Patents
Literature
105 results about "Token ring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
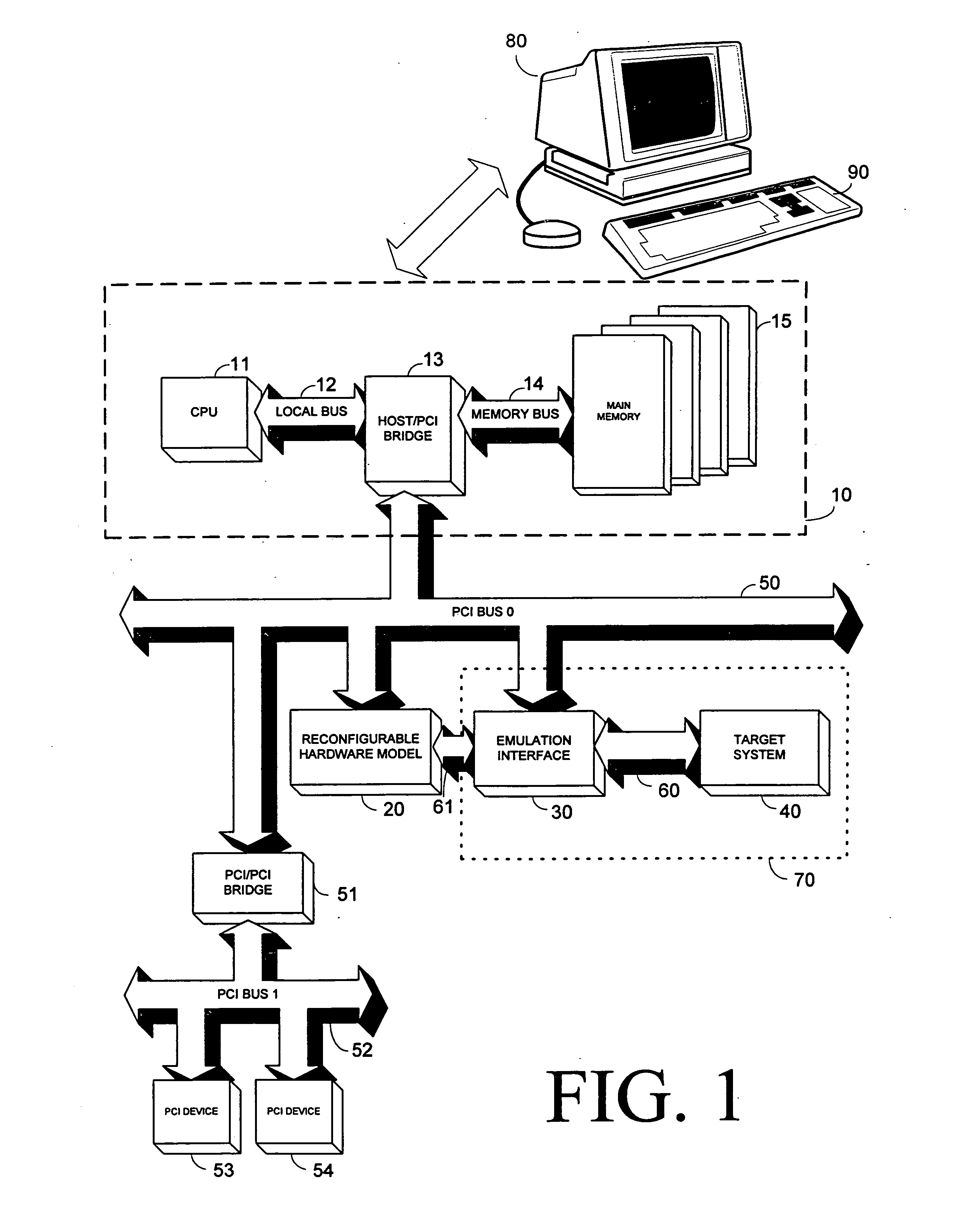
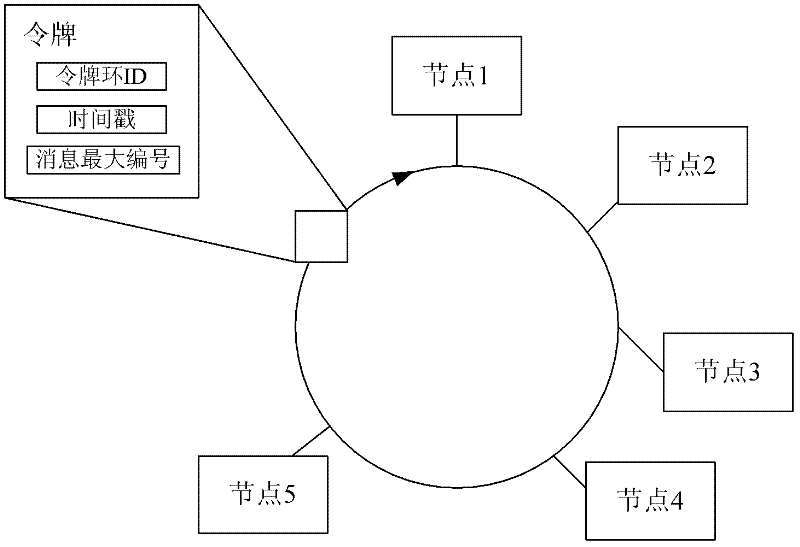
Token Ring local area network (LAN) technology is a communications protocol for local area networks. It uses a special three-byte frame called a "token" that travels around a logical "ring" of workstations or servers. This token passing is a channel access method providing fair access for all stations, and eliminating the collisions of contention-based access methods.
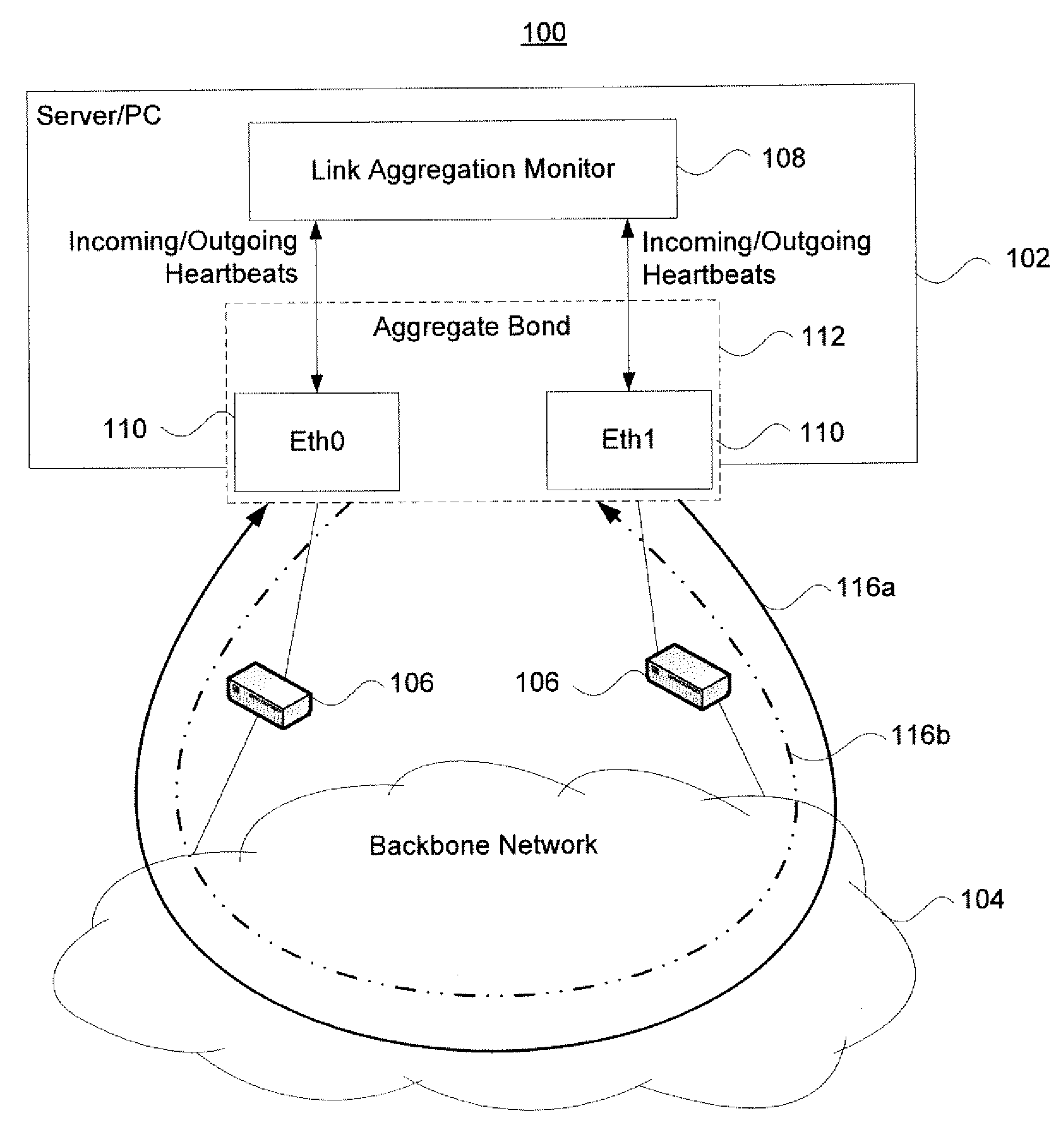
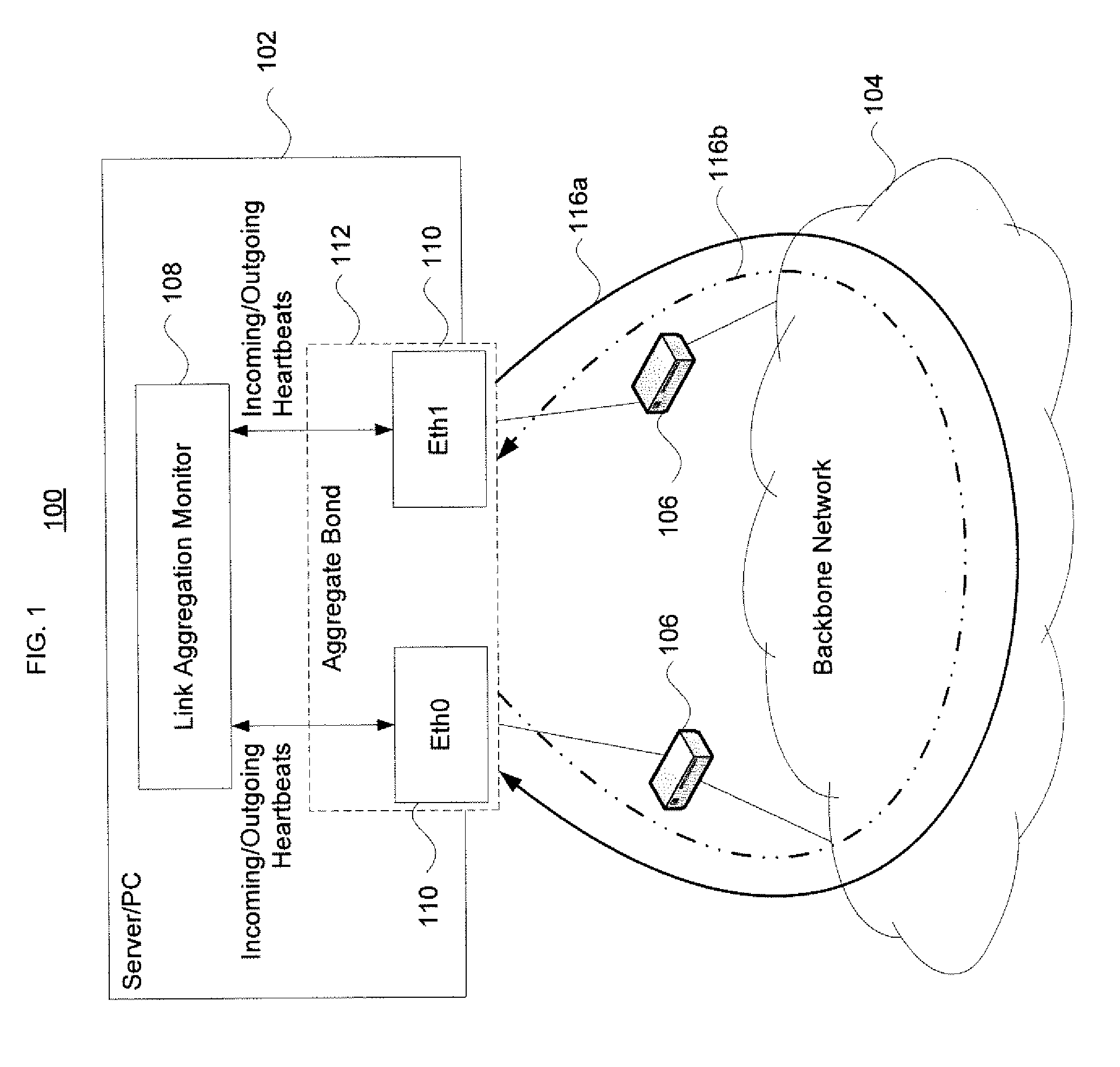
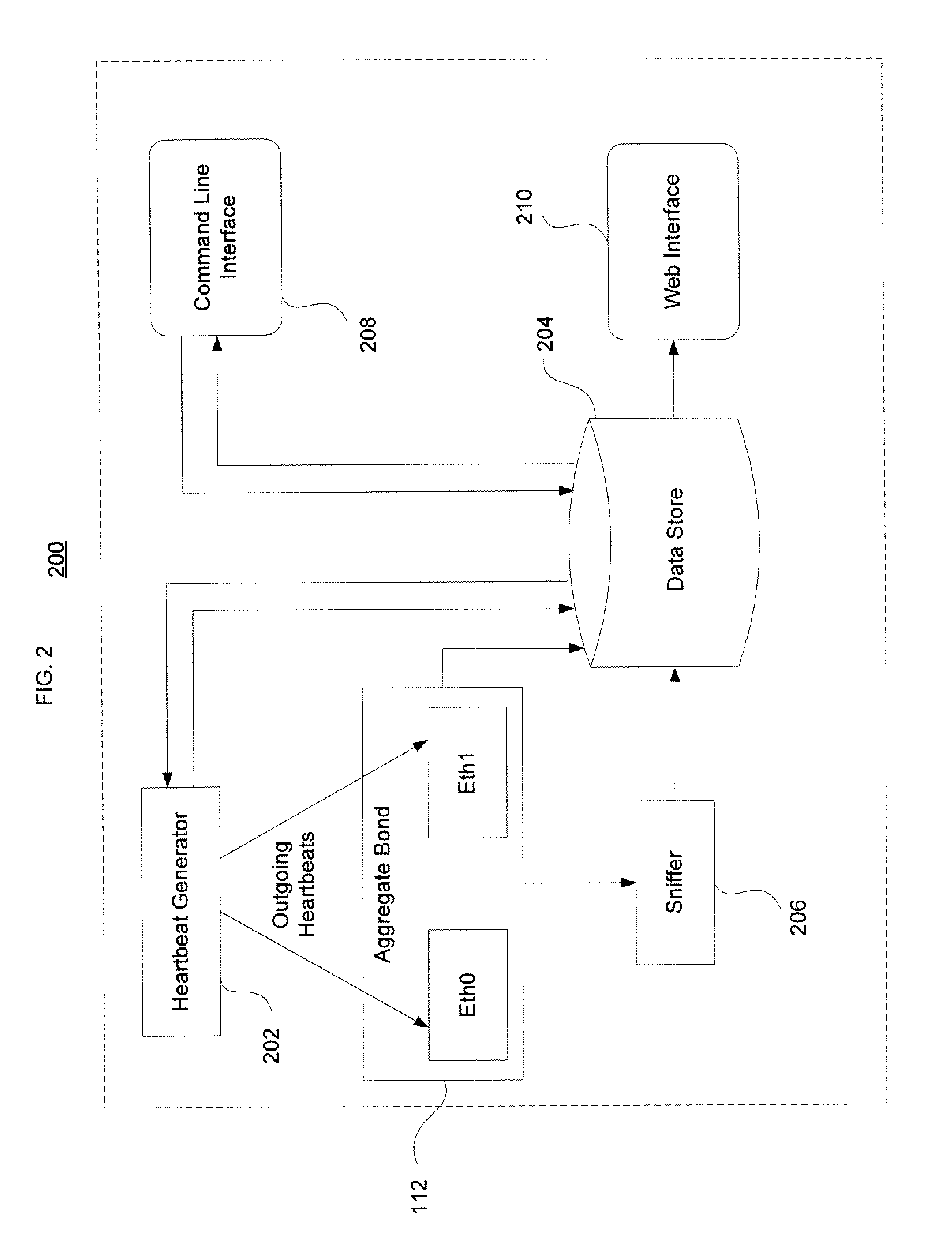
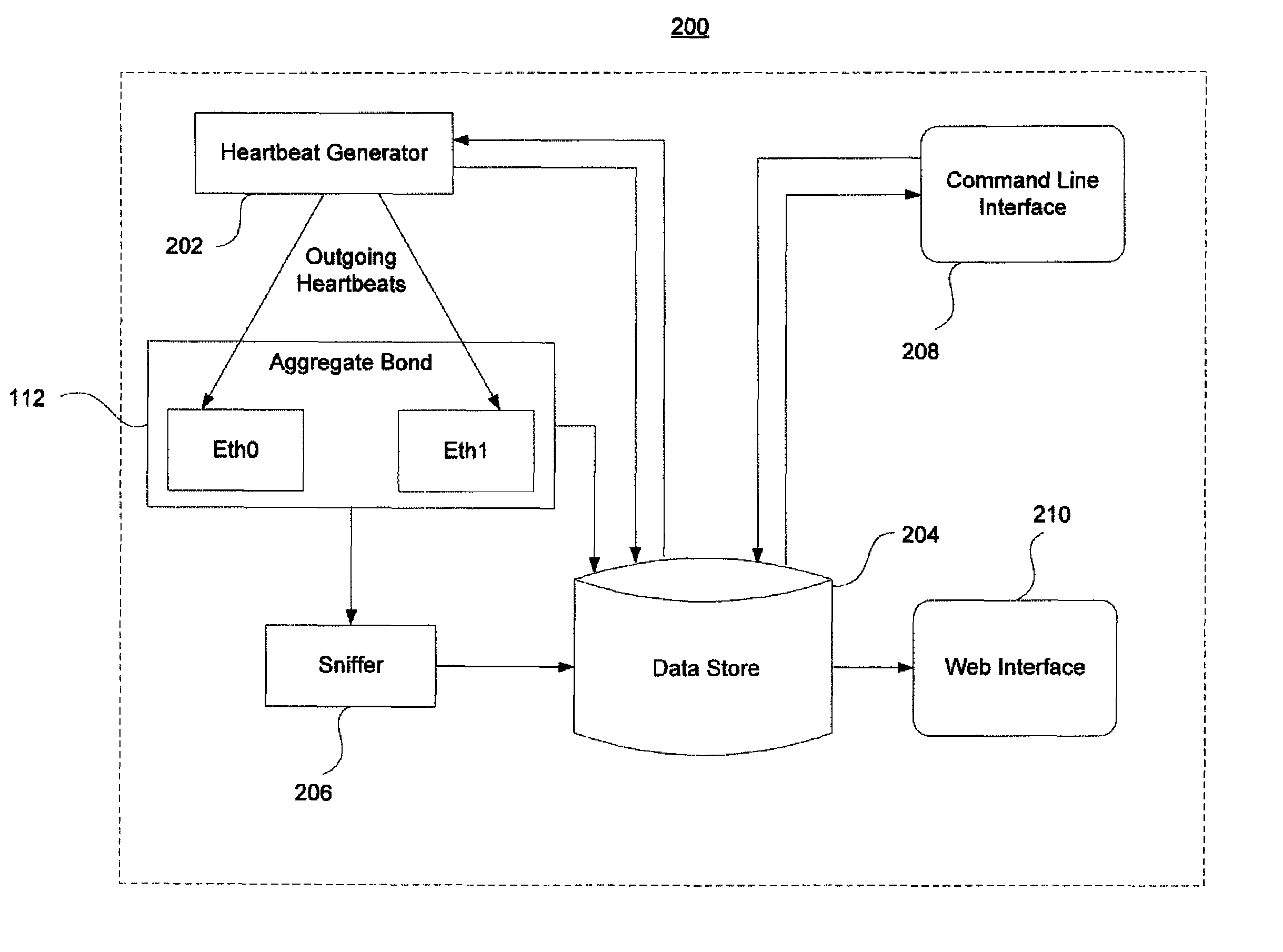
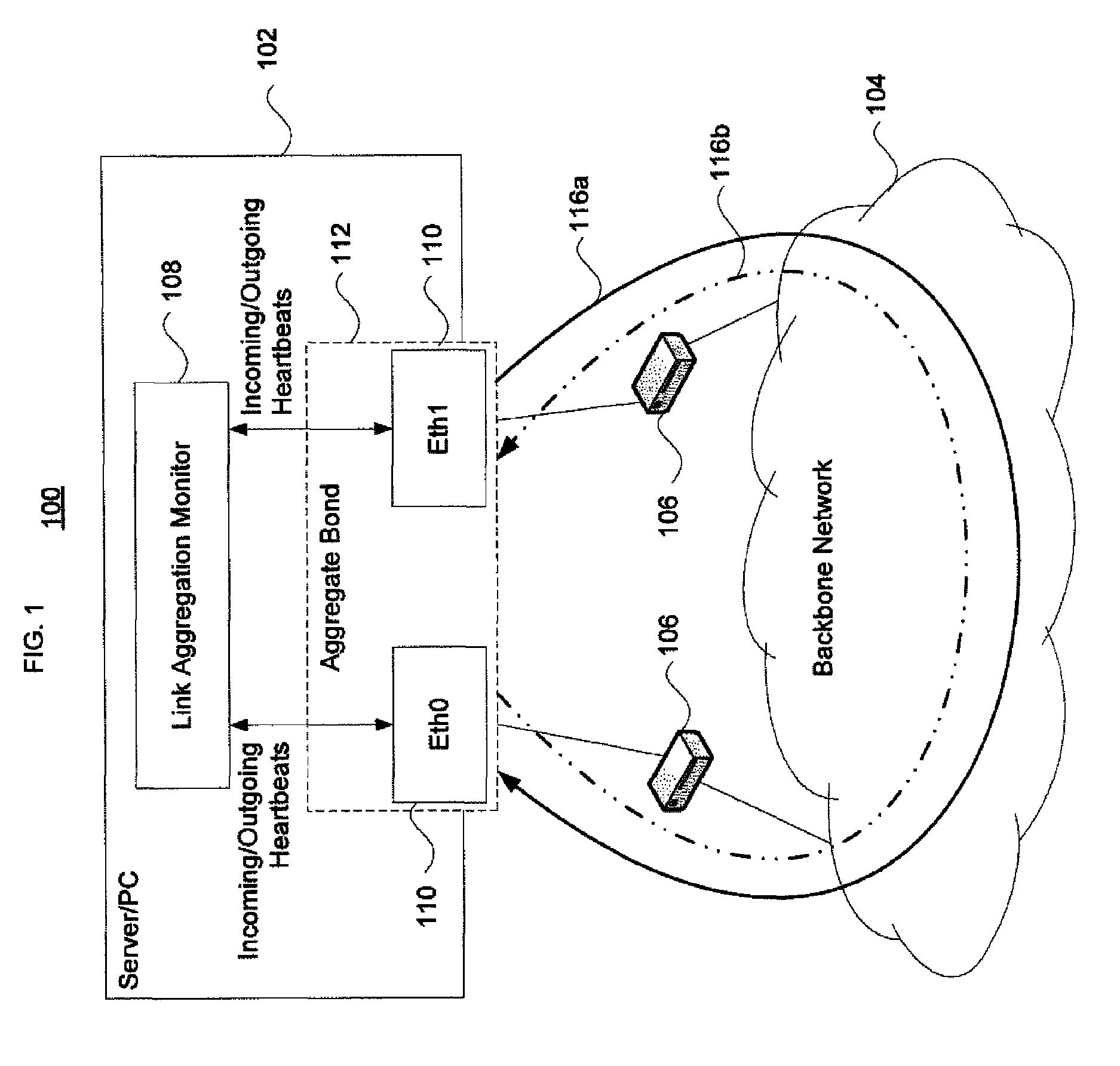
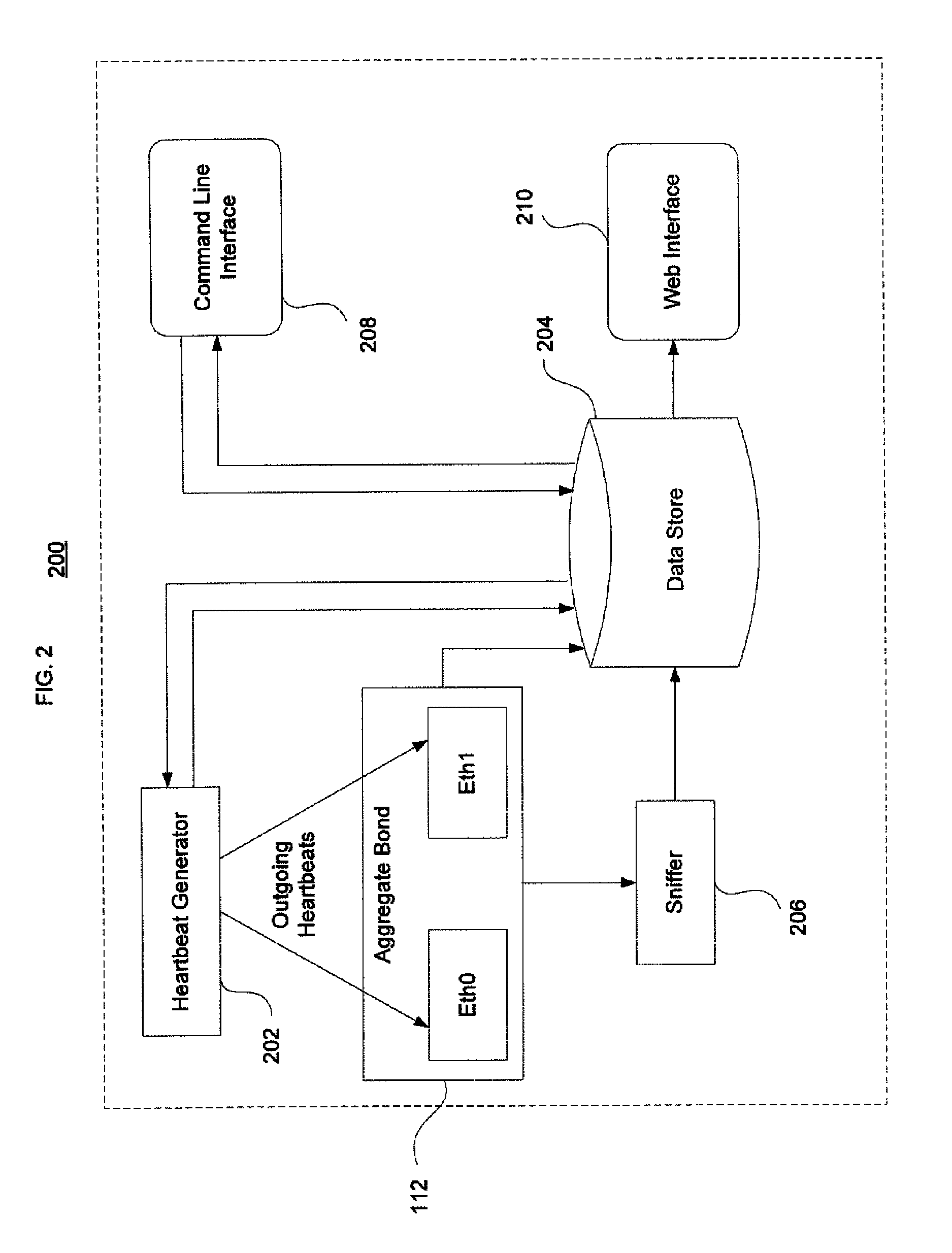
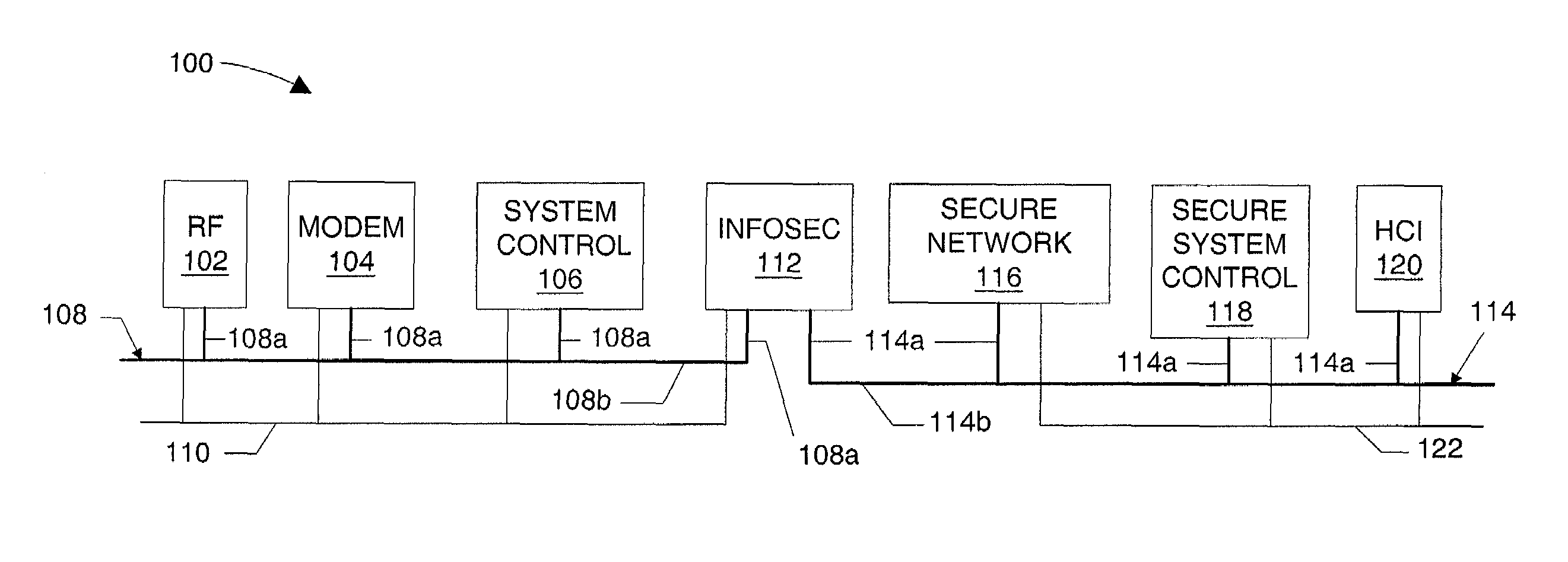
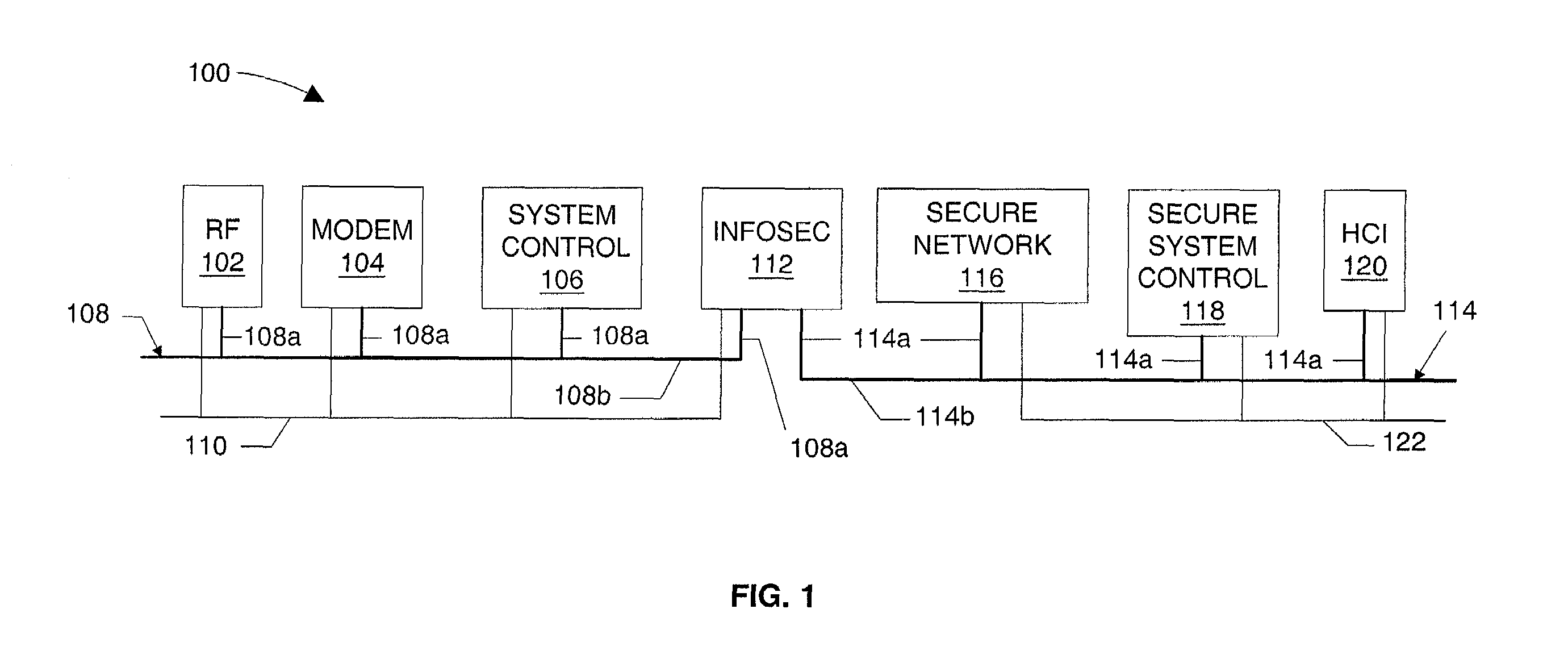
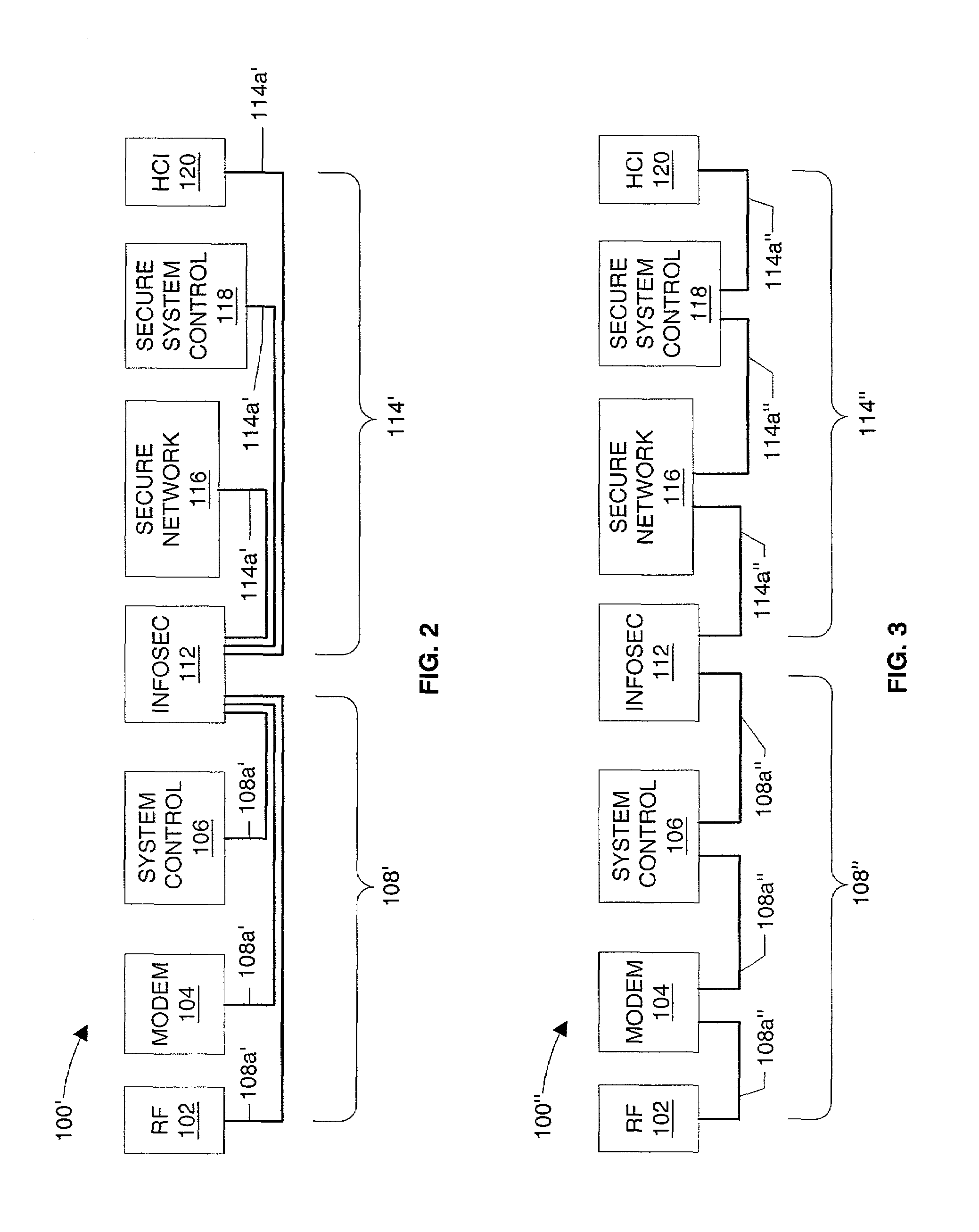
Interface monitoring for link aggregation
The present invention provides network interface monitoring and management that may be employed with link aggregation technologies. Multiple network interfaces may be aggregated into a single bond and data may be transferred to and from a backbone network via this aggregated bond. A link aggregation monitor employs a heartbeat generator, sniffer and data store to keep track of health and availability of network interfaces. The heartbeat generator sends heartbeats to the network interfaces, which pass the heartbeats around in a token ring configuration. If a network interface fails or otherwise goes offline, detection of this condition causes the monitor and heartbeat generator to prepare new or modified heartbeats so that data may be efficiently and accurately routed around the token ring and health of all remaining alive interfaces can be monitored properly. If a network interface re-enters or is added to the aggregate bond, new / modified heartbeats are then employed.
Owner:GOOGLE LLC
Inter-chip communication system
InactiveUS20050102125A1Decrease in performanceMultiple digital computer combinationsCAD circuit designData packCommunications system
Owner:CADENCE DESIGN SYST INC
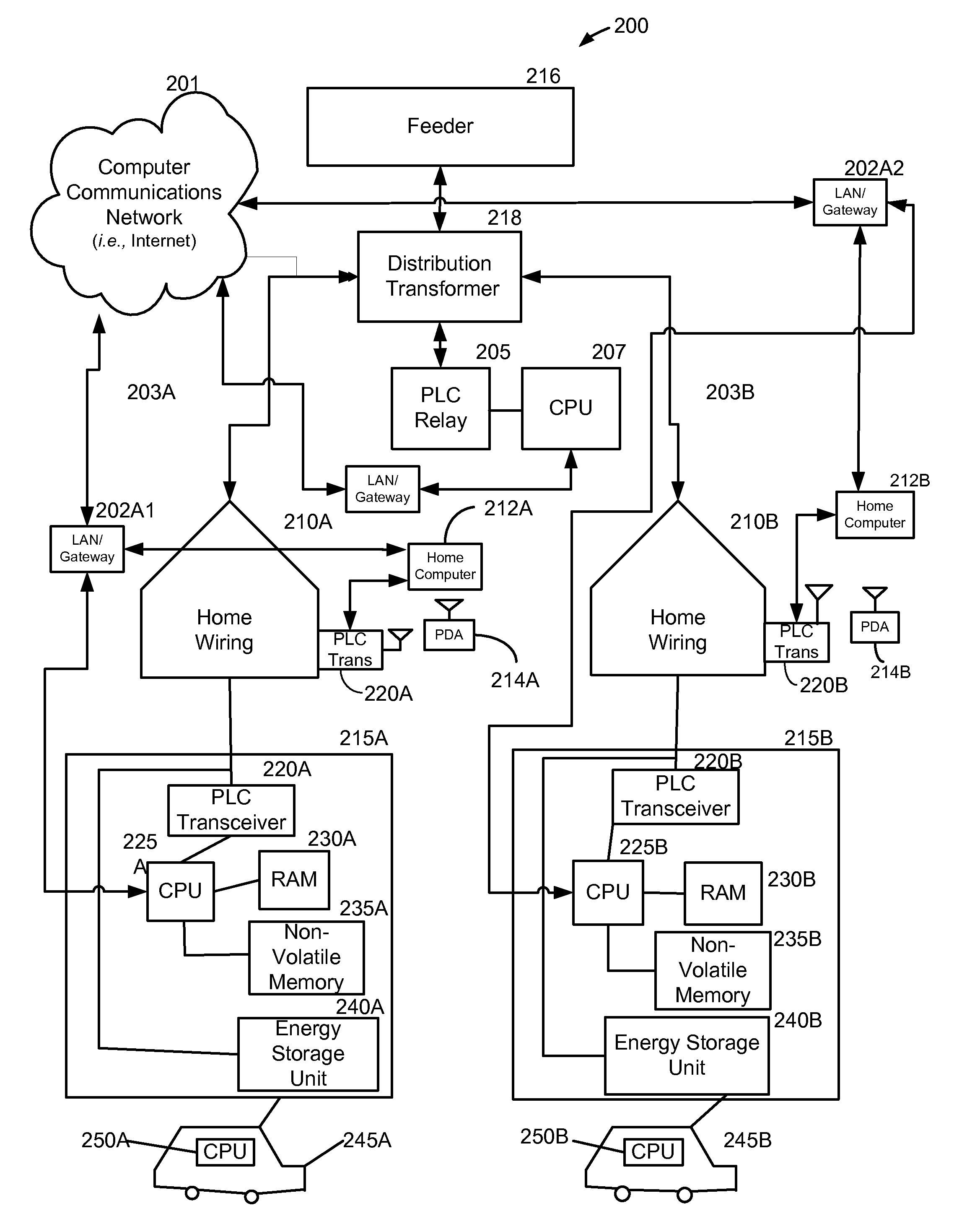
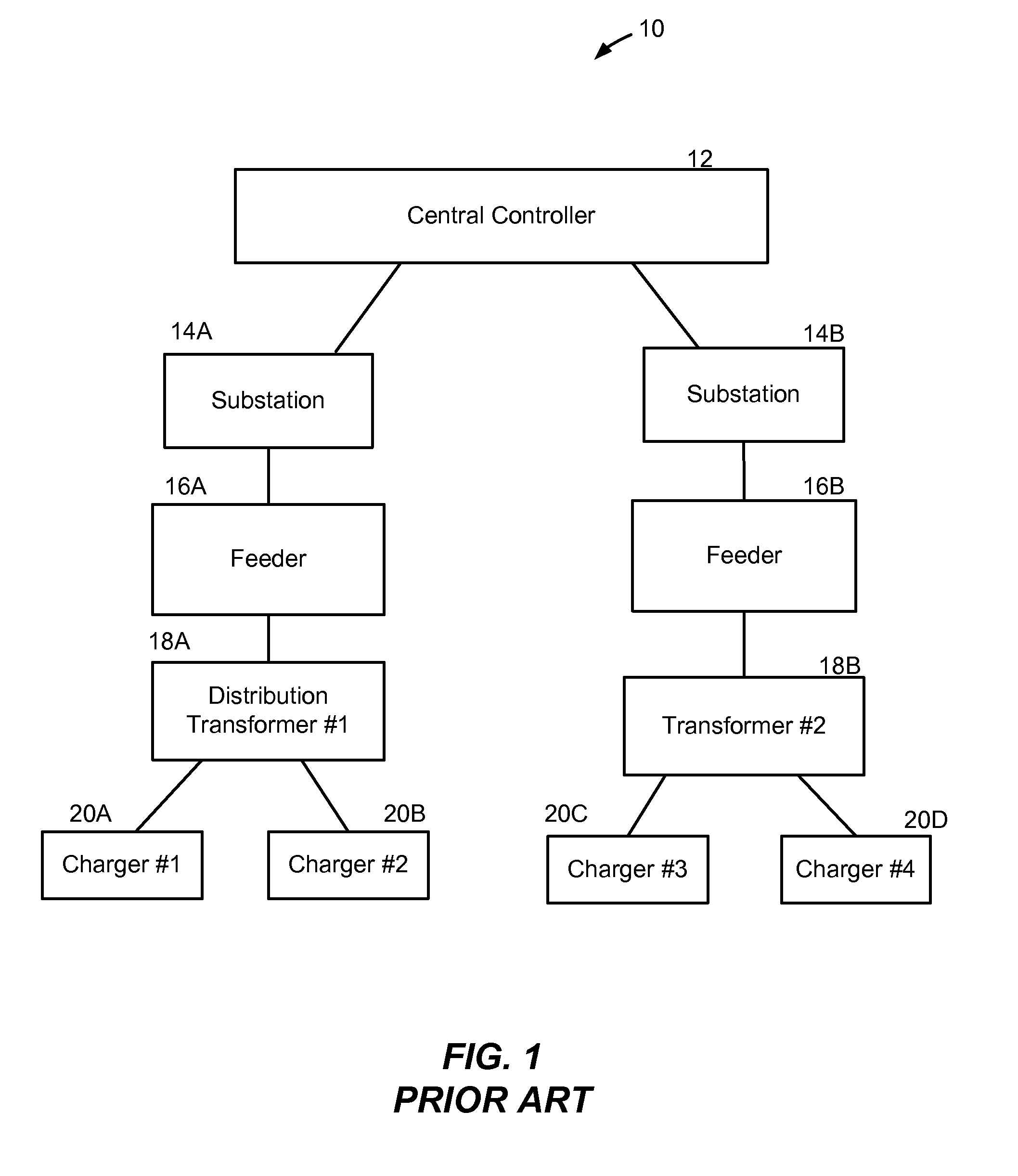
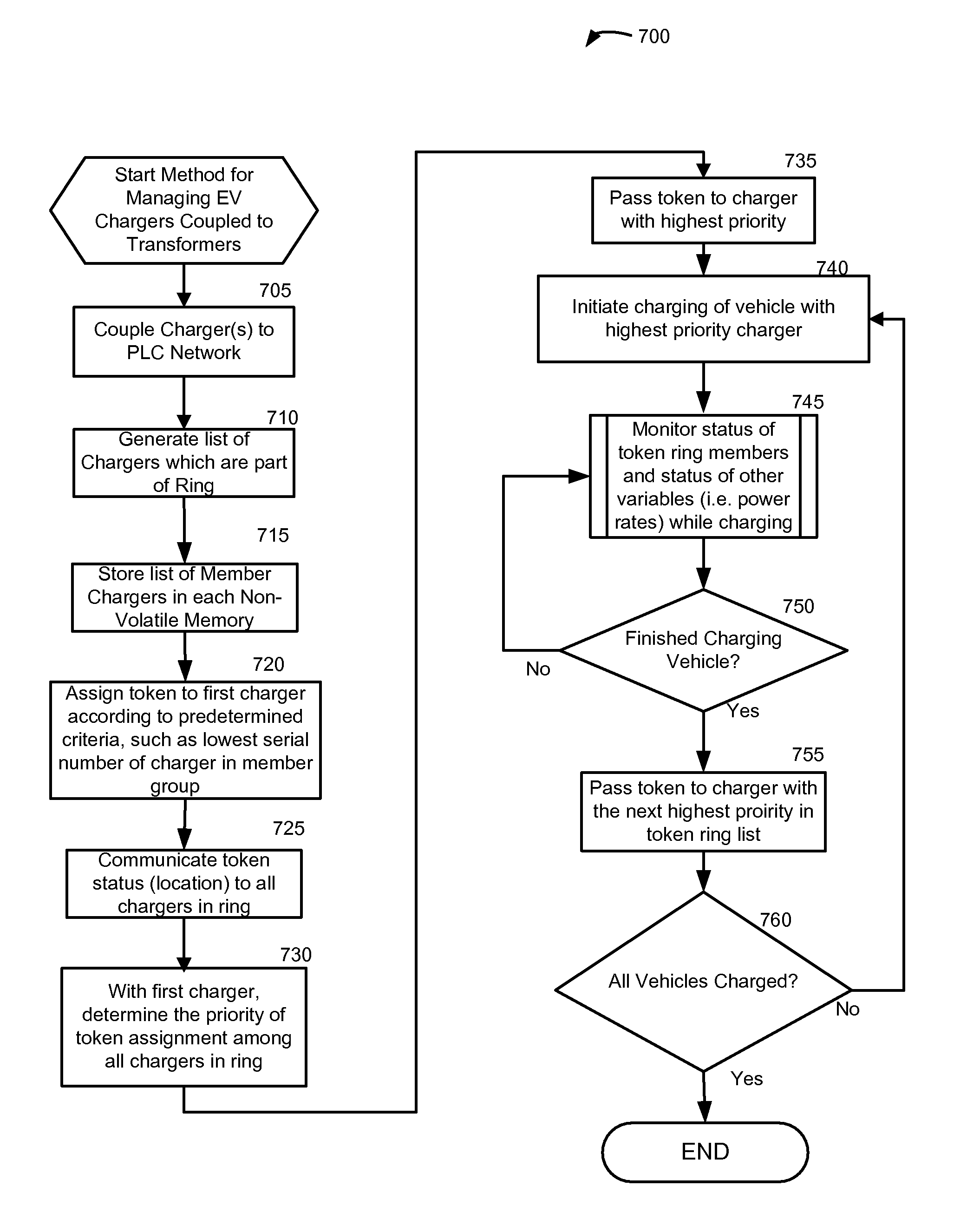
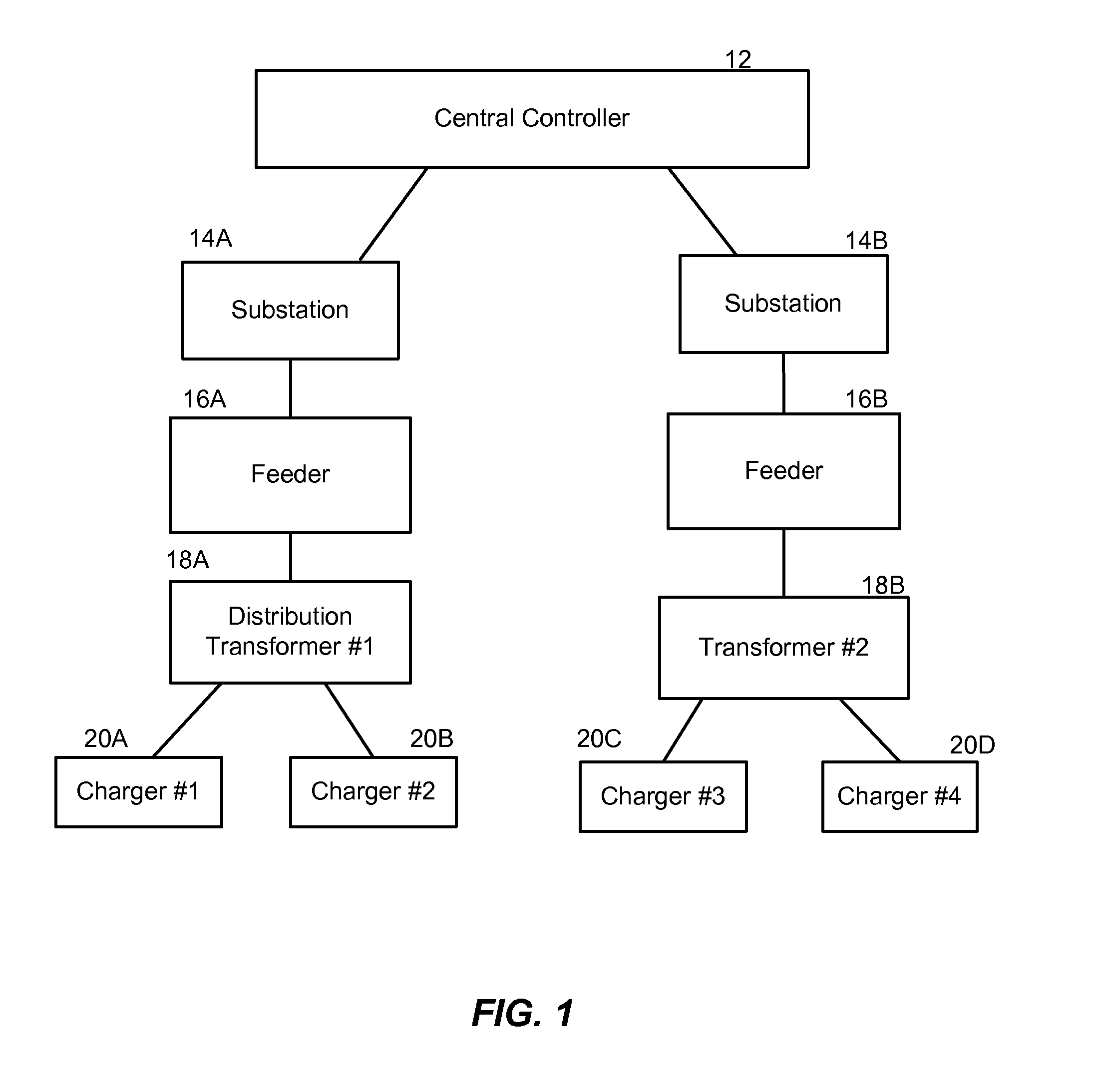
Method and system for co-operative charging of electric vehicles
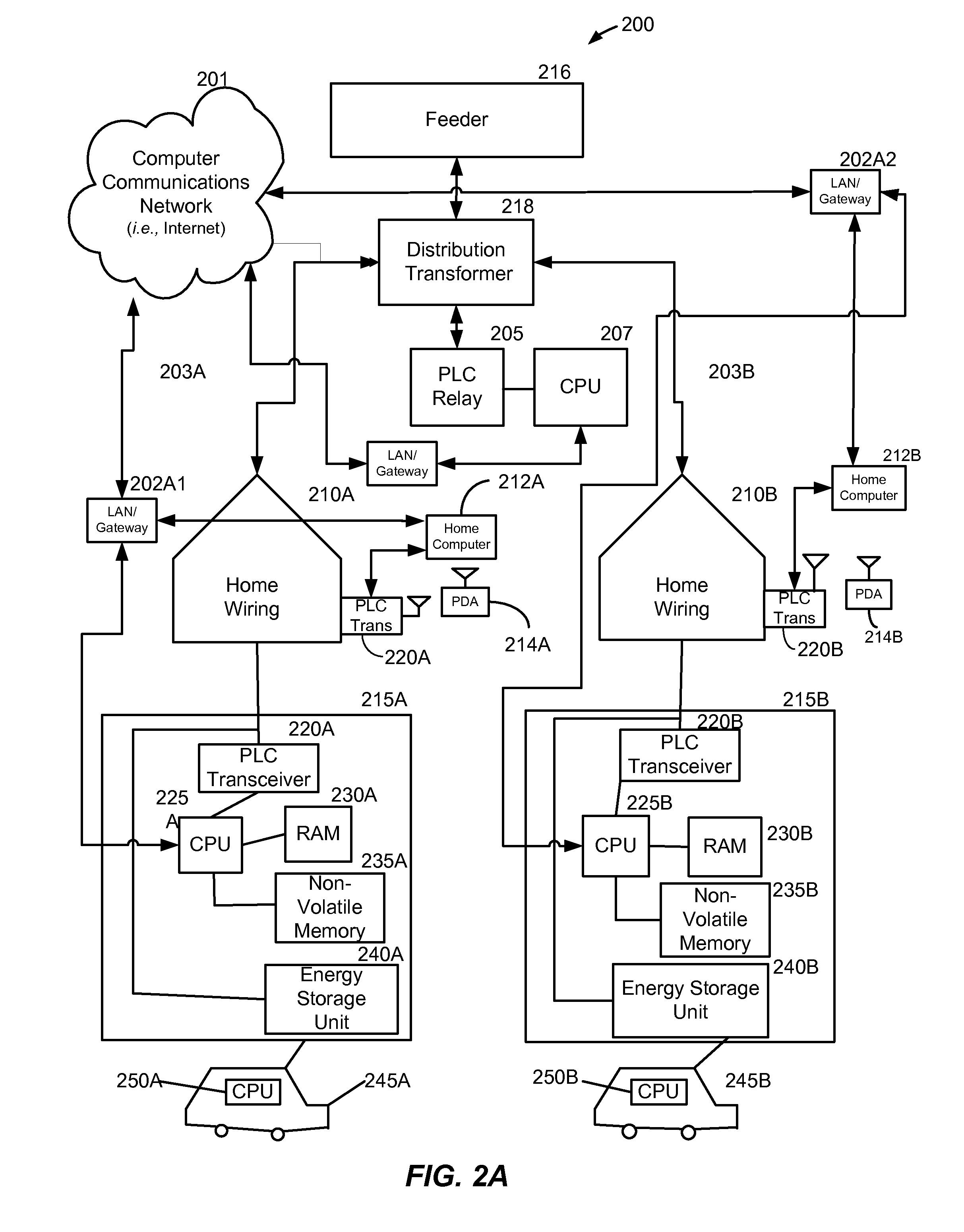
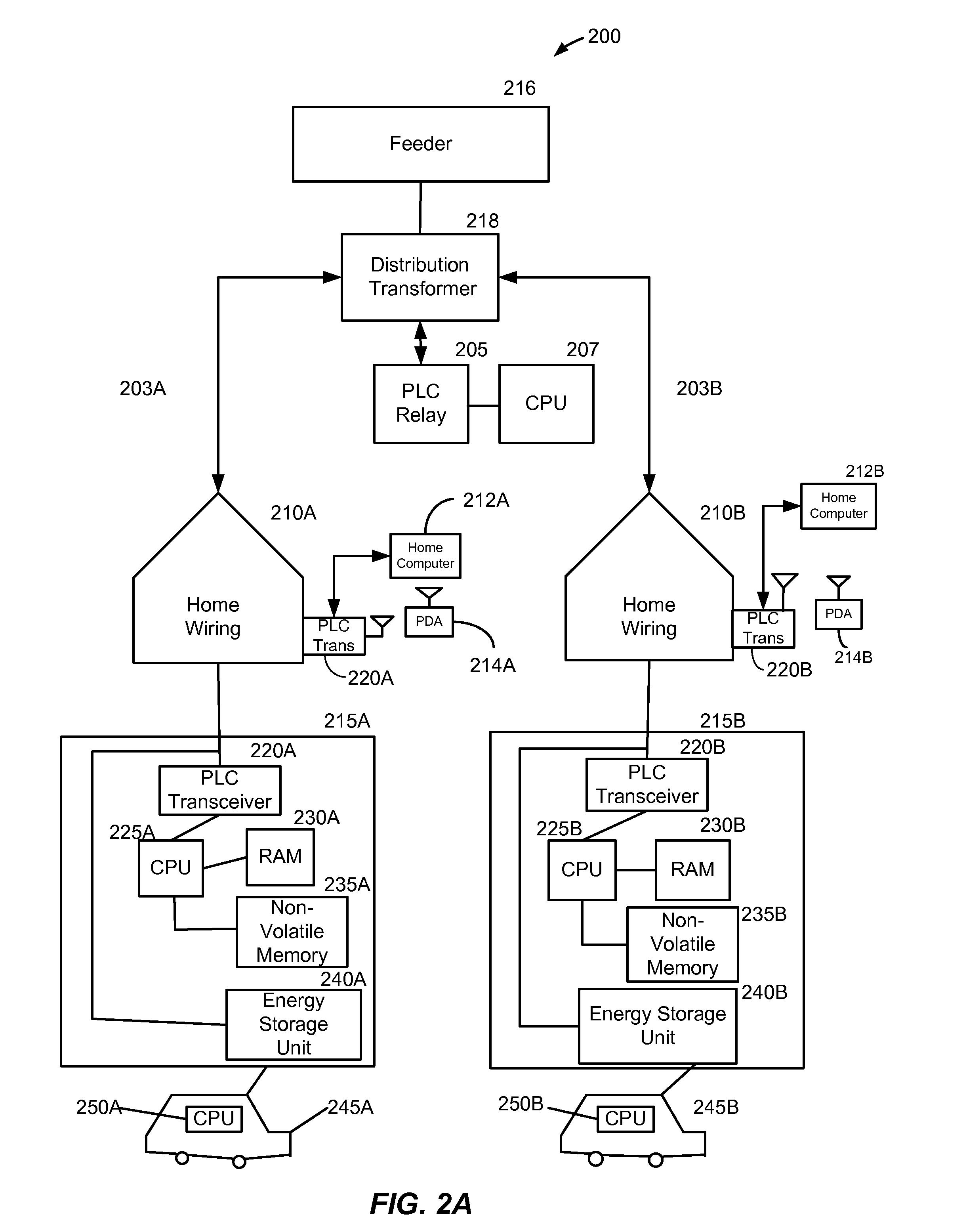
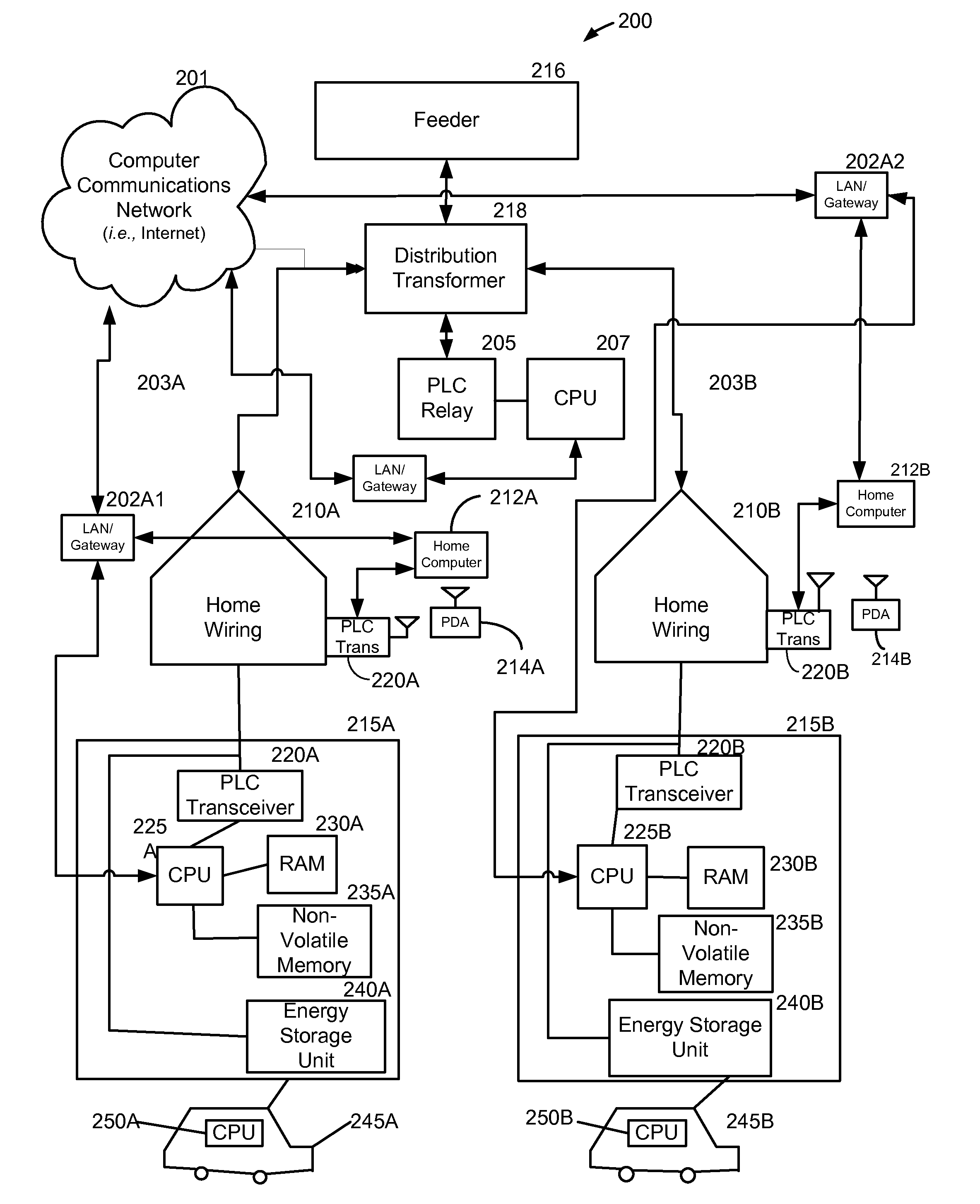
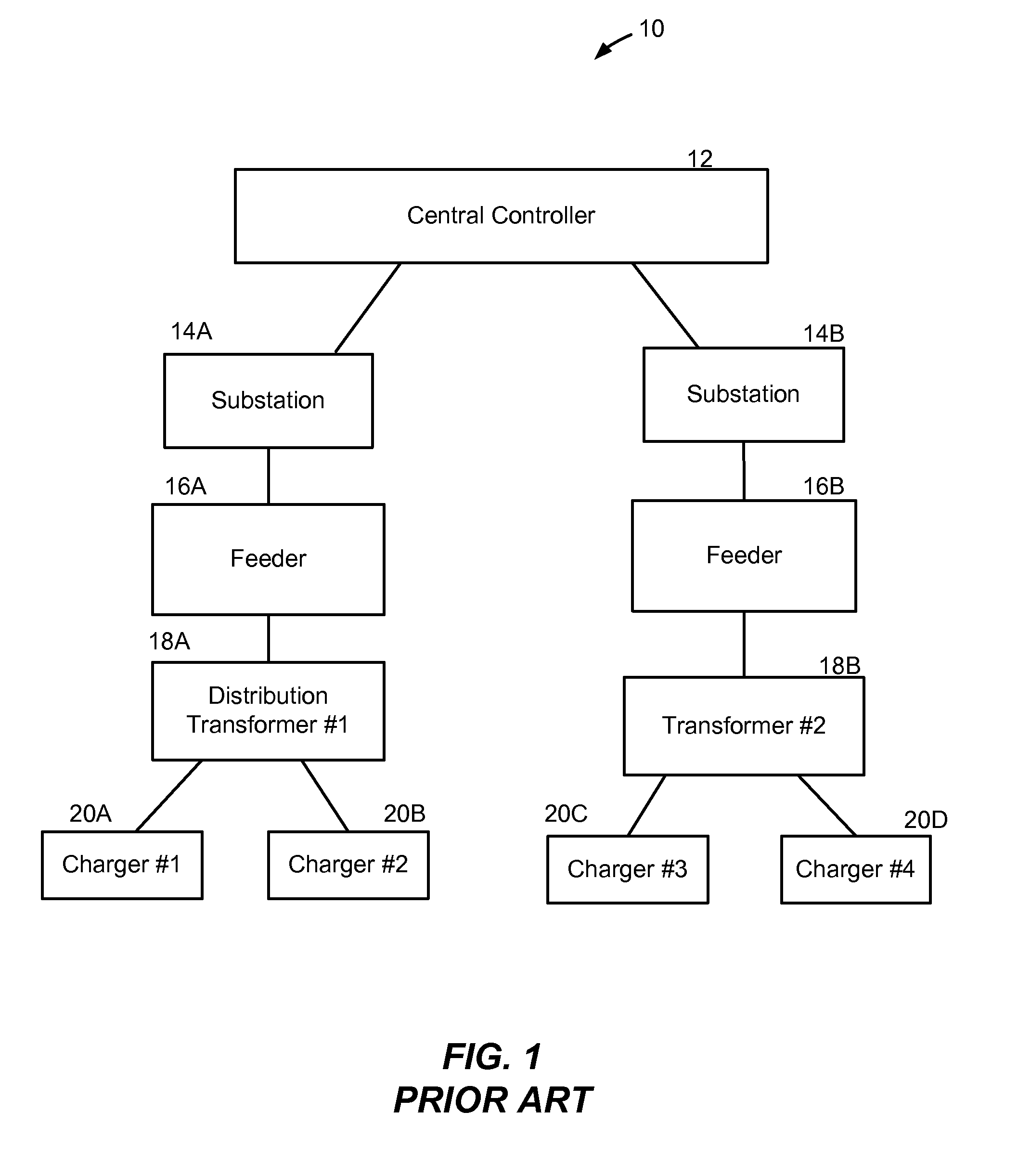
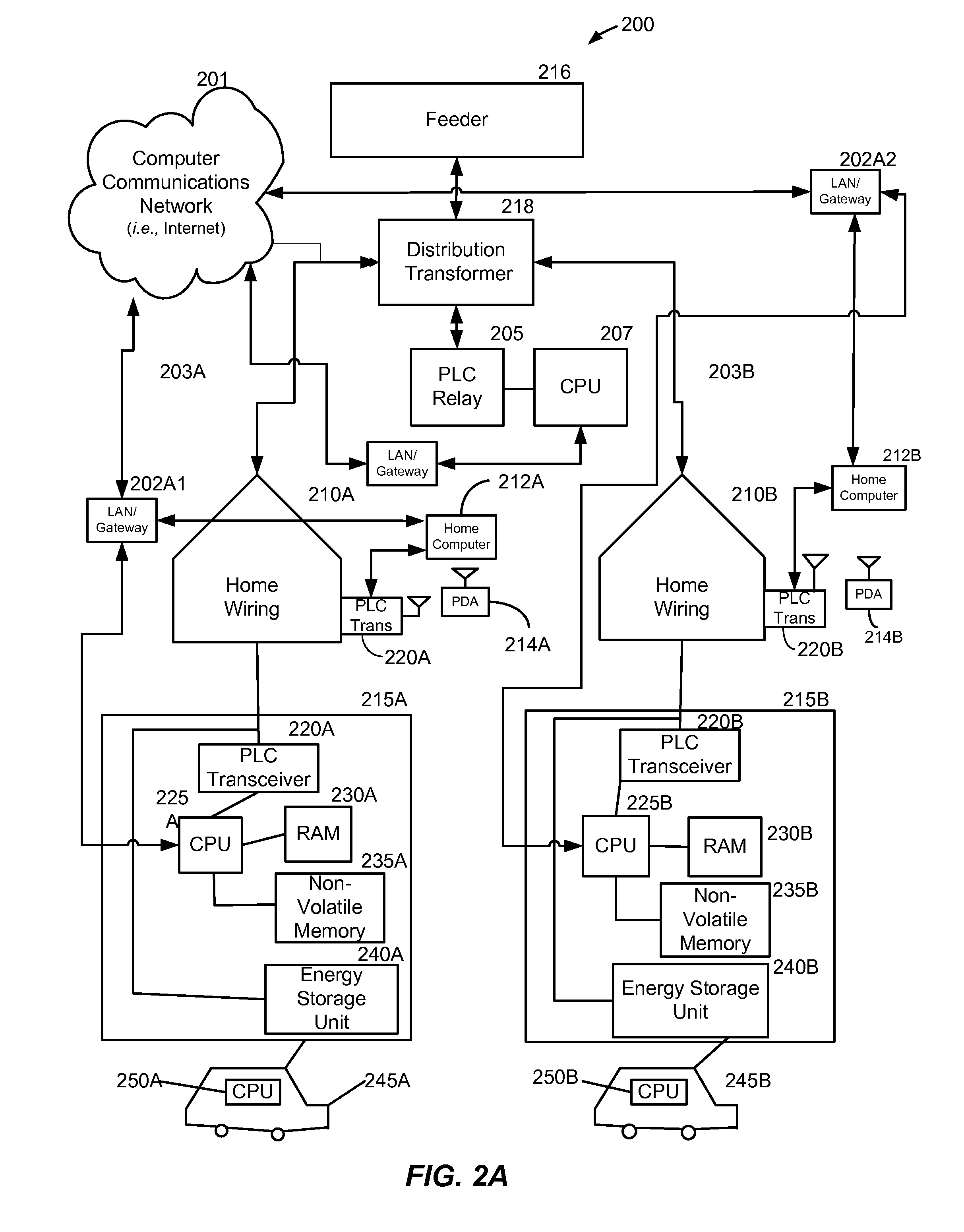
ActiveUS20110109266A1Possible failureDc source parallel operationPower to auxillary motorsDistribution transformerThe Internet
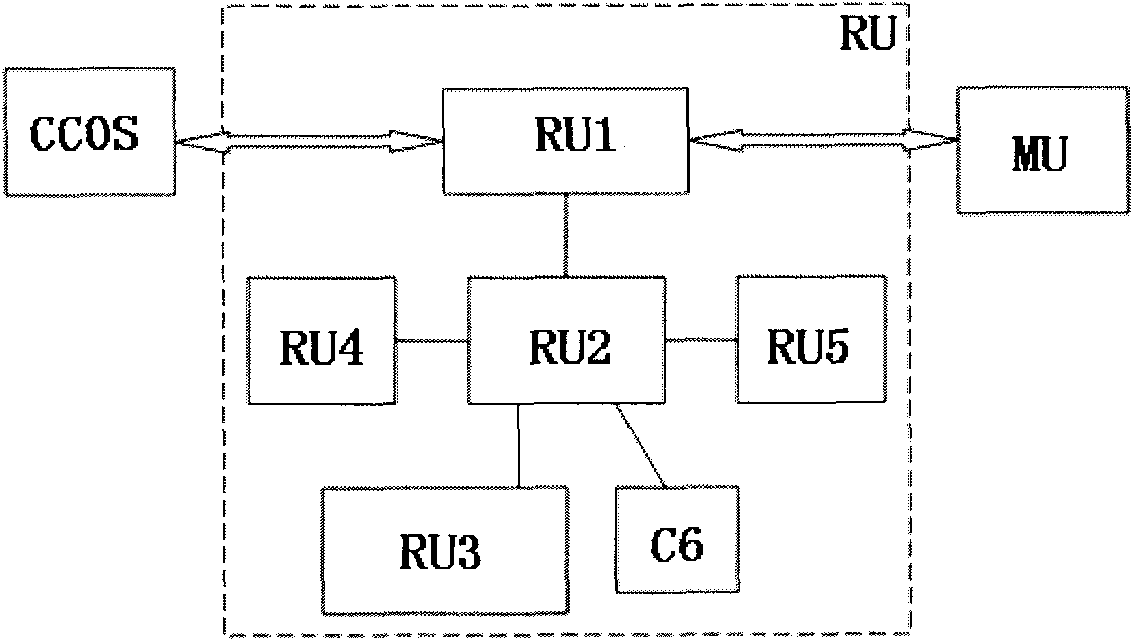
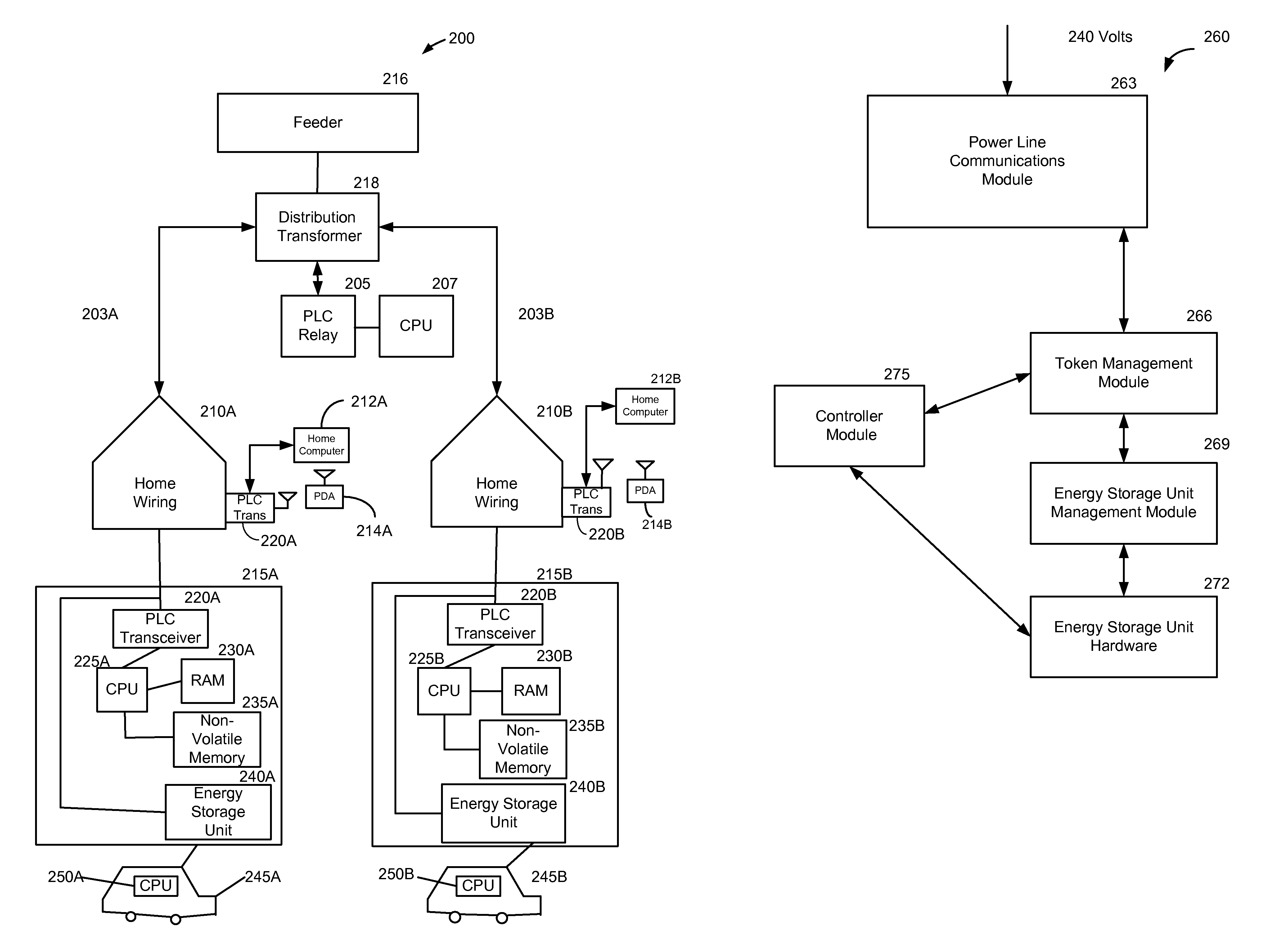
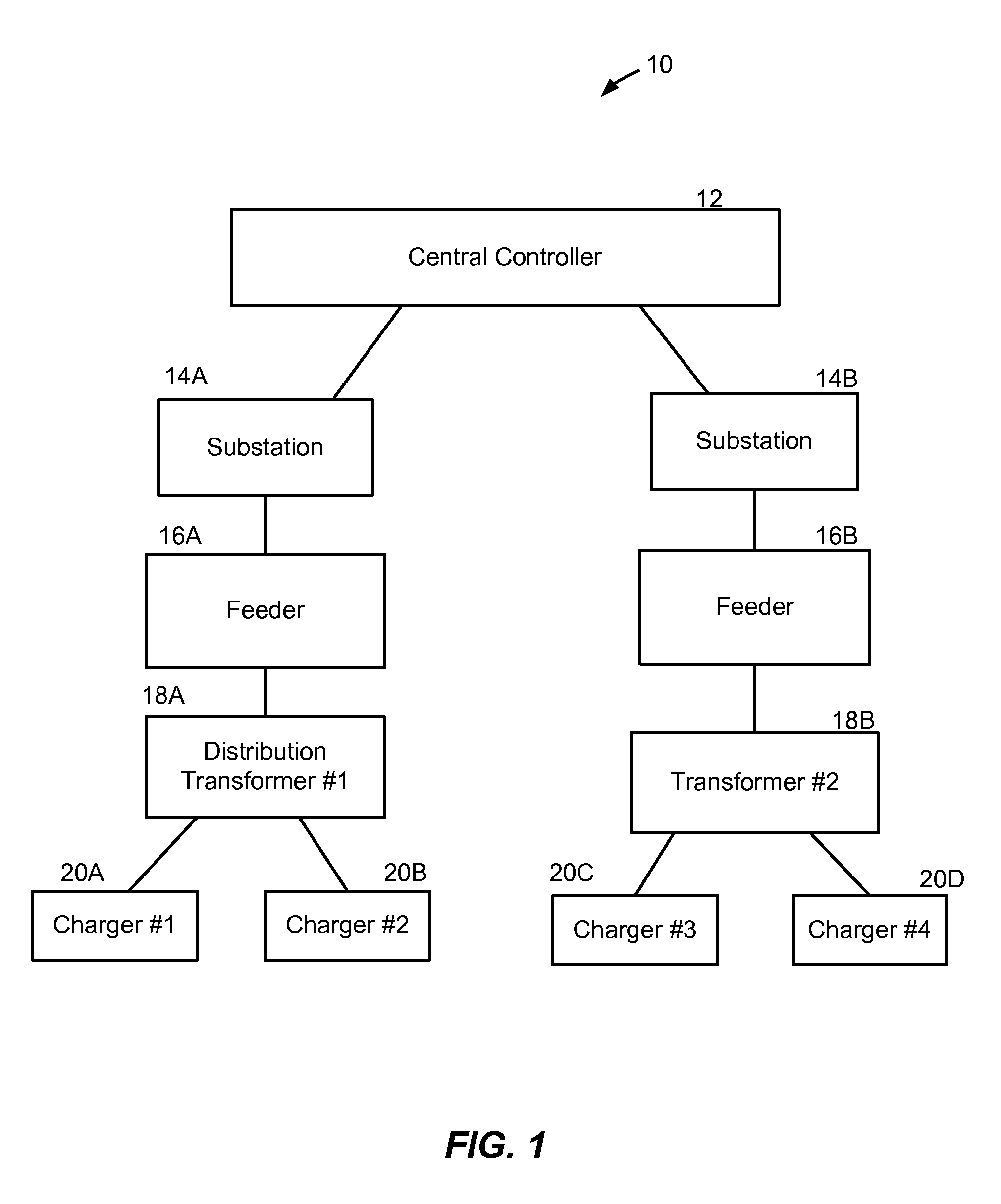
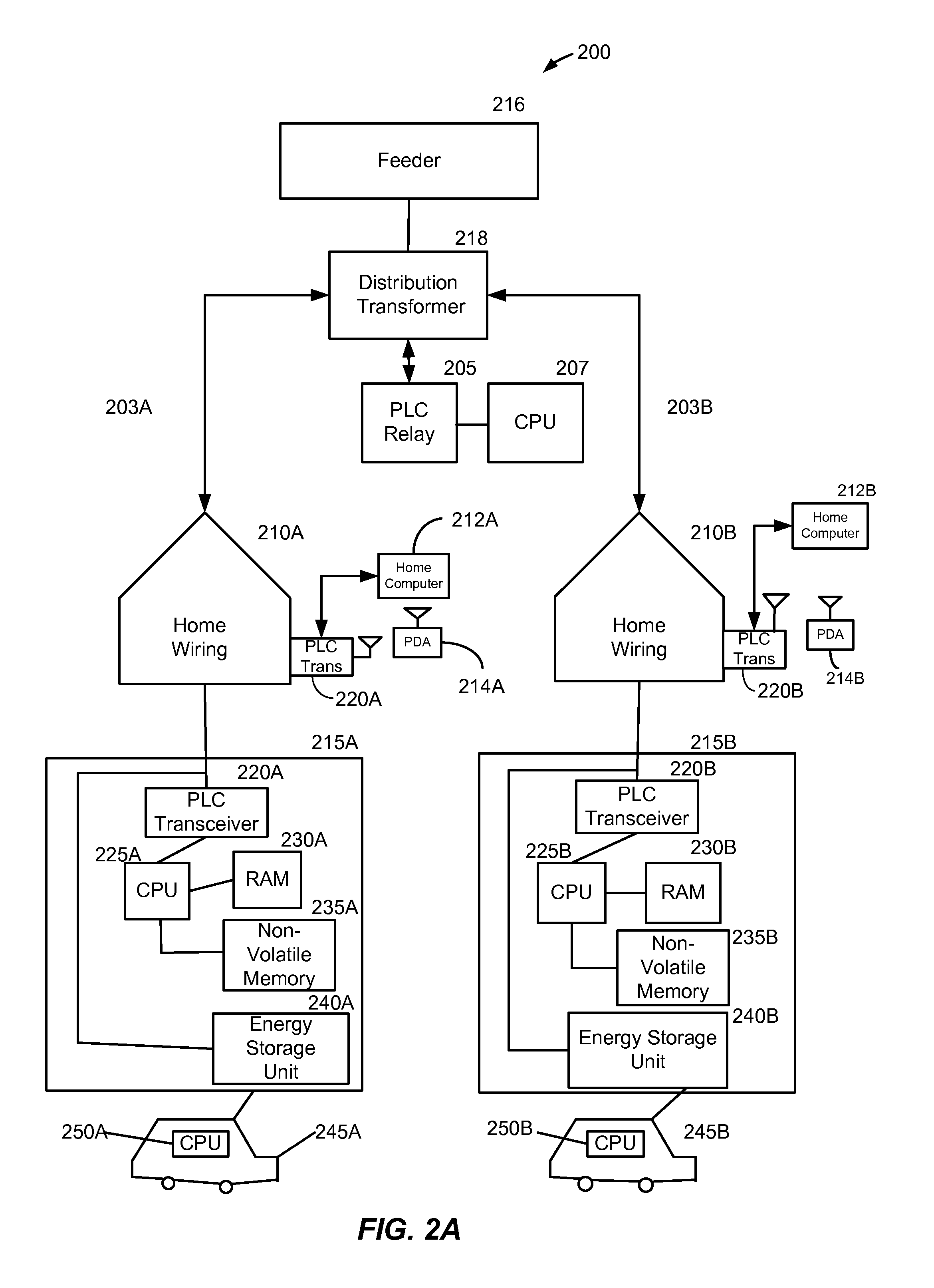
A method and system provide for the cooperative charging of electric vehicles. By using power line communications, chargers of the electric vehicles who are serviced by the same distribution transformer can form self-contained local area networks due to the nature of power line communications (PLCs). Alternatively, or in addition to the PLCs, other communication networks, such as the Internet and local area networks, may be used as part of the communications infrastructure for the chargers. After the chargers of the electric vehicles are coupled to one another through power line communications or traditional communications networks, they can form a logical token ring network. According to this token ring network, a predetermined number of tokens can be assigned within the token ring network for permitting chargers with tokens to charge respective electric vehicles while chargers without tokens must wait until they receive a token to initiate charging.
Owner:ITRON
Inter-chip communication system
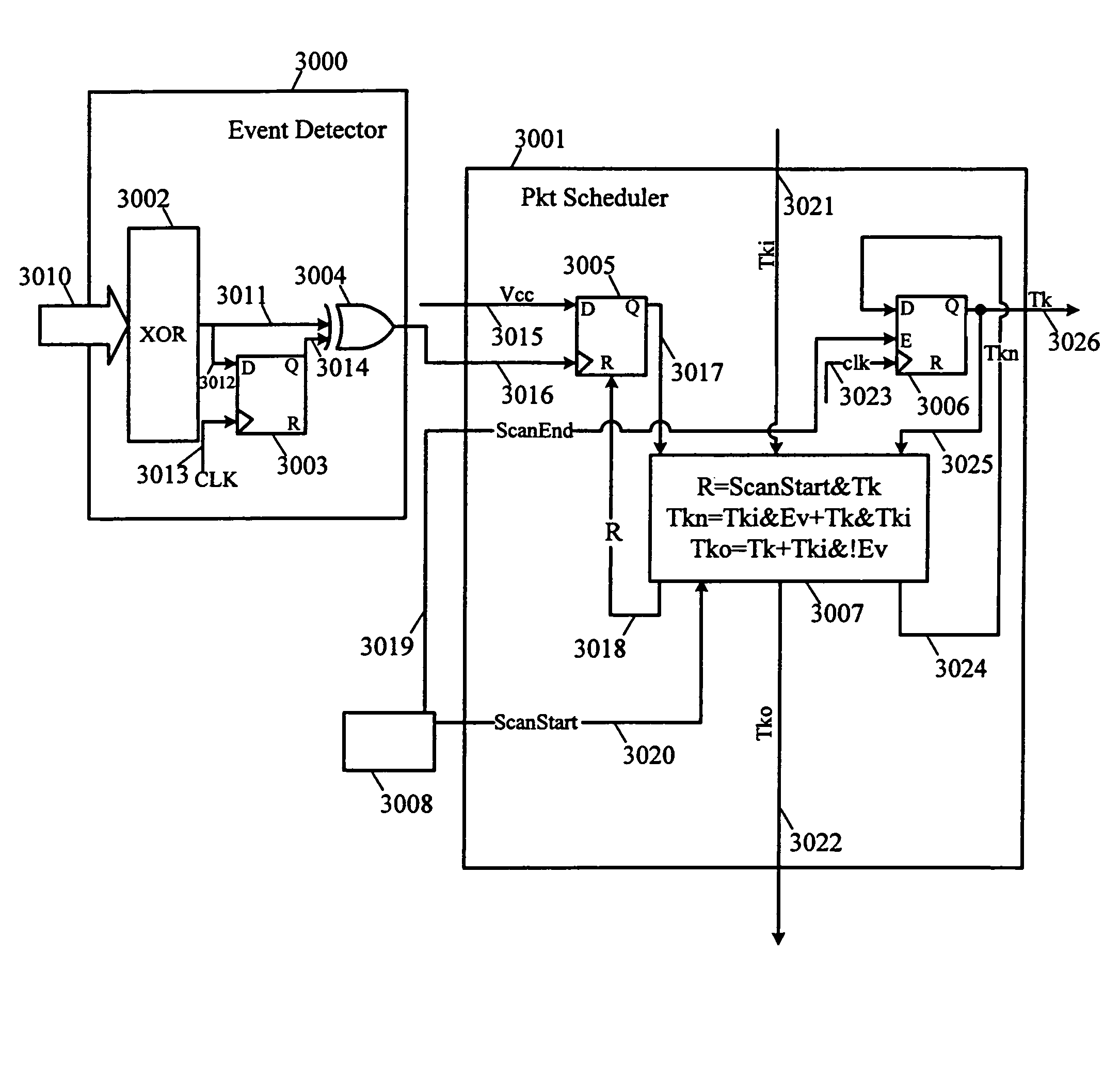
InactiveUS7512728B2Decrease in performanceMultiple digital computer combinationsCAD circuit designCommunications systemPacket scheduling
The complexity of user designs, the limited capacity of FPGA chips, and the limited number of chip pinouts have resulted in the development of inter-chip communication technology that necessitates the transfer of a large amount of data across a limited number of pins in the shortest amount of time. The inter-chip communication system transfers signals across FPGA chip boundaries only when these signals change values. Thus, no cycles are wasted and every event signal has a fair chance of achieving communication across chip boundaries. The inter-chip communication system includes a series of event detectors that detect changes in signal values and packet schedulers which can then schedule the transfer of these changed signal values to another designated chip. Working with a plurality of signal groups that represents signals at the separated connections, the event detector detects events (or changes in signal values). When an event has been detected, the event detector alerts the packet scheduler. The packet scheduler employs a token ring scheme as follows. When the packet scheduler receives a token and detects an event, the packet scheduler “grabs” the token and schedules the transmission of this packet in the next packet cycle. If, however, the packet scheduler receives the token but does not detect an event, it will pass the token to the next packet scheduler. At the end of each packet cycle, the packet scheduler that grabbed the token will pass the token to the next logic associated with another packet.
Owner:CADENCE DESIGN SYST INC
Method and system for improving high speed internetwork data transfers
InactiveUS6631137B1Improving high speed traffic operationHigh speed data transmissionNetworks interconnectionSecuring communicationVirtual LANIp address
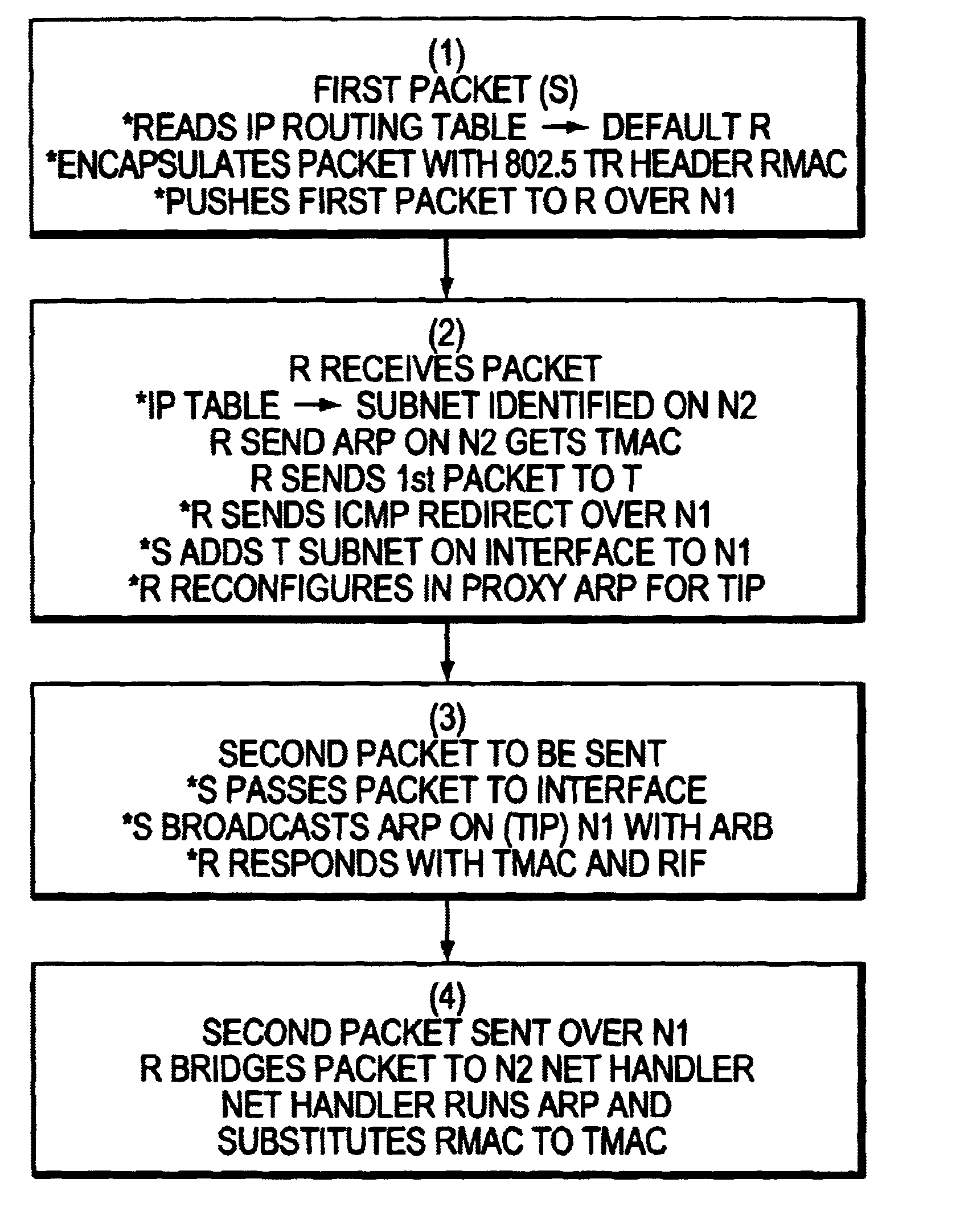
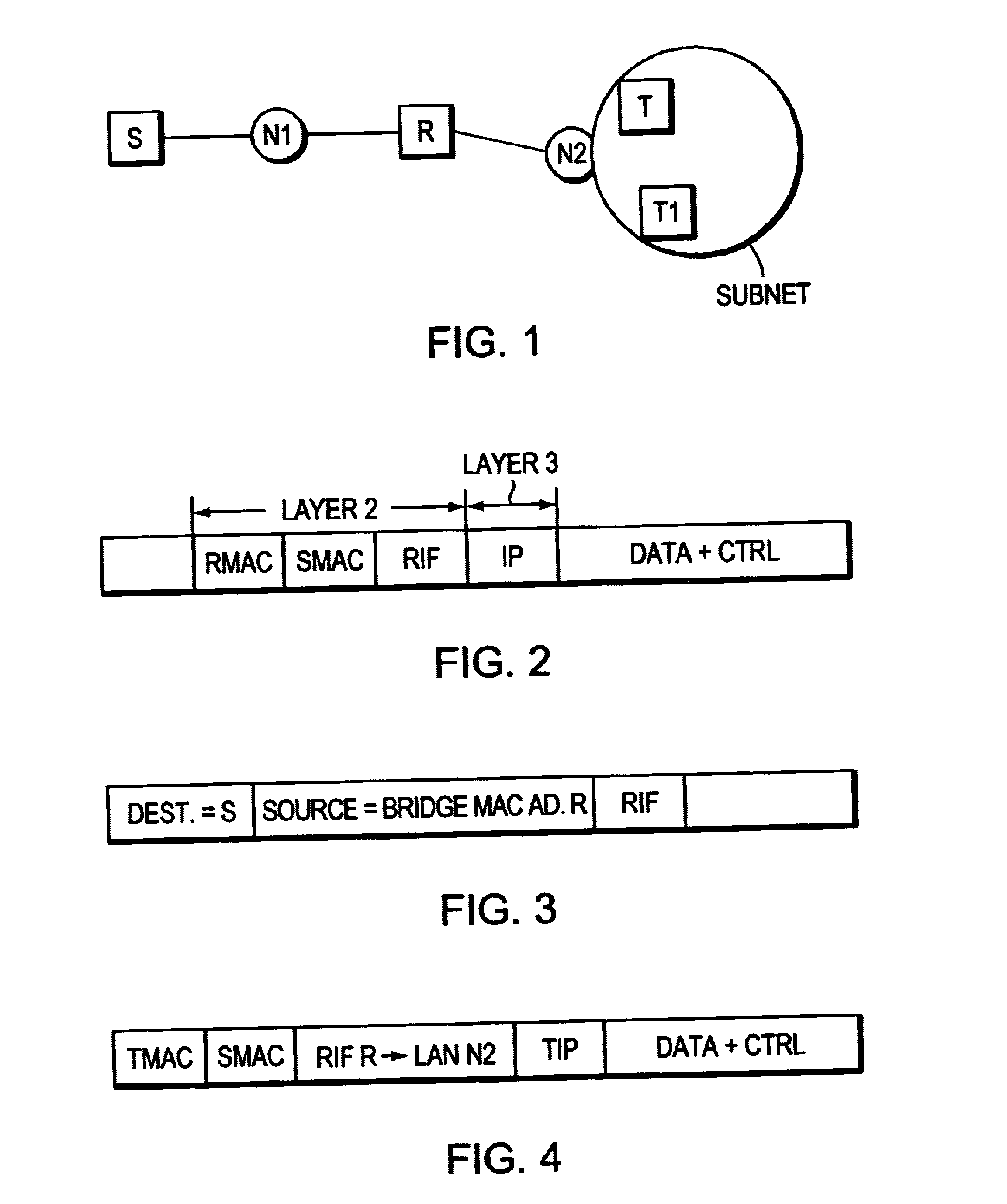
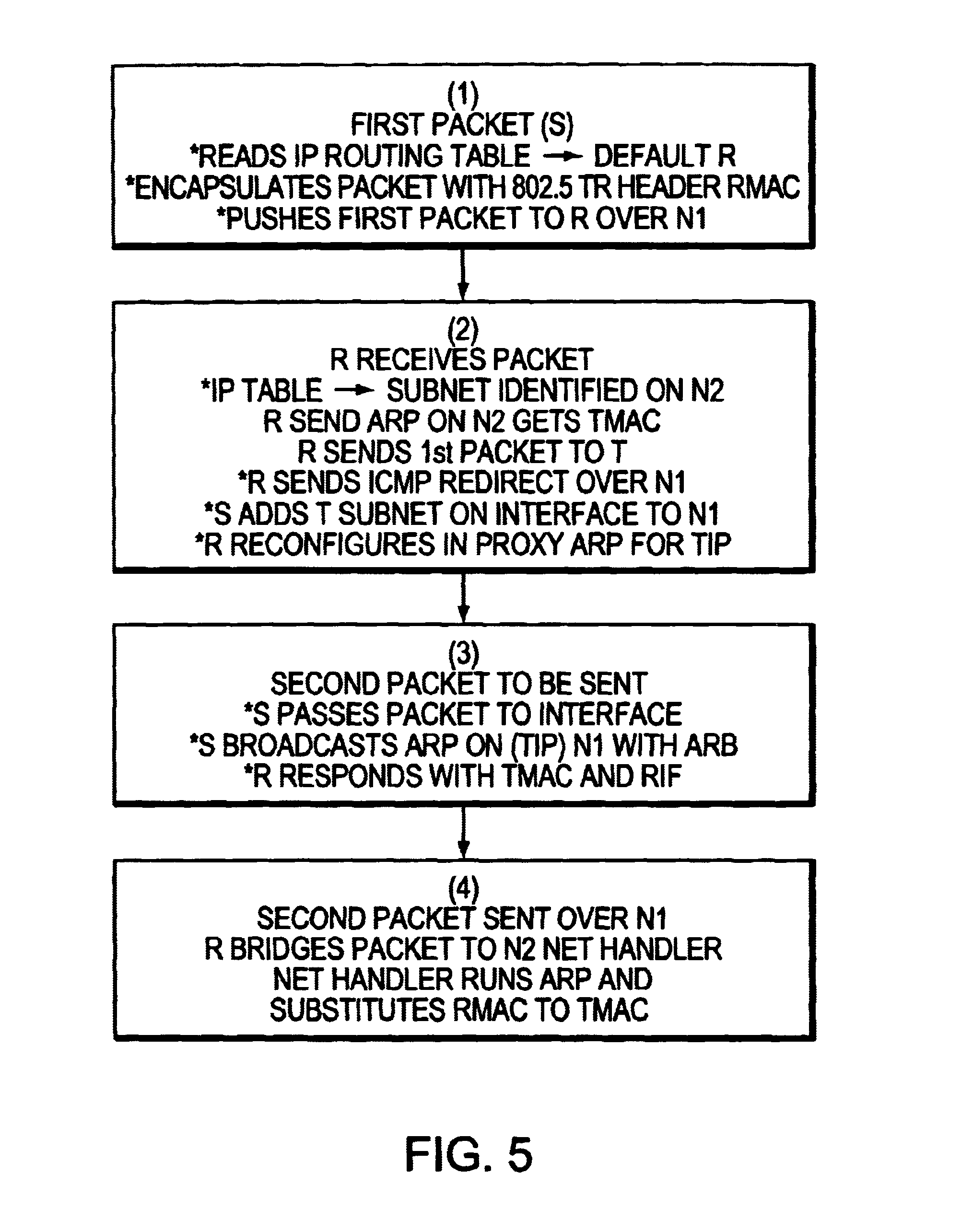
A method for creating a single virtual LAN including a source (S) attached to a first Token ring LAN (N1), a target (T) within a subnet attached to a different Token ring LAN (N2), and an interconnecting router (R). The source (S) encapsulates the first packet with a Token ring header including the router MAC address (RMAC), SMAC as source MAC address as layer 2 information, and IP address of T (TIP) as layer 3 data and sends this packet over N1 toward the router. When receiving the first packet, R reads its IP table for best match with TIP address to identify the subnet including T. The net handler runs an ARP protocol to identify TMAC address, substitutes the MAC header with said TMAC address into said first packet destination MAC address field and forwards said first packet over N2. R then sends a conventional ICMP message over N1 limited broadcast and reconfigures itself in proxy ARP for the defined subnet. For the second packet, S runs an ARP and R answers with RMAC address and the RIF data to be used for next packets.
Owner:CISCO TECH INC
Real time control of hardware and software via communications network
InactiveUS20050125150A1Eliminate the effects ofProgramme controlProgramme-controlled manipulatorTime delaysGlobal Positioning System
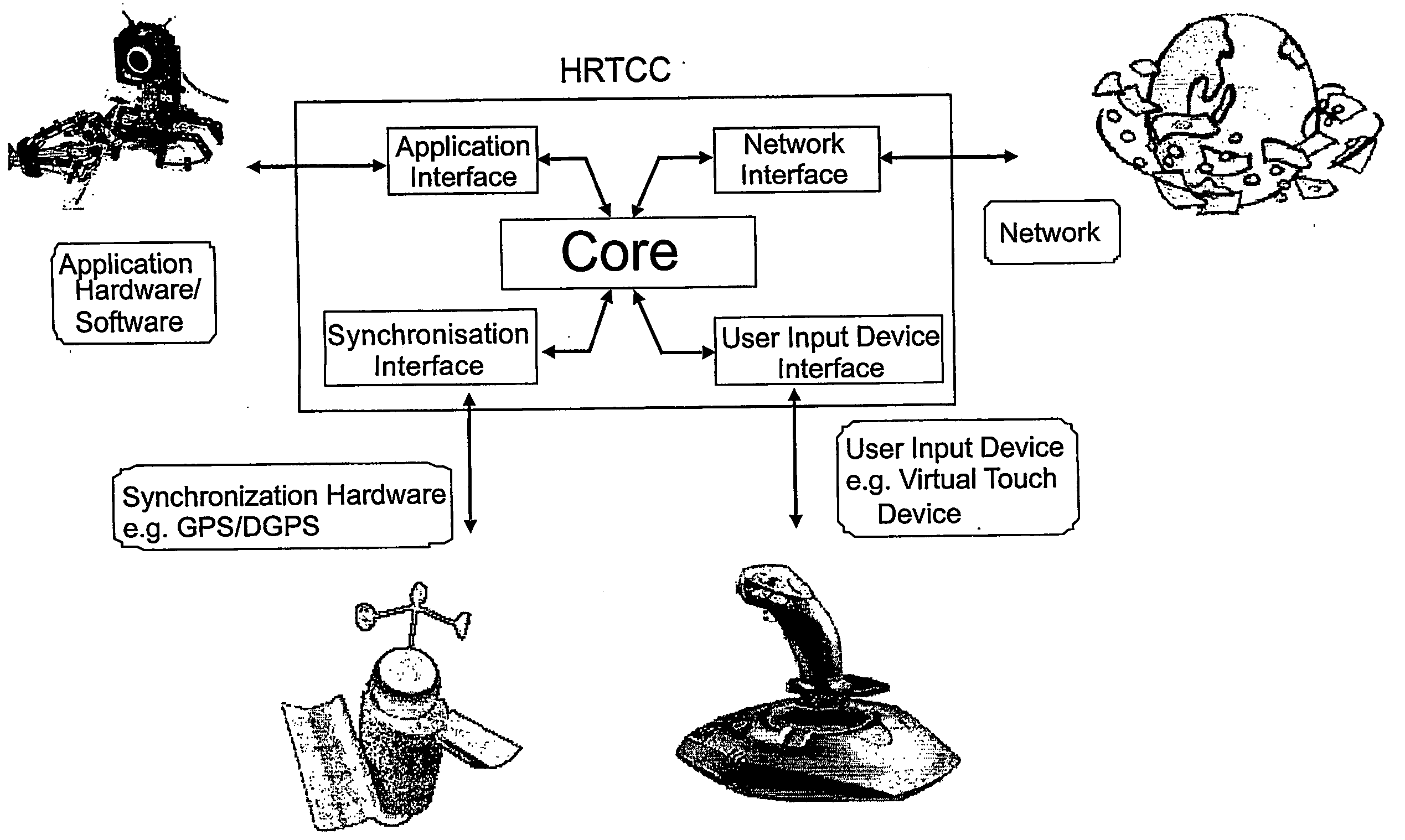
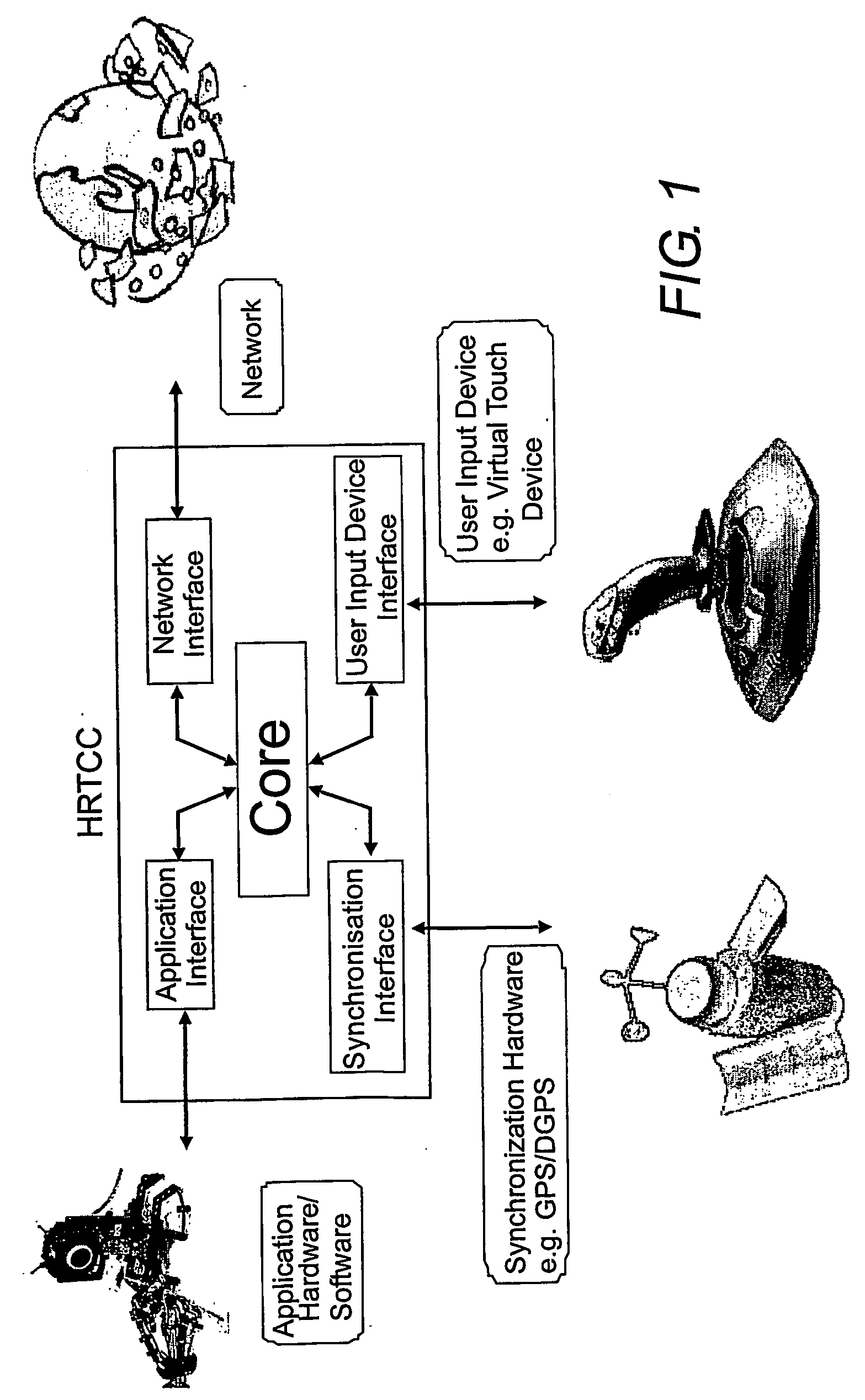
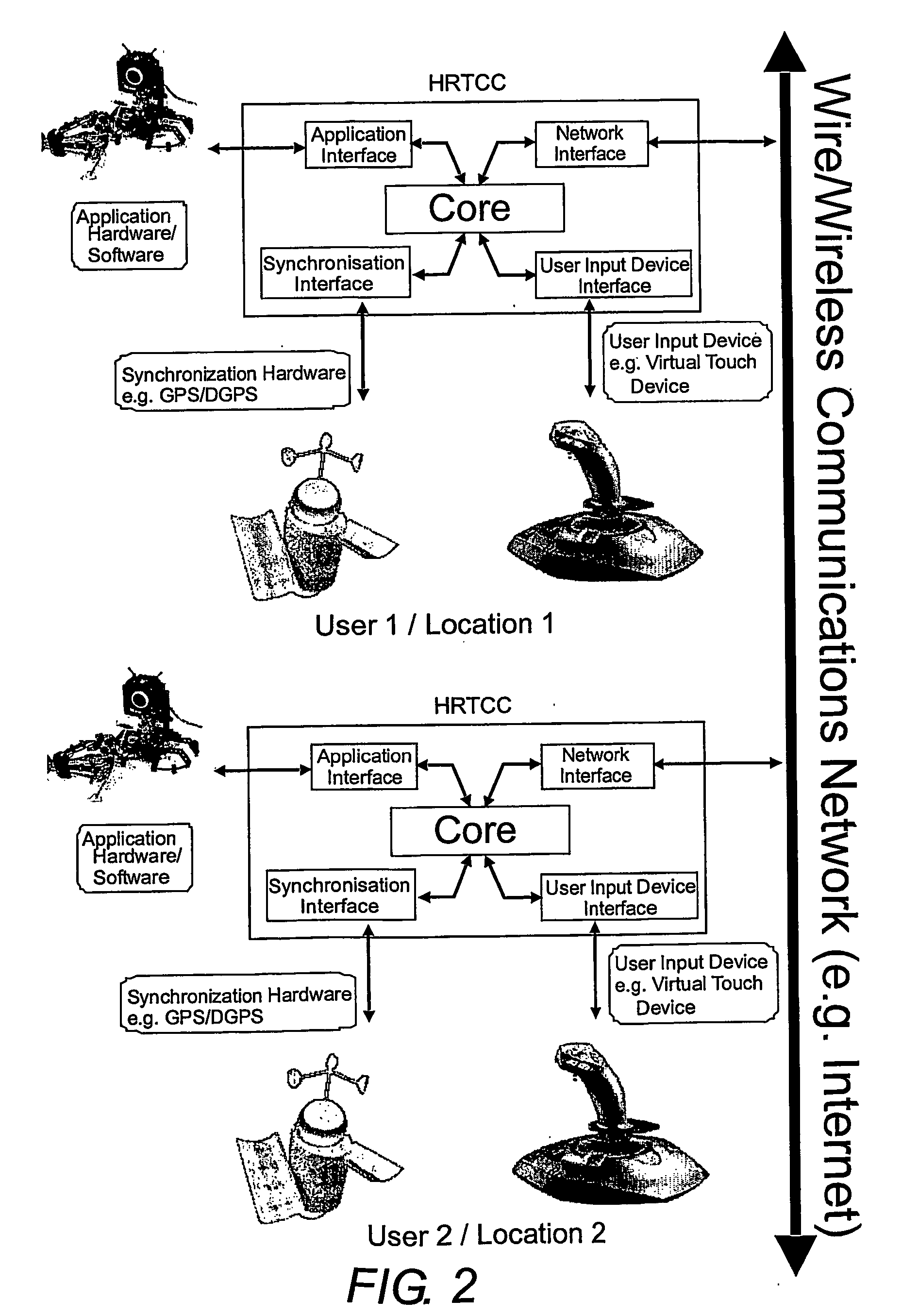
A Hard Real Time Control Center (HRTCC), comprised of hardware, software and firmware, with time synchronisation and time delay compensation methodologies that allows Application Hardware and / or User Input Devices to be networked together on any communications network as if there were negligible network delays in the system, is disclosed. This will allow Application Hardware and / or User Input Devices (connected to an HRTCC at one location (node) on the network) to control or operate Application Hardware and / or User Input Devices connected to another HRTCC at a remote location without the detrimental effects of network time delays. The time synchronisation of the various HRTCCs on the network can be enabled using hardware (e.g. a global positioning system (GPS)) or any other software method (e.g. Network Time Protocol). Using time stamps from the time synchronisation, the time delay of the signals (data) transferred over the network can be determined. The main embodiment of the time delay compensation methodology is an estimator / predictor algorithm. The estimator generates signal information that allows the predictor, using the time delay, to project the signal information characteristics into the future by an amount equal to the time delay. If this predicted signal is used rather than the delayed signal, there will be no readily apparent time delay in the system thereby significantly improving the stability and performance of the associated application. Any software architecture can be used such as servant-client, token ring or peer to peer.
Owner:HANDSHAKE VR
Method and system for co-operative charging of electric vehicles
ActiveUS8106627B1Possible failureElectric signal transmission systemsCharging stationsDistribution transformerEngineering
A method and system provide for the cooperative charging of electric vehicles. By using power line communications, chargers of the electric vehicles who are serviced by the same distribution transformer can form self-contained local area networks due to the nature of power line communications. After the chargers of the electric vehicles are coupled to one another through power line communications, they can form a token ring network. According to this token ring network, a predetermined number of tokens can be assigned within the token ring network for permitting chargers with tokens to charge respective electric vehicles while chargers without tokens must wait until they receive a token to initiate charging.
Owner:ITRON
Token ring network topology discovery and display
InactiveUS6483812B1Efficient collectionReduce network trafficError preventionTransmission systemsInterconnect topologyData transmission
A method and system for determining the topology of a communications network that utilizes routing information fields contained within transmission frames for controlling routine transmissions. First, a plurality of transmission frames associated with routine data transmissions are collected. Next, a plurality of routing information fields are extracted from the plurality of transmission frames. Thereafter, the plurality of routing information frames are analyzed and parsed, thereby yielding interconnected topology data. Finally, the interconnected topology data from the plurality of routing information fields is converted and stored into programming language data objects, such that the data objects may thereafter be utilized to display the interconnected topology of the communications network.
Owner:IBM CORP
Method and apparatus for performing frame processing for a network
InactiveUS20020010793A1Easy to handleError preventionFrequency-division multiplex detailsMedia access controlProgrammable hardware
An improved frame processing apparatus for a network that supports high speed frame processing is disclosed. The frame processing apparatus uses a combination of fixed hardware and programmable hardware to implement network processing, including frame processing and media access control (MAC) processing. Although generally applicable to frame processing for networks, the improved frame processing apparatus is particular suited for token-ring networks and ethernet networks. The invention can be implemented in numerous ways, including as an apparatus, an integrated circuit and network equipment.
Owner:AVAYA MANAGEMENT LP
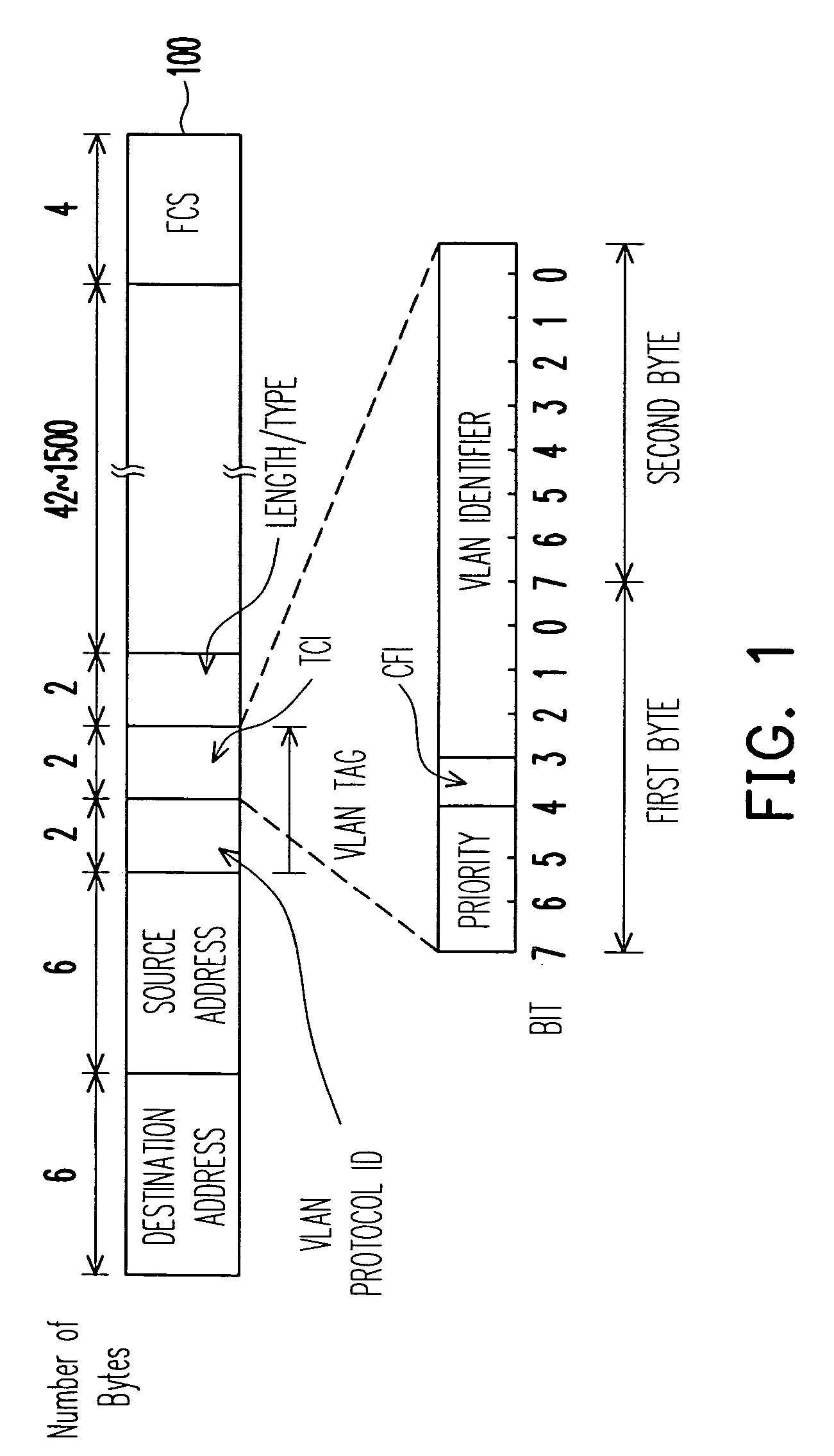
End-to-end mapping of VLAN ID and 802.1P COS to multiple BSSID for wired and wireless LAN
A quality of service (QoS) based load-balancing scheme in network communication between a local area network (LAN) and a wireless local area network (WLAN) is provided. The load balancing decision is made by a load balancing module according to traffic conditions and bandwidth availability of each traffic priority class based on a corresponding class of service. The load balancing module also maps an identifier in the LAN to one or more identifiers (BSSIDs or SSIDs) in the WLAN for accommodating the communication between LAN and WLAN for maintaining the quality of service (QoS). The identifier in the LAN can be a VLAN tag at the LAN, or identity of the port, physical address of terminals including MAC address, Token Ring or etc. protocols, or Internet address (IP) according to LAN standards.
Owner:WANG SHIWEI
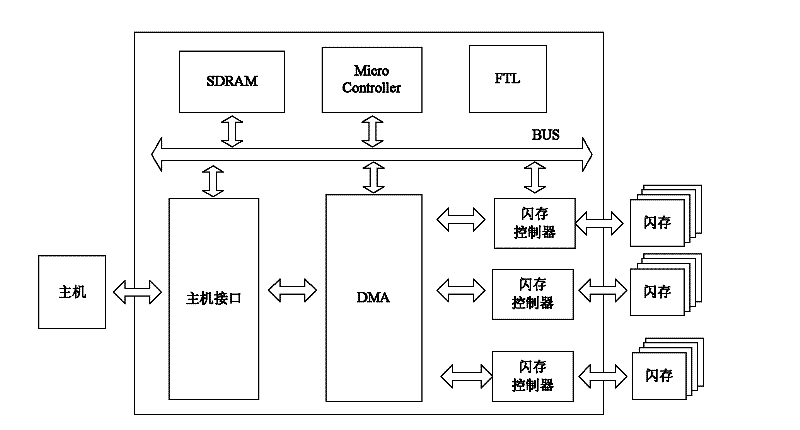
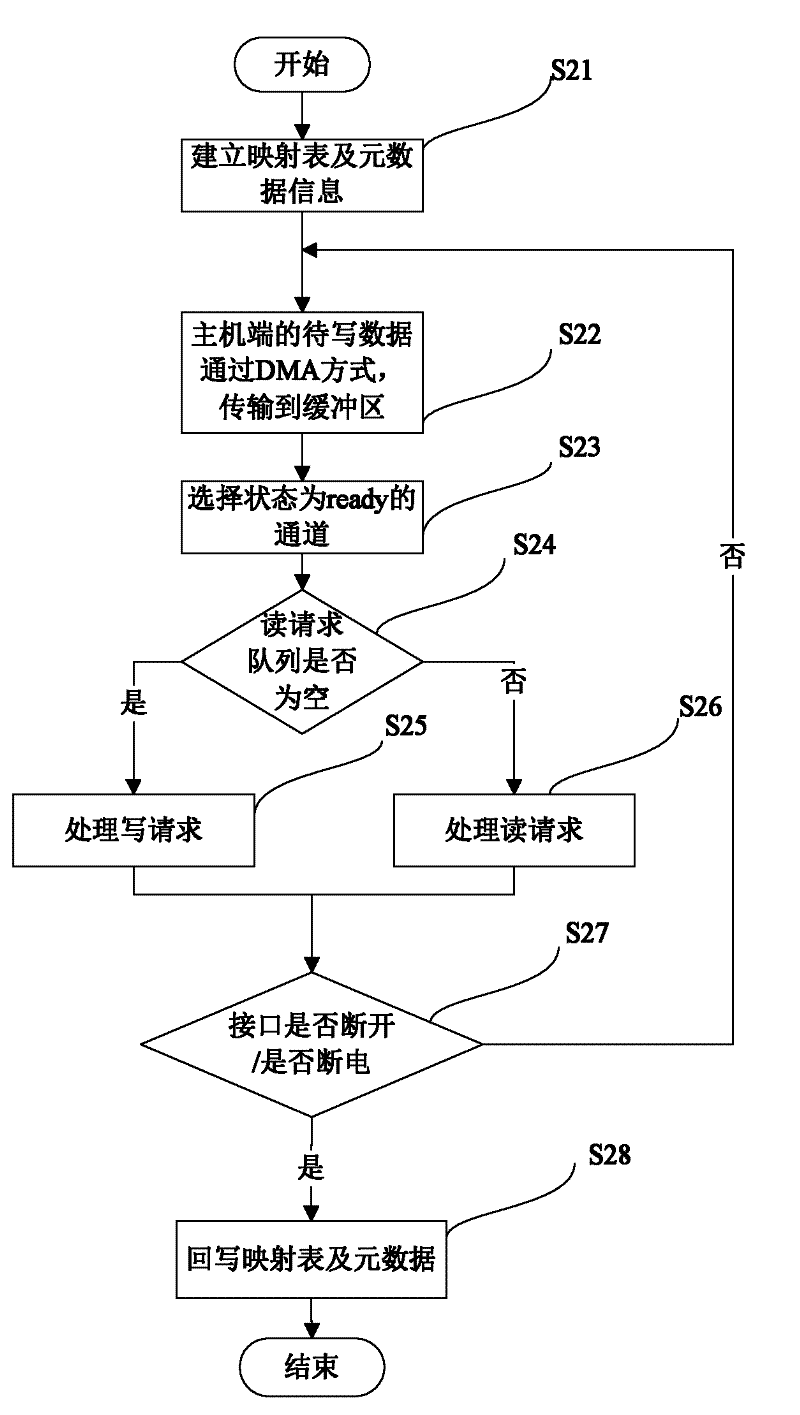
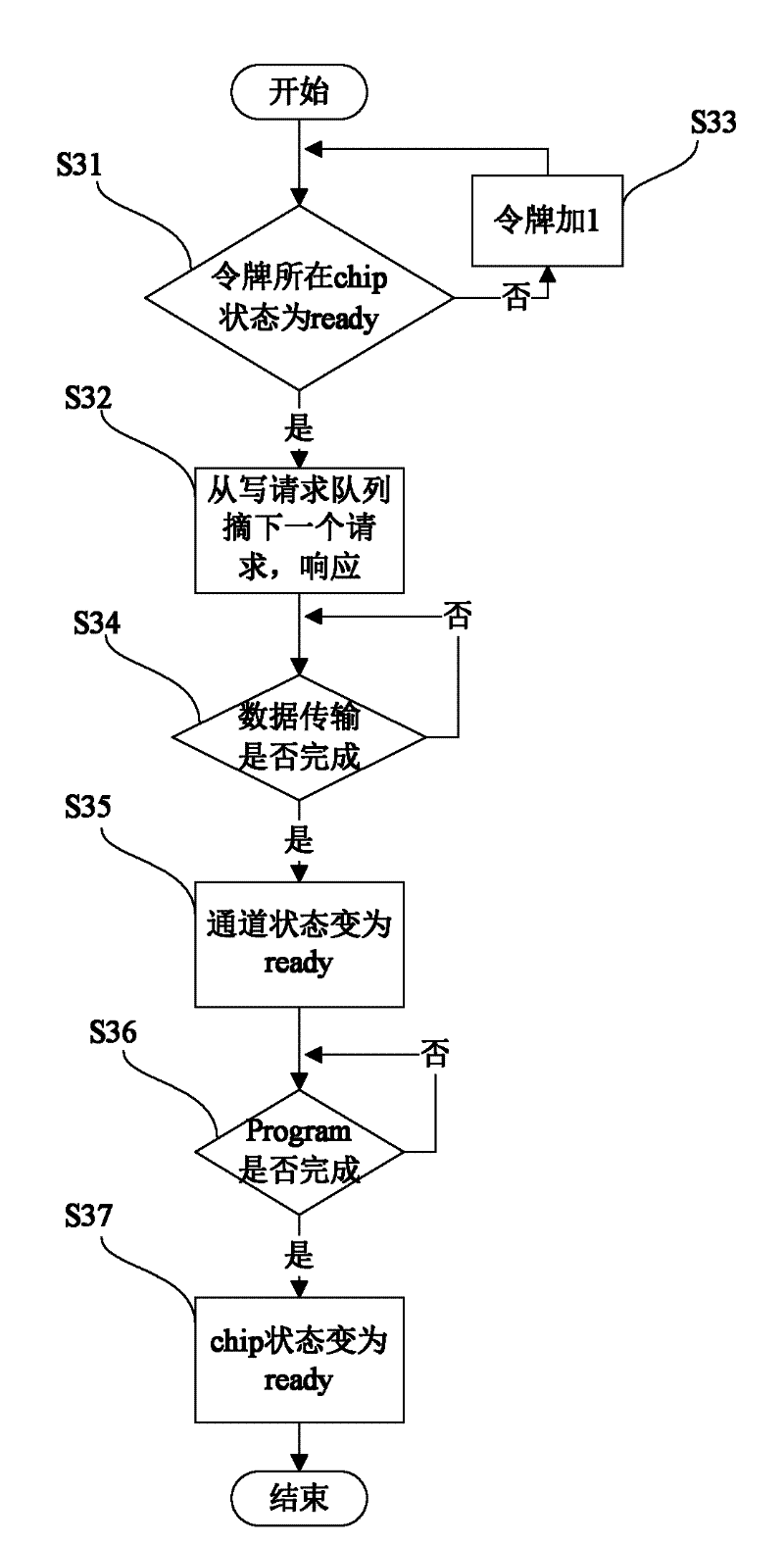
Method for controlling data reading and writing of multi-channel solid-state disc
ActiveCN102567257AFast transferUniform wearInput/output to record carriersDirect memory accessComputer science
The invention discloses a method for controlling data reading and writing of a multi-channel solid-state disc, comprising the steps of: (1) building a mapping table to store a mapping relationship of a solid-state disc logic address and a physical address, (2) transmitting a data to be written of a host terminal to a buffer area of a channel controller through a DMA (Direct Memory Access), (3) selecting a channel of which a channel state is ready, (4) finding out a reading request in a chip state which is ready from a reading request queue of the channel of which the state is ready and serving the reading request, (5) finding out a writing request in the chip state which is ready from a writing request queue if the reading request queue is null, writing the data of the buffer area into a free page of the chip, and then modifying corresponding relationship between a corresponding logic address and a physical address in the mapping table so as to finish writing operation. According to the method disclosed by the invention, fast transfer of an interface data is realized, and parallel communication among the channels and serial pipeline operation inside the channels are also realized. Abrasions among all the chips of SSD (solid state disks) are also uniform due to mode adoption of a token ring.
Owner:HUAZHONG UNIV OF SCI & TECH
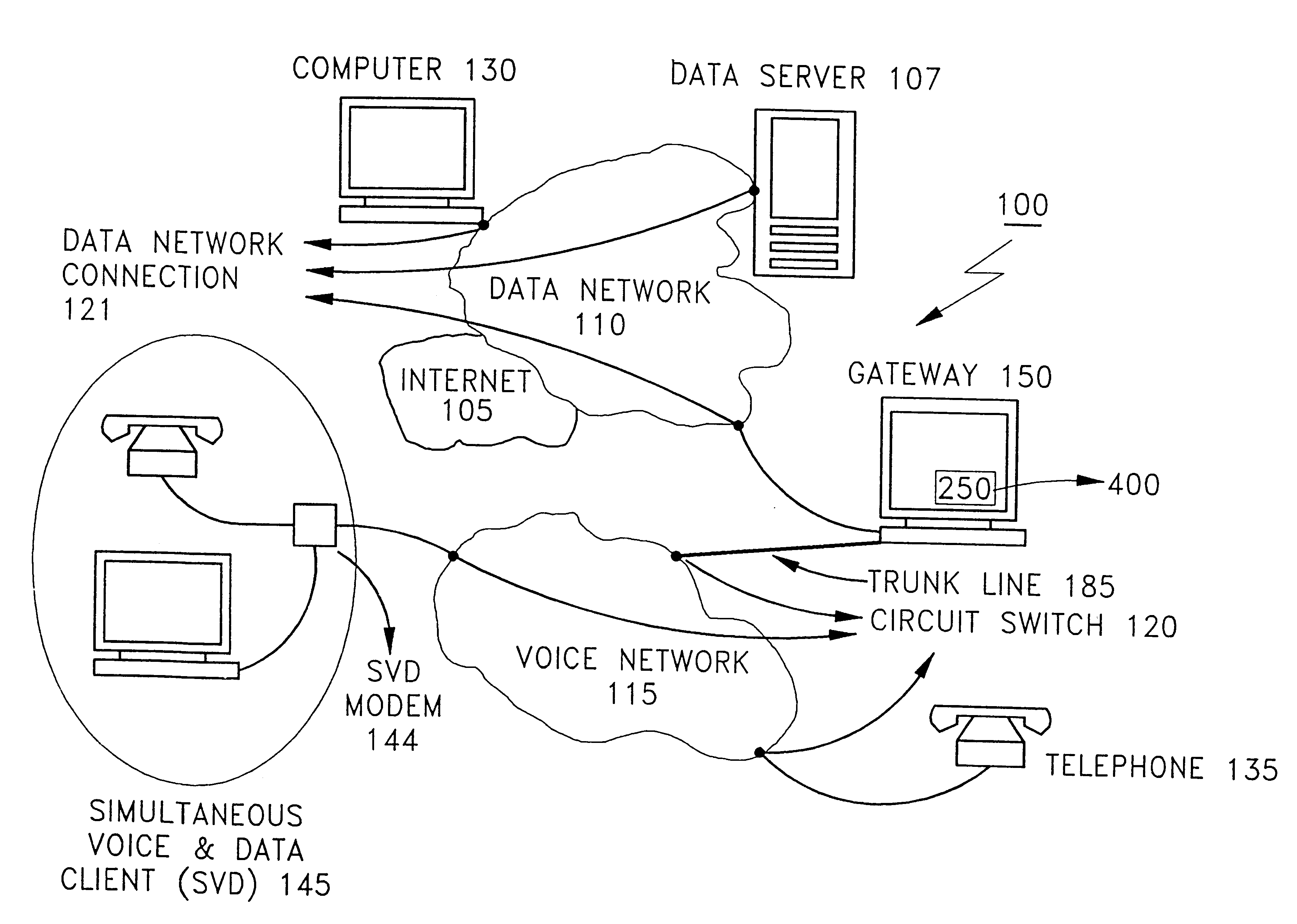
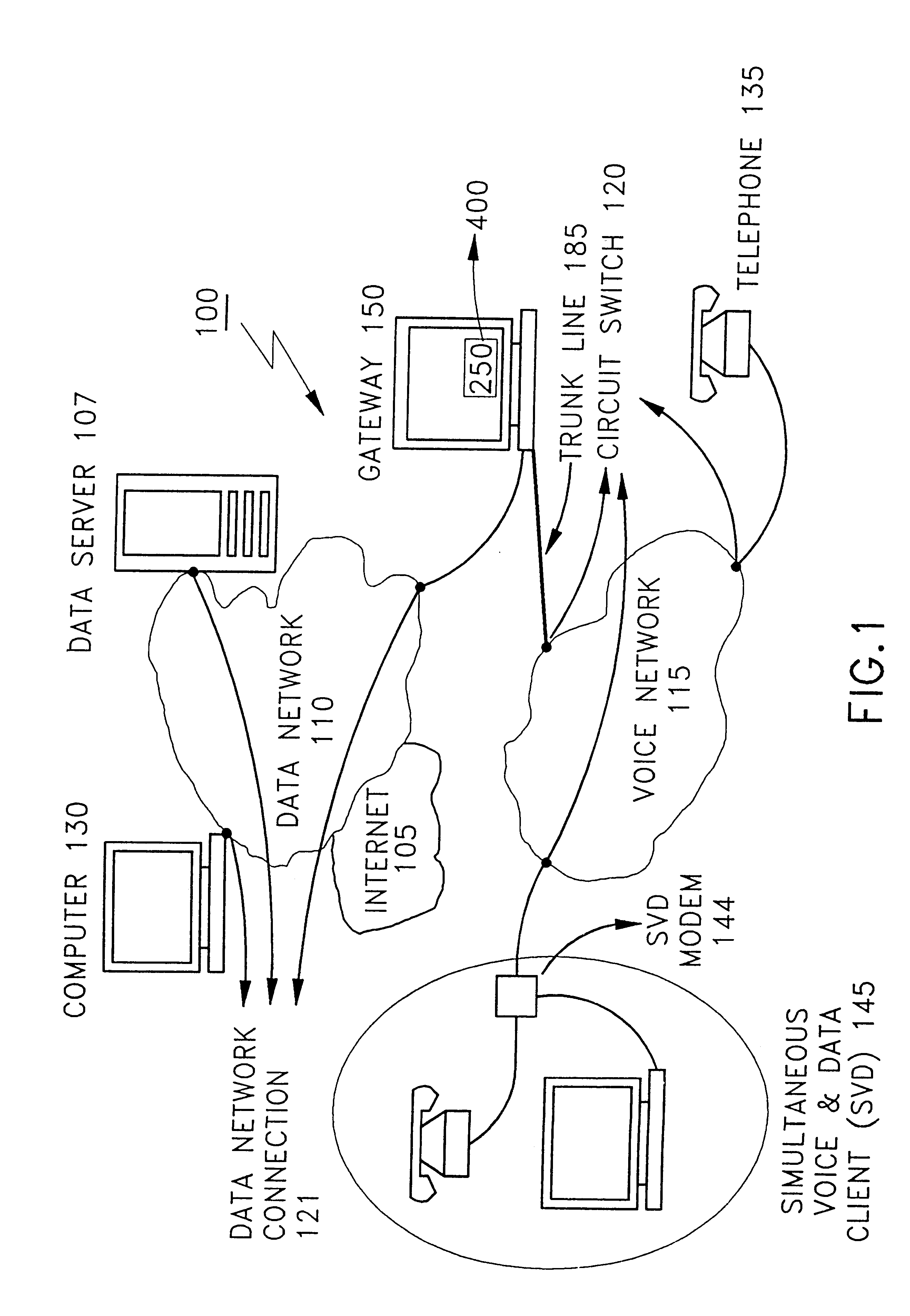
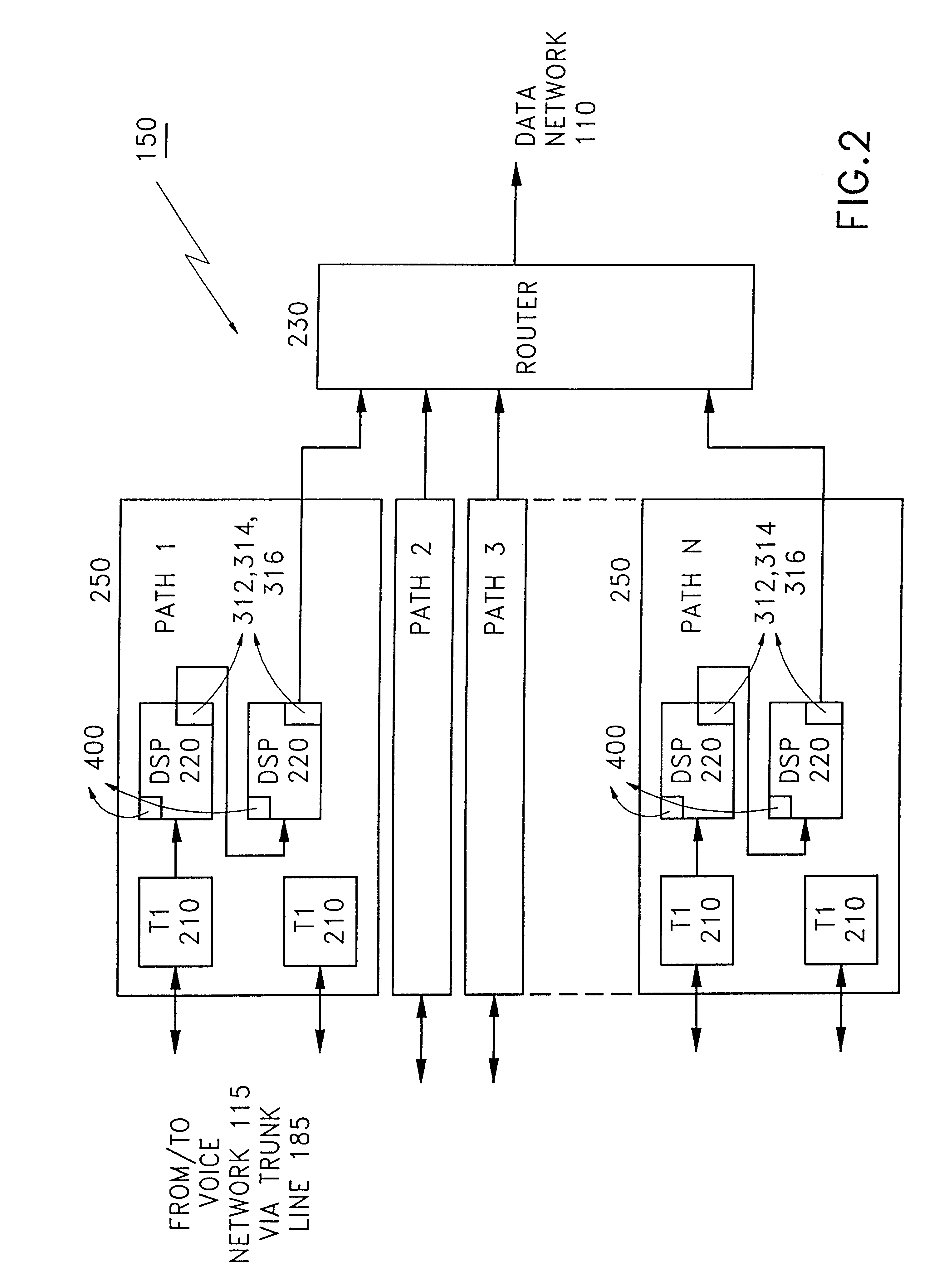
Multipoint simultaneous voice and data services using a media splitter gateway architecture
InactiveUS6173044B1Multiplex system selection arrangementsTelephone data network interconnectionsData streamModem device
A gateway enables point to multipoint connectivity from voice, data, or SVD clients over voice and data networks. The gateway connects one or more known voice networks (e.g. telephone networks) and one or more data networks (e.g. LANs, WANs, and internet) so that clients on either network may access any of the networks via various devices like analog telephones, data modems, SVD modems, or direct data network connections (e.g., ethernet, token ring). The gateway has connections to both the data network(s) as well as the voice network(s). The gateway is capable of splitting a signal with both voice and data streams and routing either and / or both of these streams over the voice network alone, the data network, or both. A process, executing on the gateway enables the gateway to establish connections on gateway paths and to control and direct a flow of voice and data information between the destinations on these networks.
Owner:IBM CORP
Universal network interface connection
InactiveUS7171505B2Wide flexibilityDigital computer detailsElectric digital data processingModem deviceProgrammable logic device
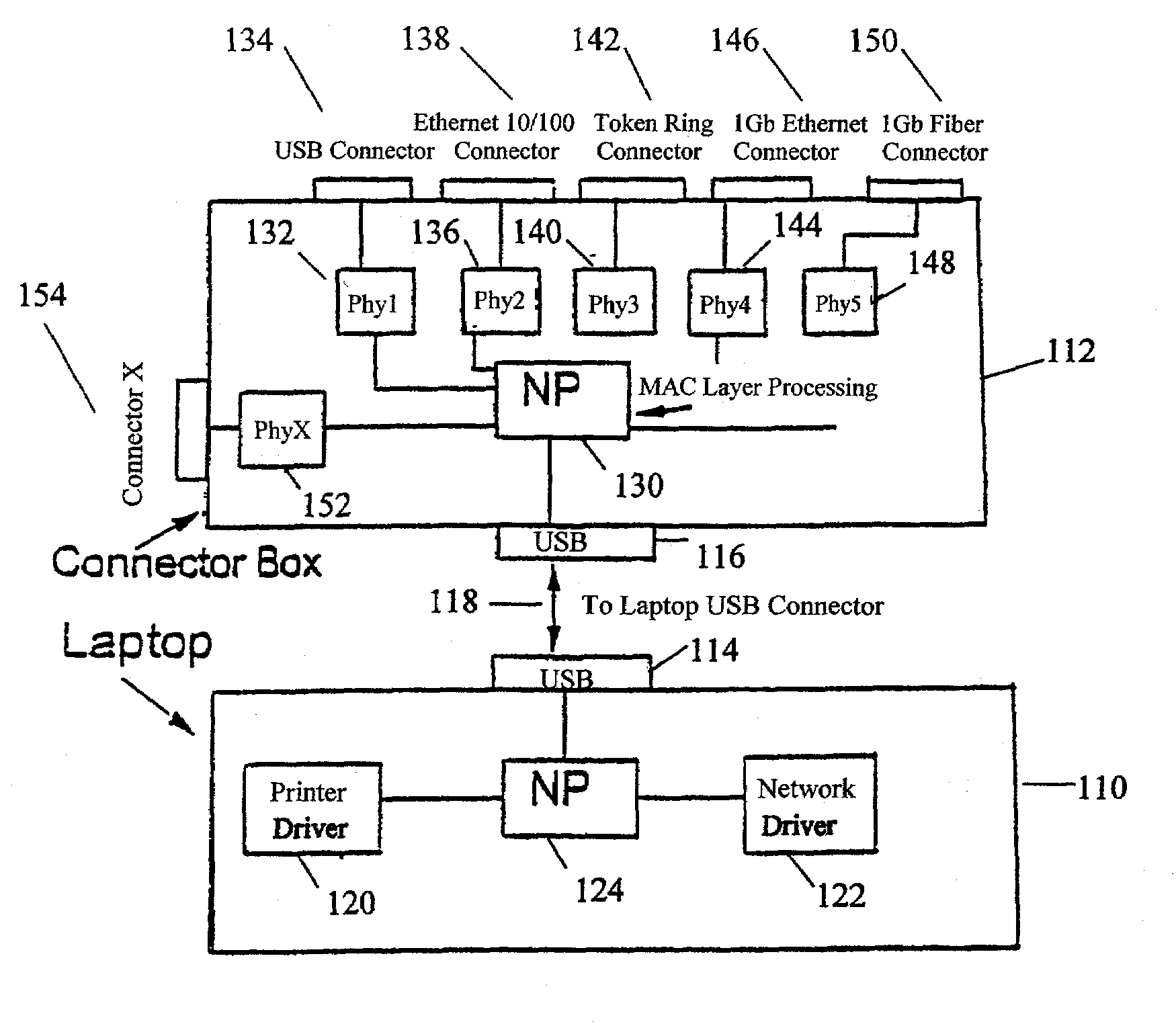
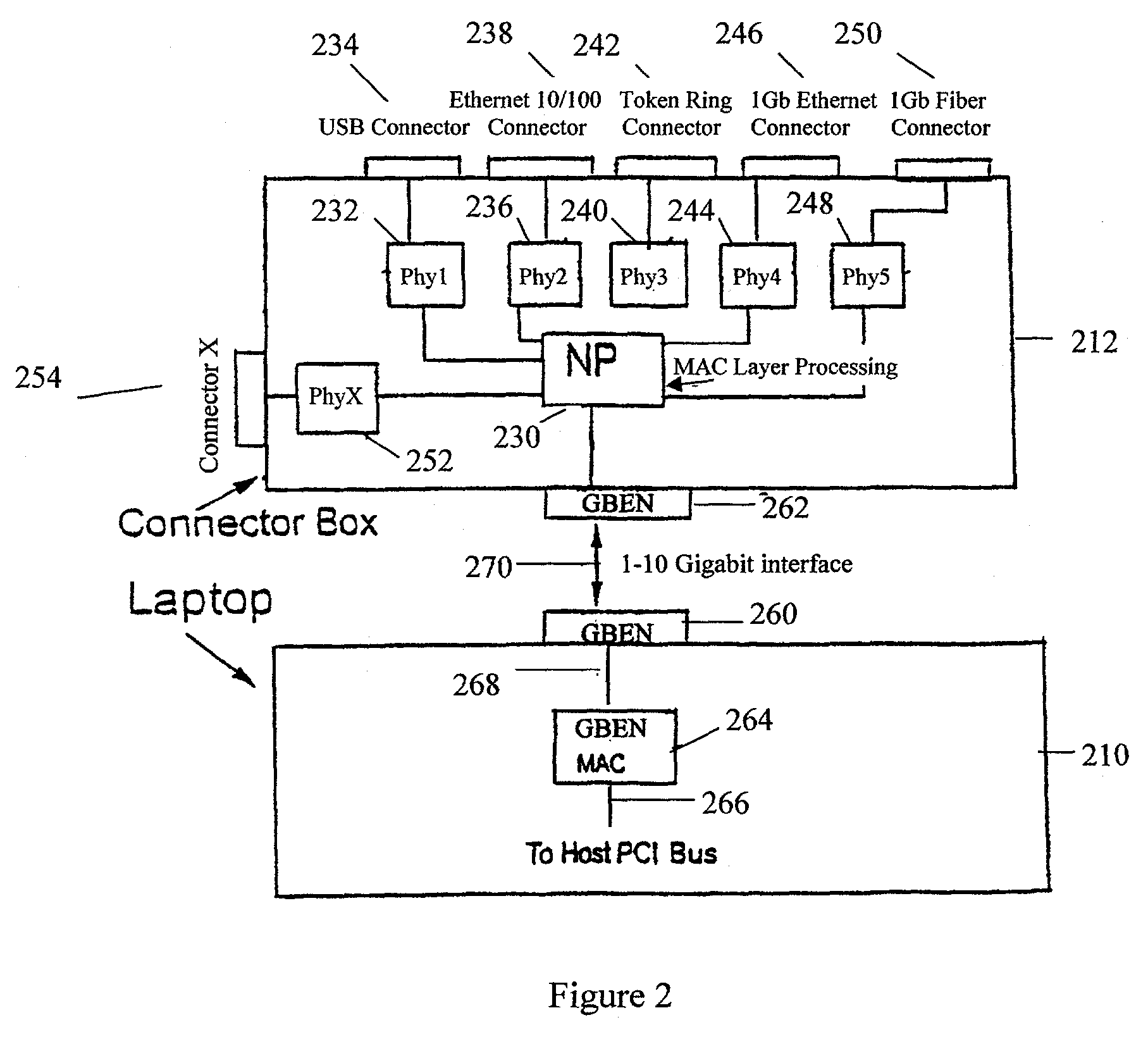
An interface connection is described for joining a host device, such as a Network Processor, to peripherals such as modems, printers, local area networks, Ethernets and Token-Ring interfaces. The connection is particularly useful for joining portable computers, such as laptops, to these peripherals. The connector utilizes a programmable Network Processor (NP) either in the host device or in an external fan-out box. This programmable Network Processor adapts the host device to a variety of peripheral devices utilizing different protocols and I / O speeds. The NP can use a Digital Signal Processor to provide programmable services to the physical layers. The host device may contain a high-speed communication interface with the NP contained in the external connection box.
Owner:IBM CORP
Interface monitoring for link aggregation
The present invention provides network interface monitoring and management that may be employed with link aggregation technologies. Multiple network interfaces may be aggregated into a single bond and data may be transferred to and from a backbone network via this aggregated bond. A link aggregation monitor employs a heartbeat generator, sniffer and data store to keep track of health and availability of network interfaces. The heartbeat generator sends heartbeats to the network interfaces, which pass the heartbeats around in a token ring configuration. If a network interface fails or otherwise goes offline, detection of this condition causes the monitor and heartbeat generator to prepare new or modified heartbeats so that data may be efficiently and accurately routed around the token ring and health of all remaining alive interfaces can be monitored properly. If a network interface re-enters or is added to the aggregate bond, new / modified heartbeats are then employed.
Owner:GOOGLE LLC
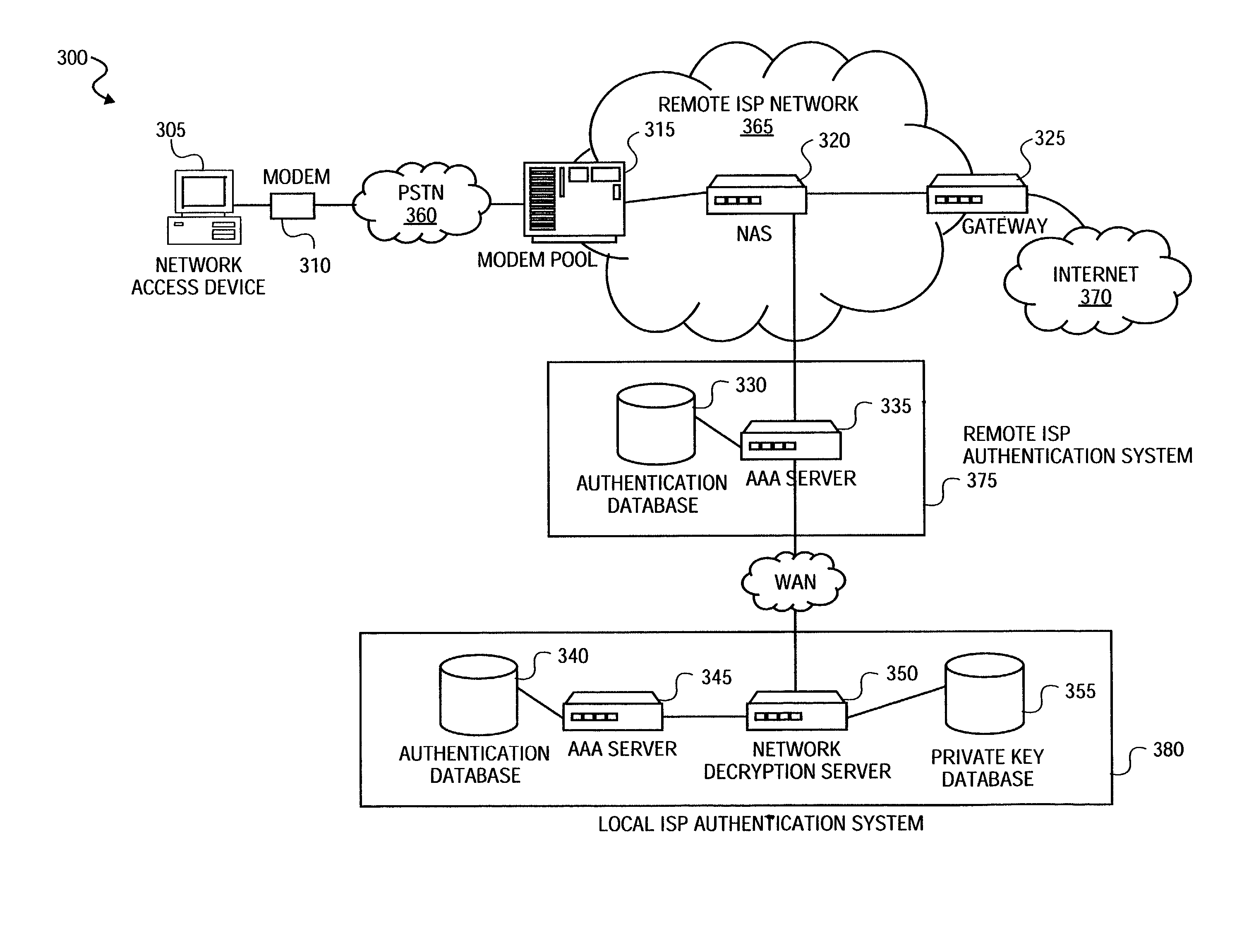
Method and system for securely authenticating network access credentials for users
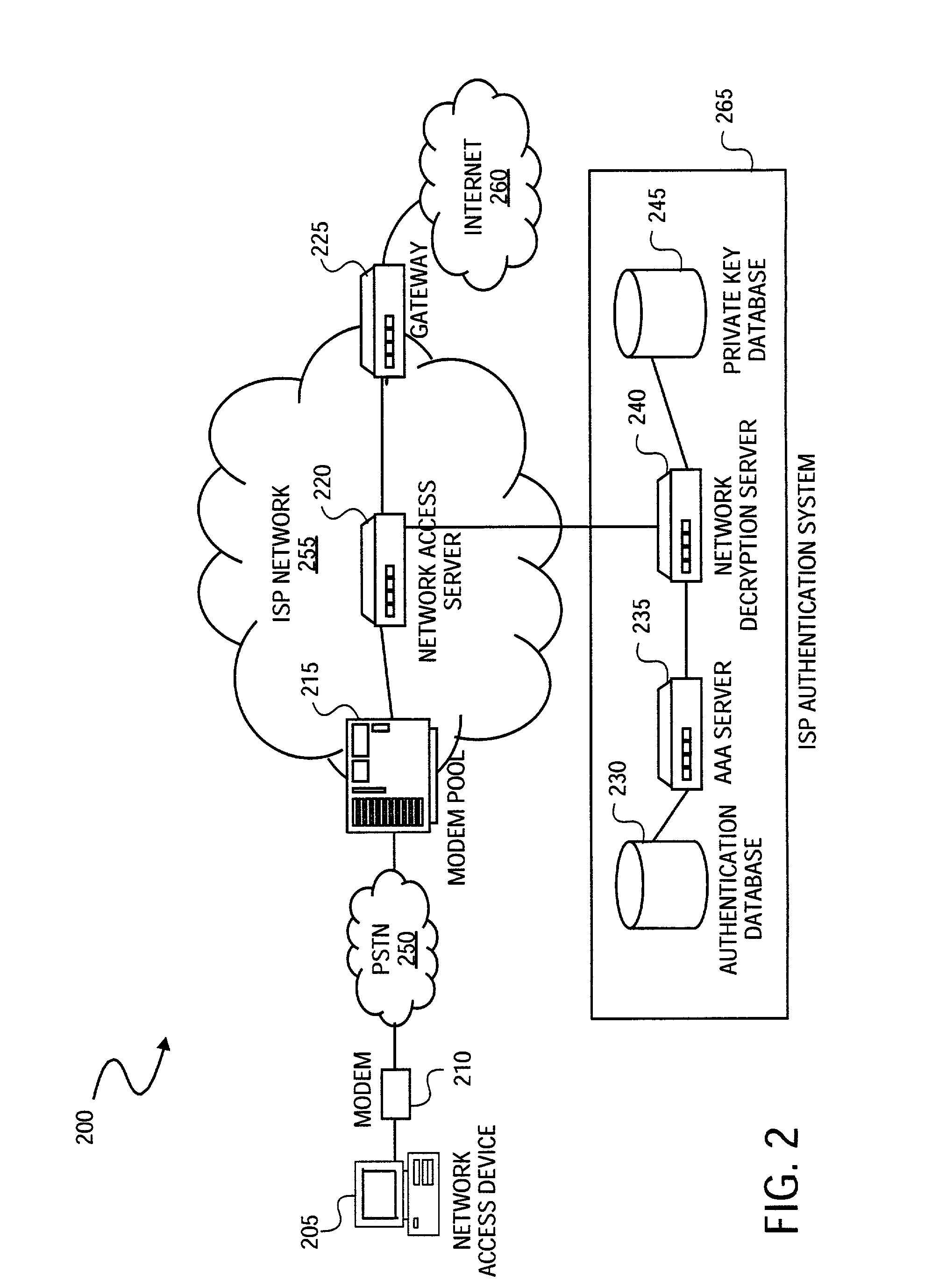
InactiveUS7921290B2Digital data processing detailsUser identity/authority verificationHypertext Transfer Protocol over Secure Socket LayerDirectory Access Protocol
A method is provided to securely authenticate user credentials. The method includes encrypting a user credential with a public key at an access device wherein the public key is part of a public / private key pair suitable for use with an encryption algorithm. The encrypted network user credential is transmitted from the access device to a decryption server where it is decrypted with a private key, the private key being part of the public / private key pair suitable for use with the encryption algorithm. The decrypted user credential is then transmitted from the decryption server to an authentication server for verification. The decryption server typically forms part of a multi-party service access environment including a plurality of access providers, the method including decrypting the user credential of a user proximate an access provider associated with the user credential. The method can be used in legacy protocols such as Point-to-Point protocol (PPP), Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), Remote Authentication Dial In User Service (RADIUS) protocol, Terminal Access Controller Access Control System (TACACS) protocol, Lightweight Directory Access Protocol (LDAP), NT Domain authentication protocol, Unix password authentication protocol, HyperText Transfer Protocol (HTTP), HyperText Transfer Protocol over Secure sockets layer (HTTPS), Extended Authentication Protocol (EAP), Transport Layer Security (TLS) protocol, Token Ring protocol and / or Secure Remote Password protocol (SRP).
Owner:CHANNEL IP BV
Adaptive interface apparatus and method for data terminal elements in a communication network transmitting and receiving ethernet over a shielded twisted pair cabling system
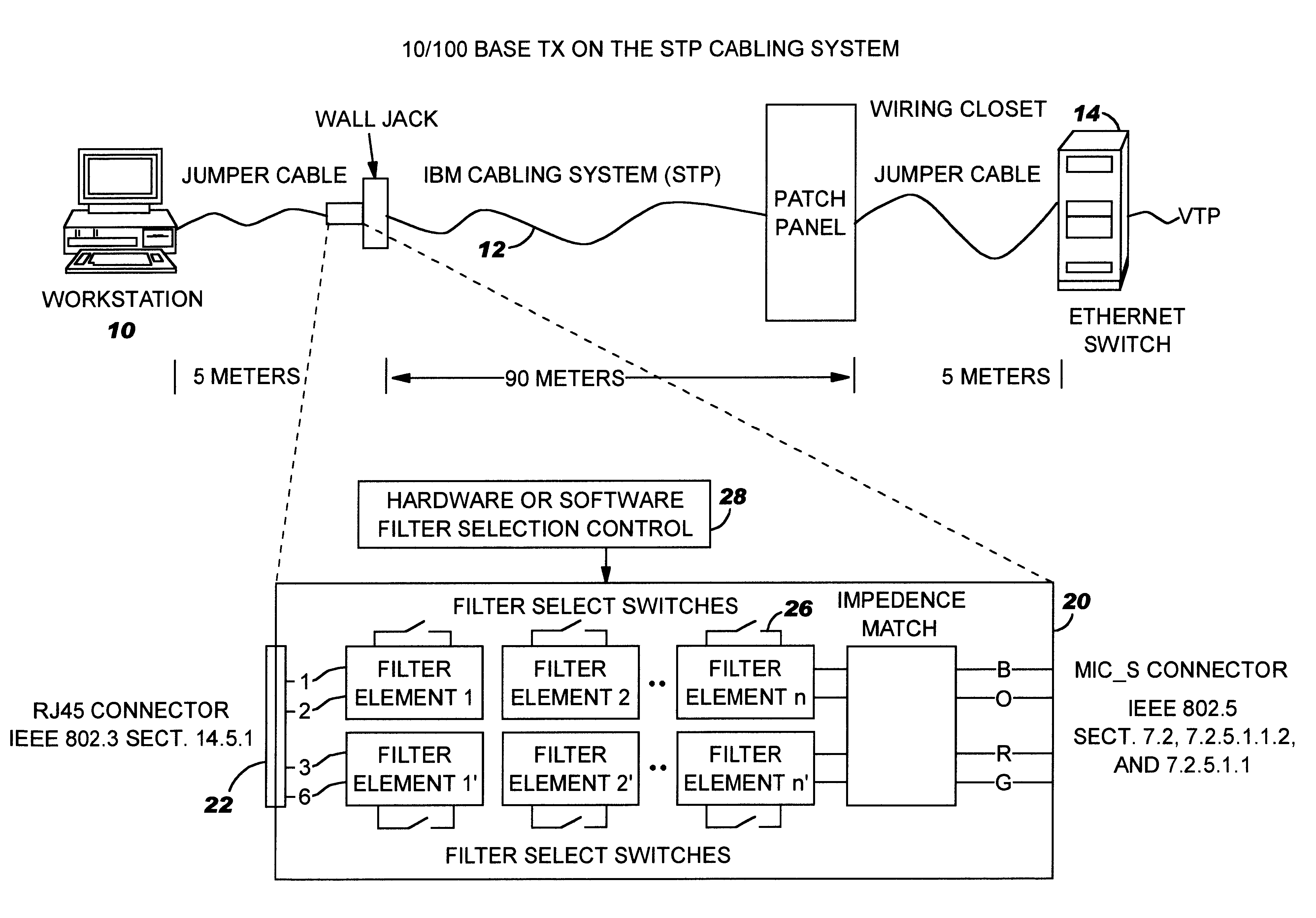
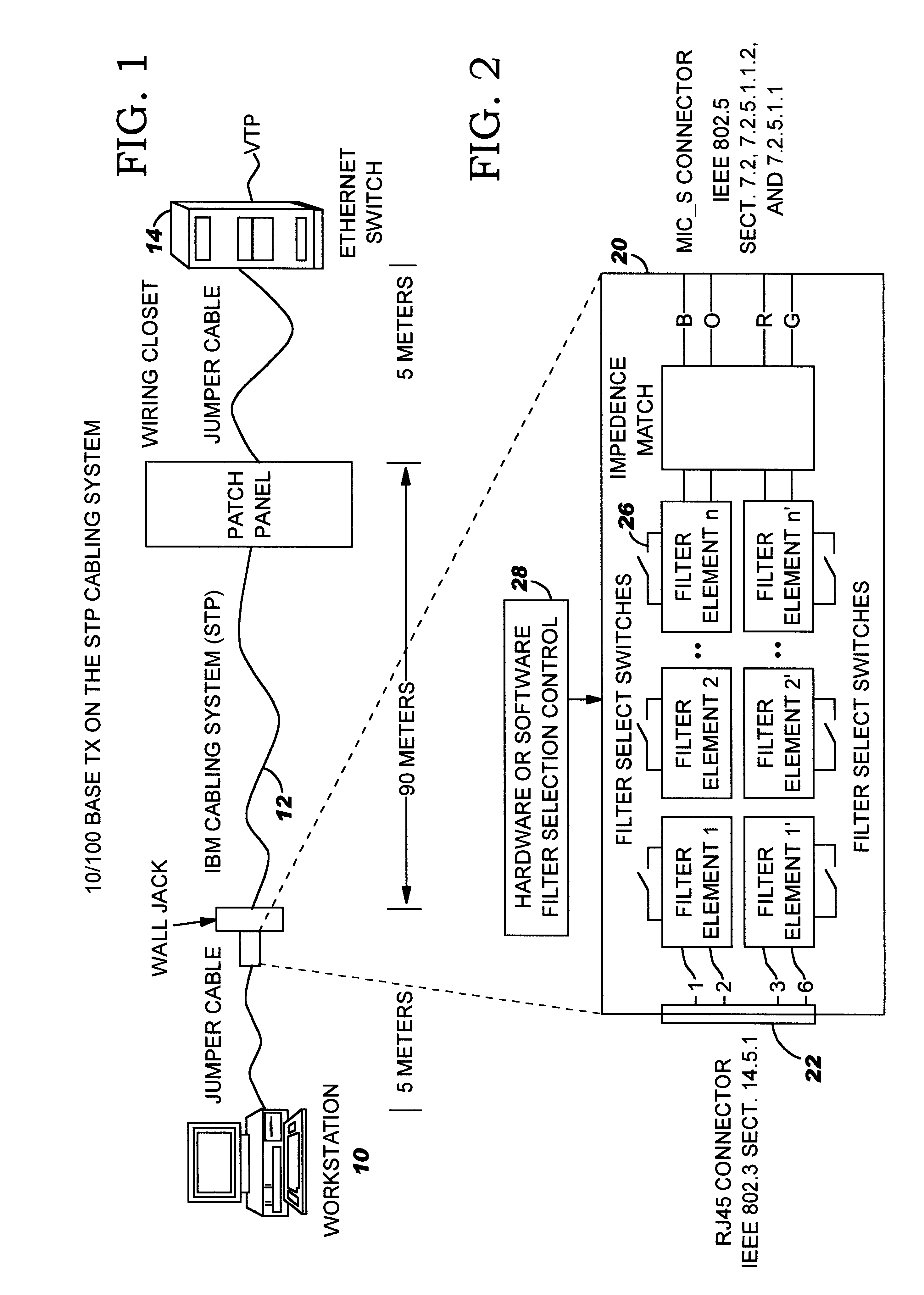
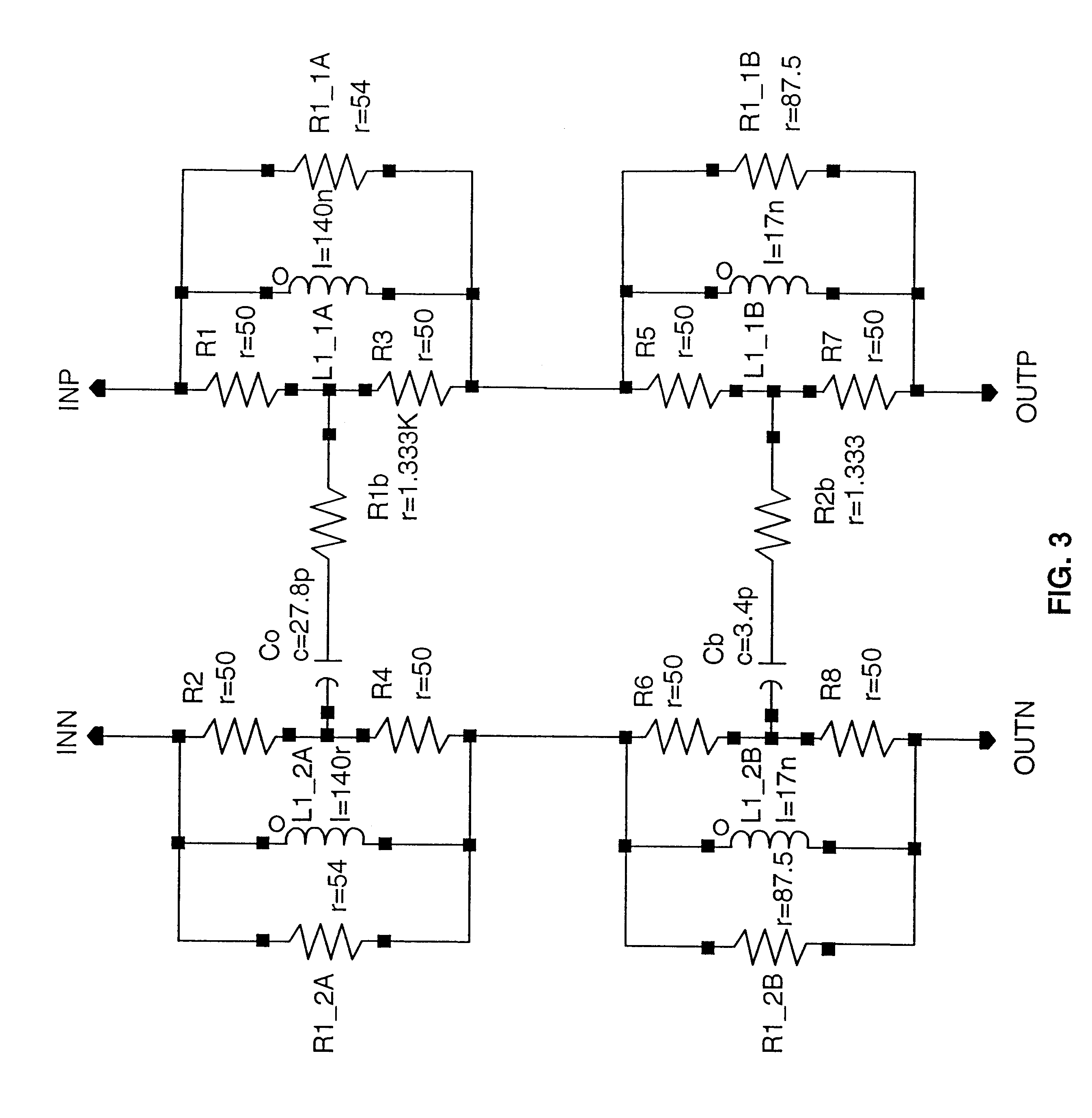
InactiveUS6332166B1Increase contactRealize automatic adjustmentBaseband system detailsTelephonic communicationWorkstationEmbedded system
An adaptive interface and method of operation facilitate connection of a work station in a Local Area Network (LAN) using Shielded Twisted Pair (STP) cabling to an Ethernet 10 / 100BASE TX installation using Unshielded Twisted Pair (UTP). The work station is coupled through the adaptive interface to the STP cabling system emulating a given number of meters of UTP cabling. The interface adapter comprises at one end a RJ 45 connector adapted for connection to the STP cabling and at the other end a MIC_S token ring connector coupled to an Ethernet adapter through the STP cabling system. The adaptive interface includes programmatically controlled filters interconnecting the RJ 45 and MIC_S connectors. The filter comprises a series of 1 . . . N switchable lumped passive element units which can be sequentially connected into the STP cabling to emulate the amplitude attenuation and phase shift of a preselected length of UTP 5 cabling, typically in the range of 20 meters. In operation, the Physical Layer (PHY) in the communication system enters a start up sequence for the various circuits and cabling in the layer. During the start up sequence, the adaptive interface is bypassed. After an appropriate delay to allow PHY convergence or a bit error rate measurement, the PHY transmit / receive signals are examined for bit errors by a test unit. If there are no bit errors, no filter element is inserted in the STP cabling by the adaptive interface and the work station is coupled to the Ethernet installation. If there are bit errors, a first filter element is switched into the STP cabling by the adaptive interface. The bit error signals are re-examined. If there are no errors, the workstation is connected to the Ethernet installation. If bit errors continue to exist, the next element(s) of the filter is inserted into the STP cabling until the "Nth" filter element is reached. If bit errors continue to exist on the STP cabling after inserting the Nth filter in the STP cabling, a re-try test sequence is initiated by the adaptive interface and the start up sequence is repeated. If re-try is not initiated, a transmit error is displayed and the workstation / Ethernet installation cannot proceed without modification. A diagnostics menu is displayed and a set-up process determines with human intervention what system changes are needed for the workstation / Ethernet connection.
Owner:IBM CORP
Method and system for co-operative charging of electric vehicles
ActiveUS8324859B2Possible failureDc source parallel operationPower to auxillary motorsDistribution transformerThe Internet
A method and system provide for the cooperative charging of electric vehicles. By using power line communications, chargers of the electric vehicles who are serviced by the same distribution transformer can form self-contained local area networks due to the nature of power line communications (PLCs). Alternatively, or in addition to the PLCs, other communication networks, such as the Internet and local area networks, may be used as part of the communications infrastructure for the chargers. After the chargers of the electric vehicles are coupled to one another through power line communications or traditional communications networks, they can form a logical token ring network. According to this token ring network, a predetermined number of tokens can be assigned within the token ring network for permitting chargers with tokens to charge respective electric vehicles while chargers without tokens must wait until they receive a token to initiate charging.
Owner:ITRON
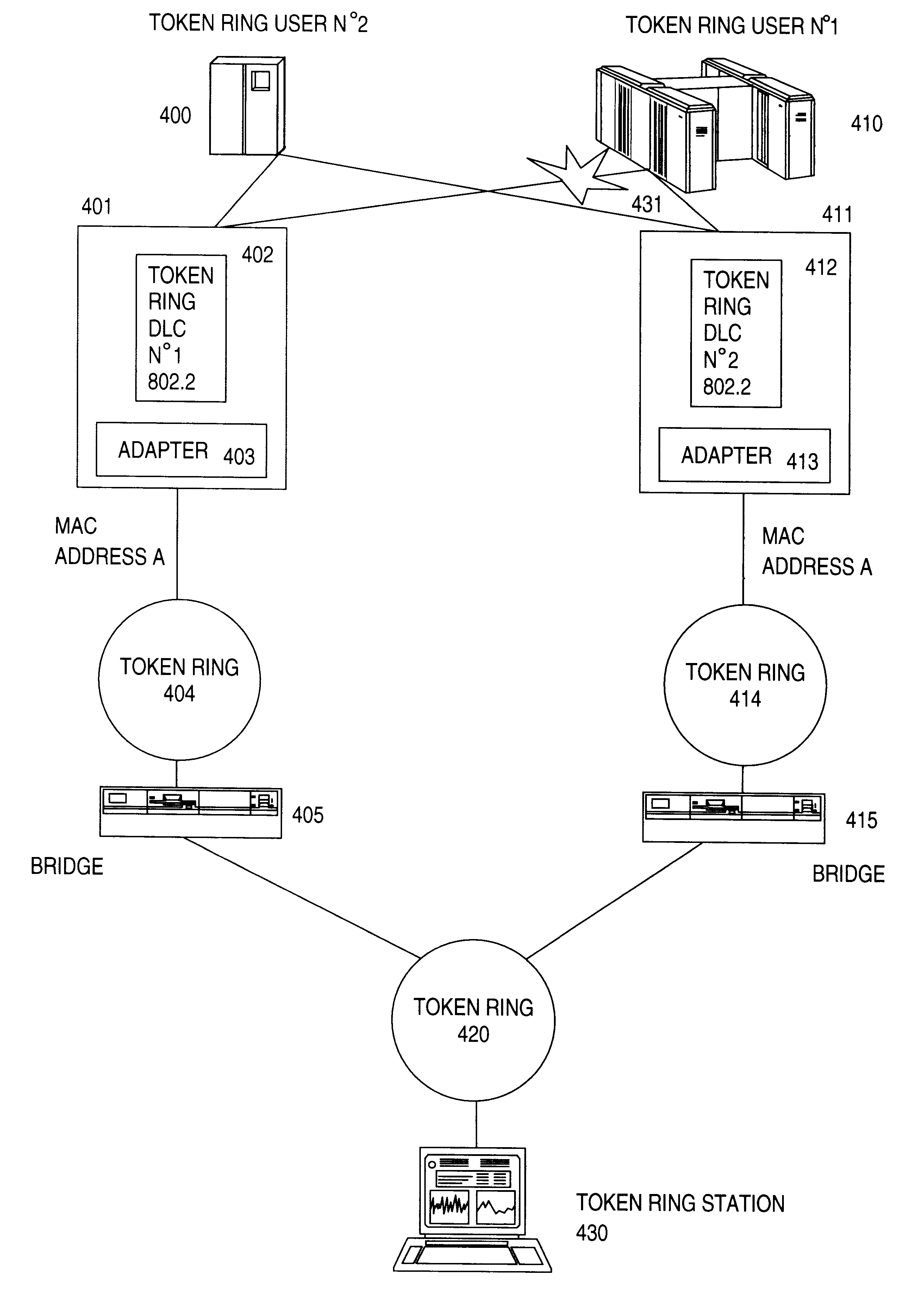
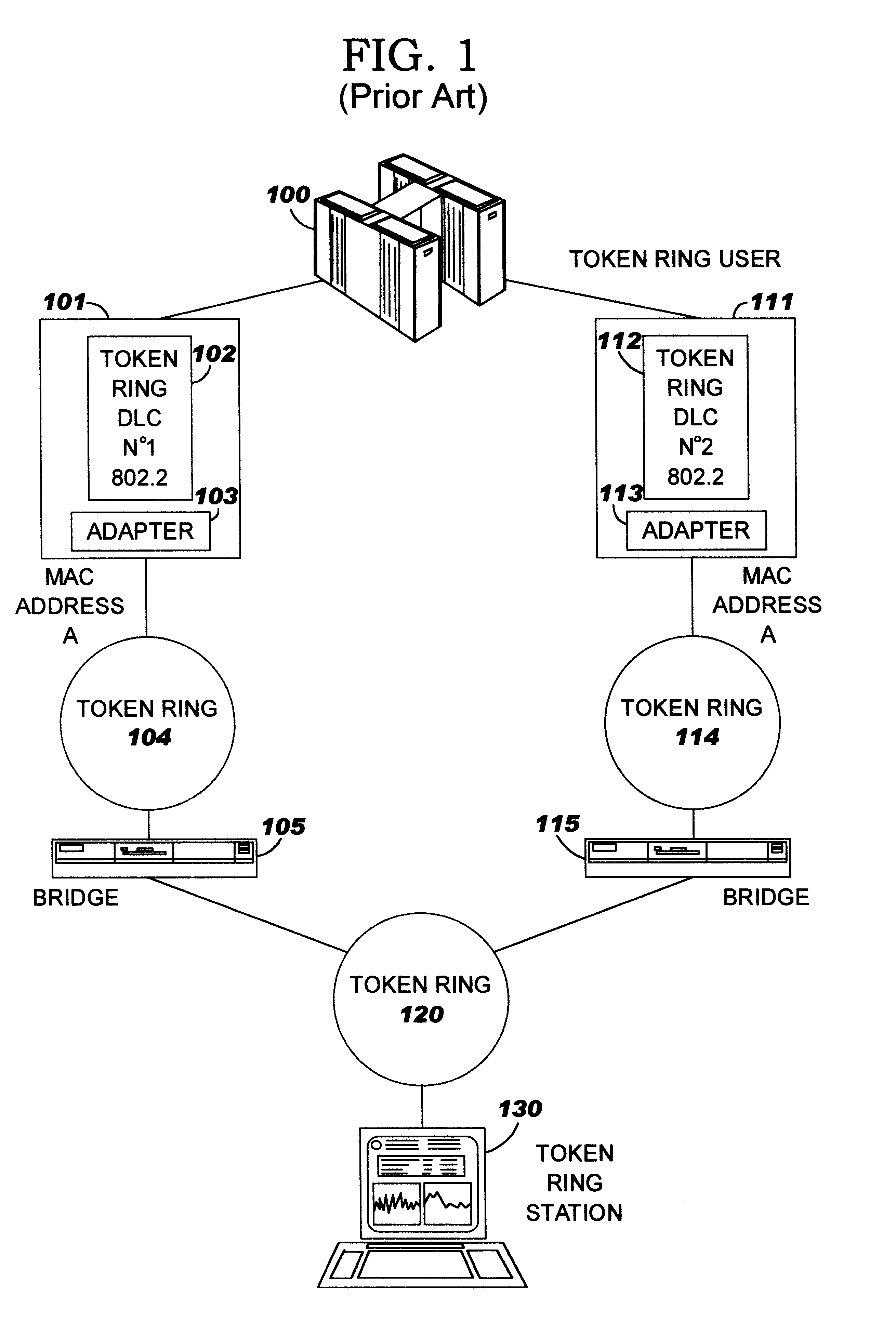
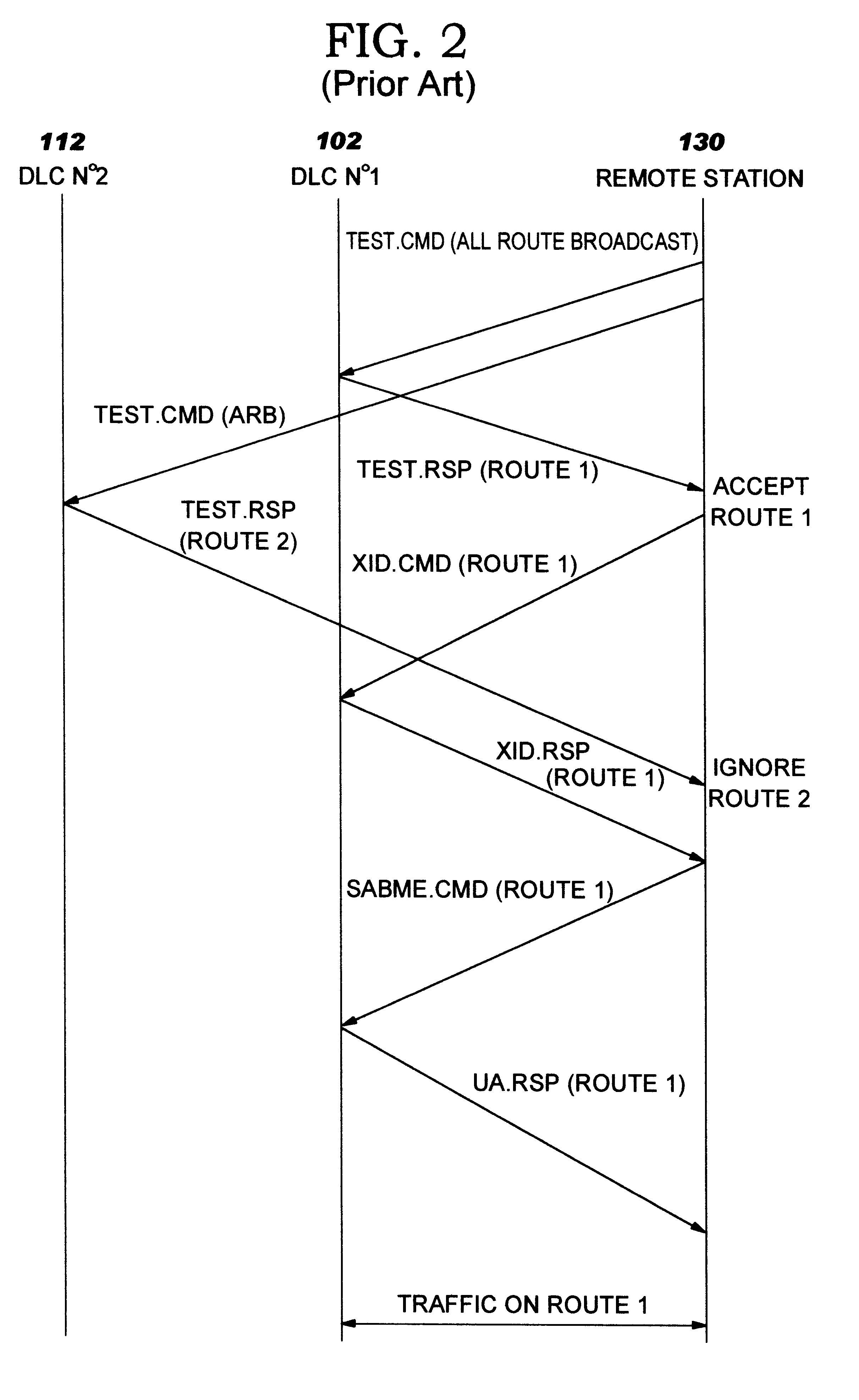
Method and apparatus for an automatic load balancing and back-up of a multi-users network
The invention aims to implement the Load Balancing / Backup function in a Multi-Users environment and to allow a remote station to have an alternate route through another Token Ring DLC to backup. By directing the connection to another route, it postpones the connection from a remote station to a Token Ring user through a first selected Token Ring DLC for a predetermined delay. For that purpose, each Token Ring DLC stores parameters of the remote station that has an unsuccessful connection in its own Connection Cache Table. In this way, when a Test frame is received in each DLC, this latter checks in the Connection Cache Table before responding to the Test frame. The Test frame is ignored and no Test response is sent back to the remote station when the remote station is identified in the table so as to allow the remote station to detect an alternate route with a backup DLC if it exists. Each Token Ring DLC manages its own Connection Cache table which contains an entry, a source MAC address and a Source SAP and a counter indicating the number of unsuccessful attempted Test frames received from that remote station. If the counter reaches a value N, then the entry corresponding to the remote station is removed from the table. Thus, the next time a Test frame is received from this remote station, it is accepted and a response is sent from the DLC. It gives a new opportunity to the remote station to establish a connection to the user in case this latter would become available again.
Owner:IBM CORP
Novel digital seismic detector based on computer network
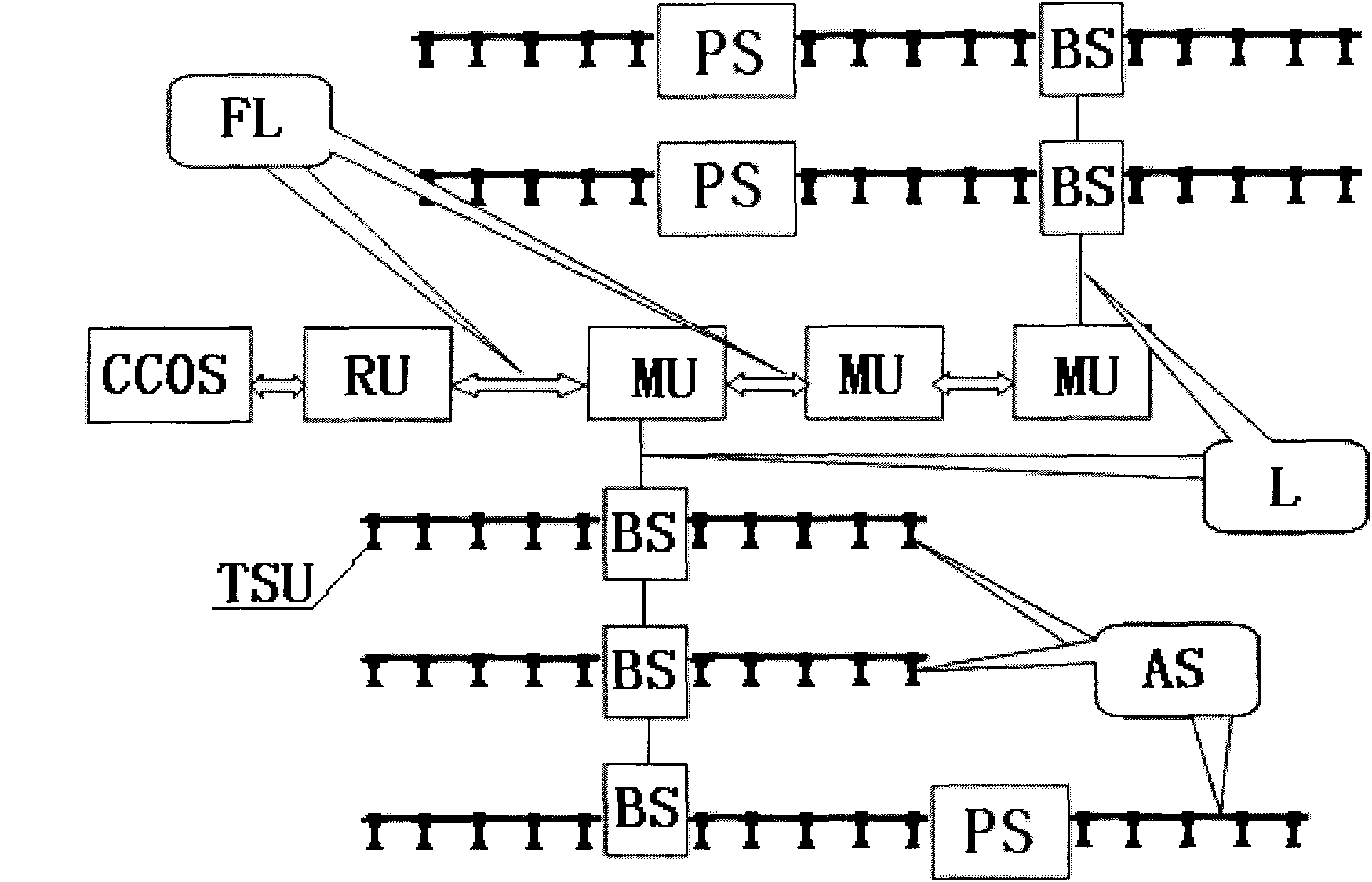
InactiveCN102213768AProcess controlMeet managementSeismic signal receiversTransmissionReal-time dataGigabit
The invention relates to a digital seismic detector based on a computer network, and is used for solving the problems of high cost, high power consumption and poor function of the traditional seismic detector. The digital seismic detector consists of a central control operating system, root nodes, main nodes, base stations, a power supply station used for supplying power to an acquisition chain, the acquisition chain, optical cables and a big-cable unit; the central control operating system is connected with the root nodes through a plurality of bonded gigabit lines; the root nodes are connected with the main nodes and other field ground equipment through a plurality of the optical cables; a plurality of the main nodes are connected through gigabit optical cables to form a backbone network; the main nodes are connected with the base stations through large line cables; the base stations are connected through 100M big cables to form a secondary backbone network; the base stations provide a plurality of special synchronous transmission interfaces for connecting the acquisition chain and the power supply station; the acquisition chain consists of a plurality of acquisition stations; and the base stations have the function of the power supply station and are used for supplying power to the acquisition chain. In the invention, the data transmission of the backbone network is completed by adopting gigabit optical fiber, the data transmission of the secondary backbone network is completed by adopting the 100M cables, and the real-time data transmission of the acquisition chain is realized by adopting a similar token ring. The digital seismic detector has the advantages of low cost, low power consumption, strong function and capability of realizing data transmission of a 100-thousand-grade digital seismic detector in a reliable mode.
Owner:INST OF GEOLOGY & GEOPHYSICS CHINESE ACAD OF SCI
Method and system for co-operative charging of electric vehicles
ActiveUS20120153896A1Possible failureDc network circuit arrangementsCharging stationsDistribution transformerEngineering
A method and system provide for the cooperative charging of electric vehicles. By using power line communications, chargers of the electric vehicles who are serviced by the same distribution transformer can form self-contained local area networks due to the nature of power line communications. After the chargers of the electric vehicles are coupled to one another through power line communications, they can form a token ring network. According to this token ring network, a predetermined number of tokens can be assigned within the token ring network for permitting chargers with tokens to charge respective electric vehicles while chargers without tokens must wait until they receive a token to initiate charging.
Owner:ITRON
Flow control method and device as well as clustering system
ActiveCN102647323AShorten the timeReduce sending delayData switching networksTraffic capacityCluster systems
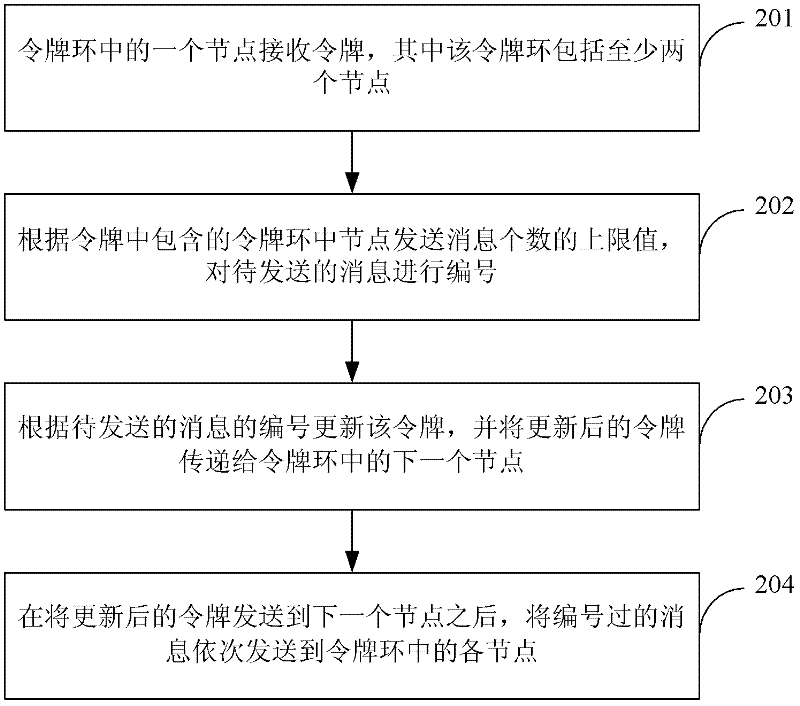
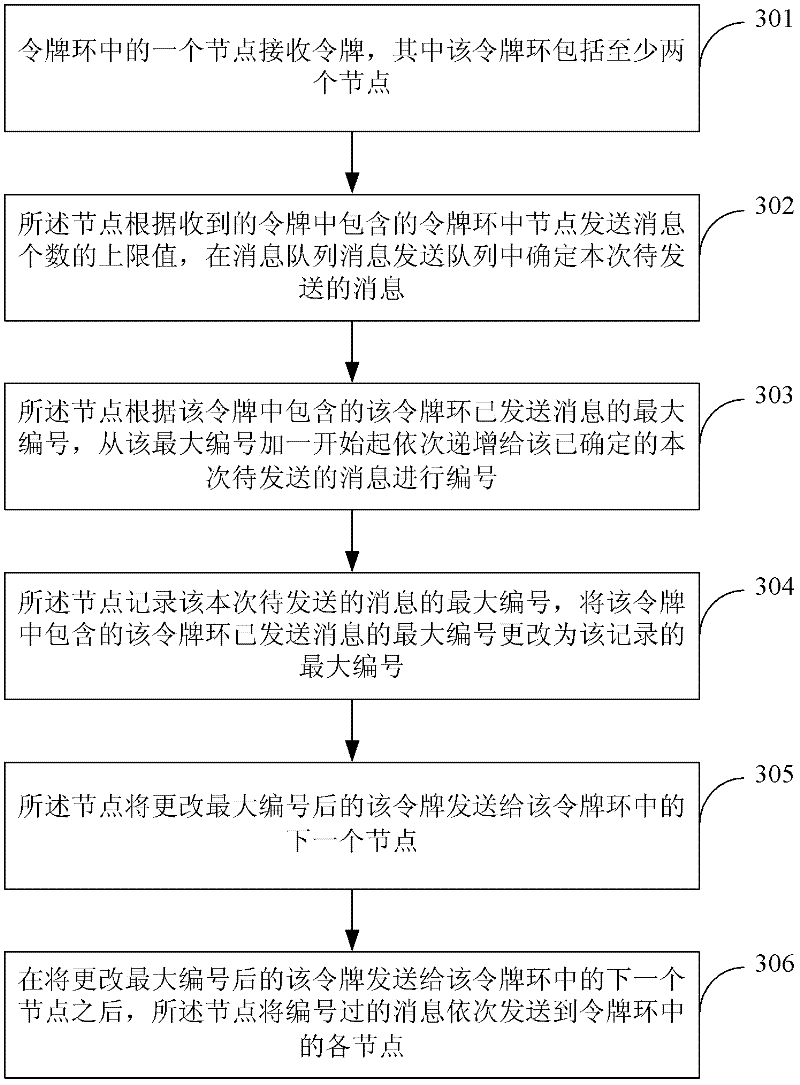
The invention discloses a flow control method and device as well as a clustering system, belonging to the technical field of a token-ring. The flow control method comprises the following steps of: receiving a token by a node in the token-ring, wherein the token-ring comprises at least two nodes; numbering information to be sent according to information relevant to node sending information in the token-ring, which is contained in the token; updating the token according to numbers of the information to be sent, and transmitting the updated token to the next node in the token-ring; and after the updated token is sent to the next node, sequentially sending the numbered information to each node in the token-ring. The flow control device comprises a receiving module, a numbering module, an updating module and a sending module. The clustering system comprises a plurality of nodes forming the token-ring. According to the flow control method and device as well as the clustering system provided by the invention, time for winding the token around the token-ring for one circle is greatly reduced; an information throughput of clustering the token-ring is improved; the transmission delay of the information is reduced; and the information instantaneity is improved.
Owner:HUAWEI TECH CO LTD
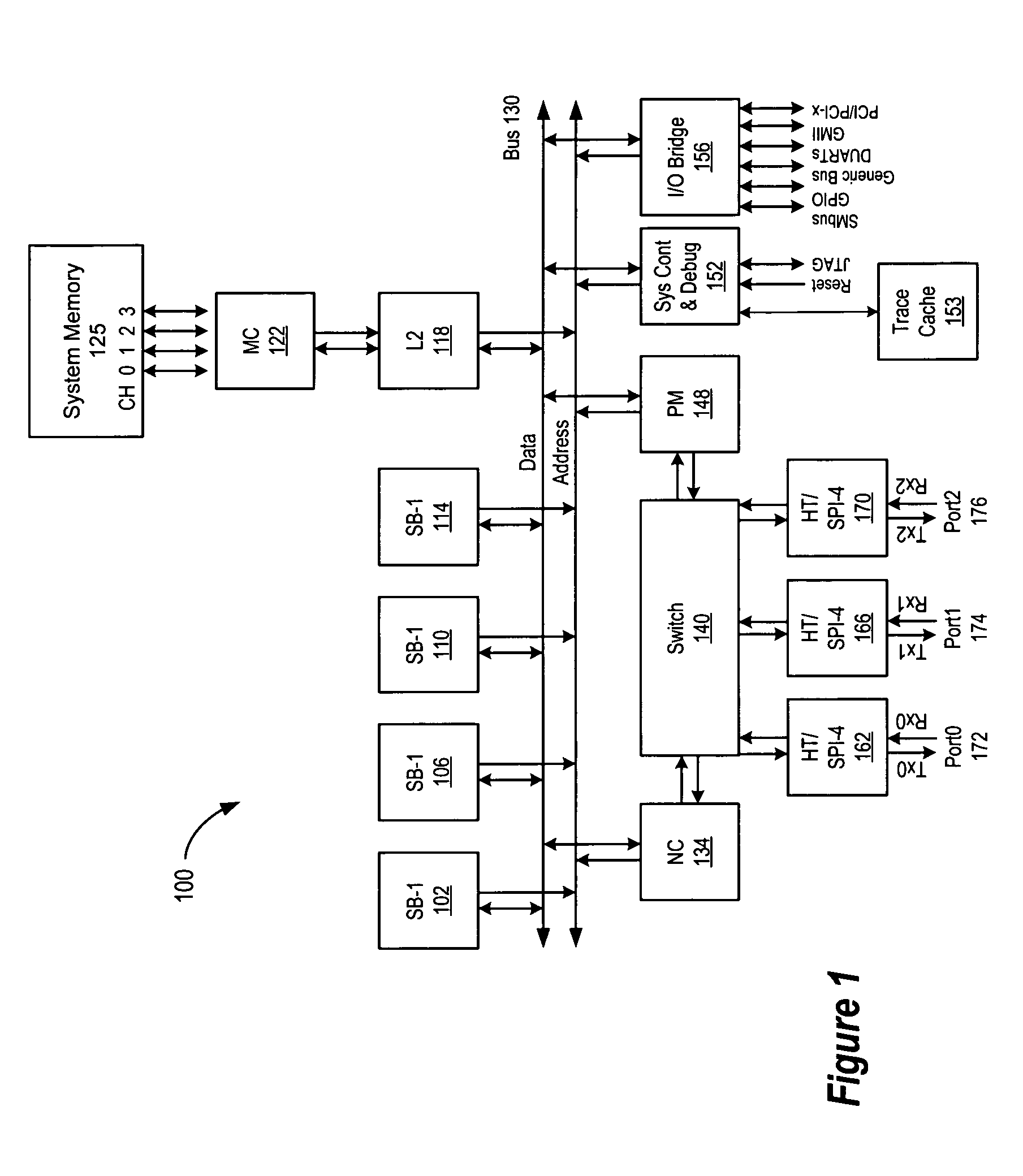
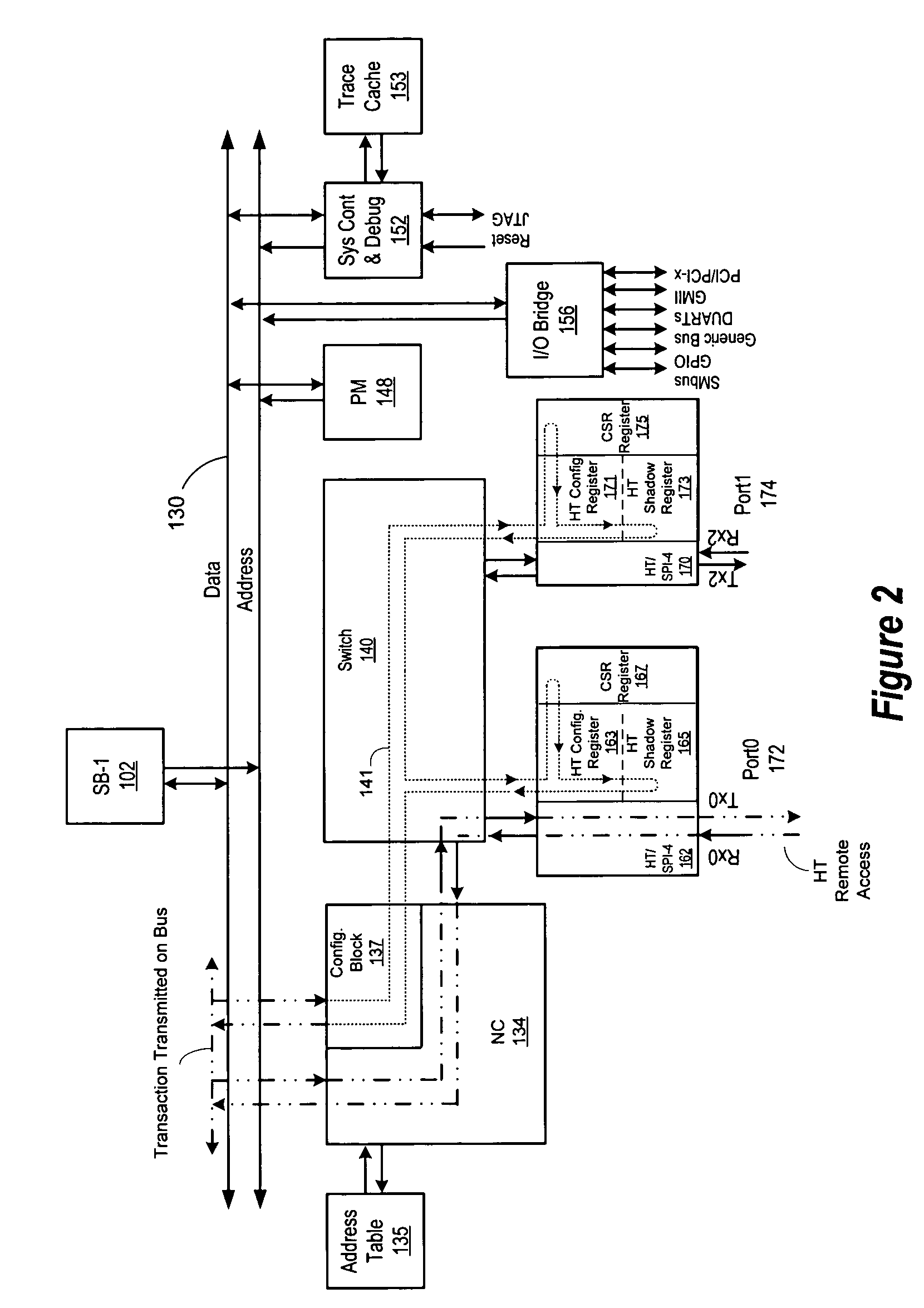
Distributed copies of configuration information using token ring
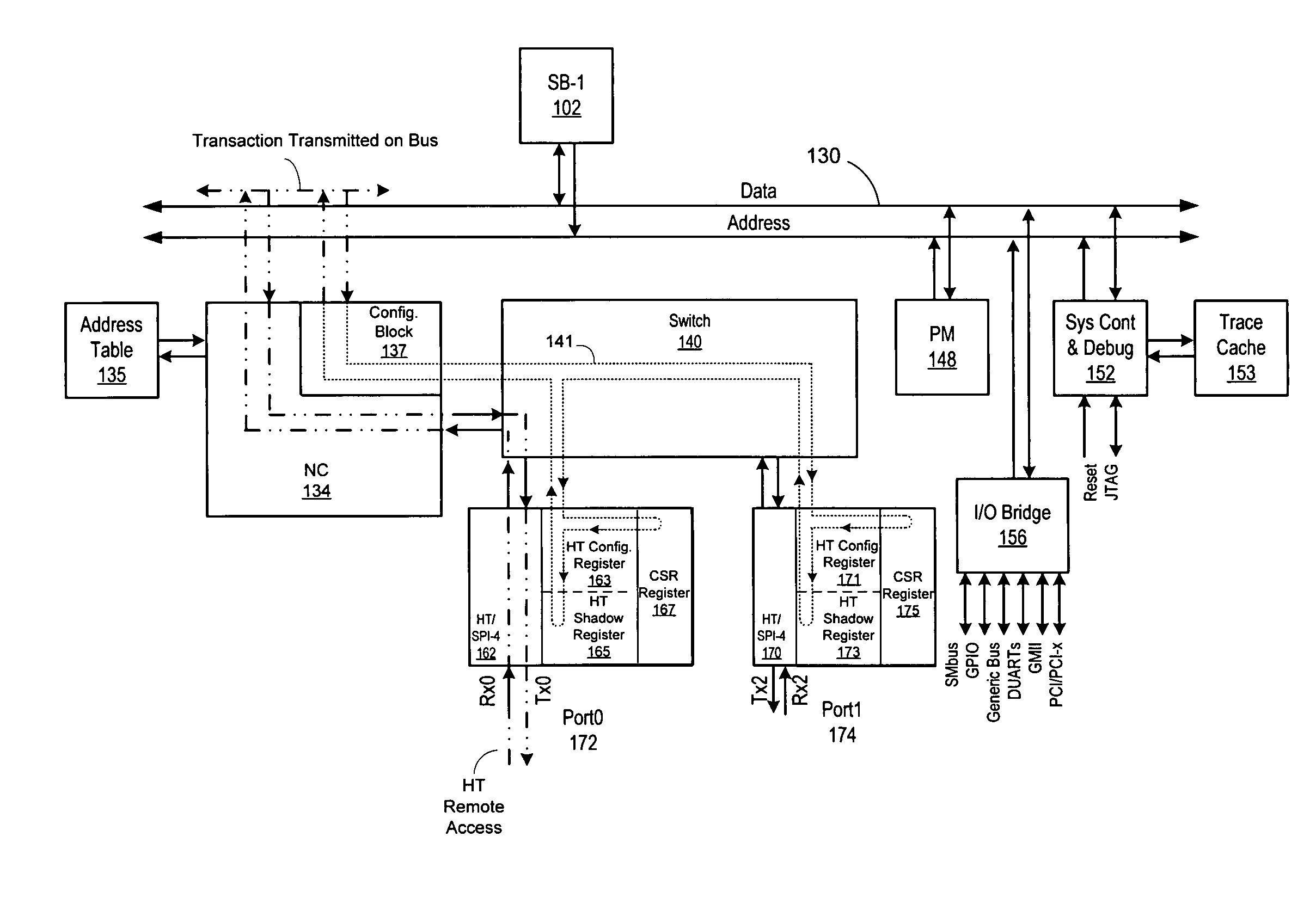
InactiveUS7131020B2Multiple digital computer combinationsGenerating/distributing signalsData processing systemProcessor register
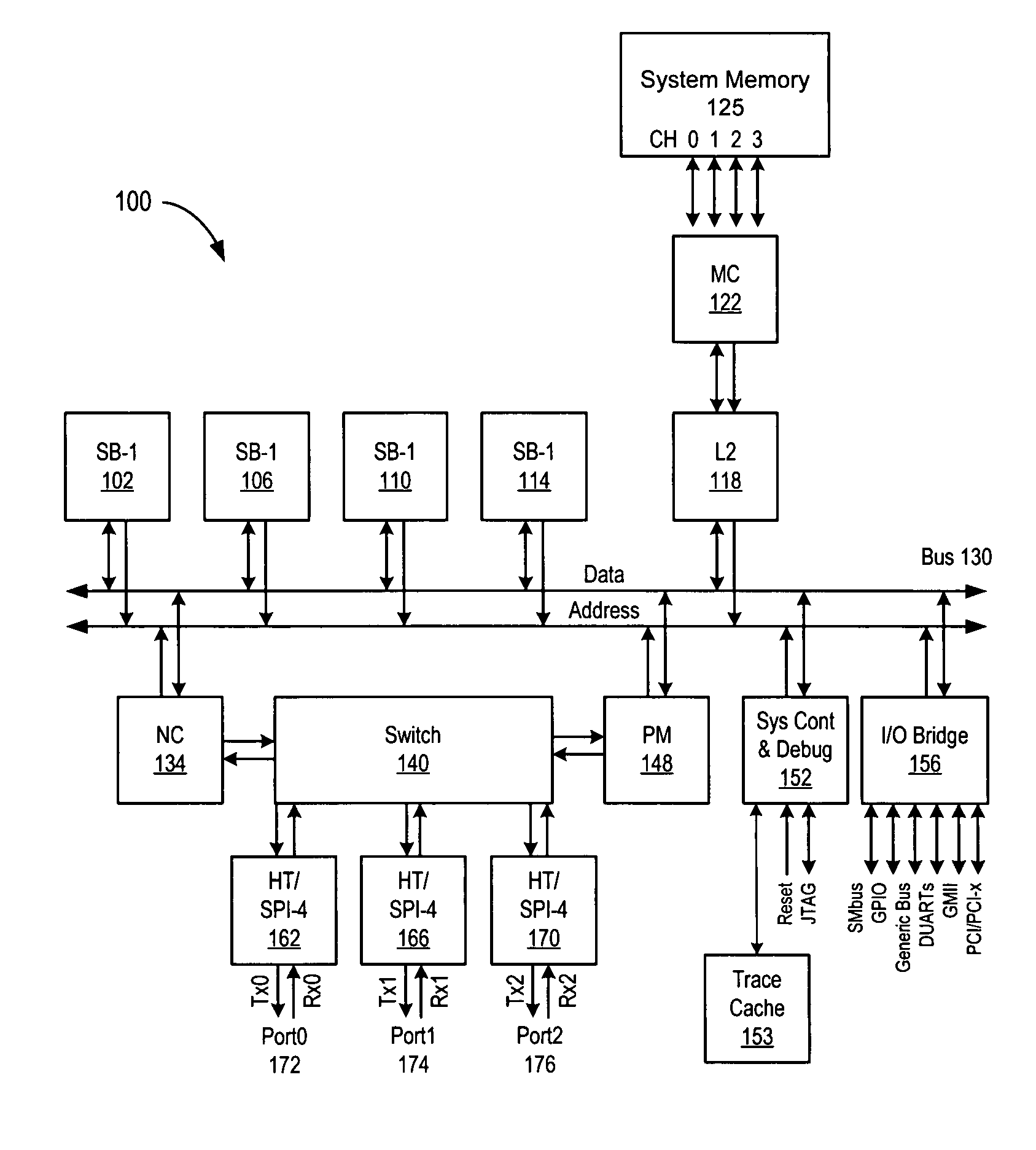
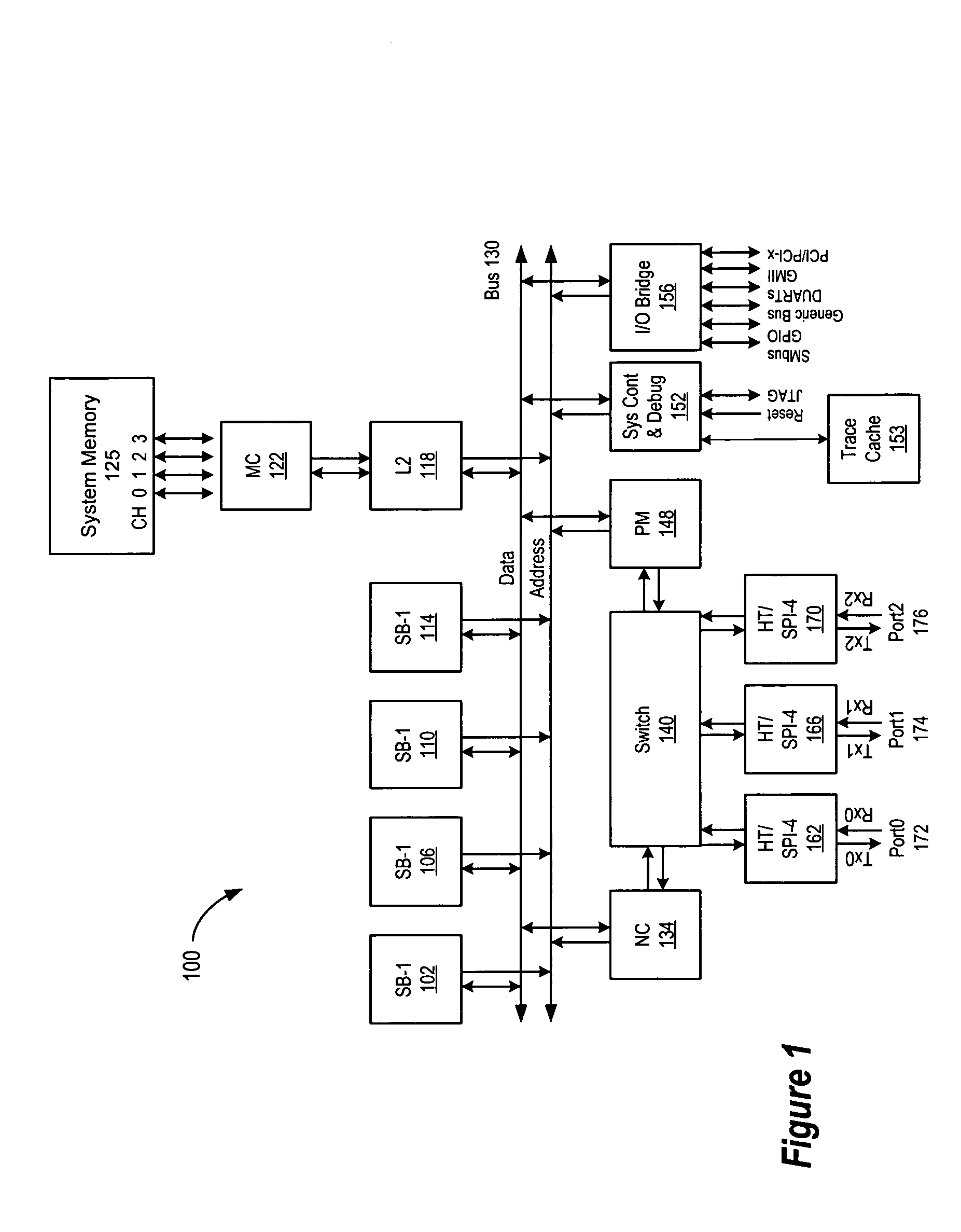
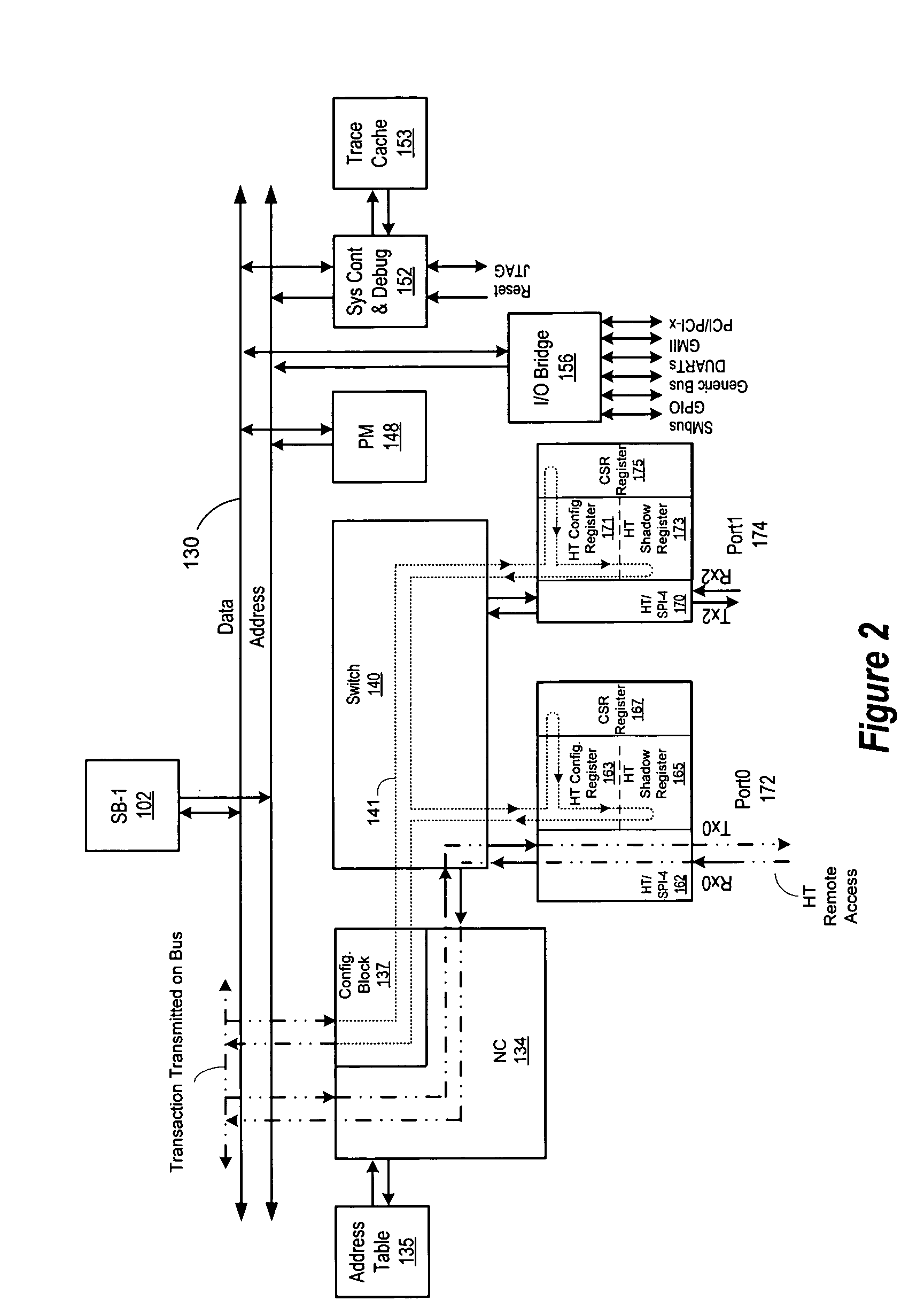
A system for synchronizing configuration information in a plurality of data processing devices using a common system interconnect bus. The present invention provides a method and apparatus for enforcing automatic updates to the configuration registers in various agents in the data processing system. A node controller is operably connected to a system interconnect bus and a switch. A plurality of interface agents are connected to the switch, with each of the interface agents comprising a configuration space register, a configuration space shadow register and a control and status register (CSR). A token ring connected to the node controller is operable to transmit data from the node controller to a plurality of interface agents connected to the token ring, thereby providing a system for updating the various configuration registers in each of the agents.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
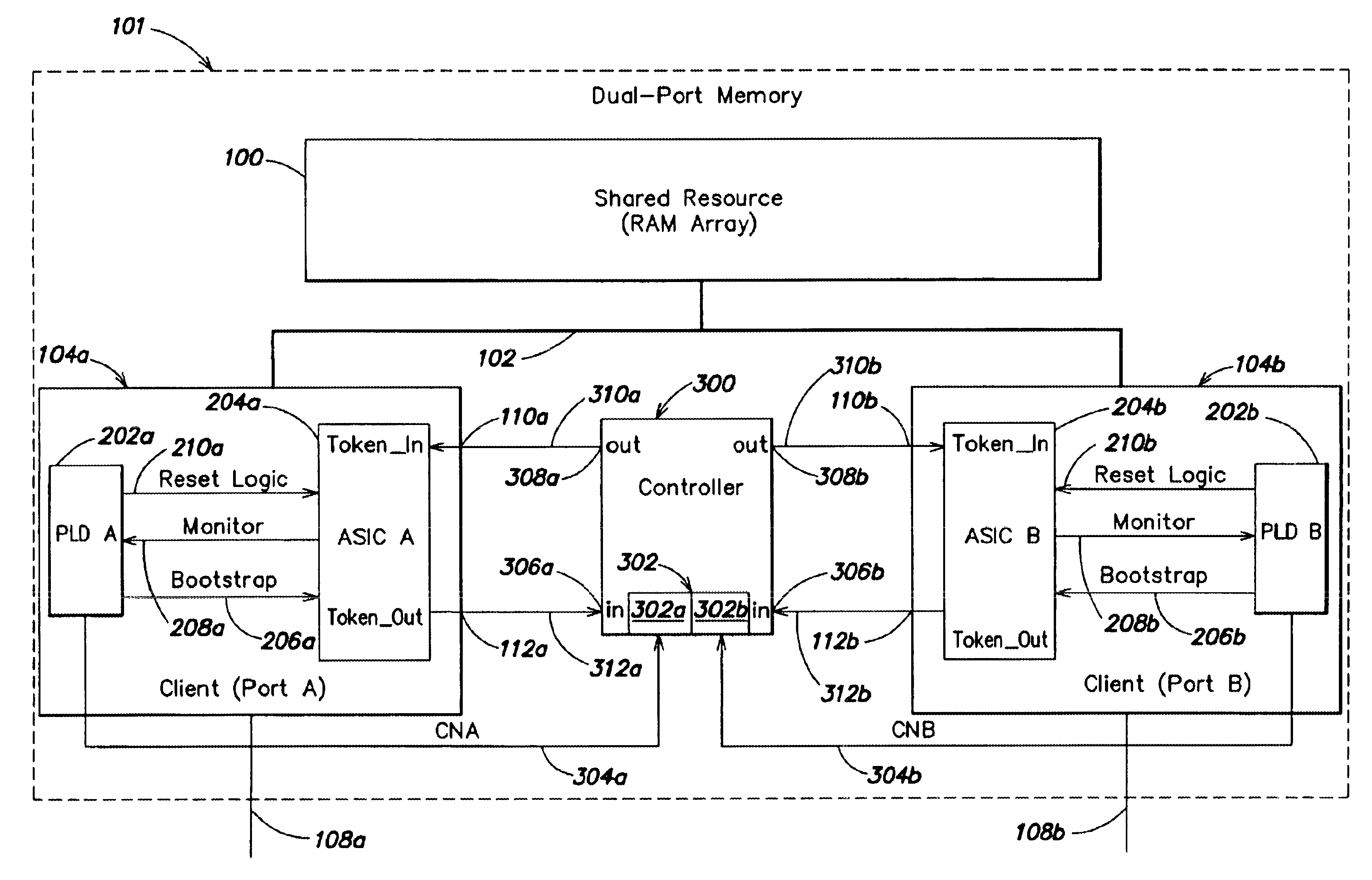
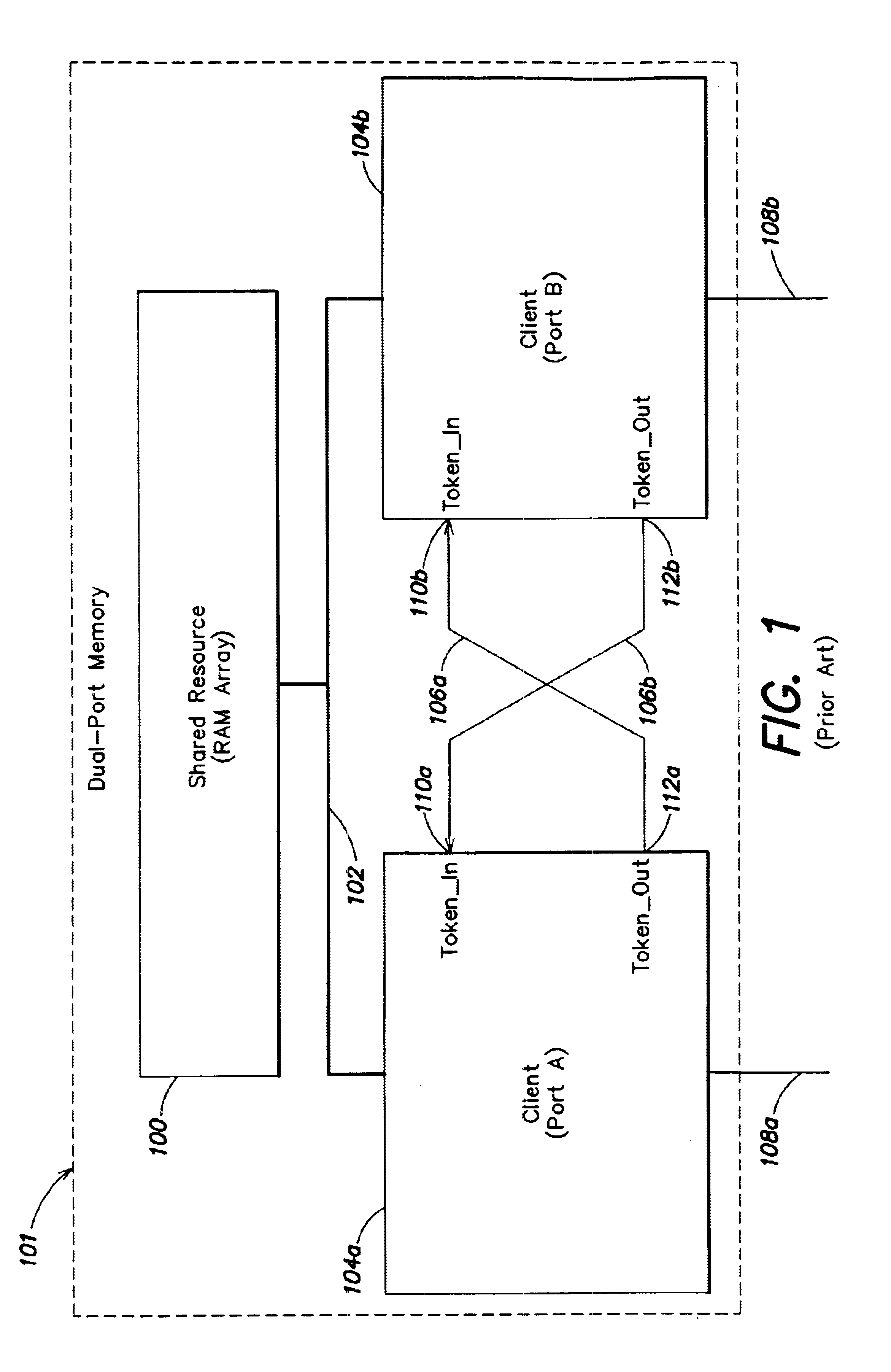
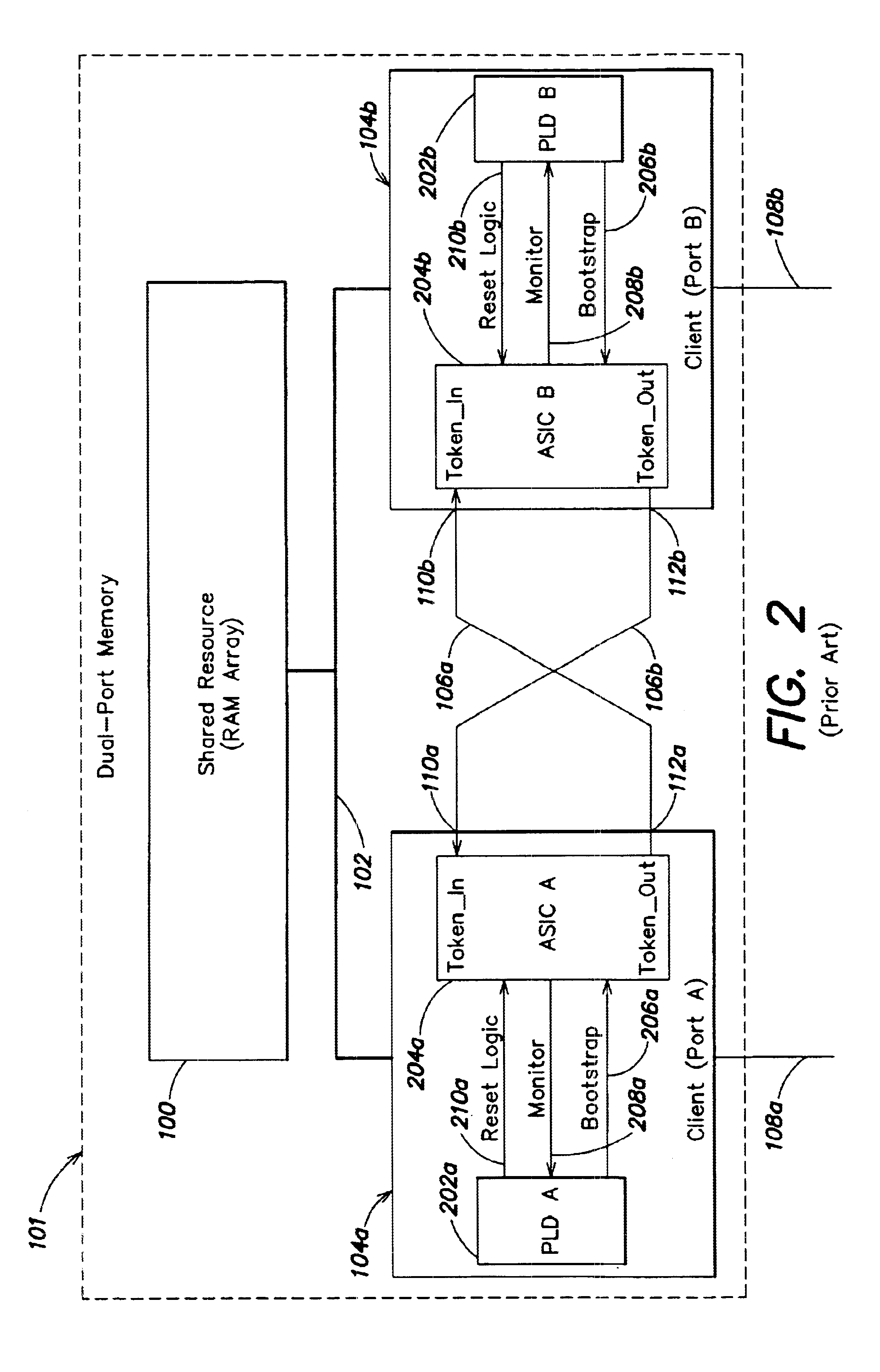
Token exchange system with fault protection
According to one embodiment, a system for controlling passing of a token among a plurality of clients that access a shared resource includes at least one controller. The at least one controller is configured to cause the token to be passed to each of the plurality of clients when the system is in a first state, and to cause the token to be passed to fewer than all of the plurality of clients when the system is in a second state. According to another embodiment, a token-ring system includes a shared resource, at least first and second clients that access the shared resource, and error detection logic. The first client includes a primary device and a secondary device which provides bootstrap information to the primary device. The error detection is configured to directly monitor the secondary device for an anomaly in the operation thereof. According to yet another embodiment, a method is disclosed for operating a multi-port memory including at least first and second memory ports that access a shared memory. The first memory port includes a primary device and a secondary device which provides bootstrap information to the primary device. The method includes steps of: (a) permitting each of the first and second memory ports to access the memory when it is in possession of a token, and (b) continuously monitoring the secondary device for an anomaly in operation thereof.
Owner:EMC IP HLDG CO LLC
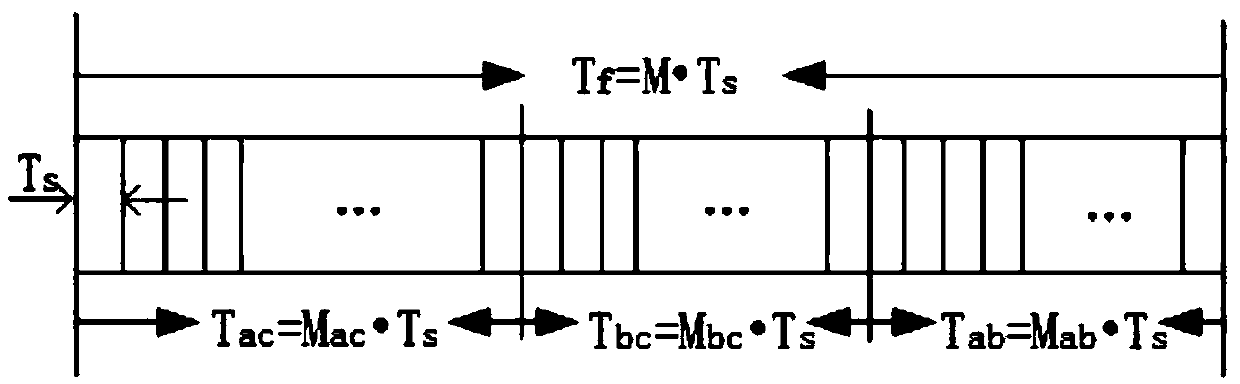
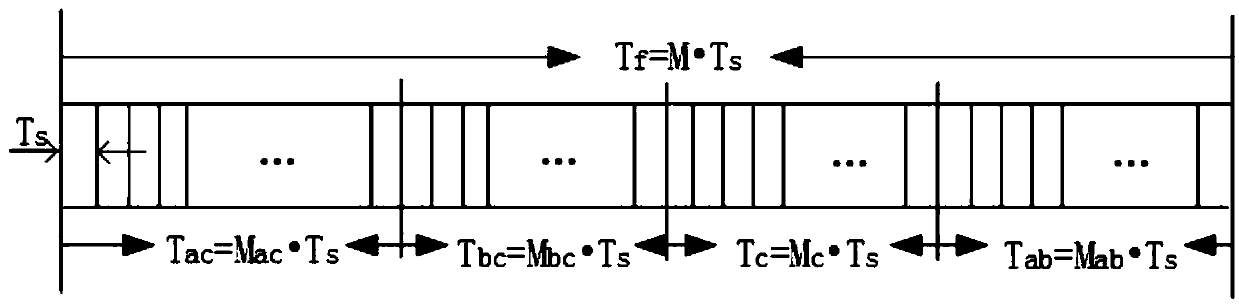
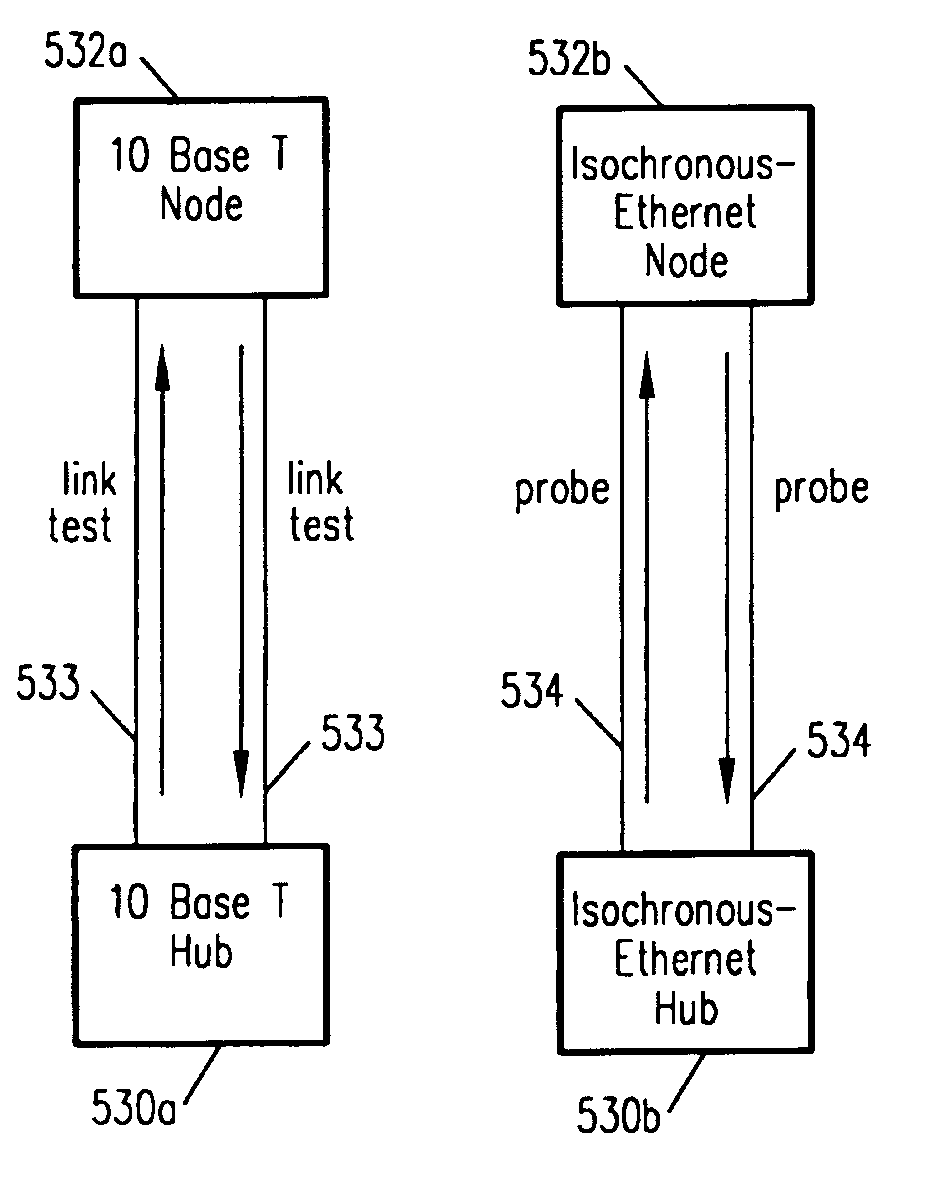
Network link detection and generation
InactiveUSRE39116E1Frequency-division multiplex detailsTime-division multiplexMix networkNetwork link
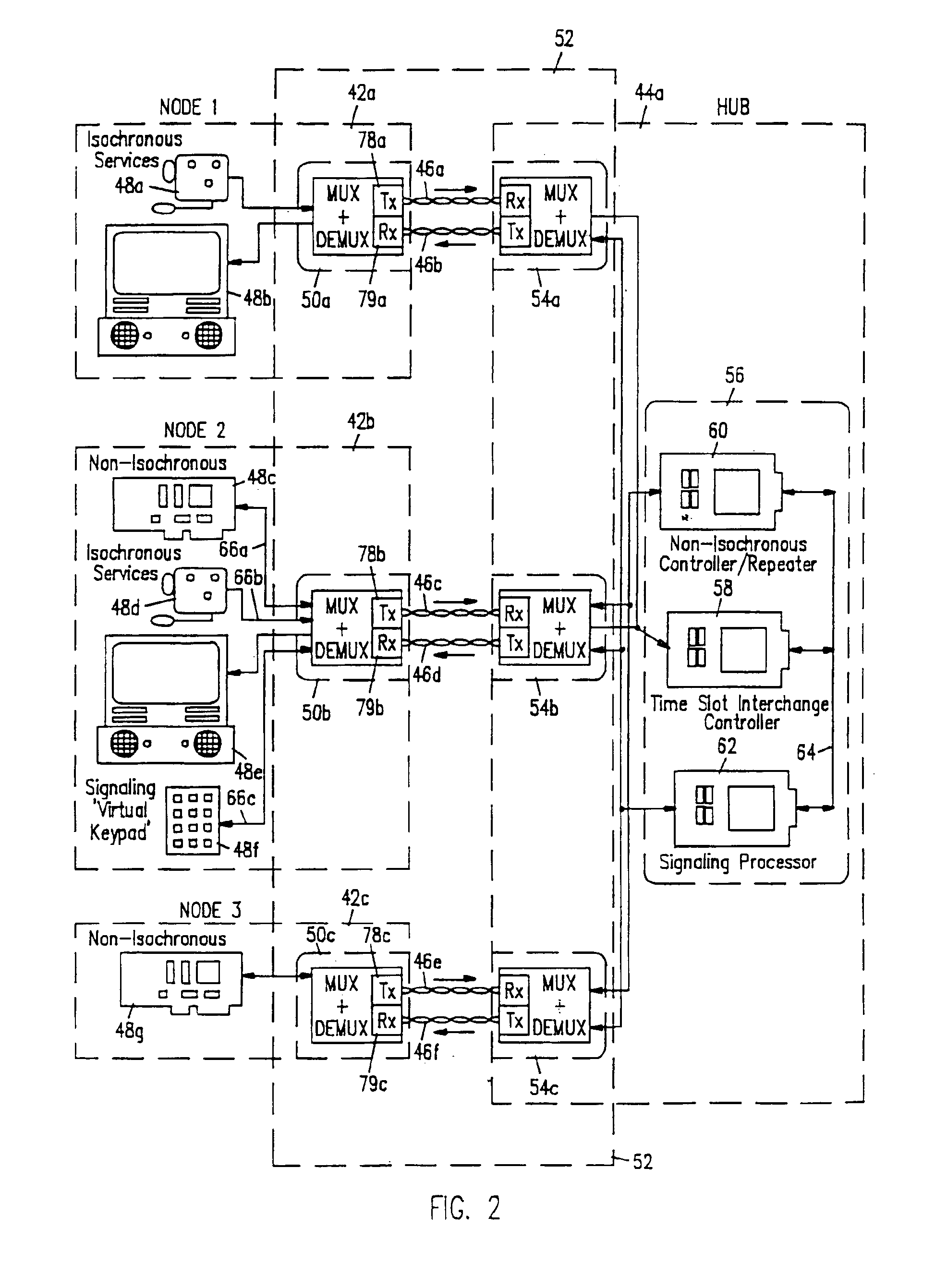
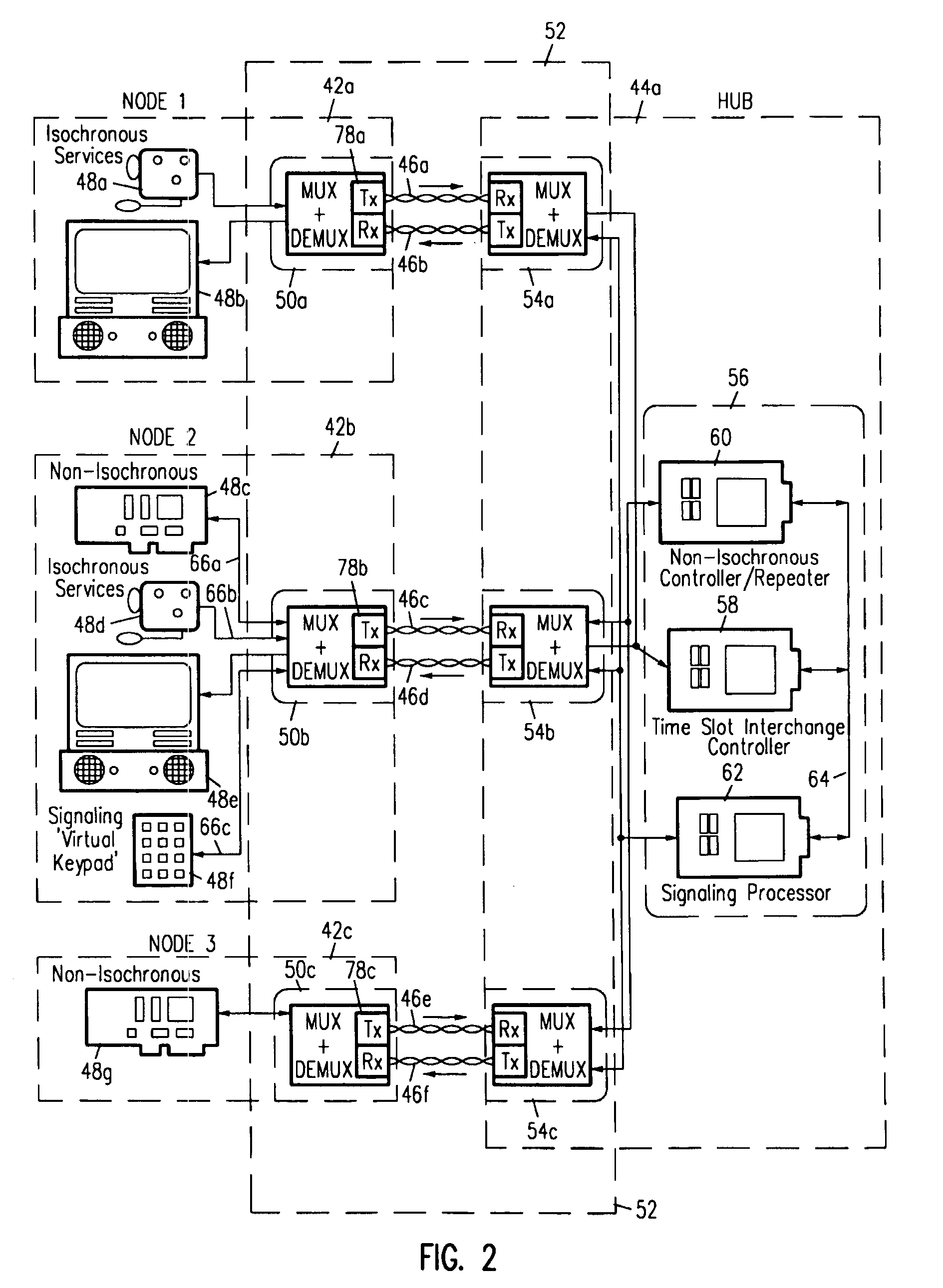
Support for a mixed network environment is provided which can contain multiple isochronous and / or non-isochronous LAN protocols such as Isochronous-Ethernet. Ethernet, isochronous-token ring, token ring, other isochronous-LAN or other LAN Systems. Support for a mixed environment includes a protocol detection mechanism which is embodied in a handshaking scheme. This handshaking scheme determines the signalling capability at the end points of the link and implements the correct protocol. This enables isochronous nodes and hubs to automatically detect the presence of Ethernet, token ring, or other LAN equipment at the other and of the network cable. If this detection occurs, the isochronous LAN equipment will fall-back to a LAN compliant mode of operation. Typically, only the hub will have the capability of operating at different networking modes, such as Ethernet, Token Ring isochronous modes. The hub will listen for some form of identification from the attached nodes as to the type of service to provide—isochronous or non-isochronous: Ethernet, token ring or other LAN service.
Owner:NEGOTIATED DATA SOLUTIONS
Distributed copies of configuration information using token ring
InactiveUS20050080941A1Multiple digital computer combinationsGenerating/distributing signalsData processing systemTransmission protocol
A system for synchronizing configuration information in a plurality of data processing devices using a common system interconnect bus. The present invention provides a method and apparatus for enforcing automatic updates to the configuration registers in various agents in the data processing system. The interface agent are not required to have target / response logic to respond to internal and external configuration accesses. In and embodiment of the present invention, a node controller, which may comprise a configuration block, is operably connected to a system interconnect bus and a switch. A plurality of interface agents are connected to the switch, with each of the interface agents comprising a configuration space register, a configuration space shadow register and a control and status register (CSR). A token ring connected to the node controller is operable to transmit data from the node controller to a plurality of interface agents connected to the token ring, thereby providing a system for updating the various configuration registers in each of the agents. A transaction from an interface agent is transferred to the node controller which transfers the transaction onto the system interconnect bus. The transaction on the system interconnected bus is detected by the configuration block of the node controller and is then transmitted on the token ring to each of the agents connected thereto. The information transmitted on the token ring is used to update the information in the configuration space registers and configuration space shadow registers of each of the agents connected to the token ring. In an embodiment of the invention the interface agents are configured in accordance with the Hypertransport protocol. In this embodiment, the configuration comprises a HT configuration space register and the configuration space shadow register comprise a HT configuration space shadow register.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
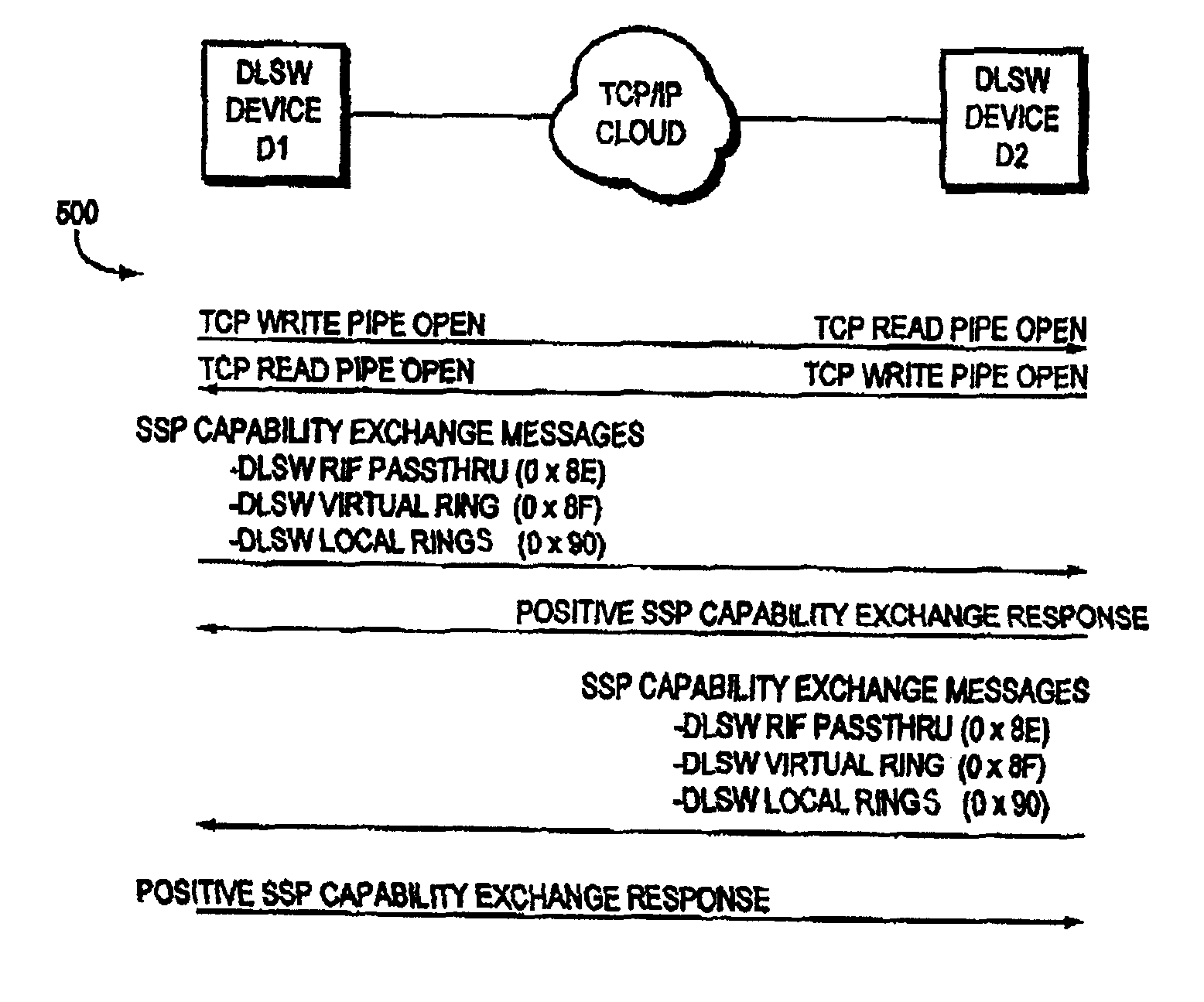
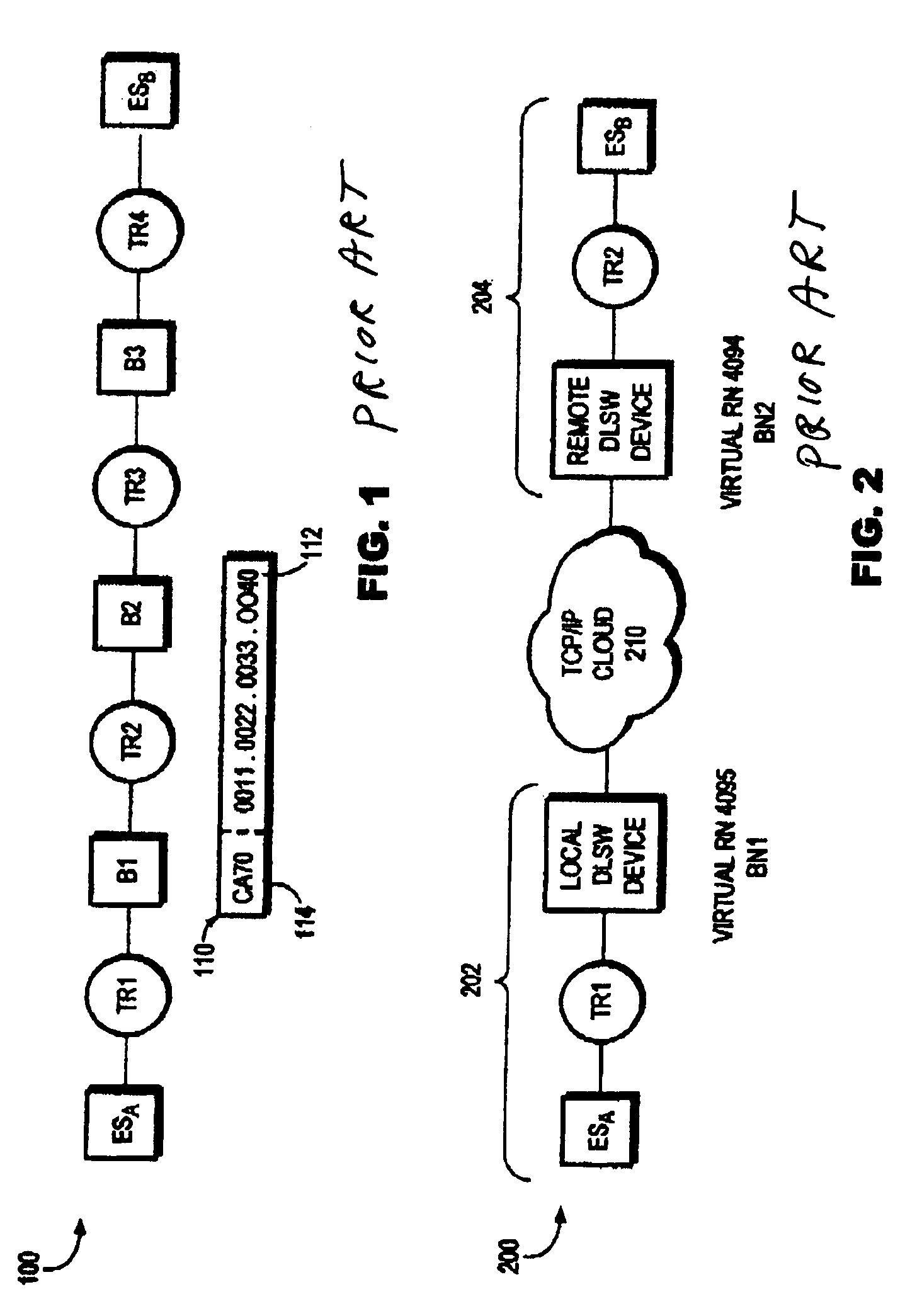
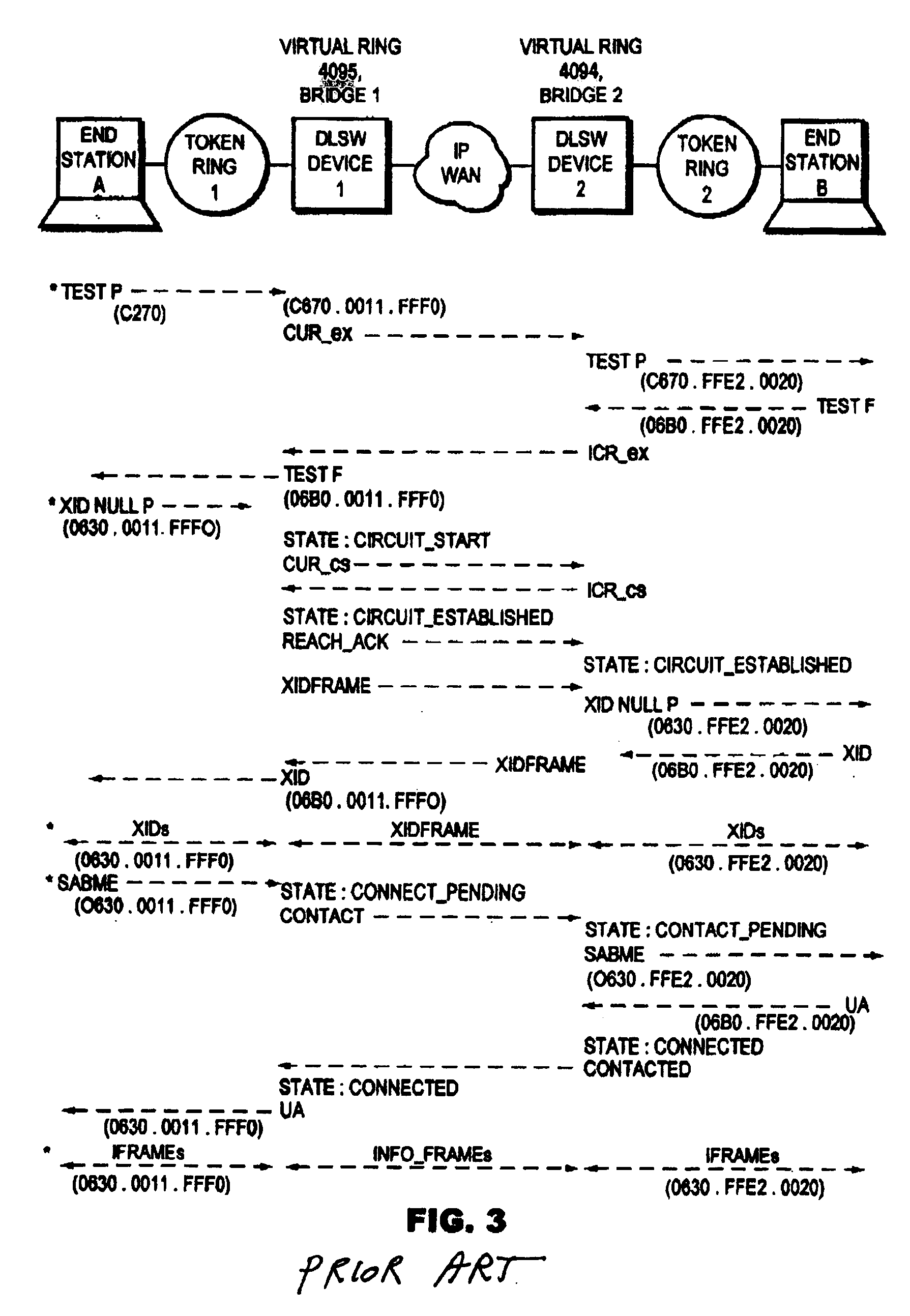
DLSw RIF passthru technique for providing end-to-end source route information to end stations of a data link switching network
A data link switching (DLSw) routing information field (RIF) passthru technique provides end-to-end source route information to source and destination endstations coupled to respective local and remote source-route bridge (SRB) subnetworks of a DLSw network. The local and remote SRB subnetworks include respective local and remote DLSw peer switches that communicate over an intermediate wide area nework to form the DLSw network. The source route information describes a complete path between the source endstation and the local DLSw switch on the local SRB subnetwork, and the remote DLSw switch and destination endstation on the remote SRB subnetwork. The DLSw RIF passthru technique enables token ring frame exchanges between the source and destination endstations with end-to-end source route information that is transparently forwarded between the DLSw peer switches.
Owner:CISCO TECH INC
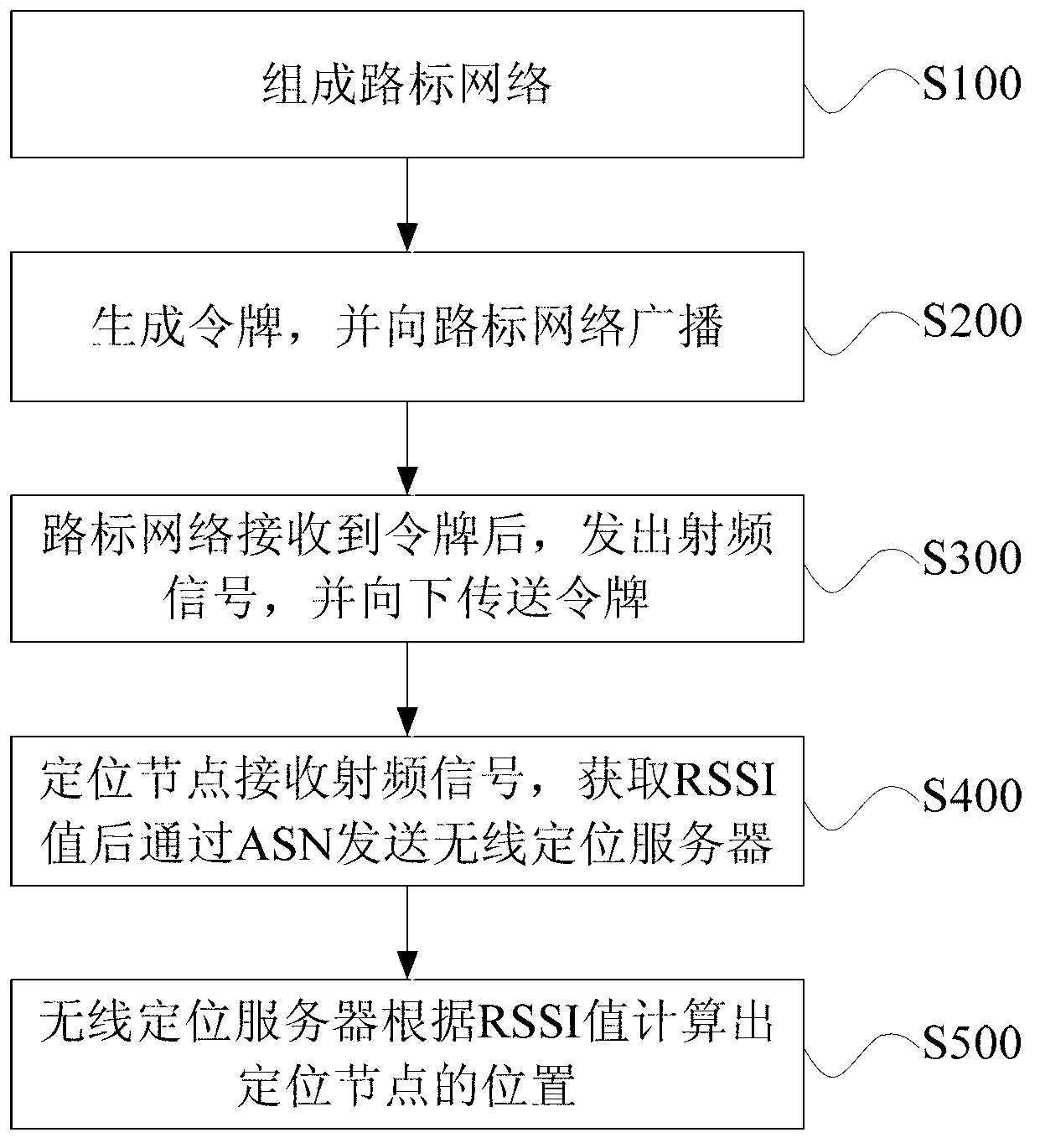
Method and system for radio frequency location based on token ring under Internet of things environment
The invention discloses a method and system for radio frequency location based on a token ring under an Internet of things environment. The method comprises the steps that a road sign network is composed of road sign nodes in a locating zone; after a token is generated by ASN, the token is broadcasted to the road sign network through a downlink channel; after the token is obtained by the road sign nodes in the road sign network, radio frequency signals are sent to locating nodes entering the locating zone through the downlink channel and the token is sent out; the radio frequency signals sent by the road sign nodes are received by the locating nodes, an RSSI value of each road sign node is obtained and sent to an ASN through an uplink channel, and each RSSI value is sent to a wireless locating server through the Internet by the ASN; the positions of the locating nodes are calculated through the wireless locating server according to the received RSSI values. The token is maintained by the ASN and transmitted among the road sign nodes, locating frames can be sent only after the token is obtained by the road sign nodes, and conflict is effectively avoided when data are sent among the road sign nodes.
Owner:WUHAN UNIV OF TECH +1
Radio with internal packet network
The invention relates to a programmable radio having an internal packet network for communicating between the functional modules of the radio. Modules may have a network controller, a network connector, memory for storing the instructions and processors to execute the instructions to implement the functional aspects of the radio, such as signal reception and conversion, internal data routing and output signal transmission. The network may be configured as a bus, a daisy chain or a central hub, and may be implemented using twisted pair, cable, fiber, or a wireless link. The network itself may use standard network protocols applicable to Ethernets, asynchronous transfer mode networks, token ring networks, resilient packet ring networks, or other similar “internet” networks.
Owner:RAYTHEON BBN TECH CORP
Token ring based Adhoc network MAC layer channel access and resource reservation method
InactiveCN108834182AReduce conflictImprove throughputNetwork traffic/resource managementAlgorithmData transmission
The invention relates to a token ring based Adhoc network MAC layer channel access and resource reservation method. The method specifically includes: time slot resources are divided into superframes,each superframe is divided into four subframes, and the data transmission direction of each subframe is specified so as to avoid the influence of hidden terminals; and an optimization model is established, the number of time slots and the total number of time slots of each subframe are obtained through a time slot number optimization algorithm, and comparatively small end-to-end delay is obtained.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI +1
Network link endpoint capability detection
Support for a mixed network environment is provided which can contain multiple isochronous and / or non-isochronous LAN protocols such as isochronous-ethernet, ethernet, isochronous-token ring, token ring, other isochronous-LAN or other LAN systems. Support for a mixed environment includes a protocol detection mechanism which is embodied in a handshaking scheme. This handshaking scheme determines the signalling capability at the end points of the link and implements the correct protocol. This enables isochronous nodes and hubs to automatically detect the presence of ethernet, token ring, or other LAN equipment at the other end of the network cable. If this detection occurs, the isochronous LAN equipment will fall-back to a LAN compliant mode of operation. Typically, only the hub will have the capability of operating in different networking modes, such as ethernet, Token Ring isochronous modes. The hub will listen for some form of identification from the attached nodes as to the type of service to provide—isochronous or non-isochronous; ethernet, token ring or other LAN service.
Owner:NEGOTIATED DATA SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com