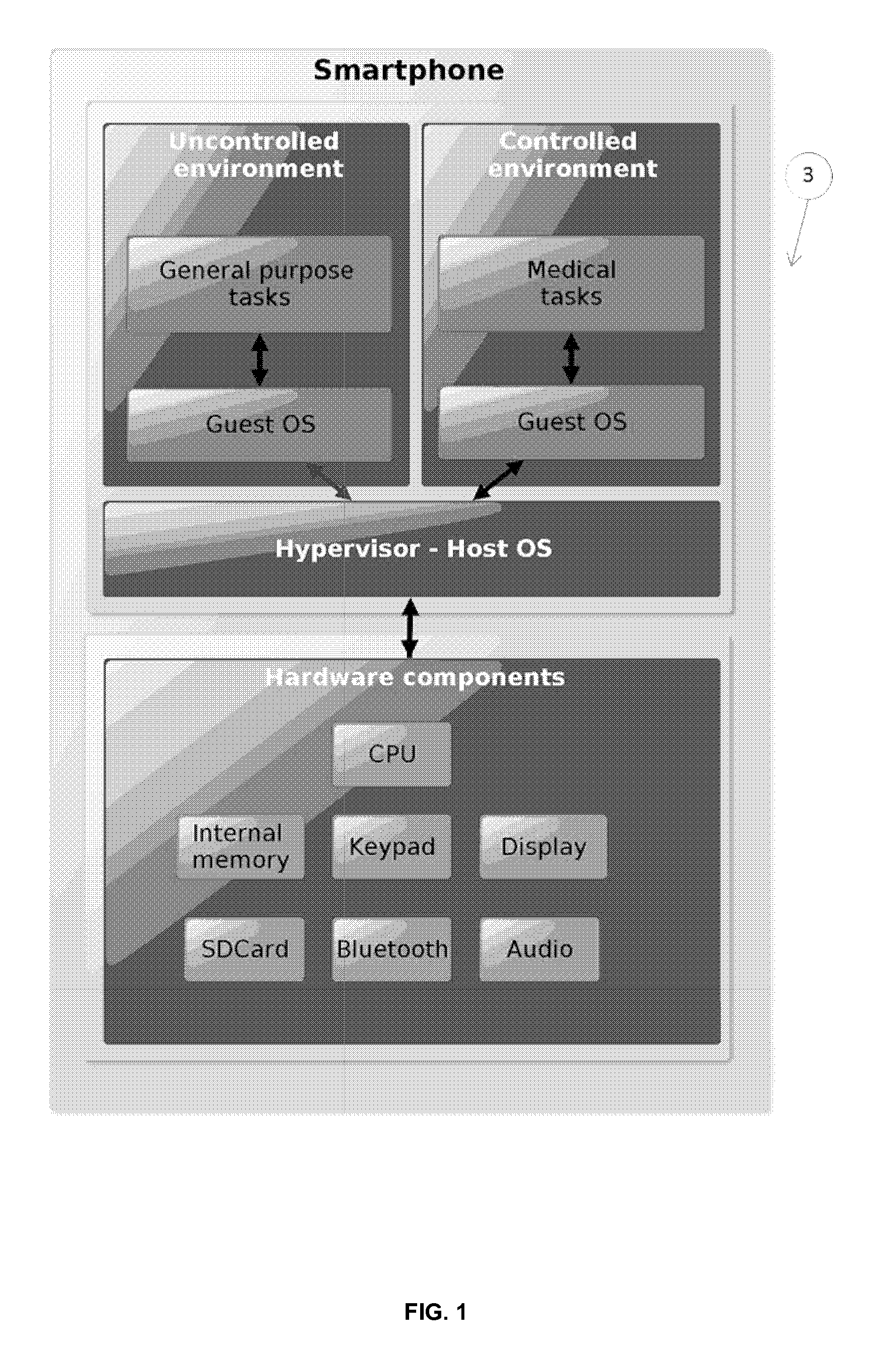
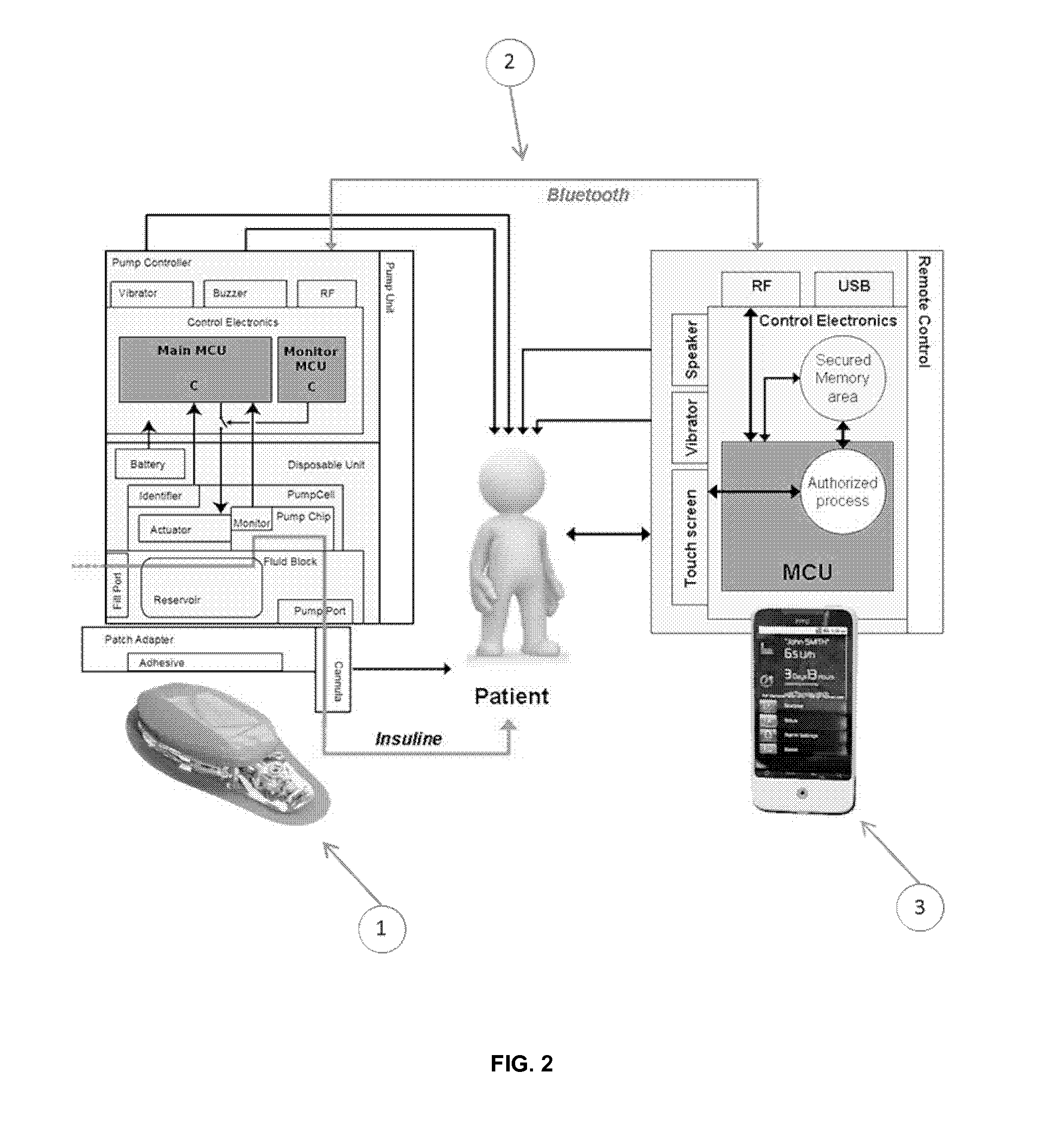
The invention comprises a medical assembly composed by a medical device and a remote control which communicate in a secure and wireless manner. The remote control is connected to at least one security token. Key information stored in the medical device and the security token is used to establish a connection and to communicate in a secure manner.
Owner:DEBIOTECH SA
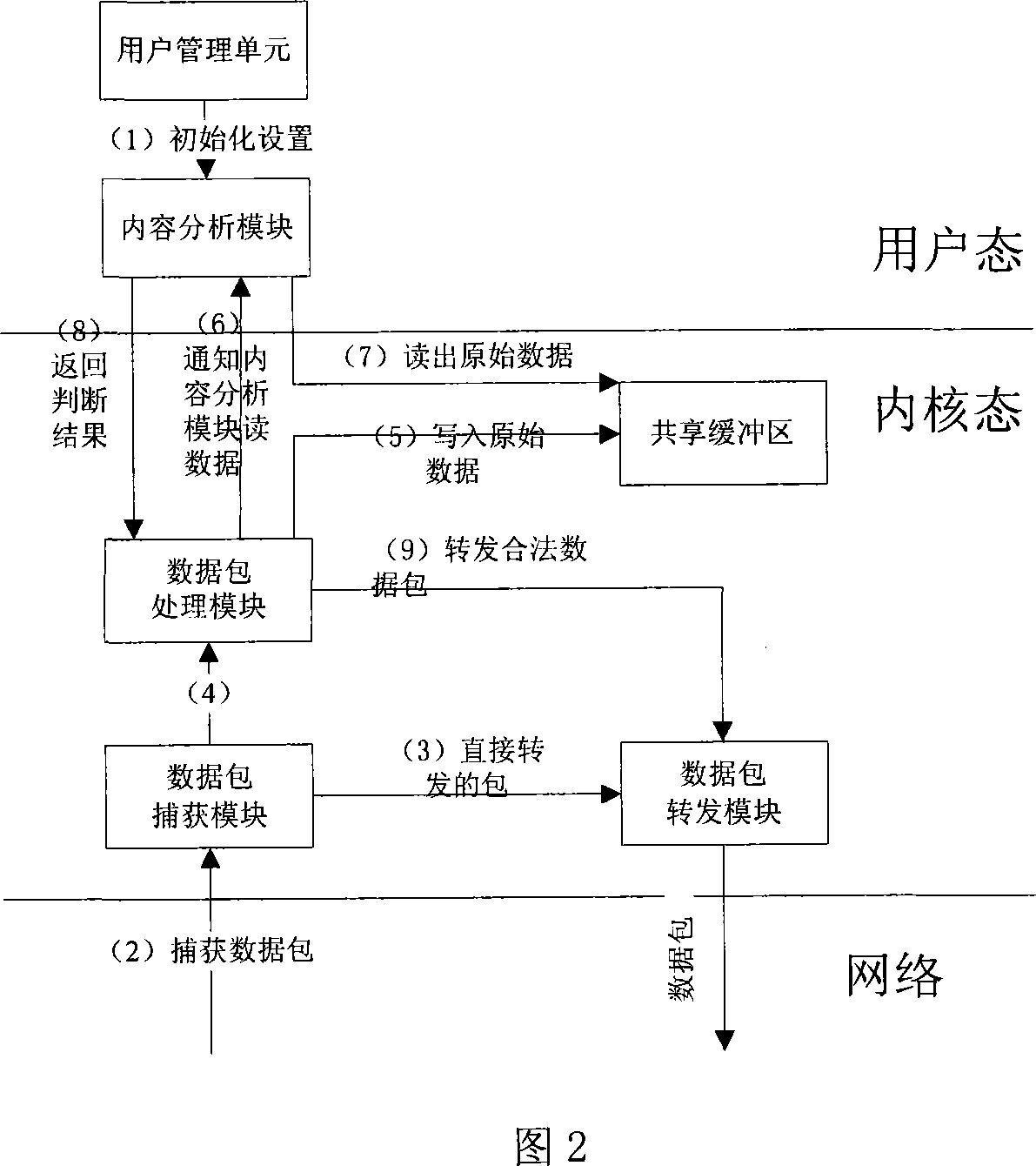
Content filtering gateway realizing method based on network filter
InactiveCN101068229AEasy maintenanceNot easy to attackNetwork connectionsInternal memoryCommunications security
A method for realizing content filtering gateway based on network filter includes realizing network content analysis and real time monitor as well as realizing purpose of filtering application layer information at network layer based on Linux system platform, utilizing network filter Net-filter frame to carry out collection and filtering on data packet under kernel state for optimizing network path of data packet and for raising collection efficiency of data, furthermore using shared internal memory technique of user space and kernel space to submit session content from kernel state to content filtering module of user state.
Owner:BEIJING UNIV OF TECH
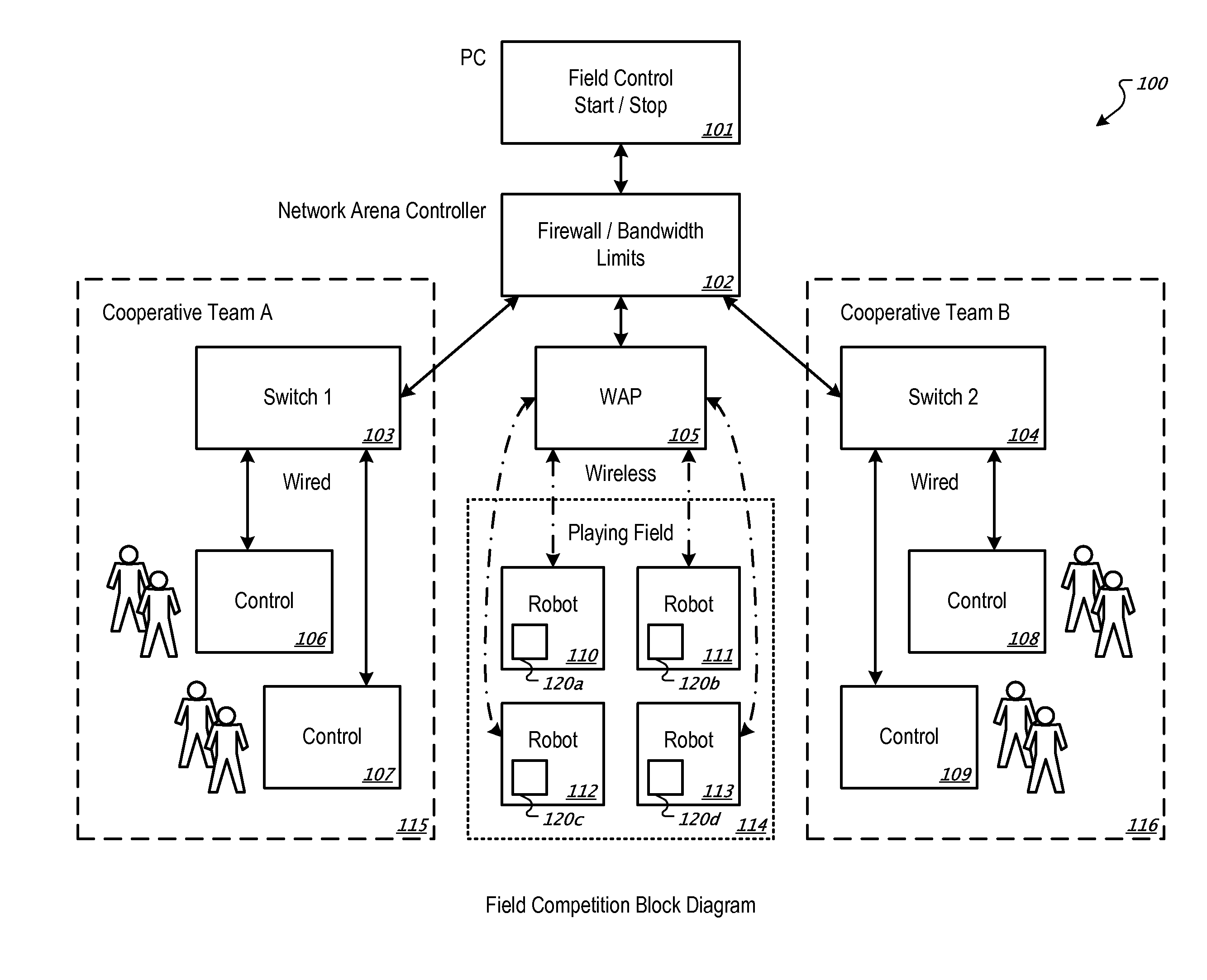
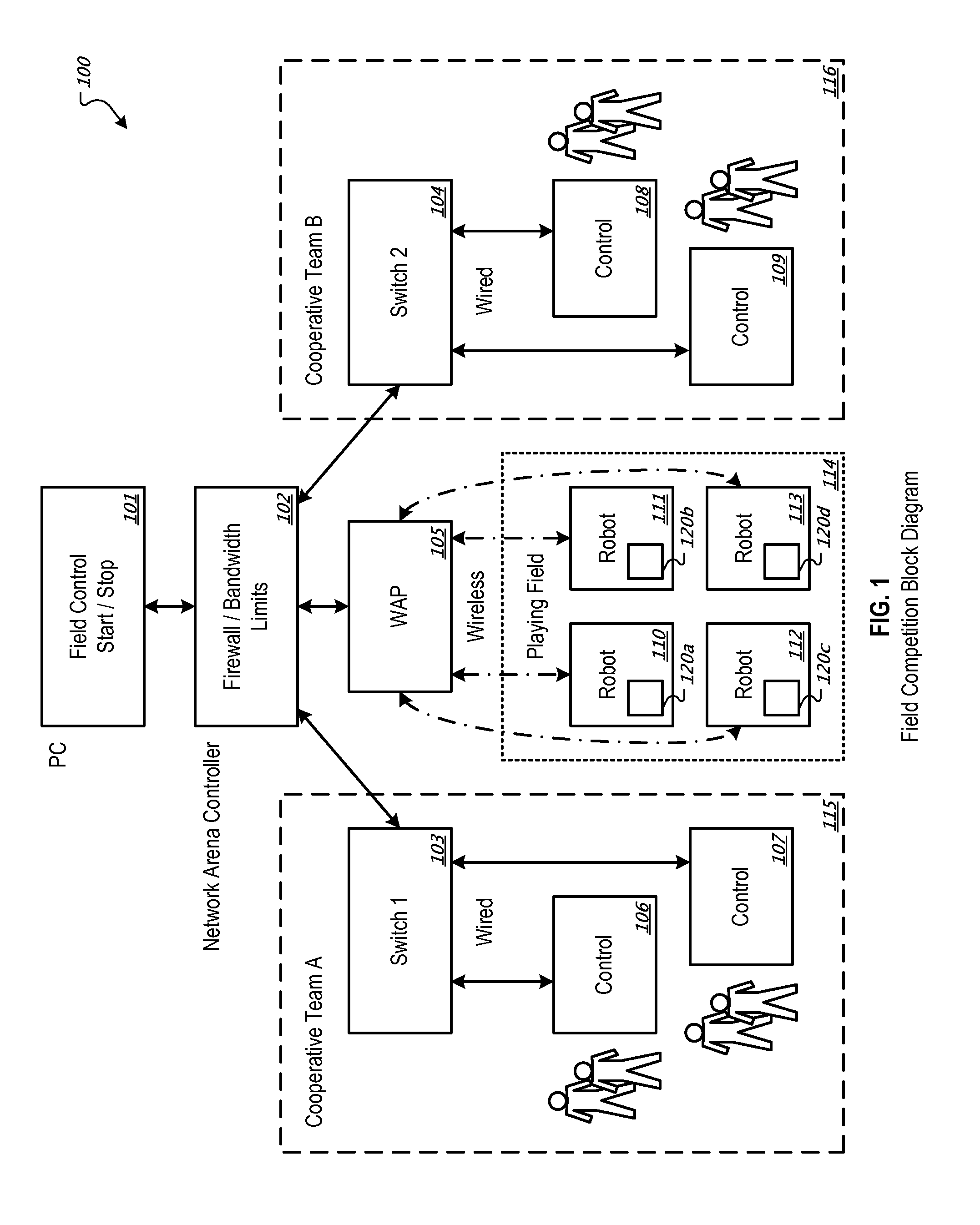
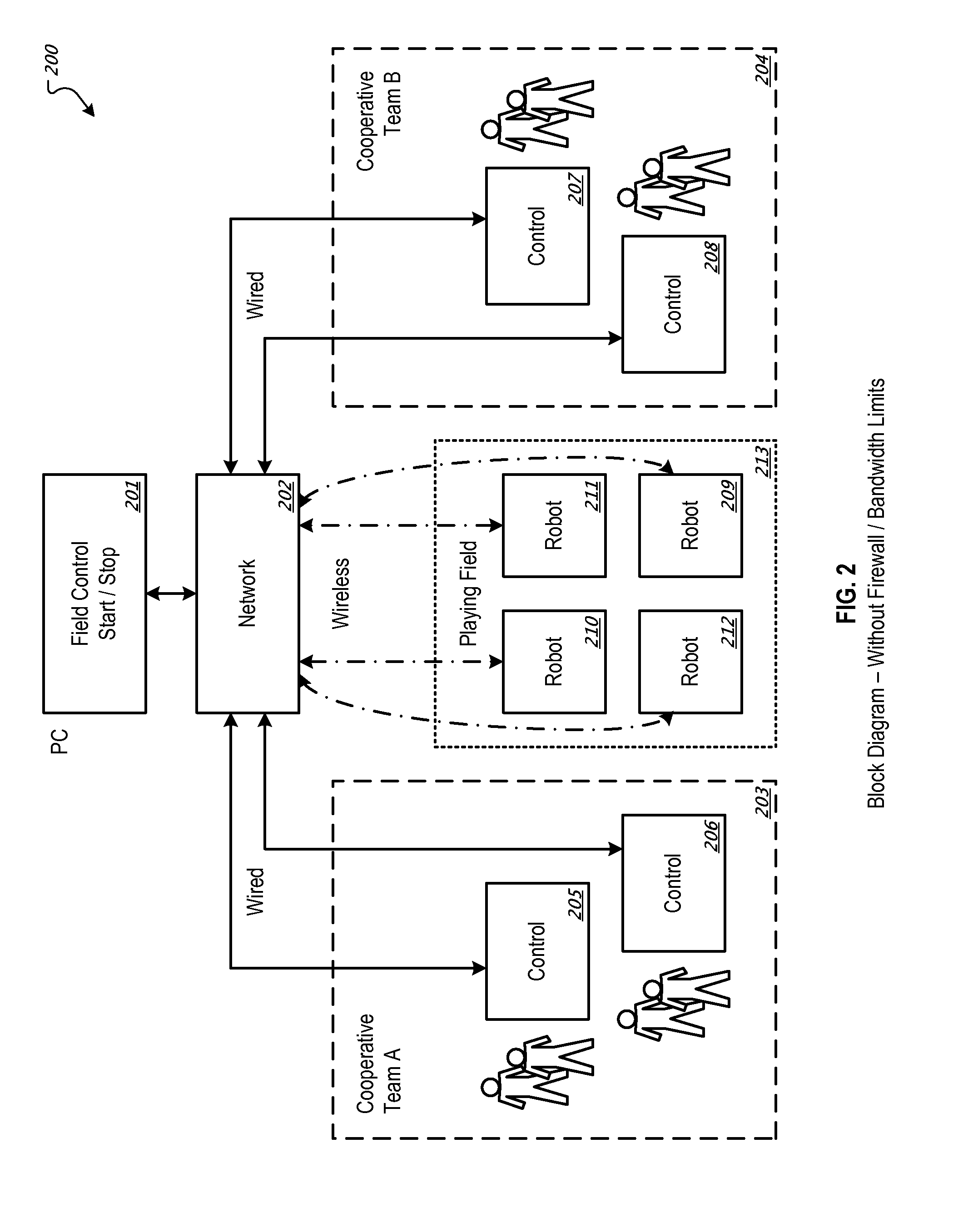
Securing communications with robots
The present disclosure is directed to a system and method for managing communications with robots. In some implementations, a computer network, where operators interface with the network to control movement of robots on a wireless computer network includes a network arena controller and a plurality of robot controllers. The network arena controller is configured to provide firewall policies to substantially secure communication between robot controllers and the associated robots. Each controller is included in a different robot and configured to wirelessly communicate with the network arena controller. Each robot controller executes firewall policies to substantially secure wireless communication.
Owner:INNOVATION FIRST INC
Identity authentication method and system
ActiveCN104579694AFull assurance of authenticityDynamicUser identity/authority verificationCommunications securityPassword
The invention discloses an identity authentication method and an identity authentication system. The method comprises the following steps: fixed identity identification information, a key schedule and a dynamic identity function are exchanged between a server and a client; a first random number is transmitted to the server and first response information transmitted by the client and second random number are received; the hash values of the first random number, the first dynamic identity information and the fixed client identity identification information as original texts are calculated and compared with the first response information, if the same hash values are present, the authentication is qualified; second response information is calculated and transmitted to the client, so that the hash values of the second random number, the second dynamic identity information and the fixed server identity identification information as the original texts are calculated by the client and compared with the second response information; if the same hash values are present, the authentication is qualified. The method is characterized in that the dynamic identity information is flexible and changeable, the information can be prevented from being revealed, the password encoding difficulty is increased and the security of the identity authentication is improved. Besides the method further comprises the following steps of key negotiation, heartbeat authentication and key schedule update, and thus the communication security and the periodic identity authentication are ensured.
Owner:ZHEJIANG UNIV
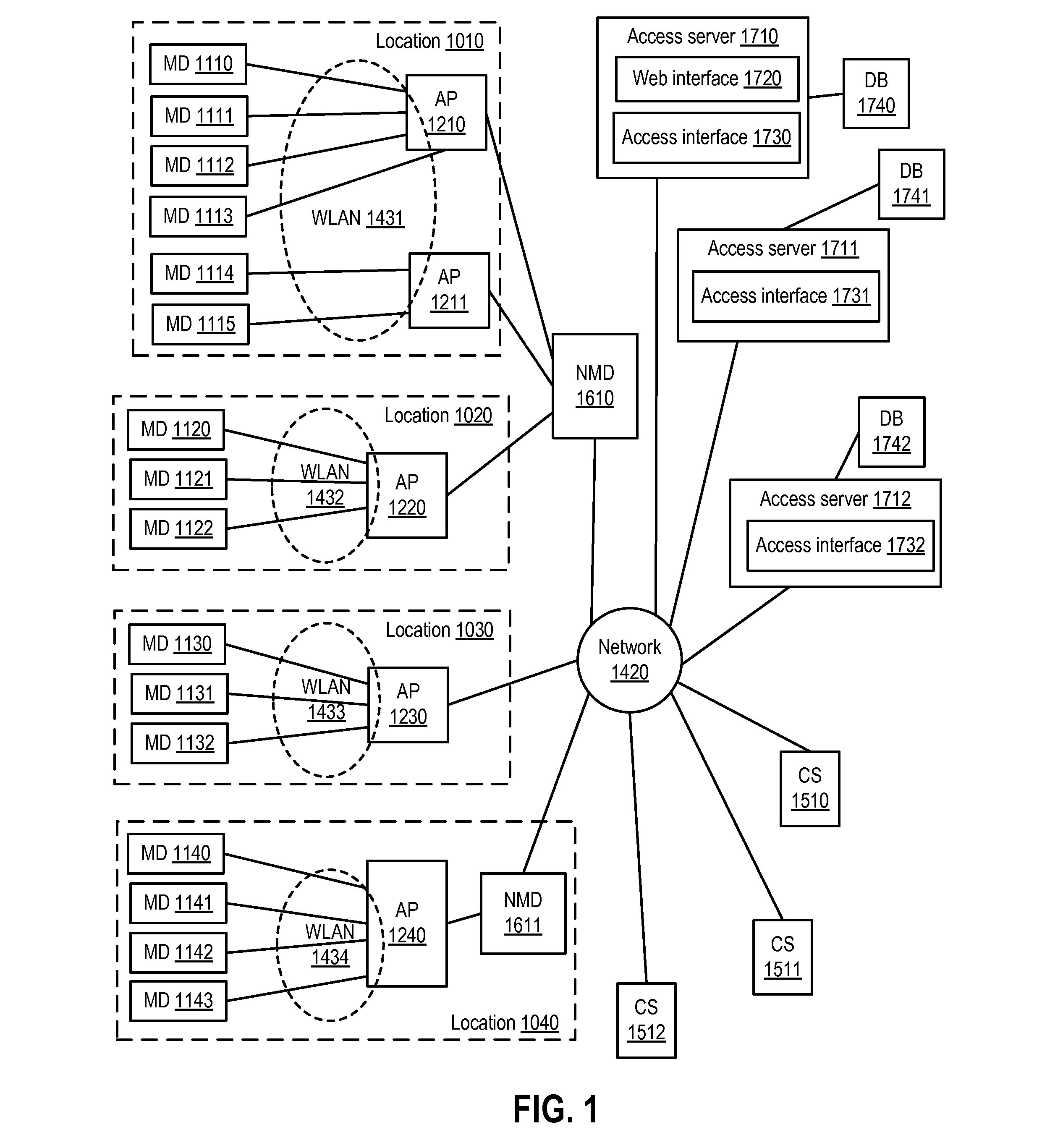
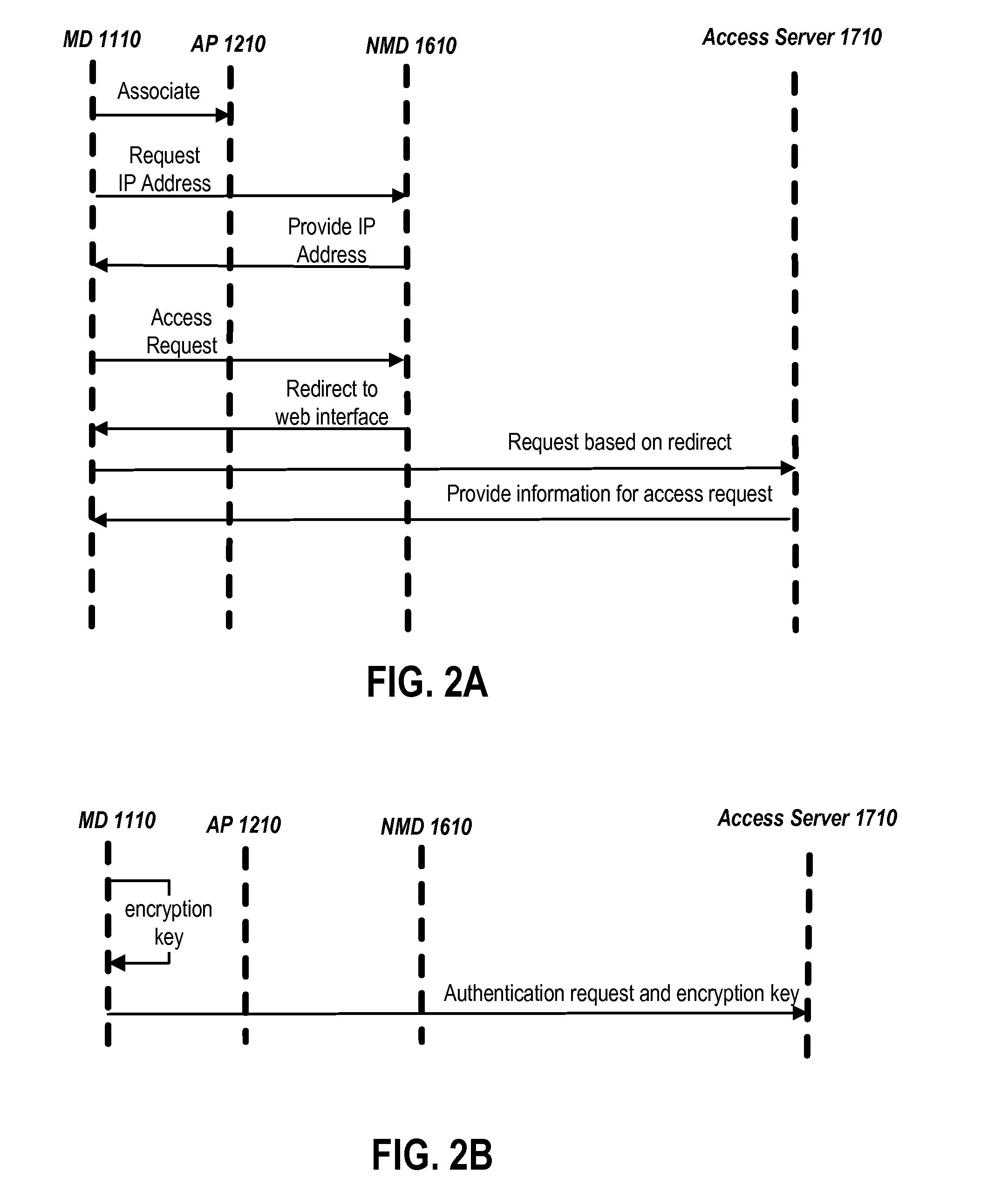
Securing Communications of a Wireless Access Point and a Mobile Device
ActiveUS20130103939A1User identity/authority verificationNetwork topologiesSecure communicationCommunications security
In one or more embodiments, a network provider can receive a request to access a public network via a wireless network implemented via one or more wireless access points. The network provider can receive, via an unsecured wireless communication from a mobile device utilizing the wireless network and via a hypertext transfer protocol secure (HTTPS), an encryption key usable to secure wireless communications from the mobile device utilizing the wireless network. The encryption key can be encrypted via a public encryption key, received from the network provider or previously stored by the mobile device, associated with the network provider. The network provider can decrypt the encryption key and can provide the encryption key to a wireless access point implementing the wireless network and communicating with the mobile device. The wireless access point and the mobile device can communicate in a secure fashion based on the encryption key.
Owner:AT&T INTPROP I L P
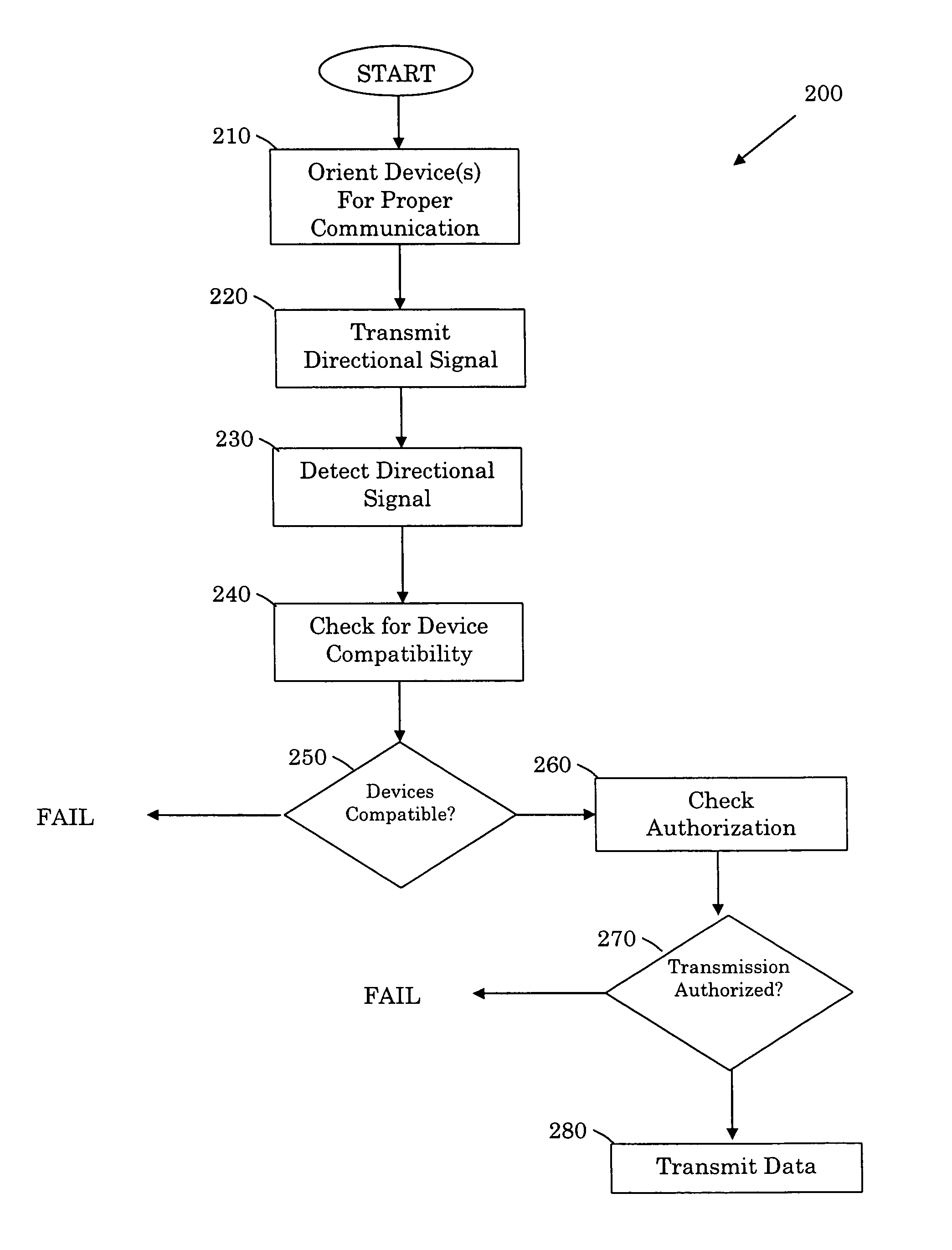
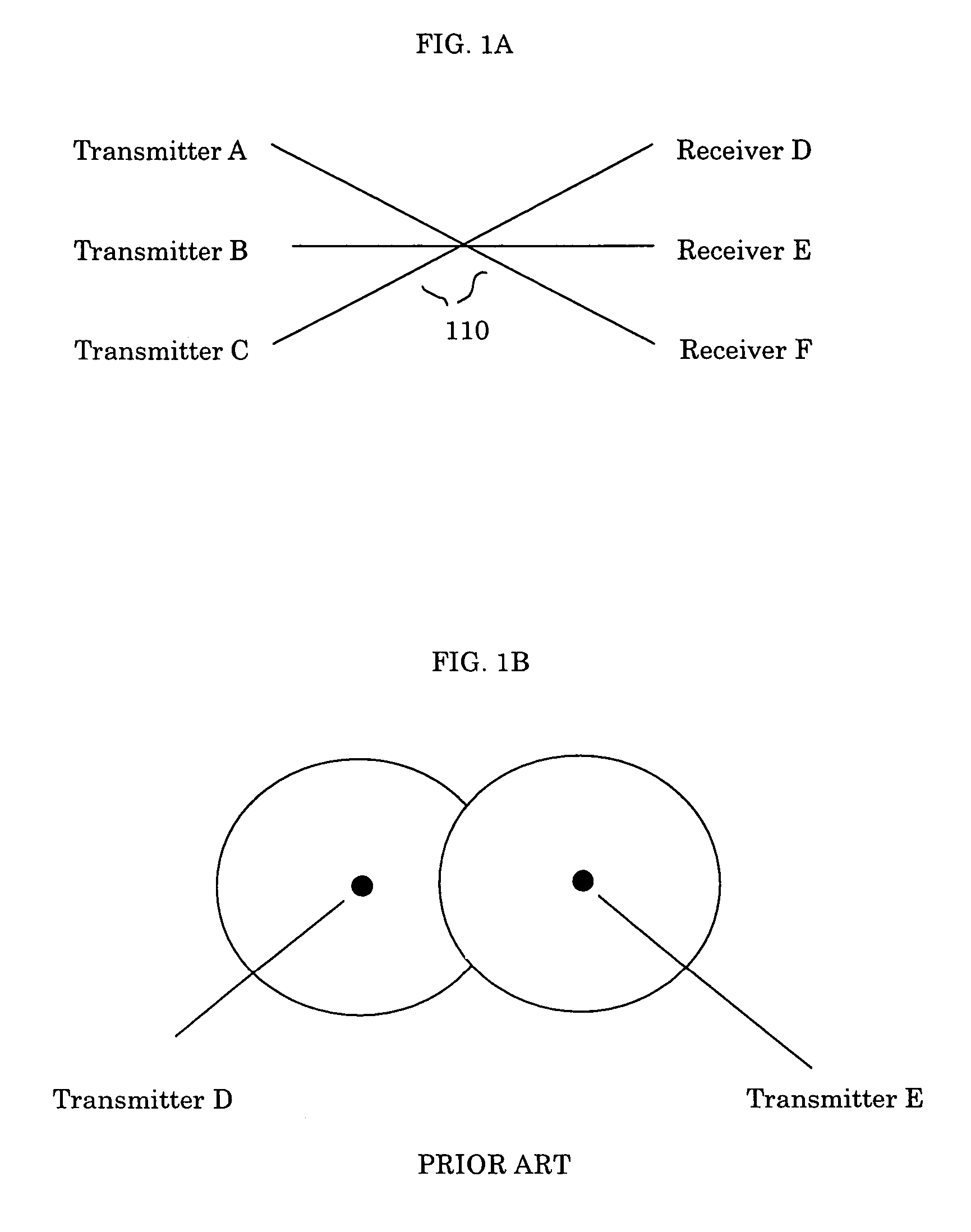
Systems and methods for communicating with multiple devices
InactiveUS7761092B2Data switching by path configurationSubstation equipmentCommunications securityHigh rate
Disclosed are systems and methods for communicating with multiple devices. In one embodiment, a plurality of wireless devices in close proximity are able to transmit data at a high rate using a secure connection. While in one embodiment this data is transmitted using a high speed, directional signal at a 60 GHz frequency. In a further embodiment, data is transmitted at a 60 GHz frequency between a personal computing device and a plurality of consumer electronic devices that are in relative close proximity to one another. The directional nature of this high frequency signal permits a large number of devices in a close proximity to communicate without interfering with each other. Moreover, the directional nature of such a high frequency signal provides added communications security since the receiver will typically be in the line of sight of the transmitter.
Owner:SONY CORP +1
Key processing method and device in double-connection mode
Embodiments of the present invention disclose a key processing method and device in a double-connection module, which guarantee communication security of UE in a double-connection mode. The method of the embodiments of the invention comprises a step in which according to a first base station and a second station where communication connection with a terminal exists, the second station receives a first request message which is used for requesting the second base station to generate a key used in communicating with the terminal and sent by the first base station; and a step in which the second base station, based on a security key carried in the first request message, generates a key used in communicating with the terminal.
Owner:HUAWEI TECH CO LTD
Data communication security arrangement and method
InactiveUS20050154896A1Improve security levelSmall sizeSynchronising transmission/receiving encryption devicesComputer security arrangementsCommunications securityComputer science
A novel and efficient encryption and decryption method and arrangement is presented for synchronization of a communication session for encrypted transmission or authentication between at least two communicating units, a first unit and a second unit communicating via a communication channel. Each unit comprises a session counter (X, Y). The method comprises a handshake procedure whereby the synchronization of session counters is obtained by successively communicated signatures between said communicating units.
Owner:IMPSYS DIGITAL SECURITY
Method for securing a communication
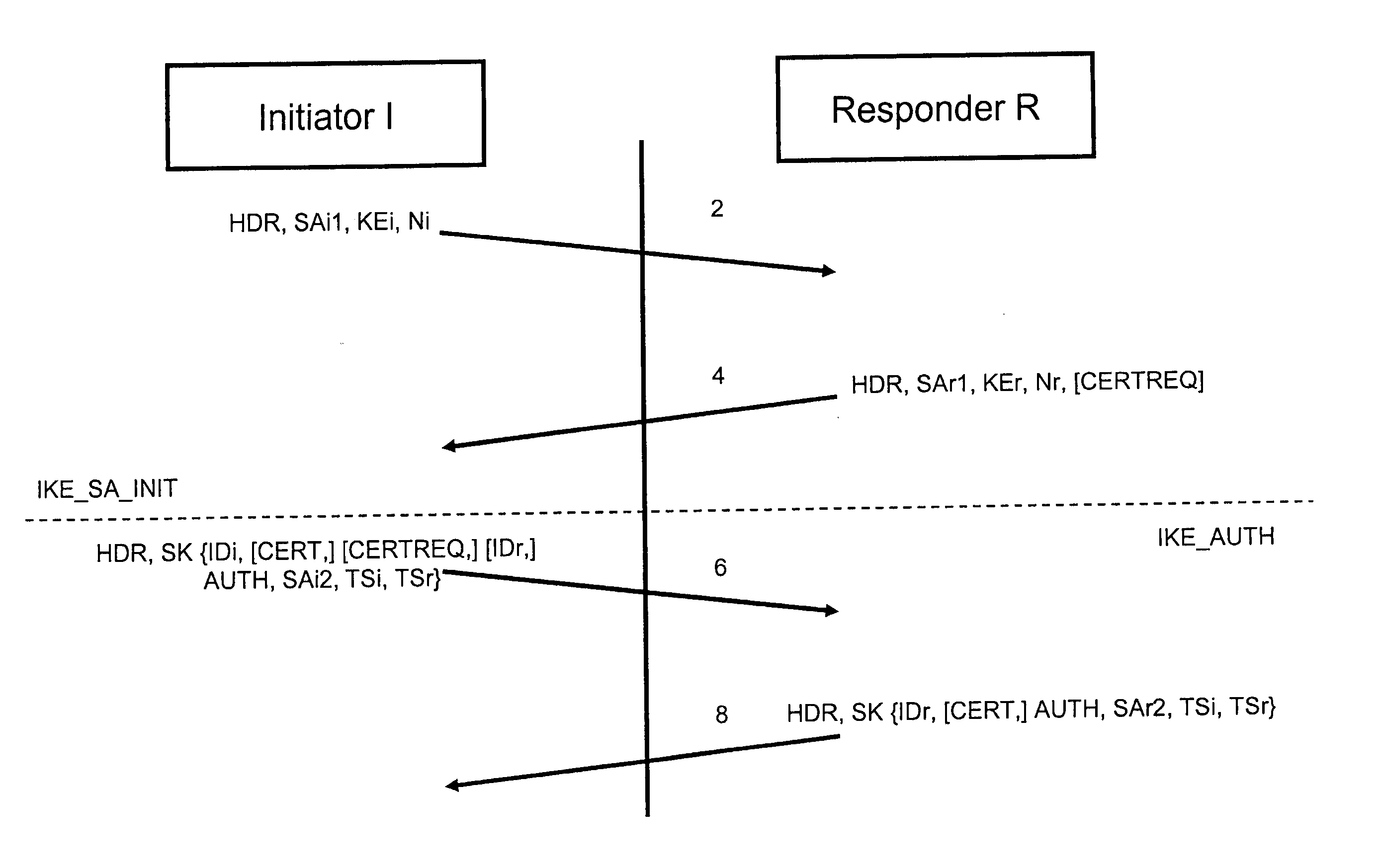
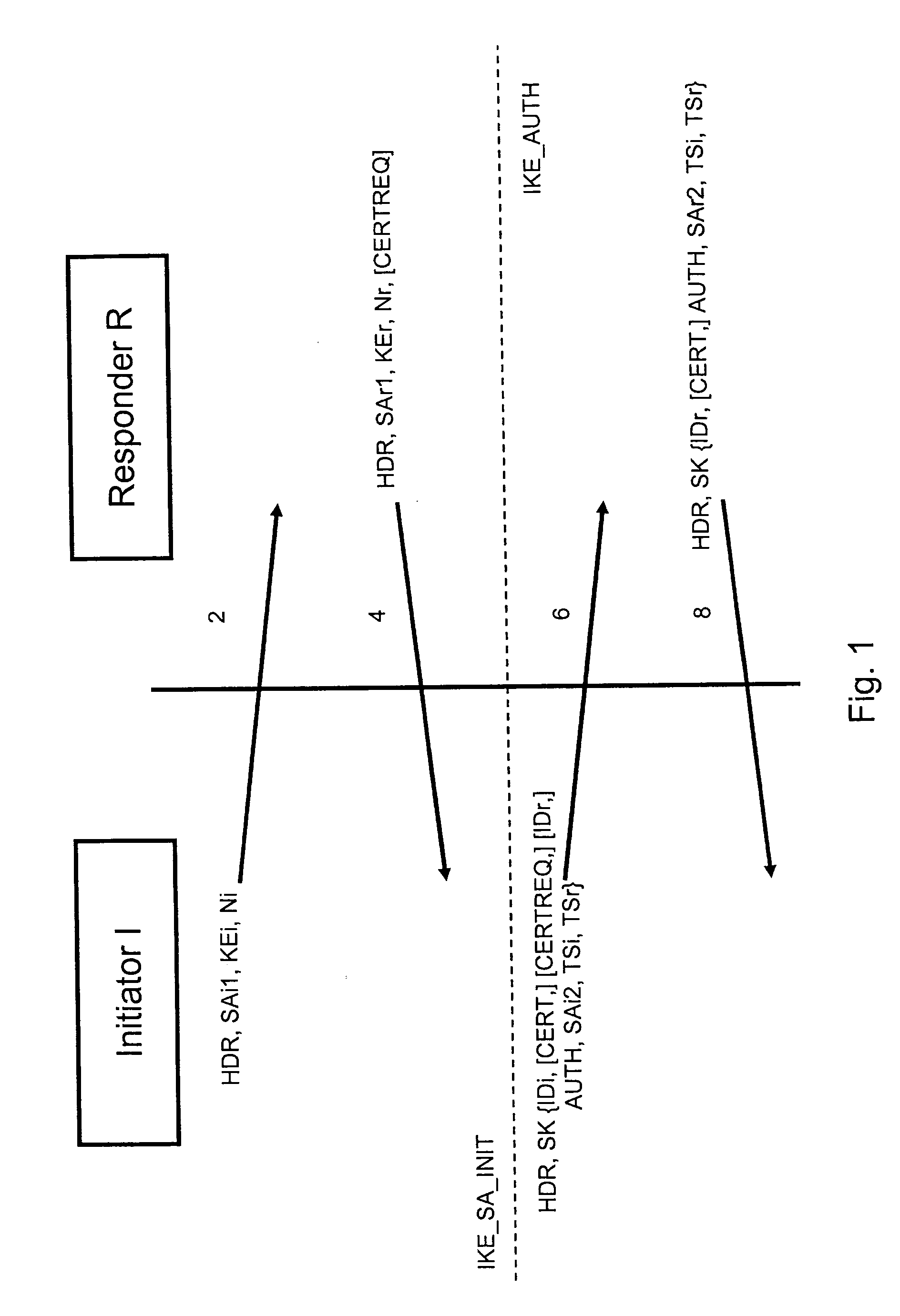
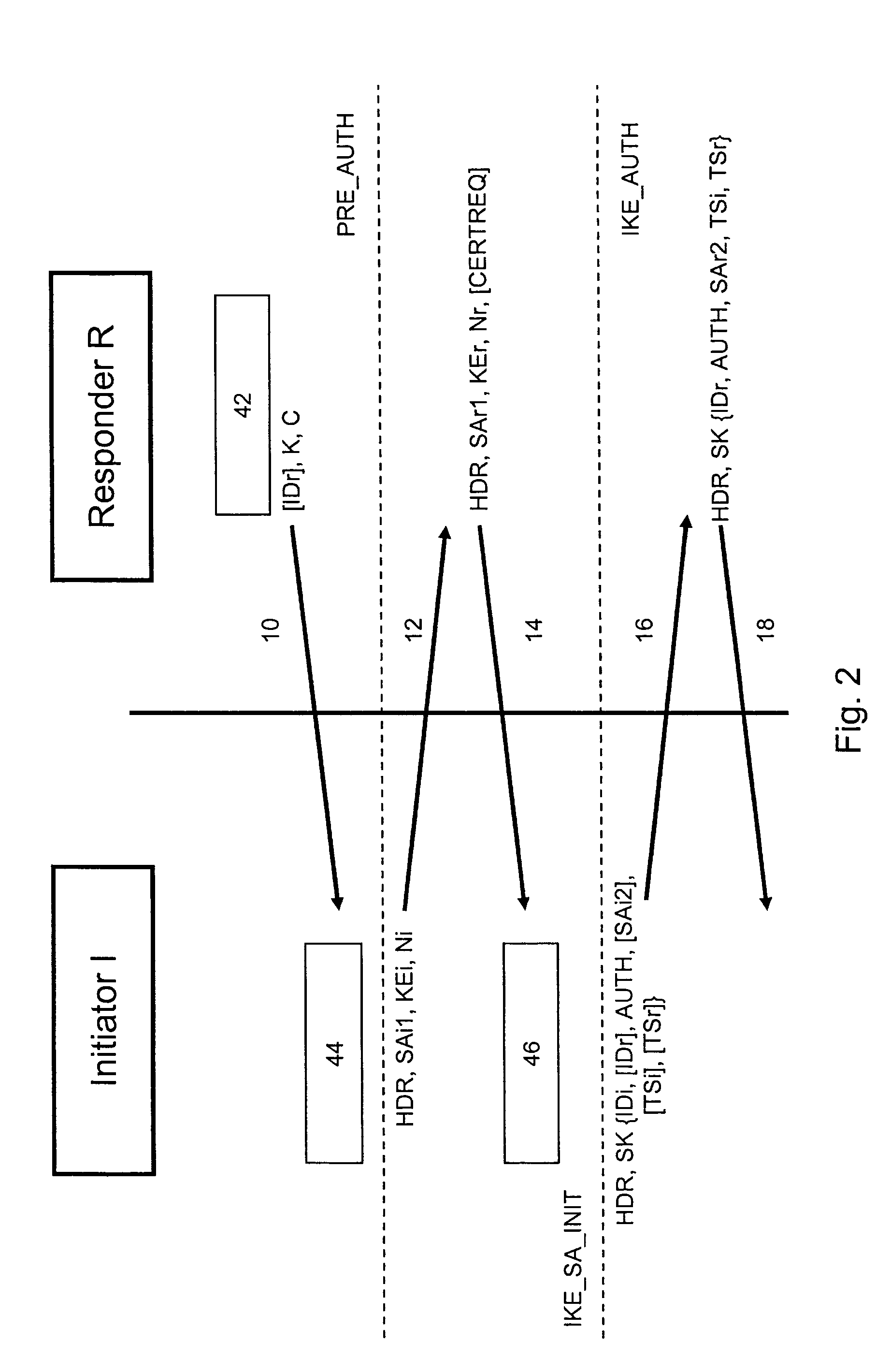
ActiveUS20050076216A1Easy to useSecure transmissionKey distribution for secure communicationUser identity/authority verificationCommunications securityEngineering
A method for securing a communication between at least one initiator (I) and one responder (R) generates a first key (KEr) within the responder (R), generates a second key (K) within the responder (R), computes an authentication code (C) using the first key (KEr) and the second key within said responder (R), transmits the second key (K) and the authentication code (C) from the responder (R) to the initiator (I) using a first communication channel, transmits the first key (KEr) from the responder (R) to the initiator (I) using a second communication channel, computes a verification code (C′) using the first key (KEr) and the second key (K) within the initiator (I), and compares the verification code (C′) with the authentication code (C) within the initiator.
Owner:III HLDG 3
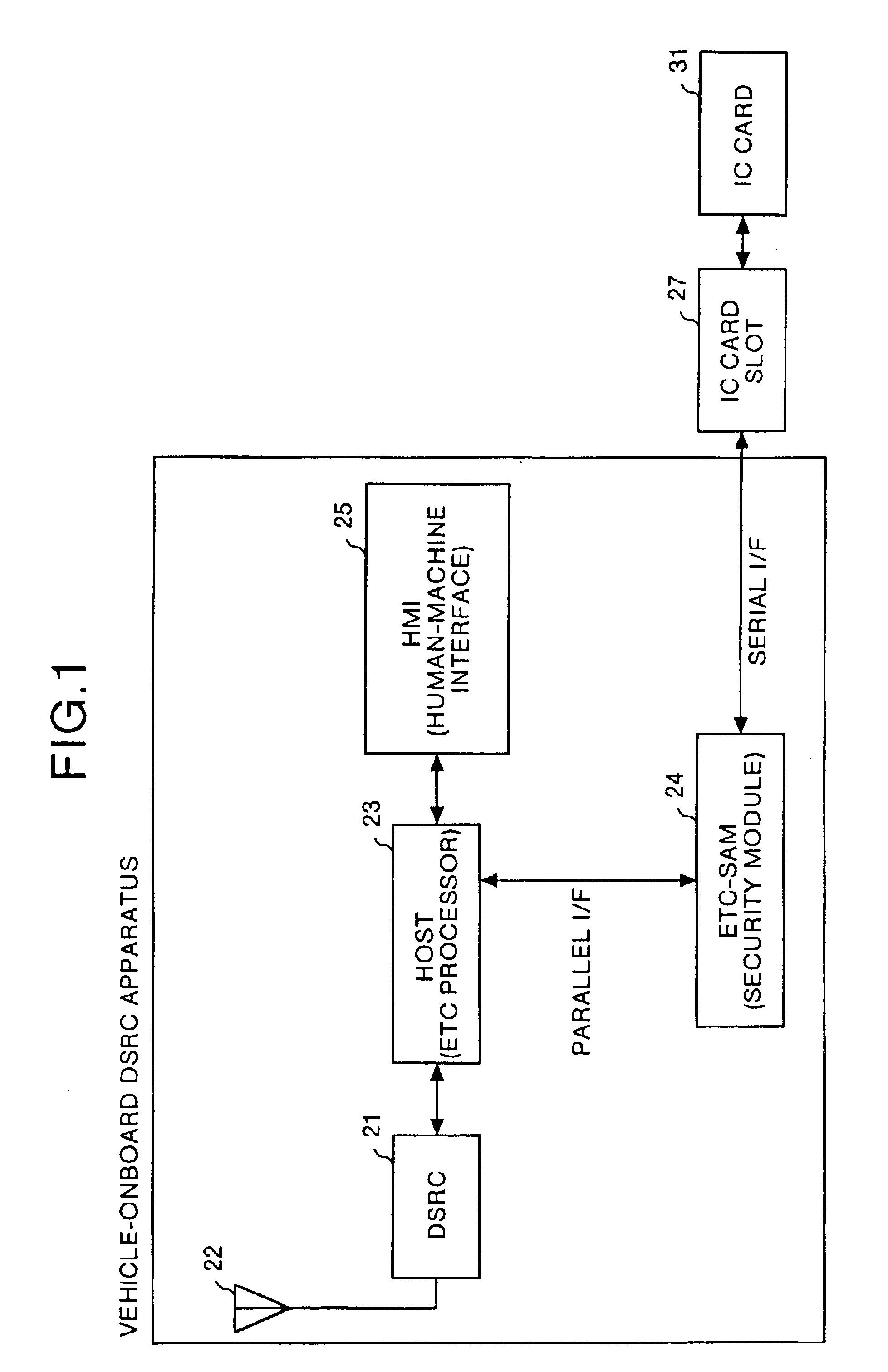
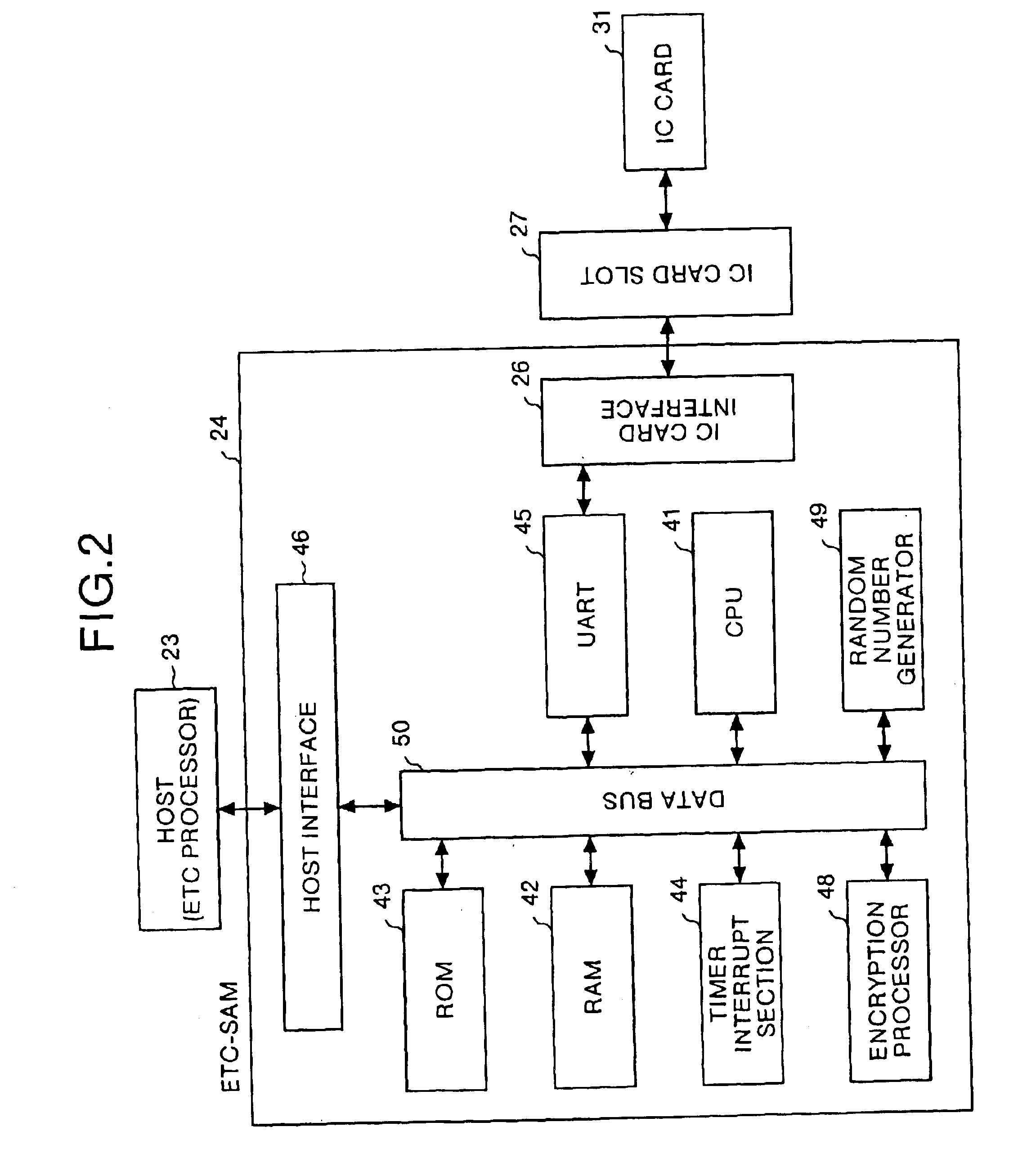
Vehicle-onboard DSRC apparatus
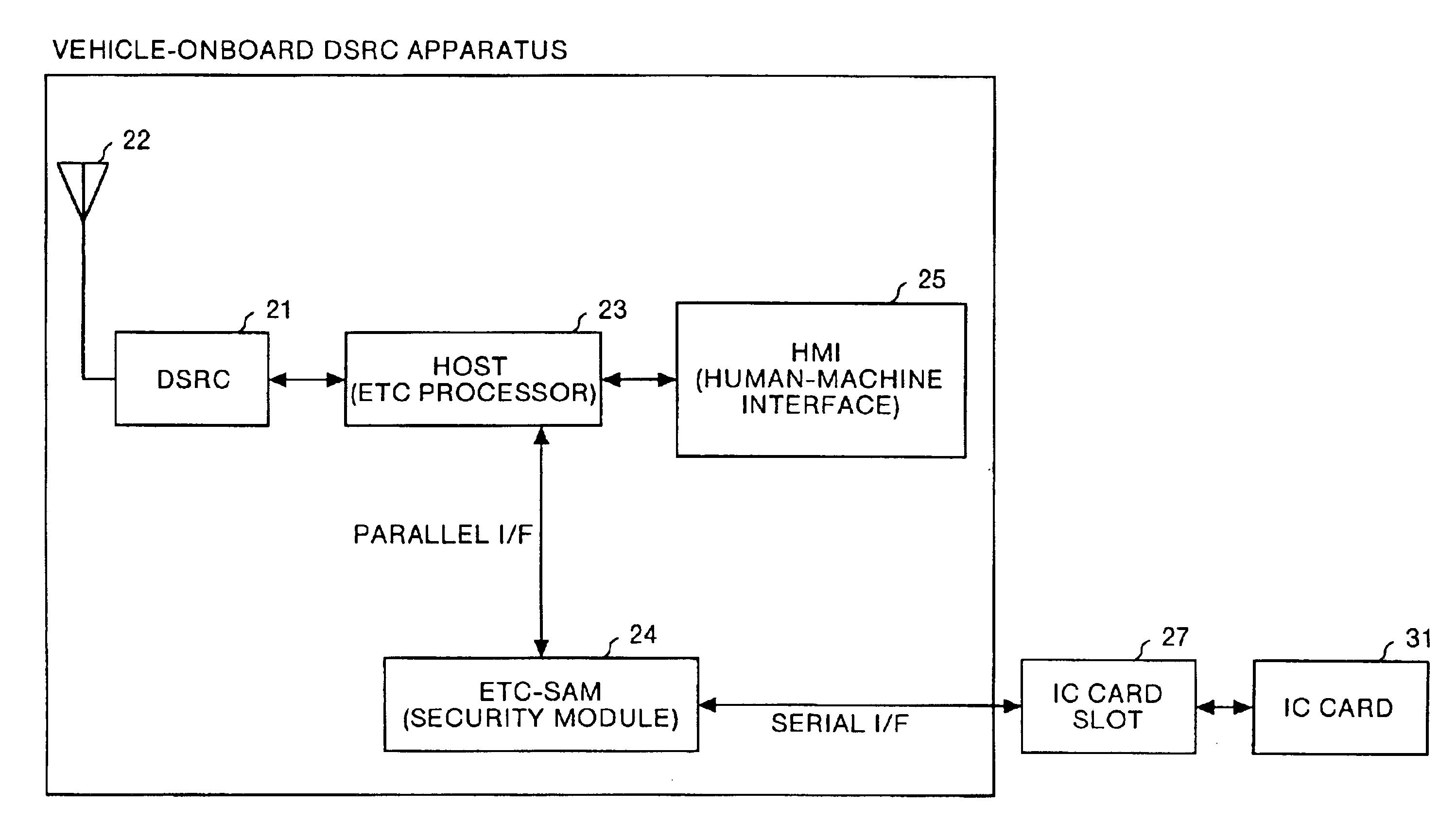
InactiveUS6920379B2Simple procedureShorten communication timeElectric signal transmission systemsTicket-issuing apparatusCommunications securityCommunications system
In a vehicle-onboard dedicated short-range communication (DSRC) apparatus for the DSRC communication system, a command judgment unit of an electronic toll communication-security application module (ETC-SAM) judges the type of command included in a communication signal transmitted between a HOST and an IC card with user information held therein. A command control unit of the ETC-SAM controls whether the command is to be analyzed, according to a result of judgment by the command judgment unit. Therefore, it is possible to simplify a communication procedure and reduce a communication time.
Owner:RENESAS TECH CORP
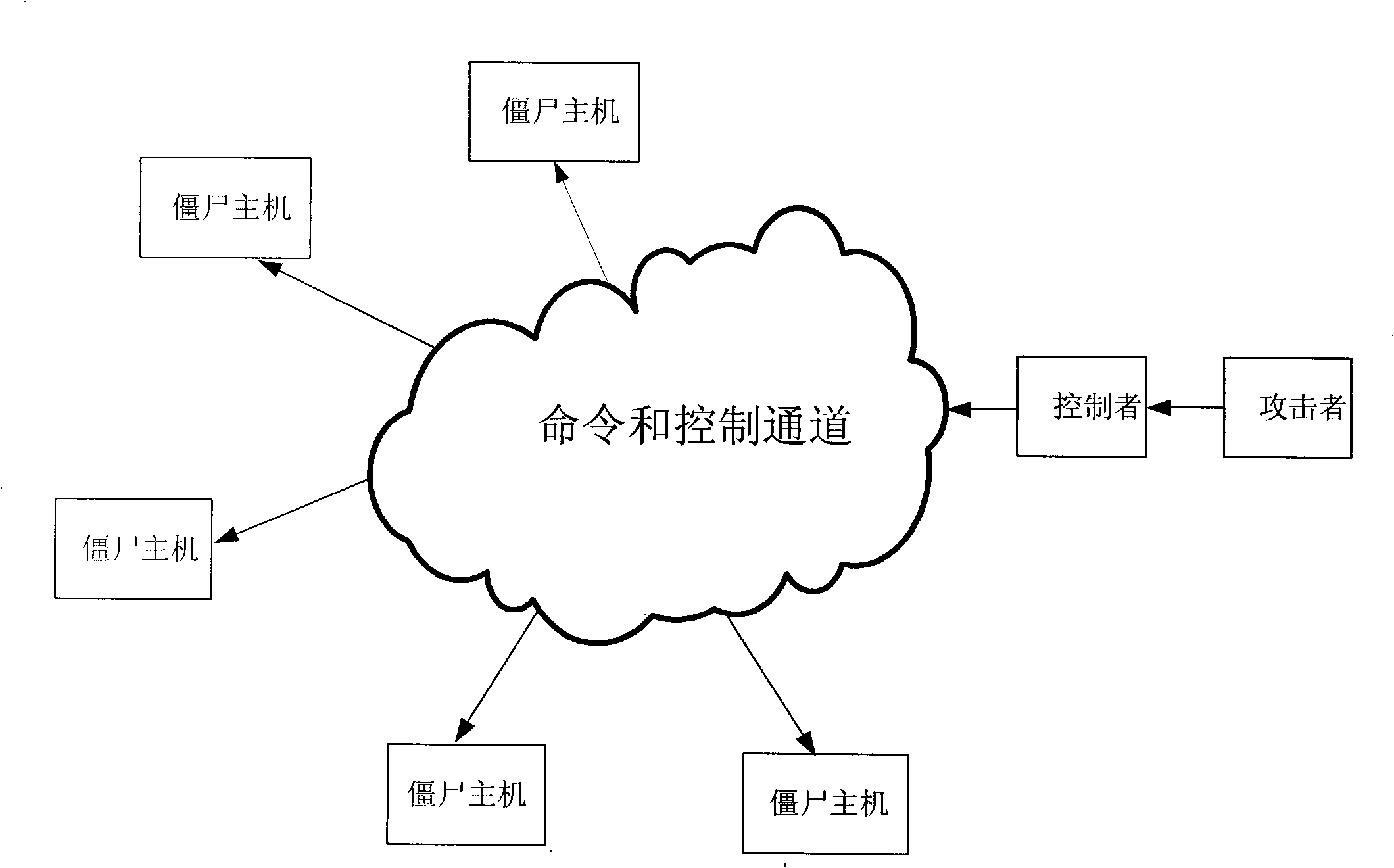
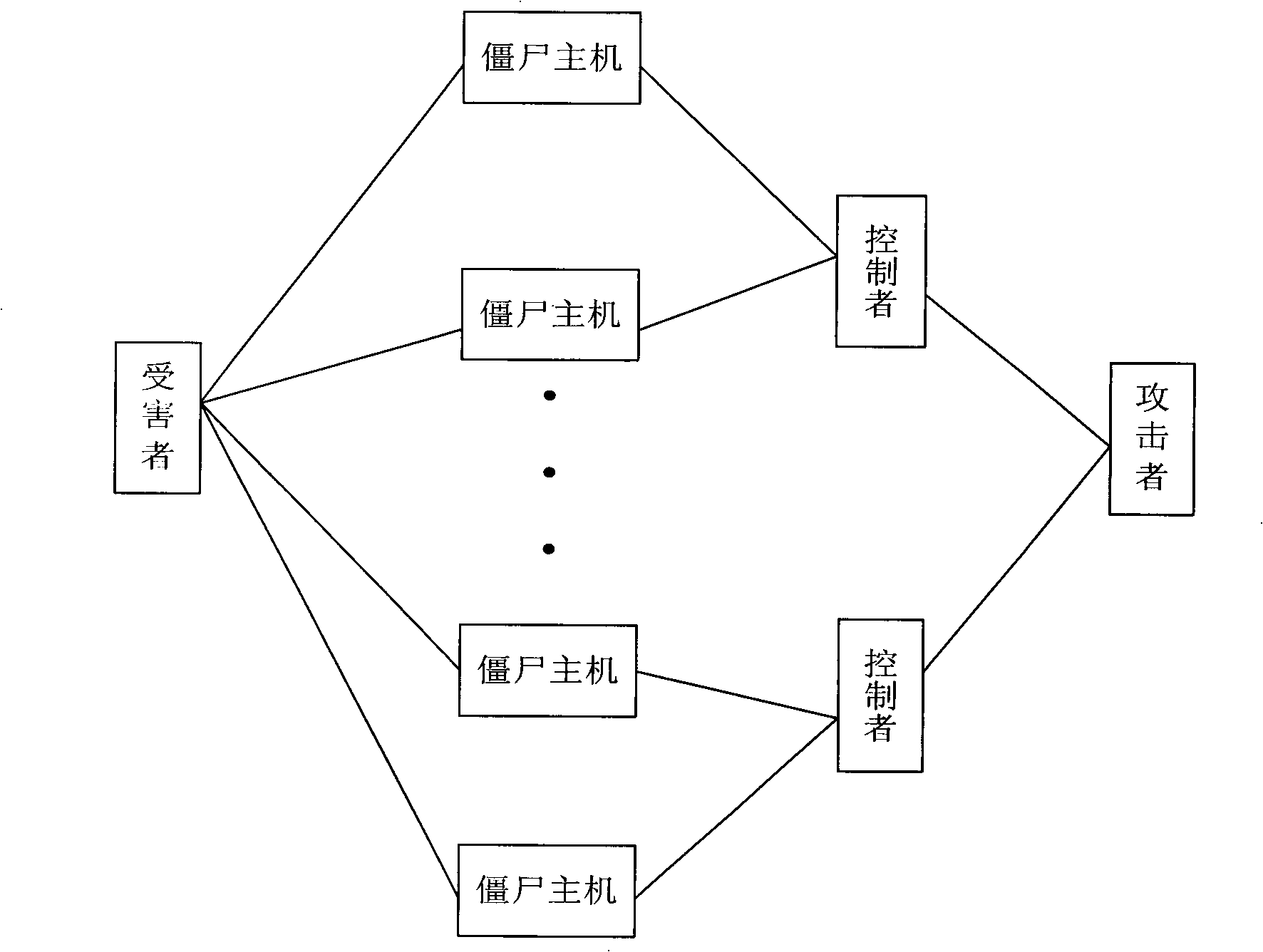
Detection method, system and apparatus of zombie network
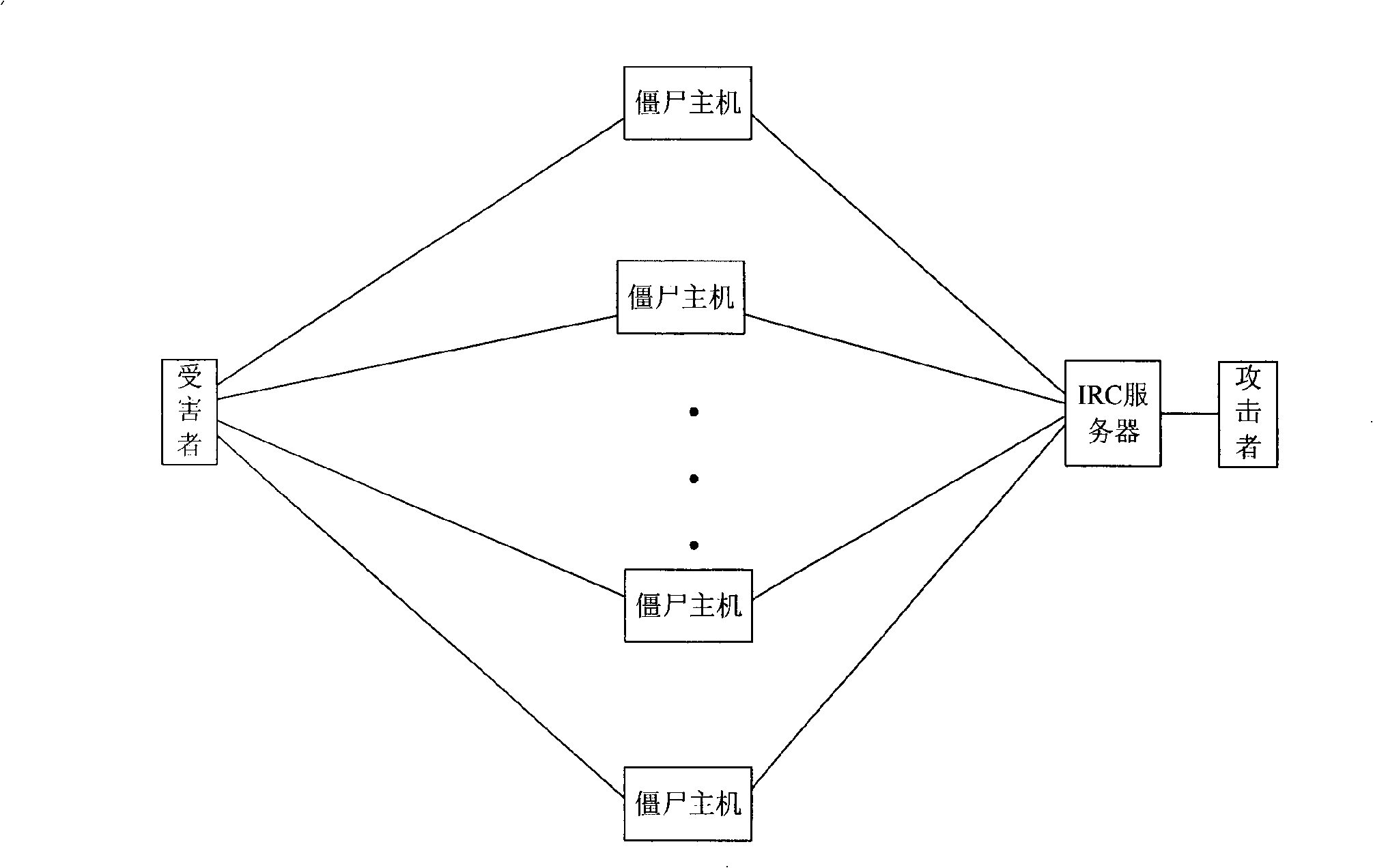
ActiveCN101360019AAvoid harmResolve detectionData switching networksCommunications securityAnalysis center
Embodiments of the invention disclose a method, a system and a device for detecting botnet, belonging to the network communication security field. The method comprises: receiving a communication message of the network under test; picking up a botnet information message of the communication message according to the communication message; picking up a bot host IP and a controller IP according to the botnet information message; and inquiring about account numbers corresponding to the bot host IP and the controller IP according to the picked bot host IP and the controller IP. The system comprises: a network probe, a monitoring and analysis center and an authentication server. The device includes a monitoring and analysis center. The botnet detection method can detect the botnet in real time, and can also respond to the botnet in real time, thereby solving the problem that the prior art based on the ex post analysis can not detect and respond to the botnet in real time, avoiding the harm of botnet, and making the network communications more secure.
Owner:CHENGDU HUAWEI TECH
Certifying and key consulting method and its device based on TTP
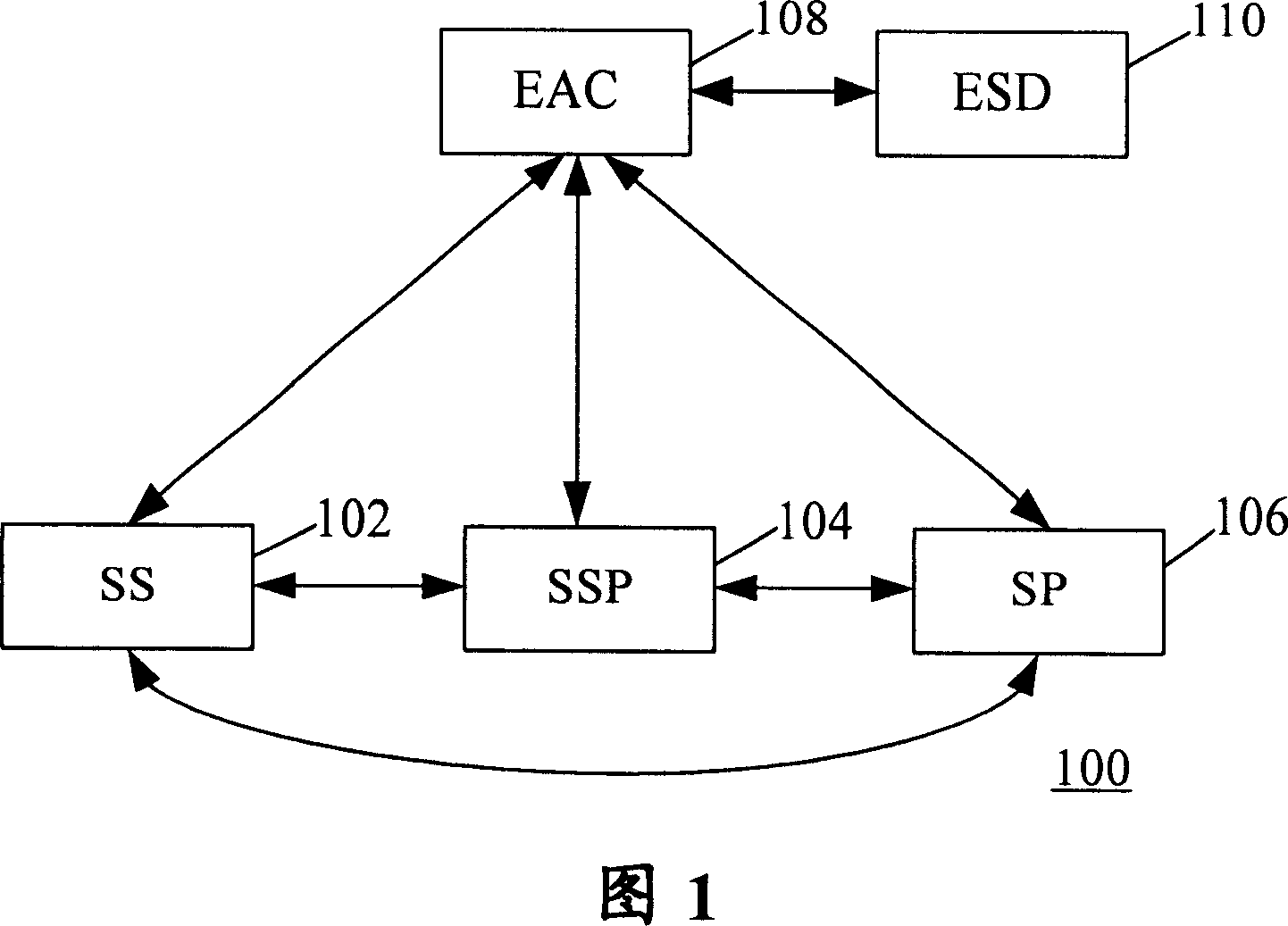
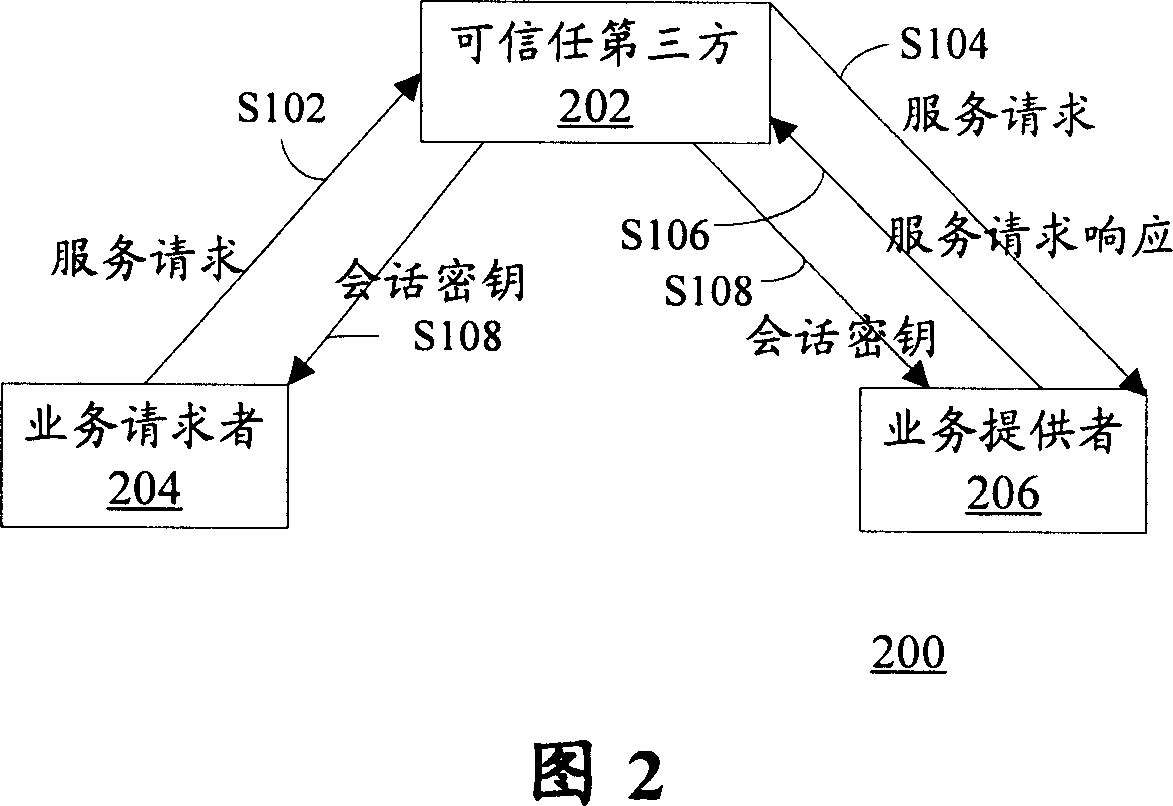
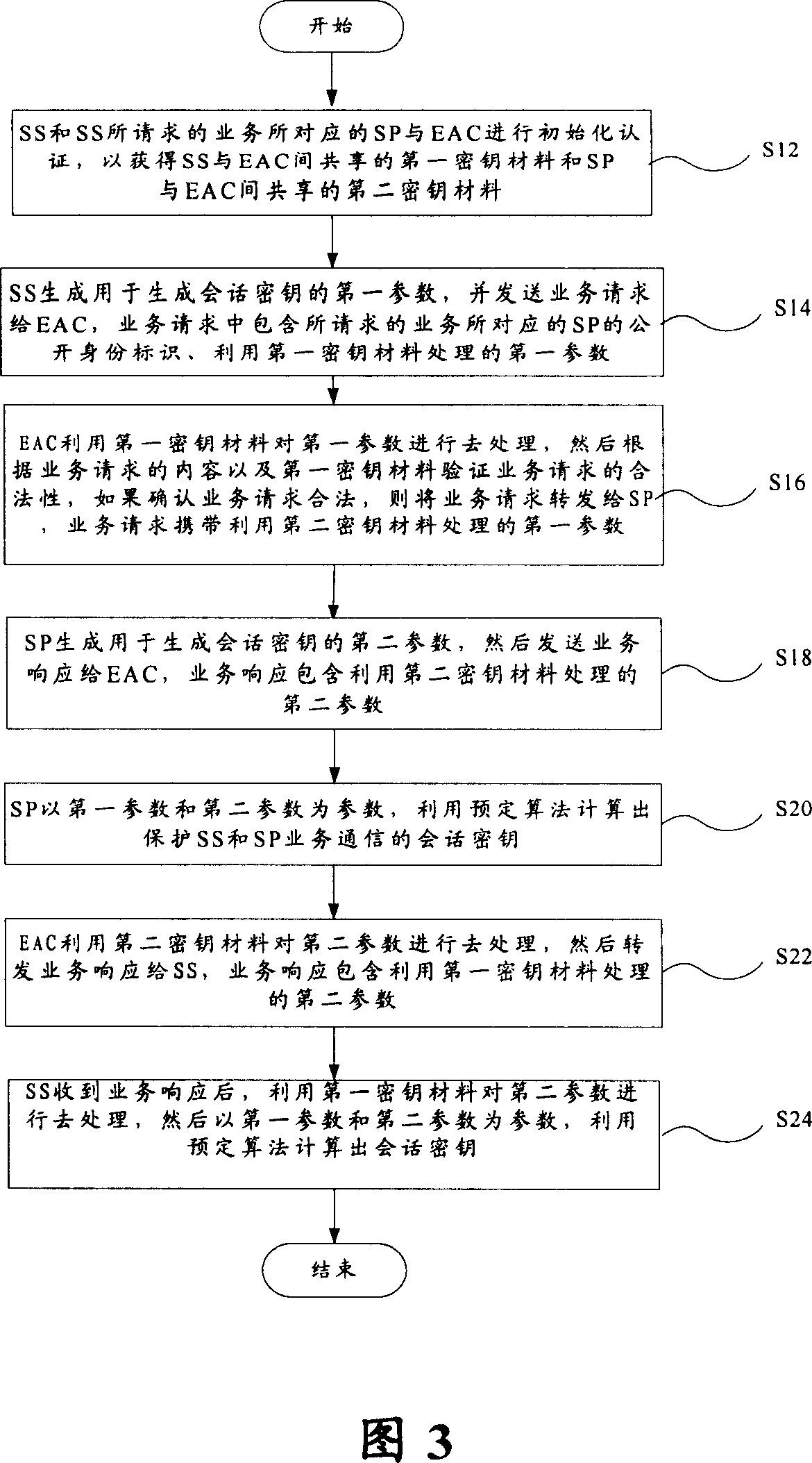
InactiveCN101052033APrevent midway interceptionPrevent leakageTransmissionCommunications securitySession key
The method comprises: a) the service subscriber generates a first parameter used in generating a session key, and sends a service request containing the first parameter to the entity authentication center; b) according to the content of the request, the entity authentication center relays the service requested in the service request to its corresponding service provider; c) the service provider generates a second parameter used in generating a session key, and sends a service confirmation containing the second parameter to the entity authentication center; d) with the first and second parameters, the service provider uses a predetermined algorithm to generate a session key; e) the entity authentication center relays the service confirmation to the service subscriber; f) after receiving the service confirmation, with the first and second parameters, the service subscriber uses a predetermined algorithm to calculate a session key.
Owner:HUAWEI TECH CO LTD
Method for a Dynamic Perpetual Encryption Cryptosystem
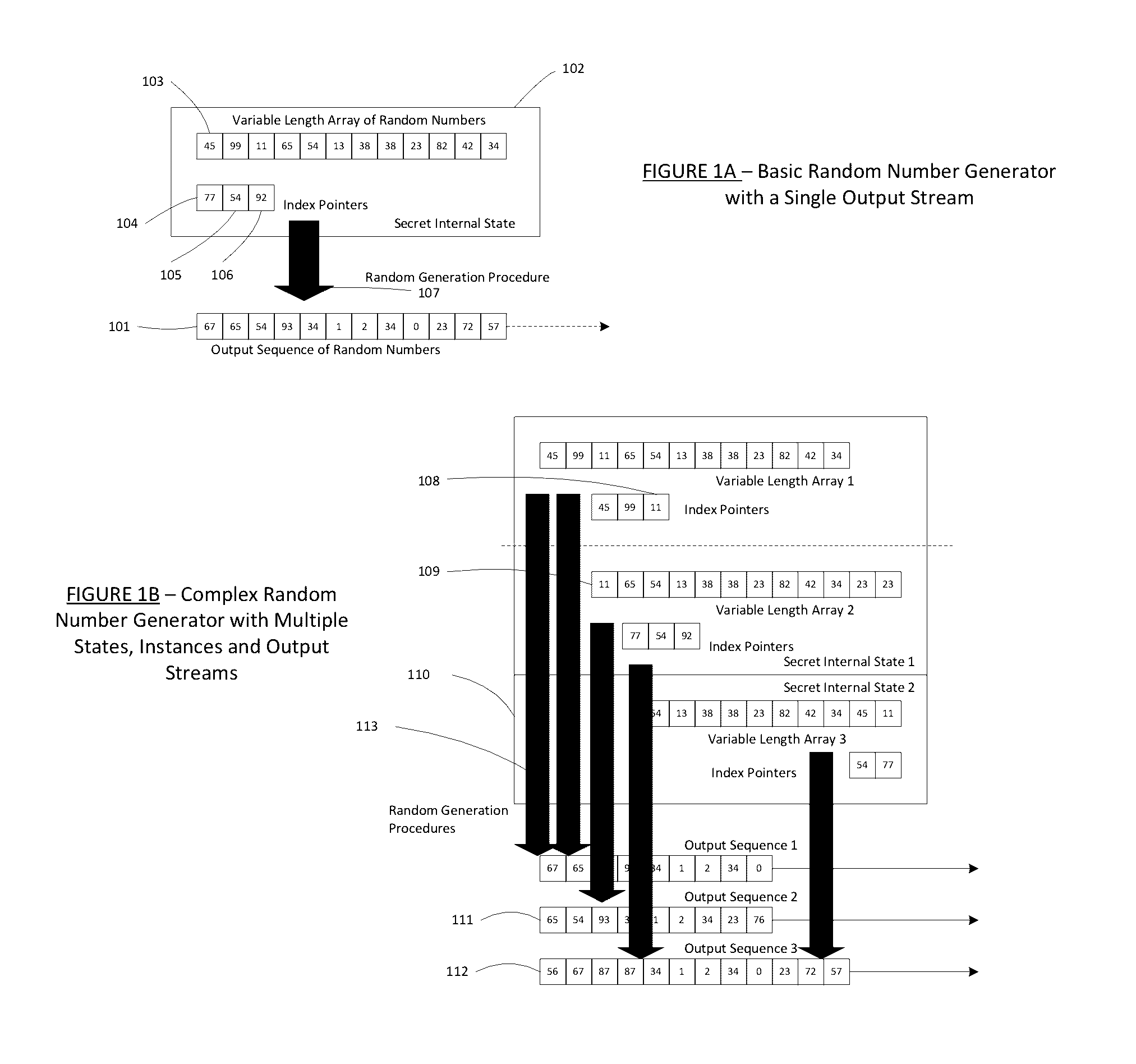
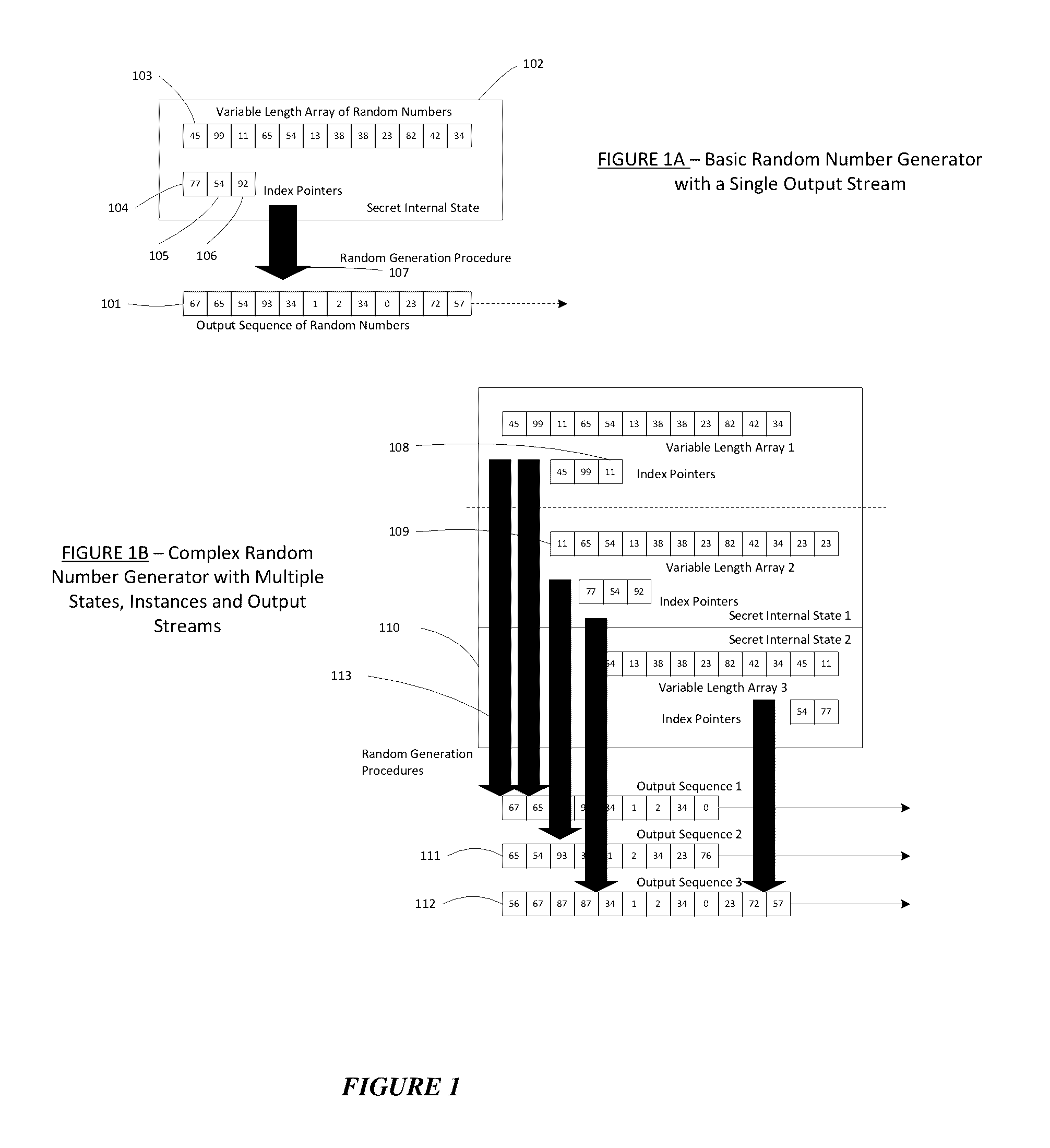
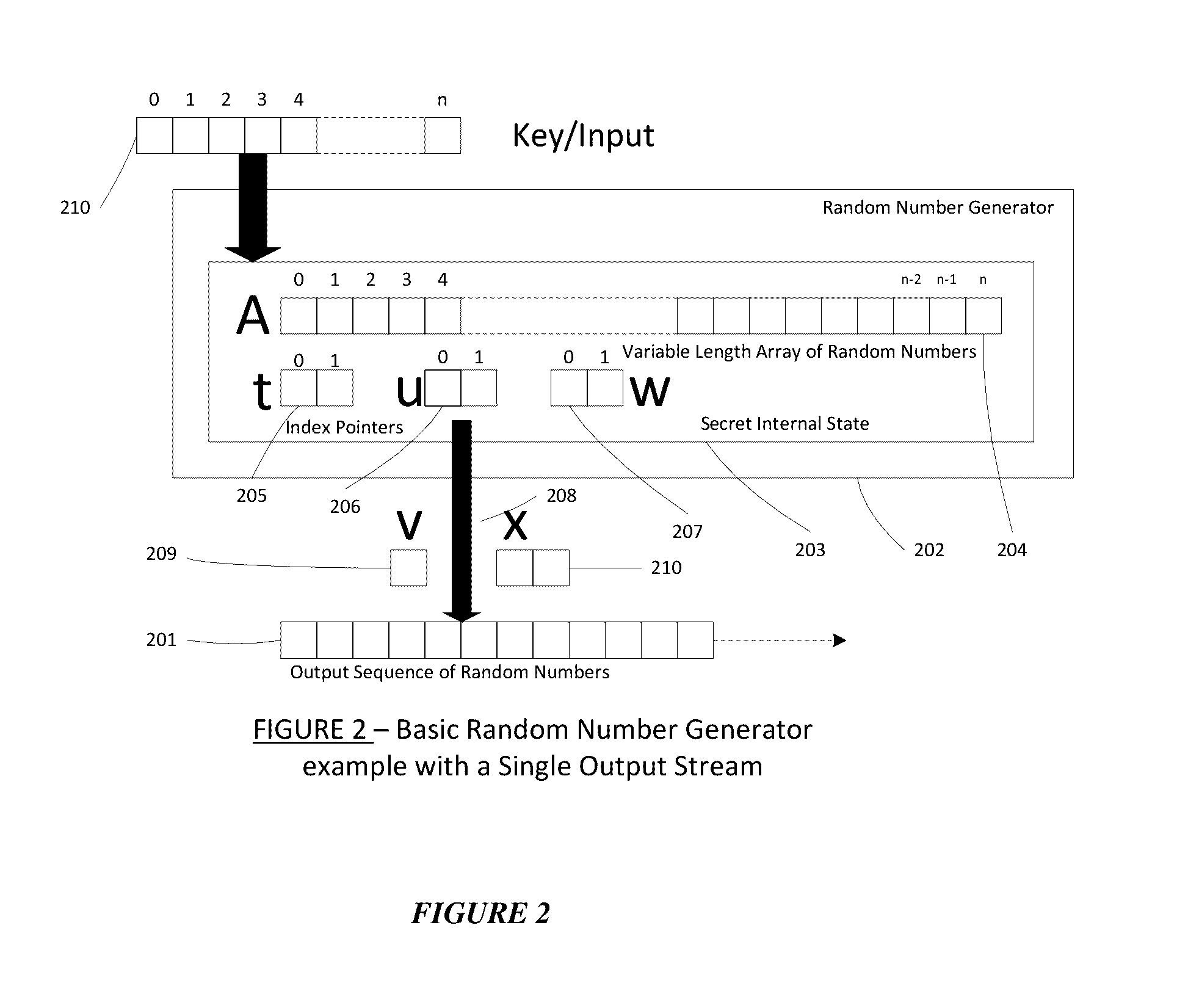
A dynamic computer communication security encryption method or system using an initial seed key and multiple random number generators of a specific design, whereby a sequence of independent random entropy values is produced by one set of random number generators and encrypted along with the message stream using the initial seed key, or the output of a second set of random number generators initialized with the initial seed key, and following the subsequent transmission of the variable encrypted entropy / message block, the entropy values are used to symmetrically or identically augment or increase the current uncertainty or entropy of the cryptosystem at both the sender and the receiver, prior to the next encryption block operation. The encryption process effectively entailing the use of multiple encryption ciphers, and the entropy augmentation process entailing the encryption or application of various logical mathematical operations on the already dynamic but deterministic internal state values of the second set of random number generators, effectively altering their deterministic outputs in a random probabilistic manner.Random length message value sequences from one or more data sources is combined with one or more random length entropy value sequences from an independent source, following which the entropy “updates” may also be used to alter, or change any cryptosystem variable, value or component in a randomly determined manner. In addition, whilst ensuring synchronization, the random entropy sequences also serve to “pollute” the cipher-stream and thereby hinder most current forms of cryptanalysis, whilst simultaneously injecting additional entropy into the cryptographic system and allowing for its propagation to affect any connected system nodes, and thereby introducing unpredictable entropy into the system pseudorandom number generator outputs, and thereby ensuring the perpetual generation of unpredictable random numbers.Super-encryption mechanics are independent of the user data, simple, fast and efficient, and can incorporate compression, error correction and asymmetric encryption authentication routines. But most importantly, super-encryption ensures resistance to brute force attacks (not possible to verify if a message was even sent), an ability to exceed “perfect secrecy” requirements, and an improvement on previous super-encipherment design, since overhead can be dramatically reduced from 100% overhead.Communication links previously established by system nodes with central authorities may be used for secure node authentication and registration, whilst allowing the central authority to broker and synchronize communication channels and providing mutual authentication and other security functions between the system nodes.
Owner:FIGUEIRA HELDER SILVESTRE PAIVA
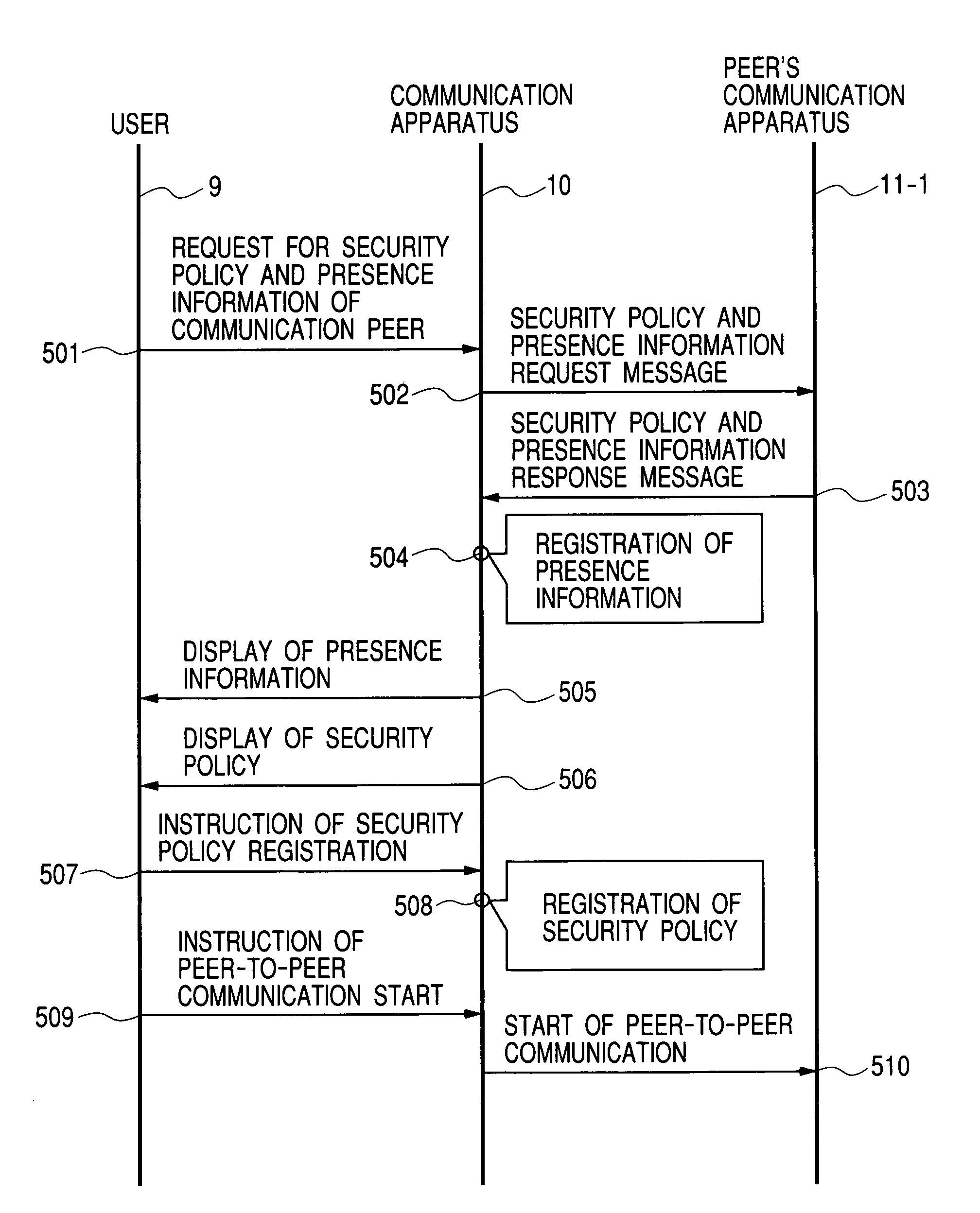
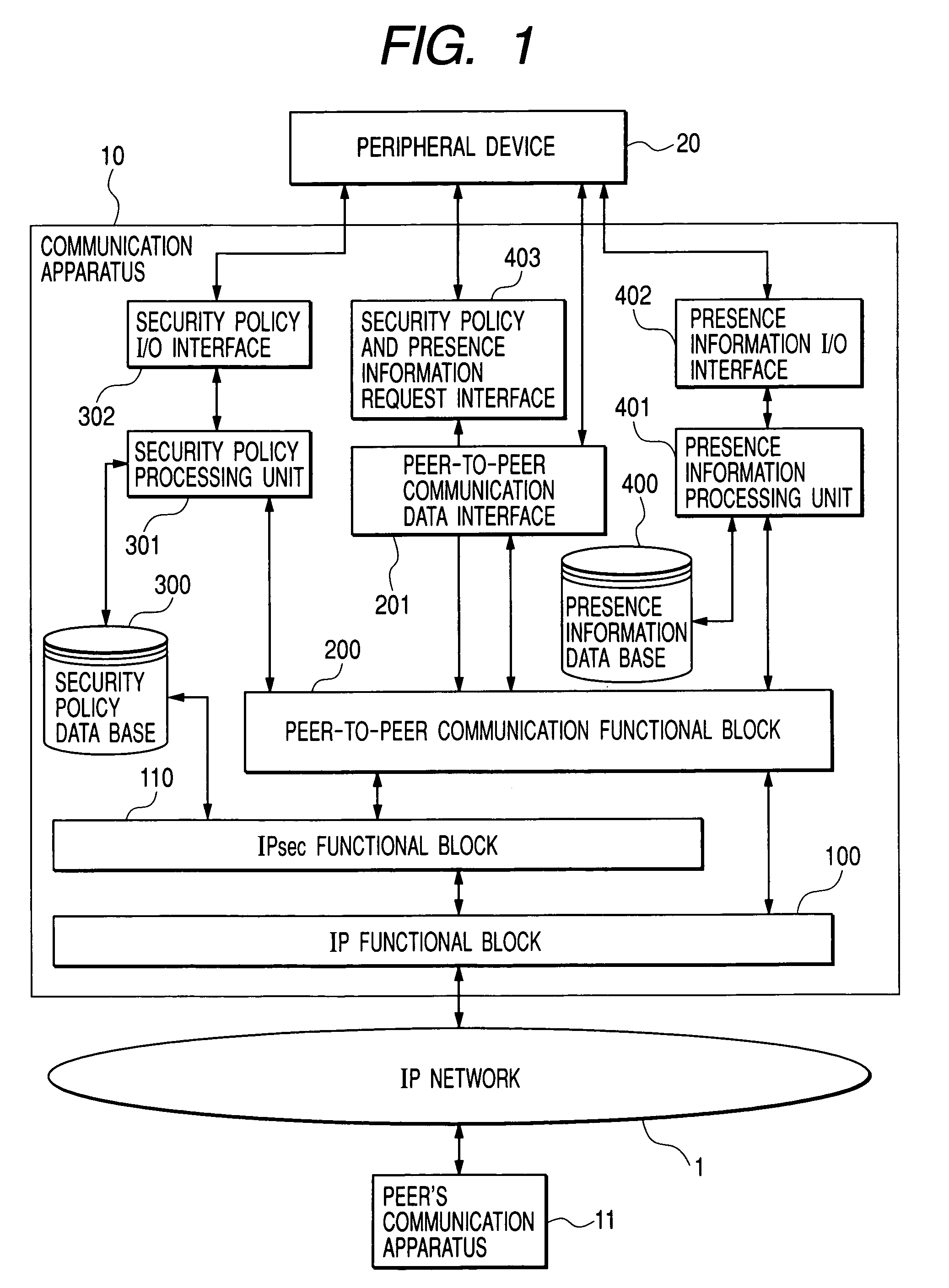
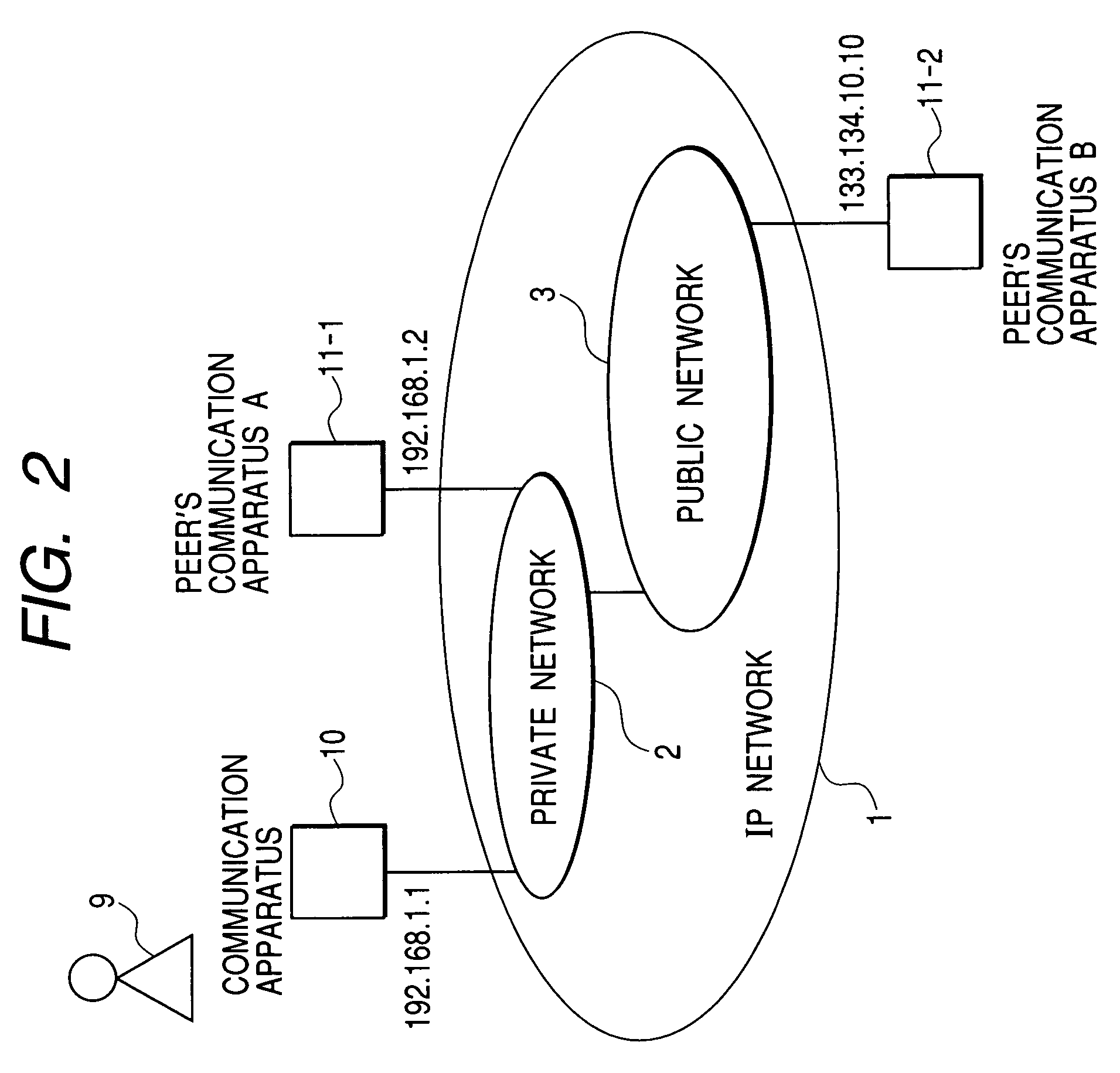
Peer-to-peer communication apparatus and communication method
InactiveUS7337465B2Ensure safetyDigital data processing detailsUser identity/authority verificationCommunications securityNetwork packet
A peer-to-peer communication apparatus connected to an IP network acquires, from a peer's communication apparatus, presence information including information for judging a communication security environment of the peer's communication apparatus and a security policy to be applied by the peer's communication apparatus to a packet, displays the presence information and security policy information such that a user can judge the prosperity of the security policy information based on the presence information, and processes a data packet to be transmitted to the peer's communication apparatus in accordance with the security policy approved by the user.
Owner:HITACHI LTD
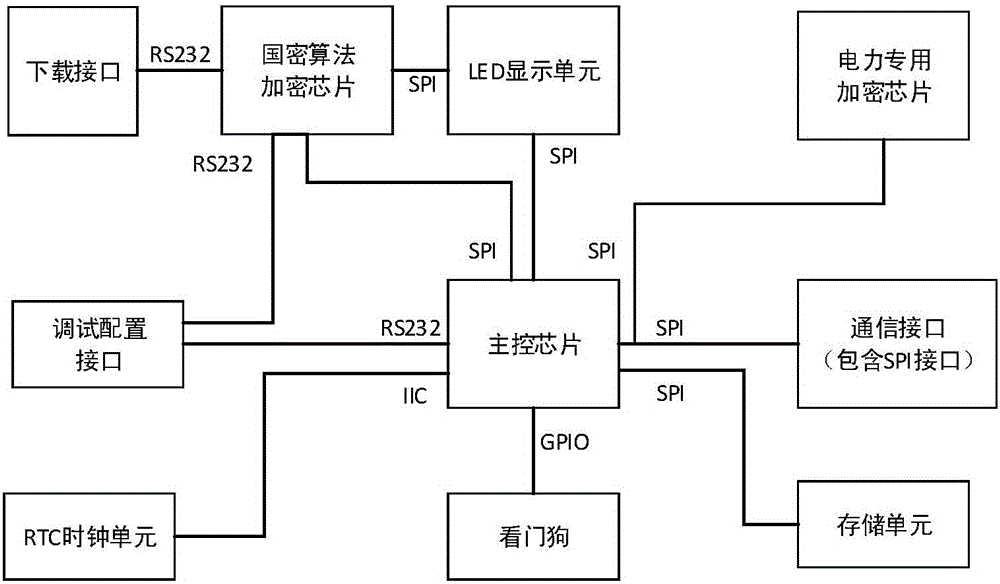
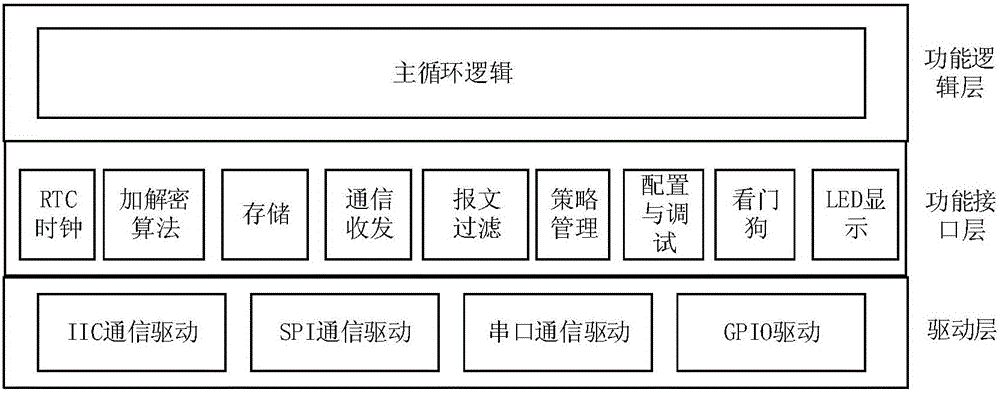
Security encryption authentication module for power distribution terminal communication and method thereof
InactiveCN105871873ASpeed up encryption/decryption timeReduce dependenceKey distribution for secure communicationUser identity/authority verificationCommunication interfaceCommunications security
The invention discloses a security encryption authentication module for power distribution terminal communication and a method thereof. The security encryption authentication module comprises a main control chip, a commercial code algorithm encryption chip, a communication interface and a storage unit; the main control chip is connected with the commercial code algorithm encryption chip, the communication interface and the storage unit and receives message information of a front-end processor of a distribution master station and a distribution terminal through safe interface software of the distribution terminal to overall manages the other modules, and the commercial code algorithm encryption chip encrypts or decrypts the message information received by the main control chip. The special encryption chip is adopted in the security encryption authentication module, response speed is increased, and dependence on a CPU and an internal storage is reduced. Besides, communication security is greatly improved by means of bidirectional authentication of verifying each other's identity between the security encryption authentication module and a distribution security interaction gateway.
Owner:STATE GRID CORP OF CHINA +4
Method for secure user and site authentication
ActiveUS8549601B2Not easily defeatedImprove securityDigital data processing detailsMultiple digital computer combinationsUser authenticationOne-time password
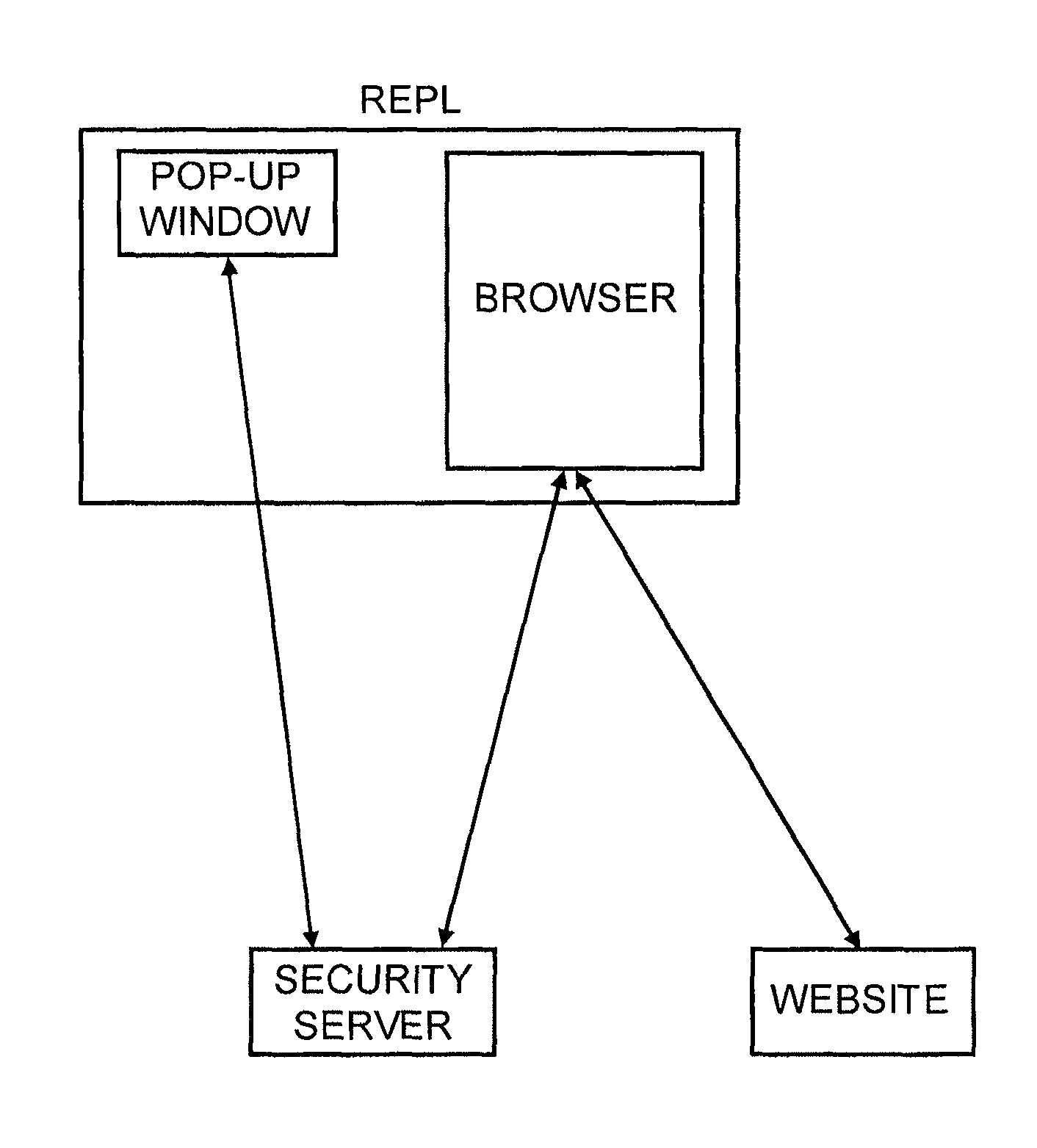
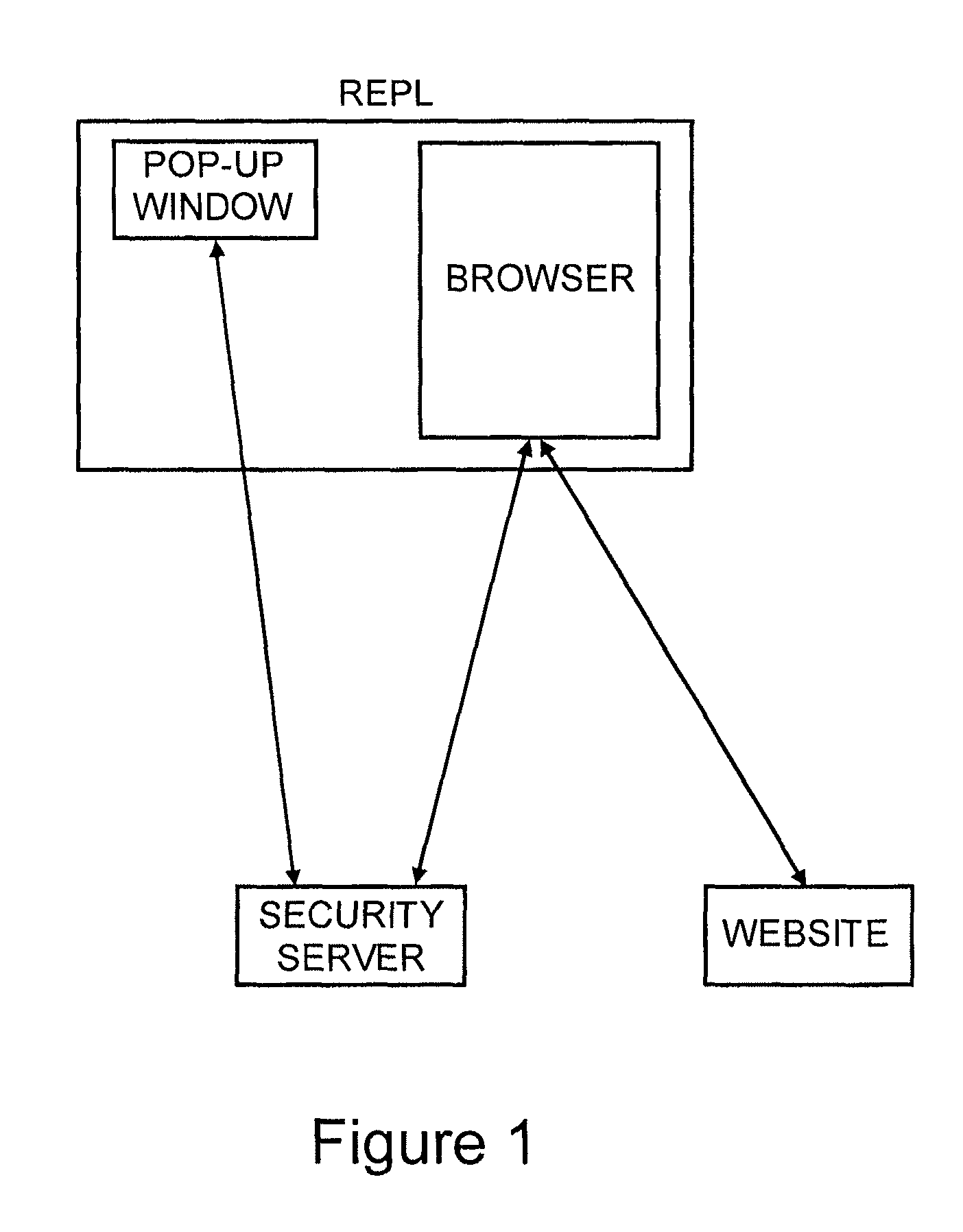
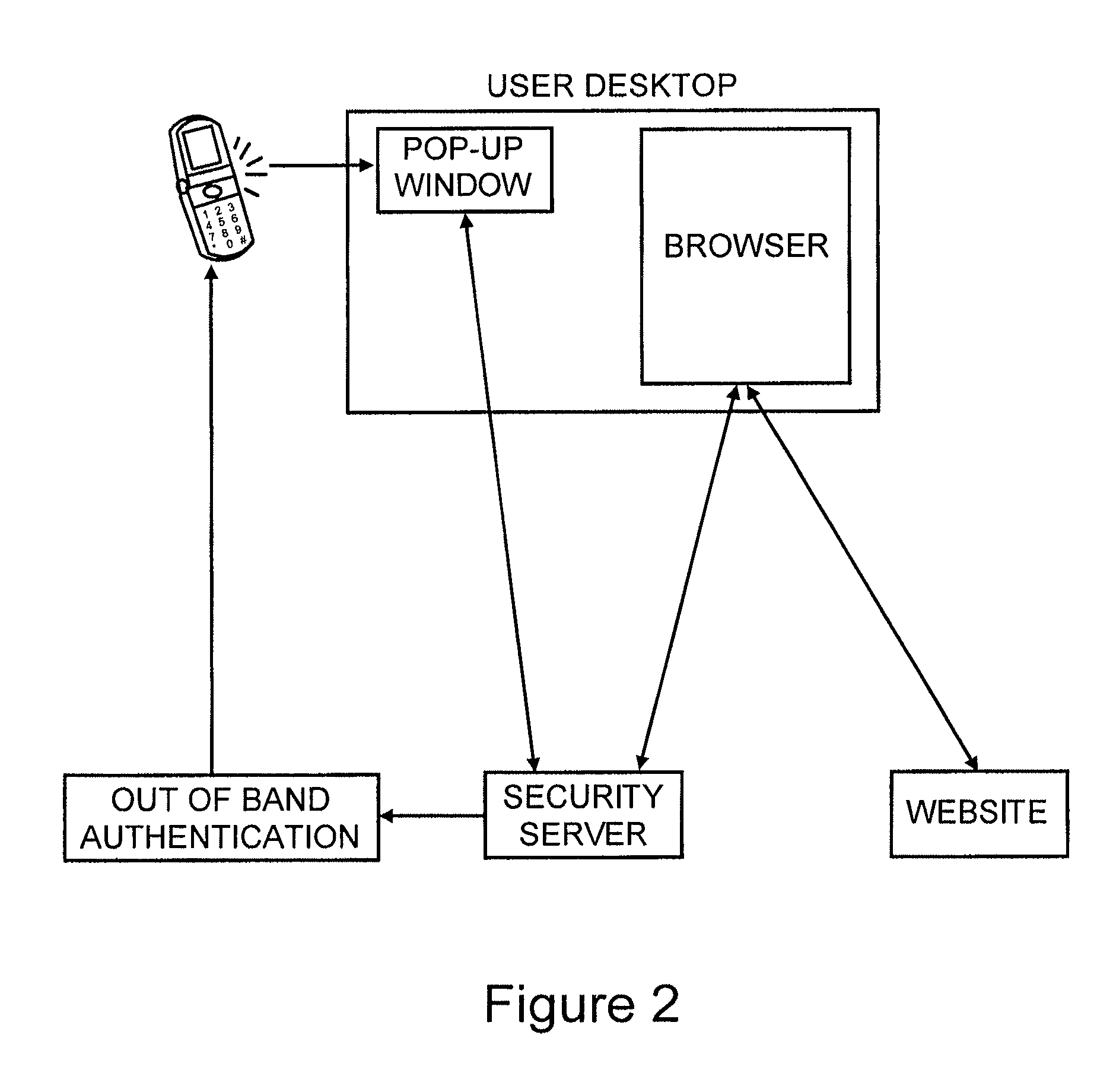
User authentication is achieved by creating a window on the user's PC that is in communication with a security server, where this communication channel is separate from the communication channel between the user's browser and whichever web site they are at. A legitimate web site embeds code in the web page which communicates to the security server from the user's desktop. The security server signals both the web page on the user's browser and the window to which it has a separate channel. If user authentication is requested by the web site, the security server computes a one time password based on a secret which it shares with the web site, but not with the user, and which is not associated with any particular user, and the web site can re-compute the one time password to authenticate the user.
Owner:PAYFONE
Intrusion detection system facing cloud calculating environment
InactiveCN102724176ASolve the large-scale dynamic number of usersEnsure application securityTransmissionCommunications securityService domain
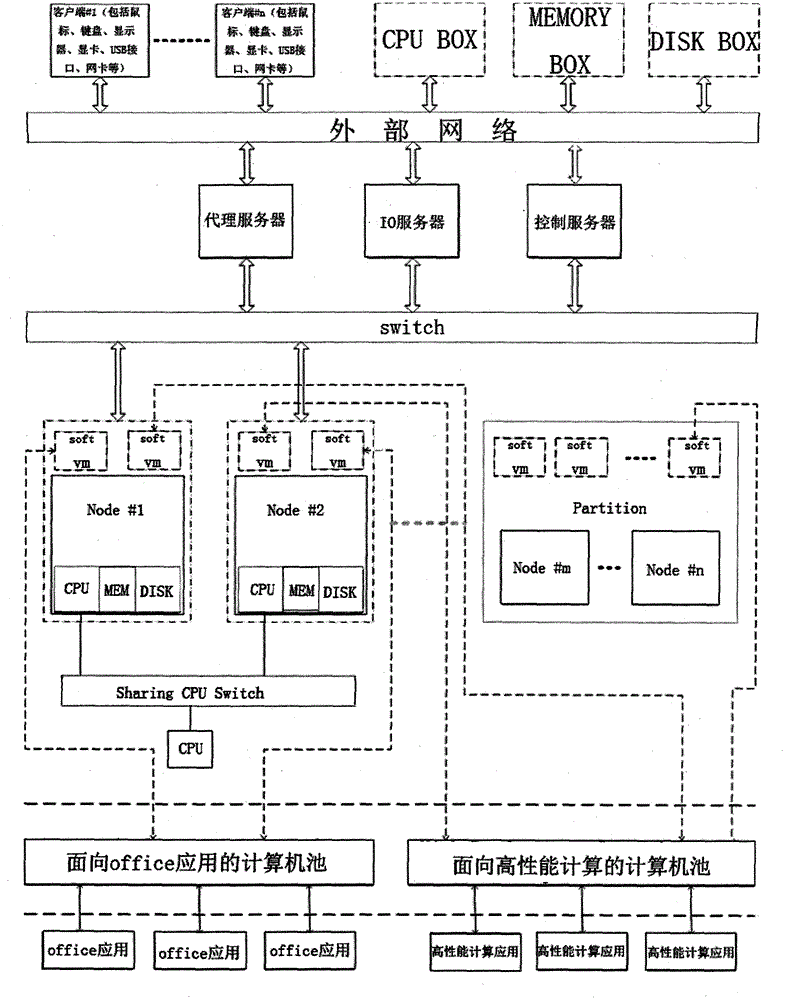
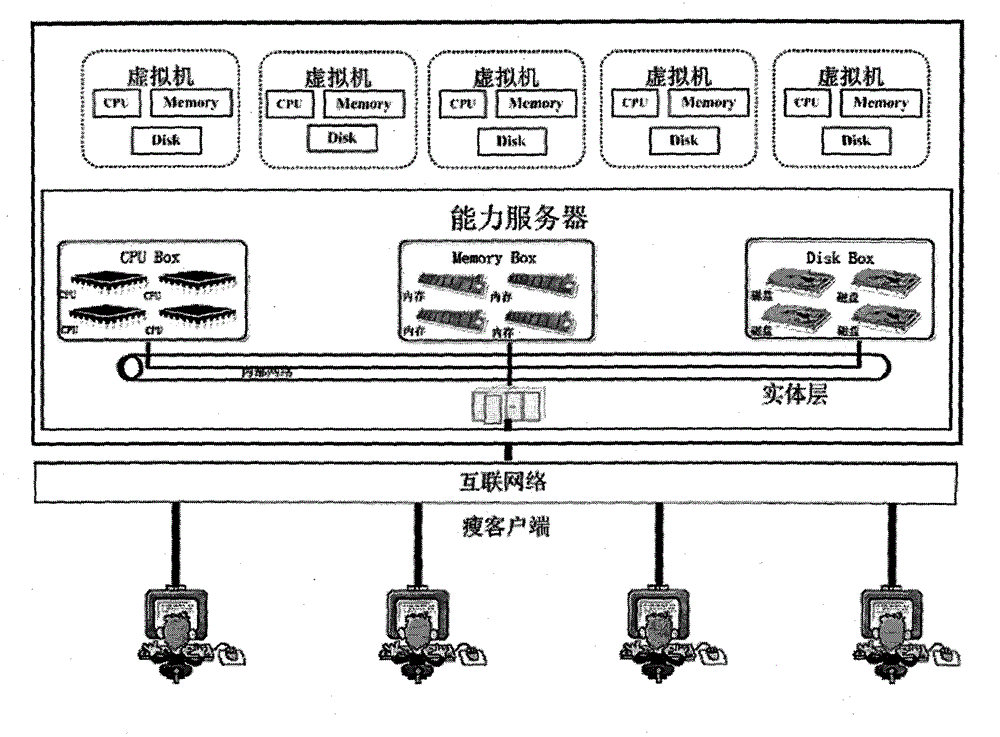
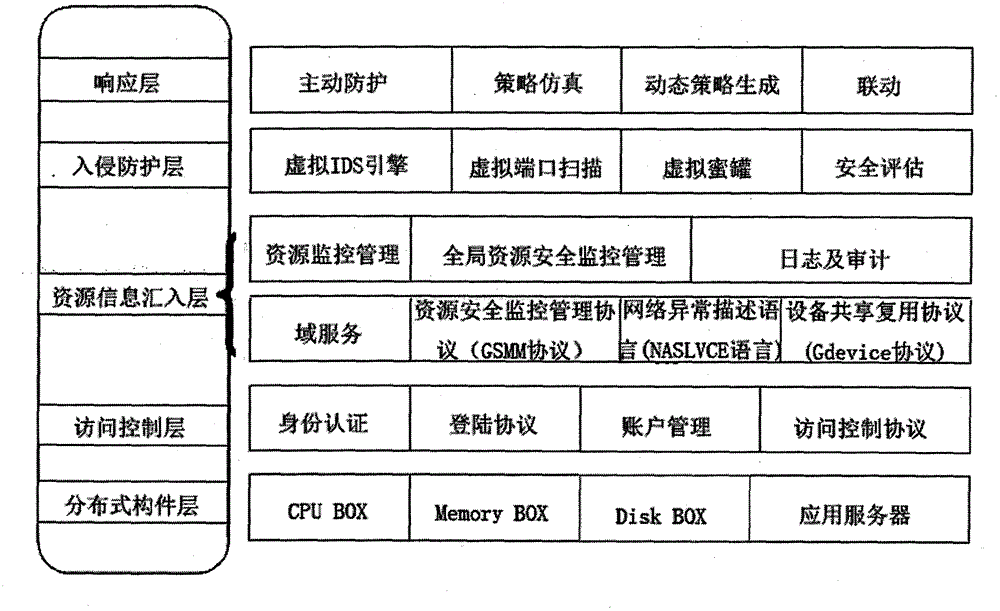
According to the invention, a safety problem based on splitting and under large-scale shared virtual calculating environment is discussed. And the invention provides a safety framework based on a virtual machine and facing the virtual calculating environment and a large-scale distributed extensible intrusion detection system. The system provides resource access monitoring identity authentication inside and outside an ability service domain and an encrypted data transmission channel for a user, provides isolation and protection of a user space and a system space and finally guarantees application safety based on an ability server. By using the system of the invention, many safety problems under the ability server, such as, a large-scale dynamic user quantity, large-scale dynamic virtual resource objects, a calculating load of dynamic increase and reduction, user space isolation, user system isolation and protection, internal and external network attack prevention, equipment safety reuse and sharing, communication safety, uniform authentication, access control and the like, are solved.
Owner:BEIJING COMPUTING CENT
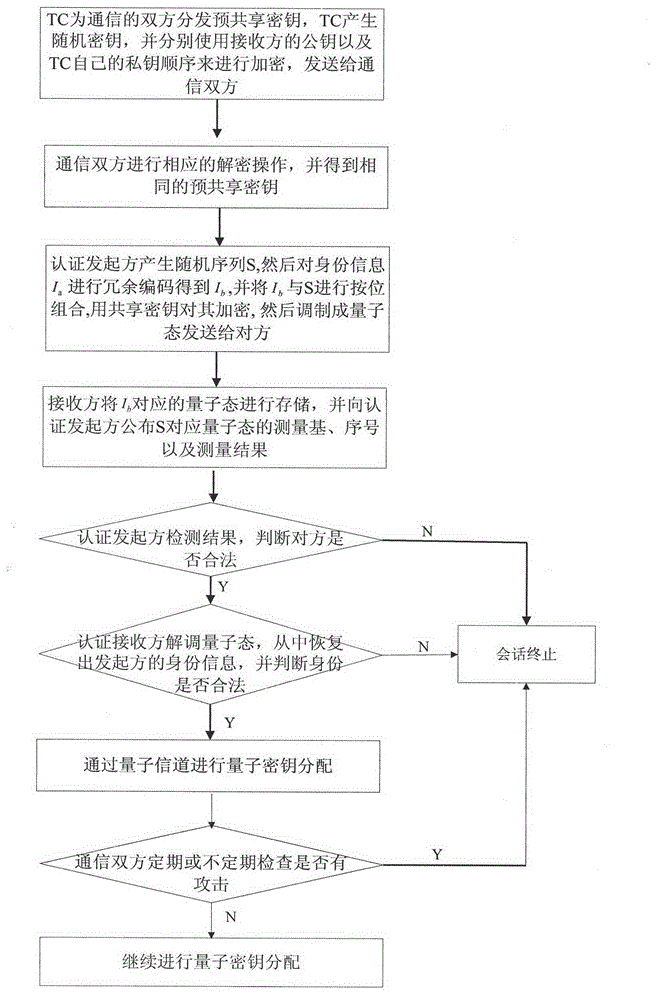
Model and method for user authentication for quantum key distribution network
ActiveCN102946313AAvoid Intermittent AttacksPrevent theftKey distribution for secure communicationUser identity/authority verificationCommunications securityMan-in-the-middle attack
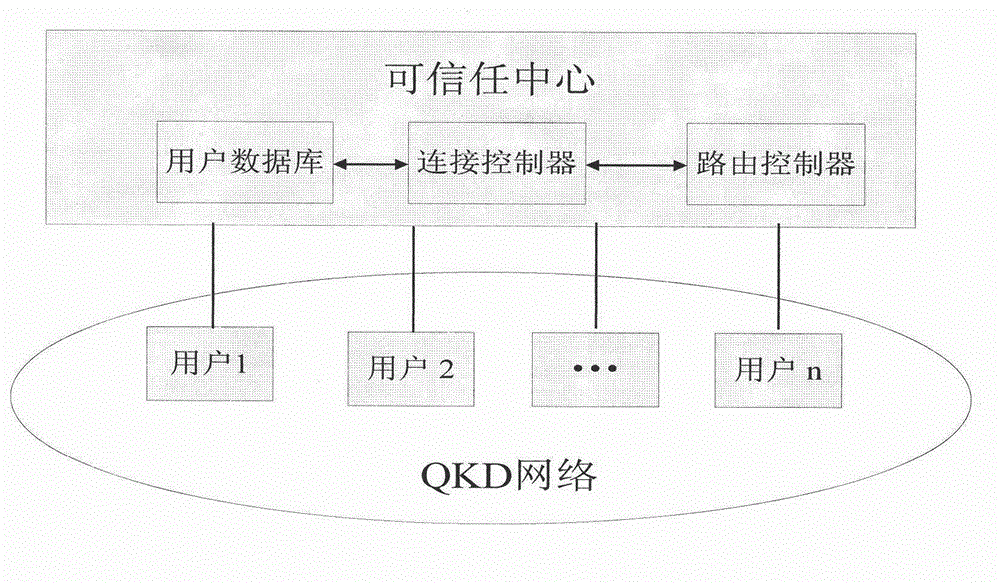
The invention provides a model and a method for user authentication based on a trusted center in a quantum key distribution network, specifically, a user authentication model based on the trusted center is provided and an implementation method is described in detail, in order to realize the communication security between any two users in the network and prevent a man-in-the-middle attack. Based on the model, the invention further provides a method for user authentication, which comprises the following steps that: 1, any user requesting for communication in the network sends a connection request to the trusted center; 2, the trusted center sends a pre-shared key to the two communication parties respectively; 3, the two communication parties set up a quantum channel and are authenticated; and 4, the two parties are authenticated regularly or irregularly in the subsequent communication process. According to the invention, by fully considering the development status of the current quantum key distribution network and by combining with the actual requirement, a quantum communication channel can be set up securely between any two nodes in the network, so that the communication security between users can be realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
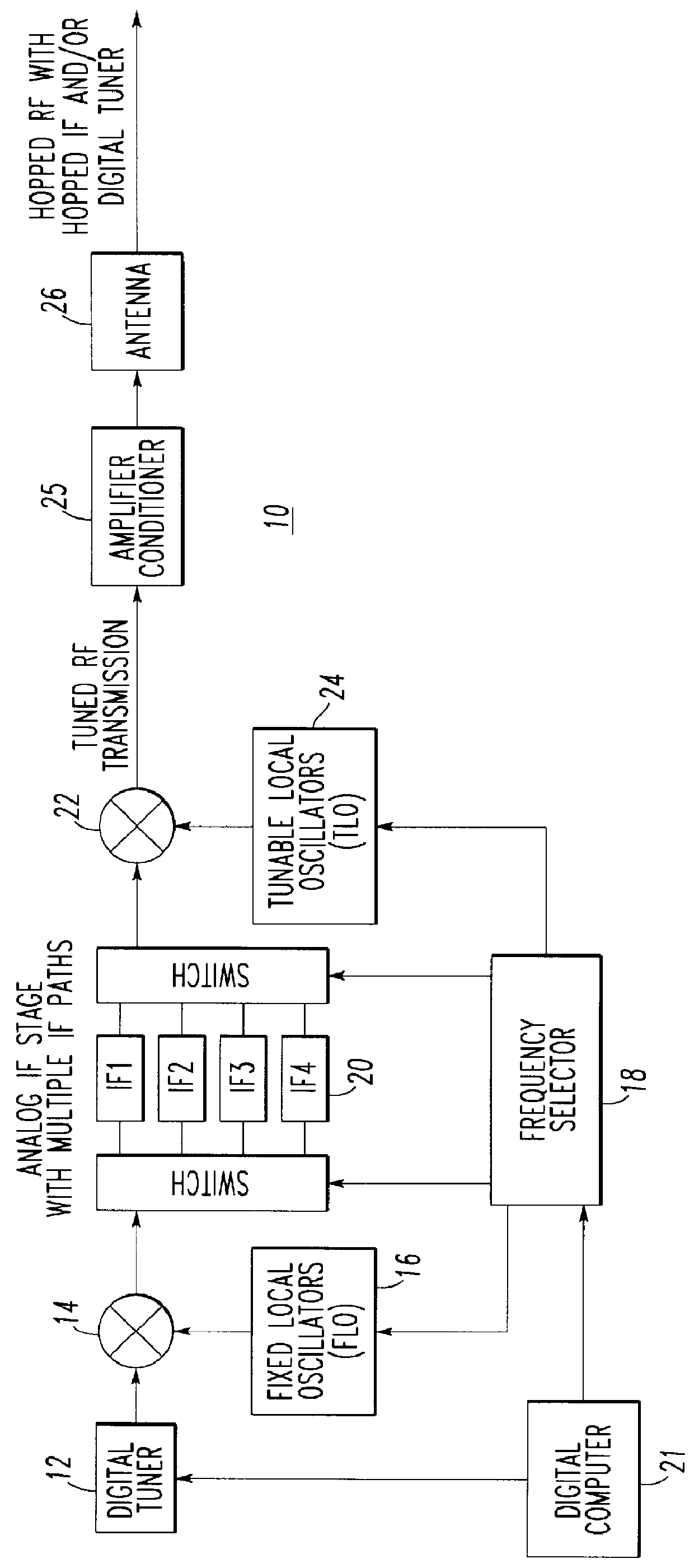
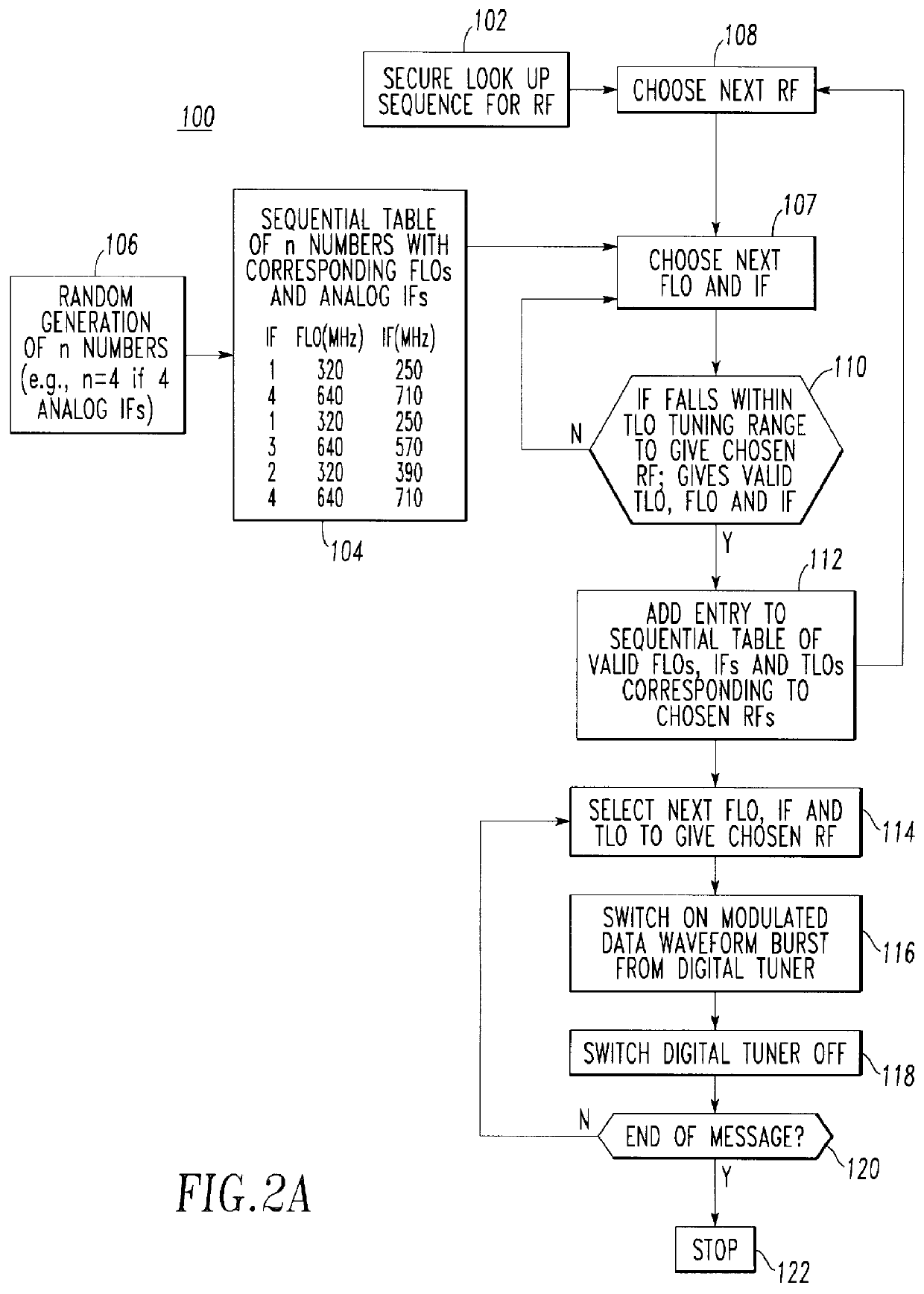
Frequency hopping radio transmitter apparatus and method providing very high communication security
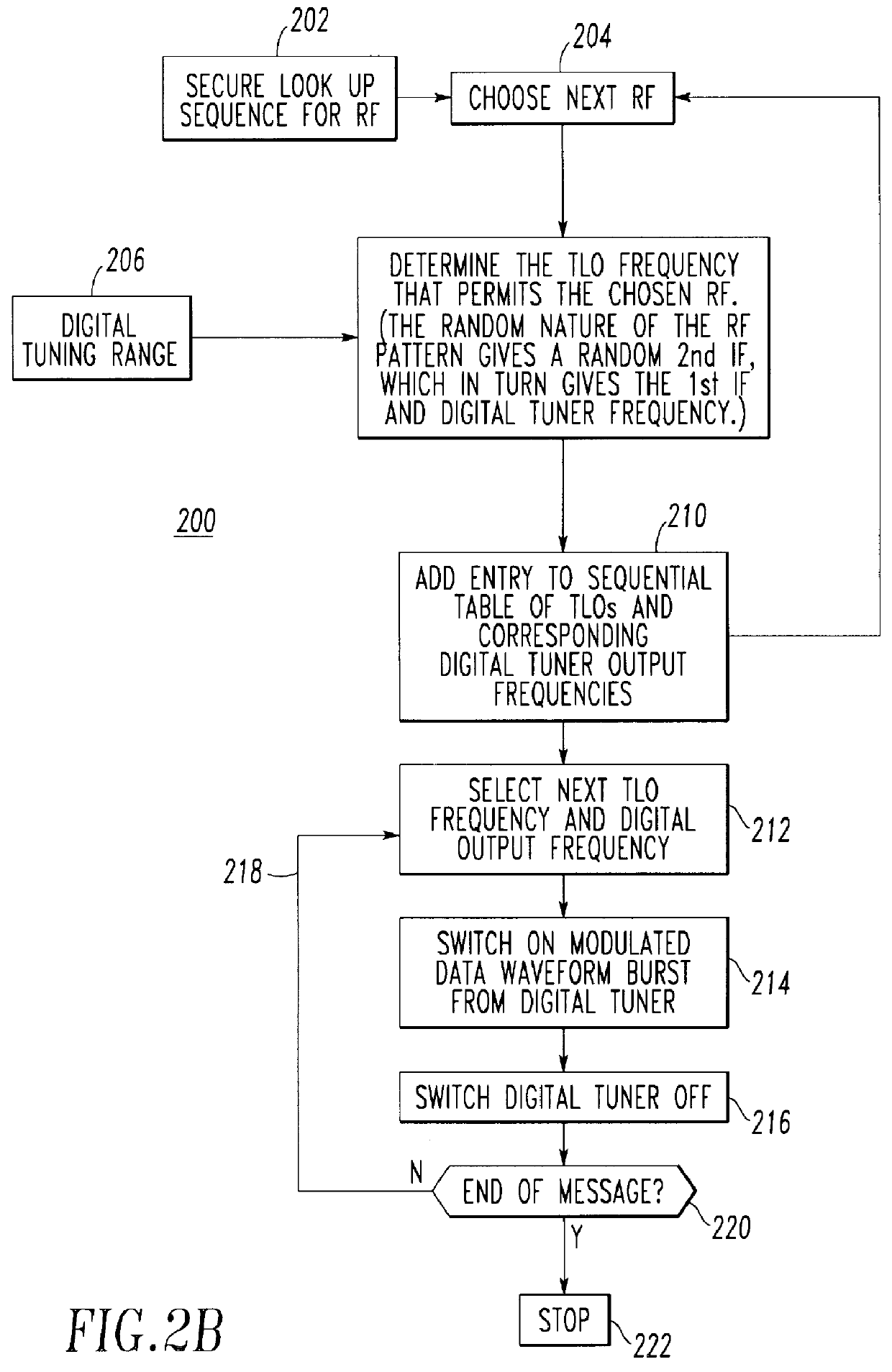
InactiveUS6028885AAngle modulationFrequency-modulated carrier systemsDigital tuningCommunications security
A radio transmitter is structured to provide frequency hopping of transmitted leakage signals in addition to RF hopping of the RF output signal. A digital computer controls a digital tuner, a TLO, a FLO, and an IF unit to provide the RF hopping and to provide digital-tuner frequency hopping and IF hopping thereby enabling the frequency hopping of transmitted leakage digital tuner and IF signals.
Owner:NORTHROP GRUMMAN SYST CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com