Patents
Literature
5010 results about "Wireless access point" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
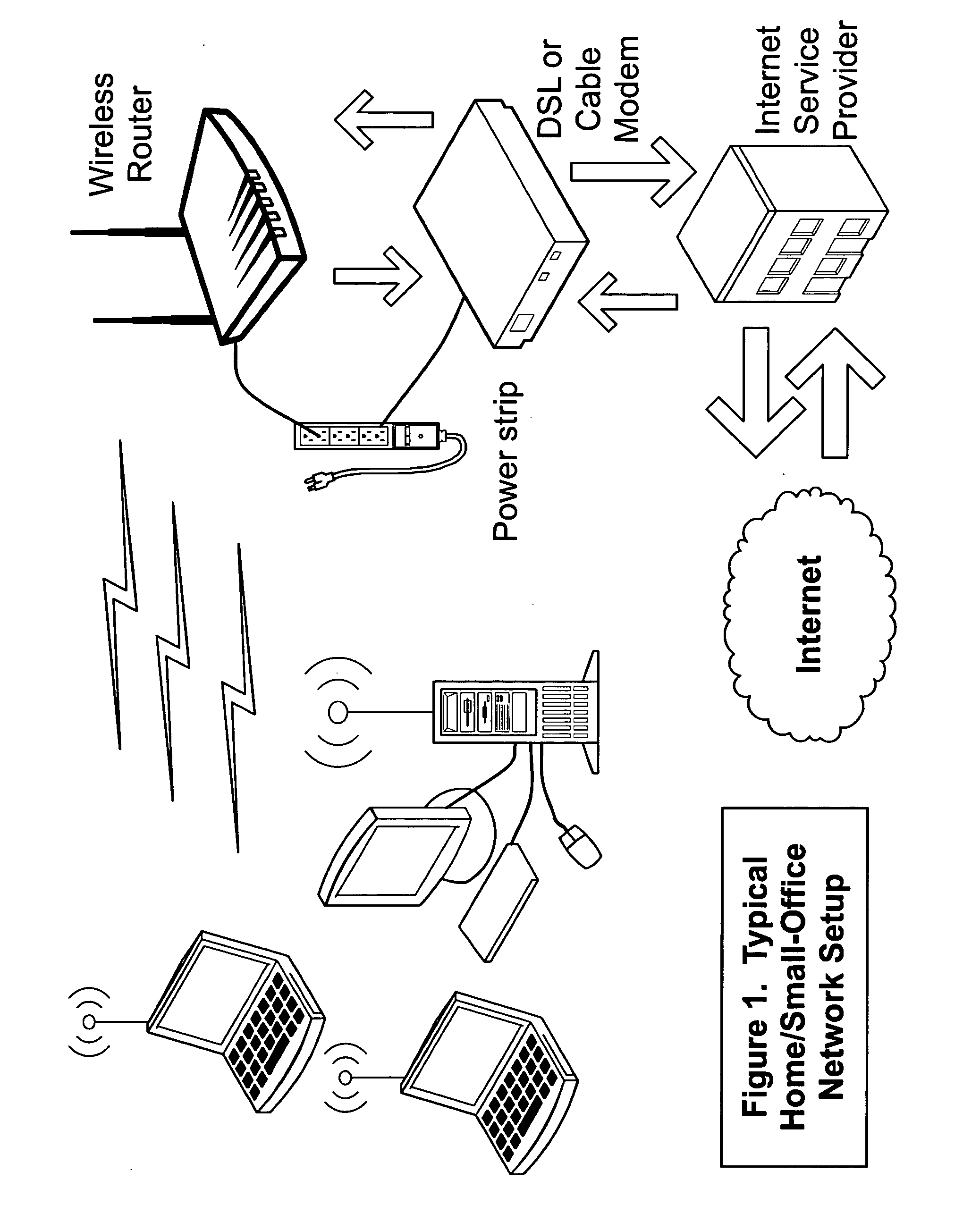
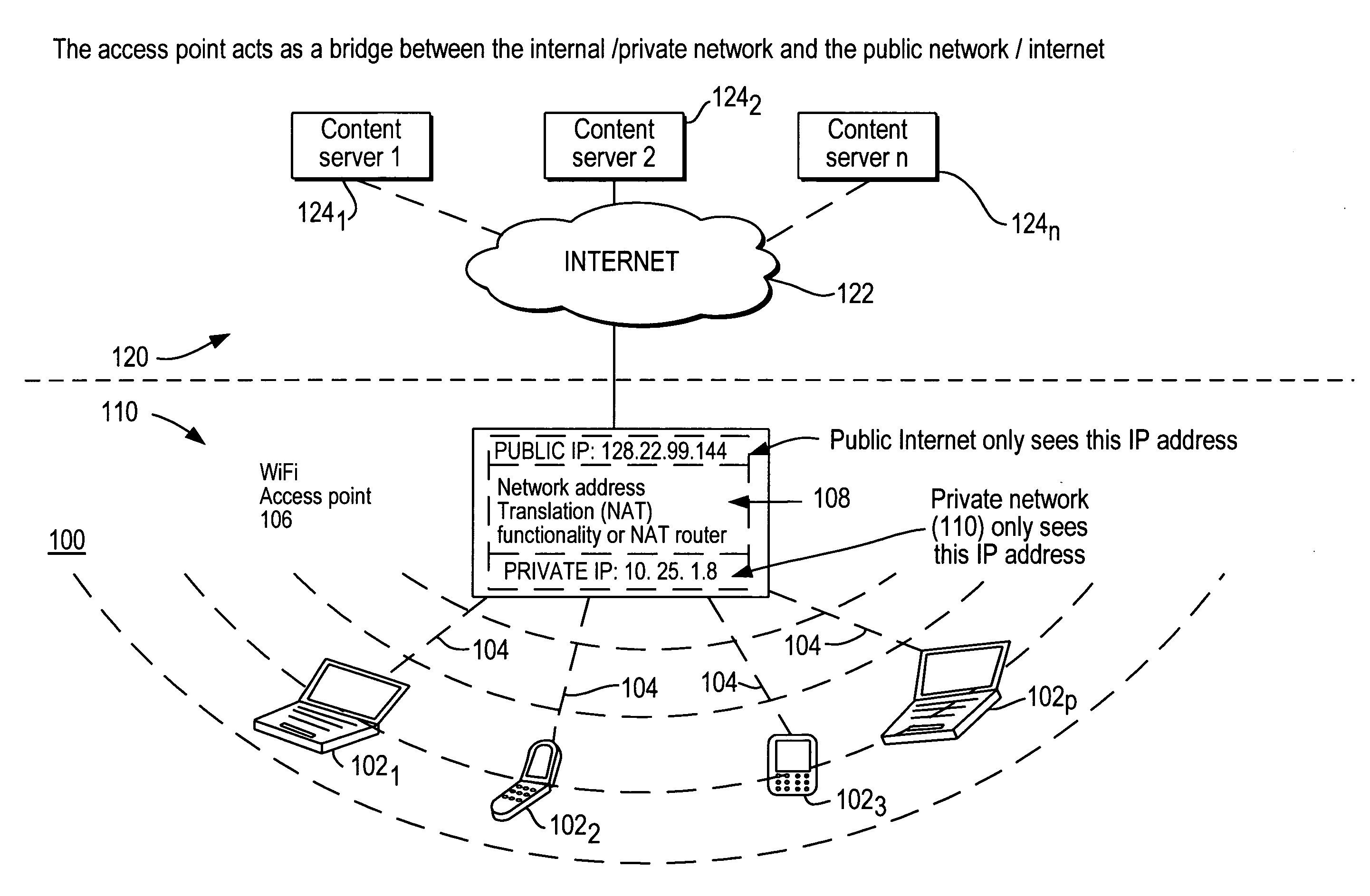
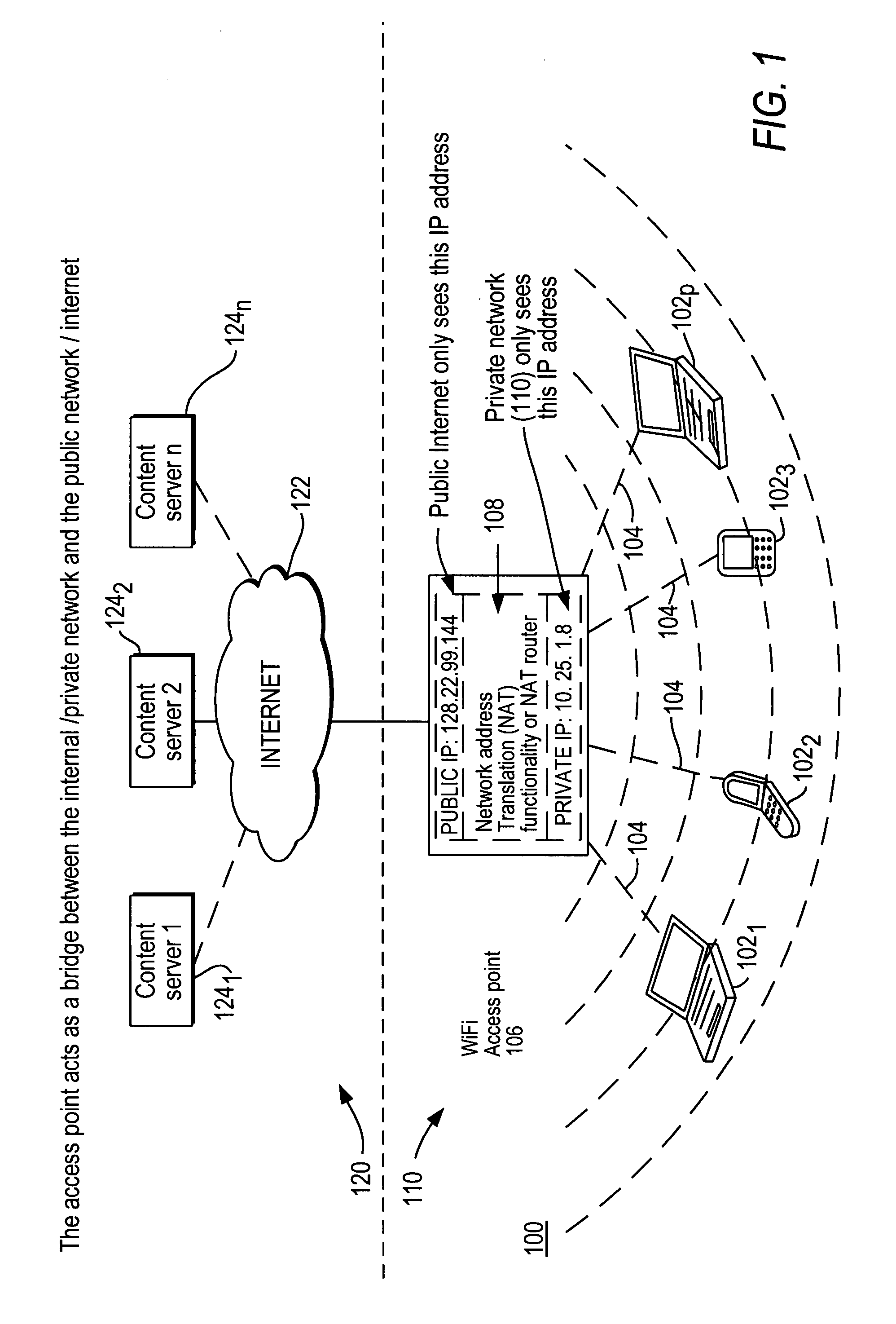
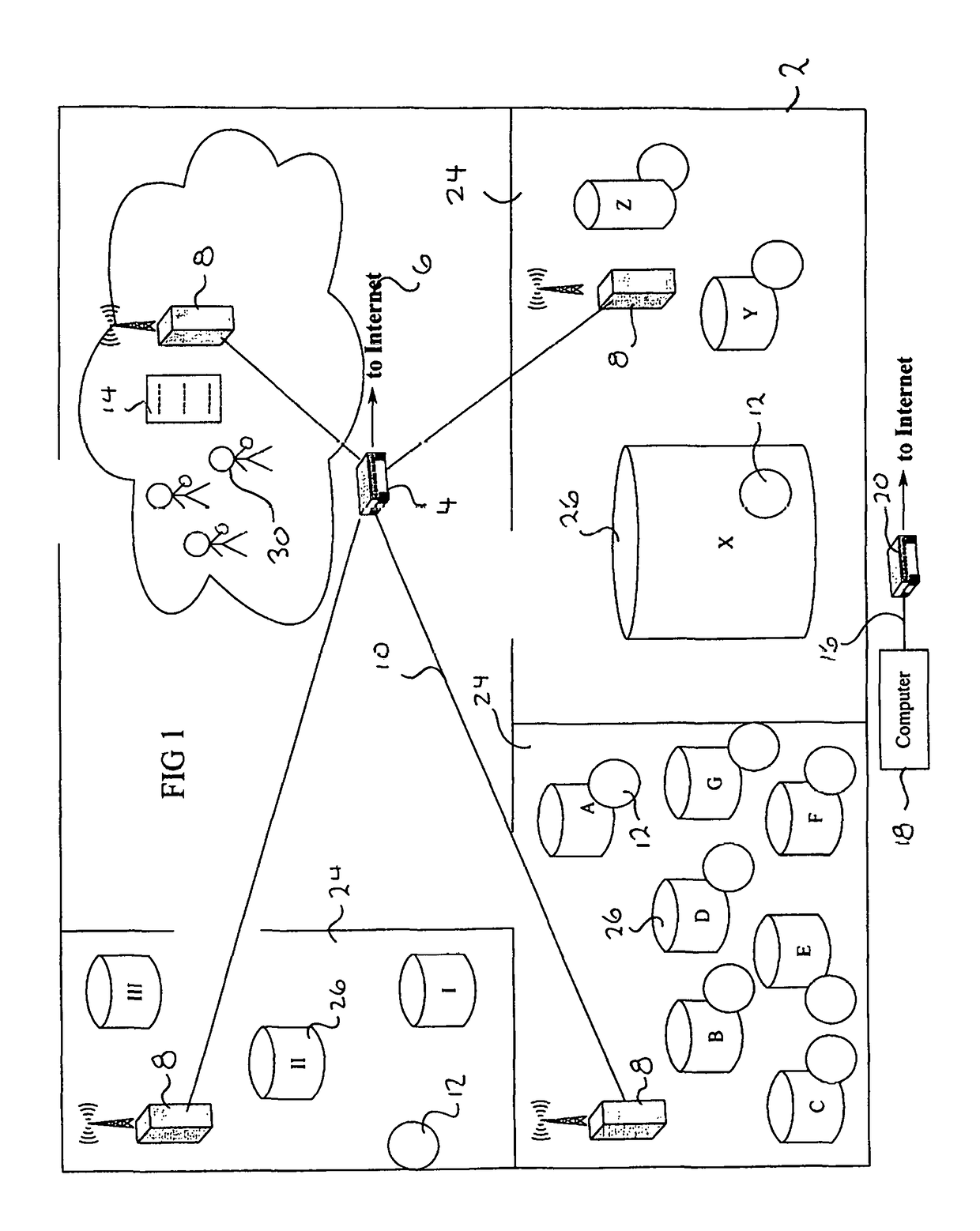
In computer networking, a wireless access point (WAP), or more generally just access point (AP), is a networking hardware device that allows other Wi-Fi devices to connect to a wired network. The AP usually connects to a router (via a wired network) as a standalone device, but it can also be an integral component of the router itself. An AP is differentiated from a hotspot, which is the physical location where Wi-Fi access to a WLAN is available.
Power receptacle wireless access point devices for networked living and work spaces
Owner:UBIQUITI INC
Systems, devices, agents and methods for monitoring and automatic reboot and restoration of computers, local area networks, wireless access points, modems and other hardware
ActiveUS20090013210A1Data switching networksRedundant operation error correctionDomain nameFully qualified domain name
An embodiment of the invention is a client on a local area network that periodically and automatically evaluates its physical connectivity with the local area network, exercises local-network services such as DHCP, and verifies Internet connectivity and function by pinging one or more numerically specified IP addresses and by pinging one or more IP addresses specified by an FQDN (Fully Qualified Domain Name) known to the assigned DNS servers. An embodiment of the invention may include a plurality of client elements monitoring one or more networks. Functionality according to embodiments of the invention can send notices, automatically initiate action, and otherwise assist in, among other things, remote monitoring and administration of networks, and particularly wireless networks.
Owner:SAND HLDG LLC
Method and system for managing data traffic in wireless networks
ActiveUS7042988B2Facilitate secure integrationExtensive controlError preventionUnauthorised/fraudulent call preventionWireless mesh networkNetwork architecture
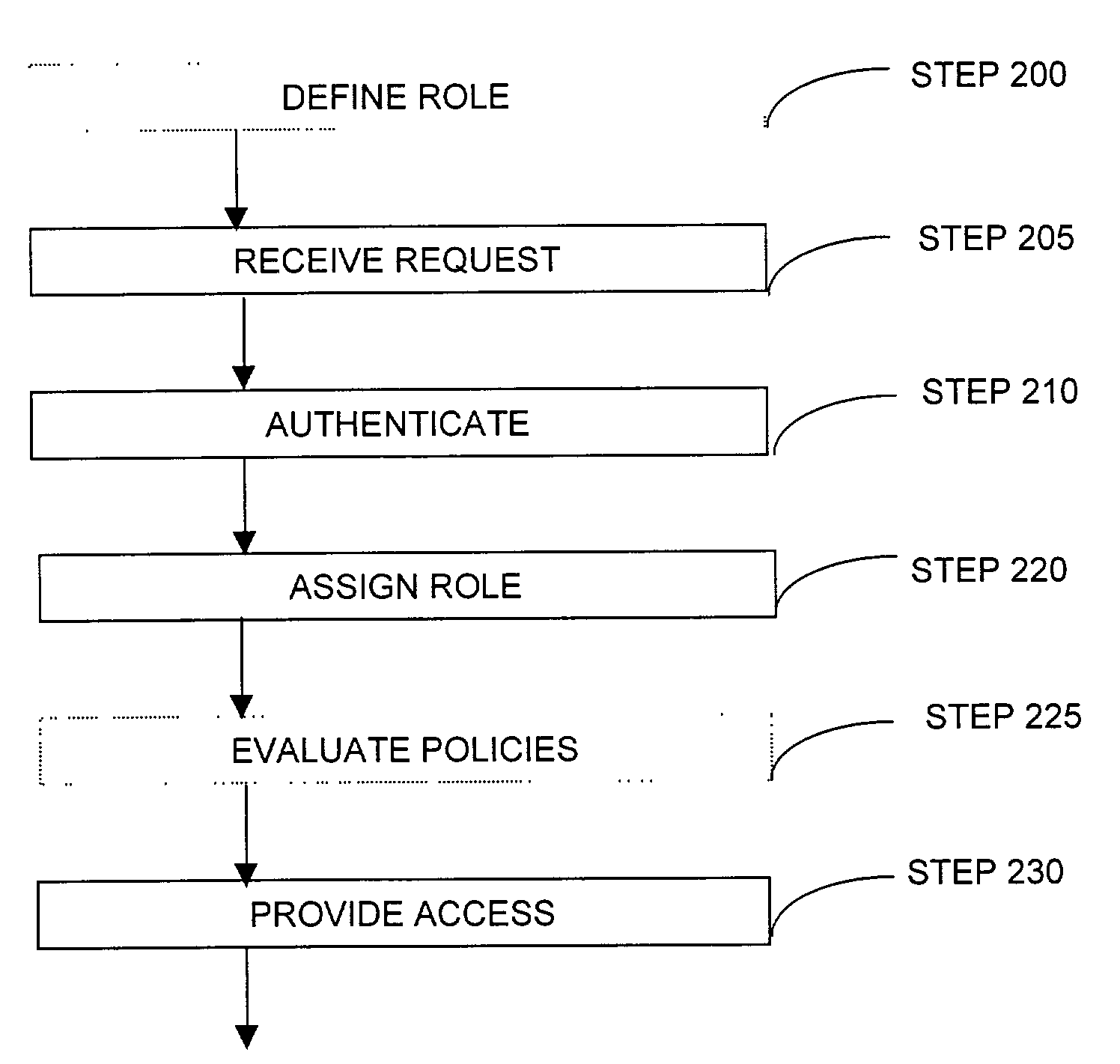
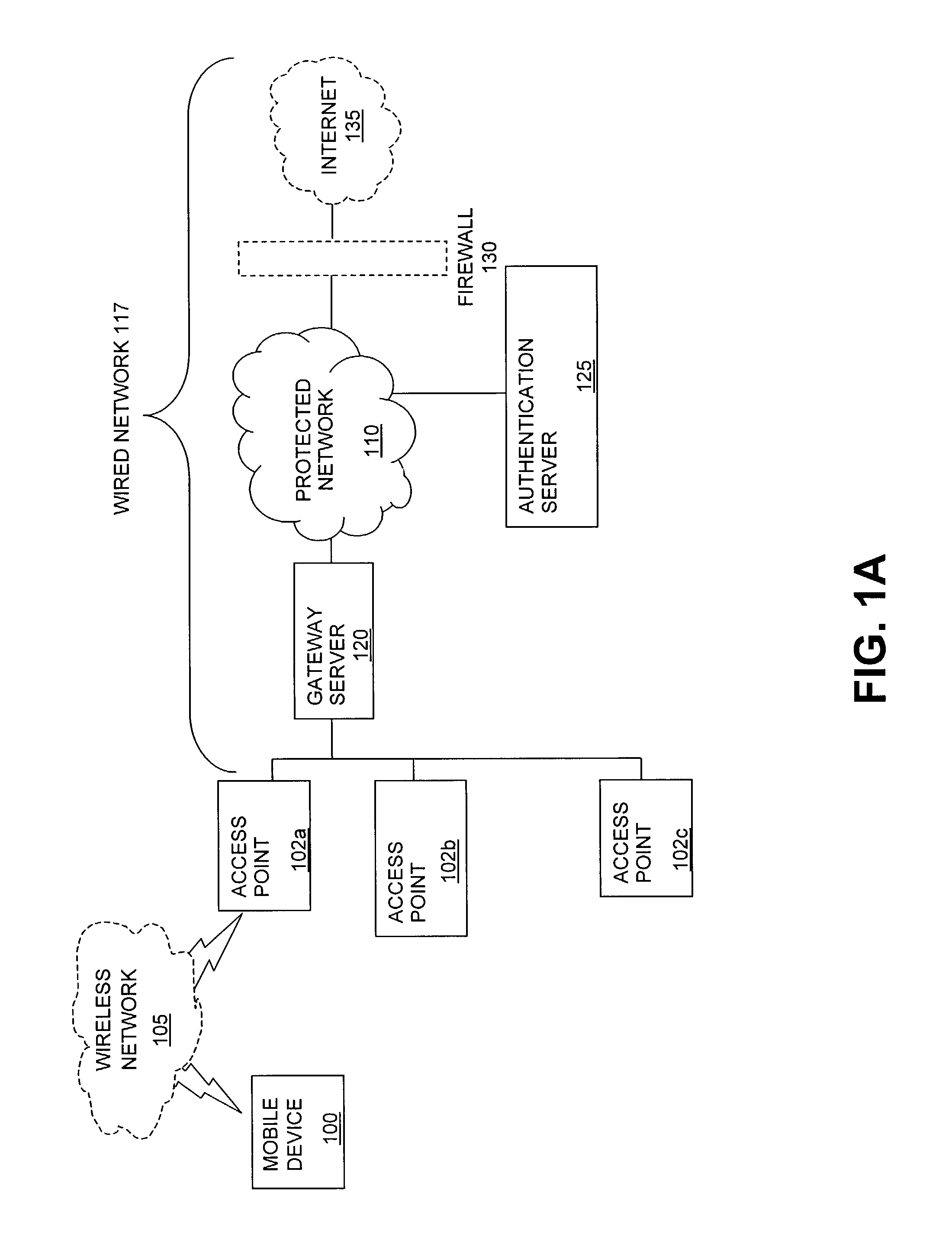
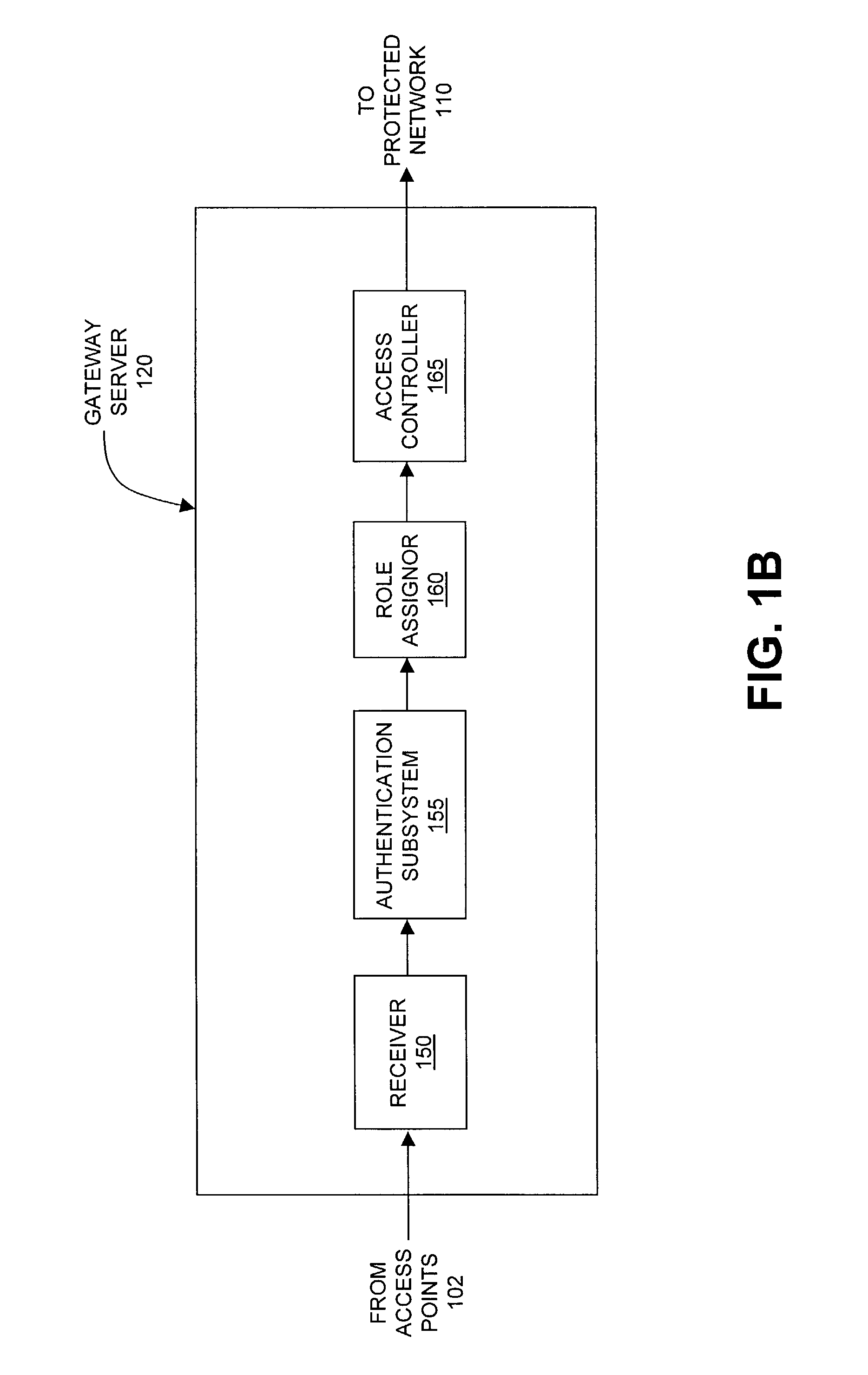
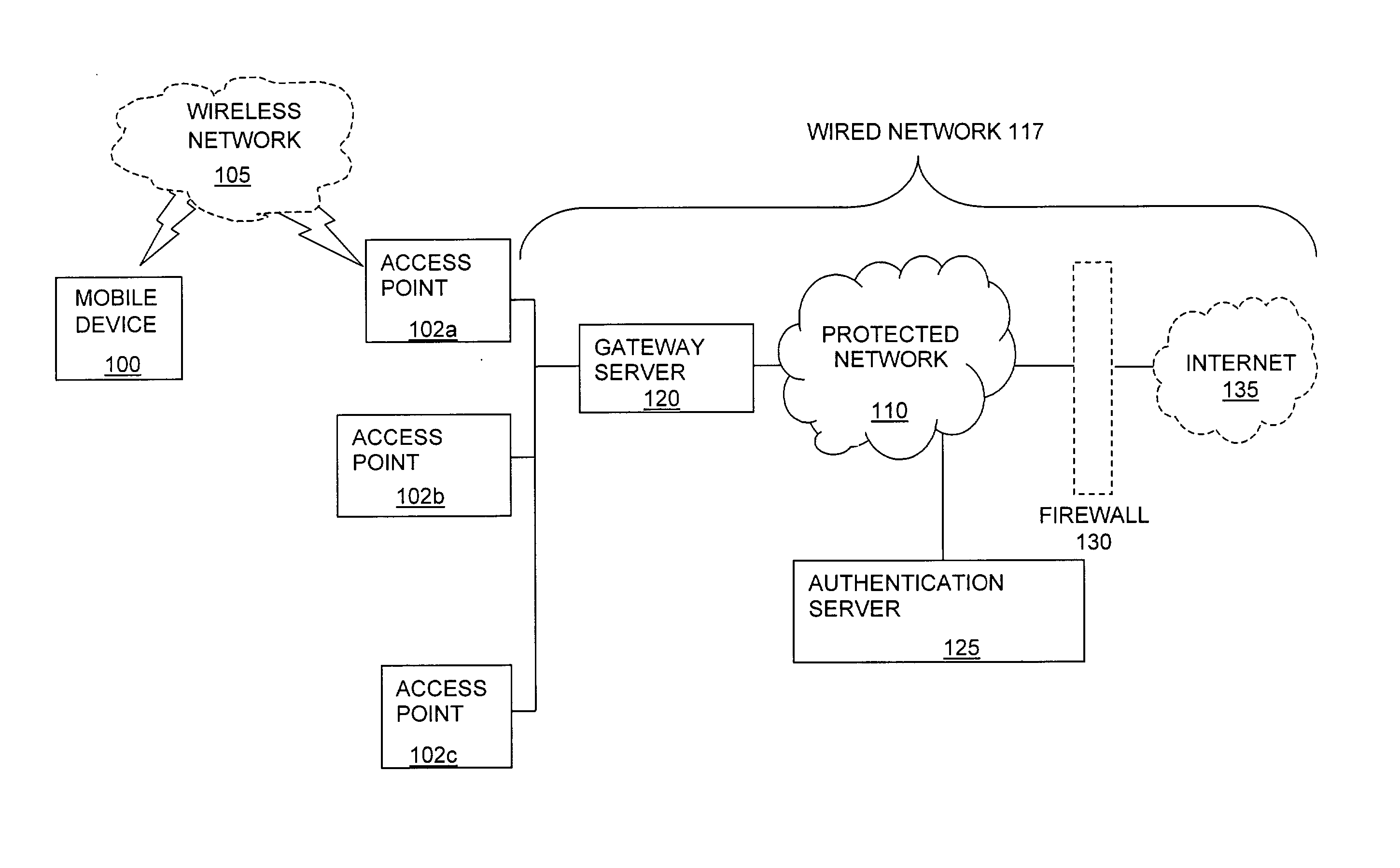
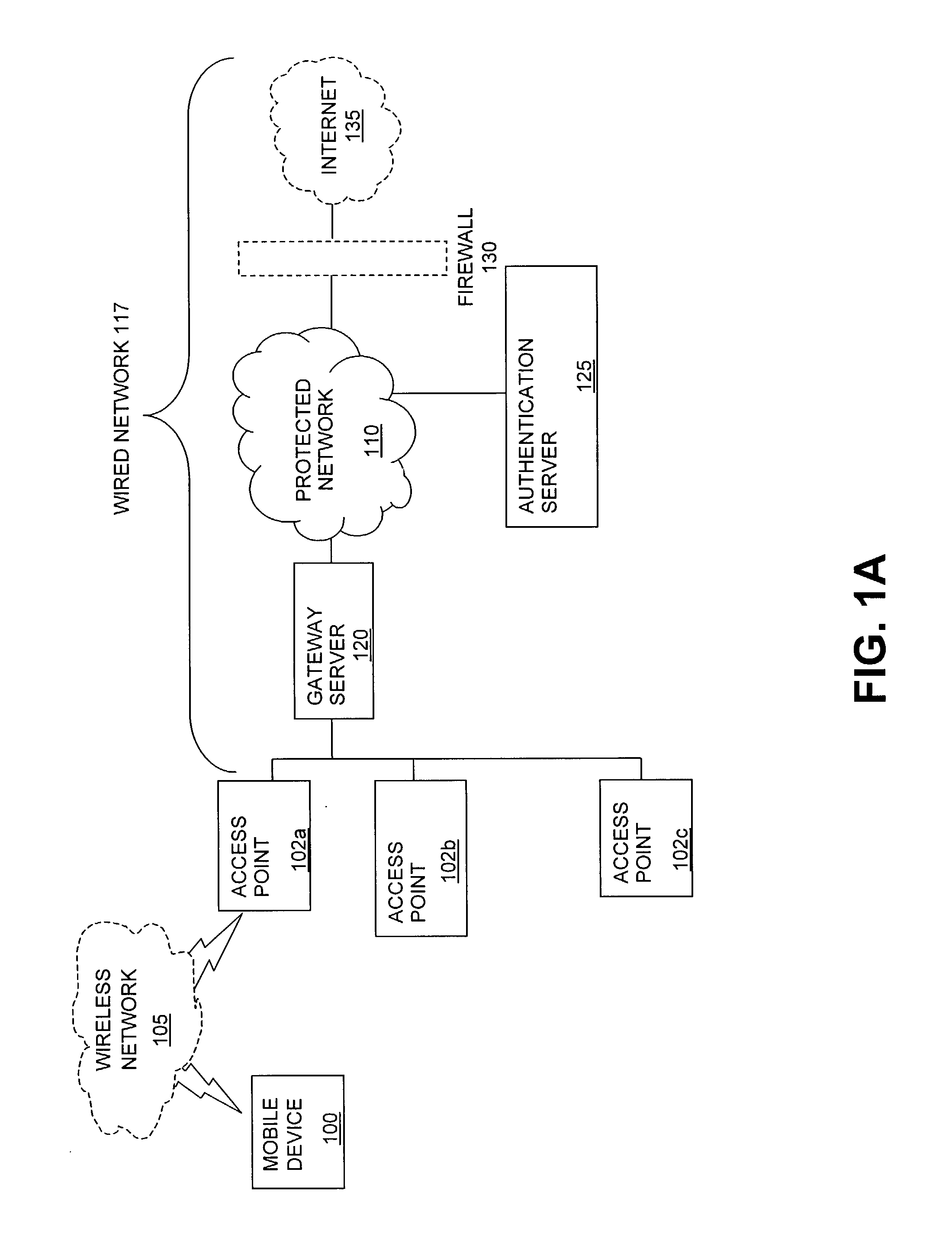
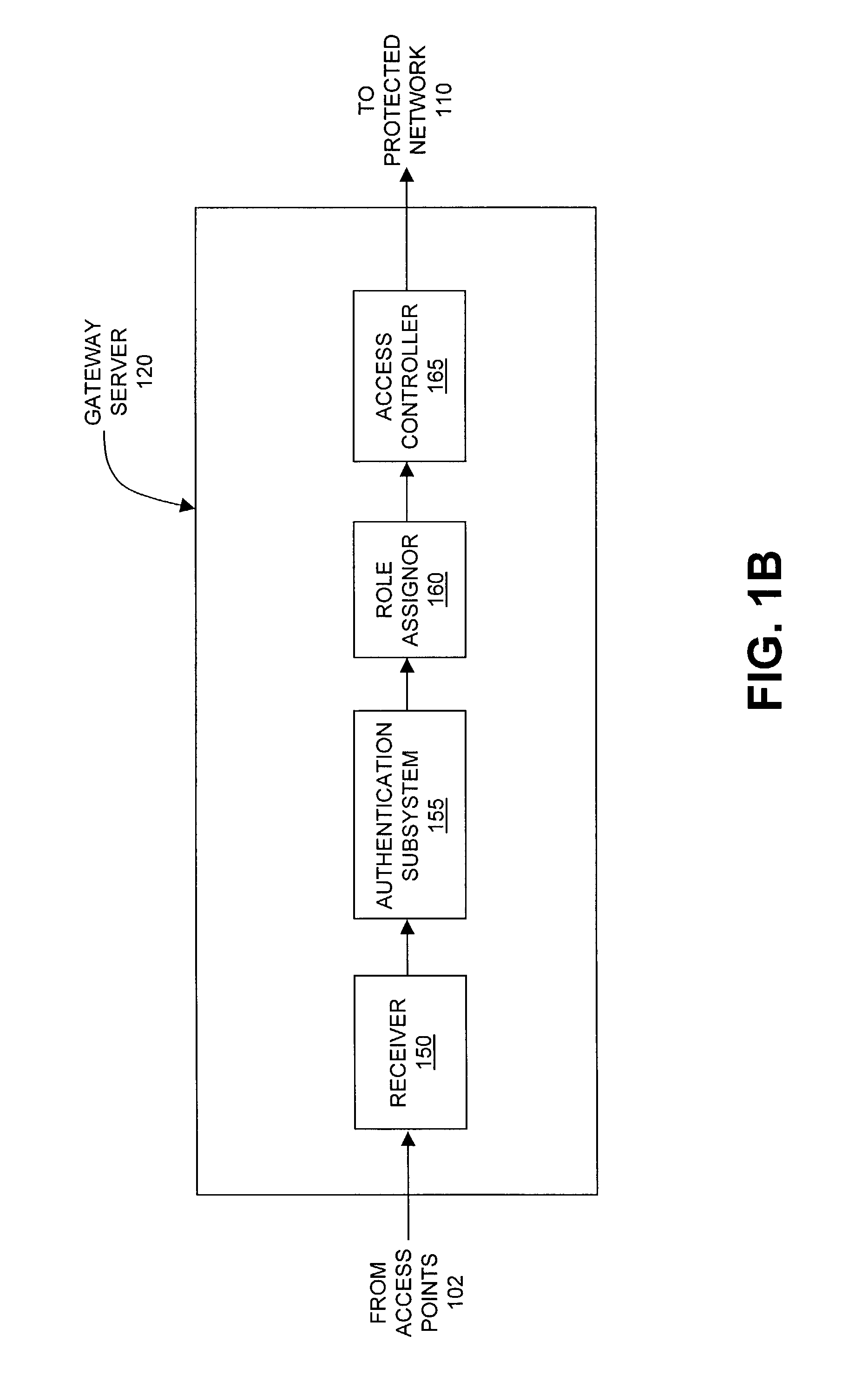
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
Method and system for managing data traffic in wireless networks
ActiveUS20030087629A1Reduce capacityEasy networkingError preventionUnauthorised/fraudulent call preventionEnterprise computingNetwork architecture
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
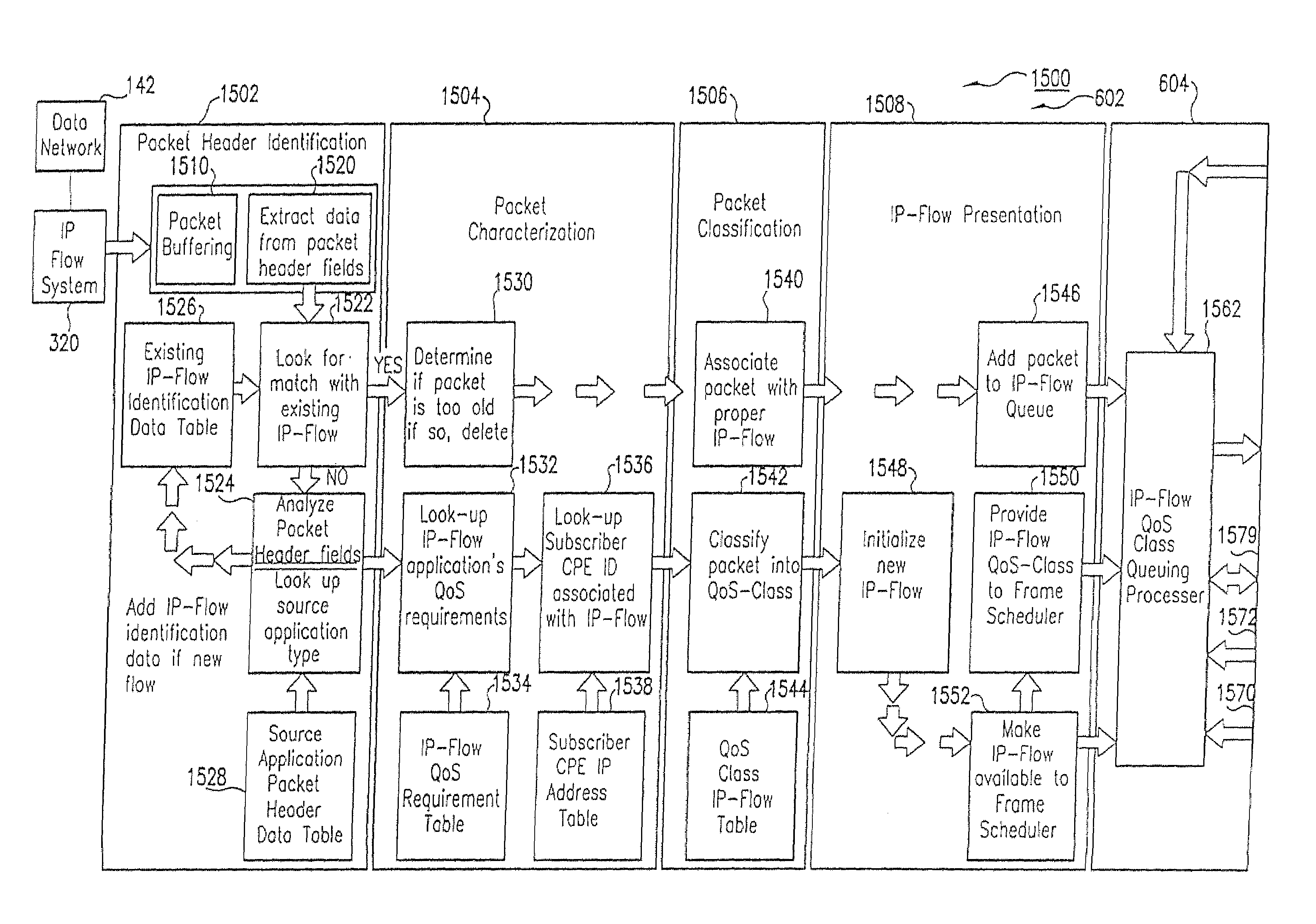
Method and computer program product for internet protocol (IP)-flow classification in a wireless point to multi-point (PtMP) transmission system
InactiveUS7251218B2Special service provision for substationError detection/prevention using signal quality detectorQuality of serviceWireless access point
A system and method for Internet Protocol (IP) flow classification group IP flows in a packet-centric wireless point to multi-point telecommunications system is disclosed. The method comprises analyzing an IP flow in a packet-centric manner, classifying the IP flow, scheduling the IP flow for transmission over a shared wireless bandwidth between a wireless base station and at least one subscriber customer premises equipment (CPE) station, allocating the shared wireless bandwidth to a communication of the IP flow between the wireless base station and a subscriber CPE station so as to optimize end-user quality of service (QoS) associated with the IP flow.
Owner:INTELLECTUAL VENTURES I LLC
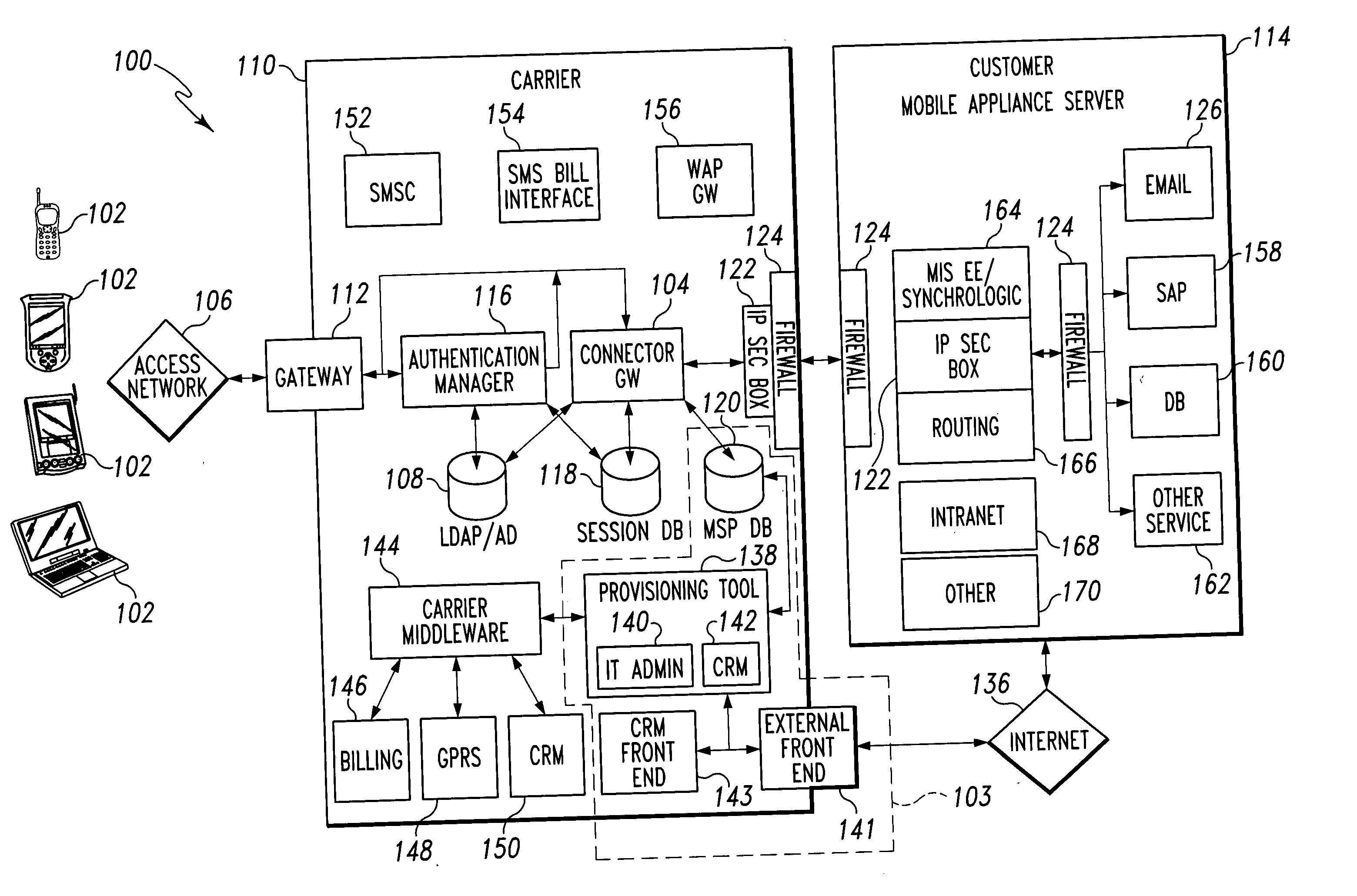
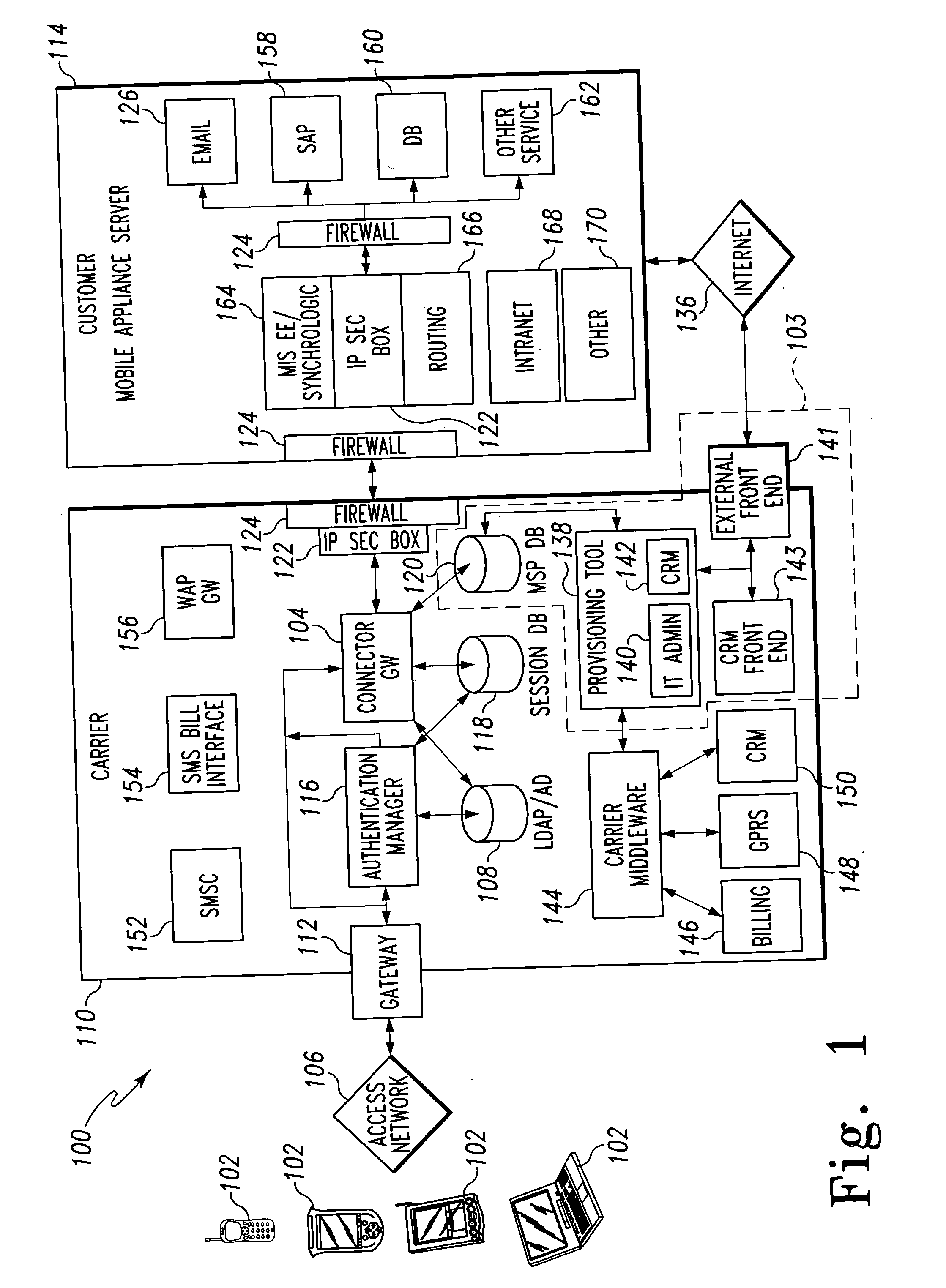
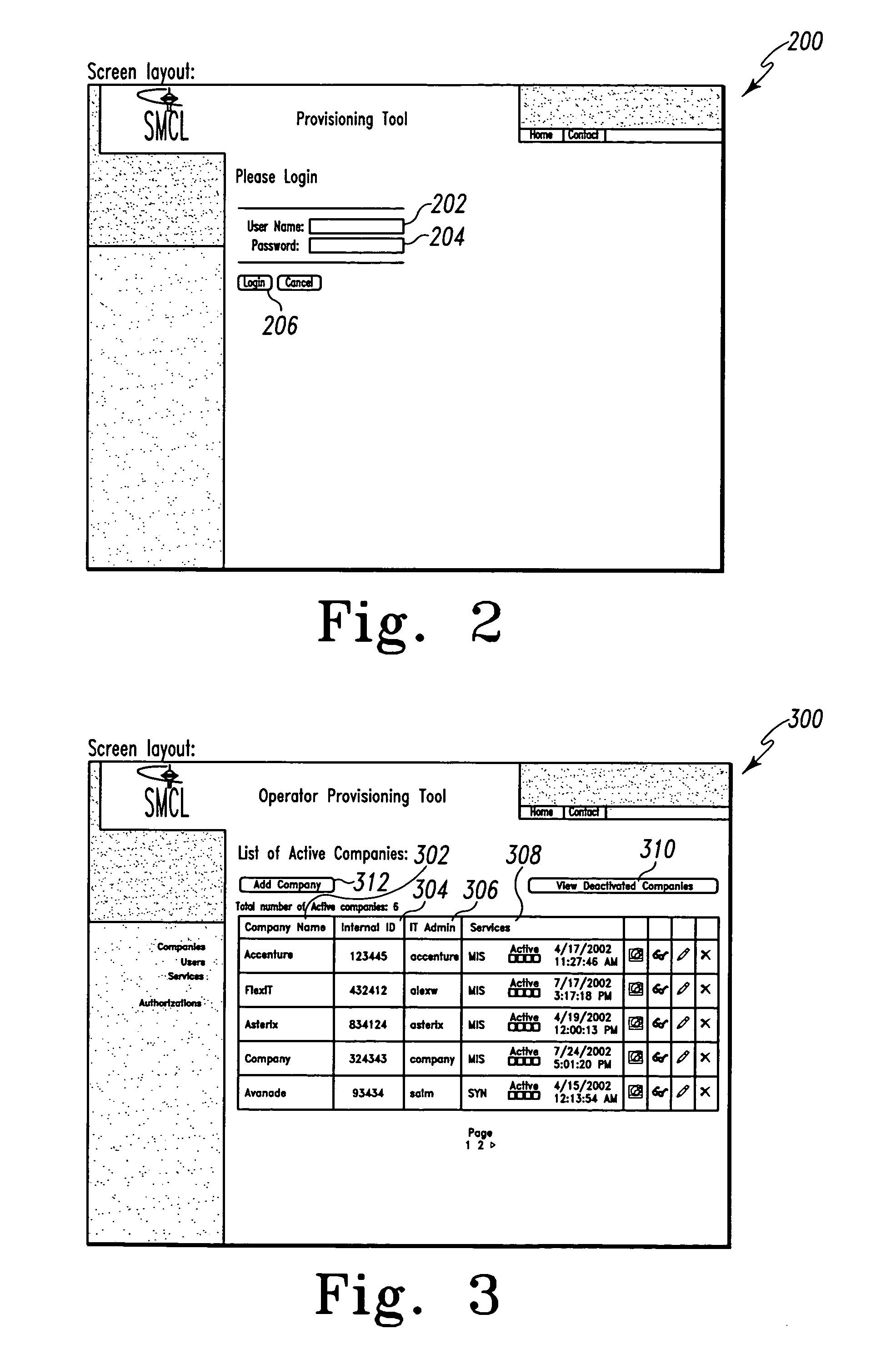
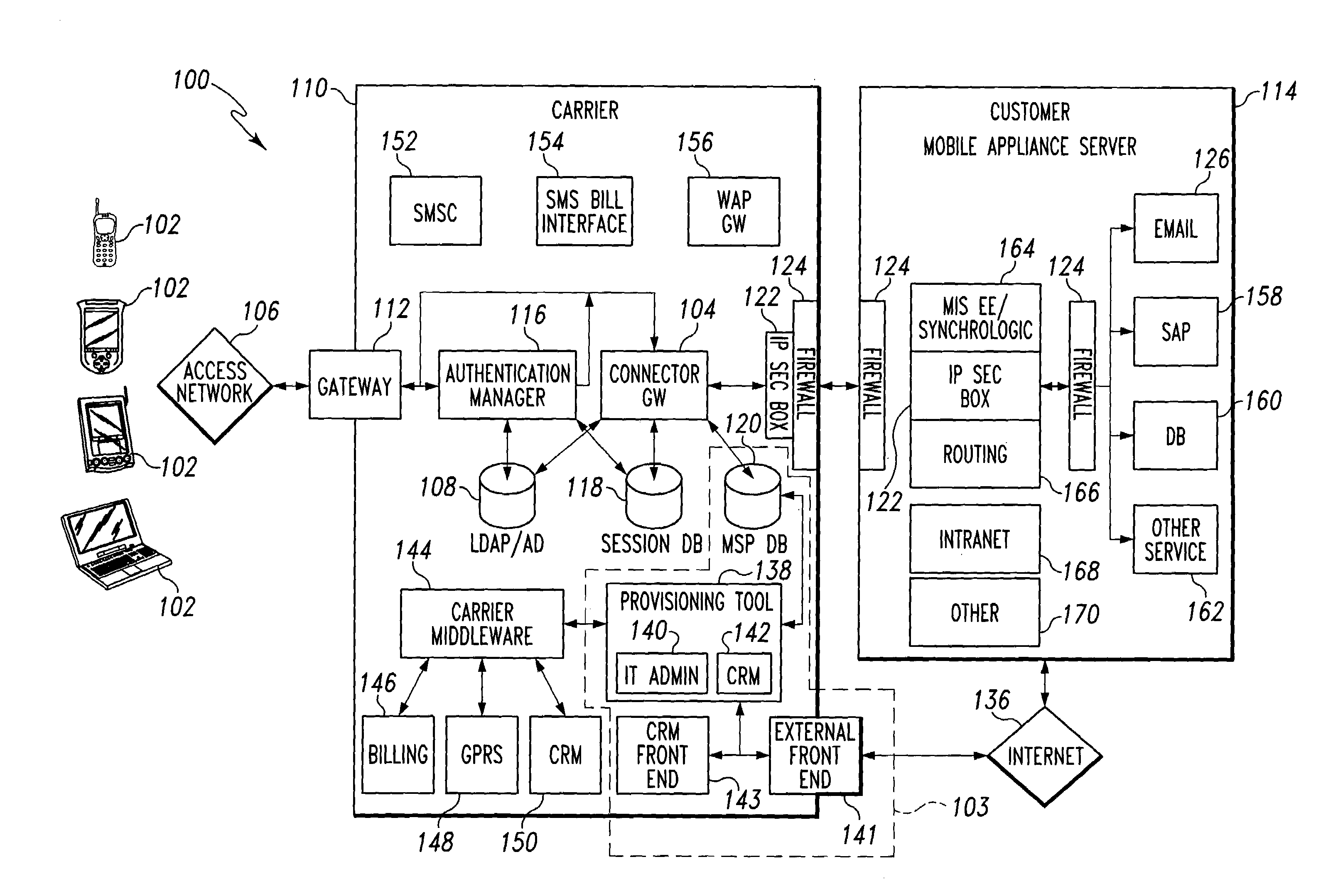
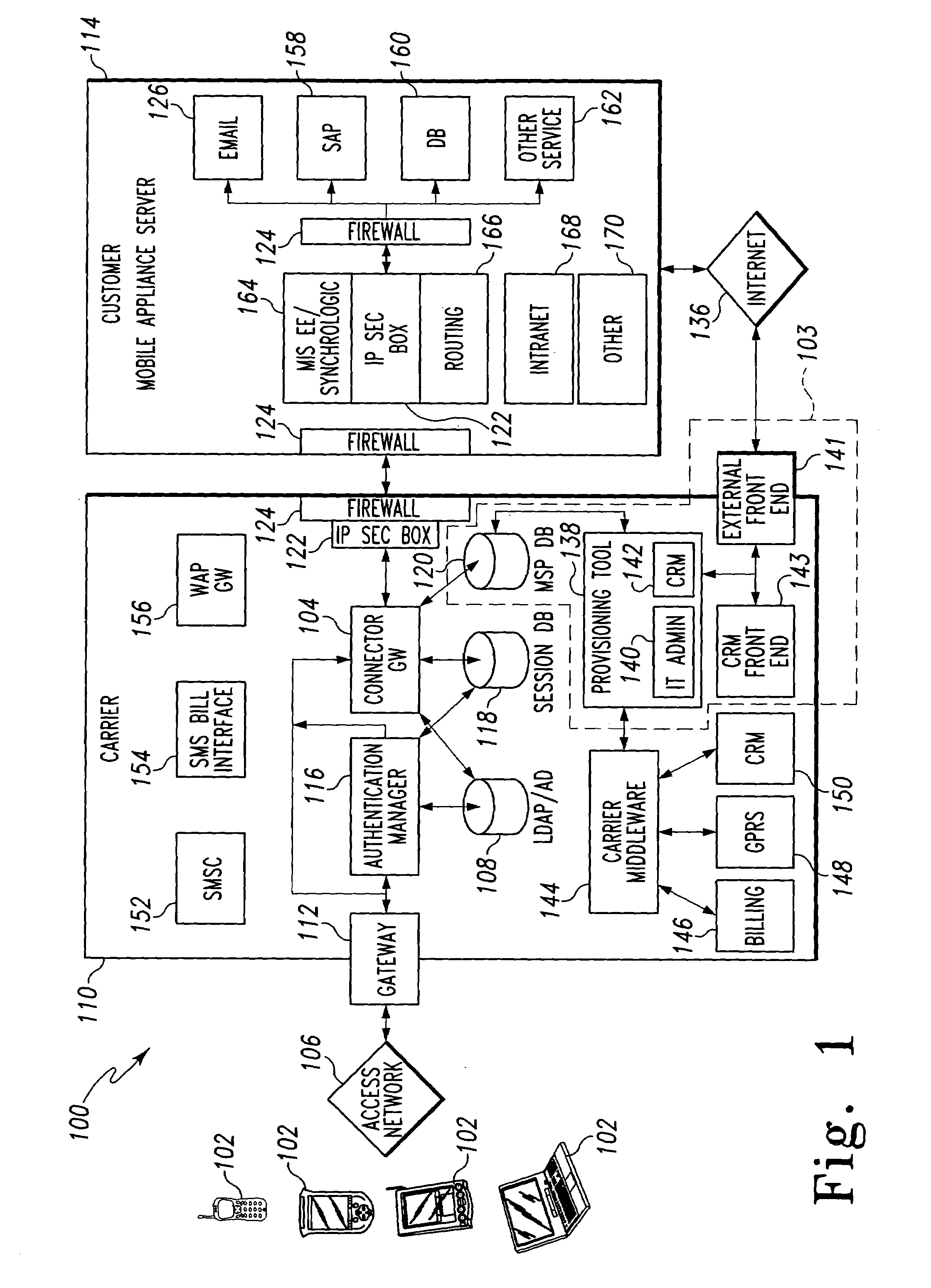
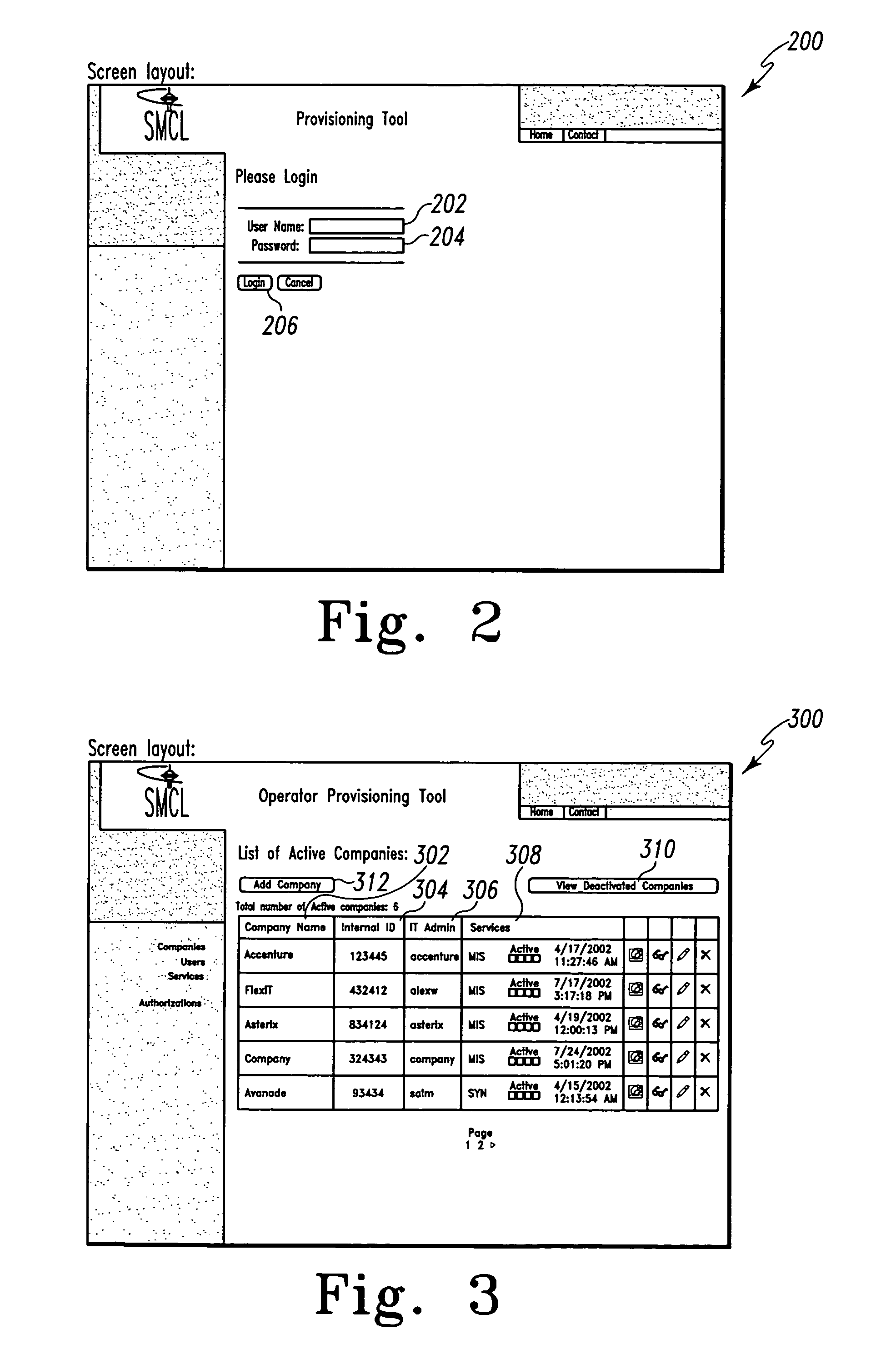
Mobile provisioning tool system
ActiveUS20050075115A1Simple processLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessWorkstation
A mobile provisioning tool system including a software provisioning tool application. The mobile provisioning tool system includes mobile devices capable of conducting wireless communication with wireless access points. A carrier network is connected with the wireless access points and a customer network that includes at least one business application. A provisioning tool application is located on a provisioning server. The provisioning tool application includes a CRM Rep component and an IT Admin component. A software provisioning tool application allows the provisioning workstation to automatically install mobile business services and configure network configuration settings on the mobile device.
Owner:ACCENTURE GLOBAL SERVICES LTD
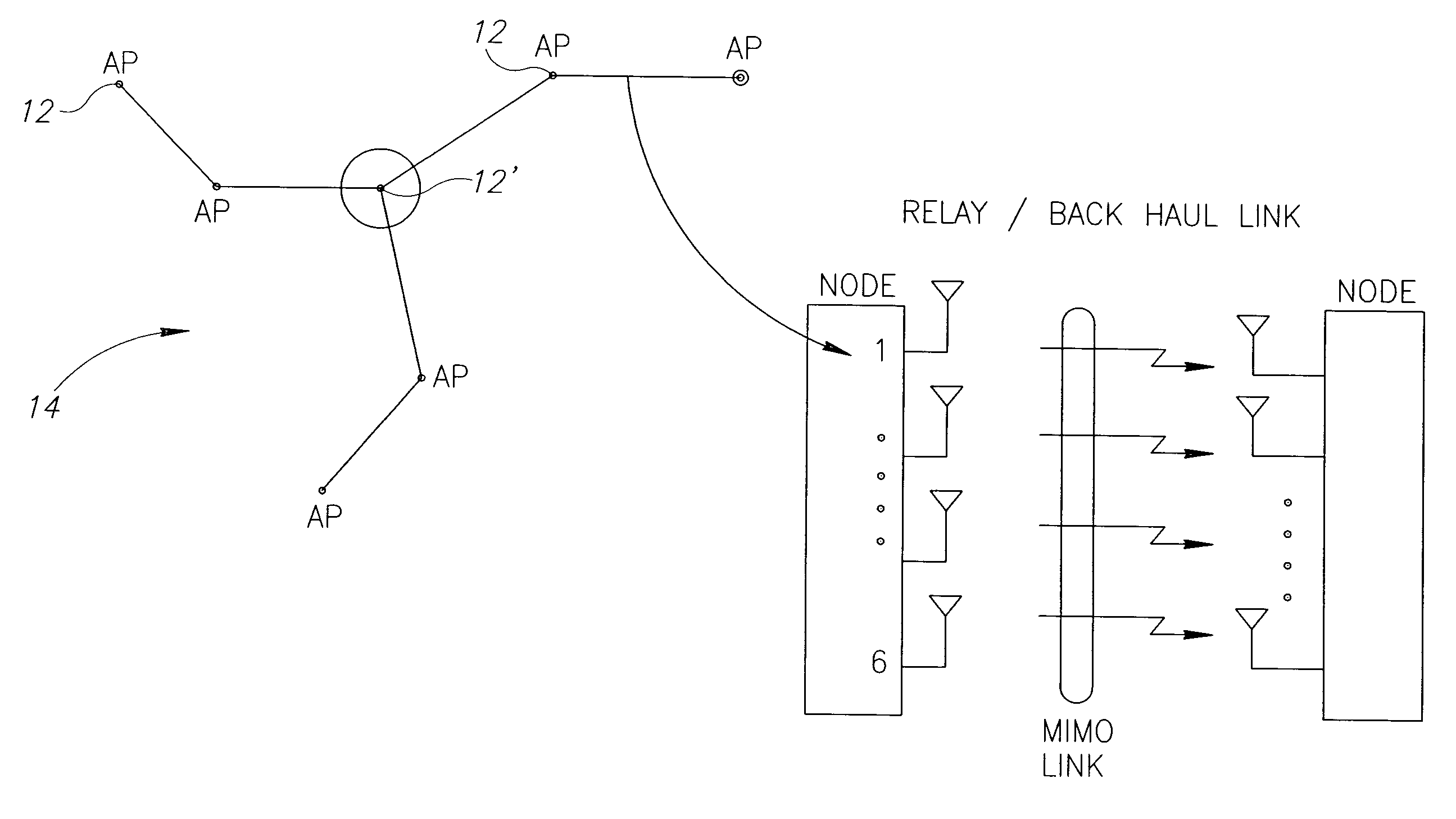
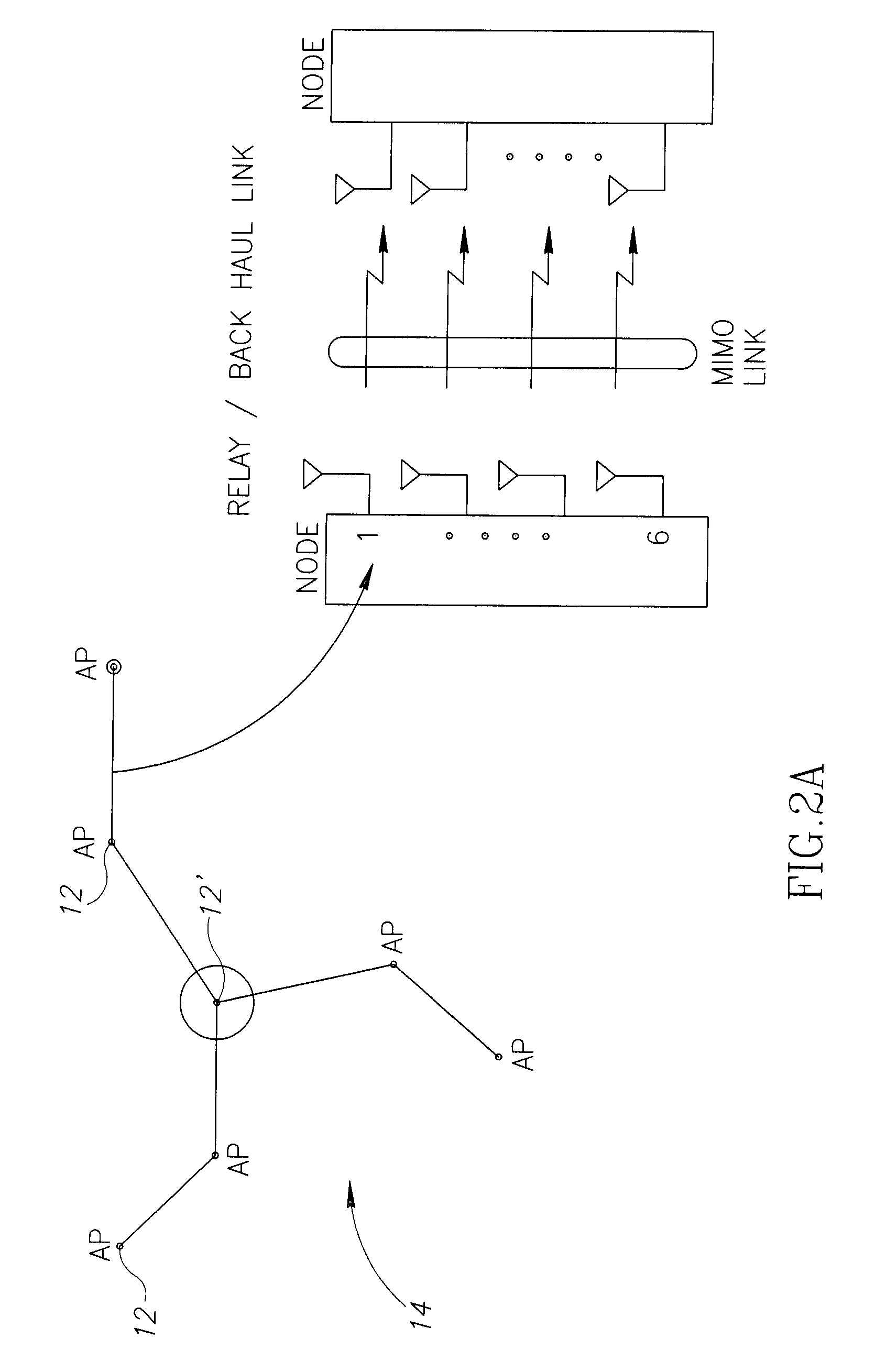
Mobile broadband wireless access point network with wireless backhaul
ActiveUS7620370B2Low costLarge capacityPower managementNetwork traffic/resource managementTransceiverModem device
A WiMAX network and communication method, the network including a plurality of WiMAX nodes deployed in micro or pico cells for providing access service to a plurality of mobile subscribers, a plurality of these nodes being arranged in a cluster, one of the nodes in each cluster being a feeder node coupled to a core network, the nodes in each cluster being coupled for multi-hop transmission to the feeder node. According to a preferred embodiment, each node includes a transceiver with associated modem, an antenna arrangement coupled to the modem and arranged for multiple concurrent transmissions, and a MAC controller for controlling the transceiver, modem and antenna arrangement for providing both access and backhaul communication.
Owner:QUALCOMM INC
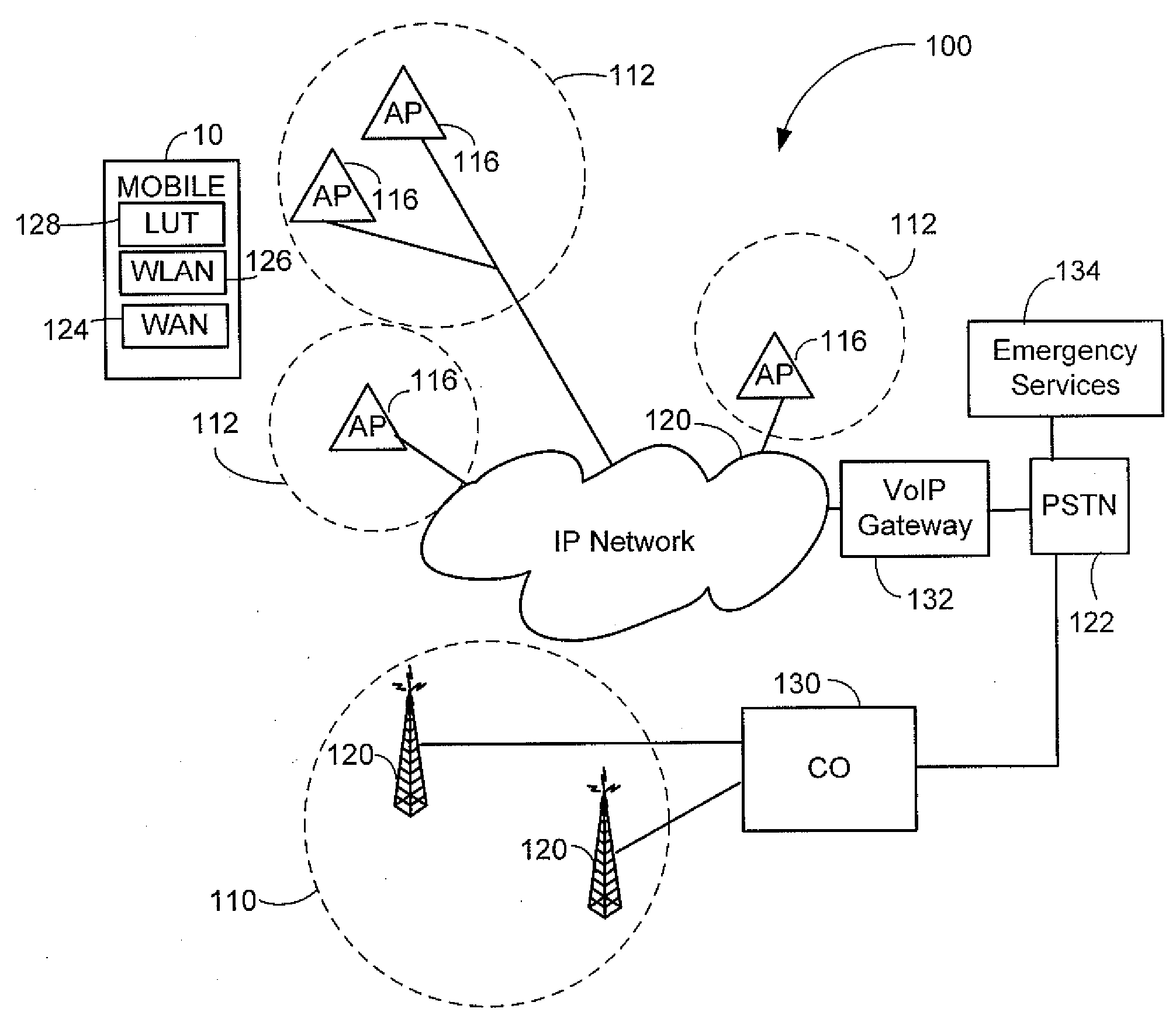
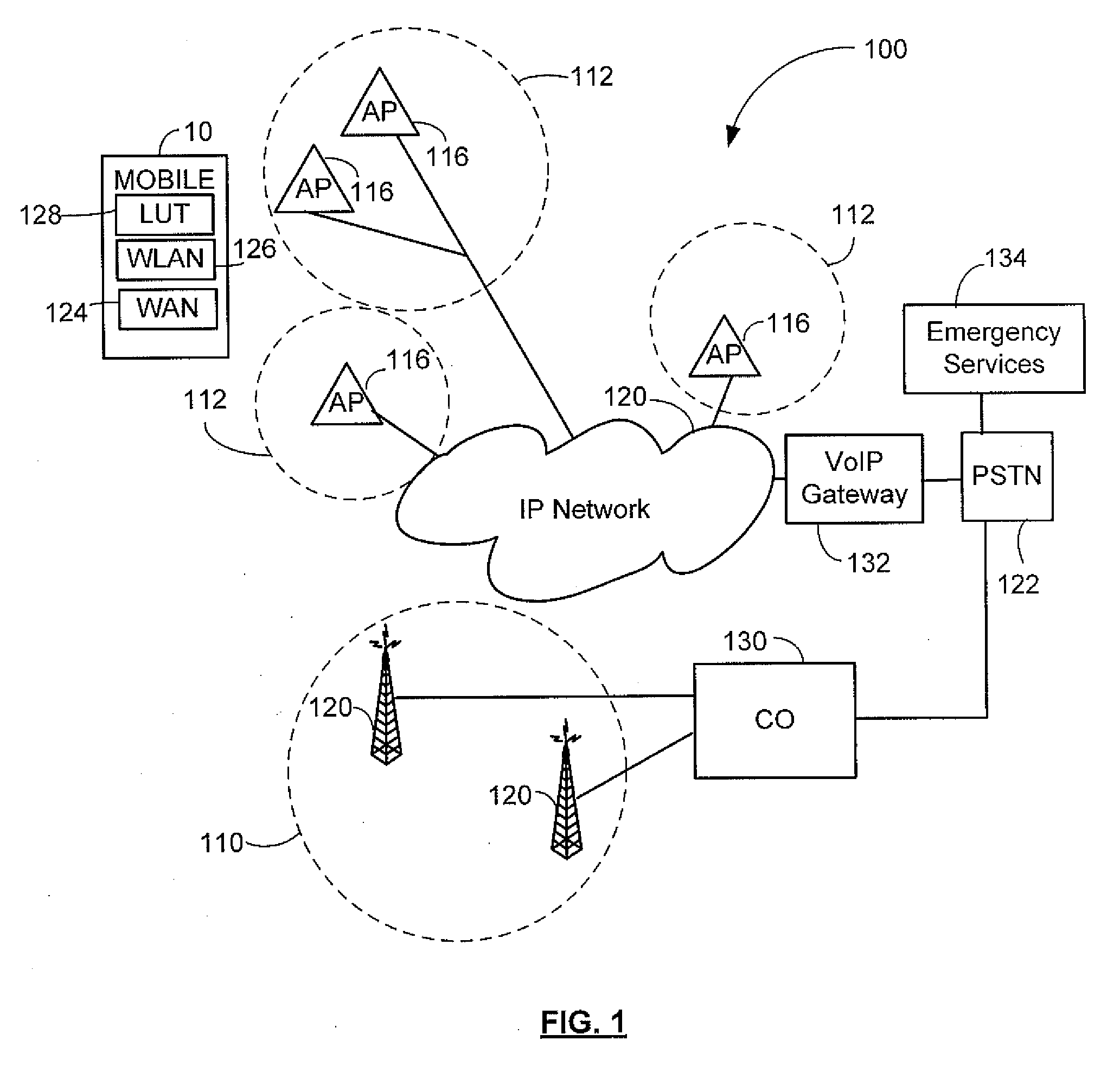
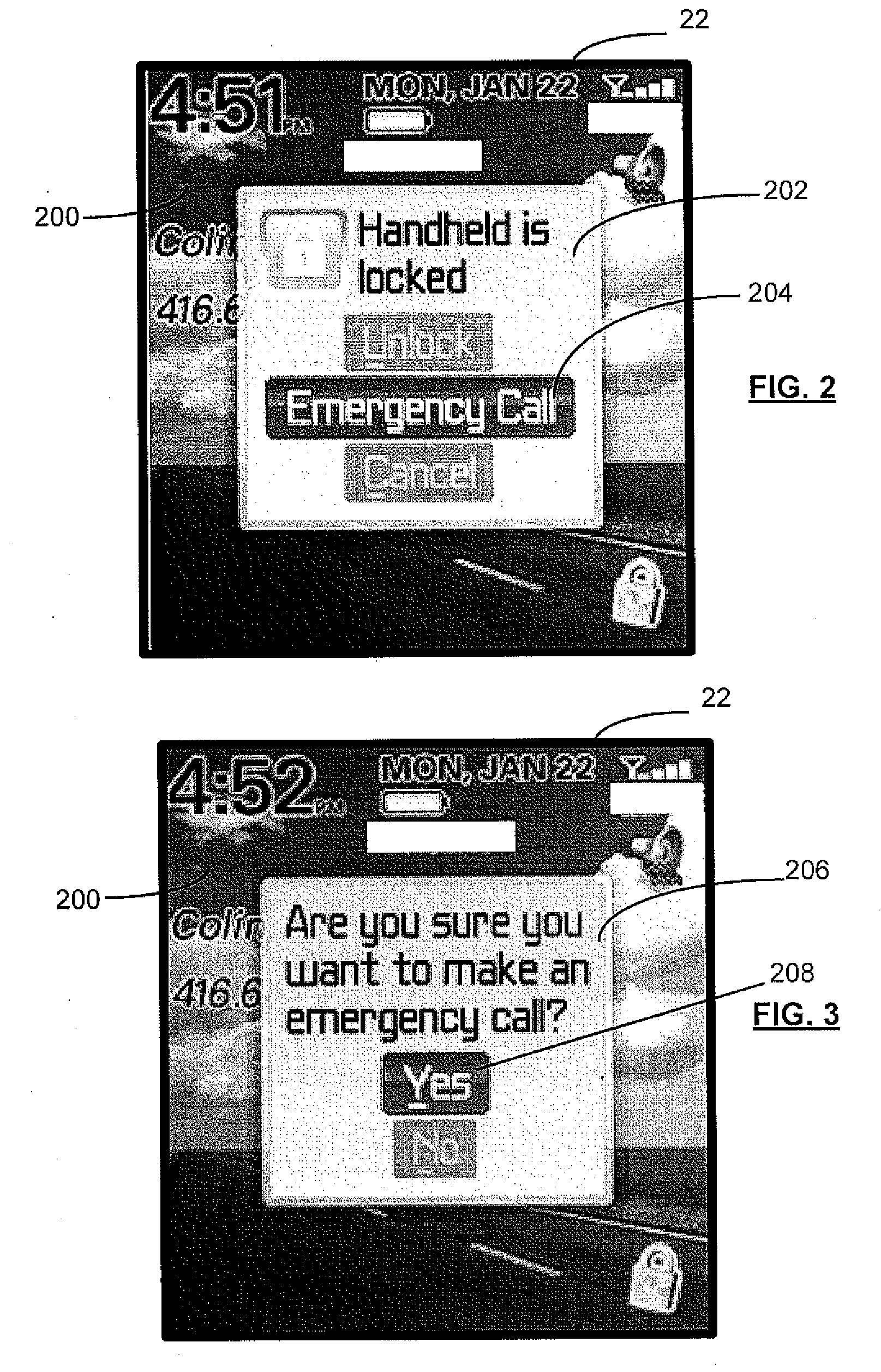
Emergency number selection for mobile communications device
ActiveUS20080200142A1Devices with wireless LAN interfaceSubstation equipmentTelecommunicationsBeacon frame
Automatically selecting an emergency number for use by a mobile communications device enabled for Voice Over Internet Protocol (VoIP) communications, including: receiving at the mobile communications device a geographic indicator in a beacon frame transmitted from a wireless access point of a wireless local area network that is connected to an Internet Protocol network; and determining from a plurality of emergency numbers stored in a storage element of the mobile communications device a selected emergency number in dependence on the received geographic indicator.
Owner:MALIKIE INNOVATIONS LTD
Provisioning and controlling medical instruments using wireless data communication
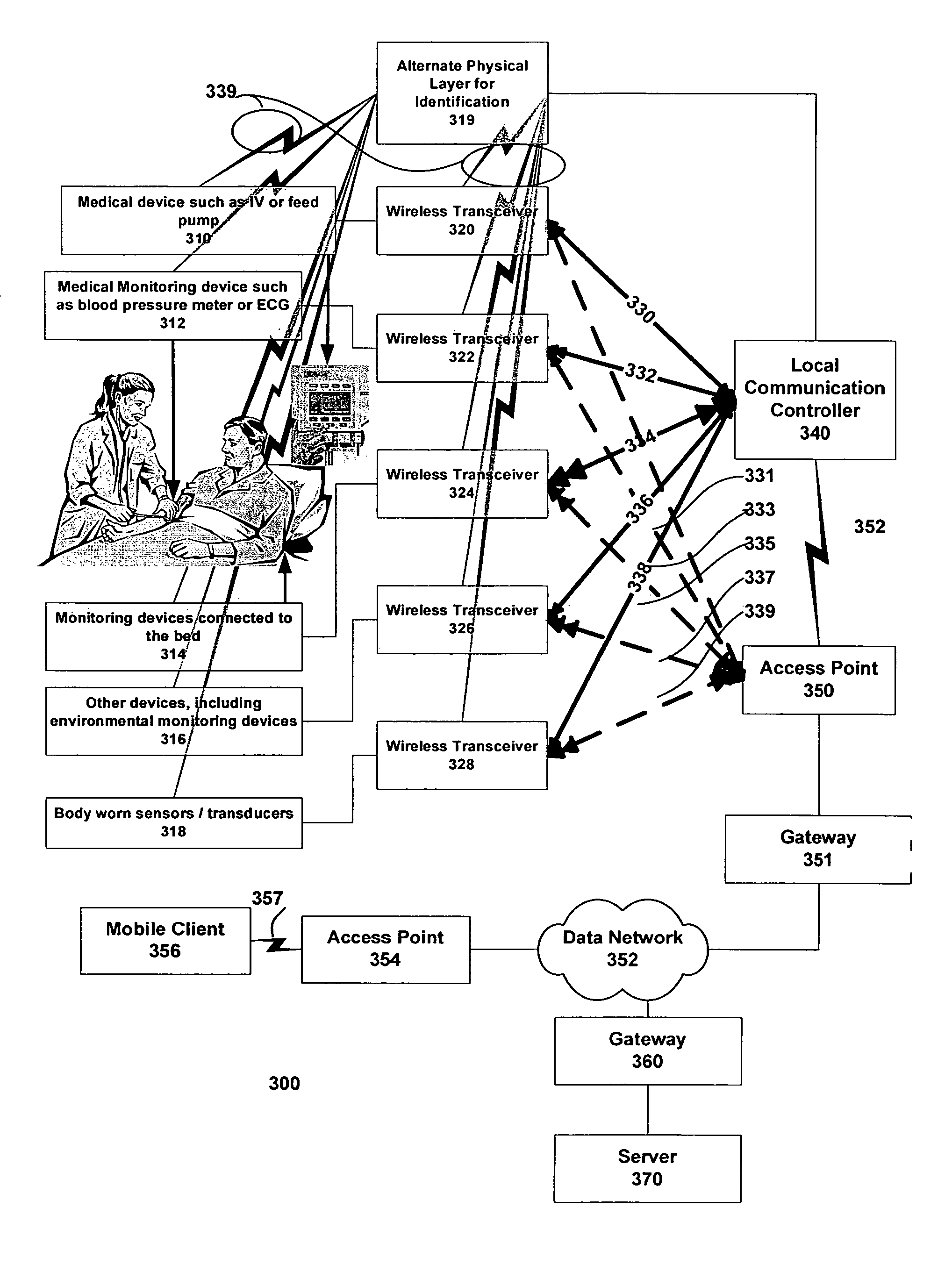
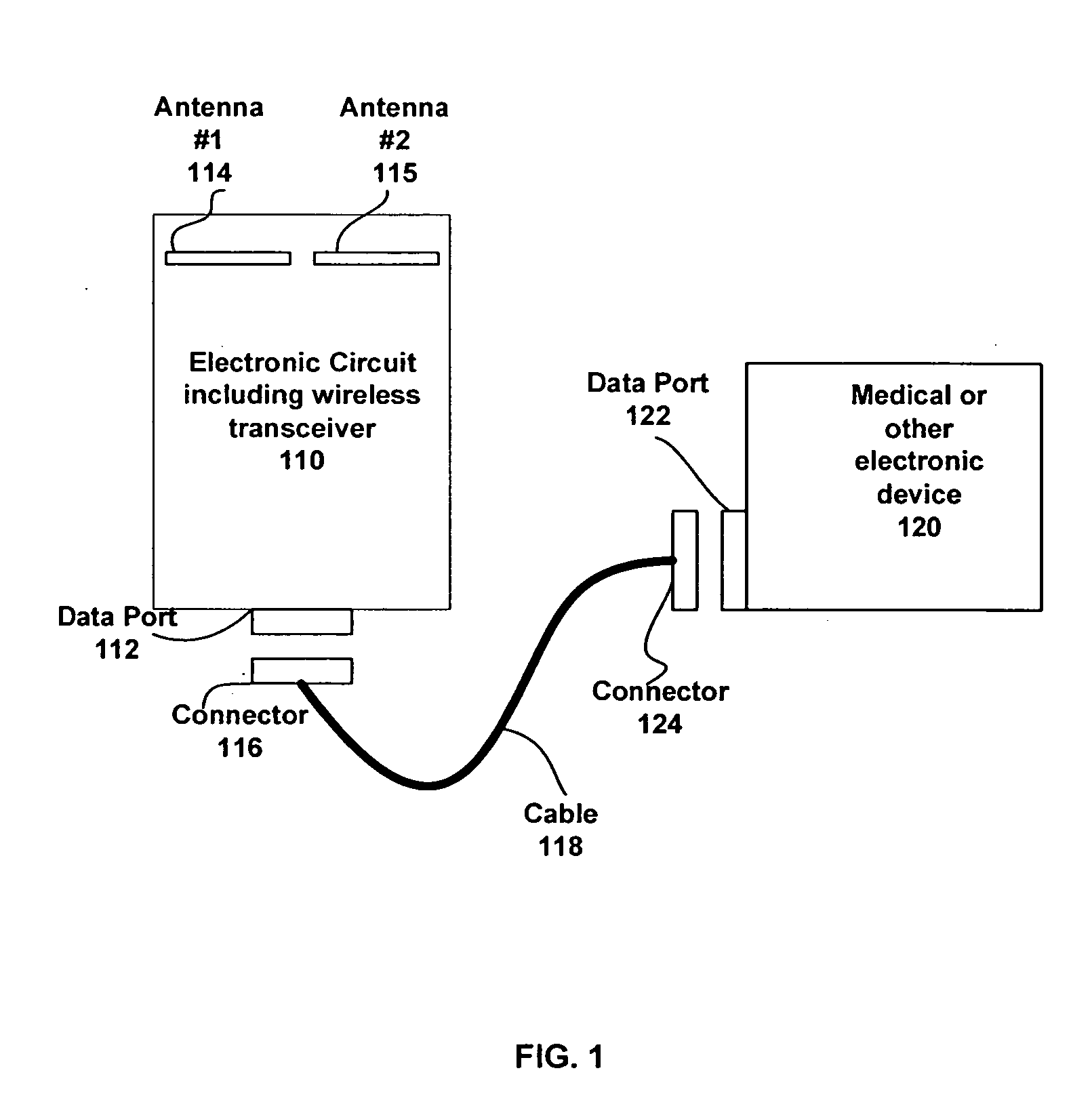
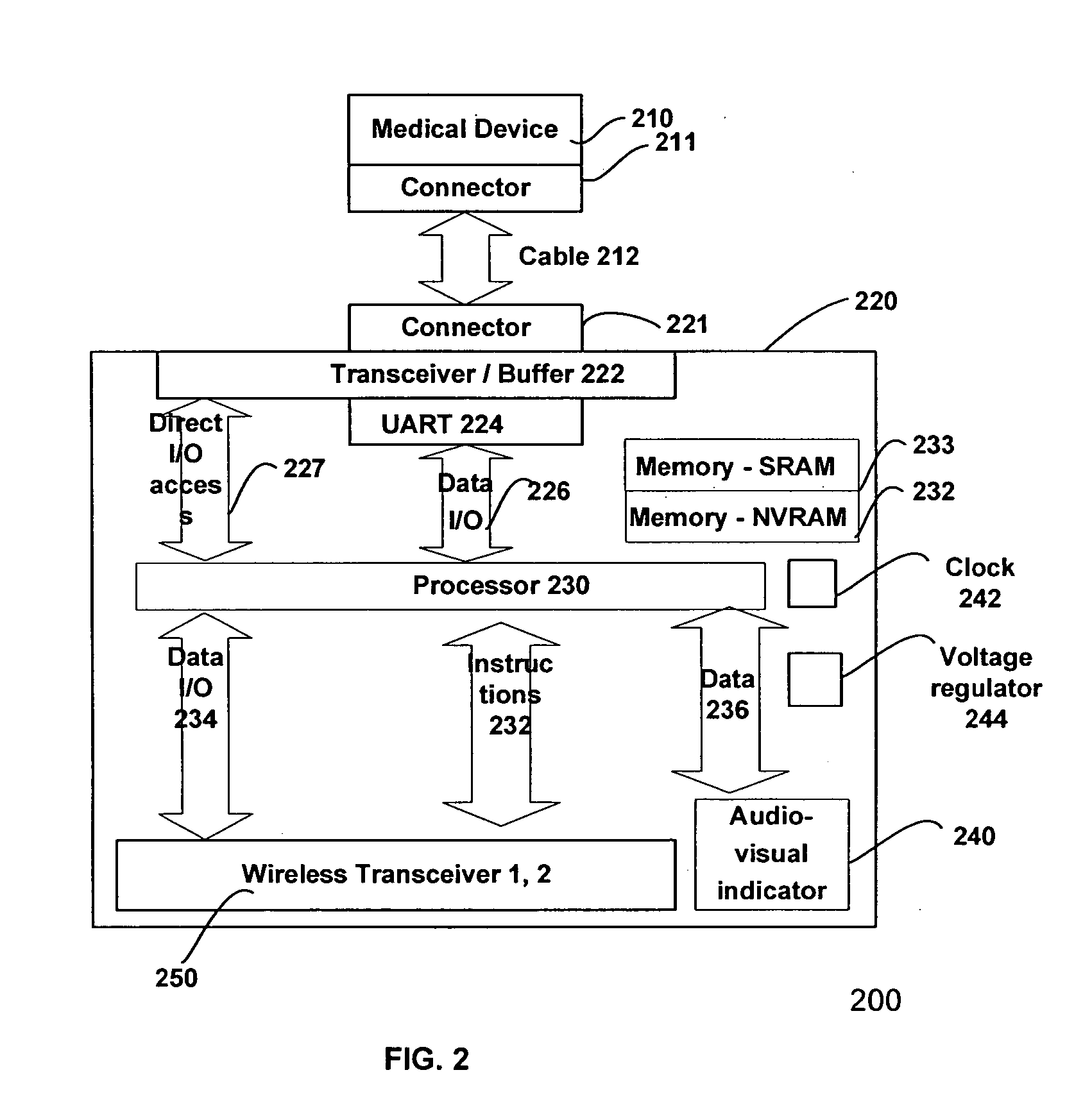
This invention teaches a method of automating some of the tasks requiring continuous data collection at the patient bedside in a hospital in a manner which significantly reduces the chances of error in providing treatment. These tasks include provisioning of the IV pumps or other fluid infusion pumps, feed pumps, oxygen delivery systems, gathering, recording, storing, and analyzing signals from ECG machine or pulse oxymeter or any other medical device. This invention teaches the use of wireless transceiver modules which are connected to the data ports on the medical instrument to gather the data and transmit the data to a wireless access point. Protocols to identify the patient, care provider, medicine, equipment, and treatment are described. Use of an external means for verifying the identity of the medical device and the medicine is also described.
Owner:CARETRENDS
Method and System for Selecting A Wireless Network
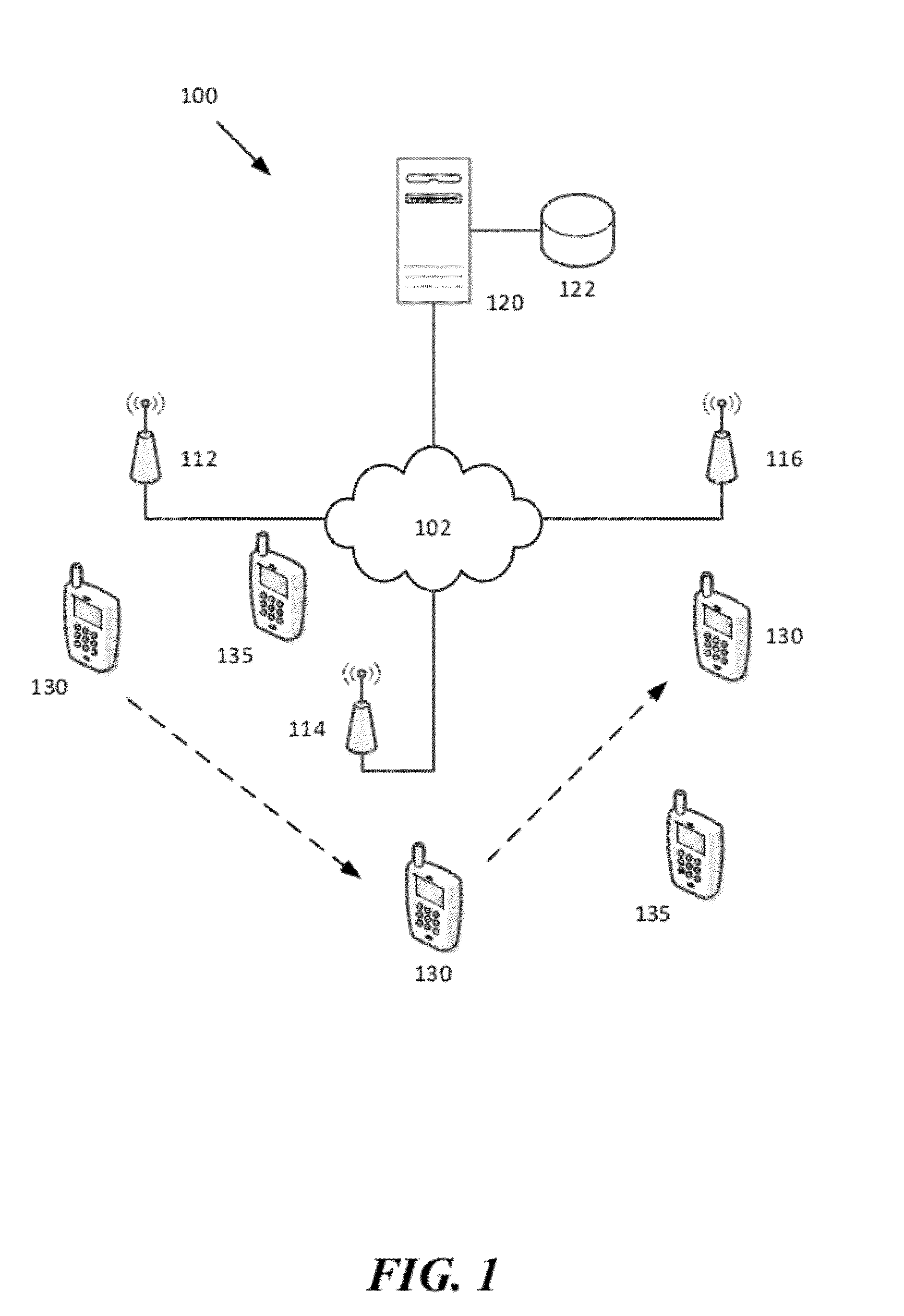
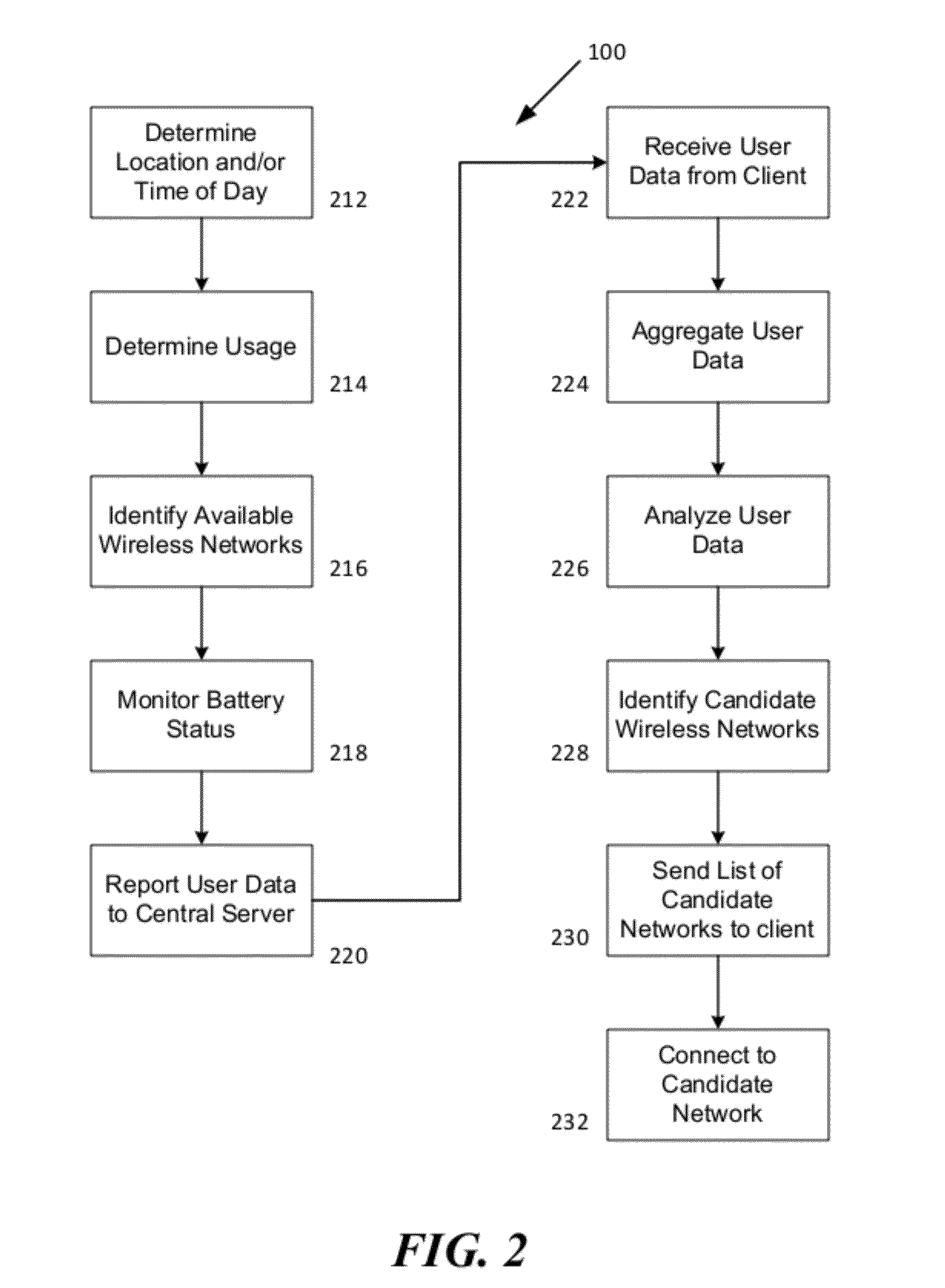
ActiveUS20120238287A1Convenient wireless connectionRaise priorityAssess restrictionConnection managementTelecommunicationsNetwork service
A method and system for selecting alternative wireless networks to establish a connection to, based on pattern information concerning determined relationships between the wireless user and the wireless network location. By monitoring location information and available wireless networks within range of a wireless user terminal, patterns of frequent and recurring locations and available wireless access points can be used to identify the wireless access points for alternative wireless networks that provide the best opportunity for offloading. People tend to frequent certain locations during their daily lives, such as their home and their place of employ, as well as the homes of relatives and friends and other favorite places like restaurants, coffee shops, shopping and sporting venues. Assumptions can be derived by monitoring available wireless networks to identify those wireless networks that provide a beneficial opportunity to offload primary (e.g., cellular) network services onto other local networks.
Owner:WEFI
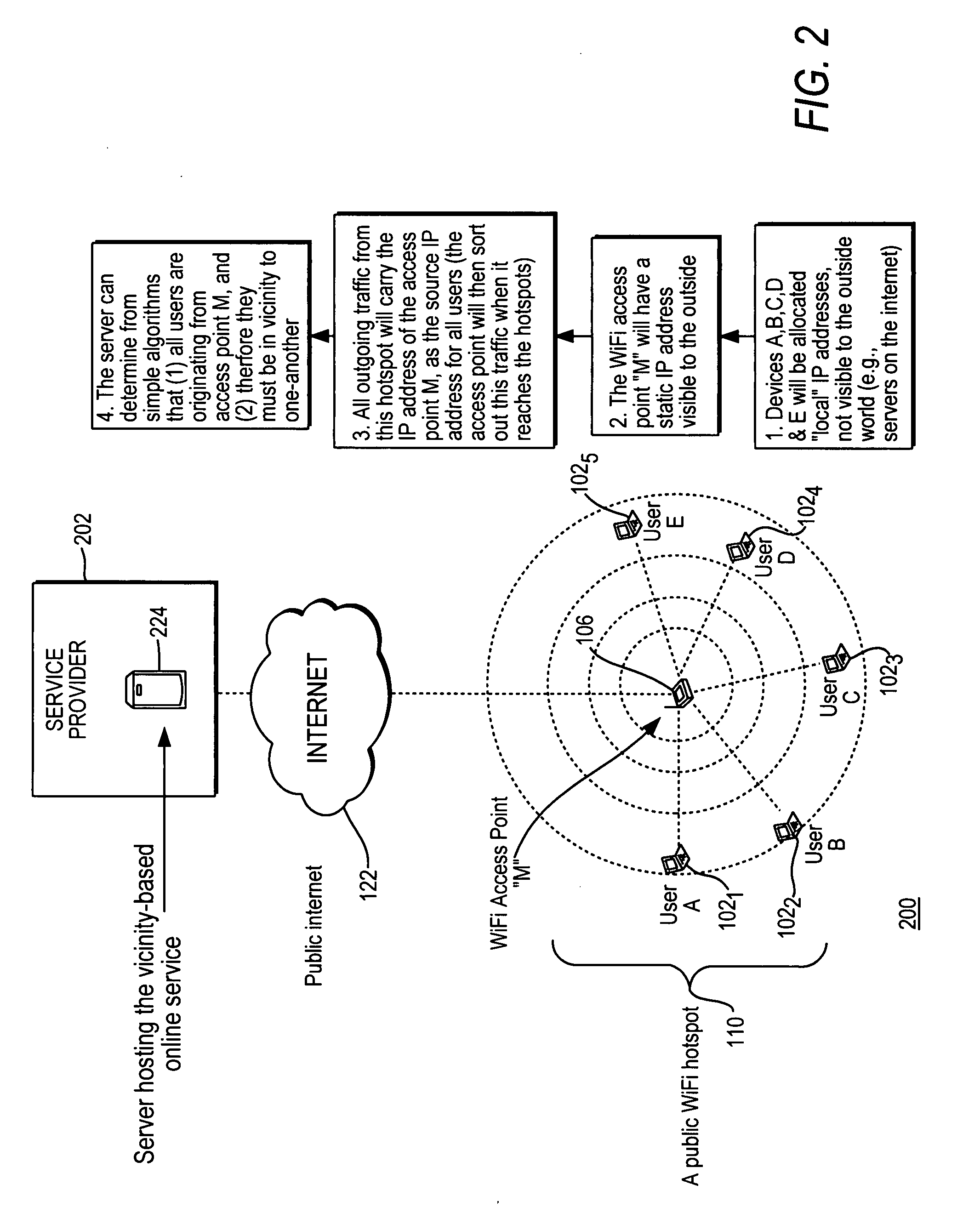
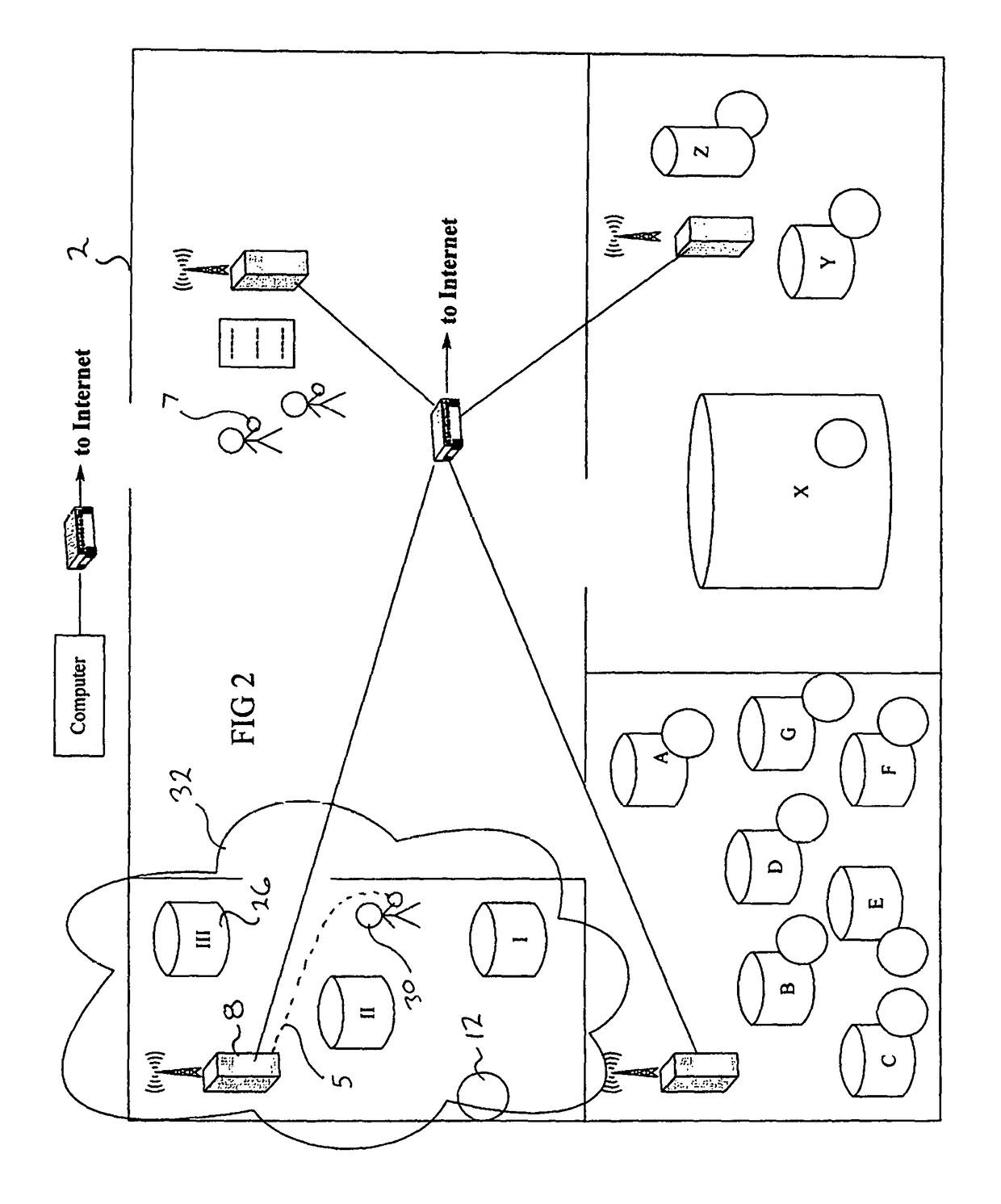
Vicinity-based community for wireless users
InactiveUS20080113674A1Network topologiesBroadcast service distributionCommunity basedPublic network
A method and apparatus for providing vicinity-based community services at a wireless access location by a public network service provider. The method includes the steps of receiving over a public network, at least one request for vicinity-based community services from at least one end-user accessing the wireless access point, grouping end-users accessing common wireless access points, and providing the vicinity-based community services in real time to end-users accessing the public network service provider from the wireless access point. The apparatus includes devices for carrying out the method described above.
Owner:BAIG MOHAMMAD FAISAL
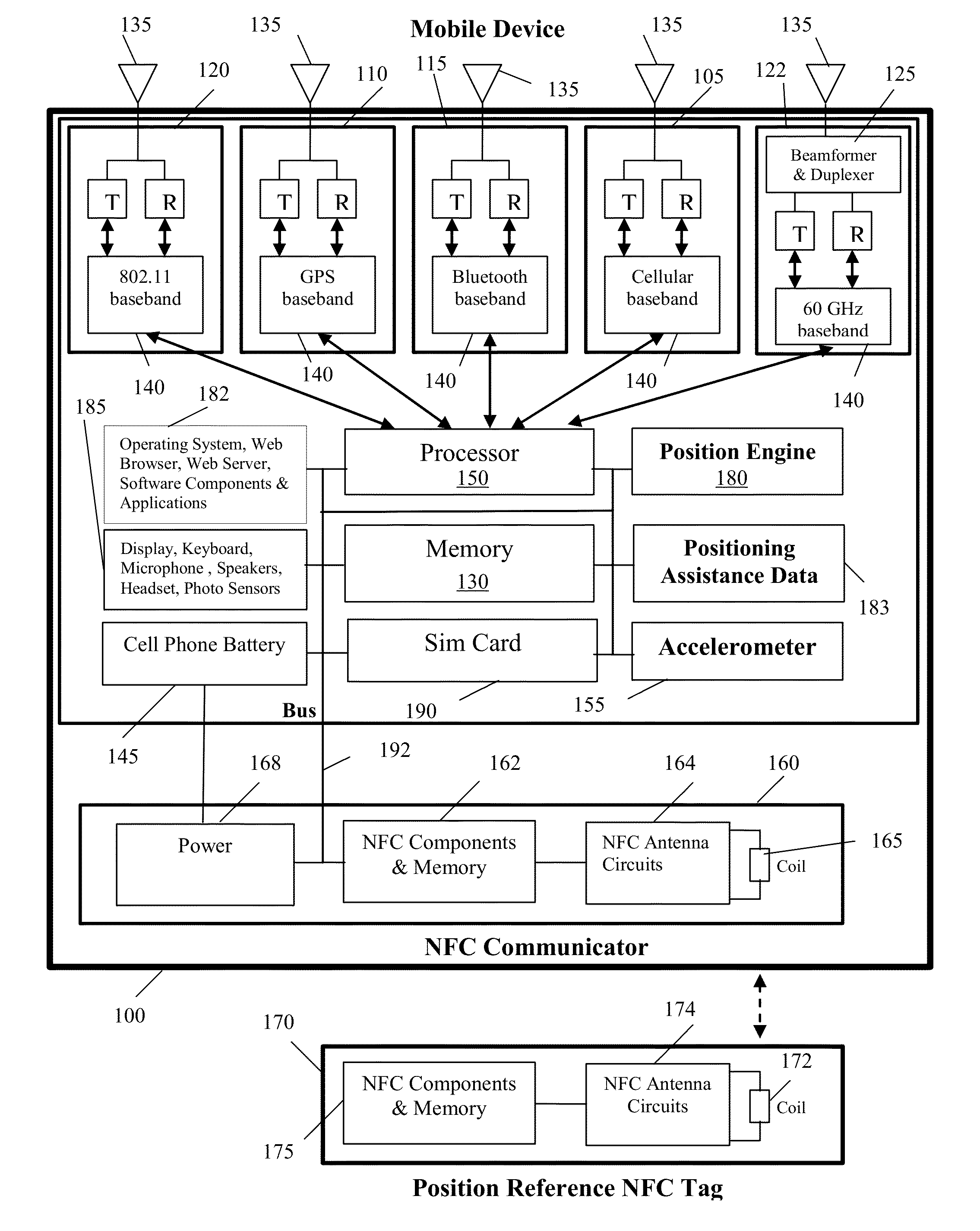
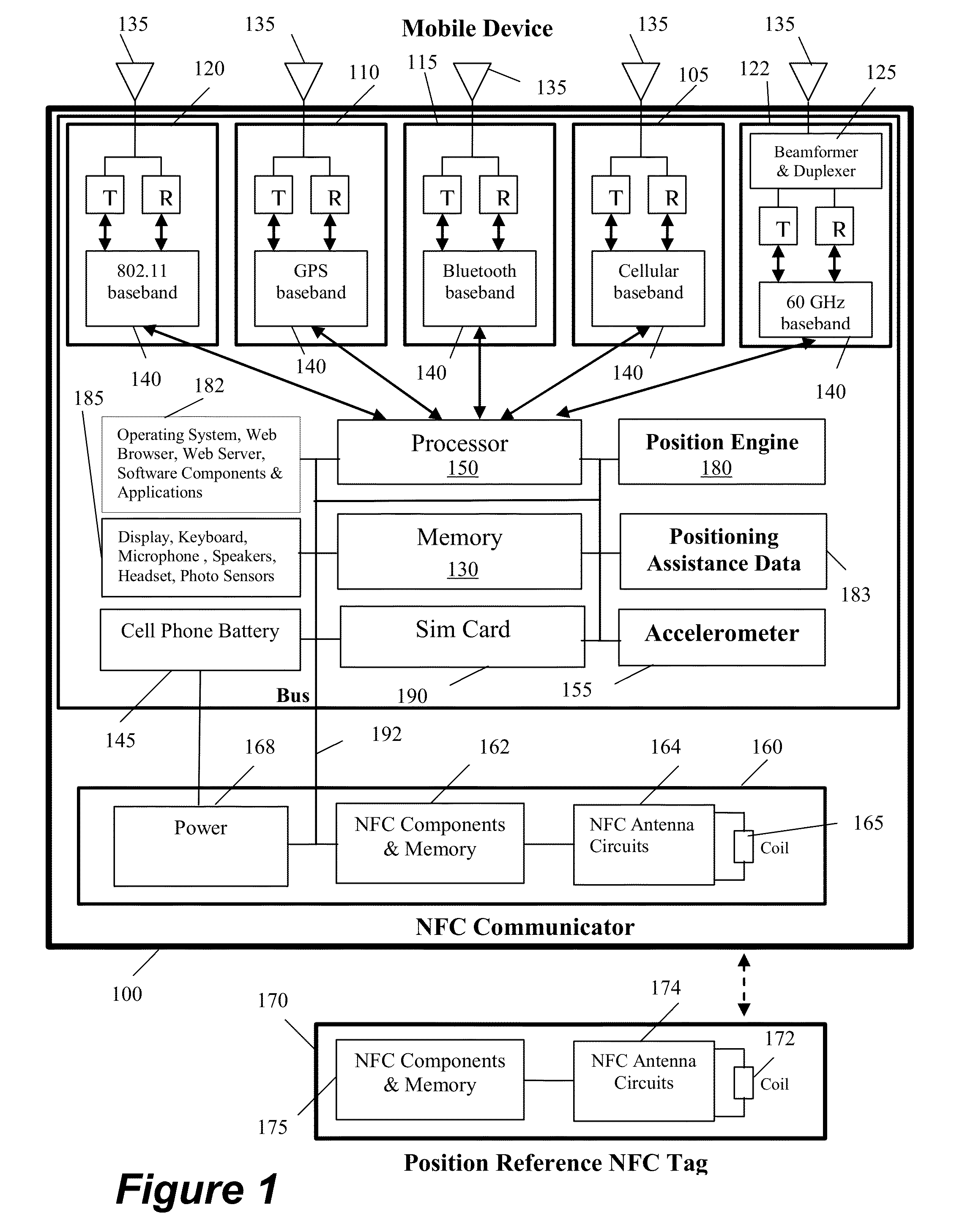
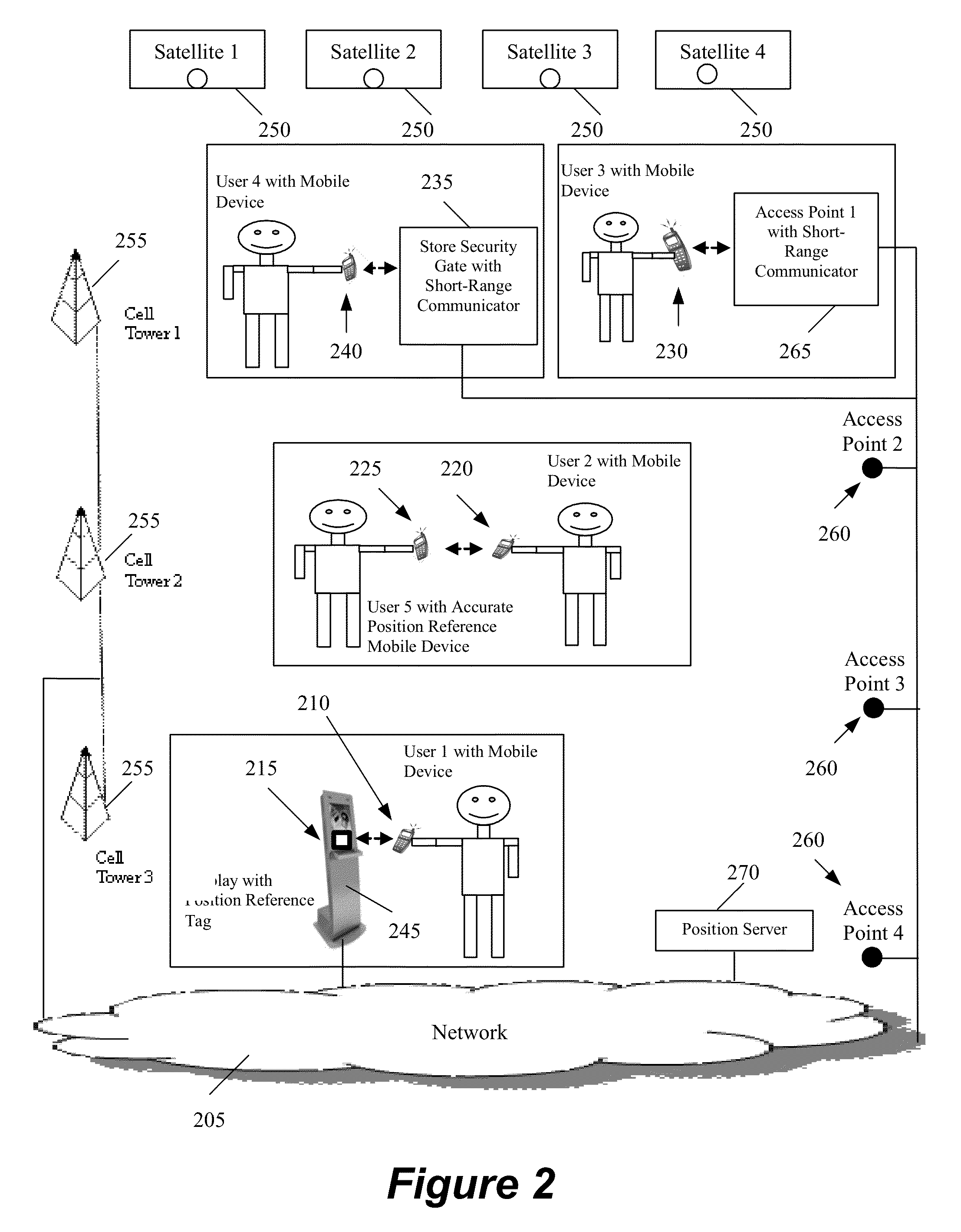
Distributed method and system for determining the position of a mobile device using long-range signals and calibrating the position using short-range signals
InactiveUS20130029685A1Energy efficient ICTNear-field transmissionWireless communication protocolTraffic signal
A method and system is described where a plurality of position reference devices use short-range wireless communication protocols to transmit positioning assistance data to nearby mobile devices, and the mobile devices use the assistance data to model errors and re-calibrate their positioning systems. The short-range communication methods include NFC, RFID, Bluetooth®, short-range 802.11, Wi-Fi Direct, and high frequency focused beams such as 60 GHz. The position reference devices are passive or active NFC tags, passive or active RFID tags, other devices that include such tags as their components, Bluetooth®-enabled devices, 60 GHz-enabled devices, and 802.11 access points that can lower their transmit power. The reference devices are located at various indoor and outdoor locations such as smart posters, kiosks, ATM machines, malls, store checkout counters, store security gates, wireless access points, cellular base-stations, tollbooths, traffic lights, and street lamp posts.
Owner:GOLBA LLC
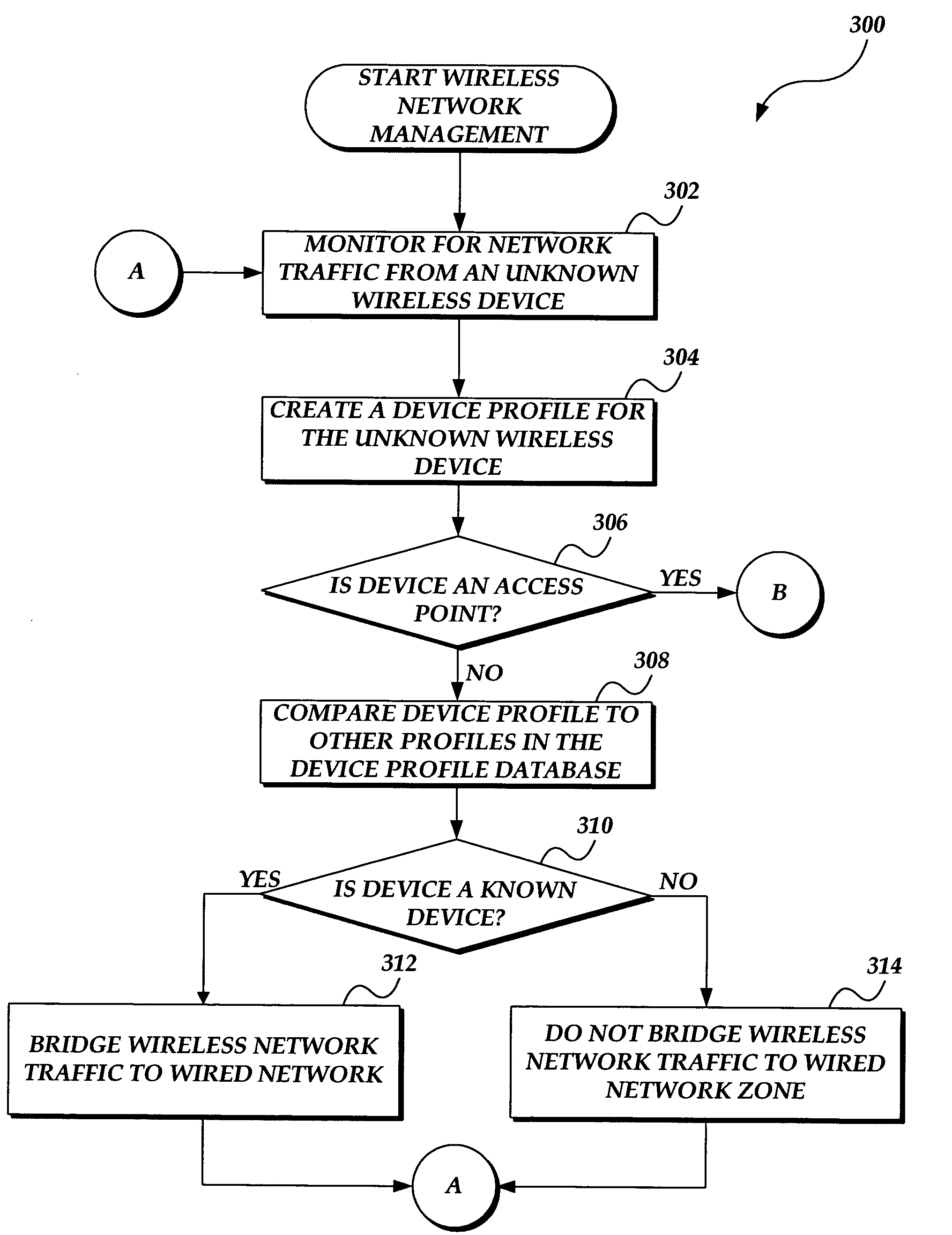
System and method for wireless local area network monitoring and intrusion detection
InactiveUS7340768B2Memory loss protectionDigital data processing detailsThreat levelNotification system
The present invention provides a system and method for providing real-time wireless network monitoring and intrusion detection. The present invention profiles wireless devices and maintains a database of known / authorized wireless device profiles. Wireless devices are analyzed to determine the threat level they pose to the network, and if the threat level exceeds a predetermined threshold, the invention refuses to bridge the network traffic from the wireless devices to the wired network. The present invention provides reporting of the wireless network activity, the known and unknown wireless devices, and the threat levels posed by the wireless devices. If an unknown wireless device is determined to be, or may be, a wireless access point, an alert is generated, such as notifying a system administrator to take appropriate action.
Owner:WIMETRICS CORP
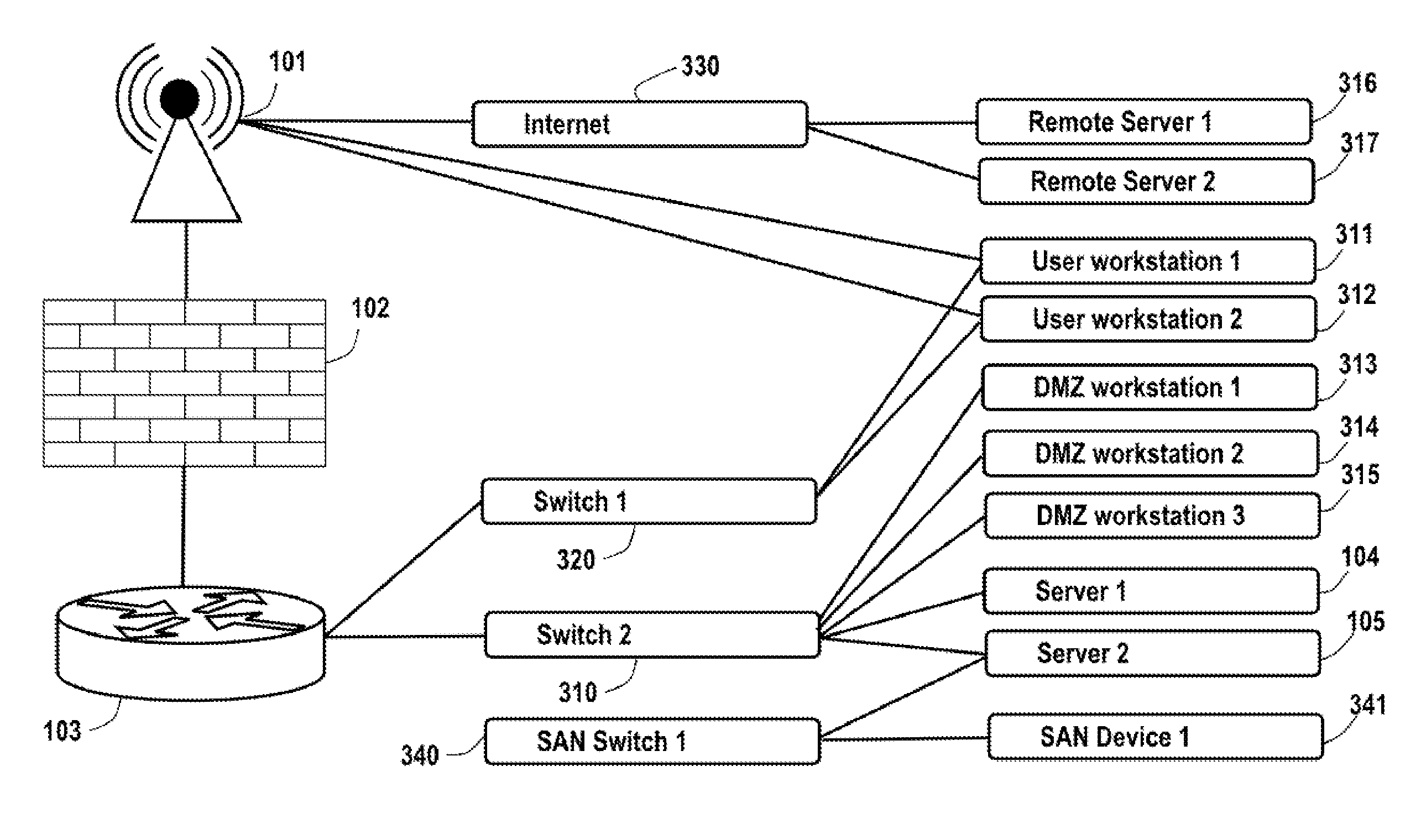
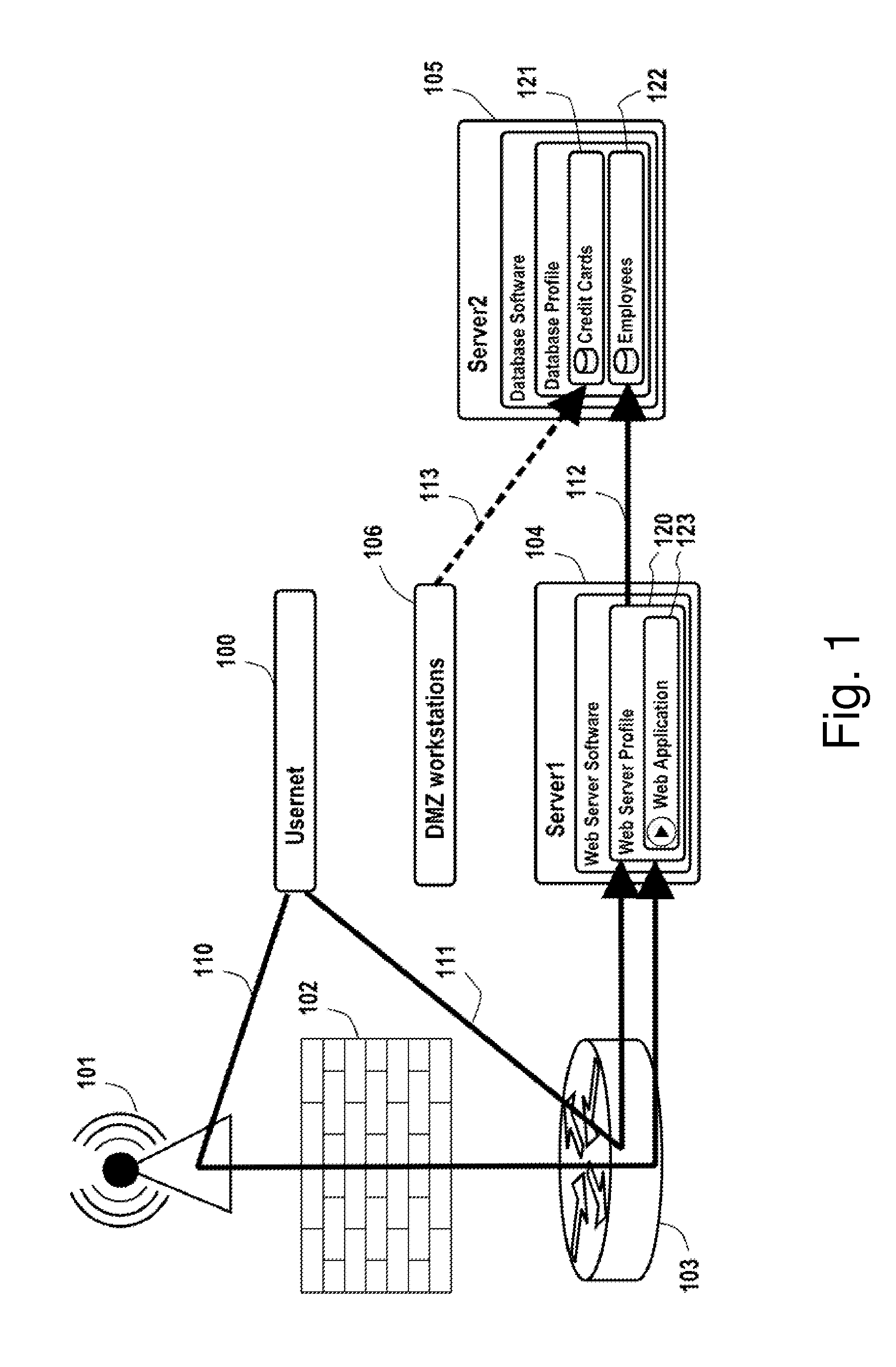
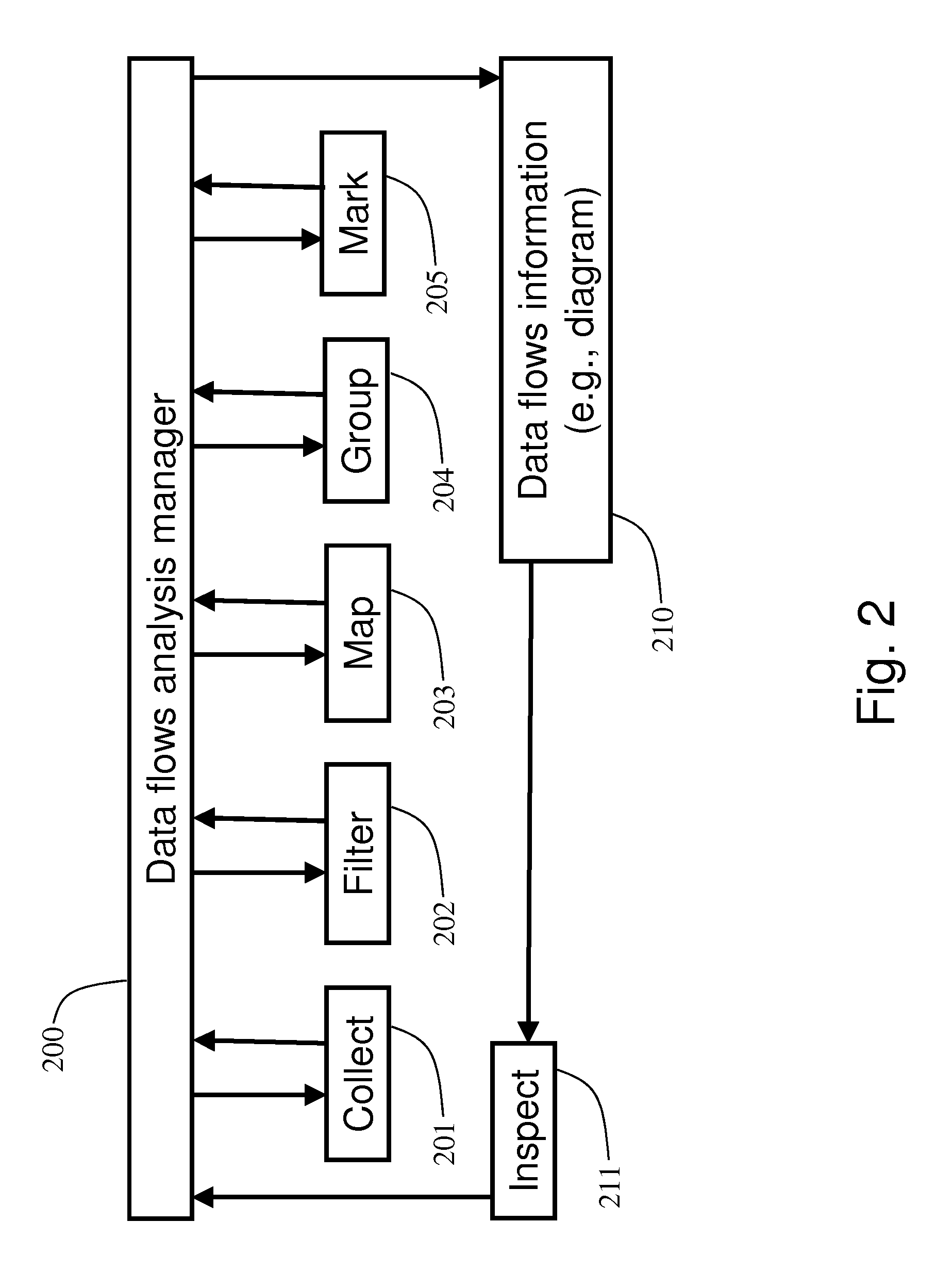
Analysis of data flows in complex enterprise it environments
The present technology enables identification, visualization, and analysis of data flows via network components in complex enterprise IT environments including but not limited to servers, workstations, switches, routers, wireless access points, traffic shapers, firewalls, storage systems and SAN systems. The technology is based on a combination of information collection, information filtering, mapping, grouping, marking, report generation, and verification.
Owner:MODELIZEIT INC
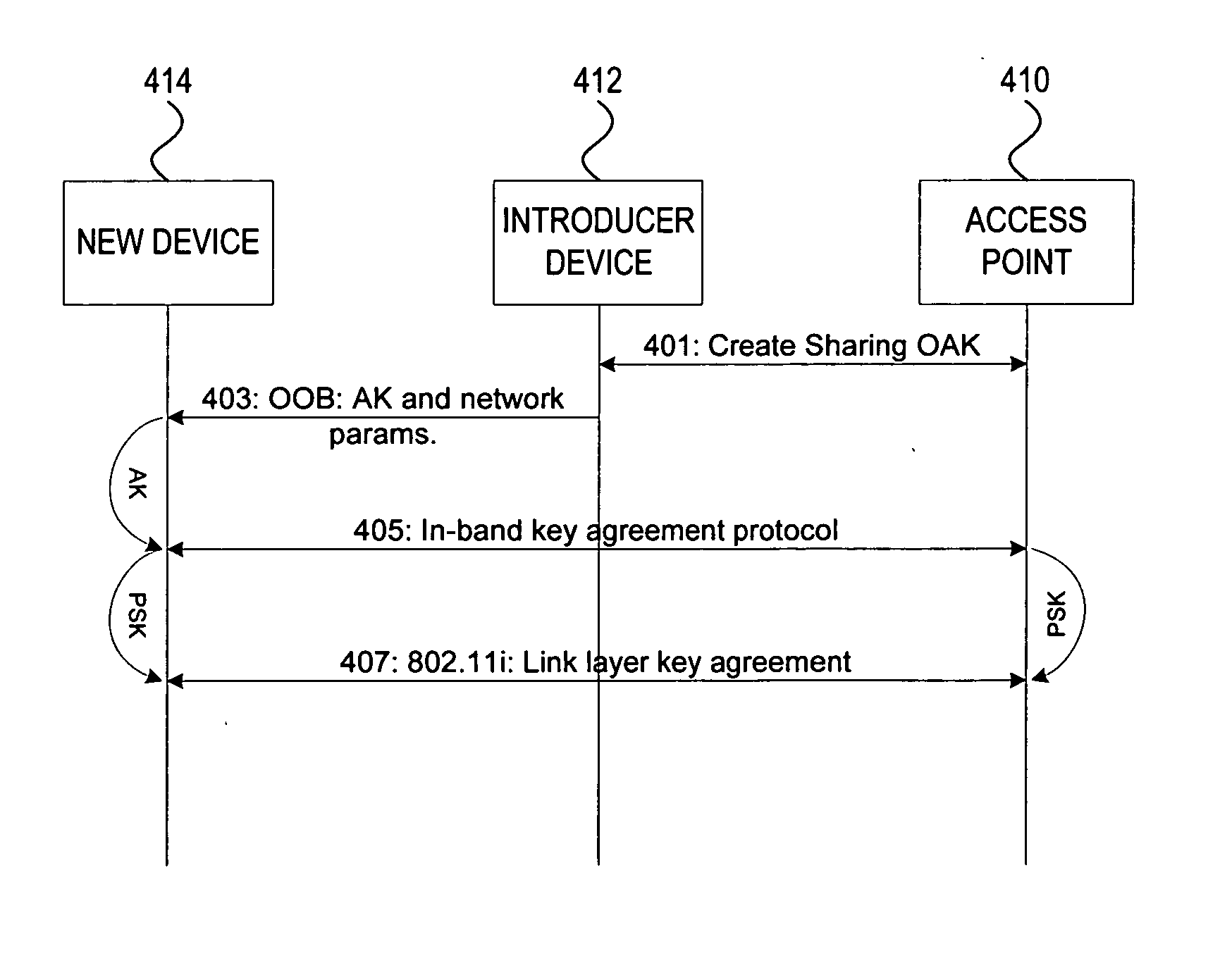
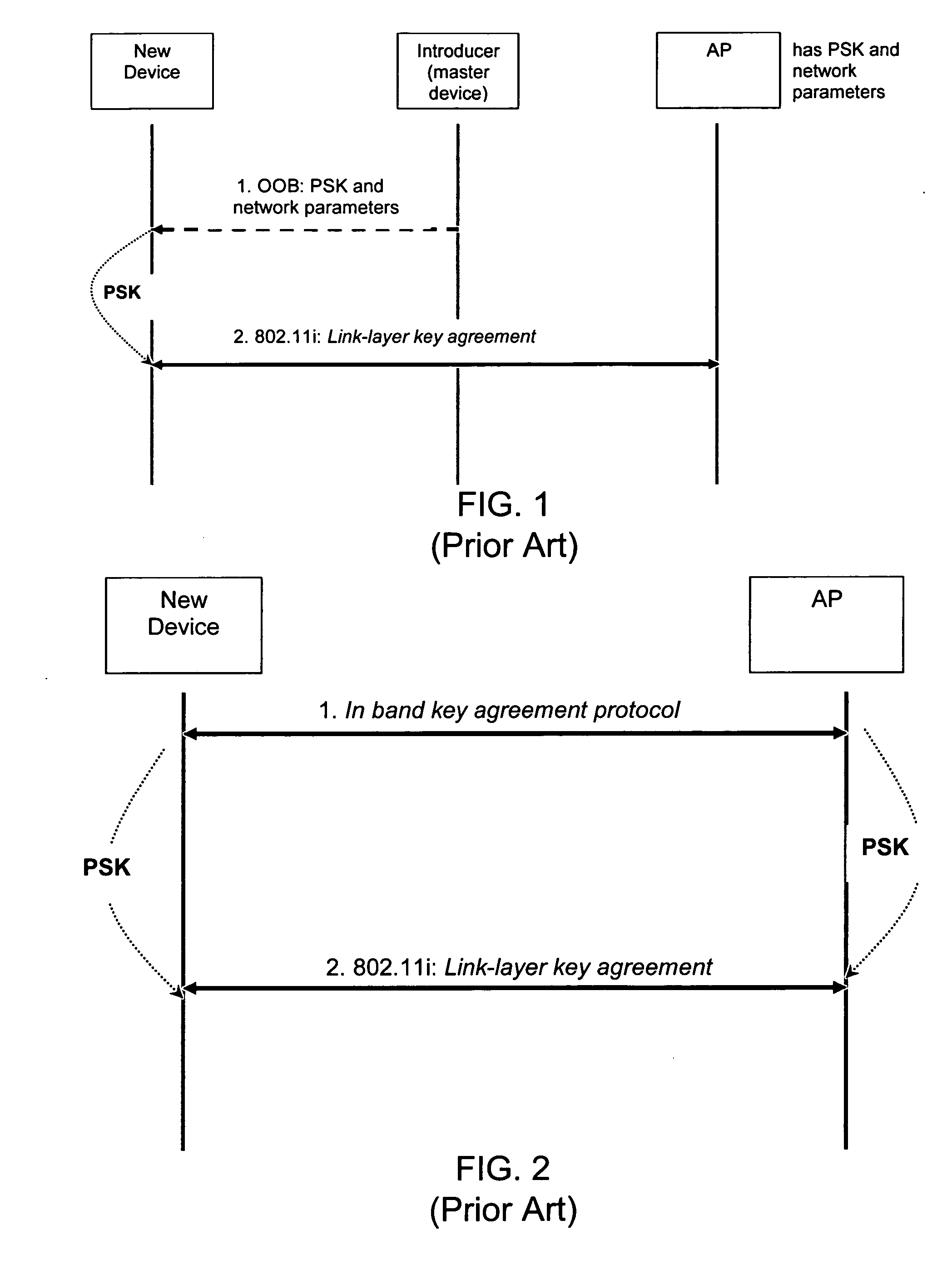
Administration of wireless local area networks
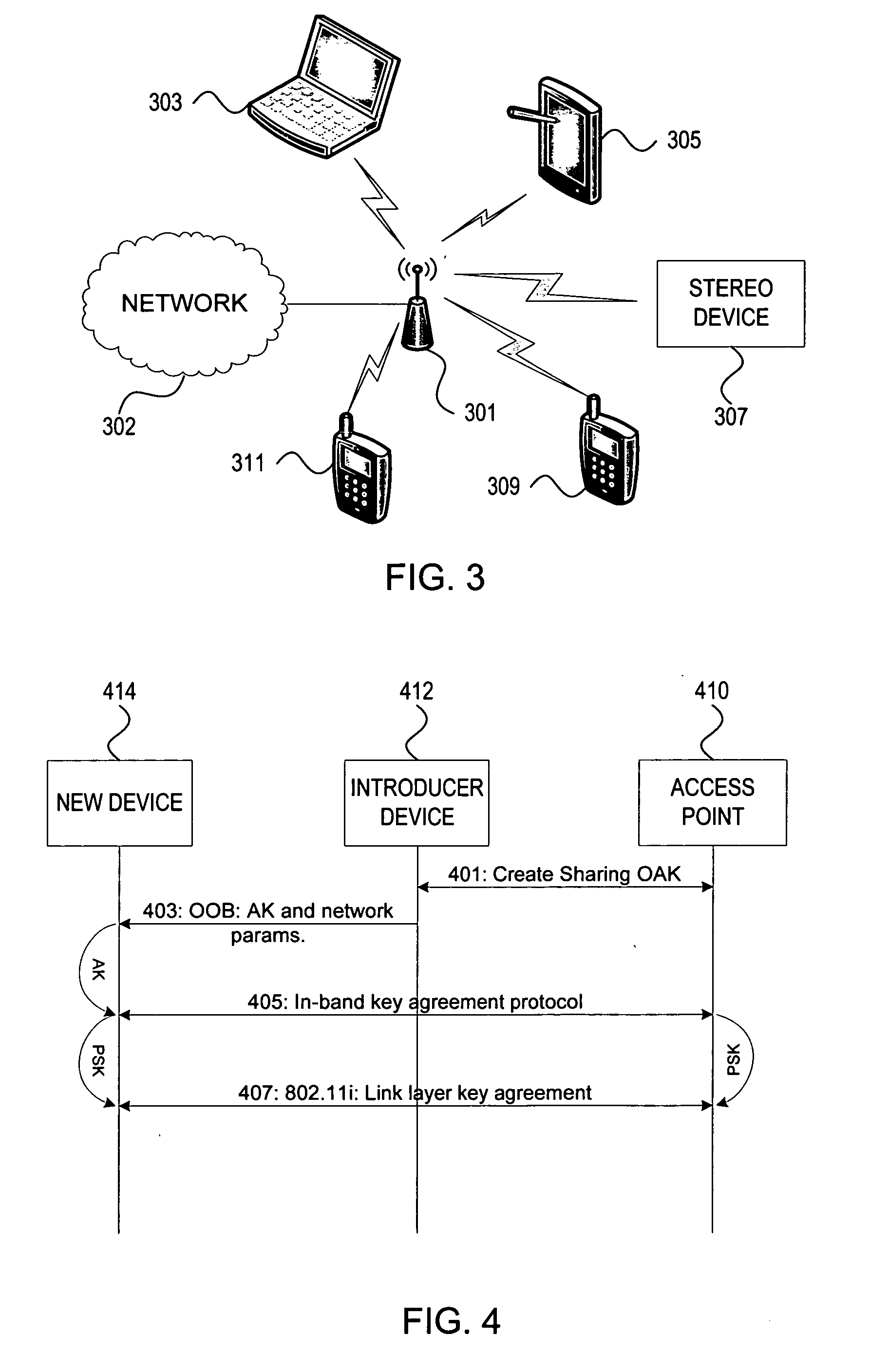
ActiveUS20060251256A1Improve securityImprove usabilityKey distribution for secure communicationAssess restrictionProbable CaseNetwork addressing
Methods and systems for managing access to a wireless local area network are provided. A wireless access point (AP) may use a unified approach that utilizes an out-of-band channel to communicate authentication key and network address information to a guest device, and utilizes an in-band channel to establish communications with the guest device, and also provides support for in-band setup on all devices. The ability to use out-of-band where possible provides for an increase to security and usability, and the possibility of delegating access from one device to another. The unified approach thereby also provides easy management of guest access to the WLAN.
Owner:NOKIA TECHNOLOGLES OY
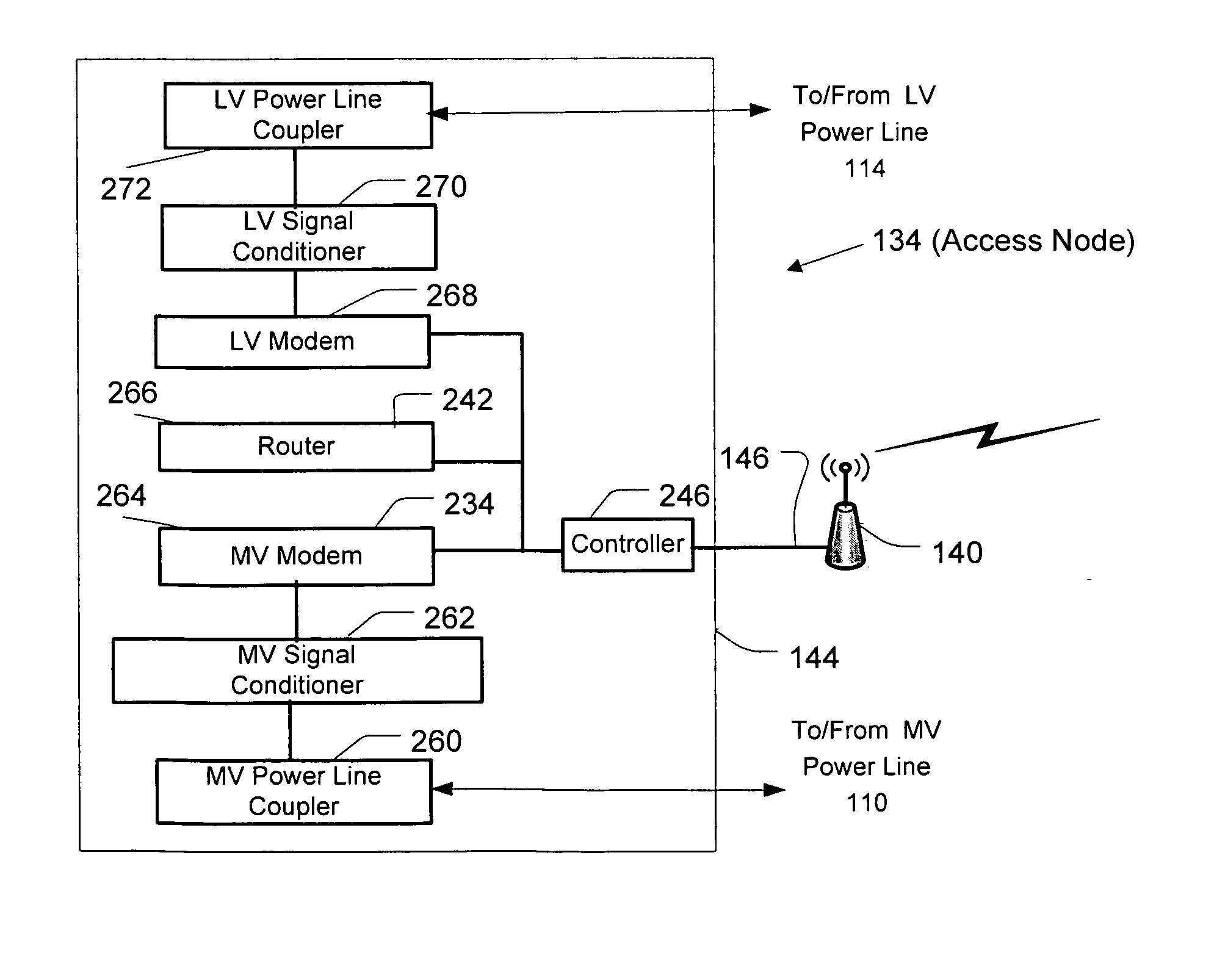
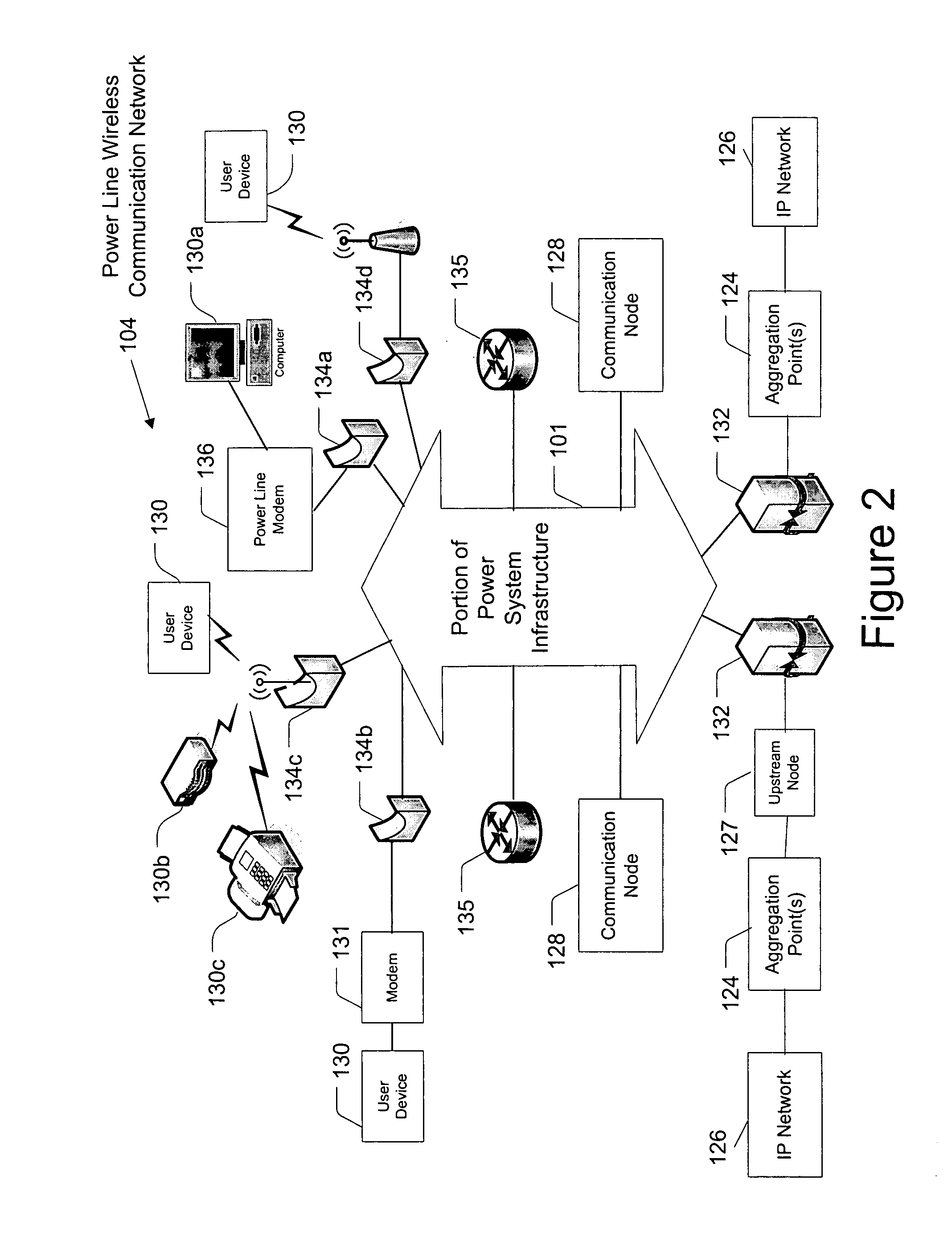
Hybrid power line wireless communication network
InactiveUS20070201540A1Wireless systems/telephoneLock network applicationsCommunications systemLow voltage
A hybrid power line wireless communication system may include an access controller and plurality of communication nodes that each may include a wireless access point coupled to a power line communication device. The wireless access points may provide wireless broadband communications to one or more user devices while the power line communication devices may provide low voltage power line broadband communications. The access controller remotely manages the wireless access points by sending control messages to the communication nodes. Control messages may traverse a power line, a non-power line medium, and / or a wireless medium. Control messages may include information relating to encryption parameters, transmission power levels, communication channels, access control, and other such parameters.
Owner:CURRENT TECH
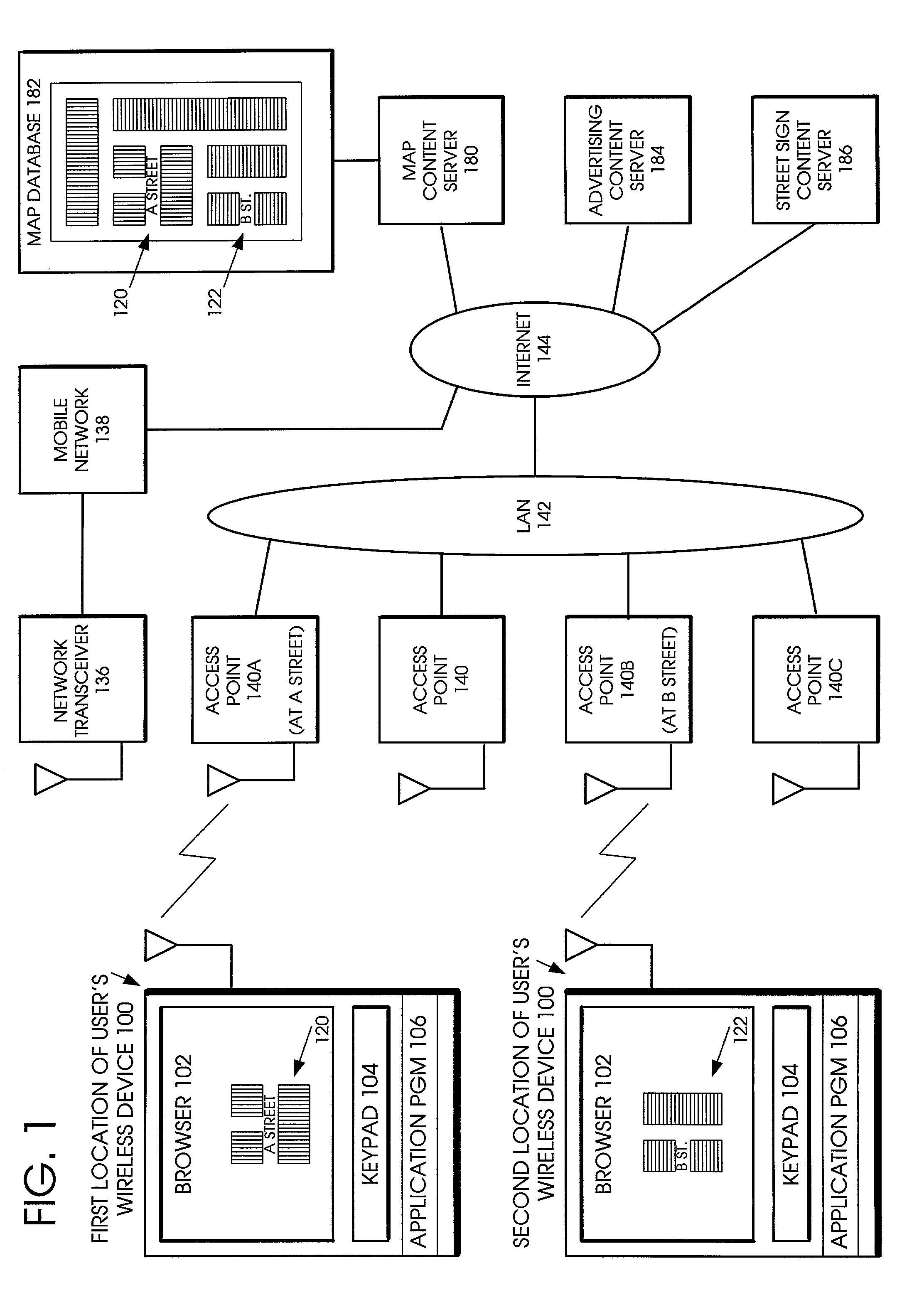
Method and apparatus for accessing networks by a mobile device
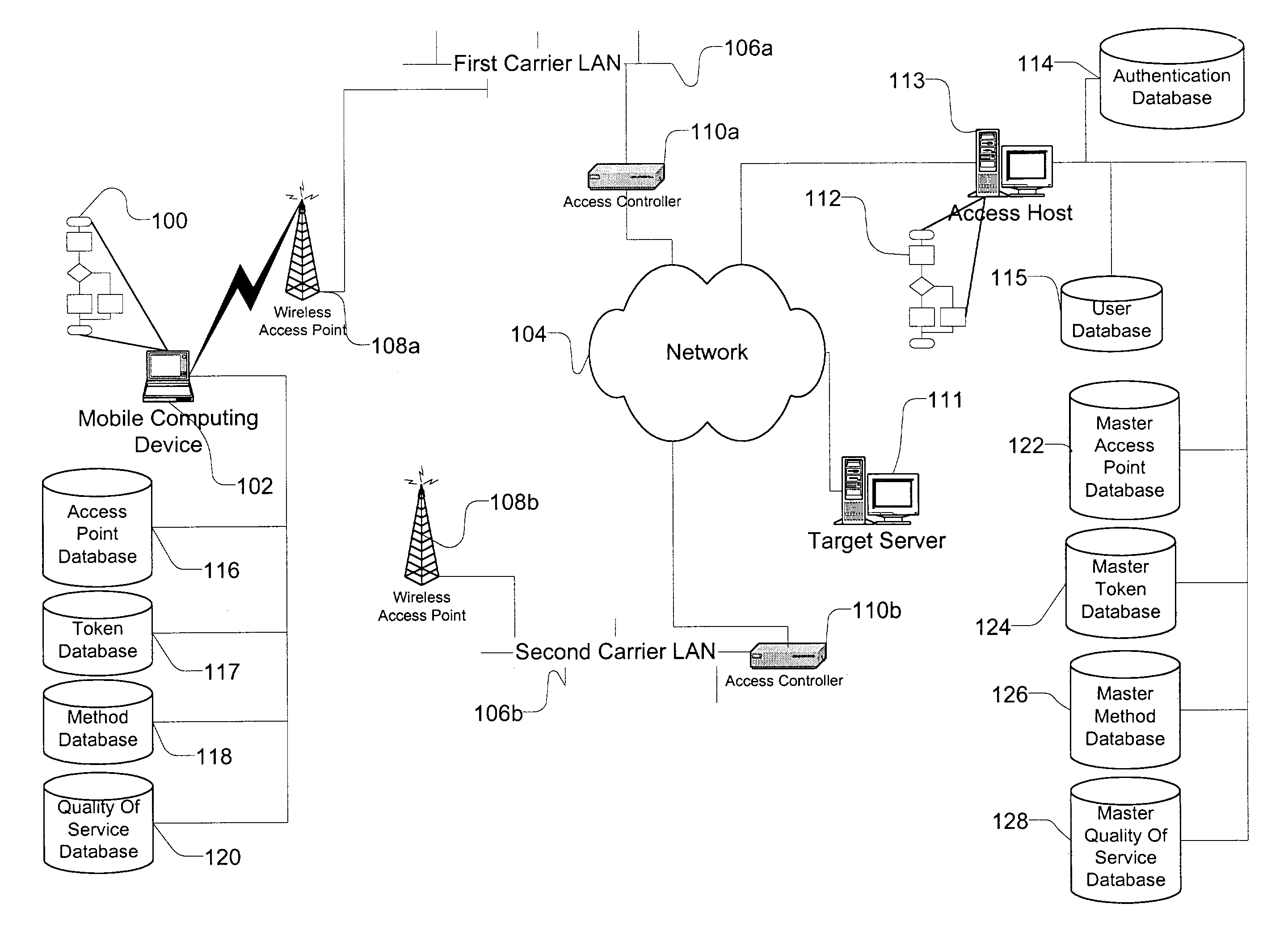
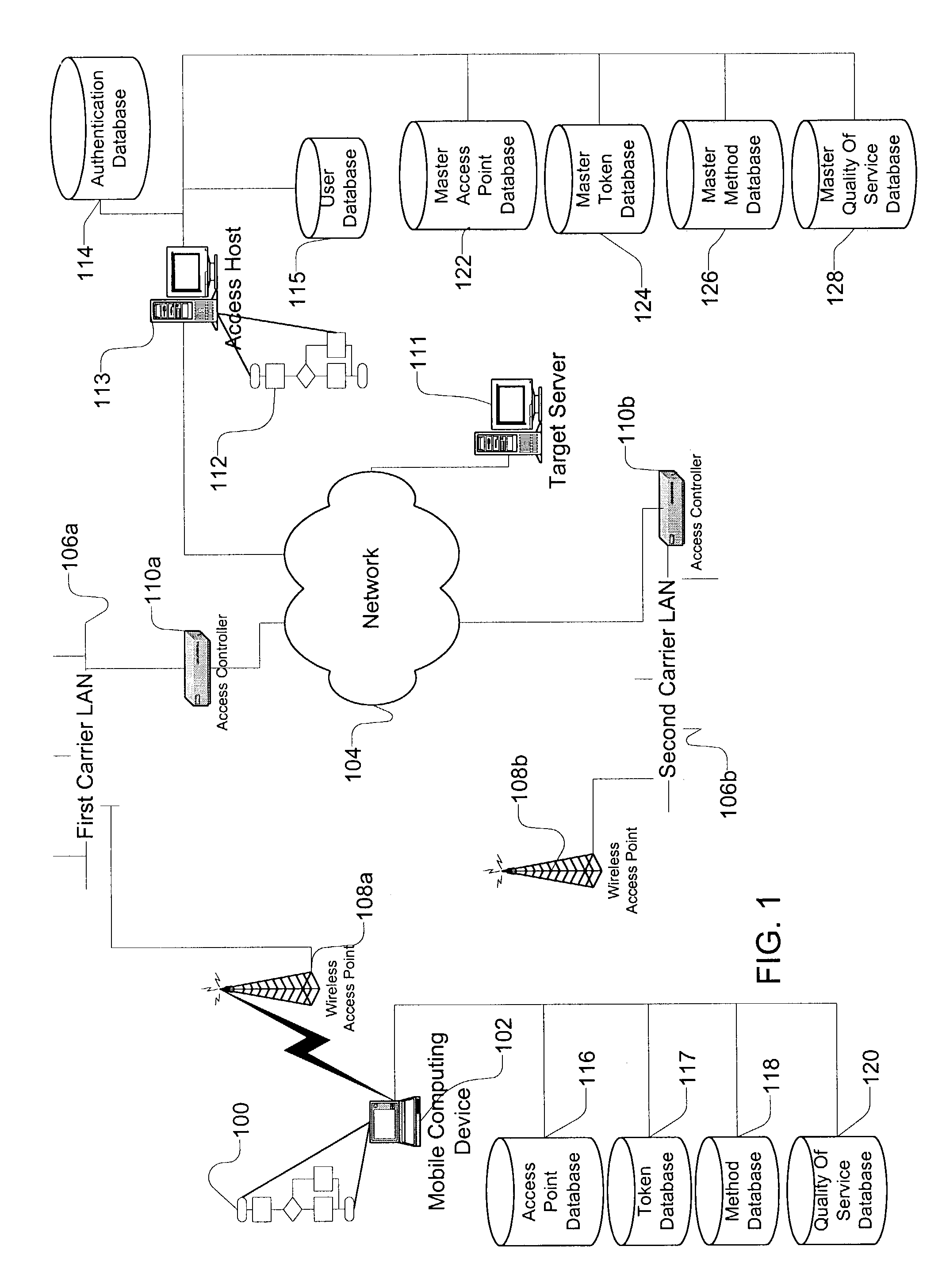
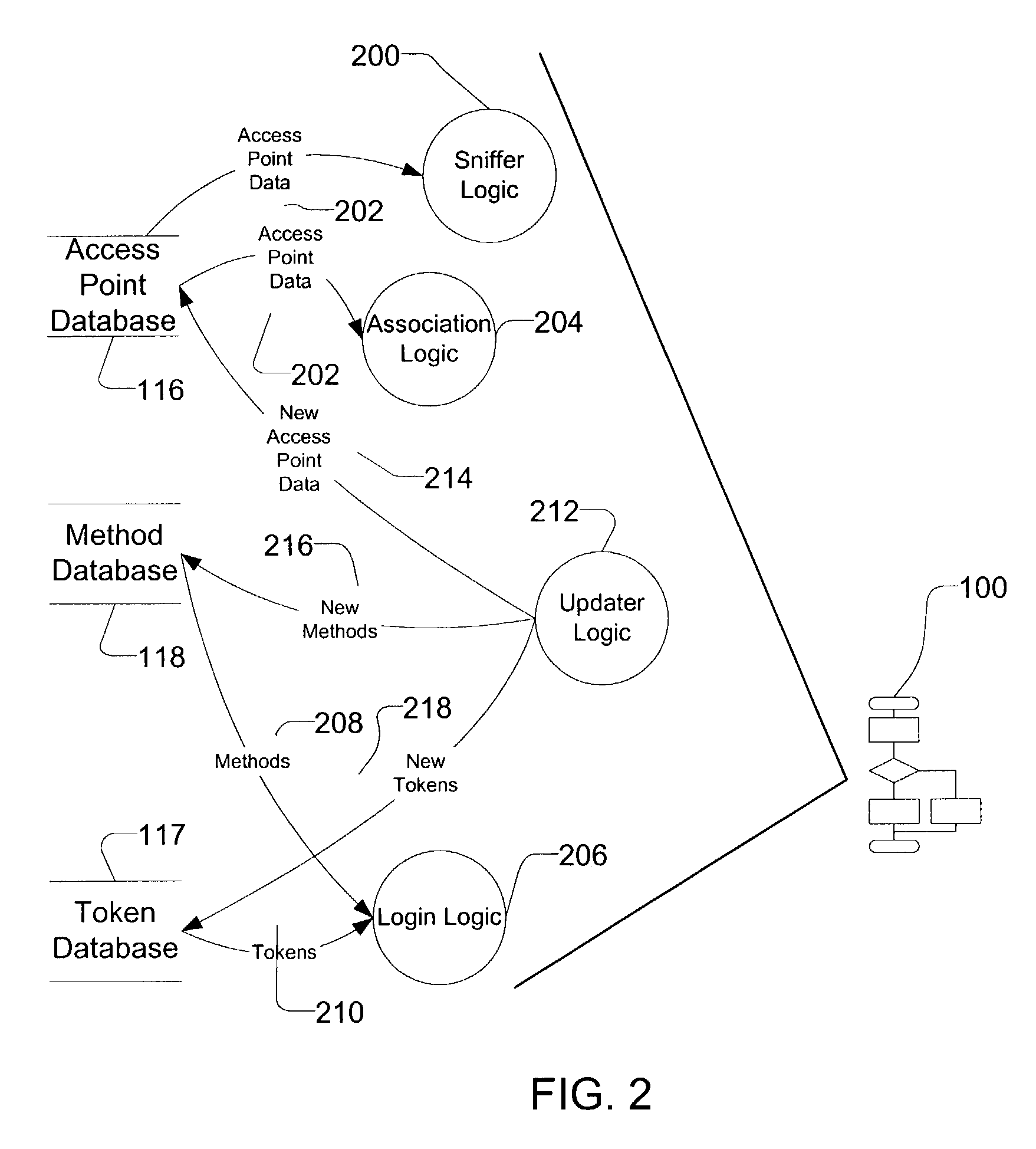
InactiveUS7483984B1Assess restrictionMultiple digital computer combinationsAccess networkNetwork generation
A method and apparatus for accessing wireless carrier networks by mobile computing devices. An access client hosted by a mobile computing device accesses carrier networks using wireless access points. The access client uses an access point database to identify access points and carrier networks. The access client uses a methods database and a tokens database to access the carrier networks. The access client updates the access point database, the methods database, and the token database using an access server when the access client is operably coupled to a carrier network. The access client transmits user information to the carrier network. The carrier network uses the user information to authenticate the user and to generate session data while the user is accessing the carrier network. The carrier network transmits the session data to the access server. The access server uses the session data to generate billing information for the user. The access client also collects network performance data for individual access points and carrier networks. The access client transmits the network performance data to the access server. The access server aggregates network performance data from a plurality of access clients to generate quality of server reports for both individual access points and carrier networks. The access client further includes access point detection and evaluation features for use by a user in selecting access points available at a single location.
Owner:BOINGO WIRELESS
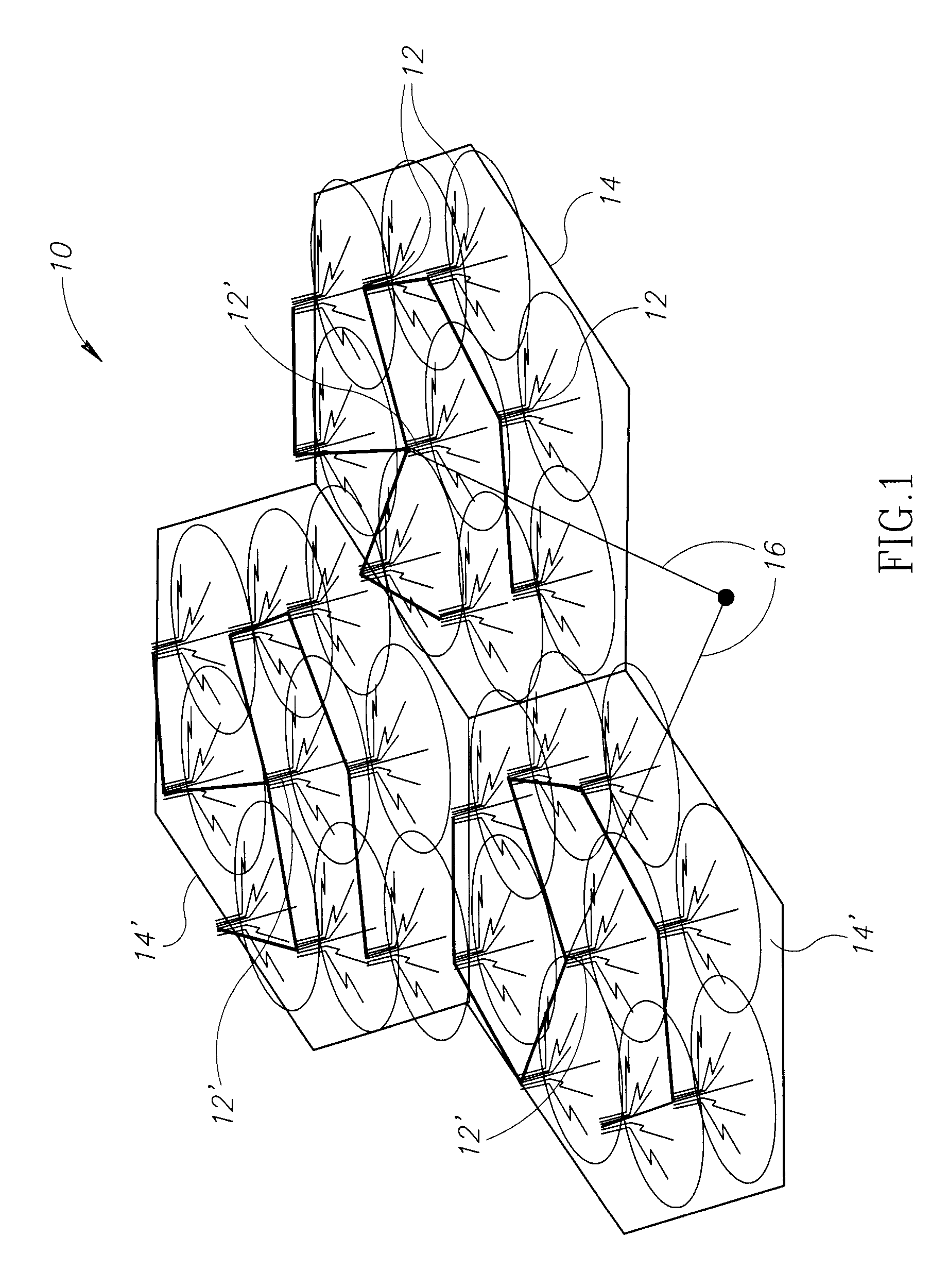
Reconfigureable arrays of wireless access points
ActiveUS20060002326A1Meet real-timeBroadcast with distributionNetwork topologiesQuality of serviceGeographic distribution
A wireless communications network includes a reconfigurable array of access points for linking wireless devices in an infrastructure mode. One or more of the access points are mobile. The mobile access points in the network can be repositioned to change the geographic distribution of the bandwidth coverage provided by the wireless network. The mobile access points may be repositioned to redistribute available network bandwidth heterogeneously according to the demand for bandwidth in local areas and to meet quality of service standards.
Owner:EXTREME NETWORKS INC
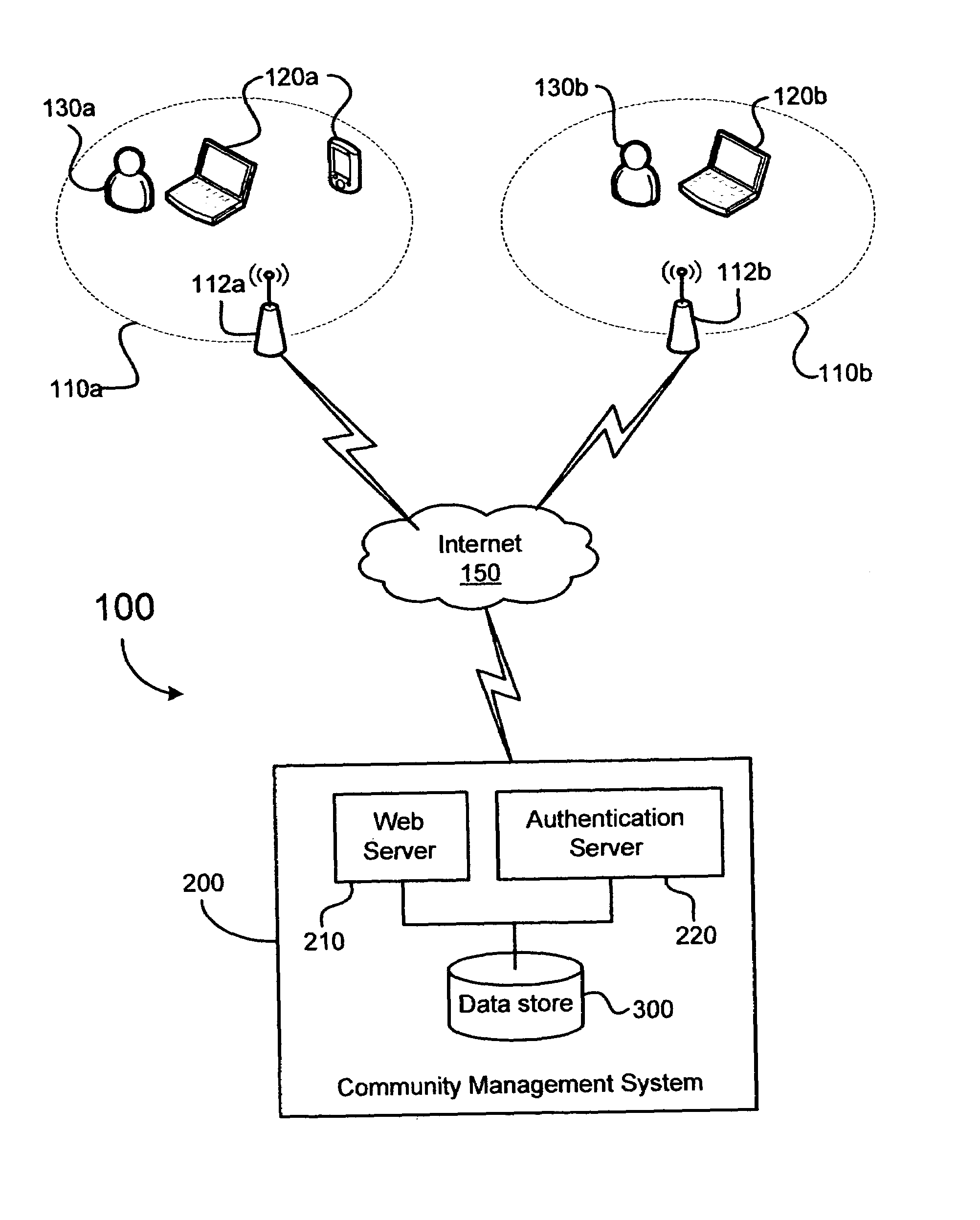
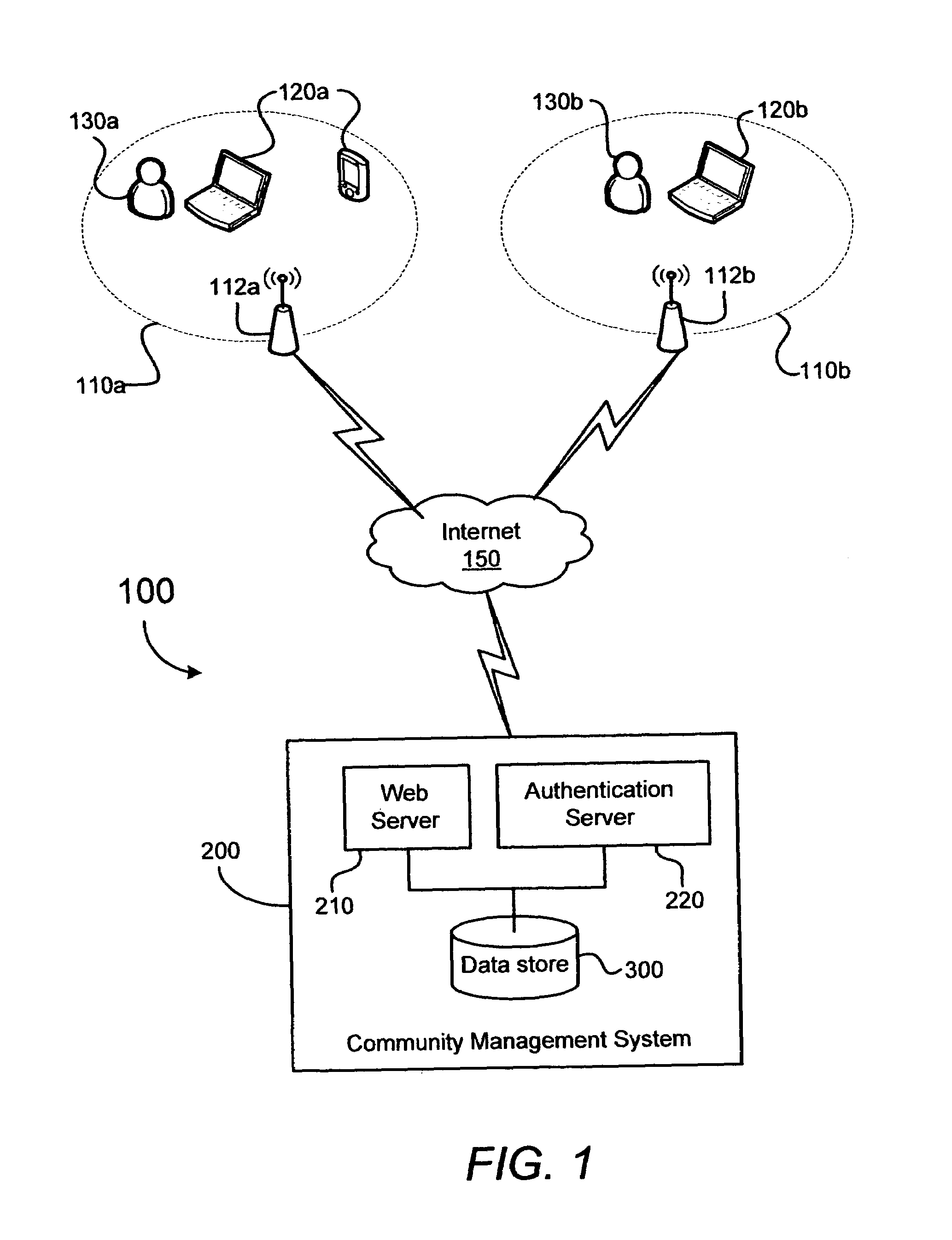
System and method for managing a wireless network community
ActiveUS7263076B1Improve abilitiesPreserving level of securityUnauthorised/fraudulent call preventionDigital data processing detailsComputer networkWeb service
A wireless network community includes a plurality of wireless access points associated with a plurality of owners and a community management system in communication with each of the plurality of wireless access points via an Internet. The community management system includes a web server for interacting with the owners and for allowing each of the owners to register as a member of the network community. The community management system also includes an authentication server, and a data store coupled to the web server and to the authentication server. The community management system is configured to allow each registered member to register an associated wireless access point and to control which of the other members is authorized to access the wireless access point.
Owner:RATEZE REMOTE MGMT LLC
Wireless access of packet based networks
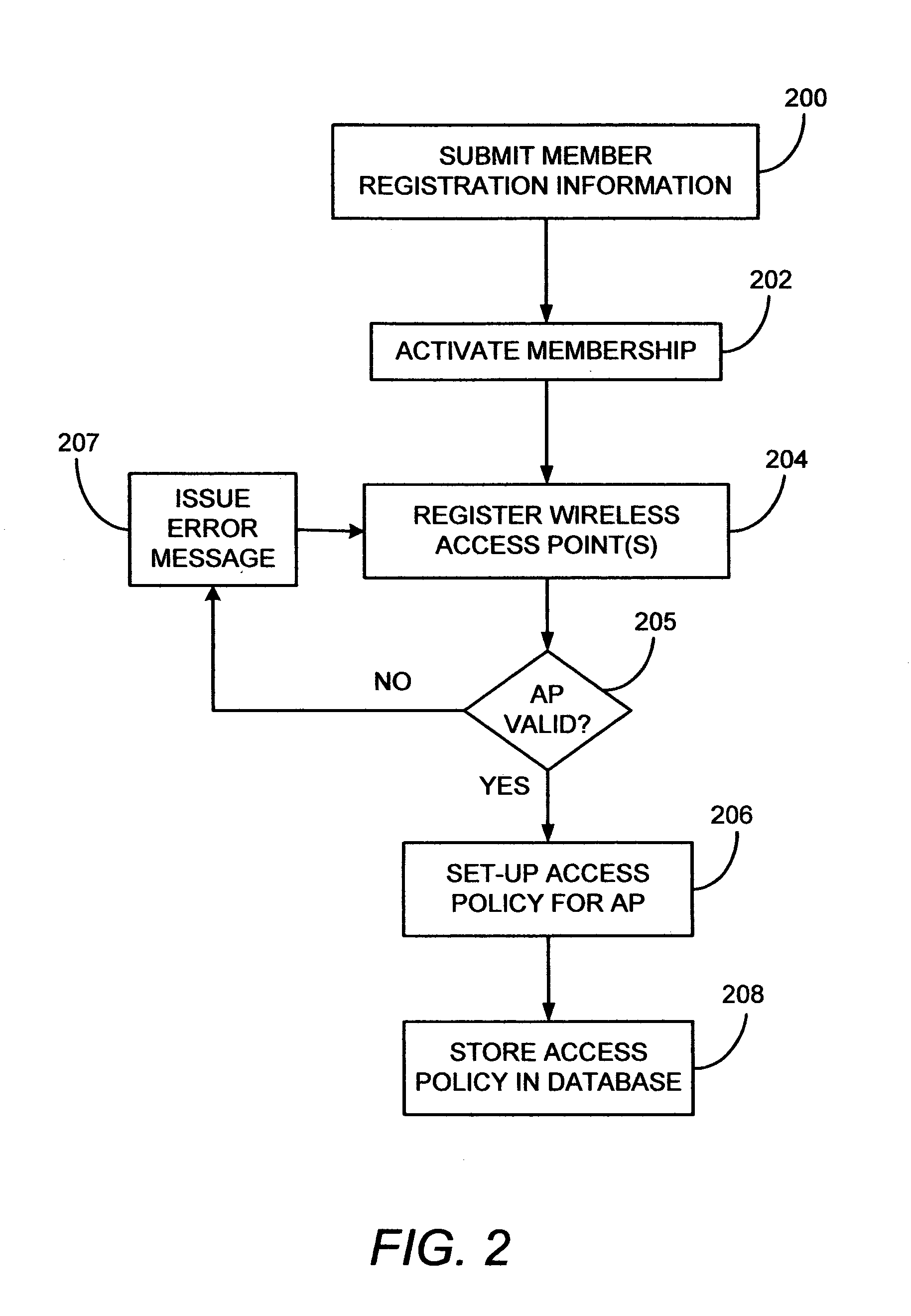
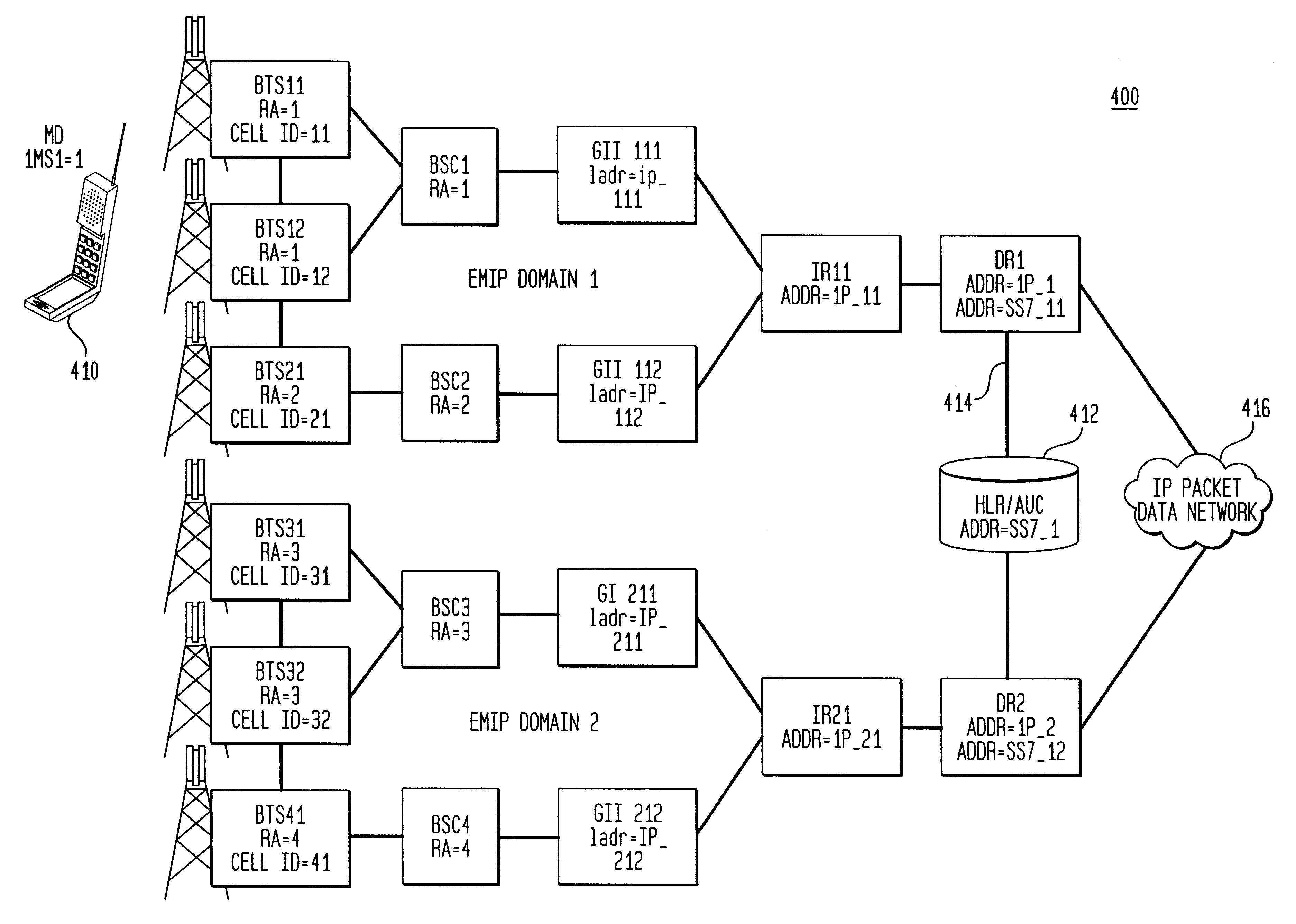
A General Packet Radio Service (GPRS) Accessed Extended Mobile Internet Protocol (EMIP) [G-EMIP] network is provided for wireless mobile device access to external packet data networks. Domains are defined to incorporate a subnet of standard GPRS and EMIP network entities accessed through a Domain Router. Packet access at the radio interface is provided using the base station portion of a GPRS network. Wireless link specific processing is relegated to this potion of the G-EMIP network. EMIP is utilized as a backbone network to provide mobility and service management and interconnection to external networks. A GPRS-IP Interworking entity (GII) interworks IP and GPRS protocols between GPRS and IP addressable network entities (i.e., translates messages of each protocol to corresponding messages of the other protocol). Mobility-related functionality is handled at the IP (network) layer. Mobile IP is used to support the macro-mobility and Handoff-Aware Wireless Access Internet Infrastructure (HAWAII) is used to support micro-mobility and paging. The Domain Router provides packet service management and interacts with a Home Location Register / Authentication Center, which provides GRPS registration, authentication and encryption.
Owner:LUCENT TECH INC +1
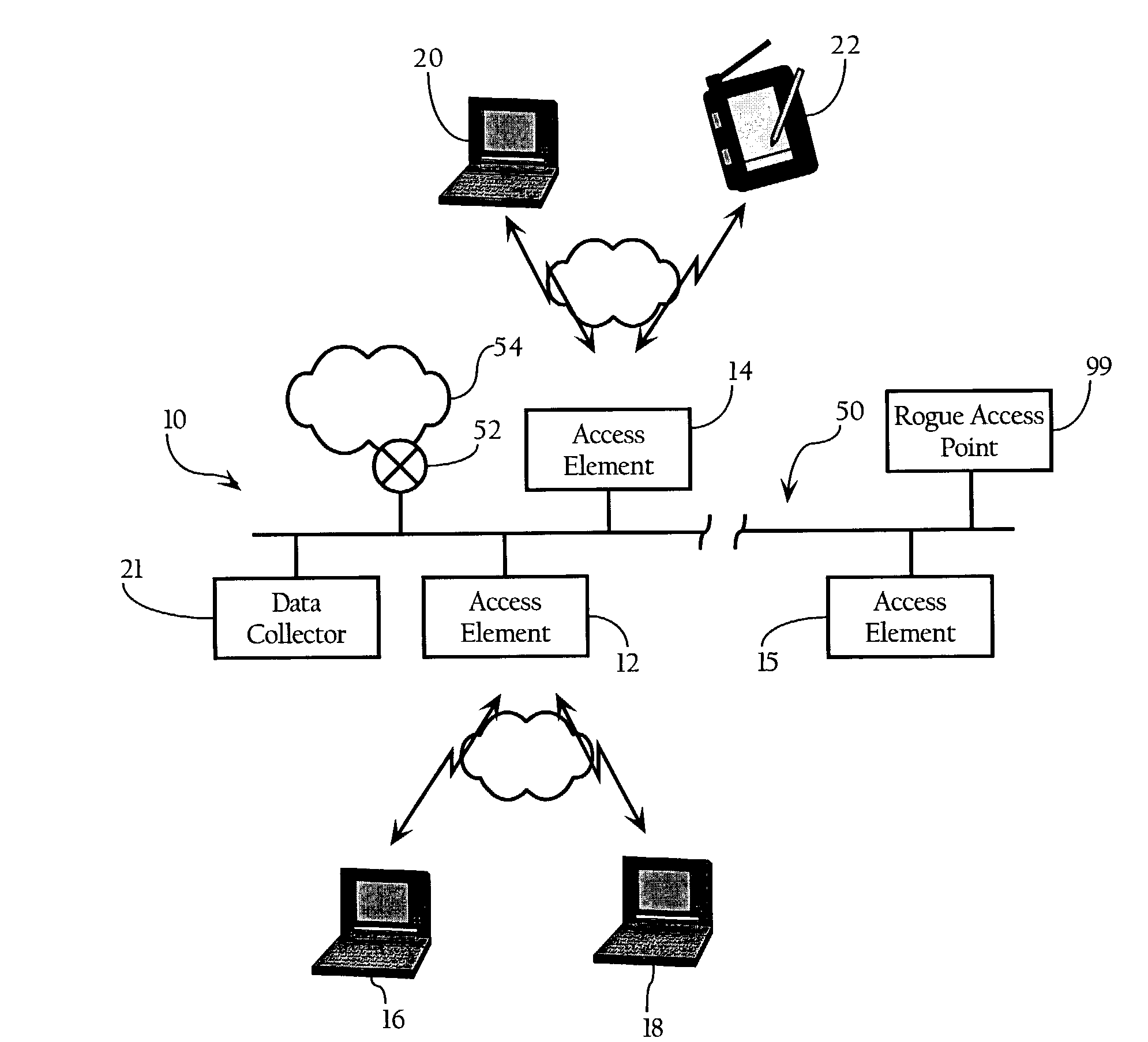
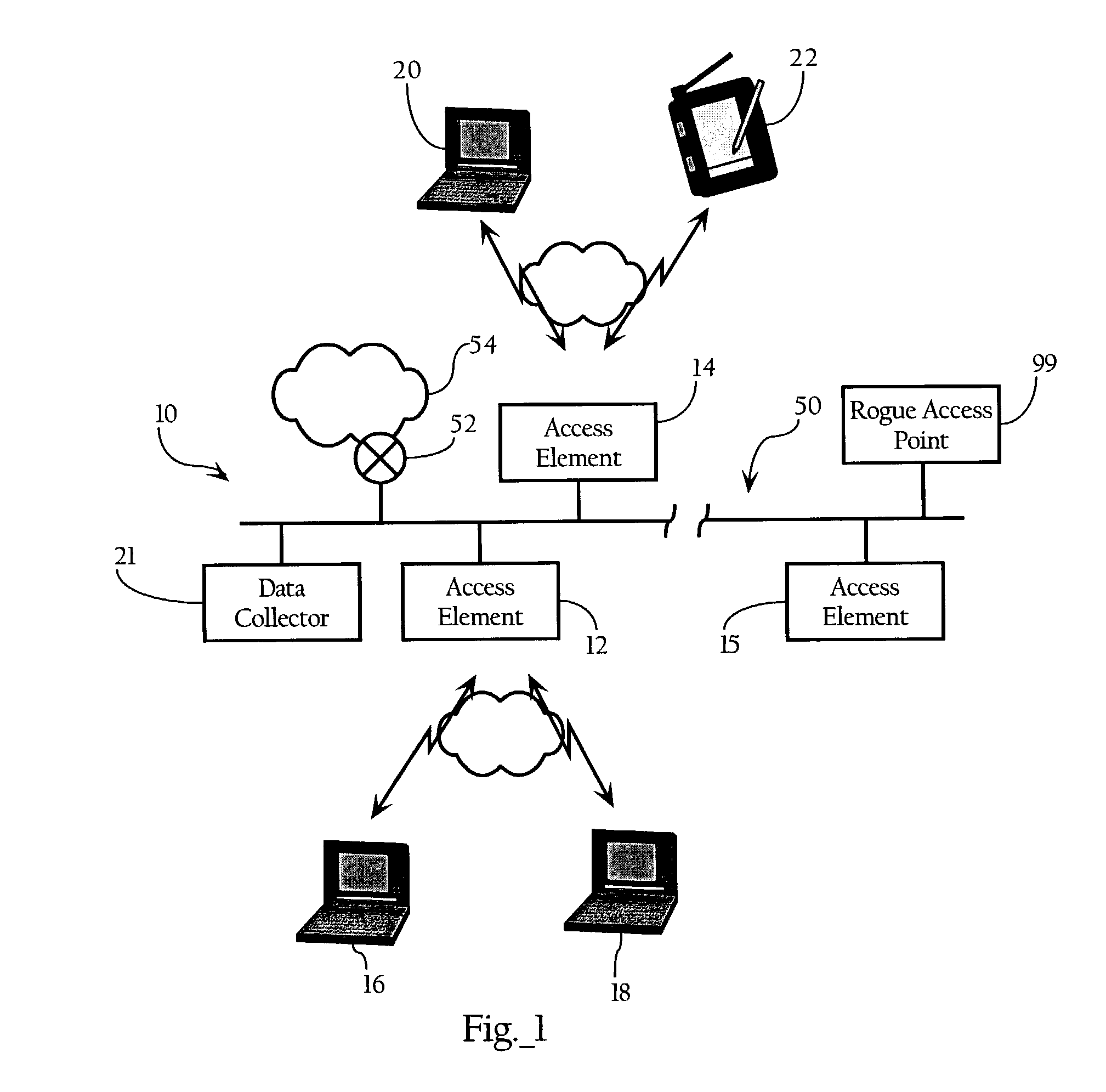
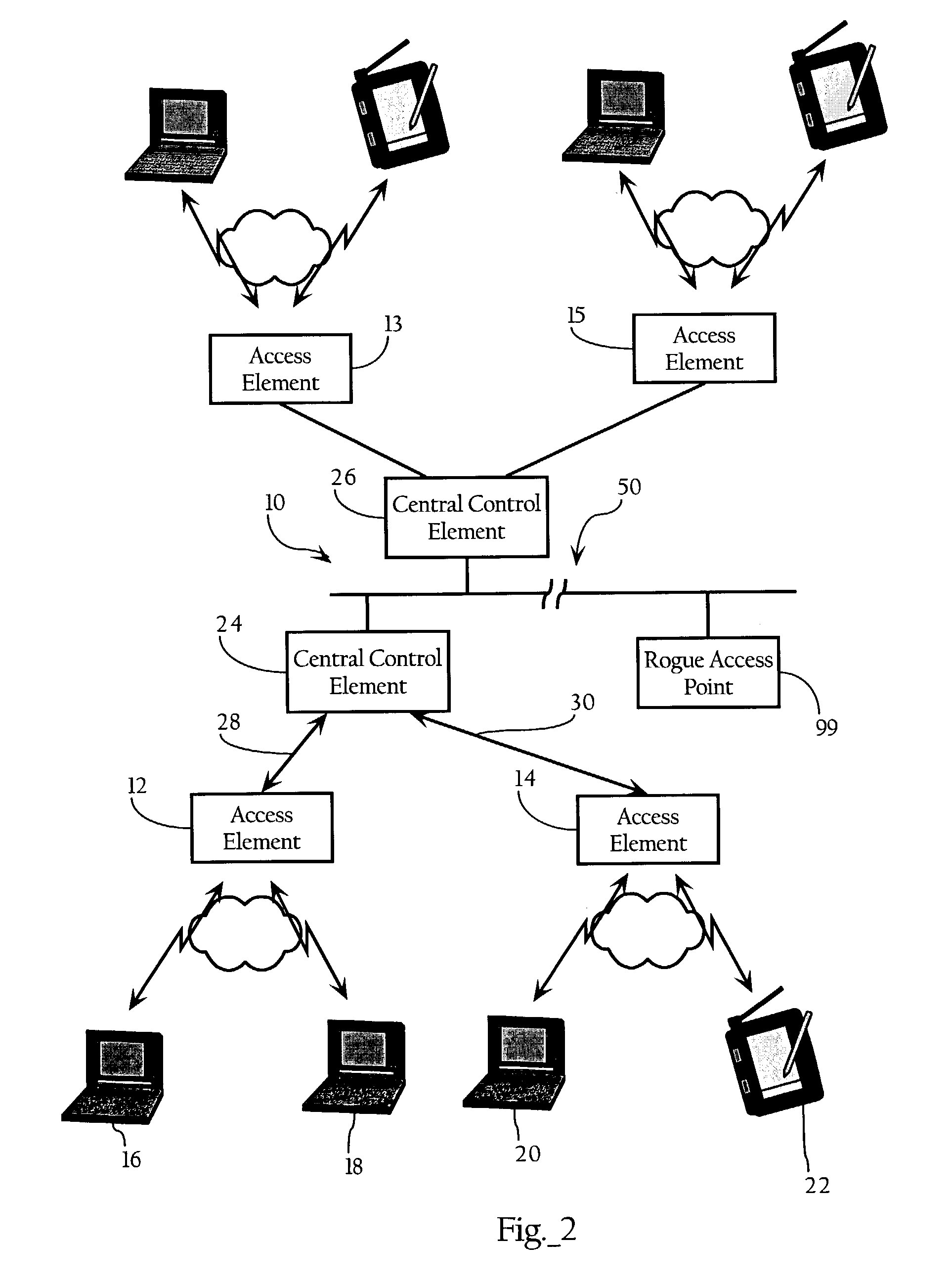
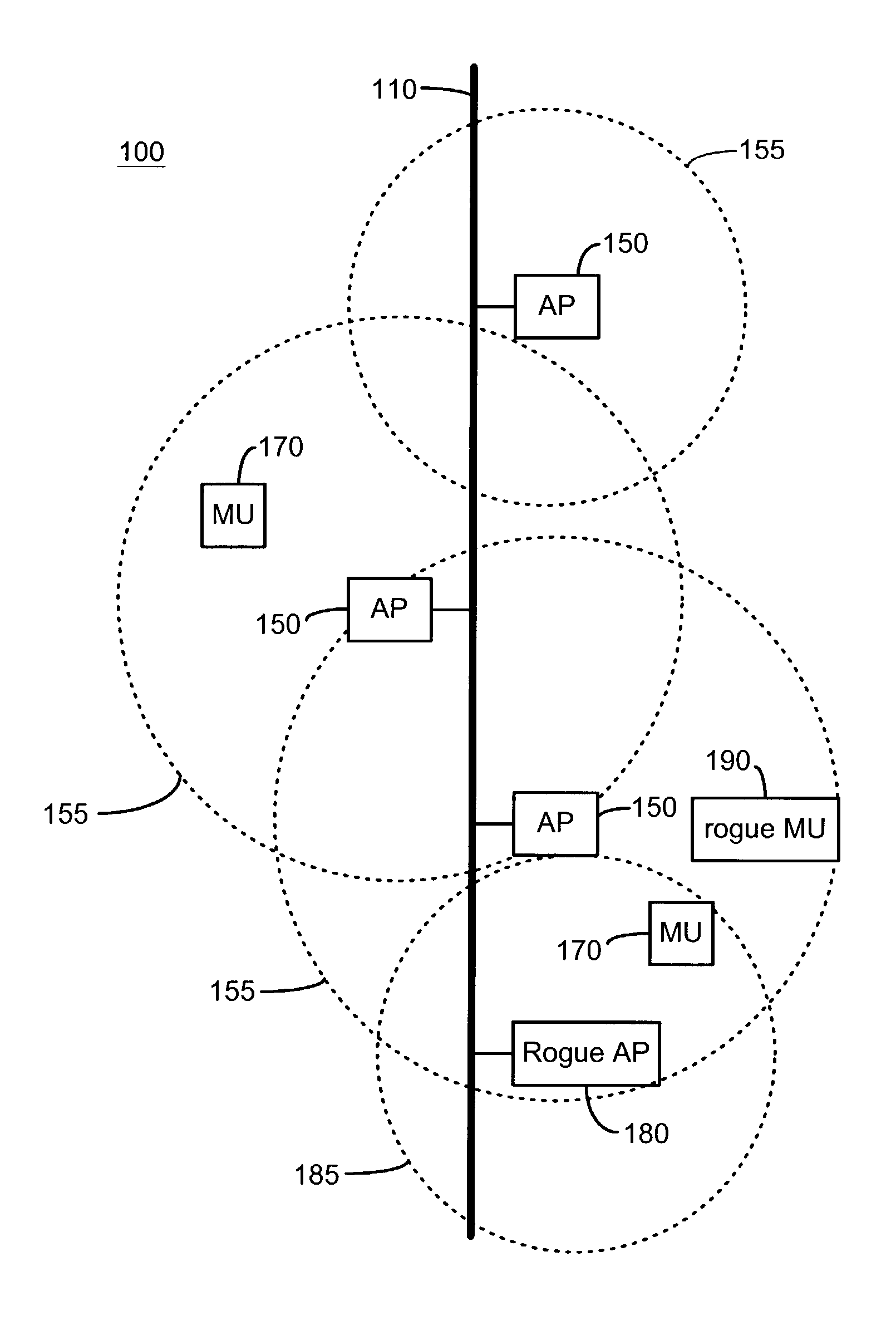
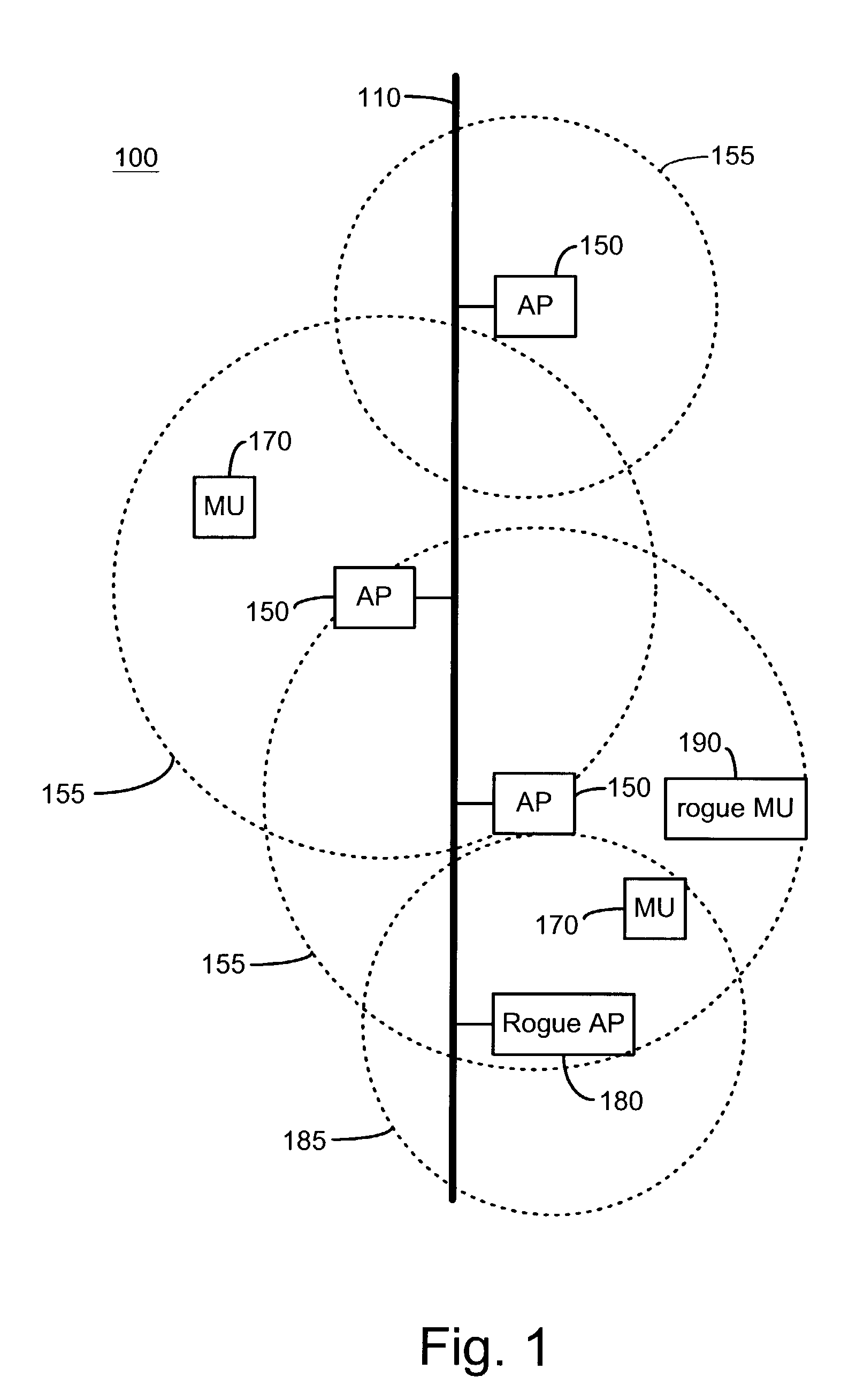
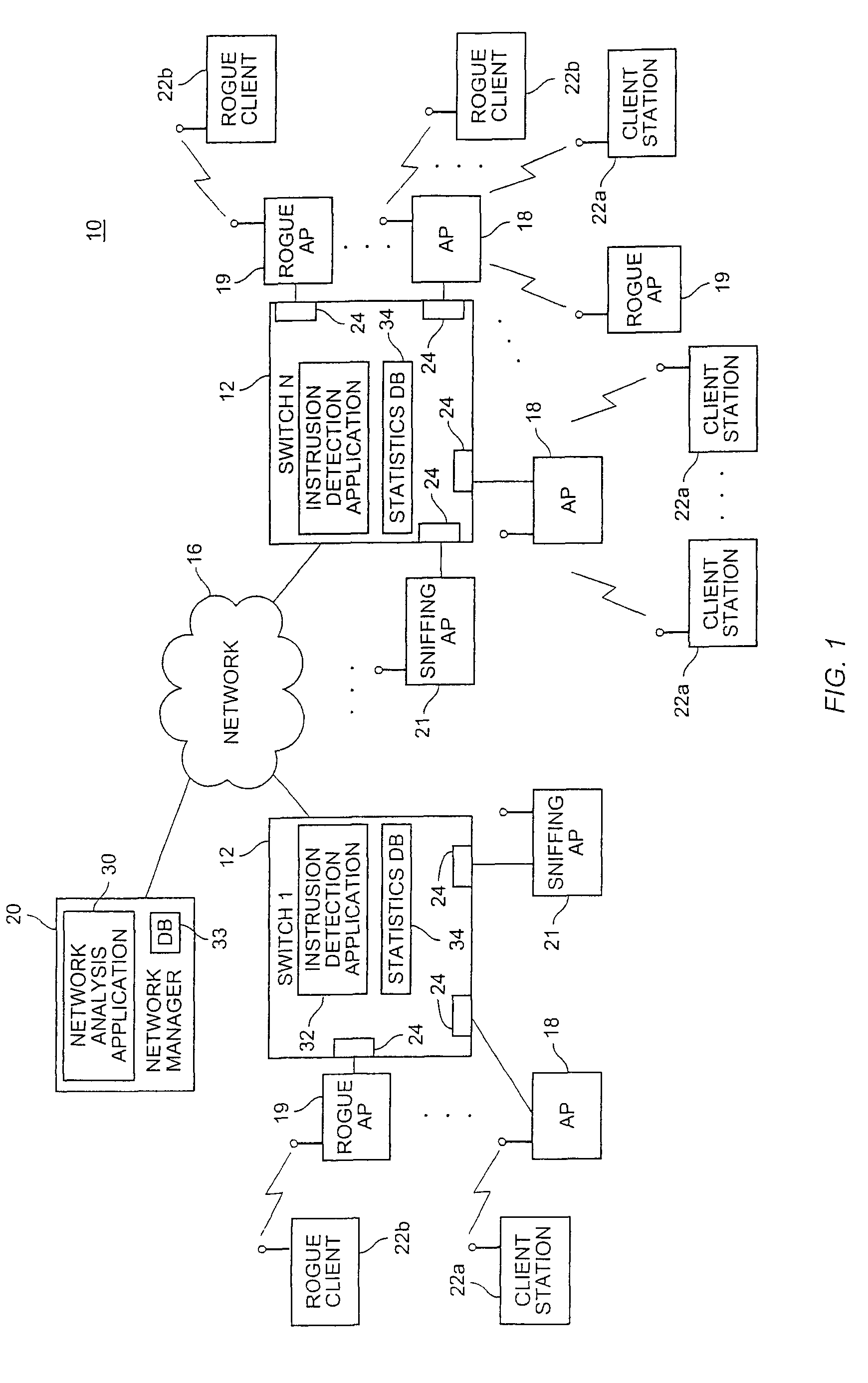
Wireless network system including integrated rogue access point detection
ActiveUS7346338B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsRogue access pointWireless access point
Methods, apparatuses and systems facilitating automated detection of rogue wireless access points in a wireless network environment. The present invention, in one embodiment, integrates automated detection of rogue access points into wireless network systems. As discussed more fully below, the present invention can be applied to a variety of wireless network system architectures.
Owner:CISCO TECH INC
Method and system for localized data retrieval
ActiveUS9877138B1Easy programmingQuick SetupNetwork topologiesConnection managementData retrievalMobile device
A system and method for localized data retrieval to disseminate data about points of interest at a display venue, based on a local area network established with a series of commonly named wireless access points operatively connected to a main router. The system is connected to a user's mobile device through an application they are directed to download. Each WAP has a common name and is located about the display venue in close enough proximity to other WAPs so as to constitute an uninterrupted communication platform with the main LDRS computer from which data about the points of interest is polled. Interspersed about the display venue is a series of tracking devices causing nearby mobile devices to self report their location to the LDRS computer.
Owner:FRANKLIN WARREN LEE
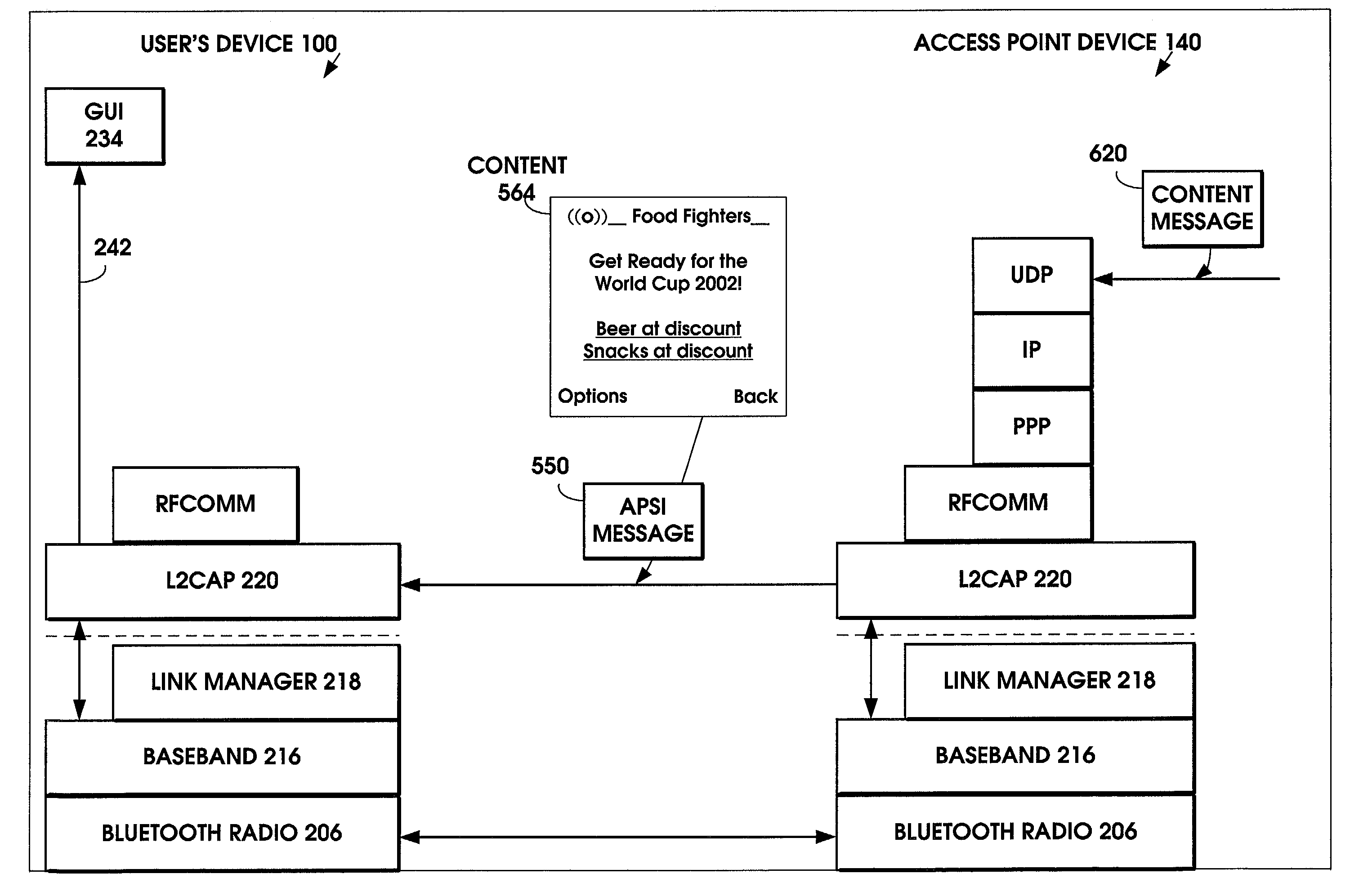
Service notification on a low bluetooth layer
InactiveUS7151764B1Fast contentFast processingAssess restrictionNetwork topologiesPointing deviceProtocol Application
A method is provided to minimize the protocol stacks needed for a short range wireless access point to rapidly communicate a message to a short range wireless mobile device and display it to the user. The short range wireless access point device stores an Access Point Service Indicator (APSI) message characterizing the service platform offerings. The APSI message has a unique message ID in its header. The user device's transport protocol layer is modified to detect the unique message ID and load it into an APSI message buffer. The transport protocol layer passes the APSI message directly to the application layer, bypassing the middleware protocol layers. The method can be applied to communications between various types of wireless devices to enable rapid communication, such as between two mobile devices, between fixed and mobile devices, between short range devices or between long range devices.
Owner:NOKIA CORP
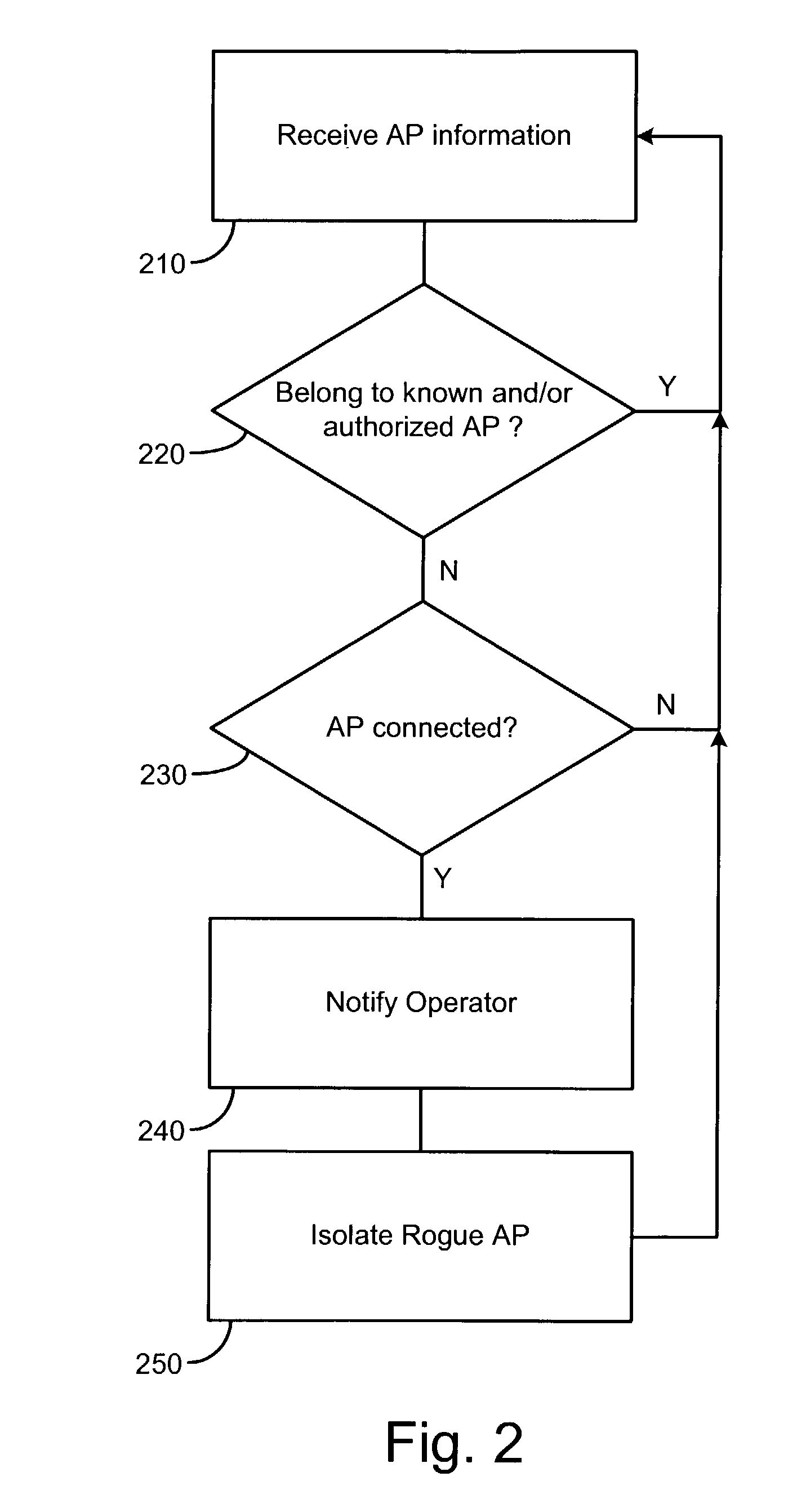
System and method for detecting unauthorized wireless access points
InactiveUS7965842B2Data switching by path configurationSecret communicationCyber operationsInternet privacy
Unauthorized wireless access points are detected by configuring authorized access points and mobile units to listen to all wireless traffic in its cell and report all detected wireless devices to a monitor. The monitor checks the reported devices against a list of authorized network devices. If the reported wireless device is not an authorized device, the monitor determines if the reported device is connected to the network. If the reported device is connected to the network and is not an authorized device, the monitor alerts the network operator or network manager of a rogue device connected to the network and attempts to locate and isolate the rogue device.
Owner:IVANTI INC
Mobile provisioning tool system
ActiveUS7239877B2Significant processingLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessNetwork connection
Owner:ACCENTURE GLOBAL SERVICES LTD
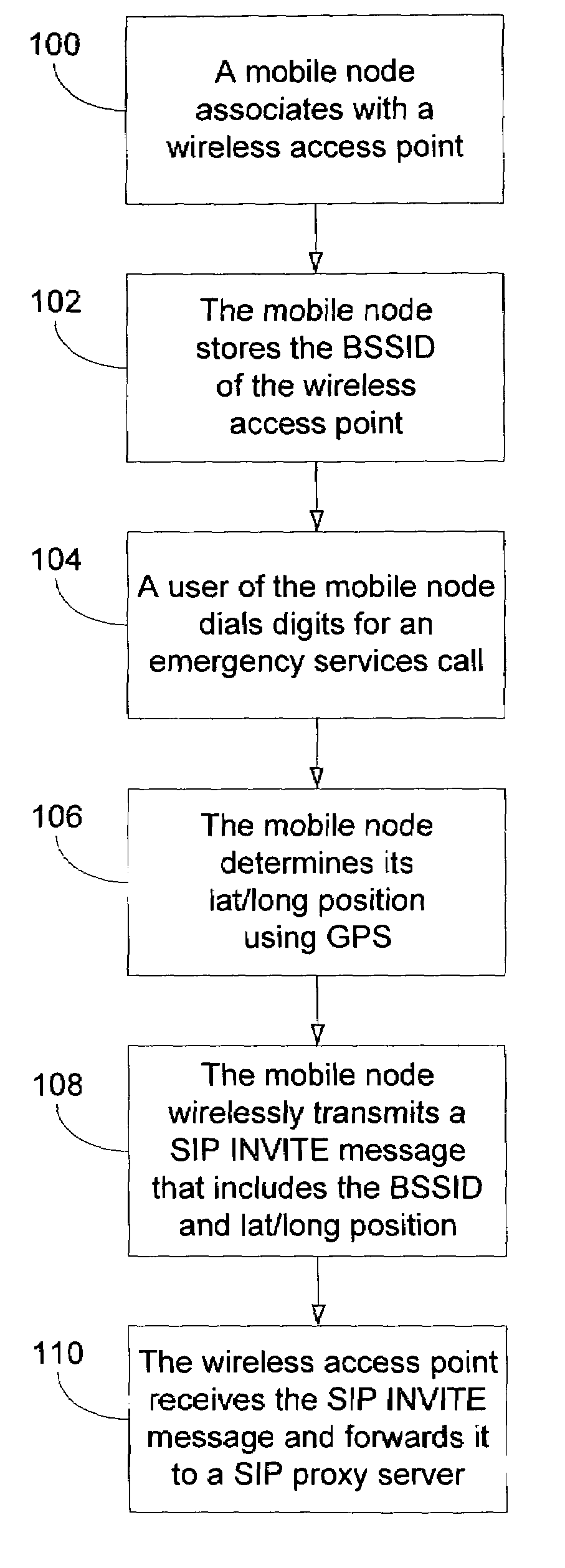
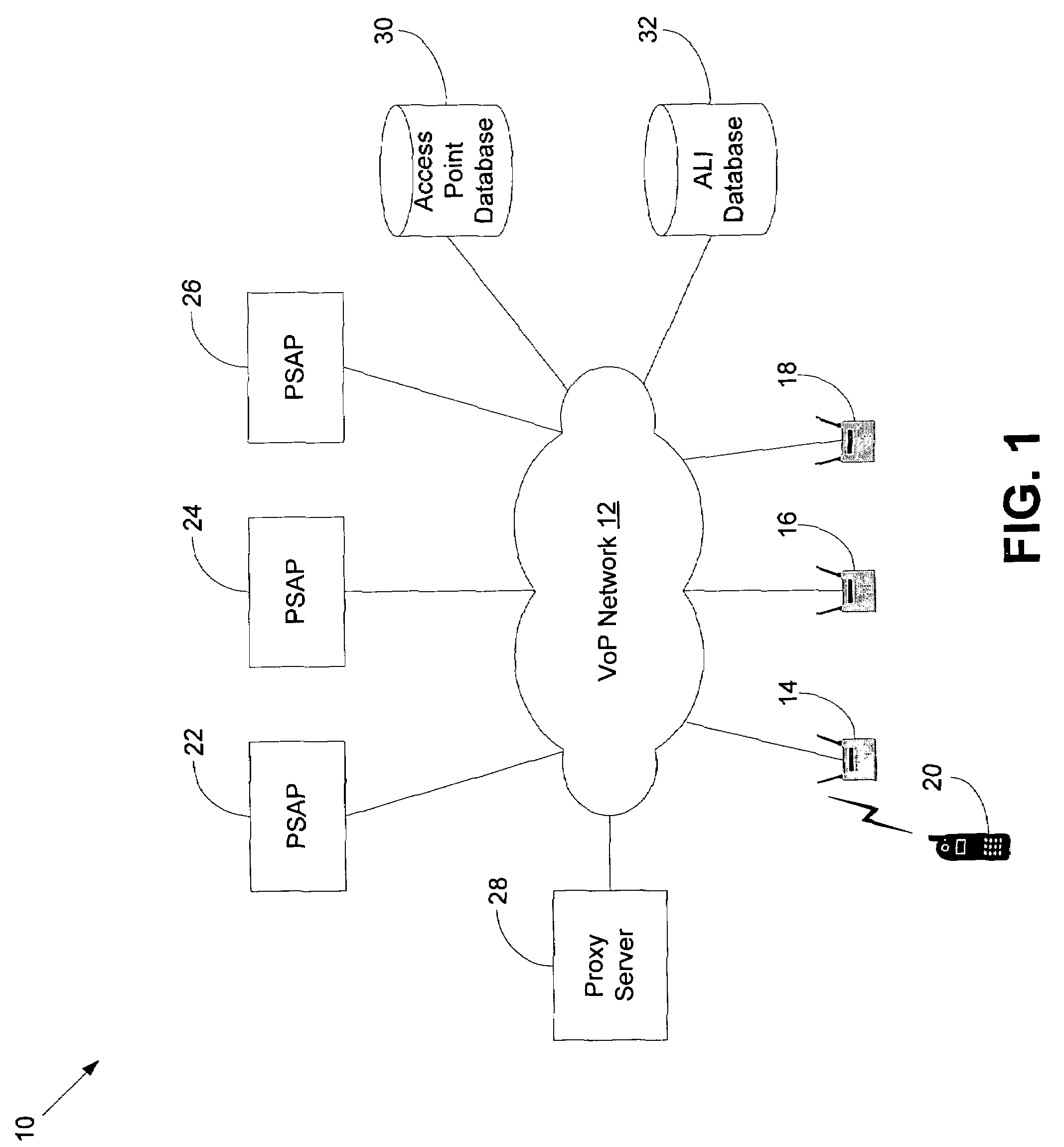
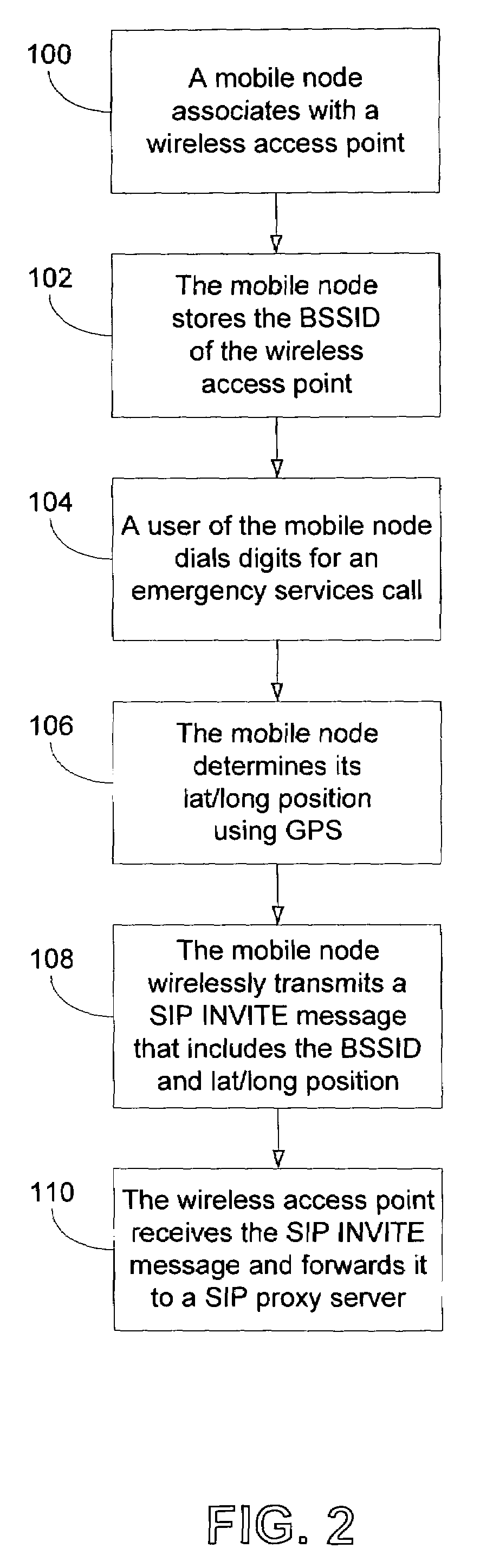
Method and system for using basic service set identifiers (BSSIDs) for emergency services routing
A plurality of public safety answering points (PSAPs) are accessible via a voice-over-packet (VoP) network. Each wireless access point of the VoP network is identified by a basic service set identifier (BSSID). A mobile node associates with a wireless access point and stores the wireless access point's BSSID as an indicator of the mobile node's location. A user of the mobile node dials digits for an emergency services call. In response, the mobile node transmits a SIP INVITE message that includes the BSSID and an additional indicator of the mobile node's location, e.g., determined using GPS or tower triangulation. A SIP proxy server receives the SIP INVITE message and attempts to determine the appropriate PSAP to answer the call based on the BSSID. If the attempt is unsuccessful, the SIP proxy server determines the appropriate PSAP based on the additional indicator.
Owner:SPRINT SPECTRUM LLC
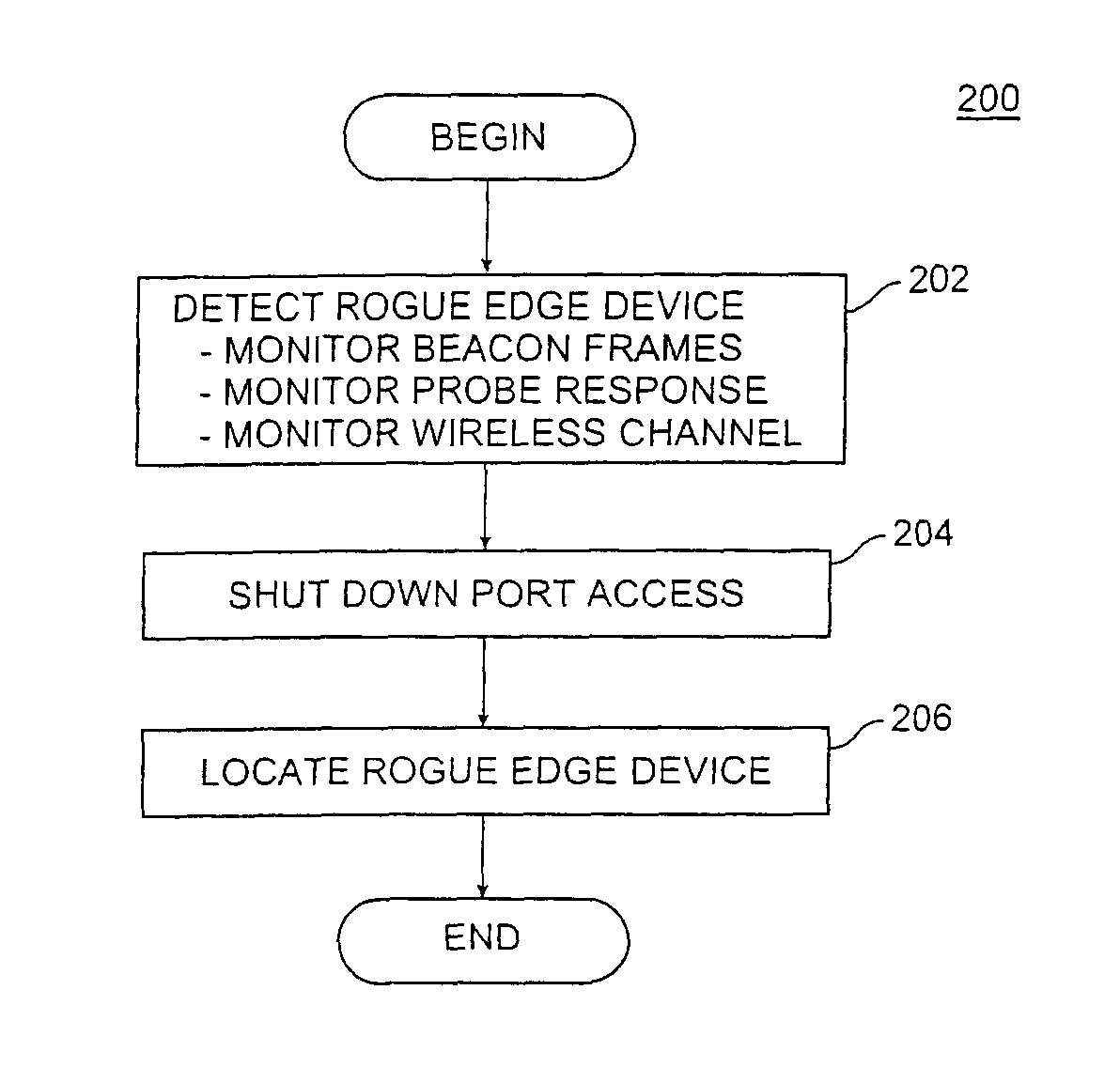
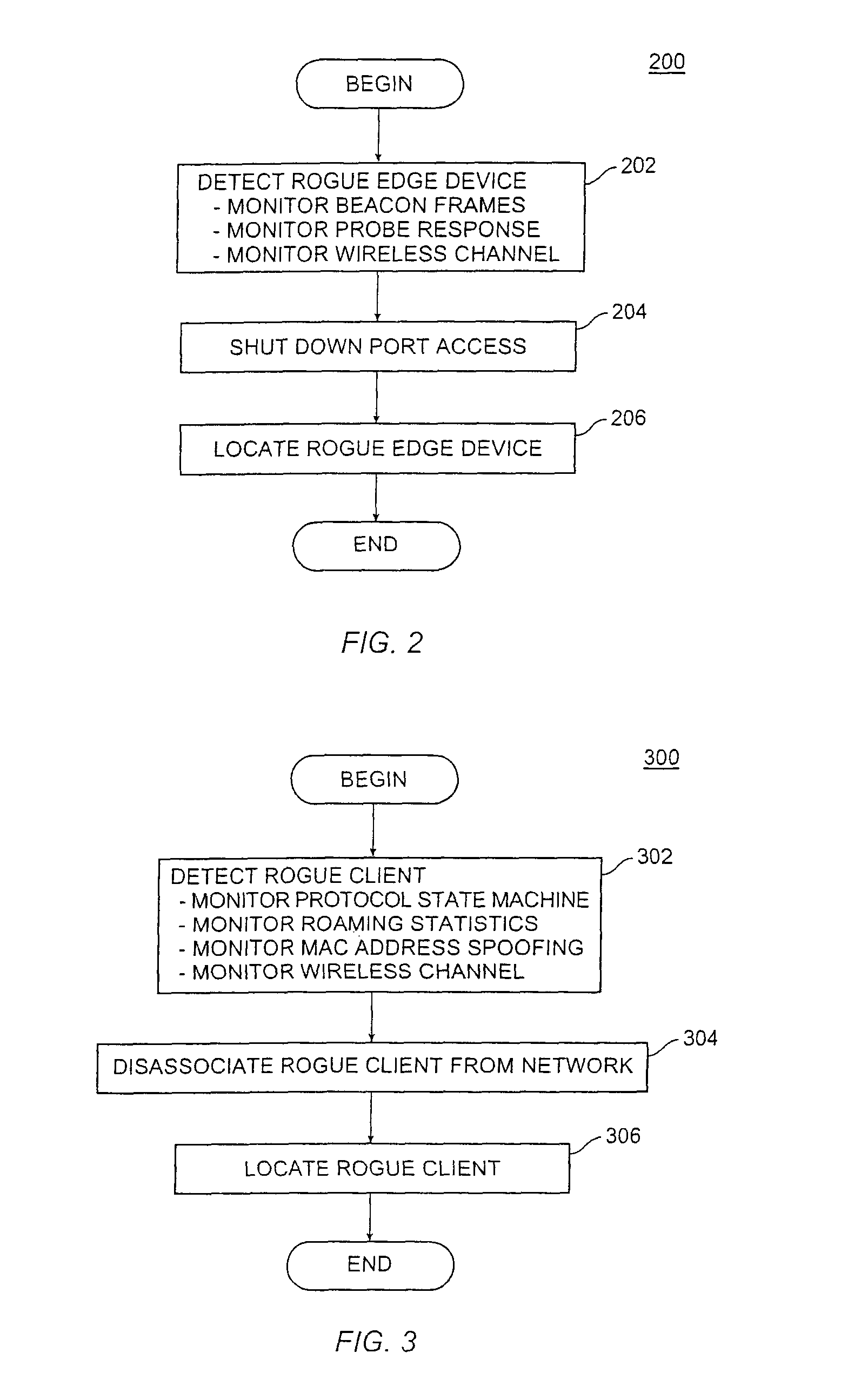
Method and system for detecting and preventing access intrusion in a network
ActiveUS8707432B1Memory loss protectionError detection/correctionNetwork connectionNetwork addressing
A wireless computer network includes components cooperating together to prevent access intrusions by detecting unauthorized devices connected to the network, disabling the network connections to the devices, and then physically locating the devices. The network can detect both unauthorized client stations and unauthorized edge devices such as wireless access points (APs). The network can detect intruders by monitoring information transferred over wireless channels, identifying protocol state machine violations, tracking roaming behavior of clients, and detecting network addresses being improperly used in multiple locations. Upon detecting an intruder, the network can automatically locate and shut off the physical / logical port to which the intruder is connected.
Owner:EXTREME NETWORKS INC
Mobile virtual LAN
InactiveUS6847620B1Not burdened with associated computational overheadNetwork topologiesWireless network protocolsCommunications systemVirtual LAN
A communication system in which multiple protocols and proxy services are executed by an access point. In one embodiment of the invention, GVRP and GMRP registrations are combined in a single packet when a wireless device roams to a different VLAN. In addition, outbound GVRP and GMRP multicast messages are handled by an access point (also referred to as a GVRP and GMRP “gateway”) such that the wireless device is not burdened with the associated computational overhead. In a further embodiment, a wireless device may dynamically switch between a VLAN-aware state and a VLAN-unaware state depending on the nature of a detected access point. For example, if a relevant access point supports GVRP, the wireless device may operate as a VLAN terminal. If a wireless device is not attached to an access point with a matching VLAN ID, the wireless device sends and receives VLAN tagged frames. If a wireless device configured with a VLAN ID is attached to an access point with a matching VLAN ID, or if the wireless device is attached to a non-VLAN access point, then the wireless device may send and receive raw / untagged frames. In addition to the gateways described below, the ability of a wireless device to detect when it can send untagged frames is considered novel. In another embodiment of the invention, a special ID that is different than the native VLAN ID for a switch port is used for VLAN-unaware devices. This allows such devices that do not issue tagged frames to belong to a single VLAN ID.
Owner:AVAGO TECH INT SALES PTE LTD
Two-tier wireless broadband access network
ActiveUS8625547B1Quality improvementEasy to installSite diversityNetwork topologiesAccess networkWireless mesh network
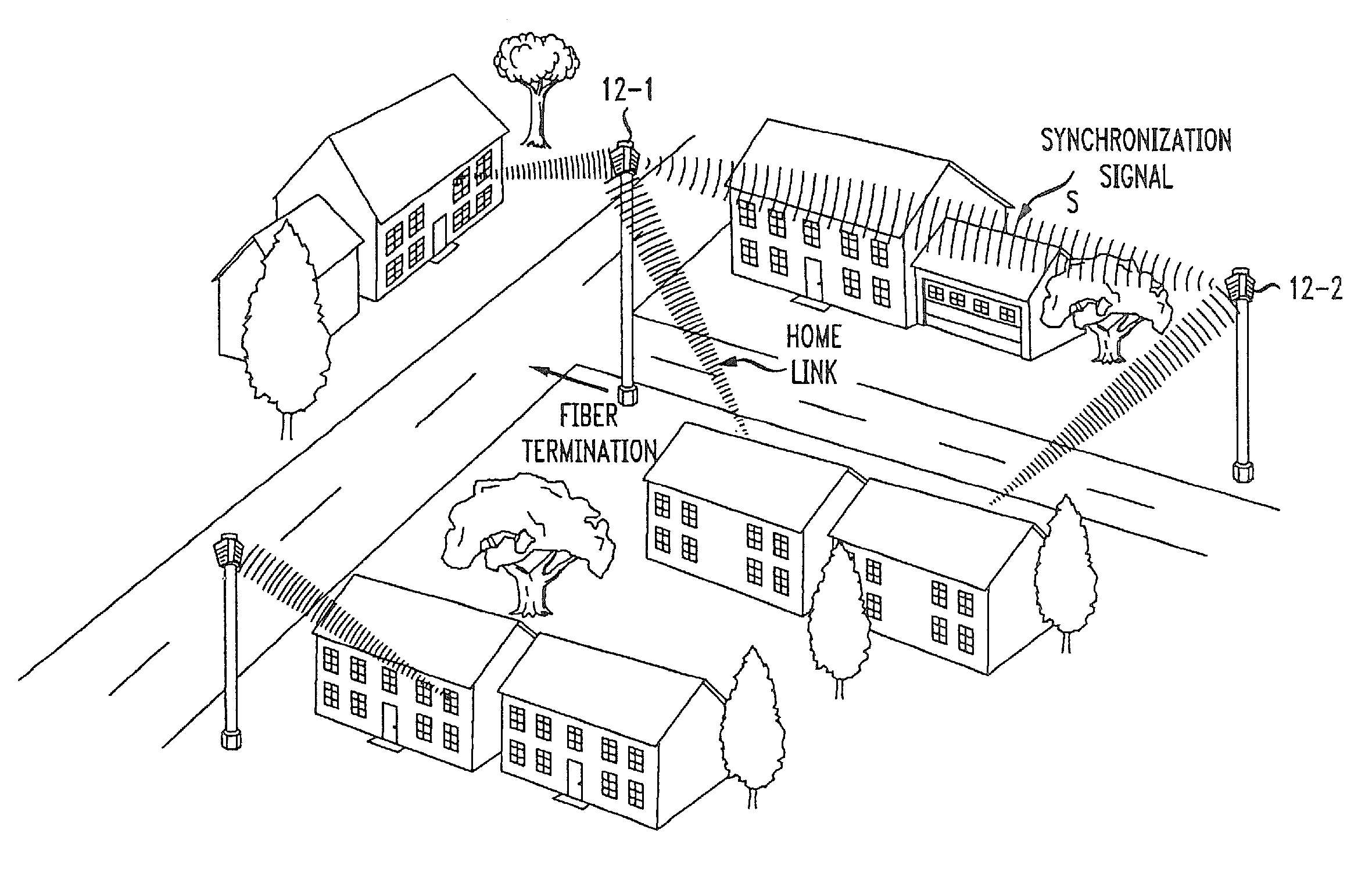
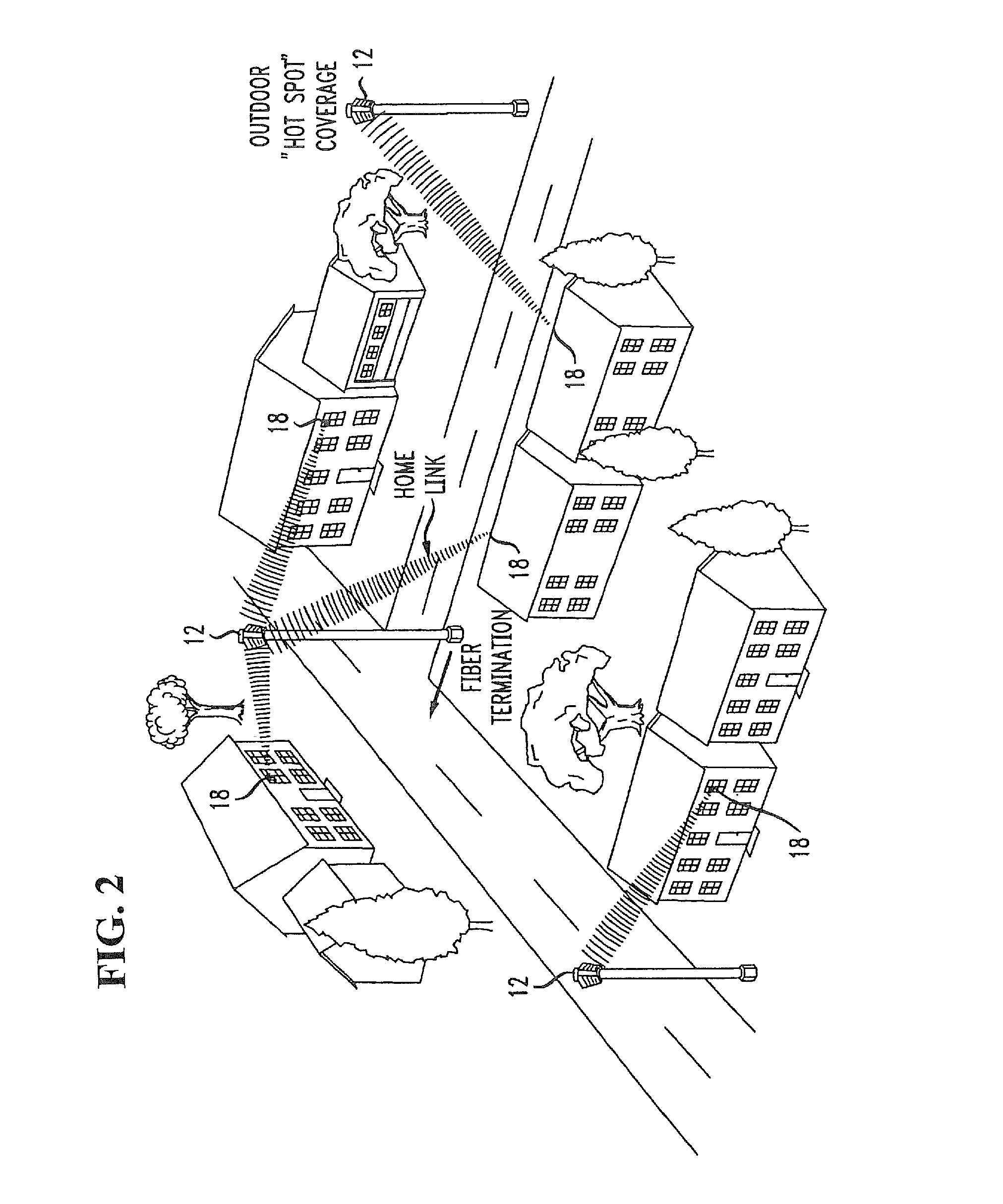
A wireless access network is based on a two-tier access point (AP) structure to provide effective and efficient wireless communication into an individual home / office building. A first tier of the network utilizes “neighborhood” APs, relatively low power, and utilized to provide wireless communication with a “nanocell” boundary (e.g., 300-1000 feet). A second tier of the network utilizes a set of “network concatenation devices” (window bridge), with a separate network concatenation device at each permanent facility in the nanocell that houses wireless devices. The network concatenation device is attached to a window, for example, of a home in communication with the neighborhood AP. The network concatenation device functions as a bridge to couple to each of the wireless devices within the home. This communication is then relayed in an efficient manner between the network concatenation device and the neighborhood AP. By using a number of neighborhood APs, rather extensive wireless coverage can be obtained.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
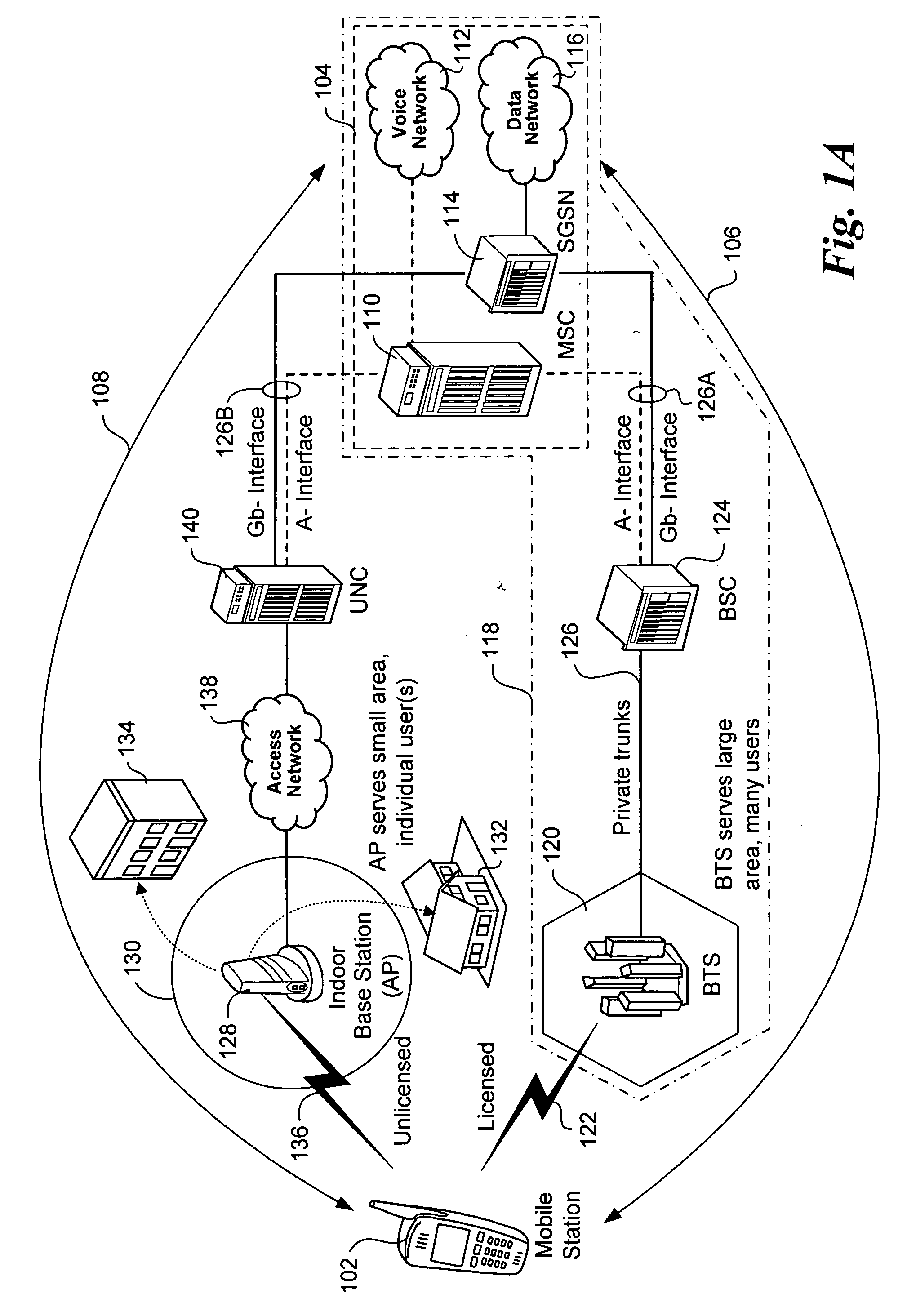
Apparatus and messages for interworking between unlicensed access network and GPRS network for data services
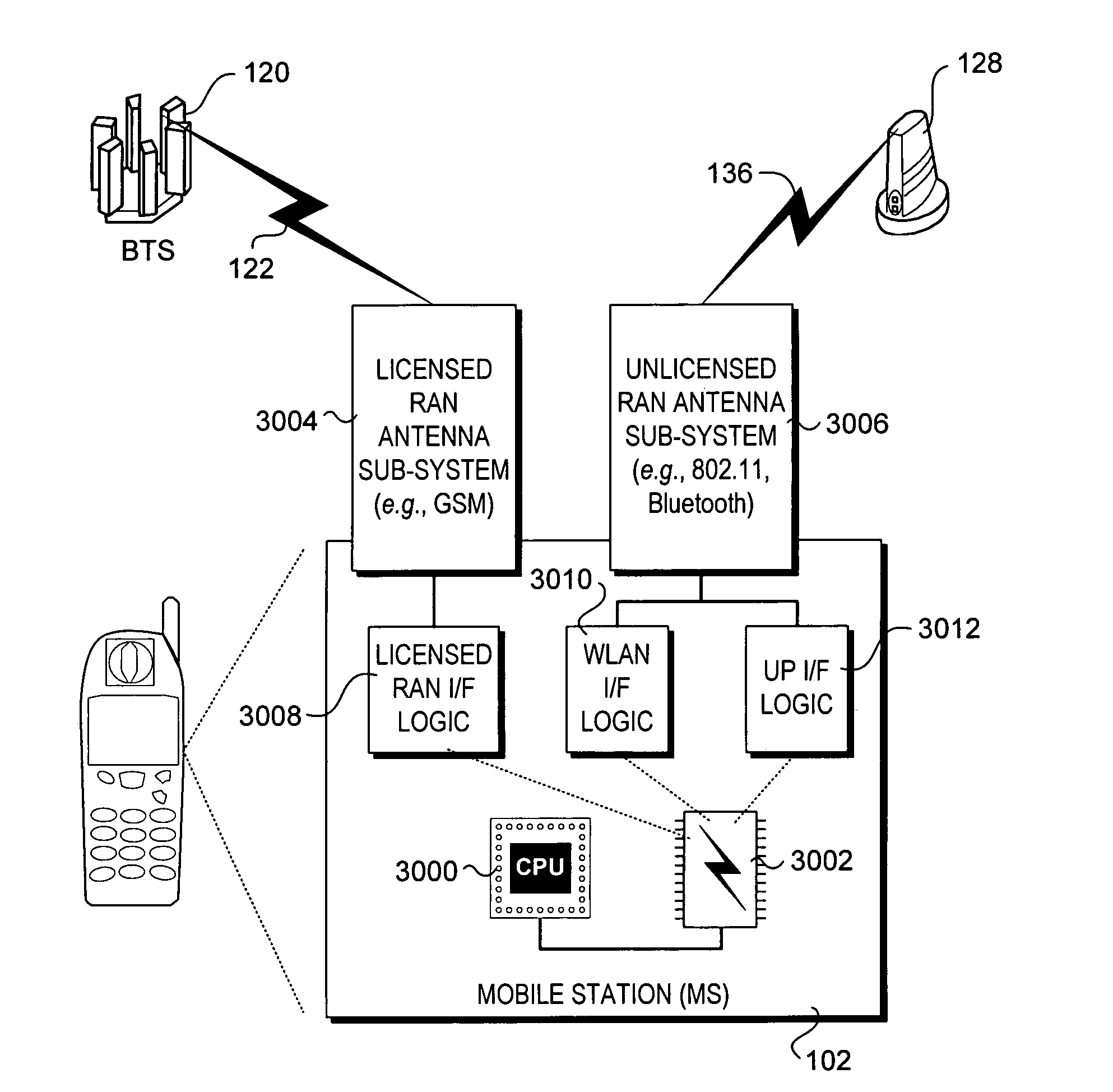
Methods for performing various operations via unlicensed mobile access (UMA) radio link control (URLC) messages in an unlicensed mobile access network (UMAN). The UMAN comprises a first radio access network that may be employed for accessing data services provided by a core network comprising a second radio access network. URLC messages are exchanged between mobile stations (MSs) and UMA network controllers (UNCs) to perform various operations associated with the UMAN. An MS may access the UMAN via a wireless access point (AP) that is communicatively coupled to a UNC via an IP network. The URLC messages are sent between MSs and UNCs using an Up interface comprising a set of layered protocols over an underlying IP transport.
Owner:RIBBON COMM OPERATING CO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com