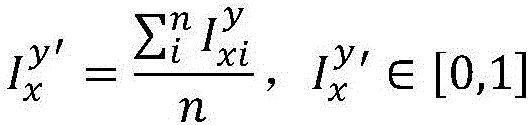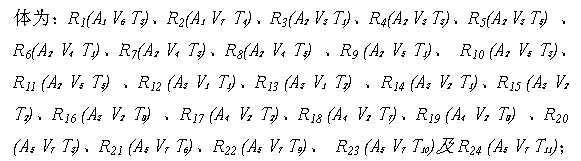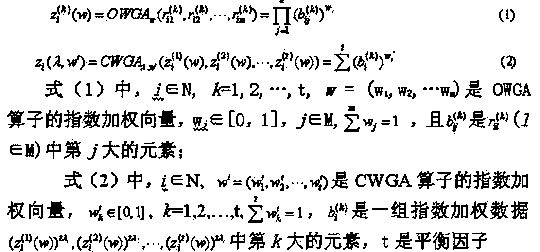Patents
Literature
635 results about "Security assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
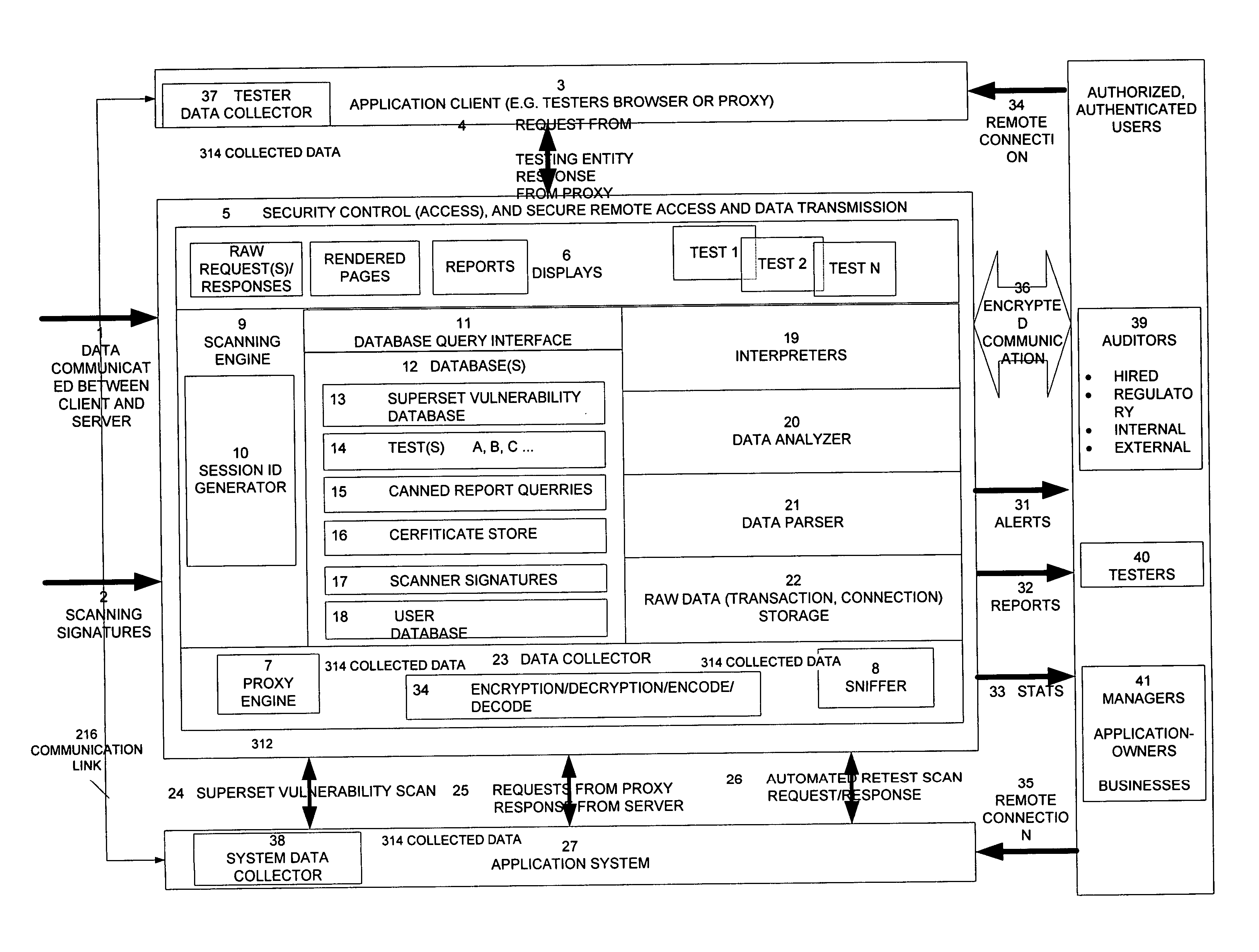
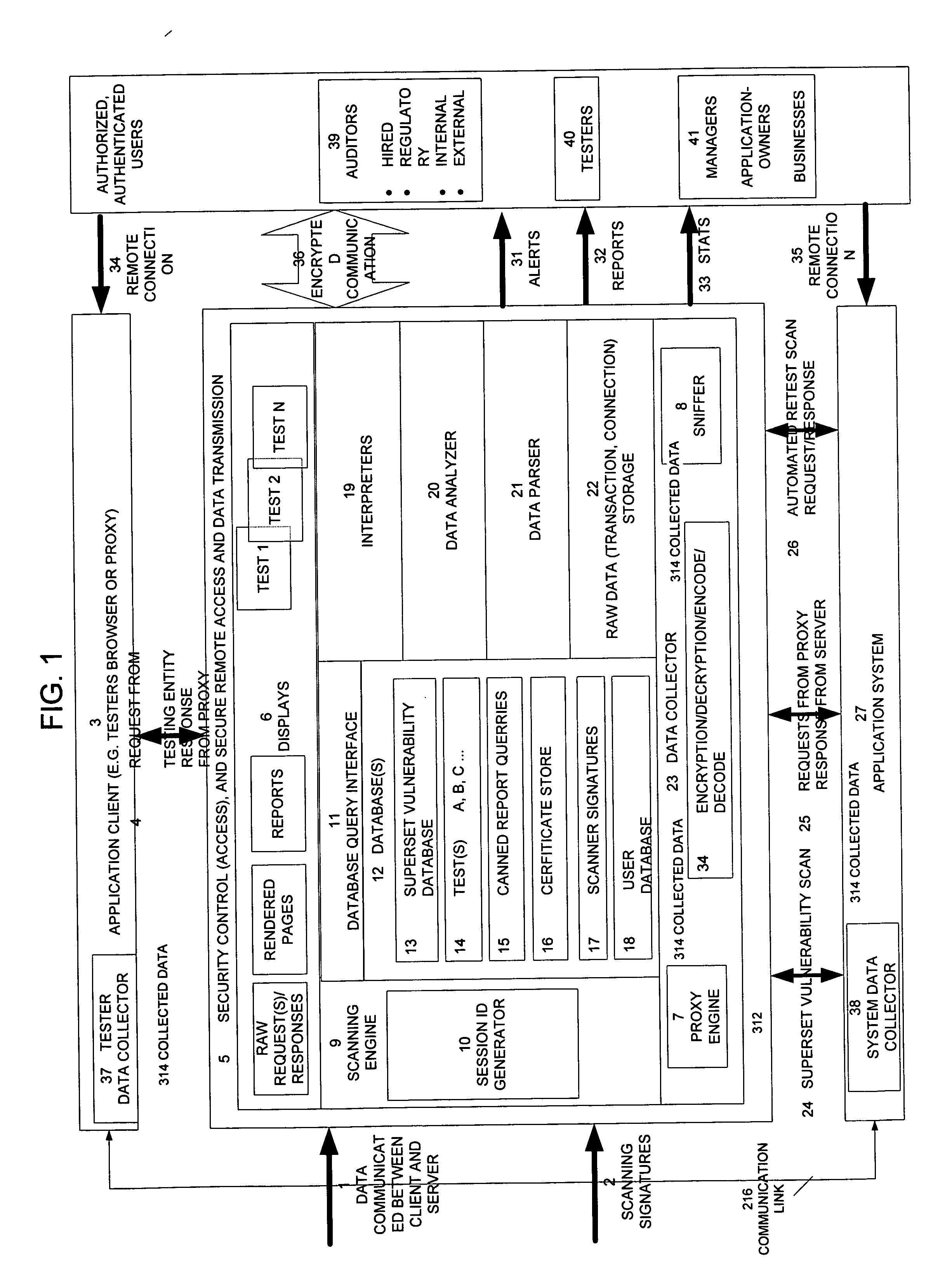
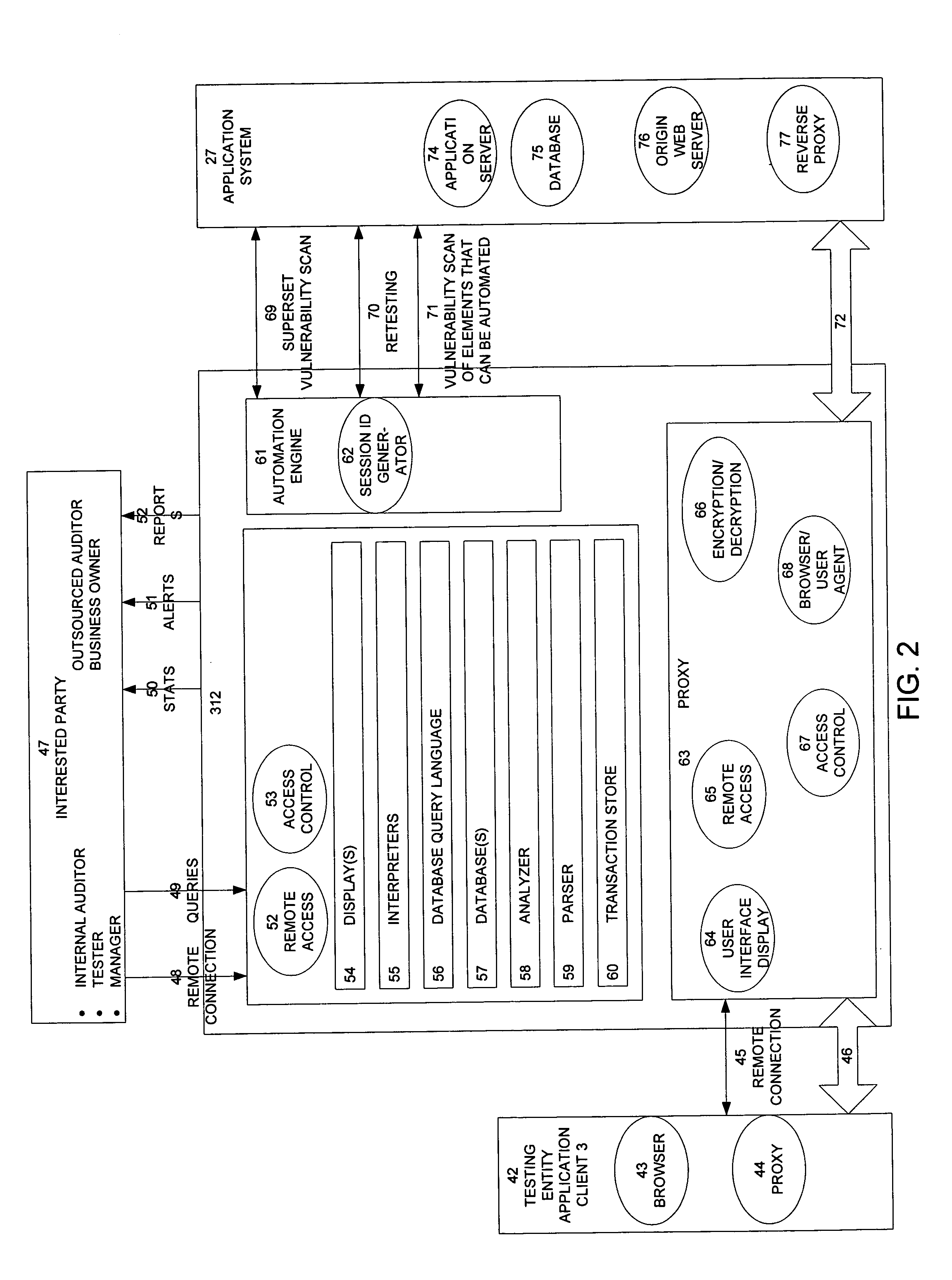
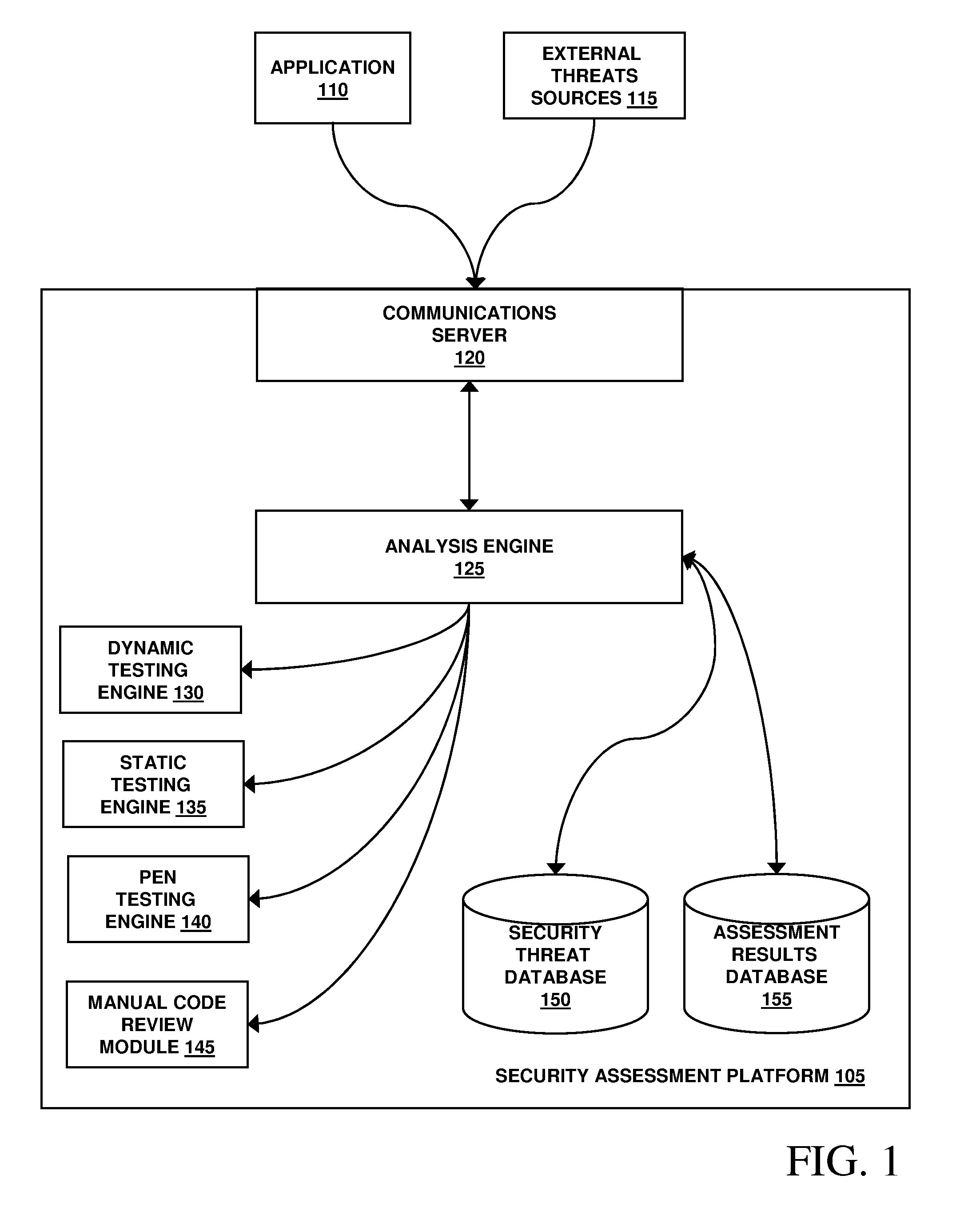
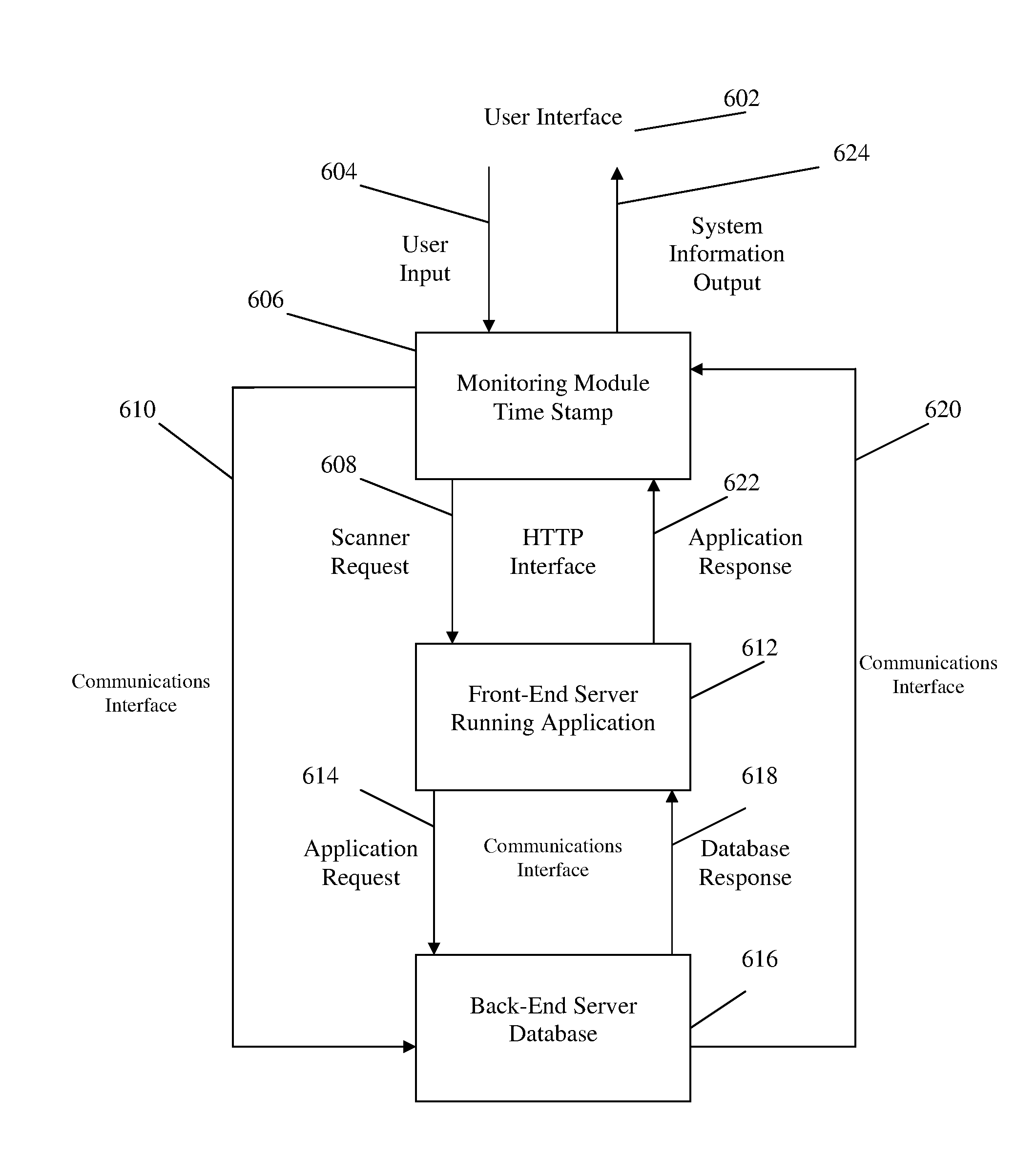
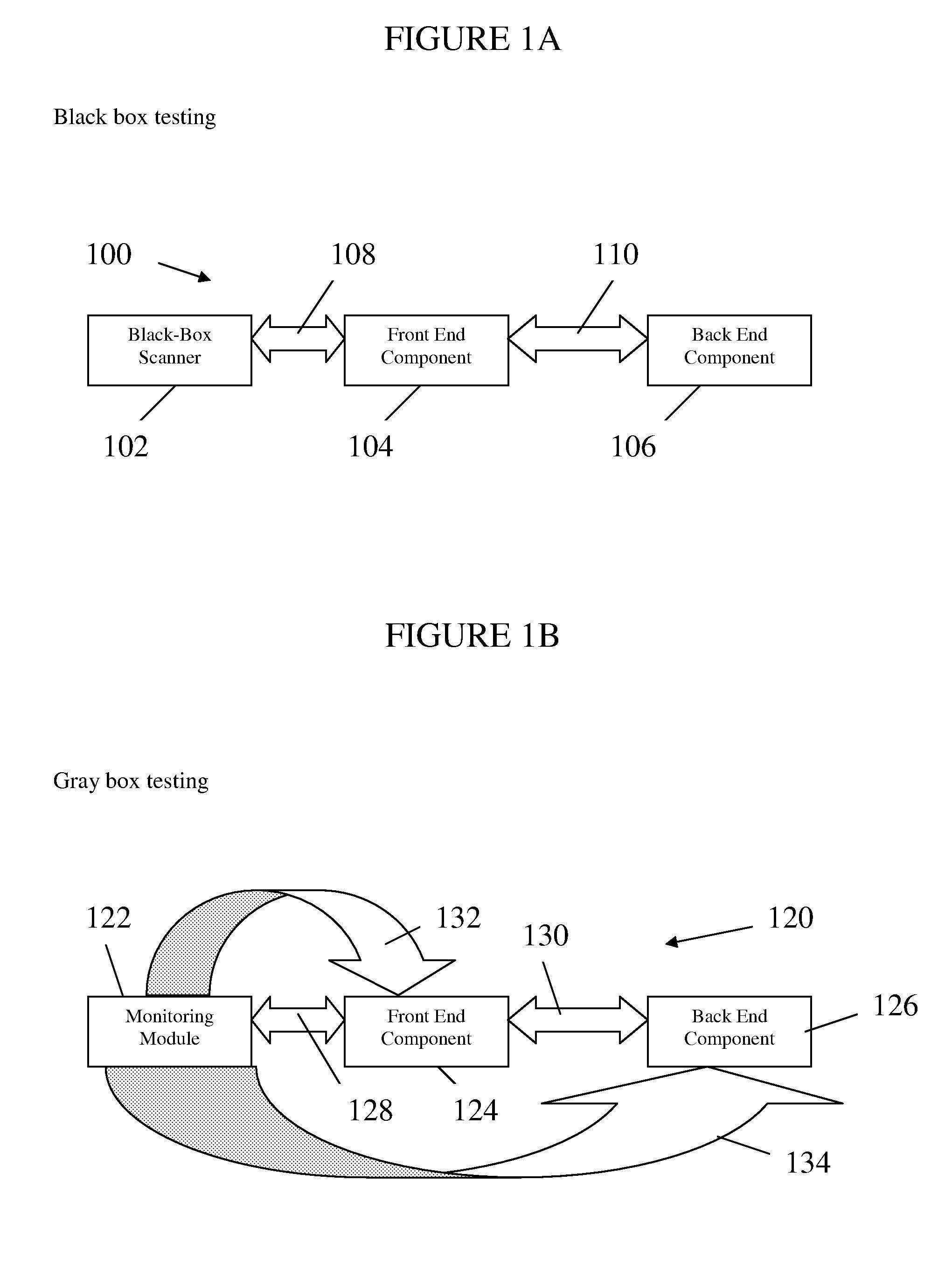
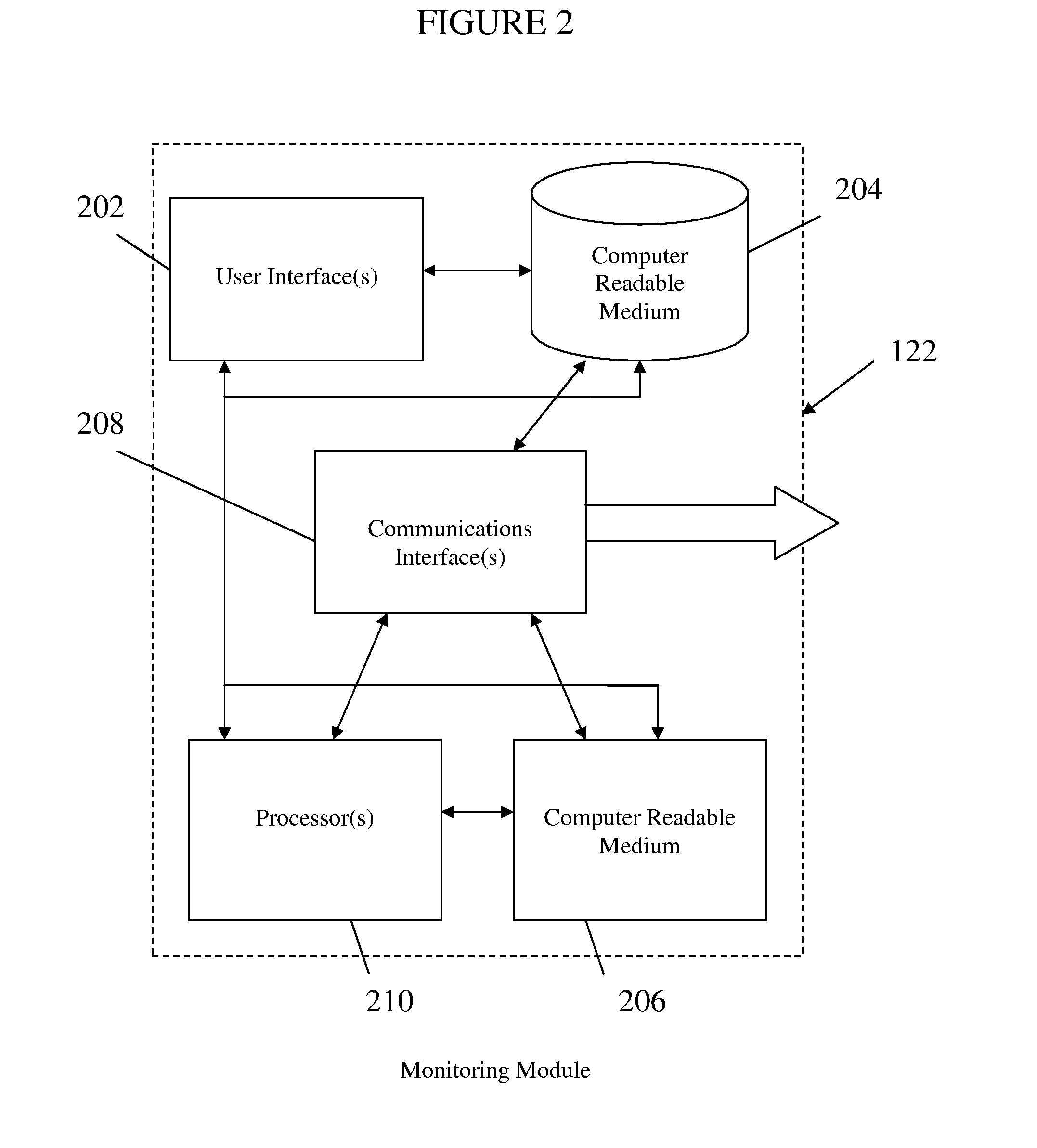
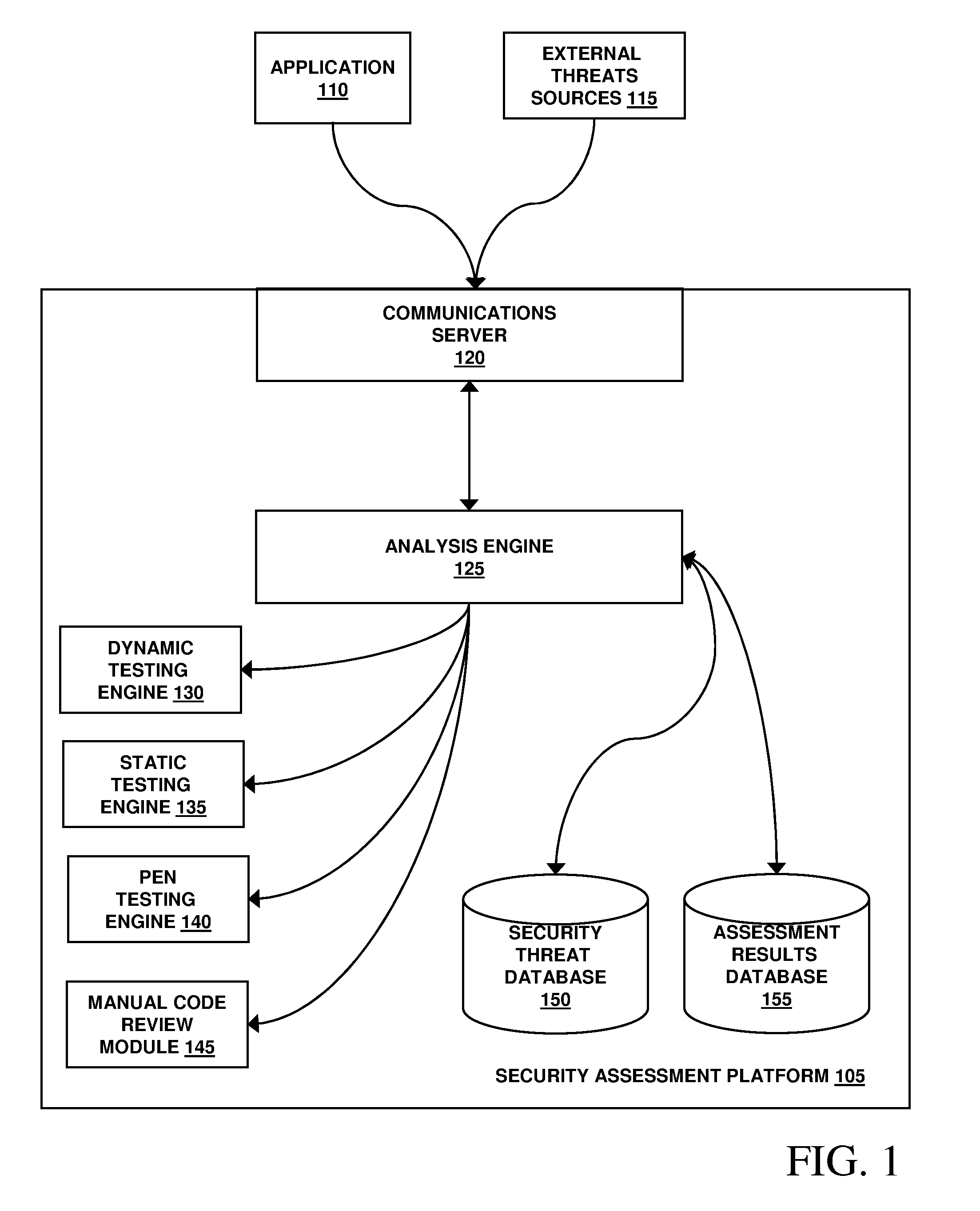
Method, system, and apparatus for managing, monitoring, auditing, cataloging, scoring, and improving vulnerability assessment tests, as well as automating retesting efforts and elements of tests
InactiveUS20050138426A1Streamline and improve test effortImprove consistencyDigital data processing detailsHardware monitoringAnalysis dataWeb application
A scalable method, system, and apparatus for non-intrusively auditing and improving security assessments includes capturing, storing, presenting, displaying, inspecting, monitoring, and analyzing data flow in client-server security assessments and / or network / infrastructure security assessments. The invention provides interested parties with a mechanism to non-intrusively audit in real-time the vulnerability test effort, as well as review, replay, and analyze all aspects of the security assessment during and after the test. For web application assessments, the data capture includes one of the following or some combination: an intermediary with all data passing through the intermediary; a sniffer that can passively extract all data being communicated between the application and tester; and a plurality of computing modules (e.g., software, appliances, etc.) installed in the tester environment or within the application system environment (e.g., software installed on the tester's computer, or on the computer where the intermediary is running, or software installed on the application systems proxy or web server, or an appliance in either environment) for storing, processing, analyzing, reporting, and displaying the data.
Owner:STYSLINGER BRIAN
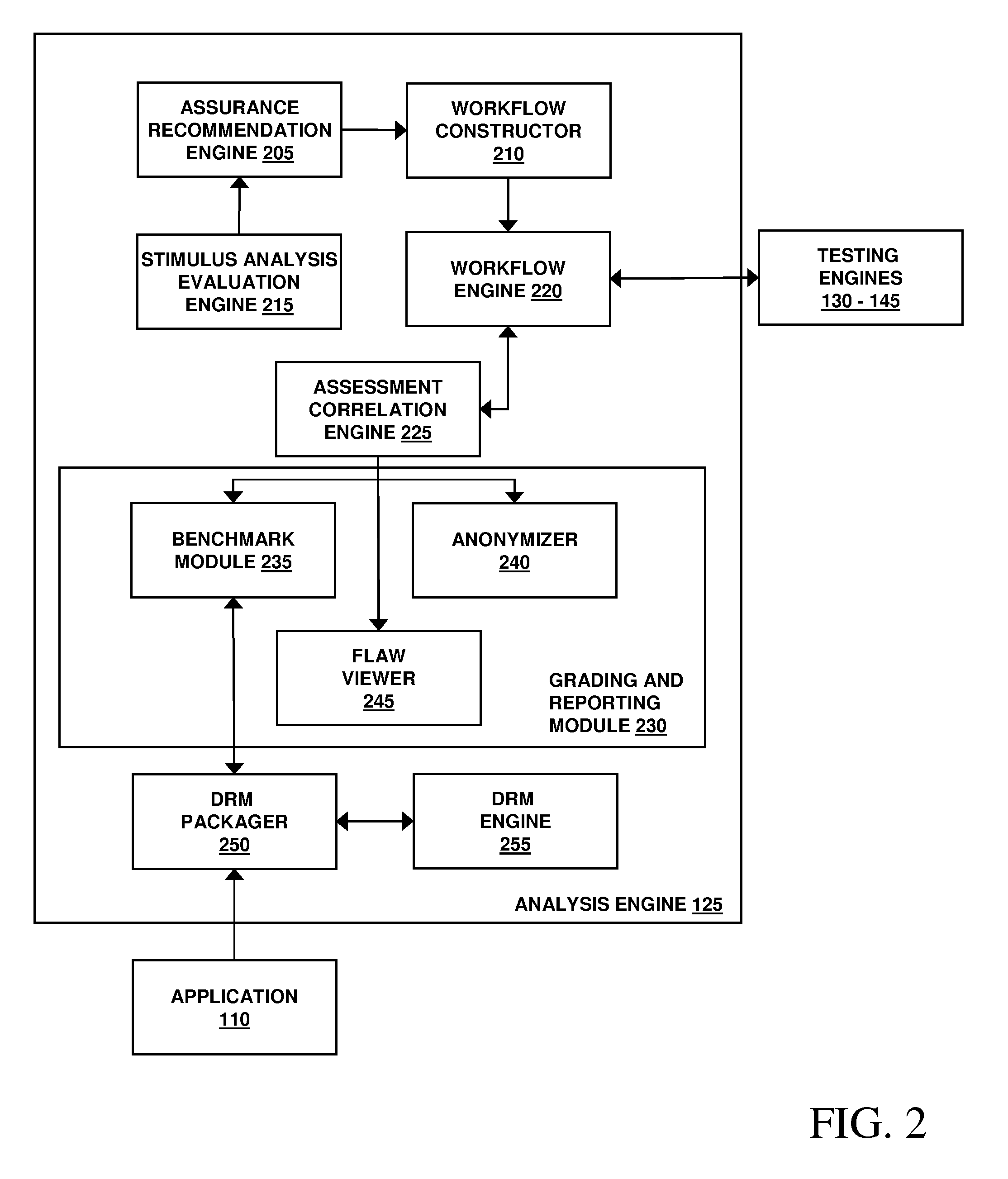
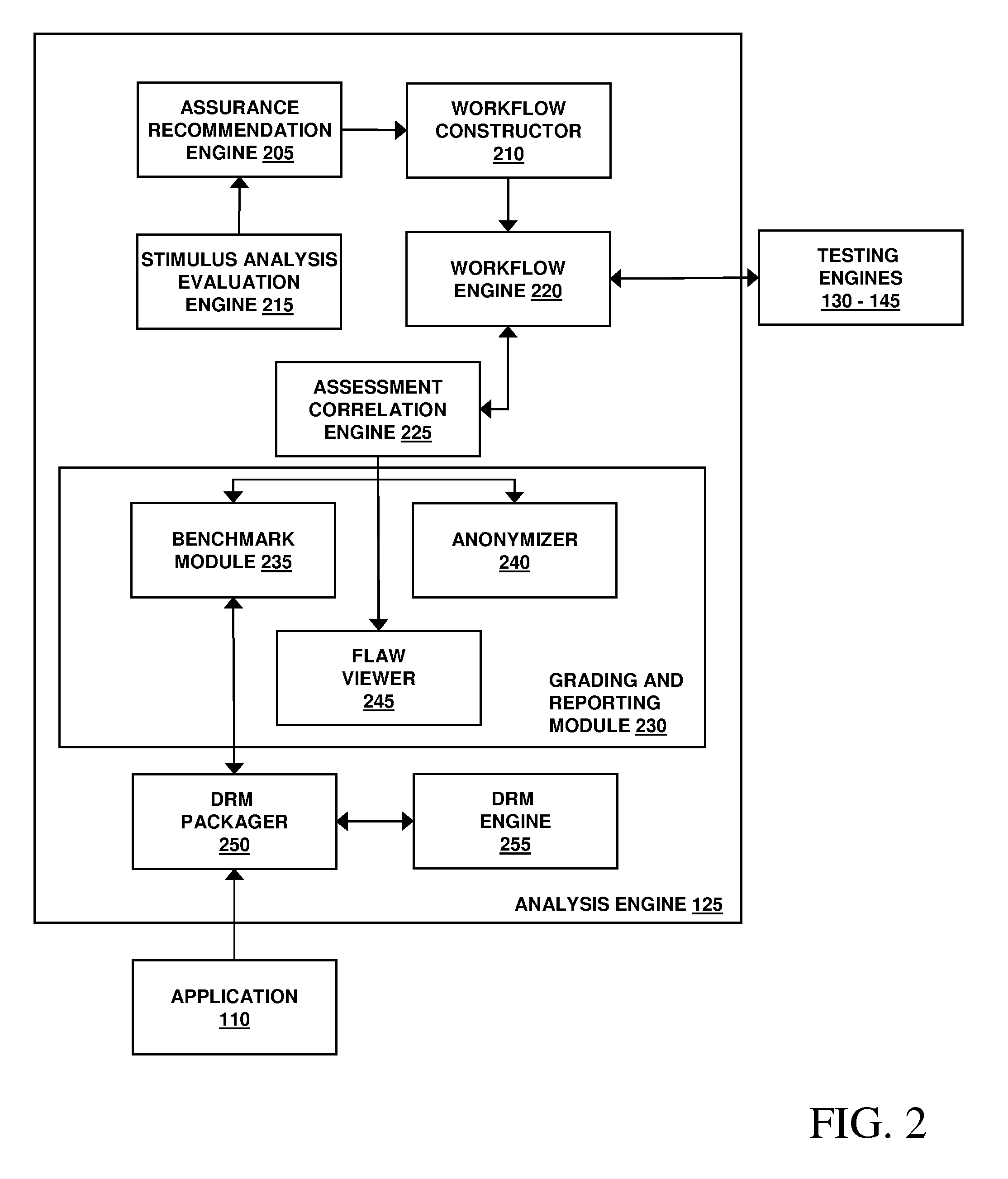
Assessment and analysis of software security flaws
ActiveUS20080209567A1Facilitates security assessment and vulnerability testingFacilitates benchmarkingMemory loss protectionUnauthorized memory use protectionApplication specificApplication software
Security assessment and vulnerability testing of software applications is performed based at least in part on application metadata in order to determine an appropriate assurance level and associated test plan that includes multiple types of analysis. Steps from each test are combined into a “custom” or “application-specific” workflow, and the results of each test may then be correlated with other results to identify potential vulnerabilities and / or faults.
Owner:VERACODE
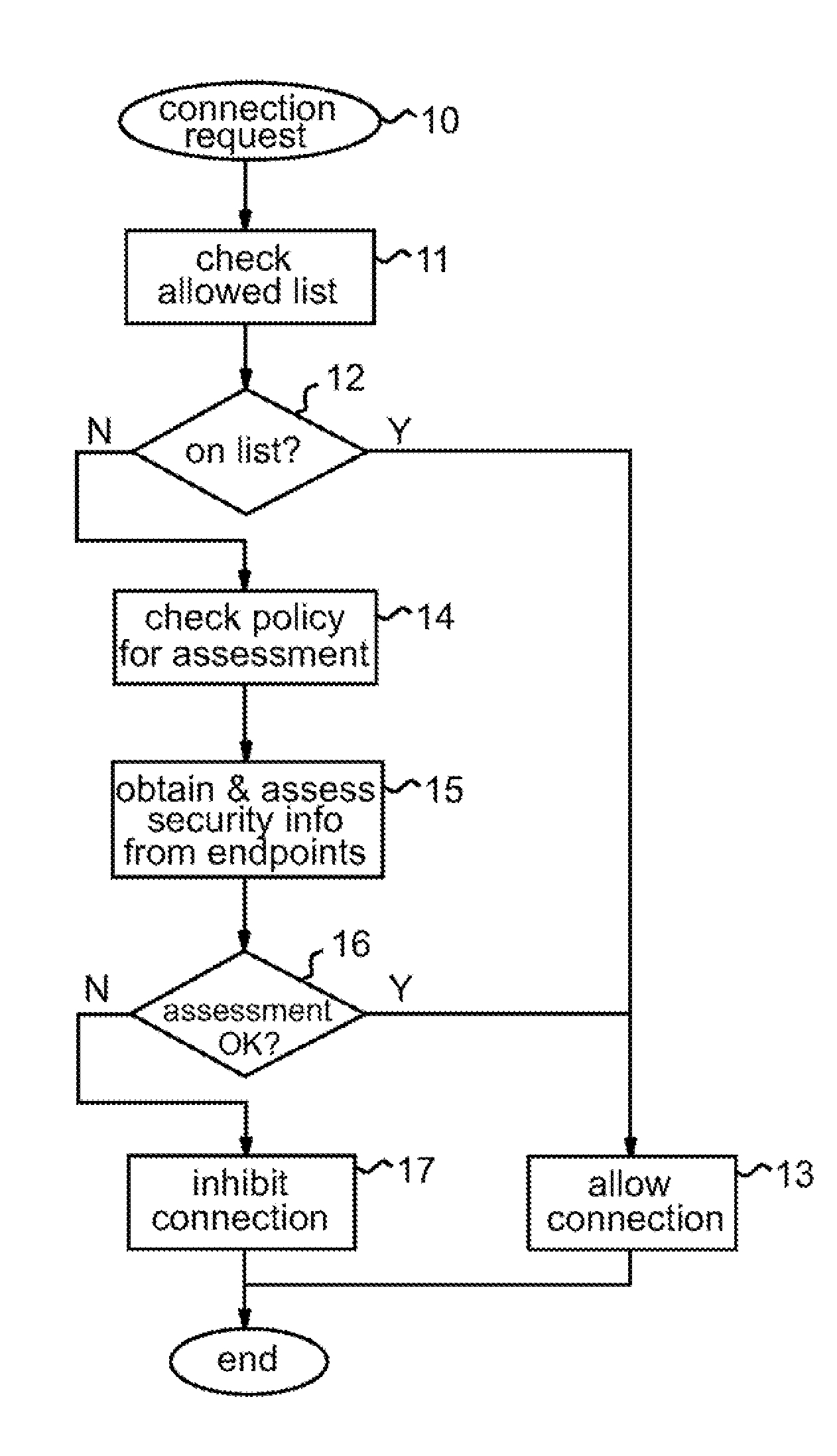
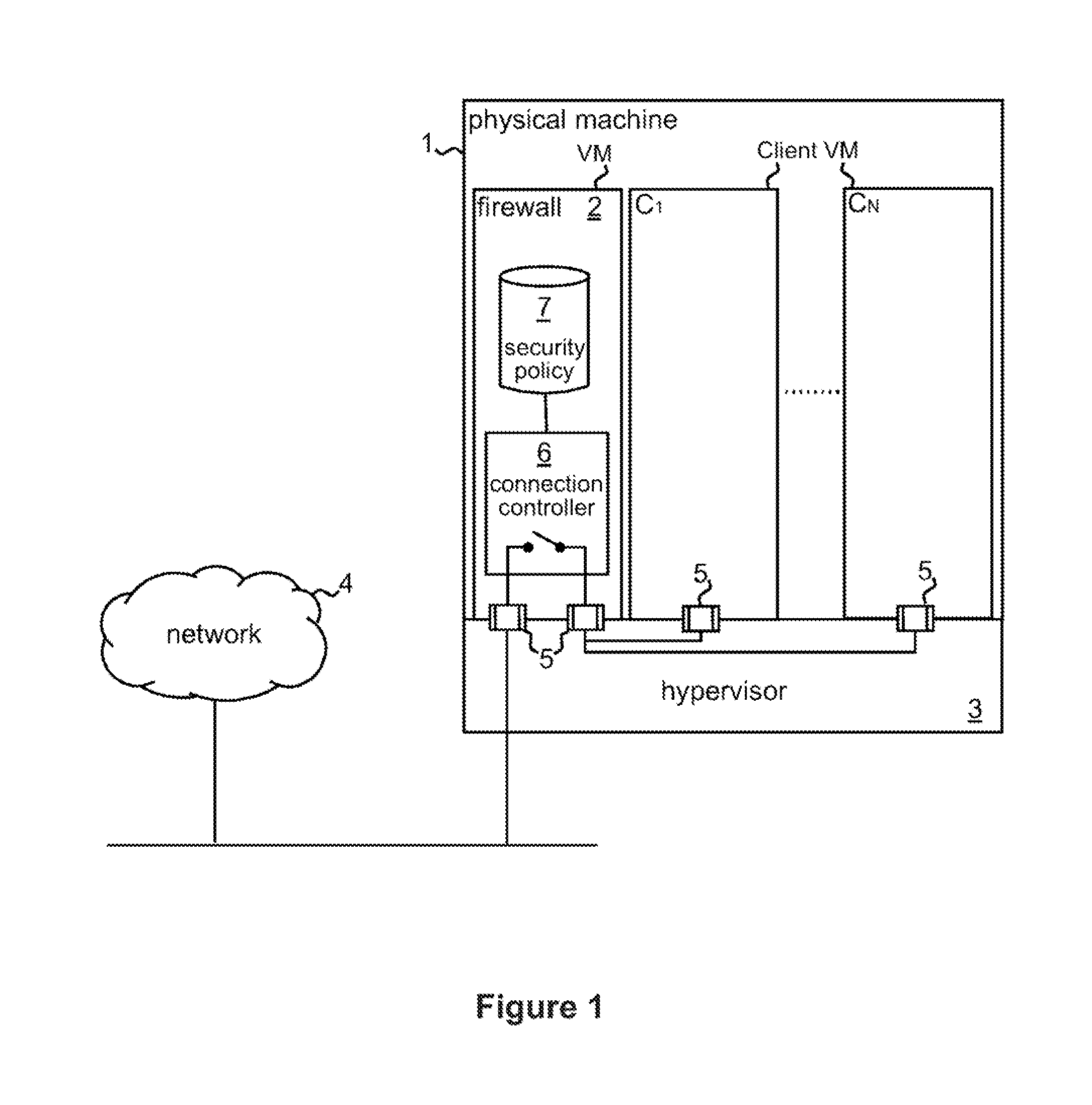
Firewall for controlling connections between a client machine and a network
ActiveUS20080289028A1Function increaseAvoid problemsComputer security arrangementsMultiple digital computer combinationsSecure stateClient-side
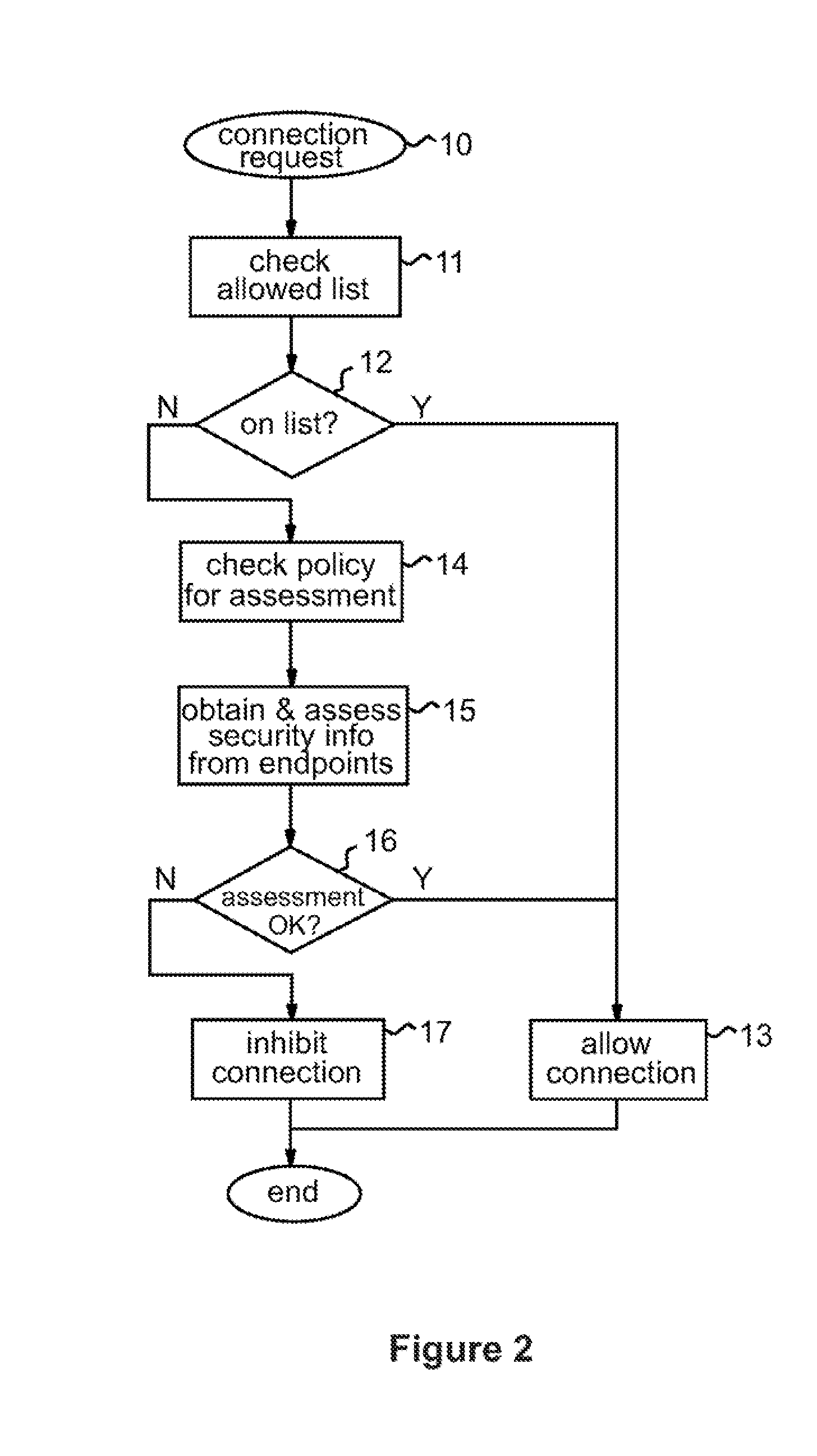
A firewall system adapted for location outside the client machine, preferably in the same data processing device as the client machine but outside a virtual machine containing the client machine. Control logic of the firewall system receives incoming and outgoing connections from the network and client machine respectively. In response to a connection request initiating a connection between respective endpoints in the network and client machine, the control logic performs a security assessment comprising obtaining from at least one of the network and client machine information indicative of the security state of the endpoint therein, and allows or inhibits the connection in dependence on the result of the security assessment. The security assessment may be performed in accordance with a security policy of the system, and different security assessments may be performed for different connection requests in accordance with the security policy.
Owner:GLOBALFOUNDRIES US INC
Method and system for cyber-security vulnerability detection and compliance measurement (CDCM)
InactiveUS20050132225A1Improve abilitiesDigital data processing detailsUser identity/authority verificationProgram planningHandling system
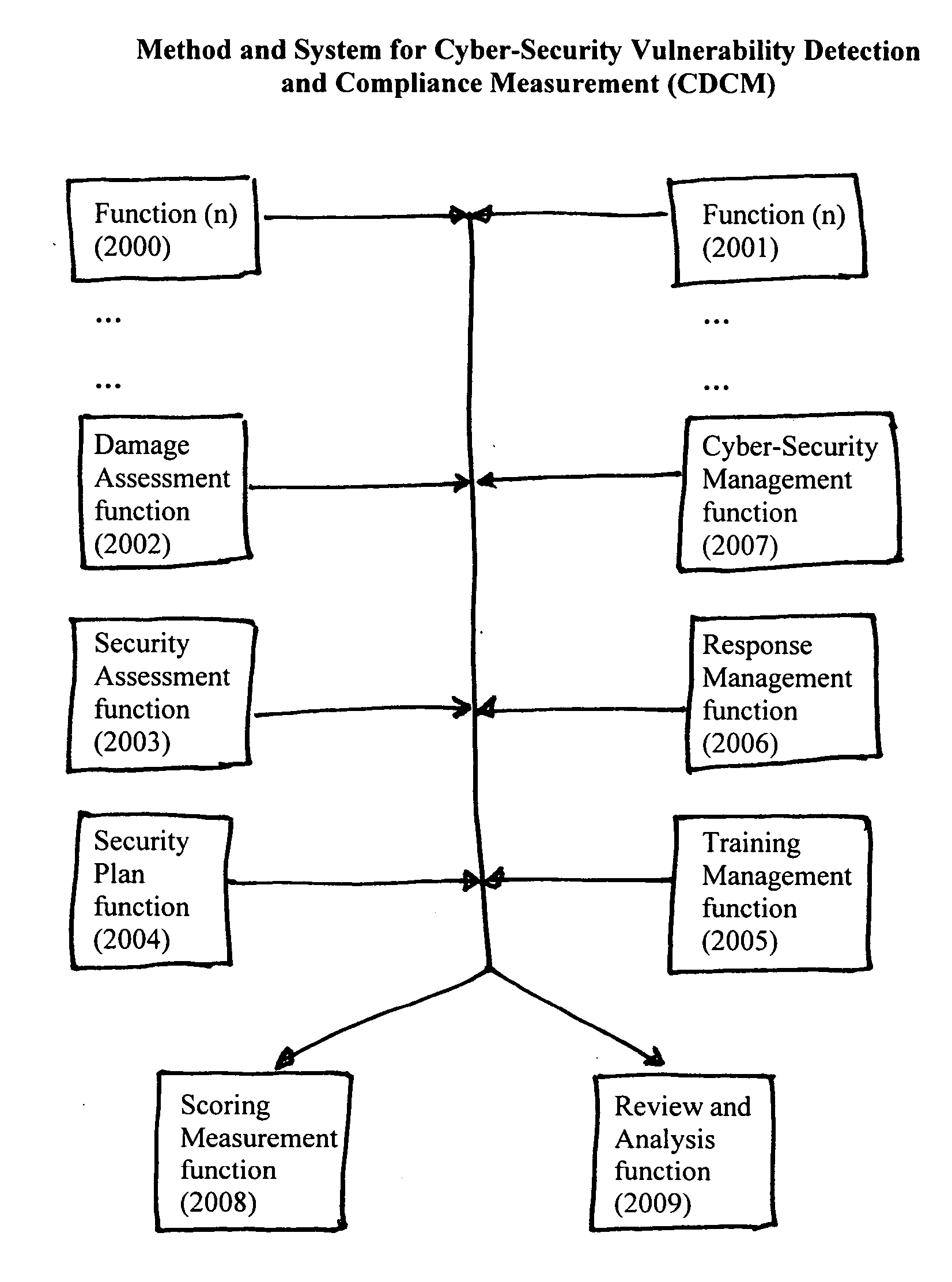
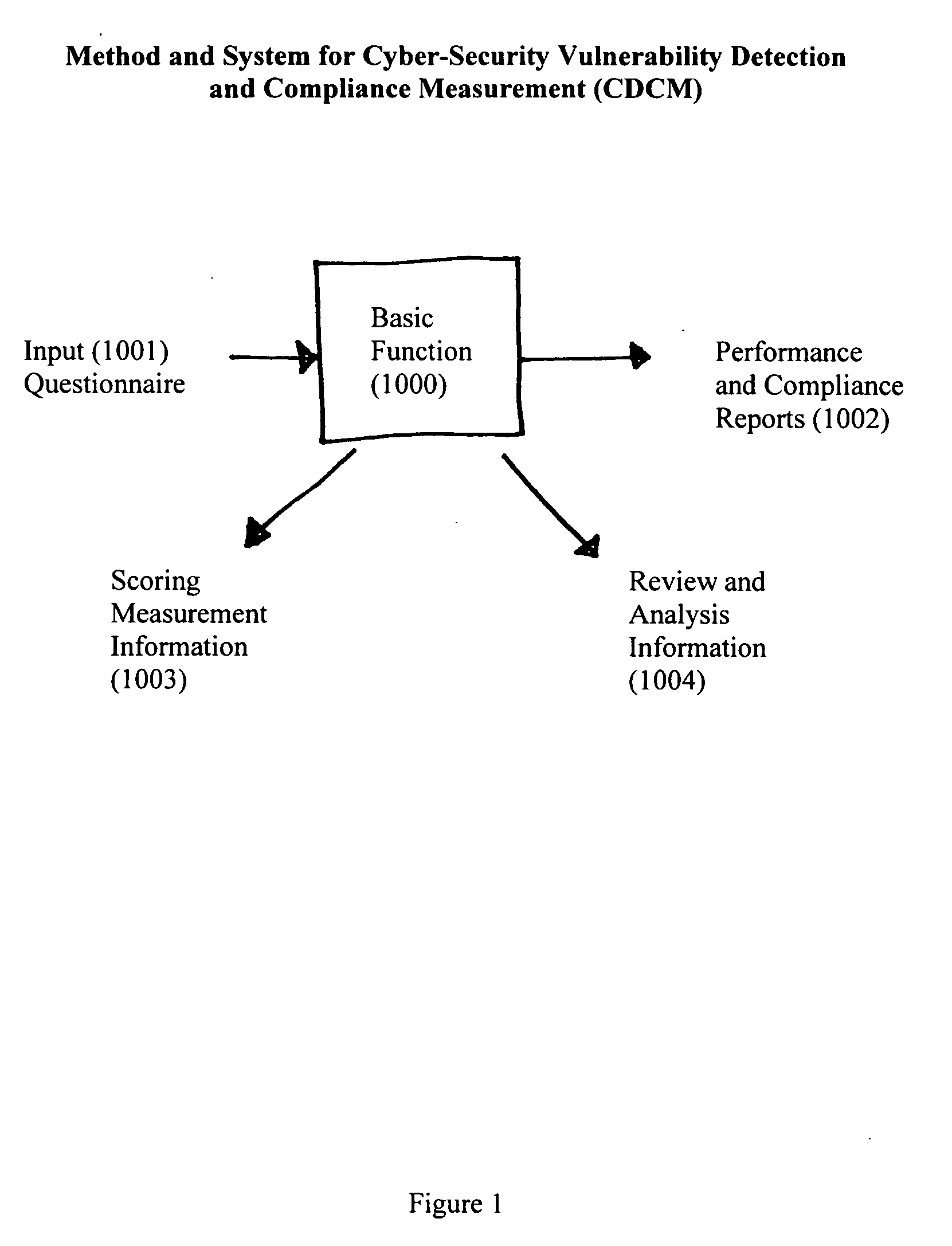
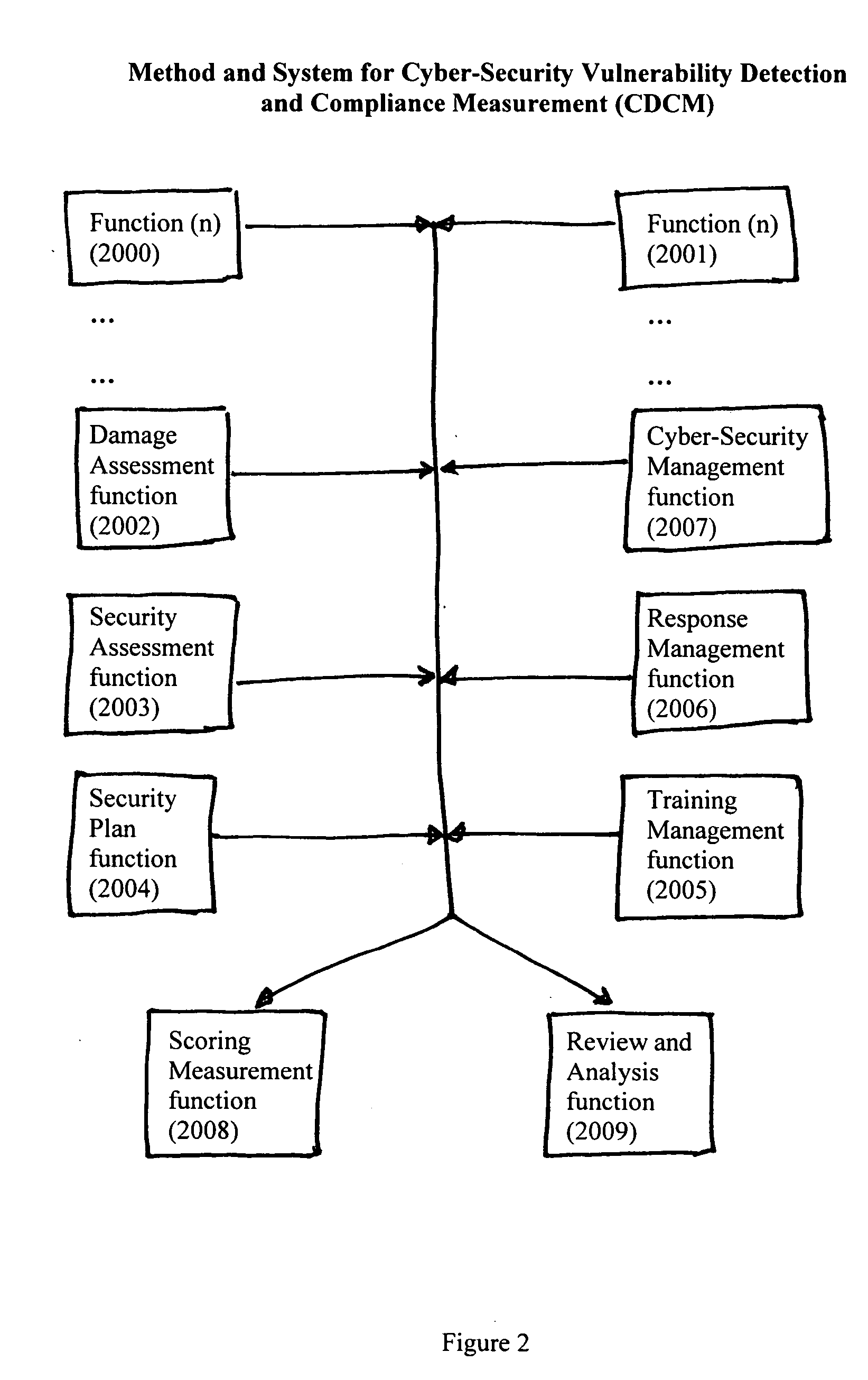
Method and System for Cyber-Security Vulnerability Detection and Compliance Measurement (CDCM) provides any entity, organization or individual with access to or possession of sensitive, confidential or secret information, defined as “protected information,” in digital format that is received, processed, stored or distributed by a computer, computer system or digital processing equipment with the capability to detect and respond to cyber security vulnerabilities and to measure compliance with cyber-security requirements as established by the Federal Security Information Management Act (FISMA) for the security of protected information and certain additional related desirable or mandatory cyber-security requirements. In one sample embodiment of the invention, the method utilizes a damage assessment function; a security assessment function; a security plan or planning function; a training management function; a response management function; a cyber-security management function; a scoring measurement function; and a review and analysis function; to establish a quantifiable and definitive numerical measurement of the relative compliance of a specific processing system, at a specific point in time, to a defined and established threshold value of performance, or compliance acceptance, and to provide, assemble and be capable of archiving the supporting parameters, status, states and analysis that is specifically associated with the numerical value which represents the specific processing system's state of compliance at the specified time and to utilize various intermediate values and parameters to manage and enhance the performance of the specific system thereby improving the systems compliance score and numerical performance measurement value.
Owner:GEARHART GLENN
Security based network access selection
ActiveUS9325737B2Digital data processing detailsMultiple digital computer combinationsCommunications systemNetwork connection
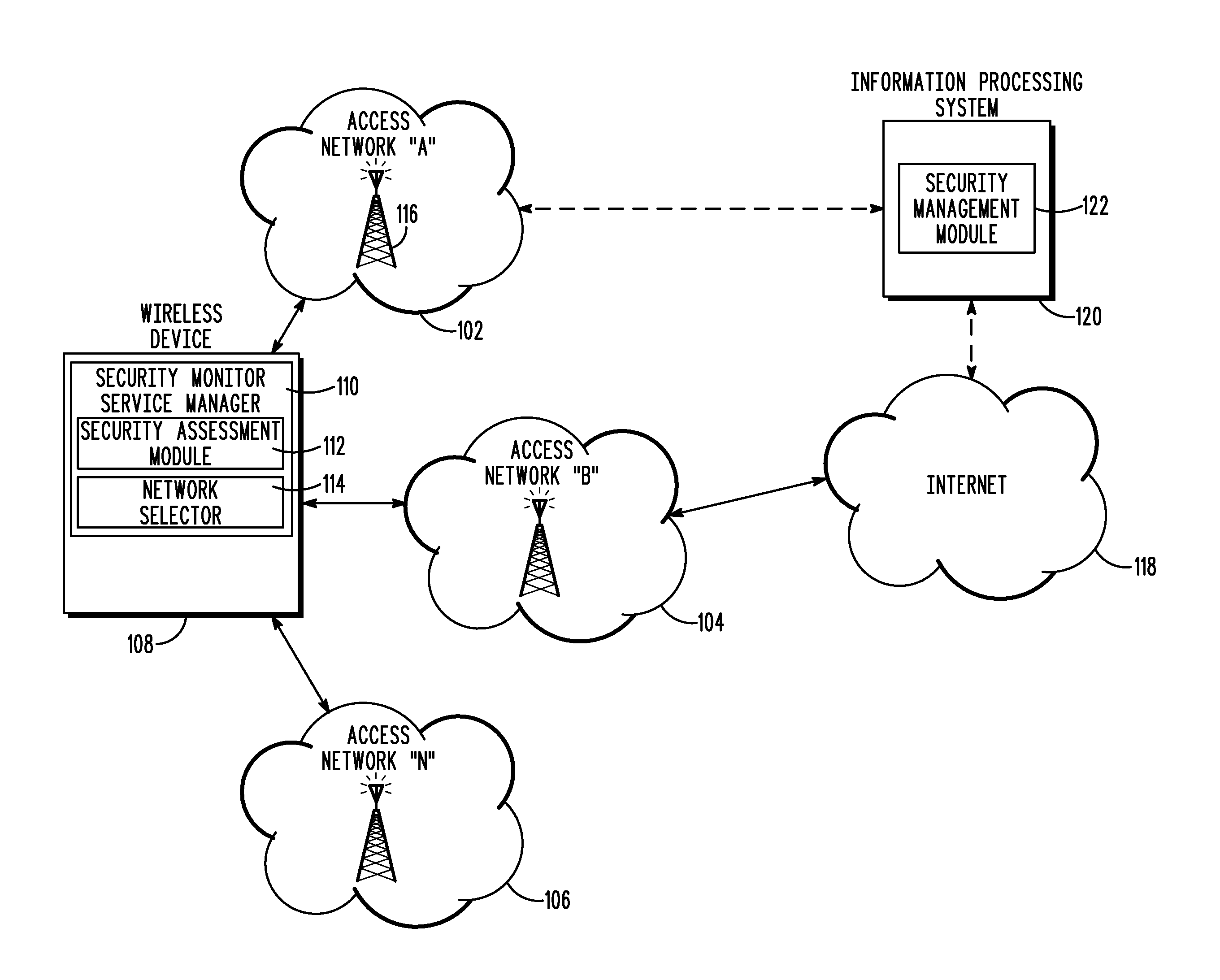
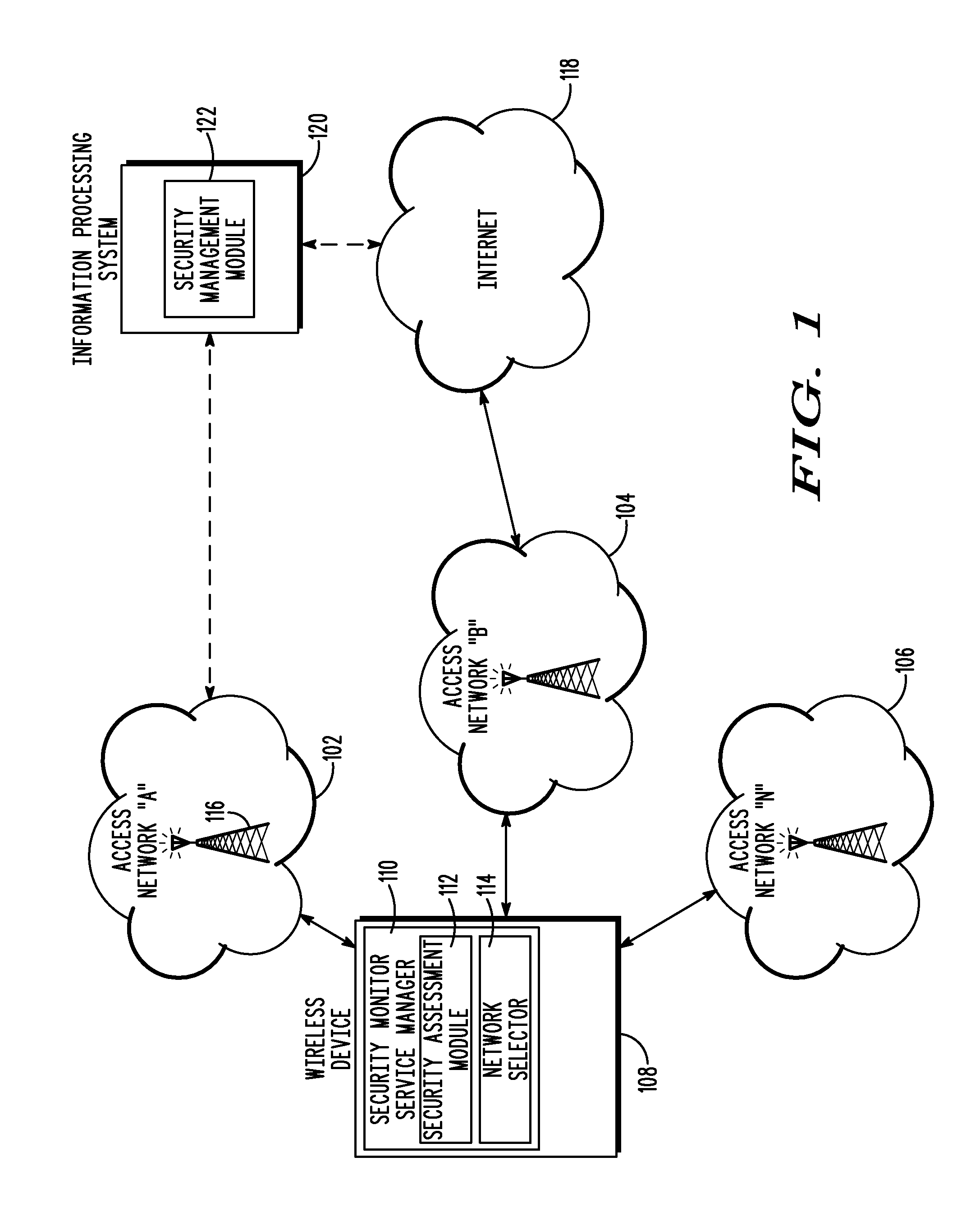
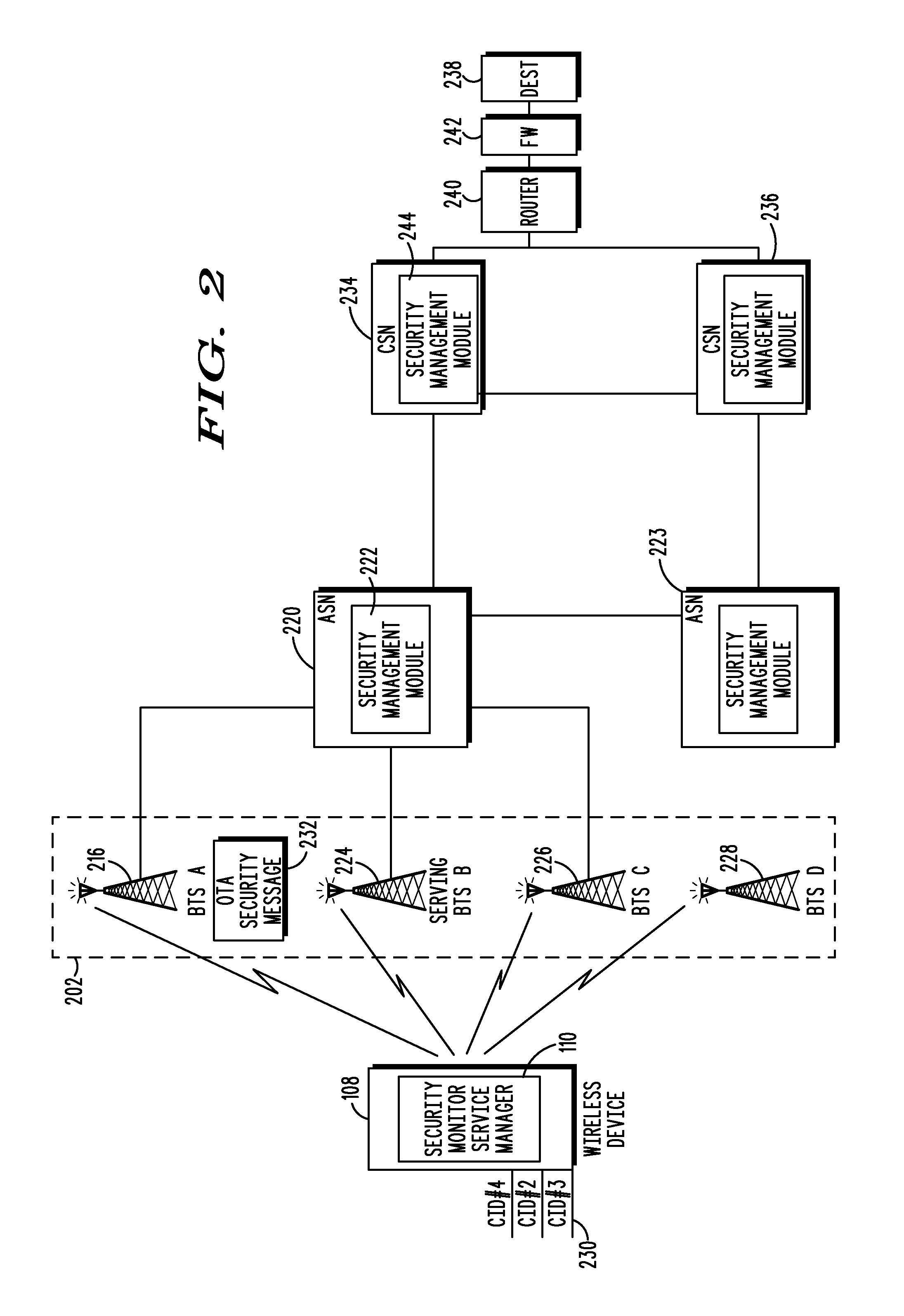
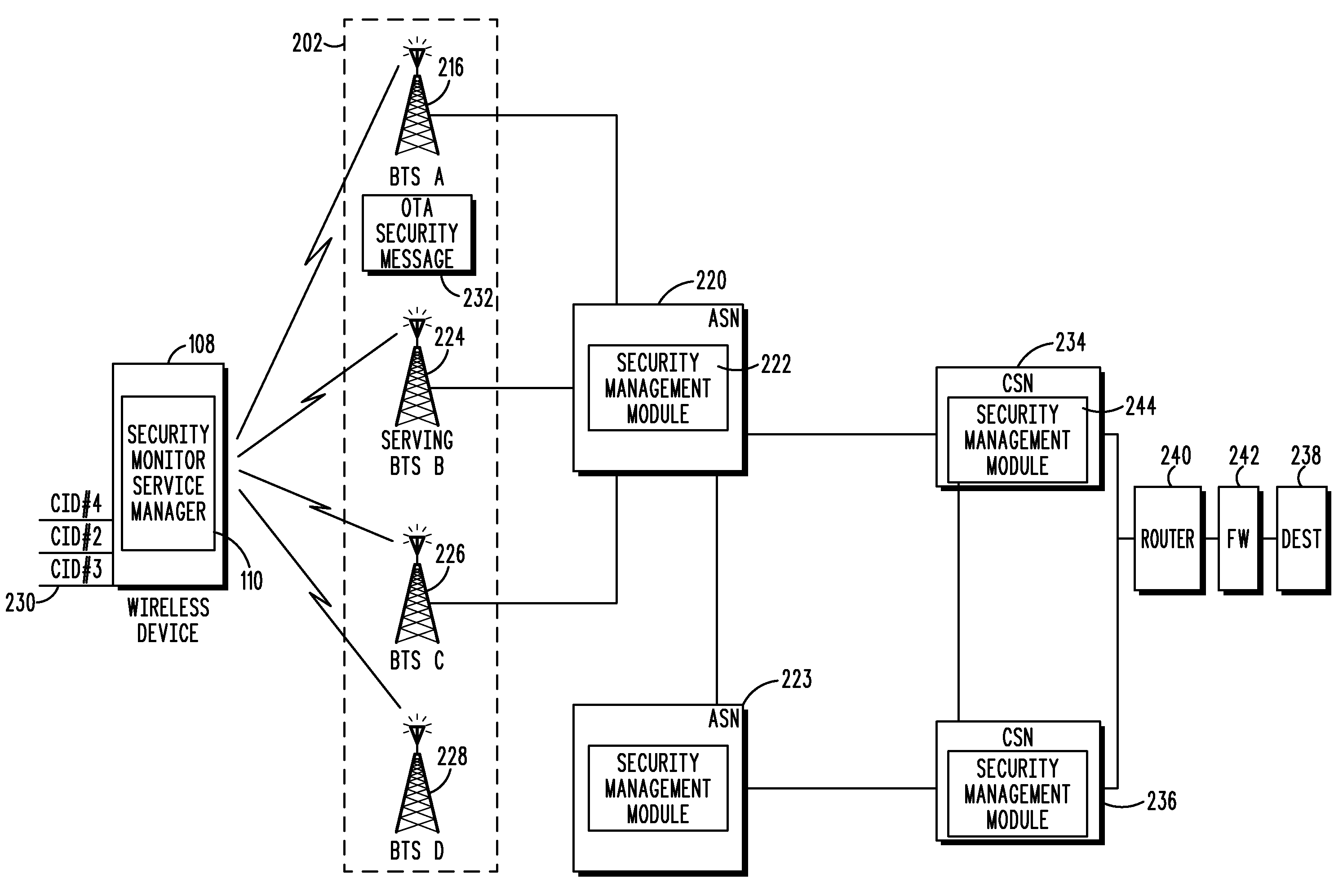
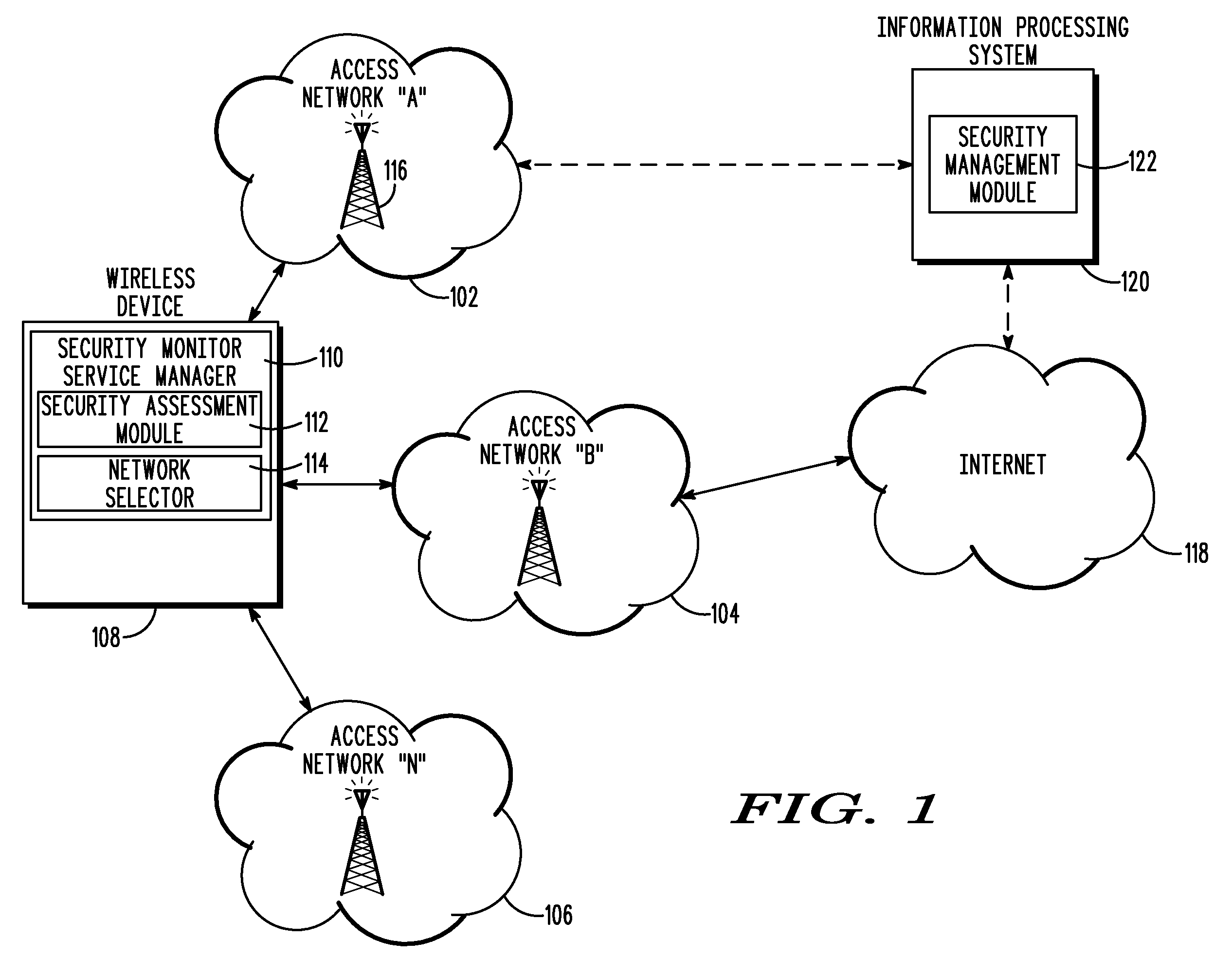
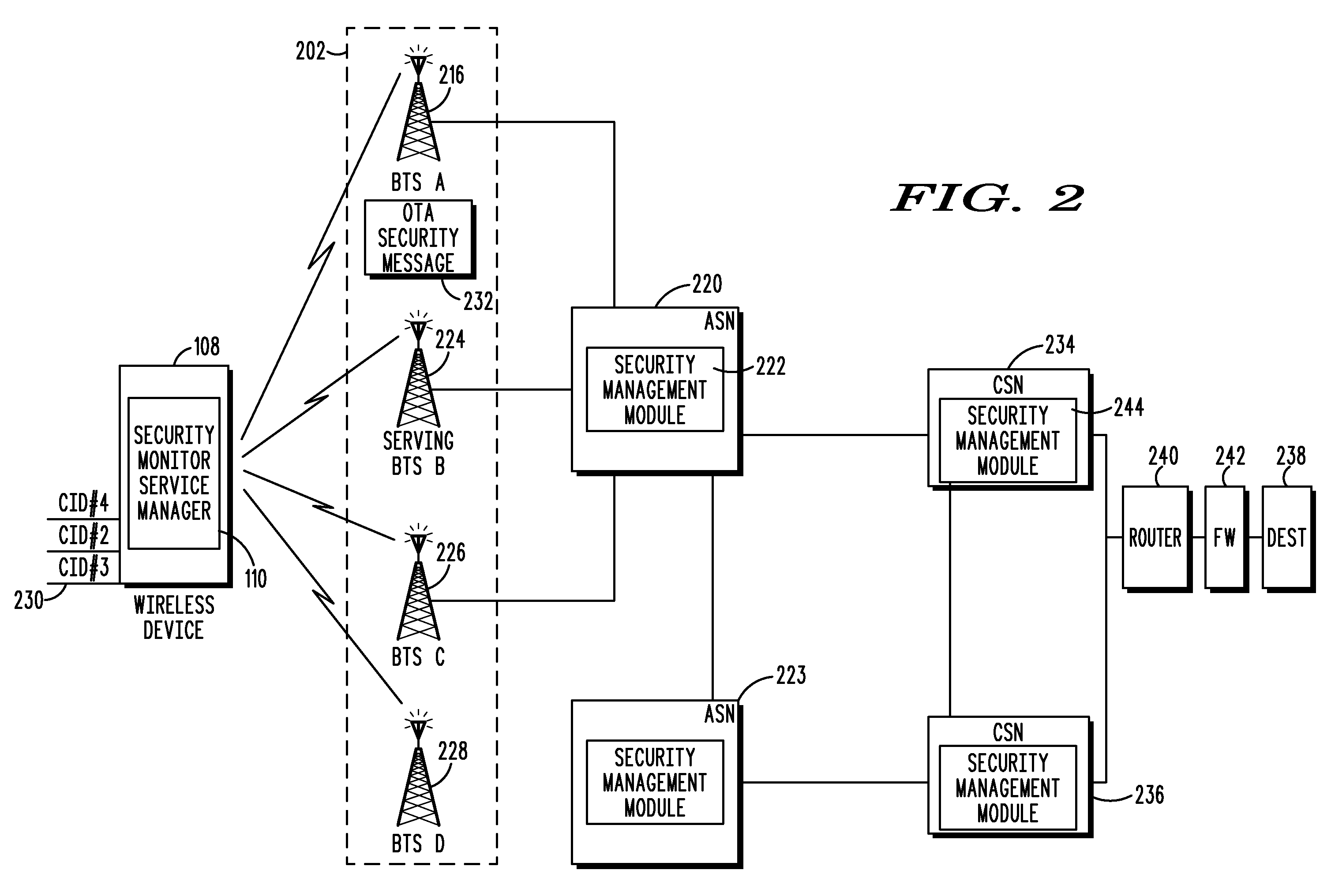
A method and wireless device select a set of secure network connections (230) between a wireless device (108) in a wireless communication system and a target destination system (238). A first security assessment (708) associated with each of a plurality of base station connections associated with respective each of a plurality of base stations (116) available for wireless communications with the wireless device (108) is performed. A second security assessment (716) associated with each of a plurality of subsequent network connections available between the plurality of base stations (116) and a target destination system (238) is performed. A set of base station connections from the plurality of base station connections are prioritized according to predetermined security criteria associated with the wireless device (108). A set of subsequent network connections from the plurality of subsequent network connections (230) are prioritized according to predetermined security criteria associated with the wireless device (108).
Owner:MOTOROLA SOLUTIONS INC
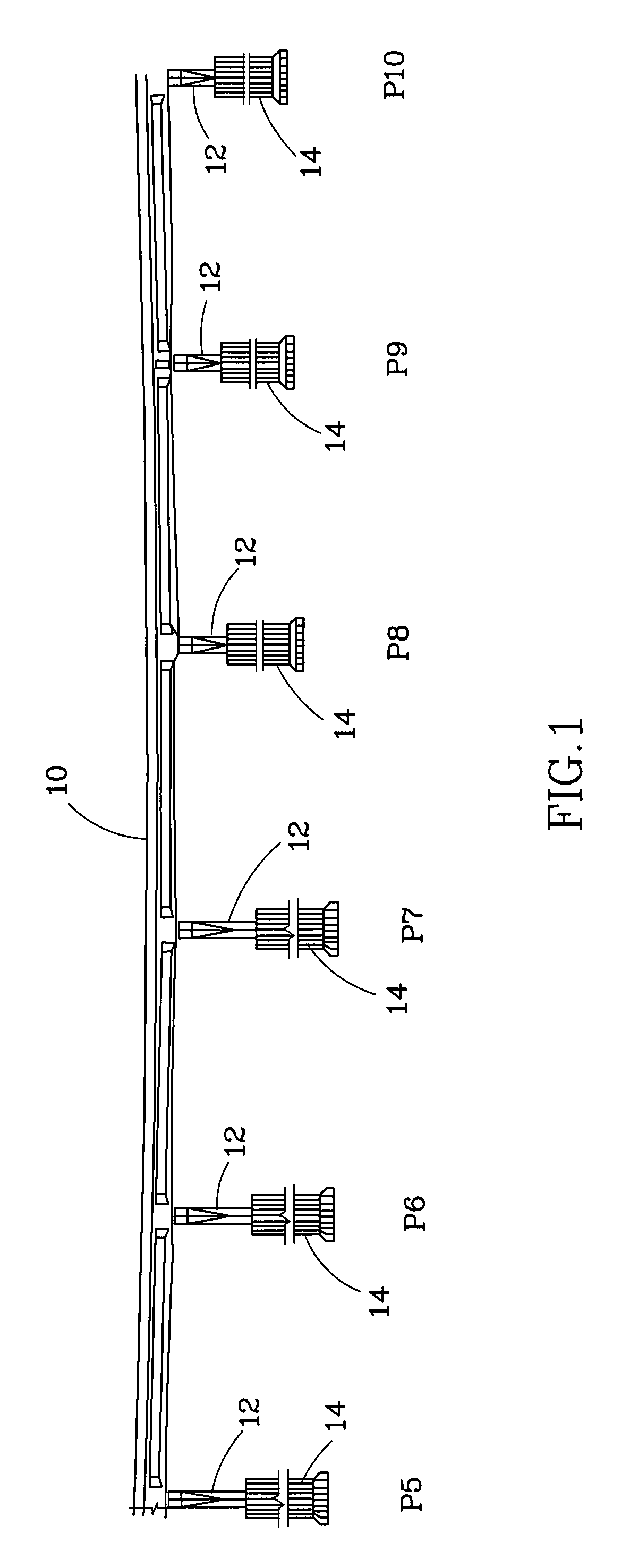
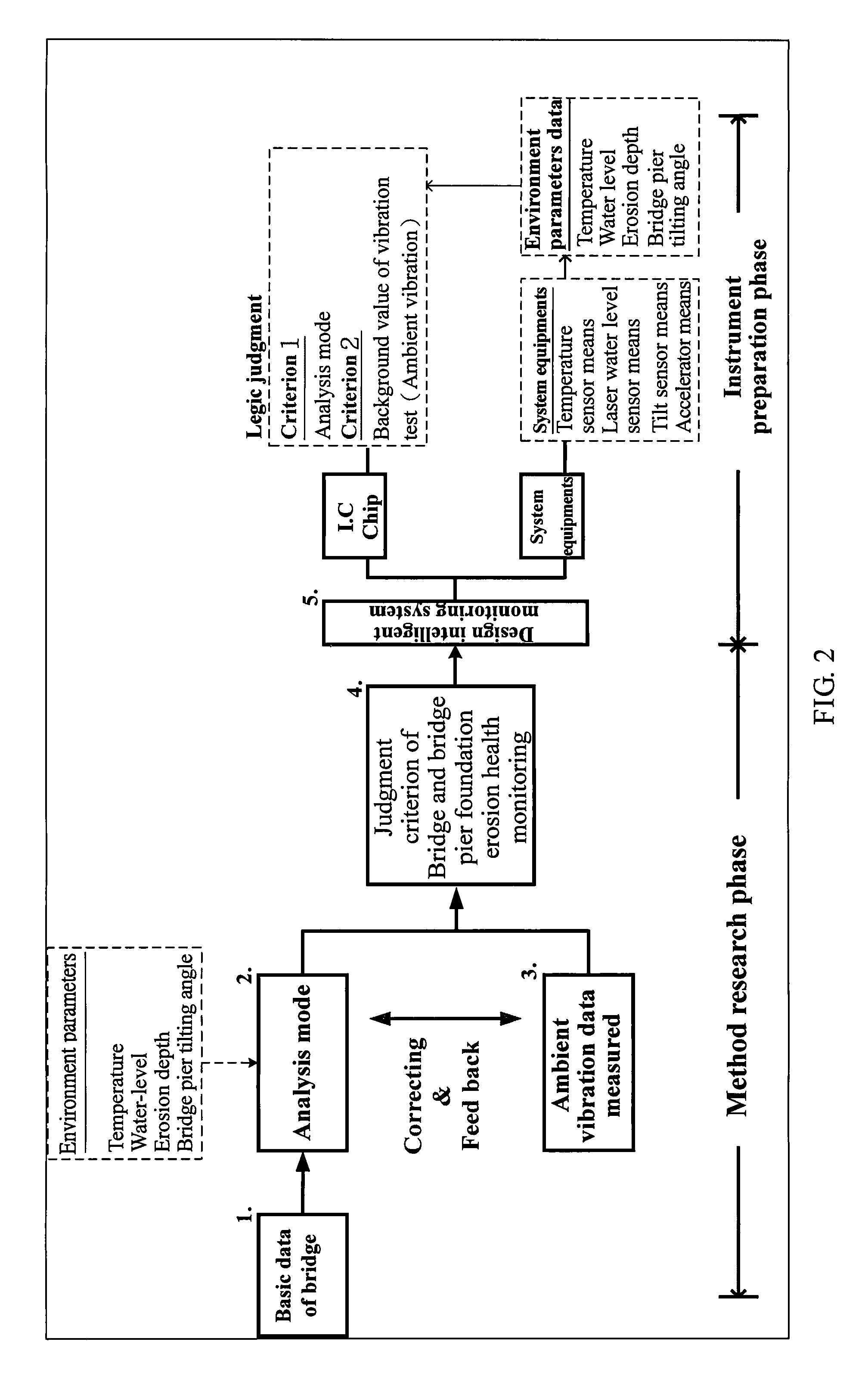
Bridge monitoring and safety evaluation method using a vibration technique
ActiveUS20100242609A1Easy system maintenanceImprove the level ofVehicle testingFluid-tightness measurementStructural monitoringEngineering
The invention relates bridge structure safety evaluation technology by means of combining vibration measuring and structural model analysis techniques for bridge erosion evaluation and pre-warning monitoring applications. This technology can also be applied for long-term bridge structure monitoring and safety evaluation as well as judgment and evaluation of rail structure abnormality.
Owner:LEE WEI FENG
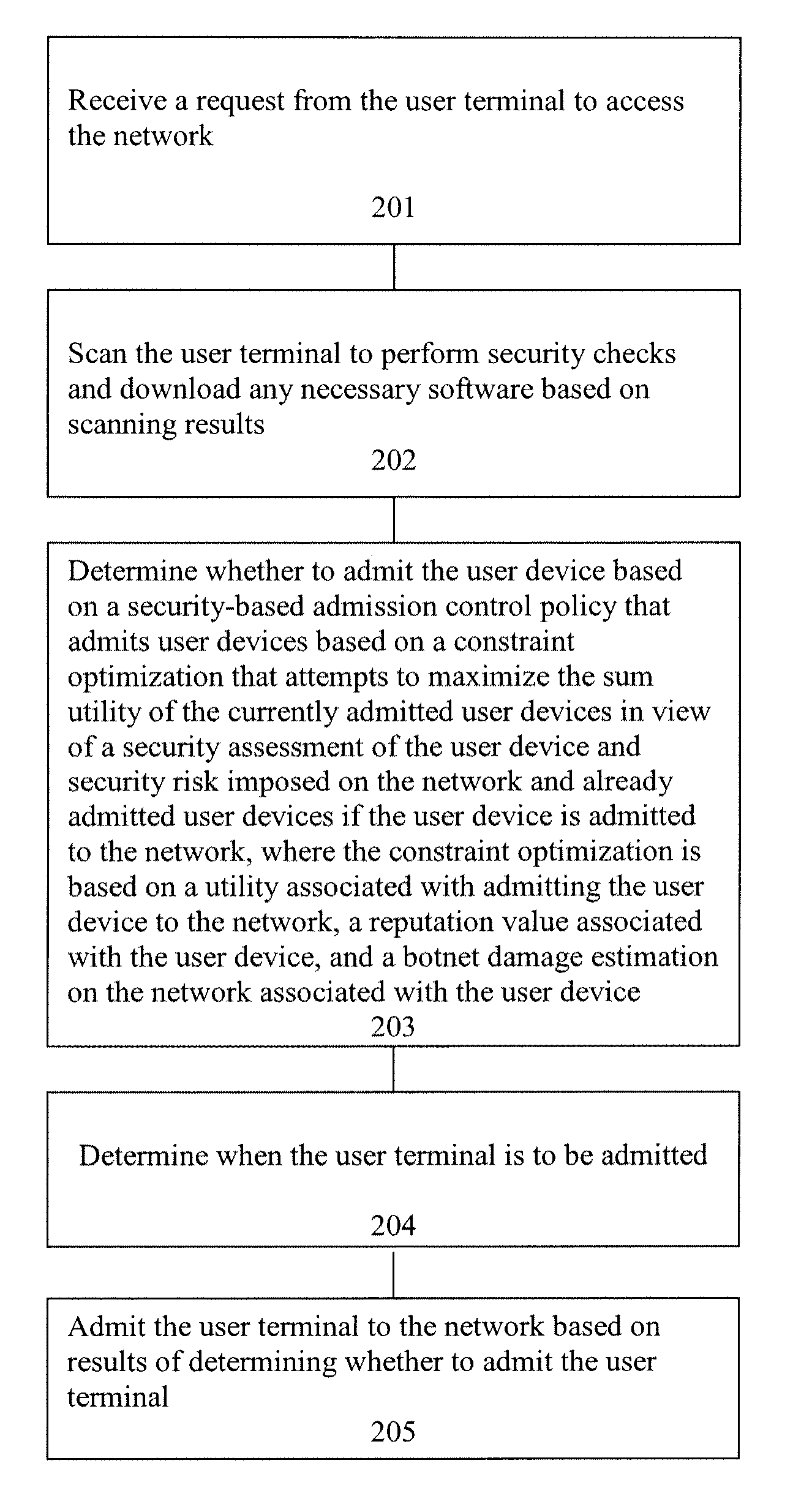
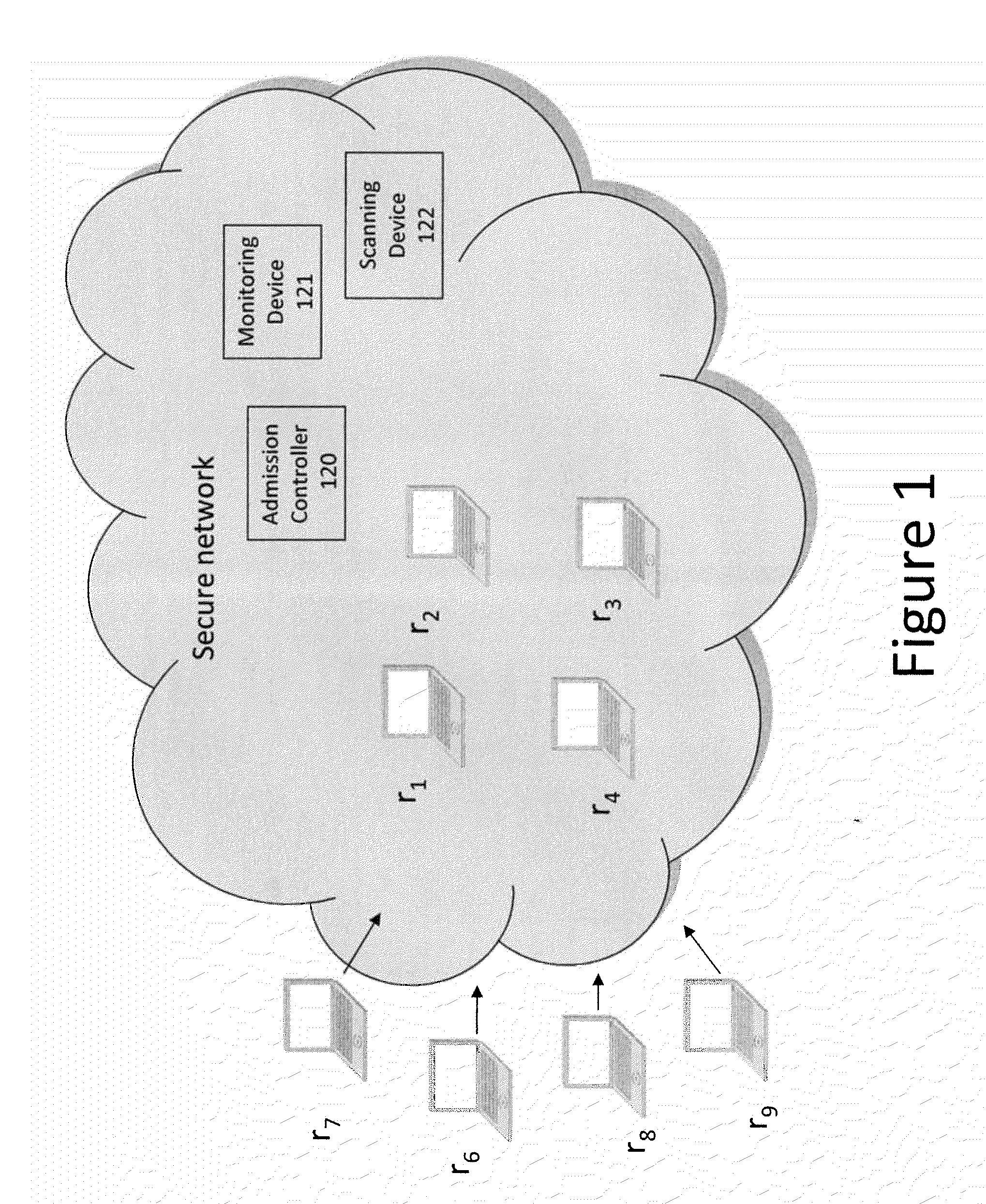
Method and apparatus for security-risk based admission control
A method and apparatus is disclosed herein for security risk-based admission control. In one embodiment, the method comprises: receiving a request from the user device to access the network; determining whether to admit the user device based on a security-based admission control policy that admits user devices based on a constraint optimization that attempts to maximize the sum utility of the currently admitted user devices in view of a security assessment of the user device and security risk imposed on the network and already admitted user devices if the user device is admitted to the network, wherein the constraint optimization is based on a utility associated with admitting the user device to the network, a reputation value associated with the user device, and a botnet damage estimation on the network associated with the user device; and admitting the user device to the network based on results of determining whether to admit the user device.
Owner:NTT DOCOMO INC
Security based network access selection
ActiveUS20090007246A1Digital data processing detailsMultiple digital computer combinationsCommunications systemNetwork connection
A method and wireless device select a set of secure network connections (230) between a wireless device (108) in a wireless communication system and a target destination system (238). A first security assessment (708) associated with each of a plurality of base station connections associated with respective each of a plurality of base stations (116) available for wireless communications with the wireless device (108) is performed. A second security assessment (716) associated with each of a plurality of subsequent network connections available between the plurality of base stations (116) and a target destination system (238) is performed. A set of base station connections from the plurality of base station connections are prioritized according to predetermined security criteria associated with the wireless device (108). A set of subsequent network connections from the plurality of subsequent network connections (230) are prioritized according to predetermined security criteria associated with the wireless device (108).
Owner:MOTOROLA SOLUTIONS INC
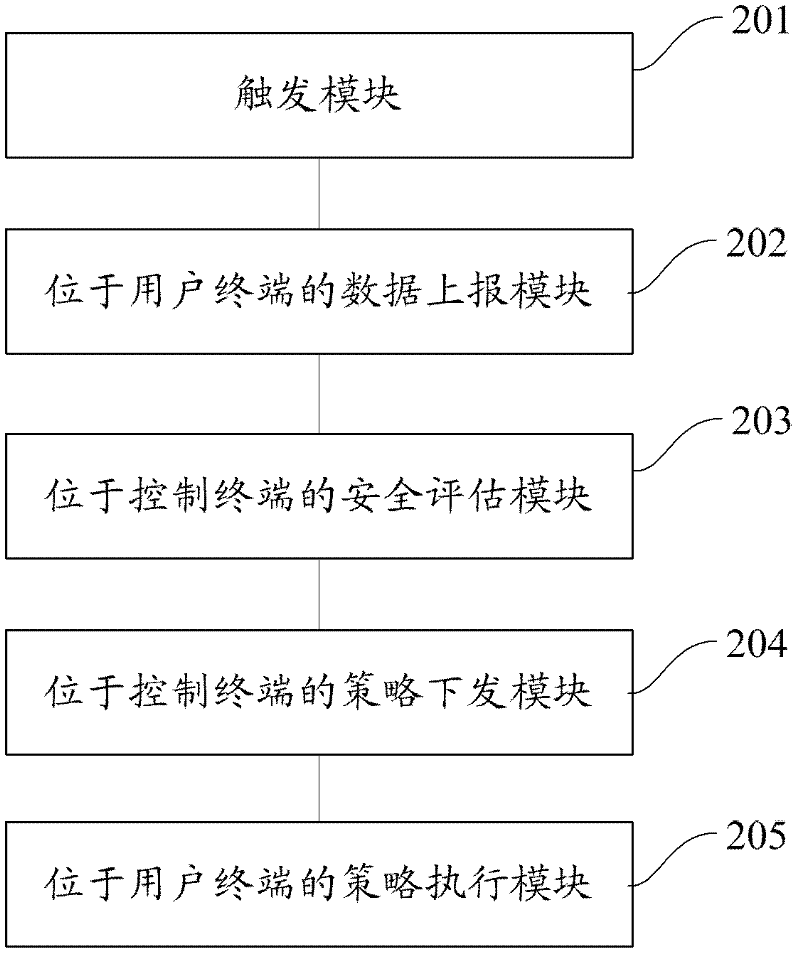
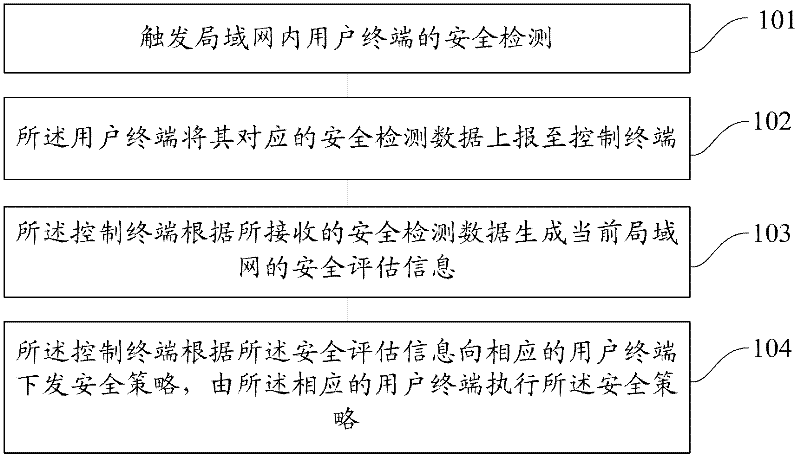
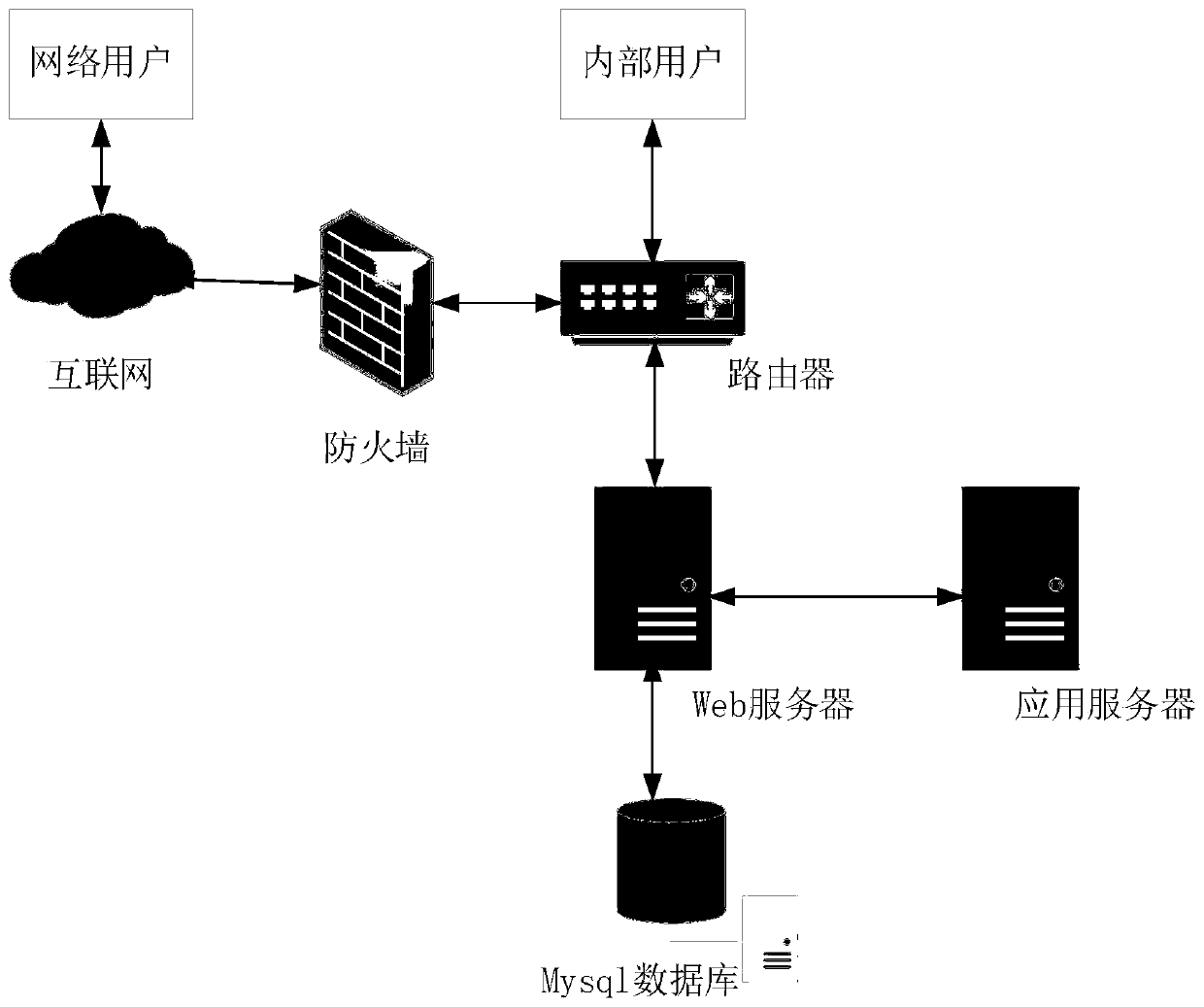
Local area network (LAN) security evaluation method and system
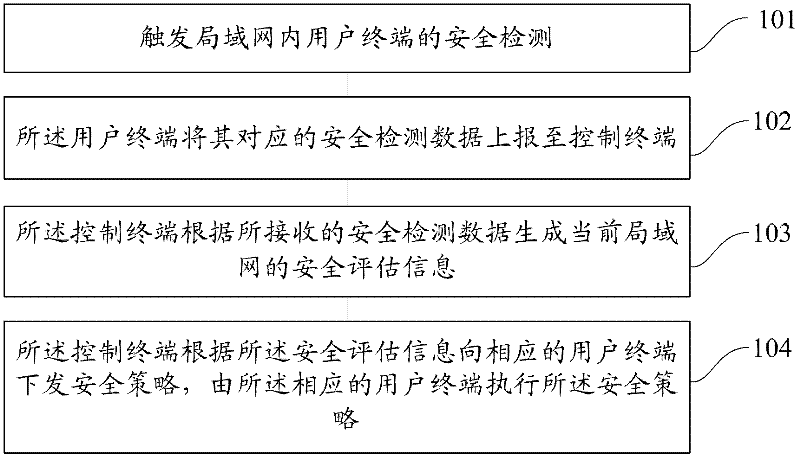
ActiveCN102413011AFull feedbackReal feedbackData switching networksSecurity assessmentLocal area network
The invention provides a local area network (LAN) security evaluation method and system. Terminals in an LAN comprise a control terminal and a user terminal, and the method comprises the steps of: triggering security detection on the user terminal in the LAN; reporting security detection data corresponding to the user terminal to the control terminal by the user terminal; and generating security evaluation information of the current LAN by the control terminal according to the received security detection data. The method and system provided by the invention can be used for completely and truly feeding back the security state of an enterprise network.
Owner:奇安信网神信息技术(北京)股份有限公司 +1
Systems and methods for providing virtual currencies
Systems and methods for conducting reliable financial transactions, credit decisions, and security assessments are provided. Connectivity values may be assigned to members of a community by users, third parties, or automatically based on the frequency of interactions between members of the community. Connectivity values may represent such factors as alignment, reputation within the network community, or the degree of trust. Information about a financial transaction may be automatically published to other qualifying members of the community based on connectivity values. The other qualifying members may then be given the opportunity to participate in the same financial transaction or access the same financial application in order to initiate their own financial transaction, or to take action based on information about the financial transaction, credit decision, and / or security assessment. These transactions may also be based on virtual and / or electronic currencies.
Owner:WWW TRUSTSCI COM INC
Systems and methods for conducting more reliable financial transactions, credit decisions, and security assessments
Systems and methods for conducting more reliable financial transactions, credit decisions, and security assessments are provided. A user may assign user connectivity values to other members of the community, or connectivity values may be automatically harvested or assigned from third parties or based on the frequency of interactions between members of the community. Connectivity values may represent alignment, reputation within the network community, or the degree of trust. Information about a financial transaction initiated by a first member of the community, a credit decision, and / or a security assessment may be automatically published to other qualifying members of the community based on connectivity values. The other qualifying members may then be given the opportunity to participate in the same financial transaction or access the same financial application in order to initiate their own financial transaction, or to take action based on information about the financial transaction, credit decision, and / or security assessment.
Owner:WWW TRUSTSCI COM INC
Region-based security evaluation method for the electric power distribution system
ActiveUS20140236513A1Effective controlWidely distributedData processing applicationsResistance/reactance/impedenceOperating pointTransformer
The invention discloses a region-based security evaluation method for the distribution system, which belongs to the field of electric power distribution system operation. The method contains the following steps: a. acquiring distribution system security region and security boundaries according to substation transformer capacity of the distribution system and link relationships among the substation transformers (101); b. acquiring the distance between operating point and the security boundaries (102); c. judging whether the operating point is within the distribution system security region according to the distance between the operating point and security boundaries (103); if yes, performing step (4), otherwise, performing step (5); d. acquiring the load shortage or excess Li of a link unit (104); e. adjusting the load of the substation transformers until the operating point comes back to the distribution system security region, then performing step (4) (105). The method provides more information than traditional N−1 simulation in distribution system security assessment; and reduces calculation, increases the operating speed and satisfies the requirement of real-time and on-line operation.
Owner:TIANJIN UNIV
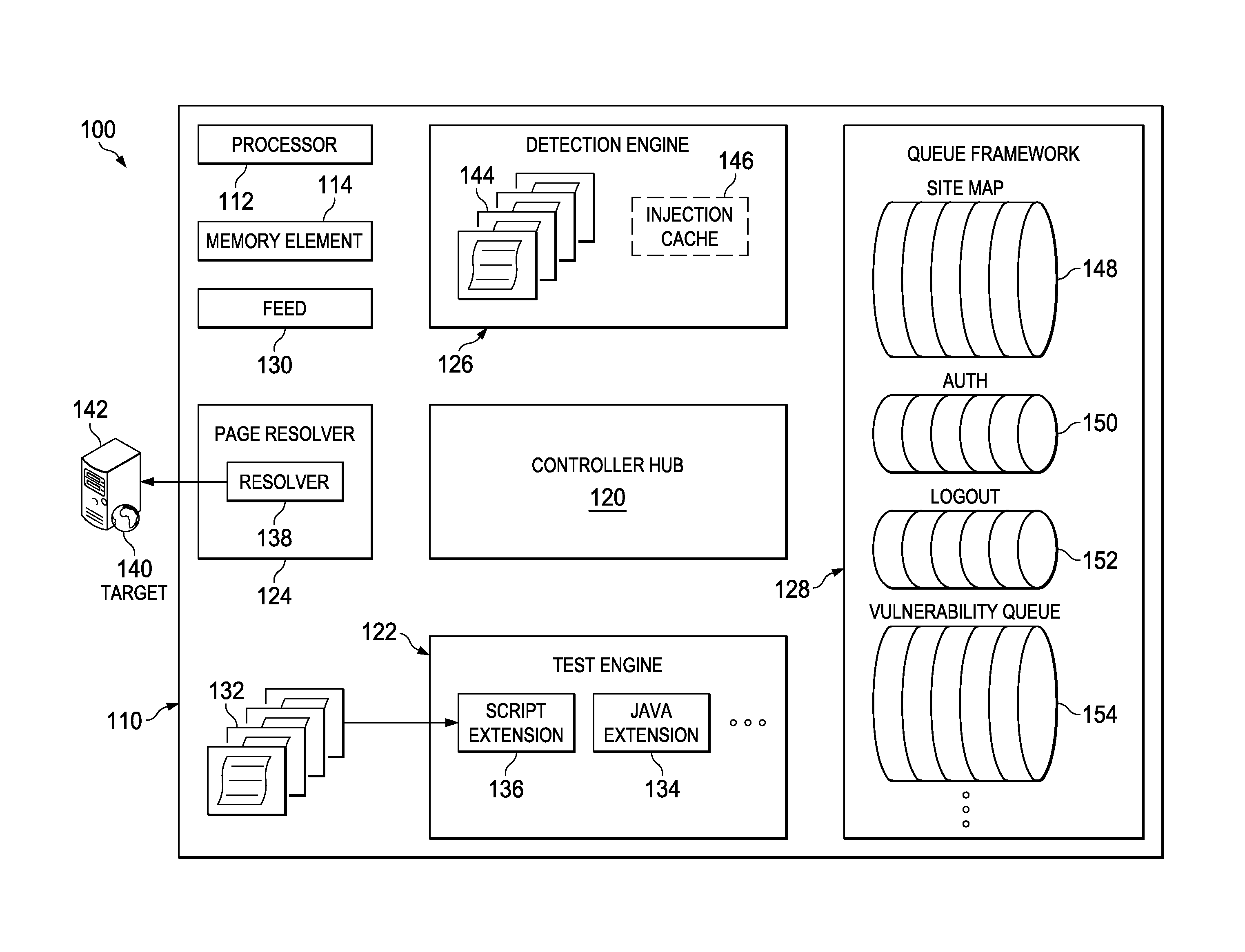
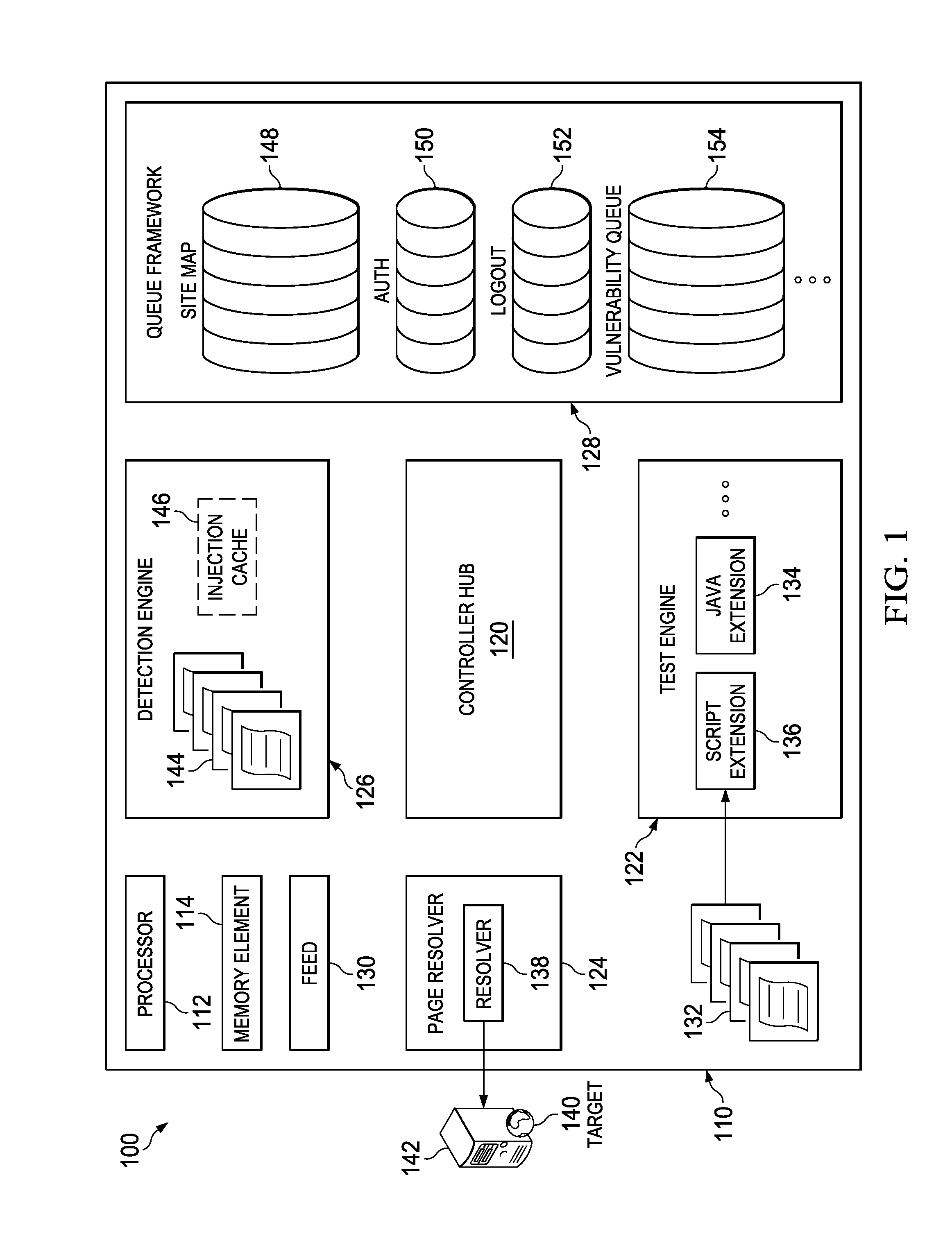
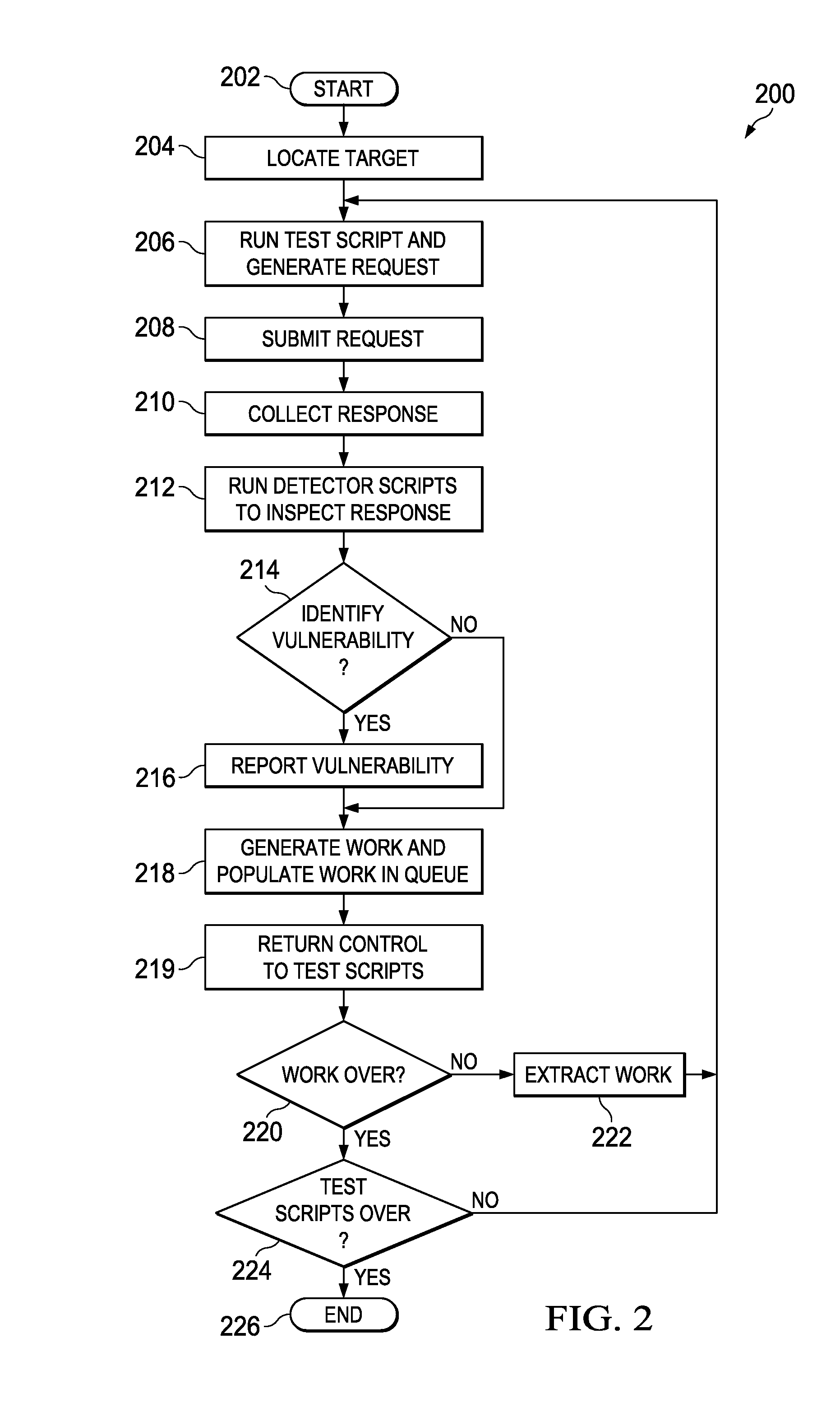
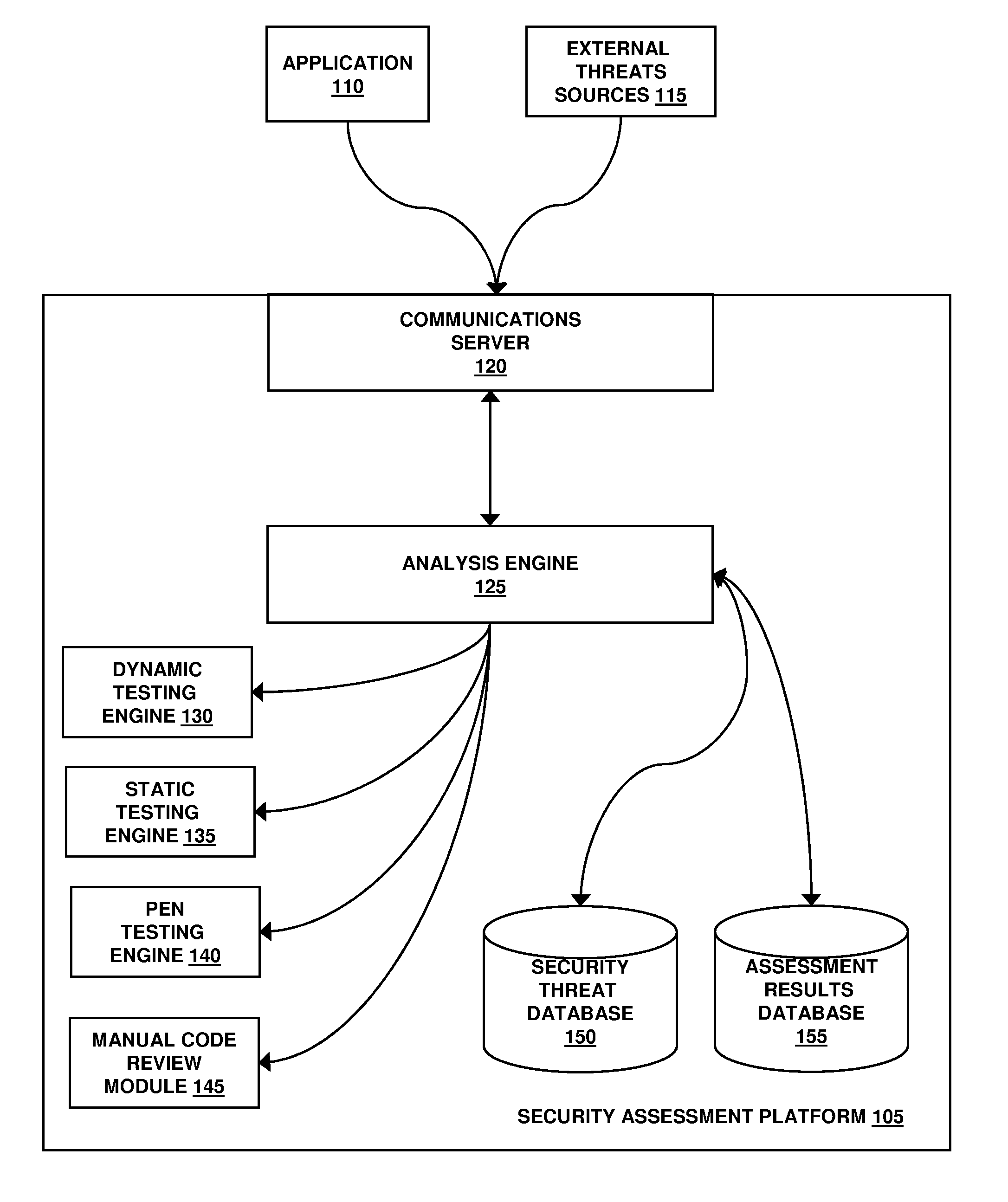
System and method for application security assessment
ActiveUS20130247204A1Memory loss protectionError detection/correctionTest scriptApplication security
A system and method in one embodiment includes modules for running a test script to generate a request to a target application, receiving a response from the target application, and running a detector script to inspect the response for a vulnerability. More specific embodiments include a target web site, populating a work in a queue, where the work corresponds to content in the response, and running a second test script or detector script to generate a follow-up request to the application if the vulnerability has been identified in the response. Other embodiments include extracting the work from the queue, and running a second test script corresponding to the extracted work. Other embodiments include storing an injection in an injection cache, de-registering the injection from the injection cache if it is identified in the response, and re-crawling the application, if the injection has not been de-registered from the injection cache.
Owner:MCAFEE LLC
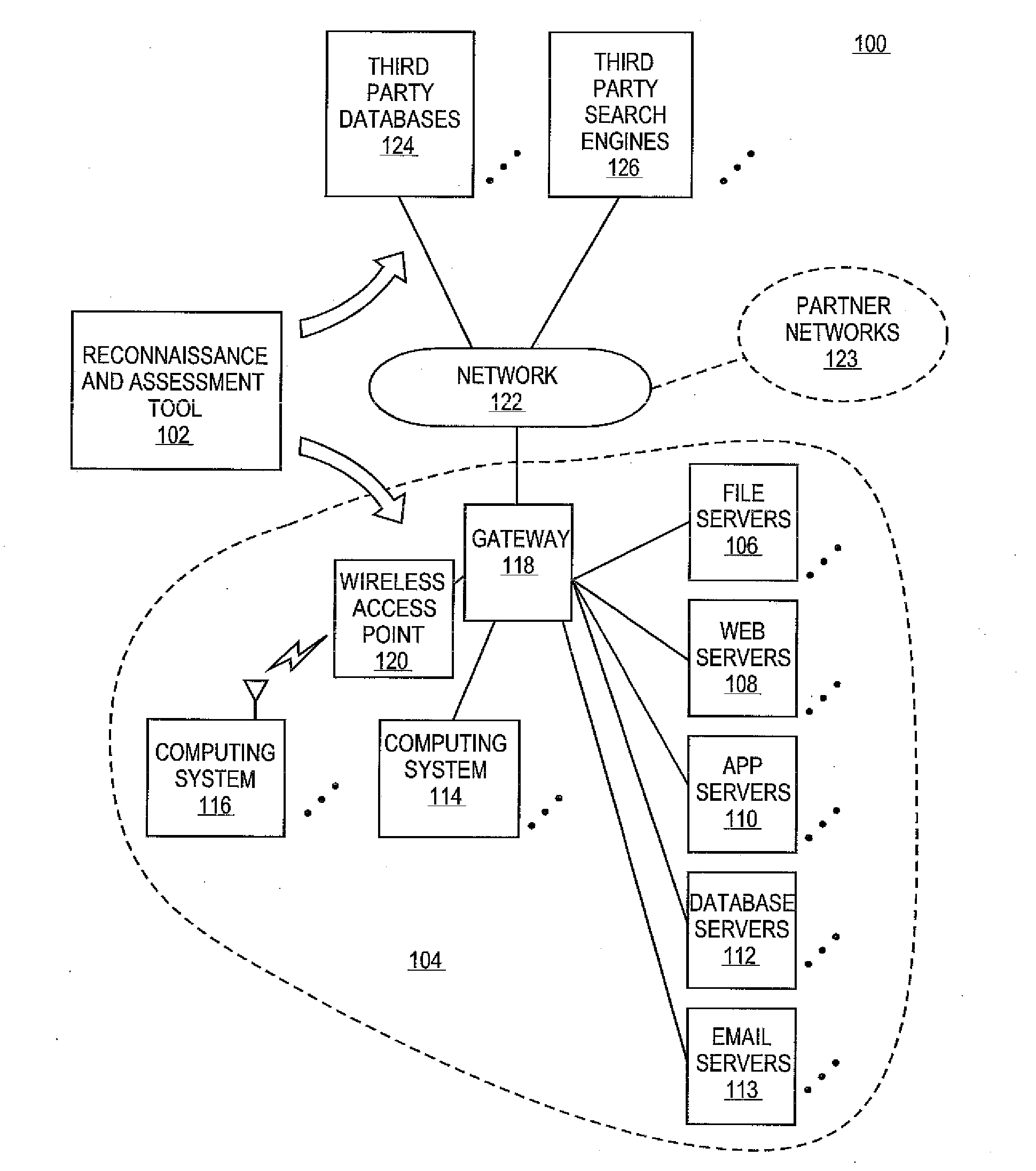
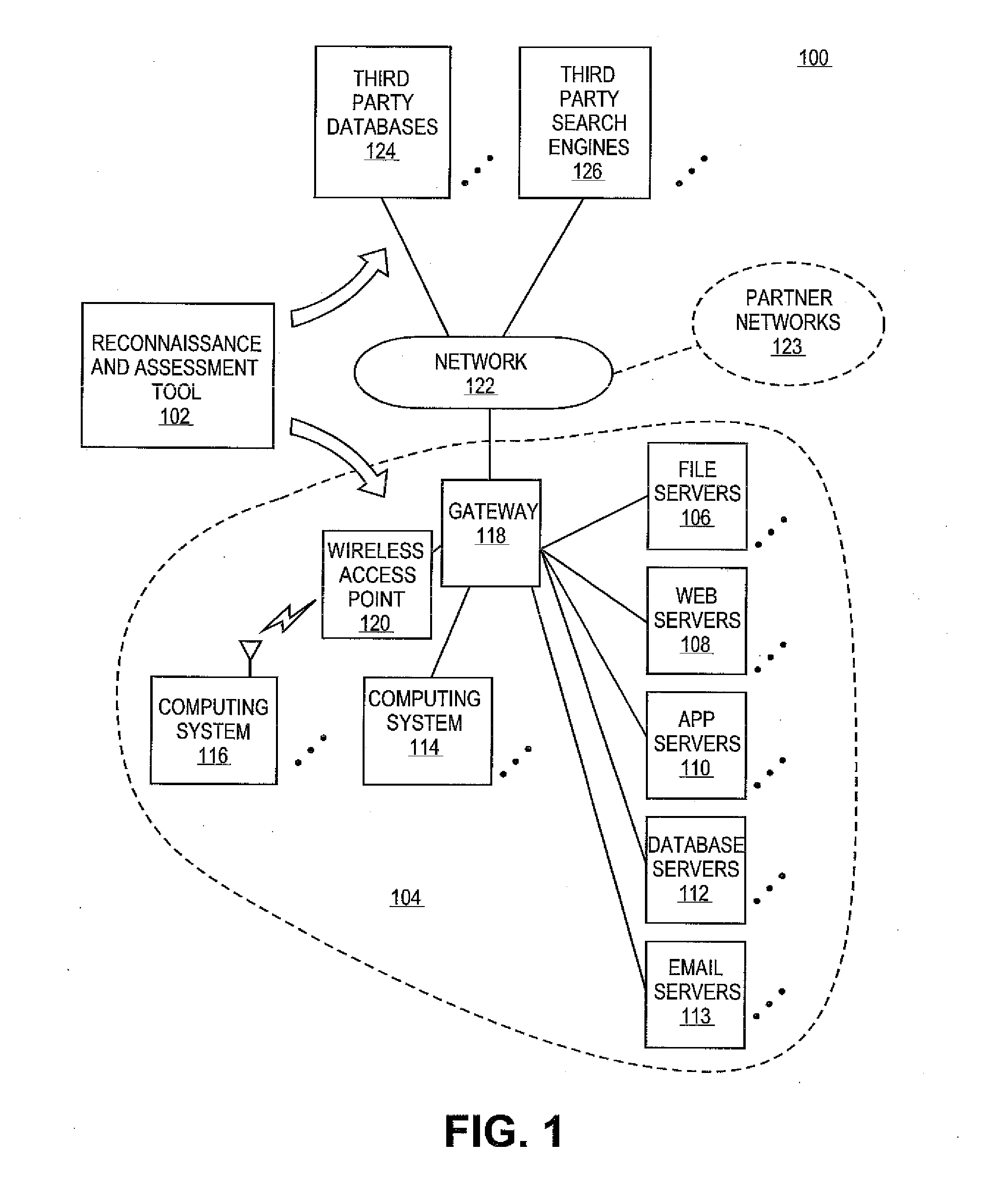
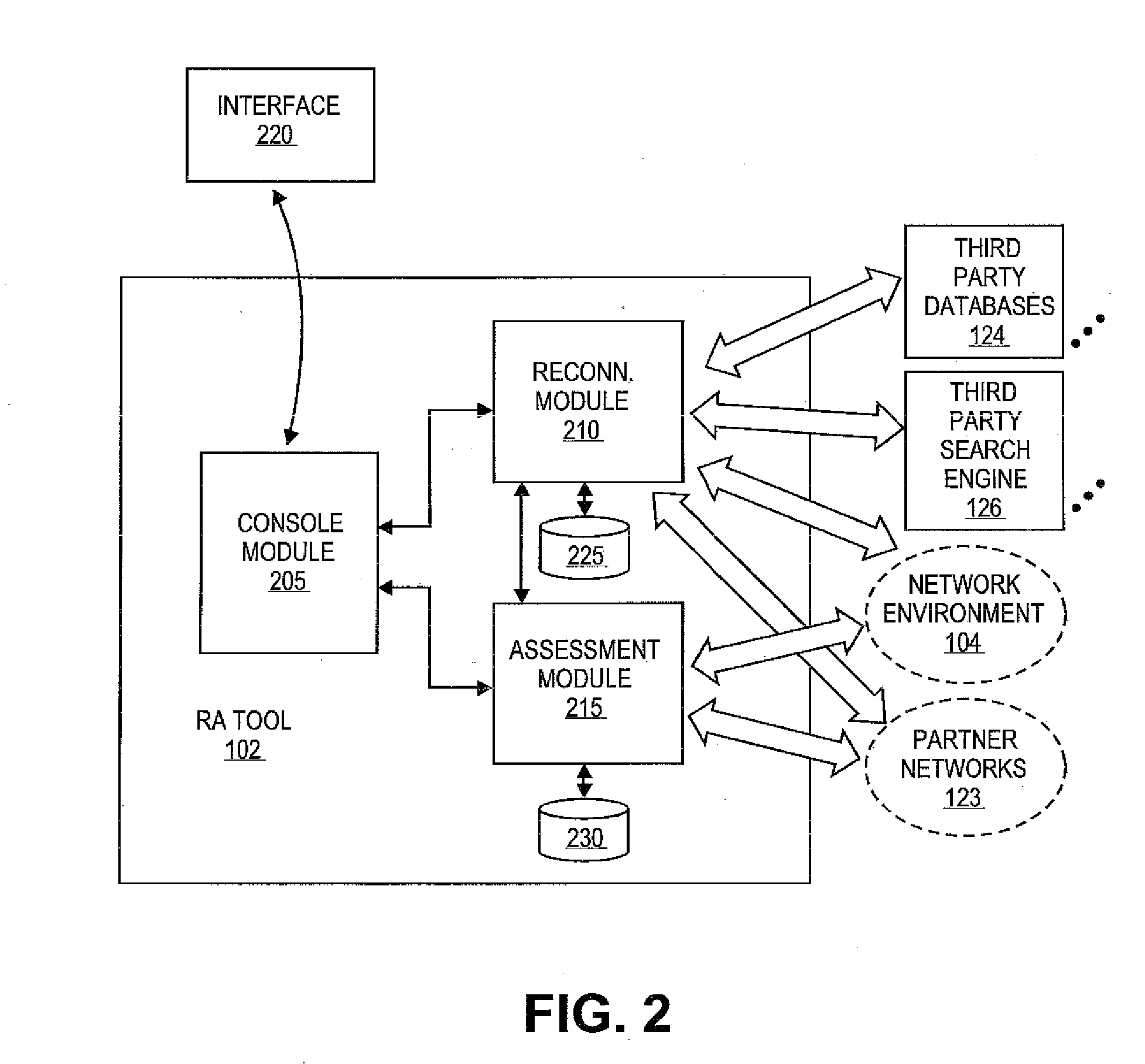
Methods and systems for integrating reconnaissance with security assessments for computing networks
A reconnaissance and assessment (RA) tool can receive base information about the network, such as basic network information and details about an entity and personnel associated with network. The RA tool can utilize the base information to perform reconnaissance procedures on the network to identify the attack surface of the network. The RA tool can perform reconnaissance on the network, itself, and on other external sources, such as third party databases, search engines, and partner networks. Once the attack surface is identified, the RA tool can automatically perform appropriate security assessments on the attack surface. Additionally, if additional information is determined about the network during the security assessments, the RA tool can perform additional reconnaissance and security assessments based on the additional information.
Owner:RAPID7
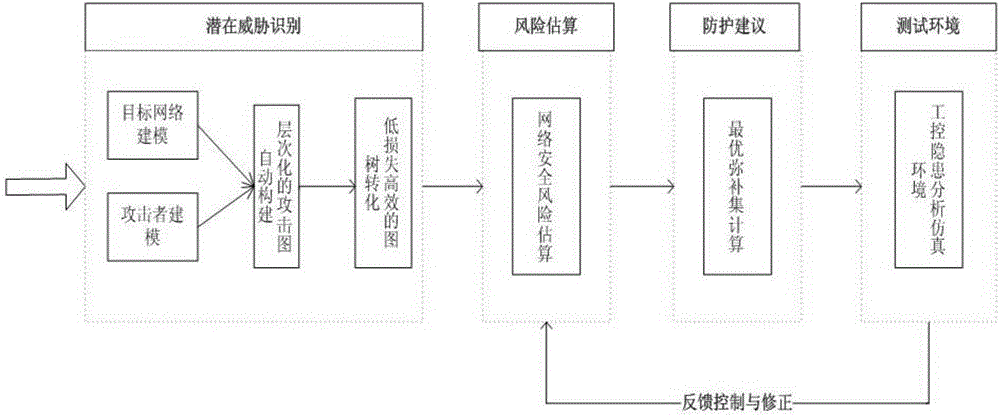
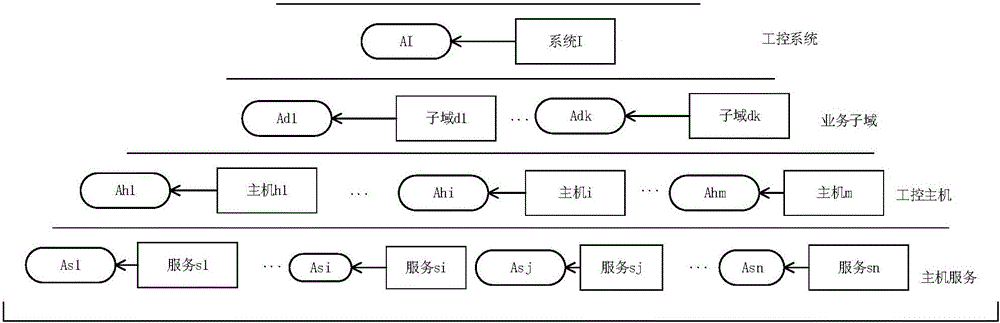
Risk assessment method suitable for industrial control system
ActiveCN106709613ARealize safety hazardDiscovery of potential safety hazardsResourcesSecurity assessmentIndex system
The invention relates to a risk assessment method suitable for an industrial control system. According to the method, modeling is performed on a target network by using a hierarchical modeling method based on the security attribute, and modeling is performed on the capacity of an attacker in the attack process by using an attack mode knowledge base; then a hierarchical attack graph is constructed according to the security model of the target network and the attacker, and the attack graph is converted into an attack tree; and then a hierarchical risk evaluation index system is constructed by using a hierarchical index analysis method, and comprehensive judgment is performed by using a layer-by-layer weighing method so that the risk assessment result of the industrial control system can be obtained. The system or equipment does not need to be offline in the analysis method, and the method is a risk assessment and management tool based on combination of qualitative and quantitative analysis of the model so that the security hidden trouble in the industrial control system can be discovered, and the security assessment level of the industrial control system can be enhanced.
Owner:INST OF INFORMATION ENG CAS
Software running security measurement and estimation method based on network environment
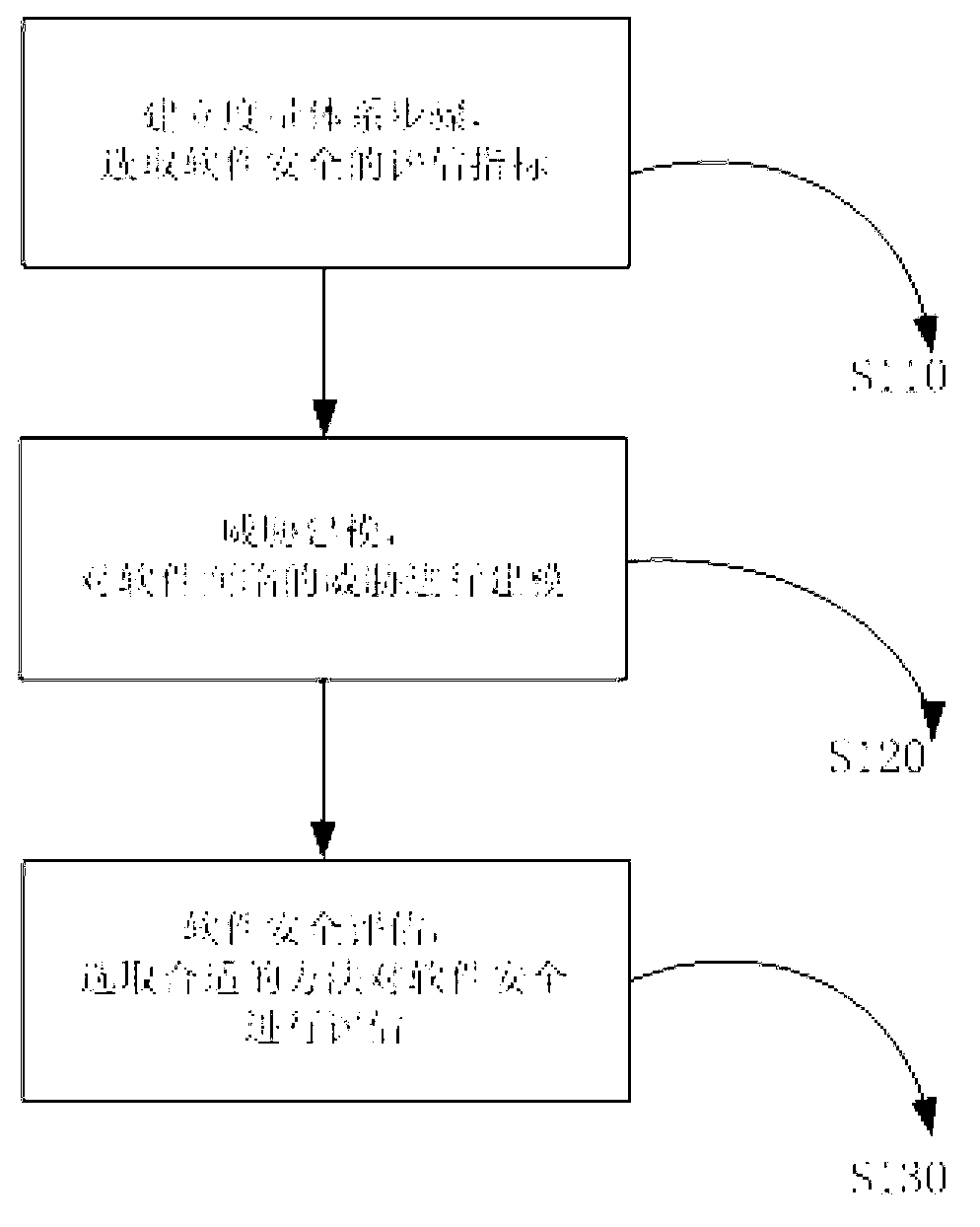
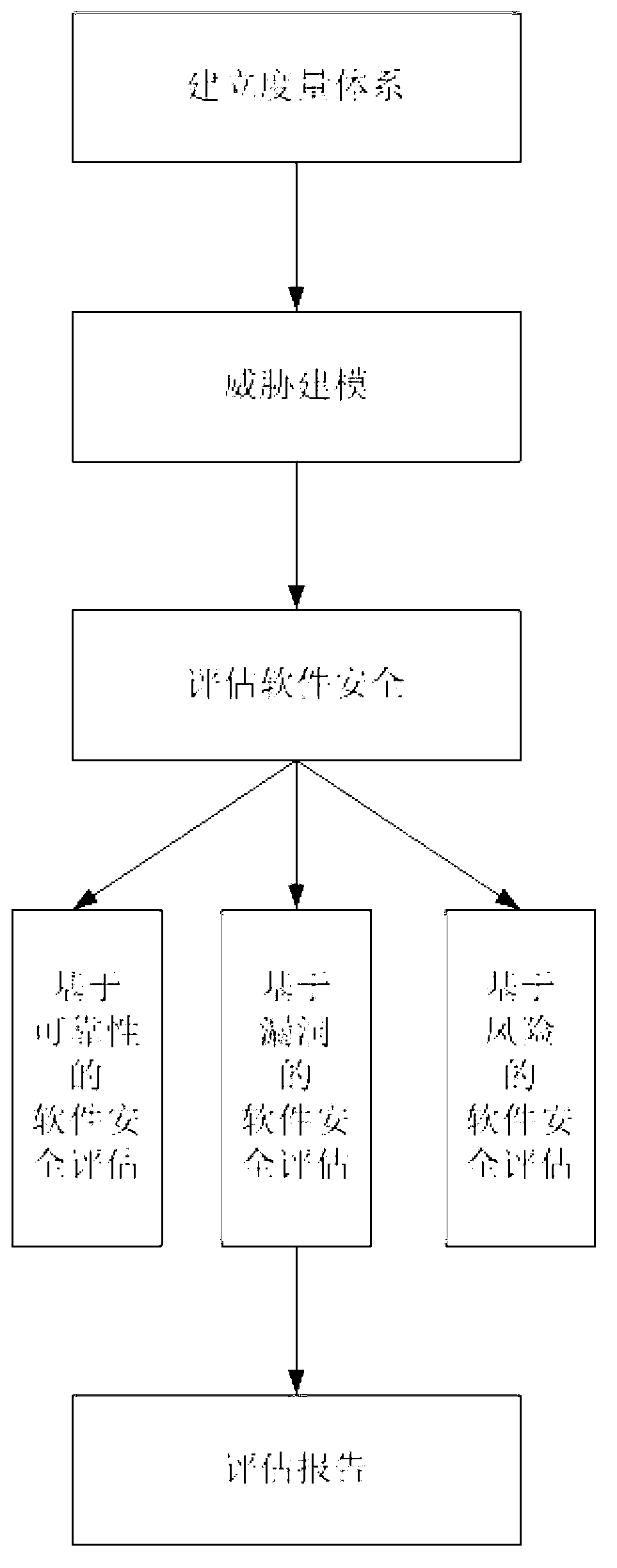
ActiveCN102799822AObjective selectionFull selectionComputer security arrangementsConfidentialityInformation security
The invention discloses a software running security measurement and estimation method based on a network environment, and belongs to a network information security analysis and estimation technology. The method comprises the following steps of: constructing a measurement system, namely selecting a software security estimation index; performing threat modeling, namely modeling a threat of software under the network environment; and estimating the security of the software, namely performing security estimation on the software facing the threat under the network environment according to the estimation index through a software security estimation method based on reliability, a software security estimation method based on bug and a software security estimation method based on risk. The step of constructing the measurement system also comprises a substep of selecting the completeness, the non-repudiation, the confidentiality, the authorization, the availability and the identity checkability as the software security estimation indexes. By the method, the security bug and the risk of the software can be estimated in advance, so that a function and security module of the software can be immediately adjusted, and dangerous events can be effectively controlled and prevented.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
Environment risk source pre-warning system
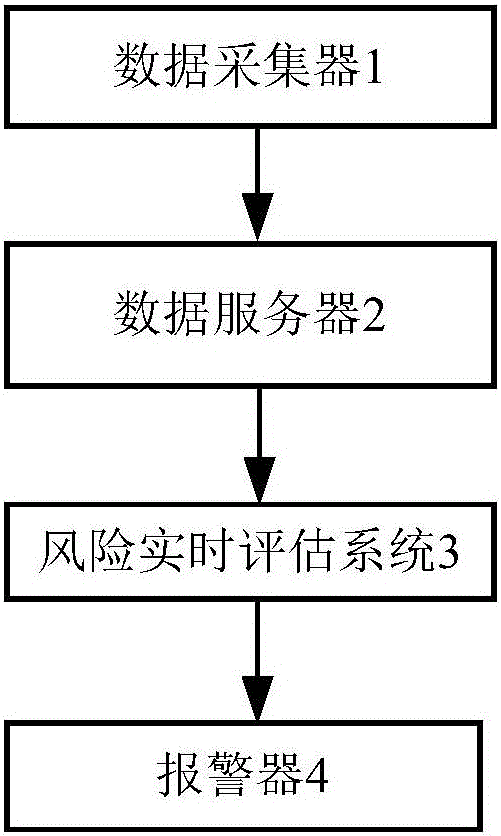
InactiveCN106204392ARealization riskReduce lossesData processing applicationsSpecial data processing applicationsCountermeasureData acquisition
The invention discloses an environment risk source pre-warning system, comprising a data collector, a data server, a risk real-time evaluation system and a warner. The data collector is used for collecting real-time monitoring data of detection points in an environment risk source. An environment risk source information database for recording environment risk source basic information and a threshold value database for recording the threshold values corresponding to the real-time monitoring data of the detection points are installed in the data server. The risk real-time evaluation system is used for carrying out security evaluation on the environment risk source and calculating the risk degree of the environment risk source. The warner is used for carrying out selective warning according to the risk degree of the environment risk source. According to the system, the risk evaluation and pre-warning can be carried out on the environment risk source, a monitor can be helped to take countermeasures effectively and timely, and losses resulting from a risk event can be reduced to the lowest.
Owner:林杨
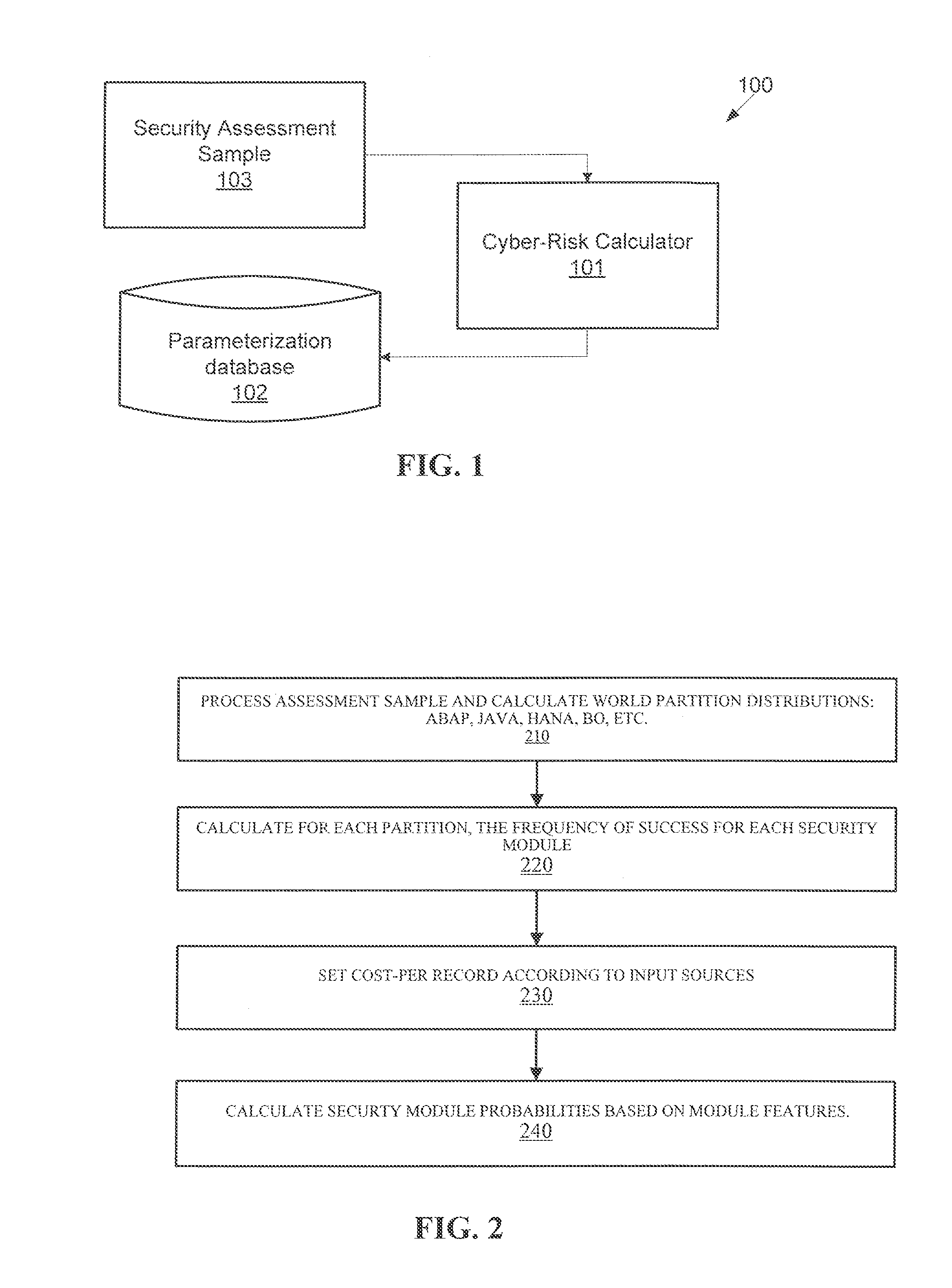
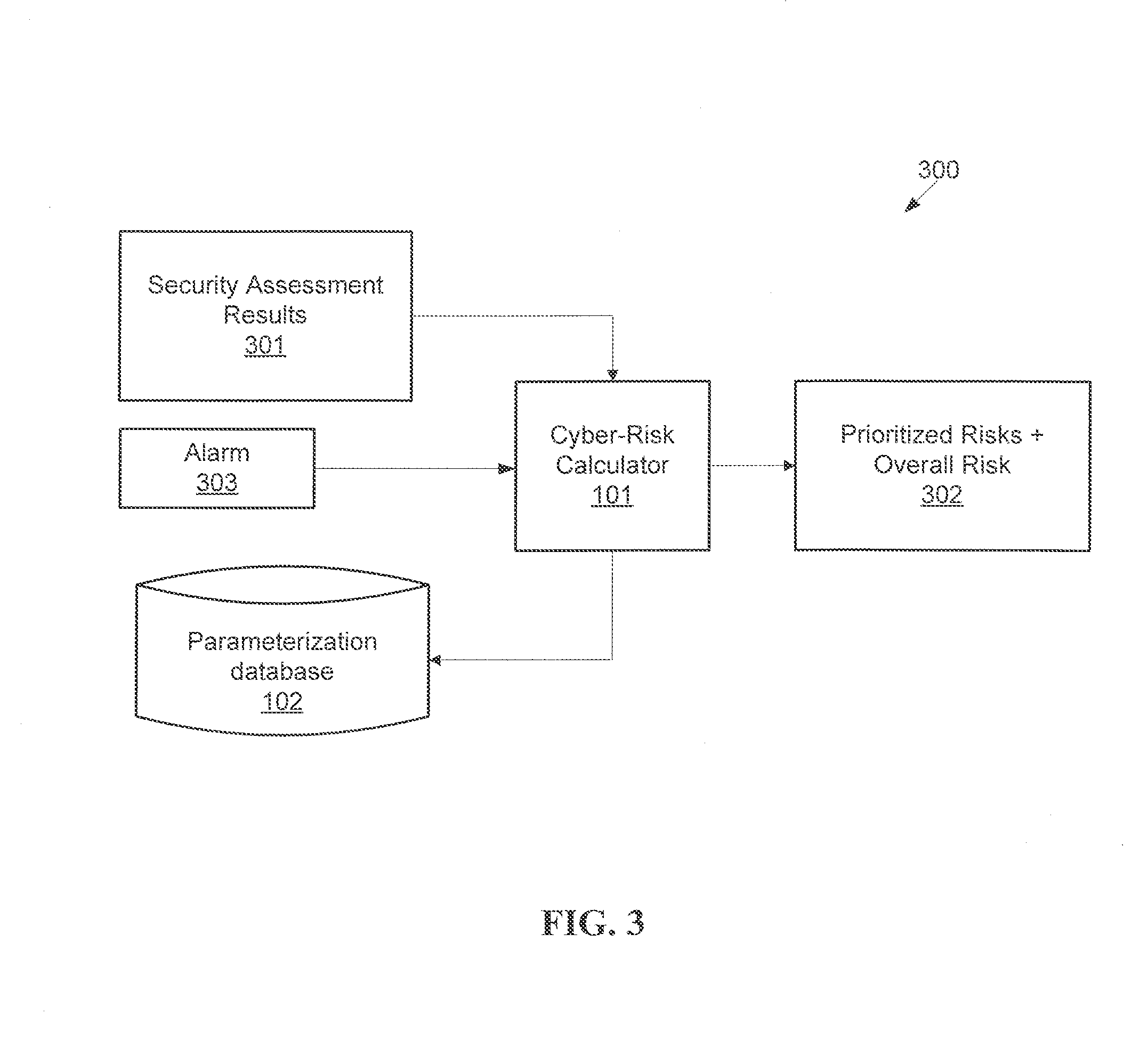
System and method for automatic calculation of cyber-risk in business-critical applications
ActiveUS20160119373A1Automatically calculateWeb data indexingMemory loss protectionRisk exposureComputer science
A system for calculating cyber-risk in a software application includes a cyber-risk calculator. The cyber-risk calculator receives a security assessment result sample having a list of security modules, each security module listing including a respective result of a security assessment of the application identifying a vulnerability and / or misconfiguration capable of being exploited and / or abused. When run in a risk calculation mode, the cyber-risk calculator determines a world partition of the application in the security assessment result sample belongs to, references a set of parameters from a parametrization database according to the world partition corresponding to the application, determines a cyber-risk exposure level for the application based upon the security assessment result sample and the set of parameters, and reports results of the cyber-risk calculation.
Owner:ONAPSIS
Automated security assessment of business-critical systems and applications
ActiveUS20130174263A1Reduce the risk of fraudReduce audit costsMemory loss protectionWeb data indexingApplication softwareApplication security
Systems and methods which provide a new application security assessment framework that allows auditing and testing systems to automatically perform security and compliance audits, detect technical security vulnerabilities, and illustrate the associated security risks affecting business-critical applications.
Owner:ONAPSIS
Method and apparatus for security assessment of a computing platform
InactiveUS8650651B2Memory loss protectionError detection/correctionCommunication interfaceSecurity testing
Owner:INT BUSINESS MASCH CORP
Assessment and analysis of software security flaws
ActiveUS8499353B2Facilitates security assessment and vulnerability testingFacilitates benchmarkingMemory loss protectionUnauthorized memory use protectionApplication specificApplication software
Security assessment and vulnerability testing of software applications is performed based at least in part on application metadata in order to determine an appropriate assurance level and associated test plan that includes multiple types of analysis. Steps from each test are combined into a “custom” or “application-specific” workflow, and the results of each test may then be correlated with other results to identify potential vulnerabilities and / or faults.
Owner:VERACODE
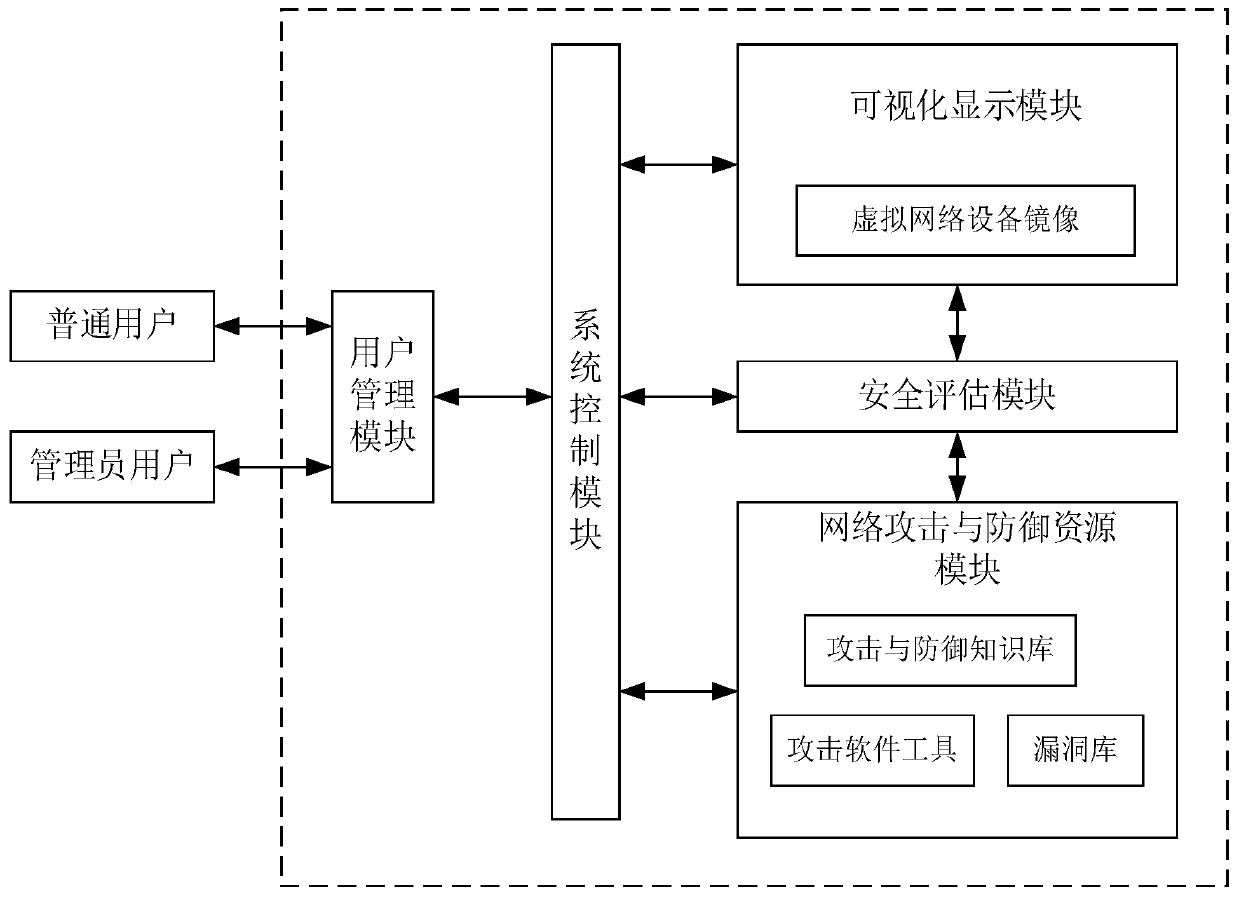
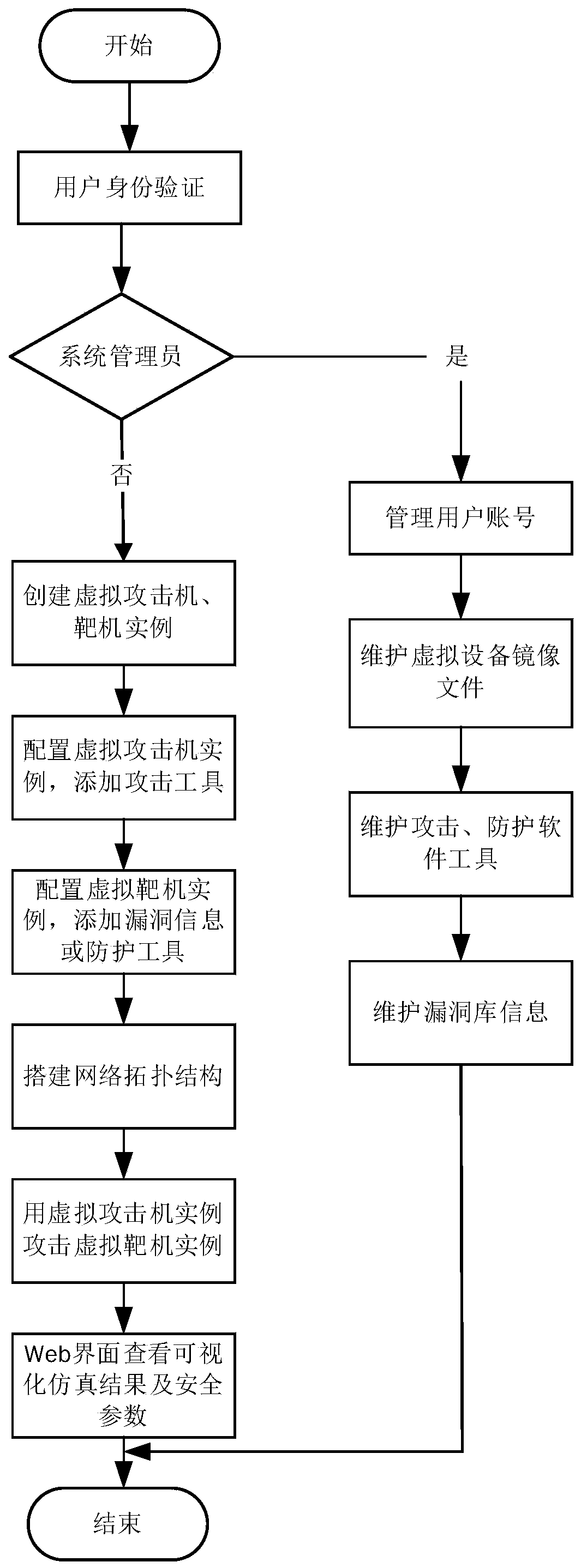
Network attack and defense virtual simulation and security evaluation method and system based on virtualization technology
InactiveCN110098951ARealize simulationRealize remote sharingData switching networksVirtual targetVirtualization
The invention discloses a network attack and defense virtual simulation and security evaluation method and system based on a virtualization technology. The method comprises: (1) a visual display module sending a received instruction for creating a network topological graph to a system control module, creating virtual network equipment, and a network attack and defense resource library module configuring the virtual equipment according to a performed experiment category; 2) the system control module creating a network topological structure according to the instruction of creating the network topological graph; 3) after the network attack starts, the visual display module capturing the position of the data packet sent by the virtual attacker, and dynamically displaying the position of the current attack; the system control module capturing a communication network data packet between the virtual attack machine and the virtual target machine; and 4) a security evaluation module being usedfor acquiring real-time security parameters of the virtual target drone during network attack and defense simulation, displaying the real-time security parameters in real time through a visual displaymodule, and evaluating the security of the virtual target drone.
Owner:XIDIAN UNIV +1
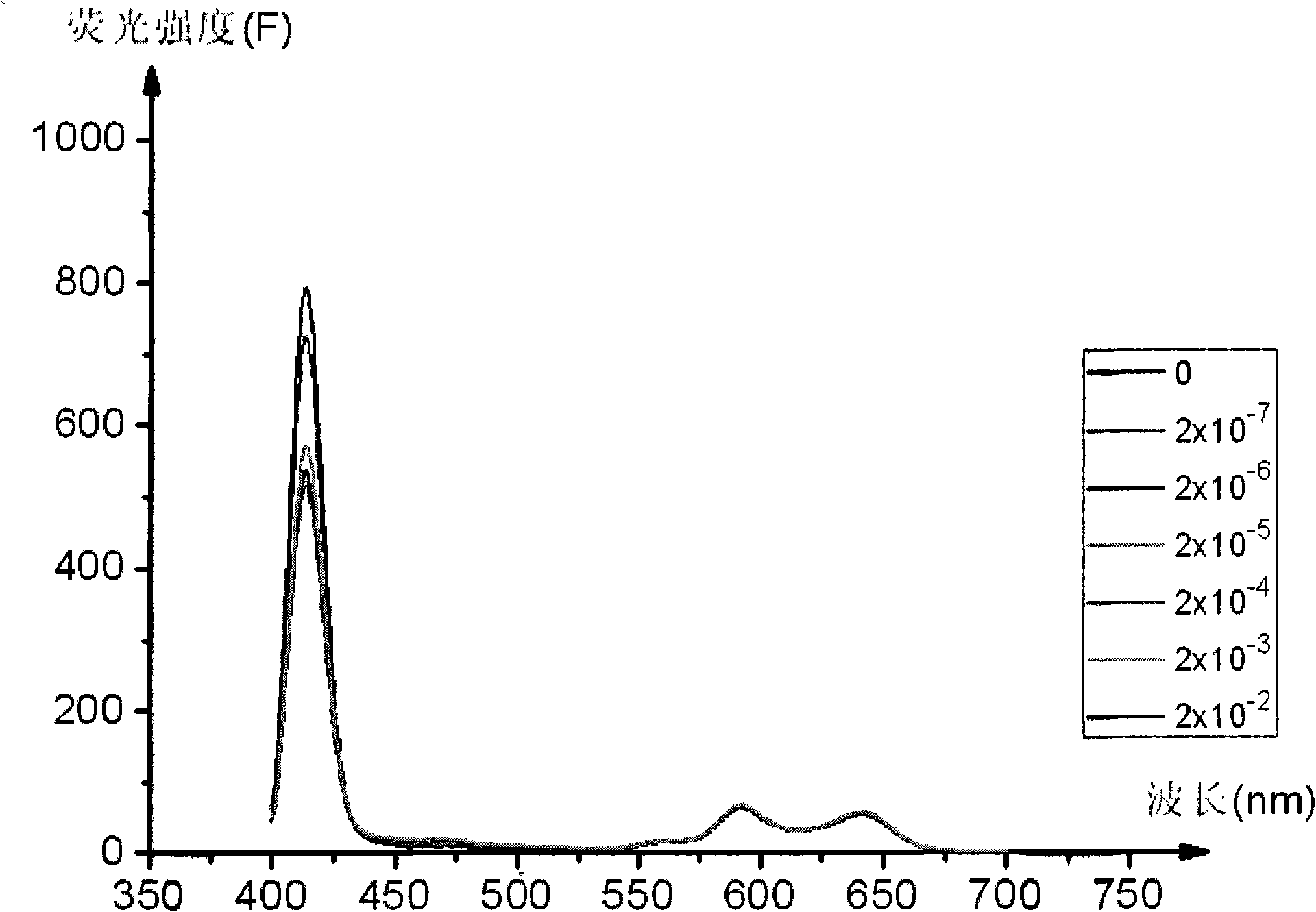
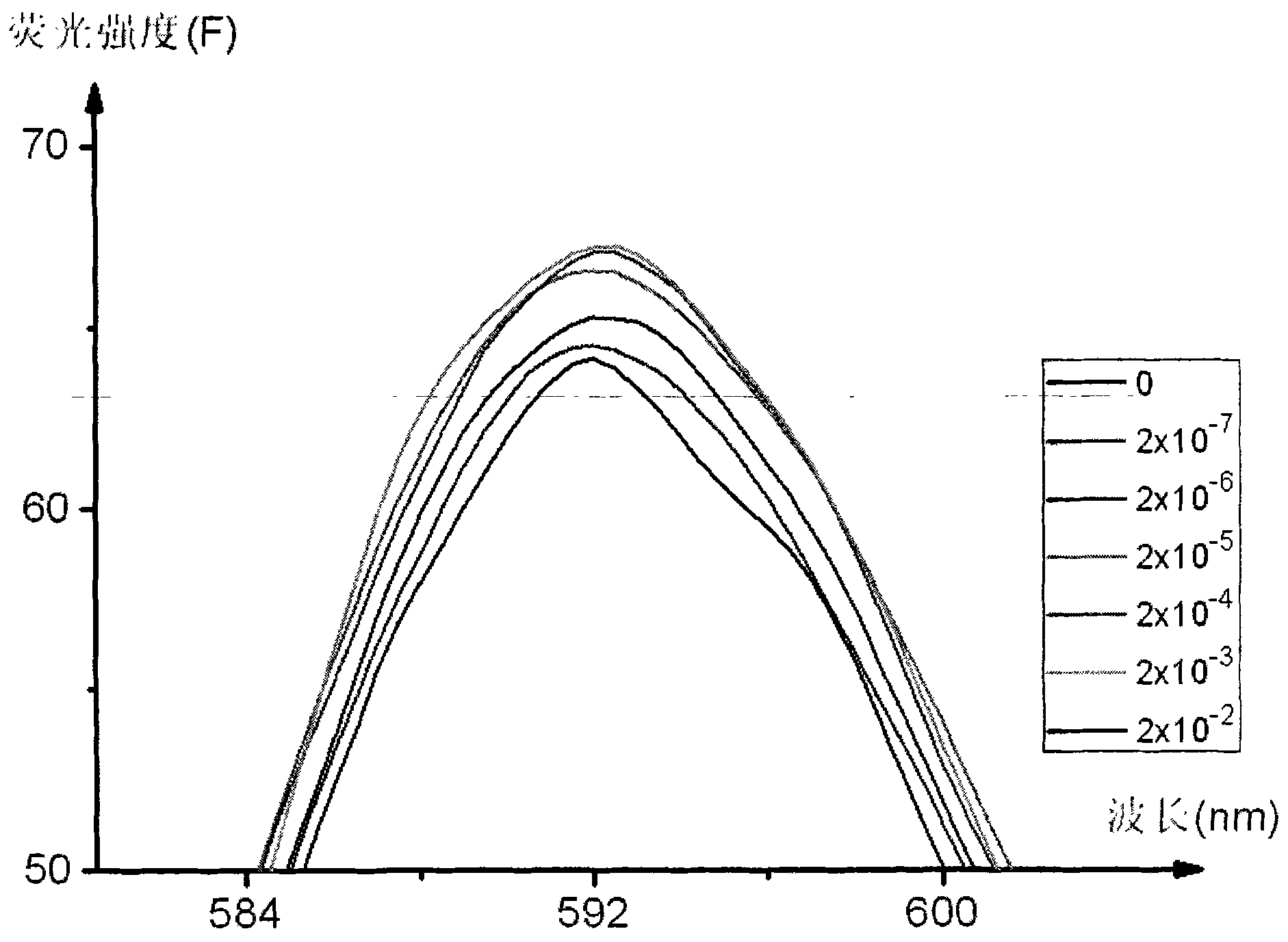
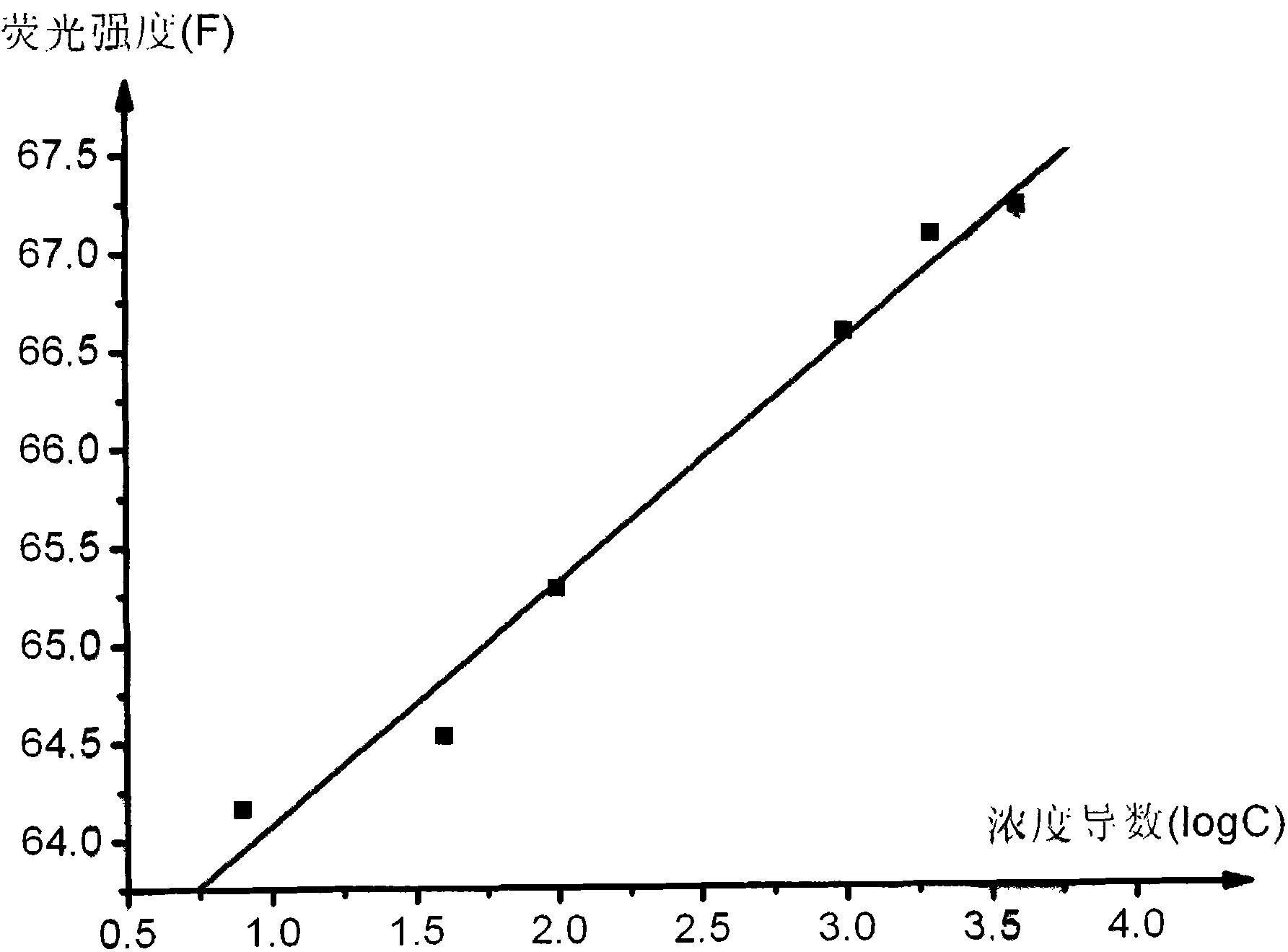
Method for fast detecting pesticide residue
ActiveCN101776601AEasy to operateEasy to detectPreparing sample for investigationFluorescence/phosphorescencePesticide residueLiquid state
The invention provides a method for fast detecting pesticide residue, which relates to a fluoroscopic detection method of organic phosphor pesticide. The invention utilizes a fluorescence spectrophotometer with program, uses porphyrin compounds as fluorescence indicating agents and developers, and detects the organic phosphor pesticide in the liquid state porphyrin detection solution through preparing a porphyrin solution, an organic phosphor pesticide solution and a liquid state detection solution. The invention has the characteristics of high detection sensitivity, low detection limitation, high accuracy, simple and convenient operation, convenient and fast in-site detection, high economical efficiency, convenient popularization and application and the like. The invention can be widely used for the trace amount detection of foodgrain, food and the like which easily contain the organic phosphor pesticide residue, and can also be used in the security assessment of food such as vegetables, fruit and the like and the environment detection.
Owner:LUZHOU LAOJIAO GRP CO LTD +1
Quarantine of software based on analysis of updated device data
ActiveUS20200285752A1Platform integrity maintainanceSoftware deploymentSoftware engineeringData profiling
A method includes: after installation of software on a first mobile device, receiving new data from a second mobile device; analyzing, using a data repository, the new data to provide a security assessment; determining, based on the security assessment, a new security threat associated with the software; and in response to determining the new security threat, causing the first mobile device to implement a quarantine of the software.
Owner:LOOKOUT MOBILE SECURITY
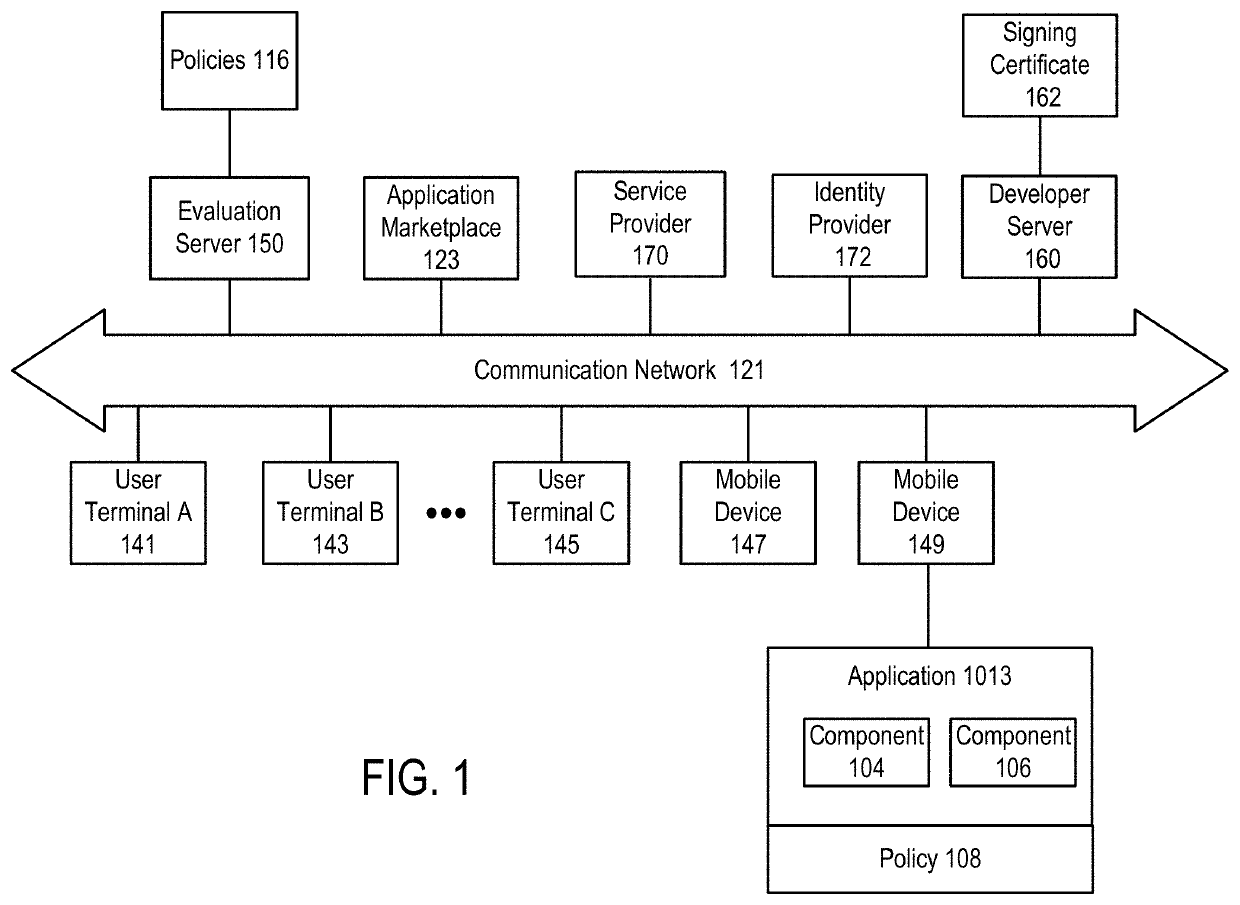
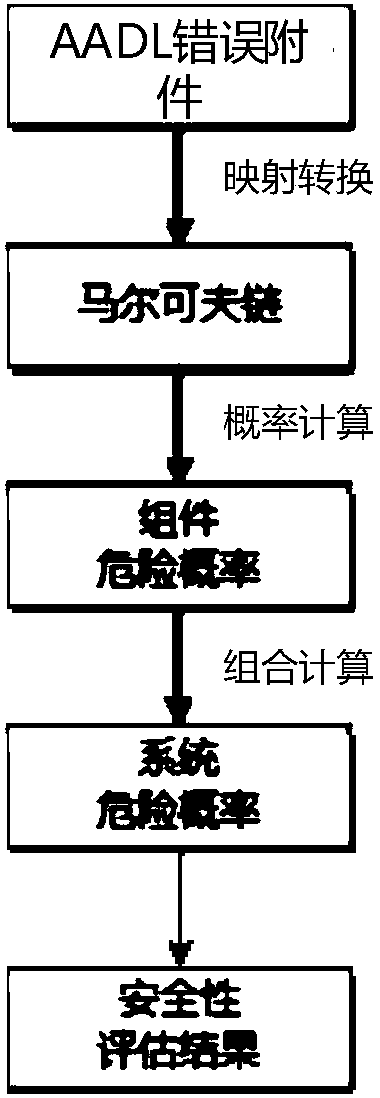
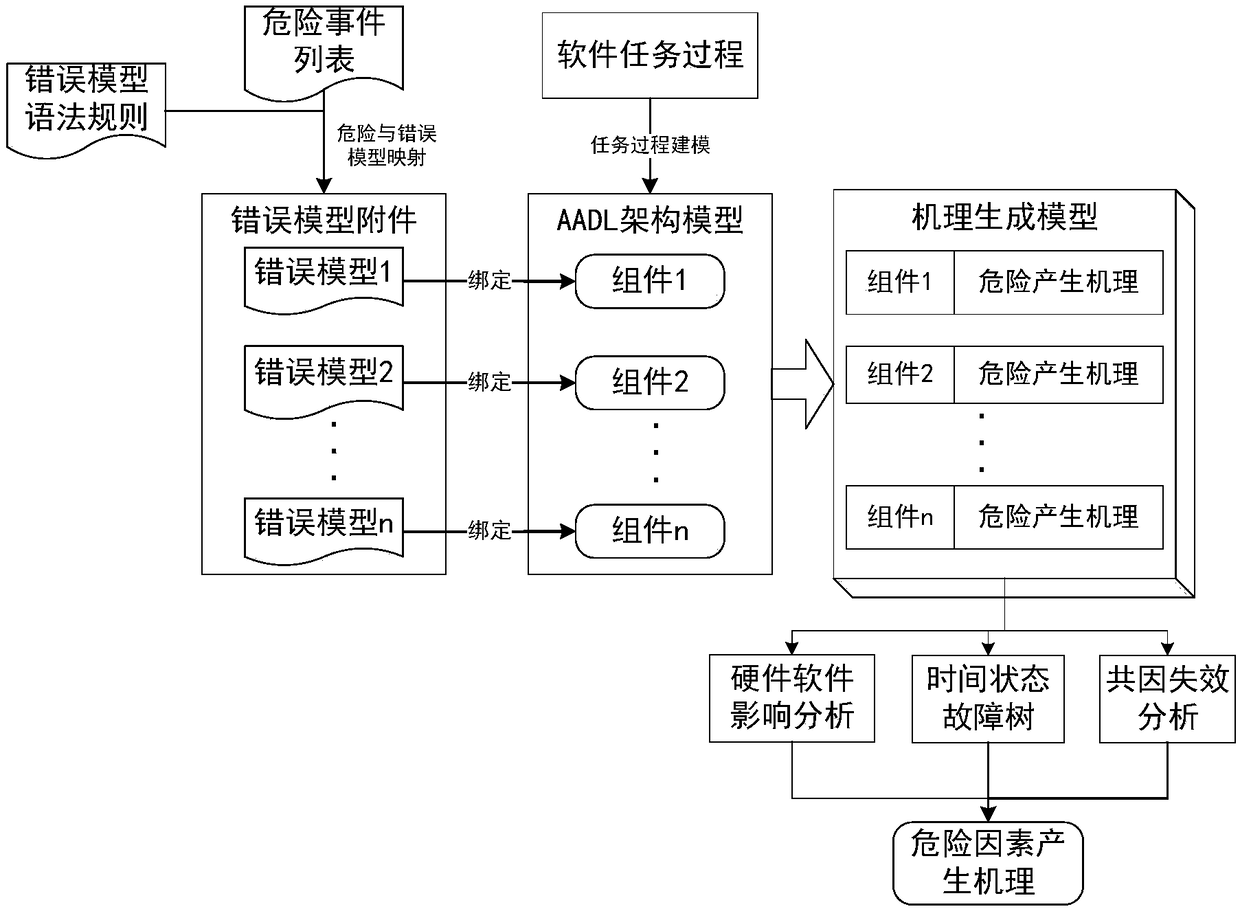
AADL (architecture analysis and design language) model extension based software system security verification and assessment method
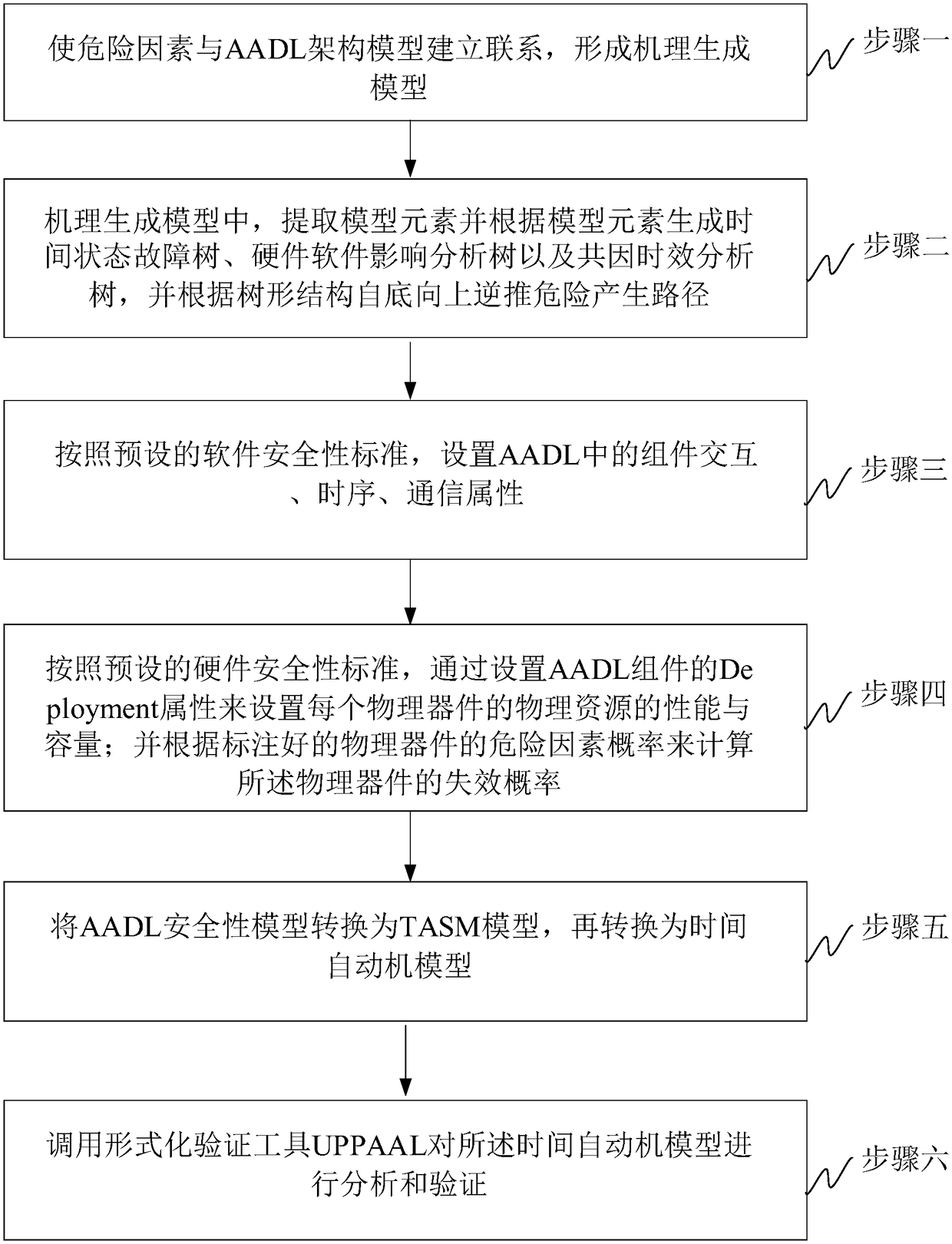
ActiveCN108376221AImplement security assessmentImprove assessment accuracyPlatform integrity maintainanceSoftware systemAutomaton
The invention relates to an AADL (architecture analysis and design language) model extension based software system security verification and assessment method, which is provided in order to overcome defect of difficulty in direct processing of system models, high computation cost and high redundancy in computation in existing AADL model based verification and assessment. The method includes: establishing relationship between risk factors and an AADL architecture model to form a mechanism generating model; extracting model elements, generating a time state fault tree, a hardware software impactanalysis tree and a common cause time-dependent analysis tree according to the model elements, and backstepping a risk generation route according to the tree structure from bottom to top; setting physical resource properties and capacity of each physical device; calculating the failure probability of each physical device according to labeled risk factor probability of each physical device; converting an AADL security model into a timed automata; calling a formal verification tool UPPAAL for analysis and verification of the timed automata. The method is applicable to security assessment of software and hardware systems.
Owner:HARBIN INST OF TECH
Risk assessment algorithm for information system
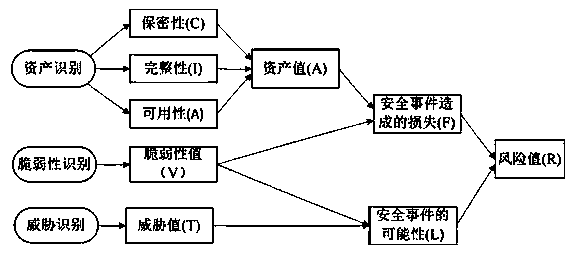
InactiveCN103400027AEliminate the effects ofReduce the impactSpecial data processing applicationsAlgorithmFactor selection
The invention discloses a risk assessment algorithm for an information system. According to the GB / T20984-2007 standard, a correlation between the assessment factors of assets, the assessment factors of vulnerability and the assessment factors of threats of the information system is established, a safety assessment indicator system is achieved, and 24 pairs of risk relations are achieved. The 24 pairs of achieved risk relations are substituted into a formula (1), an asset comprehensive value A is obtained through calculation. According to asset comprehensive value A and a vulnerability value V, the comprehensive value F of the loss caused by security events is worked out. According to the vulnerability value V and a threat value T, a security event possibility comprehensive value L is worked out. The comprehensive value F of the loss caused by the security events and the security event possibility comprehensive value L are substituted into a formula (2), and then a risk comprehensive value R is worked out and obtained. The risk assessment algorithm for the information system can eliminate the influence caused by the facts that assessment factor selection is unreasonable and risk correlation analysis cannot objectively reflect the system state, and improve the objectivity and the accuracy of risk assessment.
Owner:GUIZHOU UNIV
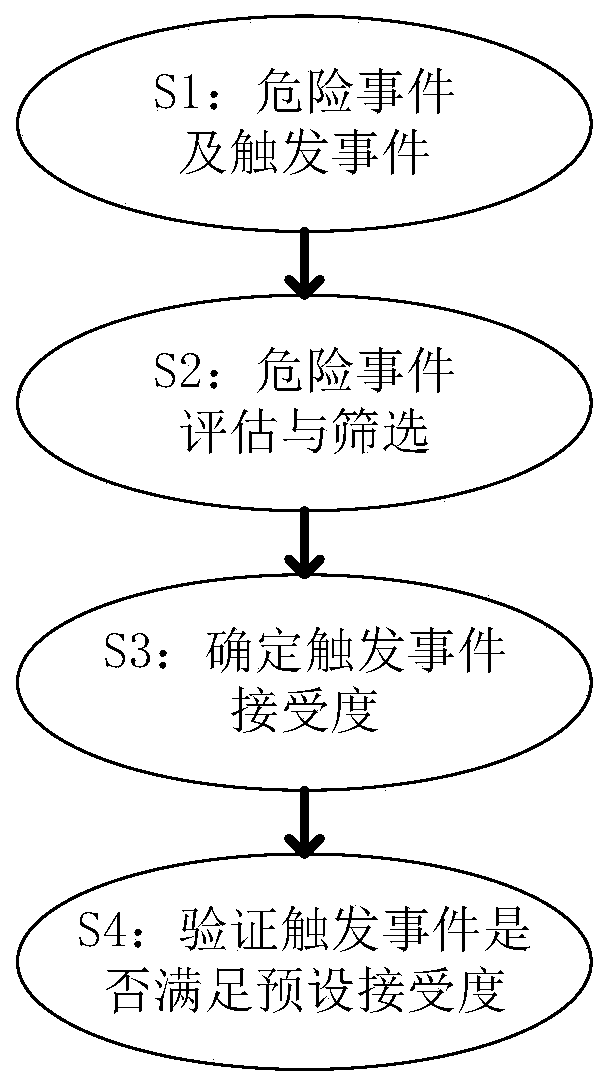
A verification method and system for safety of expected functions of an autonomous vehicle
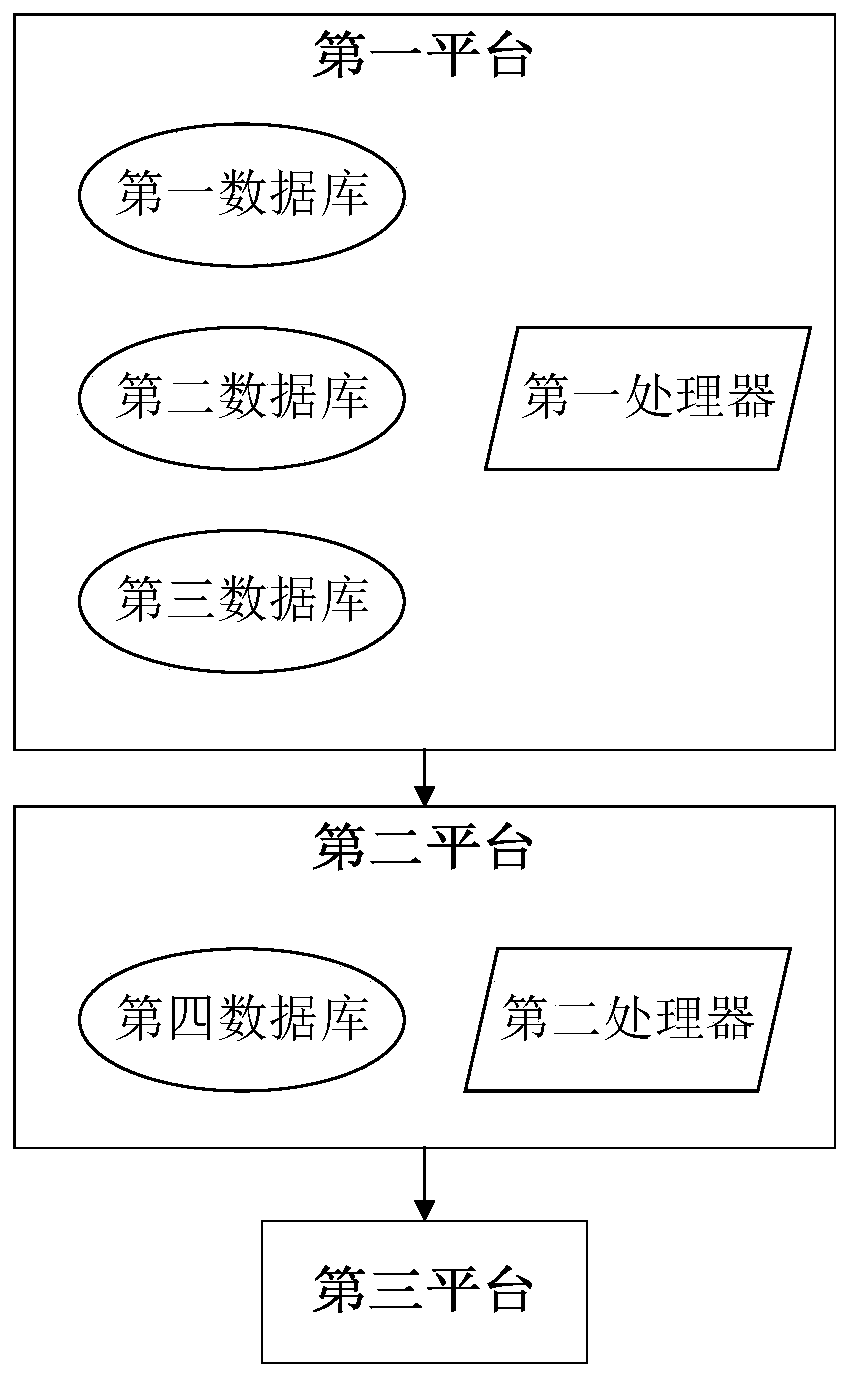
PendingCN109885870AEasy to operateEasy to implementSpecial data processing applicationsObject basedValidation methods
The invention relates to a verification method and system for safety of expected functions of an autonomous vehicle, and the method comprises the steps of determining a dangerous event and a trigger event based on a system framework of a target vehicle; assessing and screening dangerous events; determining the acceptance degree of the trigger event; and verifying whether the trigger event satisfies the preset acceptance degree. The system comprises a first platform which is used for identifying a dangerous event of the autonomous vehicle and exporting a corresponding trigger event and a trigger event probability, and a second platform which is used for exporting a dangerous event of the autonomous vehicle, determining the ASIL level of the dangerous event and determining a corresponding trigger event tolerance or error rate target according to the ASIL level and the corresponding trigger event probability; a third platform which is used for reproducing the trigger event, testing the autonomous vehicle and verifying whether the trigger event reaches a set target or not. According to the present invention, the requirement for expected function safety assessment in the function development of the autonomous vehicle is met; the quantitative and verifiable evaluation requirements are provided, and the operability is high.
Owner:TONGJI UNIV
Evaluation system and evaluation method for deformation monitoring safety
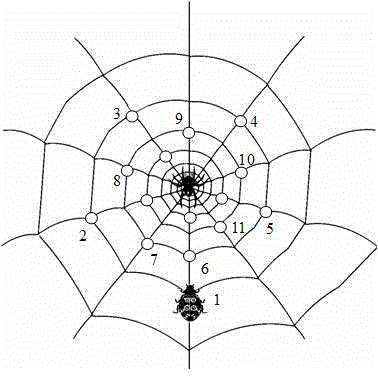
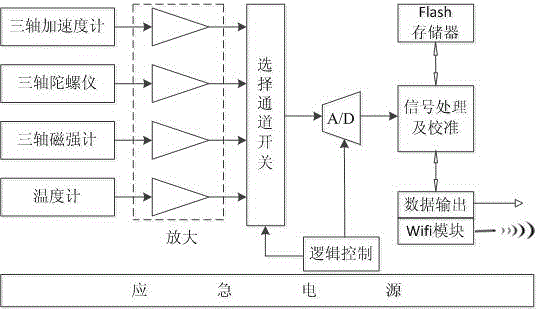
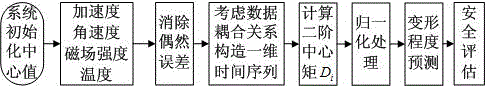
The invention discloses an evaluation system and an evaluation method for deformation monitoring safety based on MIMUs. The MIMUs which are used as monitoring pitch points are structured by MEME accelerometers, gyroscopes, magnetometers and thermometers and are arranged on a bionic spider network which is structured by electric optical fiber cables, the electric optical fiber cables are used for supplying electric power and transferring a data, a WIFI module is used for transferring the data in an emergency, and an integrated data processing device is used for processing the data and evaluating the safety. When the effect of a temperature is considered, the deformation can cause a data change, and through the variation degree of the data, the deformation degree is evaluated. Besides, through calculating a second-order central moment of a monitoring data, normalized deformation degree evaluation is performed, and the safety level is evaluated in a real-time manner. The deformation monitoring safety evaluation system is easy to realize, high in reliability and more accurate.
Owner:HENAN POLYTECHNIC UNIV
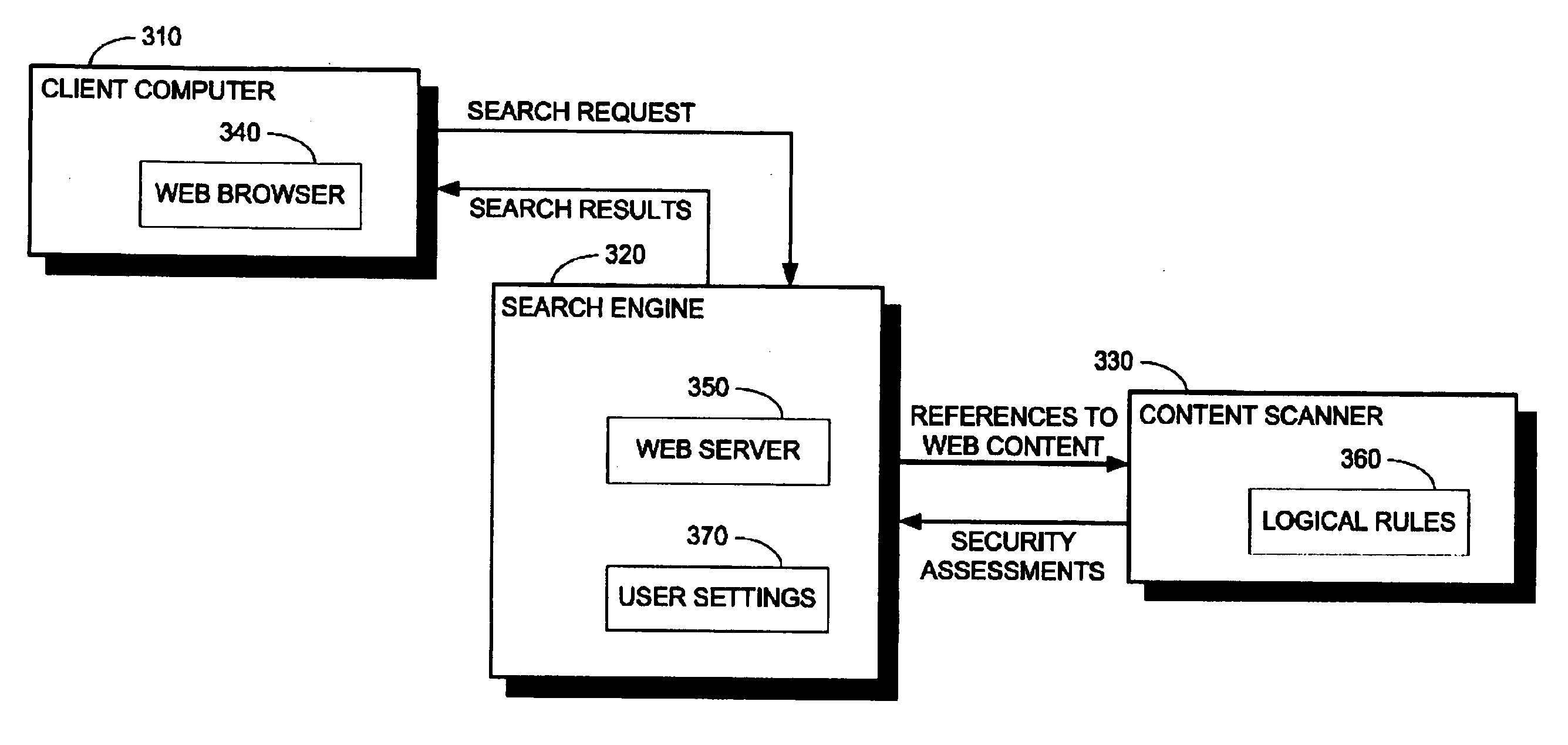
System and method for appending security information to search engine results
A system for appending security information to search engine results, including a search engine for locating, in a computer network, web pages that include at least one designated search term, for issuing a security analysis request to a content security scanner to assess at least one designated web page for potential security risks, and for preparing a search results summary that includes links to the located web pages and security assessments for the located web pages, a client computer communicatively coupled with the search engine for issuing a search request with at least one user designated search term, to the search engine, and for receiving the search results summary from the search engine, and a content security scanner communicatively coupled with the search engine for assessing security of content in at least one designated web page. A method and computer-readable storage media are also described and claimed.
Owner:FINJAN LLC
Method for simplifying rail transit train operation control system
ActiveCN103612650AChange the way the implementationChange the way of beingRailway traffic control systemsControl systemWorkload
The invention discloses a method for simplifying a rail transit train operation control system, and belongs to the technical field of rail transit control. The method particularly includes 1), improving a process for designing a universal safety computer platform; 2), simplifying vehicular application or ground application of the rail transit train operation control system. The method has the advantages that the designed universal safety computer platform is implemented on the basis of hardware / software difference design principles and hierarchical diagnosis principles, and functions for simultaneously implementing a plurality of application control logics are supported in the aspect of software on the basis of double-determinacy principles; a plurality of traditional rail transit operation control logic processing functions can be simultaneously supported by a logic processing layer of the universal safety computer platform designed by the process, so that the quantity of equipment of the traditional rail transit train operation control system can be reduced, and the reliability of the operation control system can be improved; the universal safety computer platform designed by the process can be migrated to rail transit train operation control systems with different requirements, so that development and safety assessment workload can be reduced, and the development and safety assessment cost can be lowered.
Owner:BEIJING JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com