Patents
Literature
3044 results about "Backbone network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
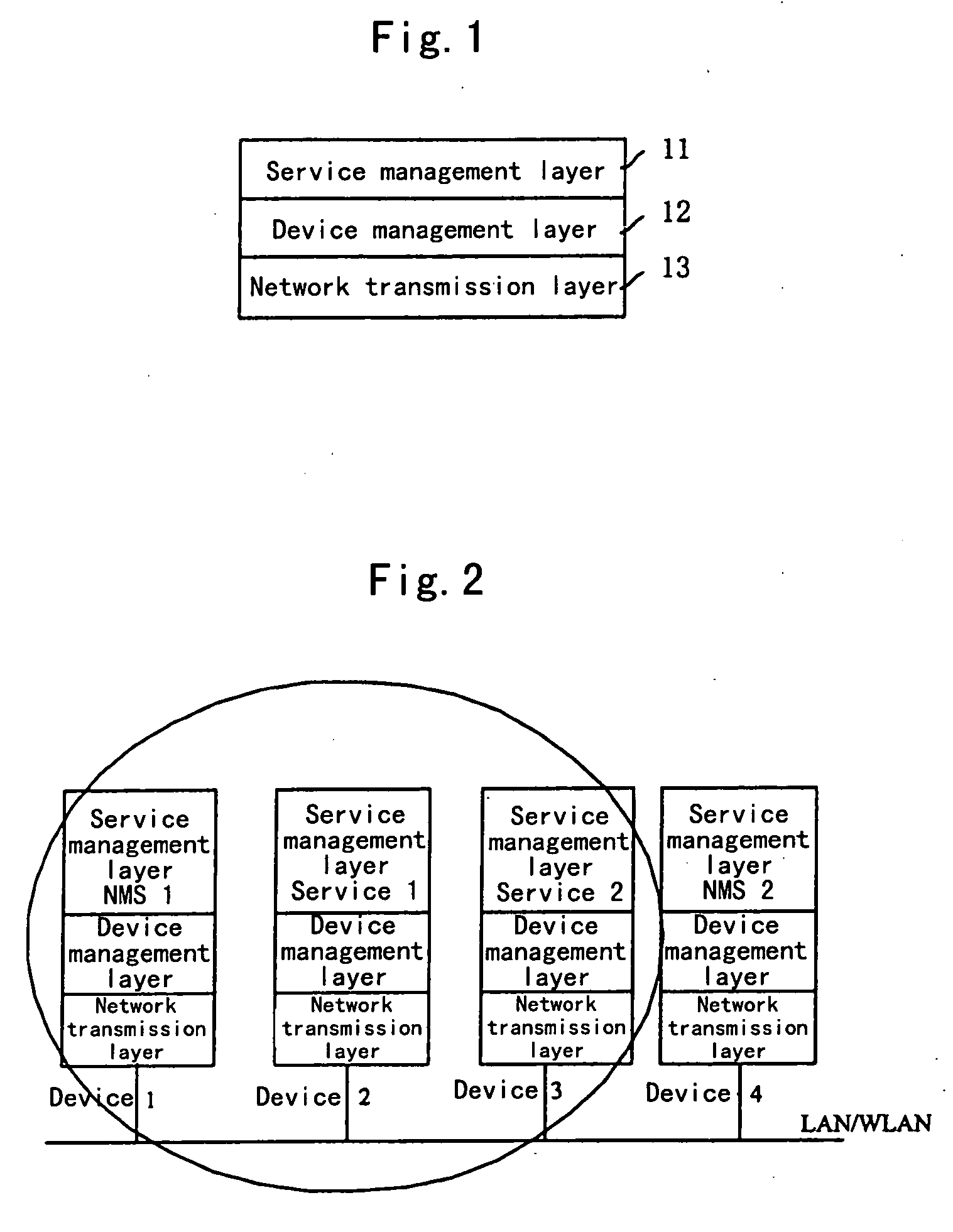
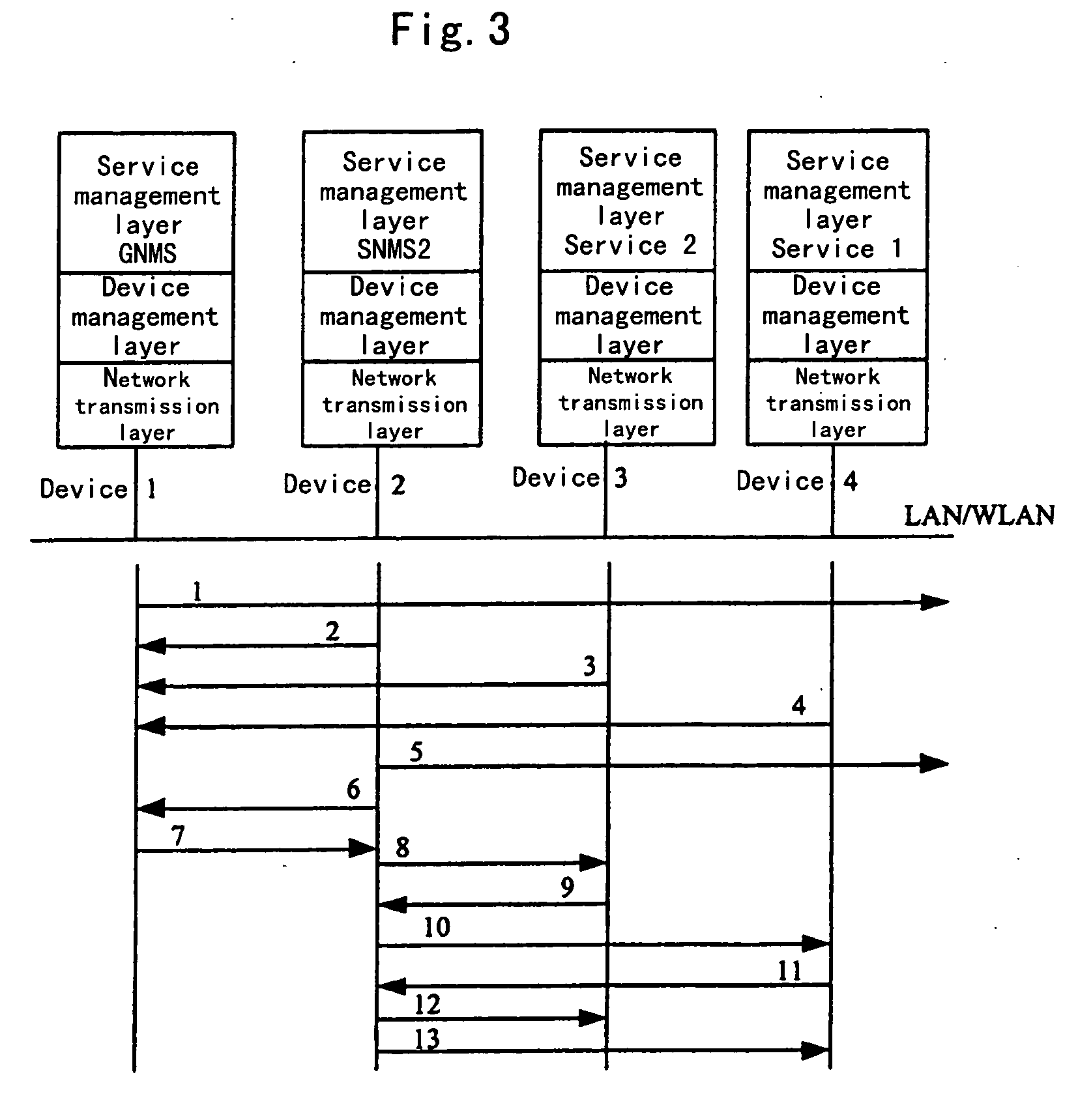
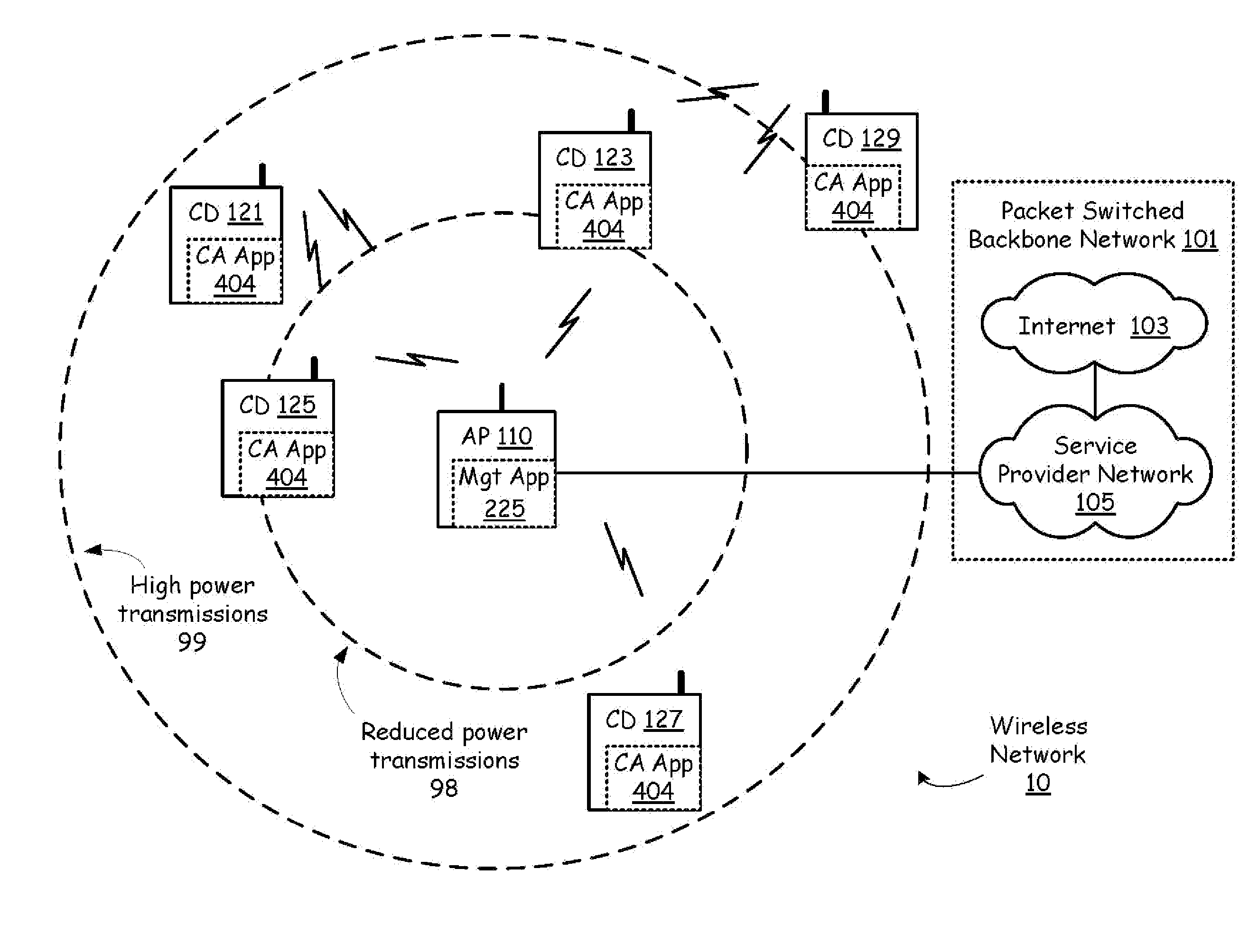
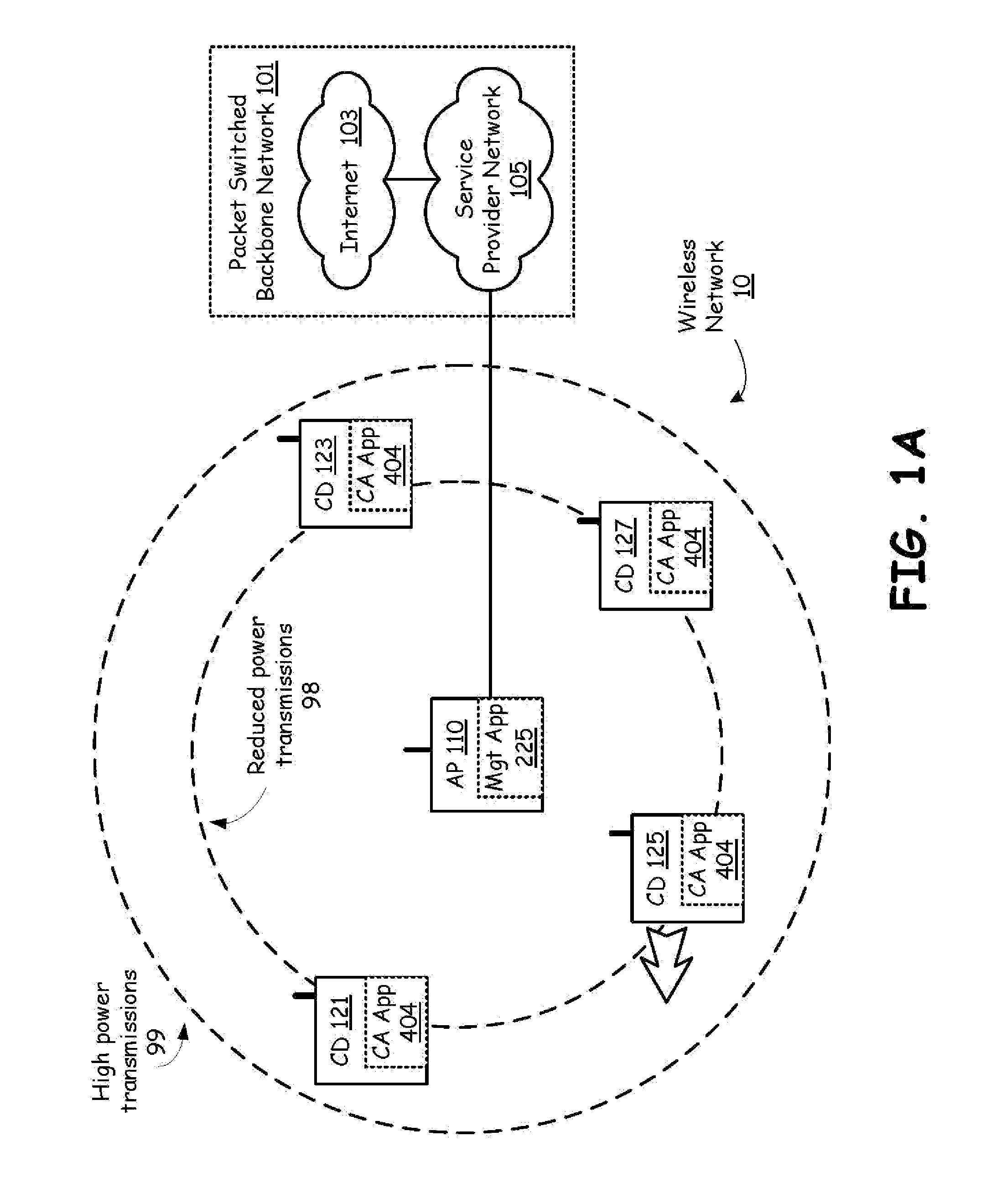
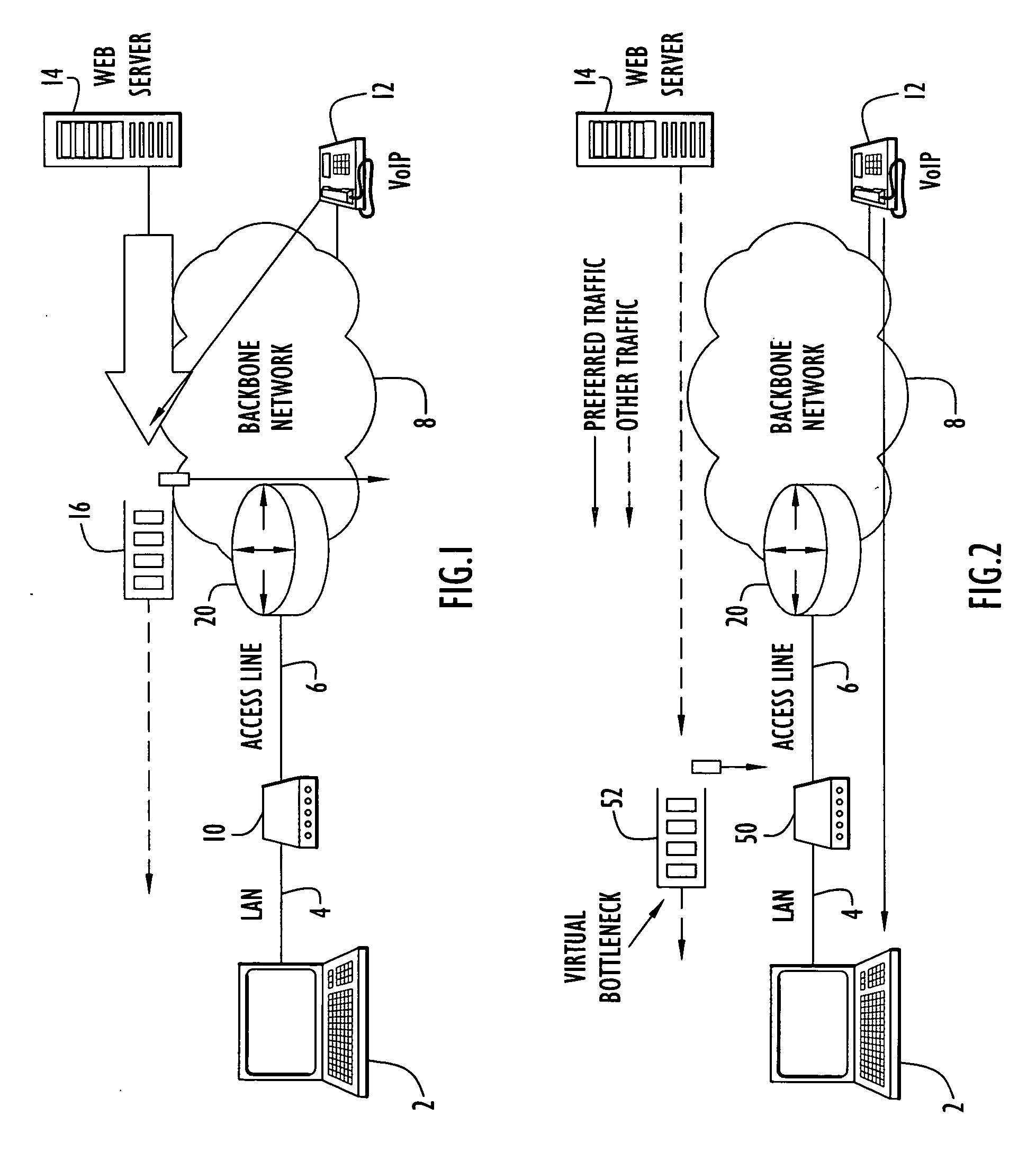
A backbone is a part of computer network that interconnects various pieces of network, providing a path for the exchange of information between different LANs or subnetworks. A backbone can tie together diverse networks in the same building, in different buildings in a campus environment, or over wide areas. Normally, the backbone's capacity is greater than the networks connected to it.
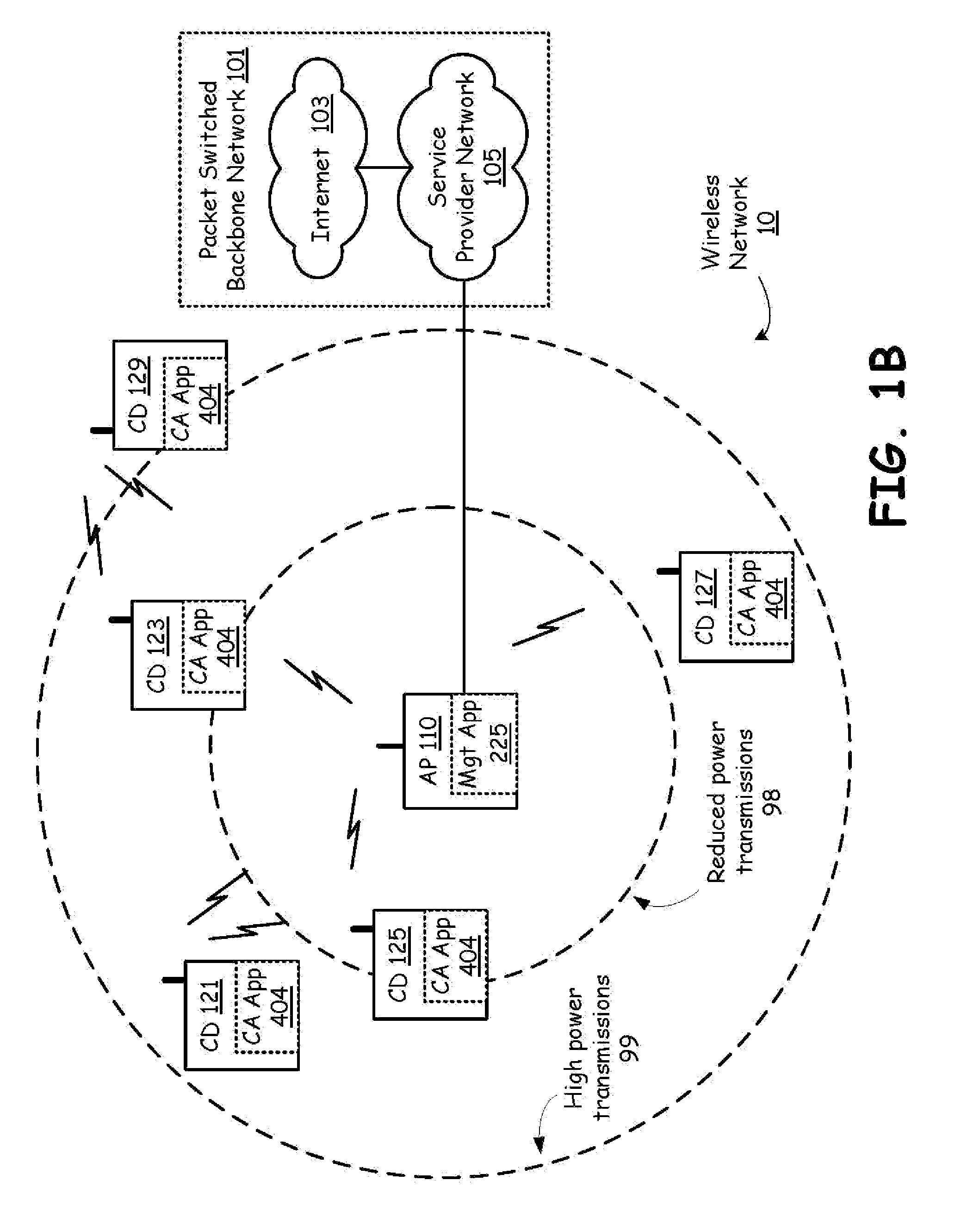
Wireless access of packet based networks
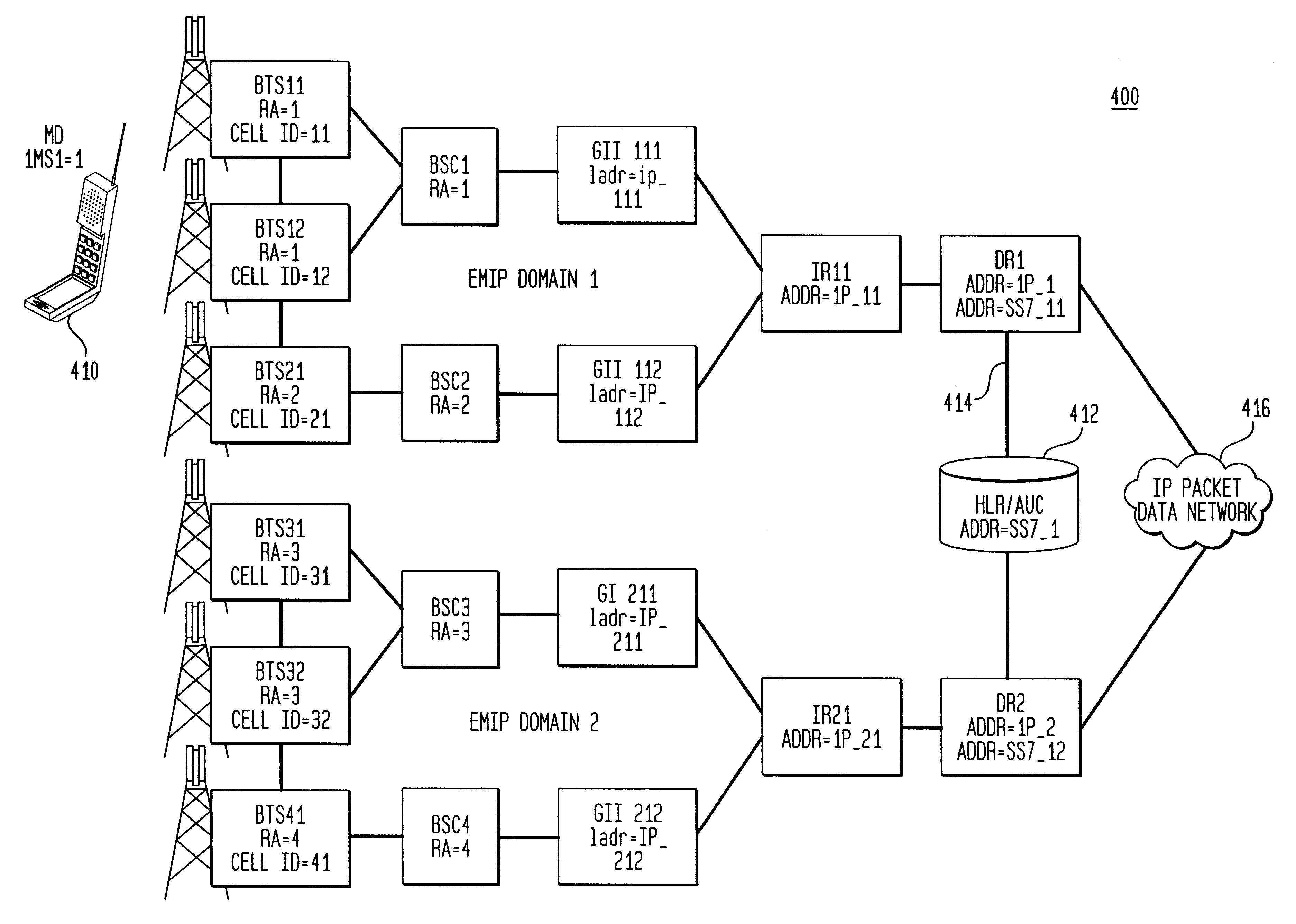
A General Packet Radio Service (GPRS) Accessed Extended Mobile Internet Protocol (EMIP) [G-EMIP] network is provided for wireless mobile device access to external packet data networks. Domains are defined to incorporate a subnet of standard GPRS and EMIP network entities accessed through a Domain Router. Packet access at the radio interface is provided using the base station portion of a GPRS network. Wireless link specific processing is relegated to this potion of the G-EMIP network. EMIP is utilized as a backbone network to provide mobility and service management and interconnection to external networks. A GPRS-IP Interworking entity (GII) interworks IP and GPRS protocols between GPRS and IP addressable network entities (i.e., translates messages of each protocol to corresponding messages of the other protocol). Mobility-related functionality is handled at the IP (network) layer. Mobile IP is used to support the macro-mobility and Handoff-Aware Wireless Access Internet Infrastructure (HAWAII) is used to support micro-mobility and paging. The Domain Router provides packet service management and interacts with a Home Location Register / Authentication Center, which provides GRPS registration, authentication and encryption.
Owner:LUCENT TECH INC +1
Transparent, look-up-free packet forwarding method for optimizing global network throughput based on real-time route status
ActiveUS20040032856A1Fast protection re-routingEfficient multicastingData switching by path configurationPrivate networkOSI model
A packet forwarding method for optimizing packet traffic flow across communications networks and simplifying network management. The invention provides look-up-free and packet-layer-protocol transparent forwarding of multi-protocol packet traffic among Layer-N (N=2 or upper in the ISO OSI model) nodes. The invention enables flexible and efficient packet multicast and anycast capabilities along with real-time dynamic load balancing and fast packet-level traffic protection rerouting. Applications include fast and efficient packet traffic forwarding across administrative domains of Internet, such as an ISP's backbone or an enterprise virtual private network, as well as passing packet traffic over a neutral Internet exchange facility between different administrative domains.
Owner:XENOGENIC DEV LLC
System and method for delivering high-performance online multimedia services
InactiveUS6370571B1Easy to scaleIncrease speedSpecial service provision for substationResource allocationFiberCoaxial cable
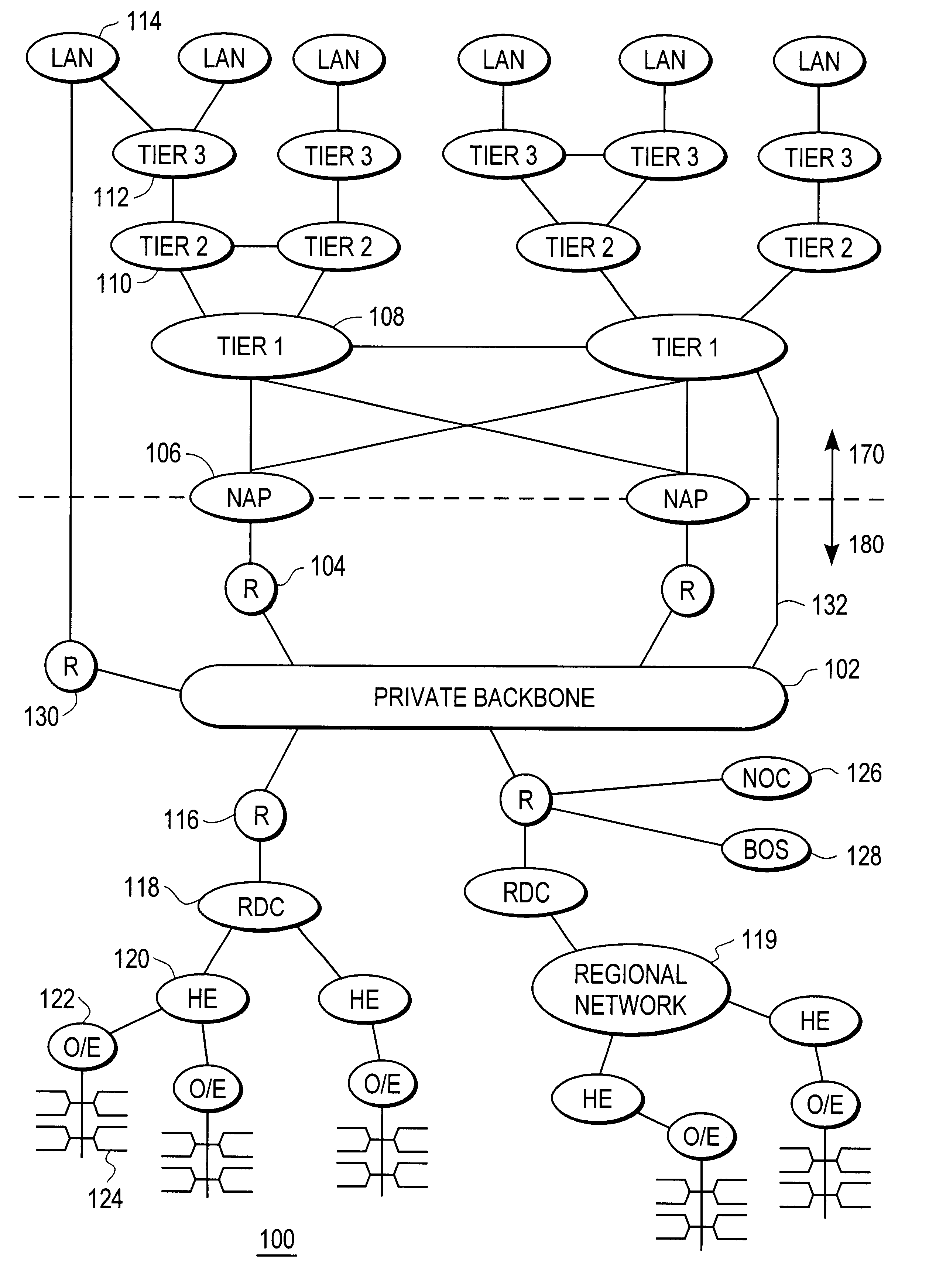
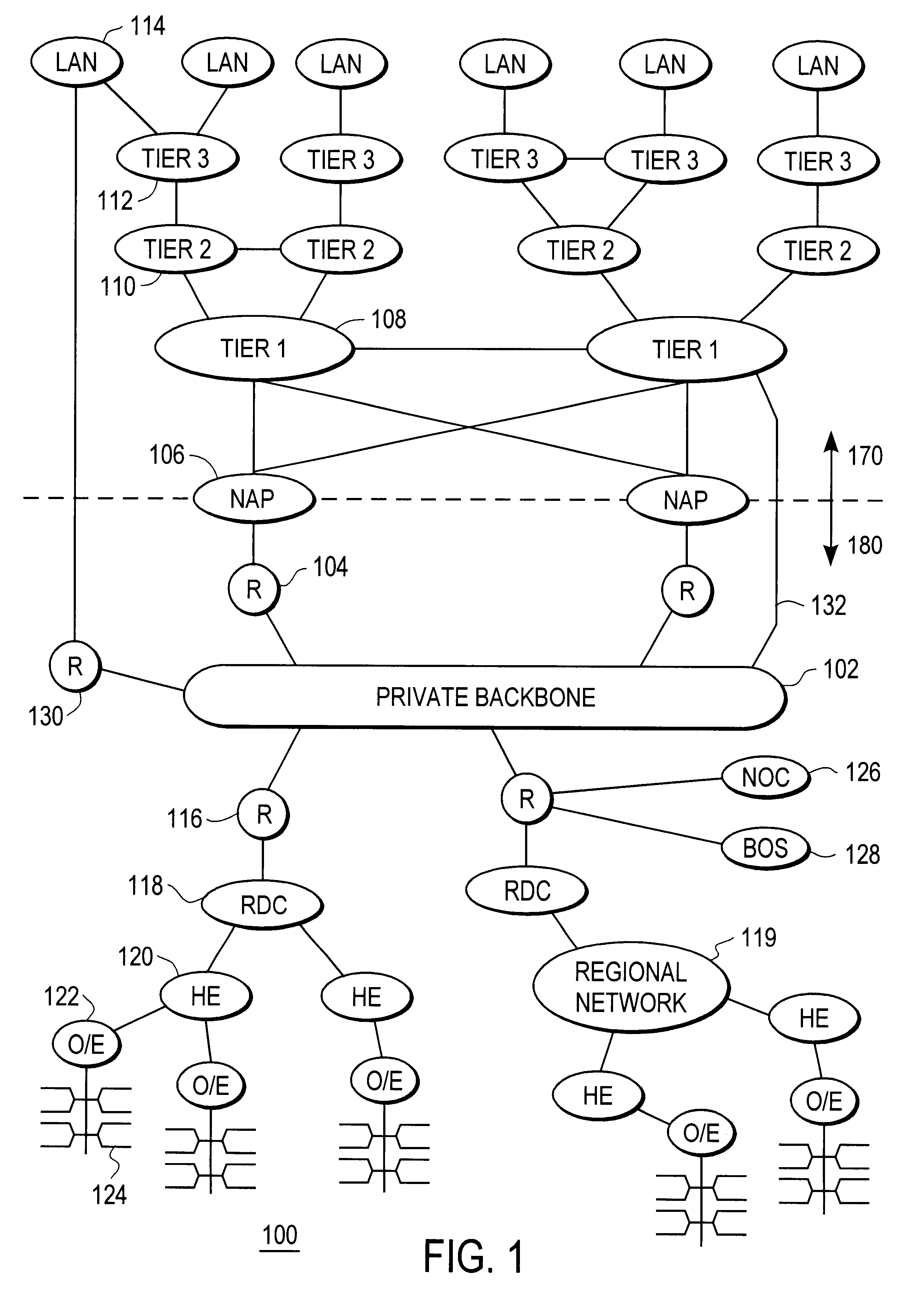
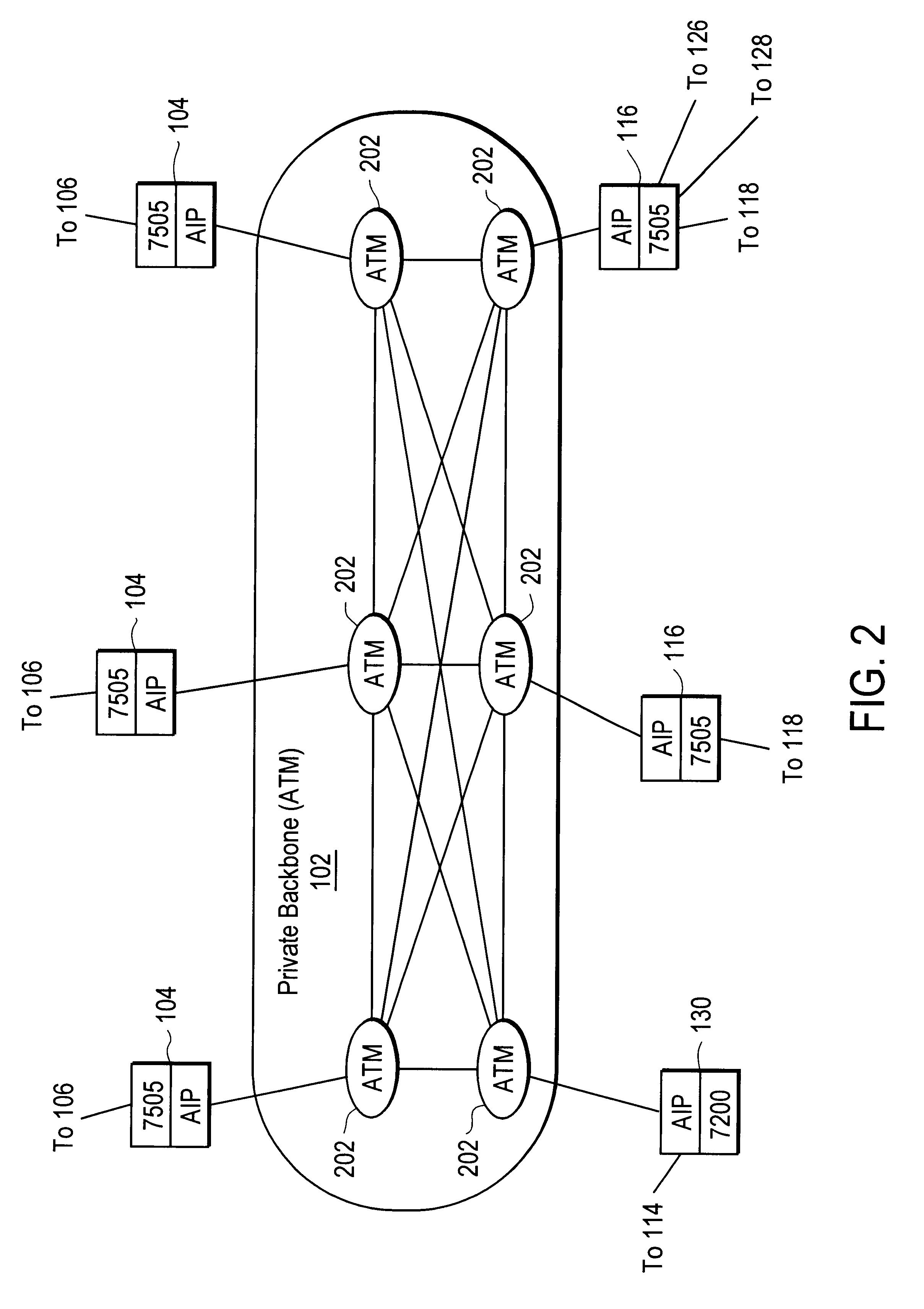
Disclosed is a scalable, hierarchical, distributed network architecture and processes for the delivery of high-performance, end-to-end online multimedia services, including Internet services such as World Wide Web access. The network architecture connects a high-speed private backbone to multiple network access points of the Internet, to a network operation center, to a back office system, and to multiple regional servers in regional data centers. Each of the regional servers connects to several caching servers in modified head-ends, which in turn connect via fiber optics to many neighborhood nodes. Finally, each node connects via coaxial cable to multiple end-user systems. The processes include those for replicating and caching frequently-accessed content, and multicasting content customized per region or locality.
Owner:AT HOME BONDHOLDERS LIQUIDATING TRUST +1
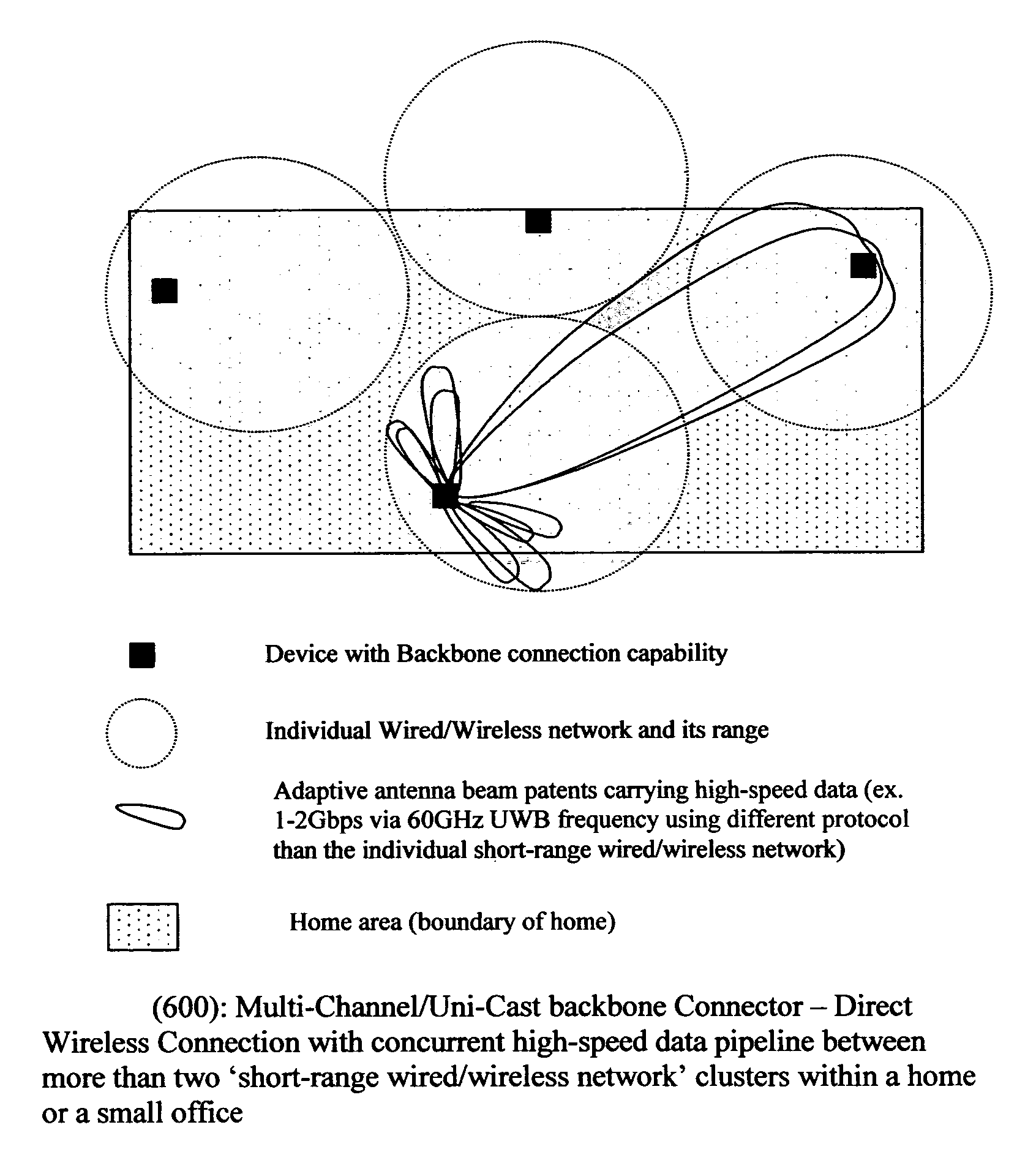
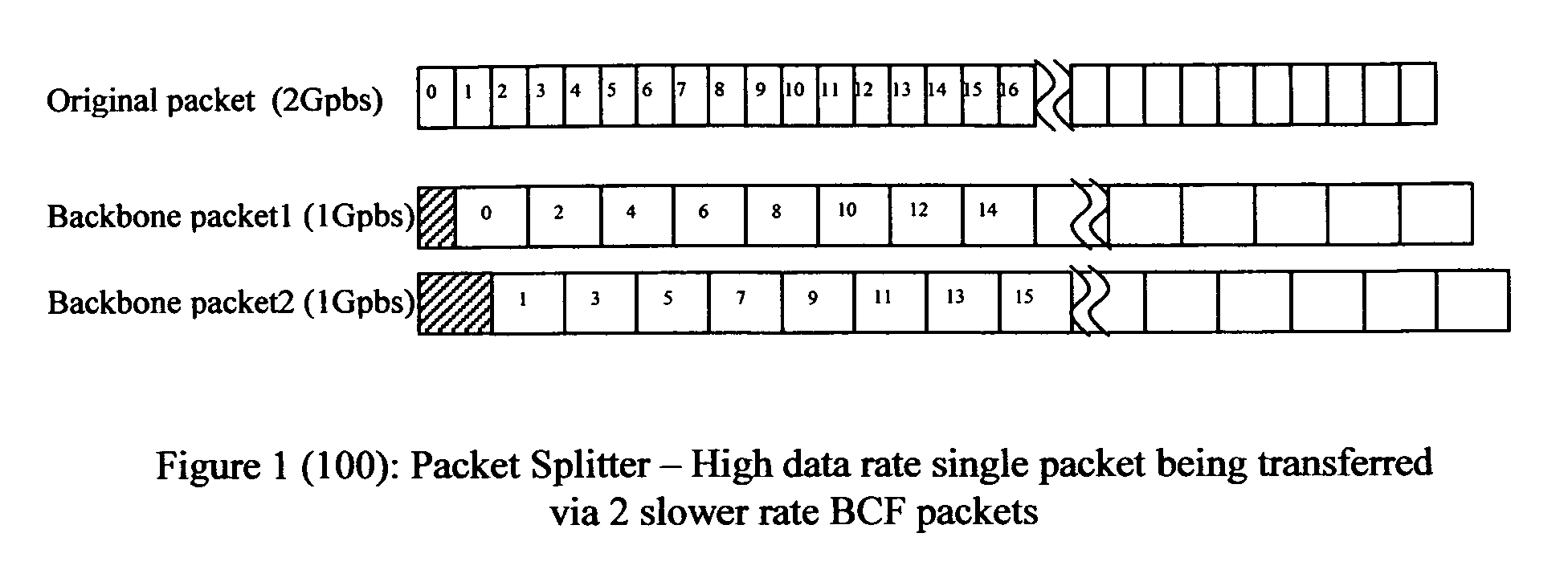
Method of constructing wireless high speed backbone connection that unifies various wired/wireless network clusters by means of employing the smart/adaptive antenna technique and dynamically creating concurrent data pipelines
InactiveUS7672271B2Reduce distractionsMinimize powerMultiplex system selection arrangementsEnergy efficient ICTTransmitted powerData link layer
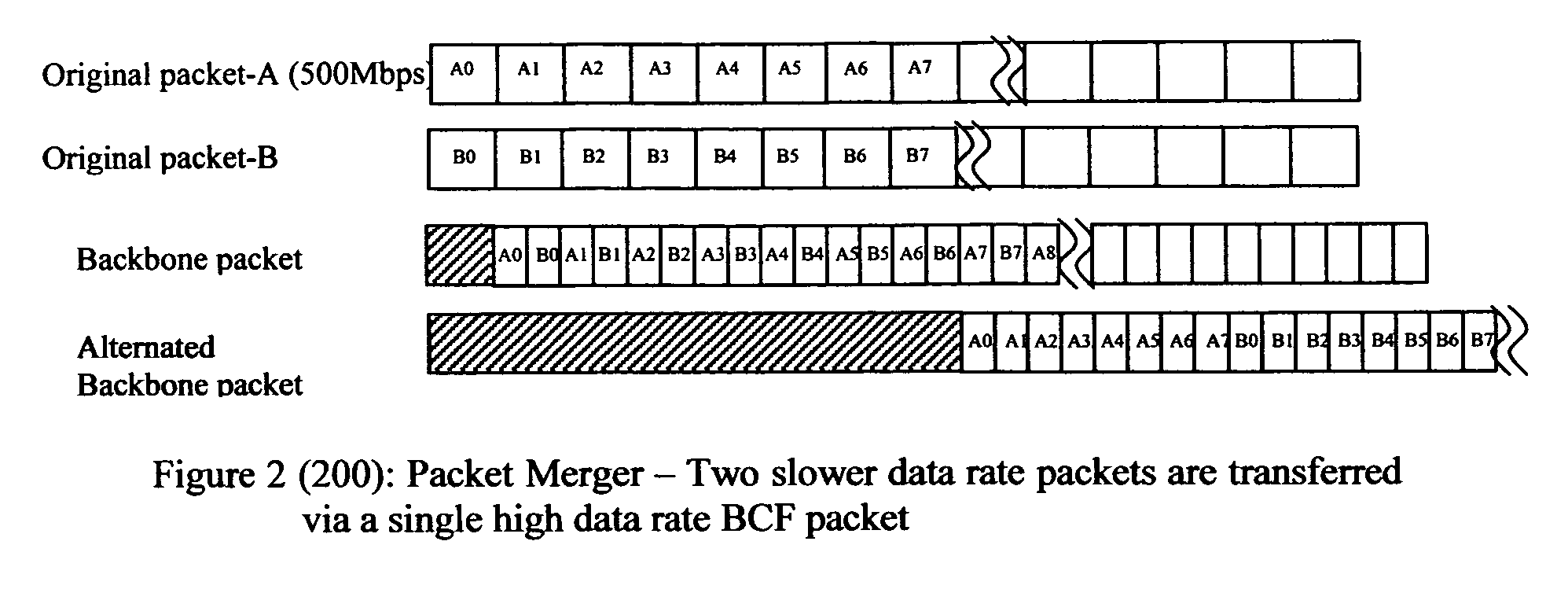
In accordance with the present invention, there is provided a high-speed wireless backbone connection, Backbone Connection Facilitator (BCF), to create a wireless home network, which may consist of many short-range wired / wireless networks. BCF dynamically creates concurrent data pipelines to meet the data bandwidth demand to transfer packets from one short-range wired / wireless network to another. BCF employs the newly developed antenna technologies (ex. MIMO, SDMA) to minimize the transmit power, to reduce the interferences, and to support the real time communication.BCF contains the BCF-PHY layer, the BCF-Data-Link-Layer, and the BCF-Network-Layer. The BCF-PHY layer consists of antenna array, a PHY Base Band controller, and a digital beam former. The BCF-Data-Link-Layer provides the MAC functionality. The BCF-Network-Layer assembles the packet, provides the source and destination address, and provides the BCF-PHY beam forming information. The BCF-Network-Layer is also responsible for parsing and assembling the packet payloads for the high-speed backbone connection.
Owner:LEE HYUN
Transparent, look-up-free packet forwarding method for optimizing global network throughput based on real-time route status
ActiveUS7254138B2Improve performanceFast and efficient packet-level traffic protection re-routingError preventionTransmission systemsPrivate networkOSI model
Owner:XENOGENIC DEV LLC
Integrated mobility management
InactiveUS20040122976A1Avoid disadvantagesPrecise routingConnection managementMultiple digital computer combinationsIp addressNetwork packet
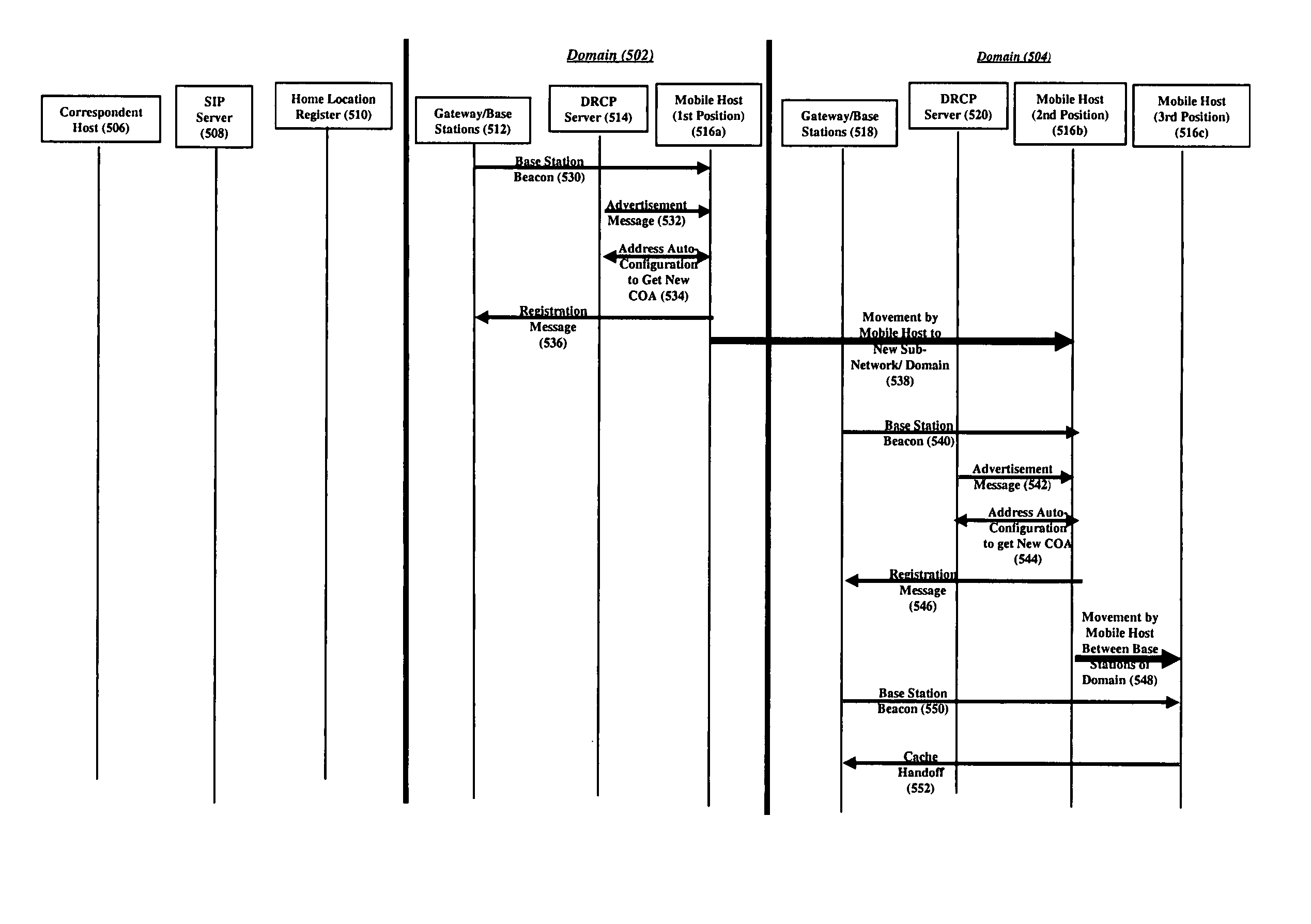
Integrated mobility management mechanisms monitor a mobile host's degree of mobility and the applications it executes. Mobile hosts move between wireless-access, micro-mobility domains interconnected through a backbone network. While the mobile host is stationary, MIP-LR and SIP systems operate to ensure TCP and RTP / UDP packets, respectively, traveling to / from the mobile host are properly routed through the backbone to the host's current domain. An MMP system routes packets through this domain. As the host moves within a domain, the MMP system updates the domain routing to the mobile host's new location. As the mobile host moves between domains, the host obtains a new IP address and the MMP system establishes routing within the new domain to the mobile host's new location. In addition, the MIP-LR and SIP systems activate to ensure the TCP and RTP / UDP packets, respectively, are automatically re-routed through the backbone to the new domain.
Owner:TELCORDIA TECHNOLOGIES INC
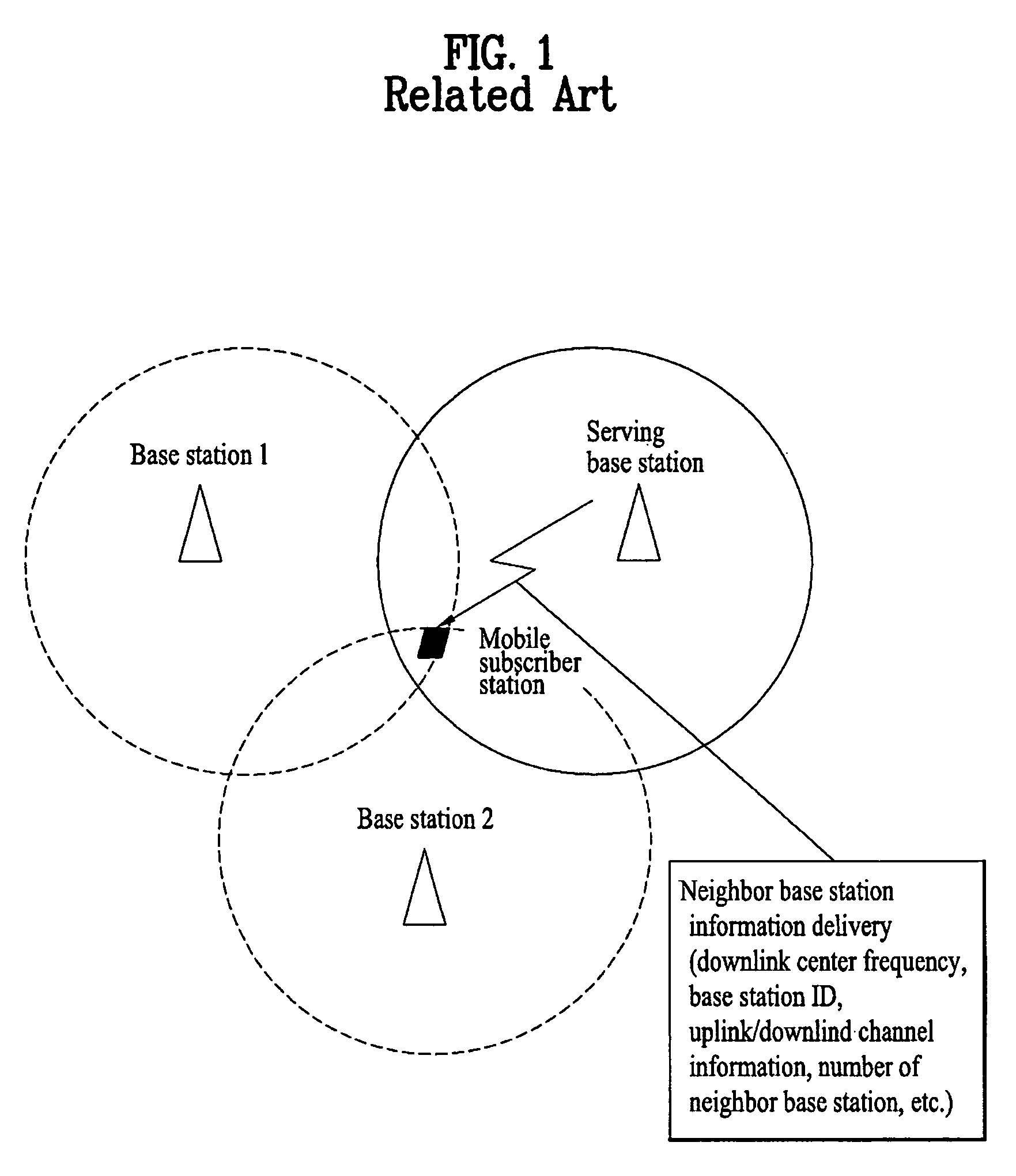
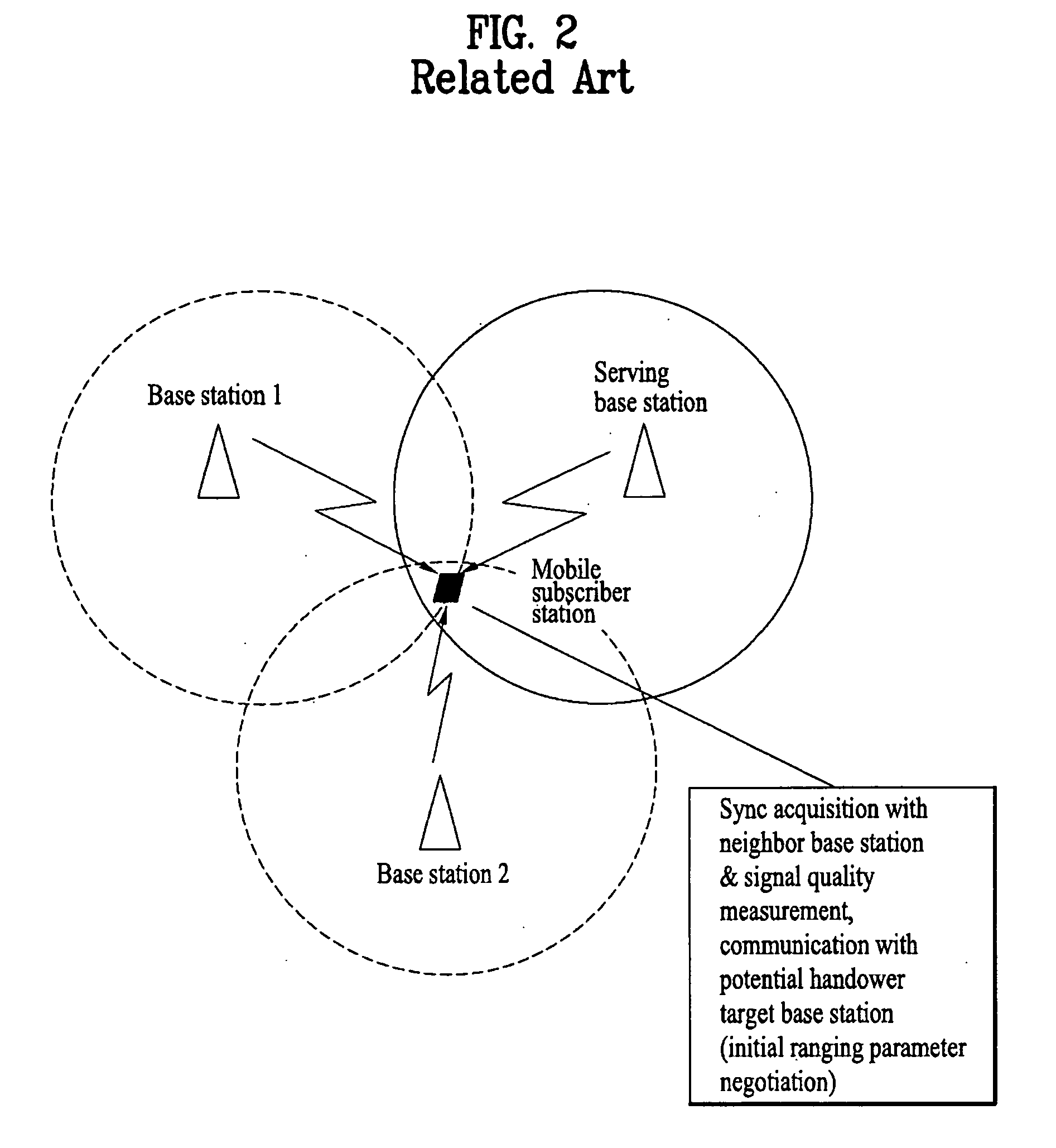
Method of communicating neighbor base station information
InactiveUS20050272403A1Engine sealsJoints with sealing surfacesSignal qualityMobile communication systems
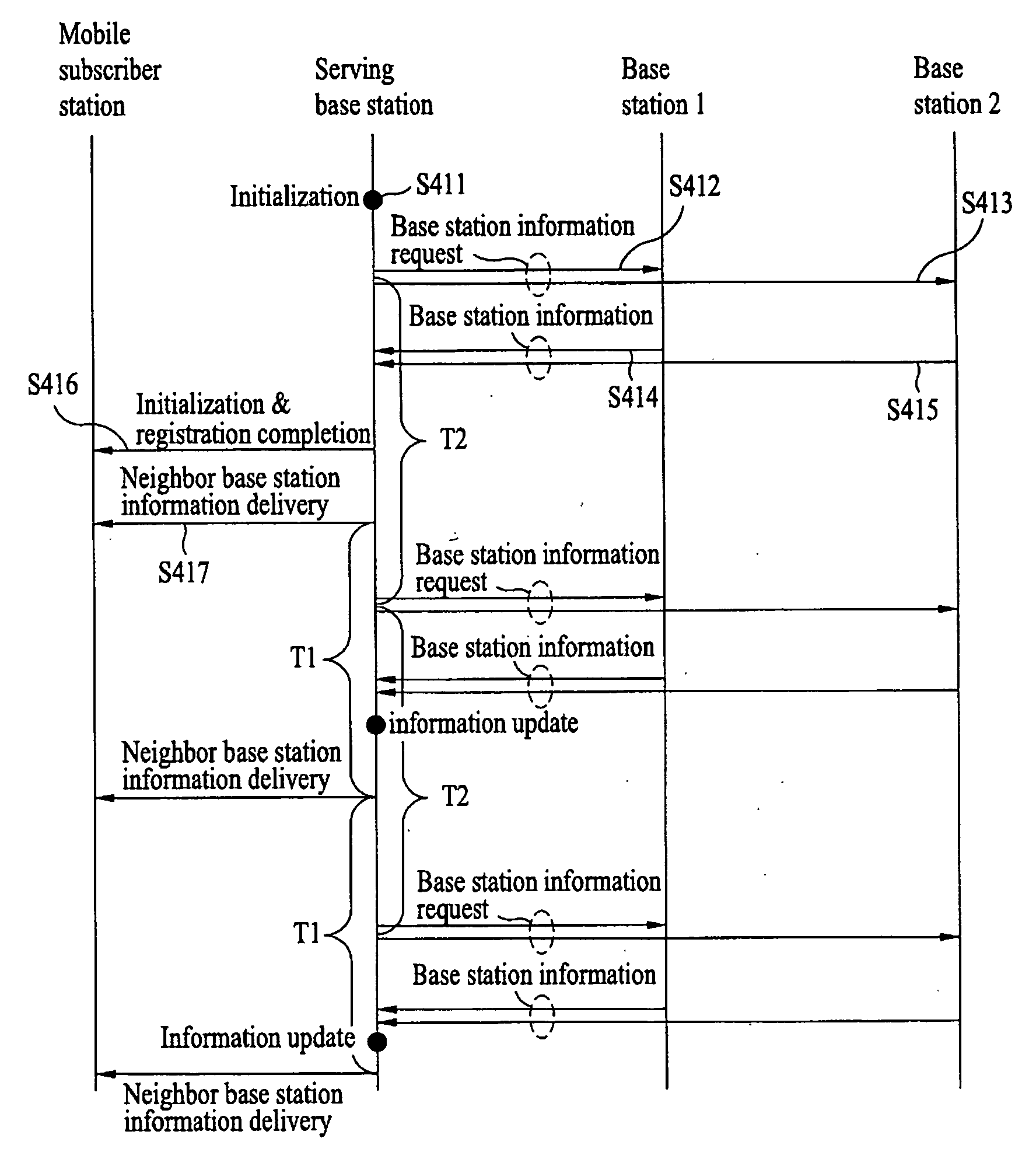
A method uses inter-base station control messages to provide neighbor base station information to mobile subscriber stations in a mobile communication system. The method includes obtaining, at a serving base station, physical channel information of neighbor base stations over a backbone network via, either directly or via a server; periodically transmitting the obtained physical channel information from the serving base station to a mobile subscriber station connected to the serving base station; and measuring, based on the updated physical channel information, signal quality of the at least one neighbor base station at the mobile subscriber station. Thus, the serving base station receives from the neighbor base stations the inter-base station control messages containing the neighbor base station information, updates the information, and provides the updated information to the corresponding mobile subscriber station(s), to be used for a specific purpose such as handover or network entry.
Owner:LG ELECTRONICS INC
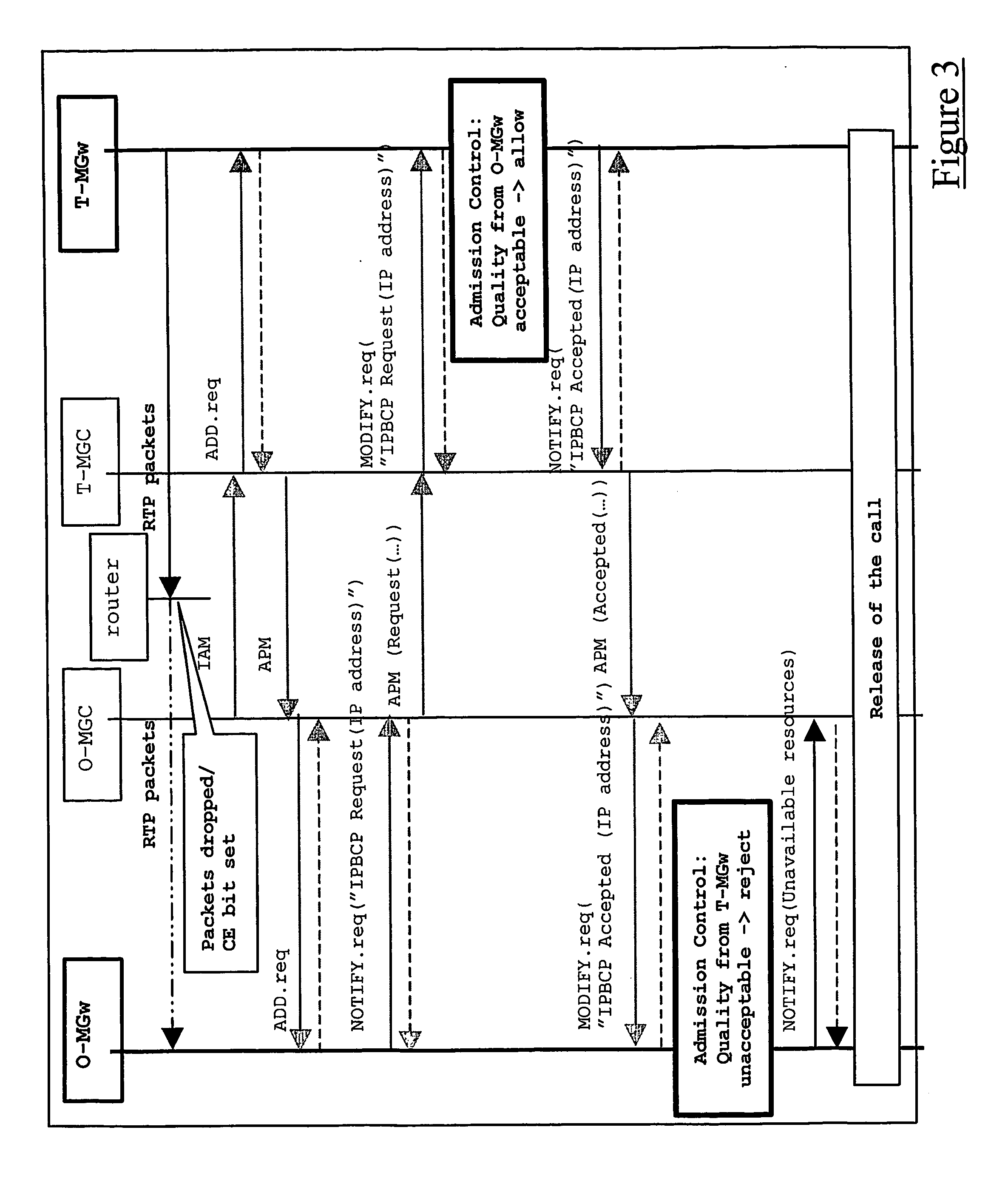
Call admission control in voip systems
InactiveUS20060251050A1Interconnection arrangementsNetwork traffic/resource managementControl systemNetwork packet
A method of controlling call admission within a system comprising a plurality of media gateways (8, 9) interconnected by a packet switched backbone (5). The method comprises, at least one media gateway (8, 9), monitoring the level of congestion suffered by incoming packets to that gateway from each other media gateway over said backbone. Following receipt of a request for a media gateway (8, 9) to terminate a bearer extending over said backbone (5) from a peer media gateway, making a decision on the admissibility of that request based upon the previously monitored level of congestion suffered by incoming packets from that peer media gateway.
Owner:UNWIRED PLANET
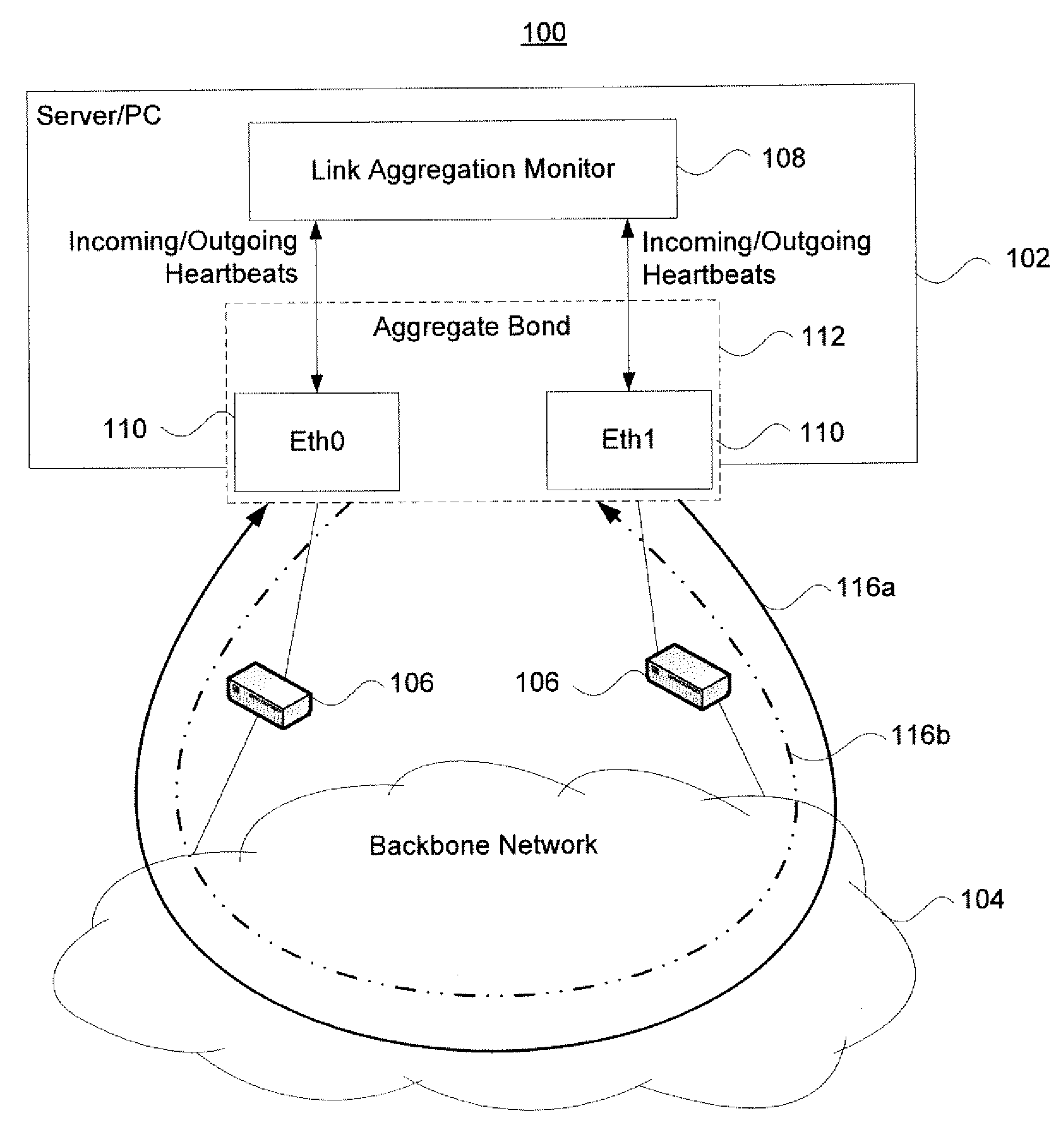
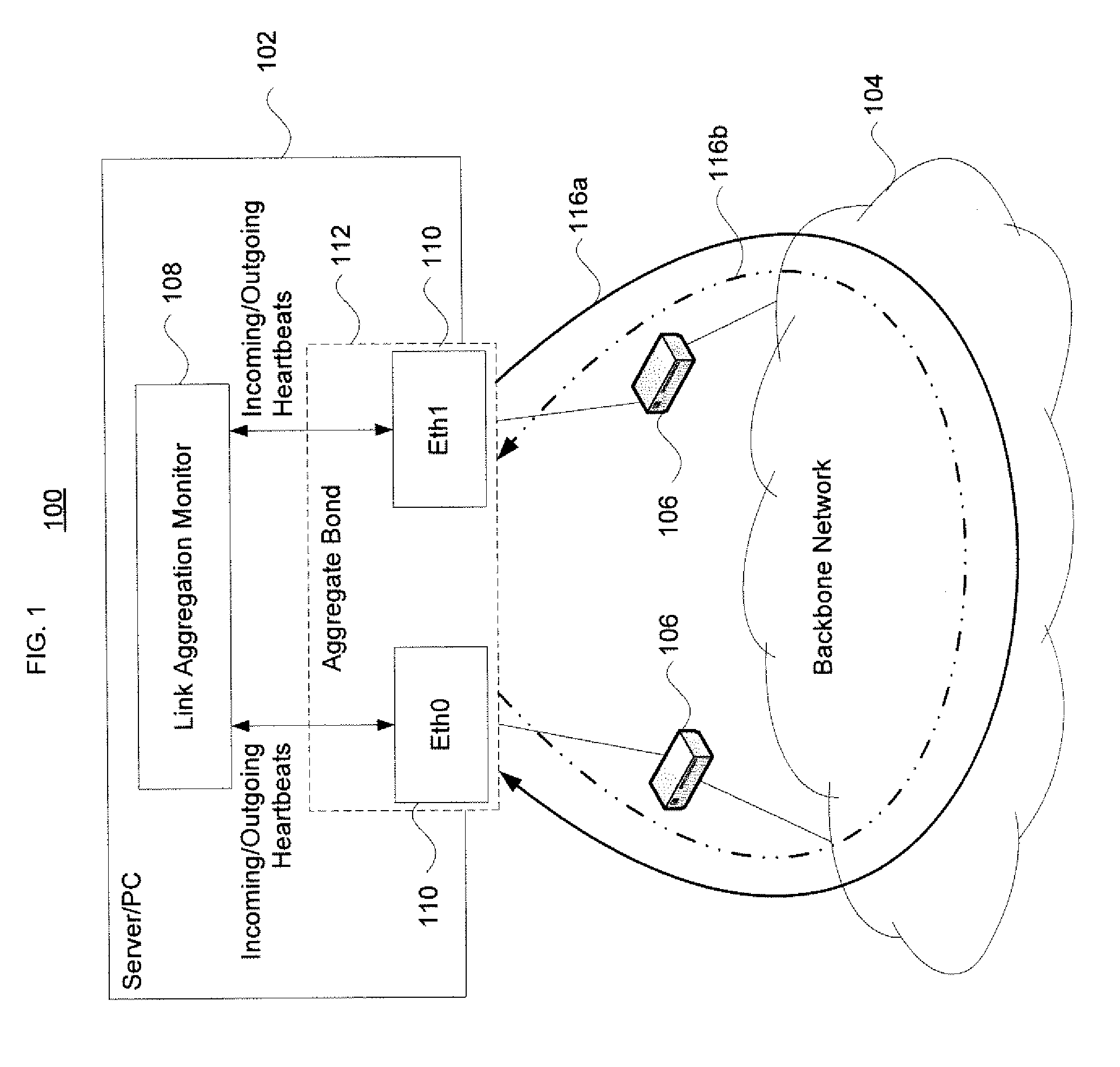
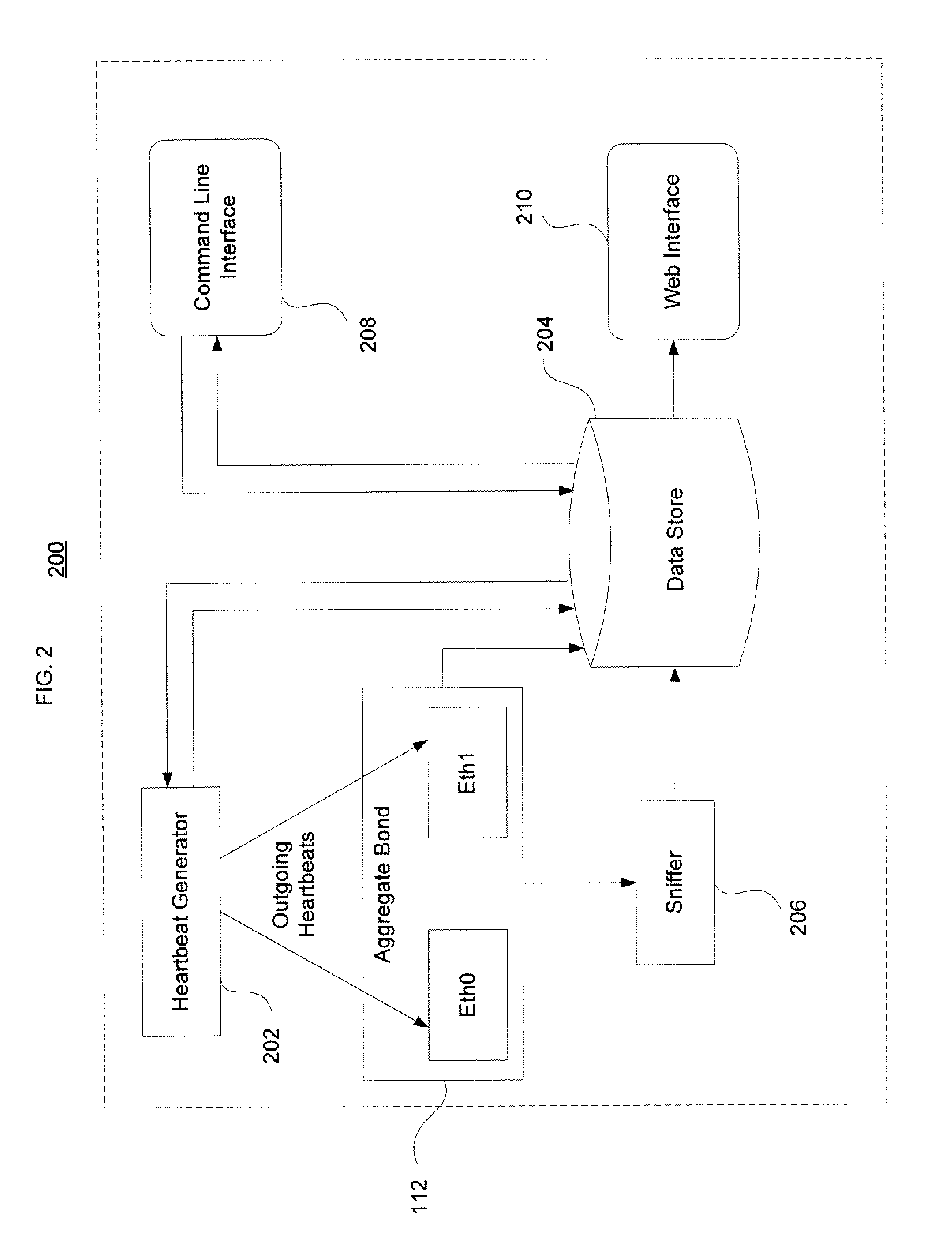
Interface monitoring for link aggregation
The present invention provides network interface monitoring and management that may be employed with link aggregation technologies. Multiple network interfaces may be aggregated into a single bond and data may be transferred to and from a backbone network via this aggregated bond. A link aggregation monitor employs a heartbeat generator, sniffer and data store to keep track of health and availability of network interfaces. The heartbeat generator sends heartbeats to the network interfaces, which pass the heartbeats around in a token ring configuration. If a network interface fails or otherwise goes offline, detection of this condition causes the monitor and heartbeat generator to prepare new or modified heartbeats so that data may be efficiently and accurately routed around the token ring and health of all remaining alive interfaces can be monitored properly. If a network interface re-enters or is added to the aggregate bond, new / modified heartbeats are then employed.
Owner:GOOGLE LLC
Unauthorized access blocking apparatus, method, program and system
ActiveUS20050198519A1Minimize impactUser identity/authority verificationUnauthorized memory use protectionIngress filteringComputer security
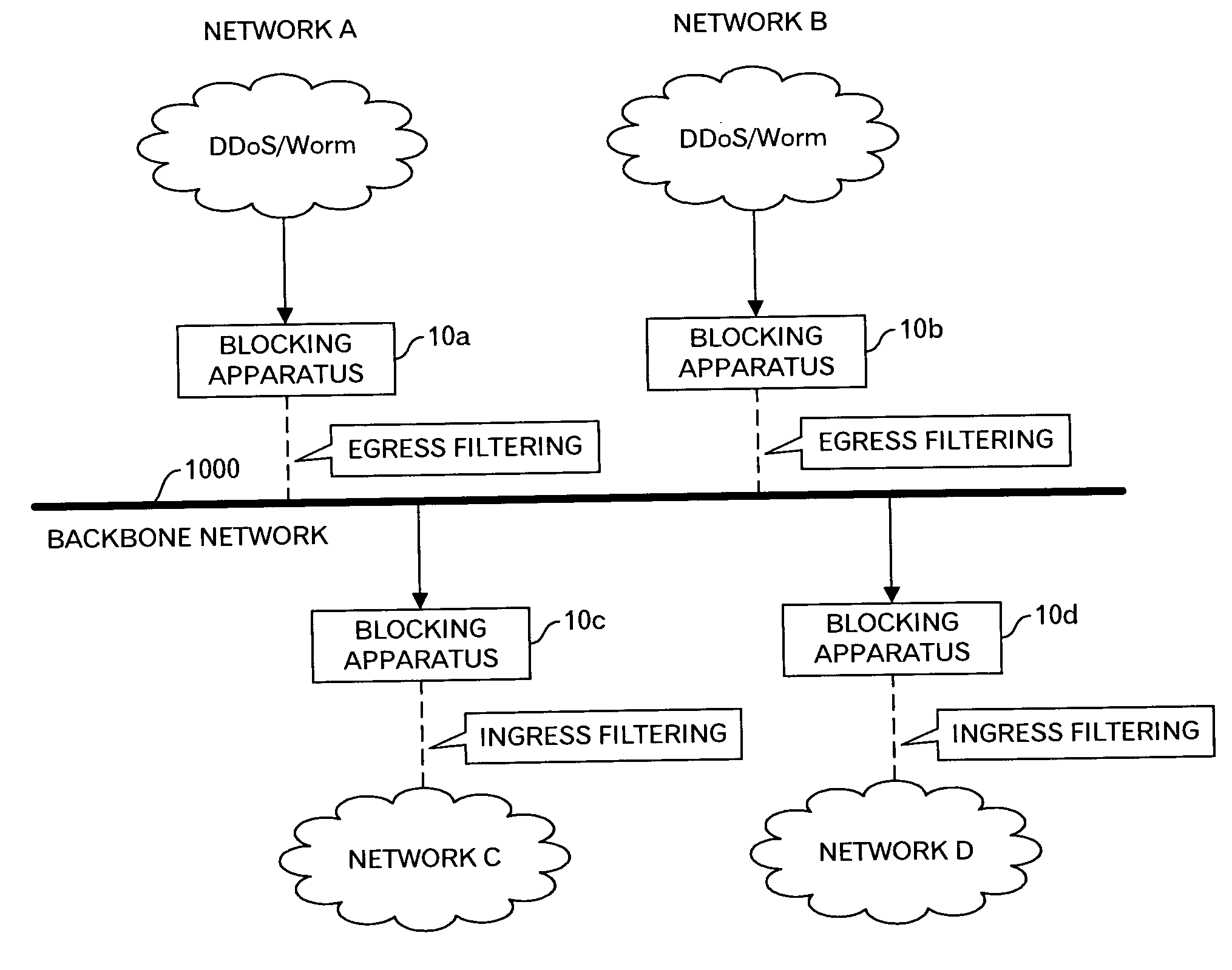
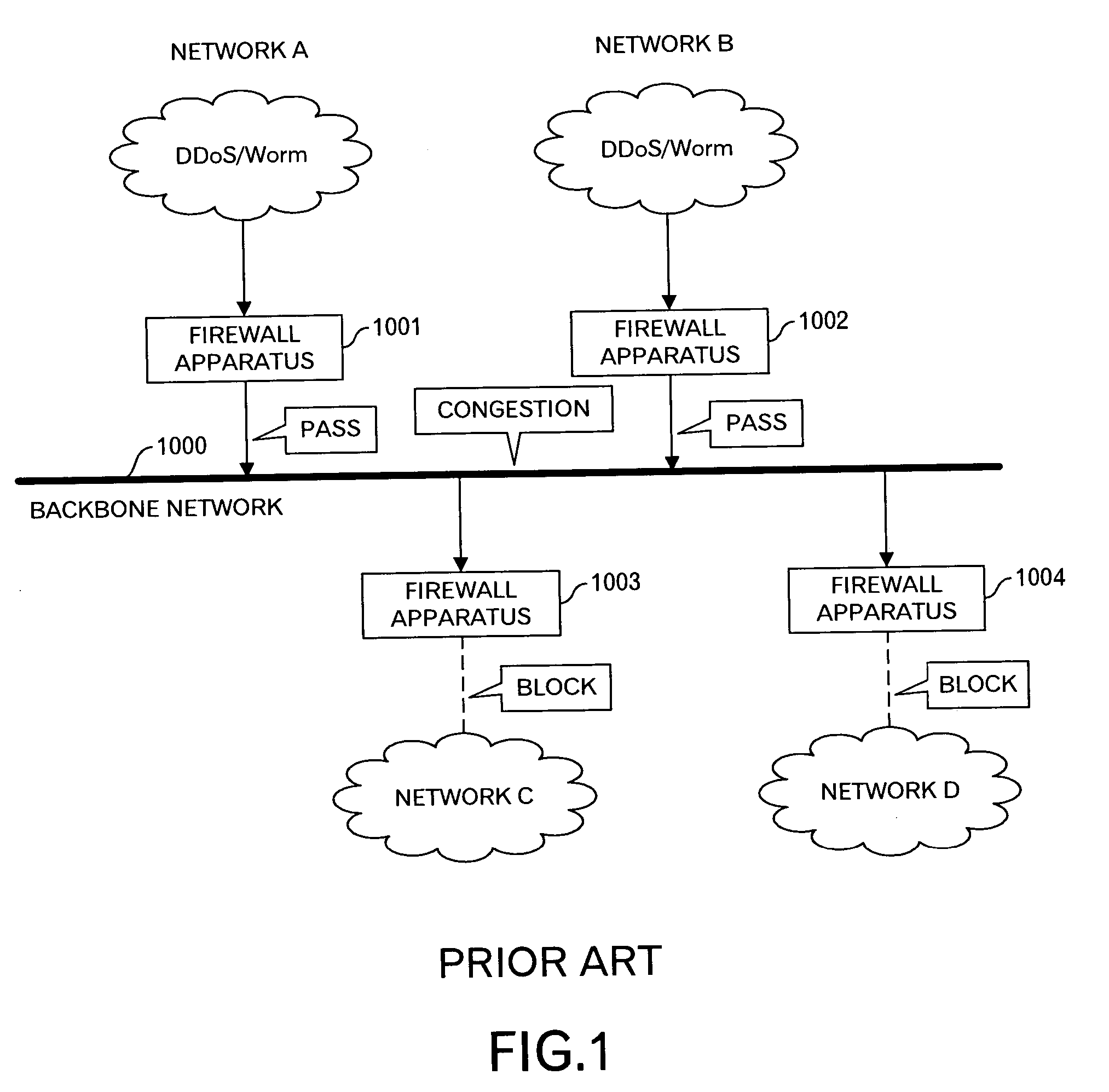
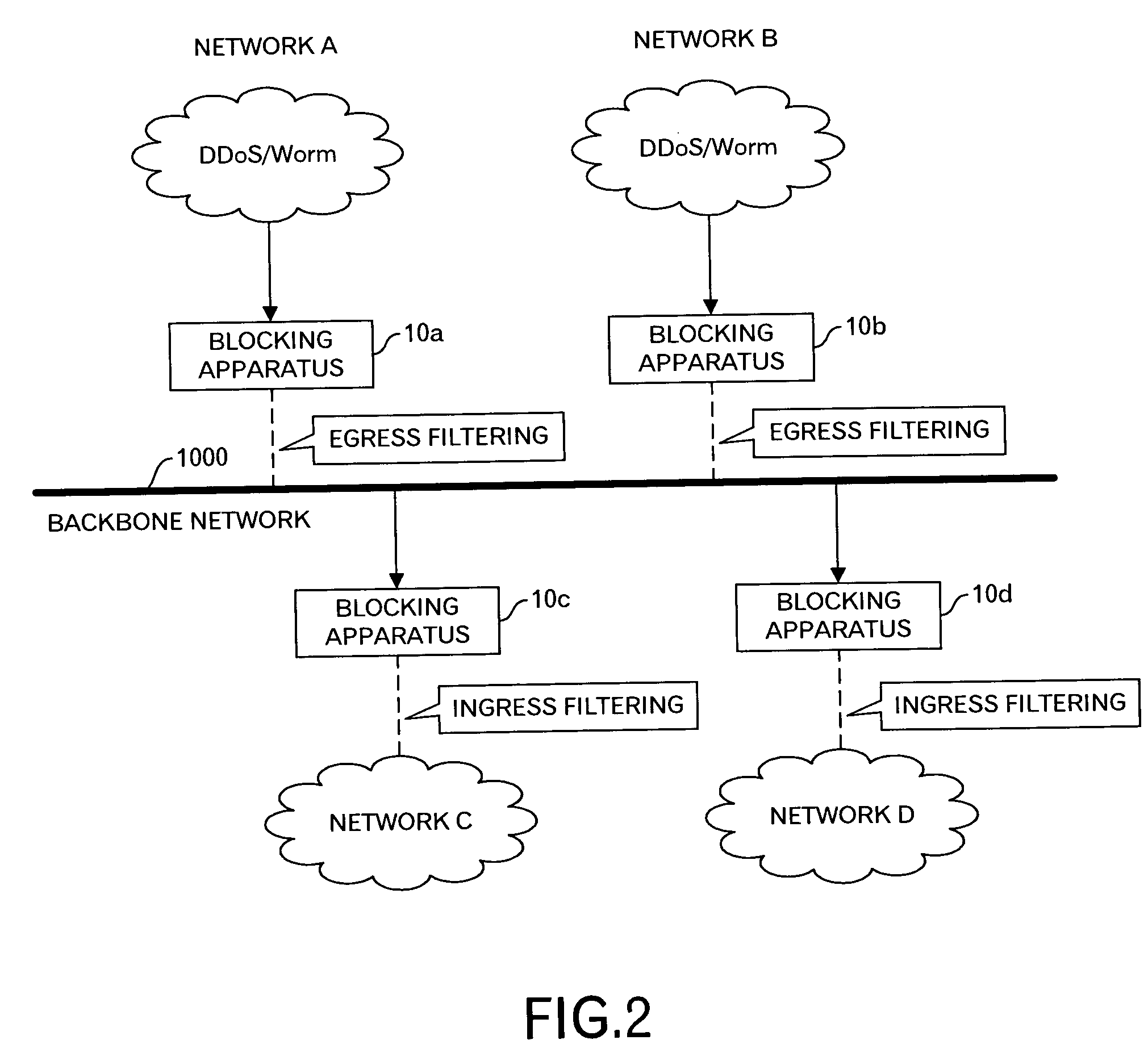
This invention is to minimize influence to other network by preventing unauthorized accesses such as DDoS attacks and probing by worms. When the blocking apparatuses 10a and 10b detect outbound packets by the DDoS attacks or by the probing by the worm, they carry out the Egress filtering for such outbound packets to prevent the packets relating to the unauthorized access from being sent to the backbone network 1000. Moreover, because a notice to the effect that the unauthorized access is detected is sent to other blocking apparatuses 10c and 10d via the management apparatus 16, for example, the blocking apparatuses 10c and 10d precautionarily carry out the Ingress filtering to prevent the packets relating to the unauthorized access from being sent to the network C and D.
Owner:FUJITSU LTD
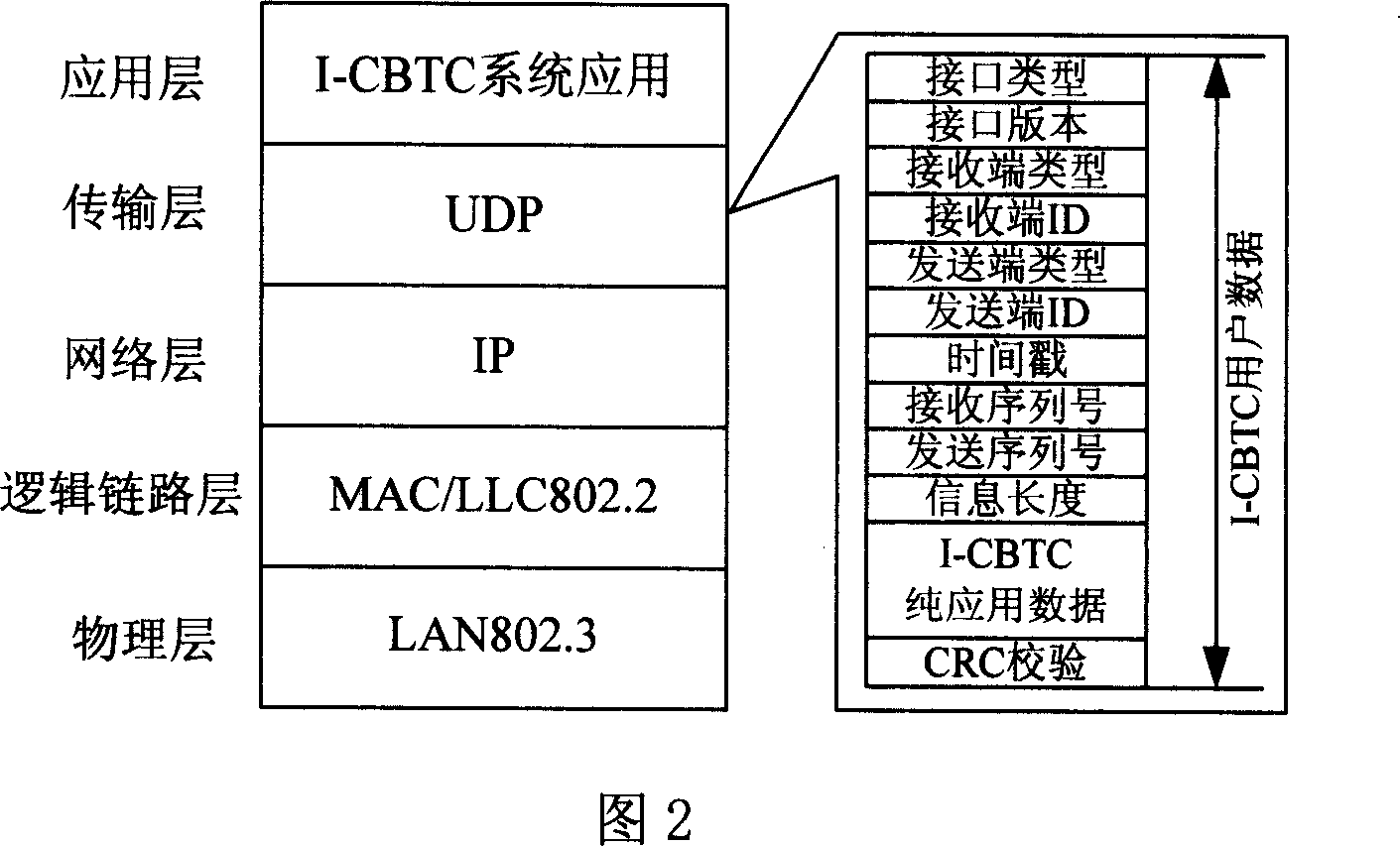
Communication-based interconnected and intercommunicated I-CBIT train operation control system
ActiveCN101009679AFacilitate resource sharingMaintain "transparencyVehicle route interaction devicesTransmissionOperational costsControl system
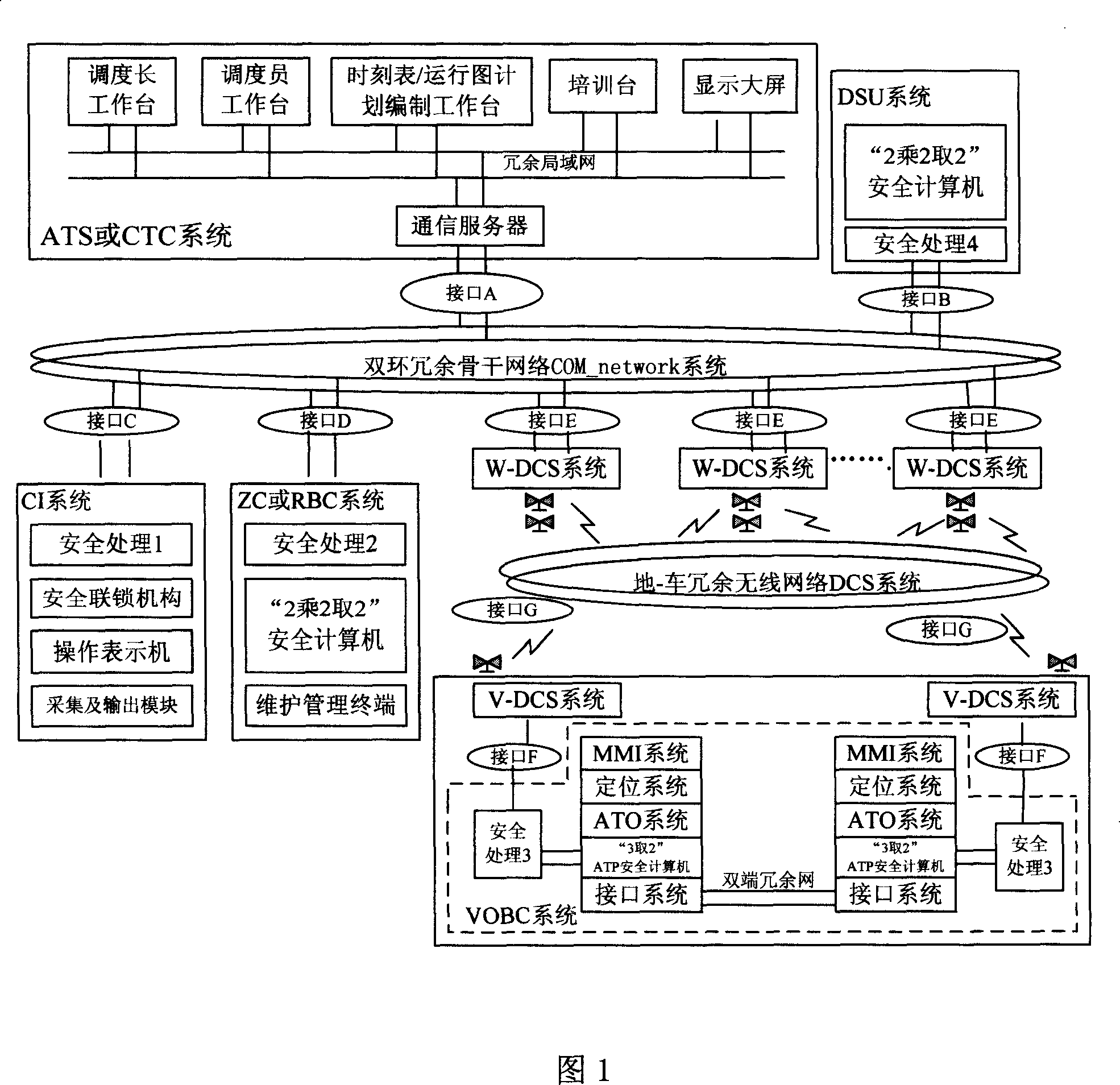
The disclosed I-CBTC mobile closed train operation control system applies wireless communication way to transmit information between ground control center and train, and comprises an ATS or CTC system, a DSU system, a CI system, a ZC or RBC system, a VOBC system, a dual-ring redundant backbone network COM_network system, a ground-train redundant wireless network DCS system, and interfaces among nodes. This invention normalizes and standardizes former function, performance index and interfaces, and reduces cost greatly.
Owner:TRAFFIC CONTROL TECH CO LTD
System and method for a wireless unit acquiring a new internet protocol address when roaming between two subnets
InactiveUS7082114B1Wireless network protocolsRadio/inductive link selection arrangementsSignal qualityWireless transmission
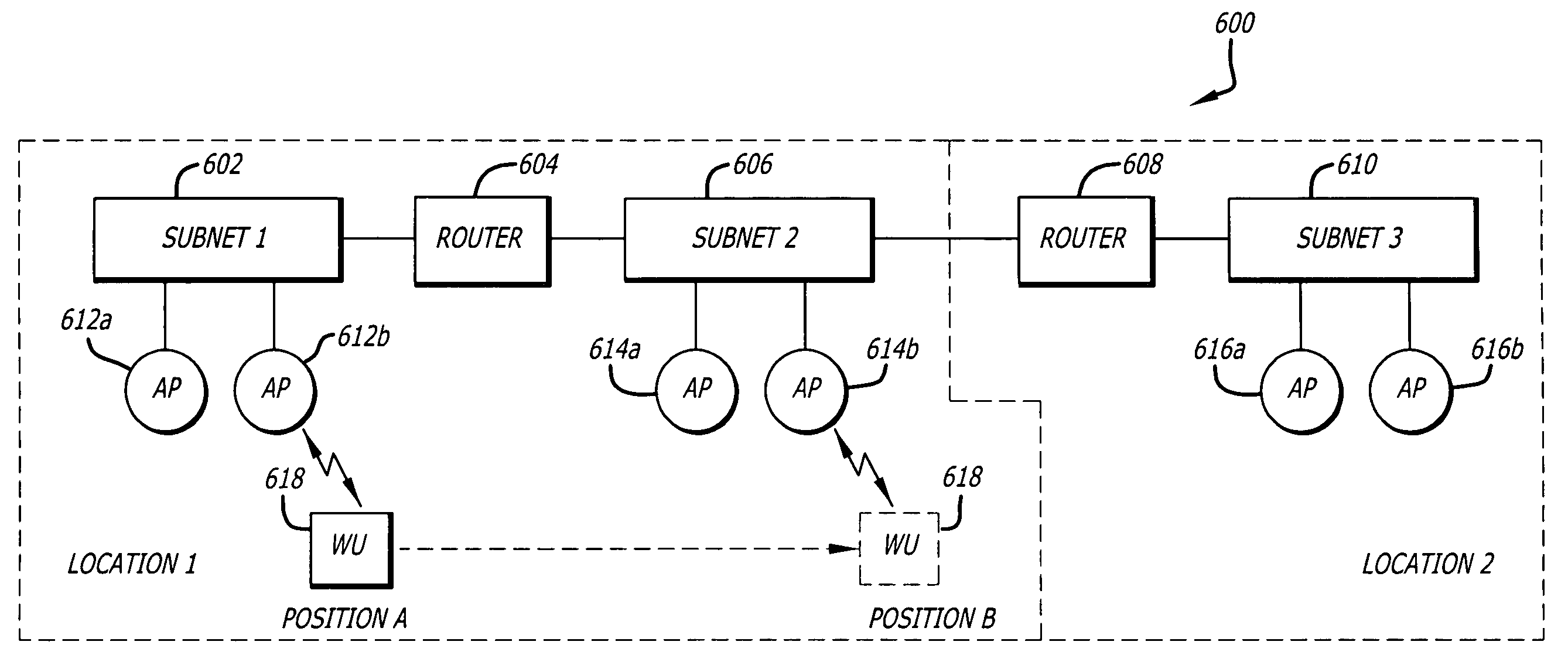
In a wireless network system having a wired backbone network with two or more sub-networks, each having one or more access points for communicating with wireless units via a wireless transmission medium, a system, apparatus and method for a wireless unit to determine whether a candidate access point is on a different sub-network than its current access point. If the wireless unit determines that the candidate access point is on a different sub-network, then the wireless unit releases its current network protocol address which was valid for the current sub-network, and obtains a new network protocol address valid for the new sub-network. This is accomplished by the candidate access point transmitting a multicast packet that includes the network protocol address of the access point and the subnet mask of the sub-network which the access point is on. By receiving this multicast packet, the wireless unit can determine if the candidate access point is on a different sub-network than its current sub-network. Also disclosed is a technique for a wireless unit to determine whether to roam to a candidate access point based on the signal qualities to its current and candidate access points, and whether the candidate access point is on a different sub-network or a designated restricted sub-network.
Owner:MICROSOFT TECH LICENSING LLC
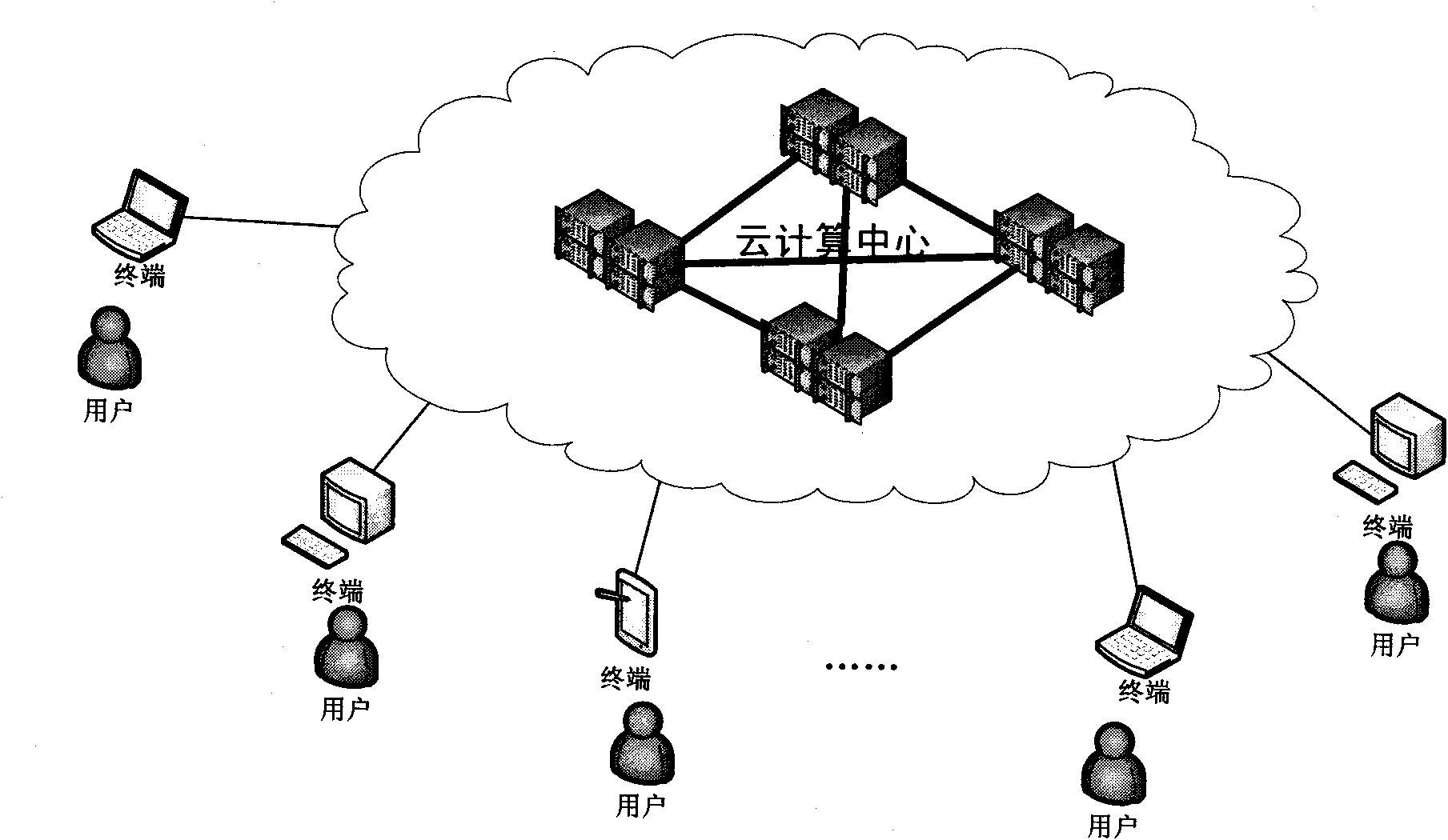
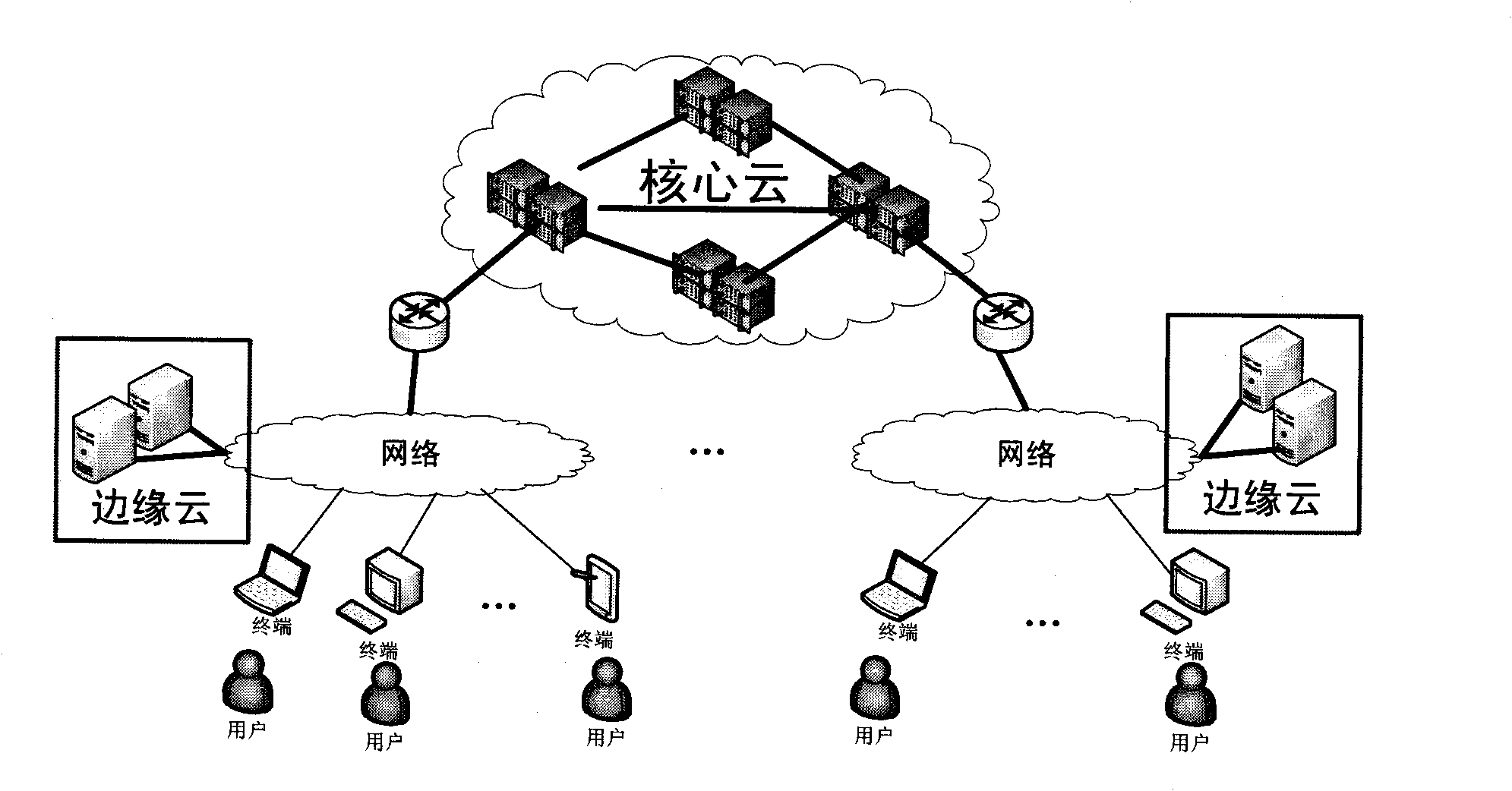
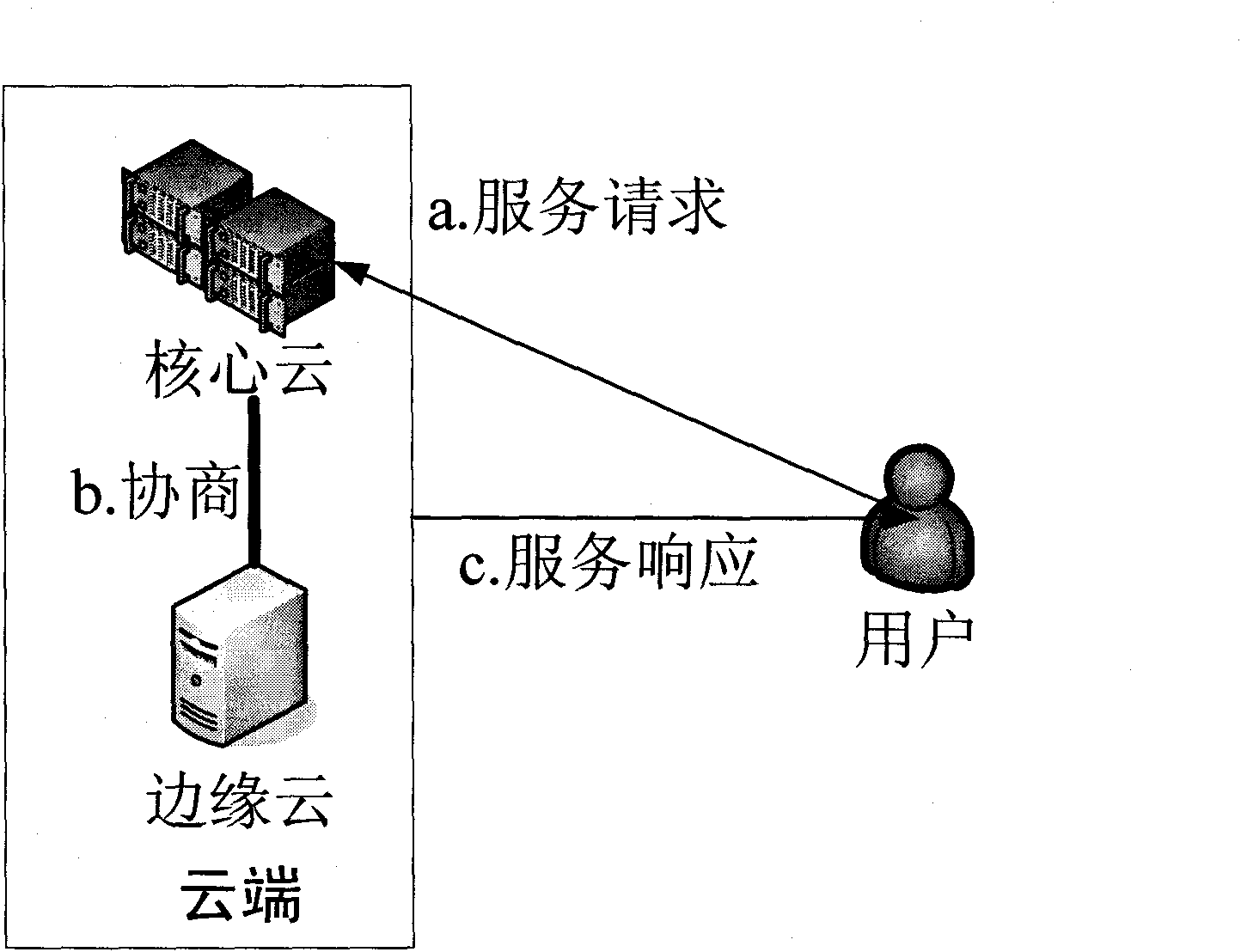
Layered distributed cloud computing architecture and service delivery method
The invention discloses a layered distributed cloud computing architecture and a service delivery method. The architecture is composed of a core cloud, an edge cloud and a terminal. The core cloud is a cloud computing service center composed of servers with powerful storage and computing capacity; the edge cloud is composed of server nodes distributed in different networks and regions and is connected with the core cloud by backbone network, and the terminal is an entity which uses a cloud computing service provided by the core cloud and edge cloud. The core cloud and the edge cloud work together to provide the cloud computing service for terminal users and uses relevance of data transmitted by the core edge and the terminal to process the data so as to reduce traffic. In the invention, network flow in most of cloud computing is confined to the local network between the edge and the terminal, thus lowering traffic of the backbone network, effectively avoiding the problems of network congestion, high latency and the like in the existing centralized cloud computing mode and improving user experience.
Owner:XIDIAN UNIV
Method to realize dynamic networking and resource sharing among equipments
InactiveUS20060155802A1Implement resourcesEasy to useResource allocationMultiple digital computer combinationsDevice registerInode
The invention relates to a method allowing dynamically networking among a plurality of devices to share resource. It includes: installing a software of dynamic networking and resource sharing on each of devices to realize dynamic networking and resource sharing. These devices periodically announce information with multicasting. A device serves as node control device, and announces the message of the existence of the device through multicasting, creates a node. A device can find the node by monitoring announcement message from the node. The device which requests to join into the node device registers its service information that can be provided by the device to the node control device. The device which has joined into the node finds the device providing service by indexing the nodal control device, and obtains desired service from the device by sending a service calling information. The method is applied to home backbone network for performing networking in home network. Then a topology connection structure with master / slave and peer-to-peer modes can be realized. The dynamic networking and resource sharing between the service providing device and the service utilizing device in the home backbone network can be realized.
Owner:LENOVO (BEIJING) LTD
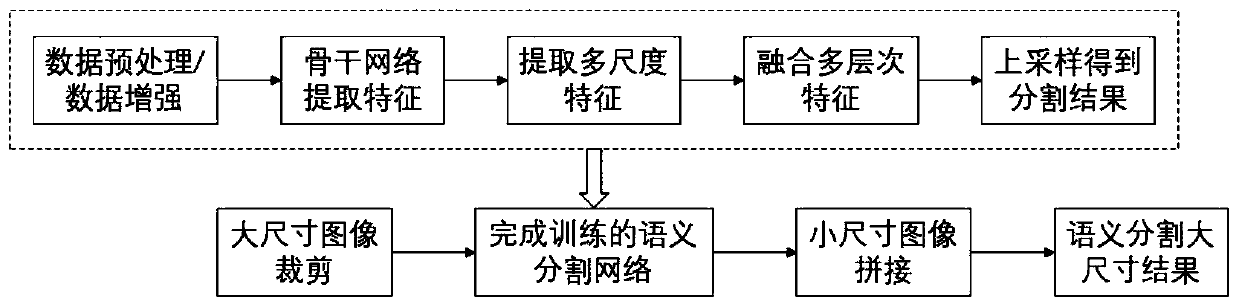
Conversational bearer negotiation
InactiveUS20070053343A1Interconnection arrangementsHybrid switching systemsAccess networkCommunications system
A method of setting up a call between first and second nodes of a communication system, said call extending across at least one circuit switched access network and a packet switched backbone network, the networks being interconnected by at least one Media Gateway. The method comprises, at a control node, obtaining ftoin a Home Subscriber Server the identity of a Media Gateway Control Function controlling that Media Gateway which will terminate the call within the circuit switched access network. The first node calls an access number notified to it by the Media Gateway Control Function, and as part of the call set-up procedure the identity of the Media Gateway selected to terminate the call is communicated to the Media Gateway Control Function.
Owner:TELEFON AB LM ERICSSON (PUBL)
Network server platform/facilities management platform caching server
InactiveUS6385693B1Digital data information retrievalSpecial data processing applicationsTraffic capacityCache server
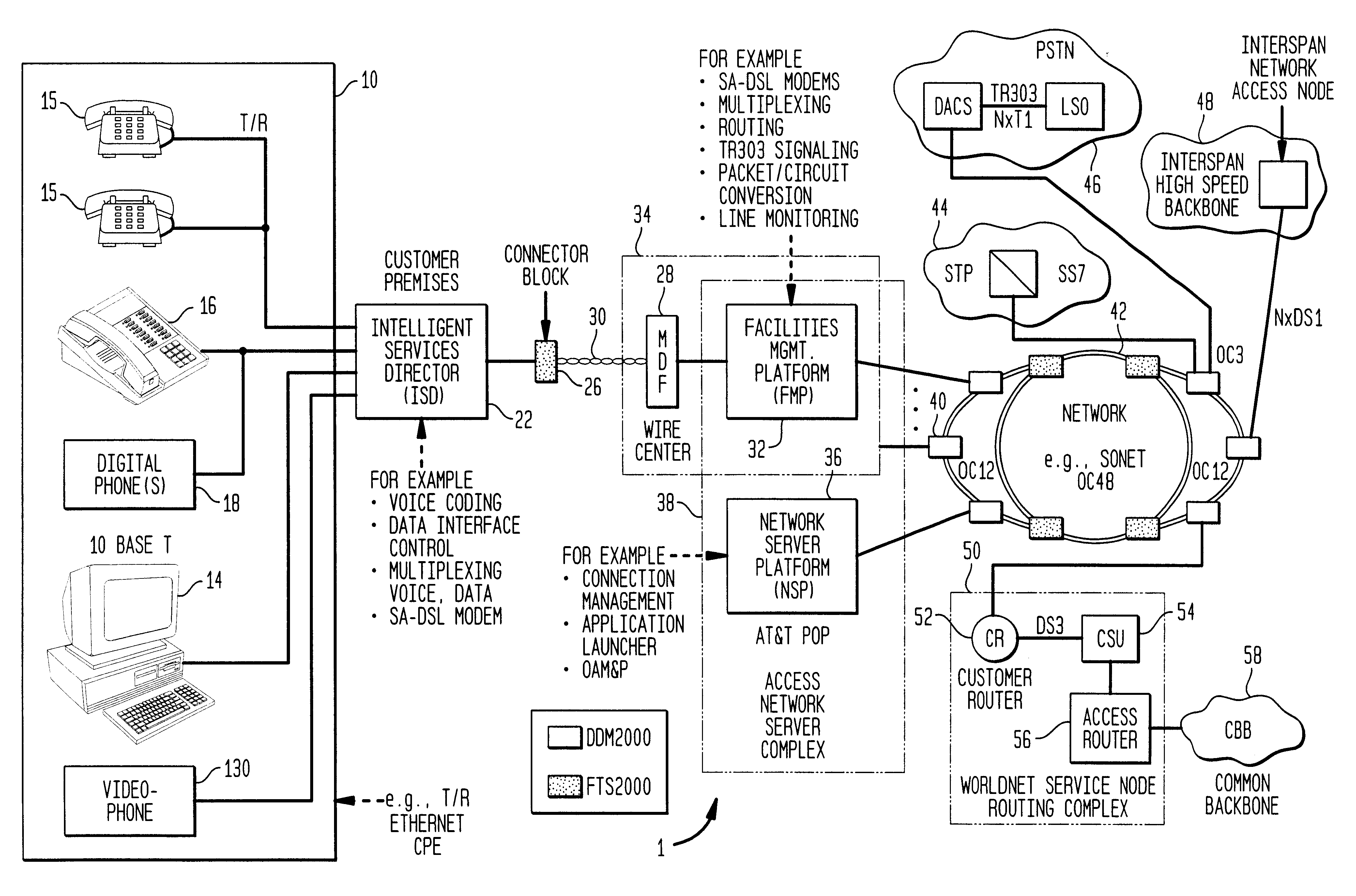
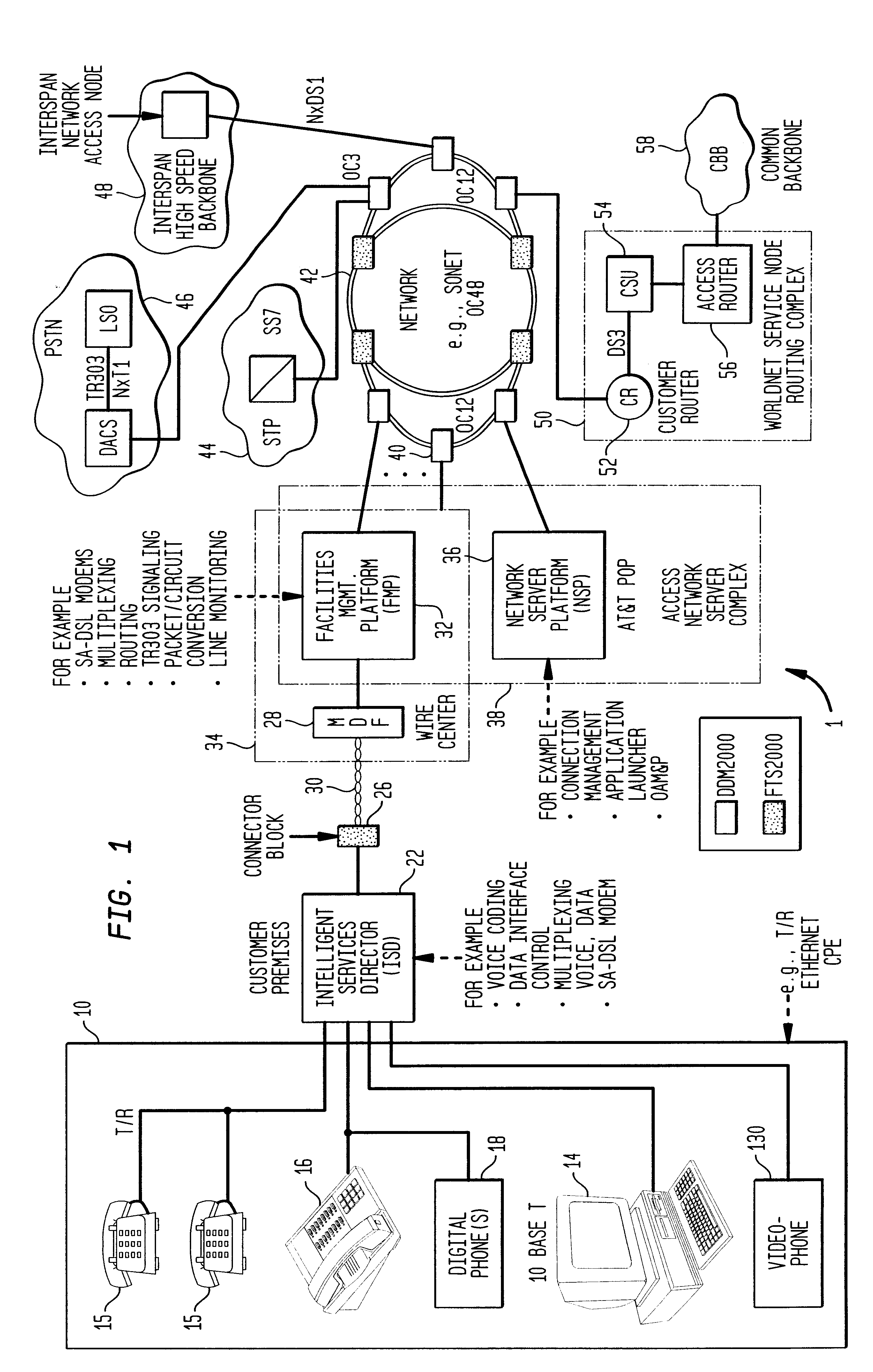
The location of large caches of memory located at the network server platform can reduce traffic on the network trunks or Internet backbone. In some instances these memory caches might be located at the facilities management platform. Those users supported on a specific network server platform no longer would be required to download regularly used information from the Internet backbone minimizing congestion on the network. These memory caches can be supplemented or refreshed with new data on a regular basis based on the requirements or changing requirements of the users. The close location of regularly accessed data allows for faster downloads and minimizes congestion on the communication network. In addition to user requested information, push information can be stored in these caches for fast downloading to the users.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
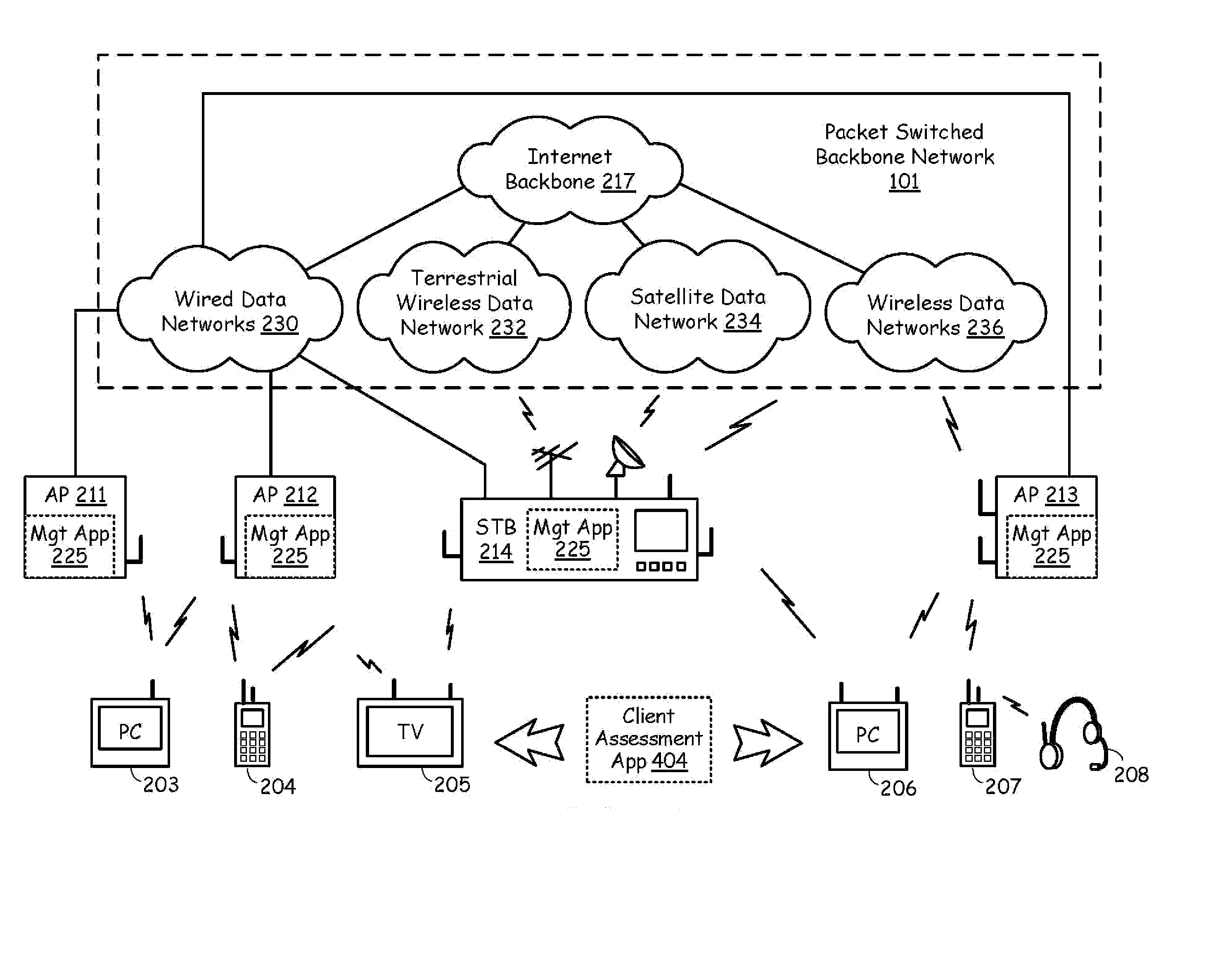
Interference parameter reporting from client devices to access point for use in modifying wireless operations
InactiveUS20080056201A1Network traffic/resource managementRadio/inductive link selection arrangementsTransceiverWireless transceiver
A wireless network in a communication infrastructure has a packet switched backbone network and includes a plurality of access points and services a plurality of client devices. The plurality of access points communicatively coupled to the packet switched backbone network and each have access point processing circuitry and access point wireless transceiver circuitry. The plurality of client devices each have client processing circuitry and client wireless transceiver circuitry. A client device of the plurality of client devices, using respective client processing circuitry and respective client wireless transceiver circuitry, determines interference parameters regarding wirelessly communicating within the wireless network. The client device then transmits the interference parameters to an access point of the plurality of access points. The access point of the plurality of access points, using respective access point processing circuitry and respective access point wireless transceiver circuitry, receives the interference parameters and alters wireless interface operations within a service area of the wireless network based upon the received interference parameters.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
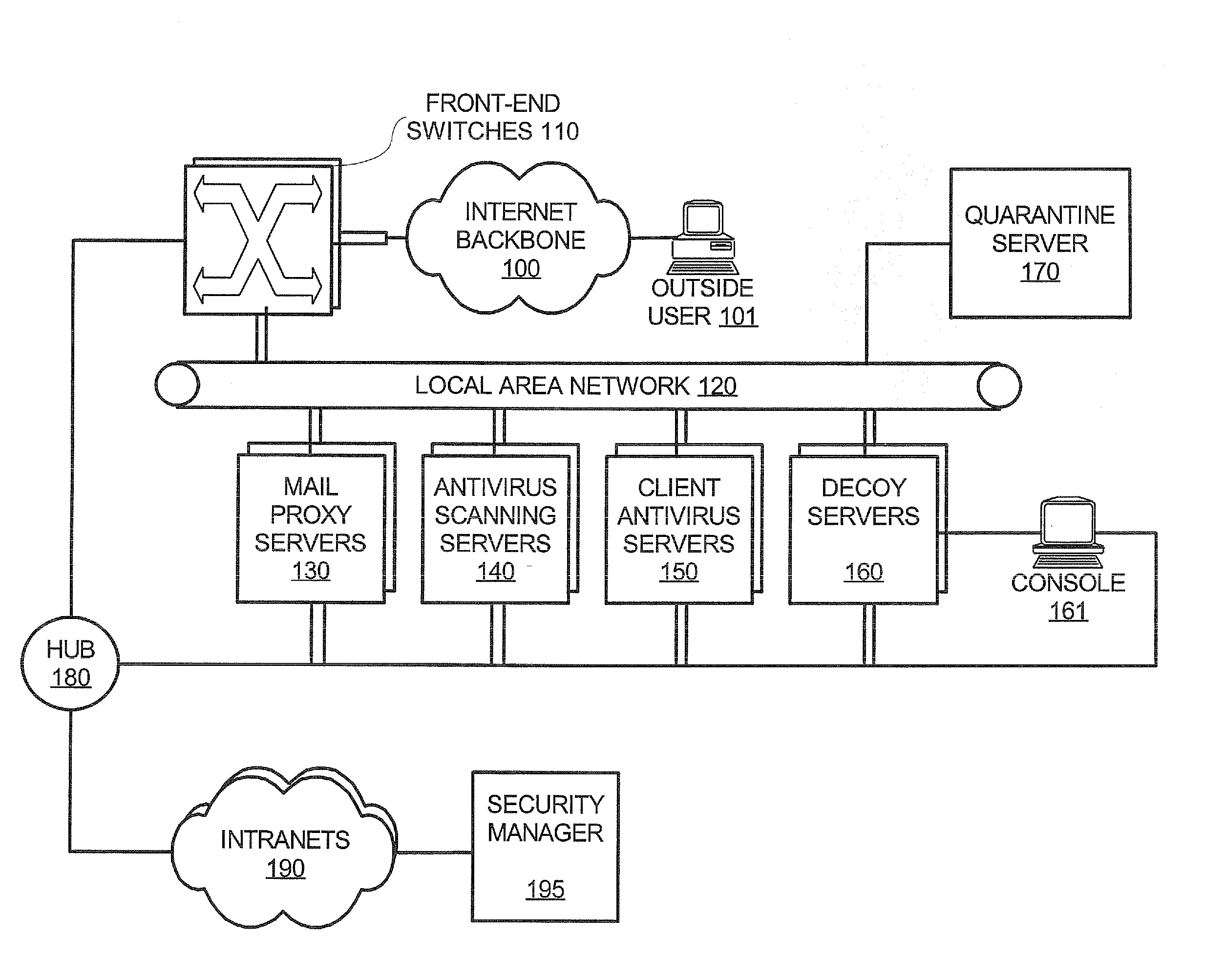
Network security architecture
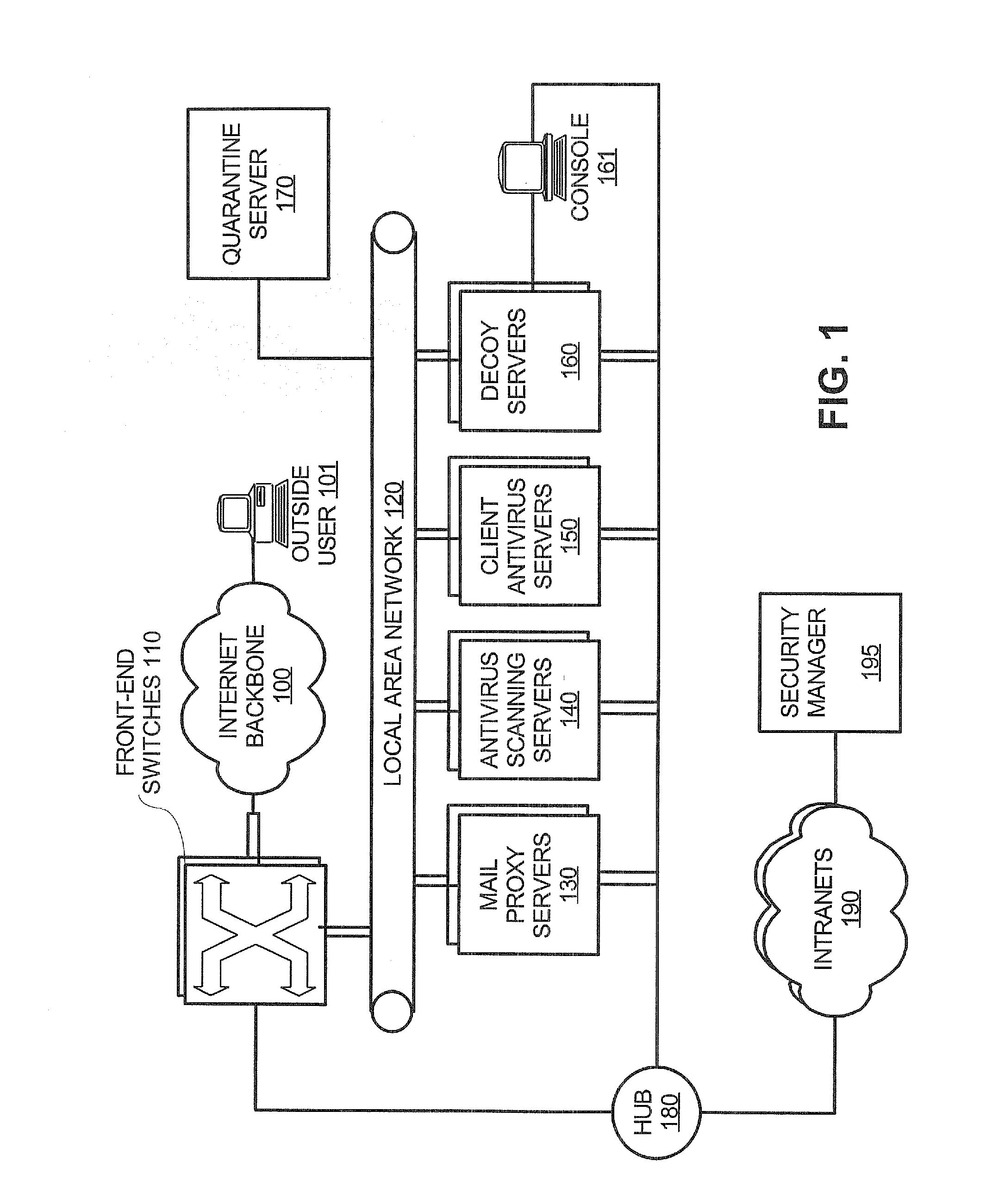
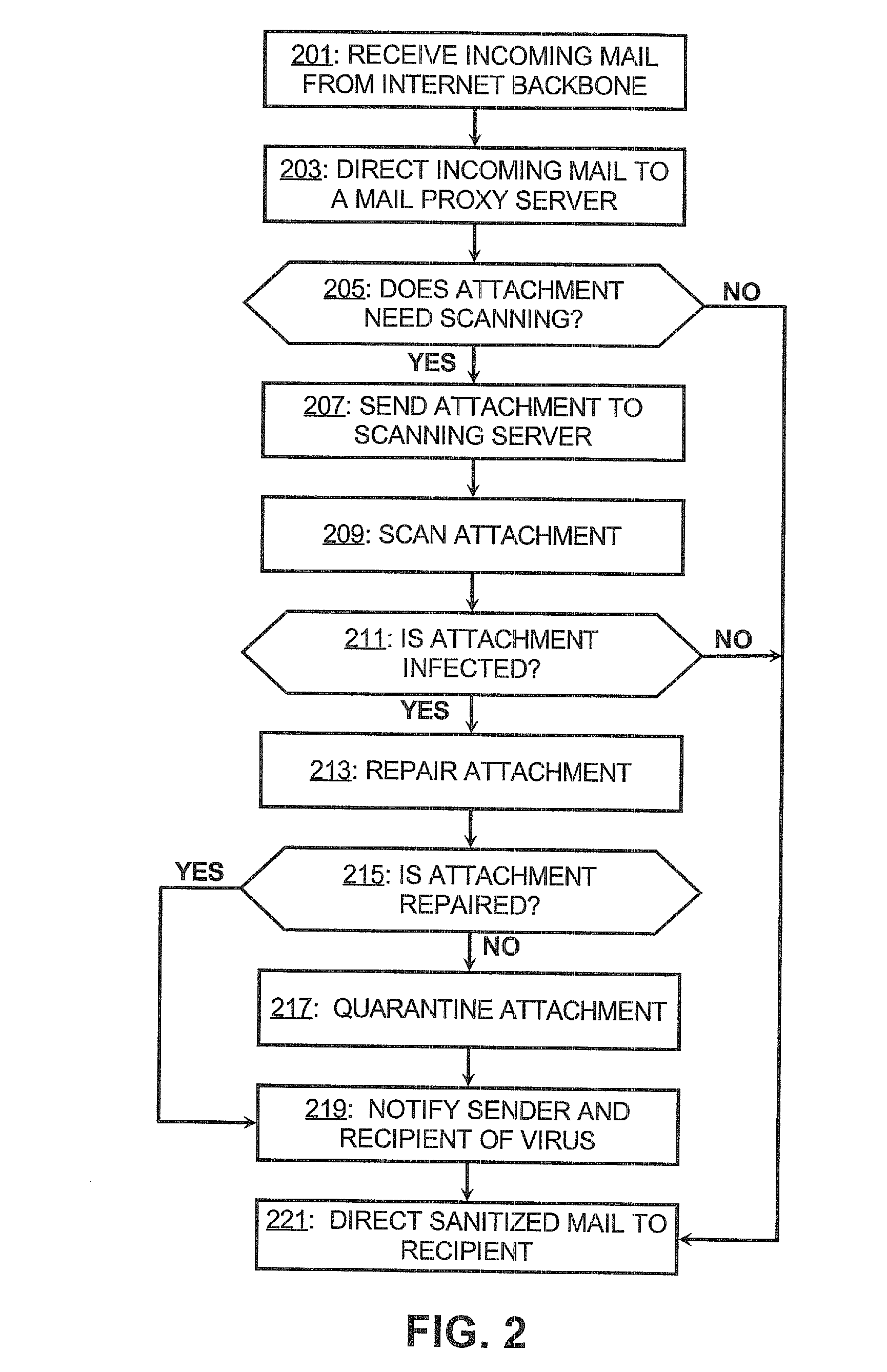
InactiveUS20120005756A1Memory loss protectionUnauthorized memory use protectionAnti virusInternet privacy
A network security system is deployed between an internet backbone and intranets that belong to subscribing organizations. The system includes a scanning system that scans incoming electronic mail for malicious code and an anti-virus server for downloading anti-virus code to clients on the intranets. A switch is provided for directing incoming electronic mail from the internet backbone to the scanning system so that the electronic mail can be scanned. In one embodiment, a decoy server is also provided for masquerading as a legitimate server and logging suspicious activity from communications received from the internet backbone.
Owner:VERIZON PATENT & LICENSING INC
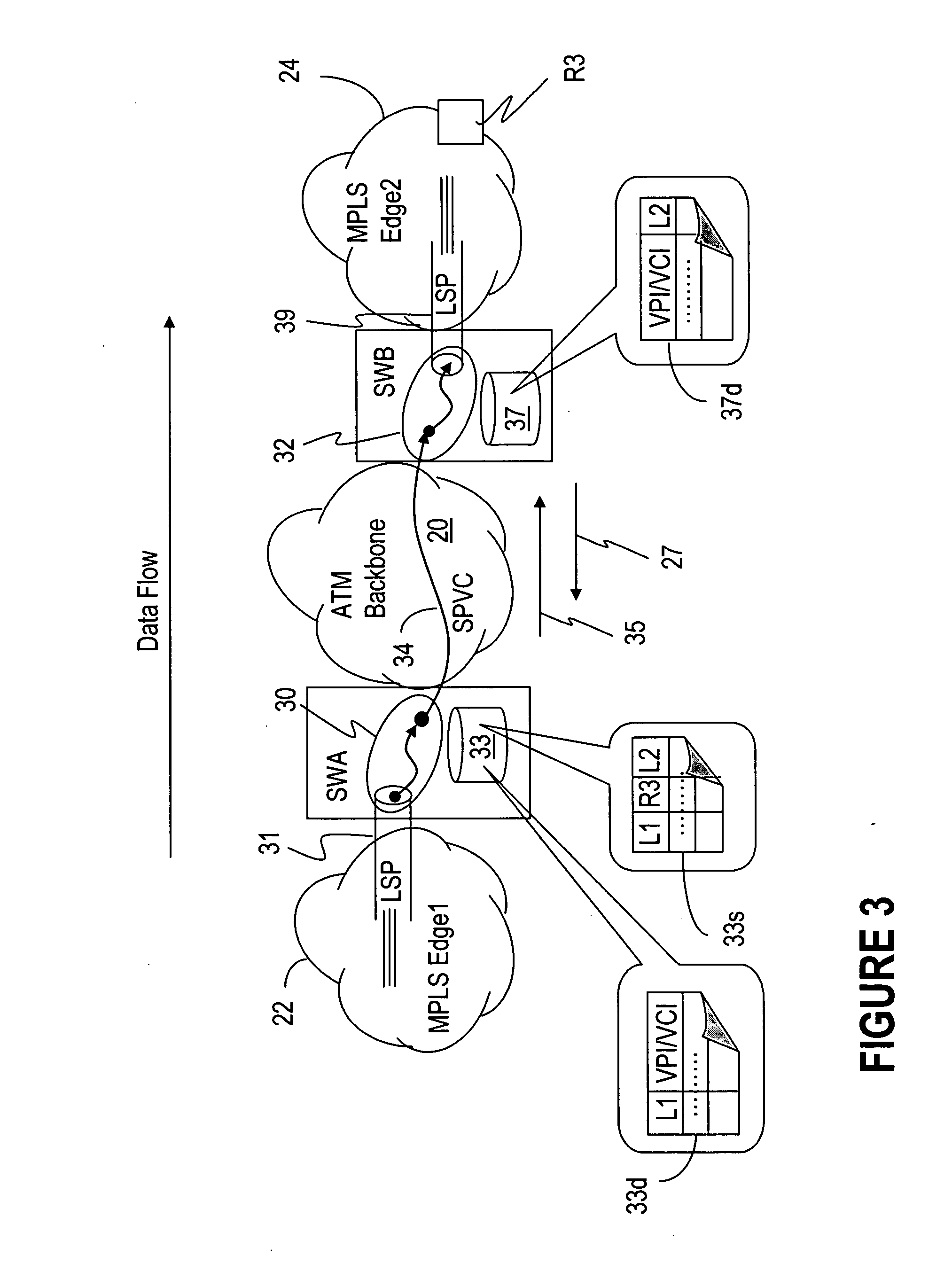
Extending IP/MPLS services reachability over ATM backbone networks
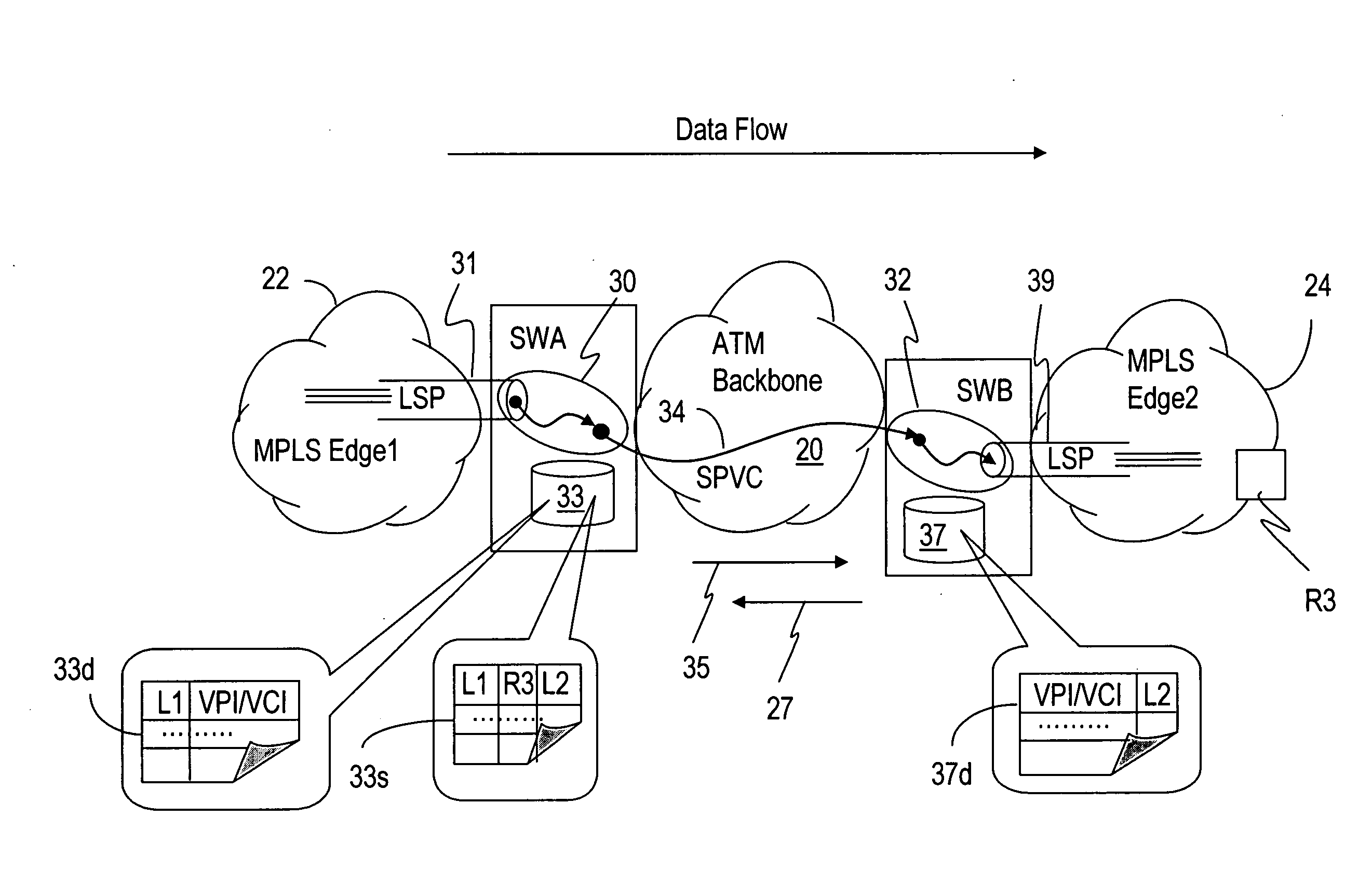
The invention enables an LSP or embedded LSPs to be mapped directly to an SPVC and carried over the ATM network. A unidirectional SPVC is established by associating it to a particular ingress LSP at the SPVC source endpoint on a multi-service switch, and to an egress LSP on the SPVC destination endpoint on another multi-service switch. The information necessary to establish the SPVC is appended in the SPVC setup message and includes LSP specific information such as the far end router ID and LSP label information, be it transport label or the full label stack. The information in the modified setup message is then used by the destination endpoint to find and connect the SPVC to the correct LSP. Incoming traffic from the LSP is switched to the SPVC at the source endpoint. The SPVC carries this traffic through the ATM network, and then the traffic is switched to the egress LSP when it emerges from the ATM network at the destination endpoint.
Owner:SOUND VIEW INNOVATIONS
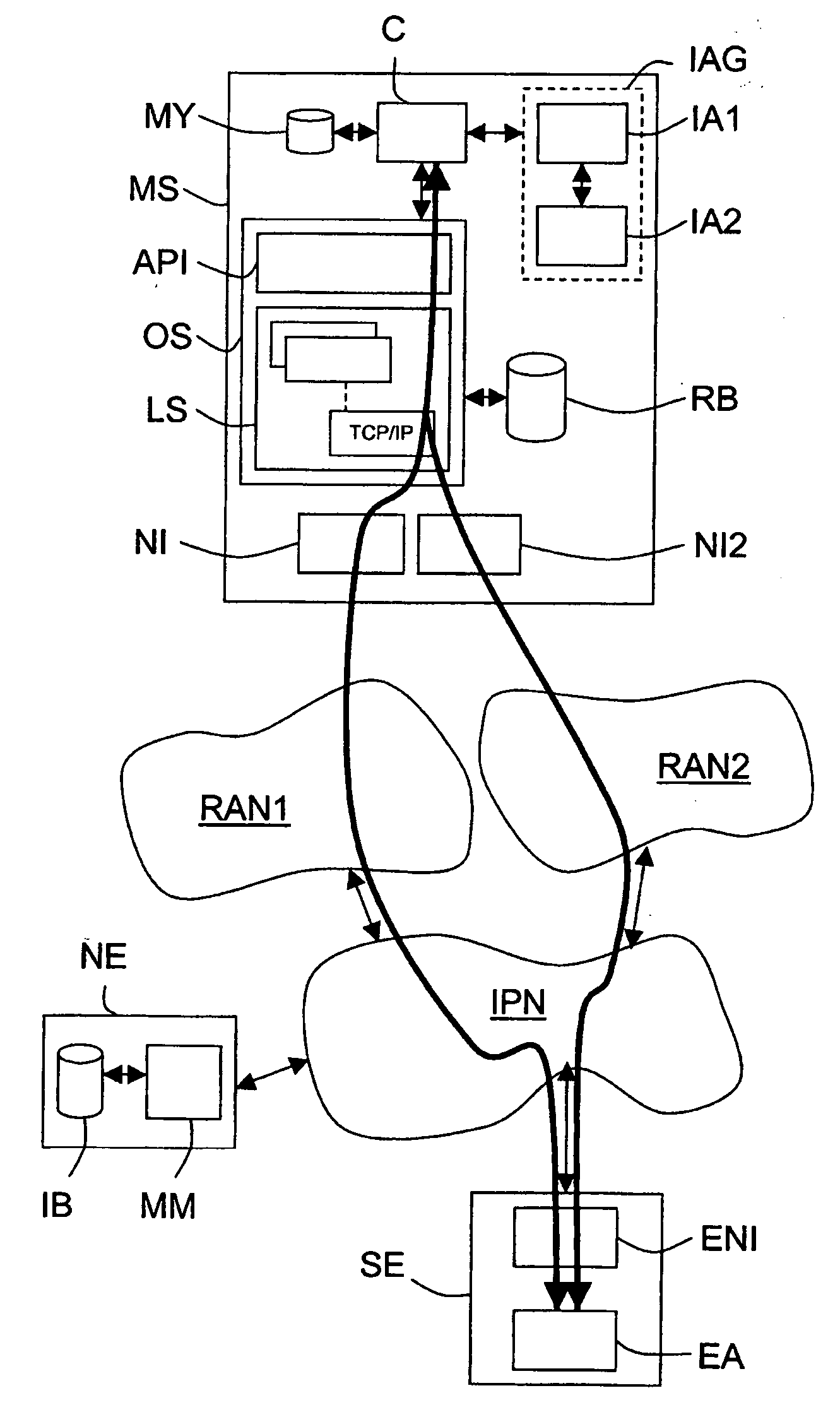
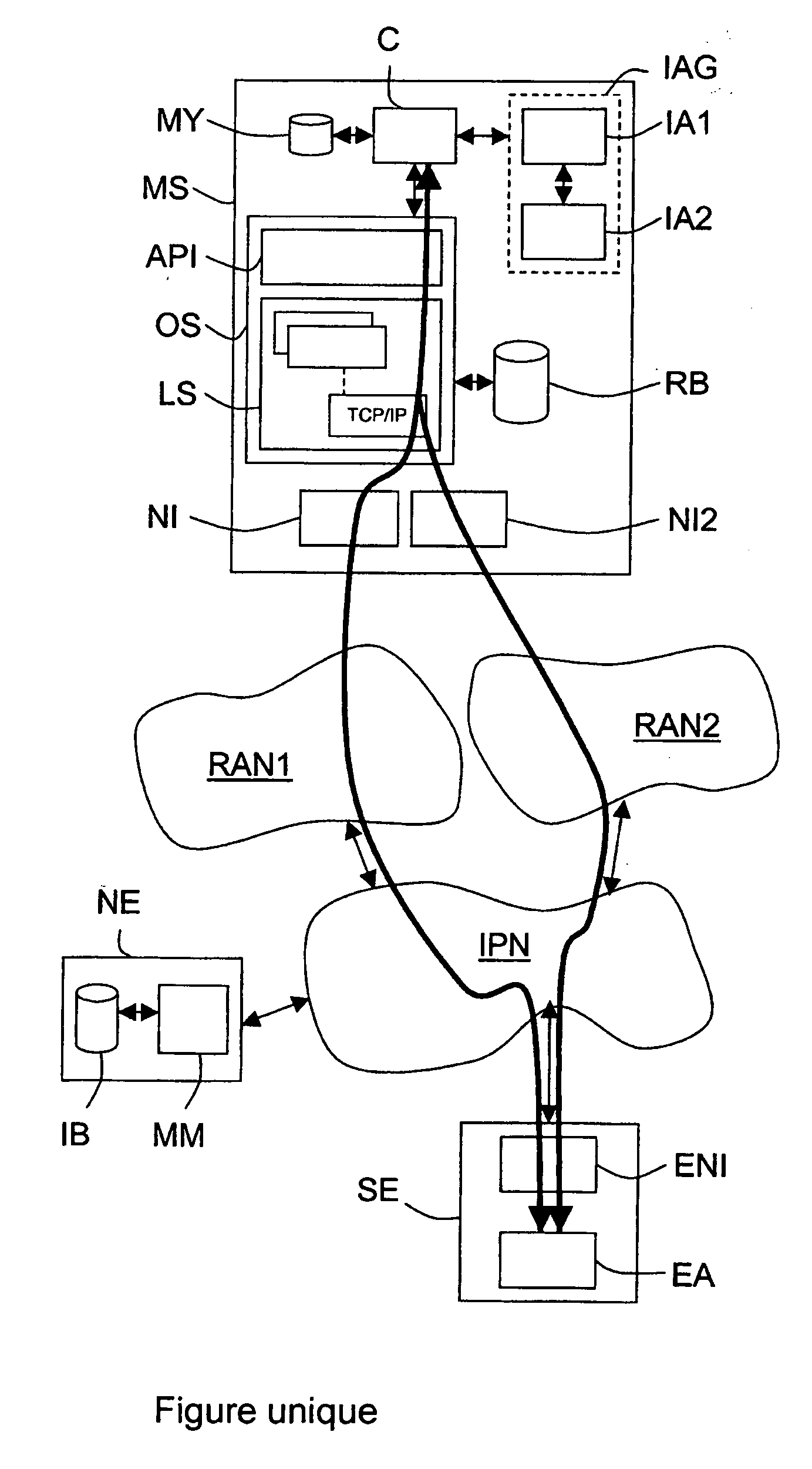
Network equipment for supplying multimode mobile terminals with data necessary for automatically selecting radio access network interfaces during service sessions
InactiveUS20070038764A1Network topologiesDevices with wireless LAN interfaceExternal applicationOperational system
A network equipment is dedicated to radio access networks of different types connected to a backbone network to which is coupled at least one application equipment including at least one external application adapted to exchange data with at least one internal application installed on multimode mobile terminals and further comprising at least two network interfaces adapted to be connected to radio access networks. The equipment comprises management means adapted to transmit to a designated terminal a control software module adapted once installed to provide a proxy interface function between internal and external applications adapted each time that it receives a transaction request designating an external application from an internal application of the terminal to determine which of the network interfaces of the terminal is suited to the transaction as a function of control information and routing information and then to instruct the operating system of the terminal to transmit the transaction request to the designated external application via a transport level connection between the determined network interface and the application equipment containing the external application.
Owner:ALCATEL LUCENT SAS
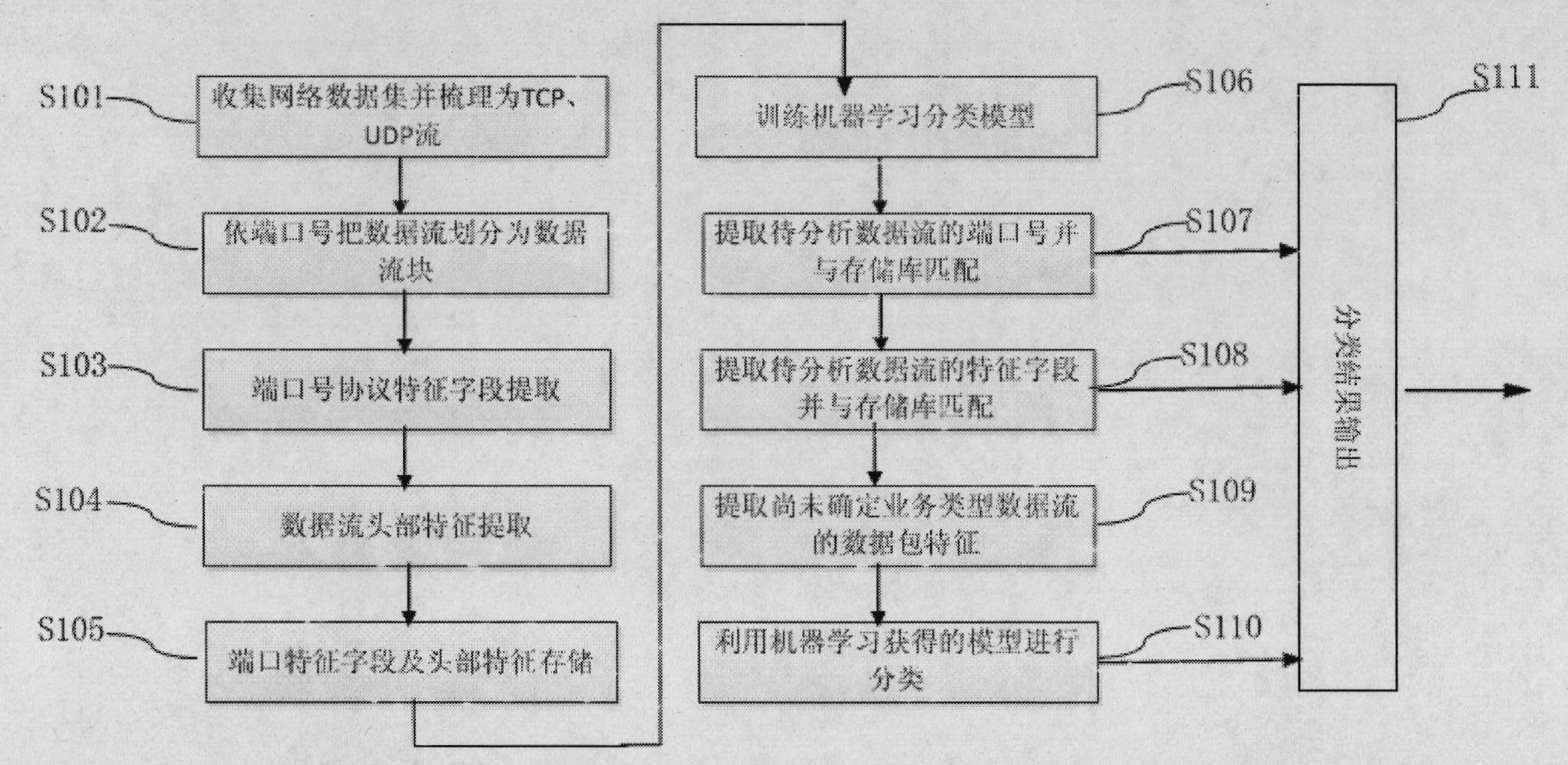
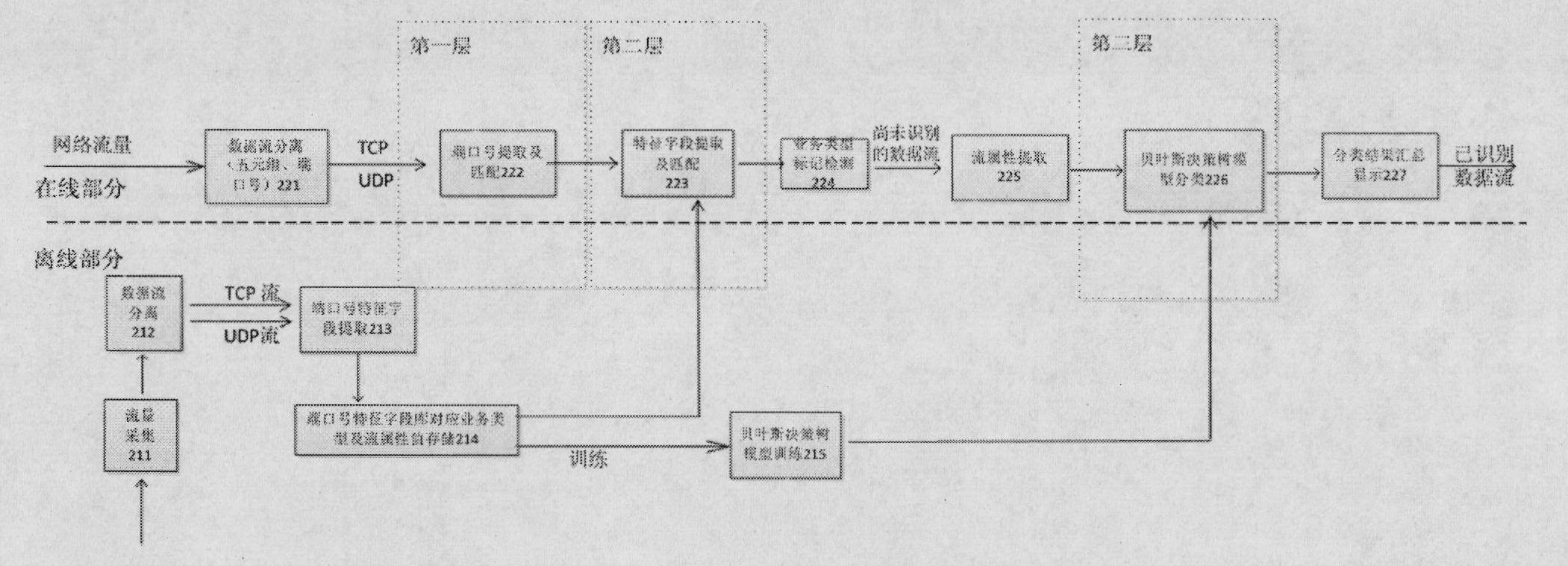
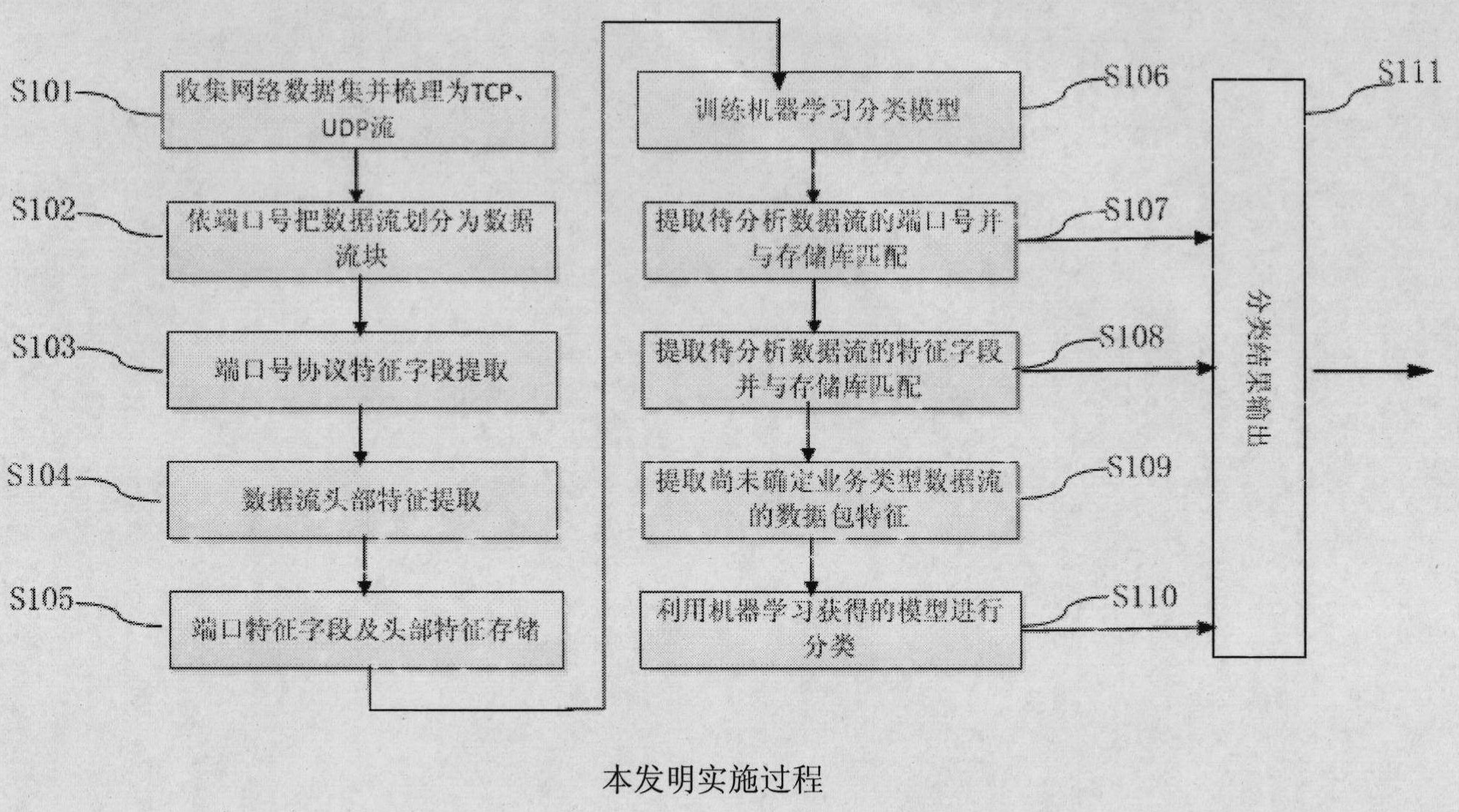
Stratification characteristic analysis-based method and apparatus thereof for on-line identification for TCP, UDP flows
The invention relates to a stratification characteristic analysis-based method and an apparatus thereof for on-line identification for TCP, UDP flows. The method comprises the following steps that: an off-line phase determines a common port number of a first layer to-be-identified service type and a characteristic field of a second layer to-be-identified service data flow through a protocol analysis; a port number and characteristic field database is constructed; meanwhile, a third layer Bayesian decision tree model is obtained by training by employing a machine study method; and service type identification on a flow is completed by utilizing the characteristic database and a study model at an on-line classification phase. In addition, the apparatus provided in the invention comprises a data flow separating module, a characteristic extraction module, a characteristic storage module, a characteristic matching module, an attribute extraction module, a model construction and classification module and a classification result display module. According to the embodiment of the invention, various application layer services based on TCP and UDP are accurately identified; moreover, the identification process is simple and highly efficient; therefore, the method and the apparatus are suitable for realization of a hardware apparatus and can be applied for equipment and systems that require on-line flow identification in a high speed backbone network and an access network.
Owner:BEIJING UNIV OF POSTS & TELECOMM
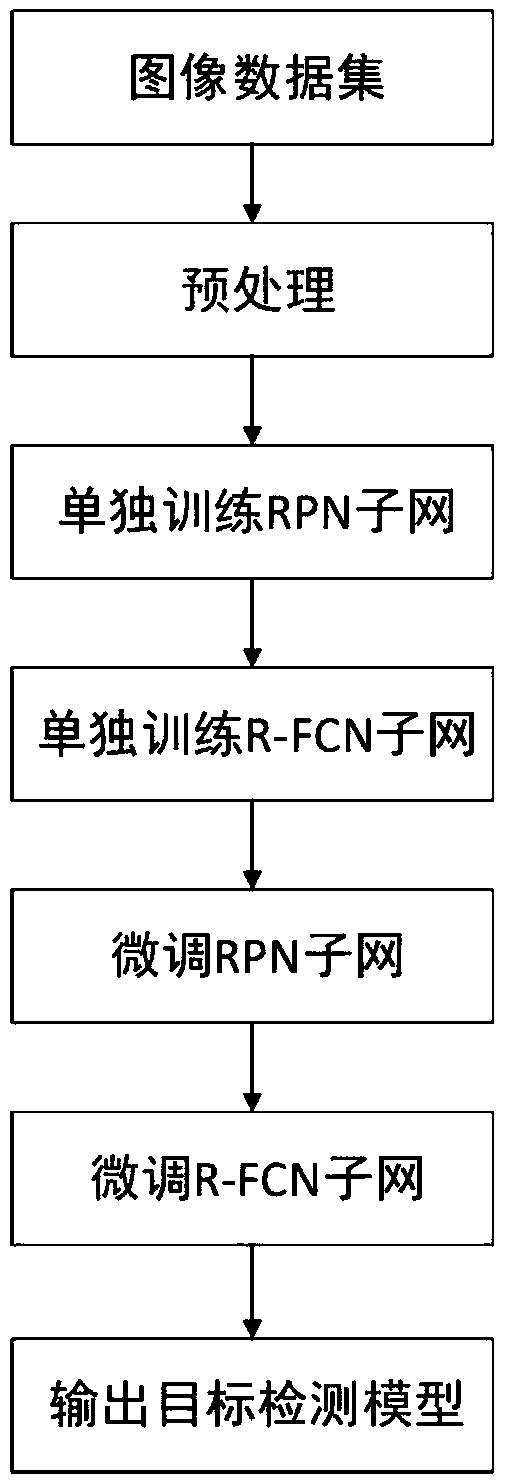
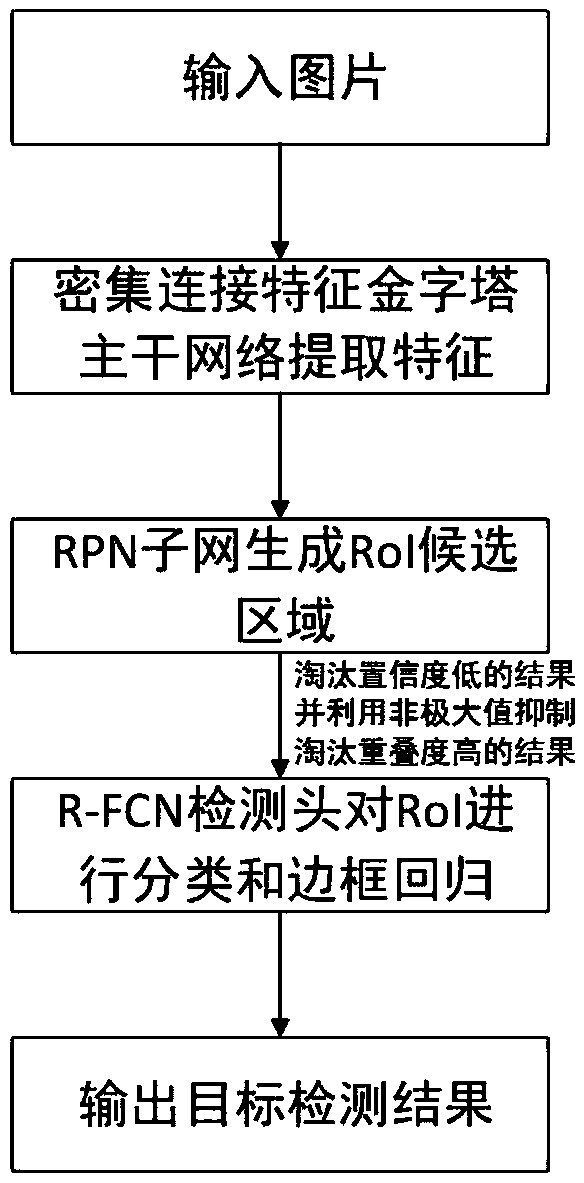
Target detection method based on a dense connection characteristic pyramid network
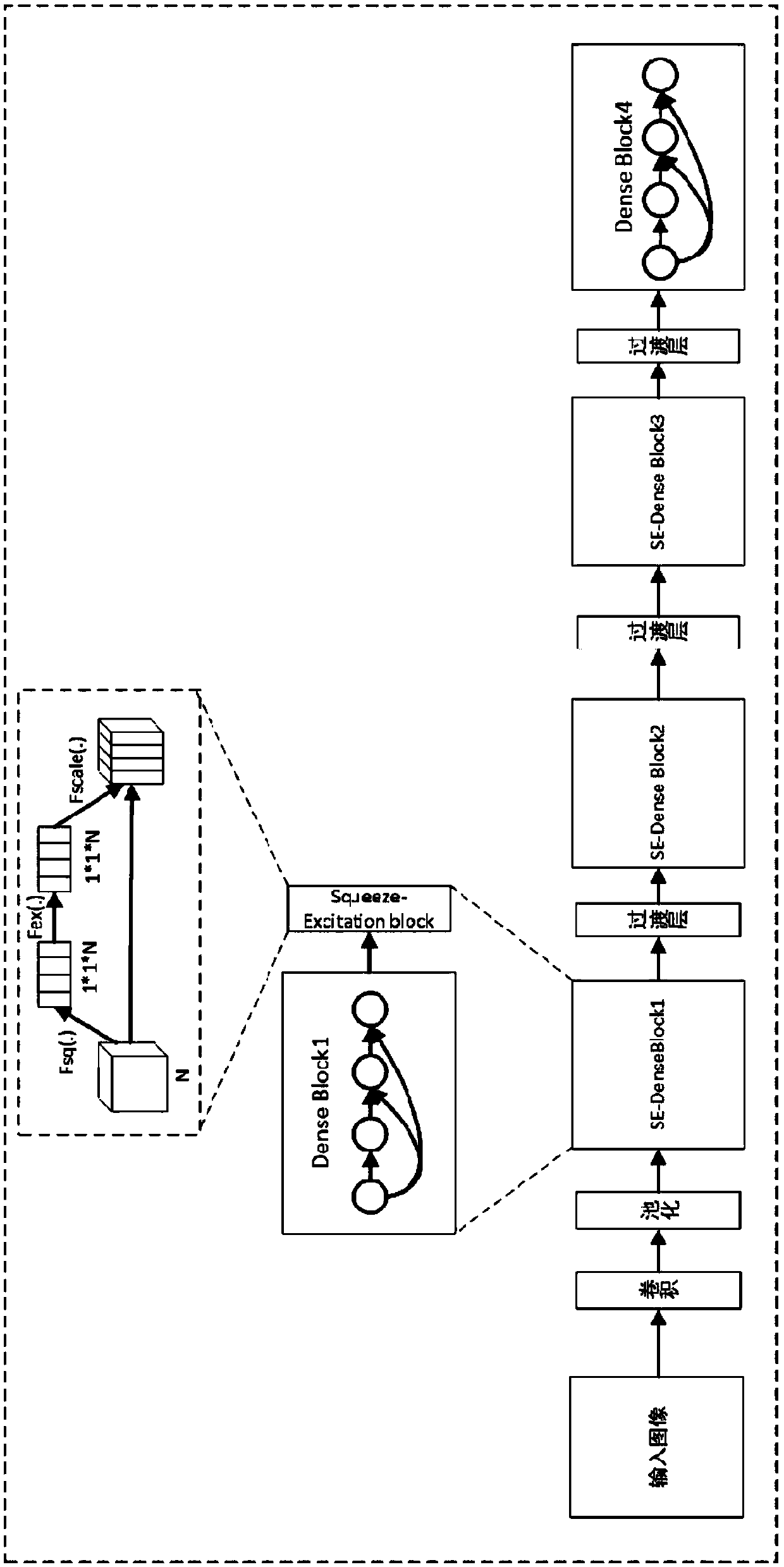
ActiveCN109614985AEnhanced Representational CapabilitiesImprove adaptabilityCharacter and pattern recognitionNeural architecturesData setImaging processing
The invention discloses a target detection method based on a dense connection characteristic pyramid network, and relates to the image processing and computer vision technology. The method comprises the steps of collecting an image data set labeled with a target bounding box and category information; constructing a dense connection feature pyramid network containing a Squeeze-Exciton structure capable of learning a dependency relationship between feature channels as a feature extraction backbone network; alternately training the RPN subnet and the R-FCN subnet to obtain a target detection model; and detecting a specific target in the image by using the model. The squeeze-Exciton structure and a dense connection structure are introduced into a feature extraction trunk network, characterization capability of the model is enhanced, adaptability of the model to targets of different sizes is enhanced through the feature pyramid structure, calculation sharing of the whole network model is achieved to the maximum degree through the R-FCN detection head, calculation resources are saved, and performance of the whole target detection model is improved. .
Owner:SOUTH CHINA UNIV OF TECH
Method of setting up ad hoc local network, method of communicating using said network, and terminal for use with said network
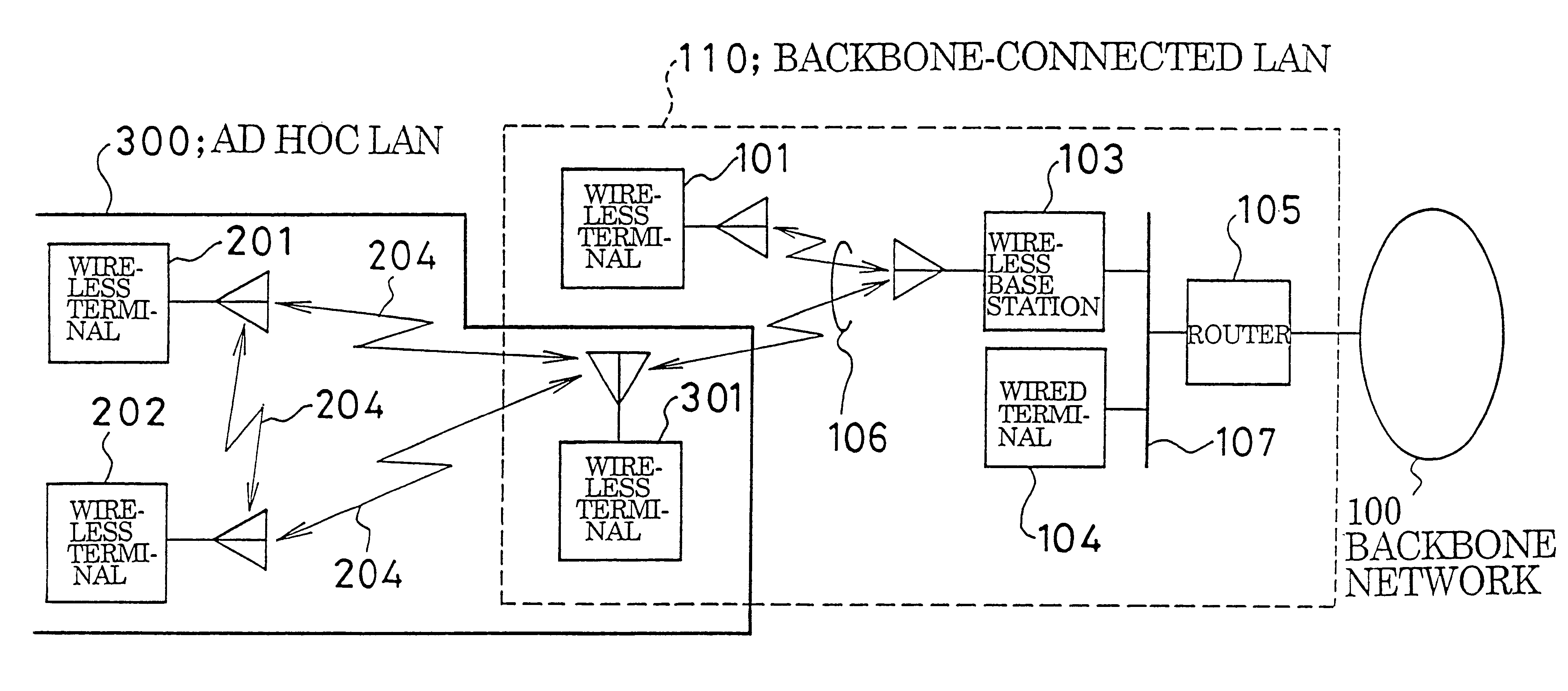
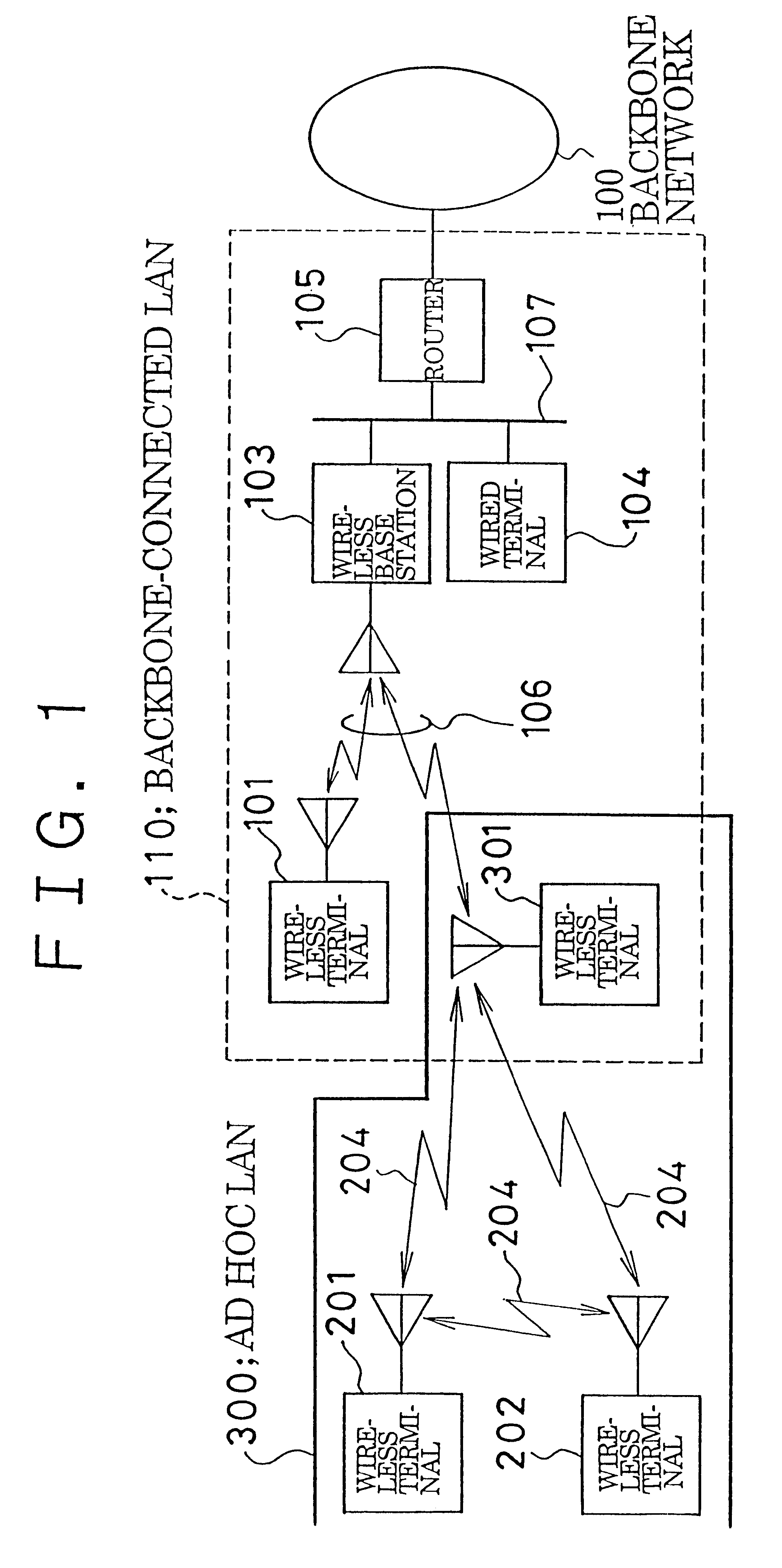
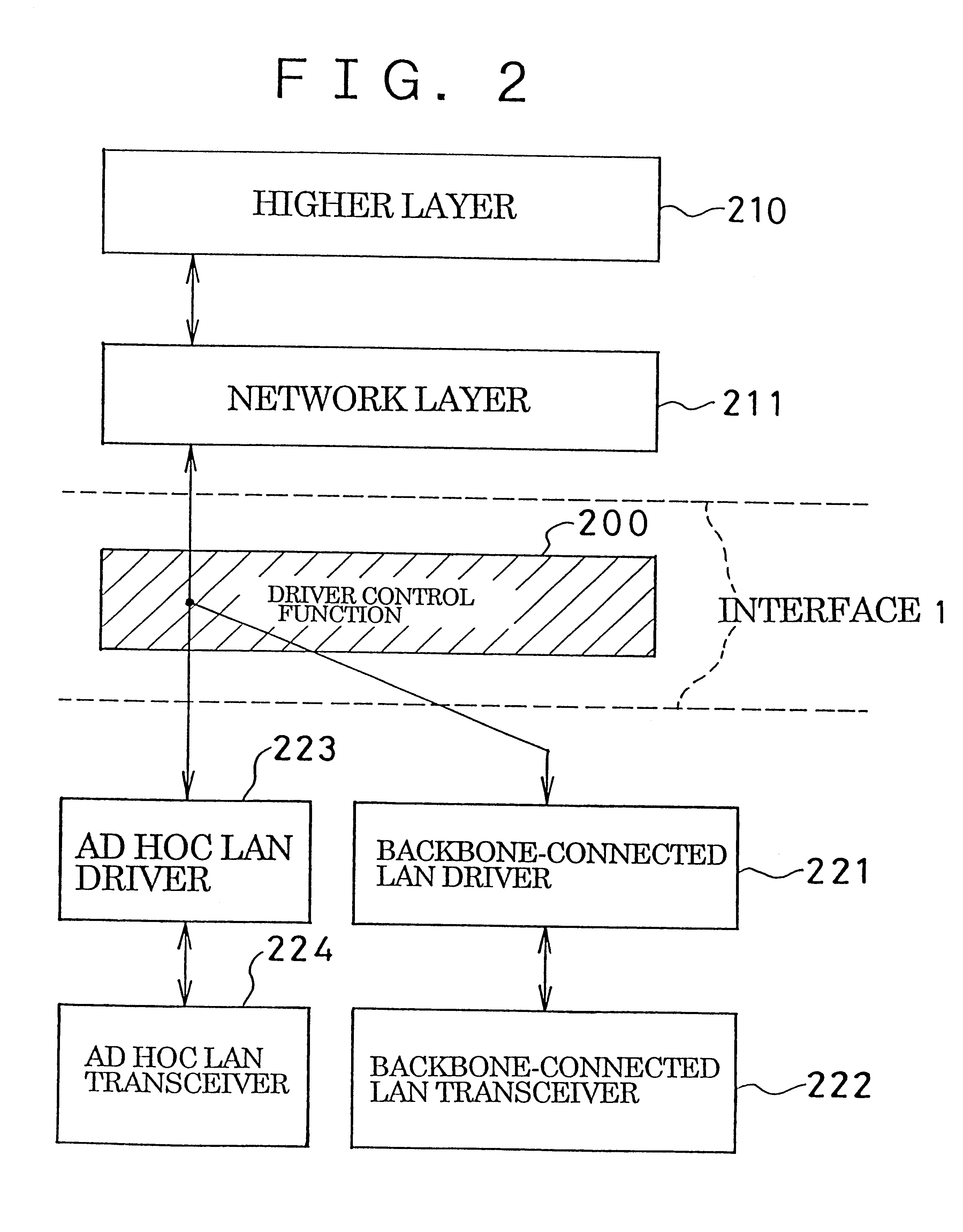
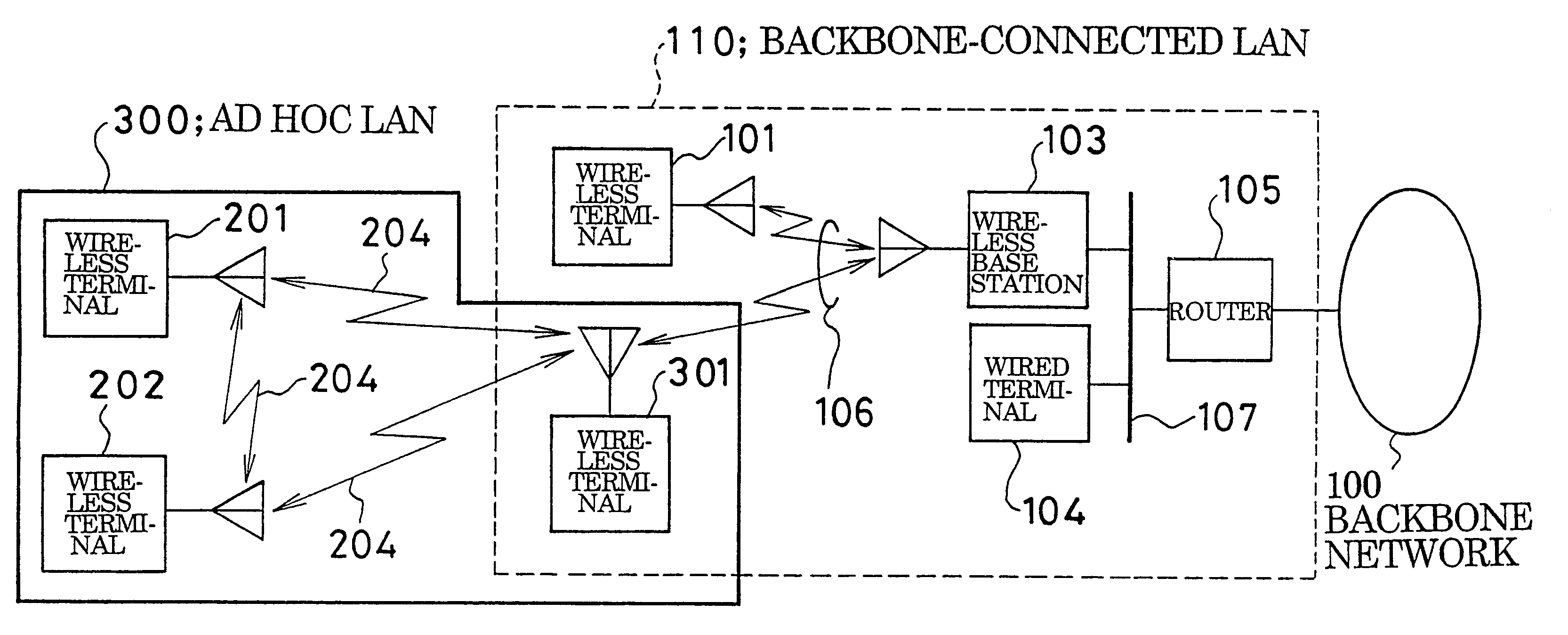
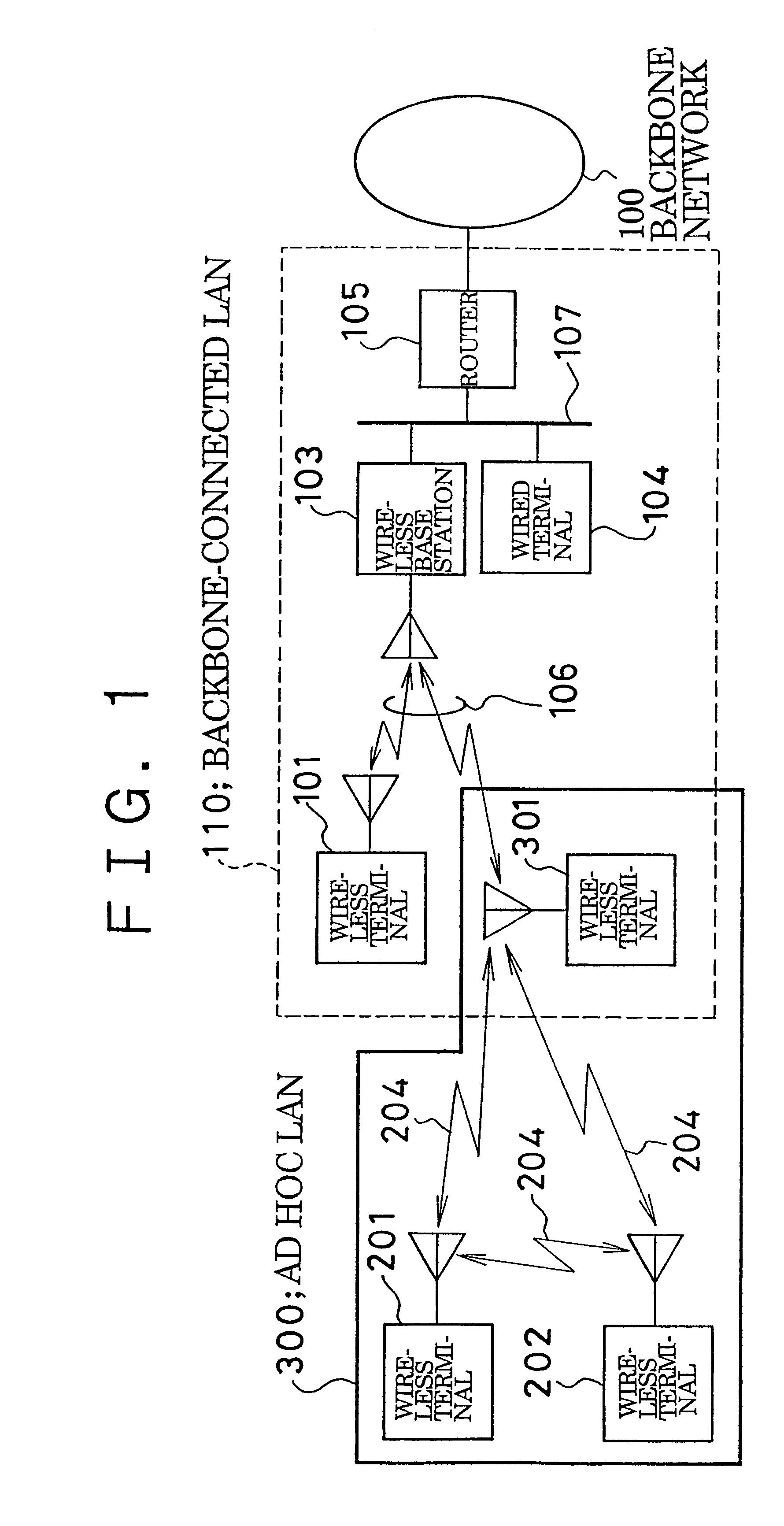
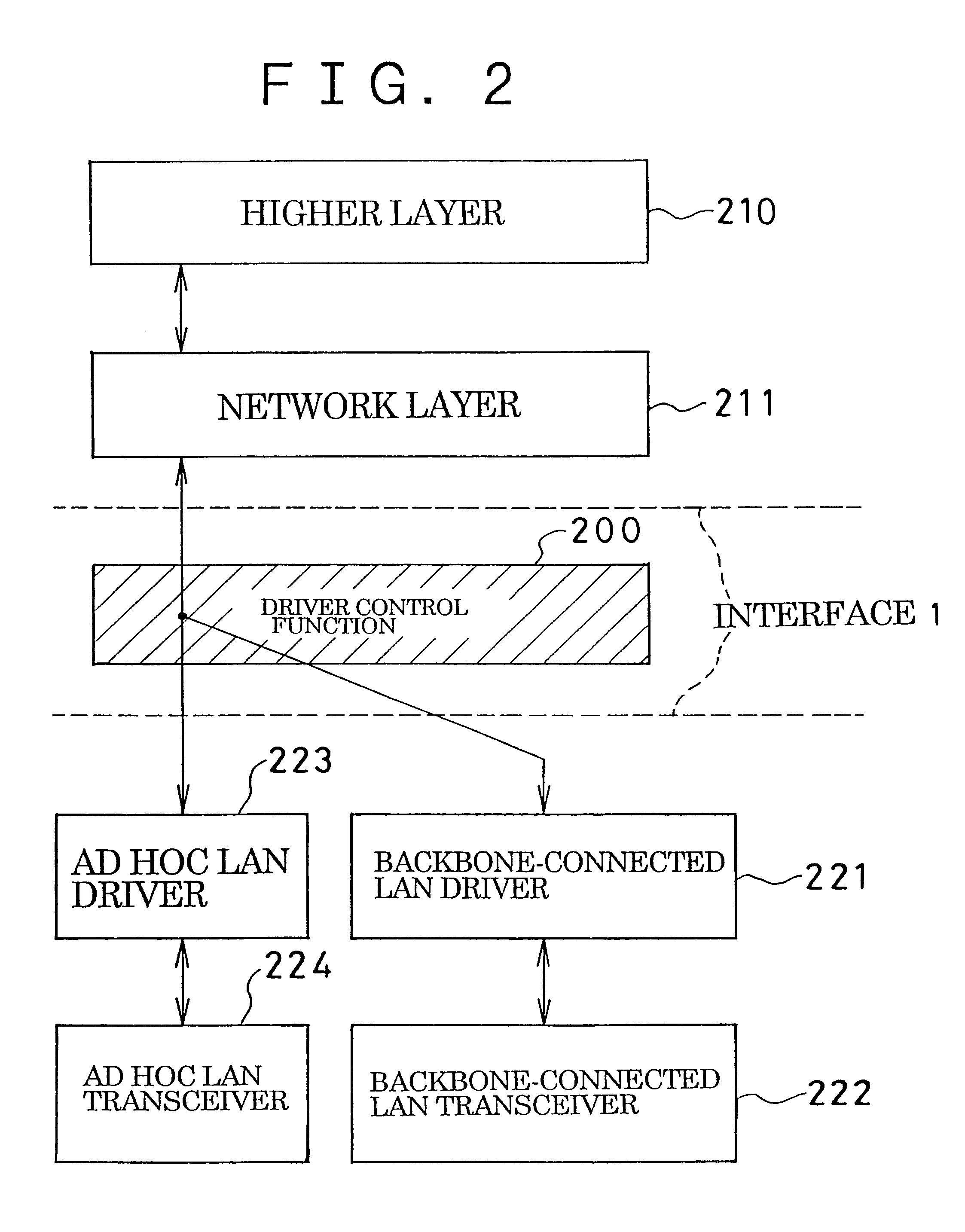
InactiveUS6338087B1Special service provision for substationNetwork topologiesLocal area networkBackbone network
An ad hoc LAN is set up in an environment in which there simultaneously exist a backbone-connected LAN connected by a high-speed backbone network and an ad hoc LAN not connected to the backbone network, wherein the ad hoc LAN is capable of communicating simultaneously with both LANs. An ad hoc LAN is defined as one multicast group used within the backbone network and backbone-connected LAN. This makes it possible for a terminal, which is connected to the ad hoc LAN and backbone-connected LAN simultaneously so that it may communicate with both LANs, to participate in the ad hoc LAN in the same manner as it would participate in a multicast group of a conventional backbone-connected LAN. As a result, the terminal construction is simplified and the terminal can be connected to an ad hoc LAN and backbone-connected LAN simultaneously.
Owner:NEC CORP
Wireless Home Network Routing Protocol
ActiveUS20100188971A1Error preventionFrequency-division multiplex detailsWireless mesh networkFamily network
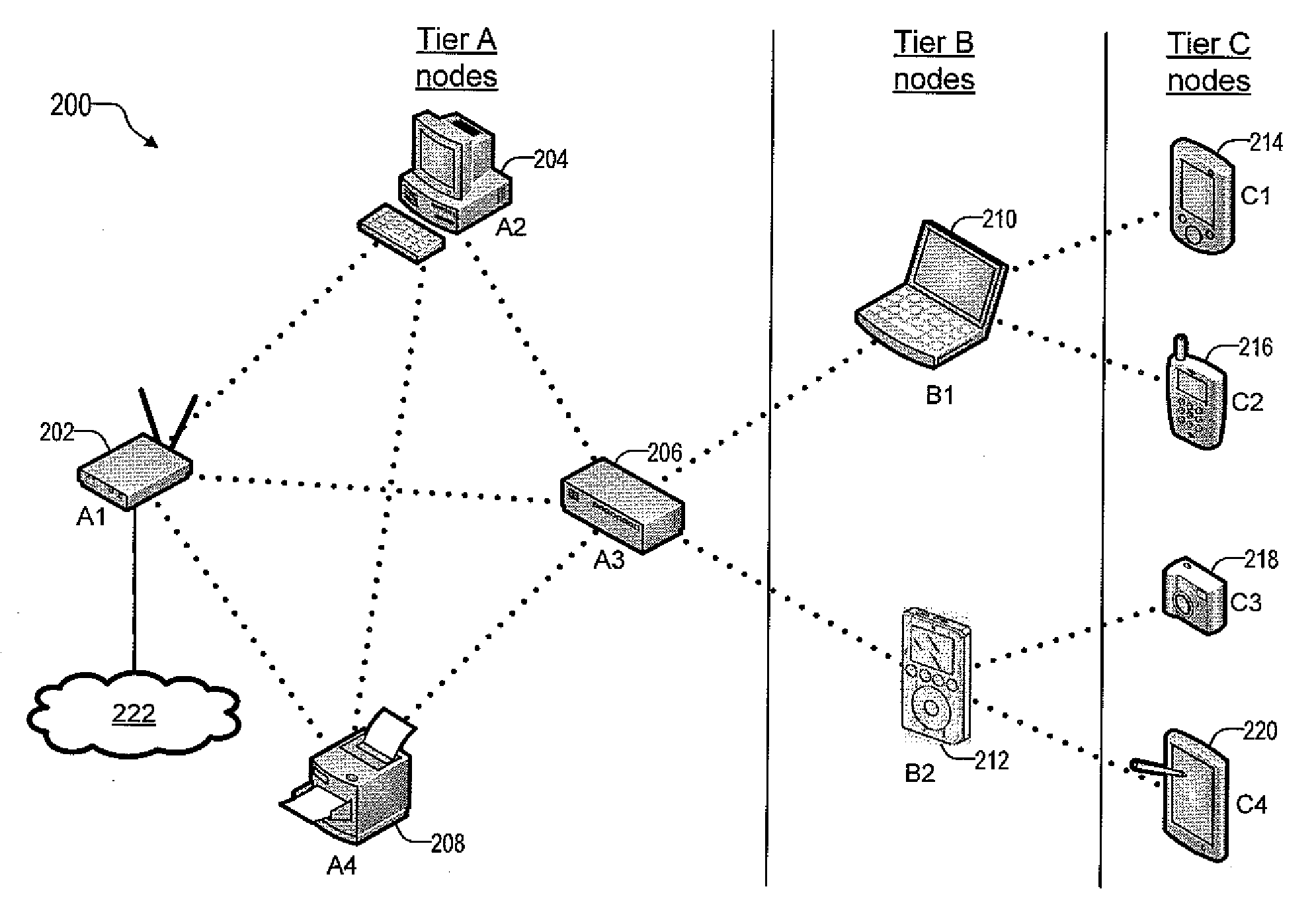
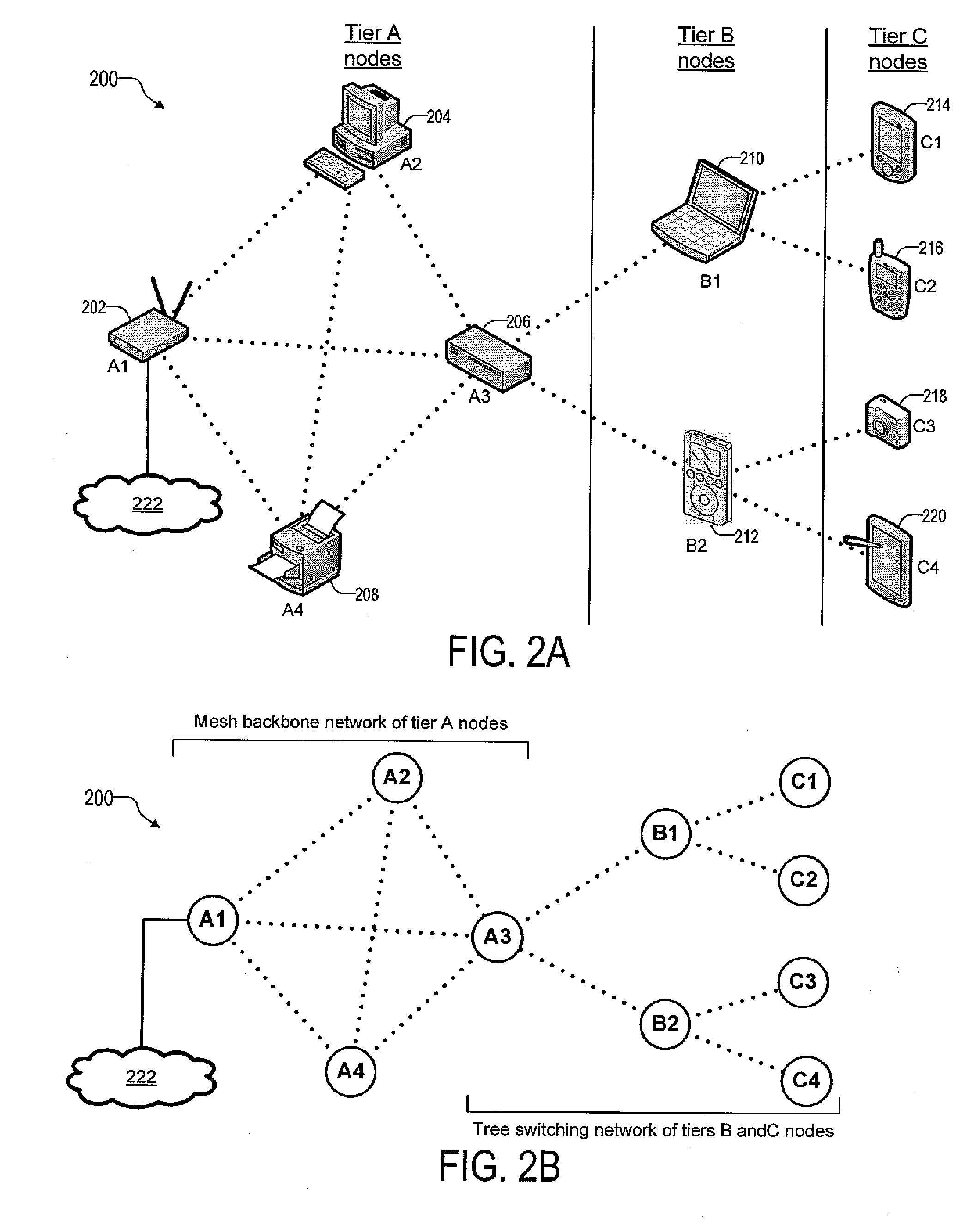
A hierarchical wireless network is provided with a mesh backbone network portion and a switching tree network portion. The mesh backbone network portion includes first tier nodes each having at least one wireless link to another first tier node. The first tier nodes execute a link-state protocol for routing packets. The switching tree network portion includes second tier nodes each having a single wireless link to one first tier node and at least one wireless link to one third tier node, and third tier nodes each having a single wireless link to one second tier node. The second tier and the third tier nodes execute switching rules for switching packets.
Owner:GOOGLE LLC
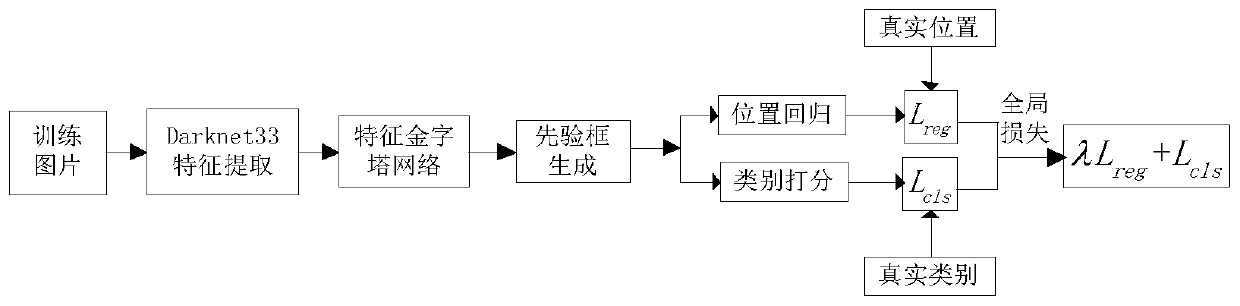
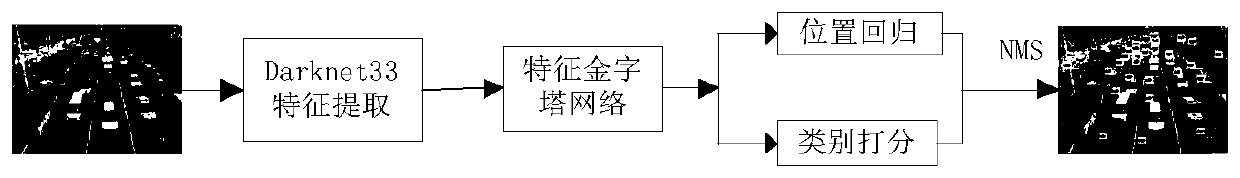
A pedestrian and vehicle detection method and system based on improved YOLOv3
ActiveCN109815886ADetection matchHigh speedCharacter and pattern recognitionNeural architecturesMulti-label classificationVehicle detection
The invention discloses a pedestrian and vehicle detection method and system based on improved YOLOv3. According to the method, an improved YOLOv3 network based on Darknet-33 is adopted as a main network to extract features; the cross-layer fusion and reuse of multi-scale features in the backbone network are carried out by adopting a transmittable feature map scale reduction method; and then a feature pyramid network is constructed by adopting a scale amplification method. In the training stage, a K-means clustering method is used for clustering the training set, and the cross-to-parallel ratio of a prediction frame to a real frame is used as a similarity standard to select a priori frame; and then the BBox regression and the multi-label classification are performed according to the loss function. And in the detection stage, for all the detection frames, a non-maximum suppression method is adopted to remove redundant detection frames according to confidence scores and IOU values, and an optimal target object is predicted. According to the method, a feature extraction network Darknet-33 of feature map scale reduction fusion is adopted, a feature pyramid is constructed through feature map scale amplification migration fusion, and a priori frame is selected through clustering, so that the speed and precision of the pedestrian and vehicle detection can be improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Client device characterization of other client device transmissions and reporting of signal qualities to access point(s)
A wireless network in a communication infrastructure has a packet switched backbone network and includes a plurality of access points and services at least one client device. The access points communicatively couple to the packet switched backbone network and each include access point processing circuitry and access point wireless transceiver circuitry. Each client device has client processing circuitry and client wireless transceiver circuitry. The client devices receive transmissions from other client devices serviced by the plurality of access points and characterize the received transmissions to determine signal qualities of the plurality of transmissions received from the other client devices. The client devices then report the signal qualities of the plurality of transmissions to at least one of the plurality of access points. The access points may forward the signal qualities to other access points, to other client devices, and may alter operation of the wireless network based upon the signal qualities.
Owner:AVAGO TECH INT SALES PTE LTD
Method and system based on mobile prediction and group switching
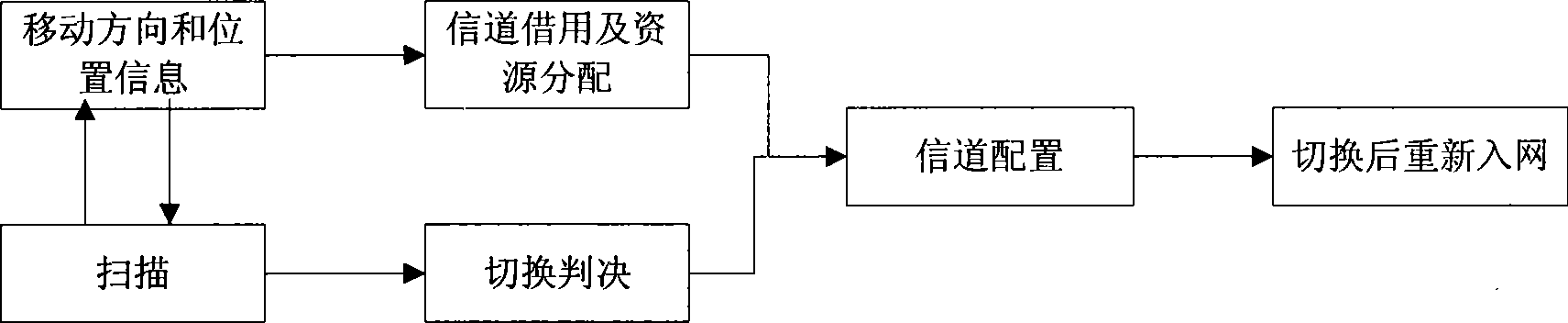
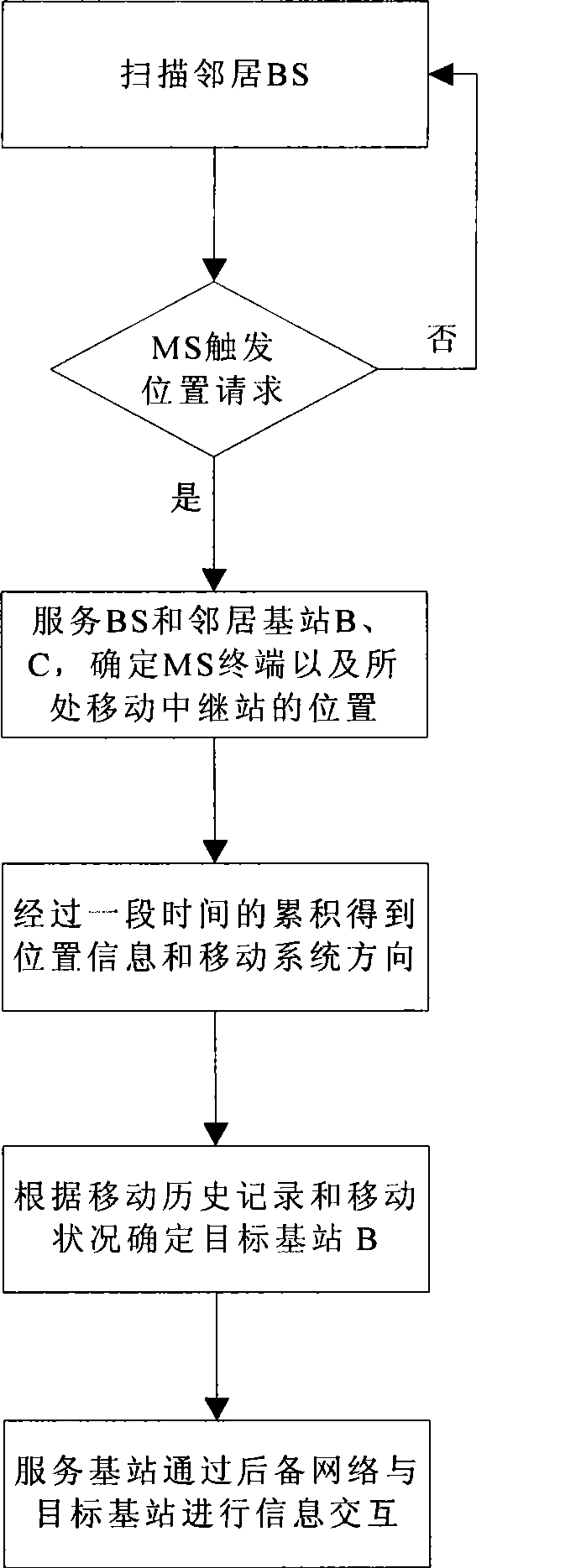
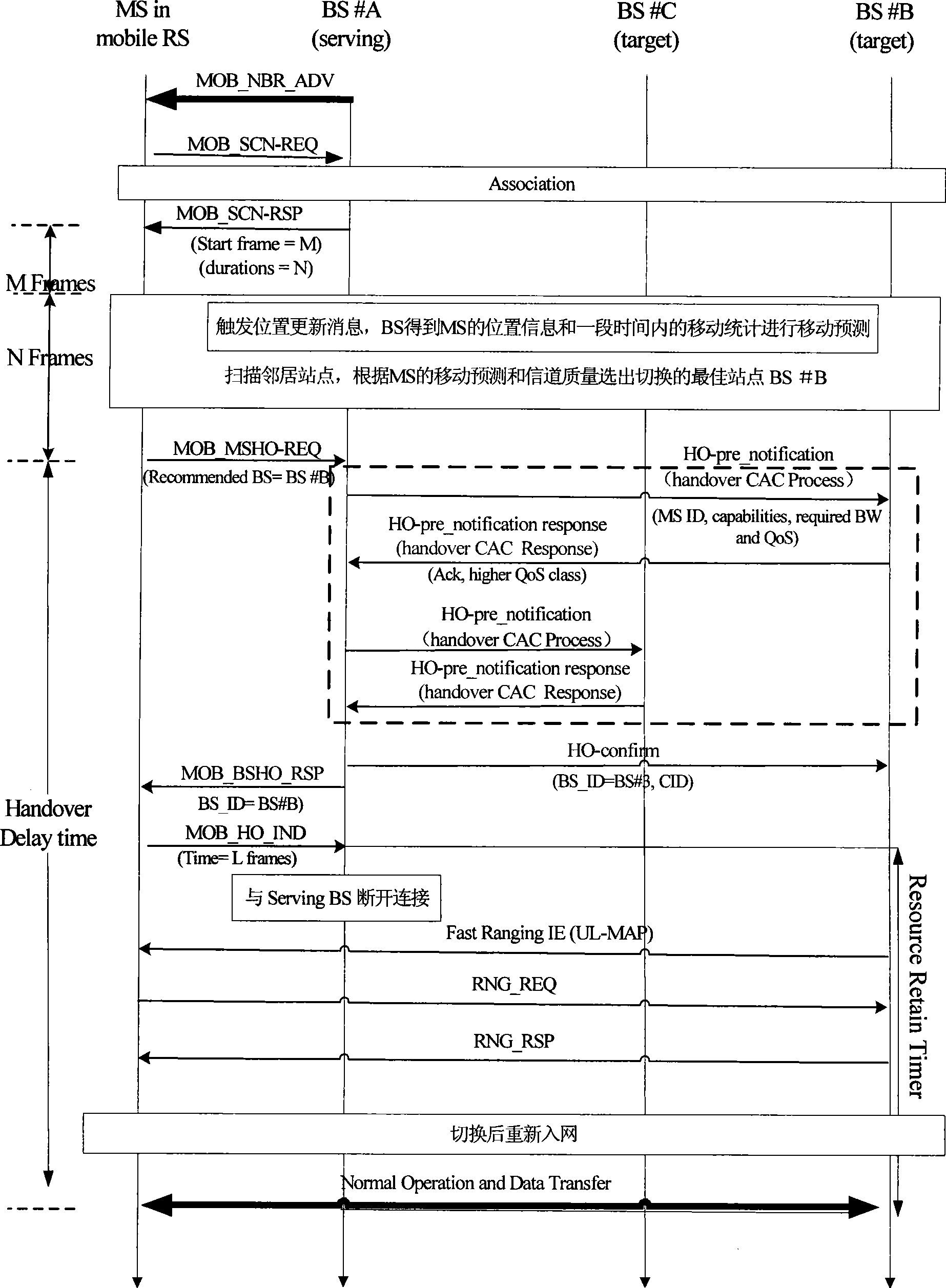
InactiveCN101365242ASave switching delay timeReduce congestionRadio/inductive link selection arrangementsData switching networksQuality of serviceRelevant information
The invention discloses a group switch method based on a mobility prediction. Multi-service group user ends which move along fixed routes in a major public transportation system need to apply to a target base station for group switch according to detected changes of a wireless channel. The method further provides a mobility prediction based on location information, which comprises the following steps: the process of reselecting a target cell is simplified by using a mobile historical database; and the target cell is enabled to obtain relative information of all group users in advance through a backup backbone network. Required channel resources are reallocated through strategies such as borrowing channels, etc. Therefore, the system switch speed of the group user terminal is greatly improved, and QoS of broadband wireless communications in the switch process is guaranteed. The method further discloses a group switch system based on the mobility prediction, which mainly comprises a location information unit, a switch judging unit, a channel borrowing and resource allocating unit and a channel allocating unit.
Owner:TONGJI UNIV
Method of setting up AD HOC local area network, method of communicating using said network, and terminal for use with said network
InactiveUS6415330B1Special service provision for substationNetwork topologiesComputer scienceNetwork connectivity
An ad hoc LAN is set up in an environment in which there simultaneously exist a backbone-connected LAN connected by a high-speed backbone network and an ad hoc LAN not connected to the backbone network, wherein the ad hoc LAN is capable of communicating simultaneously with both LANs. An ad hoc LAN is defined as one multicast group used within the backbone network and backbone-connected LAN. This makes it possible for a terminal, which is connected to the ad hoc LAN and backbone-connected LAN simultaneously so that it may communicate with both LANs, to participate in the ad hoc LAN in the same manner as it would participate in a multicast group of a conventional backbone-connected LAN. As a result, the terminal construction is simplified and the terminal can be connected to an ad hoc LAN and backbone-connected LAN simultaneously.
Owner:NEC CORP
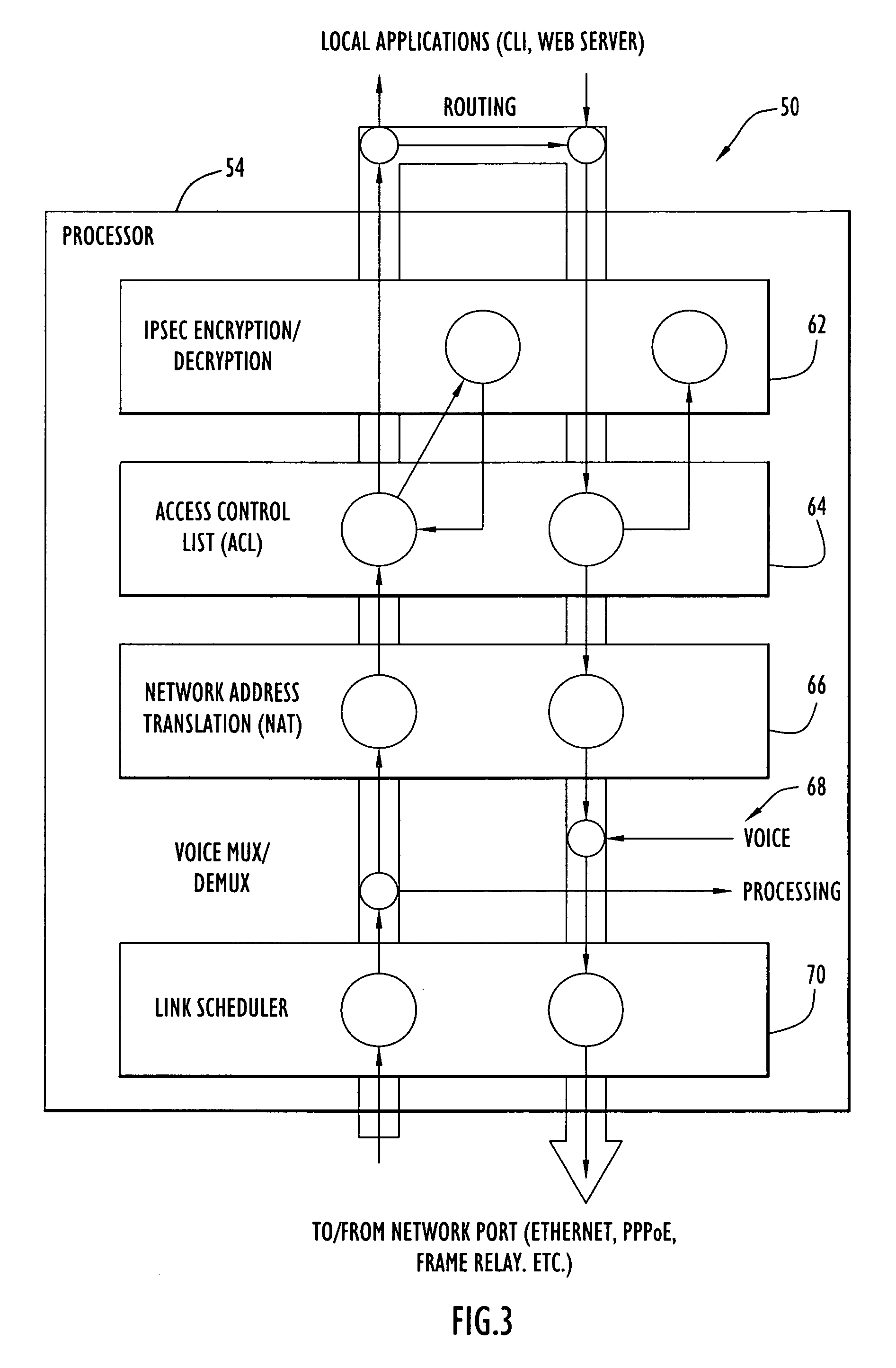
Communication device and method of prioritizing transference of time-critical data
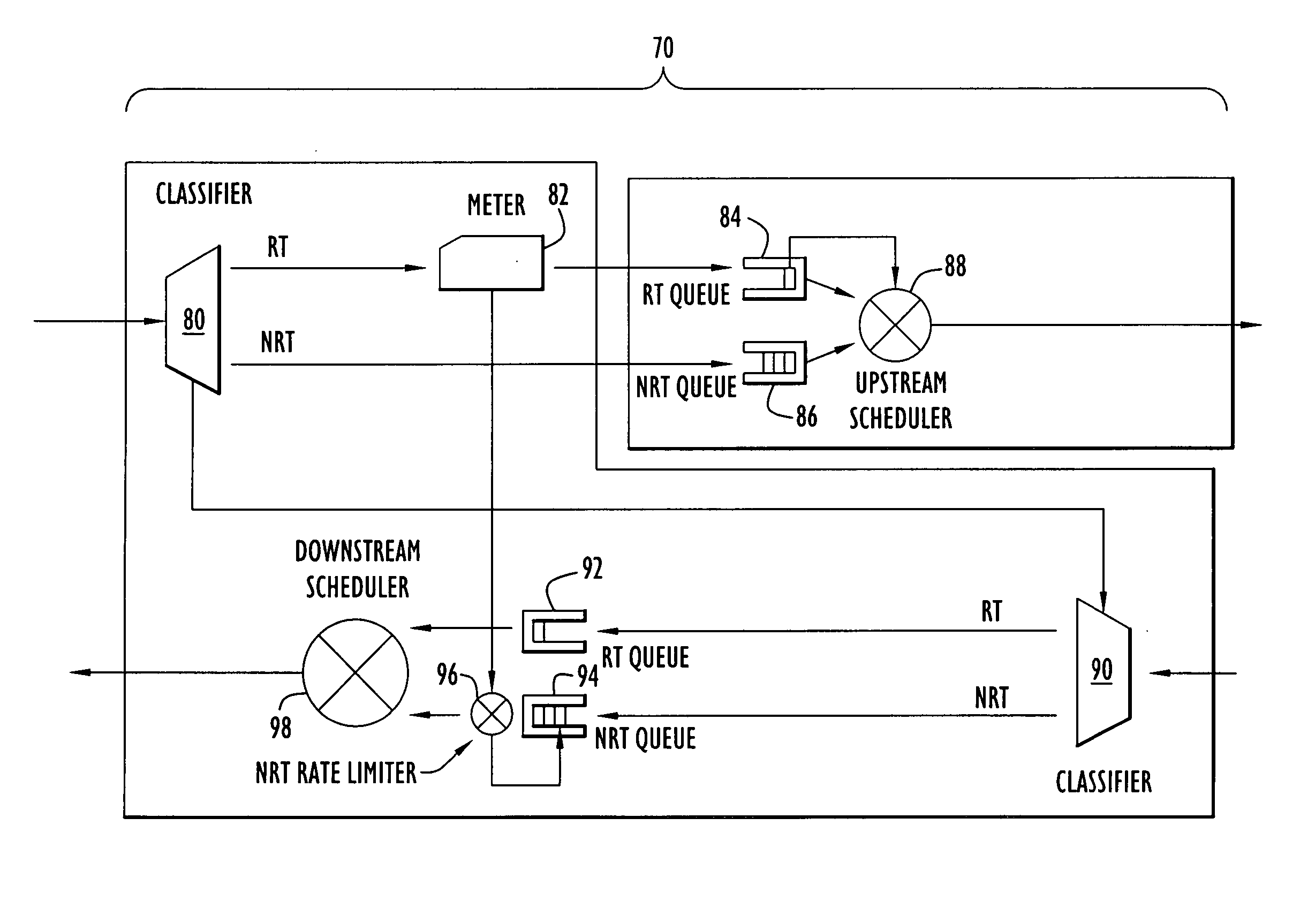
InactiveUS20060187836A1Raise transfer toSolve insufficient bandwidthError preventionTransmission systemsData packTime critical
A communication device according to the present invention enhances transfer of time-critical data between one or more LANs and a device (e.g., edge router, etc.) coupled to a backbone network. A virtual bottleneck in the form of a queue is introduced by the communication device at the customer premises or customer end of a backbone network access line where the network congestion or bottleneck resides. The virtual bottleneck delays and / or discards time insensitive traffic prior to time-critical or voice traffic being delayed in the edge router. This is accomplished by the virtual bottleneck queue including a storage capacity or length less than that of a queue utilized by the edge router. A traffic manager or scheduler controlling the virtual bottleneck dynamically adjusts the virtual bottleneck based on the bandwidth required for time-critical packets to ensure sufficient bandwidth is available for those packets.
Owner:PATTON ELECTRONICS
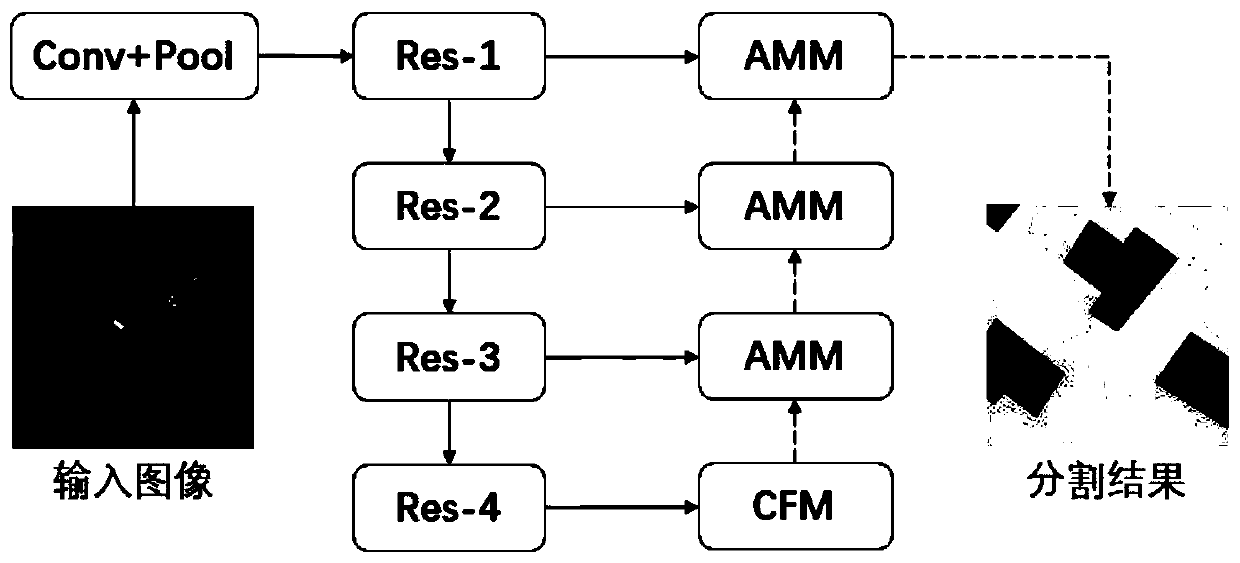
Remote sensing image semantic segmentation method based on context information and attention mechanism
The invention provides a remote sensing image semantic segmentation method based on context information and an attention mechanism. For a to-be-labeled high-resolution remote sensing image, data preprocessing and data amplification are firstly carried out, and then the amplified data is used for training a remote sensing image semantic segmentation model. In the training process, preliminary features are extracted from the image through a backbone network, then multi-scale features are extracted and fused through a multi-scale context information module, then features of different levels are combined with an attention fusion module, and finally bilinear interpolation up-sampling is directly utilized to obtain a final segmentation result. For an unlabeled image, firstly the unlabeled imageis segmented into small image blocks, the small image blocks are input into a semantic segmentation network to obtain a corresponding result, and then the small image blocks are spliced to obtain a final large-size segmentation result graph.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com