Patents
Literature
691 results about "Revocation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Revocation is the act of recall or annulment. It is the cancelling of an act, the recalling of a grant or privilege, or the making void of some deed previously existing. A temporary revocation of a grant or privilege is called a suspension.
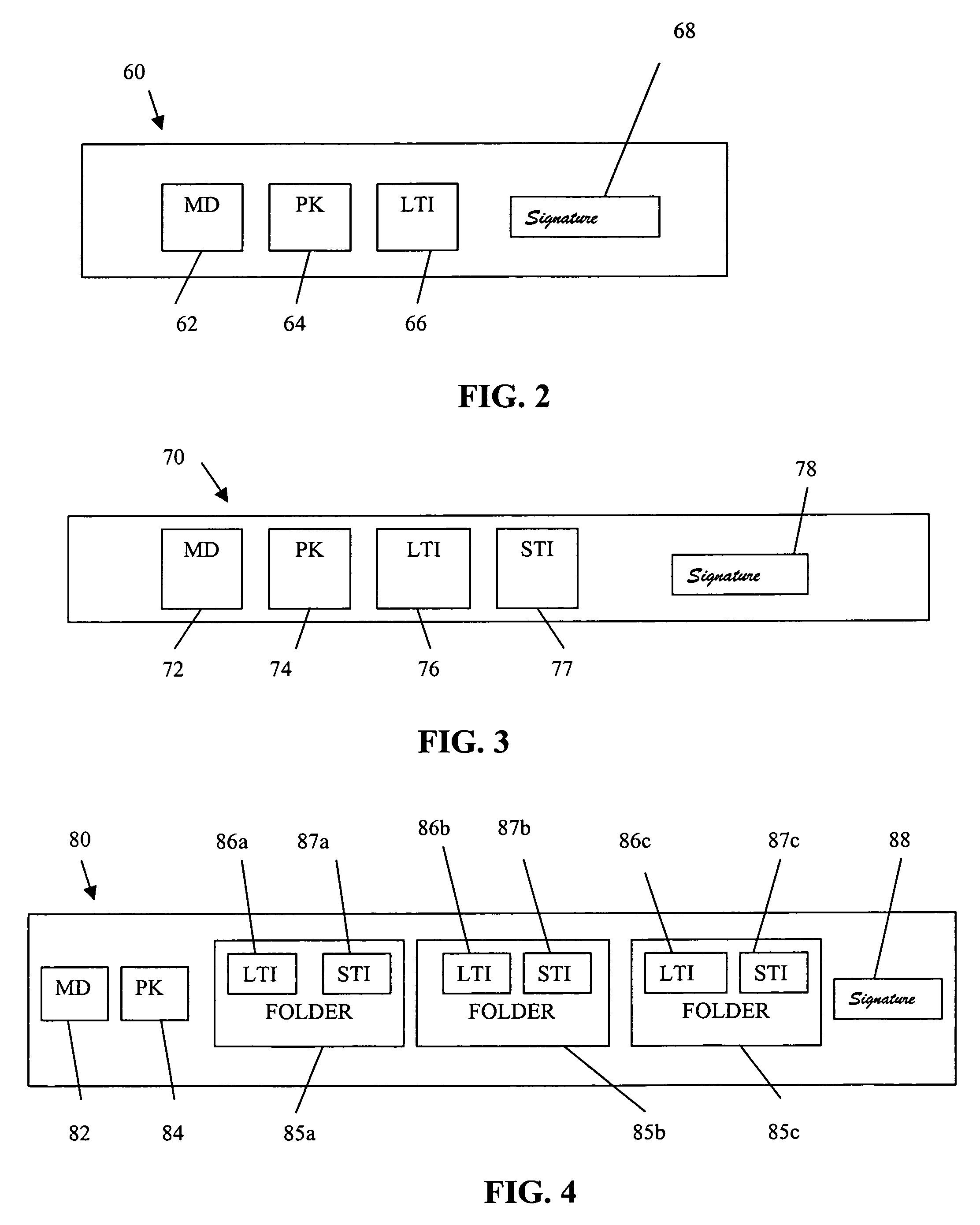
Secure digital content licensing system and method
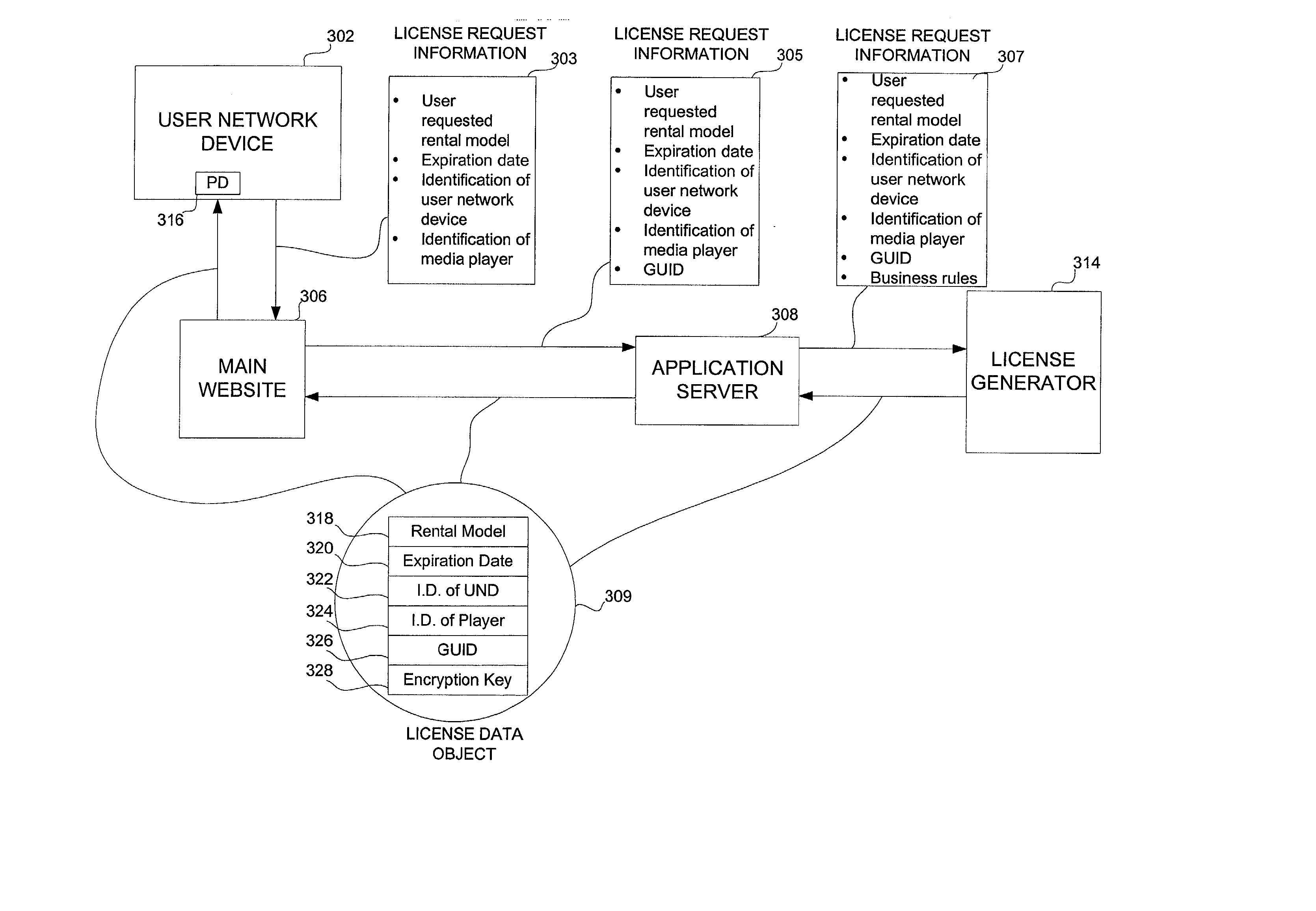
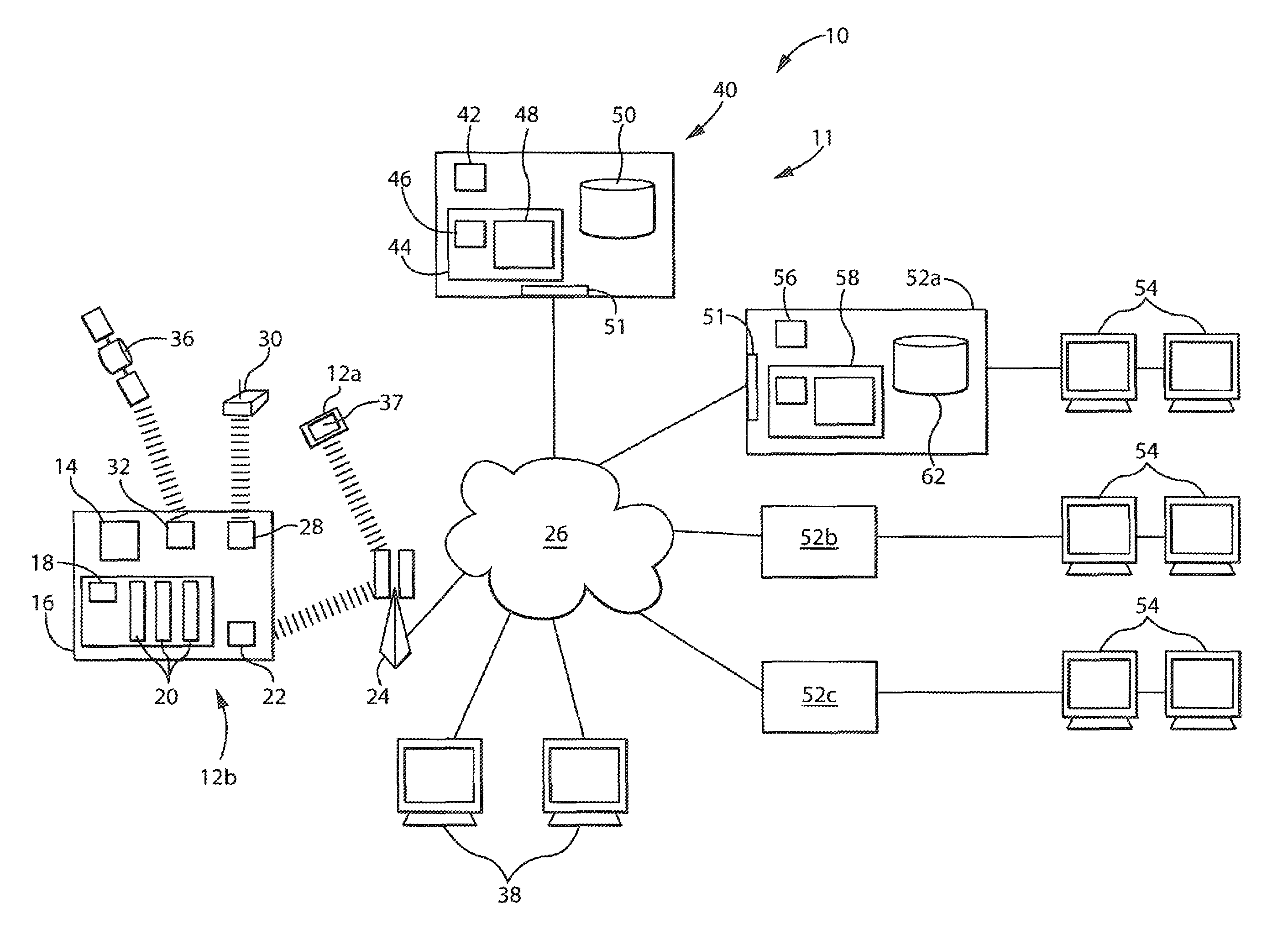
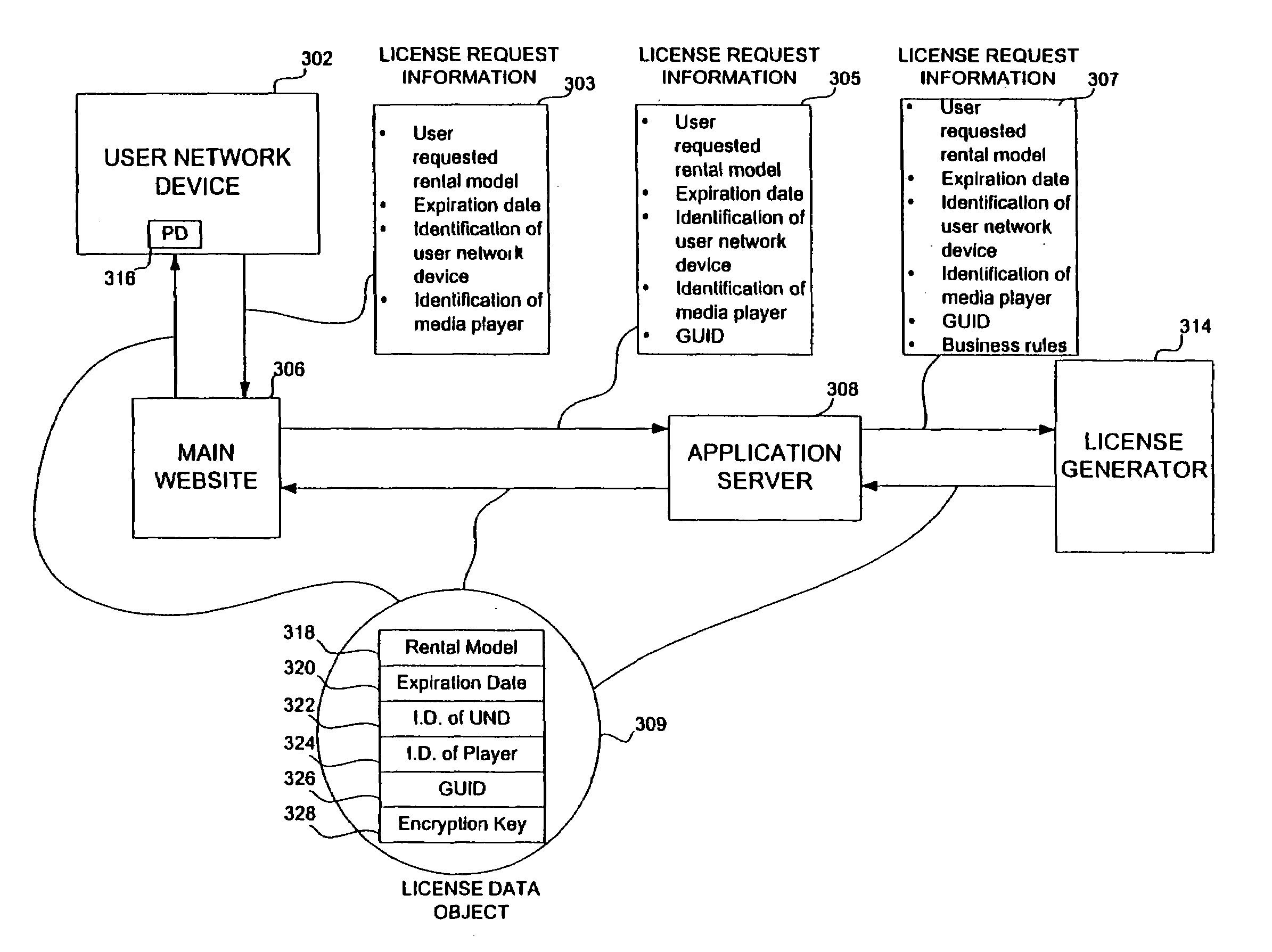
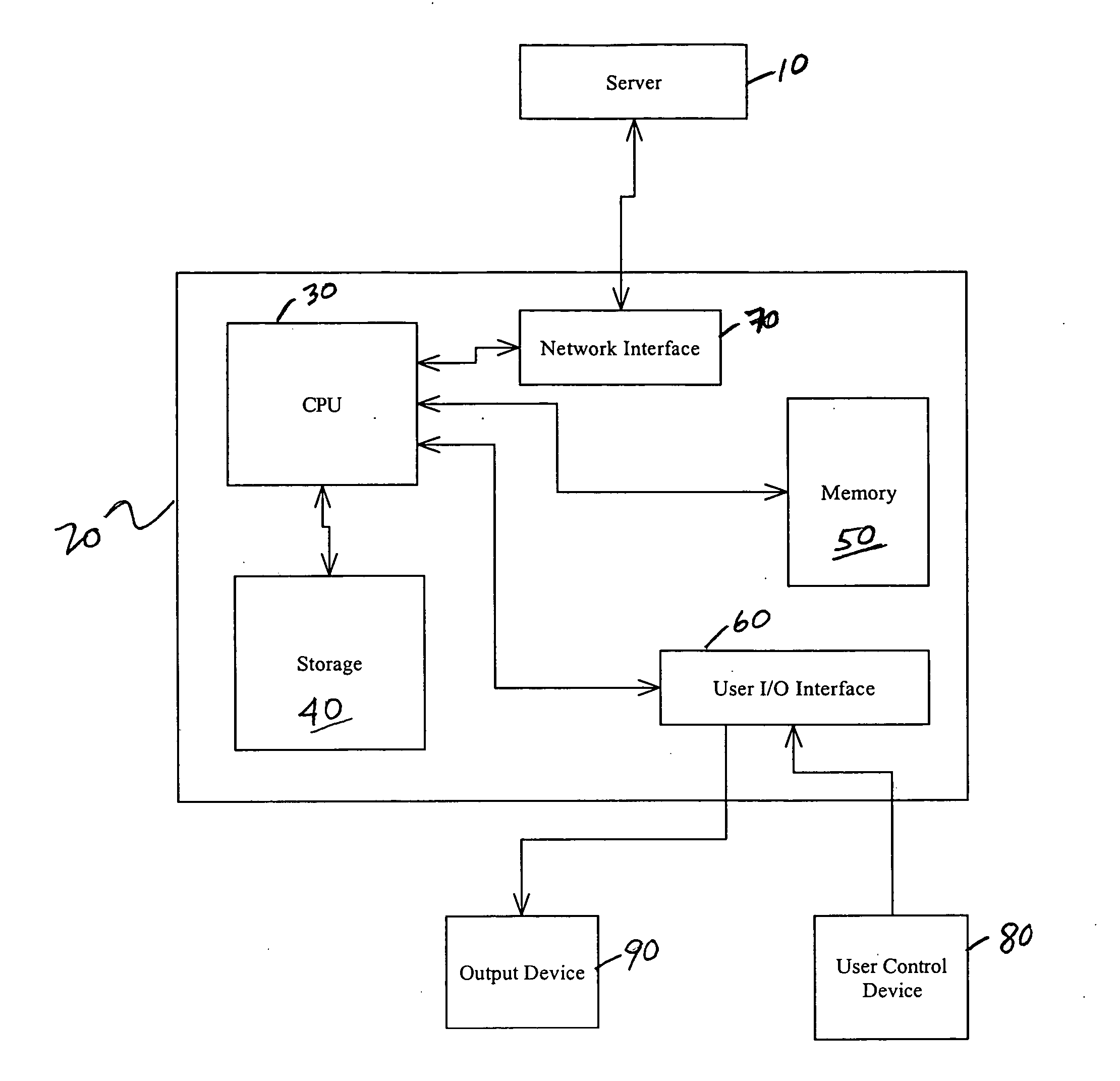
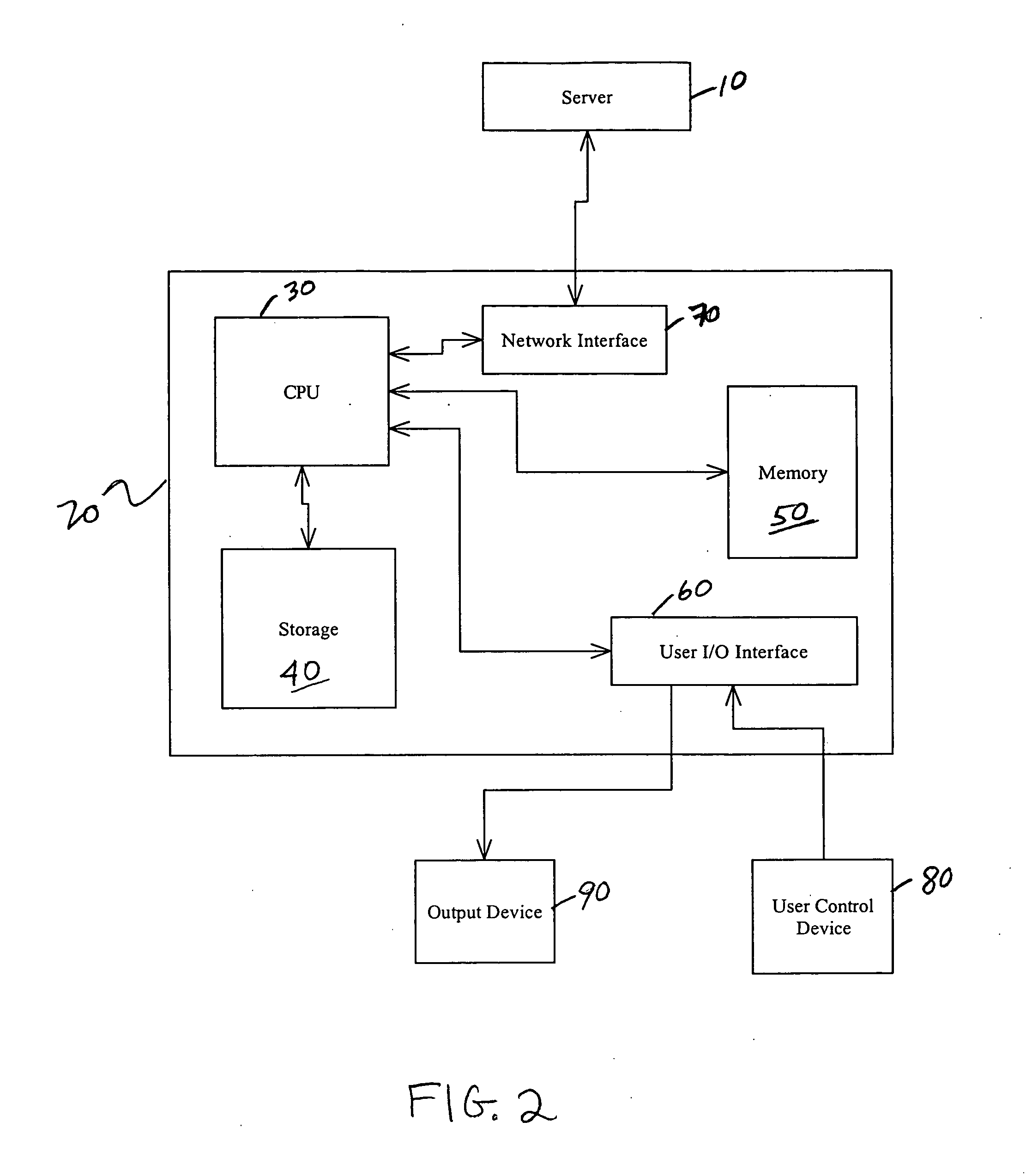
Embodiments of the present invention overcome the problems in the existing art described above by providing a secure digital content licensing system and method. Rental of the digital content occurs within an online environment including one or more user network-enabled devices and one or more server network devices connected by a communications link to the one or more user network-enabled devices. A user selects content displayed on a main website and requests download of the selected content to the user network-enabled device. To be able to access the content the user must obtain a license. The user's request for a license for specific content comprises information about a desired rental model, an expiration date for the rental model, and information that identifies the user's user network-enabled device, along with other information. A license for the content is generated which comprises the above information and also includes an encryption key for the selected movie. Media player and security technology residing on the user network-enabled device provides protection against unauthorized access to the content by ensuring that only licensed content is viewed and is accessed according to the rental model contained in the license. Media player and security technology also provides security against tampering by performing integrity checks on its various components and other components within the user network-enabled device. Revocation of access rights is made possible by revocation certificates that inhibit accessing of particular content for various reasons including compromised files or components.
Owner:BLOCKBUSTER LLC
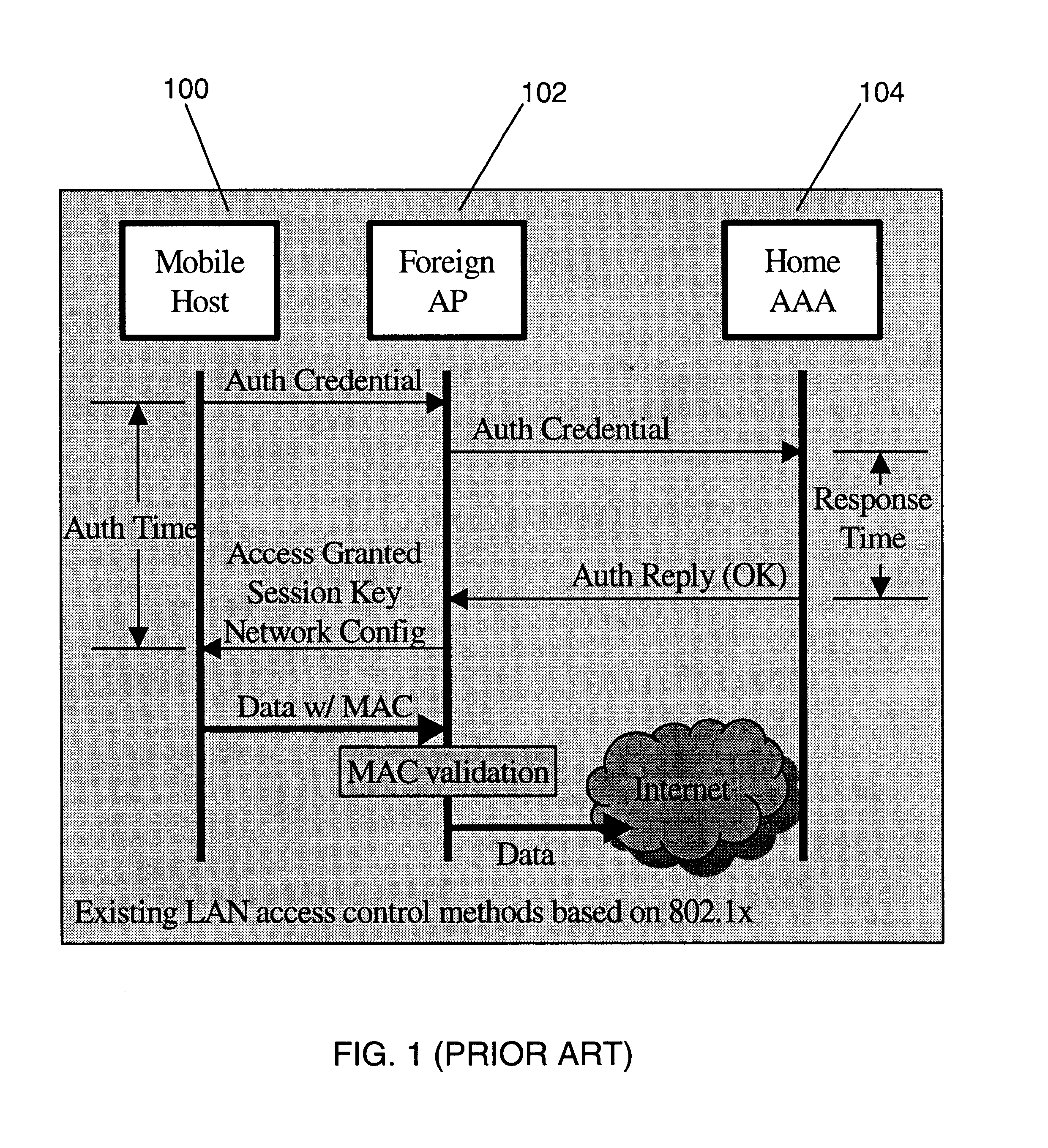
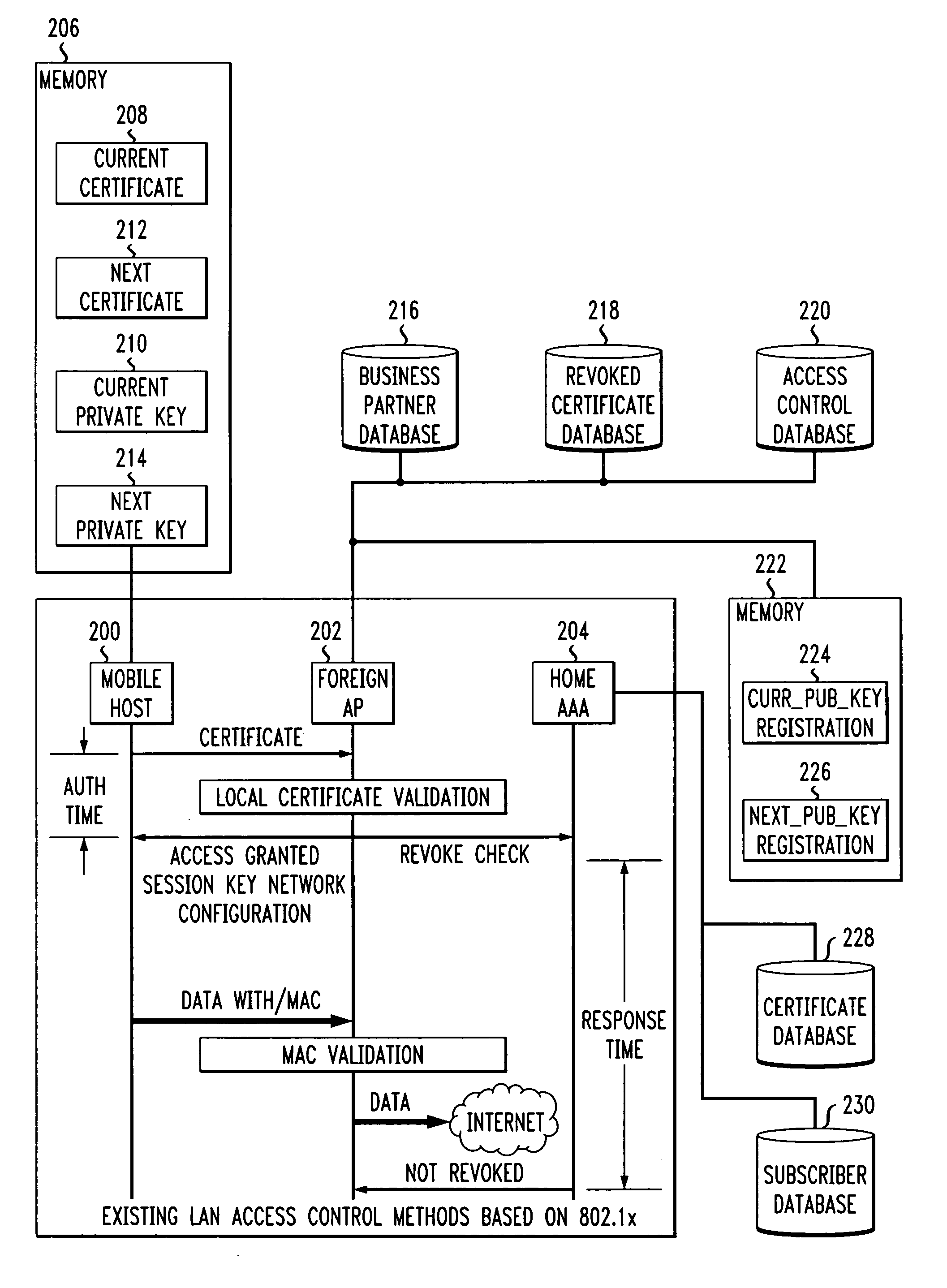
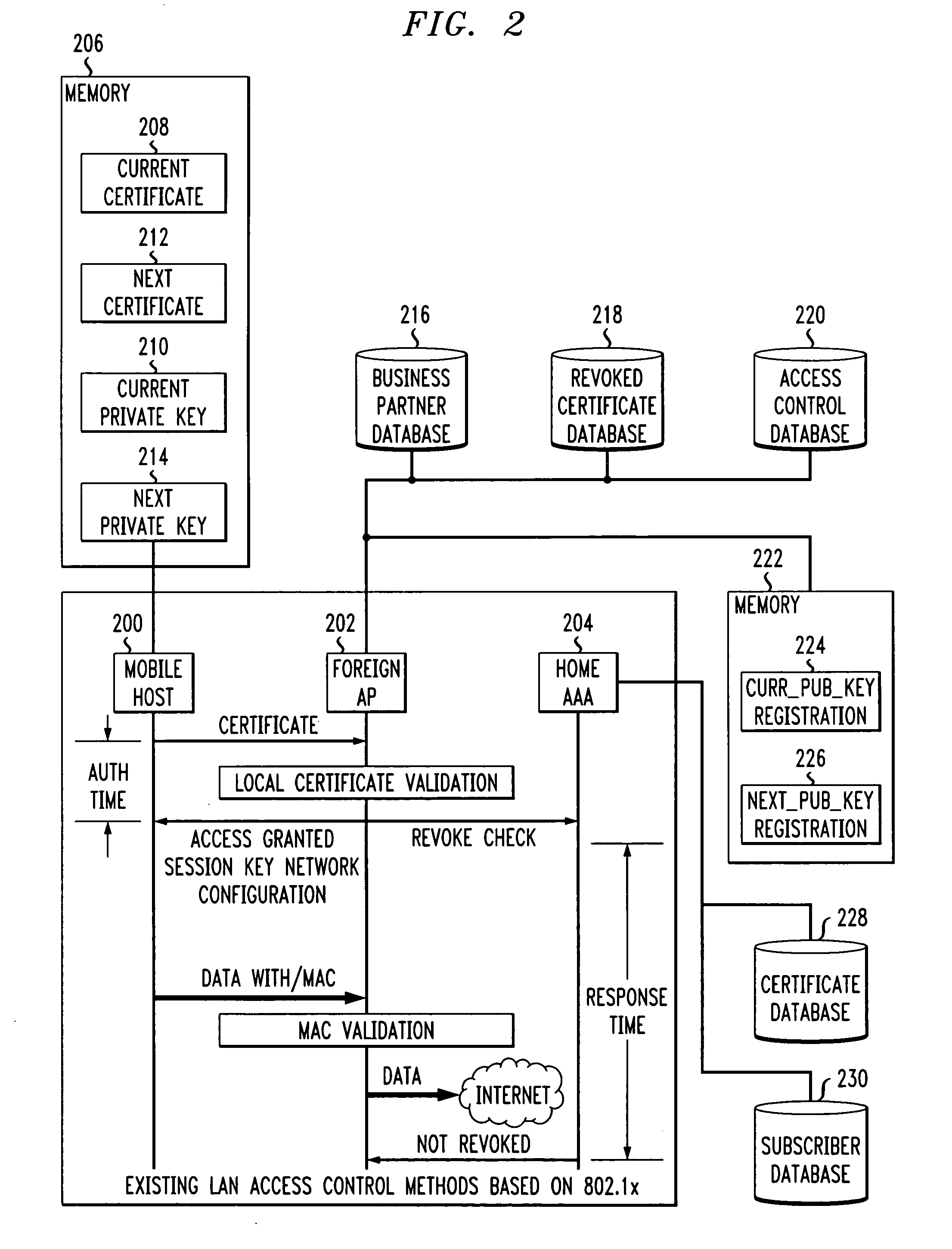
Fast authentication and access control system for mobile networking
InactiveUS6856800B1Easy to switchReduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsExpiration TimeWeb authentication
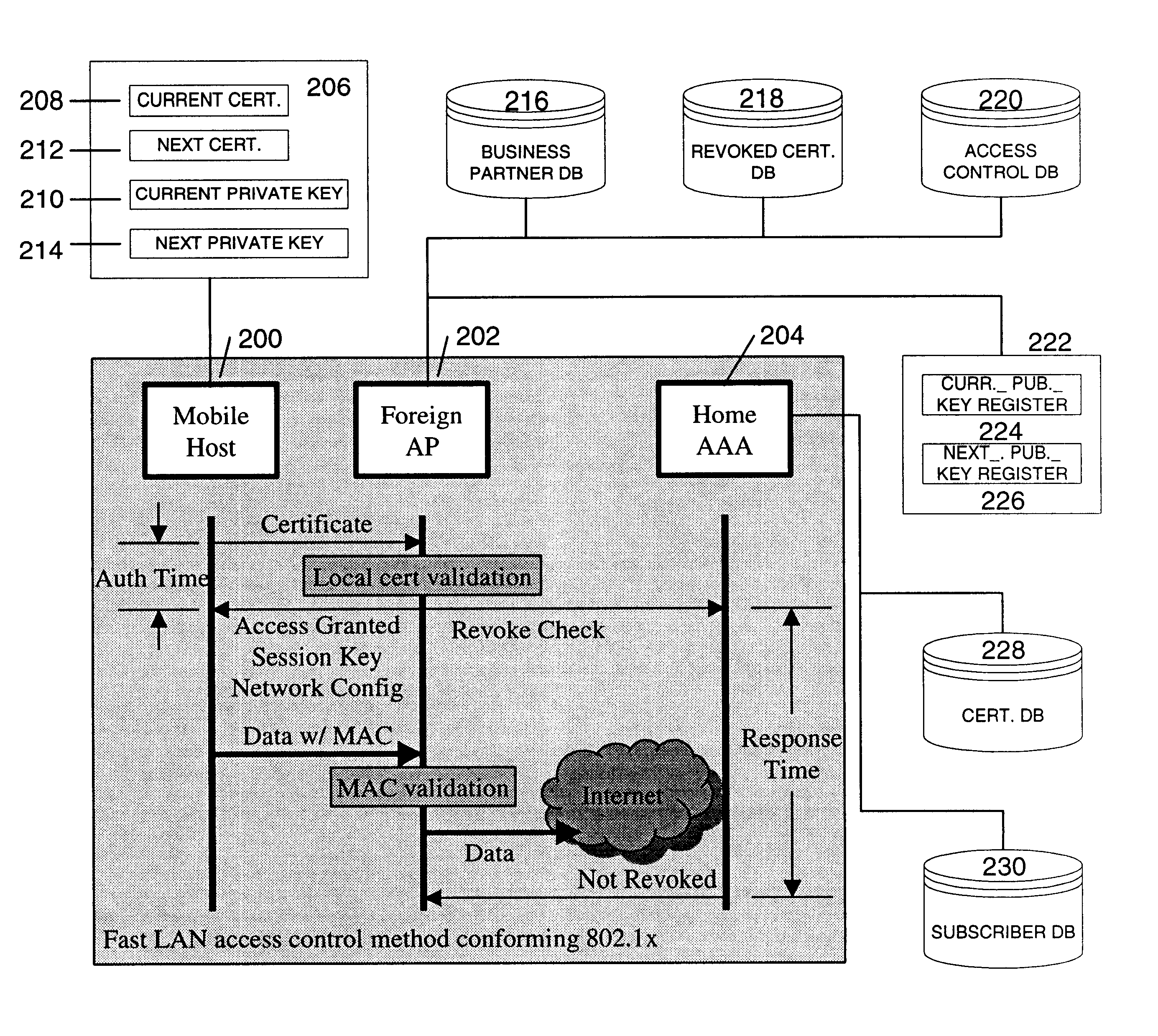
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
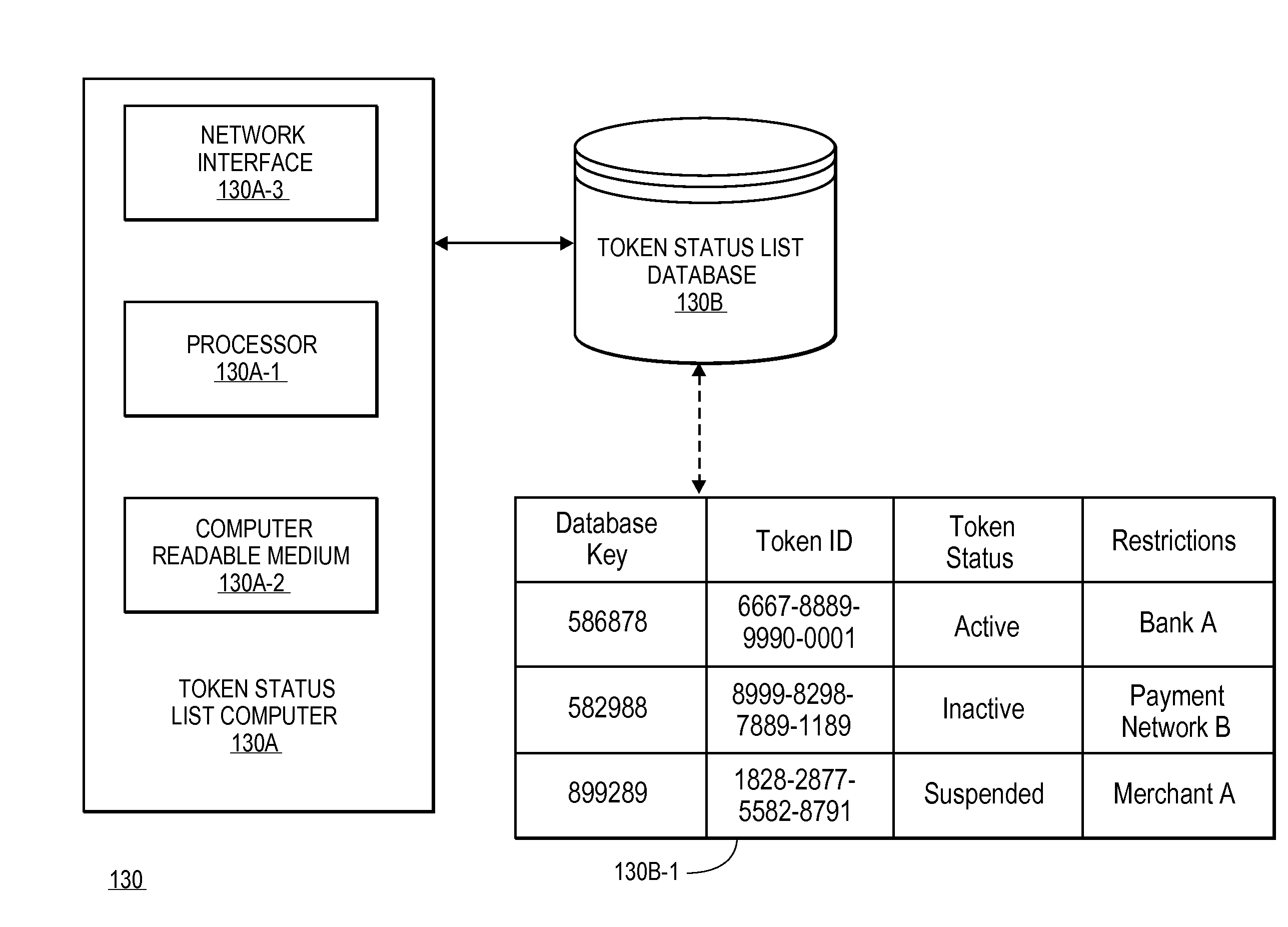
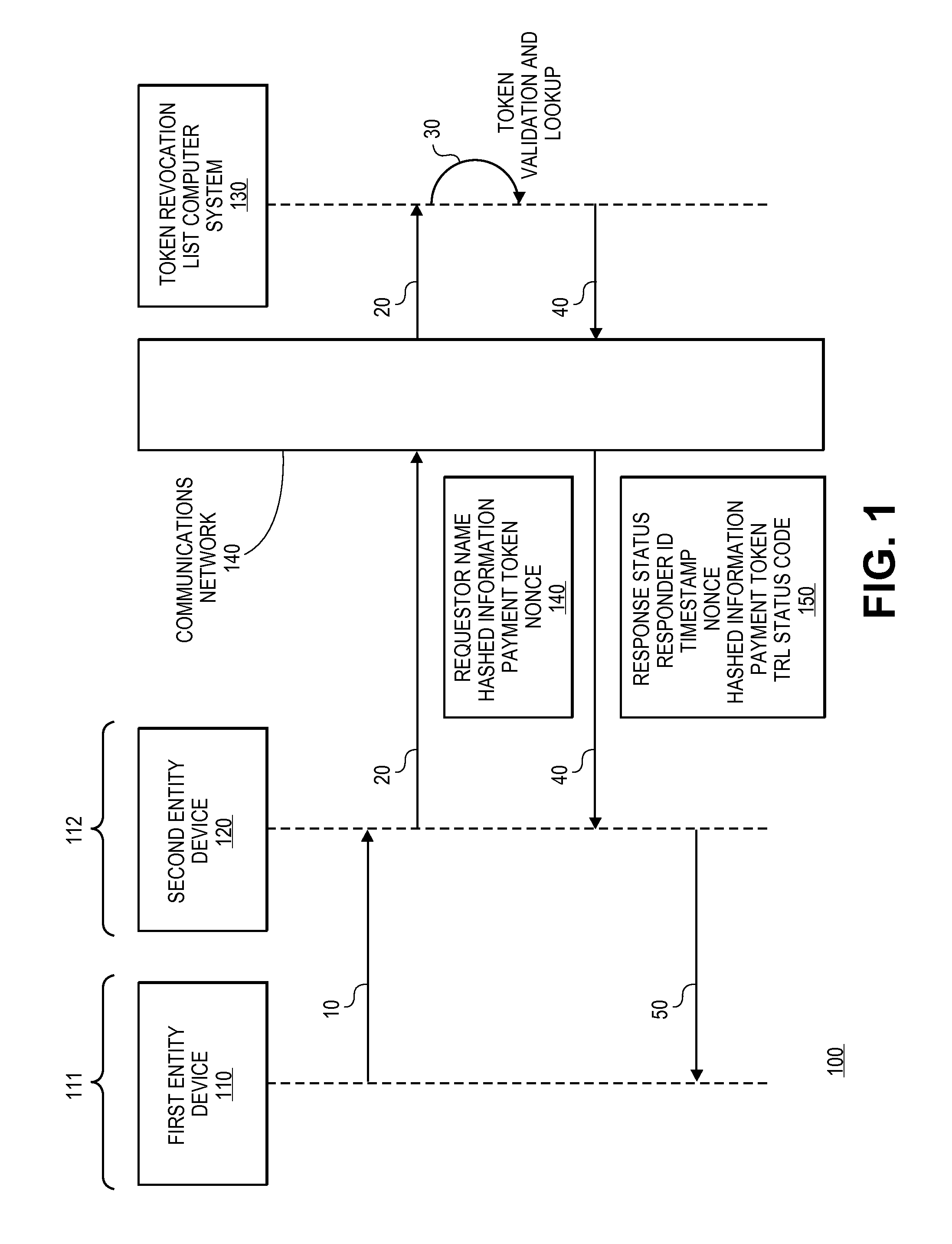
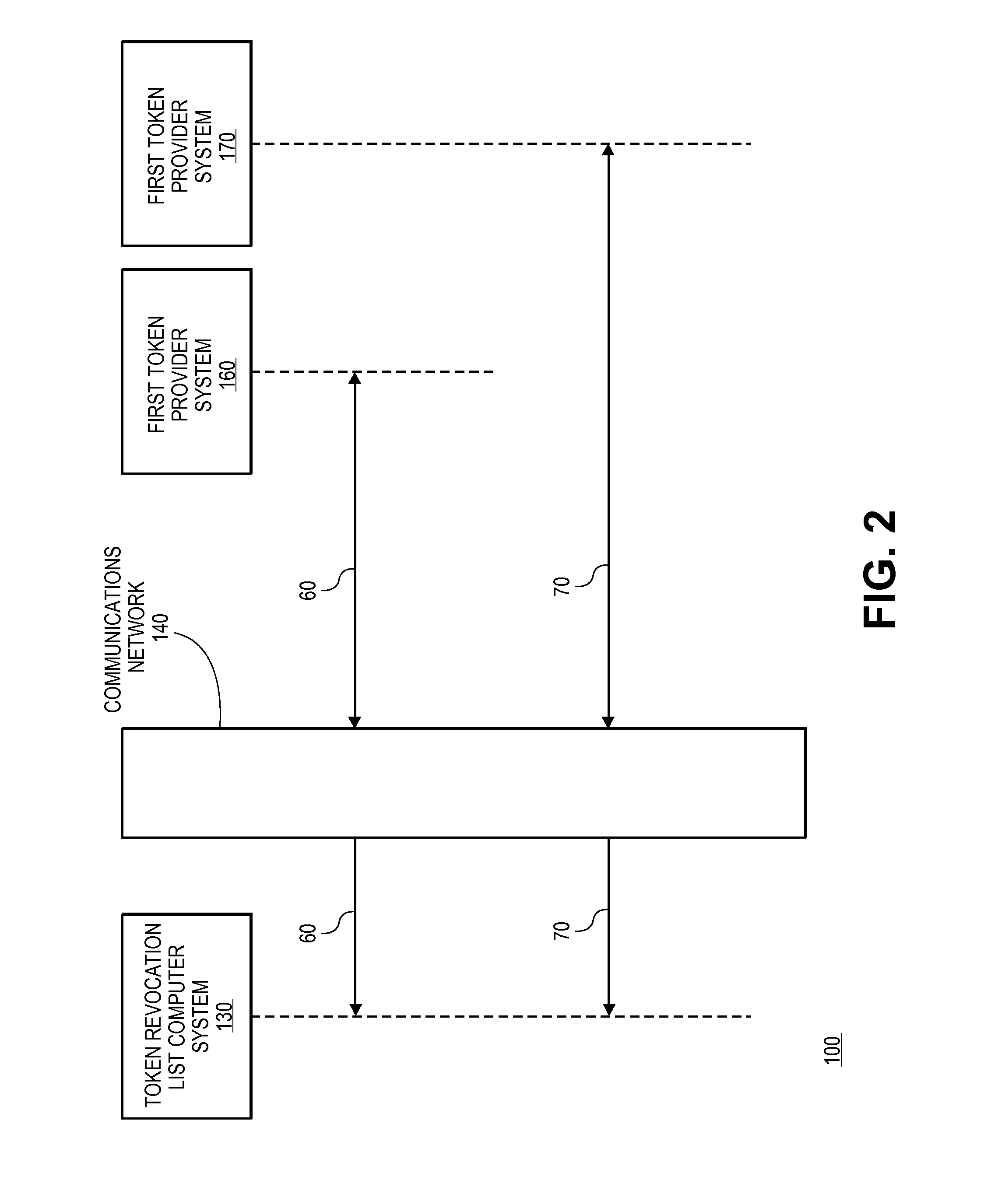
Tokenization revocation list
A method for providing a token revocation list is disclosed. The method includes maintaining a status for each of a plurality of tokens in a token revocation database. Token validation requests are received, and the statuses of payment tokens can be determined. Response messages with the statuses of the payment tokens are then sent to token status requesters so that they may make decisions on whether or not to use them to process transactions.
Owner:VISA INT SERVICE ASSOC
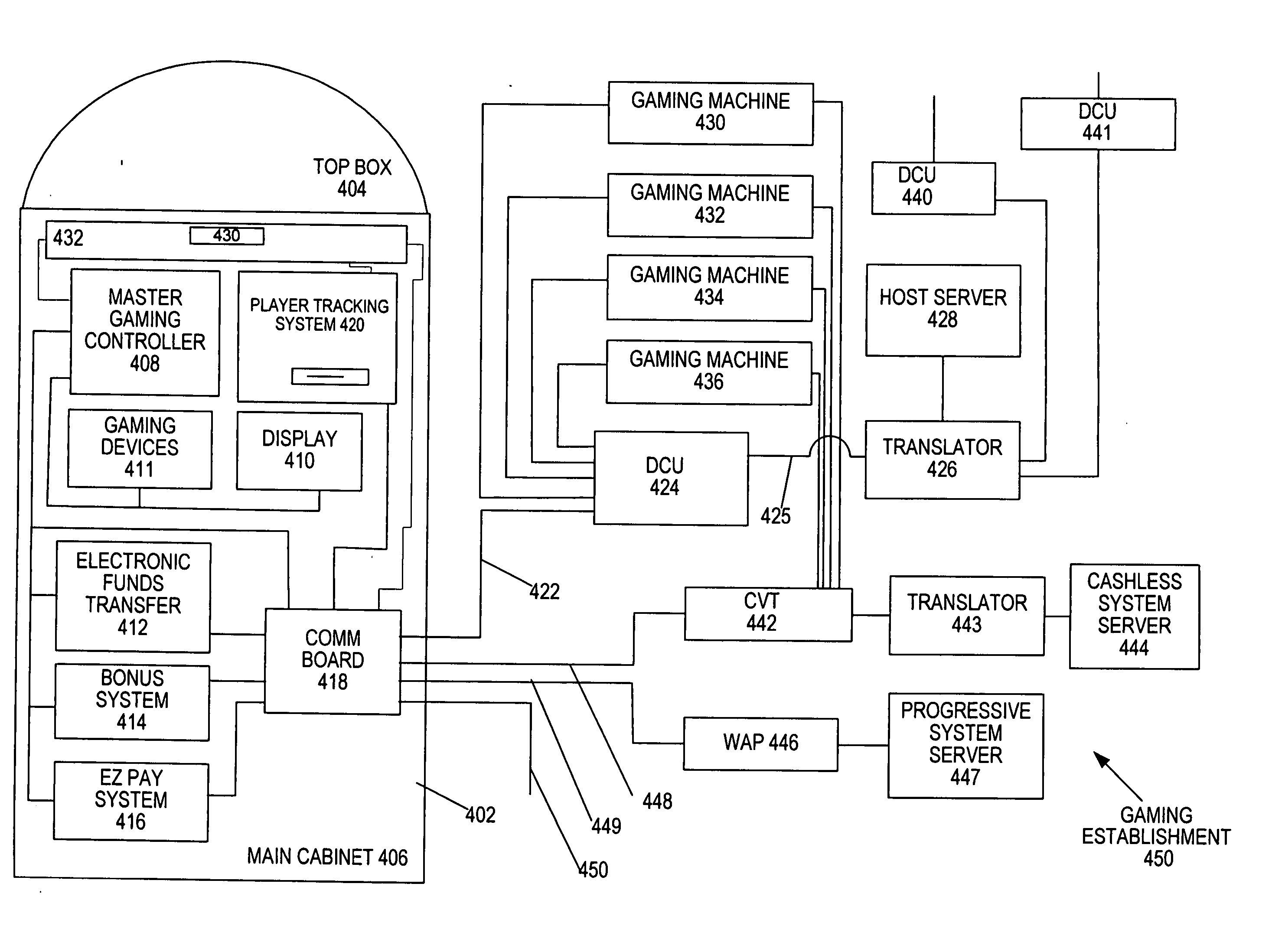
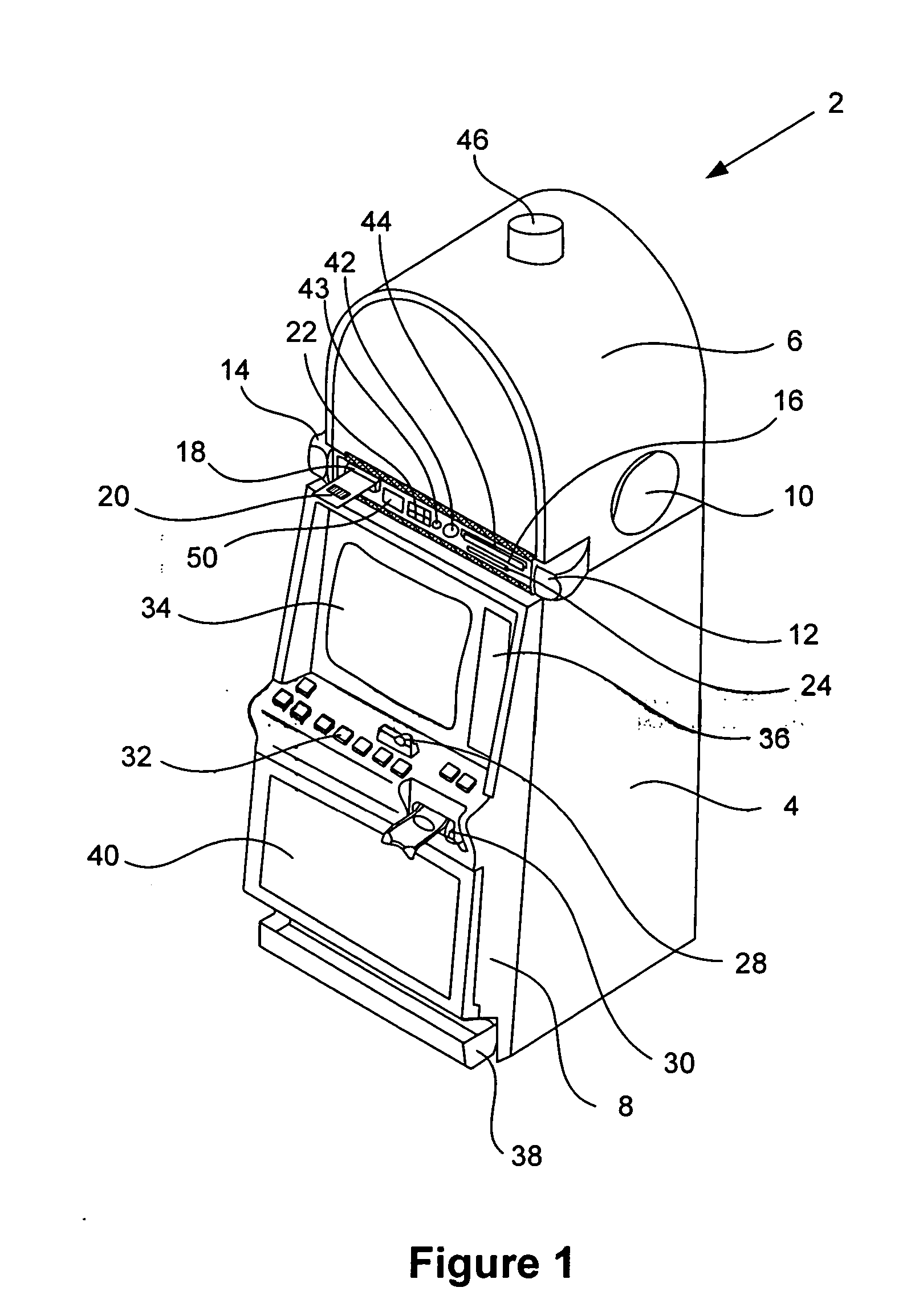
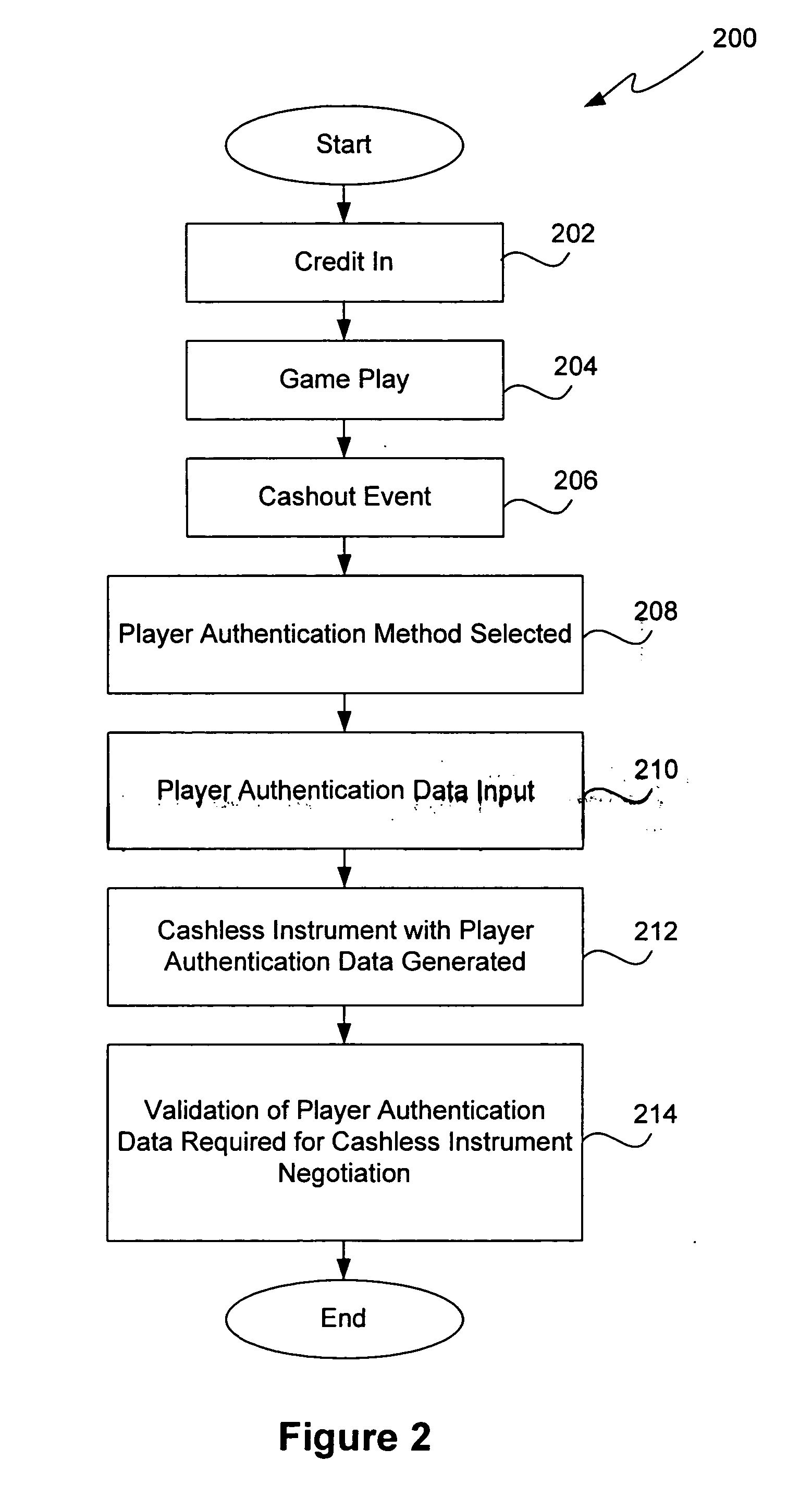
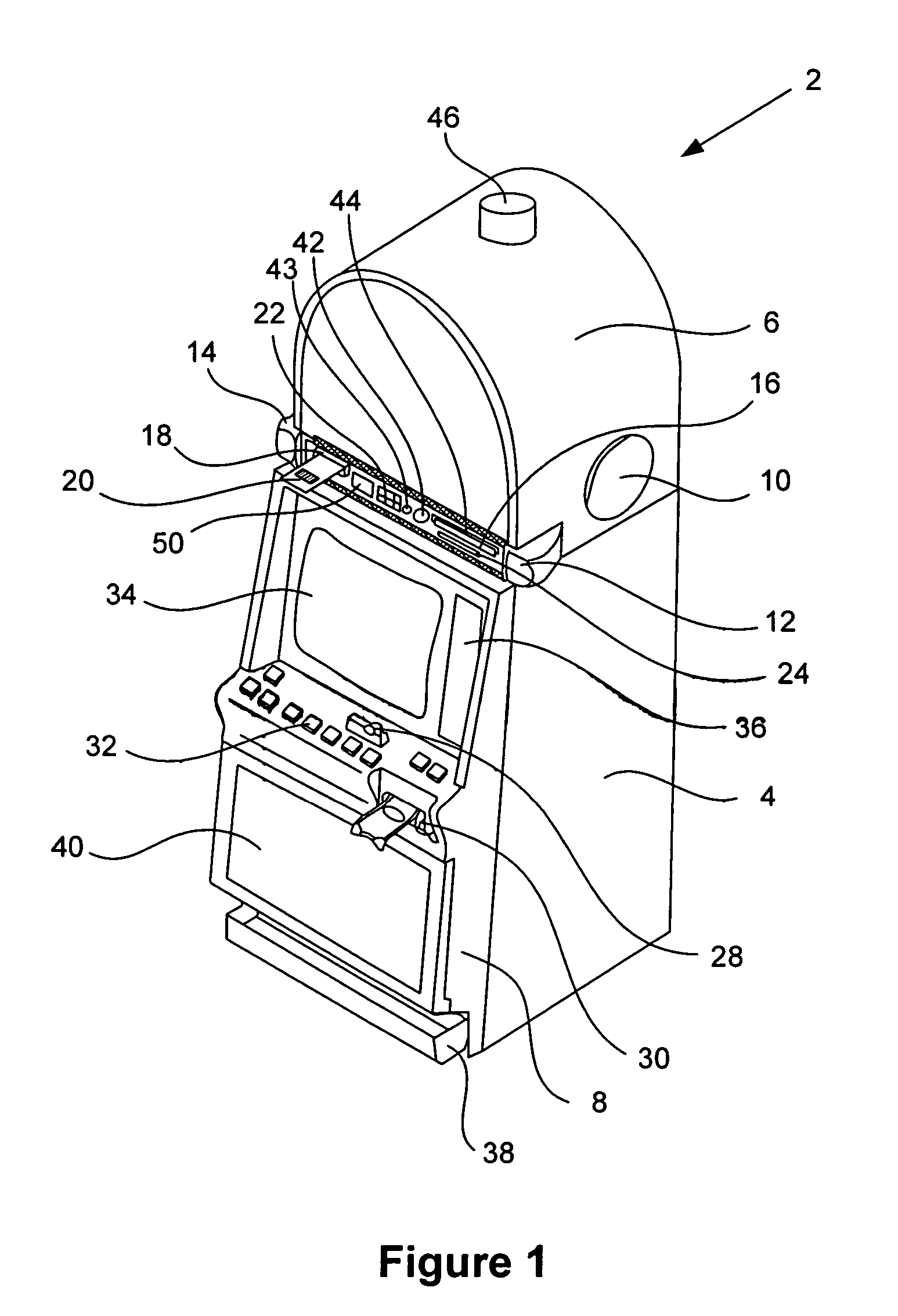
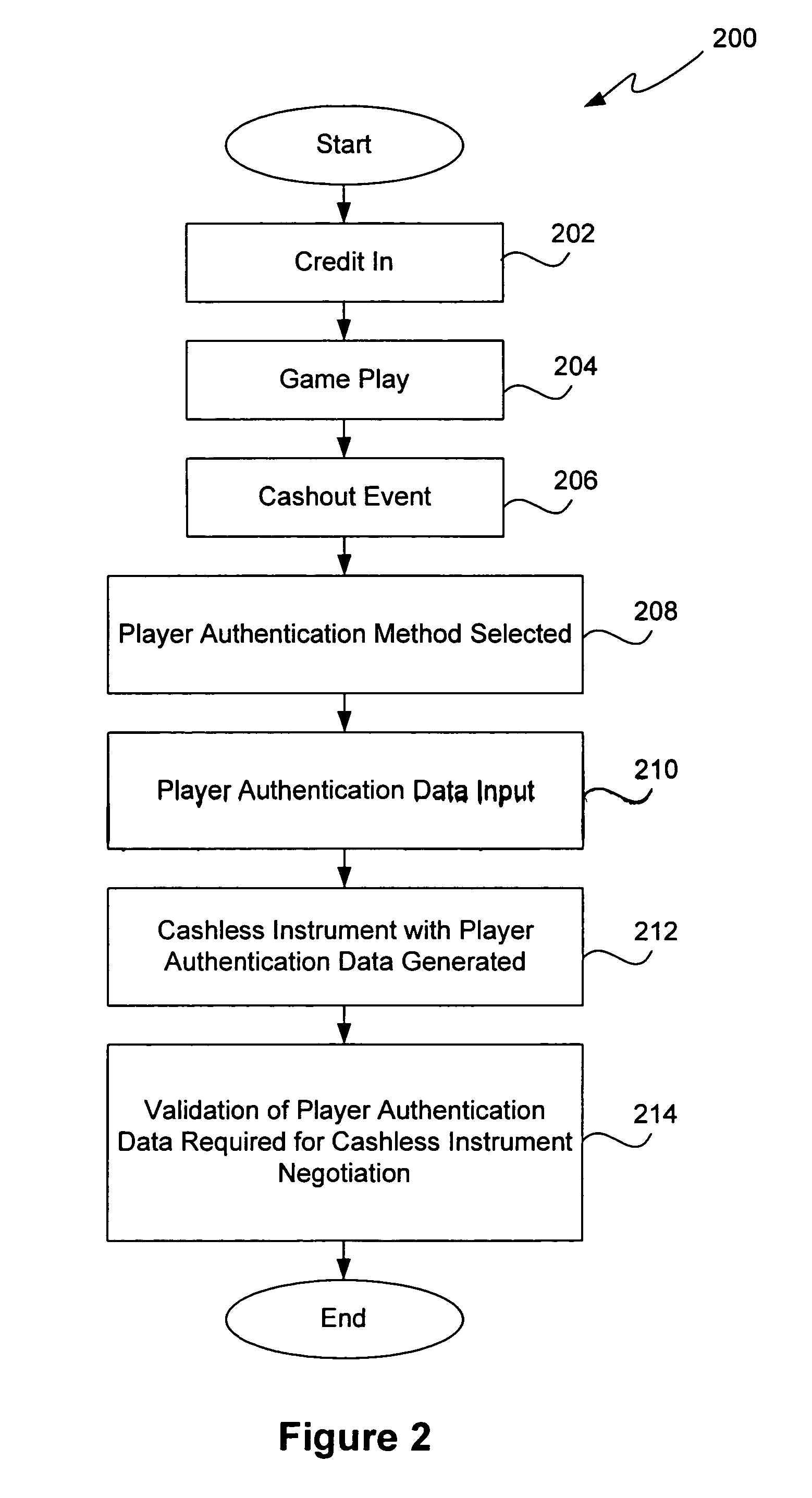
Methods and devices for gaming account management
InactiveUS20050020354A1Flexible redemptionFinanceCash registersFinancial transactionHuman–computer interaction
Methods and devices are provided for managing gaming accounts. Some aspects of the invention provide for the cancellation, revocation or consolidation of cashless gaming instruments. For example, if a player has lost a cashless gaming instrument, the player could request that the cashless gaming instrument be cancelled. The request could be made in response to information (such as an activity log, an account statement, etc.) presented by a central network device. The information could be presented on a screen, printed on paper, etc. In order for such a request to be acted upon, it is preferable that the player, the gaming establishment that issued the cashless gaming instrument and the cashless gaming instrument itself be positively identified. Some implementations of the present invention provide for more flexible redemption in a cashless gaming system. Some such implementations allow a player to “cash out,” preferably in a single transaction, after one or more gaming sessions. The gaming sessions may have been conducted at different gaming machines and / or at different casinos. Some implementations allow a player to cash out without a cashless gaming instrument.
Owner:IGT
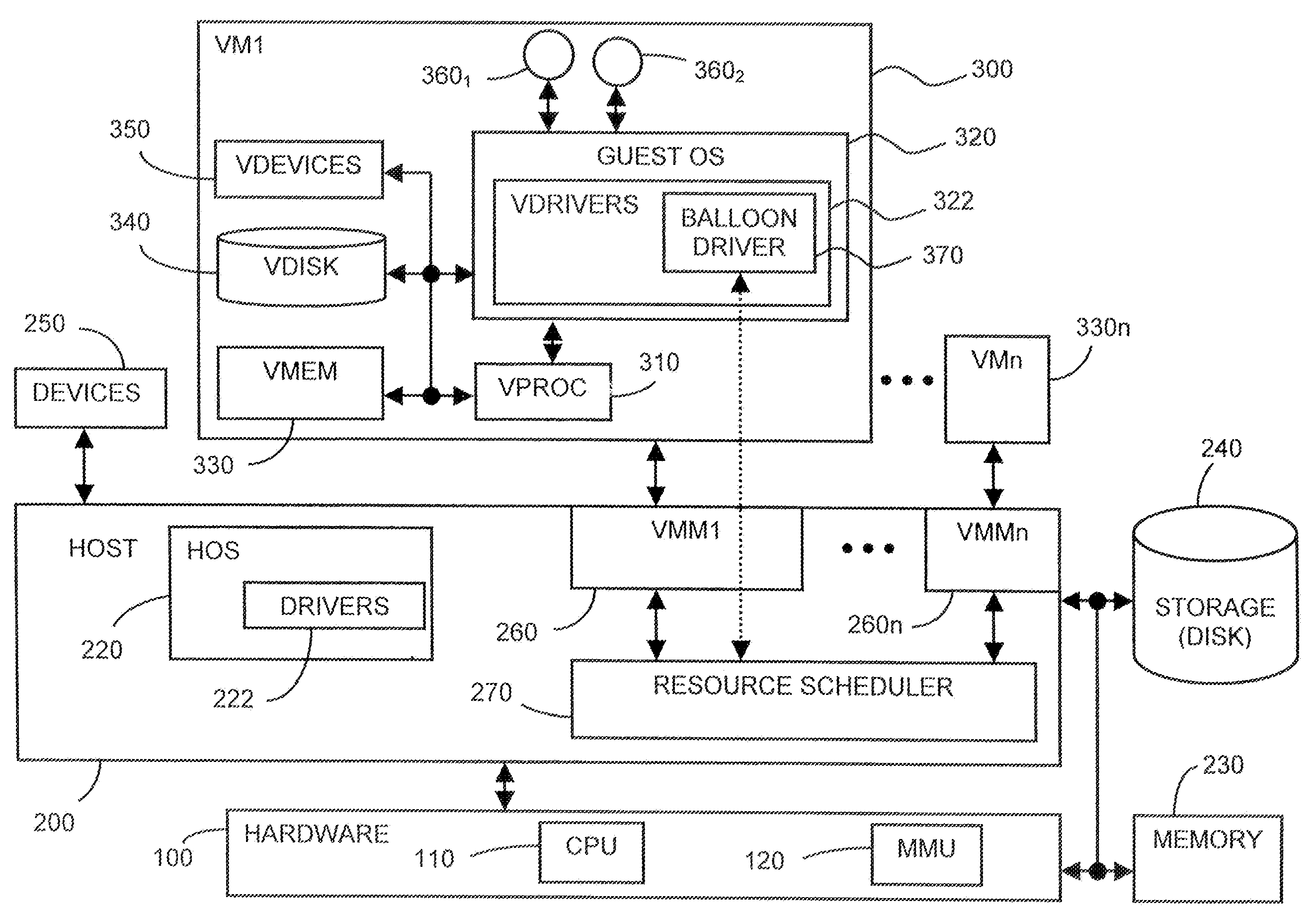
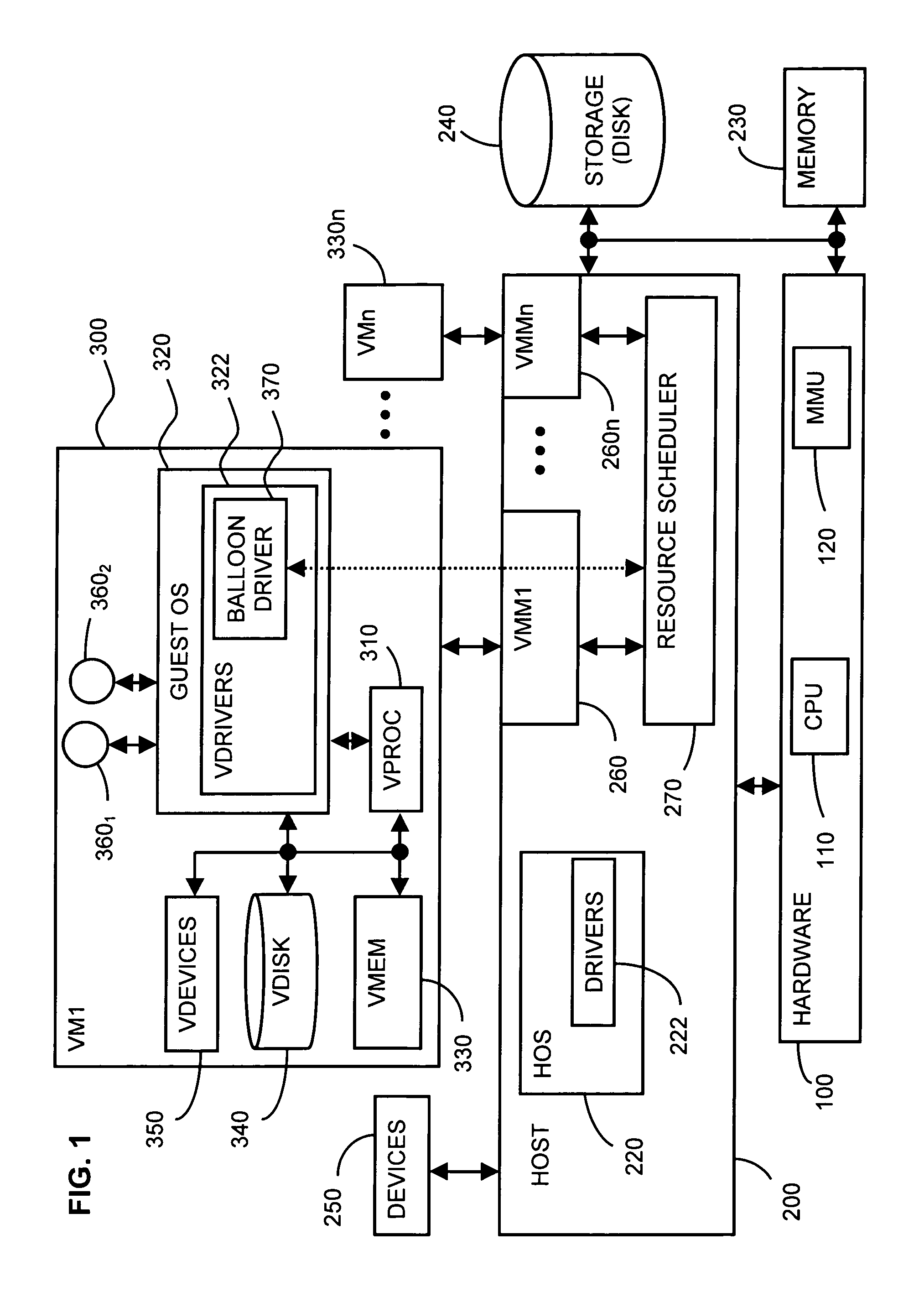
System and method for controlling resource revocation in a multi-guest computer system
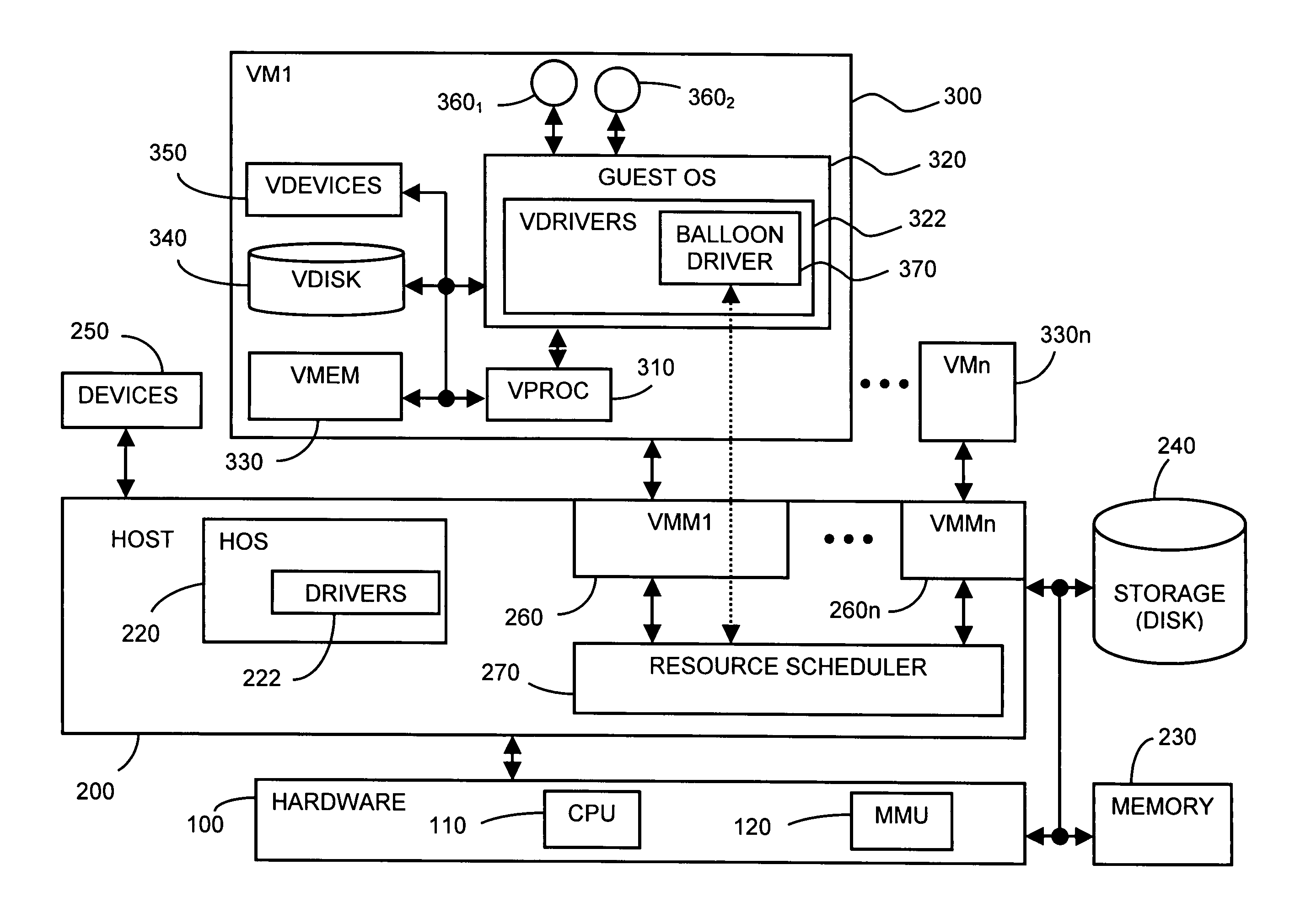
InactiveUS20090025006A1Memory architecture accessing/allocationResource allocationOperational systemDEFLATE
At least one guest system, for example, a virtual machine, is connected to a host system, which includes a system resource such as system machine memory. Each guest system includes a guest operating system (OS). A resource requesting mechanism, preferably a driver, is installed within each guest OS and communicates with a resource scheduler included within the host system. If the host system needs any one the guest systems to relinquish some of the system resource it currently is allocated, then the resource scheduler instructs the driver within that guest system's OS to reserve more of the resource, using the guest OS's own, native resource allocation mechanisms. The driver thus frees this resource for use by the host, since the driver does not itself actually need the requested amount of the resource. The driver in each guest OS thus acts as a hollow “balloon” to “inflate” or “deflate,” that is, reserve more or less of the system resource via the corresponding guest OS. The resource scheduler, however, remains transparent to the guest systems.
Owner:VMWARE INC
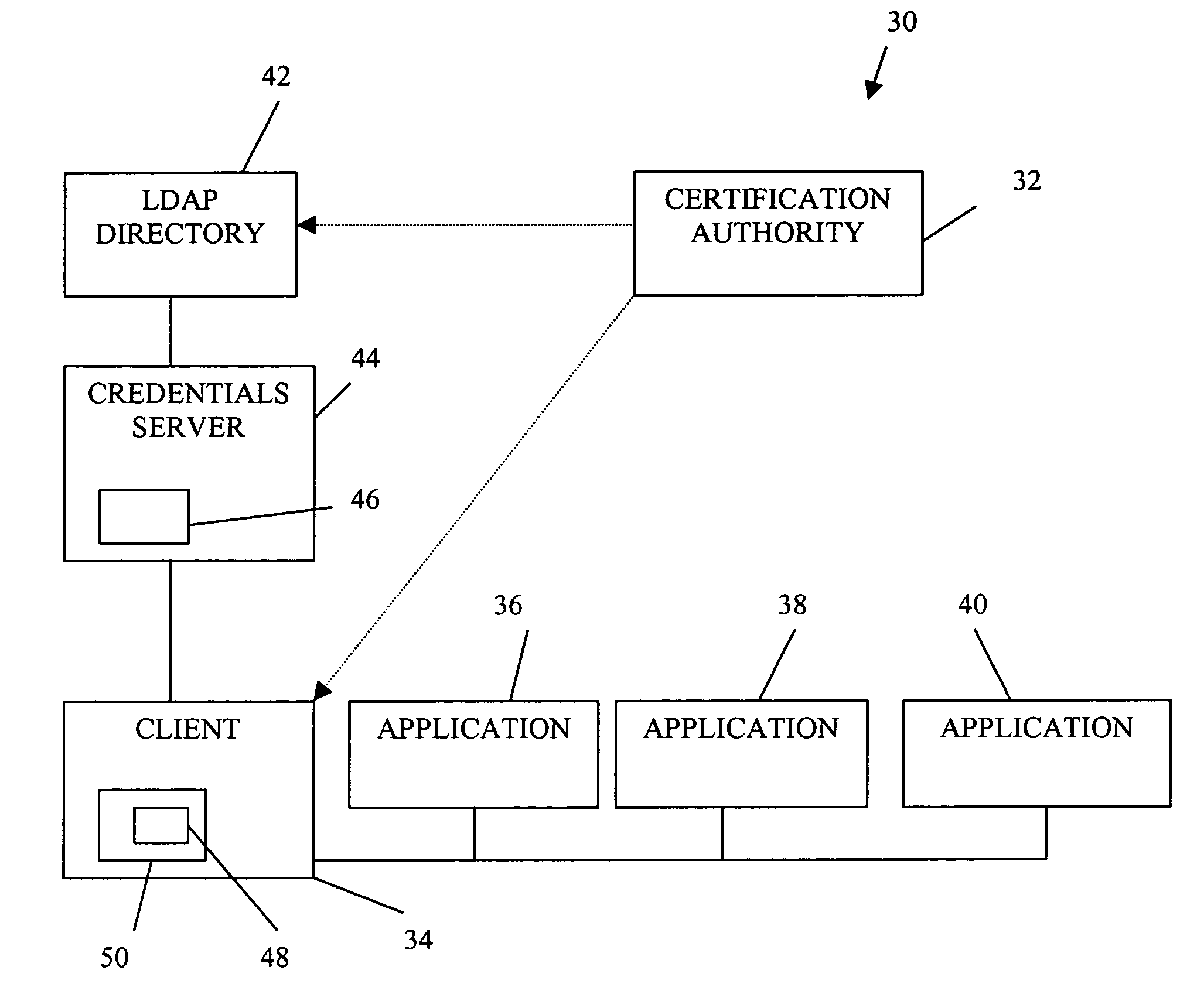
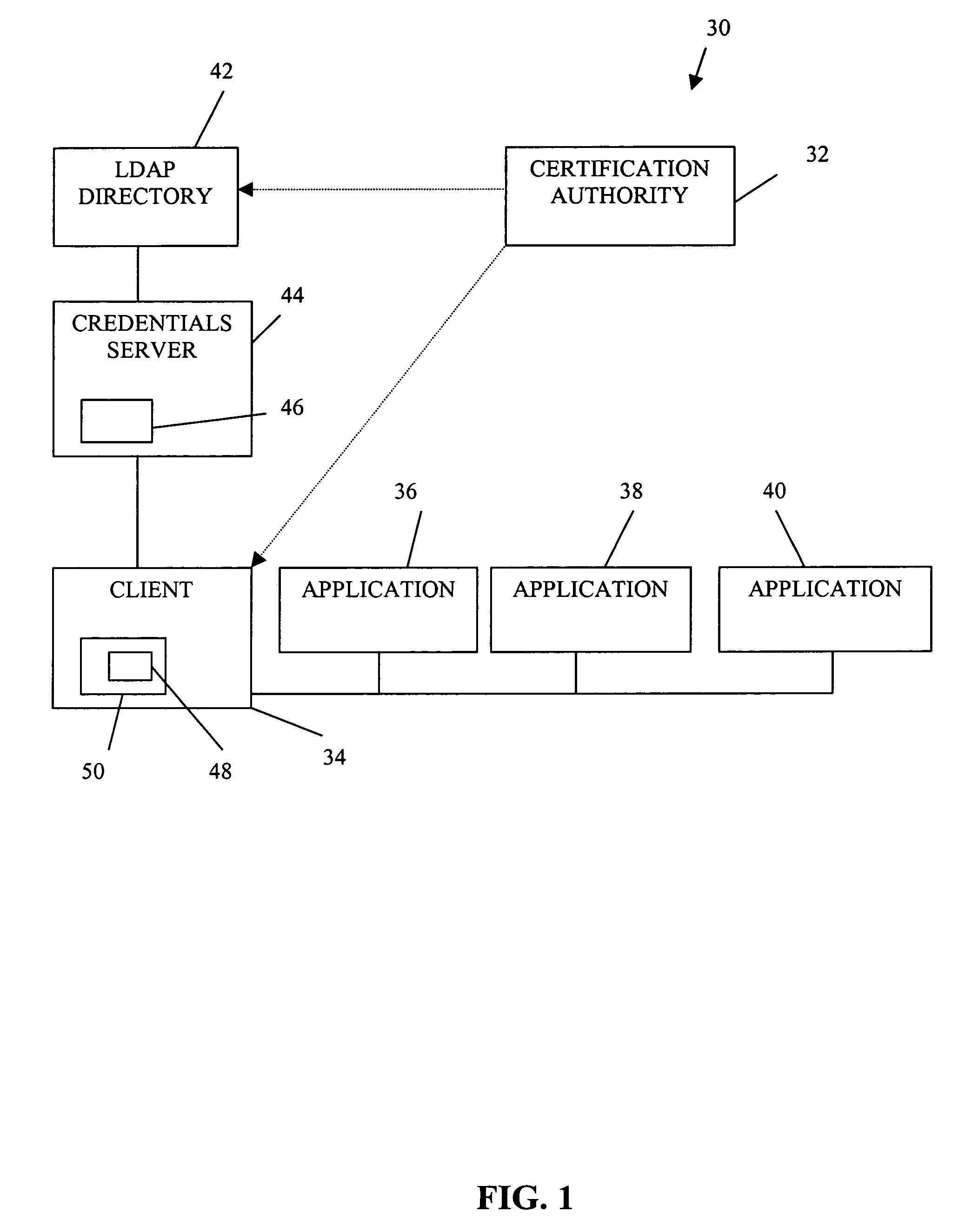
Authorization infrastructure based on public key cryptography
InactiveUS7340600B1Random number generatorsUser identity/authority verificationRoot certificateClient-side
A public key authorization infrastructure includes a client program accessible by a user and an application program. A certificate authority issues a long-term certificate that binds a public key of the user to long-term identification information related to the user. A directory stores the issued long-term certificate and short-term authorization information related to the user. A credentials server issues a short-term certificate to the client. The short-term certificate binds the public key to the long-term identification information and to the short-term authorization information. The client presents the short-term certificate to the application program for authorization and demonstrates that the user has knowledge of a private key corresponding to the public key in the short-term certificate. The short-term certificate includes an expiration date, and is not subject to revocation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
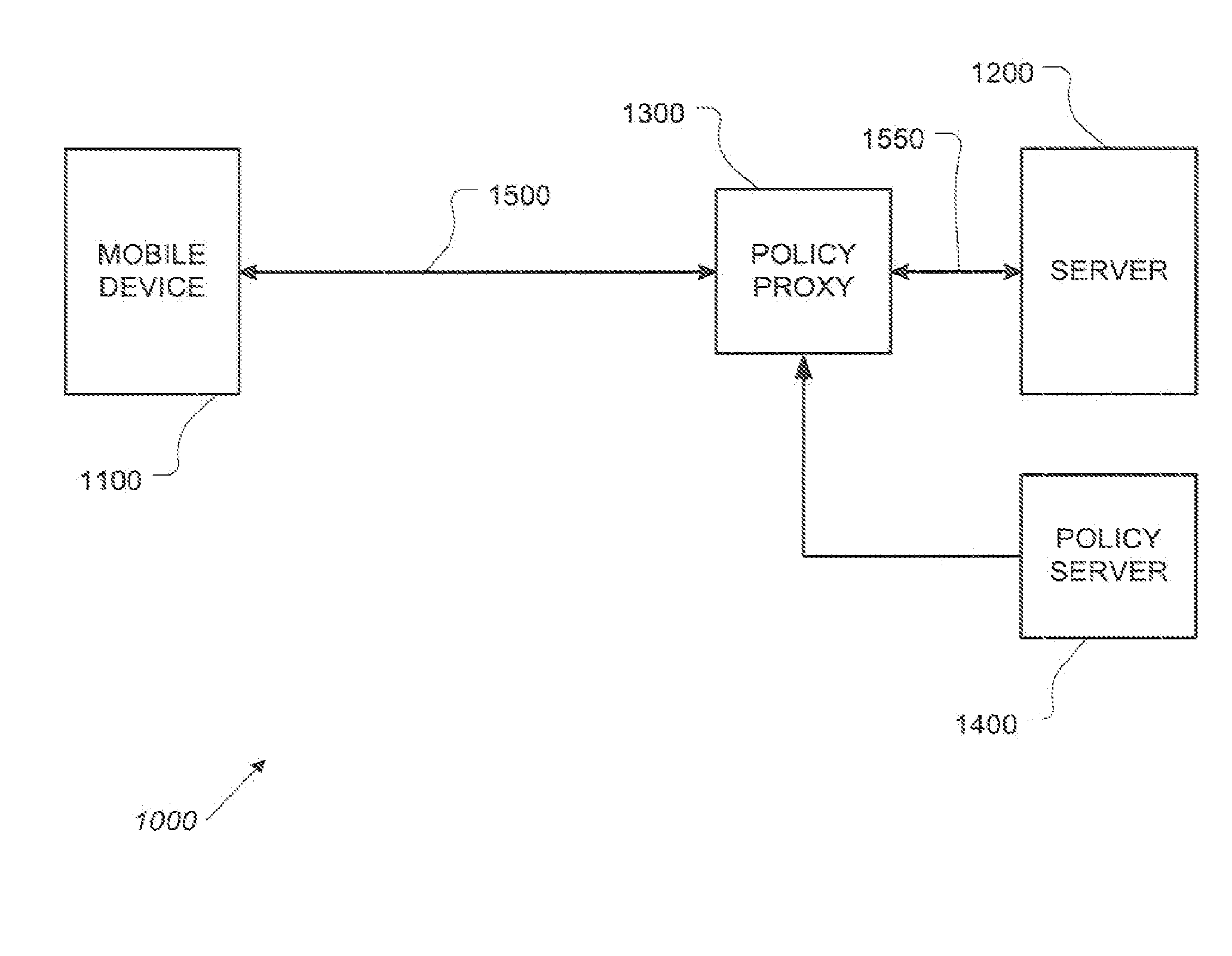
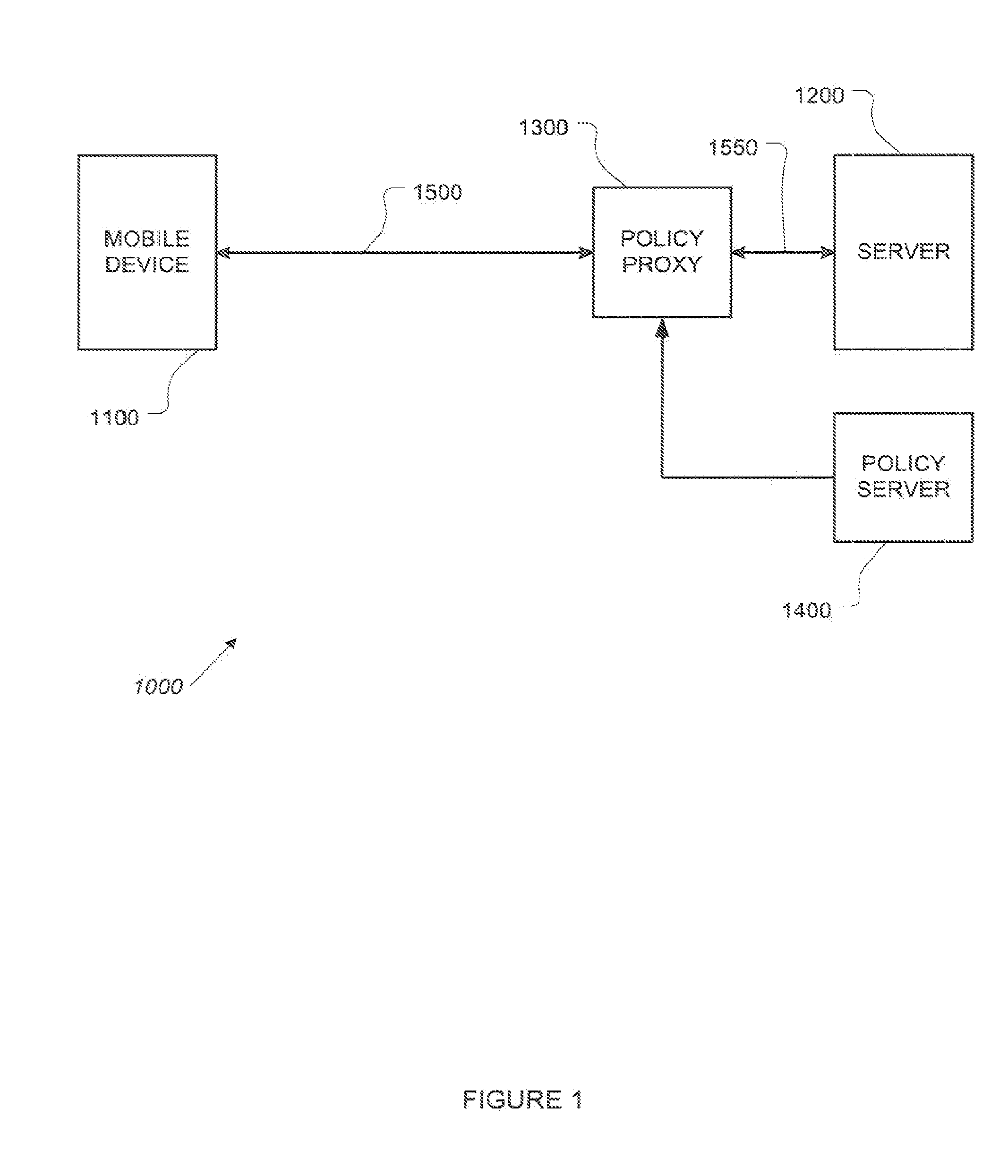
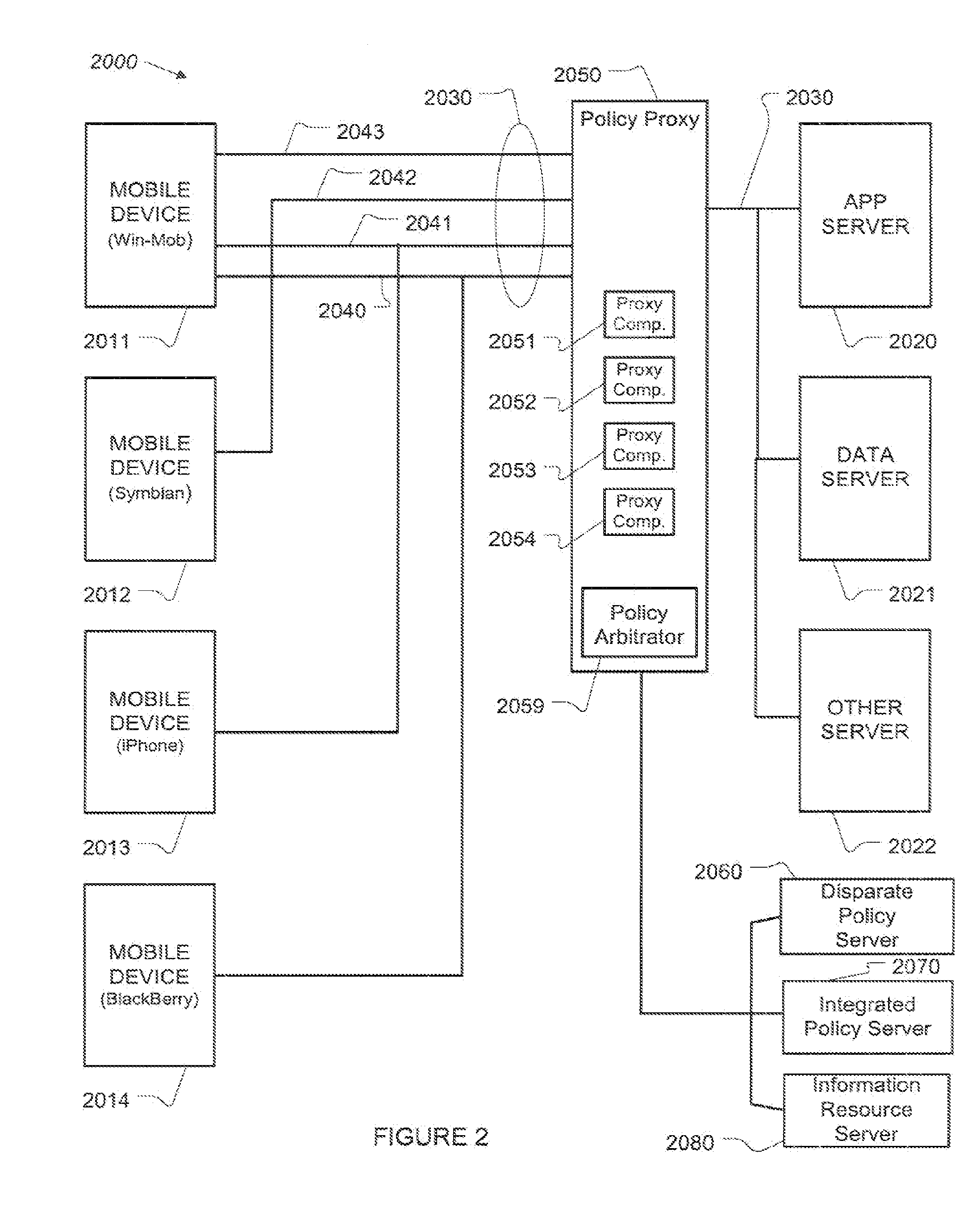
Distributed data revocation using data commands
ActiveUS20110276683A1Increase flexibilityIncrease productivityMultiple digital computer combinationsMobile application execution environmentsData streamUser device
A policy proxy intercepts a data stream between a data server and a user or other device, identifies the user device, and identifies a policy in an integrated policy server applicable to the user device based on the identity of the user device. The policy proxy may identify one or more of the policy elements based on the user device, and translate the policy elements into actions involving the data stream between the data server and the user device so as to implement at least one aspect of the identified policy. The actions can comprise permitting normal exchange of data between the data server and the user device, preventing communication between the data server and the user device, or modifying the data stream between the data server and the user device.
Owner:SKYHIGH SECURITY LLC +1
Personal data management system with sharing revocation
InactiveUS8893297B2Reduce transaction costsRedundant data entryDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyData management
A data vault system allows for centralized storage of personal data about a consumer associated with sharing permissions designating how that data may be shared and including an option to revoke permission of previously shared data. Data may be collected into cards describing a subset of globally stored data to be shared with individual vendors and providing separate sharing statuses for fine resolution control. Both intentionally entered personal data and data collected about the consumer may be protected in this data vault system.
Owner:SOLOMO IDENTITY
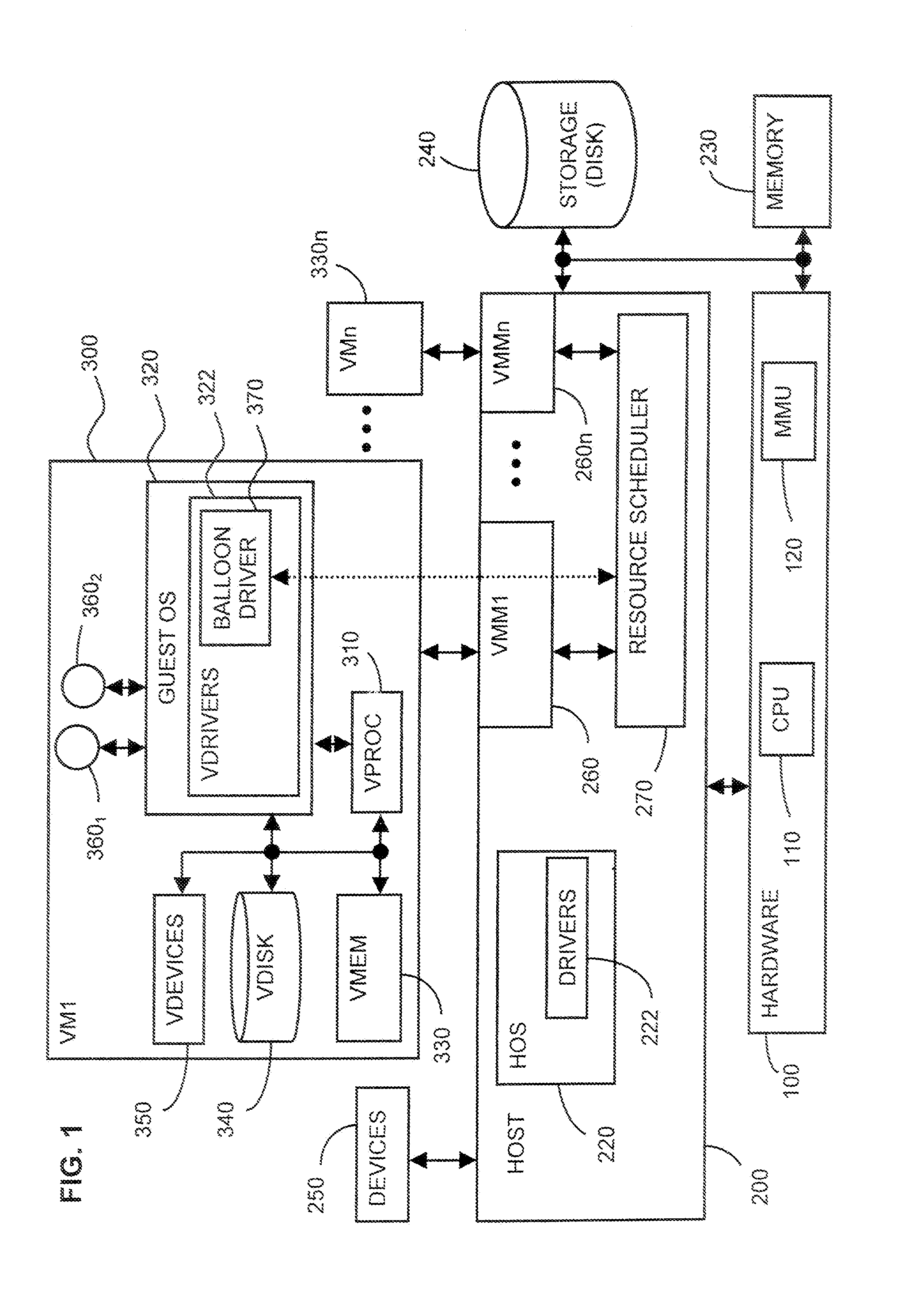
System and method for controlling resource revocation in a multi-guest computer system
ActiveUS7433951B1Effective distributionMemory architecture accessing/allocationSoftware engineeringOperational systemDEFLATE
At least one guest system, for example, a virtual machine, is connected to a host system, which includes a system resource such as system machine memory. Each guest system includes a guest operating system (OS). A resource requesting mechanism, preferably a driver, is installed within each guest OS and communicates with a resource scheduler included within the host system. If the host system needs any one the guest systems to relinquish some of the system resource it currently is allocated, then the resource scheduler instructs the driver within that guest system's OS to reserve more of the resource, using the guest OS's own, native resource allocation mechanisms. The driver thus frees this resource for use by the host, since the driver does not itself actually need the requested amount of the resource. The driver in each guest OS thus acts as a hollow “balloon” to “inflate” or “deflate,” that is, reserve more or less of the system resource via the corresponding guest OS. The resource scheduler, however, remains transparent to the guest systems.
Owner:VMWARE INC
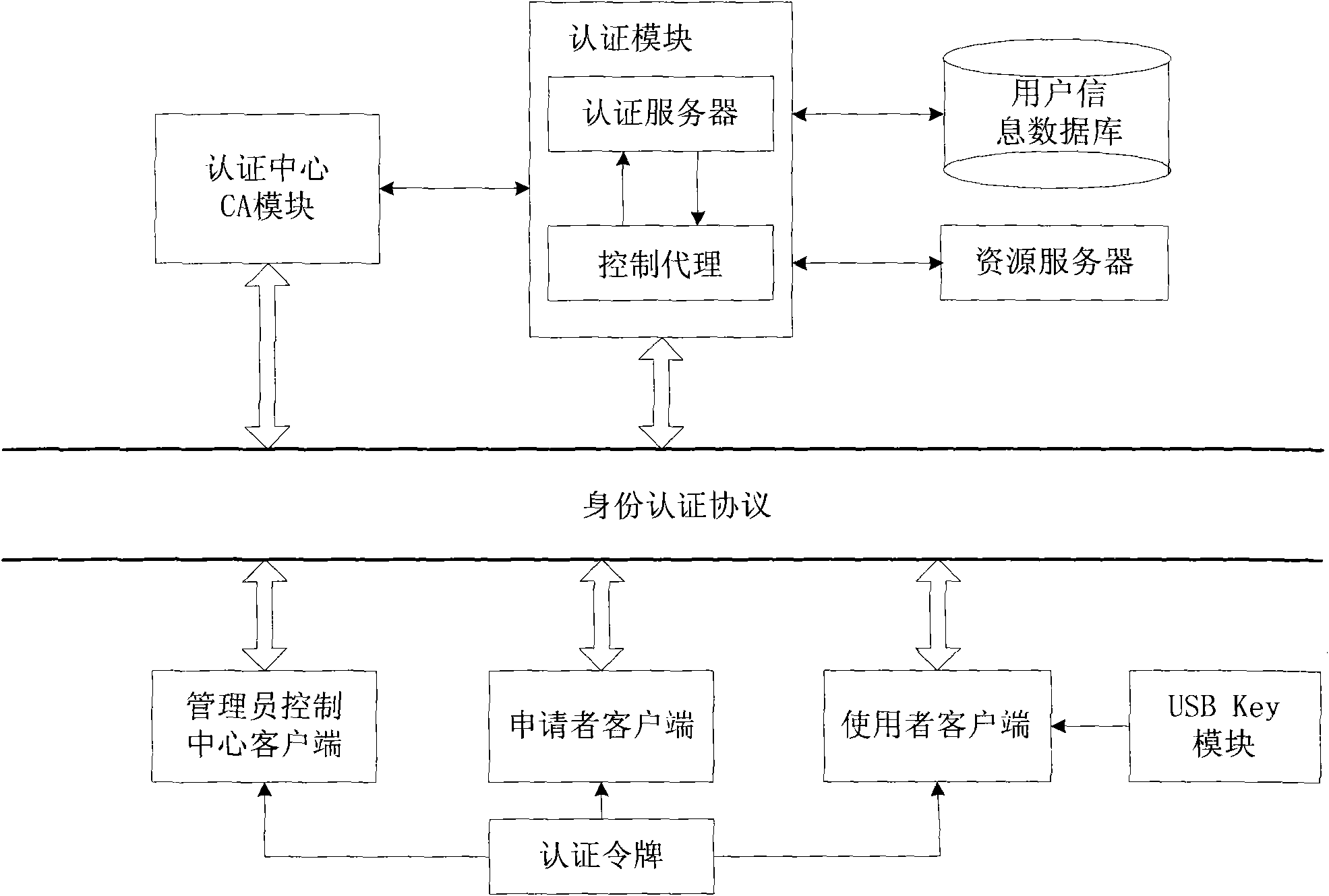
Network identity authentication system and method
InactiveCN101674304AEnsure safetyAchieve separationUser identity/authority verificationConfidentialityAuthentication server
The invention relates to an identity authentication system and an authentication method. The identity authentication system comprises an authentication center CA module, an authentication module, a client side and a USB Key module, wherein the authentication center CA module is responsible for the functions of application, examination and approval, issuing, updating and revocation of a certificate; the authentication module respectively carries out the generation of a digital envelope and the authentication of a digital certificate to the client side and a server side; the client side mainly realizes the management of the system and the clients; and the USB Key module mainly provides a medium for storing the digital certificate and a user private key to the user. The invention adopts a digital envelope technology, and can meet the high-confidentiality requirement of data transmission; an authentication token is used for sending a request to the authentication server by the client sidefor authentication and realizing the security of the authentication process; and the client side and the authentication server respectively carry out the generation of the digital envelope and the digital certificate, thus being capable of realizing the mutual authentication between the client side and the authentication server.
Owner:ZHEJIANG NORMAL UNIVERSITY
Authentication system and process
InactiveUS6230266B1Reducing authentication system securityEliminate needUser identity/authority verificationAuthentication systemCertificate authority
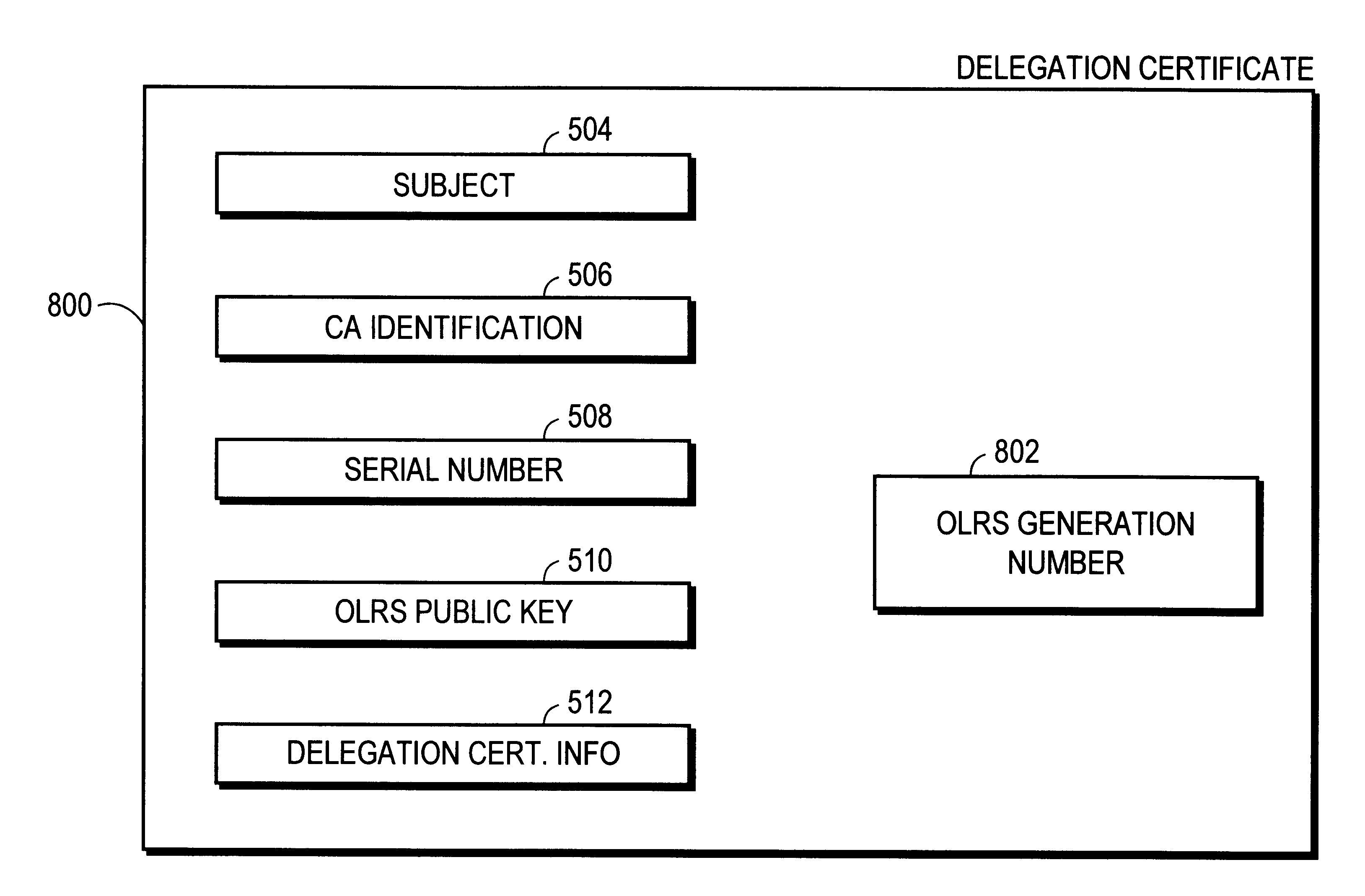
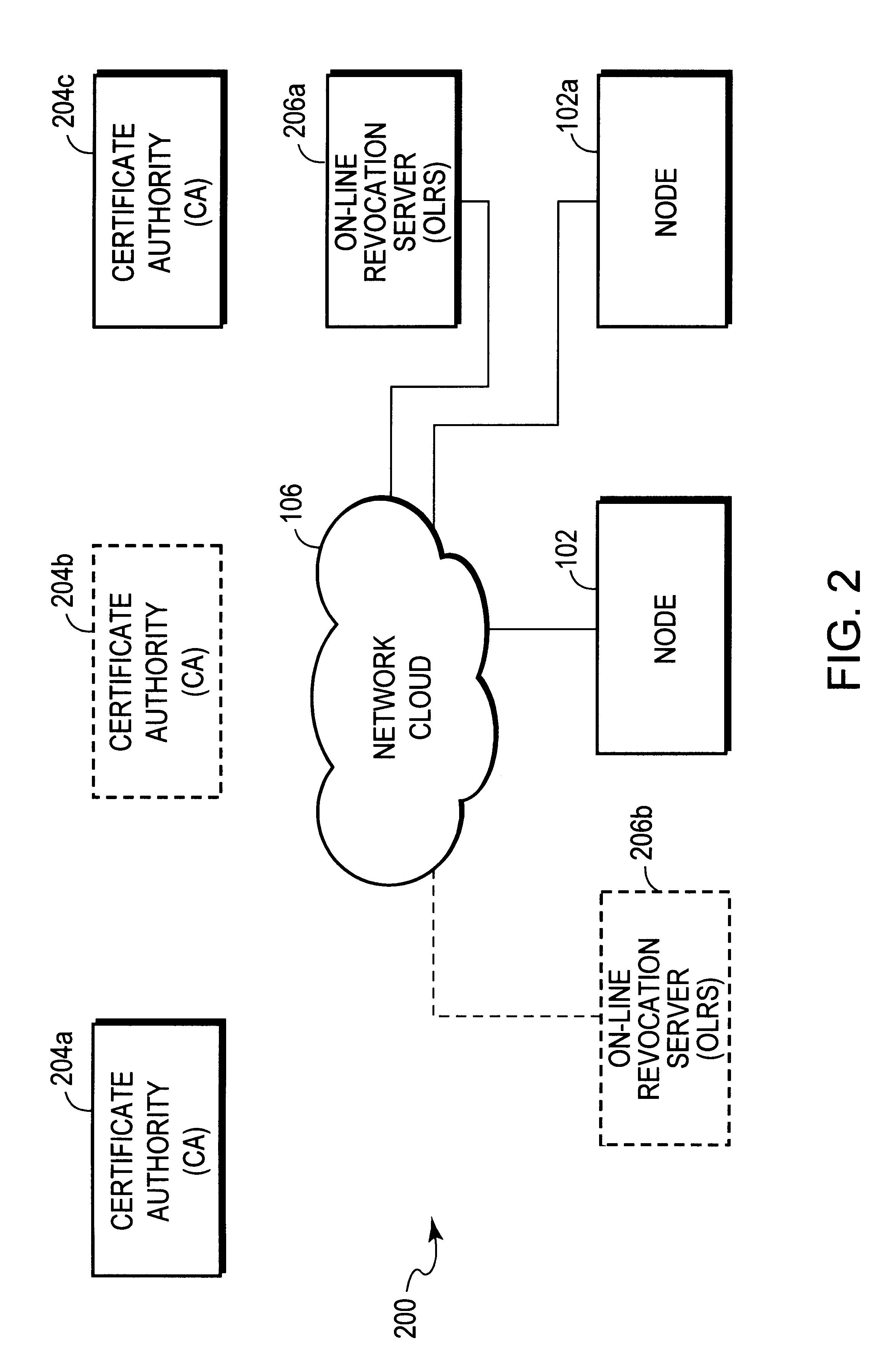
An authentication method and process are provided. One aspect of the process of the present invention includes authorizing a first on-line revocation server (OLRS) to provide information concerning certificates issued by a certificate authority (CA) that have been revoked. If the first OLRS is compromised, a second OLRS is authorized to provide certificate revocation information, but certificates issued by the CA remain valid unless indicated by the second OLRS to be revoked.
Owner:ORACLE INT CORP
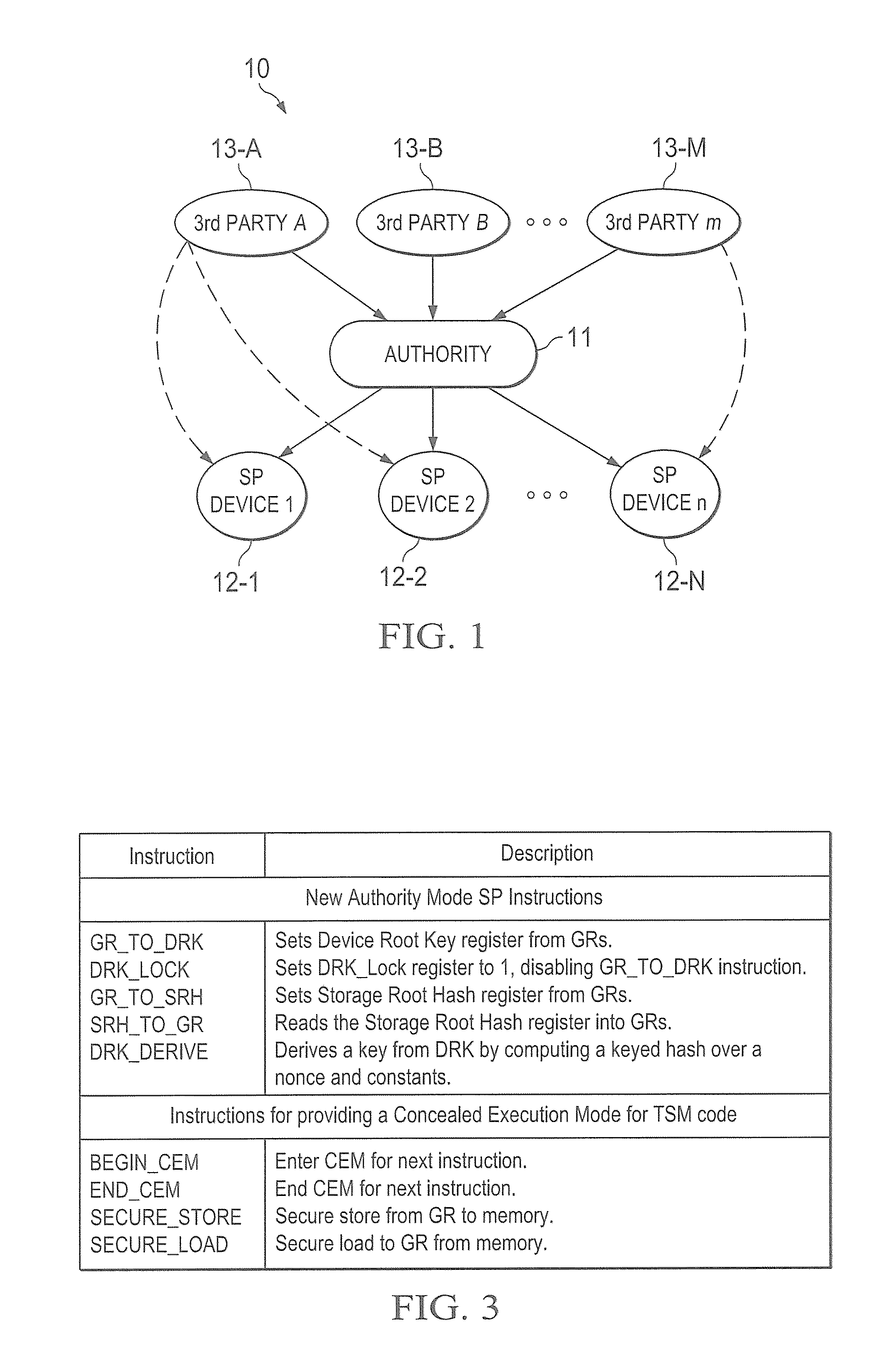
Hardware trust anchors in sp-enabled processors
ActiveUS20100042824A1User identity/authority verificationDigital computer detailsOperational systemConfidentiality
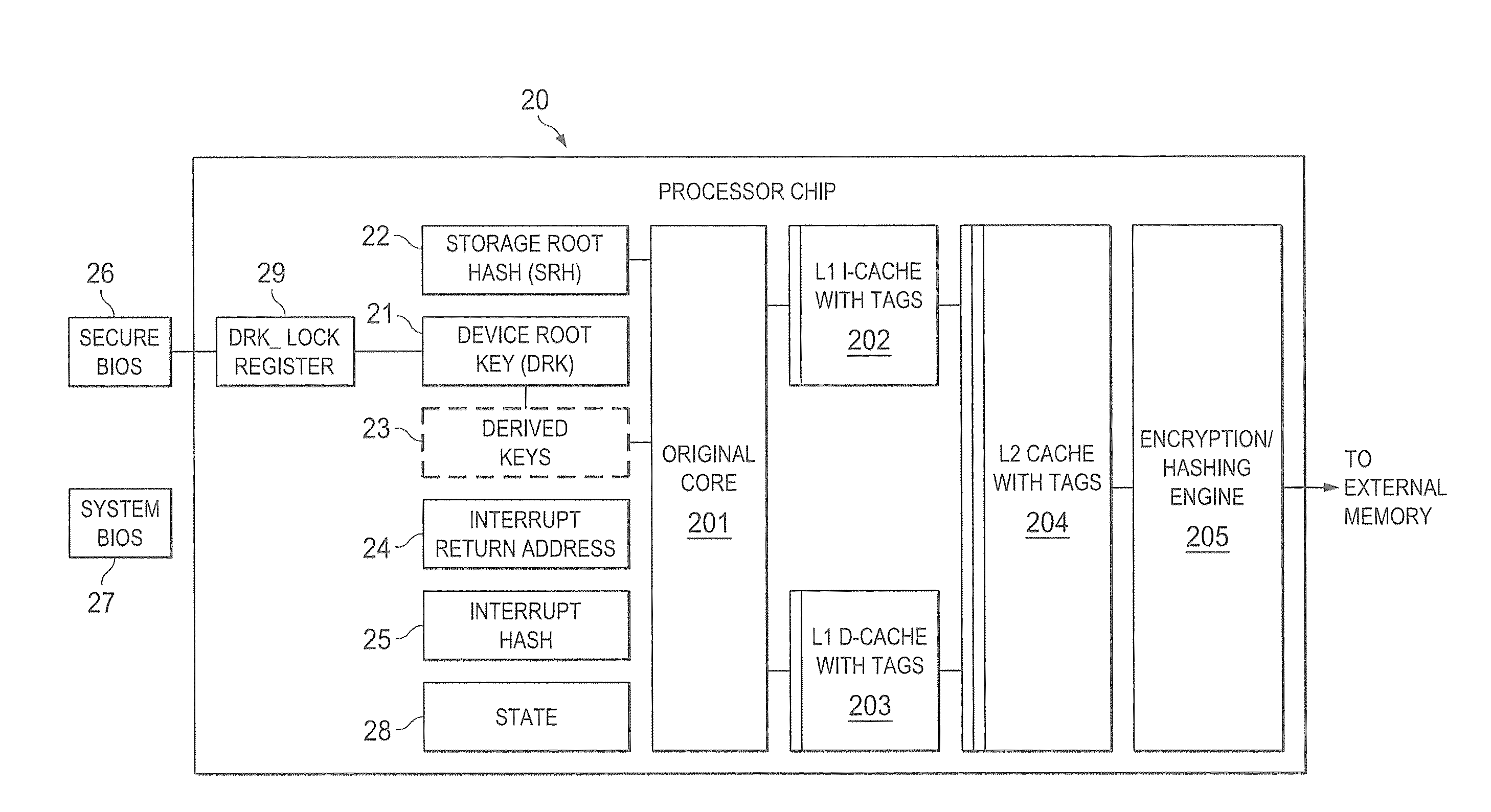
A trust system and method is disclosed for use in computing devices, particularly portable devices, in which a central Authority shares secrets and sensitive data with users of the respective devices. The central Authority maintains control over how and when shared secrets and data are used. In one embodiment, the secrets and data are protected by hardware-rooted encryption and cryptographic hashing, and can be stored securely in untrusted storage. The problem of transient trust and revocation of data is reduced to that of secure key management and keeping a runtime check of the integrity of the secure storage areas containing these keys (and other secrets). These hardware-protected keys and other secrets can further protect the confidentiality and / or integrity of any amount of other information of arbitrary size (e.g., files, programs, data) by the use of strong encryption and / or keyed-hashing, respectively. In addition to secrets the Authority owns, the system provides access to third party secrets from the computing devices. In one embodiment, the hardware-rooted encryption and hashing each use a single hardware register fabricated as part of the computing device's processor or System-on-Chip (SoC) and protected from external probing. The secret data is protected while in the device even during operating system malfunctions and becomes non-accessible from storage according to various rules, one of the rules being the passage of a certain time period. The use of the keys (or other secrets) can be bound to security policies that cannot be separated from the keys (or other secrets). The Authority is also able to establish remote trust and secure communications to the devices after deployment in the field using a special tamper-resistant hardware register in the device, to enable, disable or update the keys or secrets stored securely by the device.
Owner:THE TRUSTEES FOR PRINCETON UNIV +1
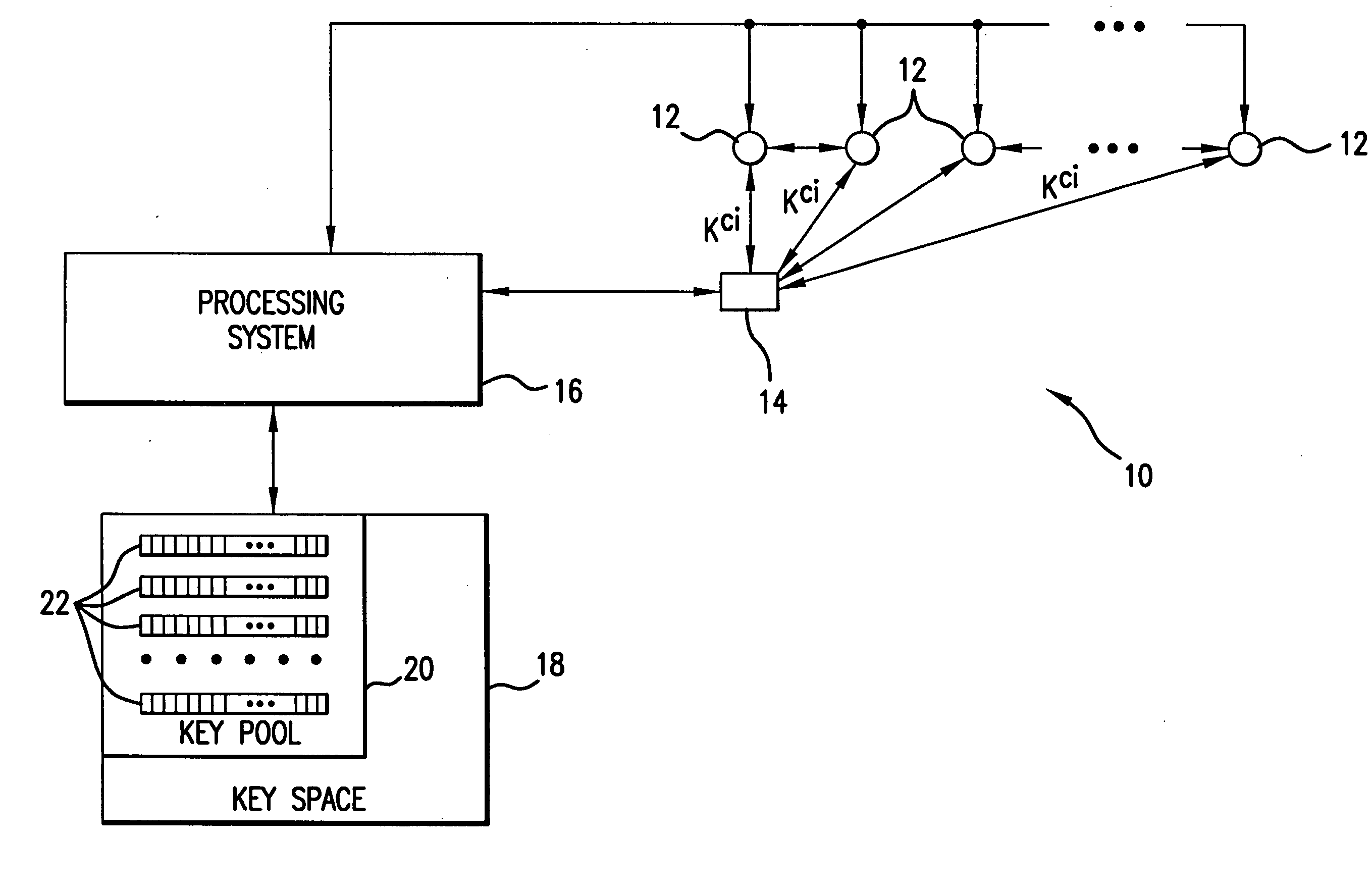
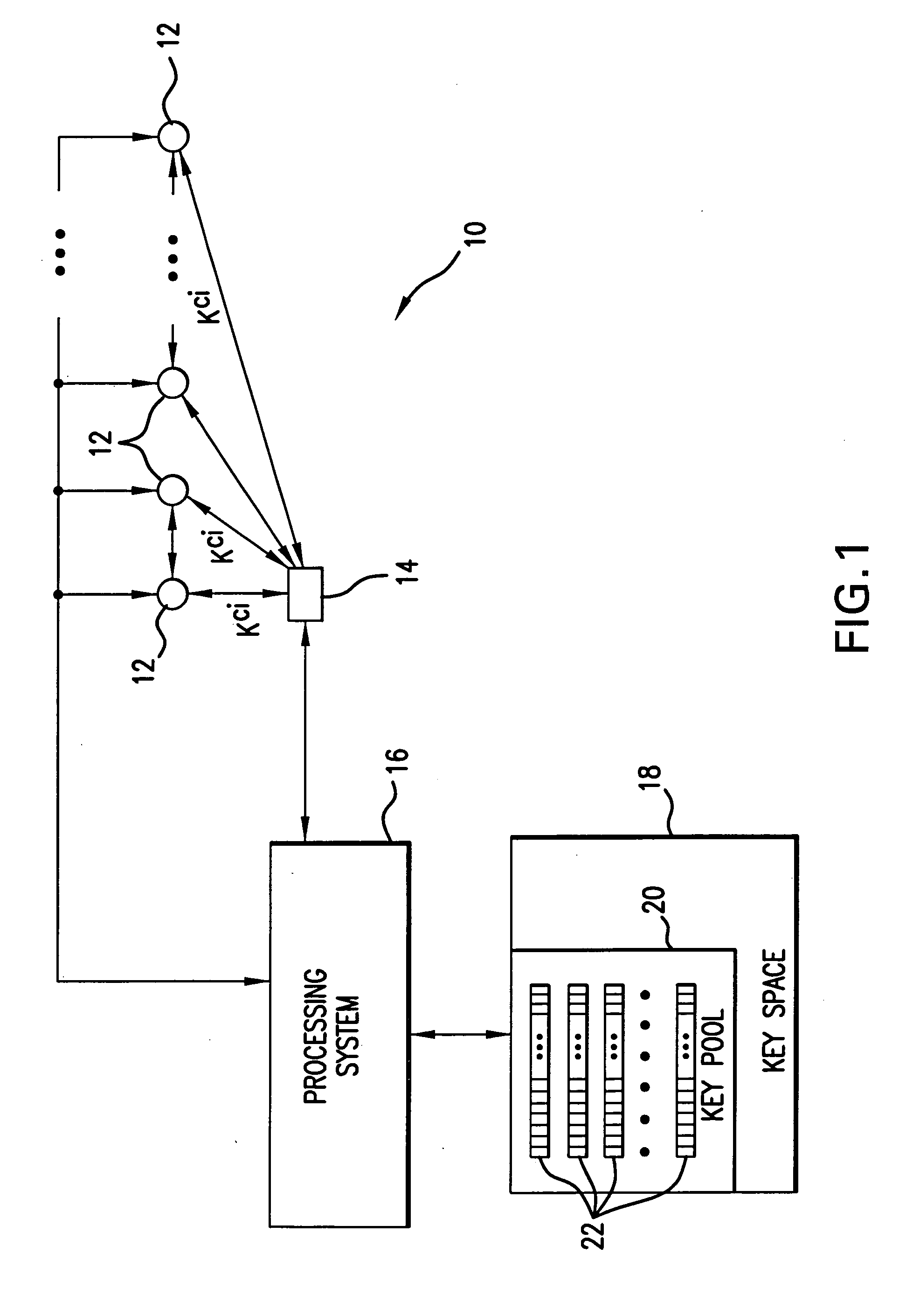
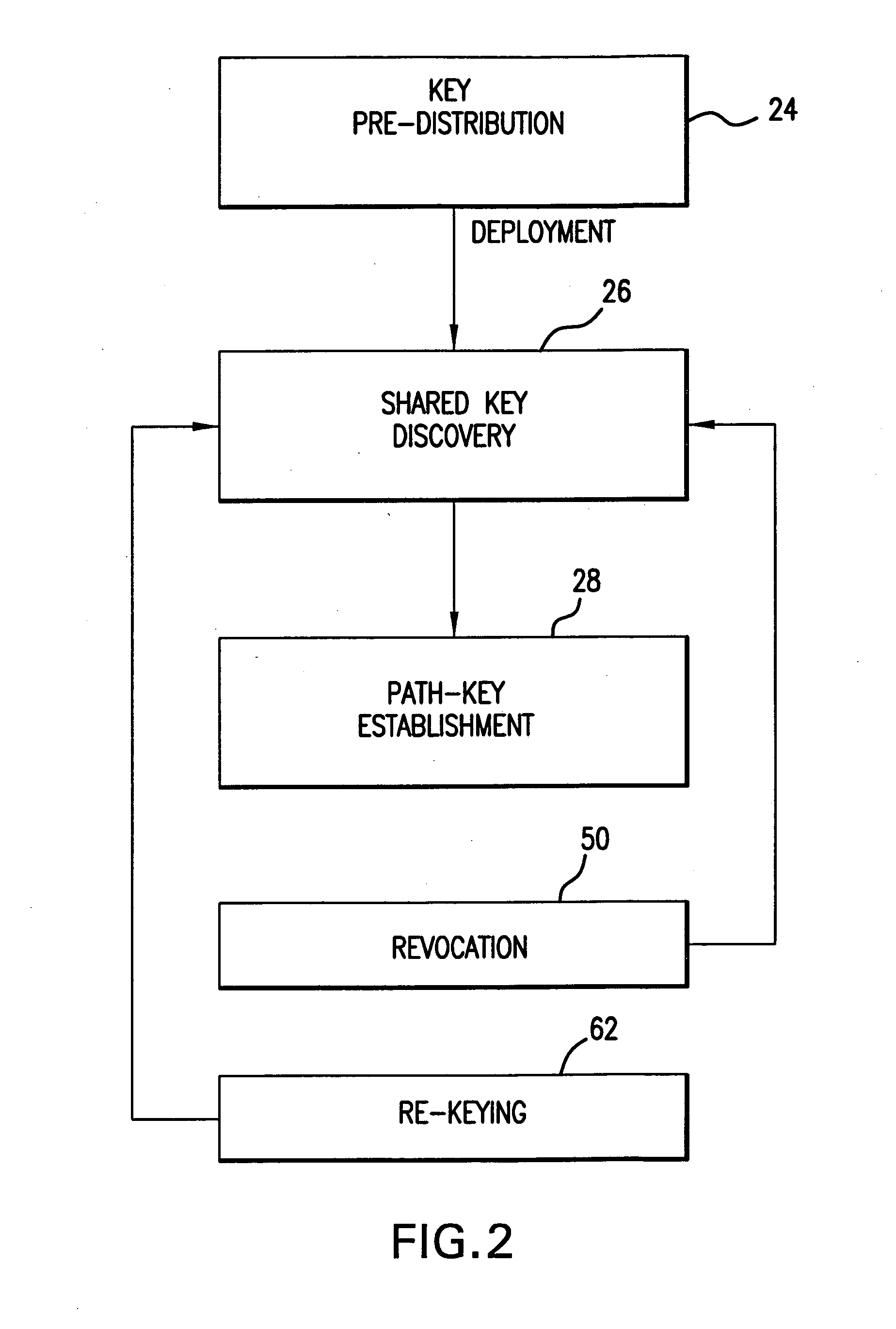
Method and apparatus for key management in distributed sensor networks
InactiveUS20050140964A1Key distribution for secure communicationOptical rangefindersRe keyingRevocation
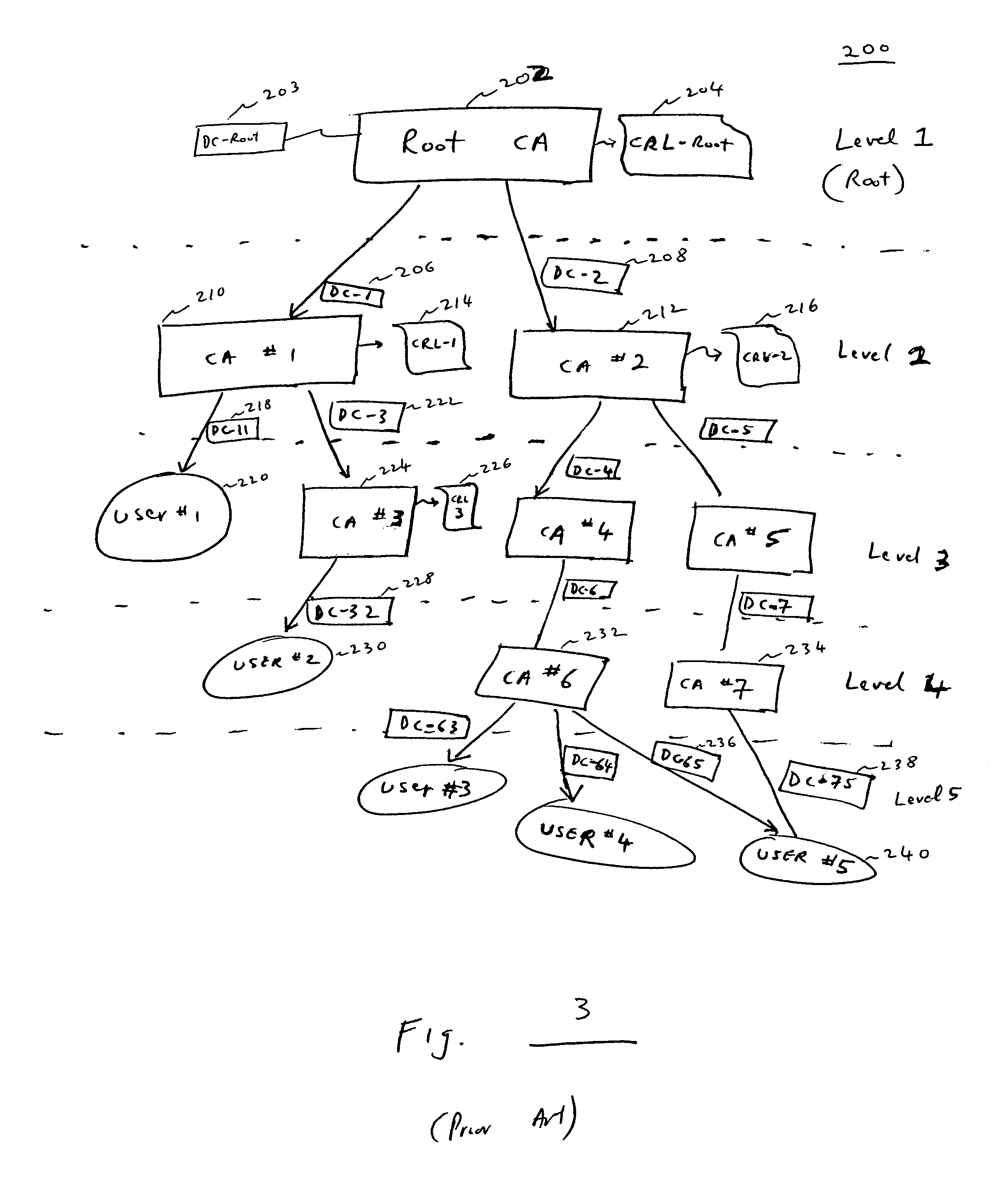
In a distributed sensor network, a method of key management is carried out in several phases, particularly key pre-distribution phase, shared key discovery phase, and as needed, a path key establishment phase. In the key pre-distribution phase, prior to DSN deployment, a ring of keys is distributed to each sensor node, each key ring consisting of randomly chosen keys from a large pool of keys which is generated off-line. A shared key exists between each two key rings with a predetermined probability. In the shared key discovery phase, which takes place upon deployment of the DSN, every sensor node discovers its neighbors in wireless communication range with which it shares keys, and the topology of the sensor array is established by forming secure communication links between respective sensor nodes. The path key establishment phase assigns a path key to selected pairs of sensor nodes in wireless communication range that do not share a key but are connected by two or more links at the end of the shared key discovery phase. The key management scheme also assumes a revocation phase for removal of the key ring of the compromised sensor node from the network. Also, re-keying phase is assumed for removal of those keys with the expired lifetime.
Owner:MARYLAND UNIV OF
Multi-channel user authentication apparatus system and method
InactiveUS20070289002A1Improve securityLess reliableRandom number generatorsMemory loss protectionPasswordUser authentication
An apparatus, system, and method are disclosed for authenticating users through multiple communication channels. The authentication method of the present invention may be used to supplement password systems or replace password authentication, effectively enabling secure sharing, auditing, delegation, and revocation of authority.
Owner:BRIGHAM YOUNG UNIV
Secure digital content licensing system and method
InactiveUS7155415B2Office automationProgram/content distribution protectionWeb siteTelecommunications link
Owner:BLOCKBUSTER LLC
Methods and devices for gaming account management
InactiveUS7950996B2Flexible redemptionFinanceCash registersFinancial transactionHuman–computer interaction
Methods and devices are provided for managing gaming accounts. Some aspects of the invention provide for the cancellation, revocation or consolidation of cashless gaming instruments. For example, if a player has lost a cashless gaming instrument, the player could request that the cashless gaming instrument be cancelled. The request could be made in response to information (such as an activity log, an account statement, etc.) presented by a central network device. The information could be presented on a screen, printed on paper, etc. In order for such a request to be acted upon, it is preferable that the player, the gaming establishment that issued the cashless gaming instrument and the cashless gaming instrument itself be positively identified. Some implementations of the present invention provide for more flexible redemption in a cashless gaming system. Some such implementations allow a player to “cash out,” preferably in a single transaction, after one or more gaming sessions. The gaming sessions may have been conducted at different gaming machines and / or at different casinos. Some implementations allow a player to cash out without a cashless gaming instrument.
Owner:IGT
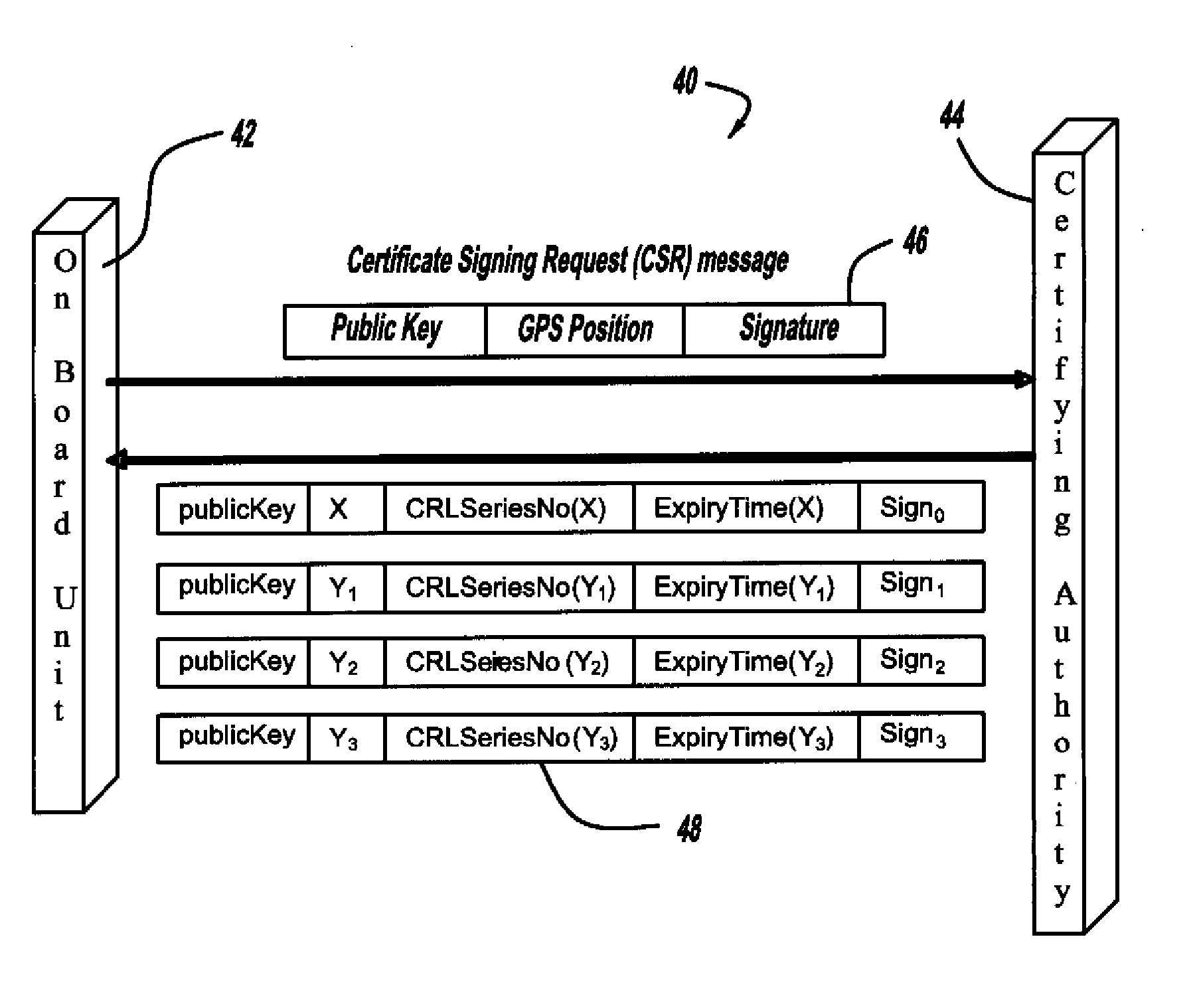
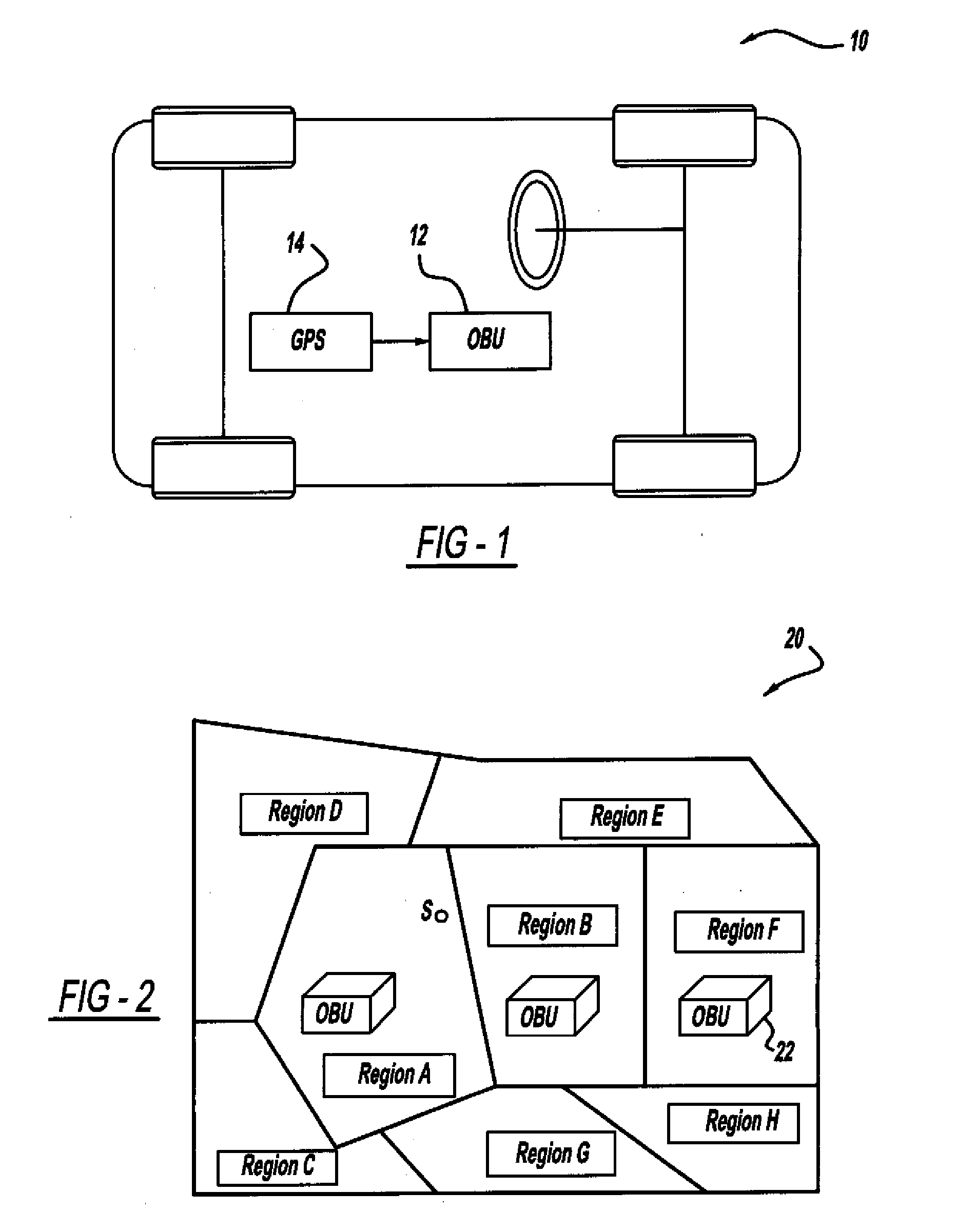
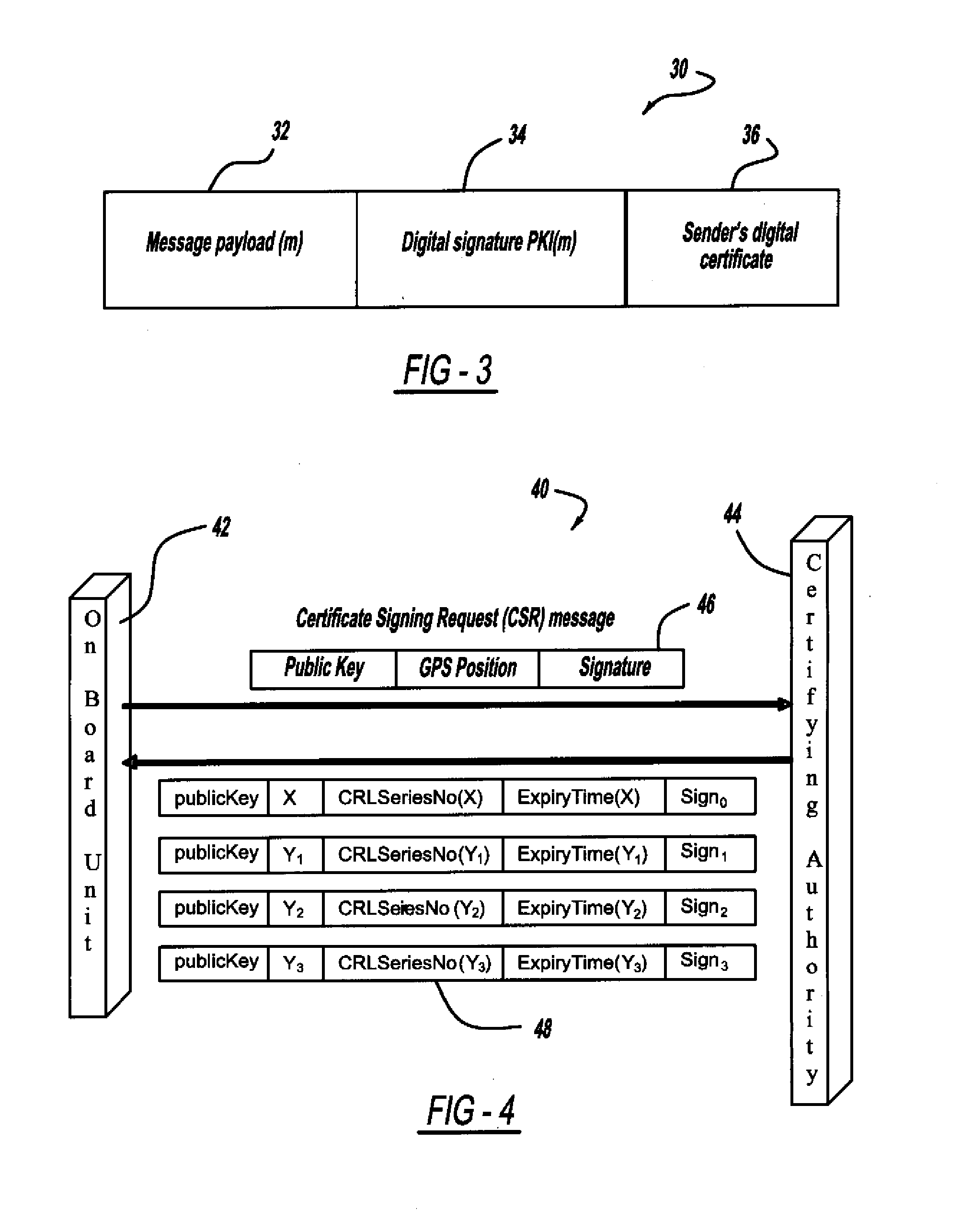
Certificate assignment strategies for efficient operation of the pki-based security architecture in a vehicular network
InactiveUS20090235071A1Small sizeReduce complexityTemperatue controlUser identity/authority verificationExpiration TimeCommunications system
A system and method for assigning certificates and reducing the size of the certificate revocation lists in a PKI based architecture for a vehicle wireless communications system that includes separating a country, or other area, into geographic regions and assigning region-specific certificates to the vehicles. Therefore, a vehicle need only process certificates and certificate revocation lists for the particular region that it is traveling in. Vehicles can be assigned multiple certificates corresponding to more than one region in the vehicles vicinity as advance preparation for possible travel or transmission into nearby regions. Further, the expiration time of certificates assigned to vehicles corresponding to a given geographic region can be tailored to be inversely proportional to the distance from a registered home region of the vehicle. A scalable design for a back-end certifying authority with region-based certificates can also be provided.
Owner:GM GLOBAL TECH OPERATIONS LLC
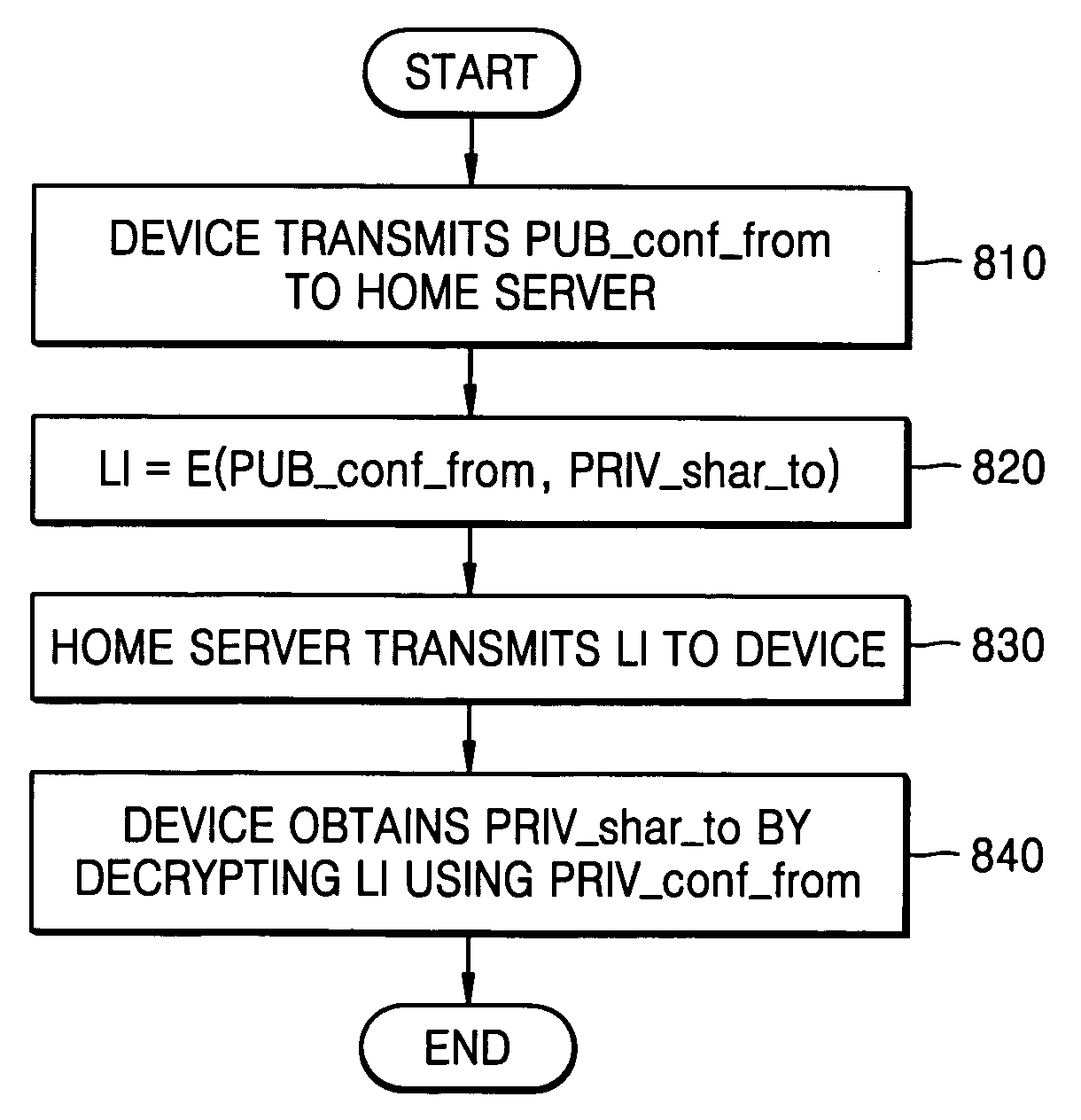
Key management method using hierarchical node topology, and method of registering and deregistering user using the same
InactiveUS20060177066A1Effectively and securely performingInstrument handpiecesTelevision systemsDigital rights management systemNetsniff-ng
A key management, user registration and deregistration for a digital rights management (DRM) system in a home network, using a hierarchical node topology. In the key management, node information is generated by allocating a pair of keys (a public key and a private key) to each node. A node tree is made by generating link information using the pair of keys and a content key. The link information is delivered from an upper node to a lower node using the node tree. The link information is obtained by encrypting a private key of a ‘TO’ node using a public key of a ‘FROM’ node. Accordingly, it is possible to realize a DRM system that protects content and easily accomplishes a binding mechanism and a revocation mechanism.
Owner:SAMSUNG ELECTRONICS CO LTD
Software conditional access system
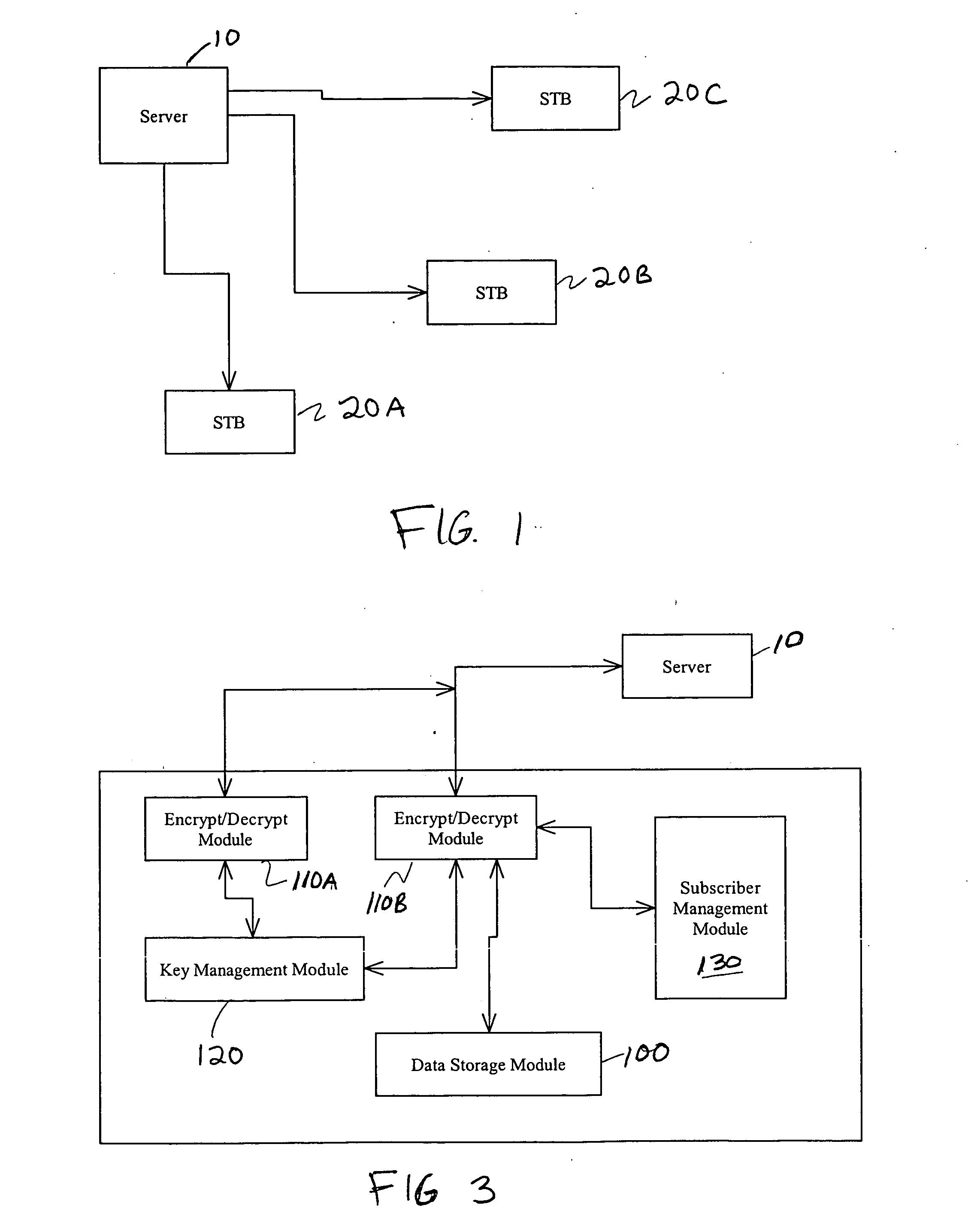
ActiveUS20050039025A1Prevent cheatingTelevision system detailsPulse modulation television signal transmissionRevocationService provider
Systems and methods which may be implemented as software to control access to content streams transmitted from a service provider's server. A software solution forces each set top box (STB) to periodically uplink to the server and to receive authentication from that server. To prevent spoofing, the server periodically loads to each STB at least one unique key that is required to access the content stream or that is required for authentication. The key or keys may be periodically revoked and / or replaced by the server. The frequency of the revocation and / or replacement of the key is ideally not fixed. Also, the server may periodically upgrade the decoding and / or authentication software on the STBs via the uplink.
Owner:IRDETO ACCESS +1
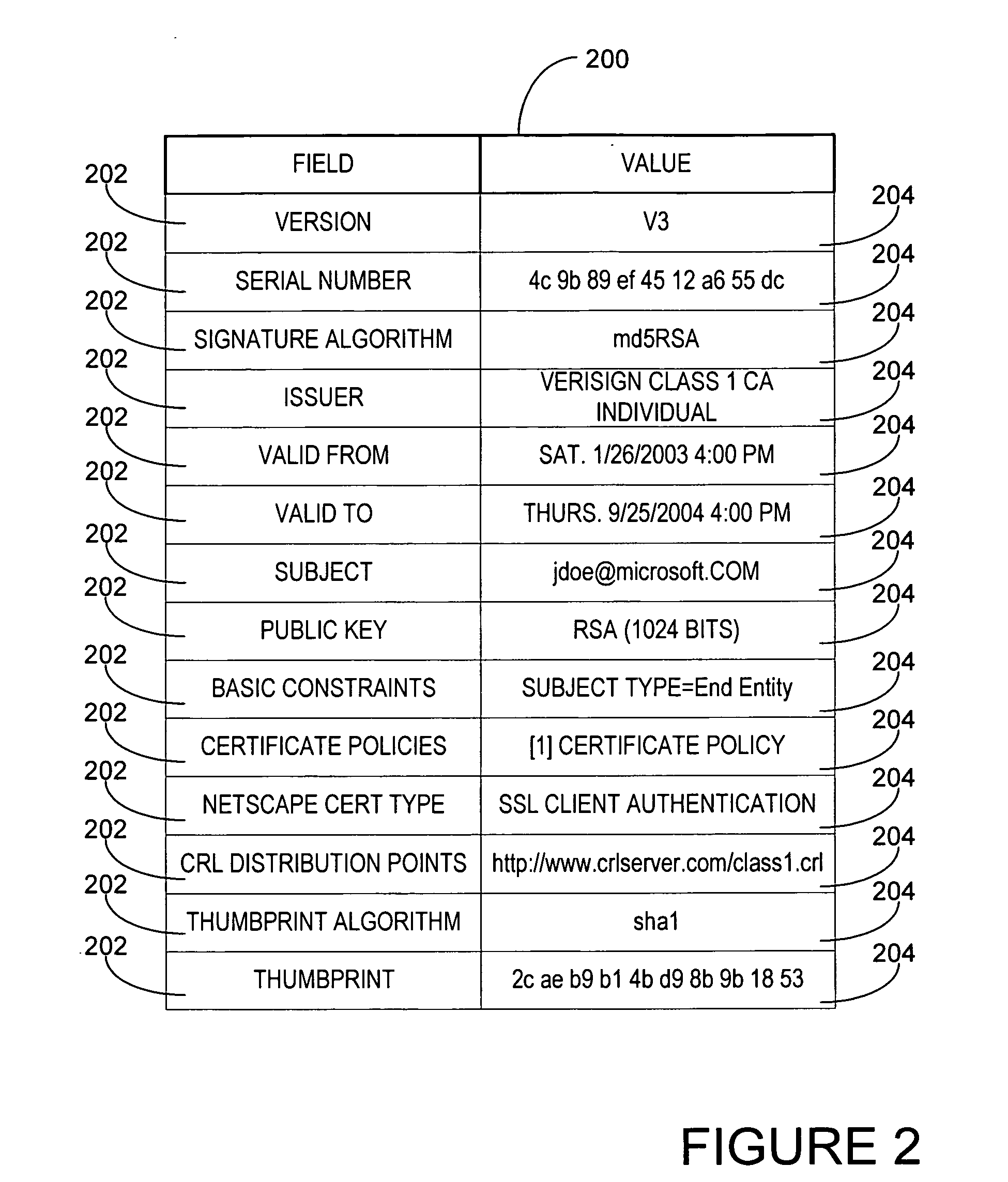
Method and apparatus for self-authenticating digital records
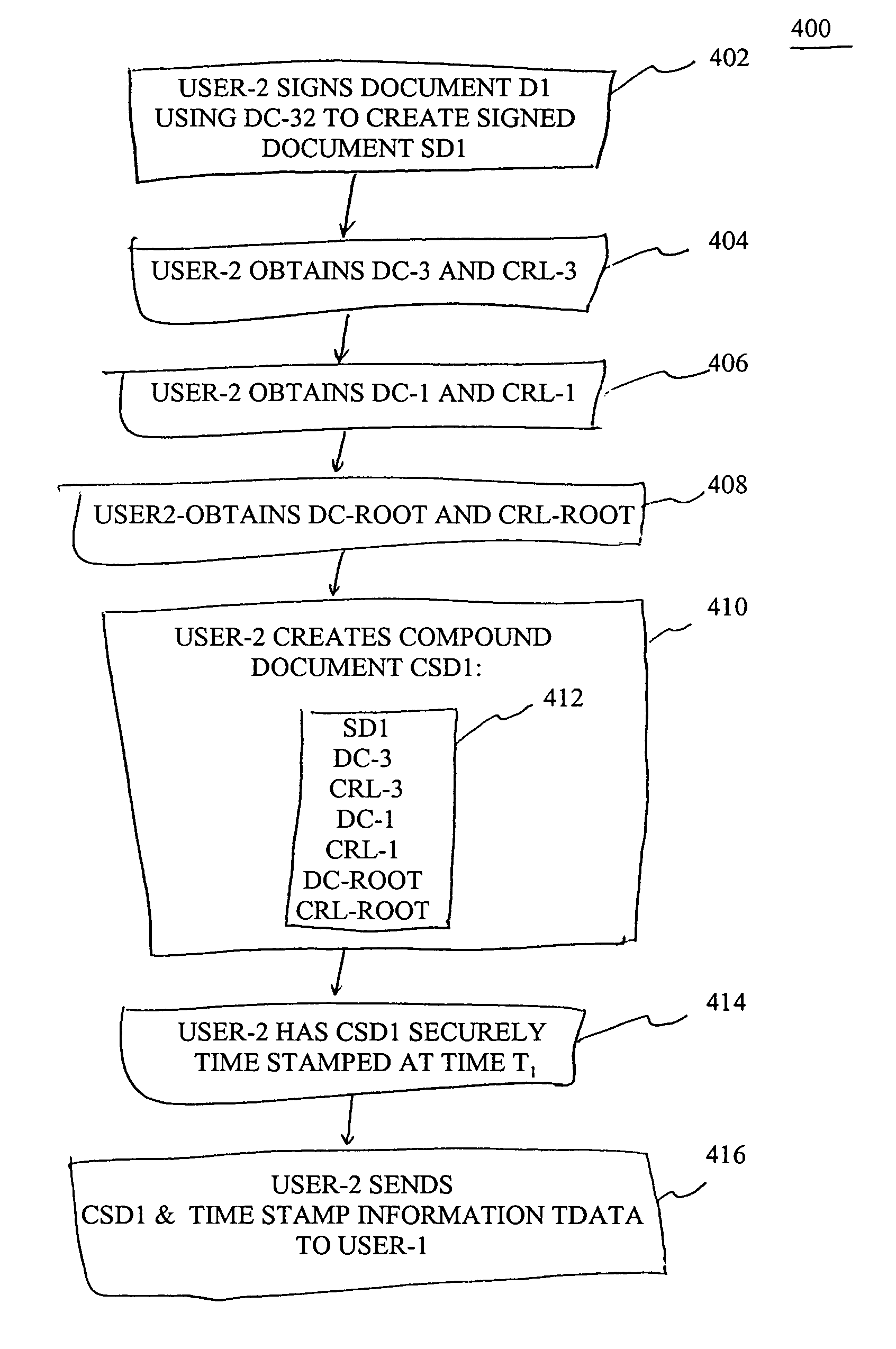
InactiveUS7047404B1Increase powerFinancePublic key for secure communicationTimestampDigital signature
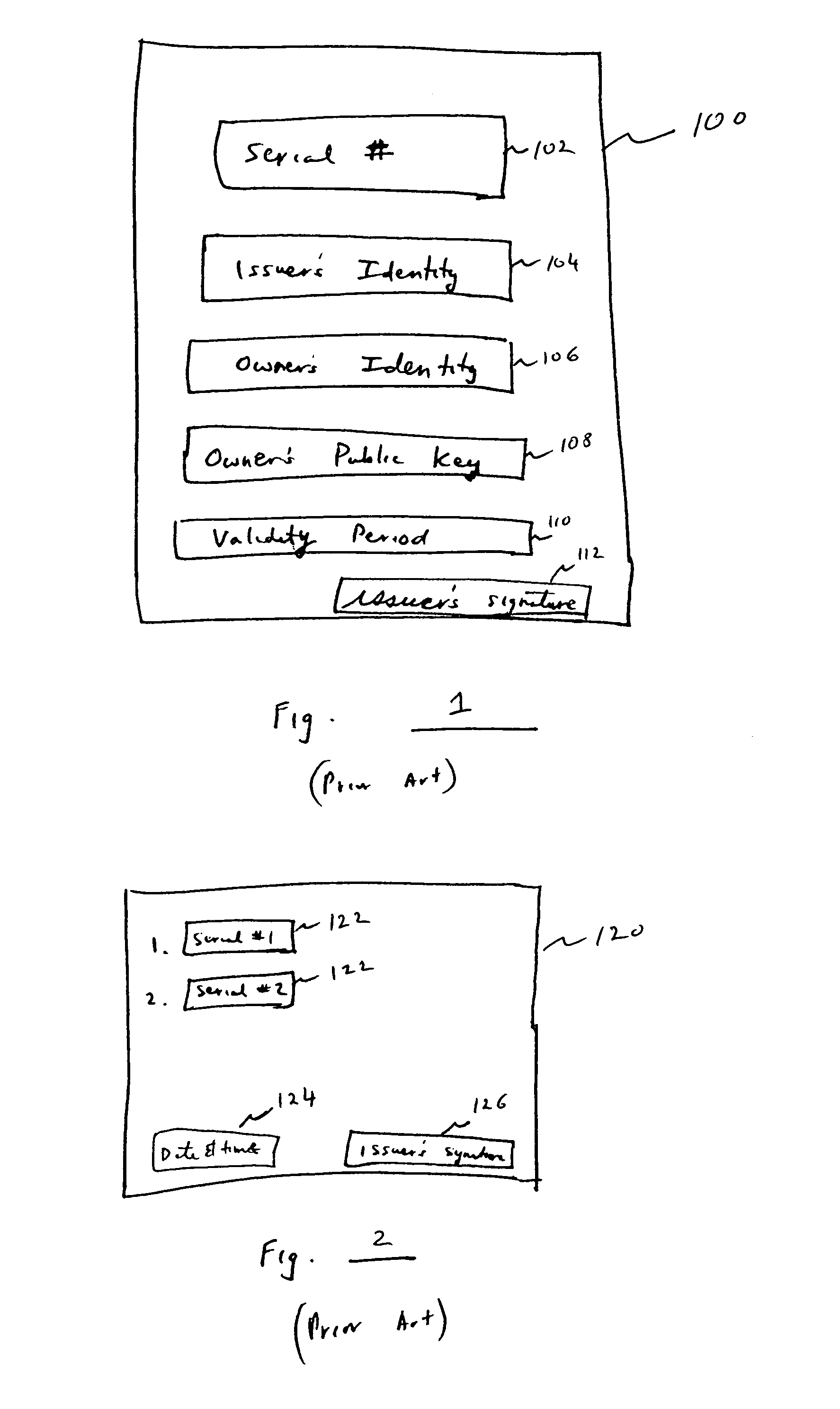
A method for proving the validity of a record digitally signed by a user having a digital certificate issued by a certification authority within a hierarchy of certification authorities. The user signs the record, and obtains the digital certificates and certificate revocation information for all the certification authorities in the chain of the hierarchy extending from the user to the root certification authority. A timestamp is applied to the record, the digital certificates and the certificate revocation information to establish a point in time in which all items were created, current and valid. If, at some later point, one or more of the digital certificates either expire or are revoked, the timestamp serves as evidence of the integrity of the signed record.
Owner:SURETY
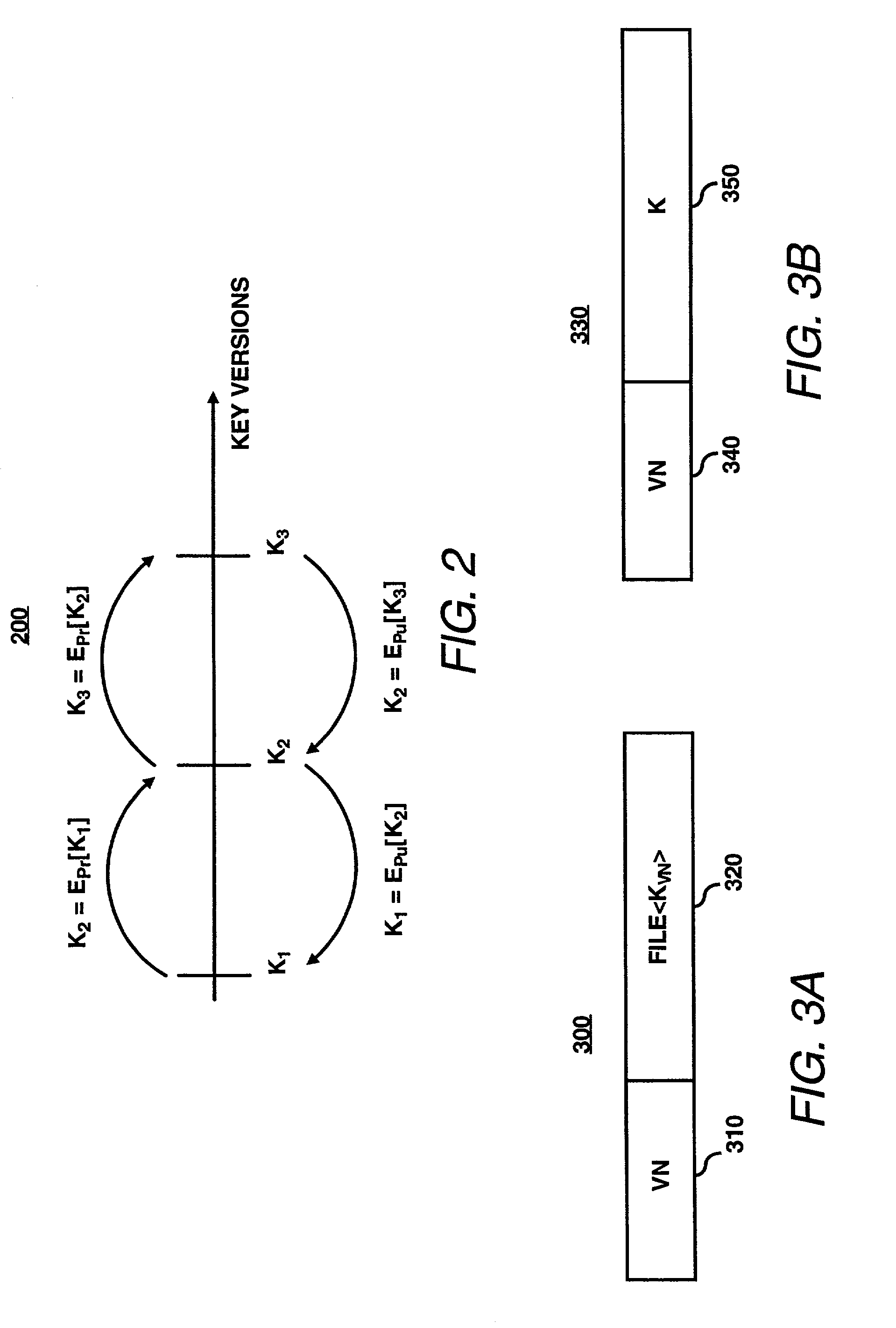
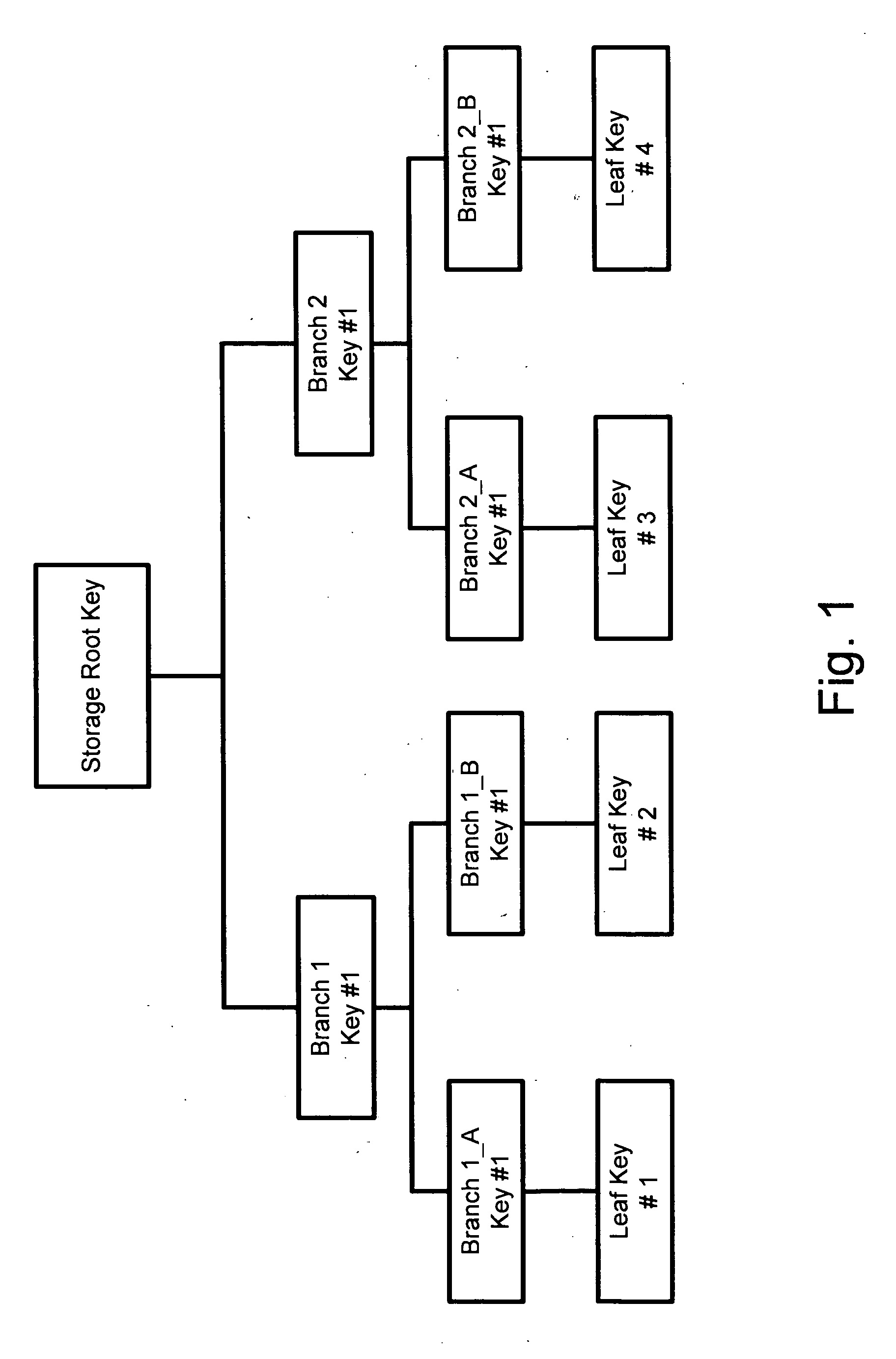
System for enabling lazy-revocation through recursive key generation
ActiveUS20030081787A1Key distribution for secure communicationComputer security arrangementsFile serverKey generation
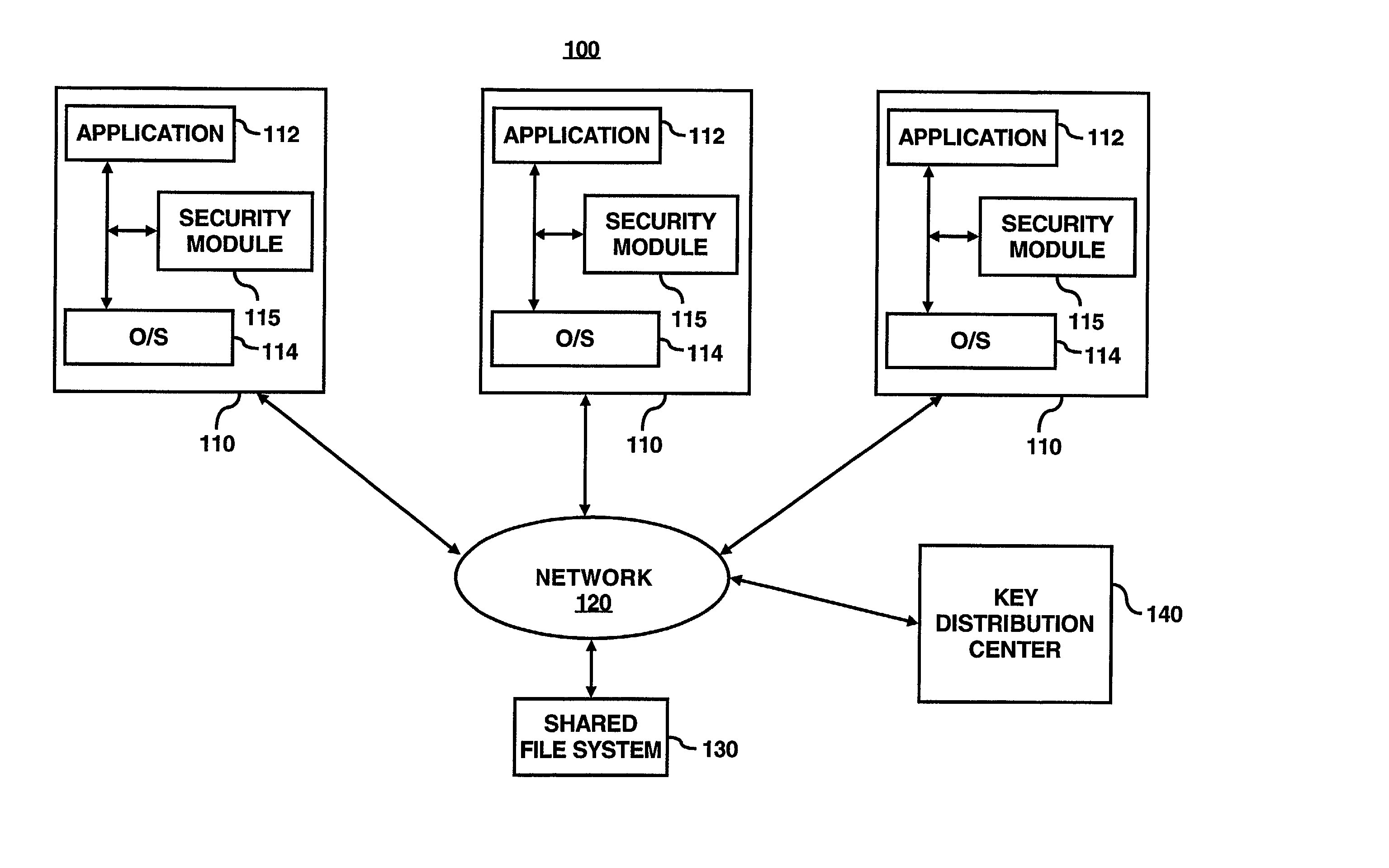
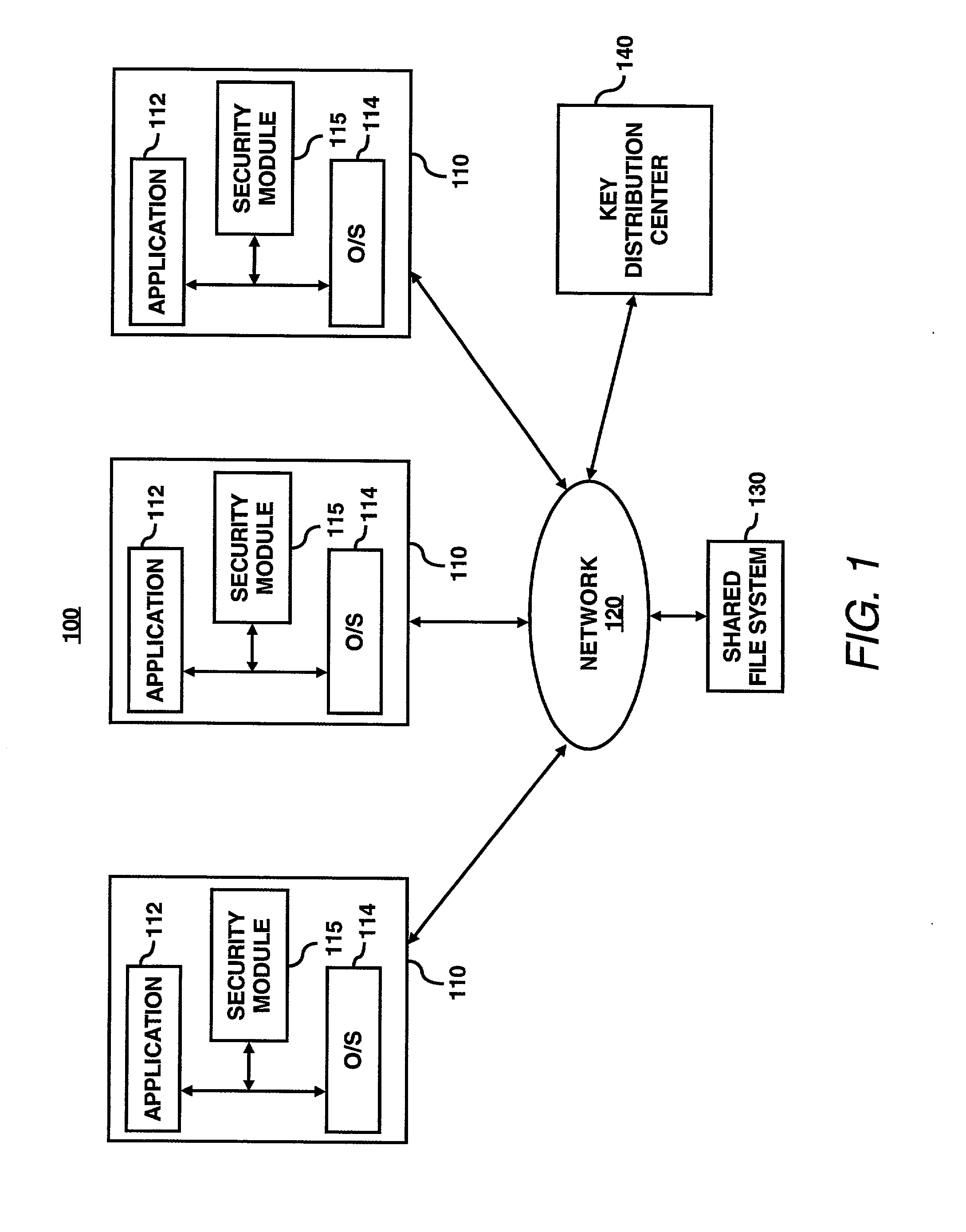
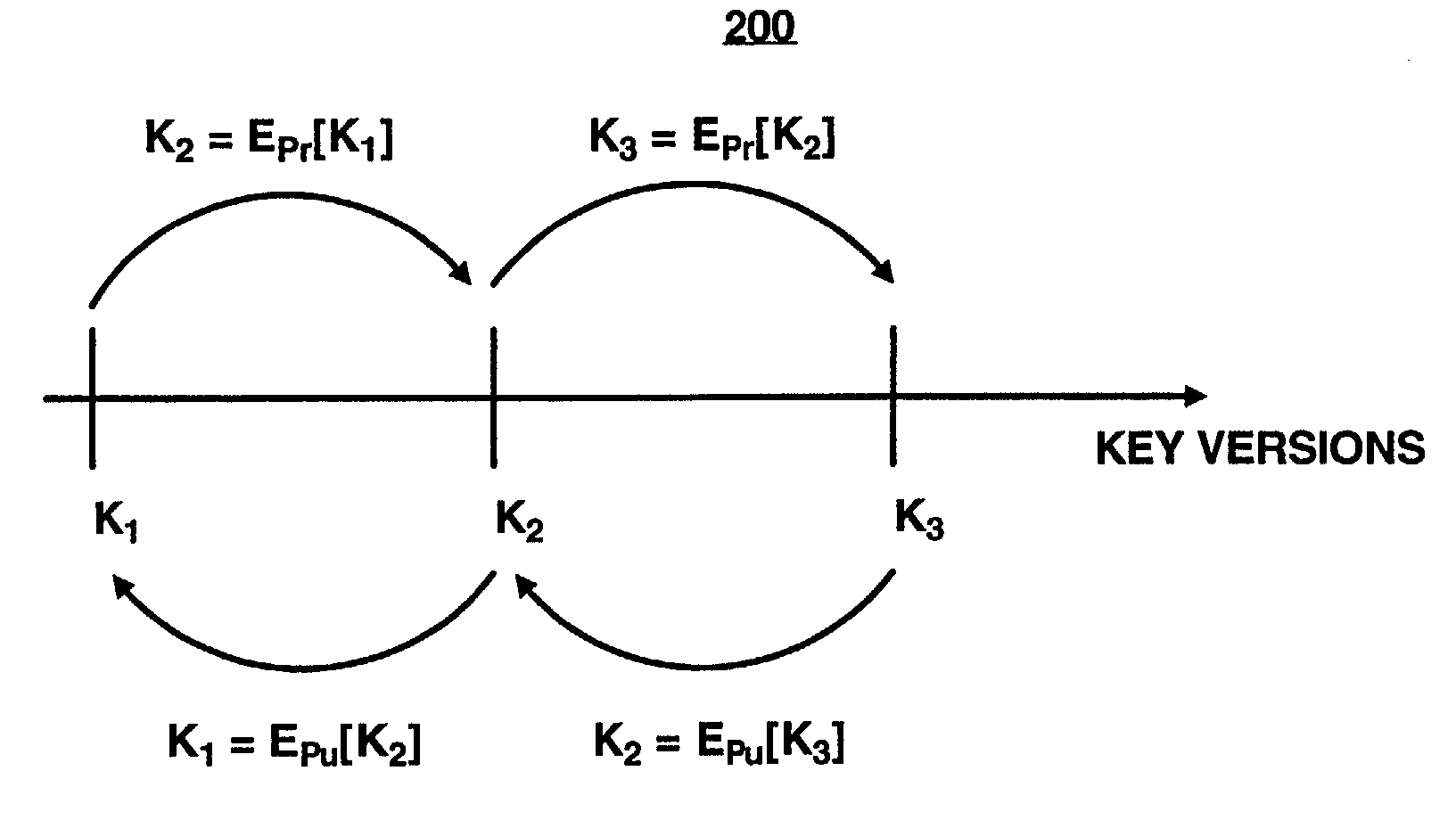
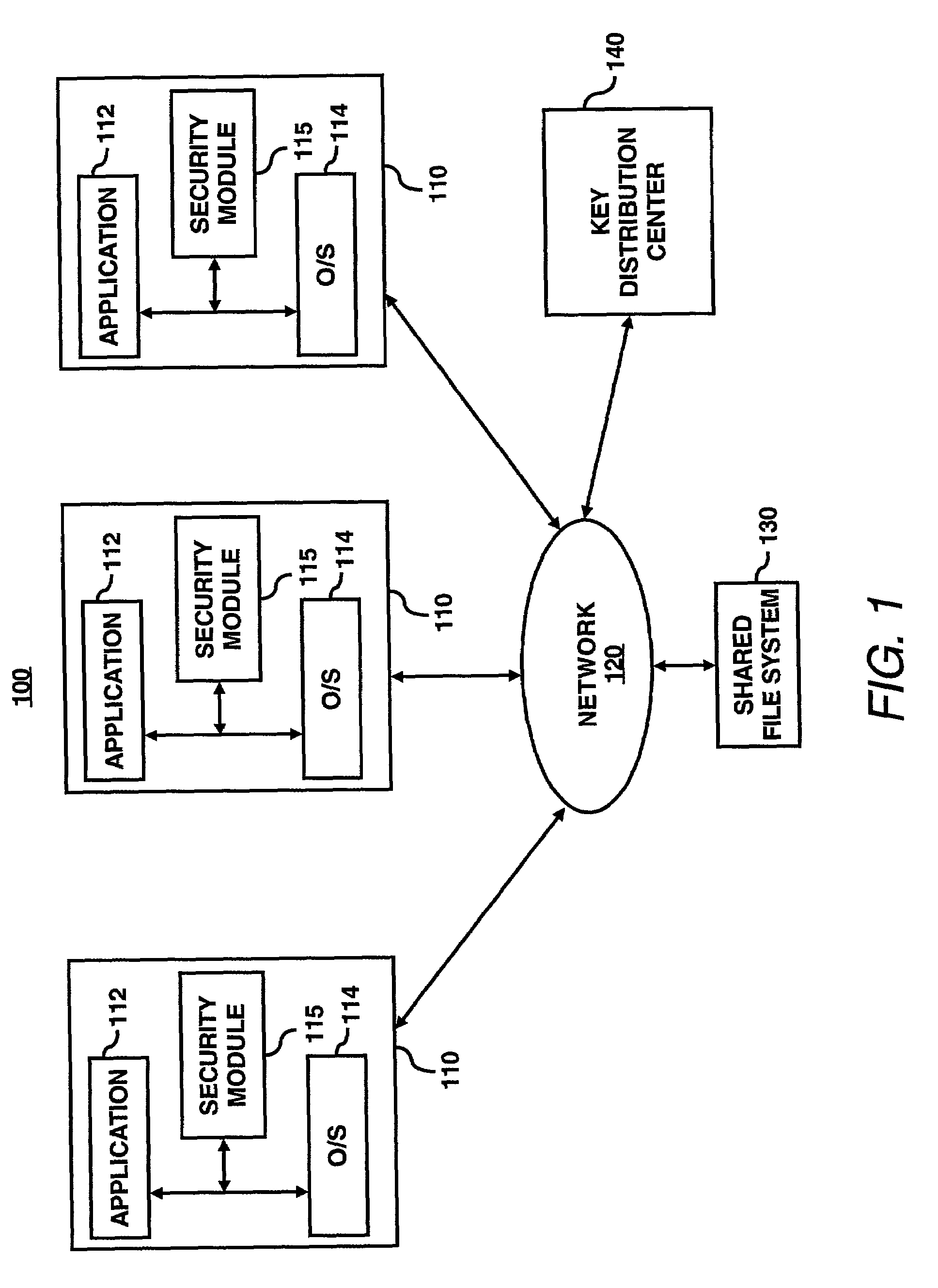
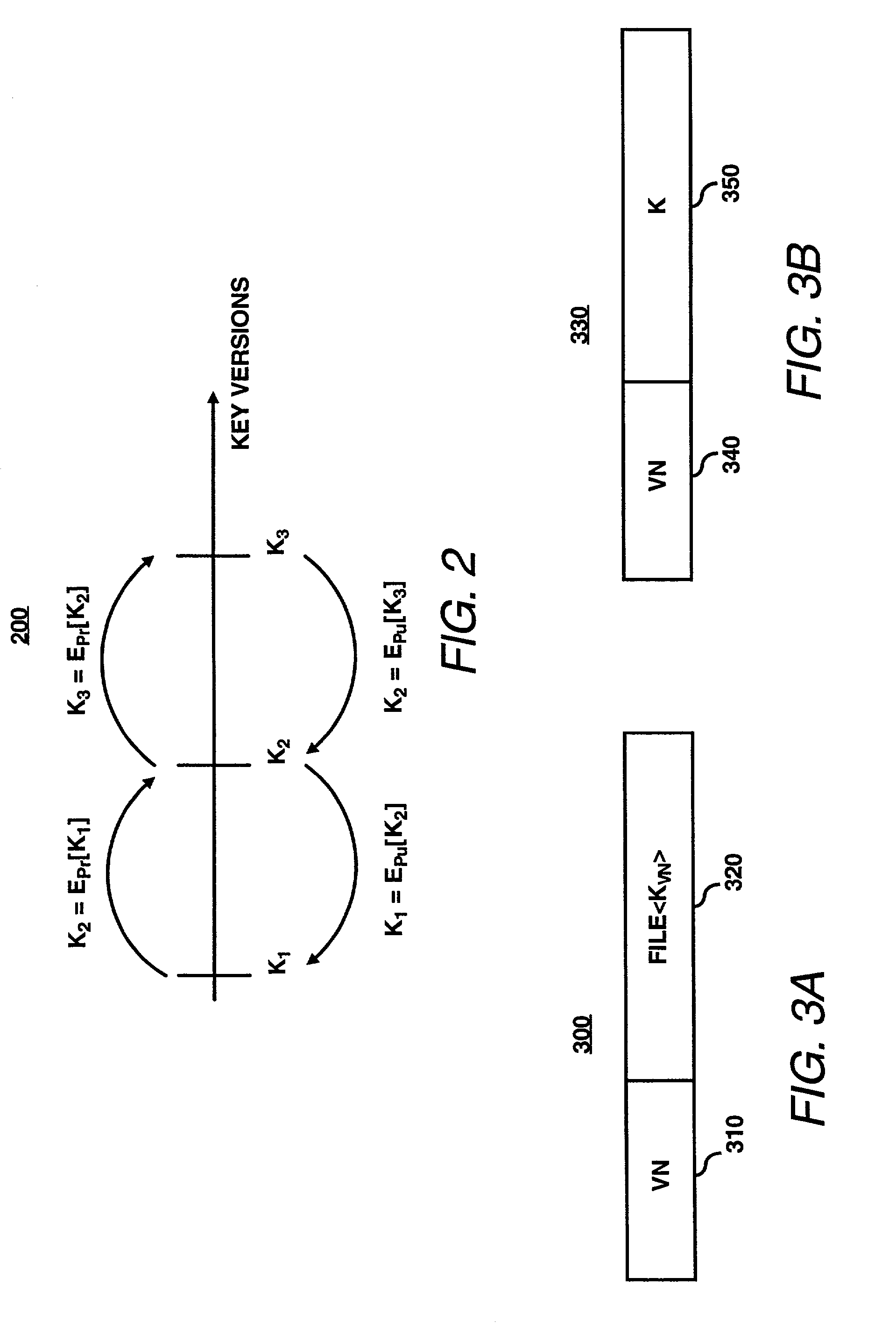
A security module is utilized to improve key management for encrypted files. In particular, multiple cryptographic keys may be used to encrypt multiple versions of a file, or to encrypt multiple separate files within a single encryption group for storage on an untrusted file server. An authorized user may require access to only a single cryptographic key to access the encrypted file or files. To revoke access of a user or to encrypt subsequent versions of a file, a file owner may utilize the security module to generate subsequent or new versions of the cryptographic key based on an asymmetric private key of the file owner. An authorized user may obtain a subsequent or new versions of the cryptographic key from the file owner or by other means. An authorized user may generate previous versions of the current cryptographic key based on an asymmetric public key of the file owner, without further contacting the owner. Accordingly, a single cryptographic key may be used to manage a group of files encrypted with the same key, or to manage multiple versions of a single file.
Owner:VALTRUS INNOVATIONS LTD +1
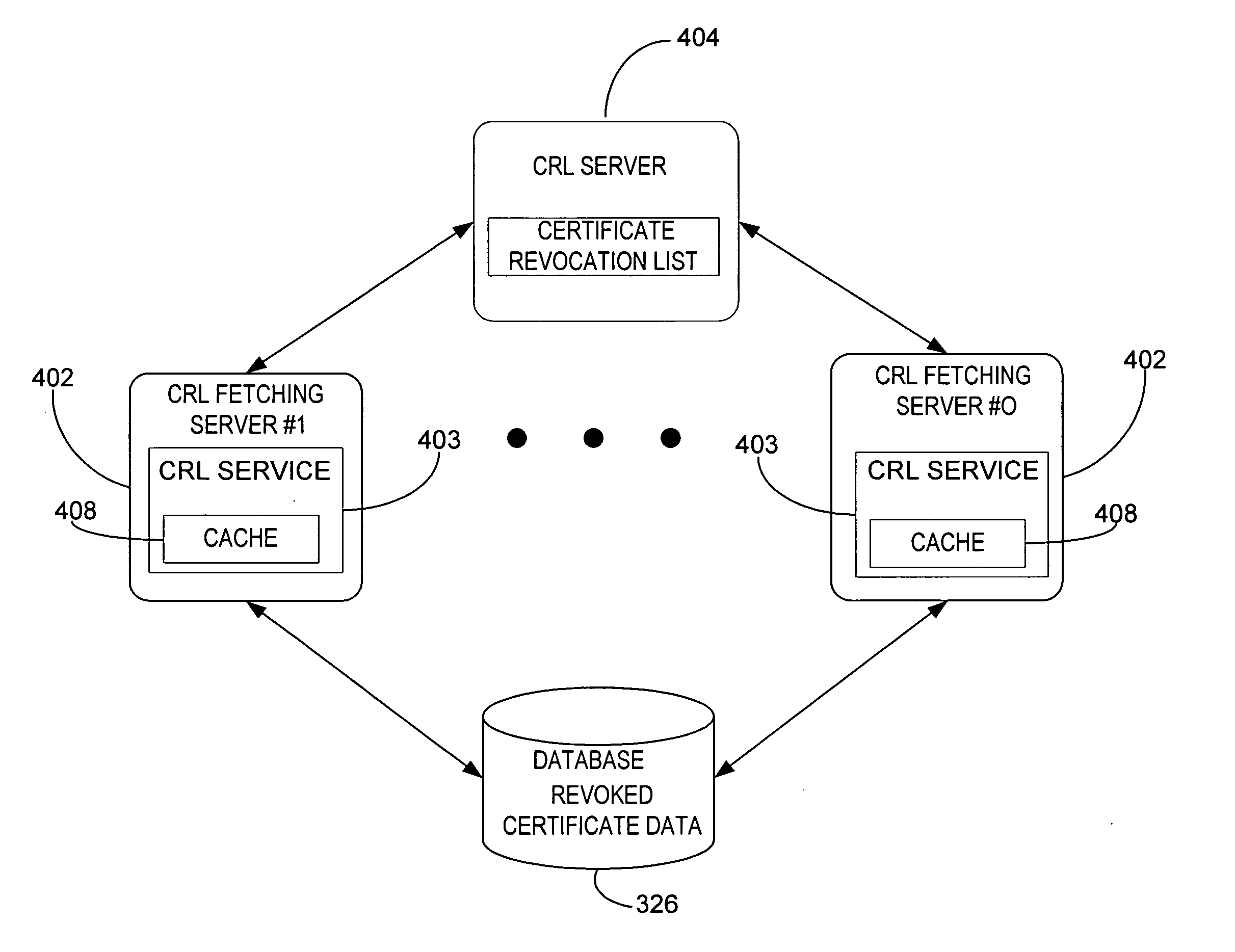
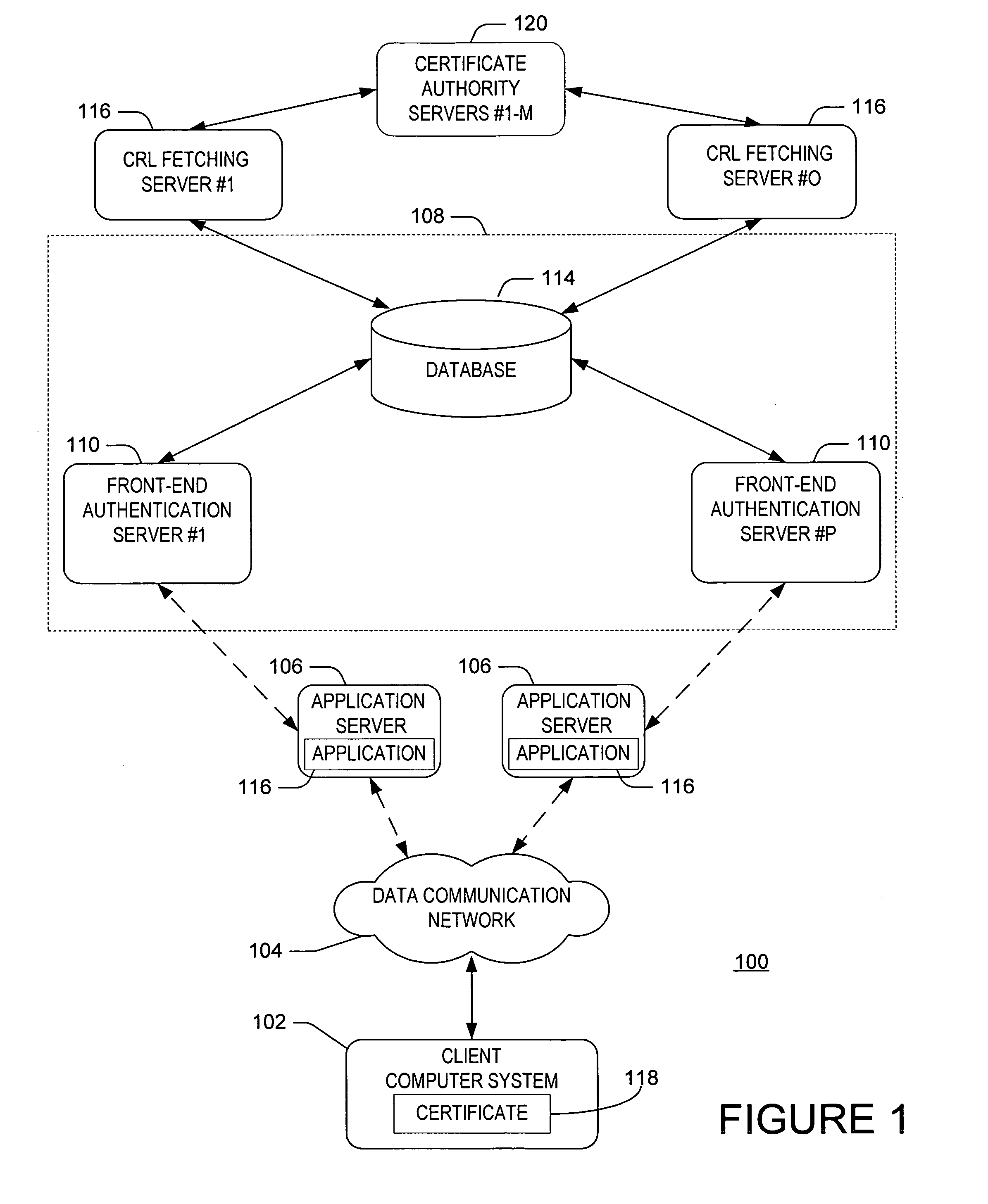
Public key infrastructure scalability certificate revocation status validation
InactiveUS20050228998A1Minimize network trafficReduce executionUser identity/authority verificationAuthentication serverCentral database
A system and method for retrieving certificate of trust information for a certificate validation process. Fetching servers periodically retrieve certificate revocation lists (CRLs) from servers maintained by various certificate issuers. The revoked certificate data included in the retrieved CRLs are stored in a central database. An authentication server receives a request from a client for access to a secure service and initiates a validation process. The authentication server retrieves revoked certificate data from the central database and compares the retrieved revoked certificate data to certificate of trust information received from the client along with the request. The authentication server denies access to the secure information if the certificate of trust information matches revoked certificate data from the central database, allows access if the certificate of trust information does not match revoked certificate data from the central database.
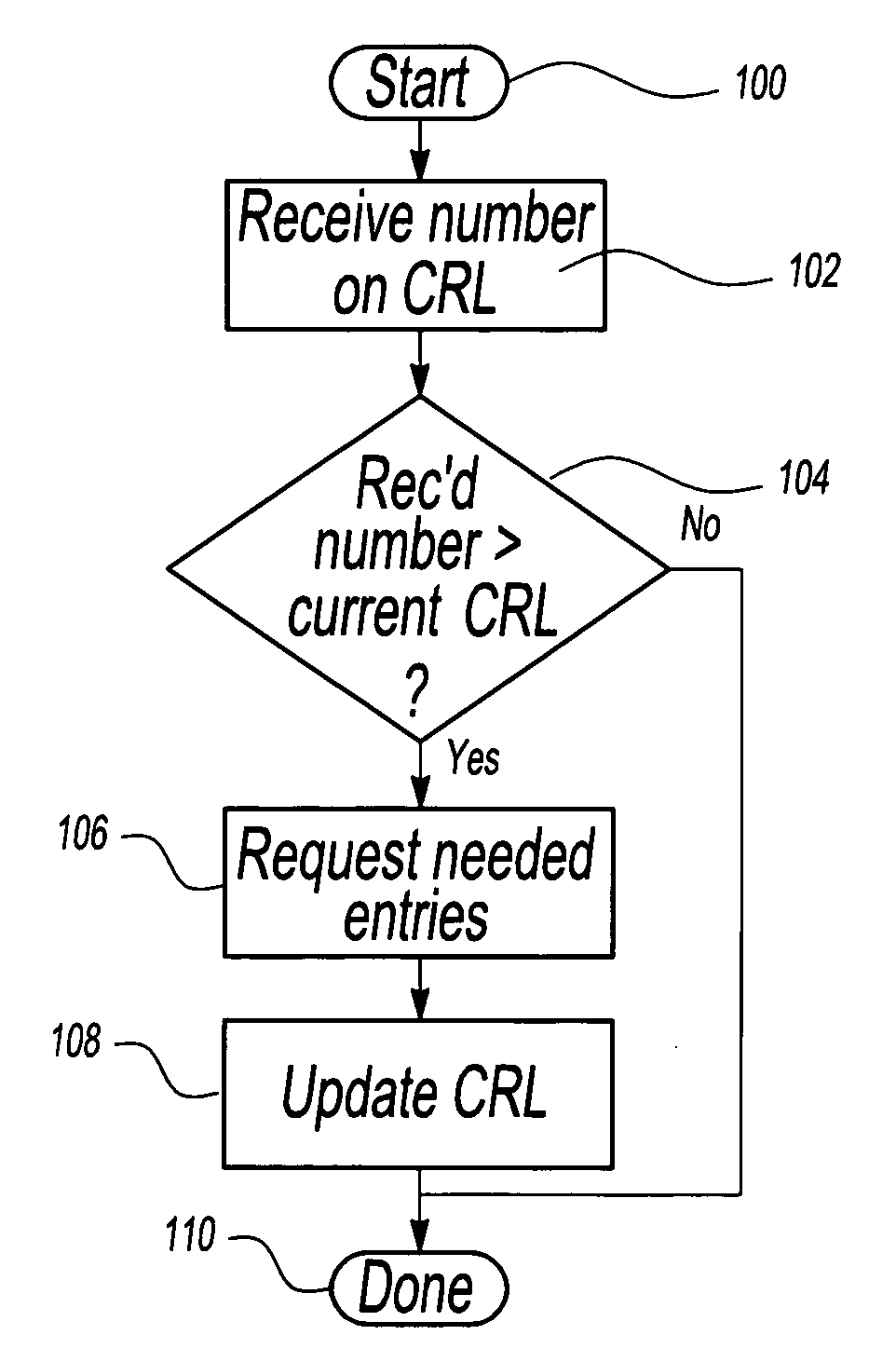
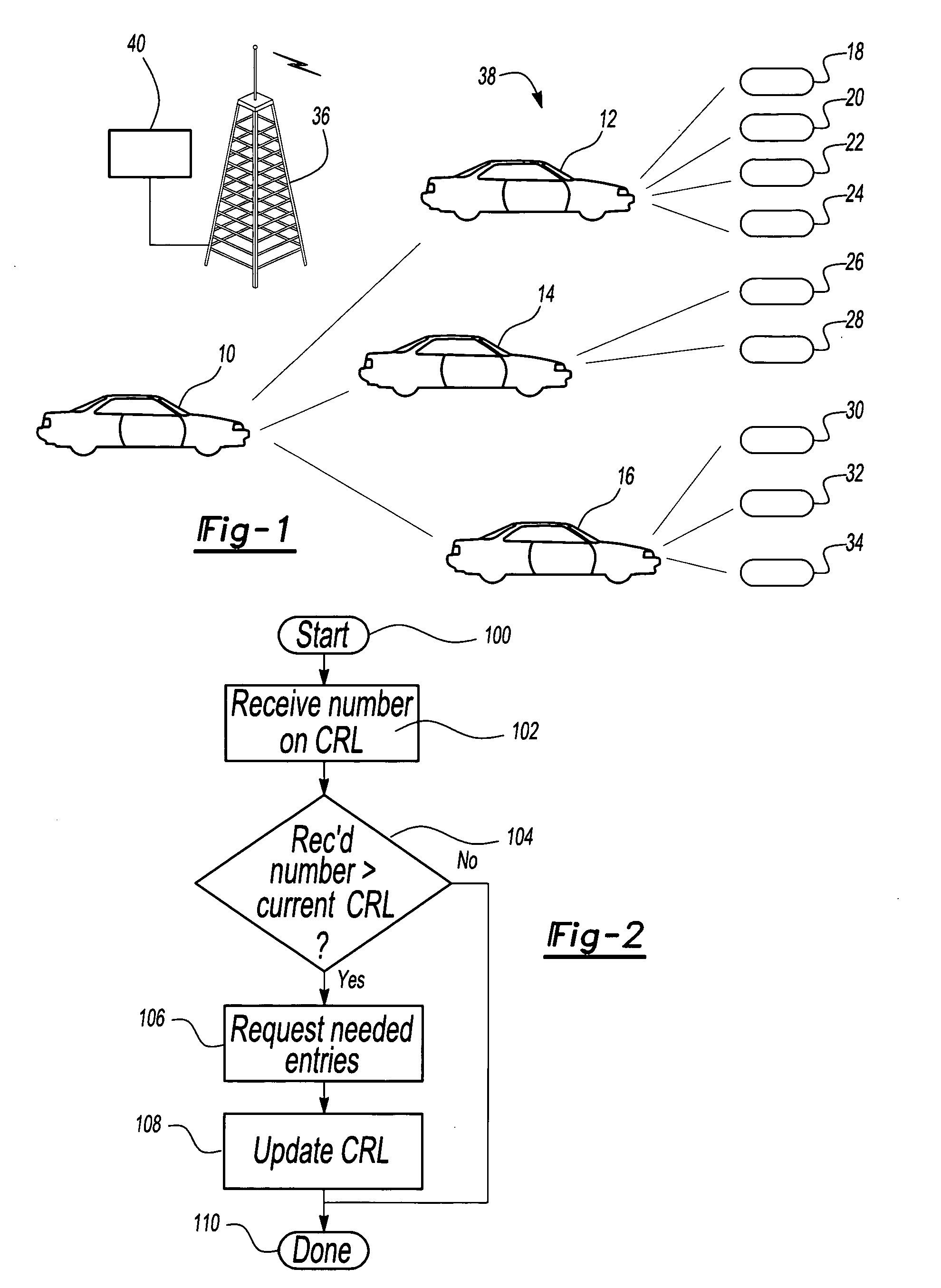
Owner:MICROSOFT TECH LICENSING LLC
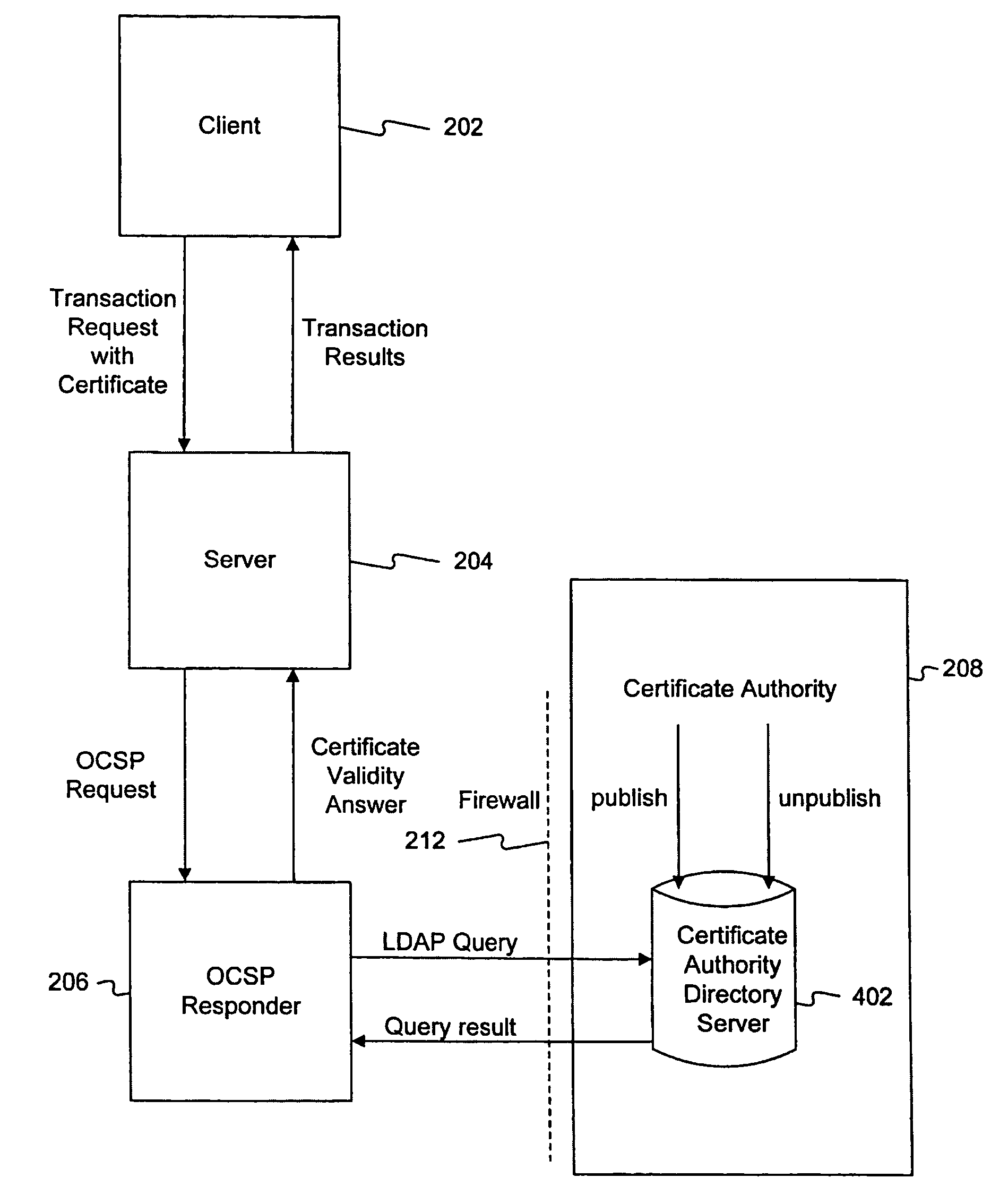
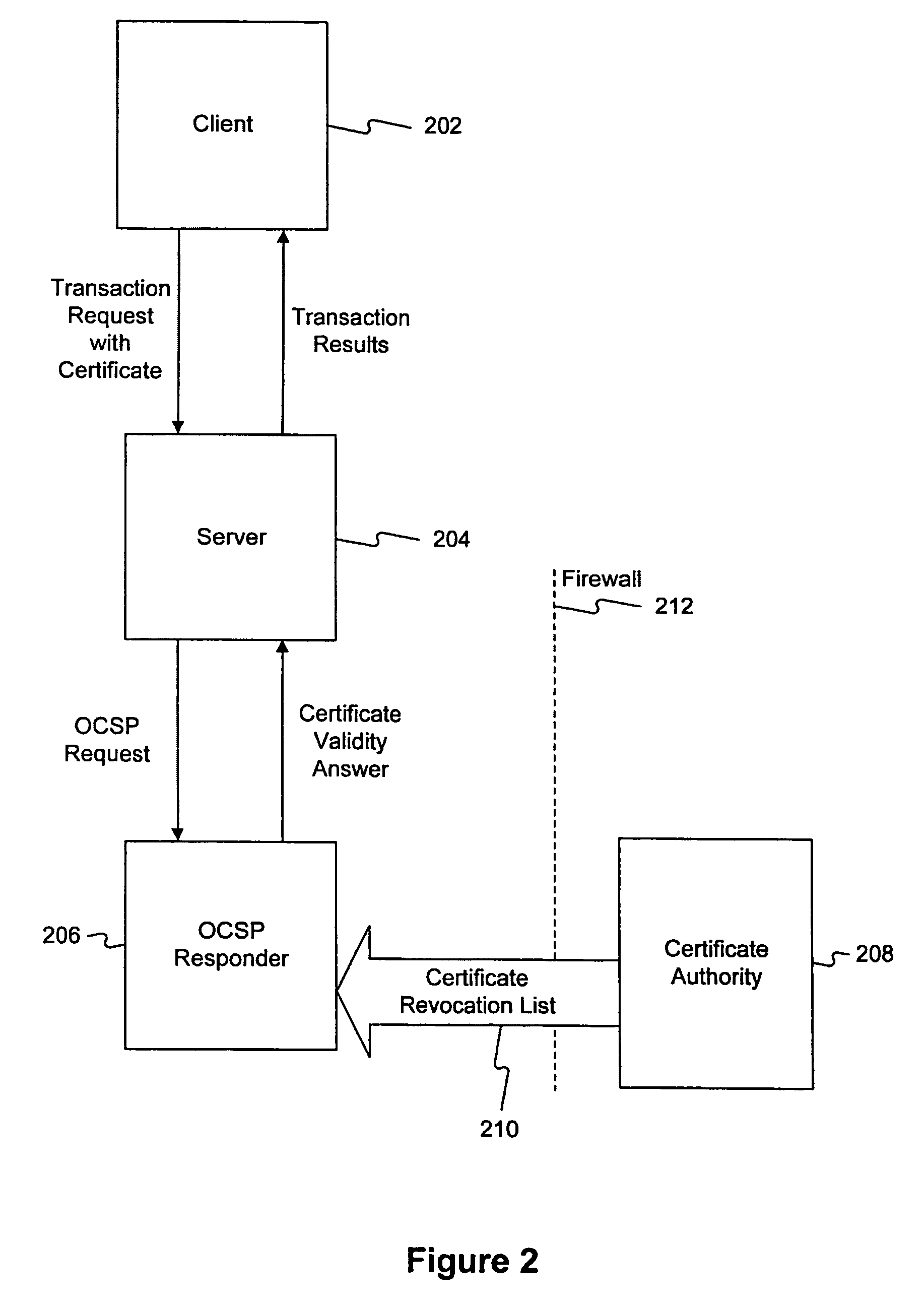
Method and system for answering online certificate status protocol (OCSP) requests without certificate revocation lists (CRL)
InactiveUS6970862B2Digital data protectionElectronic credentialsDirectory Access ProtocolClient-side
Methods and systems in accordance with the present invention efficiently validate digital certificates by answering Online Certificate Status Protocol (“OCSP”) requests without Certificate Revocation Lists (“CRL”). During validation of digital certificates, these methods and systems speed transmission, reduce required bandwidth and reduce required data storage by eliminating the need for the transmission of lengthy CRLs from a Certificate Authority (“CA”) when verifying a digital certificate from a client. In one implementation, they send a Lightweight Directory Access Protocol (“LDAP”) database query to a CA directory server to determine and pinpoint the existence of a valid digital certificate and check its validity without receiving a long list of data, such as a CRL, from a CA. The CA directory server returns the query result, and the database query in the CA directory server is performed faster than using an entire CRL, and furthermore, the transmission of the database query result is a small piece of information and does not require the large amounts of data transmission bandwidth and storage as required with transmitting CRL's.
Owner:ORACLE INT CORP
Multi-channel user authentication apparatus system and method
InactiveUS8151116B2Improve securityLess reliableMemory loss protectionDigital data processing detailsPasswordUser authentication
An apparatus, system, and method are disclosed for authenticating users through multiple communication channels. The authentication method of the present invention may be used to supplement password systems or replace password authentication, effectively enabling secure sharing, auditing, delegation, and revocation of authority.
Owner:BRIGHAM YOUNG UNIV
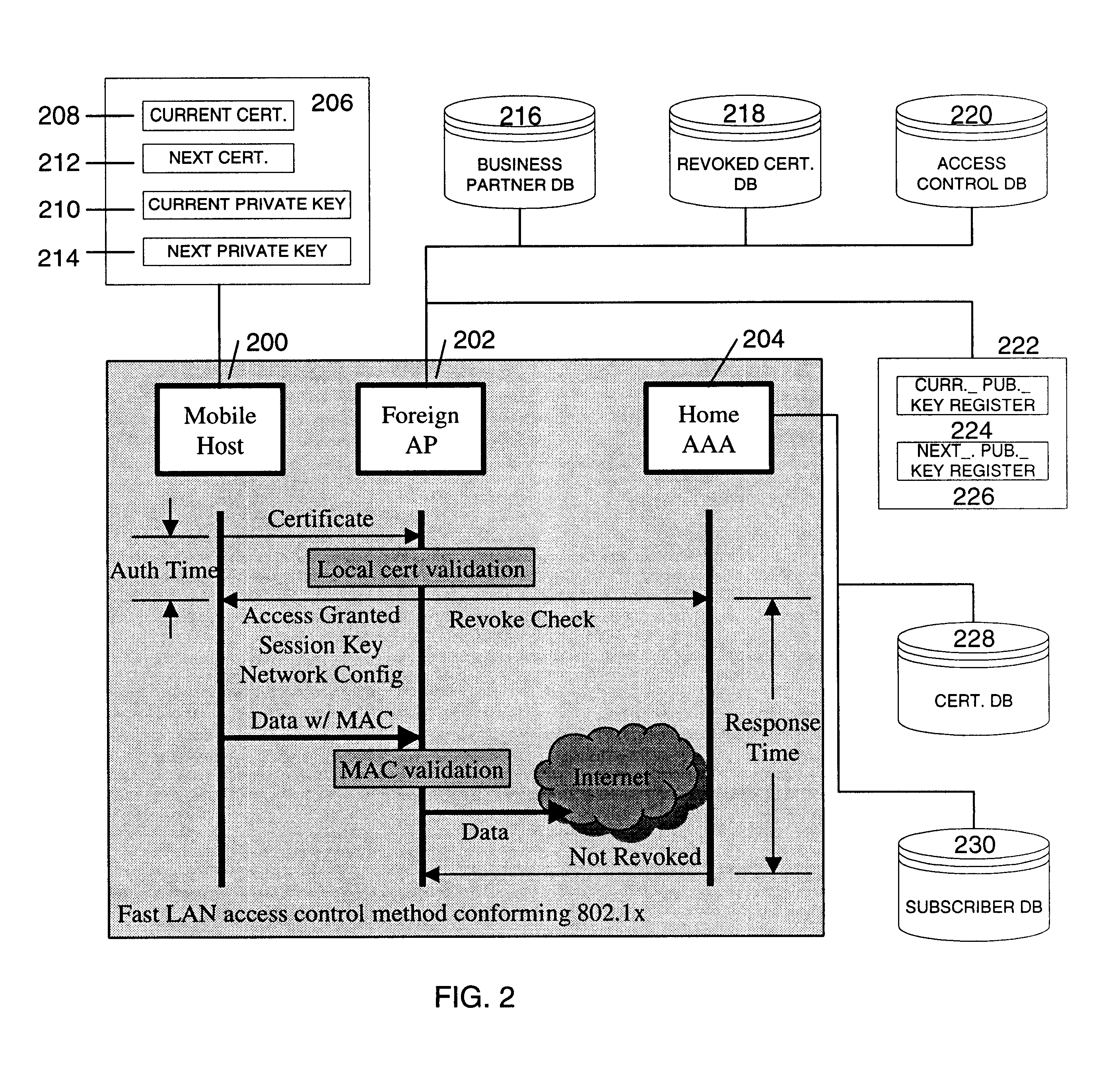
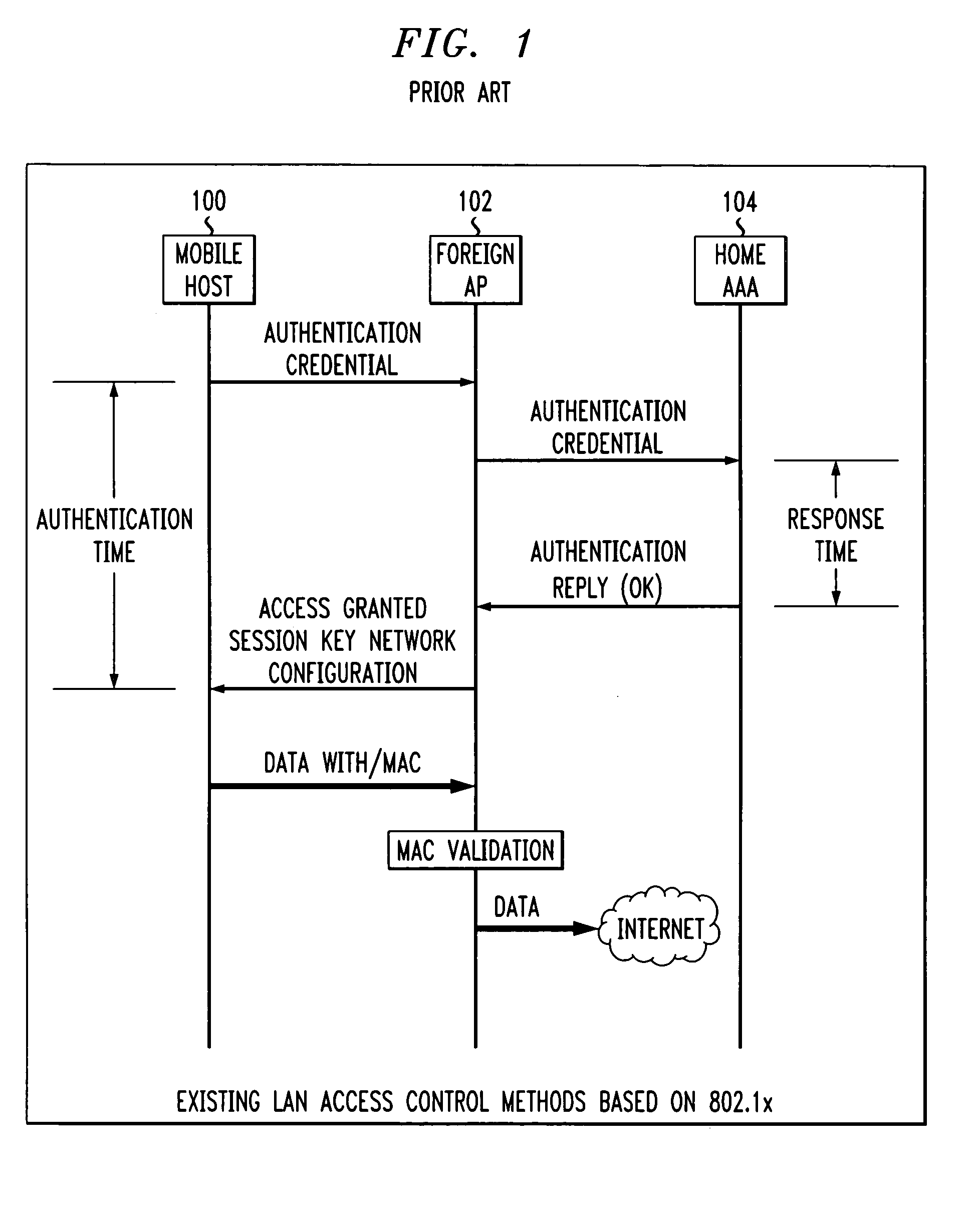
Fast authentication and access control method for mobile networking
InactiveUS7174456B1Easy to switchReduce certification timeDigital data processing detailsUser identity/authority verificationExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
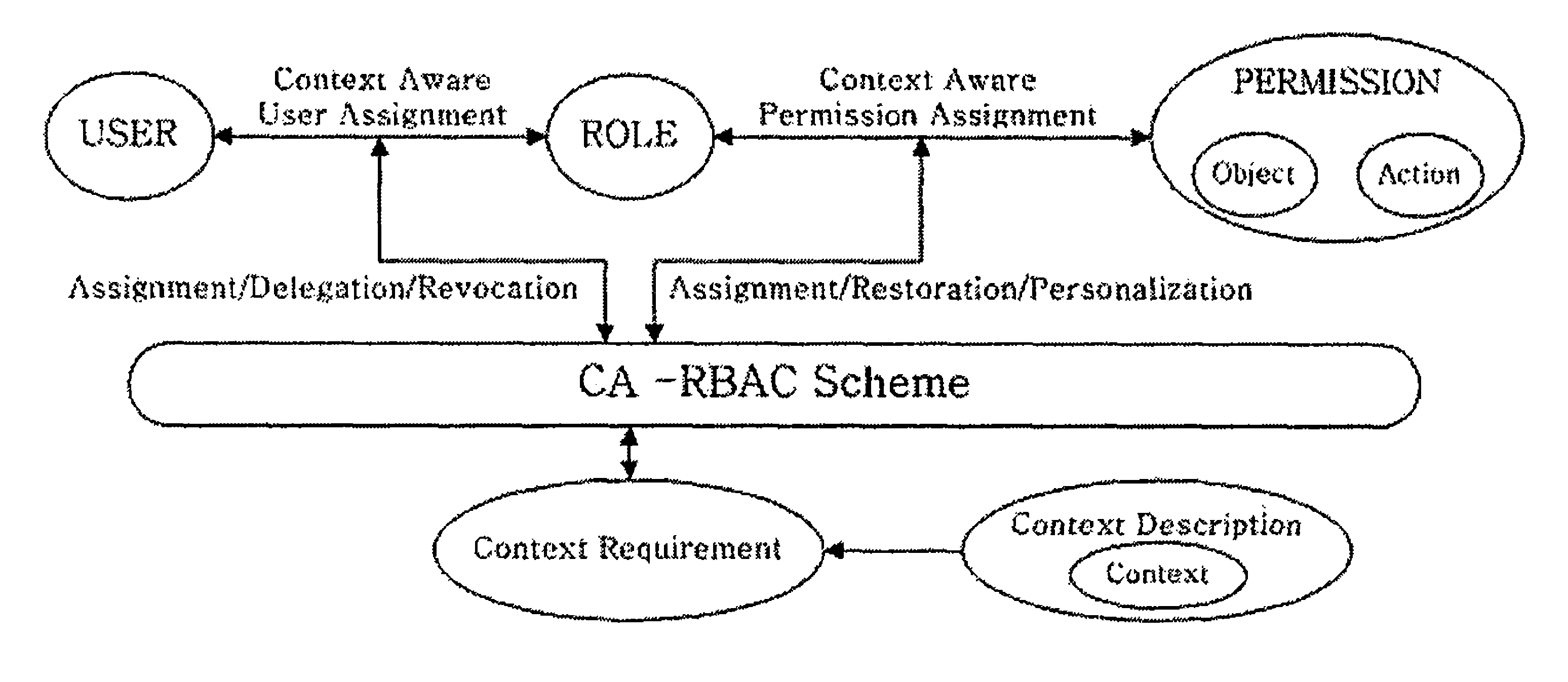
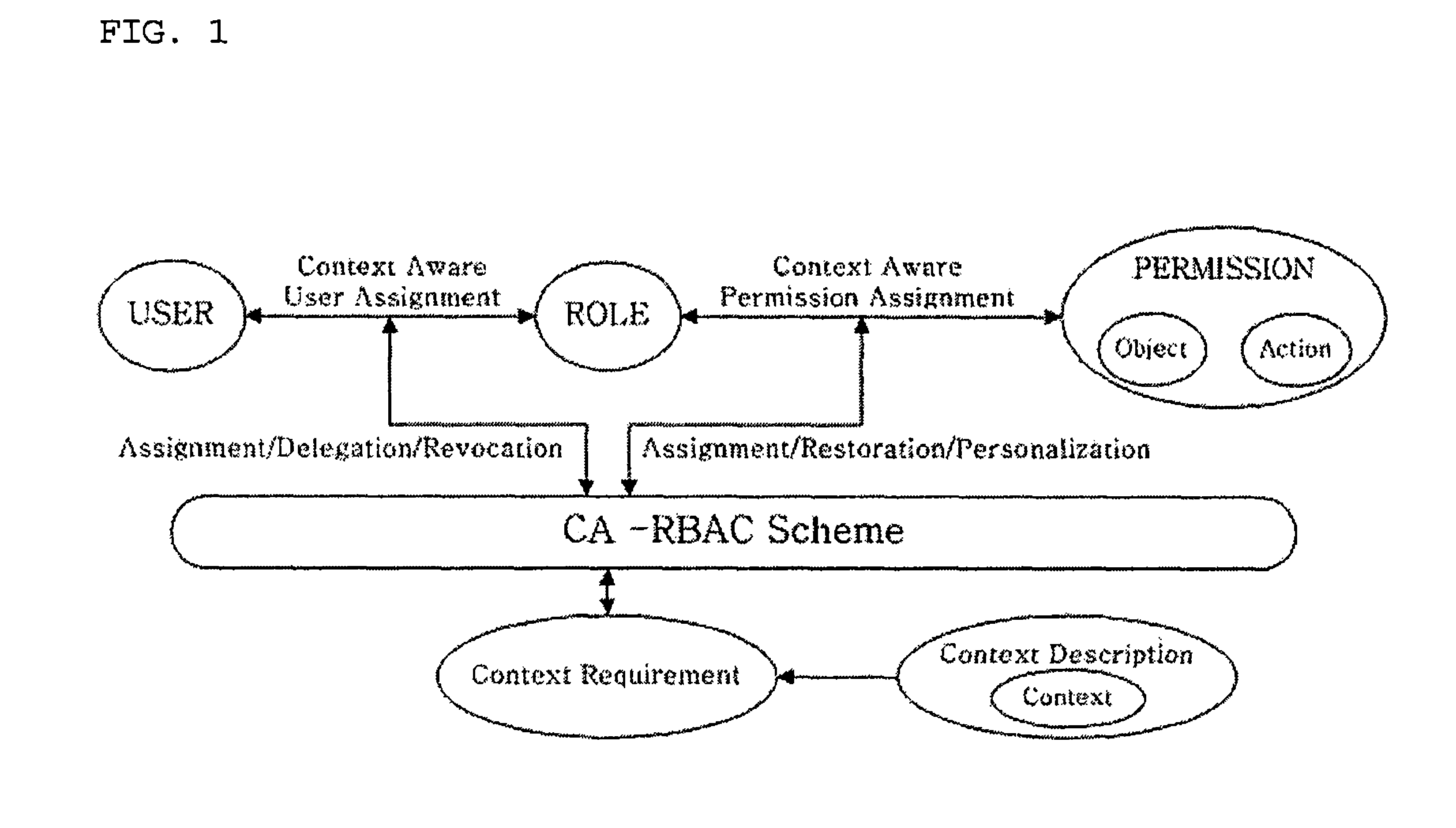
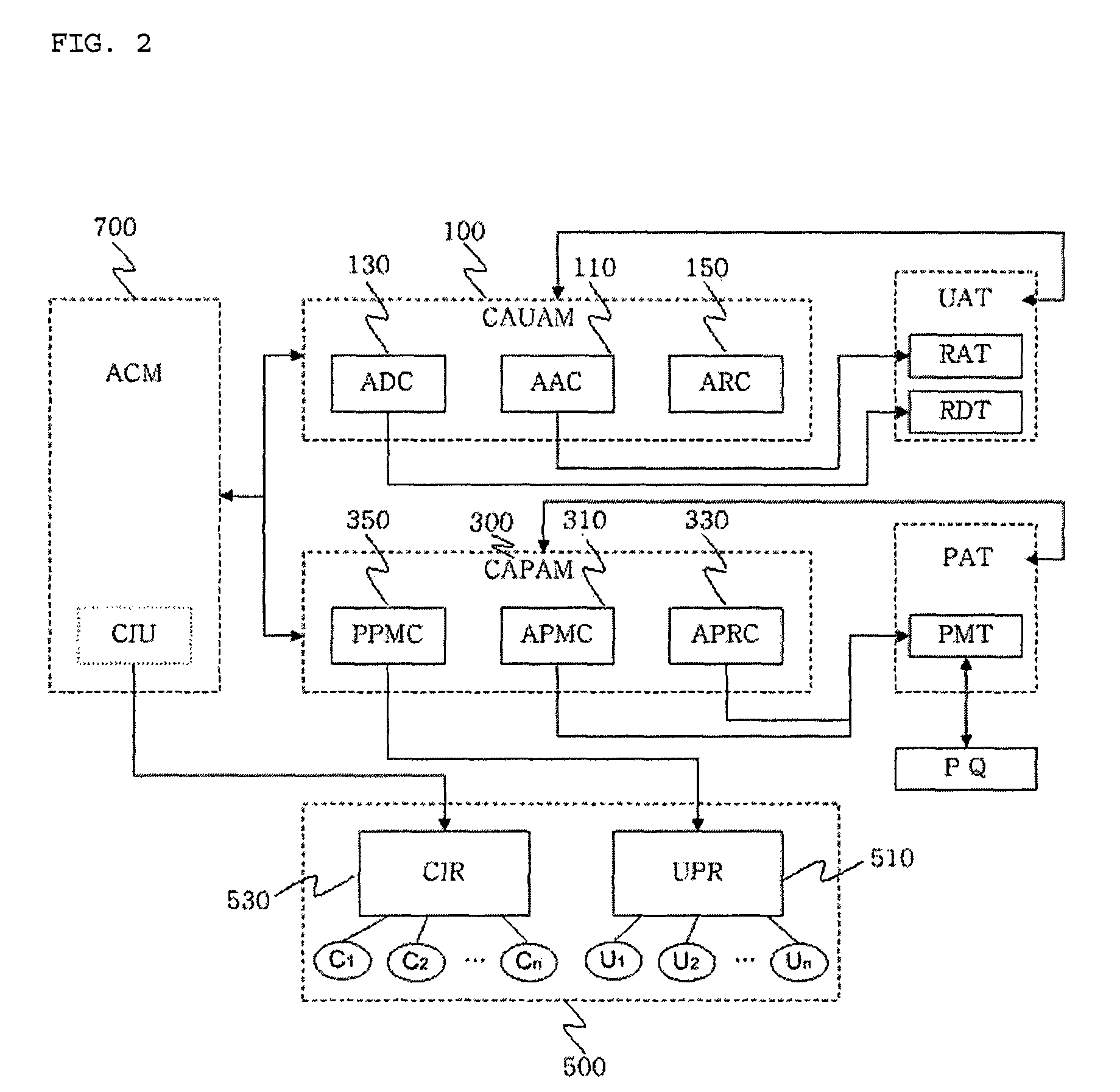
Context-aware role-based access control system and control method thereof
ActiveUS8387117B2Efficient expressionEffective controlDigital data processing detailsUser identity/authority verificationPersonalizationInformation repository
A context-aware role-based access control system and a control method thereof. The context-aware role-based access control system includes: a context-aware user assignment manager (CAUAM) for performing a role assignment function, a role delegation function, or a role revocation function for a user according to a context of the user, based on a preset context request condition; a context-aware permission assignment manager (CAPAM) for performing a permission modification, a permission restoration, and a personalized permission modification for a permission, which the role has, according to changes in the context of the user; an information repository for storing a user profile and context information; and an access control manager (ACM) for controlling the context-aware user assignment manager, the context-aware permission assignment manager, and the information repository, and processing an access control request. Accordingly, more efficient access control can be achieved in ubiquitous environments where the context of the user dynamically changes.
Owner:INTELLECTUAL DISCOVERY CO LTD
Method for distributing a list of certificate revocations in a vanet
ActiveUS20090260057A1Minimize bandwidthMinimize timeDigital data processing detailsParticular environment based servicesPrimary stationCommunications system
In a vehicle-to-vehicle wireless communication system utilizing certificates to verify trustworthiness of received communications, a method for distributing a list of certificate revocations to vehicles in the communication system. At least one main station transmits a list of certificate revocations to at least one vehicle and the vehicle thereafter transmits the list of certificate revocations to other vehicles in the communication network. Each of the other vehicles in the communication network updates its list of certificate revocations in response to the receipt of the list of certificate revocations from another vehicle in the system. The other vehicles thereafter transmit their updated list of certificate revocations to other vehicles in the system.
Owner:THE BOARD OF TRUSTEES OF THE UNIV OF ILLINOIS +1
Processing system using internal digital signatures
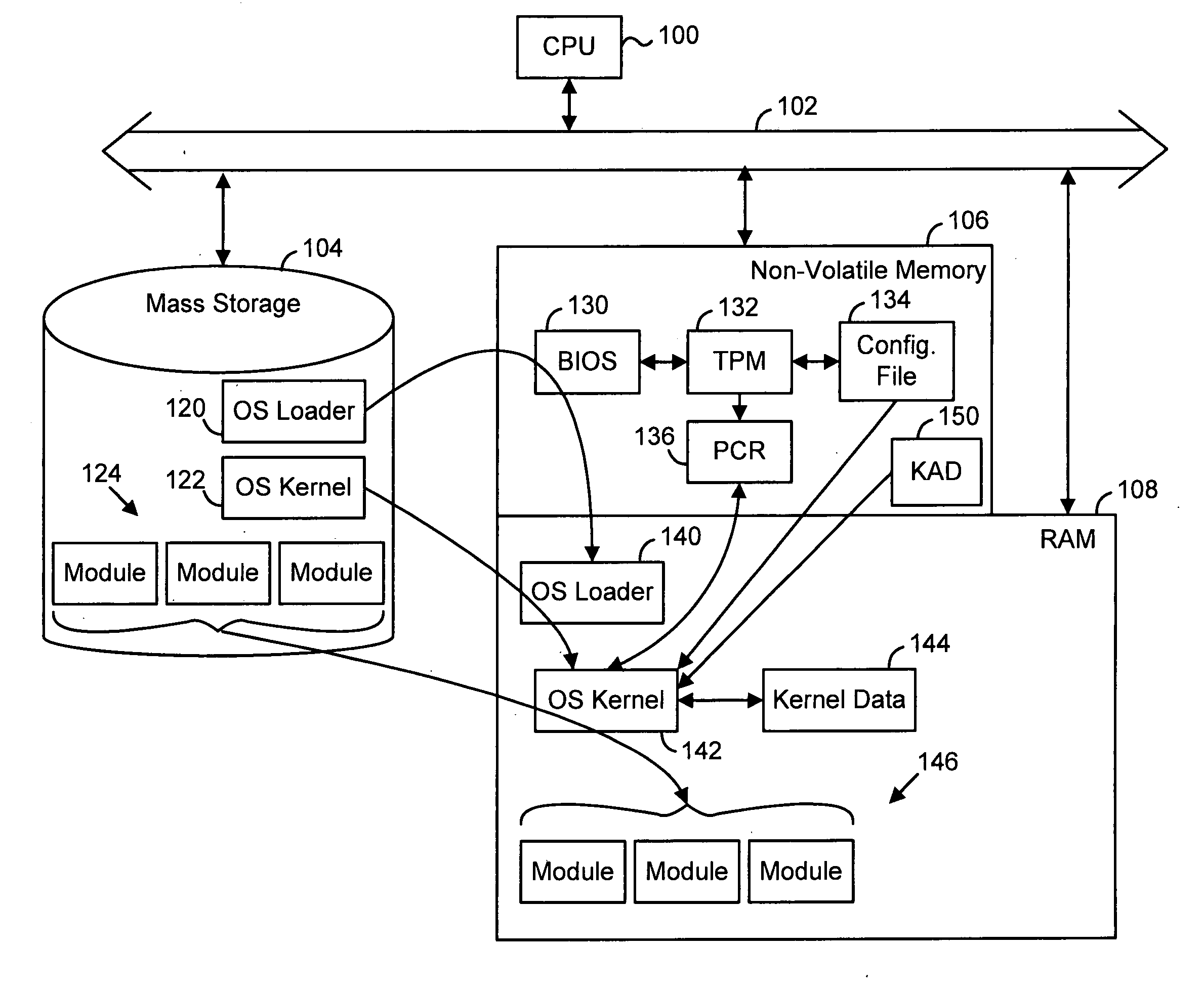
InactiveUS20060015732A1User identity/authority verificationUnauthorized memory use protectionDigital signatureHandling system
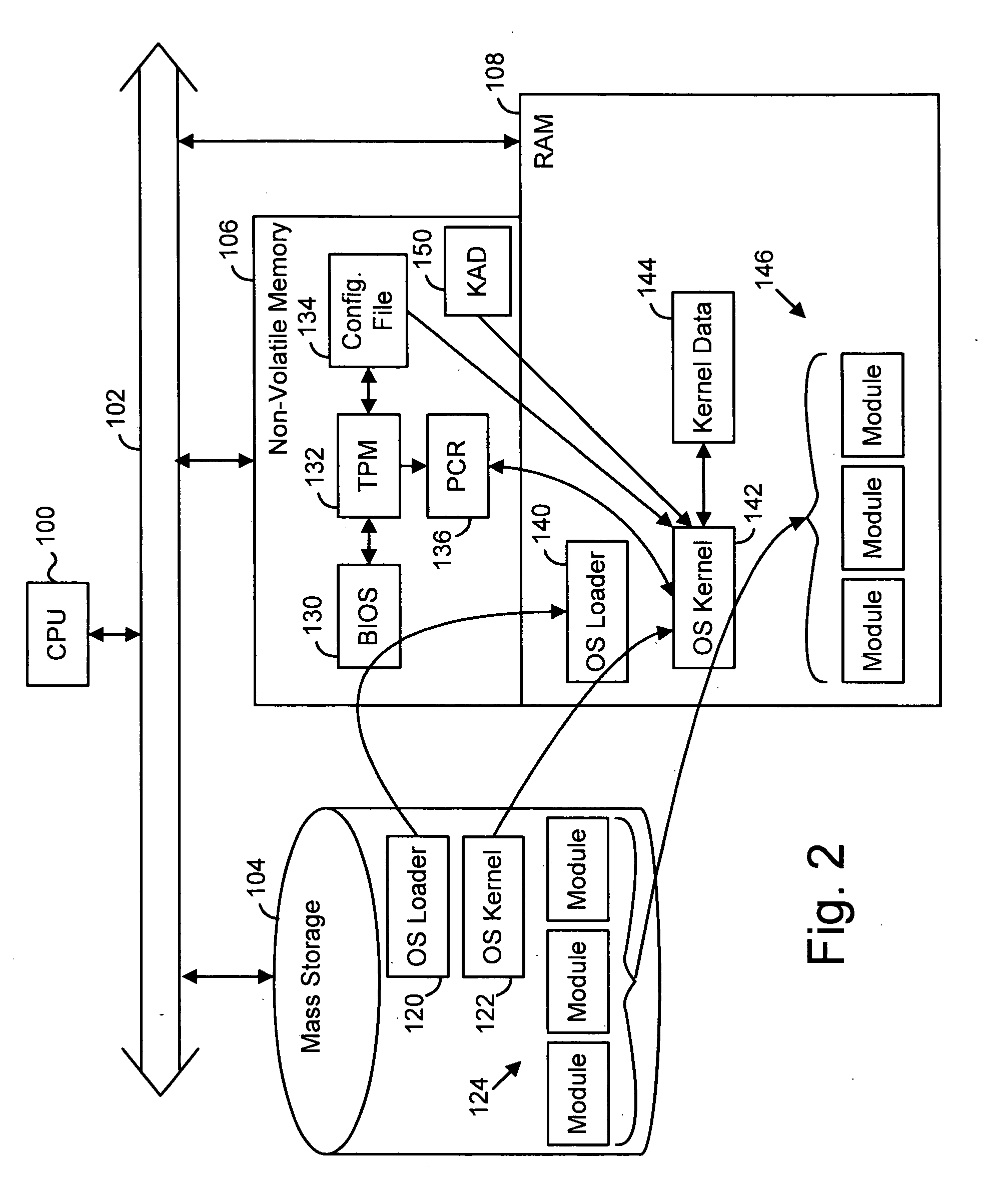
A preferred embodiment of the invention uses local or internal public and private keys for signatures. The keys are obtained and managed internally by a kernel process having access to a secure key storage area. The kernel process is booted within a trusted platform and is the only process that is allowed to access the key storage area. The internal keys can be used in addition to external keys for both internal key-based and external key-based signatures on a single digital item. In a preferred embodiment, the kernel process also maintains revocation lists and is synchronized with other entities by having the same criteria (e.g., time-based) for revoking or expiring known internal keys
Owner:SONY CORP +1
System for enabling lazy-revocation through recursive key generation
ActiveUS7203317B2Key distribution for secure communicationComputer security arrangementsComputer hardwareKey generation
Owner:VALTRUS INNOVATIONS LTD +1
Method and system for use in managing vehicle digital certificates
InactiveUS20110191581A1Effectively enables vehicle certificate managementLevel of security and privacyTransmissionSecure communicationTransceiver
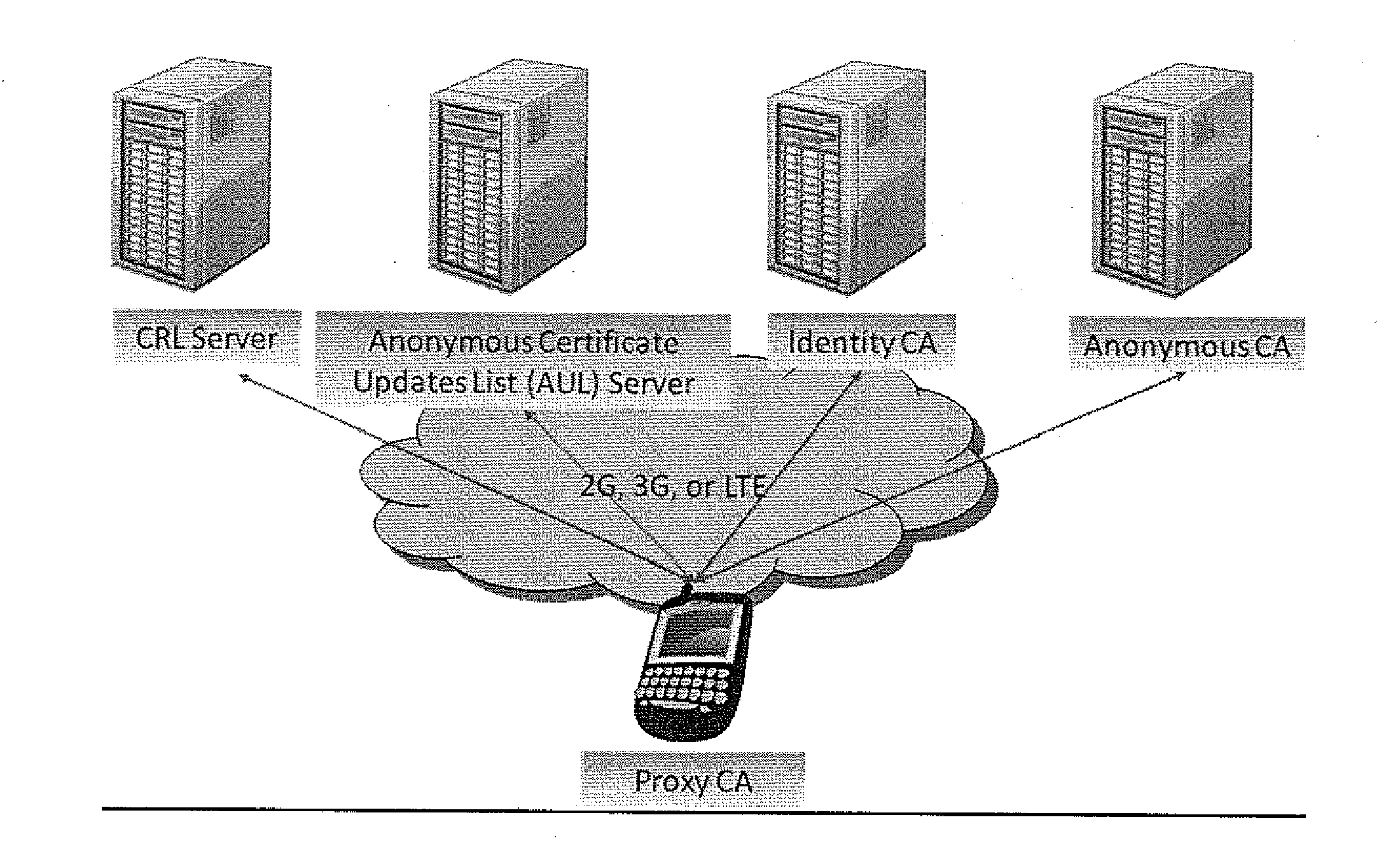
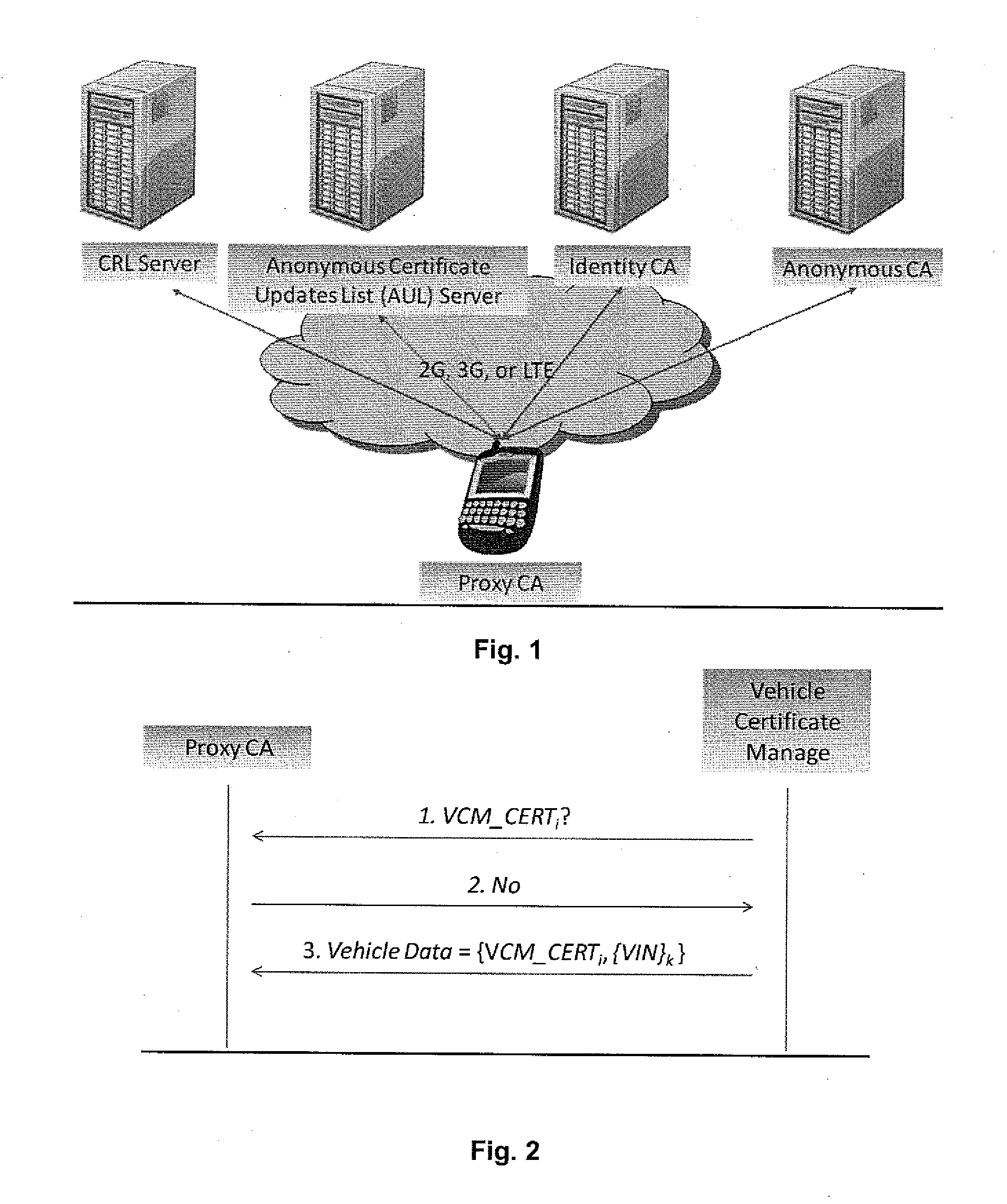
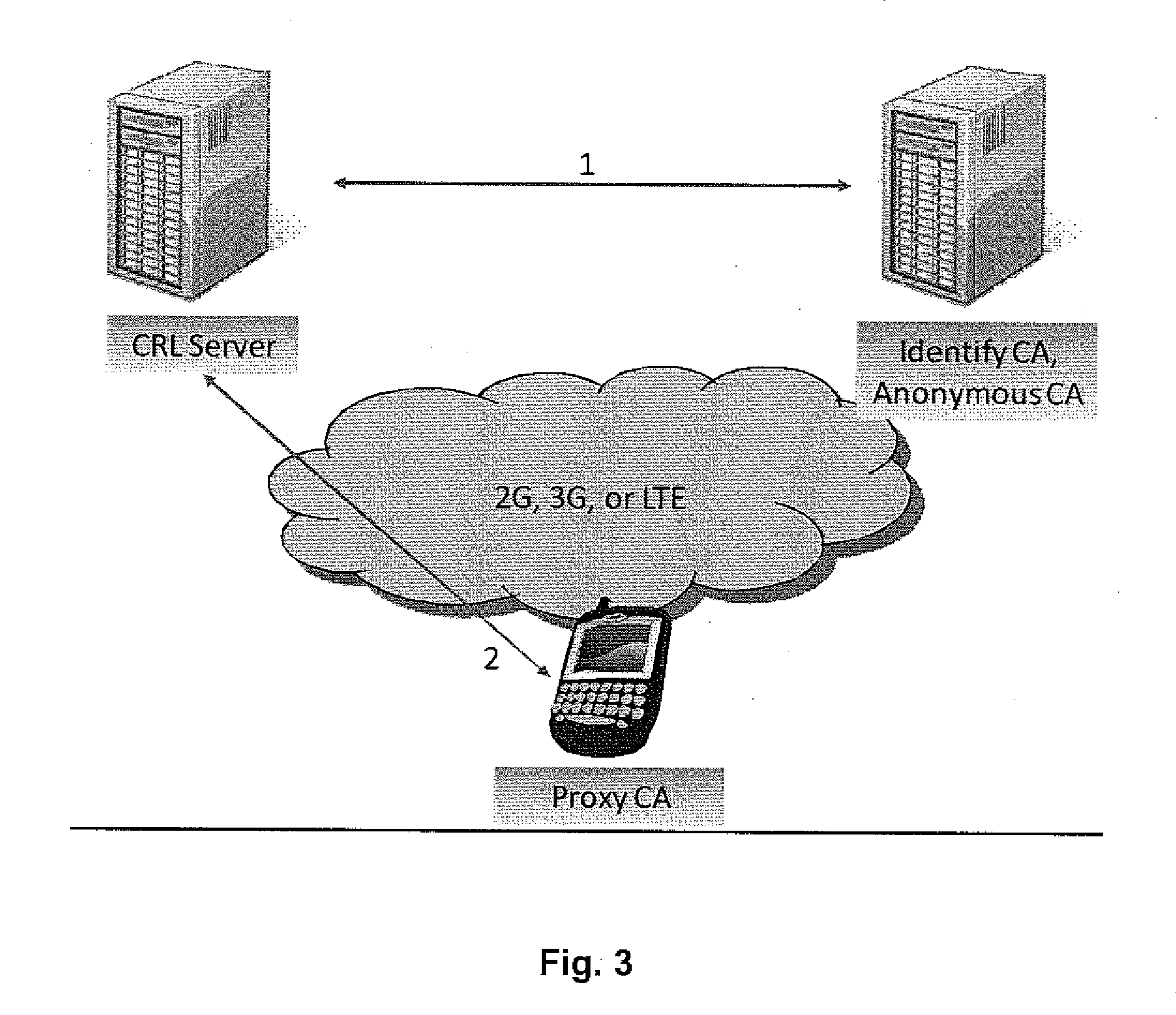
Owner:TELCORDIA TECHNOLOGIES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com