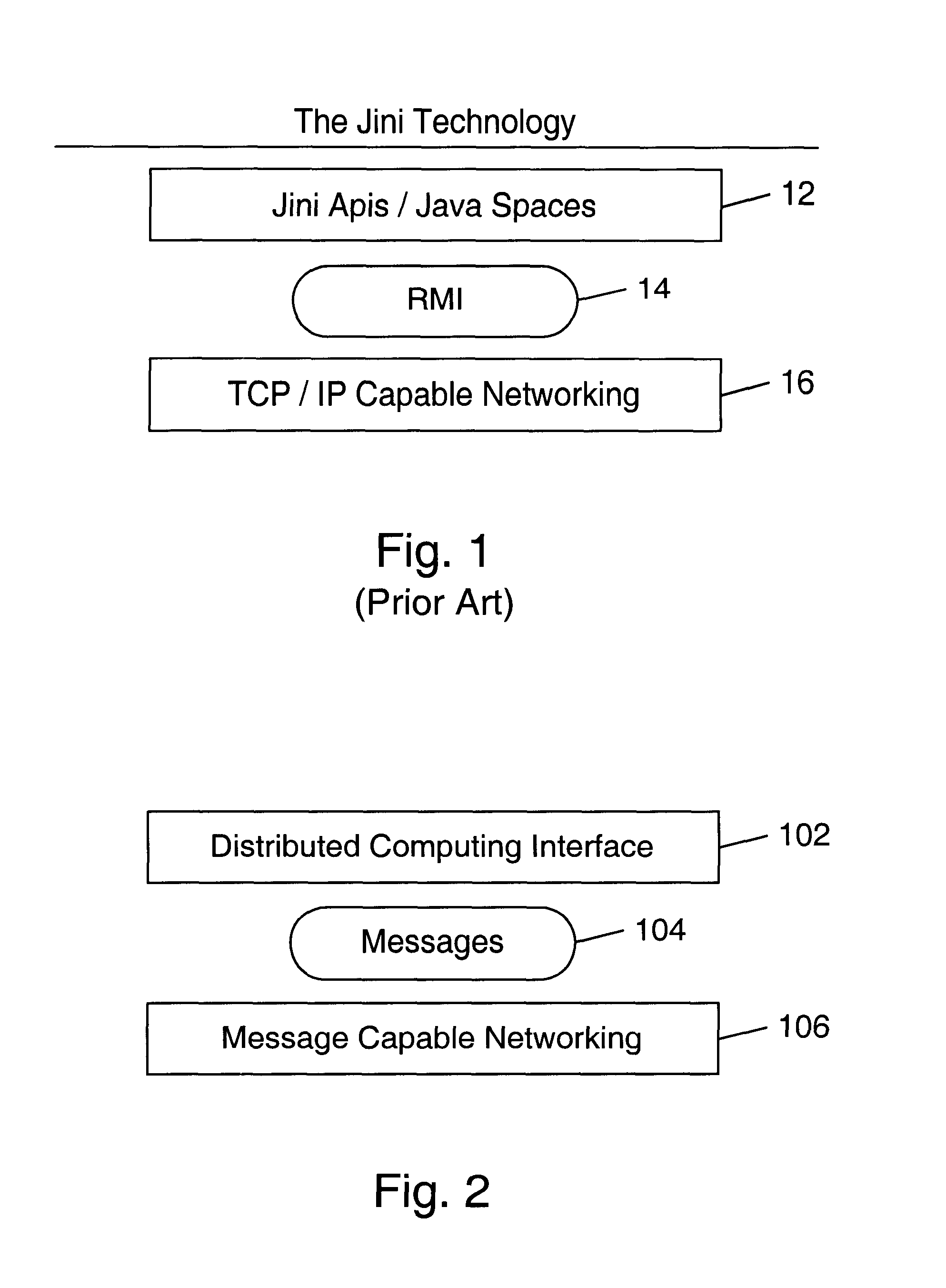
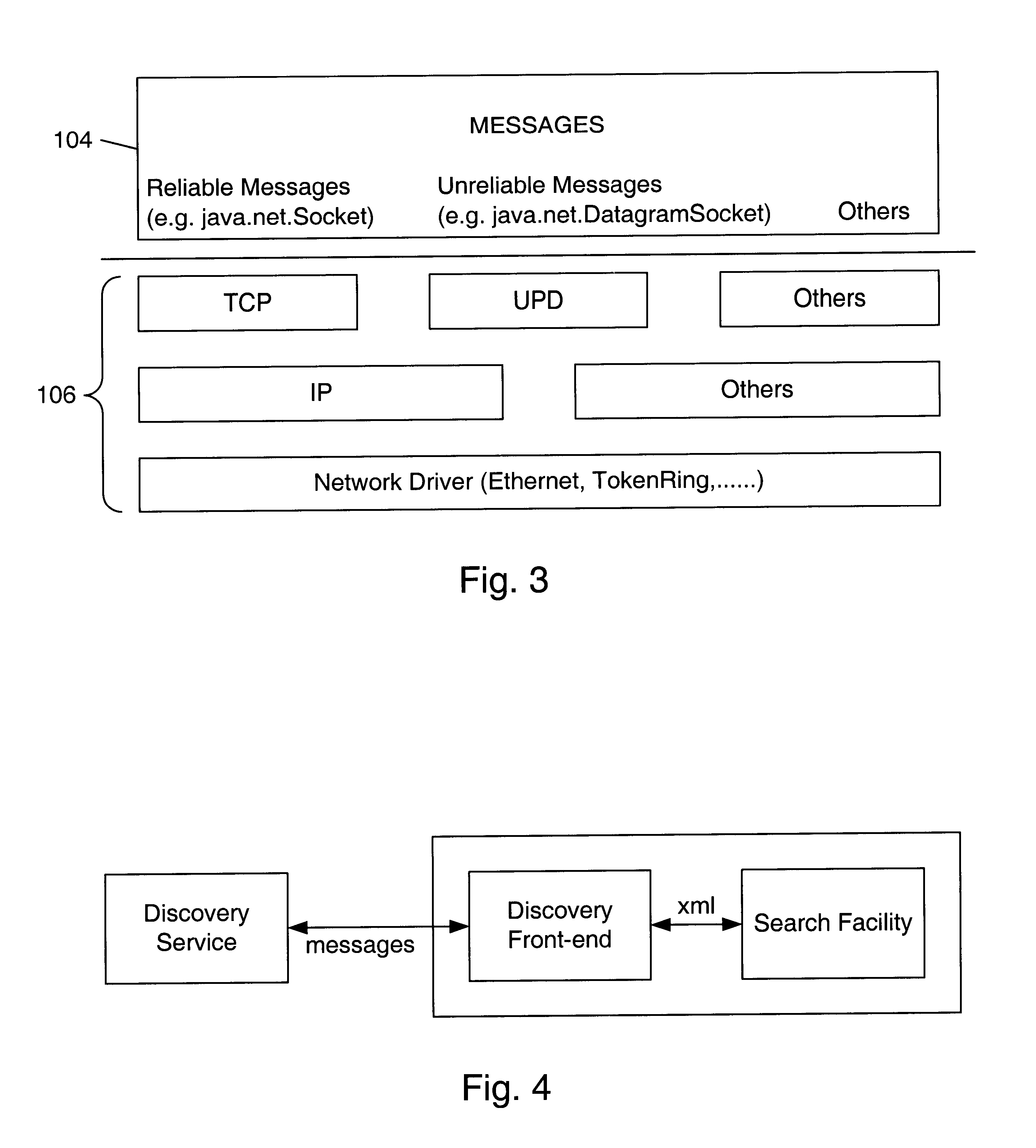
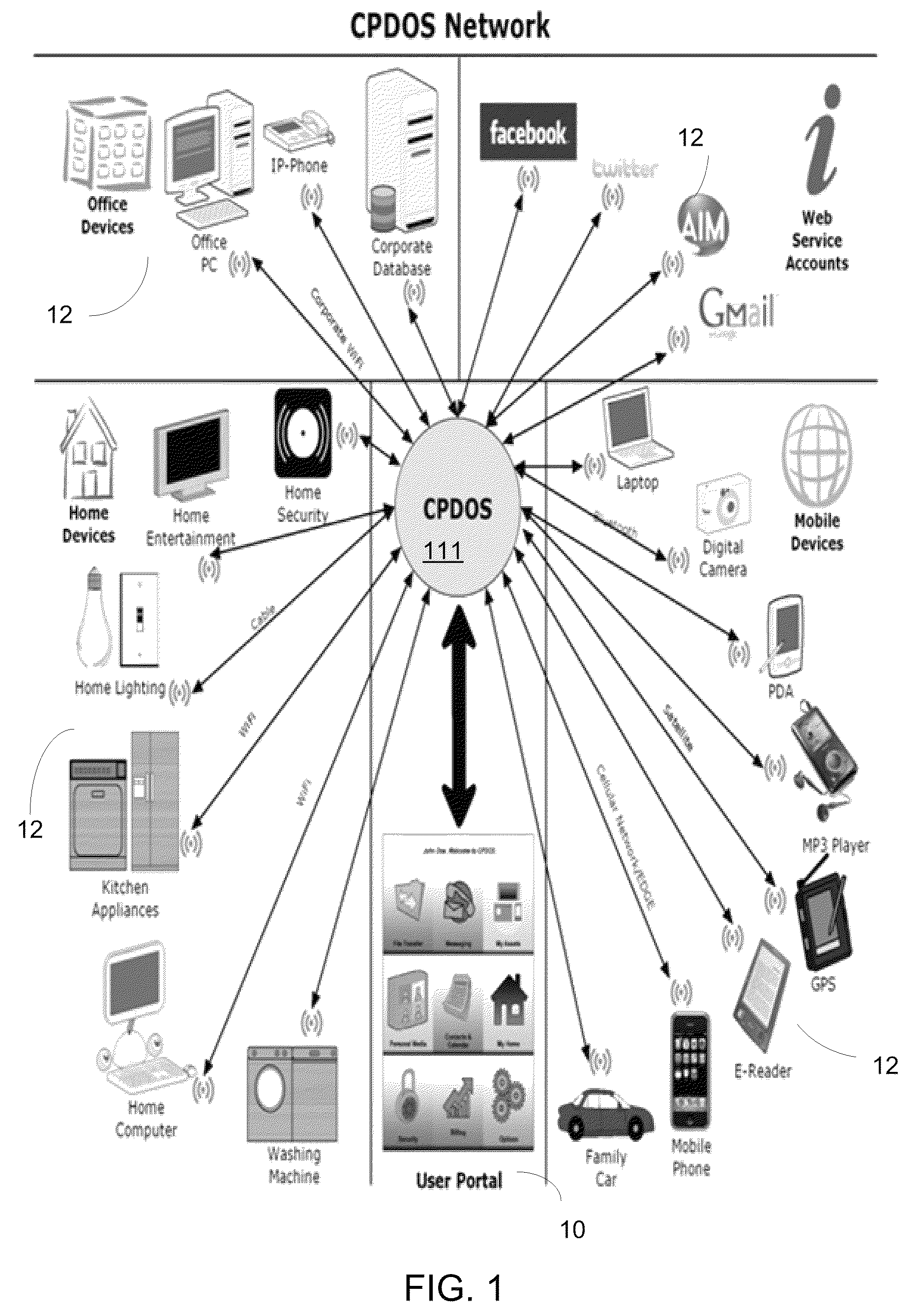
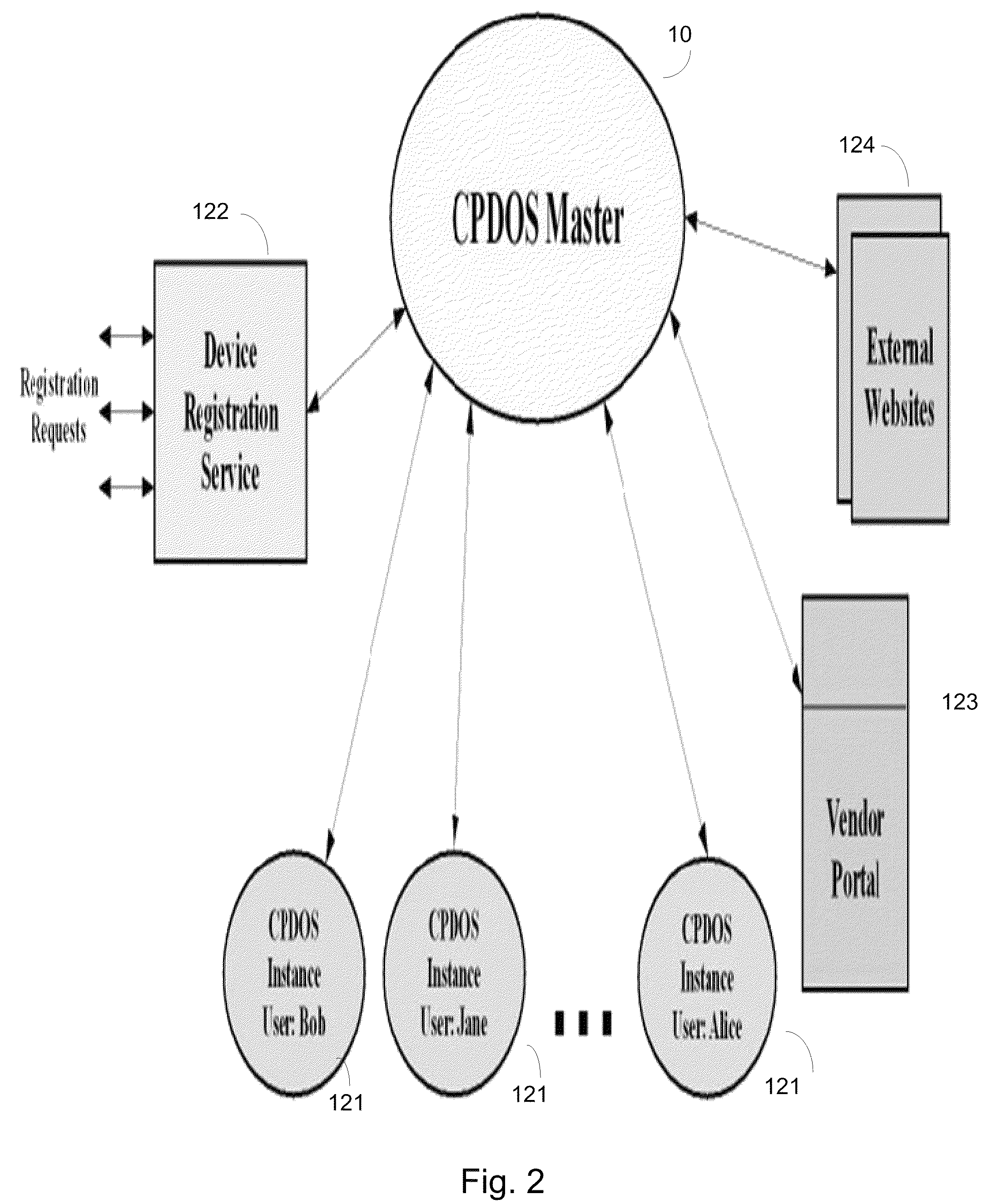
Patents
Literature
3469 results about "Security level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
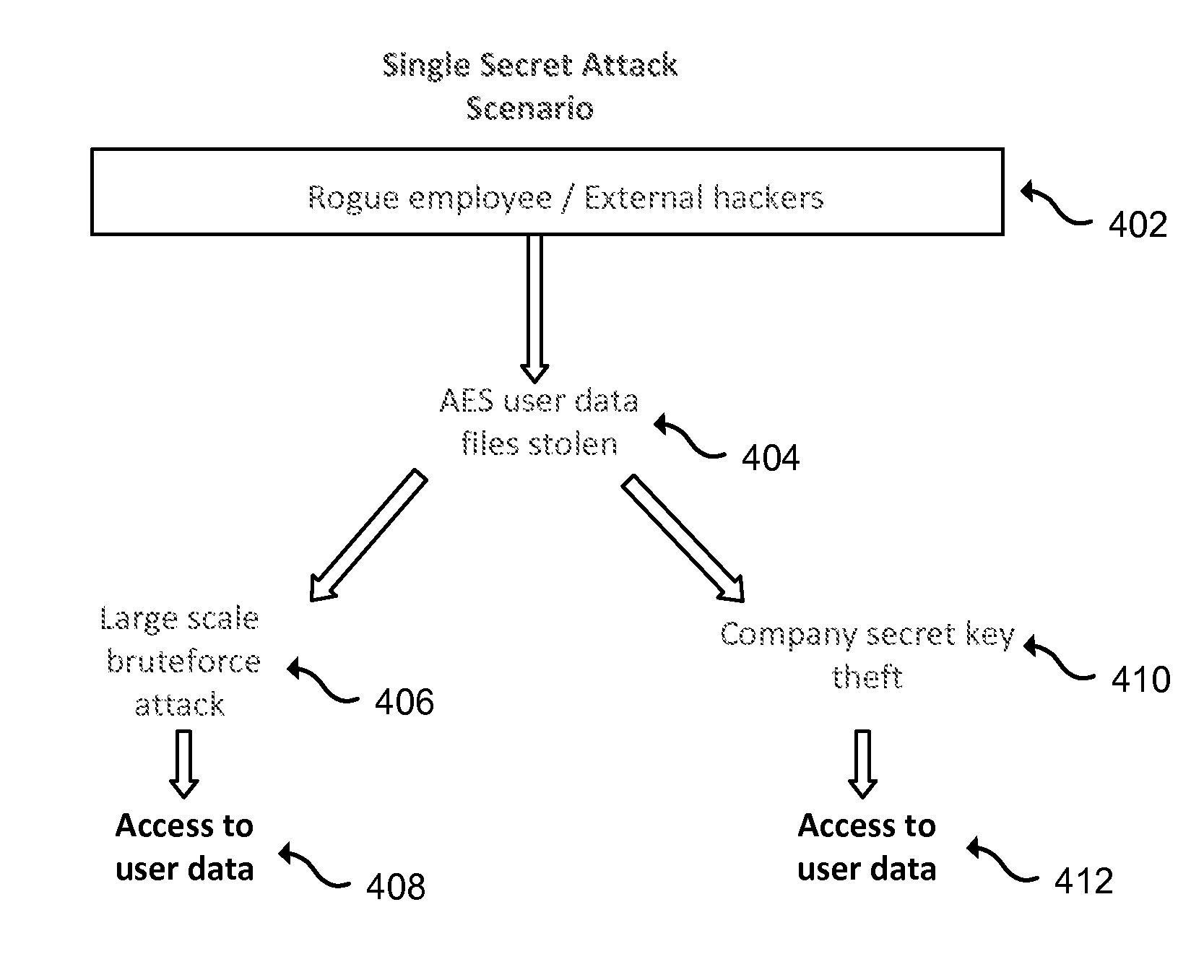
In cryptography, security level is a measure of the strength that a cryptographic primitive — such as a cipher or hash function — achieves. Security level is usually expressed in "bits", where n-bit security means that the attacker would have to perform 2 operations to break it, but other methods have been proposed that more closely model the costs for an attacker. This allows for convenient comparison between algorithms and is useful when combining multiple primitives in a hybrid cryptosystem, so there is no clear weakest link. For example, AES-128 (key size 128 bits) is designed to offer a 128-bit security level, which is considered roughly equivalent to 3072-bit RSA.
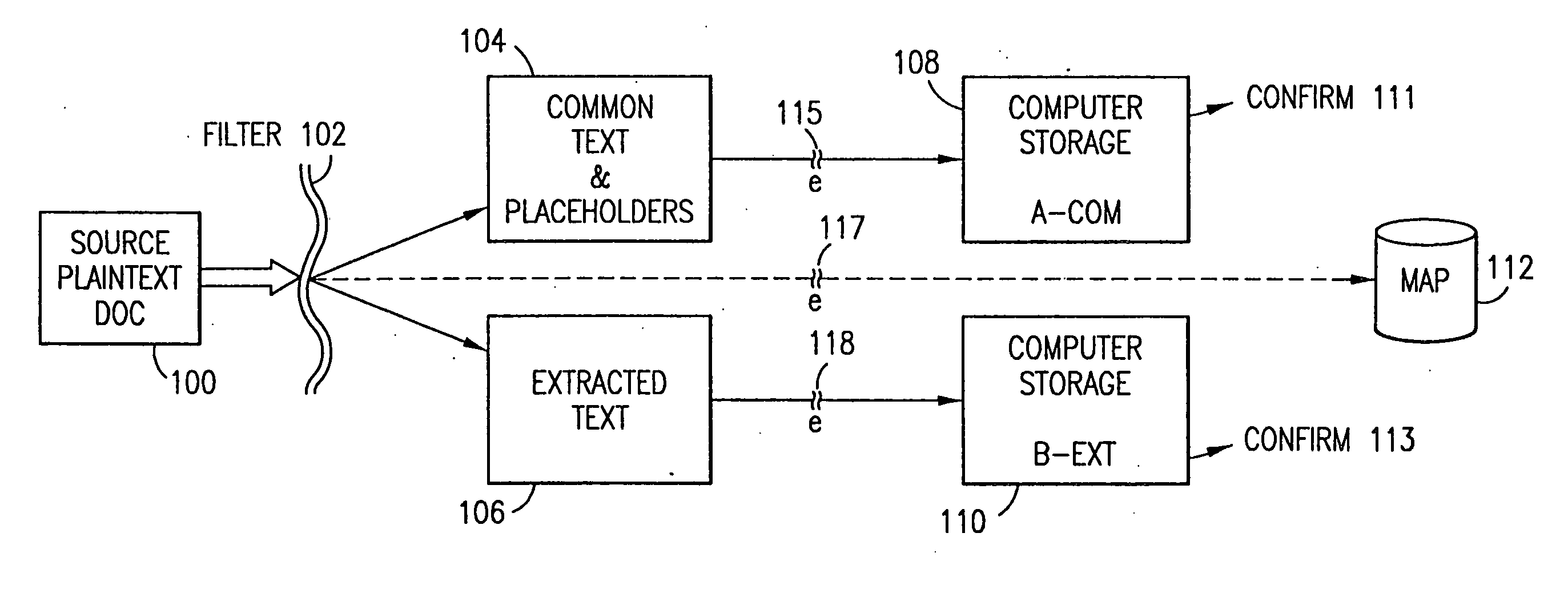
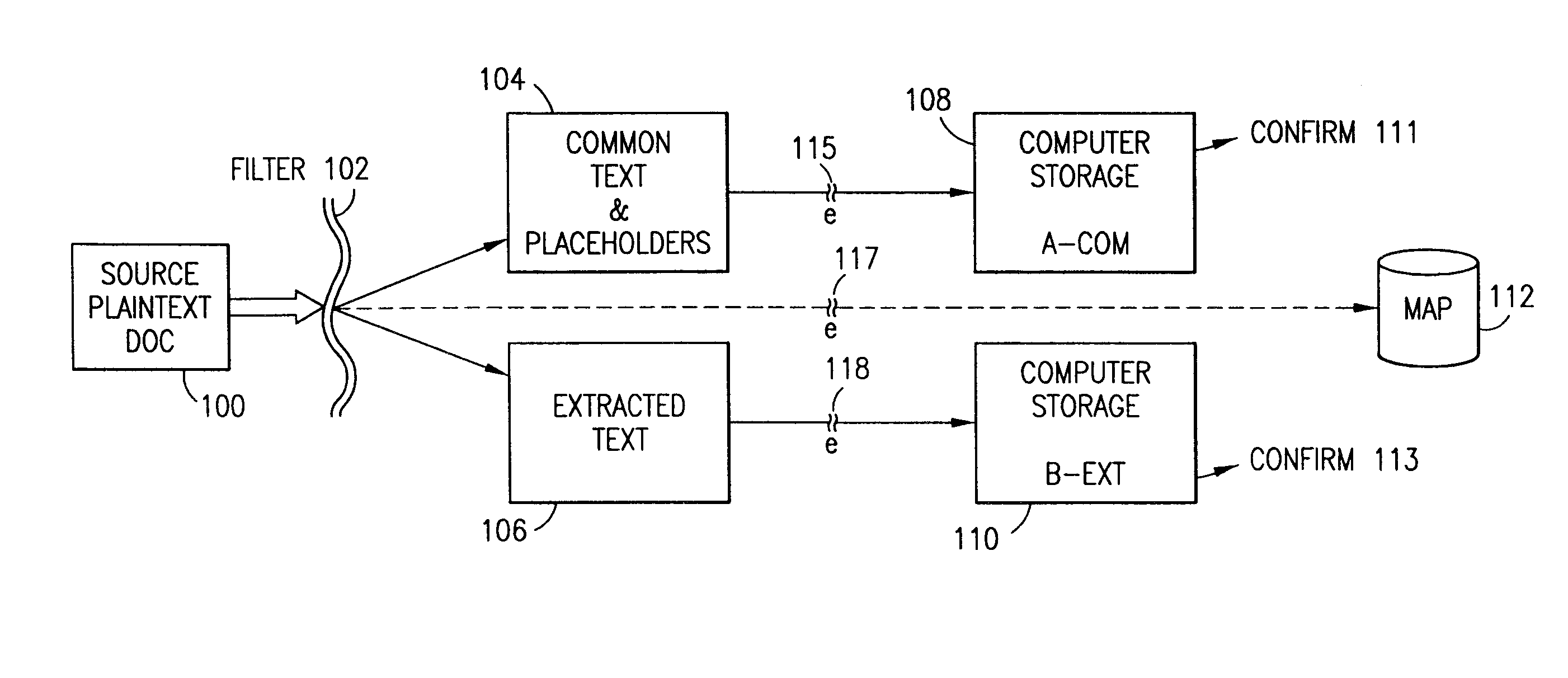
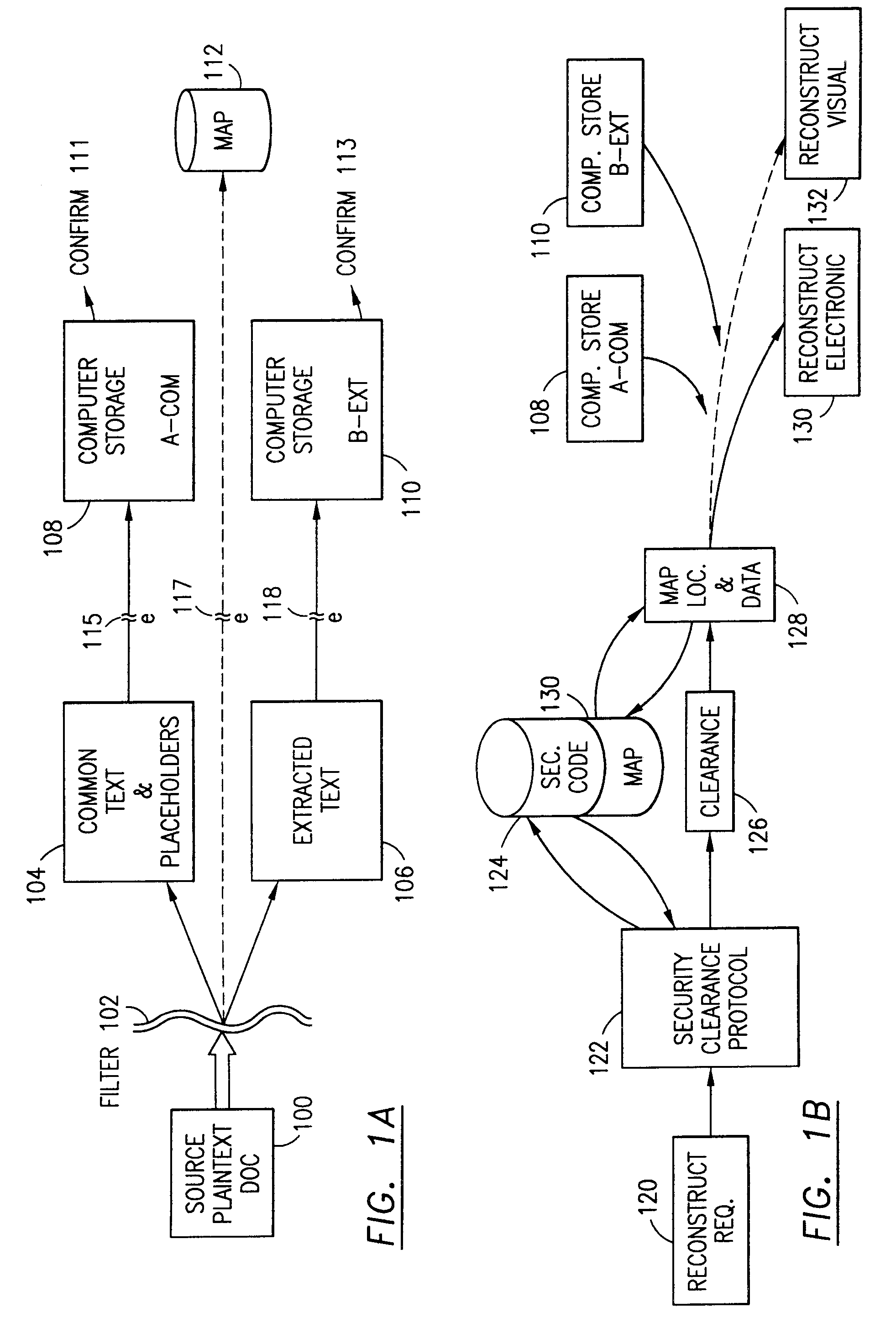
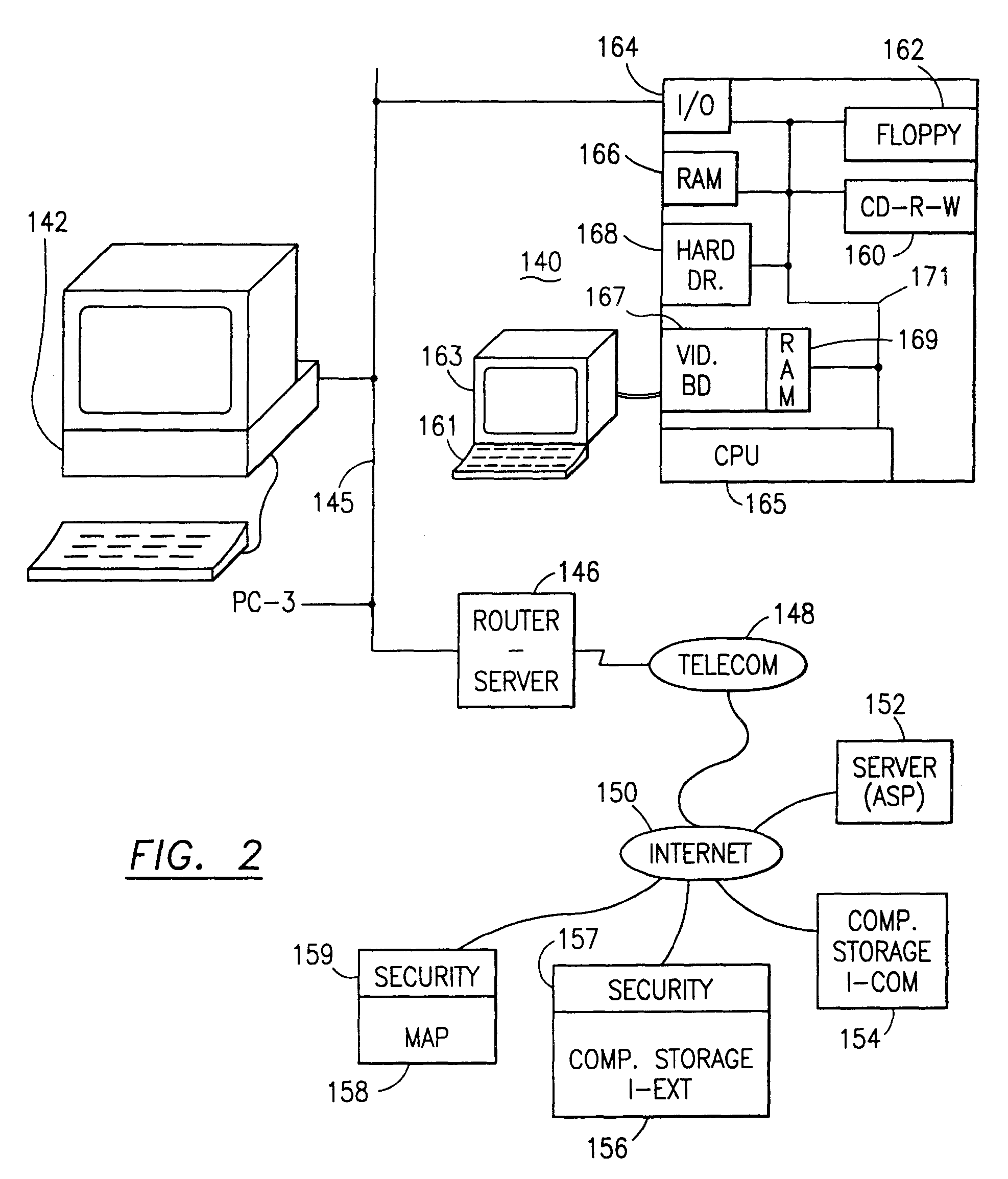
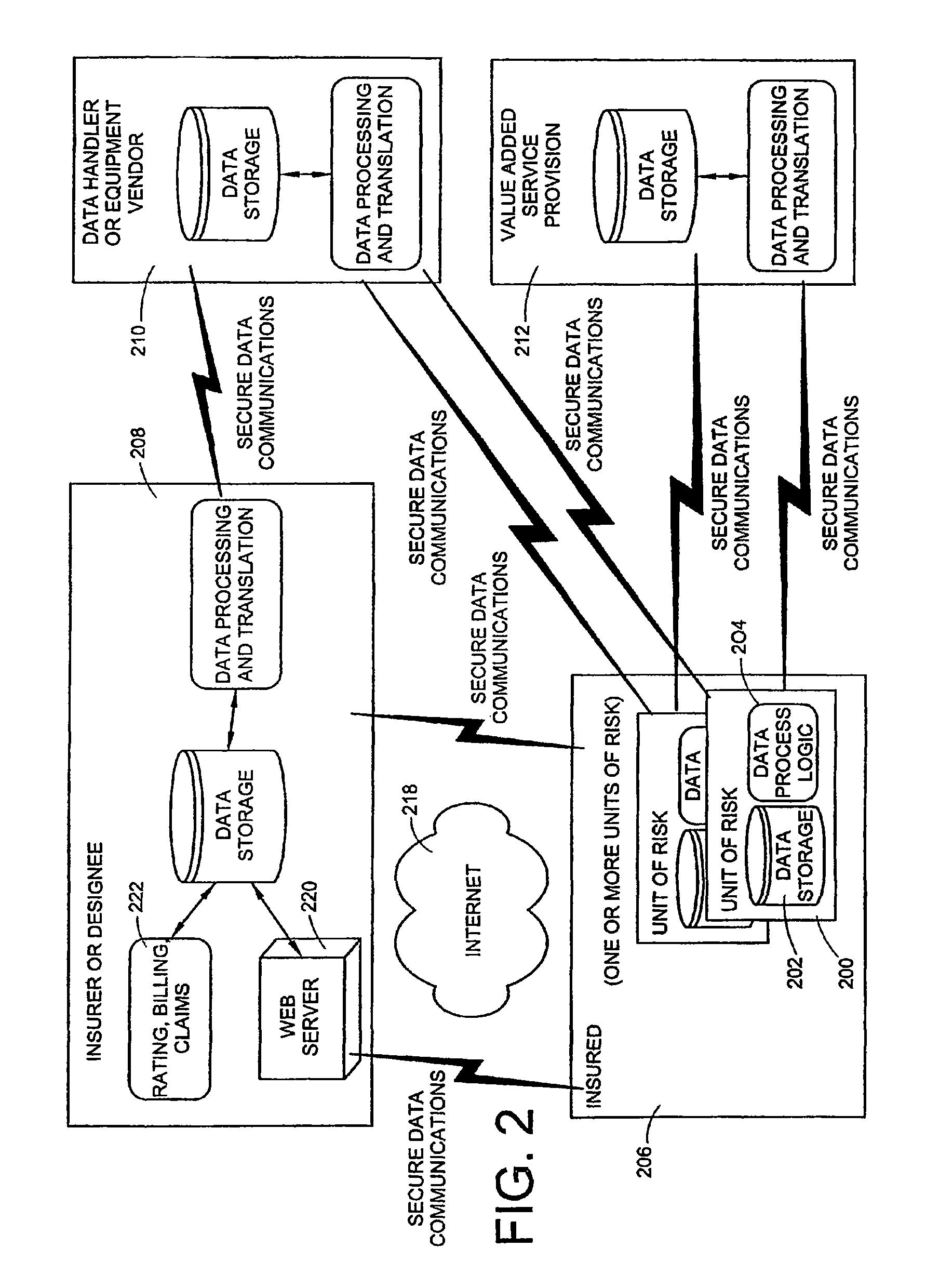
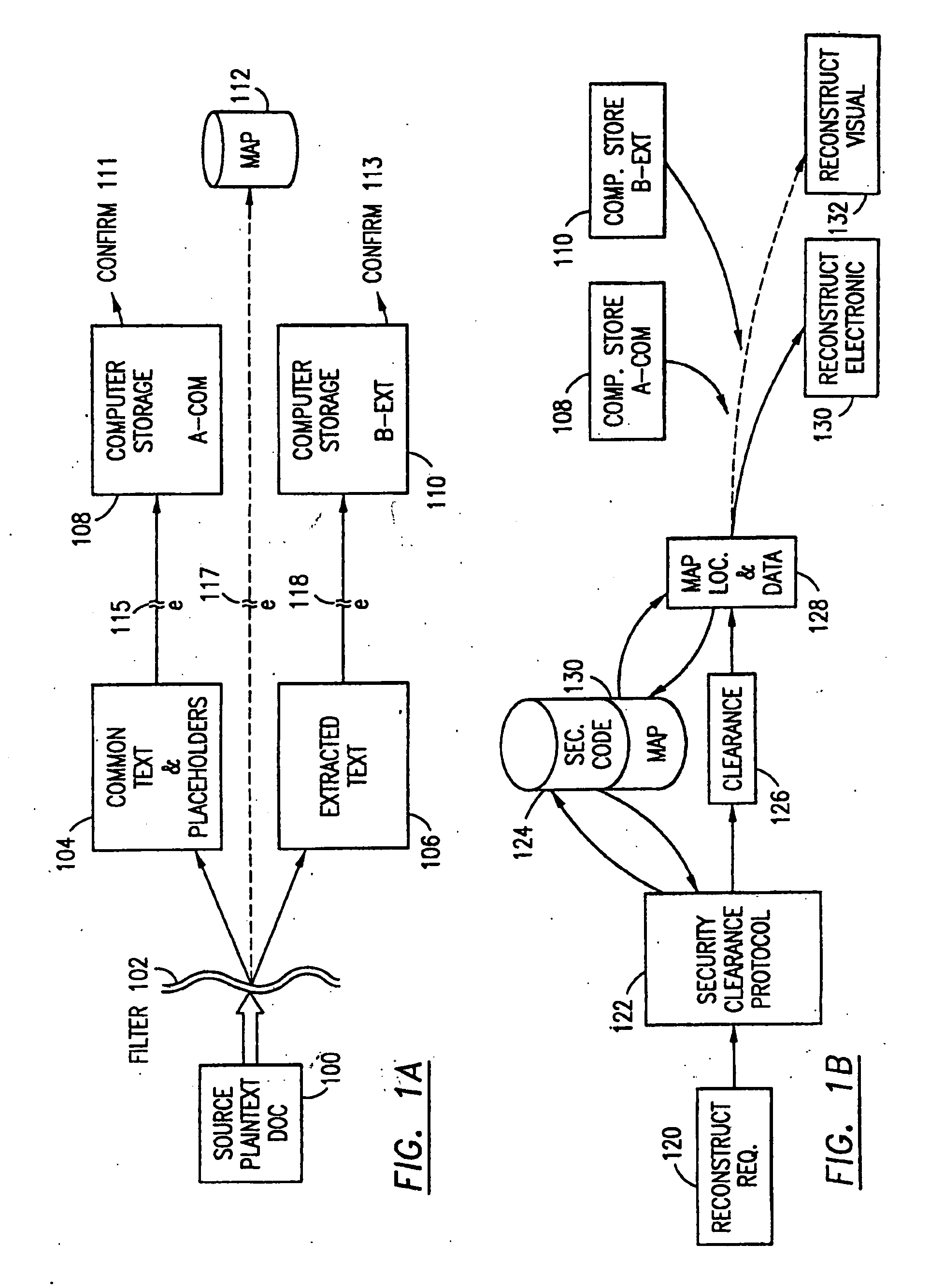
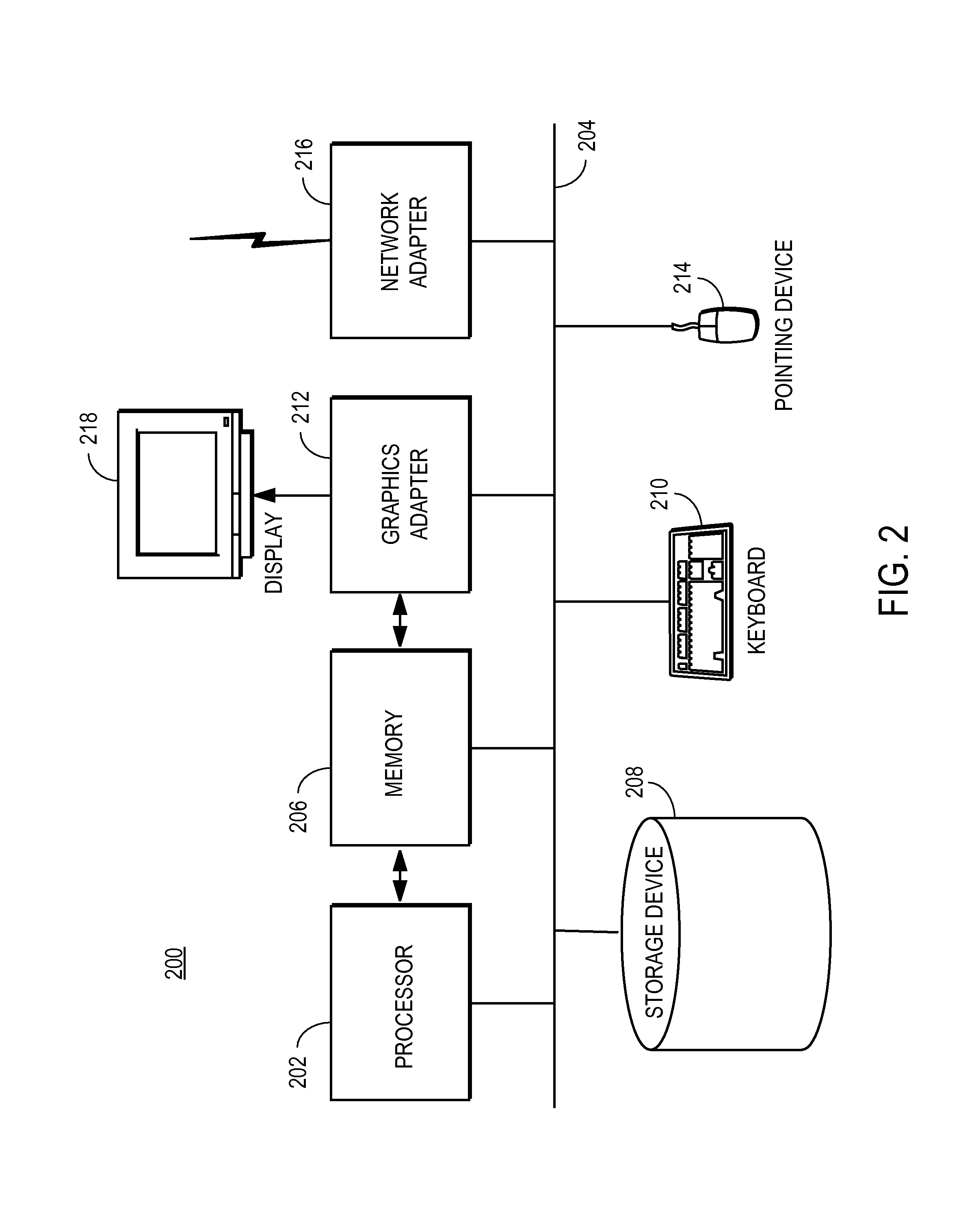
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
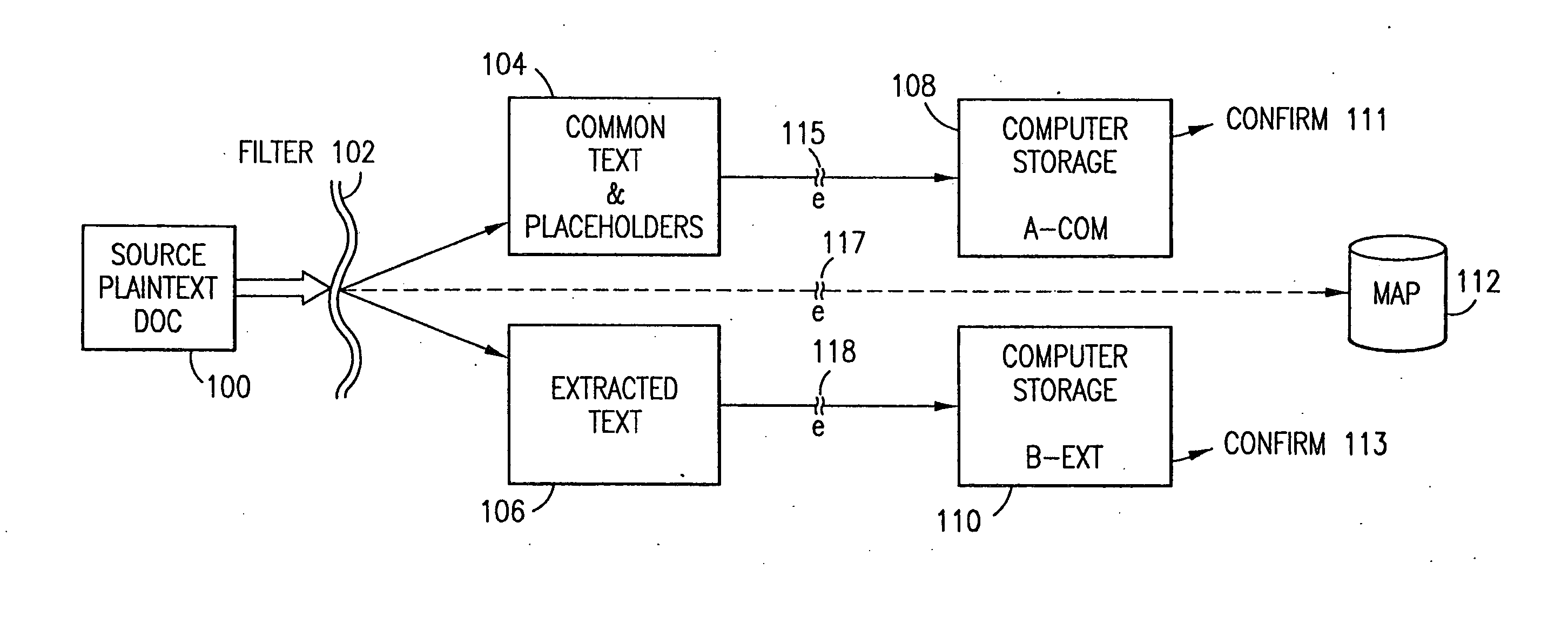
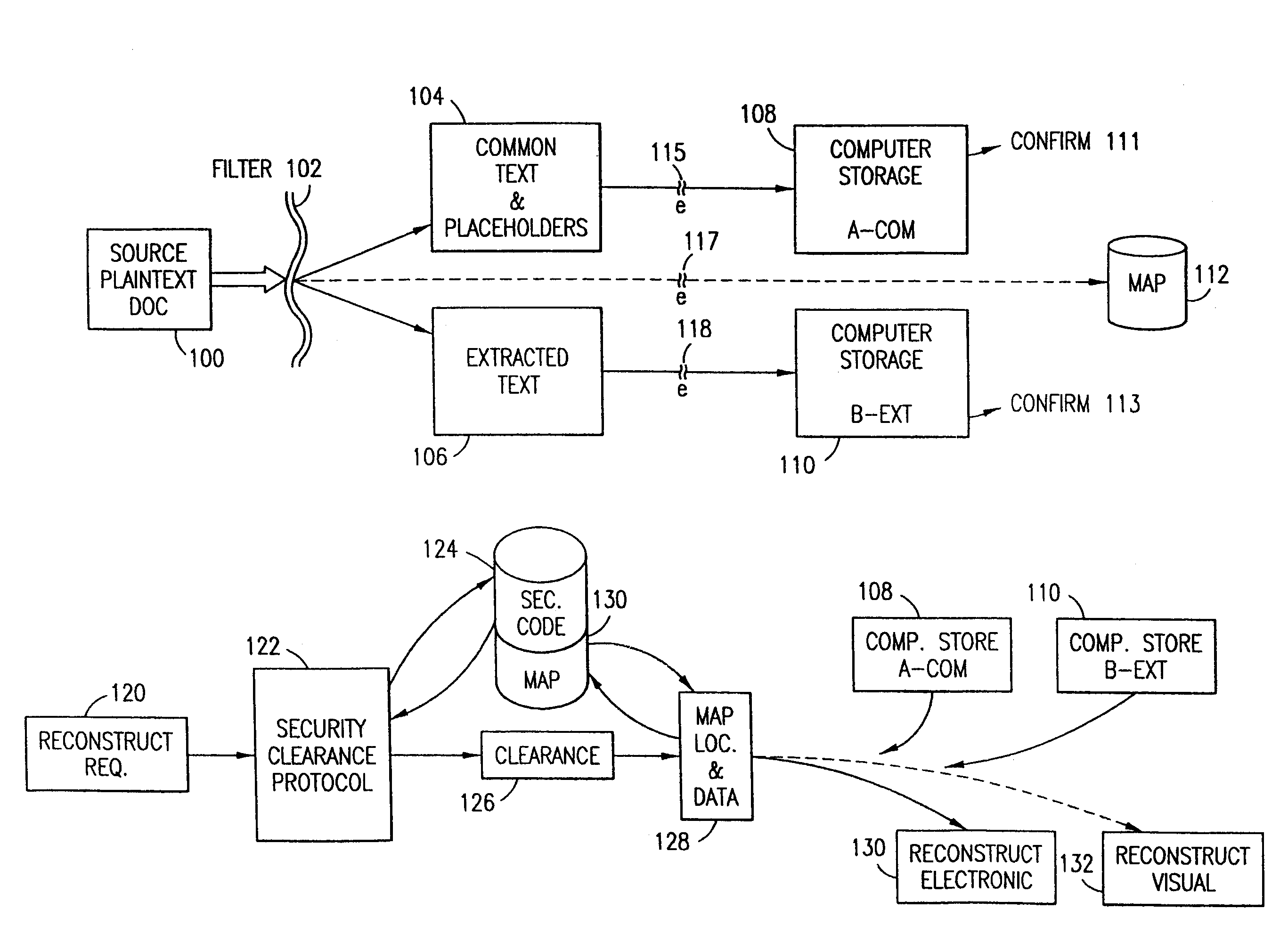
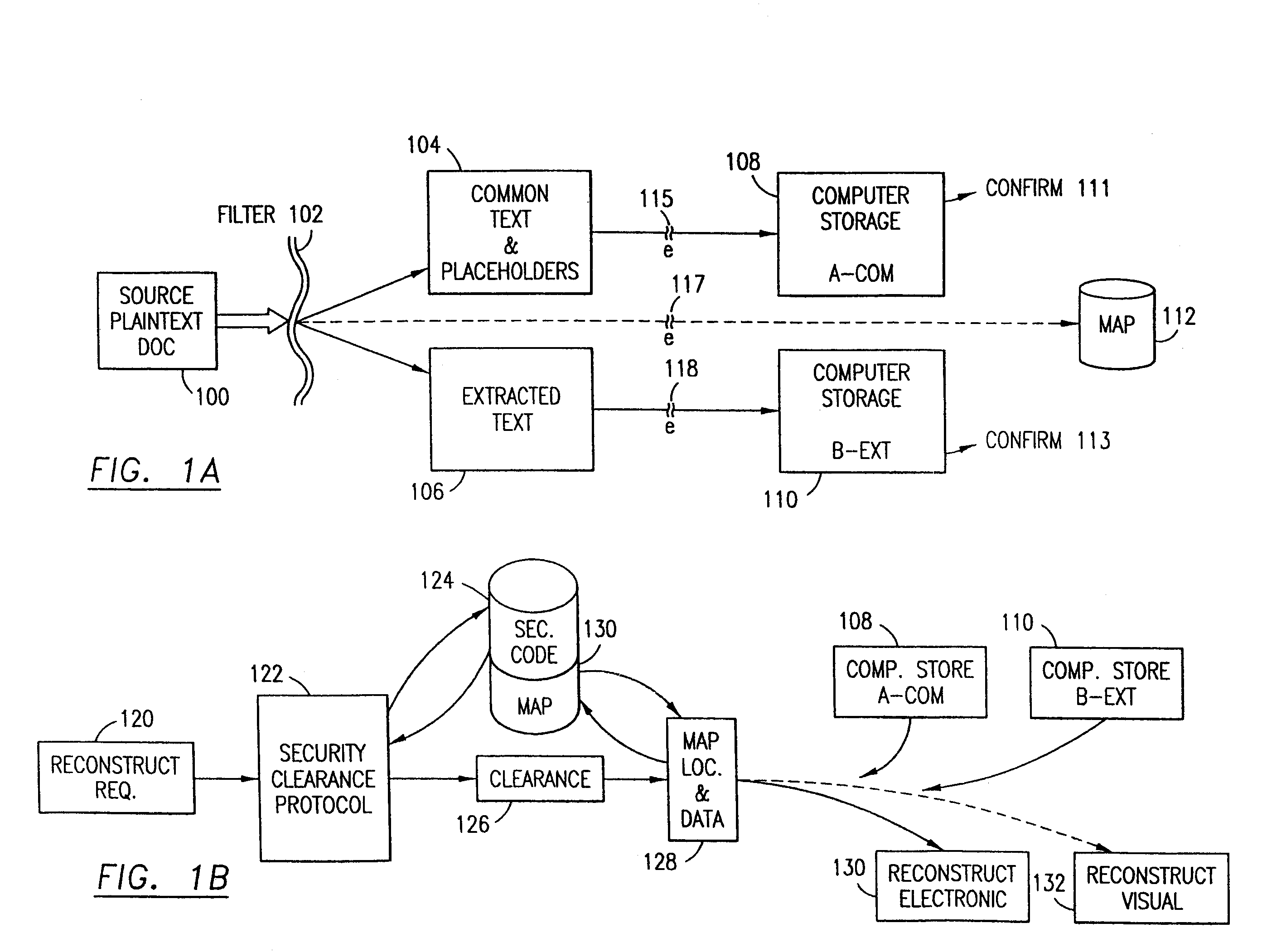
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
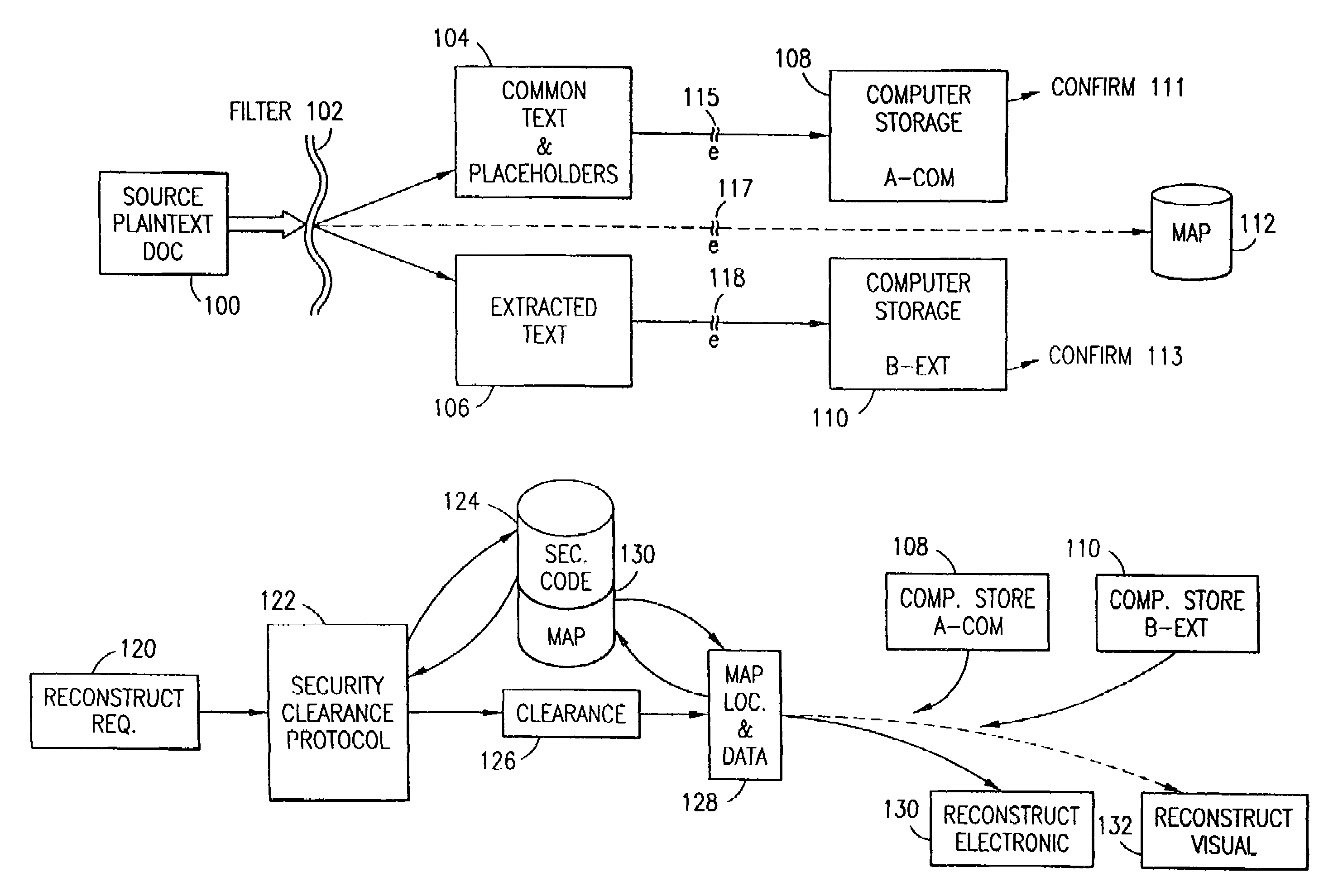
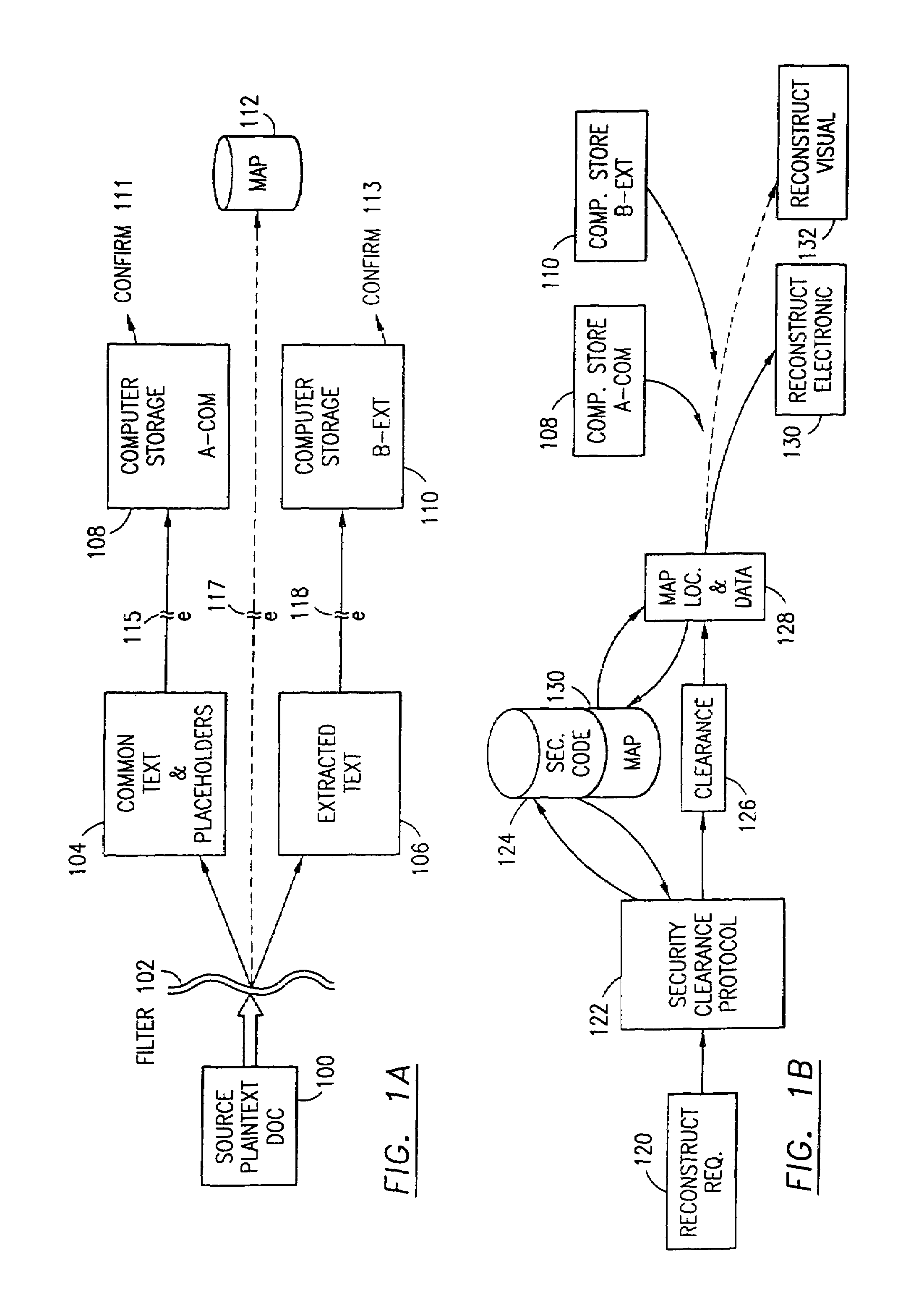
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
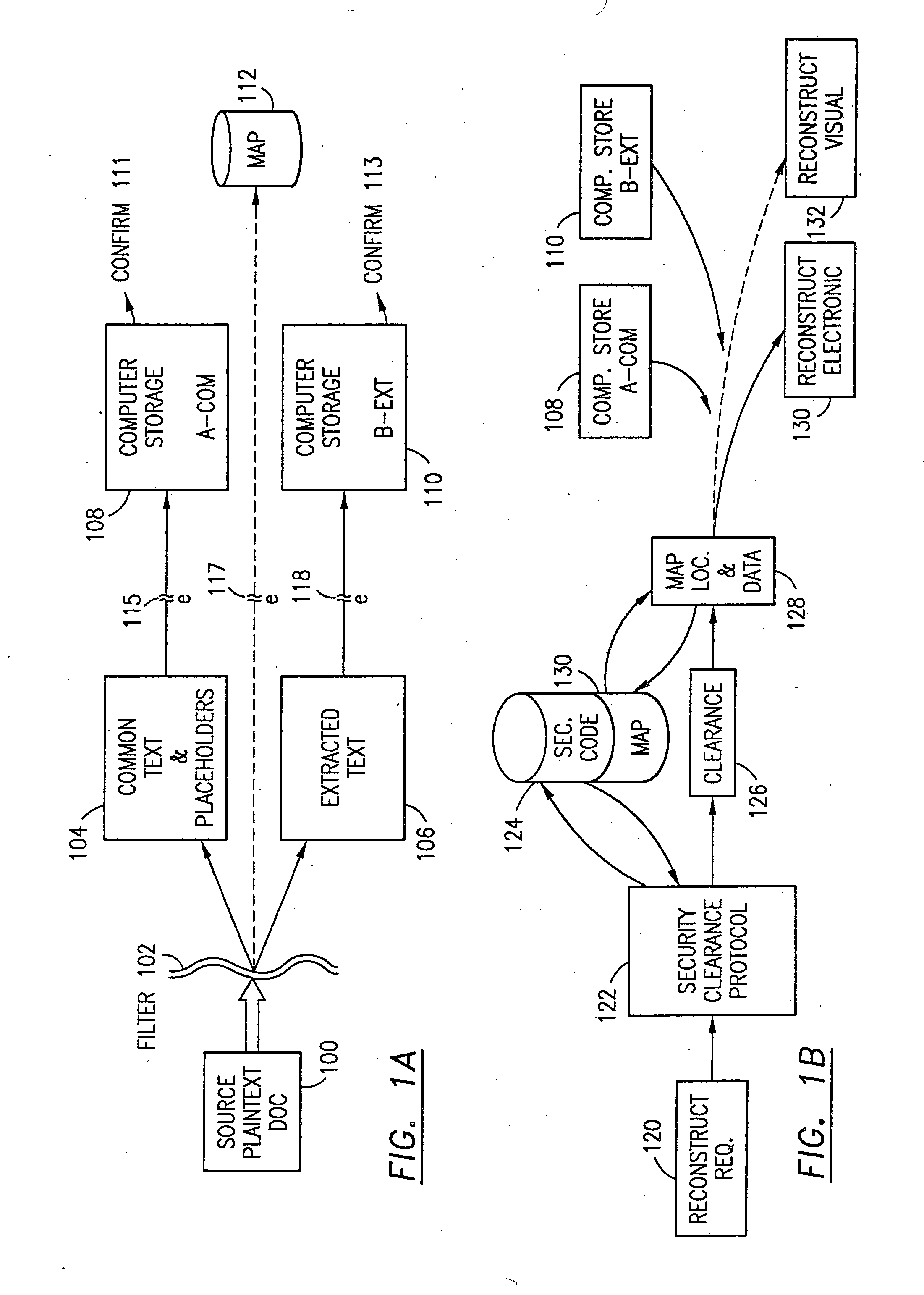
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
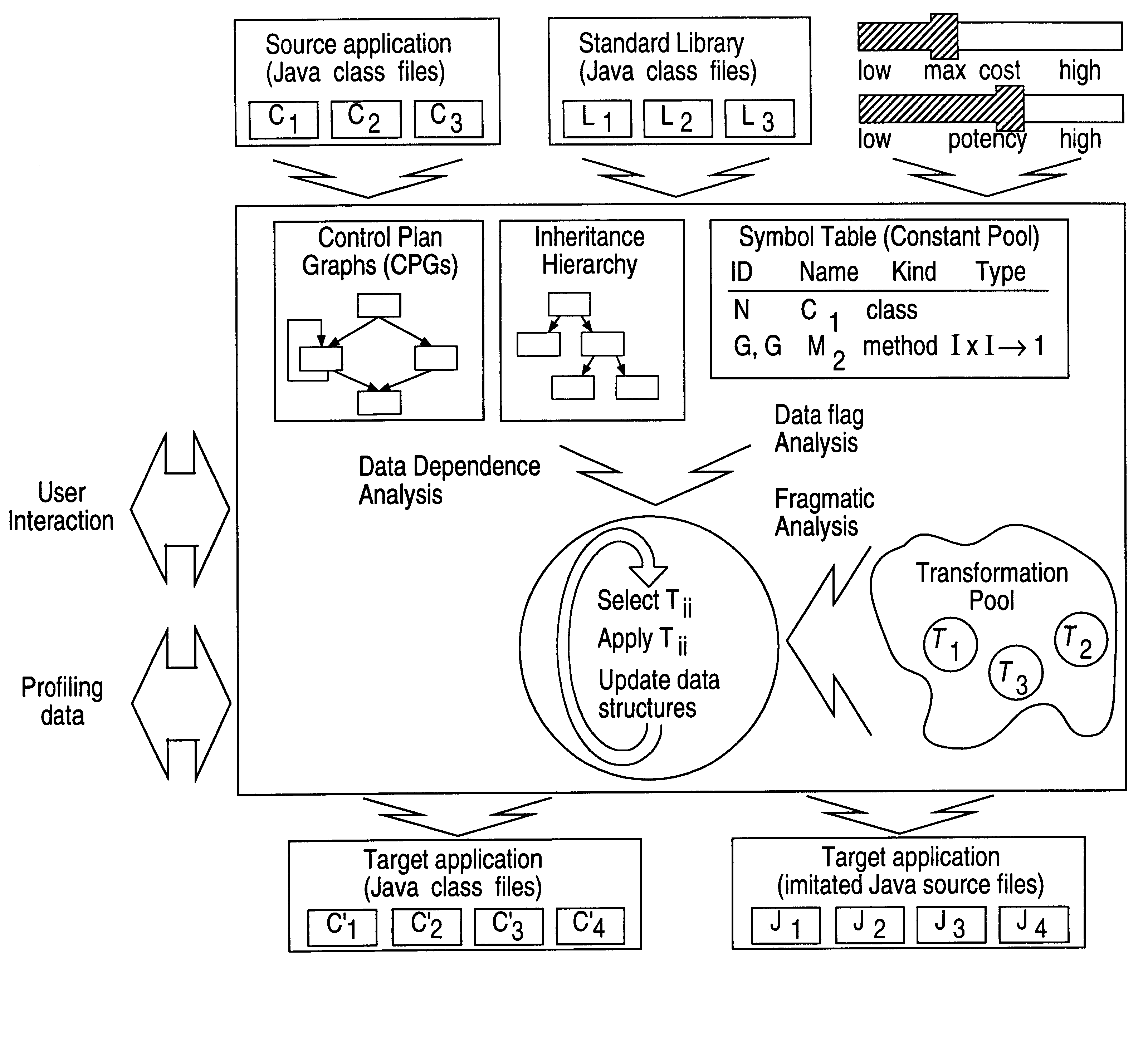
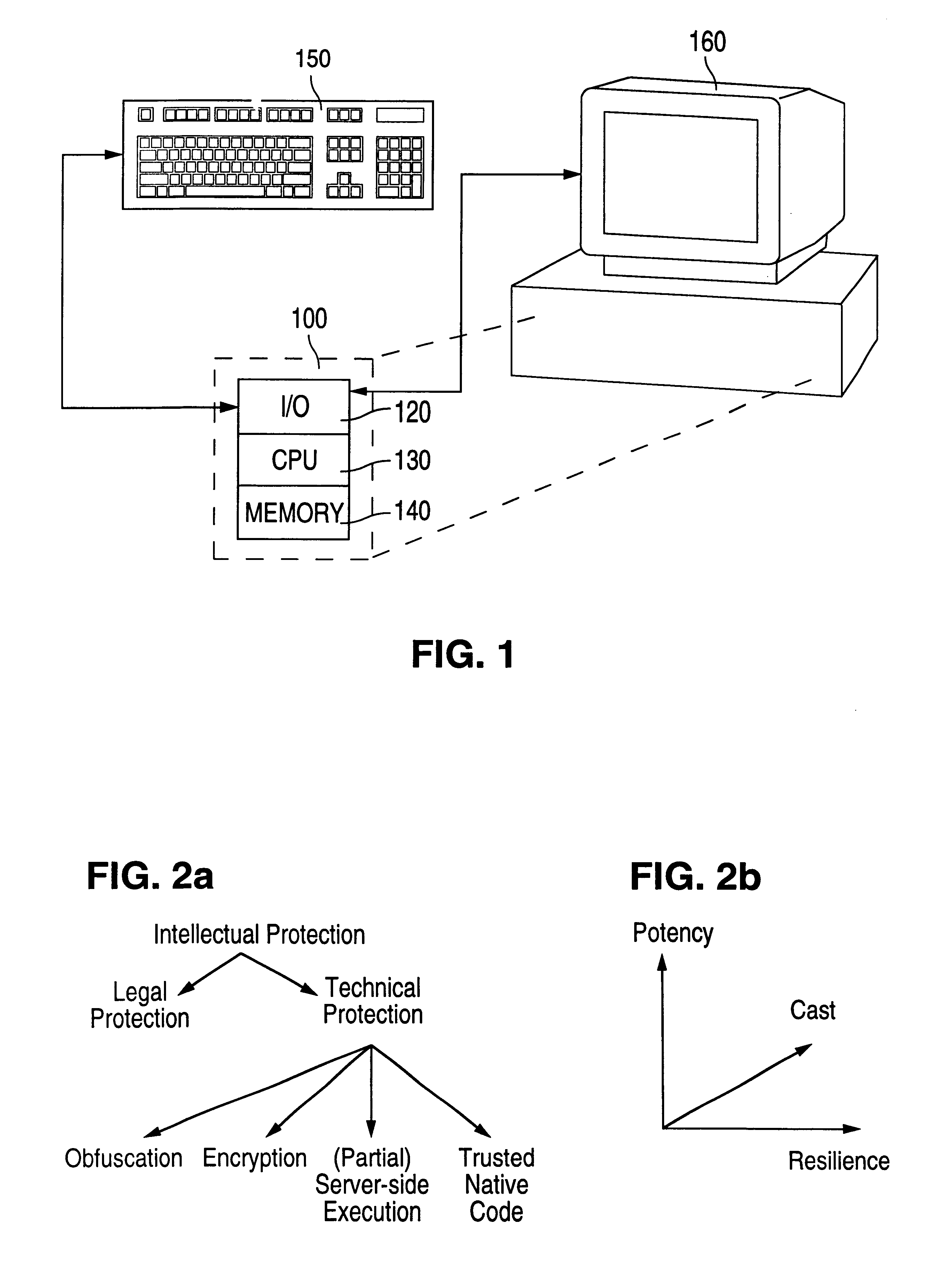
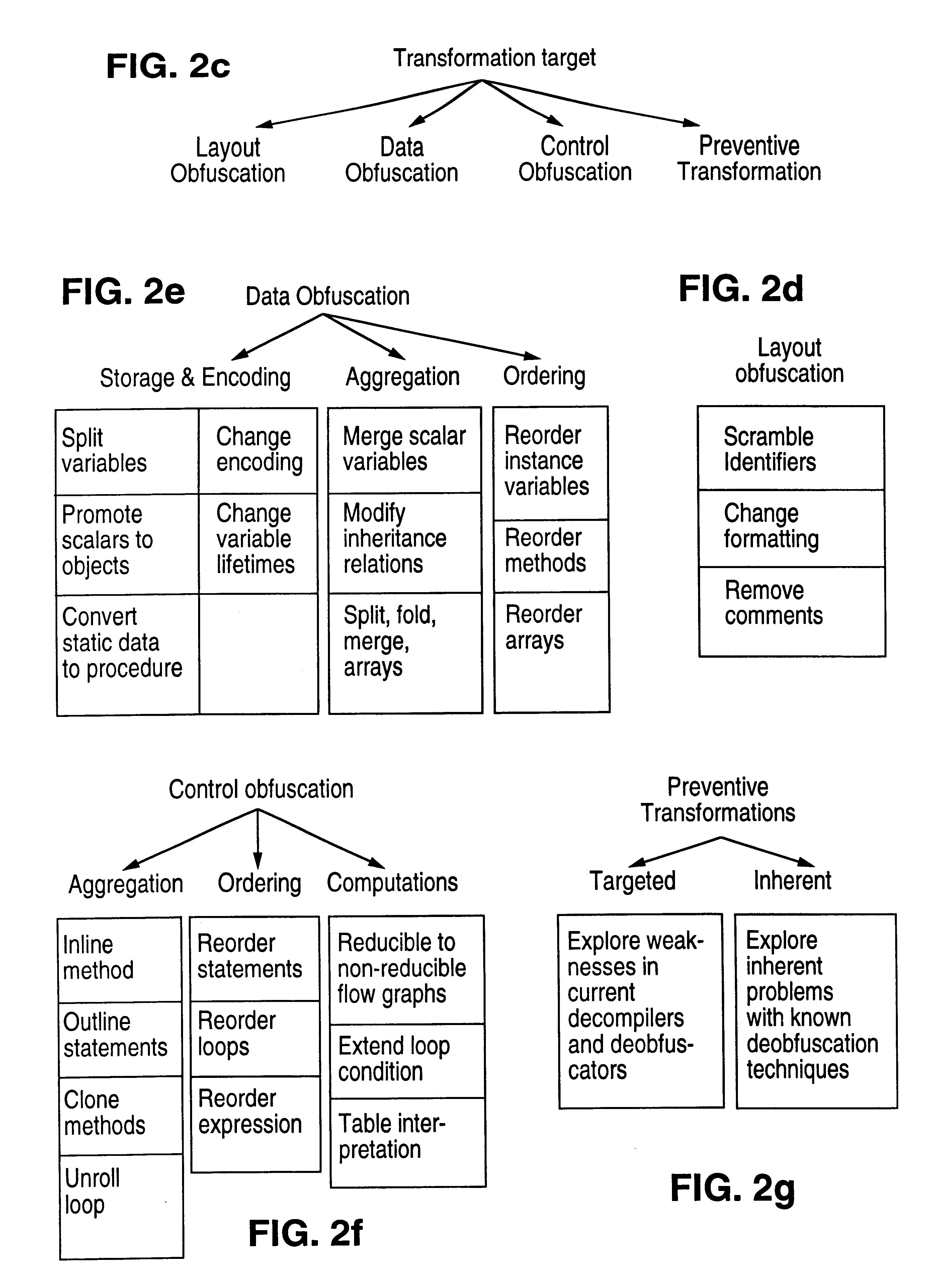
Obfuscation techniques for enhancing software security
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
Vehicle monitoring system
InactiveUS8140358B1FinanceRegistering/indicating working of vehiclesDriver/operatorMonitoring system
A data logging device tracks the operation of a vehicle or driver actions. The device includes a storage device, which may be removable or portable, having a first memory portion that may be read from and may be written to in a vehicle and a second memory portion that may be read from and may be written to in the vehicle. The second memory portion may retain data attributes associated with the data stored in the first removable storage device. A processor reads data from an automotive bus that transfers data from vehicle sensors to other automotive components. The processor writes data to the first memory portion and the second memory portion that reflect a level of risk or safety. A communication device links the storage device to a network of computers. The communication device may be accessible through software that allows a user to access files related to a level of risk or safety and other software that may be related to those files.
Owner:PROGRESSIVE CASUALTY INSURANCE
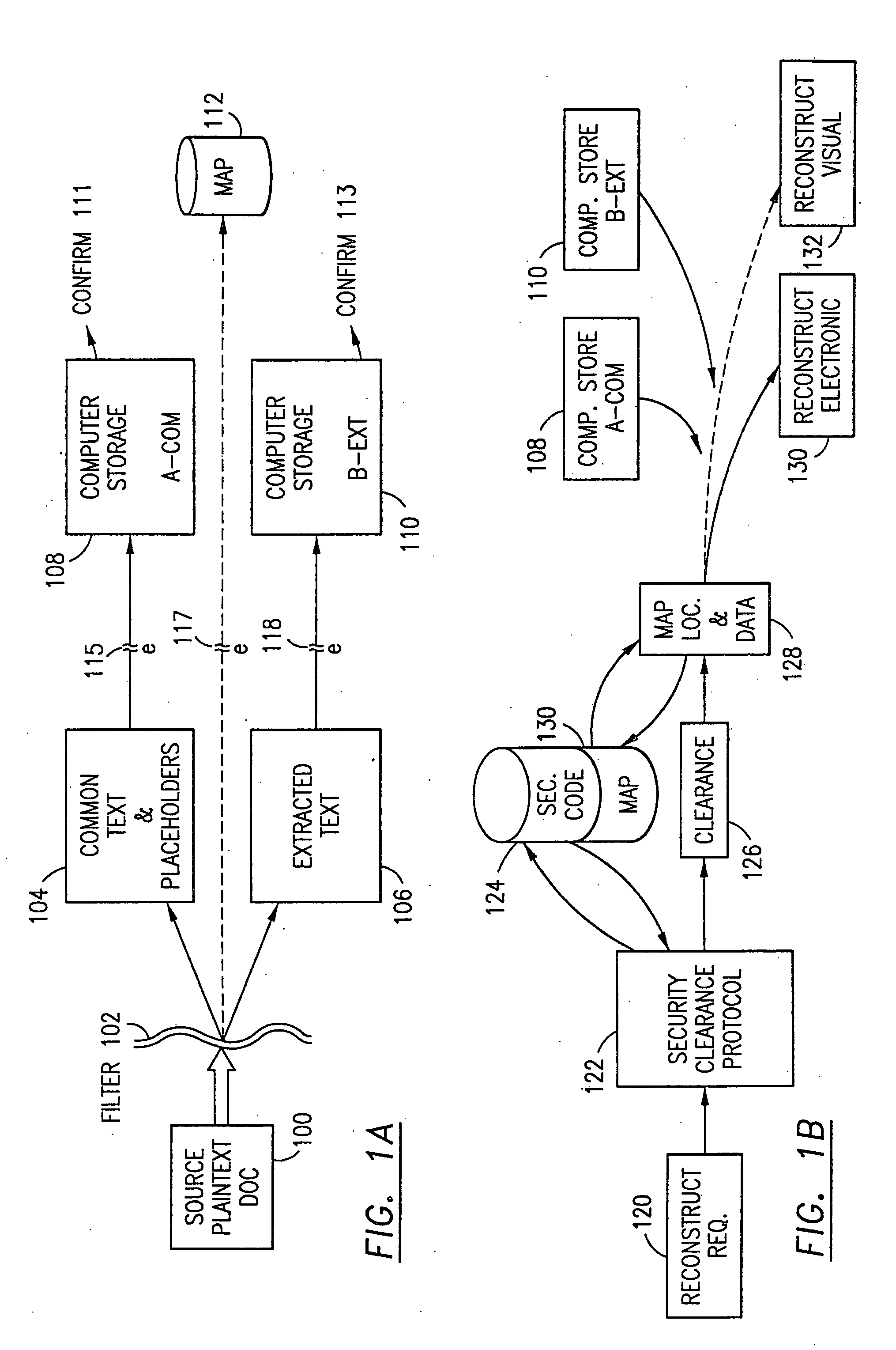
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
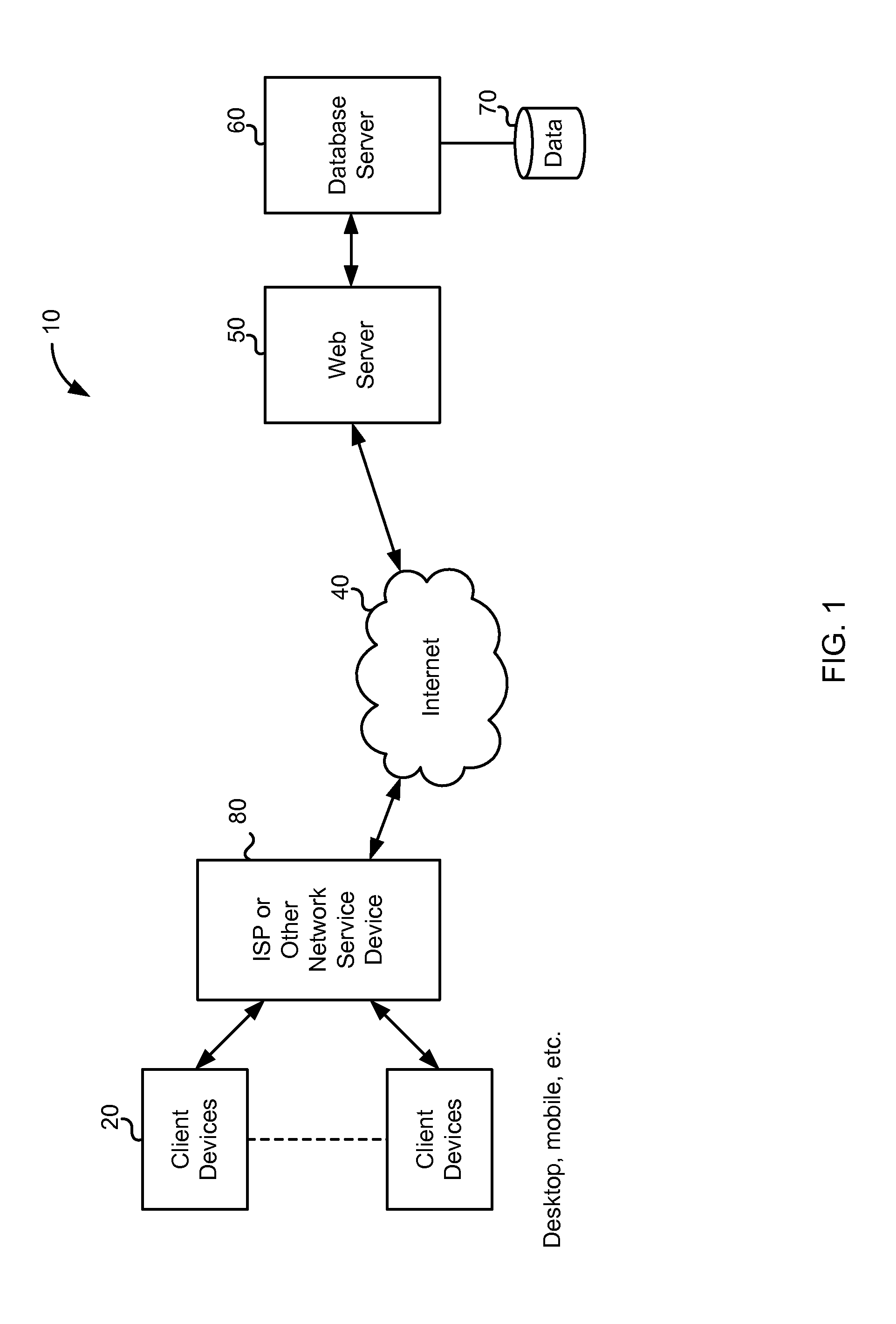
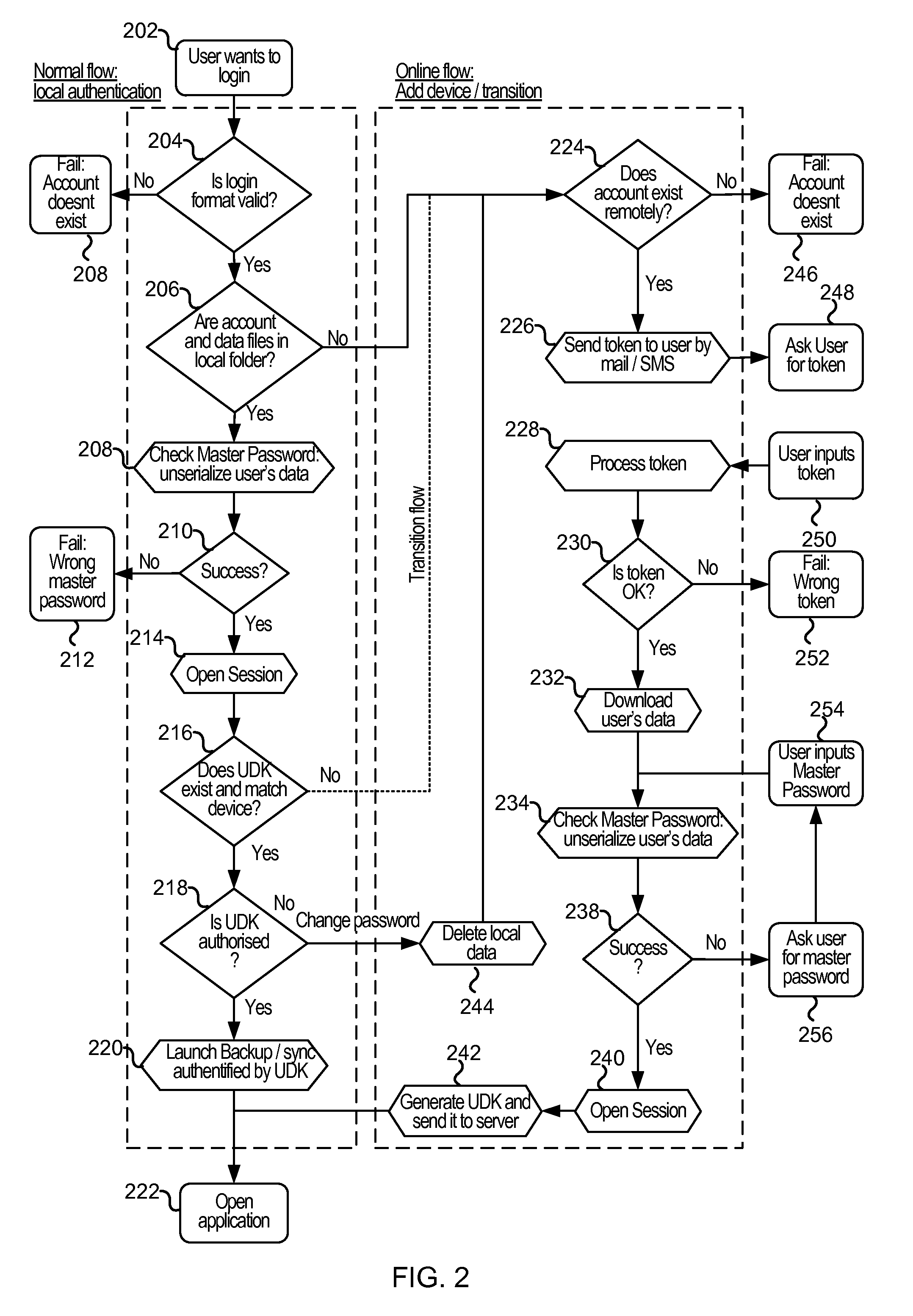
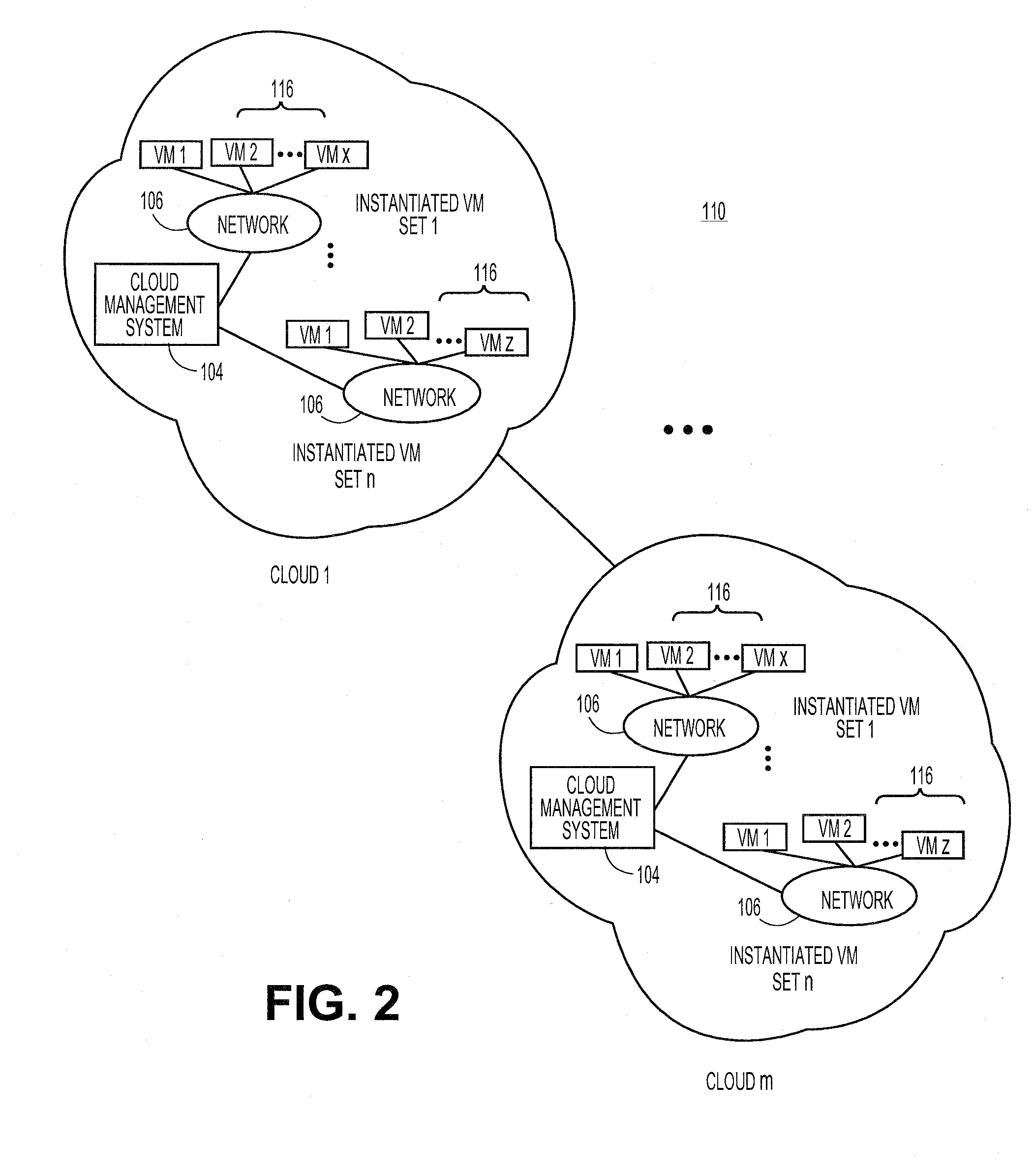
Cloud-based data backup and sync with secure local storage of access keys
ActiveUS20130145447A1Digital data processing detailsMultiple digital computer combinationsThree levelUser device
Methods and systems are provided for secure online data access. In one embodiment, three levels of security are provided where user master passwords are not required at a server. A user device may register with a storage service and receive a user device key that is stored on the device and at the service. The user device key may be used to authenticate the user device with the storage service. As data in the storage service is encrypted with a master password, the data may be protected from disclosure. As a user master key or derivative thereof is not used in authentication, the data may be protected from a disclosure or breach of the authentication credentials. Encryption and decryption may thus be performed on the user device with a user master key that may not be disclosed externally from the user device.
Owner:DASHLANE
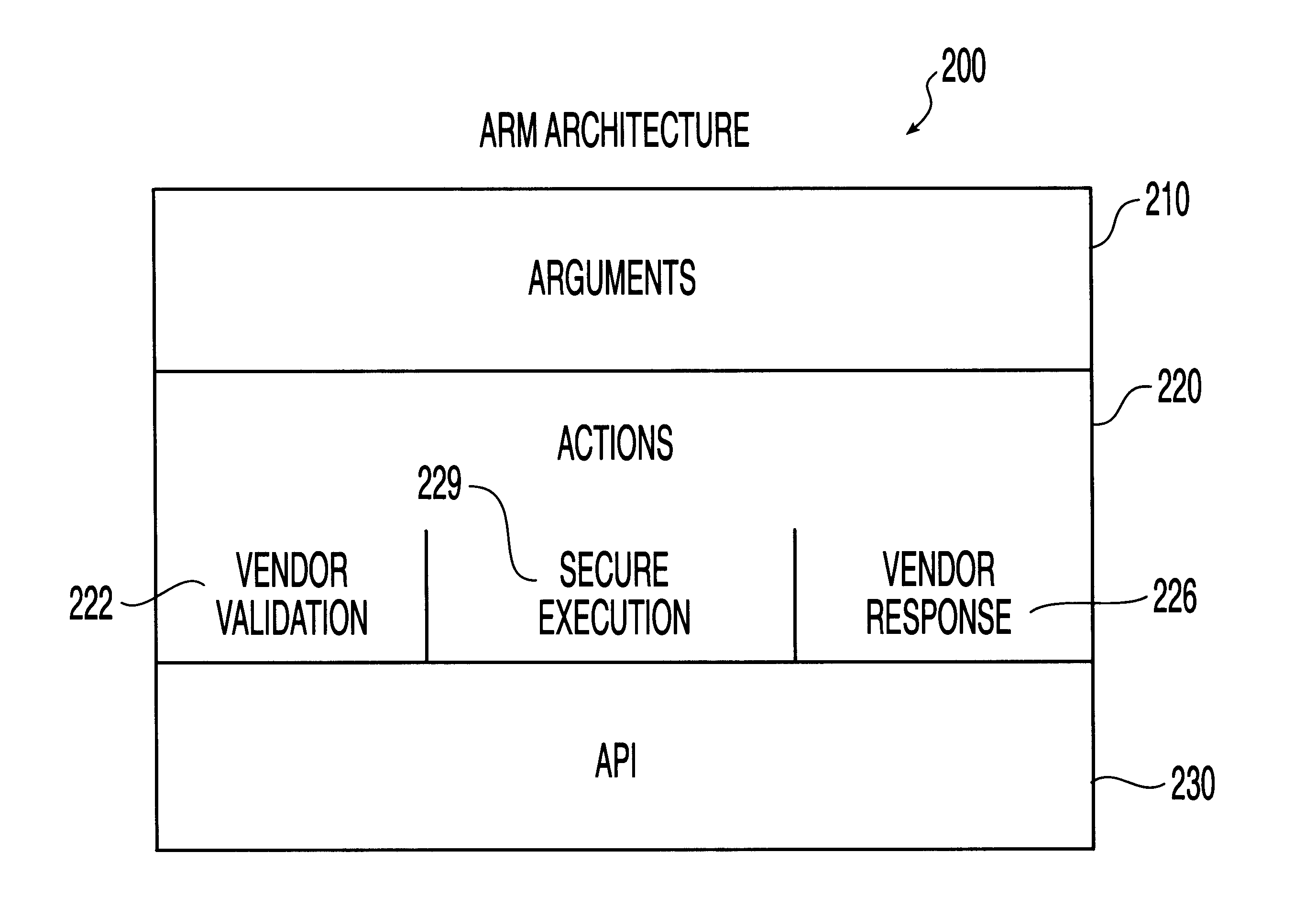
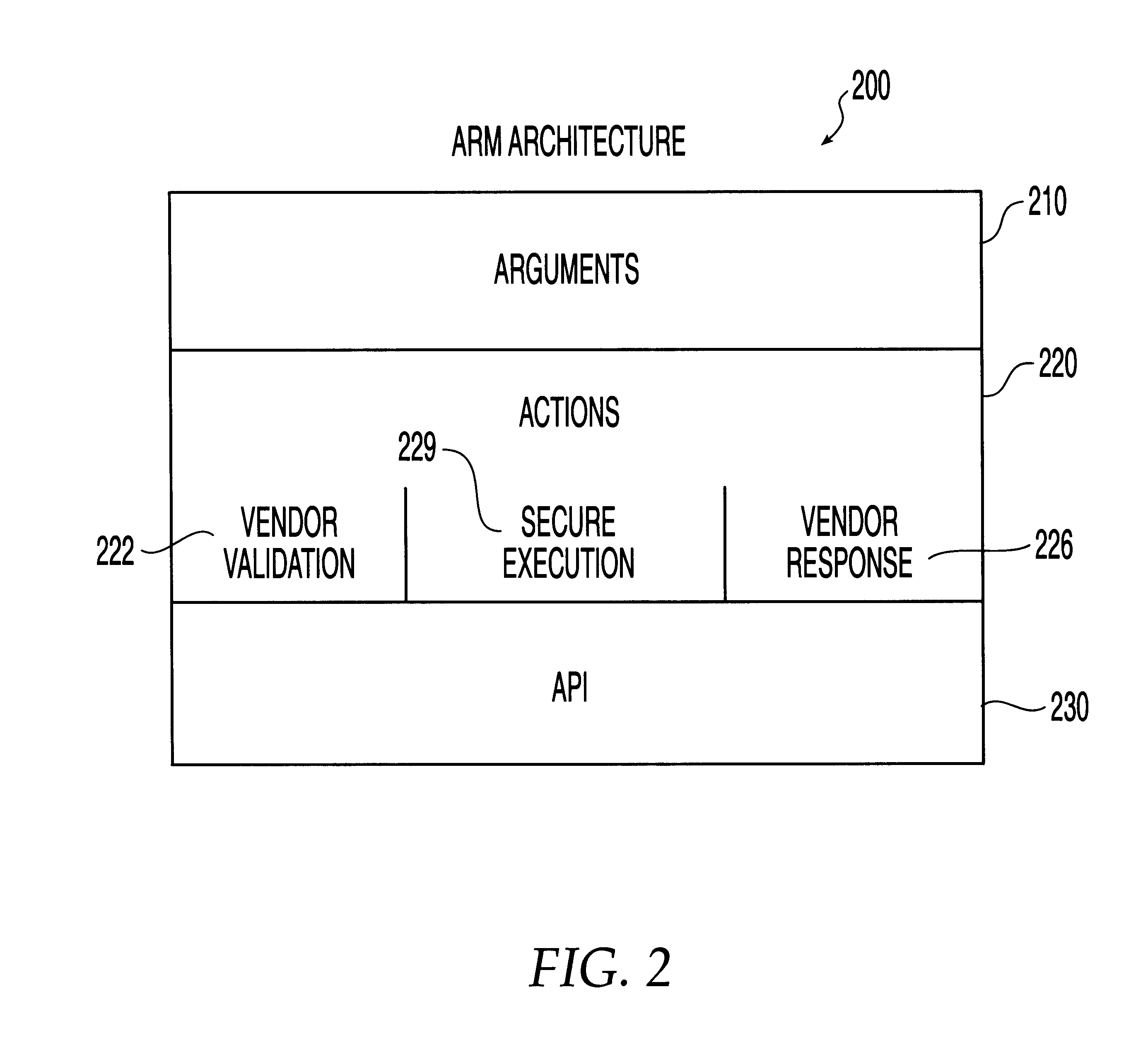
System, method and computer program product for automatic response to computer system misuse using active response modules
InactiveUS6275942B1Rapid responseMemory loss protectionDigital data processing detailsSoftware engineeringSecurity level
A system, method and computer program product for automatic response to computer system misuse using active response modules (ARMs). ARMs are tools that allow static intrusion detection system applications the ability to dynamically increase security levels by allowing real-time responses to detected instances of computer misuse. Several classes of ARMs exist which allow them to interface with several types of network elements found within a computing environment (e.g., firewalls, web servers, Kerberos severs, certificate authorities, etc.). The ARMs, once defined, are deployed in a "plug and play" manner into an existing intrusion detection system within a computing environment. A user (e.g., system administrator) may then configure the ARMs by linking them to specific computer misuses. Upon receipt of an instance of the computer misuse from the intrusion detection system, each ARM linked to the misuse collects pertinent data from the intrusion detection system and invokes a response specified by the ARM class and the collected pertinent data.
Owner:MCAFEE LLC +1
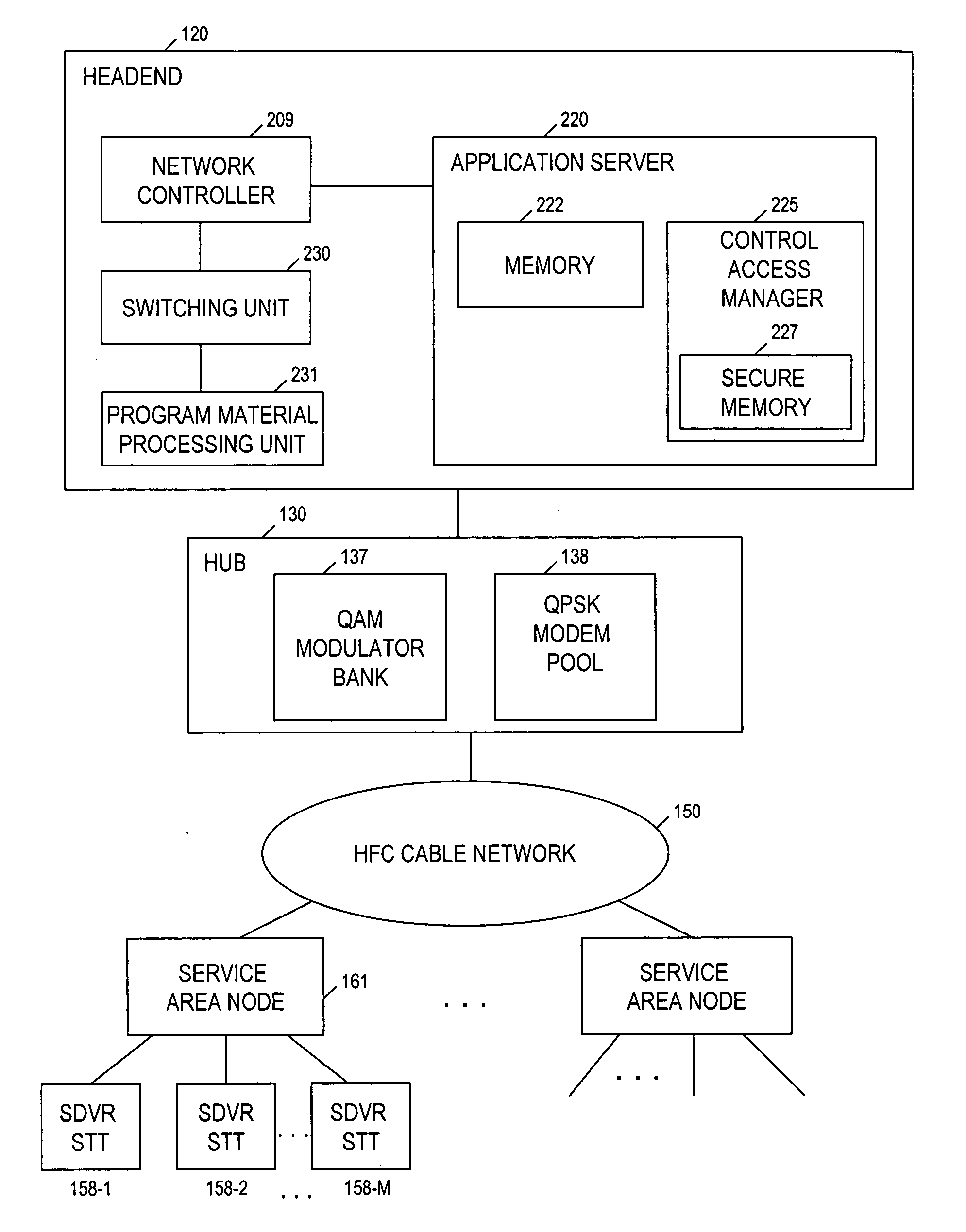
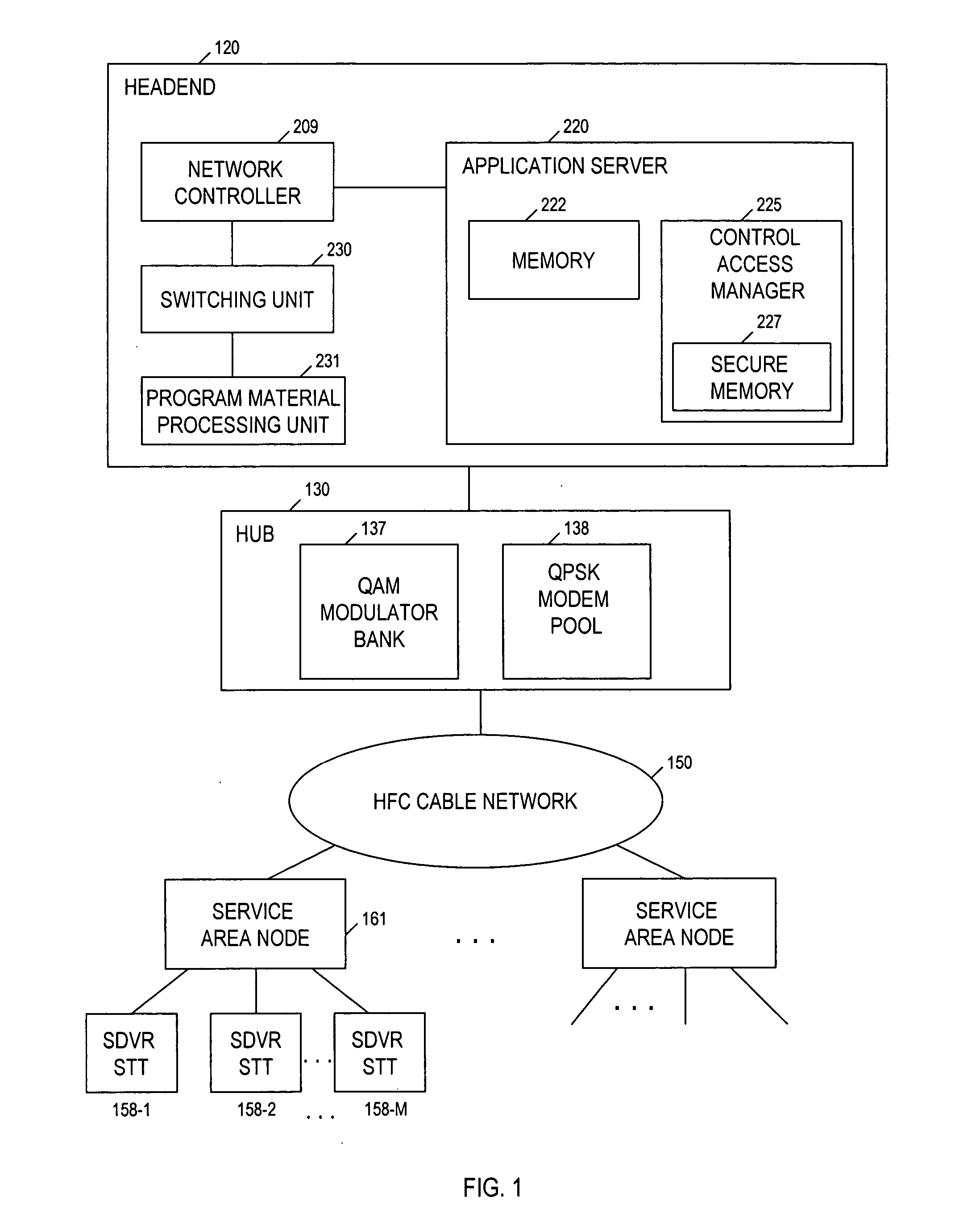
Technique for securely communicating programming content
ActiveUS20060047957A1Prevent illegal useEncryption apparatus with shift registers/memoriesDigital data processing detailsTime segmentSecurity level
A technique is provided for securely transferring programming content from a first device in a first layer, e.g., a trusted domain, to a second device in a second layer, e.g., outside the trusted domain. When a user requests that the first device transfer protected content to the second device, the first device needs to authenticate the second device. After the second device is authenticated, the first device may transfer to the second device the protected content, together with a rights file associated therewith. The rights file specifies the rights of the second device to use the protected content, according to its security level indicative of its security. These rights may concern, e.g., the number of times that the second device may subsequently transfer the protected content to other devices, the time period within which the second device may play the protected content, etc. The higher the security level of the second device is, the more rights accorded thereto. Indeed, the second device may need to meet a minimum security level requirement in order for it to receive or keep the protected content.
Owner:TIME WARNER CABLE ENTERPRISES LLC +1
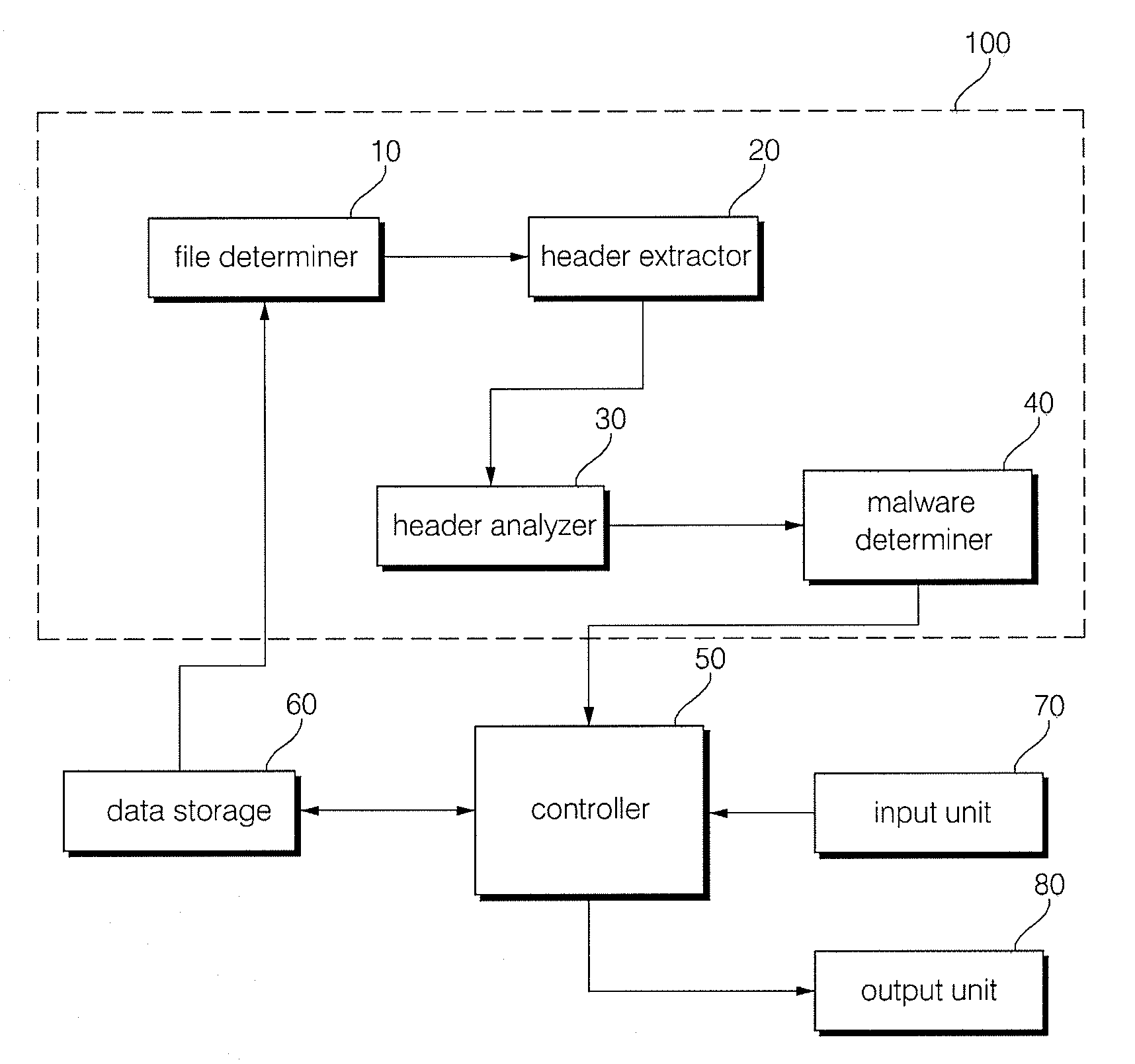
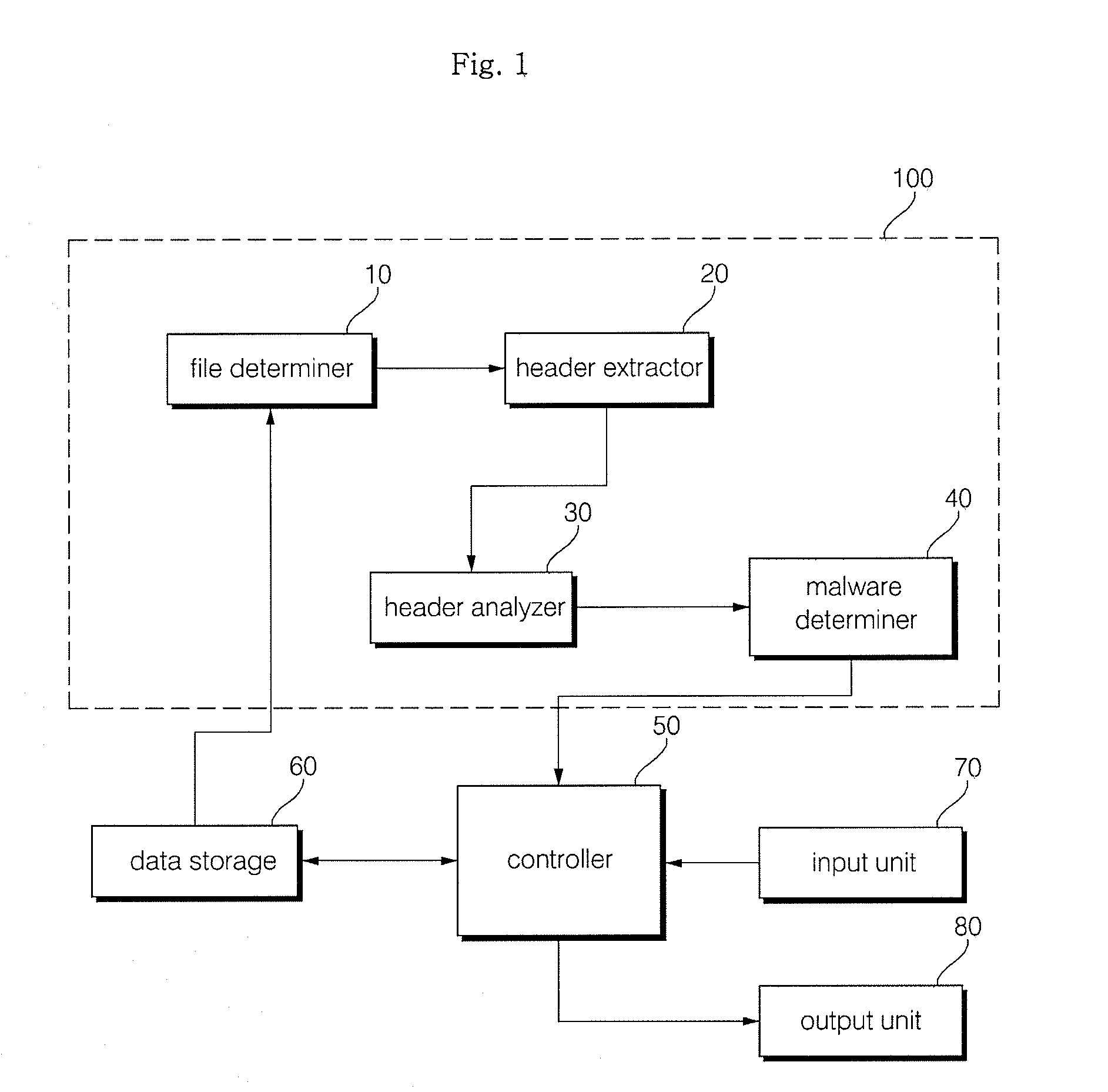
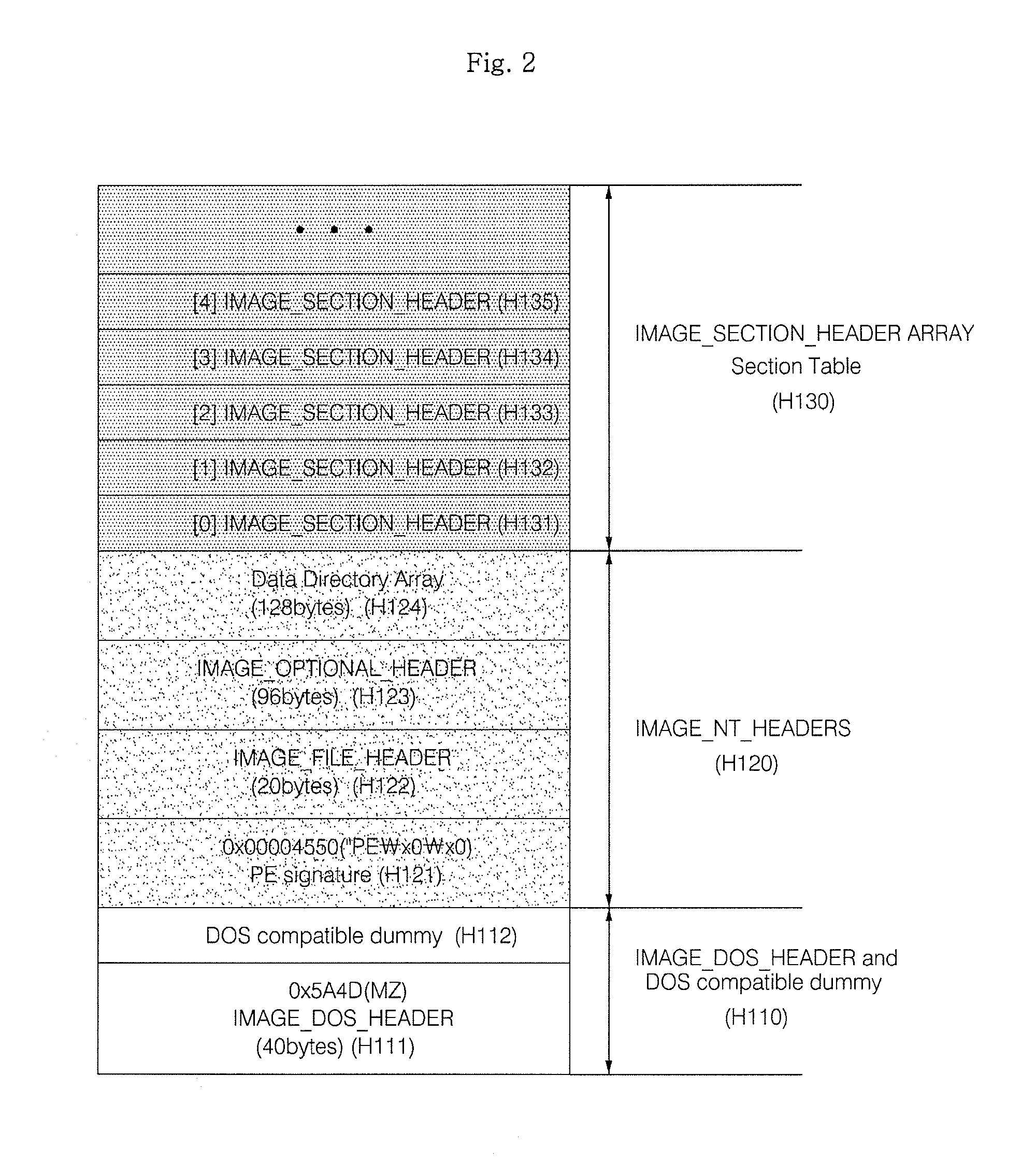
Method and apparatus for malware detection
InactiveUS20090133125A1Shorten detection timeImprove security levelMemory loss protectionUnauthorized memory use protectionMalwareProtection system
The present invention relates to an apparatus and method for detecting malware. The malware detection apparatus and method of the present invention determines whether a file is malware or not by analyzing the header of an executable file. Since the malware detection apparatus and method can quickly detect presence of malware, it can shorten detection time considerably. The malware detection apparatus and method can also detect even unknown malware as well as known malware to thereby estimate and determine presence of malware. Therefore, it is possible to cope with malware in advance, protect a system with a program, and increase security level remarkably.
Owner:ELECTRONICS & TELECOMM RES INST
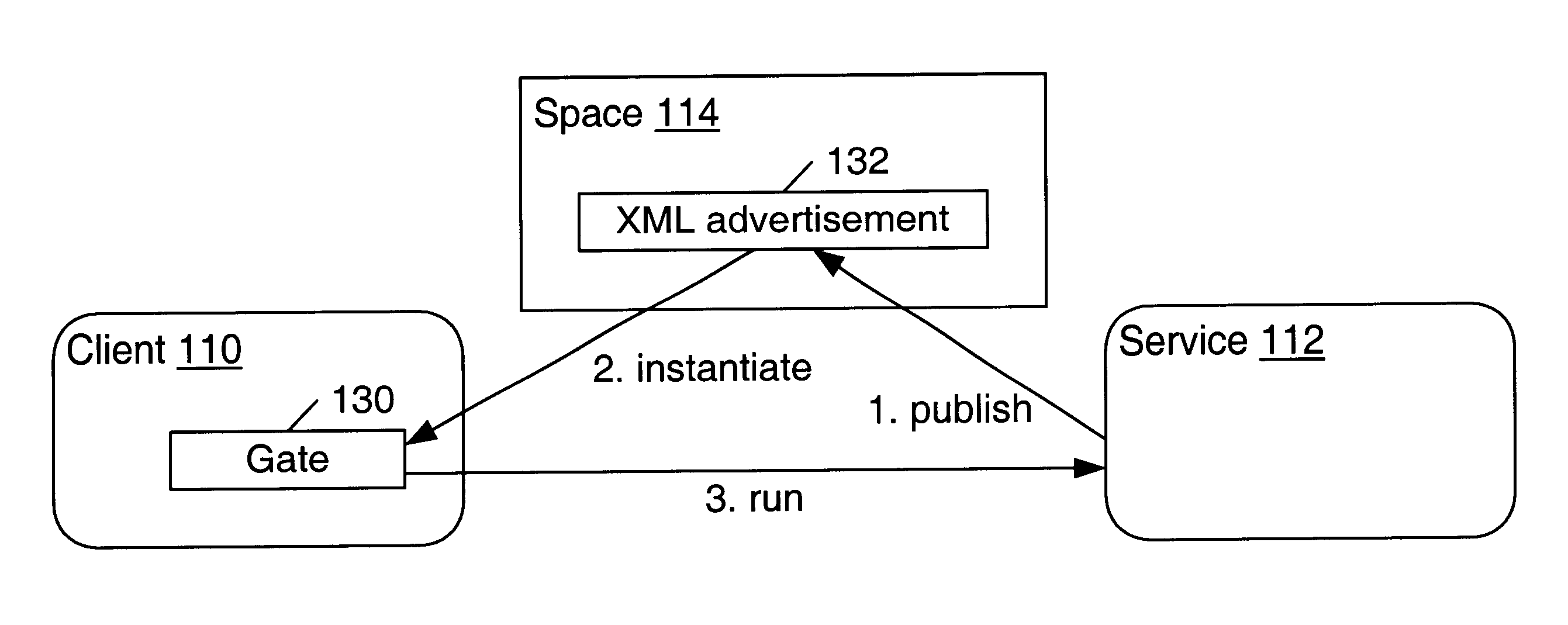
Message gates in a distributed computing environment
InactiveUS6850979B1Multiple digital computer combinationsBuying/selling/leasing transactionsDistributed Computing EnvironmentExtensible markup
Embodiments of message gates are described. A message gate is the message endpoint for a client or service in a distributed computing environment. A message gate may provide a secure endpoint that sends and receives type-safe messages. Gates may perform the sending and receiving of messages between clients and services using a protocol specified in a service advertisement. In one embodiment, the messages are eXtensible Markup Language (XML) messages. For a client, a message gate represents the authority to use some or all of a service's capabilities. Each capability may be expressed in terms of a message that may be sent to the service. Creation of a message gate may involve an authentication service that generates an authentication credential, and that may negotiate the desired level of security and the set of messages that may be passed between client and service. A message gate may perform verification of messages against a message schema to ensure that the messages are allowed. Message gates may embed the authentication credential in outgoing messages so that the receiving message gate may authenticate the message. Messages may also include information to allow the receiving gate to verify that the message has not been compromised prior to receipt.
Owner:ORACLE INT CORP
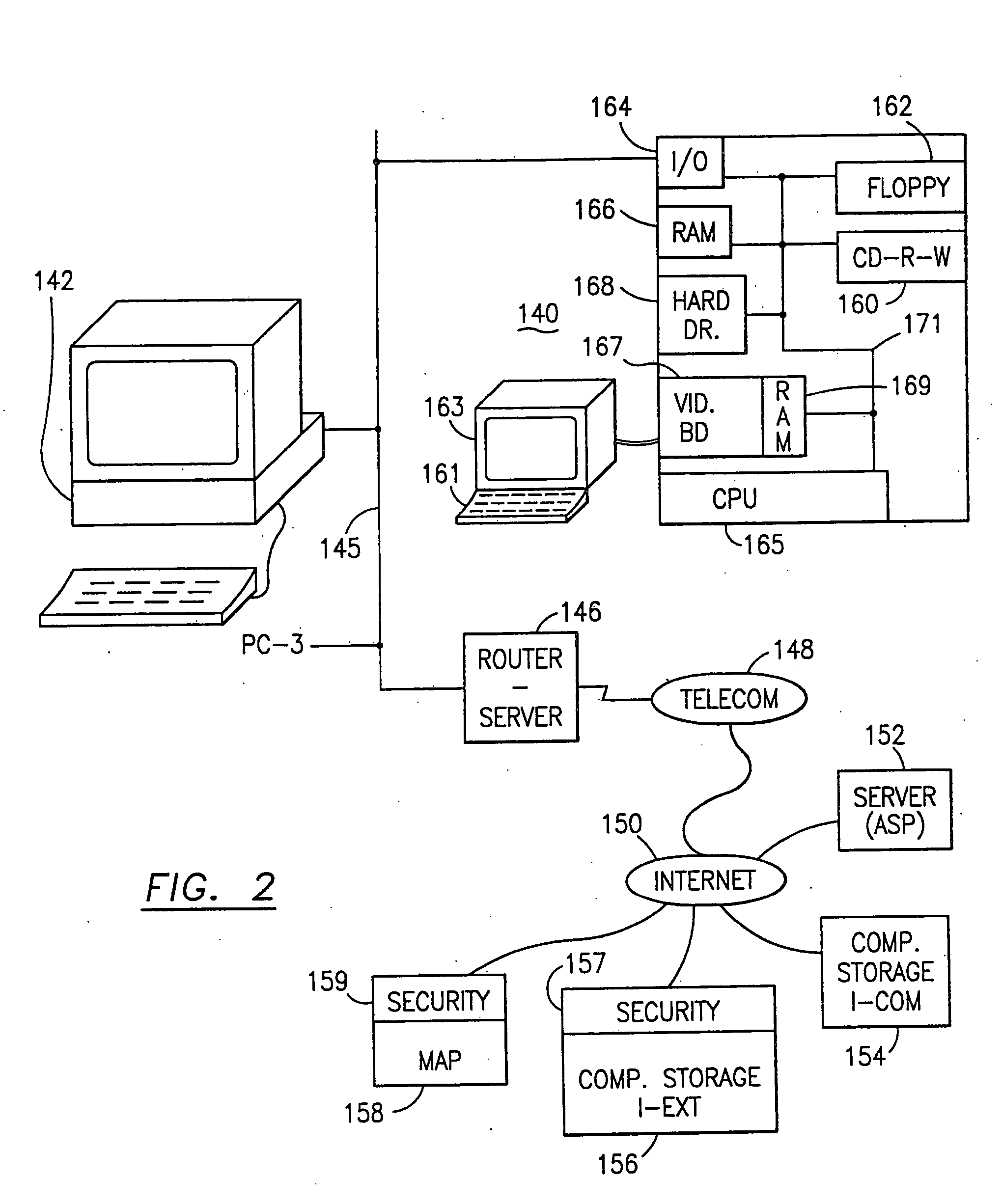
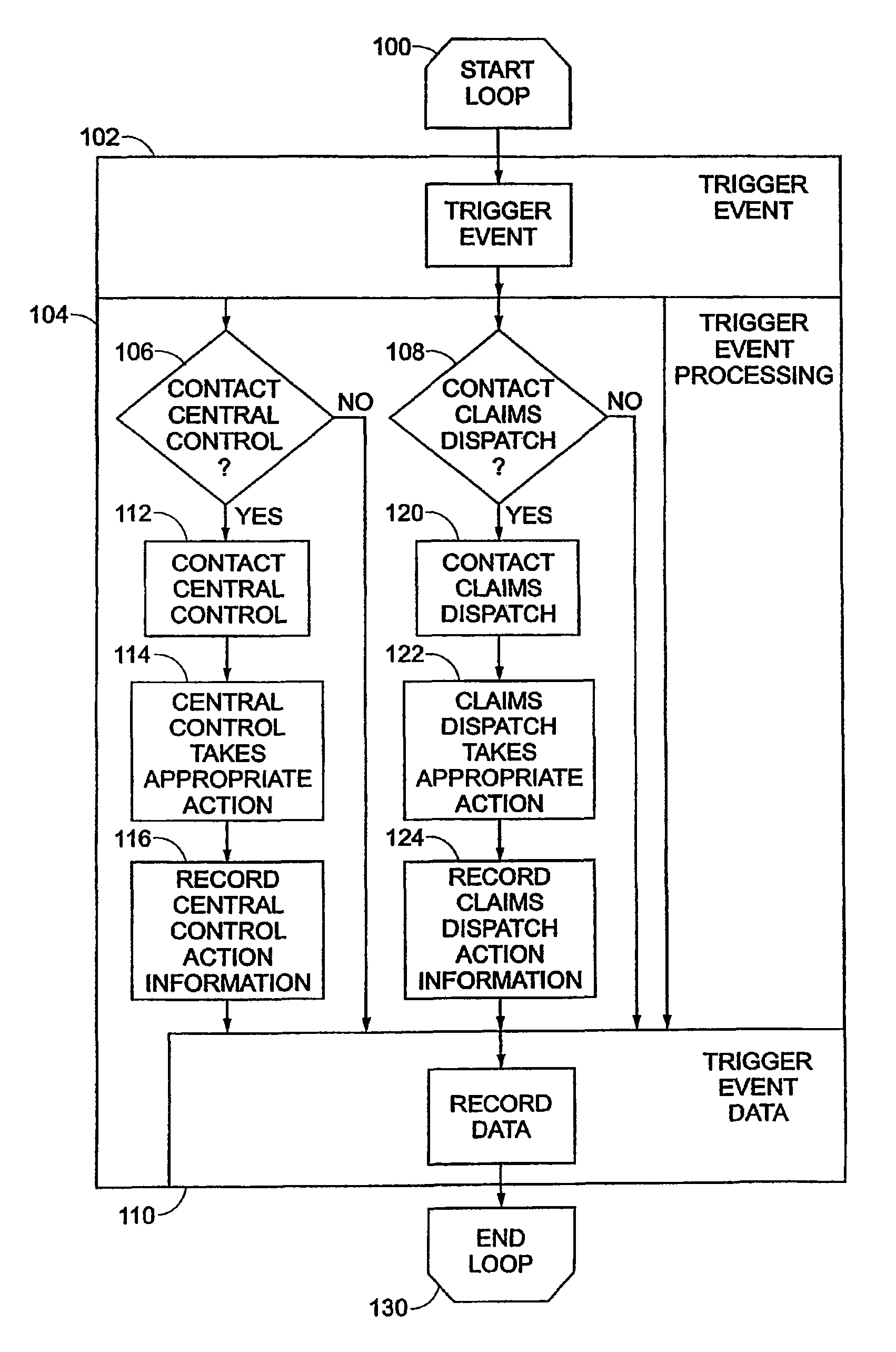
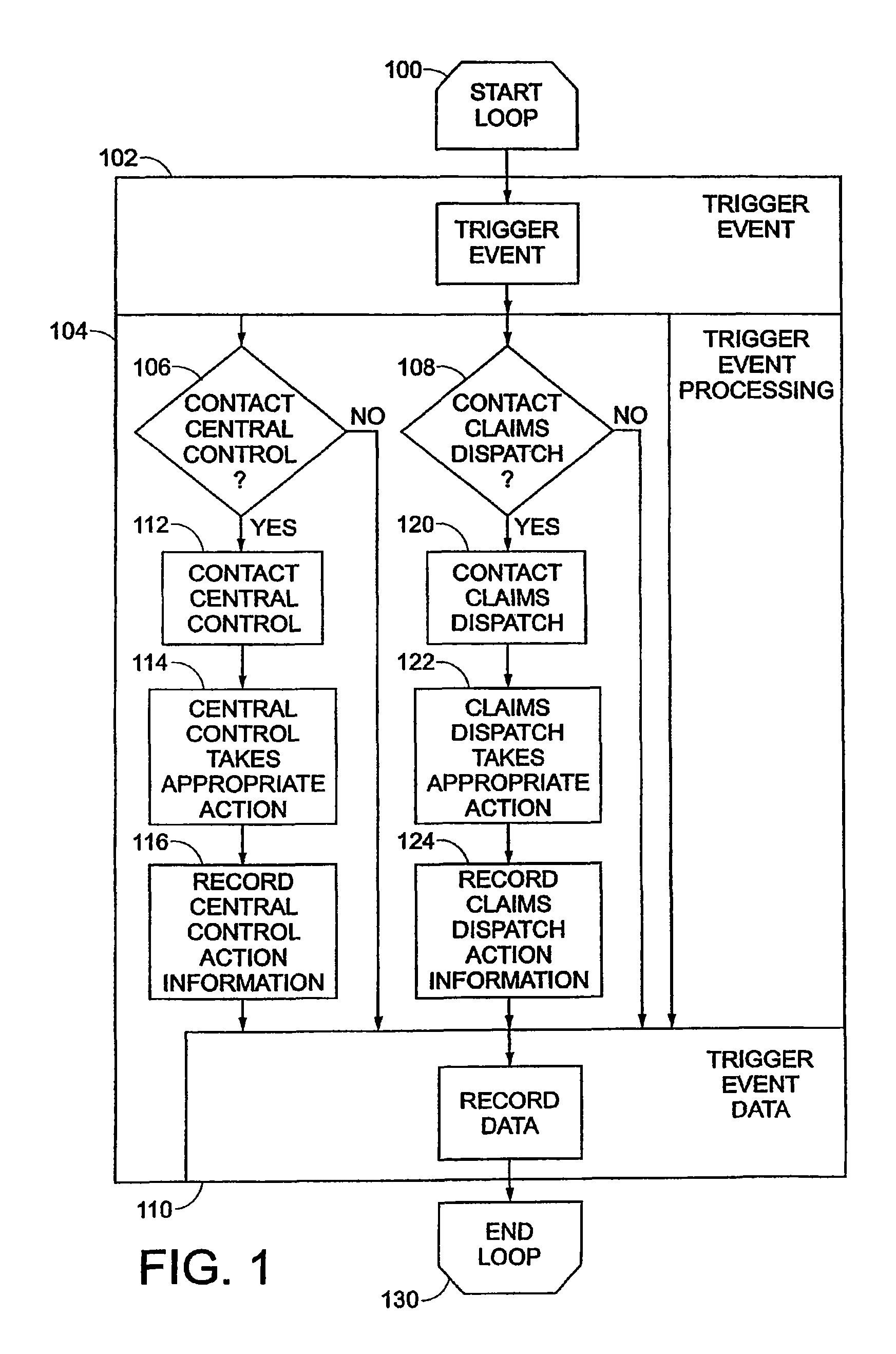
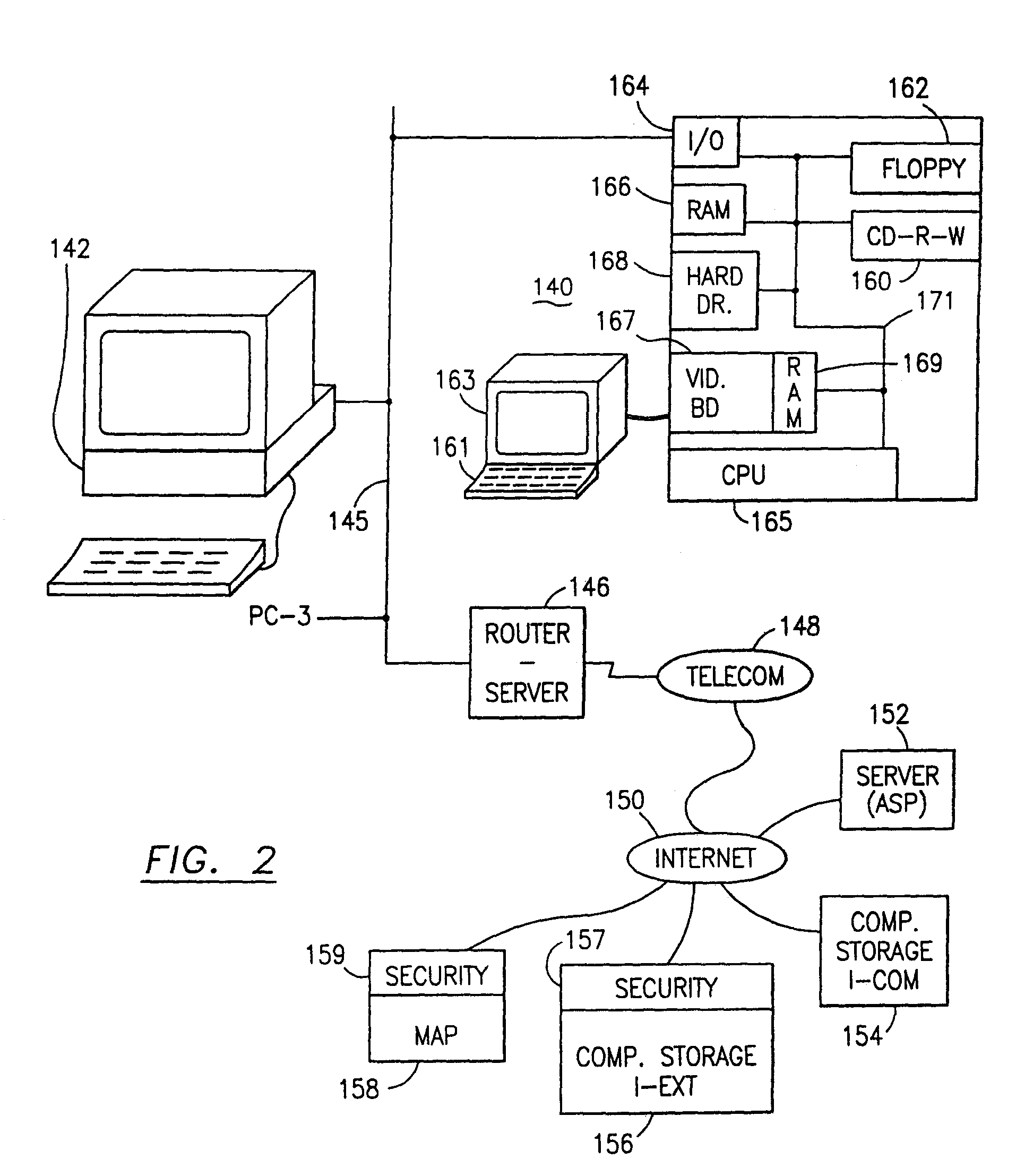
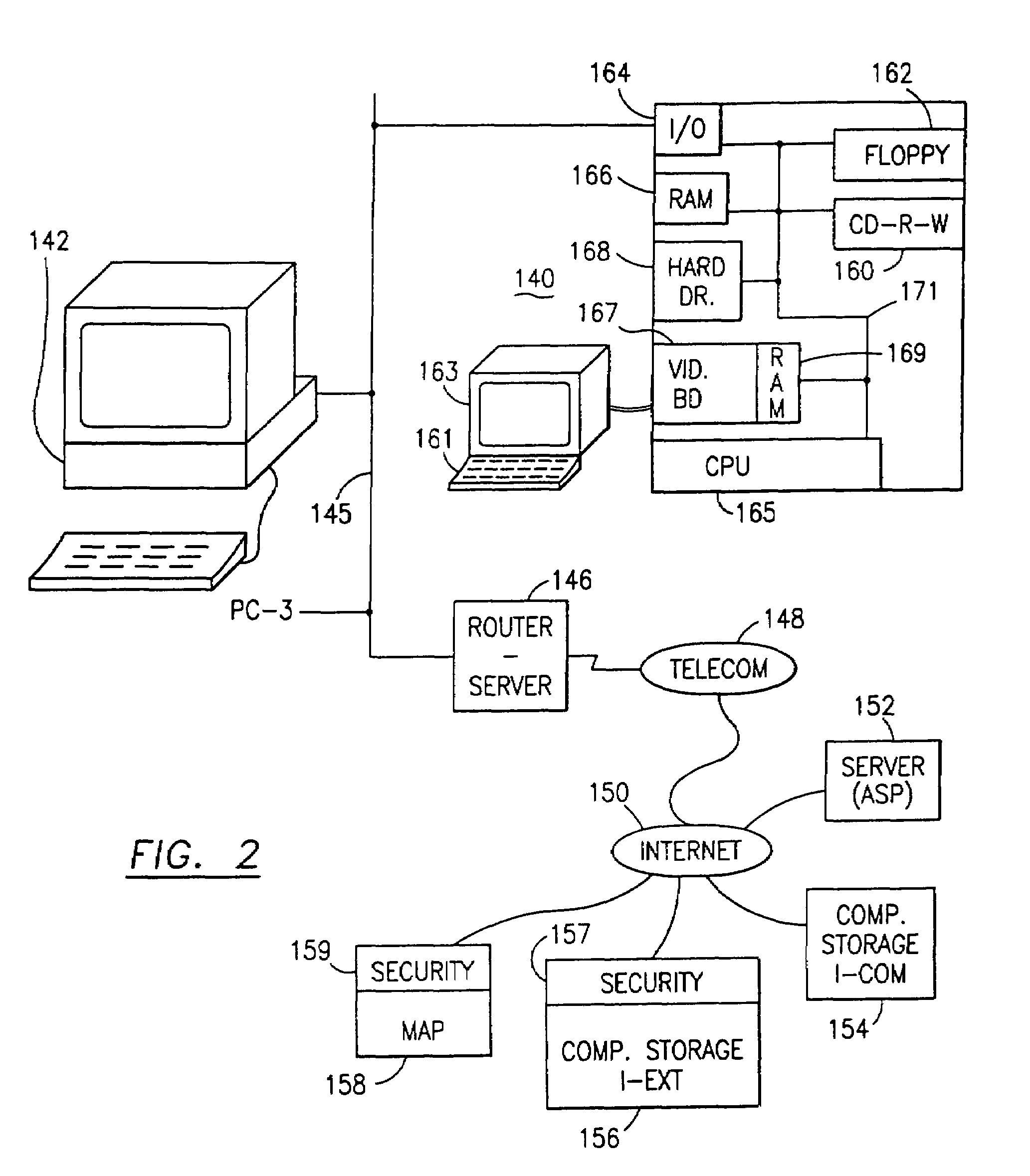
Data security system and method for portable device
ActiveUS7313825B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsDigital data processing detailsInformation processingEvent trigger
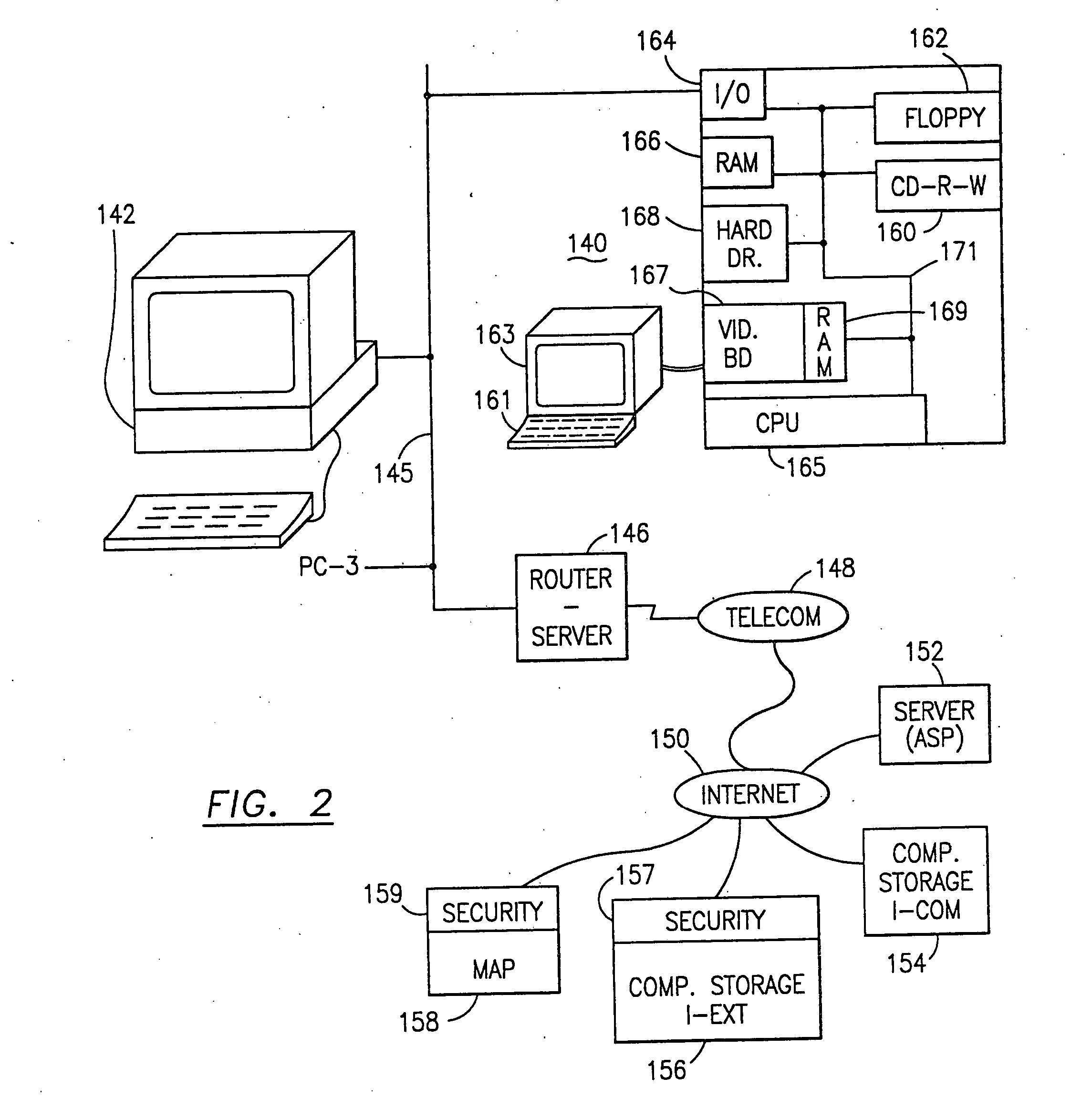
The method, used with a portable computing device, secures security sensitive words, icons, etc. by determining device location within or without a predetermined region and then extracting the security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only in the presence of a predetermined security clearance and within certain geographic territories. A computer readable medium containing programming instructions carrying out the methodology for securing data is also described herein. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
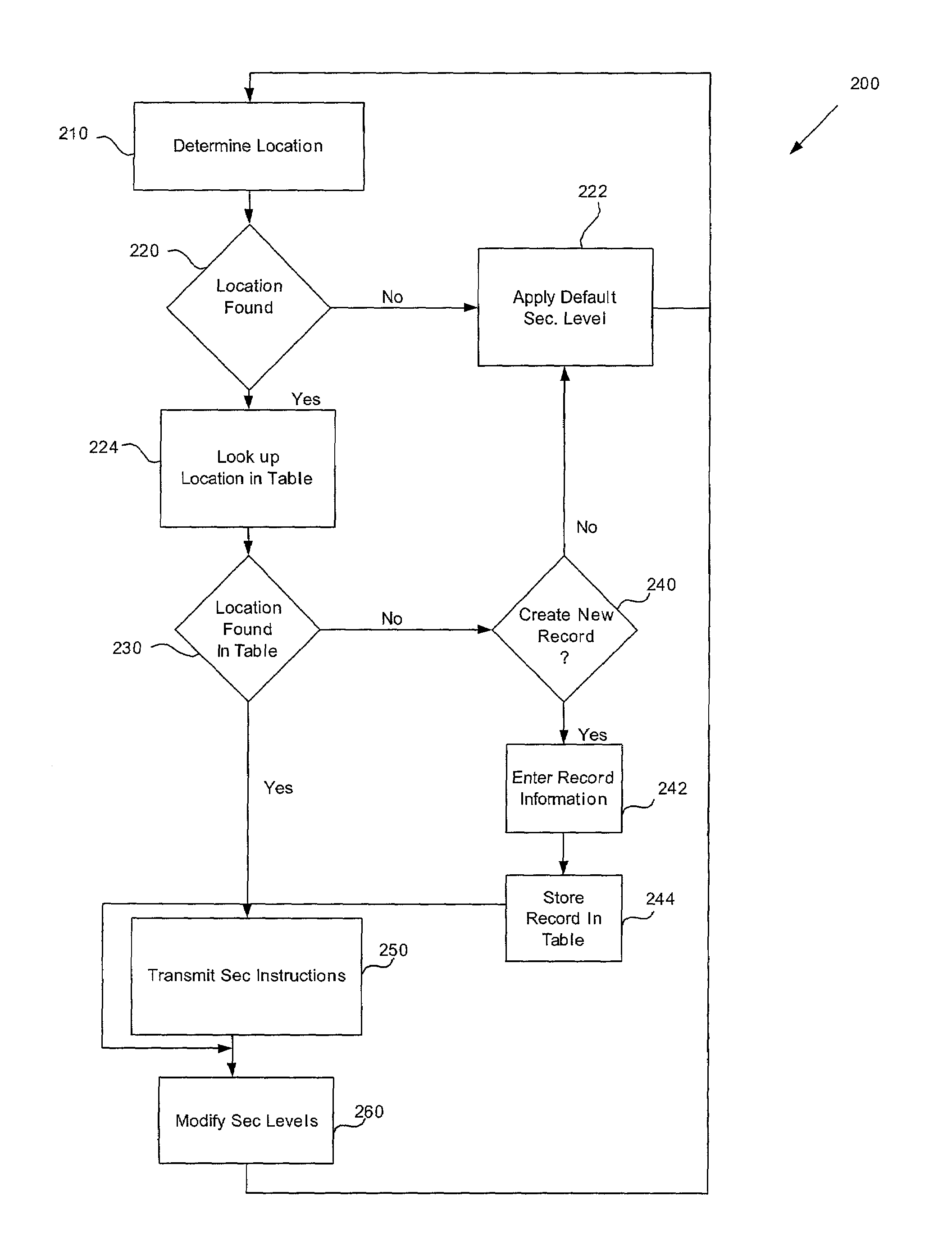
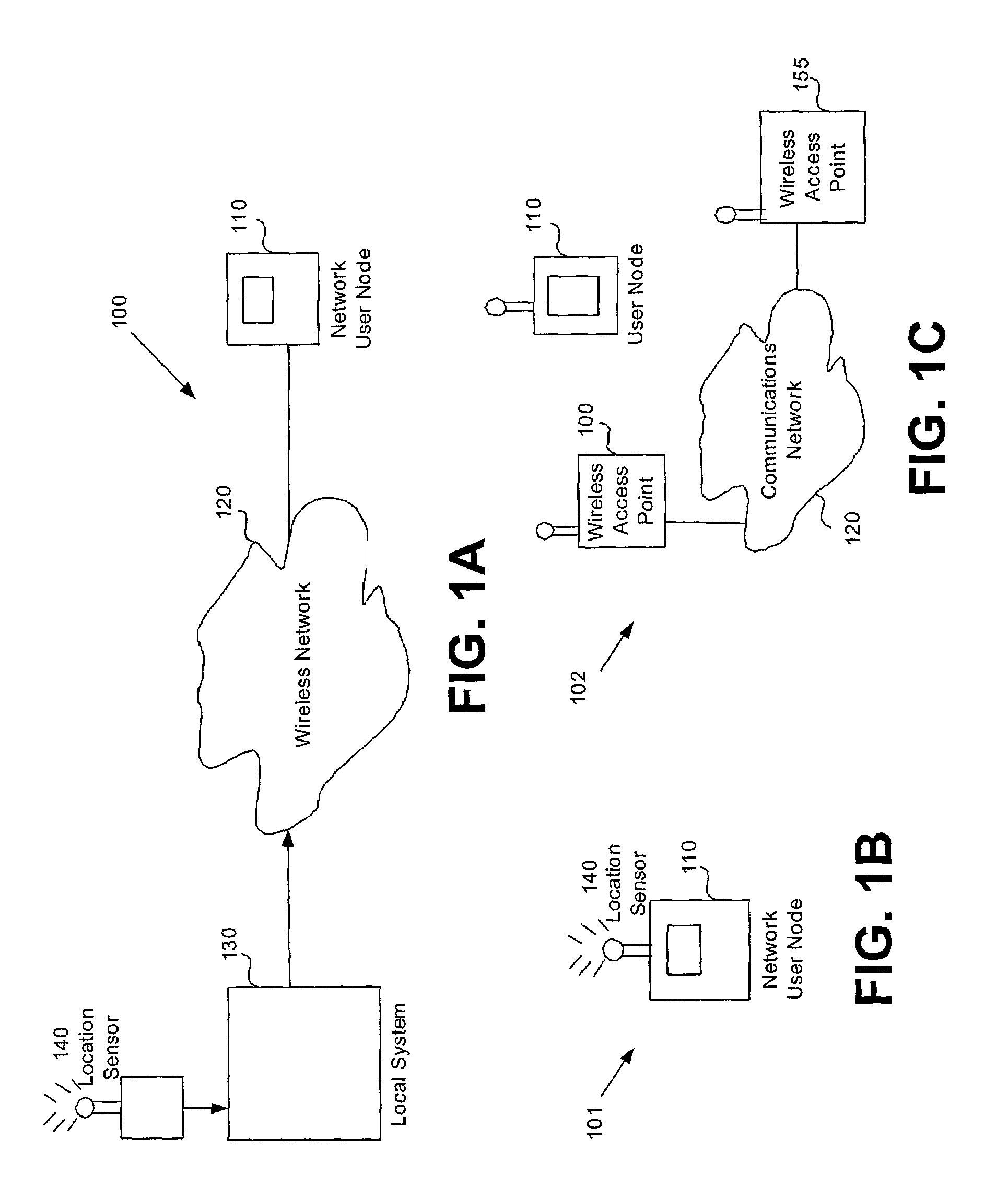
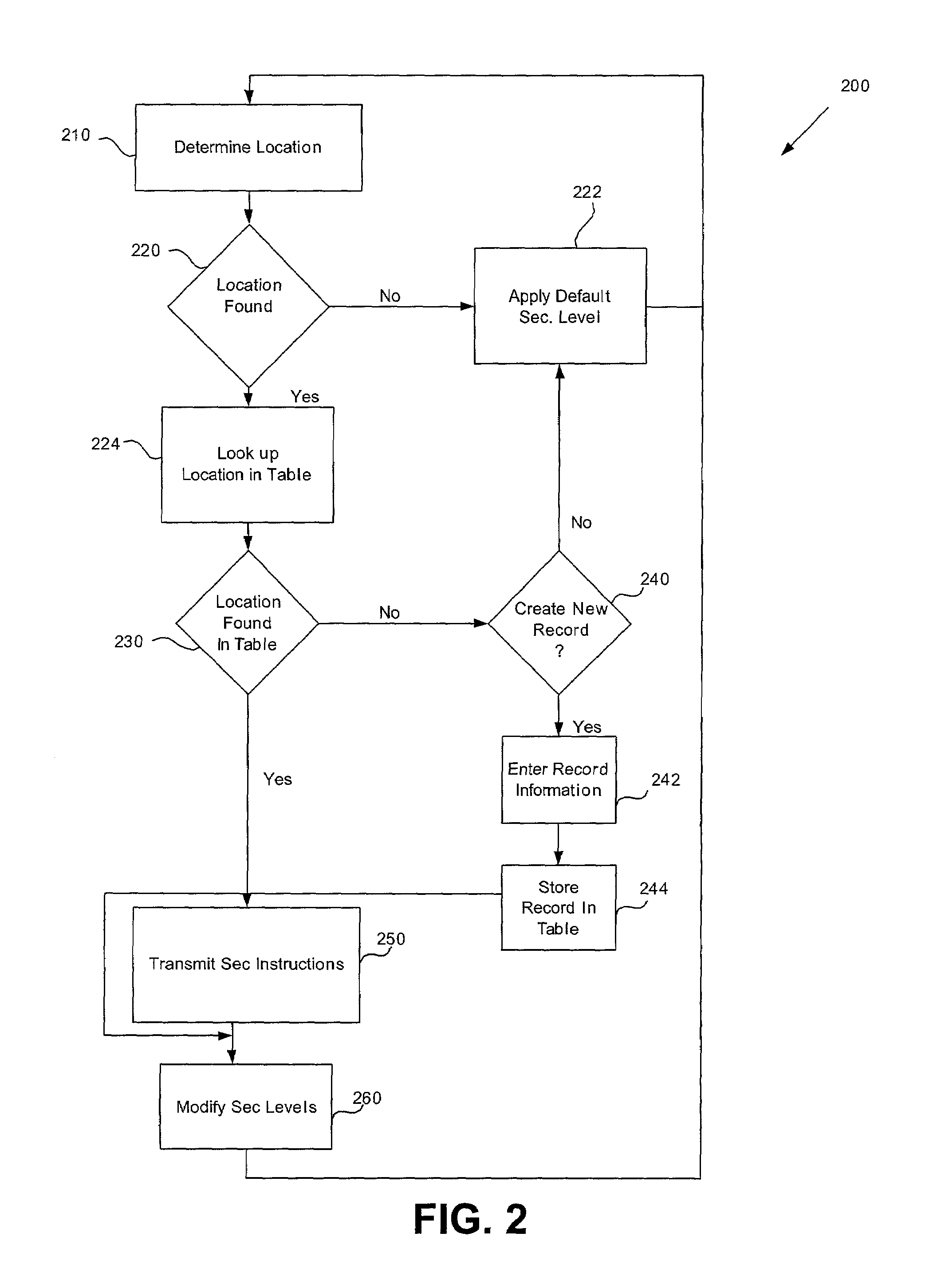
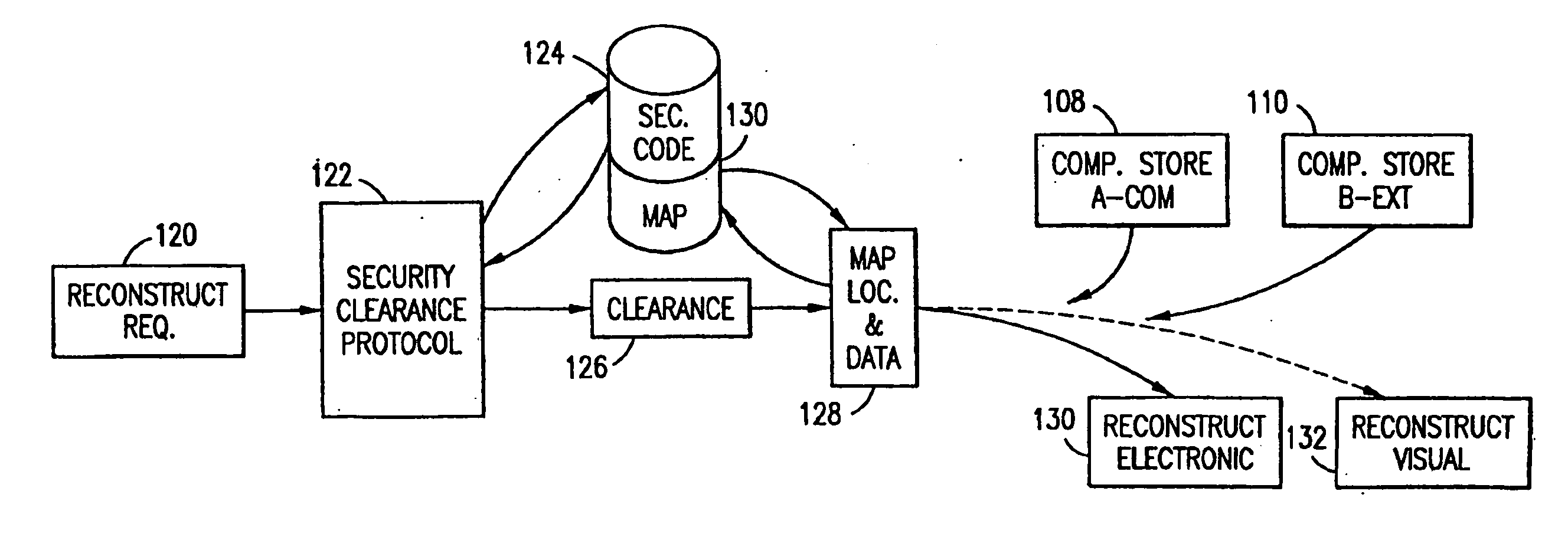
Location based security modification system and method
ActiveUS7591020B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSingle levelSecurity level
A method or system for providing a level of data security dependent on the location of the user of a wireless device is disclosed. One exemplary embodiment relates to a method of adjusting security for a network user node in communication with a network based upon the location of the node. The method is performed by determining the location of a network user node, selecting a single level of security from a group of more than two security levels based on the determined location, and modifying the security protection for the network user node based upon the selected level of security.
Owner:QUALCOMM INC
Data Security System and with territorial, geographic and triggering event protocol
ActiveUS20090178144A1Ease overhead performanceHigh overhead performanceDigital data processing detailsAnalogue secracy/subscription systemsInformation processingEvent trigger
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with territorial, geographic and triggering event protocols. The method and system determines device location within or without a predetermined region and then extracts security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only with security clearance and within certain geographic territories. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
Proactive Security for Mobile Devices
ActiveUS20110141276A1Improve security levelPrivacy protectionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsActive safetyPassword
Methods, program products, and systems for proactively securing mobile devices are described. A mobile device can proactively determine whether the mobile device is associated with a security risk and the level of the security risk. Upon determining a security risk, the mobile device can transmit coordinates of its current geographic location to a server. To protect privacy of authorized users, the transmission can be disabled by entering a password. If multiple failed password attempts are detected, the mobile device can proactively increase a security level of the device, and selectively protect files or other content stored on the mobile device. In some implementations, the mobile device can be transitioned into a surveillance mode where the mobile device records or captures information associated with one or more of user actions, ambient sound, images, a trajectory of the device, and transmits the recorded or captured information to the network resource.
Owner:APPLE INC
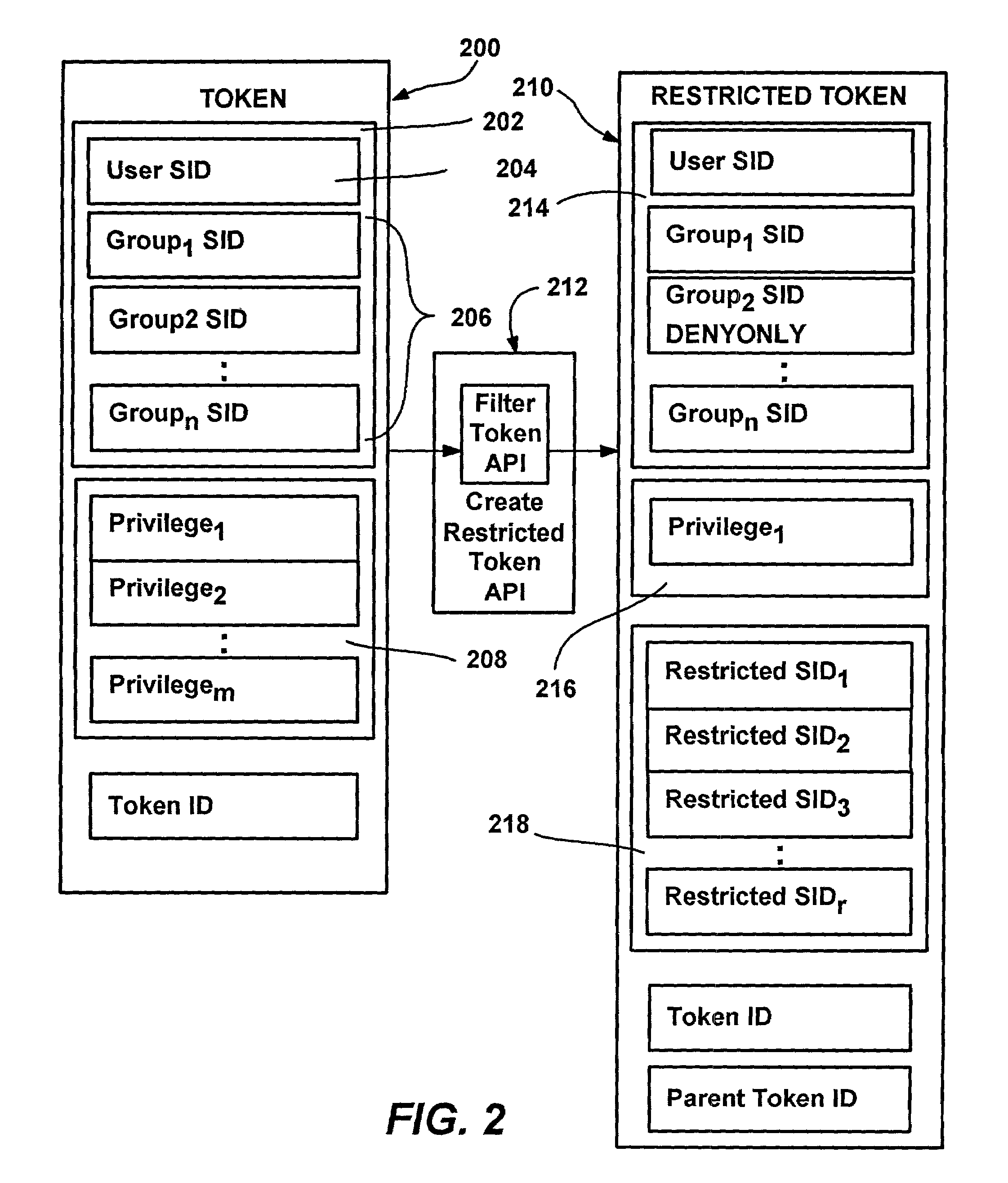
Policies for secure software execution
InactiveUS7350204B2Efficiently constrain (or prevent from running) everything on a machineDigital data processing detailsUnauthorized memory use protectionFile systemDigital signature
A system and method that automatically, transparently and securely controls software execution by identifying and classifying software, and locating a rule and associated security level for executing executable software. The security level may disallow the software's execution, restrict the execution to some extent, or allow unrestricted execution. To restrict software, a restricted access token may be computed that reduces software's access to resources, and / or removes privileges, relative to a user's normal access token. The rules that control execution for a given machine or user may be maintained in a restriction policy, e.g., locally maintained and / or in a group policy object distributable over a network. Software may be identified / classified by a hash of its content, by a digital signature, by its file system or network path, and / or by its URL zone. For software having multiple classifications, a precedence mechanism is provided to establish the applicable rule / security level.
Owner:MICROSOFT TECH LICENSING LLC
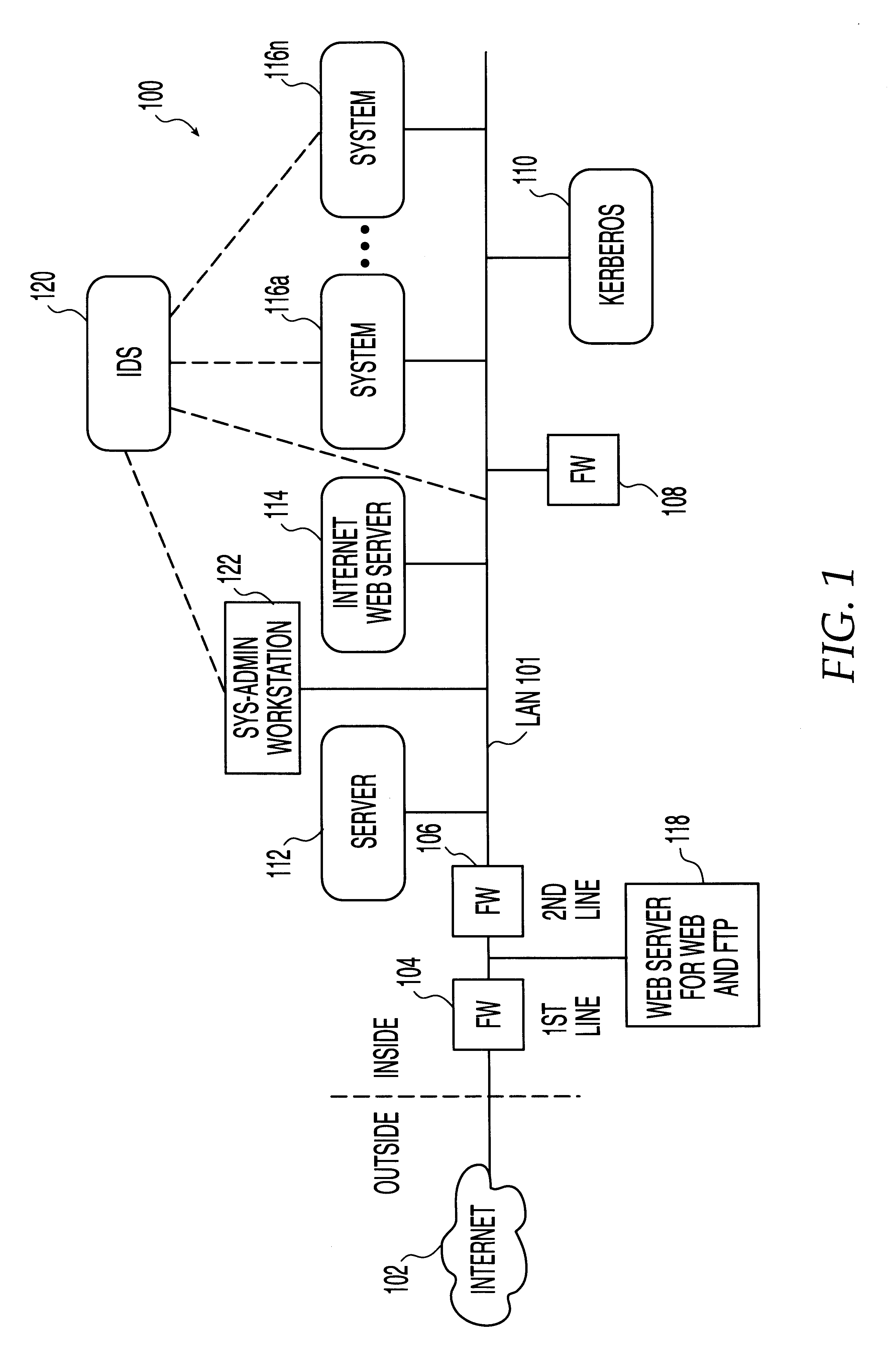
Secure enterprise network
ActiveUS8166554B2Digital data processing detailsDigital computer detailsUser authenticationApplication software
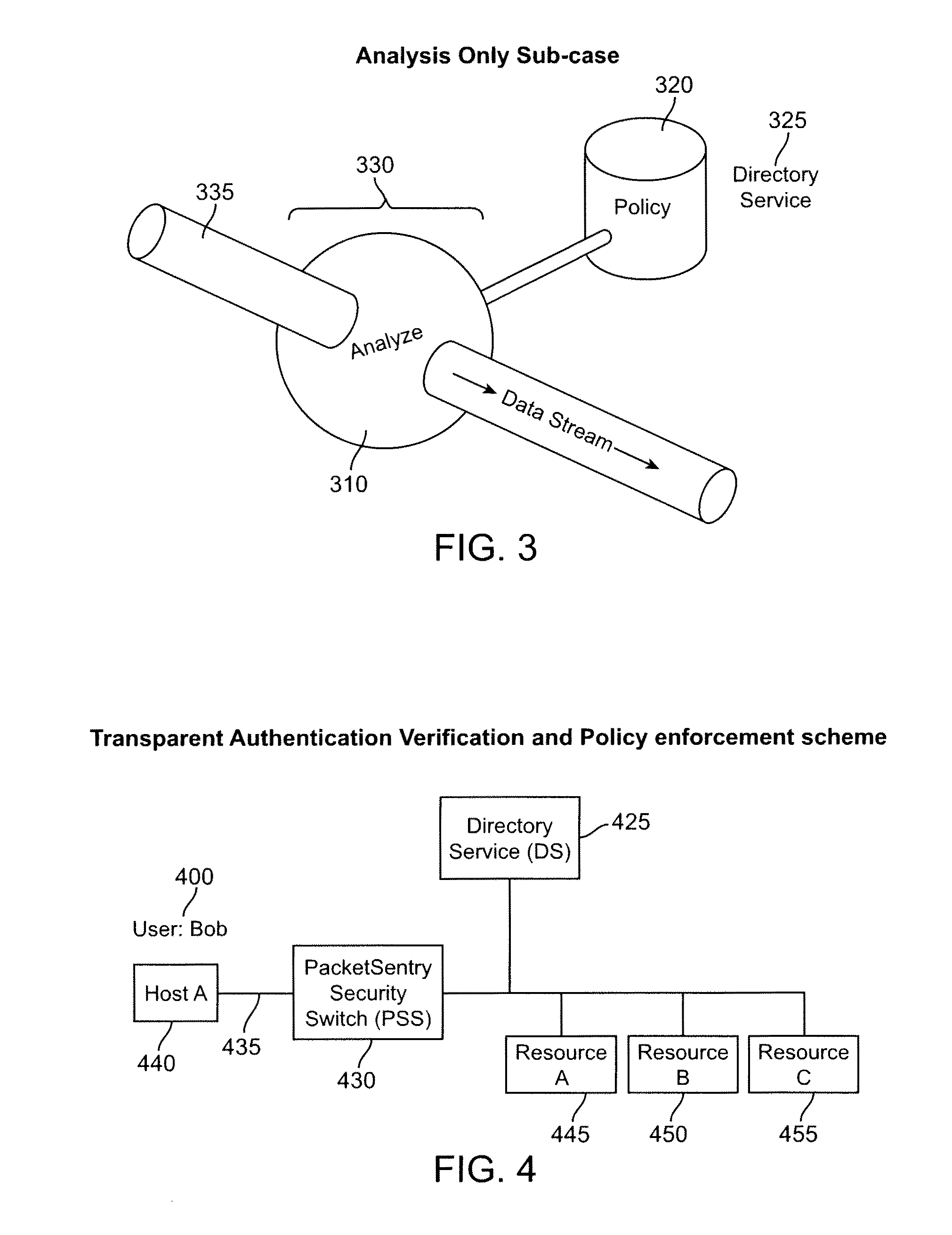
What is proposed is a method of implementing a security system (Packet Sentry) addressing the internal security problem of enterprises having a generalized approach for inferential determination and enforcement of network policy with directory service based group correlation with transparent authentication of the connected customer and the policy enforcement inside the network. The security system enables the network to analyze and enforce policy using any bit or bits in a stream or a packet, conduct Flow Vector analysis on the data traffic, provide Application Monitoring, Normalization and user authentication validation. The system enables the network to implement Group relationship Analysis and correlation using combination of Network inferences and Directory service data resulting in generation of Group norms using statistically significant relationships. These will provide a more secure enterprise environment where data security levels can be enforced and the usage monitored effectively in the infrastructure.
Owner:VMWARE INC
User validation for information system access and transaction processing
InactiveUS20030046083A1Robust methodPayment architectureDigital data authenticationUser verificationSpeech identification
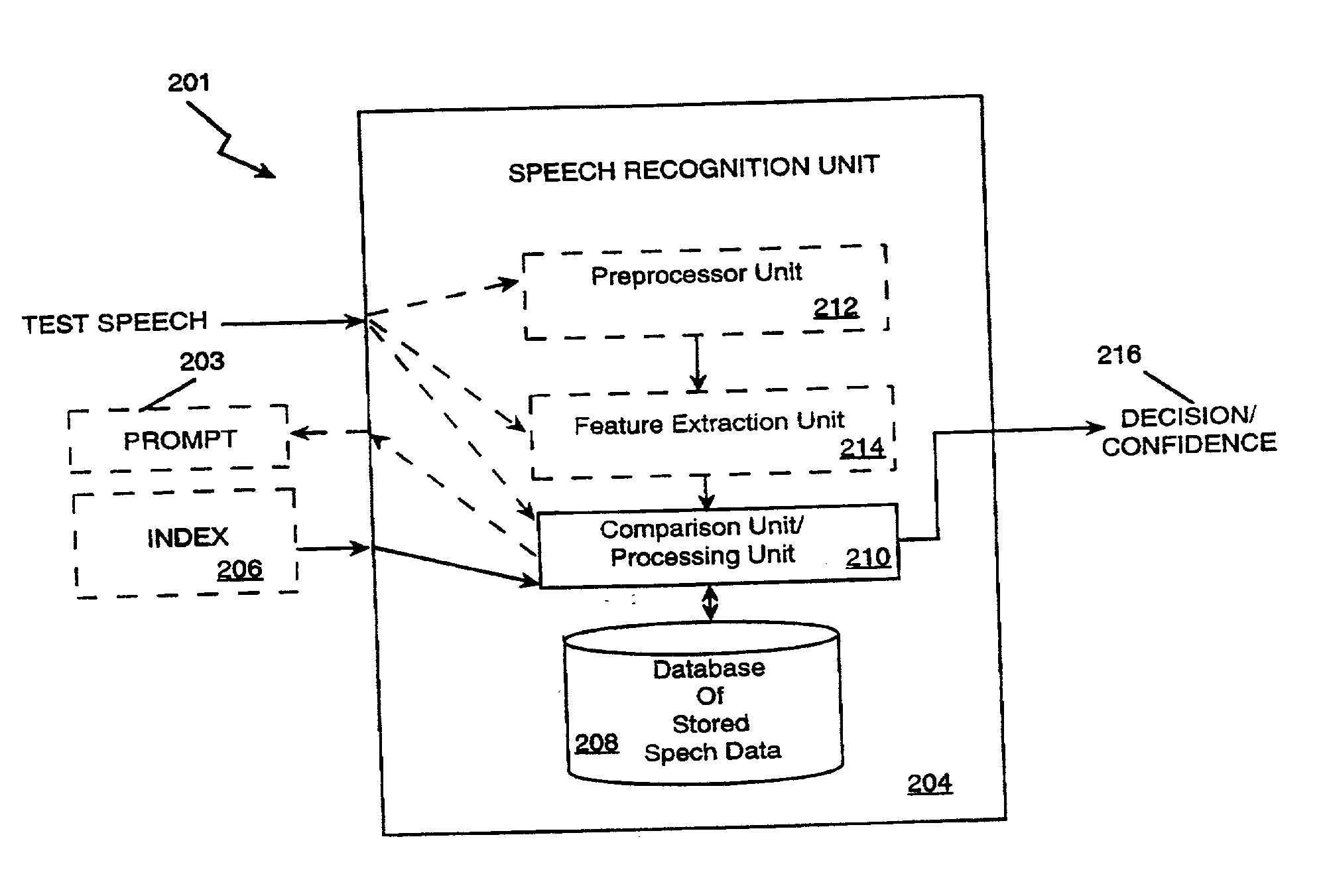
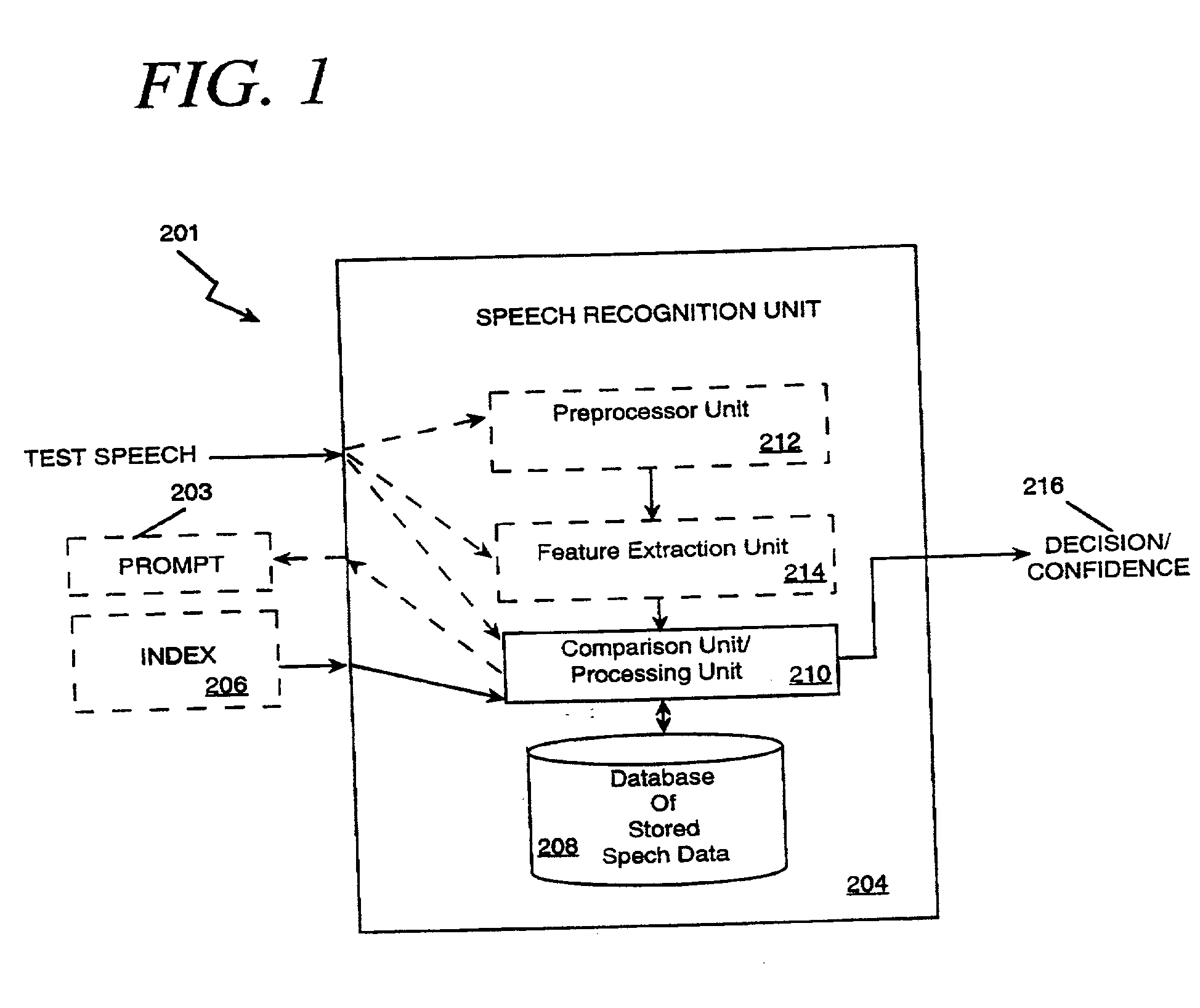
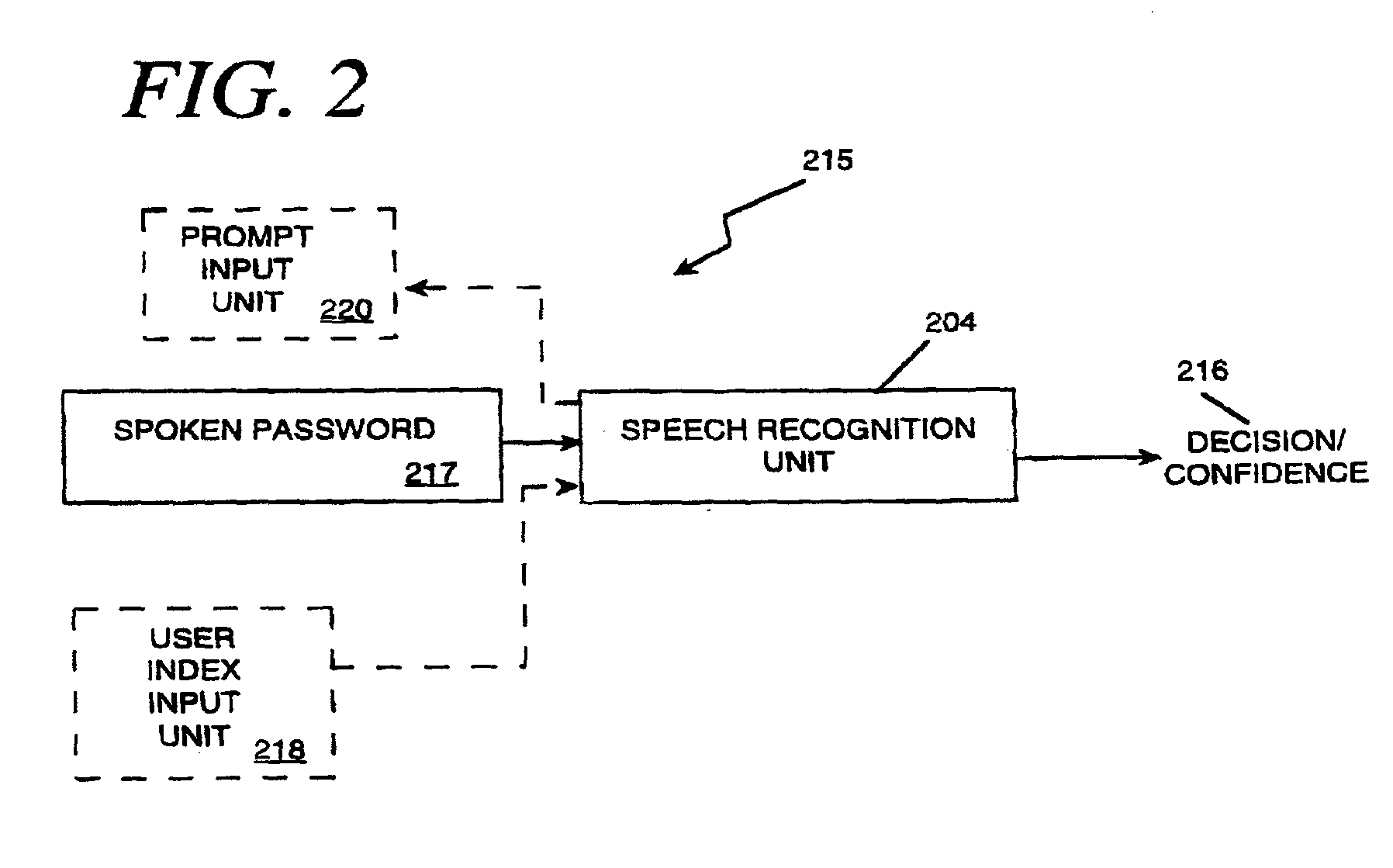
The present invention applies speech recognition technology to remote access, verification, and identification applications. Speech recognition is used to raise the security level of many types of transaction systems which previously had serious safety drawbacks, including: point of sale systems, home authorization systems, systems for establishing a call to a called party (including prison telephone systems), internet access systems, web site access systems, systems for obtaining access to protected computer networks, systems for accessing a restricted hyperlink, desktop computer security systems, and systems for gaining access to a networked server. A general speech recognition system using communication is also presented. Further, different types of speech recognition methodologies are useful with the present invention, such as "simple" security methods and systems, multi-tiered security methods and systems, conditional multi-tiered security methods and systems, and randomly prompted voice token methods and systems.
Owner:BANK ONE COLORADO NA AS AGENT +1
Cloud based operating and virtual file system
ActiveUS8527549B2Digital data information retrievalDigital data processing detailsVirtual file systemUser device
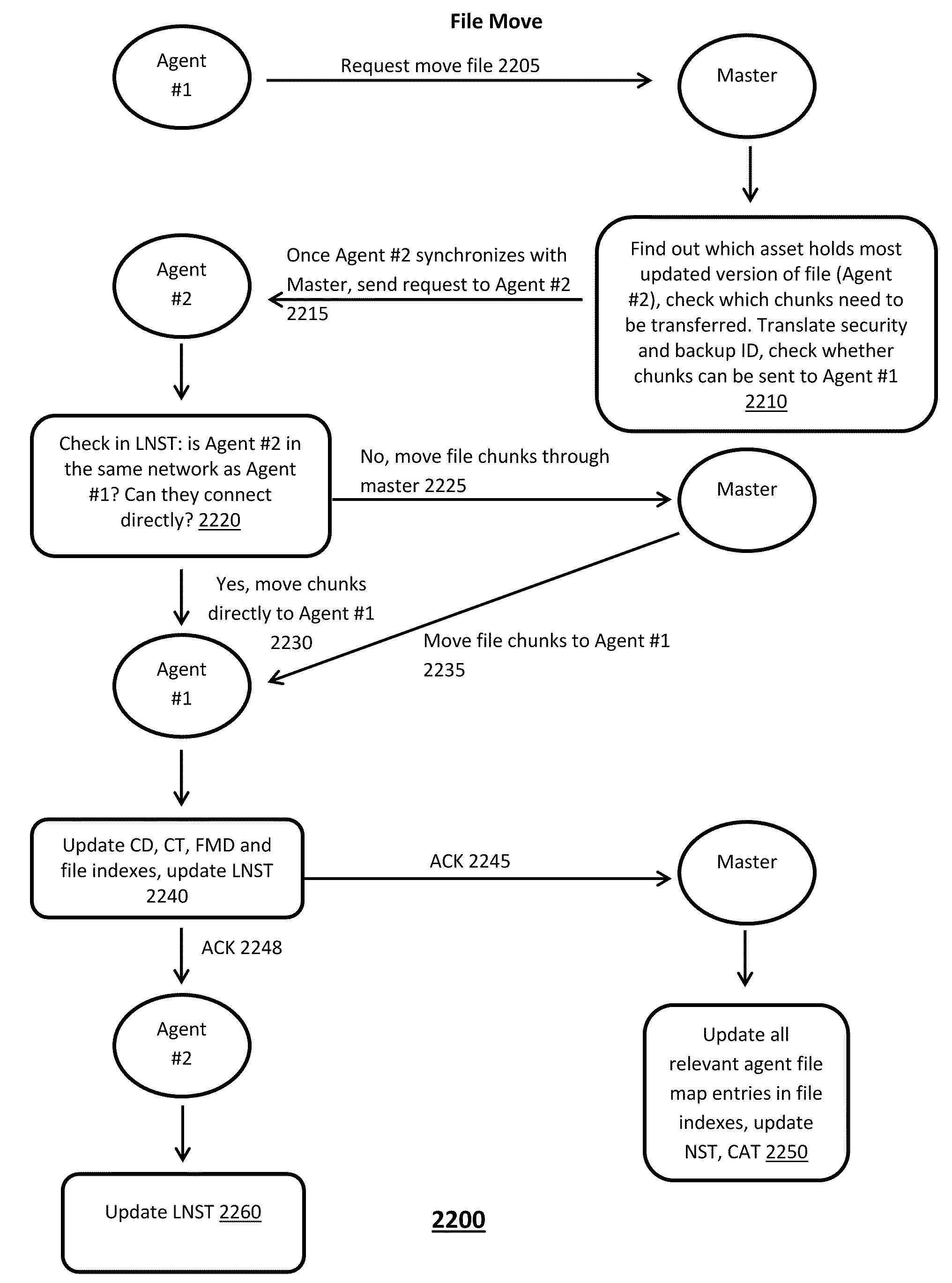
A method for managing a virtual distributed file system includes maintaining by a master device located in a cloud computing environment, a metadata data structure that stores metadata about locations of most updated versions of multiple file portions and security levels of the file portions, at least one file portion being stored at a user device coupled to the cloud computing environment, and maintaining by the master device, transaction of file portions to user entities, at least one user entity being hosted by the user device, based on at least metadata stored in the metadata data structure about the file portions.
Owner:BARRACUDA NETWORKS
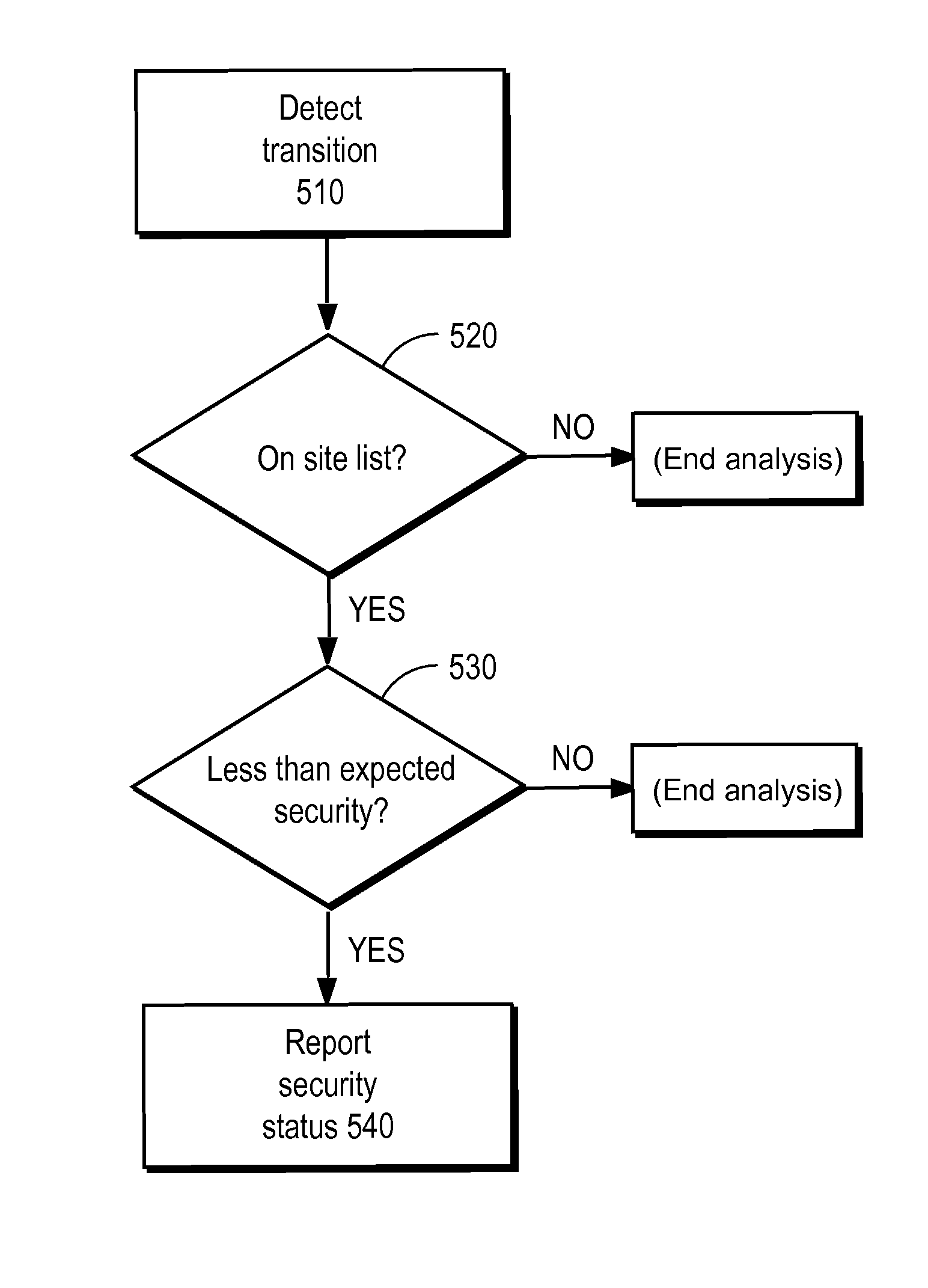
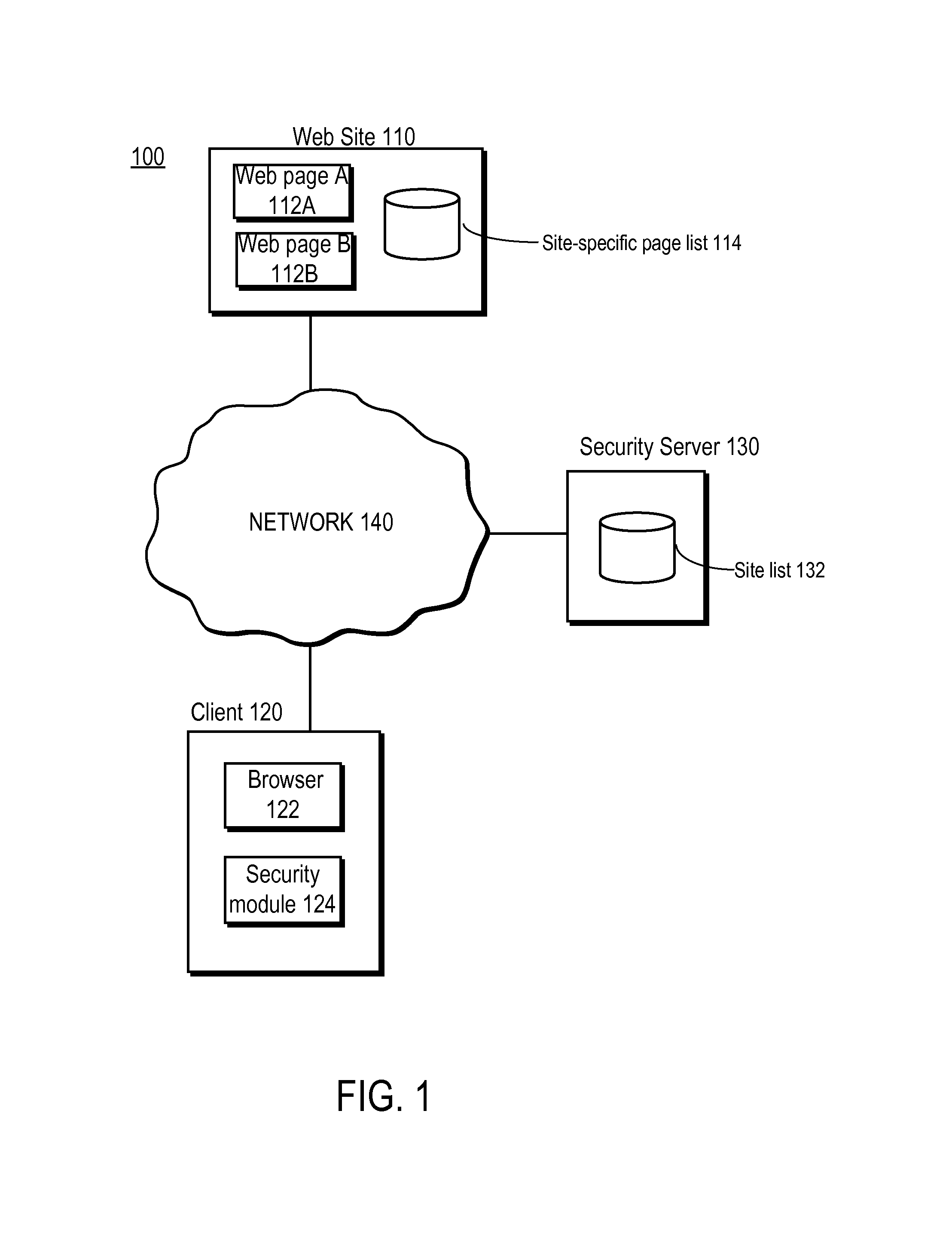
Detecting man-in-the-middle attacks via security transitions
ActiveUS8561181B1Memory loss protectionError detection/correctionMan-in-the-middle attackRemedial action
A page list comprising a list of transitions between network resources is established. Subsequently, a transition is detected between a first network resource and a second network resource. An expected security level associated with the transition is identified based on the page list. Responsive to the detected security level being determined to be lower than the expected security level, a remedial action is performed.
Owner:CA TECH INC
Data security system and method associated with data mining
ActiveUS7322047B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsMultiple keys/algorithms usagePlaintextInternet privacy
The data security method, system and associated data mining enables multiple users, each having a respective security clearance level to access security sensitive words, data objects, characters or icons. The method extracts security sensitive words, data objects, characters or icons from plaintext or other source documents to obtain (a) subsets of extracted data and (b) remainder data. The extracted data is, in one embodiment, stored in a multilevel security system (MLS) which separates extract data of different security levels with MLS guards. Some or all of the original data is reconstructed via one or more of the subsets of extracted data and remainder data only in the presence of a predetermined security level. In this manner, an inquiring party, with the proper security clearance, can data mine the data in the MLS secured storage.
Owner:DIGITAL DOORS
Adjusting security level of mobile device based on presence or absence of other mobile devices nearby
ActiveUS8095112B2Unauthorised/fraudulent call preventionDigital data processing detailsSecure stateGeolocation
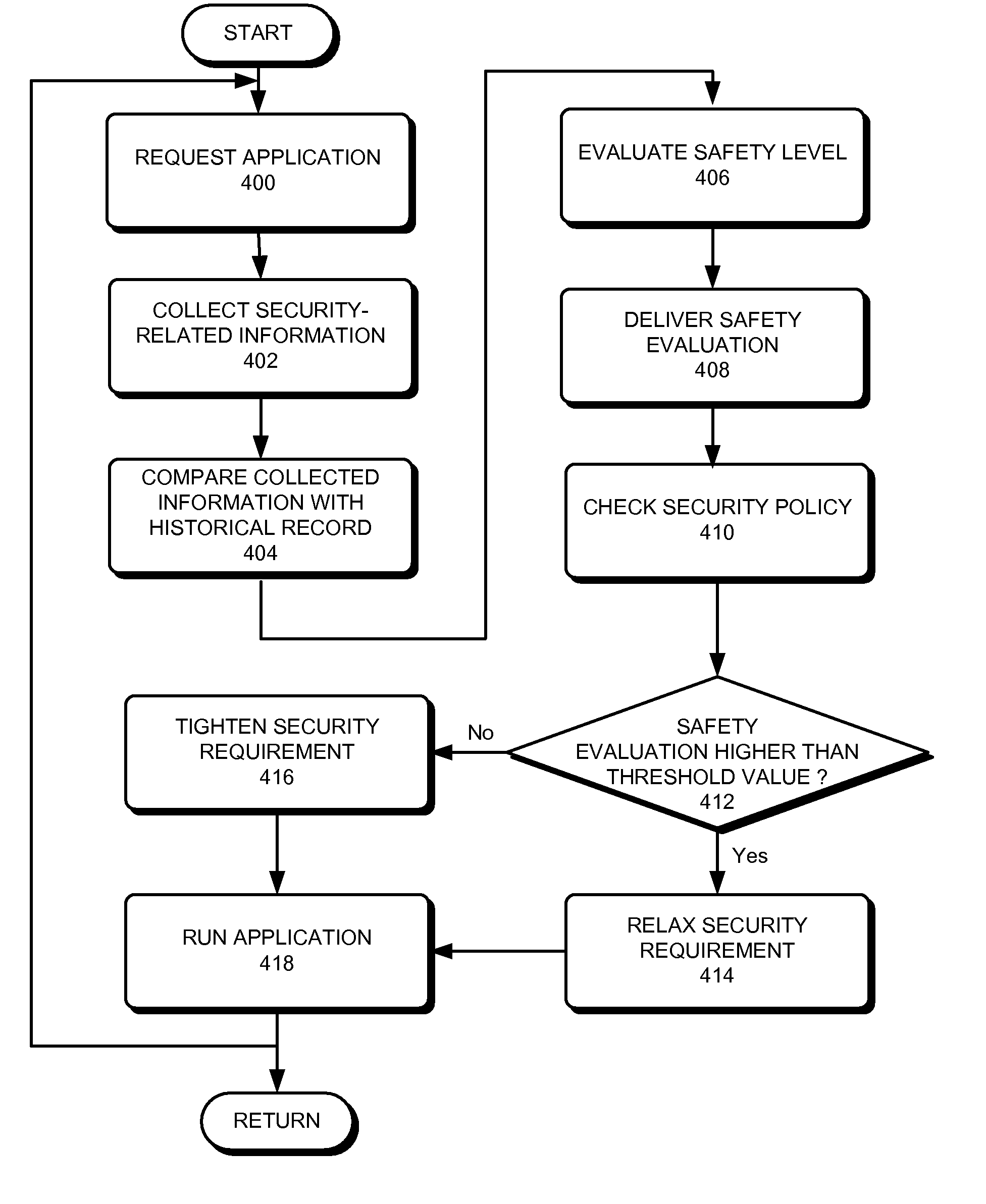
One embodiment of the present invention provides a method for adjusting security status on a mobile device, the method comprising: collecting security-related contextual information which includes information of nearby mobile devices and / or the geographic location of the intelligent mobile device; evaluating a threat level based on the collected security-related contextual information; invoking a security policy; and adjusting the security status of the mobile device based on the threat level and the security policy.
Owner:XEROX CORP
Trust spectrum for certificate distribution in distributed peer-to-peer networks
ActiveUS20030070070A1Multiprogramming arrangementsMultiple digital computer combinationsFrequency spectrumMaximum level
Embodiments of a decentralized, distributed trust mechanism that may be used in peer-to-peer platforms, to implement trust relationships based on data relevance between peers on a network and to implement trust relationships between peers and content and data (codat). In one embodiment, the trust mechanism may provide a trust spectrum of multiple levels wherein unique peer identities may be established to enable authentication and the assignment of the peers' associated access policies within a peer group. In one embodiment, the trust spectrum may have Certificate Authority signed certificates as a maximum level of security, and self-signed certificates as a minimum level of security. Since a certificate is one form of codat, in one embodiment the trust mechanism may be applied to a peer group member's collection of signed certificates for a given peer group.
Owner:ORACLE INT CORP
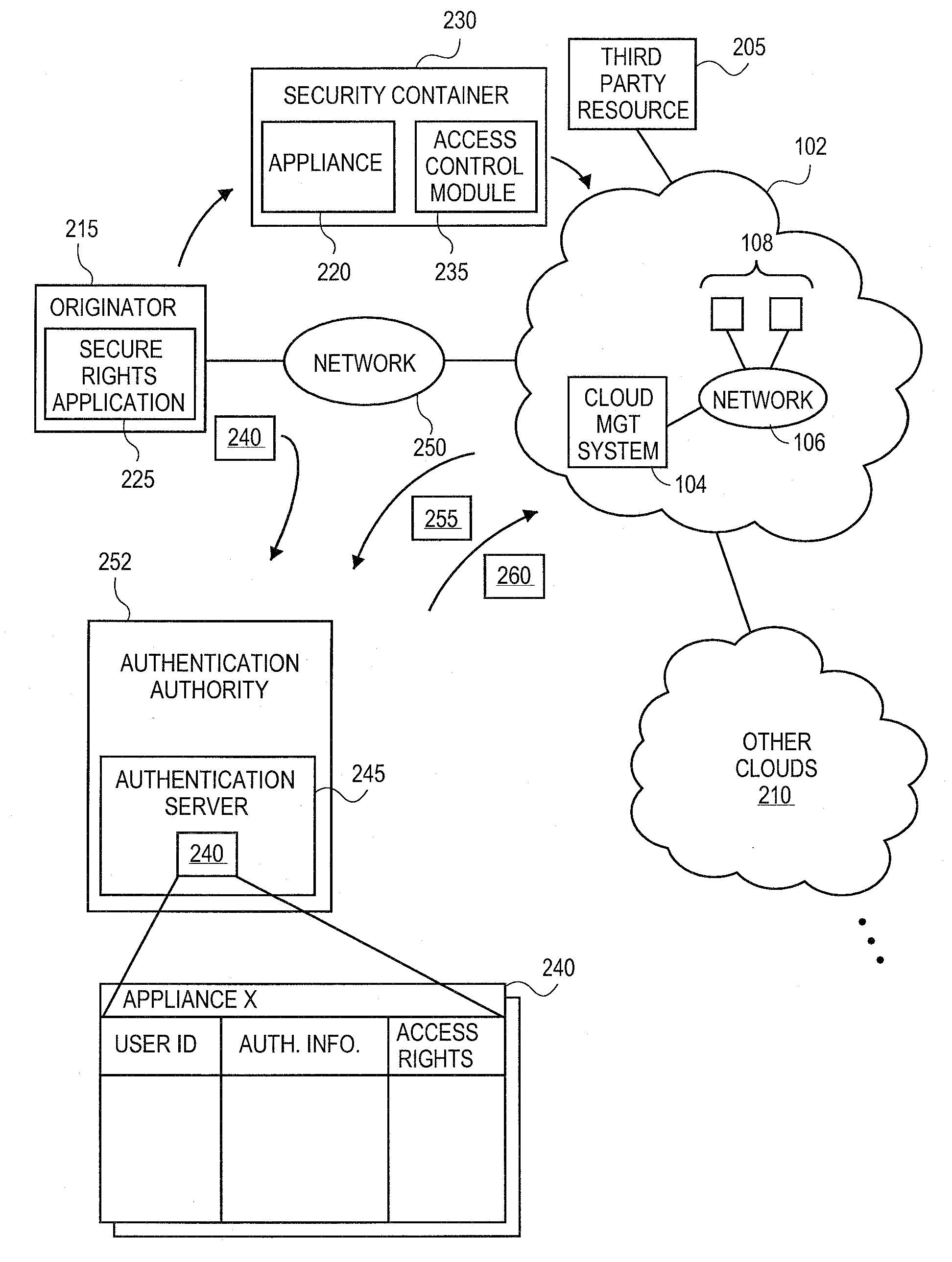
Methods and systems for securing appliances for use in a cloud computing environment
ActiveUS20100132016A1Digital data processing detailsUser identity/authority verificationOperational systemSecurity level
An originator of an appliance can independently secure the appliance for instantiation in the cloud, separate from the security level of the cloud. The originator can secure the appliance utilizing a secure rights application. The secure rights application can be configured to “wrap” an appliance in a security container. The security container can limit access to the applications and operating systems contained in the appliance, but allow the appliance to operate normally once instantiated in the cloud. The secure rights application can be configured to cryptographically secure the appliance in order limit the ability of unauthorized parties from accessing the components of the appliance while maintaining the functionality of the appliance.
Owner:RED HAT
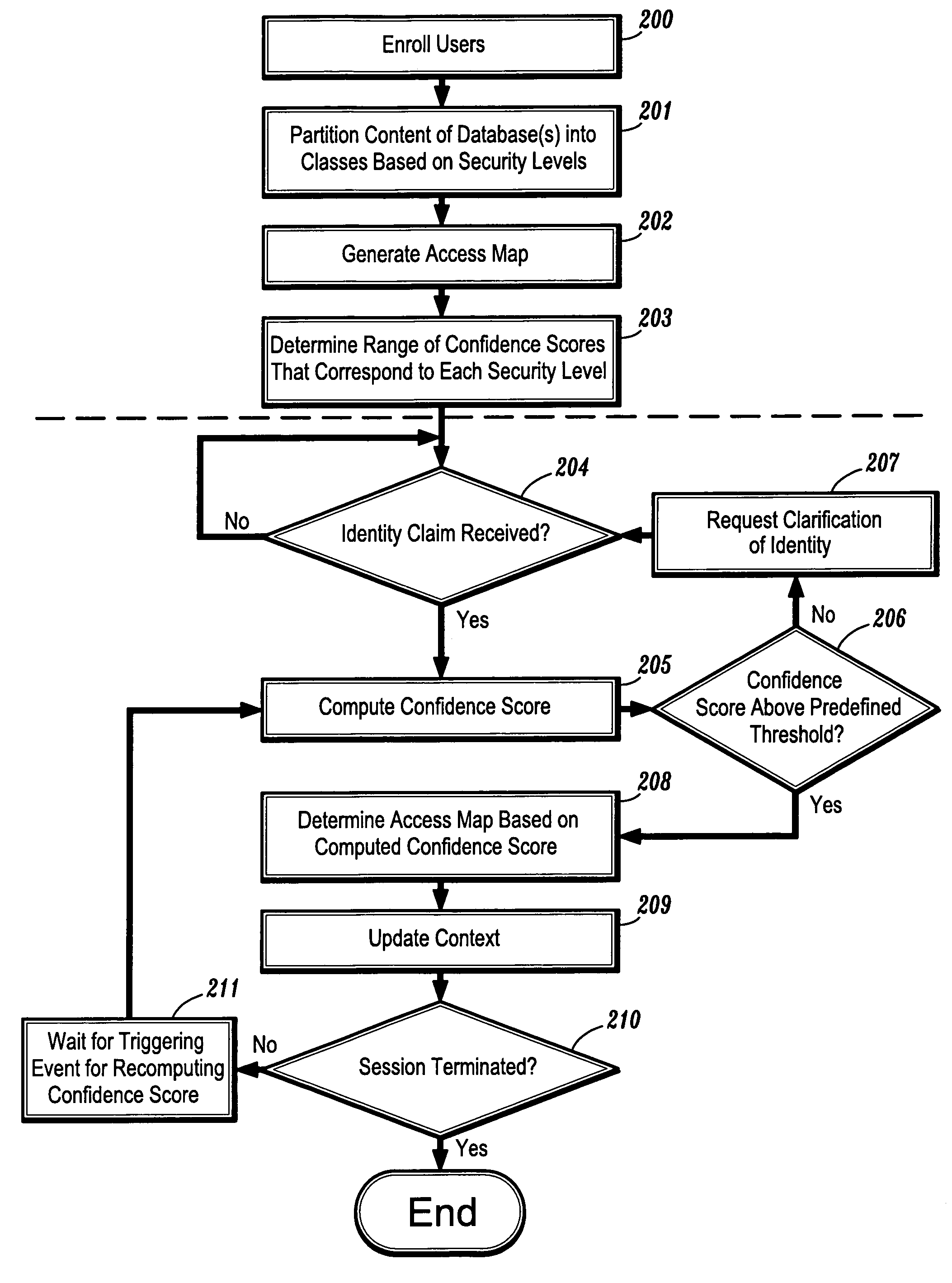
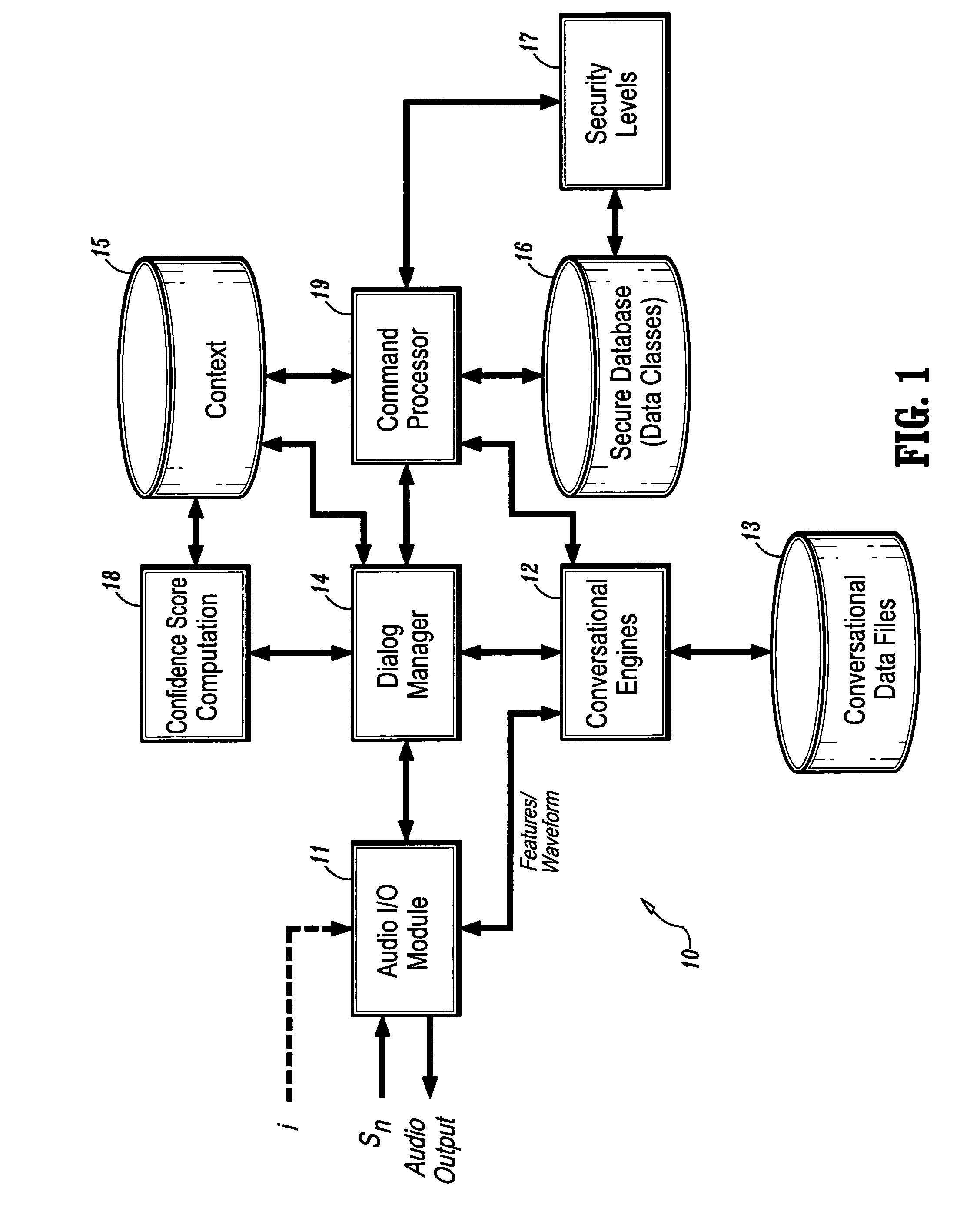
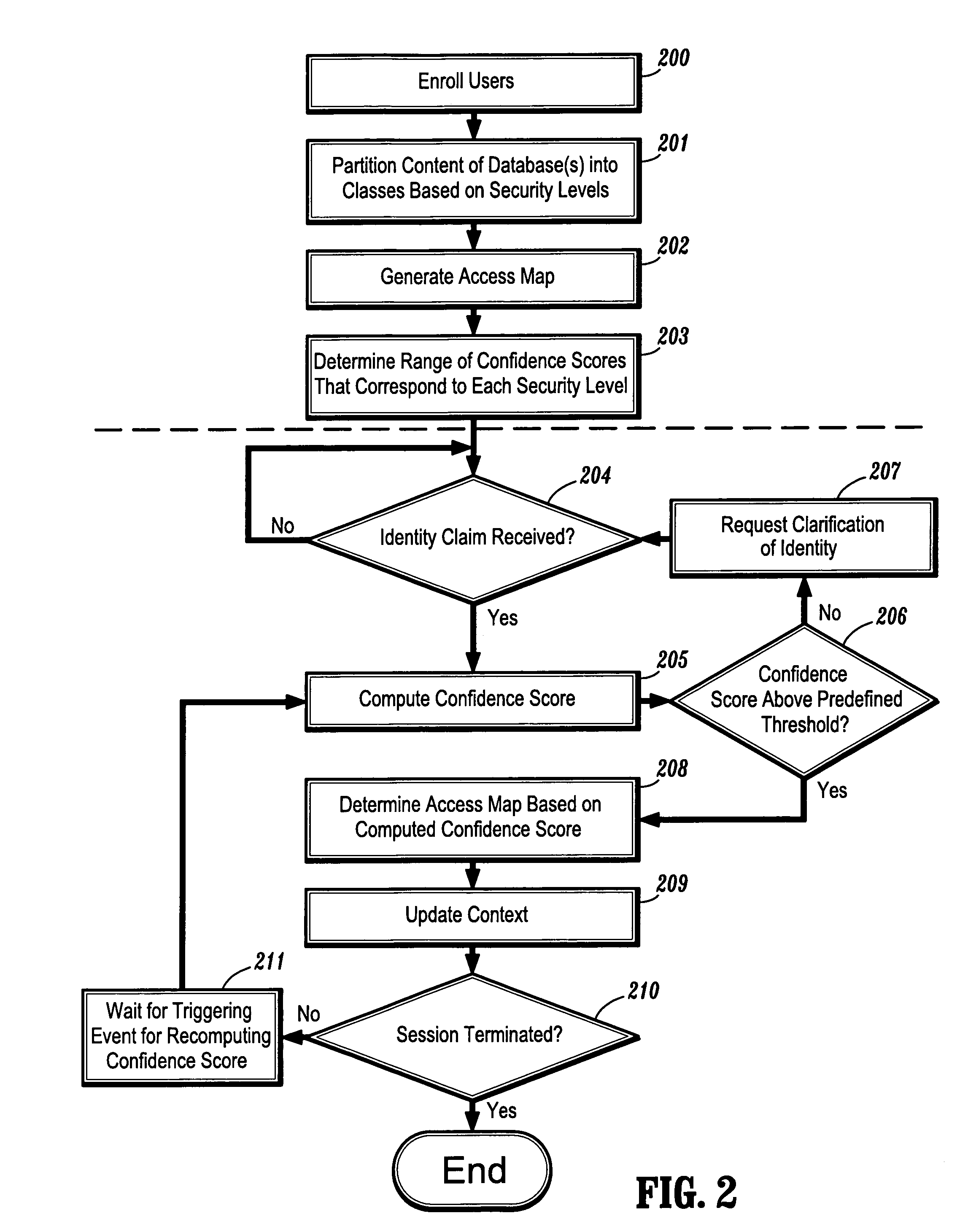
System and method for confidence based incremental access authentication
InactiveUS7039951B1Electric signal transmission systemsDigital data processing detailsSecurity levelAuthentication system
A system and method for providing continuous confidence-based authentication. The present invention may be implemented in an incremental access authentication system for controlling access to secured data having various levels of security. During the course of a conversational session between user and machine, a confidence-based authentication system according to the present invention will periodically analyze the input speech of a user interacting with the system to compute a “confidence measure” for the validity of an original identity claim i provided by the user at the commencement of the dialog session. The “confidence measure” computation process according to the present invention is seamlessly integrated into the incremental access authentication system so that the system can tailor its interaction with the user based on its confidence in the original identity claim.
Owner:NUANCE COMM INC
Smart wallet
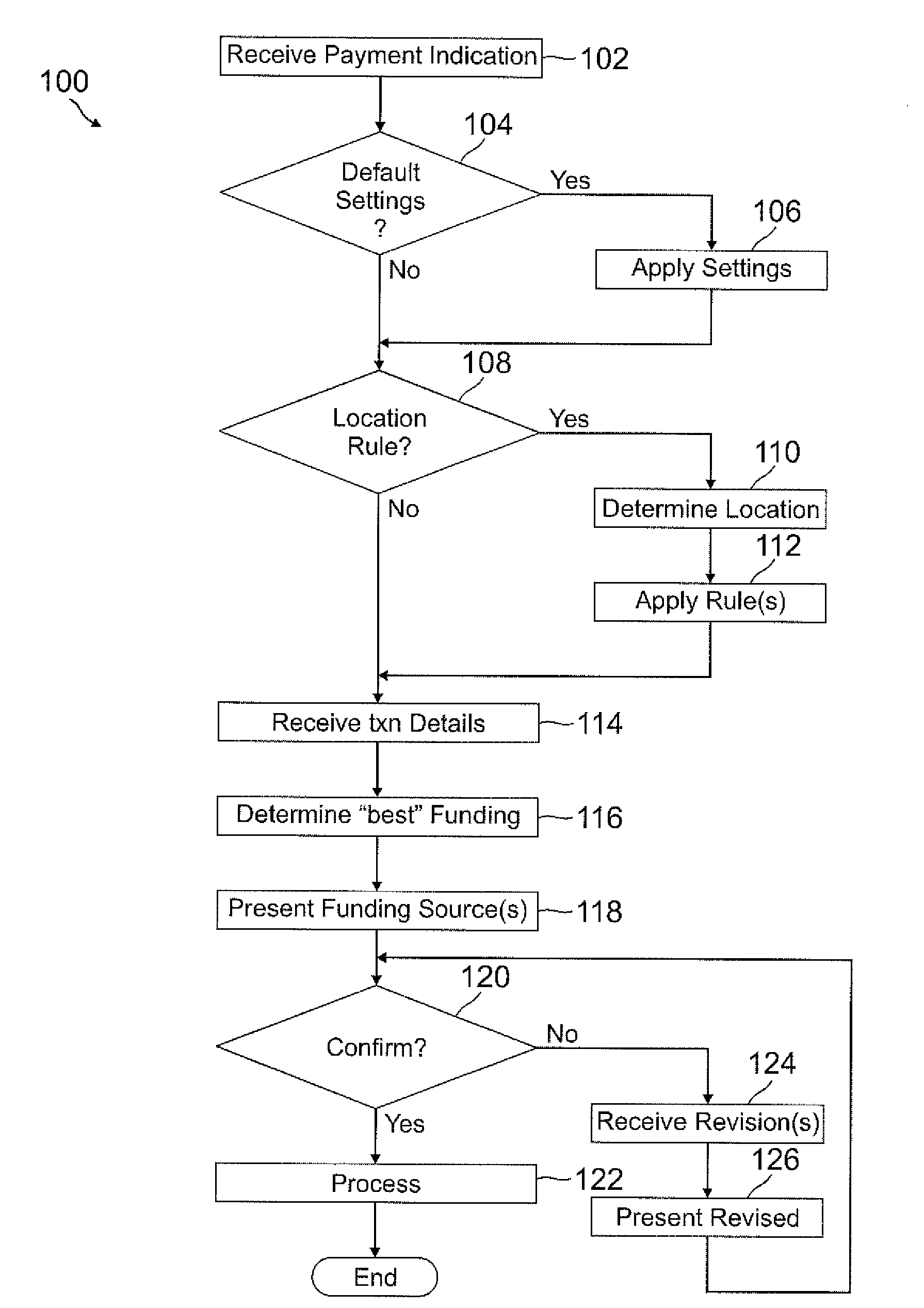
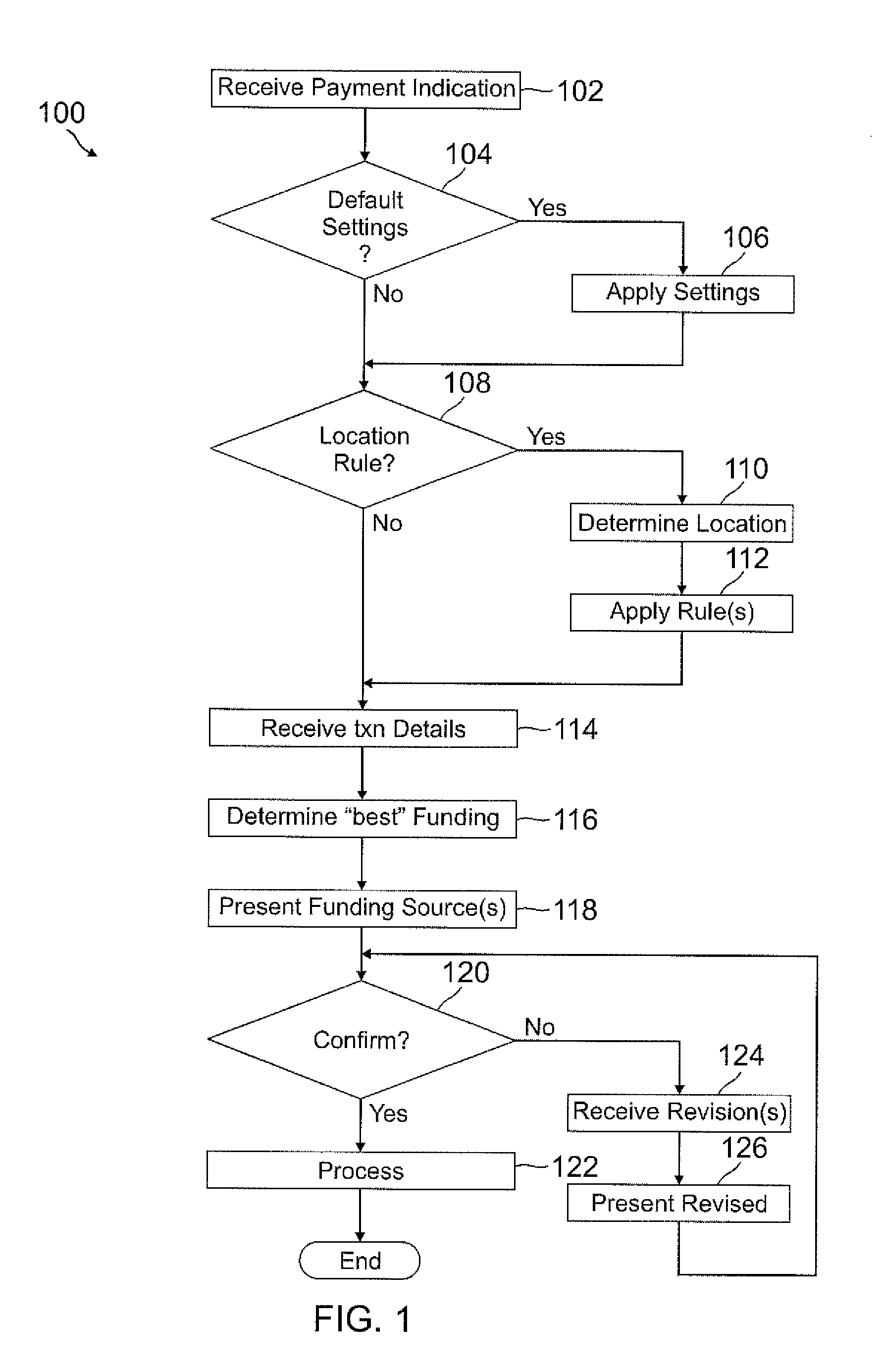
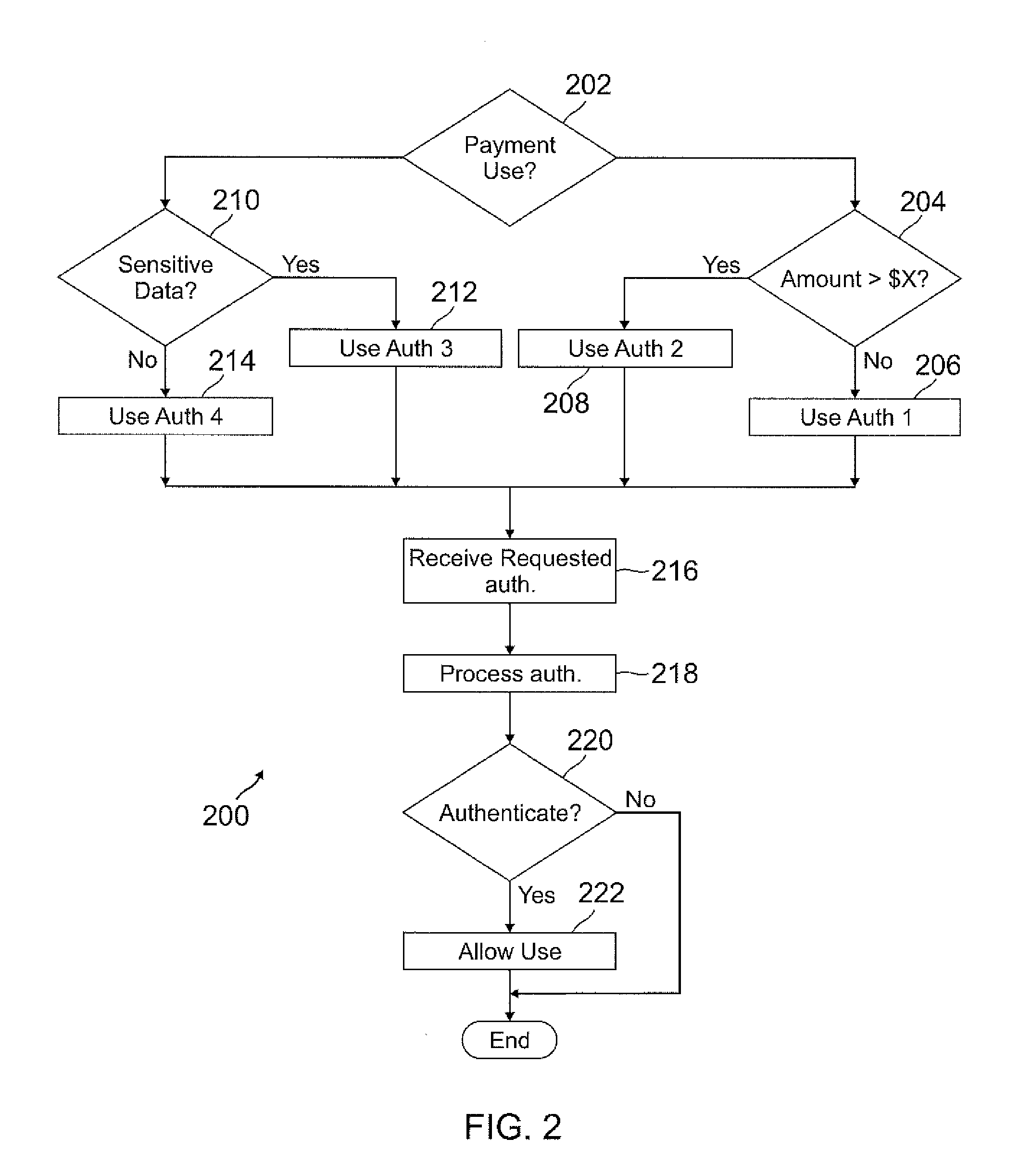
A user's smart phone is used for payments and holding information, similar to what is contained in a physical wallet. Depending on transaction details, user preferences, and location, one or more “best” funding instruments for the transaction are selected for the user, who may then revise if desired. Access to different functions or information within the phone may vary and require different authentication / security levels depending on type of use (e.g., payment or non-payment) and details of use (e.g., high payment amount vs. low payment amount, use of sensitive information vs. non-sensitive information).
Owner:PAYPAL INC
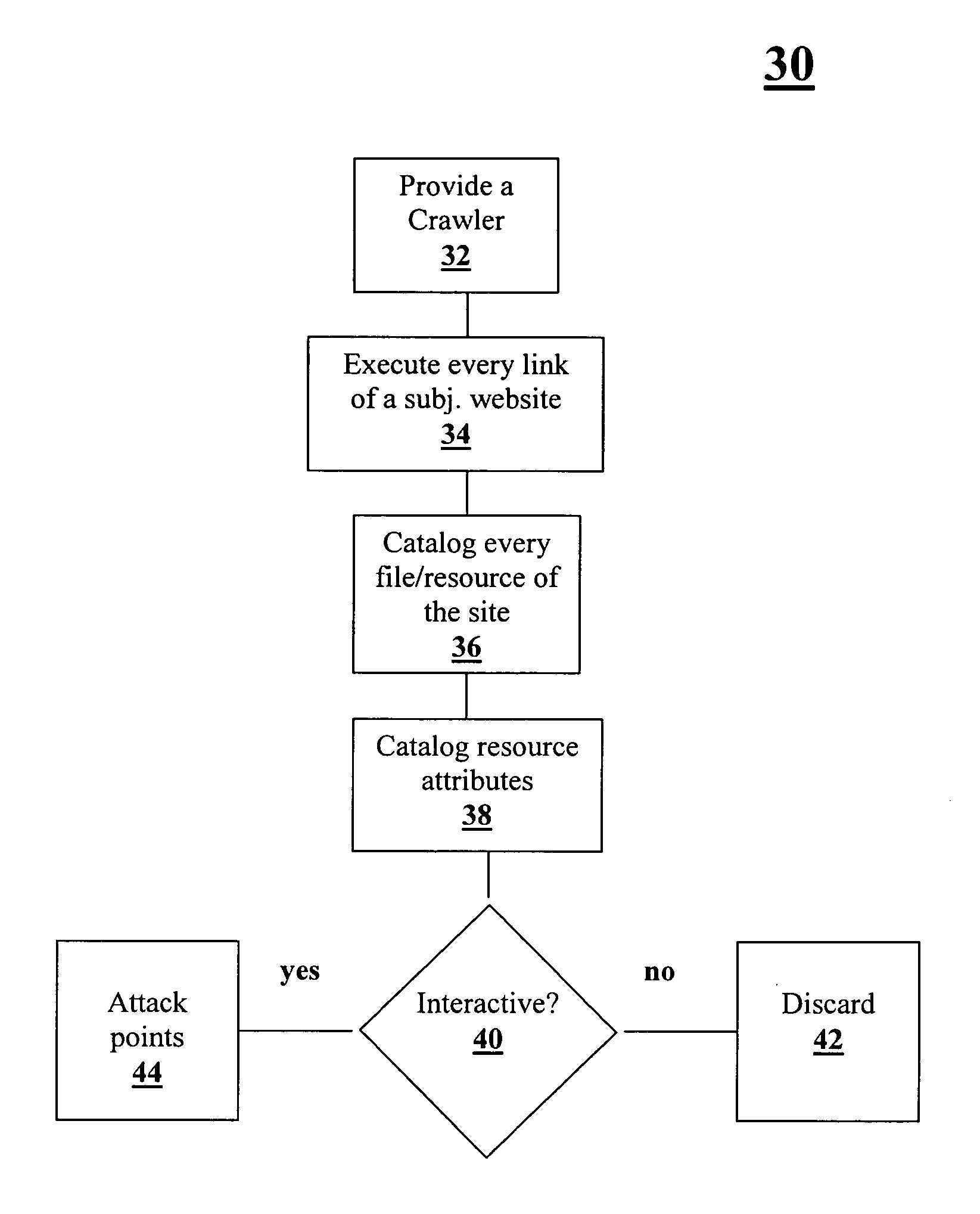
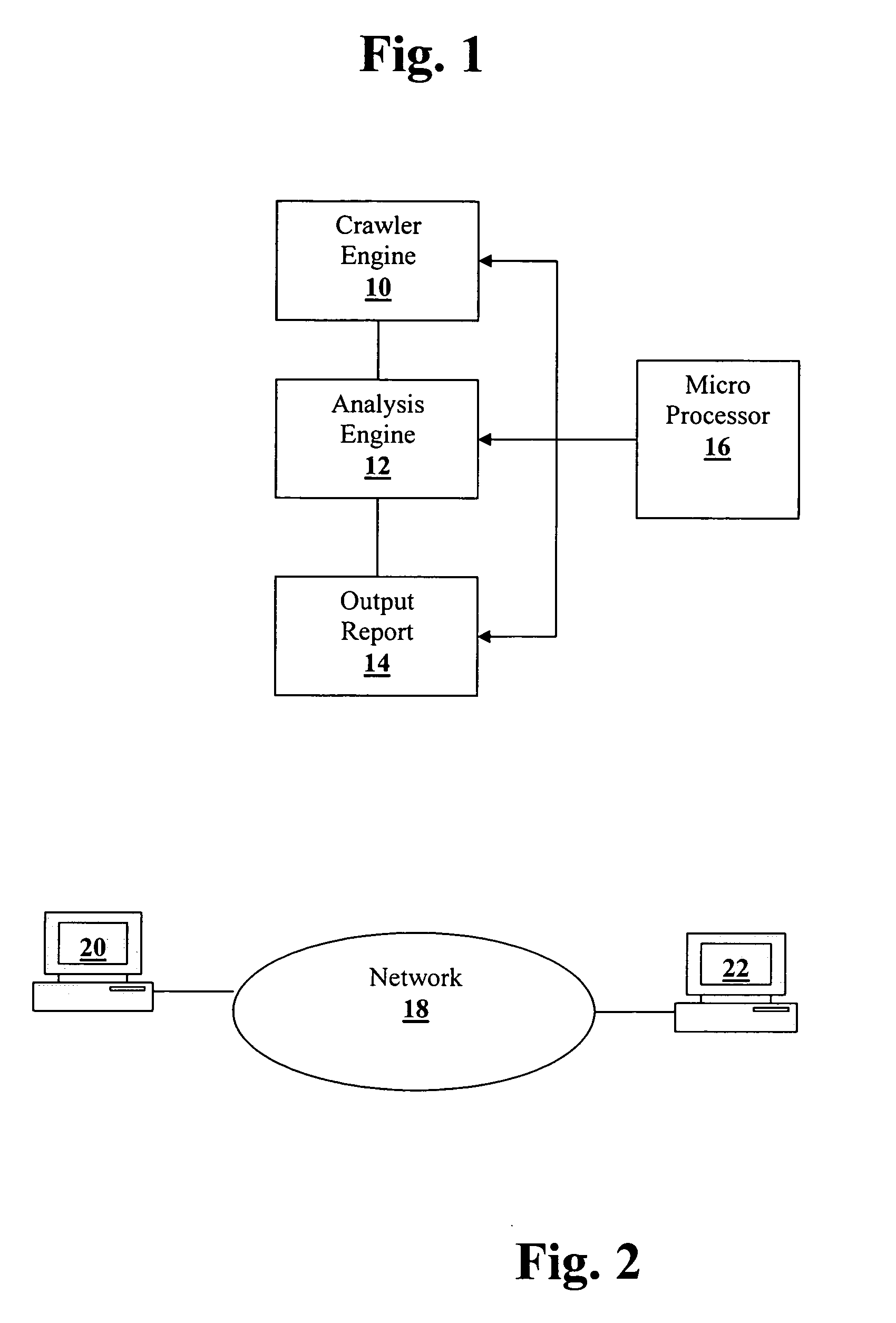
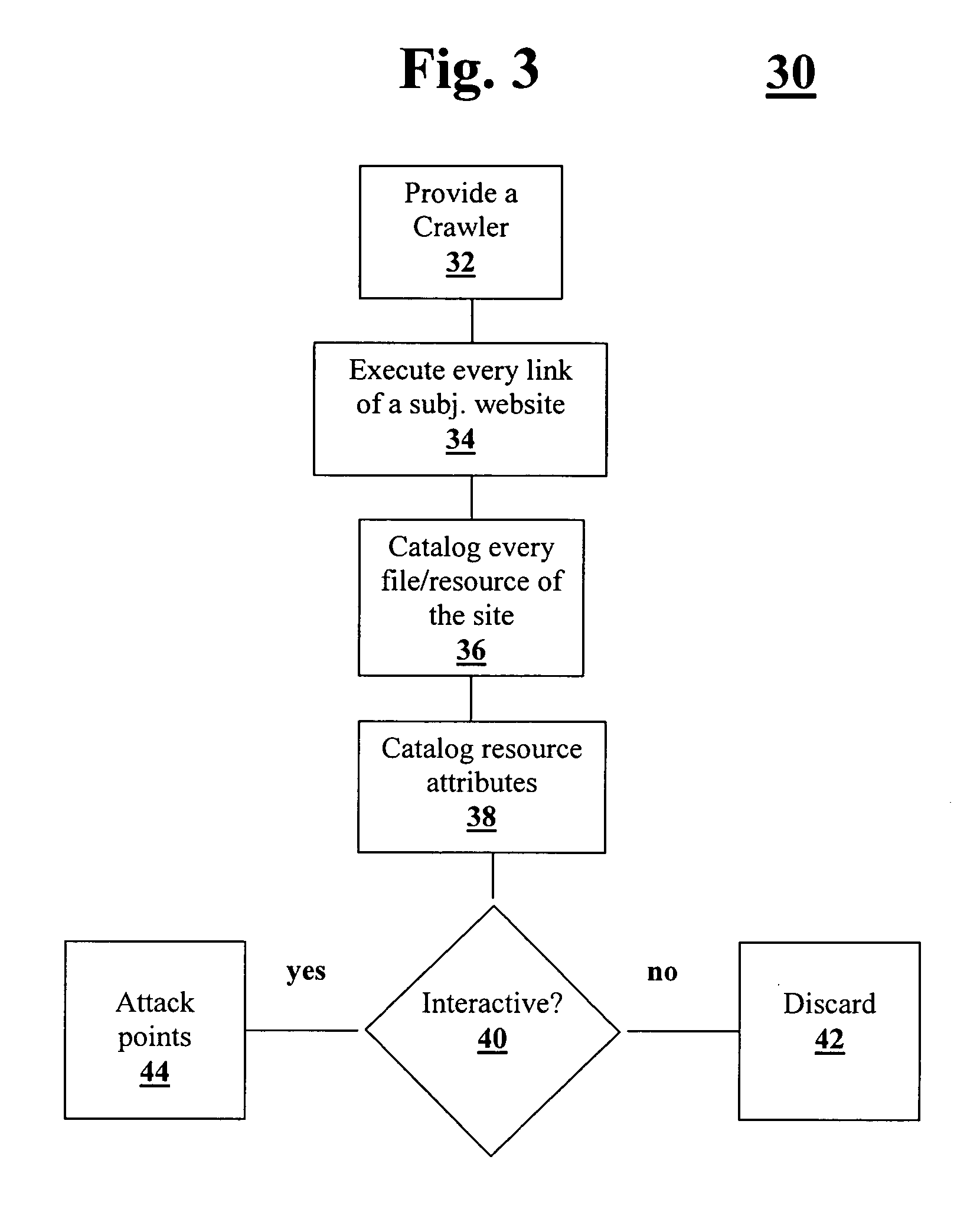
Application threat modeling
A method and system for analyzing data relating to a website including the content and architecture of the website are provided. All relevant site related information is cataloged. Then “attack points” or vectors used by a hacker within the site are determined. Based on the above, a calculation of a relevant level of security for each attack point is determined.
Owner:NT OBJECTIVES
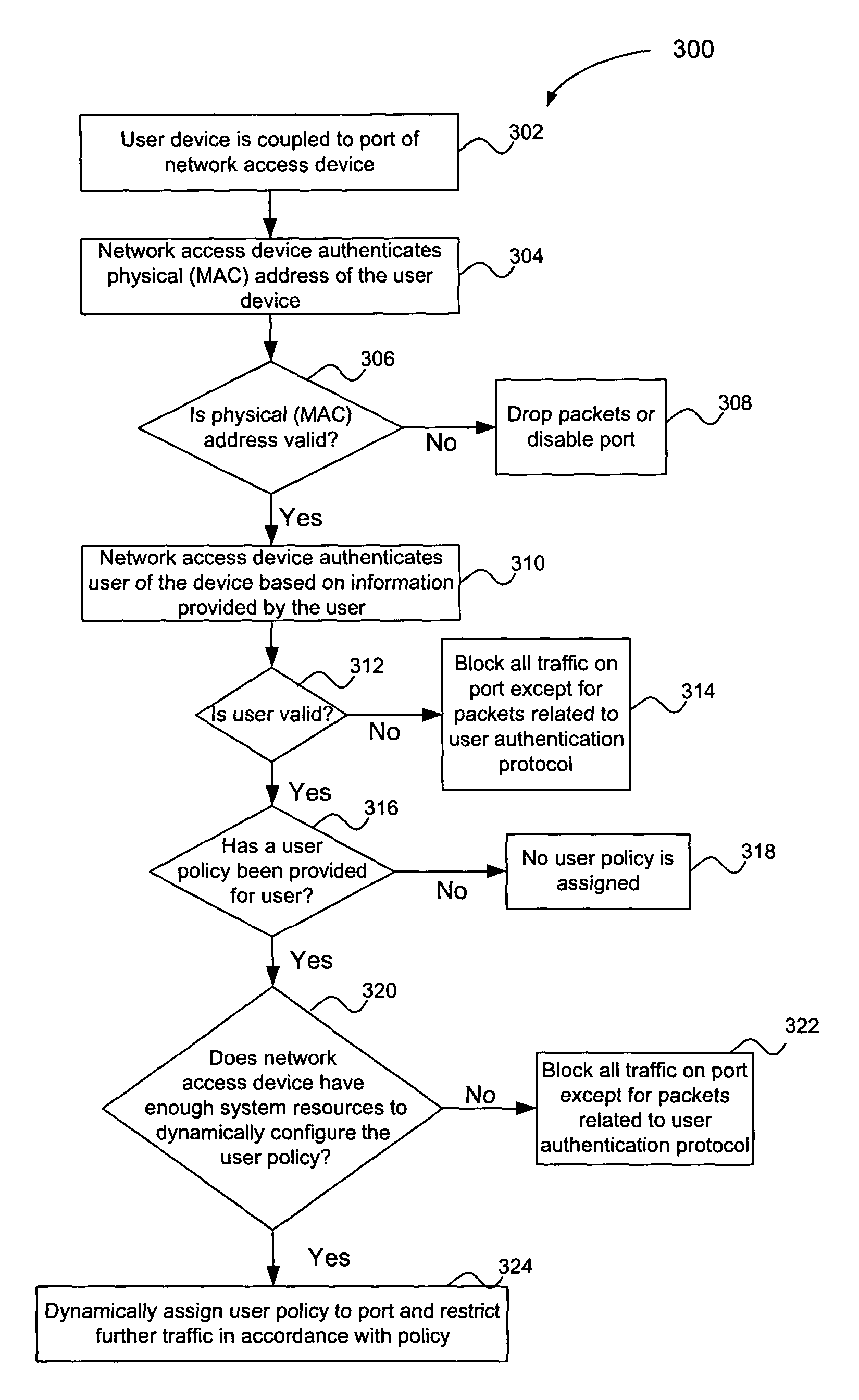
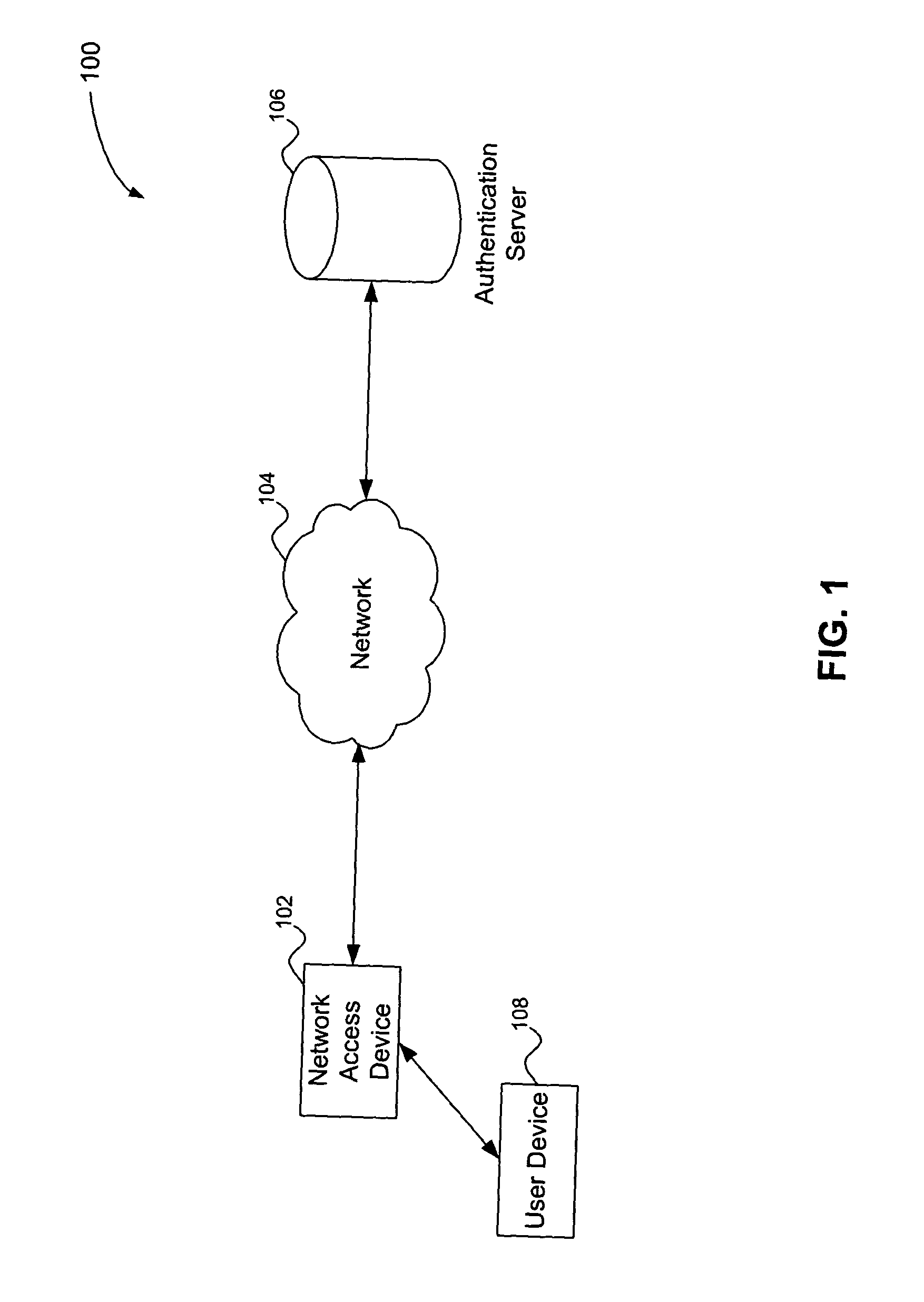
Multiple tiered network security system, method and apparatus using dynamic user policy assignment
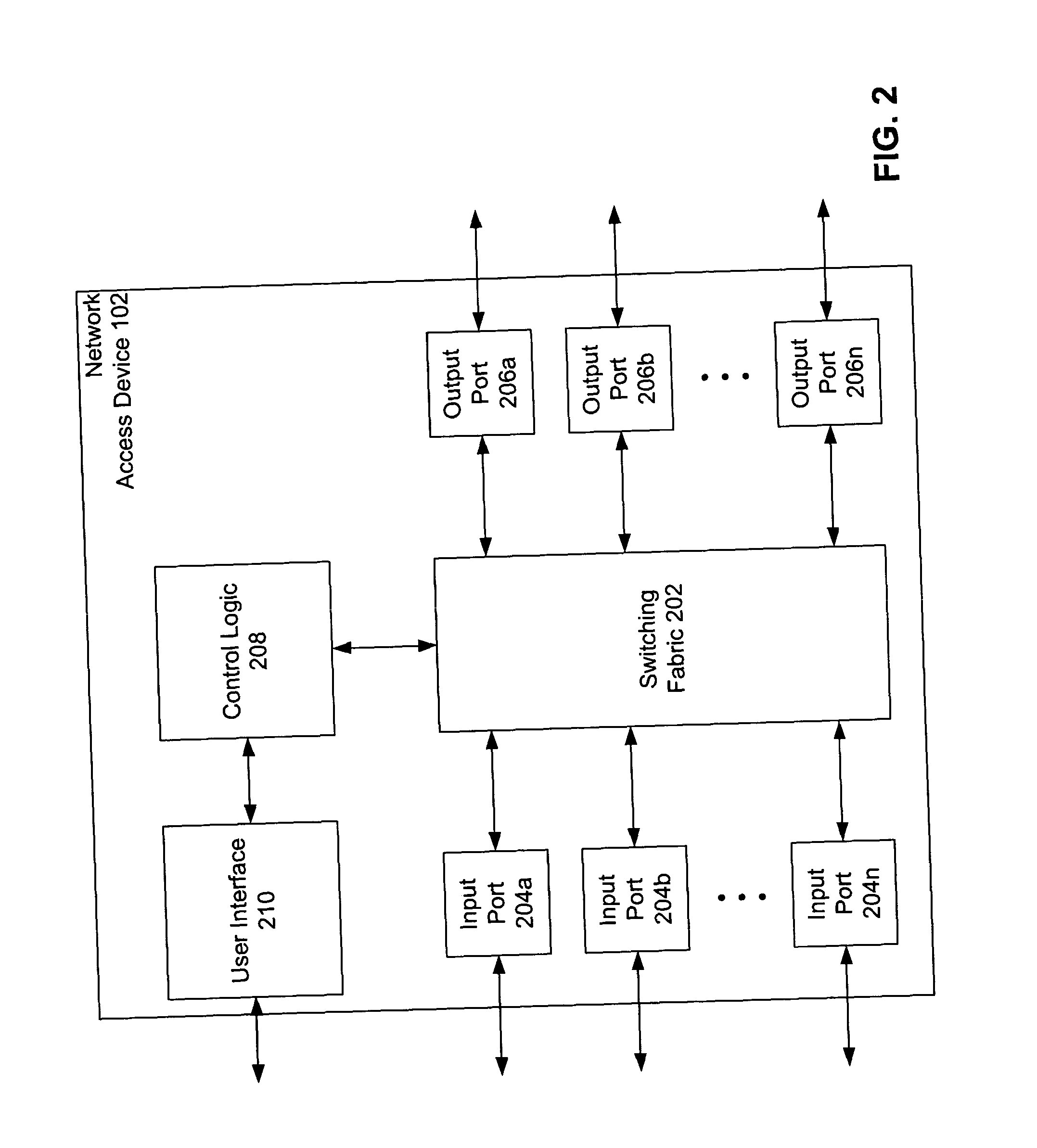
InactiveUS20050055570A1Improve network securityEfficiently provideUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThree levelPhysical address
A multiple key, multiple tiered network security system, method and apparatus provides at least three levels of security. The first level of security includes physical (MAC) address authentication of a user device being attached to the network, such as a user device being attached to a port of a network access device. The second level includes authentication of the user of the user device, such as user authentication in accordance with the IEEE 802.1x standard. The third level includes dynamic assignment of a user policy to the port based on the identity of the user, wherein the user policy is used to selectively control access to the port. The user policy may identify or include an access control list (ACL) or MAC address filter. Also, the user policy is not dynamically assigned if insufficient system resources are available to do so. Failure to pass a lower security level results in a denial of access to subsequent levels of authentication.
Owner:AVAGO TECH INT SALES PTE LTD
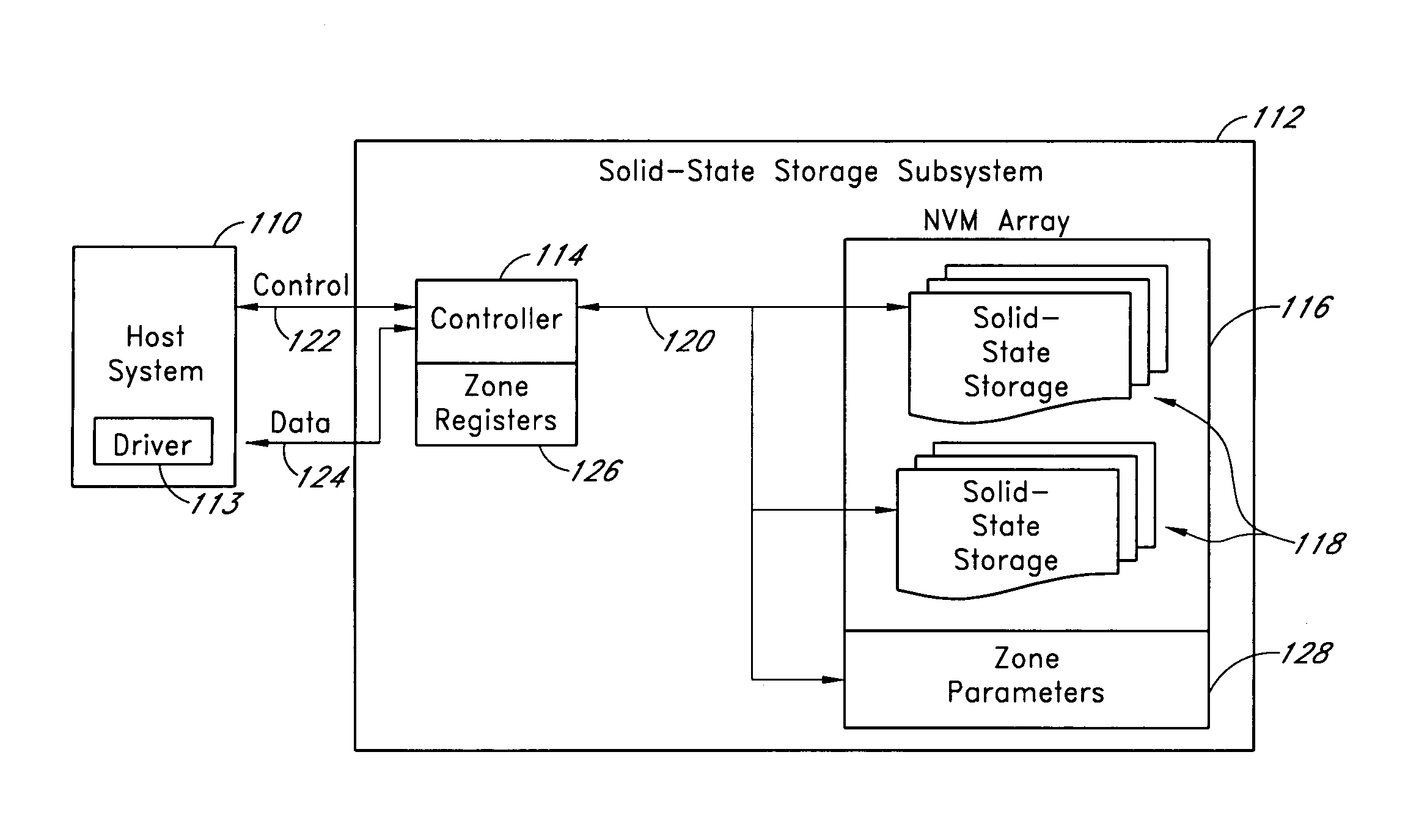
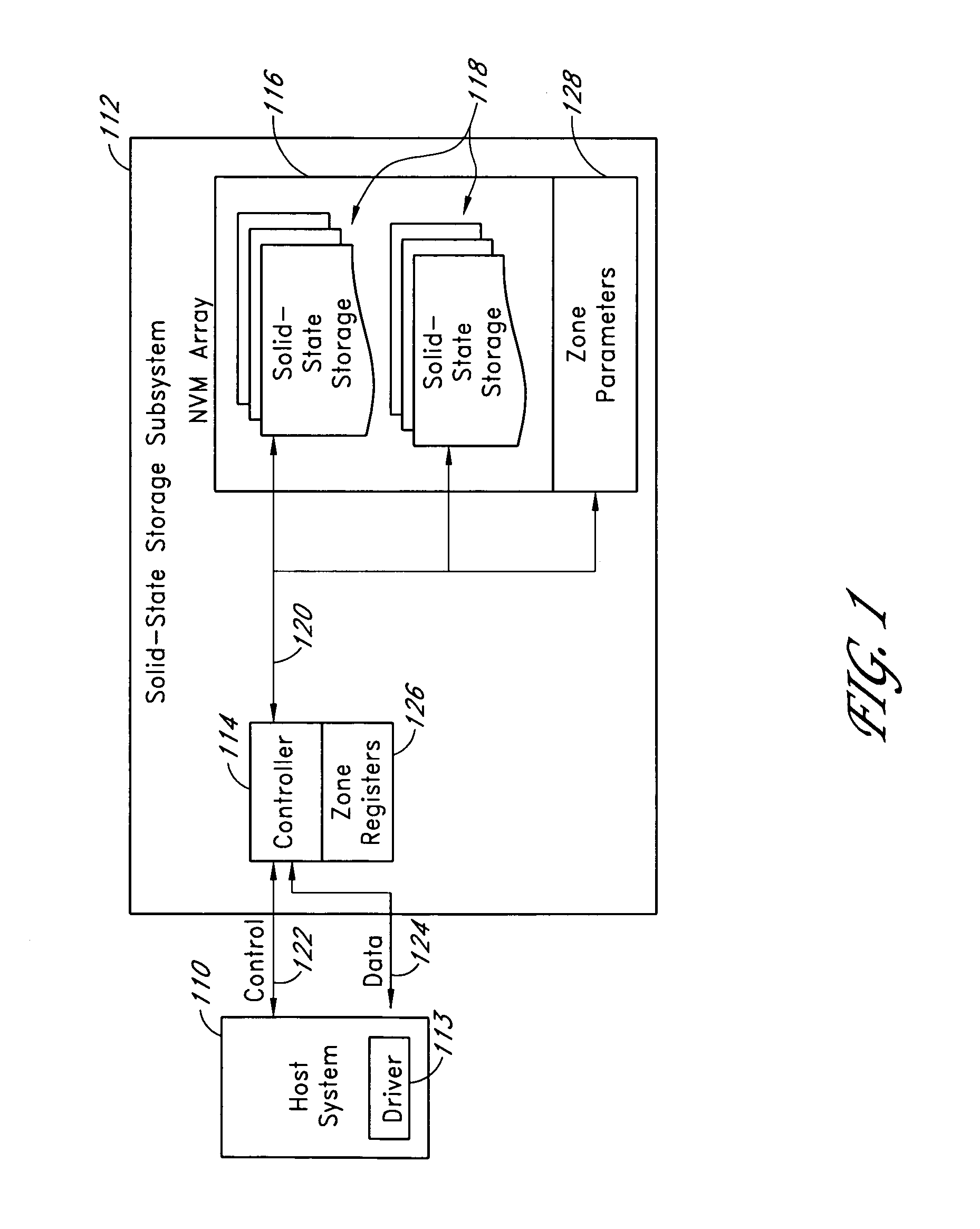
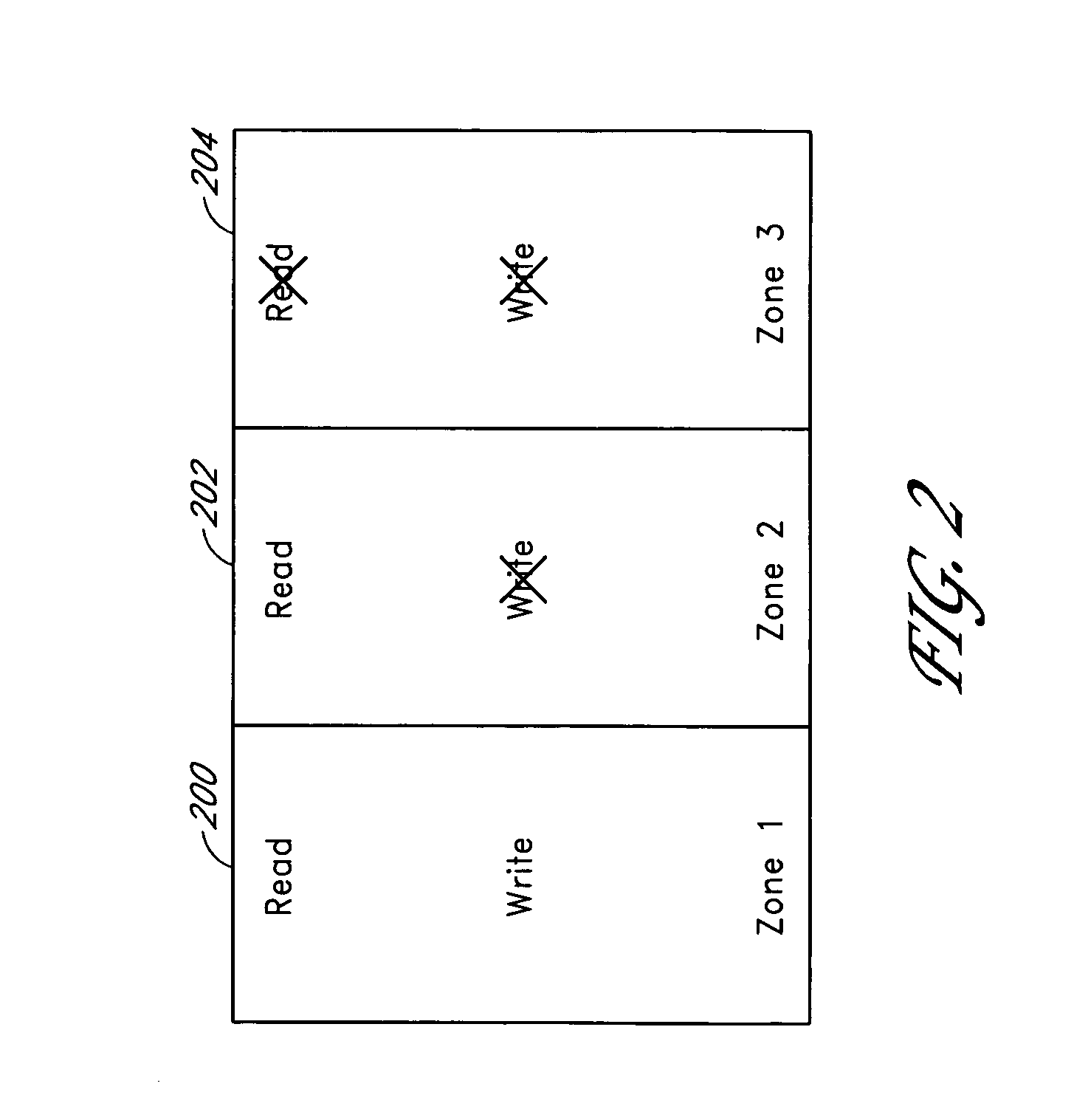
Systems and methods for storing data in segments of a storage subsystem
ActiveUS7447807B1Digital data information retrievalSpecial data processing applicationsSecurity levelData storing
A storage subsystem comprises a set of zone definitions that uses physical block addresses to divide a memory array in the storage subsystem into zones or segments. A set of zone parameters defines user access modes and security levels for each of the segments. Defining zones for the memory array provide flexibility and increased protection for data stored in the memory array. For example, data of one zone can be quickly erased without affecting data stored in other zones and critical data can be stored in read-only zones to prevent inadvertent overwrite.
Owner:WESTERN DIGITAL TECH INC
Method, system and apparatus for selecting encryption levels based on policy profiling
InactiveUS7010681B1Easily maintainable methodSelective encryptionSecuring communicationClient-sideSecurity level
The present invention depicts a method, system and program product for controlling levels of security and levels of encryption based on a predefined policy profile. This enables administrators and those who control the network to easily respond to changes in the requirements of the security levels for specific applications. It also allows for response to changes in personnel (such as someone being removed from a position that had topsecret security access) and accommodates variations in access by client devices.
Owner:IBM CORP
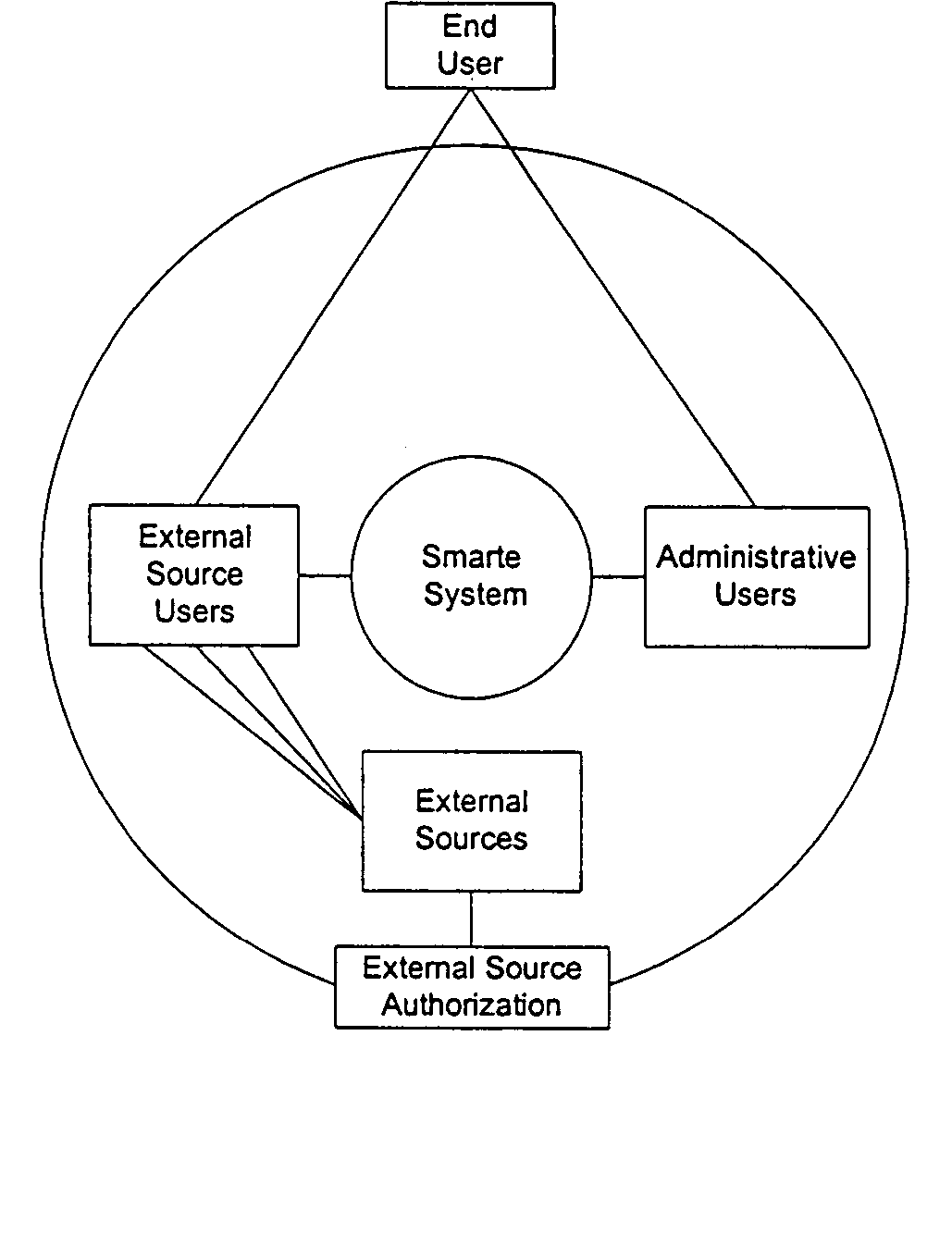
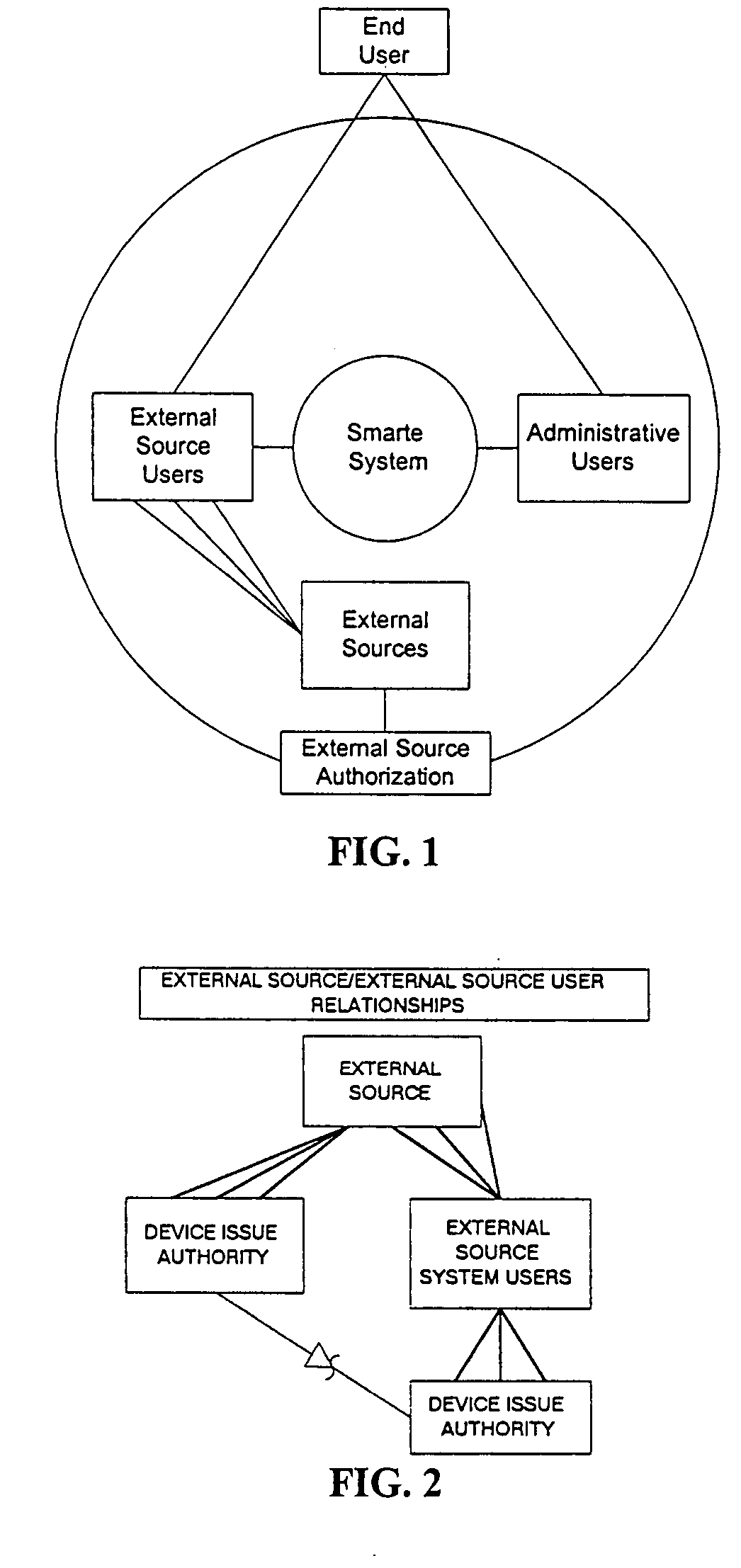
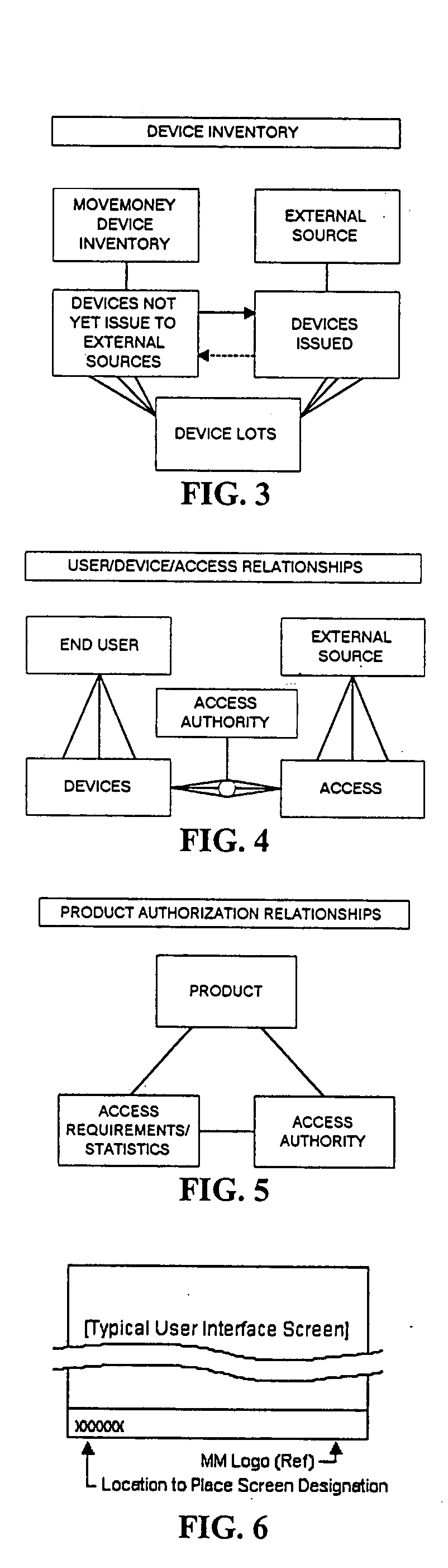
User/product authentication and piracy management system
InactiveUS20050149759A1Reduce potentialPrevent illegal useDigital data processing detailsMultiple digital computer combinationsDigital identitySerialization
A system in the form of a software solution that provides new and unique solutions to the need to secure digital environments. The present invention uses innovative and new forms of multi-factor user authentication and digital identity management, providing levels of security unmatched in the industry. In addition, the system provides new and unique methods of software piracy management including CD media-based copy protection, remote CD media validation, embedded product serialization, protection of electronically distributed software, and remote product installation tracking.
Owner:MOVEMONEY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com