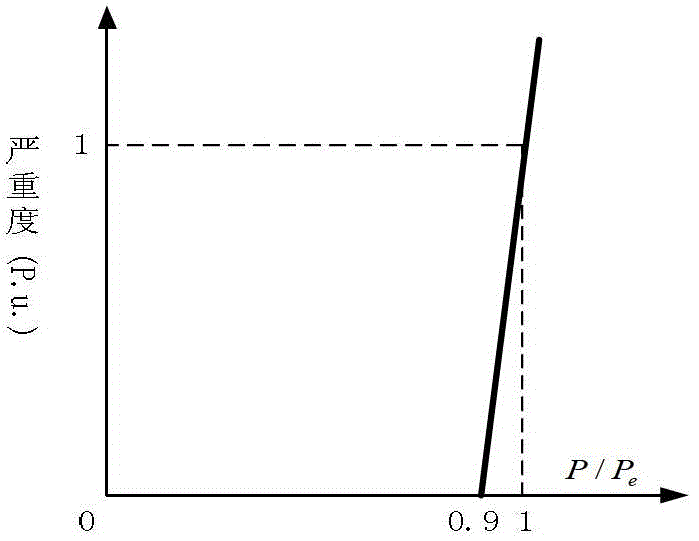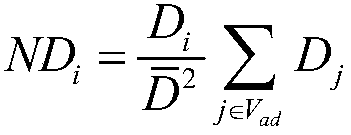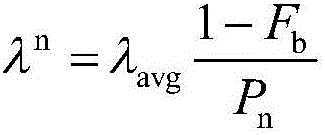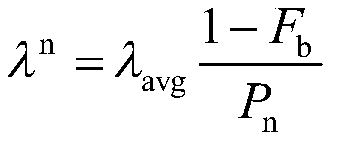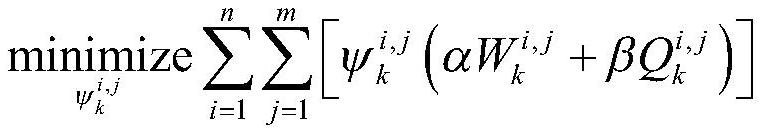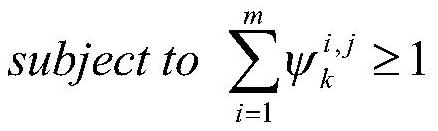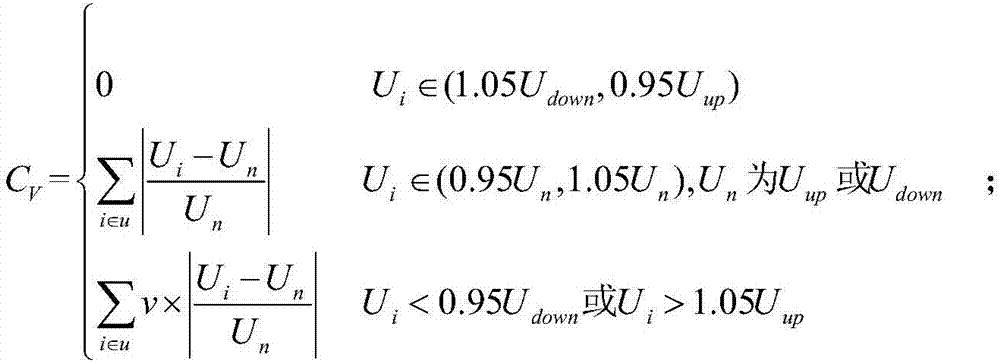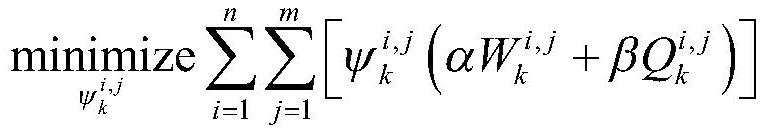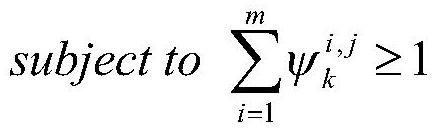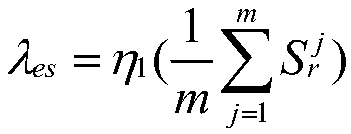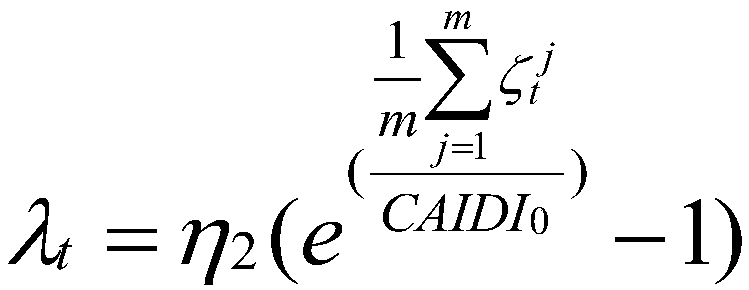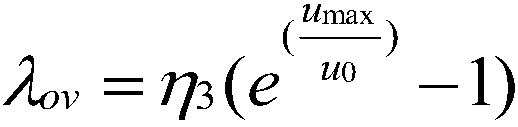Patents
Literature
34 results about "Risk theory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safety level evaluation method of power grid
ActiveCN101800426AEasy to understandPractical applicationAc network circuit arrangementsStructure analysisTotal risk
The invention relates to a safety level evaluation method a power grid, comprising the following steps of: firstly determining a supposed accident list, and sequentially disconnecting elements of the supposed accident list; after a certain element is disconnected, carrying out topological structure analysis and load flow calculation on a system, and then calculating a power grid loss load risk evaluation index, a power grid overload risk evaluation index, a power grid low voltage risk evaluation index and a power grid voltage collapse risk evaluation index; repeating the process till all the elements of the supposed accident list are completely calculated; and then calculating a system single-risk evaluation index and a system total-risk evaluation index. The invention introduces a risk theory and a utility theory to the safety evaluation of the power grid, separately diagnoses the safety of the system from different side surfaces, further obtains the risk evaluation index of the whole system by an analytic hierarchy process (AHP), obtains simple and clear results and has better discrimination and can reflect the occurrence possibility of different accidental accidents and severity degree of a consequence caused by the accidental accidents.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +1
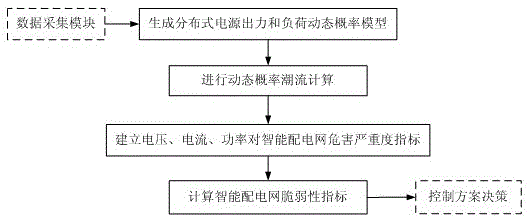
Assessment method for vulnerability of smart distribution network based on dynamic probability trend
ActiveCN102930175AImprove self-healing abilityData processing applicationsSpecial data processing applicationsRisk theoryVulnerability index
The invention relates to an assessment method for vulnerability of a smart distribution network based on a dynamic probability trend. The assessment method comprises the following steps: adopting a basic function and a random function to form probability distribution for node injection power of the smart distribution network; computing probability distribution for busbar voltage and line power according to Gram-Charlier stage number and semi invariant; utilizing a piecewise function to compute harm severity index caused by voltage, current and power on the smart distribution network; and then computing to output the vulnerability index of the smart distribution network. According to the invention, the method based on risk theory adopts the dynamic probability trend method to access the vulnerability, and enables a self-healing control scheme of the smart distribution network to adapt to change of load and operating environment of the smart distribution network, so that the smart distribution network can operate safely, reliably and economically.
Owner:HOHAI UNIV +2
Power grid differentiation-based core backbone network architecture construction method
ActiveCN103151777AHas practical significanceFast convergenceAc network circuit arrangementsNODALAlgorithm
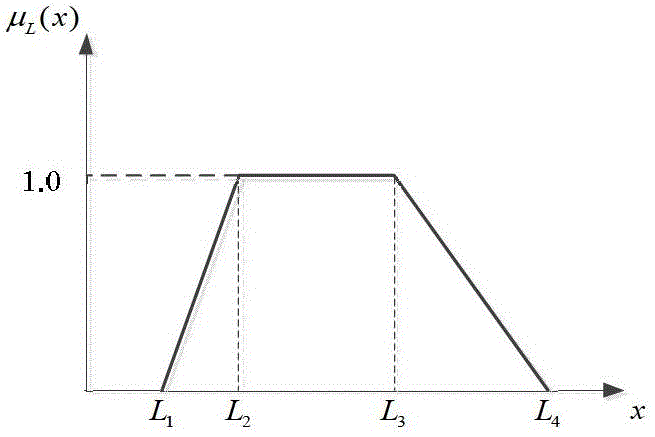
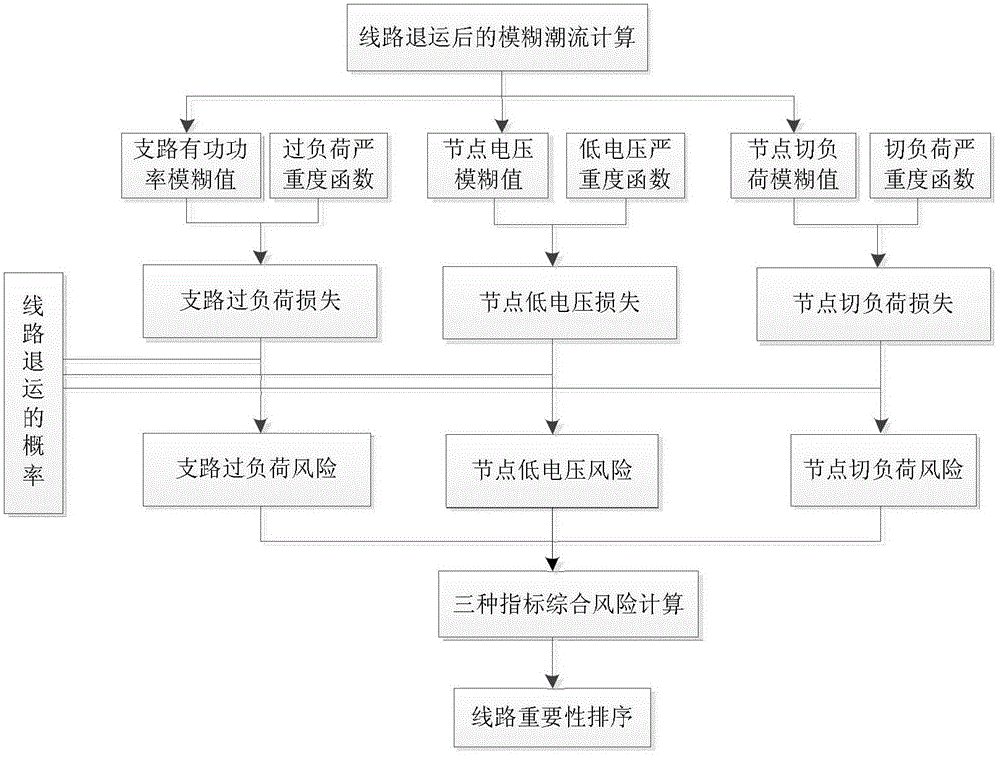
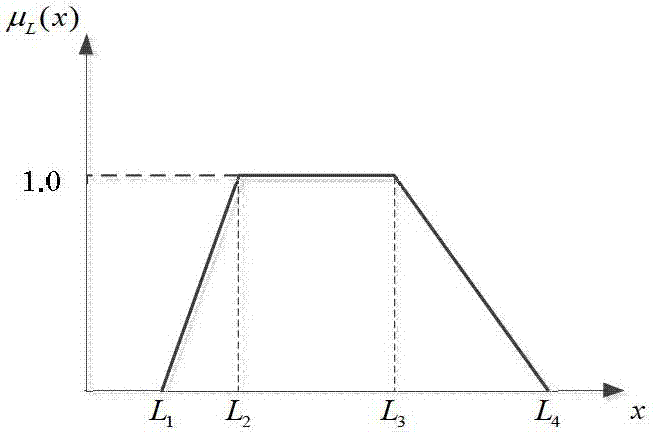
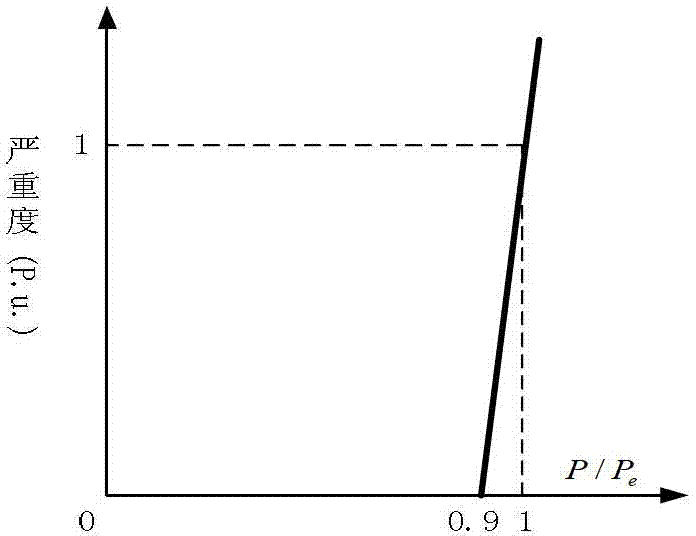
The invention discloses a power grid differentiation-based core backbone network architecture construction method. The importance of lines and nodes in a power system are taken into comprehensive account, the knowledge of a risk theory is referenced, the importance of the lines is obtained by calculating risk indicators of the lines, and the importance of the nodes is evaluated based on the knowledge of a graph theory; and a core backbone network architecture searching model is constructed based on the importance of the lines and the nodes, and network architectures are searched by a particle swarm algorithm to obtain the lines and the nodes for constructing a core backbone network architecture. The importance of the lines is evaluated by line returning risks, so that the importance of the lines can be better reflected from the point of electrical quantity variation; and a fuzzy-membership-based line returning risk evaluation method more consistent with actual conditions is provided, and the influence of uncertain factors of the power system is taken into comprehensive account.
Owner:STATE GRID CORP OF CHINA +2
Engineering-risk wireless-sensing early-warning visualization system and method
InactiveCN104167084AReal-time monitoringReal-time warningAlarmsAutomatic controlEngineering structures
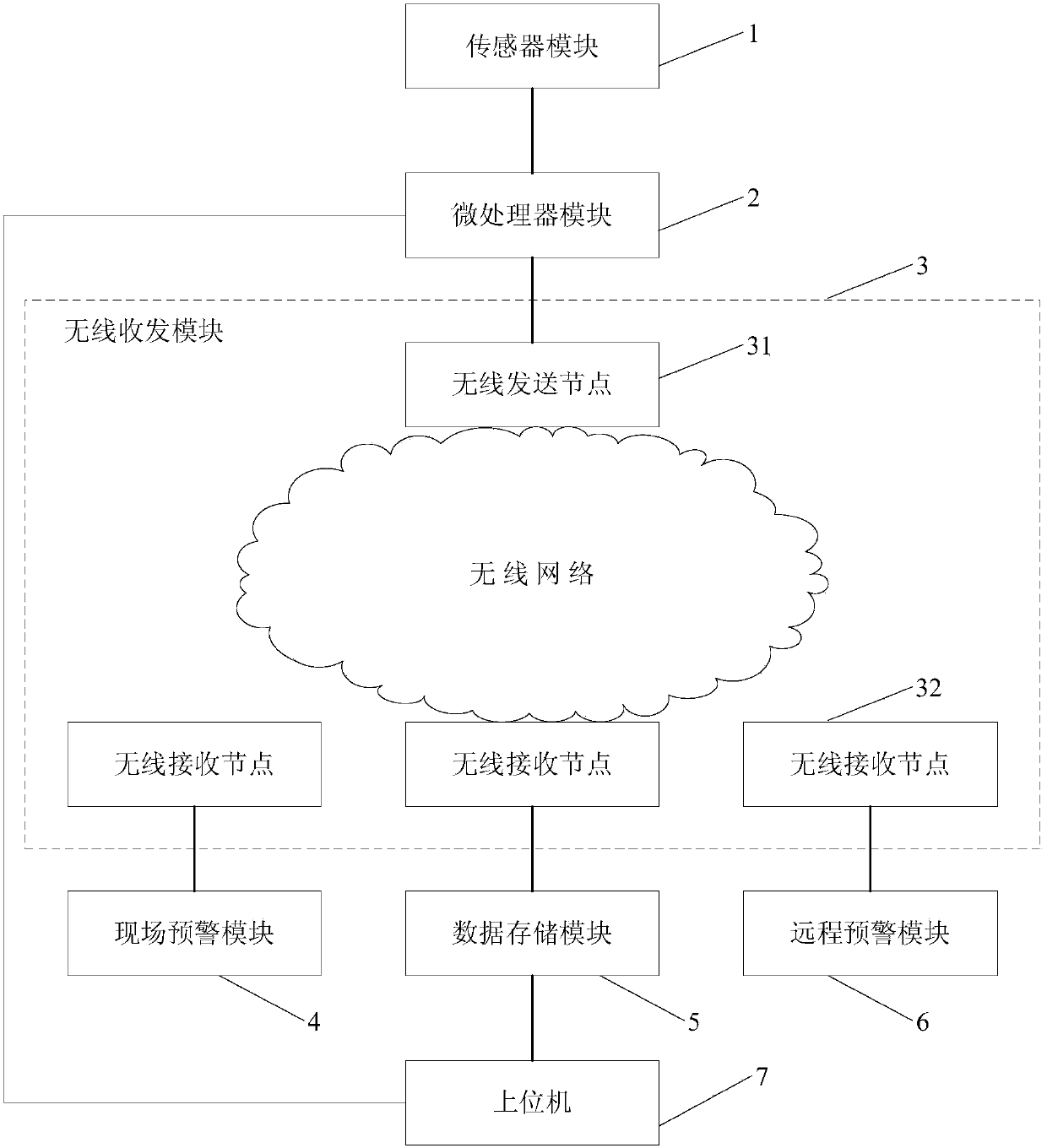
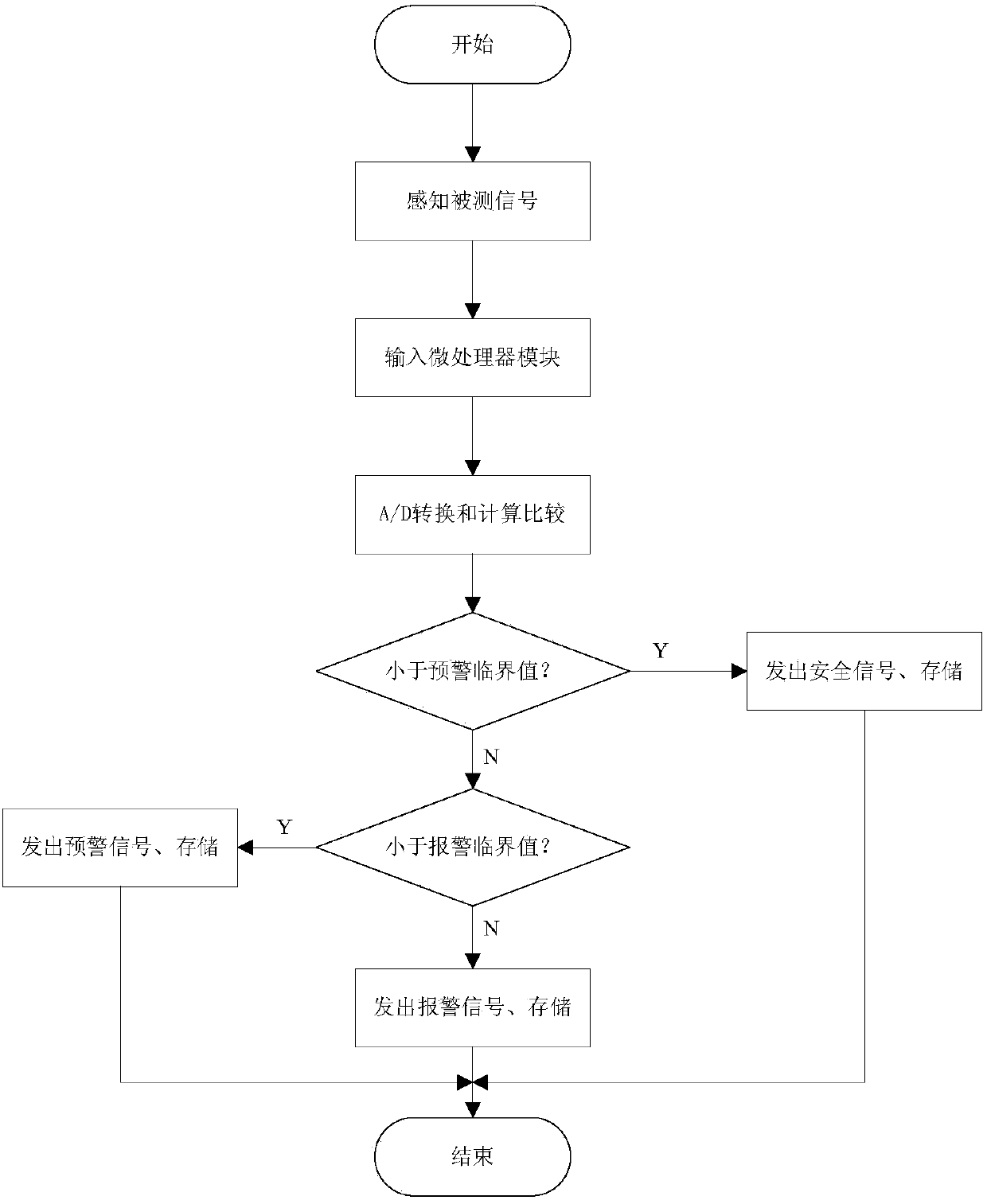
The invention relates to an engineering-risk wireless-sensing early-warning visualization system and method. The system comprises a sensor module, a microprocessor module, a wireless receiving and transmitting module, a site early-warning module, a data storage module, a long-distance early-warning module and an upper computer. The sensor module is arranged in an engineering structure and is connected with the microprocessor module. The microprocessor module is connected with the wireless receiving and transmitting module and the upper computer respectively. The wireless receiving and transmitting module is connected with the site early-warning module, the data storage module and the long-distance early-warning module respectively. The site early-warning module is arranged at an engineering site, the long-distance early-warning module is arranged in a long-distance monitoring room, and the data storage module is connected with the upper computer. Compared with the prior art, the engineering-risk wireless-sensing early-warning visualization system and method are used for safety monitoring and early-warning of the civil engineering, a monitoring theory, an engineering risk theory and an automatic control theory are combined, the limitation of an existing monitoring and early-warning method is broken through, real-time feedback and timely early warning are achieved, and safety in the engineering construction and operation process is guaranteed to the maximum degree.
Owner:TONGJI UNIV
Information security risk assessment method oriented to typical metallurgy process control system
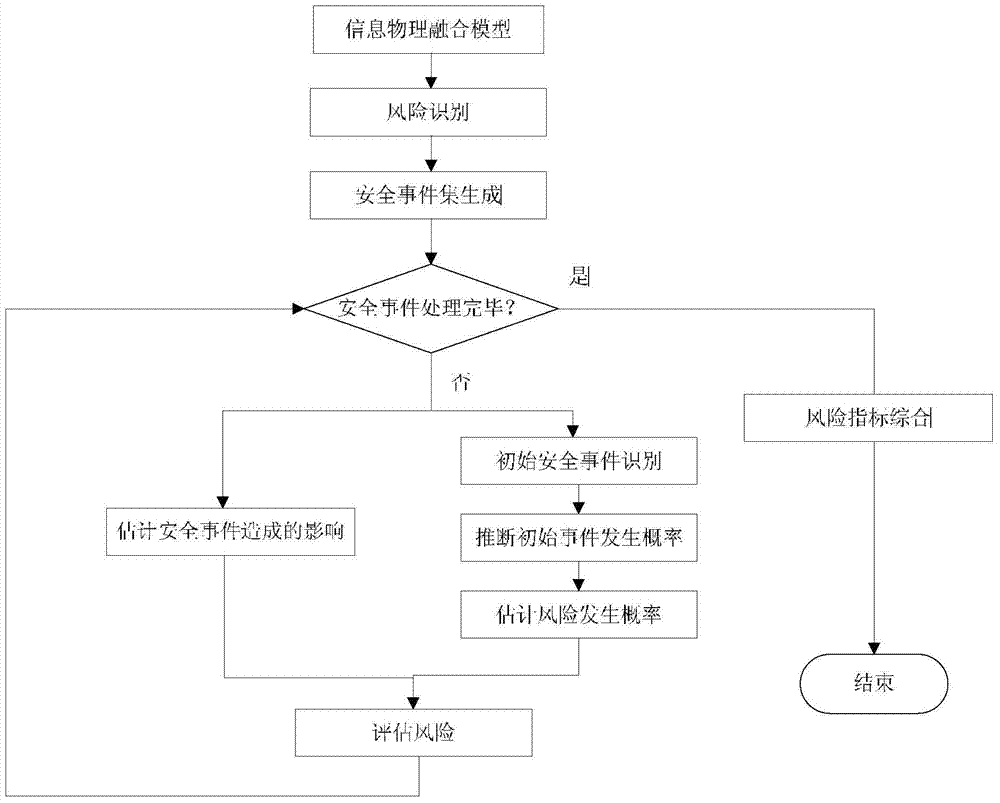
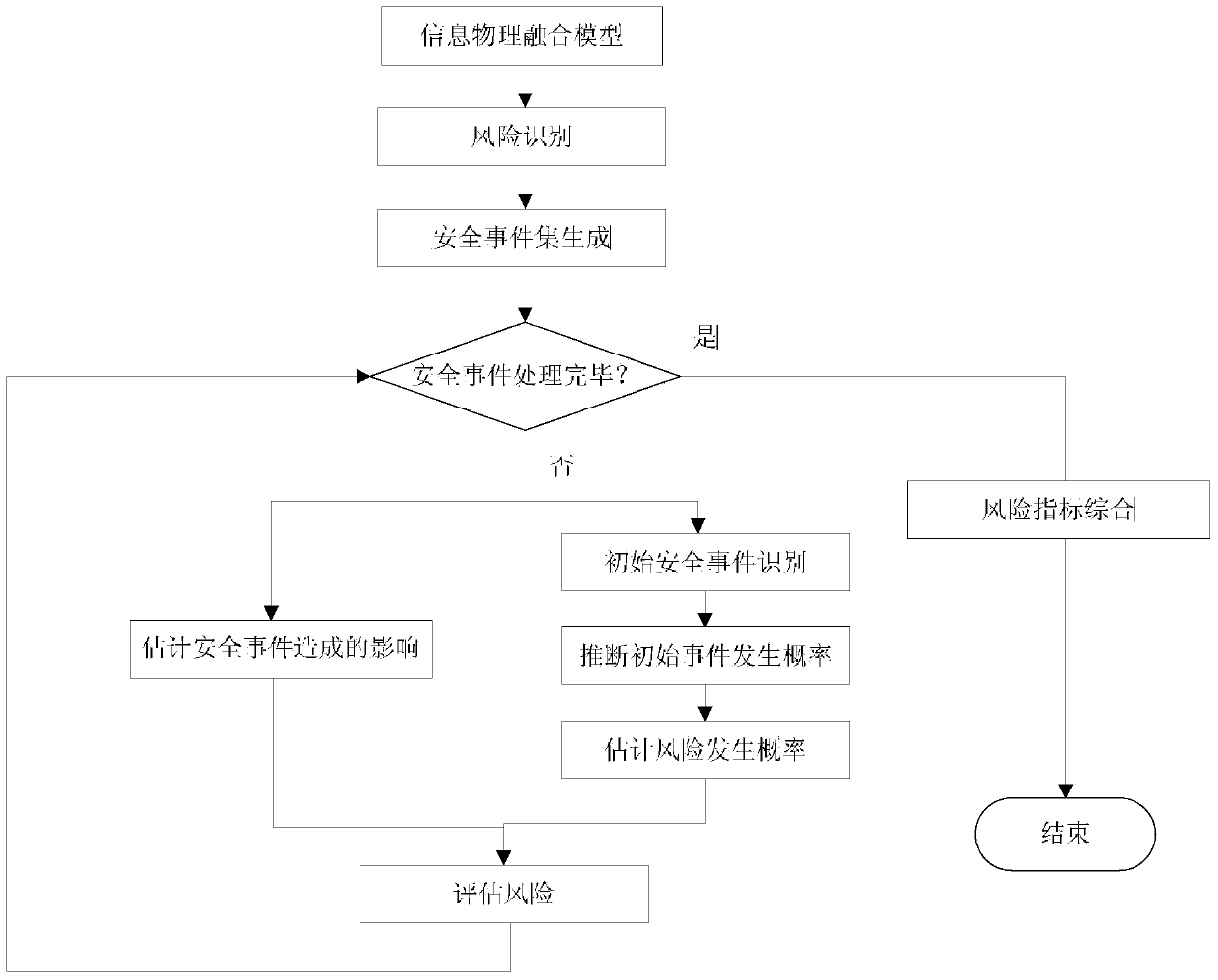
InactiveCN104331072AGuaranteed safe operationLow costElectric testing/monitoringProbabilistic methodRisk indicator
The invention provides an information security risk assessment method oriented to a typical metallurgy process control system and belongs to the technical field of industrial control system information security. The system robustness under different attack modes and policies is analyzed by establishing an attack model under the typical scenes of the metallurgy process, and therefore, the security risk assessment on the typical metallurgy process control system in different attack modes and a failure mode can be realized. Based on the risk theory, the method is used for performing the security risk assessment by use of a random probability algorithm by defining the metallurgy process control system as a physical information fusion system; from the two aspects of the occurrence probability and the influence of attack sources or failure sources, a security assessment method based on risk indexes is developed. Quantitative estimation is performed based on risk indexes; a security incident set is created based on the established physical information fusion model and attack model, and then the security incident set is combined with the calculated robustness assessment indexes for the quantitative estimation, and therefore, the weak security links in the control system can be located conveniently.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
Identification method of vulnerable nodes of distribution network
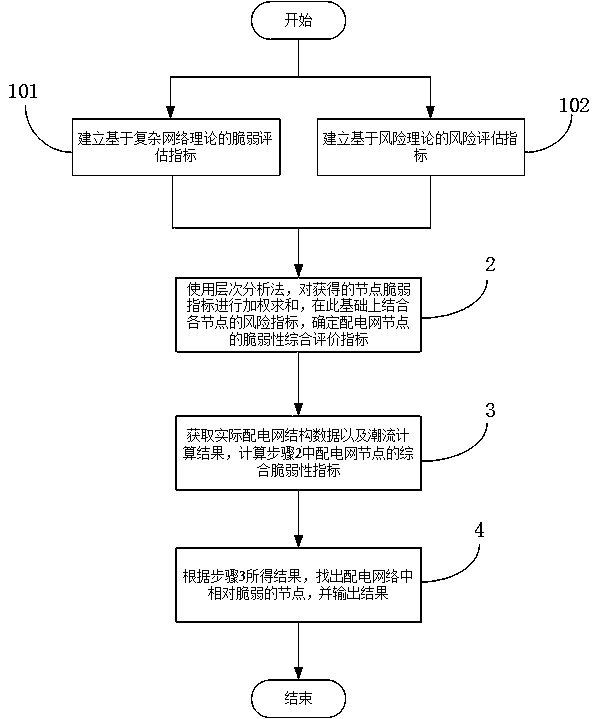
PendingCN107871216AEffectively identify vulnerable nodesFind vulnerable nodesResourcesRisk theoryRisk evaluation
The invention discloses an identification method of vulnerable nodes of a distribution network. The method includes the following steps: (1) establishing vulnerability evaluation indexes based on complex network theory, and a risk evaluation index based on risk theory; (2) using a hierarchical analysis method to carry out weighted summation on the vulnerability evaluation indexes of the distribution network and comprehensively analyze the vulnerability indexes and the risk index, and establishing a comprehensive estimation index of node vulnerability of the distribution network; (3) acquiringstructure data of the distribution network and a power flow calculation result, and calculating the comprehensive estimation index of the distribution network; and (4) outputting the relatively vulnerable nodes of the distribution network. The comprehensive estimation index has the following advantages that: the complex network theory and the risk theory are adopted, a structure of the distribution network is taken into account, fault risks are taken into account, and the identification problem of the vulnerable nodes in the distribution network is comprehensively solved.
Owner:HUIZHOU POWER SUPPLY BUREAU OF GUANGDONG POWER GRID CO LTD
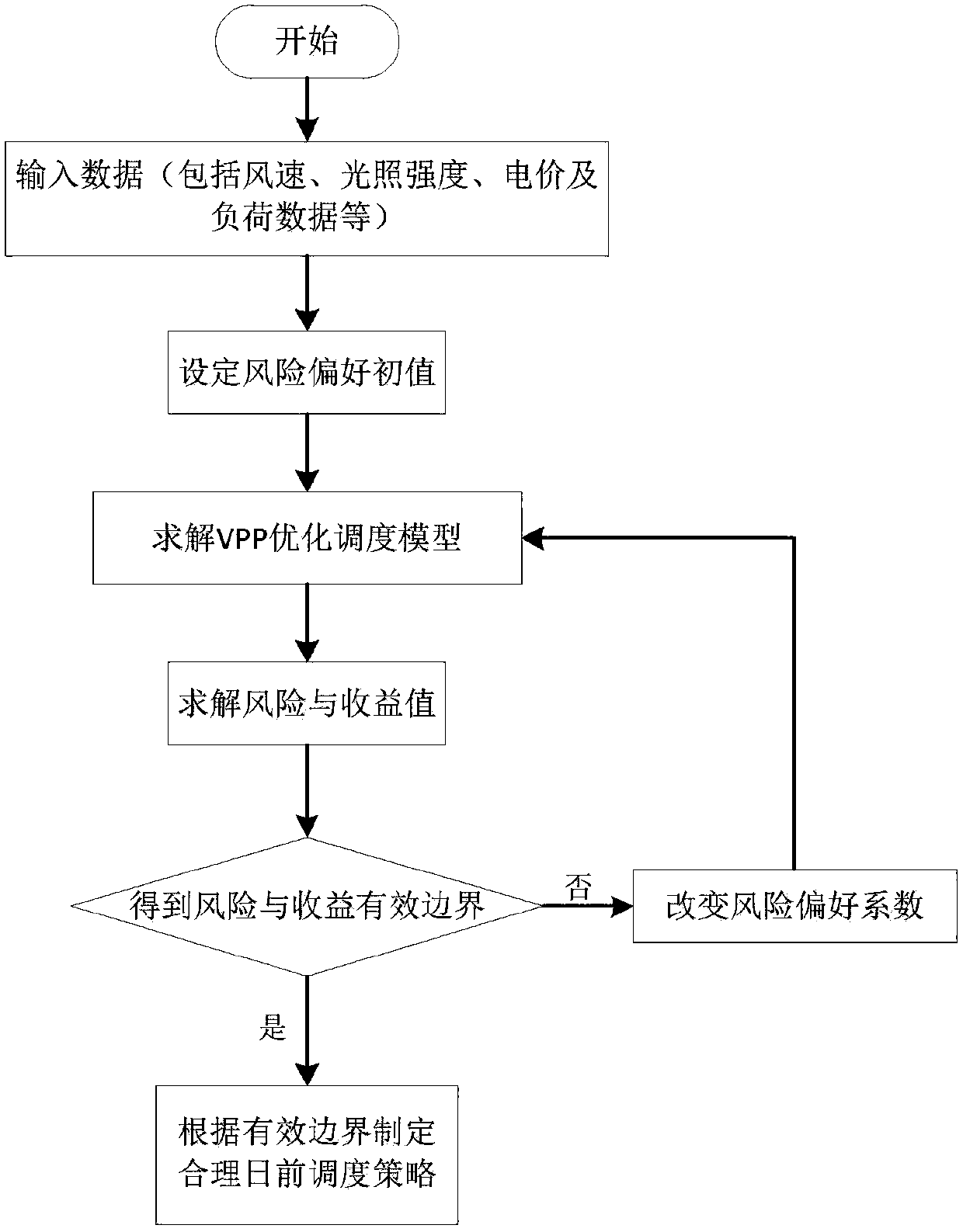
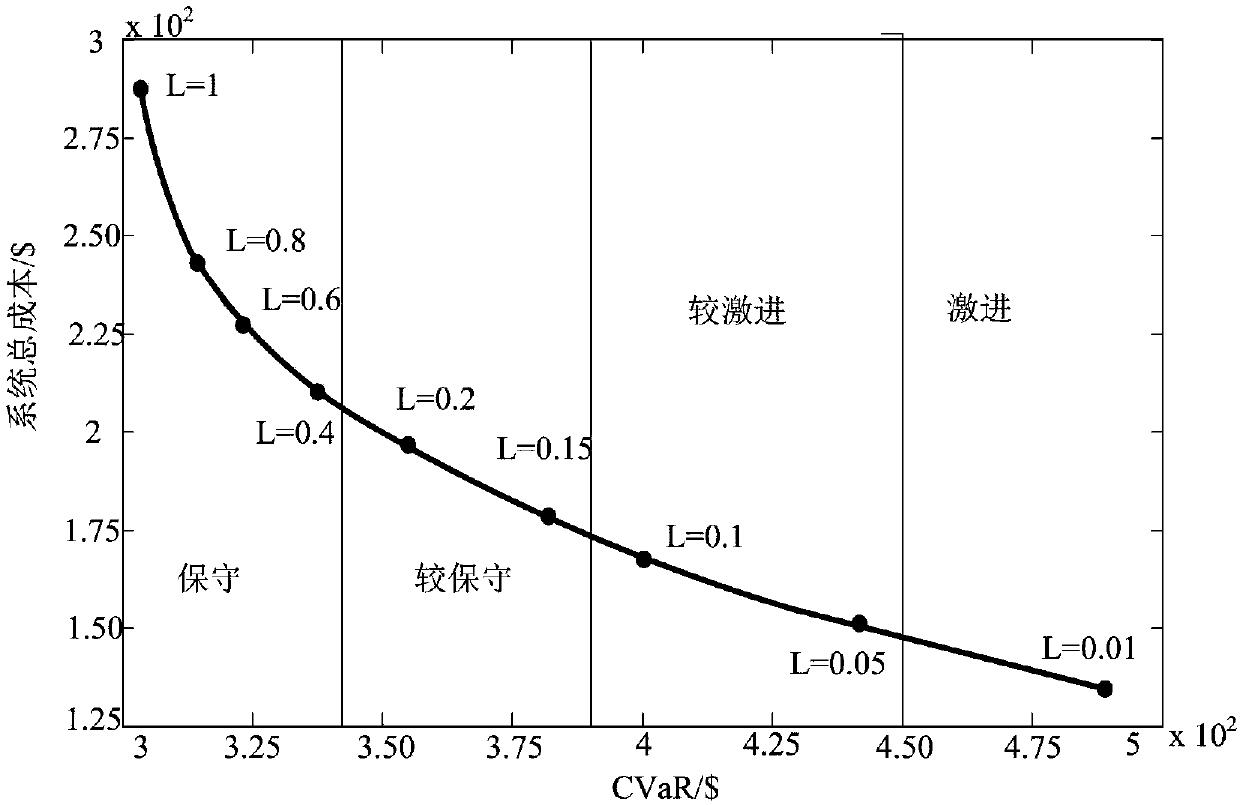
Virtual power plant optimization scheduling modeling method based on CVaR
ActiveCN108053057AReduce riskIncrease revenue from electricity salesForecastingDesign optimisation/simulationWeight coefficientMathematical model
The invention provides a virtual power plant (VPP) optimization scheduling modeling method based on a conditional risk value (CVaR). The risk theory is utilized to discuss a VPP scheduling optimization problem, the VPP contains a large number of renewable energy such as wind and light, the output is different from conventional energy, strong gap and volatility exist, a VPP scheduling optimizationproblem is an uncertainty problem, so VPP scheduling is made to face a possible risk, the CVaR theory can be utilized to accurately measure the risk of the VPP in scheduling operation, and thereby economical efficiency and the risk are balanced. In a target function of traditional VPP scheduling operation, a CVaR item for measuring the risk is added, the target function of a mathematical model ofthe problem is made to not only consider minimum total cost, but also the least risk, the CVaR is multiplied by a weight coefficient and is then added to the target function, and a multi-target problem is converted into a single-target problem for solution. The method is advantaged in that operators with different risk preferences are further graded, and instructive solutions are provided for theVPP operators with the different risk preferences.
Owner:YANCHENG POWER SUPPLY CO STATE GRID JIANGSU ELECTRIC POWER CO +3
Electric power system protection and control method based on risk assessment
InactiveCN104156879AImprove reliabilityAvoid cascading failuresData processing applicationsElectric power systemPower grid
The invention discloses an electric power system protection and control method based on a risk assessment. The method comprises the following steps: carrying out the risk assessment on an electric power system, and calculating power network risk values; establishing a protection and control object function; inputting electric power system running states and parameters; and according to the protection and control object function and the power network risk values, formulating electric power system protection and control measures. According to the invention, risk theories are applied to the protection and control of the electric power system, the problem of formulating protection and control measured by reliance on experience of dispatchers is solved, and quantifiable measures can be obtained by use of the method so as to effectively realize safety protection and control of the electric power system. Besides, the method, on the basis of the risk assessment, takes control cost into consideration in an integrated approach, draws up the protection and control object function and formulates the quantifiable protection and control measures according to the object function so as to reduce the control cost as much as possible under the condition that safety protection of the electric power network is realized.
Owner:ELECTRIC POWER SCHEDULING CONTROL CENT OF GUIZHOU POWER GRID CO LTD +1
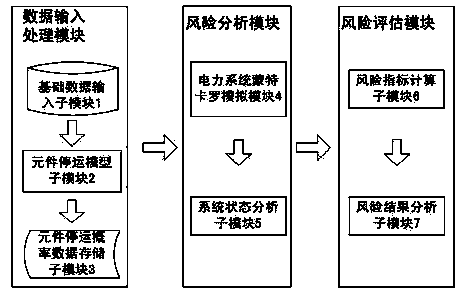
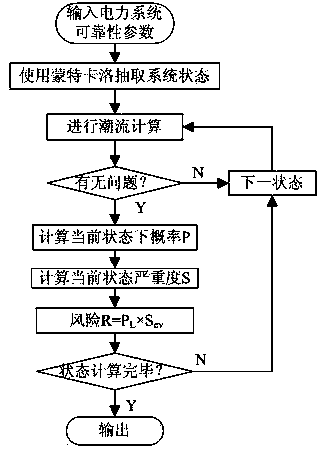
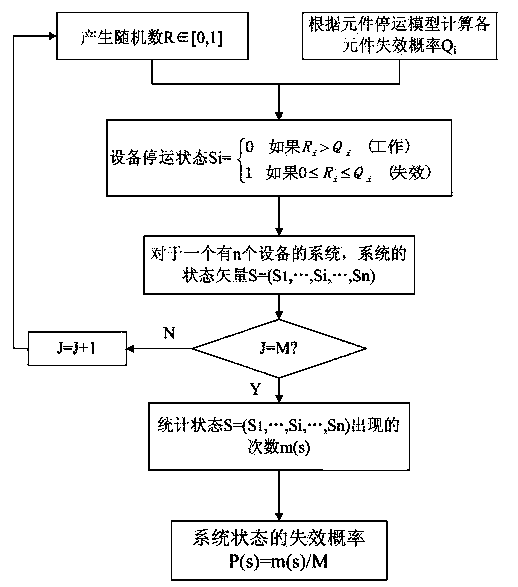
Power grid operating state assessment method based on risk theory
ActiveCN103646350AComprehensive understanding of risksData processing applicationsIslandingPower grid
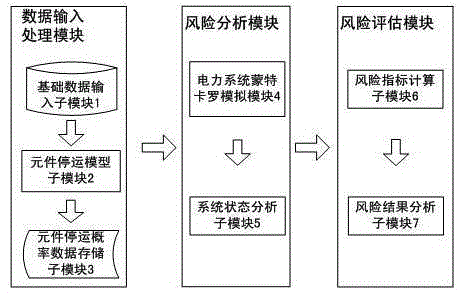
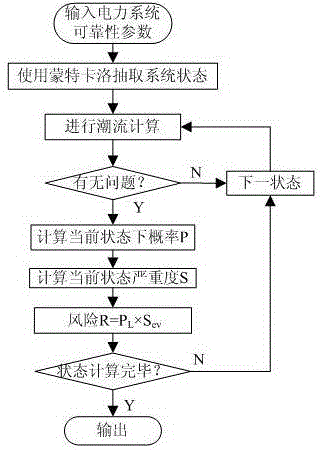
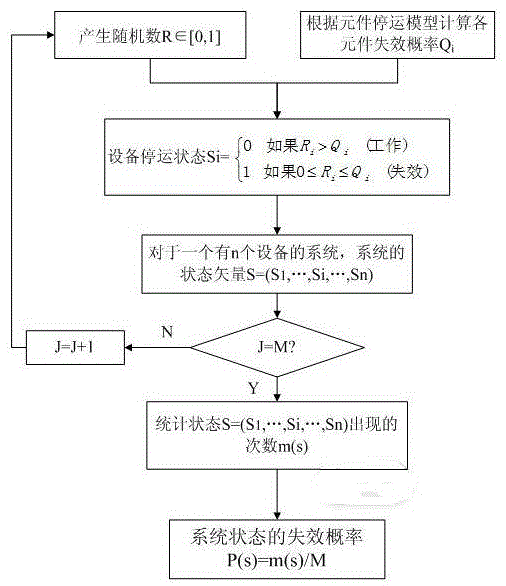
The invention discloses a power grid operating state assessment method based on the risk theory. The method comprises the following steps: data is collated, and a data processing module is established; the outage probability of power grid elements is calculated; the element outage probability data is stored; the power grid operating state is extracted through the Monte Carlo method; the system state is analyzed; system state analysis is performed through a submodule 5 to judge whether problems, such as the circuit overload problem, the voltage out-of-limit problem, the bus isolation problem, the problem that a system is separated into isolated islands, etc., occur; the power grid operating risk indicators are calculated; and the power grid operating state risk indicator result is analyzed to give out the weak link of the power grid. According to the invention, risk assessment is performed on the power grid operating state; the actual operating state of the power grid is simulated by using the Monte Carlo method, the event random nature of the power grid is taken into account reasonably; different risk indicators are used, multi-angle and multi-level assessment is performed on the power grid operating state risk; and the power grid operating state risk assessment result is analyzed to give out the weak link of the power grid.
Owner:江西汇能电力工程技术有限公司
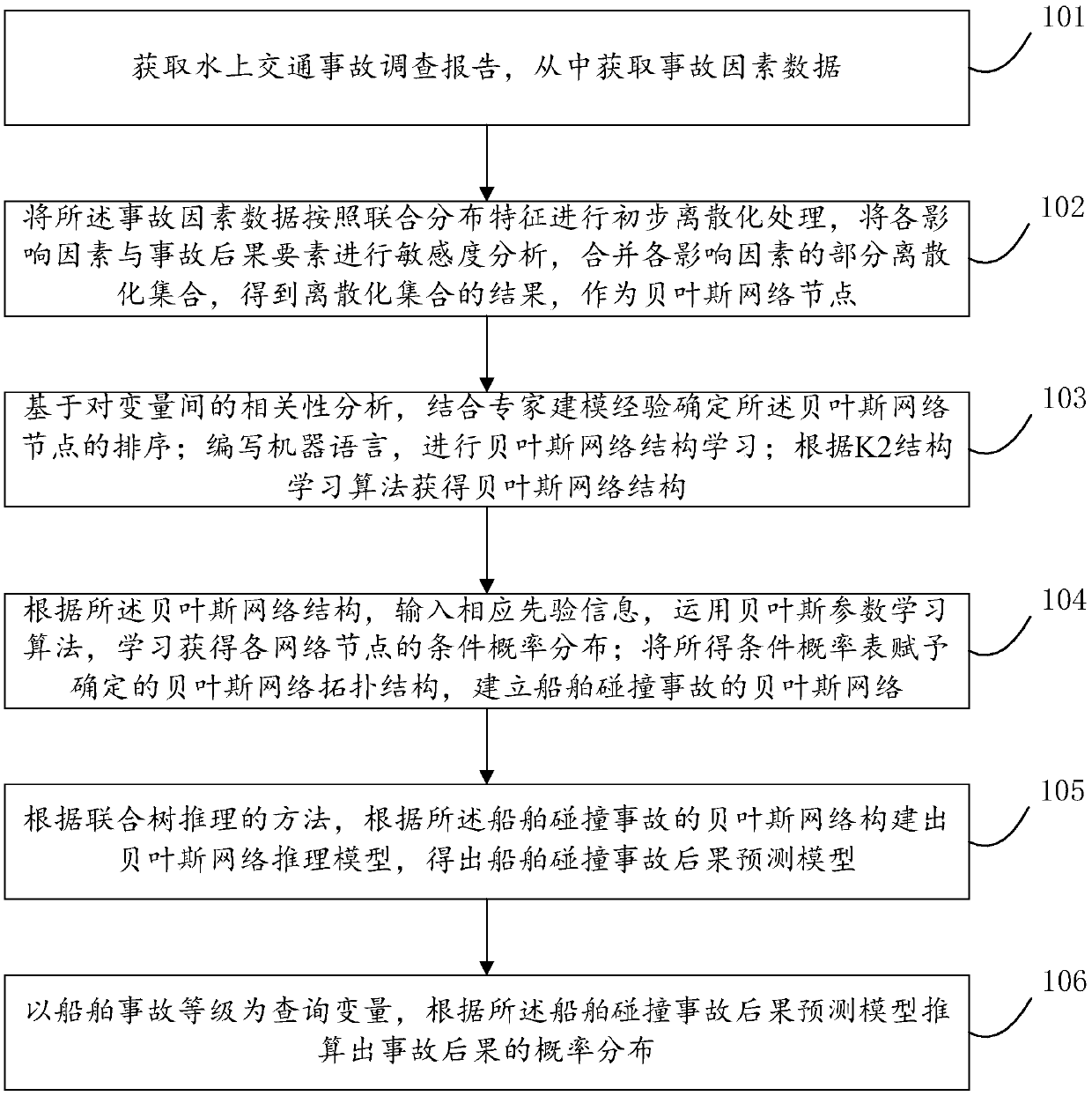
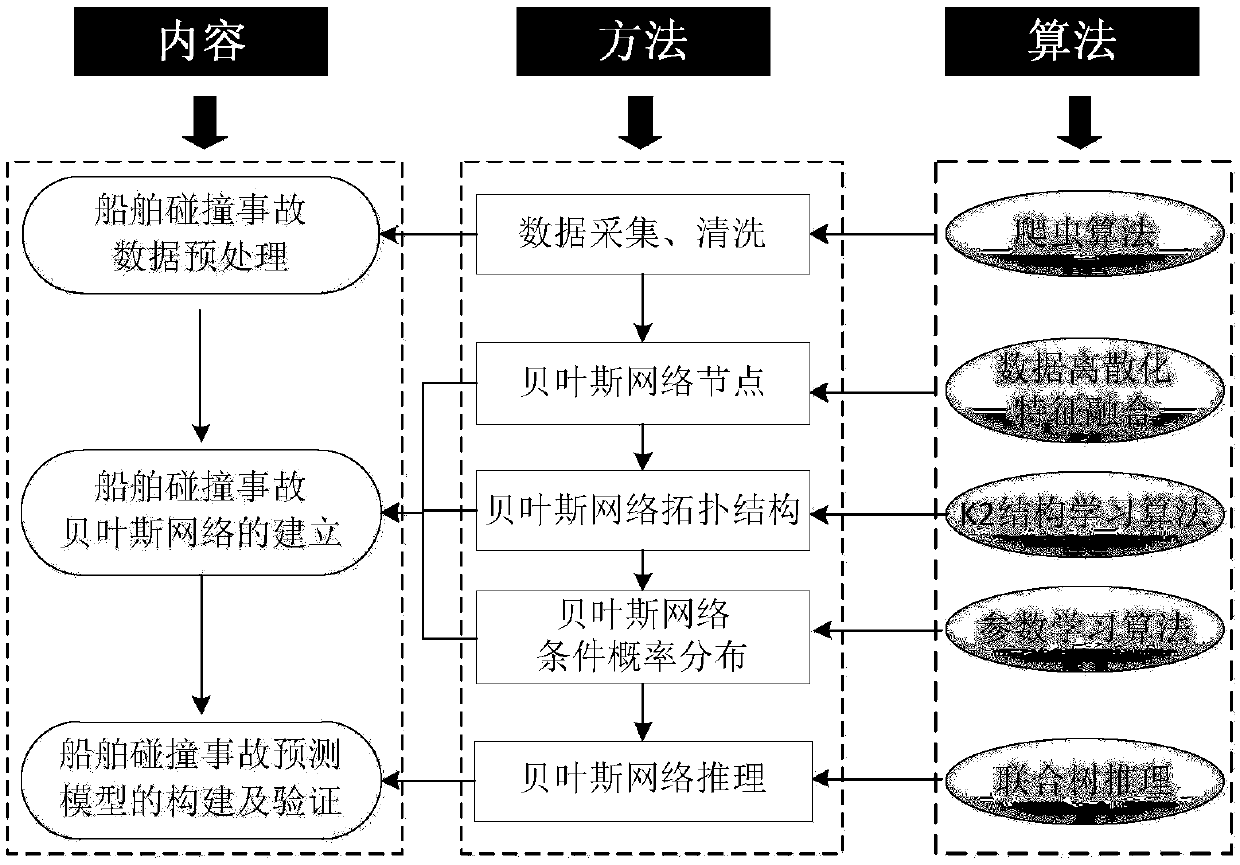
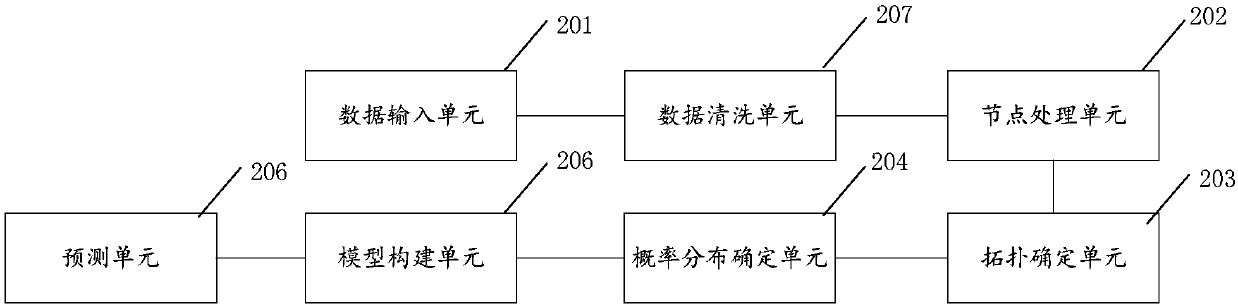
ship collision accident level prediction method and system based on a Bayesian network
InactiveCN109657880ASolve forecasting problemsAchieve Grade PredictionForecastingCharacter and pattern recognitionRisk theoryComputer science
The invention discloses a ship collision accident level prediction method and system based on a Bayesian network. According to the method, by constructing a ship collision accident prediction model, grade prediction of ship collision accidents is achieved, from the perspective of data, the law between accident factors is found by deeply mining the relation between the accident factors, an expert knowledge method with too high subjectivity is replaced, and the Bayesian network of the ship collision accidents is established. From the perspective of the method, a ship collision accident prediction model is constructed based on the Bayesian network, the ship collision accident level prediction problem is solved, and the development of the maritime risk theory is promoted. From the perspectiveof application, research results can provide scientific basis for ship navigation command and emergency decision making.
Owner:中交信息技术国家工程实验室有限公司
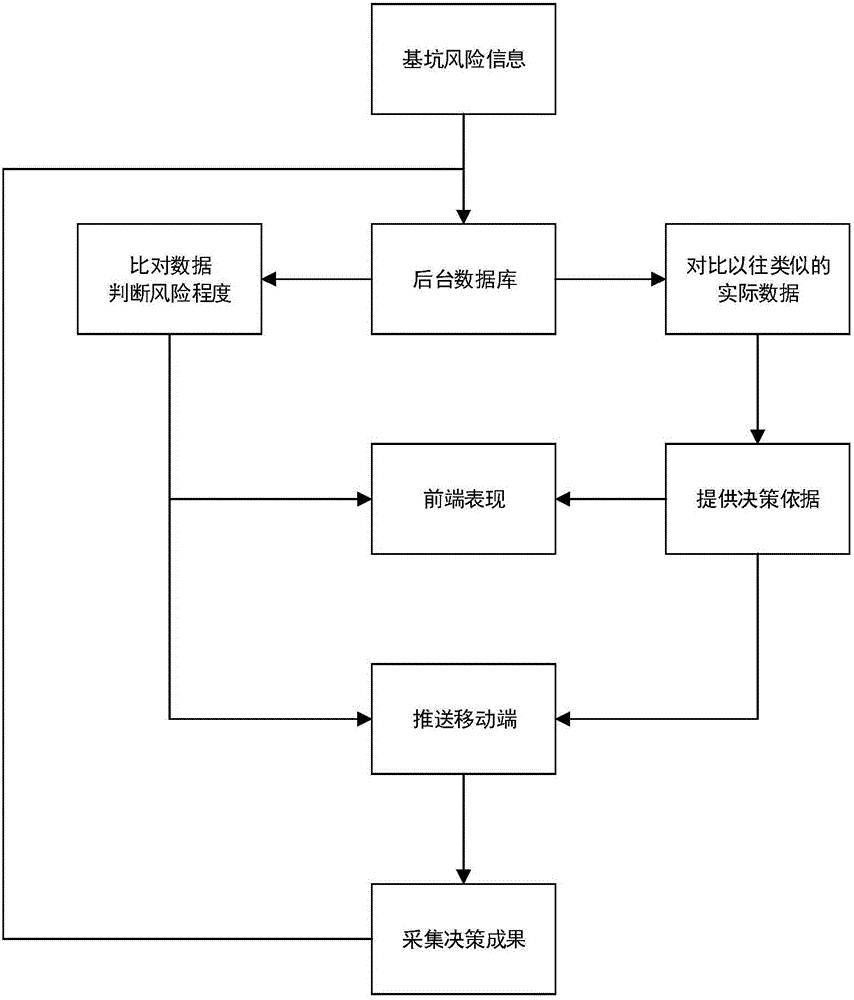
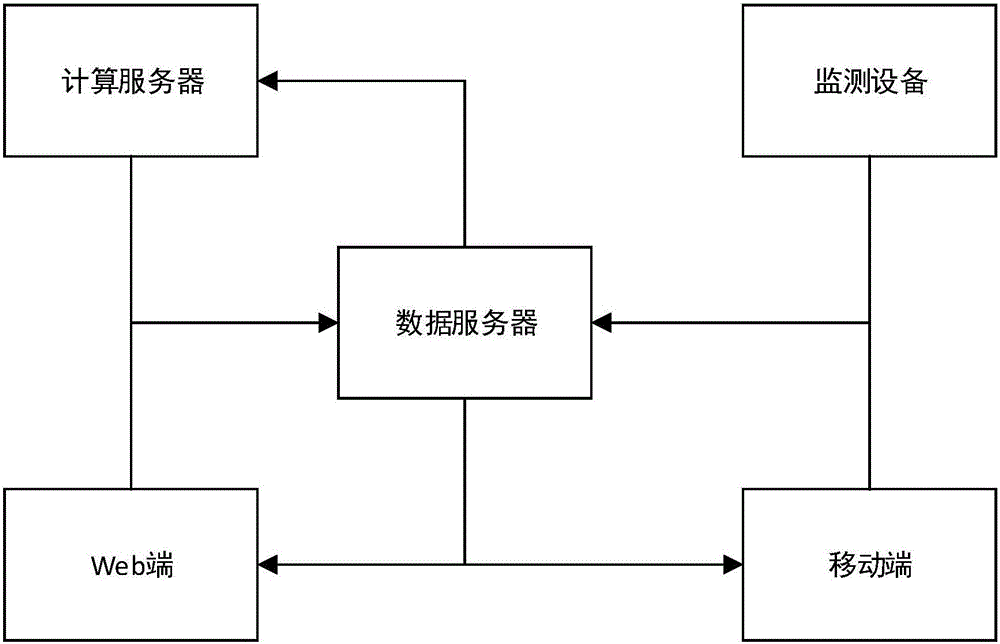
Foundation pit risk management method based on big data analysis and foundation pit risk management system based on big data analysis
The invention provides a foundation pit risk management method based on big data analysis and a foundation pit risk management system based on big data analysis. The foundation pit risk management method comprises following steps: step1, establishment of a foundation pit risk management system hardware platform; step2, acquisition of foundation pit risk related information; step 3, dynamic acquisition of foundation pit deformation data; step 4, analysis, comparison, calculation of related data information; step 5, the display of the acquired foundation pit risk related information by adopting visualization means; step6, timely transmission of effective information to information demanders by adopting an Internet way; step7, recording of risk treatment means and treatment results proposed by the information demanders. By adopting an informatization way, the foundation pit risk related information is acquired, the storage, the extraction, the arrangement, and the analysis of the above mentioned information are facilitated; foundation pit data is timely updated; by adopting the constant accumulation and analysis of the foundation pit risk related information, a foundation pit risk theory is in dynamic adjustment, and therefore the risk management is more accurate and effective; the transmission efficiency and the transmission accuracy of the information are improved, and risk prevention early warning is provided.
Owner:上海斯涵福信息科技有限公司
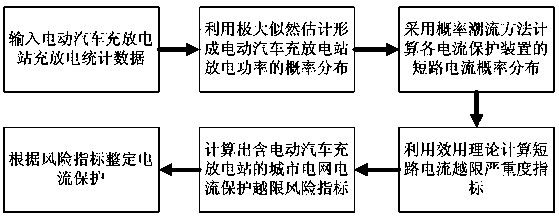
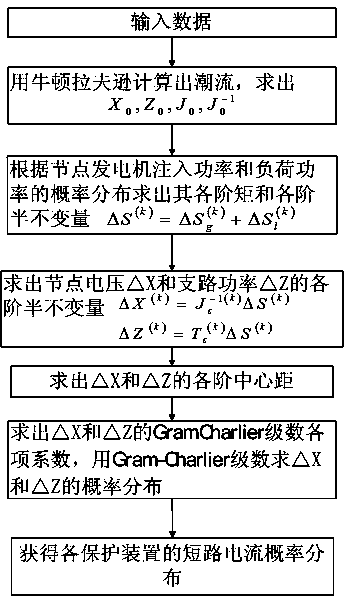
Current protection and threshold crossing risk monitoring method for urban power grid including EV (electric vehicle) charge-discharge stations
ActiveCN104182640AGuarantee the normal operation of current protectionGuaranteed uptimeSpecial data processing applicationsInformation technology support systemData informationEngineering
The invention belongs to the field of power system protection and control and particularly relates to a current protection and threshold crossing risk monitoring method for an urban power grid including EV (electric vehicle) charge-discharge stations. Probability distribution of discharge powers of the EV charge-discharge stations is formed on basis of charge-discharge data information of the EV charge-discharge stations; short circuit current probability distribution of each current protector is calculated through Gram-Charlier series and a semi-invariant; a short circuit current threshold crossing severity index is calculated through a utility theory; current protection and threshold crossing risk indexes of the urban power grid including the EV charge-discharge stations are then calculated. According to the method, risk assessment is performed by a probabilistic power flow method on basis of the utility theory and a risk theory; normal current protection is effectively guaranteed for the urban power grid including EV charge-discharge stations, and the urban power grid can run safely and reliably.
Owner:WUHAN UNIV
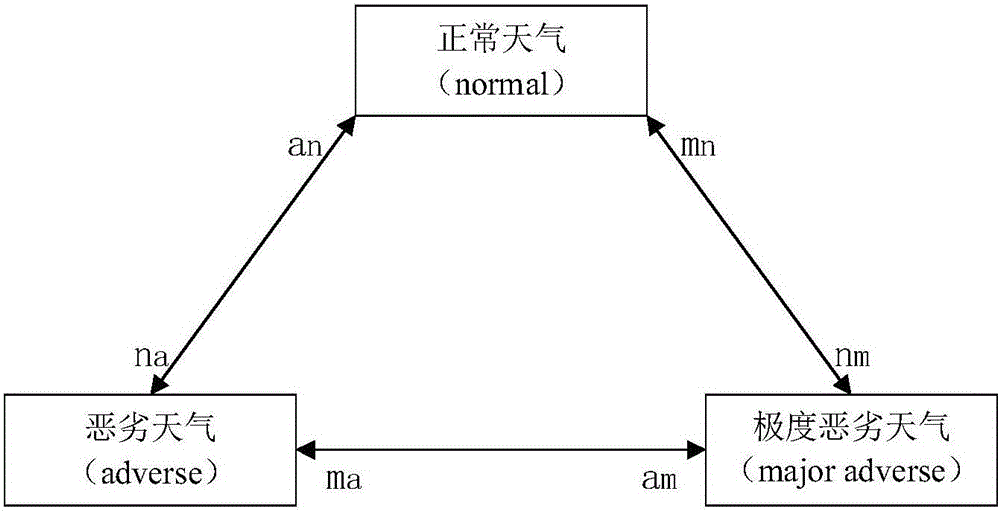
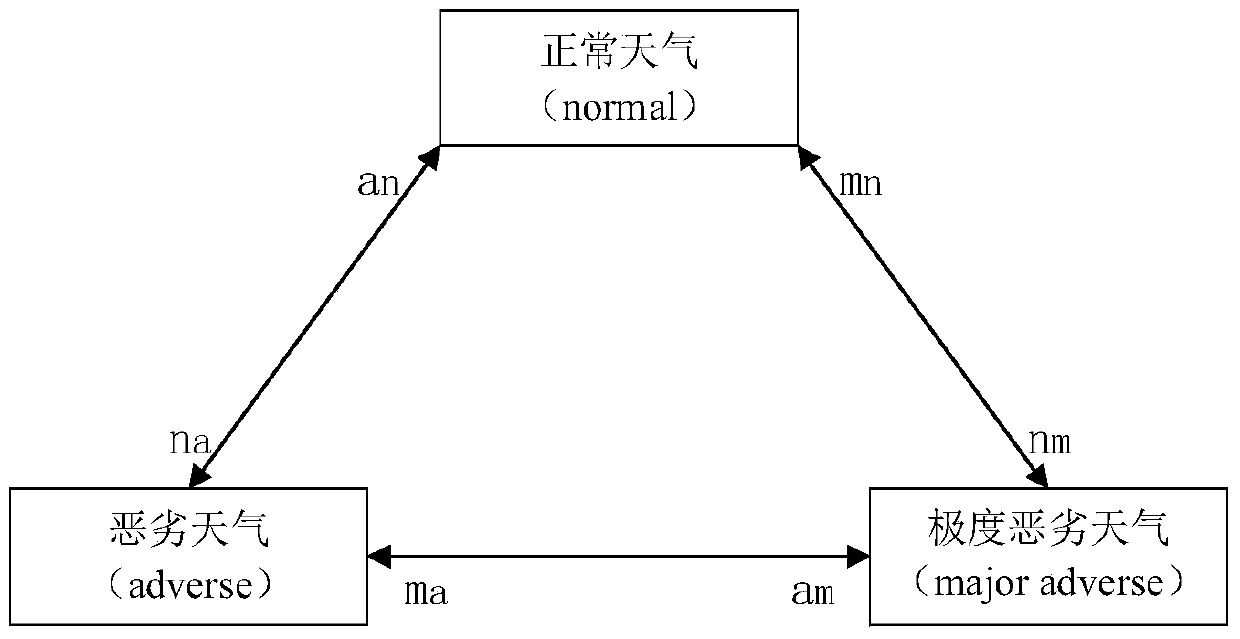
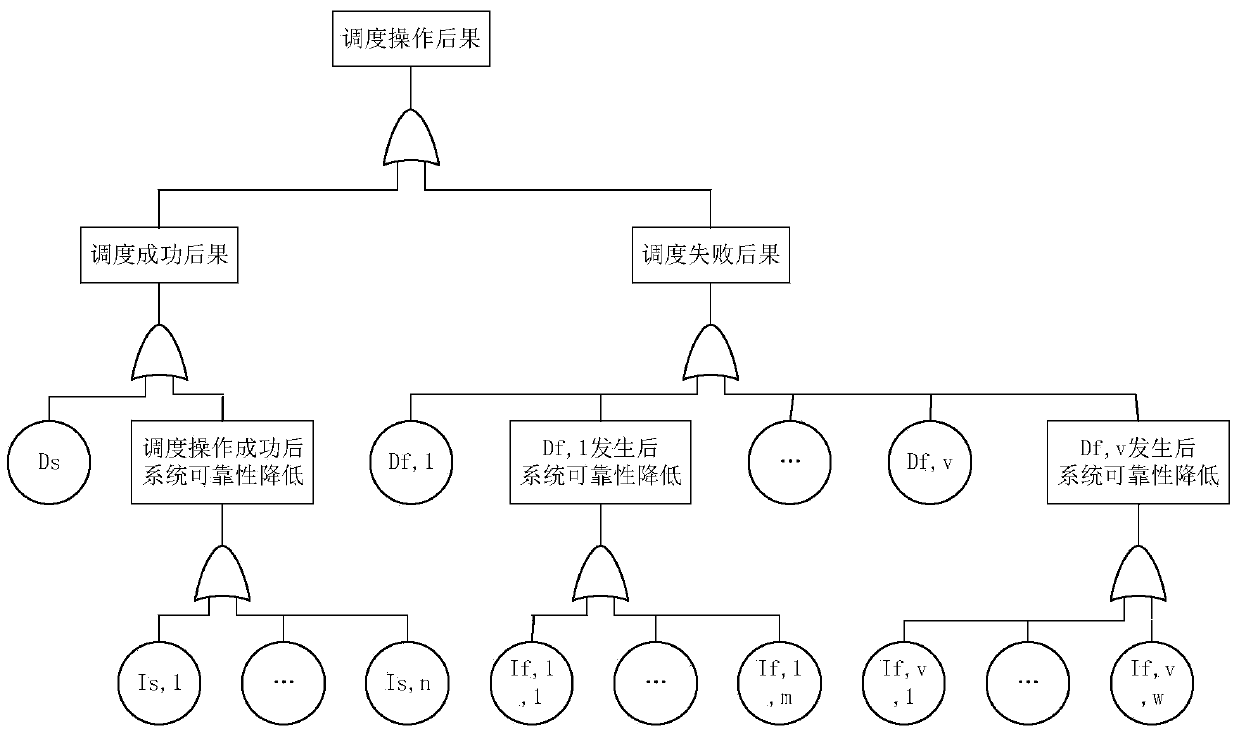
Power grid dispatching operation risk evaluation method taking weather factor into consideration
ActiveCN105869071AReliable methodSimple methodResourcesInformation technology support systemWeather factorTotal risk
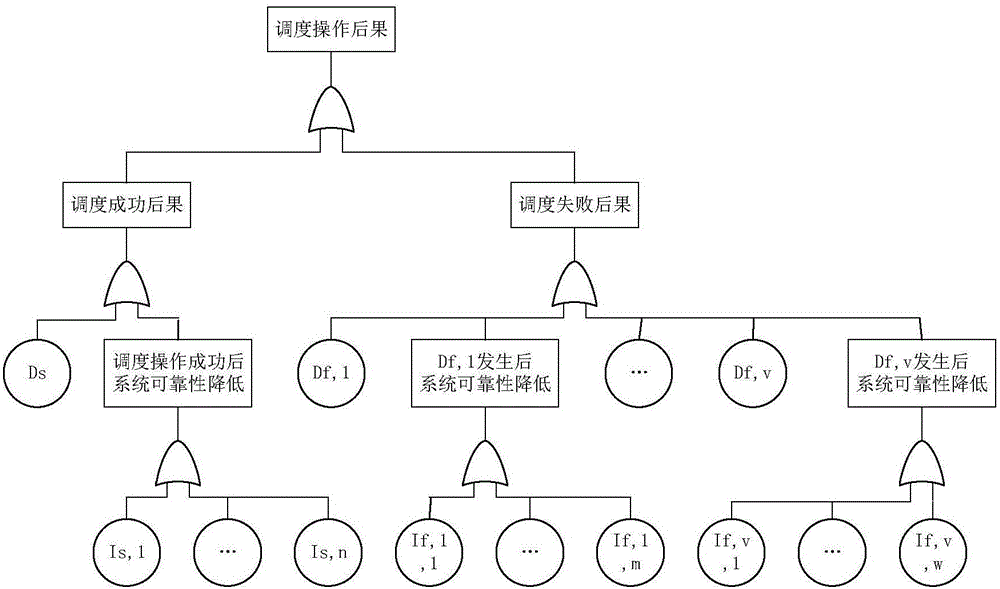
The invention discloses a power grid dispatching operation risk evaluation method taking a weather factor into consideration. The method comprises the following steps: step 1, according to weather statistical data, historical statistical data of an equipment fault rate and a three-state weather model, calculating an equipment fault probability in a dispatching operation process respectively under a normal weather condition, a bad weather condition and an extremely bad weather condition; step 2, according to a system state in the dispatching operation process, obtaining a fault tree model; step 3, according to the fault tree model and a given risk consequence index, calculating a consequence of each step of operation, and determining whether the sequence is a development fault of the last step; and step 4, according to a risk theory, calculating a risk value of each step in the dispatching operation process and a total risk value. The method is reliable, is easily implemented and is convenient to promote.
Owner:ZHEJIANG UNIV
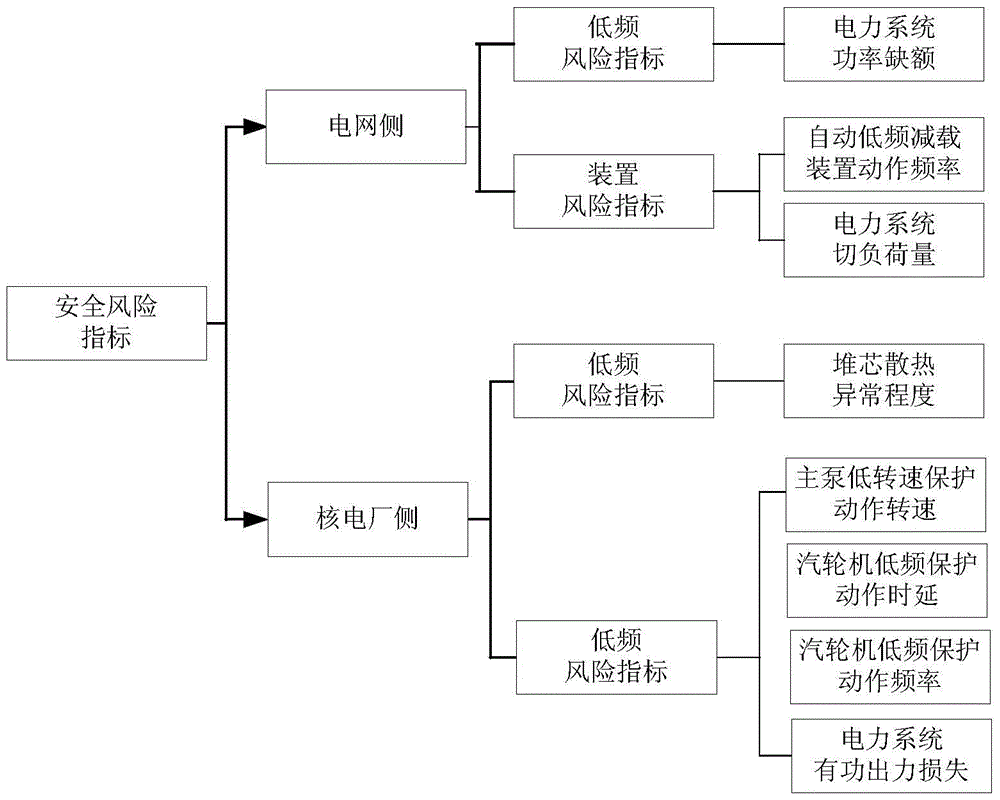
Low frequency risk comprehensive evaluation method for nuclear power accessed to grid
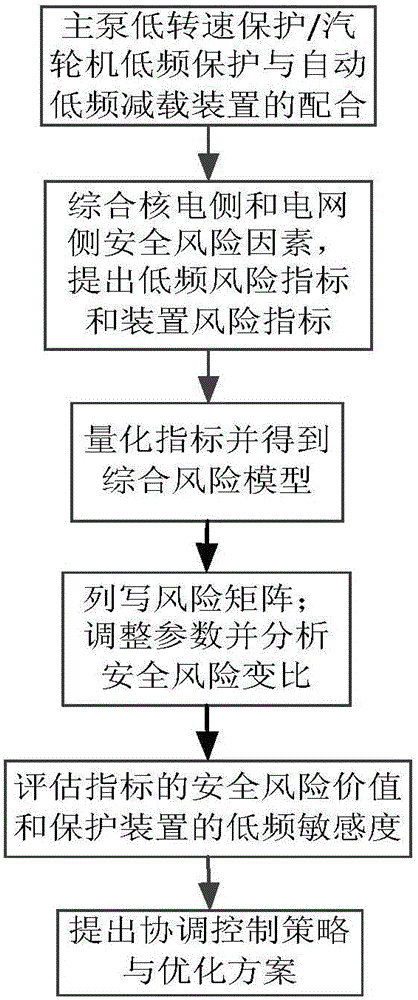
The invention discloses a low frequency risk comprehensive evaluation method for nuclear power accessed to grid, which comprises safety risk evaluation indexes with plant-grid risks combined, a low frequency risk evaluation model integrating safety and economy between the nuclear power and the power grid, and a nuclear power low frequency risk evaluation method for a low frequency safety risk transformation ratio, an index safety risk value, a device low frequency risk sensitivity and the like. The low frequency risk indexes comprise a low frequency risk index for evaluating reduction of the system frequency on the plant-grid influence degree and a device risk index based on a plant-grid low frequency protection device; the low frequency comprehensive risk model is built based on a risk theory and a plant-grid side economic index is introduced, and quantitative analysis on the low frequency risk is realized; and the risk calculation method for the safety risk transformation ratio, the index safety risk value, the device low frequency risk sensitivity and the like is easy to compare and analyze, and a basis is provided for making a protection device parameter optimization scheme and a plant-grid coordination control strategy. The structure is rigorous and clear, and requirements of risk analysis and decision are met; and model parameters have clear meaning and are easy to acquire, the modeling process is clear, quick, convenient, efficient, accuracy and strong in practicability.
Owner:WUHAN UNIV
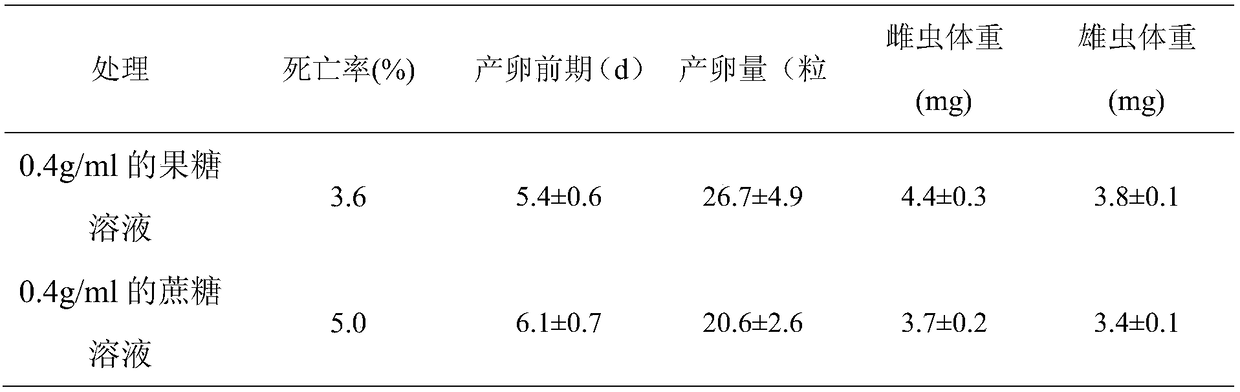
Method for evaluating the influence of insecticidal protein on adults of propylaea japonica and feeding device
InactiveCN108575912AReflect feeding patternsAccurately reflectBiological testingAnimal husbandryMortality rateSecondary metabolite
The invention discloses a method for evaluating the influence of insecticidal protein on adults of propylaea japonica and a feeding device. The invention firstly designs a feeding device for simulating the plant gland, and the suction mode of cotton flower extrafloral nectaries is simulated, and then a cotton juice extract is used as a solvent to dissolve the exogenous insecticidal protein, and fructose is added to serve as a phagostimulant of the propylaea japonica adults; a single-pair of the propylaea japonica adults are put into the feeding device with a feeding solution, and enough pea aphids are supplemented to culture in an illumination cultivation box. According to the indexes of the to-be-detected solution on the death rate of the propylaea japonica adults, the egg laying early stage, the egg laying amount and the weight, whether the insecticidal protein has the influence on the propylaea japonica adults or not is judged. On the base of establishing the risk theory of evaluating that the secondary metabolites and the insecticidal protein in the plant interact to influence the propylaea javanica, the natural environment of the insecticidal protein threat which is faced by the propylaea ladyridis can be reflected more truly, the evaluation method is simple, and the applicability is high.
Owner:INST OF COTTON RES CHINESE ACAD OF AGRI SCI
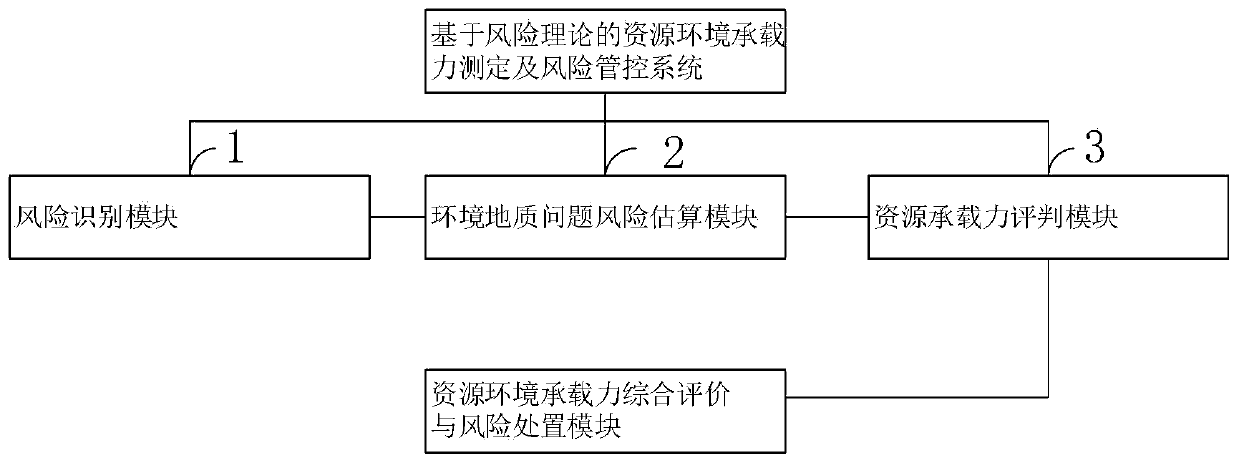
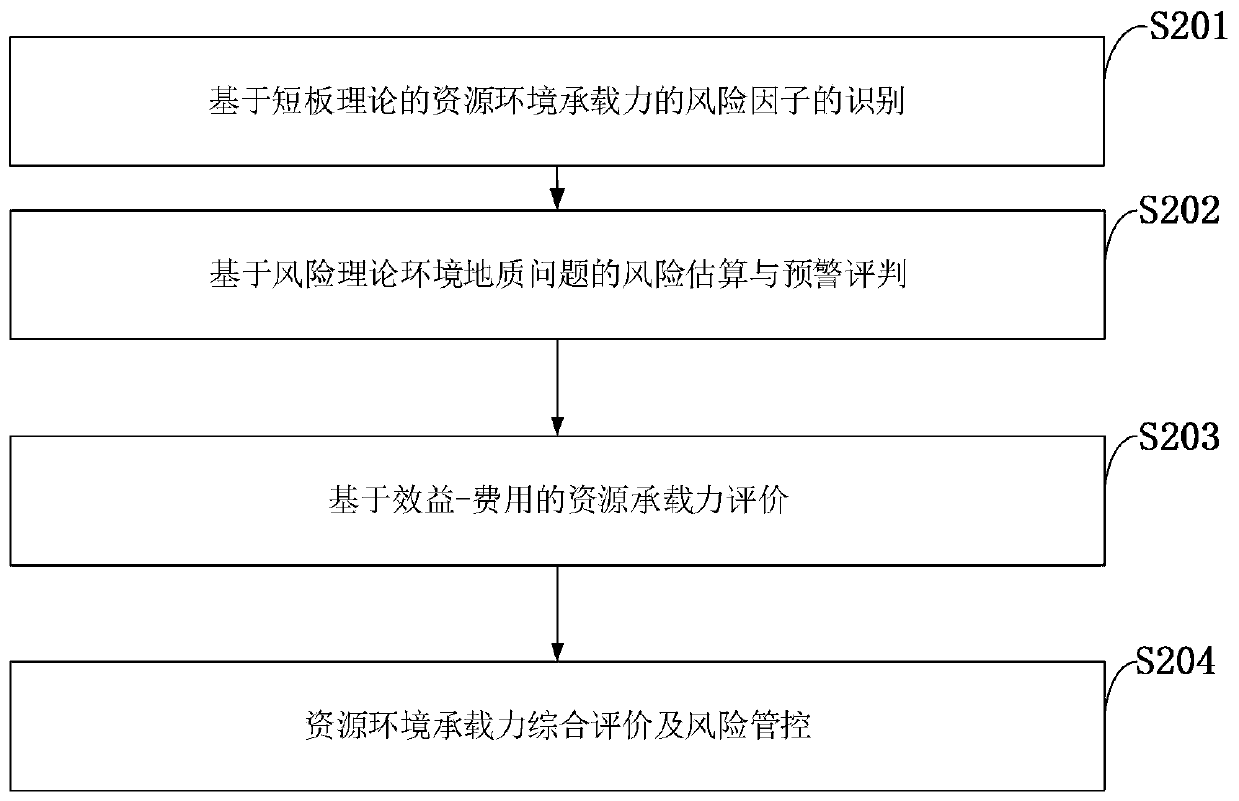
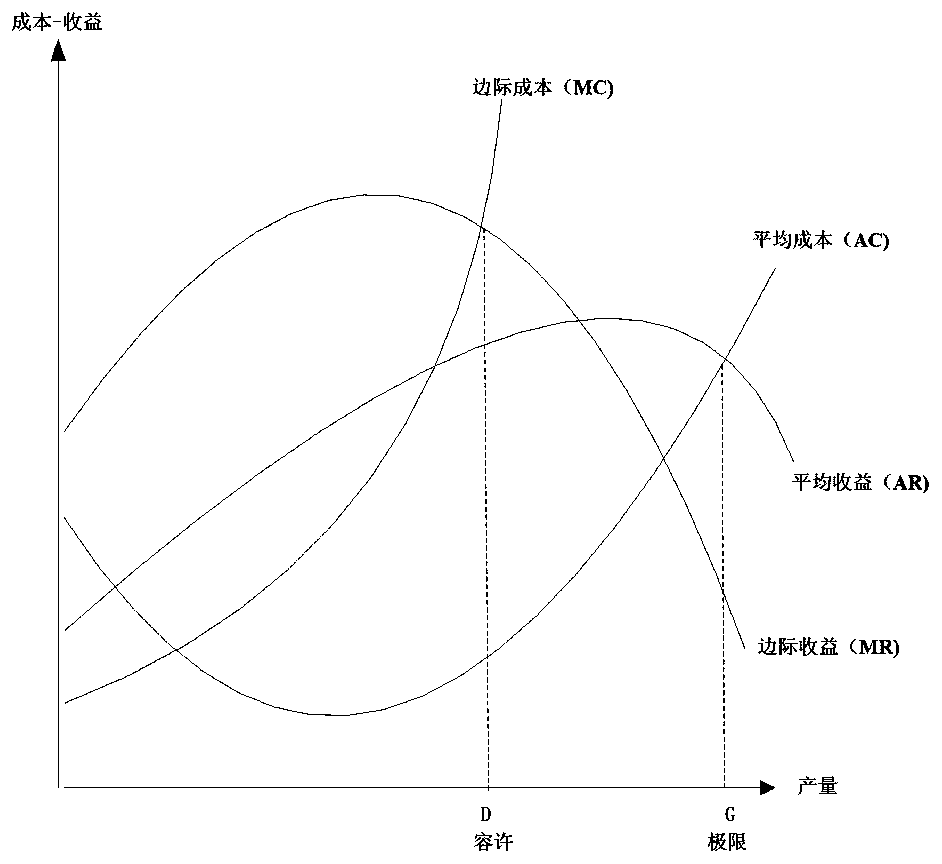
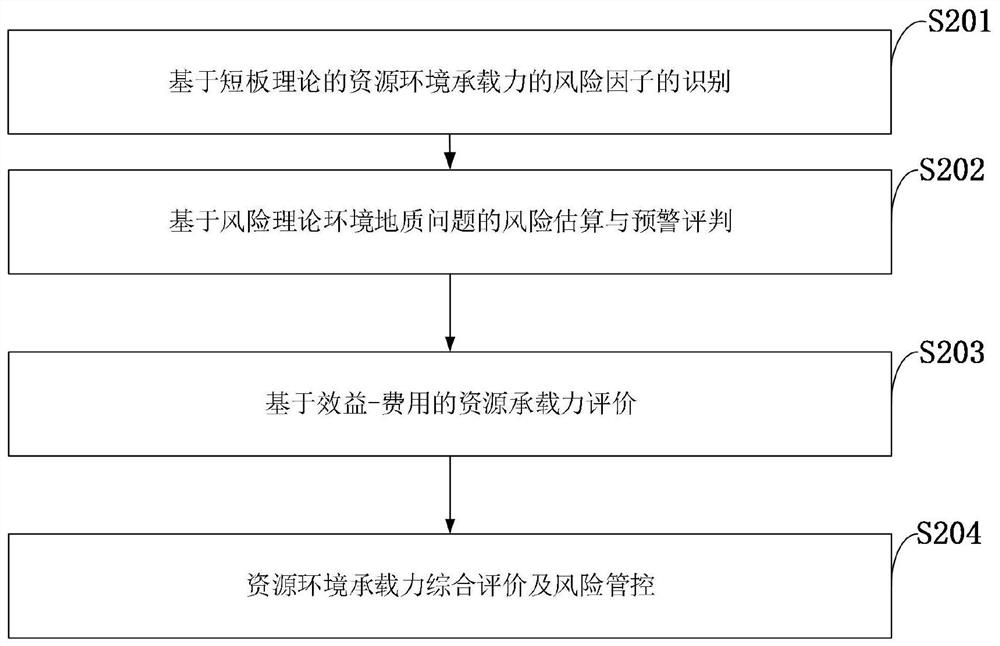
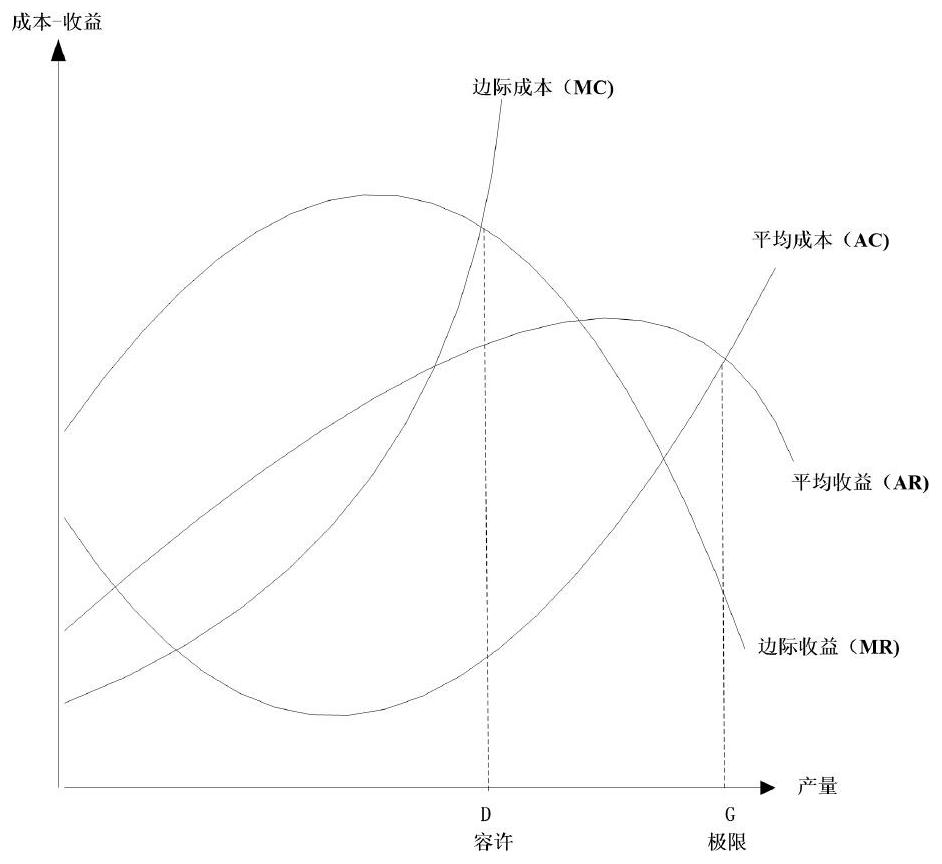
Resource environment bearing capacity measurement and risk management and control method based on risk theory
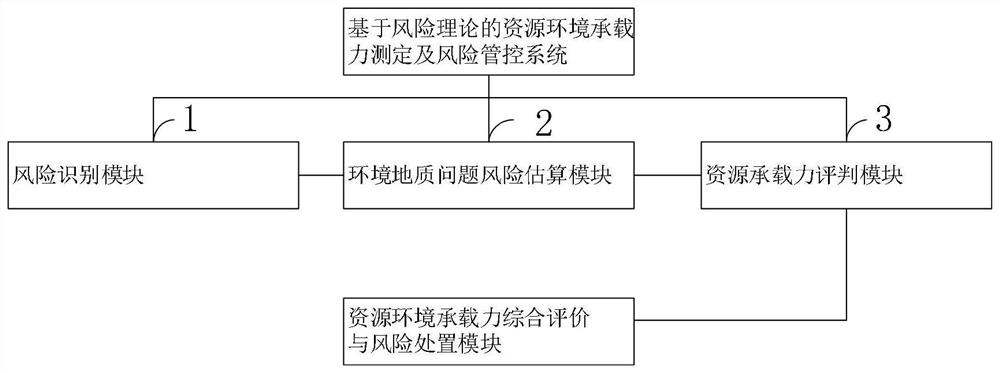
ActiveCN110288186AImprove processing efficiencyService planning and constructionResourcesData setRisk theory
The invention belongs to the technical field of computer software, and discloses a resource environment bearing capacity measurement and risk management and control method based on the risk theory, which comprises the steps that after collected data are transmitted to a computer, data preprocessing, classification and storage are carried out, risk factor recognition of a resource environment is carried out through the short board technology, and a large database of the resource environment bearing capacity is established; health, property and life risks of the resource environment are calculated and classified according to the resource environment data stored in the computer; resource environment data stored in a computer are called, and a storage data set of resource bearing capacity is established; game analysis is carried out on the basis of benefits-cost ratio, and comprehensive evaluation on resource bearing capacity is carried out; and risk adaptation, transfer and emergency disposal schemes are formulated. According to the risk-based resource environment bearing capacity evaluation principle, the risk-based resource environment bearing capacity evaluation technical method system and evaluation criteria, new theories and key technologies are provided for resource environment bearing capacity evaluation, and a basis is provided for demarcation of three red lines in territorial space development.
Owner:XIAN CENT OF GEOLOGICAL SURVEY CGS
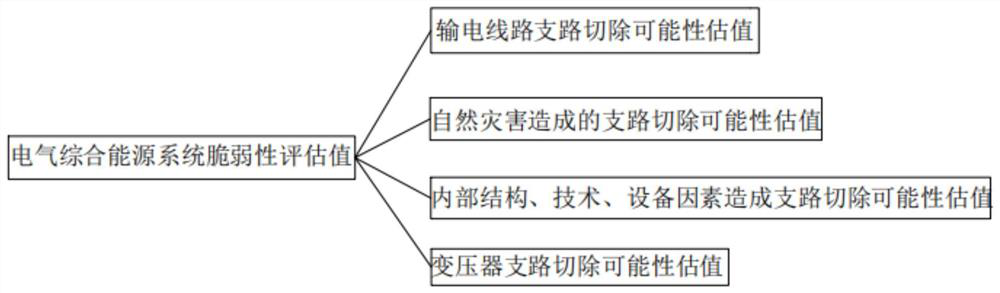
Vulnerability assessment method for electrical integrated energy system
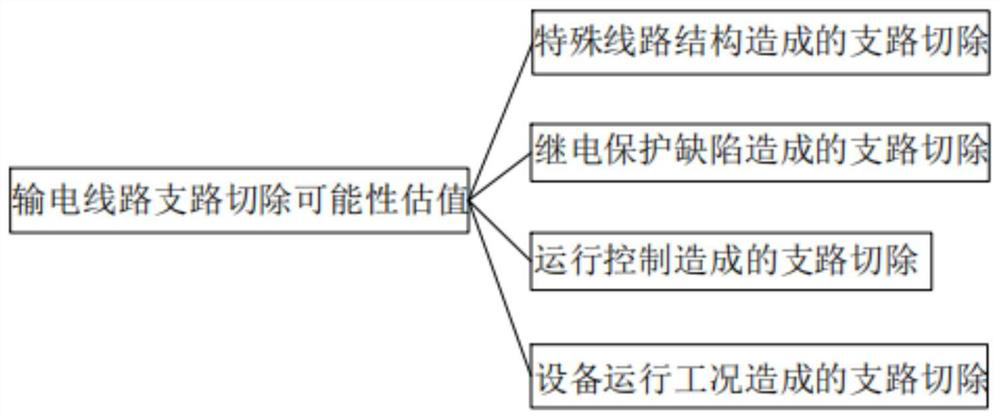
InactiveCN112836968AVerify validityTechnology managementResourcesElectric power systemIntegrated energy system
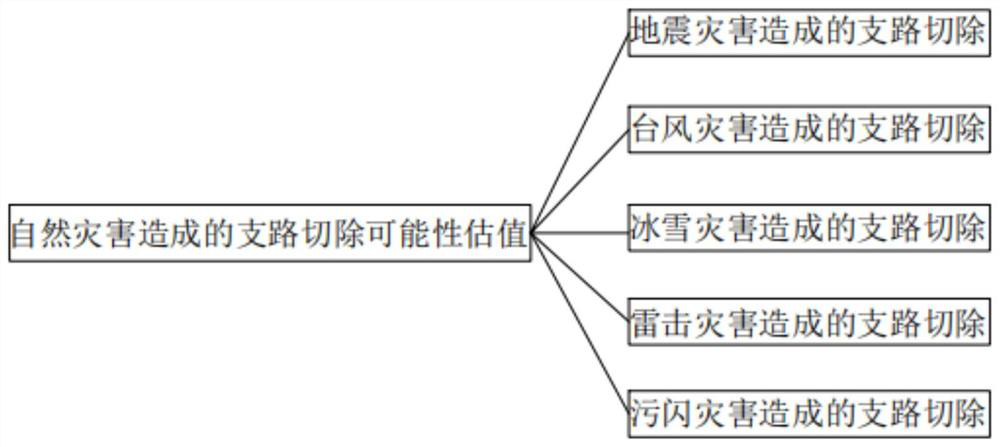
The invention discloses a vulnerability assessment method for an electrical integrated energy system. The vulnerability assessment method comprises the following steps: S1, starting assessment; S2, calculating and inputting an estimated value of the branch removal possibility of the power transmission line; S3, calculating and inputting a branch removal possibility estimated value caused by the natural disaster; S4, calculating an estimated value of the possibility of branch removal caused by internal structure, technology and equipment factors, and inputting the estimated value; S5, calculating and inputting a transformer branch removal possibility estimated value; and S6, obtaining an evaluation value of the vulnerability of the electrical integrated energy system. According to the electric power system structure vulnerability analysis method based on the electrical betweenness and the risk theory, the effectiveness of identifying the vulnerable branches and the vulnerable nodes in system structure vulnerability evaluation by the electrical betweenness is verified.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
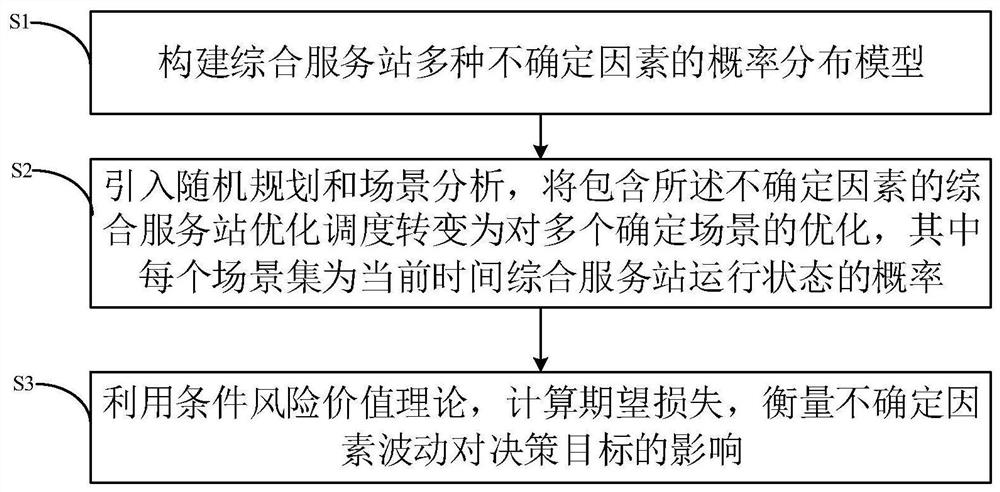
Quantitative optimization analysis method and system for uncertain factors of comprehensive service station
The invention provides a quantitative optimization analysis method and system for uncertain factors of a comprehensive service station. The method comprises the following steps: constructing a probability distribution model of various uncertain factors of the comprehensive service station; introducing stochastic programming and scene analysis, converting comprehensive service station optimization scheduling containing the uncertain factors into optimization of a plurality of determined scenes, wherein each scene set is the probability of the running state of the comprehensive service station at the current time; and calculating expected loss by using a conditional value-at-risk theory, and measuring the influence of uncertain factor fluctuation on a decision target. According to the method, the probability distribution model of various uncertain factors of the comprehensive service station is constructed, the random programming theory and the conditional value-at-risk theory are applied, the influence of uncertain factor fluctuation on a decision-making target is measured, and a bidding model of the comprehensive service station for optimizing multi-type resource output in a market environment is established; the model gives consideration to the robustness and economy of the bidding decision of the comprehensive service station, can deal with severe scenes, and is more practical.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
Risk assessment method for power grid dispatching operation considering weather factors
ActiveCN105869071BReliable methodSimple methodResourcesInformation technology support systemTotal riskRisk theory
The invention discloses a power grid dispatching operation risk evaluation method taking a weather factor into consideration. The method comprises the following steps: step 1, according to weather statistical data, historical statistical data of an equipment fault rate and a three-state weather model, calculating an equipment fault probability in a dispatching operation process respectively under a normal weather condition, a bad weather condition and an extremely bad weather condition; step 2, according to a system state in the dispatching operation process, obtaining a fault tree model; step 3, according to the fault tree model and a given risk consequence index, calculating a consequence of each step of operation, and determining whether the sequence is a development fault of the last step; and step 4, according to a risk theory, calculating a risk value of each step in the dispatching operation process and a total risk value. The method is reliable, is easily implemented and is convenient to promote.
Owner:ZHEJIANG UNIV
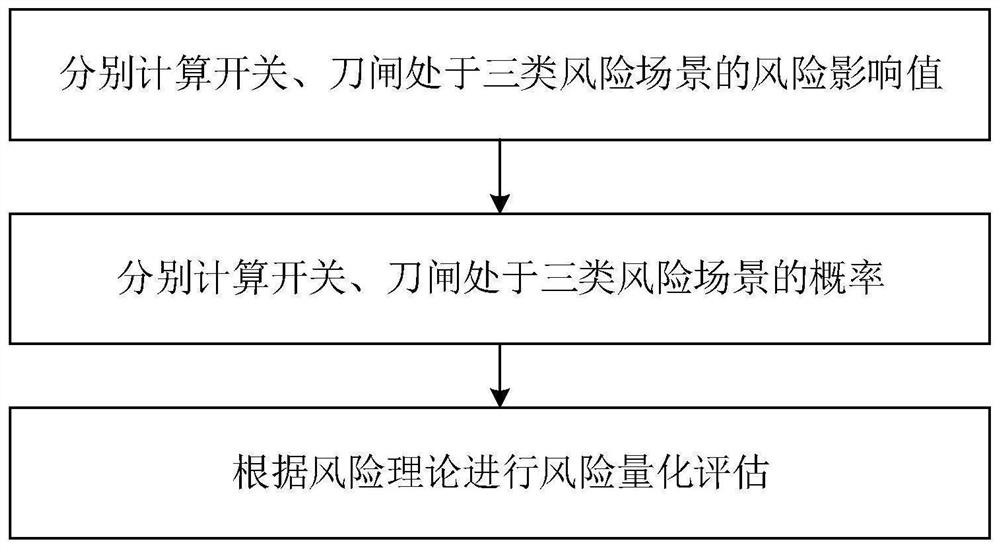
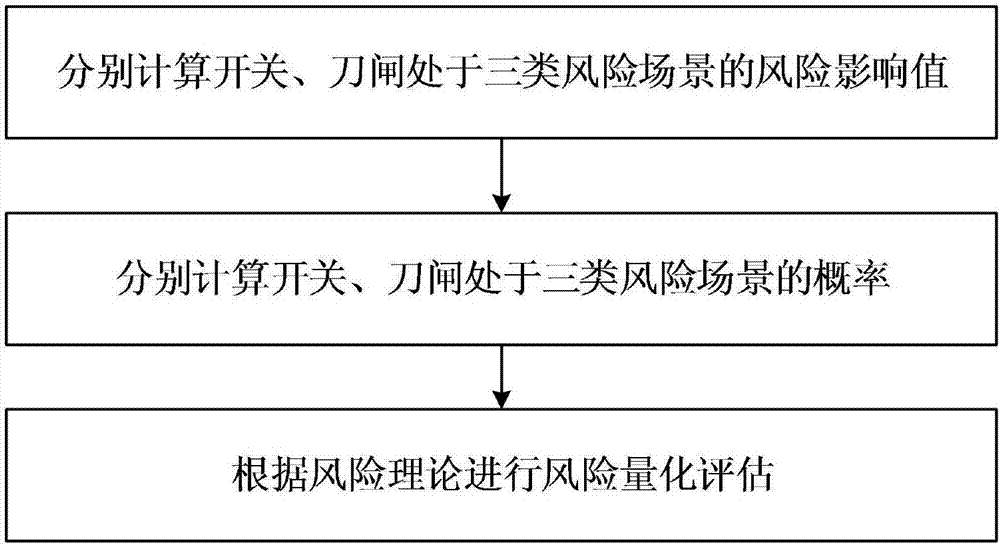
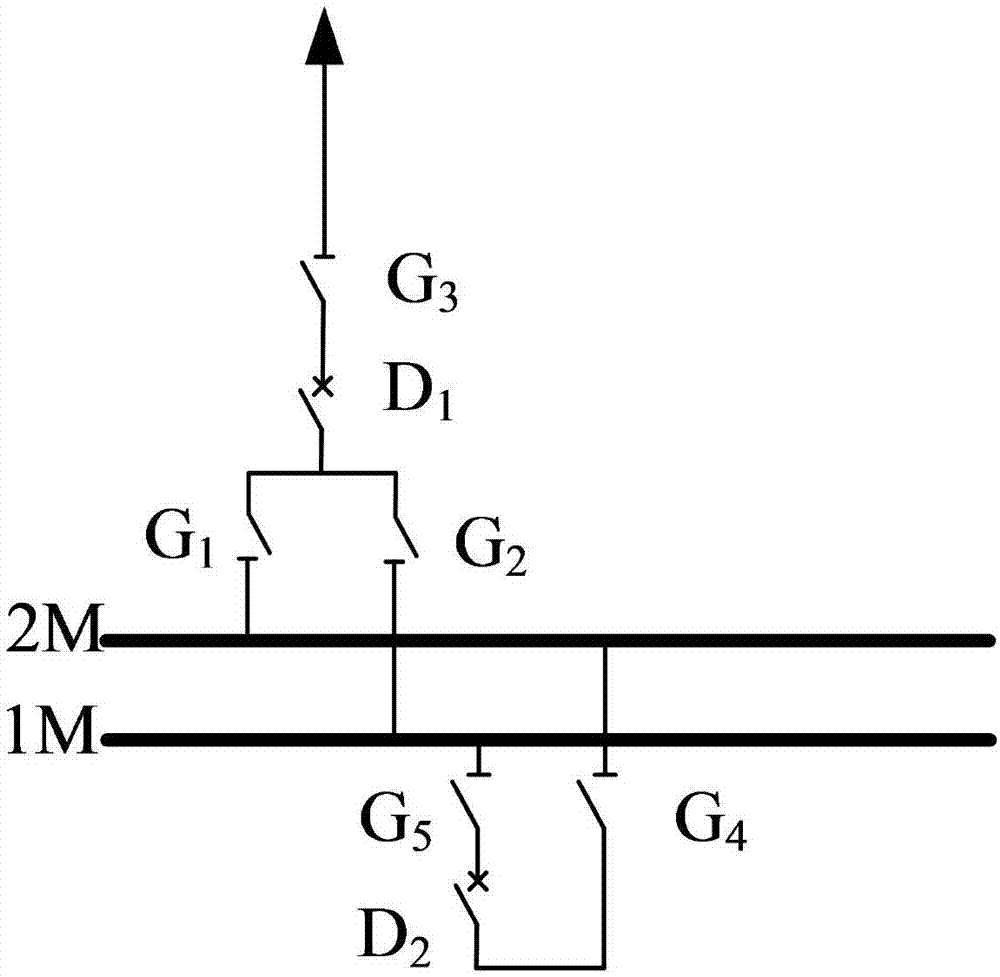
A risk quantitative assessment method for switch and knife switch operation process
InactiveCN107316135BReduce operational risk factorEnsure safetyResourcesRisk quantificationElectric power system
The invention discloses a risk quantification evaluation method for switch and knife switch operation processes. The method comprises following steps of (1), dividing operation states of a switch and a knife switch into three kinds of risk scenes of a successful state C1, an accident state C2 and a defect state C3, and calculating risk influence values of the switch and the knife switch in the successful state C1, the accident state C2 and the defect state C3; (2), calculating probabilities of the switch and the knife switch in the successful state C1, the accident state C2 and the defect state C3; and (3), carrying out risk quantification evaluation according to a risk theory. According to the invention, the actual switch and knife switch operation can be guided; and the method is very important in avoiding risks in the switch and knife switch operation, reducing risk coefficients of the switch and knife switch operation and maintaining safe, reliable and economical operation of an electric power system.
Owner:GUANGXI POWER GRID CORP
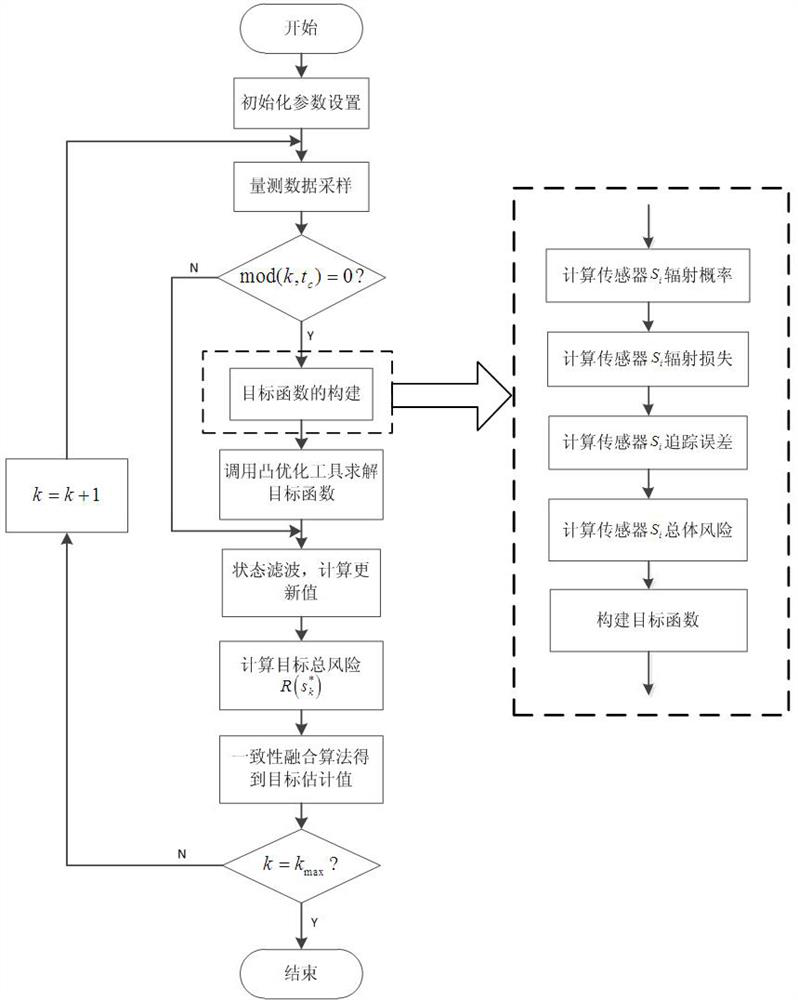
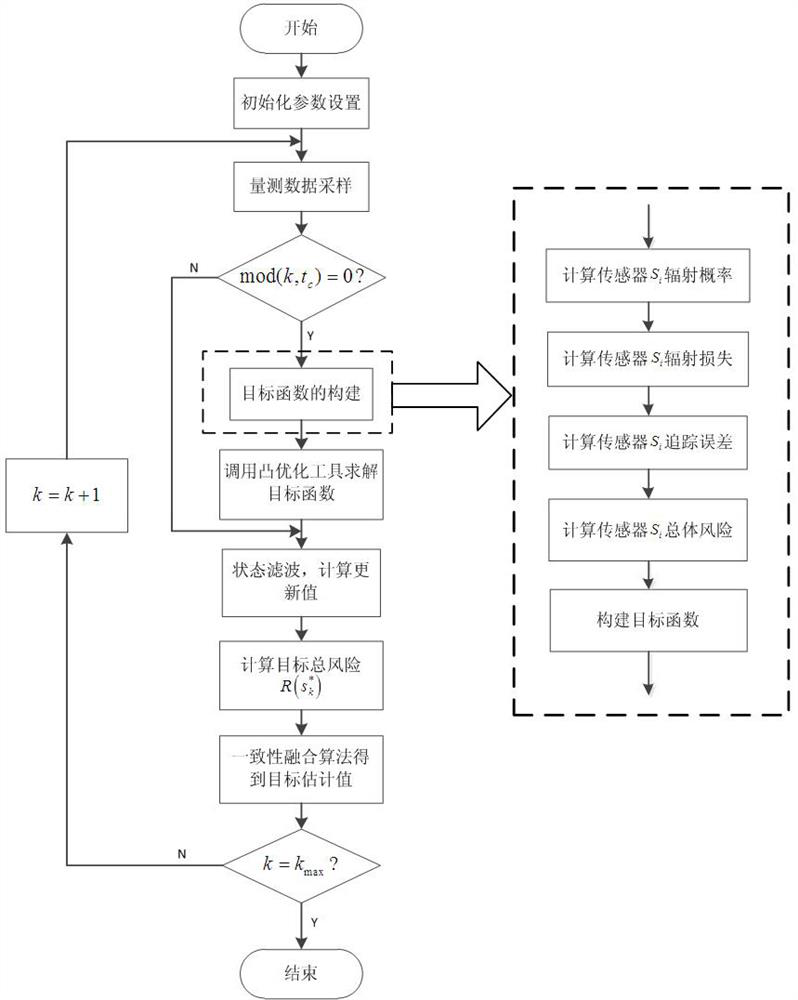
An Active Sensor Management Method Based on Risk Theory
ActiveCN113435034BImprove solution efficiencyDesign optimisation/simulationSpecial data processing applicationsRadiation riskAlgorithm
The invention discloses an active sensor management method based on risk theory, comprising the following steps: firstly, establishing a target risk model by using the risk theory; then, a calculation method of sensor radiation risk and sensor tracking error is given to quantify potential losses; The objective function is established with the minimum weighted sum of the two risks as the optimization objective. In order to obtain better combat benefits and improve the efficiency of solving the objective function, the convex optimization toolkit is used to solve the objective function. The invention uses the risk theory to build a model, builds the objective function according to the sensor radiation risk and the sensor tracking error, and uses the convex optimization theory to optimize and solve the objective function to obtain the optimal solution of the objective function, thereby improving the solving efficiency of the objective function.
Owner:HENAN UNIVERSITY
Risk quantification evaluation method for switch and knife switch operation processes
InactiveCN107316135AReduce operational risk factorEnsure safetyResourcesRisk quantificationElectric power system
The invention discloses a risk quantification evaluation method for switch and knife switch operation processes. The method comprises following steps of (1), dividing operation states of a switch and a knife switch into three kinds of risk scenes of a successful state C1, an accident state C2 and a defect state C3, and calculating risk influence values of the switch and the knife switch in the successful state C1, the accident state C2 and the defect state C3; (2), calculating probabilities of the switch and the knife switch in the successful state C1, the accident state C2 and the defect state C3; and (3), carrying out risk quantification evaluation according to a risk theory. According to the invention, the actual switch and knife switch operation can be guided; and the method is very important in avoiding risks in the switch and knife switch operation, reducing risk coefficients of the switch and knife switch operation and maintaining safe, reliable and economical operation of an electric power system.
Owner:GUANGXI POWER GRID CORP
Active sensor management method based on risk theory
ActiveCN113435034AImprove solution efficiencyDesign optimisation/simulationSpecial data processing applicationsRadiation riskAlgorithm
The invention discloses an active sensor management method based on a risk theory, and the method comprises the following steps: firstly, building a target risk model through the risk theory, and then giving a calculation method of a sensor radiation risk and a sensor tracking error to quantify potential loss, and then, establishing a target function with the minimum weighted sum of the two risks as an optimization target, and in order to obtain better combat benefits and improve the solving efficiency of the target function, using a convex optimization toolkit to solve the target function. According to the method, the model is established by using the risk theory, the target function is constructed according to the sensor radiation risk and the sensor tracking error, and the optimal solution of the target function is obtained by optimizing and solving the target function by using the convex optimization theory, so that the solving efficiency of the target function is improved.
Owner:HENAN UNIVERSITY
Risk theory-based medium and lower voltage distribution network neutral point grounding mode decision-making method
The invention discloses a risk theory-based medium and lower voltage distribution network neutral point grounding mode decision-making method. The method comprises the following steps of 1, collectingmedium and lower voltage distribution network structural characteristic and power supply region data, relay protection parameters and single-phase fault data, overvoltage statistical data, power-downtime and data information of number of households in power down; 2, calculating human body electric shock risk index <Lambda><es>; 3, calculating power down risk index <Lambda><t>; 4, calculating overvoltage risk index <Lambda><ov>; 5, calculating a power distribution system comprehensive risk index R<s> according to the human body electric shock risk index <Lambda><es>, the g power down risk index <Lambda><t> and the overvoltage risk index <Lambda><ov>; and 6, obtaining the comprehensive risk of the neutral point grounding mode according to the power distribution system comprehensive risk index R<s>. By virtue of the method, the technical problem that decision making for the medium and lower voltage distribution network neutral point grounding mode specific to the human body electric shock risk is absent in the prior art is solved.
Owner:GUIZHOU POWER GRID CO LTD
An information security risk assessment method for typical metallurgical process control systems
InactiveCN104331072BGuaranteed safe operationLow costElectric testing/monitoringProbabilistic methodRisk theory
The invention provides an information security risk assessment method oriented to a typical metallurgy process control system and belongs to the technical field of industrial control system information security. The system robustness under different attack modes and policies is analyzed by establishing an attack model under the typical scenes of the metallurgy process, and therefore, the security risk assessment on the typical metallurgy process control system in different attack modes and a failure mode can be realized. Based on the risk theory, the method is used for performing the security risk assessment by use of a random probability algorithm by defining the metallurgy process control system as a physical information fusion system; from the two aspects of the occurrence probability and the influence of attack sources or failure sources, a security assessment method based on risk indexes is developed. Quantitative estimation is performed based on risk indexes; a security incident set is created based on the established physical information fusion model and attack model, and then the security incident set is combined with the calculated robustness assessment indexes for the quantitative estimation, and therefore, the weak security links in the control system can be located conveniently.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
A Risk Theory-Based Evaluation Method of Power Grid Operational State
ActiveCN103646350BComprehensive understanding of risksSpecial data processing applicationsIslandingPower grid
The invention discloses a power grid operating state assessment method based on the risk theory. The method comprises the following steps: data is collated, and a data processing module is established; the outage probability of power grid elements is calculated; the element outage probability data is stored; the power grid operating state is extracted through the Monte Carlo method; the system state is analyzed; system state analysis is performed through a submodule 5 to judge whether problems, such as the circuit overload problem, the voltage out-of-limit problem, the bus isolation problem, the problem that a system is separated into isolated islands, etc., occur; the power grid operating risk indicators are calculated; and the power grid operating state risk indicator result is analyzed to give out the weak link of the power grid. According to the invention, risk assessment is performed on the power grid operating state; the actual operating state of the power grid is simulated by using the Monte Carlo method, the event random nature of the power grid is taken into account reasonably; different risk indicators are used, multi-angle and multi-level assessment is performed on the power grid operating state risk; and the power grid operating state risk assessment result is analyzed to give out the weak link of the power grid.
Owner:江西汇能电力工程技术有限公司
A Risk Theory-Based Method for Determination of Resource and Environment Carrying Capacity and Risk Control
ActiveCN110288186BImprove processing efficiencyService planning and constructionResourcesEnvironmental resource managementData set
The invention belongs to the technical field of computer software, and discloses a risk theory-based resource and environment bearing capacity measurement and risk control method. After the collected data is transmitted to a computer, data preprocessing, classification and storage are performed, and short board technology is used to carry out Identify the risk factors of the resource environment and establish a large database of the resource and environment carrying capacity; calculate and classify the health, property, and life risks of the resource and environment for the resource and environment data stored in the computer; use the resource and environment data stored in the computer to establish the resource carrying capacity Based on the game analysis based on the benefit-cost ratio, a comprehensive evaluation of resource carrying capacity is carried out; risk adaptation, transfer and emergency response plans are formulated. The risk-based resource and environment carrying capacity evaluation principle, technical method system and evaluation criteria of the present invention provide new theories and key technologies for the evaluation of resource and environment carrying capacity, and provide a basis for the delineation of "three red lines" for land space development.
Owner:XIAN CENT OF GEOLOGICAL SURVEY CGS
Vulnerability assessment method for smart distribution network based on dynamic probabilistic power flow
ActiveCN102930175BImprove self-healing abilityData processing applicationsSpecial data processing applicationsPower flowProbabilistic load flow
The present invention is a method for assessing the vulnerability of smart distribution network based on dynamic probabilistic power flow. The basic function and random function are used to form the probability distribution of the injected power of smart distribution network nodes, and the Gram-Charlier series and half The invariant calculates the probability distribution of the bus voltage and line power, uses the piecewise function to calculate the severity index of the damage caused by the voltage, current, and power to the smart distribution network, and then calculates the vulnerability index of the output smart distribution network; this method is based on risk Theory, using the dynamic probabilistic power flow method for vulnerability assessment, to ensure that the self-healing control scheme of the smart distribution network can always adapt to changes in the load and operating environment of the smart distribution network, so that the smart distribution network can operate safely, reliably and economically.
Owner:HOHAI UNIV +2
A Construction Method of Core Backbone Grid Based on Grid Differentiation
ActiveCN103151777BHas practical significanceFast convergenceAc network circuit arrangementsNODALAlgorithm
The invention discloses a power grid differentiation-based core backbone network architecture construction method. The importance of lines and nodes in a power system are taken into comprehensive account, the knowledge of a risk theory is referenced, the importance of the lines is obtained by calculating risk indicators of the lines, and the importance of the nodes is evaluated based on the knowledge of a graph theory; and a core backbone network architecture searching model is constructed based on the importance of the lines and the nodes, and network architectures are searched by a particle swarm algorithm to obtain the lines and the nodes for constructing a core backbone network architecture. The importance of the lines is evaluated by line returning risks, so that the importance of the lines can be better reflected from the point of electrical quantity variation; and a fuzzy-membership-based line returning risk evaluation method more consistent with actual conditions is provided, and the influence of uncertain factors of the power system is taken into comprehensive account.
Owner:STATE GRID CORP OF CHINA +2
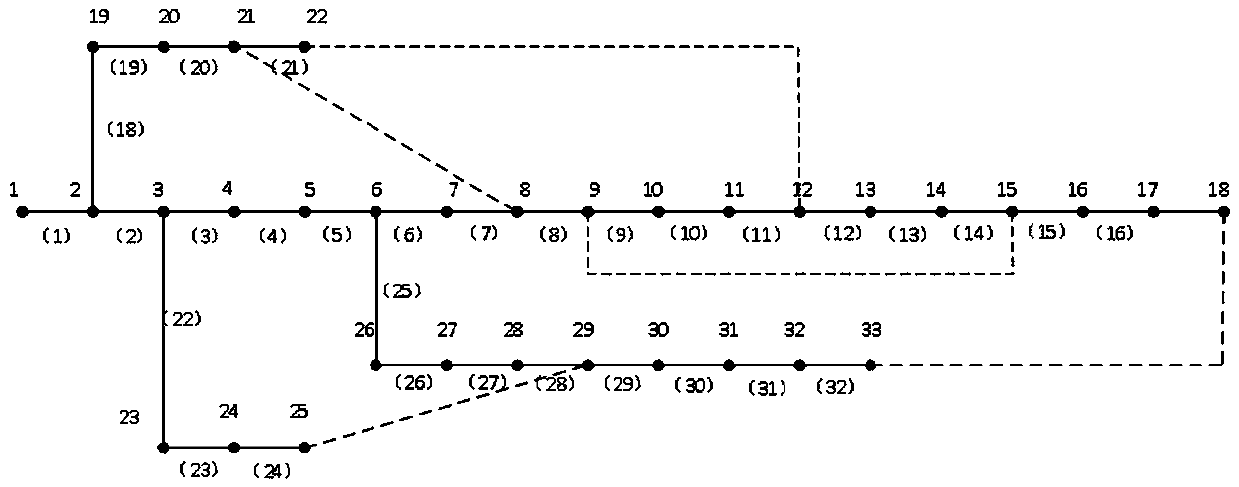
Core backbone network frame construction method based on risk theory
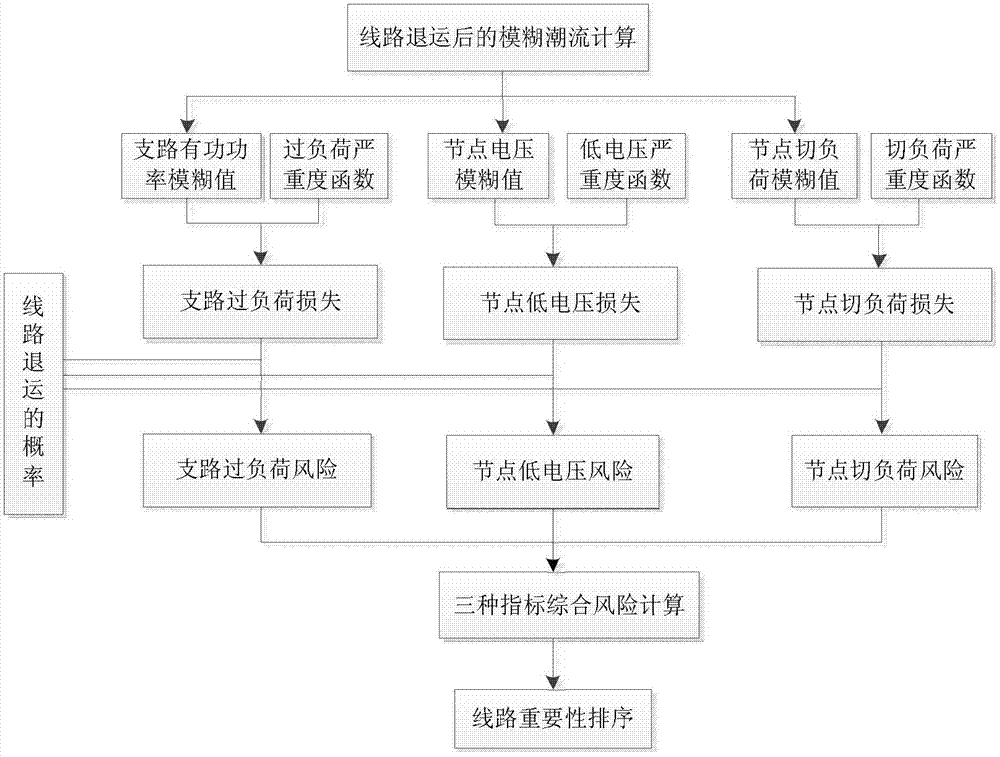
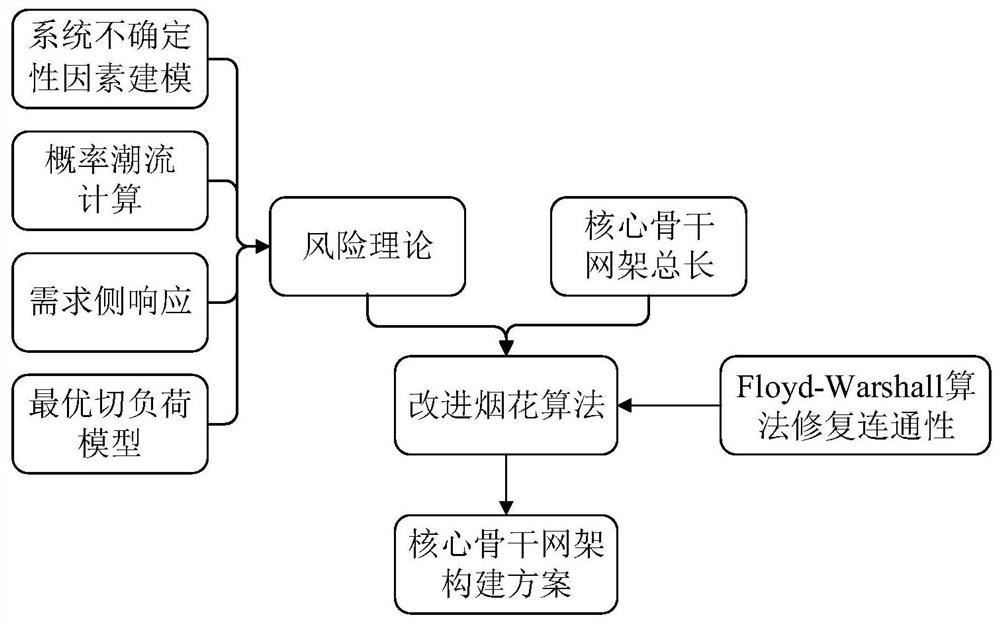
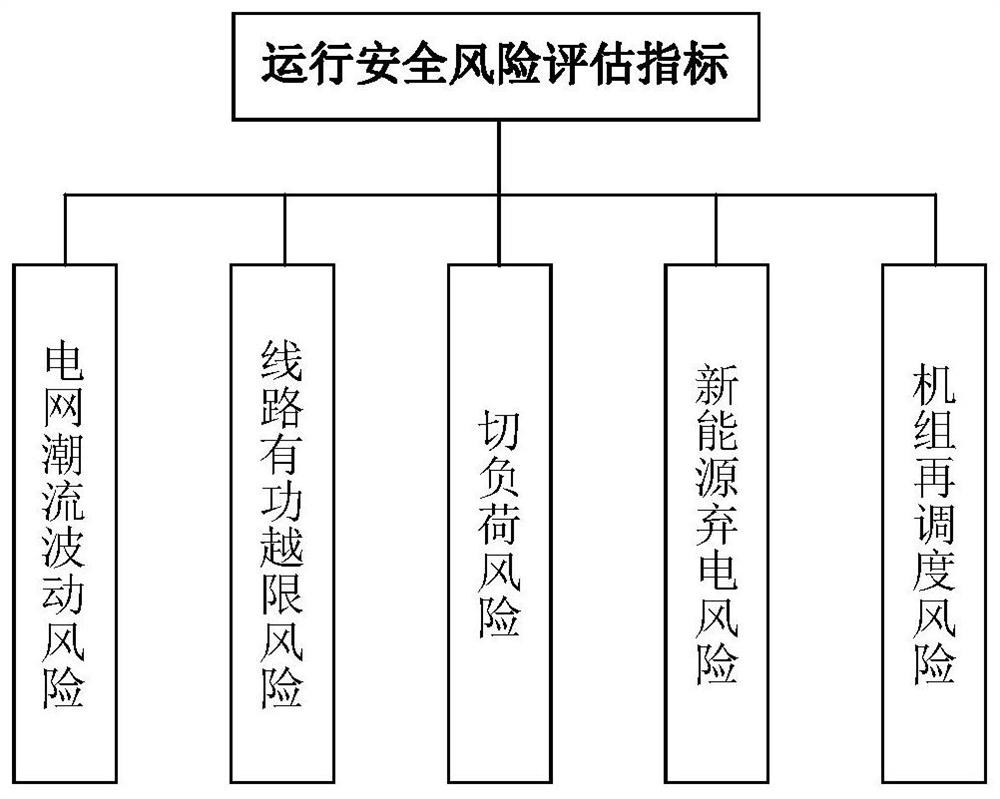
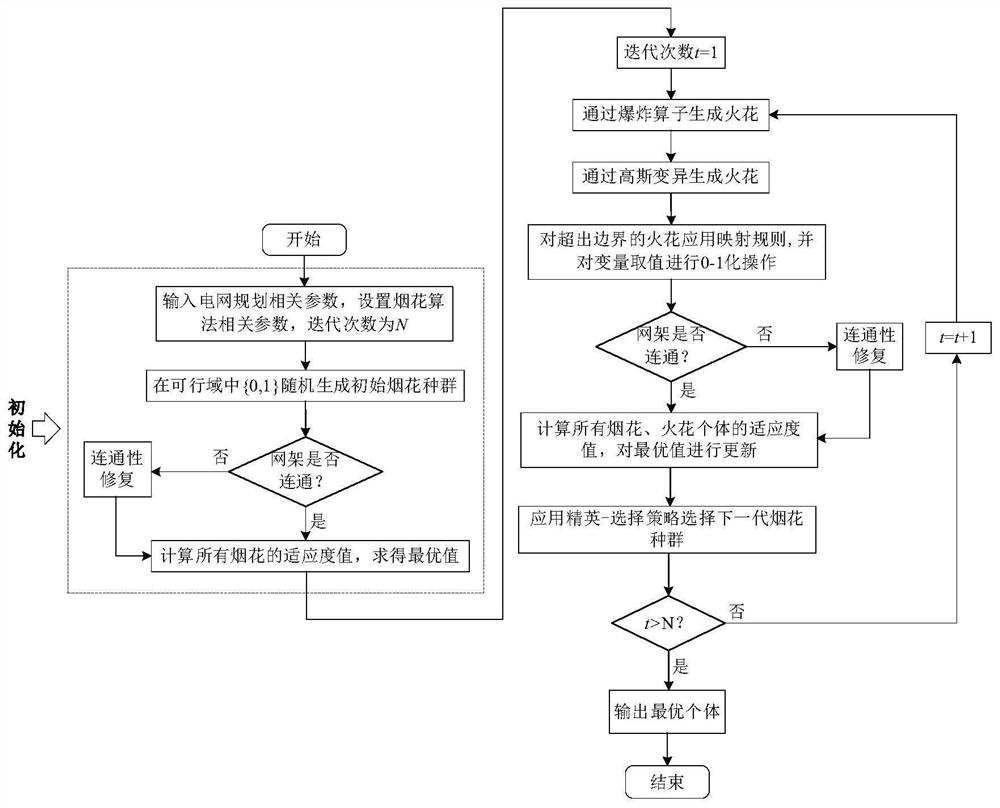
PendingCN113705986ALower risk levelImprove voltage limitResourcesInformation technology support systemAlgorithmNew energy
The invention relates to an electric power system differentiation planning technology, in particular to a core backbone network frame construction method based on a risk theory, and the method comprises the steps: constructing an electric power system safety risk assessment index system based on the risk theory; calculating the weight of each index based on a CRITIC weighting method; and completing risk assessment through a probabilistic load flow calculation result, constructing a core backbone network frame search model by taking the minimum sum of the comprehensive risk level and the length of the core backbone network frame as an objective function; solving the constructed model based on an improved fireworks algorithm, and repairing the net rack connectivity through a Floyd-Warshall algorithm to obtain a core backbone net rack construction scheme. According to the method, risk factors are fully considered in construction of the core backbone network frame, the adverse conditions of voltage out-of-limit, power out-of-limit and the like are effectively improved, and the risk level of operation of the core backbone network frame is reduced. The risk level of the power system under the large-scale new energy access trend is reduced, and the disaster resistance of the system is improved.
Owner:WUHAN UNIV +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com