Patents
Literature
158 results about "Total risk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Privacy Risk Metrics in Online Systems
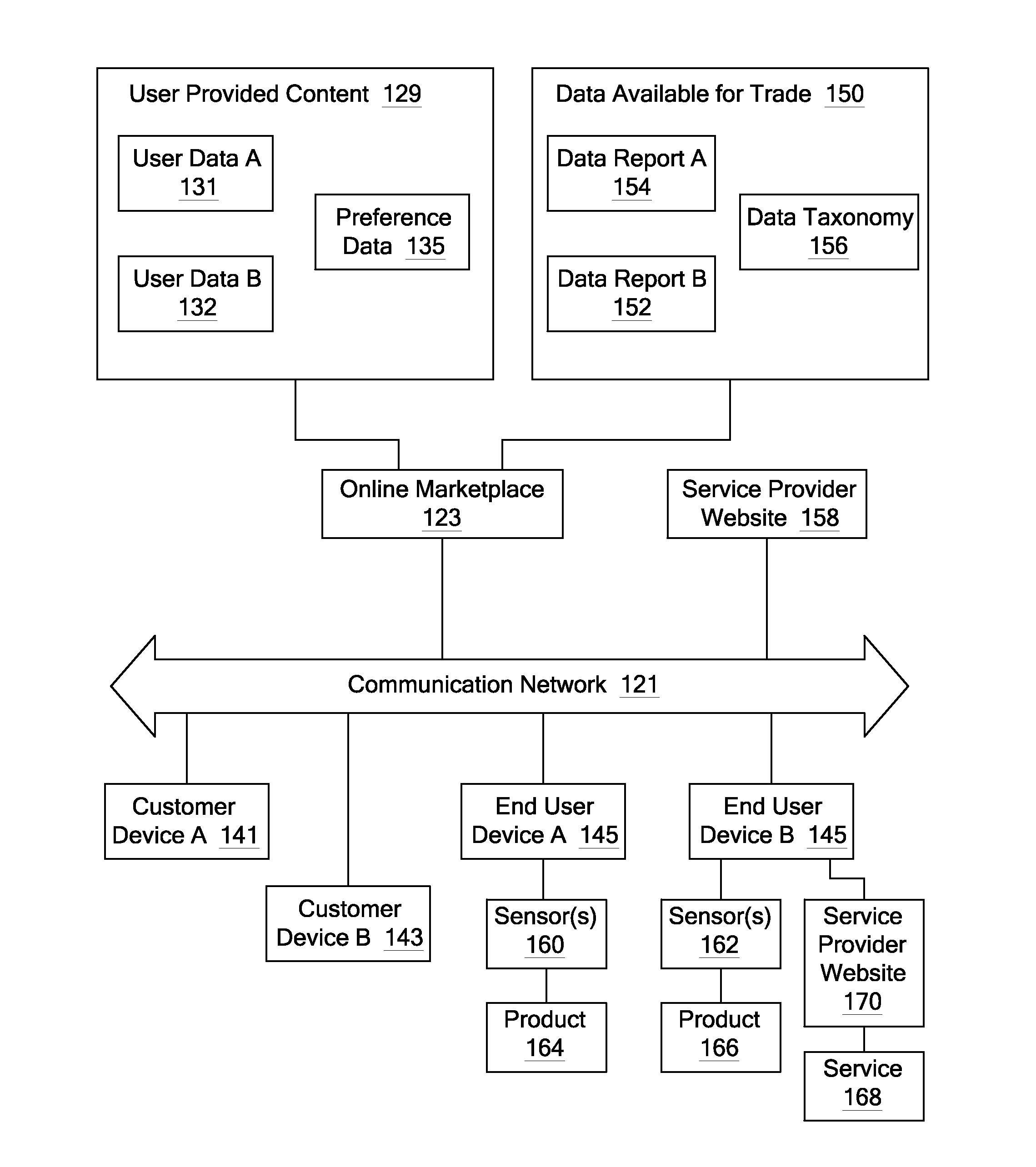
A plurality of persona attributes are identified within a data set received from a data seller. A persona privacy risk associated with the persona attributes of the dataset is determined. The persona privacy risk comprises an estimate of the potential sensitivity of the persona attributes. A plurality of identity attributes within a data set received from a data seller are identified. An identity privacy risk associated with the plurality of identity attributes is determined. The persona privacy risk comprises an estimate of the risk that the plurality of identity attributes identify the data seller. A total privacy risk is then determined using the persona privacy risk and the identity privacy risk associated with the dataset, the total privacy risk comprising an estimate of a total risk to the privacy of the data seller that disclosure of the dataset represents.
Owner:STATZ
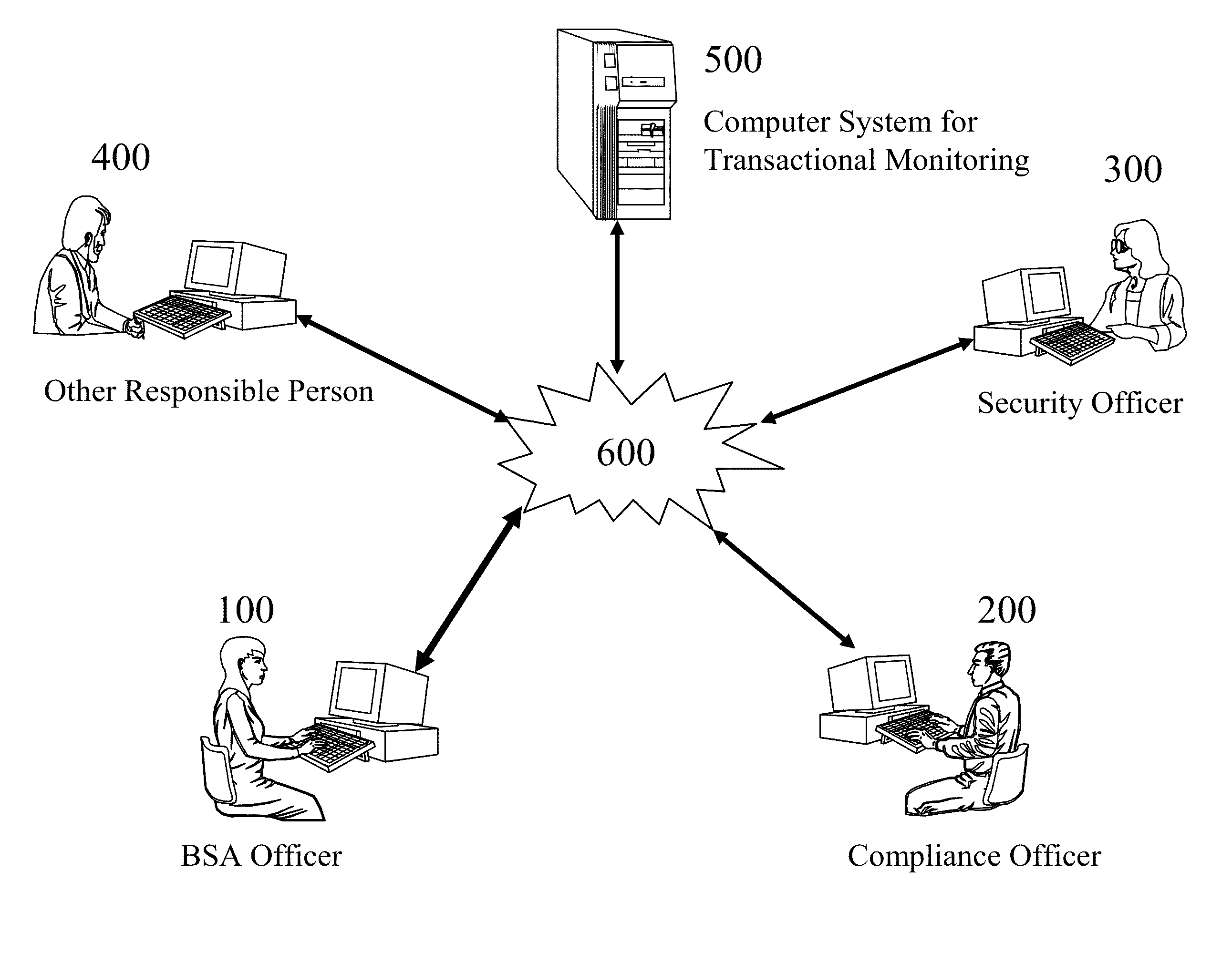
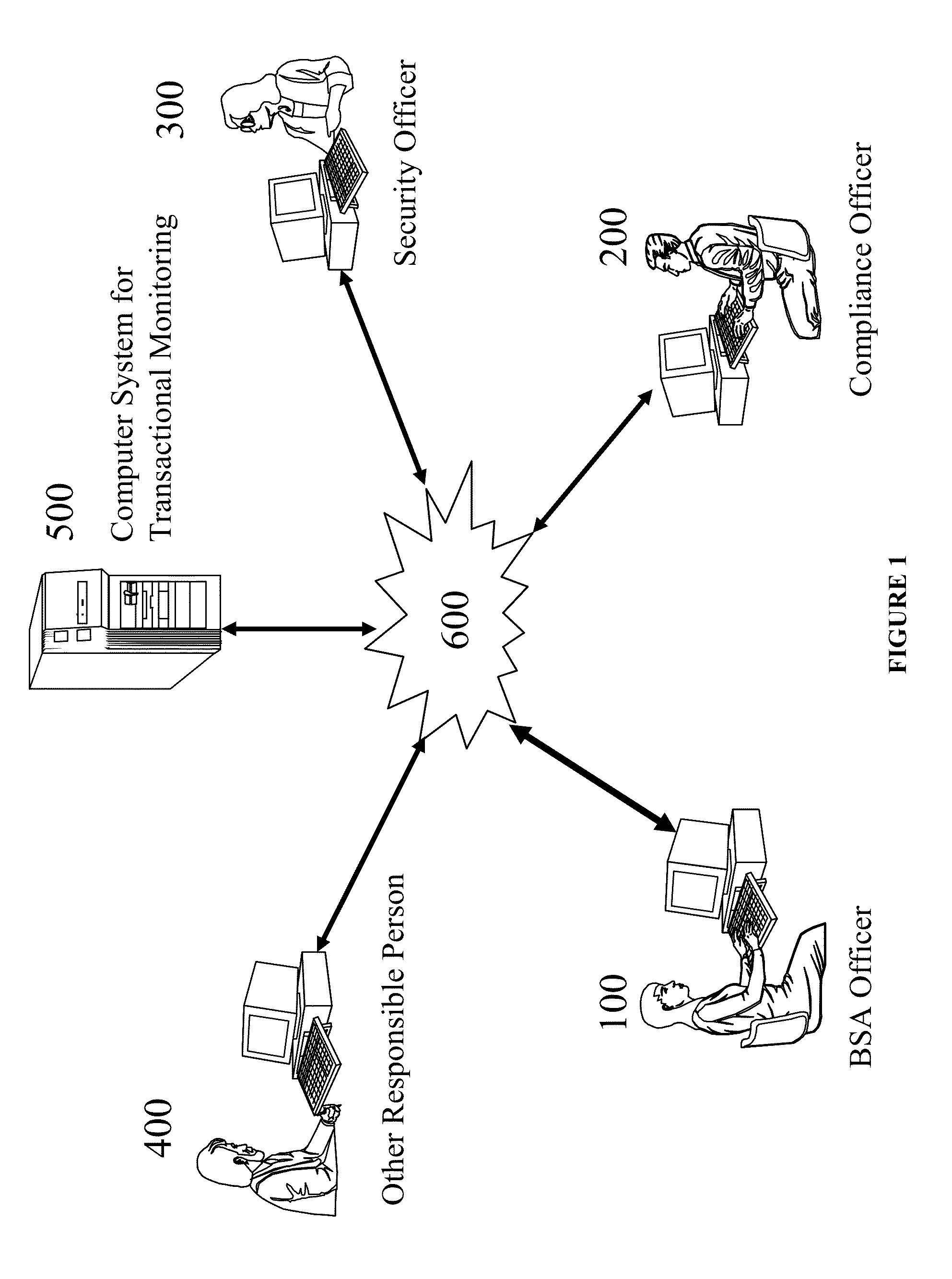
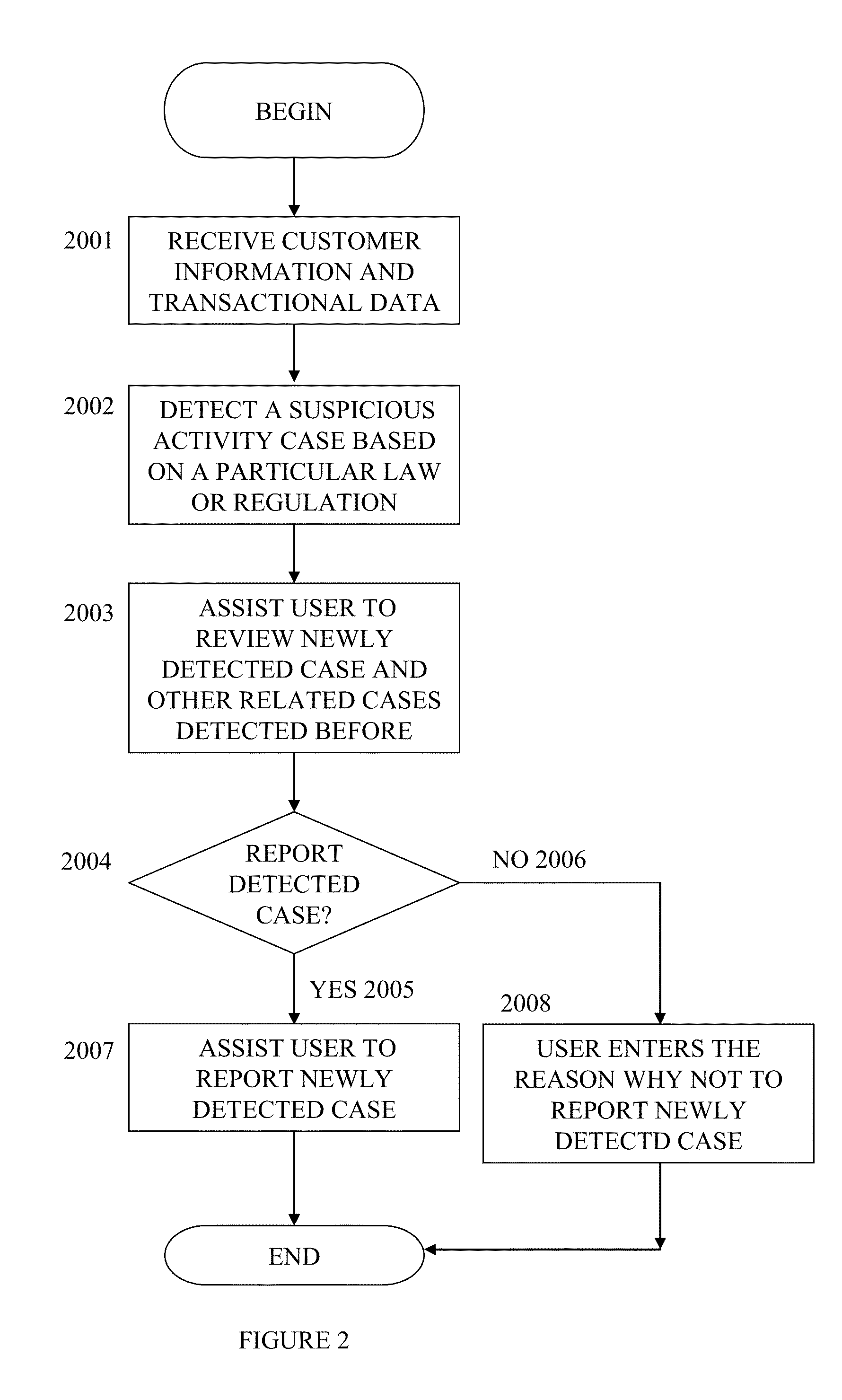
Transactional monitoring system
ActiveUS20140058914A1Promote resultsReduces or eliminates human efforts and mistakesFinancePayment architectureRisk factorTotal risk
A computer system conducts transactional monitoring to detect different types of possible cases in order to prevent financial crimes and assist businesses to comply with different types of laws and regulations. The computer system derives a total risk score for each of a group of entities based on risk factors. Each of the risk factors is assigned a risk score. The computer system also detects an entity when the total risk score of the detected entity differs from a reference derived from total risk scores of the group of entities by a pre-determined margin. The computer system also assists a user to identify at least one transaction that has caused the detected entity to have a total risk score that differs from the reference derived from the total risk scores of the group of entities.
Owner:AI OASIS INC
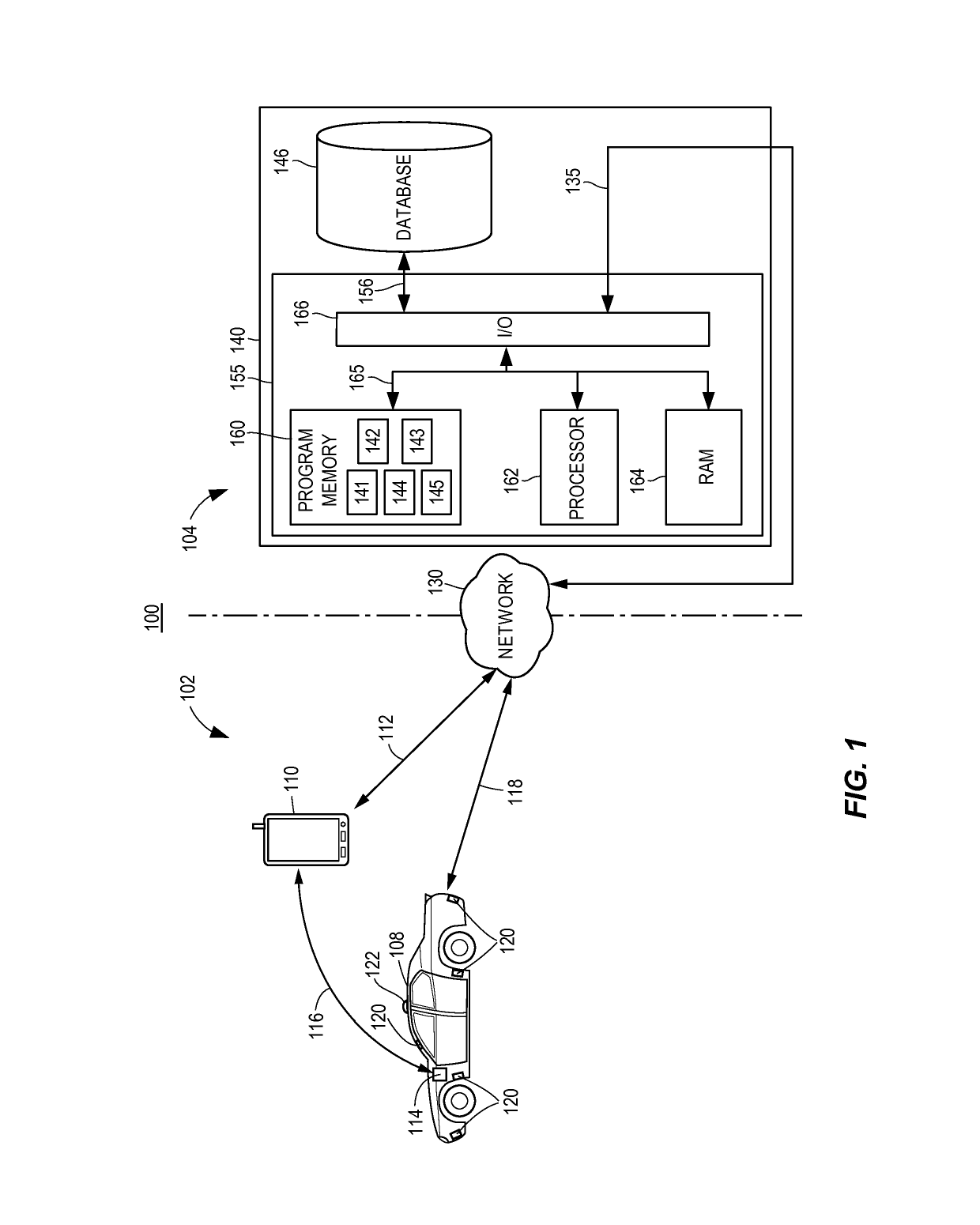
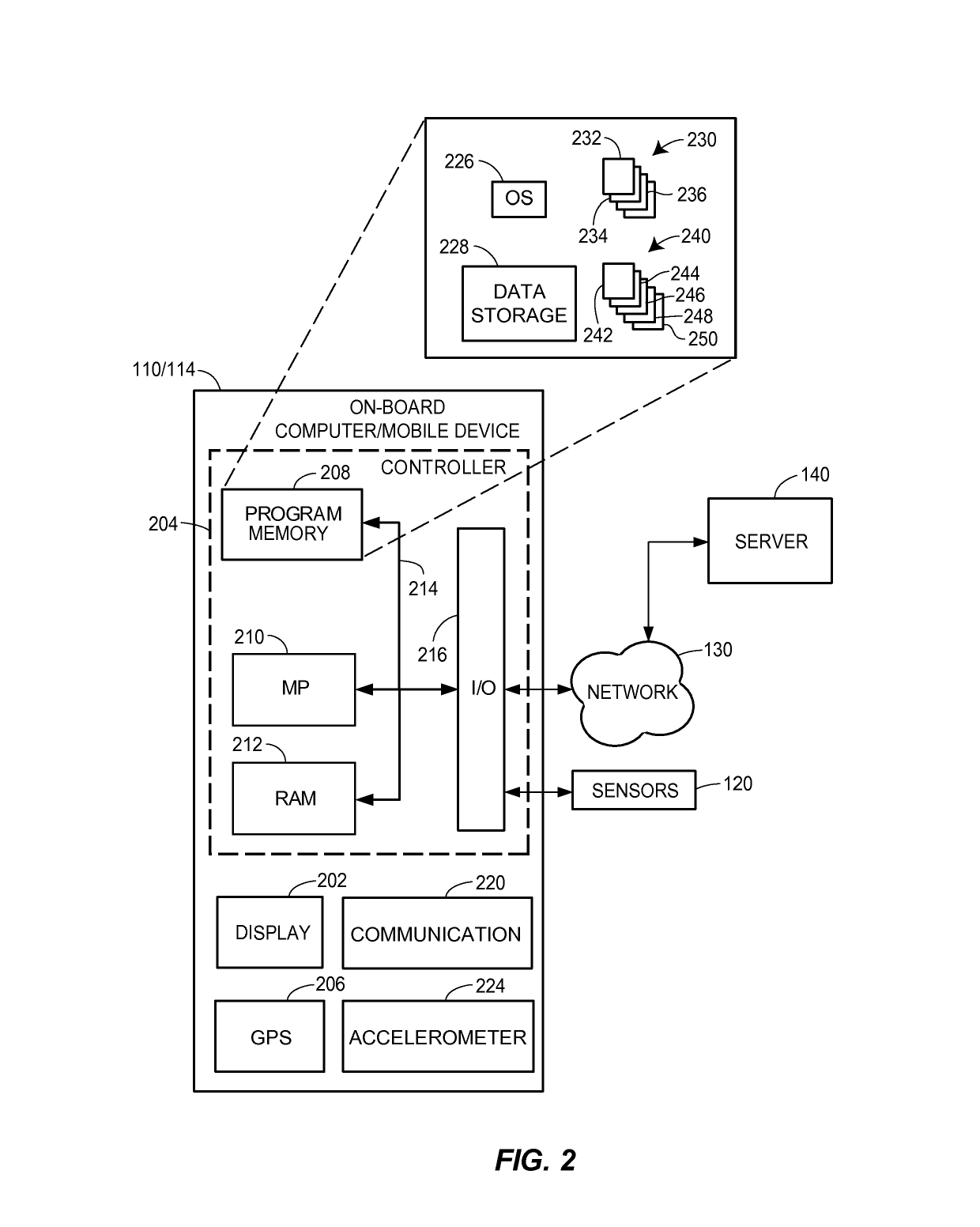
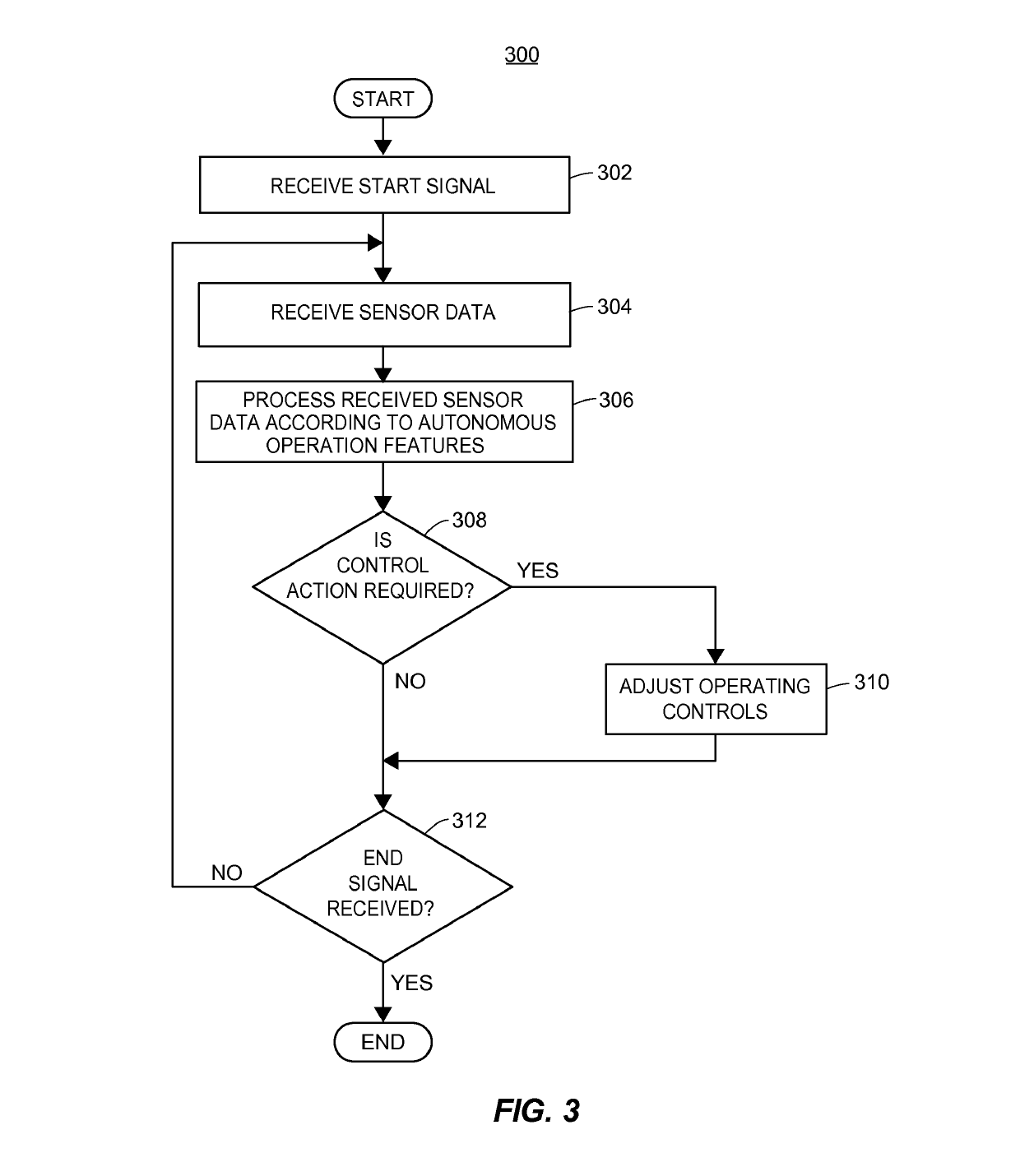
Autonomous feature use monitoring and telematics
ActiveUS10185999B1Operation moreFacilitate risk assessmentFinanceRegistering/indicating working of vehiclesRisk levelTotal risk
Methods and systems for monitoring use and determining risk associated with operation of autonomous vehicles are provided. According to certain aspects, autonomous operation features associated with a vehicle may be determined, and operating data regarding vehicle operation may be obtained. The operating data may include information regarding use levels or settings associated with use of the autonomous operation features. Risk levels associated with the features may be determined from test data or actual loss data. The risk levels and operating data may be used to determine a total risk level associated with operation of the vehicle with expected use levels of the autonomous operation features. The total risk level may further be used to determine or adjust aspects of an insurance policy associated with the vehicle.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
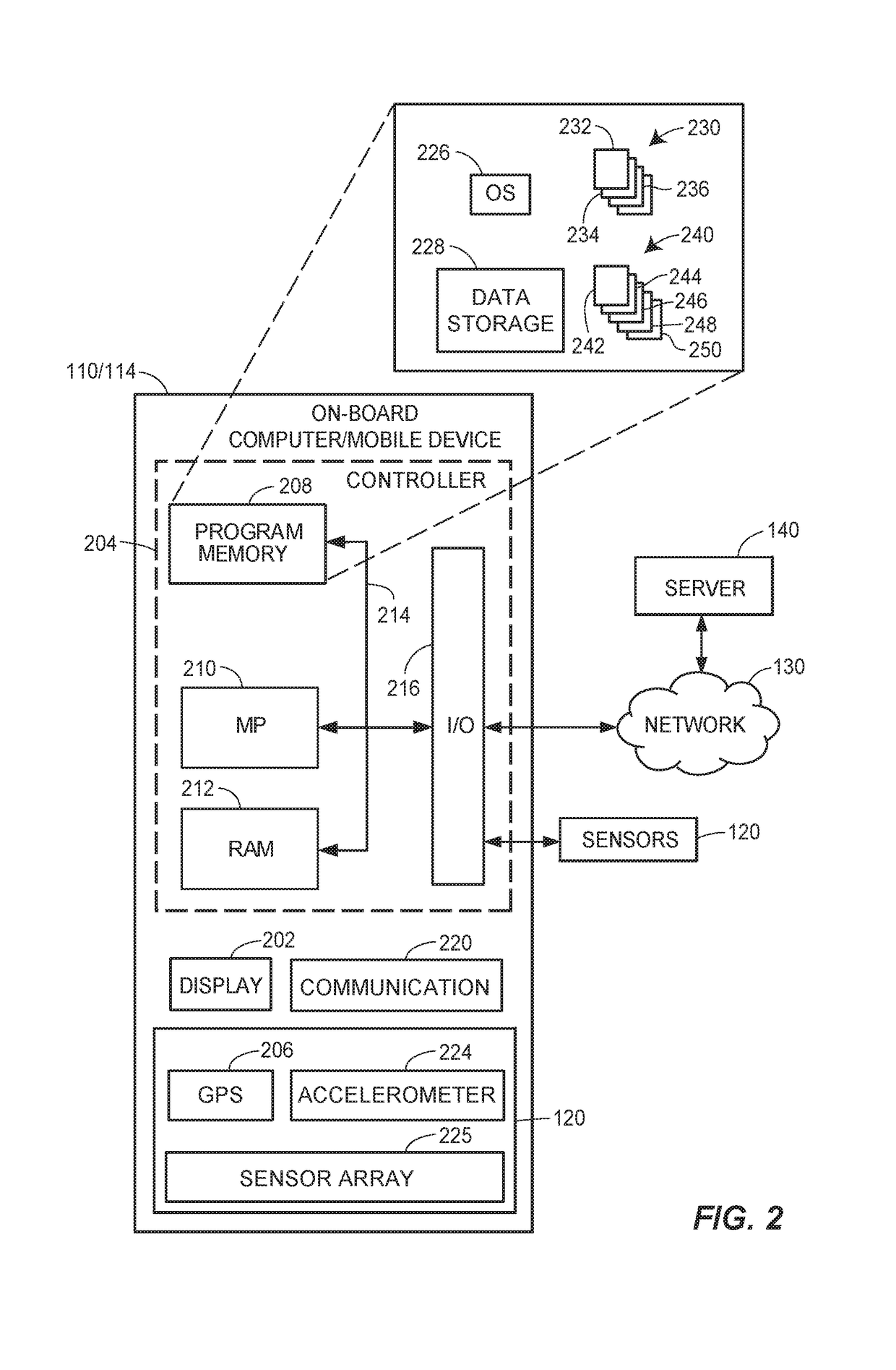
Computer based risk level monitor and patient compliance method and system
InactiveUS20050102159A1Improve compliance rateVAR reductionData processing applicationsHealth-index calculationRisk levelTotal risk
The risk monitor, as a computer-based method, program or system, monitors medical compliance by a plurality of patients having a corresponding plurality of medical compliance plans. The plans for each patient are displayed and the system accepts input from the patient indicative and / or heathcare providers of the patient's compliance with the plan. The system then assesses or analyzes the input and assigns a corresponding risk value based upon a range of risk values for various degrees of compliance. In addition, the patient's lifestyle inputs can be added to determine the risk value. The assessment continues for a plurality of patients thereby providing an indication of the risk value (a total risk value) for a patient, doctor, group of healthcare providers, a clinic or a hospital. By implementing various communication episodes (telephone calls, e-mails, letters), the system seeks to reduce the risk value for a particular patient and for the plurality of patients by altering the communication episodes and monitoring the resulting risk values both individually and as a group.
Owner:MONDSHINE ROBERT B
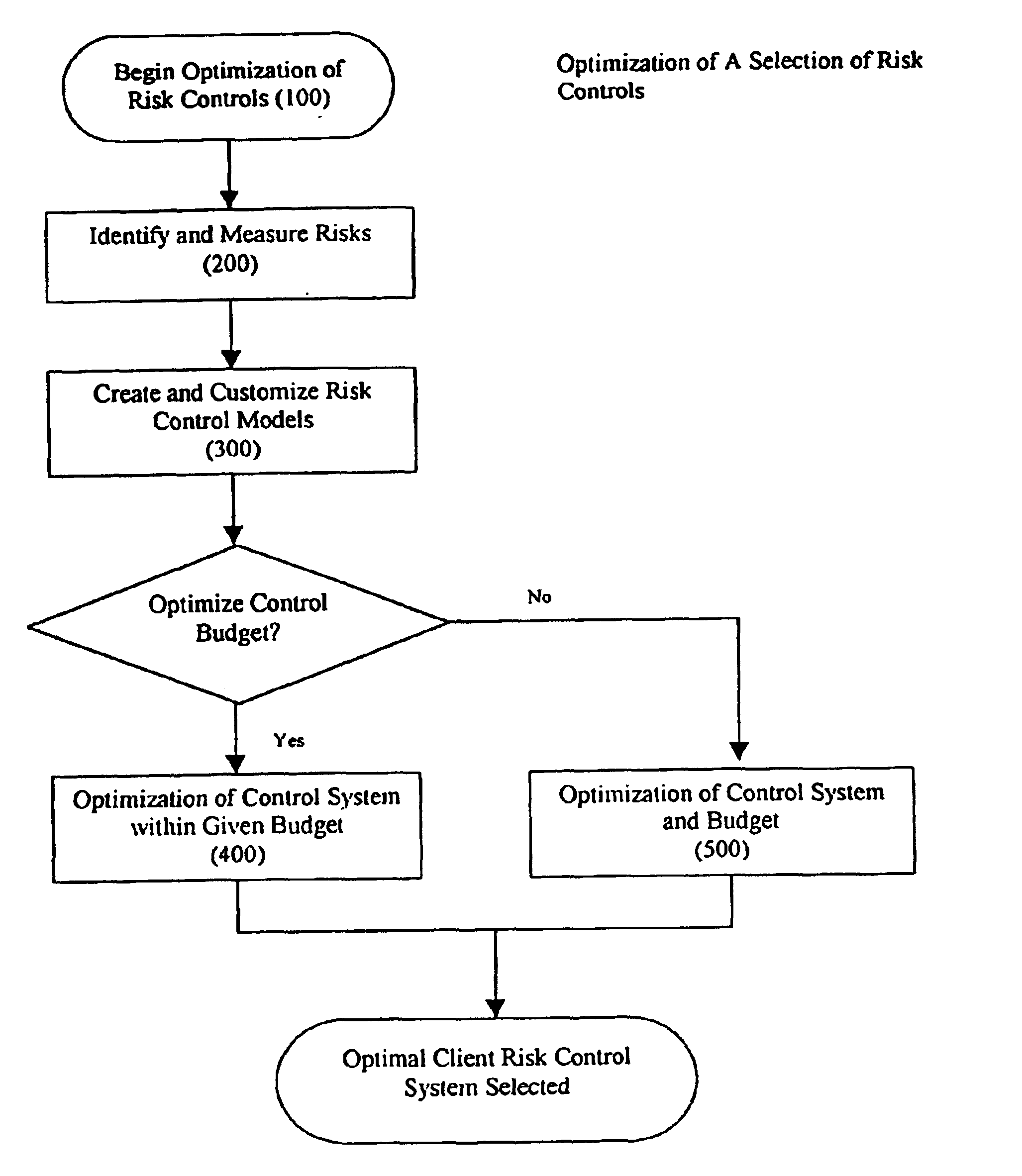
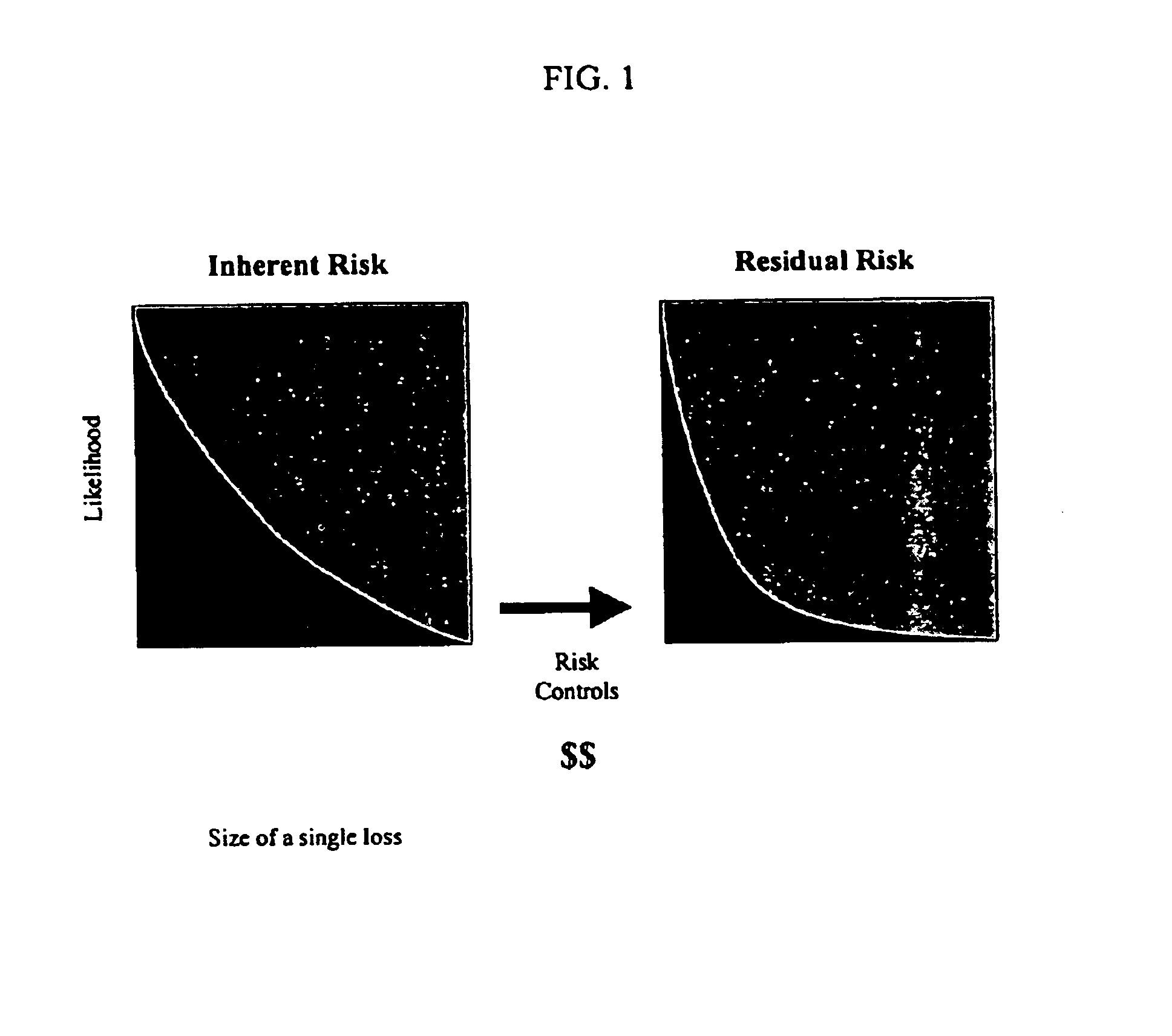
Method and system for risk control optimization
InactiveUS6876992B1Economic value maximizationHigh economic valueFinanceComputation using non-denominational number representationRisk exposureRisk Control
A method and system for selecting an optimal set of management and risk controls for a given set of risks within a variable control budget. Specifically, optimization according to the present invention is defined using a method and system to calculate the greatest reduction in an organization's risk exposure with the minimum investment in cost and time as measured by the economic value added of the risk system change. Risk control models and management risk control models are client customized into a risk control system specifically addressing a clients applicable risks and their associated exposures. An operator is able to determine which risk control system maximizes available resources while also reducing an organization's total risk exposure.
Owner:WILLIS NORTH AMERICA
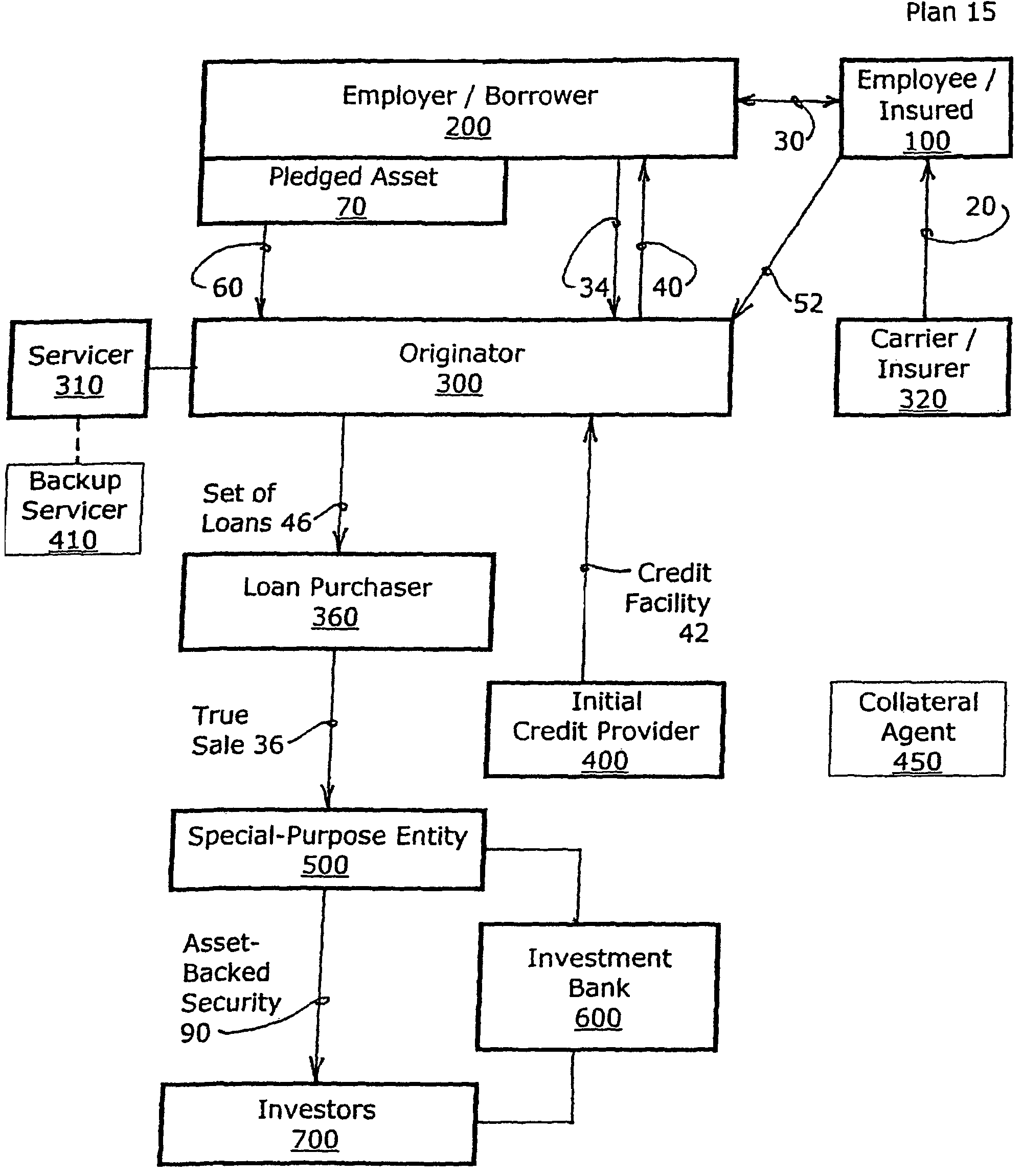
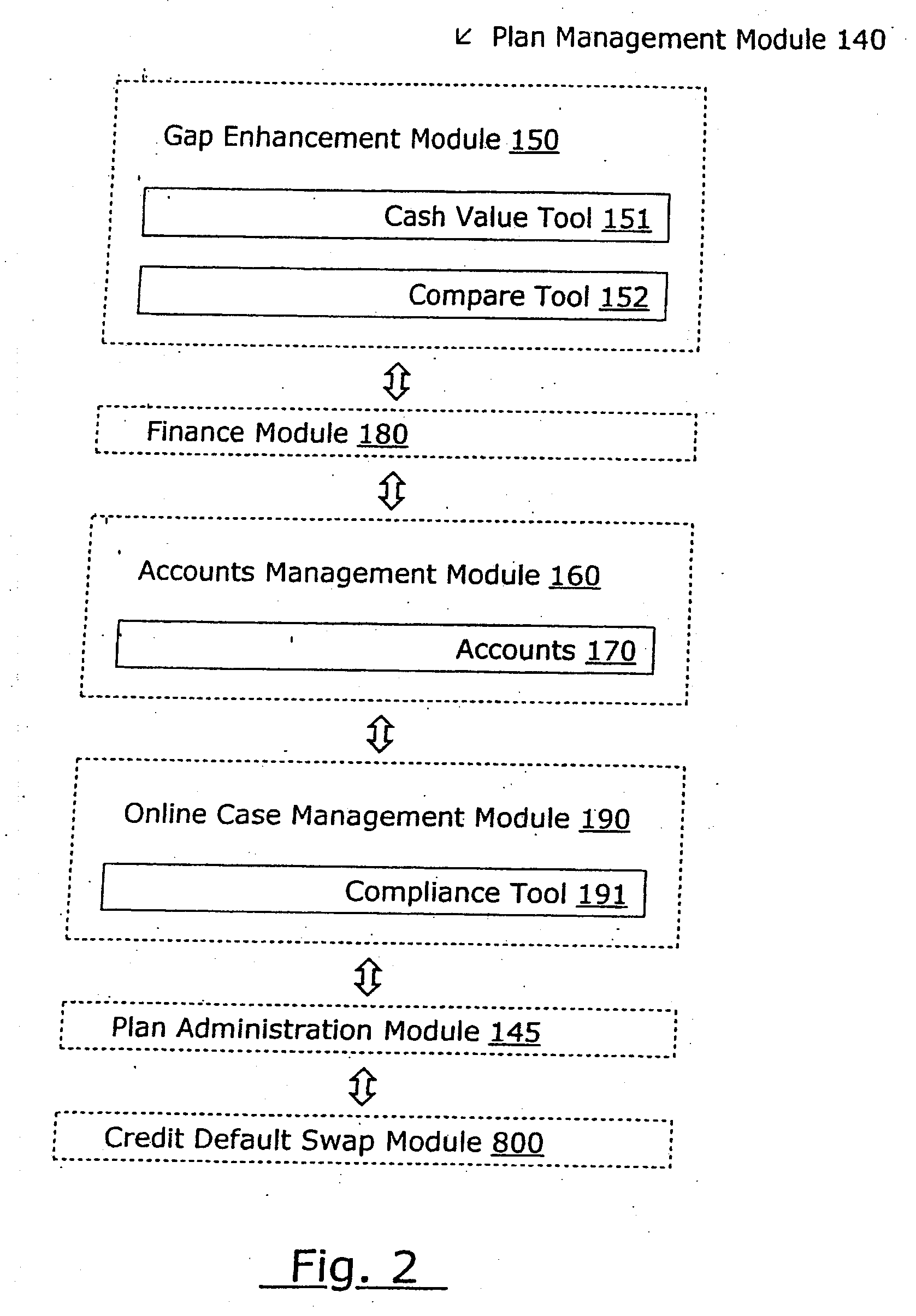
System for managing the total risk exposure for a portfolio of loans
A computer system for monitoring and enhancing the collateral security underlying a set of loans is provided, including a system for calculating the unsecured value of the set at any time and for initiating additional collateral enhancement instruments when the unsecured value exceeds a certain limit. The system may include a variety of modules in communication with a relational database for storing data about the loans and system elements. The computer system may also be configured to allocate, manage, and execute the waterfall or cascade of funds between and among the various participants in a financial plan. The invention also includes a structured finance plan and related methods for enhancing the collateral security of a loan obtained for a life insurance or annuity product, and a system and method for managing a portfolio of such loans in order to obtain favorable financing and to facilitate securitization.
Owner:ENTAIRE GLOBAL INTPROP
Method and system for assessing fall risk
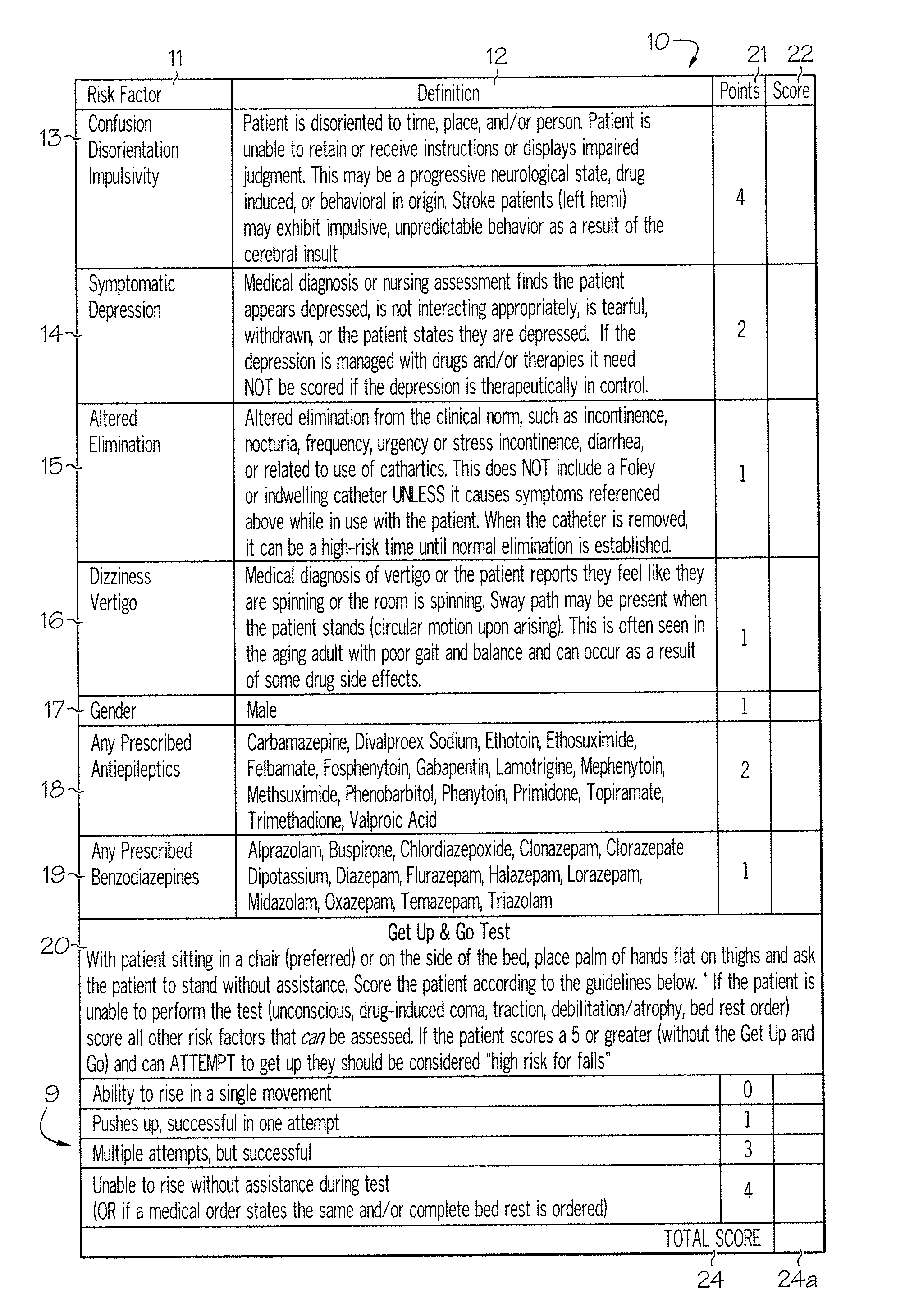
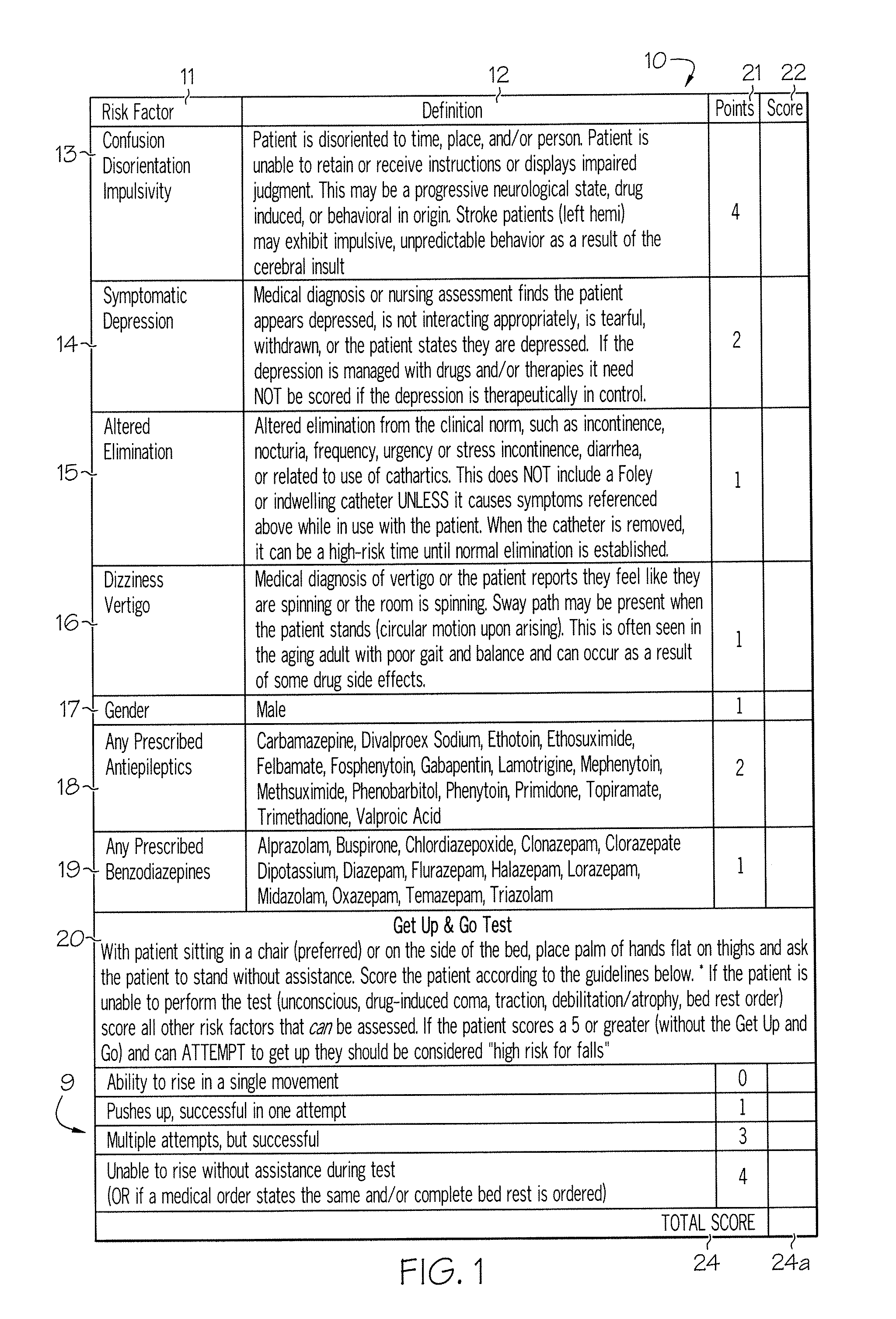
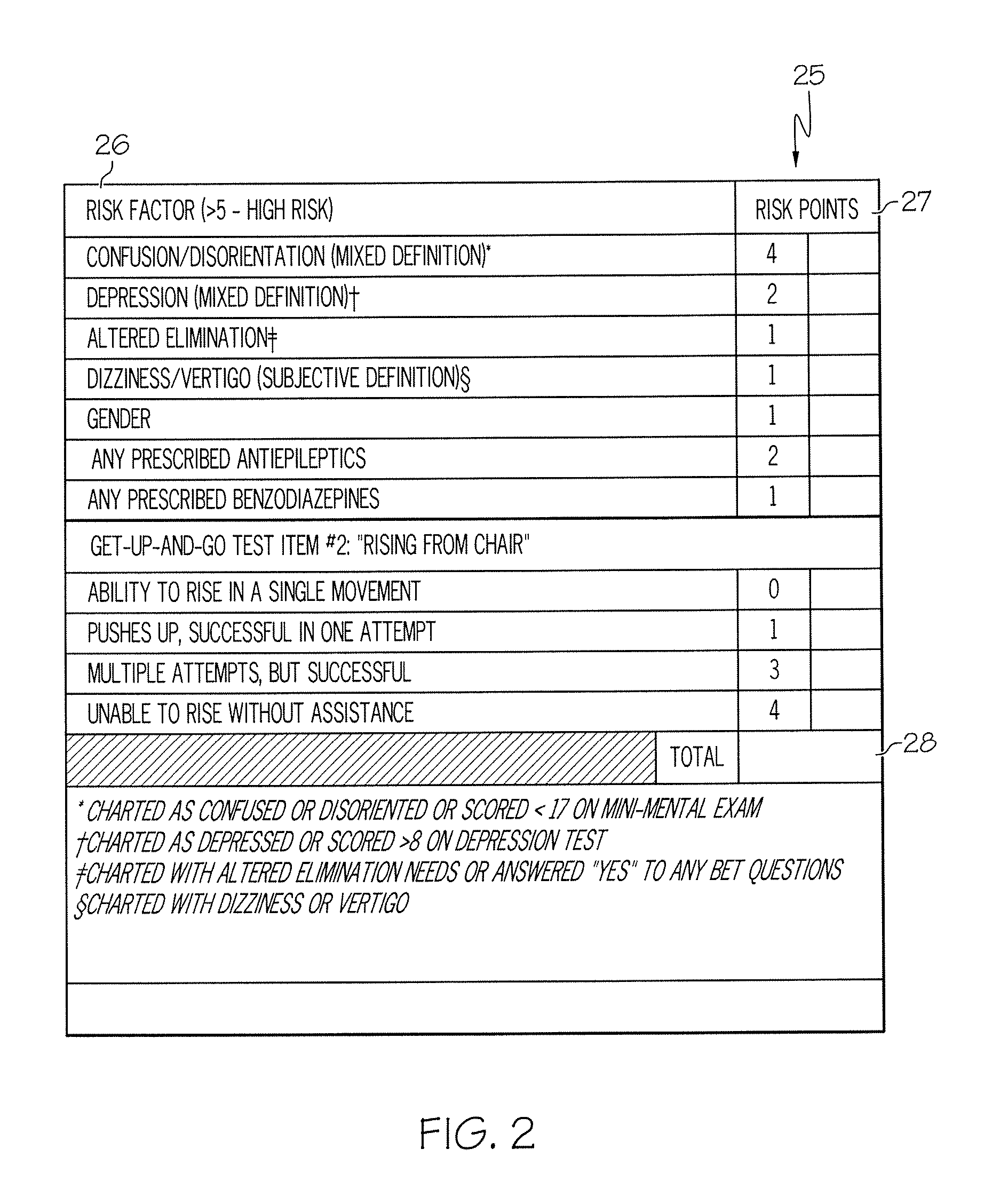
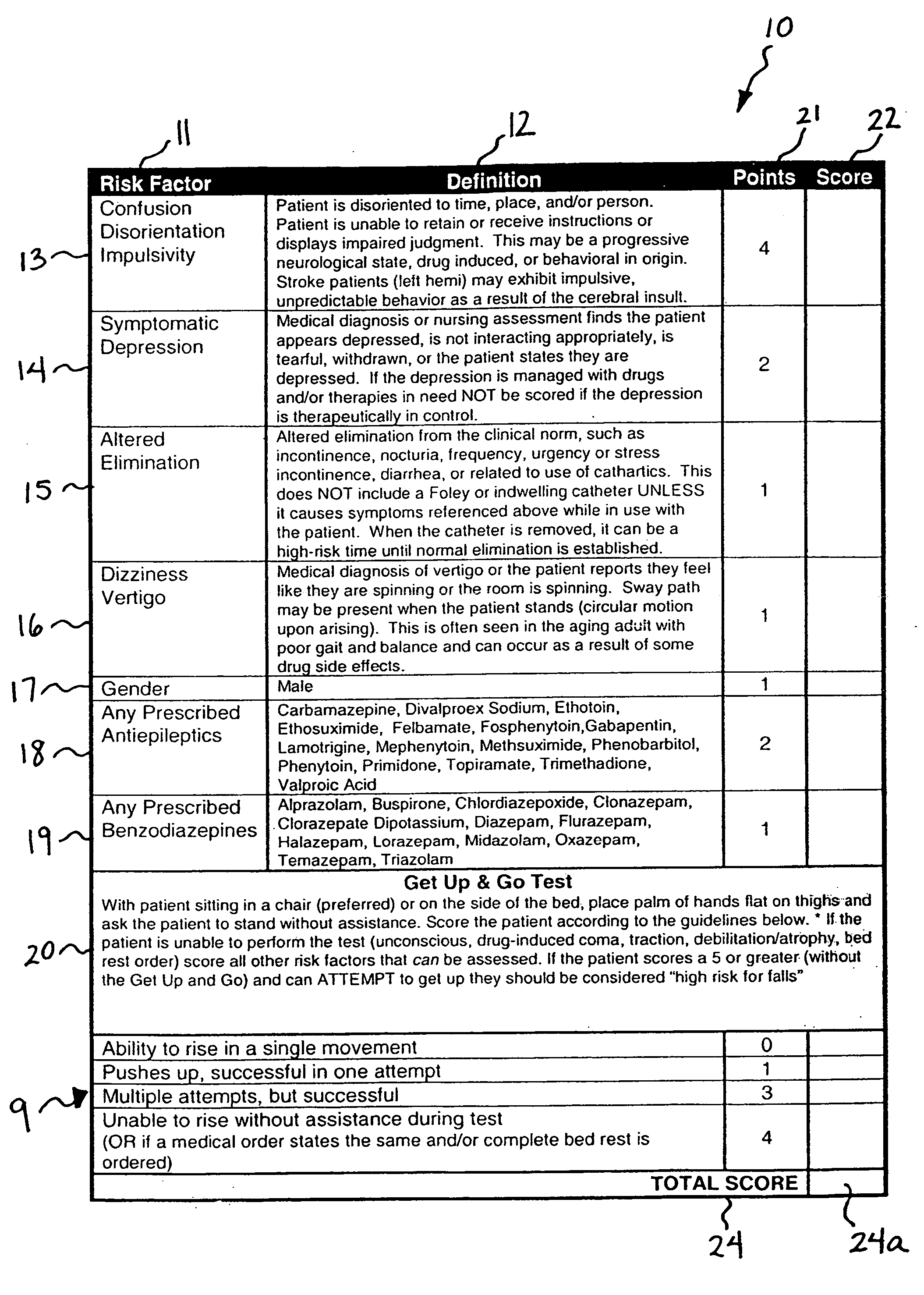
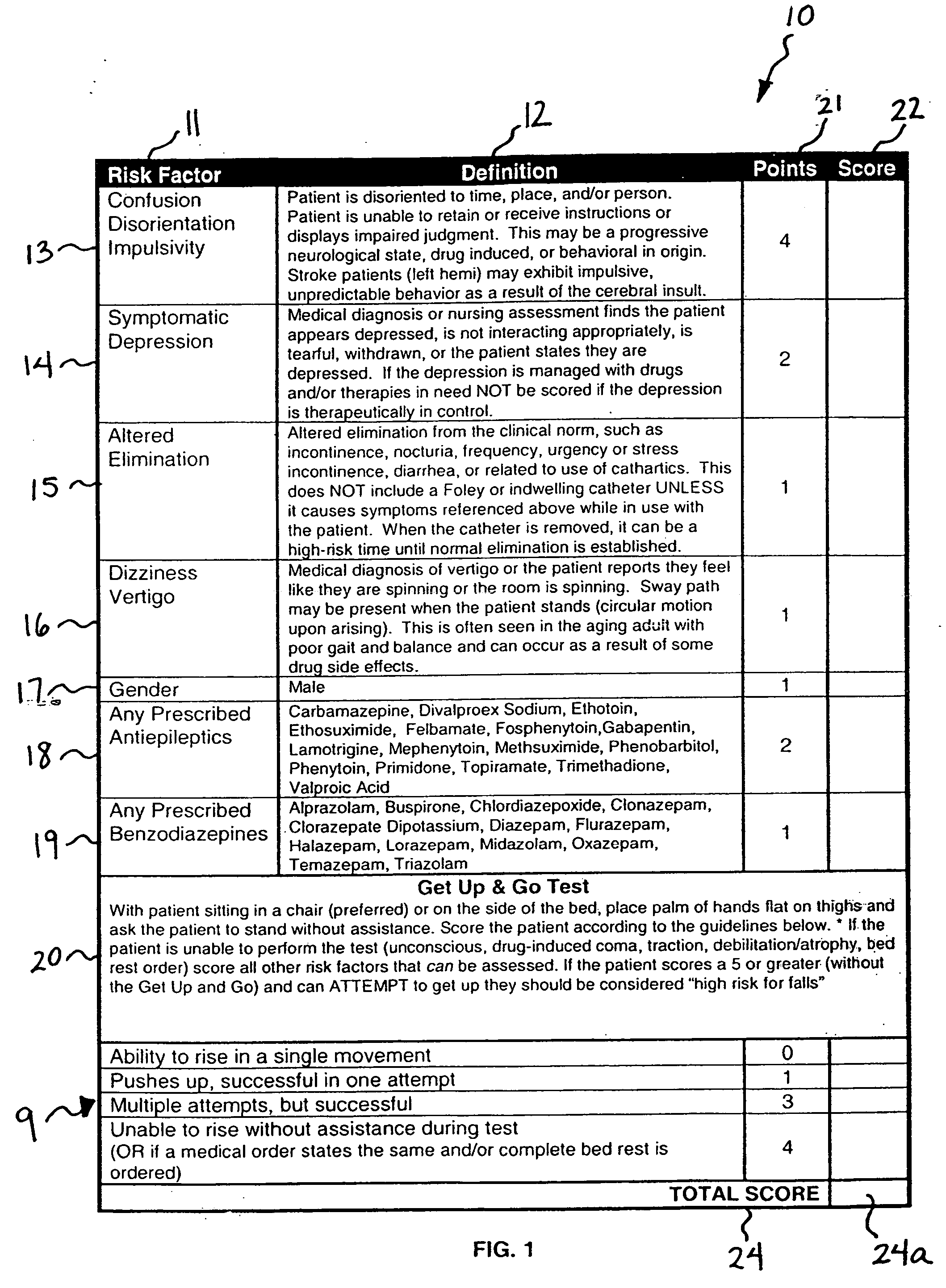
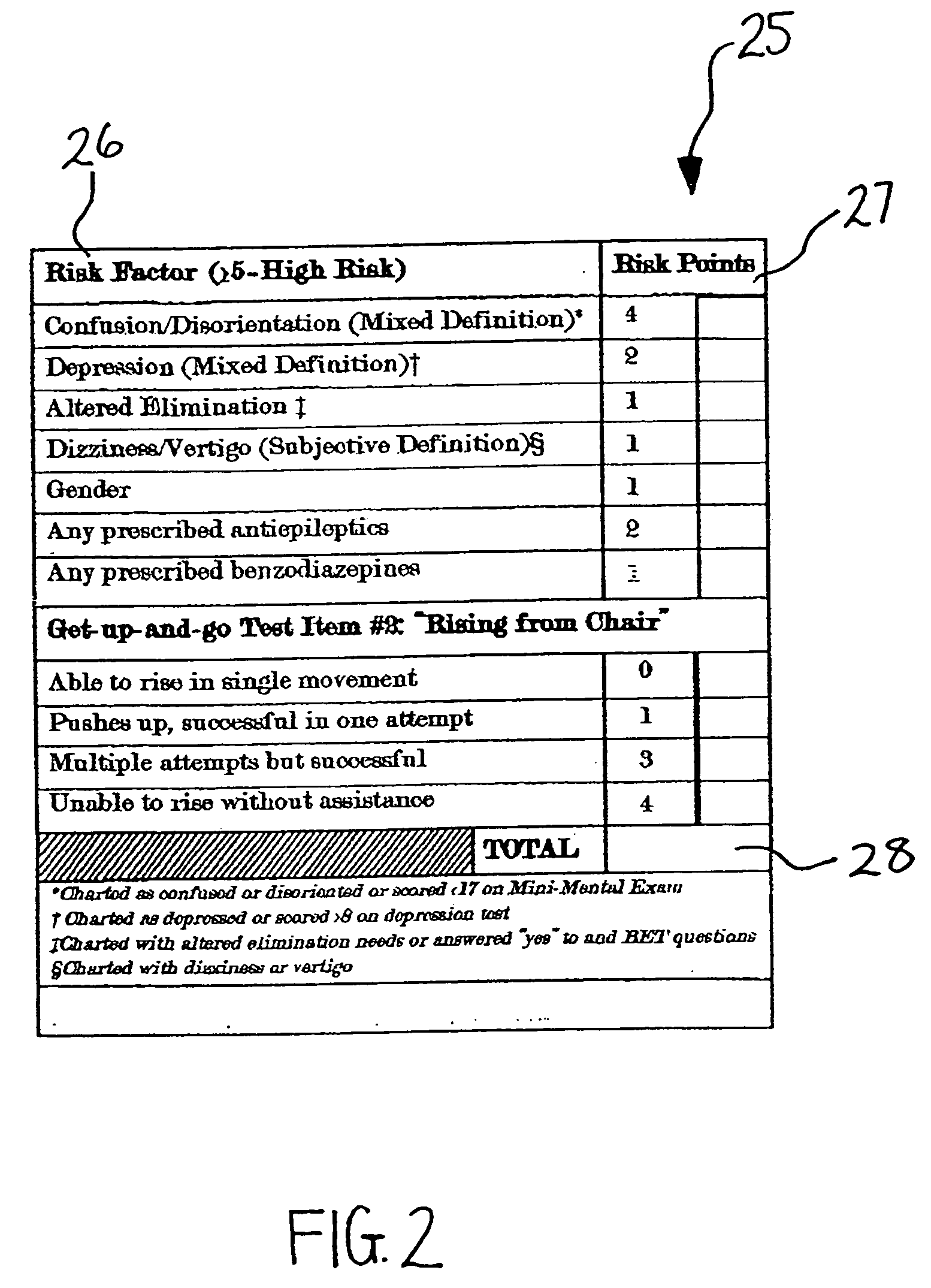
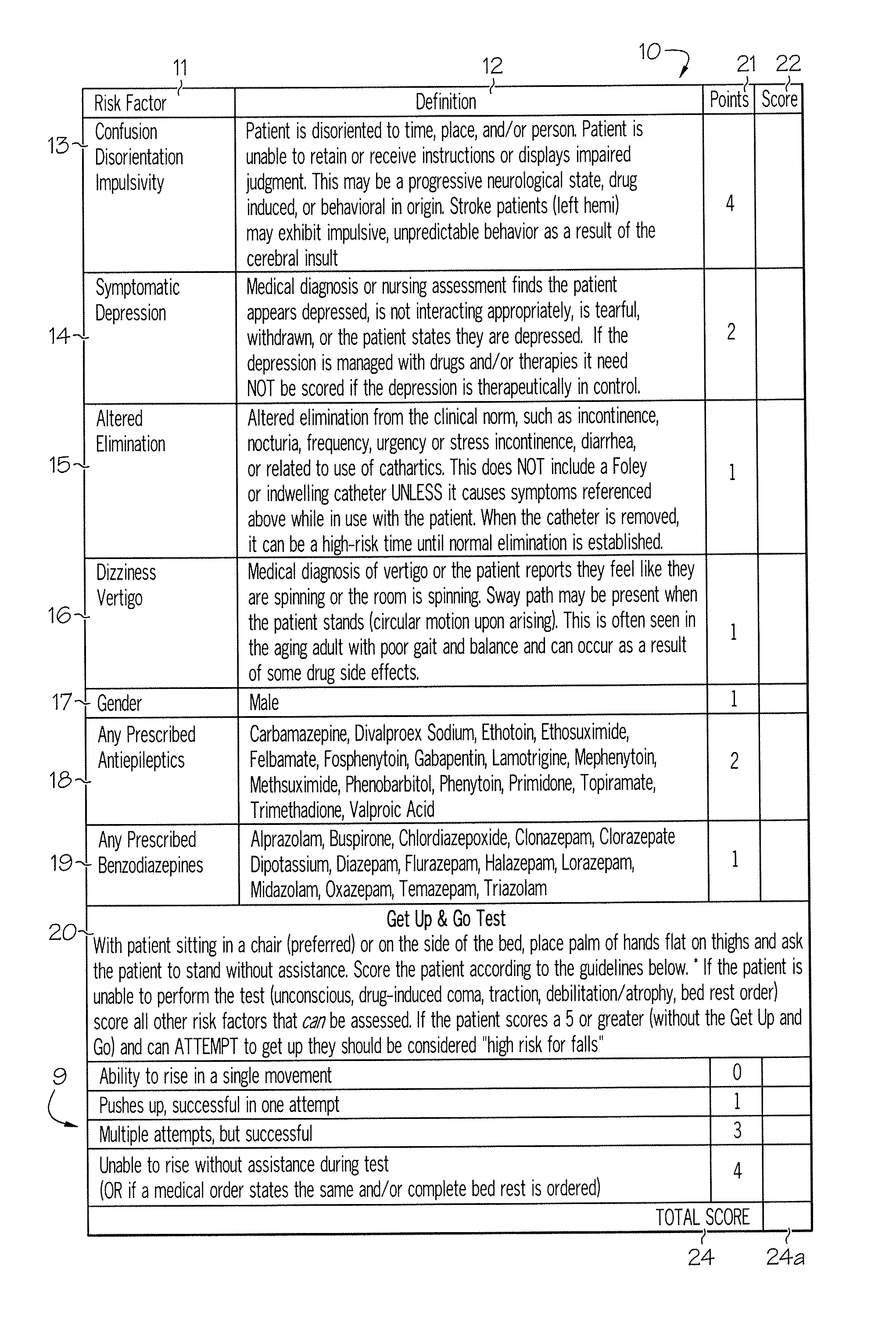
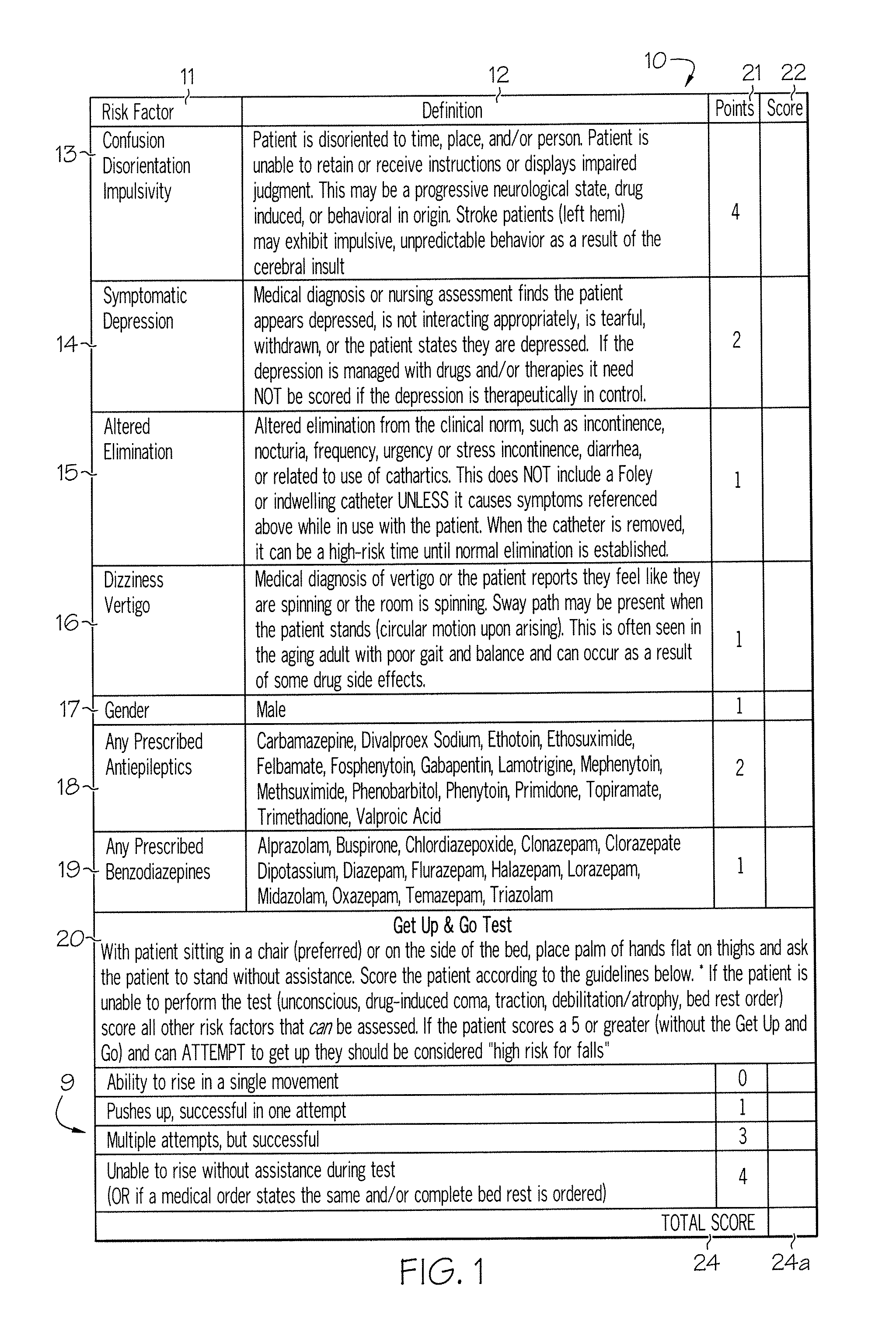
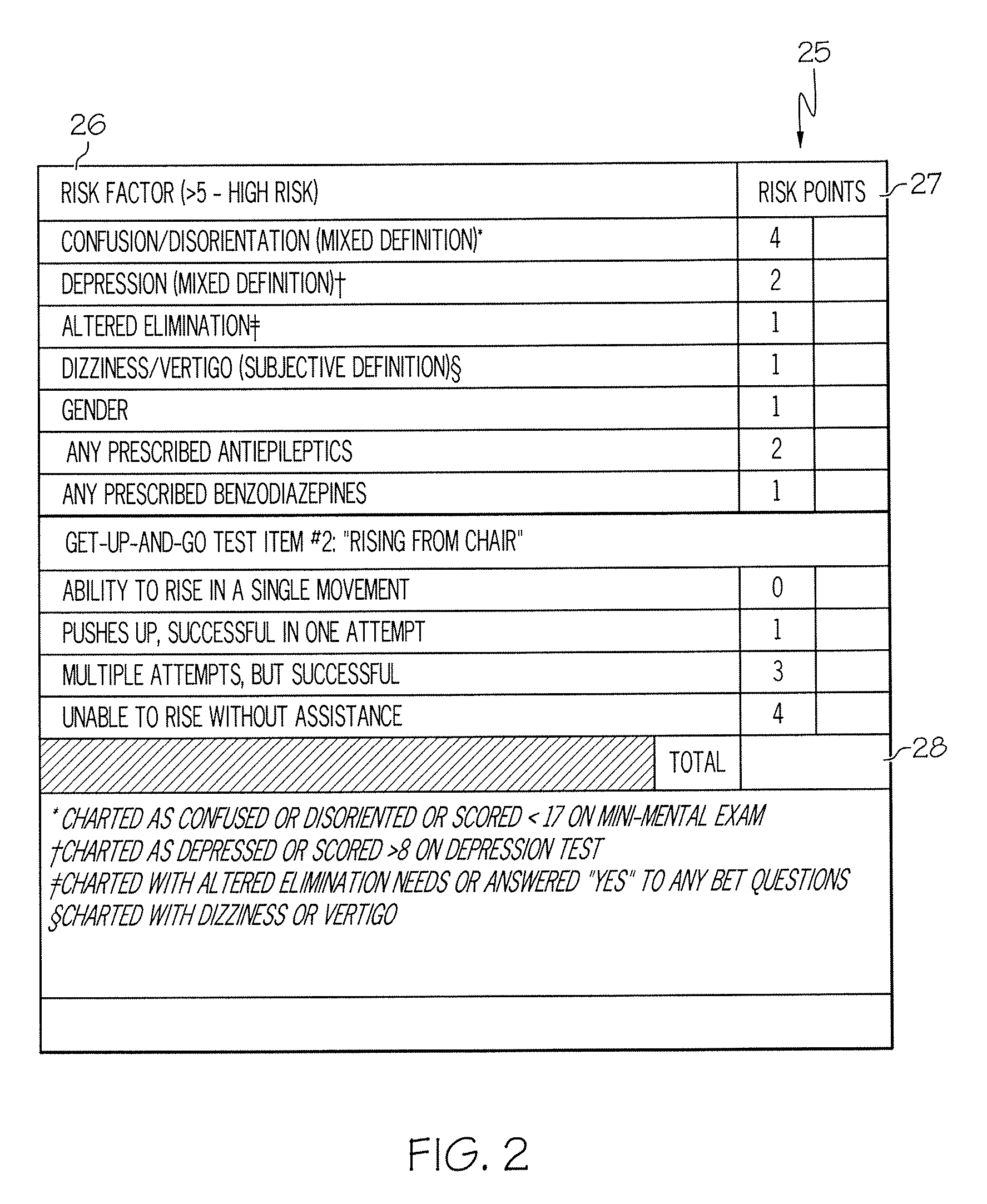
ActiveUS20080009686A1Easy to addAccurate predictionData processing applicationsTherapiesBenzodiazepineTotal risk
A method and system for determining the fall risk of a patient is provided. The method includes the evaluation of a patient to determine whether the patient exhibits one or more intrinsic fall risk factors selected from a group consisting of confusion, depression, altered elimination, dizziness, male gender, antiepileptic / anticonvulsant prescriptions and benzodiazepine prescriptions. A specific point value is assigned to each of the intrinsic risk factors found to be exhibited by the patient. A mobility test is also performed on the patient to evaluate the patient's ability to rise from a seated position, and a specific mobility test point value is assigned to the patient based upon the patient's performance of the mobility test. Each intrinsic risk factor's specific point value is then summed together with the specific mobility test point value to achieve a total risk score, and the patient's fall risk is determined based on the total risk score. An intervention process may be developed for the patient based on the patient's fall risk.
Owner:AHI OF INDIANA
Method and system for assessing fall risk
ActiveUS20050182305A1Easy to addAccurate predictionHealth-index calculationSurgeryBenzodiazepineTotal risk
A method and system for determining the fall risk of a patient is provided. The method includes the evaluation of a patient to determine whether the patient exhibits one or more intrinsic fall risk factors selected from a group consisting of confusion, depression, altered elimination, dizziness, male gender, antiepileptic / anticonvulsant prescriptions and benzodiazepine prescriptions. A specific point value is assigned to each of the intrinsic risk factors found to be exhibited by the patient. A mobility test is also performed on the patient to evaluate the patient's ability to rise from a seated position, and a specific mobility test point value is assigned to the patient based upon the patient's performance of the mobility test. Each intrinsic risk factor's specific point value is then summed together with the specific mobility test point value to achieve a total risk score, and the patient's fall risk is determined based on the total risk score. An intervention process may be developed for the patient based on the patient's fall risk.
Owner:AHI OF INDIANA
Safety level evaluation method of power grid
ActiveCN101800426AEasy to understandPractical applicationAc network circuit arrangementsStructure analysisTotal risk
The invention relates to a safety level evaluation method a power grid, comprising the following steps of: firstly determining a supposed accident list, and sequentially disconnecting elements of the supposed accident list; after a certain element is disconnected, carrying out topological structure analysis and load flow calculation on a system, and then calculating a power grid loss load risk evaluation index, a power grid overload risk evaluation index, a power grid low voltage risk evaluation index and a power grid voltage collapse risk evaluation index; repeating the process till all the elements of the supposed accident list are completely calculated; and then calculating a system single-risk evaluation index and a system total-risk evaluation index. The invention introduces a risk theory and a utility theory to the safety evaluation of the power grid, separately diagnoses the safety of the system from different side surfaces, further obtains the risk evaluation index of the whole system by an analytic hierarchy process (AHP), obtains simple and clear results and has better discrimination and can reflect the occurrence possibility of different accidental accidents and severity degree of a consequence caused by the accidental accidents.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +1
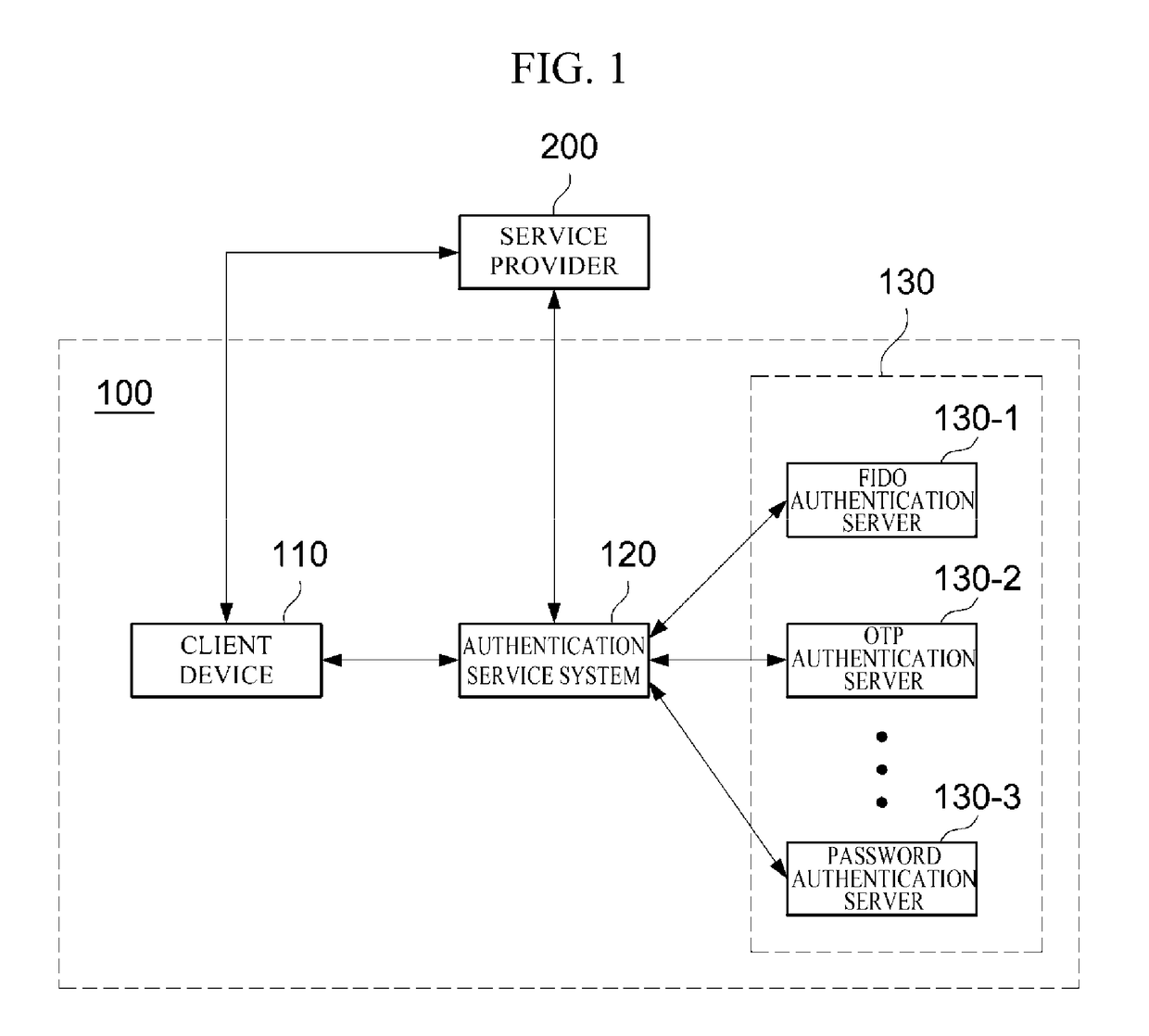
Risk analysis apparatus and method for risk based authentication
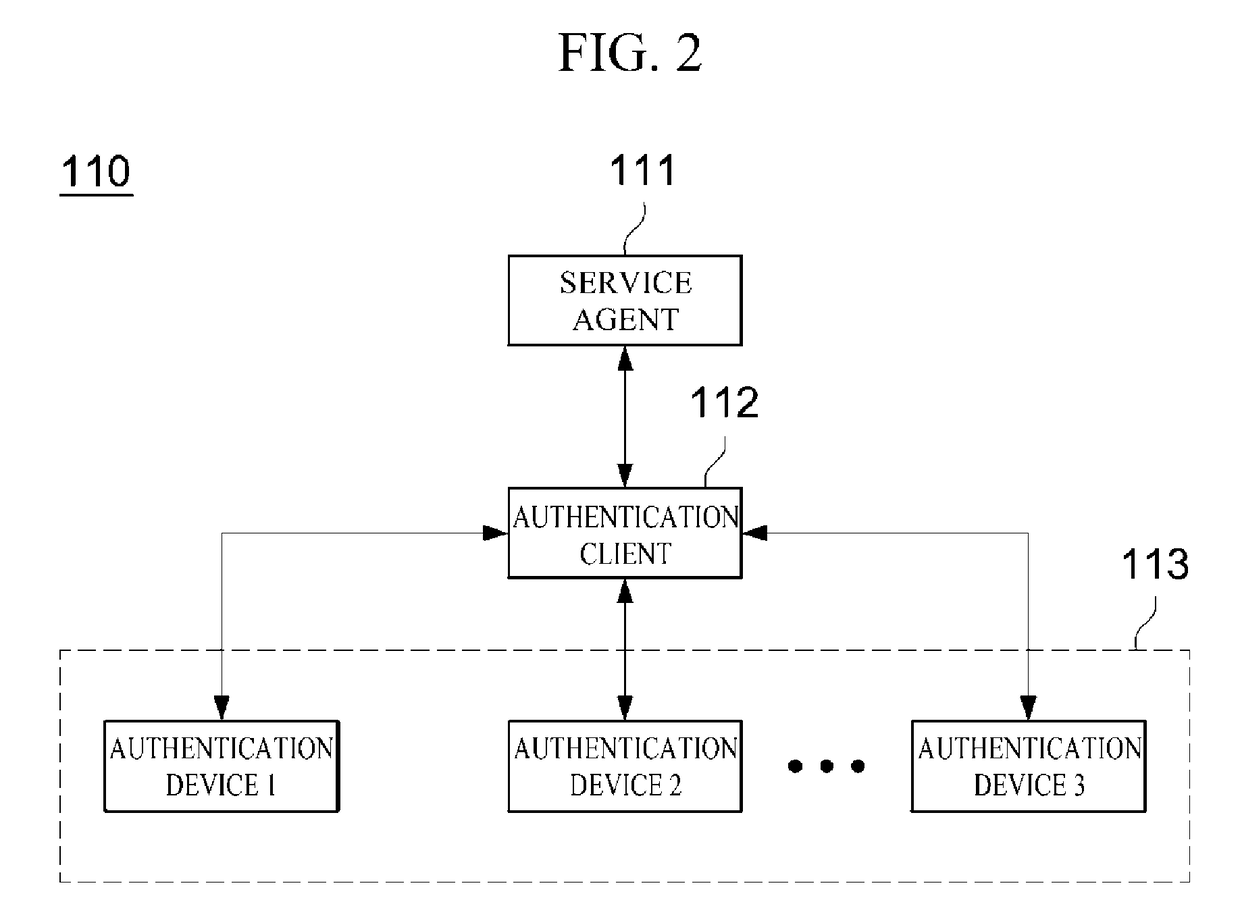
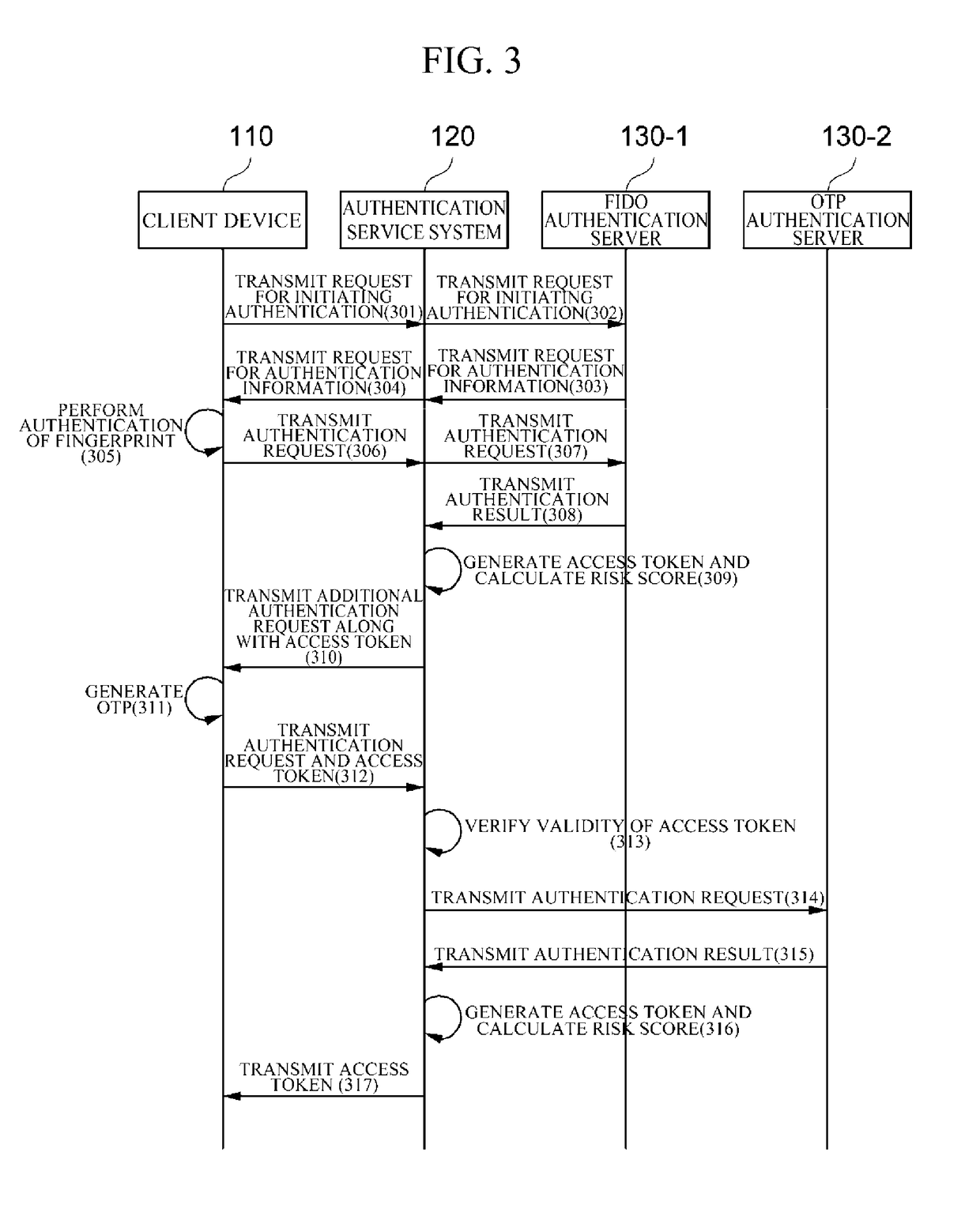
ActiveUS20180341758A1Well formedImprove system flexibilityDigital data authenticationRisk profilingTotal risk
A risk analysis apparatus and method are provided. According to one embodiment of the present disclosure, the risk analysis apparatus includes: at least one processor configured to: a risk factor collector configured to collect risk factors related to one or more authentication processes for authentication of a user of a client device in an authentication system; a risk analyzer configured to calculate a current risk score for the user based on the collected risk factors and calculate a total risk score based on a risk score history of the user and the current risk score based on the one or more authentication processes being successful; and an additional authentication requester configured to determine whether additional authentication of the user is required based on the current risk score and the total risk score and, request the client device for the additional authentication of the user based on the additional authentication being required.
Owner:SAMSUNG SDS CO LTD
System for managing the total risk exposure for a portfolio of loans
A computer system for monitoring and enhancing the collateral security underlying a set of loans is provided, including a system for calculating the unsecured value of the set at any time and for initiating additional collateral enhancement instruments when the unsecured value exceeds a certain limit. The system may include a variety of modules in communication with a relational database for storing data about the loans and system elements. The computer system may also be configured to allocate, manage, and execute the waterfall or cascade of funds between and among the various participants in a financial plan. The invention also includes a structured finance plan and related methods for enhancing the collateral security of a loan obtained for a life insurance or annuity product, and a system and method for managing a portfolio of such loans in order to obtain favorable financing and to facilitate securitization.
Owner:ENTAIRE GLOBAL INTPROP
Fully autonomous vehicle insurance pricing
ActiveUS10373259B1Facilitate risk assessmentFacilitate premium determinationFinanceRisk levelTotal risk
Methods and systems for determining risk associated with operation of fully autonomous vehicles are provided. According to certain aspects, autonomous operation features associated with a vehicle may be determined, including types and version of sensors, control systems, and software. This information may be used to determine a risk profile reflecting risk levels for a plurality of features, which may be based upon test data regarding the features or actual loss data. Expected use levels may further be determined and used with the risk profile to determine a total risk level associated with operation of the vehicle by the autonomous operation features. The expected use levels may indicate expected vehicle use, as well as traffic, weather, or other conditions in which the vehicle is likely to operate. The total risk level may be used to determine or adjust aspects of an insurance policy associated with the vehicle.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
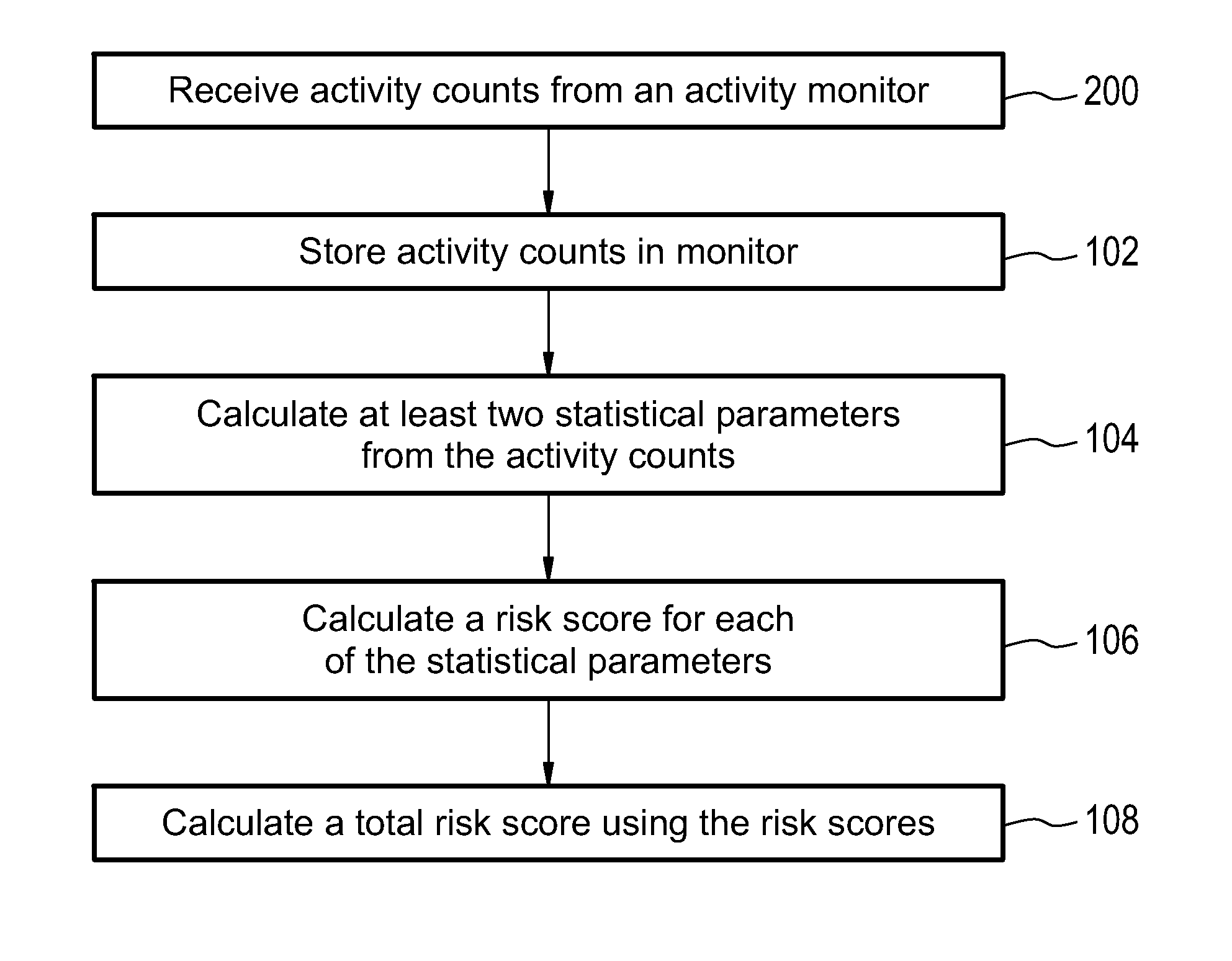
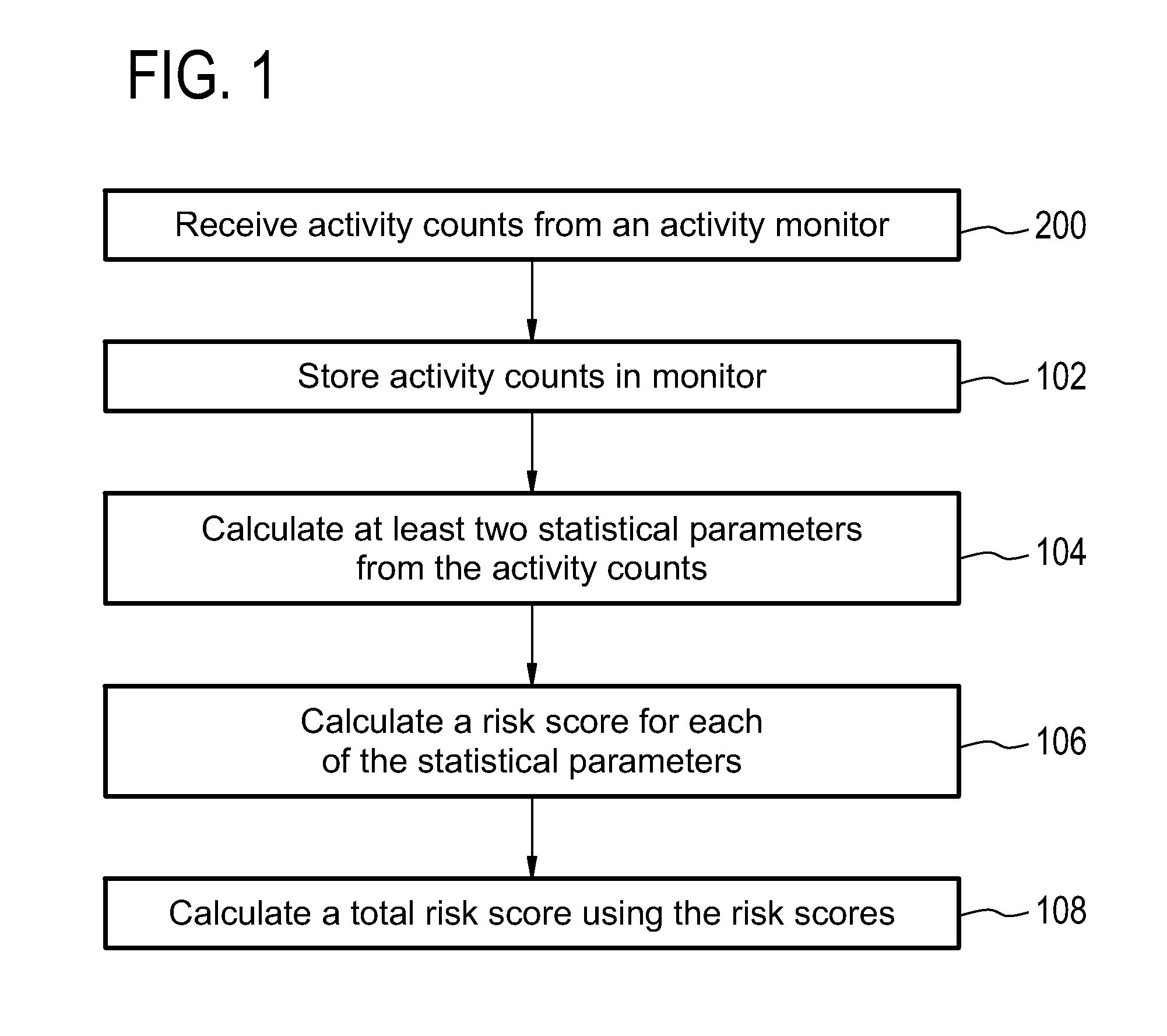
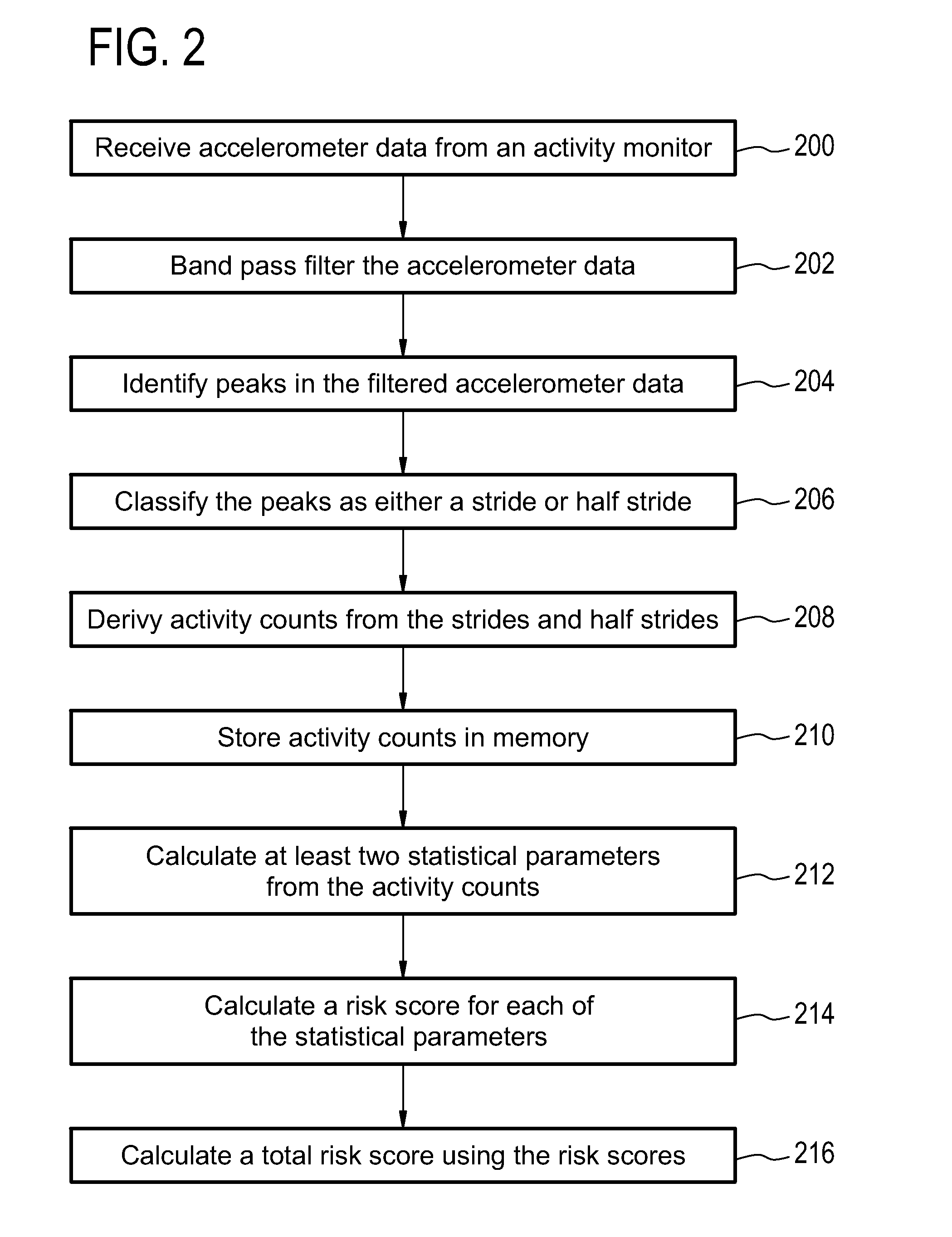
Health monitoring system for calculating a total risk score
InactiveUS20150324541A1Avoid hospitalizationData processing applicationsHealth-index calculationTotal riskMonitoring system
Embodiments of the invention provide for a health monitoring system comprising an activity monitor. The health monitoring system further comprises a processor and a memory for storing machine readable instructions. The instructions cause the processor to derive activity counts from the activity data acquired by the activity monitor. The instructions further cause the processor to store the activity counts in the memory, and are associated with a time. The instructions further cause the processor to calculate at least two statistical parameters from the activity counts, wherein the at least two statistical parameters are descriptive of the activity counts as a function of time. The instructions further causes the processor to calculate a risk score for each of the at least two statistical parameters. The instructions further cause the processor to calculate a total risk score using the risk score for each of the at least two statistical parameters.
Owner:KONINKLJIJKE PHILIPS NV
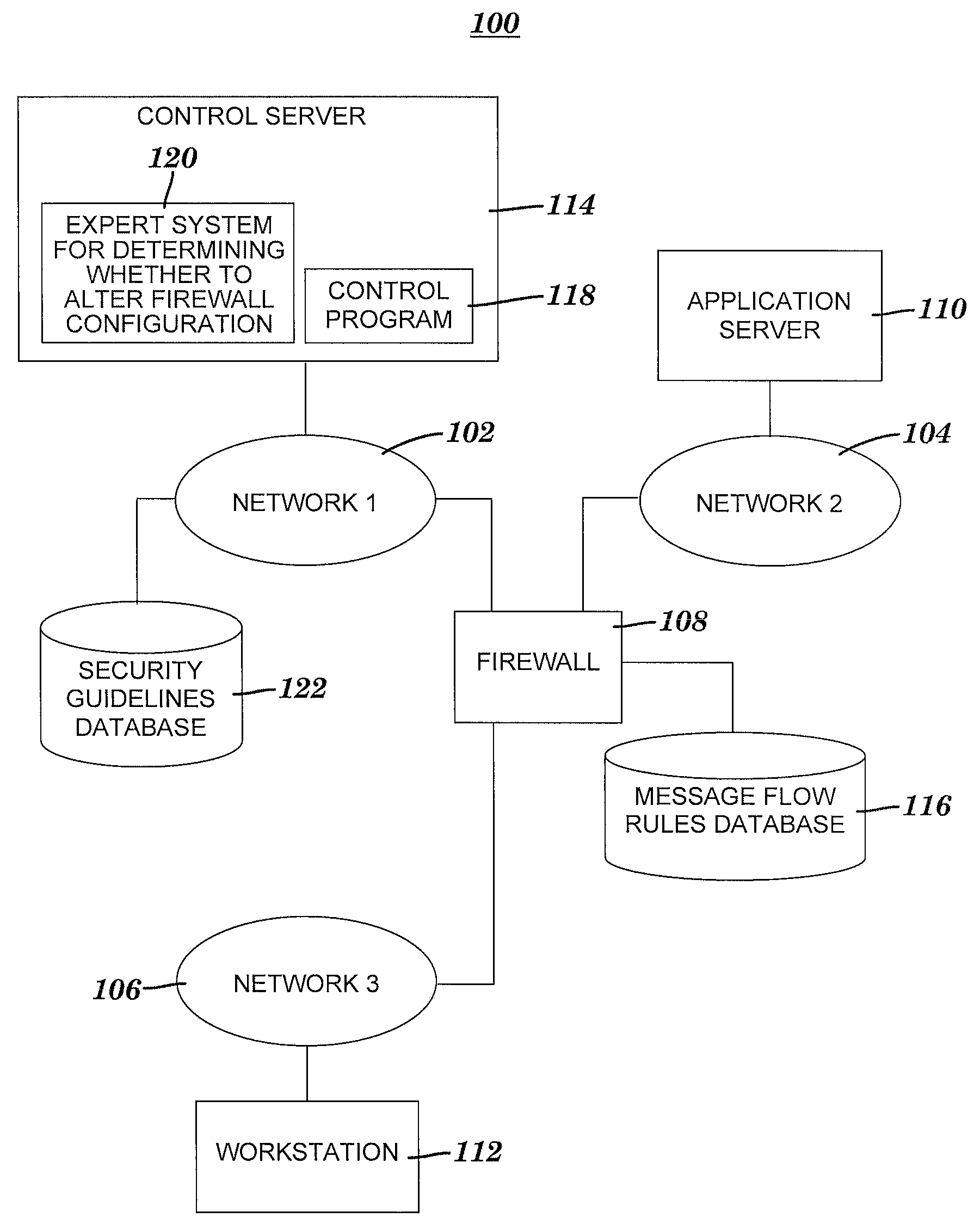
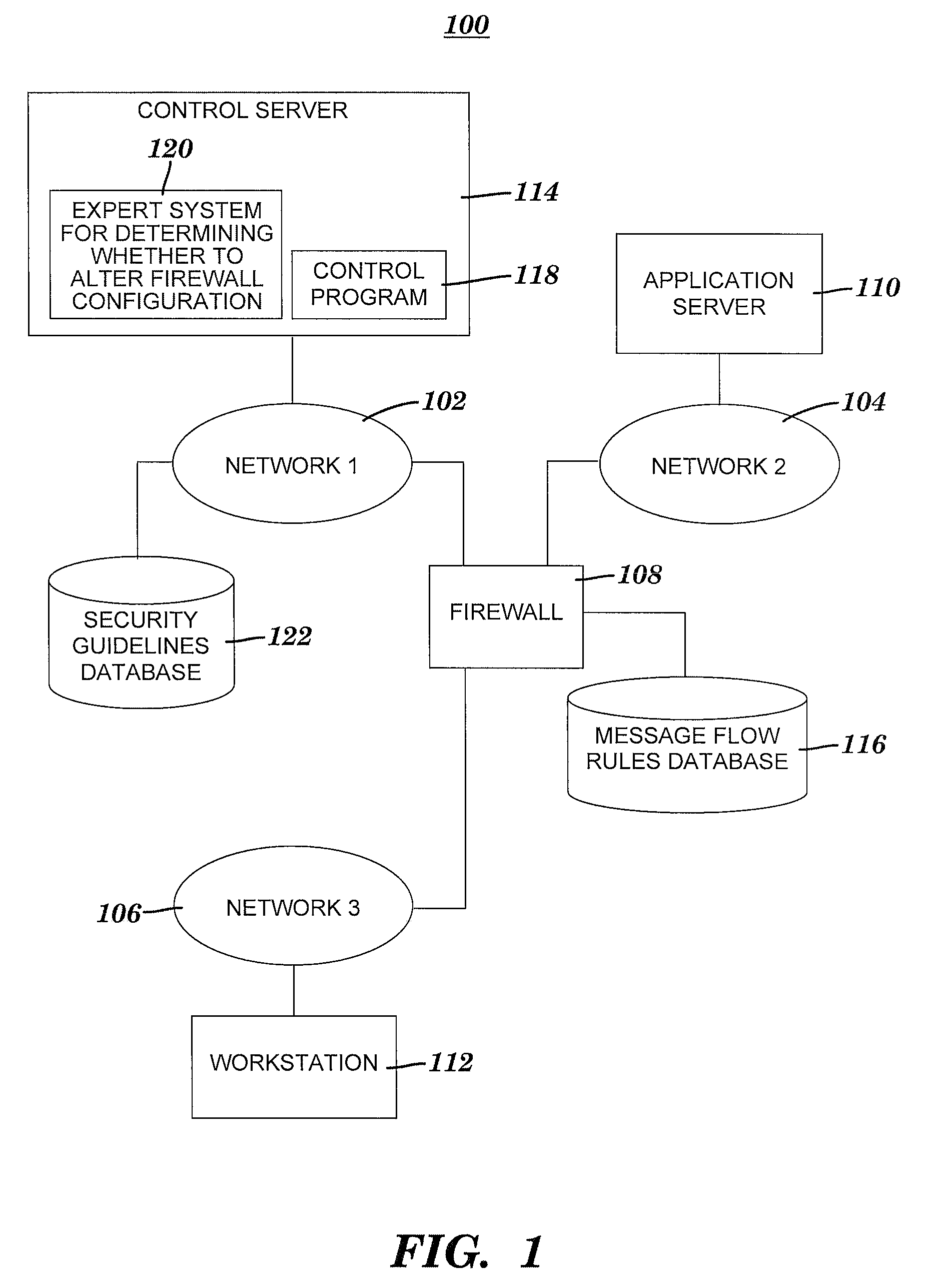
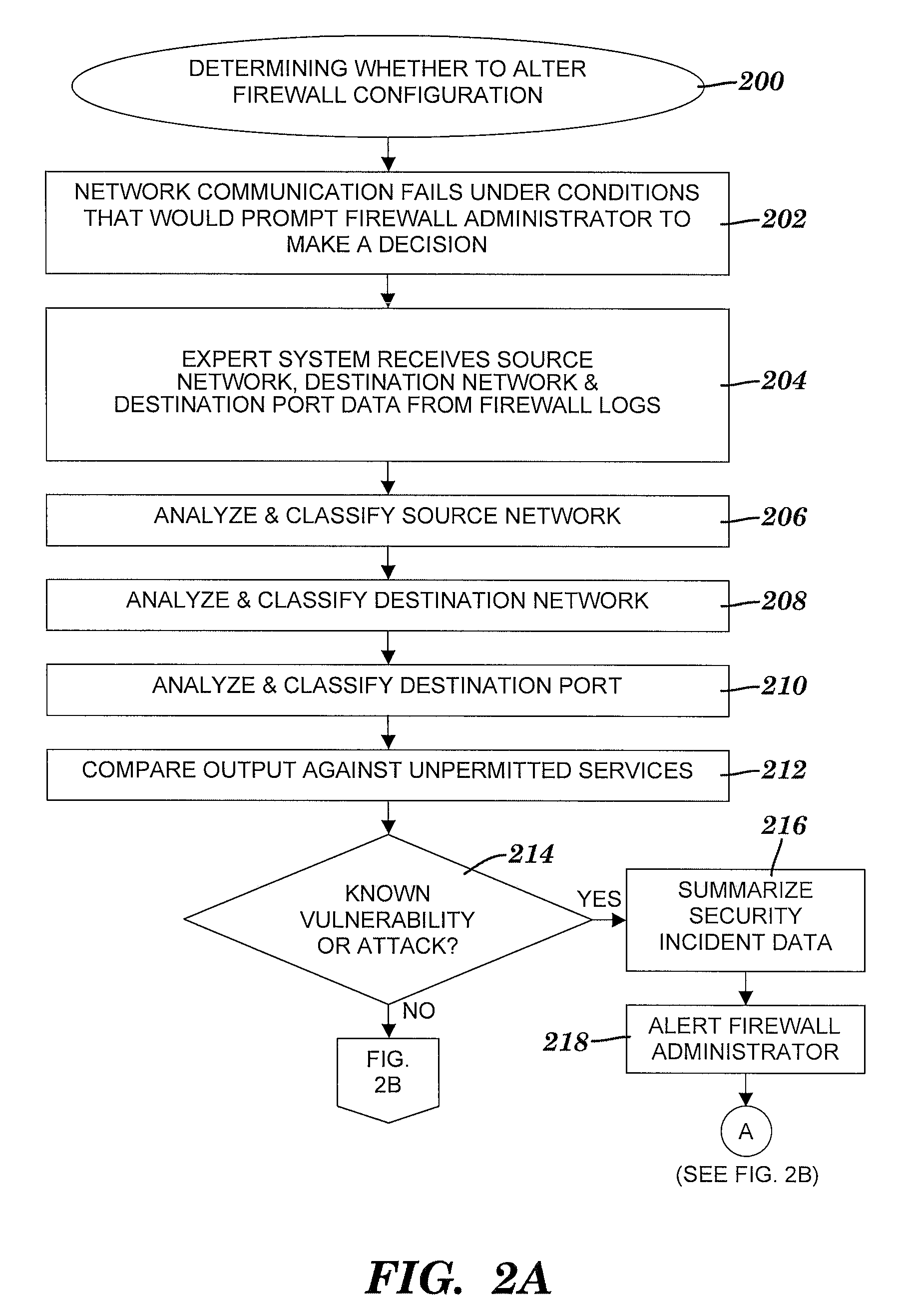
Method and sysem for utilizing an expert system to determine whether to alter a firewall configuration
ActiveUS20080172347A1Shorten the timeComputer security arrangementsMultiple digital computer combinationsTotal riskMessage flow
A method and system for utilizing an expert system to determine whether to alter a firewall configuration. The expert system receives message flow data associated with a message packet blocked by a firewall. The packet is blocked based on an associated message flow not being permitted by a set of rules. The expert system assigns predefined risk values to the message flow data so that each risk value is associated with a source network, destination network or destination port included in the message flow data. The expert system utilizes the assigned risk values to determine a total risk value associated with the message packet. Finally, the expert system generates a proposal based on the total risk value. The proposal is a recommendation for or against adding to the set of rules a message flow rule that permits the message flow.
Owner:WRP IP MANAGEMENT LLC
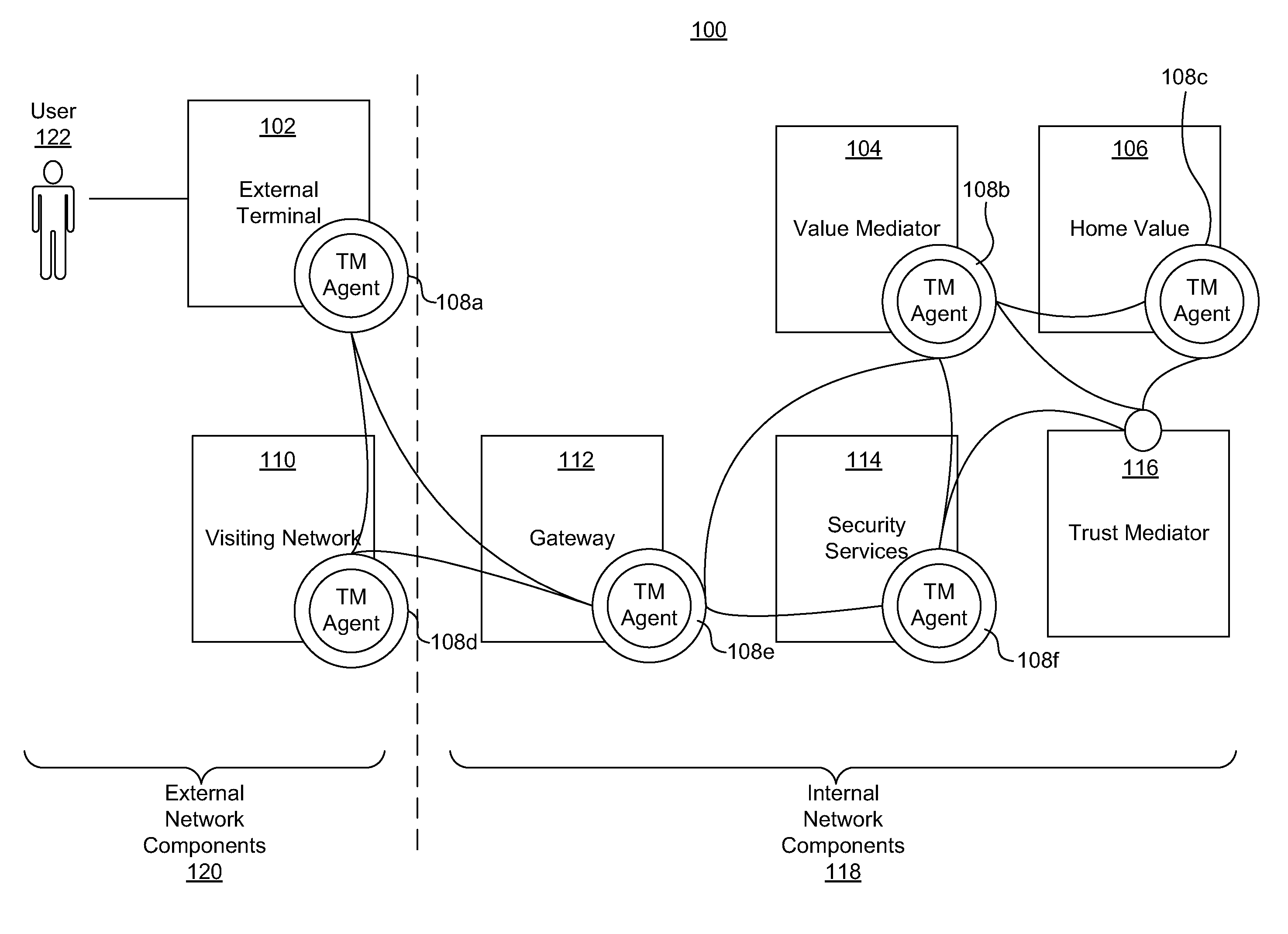
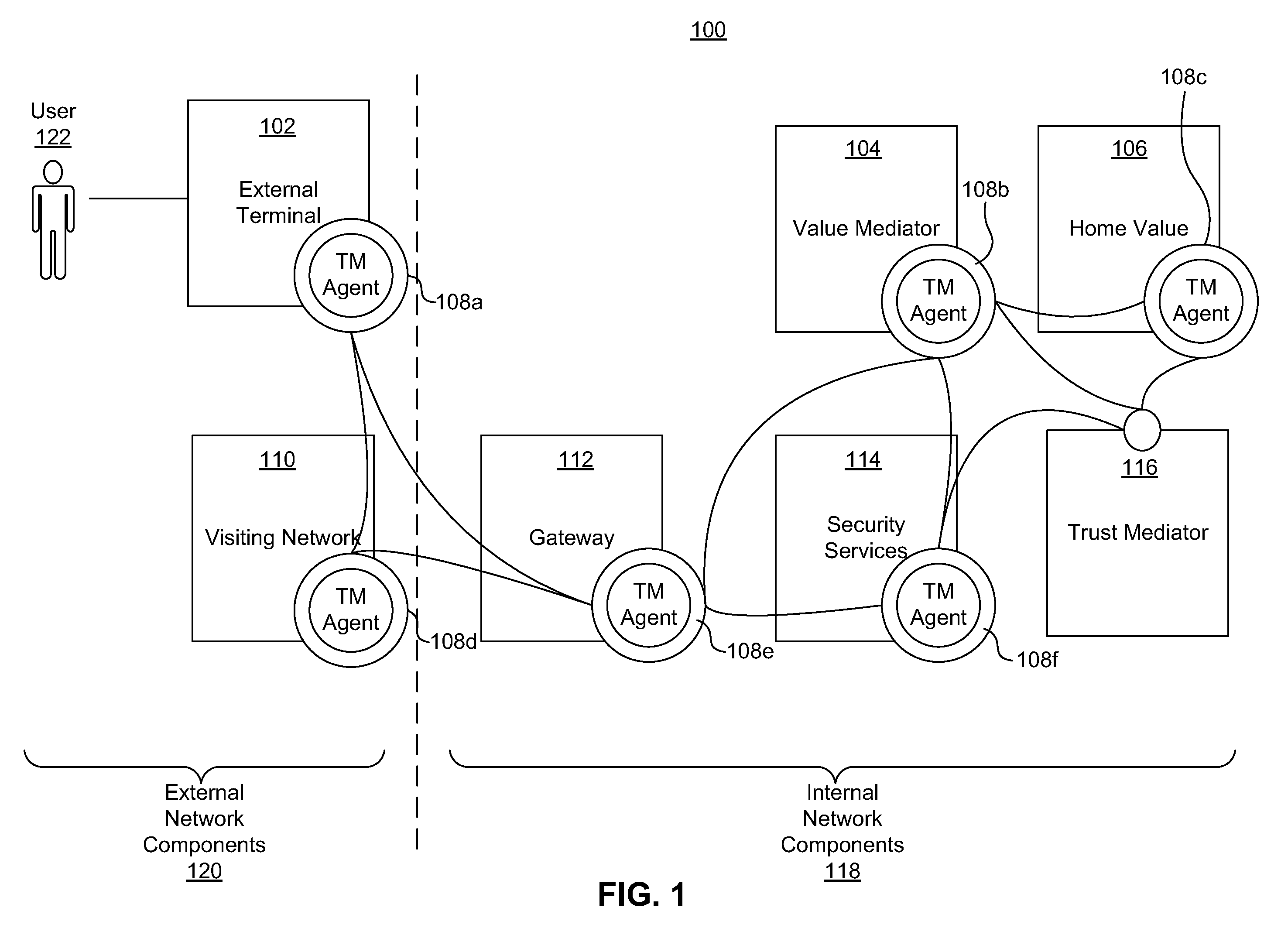
Dynamic pairing system for securing a trusted communication channel
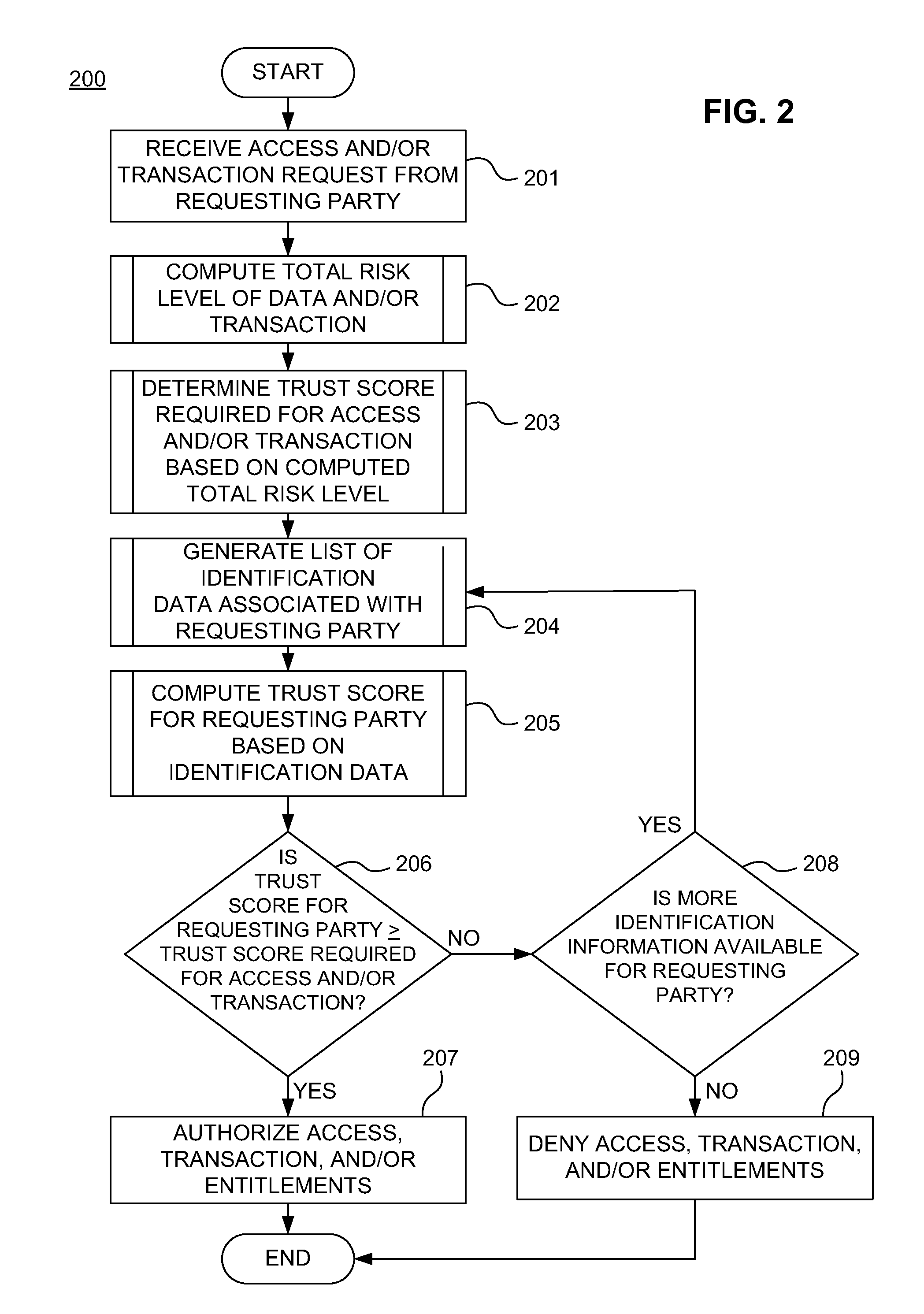
ActiveUS20110313925A1Shorten the time to marketIncrease propensityFinancePayment architectureTotal riskInternet privacy
A system for securing a trusted communications channel for a mobile financial transaction is provided by receiving, from a user via an external terminal, a request for an access control entitlement to complete a financial transaction. A total risk level associated with the financial transaction is computed. A required trust score is determined based on the total risk level. User identification data associated with the user is received from one or more data sources. The user identification data is validated. A user trust score associated with the user is computed based on the validated identification data. The user trust score is compared to the required trust score. The access control entitlement is transmitted to the user via the external terminal if the user trust score is greater than or equal to the required trust score.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
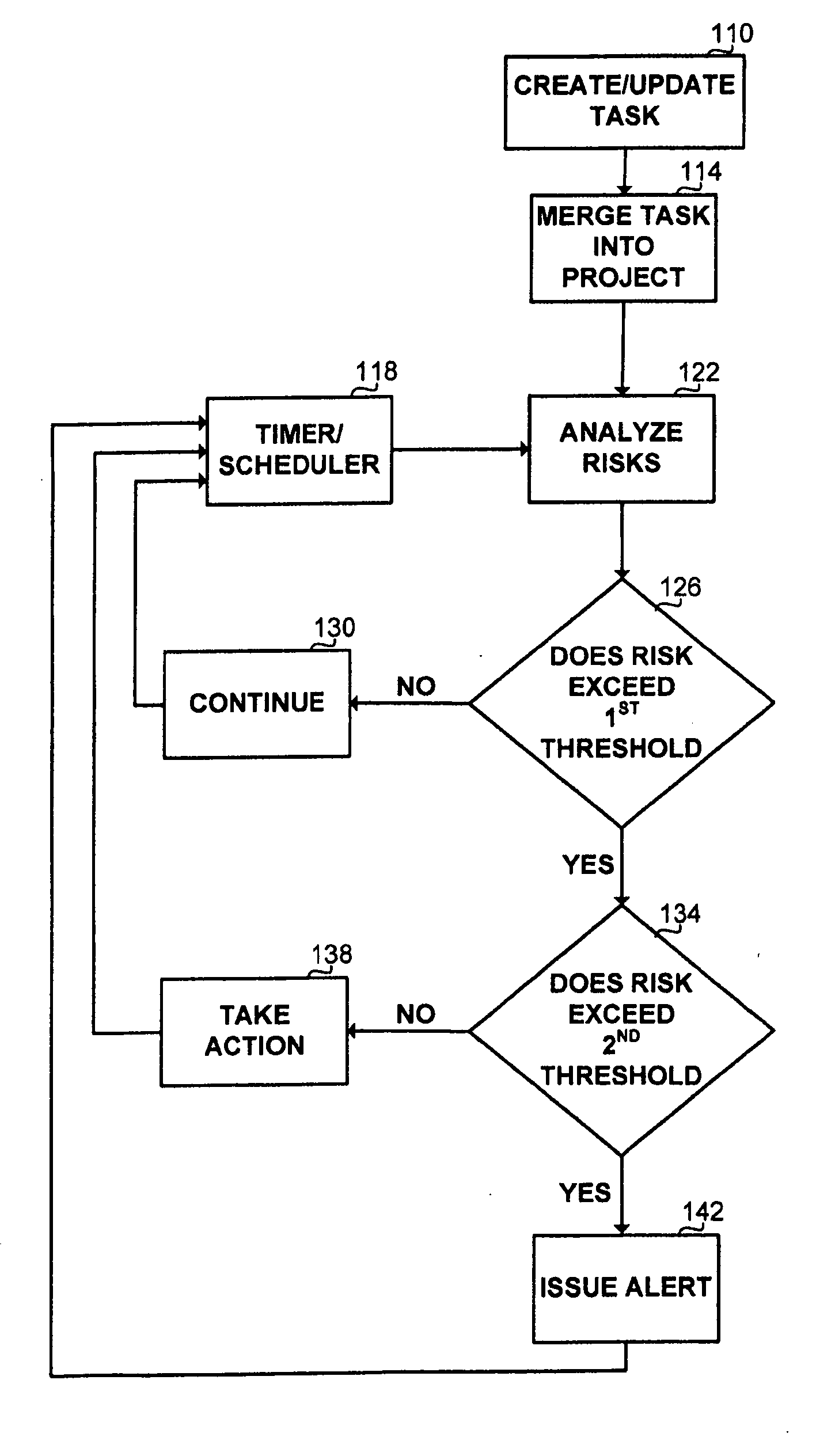
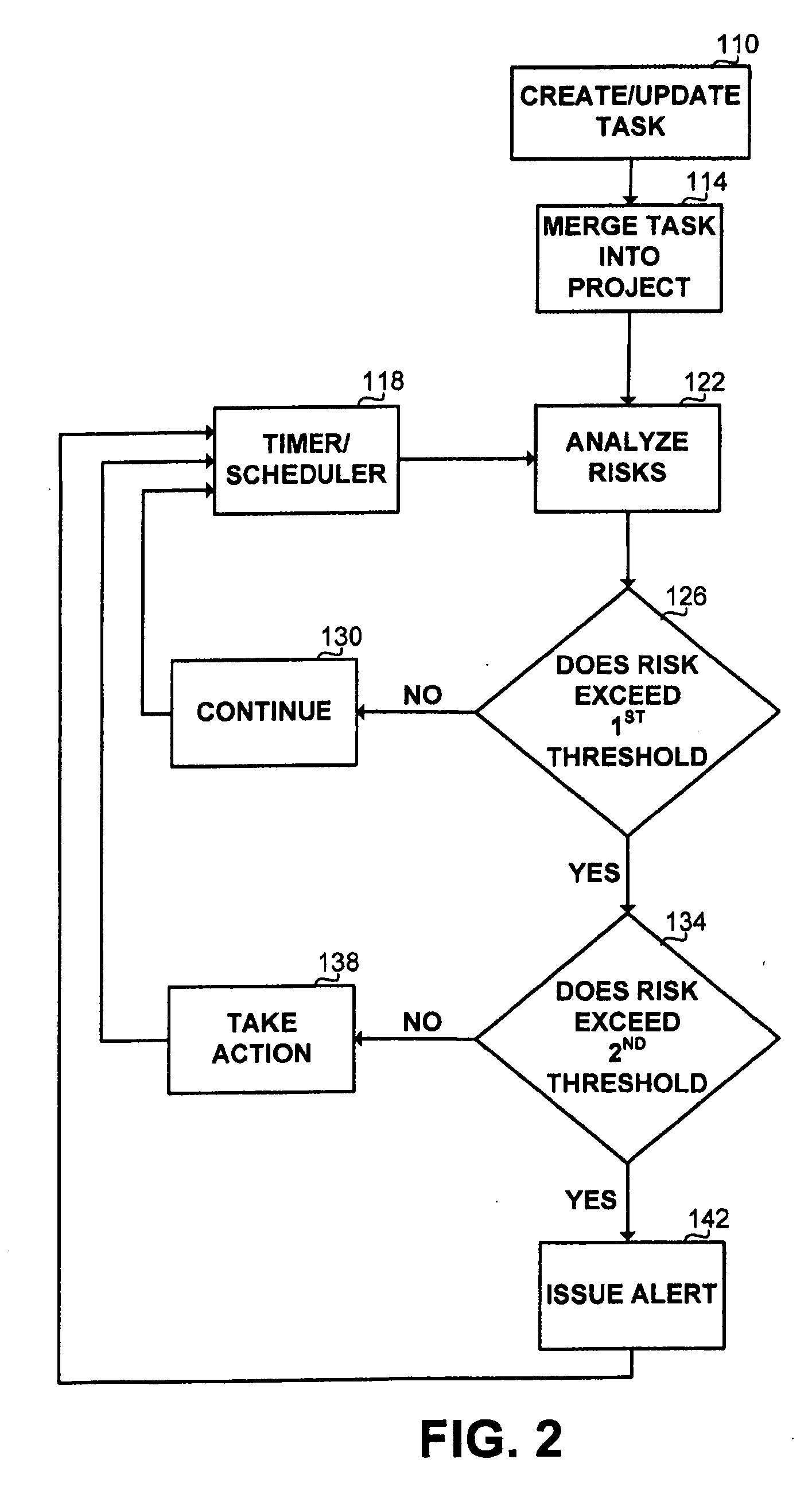
Method and apparatus for dynamic risk assessment
A method and apparatus for assessing at least one aggregate risk associated with an at least one first task associated with an at least one project, reducing said aggregate risk or alerting about said aggregate risk, the method comprising the steps of: determining a partial risk associated with said task; determining an aggregate risk associated with said task; comparing said aggregate risk a threshold; and wherein said total risk exceeds said threshold, performing at least one action. The method is executed dynamically as a response to on-going events occurring in the project. The actions taken can be notifications, inquiries and corrective actions.
Owner:PROLIFY
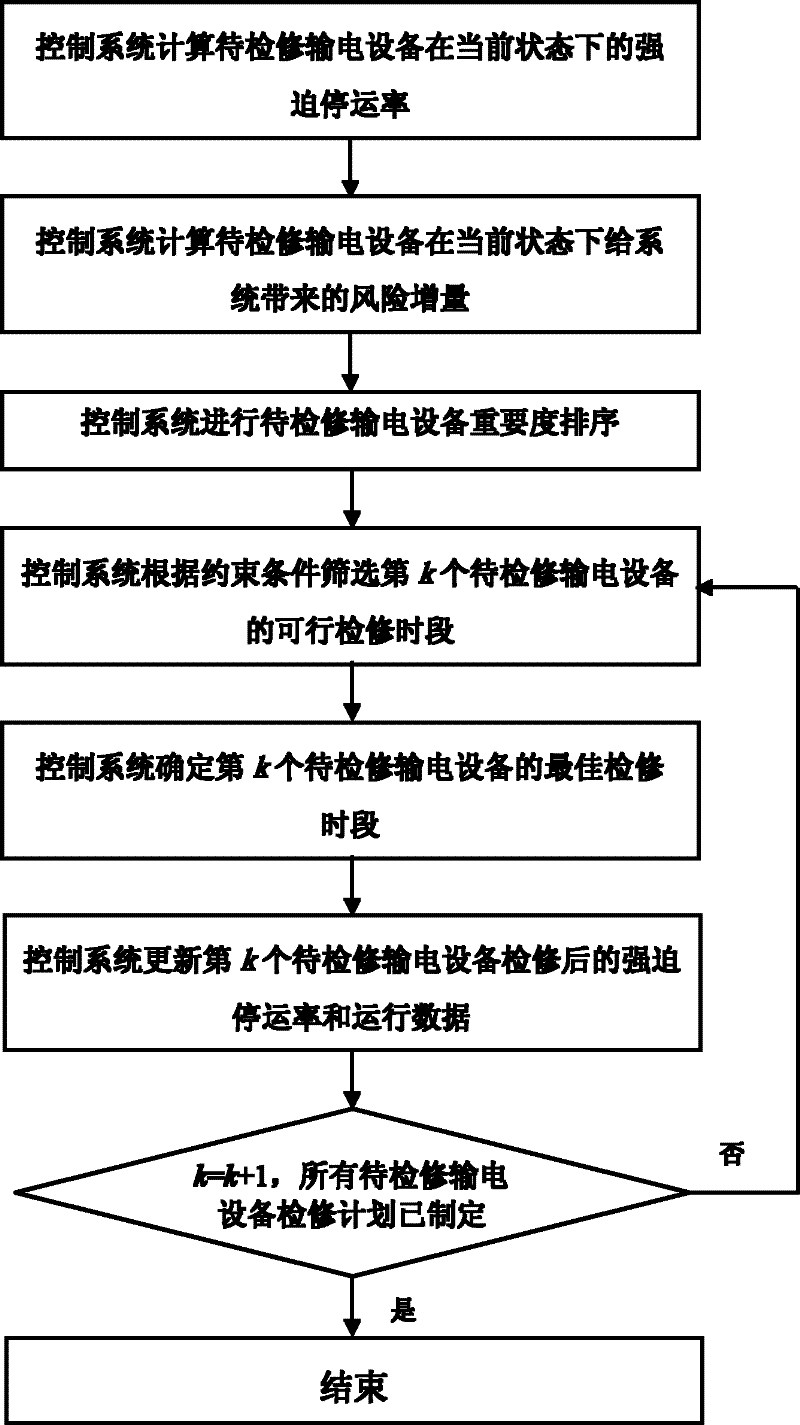
A condition-based maintenance method for power transmission equipment based on system risk
The invention discloses a method for maintaining the state of power transmission equipment based on a system risk. The method comprises the following steps that: a control system calculates the forced stoppage rate of the power transmission equipment to be maintained under the current state; the control system calculates a risk increment which is brought to the system by the power transmission equipment to be maintained under the current state; the control system sequences the importance of the power transmission equipment to be maintained; the control system screens feasible maintenance timeintervals of the kth power transmission equipment to be maintained according to restraint conditions; the control system determines the optimum maintenance time interval of the kth power transmissionequipment to be maintained; the control system updates the forced stoppage rate and operating data of the kth power transmission equipment to be maintained after maintenance, wherein k is equal to k+1; and if maintenance schedules of all pieces of power transmission equipment to be maintained are made, the system ends operation, otherwise, the system repeatedly executes the operation. By the method, a new equipment importance evaluation index is provided and can reflect the current state of the equipment and influence size of the system risk. On the premise of an operating mode of a power system and the time sequence change of the state of the equipment, the total risk of the system in investigation time is minimized.
Owner:XI AN JIAOTONG UNIV
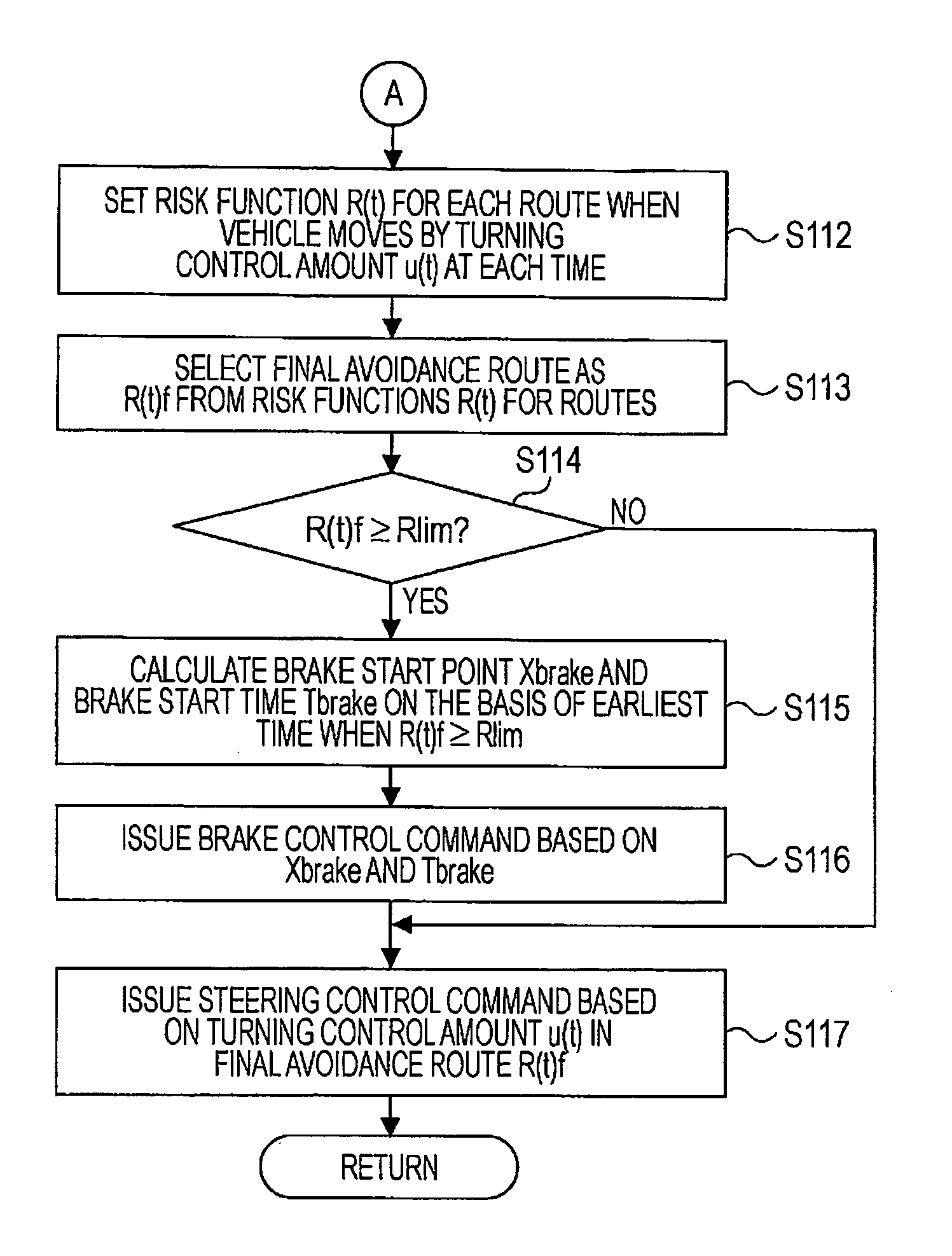
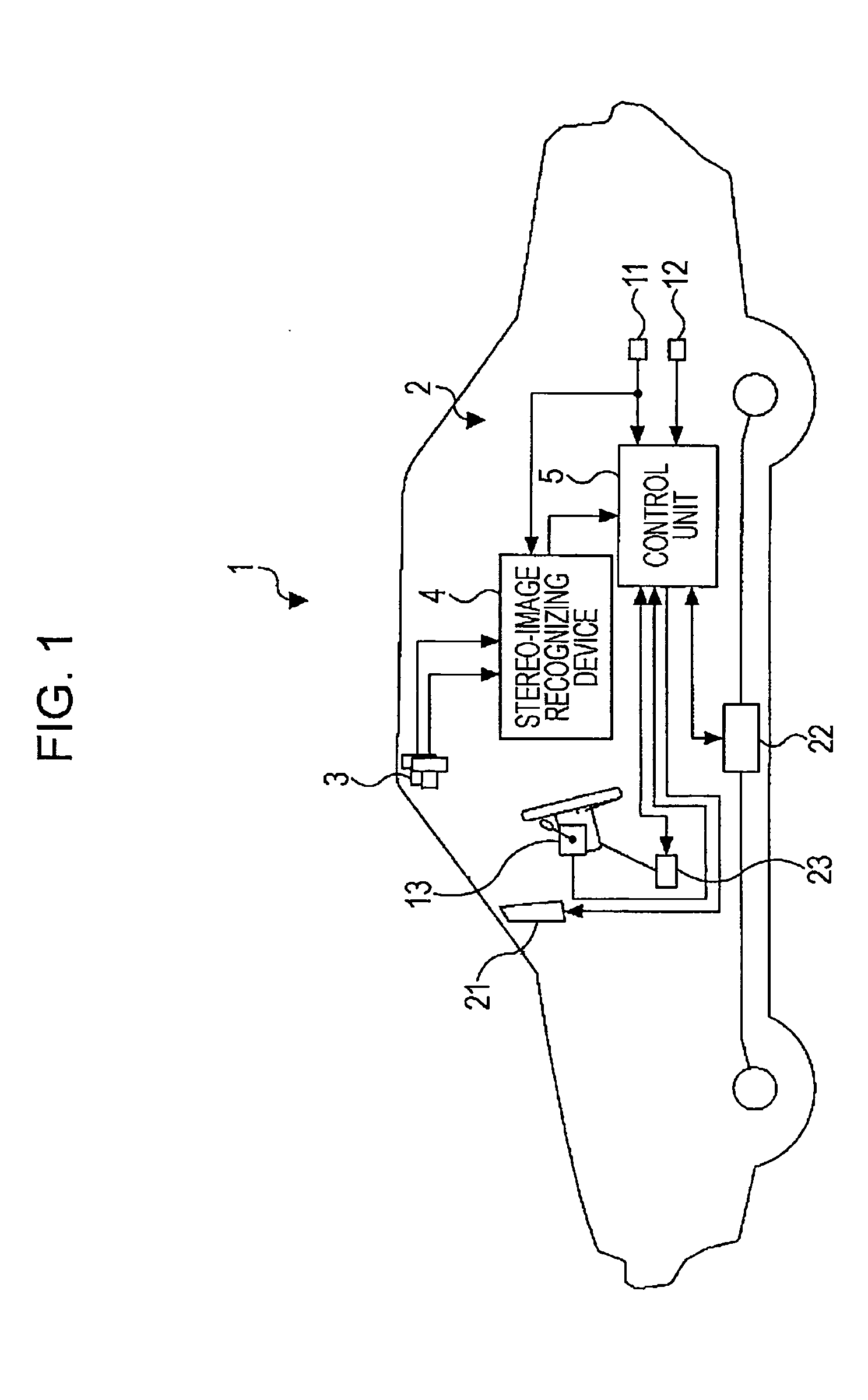
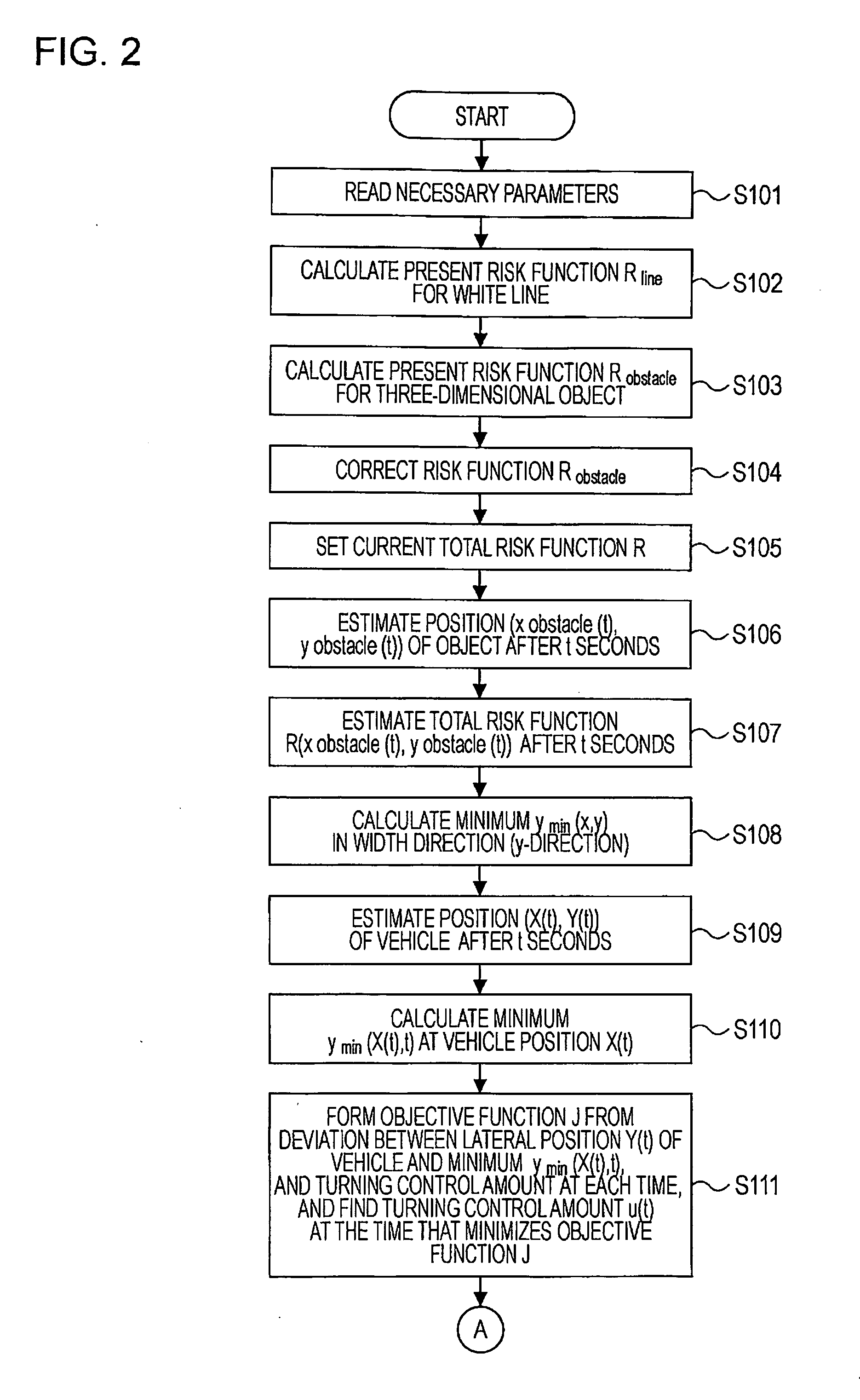
Vehicle drive assist system
ActiveUS20090037052A1Increased riskImprove securitySteering initiationsDigital data processing detailsTemporal changeTotal risk
A control unit sets a current total risk function for each of white lines, guardrails, side walls, and three-dimensional objects existing around a vehicle, estimates a temporal change in the position of each object, and calculates a minimum of the total risk function at the vehicle position for each time. An objective function is generated for the time, and a turning control amount that minimizes the objective function at the time is calculated as a turning control amount of the vehicle. Risk functions provided when the vehicle moves by the turning control amount are set for respective routes. A final avoidance route is selected from the risk functions of the routes, and steering and braking are controlled.
Owner:SUBARU CORP
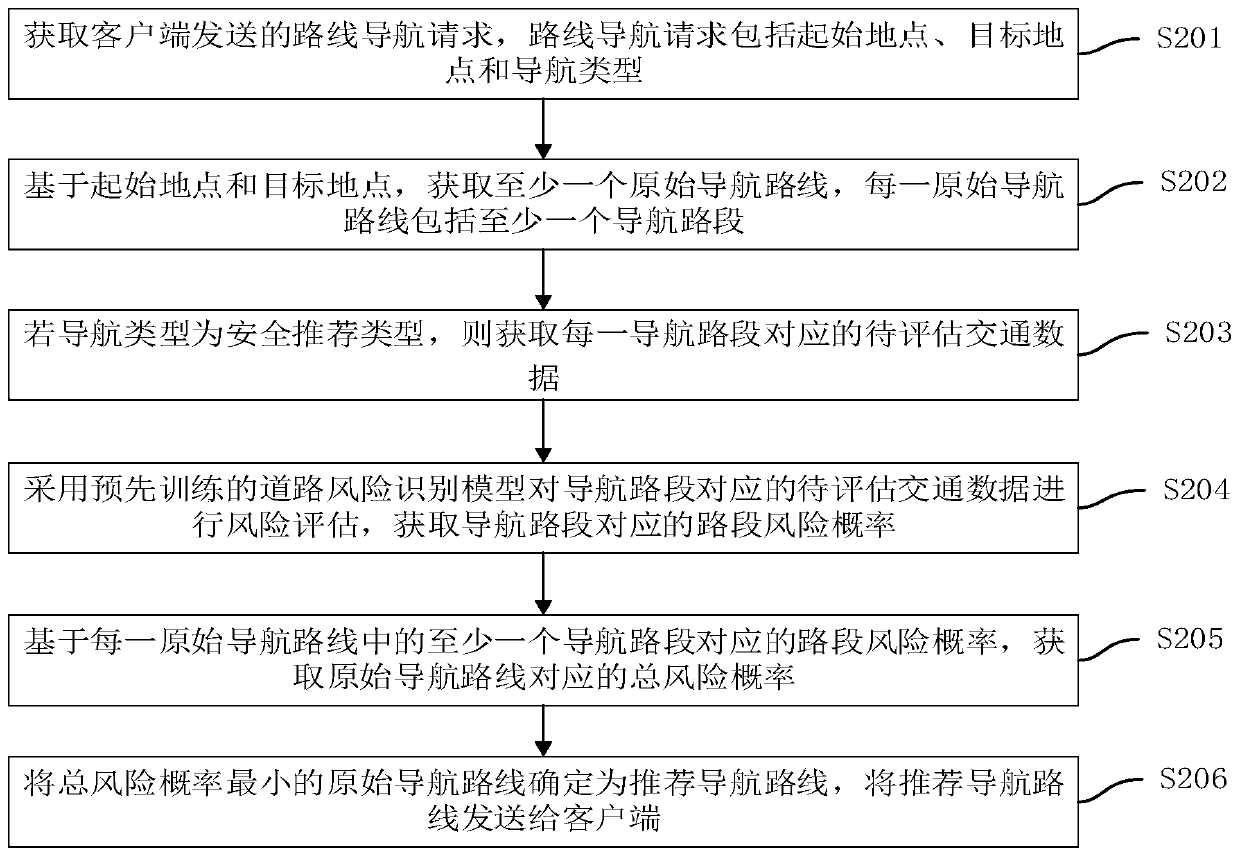
Risk assessment based intelligent navigation method and device, equipment and storage medium
ActiveCN109801491AEnsure objectivityObjectiveDetection of traffic movementResourcesTotal riskRisk identification
The invention discloses a risk assessment based intelligent navigation method and device, equipment and a storage medium. The risk assessment based intelligent navigation method includes acquiring a route and navigation request sent from a client side, acquiring multiple original navigation routes according to starting location and target location of the route navigation, further acquiring to-be-assessed traffic data corresponding to each navigation route, performing rick assessment on the to-be-assessed traffic data corresponding to each navigation route through a road rick identification model trained in advance to acquire section risk probability of the corresponding road sections, acquiring the total risk probability corresponding to the original navigation routes according to the section risk probability of at least one corresponding navigation road section of each original navigation route, and finally determining the original navigation route with the lowest total risk probability as a recommended navigation route and sending the recommended navigation route to the client side. The risk assessment based intelligent navigation method can realize route planning based on safetyfactors, thereby guaranteeing safety in driving.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Risk assessment method
InactiveUS8515783B1Cheap and practicalAccurate and efficient in practiceFinanceRisk exposureTotal risk
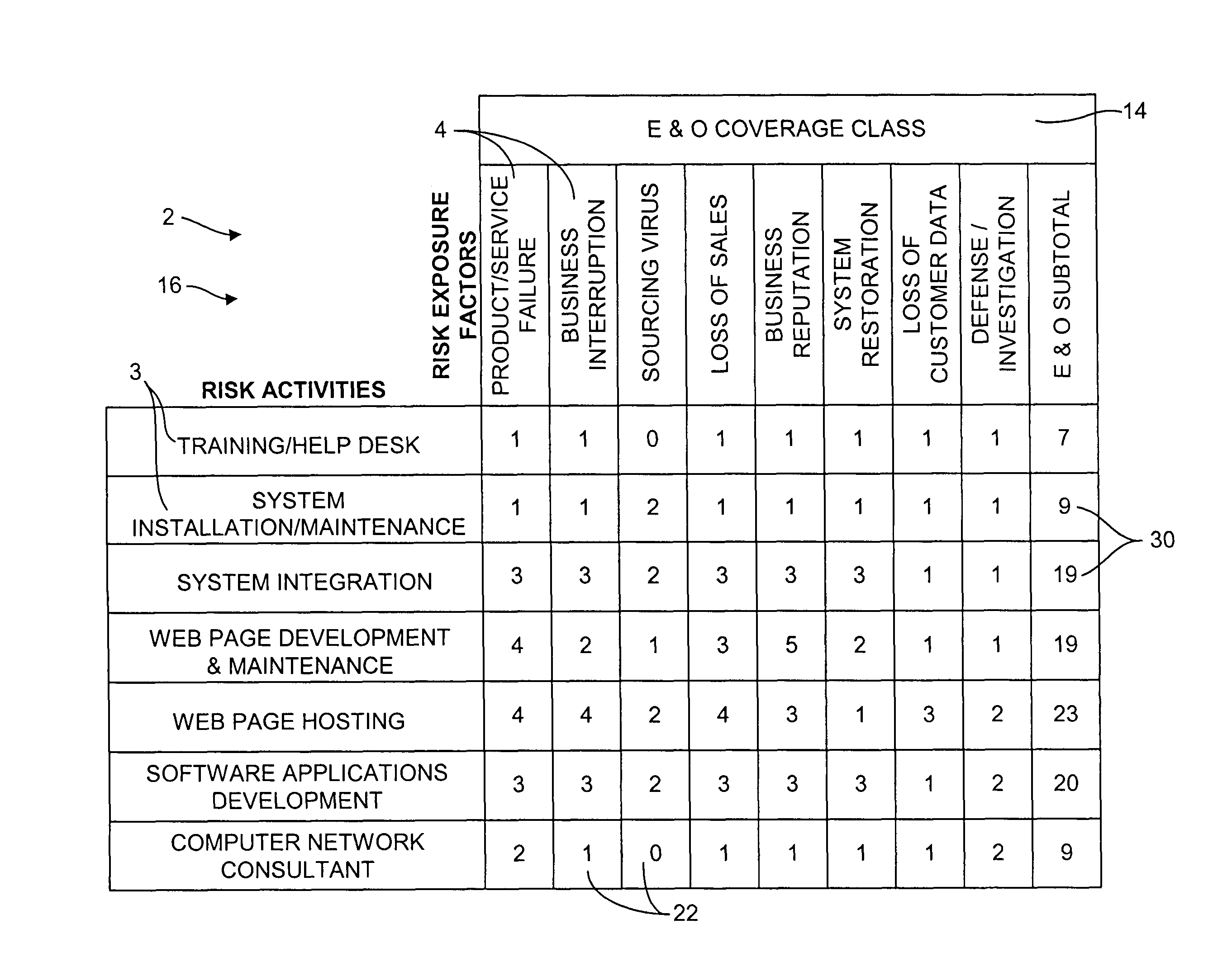
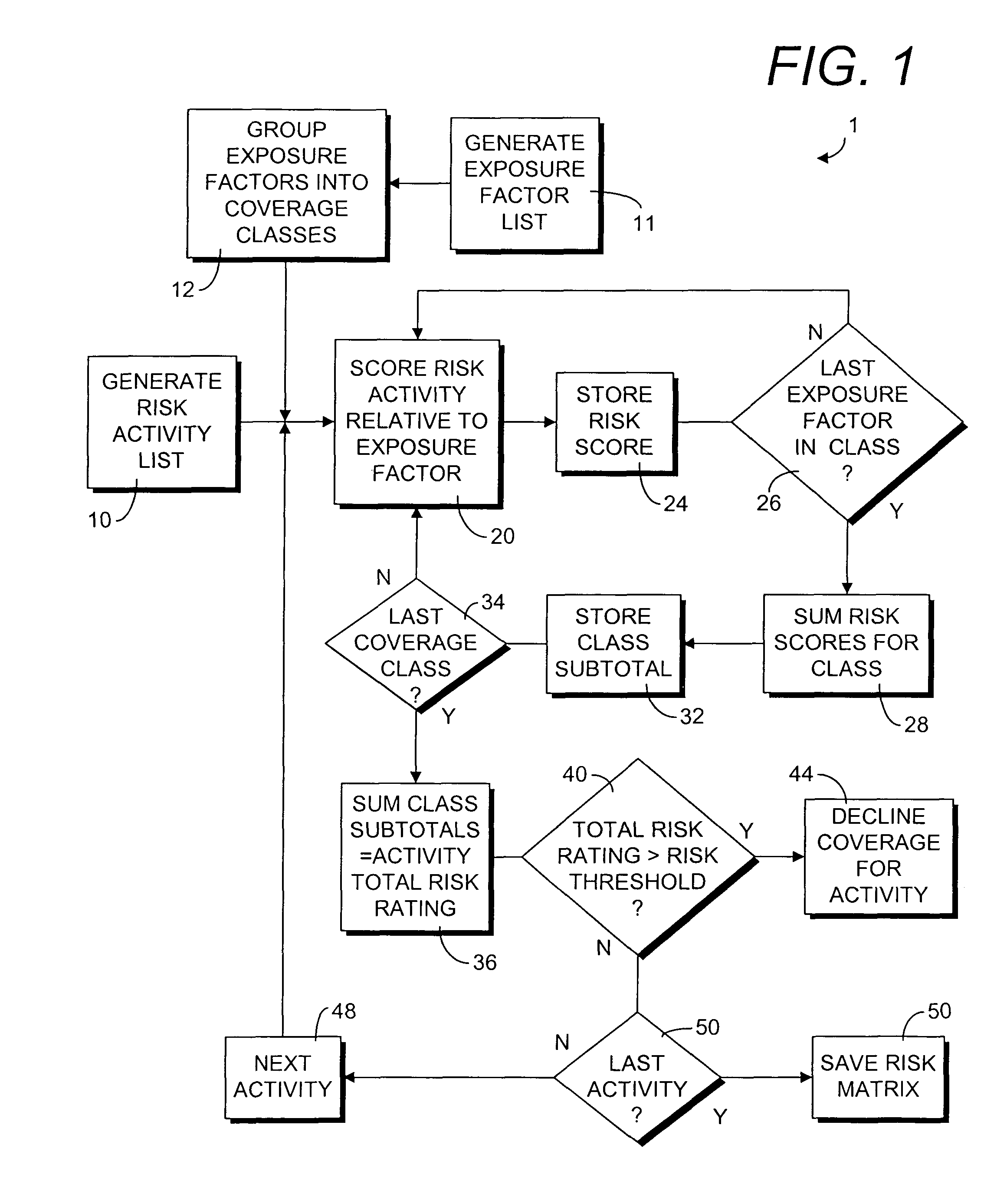
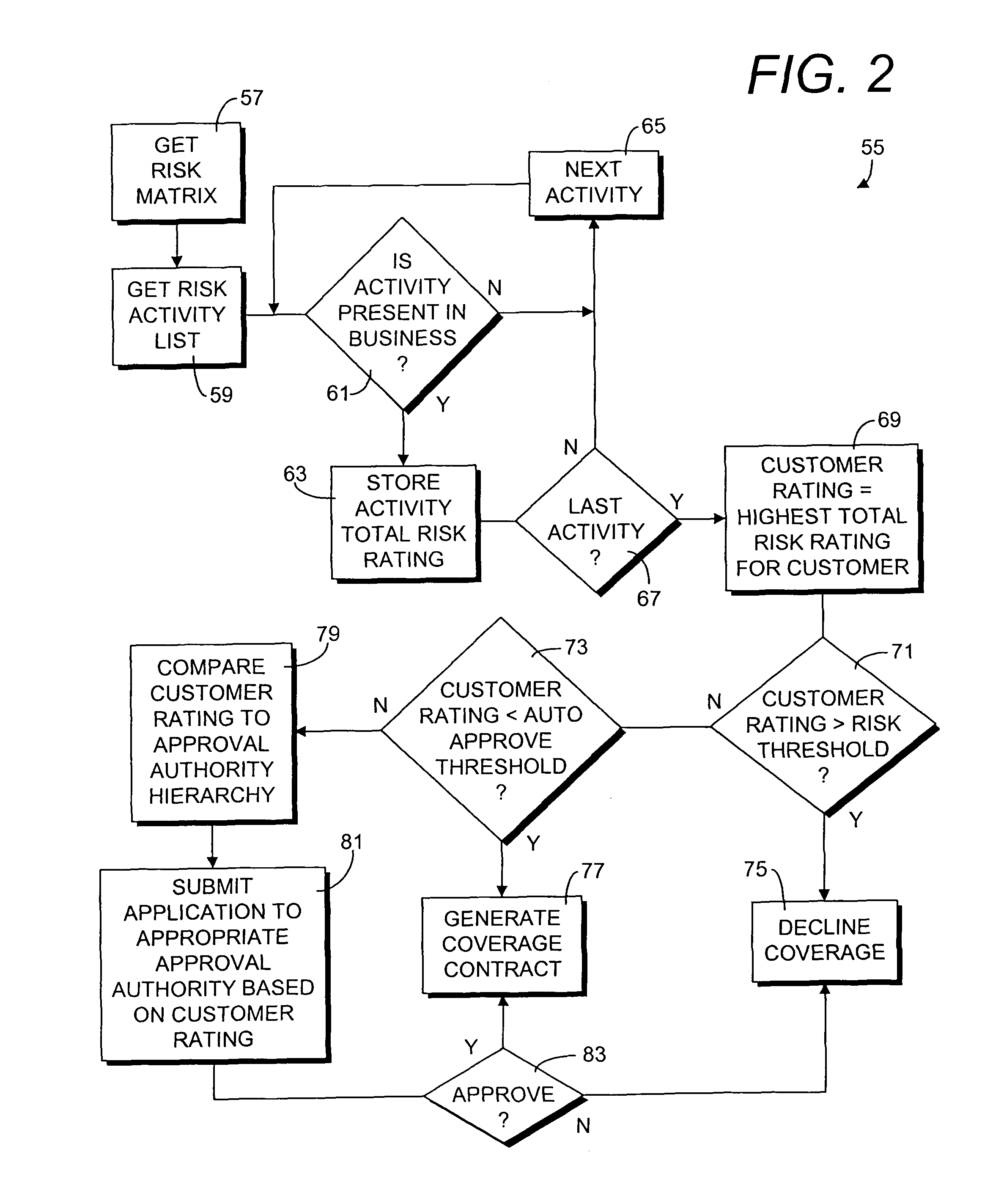
A risk assessment method for insurance coverage of an enterprise includes identifying component risk activities of the enterprise, identifying the risk exposure factors which may be applicable to such activities, numerically scoring each activity against each risk exposure factor on the frequency and severity of potential claims on the exposure factor for the activity in a risk matrix, summing all the scores for each activity to obtain a corresponding total risk rating, and analyzing each total risk rating against hierarchies of approval authority to bind coverage on the activity and the potential premium rate for the activity. The method includes identifying a highest total risk rating an applicant as a customer rating which is used as an overall measure of potential risk exposure for the applicant. The method includes the capability of automatically declining, approving, or renewing coverage based on the customer rating.
Owner:SWISS REINSURANCE CO LTD
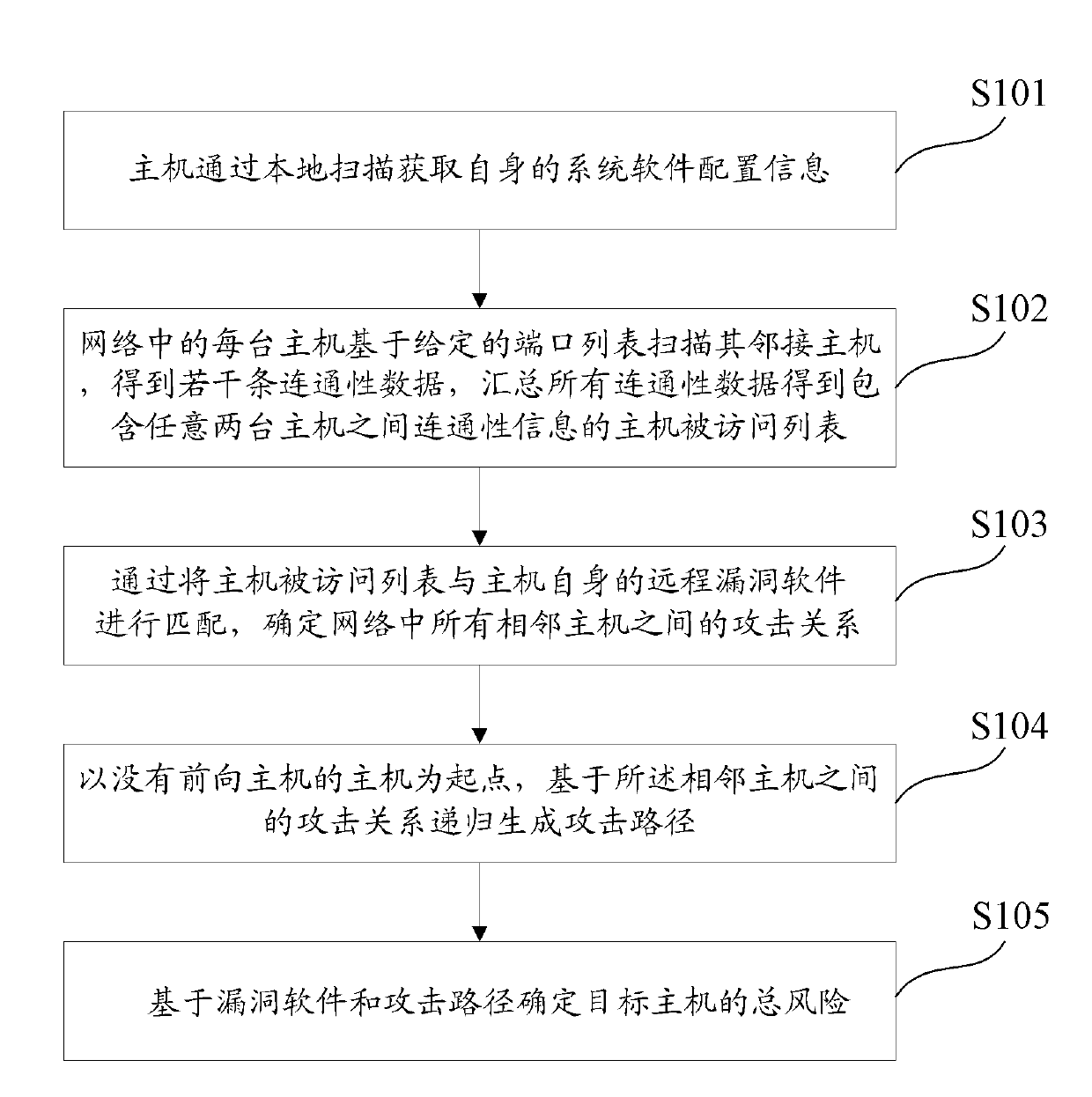
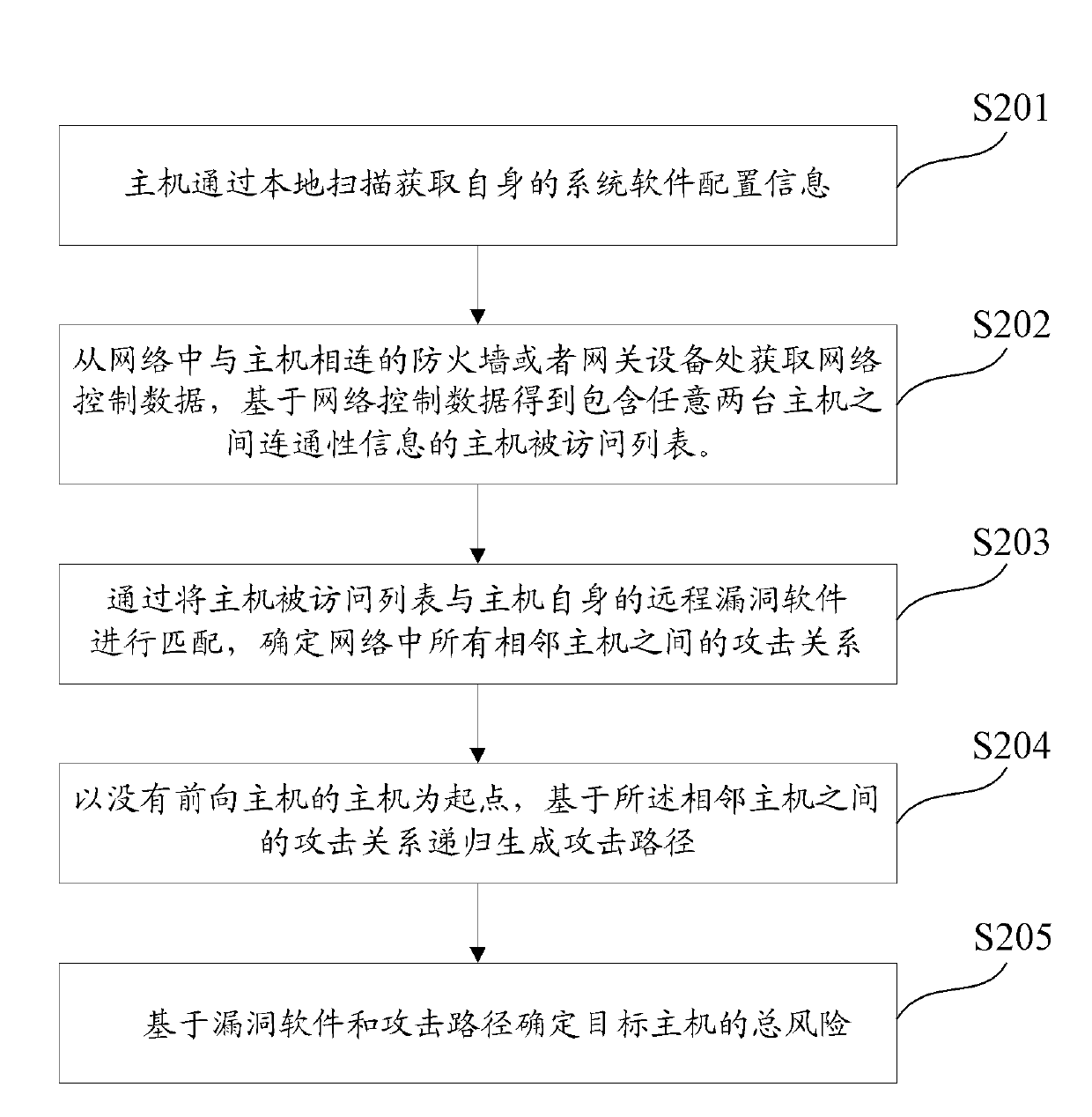
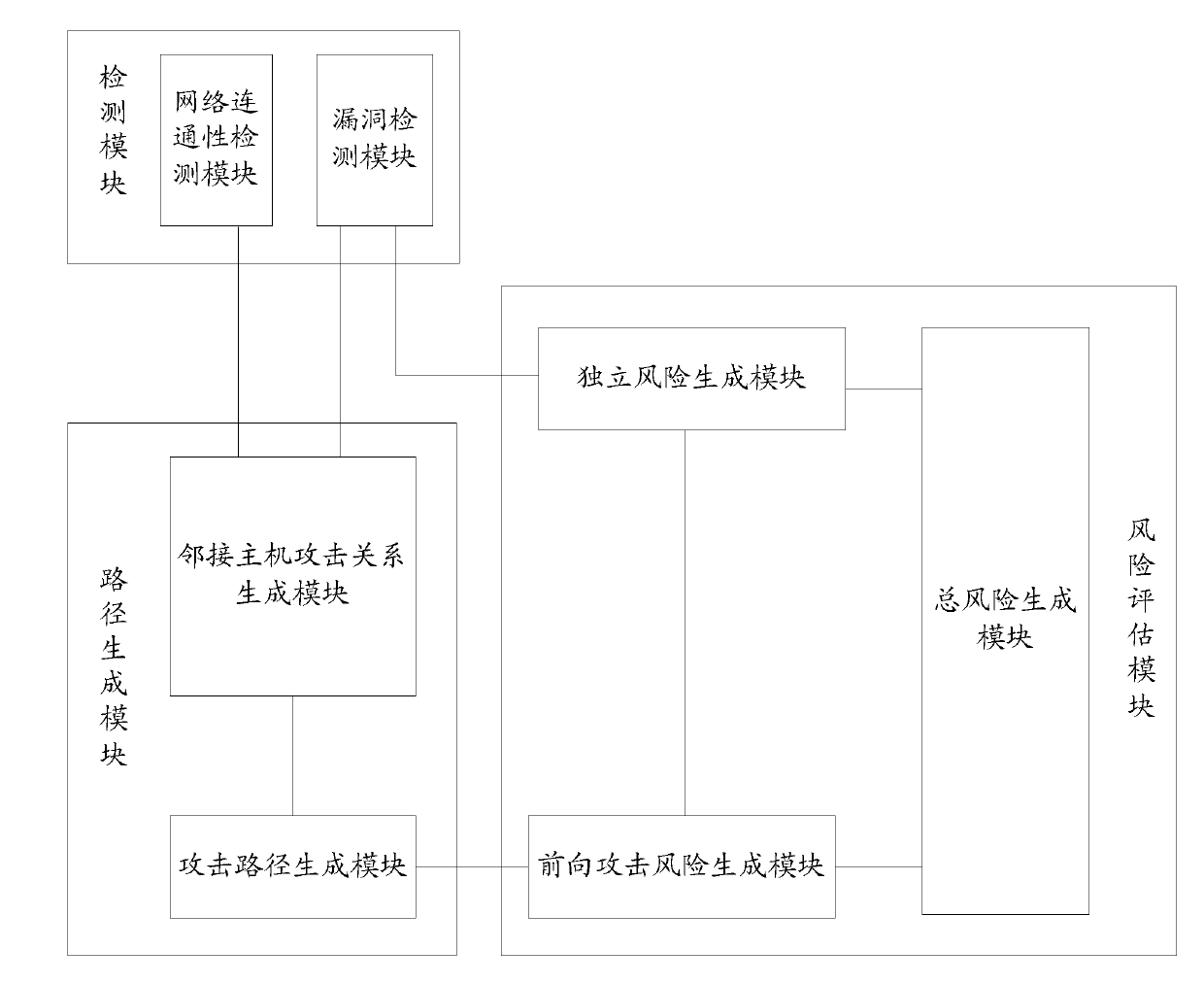
Host risk evaluation method and device
InactiveCN102170431AImprove risk assessmentComprehensive assessmentTransmissionTotal riskRisk evaluation
The invention discloses a host risk evaluation method and a host risk evaluation device. The method comprises the following steps of: detecting the bug information and network connectivity information of all hosts in a network; determining an attack path in the network according to the bug information and the network connectivity information; and determining the total risk of any target host based on the bug information and the attack path. In the method and the device, the thought of actively and dynamically evaluating potential bugs and risks by the attack path is put forward for the first time, so that host risk evaluation is more perfect, and effects are more ideal. Own bugs of the host and threats from the attack path in the network are combined, so the potential risks of the host can be explored more deeply.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
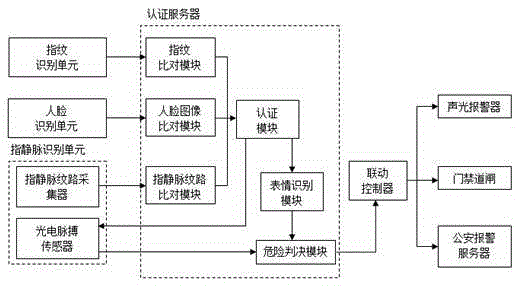
Intelligent community system and method based on fingerprint and finger-vein recognition
ActiveCN105303661AImprove accuracyImprove reliabilityCharacter and pattern recognitionIndividual entry/exit registersPattern recognitionTotal risk
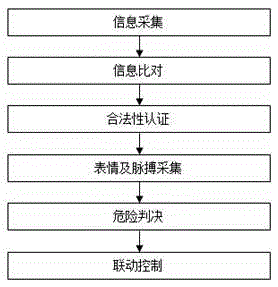
The invention discloses an intelligent community system and method based on fingerprint and finger-vein recognition. The intelligent community system comprises a fingerprint recognition unit, a face recognition unit, a finger-vein recognition unit, an authentication server, a linkage controller and a front end linkage device. The method comprises the steps that when an authentication result is illegal, an expression recognition module and a photoelectric pulse sensor driving module are started, and a risk judgment module judges a total risk value of the illegal target according to expression and pulse information of the object to be tested; the linkage controller outputs a control signal to the front end linkage device according to total risk value data and preset control logic. According to the intelligent community system and method based on the fingerprint and finger-vein recognition, fingerprint recognition, face image recognition and finger-vein lines image identification are effectively combined, when legality identification is conducted, it is required that fingerprint comparison, face image comparison and finger-vein lines comparison results all display that the object to be tested is the legal user, and the fingerprints, a face image and finger-vein lines belong to the same legal user, and the accuracy and reliability of community safe-protection management are effectively improved.
Owner:CHENGDU WISDOM SHULIAN INFORMATION TECH CO LTD
Oil-gas pipeline high-consequence area identification system and identification method
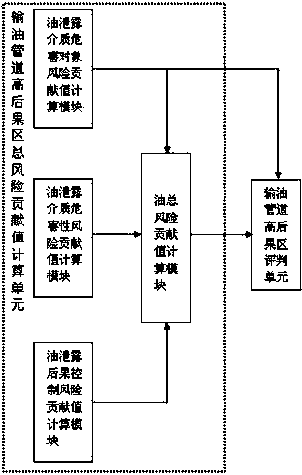
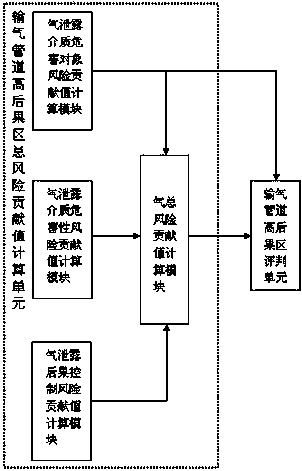
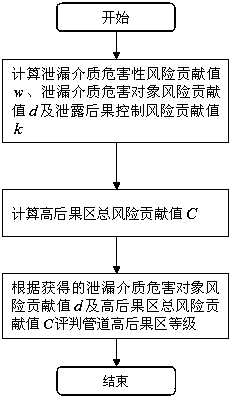
The invention discloses an oil-gas pipeline high-consequence area identification system and identification method. The identification system comprises an oil conveying pipeline high-consequence area identification subsystem and a gas conveying pipeline high-consequence area identification subsystem. The oil conveying pipeline high-consequence area identification subsystem comprises oil conveying pipeline high-consequence area total-risk contribution value computing unit and an oil conveying pipeline high-consequence area judging unit. The gas conveying pipeline high-consequence area identification subsystem comprises a gas conveying pipeline high-consequence area total-risk contribution value computing unit and a gas conveying pipeline high-consequence area judging unit. According to the identification method, existing subjective and extensive identification methods at home and abroad are abandoned, various factors influencing pipeline leakage are taken into consideration comprehensively, the systematic identification system is set up, the calculation thought and the method are simple, the site fitness of the analysis result is good, high-consequence pipe sections of different types of a whole pipeline can be identified, and engineering technical personnel can work out the scientific countermeasures according to the situations of the pipe sections.
Owner:SOUTHWEST PETROLEUM UNIV
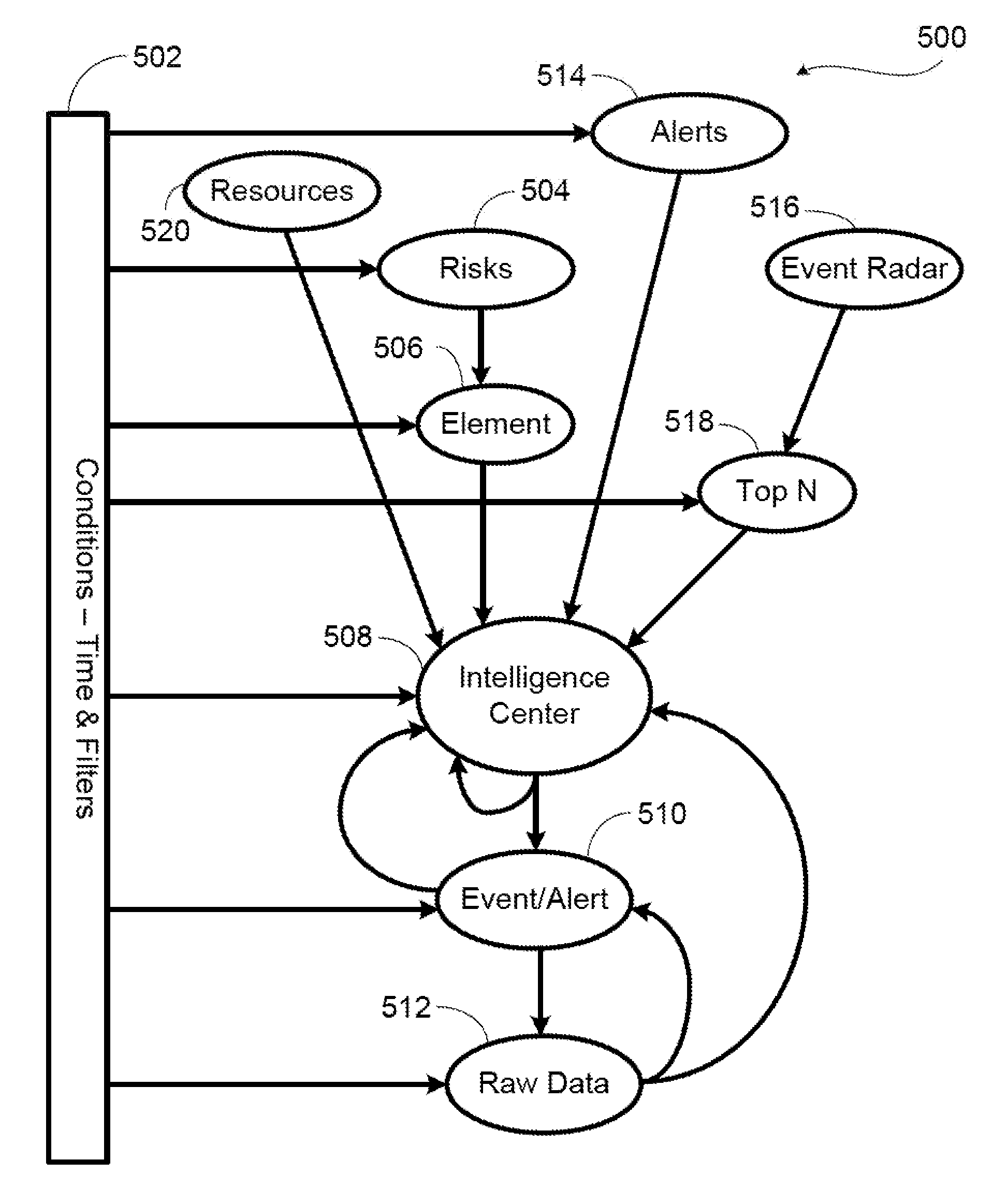
System And Method For Information Risk Management
The present invention provides a system and method for evaluating risk associated with information access requests. The information access requests are collected, assigned a risk level according to user defined policies, a total risk is calculated and presented to user. The user can select a high risk event for further analysis. The system will break down the event into basic elements, so the user can ascertain the risk. The system allows a user to customize a report and the customized report can be saved as a template for future use.
Owner:DATIPHY
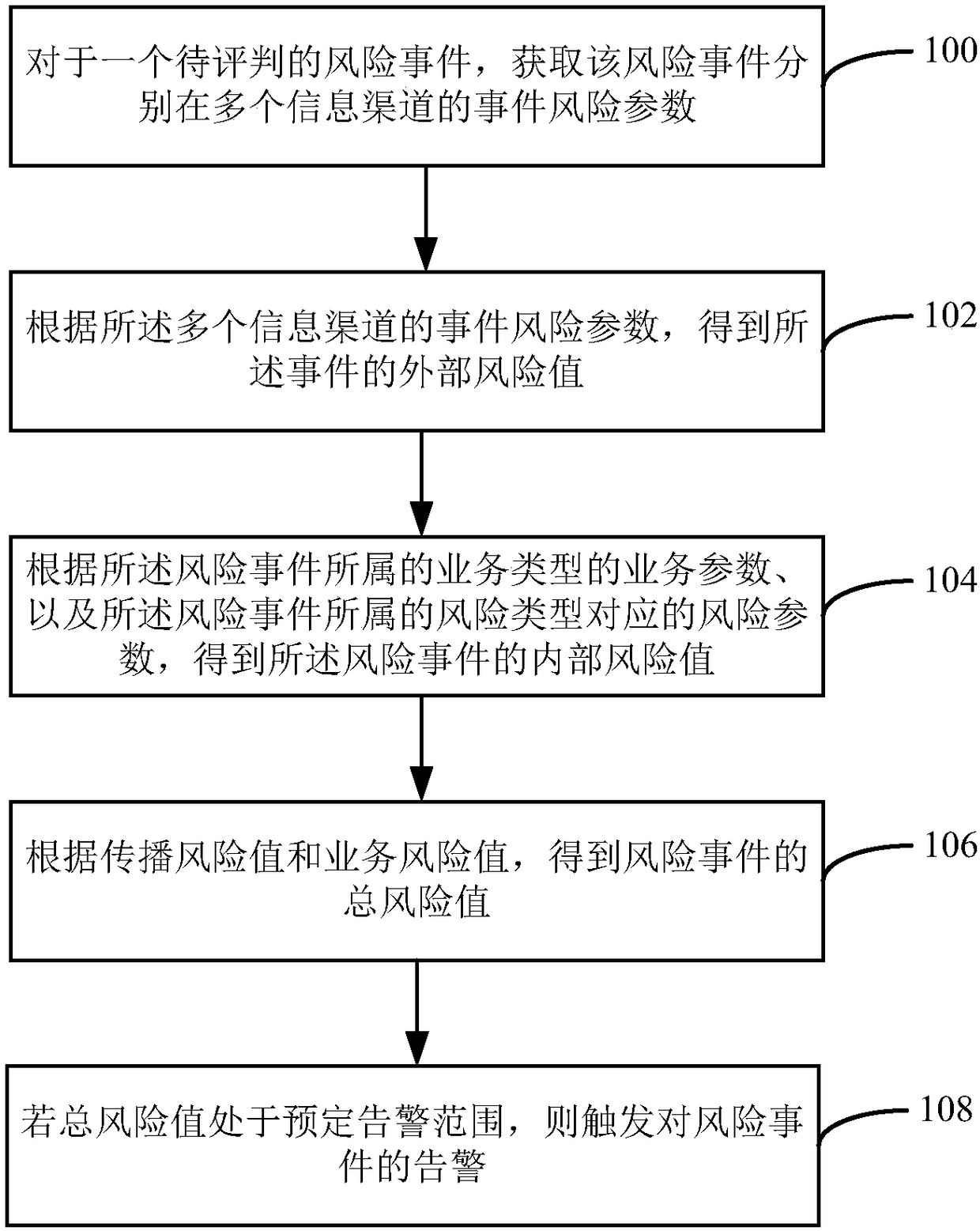
Risk event alarm method and device
The embodiment of the invention provides a risk event alarm method and device. The method comprises the steps of: obtaining event risk parameters of a risk event to be evaluated in a plurality of information channels, and obtaining a propagation risk value of the risk event according to the event risk parameters of the information channels; obtaining a business risk value corresponding to the riskevent according to the business parameter of a business type to which the risk event belongs and risk parameters corresponding to the risk type to which the risk event belongs; and obtaining a totalrisk value of the risk event according to the propagation risk value and the business risk value; and if the total risk value is located in a predetermined alarm range, triggering alarm for the risk event.
Owner:ADVANCED NEW TECH CO LTD
Device, system and method for patient monitoring to predict and prevent bed falls
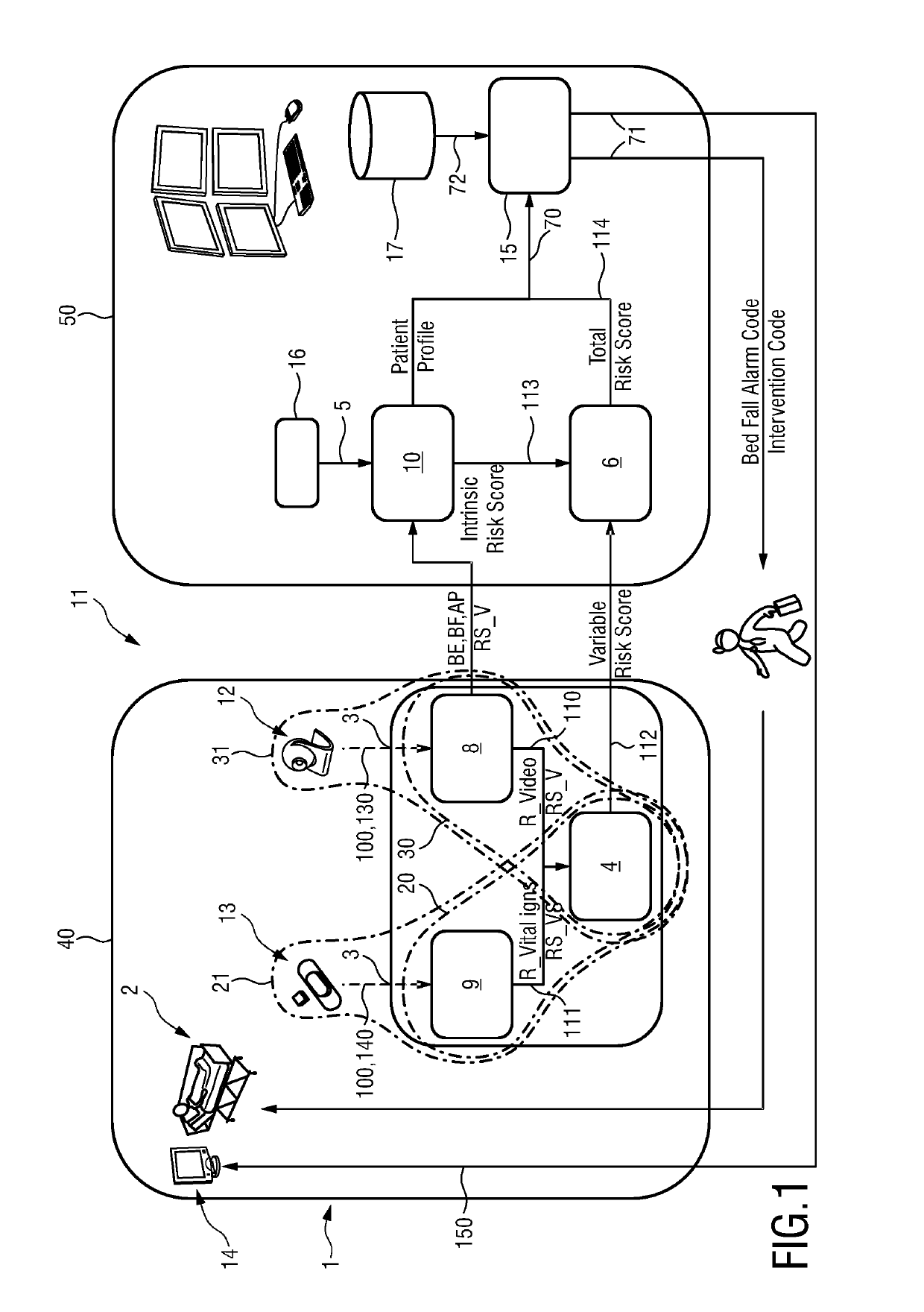
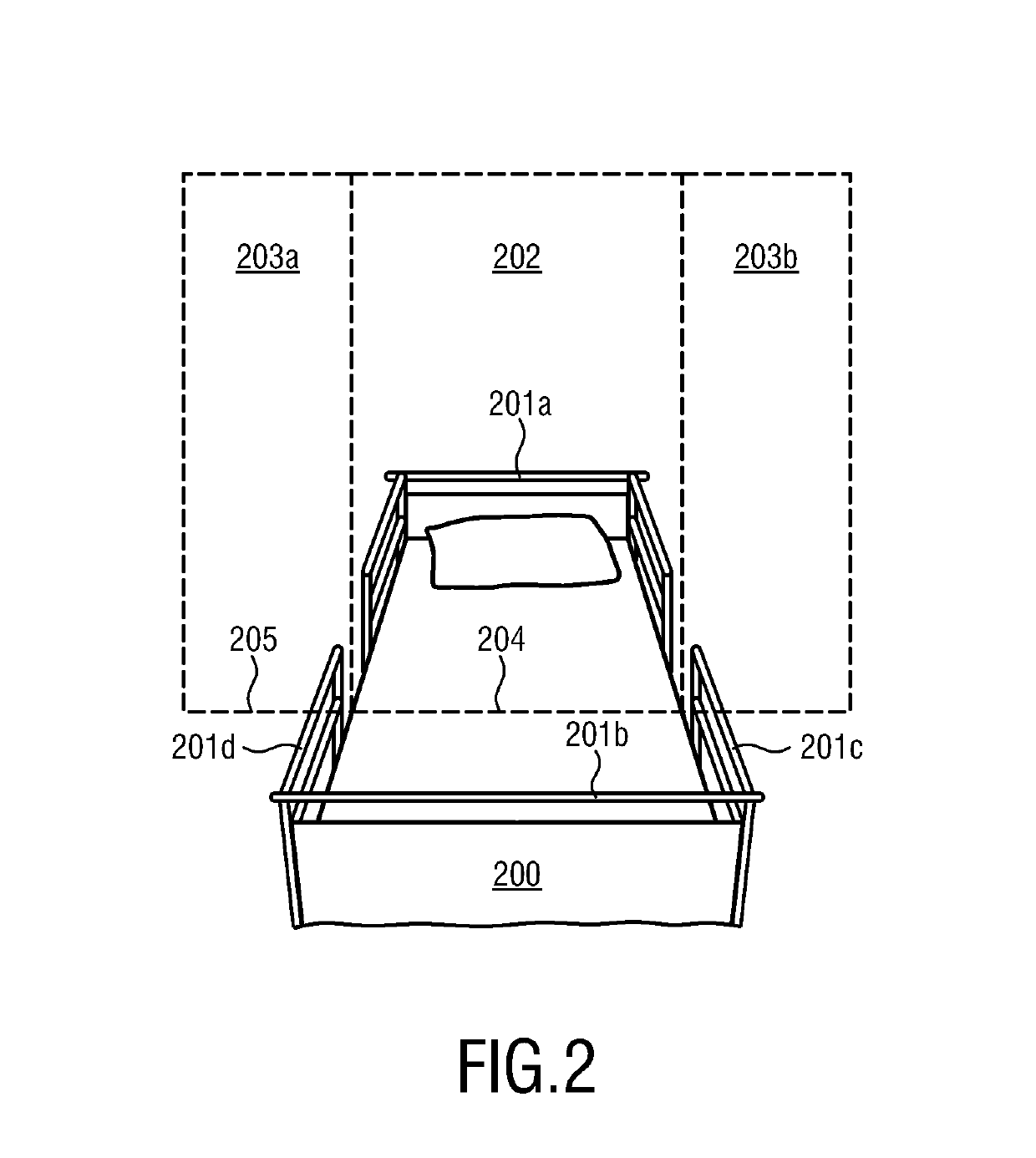
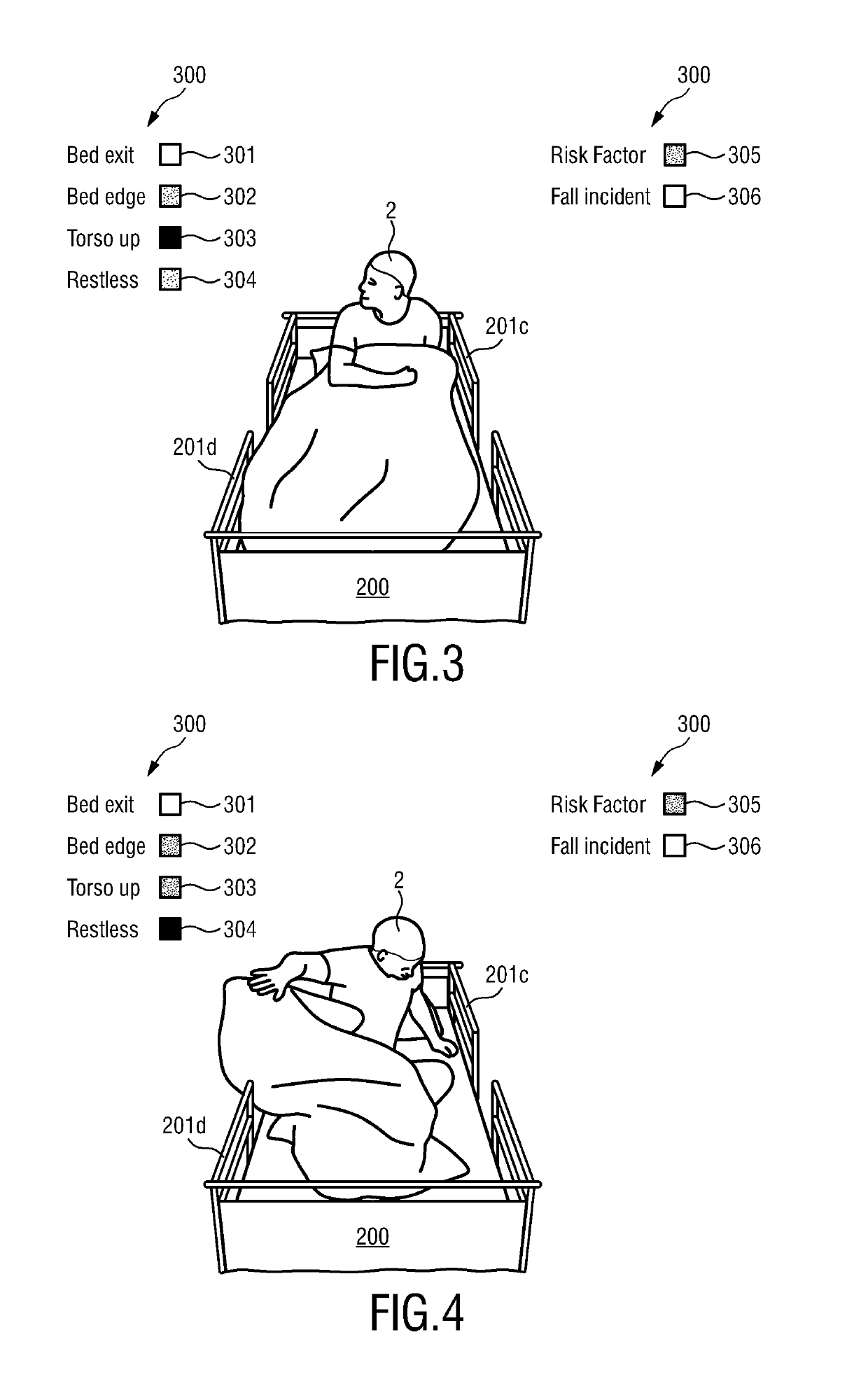
InactiveUS20190228866A1Efficient but attentive careMinimizes false alarmsHealth-index calculationMedical equipmentTotal riskFall risk
The present invention relates to a device (1) for determination of a bed fall risk of an individual (2), the device (1) comprising a first port (3) for obtaining sensor data (100) related to movement and / or a vital sign of an individual (2), an evaluation unit (4) for determining quality information indicating the quality of the sensor data (100), a second port (5) for obtaining personal data (120) of the individual (2), a calculation unit (6) for calculation of a total risk score (114) of the individual (2) based on the sensor data (100), the quality information (110) and the personal data (120), said total risk score indicating a bed fall risk of the individual (2), and a third port (7) for output of the calculated total risk score.
Owner:KONINKLJIJKE PHILIPS NV
Method and system for risk prediction for a support actuation system
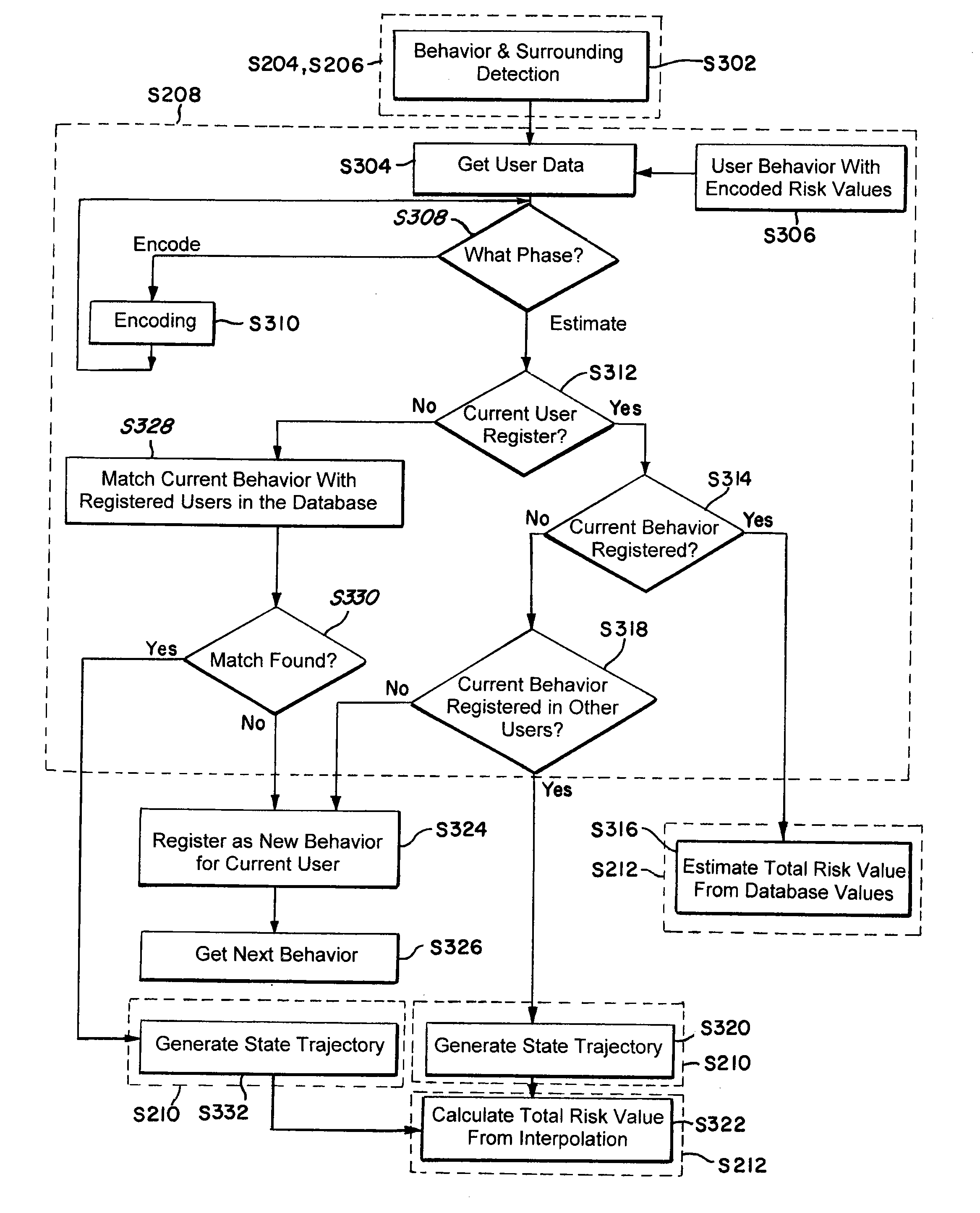
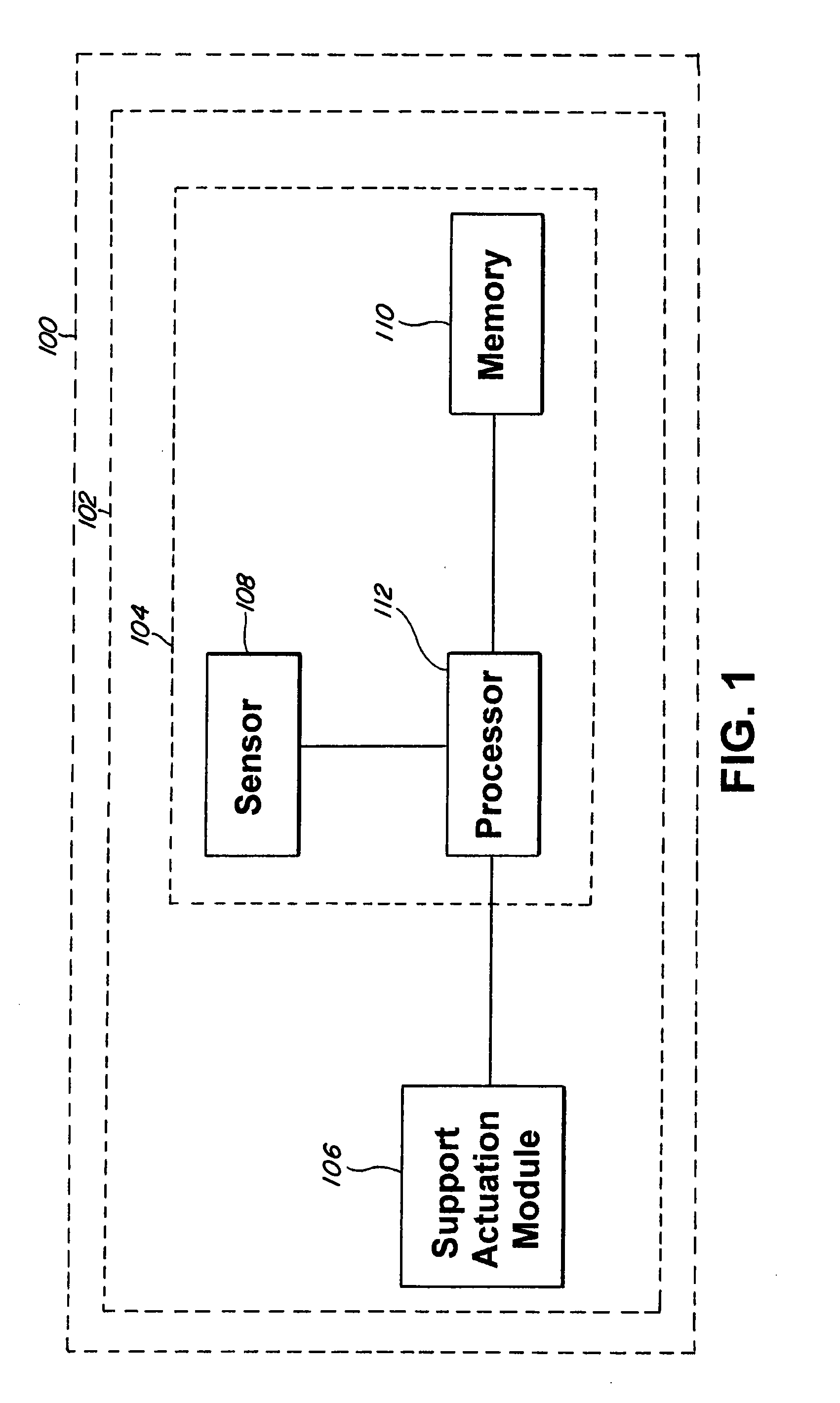
ActiveUS20120083942A1Accurate risk assessmentComputation using non-denominational number representationExternal condition input parametersTotal riskAmbient data
The present invention relates to a method and system for risk prediction for a support actuation system. The present invention includes a support actuation system for an automobile having a support actuation module and / or a risk prediction system. The risk prediction system includes a sensor, a processor, and / or a memory. The sensor detects images corresponding to identity data, environment data, event data, and / or behavior data, which are stored in the memory. The memory also stores a database including identities of users, environment risk values, event risk values, and / or behavior risk values. Using the identity data, the environment data, the event data, and / or the behavior data, the processor determines the environment risk value, the event risk value, the behavior risk value, and / or the total risk value for a user. When the total risk value is above a predetermined risk threshold, the support actuation module performs support actuation.
Owner:TOYOTA JIDOSHA KK
Method and system for assessing fall risk
ActiveUS7682308B2Easy to addAccurate predictionData processing applicationsTherapiesBenzodiazepineTotal risk
A method and system for determining the fall risk of a patient is provided. The method includes the evaluation of a patient to determine whether the patient exhibits one or more intrinsic fall risk factors selected from a group consisting of confusion, depression, altered elimination, dizziness, male gender, antiepileptic / anticonvulsant prescriptions and benzodiazepine prescriptions. A specific point value is assigned to each of the intrinsic risk factors found to be exhibited by the patient. A mobility test is also performed on the patient to evaluate the patient's ability to rise from a seated position, and a specific mobility test point value is assigned to the patient based upon the patient's performance of the mobility test. Each intrinsic risk factor's specific point value is then summed together with the specific mobility test point value to achieve a total risk score, and the patient's fall risk is determined based on the total risk score. An intervention process may be developed for the patient based on the patient's fall risk.
Owner:AHI OF INDIANA
Comprehensive evaluation method for dengue risk
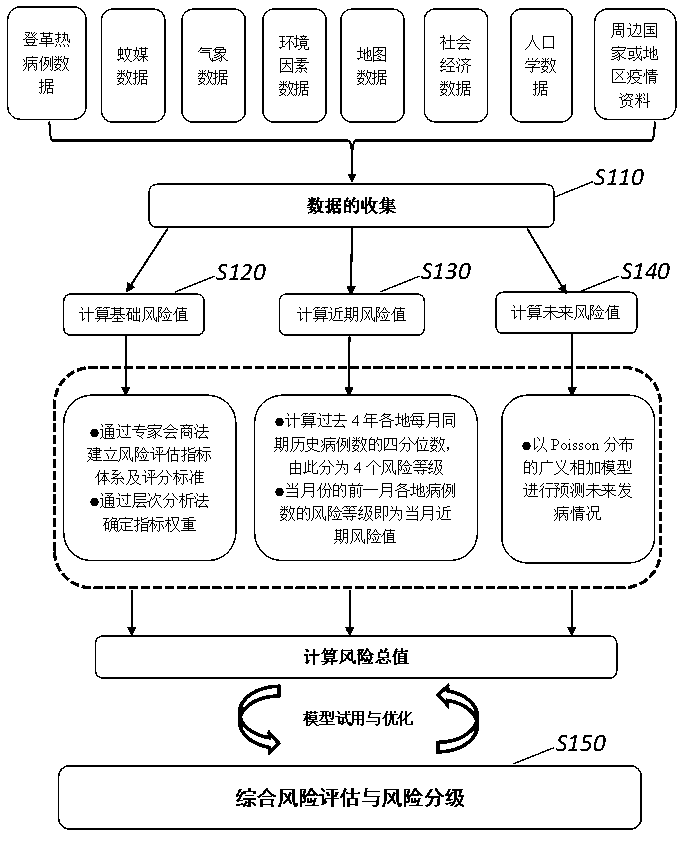
ActiveCN110459329AAccurate assessmentImprove accuracyHealth-index calculationEpidemiological alert systemsTotal riskWeight coefficient
The invention provides a comprehensive evaluation method for a dengue risk. The method comprises the steps that dengue case data, mosquito-borne data, meteorological data, map data, environment factordata, social economy data, demography data and surrounding country or area epidemic situation data are collected; a basic risk value, a nearby risk value and a future prediction risk value are calculated, and weight coefficients of the three risk values are calculated; the comprehensive evaluation method is established, and a total dengue risk value is calculated; with reference to meteorologicaldisaster level early warning, the total risk value is evaluated for the dengue risk, and grading is conducted; based on a generalized addition model, a smooth function can be used for conducting non-linear processing on variables; the variables such as meteorological factors, dengue case numbers and mosquito-borne factors are comprehensively considered and comprise more information related to attack; in combination with the three risk values, a dengue risk evaluation model is established, the dengue spreading risk is identified at multiple angles, the influence of multiple factors on dengue spreading is comprehensively considered, and the accuracy of dengue risk evaluation is effectively improved.
Owner:广东省公共卫生研究院
Risk assessment model training method and device and risk assessment method and device
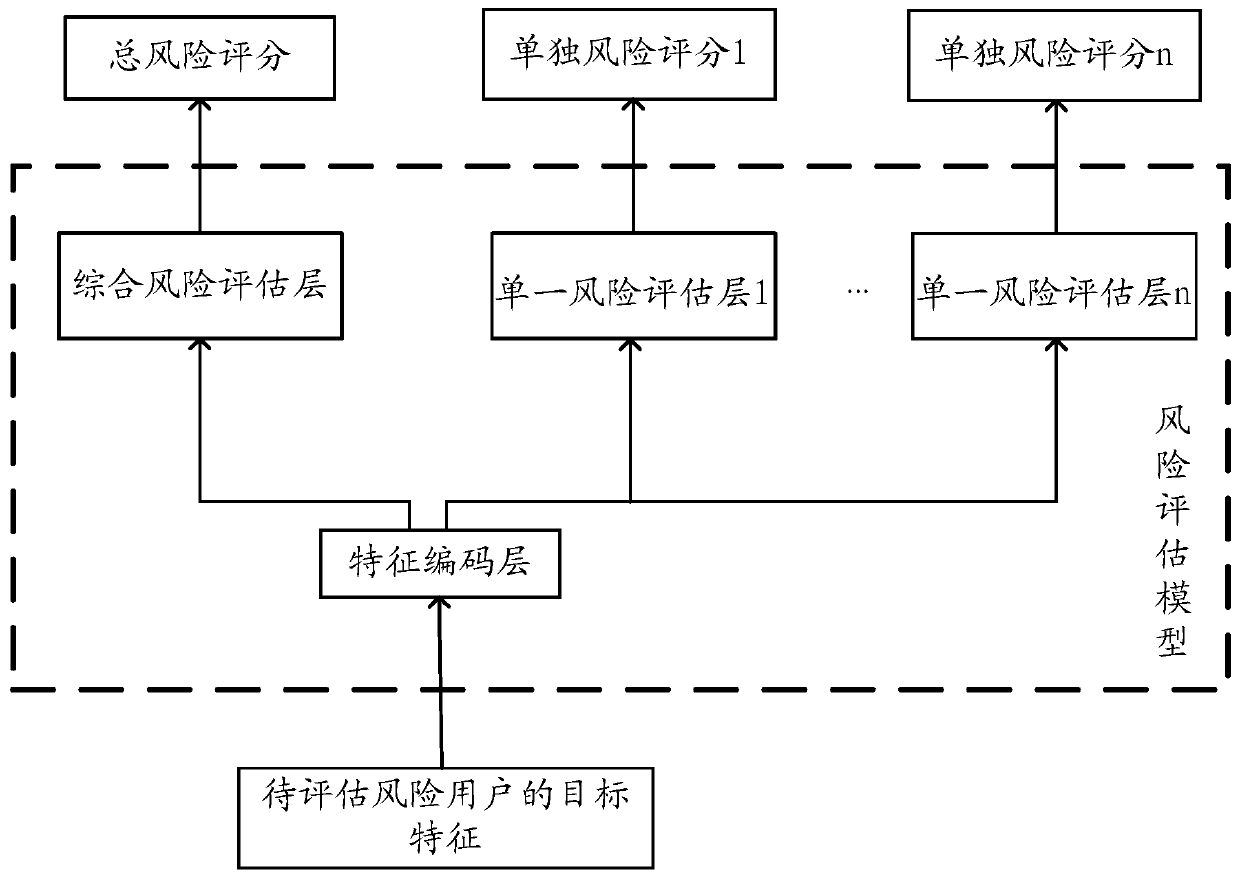
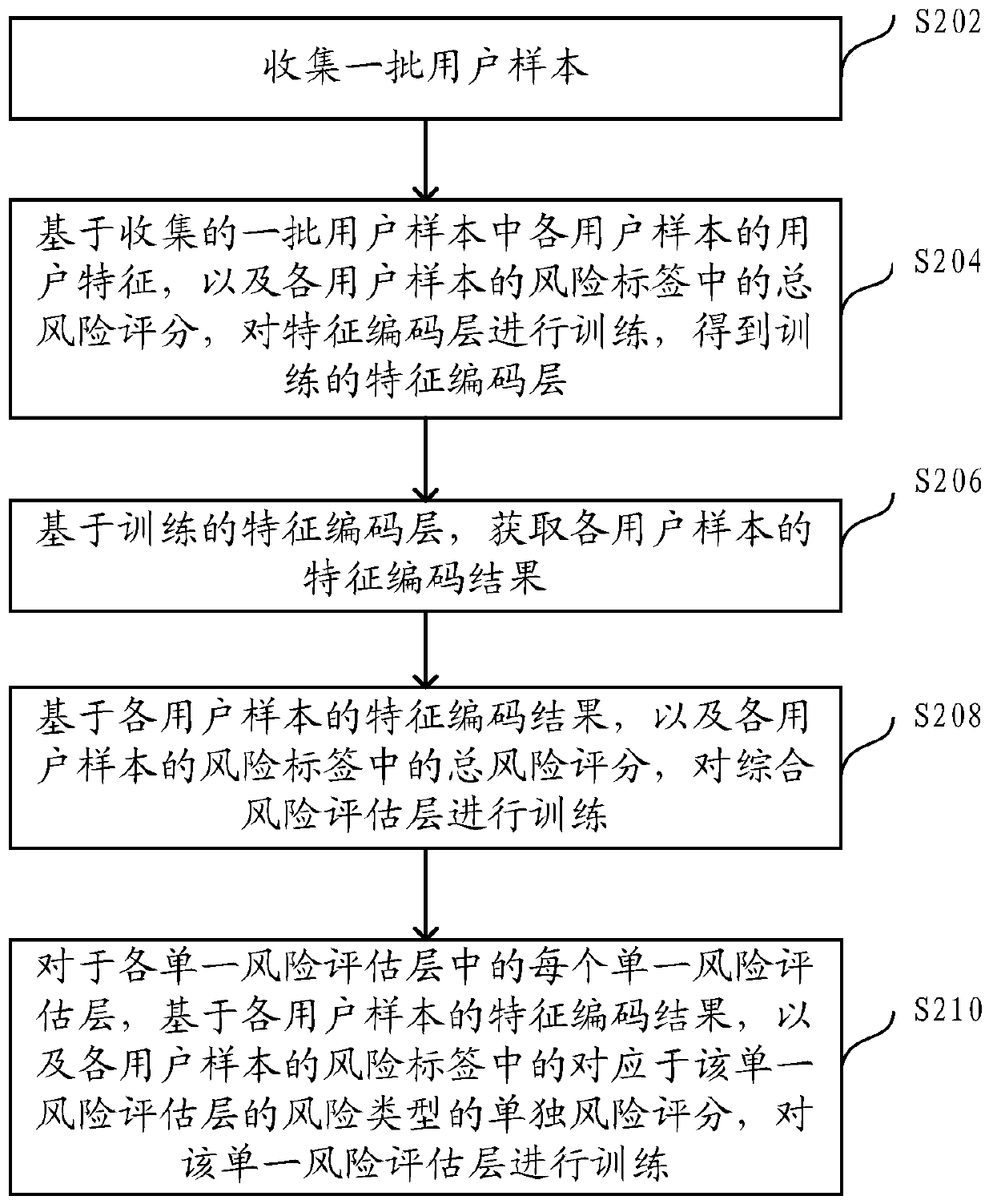
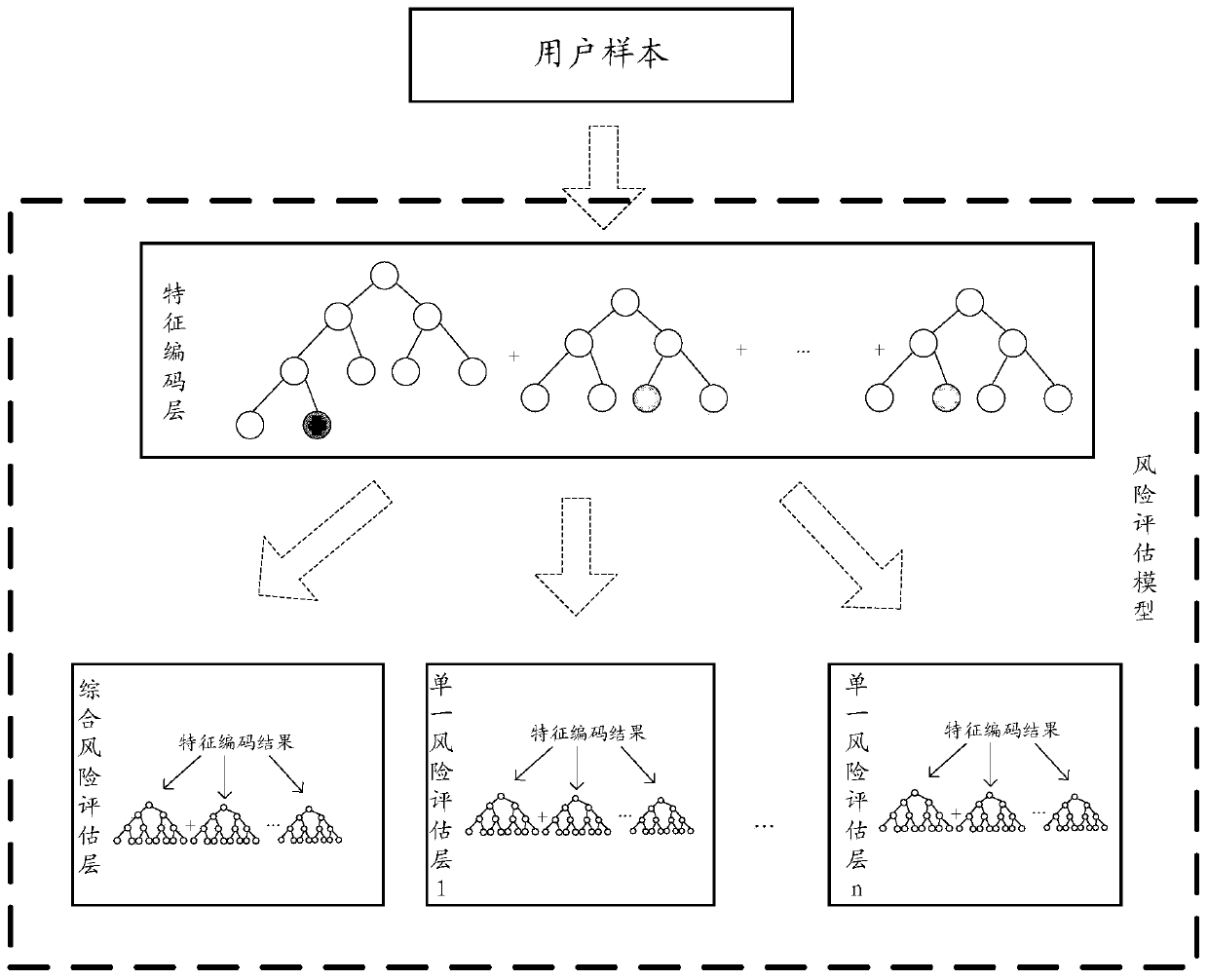
ActiveCN111401914ALow costReduce overheadCharacter and pattern recognitionProtocol authorisationPattern recognitionTotal risk
The embodiment of the invention provides a risk assessment model training method and device and a risk assessment method and device. In the training method, a batch of user samples are collected, eachuser sample comprises a user feature and a risk label, and the risk label is used for indicating a total risk score of a user and a plurality of individual risk scores corresponding to predeterminedrisk types. The feature coding layer is trained based on the user features of each user sample and the total risk score in the risk label to obtain a trained feature coding layer, and a feature codingresult of each user sample is obtained based on the trained feature coding layer. The comprehensive risk assessment layer is trained based on the feature coding result of each user sample and the total risk score in the risk label. For each single risk assessment layer in the single risk assessment layers, the single risk assessment layer is trained based on the feature coding result of each usersample and the single risk score of the corresponding risk type in the risk tag.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com