Patents
Literature
124results about How to "Lower security level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
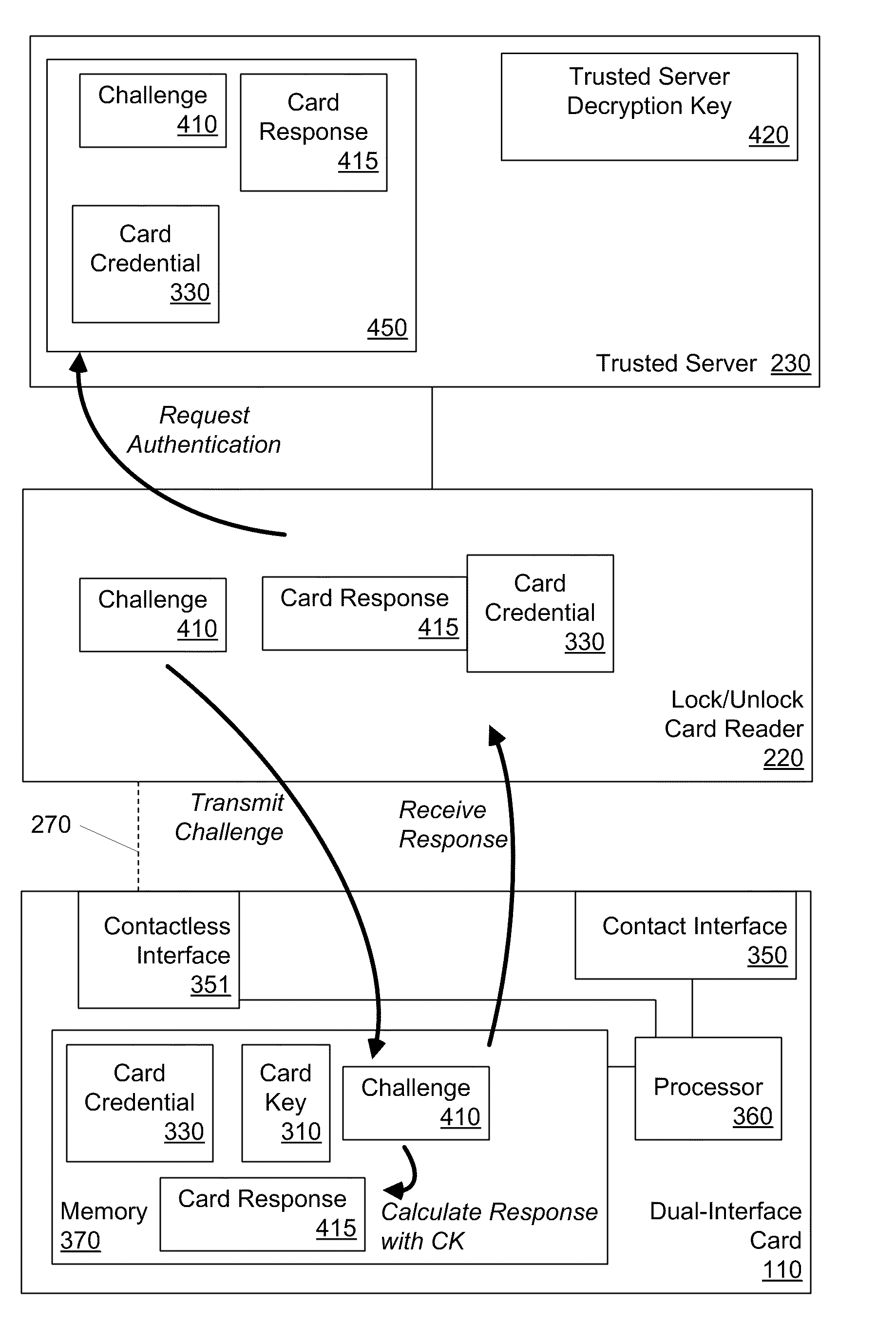
Dual-Interface Key Management
ActiveUS20110035604A1Lower security levelNear-field transmissionUnauthorized memory use protectionKey managementComputer security
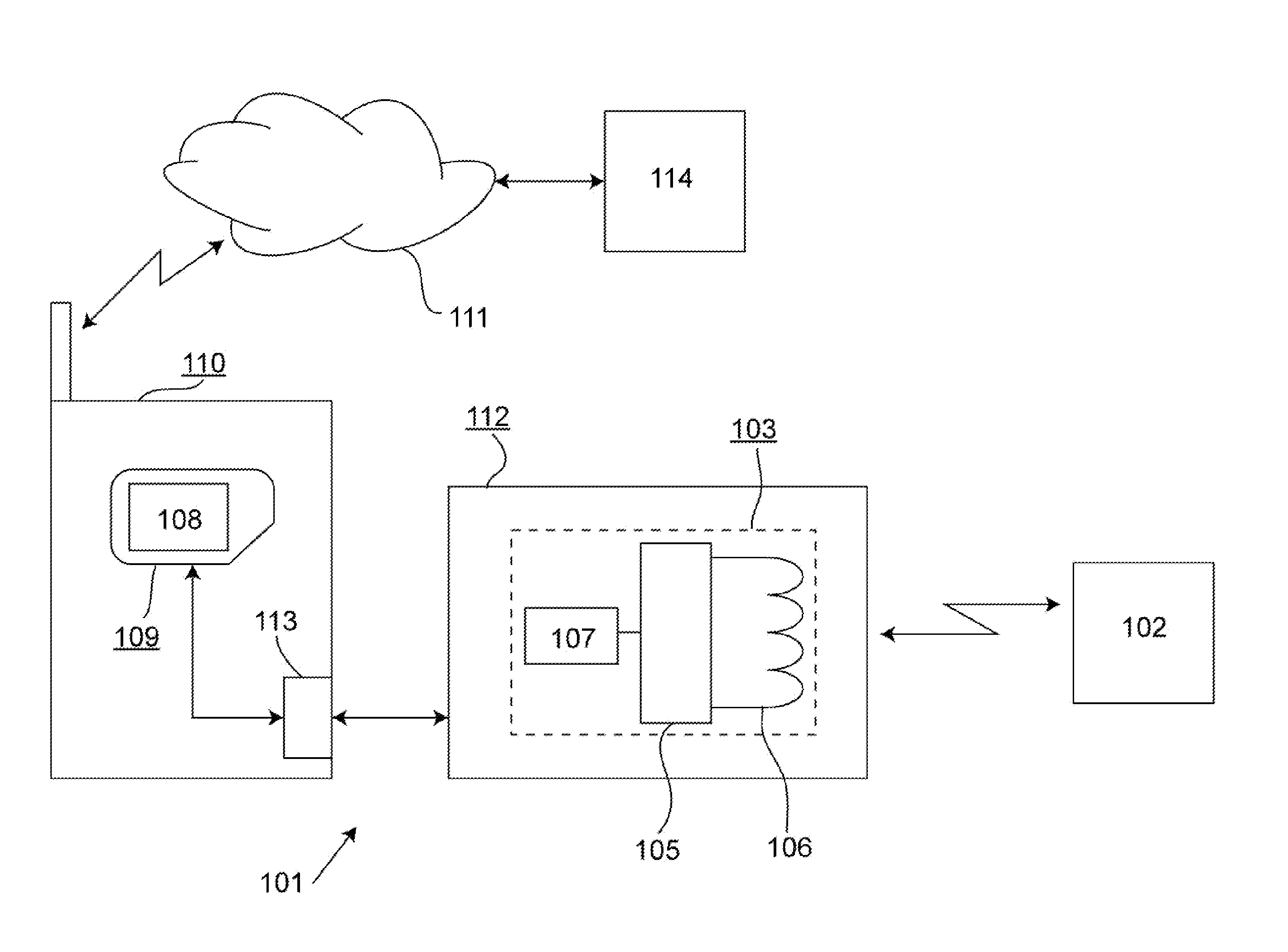
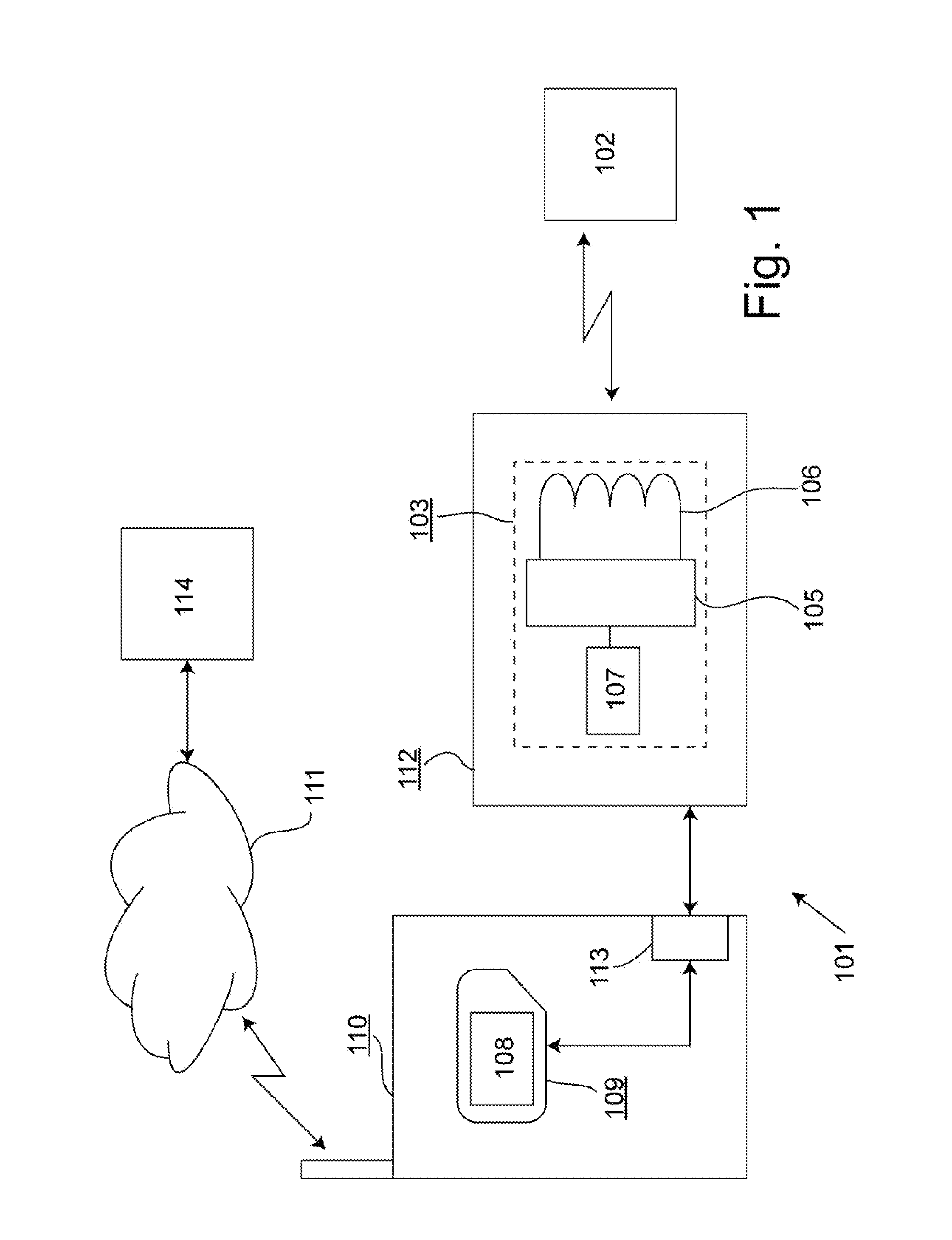
In one embodiment, a device includes a first interface, a second interface, a memory, and a processor coupled to the first and second interfaces and to the memory. The processor is configured to receive key-management information via the second interface, and to store the key-management information in a protected portion of the memory as stored key-management information. The processor is also configured to perform a challenge-response authentication interaction via the first interface. The challenge-response authentication interaction is based at least in part on the stored key-management information. The device is configured to prevent data in the protected portion of the memory from being modified in response to information received via the first interface.
Owner:HABRAKEN G WOUTER
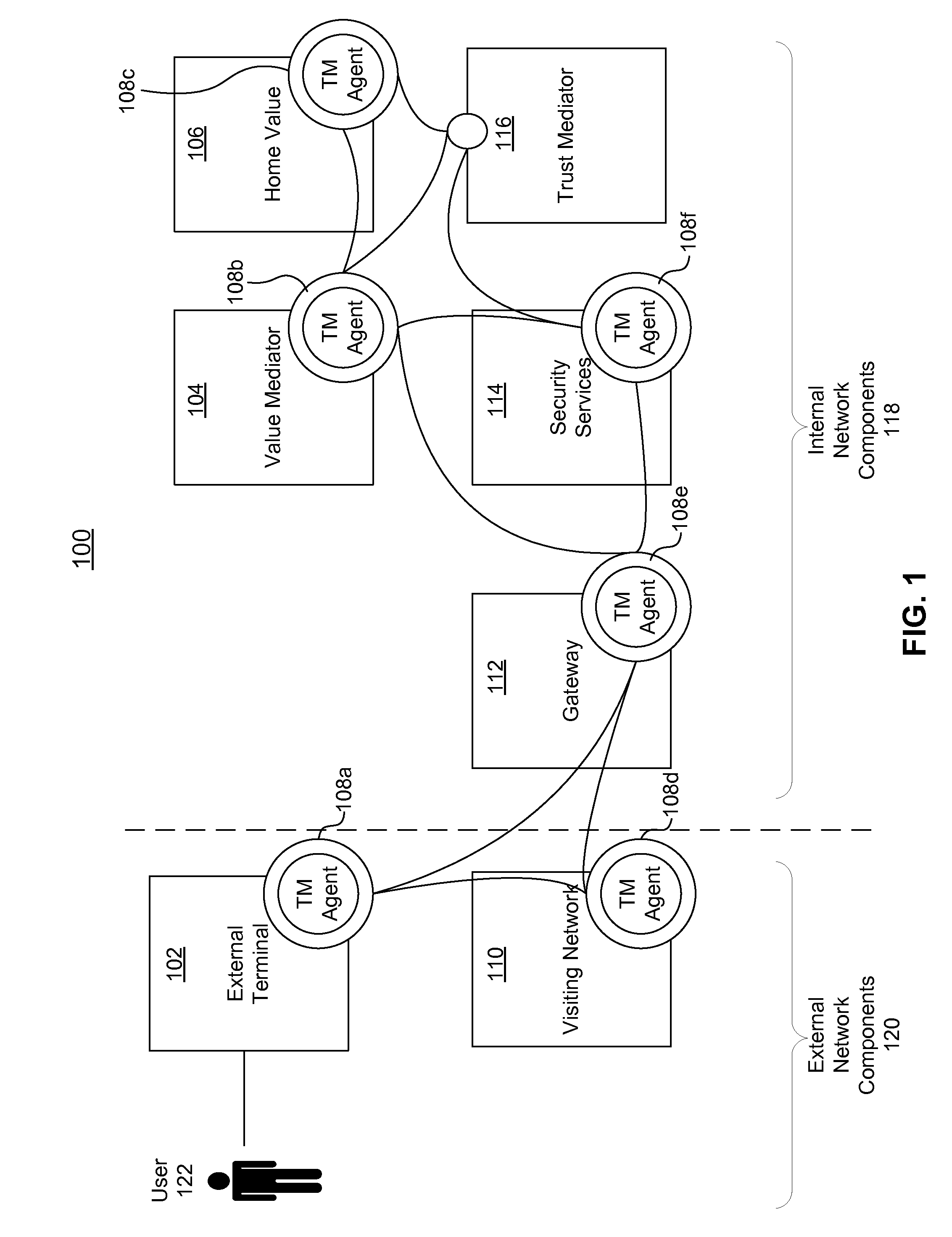
Systems, methods, and computer program products for collecting and reporting sensor data in a communication network
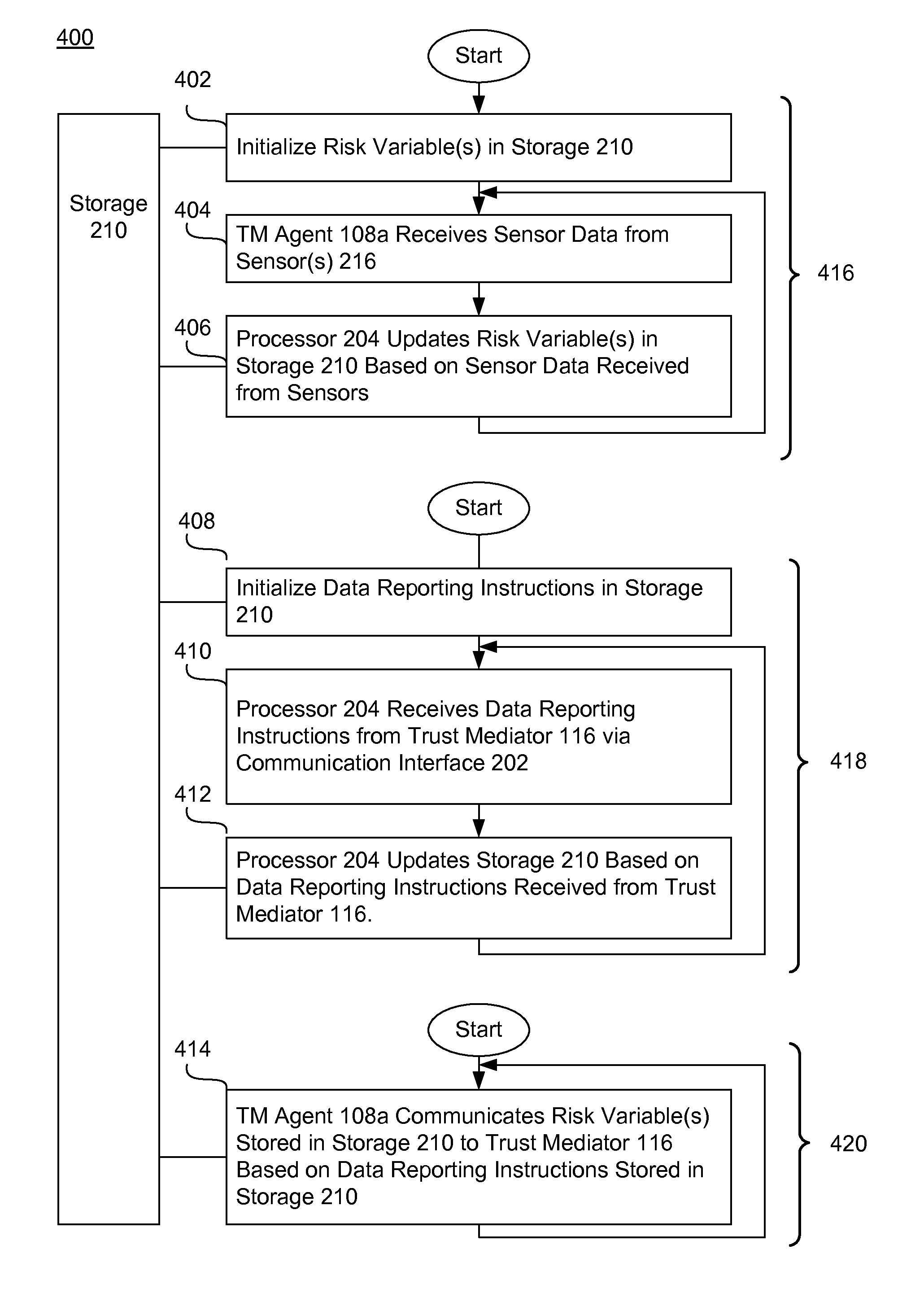
ActiveUS20110154497A1Shorten the time to marketIncrease propensityFinanceMemory loss protectionComputer networkEngineering
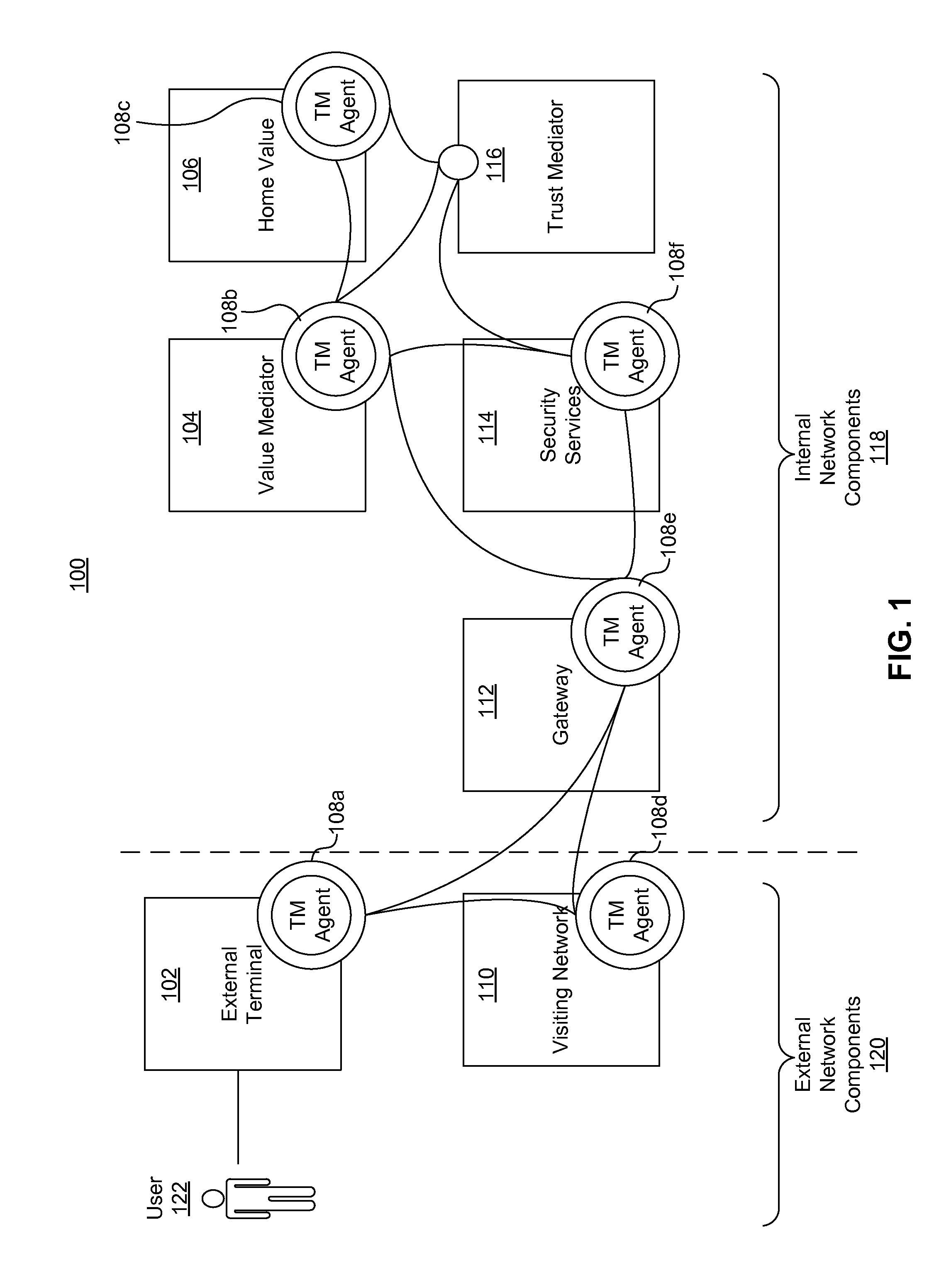
A system for collecting and reporting sensor data in a communication network includes a microprocessor coupled to a memory and an electronic storage device. The microprocessor receives sensor data from sensors, and stores the sensor data for each sensor in the electronic storage device. The microprocessor also receives, via the communication network, a data reporting instruction defining a data reporting technique corresponding to the sensor data associated with one or more of the sensors. The data reporting instruction is stored in the electronic storage device, and the microprocessor transmits, to a trust mediator over the communication network, at least a portion of the sensor data based on the data reporting instruction. The trust mediator maintains an acceptable level of security for data throughout the communication network by adjusting security safeguards based on the sensor data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
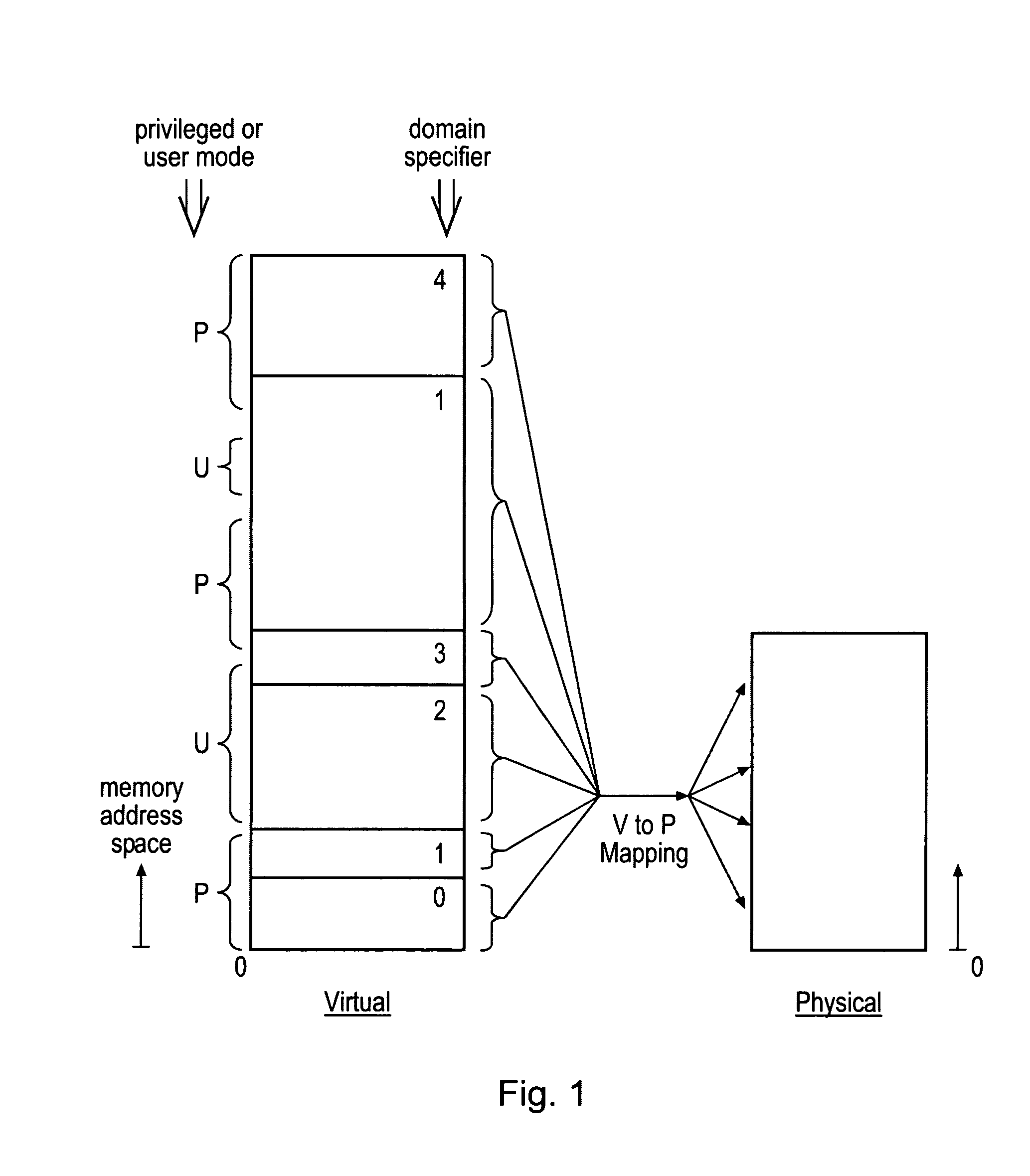
Protected function calling
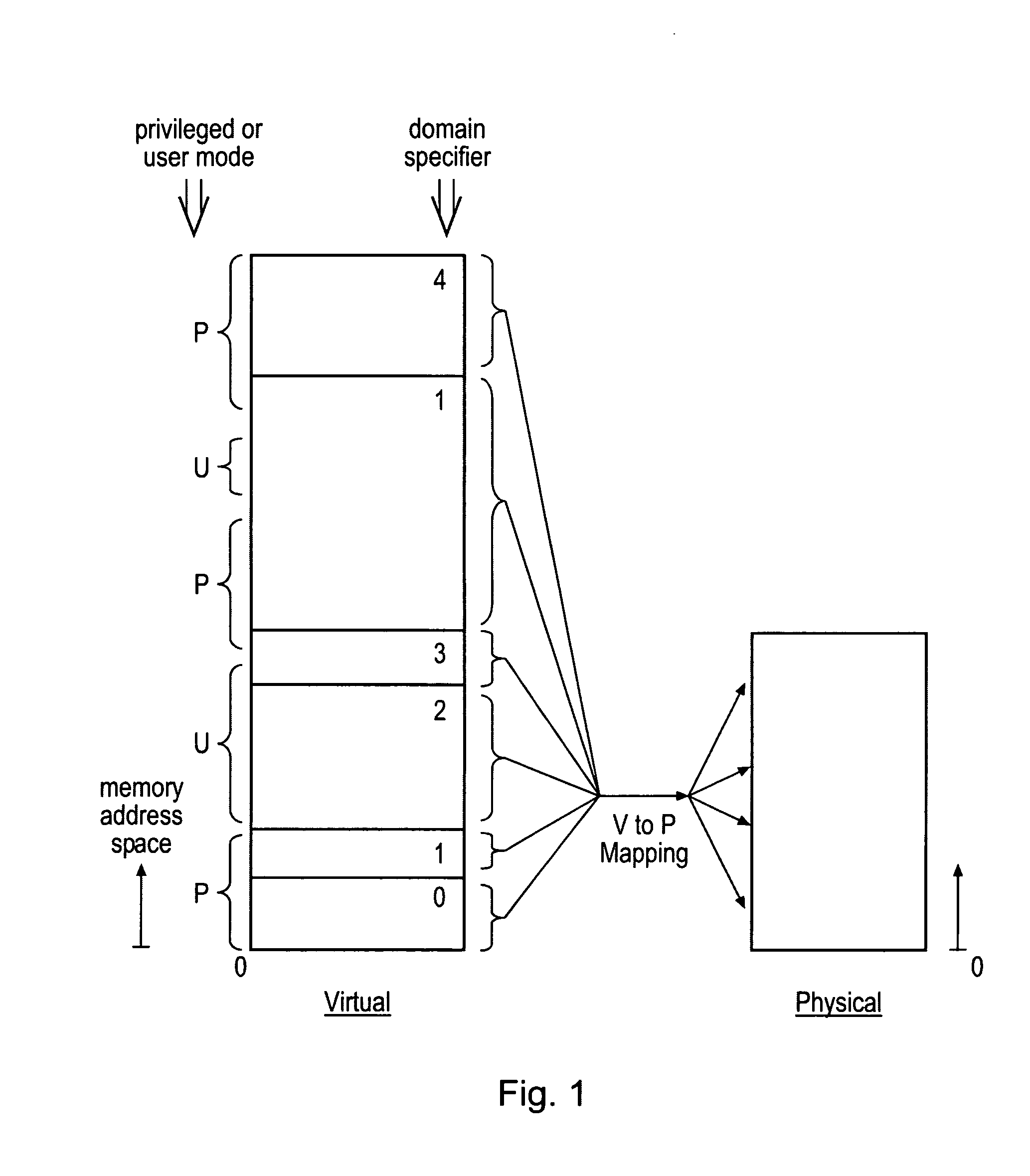
ActiveUS20080250216A1Improve securityAchieve backward compatibilityMemory architecture accessing/allocationRegister arrangementsMemory addressParallel computing
Memory address space is divided into domains and instruction access control circuitry is used to detect when the memory address from which an instruction to be executed is fetched has crossed a domain boundary and changed and in such cases to conduct a check to ensure that the instruction within the new domain is a permitted instruction of a permitted form. The permitted instruction can be arranged to be a no operation instruction other than in respect of the instruction access control circuitry, in order to assist backward compatibility.
Owner:ARM LTD
Dynamic protection of unpatched machines
ActiveUS20060218635A1Improve security levelLower security levelMemory loss protectionError detection/correctionState variationSecurity level
A system and method for protecting a computer system connected to a communication network from a potential vulnerability. The system and method protects a computer system that is about to undergo or has just undergone a change in state that may result in placing the computer system at risk to viruses, and the like, over a communication network. The system and method first detect an imminent or recent change in state. A security component and a fixing component react to the detection of the change in state. The security component may raise the security level to block incoming network information, other than information from a secure or known location, or information requested by the computer system. The fixing component implements a fixing routine, such as installing missing updates or patches, and on successfully completing the fixing routine, the security level is relaxed or lowered.
Owner:MICROSOFT TECH LICENSING LLC
Device and method for short range communication
ActiveUS20100151790A1Limited abilityLower security levelDigital data processing detailsMemory record carrier reading problemsComputer hardwareCommunication device
There is provided a communication device and method for contactless short range communication between a device and a terminal. An exemplary communication device comprises a communication component for contactless short range communication with a terminal. The exemplary device also comprises a slave element adapted to execute at least one application for executing transactions between the communication component and the terminal, wherein the slave element is coupled to the communication component via a first interface and wherein the slave element can be coupled to a secure master element via a second interface, the master element being adapted to control the slave element before a transaction is executed using the application.
Owner:VODAFONE HLDG
Security Clearance Card, System And Method Of Reading A Security Clearance Card
InactiveUS20070119924A1Large data storage capacityAvoid overwritingUser identity/authority verificationCo-operative working arrangementsBiometric dataData storing
The security clearance card, system, and method include a card that stores data to verify the identity of an owner of the card. In addition to other types of information, the card stores biometric data of the owner and other identity data. Different portions of the data may be encrypted with different encryption techniques based upon a predetermined level of security assigned to the portions of the stored data. Reader elements are then capable of reading at least a portion of the encrypted data stored on the security clearance card, and receiving at least one biometric from an individual. The biometric stored in the card is then compared with the biometric of the individual presenting the security clearance card to verify that the holder of the card is the owner of the card.
Owner:DIGITAL DATA RES
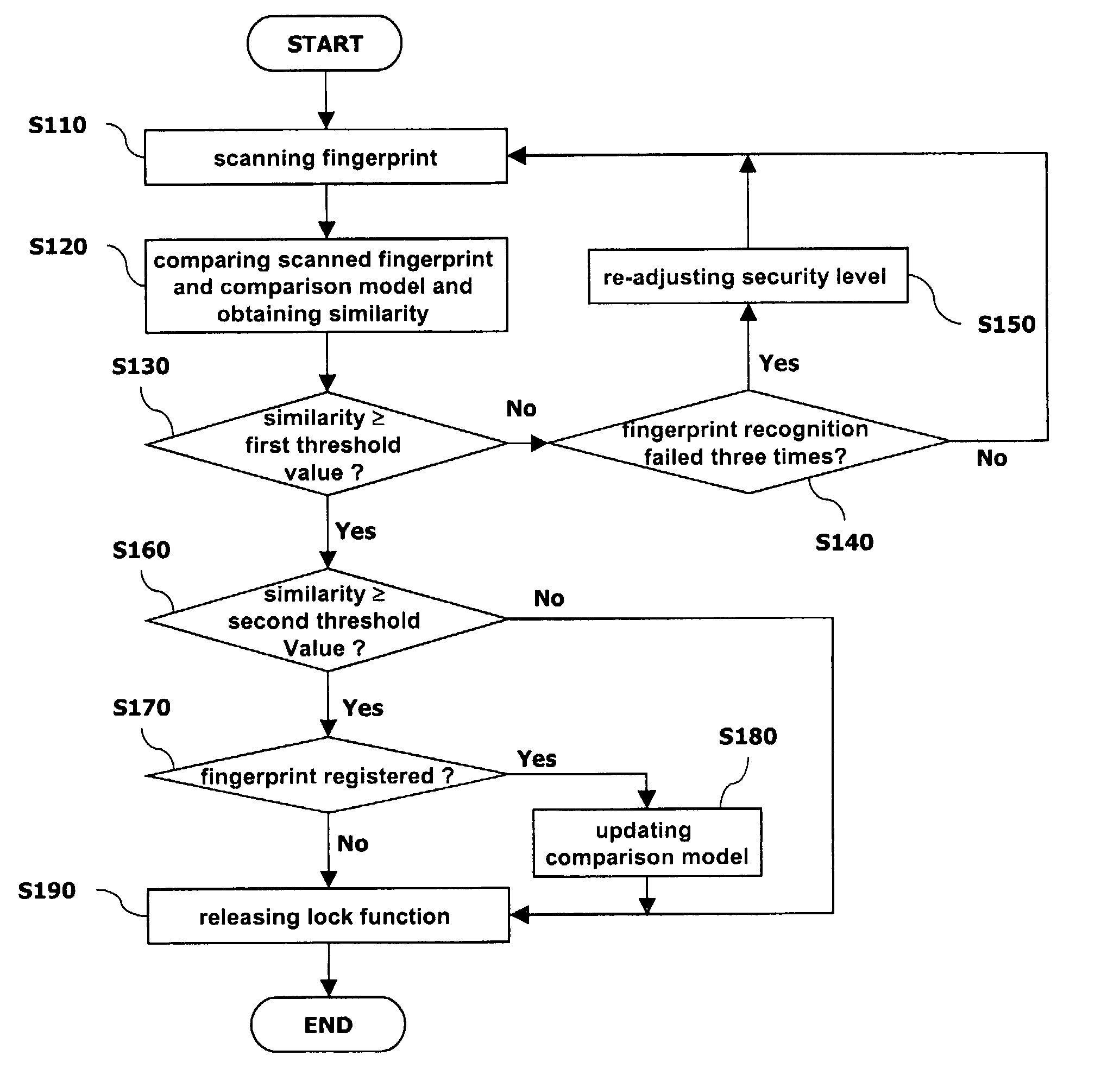
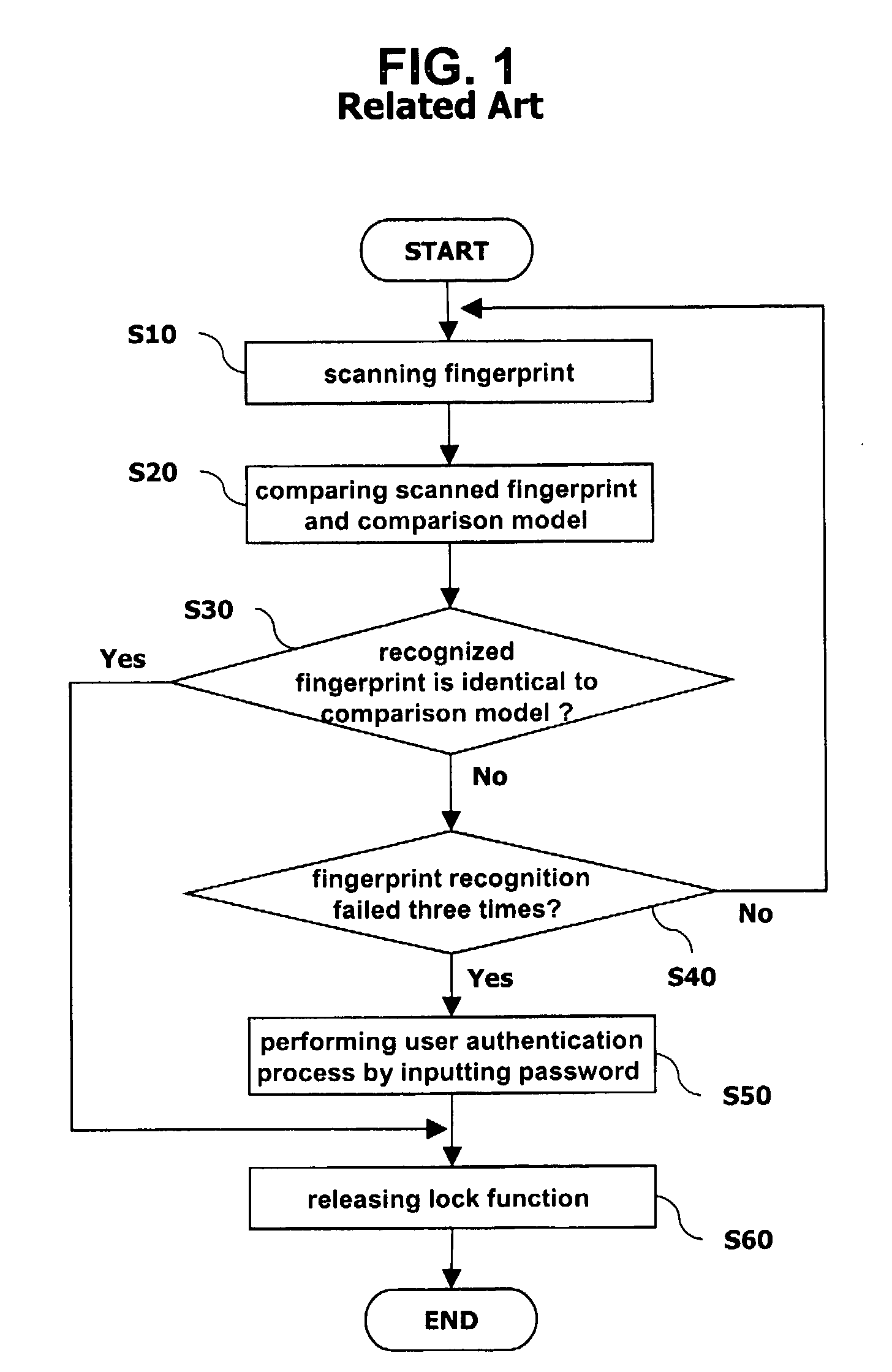
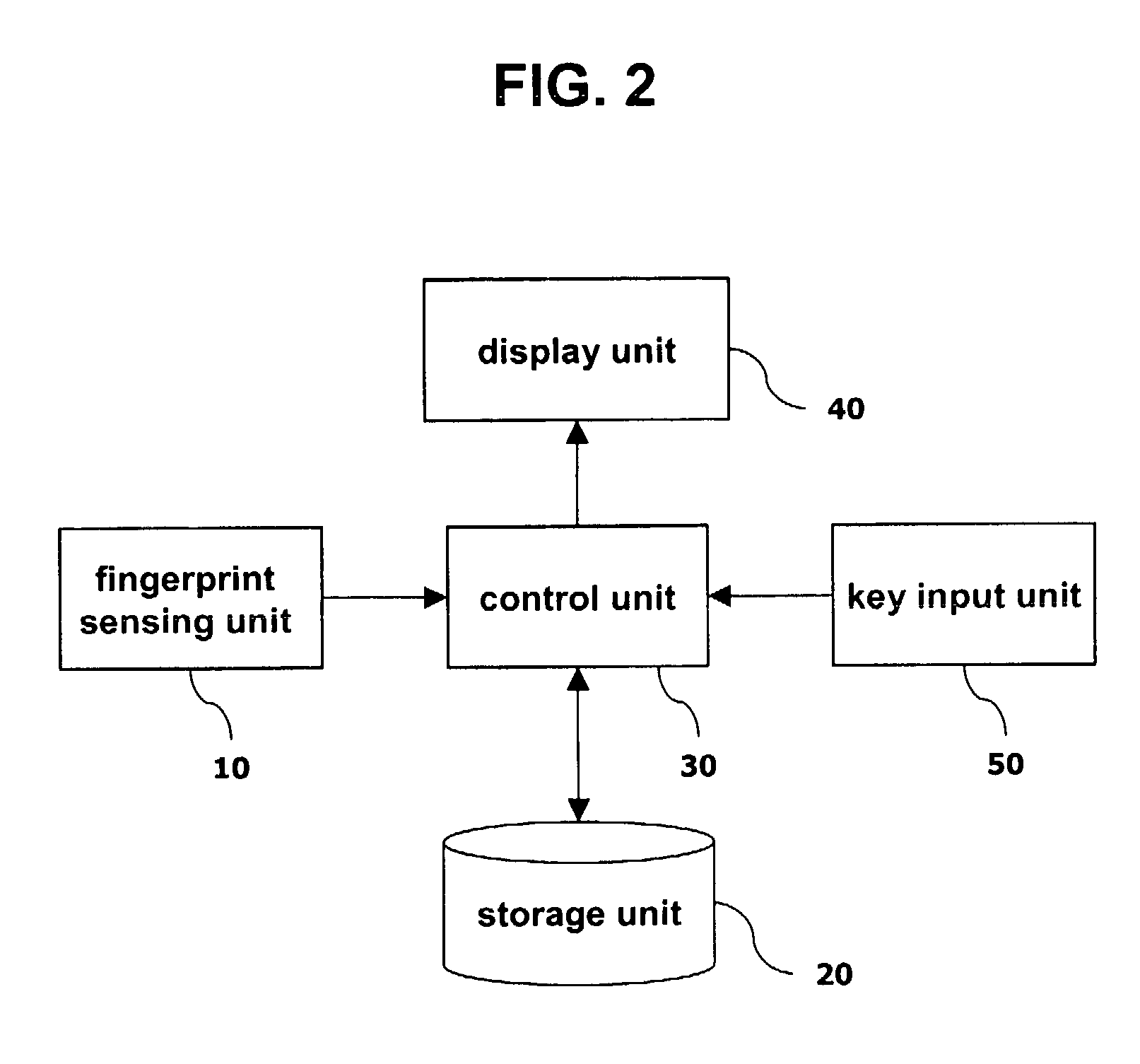
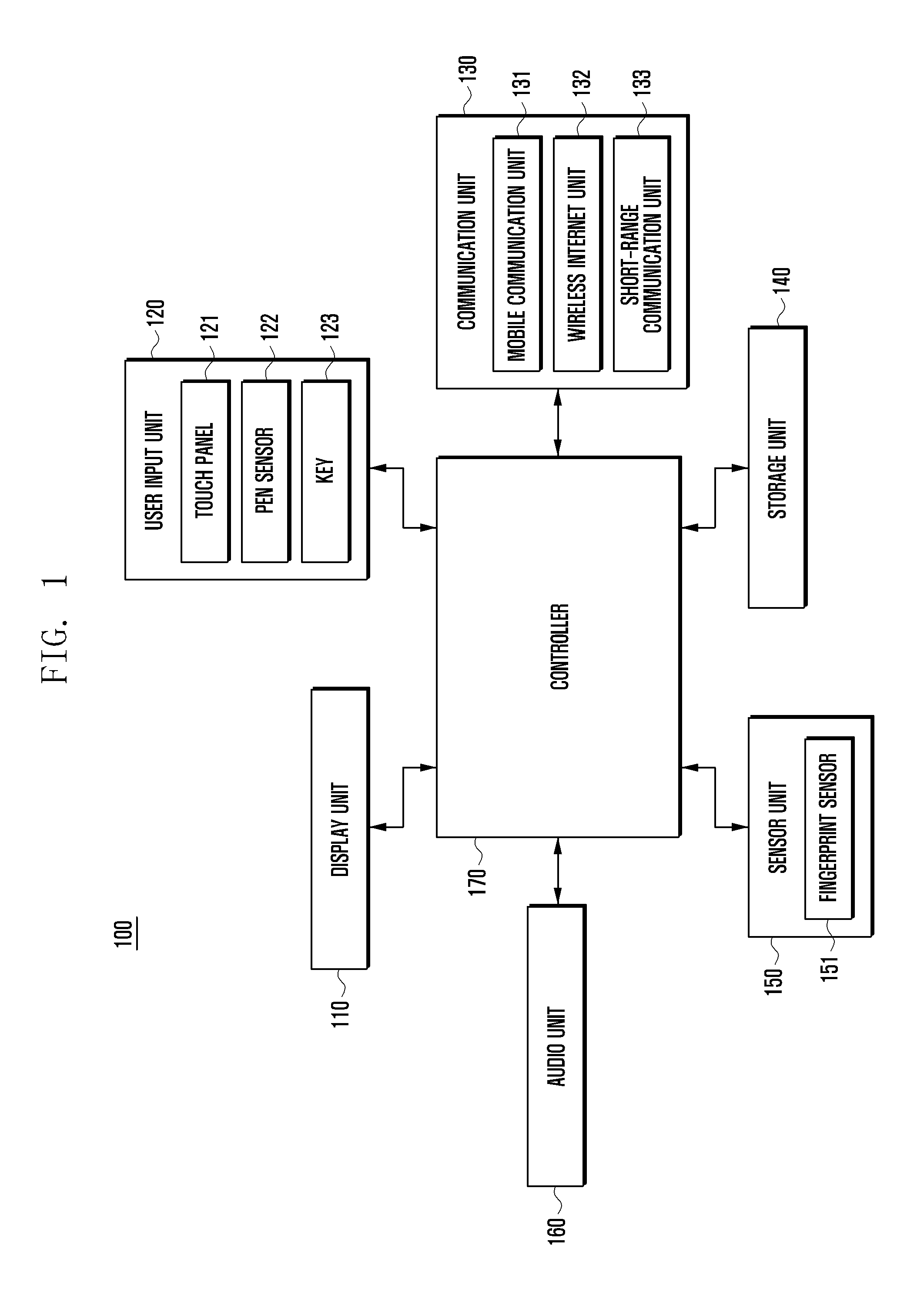
Apparatus and method of fingerprint recognition for a mobile terminal
InactiveUS7634117B2Facilitate fingerprint recognitionLower security levelCharacter and pattern recognitionDiagnostic recording/measuringPattern recognitionComputer terminal
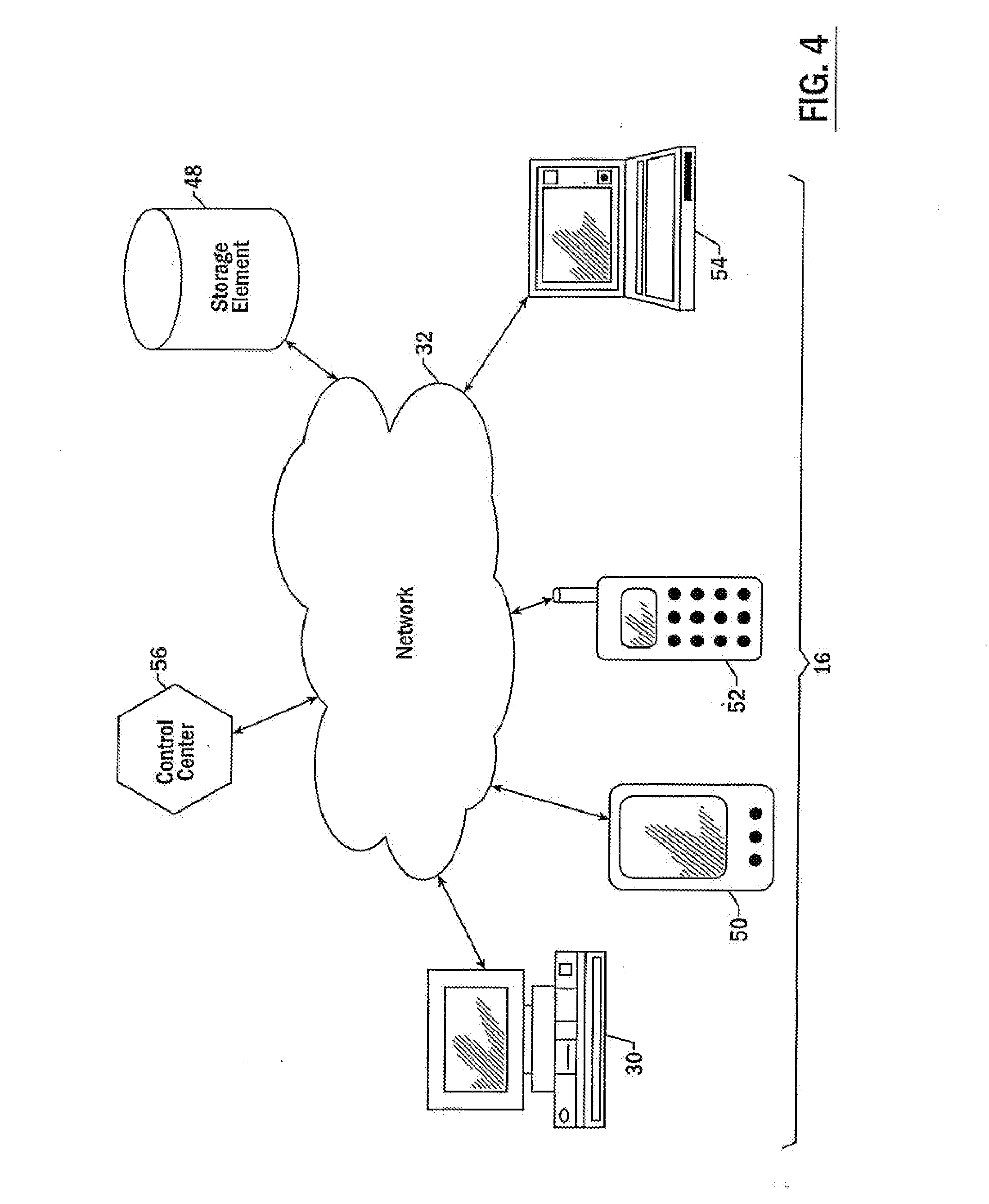
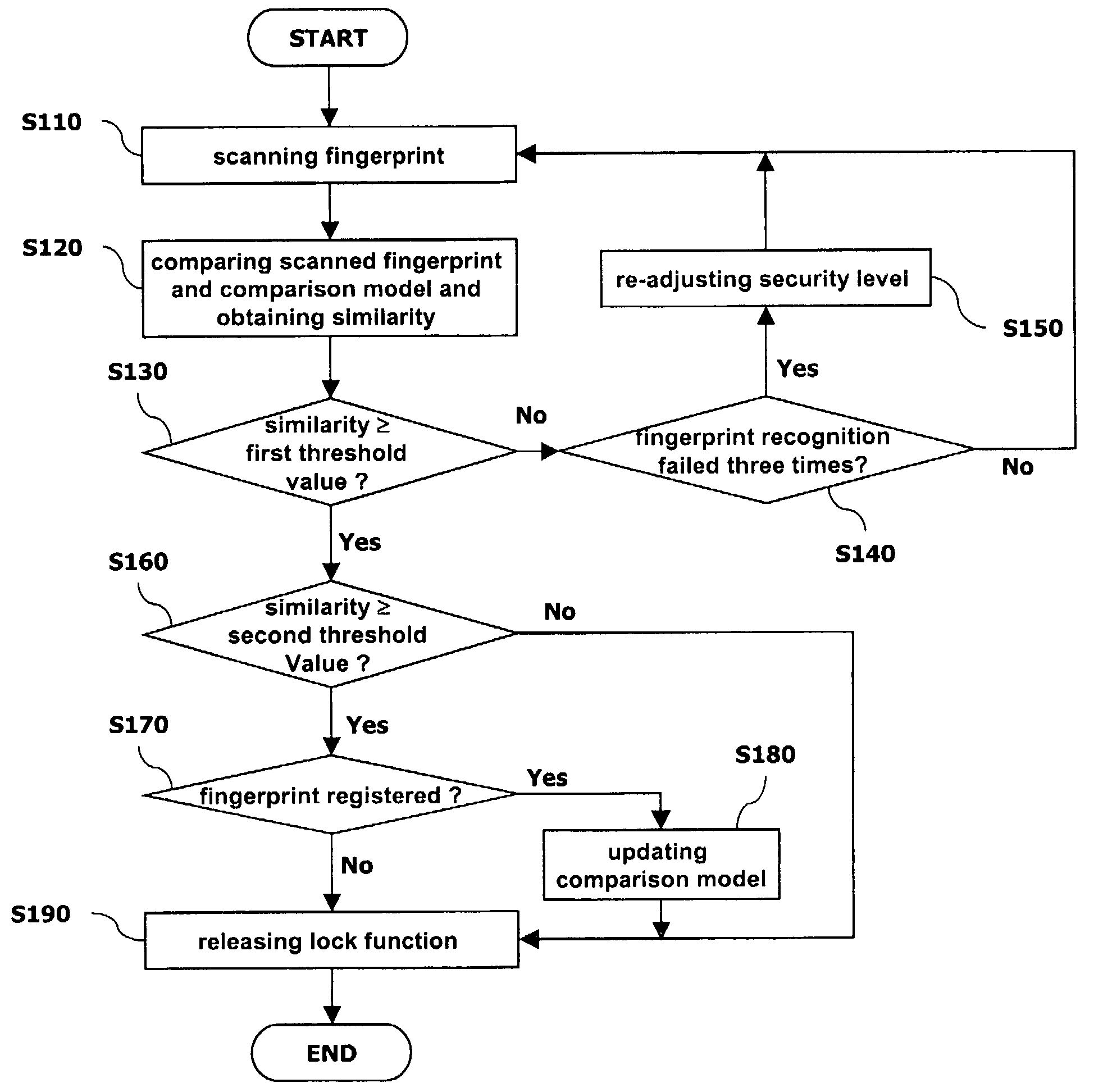
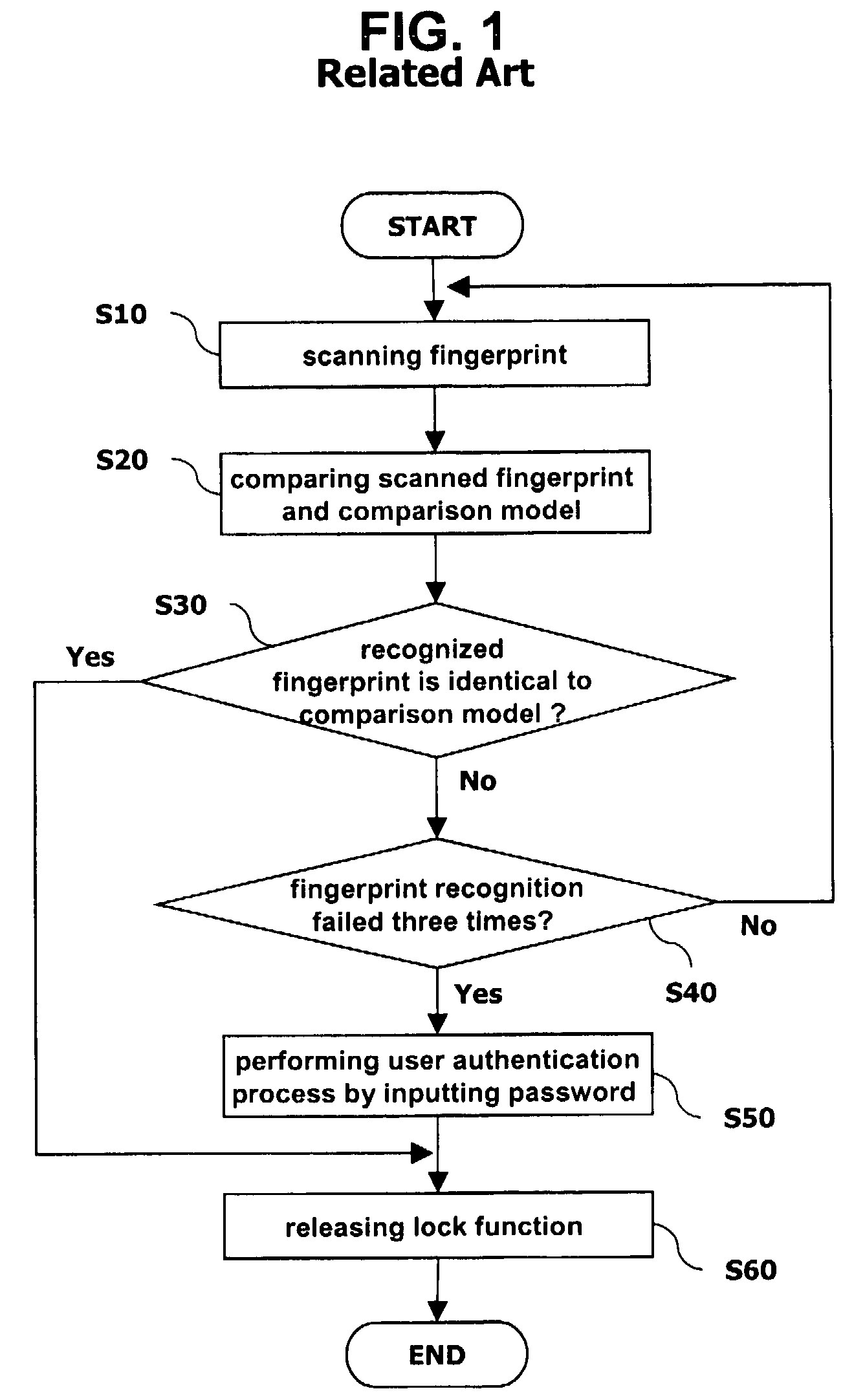
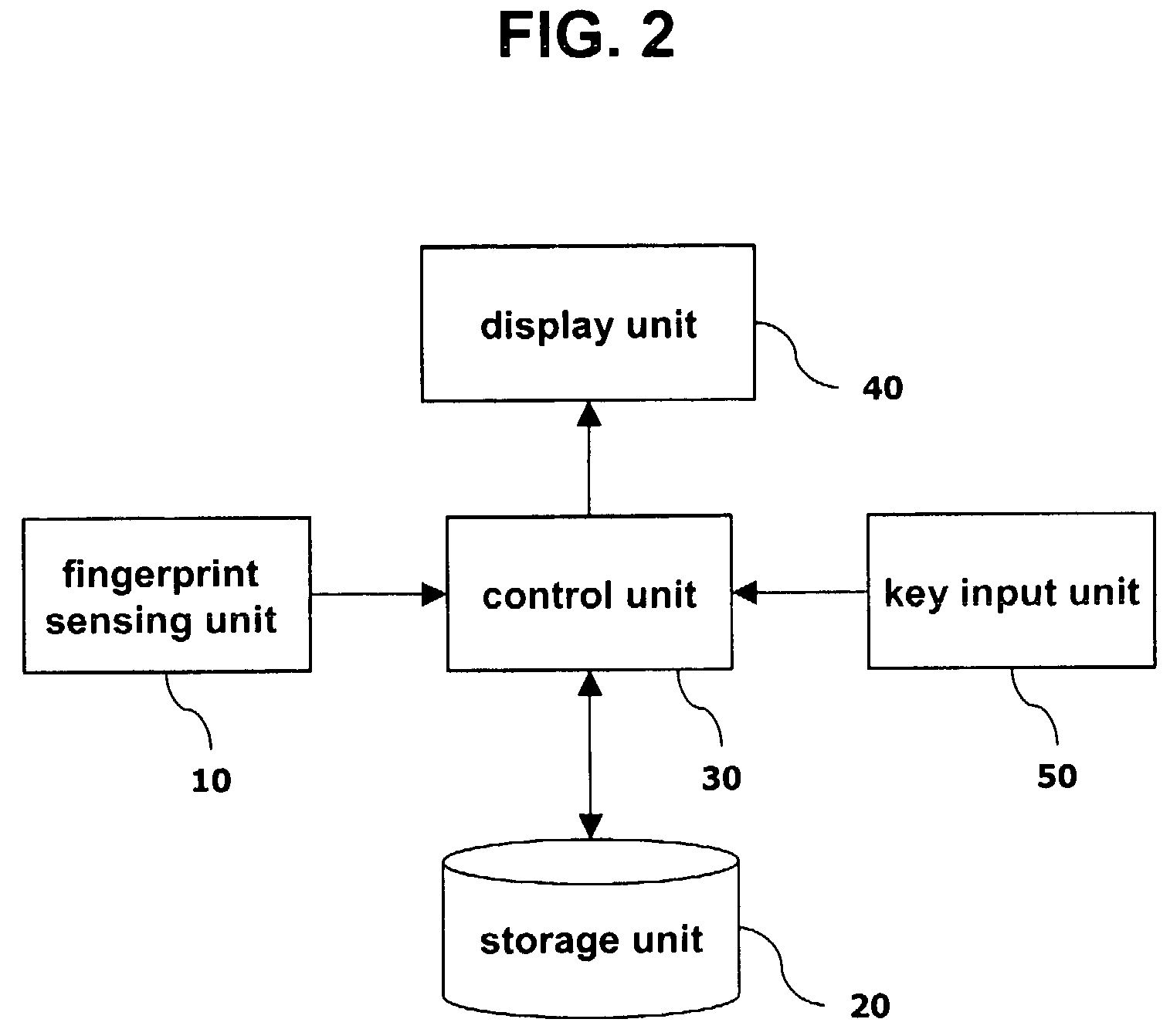
An apparatus for recognizing a fingerprint includes a fingerprint sensing unit for scanning a fingerprint of a user; a storage using for storing a comparison model of the fingerprint of the user and various threshold values; a control unit for obtaining similarity between the fingerprint of the user scanned by fingerprint sensing unit and the comparison model stored in the storage unit, comparing it with a certain threshold value, and controlling a mobile terminal according to the comparison result; and a display unit for transferring a result (success or failure) of the fingerprint recognition or a request from the control unit to the user.
Owner:LG ELECTRONICS INC
Apparatus and method of fingerprint recognition for a mobile terminal
InactiveUS20060210126A1Facilitate fingerprint recognitionLower security levelCharacter and pattern recognitionDiagnostic recording/measuringPattern recognitionModel control
An apparatus for recognizing a fingerprint includes a fingerprint sensing unit for scanning a fingerprint of a user; a storage using for storing a comparison model of the fingerprint of the user and various threshold values; a control unit for obtaining similarity between the fingerprint of the user scanned by fingerprint sensing unit and the comparison model stored in the storage unit, comparing it with a certain threshold value, and controlling a mobile terminal according to the comparison result; and a display unit for transferring a result (success or failure) of the fingerprint recognition or a request from the control unit to the user.
Owner:LG ELECTRONICS INC
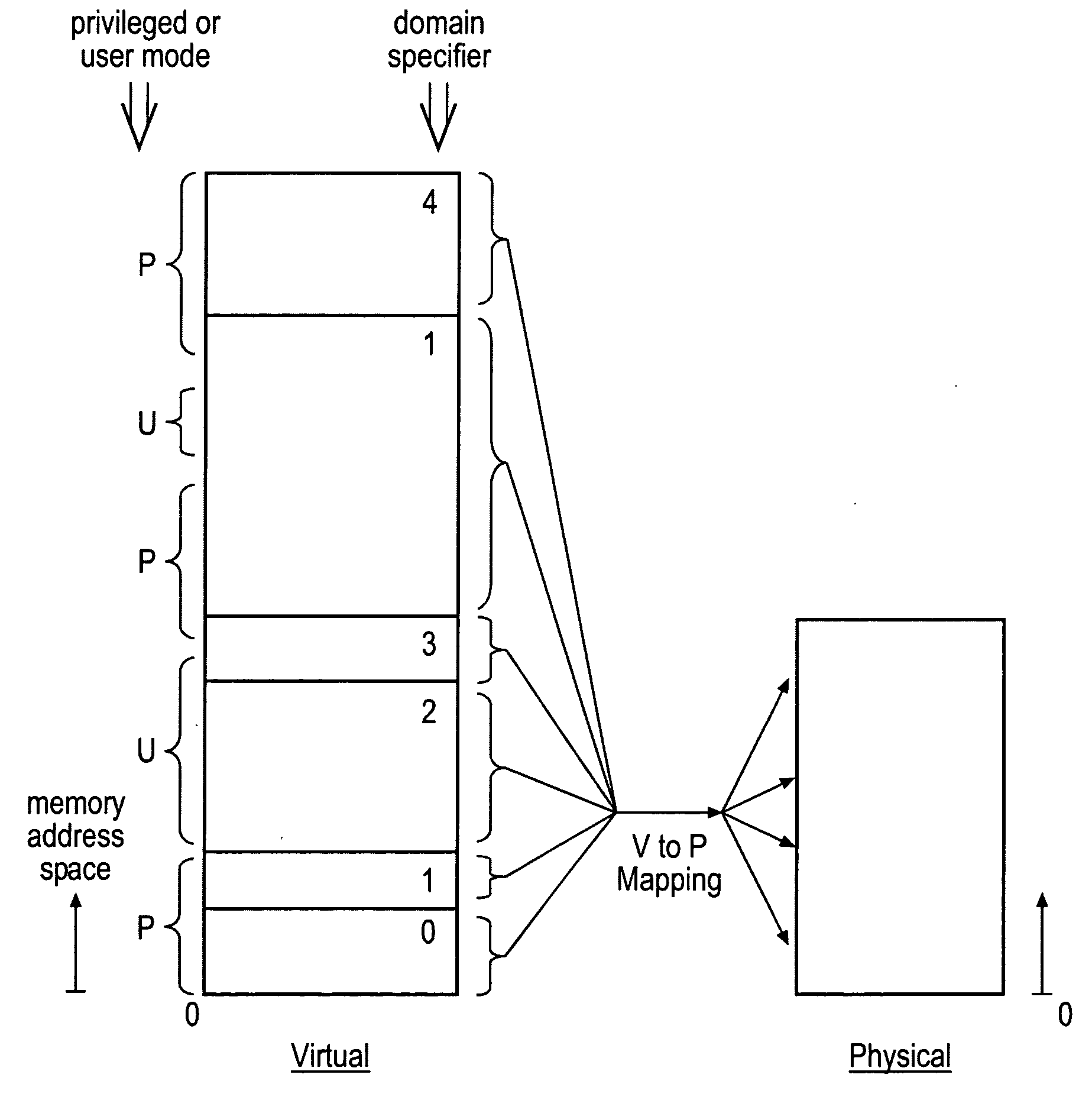
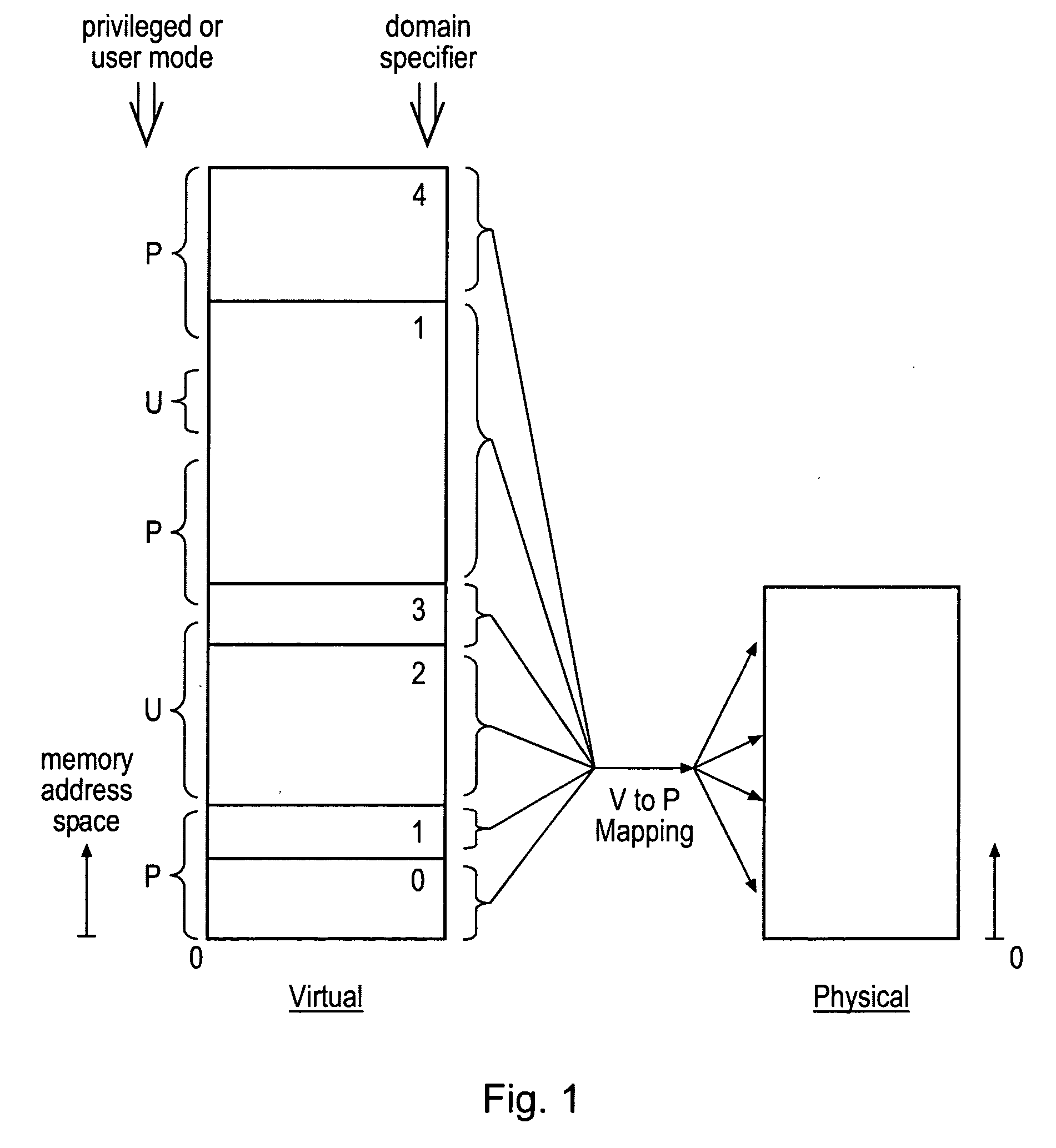
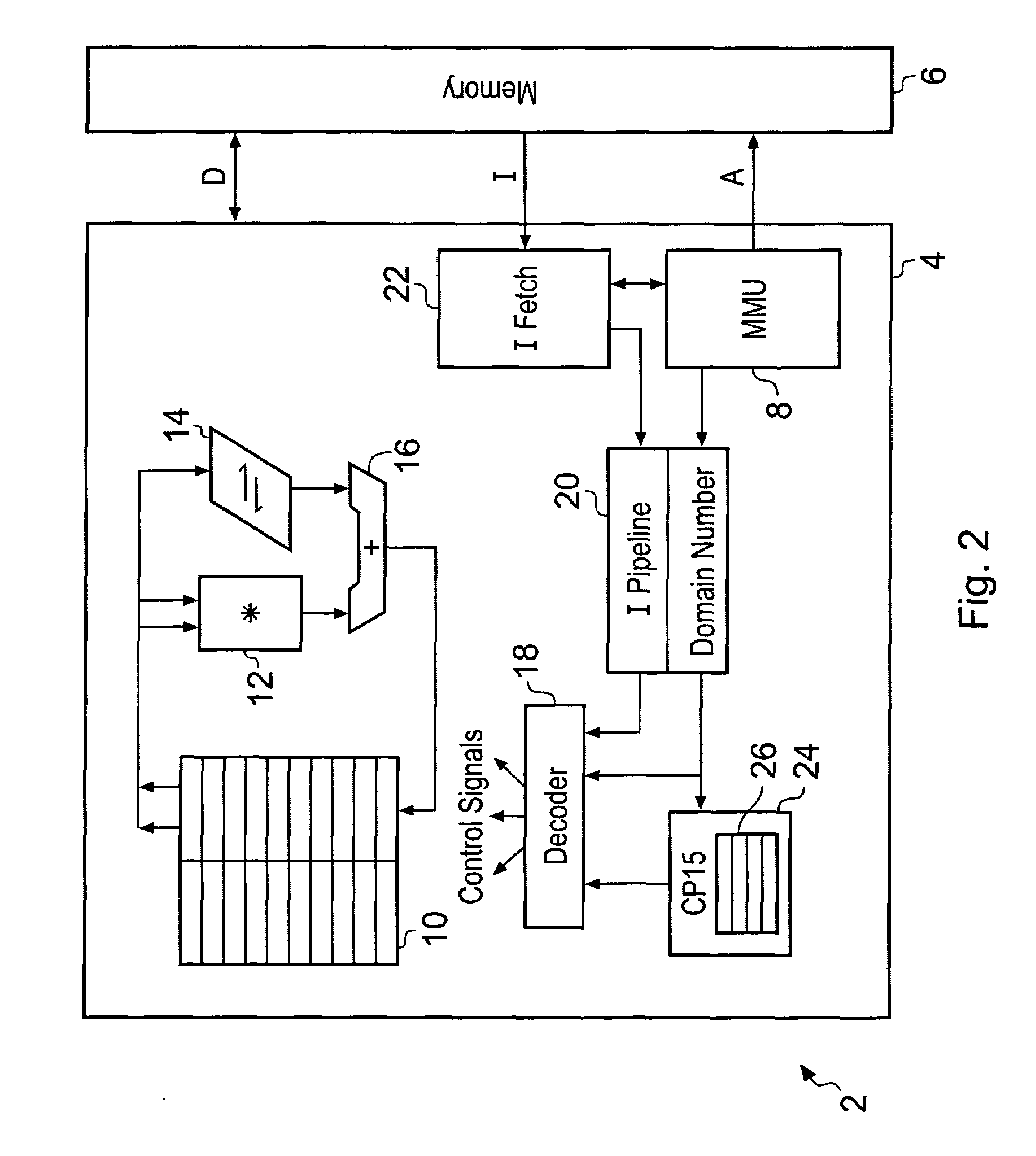
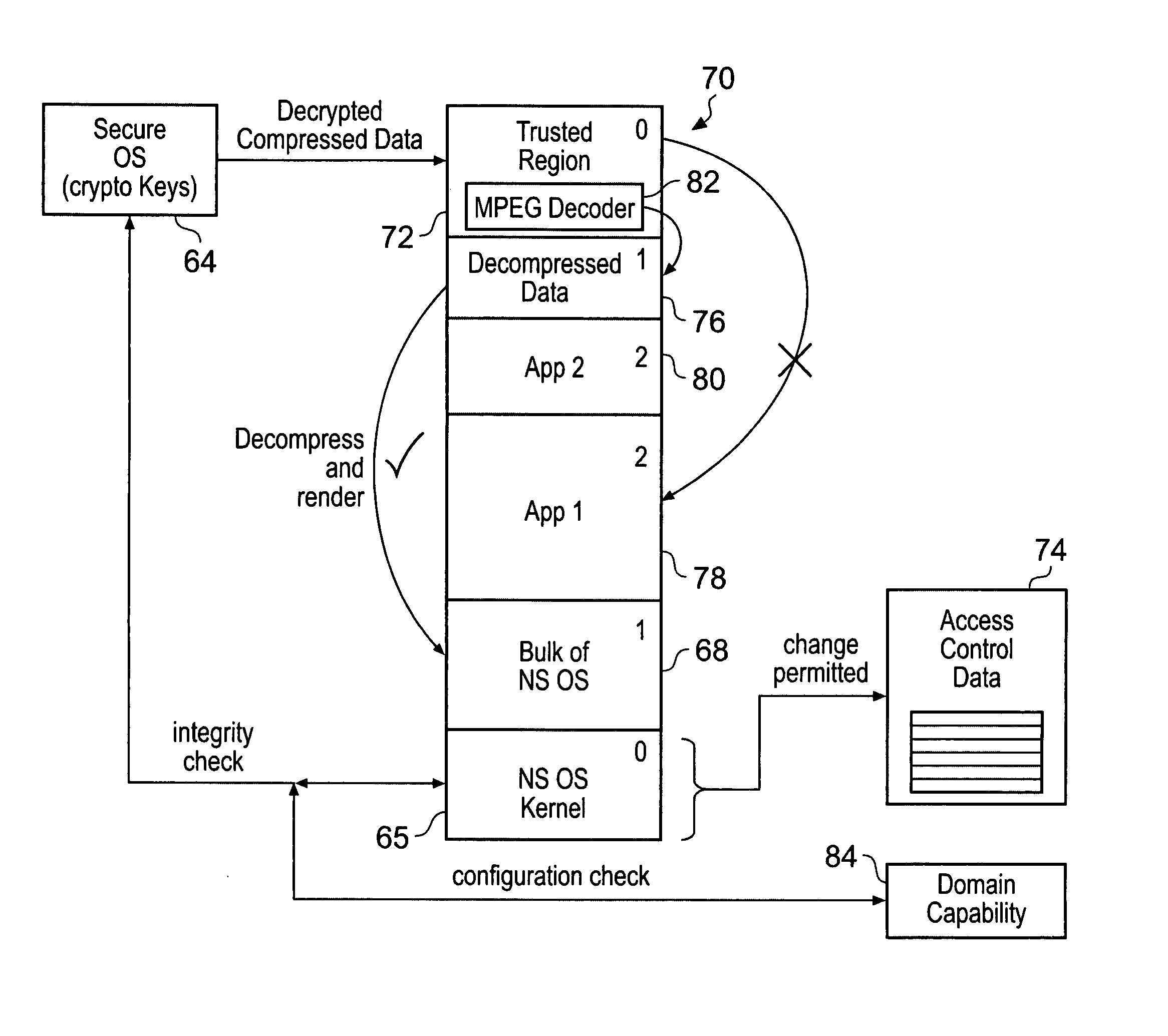
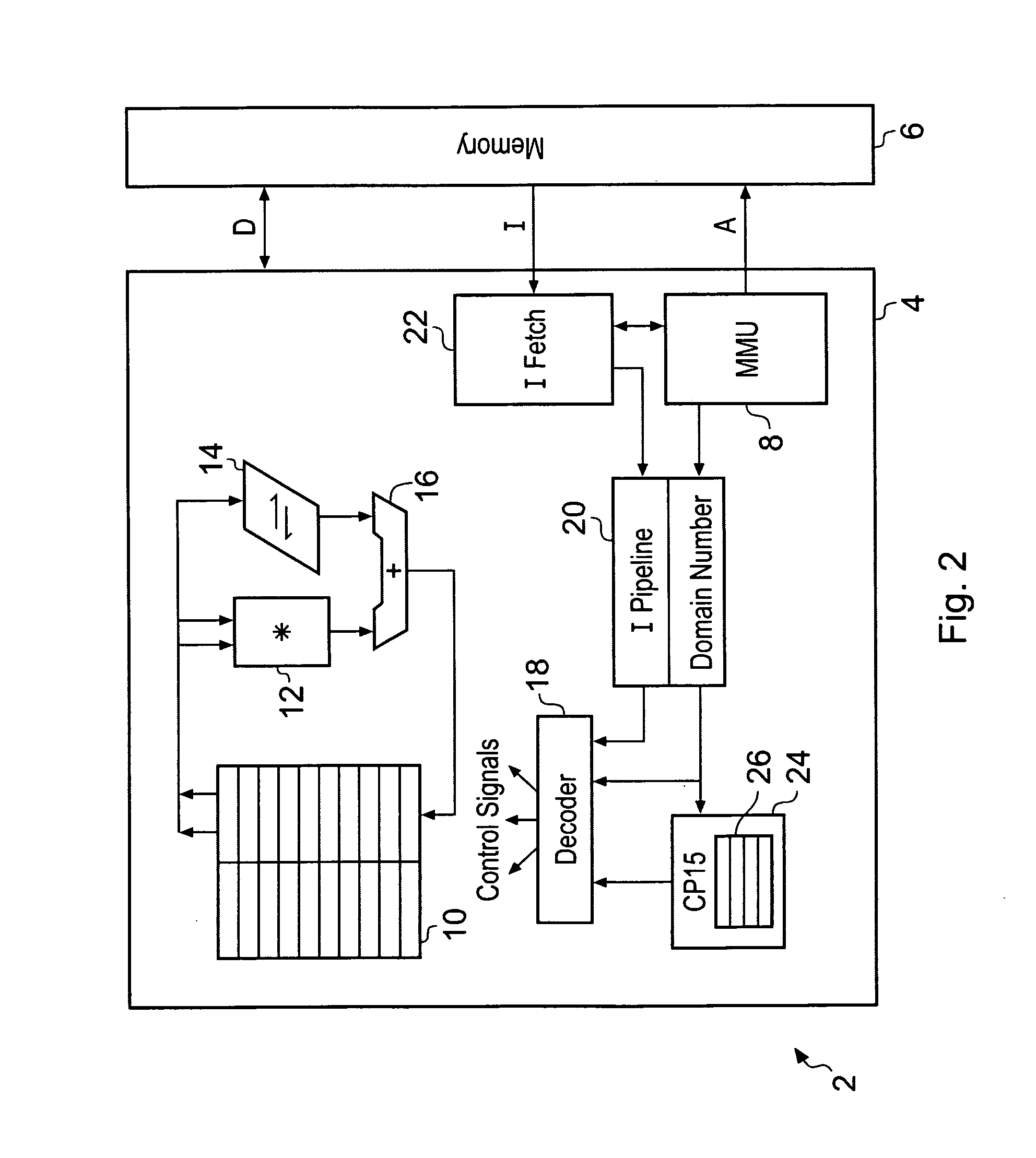
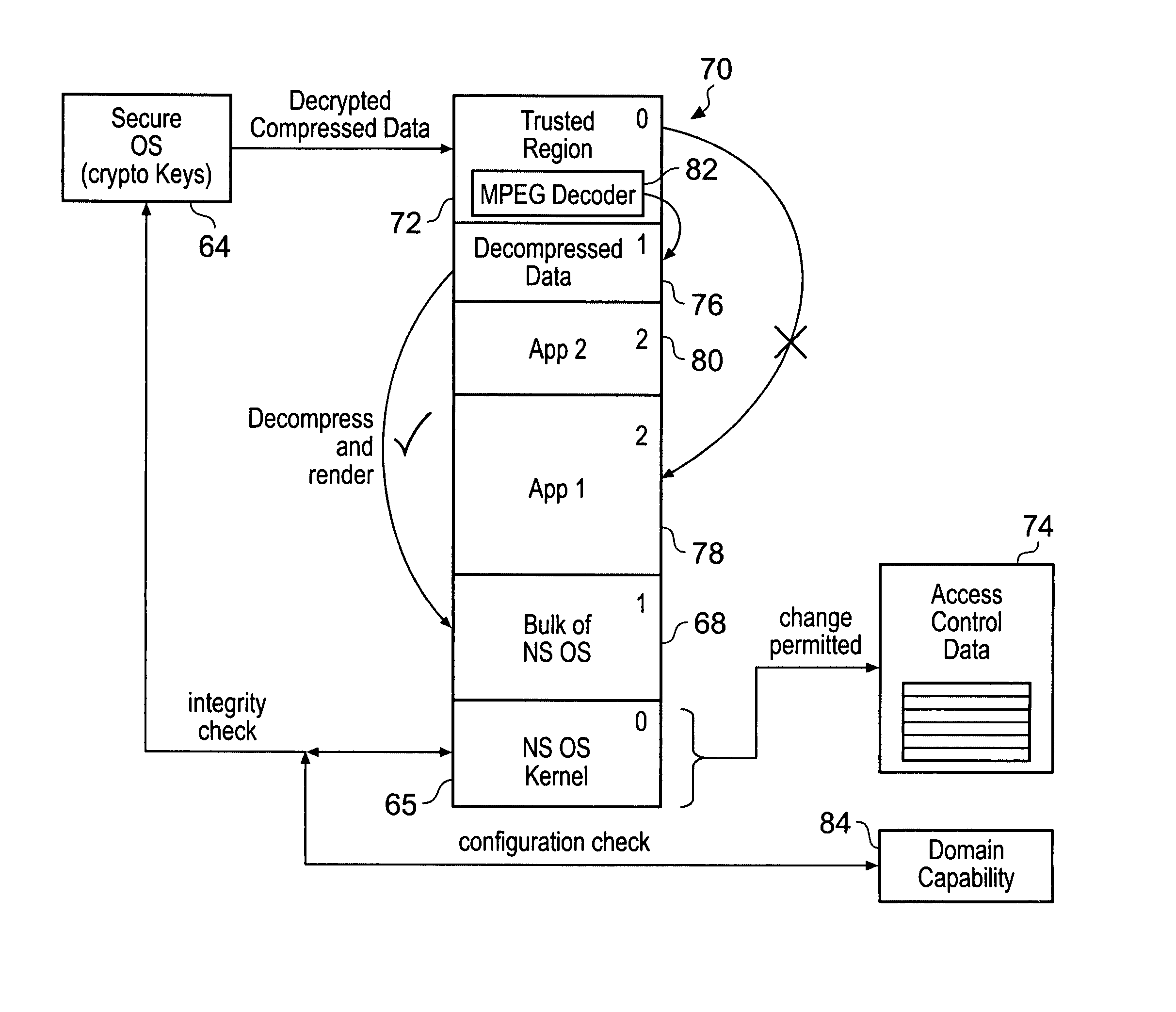
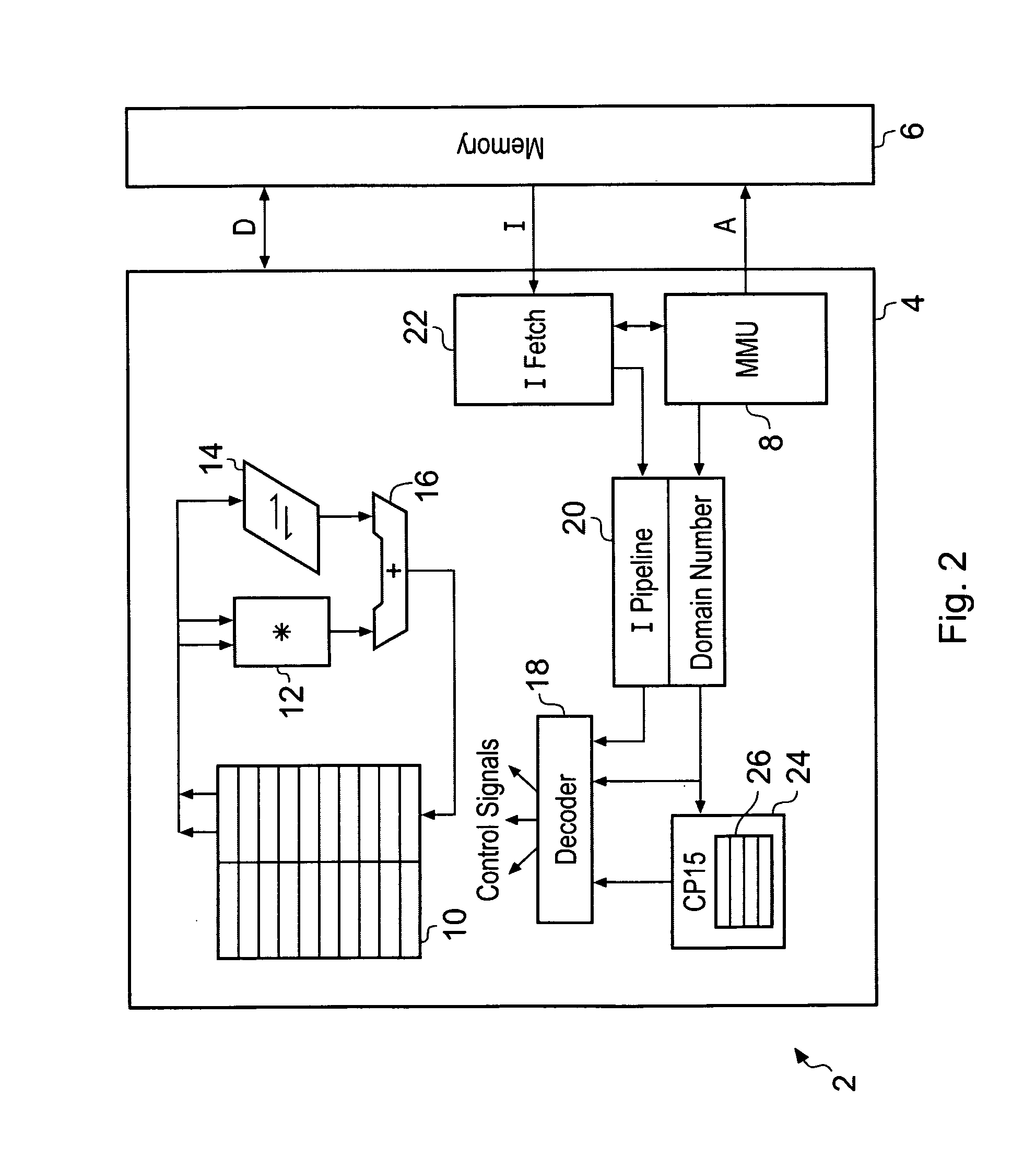
Memory domain based security control with data processing systems
ActiveUS20080250217A1Improve securityLimited abilityDigital computer detailsUnauthorized memory use protectionMemory addressOperational system
Access to memory address space is controlled by memory access control circuitry using access control data. The ability to change the access control data is controlled by domain control circuitry. Whether or not an instruction stored within a particular domain, being a set of memory addresses, is able to modify the access control data is dependent upon the domain concerned. Thus, the ability to change access control data can be restricted to instructions stored within particular defined locations within the memory address space thereby enhancing security. This capability allows systems to be provided in which call forwarding to an operating system can be enforced via call forwarding code and where trusted regions of the memory address space can be established into which a secure operating system may write data with increased confidence that that data will only be accessible by trusted software executing under control of a non-secure operating system.
Owner:ARM LTD
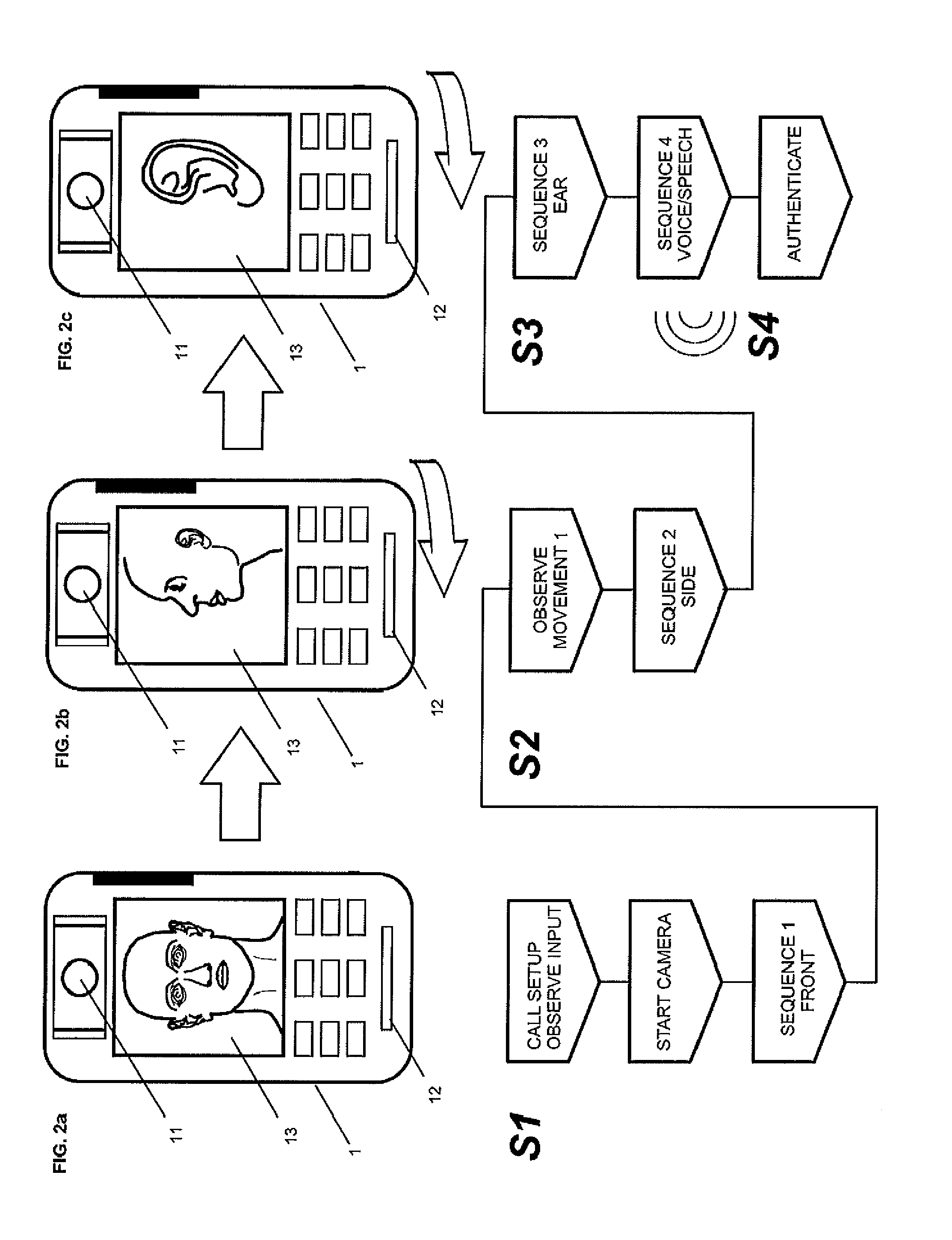
Method for sequential biometric authentication and mobile station
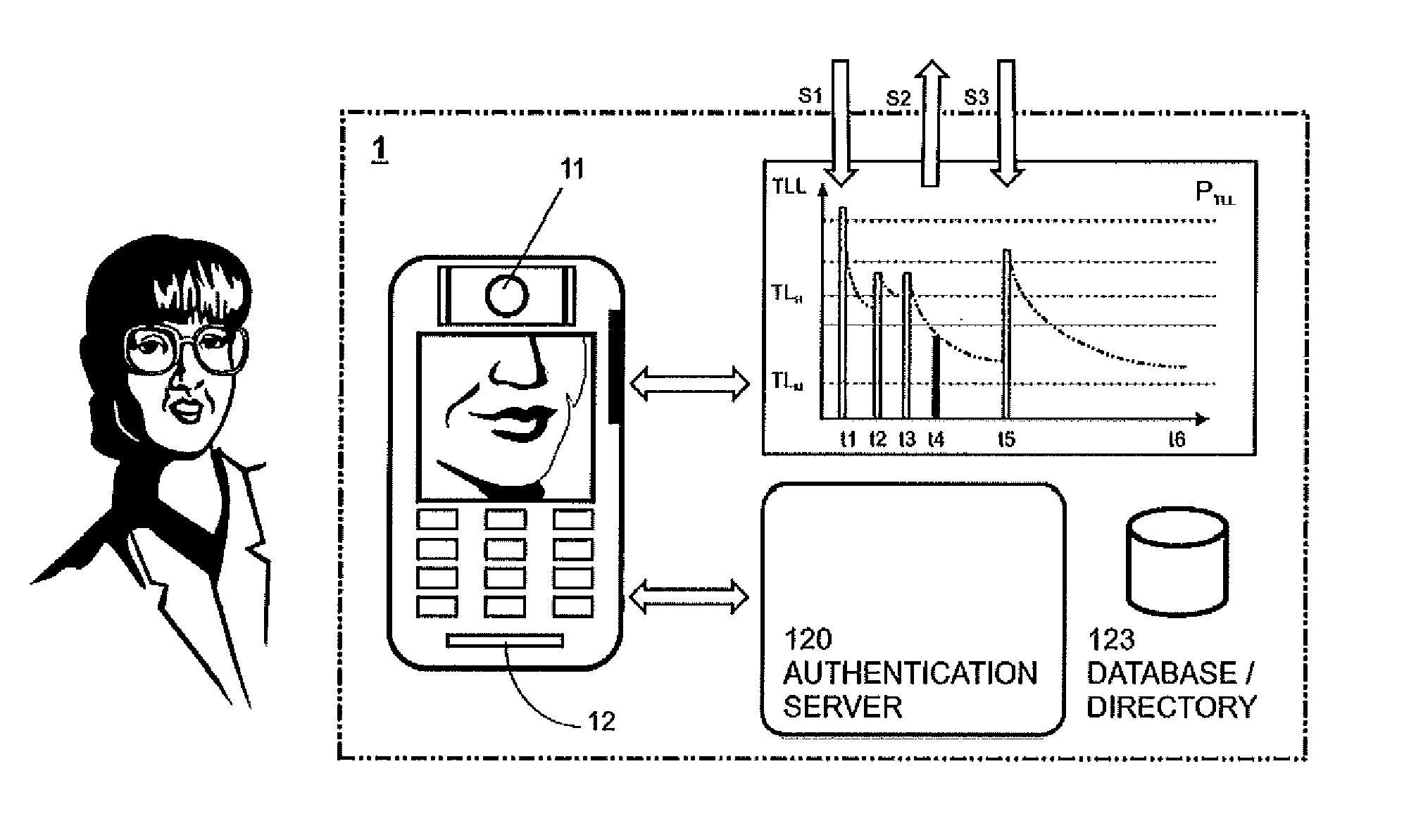
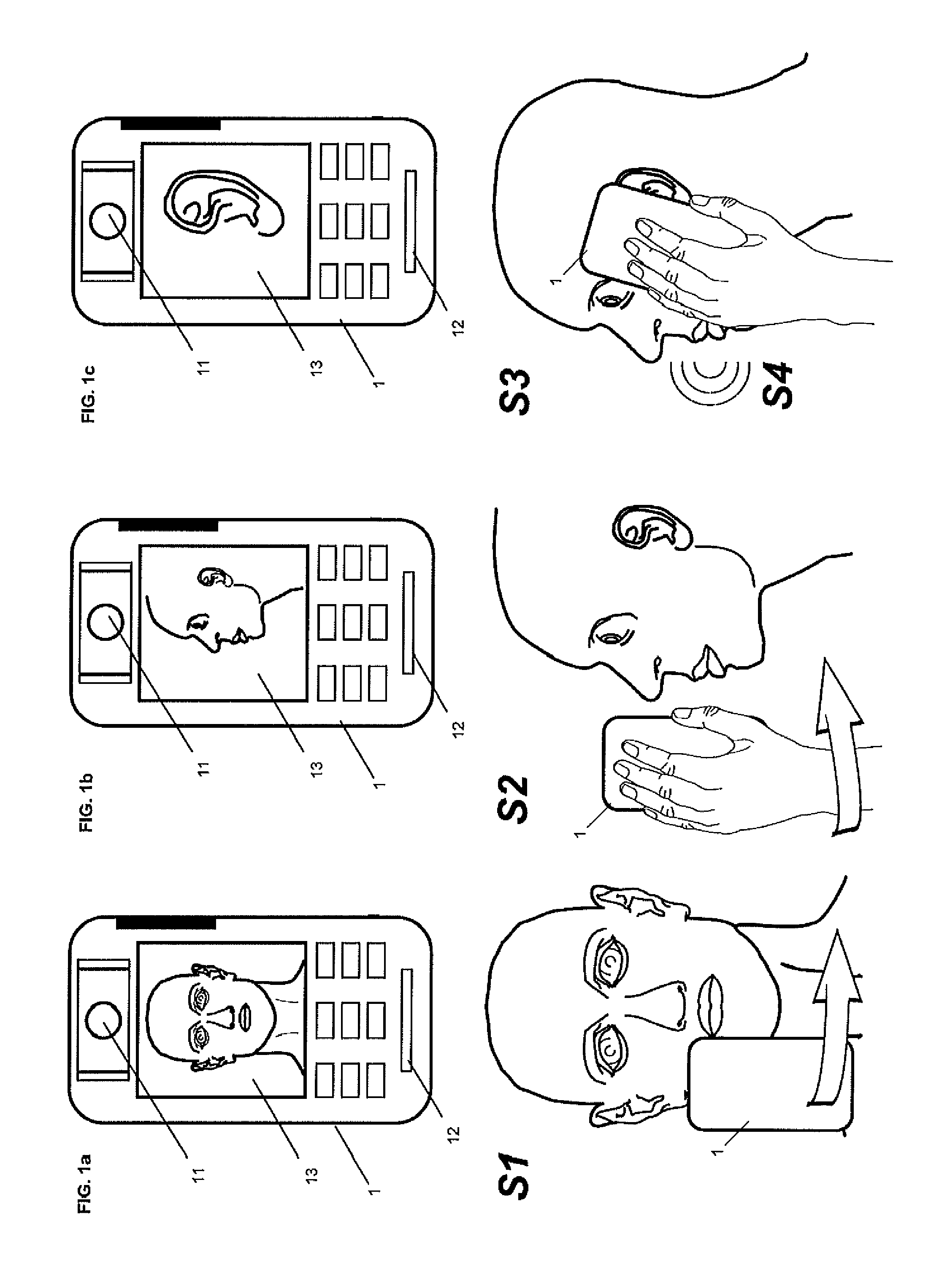
InactiveUS20130225129A1Not capture smallImprove security levelUnauthorised/fraudulent call preventionEavesdropping prevention circuitsBiometric dataDisplay device
A method of performing biometric authentication with a mobile station having a camera, front side display and integrated authentication server, or is connectable to an authentication server via a mobile communications network, includes:enrolling the user in a biometric system by capturing and storing biometric data relating to a plurality of characteristics of the user's head normally exposed to the mobile station during the process of accepting a call; activating the camera when initiating, receiving, or accepting a call and capturing optical information in one or a plurality of sequences at least between the setup or acceptance of the call and the start of the conversation and transferring the captured optical information to the authentication server; authenticating the user by comparing the optical information with the biometric data previously captured, by identifying and matching characteristics captured from different angles; and performing defined actions as a result of the authentication.
Owner:BIOMETRY COM
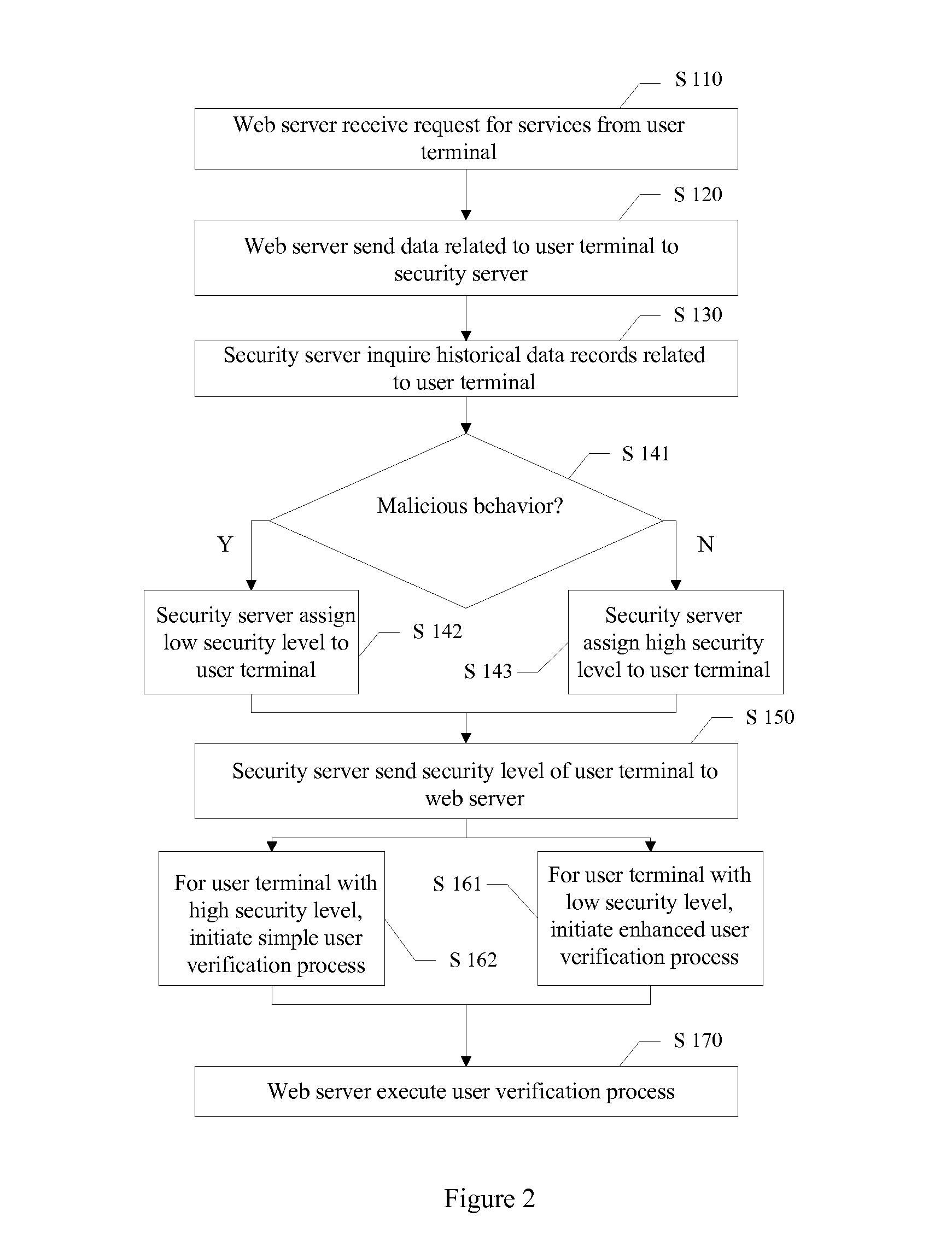
Methods and systems for secure internet access and services
ActiveUS20150135282A1Improve security levelLower security levelDigital data processing detailsMultiple digital computer combinationsCable Internet accessInternet access
A method and system for providing secure internet access and services are disclosed. The method includes receiving a request for services from a user terminal, the request including user terminal data; sending the user terminal data to a security server; and receiving a security level of the user terminal from the security server. The security server determines the security level of the user terminal based on historical user data related to the user terminal. The method further includes initiating a verification process based on the security level of the user terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD
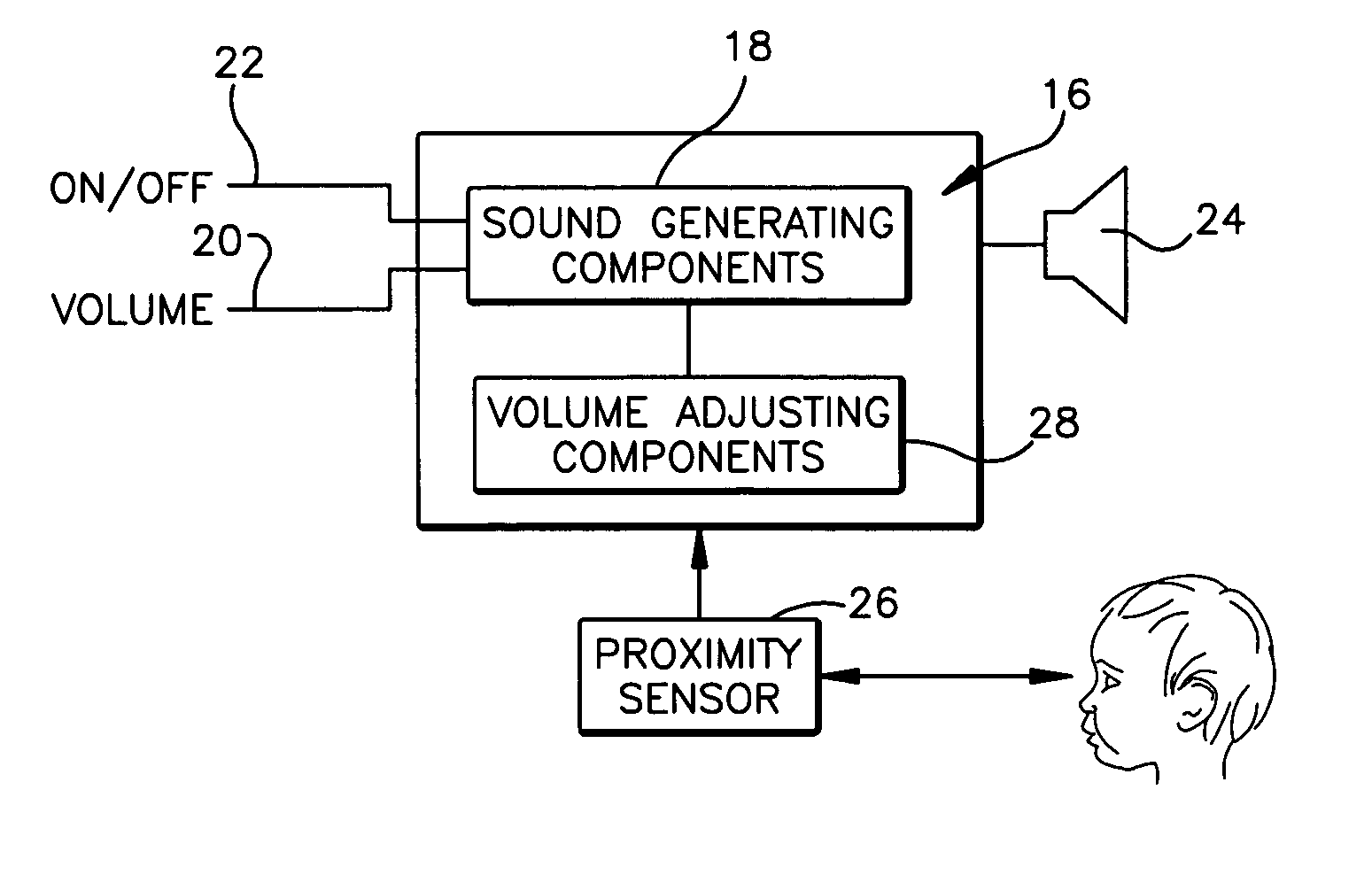
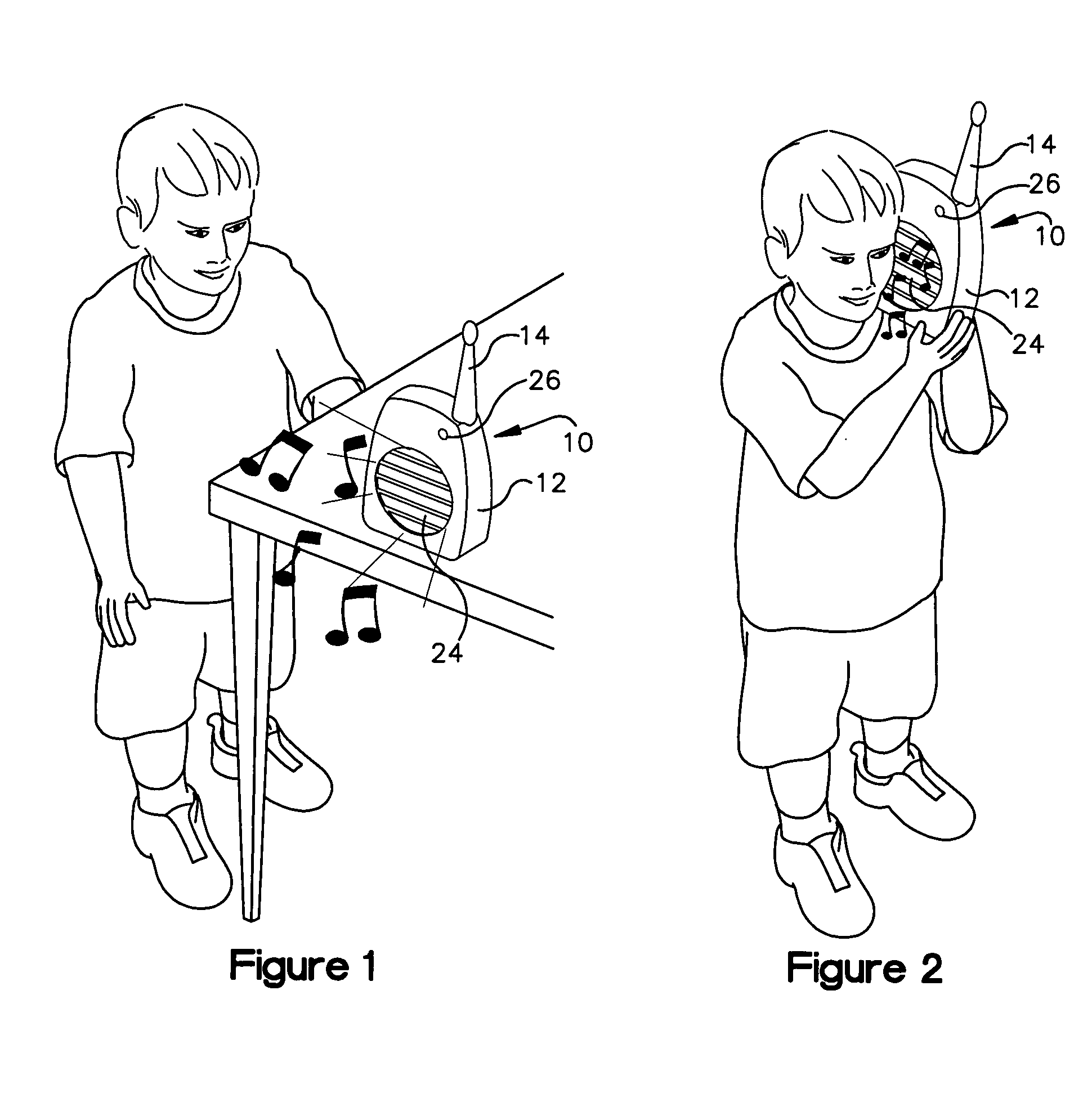
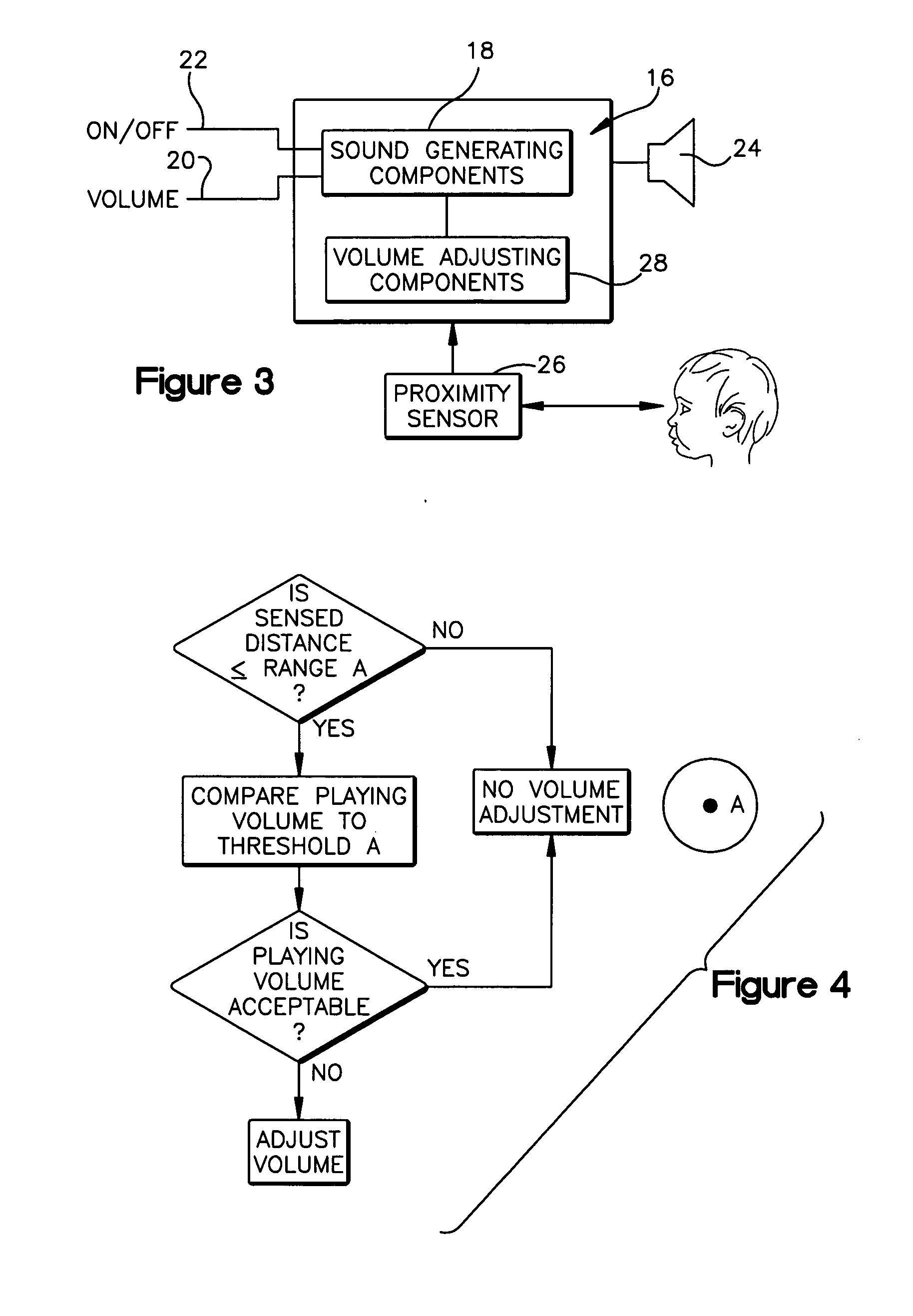
Audio device
InactiveUS20050063556A1Lower security levelDecreasing volume of playbackGain controlStereophonic systemsProximity sensorComputer science
An audio device having a primary audio purpose of producing a programmed audio output for a listener. The audio device comprises sound-generating components that generate the programmed audio output, and these components include an emitter that audibly emits this programmed output at a playing volume. A proximity sensor senses the distance to the listener, and this sensed distance corresponds to the distance between the listener and the emitter. Volume-adjusting components adjust the playing volume to prevent it from being at an unacceptable level for the sensed distance.
Owner:LITTLE TIKES
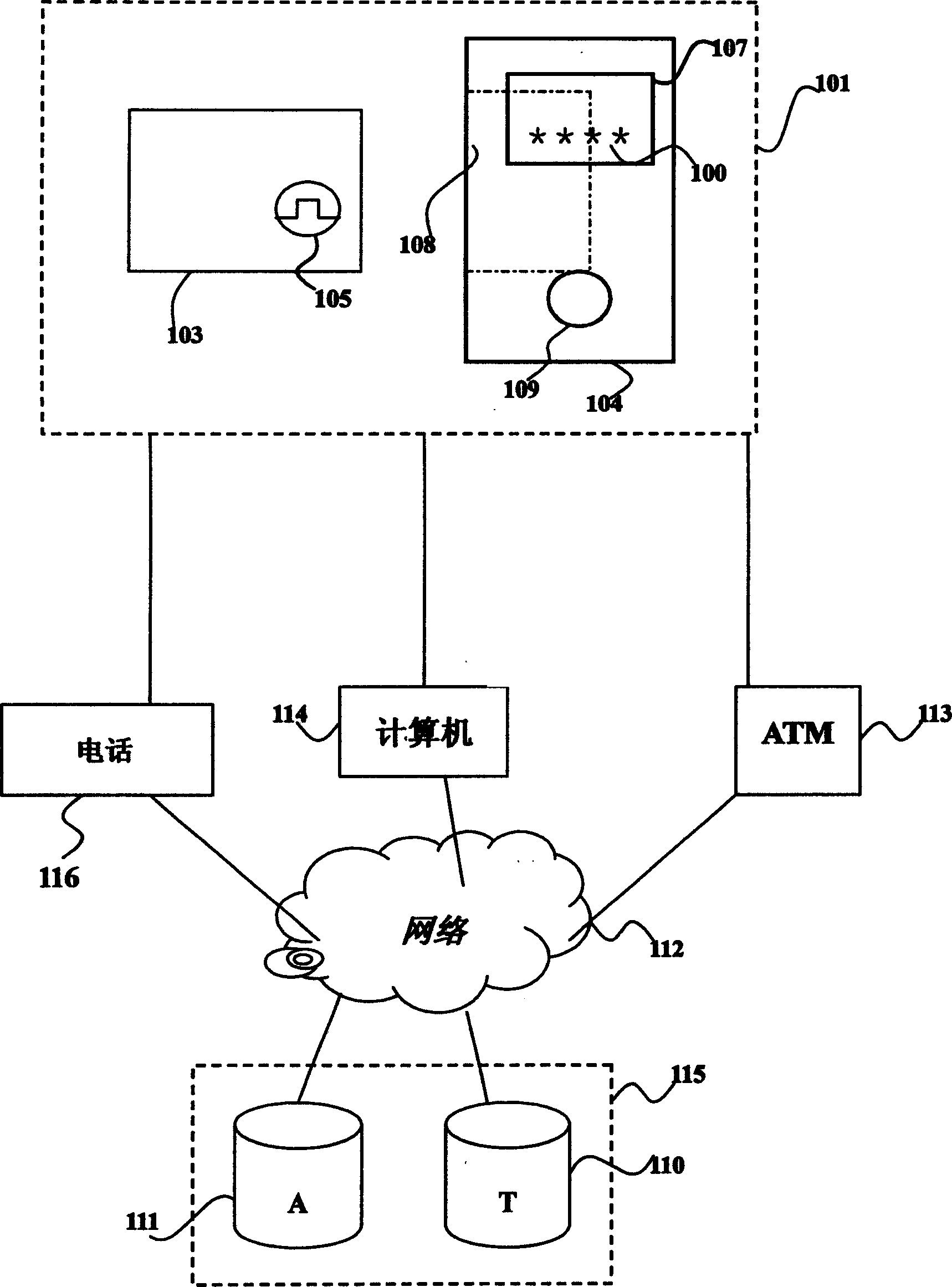
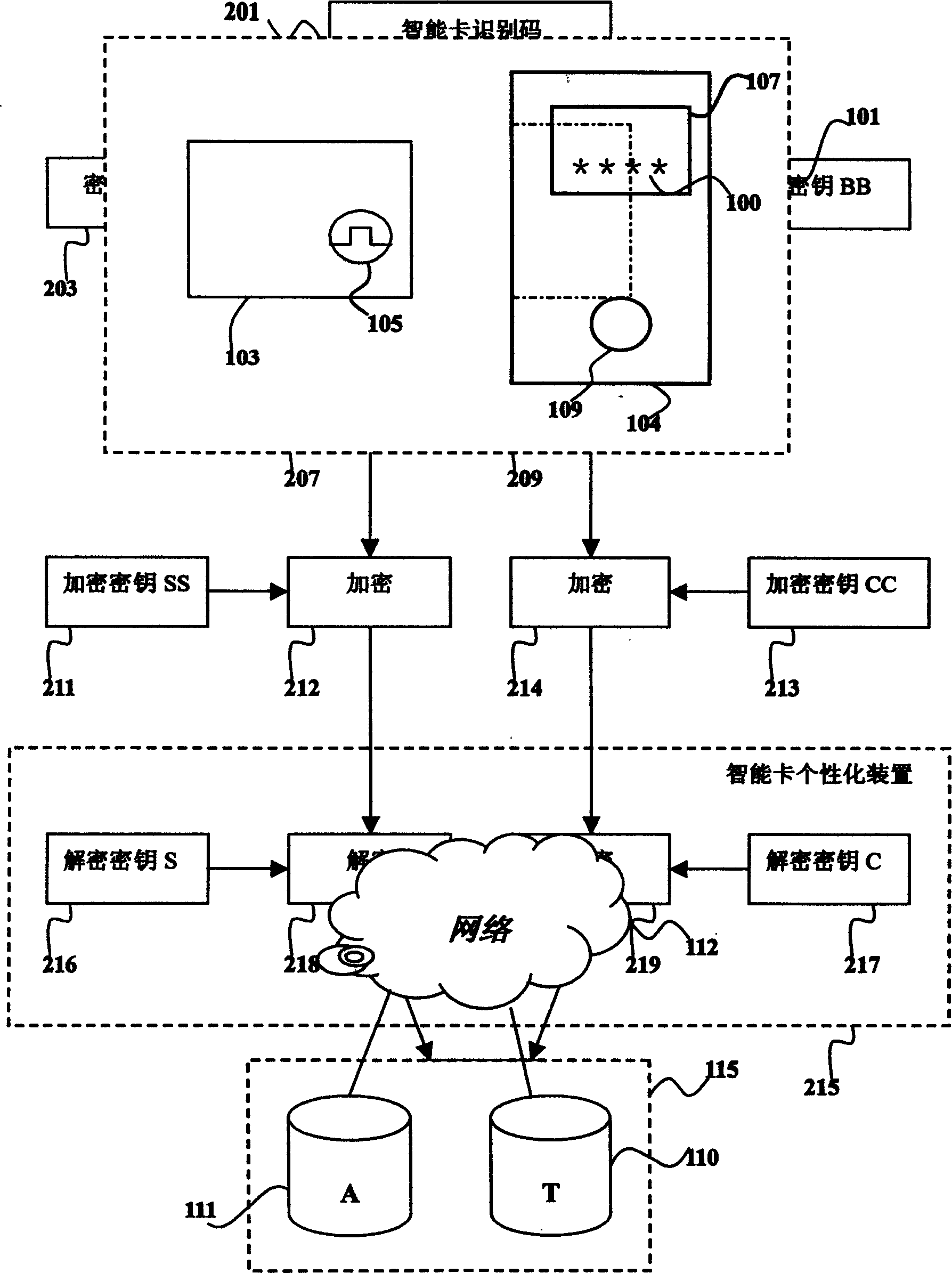
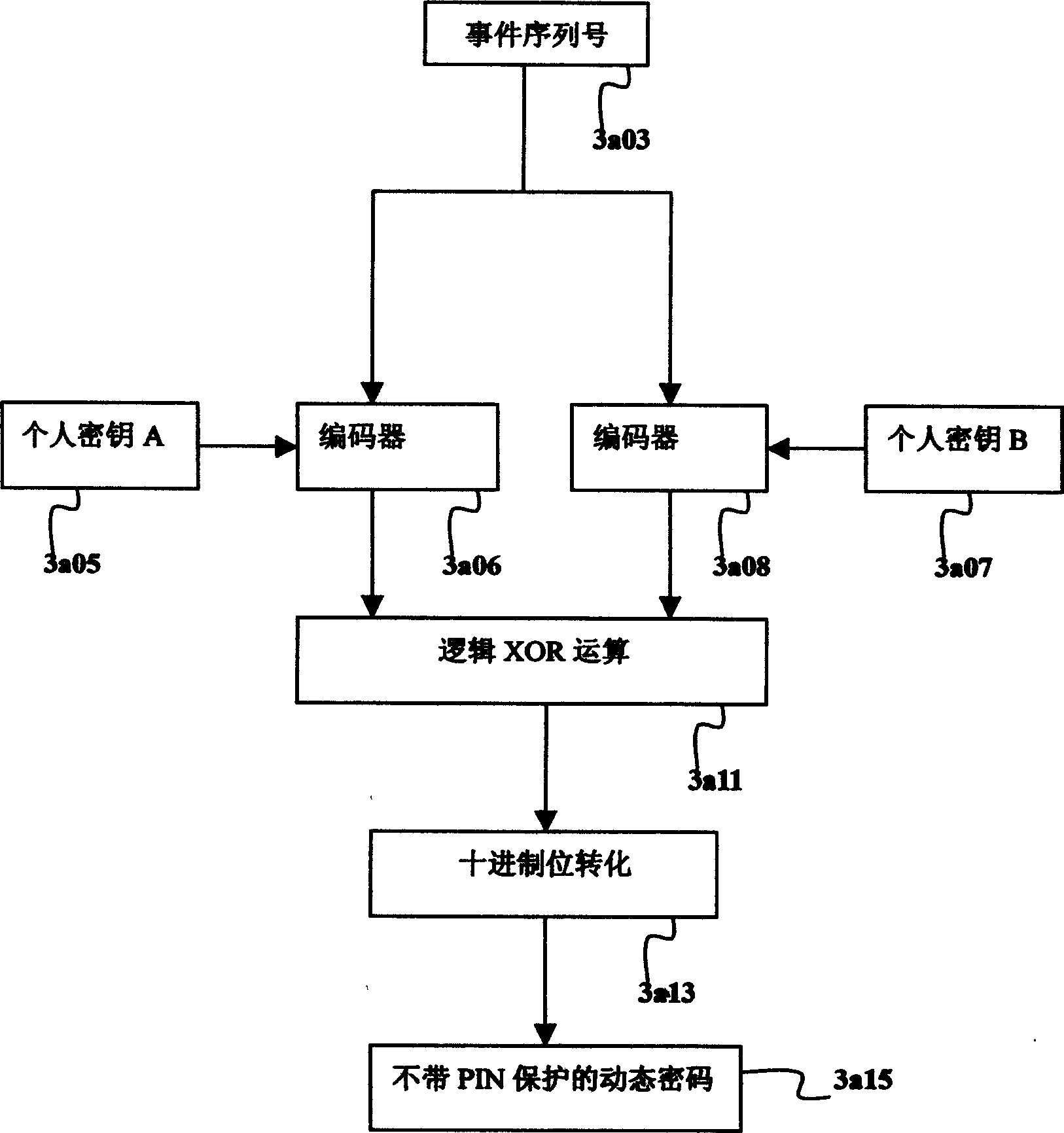
Identity certifying system based on intelligent card and dynamic coding
InactiveCN1614924AImprove securityLow costMultiple keys/algorithms usageUser identity/authority verificationFault toleranceSmart card
The system consists of smart card for generating one time password (OTP), device for creating OTP, authentication server, windows fault-tolerance authentication and synchronization method. The personal ID information and OTP are transmitted to authentication system through network. The authentication system selects one or more possible examining passwords from a large group of examining passwords to build up a smaller group of examining password. The received OTP is compared with the smaller group of examining password; if the OTP is in the smaller group the authentication of the use is passed.
Owner:王小矿
Adaptive policies and protections for securing financial transaction data at rest
ActiveUS20110314529A1Shorten the time to marketAcceptable levelDigital data processing detailsUser identity/authority verificationTransaction dataDisplay device
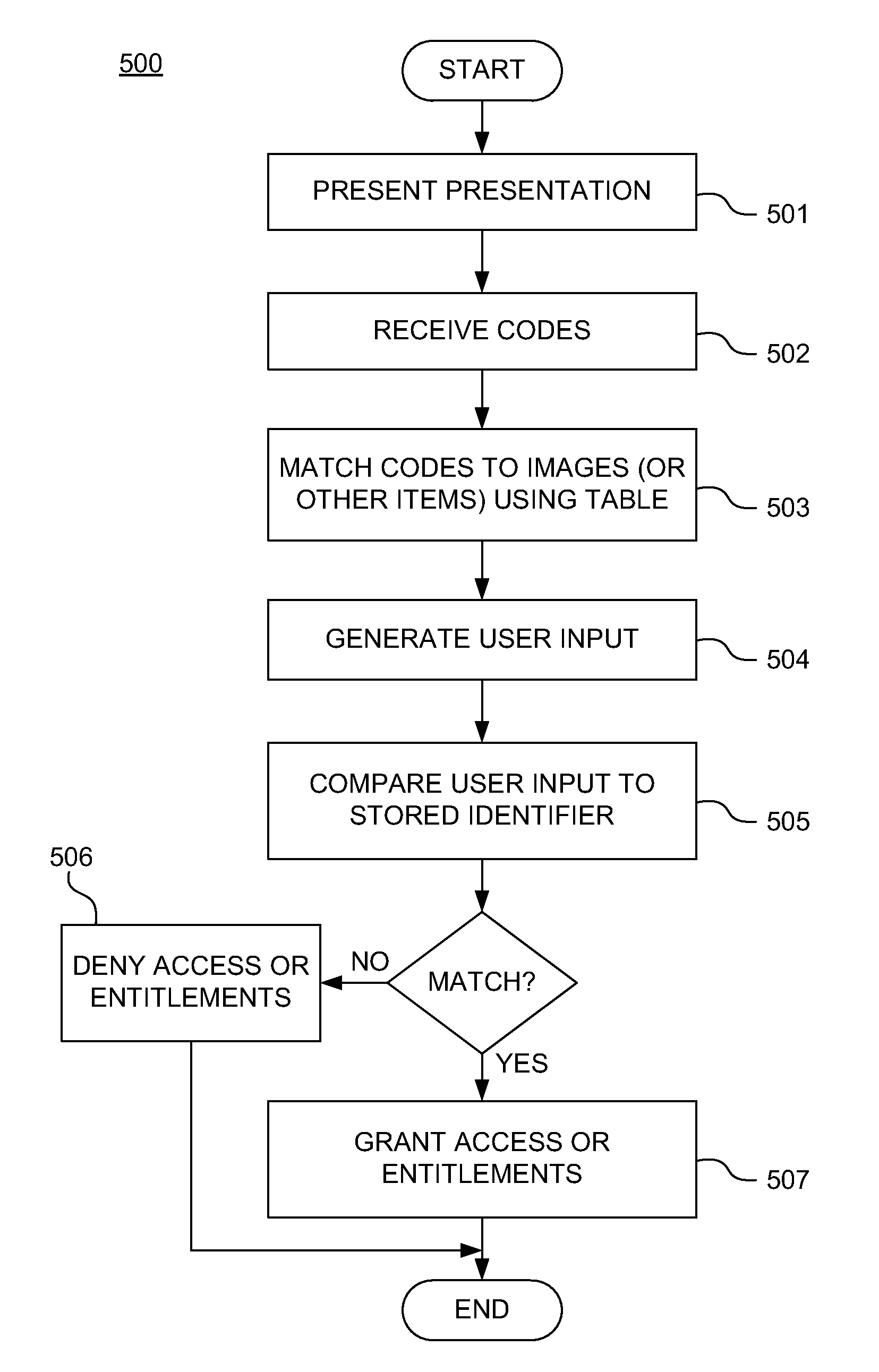
A system for challenge-response authentication is provided by receiving, from an external terminal over a communication network, a request for access to a service. A plurality of objects is presented to a user via a display. A plurality of codes is received over the communication network, each of the plurality of codes corresponding to one of the plurality of objects. The plurality of codes are matched to a plurality of alphanumeric characters according to a predetermined table. An alphanumeric string is generated from the plurality of alphanumeric characters and the alphanumeric string is compared to a user identifier stored in a database. Based on the comparing, a determination is made as to whether to grant the user access to the service.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Semiconductor memory card, and program for controlling the same
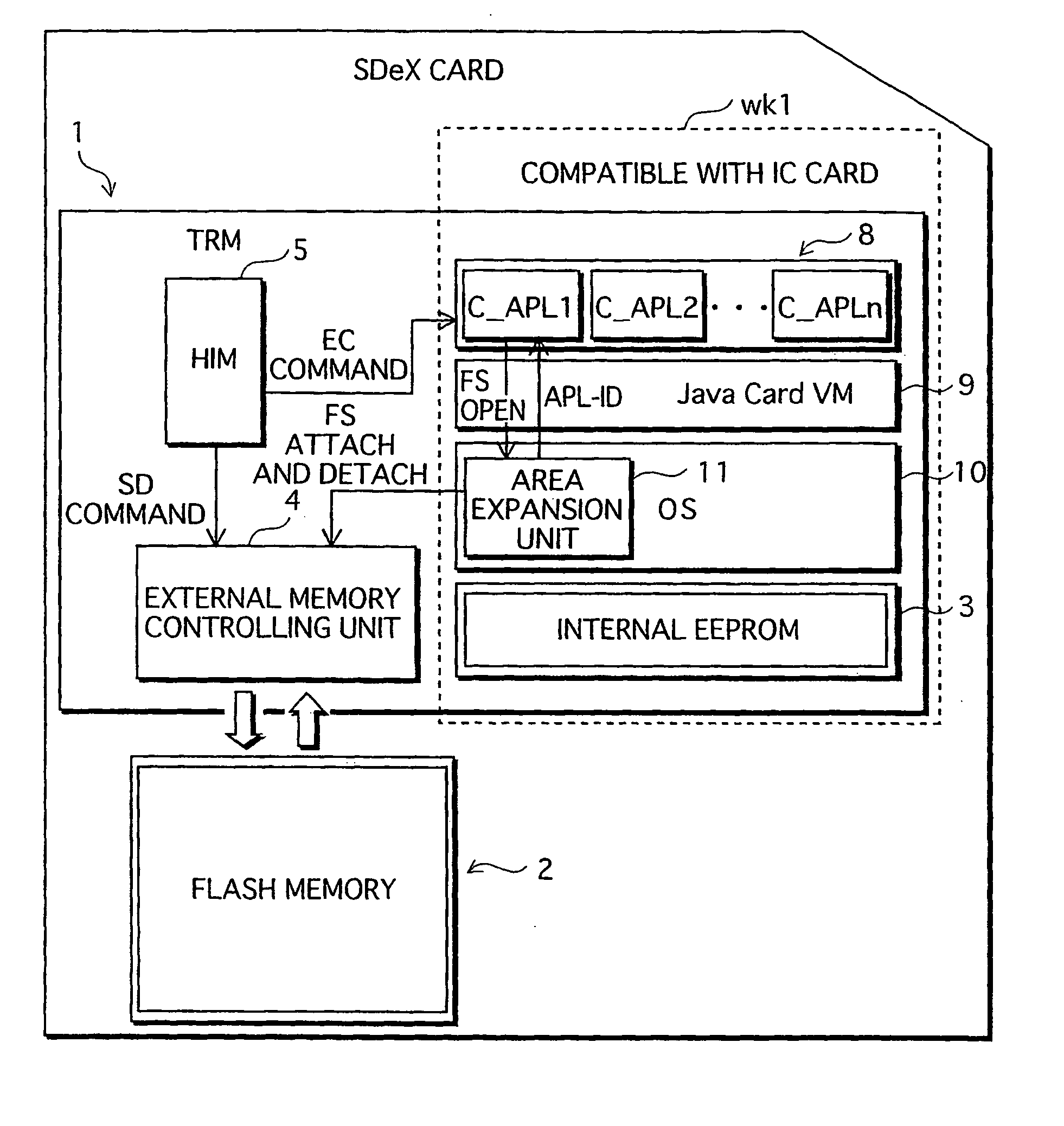
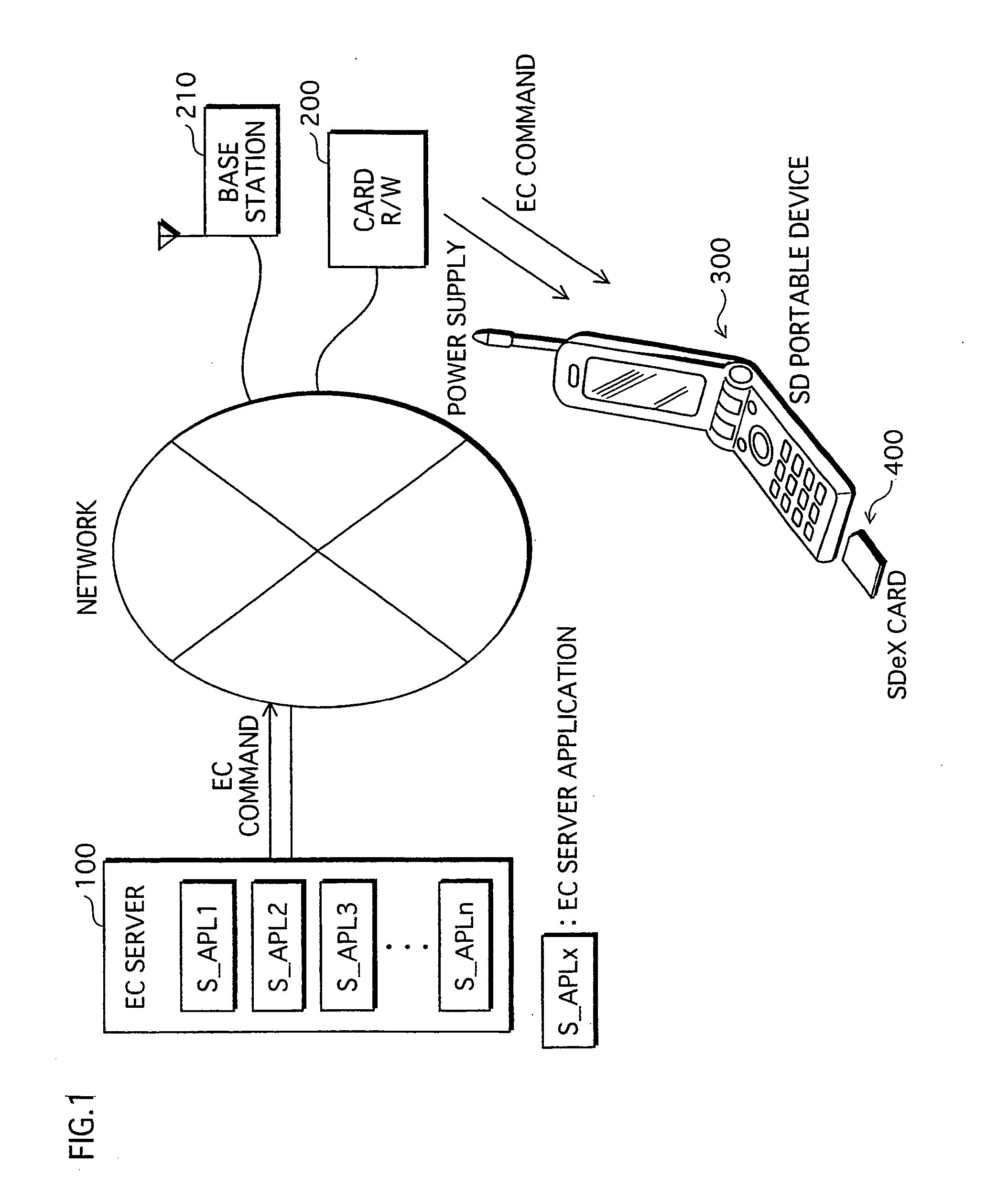
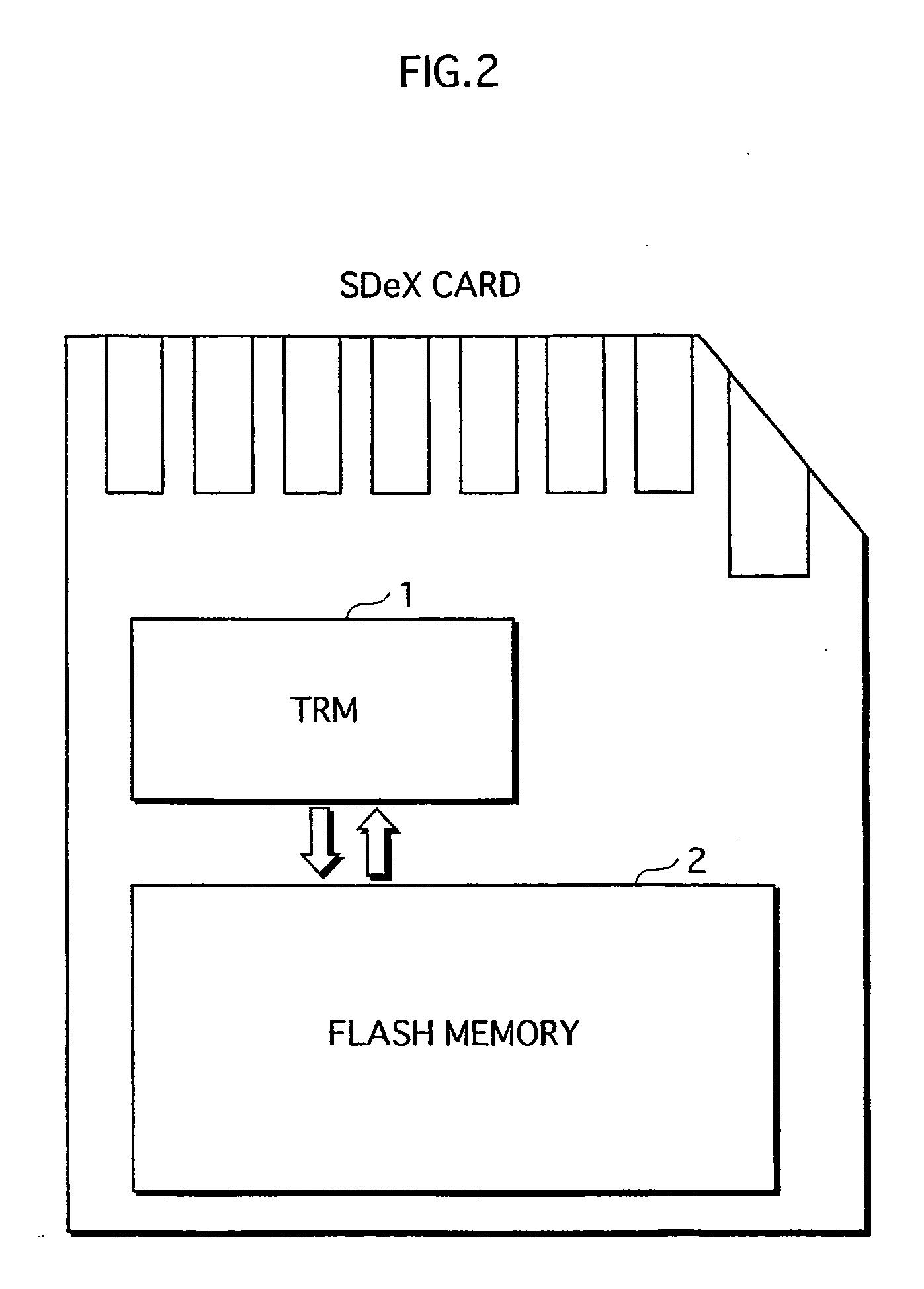
ActiveUS20060026338A1Maintaining secrecyLower security levelUnauthorized memory use protectionDigital data protectionTamper resistanceE-commerce
A semiconductor memory card that has a sufficient storage capacity when an electronic commerce (EC) application writes data to a storage is provided. A usage area for the EC application in EEPROM 3 in a tamper resistant module (TRM) 1 is expanded. The expansion is such that a partition generated in a flash memory 2 outside the TRM 1 is assigned to the EC application while a partition table is allocated in the internal EEPROM 3. Because the partition table is in the TRM 1, only a CPU 7 in the TRM 1 is able to access the generated partition table. Secrecy of stored contents increases because the access to the expanded area is limited to the CPU in the TRM 1.
Owner:PANASONIC CORP
Dynamically adaptive policy management for securing mobile financial transactions
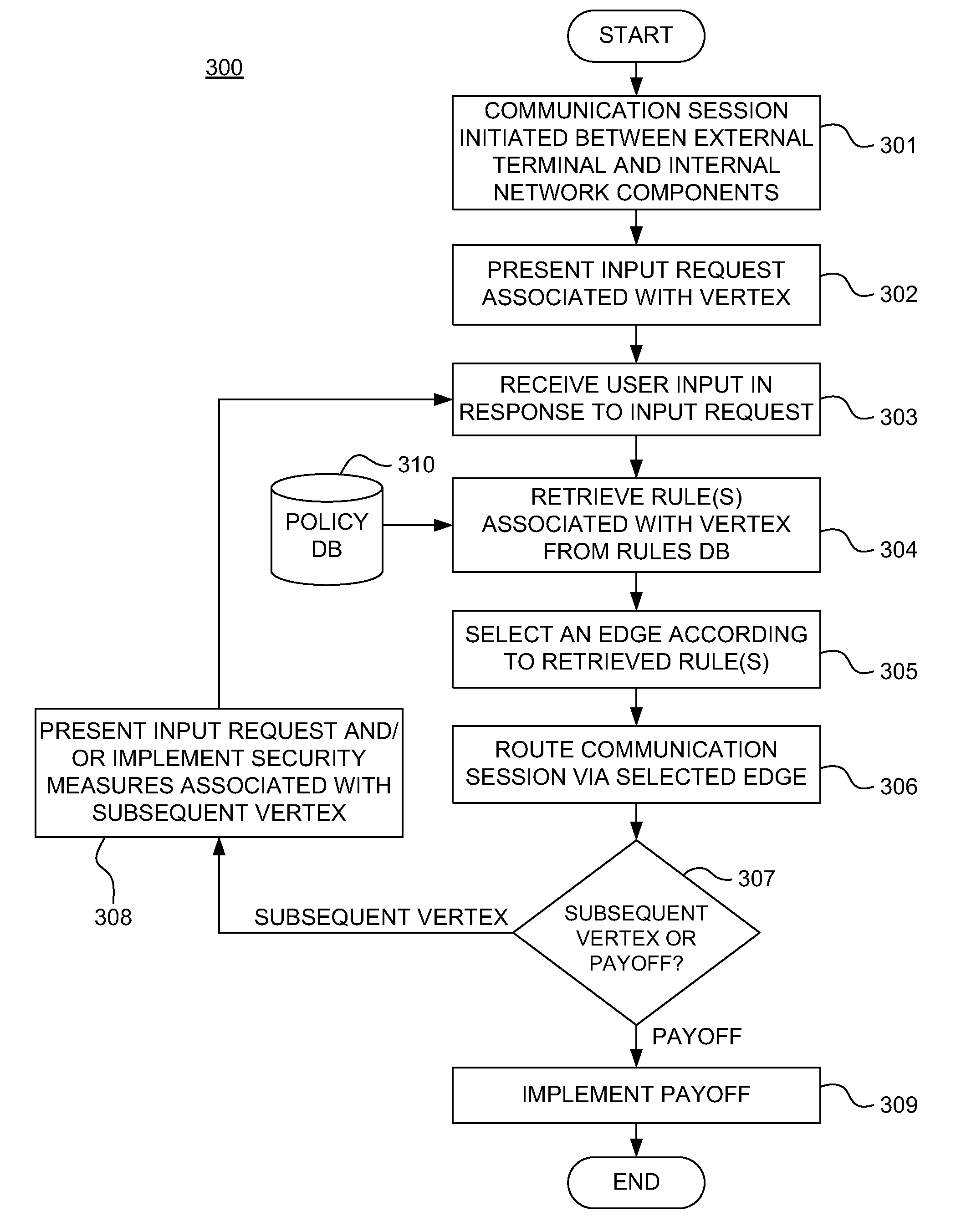
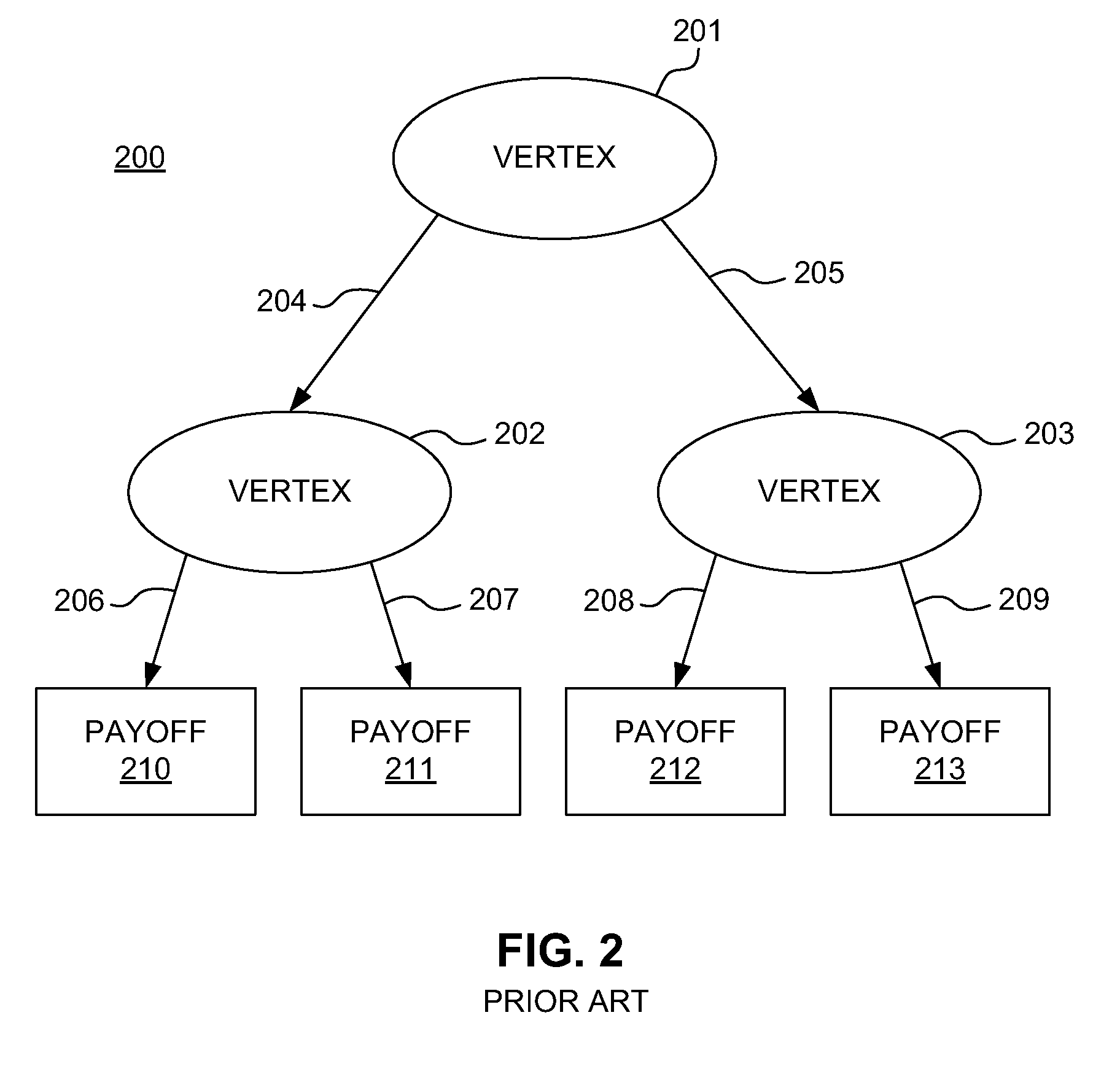
ActiveUS20110313930A1Shorten the time to marketIncrease propensityFinanceDigital data processing detailsAdaptive securityFinancial trading
A system for securing a mobile financial transaction using an adaptive security policy is provided by presenting, via an external terminal, an input request associated with a vertex of the security policy. User input is received via the external terminal in response to the input request. A rule associated with the vertex is retrieved from a database. An edge is selected from a plurality of edges associated with the vertex according to the retrieved rule. A communication session of the external terminal is routed to a subsequent vertex via the selected edge.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Security clearance card, system and method of reading a security clearance card
InactiveUS7137553B2Large data storage capacityAvoid overwritingDigital data processing detailsSensing detailsBiometric dataData storing
Owner:DIGITAL DATA RES
Dynamic pairing system for securing a trusted communication channel
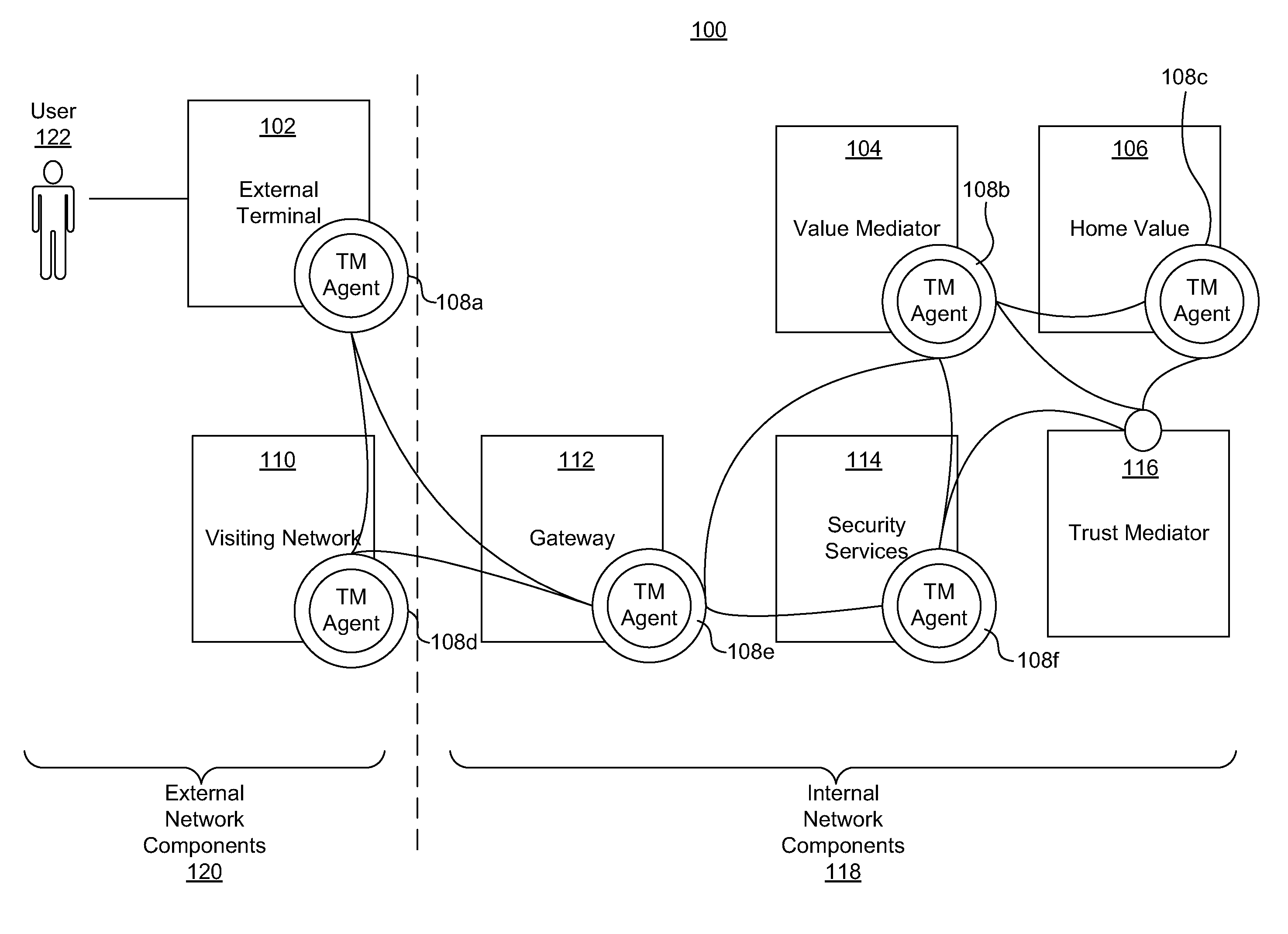
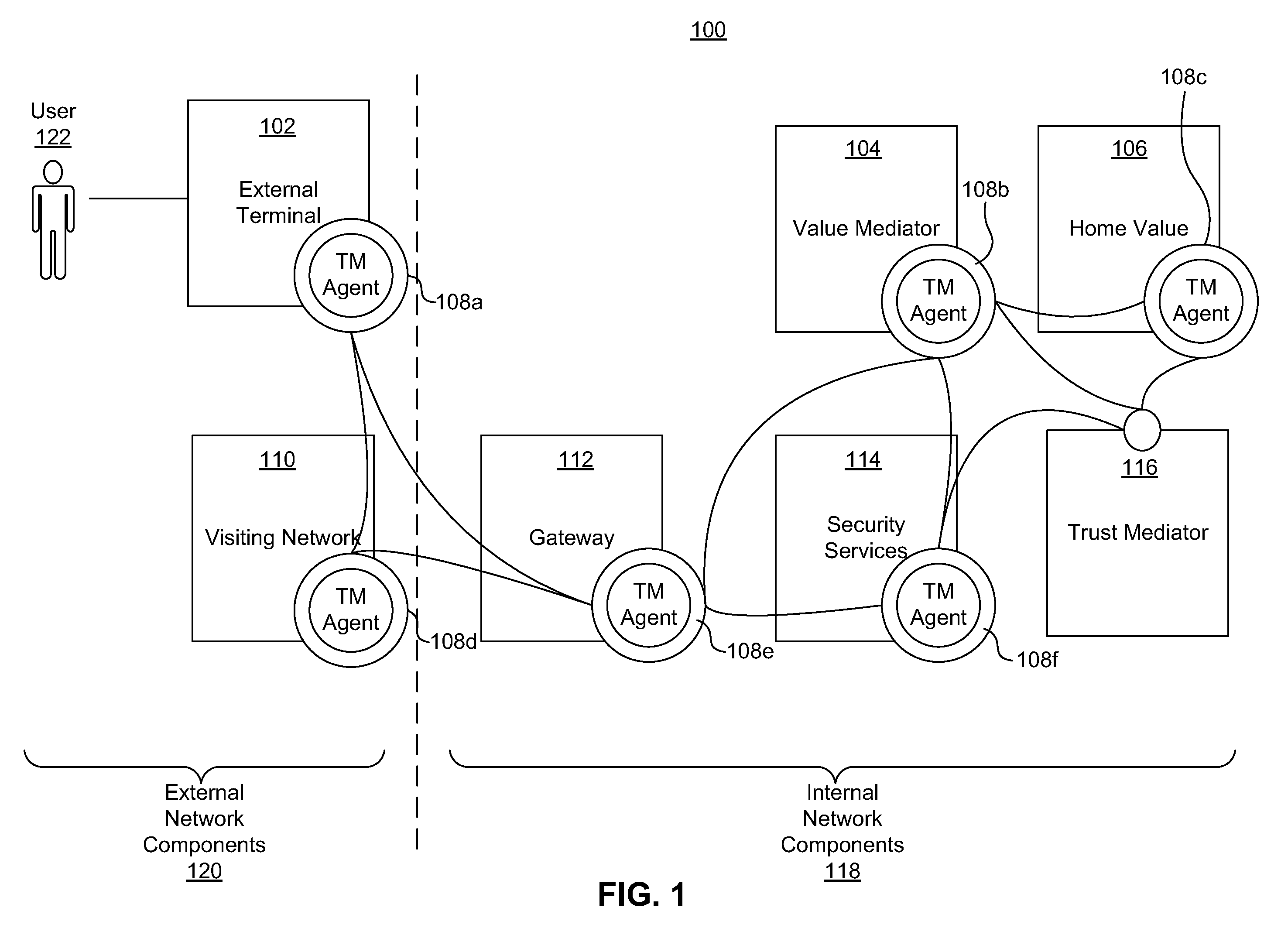
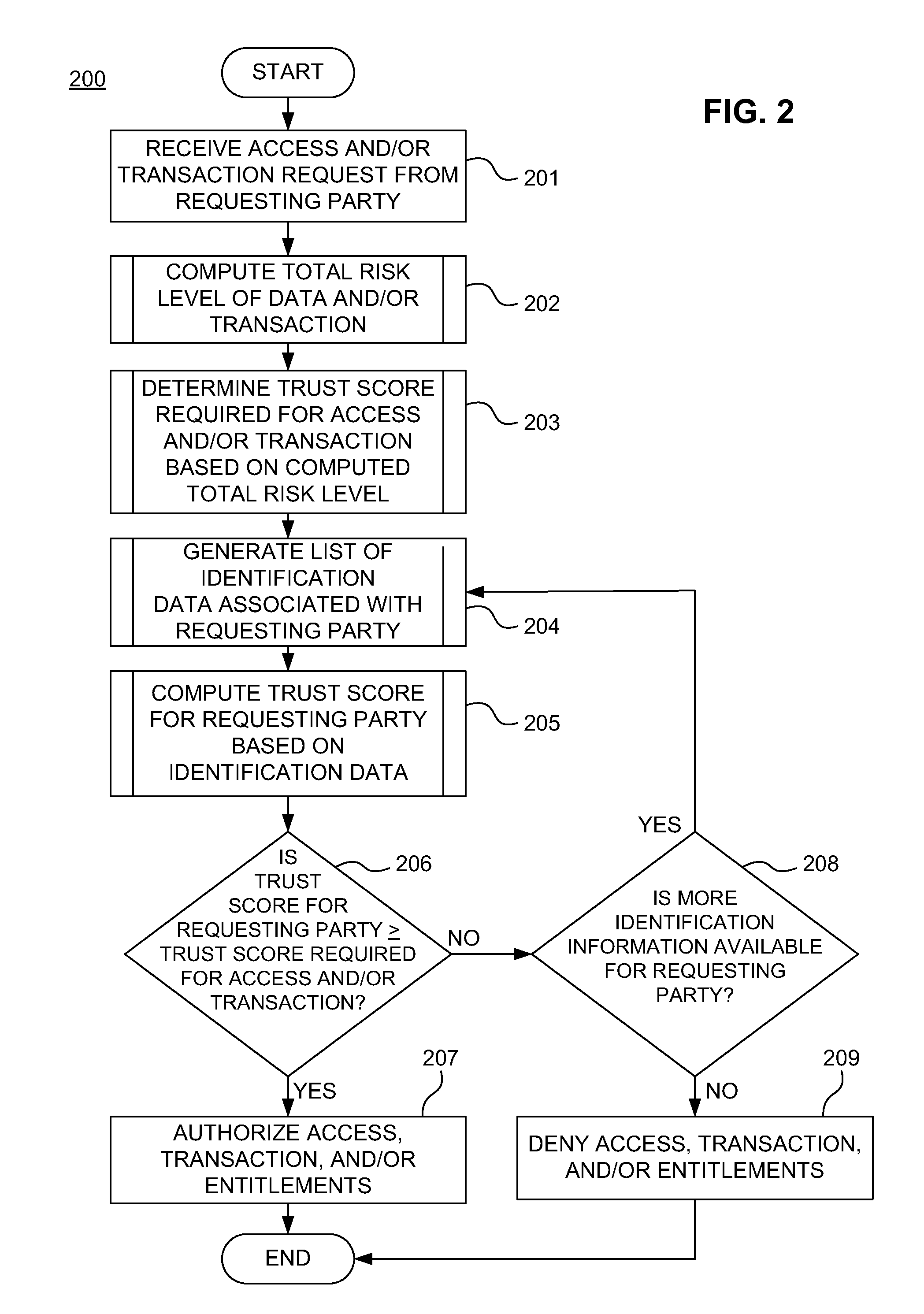
ActiveUS20110313925A1Shorten the time to marketIncrease propensityFinancePayment architectureTotal riskInternet privacy
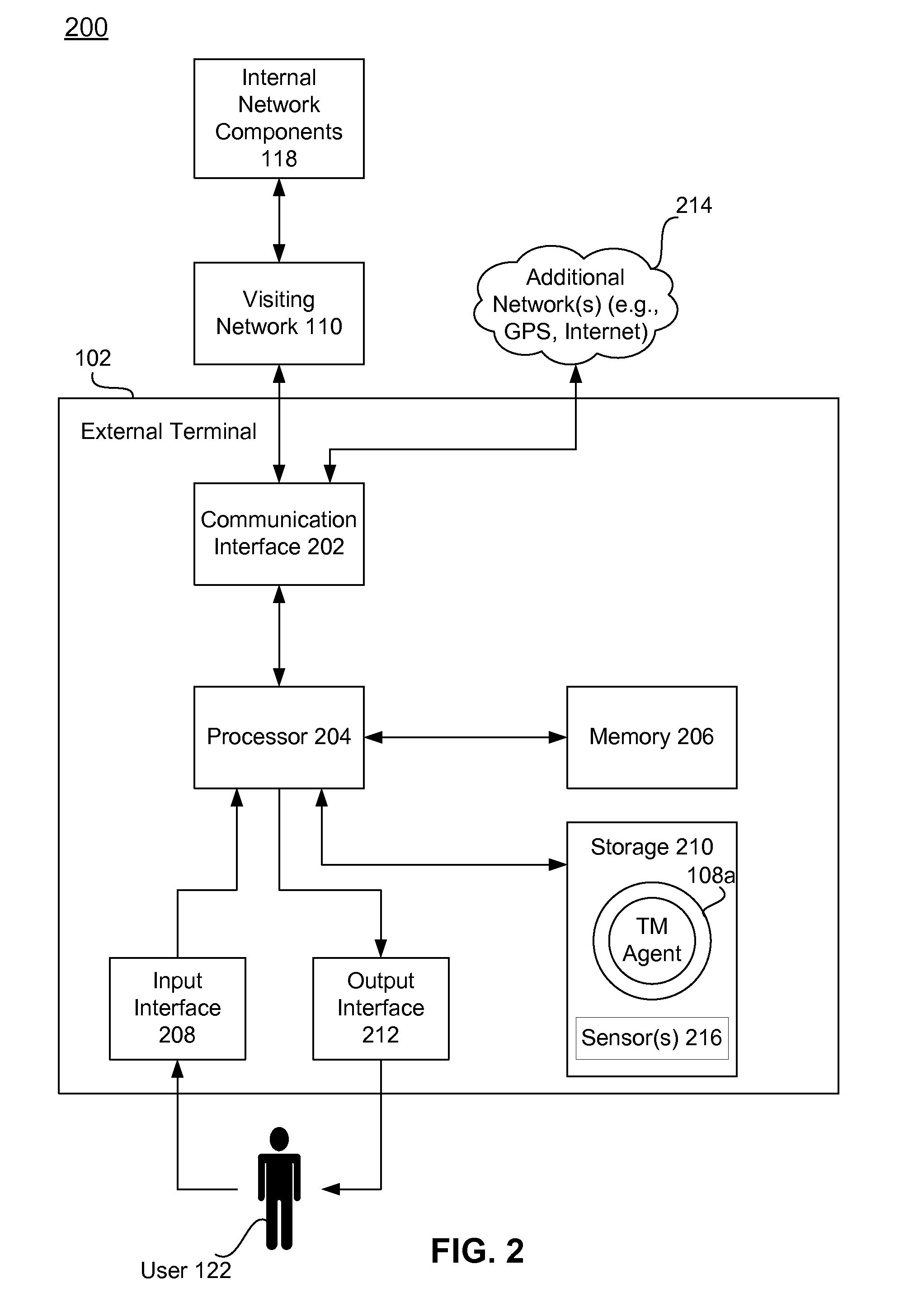
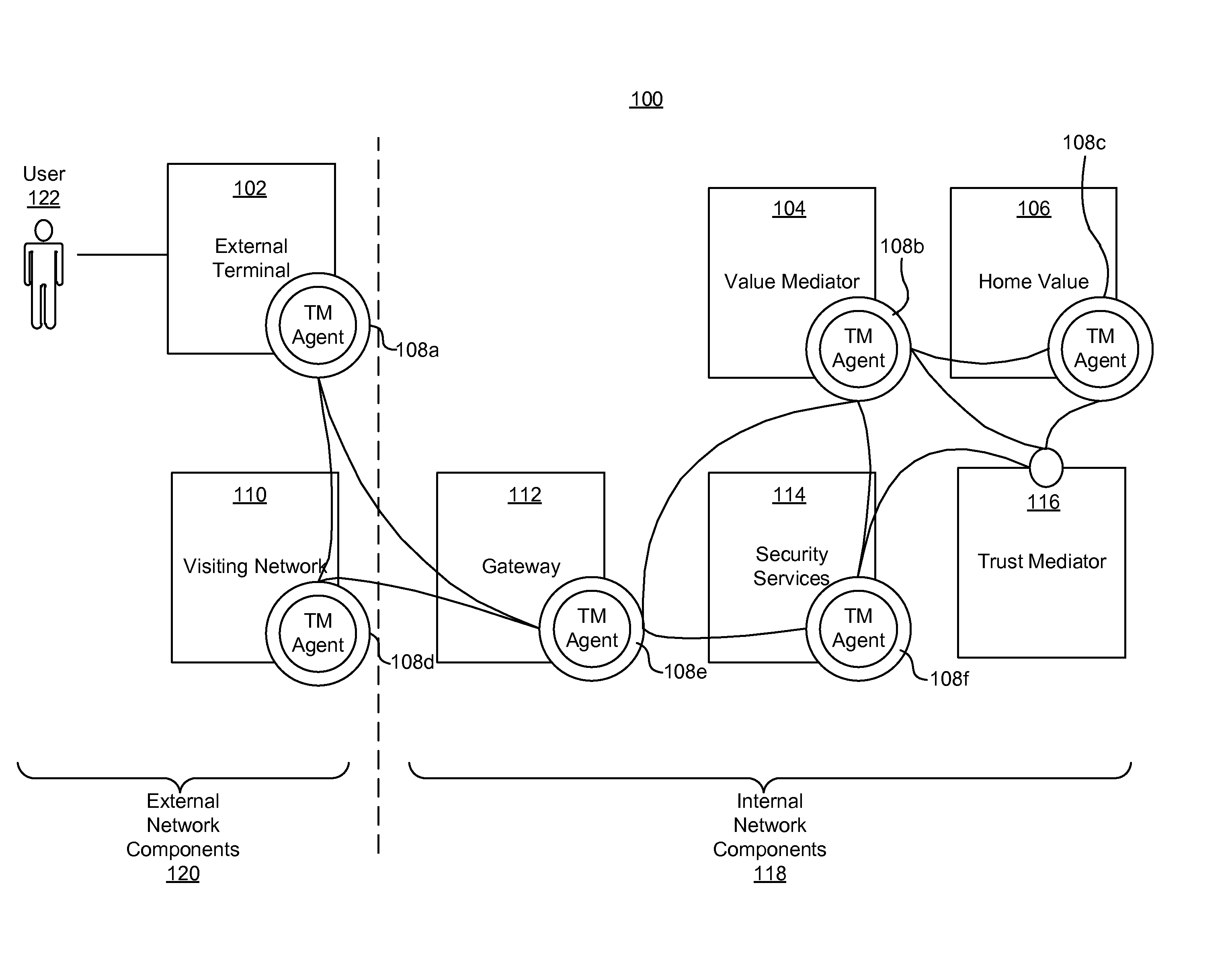
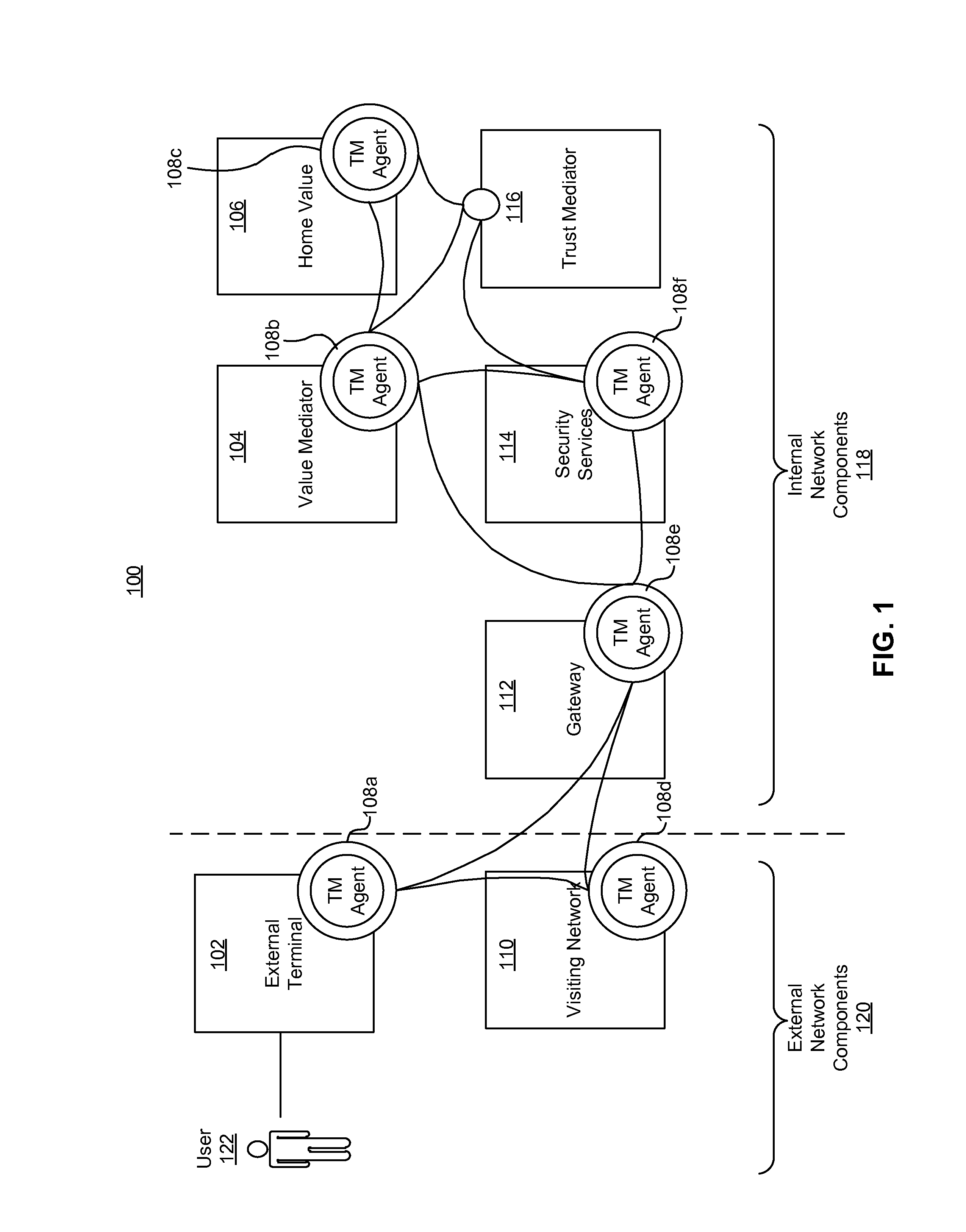
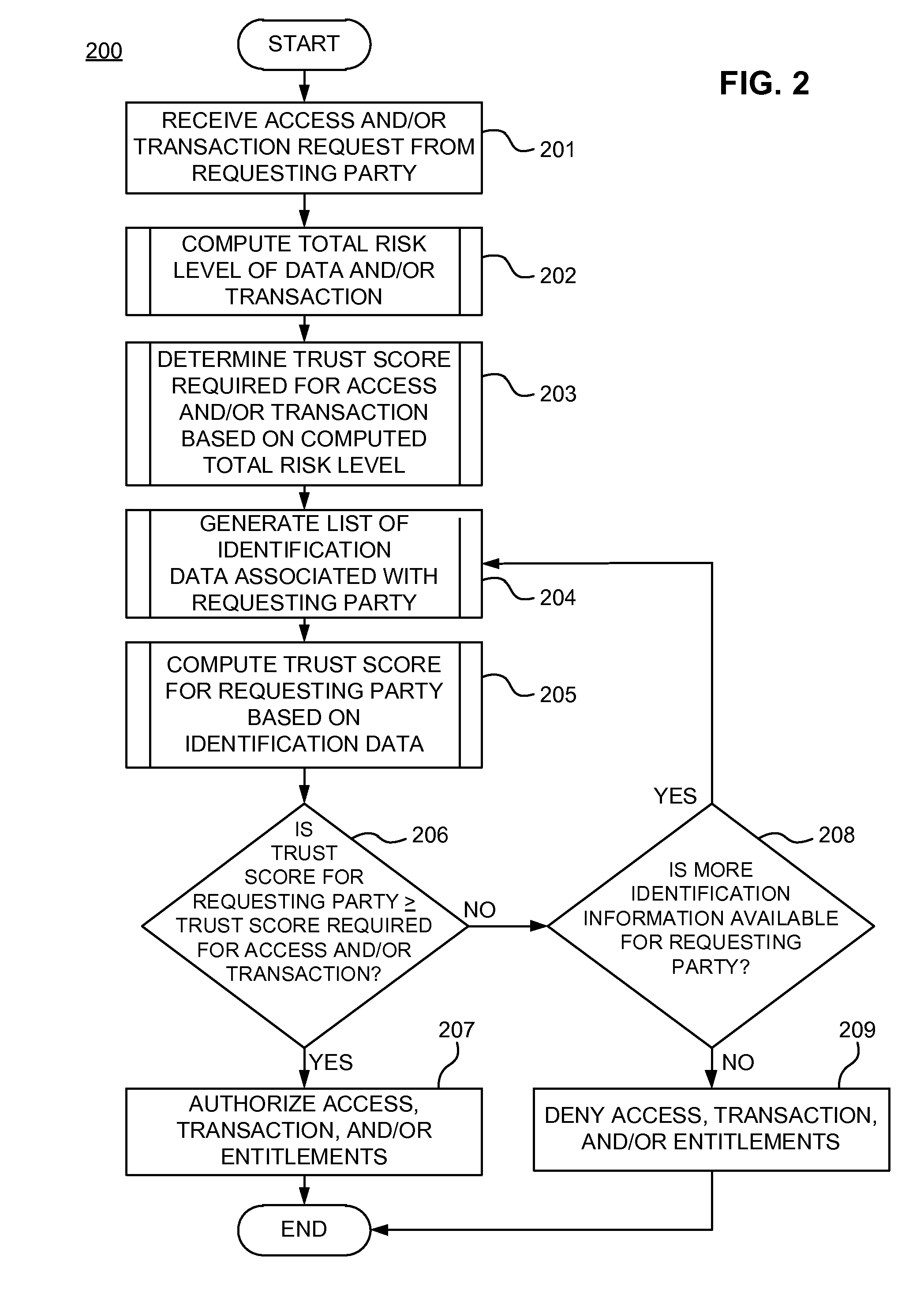
A system for securing a trusted communications channel for a mobile financial transaction is provided by receiving, from a user via an external terminal, a request for an access control entitlement to complete a financial transaction. A total risk level associated with the financial transaction is computed. A required trust score is determined based on the total risk level. User identification data associated with the user is received from one or more data sources. The user identification data is validated. A user trust score associated with the user is computed based on the validated identification data. The user trust score is compared to the required trust score. The access control entitlement is transmitted to the user via the external terminal if the user trust score is greater than or equal to the required trust score.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Memory domain based security control with data processing systems
ActiveUS7966466B2Improve securityLimited abilityDigital computer detailsUnauthorized memory use protectionMemory addressOperational system
Access to memory address space is controlled by memory access control circuitry using access control data. The ability to change the access control data is controlled by domain control circuitry. Whether or not an instruction stored within a particular domain, being a set of memory addresses, is able to modify the access control data is dependent upon the domain concerned. Thus, the ability to change access control data can be restricted to instructions stored within particular defined locations within the memory address space thereby enhancing security. This capability allows systems to be provided in which call forwarding to an operating system can be enforced via call forwarding code and where trusted regions of the memory address space can be established into which a secure operating system may write data with increased confidence that that data will only be accessible by trusted software executing under control of a non-secure operating system.
Owner:ARM LTD
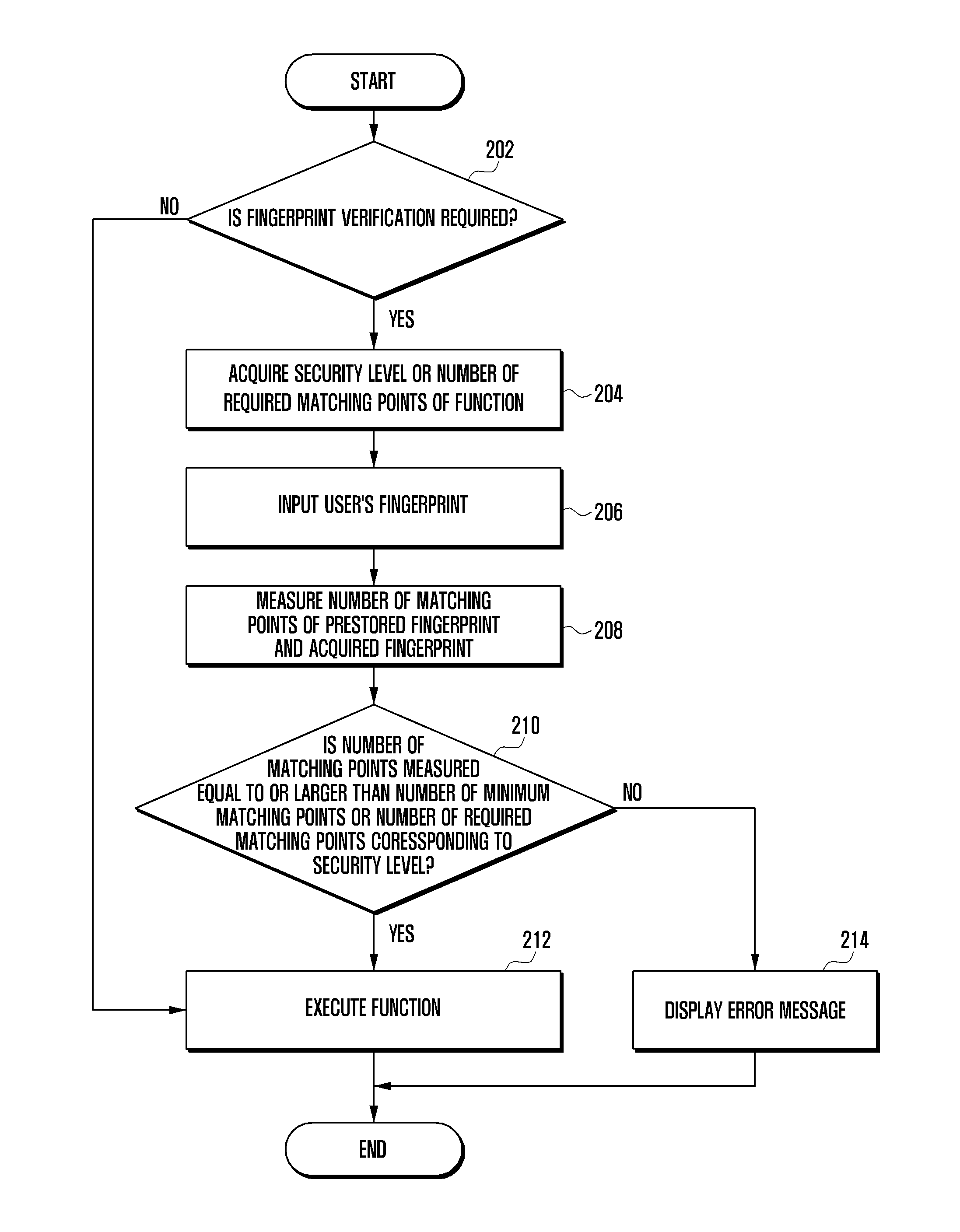
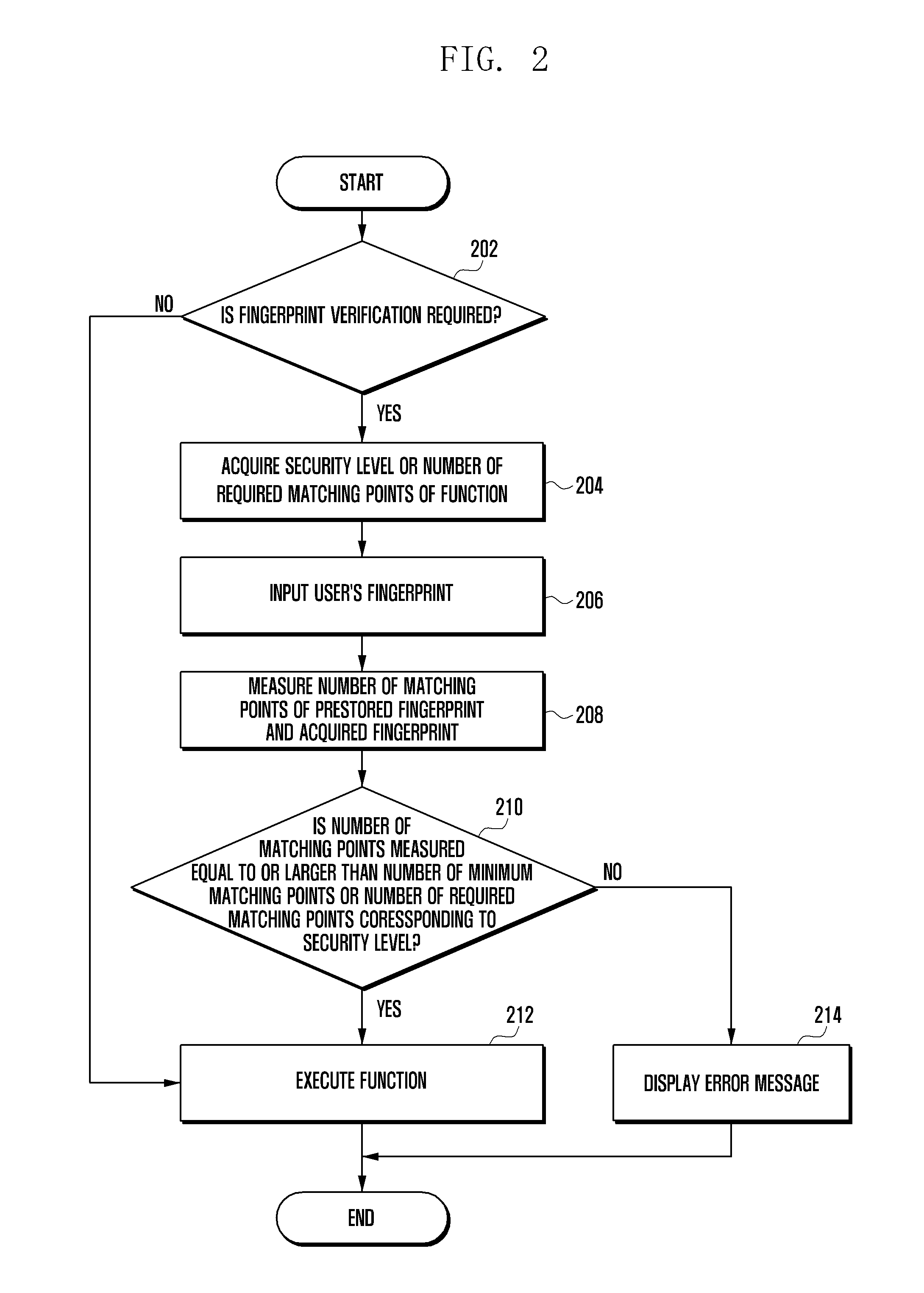
Method of executing function of electronic device and electronic device using the same
ActiveUS20150186710A1Improve usabilityLower security level2D-image generationDigital data authenticationComputer hardwareSecurity level
Methods and apparatuses are provided for executing a function of an electronic device using fingerprint verification. A security level of the function to be performed is acquired, if the function requires the fingerprint verification. A fingerprint input of a user is received. A count of a number of matching points that exist between the fingerprint input and a prestored fingerprint is determined. The count of the number of matching points is compared with a minimum number of matching points corresponding to the security level of the function.
Owner:SAMSUNG ELECTRONICS CO LTD
System for implementing dynamic access to private cloud environment via public network
InactiveUS20140337961A1Lower security levelImprove security levelMultiple digital computer combinationsProgram controlIp addressPublic network
Owner:PROMISE TECHNOLOGY
Memory device and controller
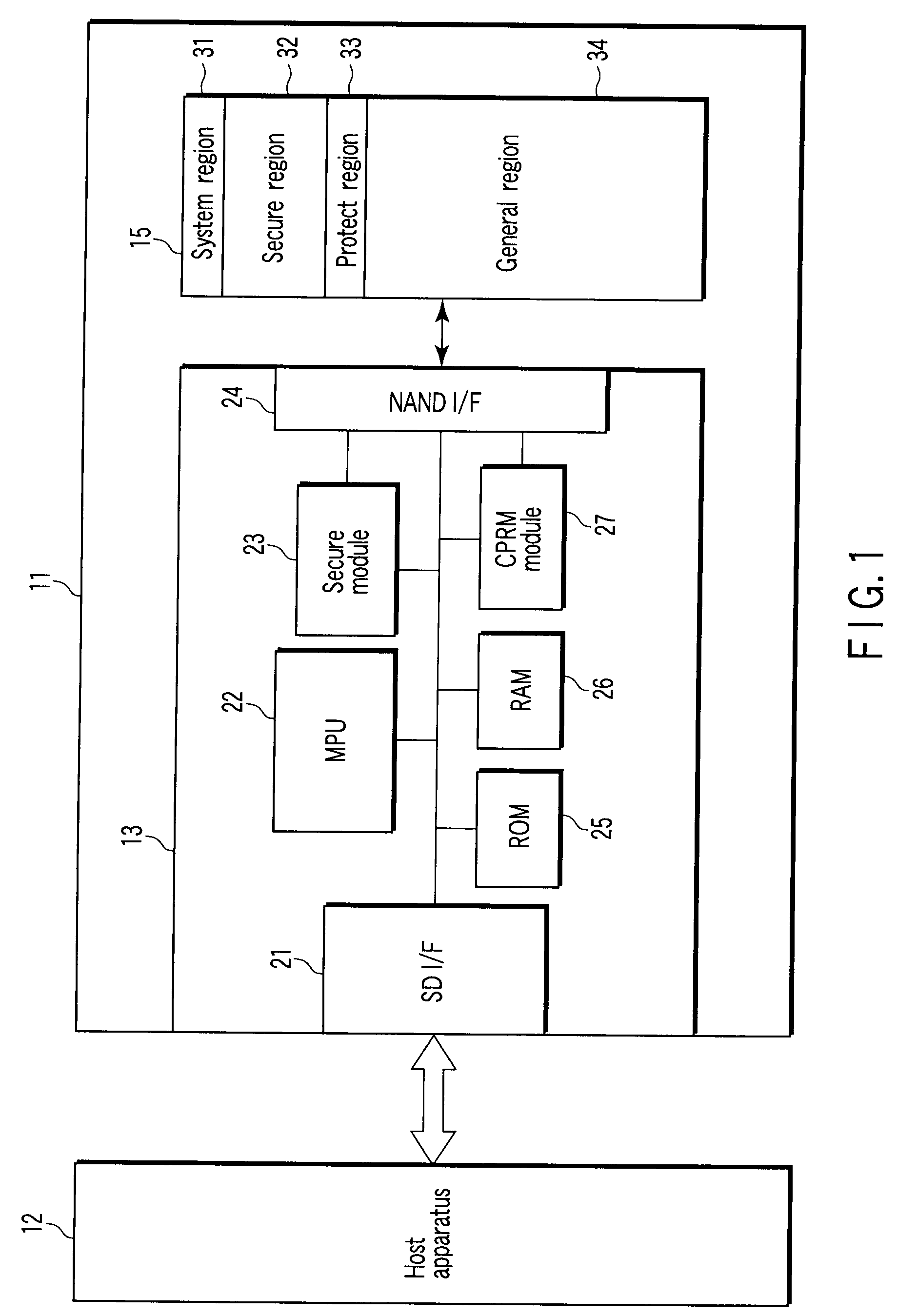
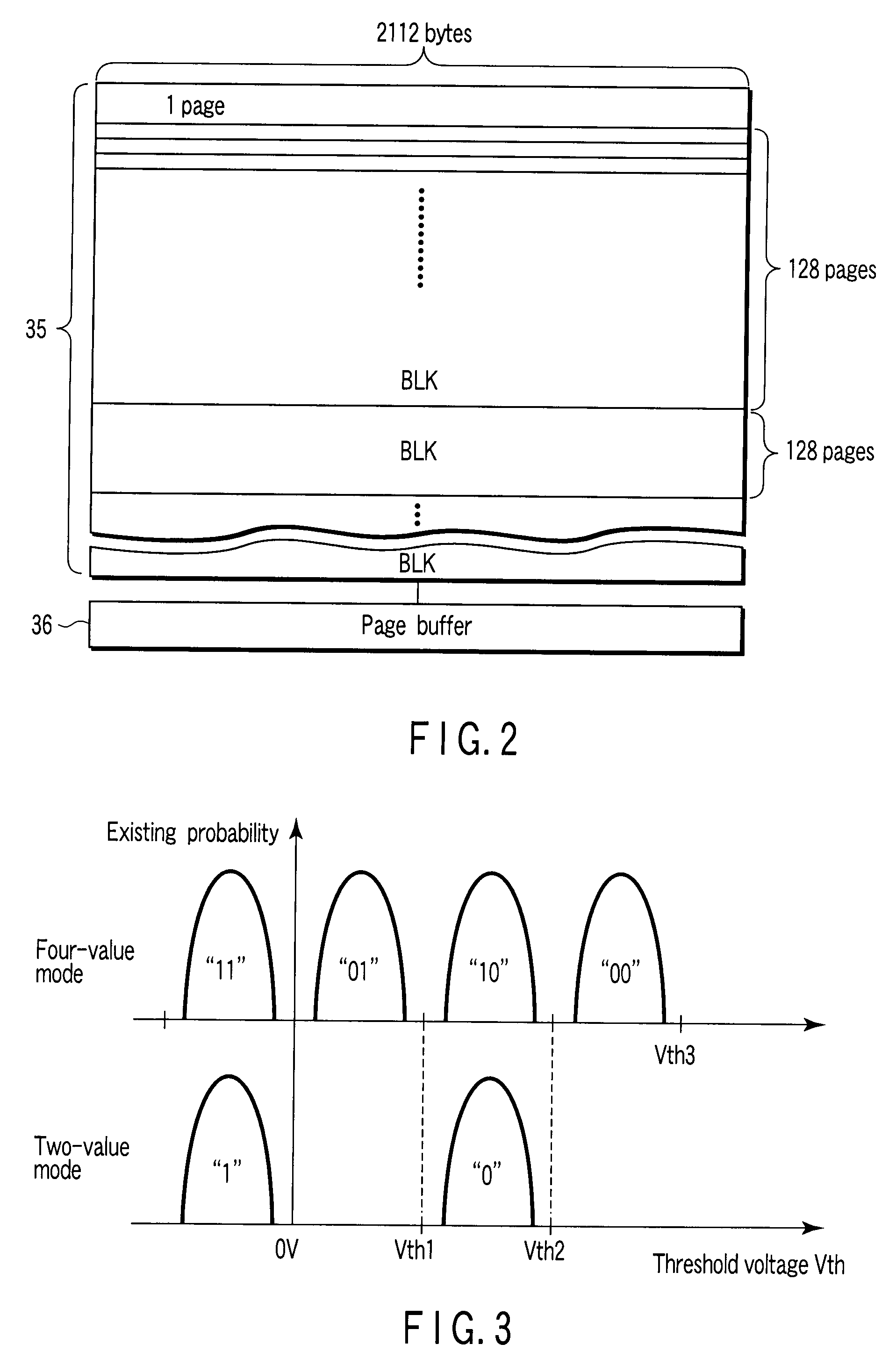
InactiveUS20080244211A1Lower security levelMemory adressing/allocation/relocationRead-only memoriesSecurity levelNon-volatile memory
A memory device comprises a nonvolatile memory including memory areas that are defined in accordance with a security levels, and a controller configured to write to a first area that is part of the memory areas in an M-value mode and to a second area that is part of the memory areas and provides lower security level than the first area in an N-value mode (N>M).
Owner:KK TOSHIBA
Systems, methods, and computer program products for collecting and reporting sensor data in a communication network
ActiveUS8621636B2Shorten the time to marketIncrease propensityFinanceMemory loss protectionComputer networkData reporting
A system for collecting and reporting sensor data in a communication network includes a microprocessor coupled to a memory and an electronic storage device. The microprocessor receives sensor data from sensors, and stores the sensor data for each sensor in the electronic storage device. The microprocessor also receives, via the communication network, a data reporting instruction defining a data reporting technique corresponding to the sensor data associated with one or more of the sensors. The data reporting instruction is stored in the electronic storage device, and the microprocessor transmits, to a trust mediator over the communication network, at least a portion of the sensor data based on the data reporting instruction. The trust mediator maintains an acceptable level of security for data throughout the communication network by adjusting security safeguards based on the sensor data.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Dynamic pairing system for securing a trusted communication channel
ActiveUS20140379581A1Shorten the time to marketIncrease propensityFinanceProtocol authorisationRisk levelComputer network
A system, method, and computer-readable medium for securing a mobile financial transaction are provided. A table matches each one of a plurality of transaction risk levels to a corresponding one of a plurality of required user trust scores, correspondingly. A financial transaction risk level associated with a financial transaction is computed. A user trust score associated with the user is computed based on user identification data associated with the user. The financial transaction risk level is matched to a corresponding one of the plurality of transaction risk levels stored in the table. The one of the plurality of required trust scores that corresponds to the corresponding one of the plurality of transaction risk levels stored in the table is identified. If the user trust score is greater than or equal to the identified one of the plurality of required trust scores, then the financial transaction is authorized.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Dynamically reacting policies and protections for securing mobile financial transaction data in transit
ActiveUS8650129B2Shorten the time to marketIncrease propensityFinanceCryptography processingSecure communicationProtection mechanism
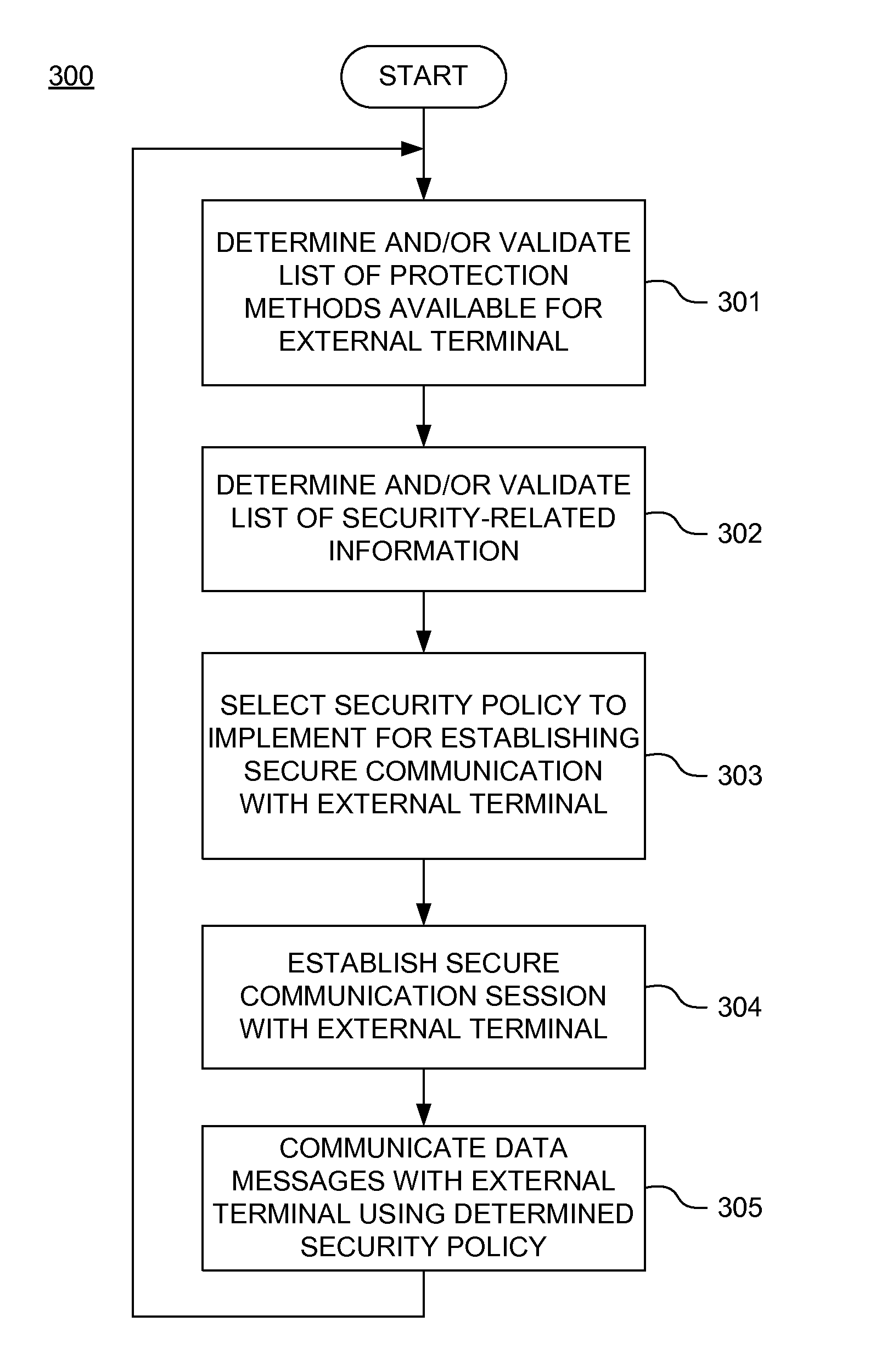
A secure mobile financial transaction is provided by receiving, over a communication network, a list of protection mechanisms available for implementation by an external terminal. Security-related data is received from one or more sensors and an attack signature is computed based on the security-related data. An appropriate security policy is selected from multiple security policies stored in a database based on the list of protection mechanisms and the attack signature. A secure communication session is established between the external terminal and an internal network component according to the selected security policy. A data message associated with a mobile financial transaction is communicated over the communication network during the communication session.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
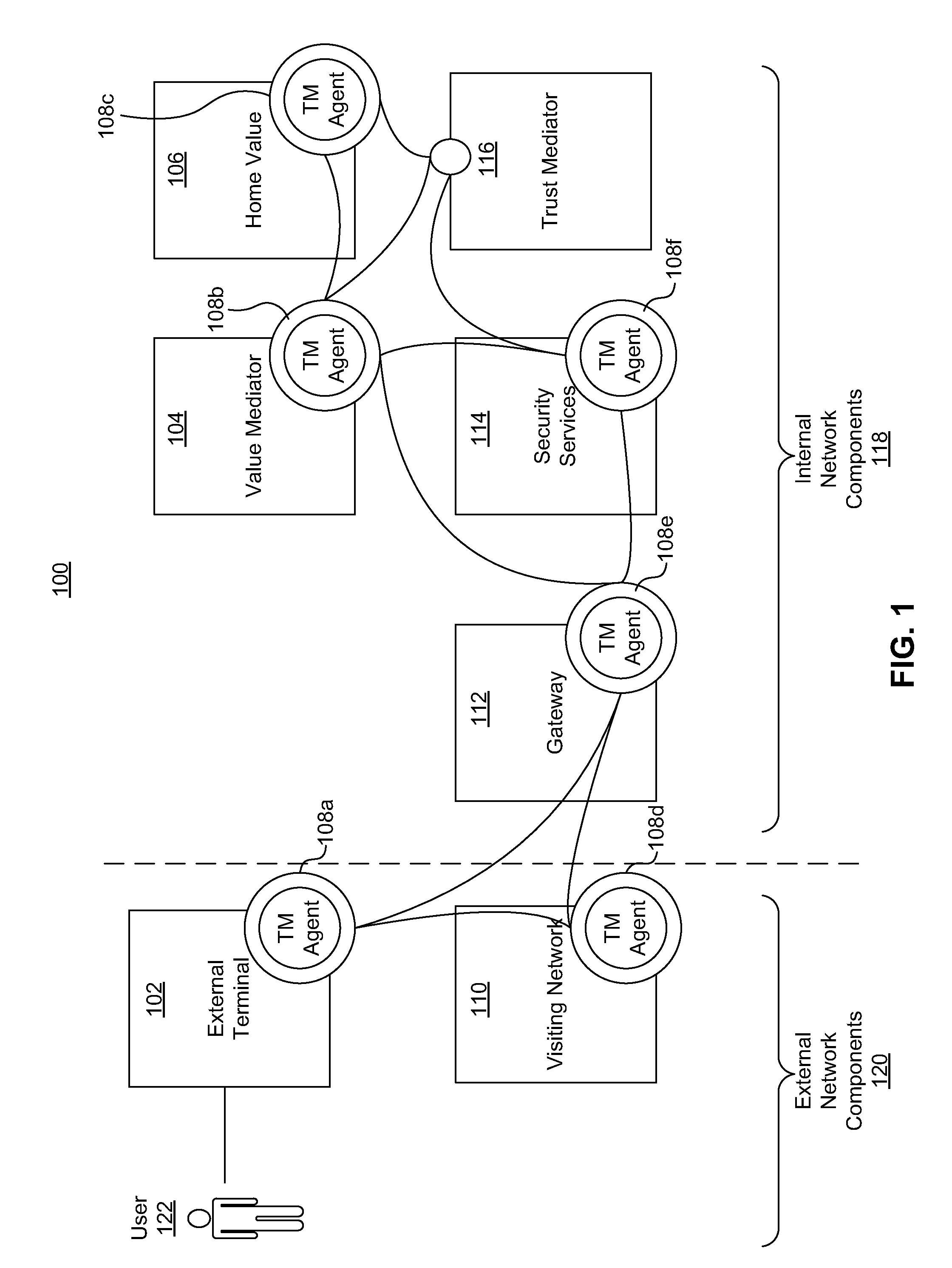
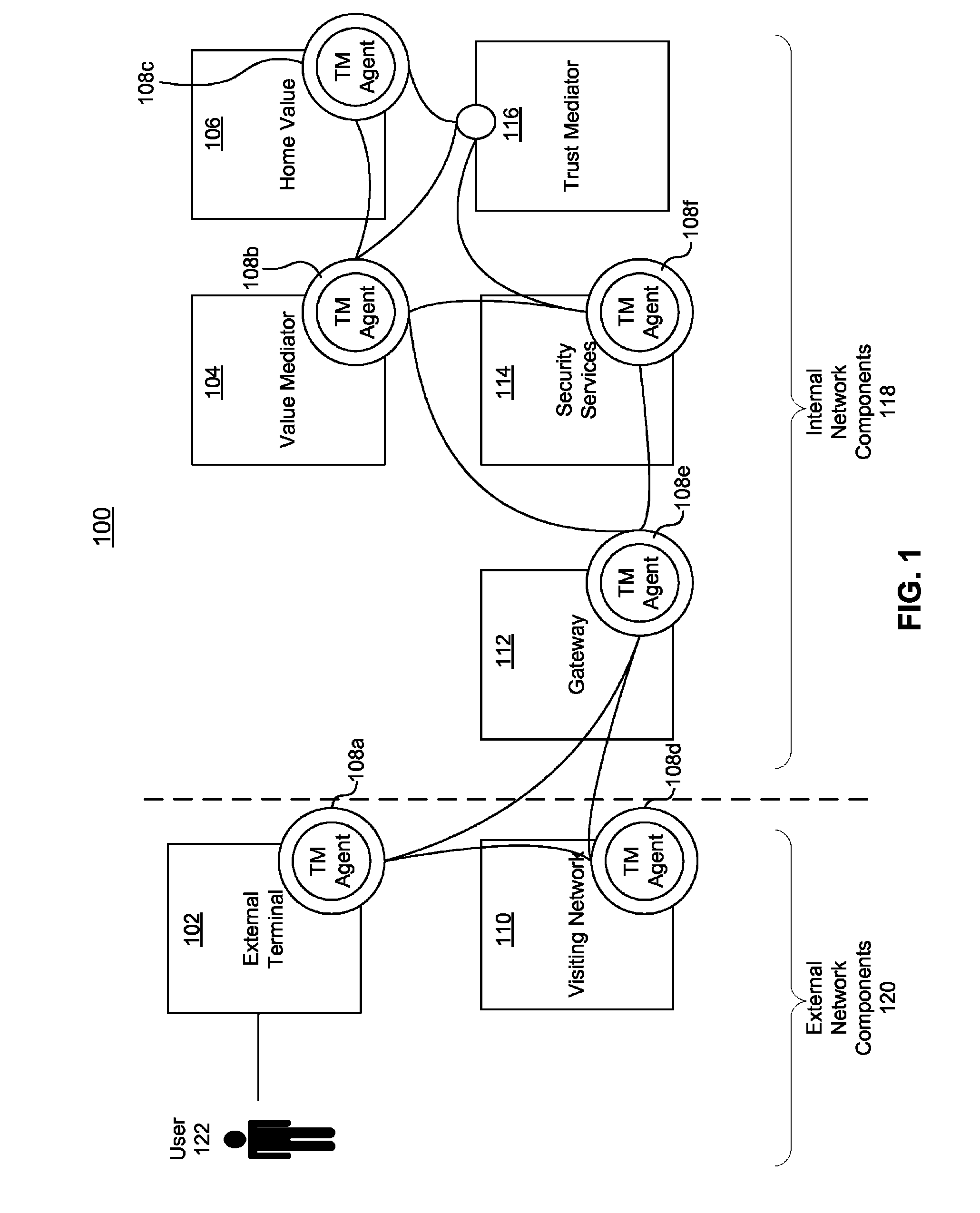
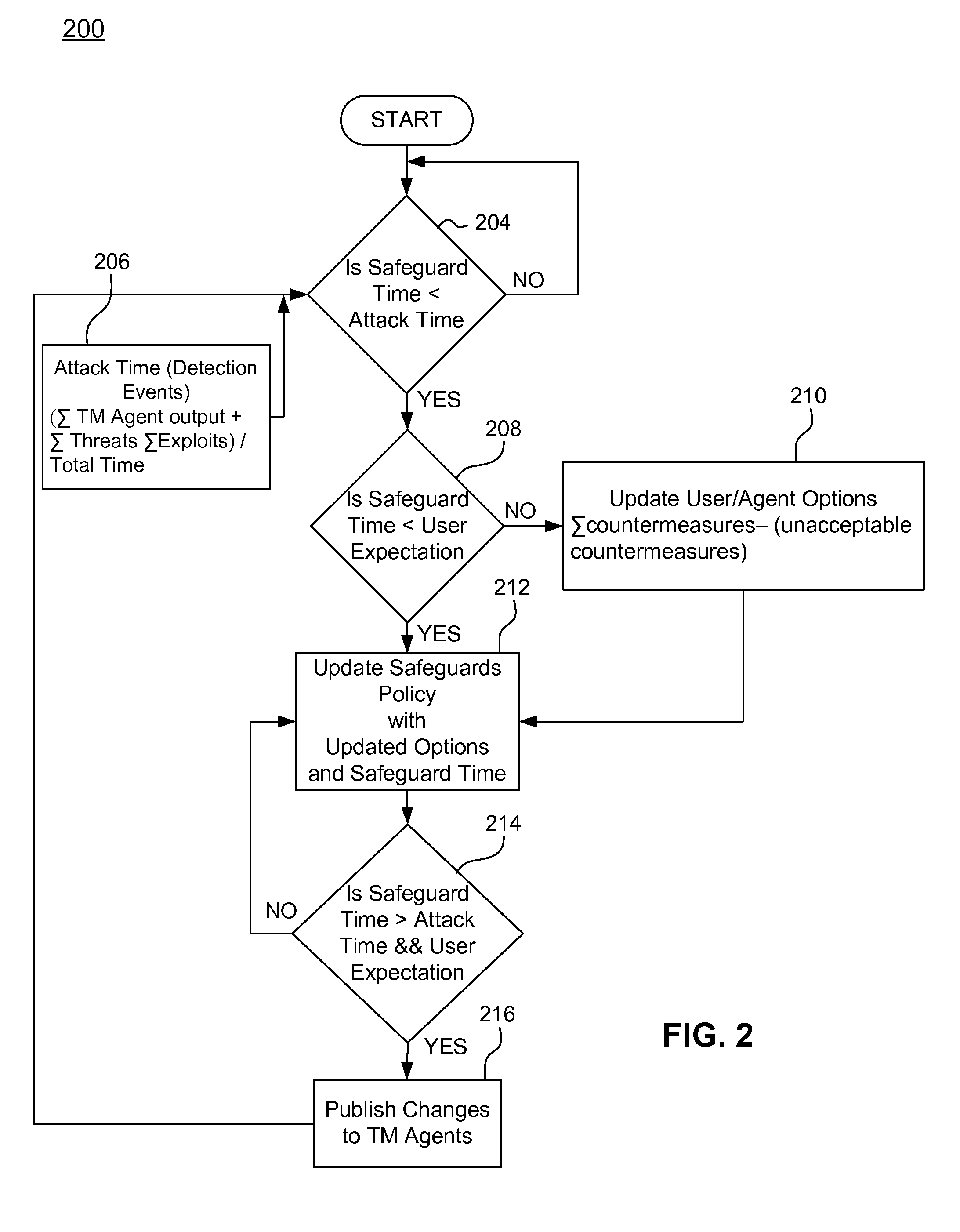
Systems, methods, and computer program products for adapting the security measures of a communication network based on feedback
ActiveUS8752142B2Shorten the time to marketIncrease propensityMemory loss protectionDigital data processing detailsSecurity MeasureSecurity level
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
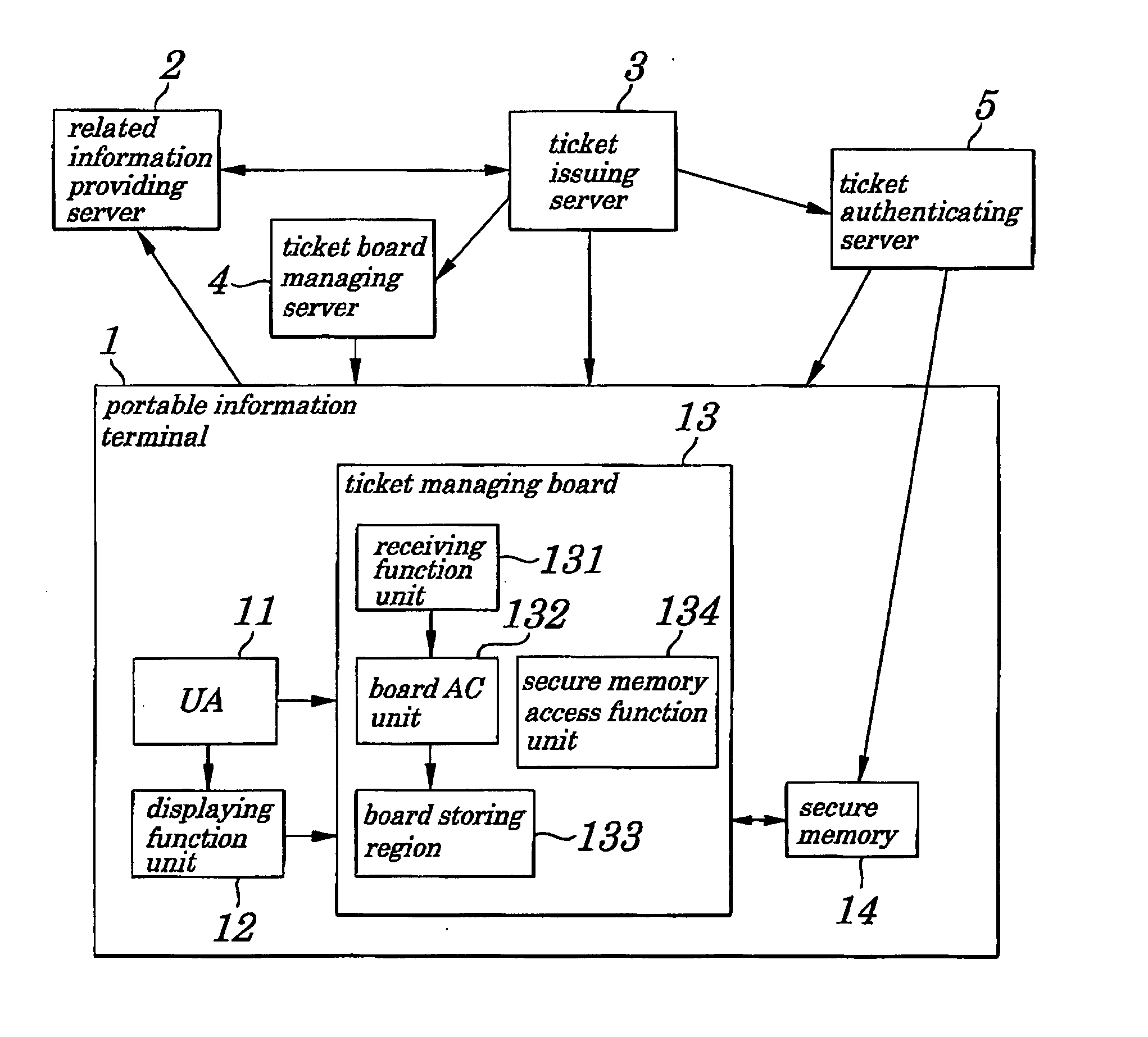
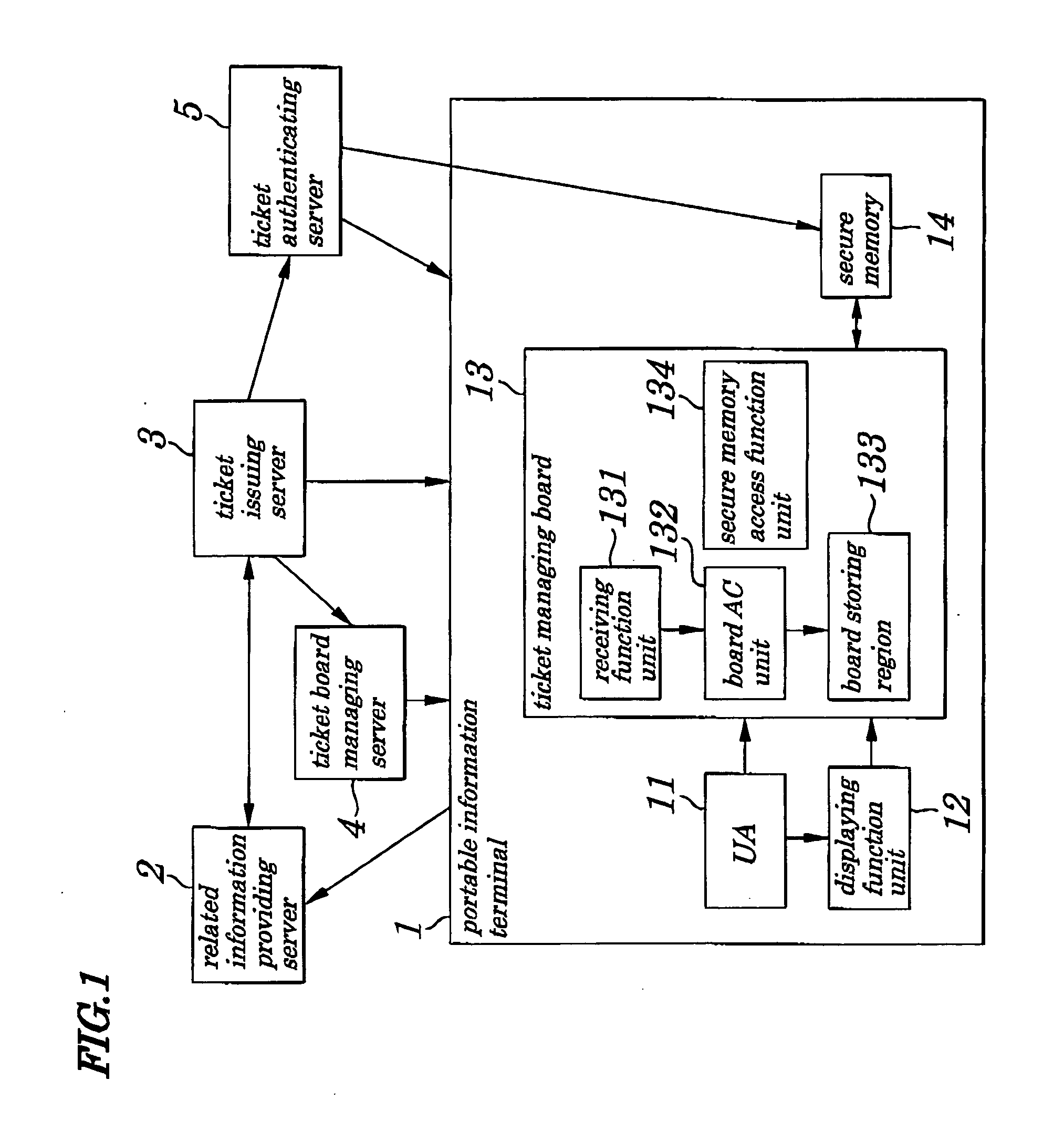
Portable information terminal, and electronic information authenticating system and method using same terminal
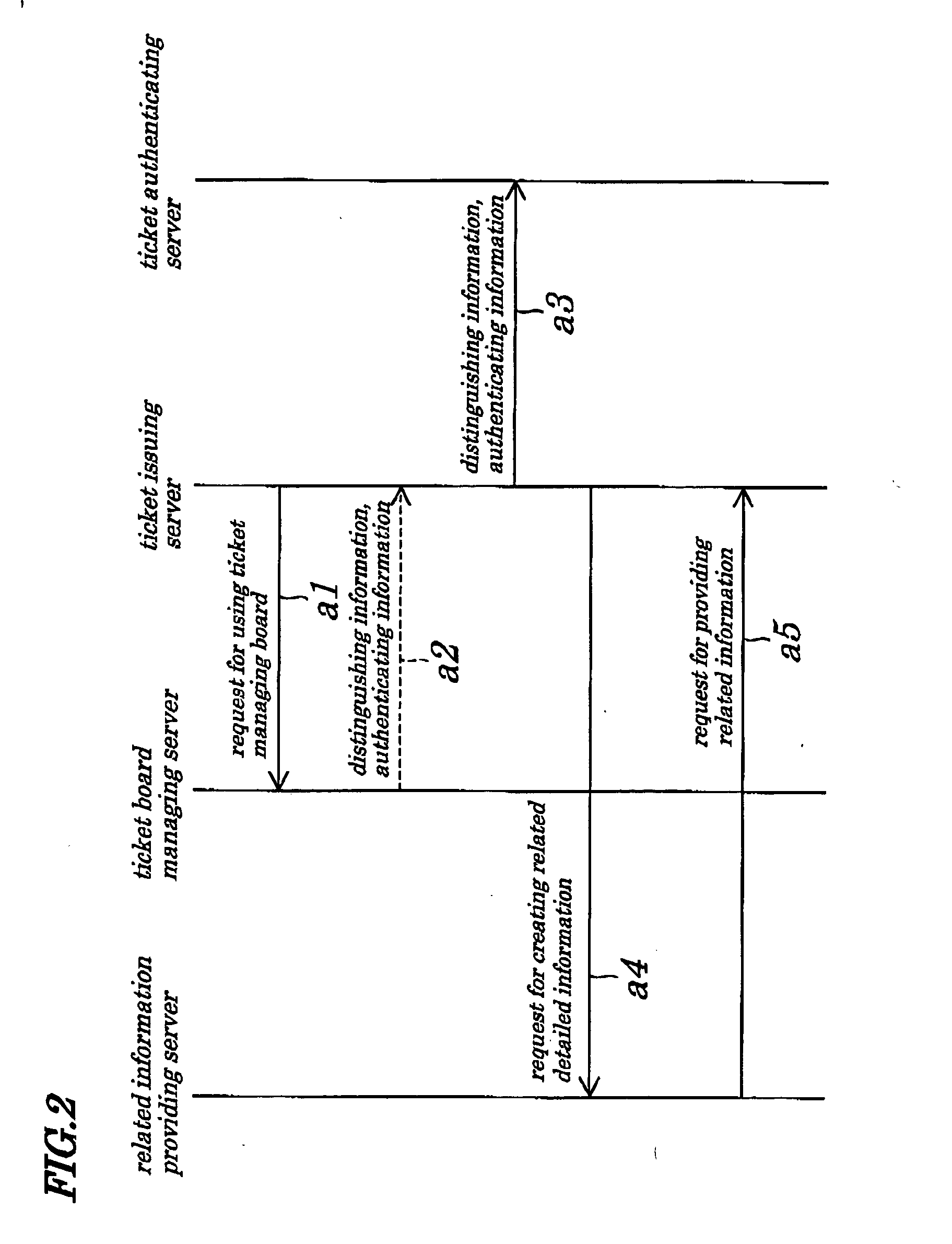
ActiveUS20050060536A1Improve securityLow costTicket-issuing apparatusDigital data processing detailsElectronic informationUser agent
An electronic information authenticating system is provided which is capable of providing enhanced security of specified electronic information and its related information in the terminal without causing high costs. In a board storing region in a ticket managing board in a portable information terminal, related information passed from a ticket issuing server to which an access is permitted by a board AC (Access Control) unit is stored. A UA (User Agent), ticket board managing server, and ticket issuing server are accessible to the board storing region. An electronic ticket to which consideration on security needs to be given is stored in a secure memory retaining enhanced security, however, the electronic ticket to which consideration on security needs not to be given is put into the board storing region being at low costs.
Owner:NEC CORP
Suppression of authorization risk feedback to mitigate risk factor manipulation in an authorization system
ActiveUS20170180339A1Lower security levelSuppress the one or more security risk factorsDigital data authenticationTransmissionInternet privacyRisk communication
Dynamic risk communication associated with a computer device may include automatically detecting one or more security risk factors for the computer device based on current context information associated with the computer device. Whether an attempt is being made via the computer device to manipulate the one or more risk factors in an attempt to reduce a security level of a computer-implemented authentication procedure may be determined. Responsive to determining that the attempt is being made to manipulate the one or more risk factors, a new challenge for additional identification may be communicated for presentation on a user interface device of the computer device while suppressing one or more security risk factors from being presented on the user interface device. Responsive to determining that an attempt is not being made to manipulate the one or more risk factors, the new challenge and one or more security risk factors may be communicated.
Owner:IBM CORP
Image processing apparatus and method for transmitting encrypted data
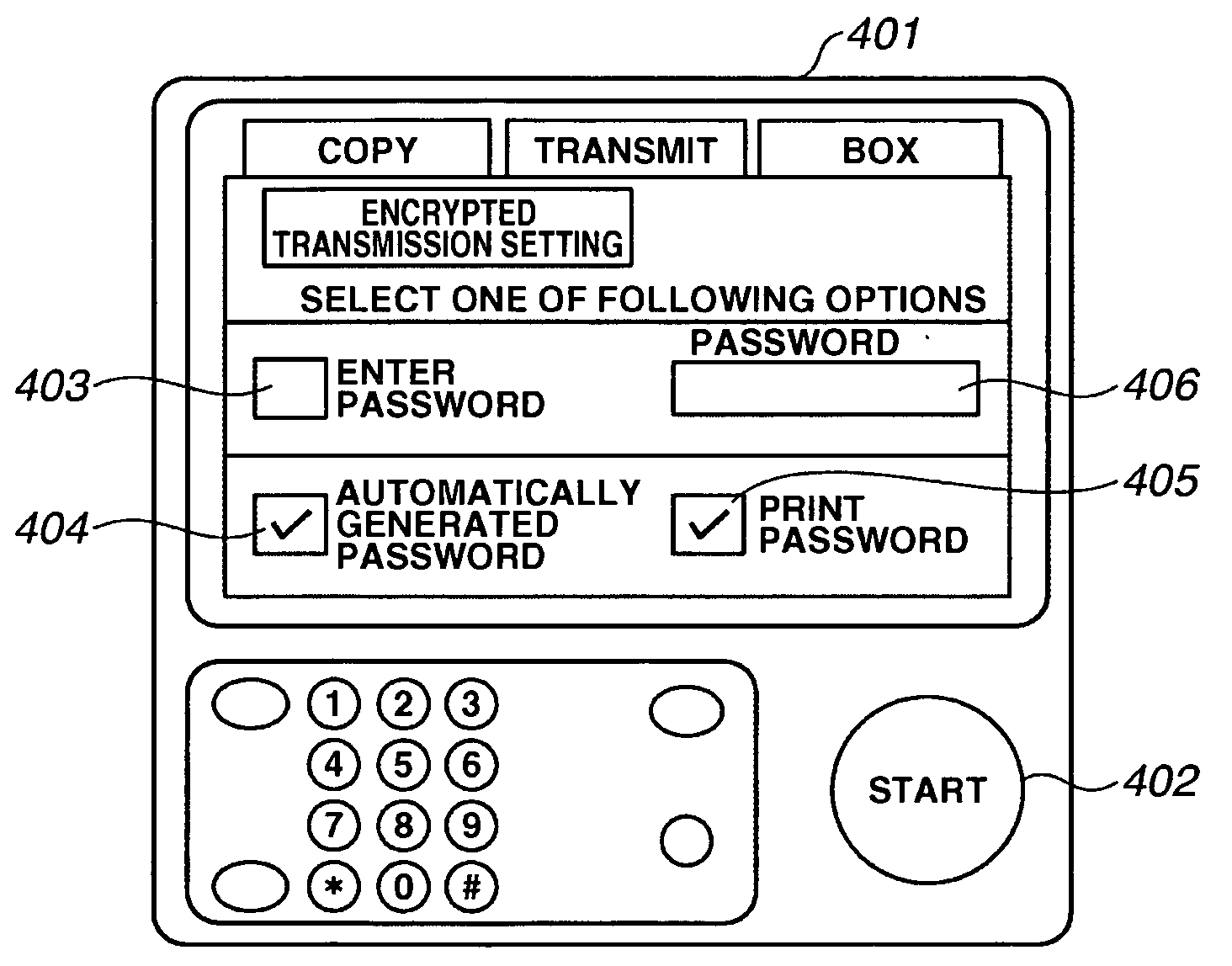
InactiveUS20060212715A1Improve security levelLower security levelDigital data authenticationSecret communicationComputer hardwareImaging processing
An image processing apparatus generates a password each time transmission of image data is instructed, encrypts the image data with the generated password, transmits the encrypted image data, and notifies the generated password.
Owner:CANON KK
Adaptive policies and protections for securing financial transaction data at rest
ActiveUS8850539B2Shorten the time to marketIncrease propensityDigital data processing detailsUser identity/authority verificationTransaction dataDisplay device
A system for challenge-response authentication is provided by receiving, from an external terminal over a communication network, a request for access to a service. A plurality of objects is presented to a user via a display. A plurality of codes is received over the communication network, each of the plurality of codes corresponding to one of the plurality of objects. The plurality of codes are matched to a plurality of alphanumeric characters according to a predetermined table. An alphanumeric string is generated from the plurality of alphanumeric characters and the alphanumeric string is compared to a user identifier stored in a database. Based on the comparing, a determination is made as to whether to grant the user access to the service.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com