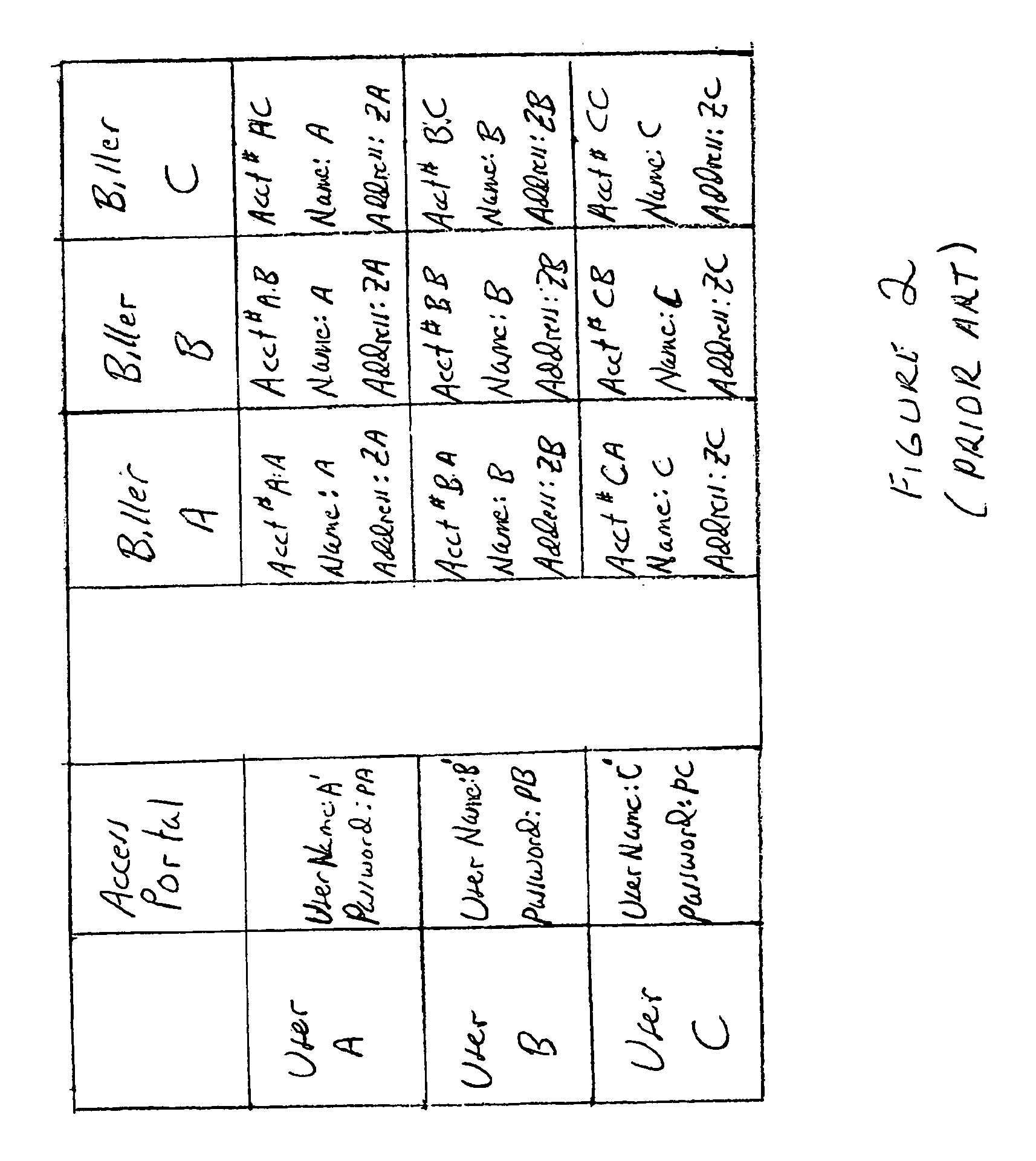
Patents
Literature
446results about How to "Enhanced authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
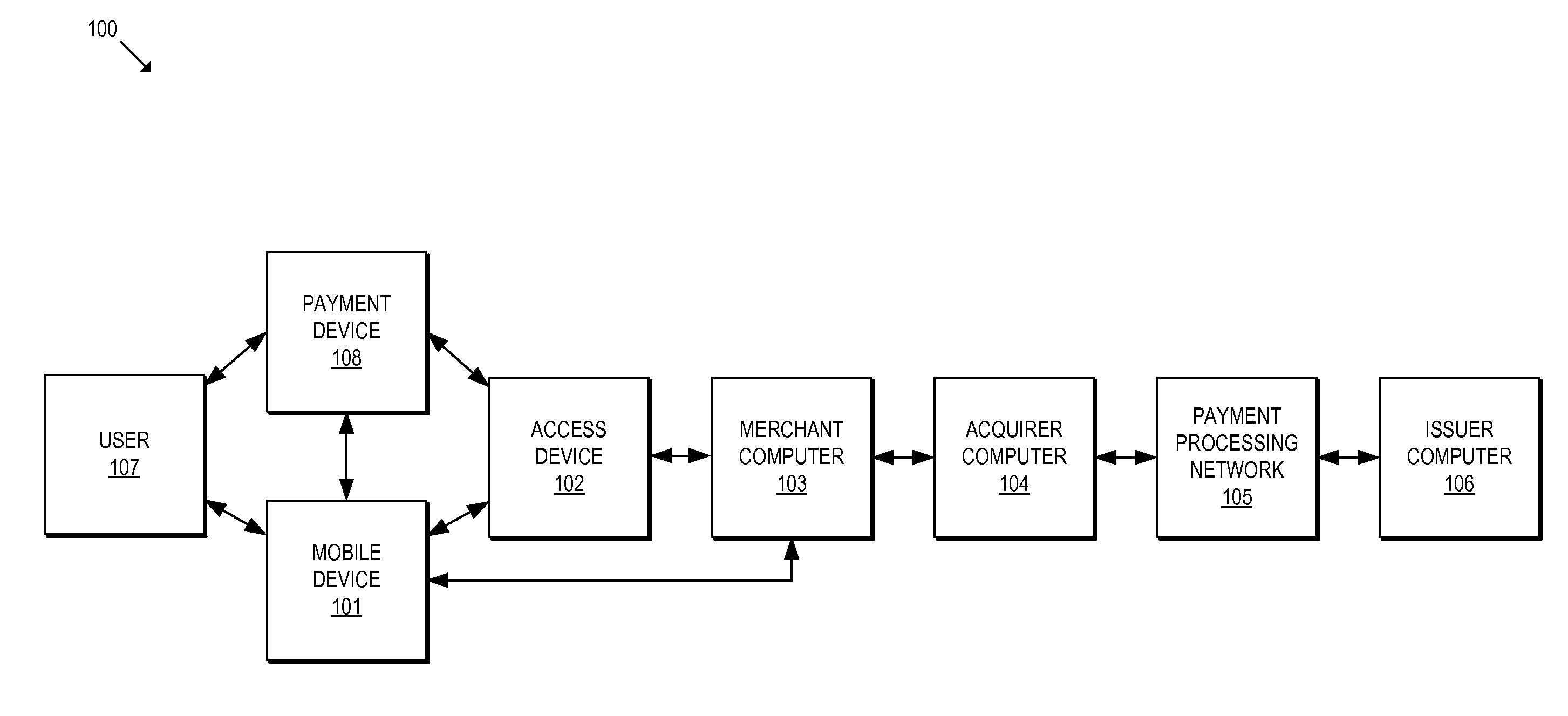
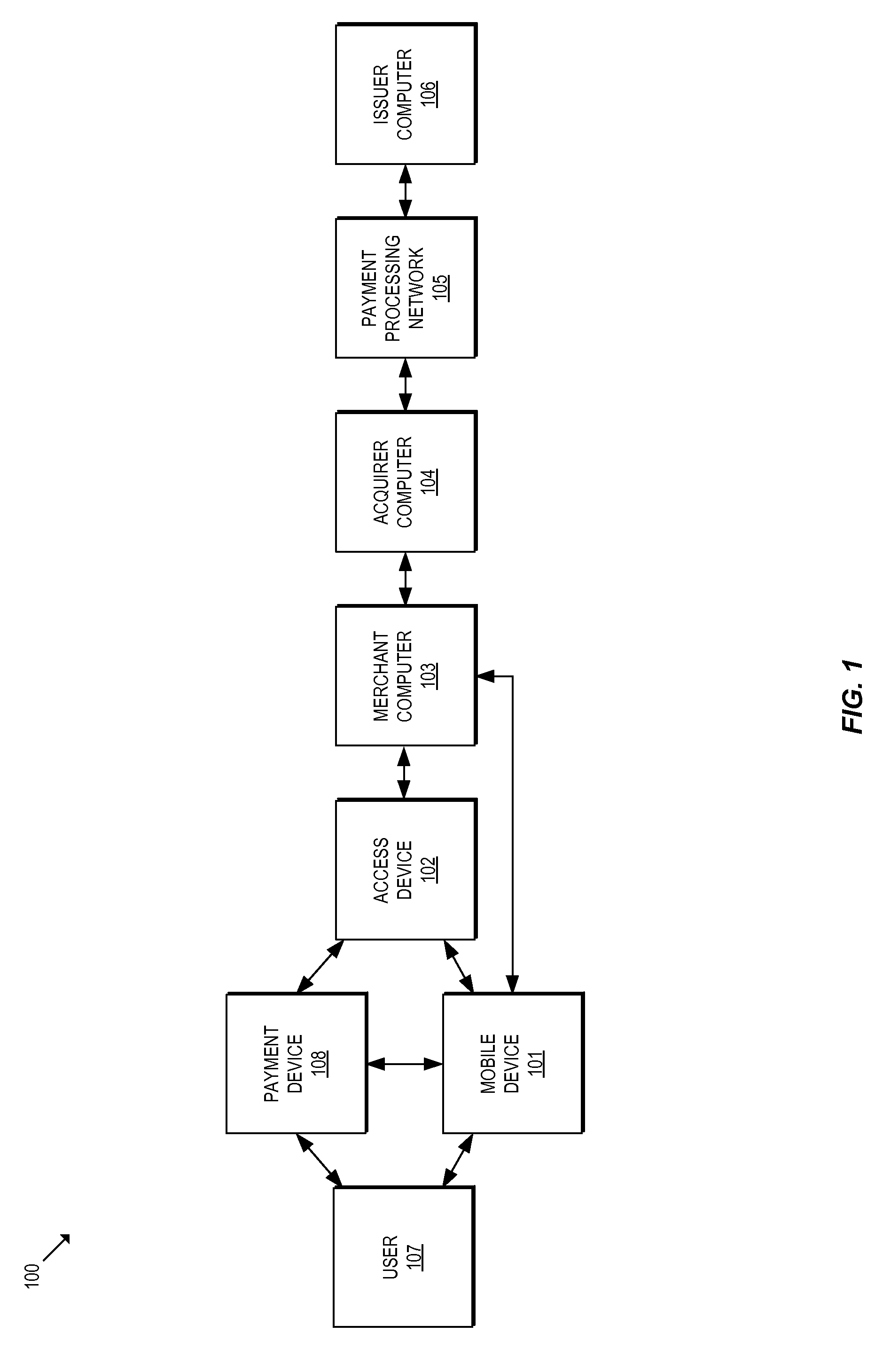
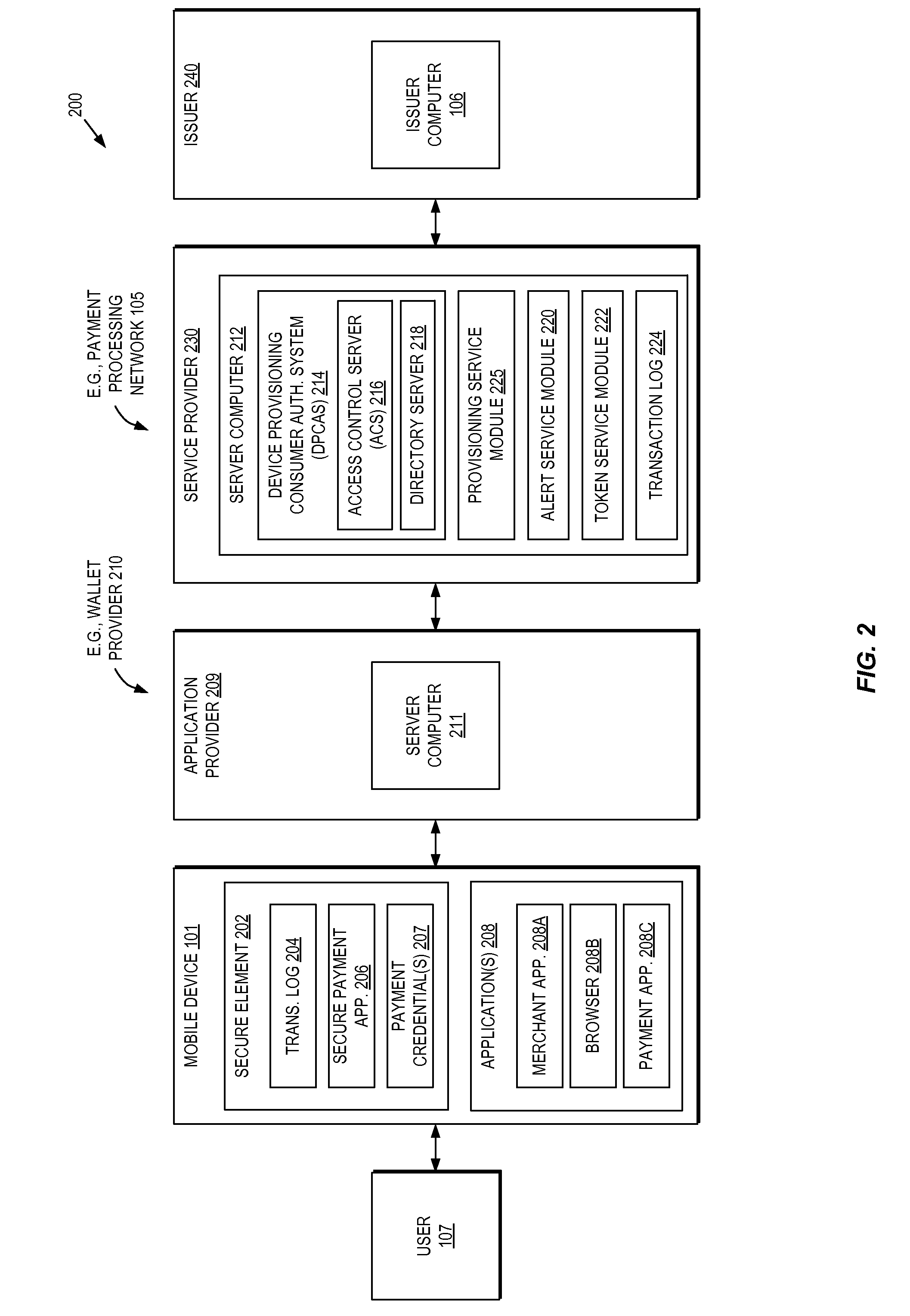
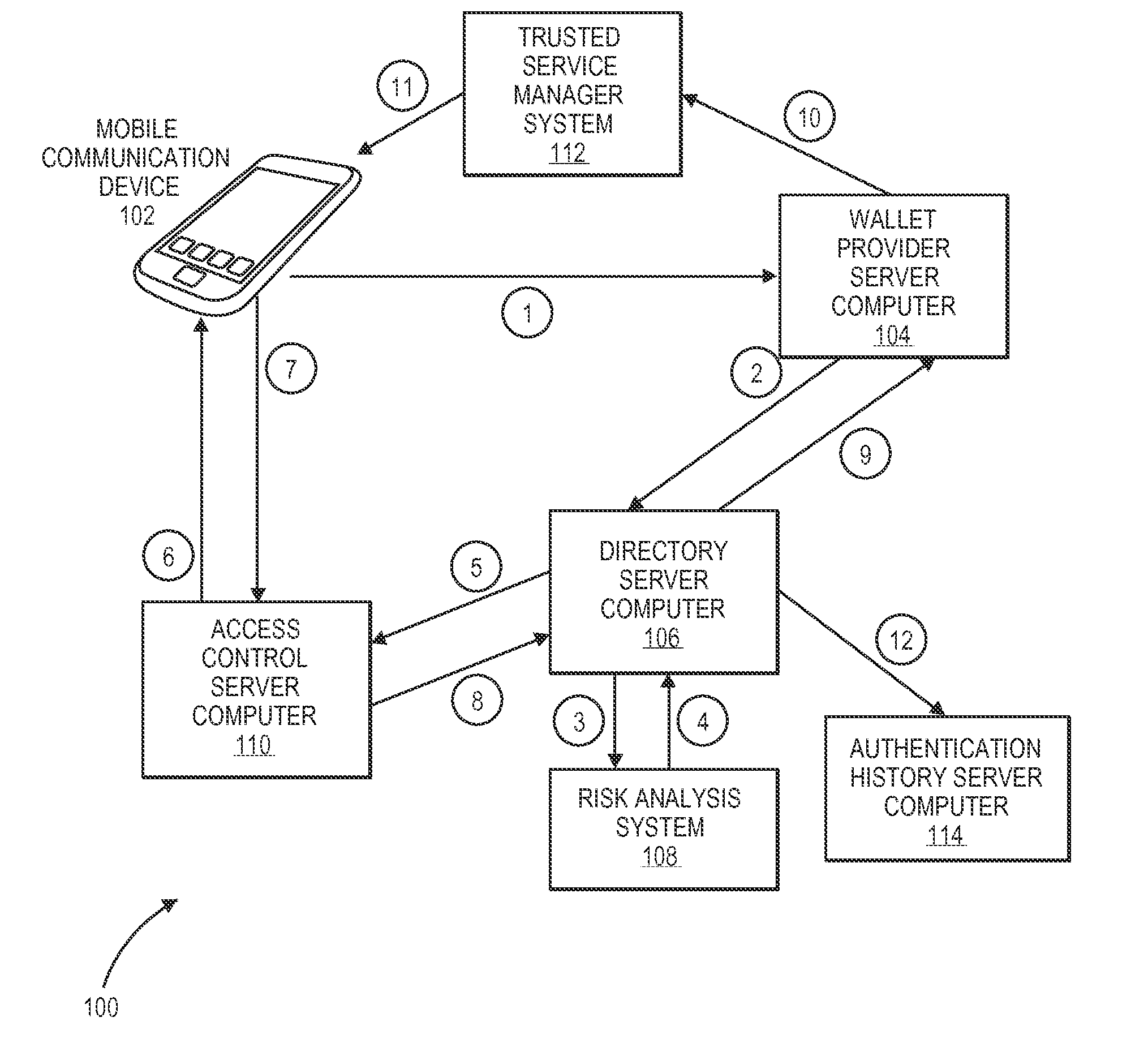
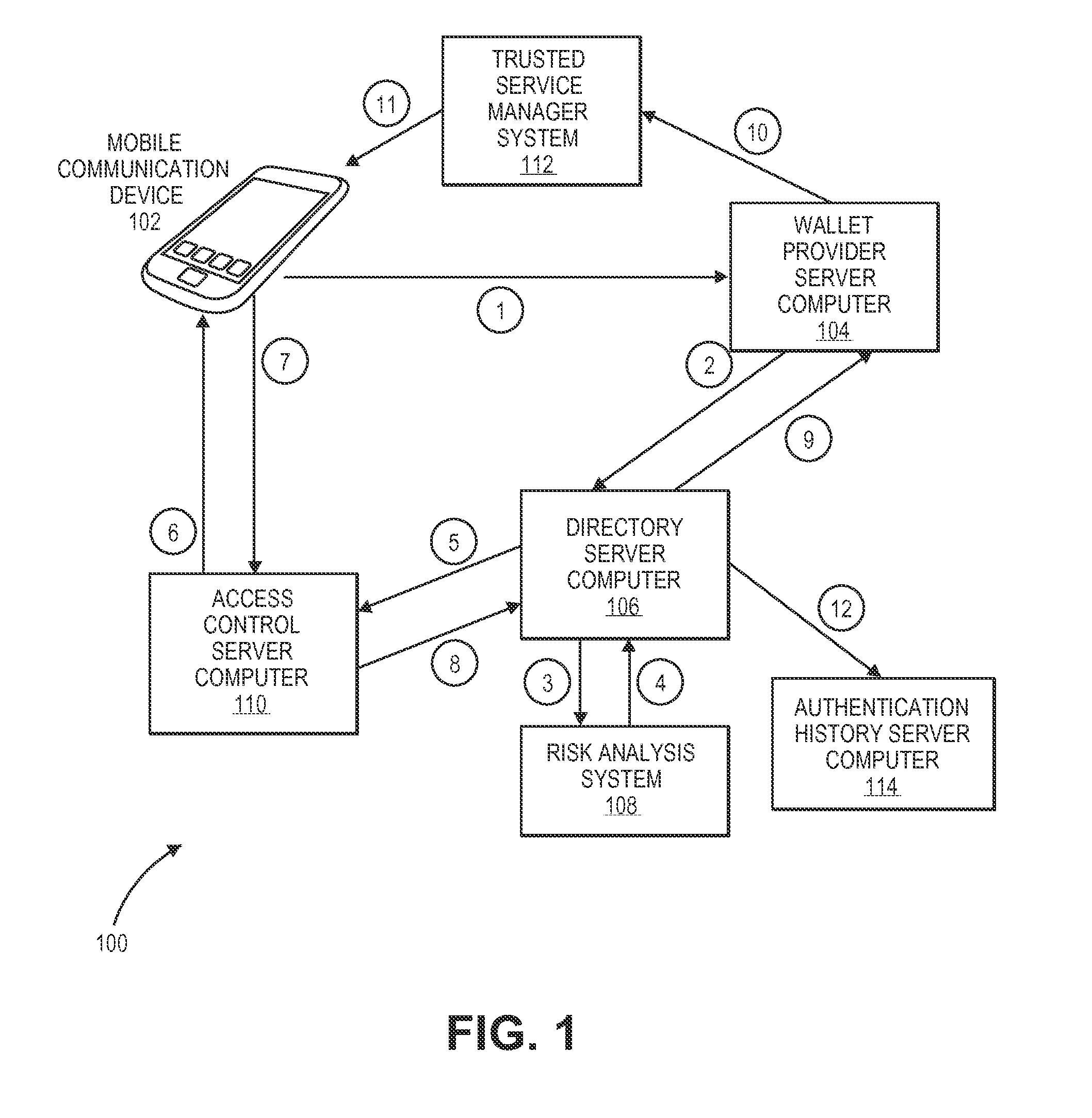
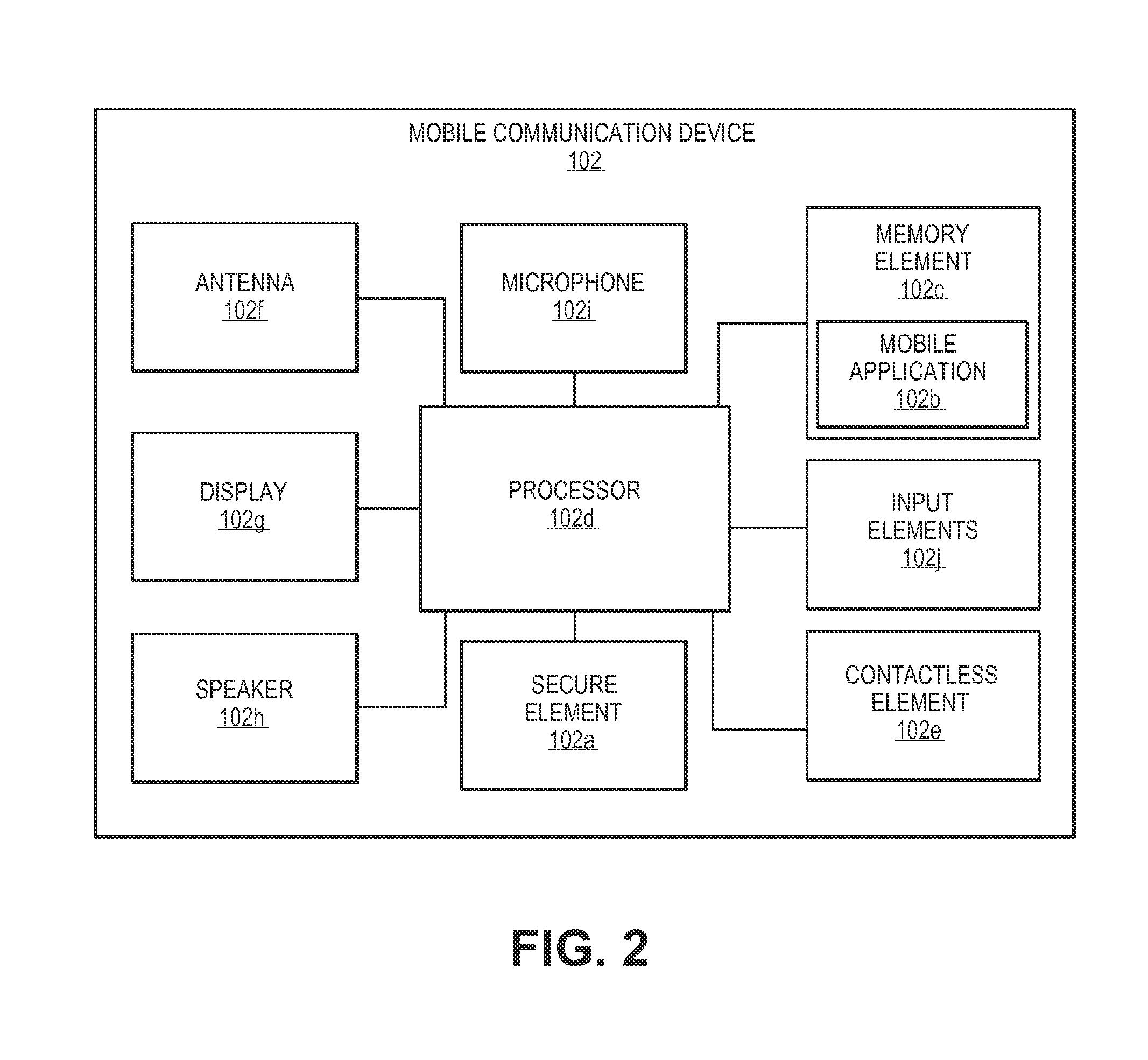
Methods and systems for provisioning mobile devices with payment credentials
ActiveUS20150046339A1Unnecessary delayProcessing speedFinanceElectronic credentialsPaymentMedium Risk
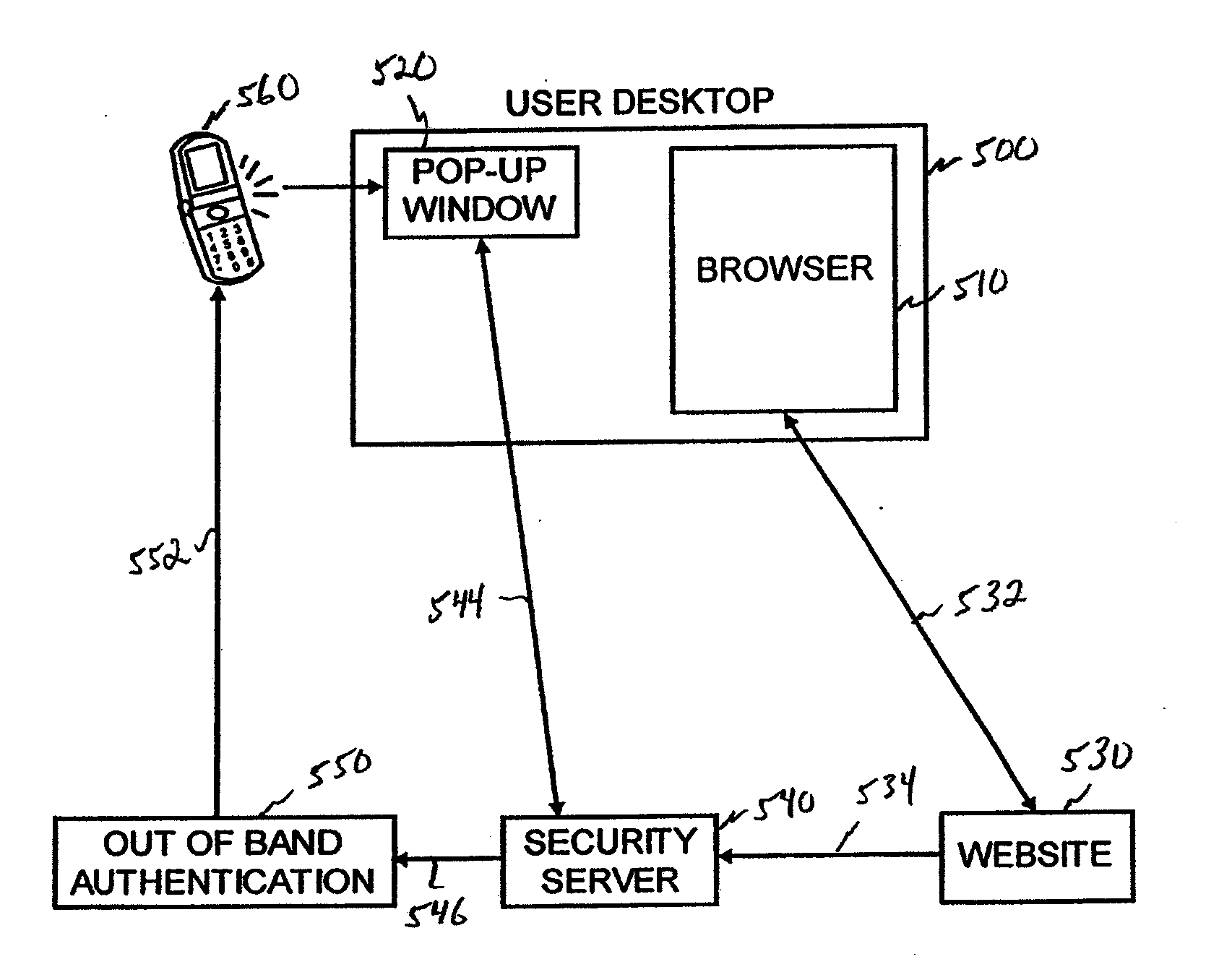
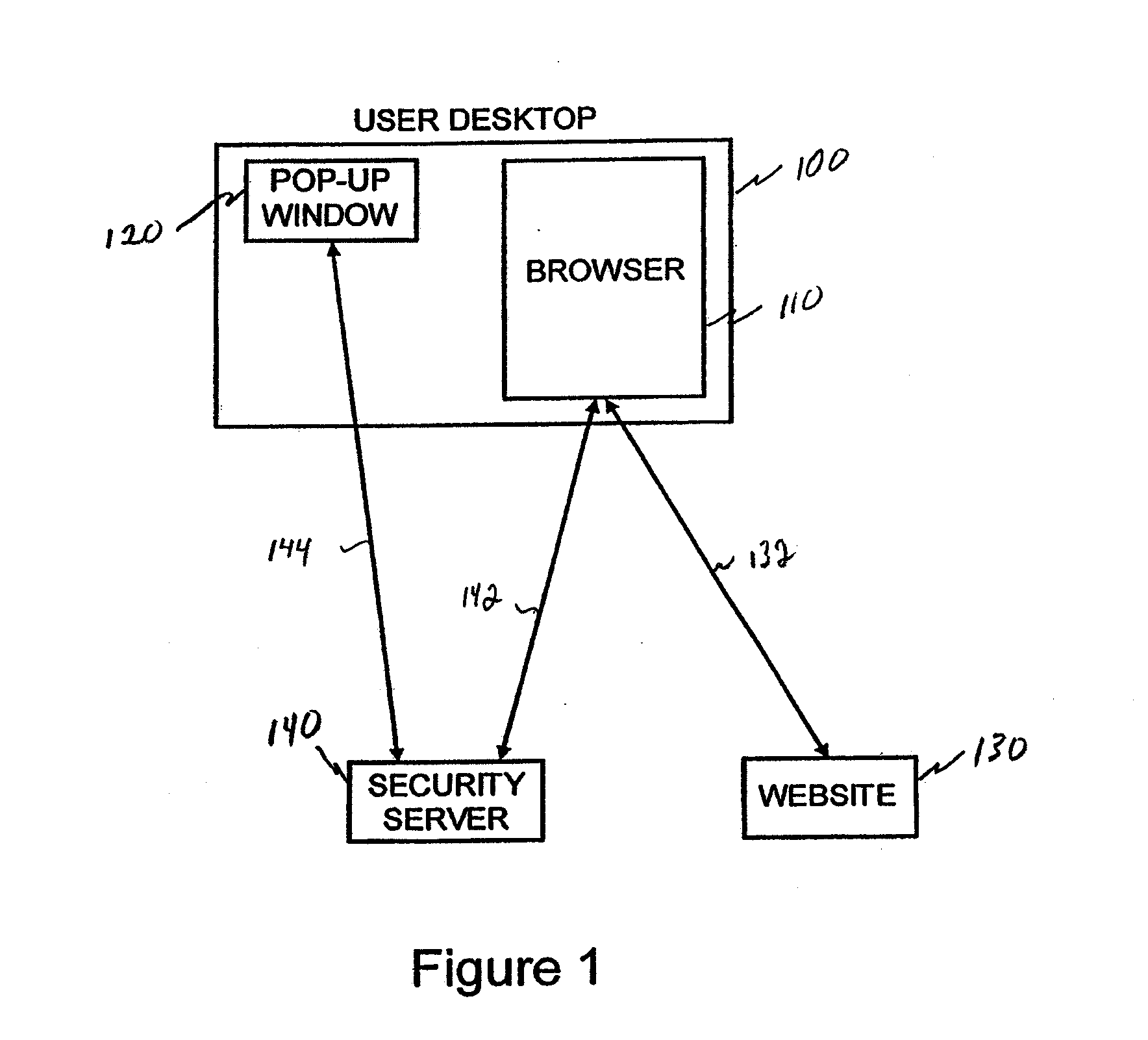
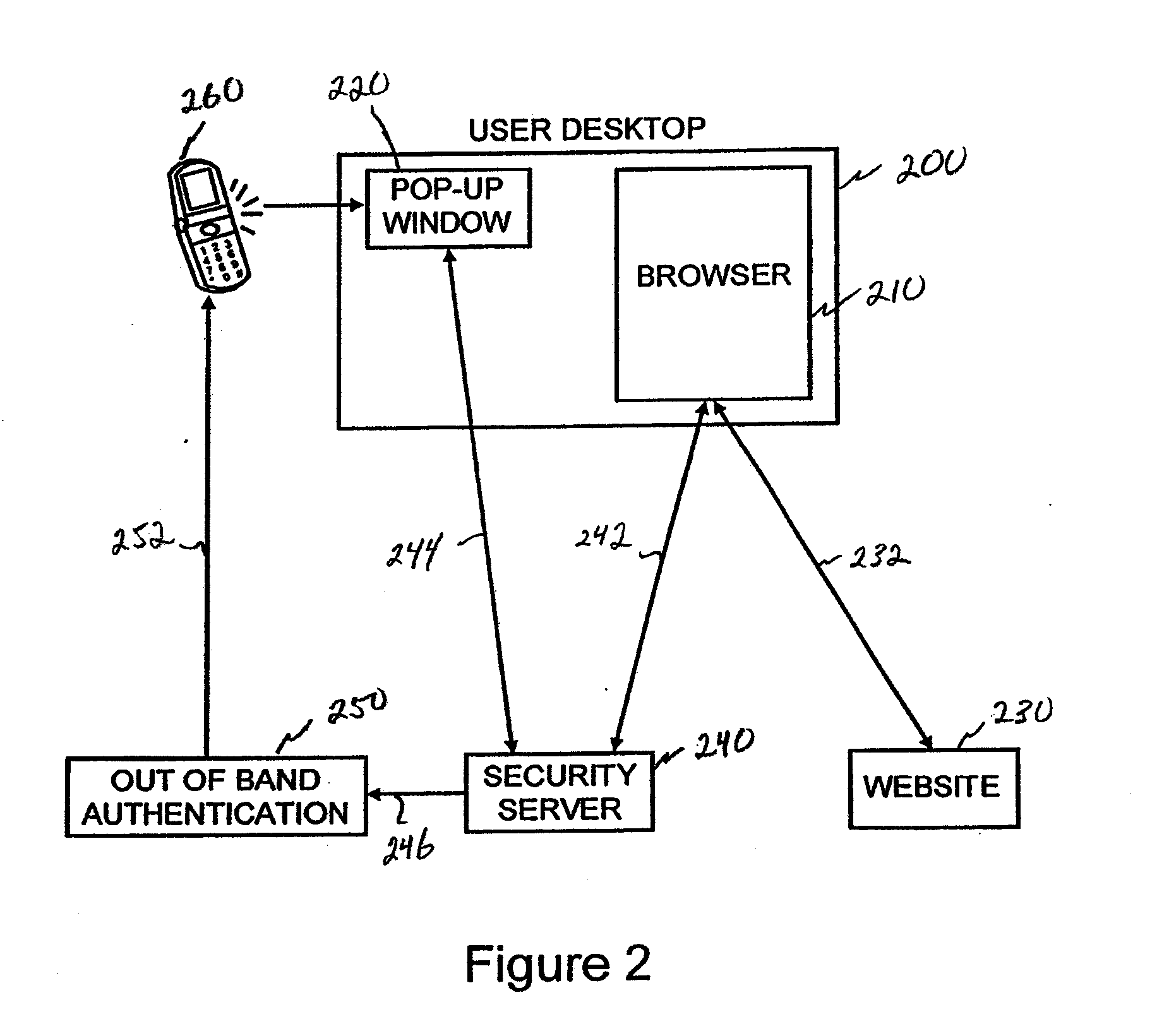
Embodiments are described that are directed to optimizing the provisioning of payment account credentials to mobile devices utilizing mobile wallets. In some embodiments, one of multiple provisioning schemes may be selectively chosen for payment account credential provisioning based upon a determined risk involved with a particular provisioning request. A low risk provisioning request leads to an immediate provisioning of a payment credential, whereas a provisioning request of high risk results in the provisioning request being denied. In some embodiments, medium risk provisioning requests will cause an additional user authentication to be performed before the payment account provisioning is finalized. The additional user authentication may occur using a separate communication channel than the channel in which the provisioning request was received.
Owner:VISA INT SERVICE ASSOC
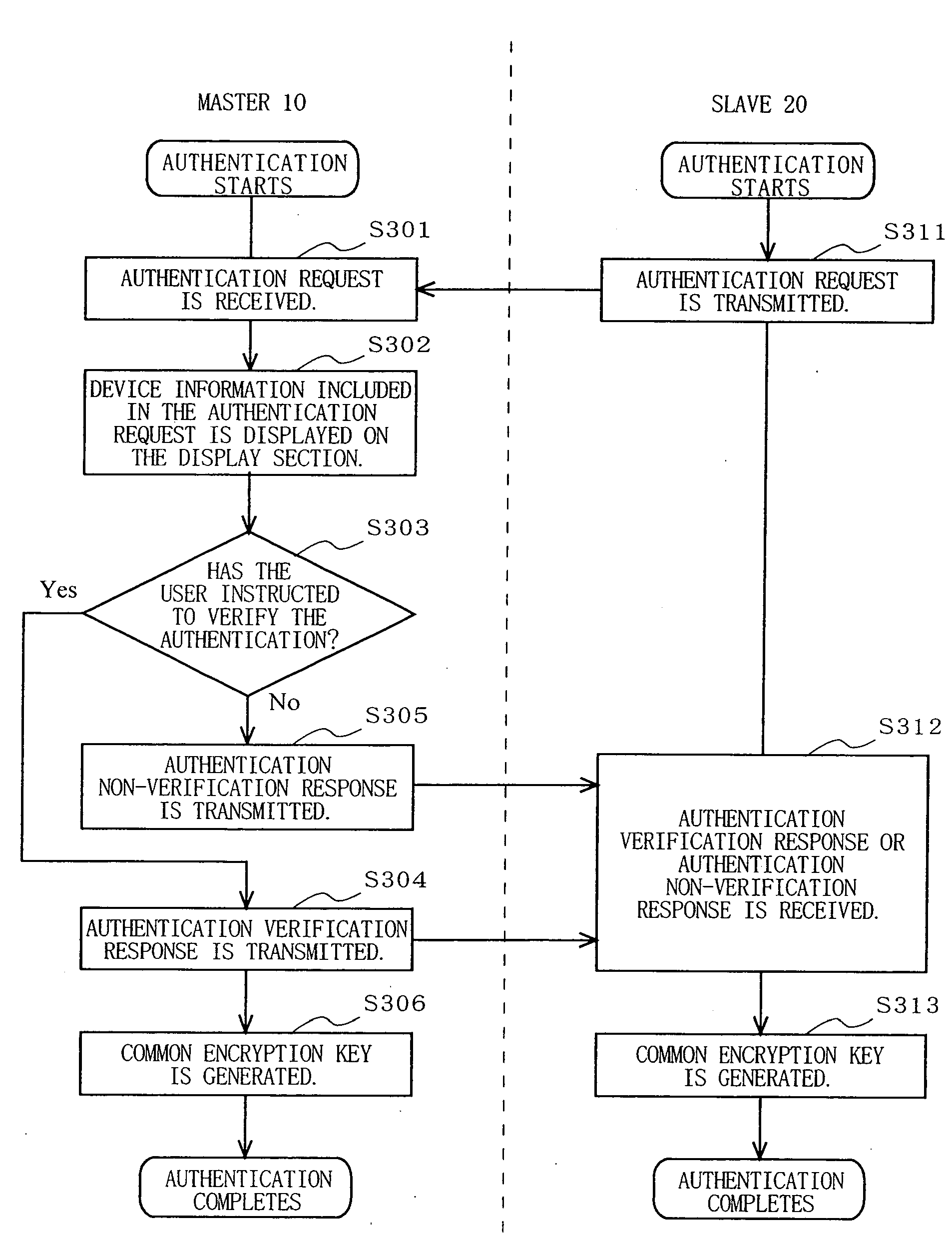
Communication device, communication system and authentication method
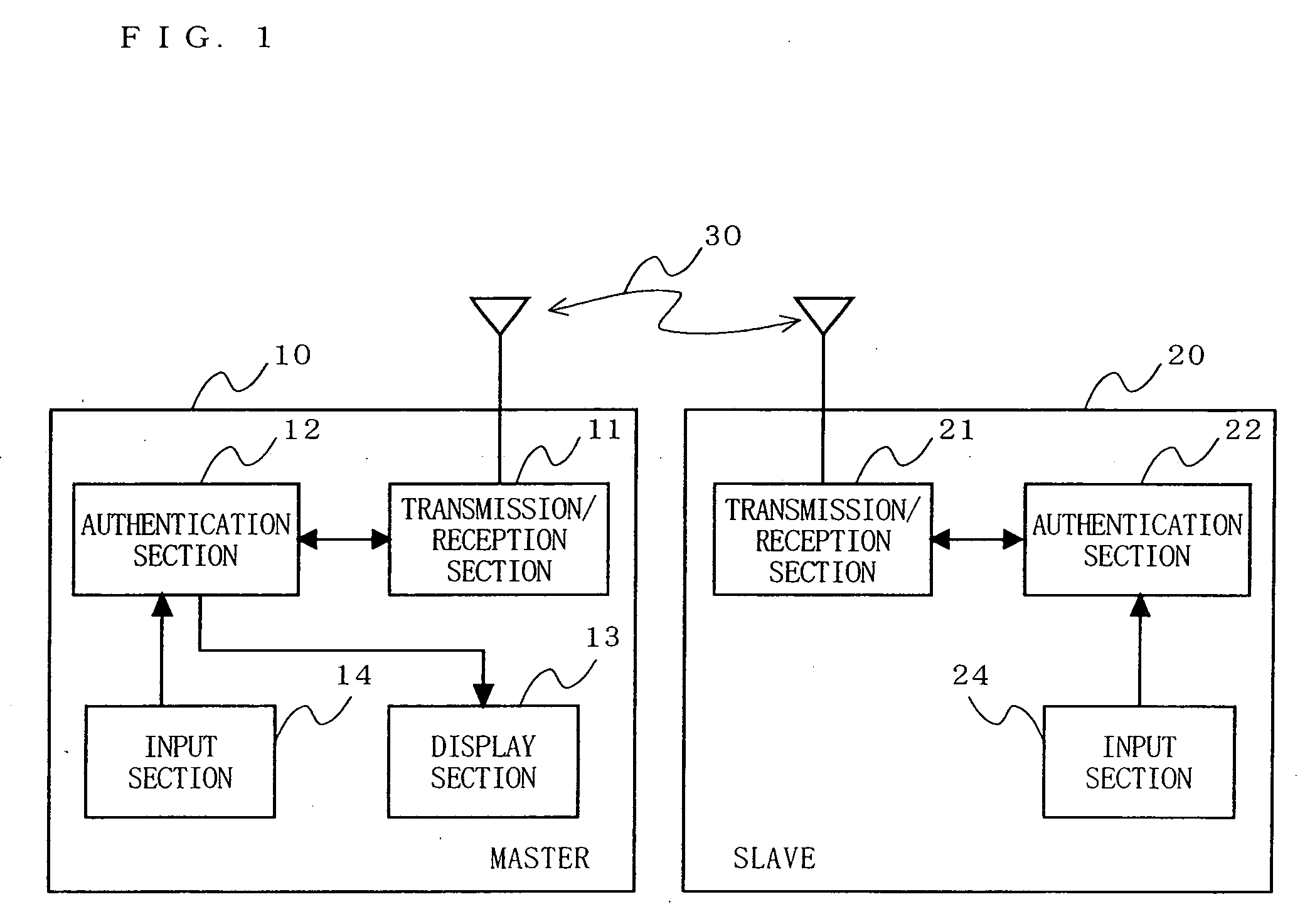
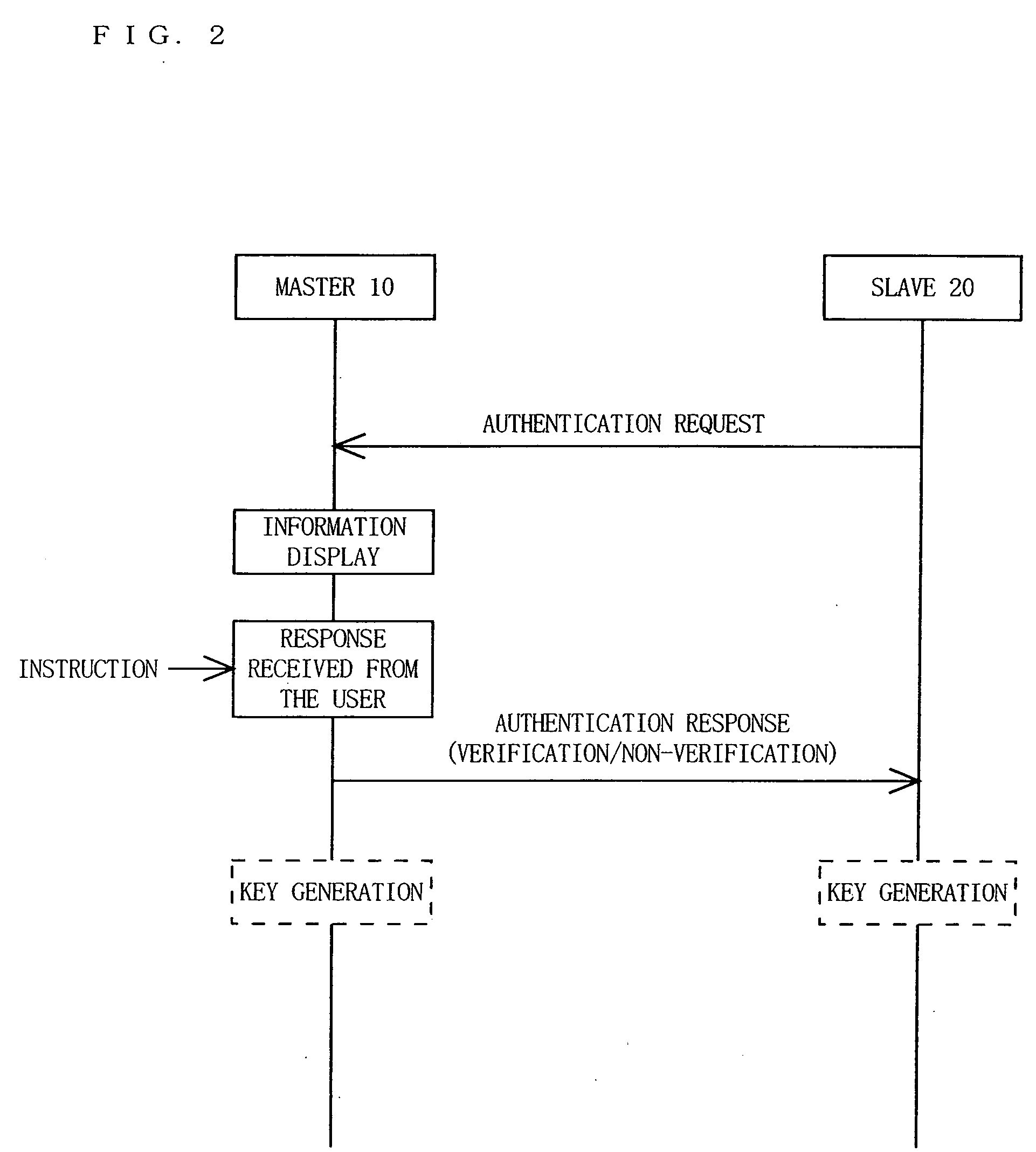
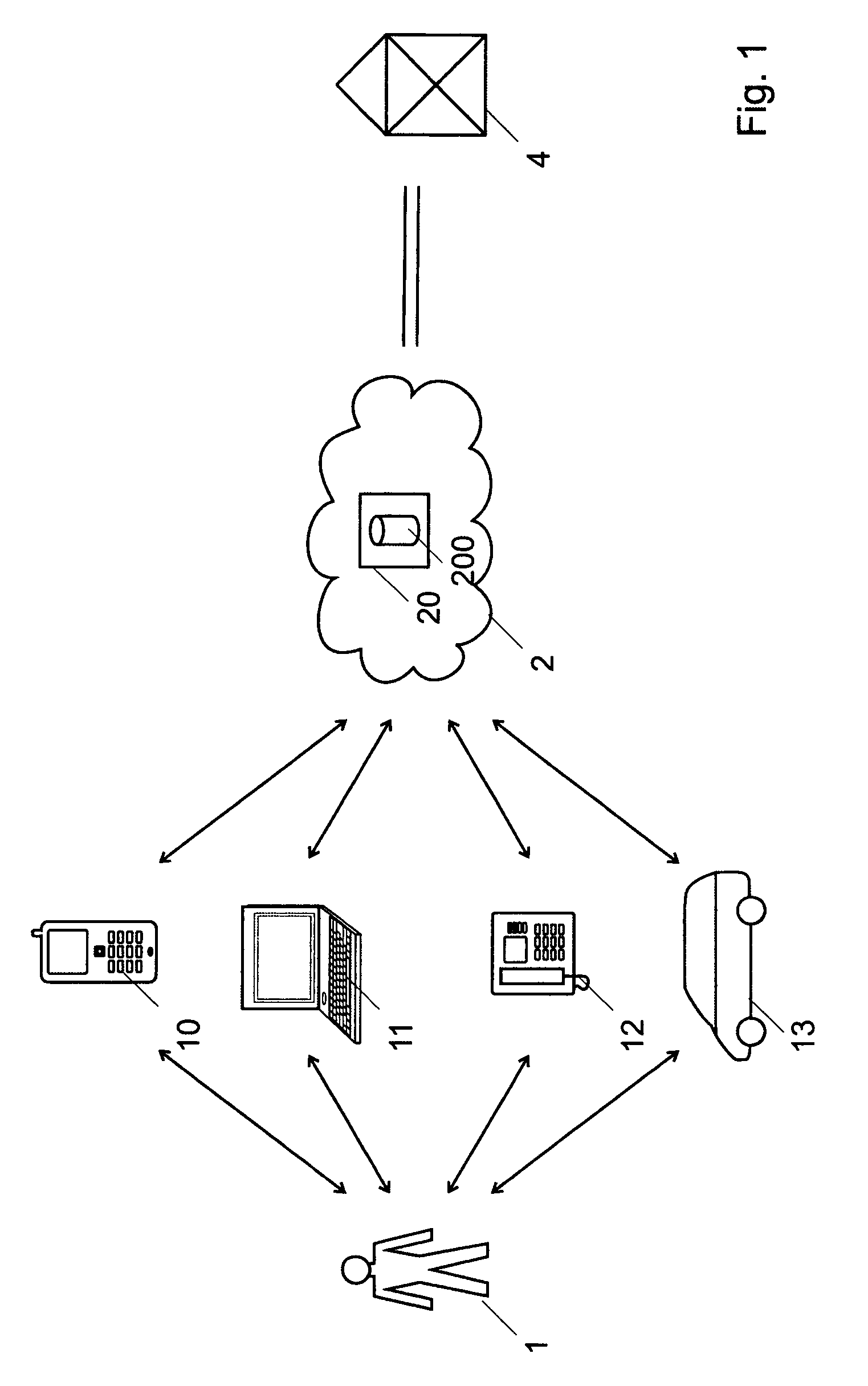
InactiveUS20070106894A1Sure easyEnhanced authenticationKey distribution for secure communicationDigital data processing detailsCommunications systemAuthentication system
A communication device, a communication system and an authentication system for preventing a disguising act by an illegal man-in-the-middle and improving the safety and certainty of authentication processing are provided. A slave (20) transmits an authentication request including device information to a master (10). The master (10) receives the authentication request and displays the device information included in the authentication request on a screen of a display section (13). The user visually checks the device information displayed on the screen of the display section 13 (13), determines whether or not to verify the authentication, and instructs the master (10) of the determination result via an input section (14). The master (10), instructed to verify or not to verify the authentication, transmits a response in accordance with the instruction to the slave (20).
Owner:SOVEREIGN PEAK VENTURES LLC
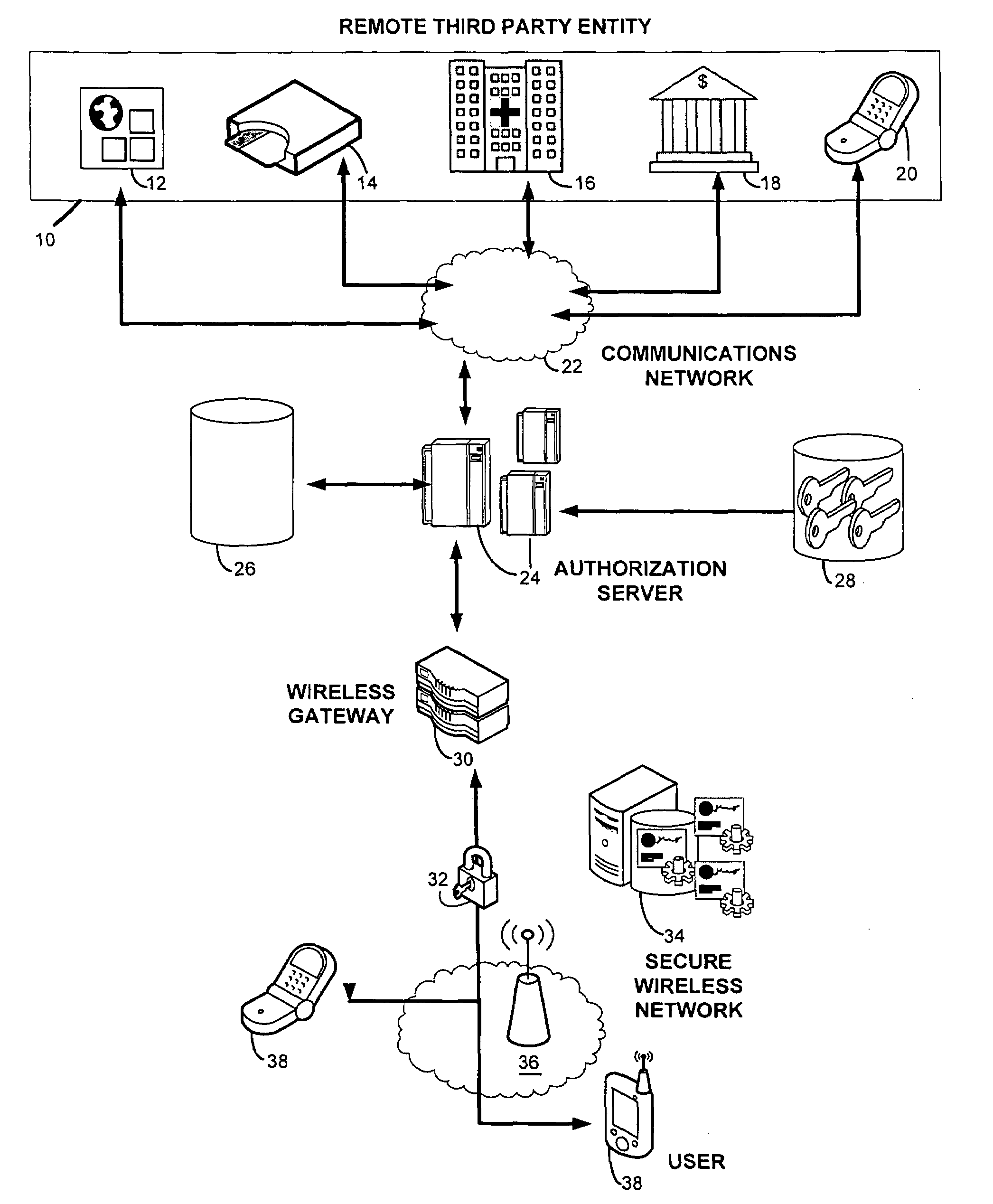
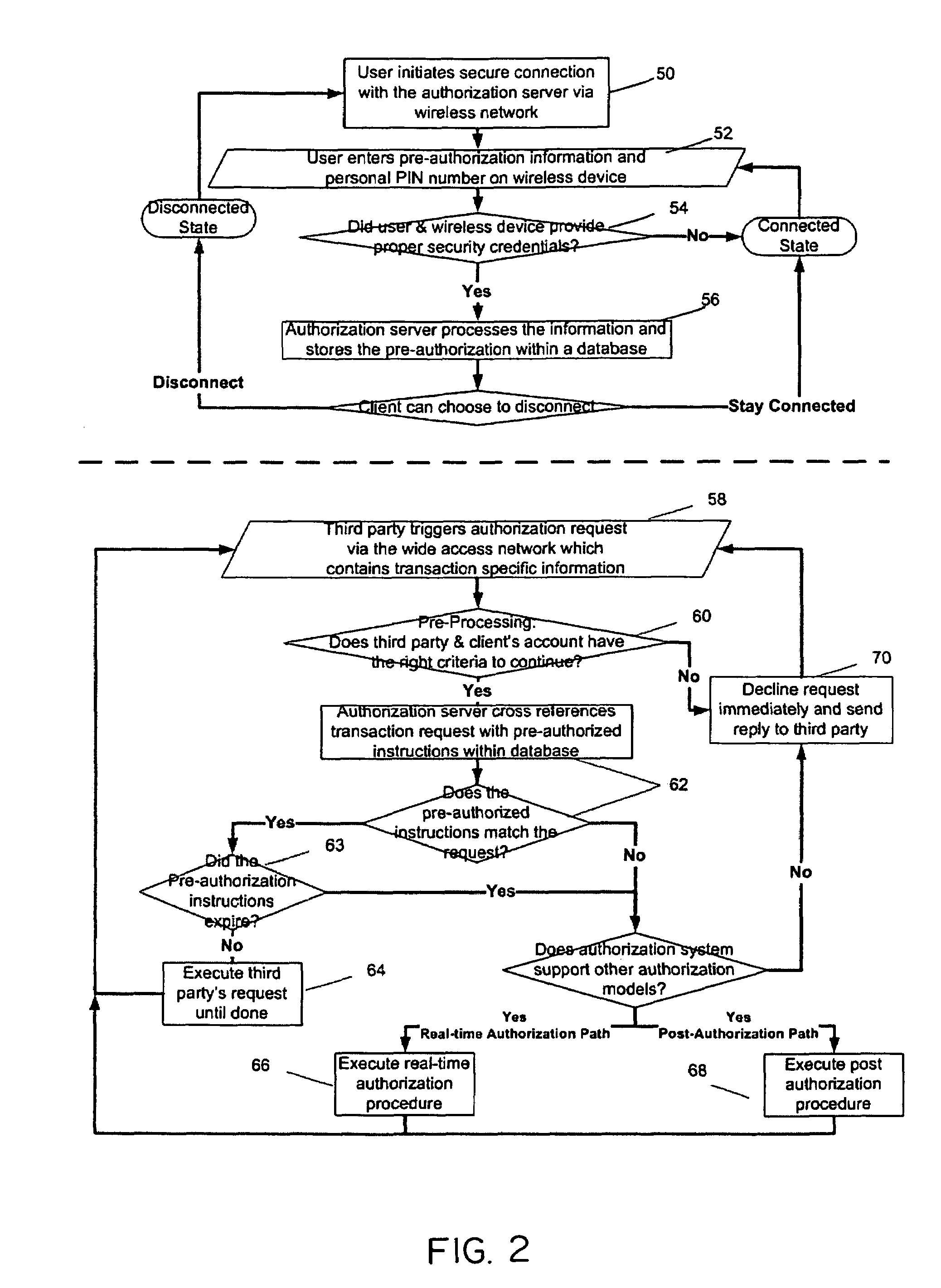
Secure wireless authorization system
ActiveUS20050184145A1Minimize the possibilityReduce financial costsFinanceUnauthorised/fraudulent call preventionThird partyAuthorization
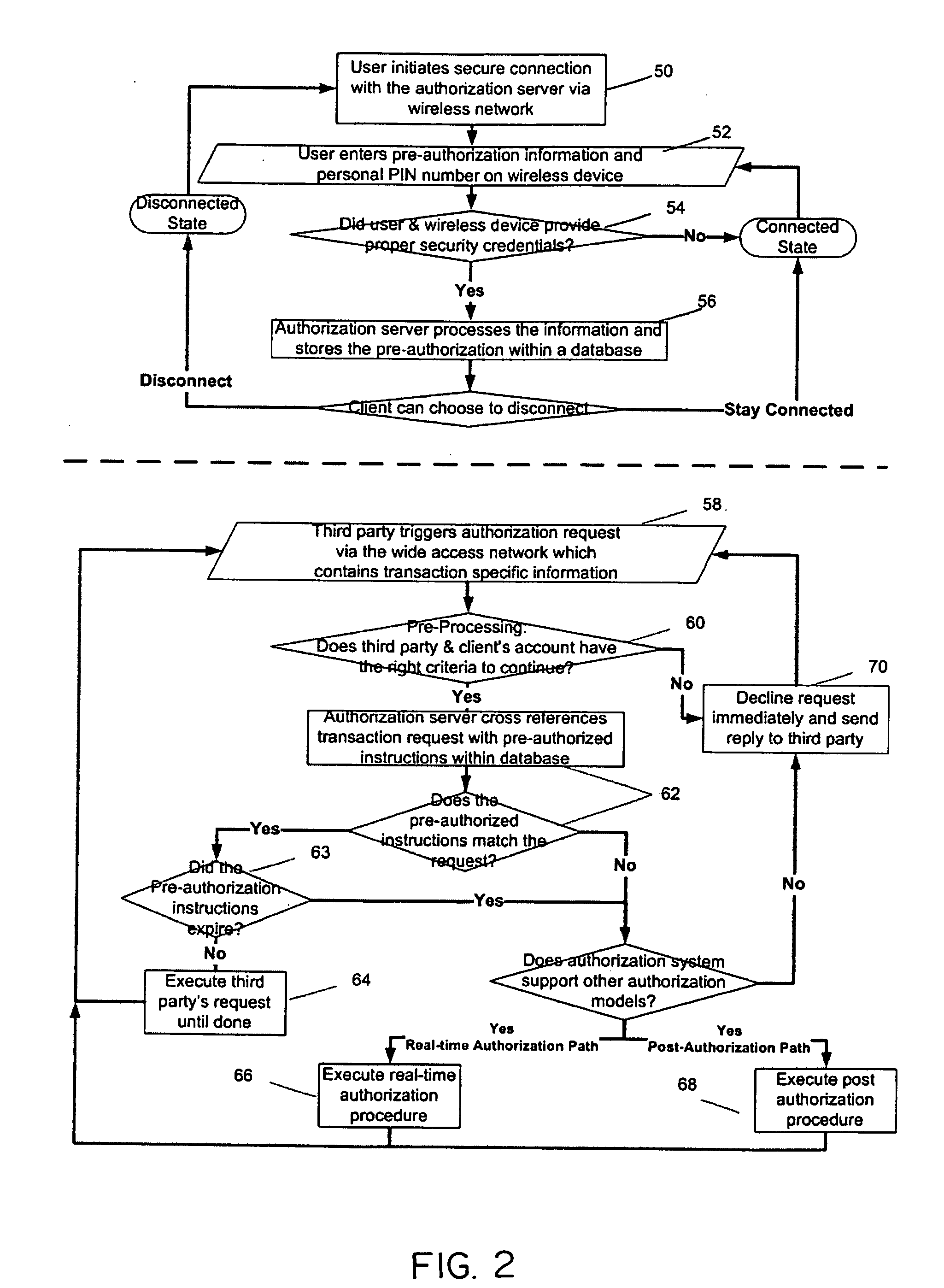
The invention relates to a secure wireless authorization system by which a user can employ a wireless device to authorize a request that is initiated by a remote third party and transmitted to the user by an authorization server. The system includes the authorization server that is linked to the third party by way of a communications connection and a wireless device that is adapted to securely store an encryption scheme and create a secure authorization from the user in response to the third party request and has the ability to establish a secure wireless connection over which the secure authorization is transmitted from the user's wireless device to the authorization server. Pre-authorization, real-time authorization and post-authorization methods are disclosed by which user authorized transactions can be completed by way of the authorization system of this invention.
Owner:7611544 CANADA
Method and system for authenticating objects and object data
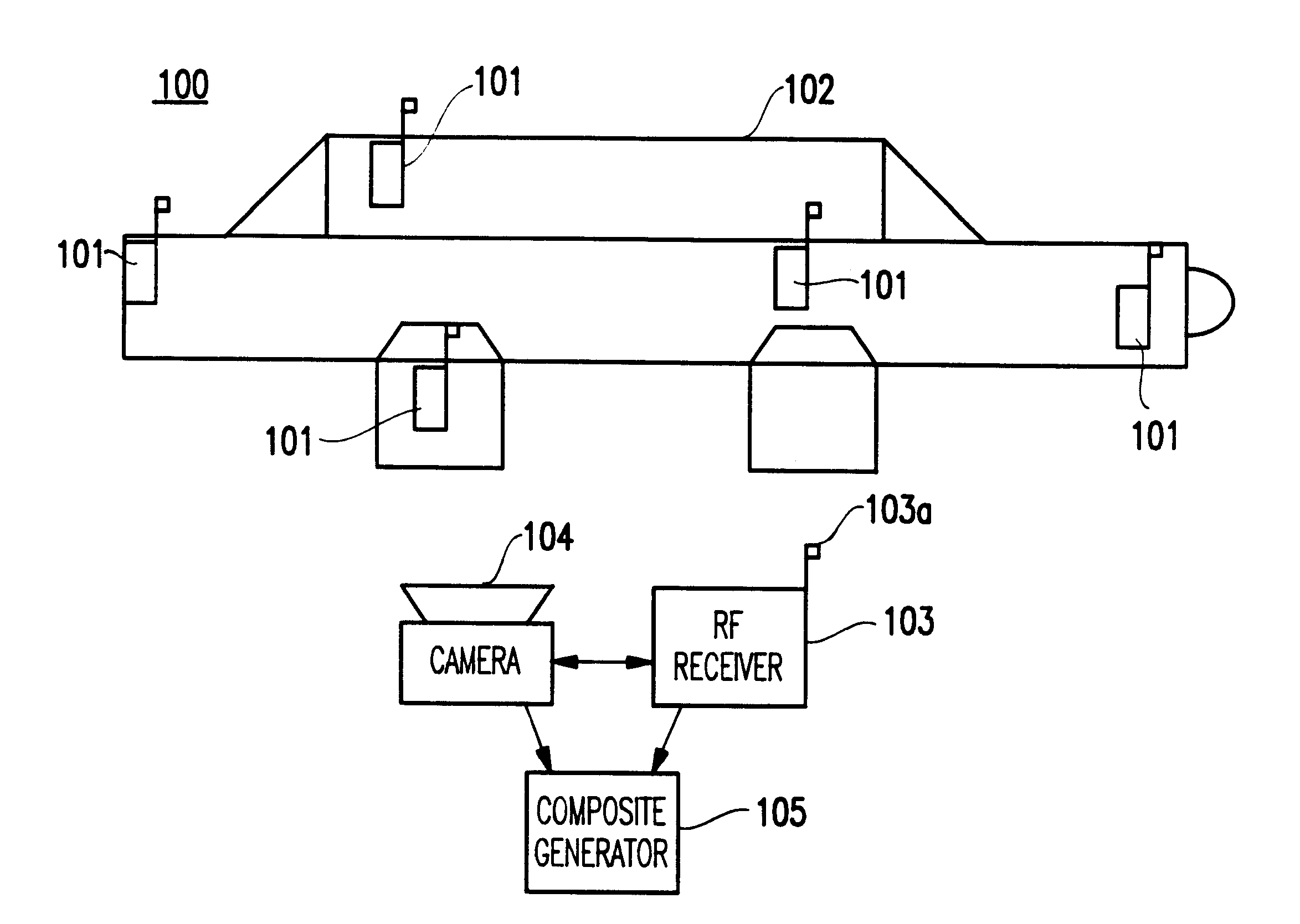
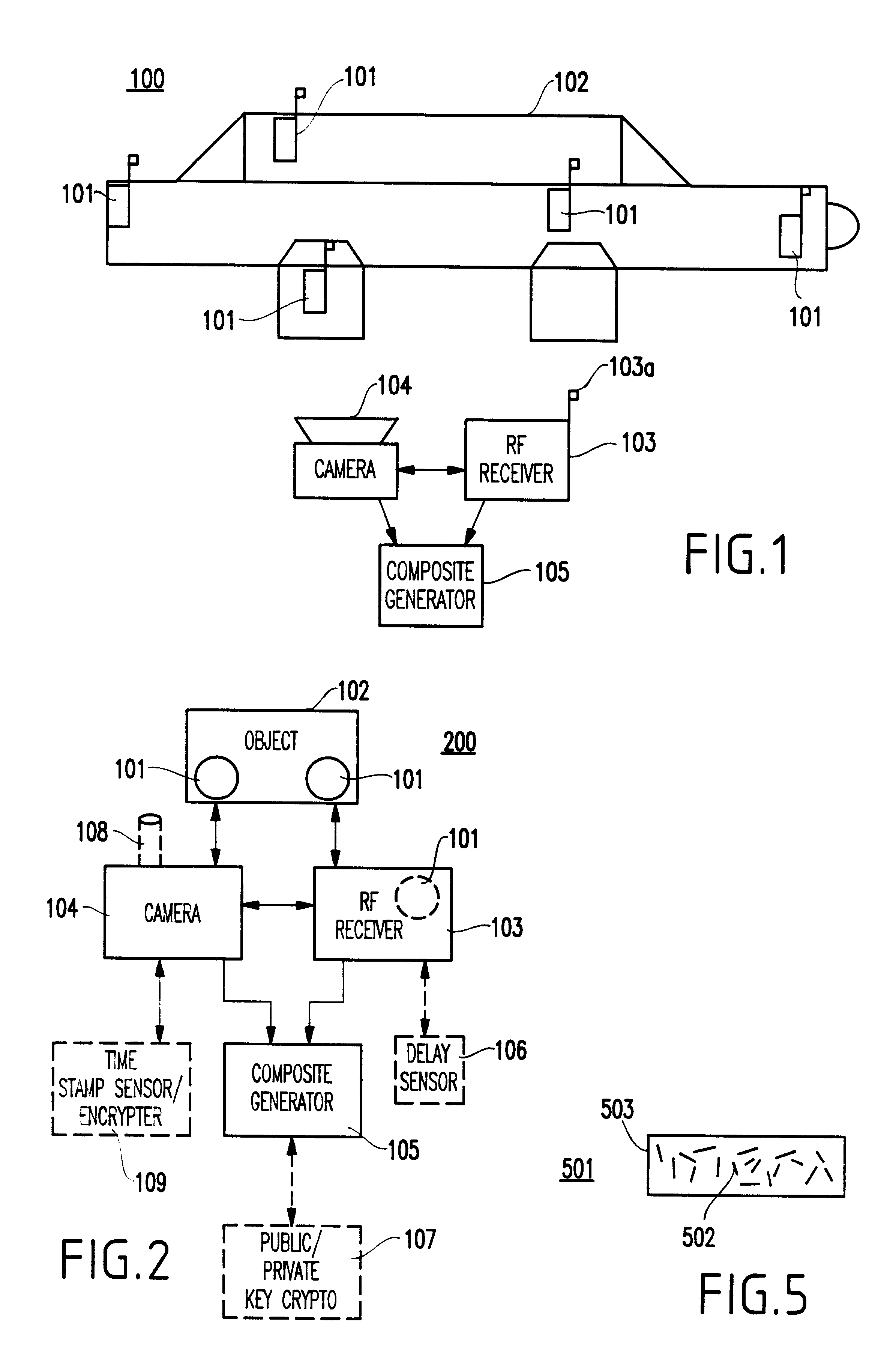
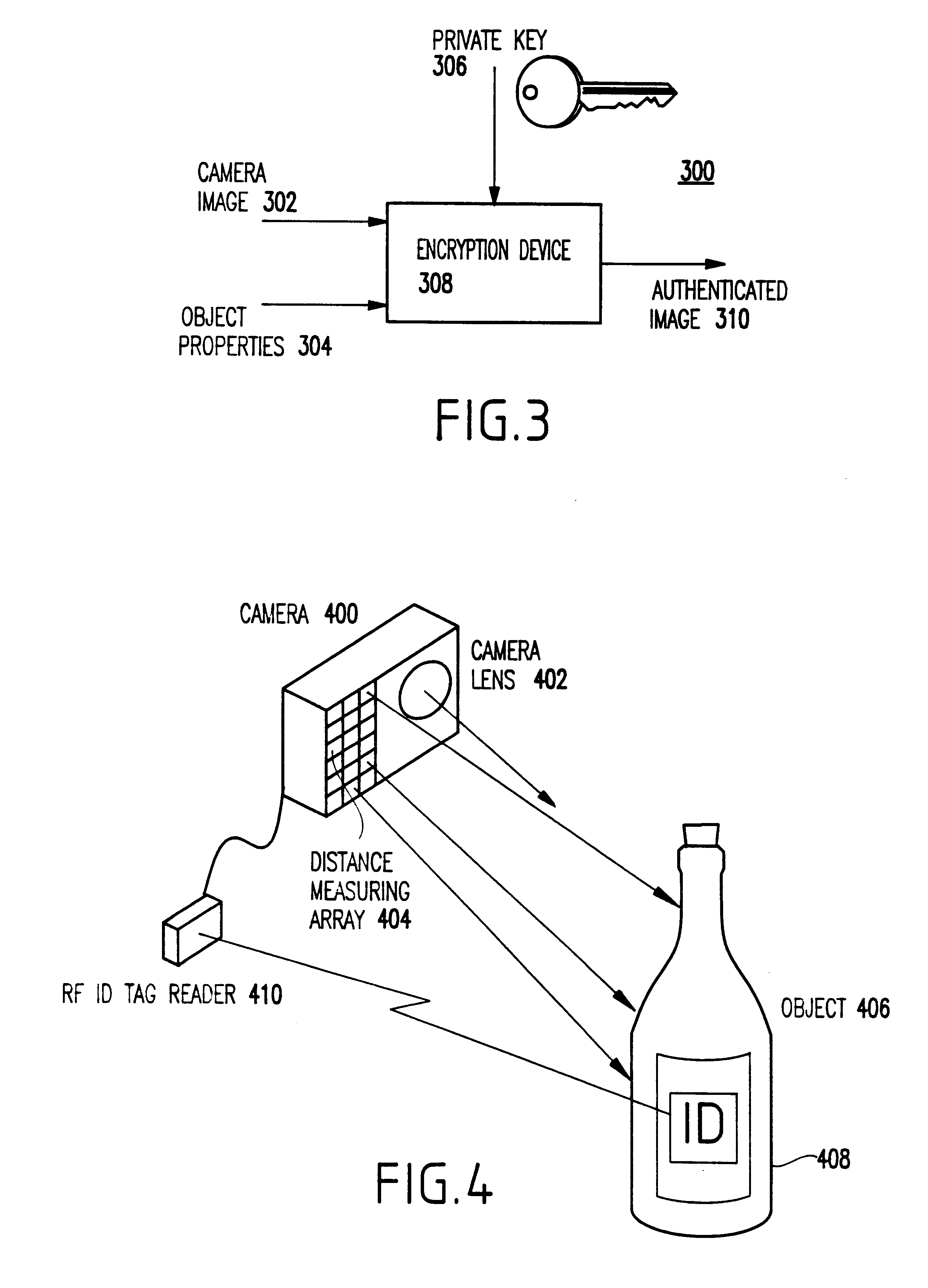
InactiveUS6397334B1Improve reliabilityIncrease credibilityTelevision system detailsFinanceVideo camera
A system and method for authenticating an image of an object, include at least one identifier associated with the object, a receiver for interrogating the at least one identifier to produce identification information, a camera system for recording an image from the object including the at least one identifier, and a composite generator for encoding the identification information from the receiver along with the image acquired by the camera system, to produce composite data.
Owner:IBM CORP
Method and system for discriminating a human action from a computerized action
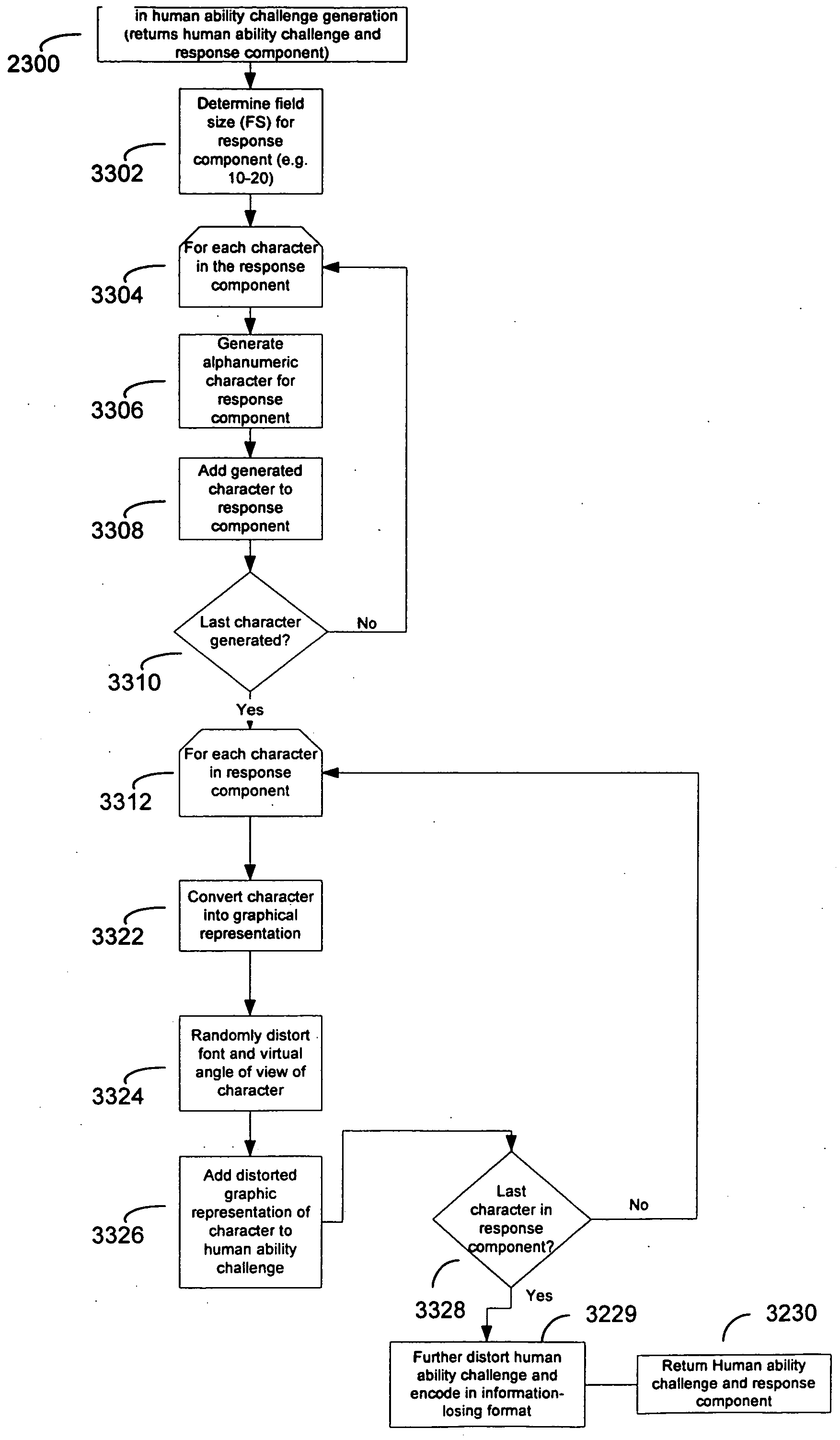
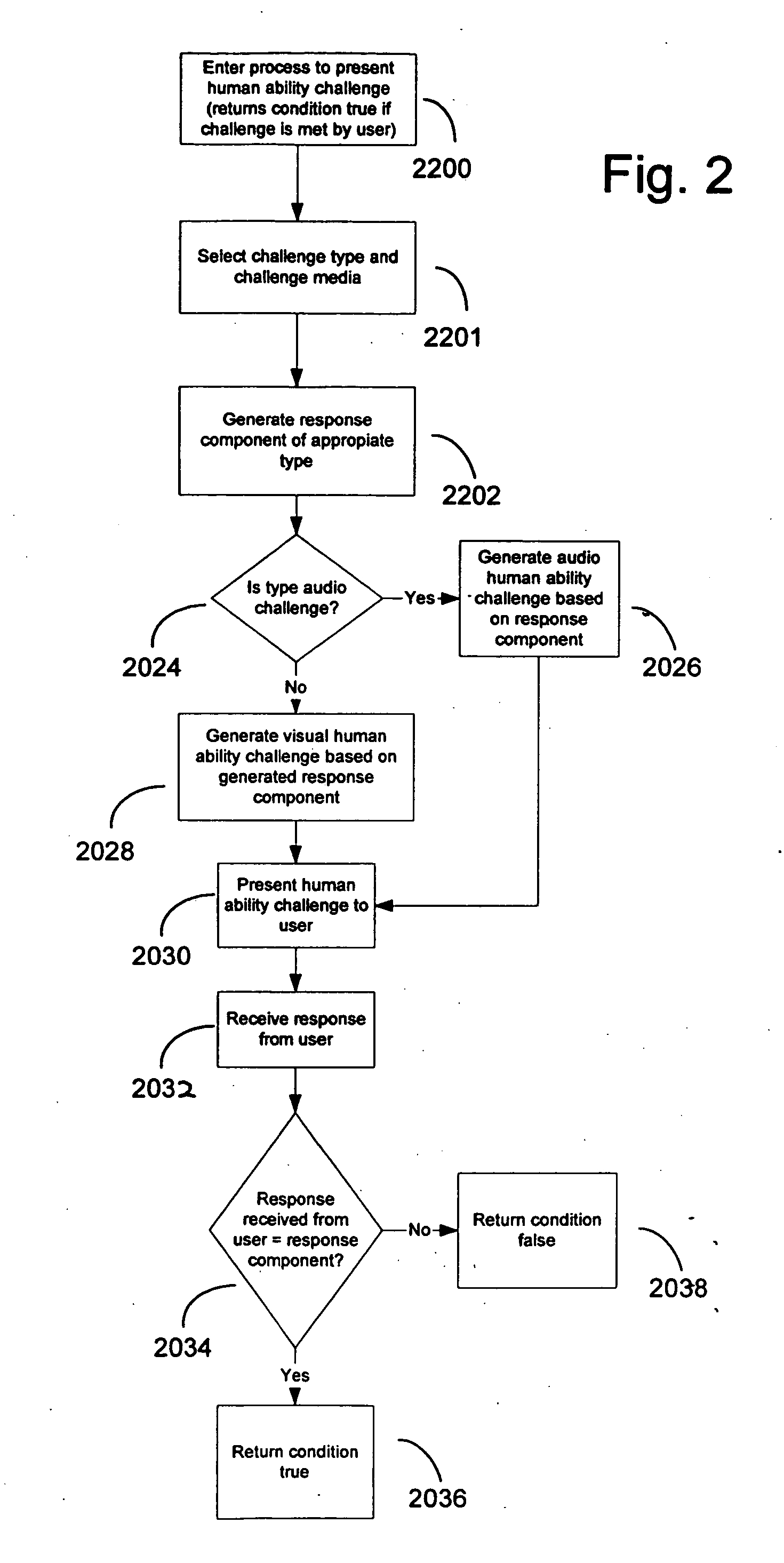
InactiveUS20050114705A1Reduce it effectivenessEnhanced authenticationDigital data processing detailsUser identity/authority verificationCognitive skillNatural language
A method and system are disclosed for discriminating automatic computerized action from a human performed action. The invention is based on applying human advantage in applying sensory and cognitive skills to solving simple problems that prove to be extremely hard for computer software. Such skills include, but are not limited to processing of sensory information such as identification of objects and letters within a noisy graphical environment, signals and speech within an auditory signal, patterns and objects within a video or animation sequence. Human skills also include higher level cognitive processing such as understanding natural language and logical assignments. The method for discriminating between humans and computerized actions can be used during authentication, to limit access by automated agents, and for confirmation of actions.
Owner:IBM CORP
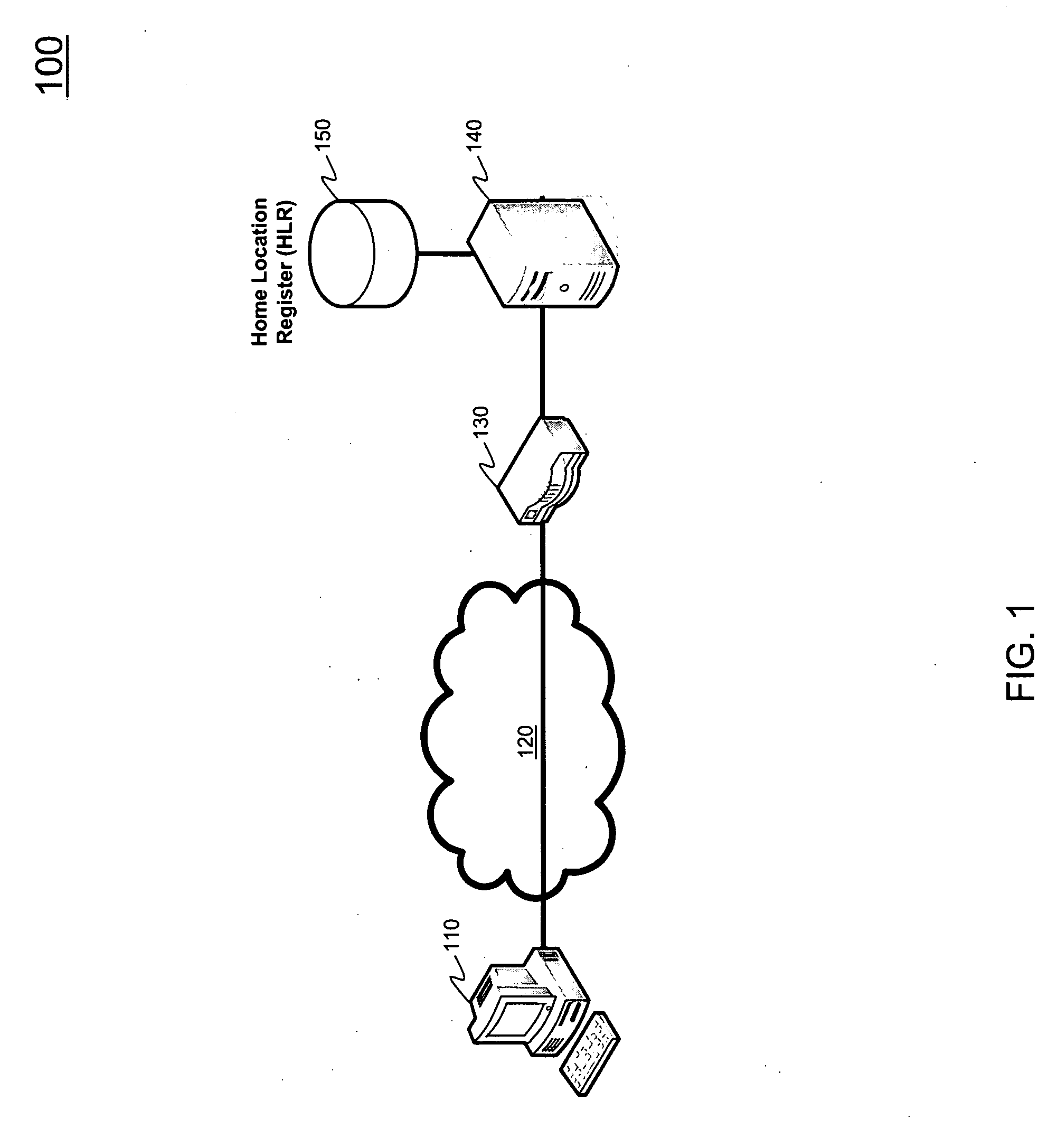
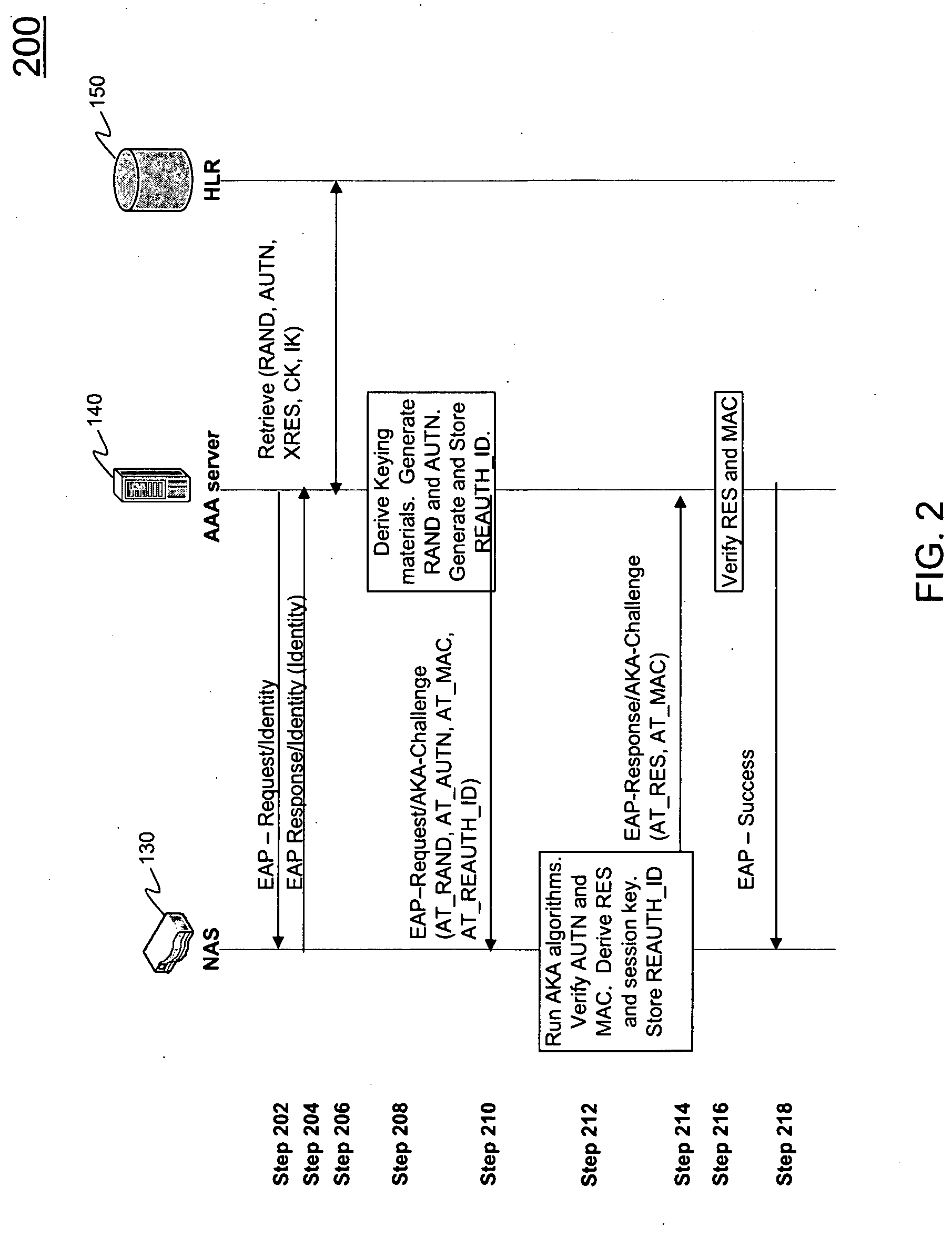
Extensible Authentication Protocol Authentication and Key Agreement (EAP-AKA) Optimization
ActiveUS20100017603A1Low costEliminate needUnauthorised/fraudulent call preventionEncryption apparatus with shift registers/memoriesClient-sideProtocol for Carrying Authentication for Network Access
Systems and methods are described for improved authentication of subscribers wishing to connect to a wireless network using the EAP-AKA protocol. Embodiments exploit the requirement that the client store and transmit the Pseudonym and Fast Re-authentication Identities upon request. By using the Fast Re-authentication Identity to store session state key information, the need for the AAA server to store and replicate the EAP-AKA key information for every session is eliminated.
Owner:AMDOCS CANADIAN MANAGED SERVICES INC +1
Securing electronic transactions over public networks
InactiveUS6948063B1Enhance authenticationEnhances secrecyMultiple keys/algorithms usageUser identity/authority verificationComputer securityNon symmetric
An electronic message for transmission over a network, such as the Internet, is created by encrypting a first component with a first crypto-key, which is associated with a first network entity, such that the encrypted first component can be decrypted by only the first network entity. The first crypto-key could, for example, be a symmetric crypto-key known only to the first network entity or the public non-symmetric crypto-key of a private-public non-symmetric key pair, where the private non-symmetric crypto key is known only to the first network entity. A second component, which is different than the first component, is encrypted with a second crypto-key, which is associated with a second network entity, such that the encrypted second component can also be decrypted by the first network entity. The second crypto-key could, for example, be a symmetric crypto-key known to both the first and second network entities or the private non-symmetric crypto-key of a private-public non-symmetric key pair of the second network entity, where the public non-symmetric crypto key is known to the first network entity. The encrypted first and second components are combined to create the electronic message.
Owner:CHECKFREE CORP
Method and apparatus for user authentication
ActiveUS20070050618A1The certification process is reliableEnhanced authenticationDigital data processing detailsUser identity/authority verificationUser inputData memory
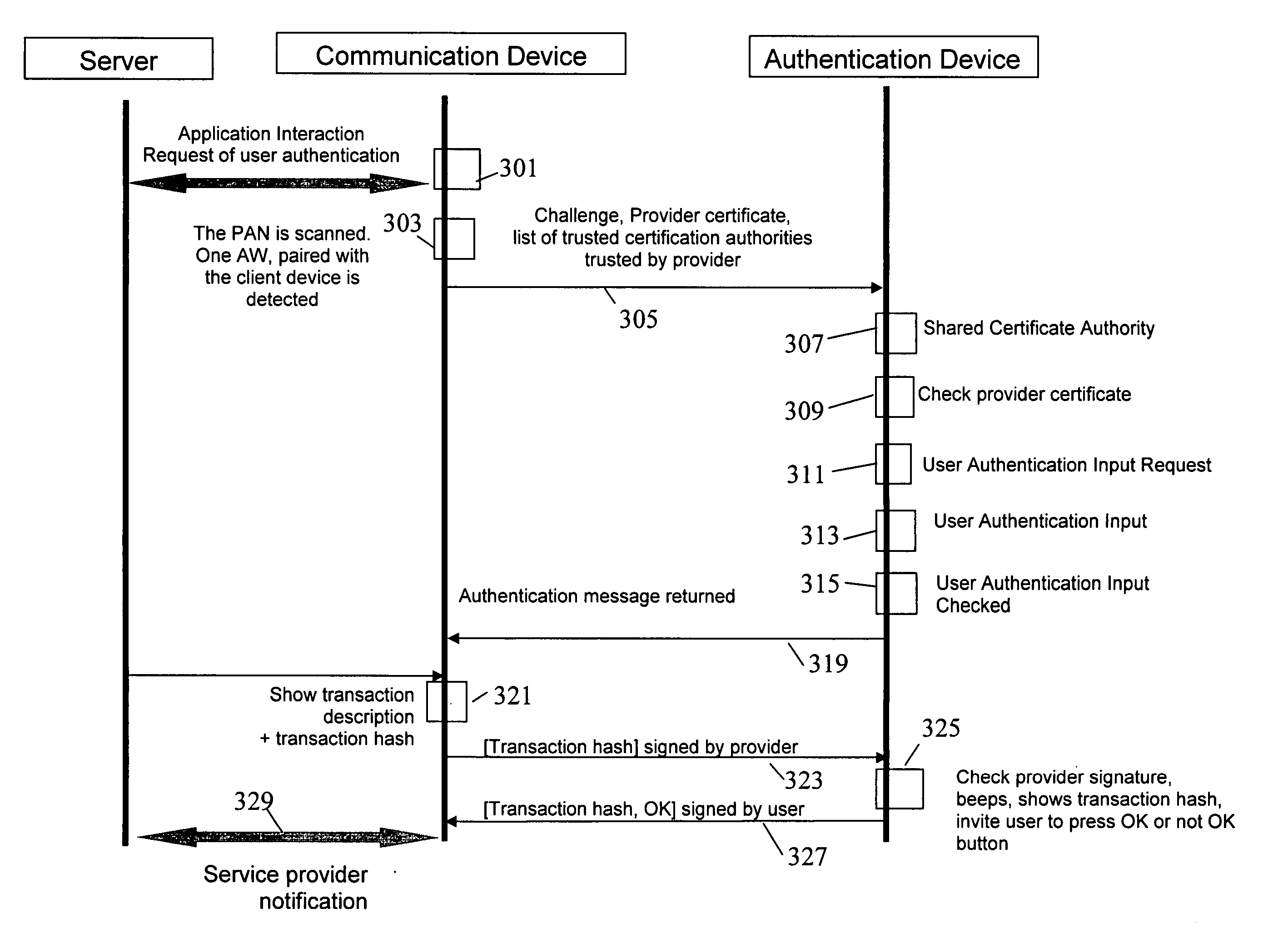
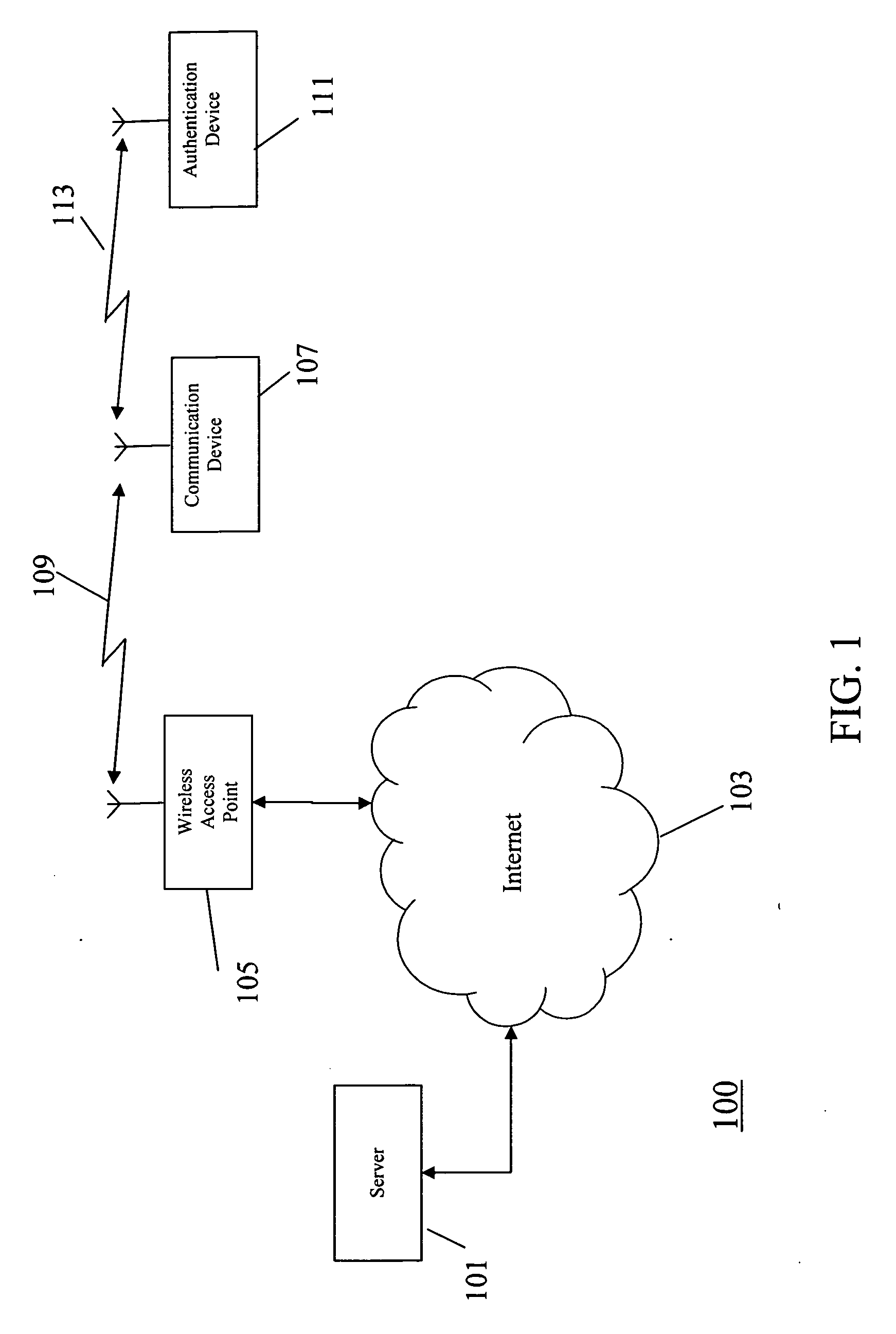
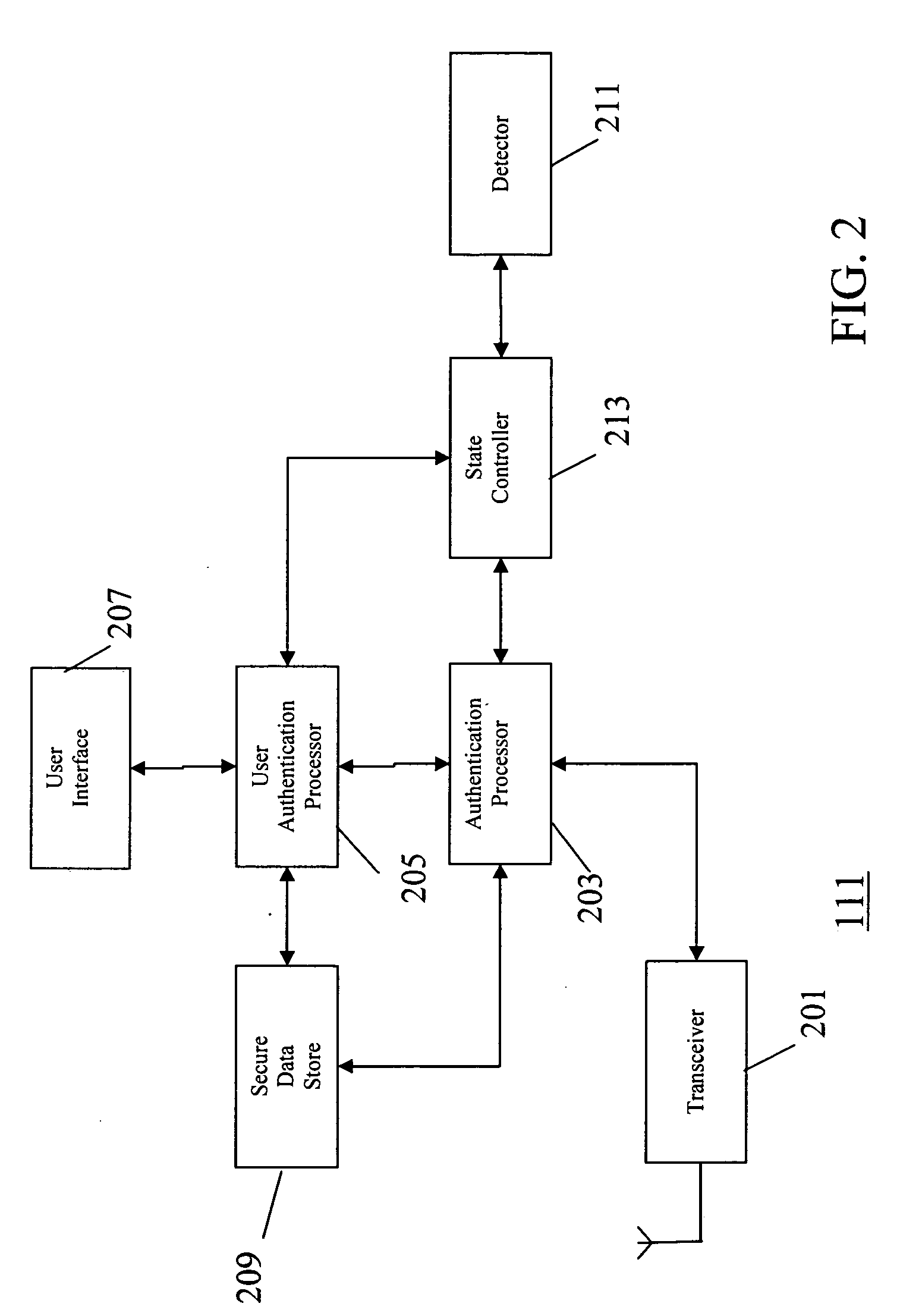
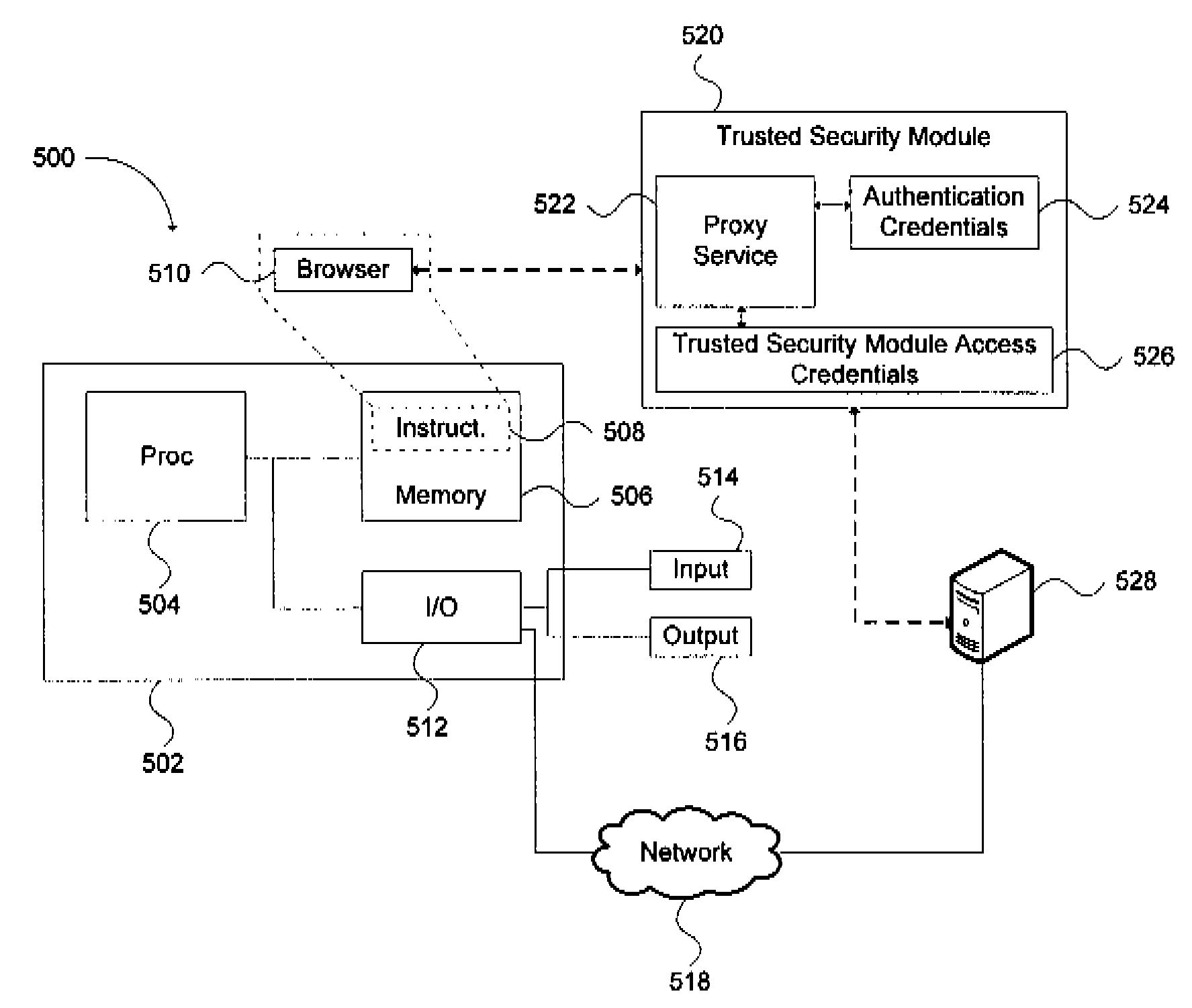
The invention provides for secure end-to-end user authentication by a remote server communicating with a communication device. The communication device further communicates with an authentication device, which provides a user authentication message to the communication device for forwarding to the remote server. The authentication device comprises a data store for storing user authentication credentials. A user authentication processor performs a local authentication of a user of the authentication device in response to a user input. An authentication processor generates the authentication message if the user authentication is valid. The authentication processor implements a cryptographic function based on the user authentication credentials. A transmitter then transmits the authentication message to the at least one communication device.
Owner:MOTOROLA SOLUTIONS INC
Secure and efficient authentication using plug-in hardware compatible with desktops, laptops and/or smart mobile communication devices such as iphones
ActiveUS20120124651A1Enhanced authenticationImproved transactionDigital data processing detailsMultiple digital computer combinationsTelecommunications linkCommunication link
A portable apparatus is removably and communicatively connectable to a network device to communicate authentication or authorization credentials of a user in connection with the user logging into or entering into a transaction with a network site. The apparatus includes a communications port to connect and disconnect the apparatus to and from the network device and to establish a communication link with the network device when connected thereto. A processor receives a secure message from the network security server via the port. The message has a PIN for authenticating the user to the network site, and is readable only by the apparatus. The processor either transfers, via the port, the received PIN to an application associated with the network site that is executing on the network device or causes the apparatus to display the received PIN for manual transfer to the application associated with the network site.
Owner:PAYFONE
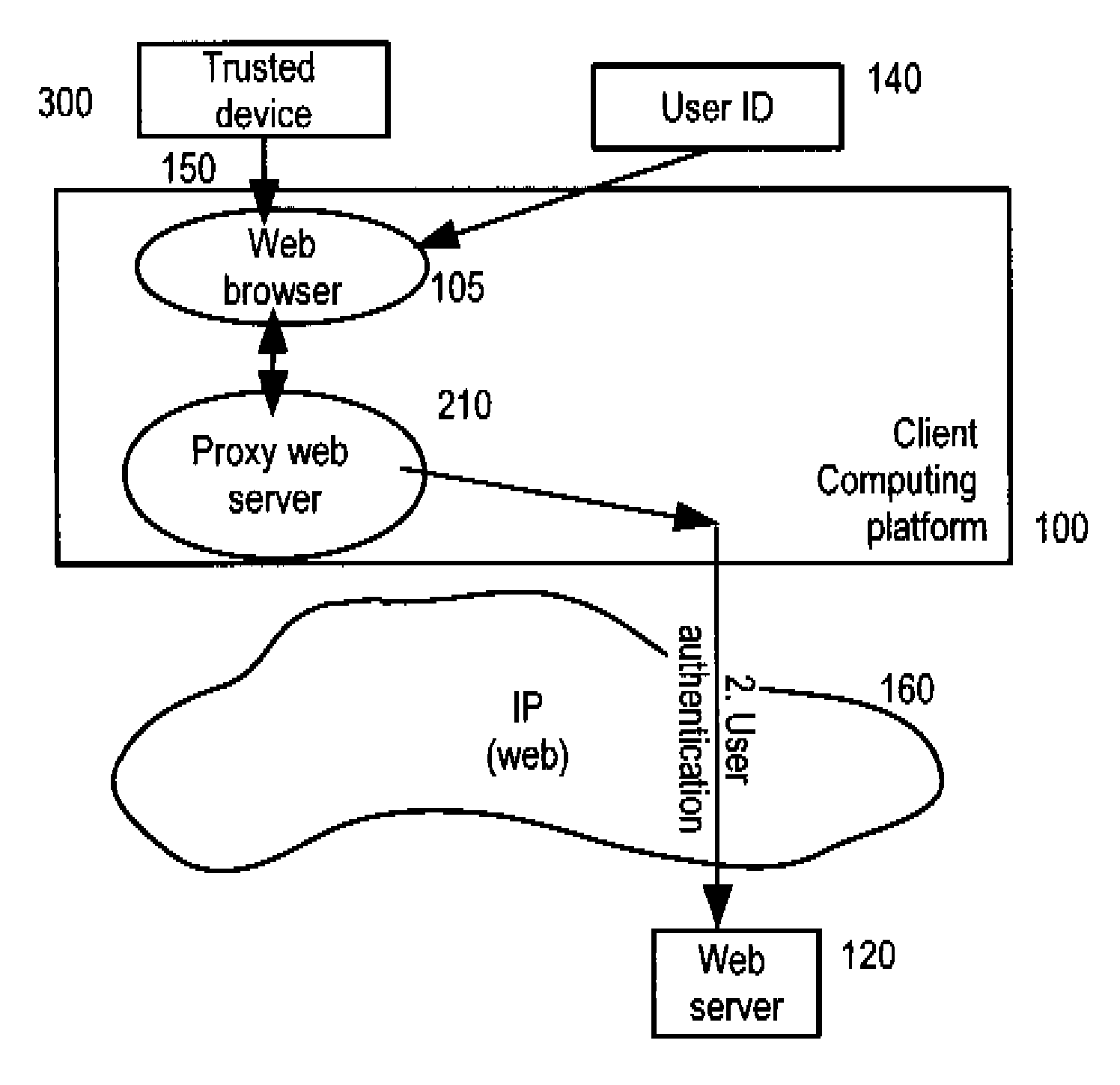
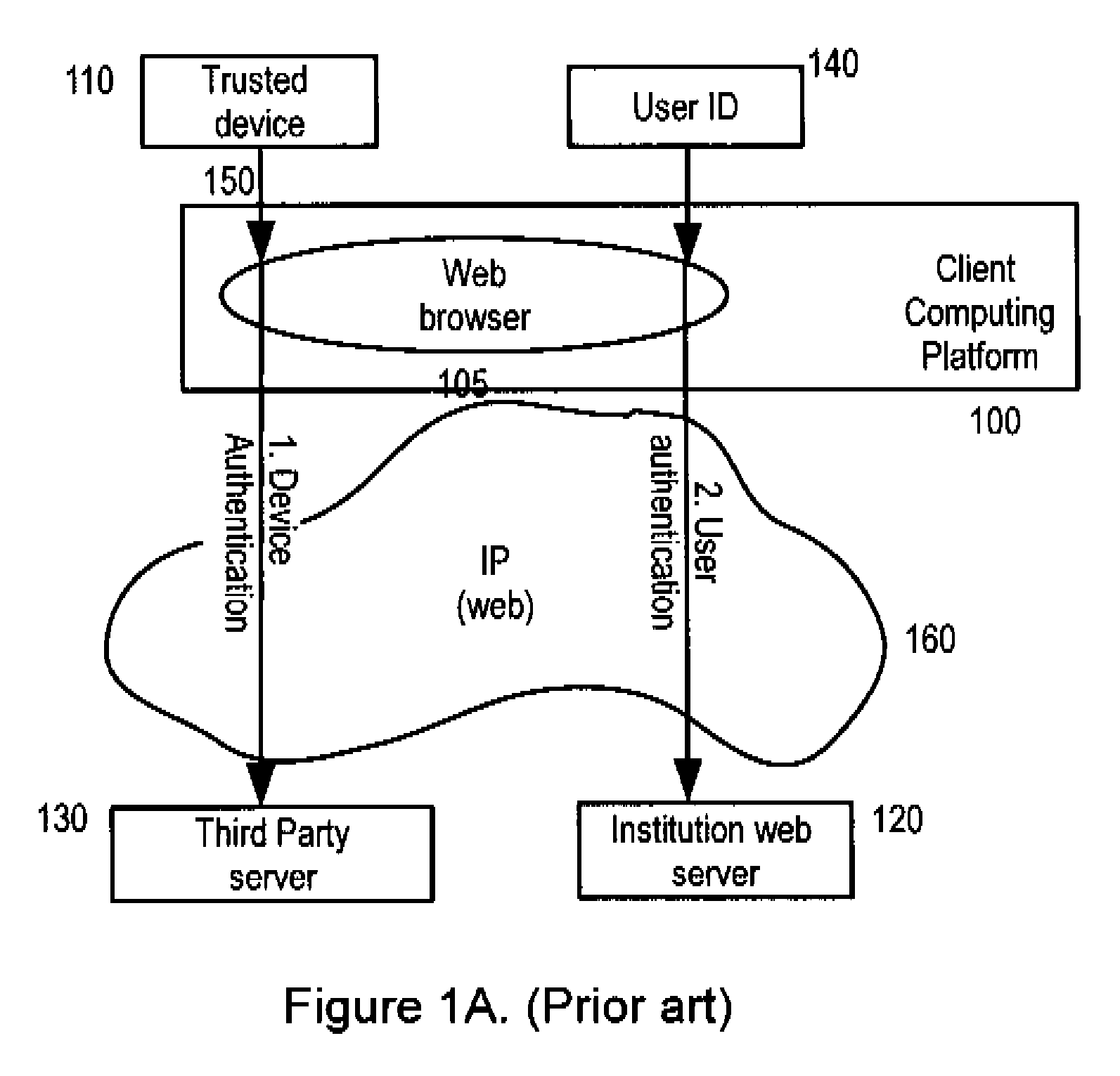
Network transaction verification and authentication
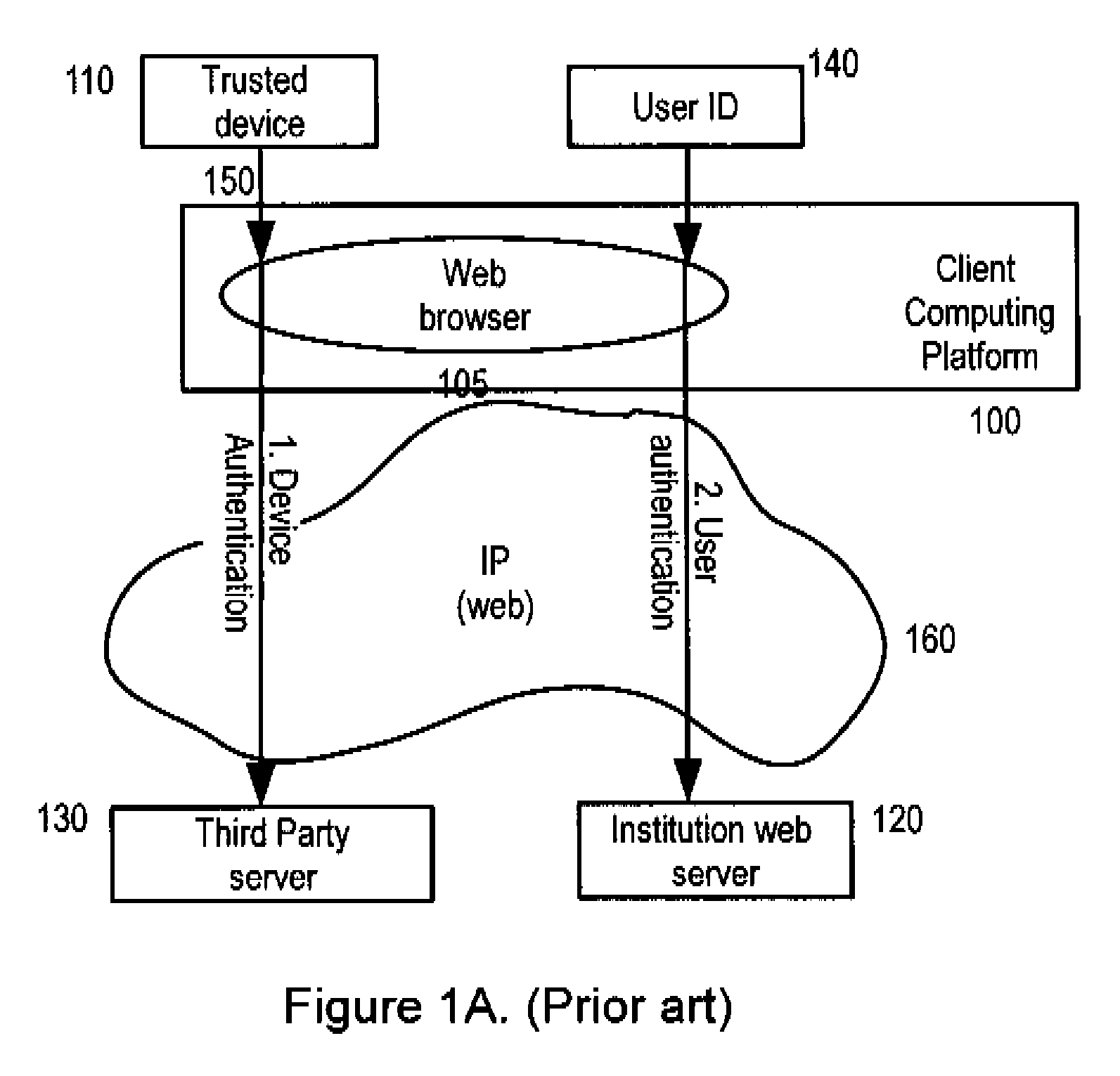
ActiveUS20100199086A1Enhanced authenticationConvenient verificationDigital data processing detailsComputer security arrangementsAuthentication serverClient-side
A two-level authentication system is described supporting two-factor authentication that offers efficient protection for secure on-line web transactions. It includes a global unique identity (UID) provided either by an institute-issued / personal trusted device, or based on client computing platform hardware attributes, and generated using institution authorized private software, institution-authorized authentication proxy software, and an institution-generated credential code which is pre-stored in the token and only accessible by the institute-authorized authentication proxy software. The institution-authorized authentication proxy software uses the user's PIN and the trusted device's UID as input and verifies the user and device identities through institution-generated credential code which was pre-stored in the trusted device. Authentication is performed in two levels: the first authenticates the user and the trusted device locally; and the second authenticates the user remotely at the institution-owned authentication server. Various embodiments add extra levels of security, including one-time-password management.
Owner:INBAY TECH
Telephony system and method with enhanced validation
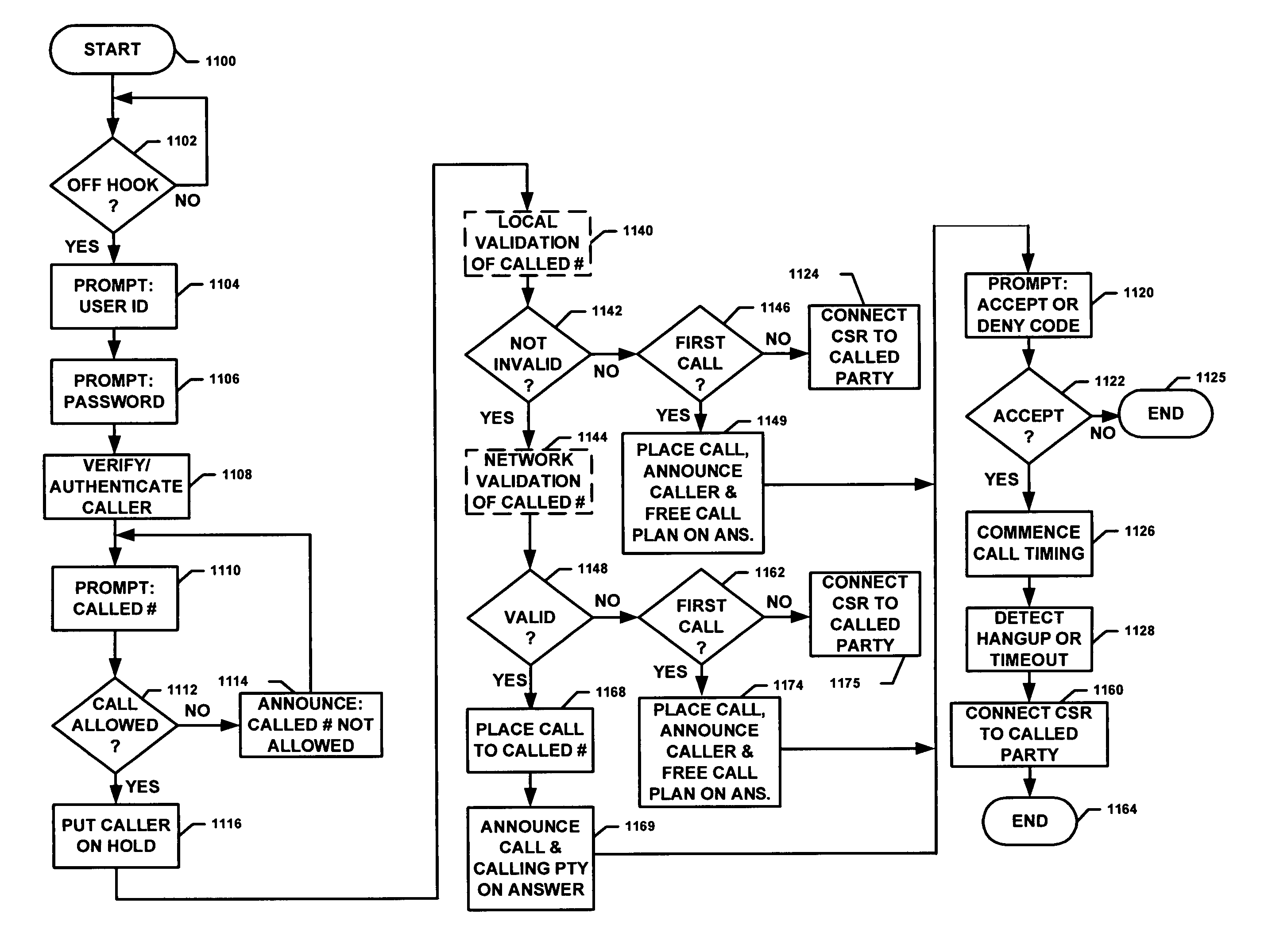
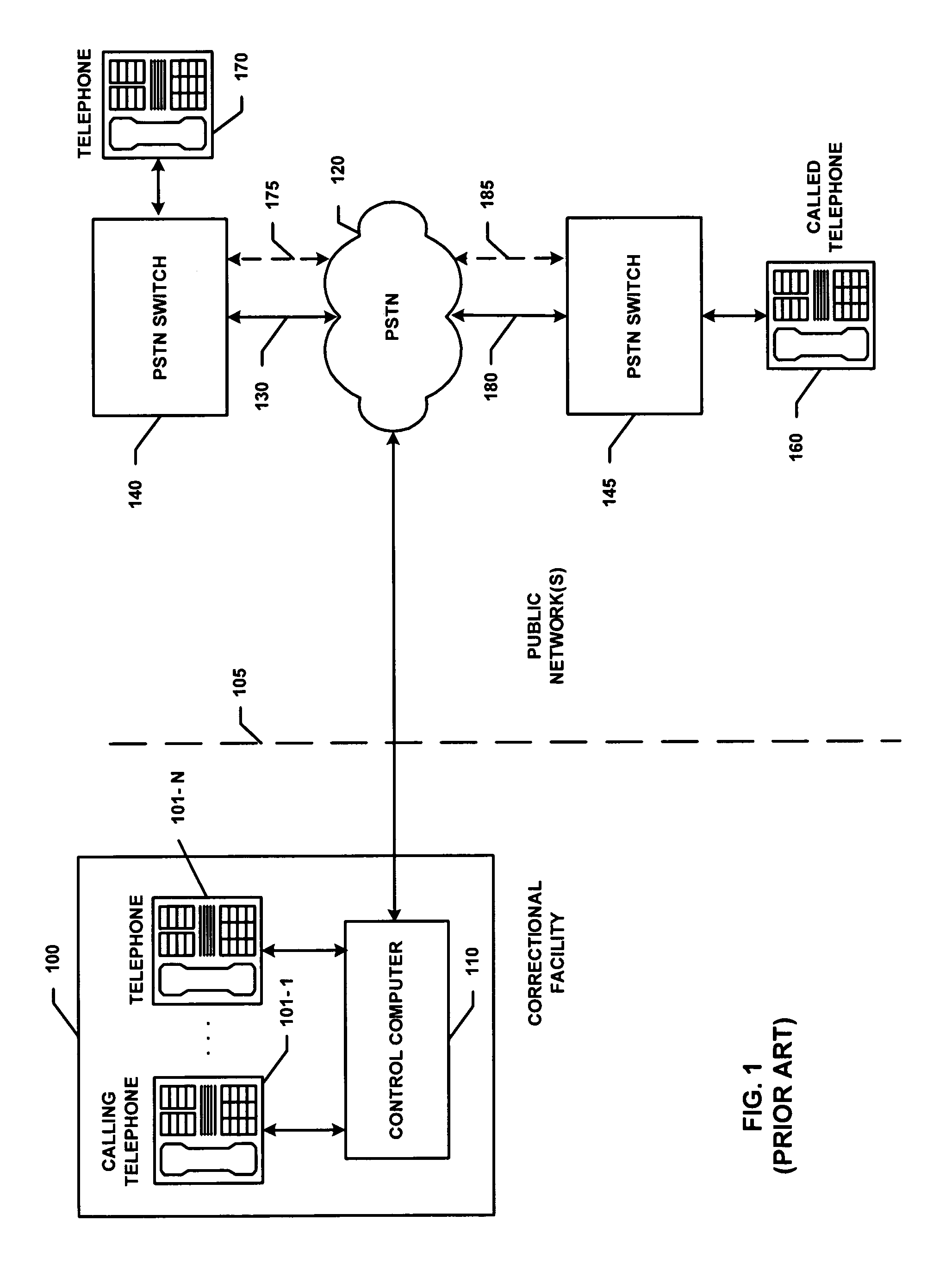
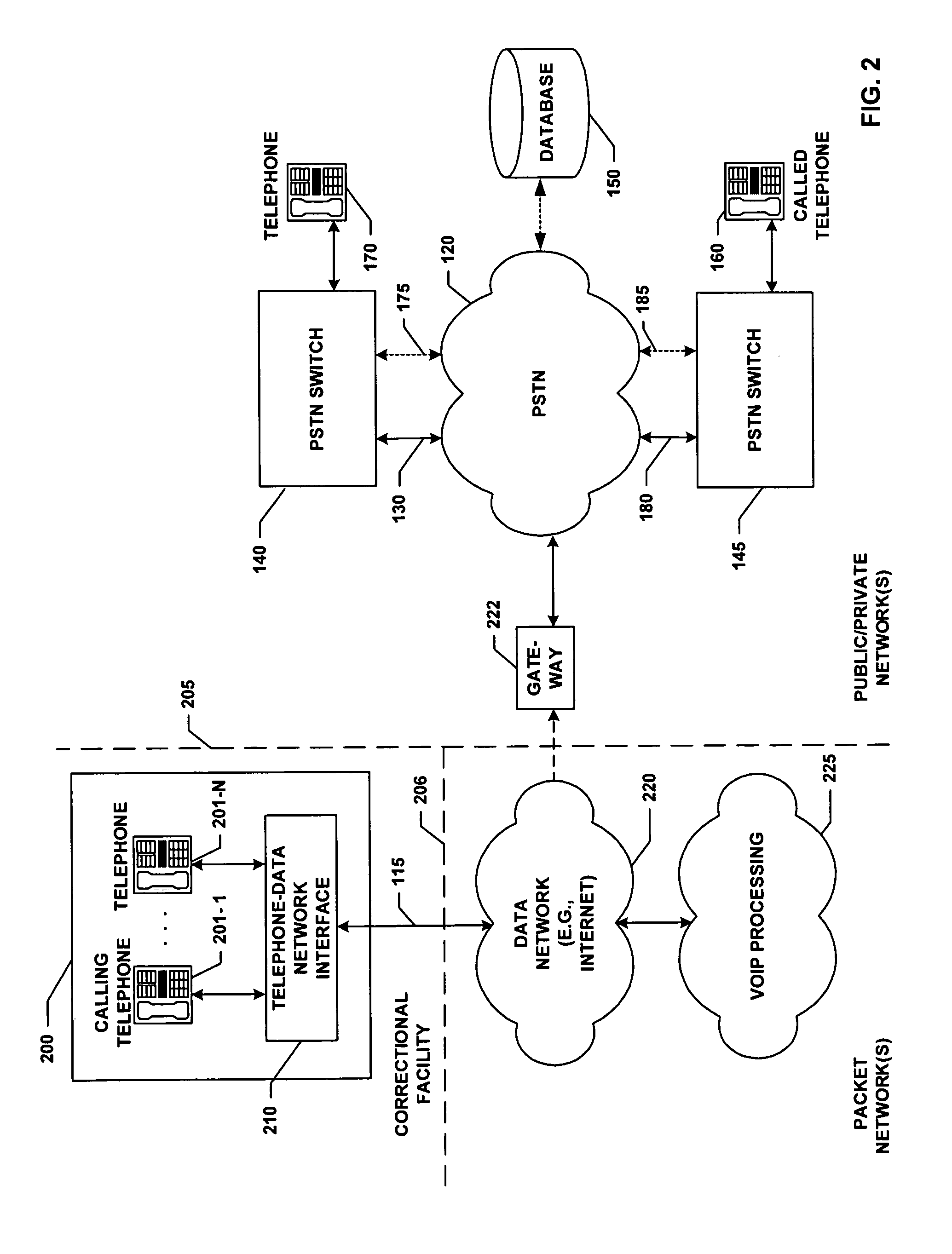
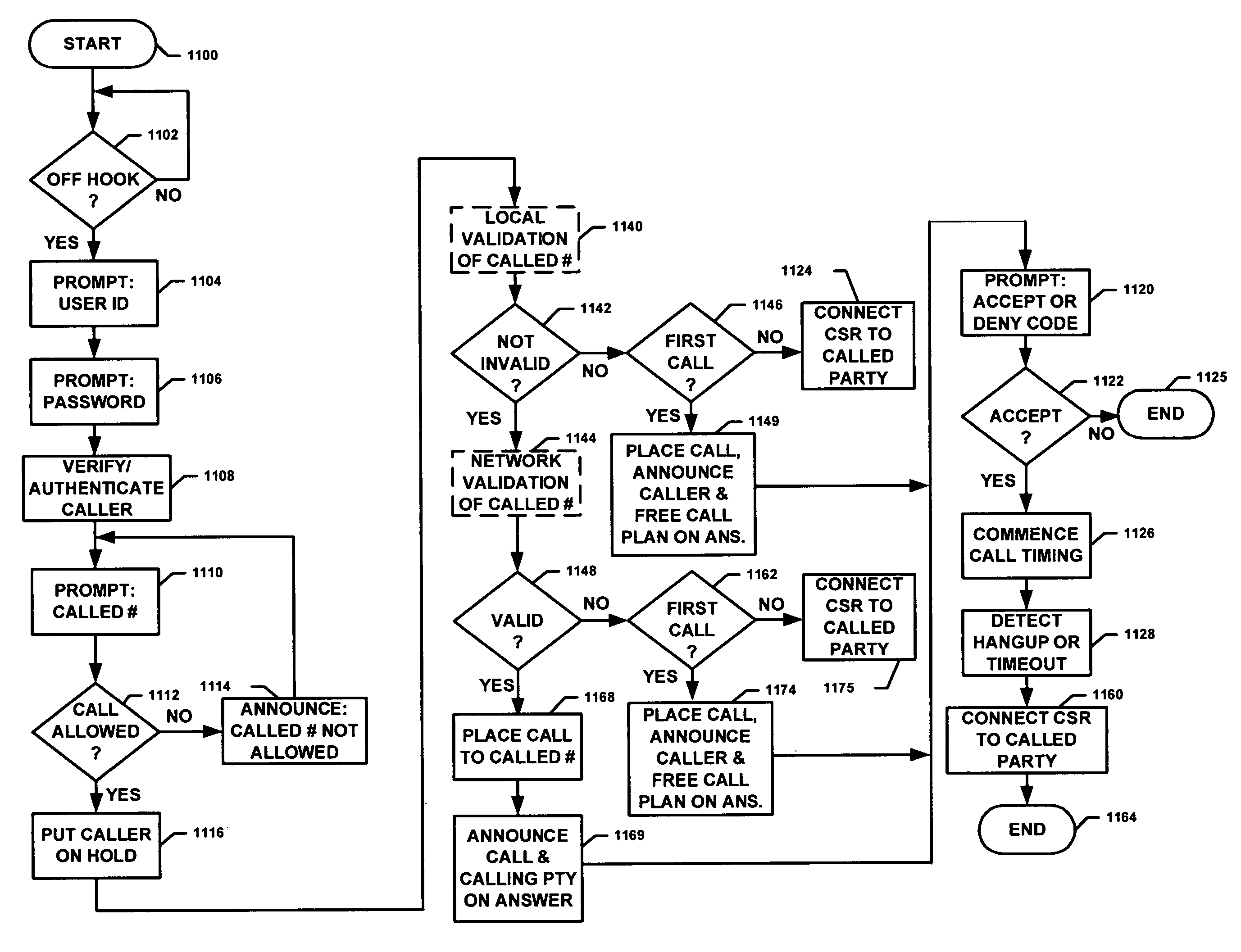
ActiveUS7881446B1Enhance identification techniqueReduce operating costsTelephonic communicationSystem administratorThird party
Inmate communications systems provide a feature-rich platform with a high degree of flexibility and security employing call control facilities located off institutional premises. Authentication processes for calling and called party verification include biometric techniques in some embodiments. Distributed processing of call control and billing provide flexible interactive call payment processes. Preferred embodiments feature voice over IP transmission and control featuring controlled access to avoid addition of unauthorized third-party call participants. Monitoring, recording and selective forwarding of calls is provided under control of system administrators.
Owner:CONFINEMENT TELEPHONY TECH +1
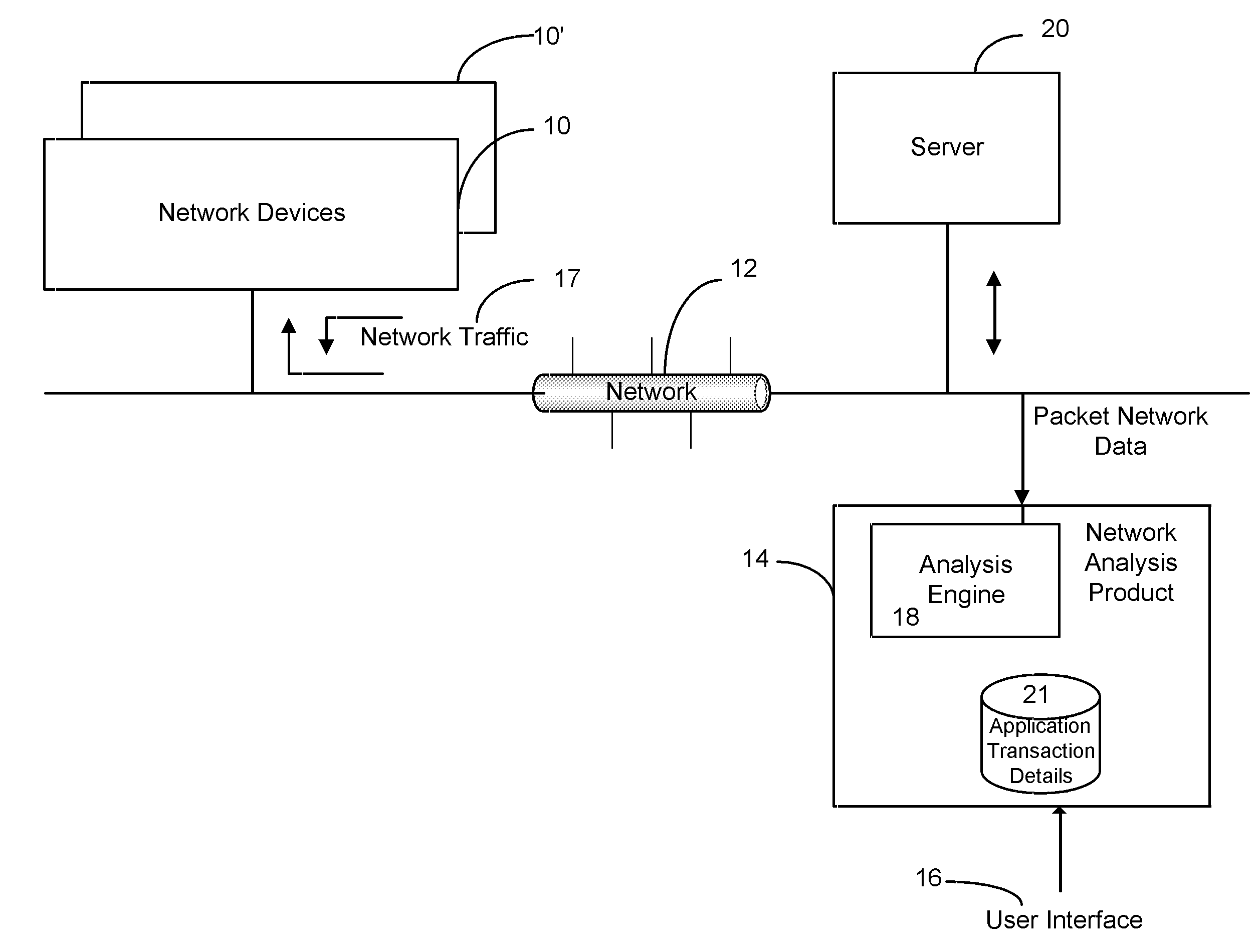
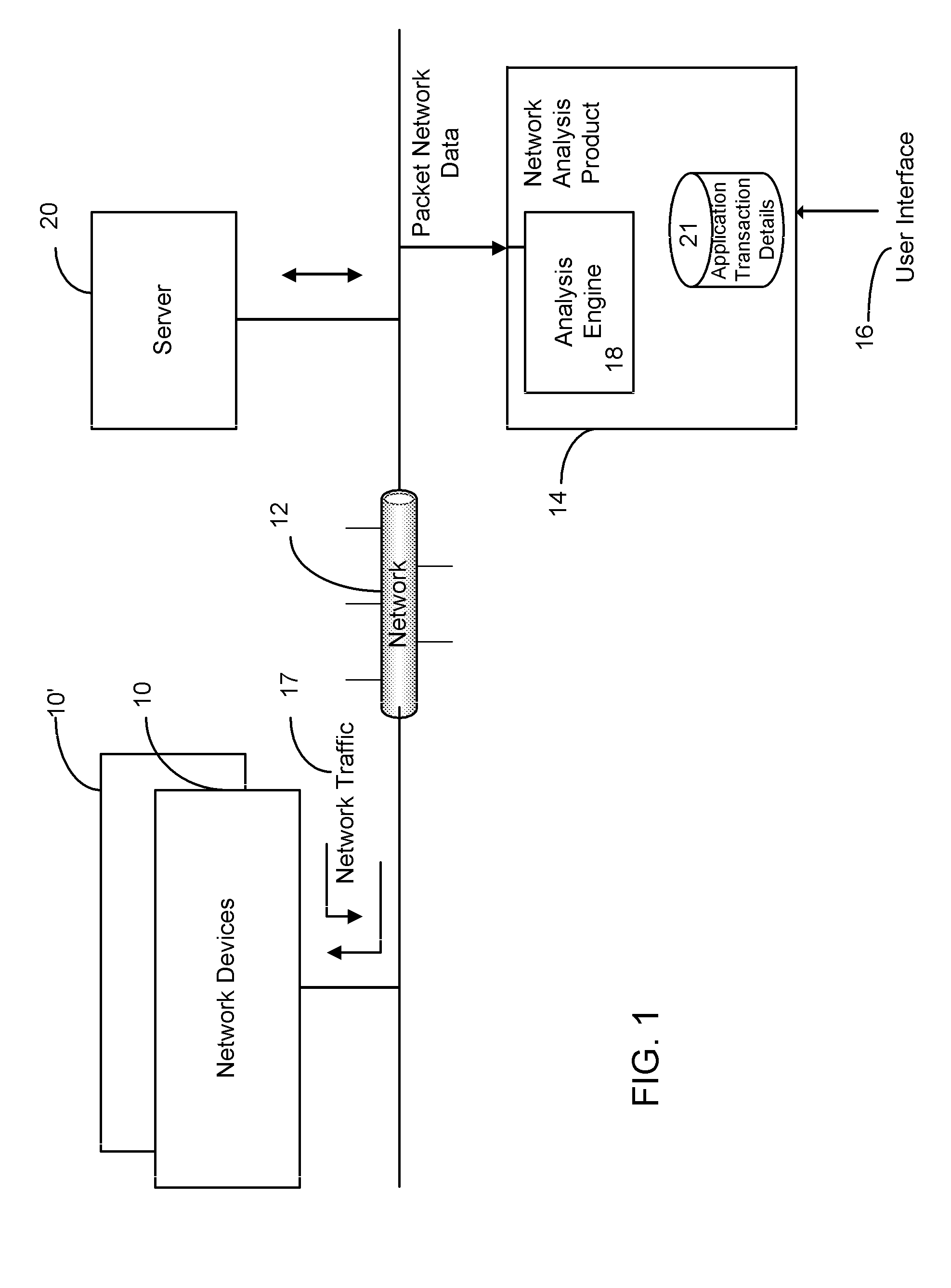
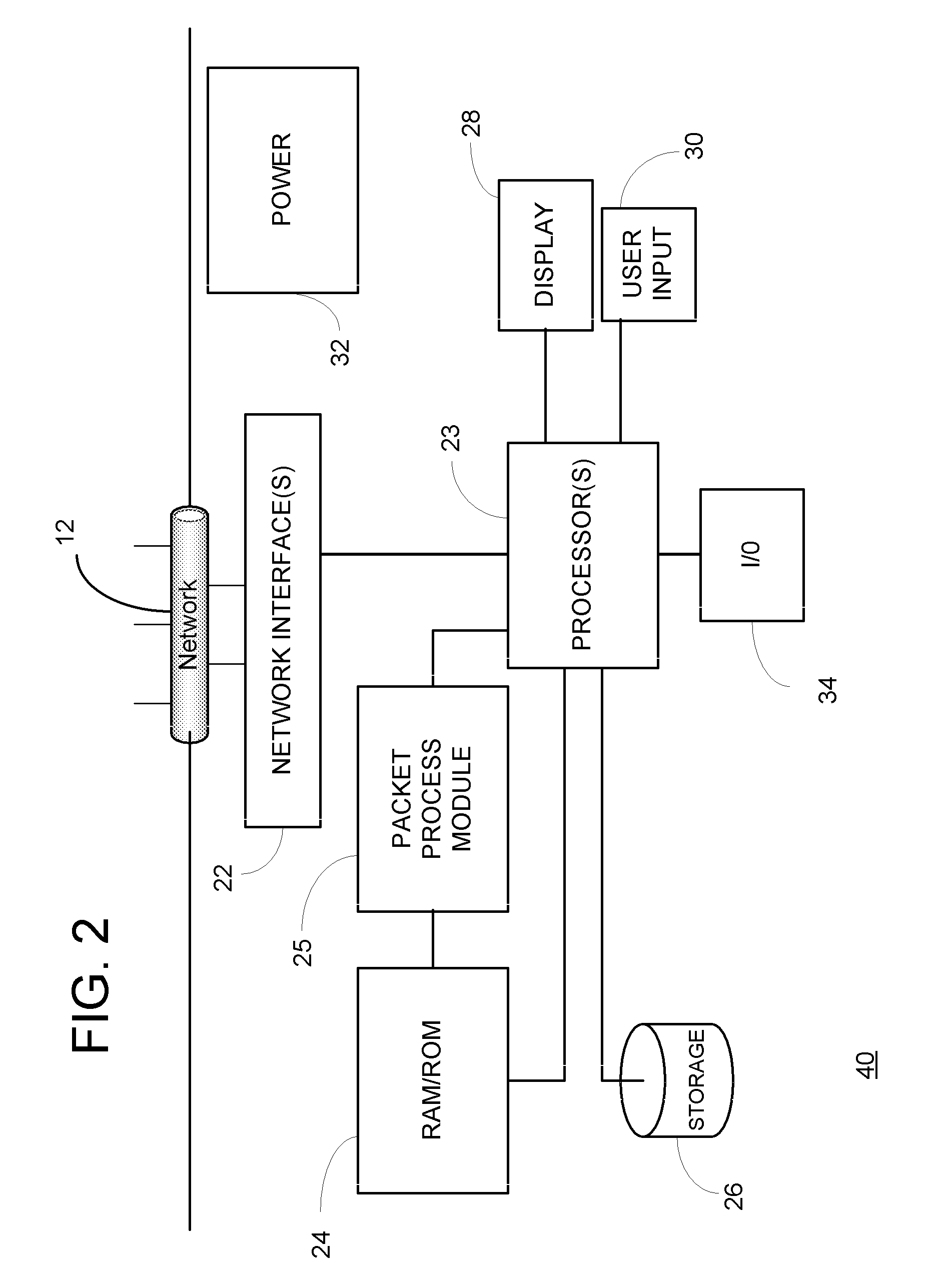
Method and apparatus of measuring and reporting data gap from within an analysis tool
ActiveUS20090296593A1Enhanced authenticationAccurately determineError preventionTransmission systemsInternet trafficNetwork tap
Network data gap is determined and reported to enable a user to validate that all the traffic that was intended to be monitored is being monitored in monitoring and / or troubleshooting tools for observation of network traffic and network installation and maintenance. Span port oversubscription, incomplete span configuration, incorrectly placed network taps and monitoring device packet drop may thereby be detected and reported as data gap.
Owner:NETSCOUT SYSTEMS
Secure wireless authorization system
ActiveUS7447494B2Theft is not still reducedEnsure safetyFinanceUnauthorised/fraudulent call preventionThird partyAuthorization
The invention relates to a secure wireless authorization system by which a user can employ a wireless device to authorize a request that is initiated by a remote third party and transmitted to the user by an authorization server. The system includes the authorization server that is linked to the third party by way of a communications connection and a wireless device that is adapted to securely store an encryption scheme and create a secure authorization from the user in response to the third party request and has the ability to establish a secure wireless connection over which the secure authorization is transmitted from the user's wireless device to the authorization server. Pre-authorization, real-time authorization and post-authorization methods are disclosed by which user authorized transactions can be completed by way of the authorization system of this invention.
Owner:7611544 CANADA
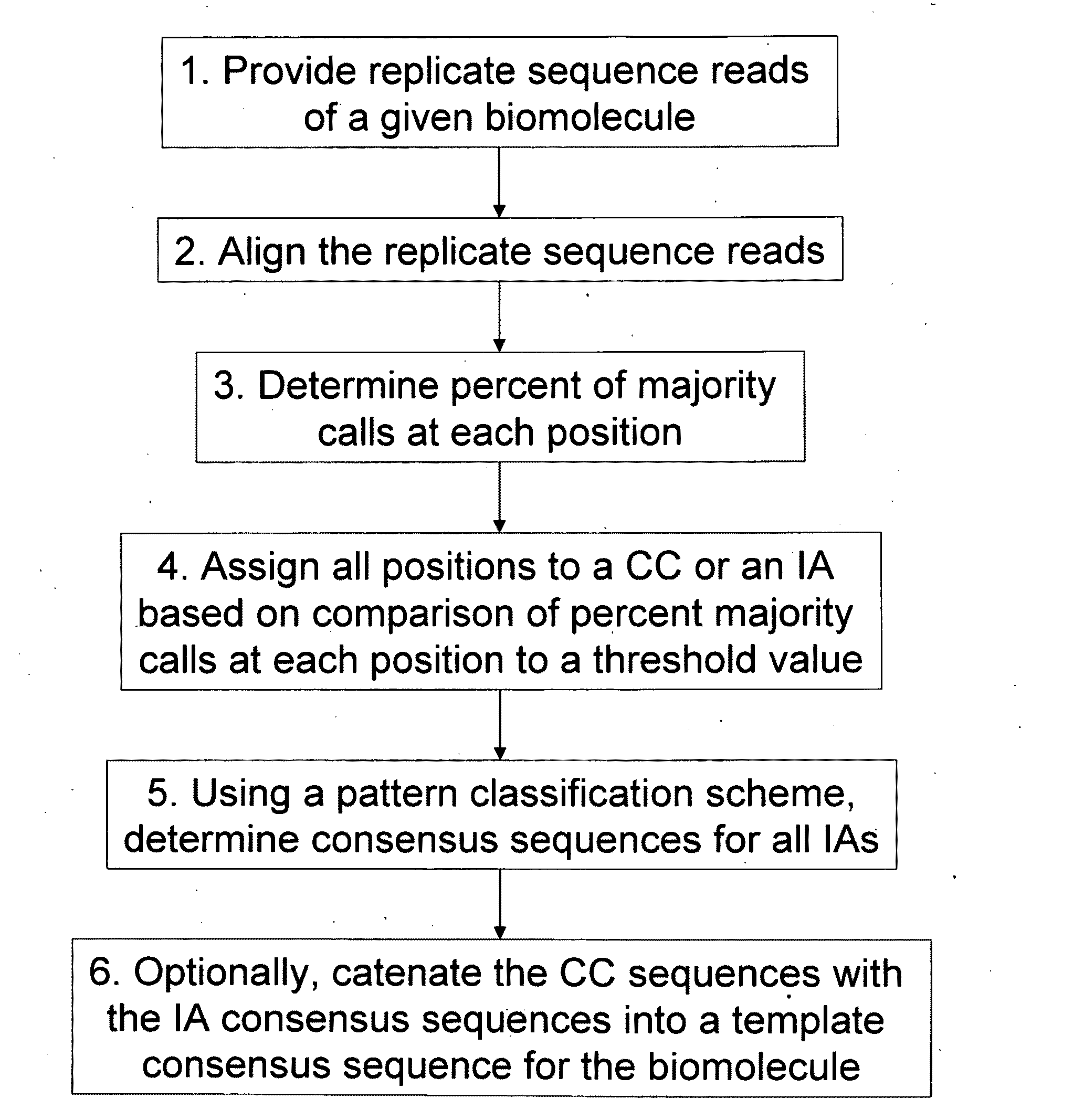
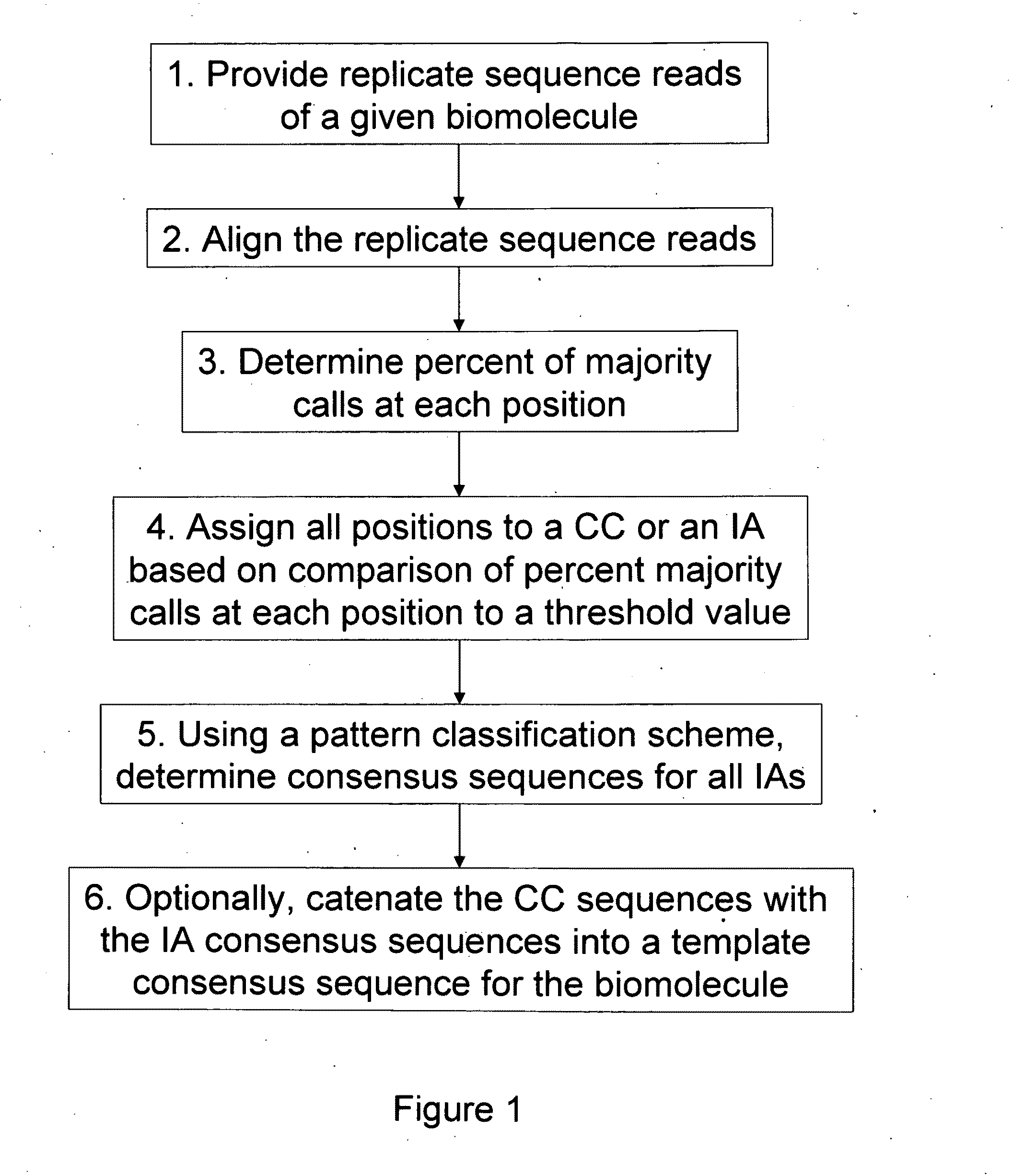
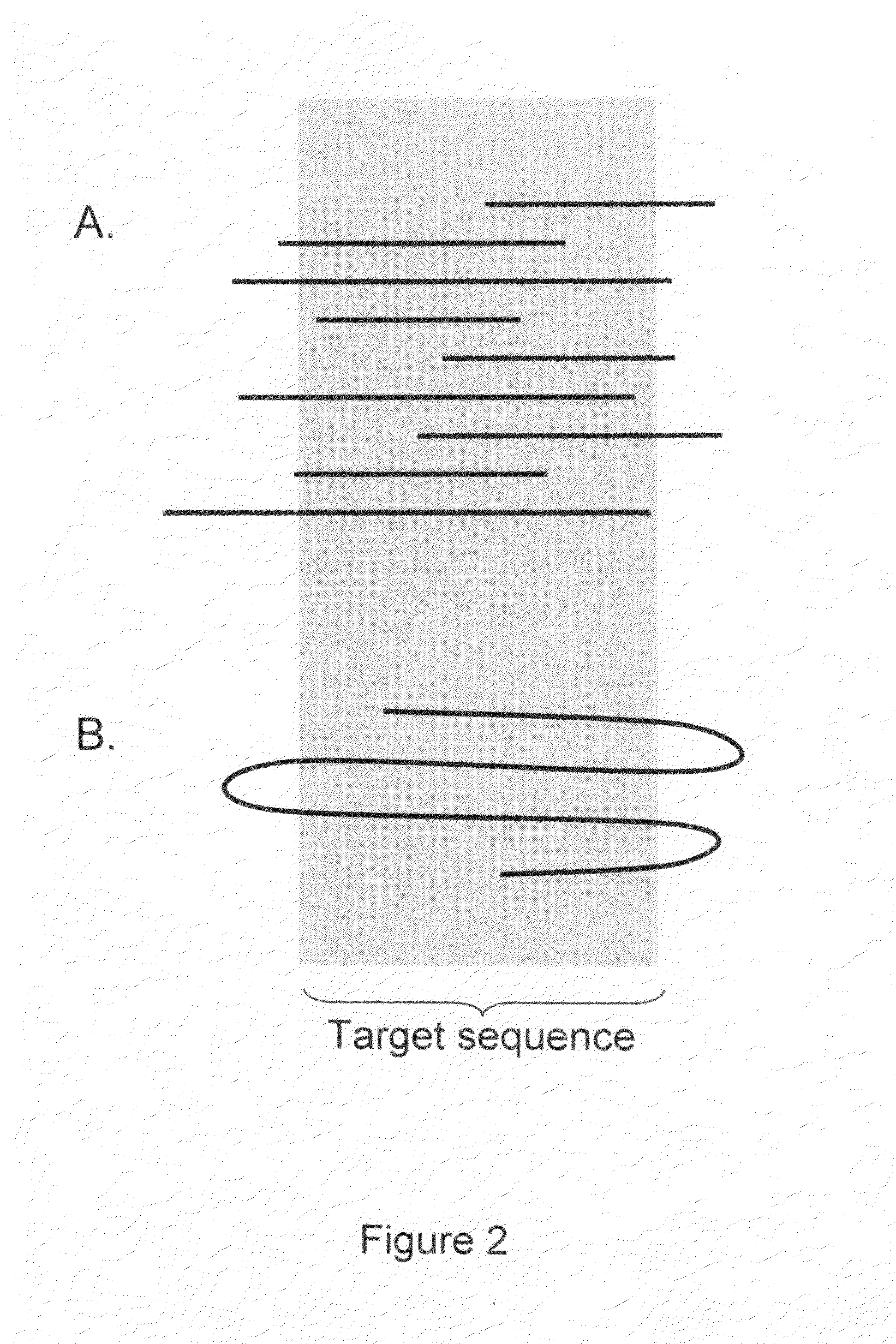
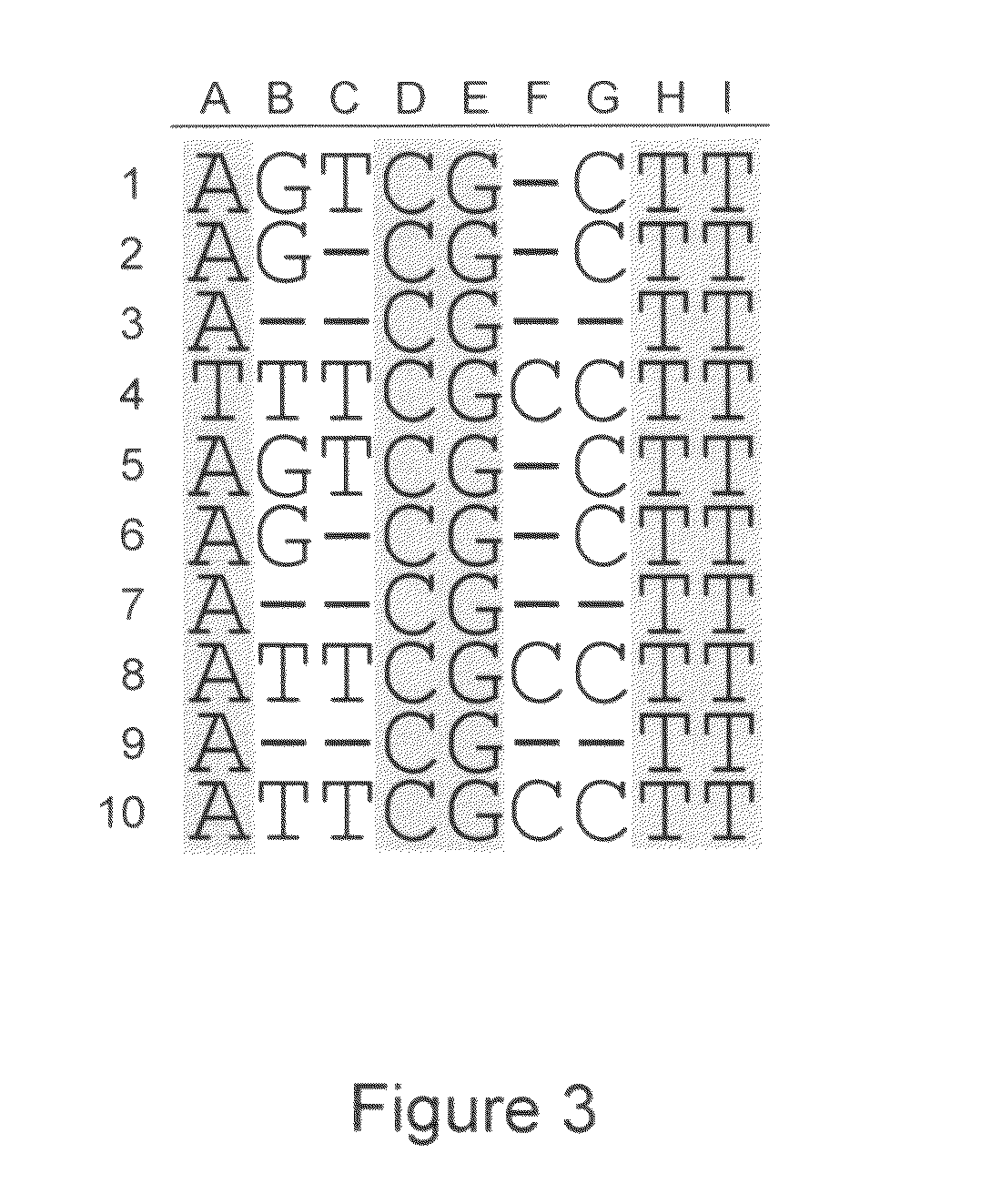
Algorithms for sequence determination
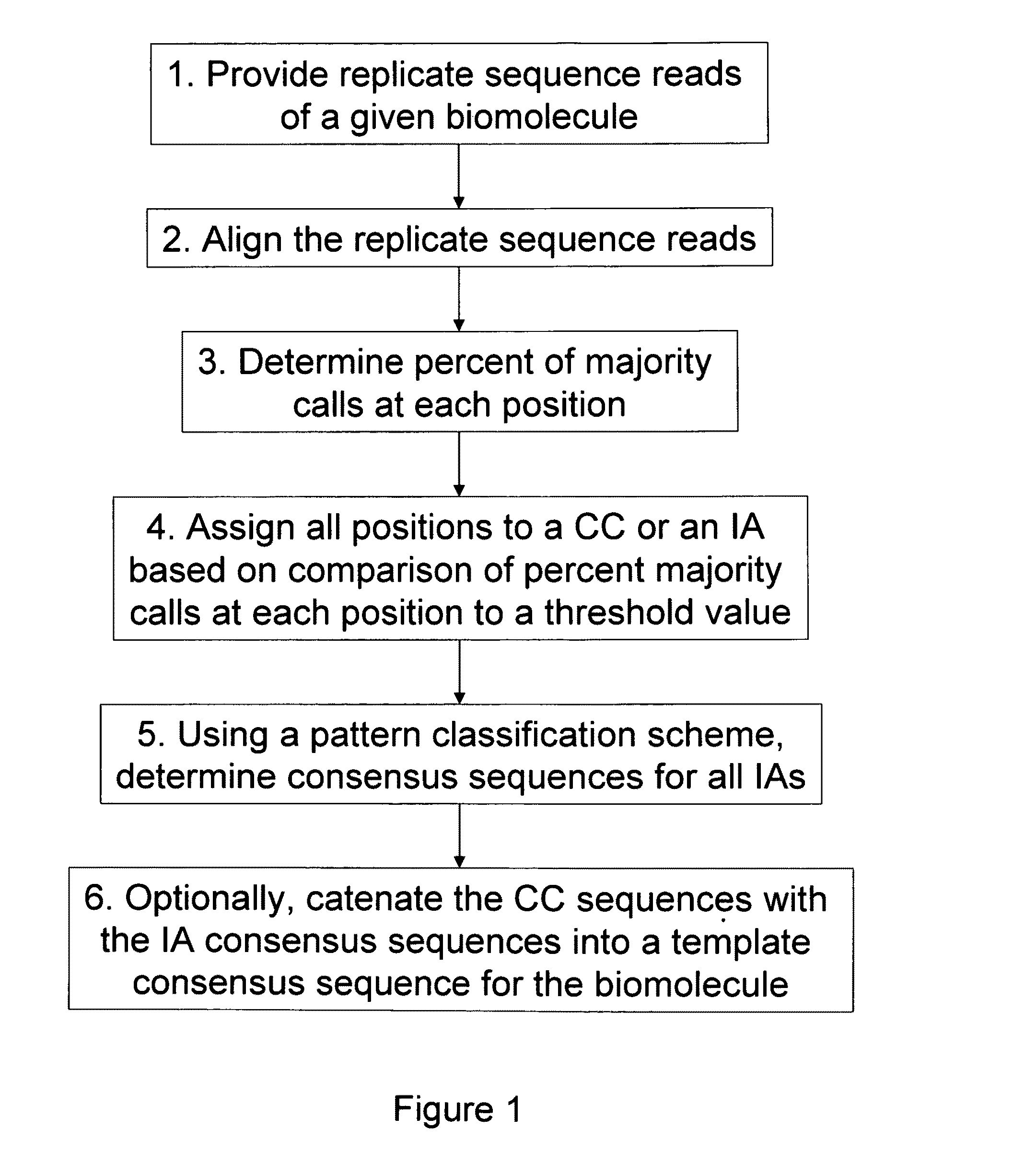
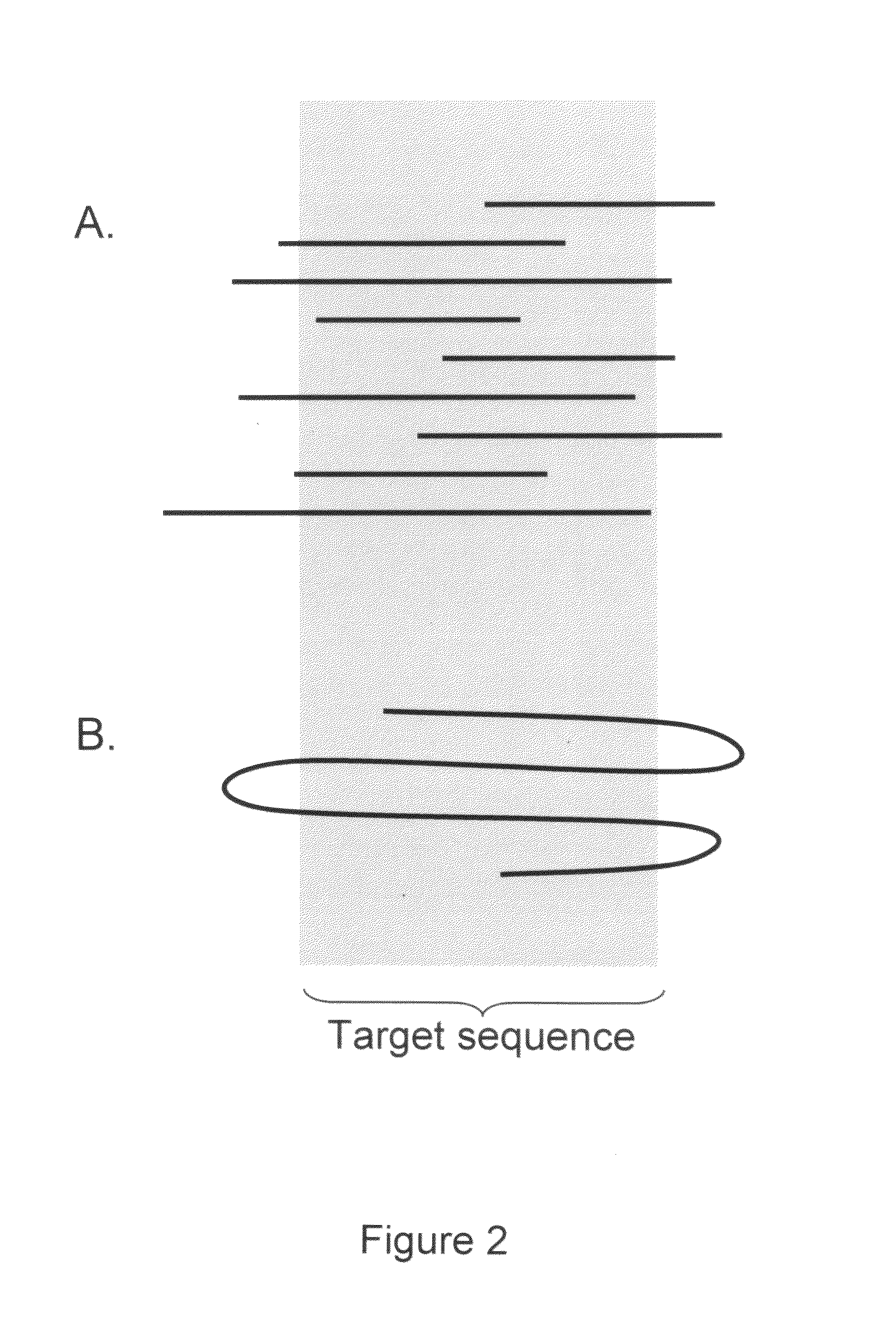
ActiveUS20100169026A1Improve validationImprove accuracyDigital computer detailsBiological testingSequencing dataSequence analysis
The present invention is generally directed to powerful and flexible methods and systems for consensus sequence determination from replicate biomolecule sequence data. It is an object of the present invention to improve the accuracy of consensus biomolecule sequence determination from replicate sequence data by providing methods for assimilating replicate sequence into a final consensus sequence more accurately than any one-pass sequence analysis system.
Owner:PACIFIC BIOSCIENCES
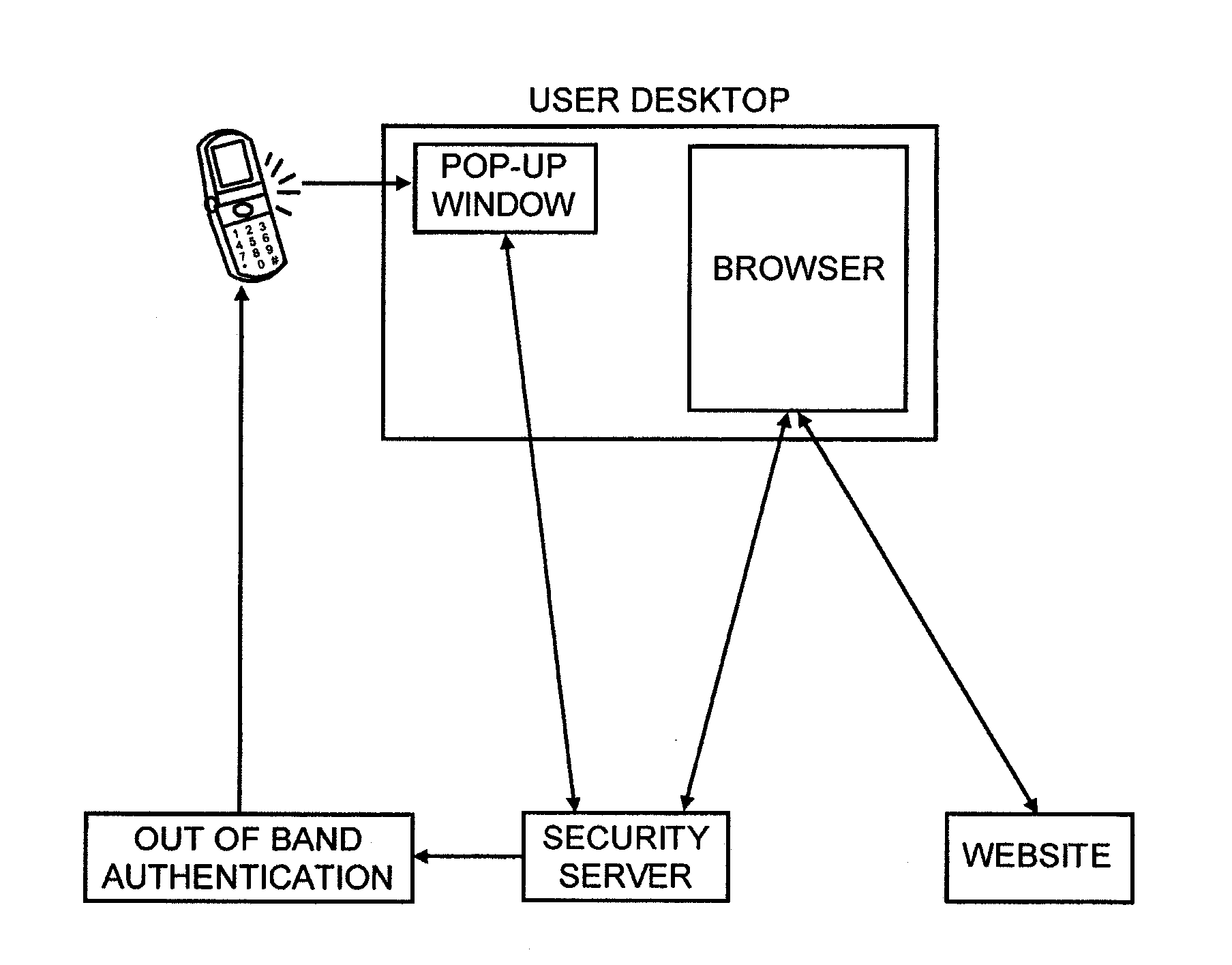
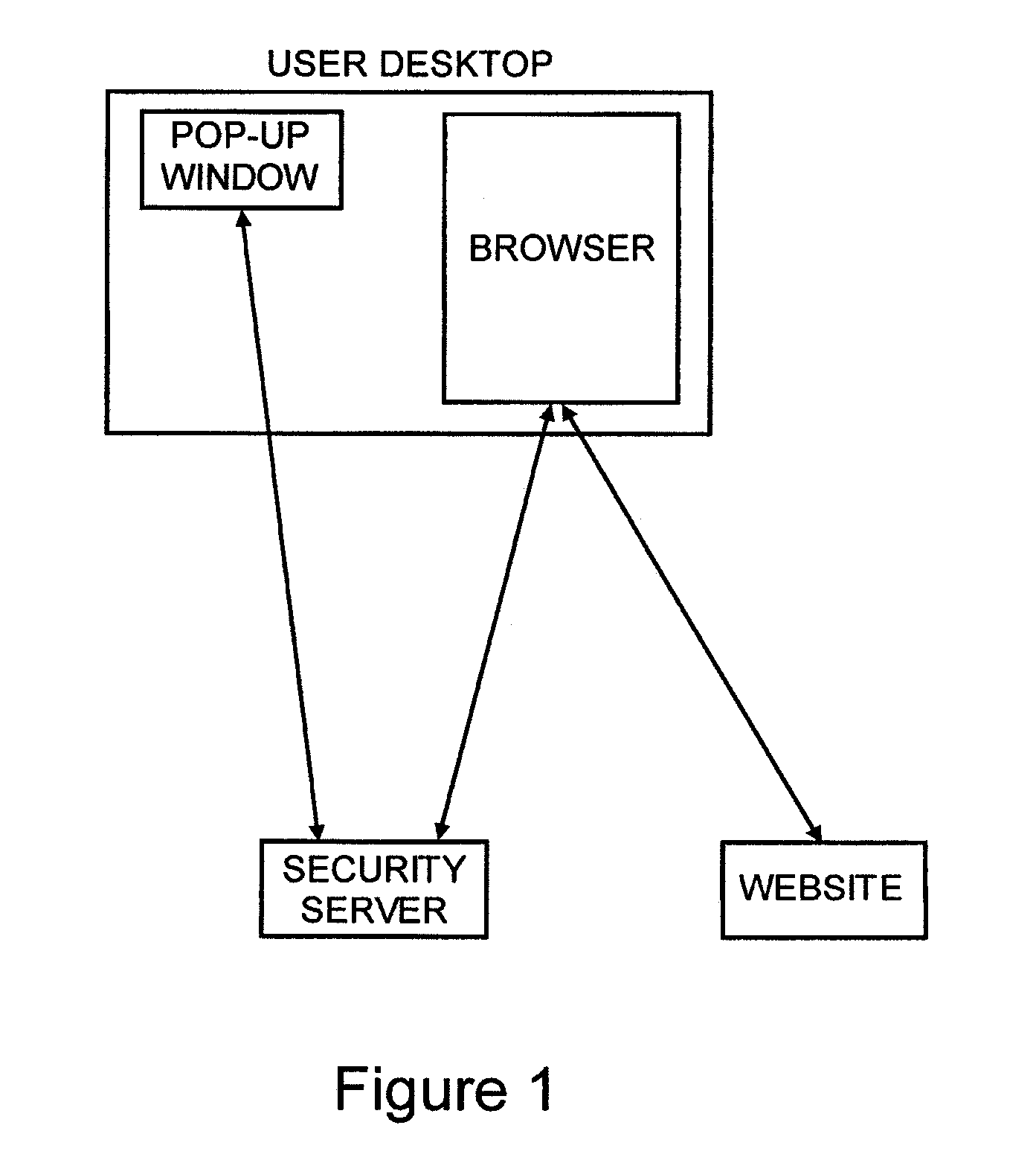
Secure and efficient login and transaction authentication using iphonestm and other smart mobile communication devices
ActiveUS20110265149A1Easy to implementEnhanced authenticationDigital data processing detailsUser identity/authority verificationUser inputAuthentication server
To authenticate a user of a mobile communication device for login or transaction authorization, a first application on the device directs transmission of a request for authentication of the user to a security server. A second application on the device receives the request for authentication from the security server and directs presentation of the received request for authentication to the user by the device. The second application receives a user input to the device indicating that the requested authentication should proceed and in response directs transmission of an indication that the requested authorization should proceed, to the security server. In response to this latter transmission, the second application receives a PIN from the authentication server. The first application directs transmission of the PIN received by the second application to the network site, which validates the transmitted PIN, in order to authenticate the user or the transaction to the network site.
Owner:PAYFONE
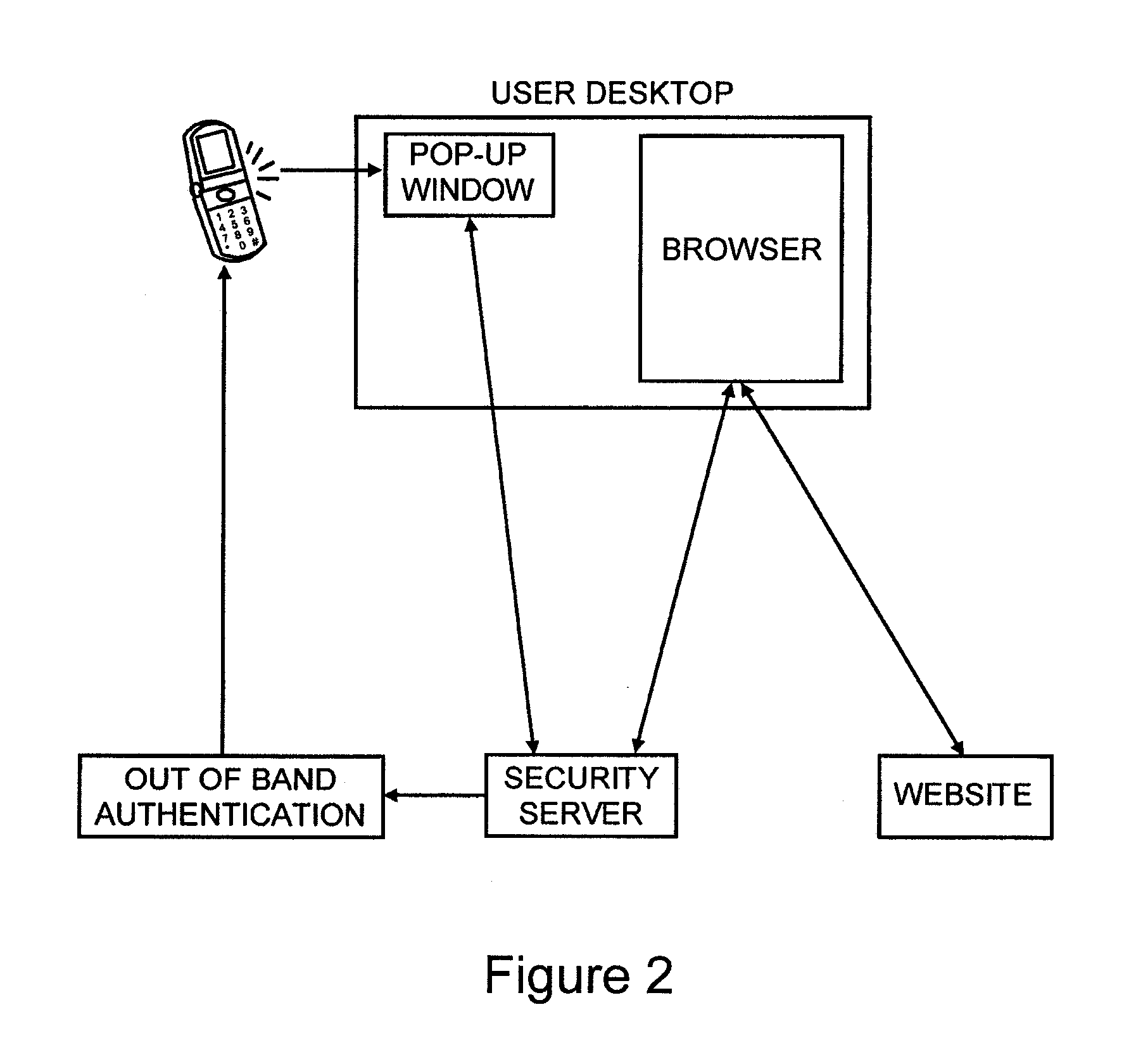
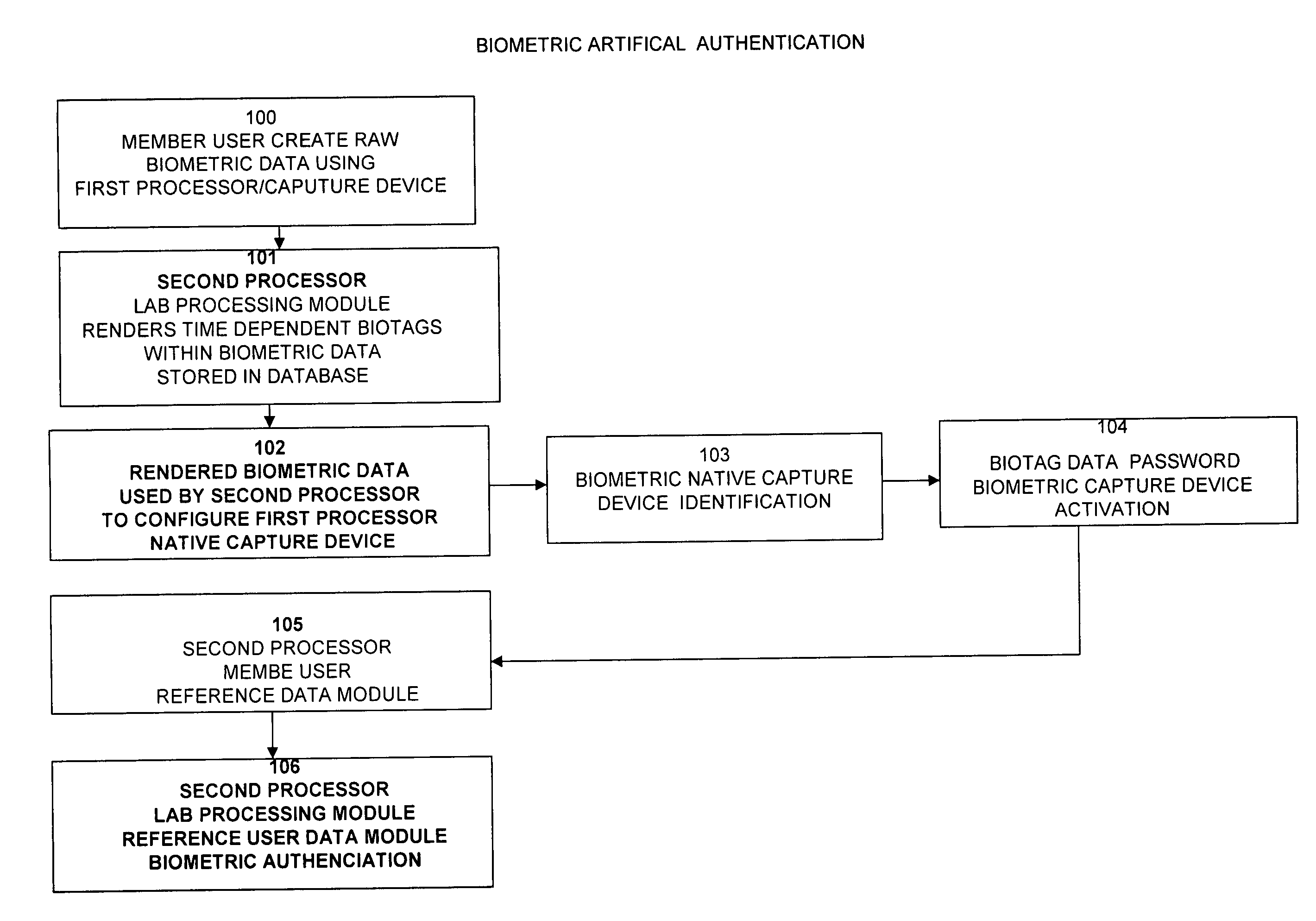
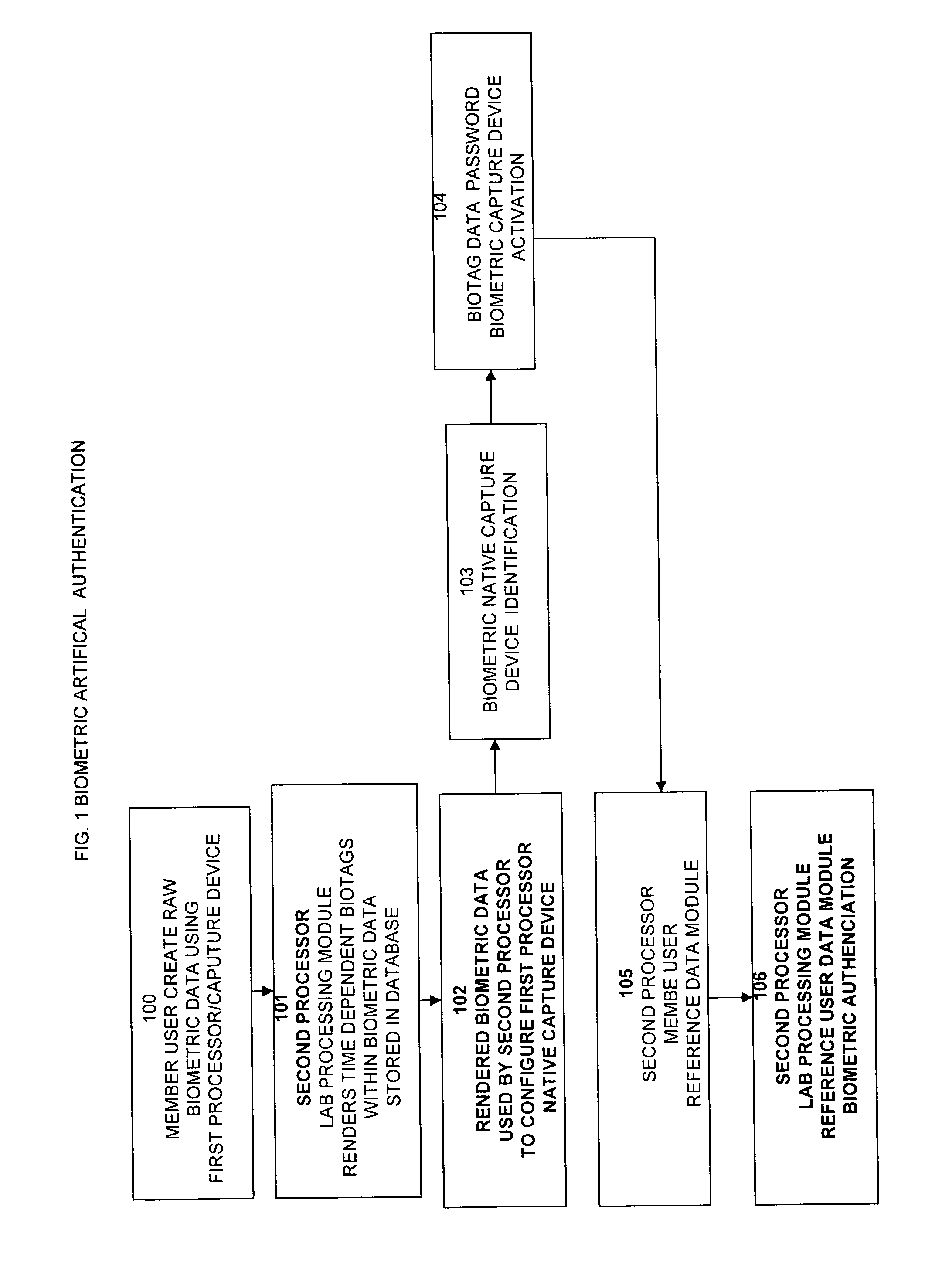
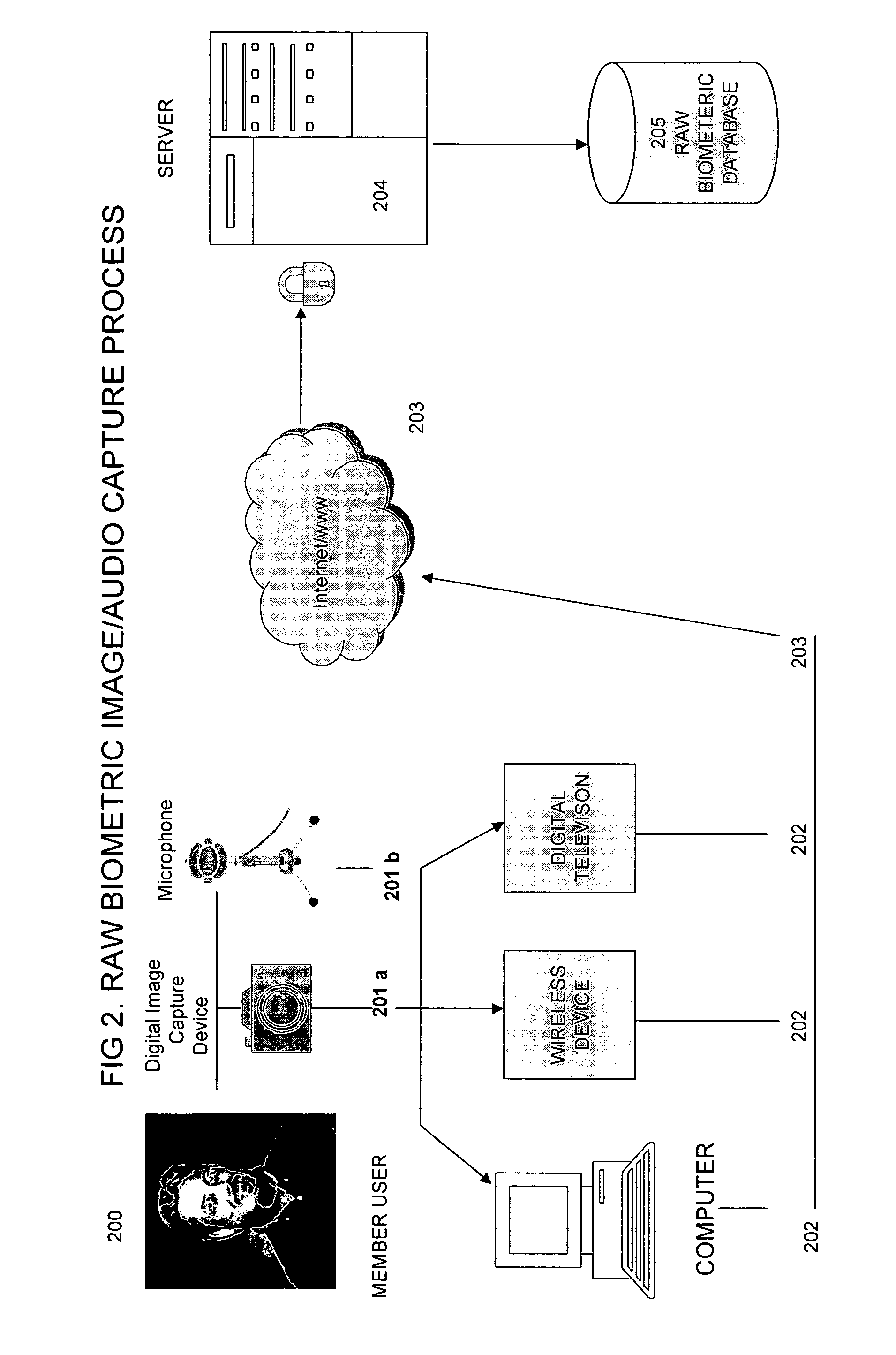
Method for user biometric artifical authentication
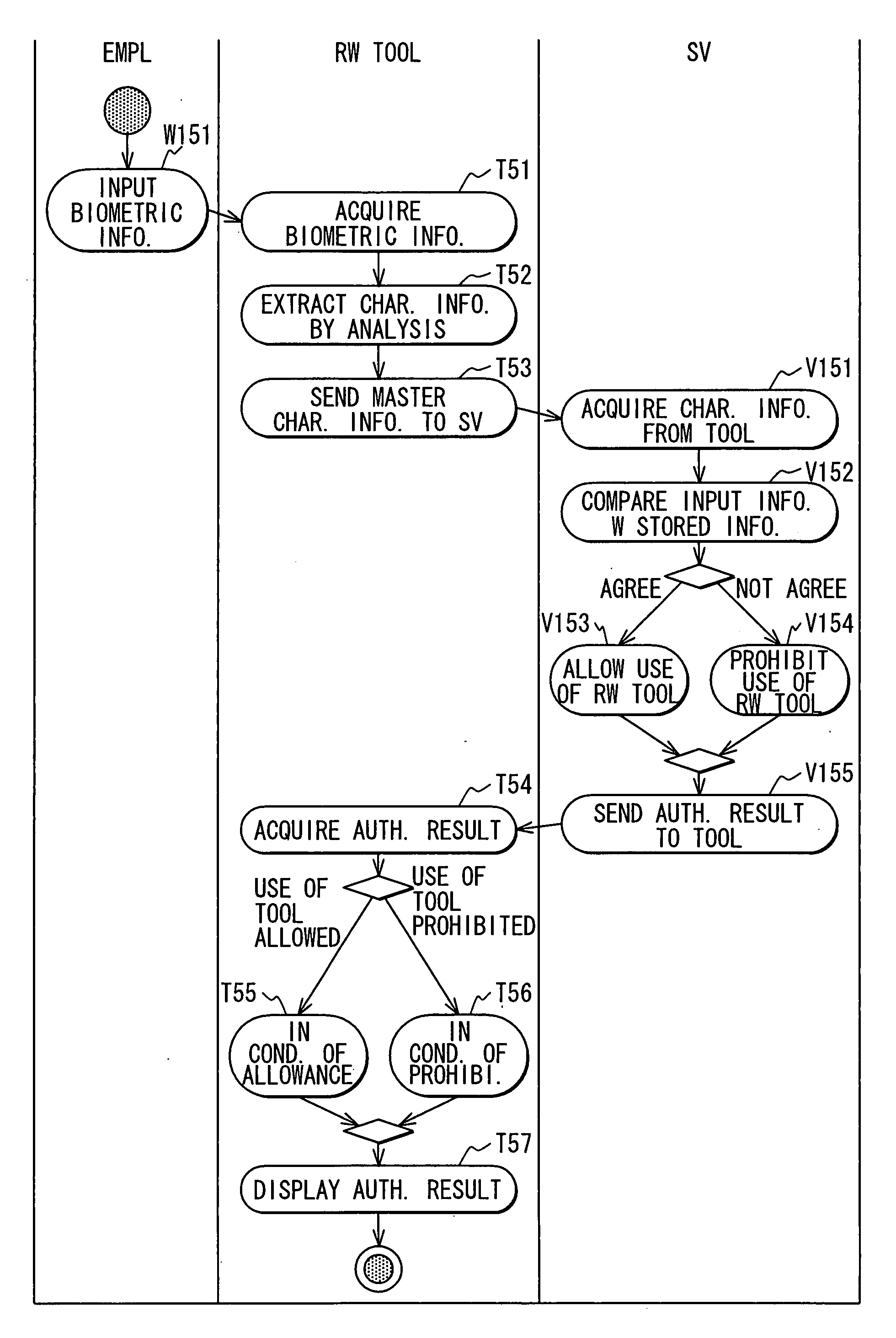
InactiveUS20070112775A1Easy accessImprove search capabilitiesDigital data authenticationBuying/selling/leasing transactionsBiometric dataReference database
A system for verifying, authenticating, and processing membership information to generate a selectively approved searchable membership database, viewable through a computer information network, such as the internet. membership verification includes a first processing unit (200) for transmitting data native biometric data to a second processing unit (204) for artificial rendering by a lab processing module (300) stores settings in a database (301). Artificially rendered biometric data is used for reference physical configuration of a first processor biometric capture device (301) Artificially rendered biometric data is used to reference the identity of a native capture device source (301) Artificial rendered biometric data is used in a pass code configuration to activate a biometric capture device (301). A custom user biometric data reference module is used for member users to create a custom biometric data reference database (303). A controlled biometric capture device by second processor is used with the custom biometric data reference database to provide multiple security encryption form identification and verification of a member user.
Owner:ACKERMAN DAVID M
Method for personalization of a service
ActiveUS20070124134A1Quality improvementImproved user authenticationDevices with voice recognitionAutomatic call-answering/message-recording/conversation-recordingSpeech soundRecognition system
Owner:HUAWEI TECH CO LTD
Method for personalization of a service
ActiveUS8005680B2Quality improvementEnhanced authenticationDevices with voice recognitionAutomatic call-answering/message-recording/conversation-recordingService provisionSpeech sound
Method for building a multimodal business channel between users, service providers and network operators. The service provided to the users is personalized with a user's profile derived from language and speech models delivered by a speech recognition system. The language and speech models are synchronized with user dependent language models stored in a central platform made accessible to various value added service providers. They may also be copied into various devices of the user. Natural language processing algorithms may be used for extracting topics from user's dialogues.
Owner:HUAWEI TECH CO LTD
Algorithms for sequence determination
ActiveUS8370079B2Enhanced authenticationImprove accuracyBiological testingSequence analysisOne passSequence analysis
The present invention is generally directed to powerful and flexible methods and systems for consensus sequence determination from replicate biomolecule sequence data. It is an object of the present invention to improve the accuracy of consensus biomolecule sequence determination from replicate sequence data by providing methods for assimilating replicate sequence into a final consensus sequence more accurately than any one-pass sequence analysis system.
Owner:PACIFIC BIOSCIENCES
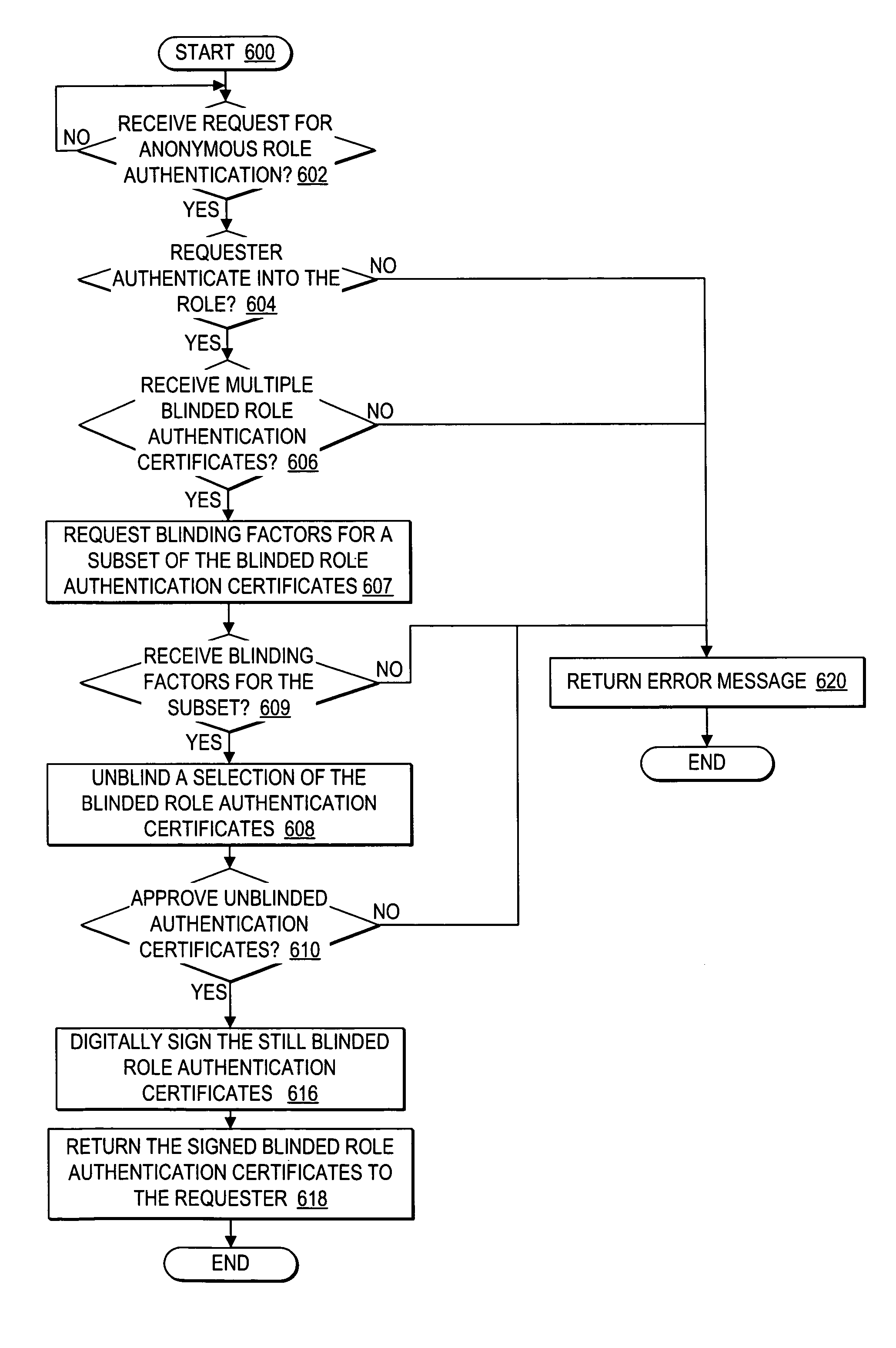
User controlled anonymity when evaluating into a role
InactiveUS20050283608A1Enhanced authenticationImprove identityDigital data processing detailsUser identity/authority verificationThird partyResource protection
A method, system, and program for user controlled anonymity when evaluating into a role are provided. An anonymous authentication controller enables a user to control anonymity of the user's identity for role based network accesses to resources, without requiring reliance on any single third party to maintain user anonymity. First, a role authentication certificate is received from a role authenticator, wherein the role authentication certificate certifies that the holder of the role authentication certificate is a member of a particular role without allowing the role authenticator issuing the role authentication certificate the ability to track an identity of a user holding the role authentication certificate. Next, an anonymous channel is established for anonymously presenting the role authentication certificate to a resource protector, wherein the resource protector requires the user to authenticate into the particular role to access a resource, wherein the role authentication certificate authenticates the user into the particular role without enabling the resource protector to ascertain the identity of the user, such that the user is in control of maintaining user anonymity for authenticated role-based accesses.
Owner:IBM CORP
Authentication system and authentication device
InactiveUS20090292918A1Enhanced authenticationImprove scalePower managementKey distribution for secure communicationAuthentication systemCryptographic nonce
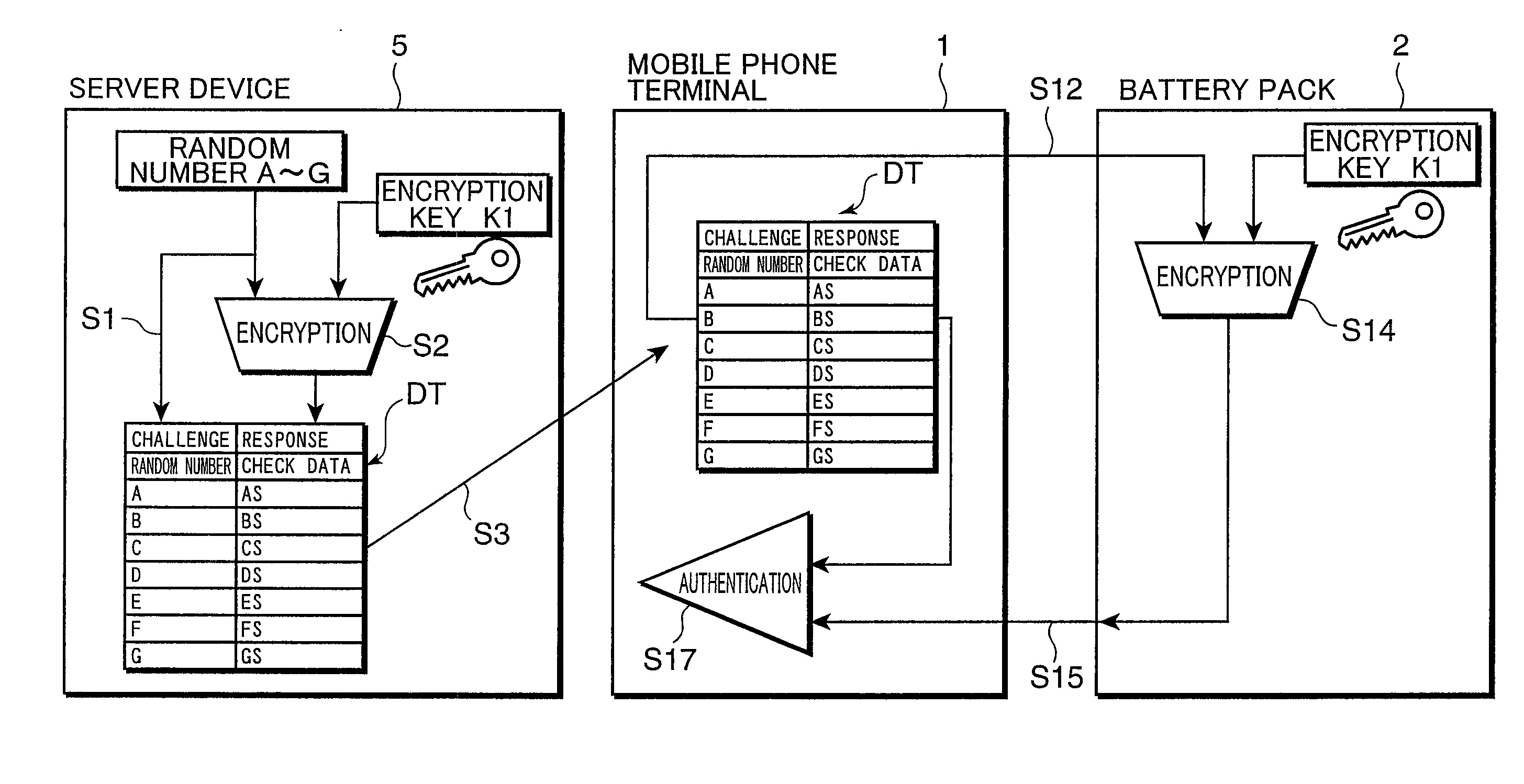
An authentication system is provided with a server device for generating a random number used for authentication and check data obtained by encrypting the random number using an encryption key, an authentication device for authenticating a device to be authenticated by transmitting the random number transmitted from the server device to the device to be authenticated and comparing reply data transmitted from the device to be authenticated with check data transmitted from the server device, and the device to be authenticated for encrypting the random number transmitted from the authentication device using the encryption key and transmitting the encrypted random number as reply data.
Owner:PANASONIC CORP
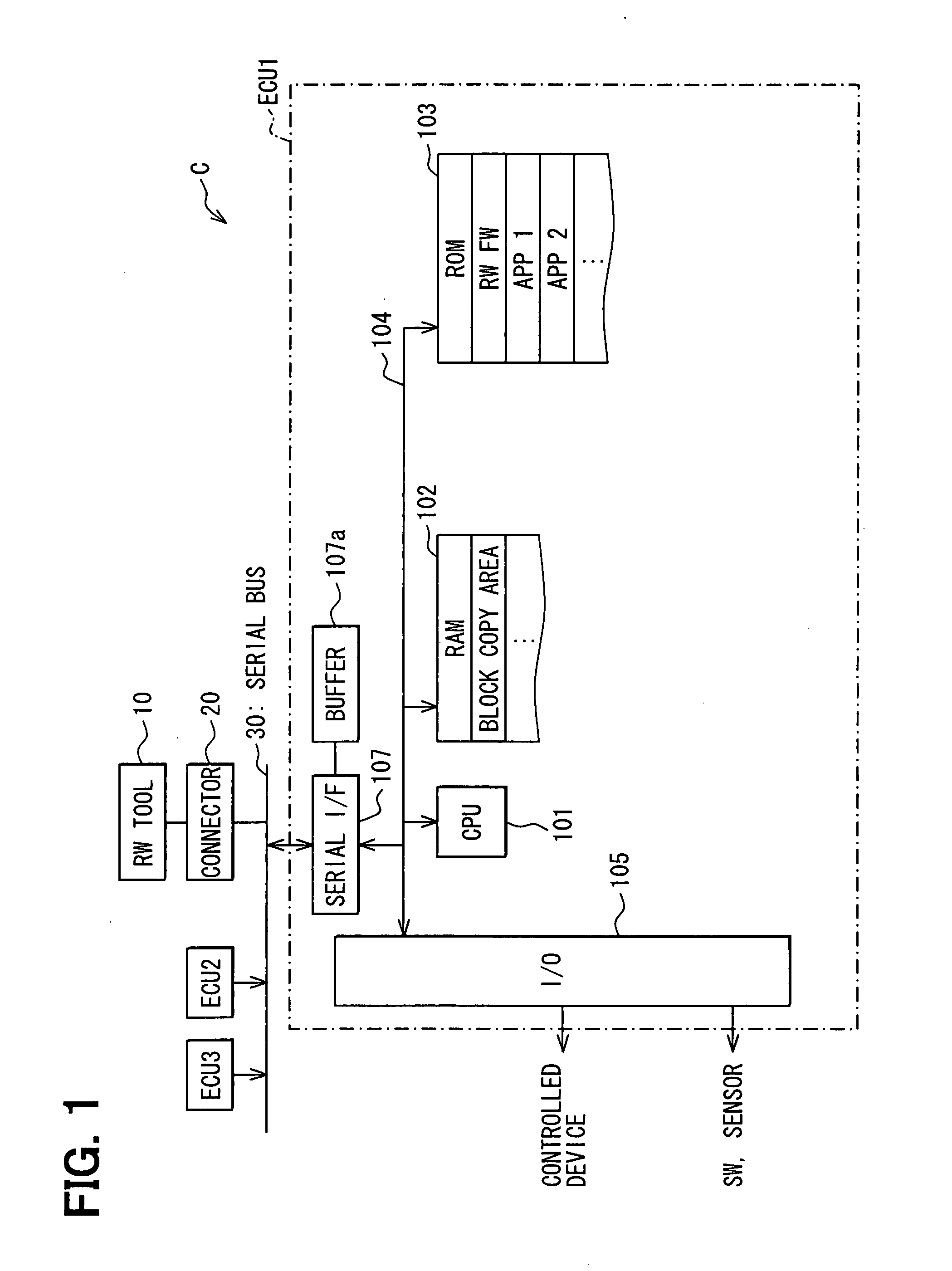
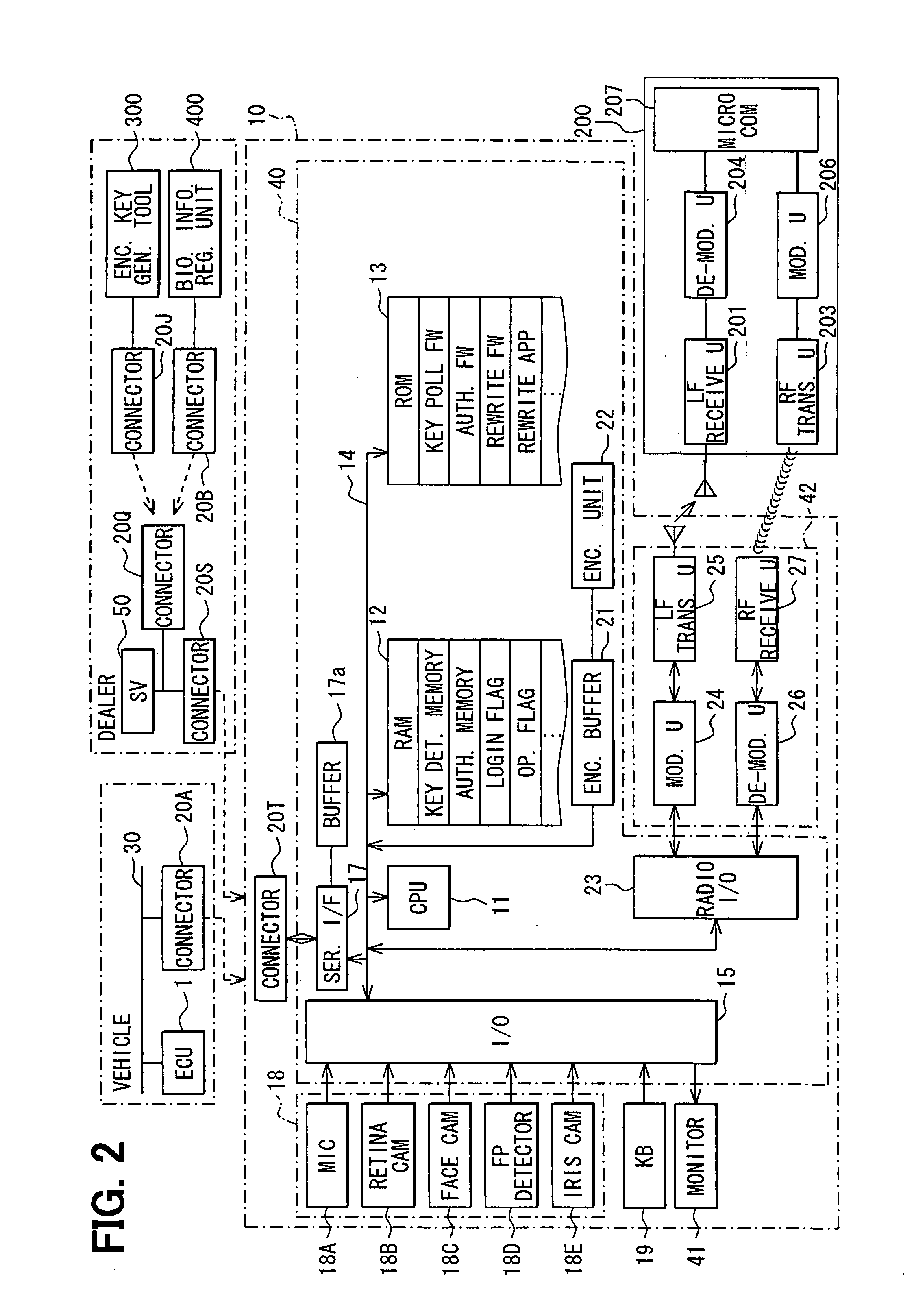
Vehicle information rewriting system
InactiveUS20080059806A1Powerful authenticationEnhanced authenticationKey distribution for secure communicationDigital data processing detailsNon-volatile memoryAuthentication
A rewriting tool for rewriting a content of a nonvolatile memory including vehicle information and the like provides a supplemental authentication process that detects a wireless authentication medium associated to an authorized rewriting tool user by wireless polling on an unconditional basis besides authenticating the authorized rewriting tool user based on an input from the rewriting tool for the purpose of an improved security.
Owner:DENSO CORP
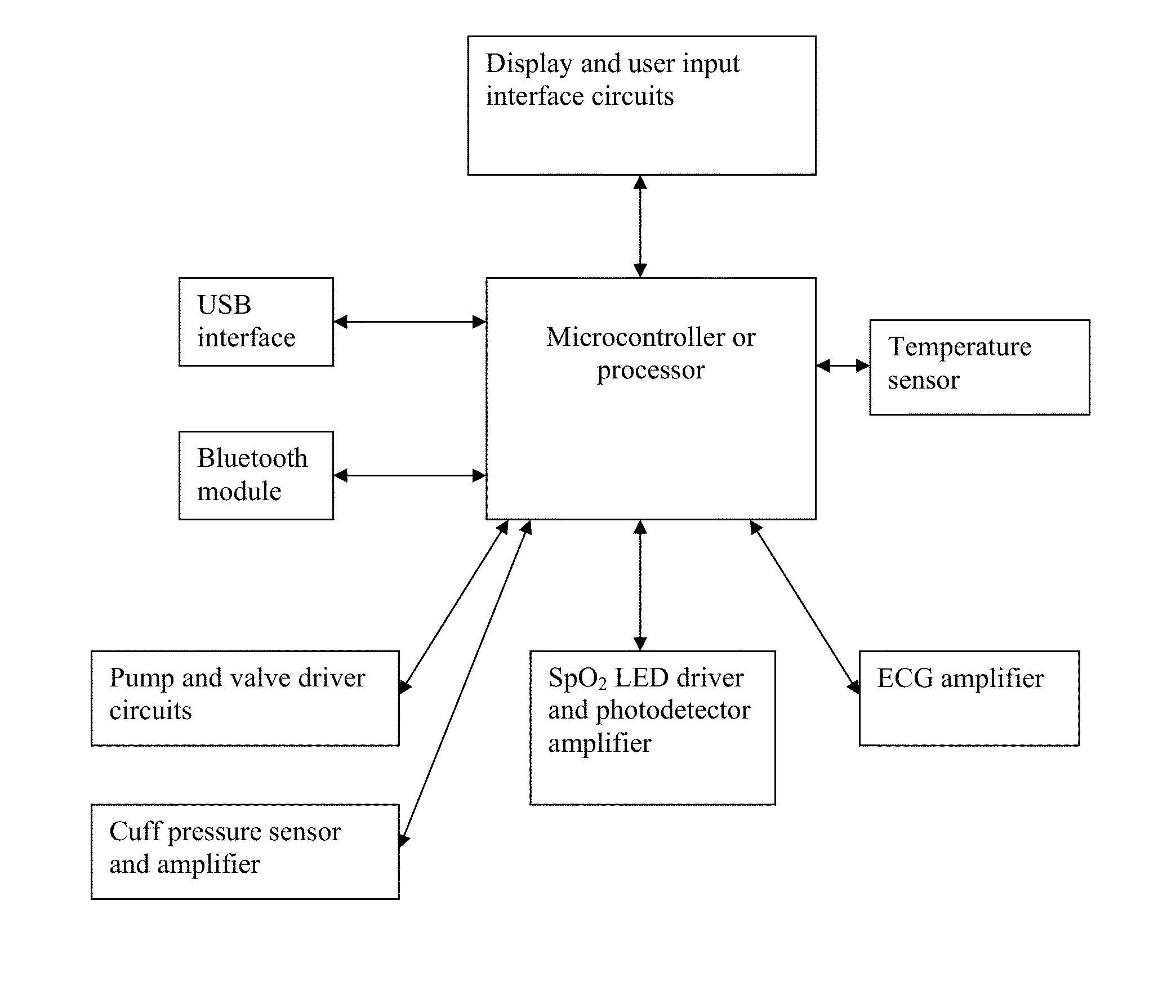
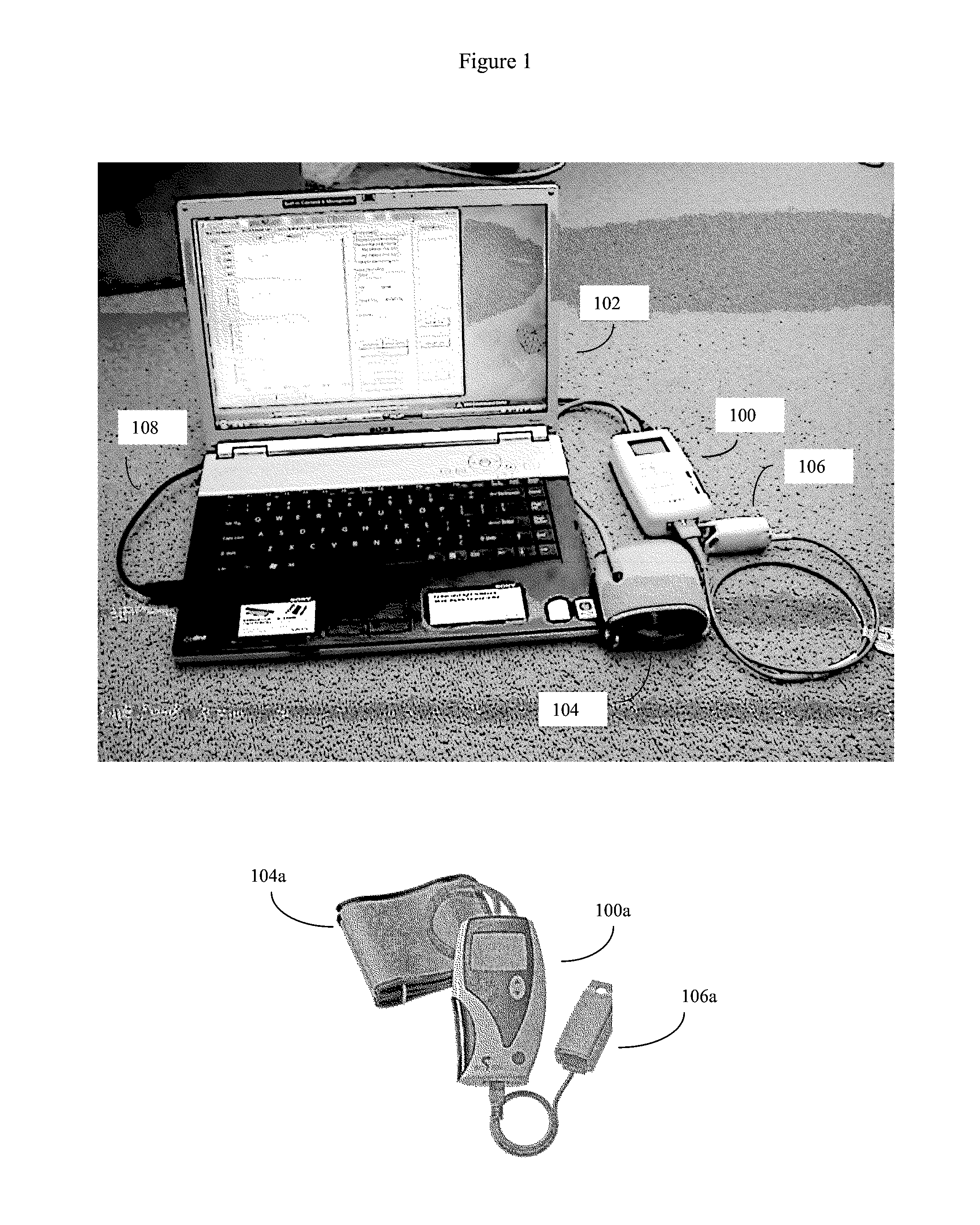
Simultanious multi-parameter physiological monitoring device with local and remote analytical capability
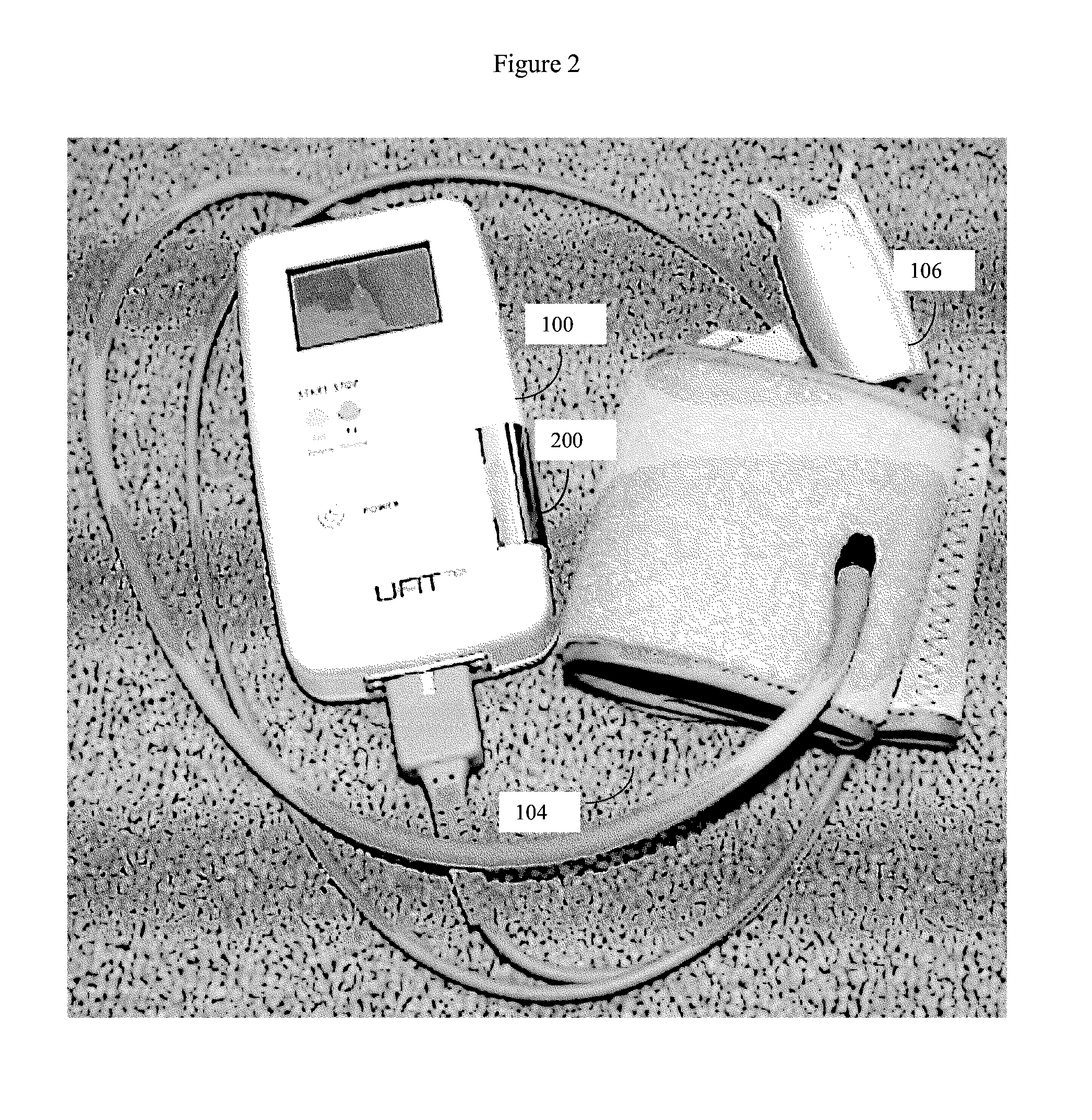
ActiveUS20140243612A1High level of quality controlEnhanced authenticationElectrocardiographyEvaluation of blood vesselsHome environmentHand held
Handheld medical diagnostic instrument that provides high time-resolution pulse waveforms associated with multiple parameters including blood pressure measurements, blood oxygen saturation levels, electrocardiograph (ECG) measurements, and temperature measurements. The device stores and analyzes the pulse waveforms simultaneously obtained from all tests, and thereby allows an unusually detailed view into the functioning of the user's cardiovascular heart-lung system. The device is designed for use by unskilled or semi-skilled users, thus enabling sophisticated cardiovascular measurements to be obtained in a home environment. Data from the device can be analyzed onboard, with local computerized devices, and with remote server based systems. The remote server may be configured to analyze this data according to various algorithms chosen by the physician to be most appropriate to that patient's particular medical condition (e.g. COPD patient algorithms). The server may be further configured to automatically provide alerts and drug recommendations.
Owner:CLOUD DS INC CORP
Methods and systems for secure internet access and services
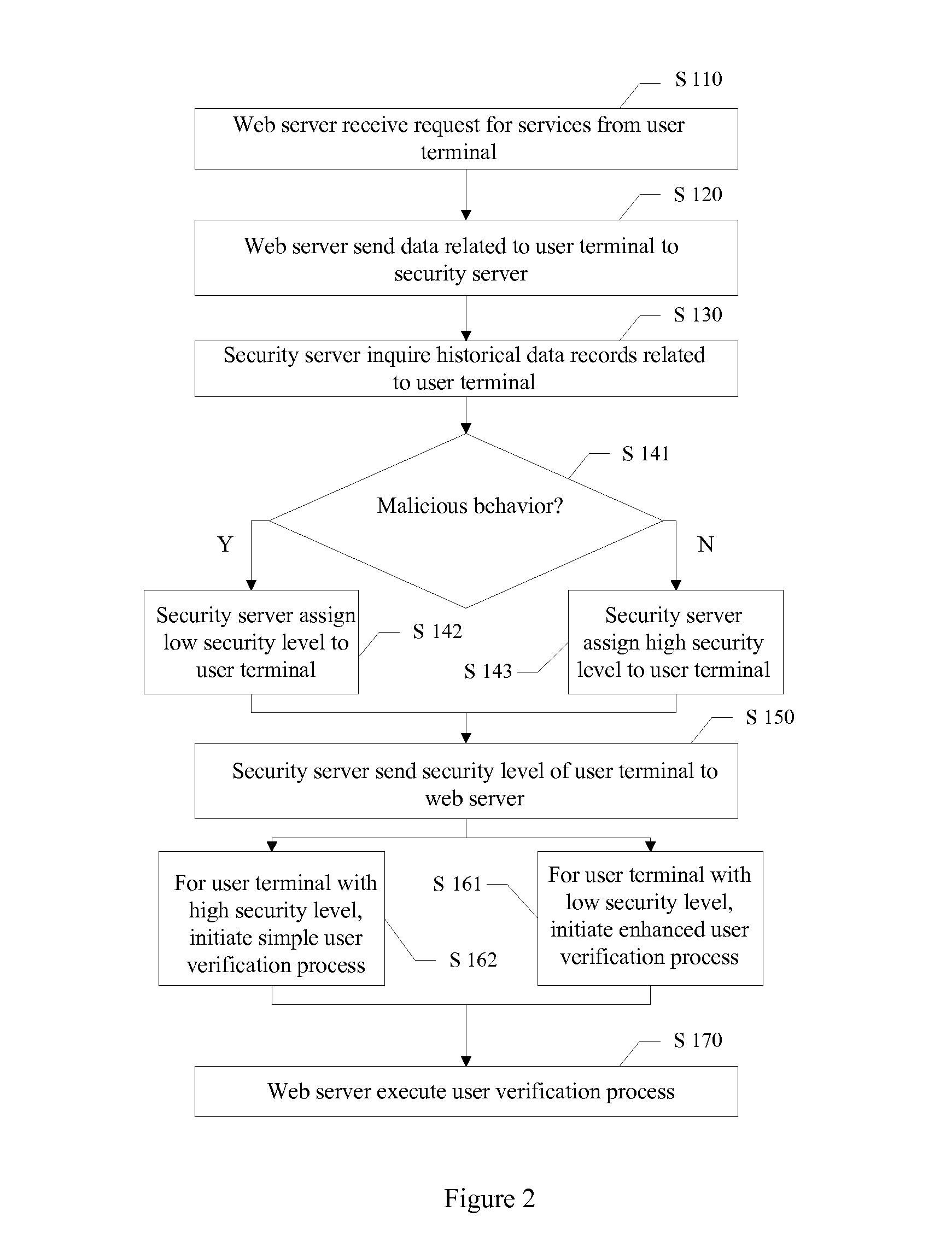
ActiveUS20150135282A1Improve security levelLower security levelDigital data processing detailsMultiple digital computer combinationsCable Internet accessInternet access
A method and system for providing secure internet access and services are disclosed. The method includes receiving a request for services from a user terminal, the request including user terminal data; sending the user terminal data to a security server; and receiving a security level of the user terminal from the security server. The security server determines the security level of the user terminal based on historical user data related to the user terminal. The method further includes initiating a verification process based on the security level of the user terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Biometric Authentication Apparatus
InactiveUS20090304237A1FocusSimple configurationCharacter and pattern recognitionDiagnostic recording/measuringImaging processingImaging lens
A biometric authentication apparatus having a simple configuration, able to easily focus on a fingerprint or a vein or other blood vessel pattern and able to clearly capture an image of the same, able to prevent forgery, and in addition able to realize high precision authentication, which biometric authentication apparatus 100 having a transparent plate 110 formed by for example glass or plastic for placement of the finger of the authenticated person, that is, the inspected specimen OBJ, downward in the figure (surface where fingerprint is located facing downward), a fingerprint capturing use illumination apparatus 120, a vein capturing use illumination apparatus 130, and an image capturing apparatus 140, which image capturing apparatus 140 has an imaging lens apparatus capturing a dispersed image of an object passing through the optical system and phase plate, an image processing apparatus generating a dispersion-free image signal from a dispersed image signal from the imaging element, and an object approximate distance information detection apparatus generating information corresponding to the distance to the object, and which the image processing apparatus generating a dispersion-free image signal from the dispersed image signal based on the information generated by the object approximate distance information detection apparatus.
Owner:KYOCERA CORP +1
Application system certification process
InactiveUS7337429B1Increase heightImprove abilitiesOffice automationSpecific program execution arrangementsTime scheduleProgram planning
Owner:LIGHTCHIP +1
Telephony system and method with enhanced fraud control
ActiveUS8031849B1Reduce operating costsImprove functionalitySpeech analysisPrepayment telephone systemsThird partyCommunications system
Inmate communications systems provide a feature-rich platform with a high degree of flexibility and security employing call control facilities located off institutional premises. Authentication processes for calling and called party verification include biometric techniques in some embodiments. Distributed processing of call control and billing provide flexible interactive call payment processes. Preferred embodiments feature voice over IP transmission and control featuring controlled access to avoid addition of unauthorized third-party call participants. Monitoring, recording and selective forwarding of calls is provided under control of system administrators.
Owner:GUMBINER KENNETH J +1
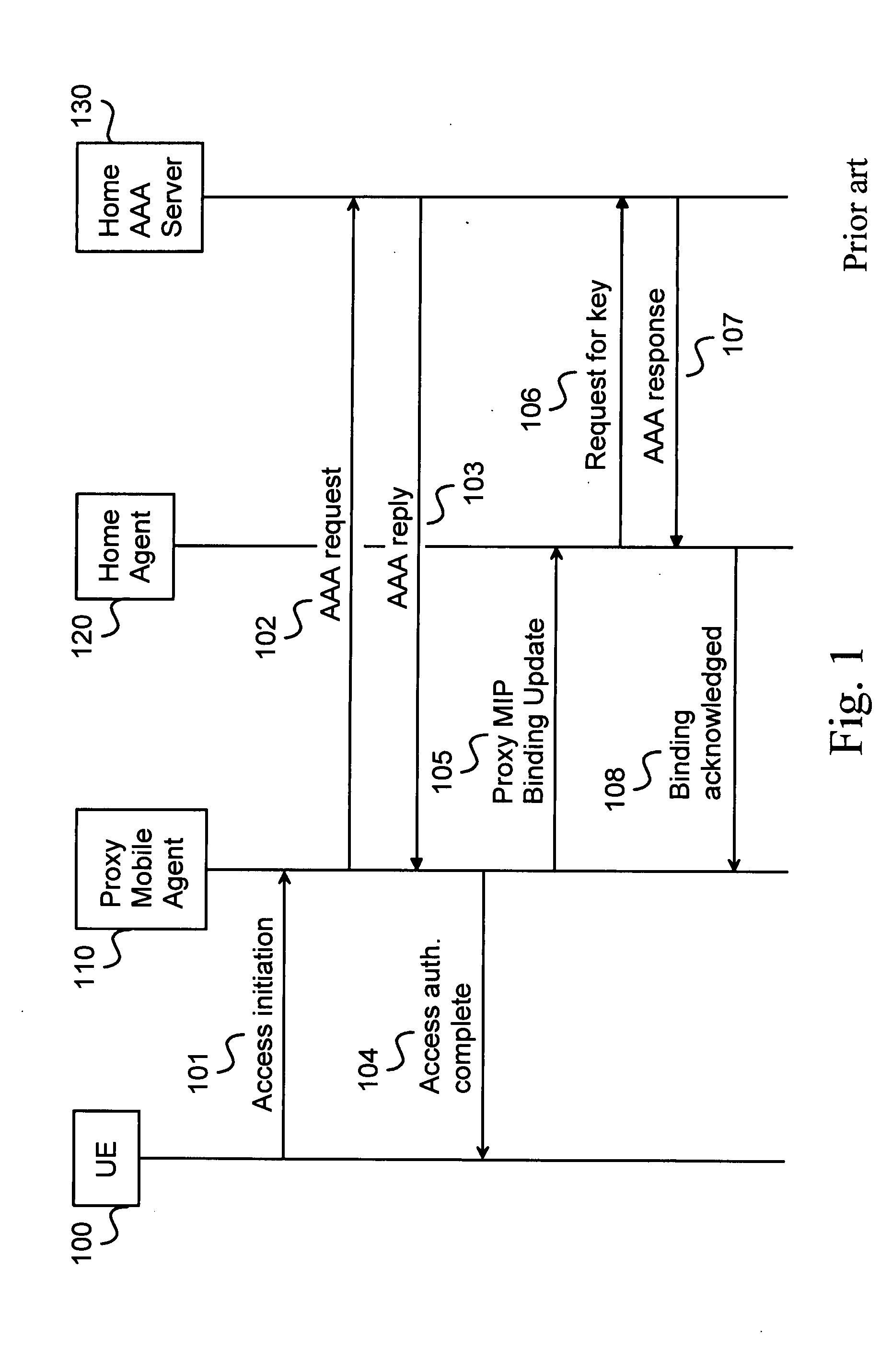
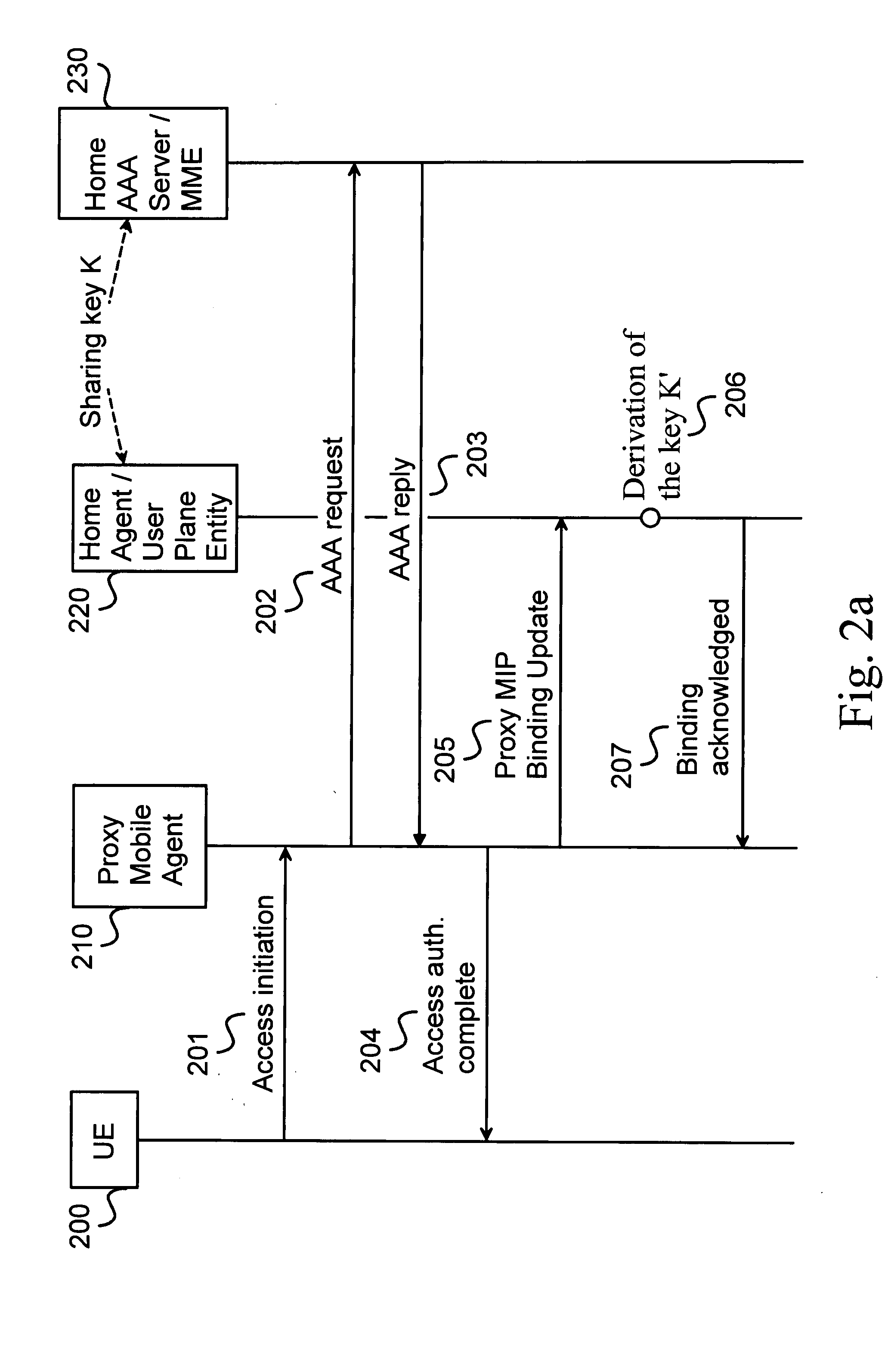
Fast update message authentication with key derivation in mobile IP systems
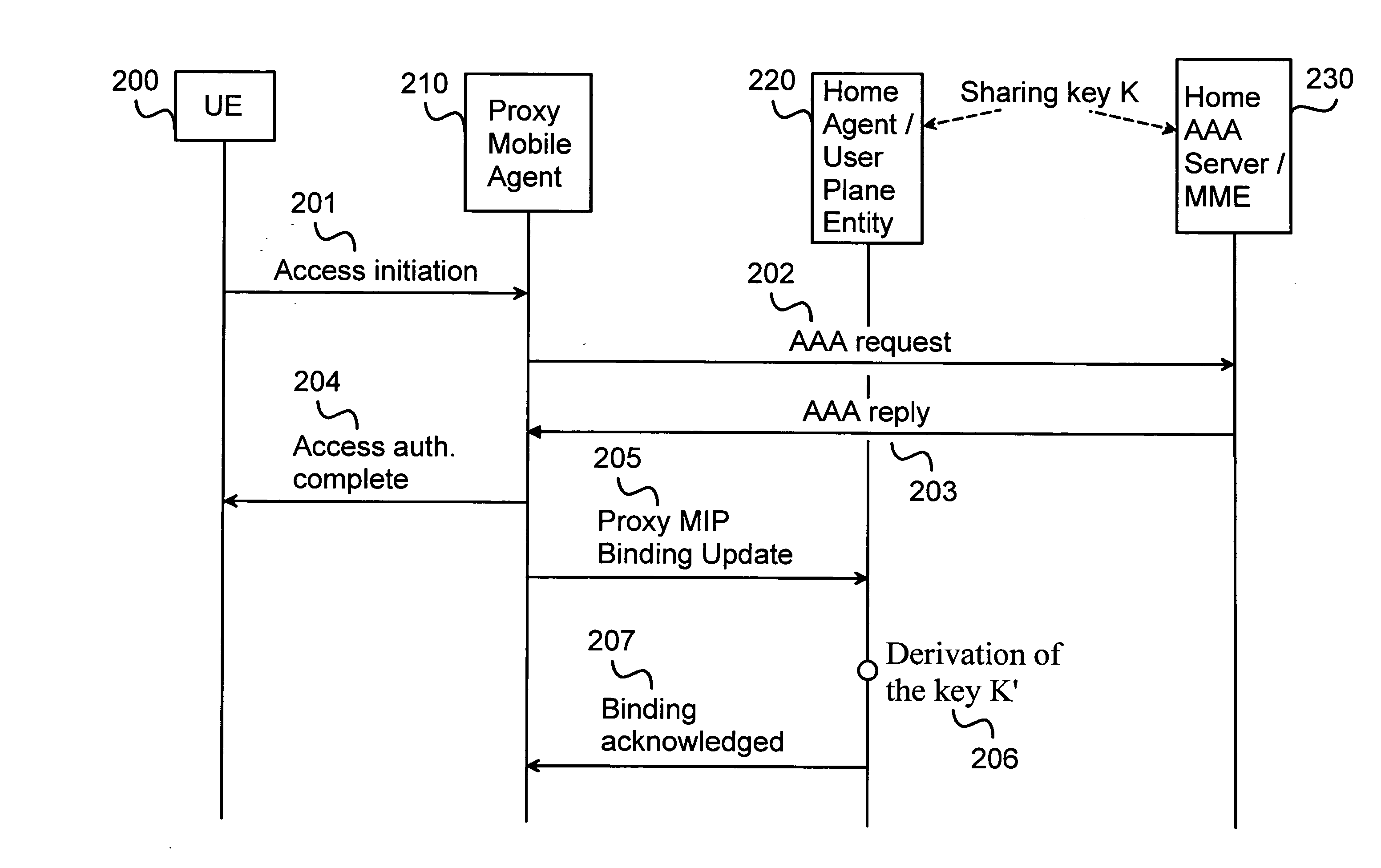
ActiveUS20080207168A1Authentication procedure is acceleratedEnhanced authenticationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsClient-sideMobile IP
The present invention performs a Binding Update or a Location Update message authentication independently and terminal-specifically in a home SAE gateway. A key, which is derived in a home AAA server from an initially set long term key, is given to a visited network for encrypting the update messages in Proxy Mobile IP. In Client Mobile IP, the key is transmitted to a mobile node for update message encryption. When the update message is received in the home SAE gateway, the key can be derived independently in the home SAE gateway without any key requests between the gateway and the home AAA server. Thus, it is possible to authenticate the binding or location update messages by verifying the two signatures. The present invention can also be implemented on a lower hierarchy of the system. The invention can be implemented in 3GPP standard releases enhanced with LTE technology, for instance.
Owner:NOKIA TECHNOLOGLES OY
Network transaction verification and authentication
ActiveUS8510811B2Enhanced authenticationConvenient verificationDigital data processing detailsComputer security arrangementsAuthentication serverClient-side
A two-level authentication system is described supporting two-factor authentication that offers efficient protection for secure on-line web transactions. It includes a global unique identity (UID) provided either by an institute-issued / personal trusted device, or based on client computing platform hardware attributes, and generated using institution authorized private software, institution-authorized authentication proxy software, and an institution-generated credential code which is pre-stored in the token and only accessible by the institute-authorized authentication proxy software. The institution-authorized authentication proxy software uses the user's PIN and the trusted device's UID as input and verifies the user and device identities through institution-generated credential code which was pre-stored in the trusted device. Authentication is performed in two levels: the first authenticates the user and the trusted device locally; and the second authenticates the user remotely at the institution-owned authentication server. Various embodiments add extra levels of security, including one-time-password management.
Owner:INBAY TECH
Account provisioning authentication
ActiveUS20140279477A1Improve securityEnhanced authenticationFinanceProtocol authorisationService provisionInternet privacy
Embodiments of the present invention are directed to methods, systems, and apparatuses for providing a secure authentication scheme for authenticating users and accounts on behalf of a service provider server computer offering services to a user. Upon determining, by the secure authentication scheme, that the user and / or account identifier associated with the user is authenticate, the service provider server computer may be provided with assurance that the user is authenticate and thereafter provide a service requested by the user.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com