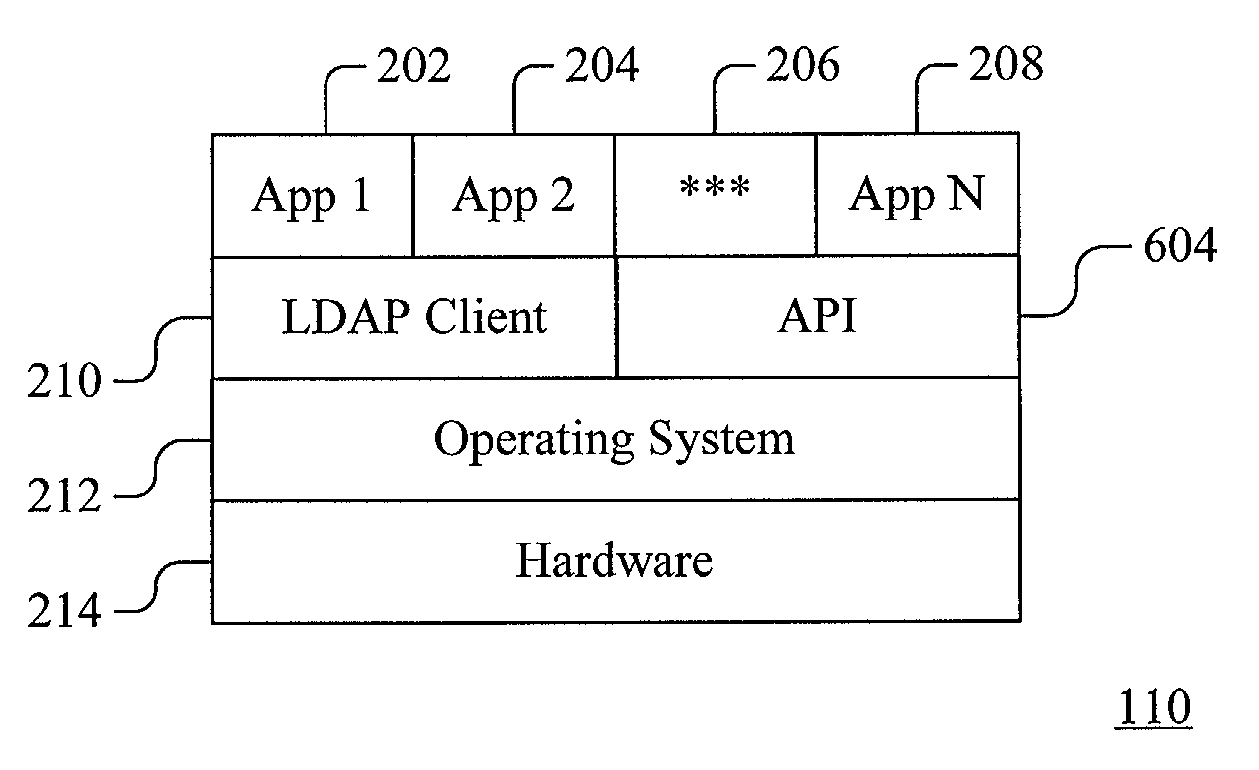
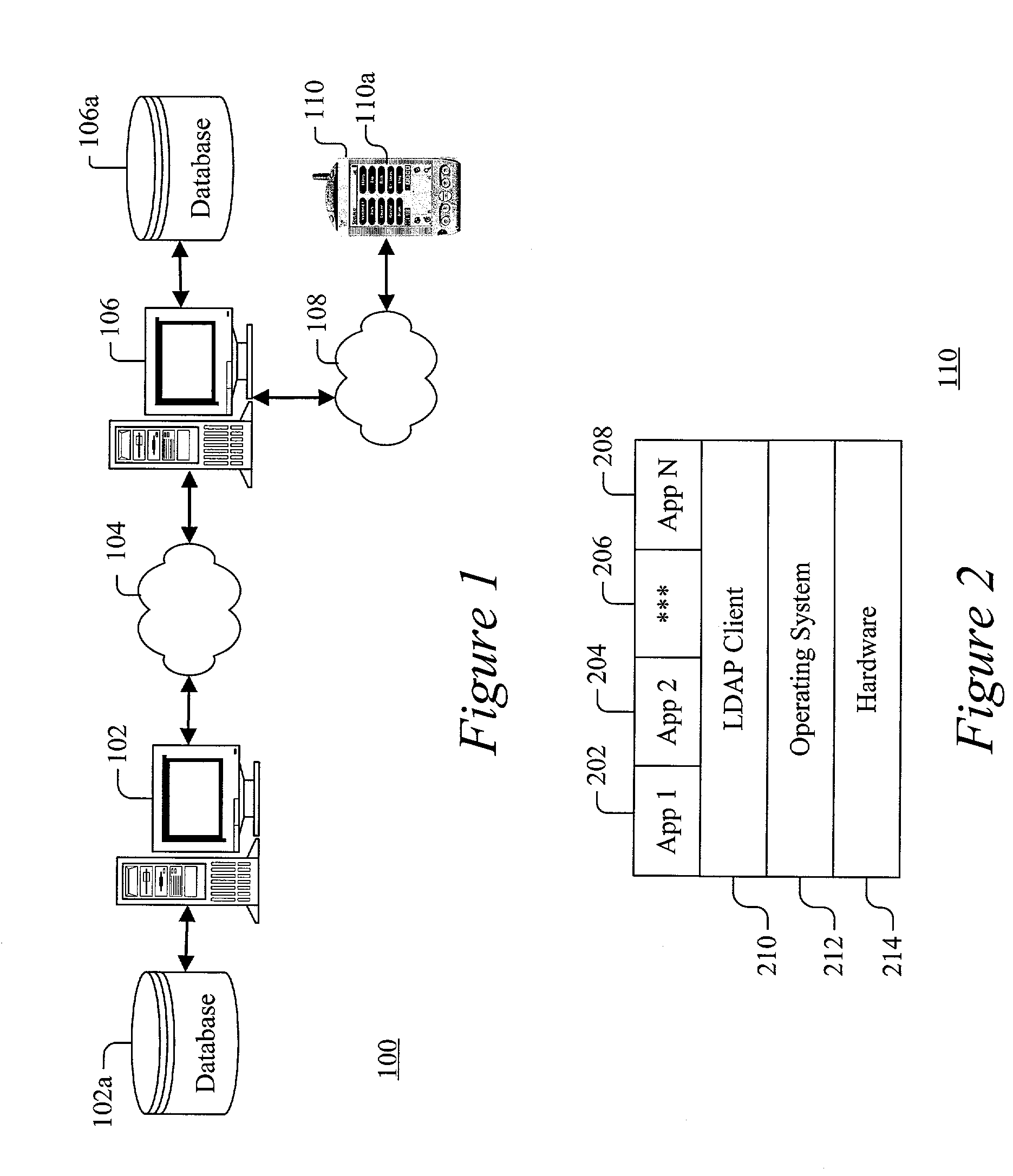
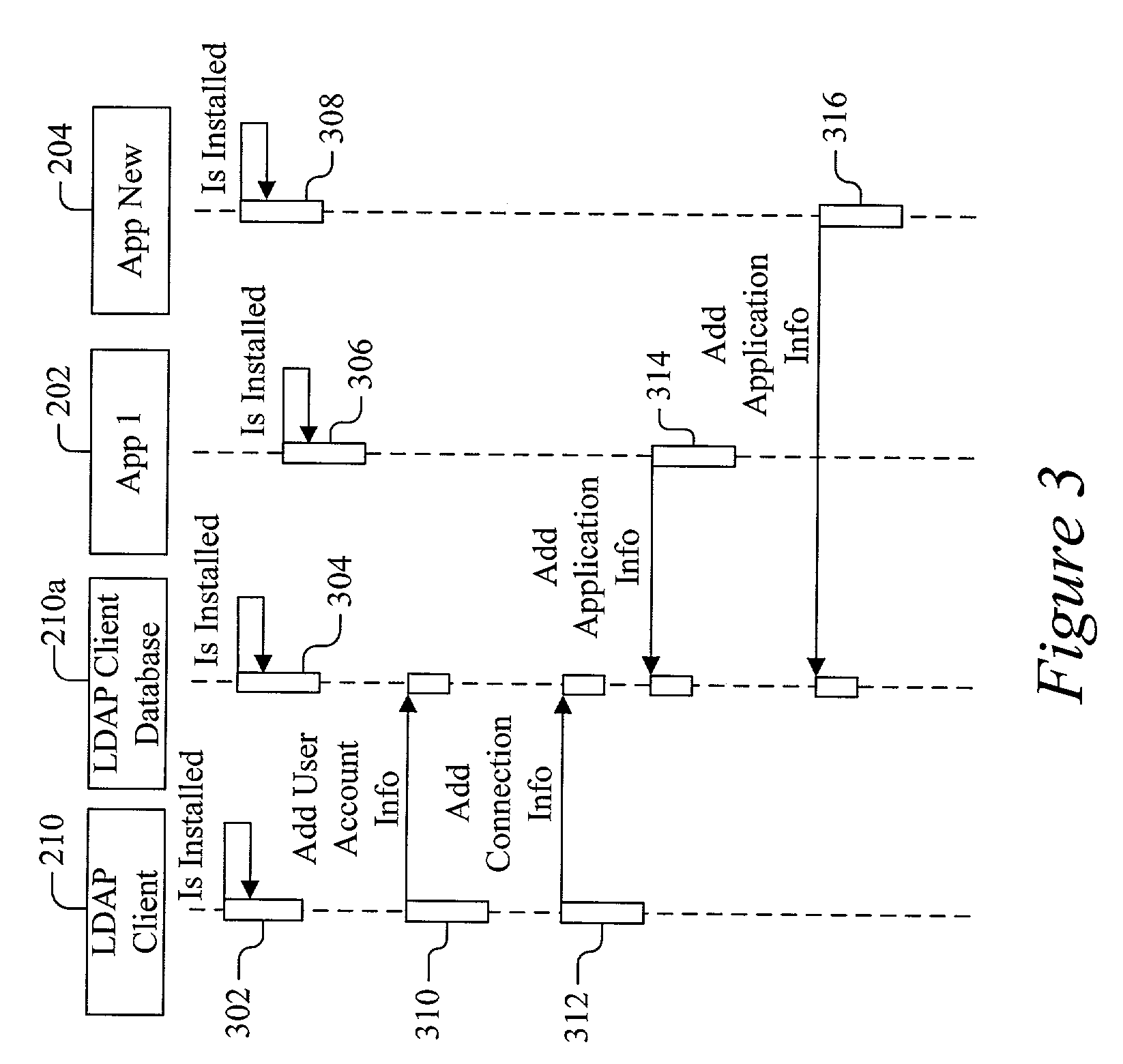
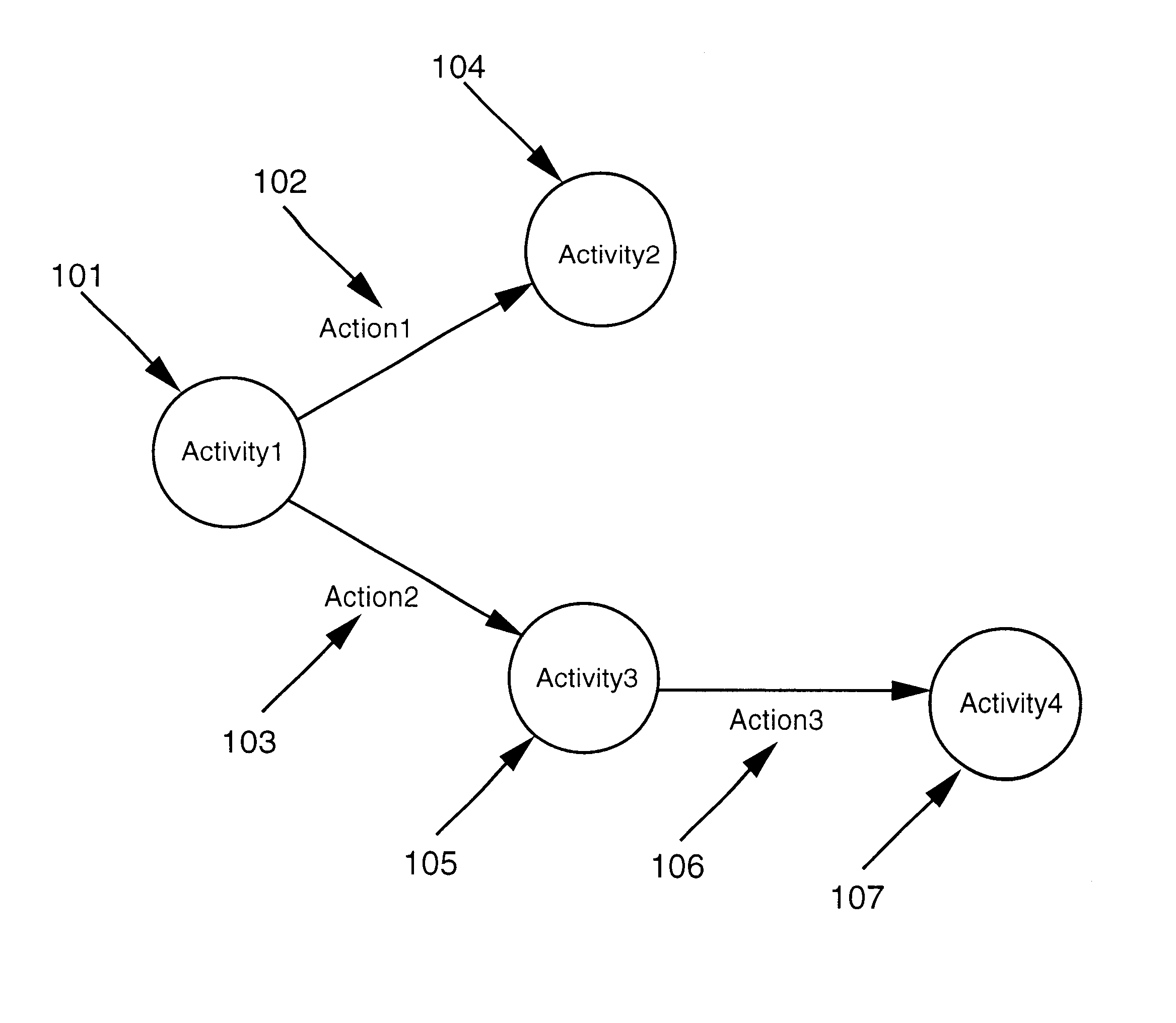
Patents
Literature
91 results about "Directory Access Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
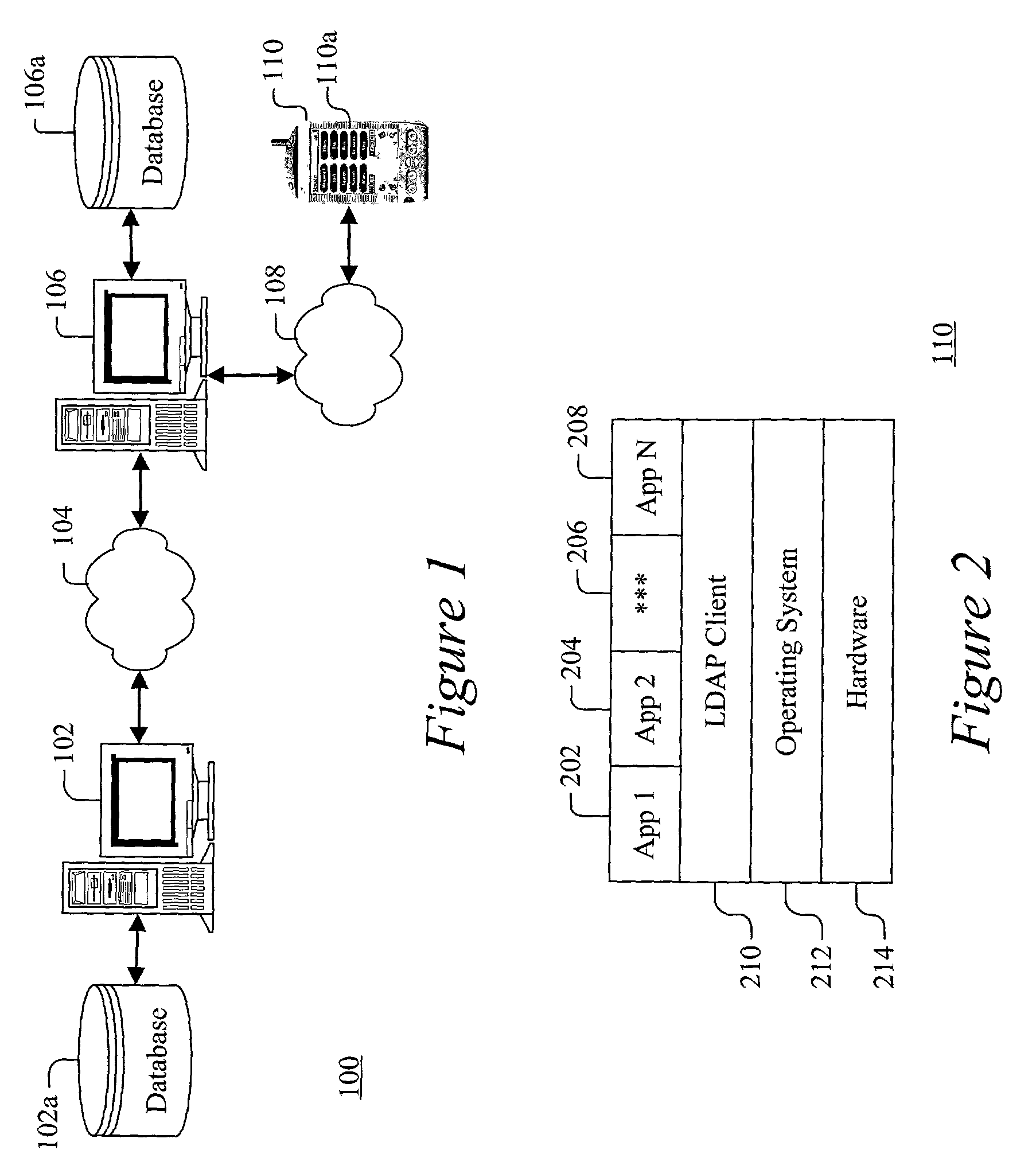
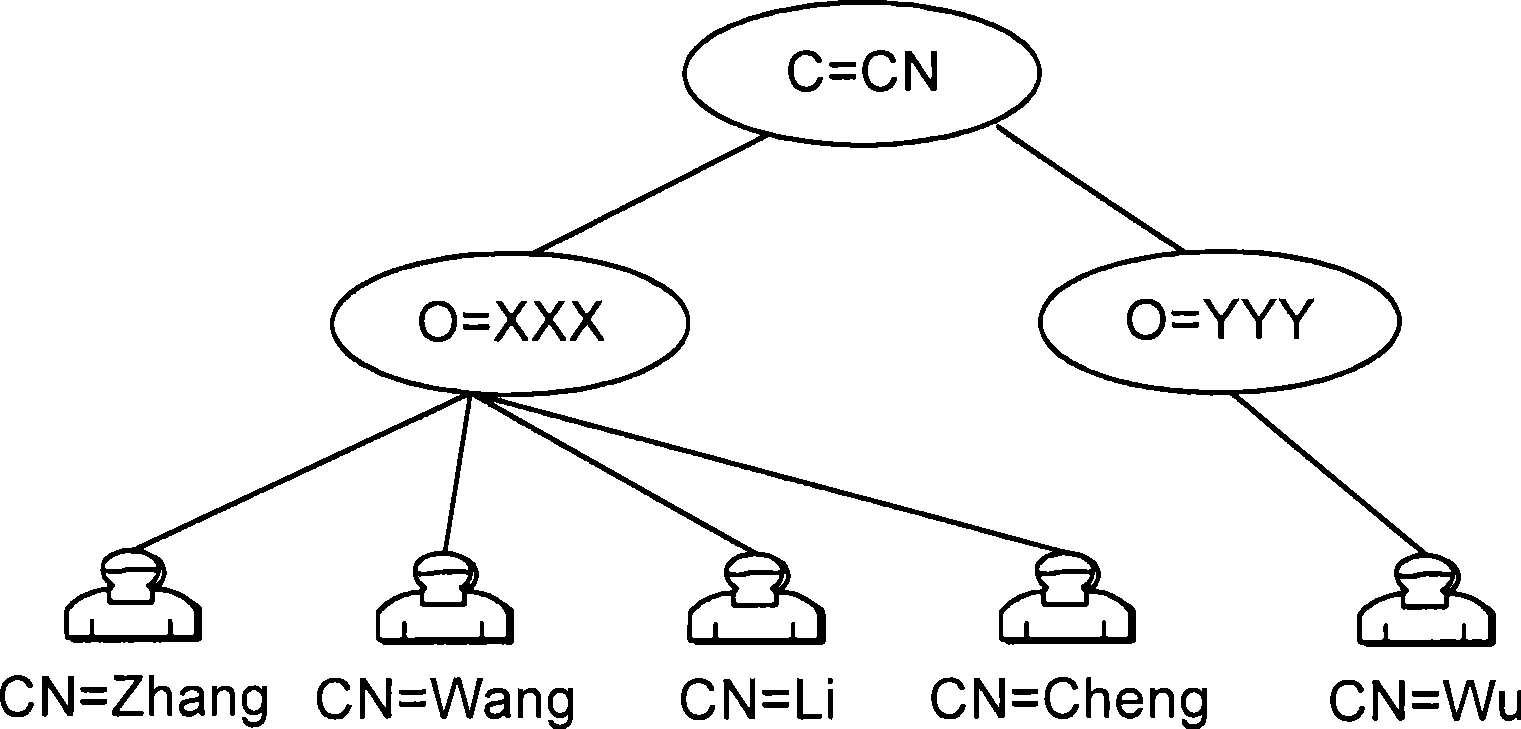
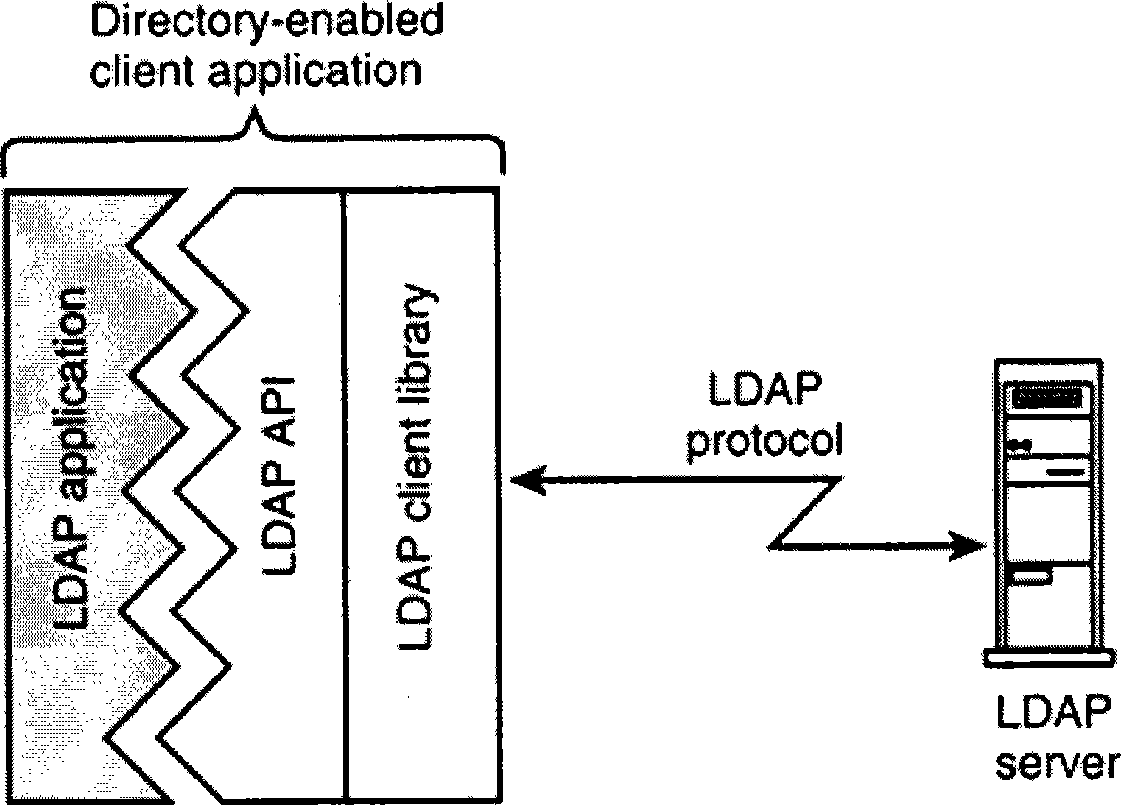
Directory Access Protocol (DAP) is a computer networking standard promulgated by ITU-T and ISO in 1988 for accessing an X.500 directory service. DAP was intended to be used by client computer systems, but was not popular as there were few implementations of the full OSI protocol stack for desktop computers available to be run on the hardware and operating systems typical of that time. The basic operations of DAP: Bind, Read, List, Search, Compare, Modify, Add, Delete and ModifyRDN, were adapted for the Novell Directory Services (NDS) and the Internet Lightweight Directory Access Protocol (LDAP).
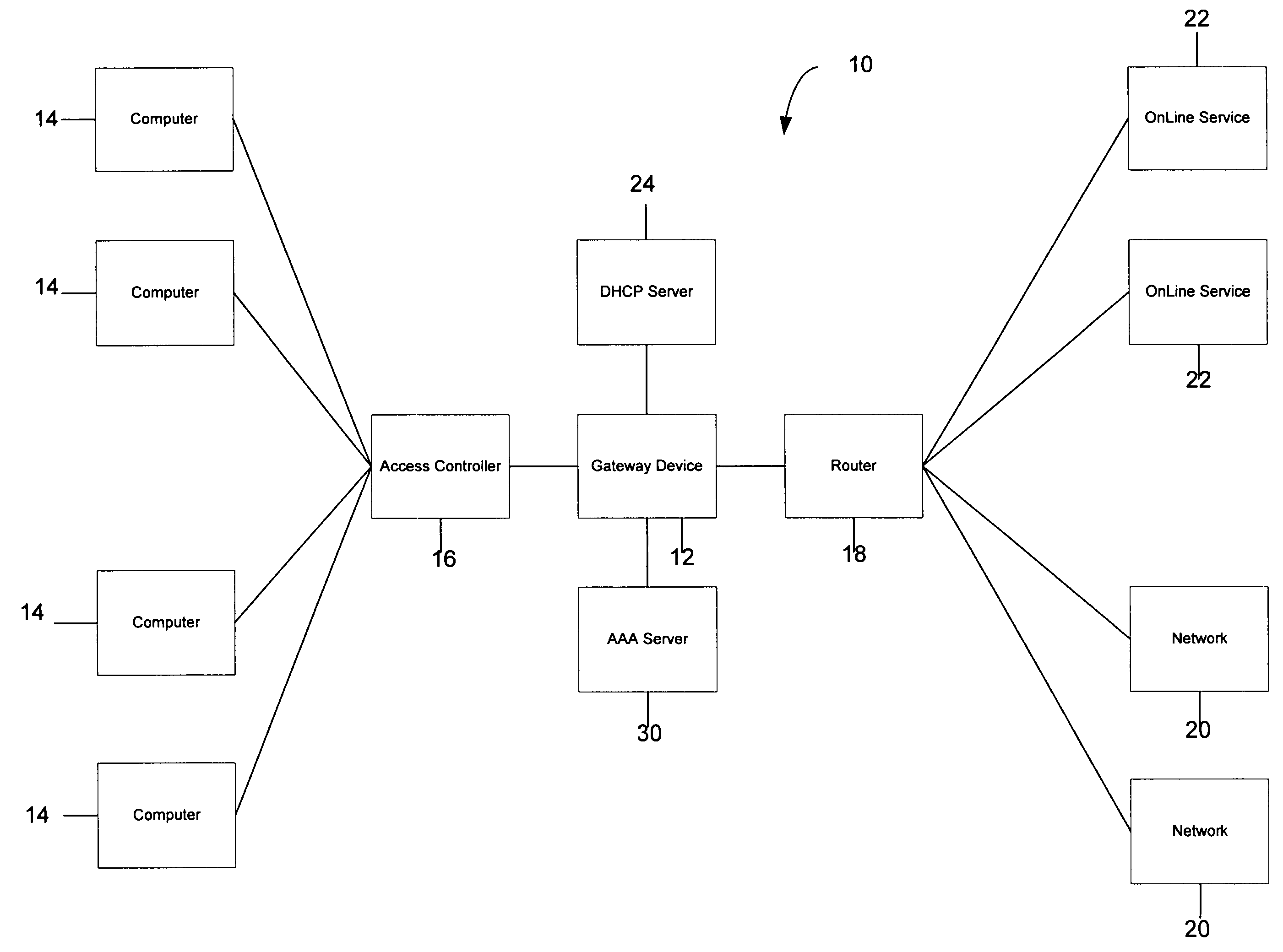
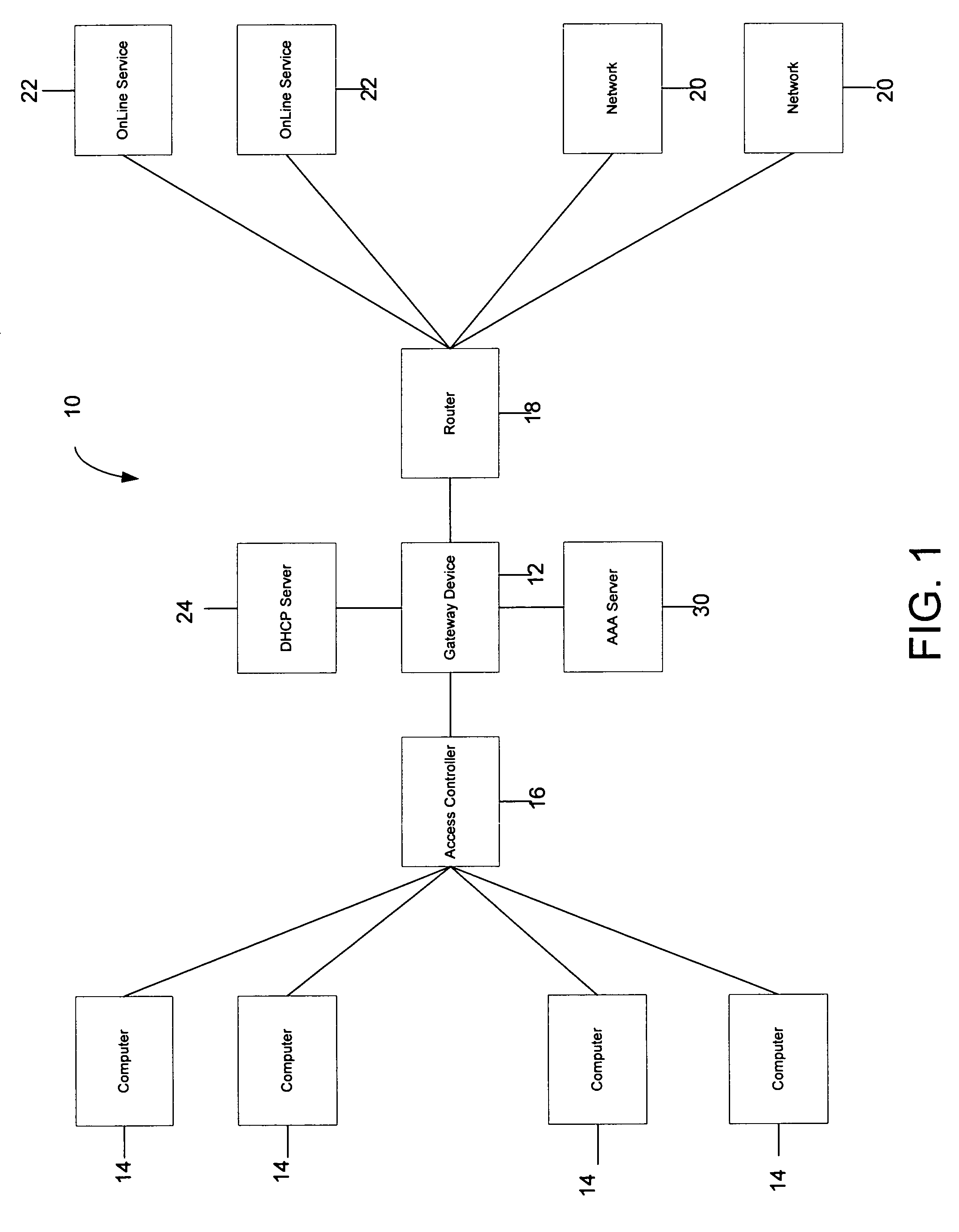
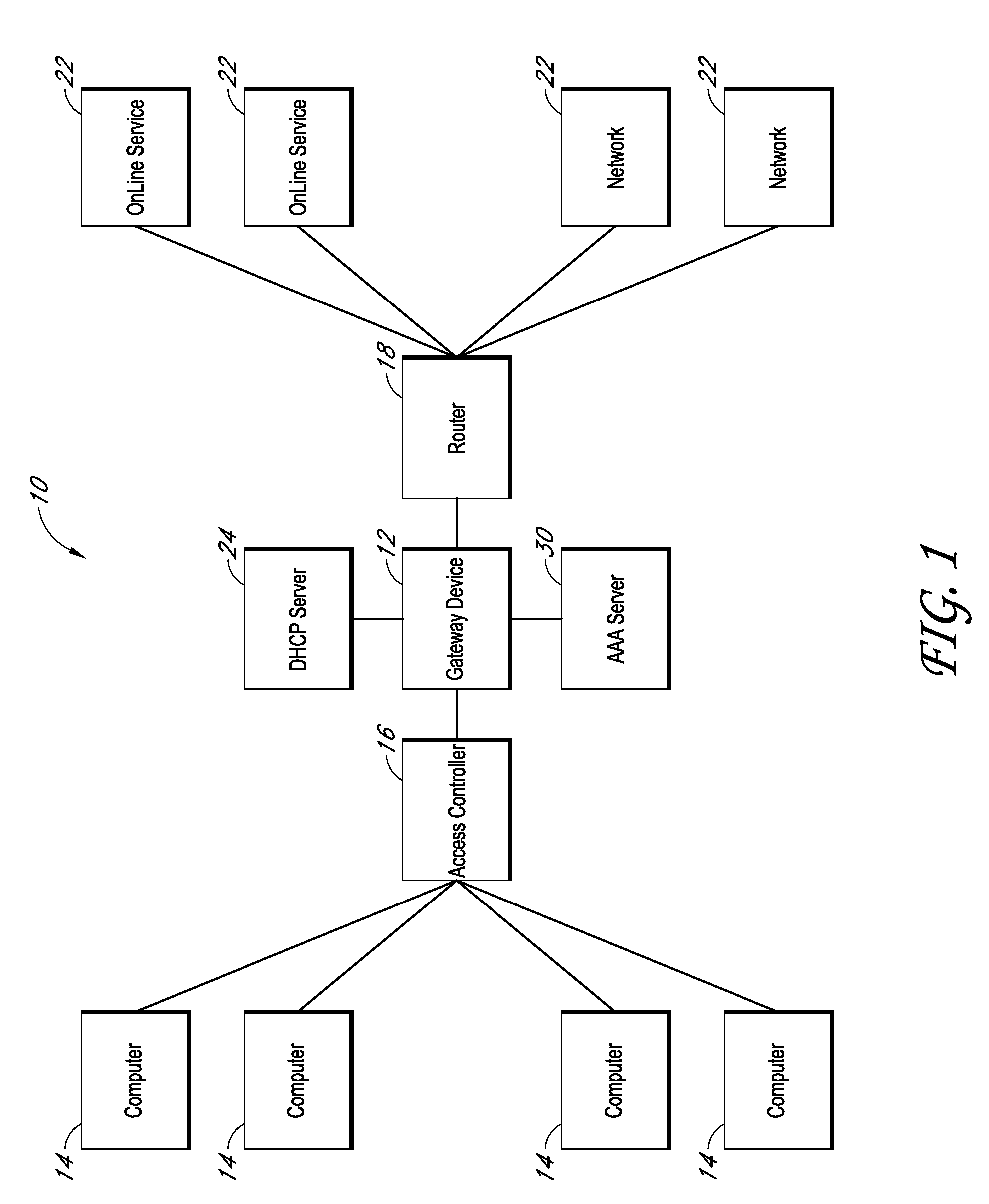
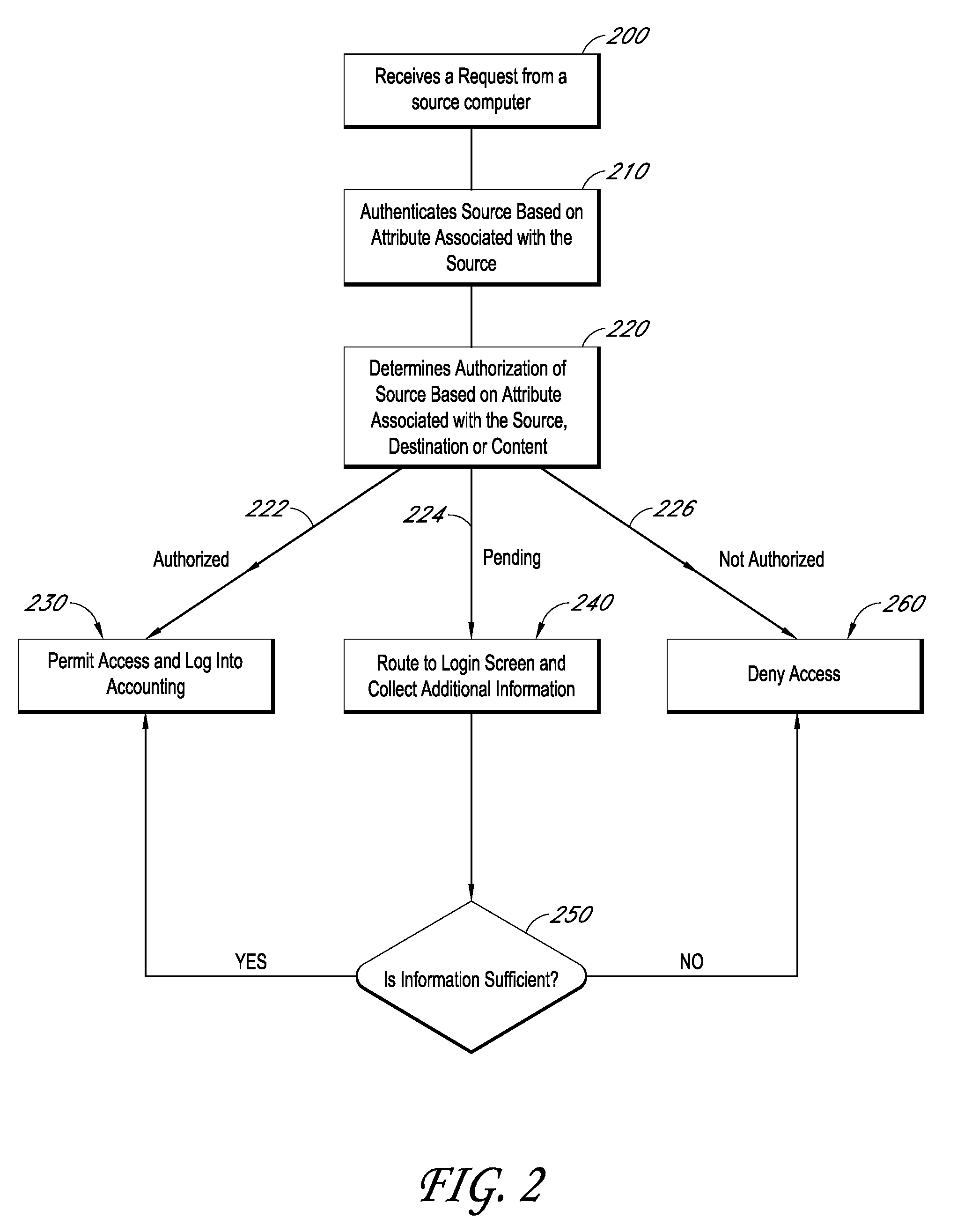
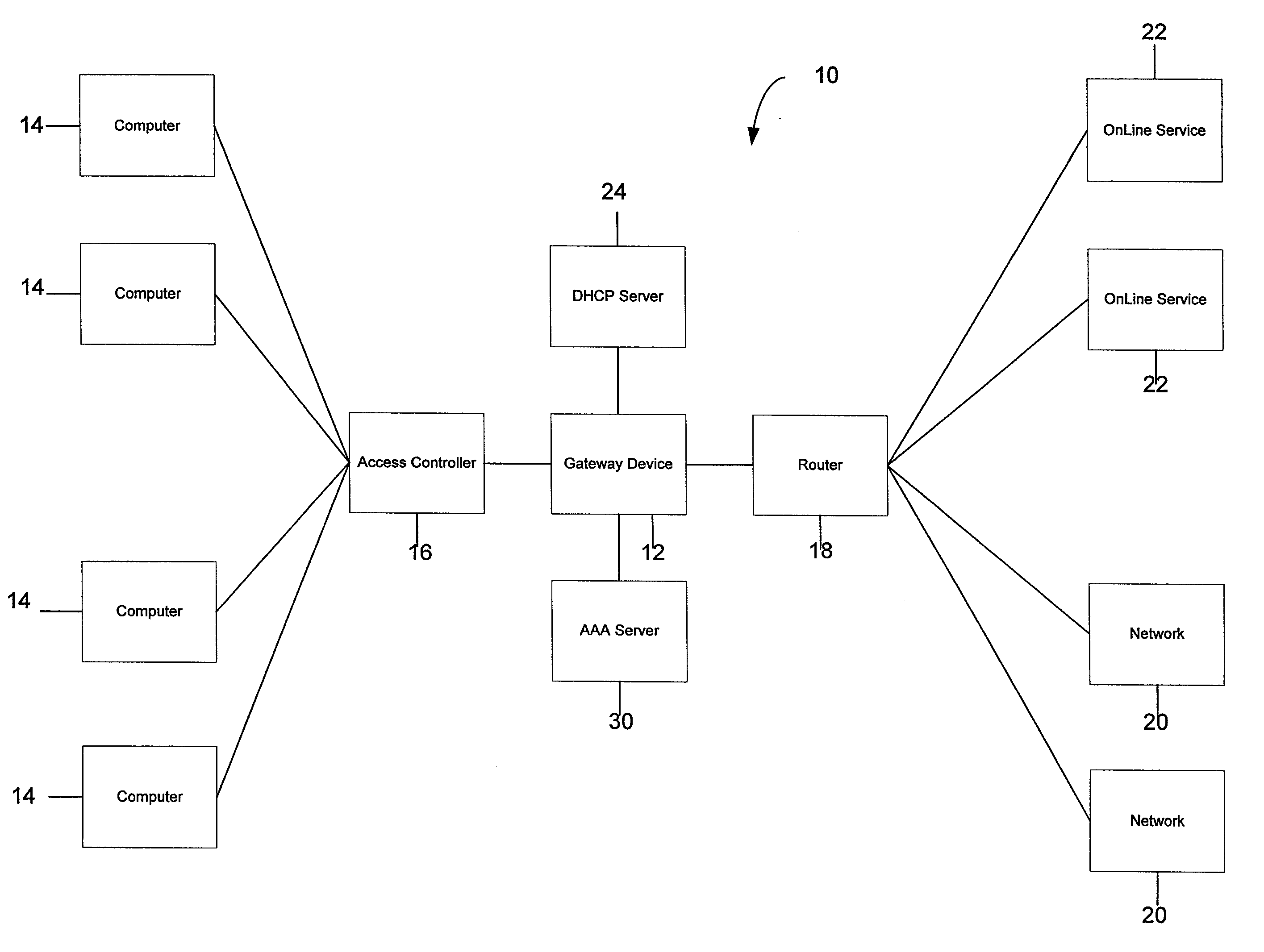
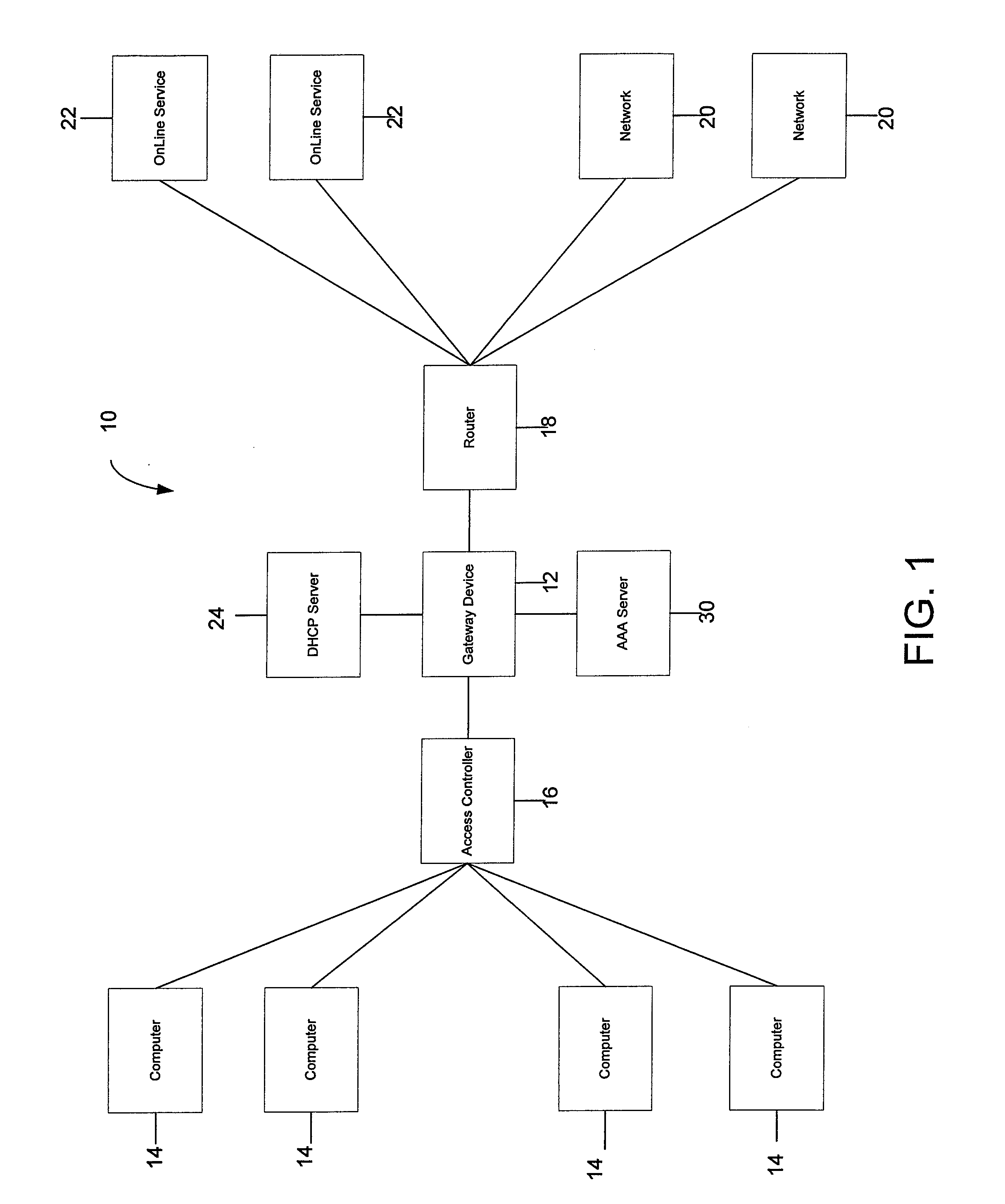
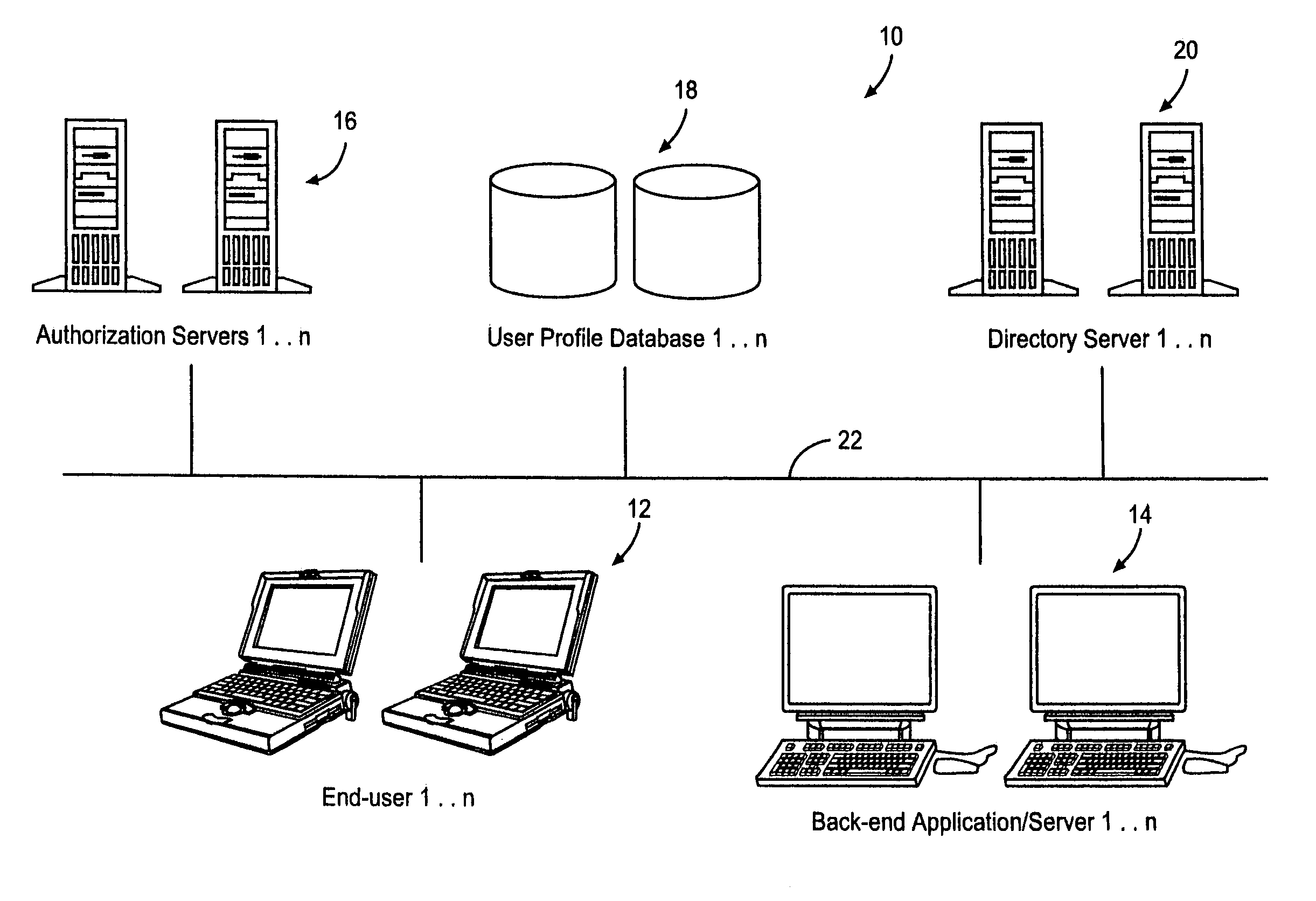
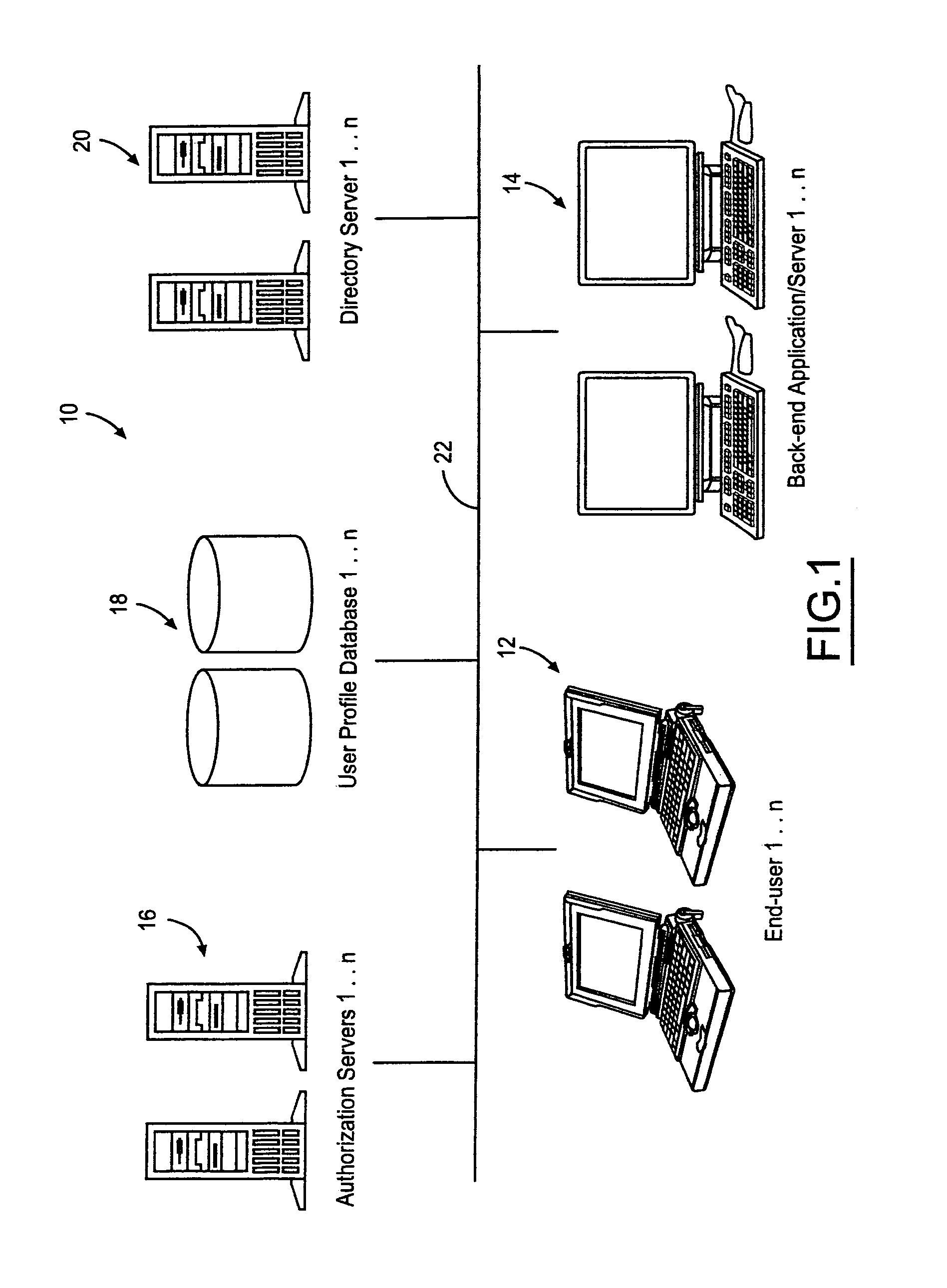
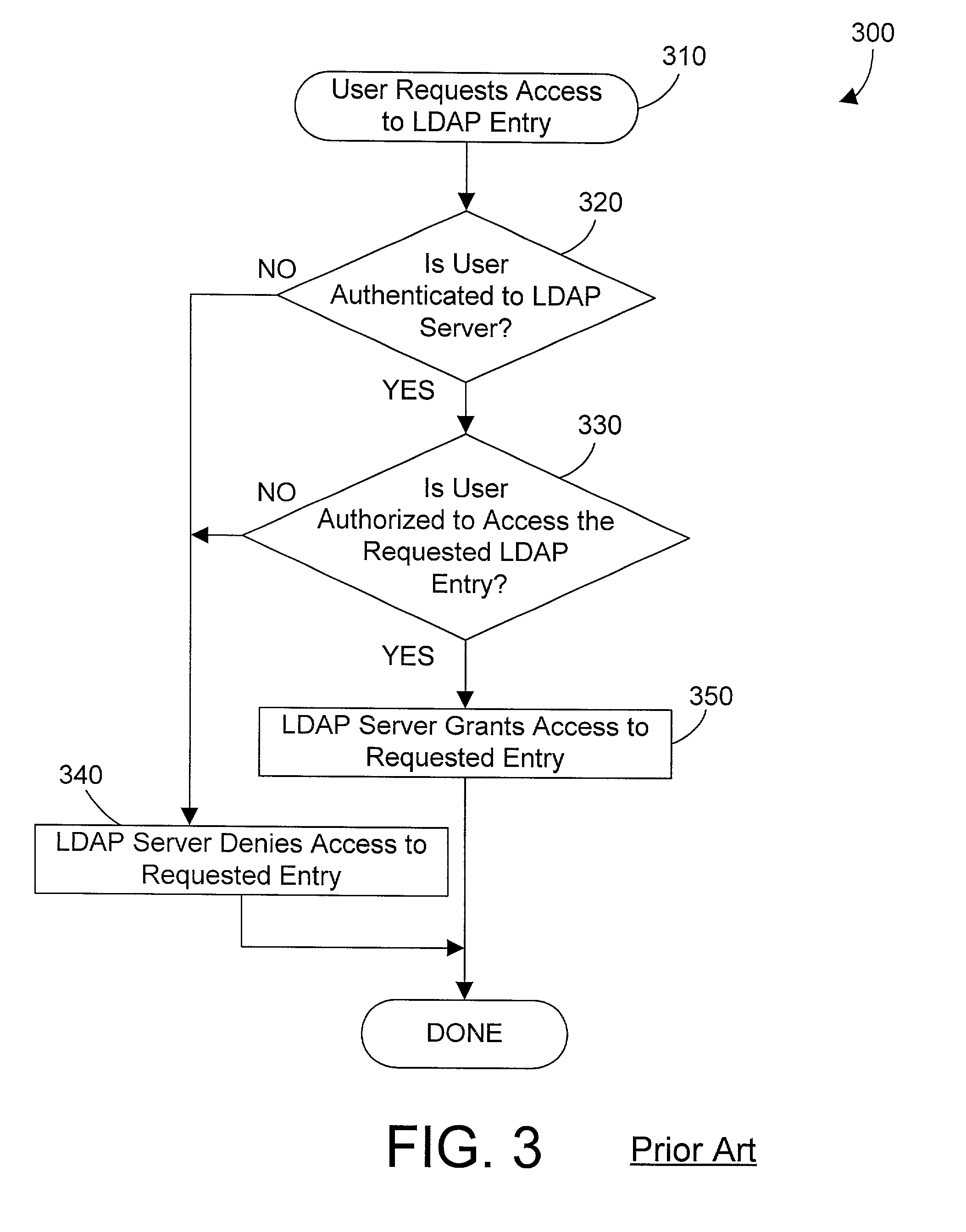
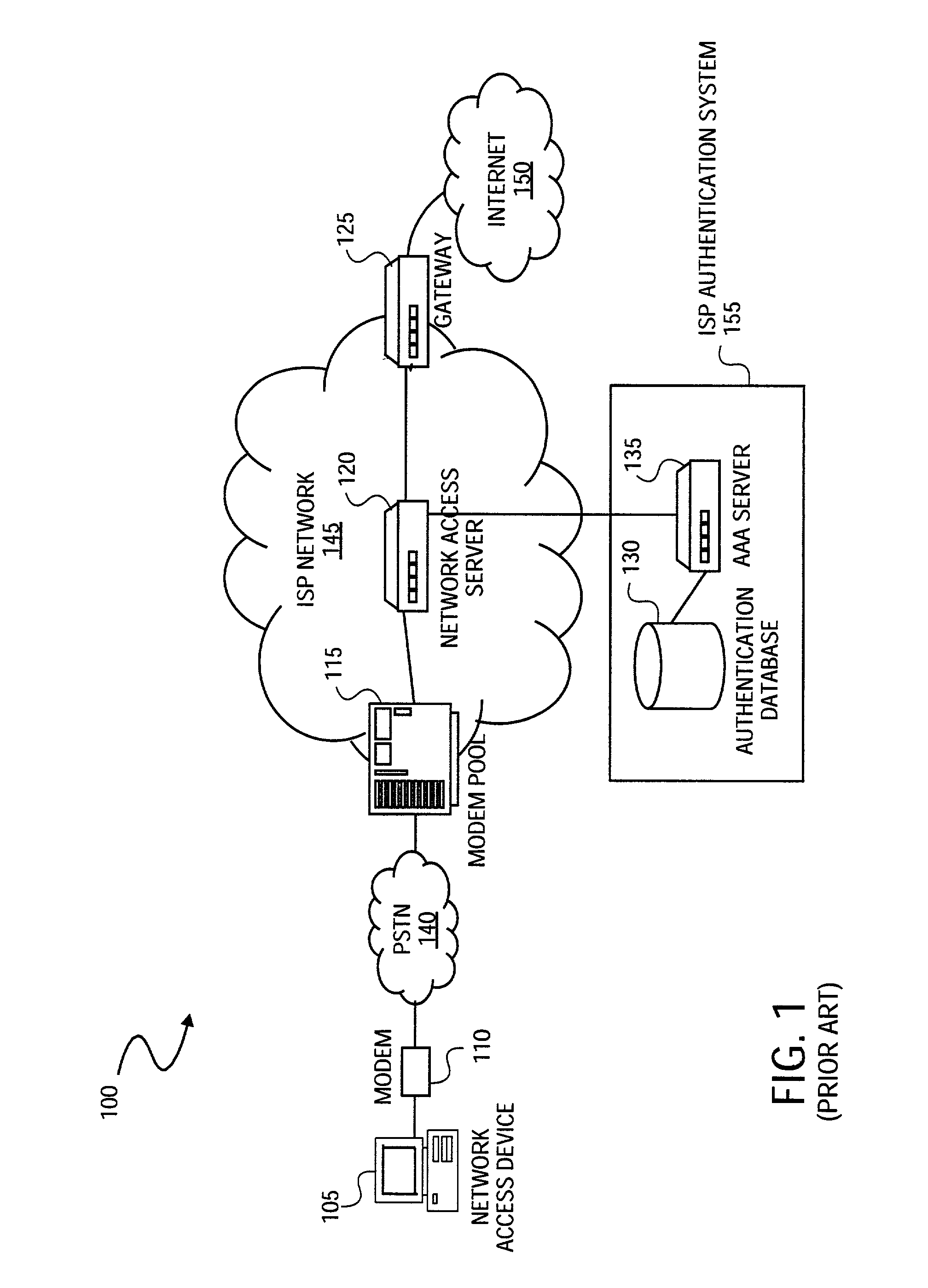
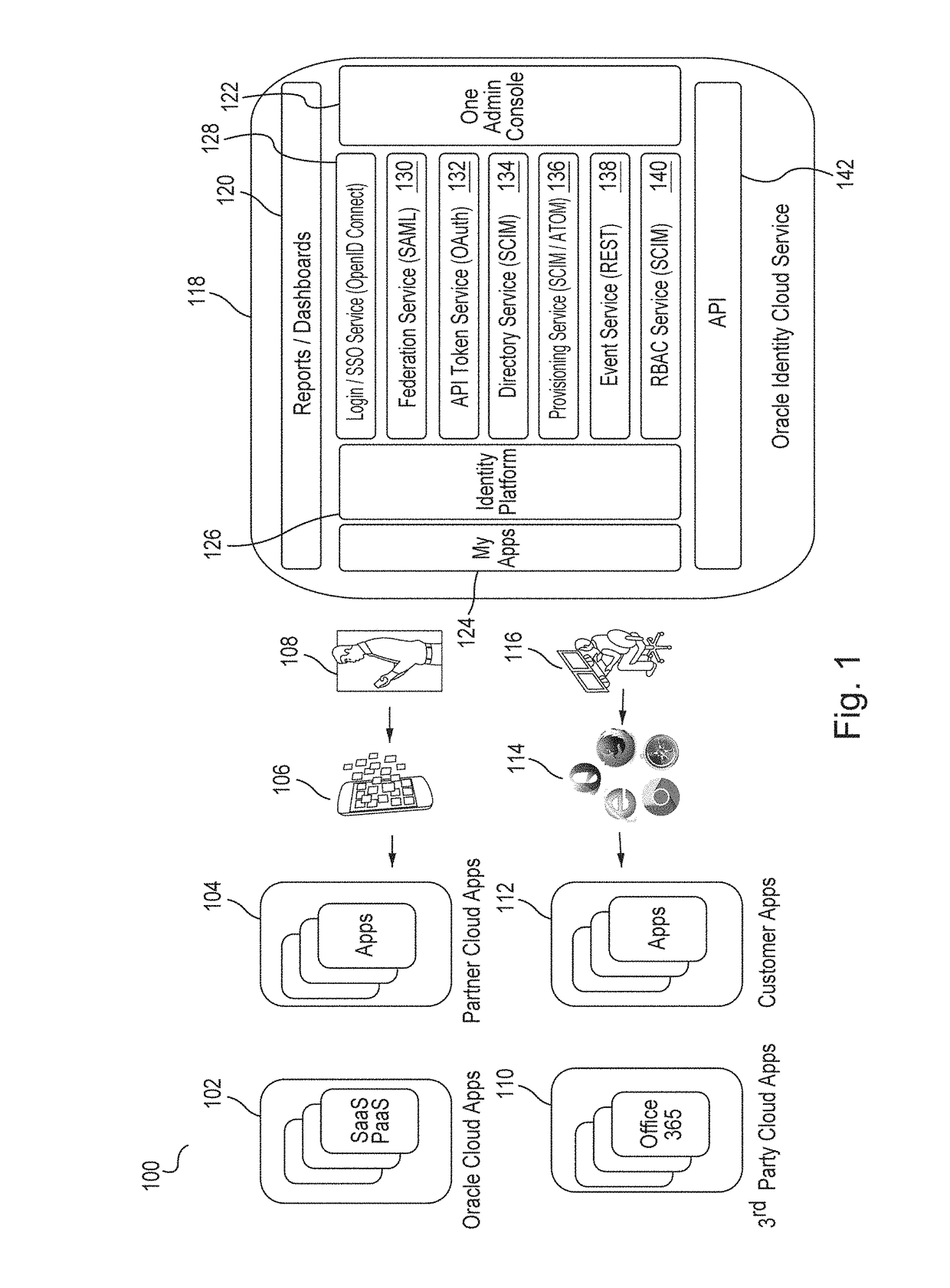
Systems and methods for providing dynamic network authorization authentication and accounting
InactiveUS7194554B1Connection managementMultiple digital computer combinationsInternet privacyDirectory Access Protocol
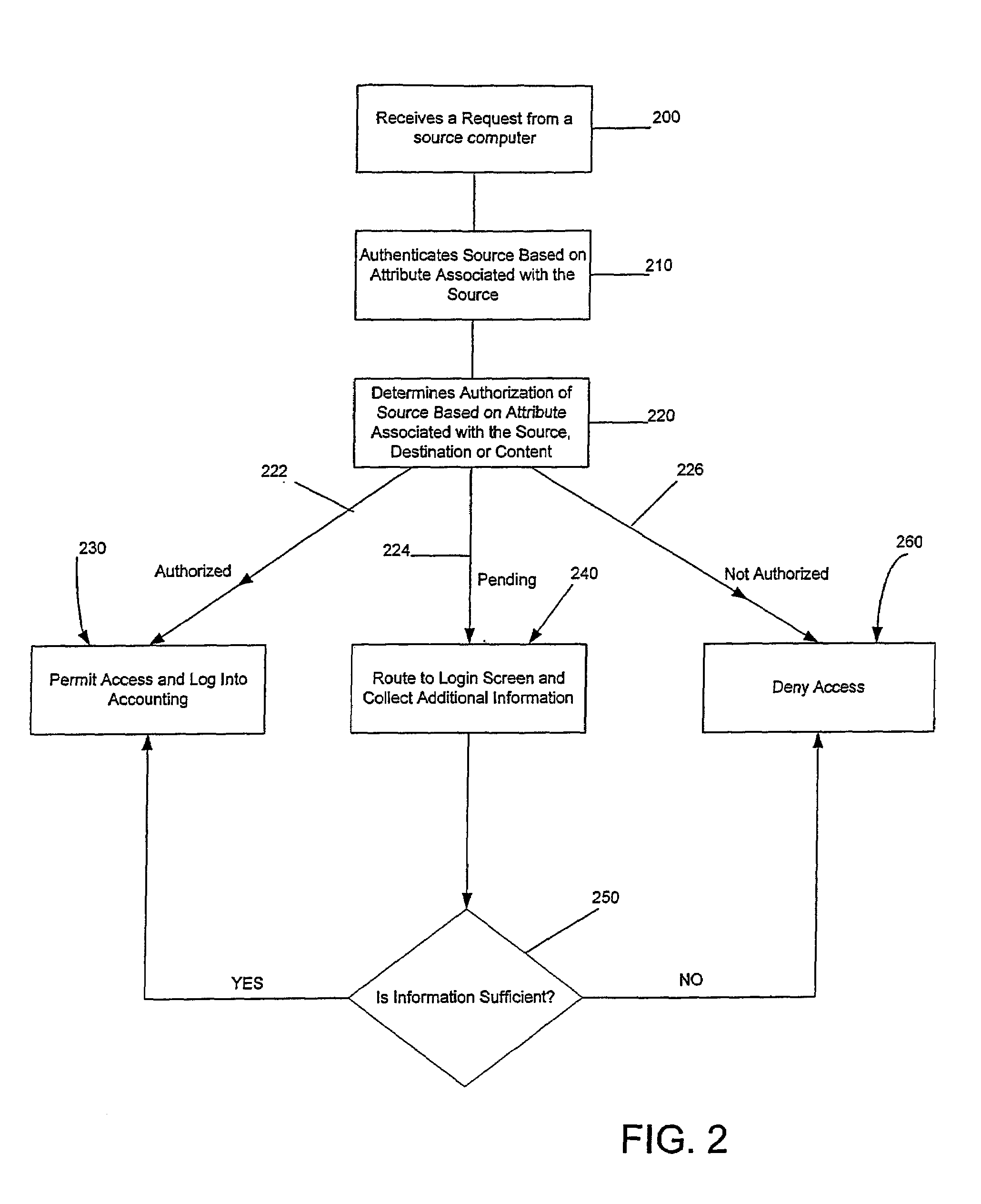
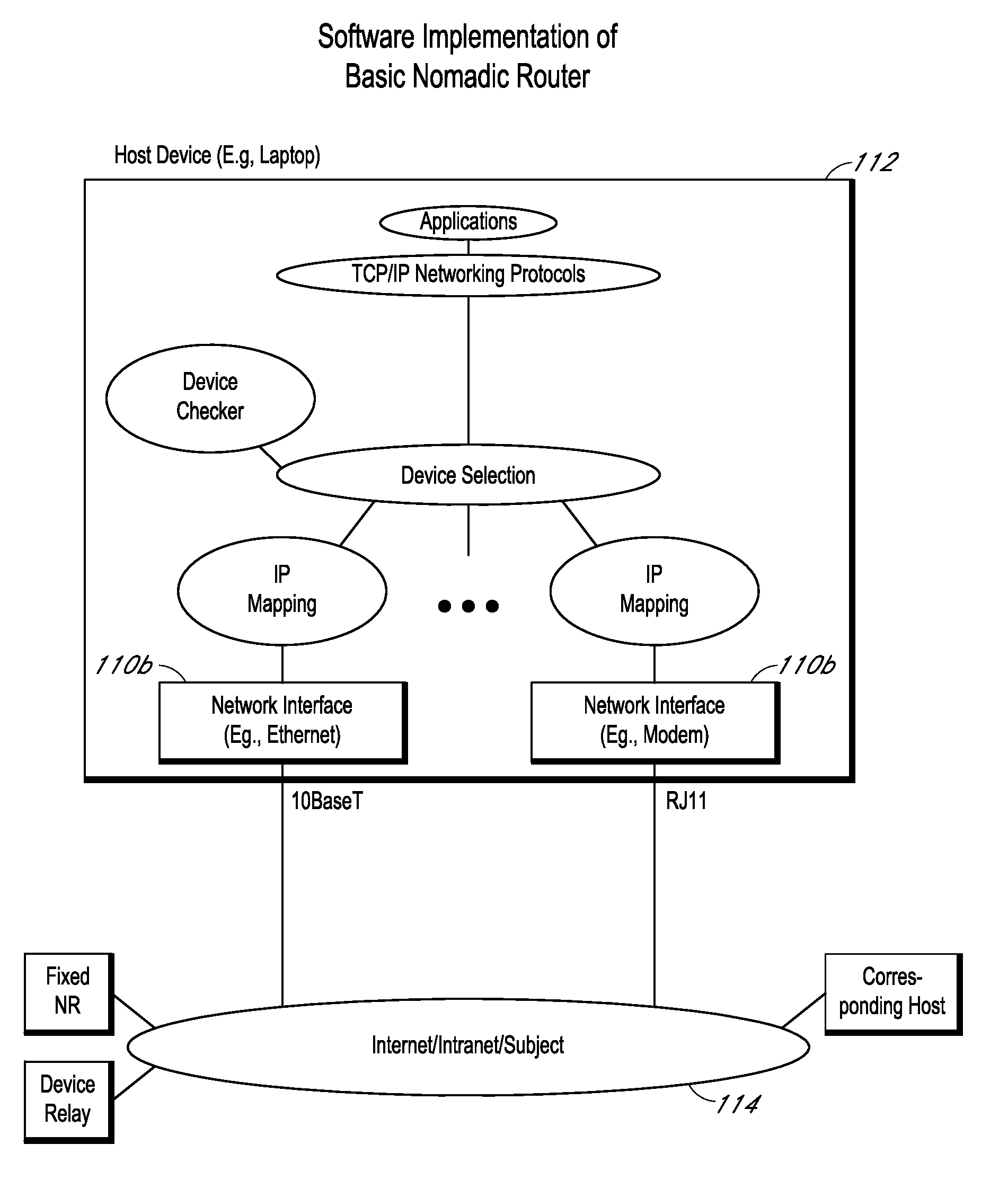
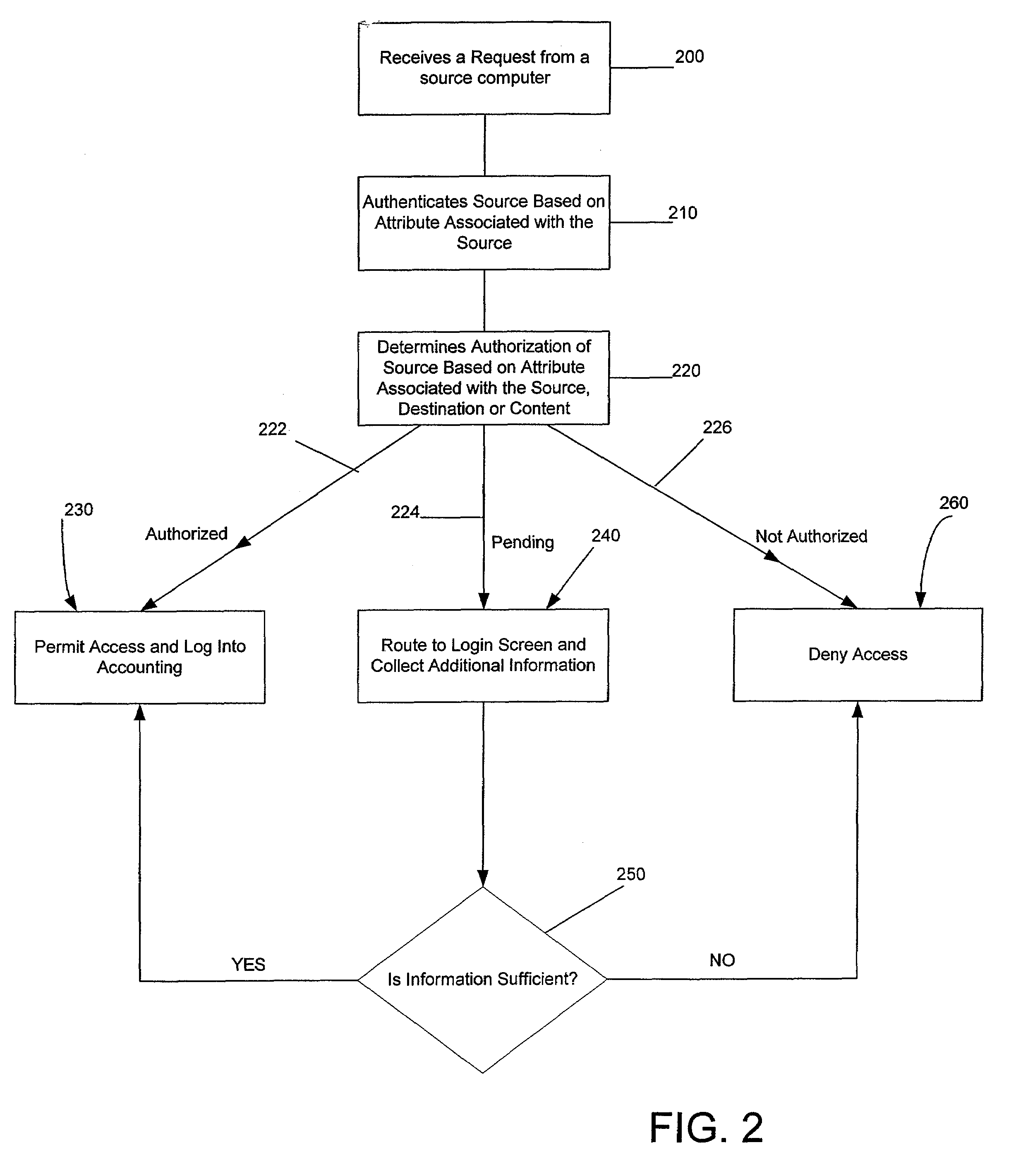
Systems and methods for selectably controlling and customizing source access to a network, where the source is associated with a source computer, and wherein the source computer has transparent access to the network via a gateway device and no configuration software need be installed on the source computer to access the network. A user may be prevented access from a particular destination or site based upon the user's authorization while being permitted to access to other sites that the method and system deems accessible. The method and system can identify a source without that source's knowledge, and can access customizable access rights corresponding to that source in a source profile database. The source profile database can be a remote authentication dial-in user service (RADIUS) or a lightweight directory access protocol (LDAP) database. The method and system use source profiles within the source profile database to dynamically authorize source access to networks and destinations via networks.
Owner:NOMADIX INC
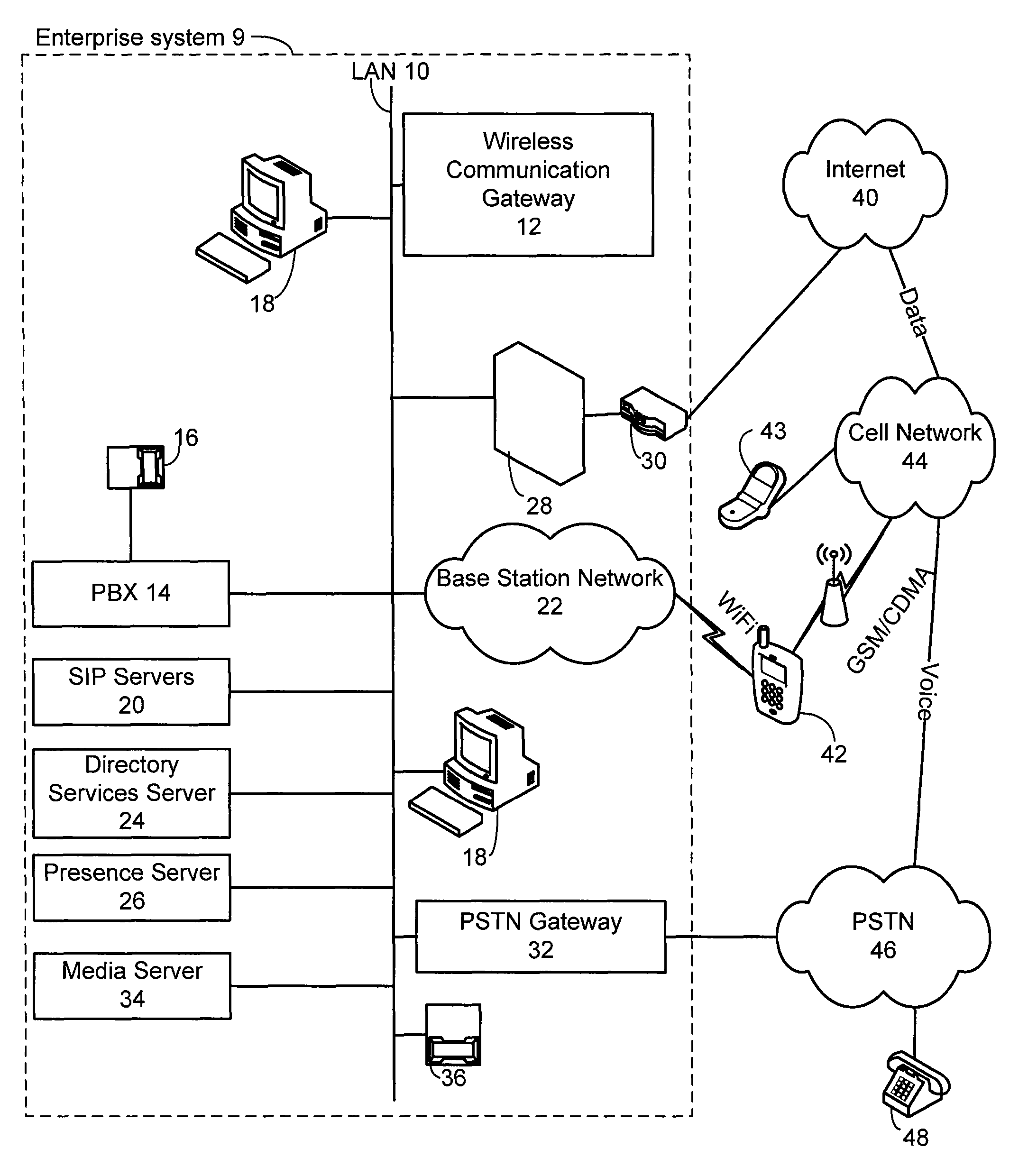
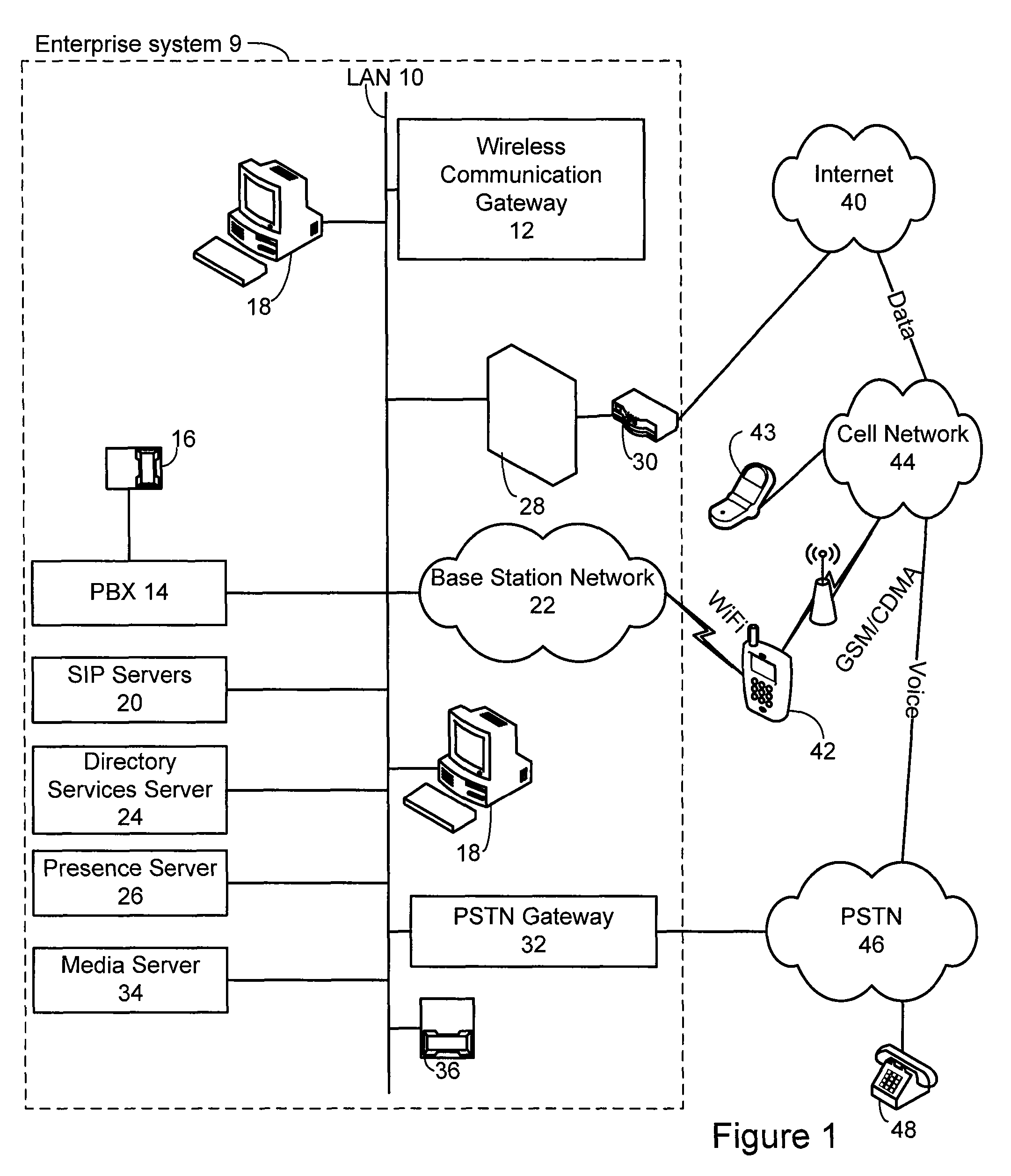
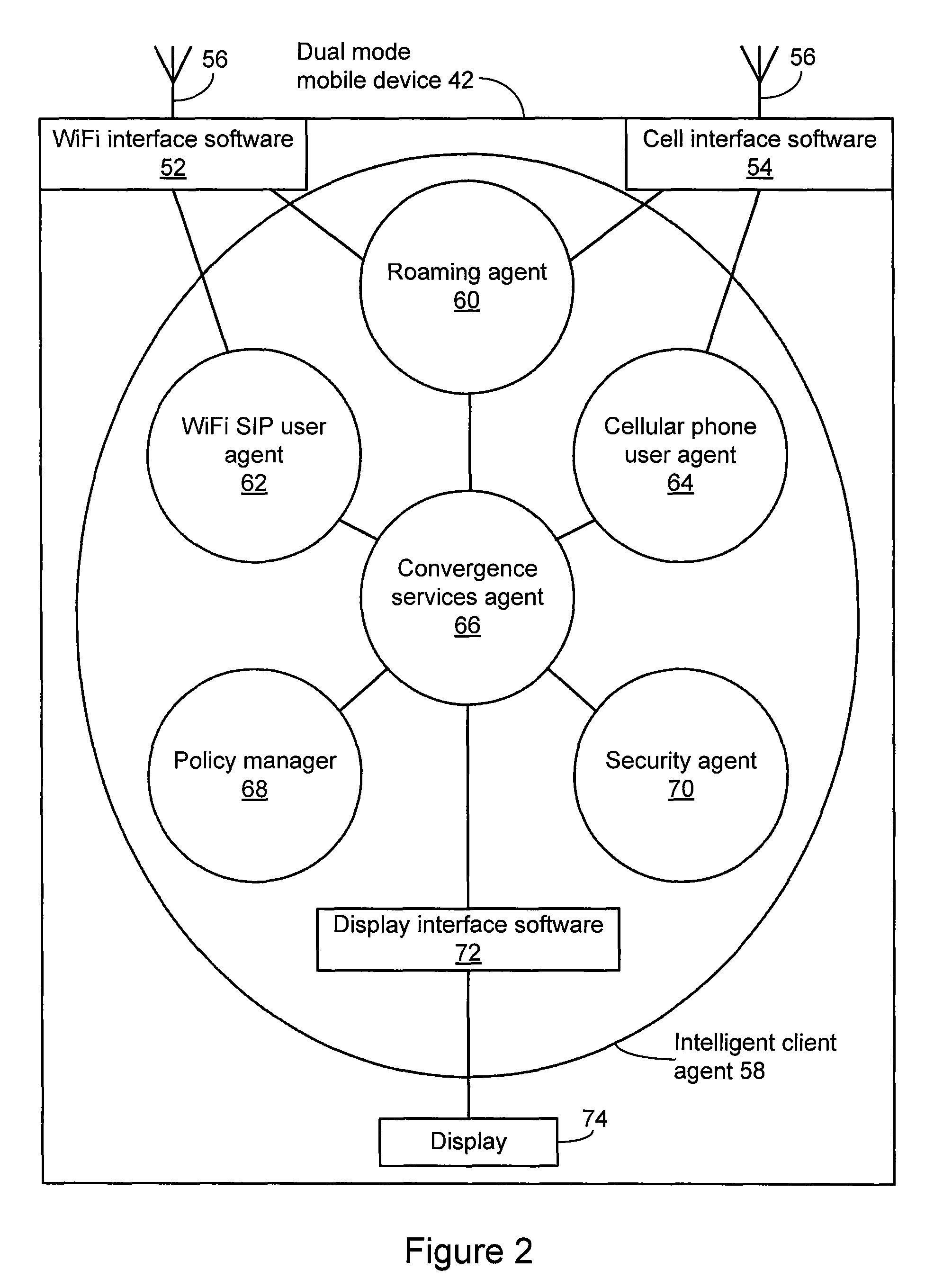
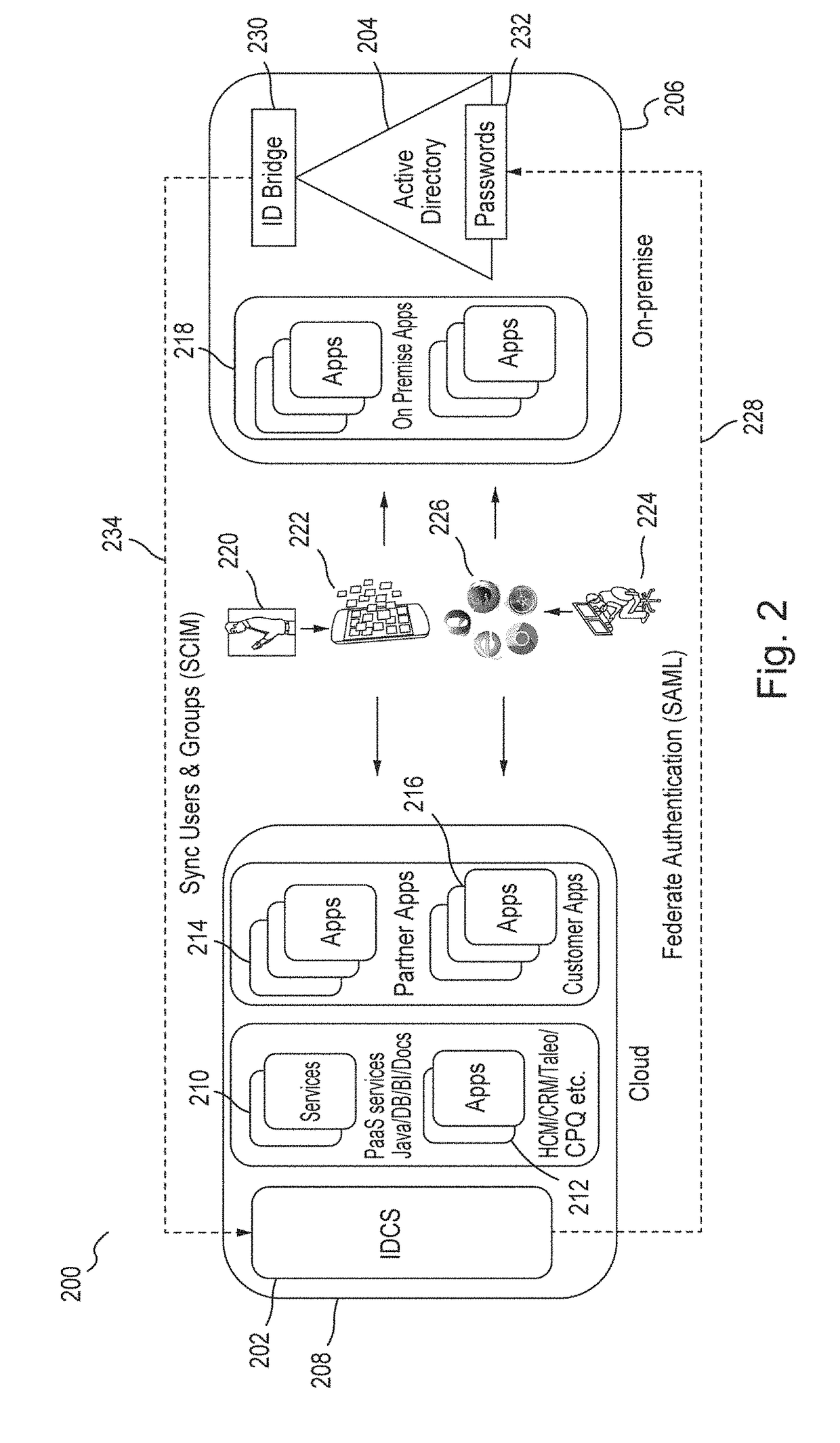
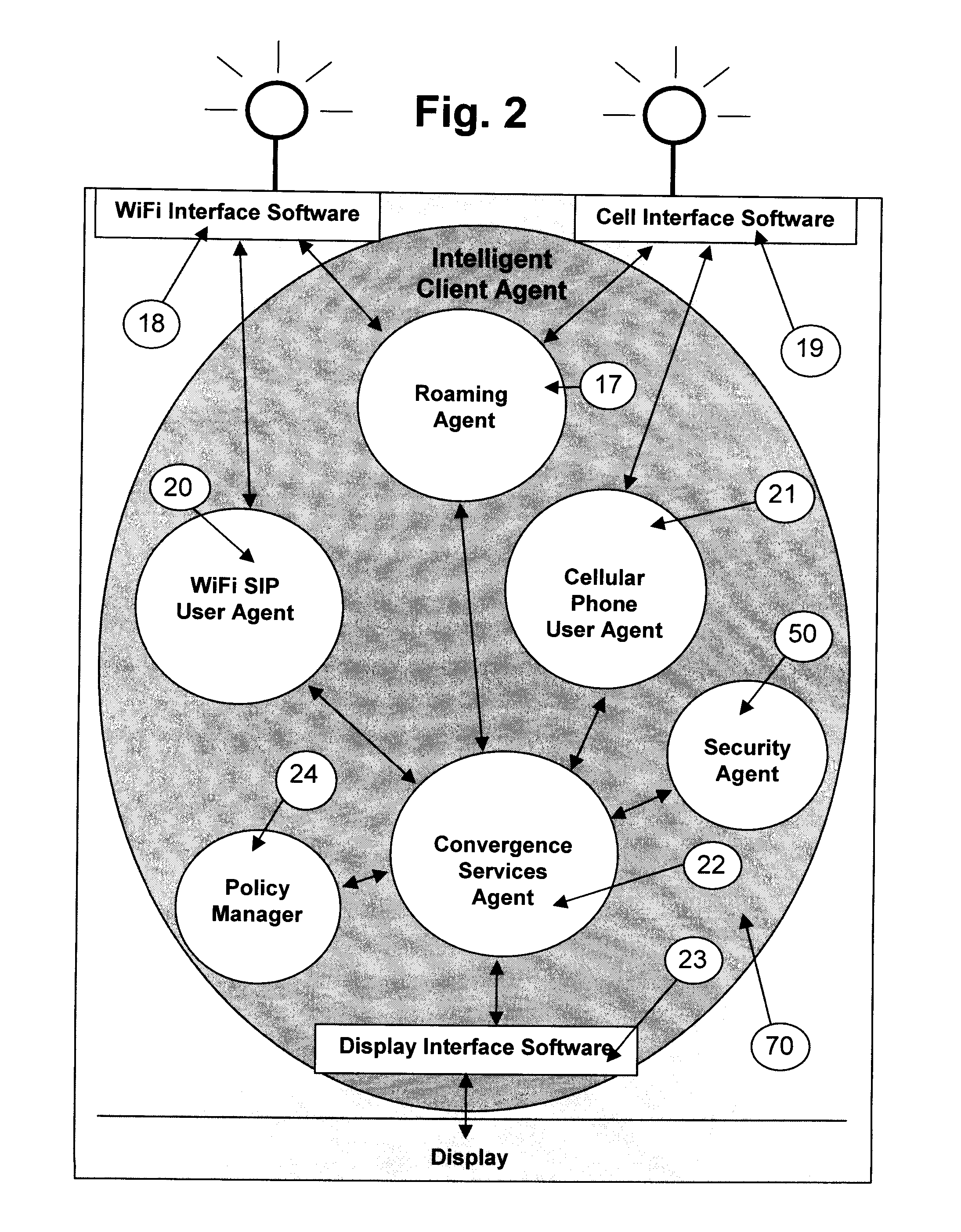
Method and system for extending services to cellular devices
A system is provide for extending services to cellular devices. The system includes a wireless gateway having a client side with an intelligent client agent and a server side with an intelligent server agent, a wireless device having a first mode operable in a cellular system and a second mode operable in a wireless local area network and including an intelligent client agent for determining operation mode and for communicating with the intelligent client agent of the wireless gateway and a communications protocol for communication between the wireless gateway intelligent client agent and the wireless device intelligent client agent to effect services. The services include one or more of voice, directory, presence, and media services. The voice service includes at least one of call waiting, call forwarding conferencing, and caller identification. The media service includes at least one of interactive voice response (IVR), text-to-speech, speech recognition, play, record. The directory service includes a public switched telephone network (PSTN) directory, a cellular network directory, an Internet directory and a private branch exchange (PBX) directory. The communications protocol includes encapsulation for at least one of directory, mobility and security services and other protocols. The other protocols include at least one of Internet protocol (IP), session initiation protocol (SIP), and lightweight directory access protocol (LDAP).
Owner:COUNTERPATH TECH
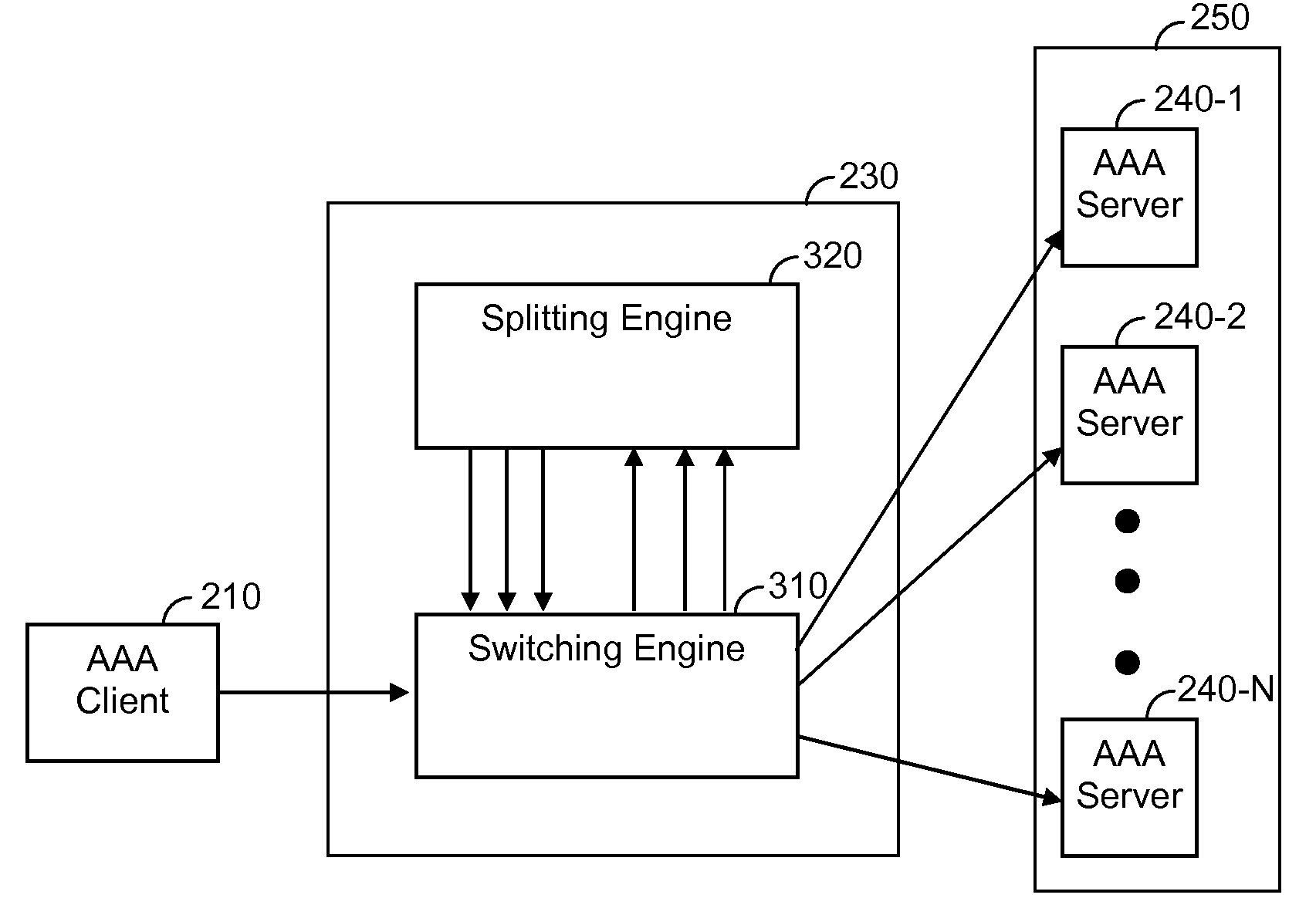
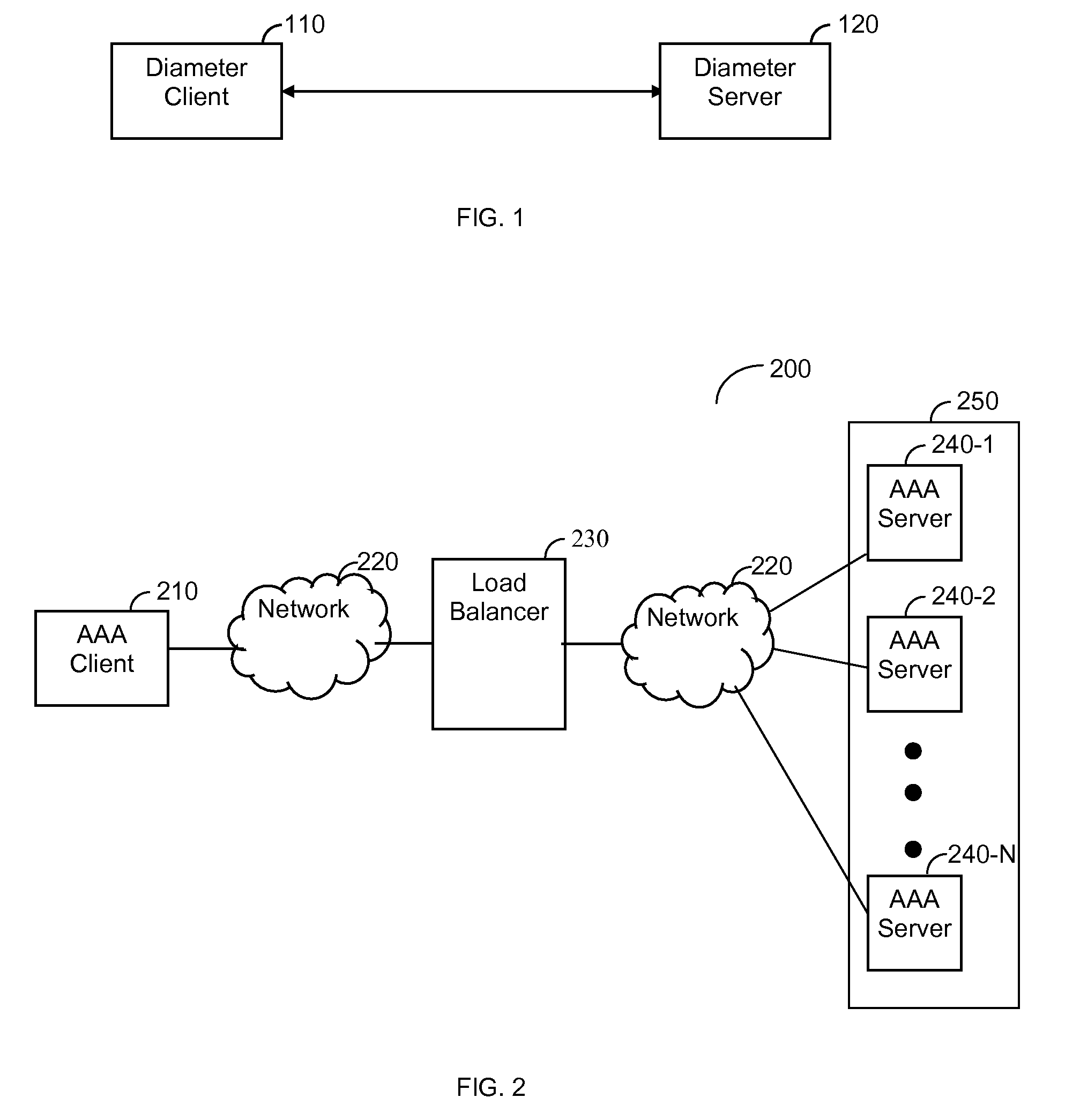
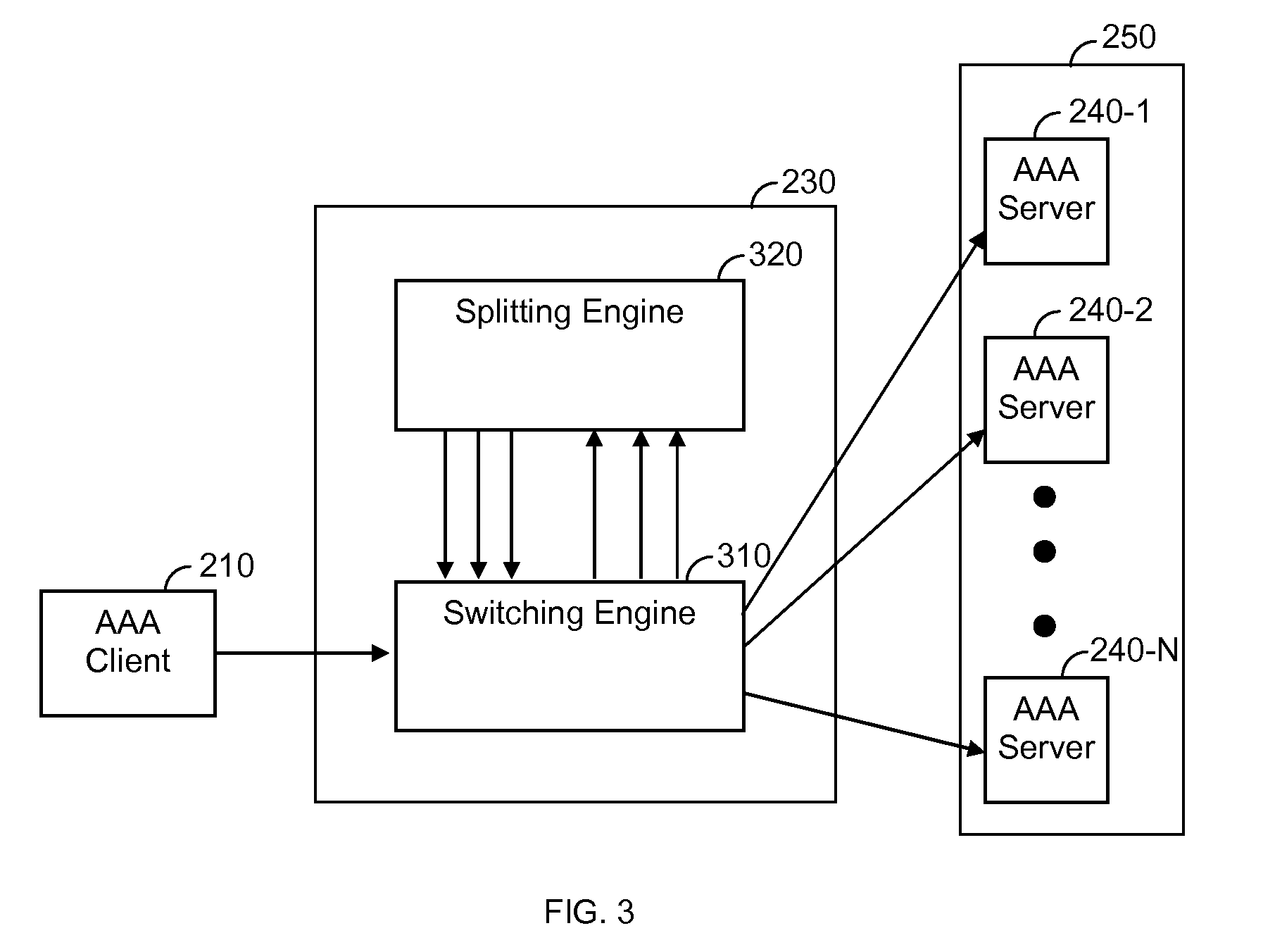
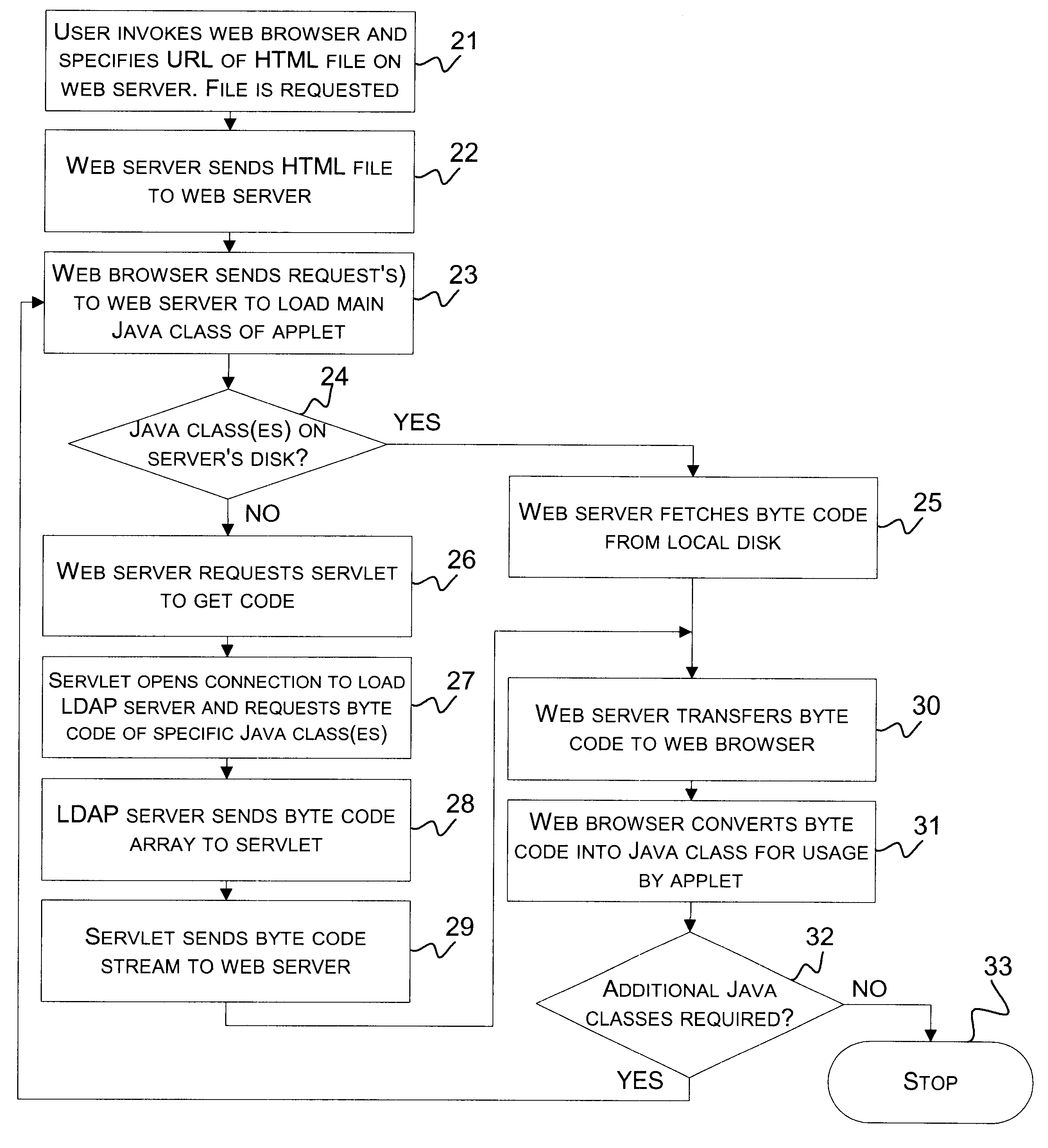
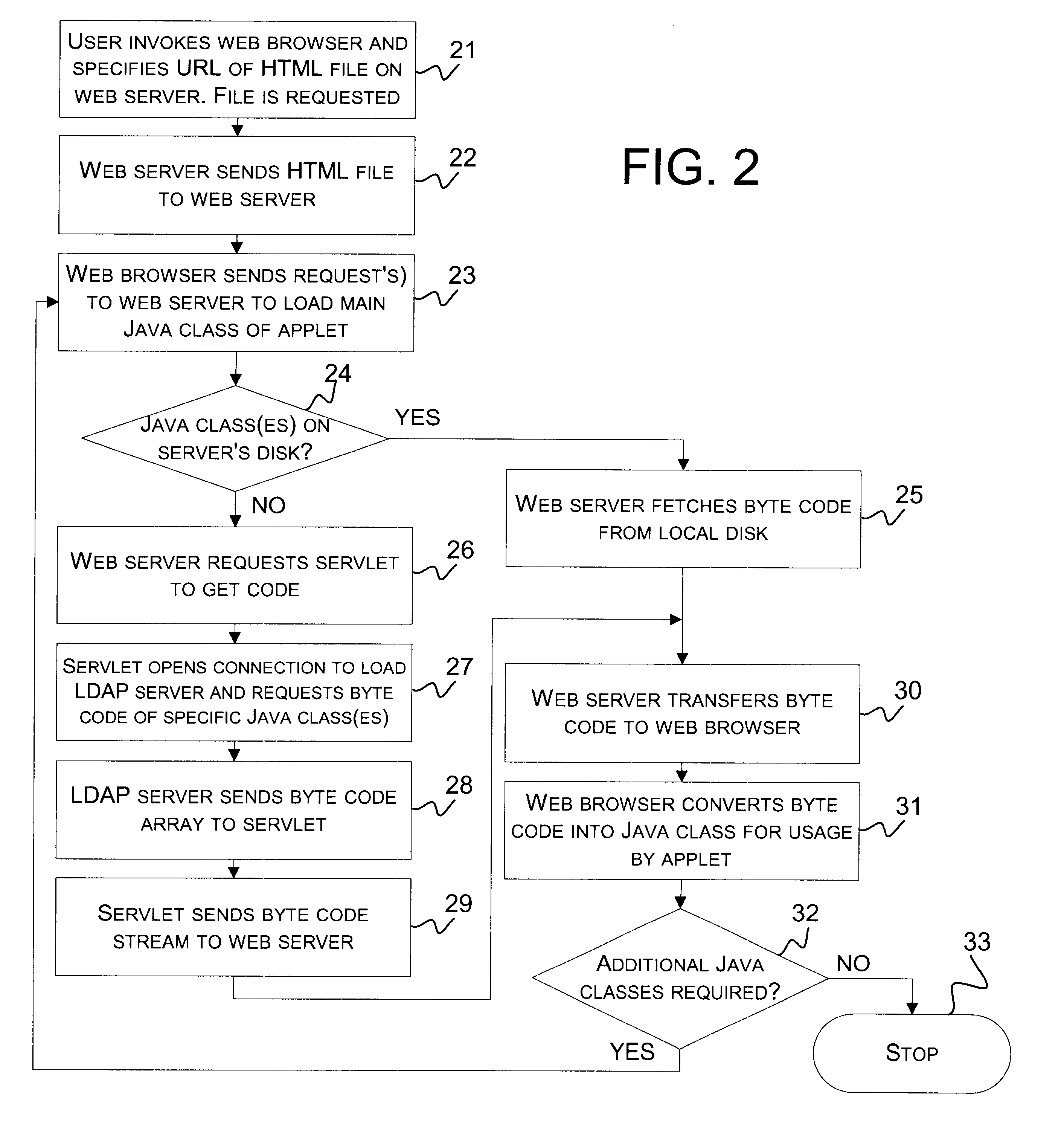
Method and System for Load Balancing over a Cluster of Authentication, Authorization and Accounting (AAA) Servers
ActiveUS20090265467A1Multiple digital computer combinationsTransmissionDirectory Access ProtocolClient-side
A method and system for load balancing over a cluster of authentication, authorization and accounting (AAA) servers. The method performs a distribution of AAA requests among AAA servers having an active AAA connection with an AAA client. The method includes establishing TCP connections with a plurality of AAA servers, using a TCP connection request received from at least one AAA client; opening AAA connections with a plurality of AAA servers, using an AAA connection request received from at least one AAA client, and distributing AAA requests to AAA servers with an active AAA connection according to a predefined load balancing algorithm. The invention is further capable of multiplexing outbound messages and requests received from a plurality of AAA servers. The AAA protocol supported by the invention includes, but is not limited to, a Diameter protocol, a lightweight directory access protocol (LDAP), and the likes.
Owner:RADWARE
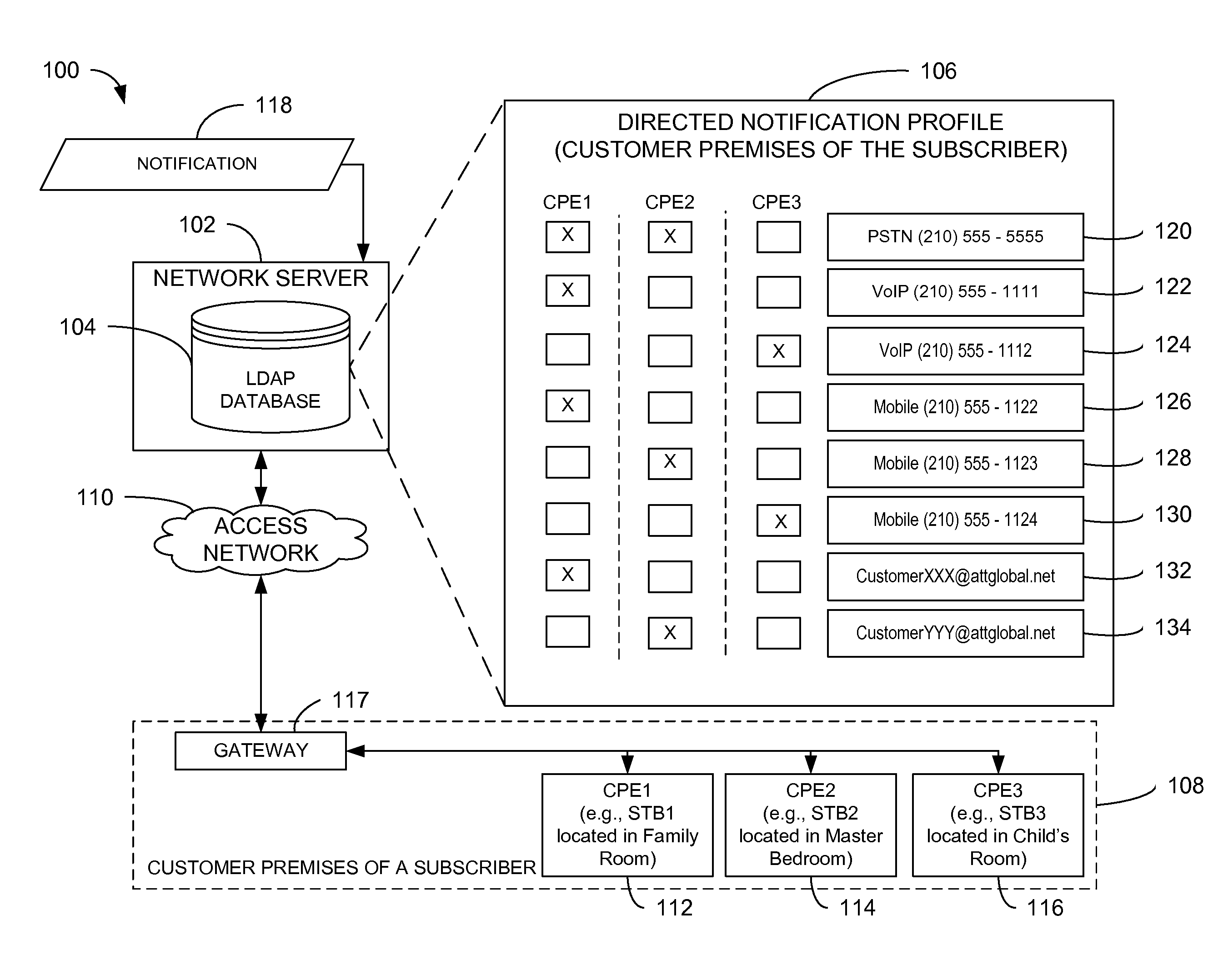
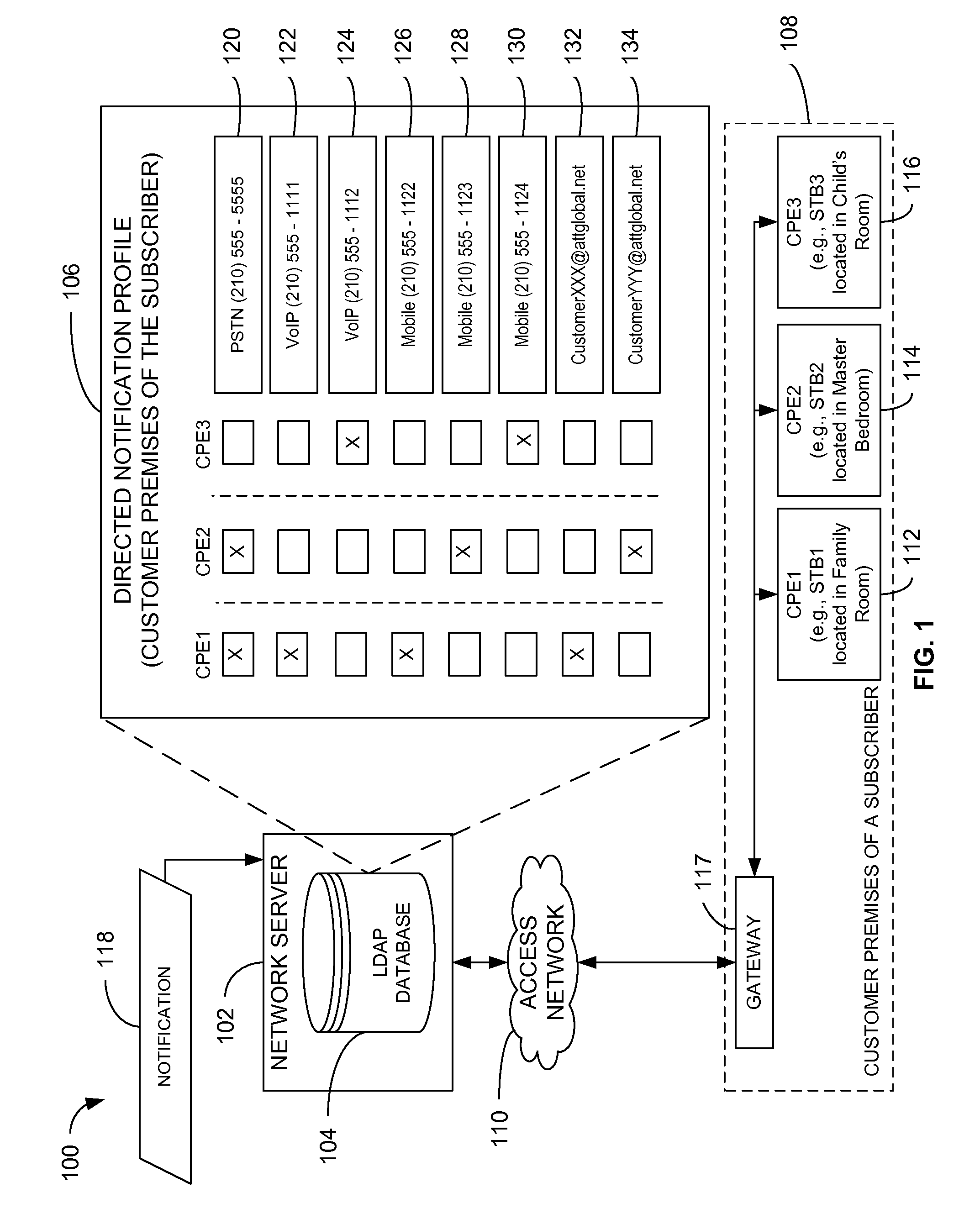
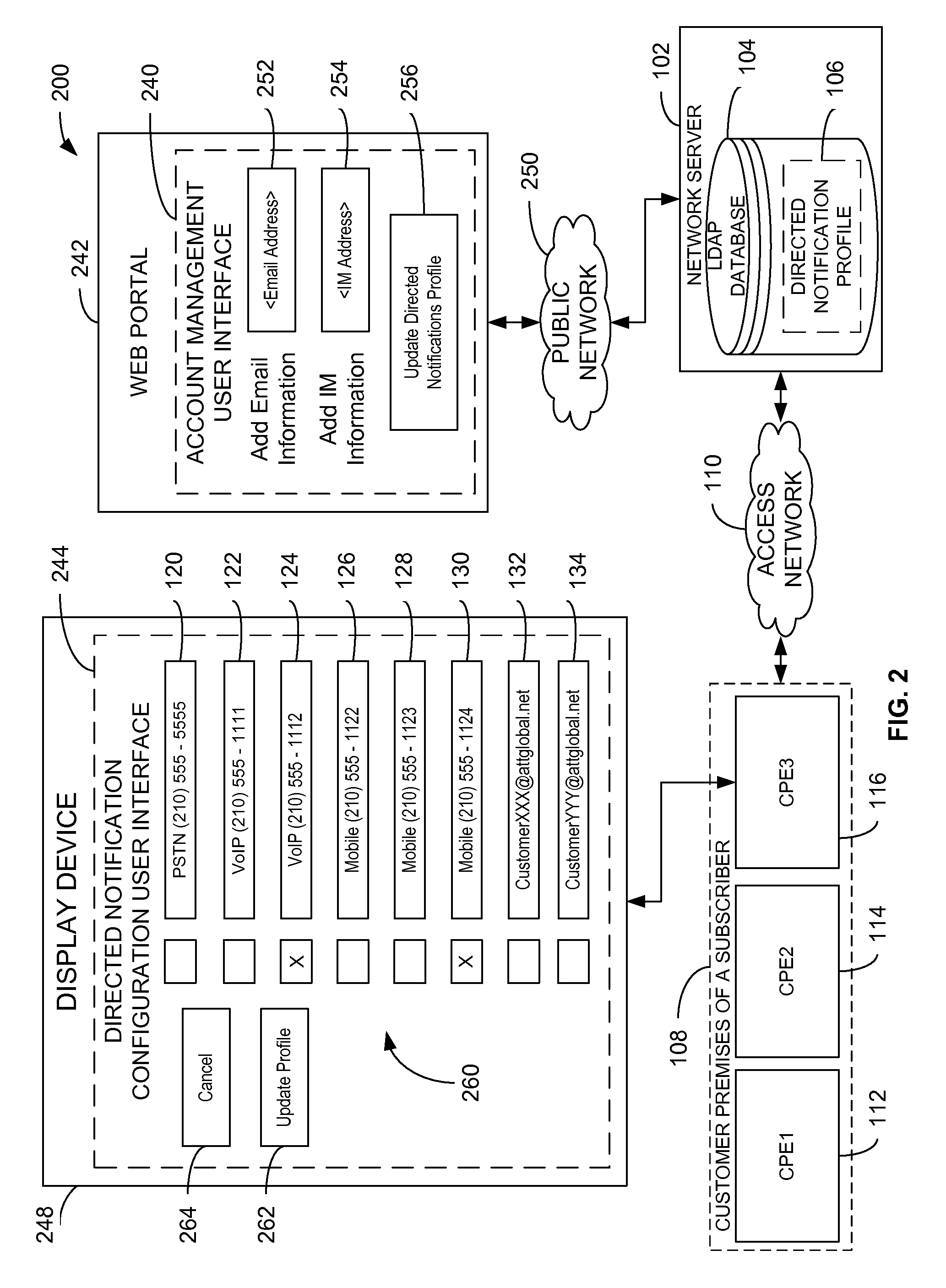
Directed notifications
InactiveUS8634533B2Interconnection arrangementsSpecial service for subscribersClient-sideDirectory Access Protocol
Owner:AT&T INTPROP I LP
Systems and methods for providing dynamic network authorization, authentication and accounting
InactiveUS20100115113A1Soft handoffImprove throughputMetering/charging/biilling arrangementsData taking preventionInternet privacyDirectory Access Protocol
Systems and methods for selectably controlling and customizing source access to a network, where the source is associated with a source computer, and wherein the source computer has transparent access to the network via a gateway device and no configuration software need be installed on the source computer to access the network. A user may be prevented access from a particular destination or site based upon the user's authorization while being permitted to access to other sites that the method and system deems accessible. The method and system can identify a source without that source's knowledge, and can access customizable access rights corresponding to that source in a source profile database. The source profile database can be a remote authentication dial-in user service (RADIUS) or a lightweight directory access protocol (LDAP) database. The method and system use source profiles within the source profile database to dynamically authorize source access to networks and destinations via networks.
Owner:NOMADIX INC
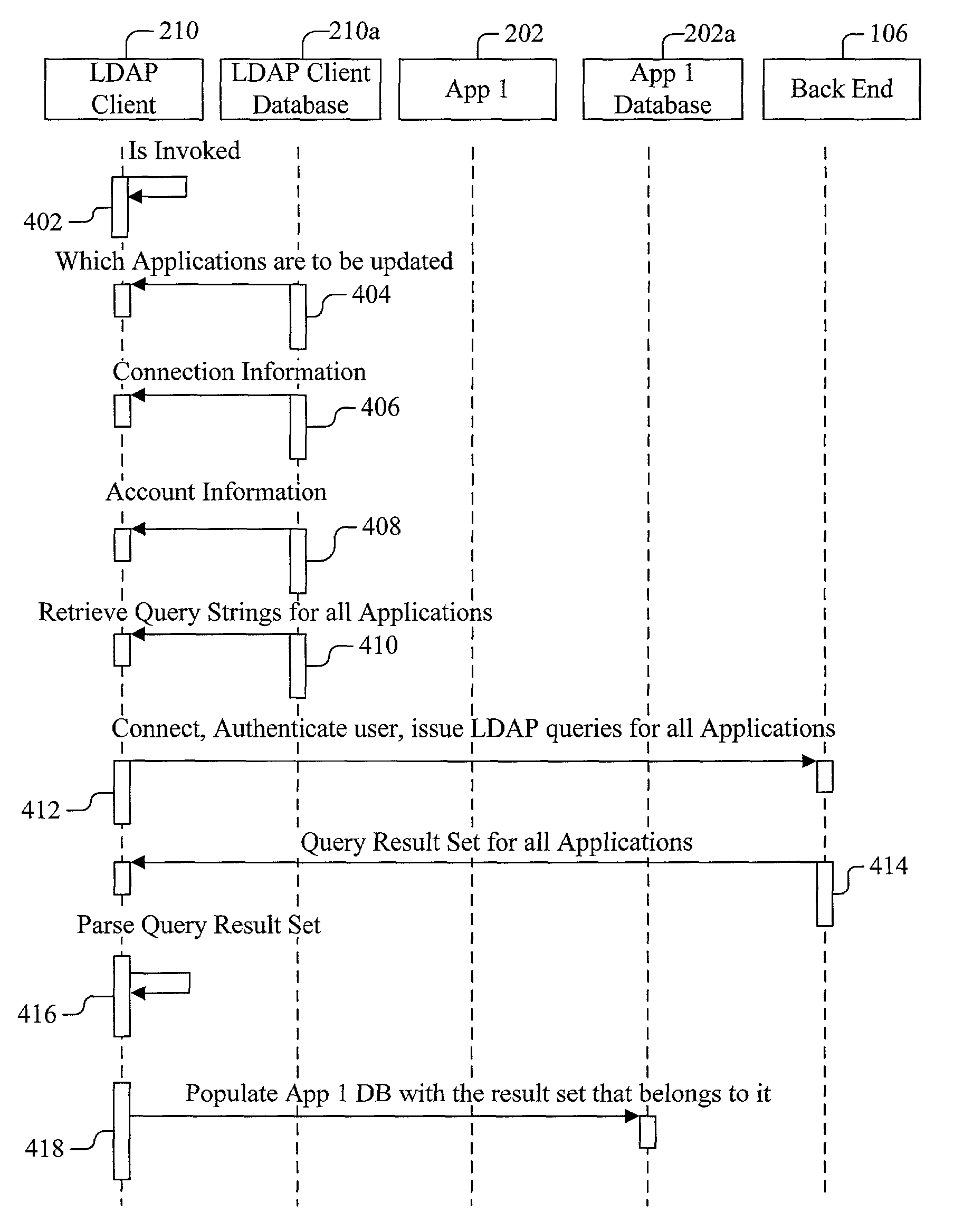
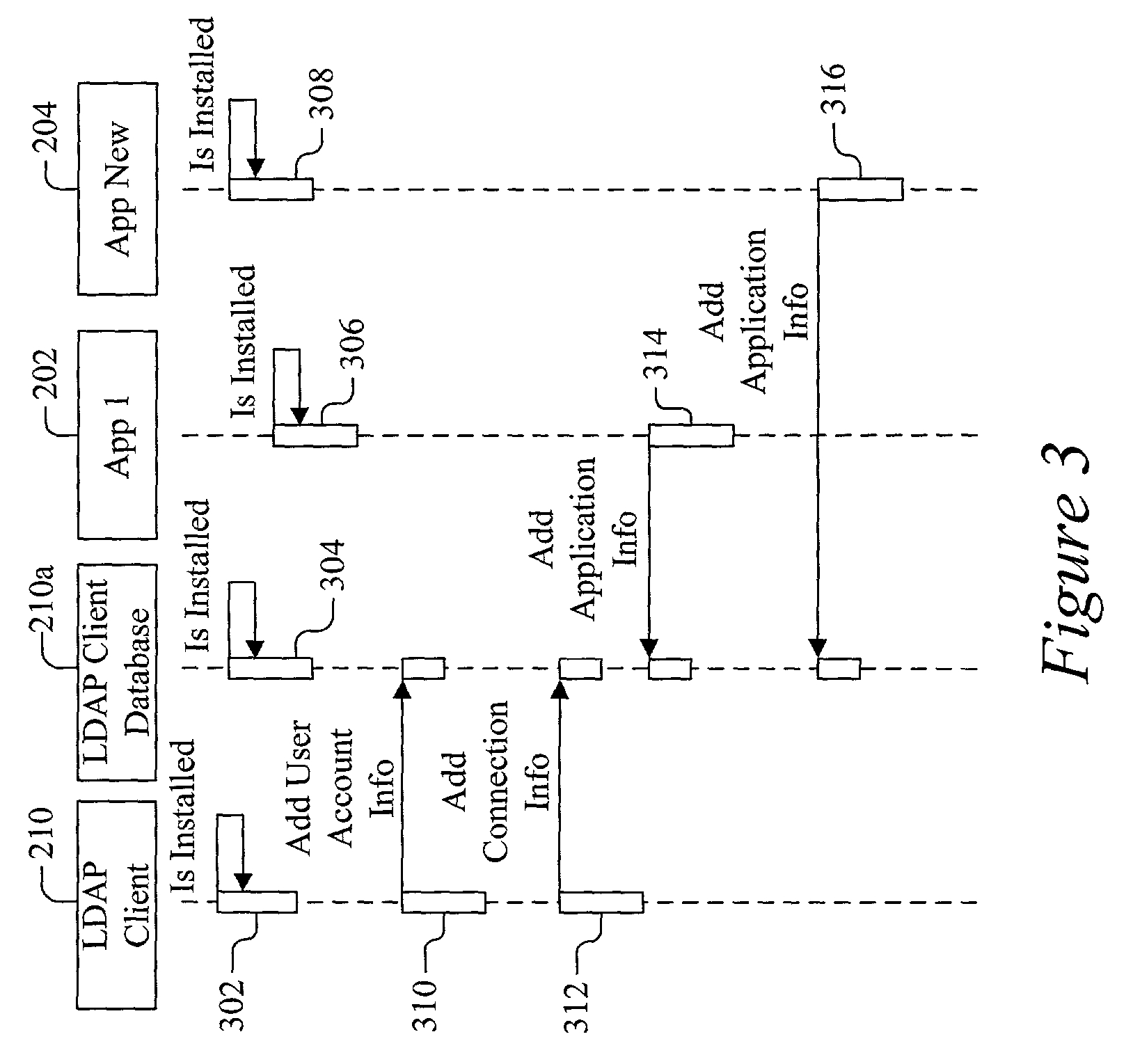
Method, device and computer program product including a lightweight directory access protocol client
InactiveUS7783593B2Digital data processing detailsSpecial service for subscribersApplication softwareClient-side
A method, apparatus and computer program product for updating data for an application, including invoking a client application; identifying an application having data to be updated; and sending a query to a directory server via the client application, the query identifying the data.
Owner:VERIZON PATENT & LICENSING INC
Systems and methods for providing dynamic network authorization, authentication and accounting
InactiveUS7689716B2Soft handoffImprove throughputConnection managementData switching by path configurationInternet privacyDirectory Access Protocol
Systems and methods for selectably controlling and customizing source access to a network, where the source is associated with a source computer, and wherein the source computer has transparent access to the network via a gateway device and no configuration software need be installed on the source computer to access the network. A user may be prevented access from a particular destination or site based upon the user's authorization while being permitted to access to other sites that the method and system deems accessible. The method and system can identify a source without that source's knowledge, and can access customizable access rights corresponding to that source in a source profile database. The source profile database can be a remote authentication dial-in user service (RADIUS) or a lightweight directory access protocol (LDAP) database. The method and system use source profiles within the source profile database to dynamically authorize source access to networks and destinations via networks.
Owner:NOMADIX INC
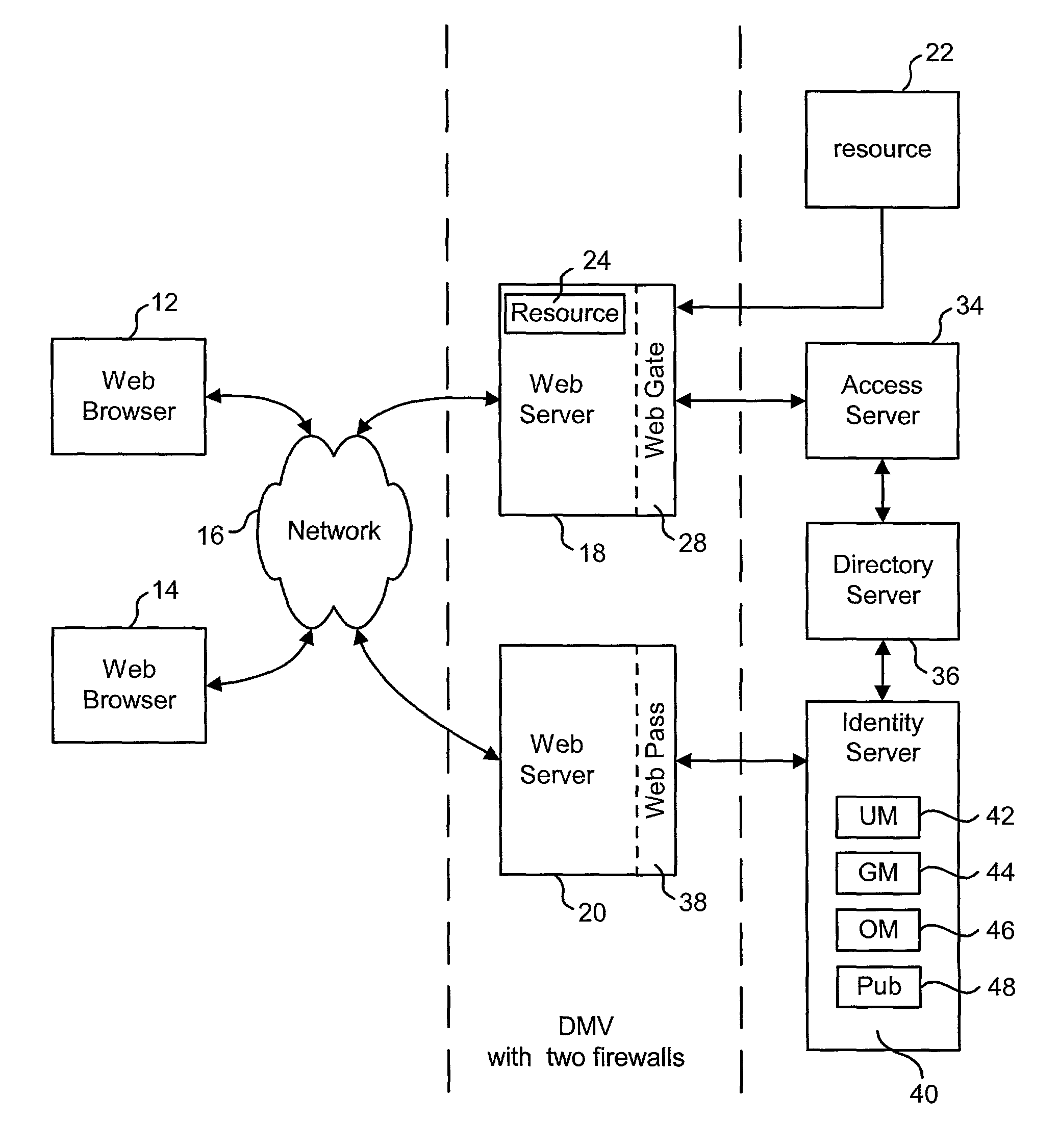
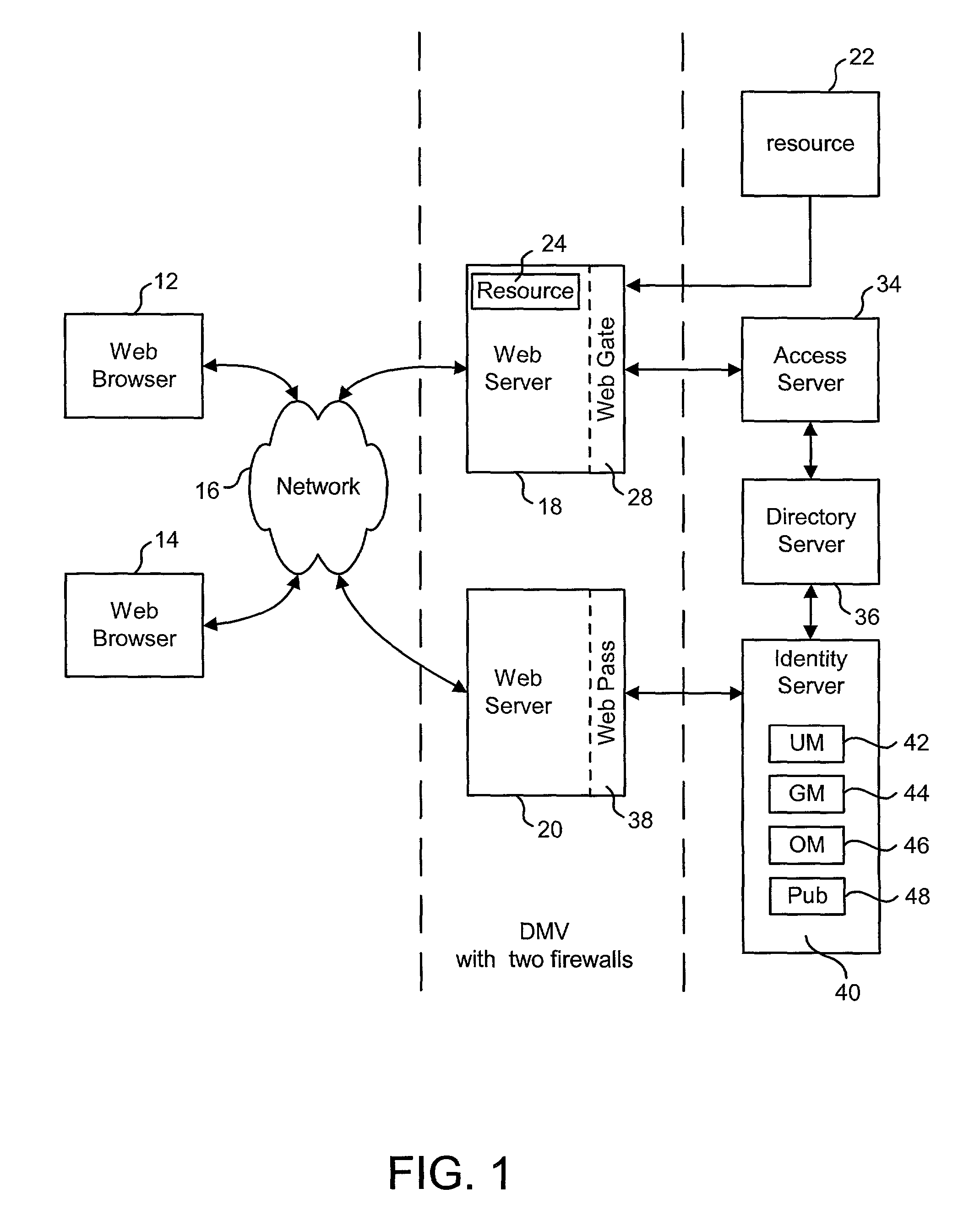
System, method and computer program product for authenticating users using a lightweight directory access protocol (LDAP) directory server
InactiveUS7185361B1Great degreeFlexible specificationsData processing applicationsDigital data processing detailsGraphicsGraphical user interface
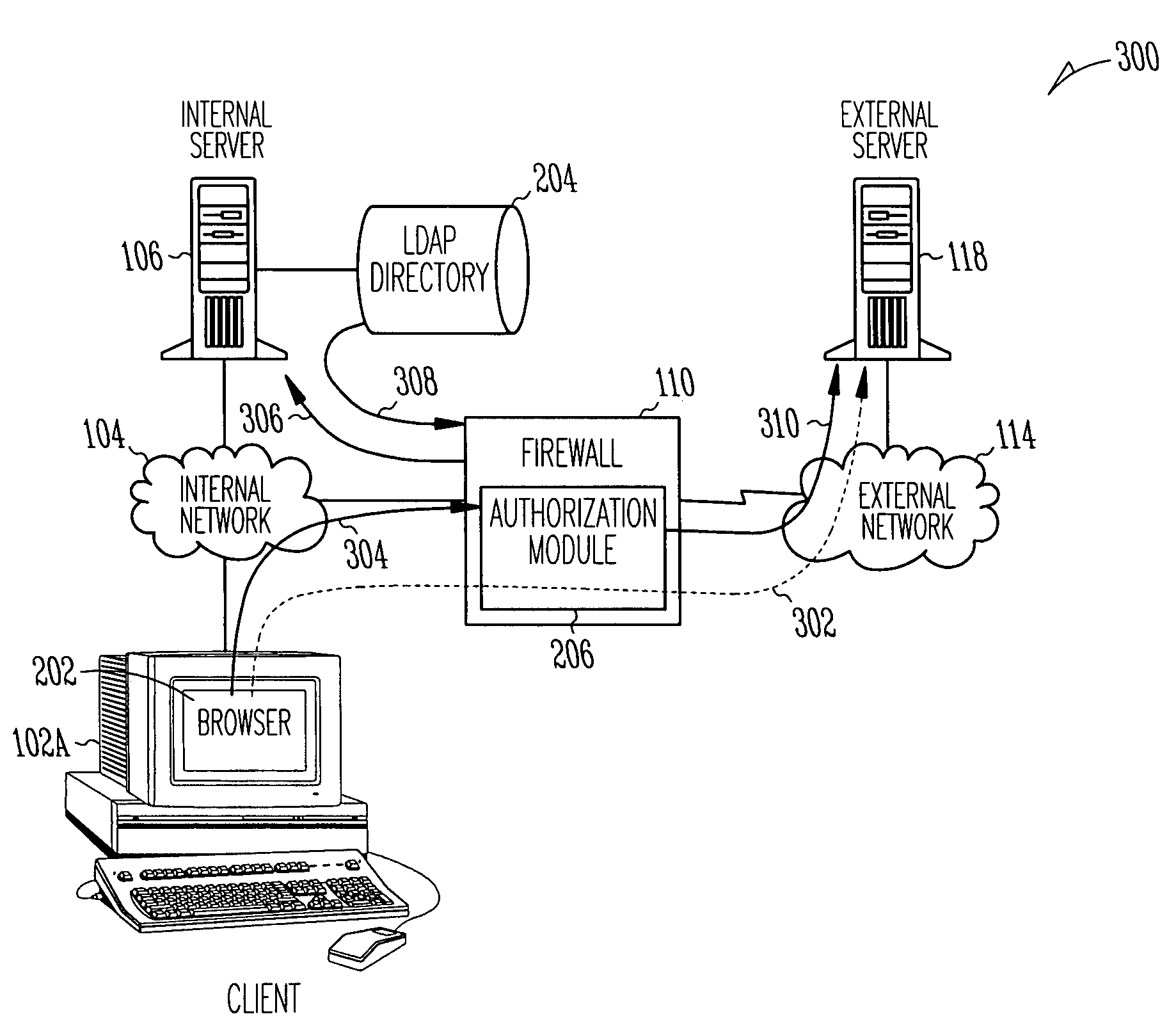
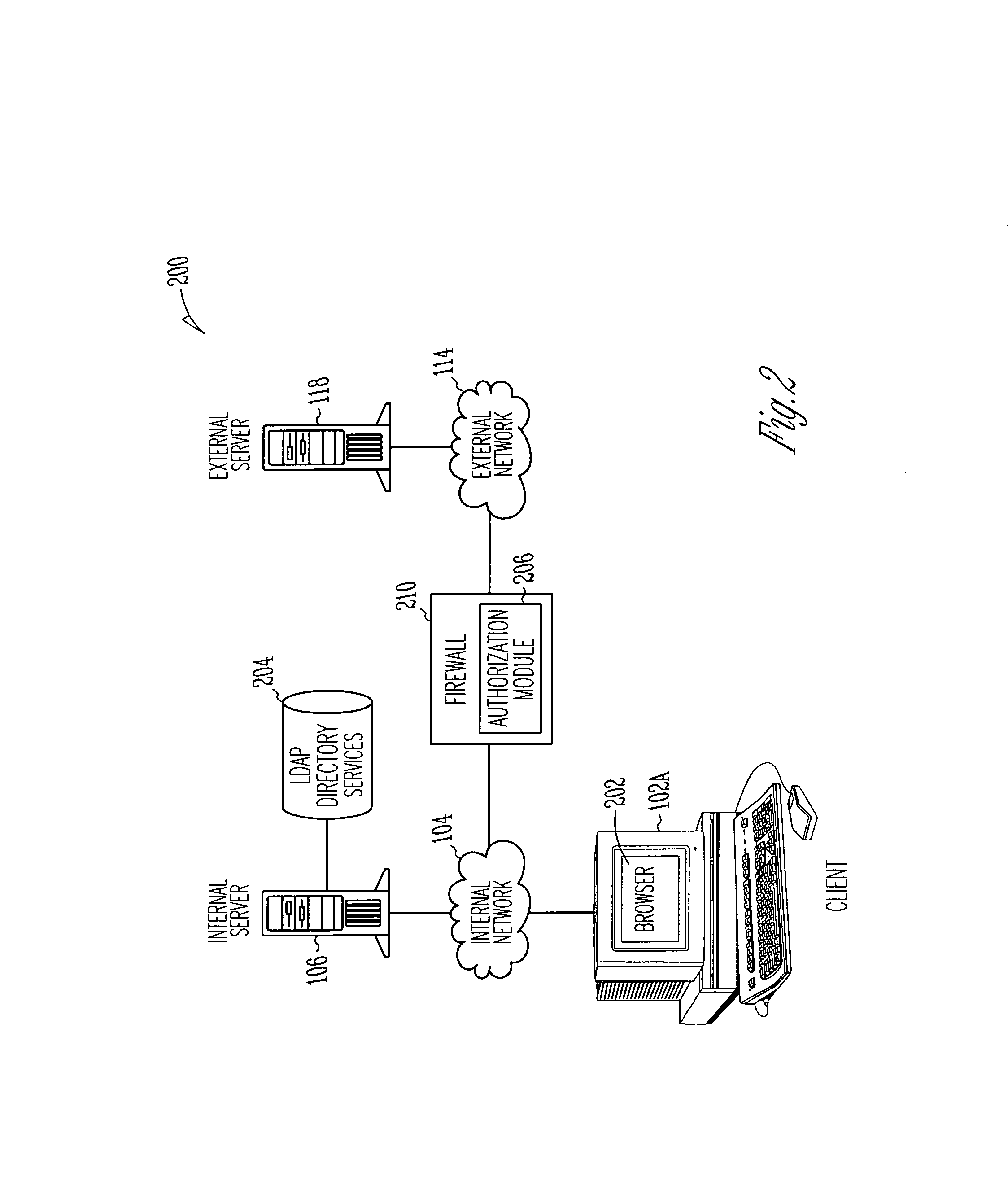
A system, method and computer program product for providing authentication to a firewall using a lightweight directory access protocol (LDAP) directory server is disclosed. The firewall can be configured through a graphical user interface to implement an authentication scheme. The authentication scheme is based upon a determination of whether at least part of one or more LDAP entries satisfy an authorization filter.
Owner:MCAFEE LLC
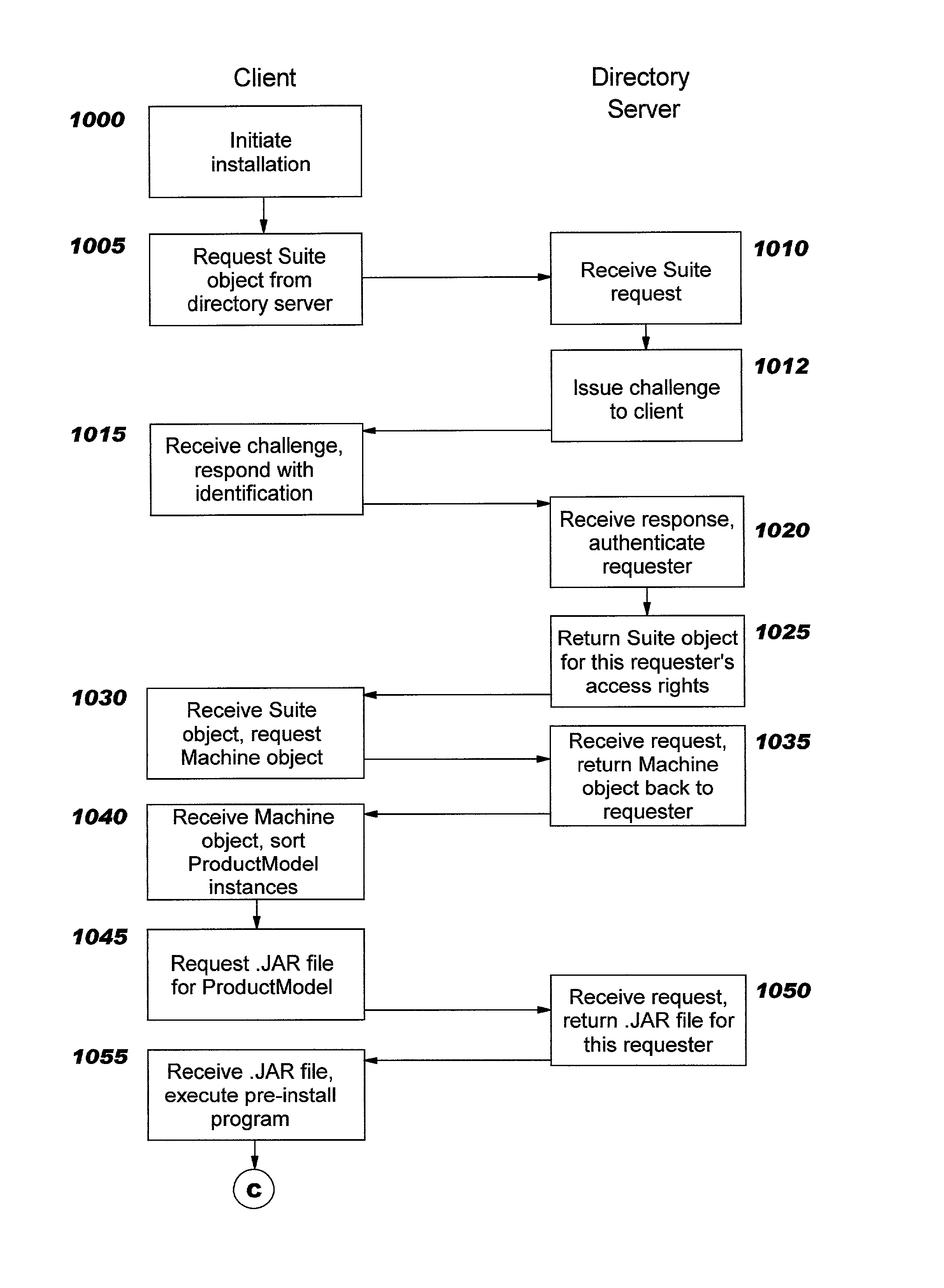
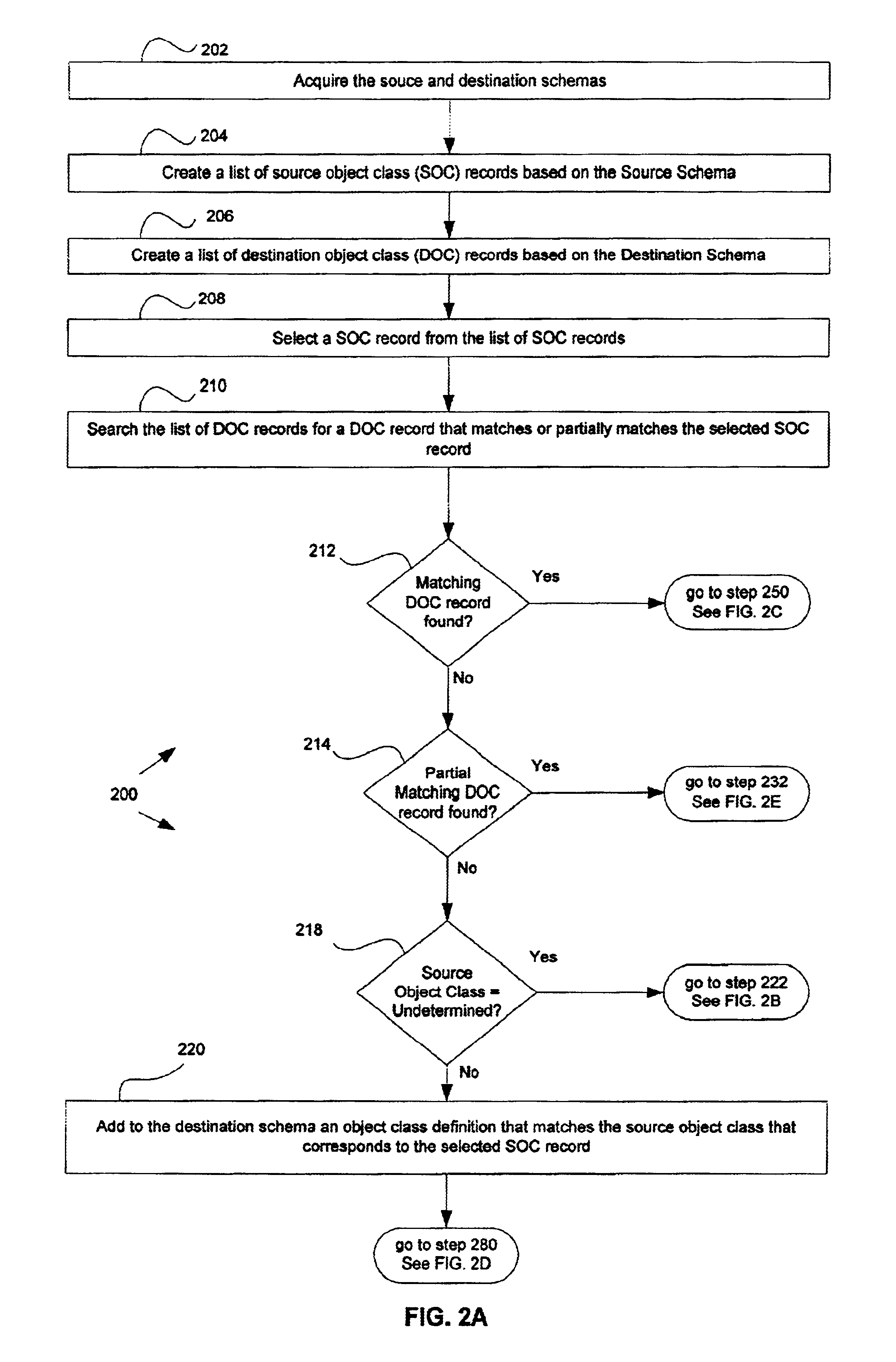
Object model and framework for installation of software packages using a distributed directory
InactiveUS20030018964A1Efficient assemblyProgram loading/initiatingMemory systemsDirectory Access ProtocolLightweight Directory Access Protocol
Methods, systems, and computer program products for improving installation of software packages using a directory (such as a Lightweight Directory Access Protocol, or "LDAP", directory). A model and framework are described, where the objects of the data model may be uncoupled from the framework, allowing individual objects to be separately stored and retrieved in the directory is association with access rights or privileges. Multiple versions of each object may therefore be created and stored, and may be easily retrieved using the built-in mechanisms of the directory, when access rights which are appropriate for a particular requester are known. Optionally, built-in authentication mechanisms of the directory may be used to authenticate the requester.
Owner:IBM CORP
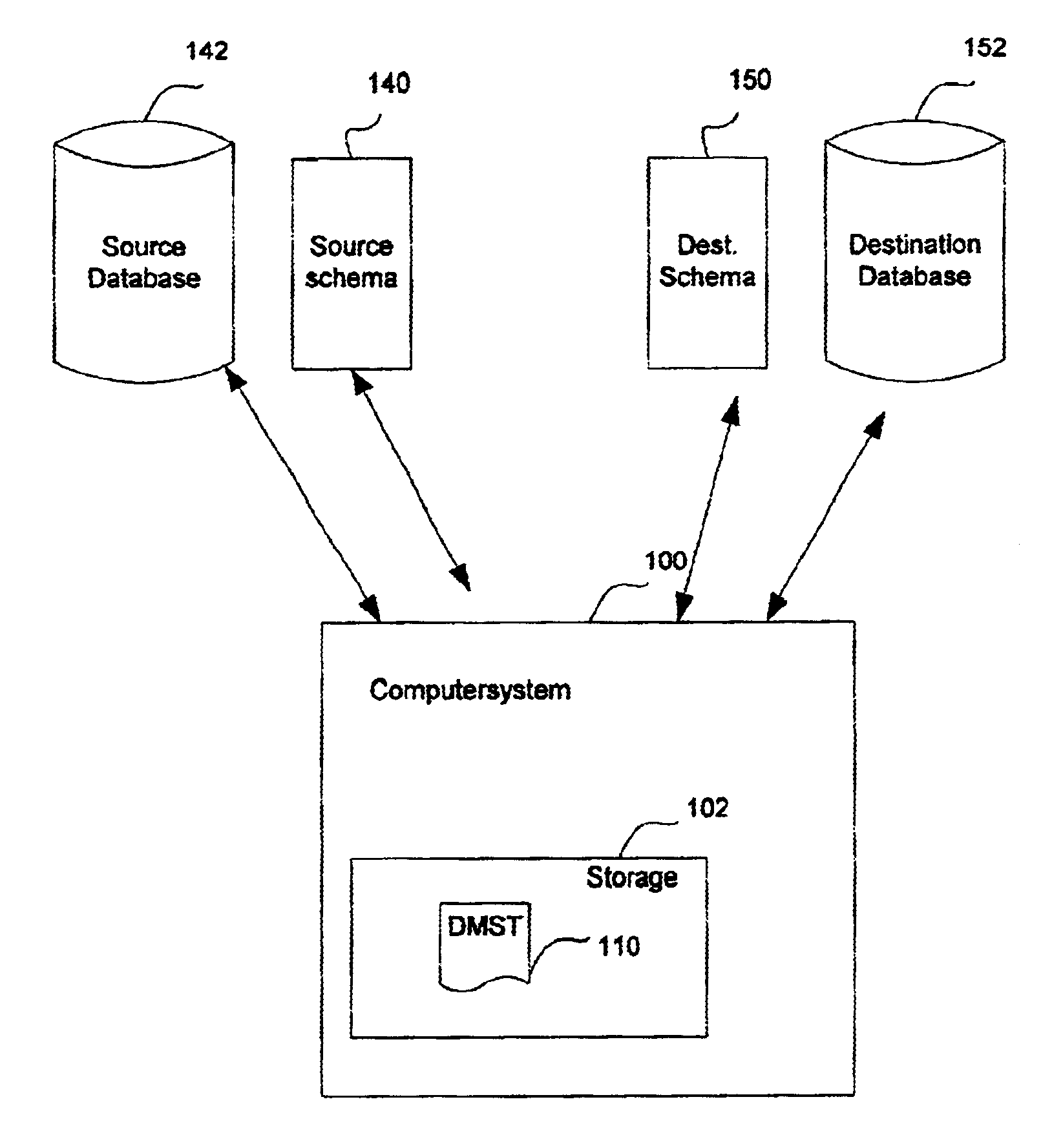
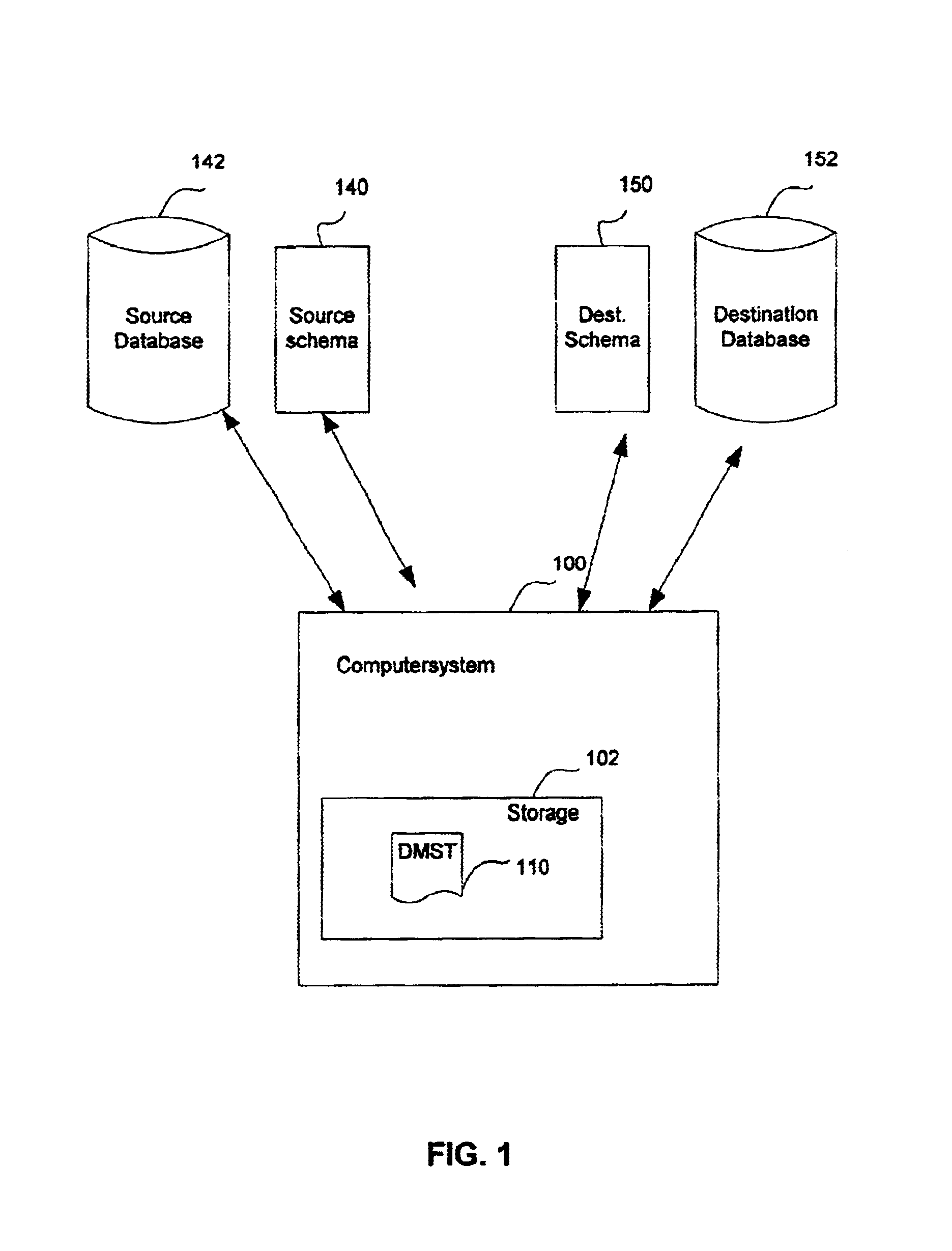
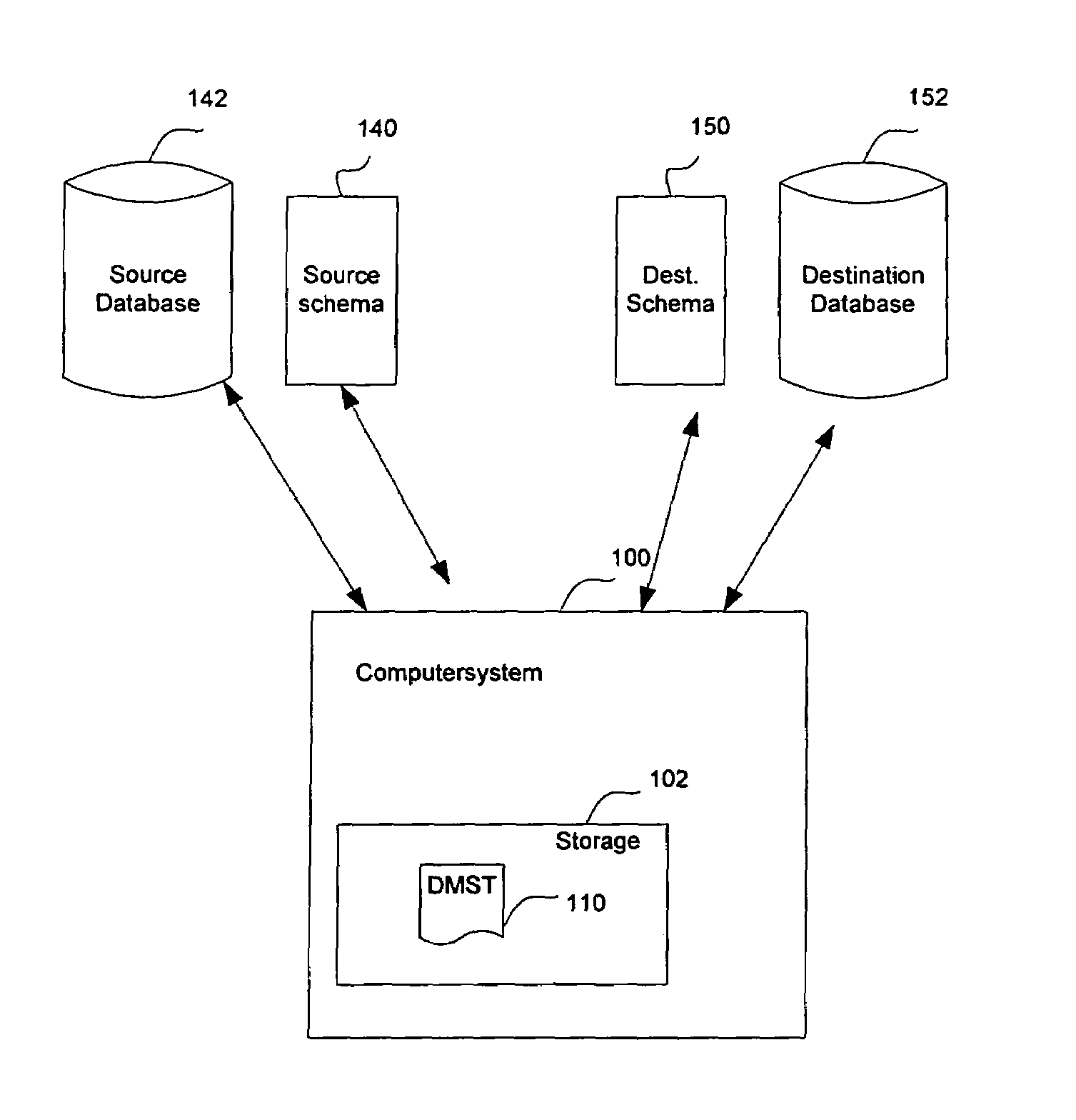
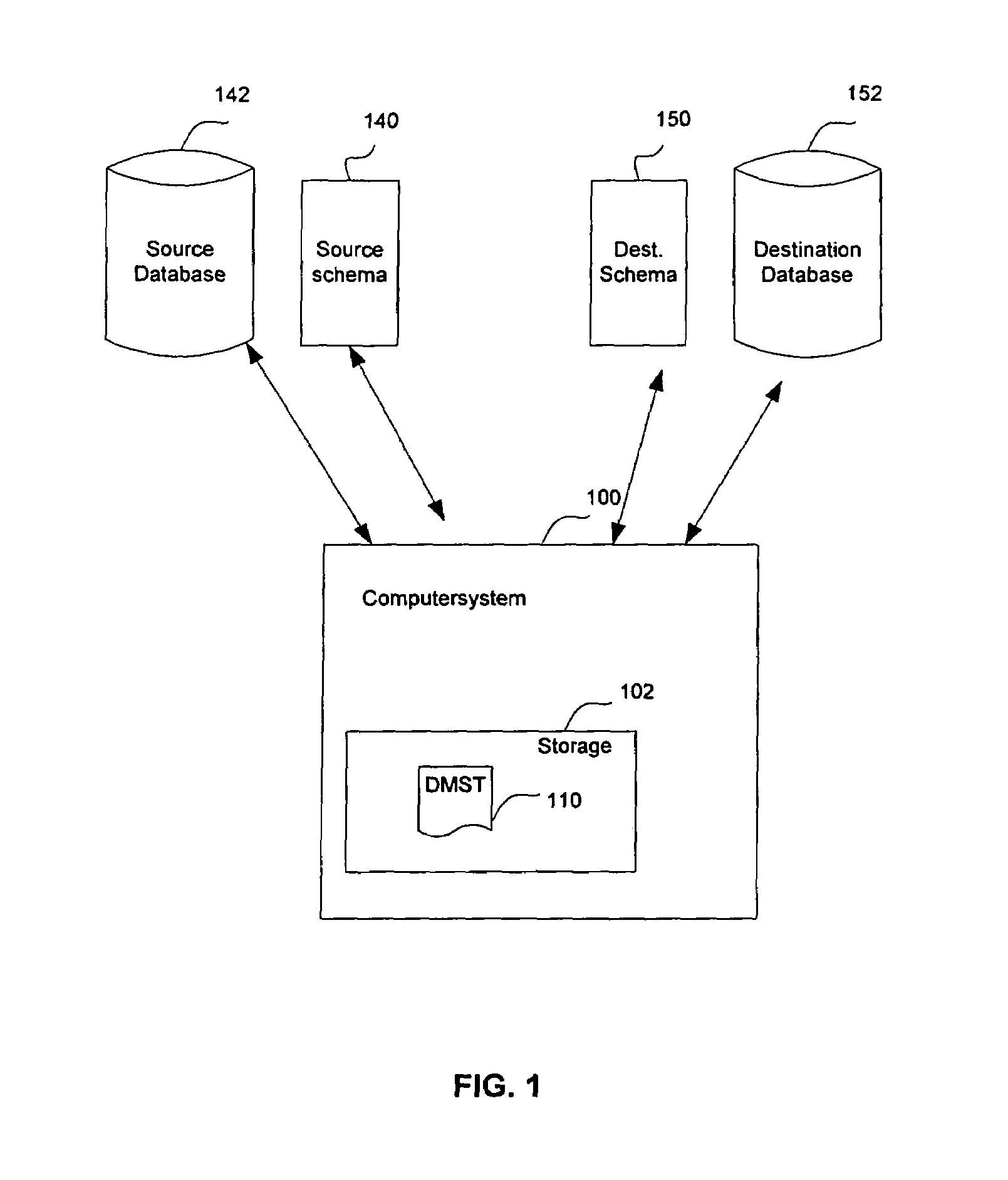
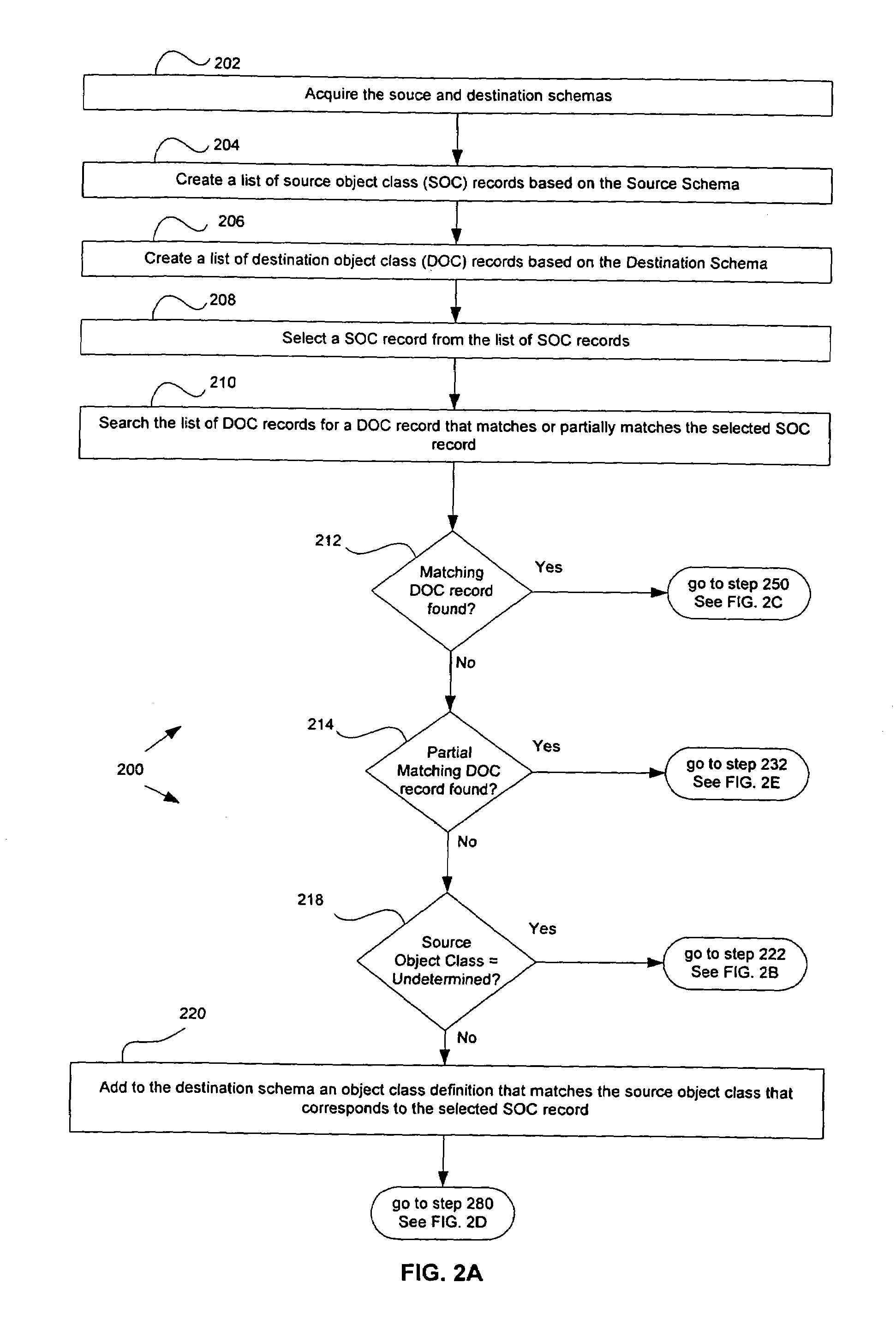
System, method and computer program product for migrating data from one database to another database
InactiveUS6915287B1Reduce complicationsData processing applicationsObject oriented databasesDirectory Access ProtocolLightweight Directory Access Protocol
A software tool that is useful when one is attempting to migrate data from one database to another database. In one aspect of the invention, the software tool reduces the complications that may arise when one attempts to migrate data from one Lightweight Directory Access Protocol (LDAP) directory to another LDAP directory, where the schemas for the two directories are not the same.
Owner:ROBERT BOSCH GMBH +1
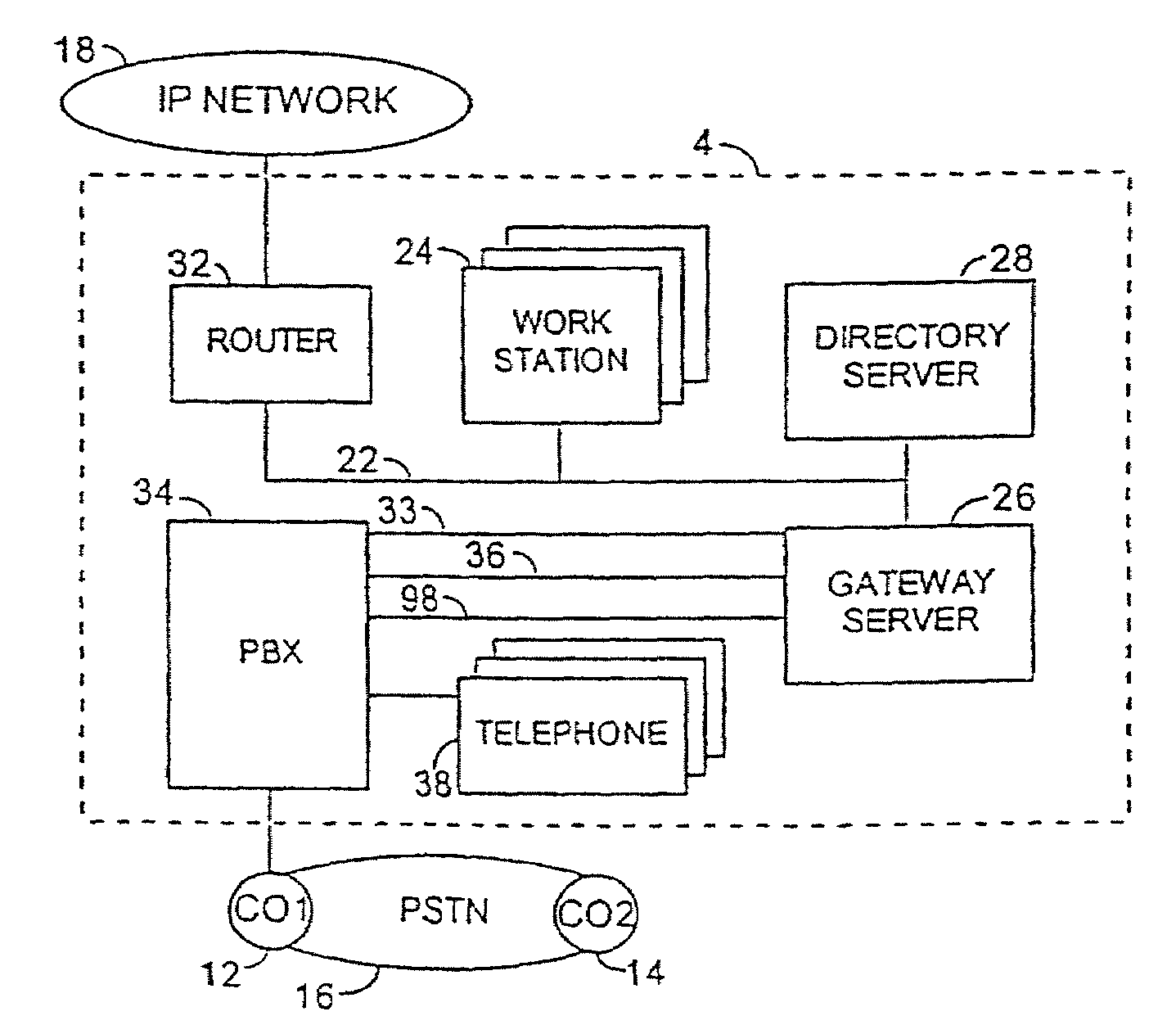
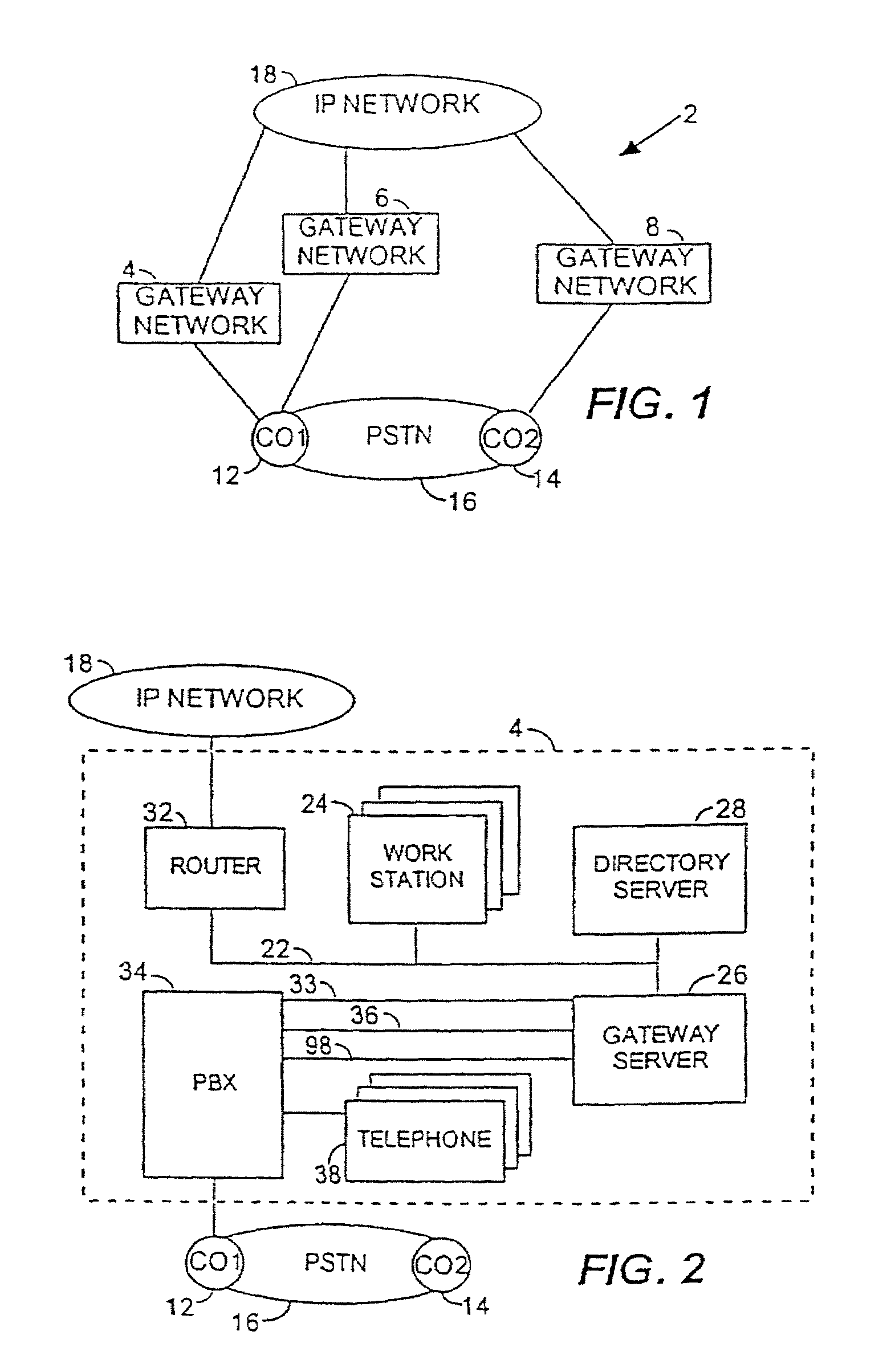
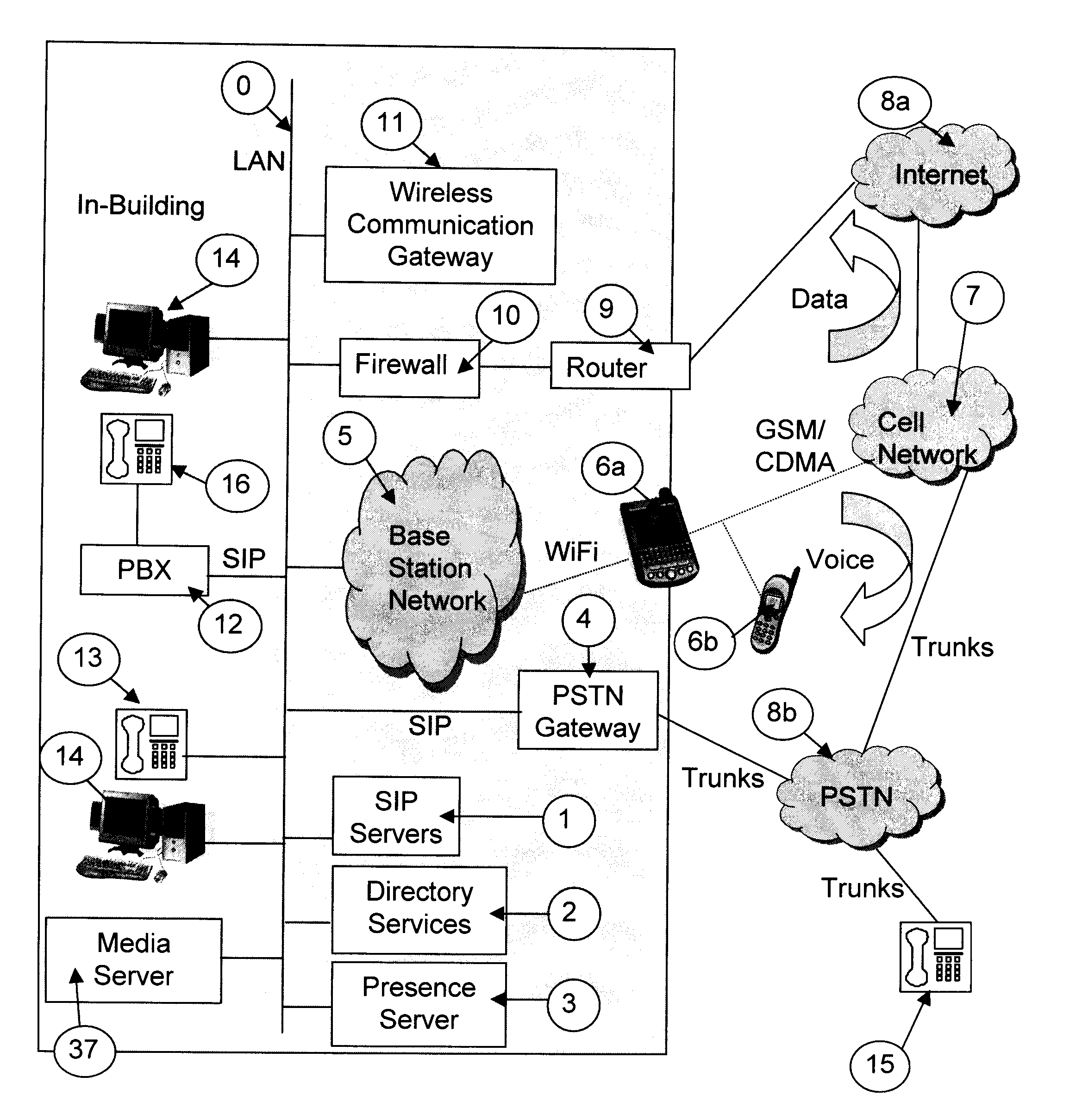
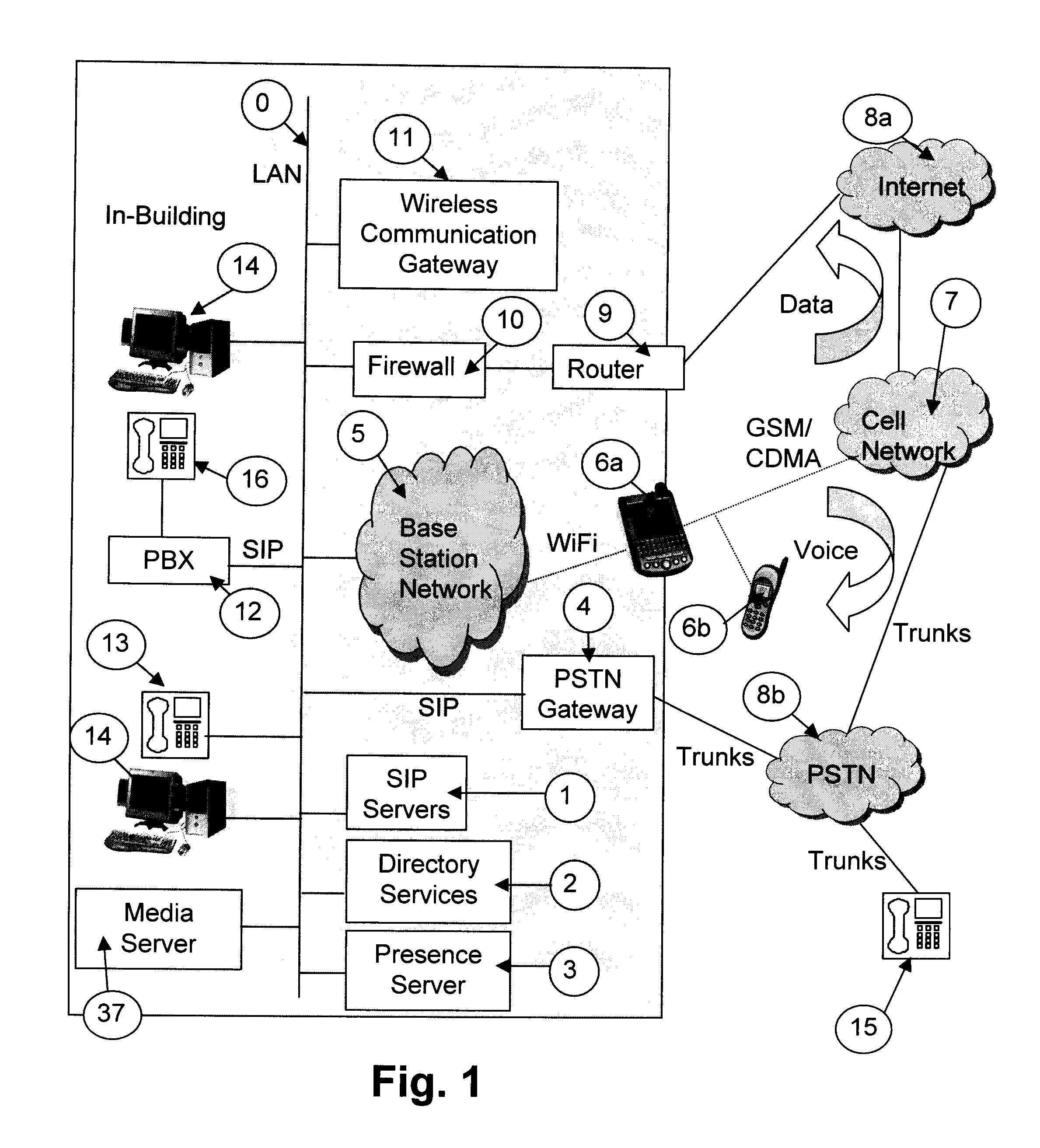
Apparatus and method for integrated voice gateway
InactiveUS7280530B2Low costFacilitate communicationInterconnection arrangementsSpecial service for subscribersMulti siteUser authentication
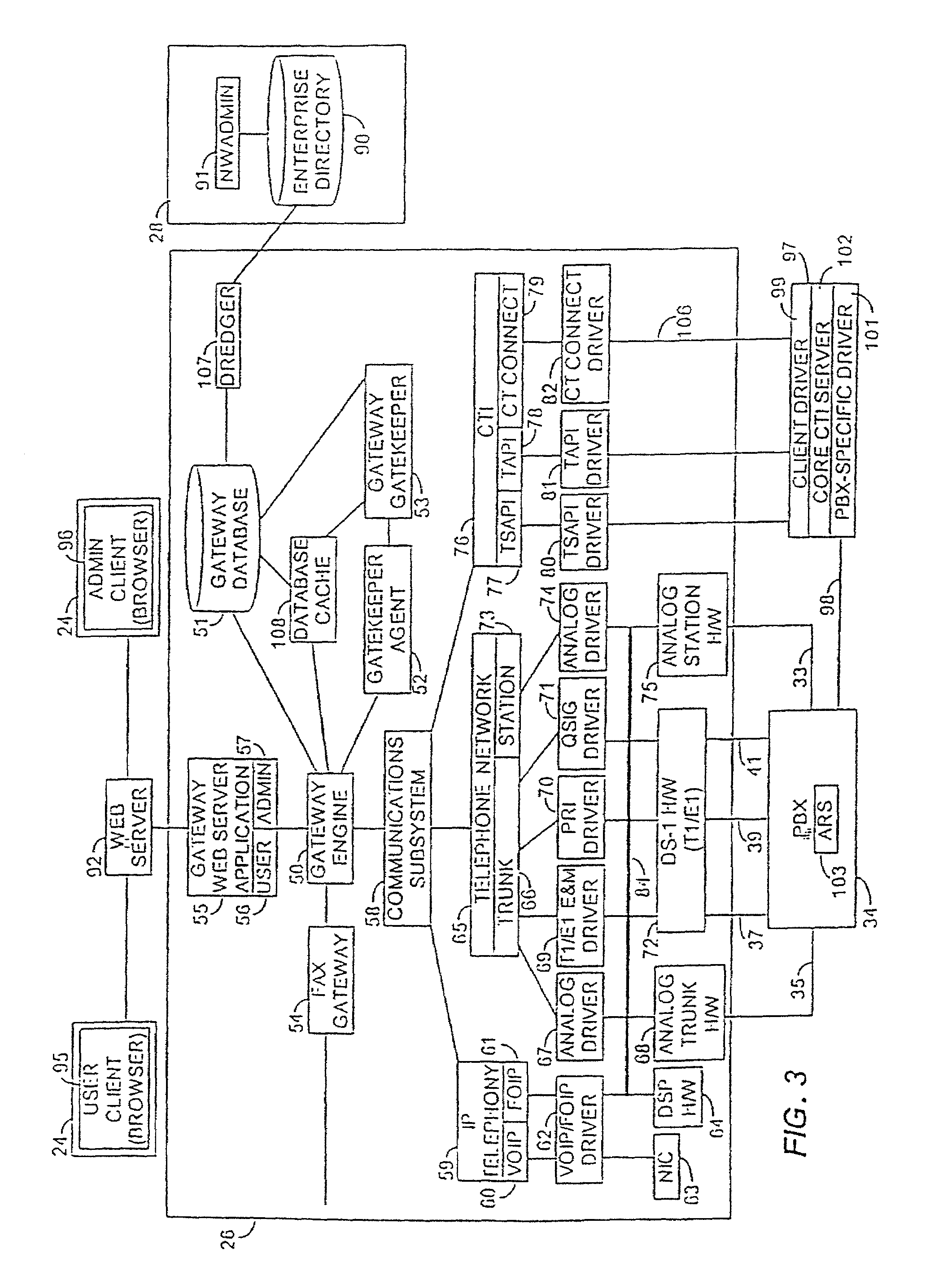
An integrated voice gateway system for use within a company which can route a voice telephone call between parties at two different locations over an IP network or over the PST NETWORK. The system can route a voice telephone call from a first location within the system to a second location within the system via the IP network, and then from the second location to a third location via the PST NETWORK. The integrated voice gateway system includes a gateway server which serves as an intranet / Internet telephony gateway. The gateway server routes intra-company voice or facsimile (fax) calls, over the company's intranet or the public Internet. The gateway server provides an alternate voice network to the PST NETWORK for a company. This alternate network is provided at a much lower cost. The gateway server is a combination of hardware and software components which reside on a PC server platform. The gateway server is coupled to a customer premise telephone system, i.e. a PBX via a T1 or E1 trunk for larger systems, or an analog trunk for smaller systems. The gateway server is coupled to the company's intranet via industry standard connections. The gateway servers in a multi-site company are coupled together via the company's intranet or wide area network (WAN) into a gateway network. The gateway server uses PBX call status links to provide many unique and useful features which are otherwise unavailable. The gateway server uses T1 inband ANI, PRI, QSIG or industry standard CTI applications programming interfaces (API) and works with any PBX which supports any of these call status links. The gateway server is equipped with a database of user and gateway objects and attributes, and provides many unique features including caller's name based on caller phone number, address translation, gateway network routing information, user authentication, etc. This database can be integrated with industry standard enterprise directory services systems including any directory which supports the Lightweight Directory Access Protocol (X.500) (LDAP) interface.
Owner:STARVOX COMM +3
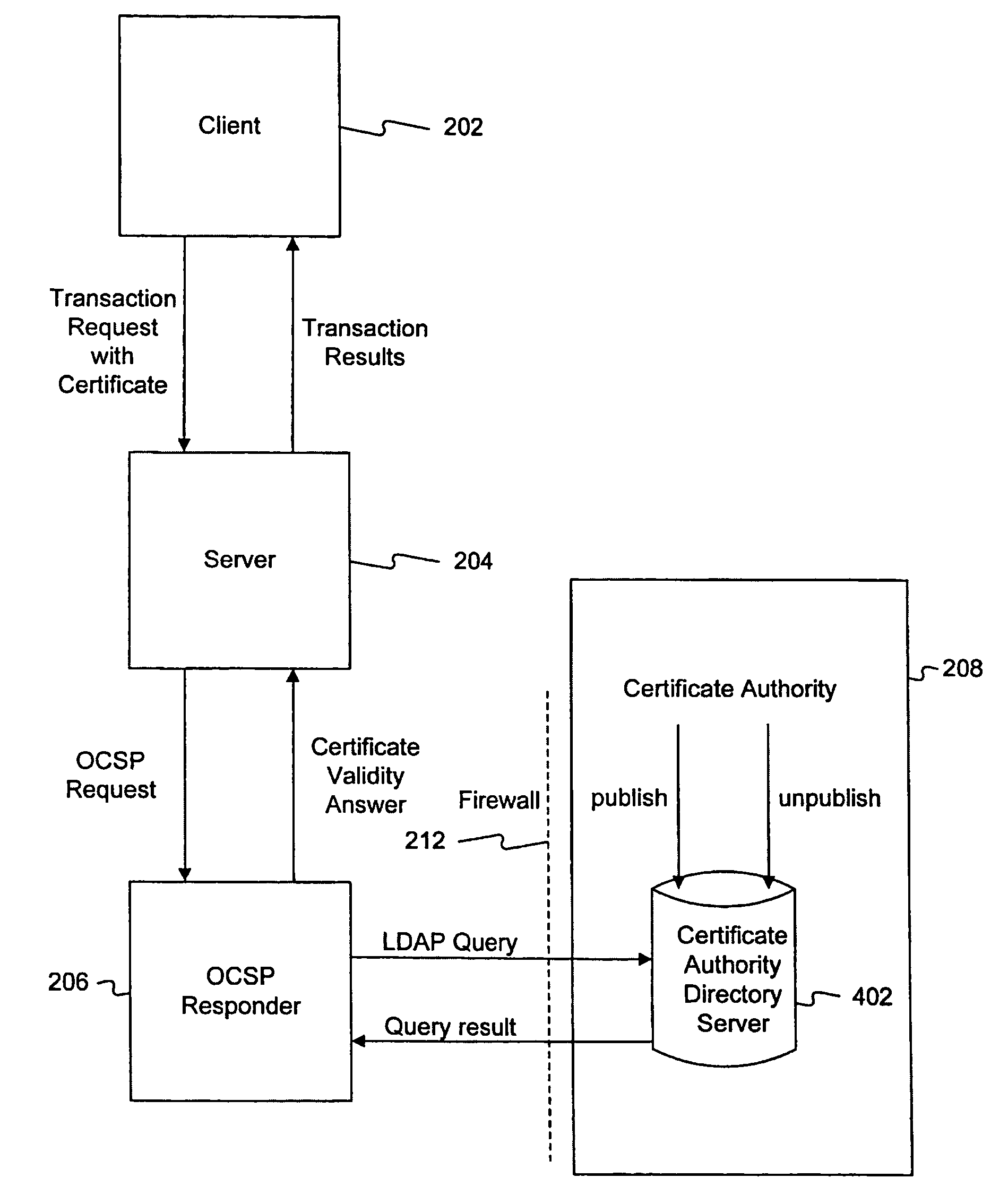
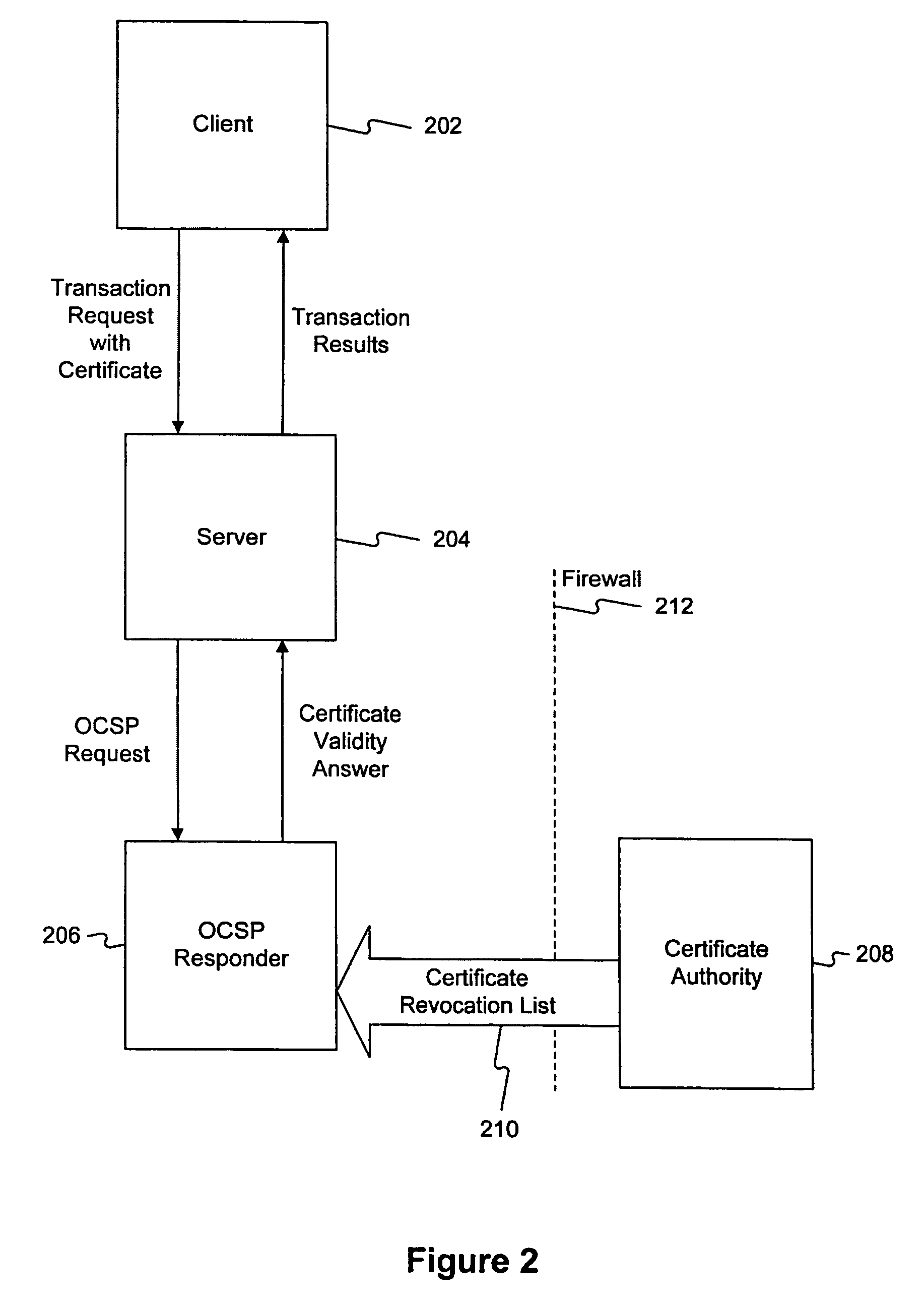
Method and system for answering online certificate status protocol (OCSP) requests without certificate revocation lists (CRL)
InactiveUS6970862B2Digital data protectionElectronic credentialsDirectory Access ProtocolClient-side
Methods and systems in accordance with the present invention efficiently validate digital certificates by answering Online Certificate Status Protocol (“OCSP”) requests without Certificate Revocation Lists (“CRL”). During validation of digital certificates, these methods and systems speed transmission, reduce required bandwidth and reduce required data storage by eliminating the need for the transmission of lengthy CRLs from a Certificate Authority (“CA”) when verifying a digital certificate from a client. In one implementation, they send a Lightweight Directory Access Protocol (“LDAP”) database query to a CA directory server to determine and pinpoint the existence of a valid digital certificate and check its validity without receiving a long list of data, such as a CRL, from a CA. The CA directory server returns the query result, and the database query in the CA directory server is performed faster than using an entire CRL, and furthermore, the transmission of the database query result is a small piece of information and does not require the large amounts of data transmission bandwidth and storage as required with transmitting CRL's.
Owner:ORACLE INT CORP
Authentication, application-authorization, and user profiling using dynamic directory services
InactiveUS7209970B1Maintenance freeMultiple digital computer combinationsTransmissionComputer usersApplication software
A system and method for authenticating and authorizing computer users with a single, standard, directory-based set of applications. The invention combines dynamic directory services (DDS) with a directory access protocol such as the light weight directory access protocol (LDAP) to provide authentication and application-authorization for secured networks, applications, and programs. Dynamic information such as session information or user ID numbers is stored in a directory each time a user logs into the systems and is maintained in the directory until the user logs out. While the information exists in the directory, it can be queried by other programs, applications, or networks that use a directory service to authenticate or authorize the user for the program, application, or network.
Owner:SPRINT SPECTRUM LLC
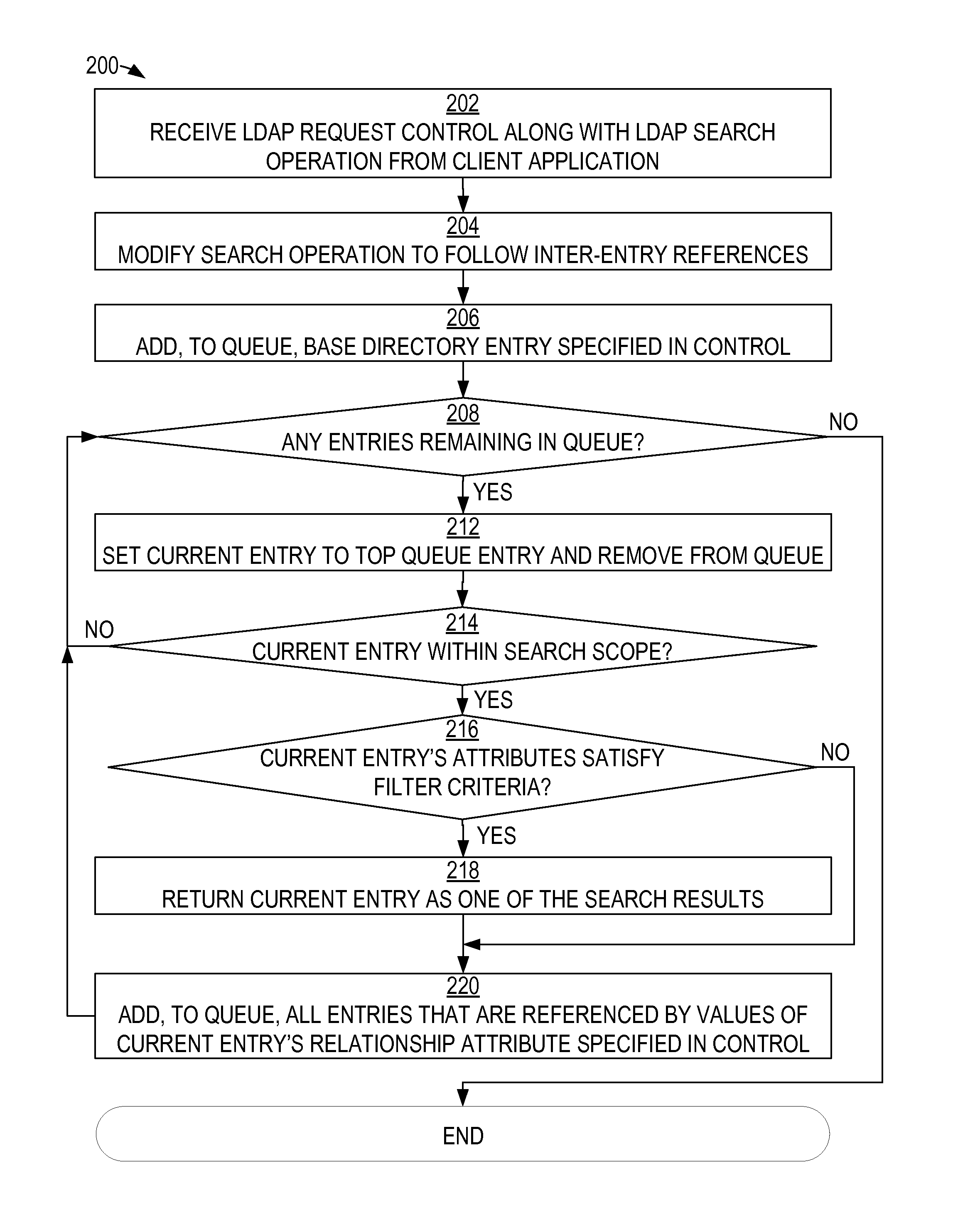
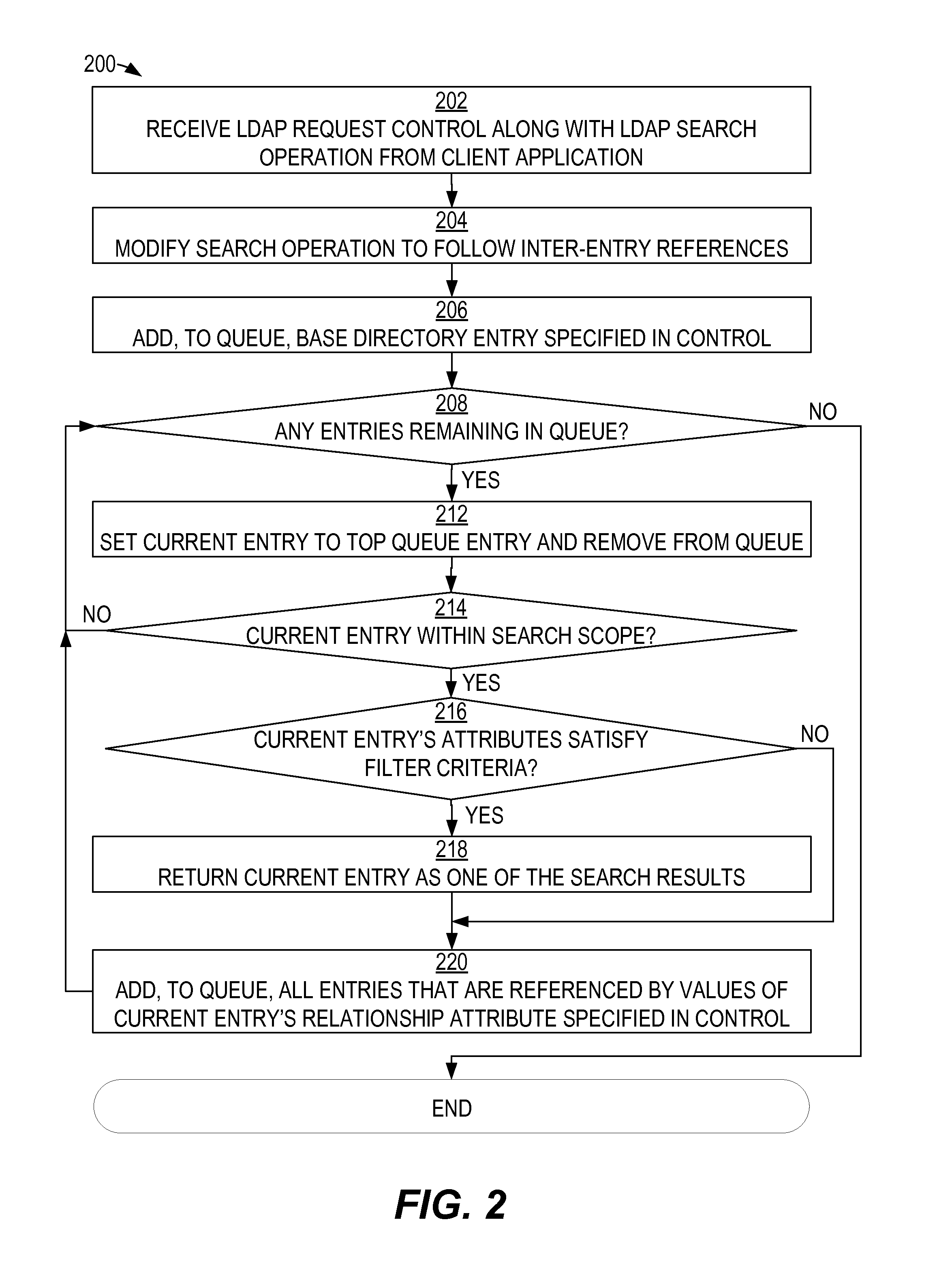
Lightweight directory access protocol (LDAP) join search mechanism
Complex search tasks are performed relative to an LDAP directory with a minimal quantity of LDAP search operations. Search tasks that follow relationships between LDAP entries can be performed, even under circumstances in which those relationships are not represented by the hierarchical structure of the LDAP directory. A client application can specify an LDAP control that the client application sends to the LDAP server along with the LDAP search operation. The LDAP server's receipt of the LDAP control can cause the LDAP server to modify the behavior of the search operation so that the LDAP server follows potentially non-hierarchical specified relationships between the LDAP entries in determining the set of entries to return as results of the search operation. As a result, the LDAP server can return a complete set of related result entries to the client application in response to a single LDAP search operation directed by the application.
Owner:ORACLE INT CORP
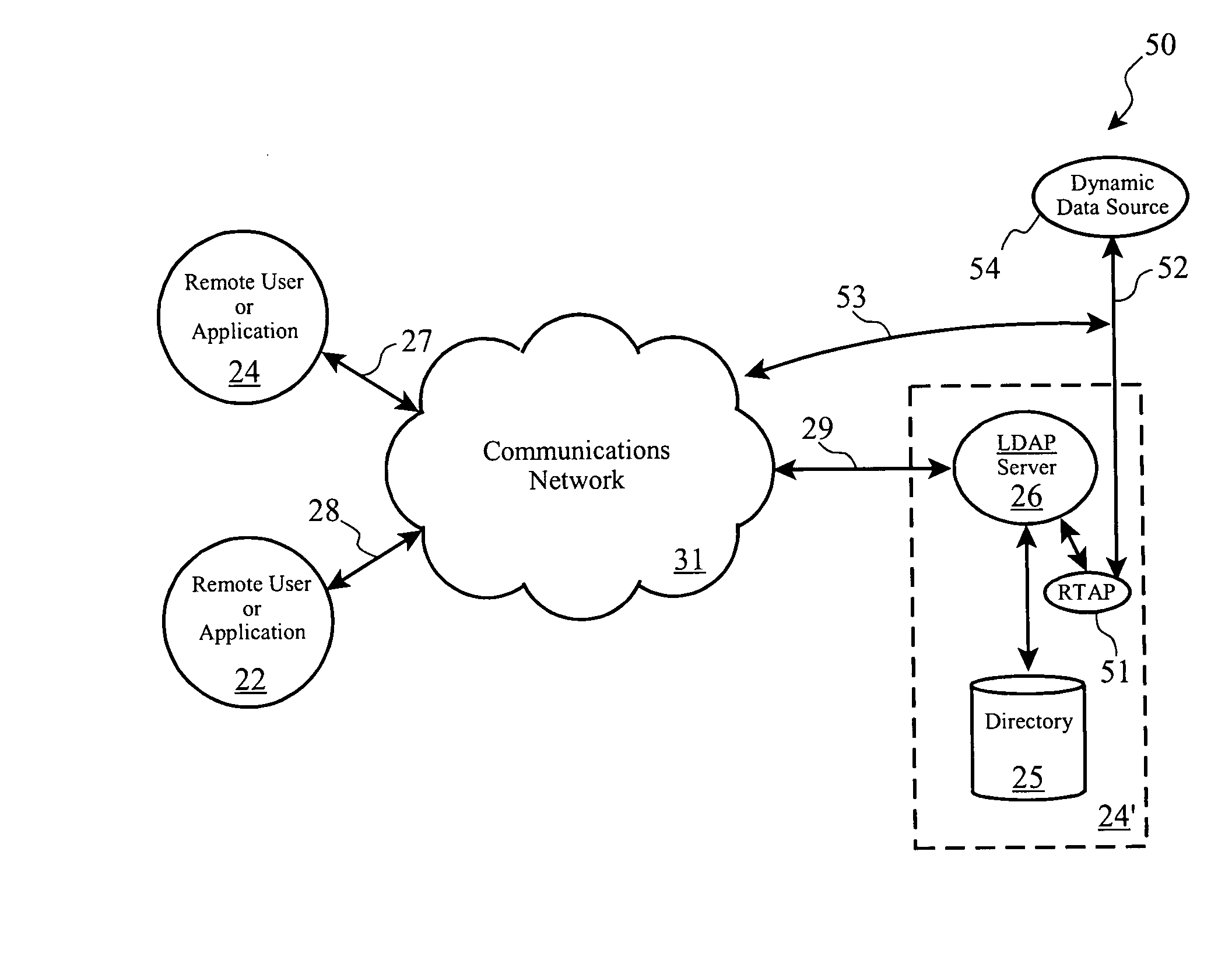
Real-time attribute processor and syntax schema for directory access protocol services
InactiveUS20050216485A1Eliminate needDigital data processing detailsTransmissionDirectory Access ProtocolDynamic data
A processor which cooperates with directory servers to handle requests for values of dynamic attributes which would otherwise present a real-time processing challenge to the directory server due to the server's dependence on the data normally being static in nature. Special schema syntax identifiers are used to identify dynamic attributes which then are not stored directly in the directory, but whose values are resolved at the time a read request is made for those attributes. This approach eliminates the need to store the dynamic information in the directory, and allows user-supplied modules to perform the resolution of the dynamic attributes in a real-time manner, including not only retrieving a value from a dynamic data source, but optionally performing calculations or manipulations on the data as well. One embodiment of the invention cooperates with Lightweight Directory Access Protocol (“LDAP”) directory servers.
Owner:IBM CORP
Method, system and computer program product for a lightweight directory access protocol client application program interface
ActiveUS7243355B2Data processing applicationsMultiprogramming arrangementsApplication softwareClient-side
A device, including a computer readable medium storing executable computer instructions for implementing an application program interface (API). The API including a function call for enabling communications between a calling application and a client on the device, the client communicating with a directory server. In another aspect, there is provided a computer-readable medium, including executable computer instructions for implementing an application program interface (API) on a device. The API, including a function call for enabling communications between a calling application and a client on the device, the client communicating with a directory server.
Owner:CDN INNOVATIONS LLC
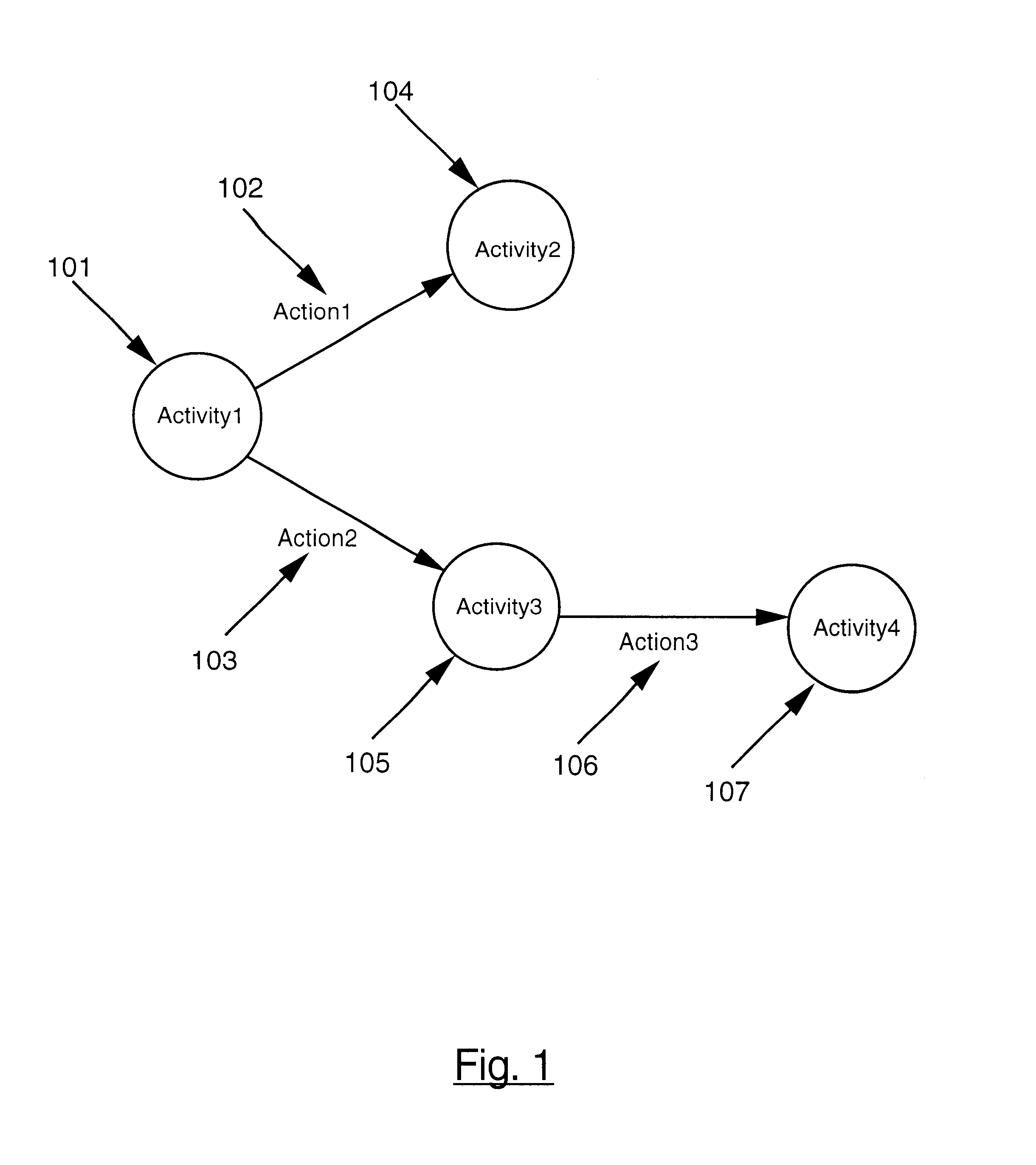
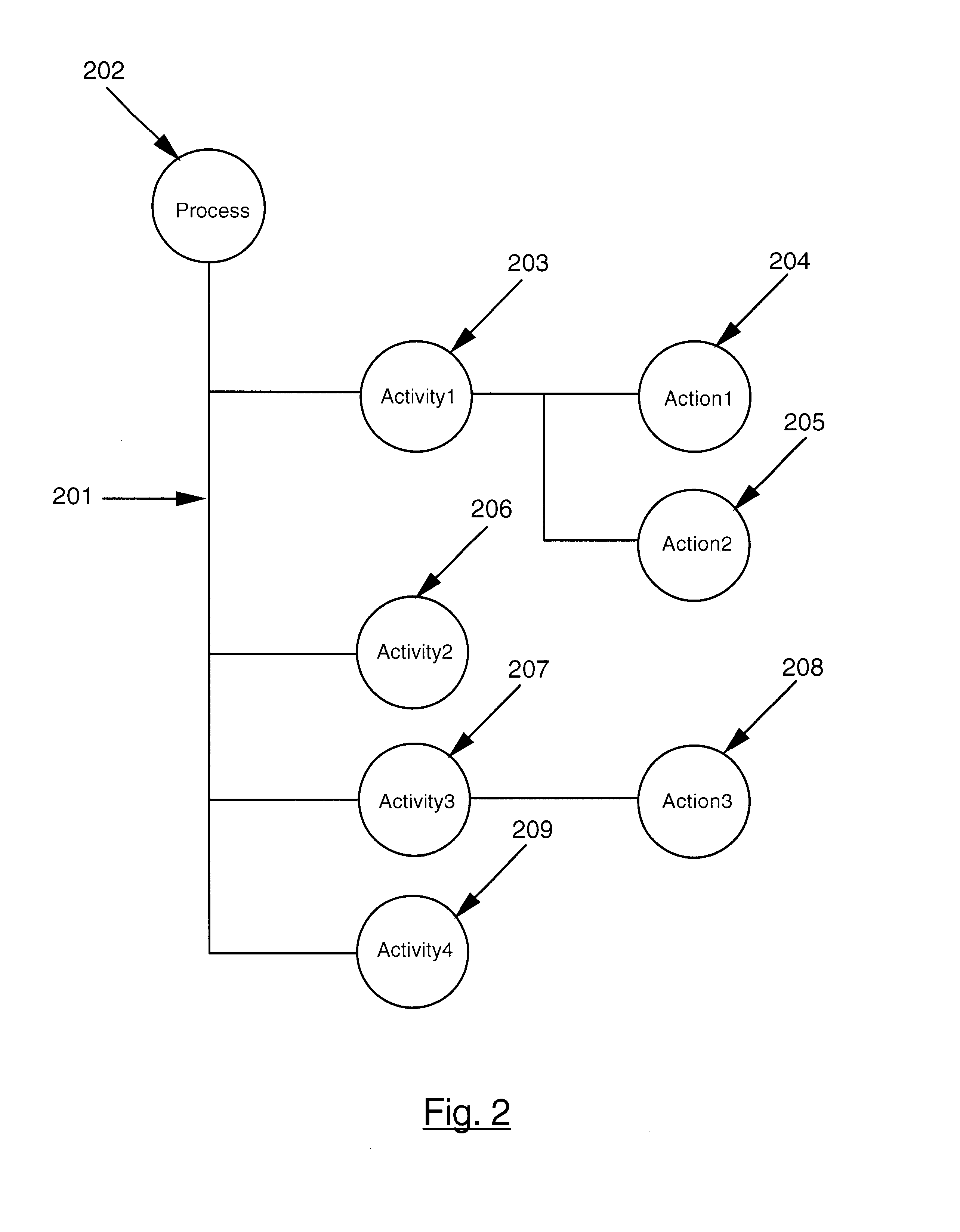
Lightweight directory access protocol workflow management system
InactiveUS7133833B1Easy to shareOffice automationSpecific program execution arrangementsLogical processDirectory Access Protocol
A lightweight directory access protocol workflow management system. The invention converts a logical process into a reusable Lightweight Directory Access Protocol (LDAP) directory representation. The directory representation is a hierarchical tree structure where each process element in the process is represented as an LDAP directory entry and is assigned a unique distinguished name and is stored in a Directory Server database or filesystem. The tree structure of the LDAP representation allows the sharing of LDAP trees or subtrees among users. The LDAP trees and subtrees can be remotely located and distributed among different LDAP servers. Another preferred embodiment of the invention provides a graphical user interface for creating a Workflow process definition which is comprised of process elements: activities; actions; and entry / exit points. The user constructs a Workflow process using the process elements, logically interrelating each activity. Once the Workflow process is defined it is converted into an LDAP directory representation and stored in a Directory Server database or filesystem.
Owner:META PLATFORMS INC
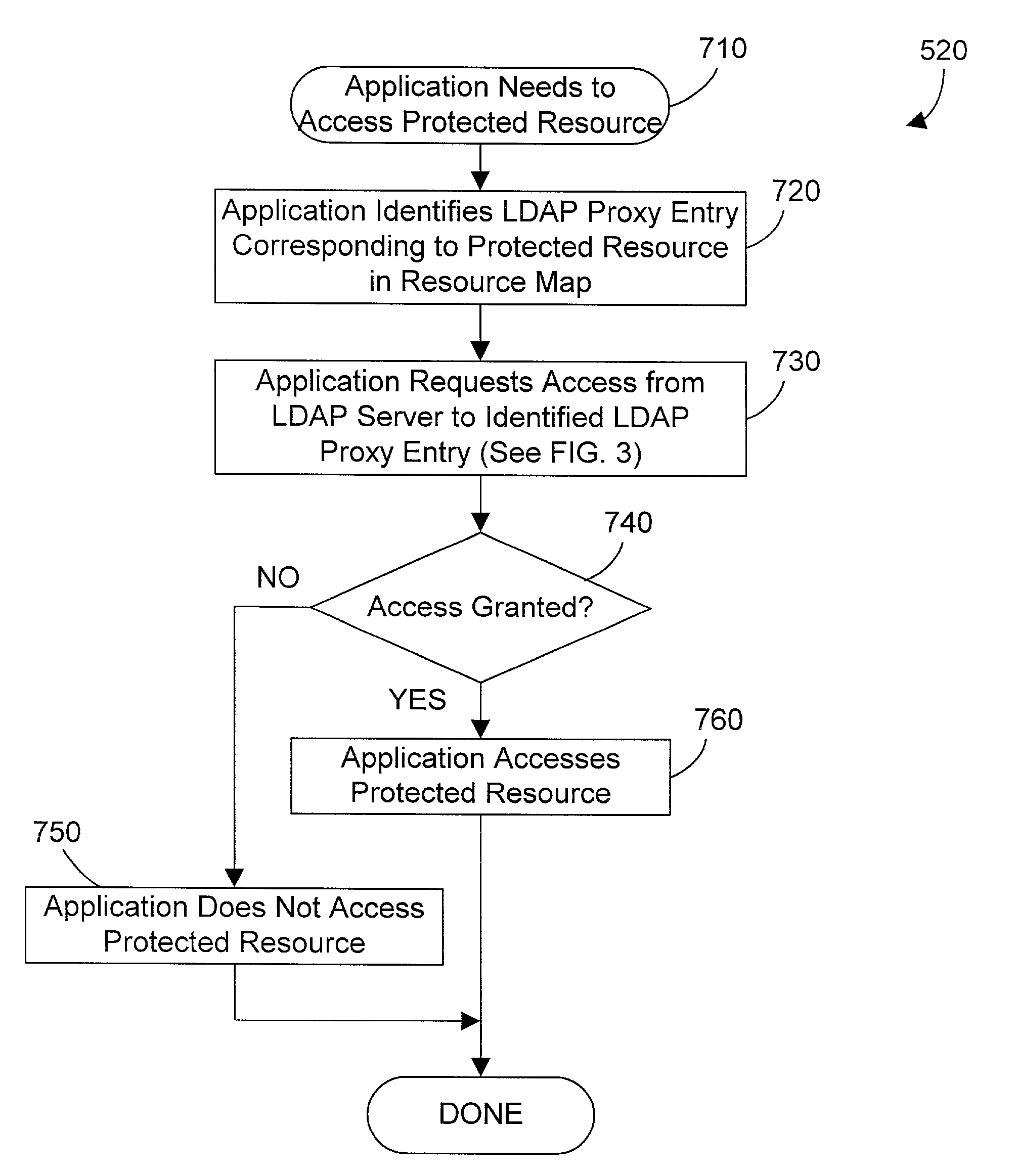
Apparatus and method for using a directory service for authentication and authorization to access resources outside of the directory service
InactiveUS7146635B2Digital data processing detailsComputer security arrangementsUser needsApplication software
An apparatus and method use the built-in authentication and authorization functions of a directory service to perform authentication and authorization for resources that are external to the directory service. A Lightweight Directory Access Protocol (LDAP) service is used in the preferred embodiments. The LDAP directory includes built-in functions for authenticating a user that requests access to an entry. Each resource that needs to be protected is mapped to an entry in the LDAP directory. These entries that correspond to protected resources external to the LDAP directory are called proxy entries. Proxy entries contain the authorization information for the corresponding protected resource in the form of an access control list for each entry that specifies the authorized users of the entry. When a user needs to access a protected resource, the user or an application uses the LDAP directory to determine whether the user is authenticated and authorized to access the proxy entry in the directory that corresponds to the resource. If the user is authenticated and authorized to access the proxy entry, the user may then access the corresponding external protected resource. The present invention thus allows the use of the internal LDAP authentication and authorization functions to determine which users are allowed to access protected resources that are external to the LDAP directory.
Owner:HCL TECH LTD
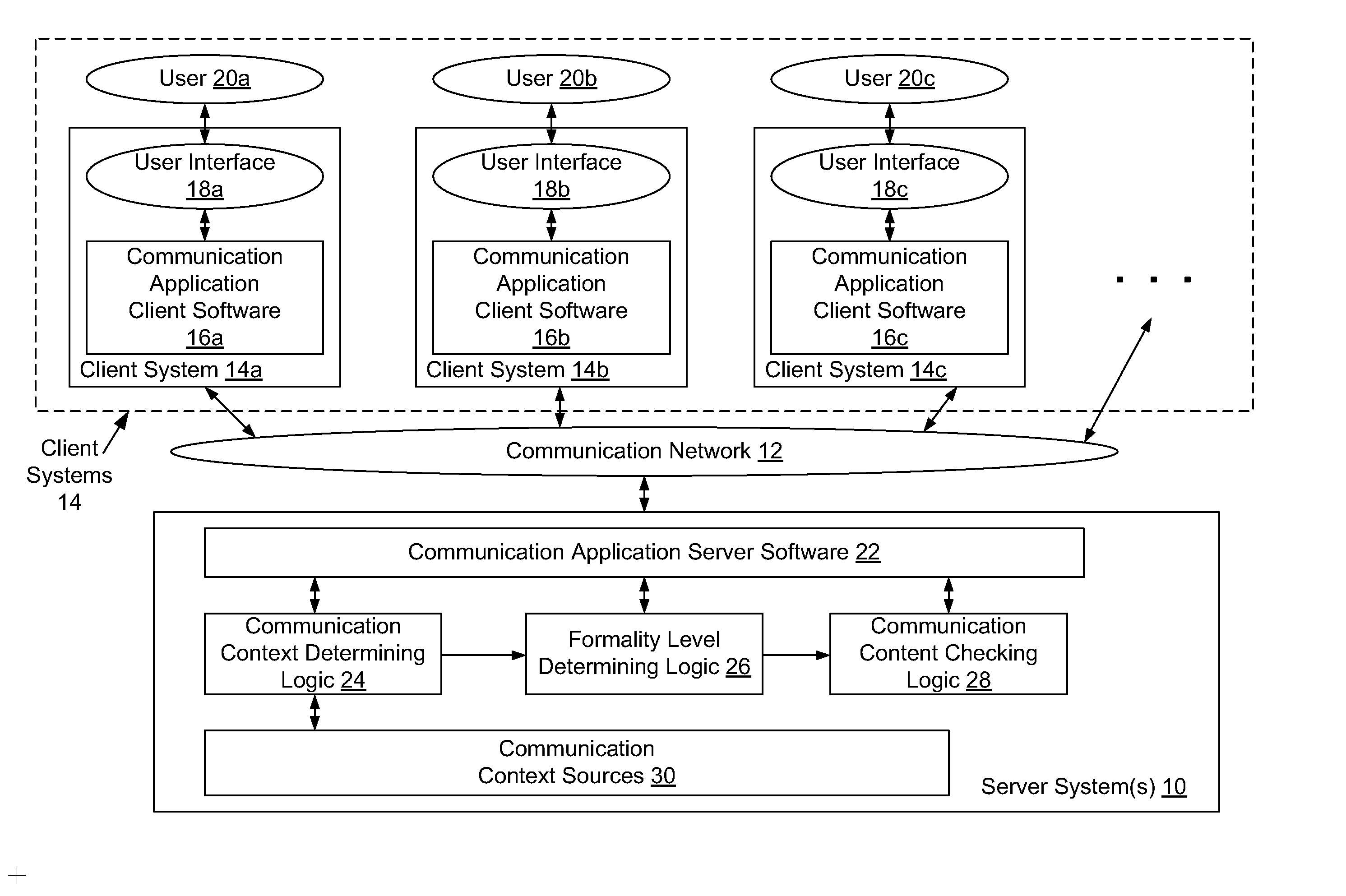
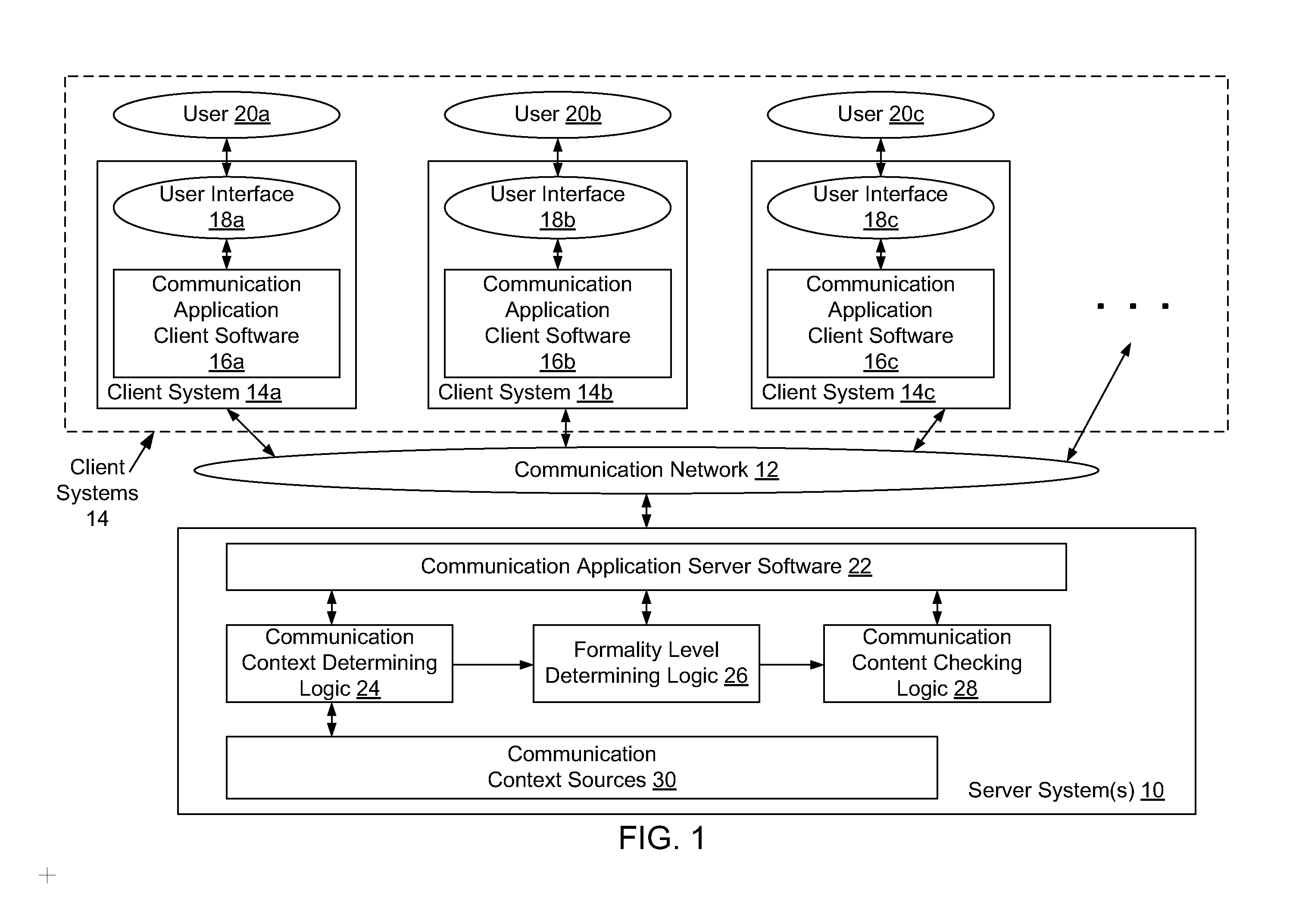
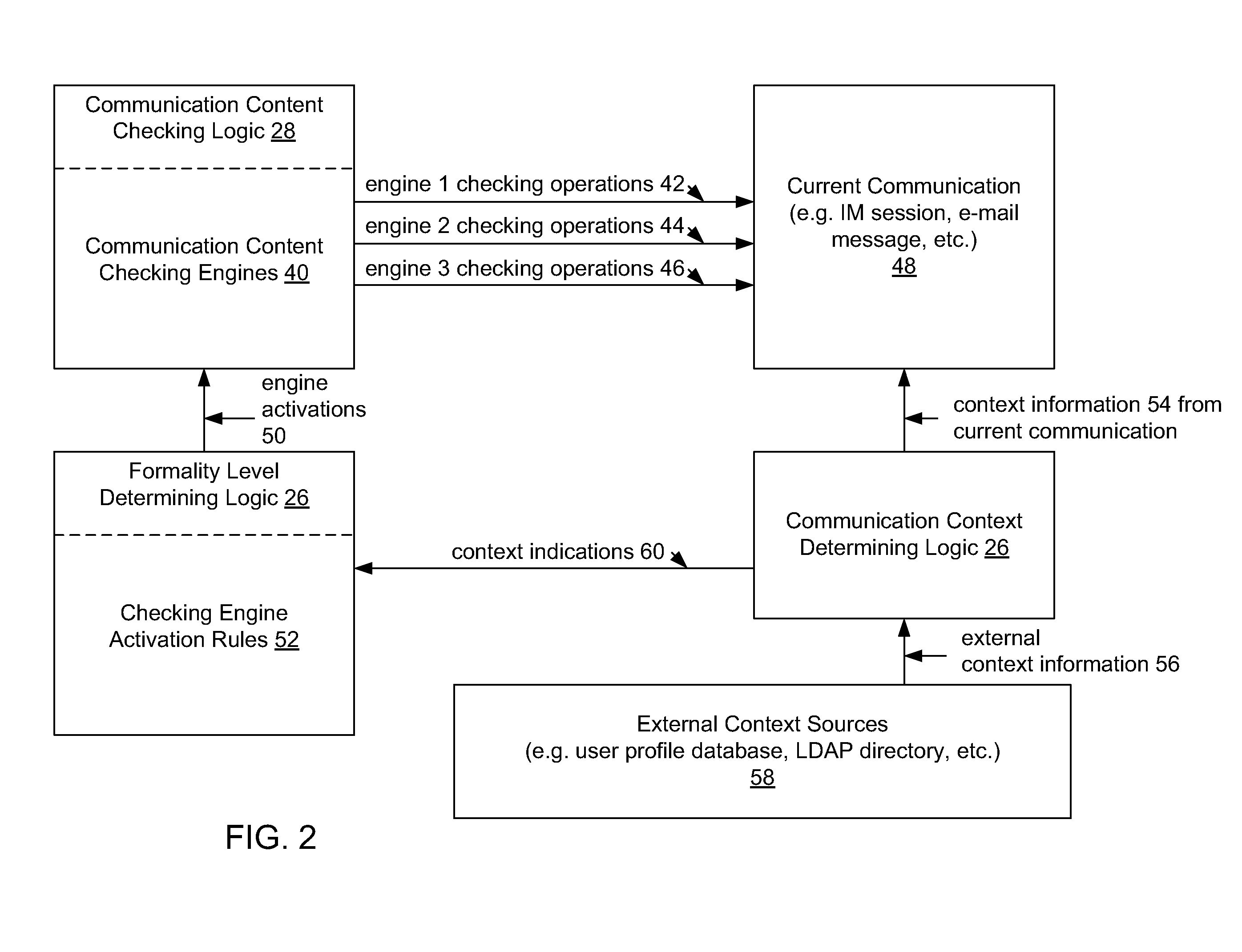
Method and system for providing communication context specific formality control
InactiveUS20080126481A1Reduce frustrationIncrease speedMultiple digital computer combinationsData switching networksProfessional relationshipGeolocation
A system for automatically providing different levels of formality controls in a communication is disclosed, in which a formality level is determined based on a current communication context. The formality level is used to enable an appropriate level of automatic checking of the communication contents. The determination of a formality level for a communication may be based on any specific context information regarding the participants and / or contents of a communication. including but not limited to the relative positions of participants within an organizational hierarchy (“organizational distance”), the professional relationships of the participants (e.g. service provider to client / customer), the frequency of communications between participants, the geographic locations of participants, the number of previous errors in the communication contents, configurable participant preferences, express communication settings by participants, etc. The determined formality level may be used to enable any specific type or level of automatic message contents checking, including but not limited to various types and levels of spell checking (e.g. location specific spell checking), grammar checking, acronym substitution, cultural filtering, etc. The disclosed system may determine organisational distances based on the contents of user directories, such as lightweight directory access protocol (LDAP) directories.
Owner:IBM CORP
Self-configurable distributed system
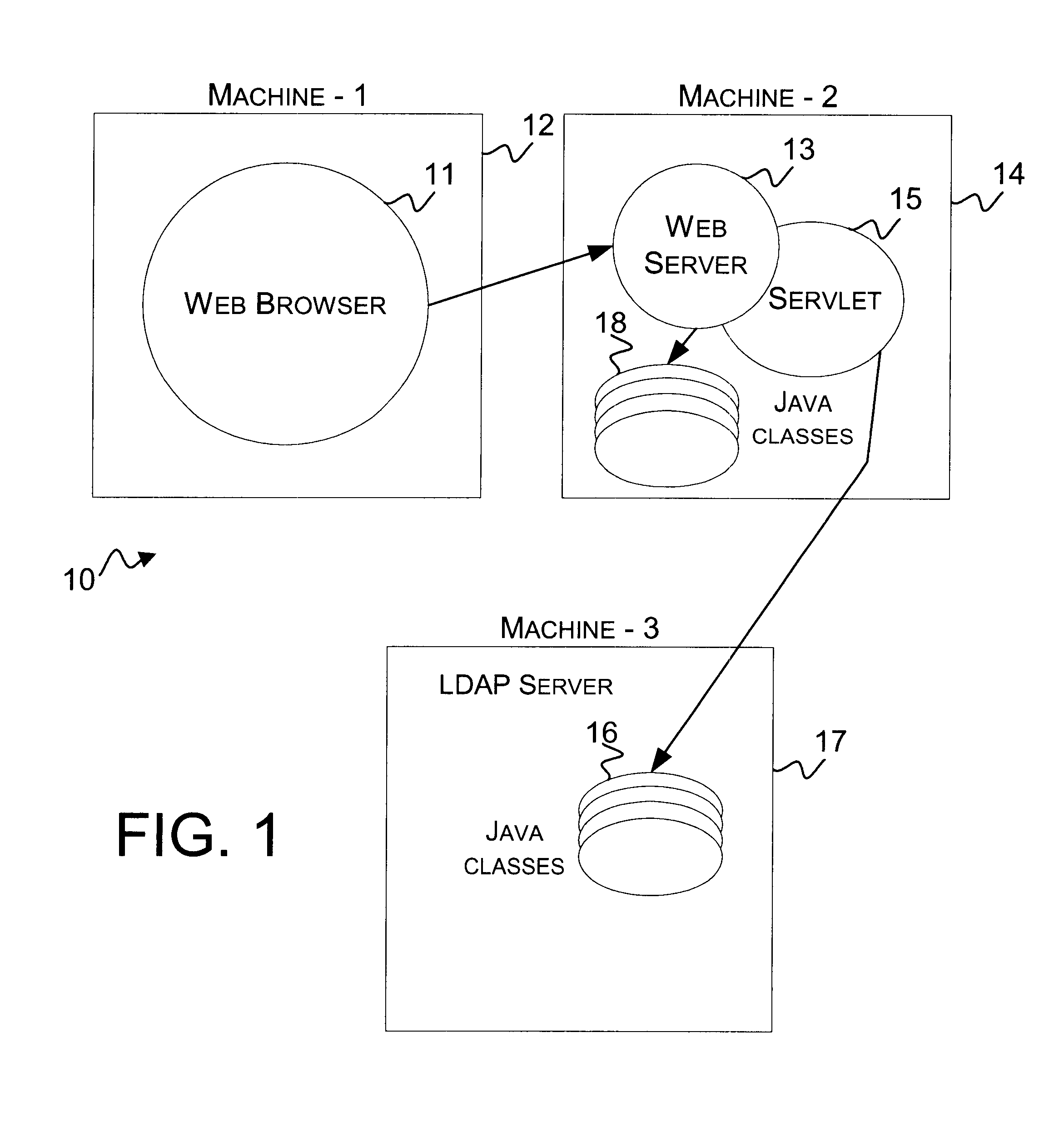
A self-configurable distributed computer software system and a method of enabling an applet running on a Web browser in the system to obtain needed software code in the form of Java classes from a machine that is not hosting the applet's originating Web server. A Lightweight Directory Access Protocol (LDAP) server stores Java classes utilized by a plurality of applets distributed throughout the system. The applet's Web server is connected to the Web browser and to the LDAP server, and includes a servlet for retrieving Java classes from the LDAP server. When the Web browser requests a needed Java class from the Web server, the Web server determines from the package name of the requested Java class whether or not the requested class is stored on the Web server's local storage disk. If not, the Web server requests the servlet to retrieve the Java class from the LDAP server. The servlet retrieves the byte code corresponding to the requested Java class, and the Web server provides it to the Web browser. The Web browser then converts the code to a Java class for use by the applet.
Owner:TELEFON AB LM ERICSSON (PUBL)
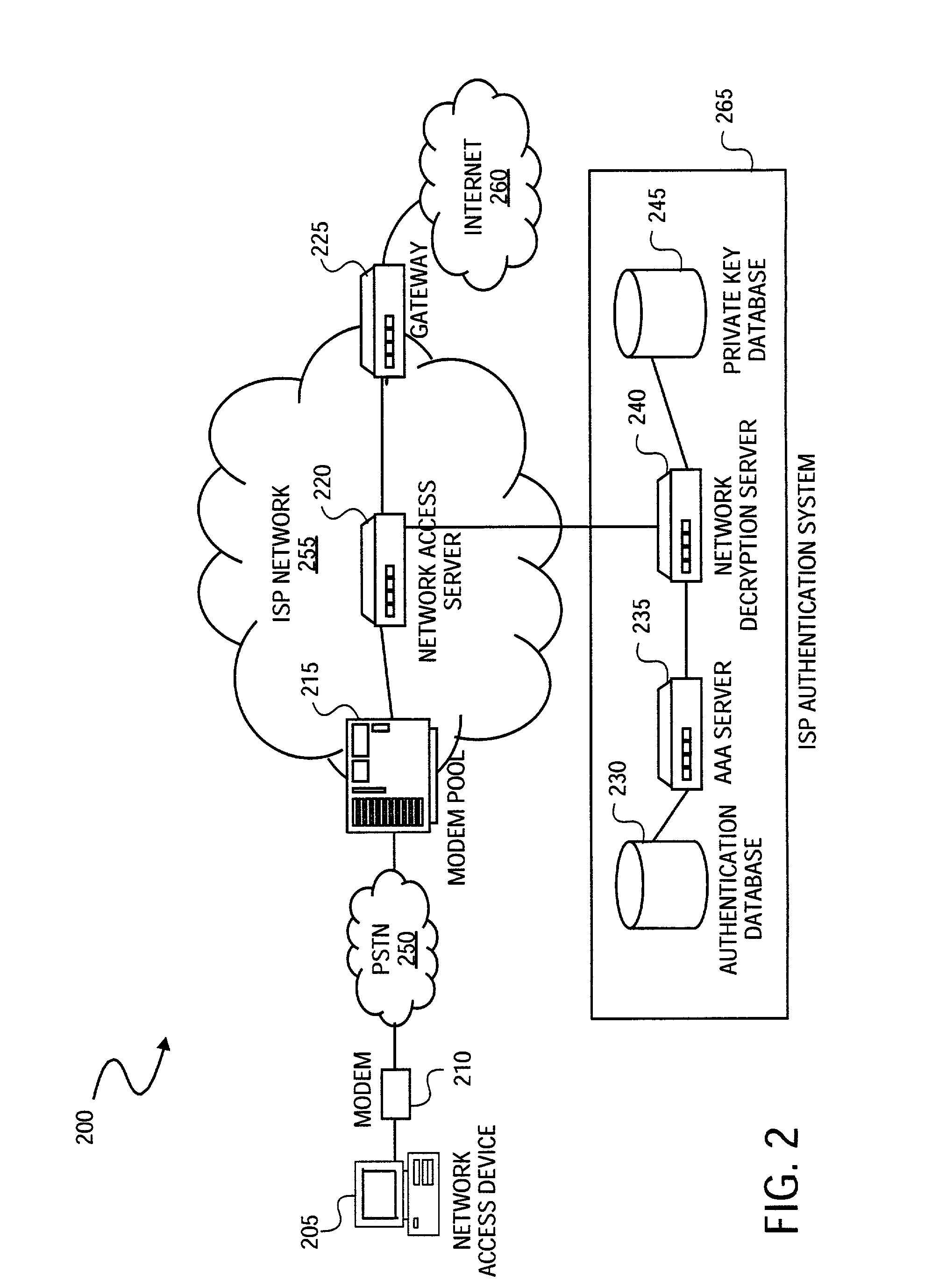
Method and system for securely authenticating network access credentials for users
InactiveUS7921290B2Digital data processing detailsUser identity/authority verificationHypertext Transfer Protocol over Secure Socket LayerDirectory Access Protocol
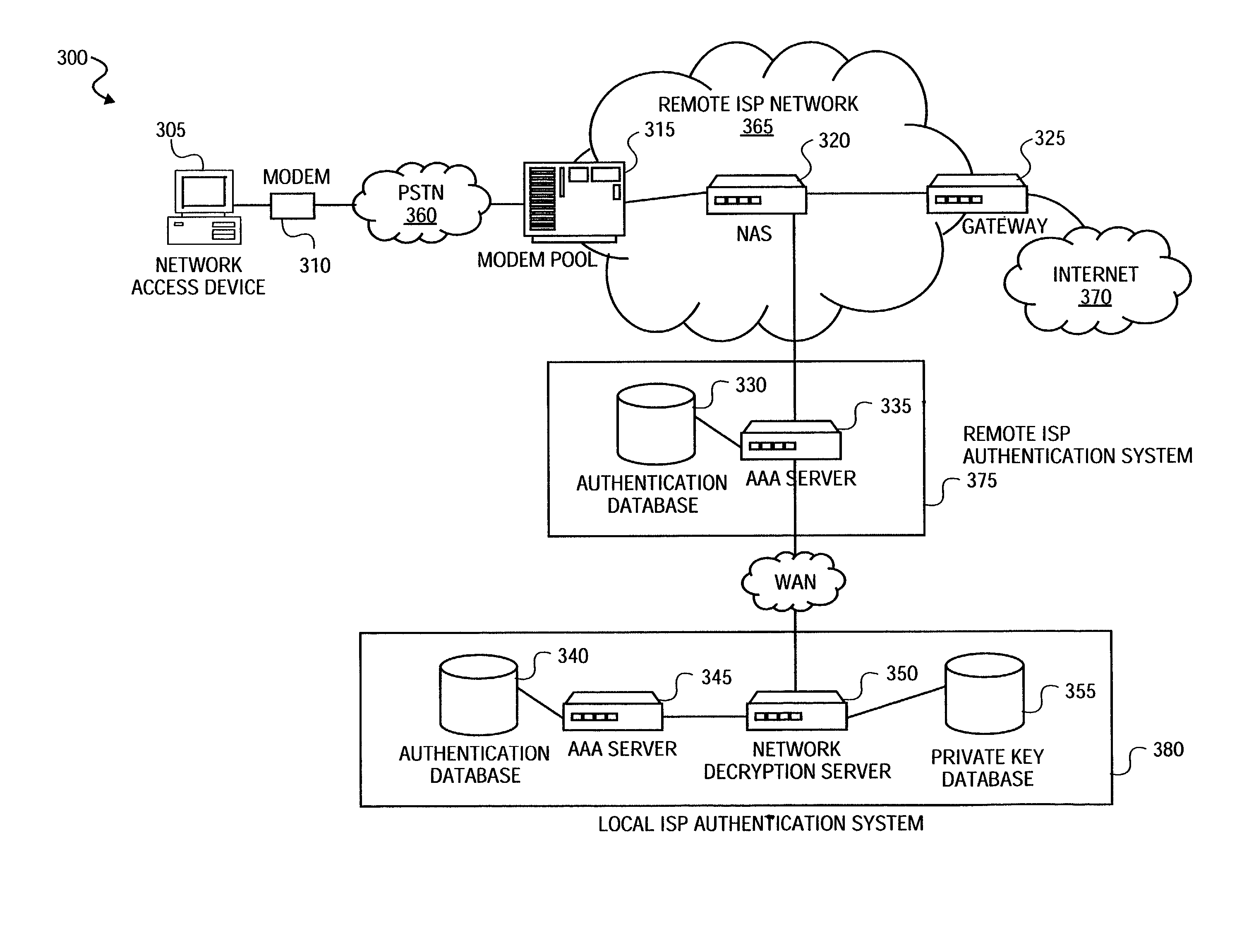
A method is provided to securely authenticate user credentials. The method includes encrypting a user credential with a public key at an access device wherein the public key is part of a public / private key pair suitable for use with an encryption algorithm. The encrypted network user credential is transmitted from the access device to a decryption server where it is decrypted with a private key, the private key being part of the public / private key pair suitable for use with the encryption algorithm. The decrypted user credential is then transmitted from the decryption server to an authentication server for verification. The decryption server typically forms part of a multi-party service access environment including a plurality of access providers, the method including decrypting the user credential of a user proximate an access provider associated with the user credential. The method can be used in legacy protocols such as Point-to-Point protocol (PPP), Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), Remote Authentication Dial In User Service (RADIUS) protocol, Terminal Access Controller Access Control System (TACACS) protocol, Lightweight Directory Access Protocol (LDAP), NT Domain authentication protocol, Unix password authentication protocol, HyperText Transfer Protocol (HTTP), HyperText Transfer Protocol over Secure sockets layer (HTTPS), Extended Authentication Protocol (EAP), Transport Layer Security (TLS) protocol, Token Ring protocol and / or Secure Remote Password protocol (SRP).
Owner:CHANNEL IP BV
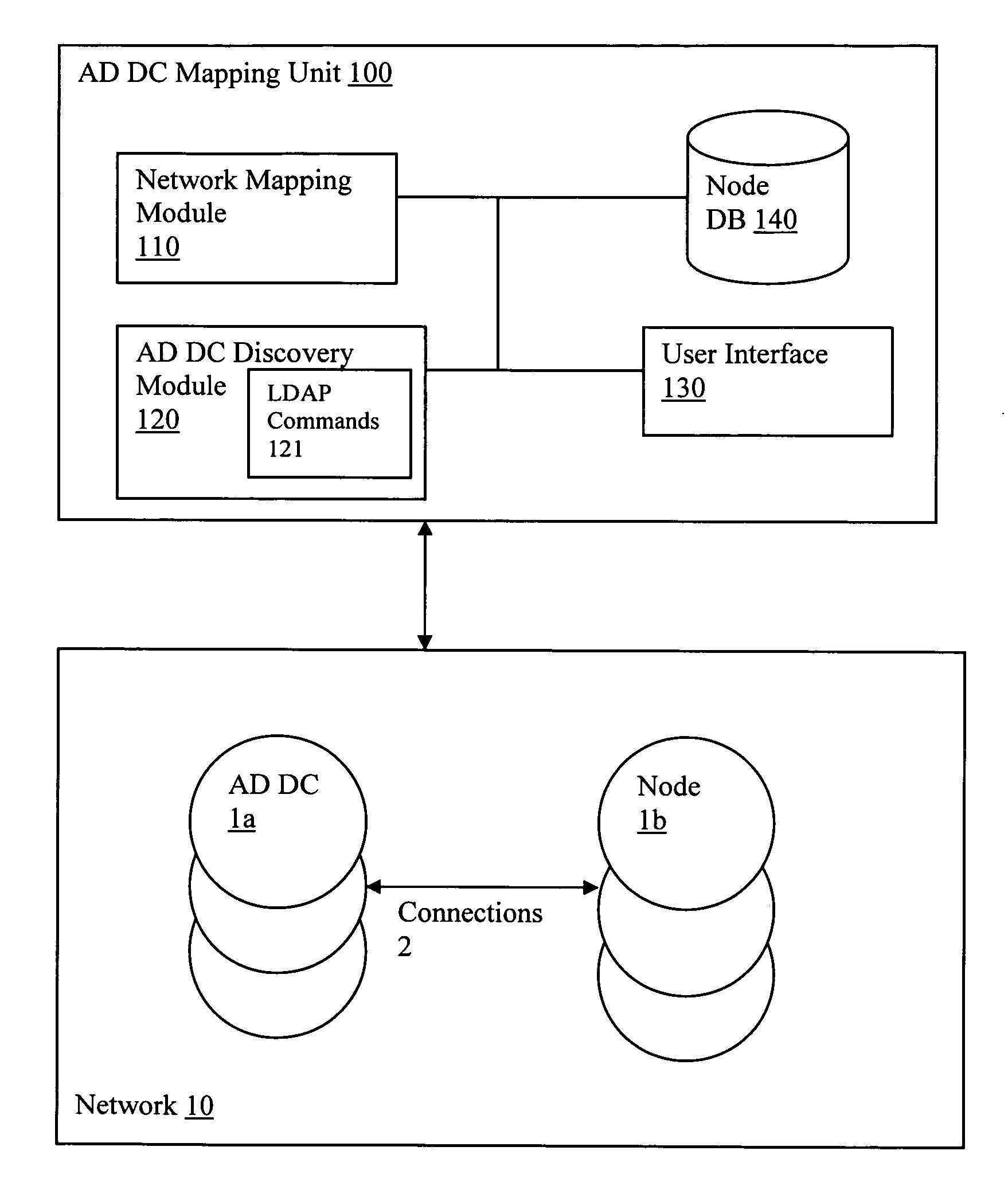
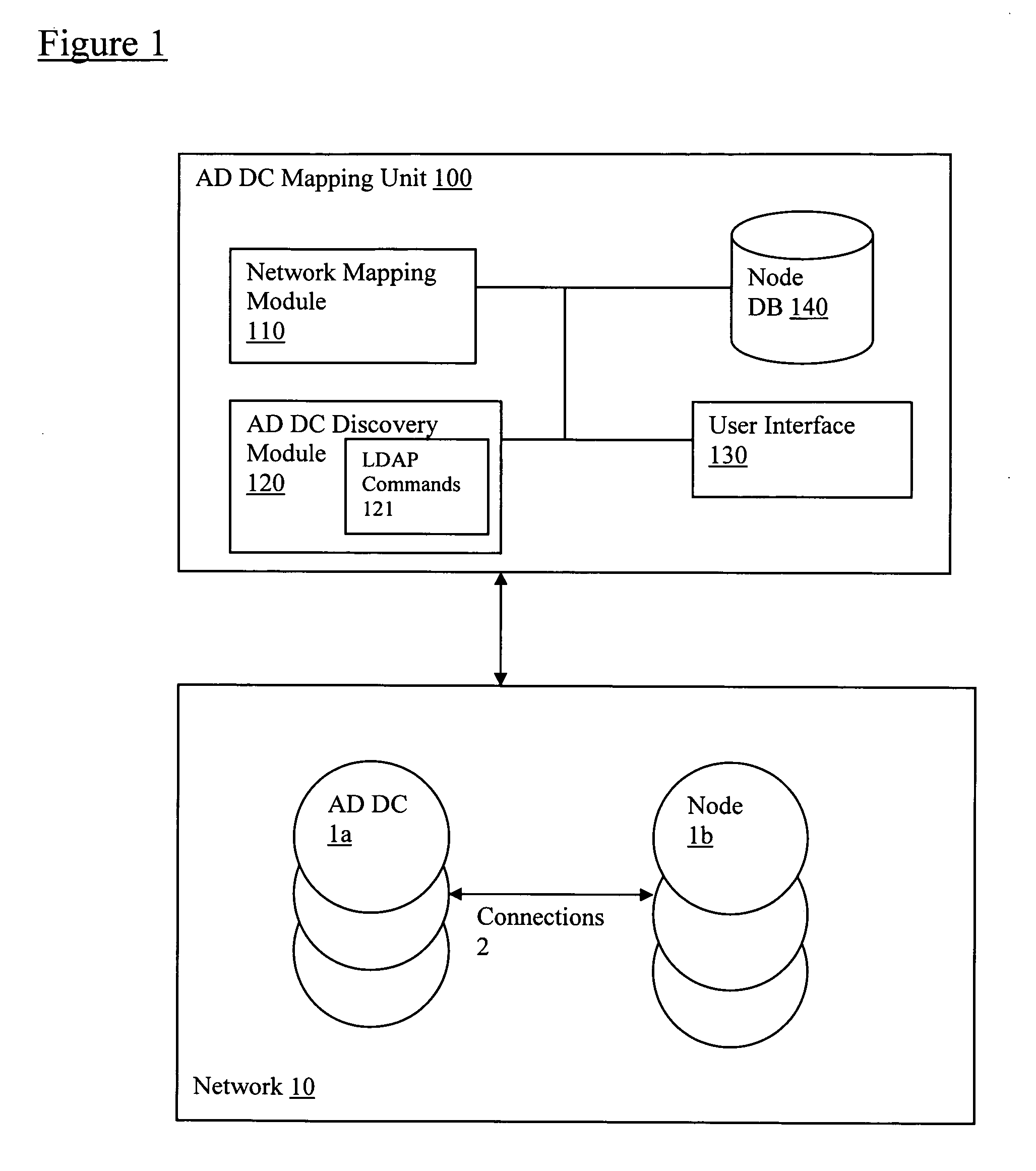
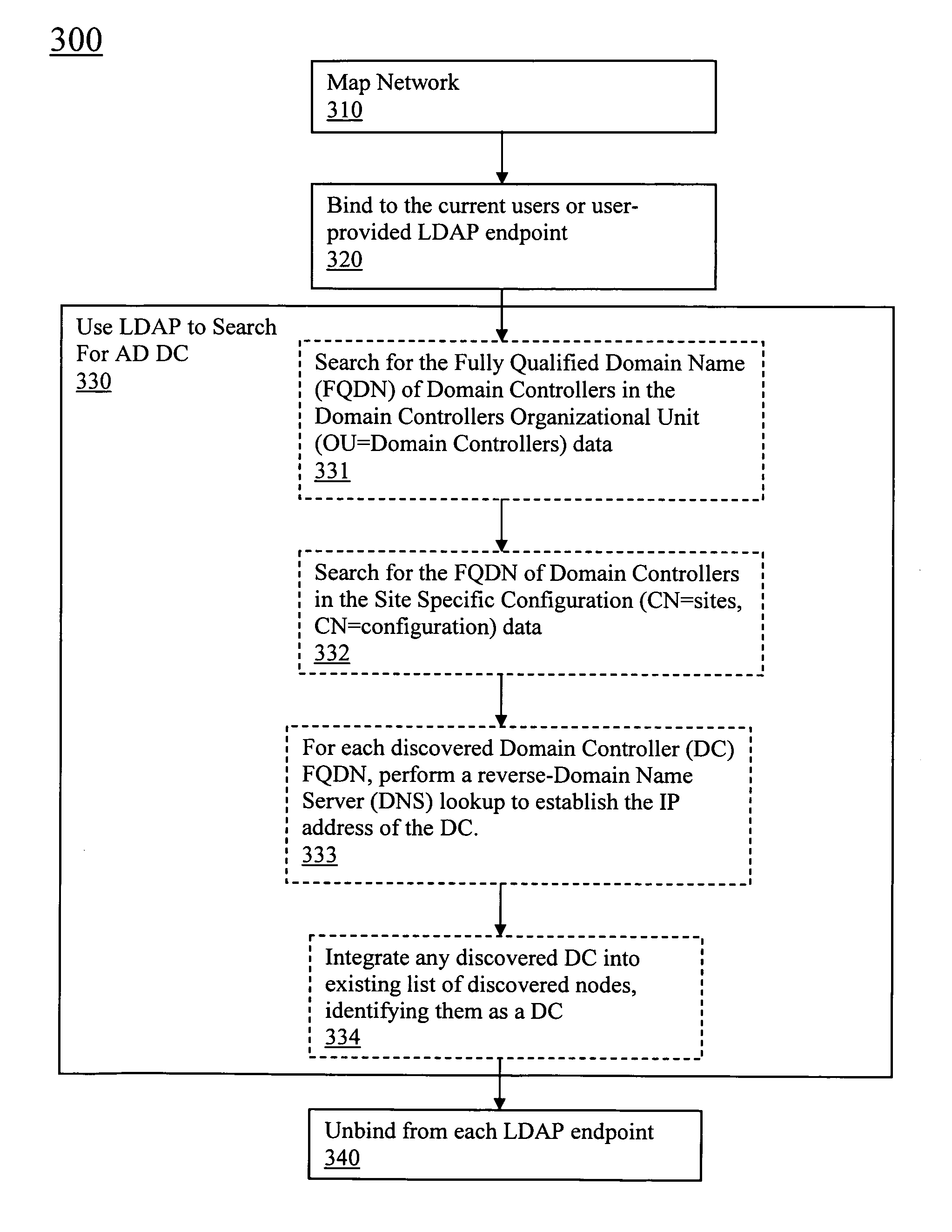
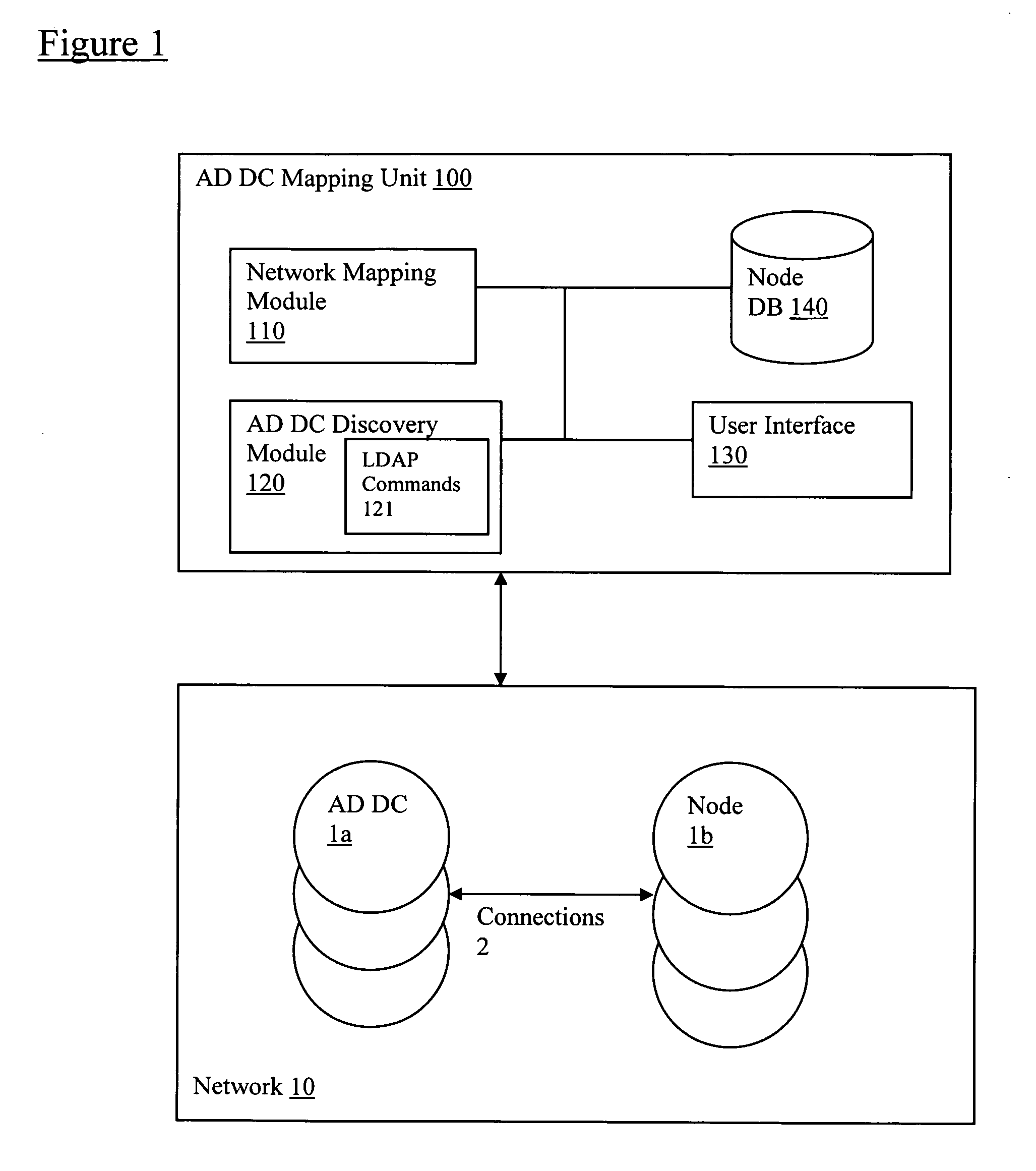
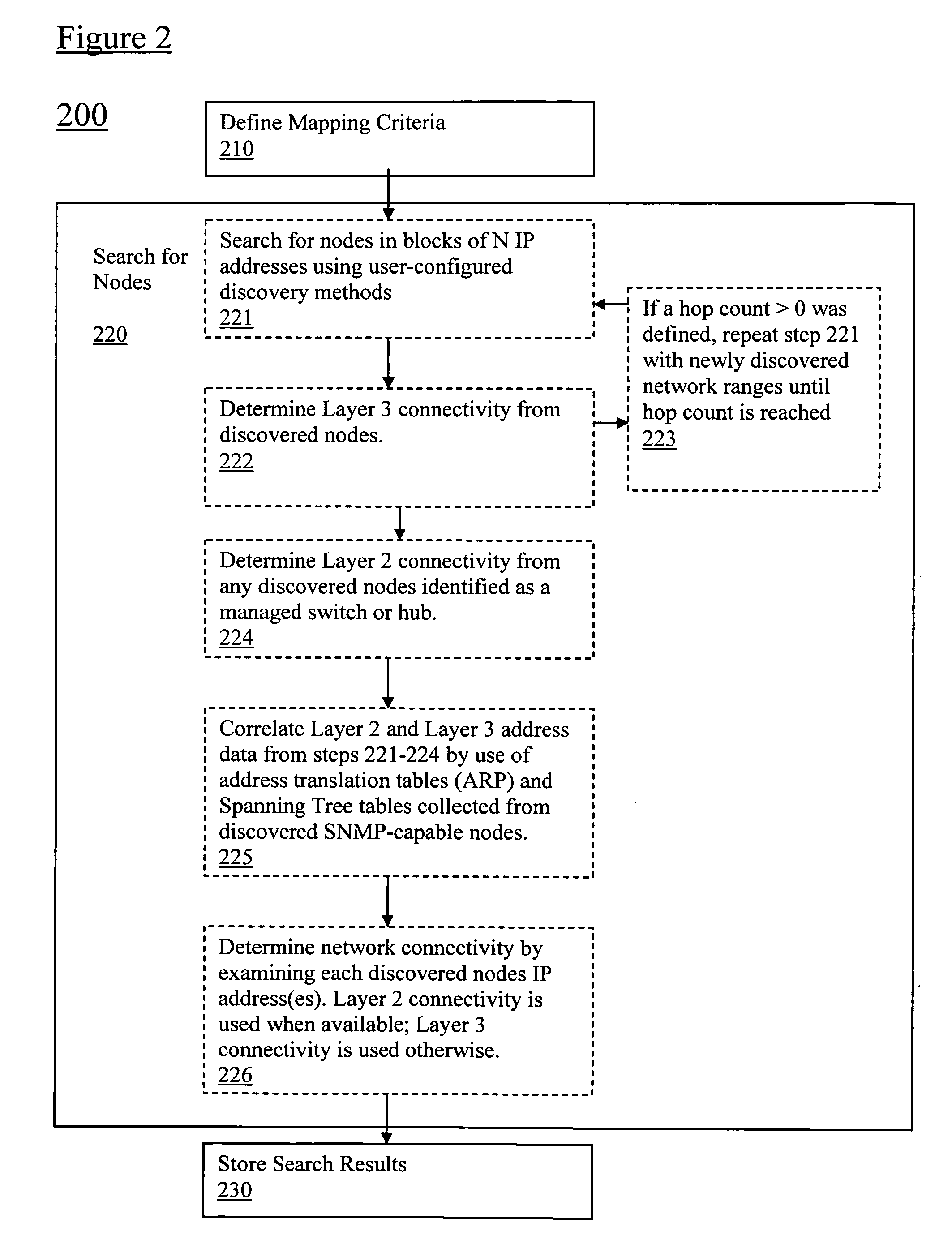
Discovery and visualization of active directory domain controllers in topological network maps
ActiveUS20090285120A1Digital computer detailsData switching by path configurationIp addressSynthetic data
Active directory (AD) Domain Controllers (DC) discovery includes determining the topology of the network, such as the nodes and connections in the network. For example, synthetic data may be transferred within the network and traced to determine the presence and relationships of the various network components. Alternatively, other mapping techniques are based upon mapping a known set of nodes to determine the relationship of the nodes. Next, Lightweight Directory Access Protocol (LDAP) commands are forwarded to the various nodes to identify the AD DC within a range of IP addresses discovered during the mapping of to the topology of the network.
Owner:SOLARWINDS WORLDWIDE
System, method and computer program product for migrating data from one database to another database
InactiveUS7310650B1Reduce complicationsData processing applicationsDigital data processing detailsDirectory Access ProtocolLightweight Directory Access Protocol
A software tool that is useful when one is attempting to migrate data from one database to another database. In one aspect of the invention, the software tool reduces the complications that may arise when one attempts to migrate data from one Lightweight Directory Access Protocol (LDAP) directory to another LDAP directory, where the schemas for the two directories are not the same.
Owner:INT BUSINESS MASCH CORP
Discovery and visualization of active directory domain controllers in topological network maps
ActiveUS8045486B2Digital computer detailsData switching by path configurationIp addressSynthetic data
Active directory (AD) Domain Controllers (DC) discovery includes determining the topology of the network, such as the nodes and connections in the network. For example, synthetic data may be transferred within the network and traced to determine the presence and relationships of the various network components. Alternatively, other mapping techniques are based upon mapping a known set of nodes to determine the relationship of the nodes. Next, Lightweight Directory Access Protocol (LDAP) commands are forwarded to the various nodes to identify the AD DC within a range of IP addresses discovered during the mapping of to the topology of the network.
Owner:SOLARWINDS WORLDWIDE
Preserving LDAP Hierarchy in a SCIM Directory Using Special Marker Groups
ActiveUS20180083944A1TransmissionHierarchical databasesApplication softwareDirectory Access Protocol
A method for hierarchically processing Lightweight Directory Access Protocol (LDAP) operations against a System for Cross-domain Identity Management (SCIM) directory is provided. The method includes providing an LDAP Directory Information Tree (DIT) including a plurality of LDAP DIT entries that describe LDAP containers, users and groups, providing a SCIM directory including a plurality of SCIM resource entries that describe SCIM users and groups, migrating the plurality of LDAP DIT entries to the SCIM directory including storing the LDAP DIT hierarchical information in the SCIM directory by mapping LDAP containers in the LDAP DIT to special marker SCIM groups in the SCIM directory, receiving, from an LDAP-based application over a network, an LDAP operation request, processing the LDAP operation request, and returning an LDAP operation response to the LDAP-based application over the network.
Owner:ORACLE INT CORP
Method and system for extending services to cellular devices
InactiveUS20070281680A1Good serviceConnection managementRadio/inductive link selection arrangementsClient agentServer agent
A system is provide for extending services to cellular devices. The system includes a wireless gateway having a client side with an intelligent client agent and a server side with an intelligent server agent, a wireless device having a first mode operable in a cellular system and a second mode operable in a wireless local area network and including an intelligent client agent for determining operation mode and for communicating with the intelligent client agent of the wireless gateway and a communications protocol for communication between the wireless gateway intelligent client agent and the wireless device intelligent client agent to effect services. The services include one or more of voice, directory, presence, and media services. The voice service includes at least one of call waiting, call forwarding conferencing, and caller identification. The media service includes at least one of interactive voice response (IVR), text-to-speech, speech recognition, play, record. The directory service includes a public switched telephone network (PSTN) directory, a cellular network directory, an Internet directory and a private branch exchange (PBX) directory. The communications protocol includes encapsulation for at least one of directory, mobility and security services and other protocols. The other protocols include at least one of Internet protocol (IP), session initiation protocol (SIP), and lightweight directory access protocol (LDAP).
Owner:COUNTERPATH TECH
Support for multiple data stores
ActiveUS7711818B2Improve performanceComplete banking machinesDigital data information retrievalData accessDirectory Access Protocol
Technology is disclosed for supporting multiple data stores. The set of data stores can be of a uniform type, or the various data stores can be different types (e.g. Lightweight Directory Access Protocol (LDAP), Structured Query Language (SQL), etc.). One implementation of the disclosed technology is with an Identity System. Another implementation is with an integrated Identity System and Access System. Various embodiments of the present invention utilize different means to separate the business logic of a system from the data access logic so that different types of data stores can be used without changing the business logic.
Owner:ORACLE INT CORP
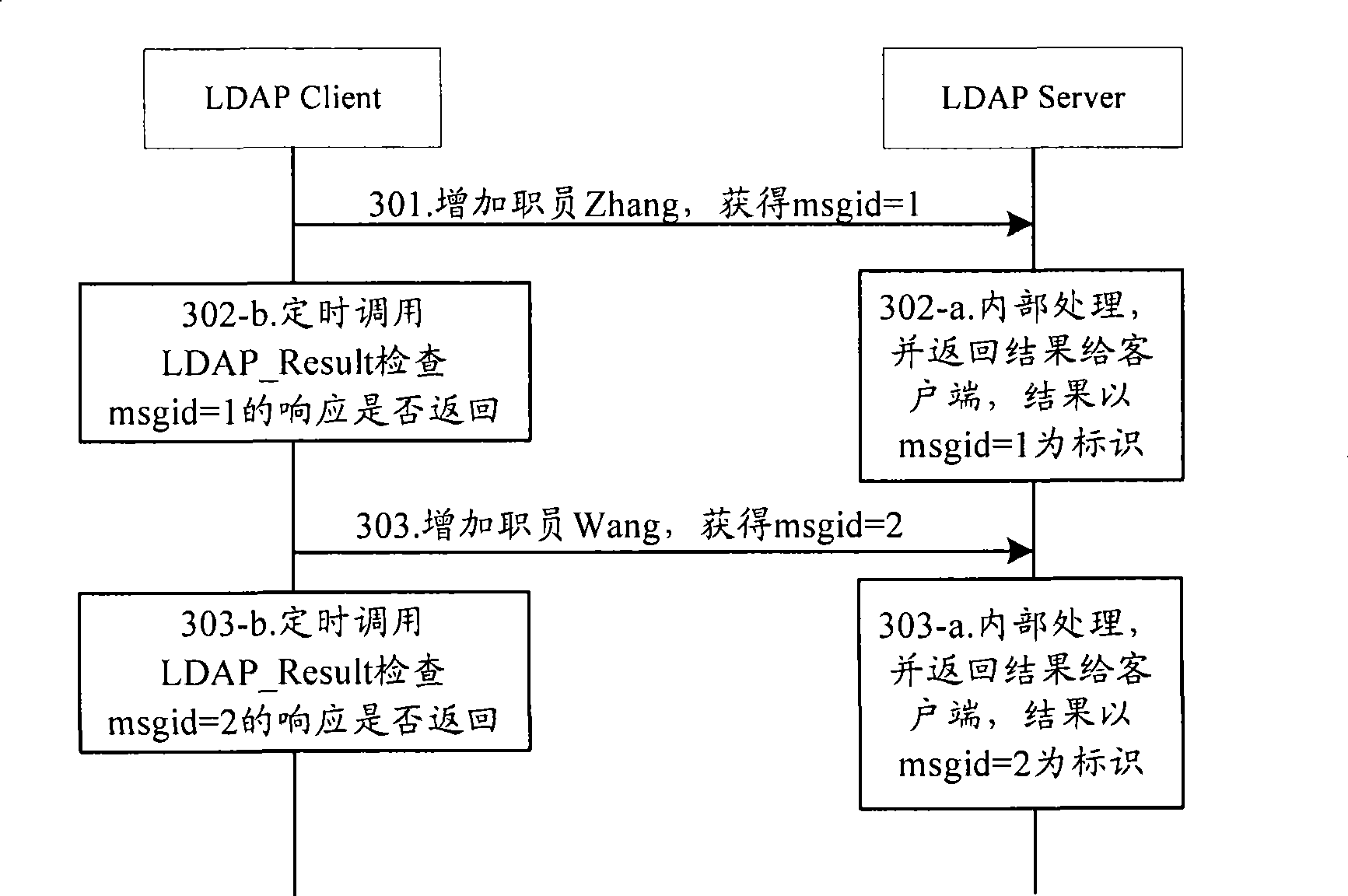
Client-server interaction method based on LDAP protocol and system thereof
ActiveCN101447981AEasy to handleSolve the problem of too many callsData switching networksSpecial data processing applicationsClient-sideDirectory Access Protocol
The invention discloses a client-server interaction method based on a lightweight directory access protocol and a system thereof. In the method, a client sends a plurality of operation item requests to a server in succession; a server asynchronously processes a plurality of operation item requests and returns corresponding request result of every operation item request to the client; and the client checks a buffer to judge whether the server returns the corresponding request results of all operation item requests. The invention solves the problem in related technology that LDAP_Result is called too frequently, so that the invention can improve the processing performance of an LDAP client.
Owner:ZTE CORP
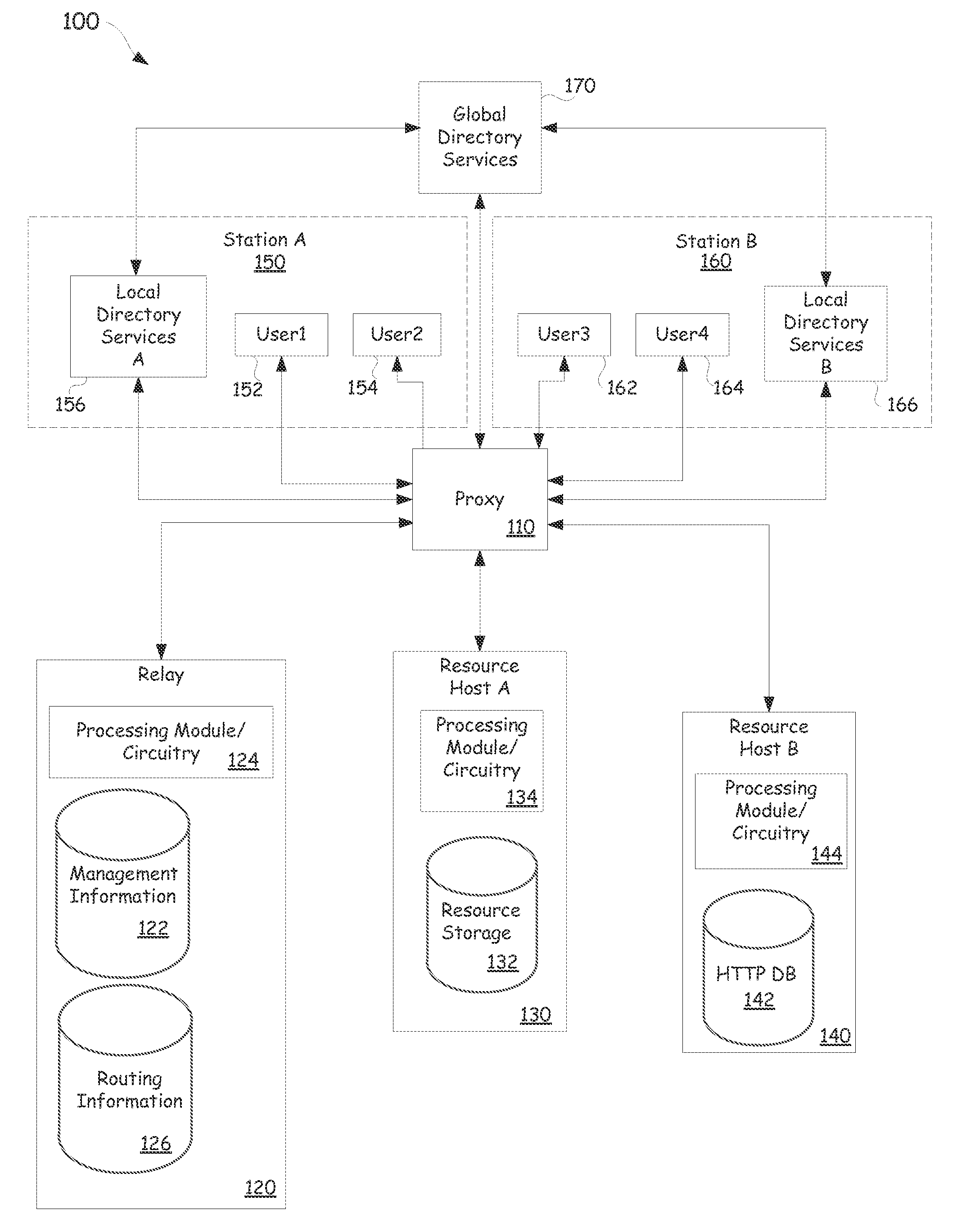
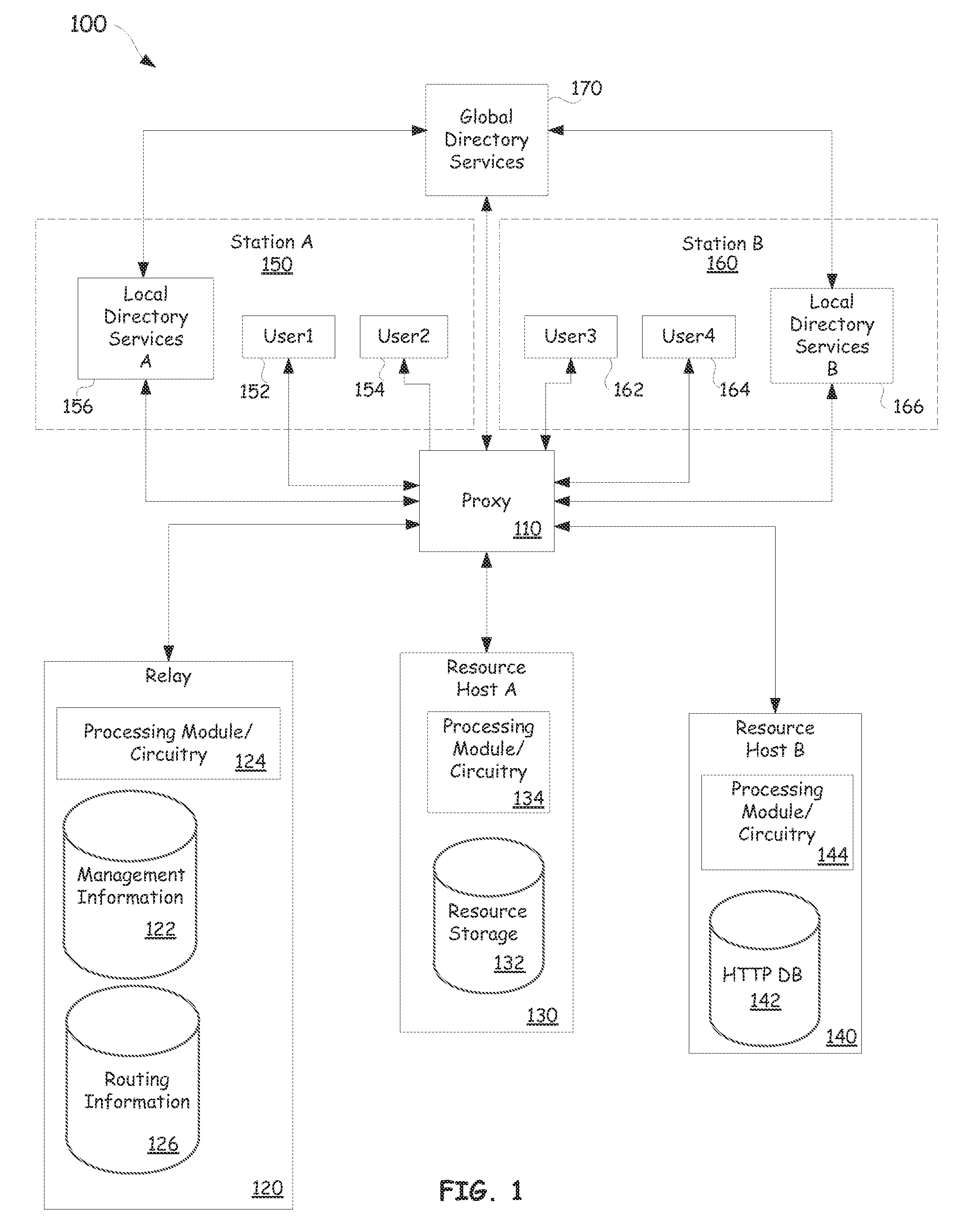
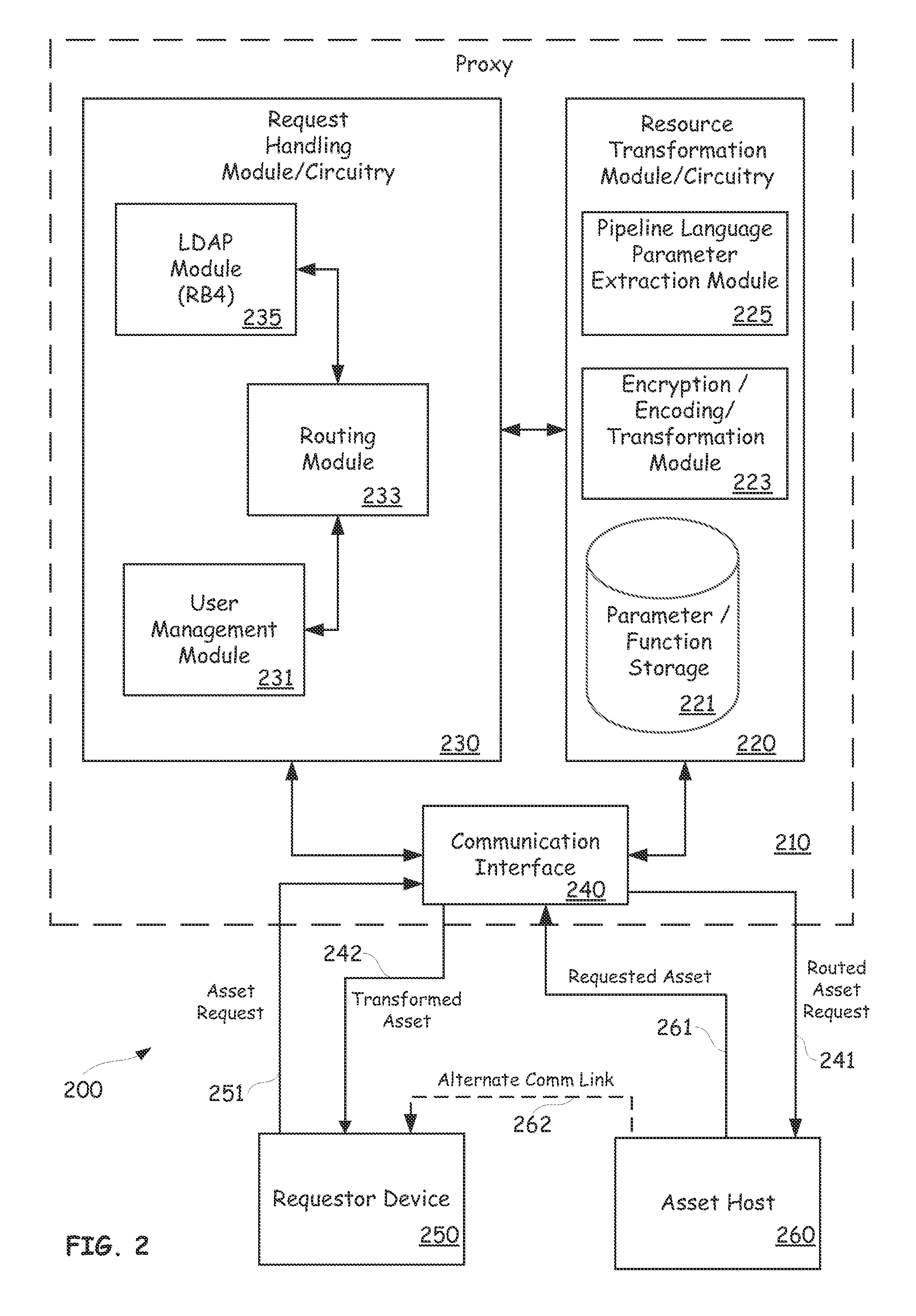
Platform-as-a-service with proxy-controlled request routing
When a user sends a request to access an asset or resource, for example a program code file or a media file, the access request can be processed by a proxy device. The proxy can use directory information obtained from a directory, for example a company-wide Lightweight Directory Access Protocol (LDAP) directory, to determine whether or not the request is from an authorized network user listed in the directory. The proxy can use management information obtained from another database to determine roles, subordinate assignment information, and access authorization information associated with the requesting user. The proxy can conditionally route the request to a resource host based on the directory information and the management information. The proxy can also transform a resource returned in response to the request by using pipeline language parameters included in a URL associated with the access request.
Owner:IHEARTMEDIA MANAGEMENT SERVICES
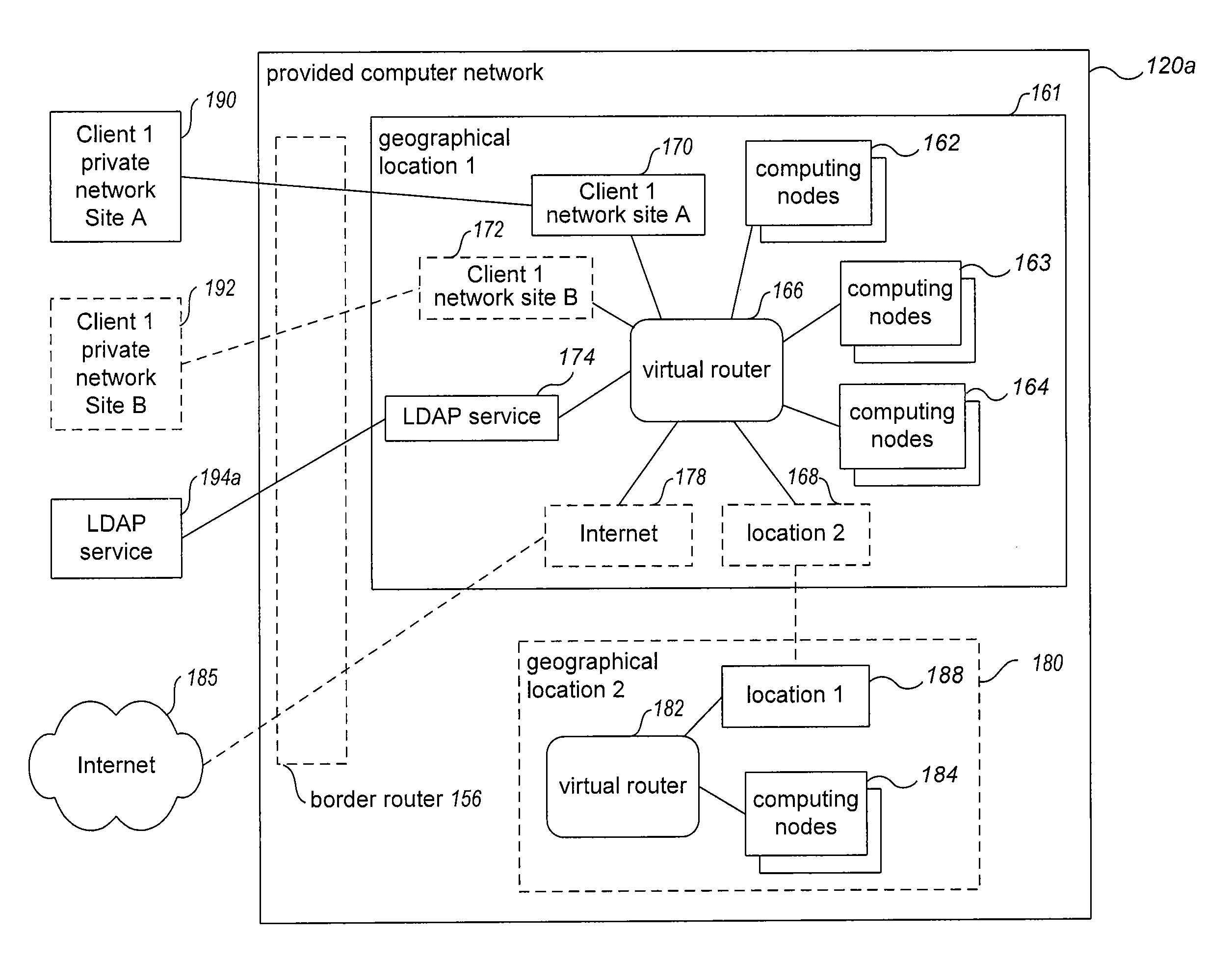
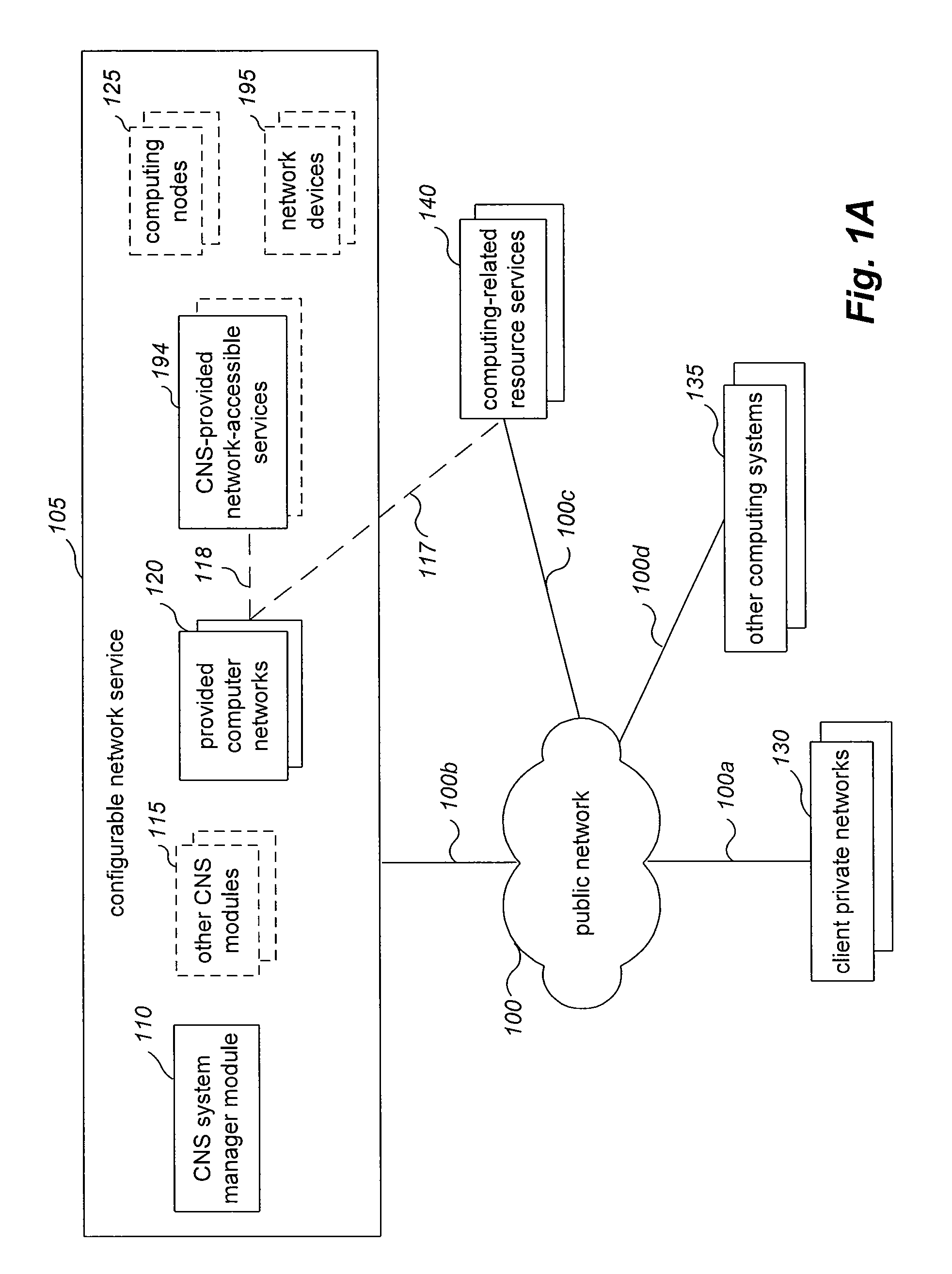
Providing private access to network-accessible services
Techniques are described for managing communications for a managed virtual computer network overlaid on a distinct substrate computer network. The techniques may be used in situations in which a configurable network service provides managed virtual computer networks for clients and also provides one or more network-accessible services that are available to the managed virtual computer networks, with particular managed virtual computer networks being configured to provide local private access to at least one of the provided network-accessible services, despite those provided network-accessible services being located externally to the particular managed virtual computer networks. In some situations, a Lightweight Directory Access Protocol (“LDAP”) network-accessible service is provided, and a logical endpoint for the LDAP service is created within a managed virtual computer network to enable the multiple computing nodes of the managed virtual computer network to communicate with one or more LDAP computer servers from the LDAP service.
Owner:AMAZON TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com