Patents
Literature
1066 results about "Minutiae" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Minutiae are, in everyday English, minor or incidental details. In biometrics and forensic science, minutiae are major features of a fingerprint, using which comparisons of one print with another can be made. Minutiae include: Ridge ending – the abrupt end of a ridge Ridge bifurcation – a single ridge that divides into two ridges Short ridge, or independent ridge – a ridge that commences, travels a short distance and then ends Island – a single small ridge inside a short ridge or ridge ending that is not connected to all other ridges Ridge enclosure – a single ridge that bifurcates and reunites shortly afterward to continue as a single ridge Spur – a bifurcation with a short ridge branching off a longer ridge Crossover or bridge – a short ridge that runs between two parallel ridges Delta – a Y-shaped ridge meeting Core – a U-turn in the ridge pattern
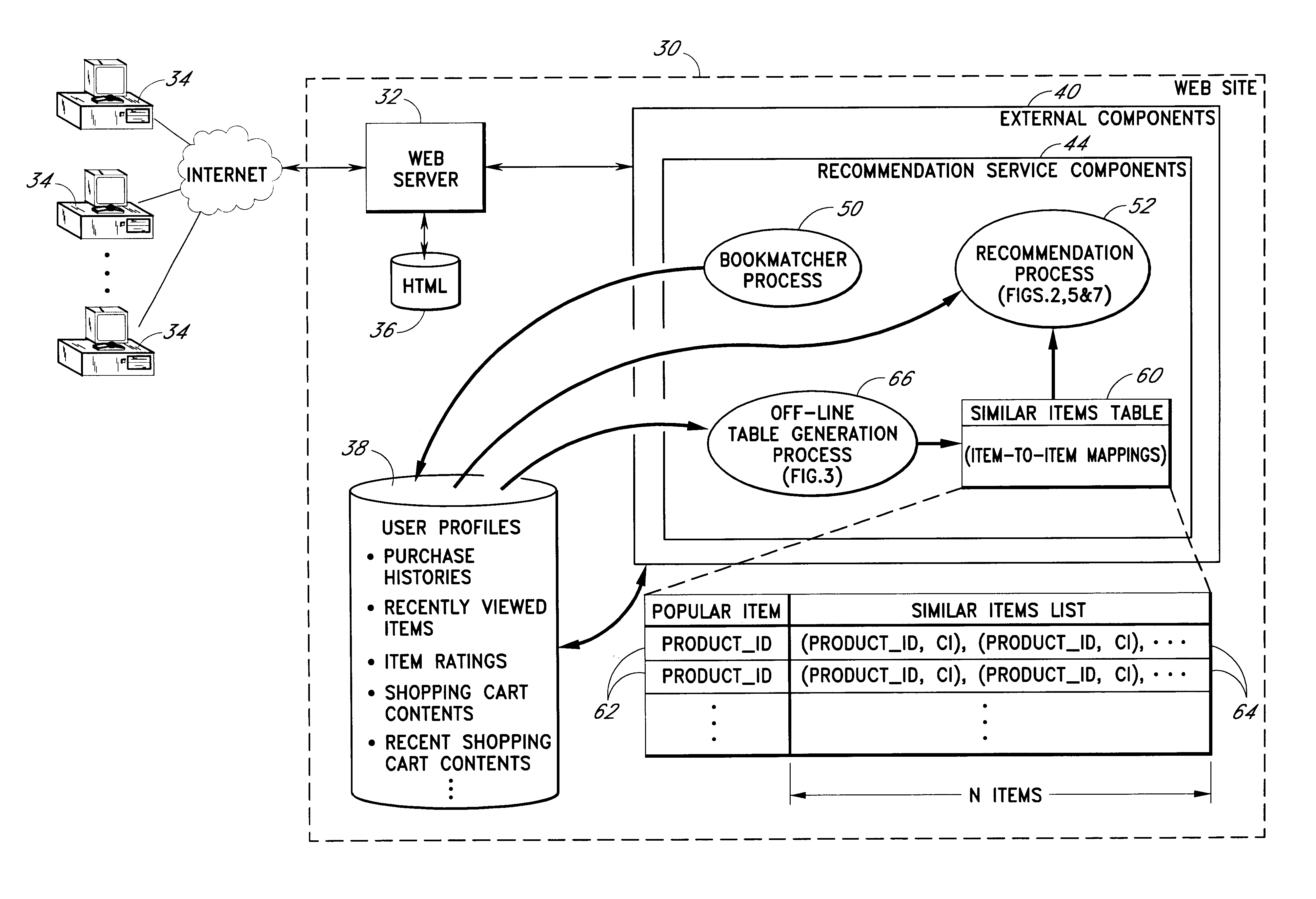
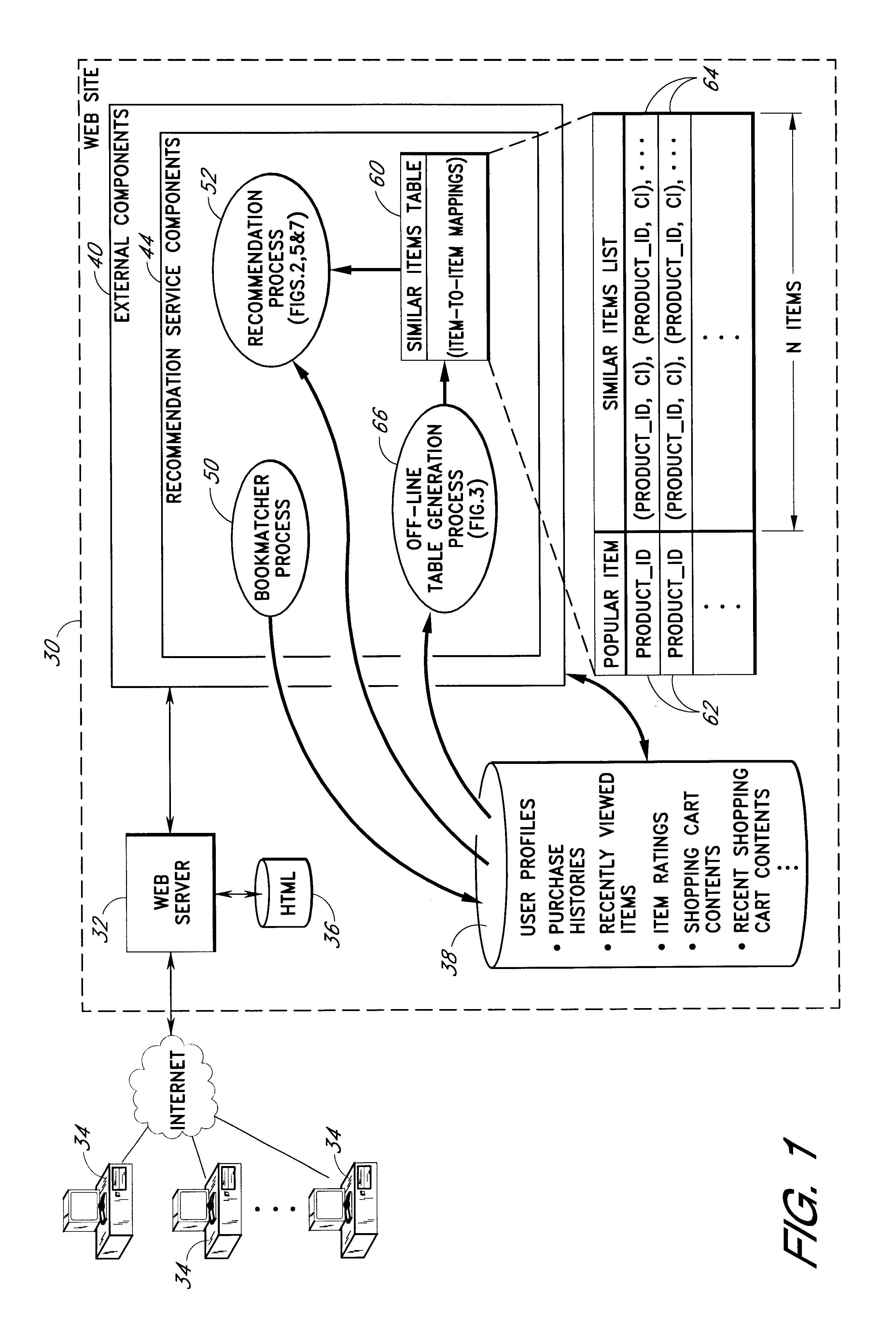
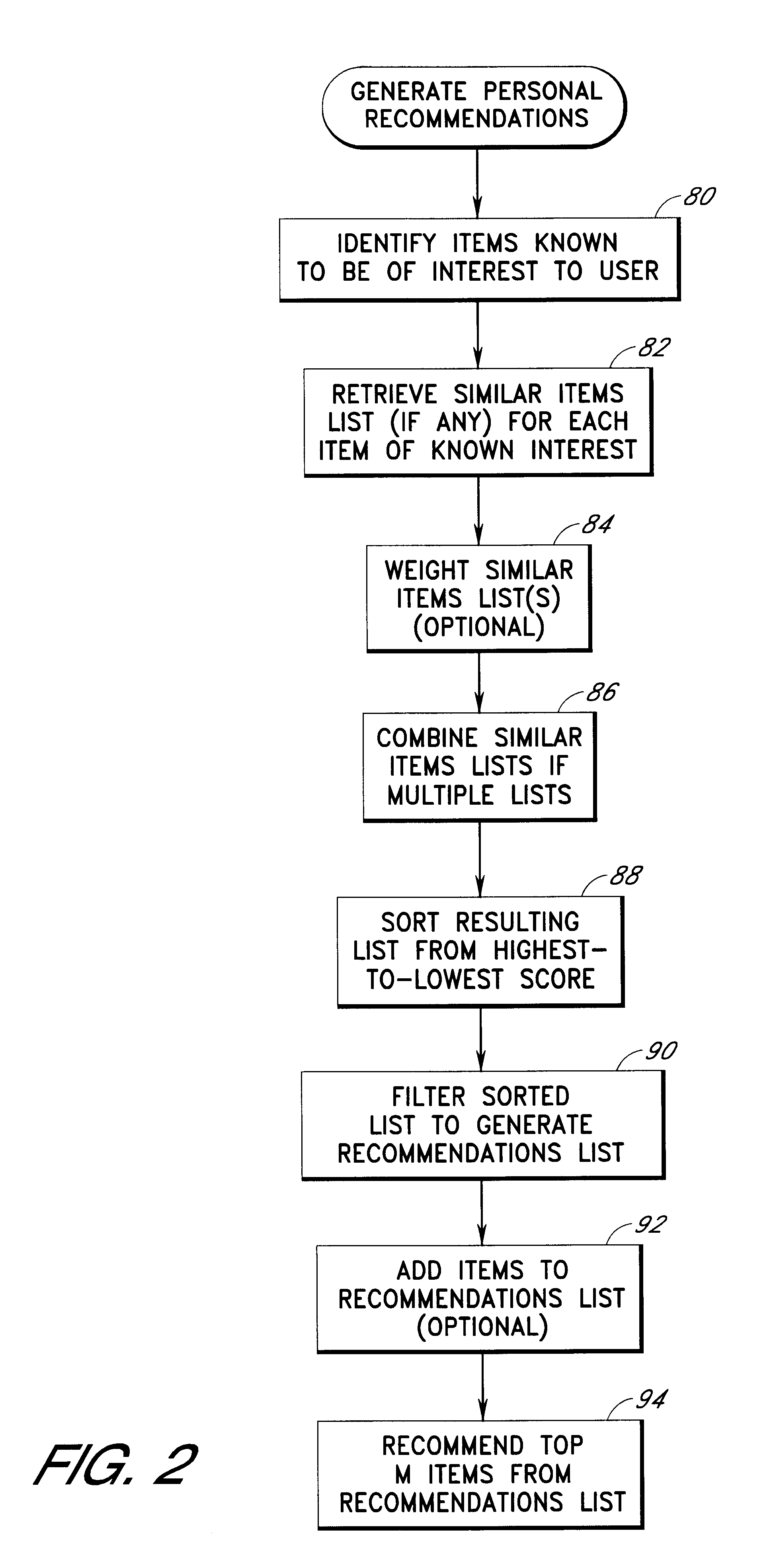
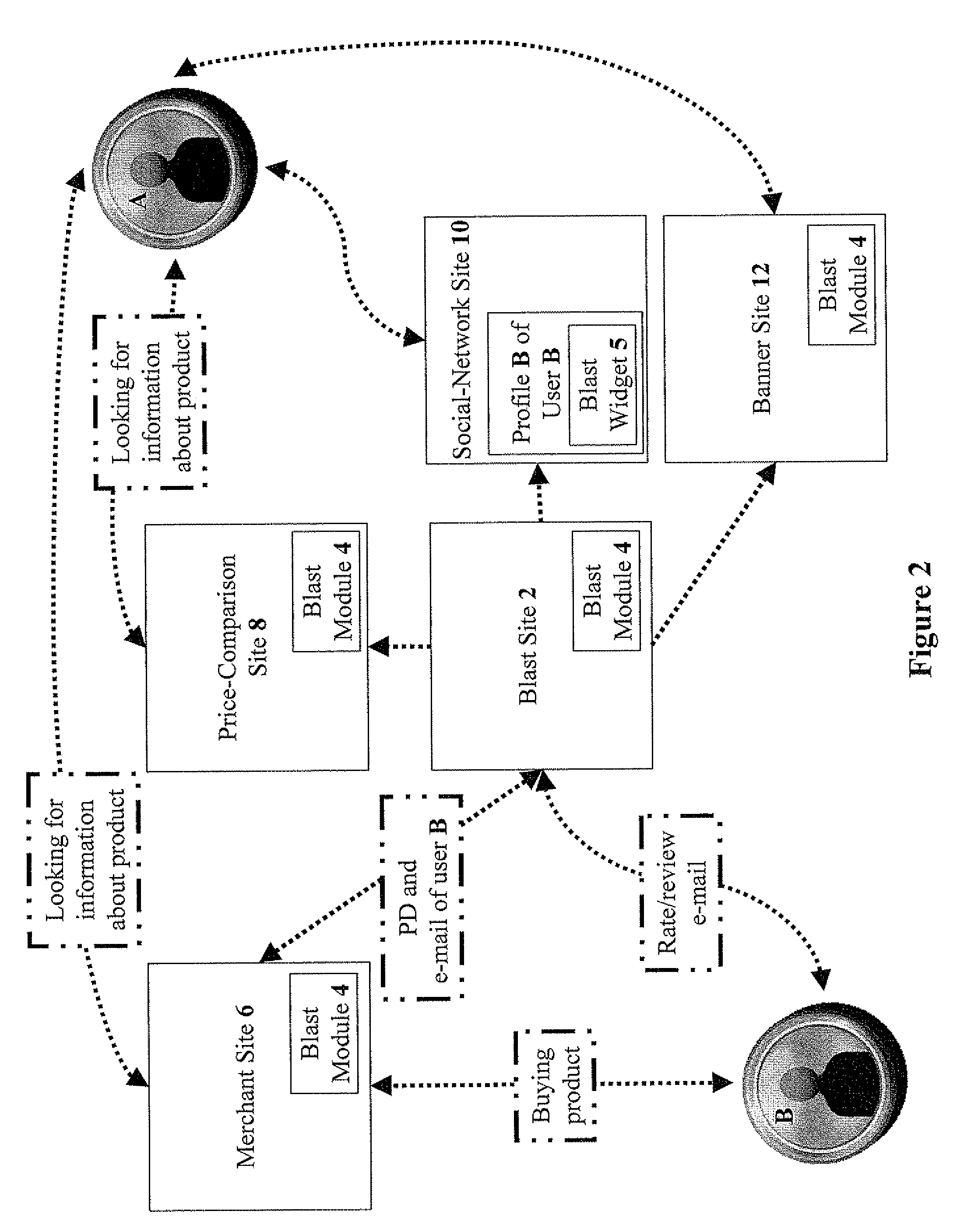
Content personalization based on actions performed during a current browsing session
InactiveUS6853982B2Without sacrificing breadthQuick buildAdvertisementsBuying/selling/leasing transactionsWeb sitePersonalization
Owner:AMAZON TECH INC
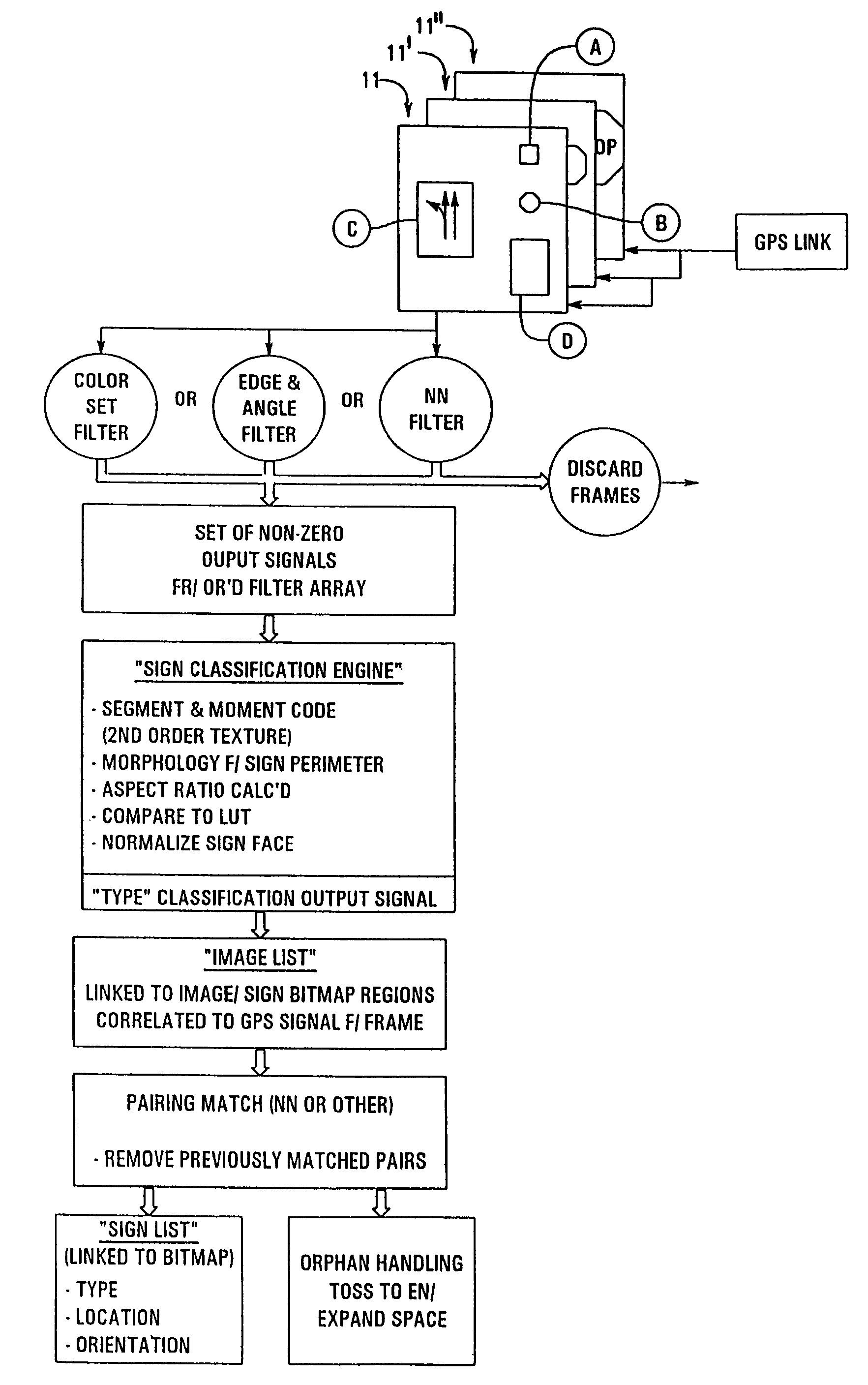
Method and apparatus for identifying objects depicted in a videostream
InactiveUS7092548B2Quick and accurate identificationAvoid processing overheadImage enhancementImage analysisPattern recognitionSemi automatic
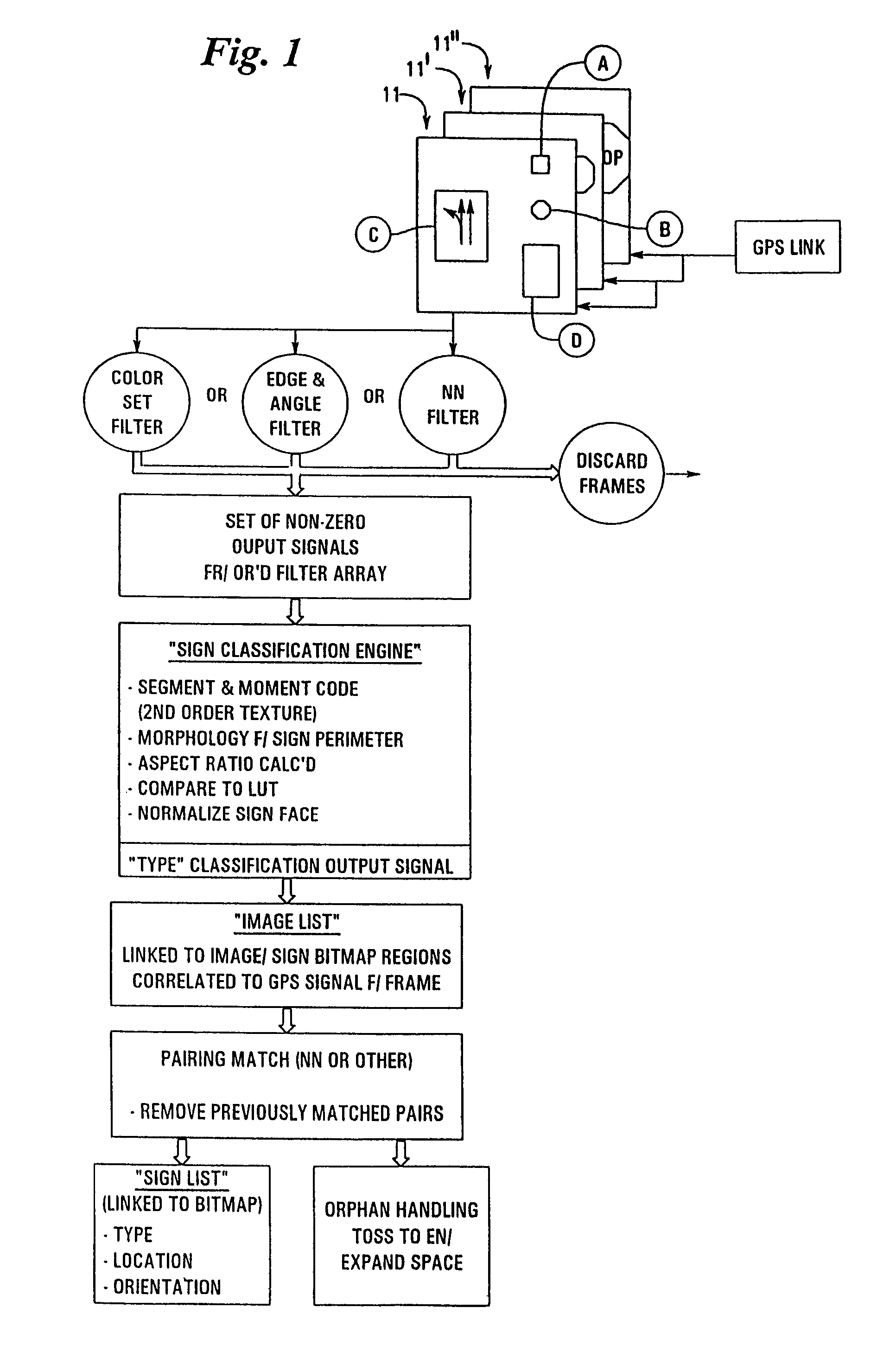
The present invention relates to an apparatus for rapidly analyzing frame(s) of digitized video data which may include objects of interest randomly distributed throughout the video data and wherein said objects are susceptible to detection, classification, and ultimately identification by filtering said video data for certain differentiable characteristics of said objects. The present invention may be practiced on pre-existing sequences of image data or may be integrated into an imaging device for real-time, dynamic, object identification, classification, logging / counting, cataloging, retention (with links to stored bitmaps of said object), retrieval, and the like. The present invention readily lends itself to the problem of automatic and semi-automatic cataloging of vast numbers of objects such as traffic control signs and utility poles disposed in myriad settings. When used in conjunction with navigational or positional inputs, such as GPS, an output from the inventative systems indicates the identity of each object, calculates object location, classifies each object by type, extracts legible text appearing on a surface of the object (if any), and stores a visual representation of the object in a form dictated by the end user / operator of the system. The output lends itself to examination and extraction of scene detail, which cannot practically be successfully accomplished with just human viewers operating video equipment, although human intervention can still be used to help judge and confirm a variety of classifications of certain instances and for types of identified objects.
Owner:GOOGLE LLC
Self-learning and self-personalizing knowledge search engine that delivers holistic results
InactiveUS6397212B1Web data indexingDigital data processing detailsPersonalizationHuman–machine interface
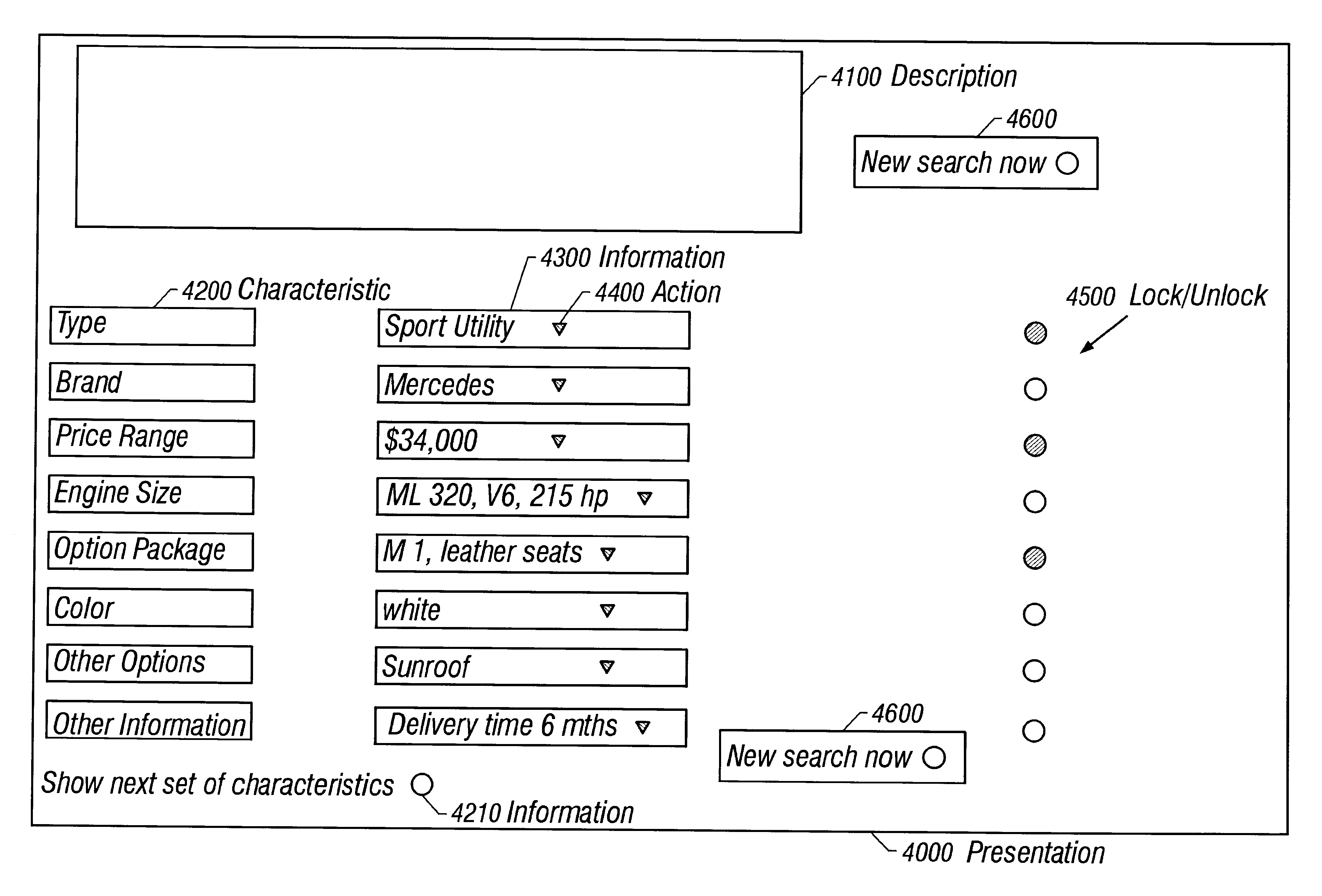
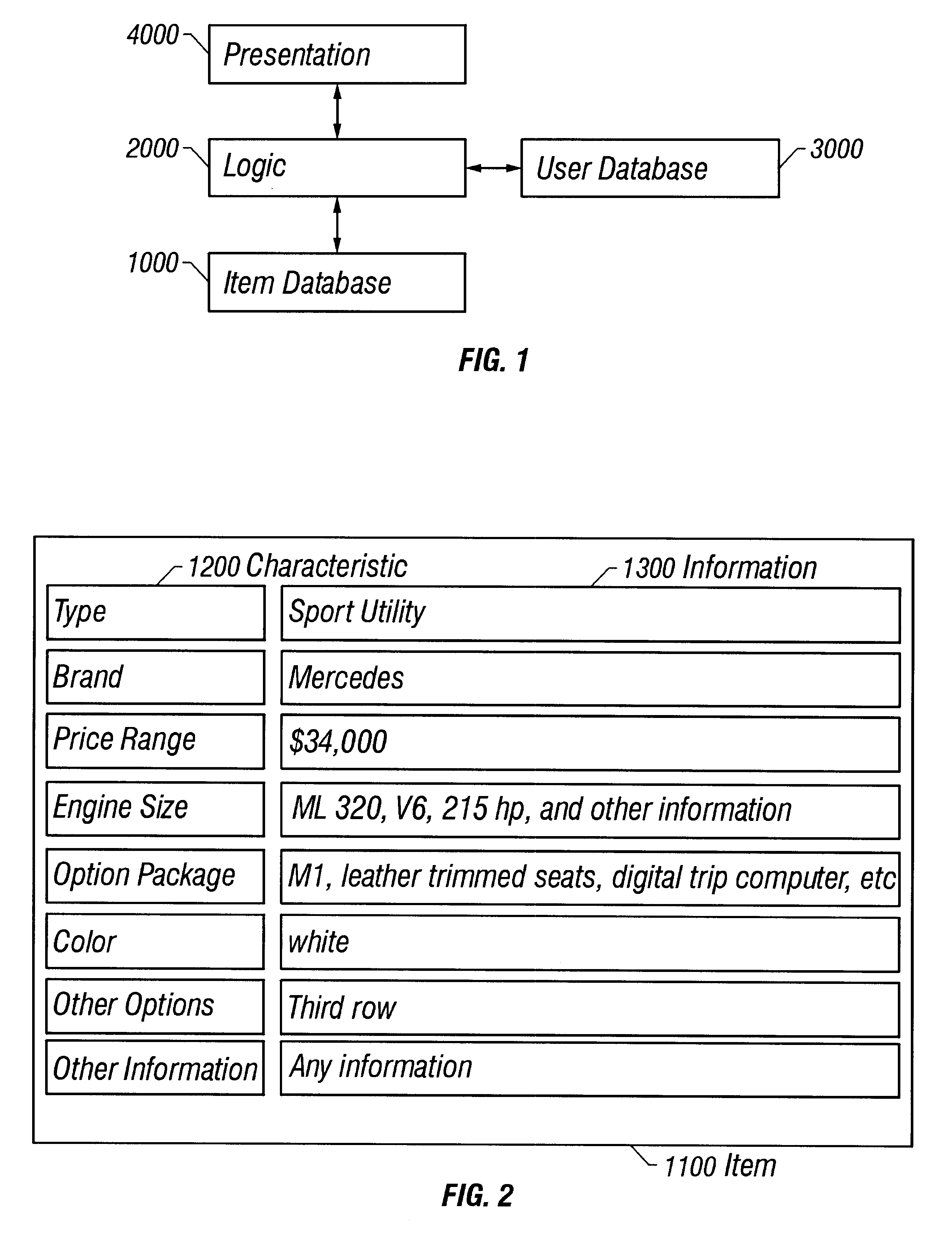
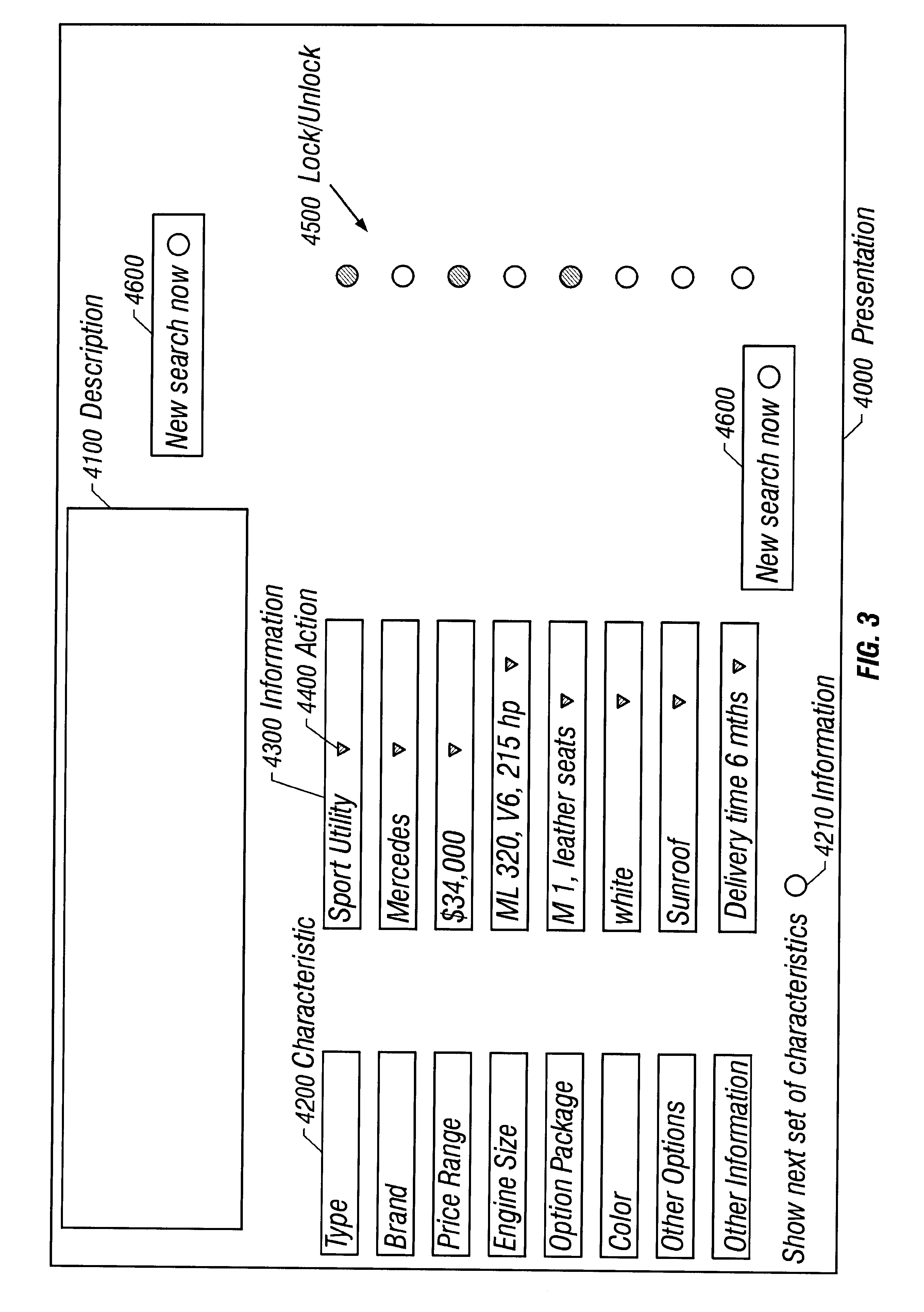
A search engine provides intelligent multi-dimensional searches, in which the search engine always presents a complete, holistic result, and in which the search engine presents knowledge (i.e. linked facts) and not just information (i.e. facts). The search engine is adaptive, such that the search results improve over time as the system learns about the user and develops a user profile. Thus, the search engine is self personalizing, i.e. it collects and analyzes the user history, and / or it has the user react to solutions and learns from such user reactions. The search engine generates profiles, e.g. it learns from all searches of all users and combines the user profiles and patterns of similar users. The search engine accepts direct user feedback to improve the next search iteration One feature of the invention is locking / unlocking, where a user may select specific attributes that are to remain locked while the search engine matches these locked attributes to all unlocked attributes. The user may also specify details about characteristics, provide and / or receive qualitative ratings of an overall result, and introduce additional criteria to the search strategy or select a search algorithm. Additionally, the system can be set up such that it does not require a keyboard and / or mouse interface, e.g. it can operate with a television remote control or other such human interface.
Owner:HANGER SOLUTIONS LLC
Mining of user event data to identify users with common interests
ActiveUS8060463B1Reduce the burden onPoor resultDatabase queryingDigital data processing detailsEvent dataElectronic catalog
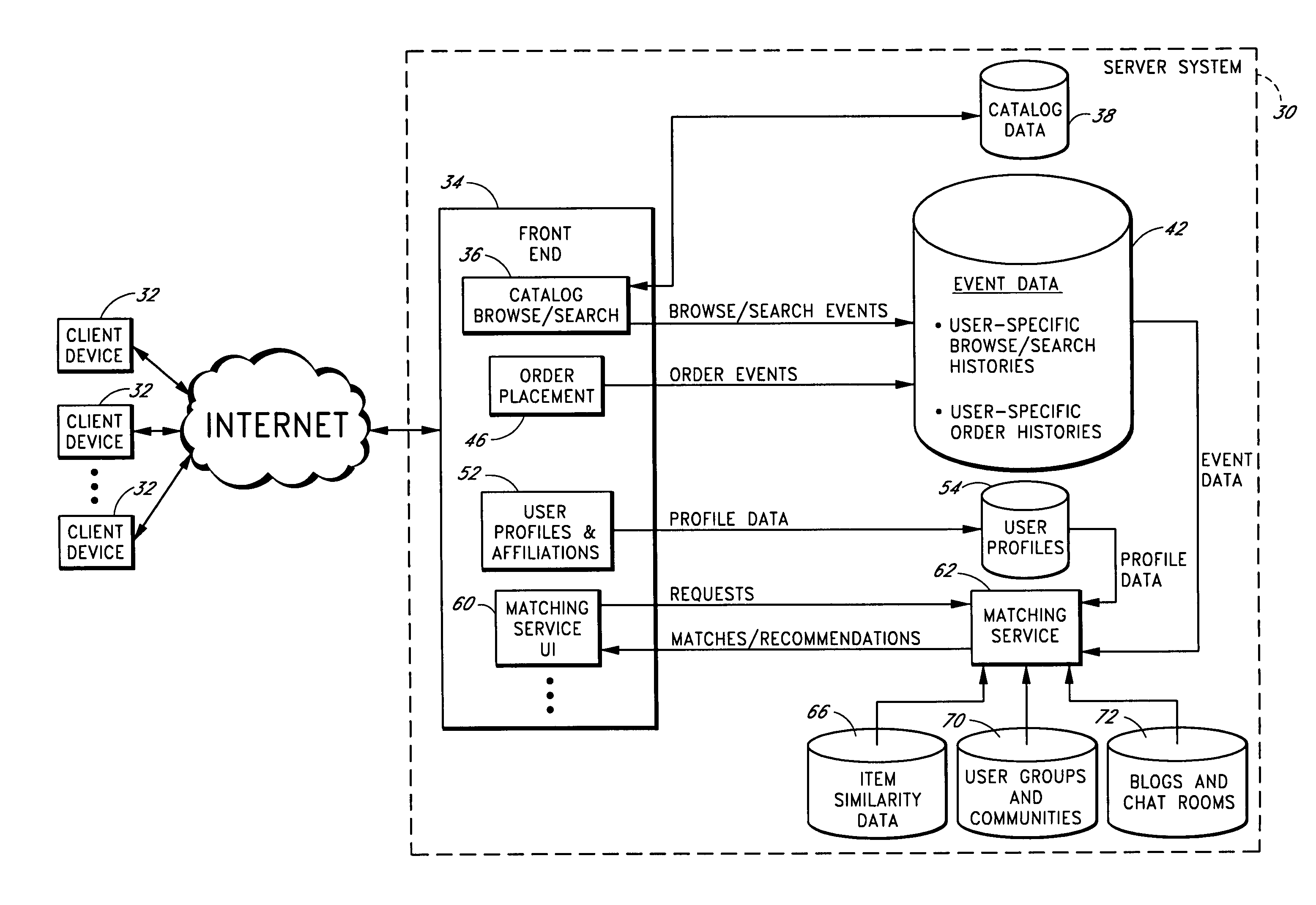
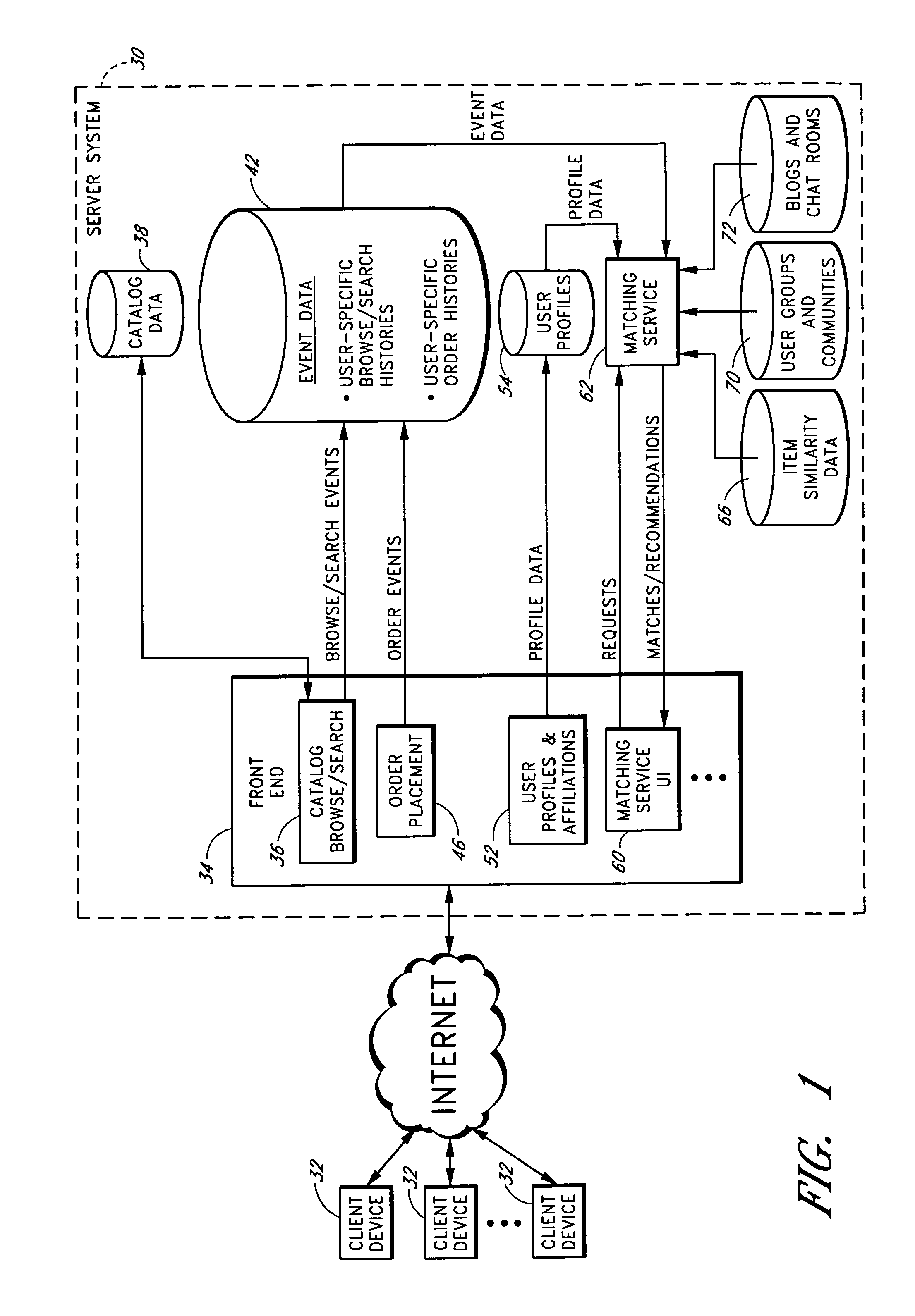
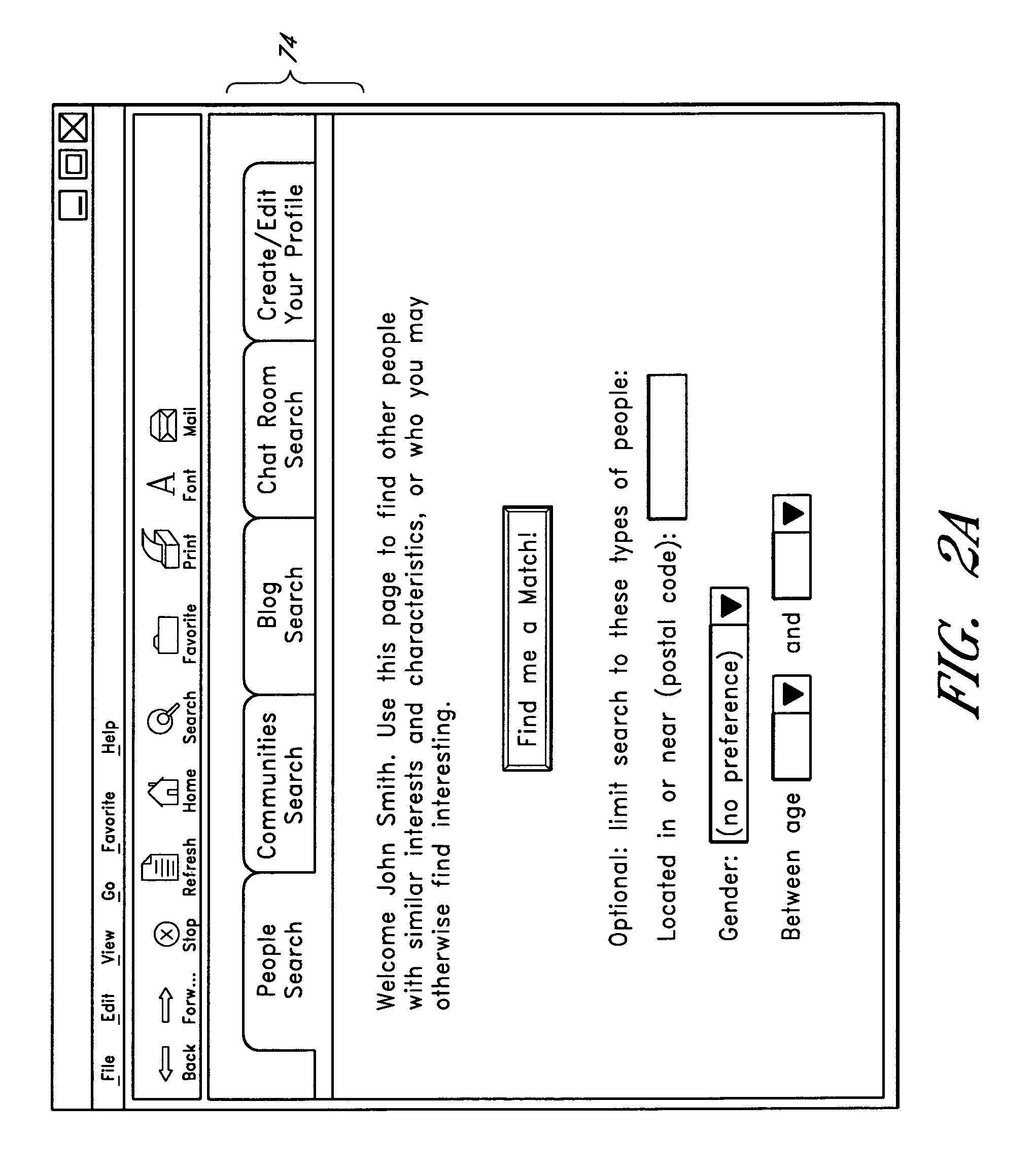
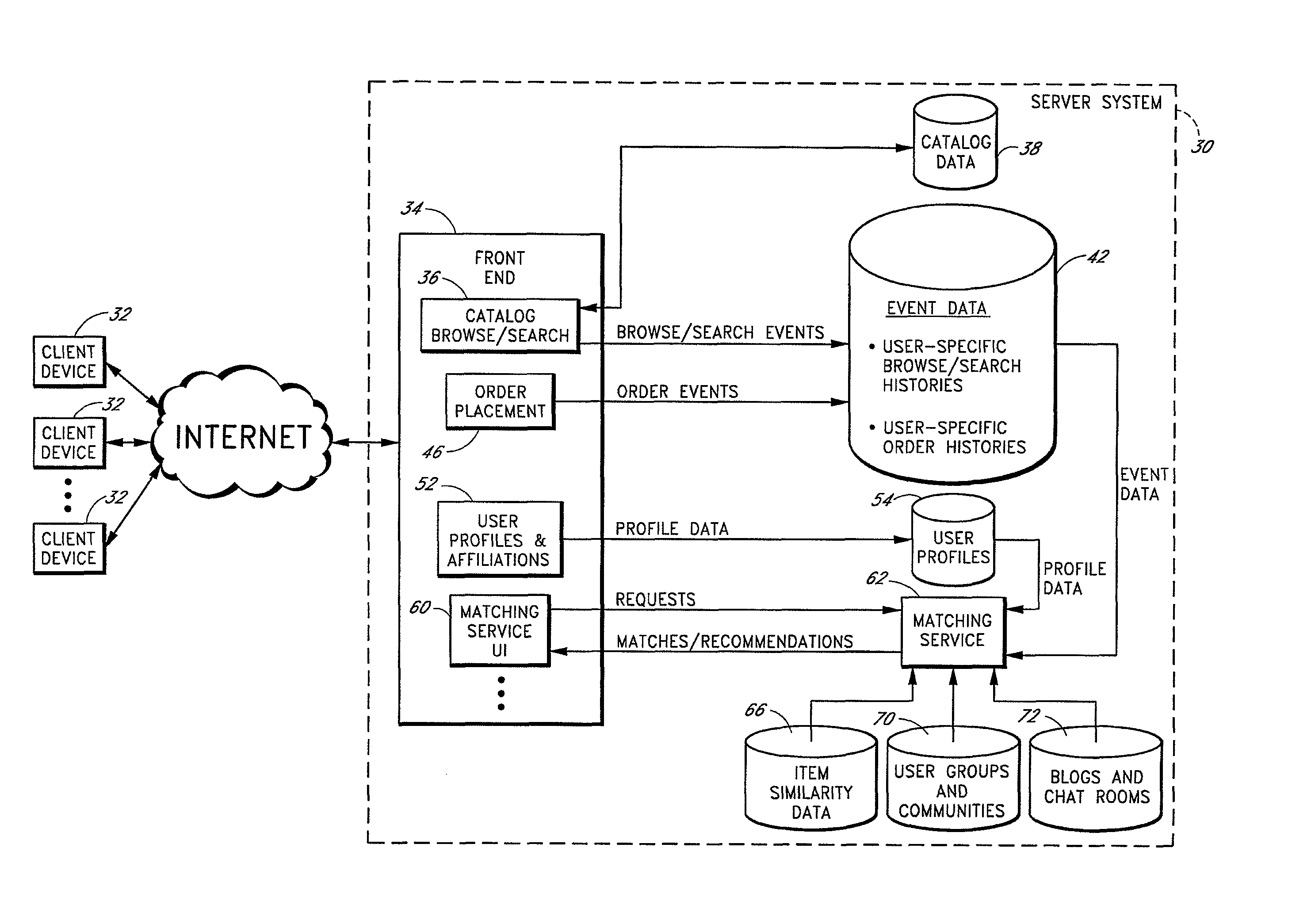
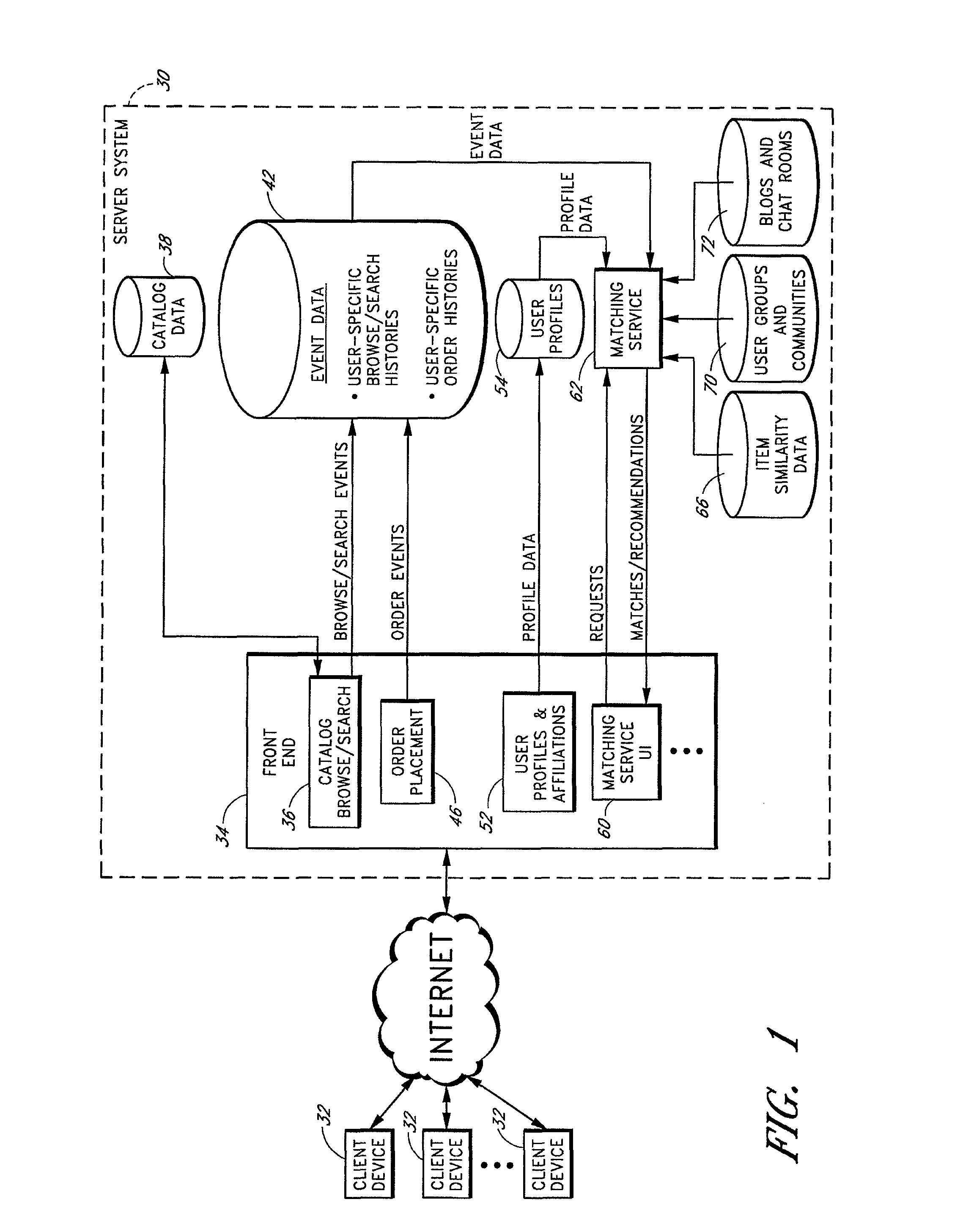
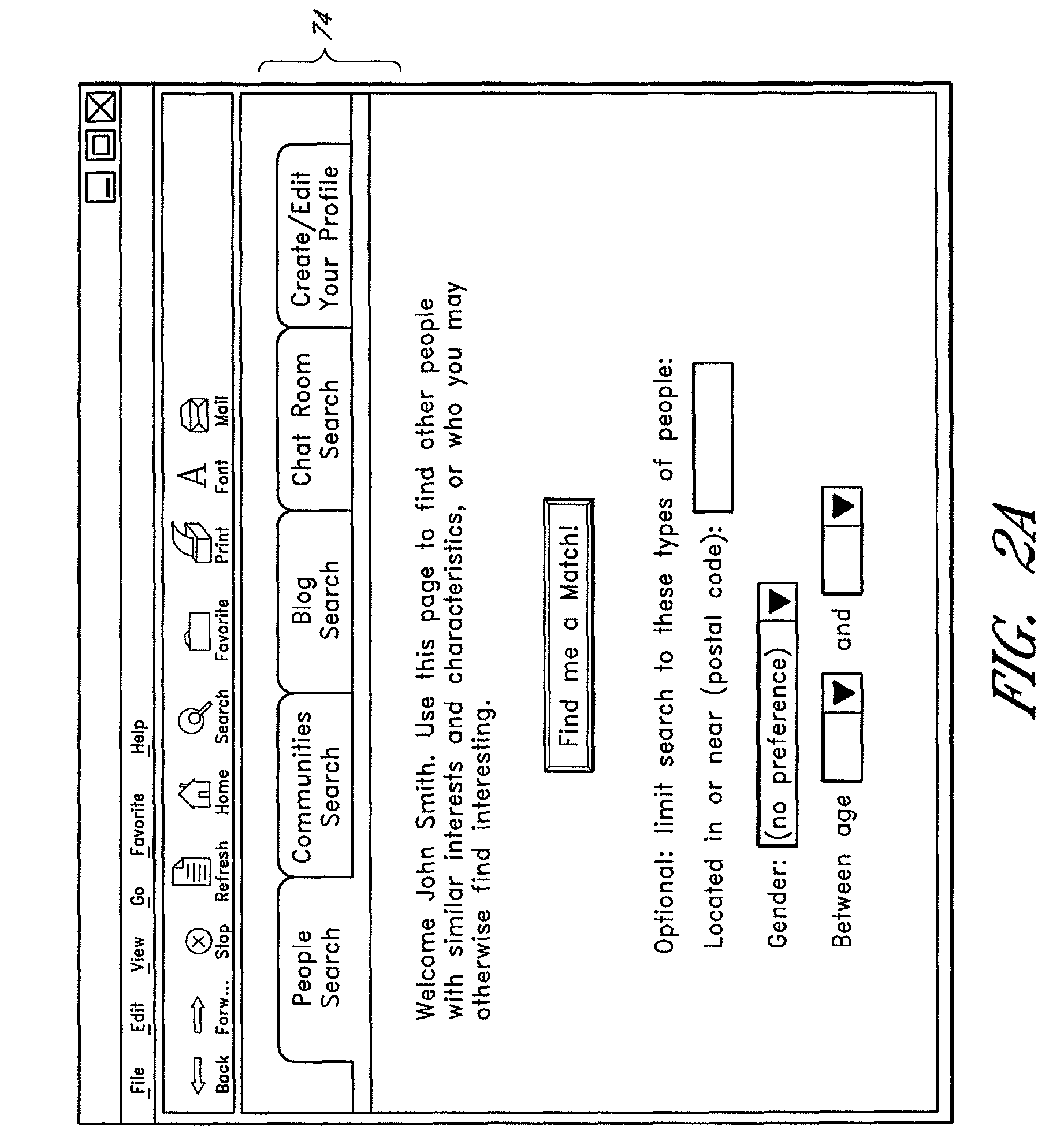
A computer-implemented matching service matches users to other users, and / or to user communities, based at least in part on a computer analysis of event data reflective of user behaviors. The event data may, for example, evidence user affinities for particular items represented in an electronic catalog, such as book titles, music titles, movie titles, and / or other types of items that tend to reflect the traits of users. Event data reflective of other types of user actions, such as item-detail-page viewing events, browse node visits, search query submissions, and / or web browsing patterns may additionally or alternatively be considered. By taking such event data into consideration, the matching service reduces the burden on users to explicitly supply personal profile information, and reduces poor results caused by exaggerations and other inaccuracies in such profile information.
Owner:AMAZON TECH INC
Social marketing and networking tool with user matching and content broadcasting / receiving capabilities
InactiveUS20100280904A1Optimization definitionMultiple digital computer combinationsData switching networksWi-FiThe Internet
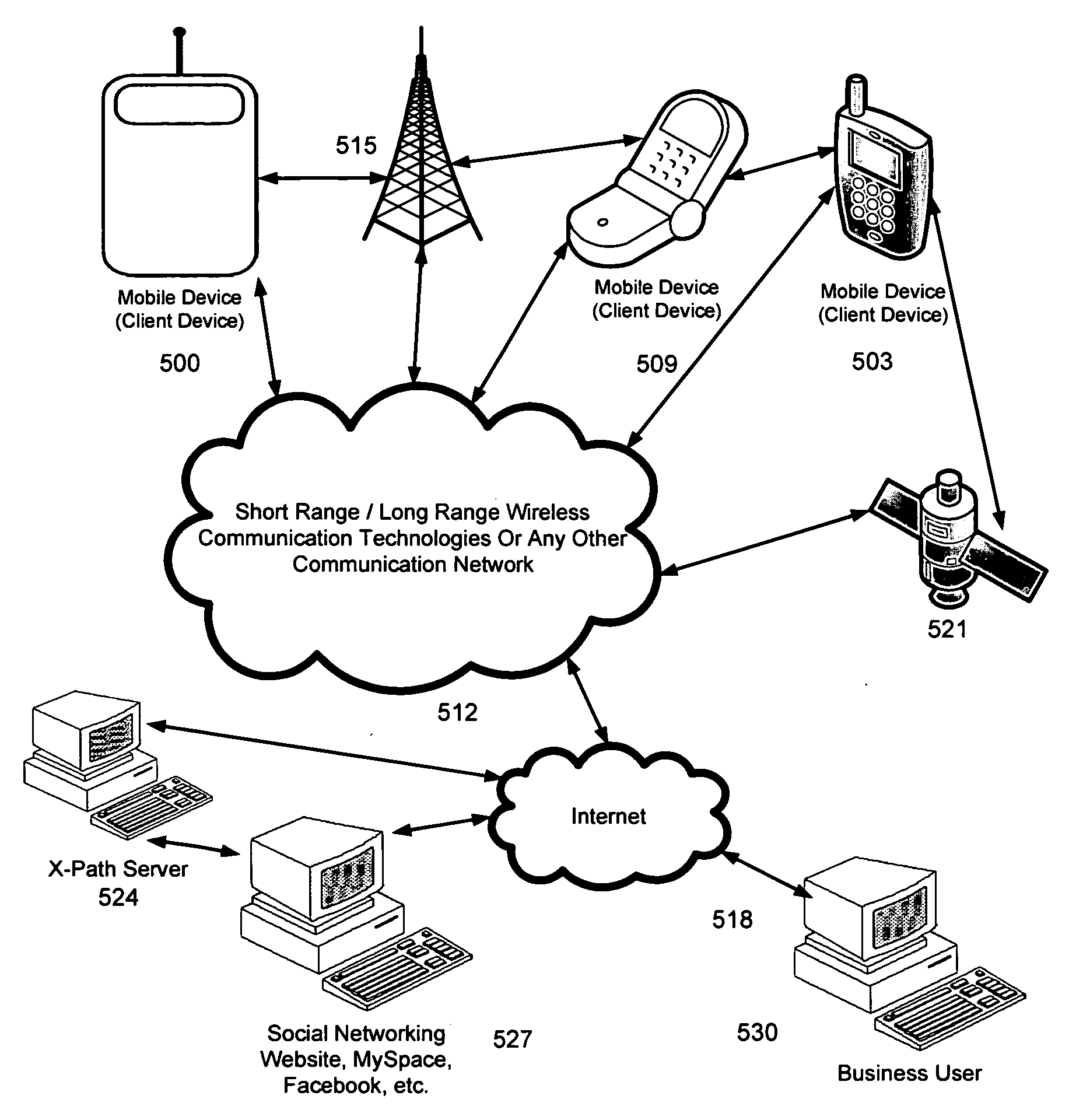
A proximity based social marketing tool / device that is free from a physical location and can be used for matching users and broadcasting messages or data to all or selected users in the proximity. These users can be searched by scanning the selected proximity range and / or by defining various keyword criteria's. And it utilizes one or more or a combination of various short-range or long-range wireless communication technologies such as Bluetooth, Wi-Fi, GPS, NFC, TransferJet, Internet, and others. The X-Path device can locate and store user's location details in the X-path server, which can be retrieved and used by users to broadcast messages to a specific category of an audience. It also makes for a great Social networking tool and takes the concept of Social Networking from the Internet out to the real Physical World.
Owner:AHUJA SUMIT PRADEEP
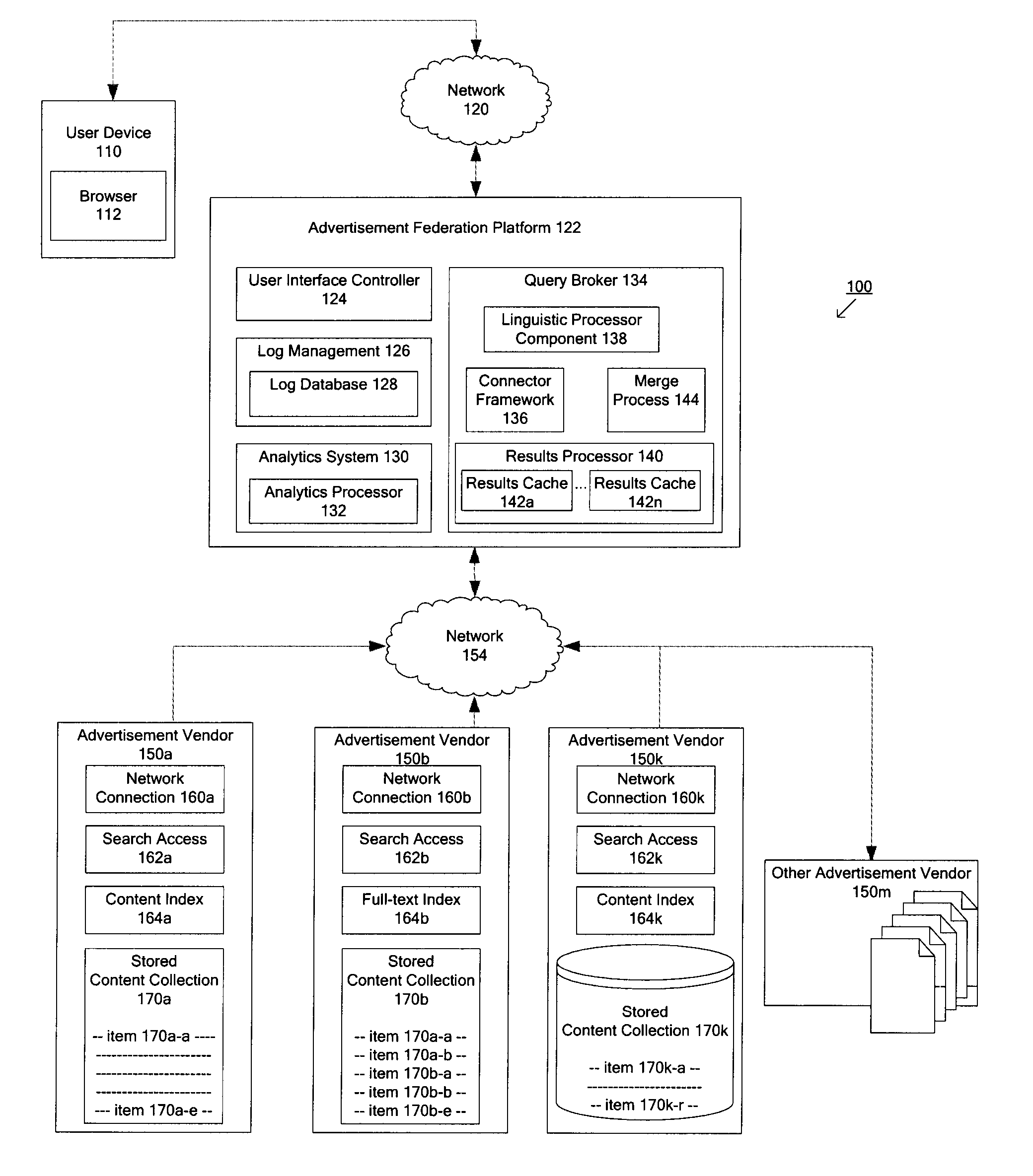
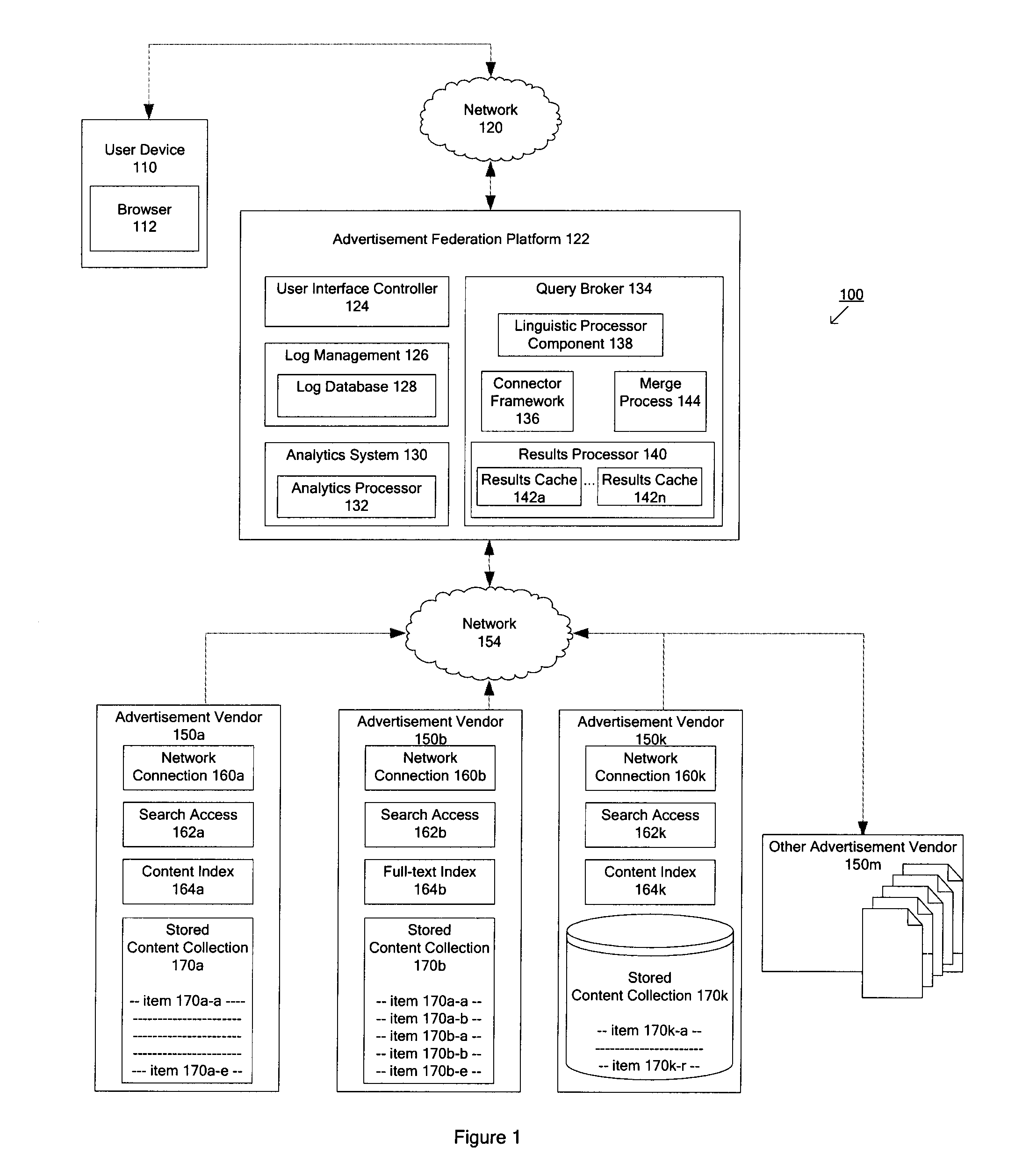
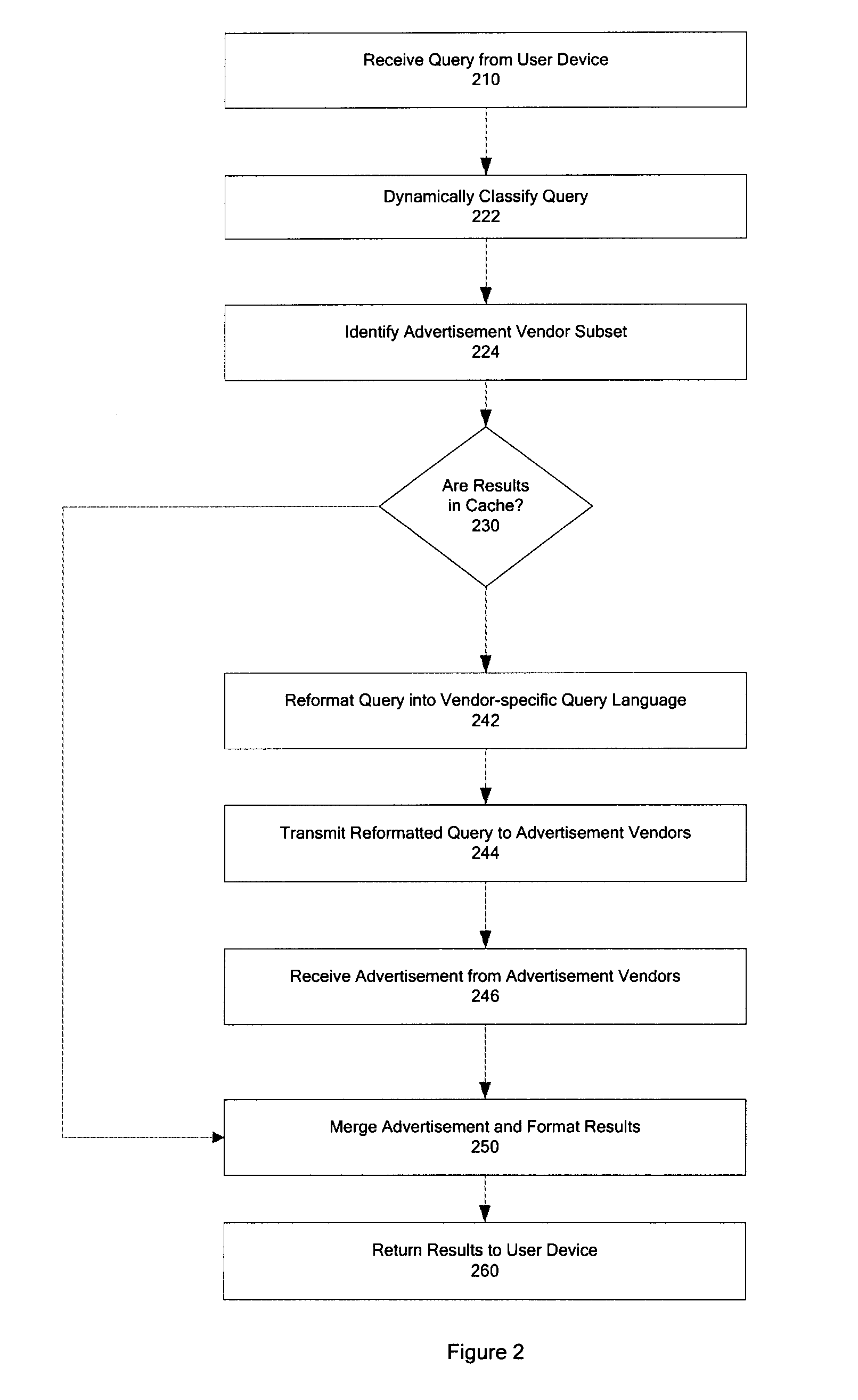
Techniques for determining relevant advertisements in response to queries
Techniques for determining relevant advertisements in response to queries is disclosed. According to an exemplary embodiment of the present disclosure, the techniques may be realized as a computer implemented method for determining relevant advertisements in response to a query. The method may comprise: receiving a query from a user device; categorizing the query to identify one or more relevant advertisement sources; formatting the query according to one or more advertisement source specifics for the one or more advertisement sources; transmitting the formatted query to the one or more advertisement sources; merging results in response to the formatted query to the one or more advertisement sources; merging results based at least in part on one or more factors; and formatting the results for delivering to the user device.
Owner:MOBILE CONTENT NETWORKS
Electronic payment systems and supporting methods and devices
ActiveUS20130060690A1Efficient transferFinanceProtocols using social networksSystems designSubject matter
Electronic payment systems and supporting methods and devices are described. For instance, the disclosed subject matter describes aggregated transactional account functionality configured to receive electronic financial transactions associated with one or more of a set of electronic identifying information such as phone ID, email, instant message, etc. for a user and related functionality. The disclosed details enable various refinements and modifications according to system design and tradeoff considerations.
Owner:RPX CORP
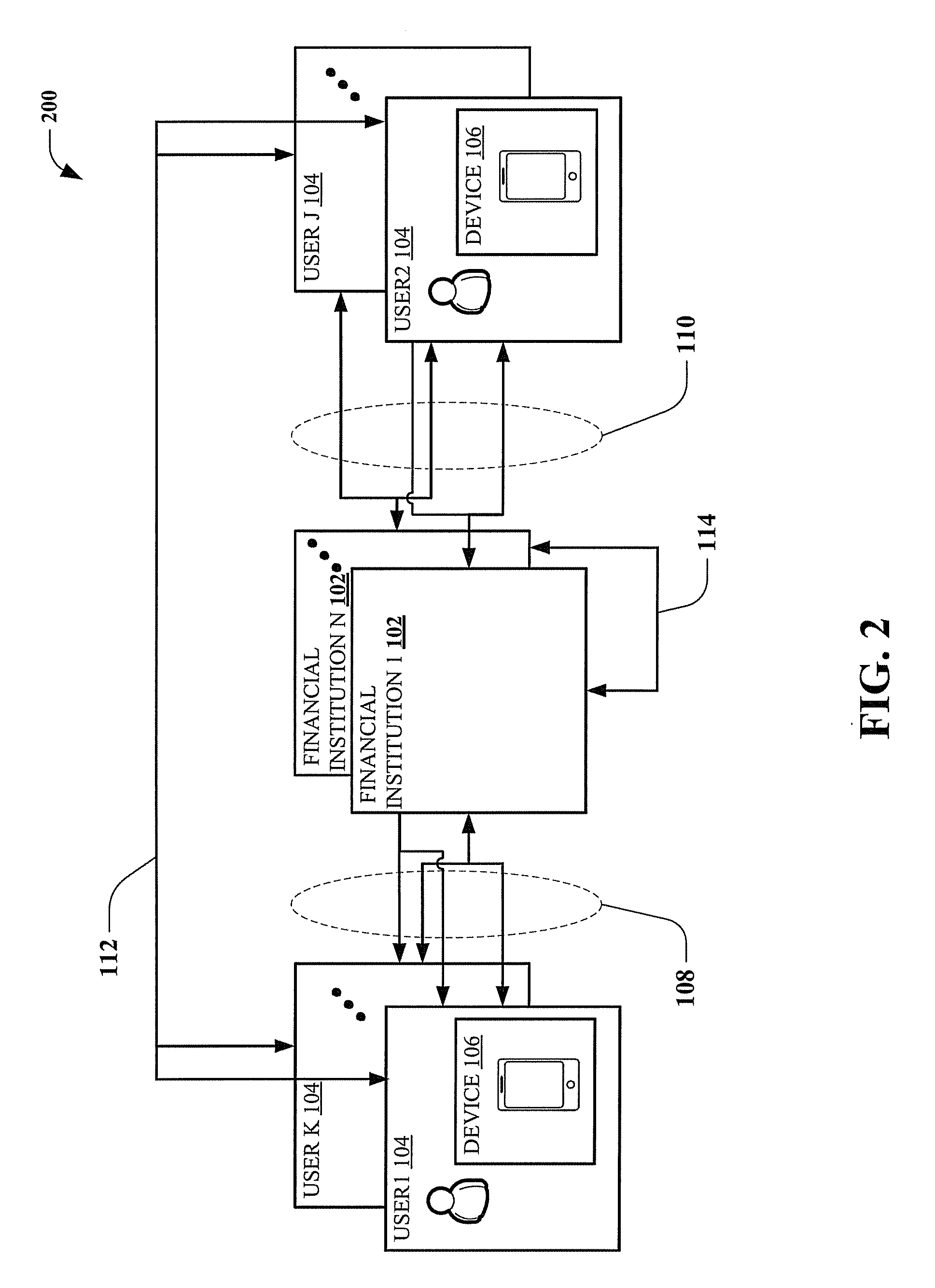
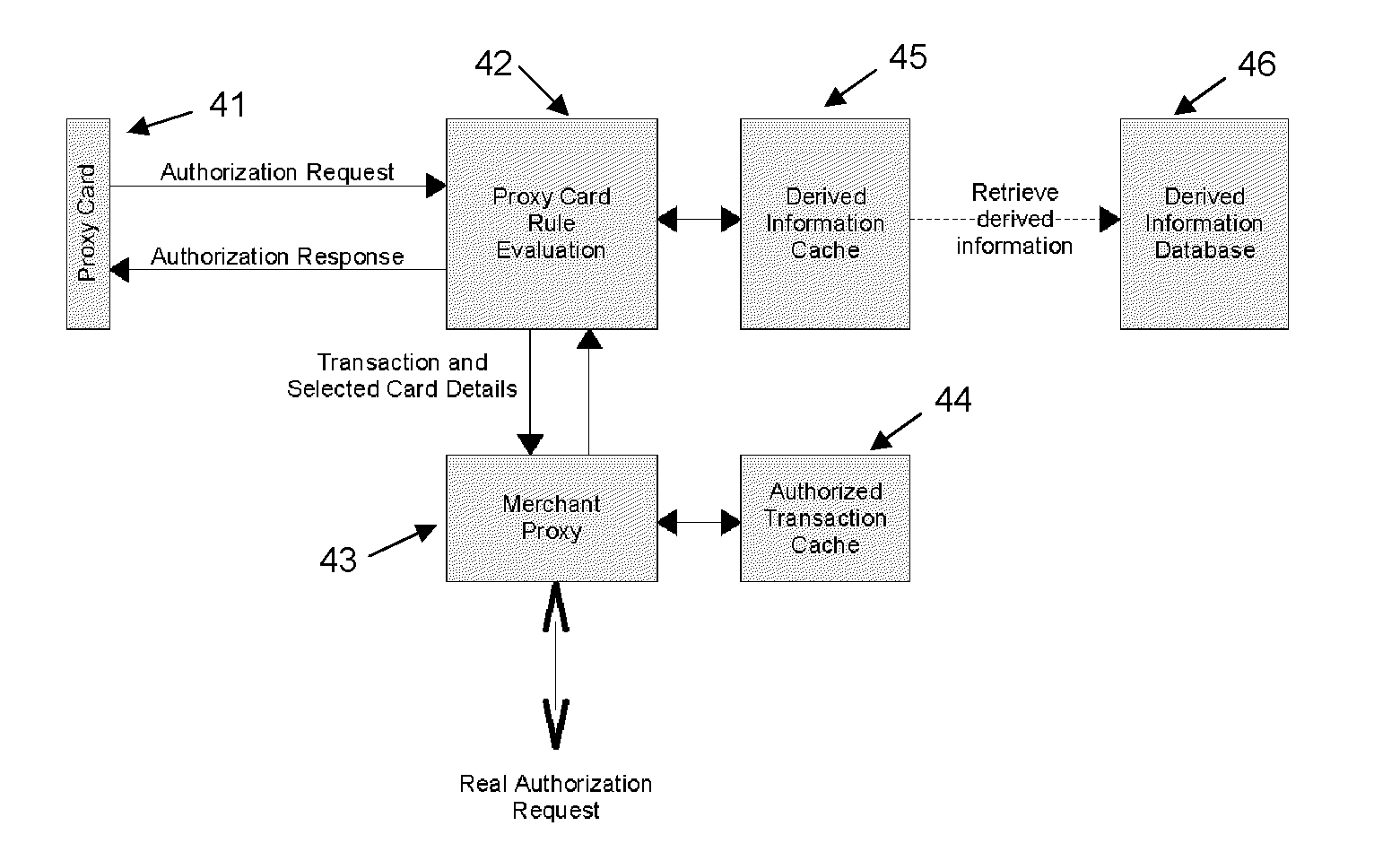
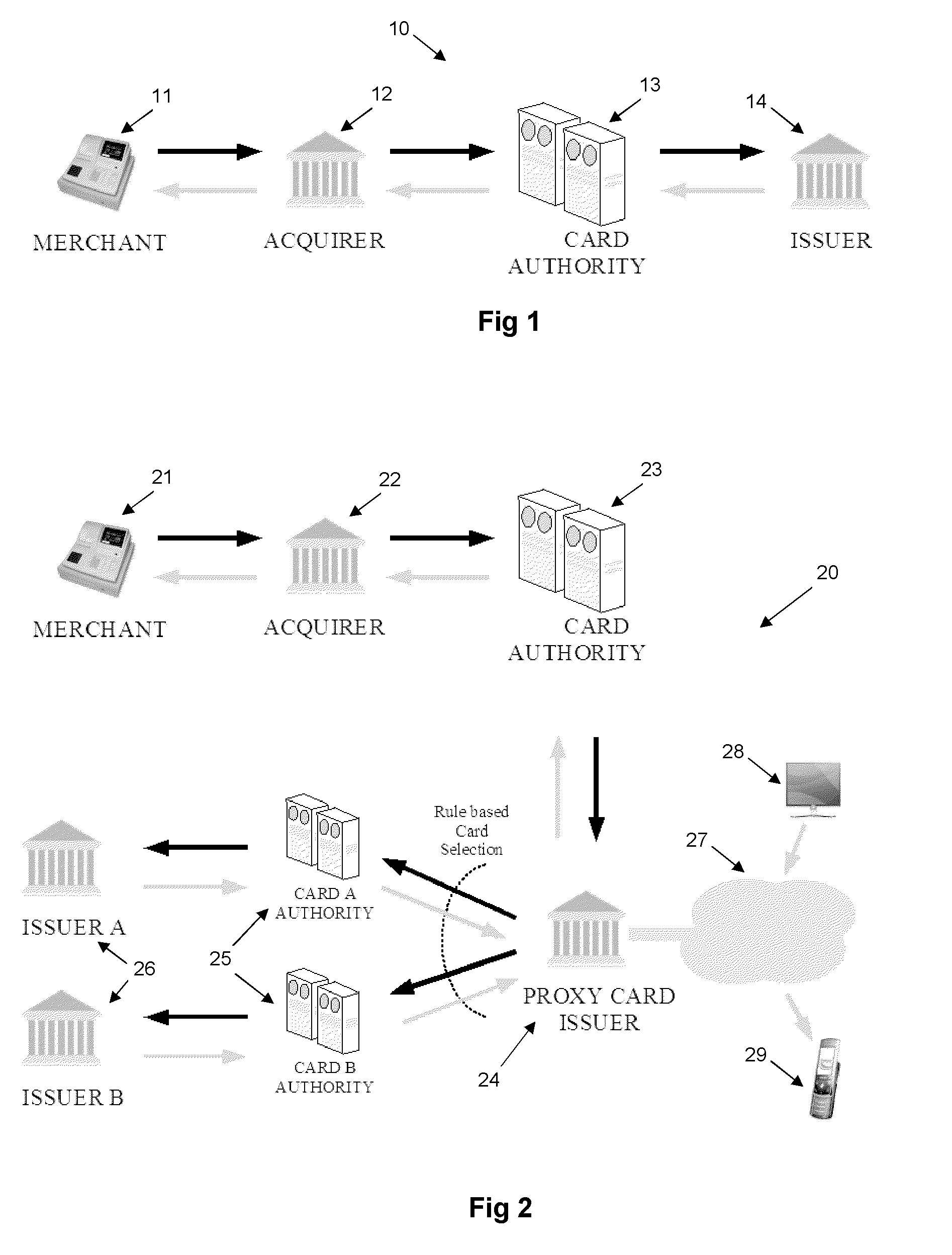
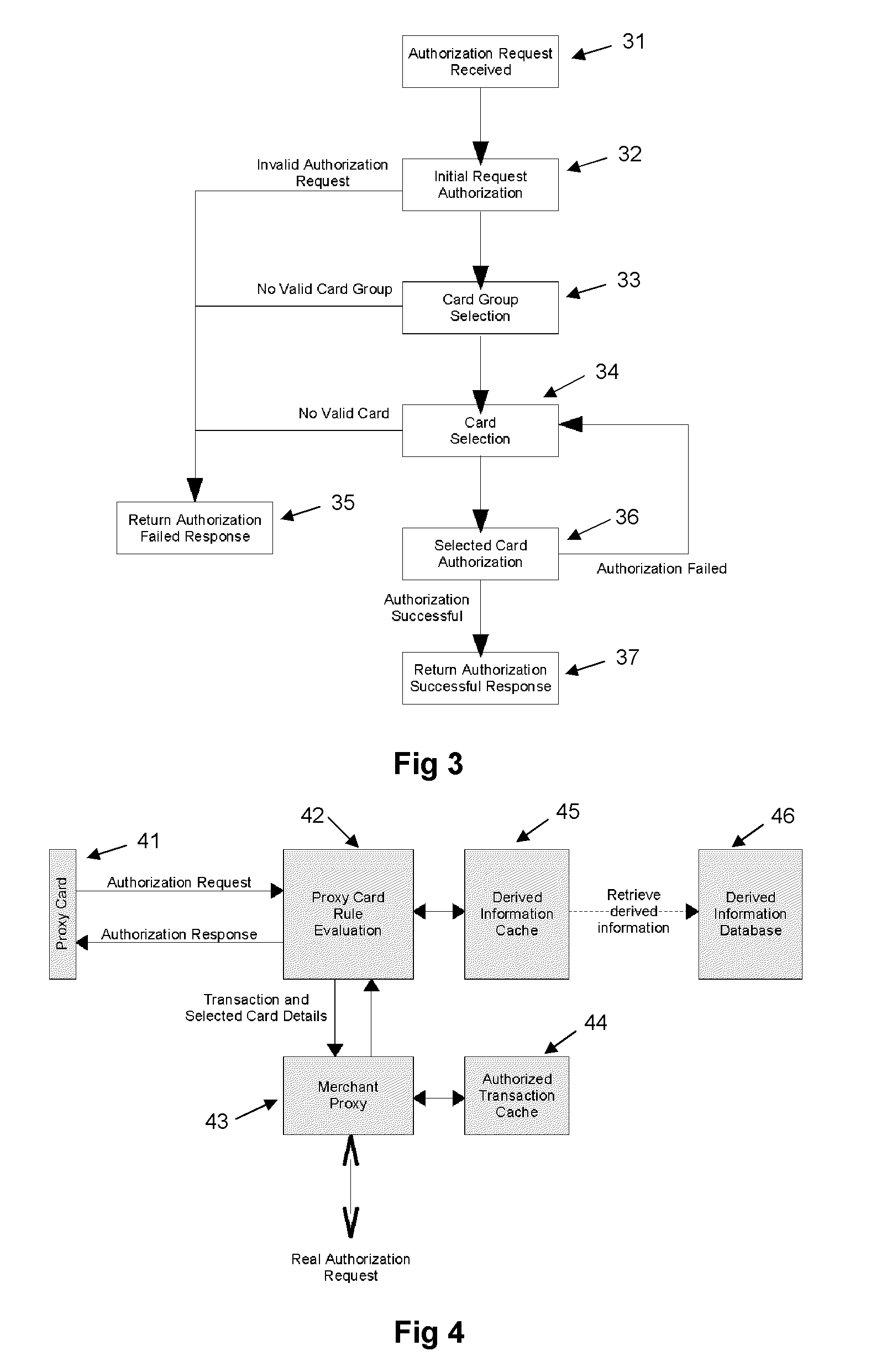
Proxy card authorization system
A system and method is provided for providing proxy access to a set of resources subject to constraints specified by the primary party having access to the resources. The system comprises one or more proxy cards associated with a proxy account that contains details on the resources available and also configurable rules for processing proxy authorization requests and returning an authorization response in dependence on the rules. The system has a particular application to payment cards and accounts, whereby the proxy card can act as proxy for one or more of the real payment cards and the proxy card authentication service may operate in a transparent manner as part of a normal overall payment authorization process.
Owner:BROWN GARY +1
Mining of user event data to identify users with common interests
InactiveUS8224773B2Reduce the burden onPoor resultDatabase queryingDigital data processing detailsEvent dataMinutiae
A computer-implemented matching service matches users to other users, and / or to user communities, based at least in part on a computer analysis of event data reflective of user behaviors. The event data may, for example, evidence user affinities for particular items represented in an electronic catalog, such as book titles, music titles, movie titles, and / or other types of items that tend to reflect the traits of users. Event data reflective of other types of user actions, such as item-detail-page viewing events, browse node visits, search query submissions, and / or web browsing patterns may additionally or alternatively be considered. By taking such event data into consideration, the matching service reduces the burden on users to explicitly supply personal profile information, and reduces poor results caused by exaggerations and other inaccuracies in such profile information.
Owner:AMAZON TECH INC
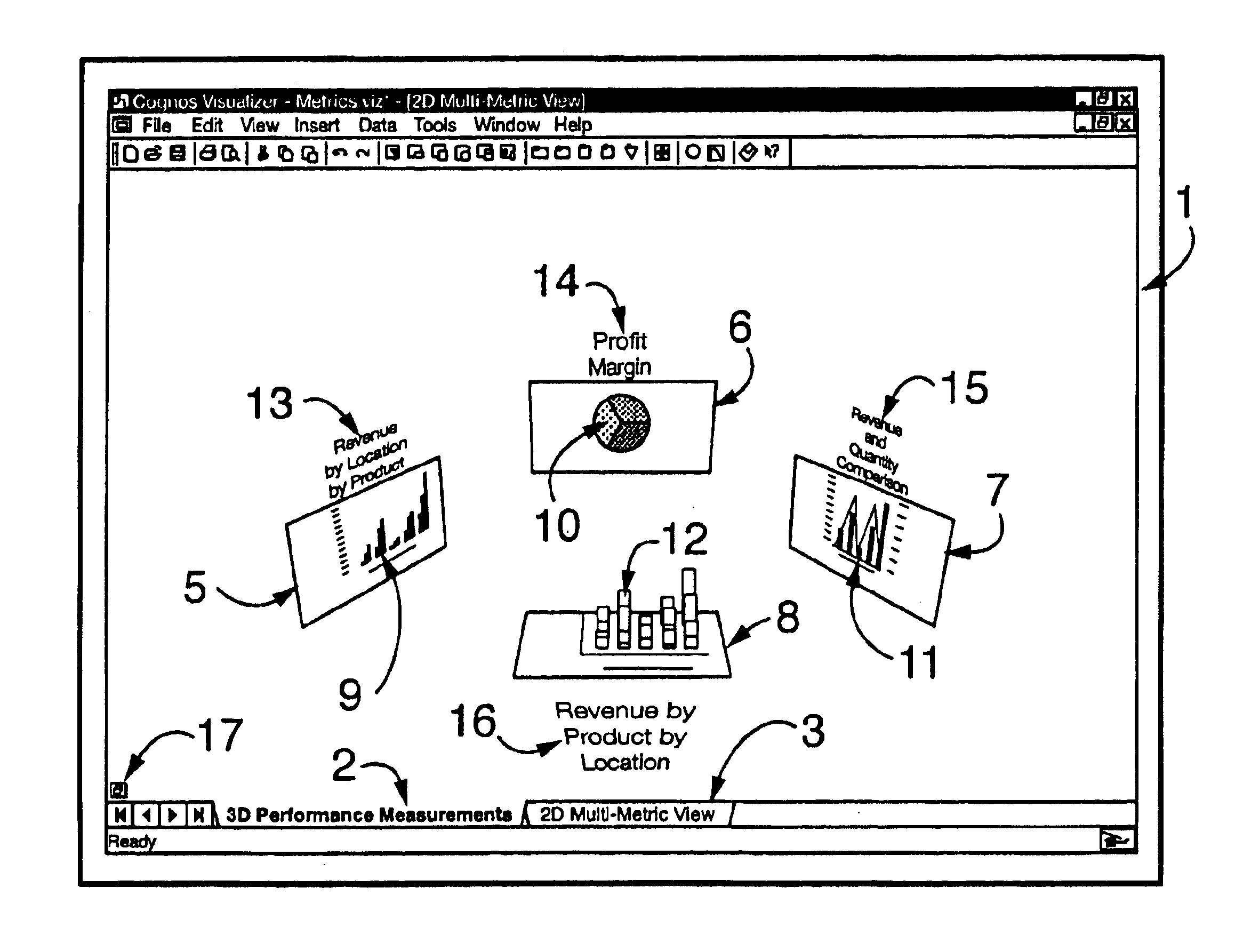
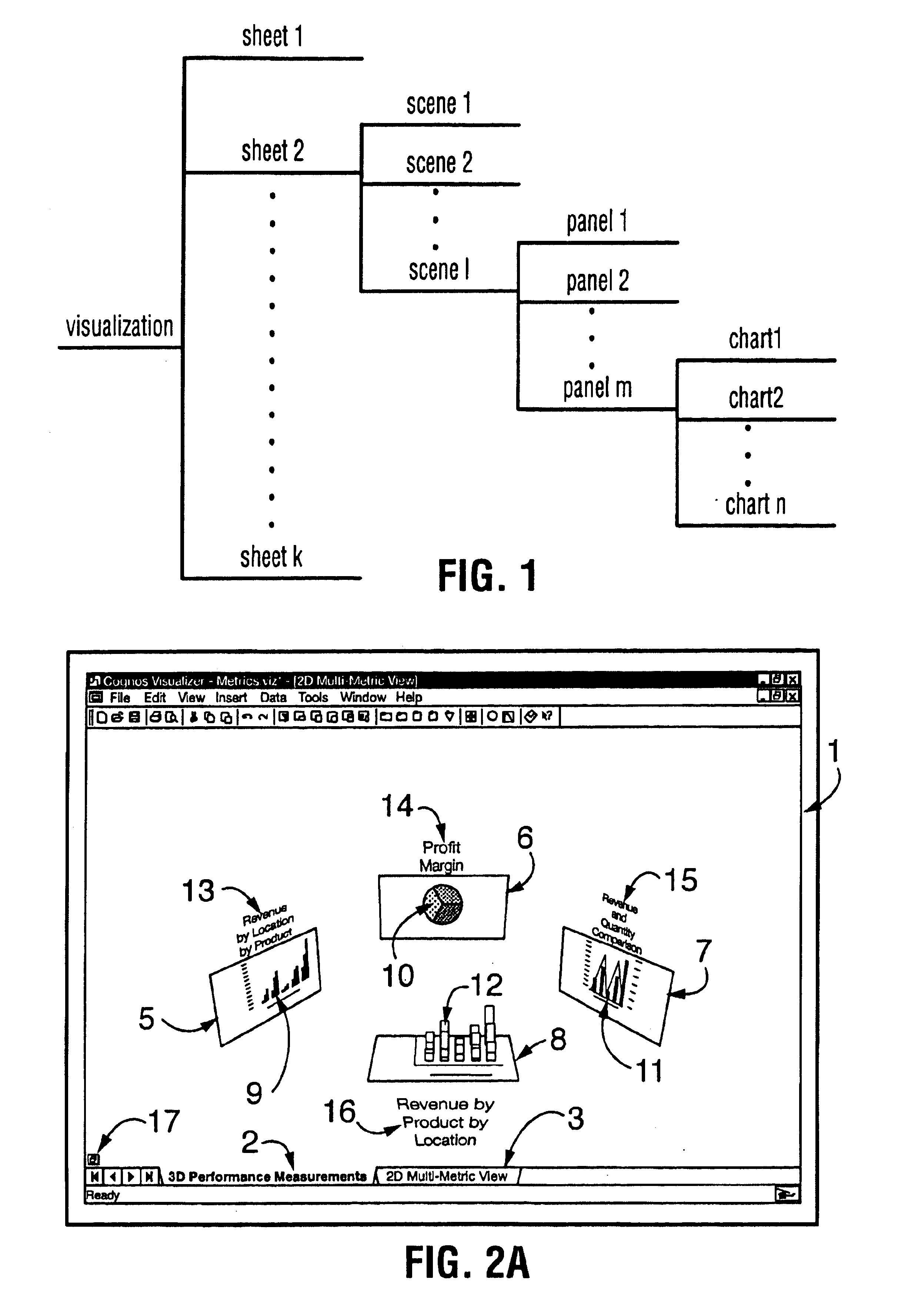
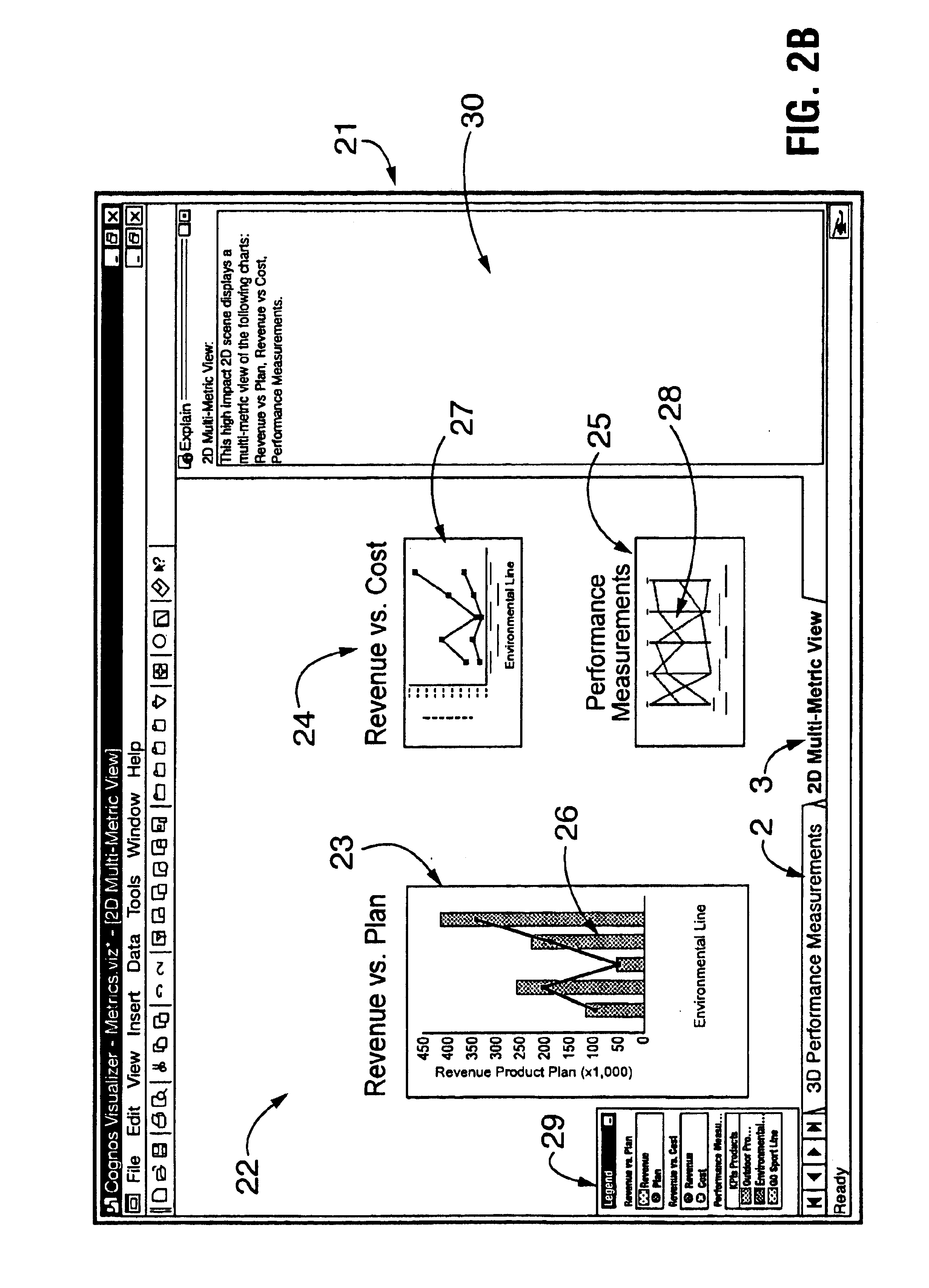
Interactive business data visualization system
Owner:DAEDALUS BLUE LLC
Gesture recognizer system architicture
ActiveUS20100199230A1Character and pattern recognitionCathode-ray tube indicatorsMinutiaeHuman–computer interaction
Systems, methods and computer readable media are disclosed for a gesture recognizer system architecture. A recognizer engine is provided, which receives user motion data and provides that data to a plurality of filters. A filter corresponds to a gesture, that may then be tuned by an application receiving information from the gesture recognizer so that the specific parameters of the gesture—such as an arm acceleration for a throwing gesture—may be set on a per-application level, or multiple times within a single application. Each filter may output to an application using it a confidence level that the corresponding gesture occurred, as well as further details about the user motion data.
Owner:MICROSOFT TECH LICENSING LLC
Compile time meta-object protocol systems and methods
InactiveUS7665073B2Software engineeringSpecial data processing applicationsDocument preparationMinutiae
The subject invention pertains to a compilation system and meta-object protocol to facilitate interaction with objects of various types including but not limited to XML documents. More specifically, a delineator or dot operator can be extended to hide idiosyncratic details of interacting with objects. Code details can be generated by a compiler behind the scenes. This enables a programmer to achieve the same results while writing much simpler and intuitive code.
Owner:MICROSOFT TECH LICENSING LLC
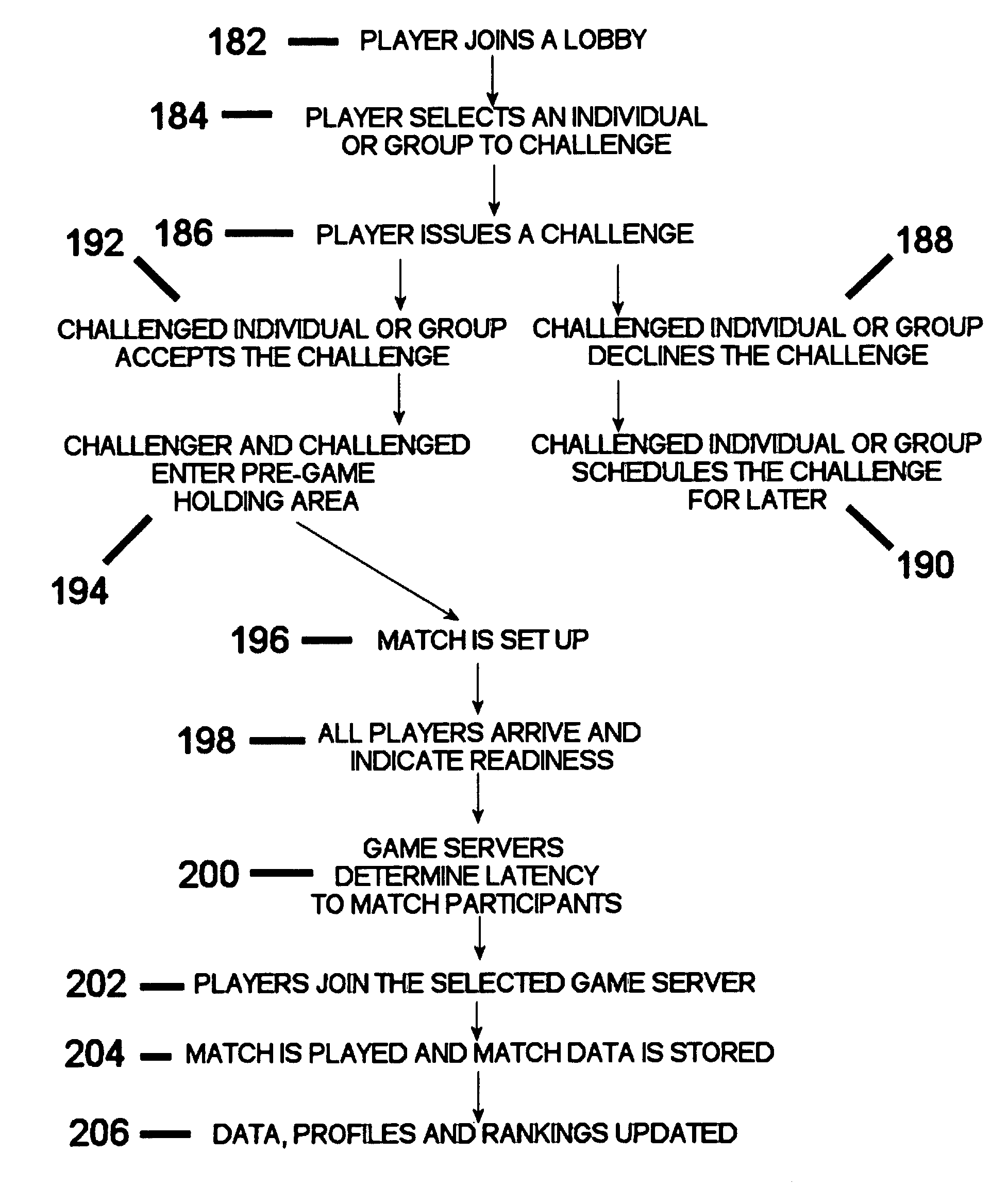
System and method for network interactive game match-up and server selection
A computer-based system and method of interactive game challenge and acceptance for finding an appropriate game server for one or more individuals to play on given skill level, latency and numerous other factors; setting up the game server with the proper parameters; connecting those individuals to that server; logging the details of the match; updating those details to a database and updating or creating statistics related to those individuals for display and ranking purposes to be used for later match-ups.
Owner:PROFESSIONAL INTERACTIVE ENTERTAINMENT
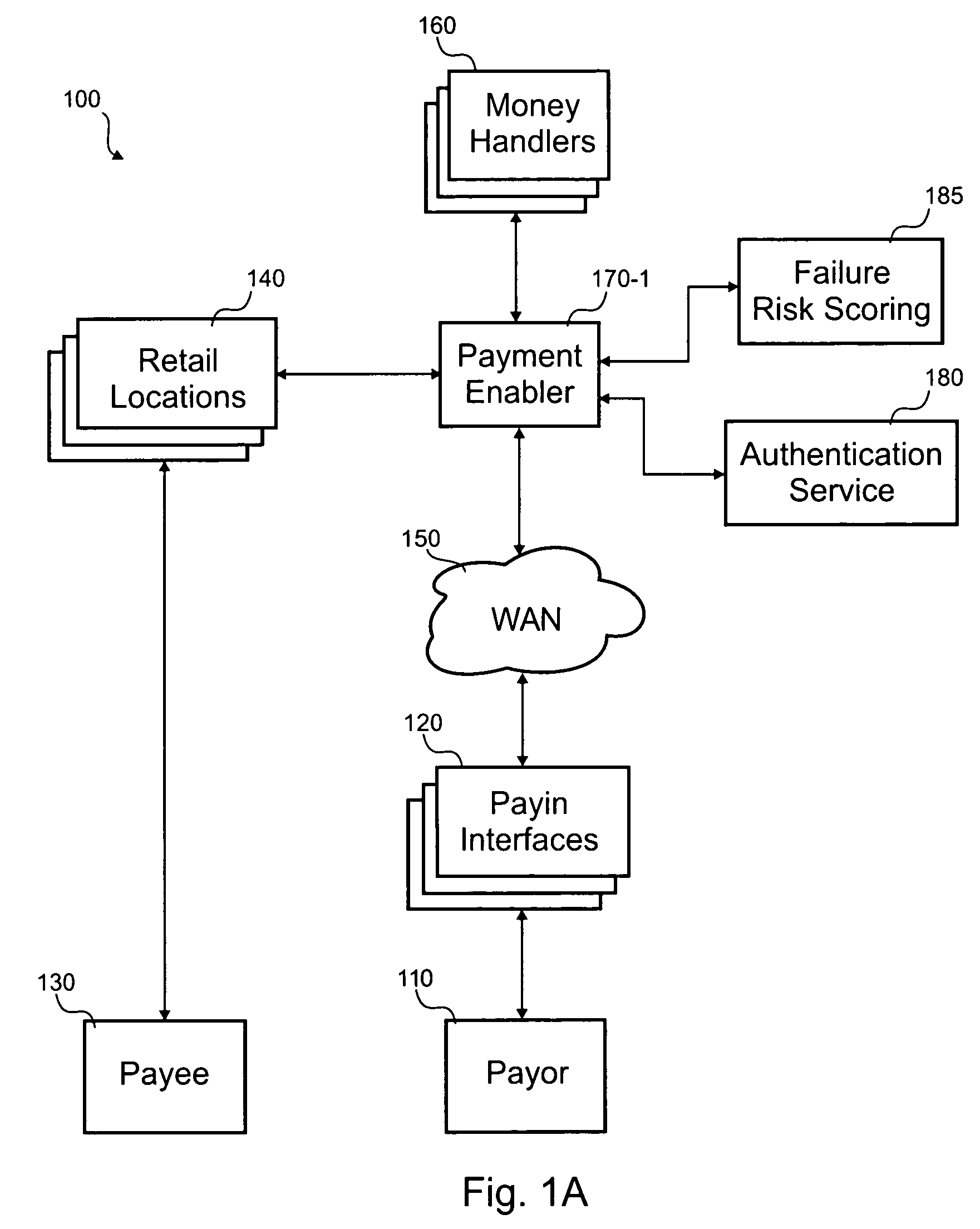
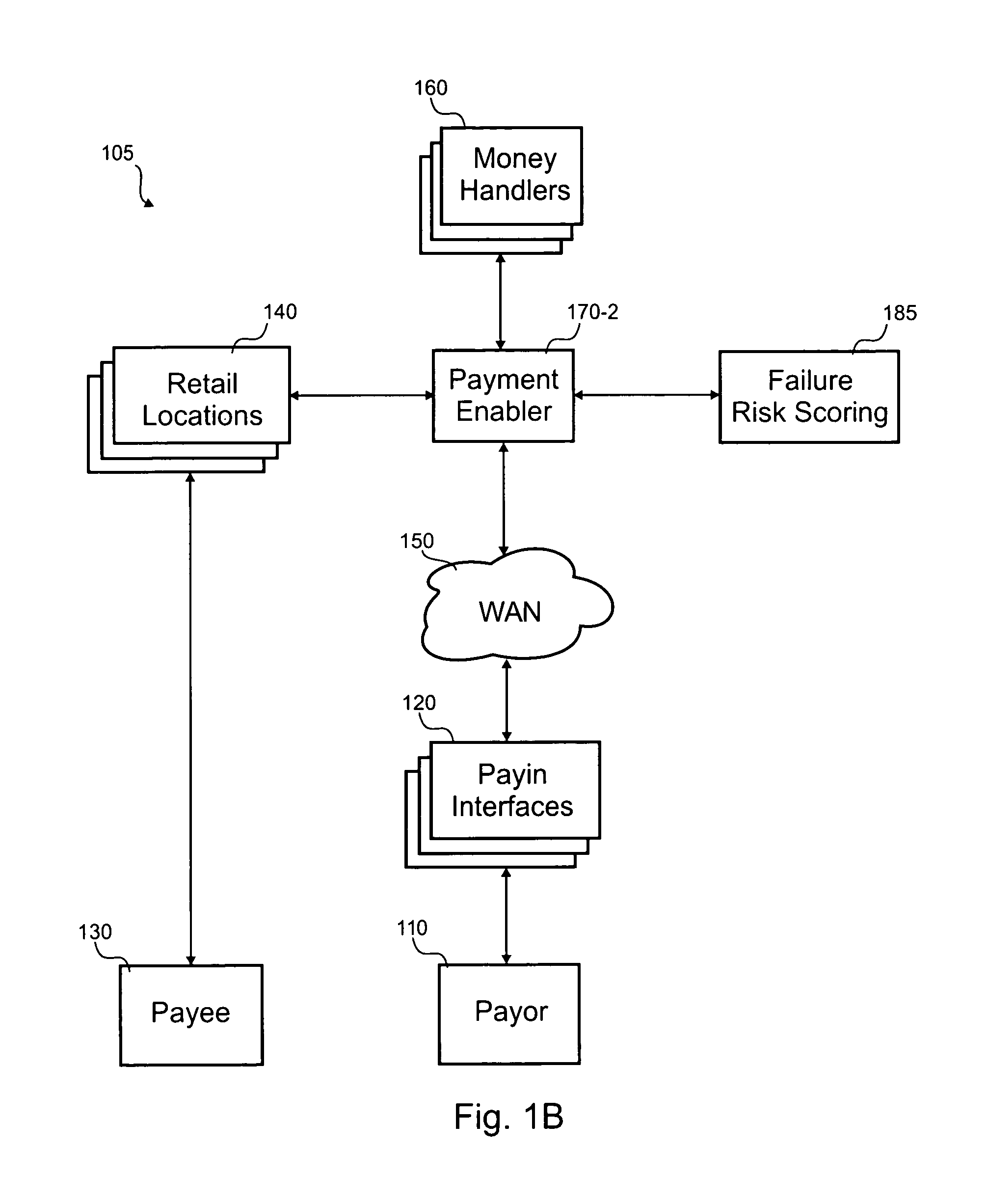
Authentication for online money transfers
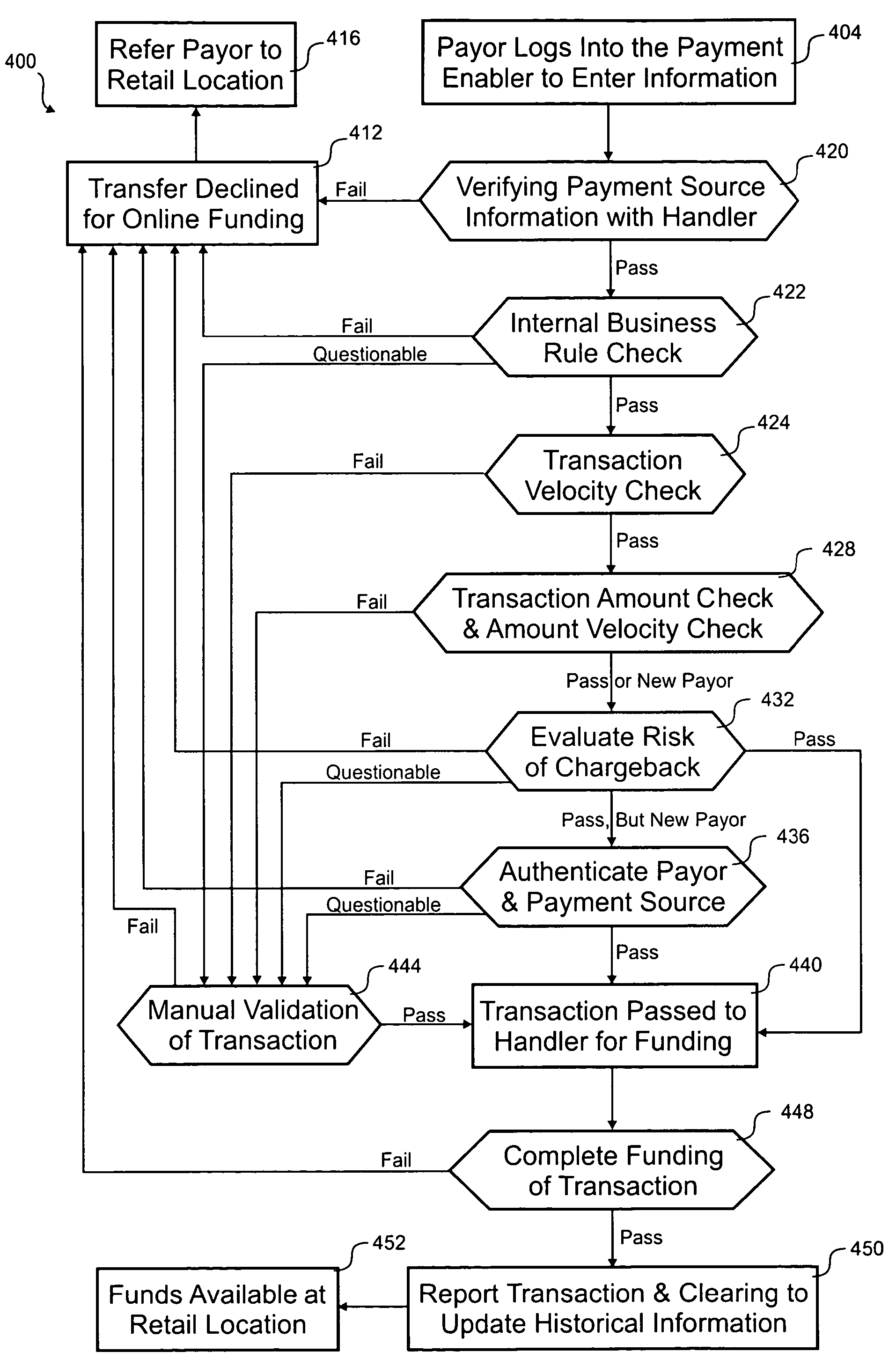
According to the invention, a method for processing a transaction where the transaction is initiated by a payor online, but paid to a payee in-person, is disclosed. In one step, payor information is accepted at a location that located across a wide area network from the payor. Transaction information and payment source information is also accepted at the location. The transaction information includes an amount and a payee identifier and the payment source information includes account details associated with an account of the payor at a money handler. A risk related to a likelihood that the transaction will complete successfully is evaluated. Validating that the payment source information is associated with the payor is manually performed if the risk is excessive. The risk can generally be reduced by the manual validation. The money handler is billed for at least the amount. It is determined if the money handler settles the amount. Historical information on the transaction is stored.
Owner:THE WESTERN UNION CO
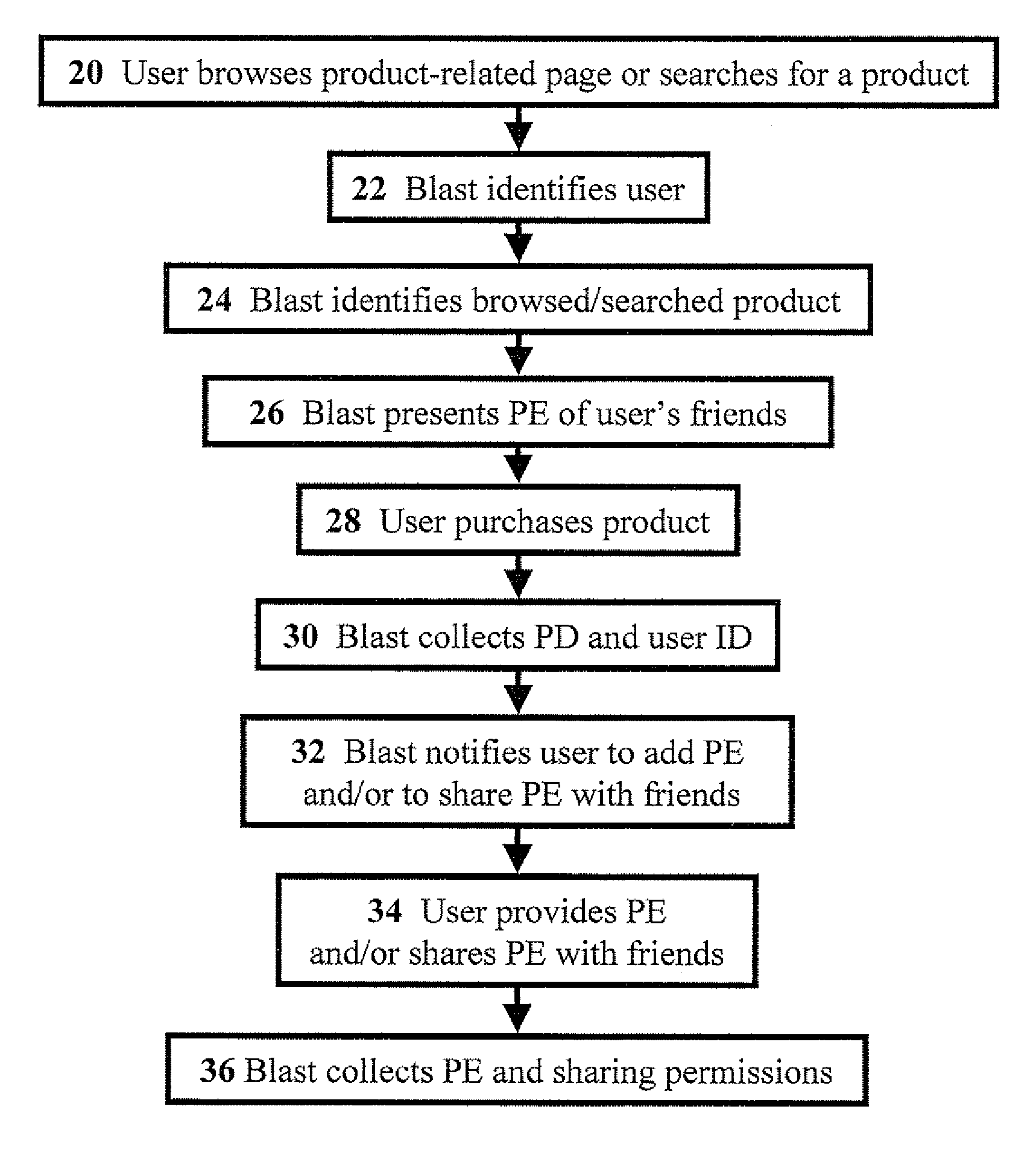
Systems and methods for e-commerce and mobile networks for providing purchase experiences of friends in a social network
InactiveUS20090070228A1Eliminate needImprove abilitiesData acquisition and loggingCommerceRelevant informationE-commerce
Methods, for facilitating electronic commerce using a social network, including: registering users on a social-network product-review site, wherein each user can be connected to other users by designating the other users as friends; identifying product purchases, of the users, made in merchant locations; collecting purchase details, and associated-user identities; sending a notification to an associated user requesting a user-specific product review from the associated user upon the associated user receiving the purchase details associated with the associated user; obtaining the user-specific product review and permissions from the associated user, wherein the permissions designate to share the user-specific product review and a relevant associated-user identity with associated-user friends; determining product-related information being accessed in various locations by a product-seeking user; ascertaining an identity of the product-seeking user; and presenting related-product reviews, based on the product-related information and related permissions, of user-related friends to the product-seeking user in the various locations.
Owner:SOCIAL FABRICS
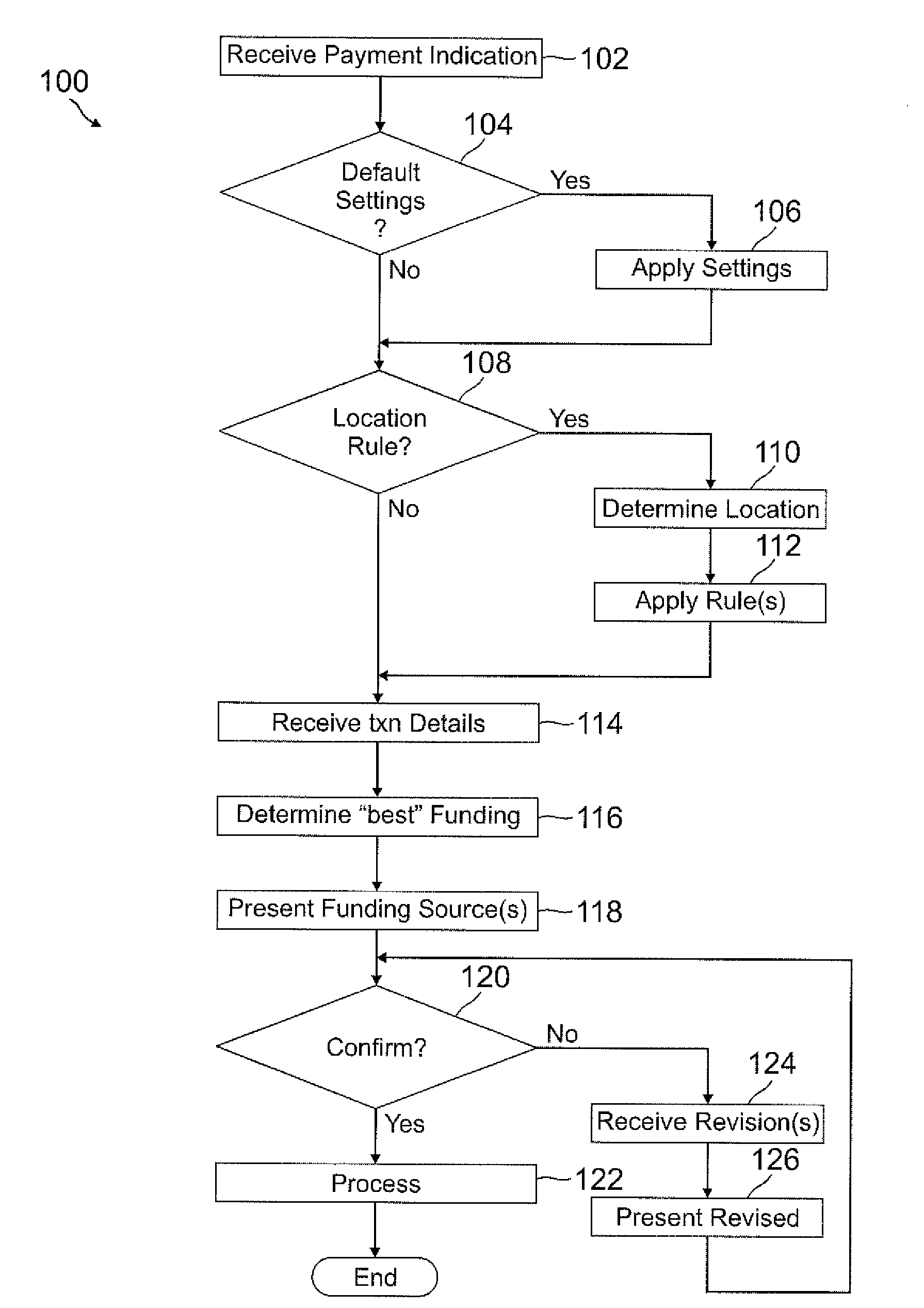
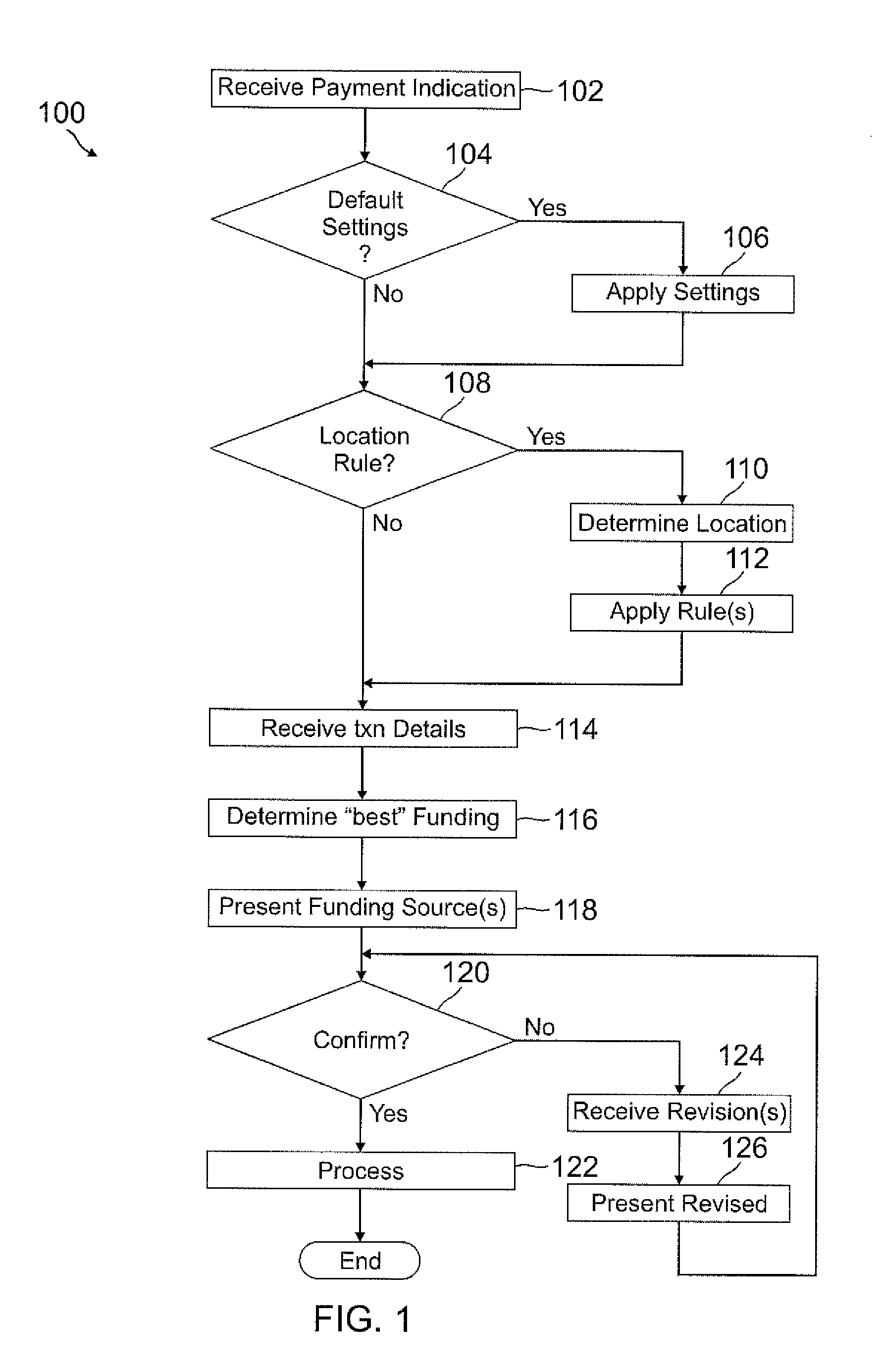
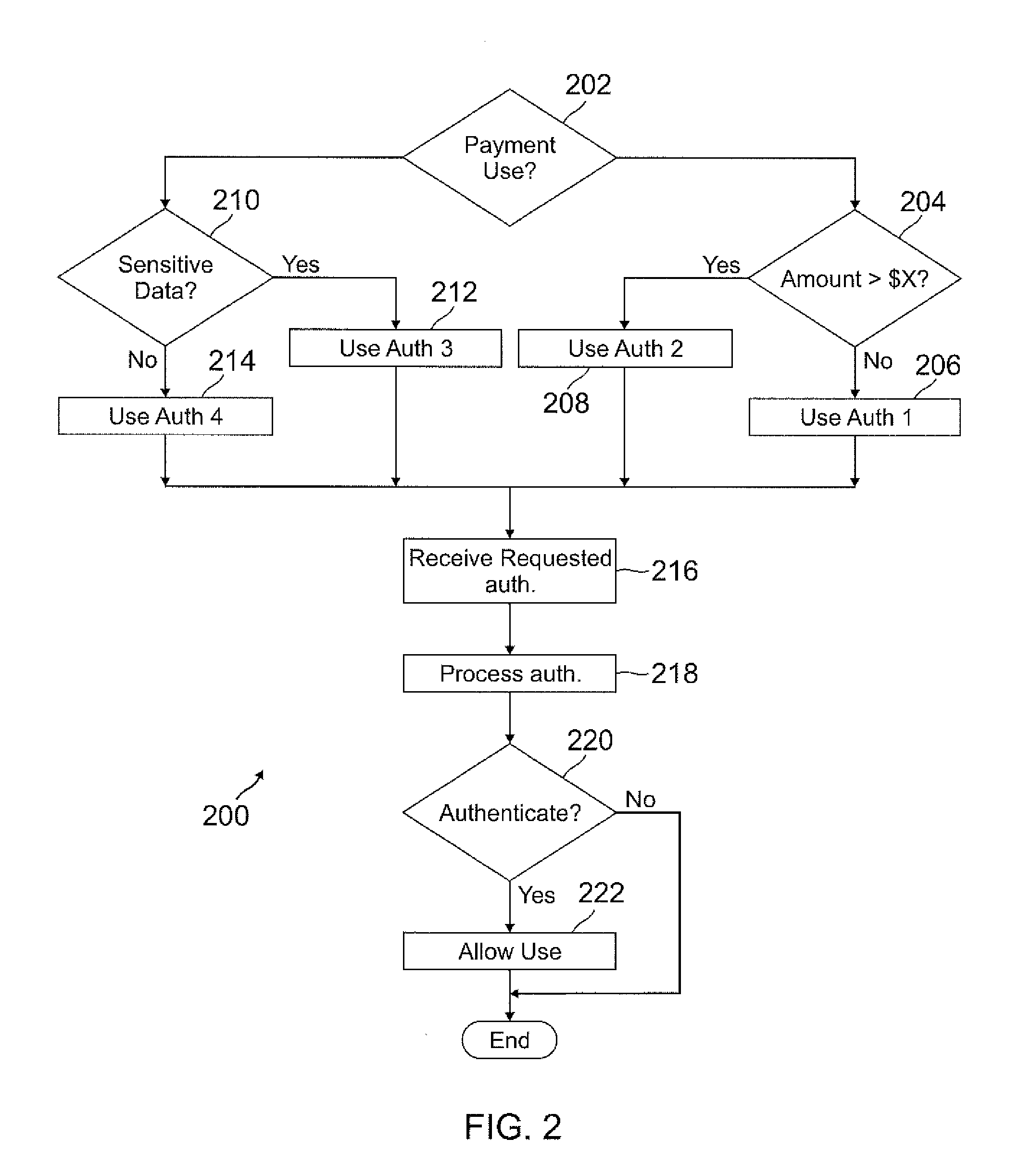
Smart wallet
A user's smart phone is used for payments and holding information, similar to what is contained in a physical wallet. Depending on transaction details, user preferences, and location, one or more “best” funding instruments for the transaction are selected for the user, who may then revise if desired. Access to different functions or information within the phone may vary and require different authentication / security levels depending on type of use (e.g., payment or non-payment) and details of use (e.g., high payment amount vs. low payment amount, use of sensitive information vs. non-sensitive information).
Owner:PAYPAL INC
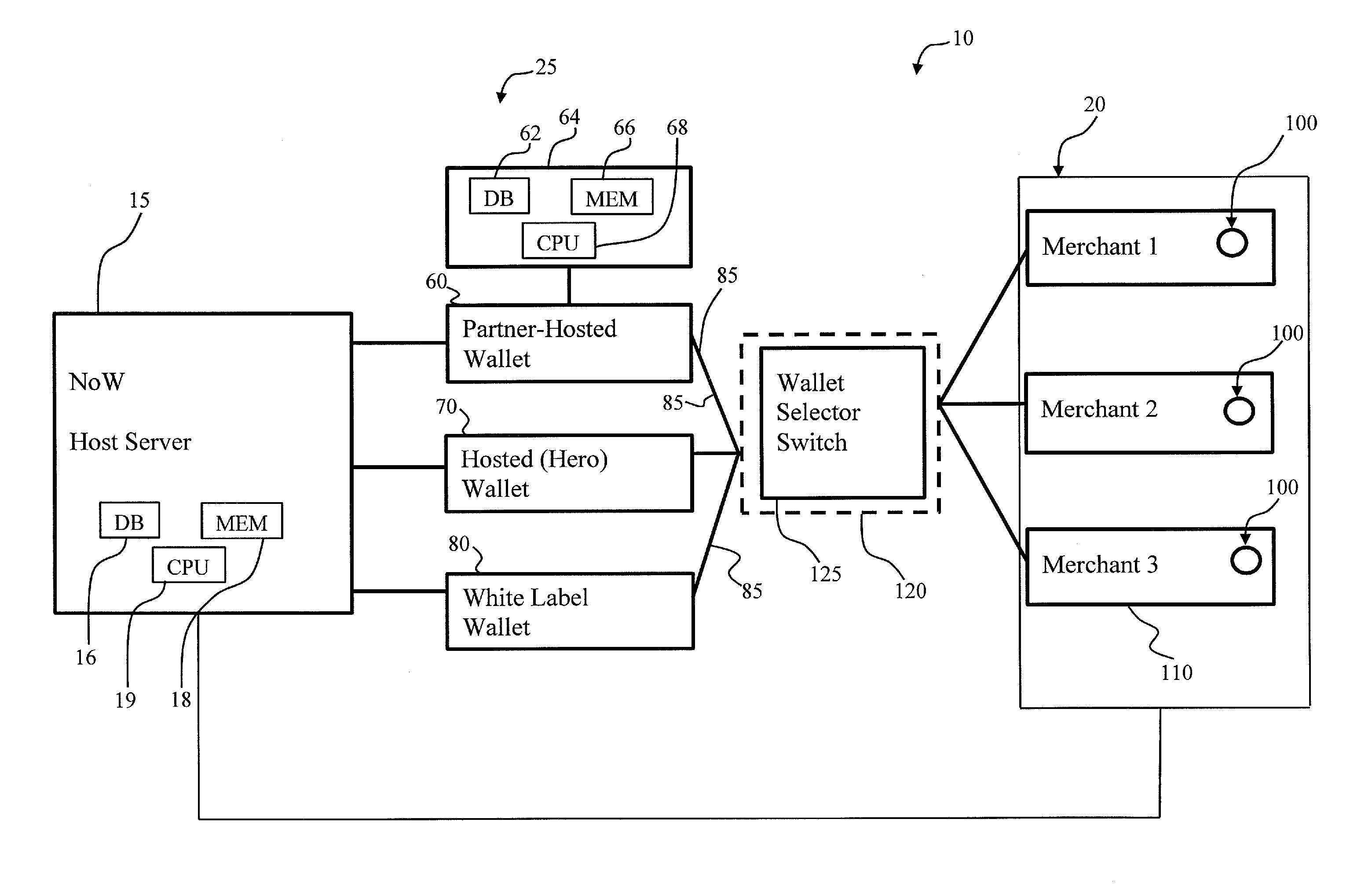
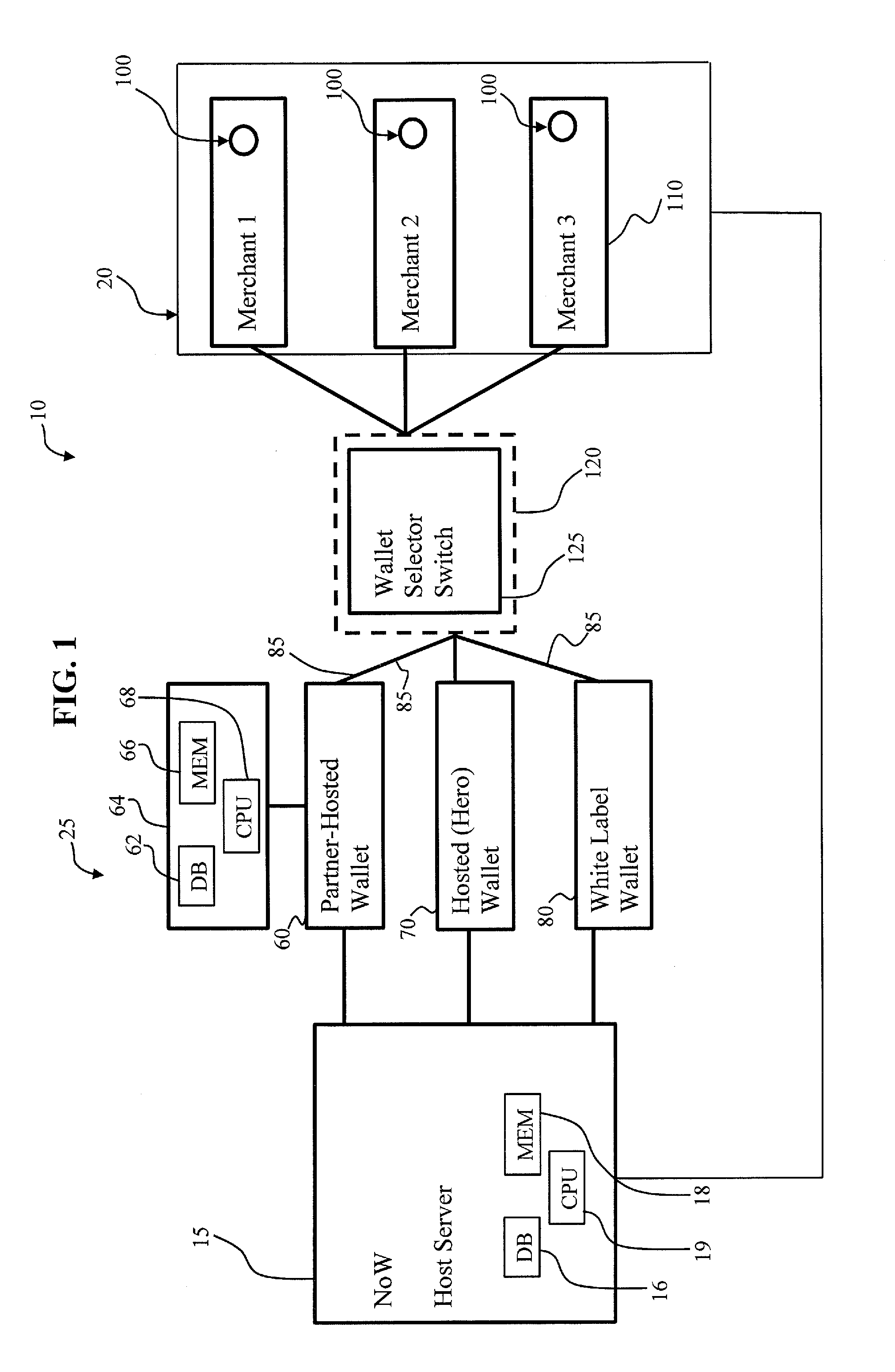
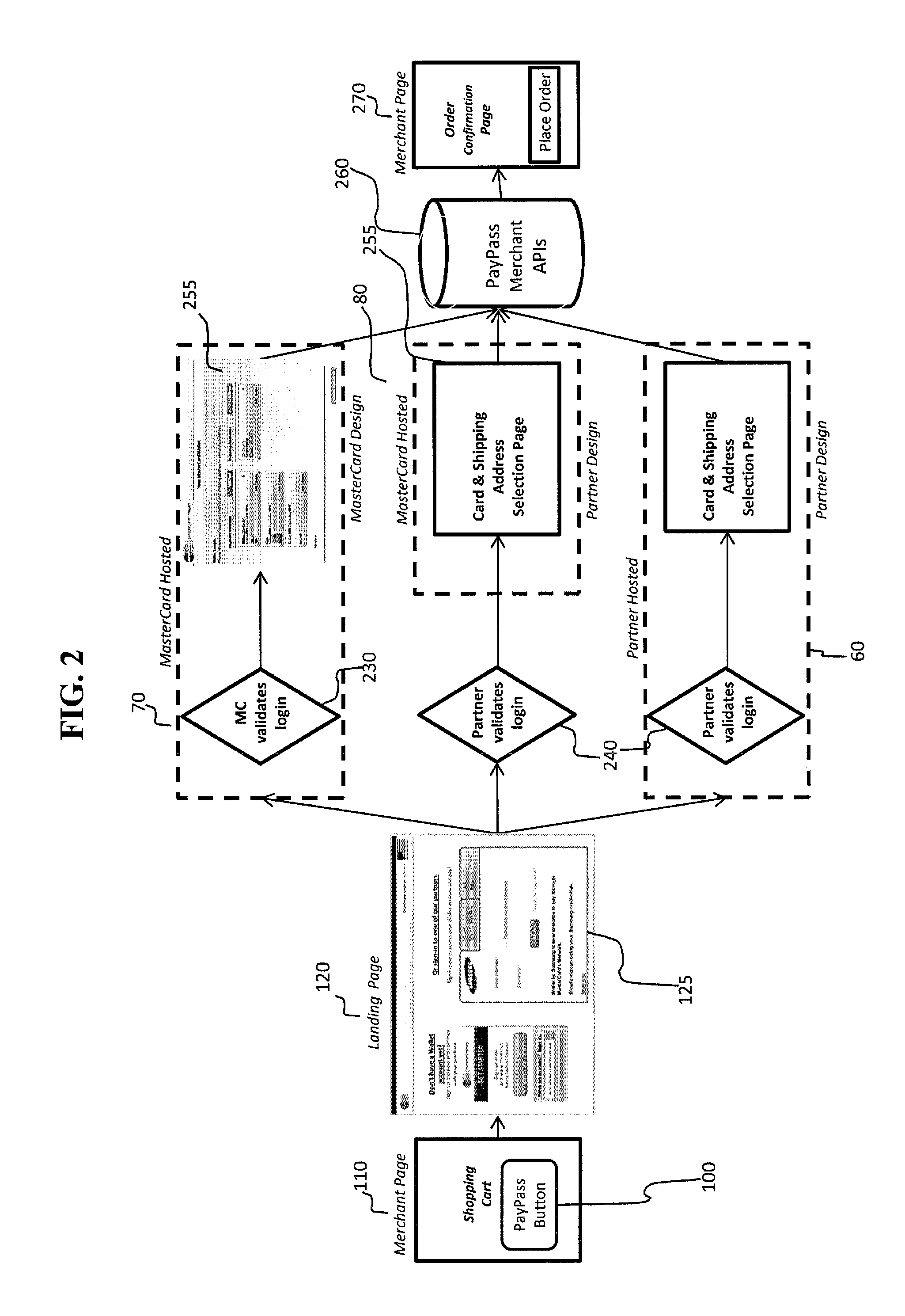
System and method to enable a network of digital wallets
A method for authorizing a digital wallet transaction initiated by a consumer from a merchant web site or app includes providing an acceptance mark on a merchant landing page associated with the merchant web site or app for initiating the digital wallet transaction, the acceptance mark comprising a link to a host server accessing an acceptance network for authorizing payment, the acceptance network comprising a plurality of digital wallets. A wallet selector switch allows selection of a wallet, the transaction is routed to the selected wallet, a payment card and shipping address are selected and the transaction is redirected back to the merchant with purchase details for authorizing and completing the digital wallet transaction. The wallets can include federated and non-federated cobranded wallets and partner-hosted wallets. Direct provisioning with partner credentials and automatic update of consumer details is provided in a federated cobranded wallet.
Owner:MASTERCARD INT INC
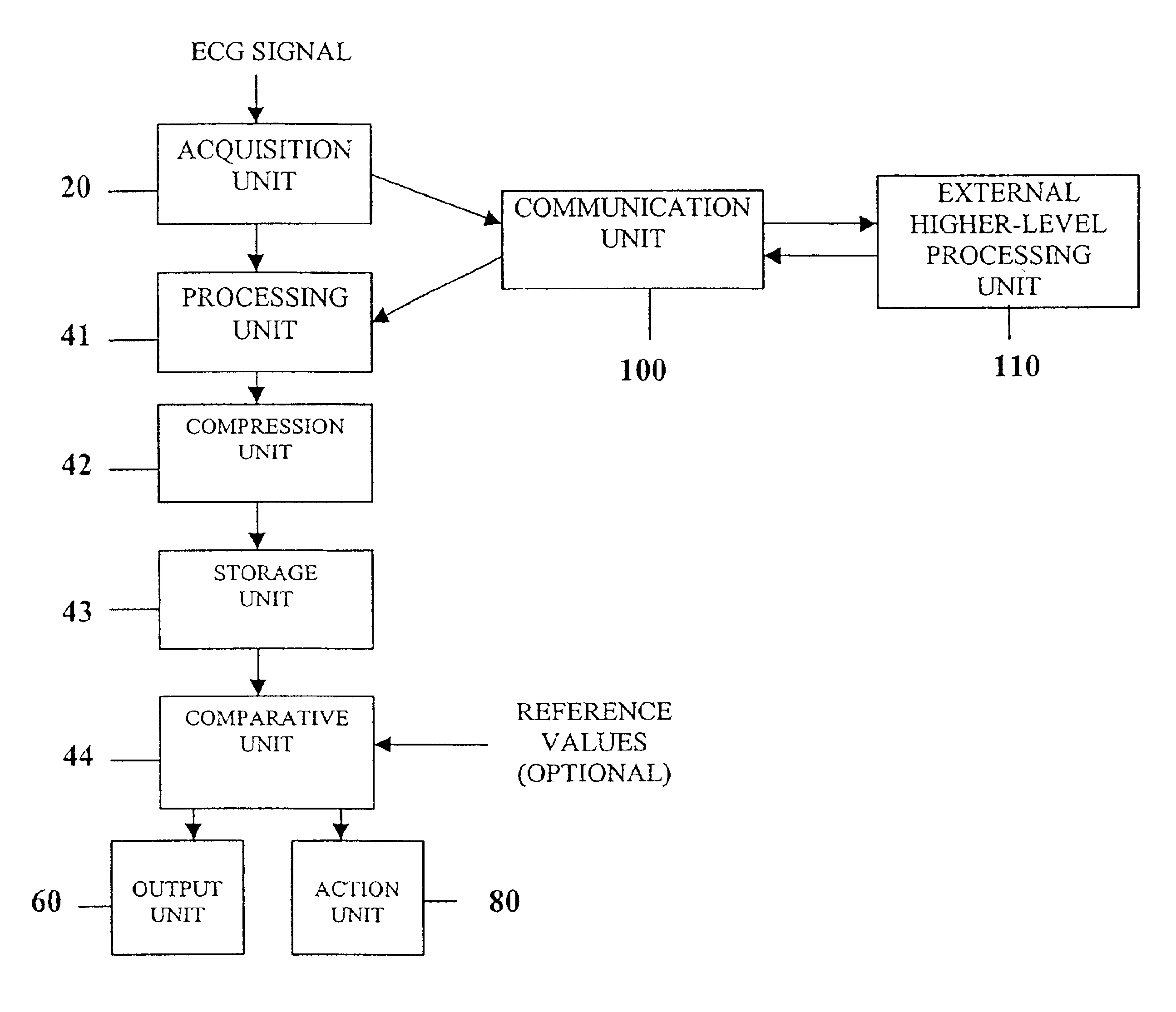
System and device for multi-scale analysis and representation of physiological data
InactiveUS6925324B2Easy to analyzeIncrease computing resourcesElectrocardiographySensorsReal time analysisT wave
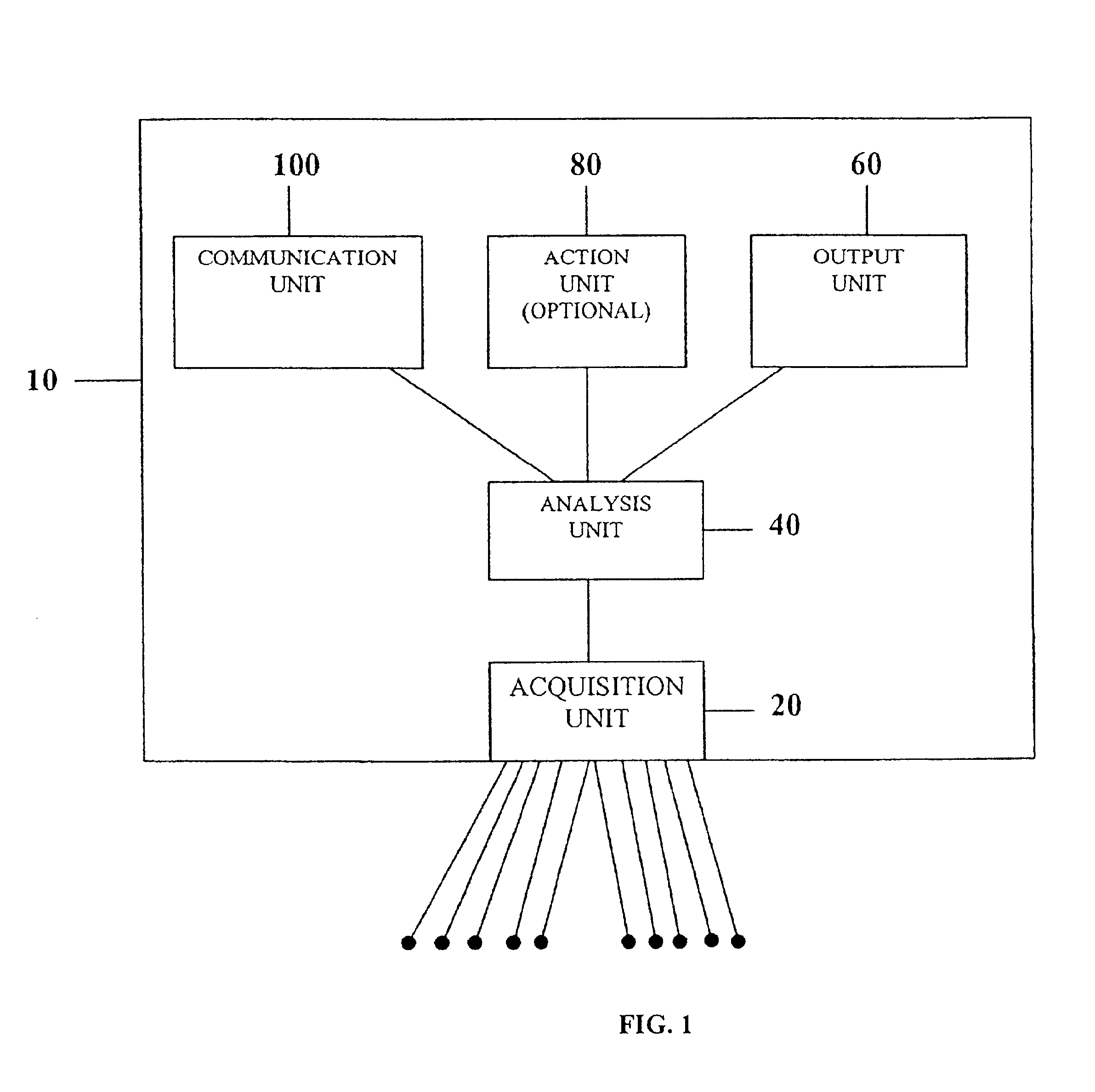
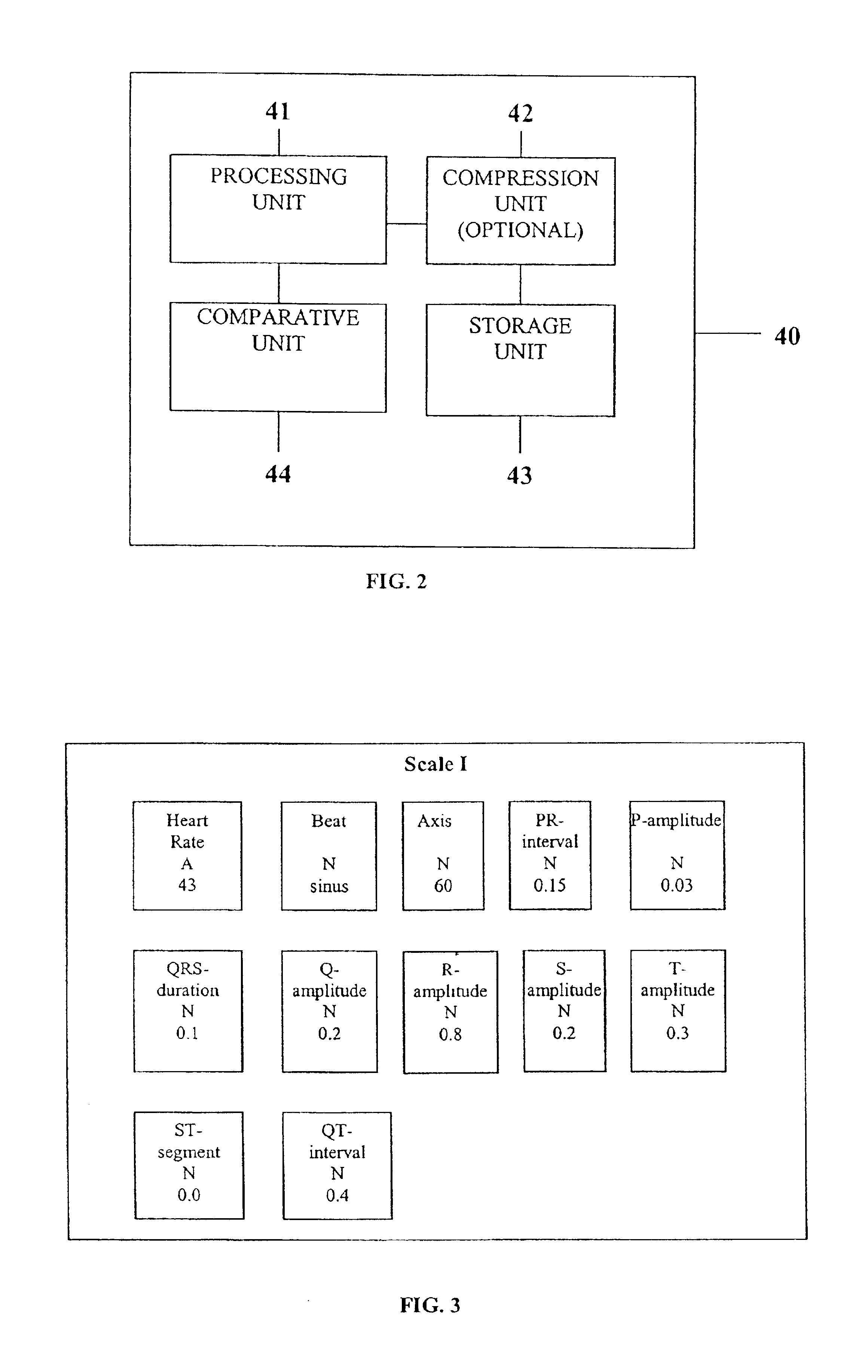
System comprised of a medical device and method for analyzing physiological and health data and representing the most significant parameters at different levels of detail which are understandable to a lay person and a medical professional. Low, intermediate and high-resolution scales can exchange information between each other for improving the analyses; the scales can be defined according to the corresponding software and hardware resources. A low-resolution Scale I represents a small number of primary elements such as intervals between the heart beats, duration of electrocardiographic PQ, QRS, and QT-intervals, amplitudes of P-, Q-, R-, S-, and T-waves. This real-time analysis is implemented in a portable device that requires minimum computational resources. The set of primary elements and their search criteria can be adjusted using intermediate or high-resolution levels. At the intermediate-resolution Scale II, serial changes in each of the said elements can be determined using a mathematical decomposition into series of basis functions and their coefficients. This scale can be implemented using a specialized processor or a computer organizer. At the high-resolution Scale III, combined serial changes in all primary elements can be determined to provide complete information about the dynamics of the signal. This scale can be implemented using a powerful processor, a network of computers or the Internet. The system can be used for personal or group self-evaluation, emergency or routine ECG analysis, or continuous event, stress-test or bed-side monitoring.
Owner:SHUSTERMAN VLADIMIR
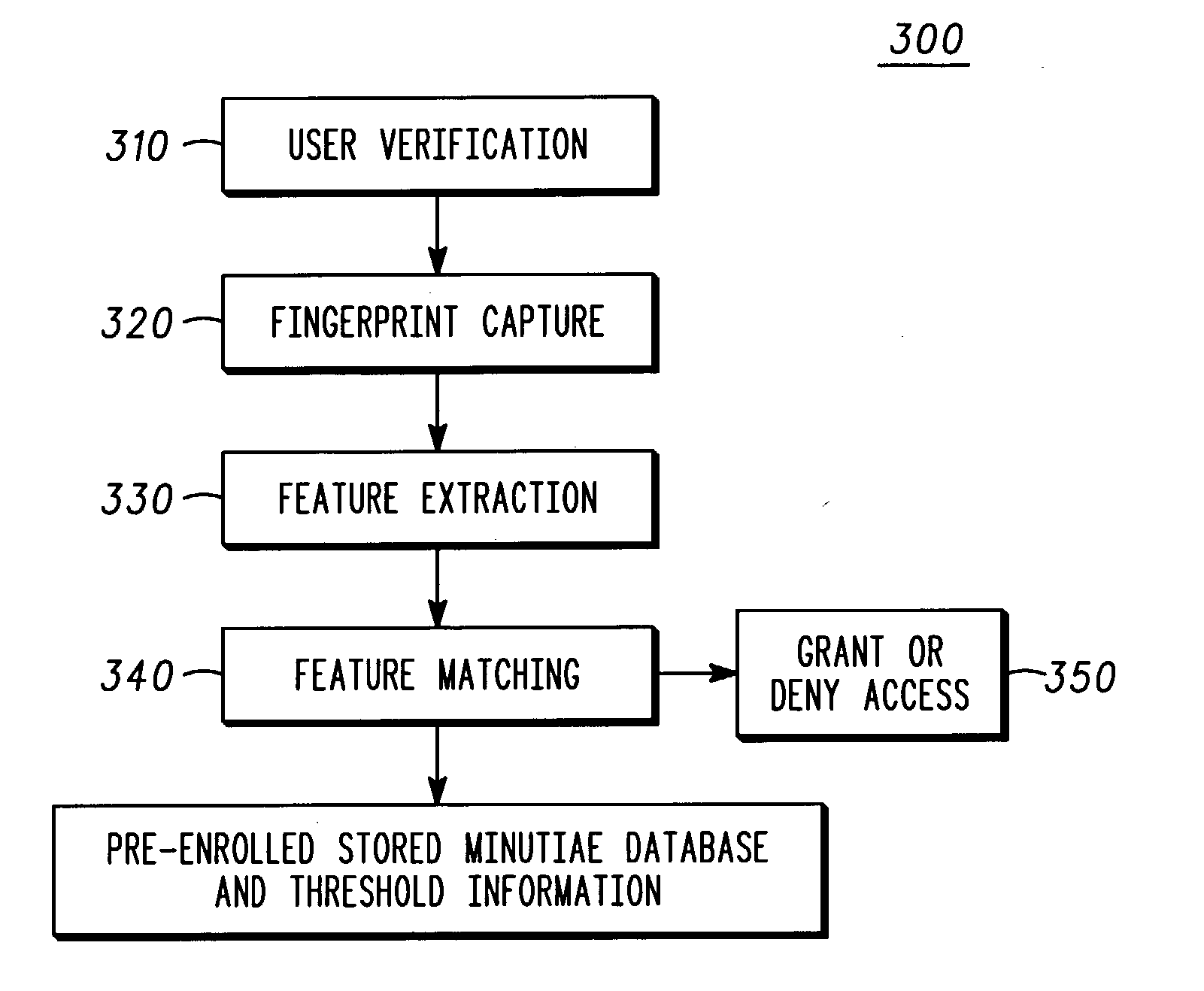
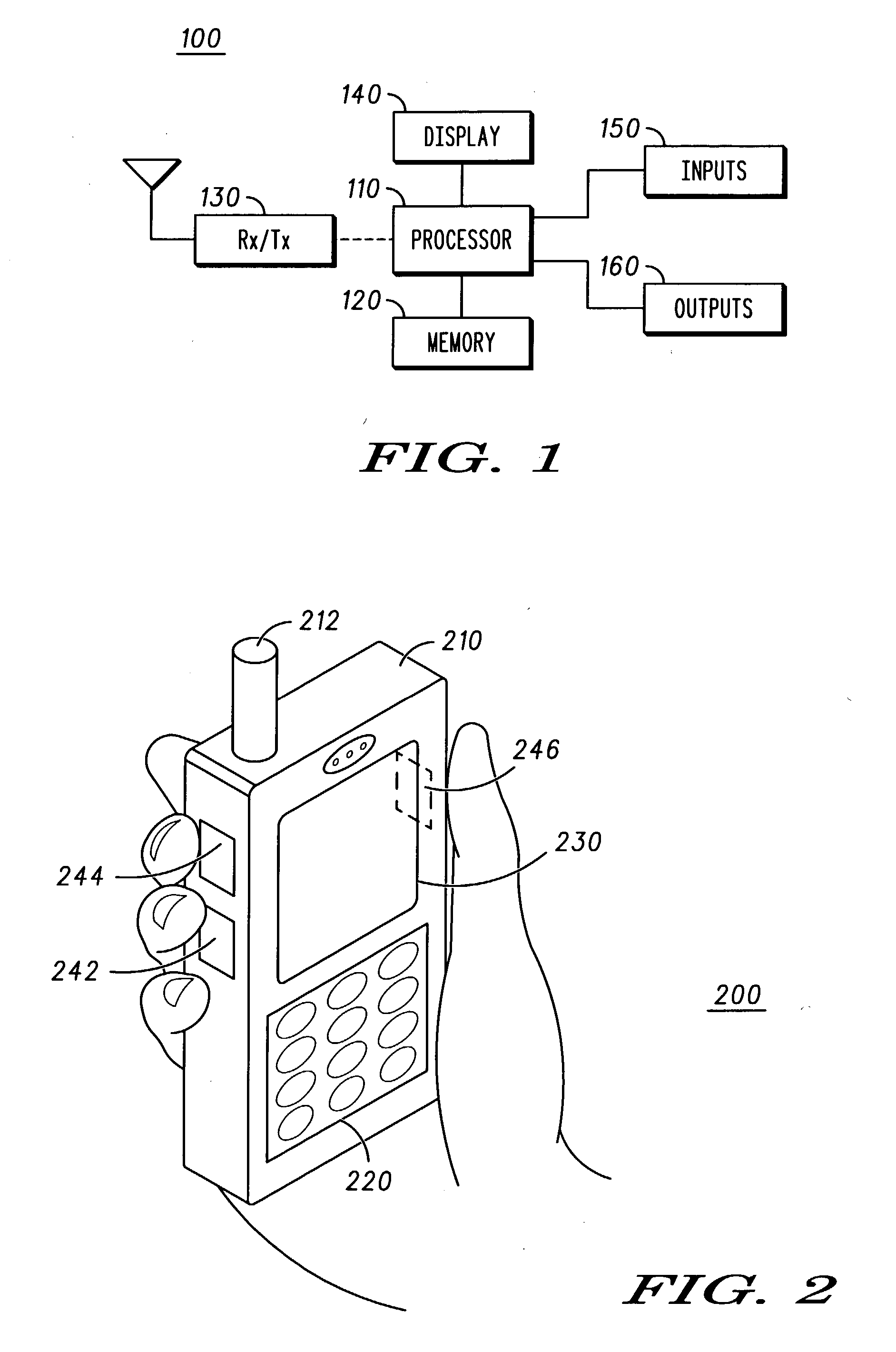
Fingerprint security systems in handheld electronic devices and methods therefor
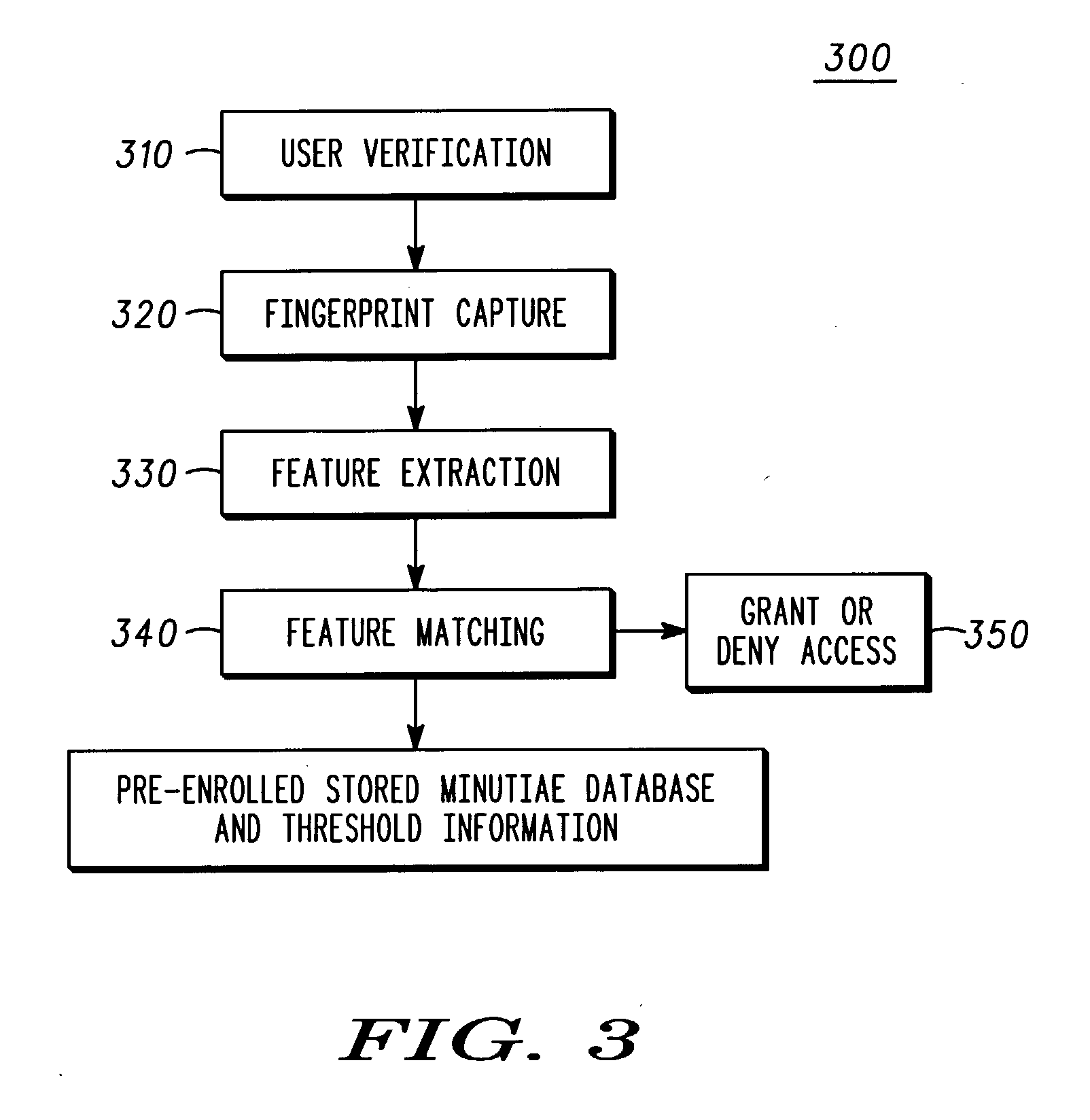
Fingerprint image processing methods for fingerprint security systems, for example, in wireless communications devices, including capturing fingerprint images (320), identifying features from images (330), matching the identified features with reference features (340), and providing access to the device based upon feature matching (350) results. In one embodiment, minutiae features are extracted from the image and matched to reference minutiae features.
Owner:MOTOROLA INC
Media Fingerprinting and Identification System
ActiveUS20100318515A1Highly accurate in findingMany typesMultimedia data indexingData processing applicationsReference databaseNumerical descriptors
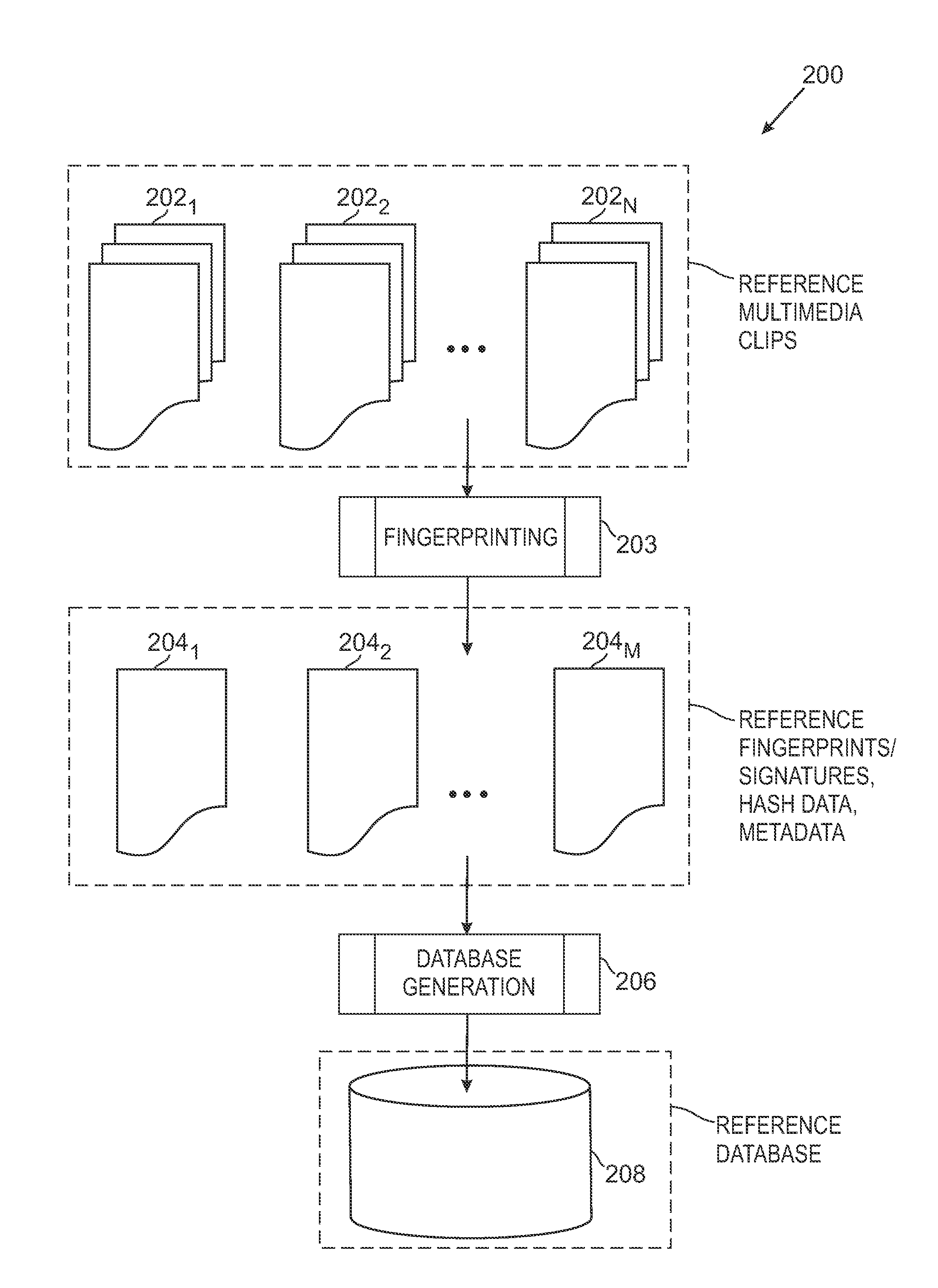
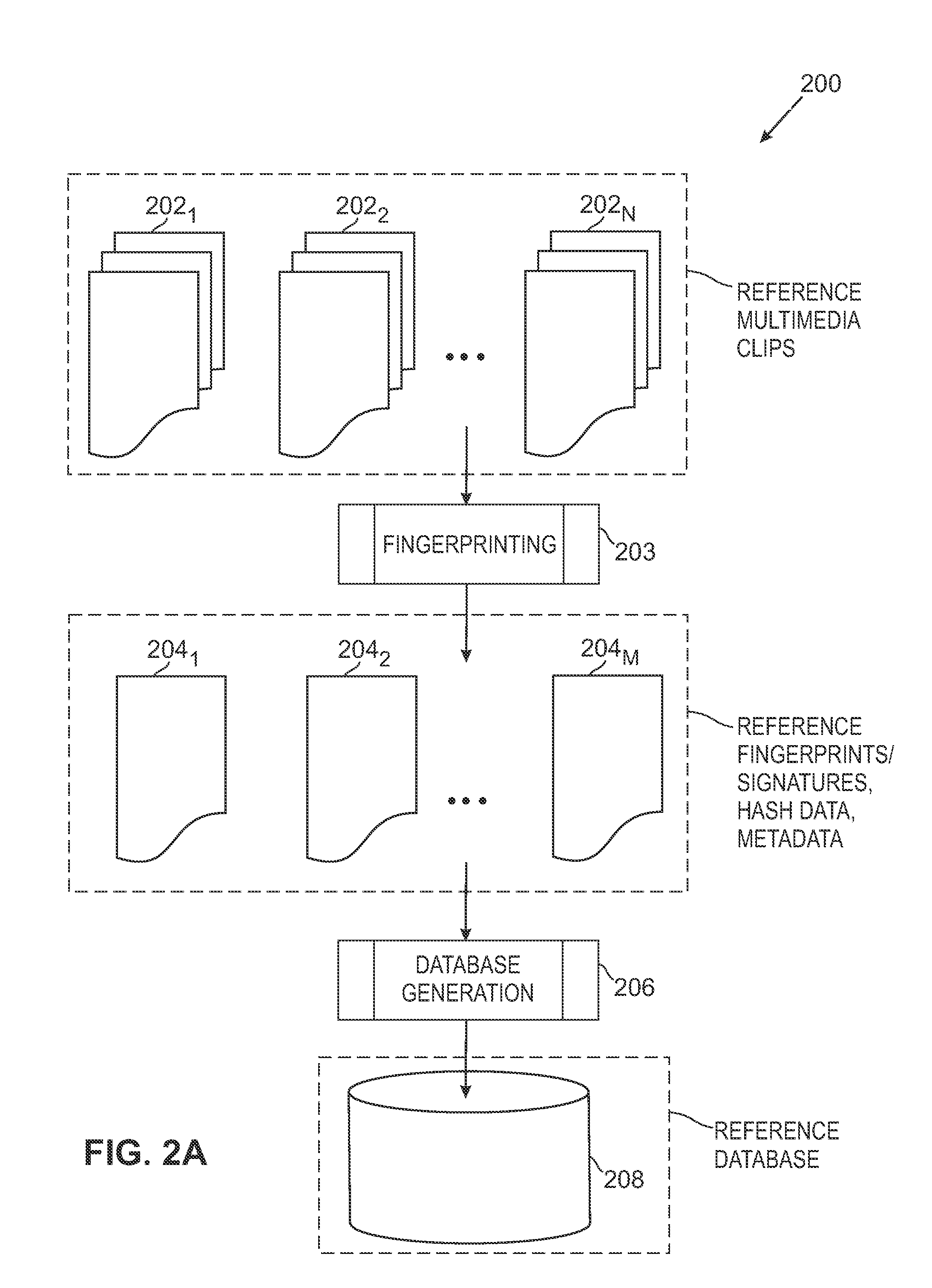
The overall architecture and details of a scalable video fingerprinting and identification system that is robust with respect to many classes of video distortions is described. In this system, a fingerprint for a piece of multimedia content is composed of a number of compact signatures, along with traversal hash signatures and associated metadata. Numerical descriptors are generated for features found in a multimedia clip, signatures are generated from these descriptors, and a reference signature database is constructed from these signatures. Query signatures are also generated for a query multimedia clip. These query signatures are searched against the reference database using a fast similarity search procedure, to produce a candidate list of matching signatures. This candidate list is further analyzed to find the most likely reference matches. Signature correlation is performed between the likely reference matches and the query clip to improve detection accuracy.
Owner:ROKU INCORPORATED
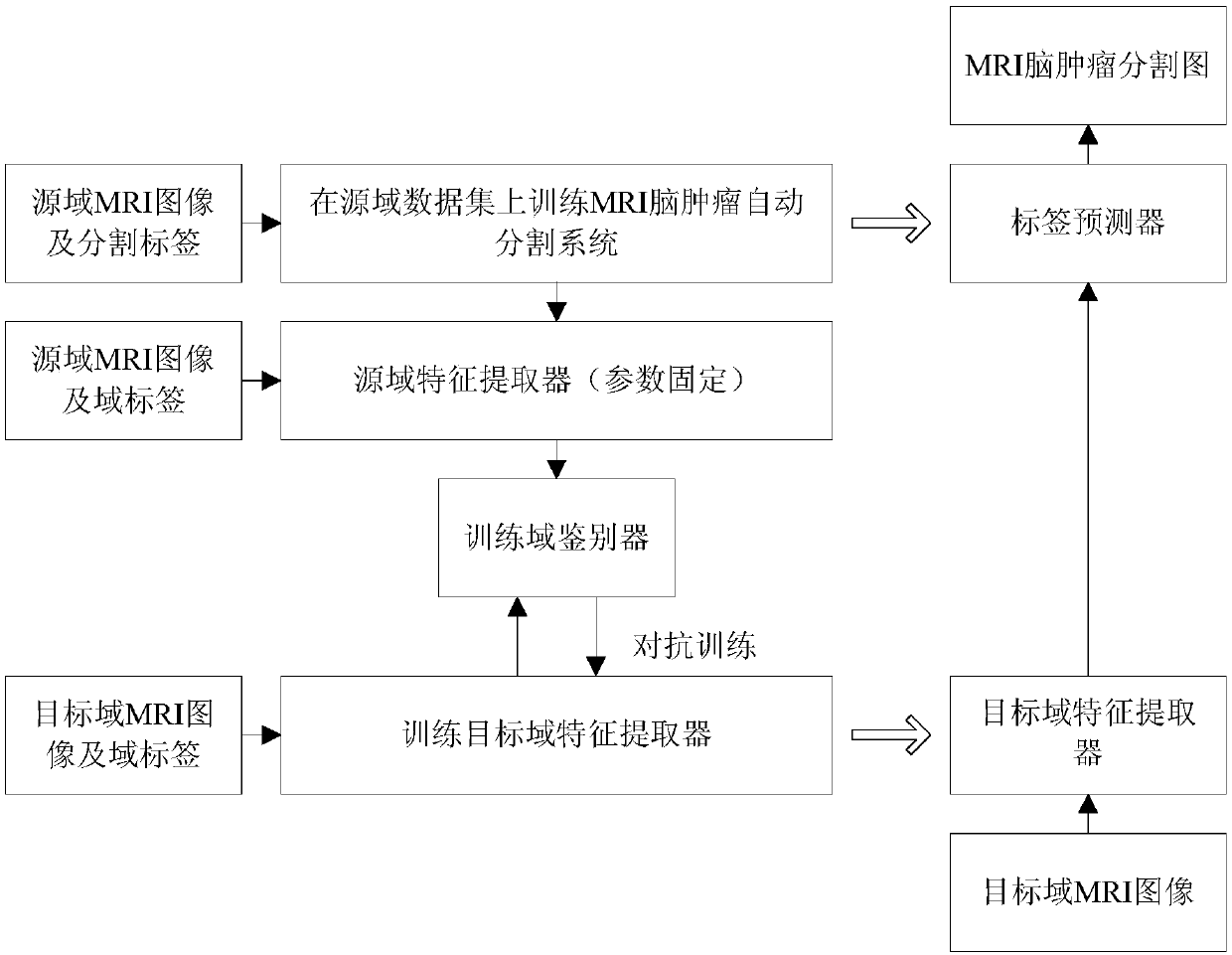
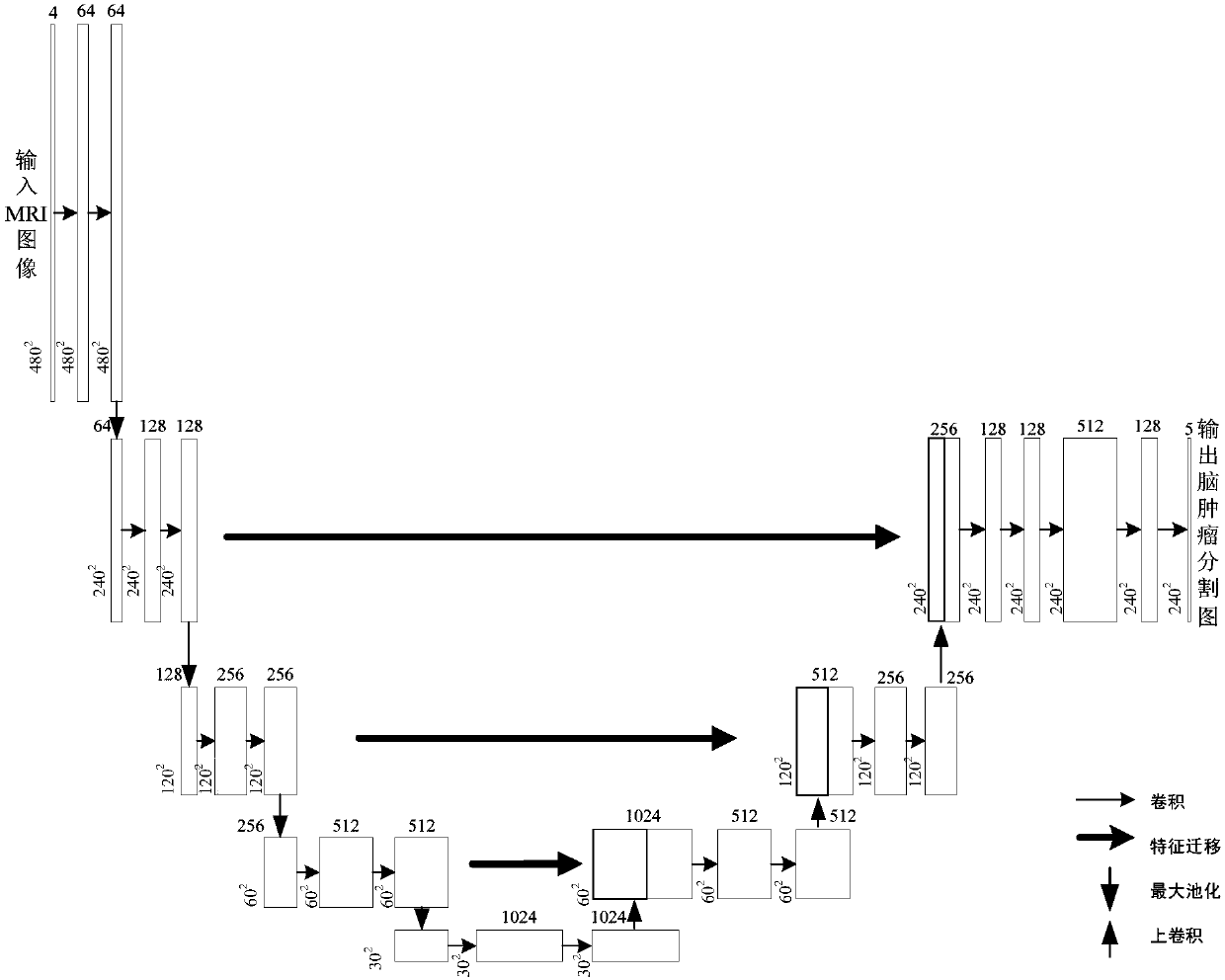
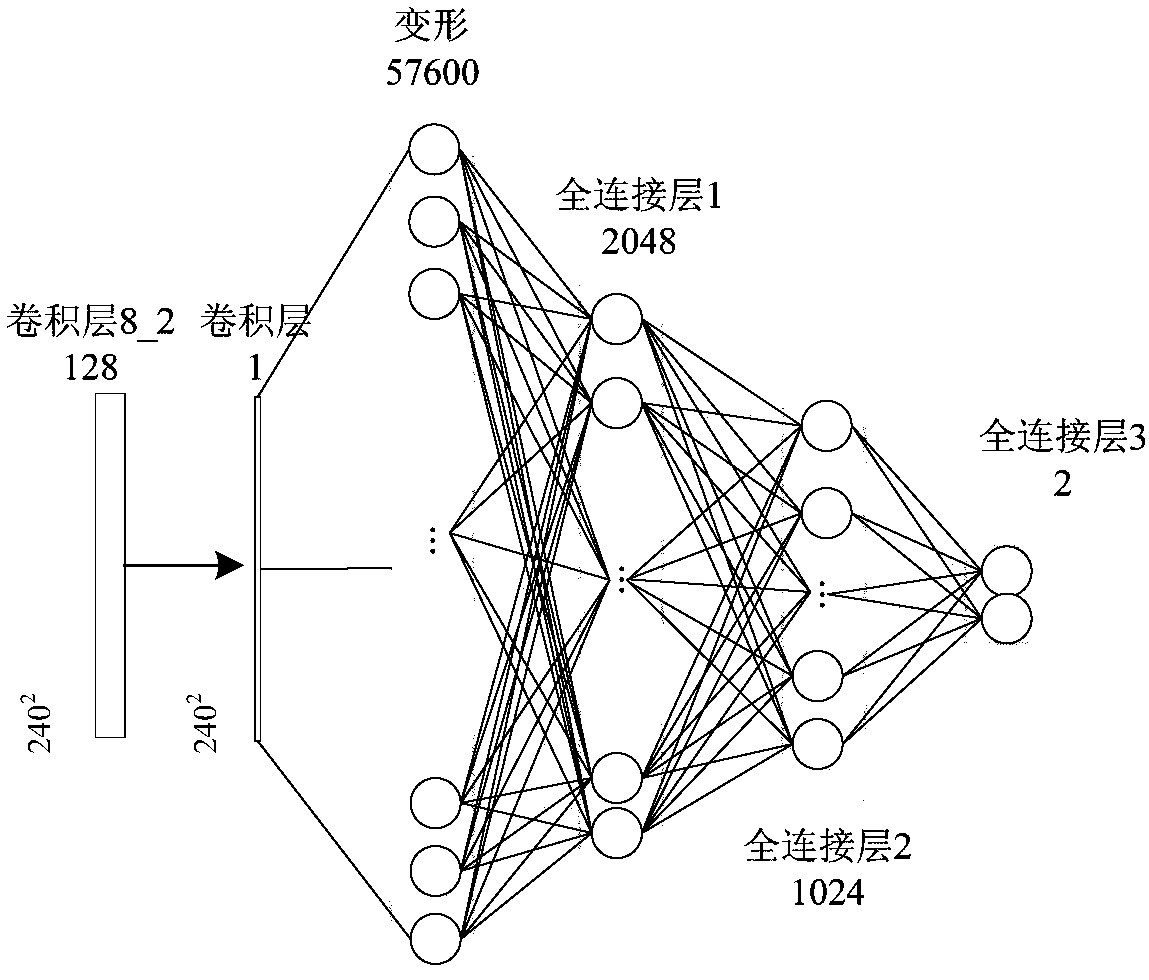
Unsupervised domain-adaptive brain tumor semantic segmentation method based on deep adversarial learning
InactiveCN108062753AAccurate predictionEasy to trainImage enhancementImage analysisDiscriminatorNetwork model
The invention provides an unsupervised domain-adaptive brain tumor semantic segmentation method based on deep adversarial learning. The method comprises the steps of deep coding-decoding full-convolution network segmentation system model setup, domain discriminator network model setup, segmentation system pre-training and parameter optimization, adversarial training and target domain feature extractor parameter optimization and target domain MRI brain tumor automatic semantic segmentation. According to the method, high-level semantic features and low-level detailed features are utilized to jointly predict pixel tags by the adoption of a deep coding-decoding full-convolution network modeling segmentation system, a domain discriminator network is adopted to guide a segmentation model to learn domain-invariable features and a strong generalization segmentation function through adversarial learning, a data distribution difference between a source domain and a target domain is minimized indirectly, and a learned segmentation system has the same segmentation precision in the target domain as in the source domain. Therefore, the cross-domain generalization performance of the MRI brain tumor full-automatic semantic segmentation method is improved, and unsupervised cross-domain adaptive MRI brain tumor precise segmentation is realized.
Owner:CHONGQING UNIV OF TECH
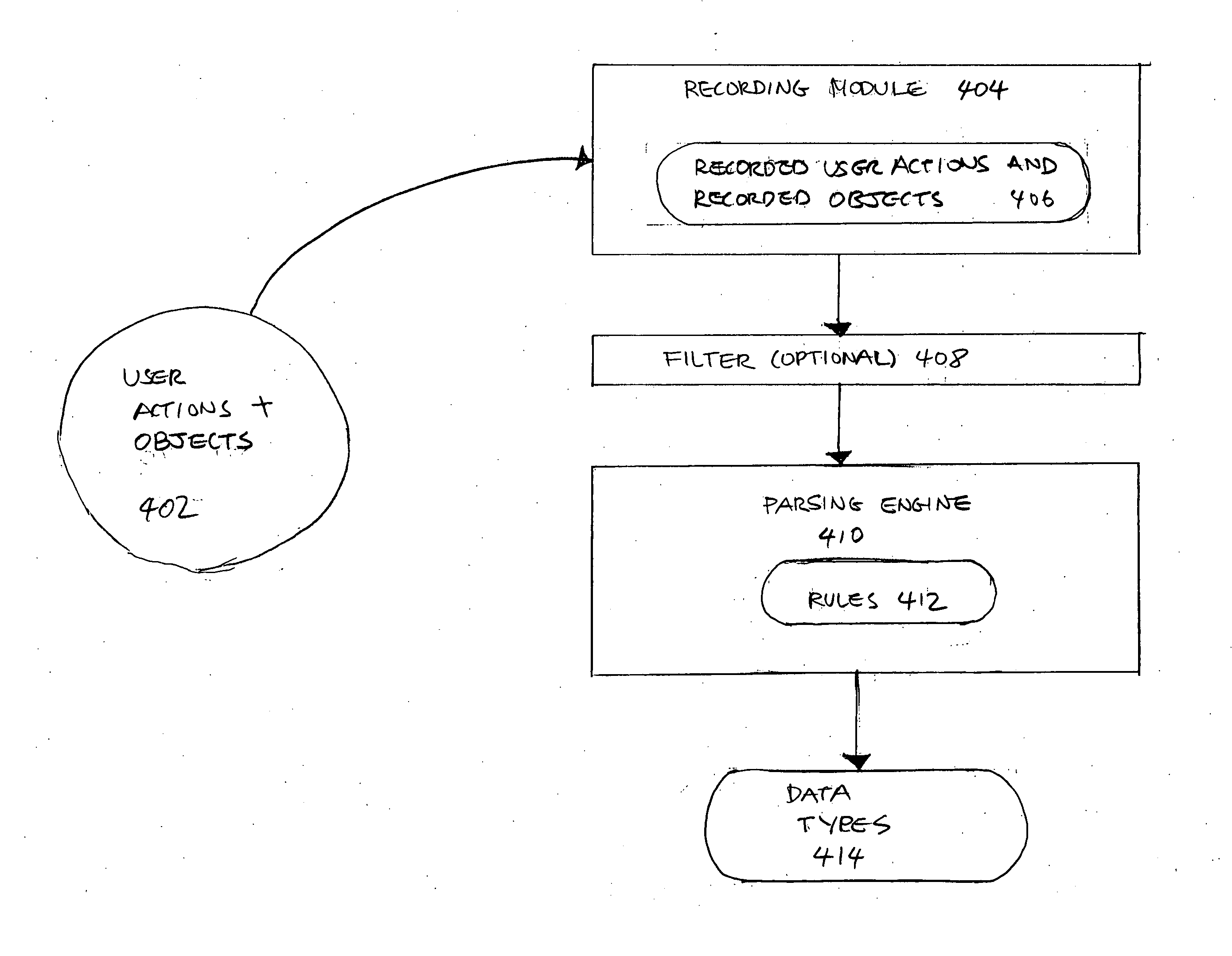
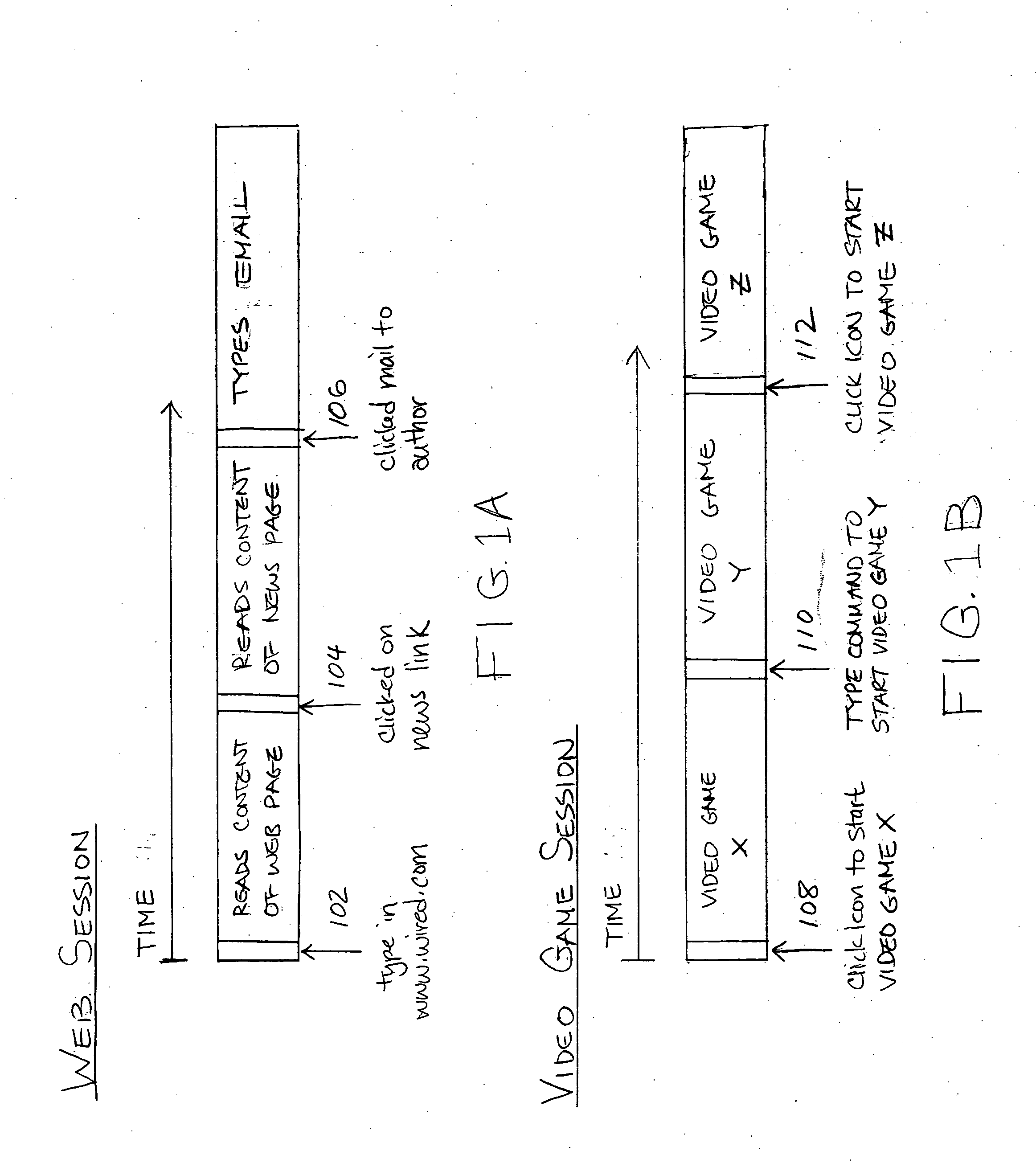
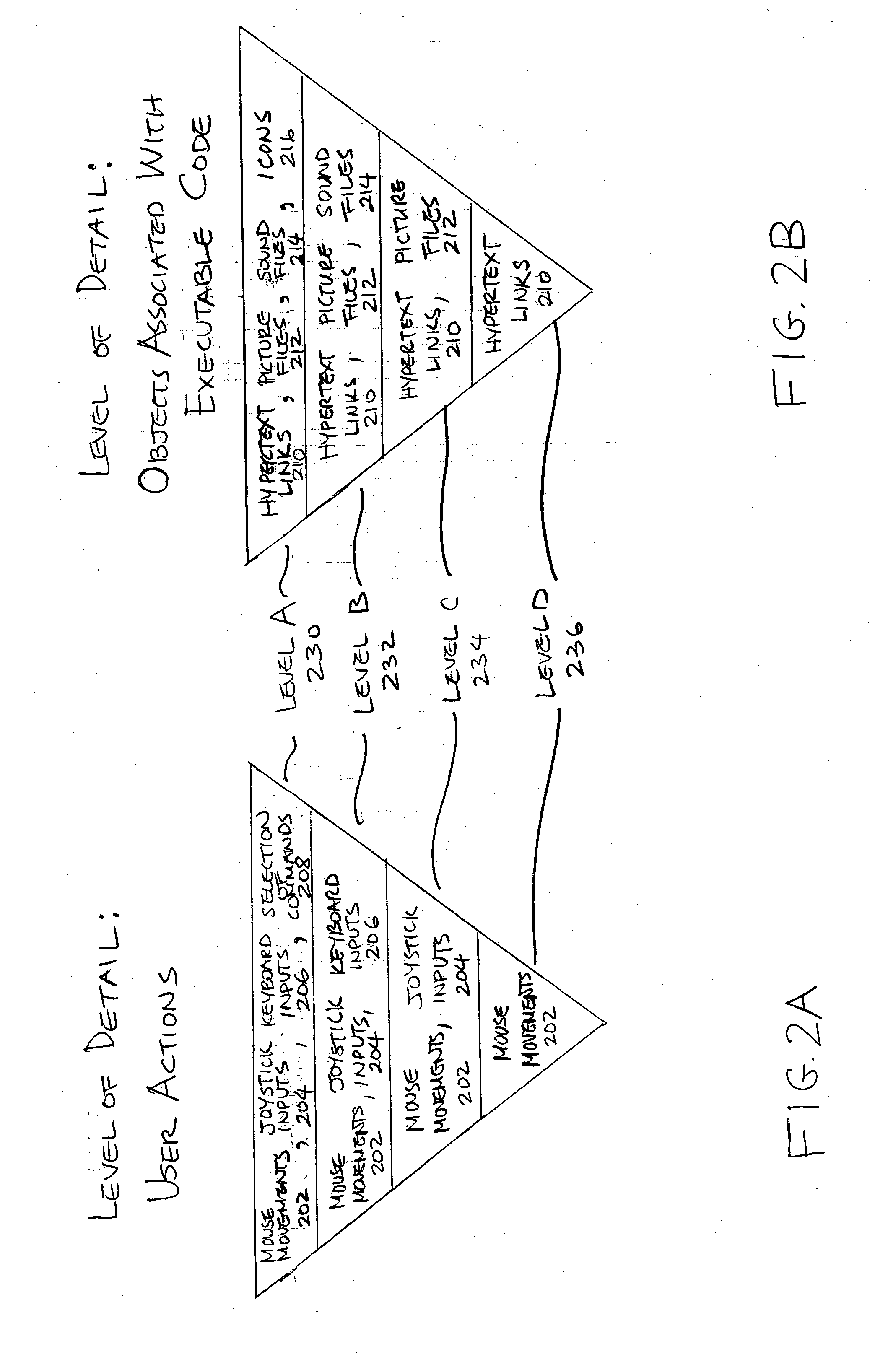
Methods and systems for recording user actions in computer programs
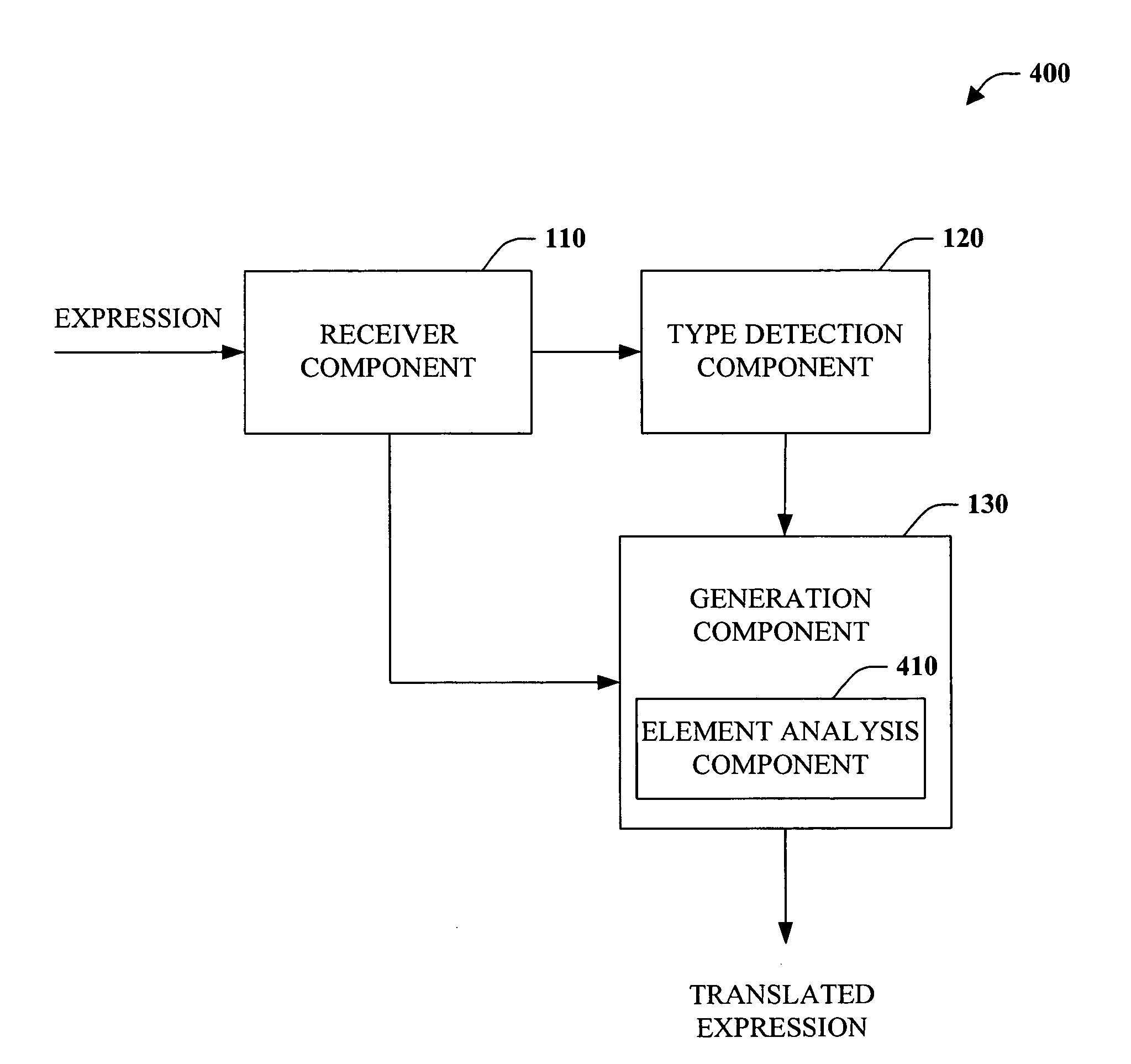
A method for recording a sequence of user actions made when interfacing with objects associated with an executable code is provided. In this method, a selection of a level of detail to record when user actions enable interfacing with the objects associated with the executable code is enabled. Subsequently, the sequence of user actions is recorded. The recorded sequence of user actions is defined by the selected level of detail. Thereafter, the recorded sequence of user actions is parsed by applying rules that enable the generation of a defined number of data types. The data types are capable of being utilized by an application that is designed to generate information that is related to one or more of the data types.
Owner:SONY COMPUTER ENTERTAINMENT INC
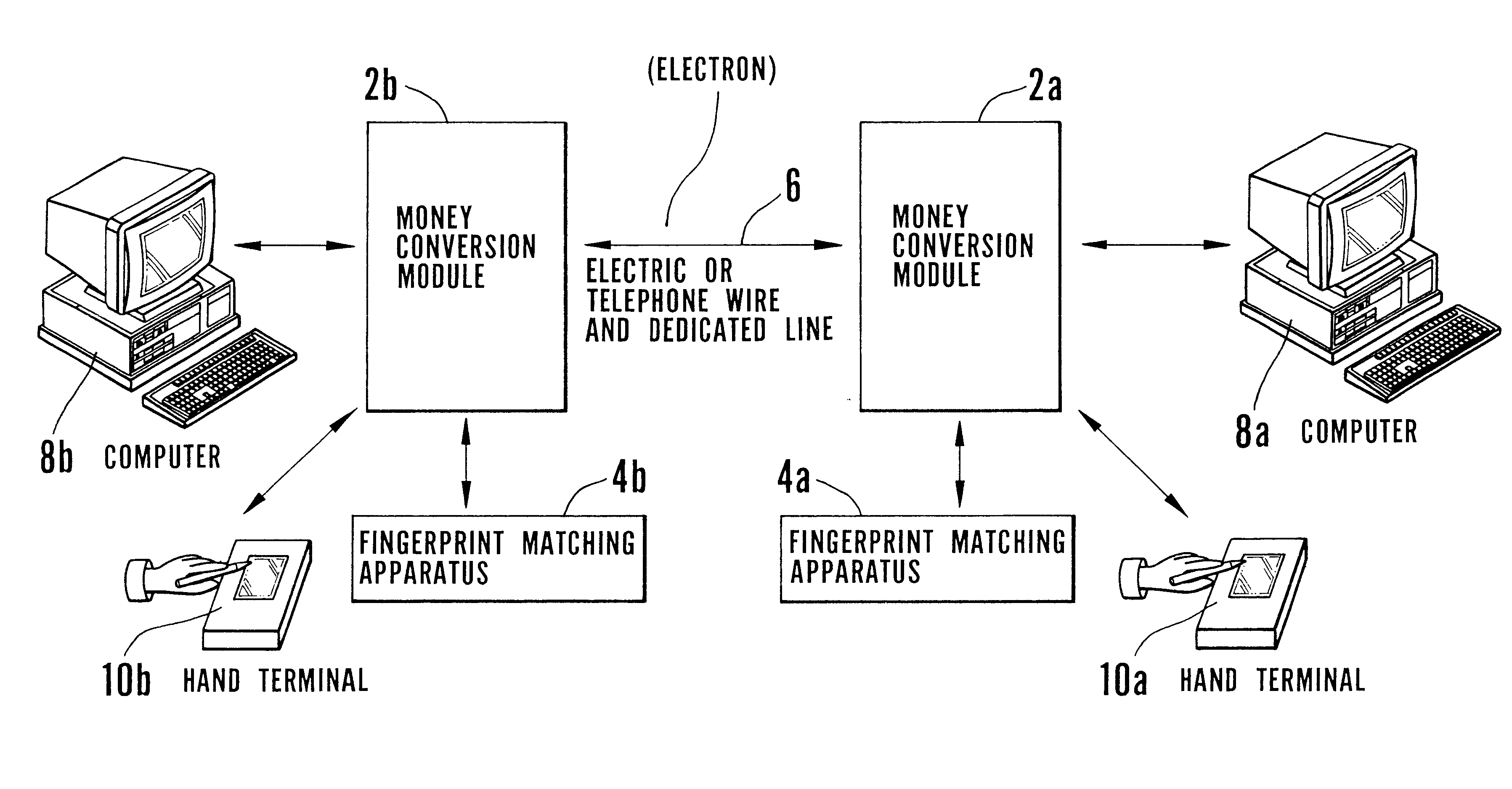
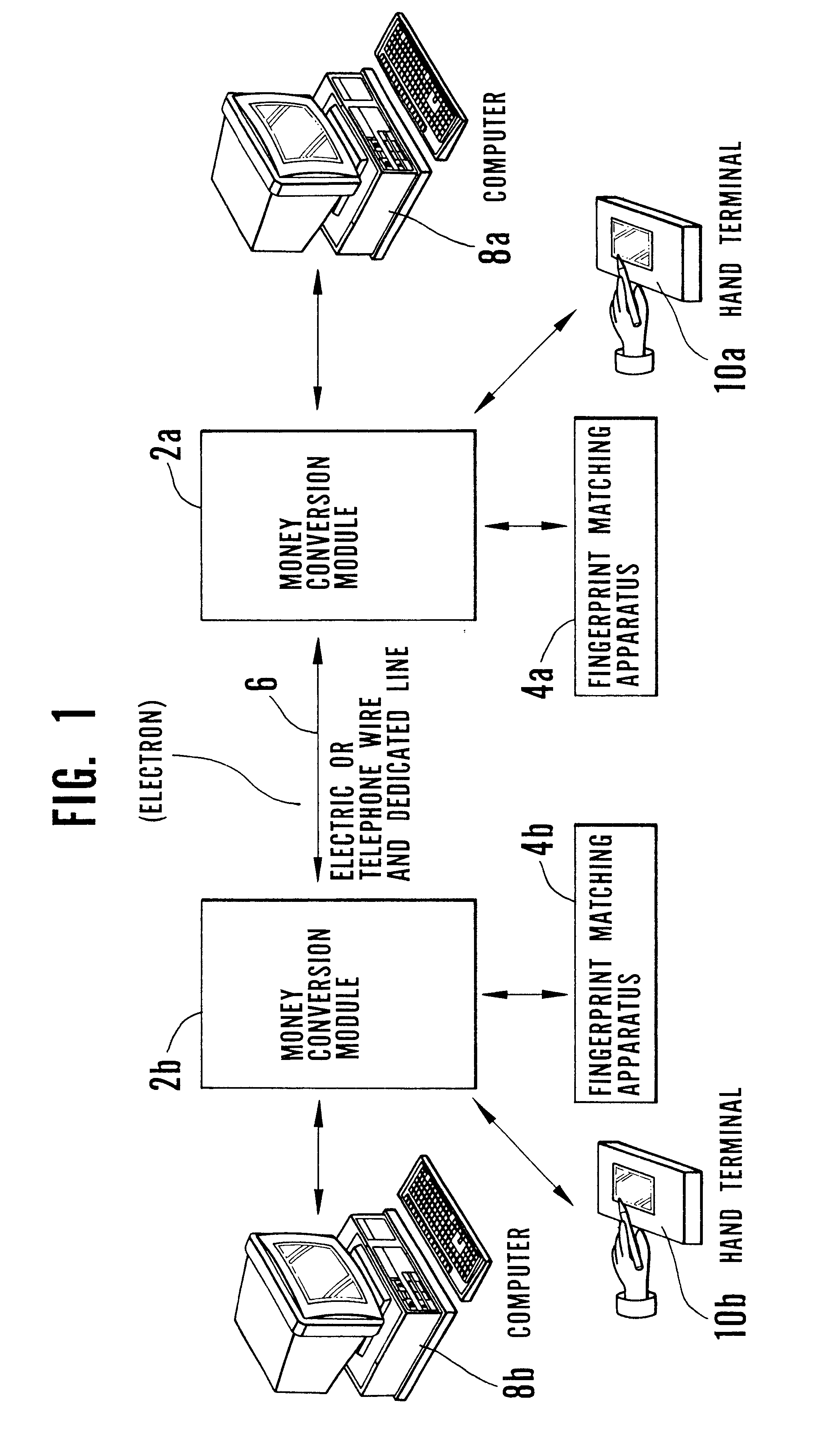
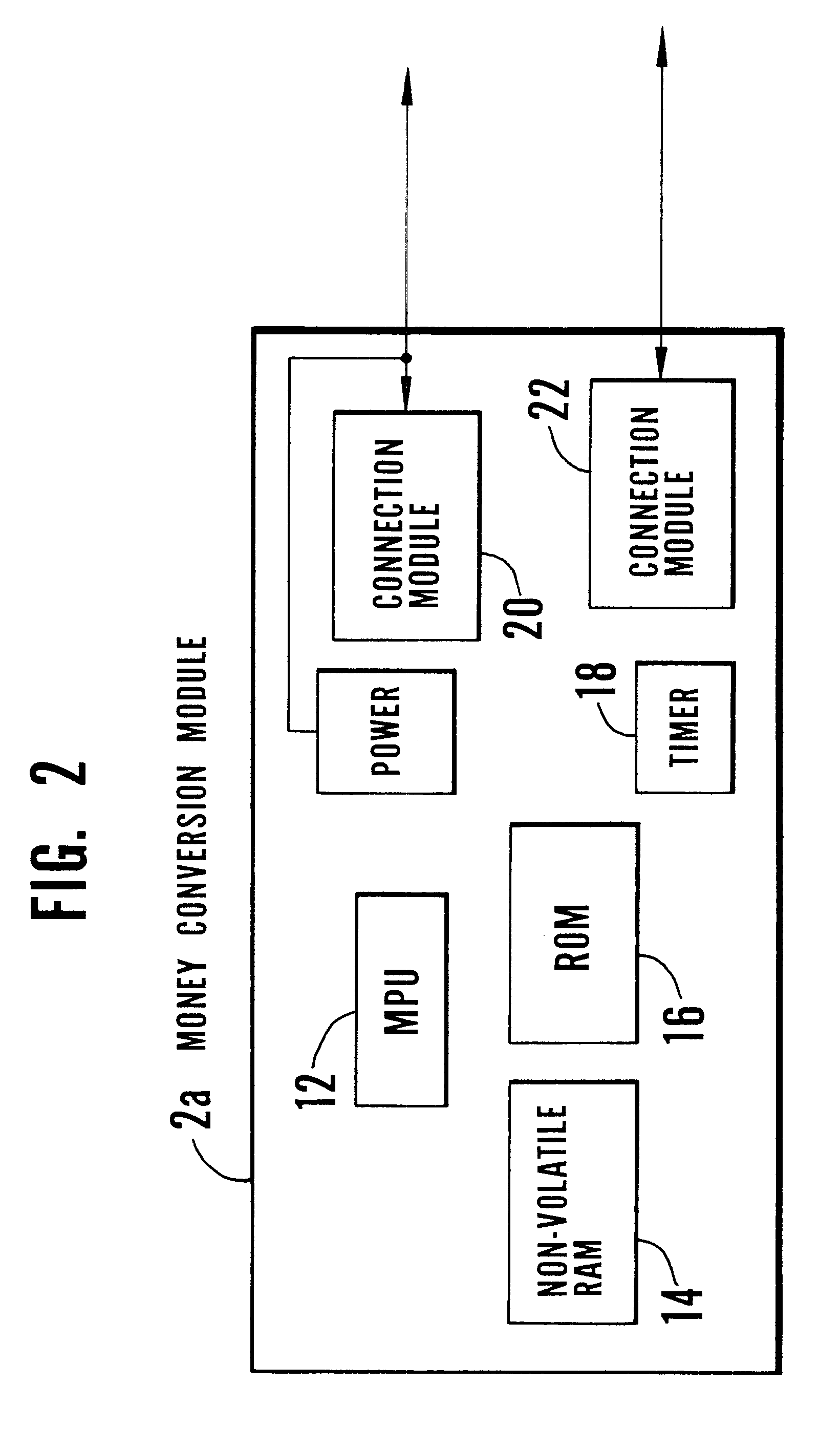
Electronic transaction system including a fingerprint identification encoding
InactiveUS6523745B1Raise security concernsEasy to useComplete banking machinesFinanceComputer moduleSoftware engineering
An apparatus and process of authorizing an electronic transaction system includes a computer located at the site of a transaction, a conversion module for enabling connection between the computer located at the site of the transaction and the conversion module to authorize the transaction, and a connection between the conversion module and the computer at the site of the transaction. The system uses fingerprint input data panel for obtaining fingerprint input data from a finger impressed on the fingerprint input data panel and converts the fingerprint input data to characteristic fingerprint points including minutiae. These characteristic fingerprint points including minutiae are used in conjunction with at least one code at the conversion module to encode messages sent across the system.
Owner:BMF CORPORATION
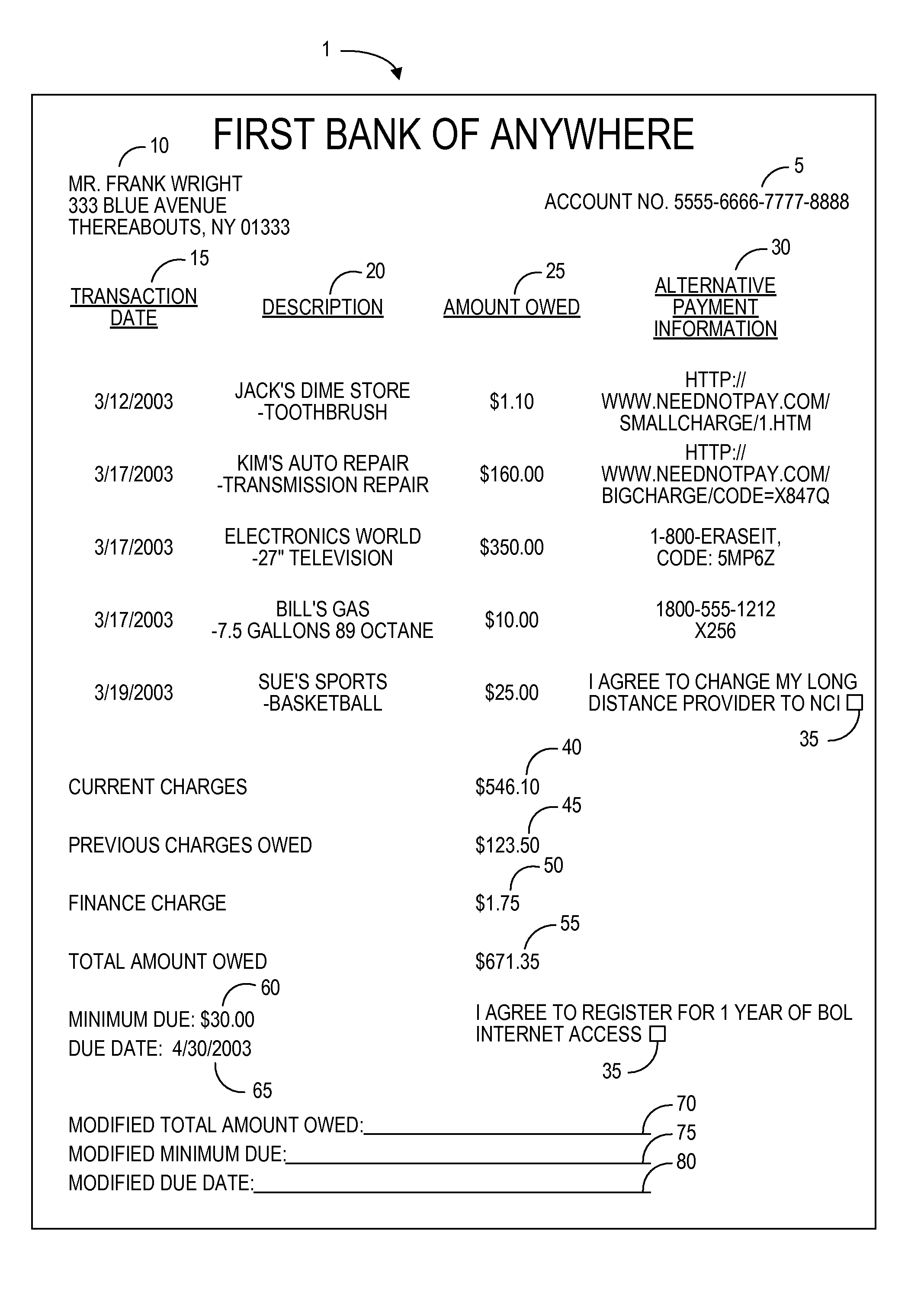
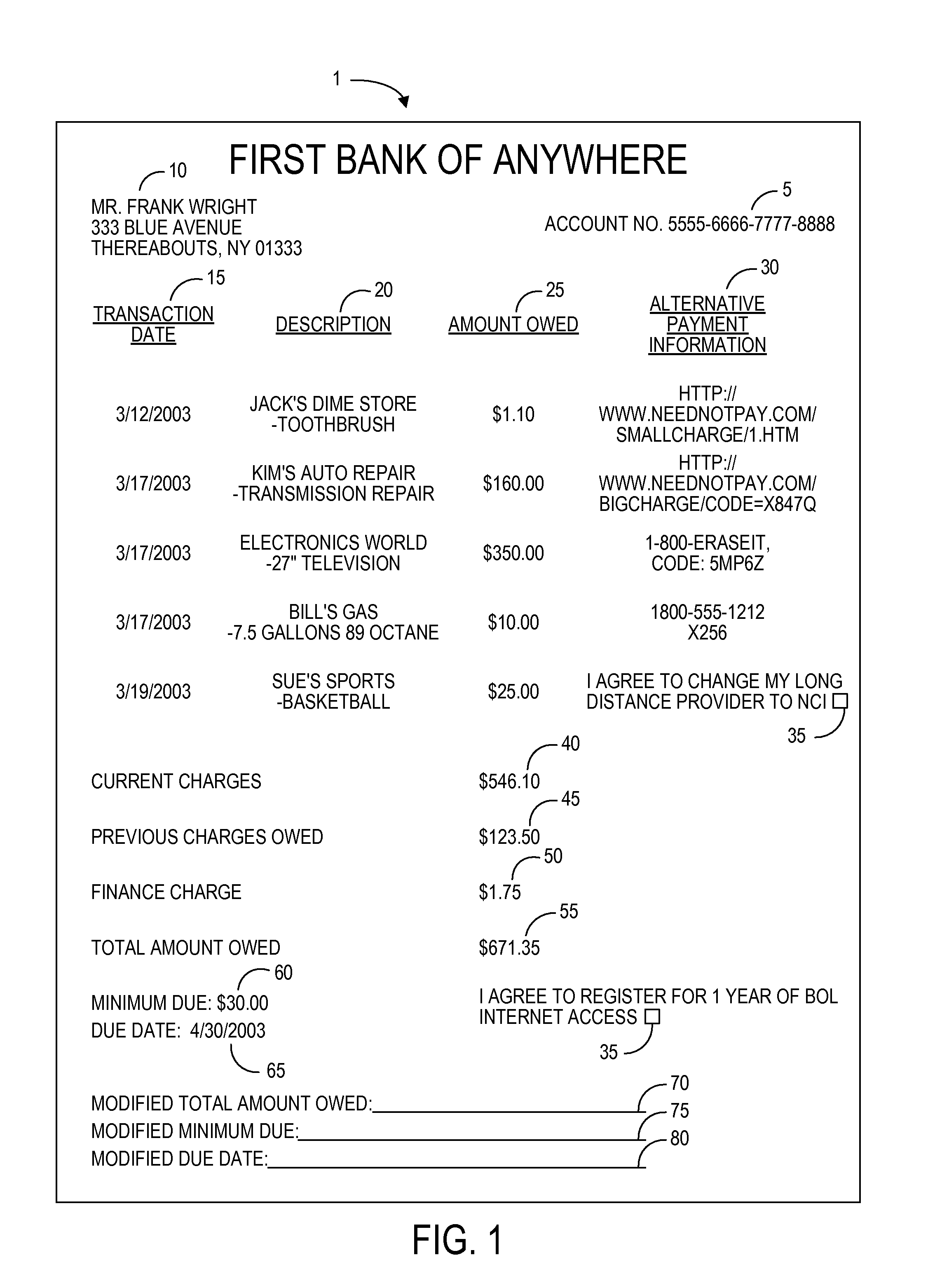
System for providing offers using a billing statement
A billing statement according to one aspect of the invention includes a description of a transaction and an offer pointer associated with the transaction, wherein the offer pointer includes information that may be used to review an offer. In one example of this aspect, the offer pointer is a telephone number printed adjacent to a description of a transaction on a credit card billing statement. The telephone number accesses a voice response system presenting conditional branches through which a consumer can navigate to review an offer. In another example, a hyperlink is positioned adjacent to a total amount owed listed on an electronically-displayed billing statement. The hyperlink may be selected to access a website presenting offers for review by the consumer. The offers reviewed in each of these examples may be customized based on details of the transaction such as the product purchased or the amount of the purchase, the identity of the consumer, and / or on other data.
Owner:PAYPAL INC
Fingerprint recognition system
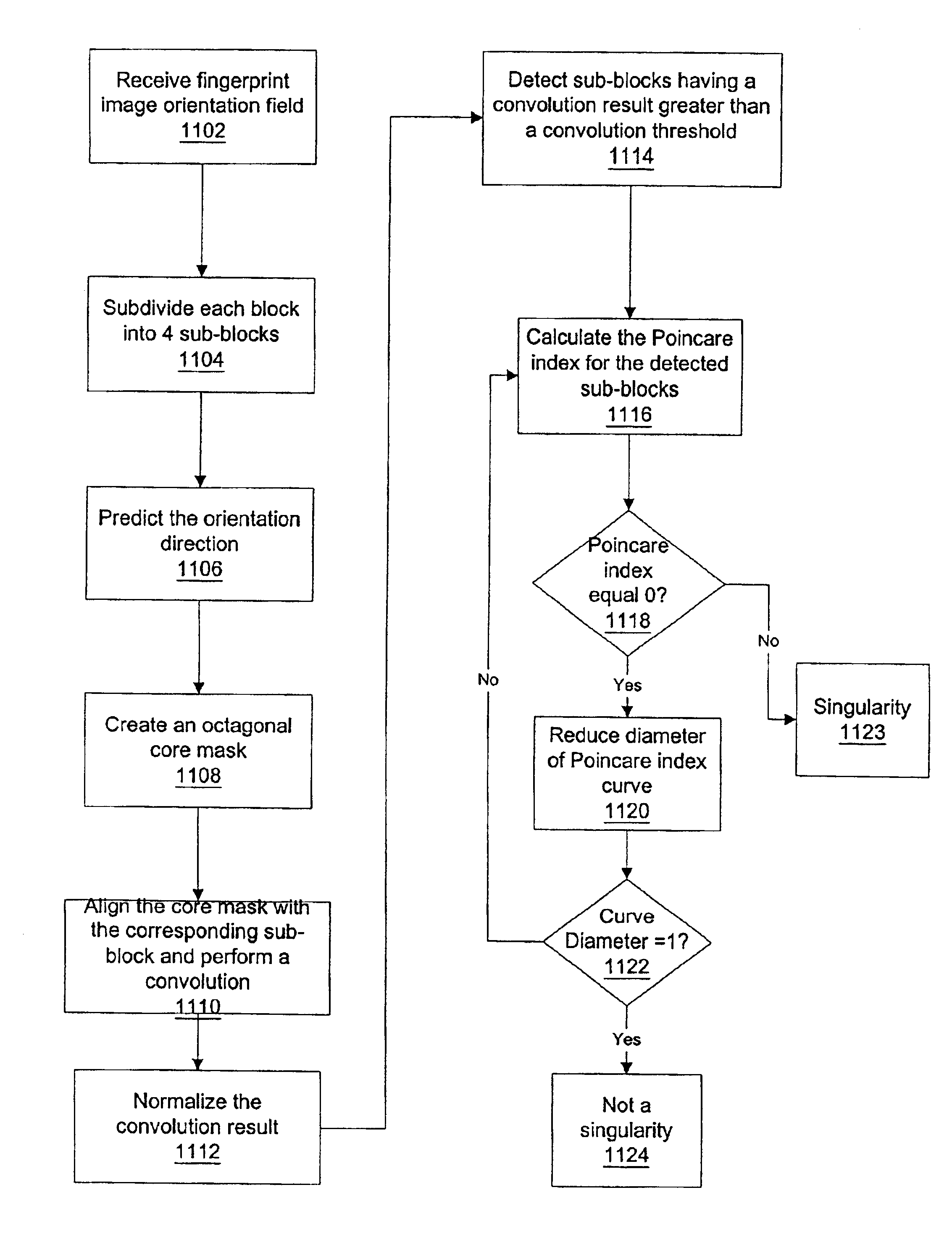
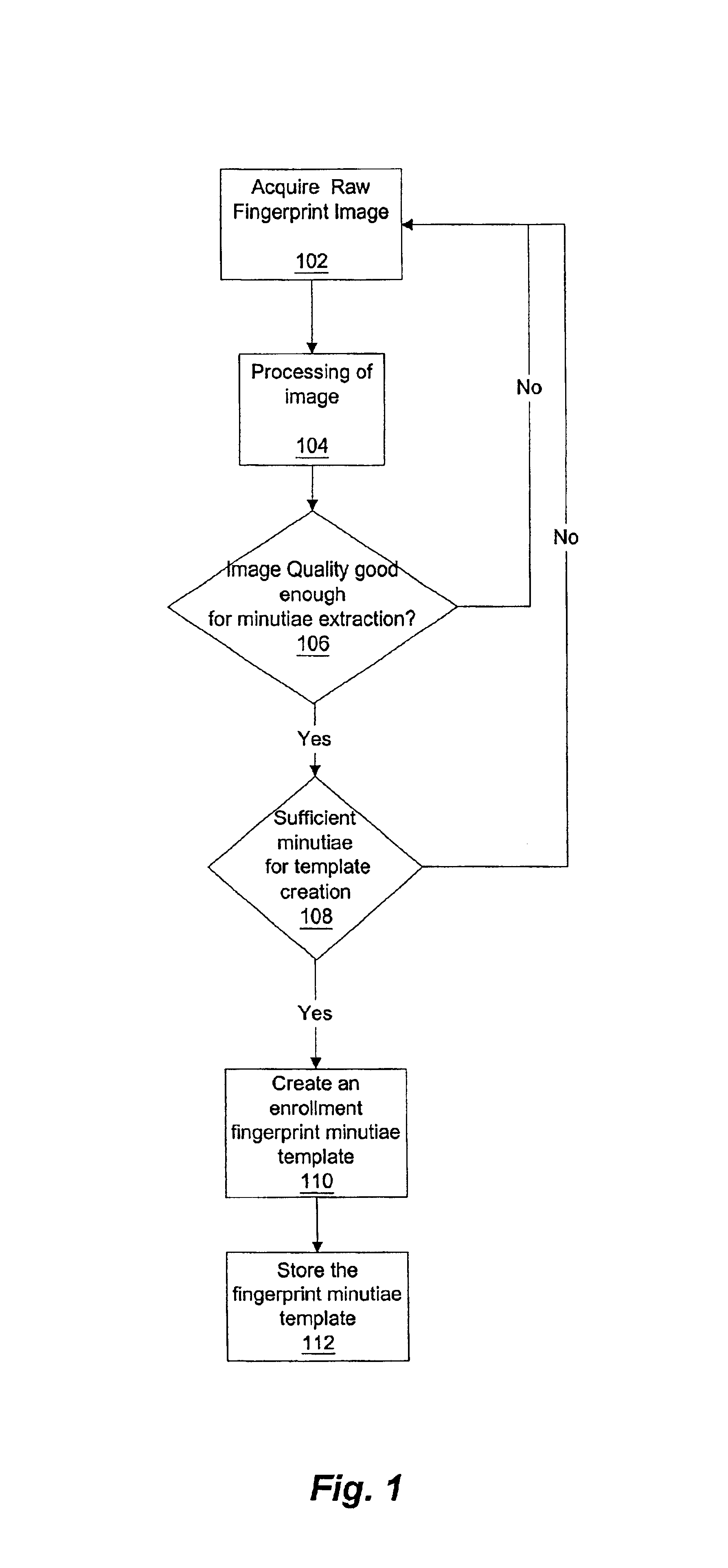
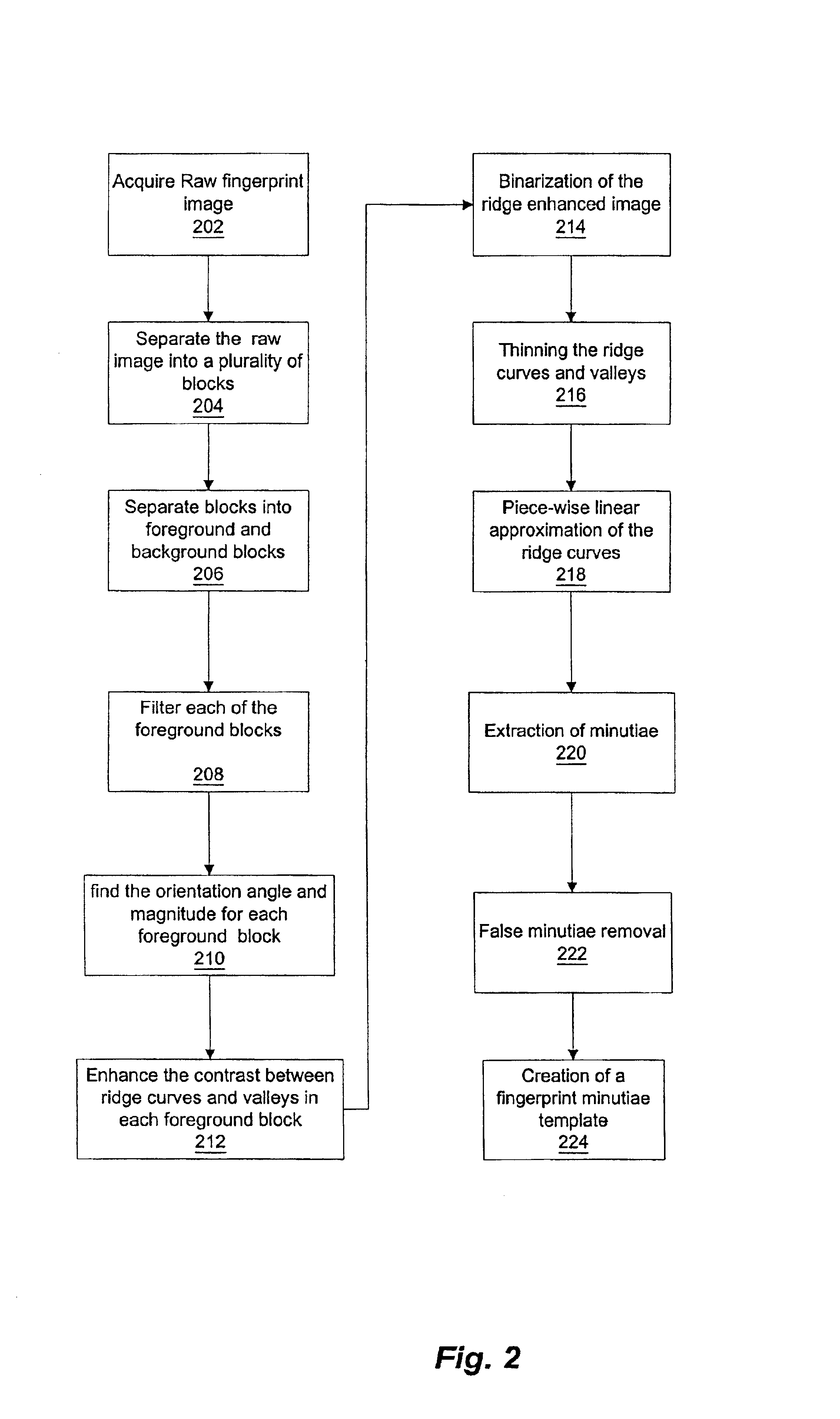
InactiveUS6876757B2Improve securityRidge curves to be enhancedProgramme controlElectric signal transmission systemsPattern recognitionMinutiae
A method of analyzing and recognizing fingerprint images that utilizes vector processing of a vector field that is defined as the tangential vector of the fingerprint ridge curves is disclosed. The raw fingerprint image is divided into blocks, filtered to remove noise, and the orientation direction of each block is found. This allows the ridge curves to be enhanced and approximated by piece-wise linear approximations. The piece-wise linear approximations to the ridge curves allow the minutiae to be extracted and classified and a fingerprint minutiae template to be constructed. An enrollment process gathers multiple fingerprint images, creates fingerprint minutiae templates corresponding to the acquired fingerprint images, and stores the templates and other data associated with the respective individual or the enrolled fingerprint in a fingerprint database. In an identification process, an unknown raw fingerprint image is obtained via a fingerprint scanner and processed similarly to the enrollment process such that the fingerprint minutiae template of the unknown fingerprint is compared to one or more previously enrolled fingerprint minutiae templates. The identity of the individual associated with the unknown fingerprint is thereby ascertained. In addition, live finger detection can be accomplished in conjunction with the verification or identification process through analysis of the fingerprint image thus enhancing the security of the overall system.
Owner:GEOMETRIC INFORMATICS INC
High-resolution, three-dimensional whole body ultrasound imaging system
InactiveUS6135960AQuality improvementHigh resolutionUltrasonic/sonic/infrasonic diagnosticsInfrasonic diagnosticsSonificationWhole body
This invention incorporates the techniques of geophysical technology into medical imaging. Ultrasound waves are generated from multiple, simultaneous sources tuned for maximum penetration, resolution, and image quality. Digitally recorded reflections from throughout the body are combined into a file available for automated interpretation and wavelet attribute analyses. Unique points within the object are imaged from multiple positions for signal-to-noise enhancement and wavelet velocity determinations. This system describes gaining critical efficiencies by reducing equation variables to known quantities. Sources and receivers are locked in invariant, known positions. Statistically valid measurements of densities and wavelet velocities are combined with object models and initial parameter assumptions. This makes possible three-dimensional images for viewing manipulation, mathematical analyses, and detailed interpretation, even of the body in motion. The invention imposes a Cartesian coordinate system on the image of the object. This makes reference to any structure within the object repeatable and precise. Finally, the invention teaches how the recording and storing of the received signals from a whole body analysis makes a subsequent search for structures and details within the object possible without reexamining the object.
Owner:HOLMBERG LINDA JEAN
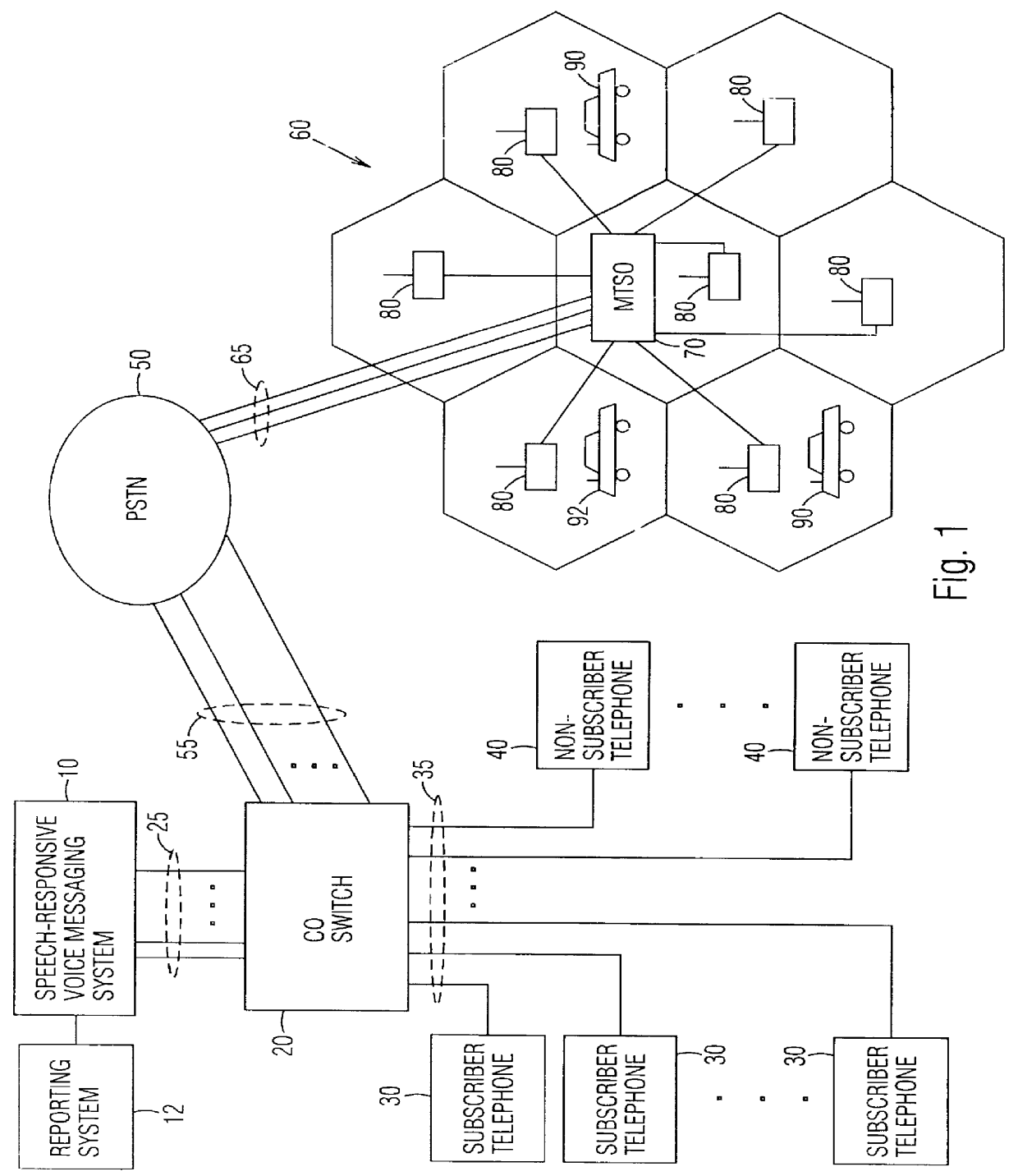
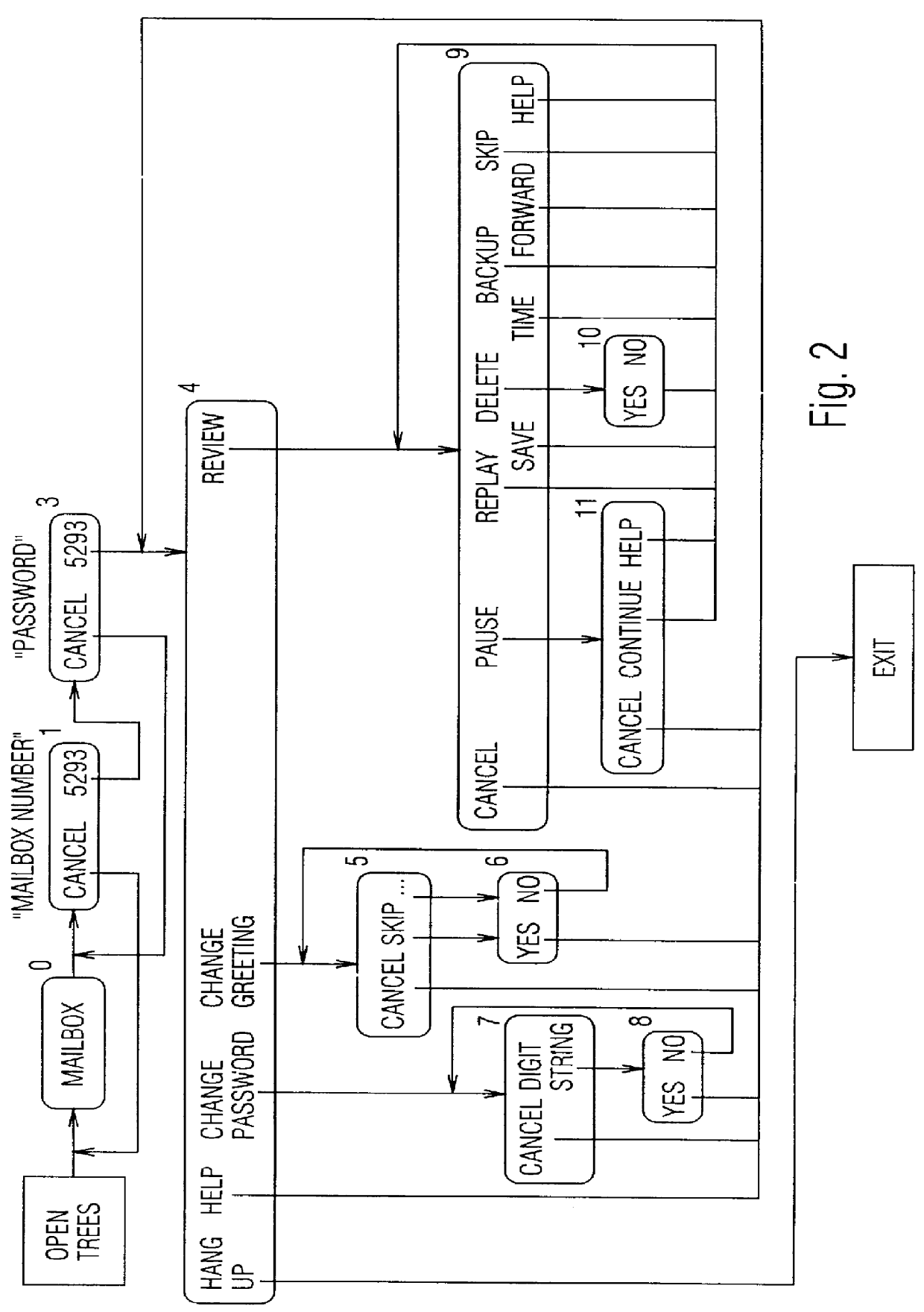
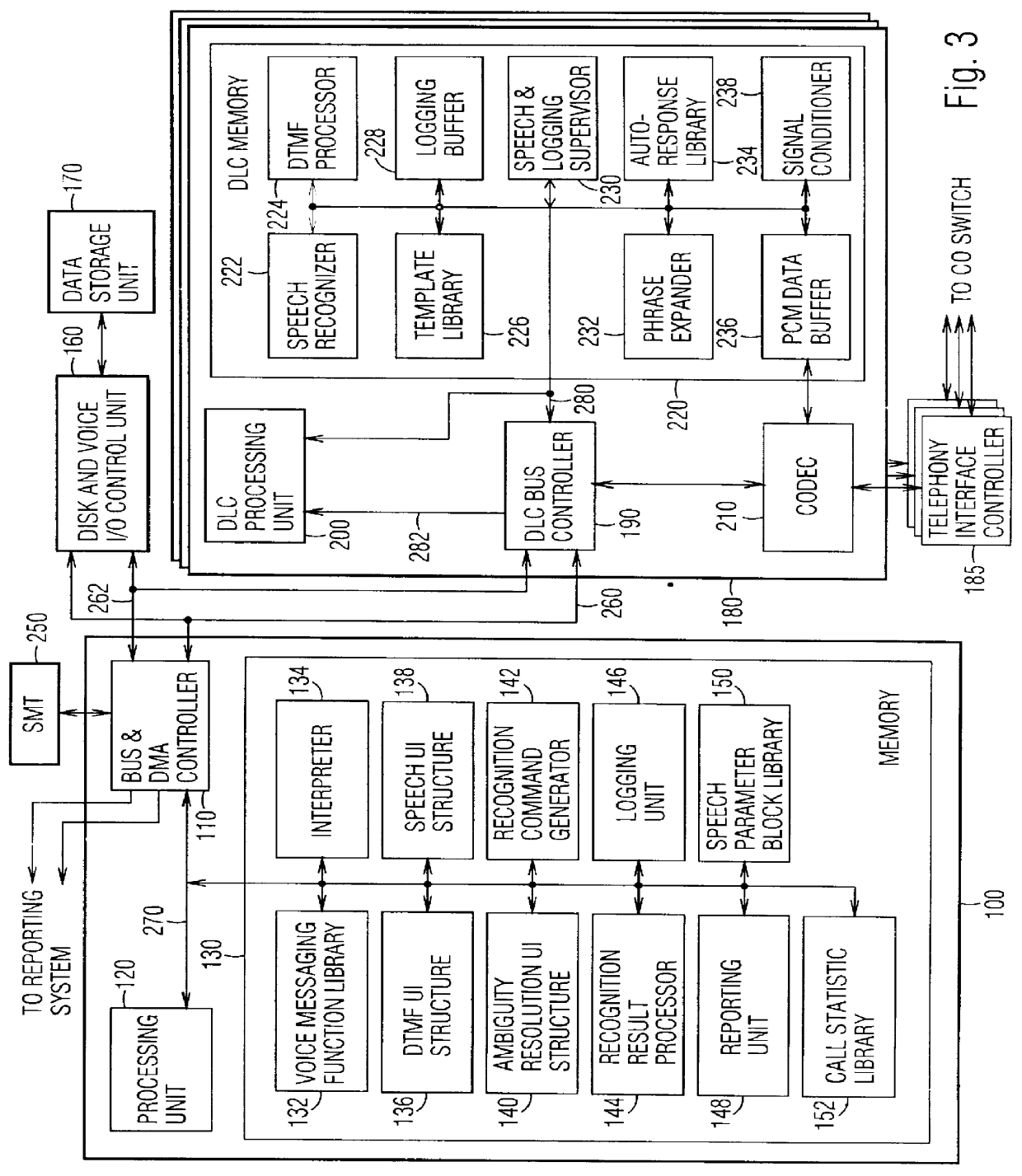
Speech-responsive voice messaging system and method
InactiveUS6094476AHigh level of error tolerance and error preventionAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersRepeated speechPassword
A system and method for speech-responsive voice messaging, in which a Speech-Responsive Voice Messaging System (SRVMS) preferably provides a hierarchically-simple speech user interface (UI) that enables subscribers to use speech to specify commands such as mailboxes, passwords, and digits. The SRVMS generates and evaluates candidate results. The SRVMS invokes a speech UI navigation operation or a voice messaging operation according to the outcome of the evaluation of the candidate results. In the preferred embodiment, the SRVMS determines whether the candidate results are good, questionable, or bad; and whether two or more candidate results are ambiguous due to a likelihood that each such result could be a valid command. If the candidate results are questionable or ambiguous, an ambiguity resolution UI prompts the subscriber to confirm whether the best candidate result is what the subscriber intended. In response to repeated speech recognition failures, the SRVMS transfers the subscriber to a Dual Tone Multi Frequency (DTMF) UI. Transfer to the DTMF UI is also performed in response to detection of predetermined DTMF signals issued by the subscriber while the speech UI is in context. The SRVMS provides a logging unit and a reporting unit which operate in parallel with the speech UI, in a manner that is transparent to subscribers. The logging unit directs the selective logging of subscriber utterances, and the reporting unit selectively generates and maintains system performance statistics on multiple detail levels.
Owner:AVAYA INC
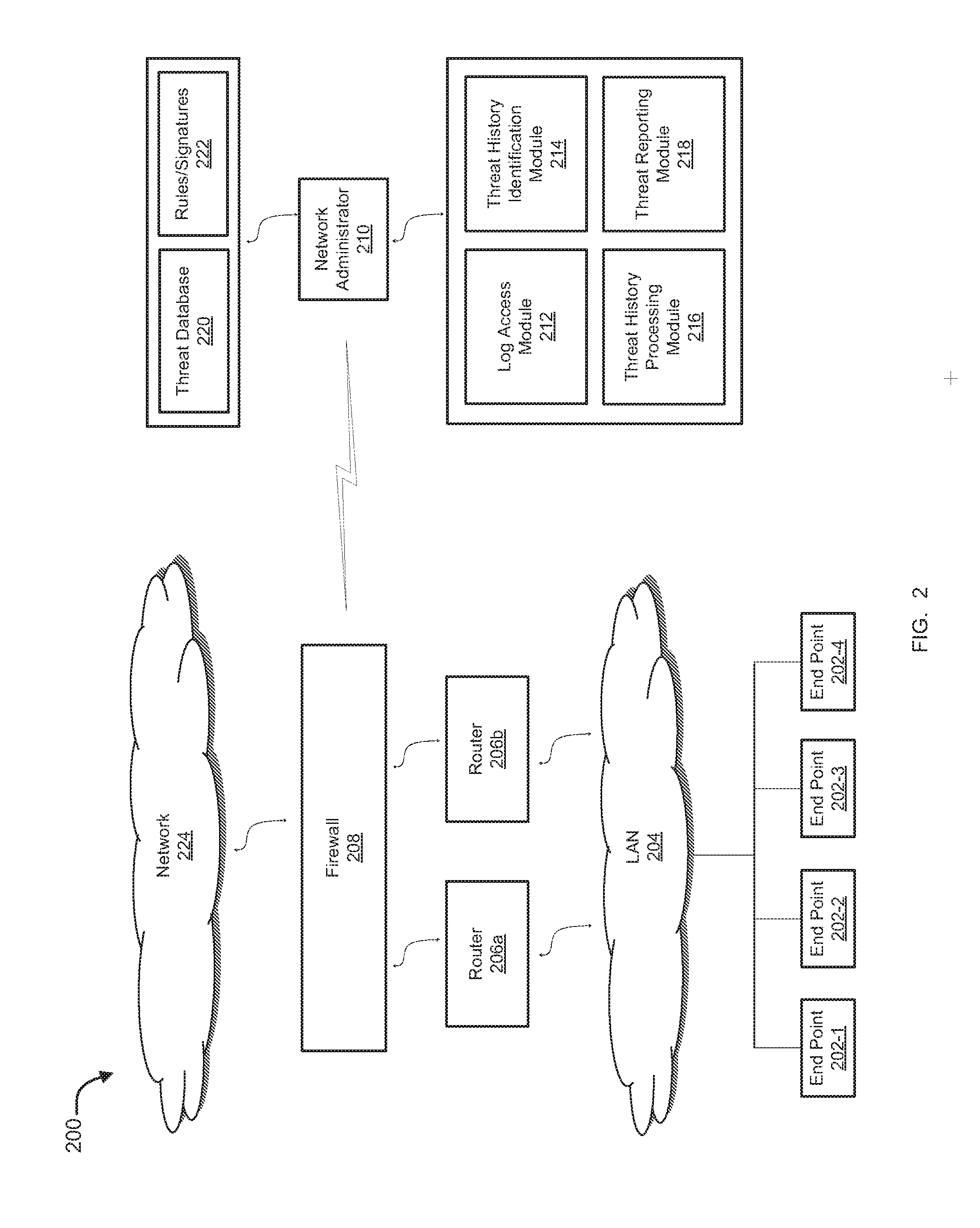
Presentation of threat history associated with network activity
ActiveUS20160173446A1Multiple digital computer combinationsProgram controlNetwork activityInternet privacy
Methods and systems for extracting, processing, displaying, and analyzing events that are associated with one or more threats are provided. According to one embodiment, threat information, including information from one or more of firewall logs and historical threat logs, is maintained in a database. Information regarding threat filtering parameters, including one or more of types of threats to be extracted from the database, parameters of the threats, network-level details of the threats, a time interval of detection of the threats and source-destination details of the threats, is received. Information regarding threats matching the threat filtering parameters are extracted from the database and is presented in a form of an interactive historical graph. Responsive to receiving from a user an indication regarding a selected subset of time in which to zoom into for further details, a list of threats within the selected subset is presented in tabular form.
Owner:FORTINET
Method and system for display of electronic mail
InactiveUS7003724B2Maintaining awarenessDigital computer detailsData switching networksLevel of detailMinutiae
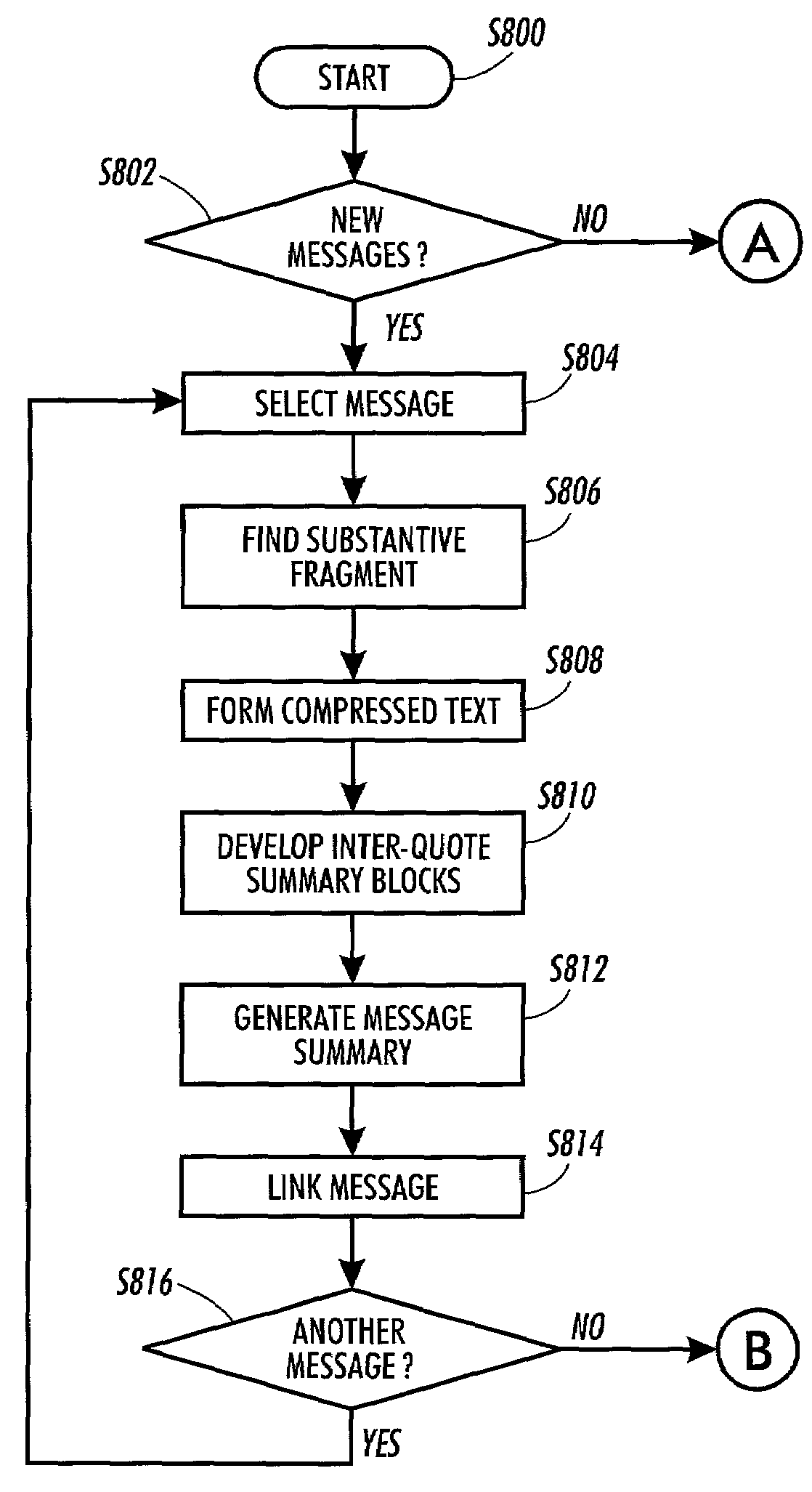
The invention provides a sequence of increasingly detailed presentation levels to assist a user in deciding whether a thread is of interest. If so, the text of the threaded messages is presented at a level of detail corresponding to the user's level of indicated interest. In particular, the invention provides a method comprising creating a message collection viewing cascade including a plurality of viewing levels for presenting one or more message threads and abbreviated forms of one or more messages, abbreviating at least one of the messages using one of a plurality of abbreviation techniques, and formatting each abbreviated message to be displayed at one of the plurality of viewing levels in the message collection viewing cascade. Each abbreviation technique specifies a manner in which the messages can be abbreviated, and each viewing level in the collection viewing cascade offers a different degree of detail for presenting the abbreviated forms of the messages.
Owner:XEROX CORP
Protection of identification documents using open cryptography
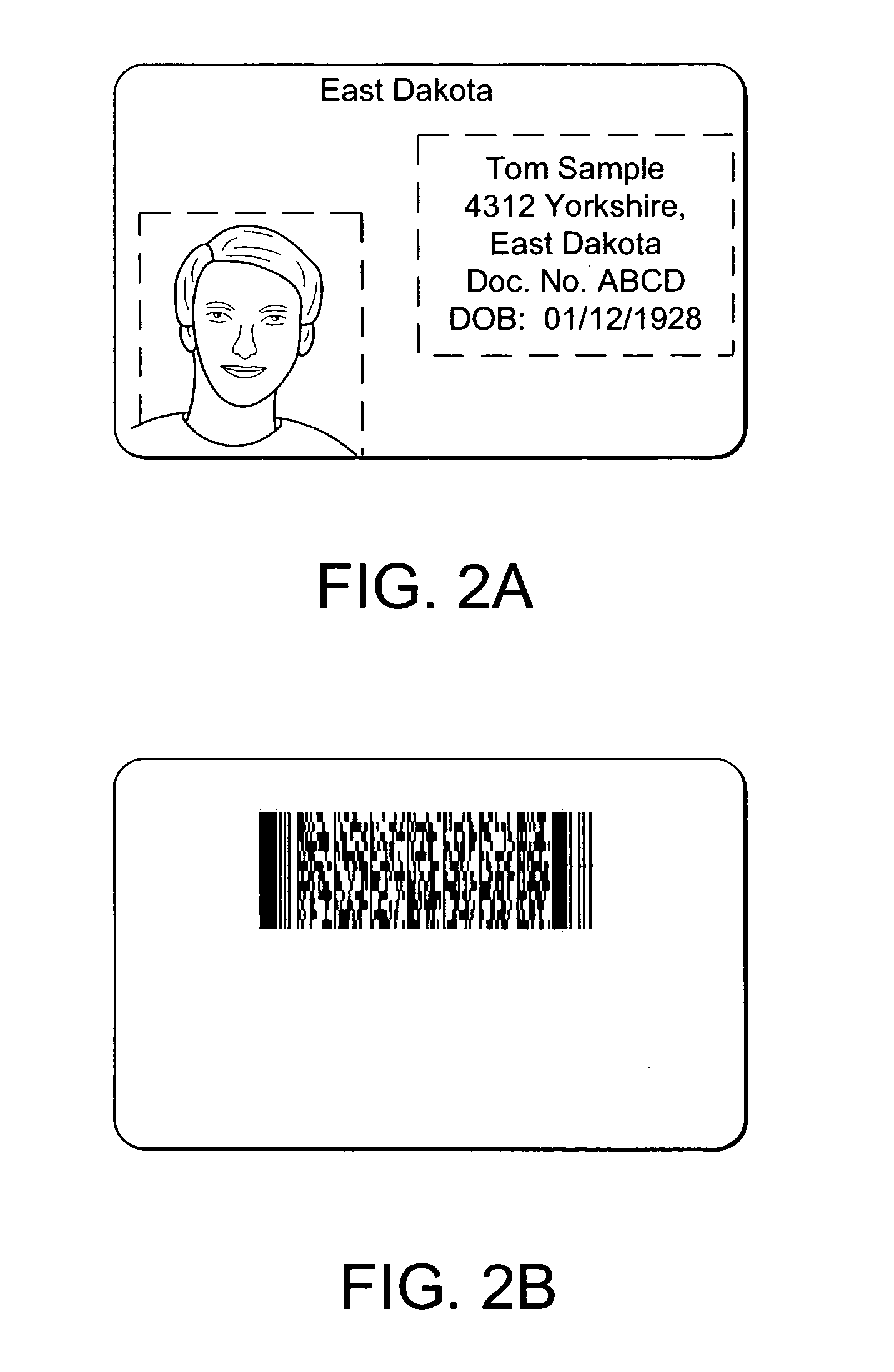
InactiveUS20050132194A1Improve security levelReduce chanceOther printing matterUser identity/authority verificationPaper documentWorkstation
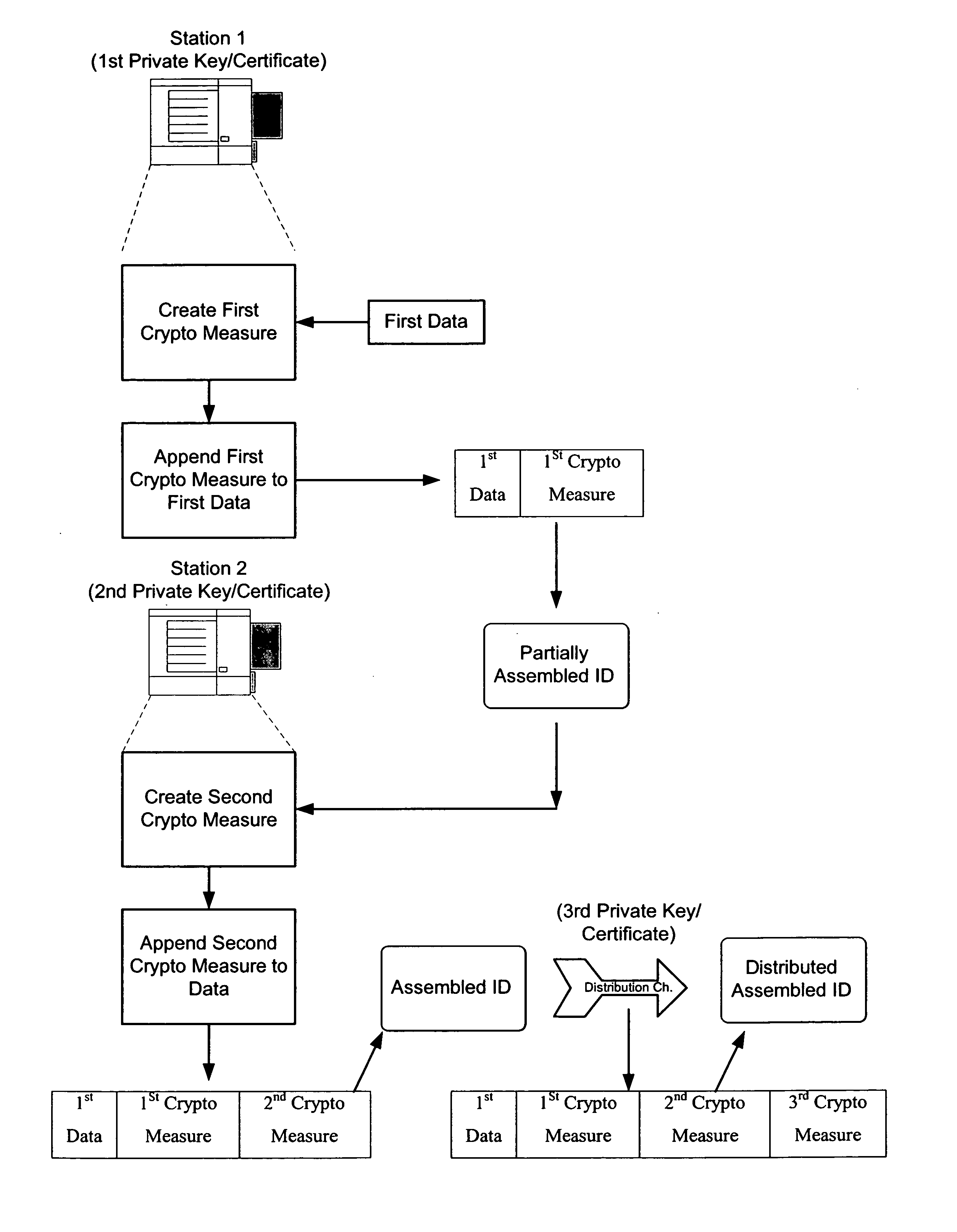
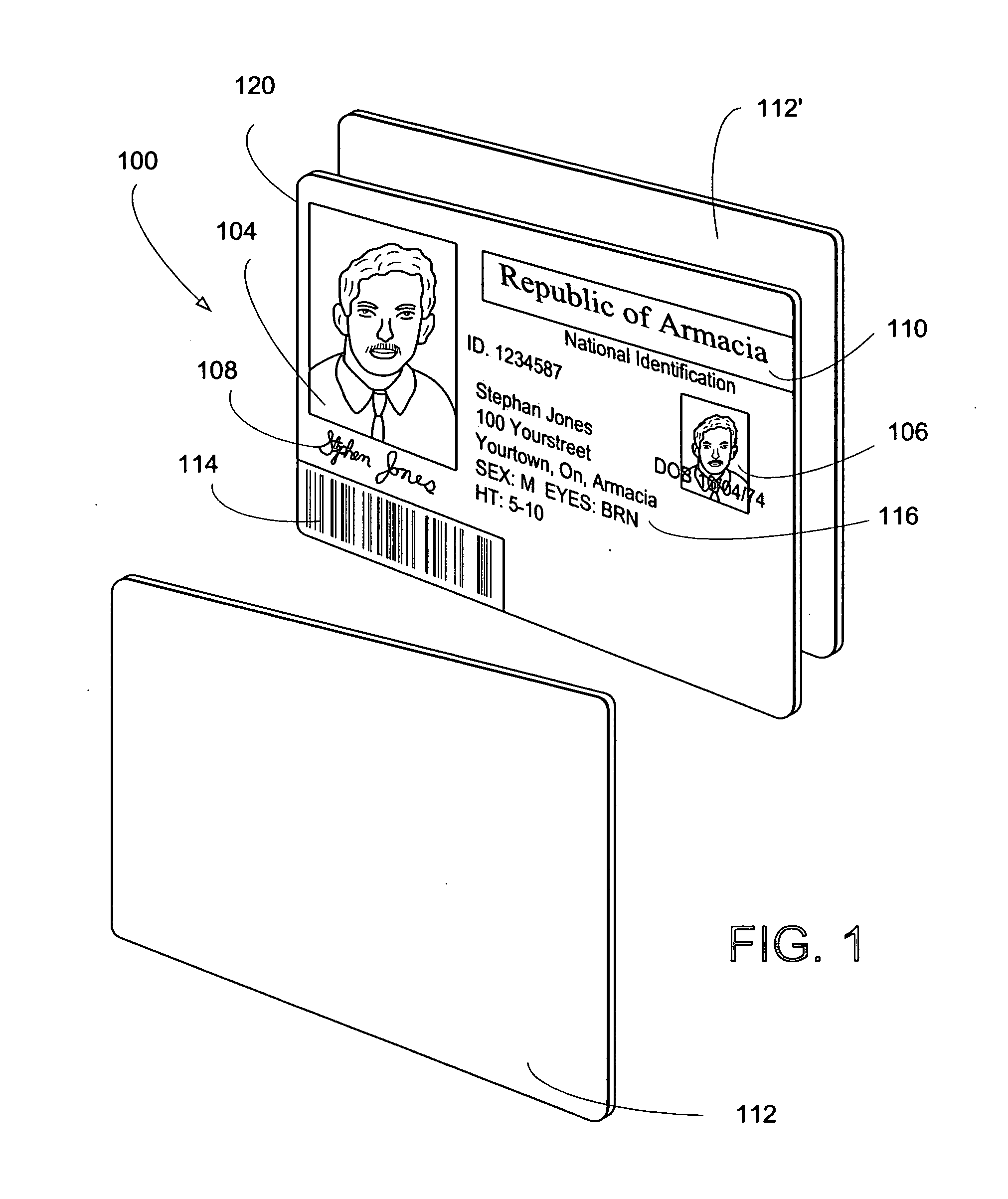
The present invention provides methods and apparatus to uniquely determine fabrication details associated with objects, such as identification documents, artwork and limited issue works, using open cryptographic techniques. A cryptographic signature is created using a private key. The private key is uniquely associated with fabrication details such as a workstation, operator, fabrication equipment, fabrication materials, etc. A public key corresponds with the private key; and therefore, the public key is associated with the fabrication details. Successfully decoding the cryptographic signature with the public key uniquely identifies the fabrication details.
Owner:L 1 SECURE CREDENTIALING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com