Patents
Literature
659results about "Mobile application execution environments" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
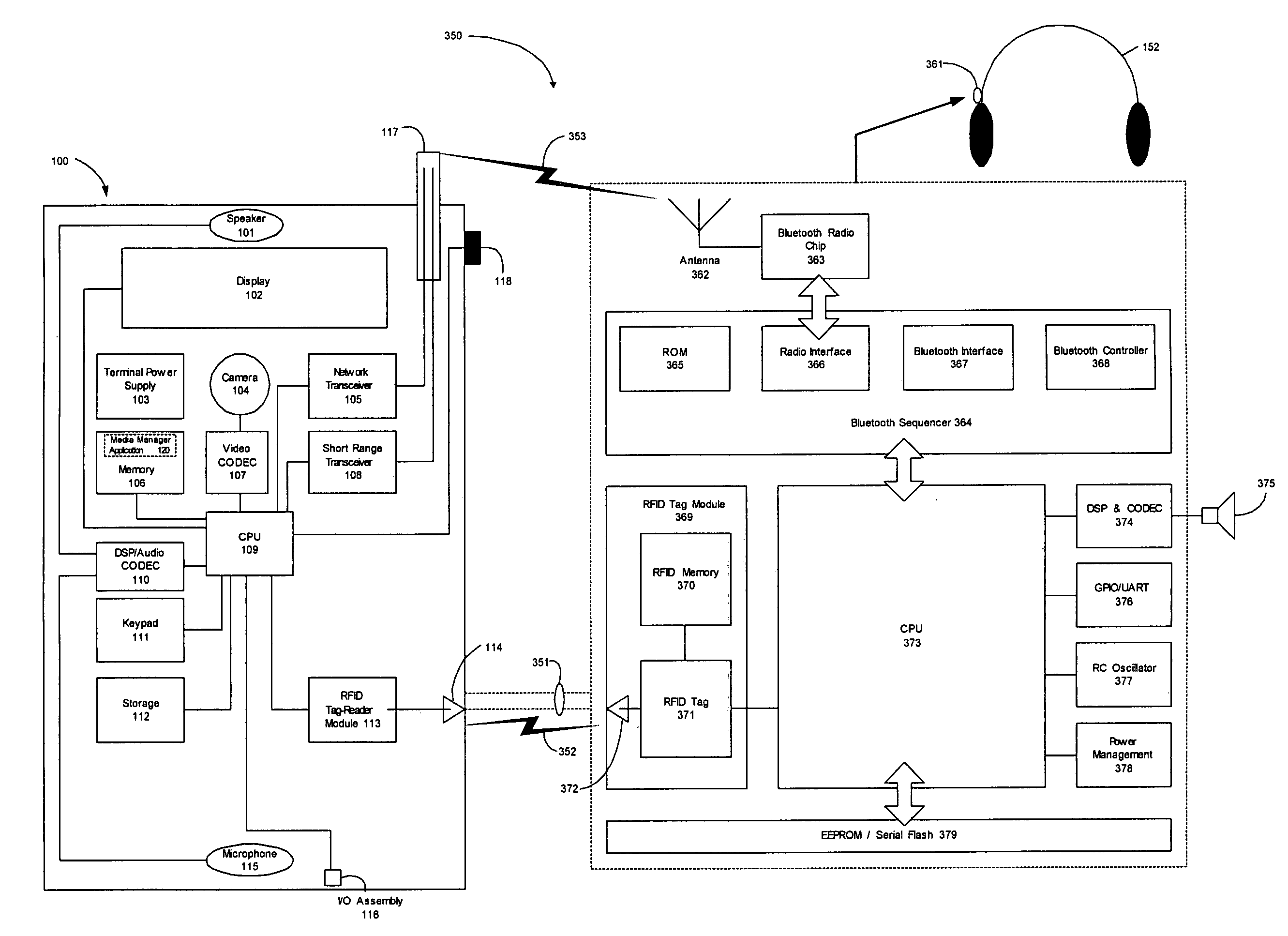
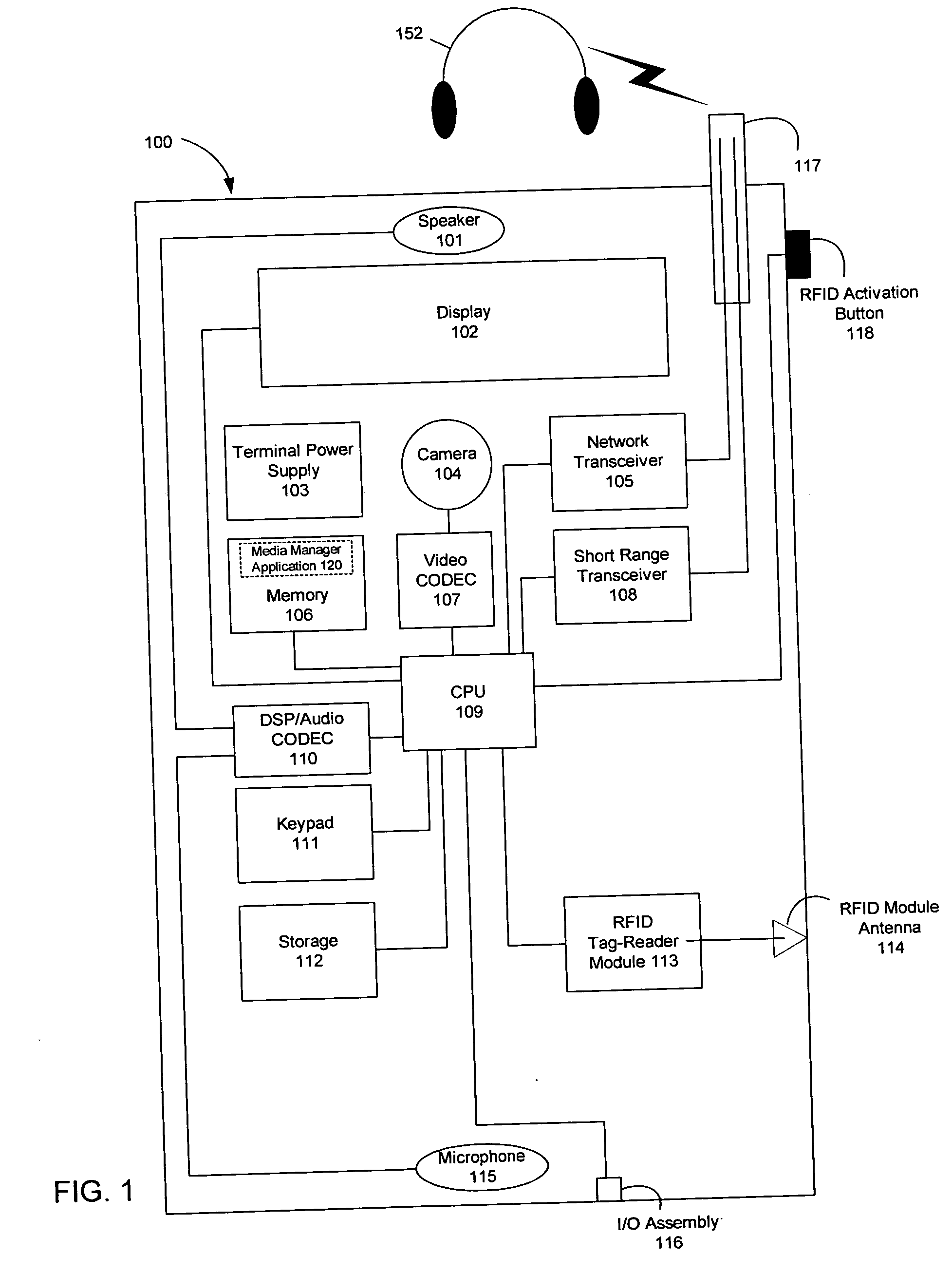
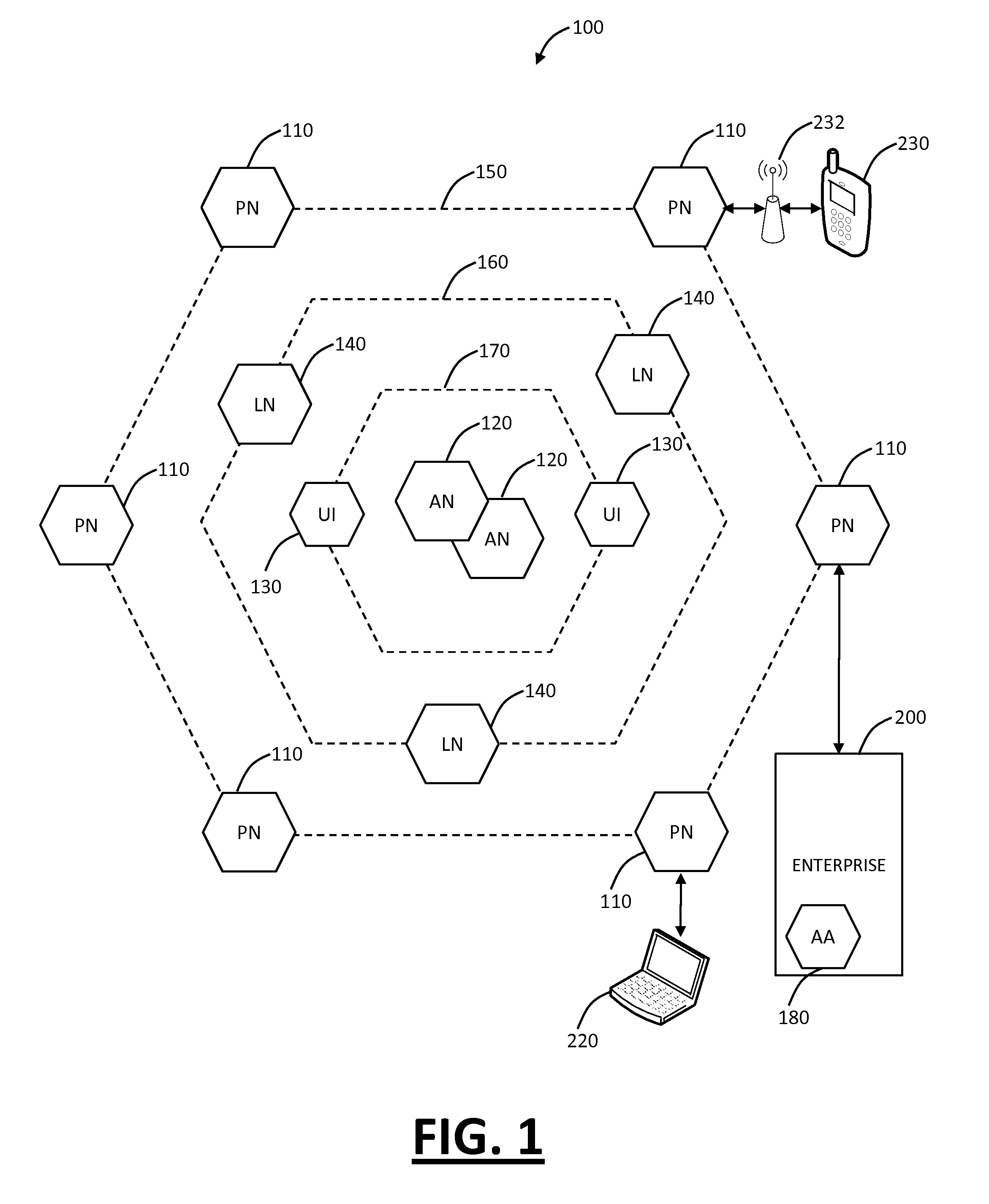
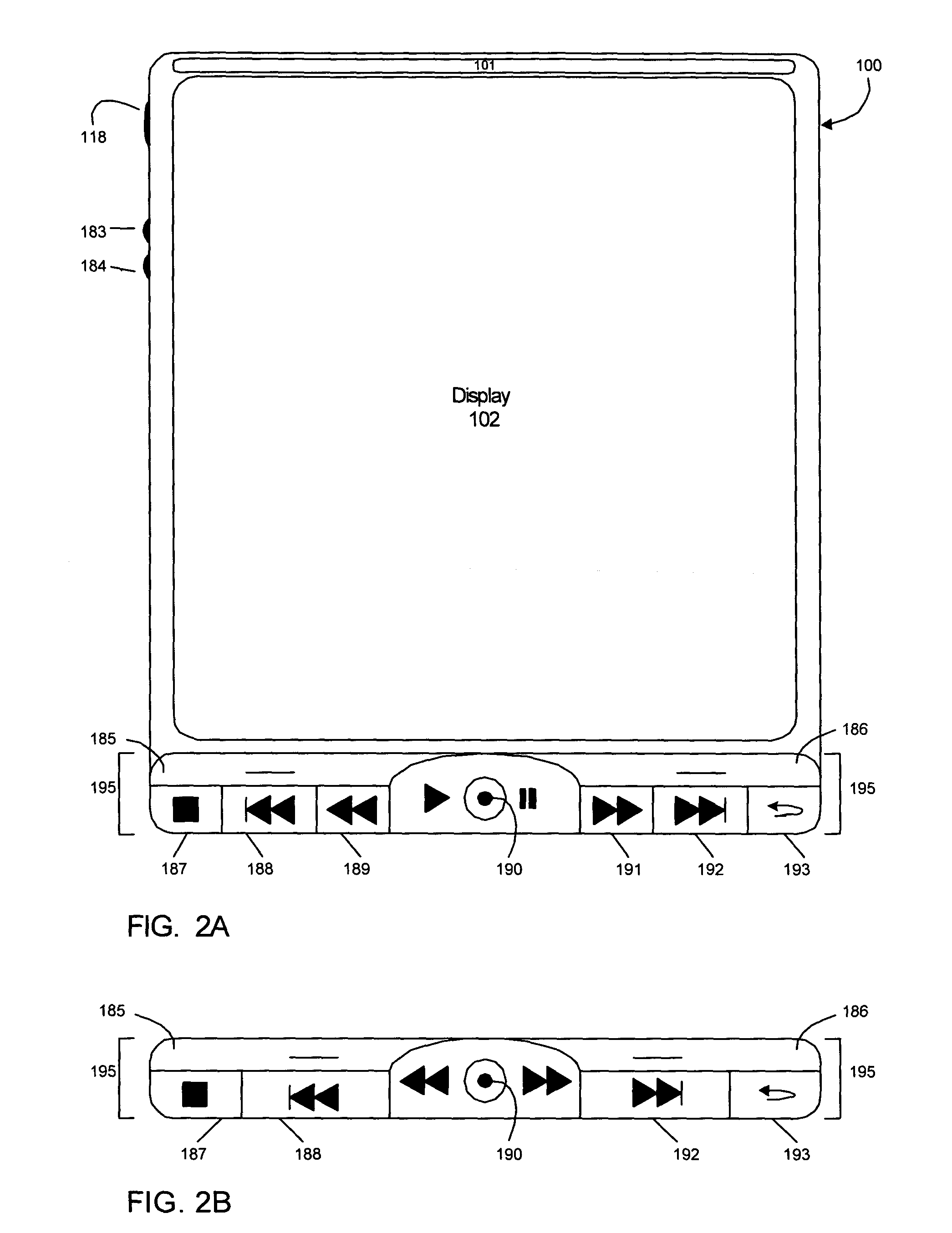
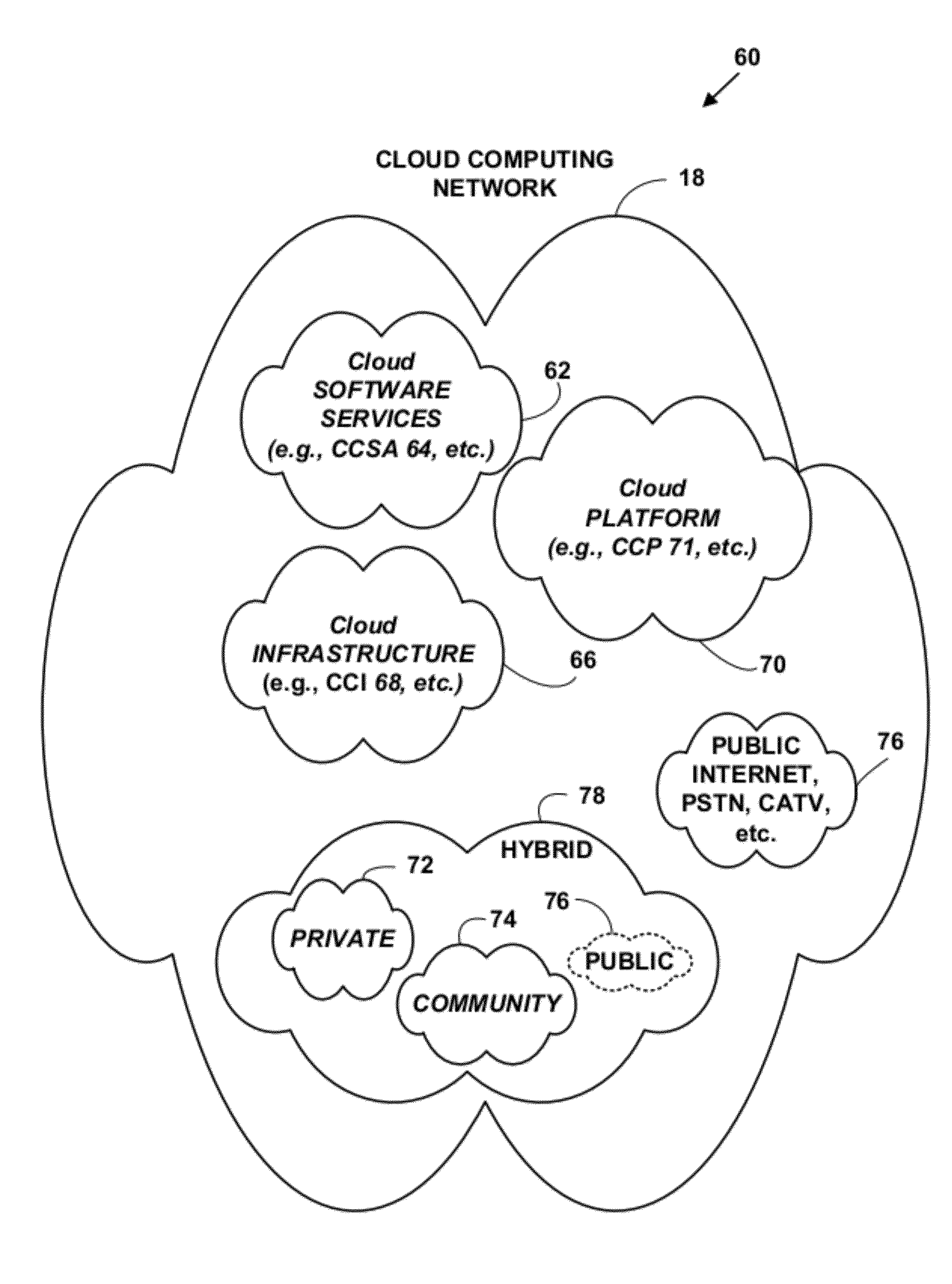
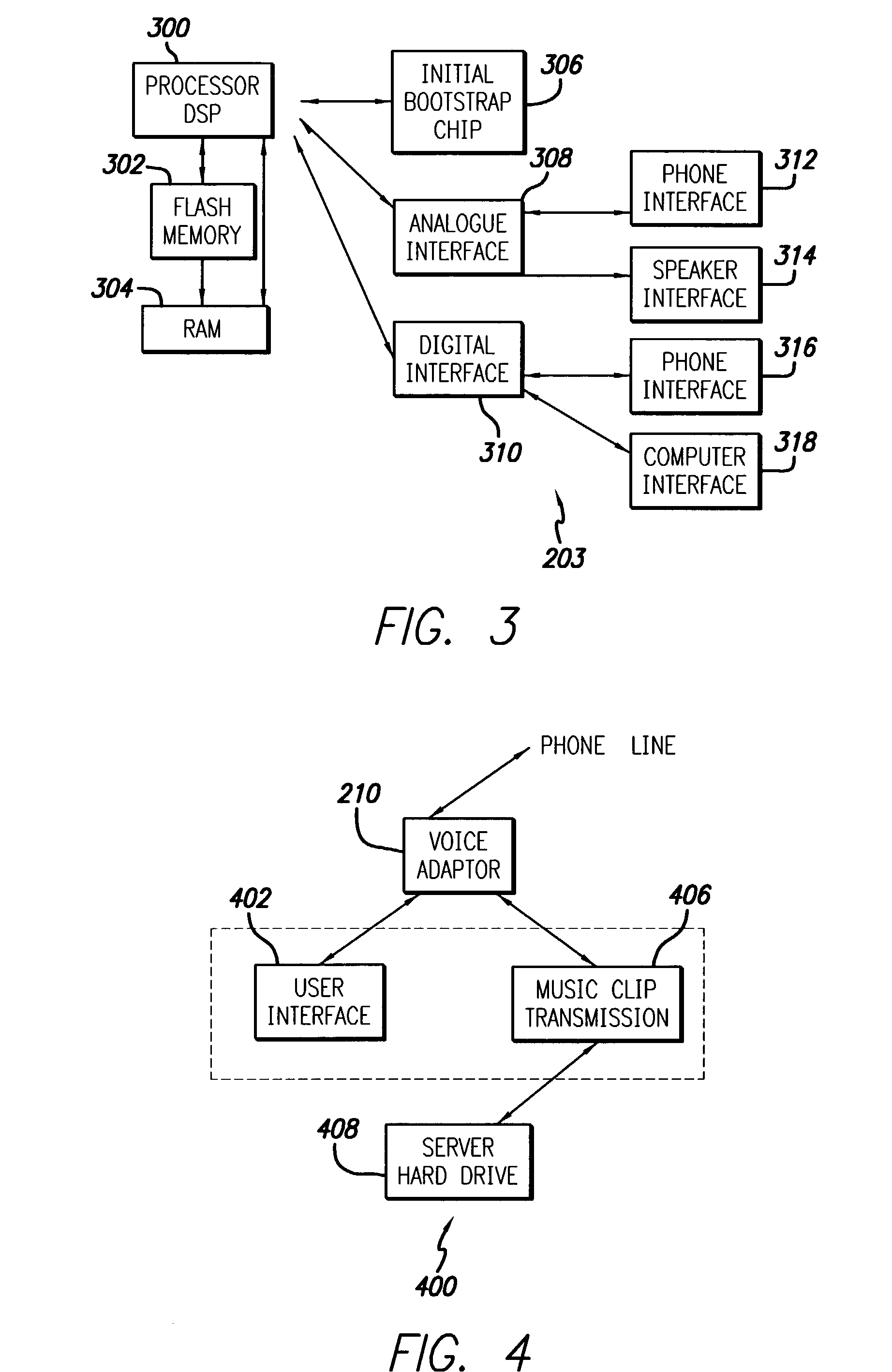
Wireless media system and player and method of operation
ActiveUS20060258289A1Easy to useMultimedia data browsing/visualisationPayment architectureUltra-widebandSecure communication
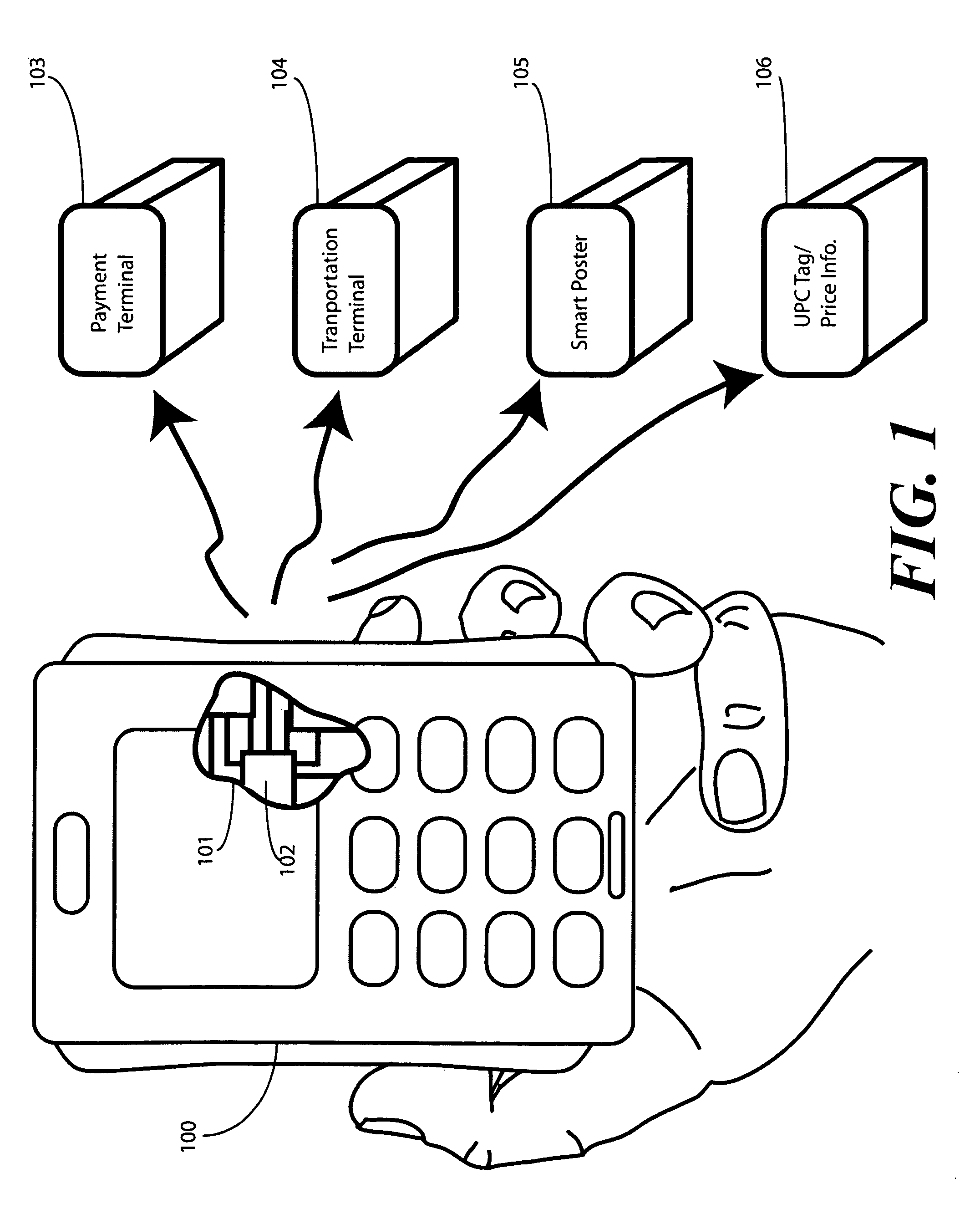
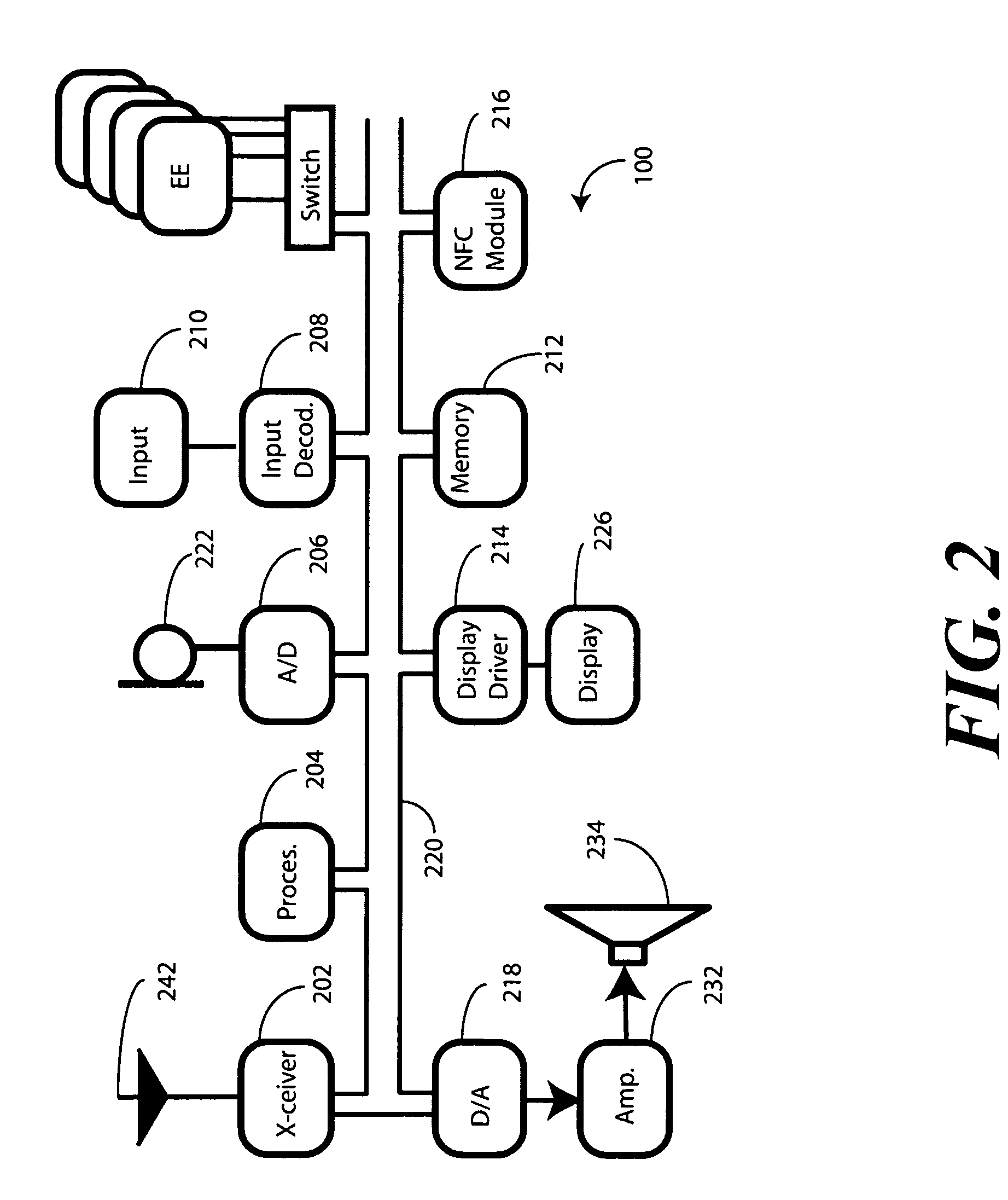
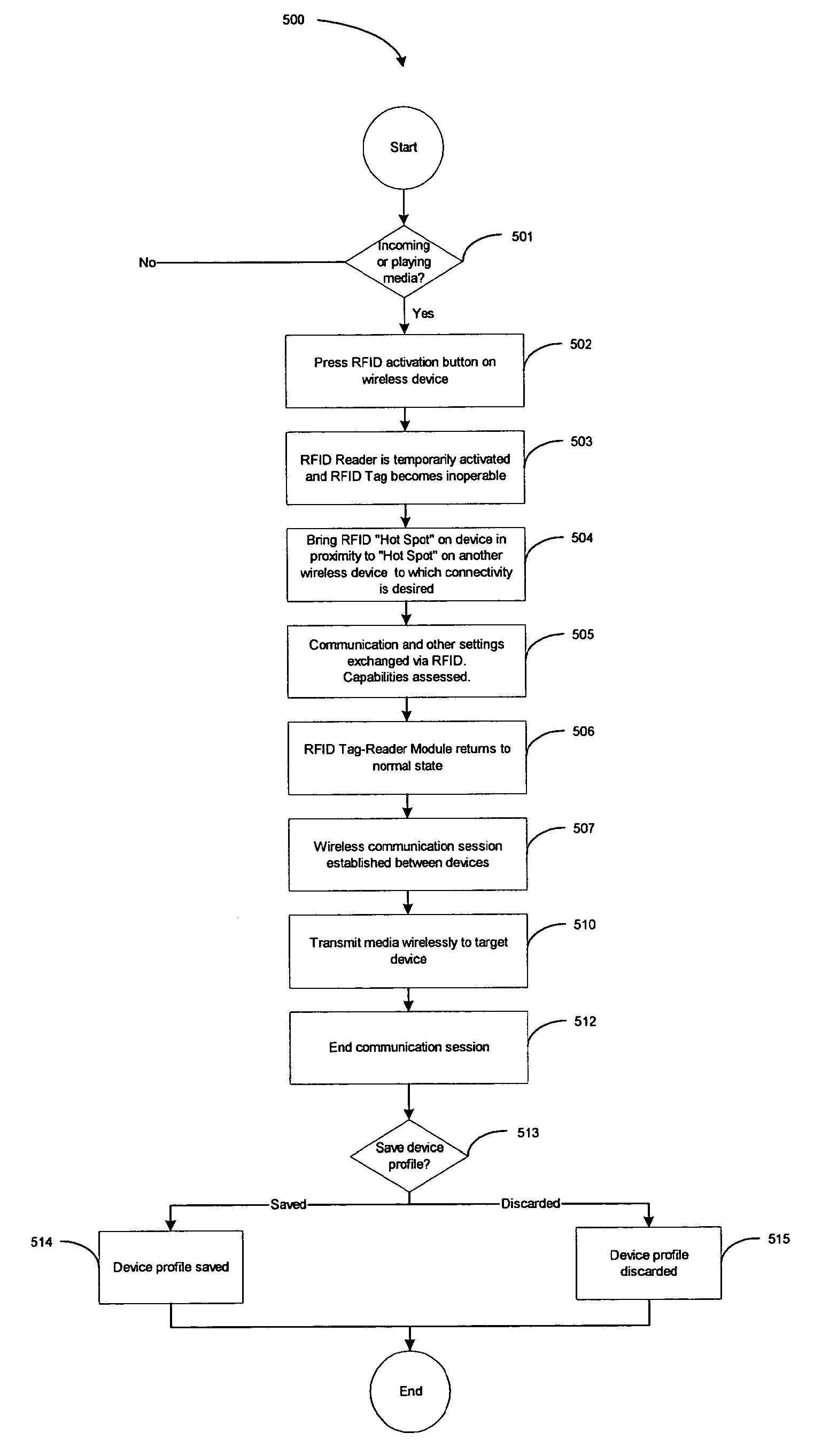
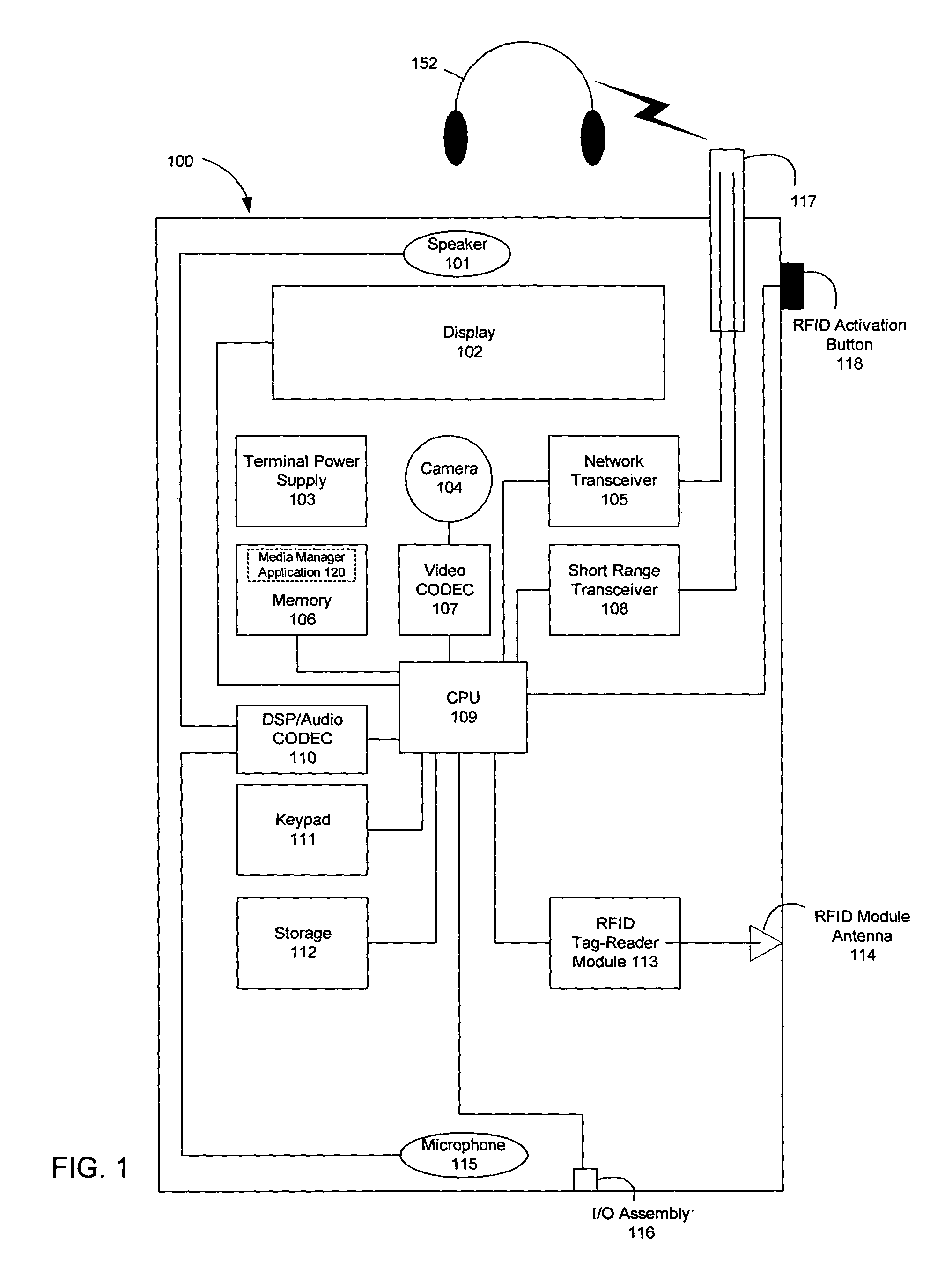
A wireless media player and a related system and methodology are disclosed. One aspect of the wireless media player system pertains to a virtual connector system, apparatus, and method for the automatic establishment of wireless connectivity with other electronic devices. In one embodiment, the media player device employs the use of integrated Radio Frequency Identification (RFID) technology to exchange communication settings, media capability, and other parameters with an external device that also has integrated RFID technology. The automatic exchange of settings and other information via a proximity-based RFID data exchange allows a media player to quickly establish a secure communication link with another device via a commonly supported wireless protocol such as Ultra Wideband (UWB) or Bluetooth. Another aspect of the media player system pertains to a method of using the captured media capability of the connecting device to customize certain menu options and software parameters in the media player.
Owner:SYNDEFENSE
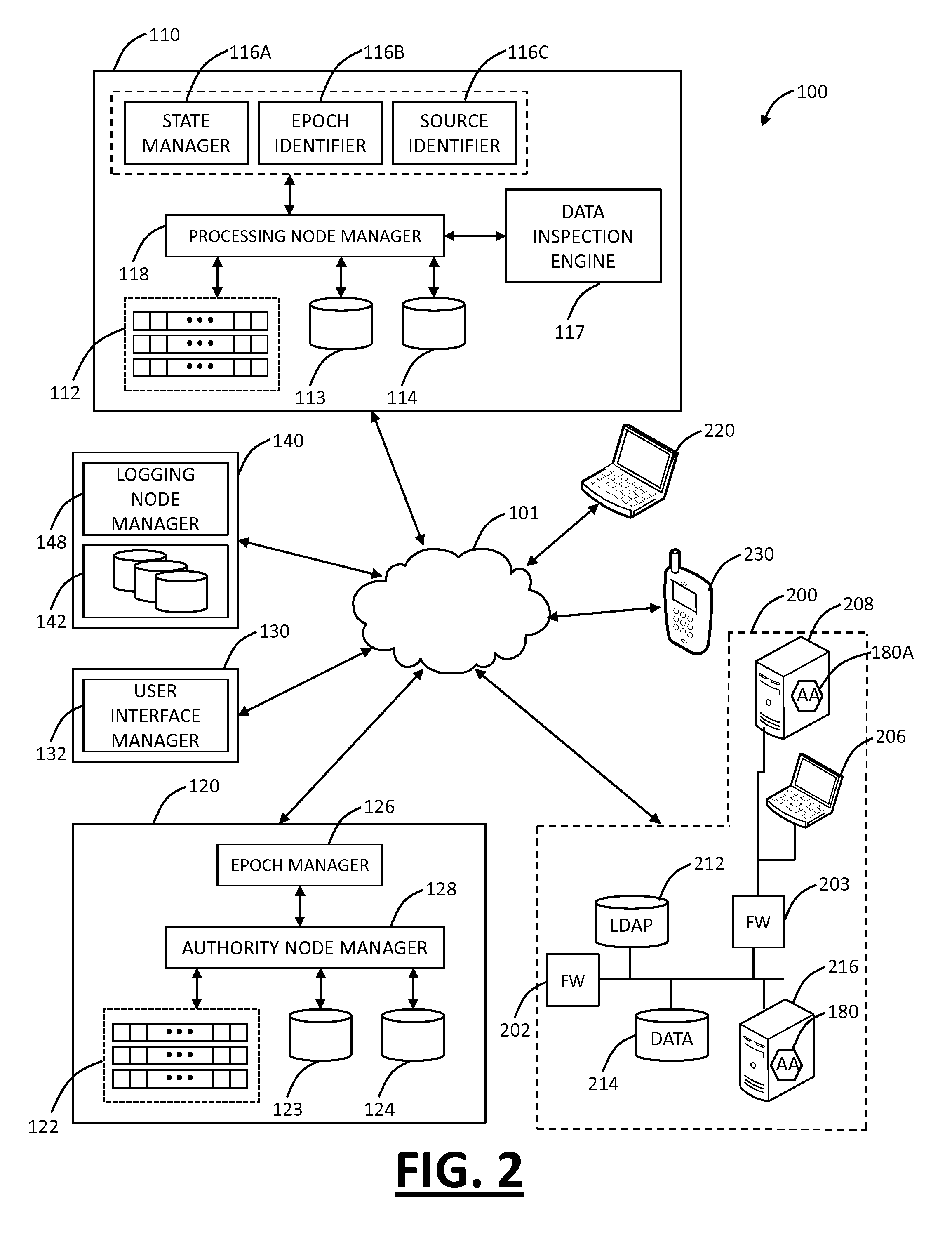
Cloud based mobile device security and policy enforcement
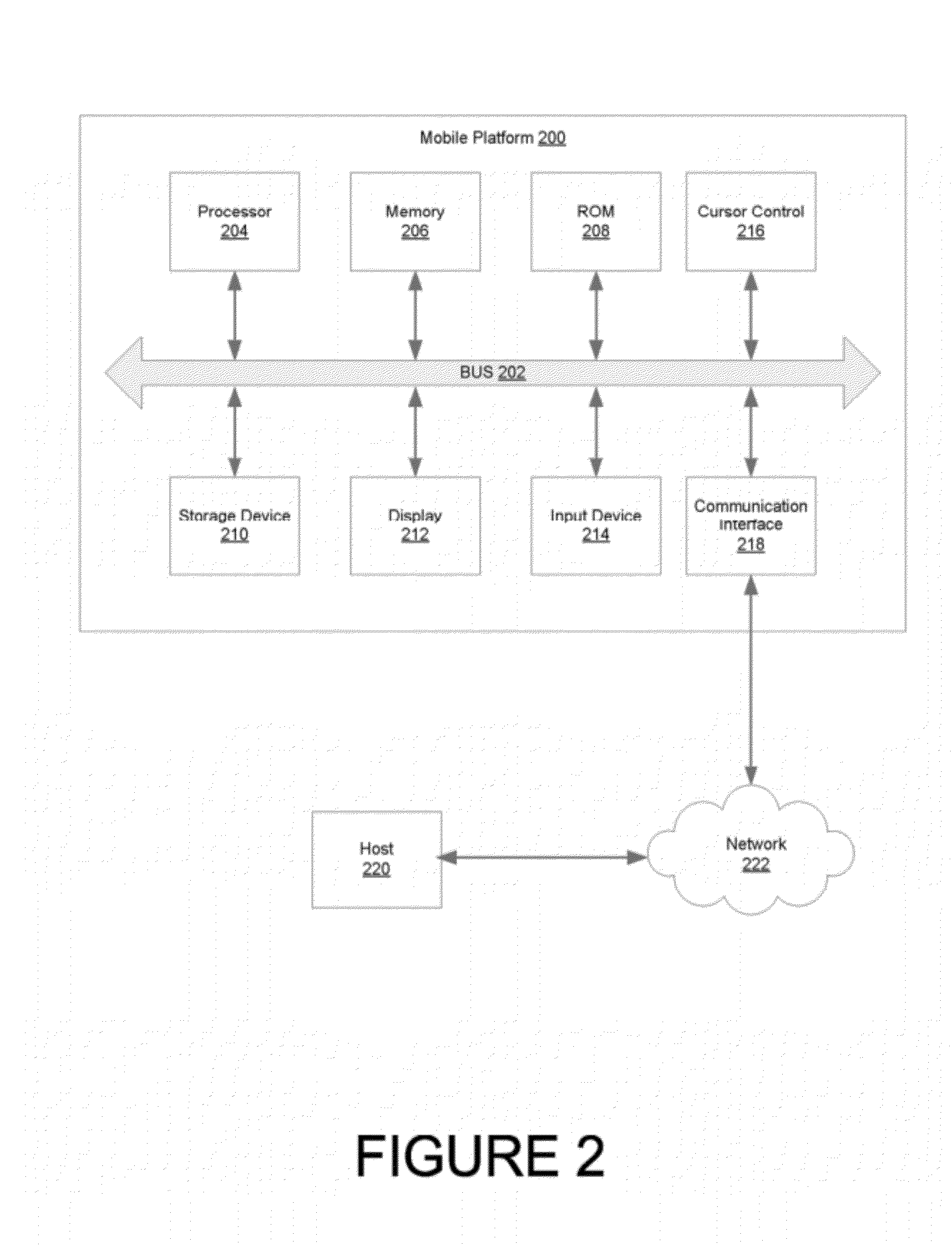
ActiveUS20120240183A1Computer security arrangementsMobile application execution environmentsTablet computerOperational system
The present disclosure relates to cloud based mobile device security and policy systems and methods to use the “cloud” to pervasively enforce security and policy on mobile devices. The cloud based mobile device security and policy systems and methods provide uniformity in securing mobile devices for small to large organizations. The cloud based mobile device security and policy systems and methods may enforce one or more policies for users wherever and whenever the users are connected across a plurality of different devices including mobile devices. This solution ensures protection across different types, brands, operating systems, etc. for smartphones, tablets, netbooks, mobile computers, and the like.
Owner:ZSCALER INC
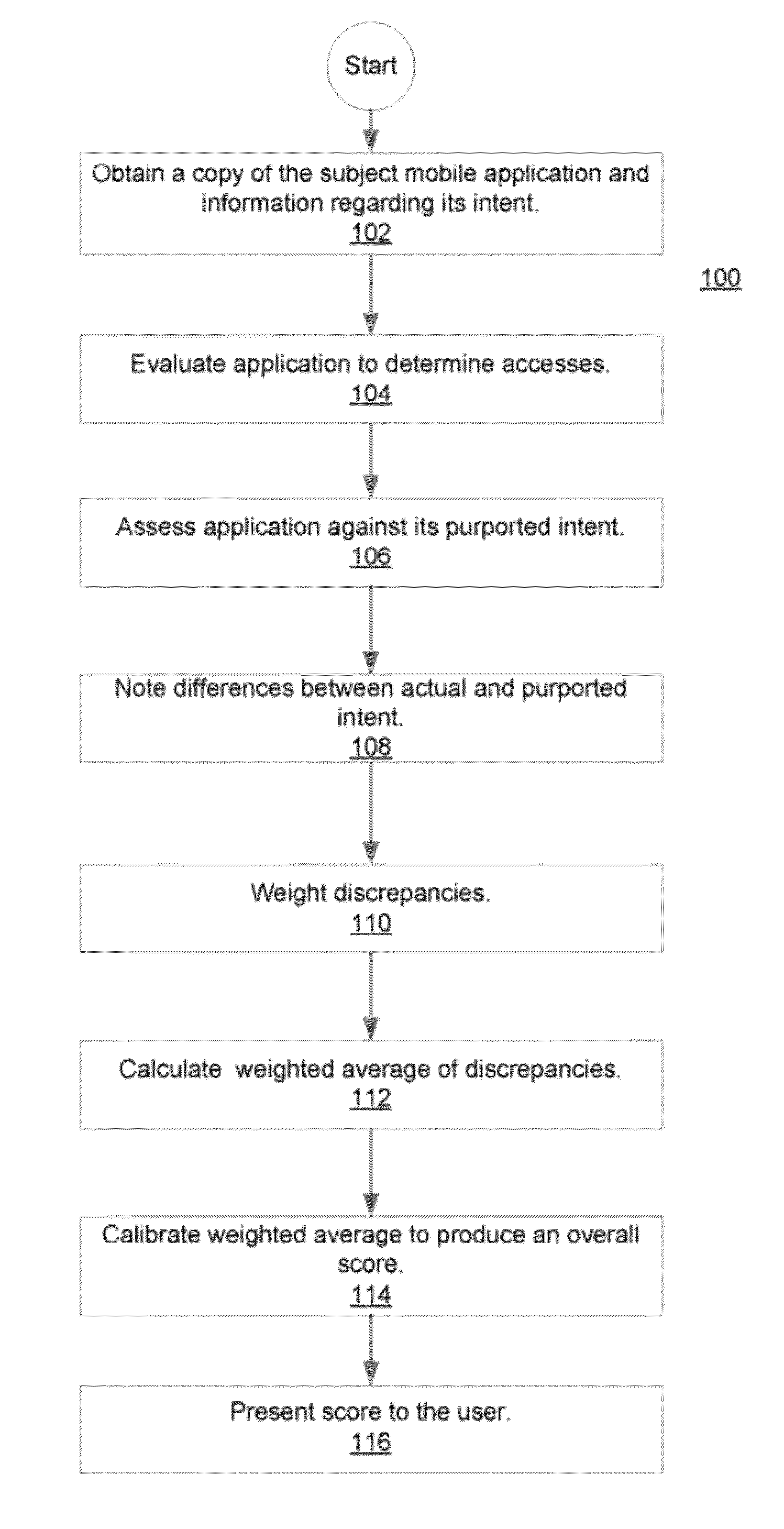
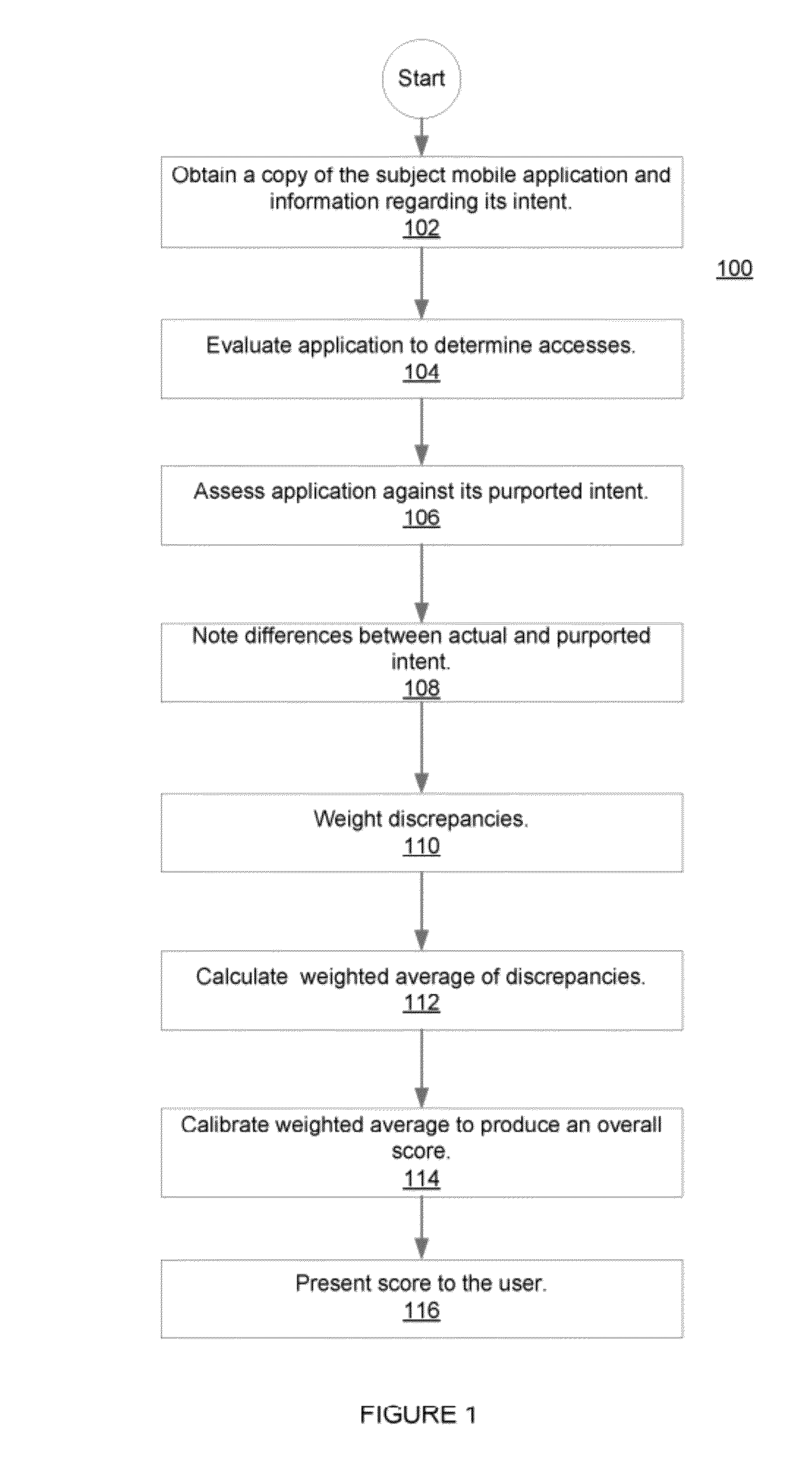
Methods and systems for rating privacy risk of applications for smart phones and other mobile platforms
InactiveUS20120110674A1Better-informed decisionService provisioningMemory loss protectionInternet privacyUser privacy
Methods and systems for evaluating and rating privacy risks posed by applications intended for deployment on mobile platforms. Validating the “intent” of a mobile platform application vis-à-vis its impact on user privacy, as viewed from an end-user's perspective allows those end-users to make better-informed decisions concerning the downloading, installation and / or operation of mobile platform applications. In making such assessments user preferences can be taken into account. Privacy scores are provided through sales channels for the applications, thereby affording potential users the opportunity to assess whether they wish to incur the associated privacy risk, before purchasing a subject application.
Owner:NCC GRP SECURITY SERVICES
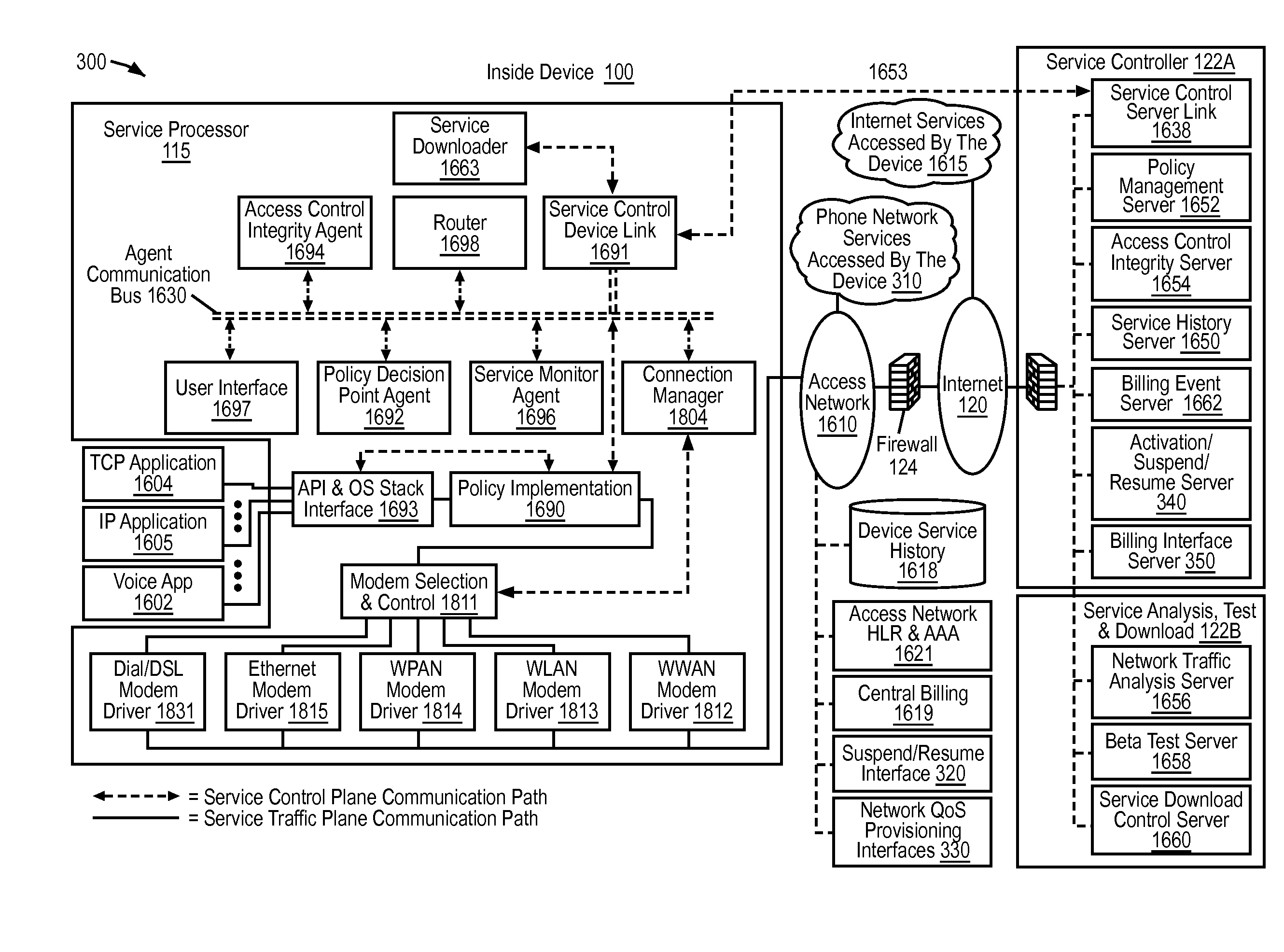
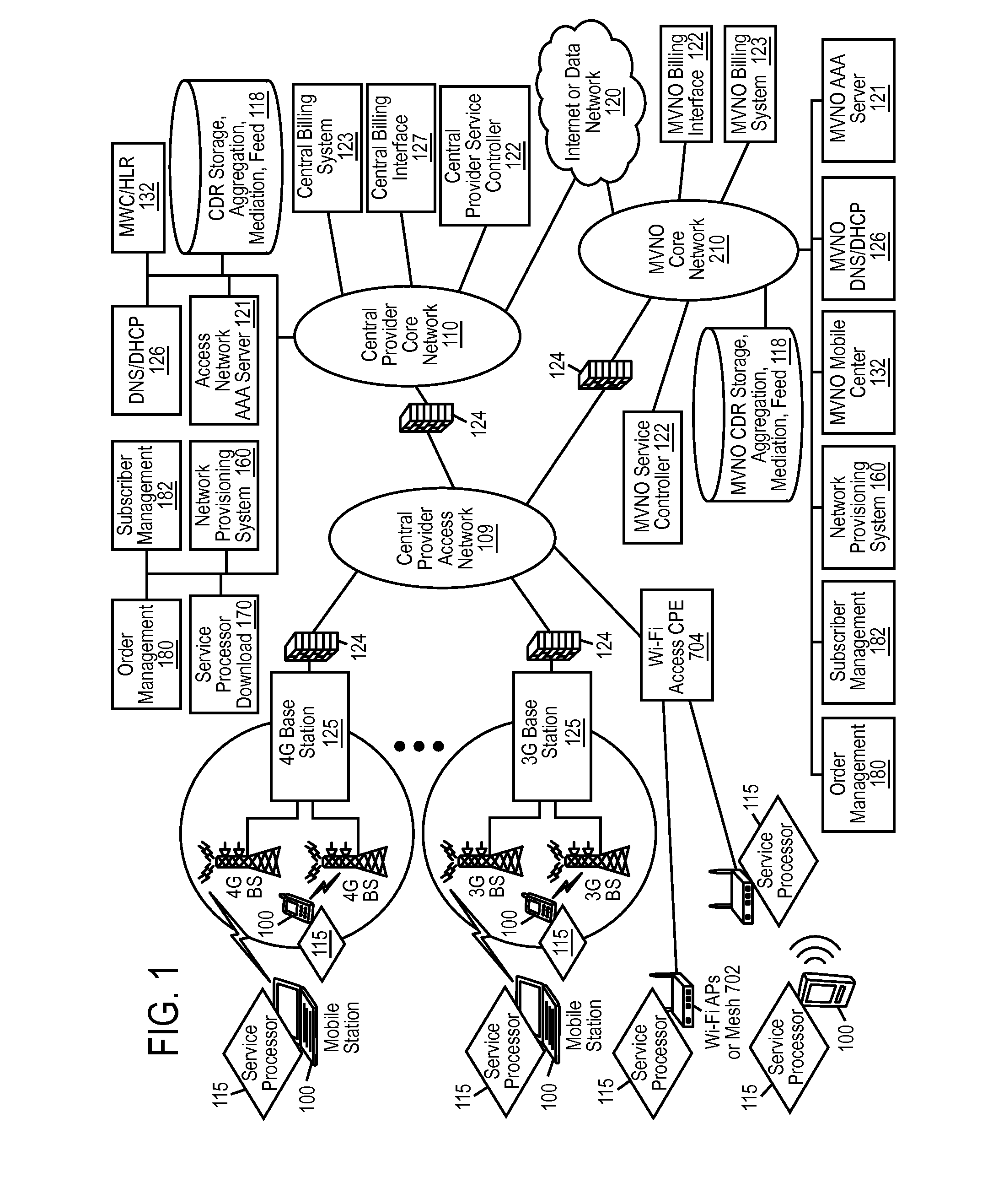
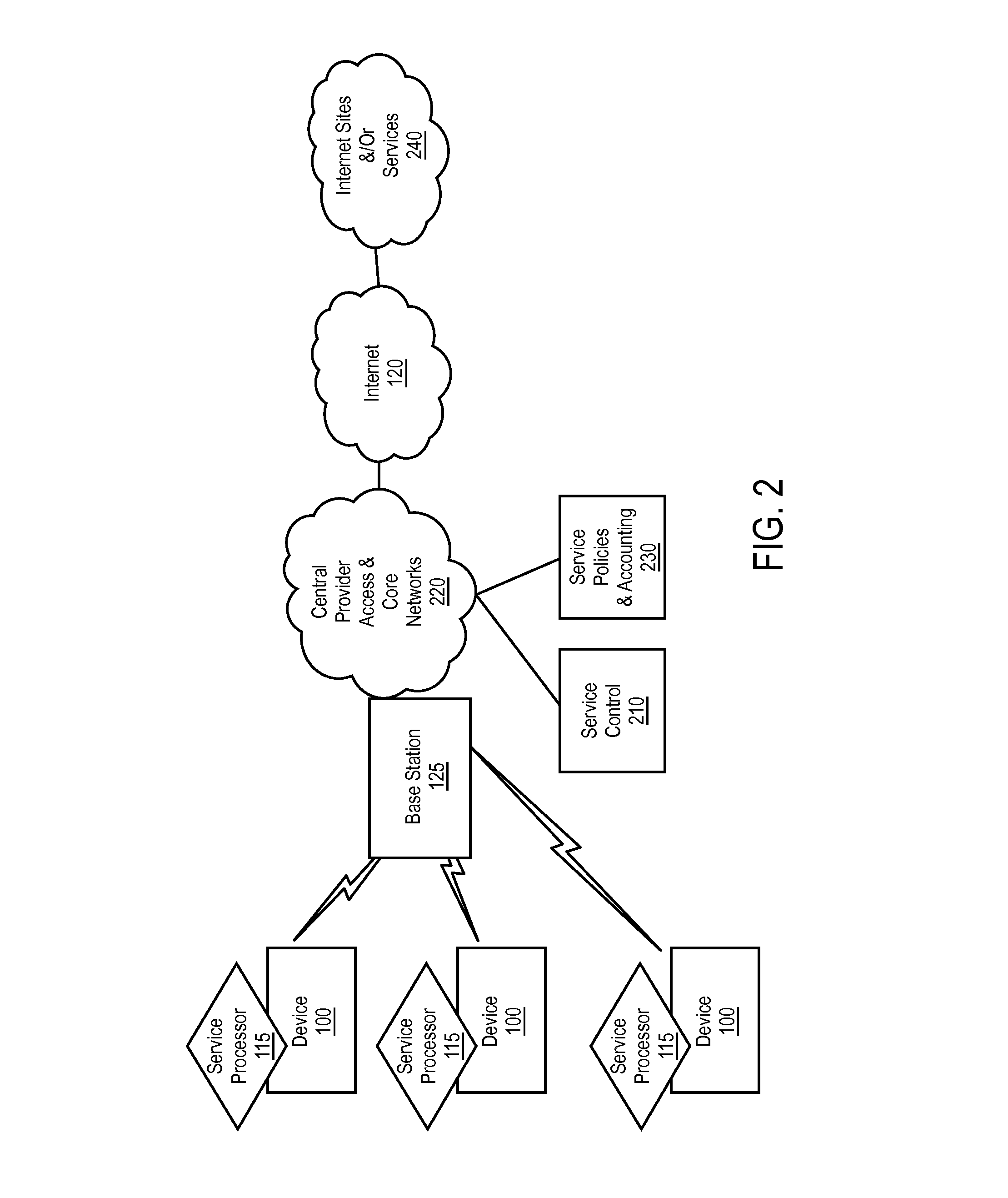
End user device that secures an association of application to service policy with an application certificate check
ActiveUS20120221955A1Input/output for user-computer interactionAccounting/billing servicesTraffic capacityApplication software
Network service provisioning is described. Network service provisioning to a device includes a mechanism for ensuring that network services are available based upon one or more of appropriate traffic control, billing, and notification policies. Ensuring that the policies are properly enforced on a device is a focus of this paper. The enforcement policies can be on the device or in the network.
Owner:HEADWATER RES LLC
Media delivery platform
InactiveUS20030033214A1Prevent intellectual propertyAccurate methodModulated-carrier systemsPayment architectureCorrection algorithmMediaFLO
An improved method for delivery and play back of sound and image files is provided. This new method includes the use of sound and / or image clips, which can be snippets or full files, as alerts for a variety of electronic devices or for playing on a handheld device, and for use as a promotion to sell items associated with the files. A collection or library of uniquely selected and / or edited clips may also be provided to the consumer in a manner far more conveniently on conventional telephone equipment than previously available. Algorithms are provided for the delivery, storage and playback of the sound files, including a delivery method algorithm (500), a parametric optimization and compression algorithm (1500), and an error correction algorithm. In contrast to the conventional ring tones or musical chimes used to ring cellular phones currently on the market, the current invention provides a method for ringing cellular phones and landline telephones with real sound recordings including real music, which may be songs lifted from copyright registered CD tracks, and may comprise human voice, various instrument sounds, and other sound effects of a high quality. A software based system for encoding the hardware of existing cellular phones at the time of manufacturing with delivery, storage, and playback capabilities in accordance with the present invention is provided, such that additional hardware is not required.
Owner:SKKY
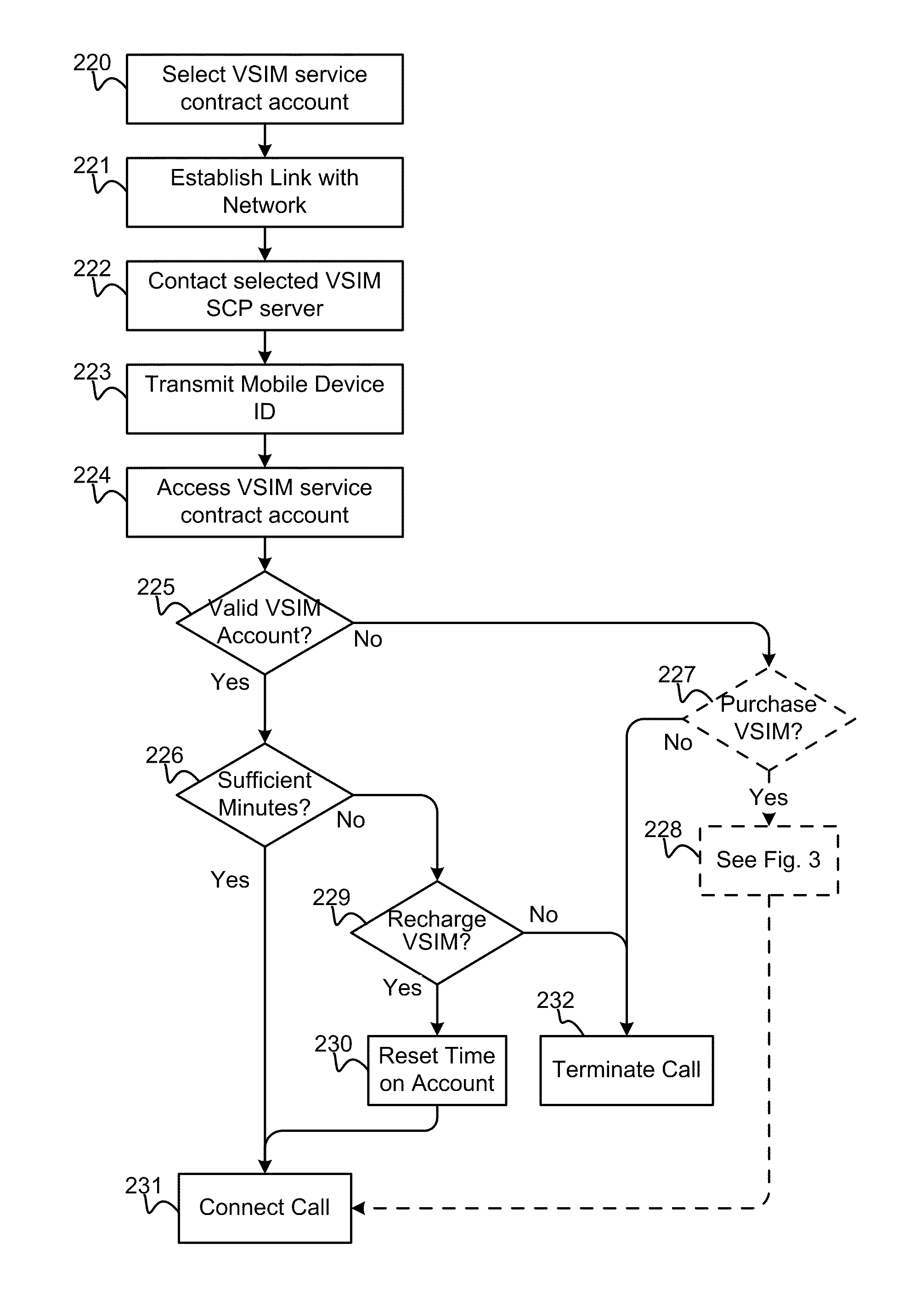
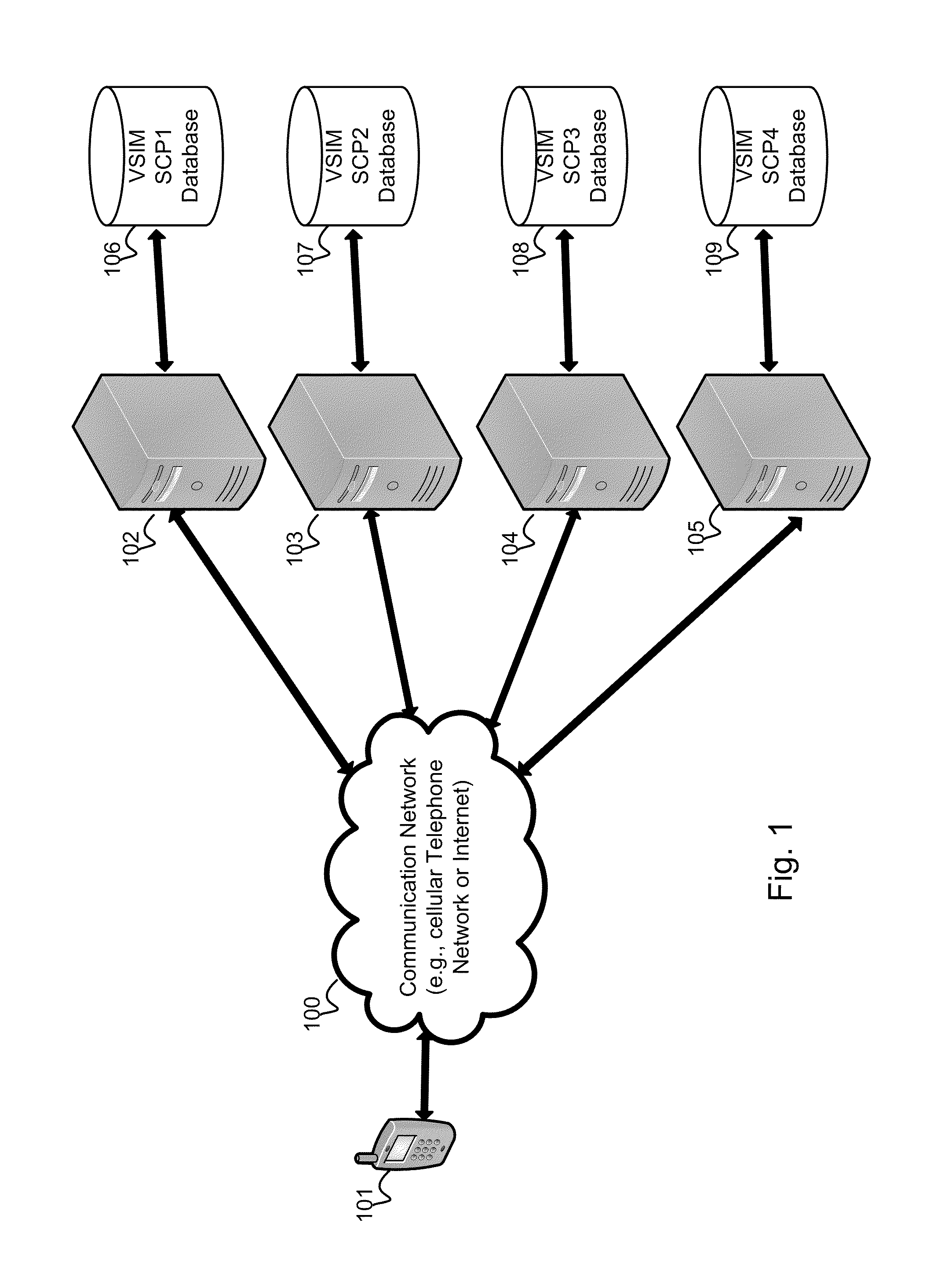
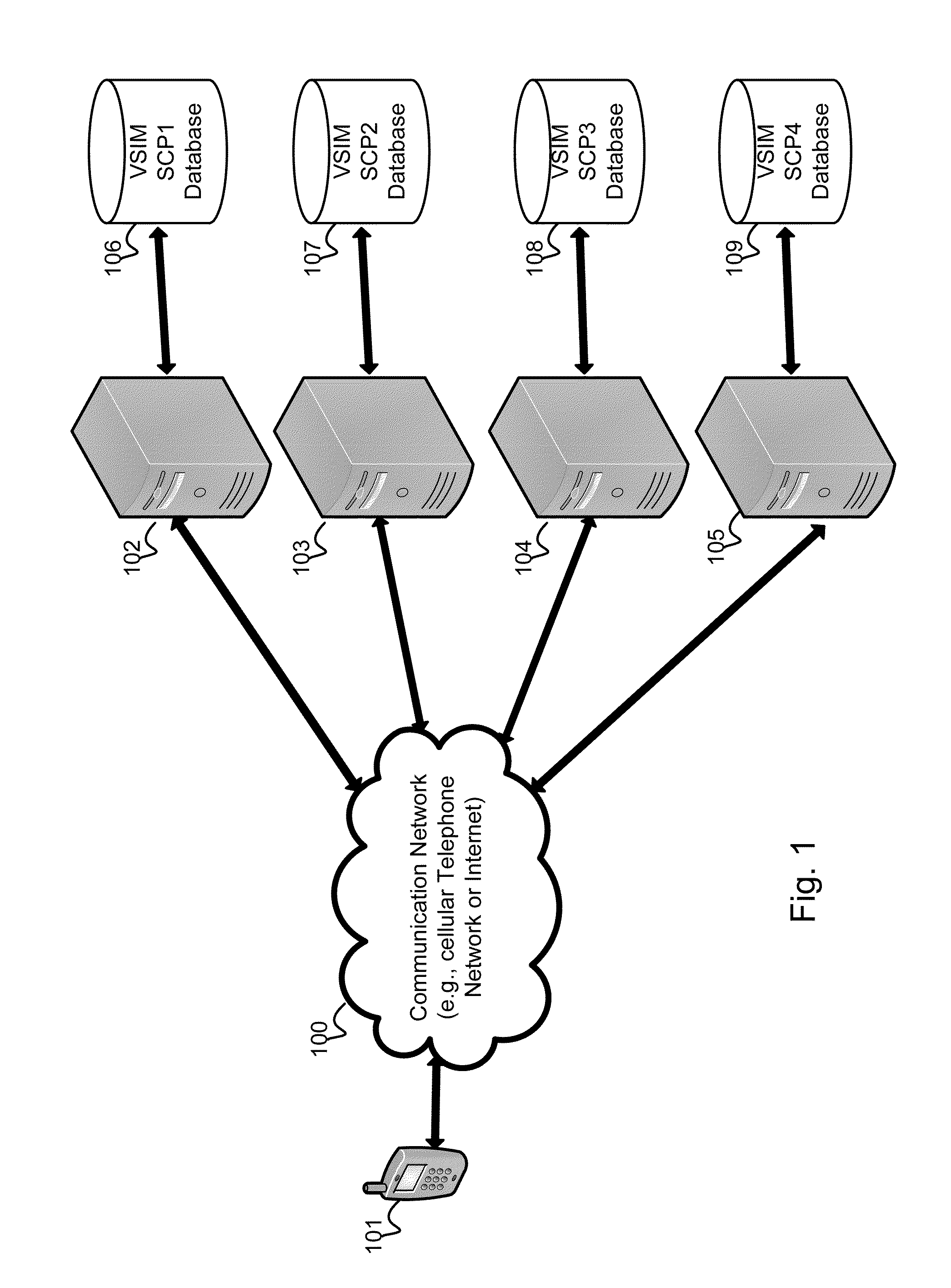
Method and apparatus for performing soft switch of virtual sim service contracts
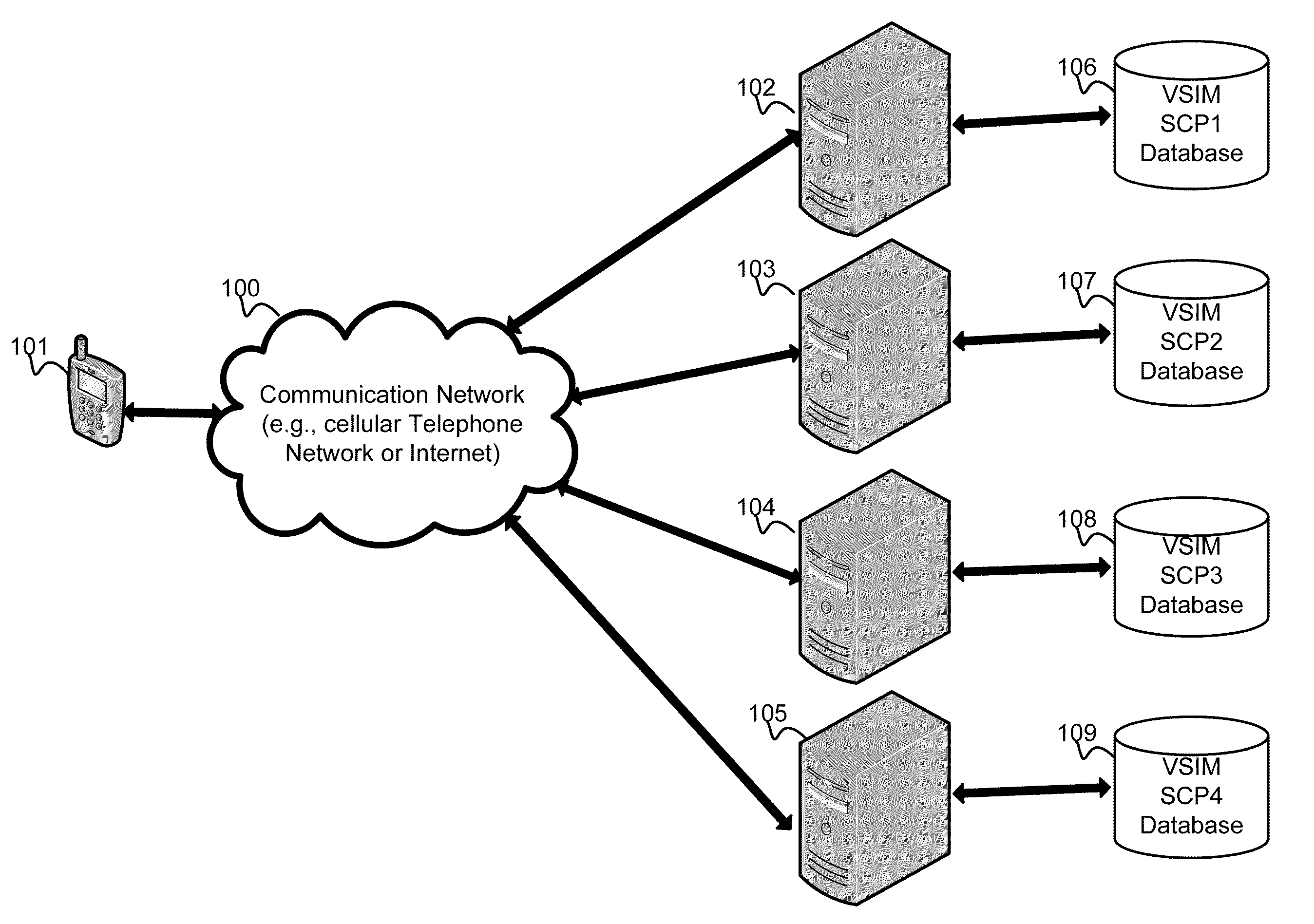
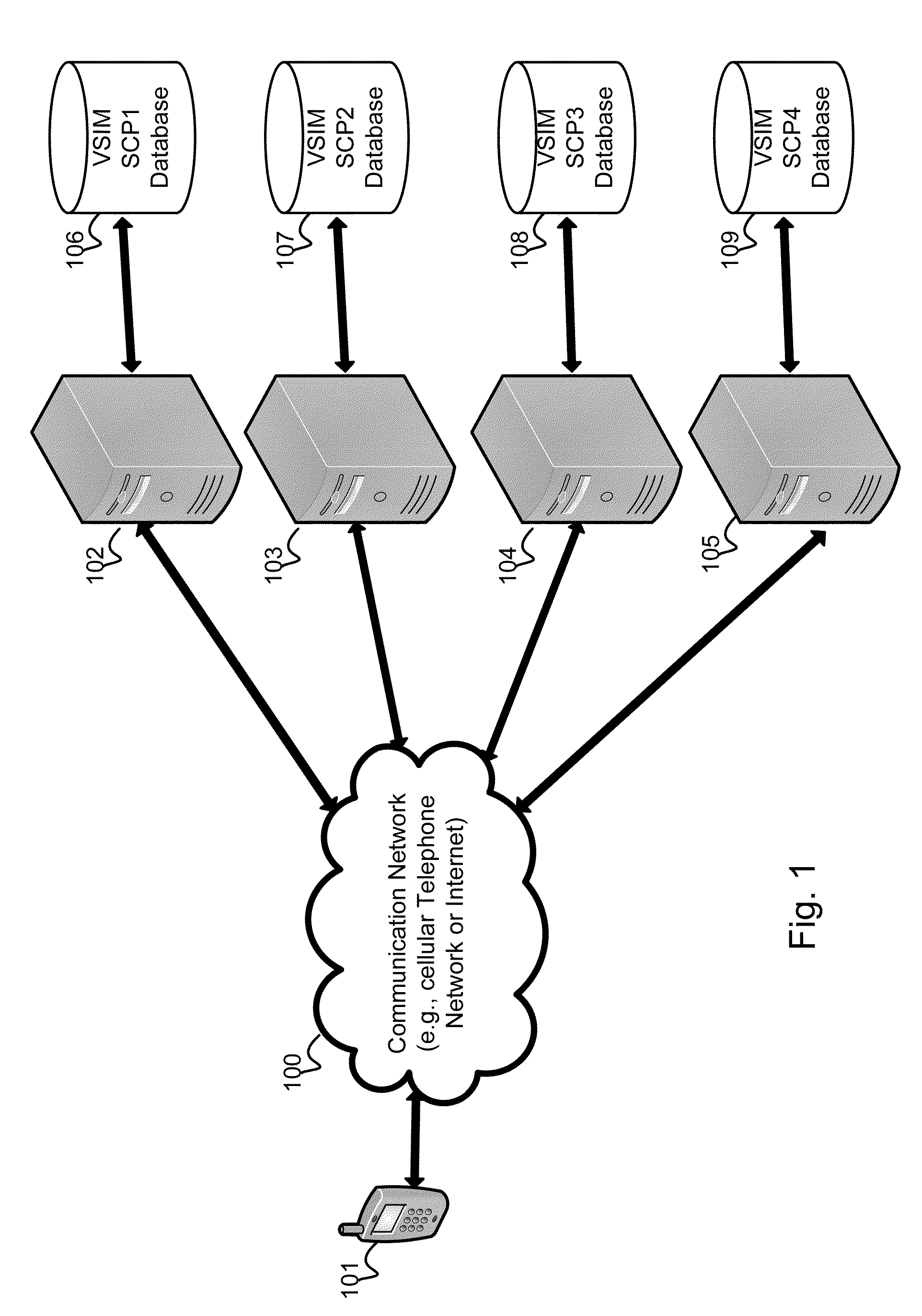
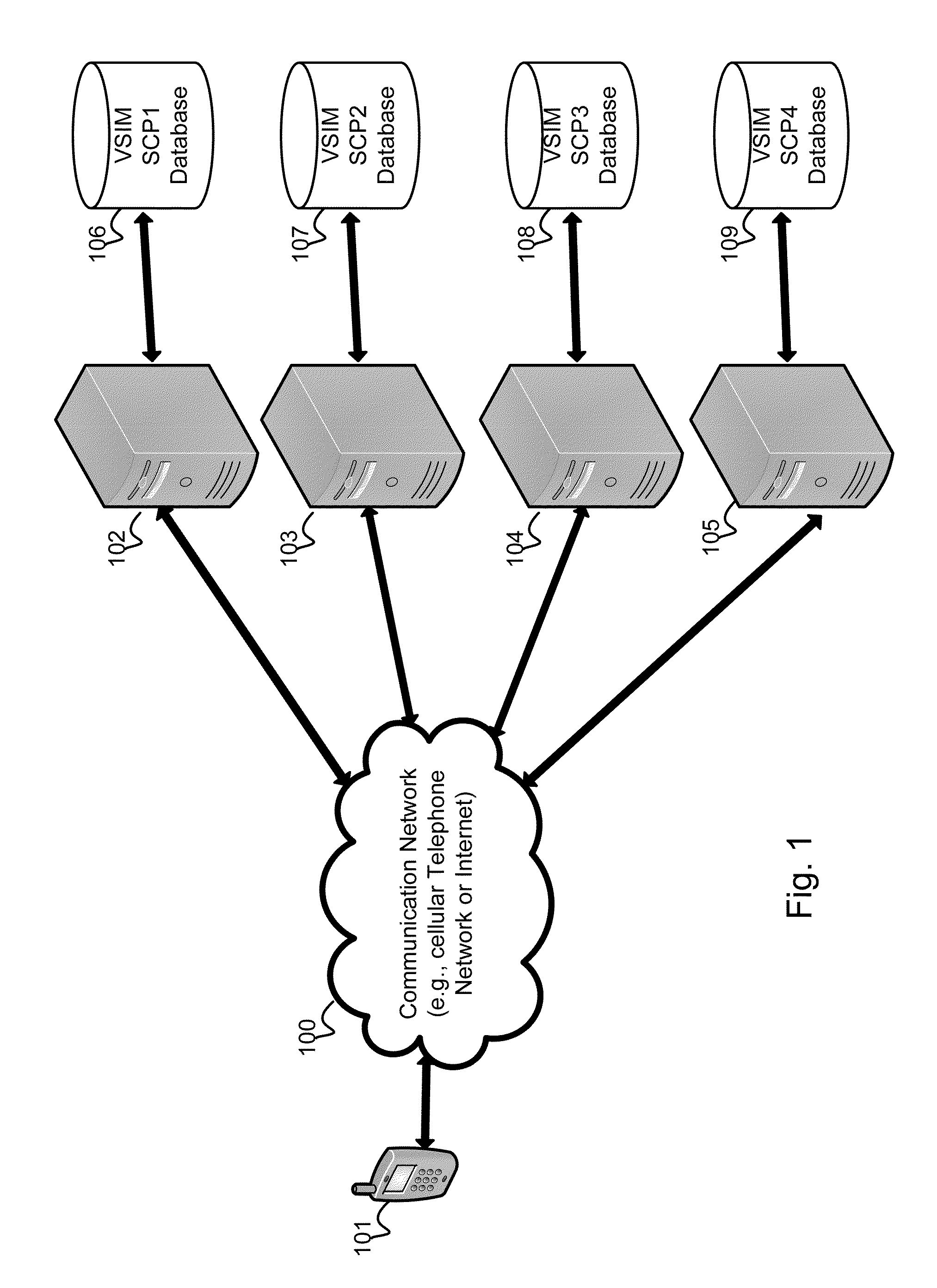
InactiveUS20100311402A1Save battery powerEffective supportService provisioningAssess restrictionInternal memoryService provision
A system and method for providing updated rules governing the switching of enabled provisioning data supporting a wireless service contract. A mobile device may be initially programmed with a profile data table and priority list index data table to automatically enable provisioning data supporting one of the plurality of service providers stored in a VSIM internal memory unit to conduct a wireless communication when certain operational parameter values are satisfied. The profile data table and priority list index data table may be automatically updated in response to a variety of triggers. The profile data table and priority list index data table may be stored remotely. Operational parameters regarding each call request are collected and transmitted to a remote service contract selection server. The selection of an optimal service provider account may be made remotely in the service contract selection server and transmitted back to the mobile device.
Owner:QUALCOMM INC
Method and apparatus for installing an application onto a smart card
Owner:ORACLE INT CORP
UICC Carrier Switching Via Over-The-Air Technology
ActiveUS20130023235A1Eliminate needService provisioningUnauthorised/fraudulent call preventionVirtual userCarrier signal
Devices, systems, and methods are disclosed which relate to provisioning a universal integrated circuit card (UICC) with multiple services. The UICC enables a wireless communication device to communicate through multiple carriers by using a unique virtual subscriber identity module (SIM) to register with each carrier. The unique virtual SIM is one of a plurality of virtual SIMs stored on and managed by the UICC. A carrier network includes a server for provisioning a new virtual SIM on a UICC over-the-air (OTA) when a new customer requests a service such as voice, data, or other type of service. These UICCs may also include logic to automatically select the best carrier for a voice call depending on the user settings.
Owner:AT&T INTPROP I L P
System and method for mobile device push communications
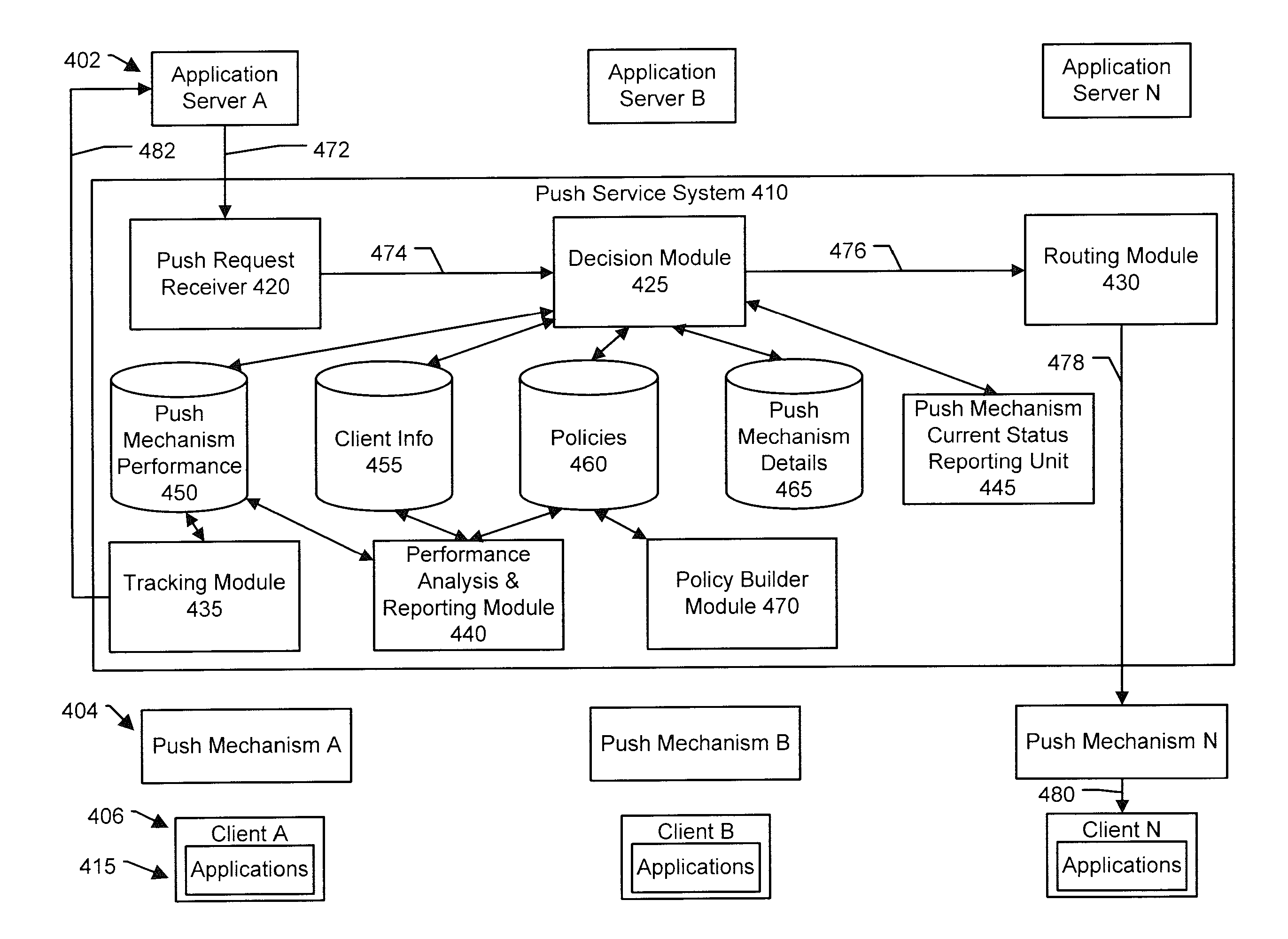
ActiveUS20130047034A1Multiple digital computer combinationsPayment architectureComputer networkMobile device
Pushing data to mobile devices can be problematic because mobile platforms may support a number push services, each of which have different cost and reliability characteristics. The problem of being able to push data to multiple different types of mobile devices from a single server is solved by a push service aggregator supporting multiple push services. Upon receiving a push request, one or more push services are selected for pushing data to a client. The selection may be based on a delivery profile included with the push request, information about the client, past performance of the push services, current status of the push services, or combinations of these. The status of the push may be tracked and monitored so as to retry in the case of non-delivery.
Owner:LOOKOUT MOBILE SECURITY
Method and system for storage and retrieval of blockchain blocks using galois fields
A method and system for storage and retrieval of blockchains with Galois Fields. One or more blocks for a blockchain are securely stored and retrieved with a modified Galois Fields on a cloud or peer-to-peer (P2P) communications network. The modified Galois Field provides at least additional layers for security and privacy for blockchains. The blocks and blockchains are securely stored and retrieved for cryptocurrency transactions including, but not limited to, BITCOIN transactions and other cryptocurrency transactions.
Owner:LESAVICH STEPHEN +1
Method and system for localized data retrieval
ActiveUS9877138B1Easy programmingQuick SetupNetwork topologiesConnection managementData retrievalMobile device
A system and method for localized data retrieval to disseminate data about points of interest at a display venue, based on a local area network established with a series of commonly named wireless access points operatively connected to a main router. The system is connected to a user's mobile device through an application they are directed to download. Each WAP has a common name and is located about the display venue in close enough proximity to other WAPs so as to constitute an uninterrupted communication platform with the main LDRS computer from which data about the points of interest is polled. Interspersed about the display venue is a series of tracking devices causing nearby mobile devices to self report their location to the LDRS computer.
Owner:FRANKLIN WARREN LEE
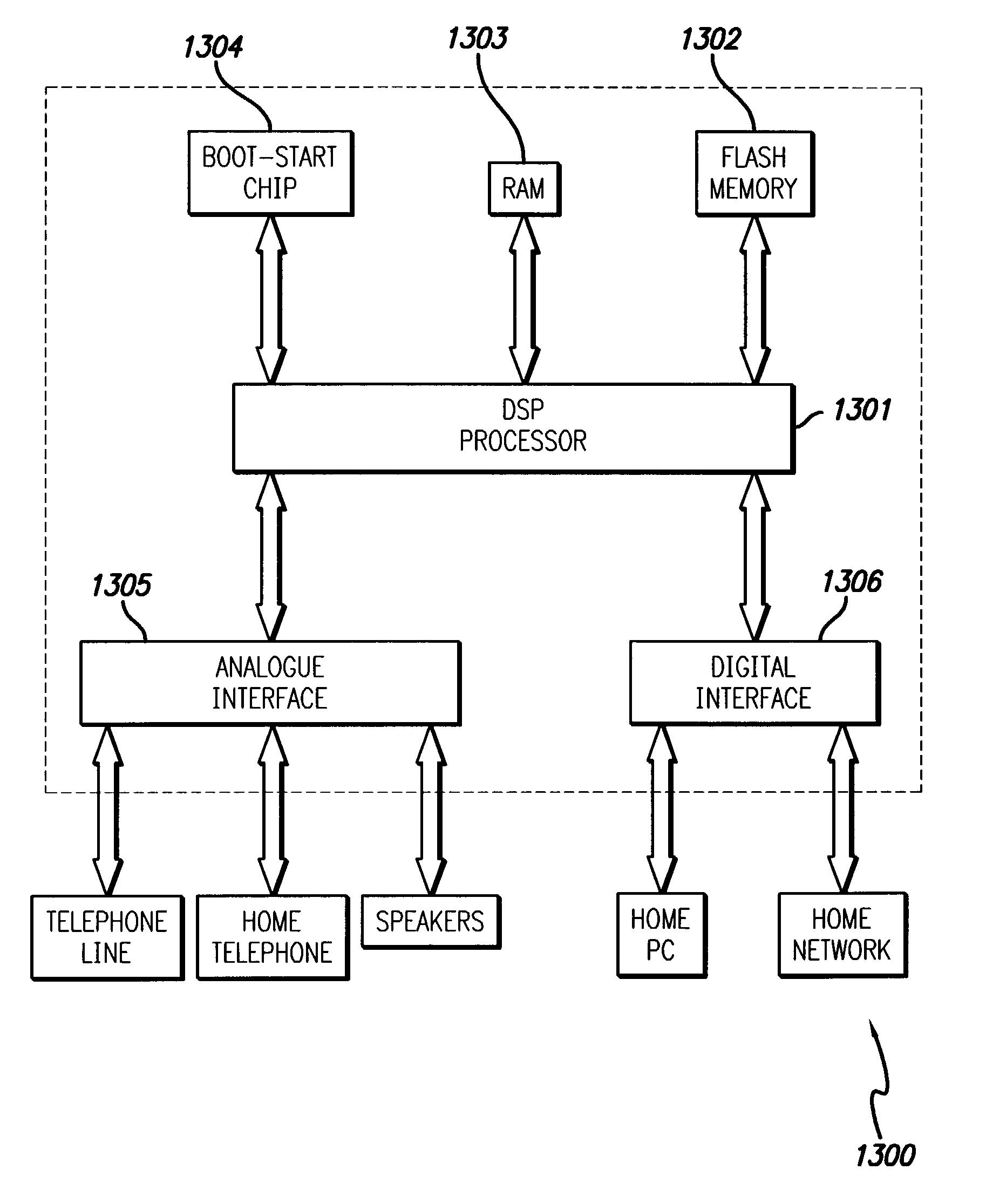
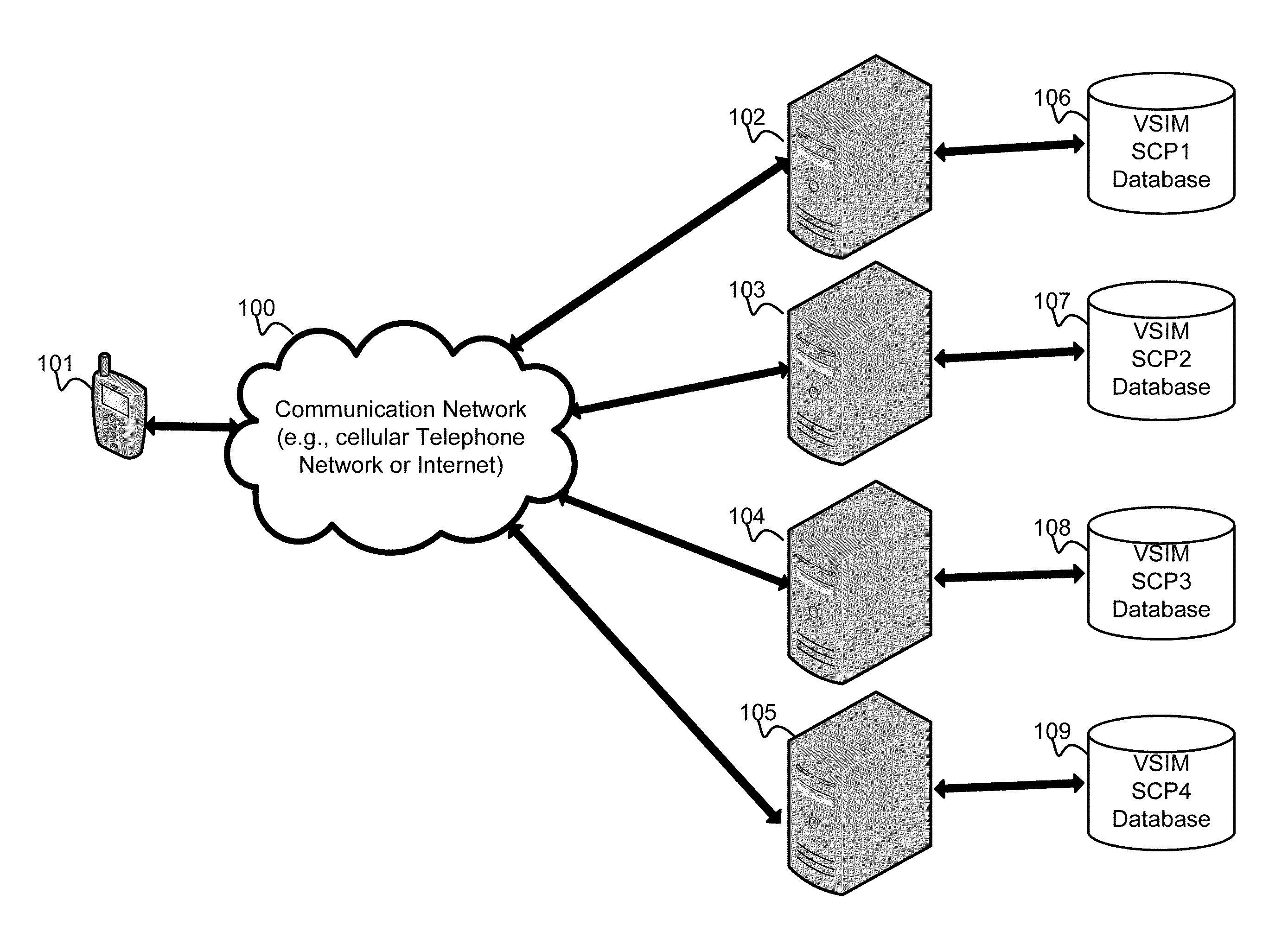
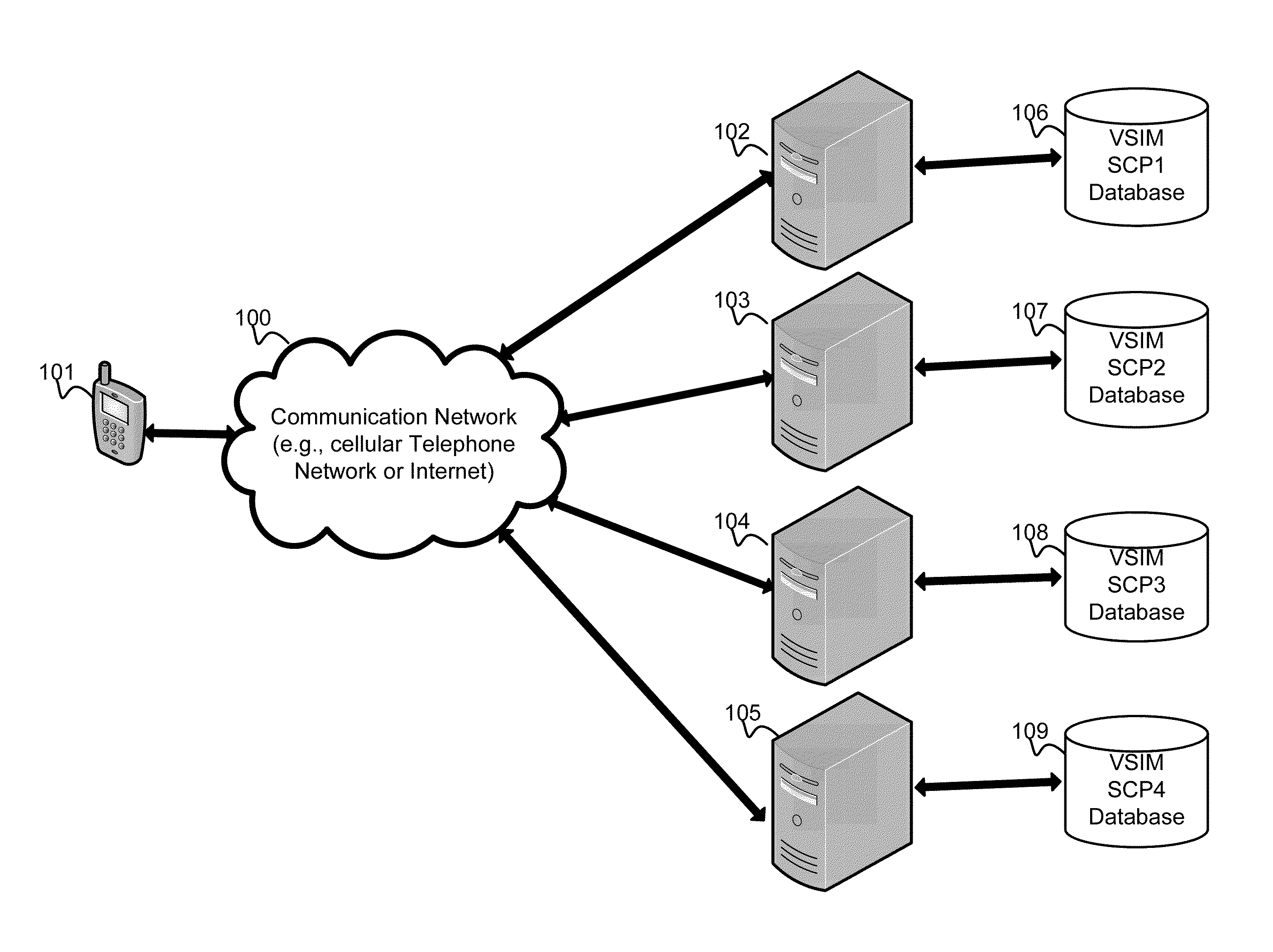
Virtual sim card for mobile handsets
A system and method store provisioning data supporting a plurality of service providers in a VSIM internal memory unit of a mobile device. A user may selectively enable provisioning data supporting one of the plurality of service providers stored in the VSIM internal memory unit to conduct a wireless communication. An embodiment permits backing up, retrieving and restoring personal data in the VSIM internal memory unit using a remote database. Another embodiment allows a mobile device to select an optimal service provider to conduct a wireless communication. The optimal service provider may be determined based upon mobile device location, communication usage request and / or time and date.
Owner:QUALCOMM INC
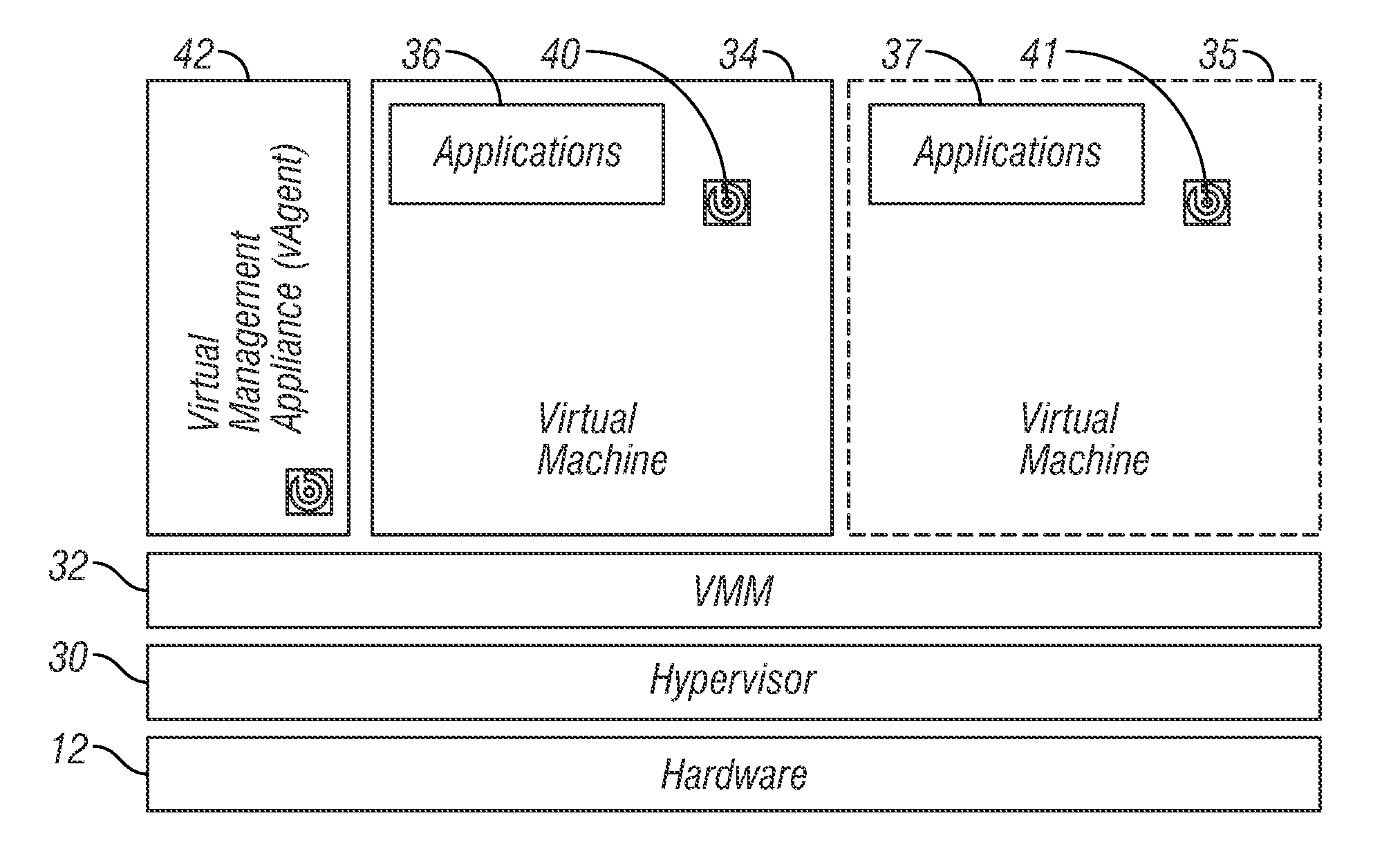
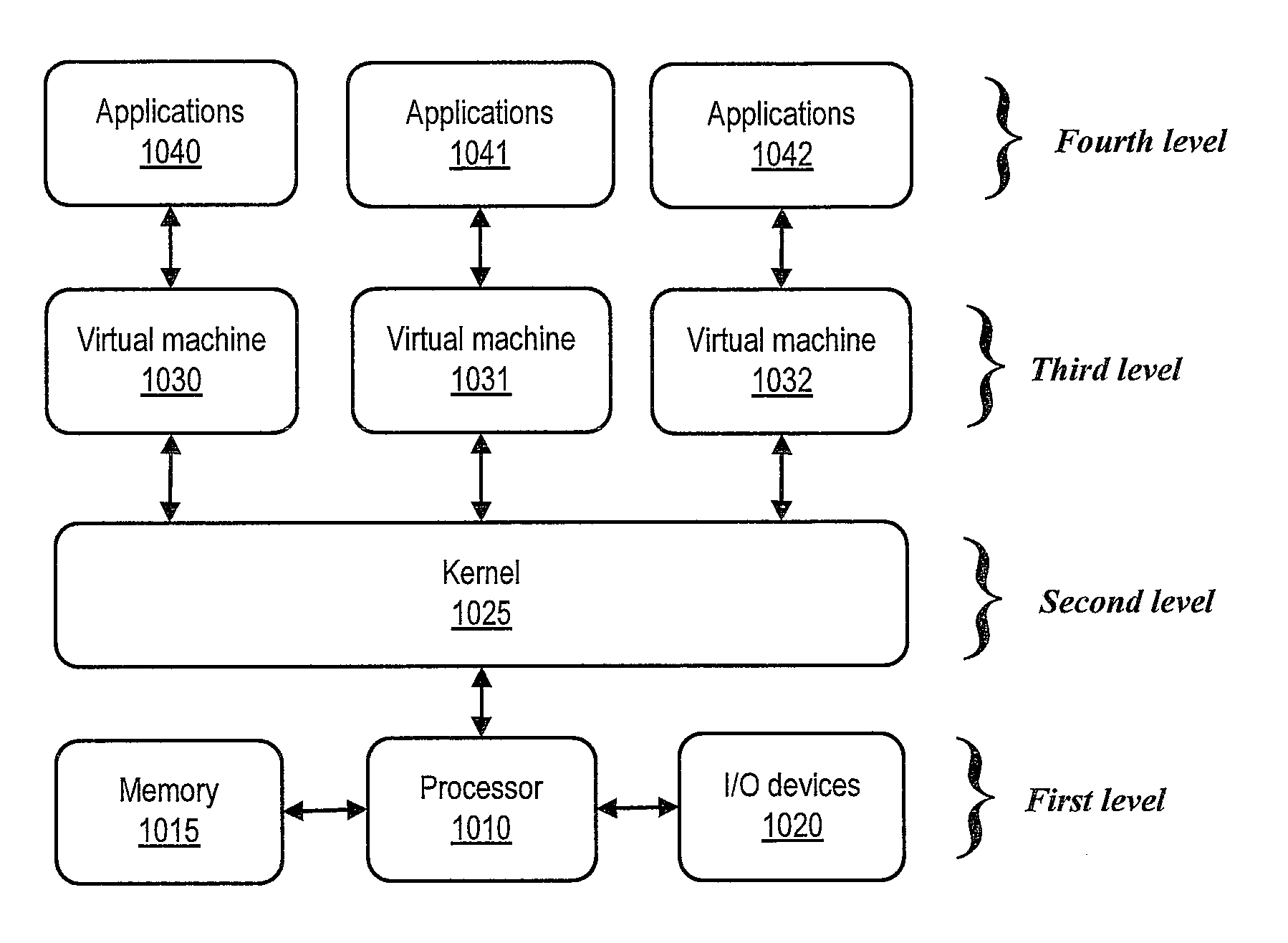
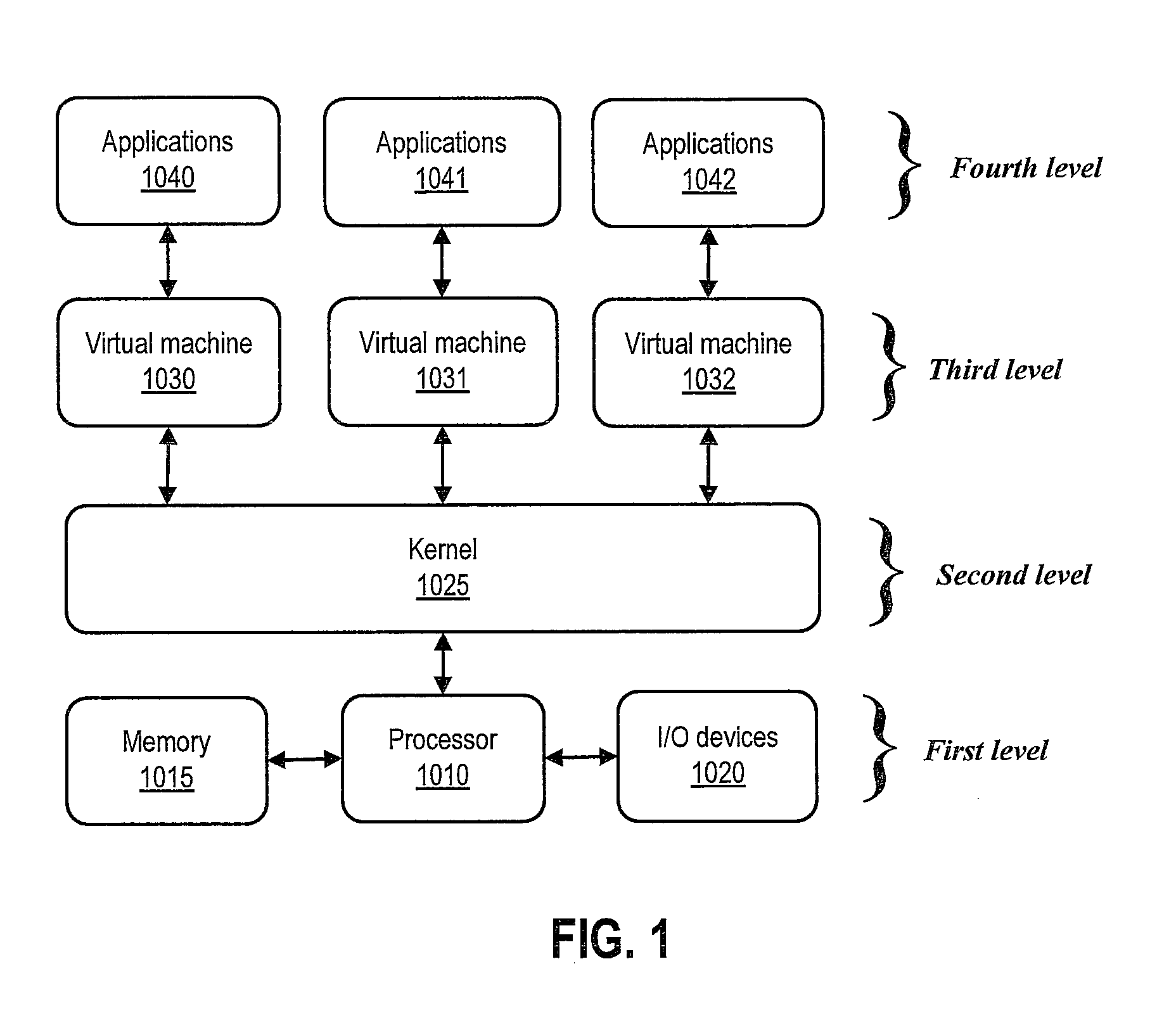
Endpoint-Hosted Hypervisor Management
InactiveUS20110107331A1New of controlNew levelService provisioningMobile application execution environmentsOperational systemClient-side
A client hypervisor comprises a virtual agent that runs outside of a system OS and that allows device management independent of the OS and user. The virtual agent is tied to a device and not a specific instance of the OS. Such client hypervisors expose new functionality to ease managing systems. Some of these capabilities come from the persistence and privileges outside the OS. In some embodiments of the invention, this new management functionality is exposed to allow device management via new virtualization concepts, such as multiple VMs per system, VM replacement, snapshot / rollback, etc.
Owner:IBM CORP
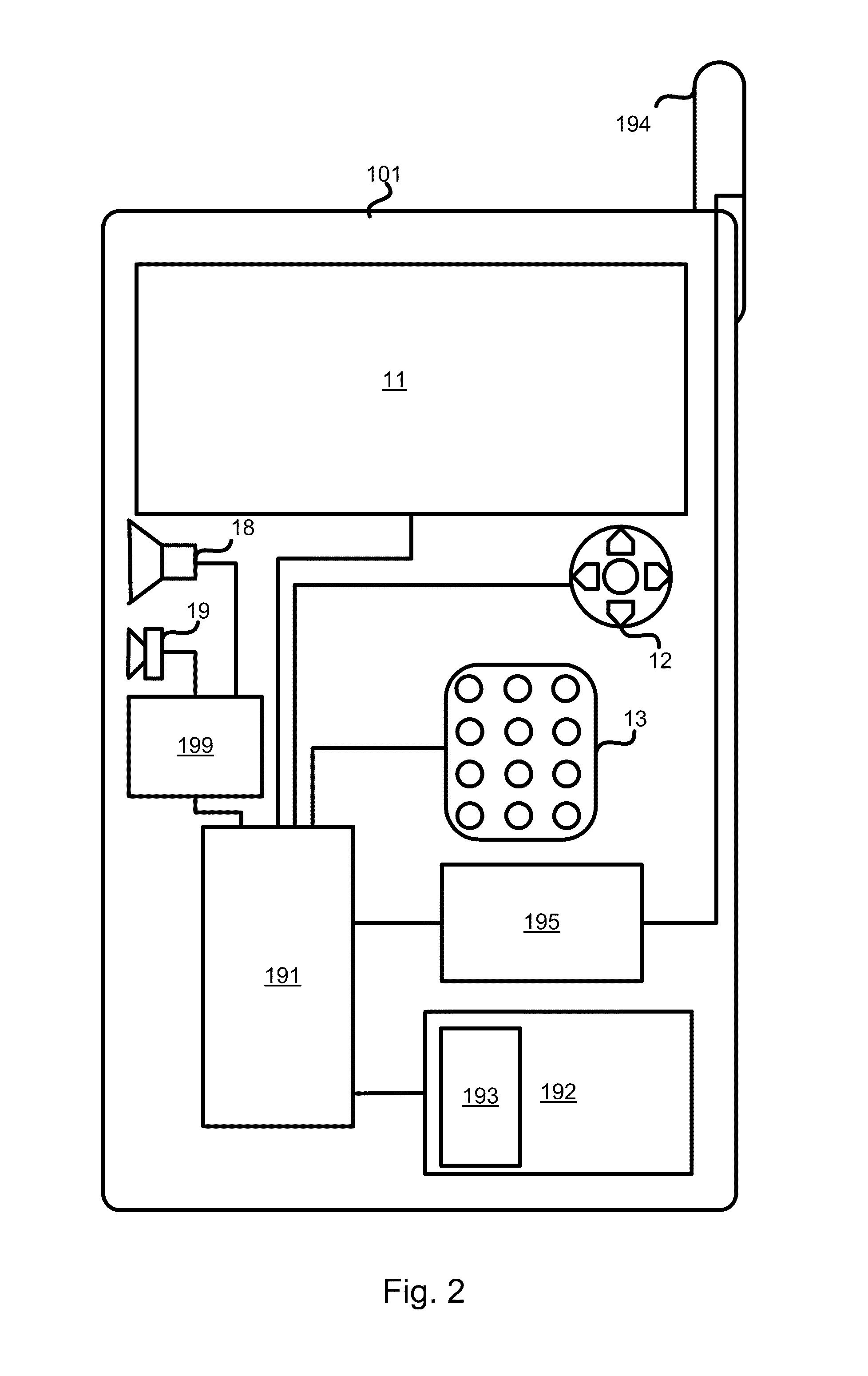
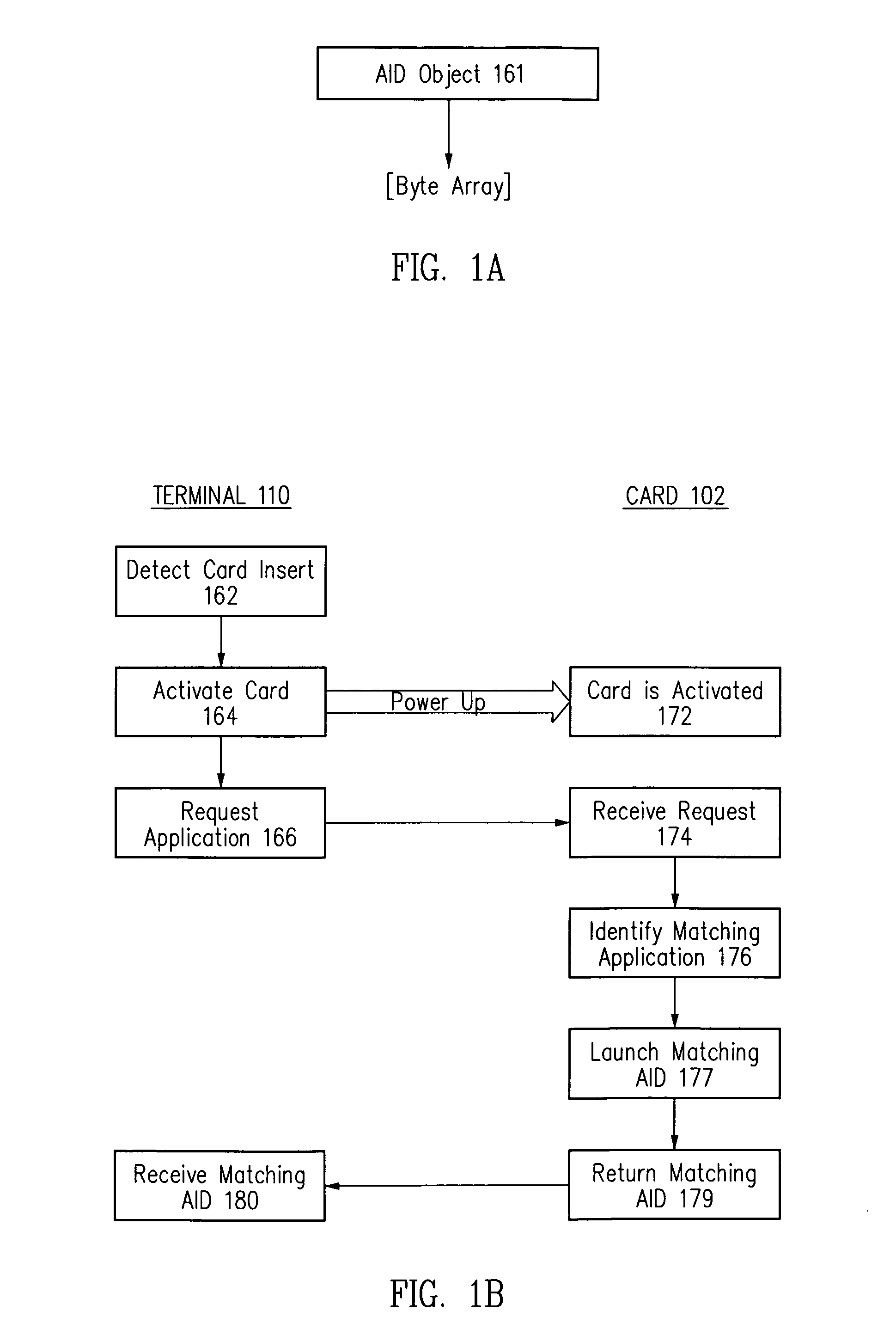
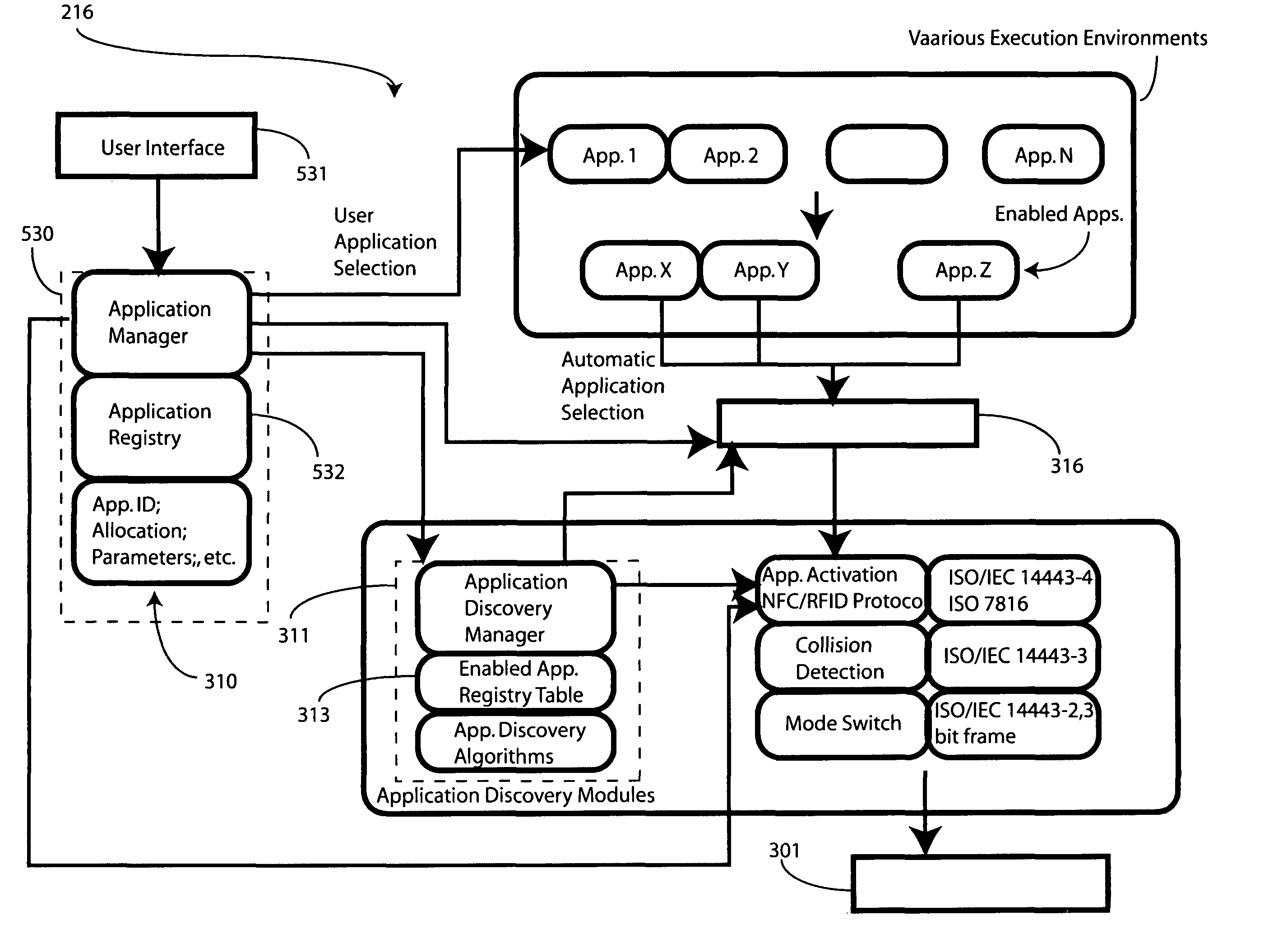
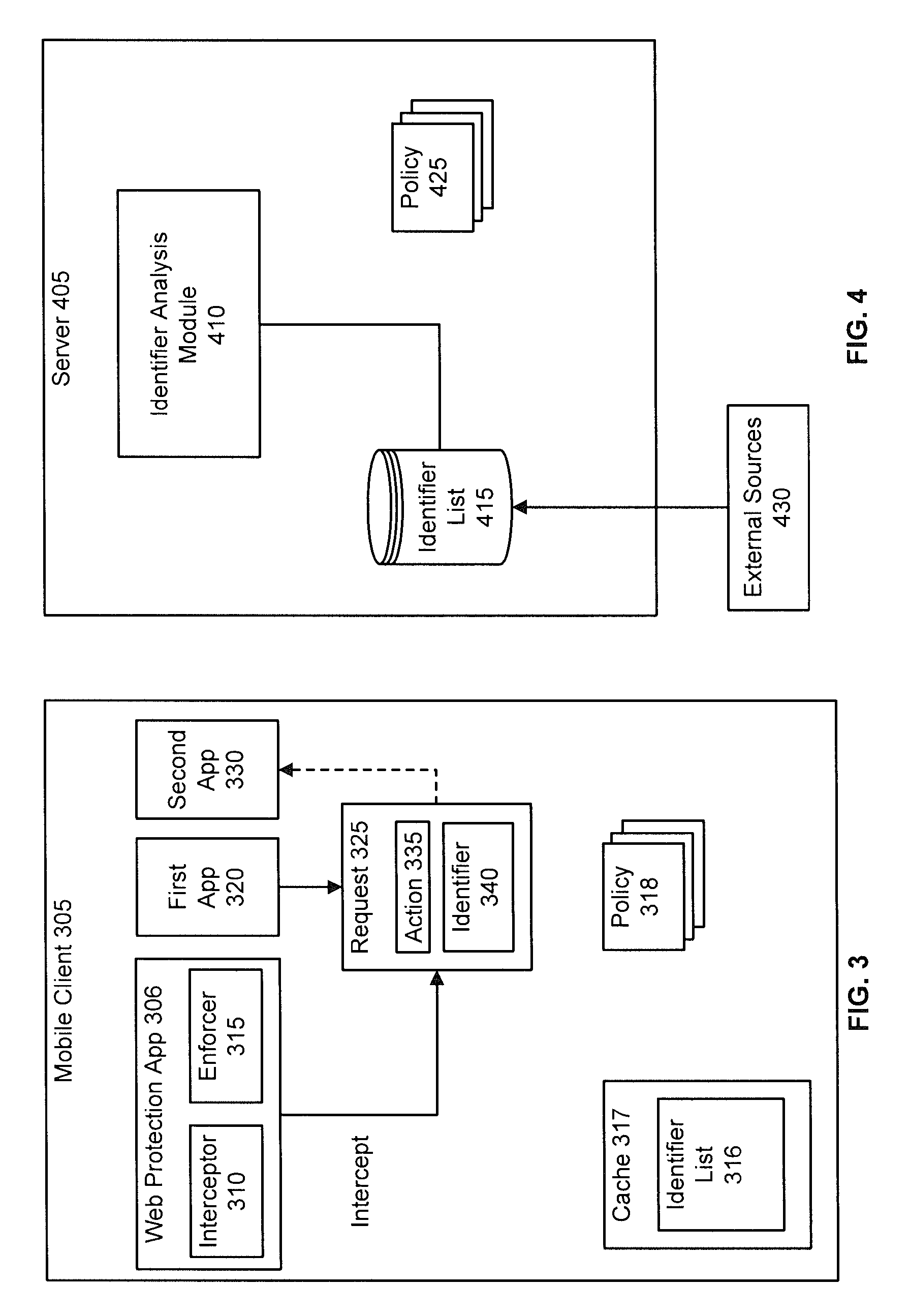
Method and apparatus for automatic near field communication application selection in an electronic device
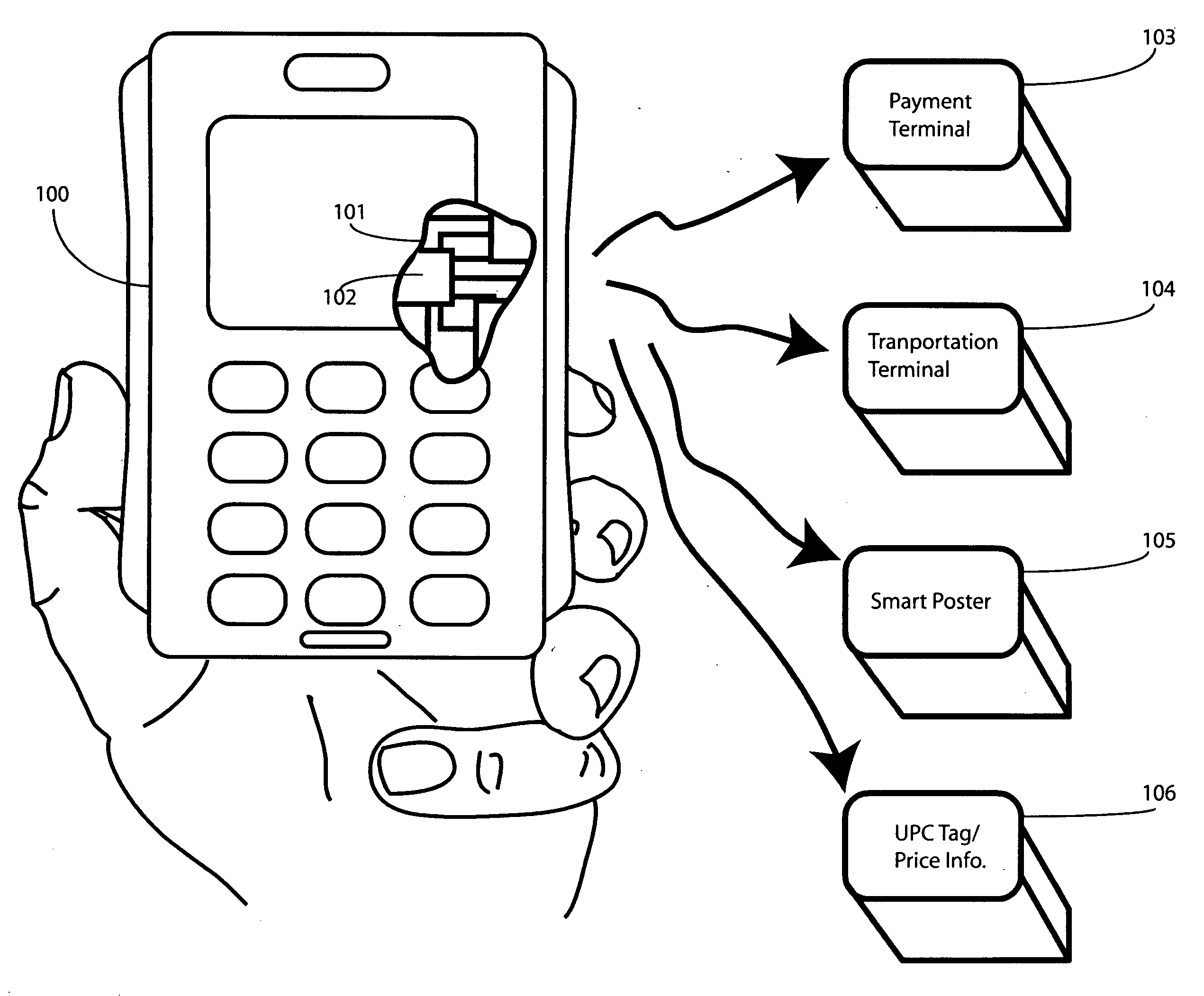
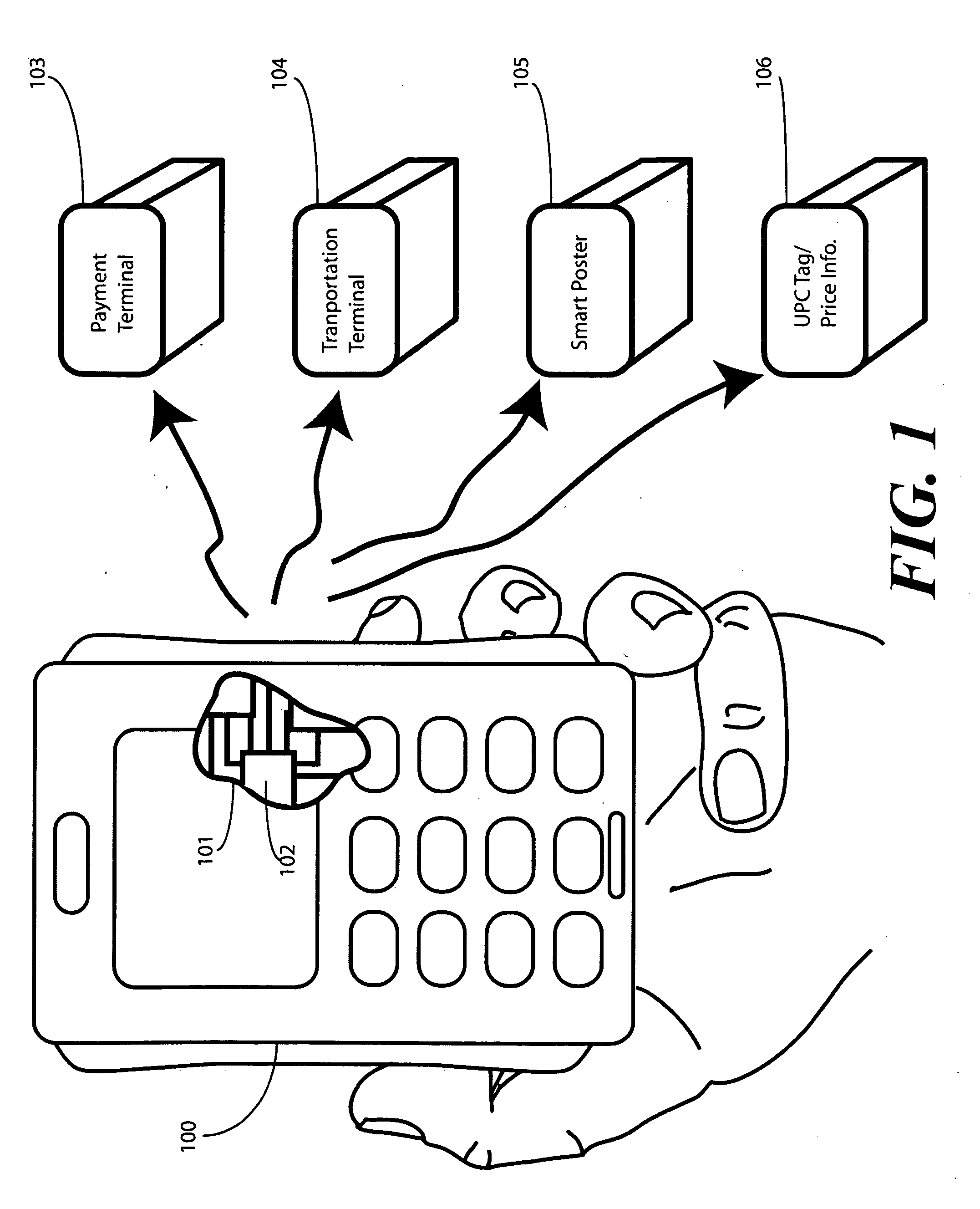
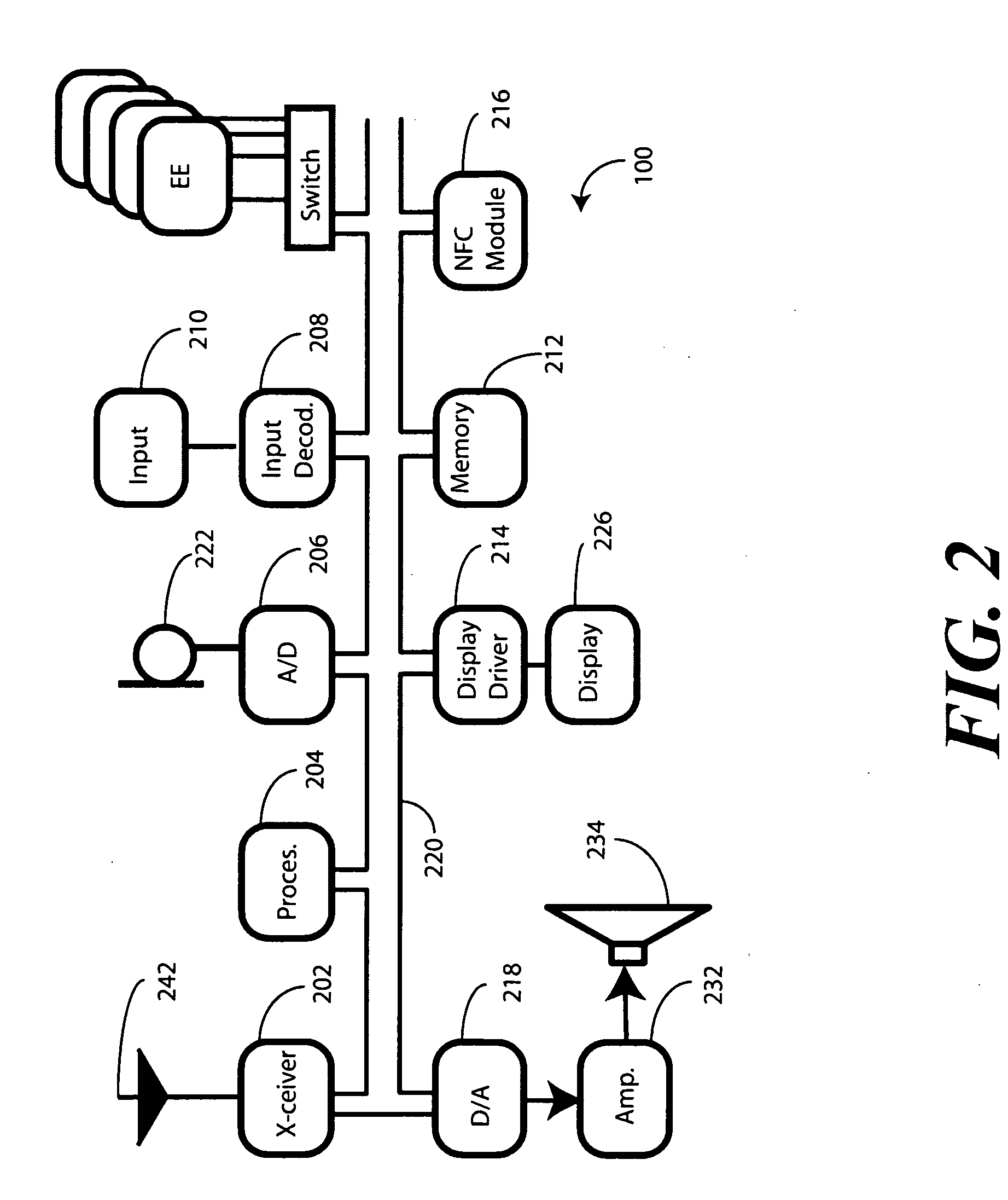
In a portable electronic device (100) having a plurality of near field communication applications stored within a plurality of execution environments, an application discovery manager (311) is configured to automatically select and launch one or more of the near field communication applications. A near field communication circuit (300) receives a near field communication request from an external near field communication device (700). The application discovery manager (311) identifies a near field communication technology, a protocol, and an application identifier and then references a registry table (313) to determine identification parameters corresponding with the identified information. The application discovery manager (311) then selects a near field communication application and launches it. The application discovery manager (311) further configures a routing switch (316) to direct data between the near field communication circuit controller (301) and the appropriate execution environment.
Owner:GOOGLE TECH HLDG LLC
Wireless inter-device data processing configured through inter-device transmitted data
ActiveUS8244179B2Near-field for read/write/interrrogation/identification systemsBroadcast services for monitoring/identification/recognitionUltra-widebandComputer hardware
A wireless media player and a related system and methodology are disclosed. One aspect of the wireless media player system pertains to a virtual connector system, apparatus, and method for the automatic establishment of wireless connectivity with other electronic devices. In one embodiment, the media player device employs the use of integrated Radio Frequency Identification (RFID) technology to exchange communication settings, media capability, and other parameters with an external device that also has integrated RFID technology. The automatic exchange of settings and other information via a proximity-based RFID data exchange allows a media player to quickly establish a secure communication link with another device via a commonly supported wireless protocol such as Ultra Wideband (UWB) or Bluetooth. Another aspect of the media player system pertains to a method of using the captured media capability of the connecting device to customize certain menu options and software parameters in the media player.
Owner:SYNDEFENSE
Scalable Secure Wireless Interaction enabling Methods, System and Framework
InactiveUS20120084364A1Avoiding self-configuringConnection securityNetwork topologiesMultiple digital computer combinationsNetwork conditionsOperation mode
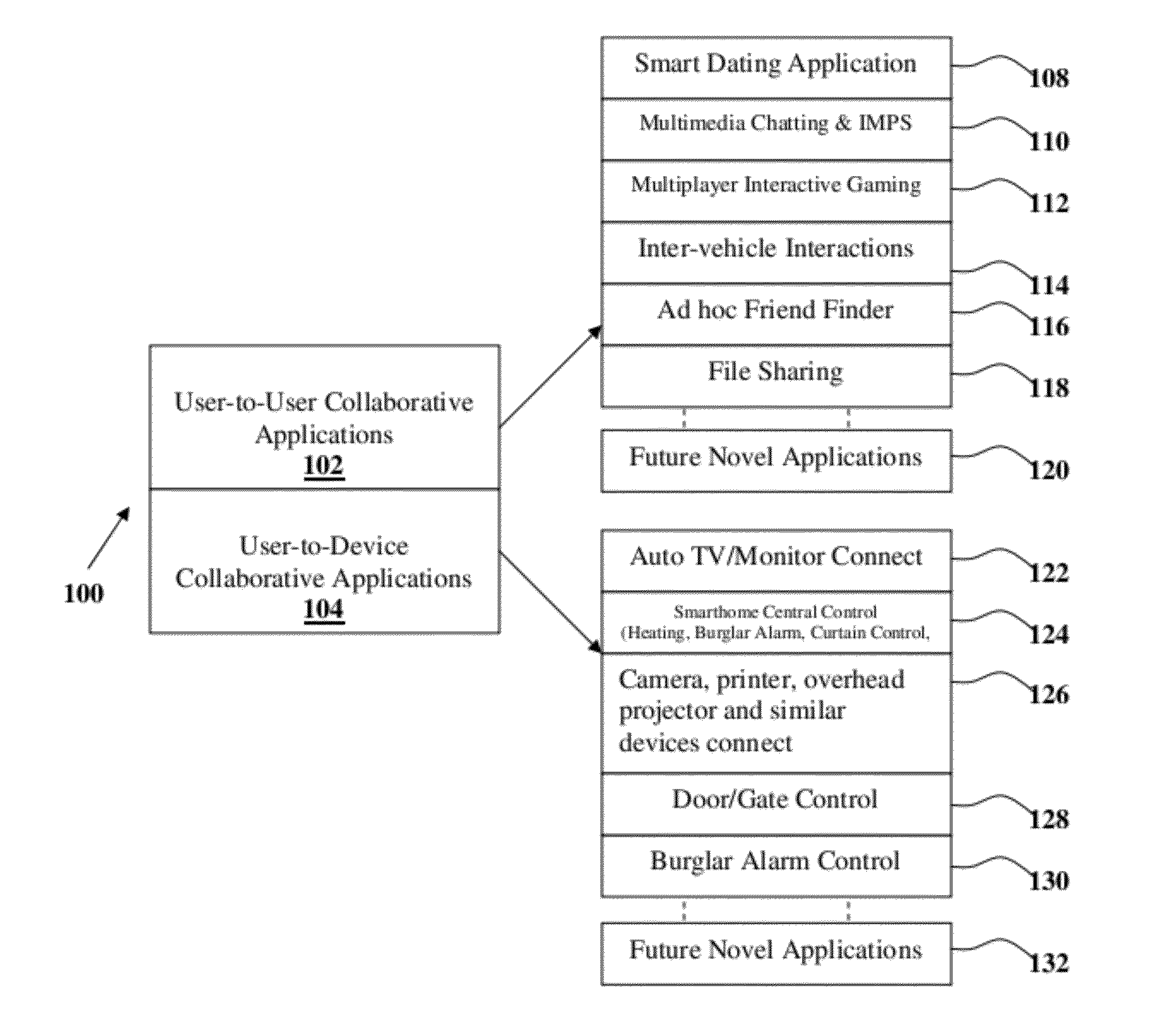
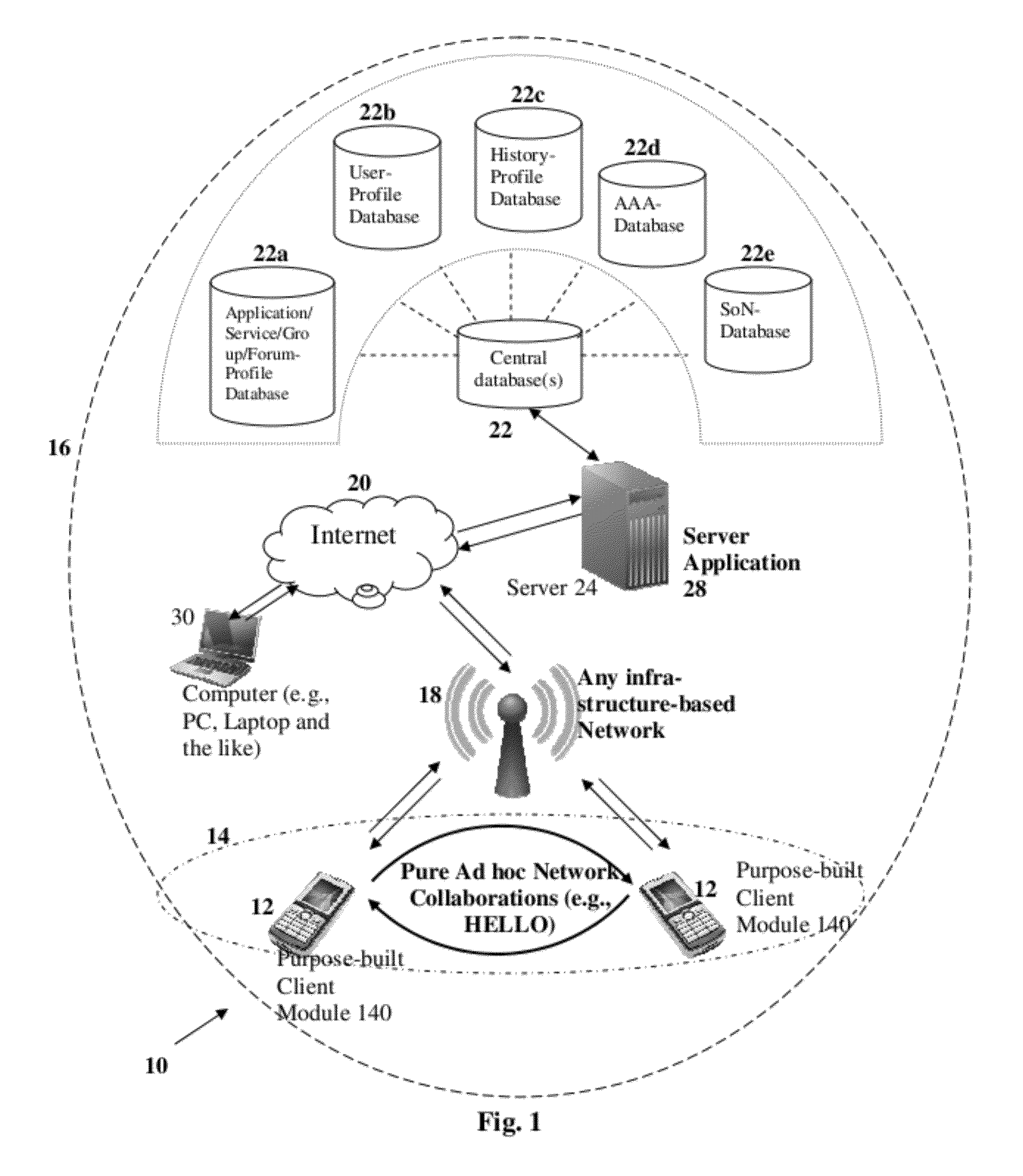
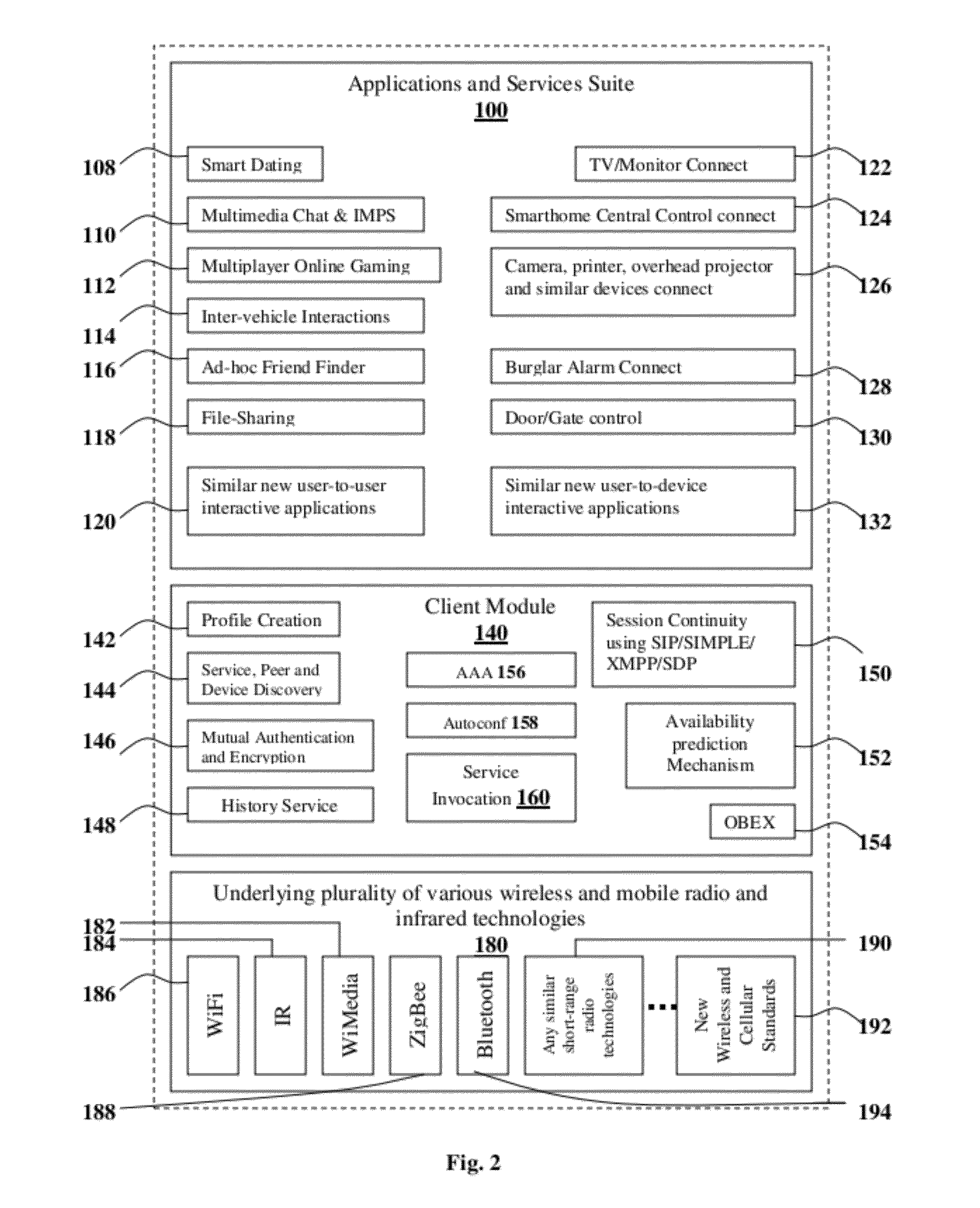
The present invention proposes methodologies, a system and a secure spontaneous collaboration framework along with a suitable application and services suite for enabling new paradigm of social networking among users of handheld devices by bridging gab between infra-structure-based networks and mobile ad hoc networks. While supporting three different operating modes for the spontaneous collaboration that suits the user preference and network conditions, the proposed solutions hide the complexity of finding the right peer / device for spontaneous collaboration, self-organising the network to be formed on-demand, mitigating the security threat, being aware of user mobility for service continuity across wide variety of networks. Binding a given user to user's handheld device and specifying the number of applications / services enabling spontaneous collaborations that a given user is interested in are possible through user-profile creations. By taking a holistic view, the proposed solutions enable very practical, scalable, secure and economical spontaneous collaborations.
Owner:SIVAVAKEESAR SIVAPATHALINGHAM
Method and system for electronic content storage and retrieval with galois fields on cloud computing networks
InactiveUS20120278622A1Web data indexingDigital data processing detailsCloud storageCloud communications
A method and system for electronic content storage and retrieval with Galois Fields on cloud computing networks. The electronic content is divided into plural portions and stored in plural cloud storage objects. Storage locations for the plural cloud storage objects are selected using a Galois field and the plural cloud storage objects are distributed across the cloud network. When the electronic content is requested, the plural portions are retrieved and transparently combined back into the original electronic content. No server network devices or target network devices can individually determine locations of all portions of the electronic content on the cloud communications network, thereby providing layers of security and privacy for the electronic content on the cloud communications network.
Owner:LESAVICH STEPHEN +1
Method and apparatus for updating rules governing the switching of virtual sim service contracts
A system and method for providing updated rules governing the switching of enabled provisioning data supporting a wireless service contract. A mobile device may be initially programmed with a profile data table and priority list index data table to automatically enable provisioning data supporting one of the plurality of service providers stored in a VSIM internal memory unit to conduct a wireless communication when certain operational parameter values are satisfied. The profile data table and priority list index data table may be automatically updated in response to a variety of triggers.
Owner:QUALCOMM INC
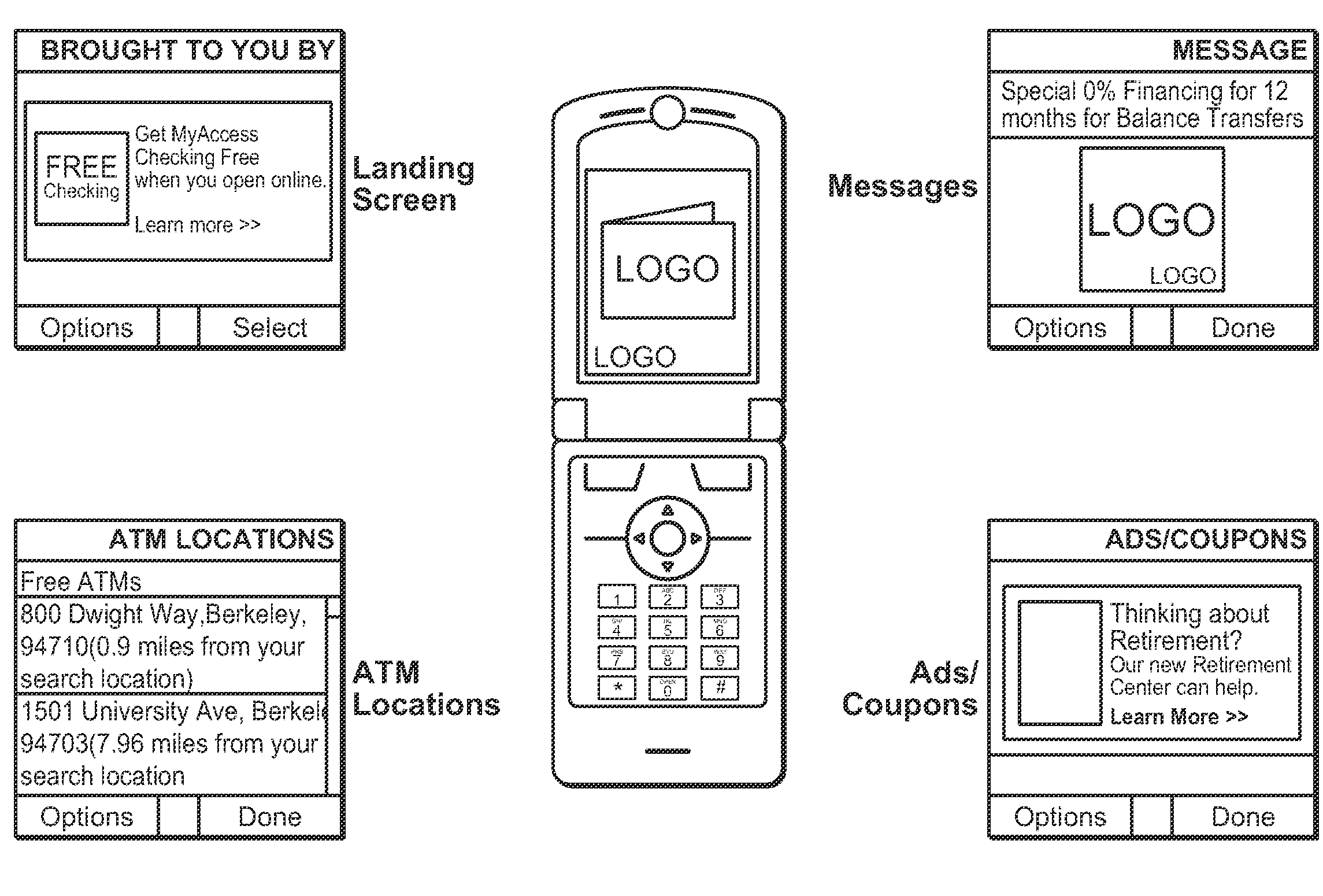
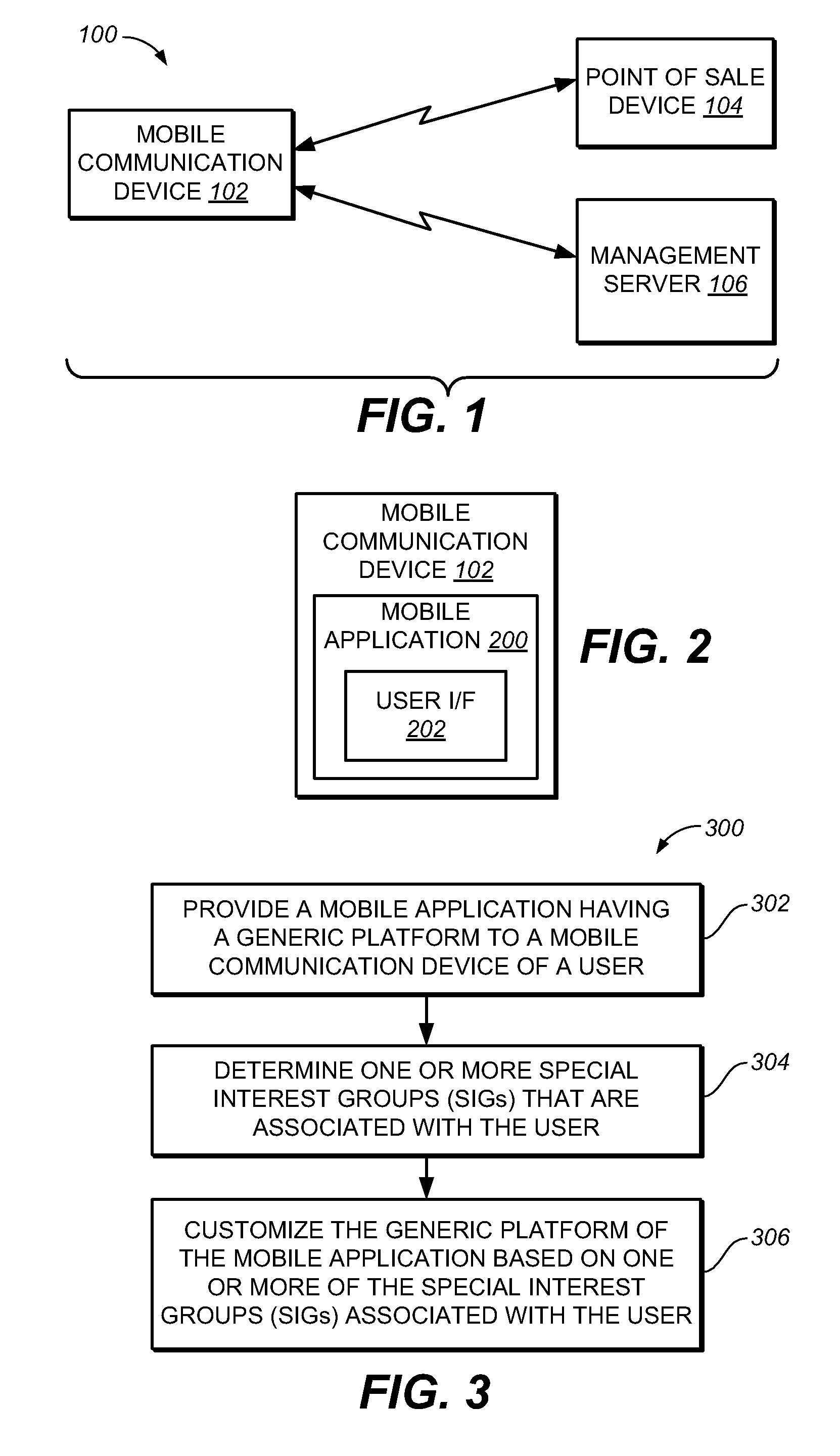
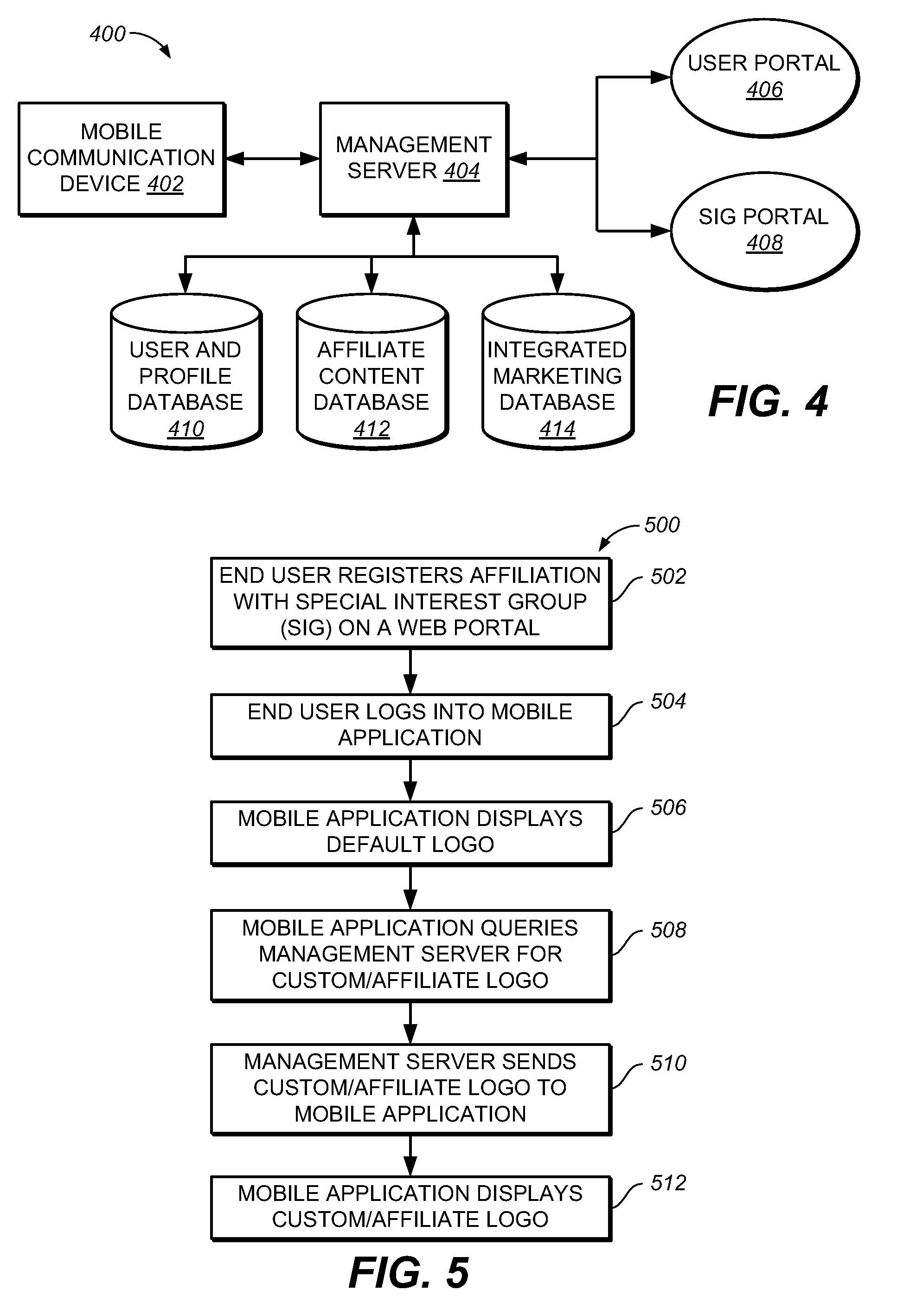
Method and system for delivering customized information to a mobile communication device based on user affiliations
A method and system for customizing a mobile application running on a mobile communication device of a user. In one implementation, the method includes providing the mobile application to the mobile communication device of the user, the mobile application having a generic platform; determining a special interest group (SIG) that is affiliated with the user; and customizing the generic platform of the mobile application based on information specific to the special interest group (SIG) that is affiliated with the user.
Owner:FISHER MICHELLE T
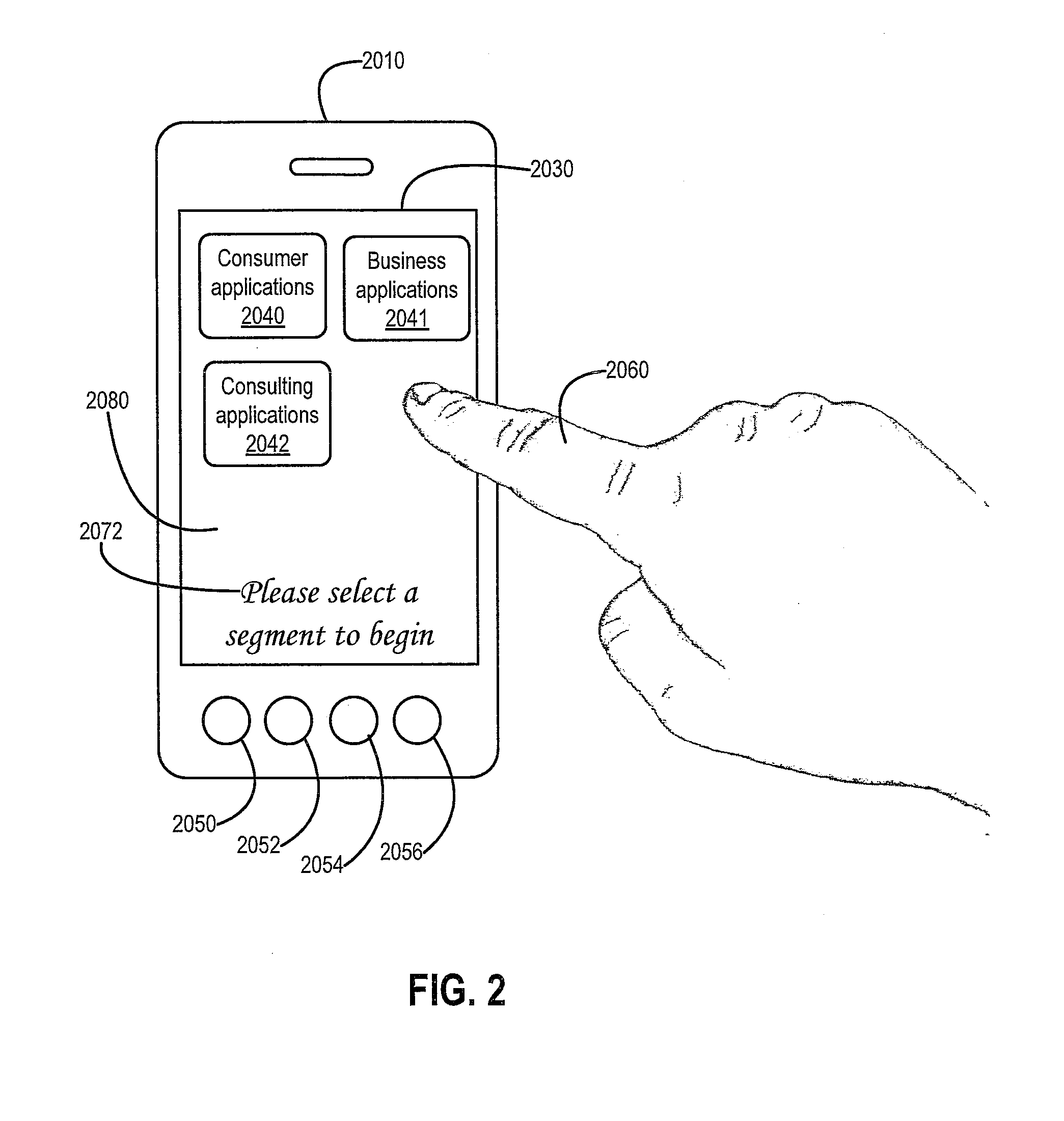
Multiple Mode Mobile Device
ActiveUS20110145833A1Unauthorised/fraudulent call preventionDigital data processing detailsUser inputPassword
In one or more embodiments, one or more methods and / or systems described can perform displaying, on a handheld device, multiple icons associated with multiple segments; receiving first user input indicating a first segment of the multiple segments; executing a first virtual machine associated with the first segment on the handheld device; executing a first application on the first virtual machine; receiving second user input indicating a second segment of the multiple segments; executing a second virtual machine associated with the second segment on the handheld device; and executing a second application on the second virtual machine. In one or more embodiments, one or more methods and / or systems described can further perform before executing the second virtual machine, receiving authentication information and determining that the user is authenticated. In one or more embodiments, the authentication information can include at least one of a user name, a password, and / or biometric information.
Owner:AT&T MOBILITY II LLC
Electronic access client distribution apparatus and methods
ActiveUS20120331292A1Effective distributionEfficiently distributedDigital data processing detailsUser identity/authority verificationElectronic accessService provision
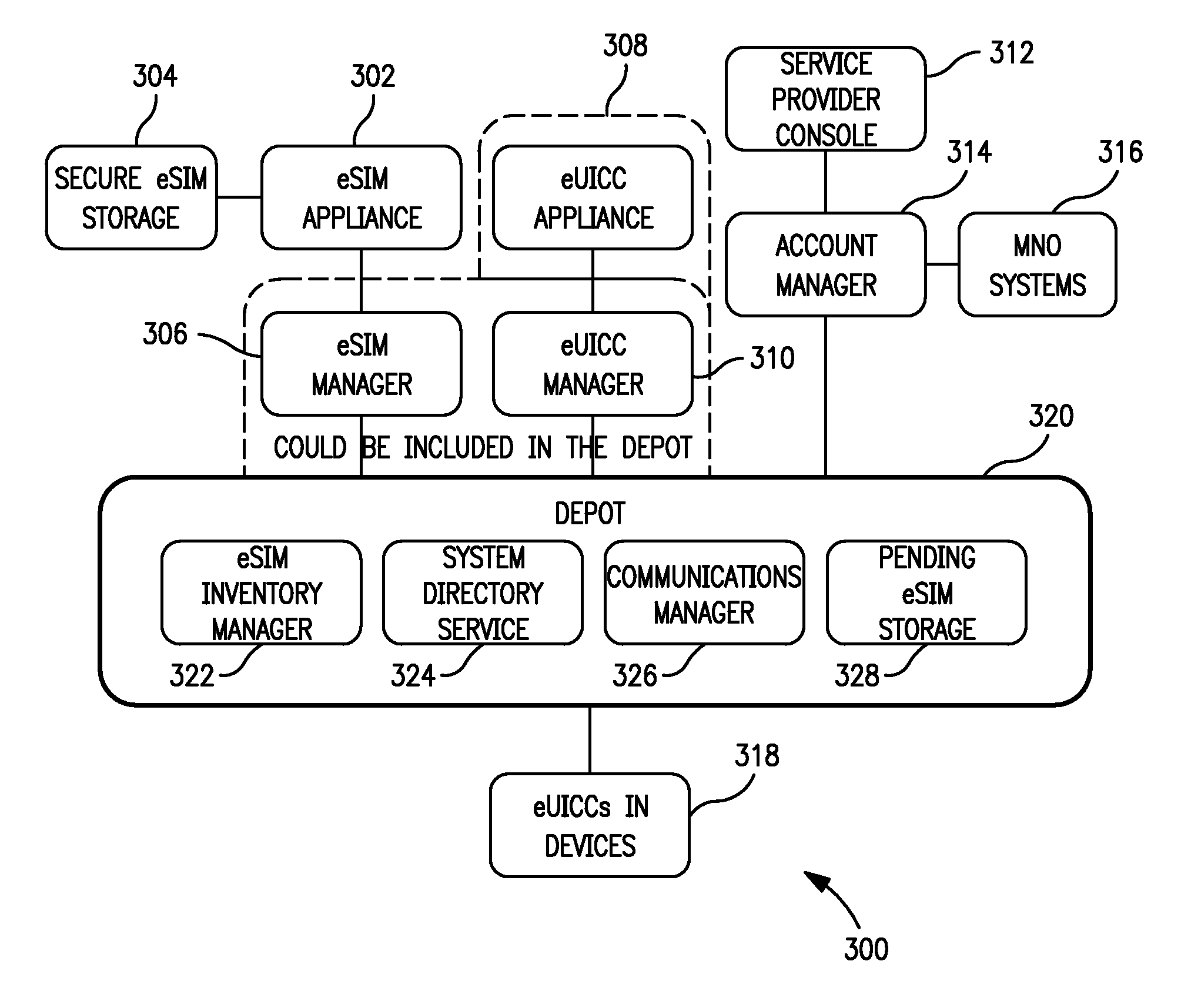
Apparatus and methods for distributing access control clients. In one exemplary embodiment, a network infrastructure is disclosed that enables delivery of electronic subscriber identity modules (eSIMs) to secure elements (e.g., electronic Universal Integrated Circuit Cards (eUICCs), etc.) The network architecture includes one or more of: (i) eSIM appliances, (ii) secure eSIM storages, (iii) eSIM managers, (iv) eUICC appliances, (v) eUICC managers, (vi) service provider consoles, (vii) account managers, (viii) Mobile Network Operator (MNO) systems, (ix) eUICCs that are local to one or more devices, and (x) depots. Moreover, each depot may include: (xi) eSIM inventory managers, (xii) system directory services, (xiii) communications managers, and / or (xiv) pending eSIM storages. Functions of the disclosed infrastructure can be flexibly partitioned and / or adapted such that individual parties can host portions of the infrastructure. Exemplary embodiments of the present invention can provide redundancy, thus ensuring maximal uptime for the overall network (or the portion thereof).
Owner:APPLE INC
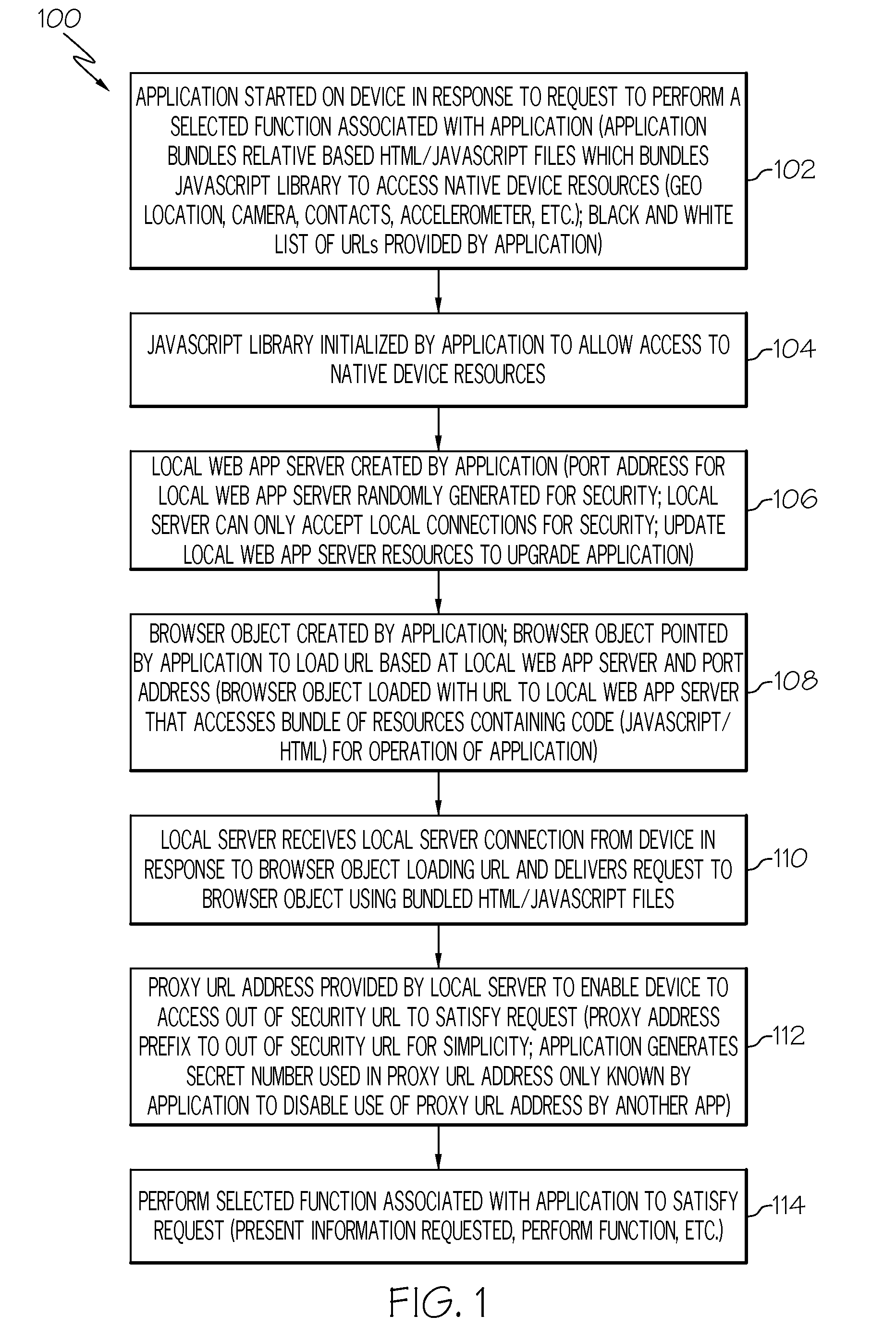
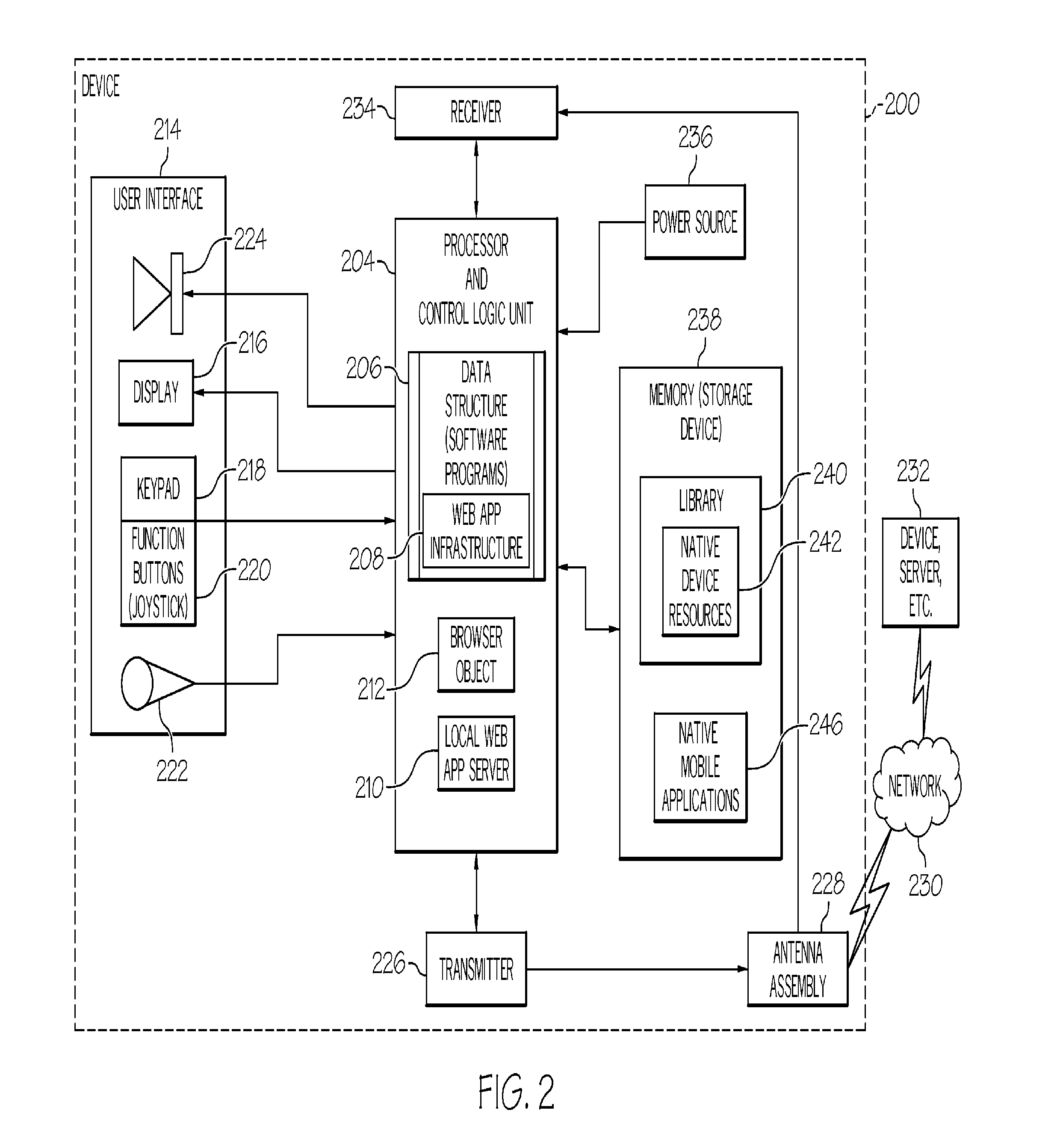
Mobile web app infrastructure
InactiveUS20120317233A1Multiple digital computer combinationsMobile application execution environmentsApplication softwareUniform resource locator
A method, device and computer program product for forming a mobile web app infrastructure on a device may include creating a local web app server on the device in response to an application being started on the device. A proxy uniform resource locator (URL) address may be provided by the local web app server that enables the device to access an out of security URL to perform a function associated with the application.
Owner:TERRACE LICENSING LLC
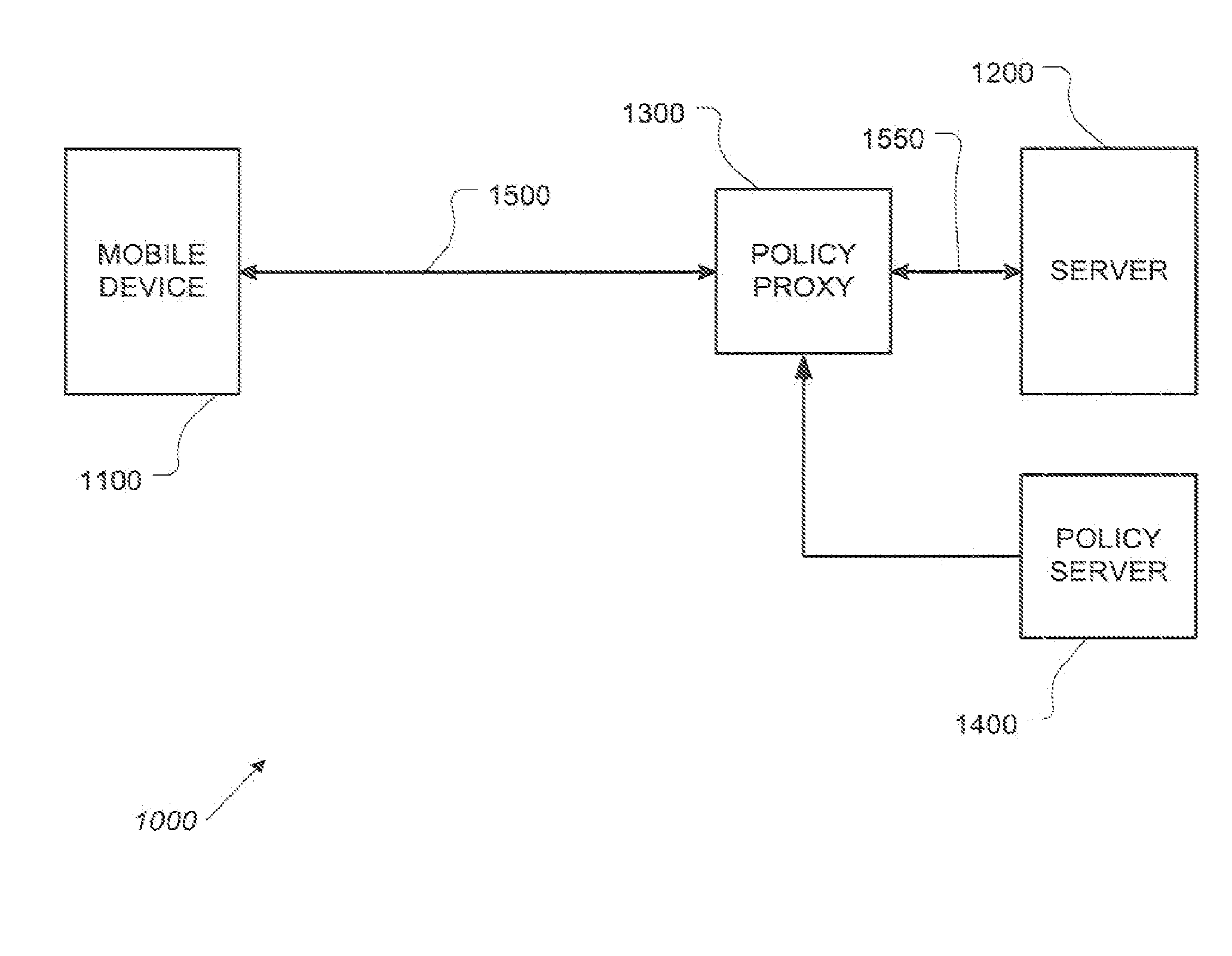
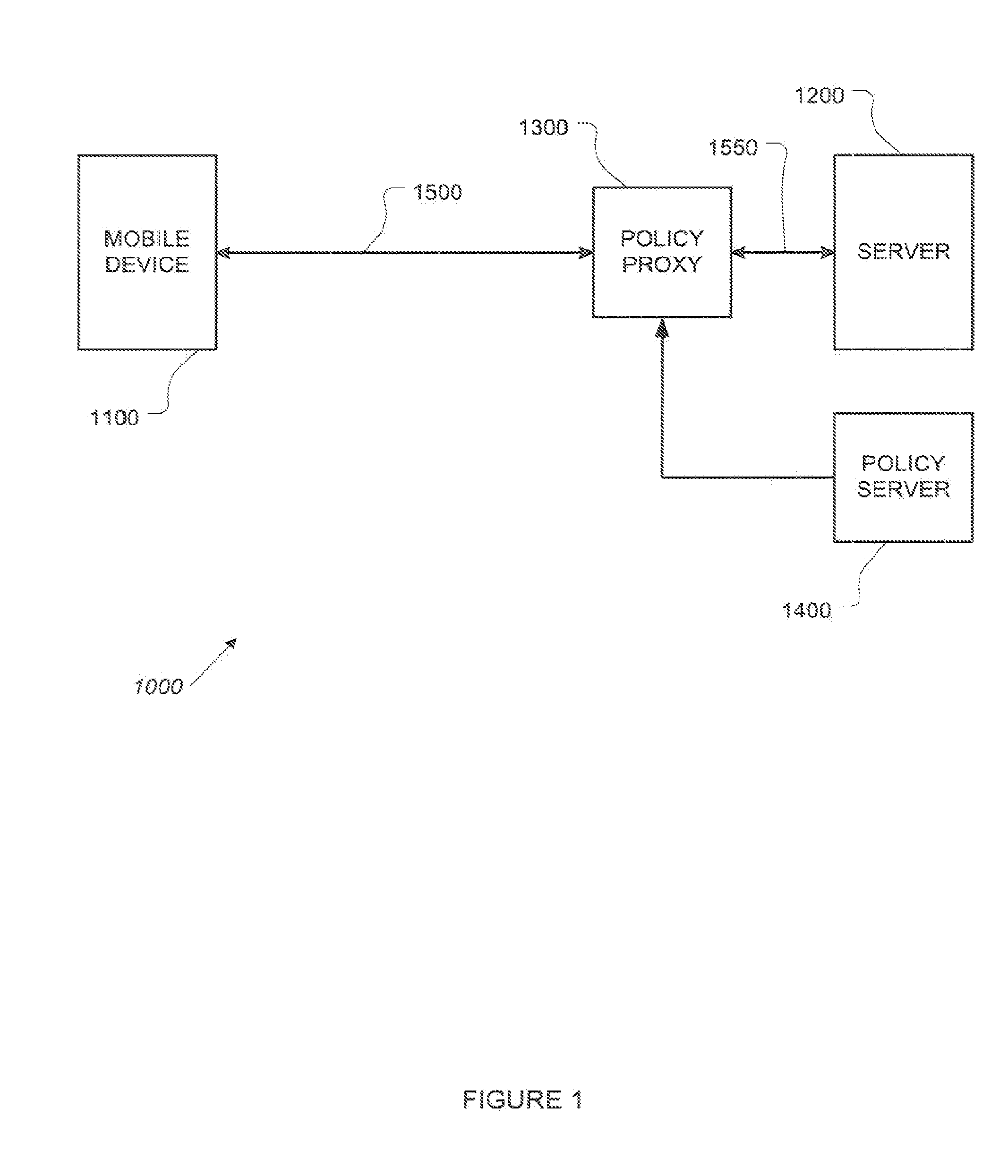
Distributed data revocation using data commands
ActiveUS20110276683A1Increase flexibilityIncrease productivityMultiple digital computer combinationsMobile application execution environmentsData streamUser device
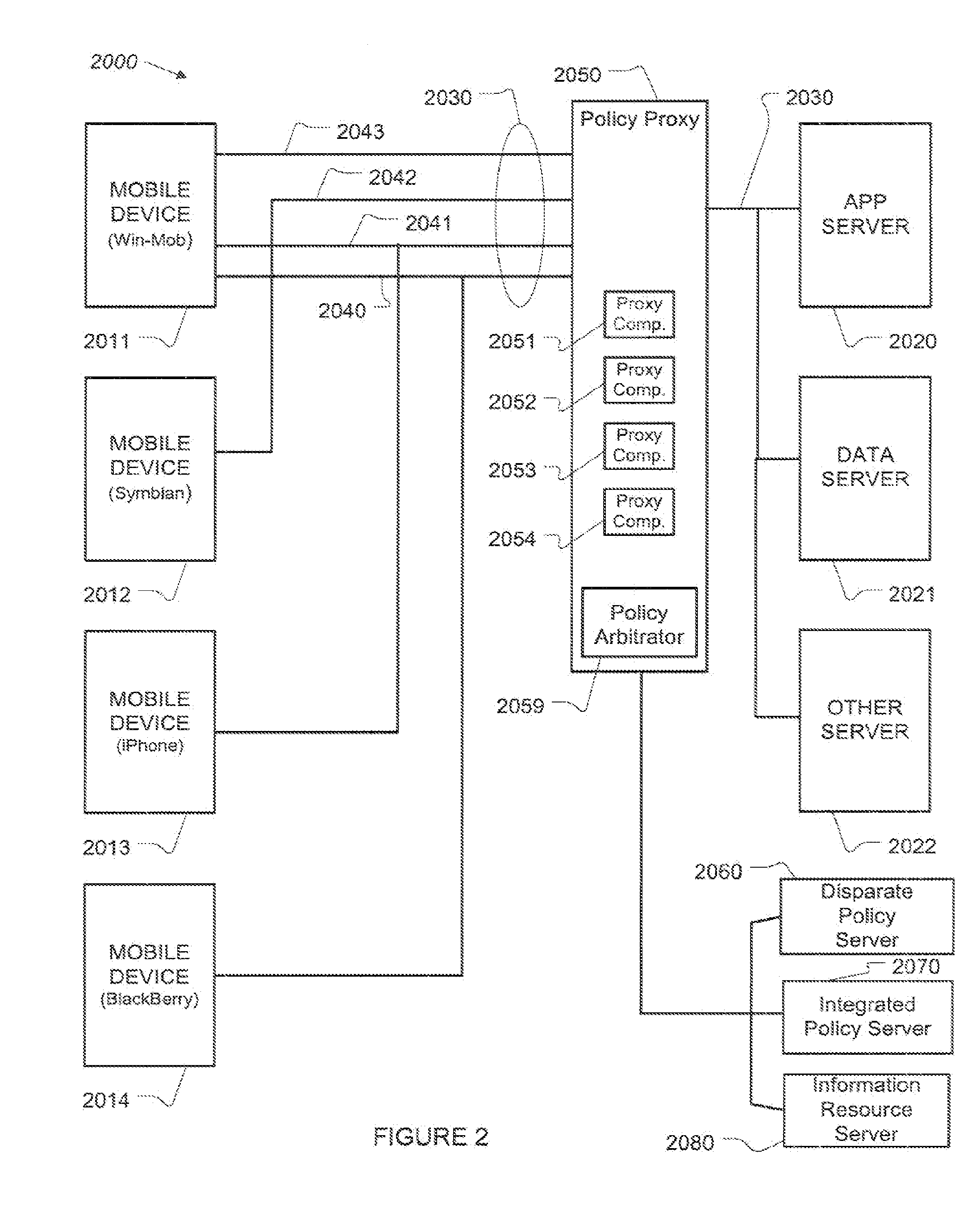
A policy proxy intercepts a data stream between a data server and a user or other device, identifies the user device, and identifies a policy in an integrated policy server applicable to the user device based on the identity of the user device. The policy proxy may identify one or more of the policy elements based on the user device, and translate the policy elements into actions involving the data stream between the data server and the user device so as to implement at least one aspect of the identified policy. The actions can comprise permitting normal exchange of data between the data server and the user device, preventing communication between the data server and the user device, or modifying the data stream between the data server and the user device.
Owner:SKYHIGH SECURITY LLC +1
Method and Apparatus for Automatic Near Field Communication Application Selection in an Electronic Device
ActiveUS20090247077A1Near-field transmissionSubstation equipmentComputer hardwareApplication Identifier
In a portable electronic device (100) having a plurality of near field communication applications stored within a plurality of execution environments, an application discovery manager (311) is configured to automatically select and launch one or more of the near field communication applications. A near field communication circuit (300) receives a near field communication request from an external near field communication device (700). The application discovery manager (311) identifies a near field communication technology, a protocol, and an application identifier and then references a registry table (313) to determine identification parameters corresponding with the identified information. The application discovery manager (311) then selects a near field communication application and launches it. The application discovery manager (311) further configures a routing switch (316) to direct data between the near field communication circuit controller (301) and the appropriate execution environment.
Owner:GOOGLE TECH HLDG LLC
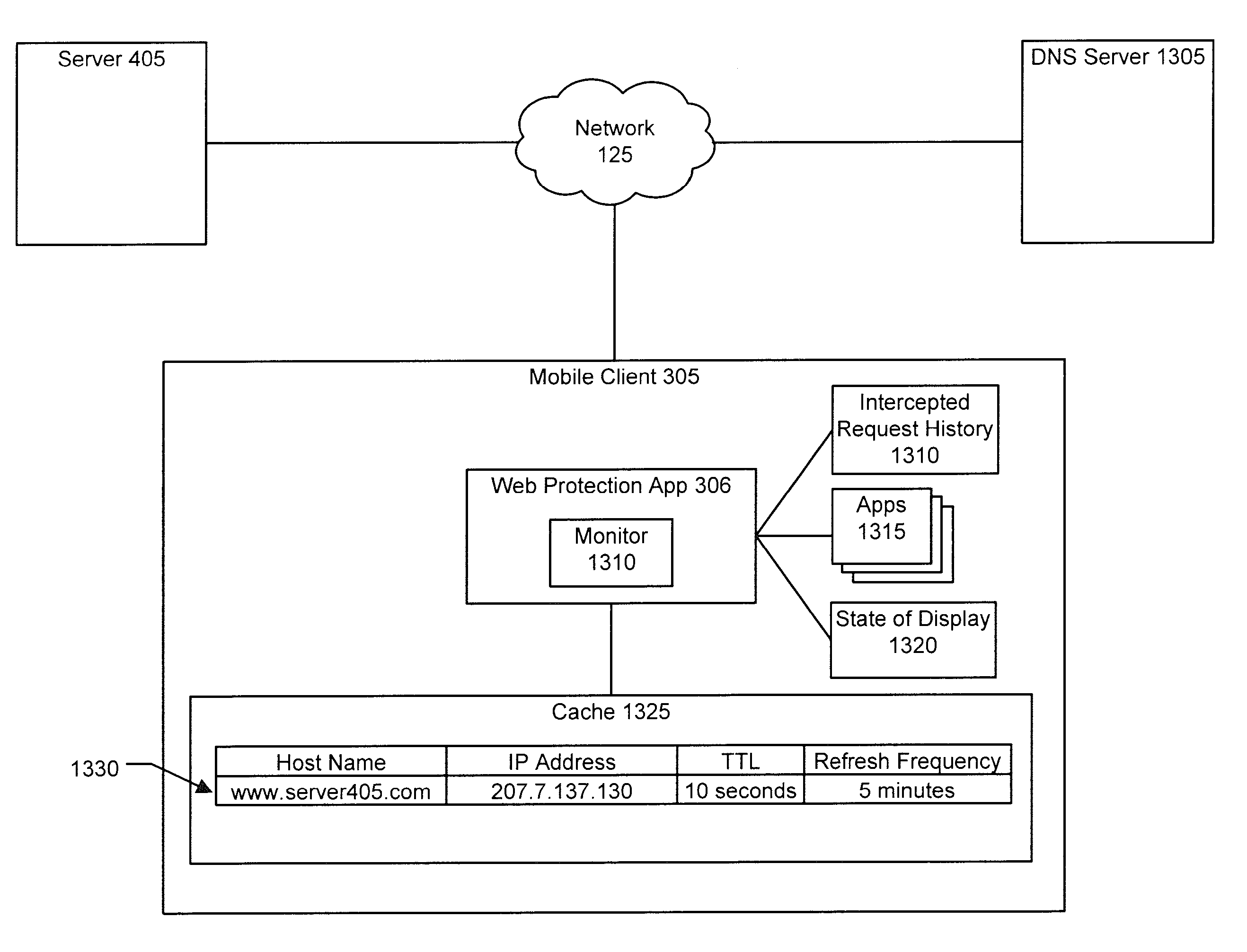
Mobile device DNS optimization
ActiveUS8738765B2Multiple digital computer combinationsMobile application execution environmentsFailoverCache server
When a mobile device interacts with a network service, synchronous DNS resolution can significantly impact user experience due to lossy or moderate-high latency conditions. Network services that rely on low-TTL DNS records for failover require a client to frequently resolve the service's host name. It is undesirable to block on these frequent resolutions. In an implementation, user activity on a mobile device is monitored to determine whether the user is engaged in an activity that would contact a server. If such an activity is in progress, then DNS requests to resolve the server's host name are periodically generated to make sure the server's IP address is cached. In an implementation, if a request to communicate with a server fails, the DNS cache expires the entry for that server so that a new DNS request can resolve the server's IP address in case the server's IP address has changed.
Owner:LOOKOUT MOBILE SECURITY
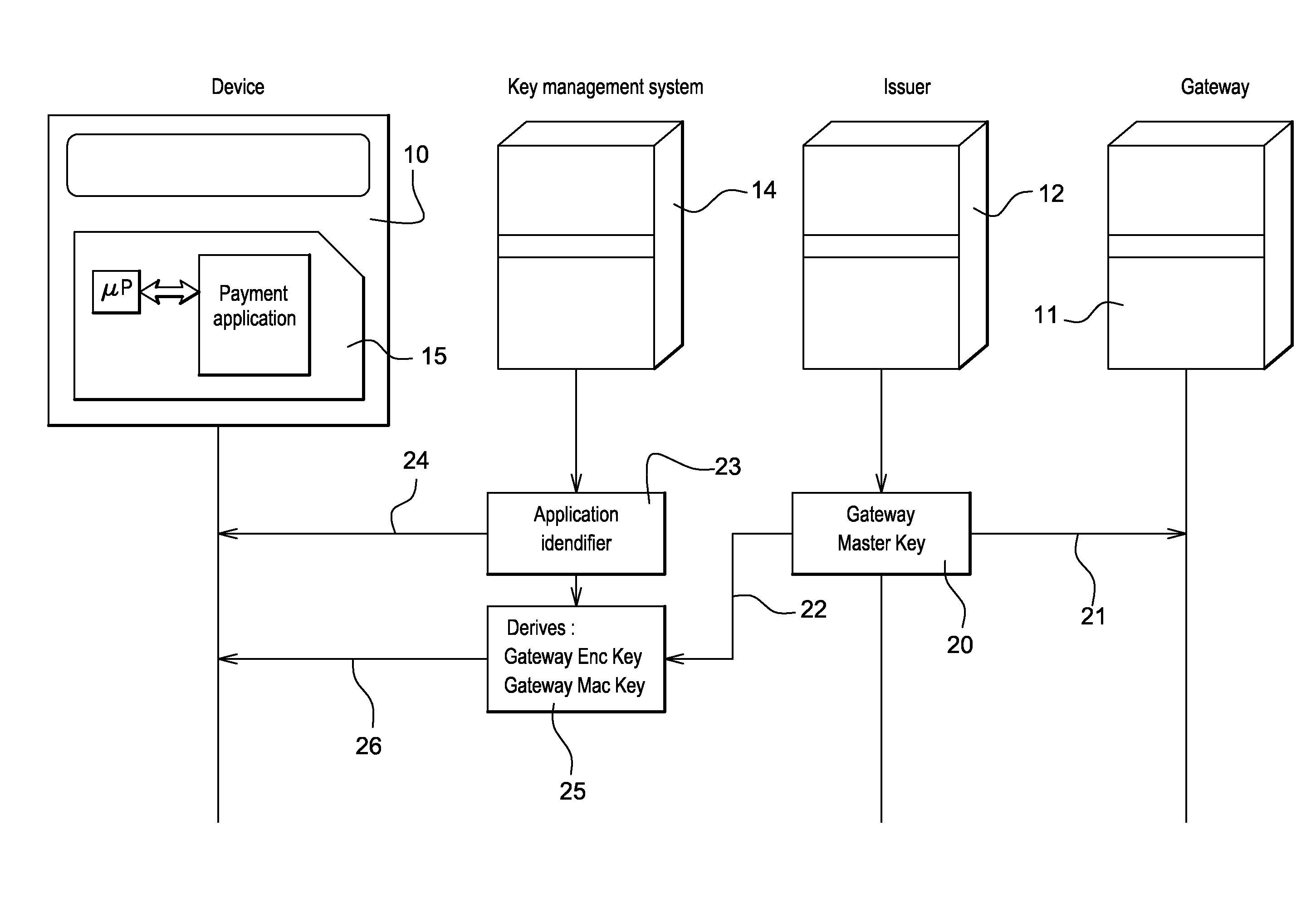
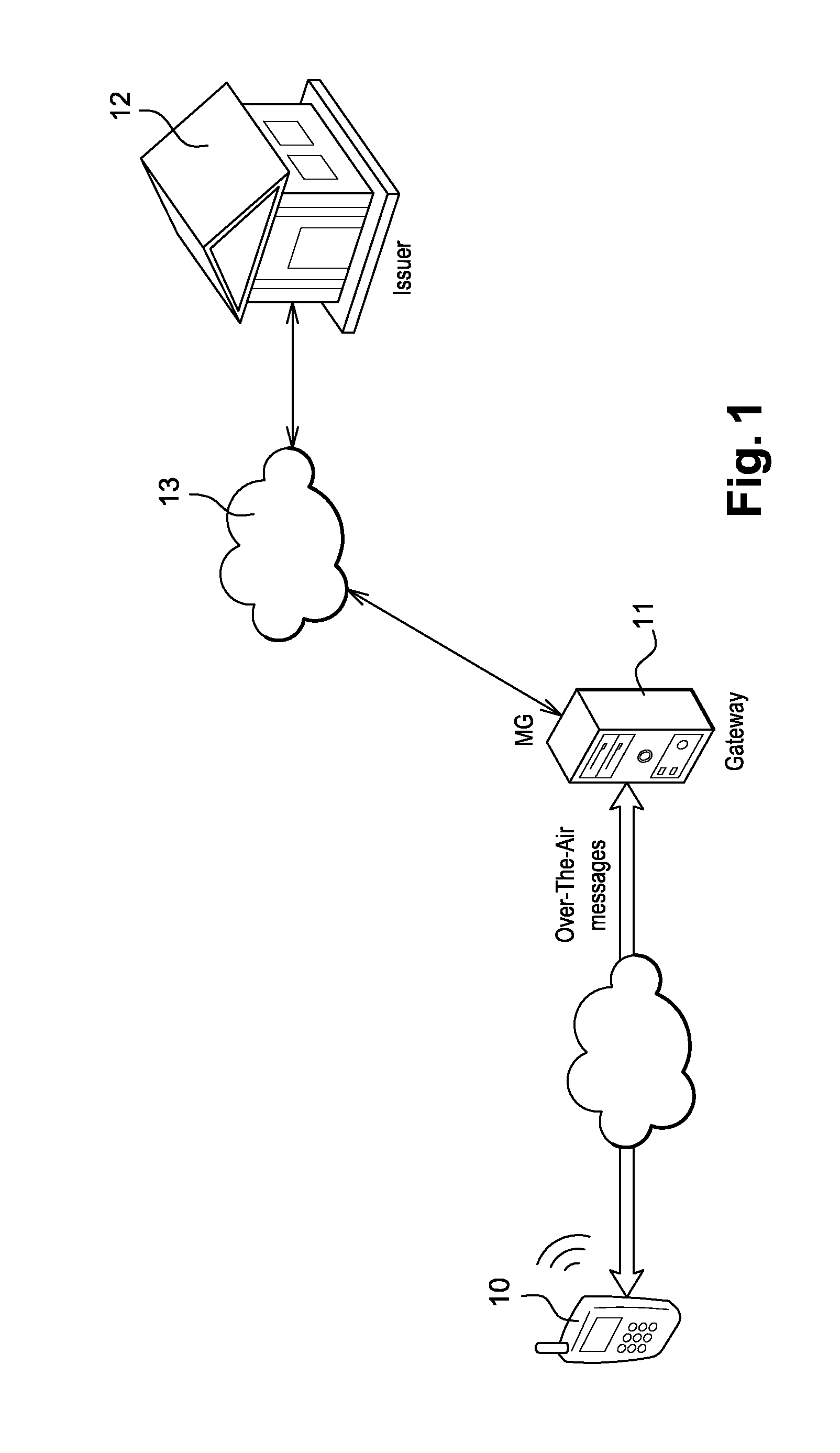
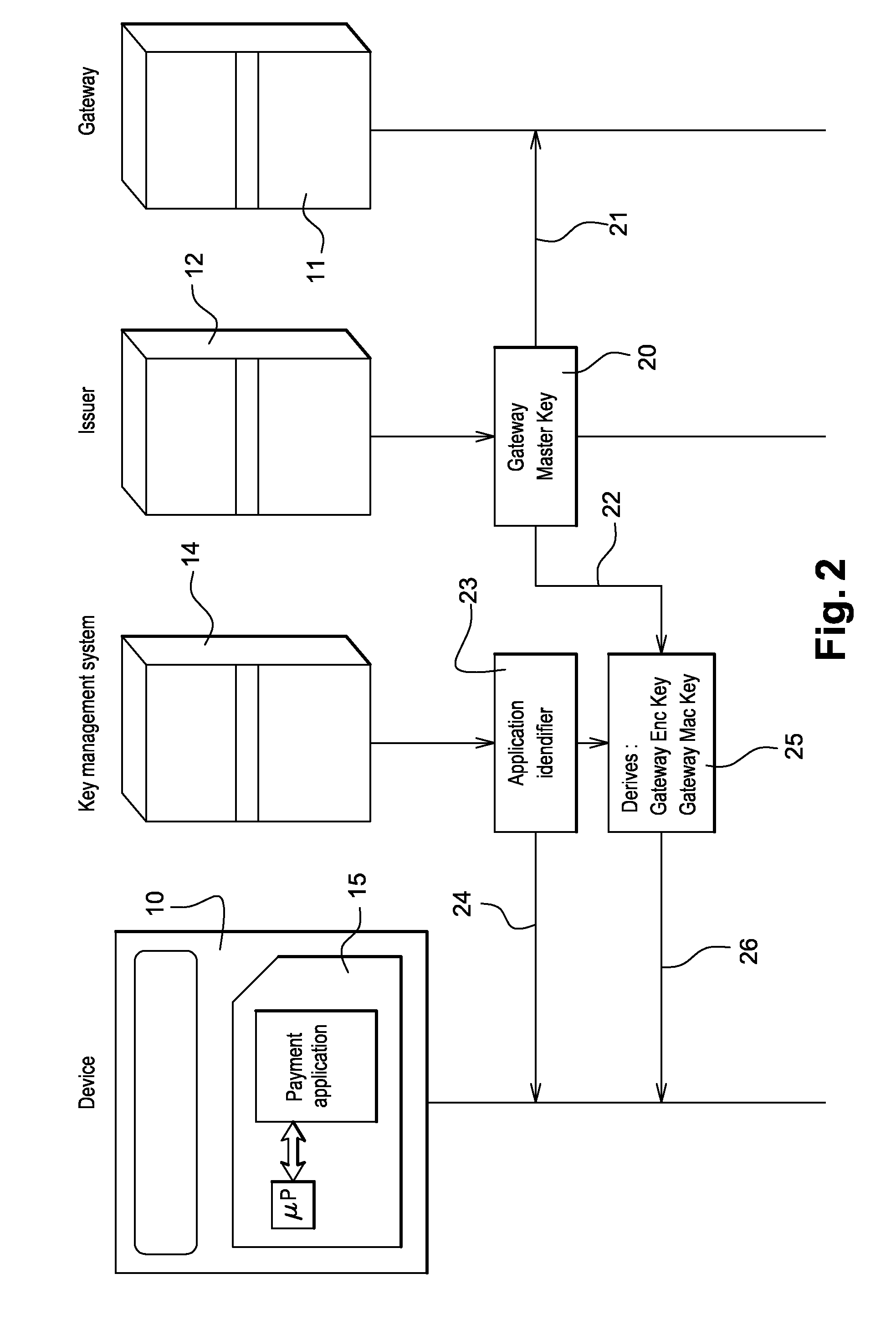
Method for securing over-the-air communication between a mobile application and a gateway
InactiveUS20160232523A1Minimize the numberSimplified generationMultiple keys/algorithms usageUser identity/authority verificationPayment transactionApplication software
The present invention generally relates to systems and methods for performing issuer updates of data stored in a mobile device, a remote authentication, a remote payment transaction or enable the configuration of mobile application functions or operations. More specifically, the present invention relates to a method and system for securing an issuer updates processing for mobile payment application. When an update transaction is initiated, the payment application increments an Application Transaction Counter ATC and derives from this ATC a session keys. Sensitive user credential data are encrypted with the computed session keys before transmission to a gateway which is configured to compute the session keys for decryption. The decrypted user credential data are forwarded to a payment application issuer for updates.
Owner:GEMPLU
Media delivery platform
InactiveUS7548875B2The process is convenient and fastEasy accessModulated-carrier systemsPayment architectureCorrection algorithmComputer hardware
A improved method for delivery and play back of sound and image files is provided, including the use of the files as alerts for various electronic devices or for playing on a handheld device. Algorithms are provided for the delivery, storage, and playback of sound files, including a delivery method algorithm, a parametric optimization and compression algorithm, and an error correction algorithm. The files may be selected from and downloaded to the electronic device with or without the use of a worldwide network connection.
Owner:SKKY
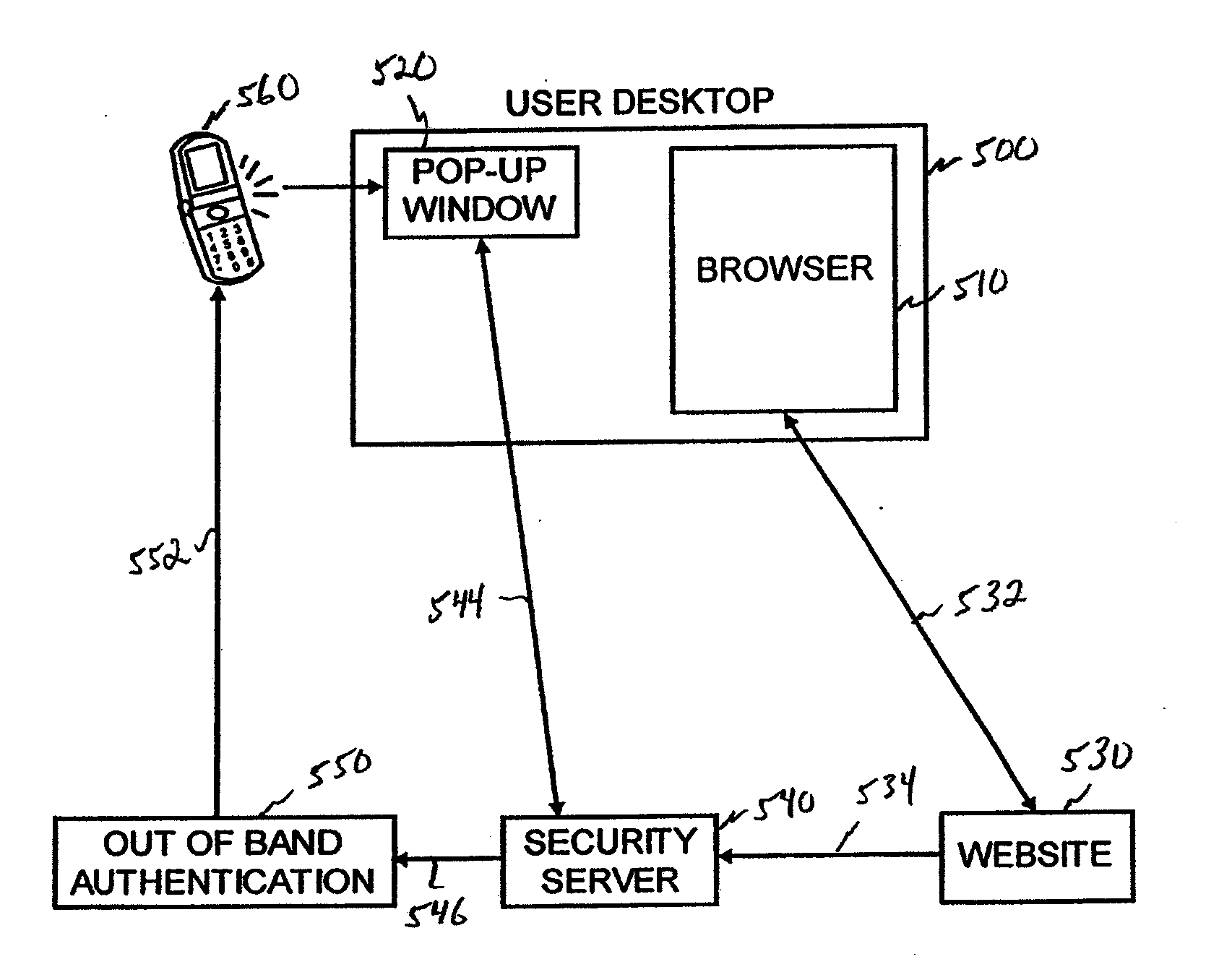
Secure and efficient authentication using plug-in hardware compatible with desktops, laptops and/or smart mobile communication devices such as iphones
ActiveUS20120124651A1Enhanced authenticationImproved transactionDigital data processing detailsMultiple digital computer combinationsTelecommunications linkCommunication link
A portable apparatus is removably and communicatively connectable to a network device to communicate authentication or authorization credentials of a user in connection with the user logging into or entering into a transaction with a network site. The apparatus includes a communications port to connect and disconnect the apparatus to and from the network device and to establish a communication link with the network device when connected thereto. A processor receives a secure message from the network security server via the port. The message has a PIN for authenticating the user to the network site, and is readable only by the apparatus. The processor either transfers, via the port, the received PIN to an application associated with the network site that is executing on the network device or causes the apparatus to display the received PIN for manual transfer to the application associated with the network site.
Owner:PAYFONE
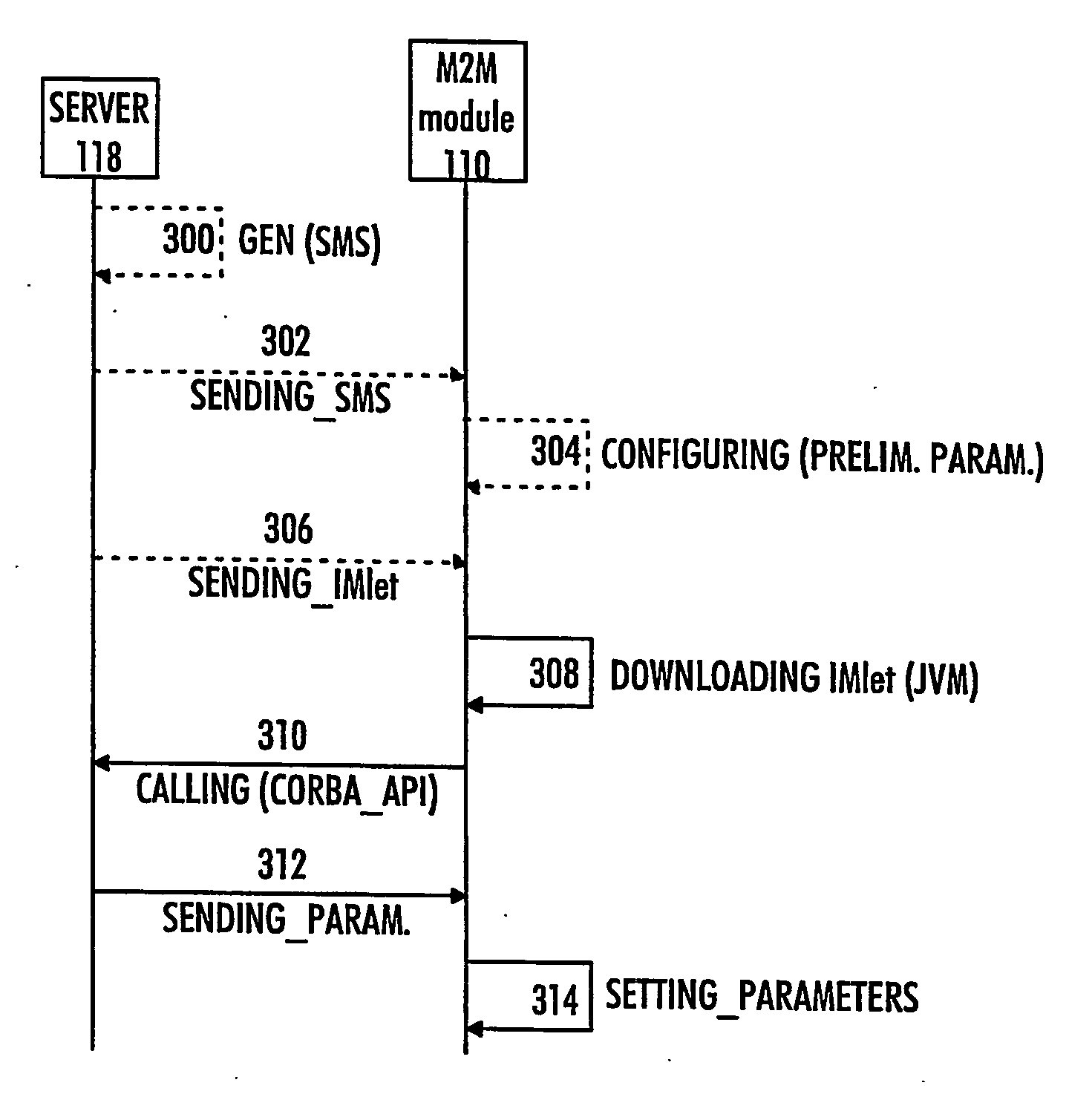
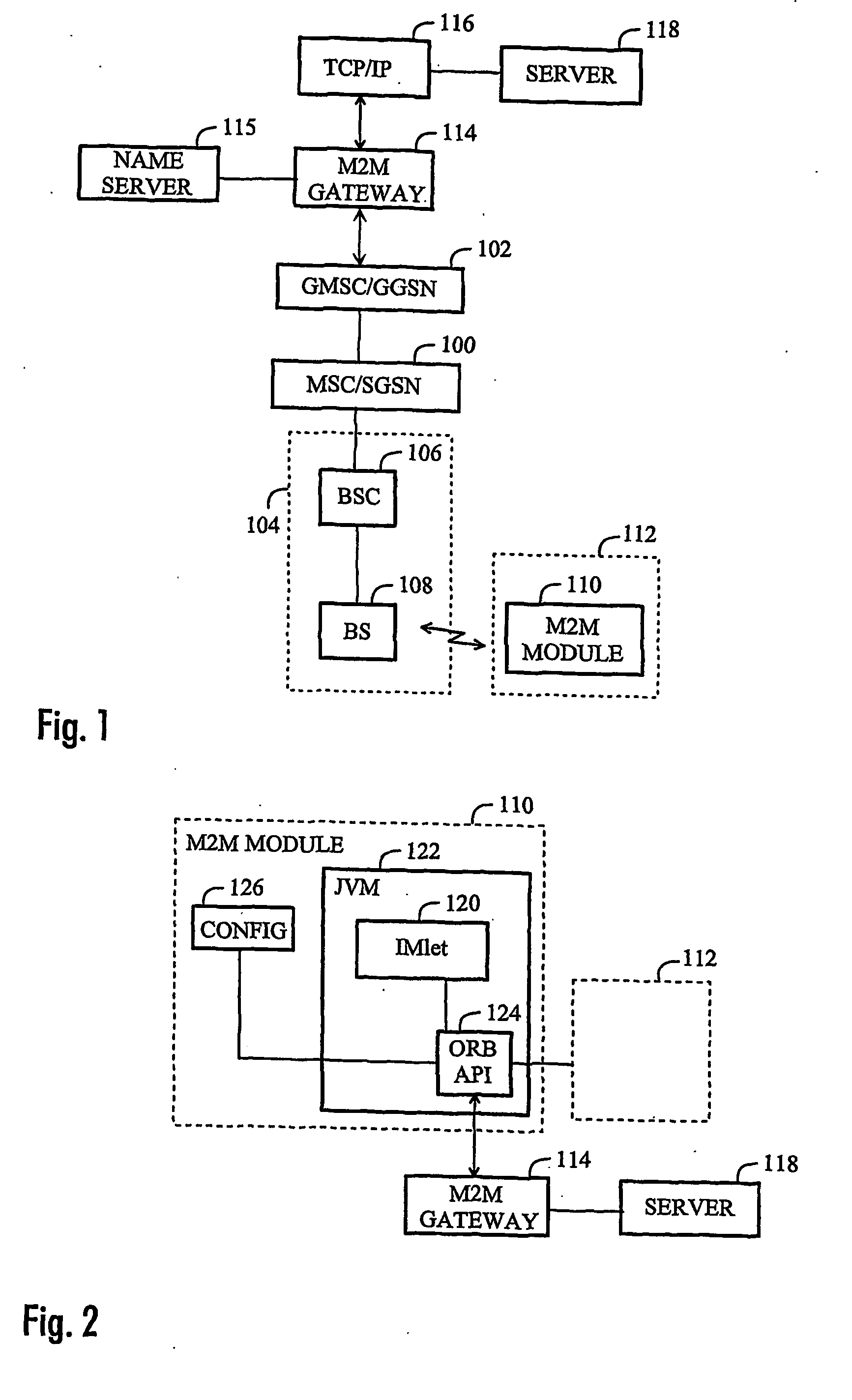
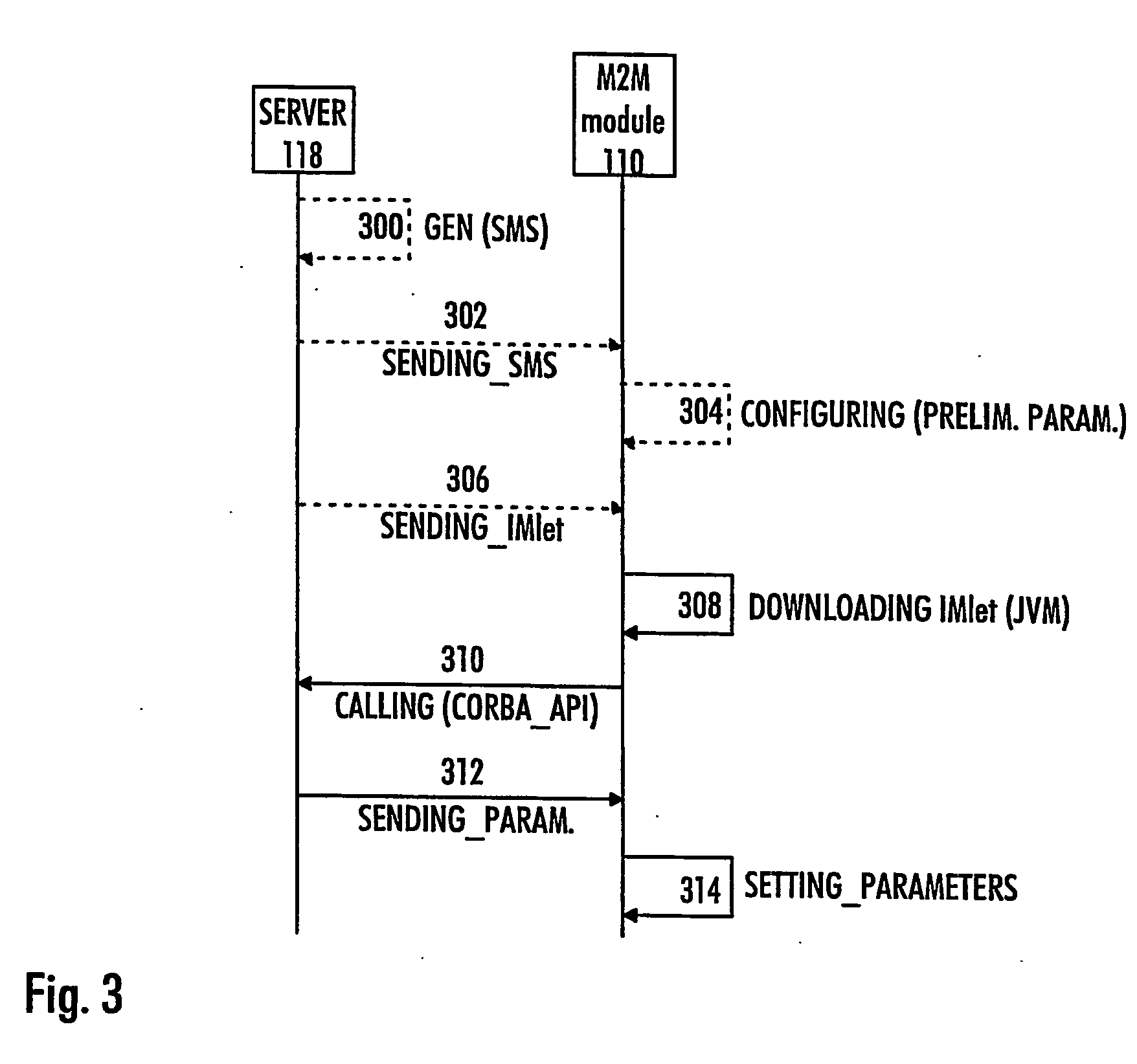
Method of configuring parameters of machine-to-machine module and machine-to-machine module
InactiveUS20070169107A1Services signallingProgram loading/initiatingApplication programming interfaceJava virtual machine
The invention relates to an M2M (machine-to-machine) module and to a method of configuring parameters of an M2M module, the method comprising establishing a connection between the M2M module and a server. The method comprises: downloading, to the M2M module, an application having an application programming interface (API) for configuring the M2M module, the application being configured to run on a Java virtual machine (JVM); communicating with the server by the application for receiving configuration parameters; and setting the parameters of the M2M module by the application based on the received configuration parameters.
Owner:NOKIA CORP
Method and apparatus for switching virtual sim service contracts based upon a user profile
A system and method store provisioning data supporting a plurality of service providers in a VSIM internal memory unit of a mobile device. A user may specify a user profile to automatically enable provisioning data supporting one of the plurality of service providers stored in the VSIM internal memory unit to conduct a wireless communication when certain criteria values are satisfied. The automatic enabling of provisioning data may be determined based upon mobile device location, communication usage request and / or time and date.
Owner:QUALCOMM INC
Popular searches
Special data processing applications Short range communication service Subscription services Machine-to-machine/machine-type communication service Near-field in RFID Near-field systems using receivers Radio transmission Home automation networks Input/output processes for data processing Network data management
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com