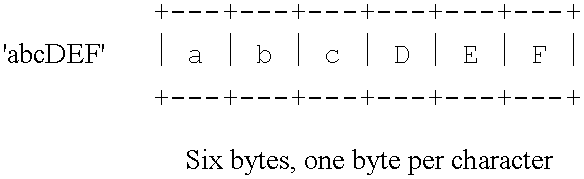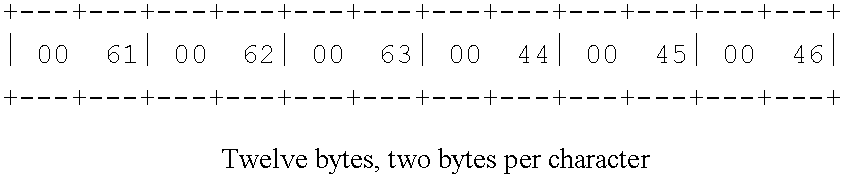Patents
Literature
5369 results about "Three level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
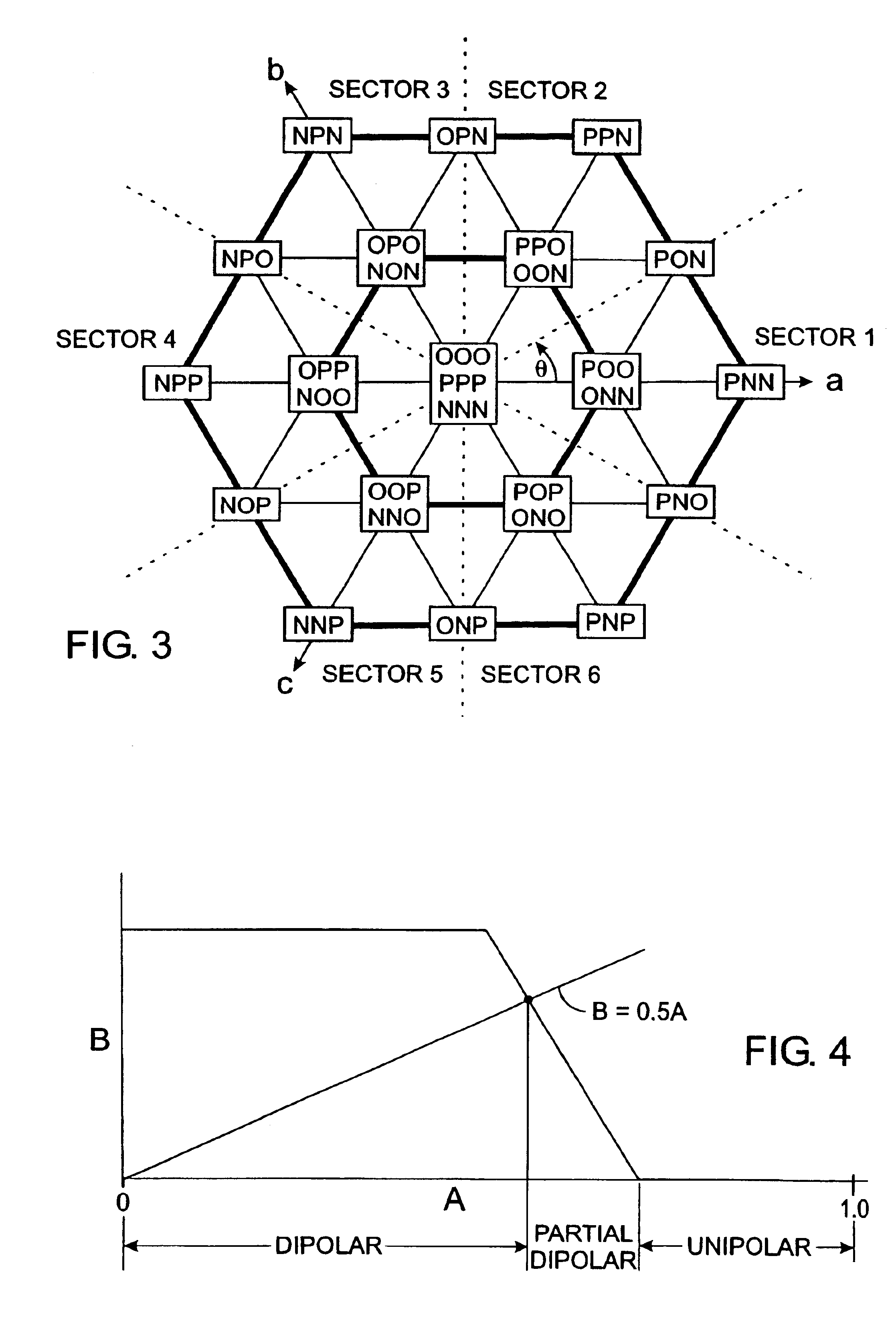
Three Levels of Leadership model. The three levels referred to in the model's name are Public, Private and Personal leadership. The model is usually presented in diagram form as three concentric circles and four outwardly directed arrows, with personal leadership in the center.
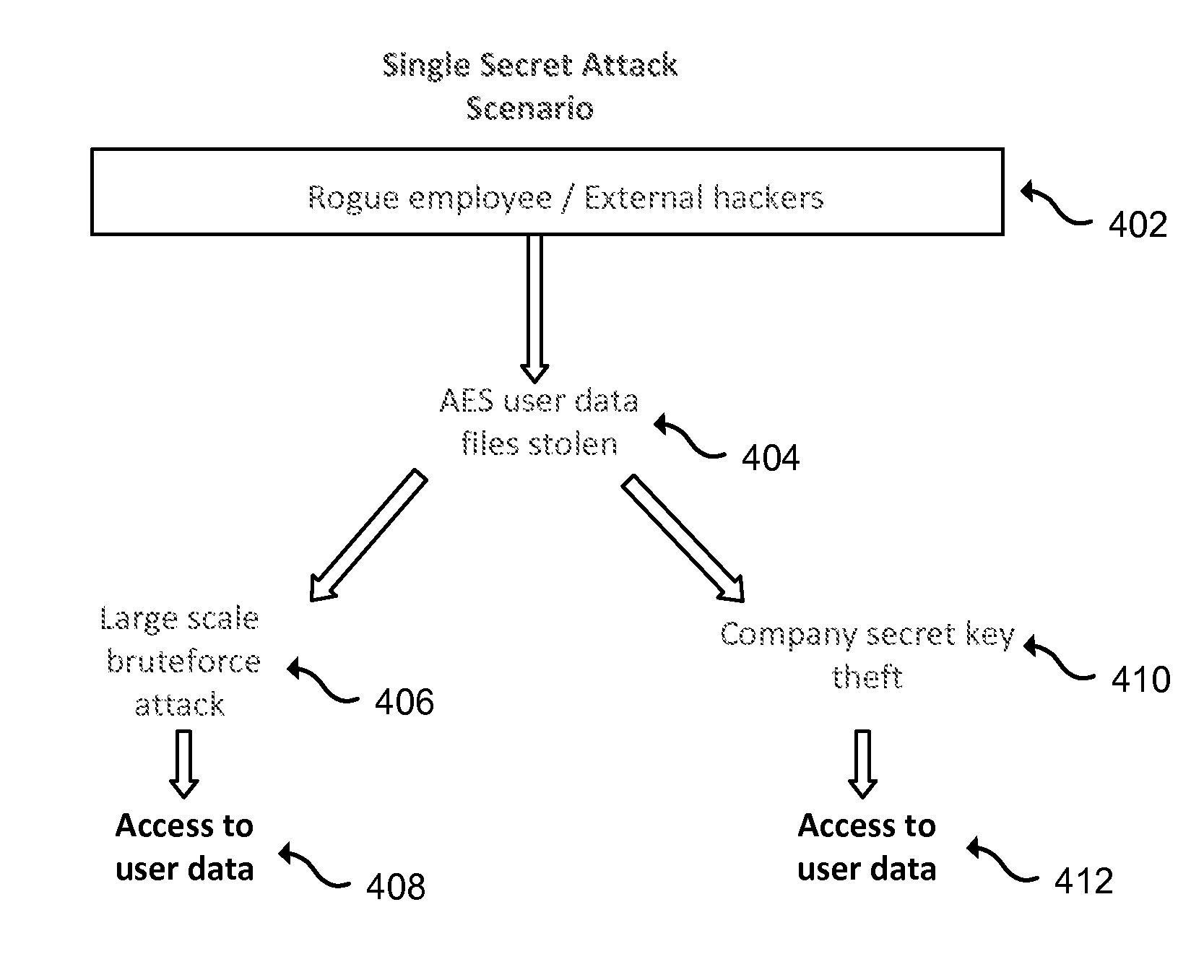
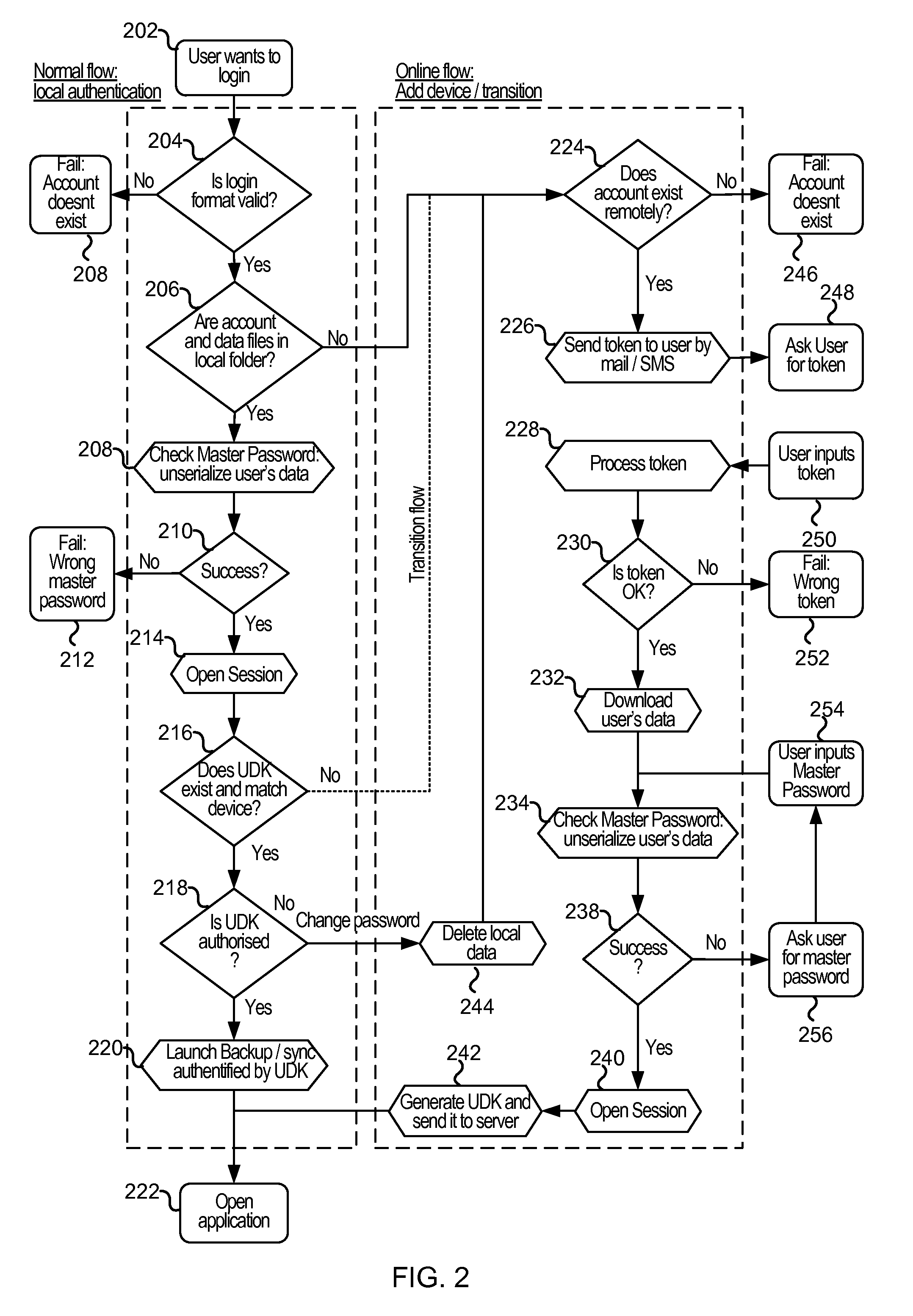
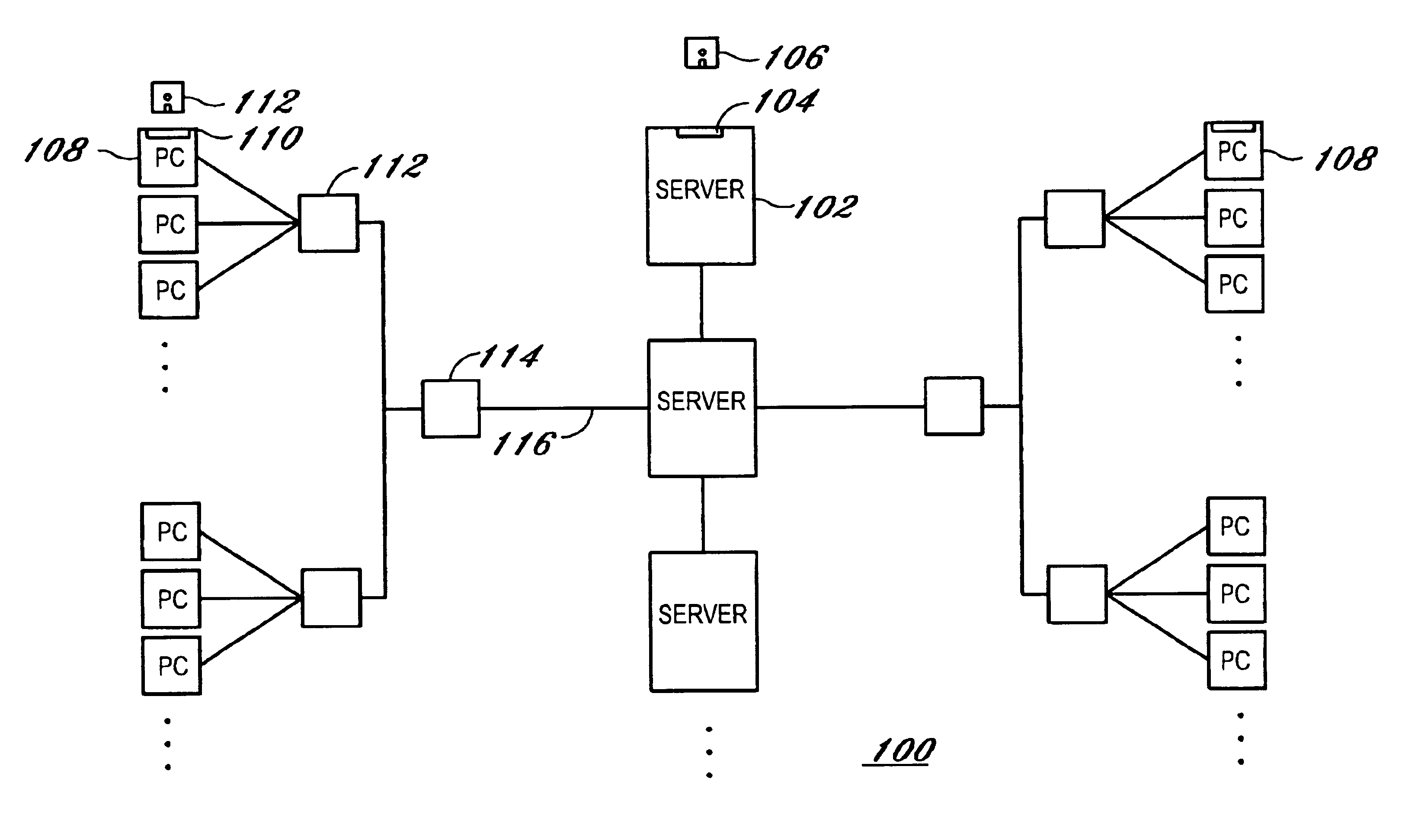
Cloud-based data backup and sync with secure local storage of access keys
ActiveUS20130145447A1Digital data processing detailsMultiple digital computer combinationsThree levelUser device
Methods and systems are provided for secure online data access. In one embodiment, three levels of security are provided where user master passwords are not required at a server. A user device may register with a storage service and receive a user device key that is stored on the device and at the service. The user device key may be used to authenticate the user device with the storage service. As data in the storage service is encrypted with a master password, the data may be protected from disclosure. As a user master key or derivative thereof is not used in authentication, the data may be protected from a disclosure or breach of the authentication credentials. Encryption and decryption may thus be performed on the user device with a user master key that may not be disclosed externally from the user device.
Owner:DASHLANE
Artificial intelligence early warning system
ActiveCN109447048APrevent overpassSemantic analysisOther databases indexingThree levelInformation resource
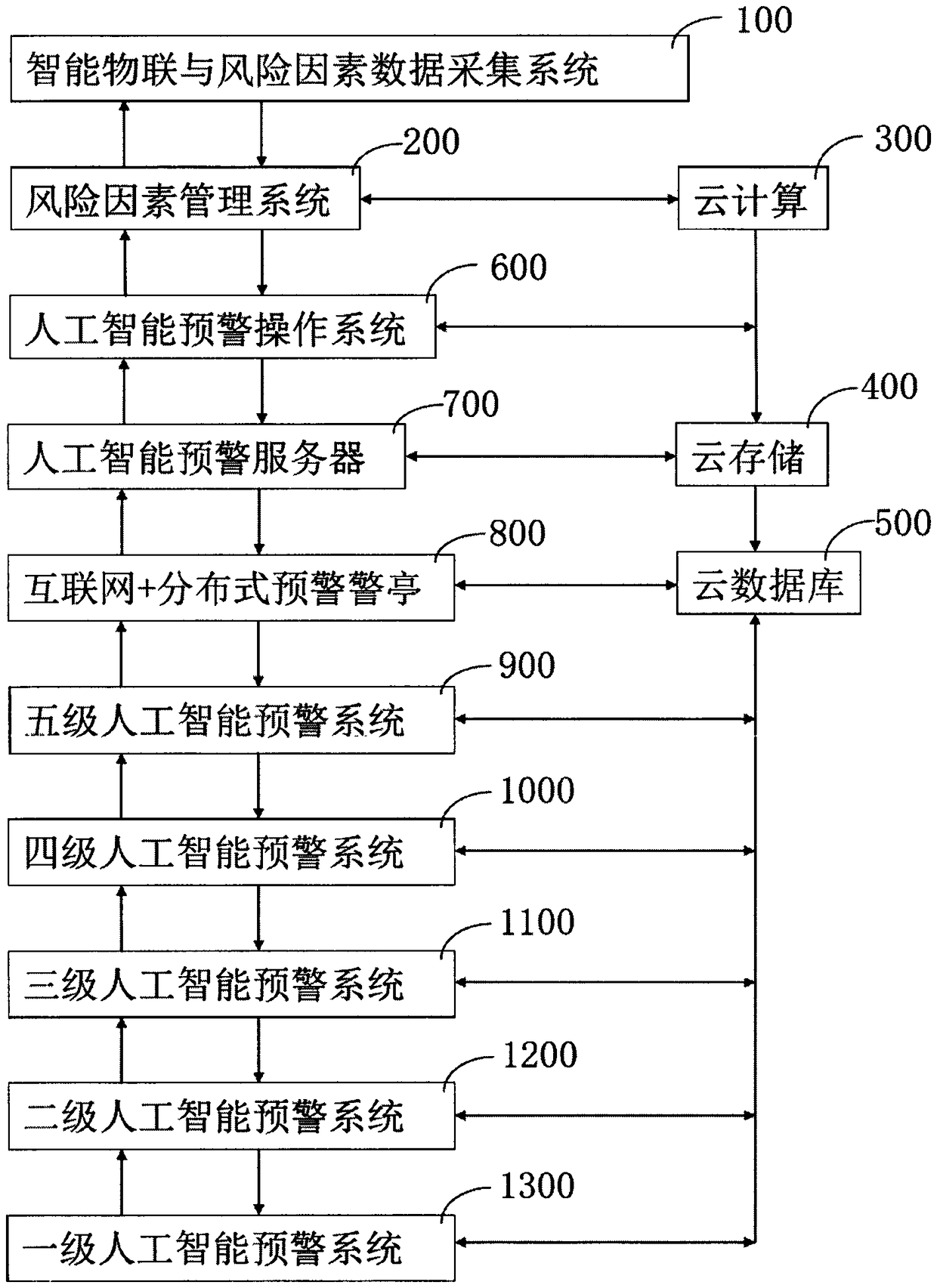
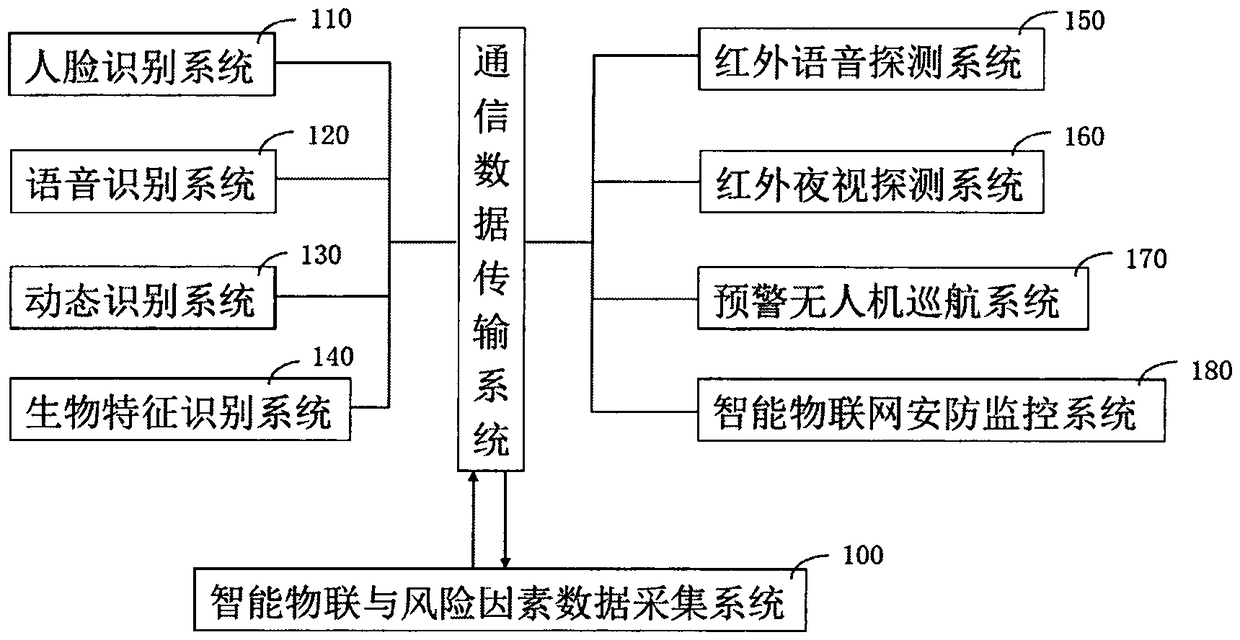
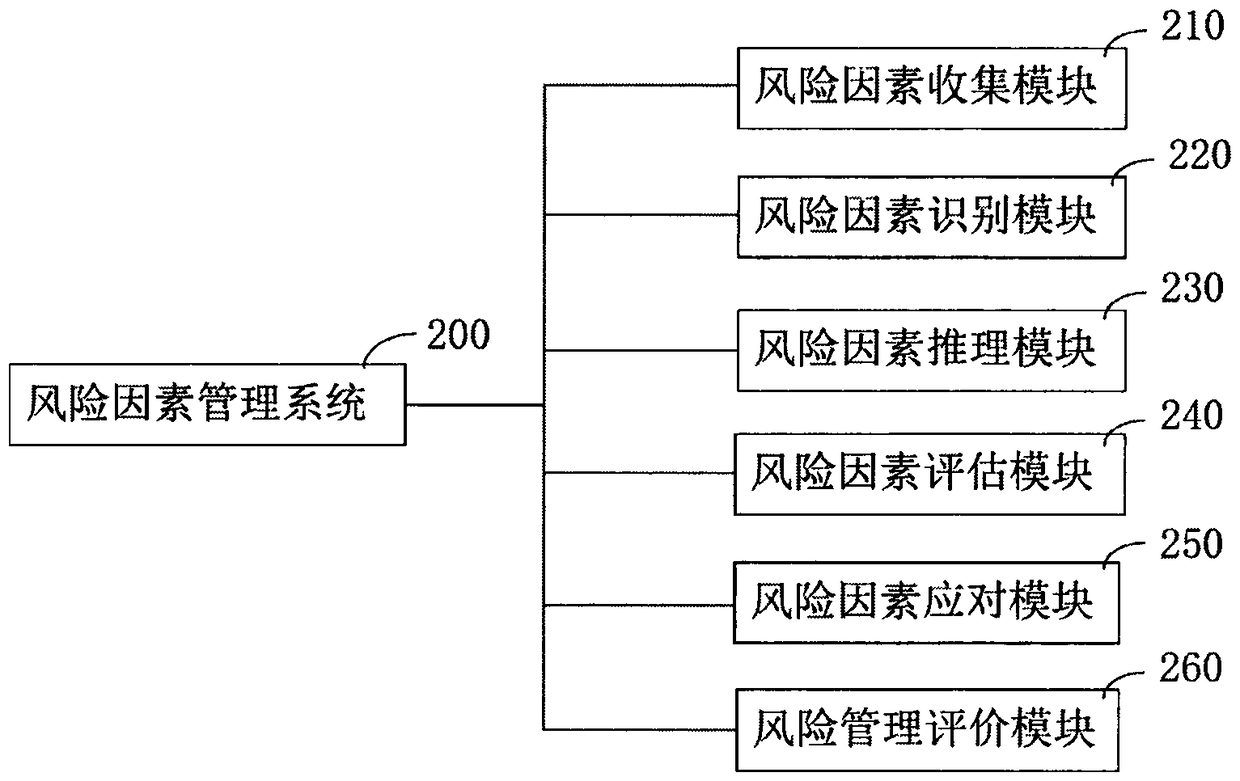
The invention relates to an artificial intelligence early warning system. The system comprises an intelligent Internet of Things and risk factor data acquisition system (100), and a risk factor management system (200), a cloud computing device (300), a cloud storage device (400), a cloud database (500), and an artificial intelligence early warning operation system (600), an artificial intelligenceearly warning server (700), an internet + distributed early warning police booth (800), a five-level artificial intelligence early warning system (900), a four-level artificial intelligence early warning system (1000), a three-level artificial intelligence early warning system (1100), a two-level artificial intelligence early warning system (1200) and a one-level artificial intelligence early warning system (1300). The artificial intelligence early warning system of the present invention collects, compares, analyzes, deduces, evaluates the risk factors, and carries out the cloud computing, cloud storage, graded alarming and prevention and control, so that all-weather 24-hour monitoring on monitoring points around the police box is achieved, a user can share information, the utilization rate of information resources is increased, and the safety guarantee is increased for maintaining the stability of the borderlands.
Owner:苏州闪驰数控系统集成有限公司
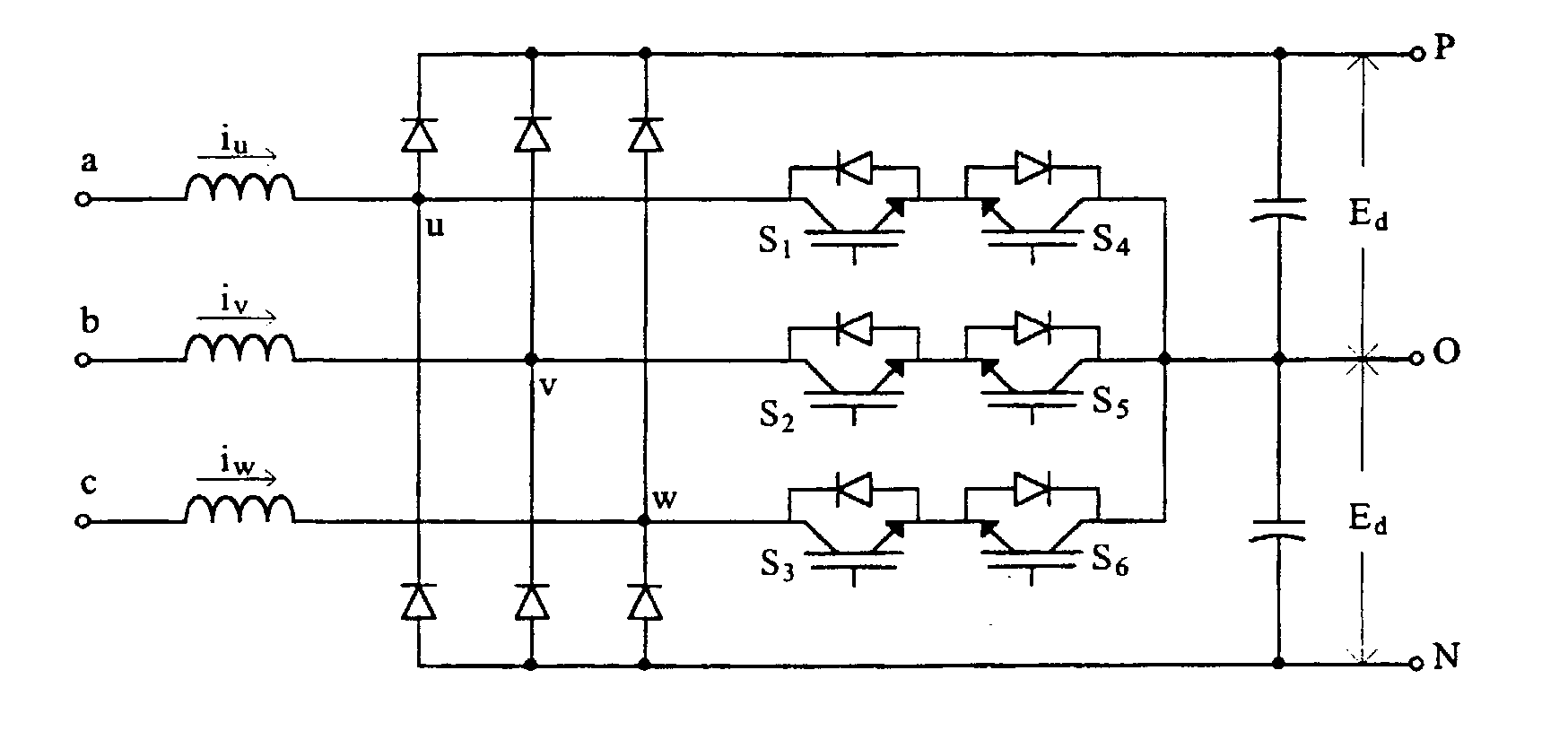
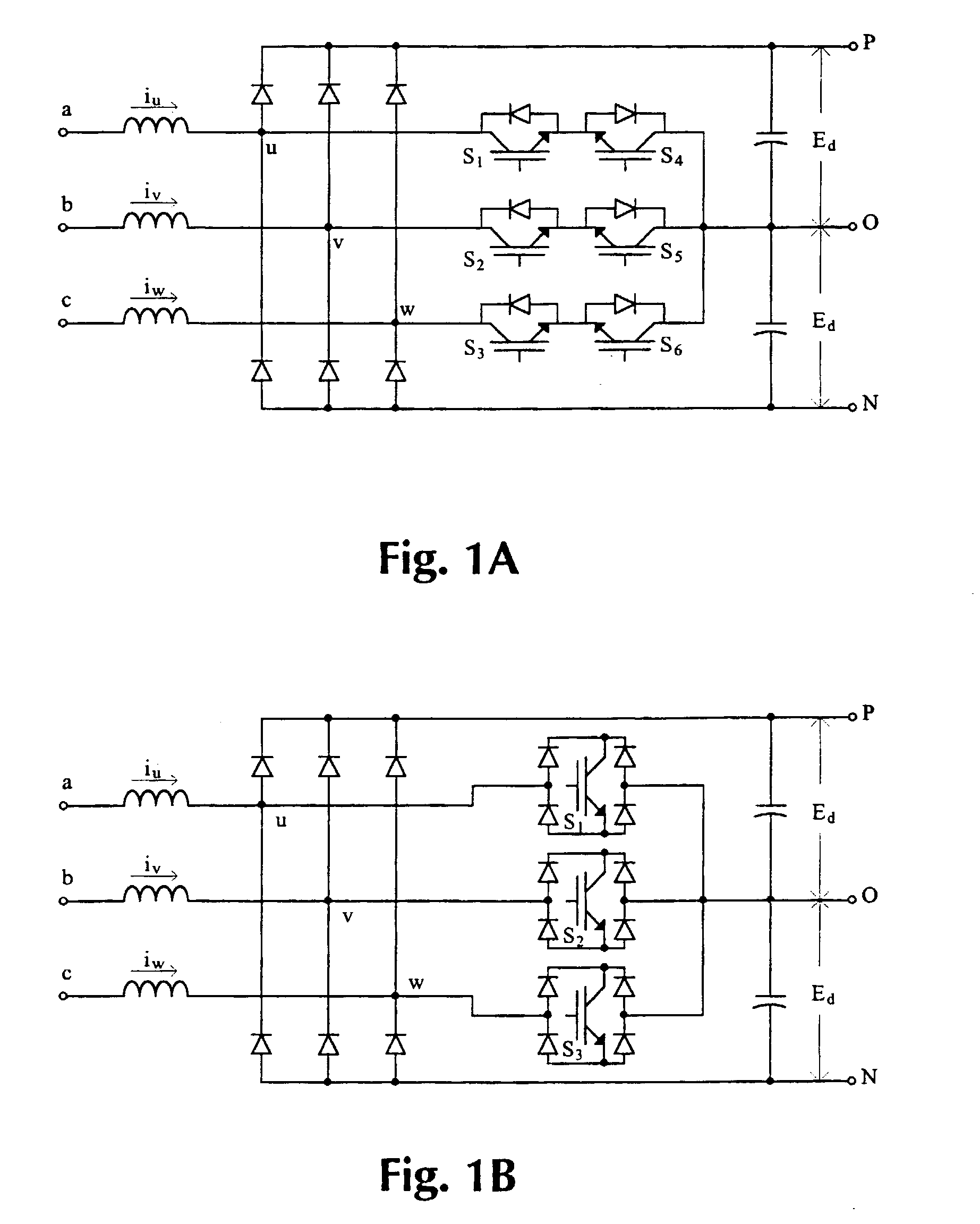
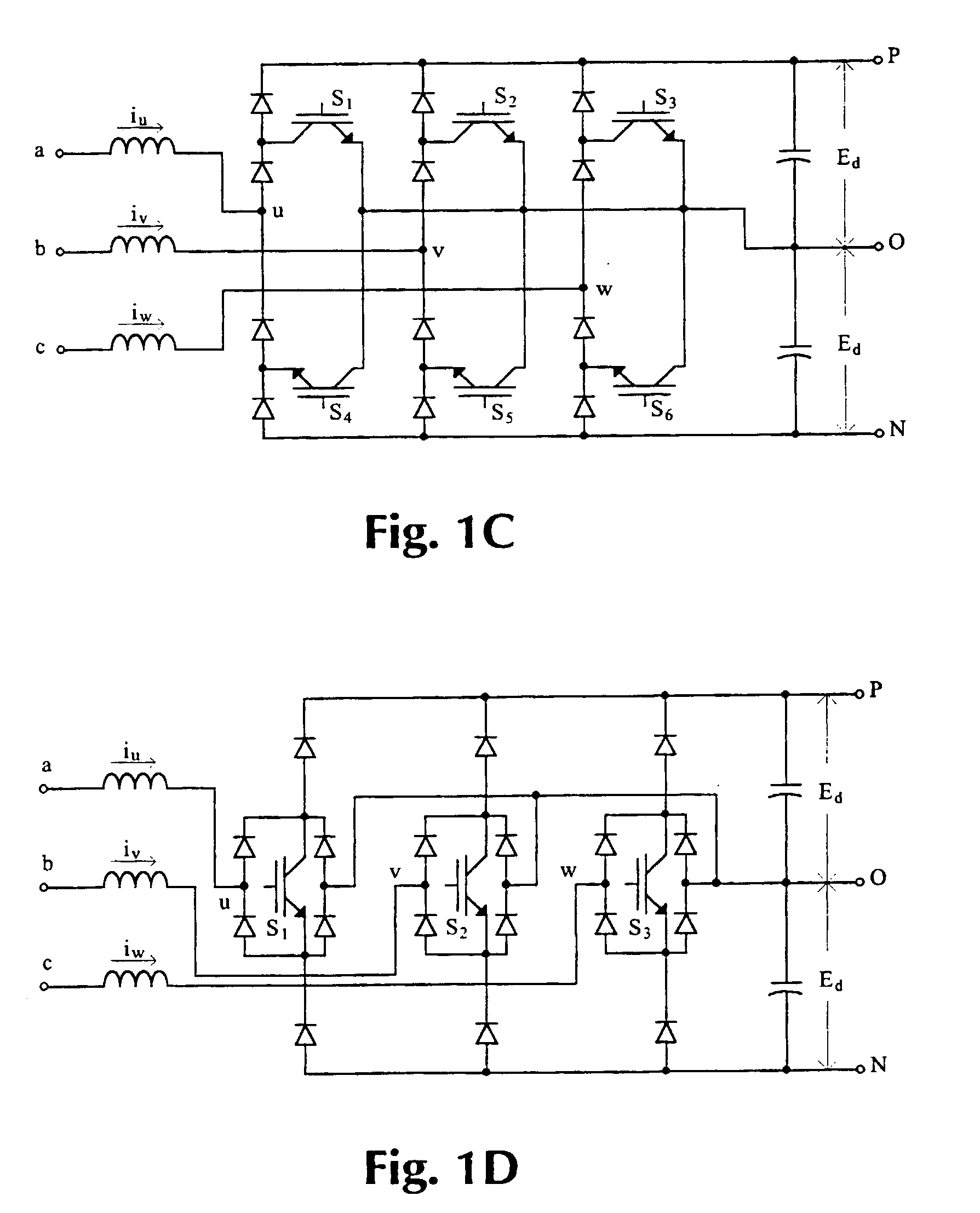
Capacitor charge balancing technique for a three-level PWM power converter
InactiveUS6842354B1Adjustable widthConversion with intermediate conversion to dcDc-dc conversionThree levelEngineering
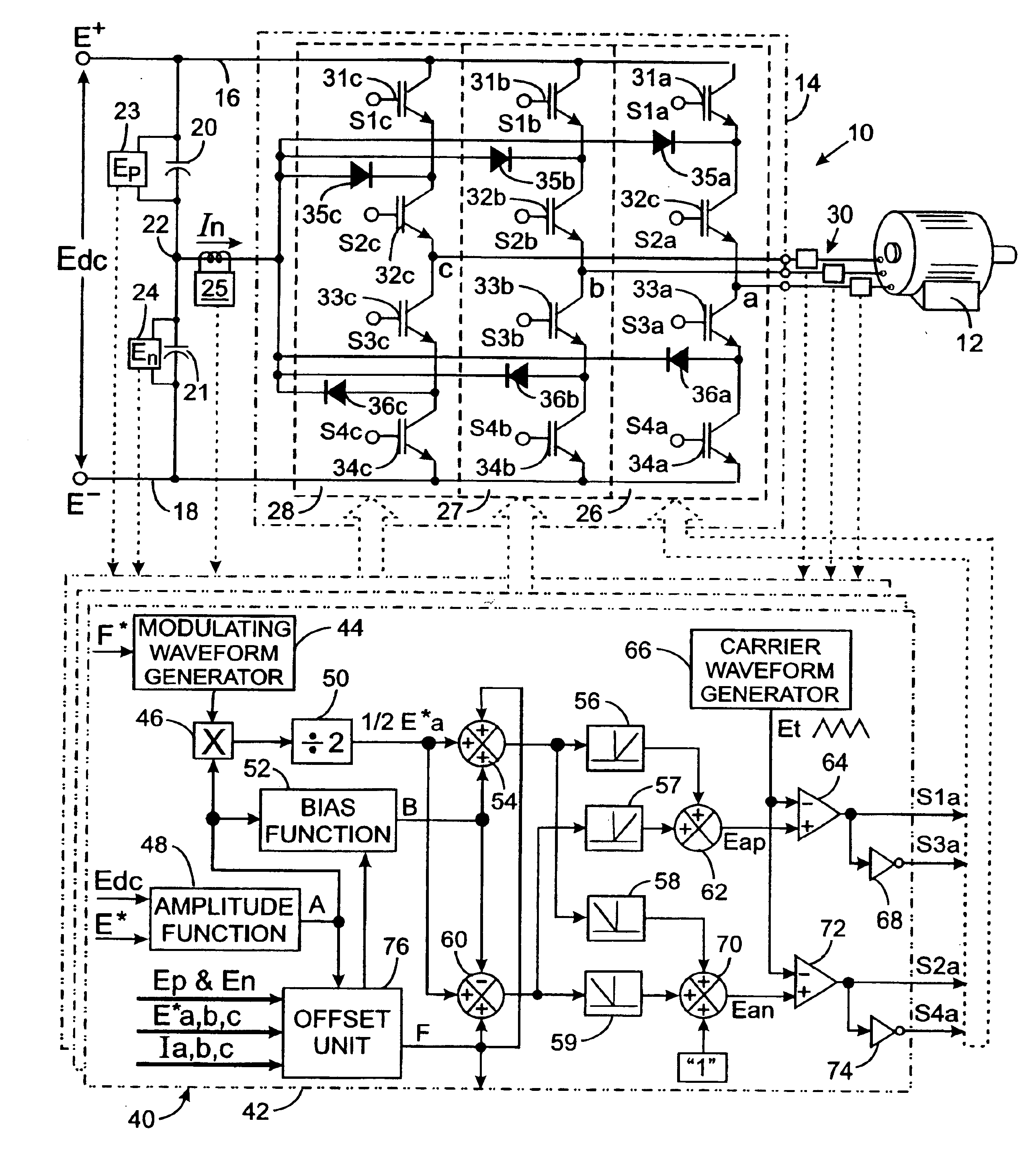
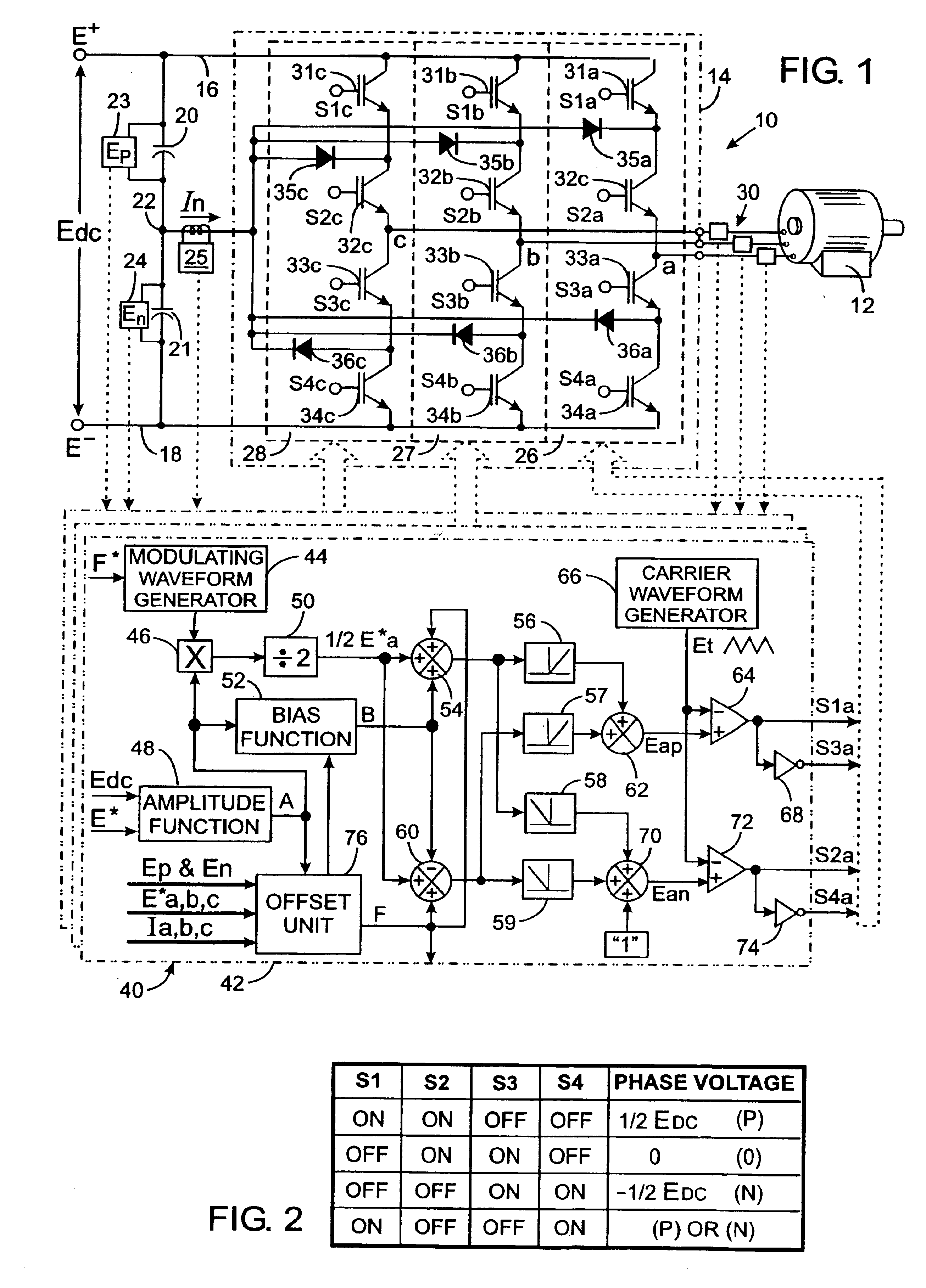
A power converter includes a DC to AC inverter that is connected to a neutral node formed between first and second capacitors connected across two DC supply lines. The inverter is operated to selectively couple the DC supply lines and the neutral node to an output terminal thereby producing an alternating voltage waveform formed by a sequence of output pulses having positive, zero and negative voltage levels. To compensate for a voltage imbalance across the capacitors, an imbalance compensation coefficient is derived from the difference in voltages across the first and second capacitors and from the direction of current between the neutral node and the inverter. The imbalance compensation coefficient is employed to adjust the width of the output pulses so as to charge and discharge the capacitors to correct the imbalance.
Owner:ROCKWELL AUTOMATION TECH
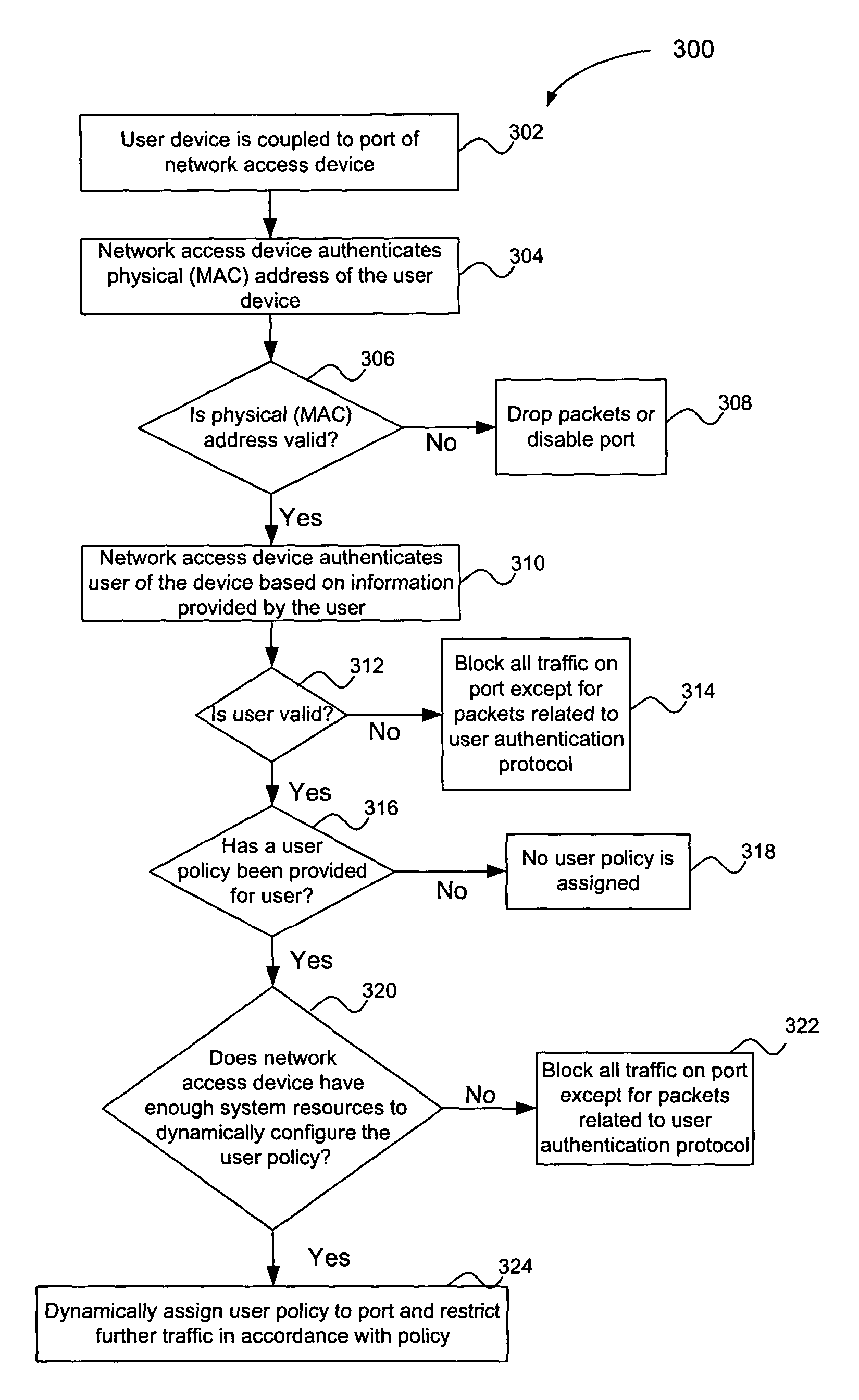
Multiple tiered network security system, method and apparatus using dynamic user policy assignment
InactiveUS20050055570A1Improve network securityEfficiently provideUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThree levelPhysical address
A multiple key, multiple tiered network security system, method and apparatus provides at least three levels of security. The first level of security includes physical (MAC) address authentication of a user device being attached to the network, such as a user device being attached to a port of a network access device. The second level includes authentication of the user of the user device, such as user authentication in accordance with the IEEE 802.1x standard. The third level includes dynamic assignment of a user policy to the port based on the identity of the user, wherein the user policy is used to selectively control access to the port. The user policy may identify or include an access control list (ACL) or MAC address filter. Also, the user policy is not dynamically assigned if insufficient system resources are available to do so. Failure to pass a lower security level results in a denial of access to subsequent levels of authentication.
Owner:AVAGO TECH INT SALES PTE LTD
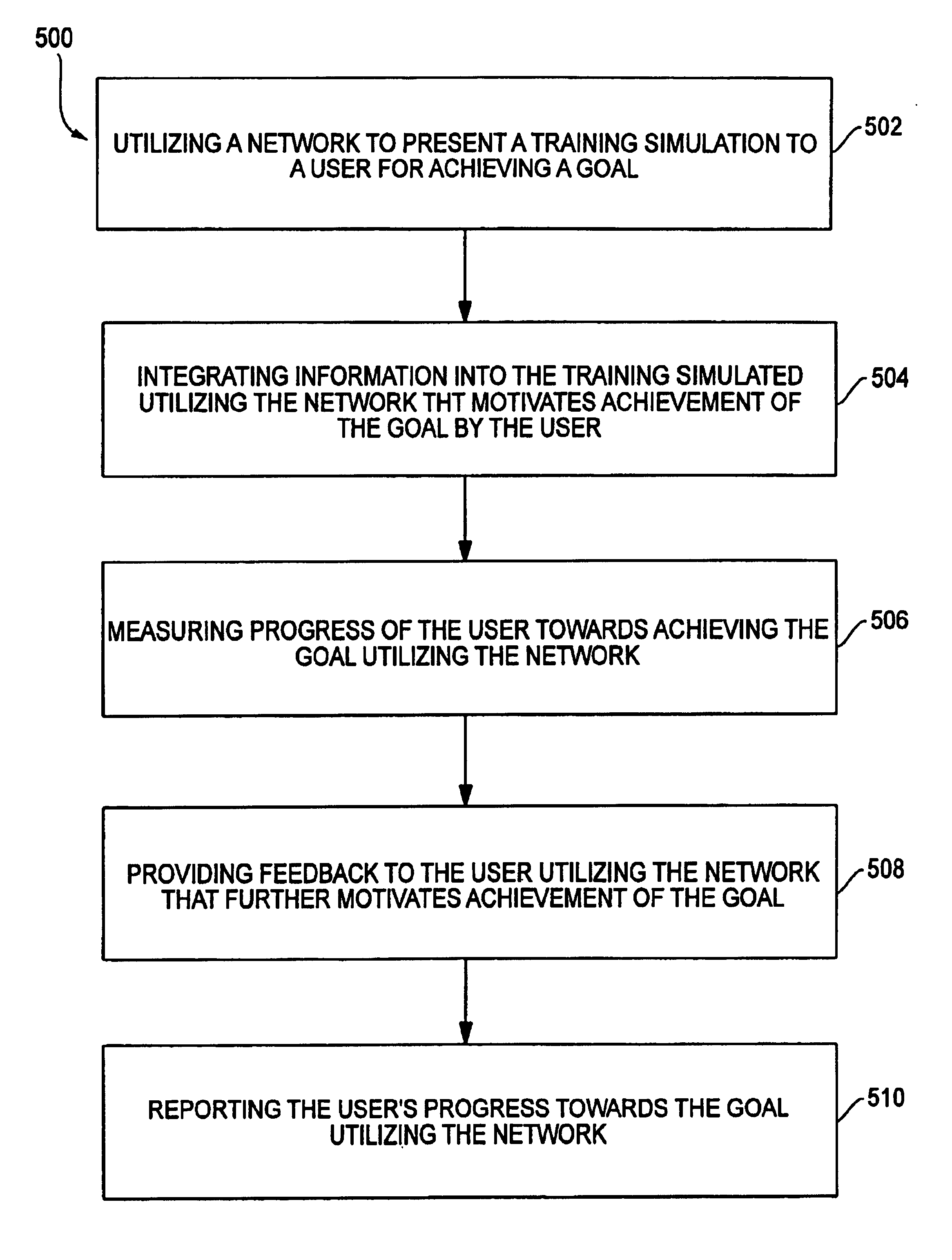
Employee analysis based on results of an education business simulation
InactiveUS6944596B1Efficient implementationProgressData processing applicationsEducational modelsThree levelConsequence analysis
Analyzing employees based on results of an education business simulation. A network is utilized to present a training simulation to a user for achieving a training goal. Information is integrated into the training simulated utilizing the network that helps motivate achievement of the goal by the user. Progress of the user towards achieving the goal is measured utilizing the network. For further motivating achievement of the goal, feedback is also provided to the user utilizing the network. There are three levels of feedback, where each is progressively more detailed and is selected based on the number of mistakes made by the user, the user's progress towards the goal is subsequently reported to the employer of the user utilizing the network.
Owner:ACCENTURE GLOBAL SERVICES LTD
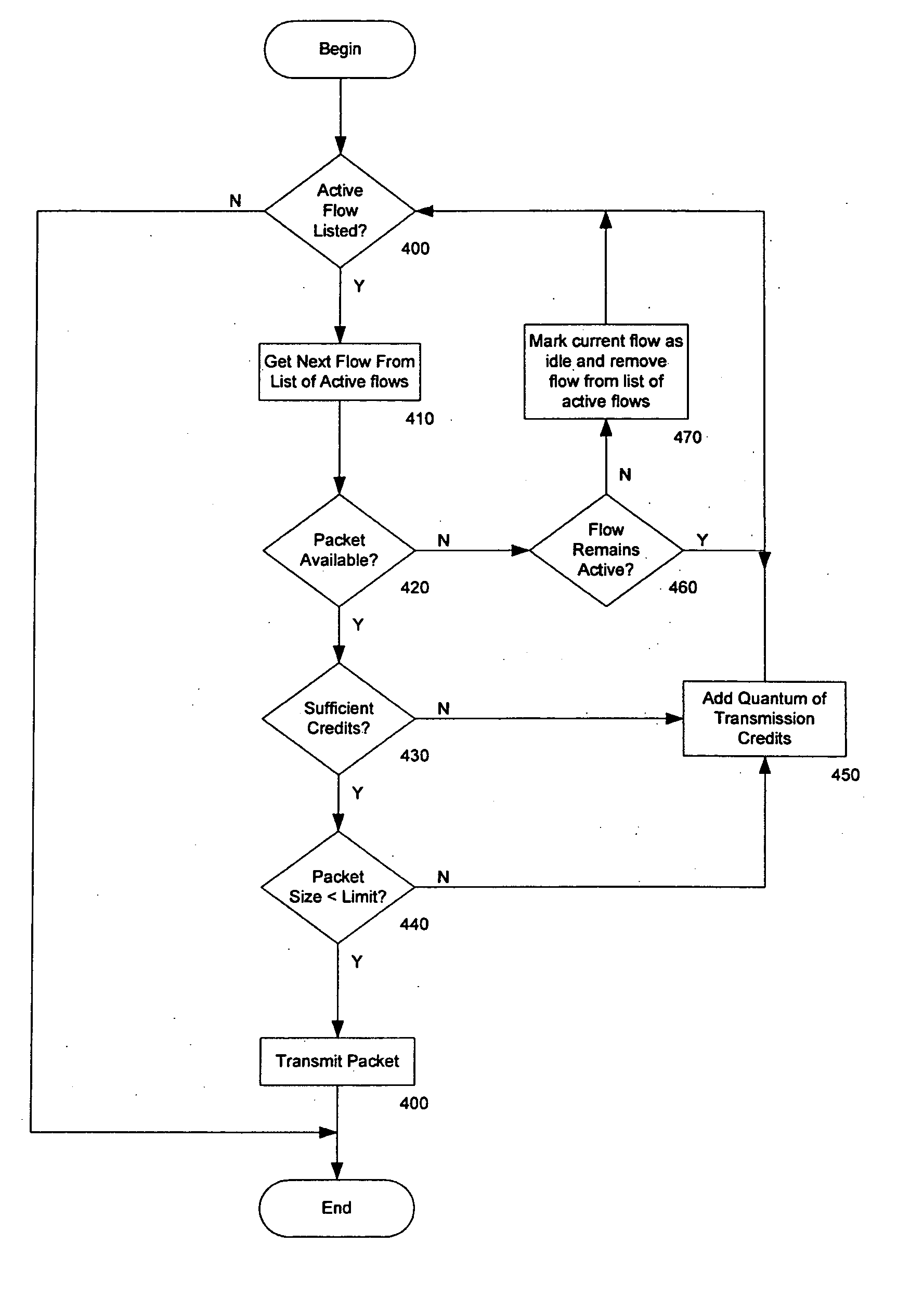
Scaleable channel scheduler system and method
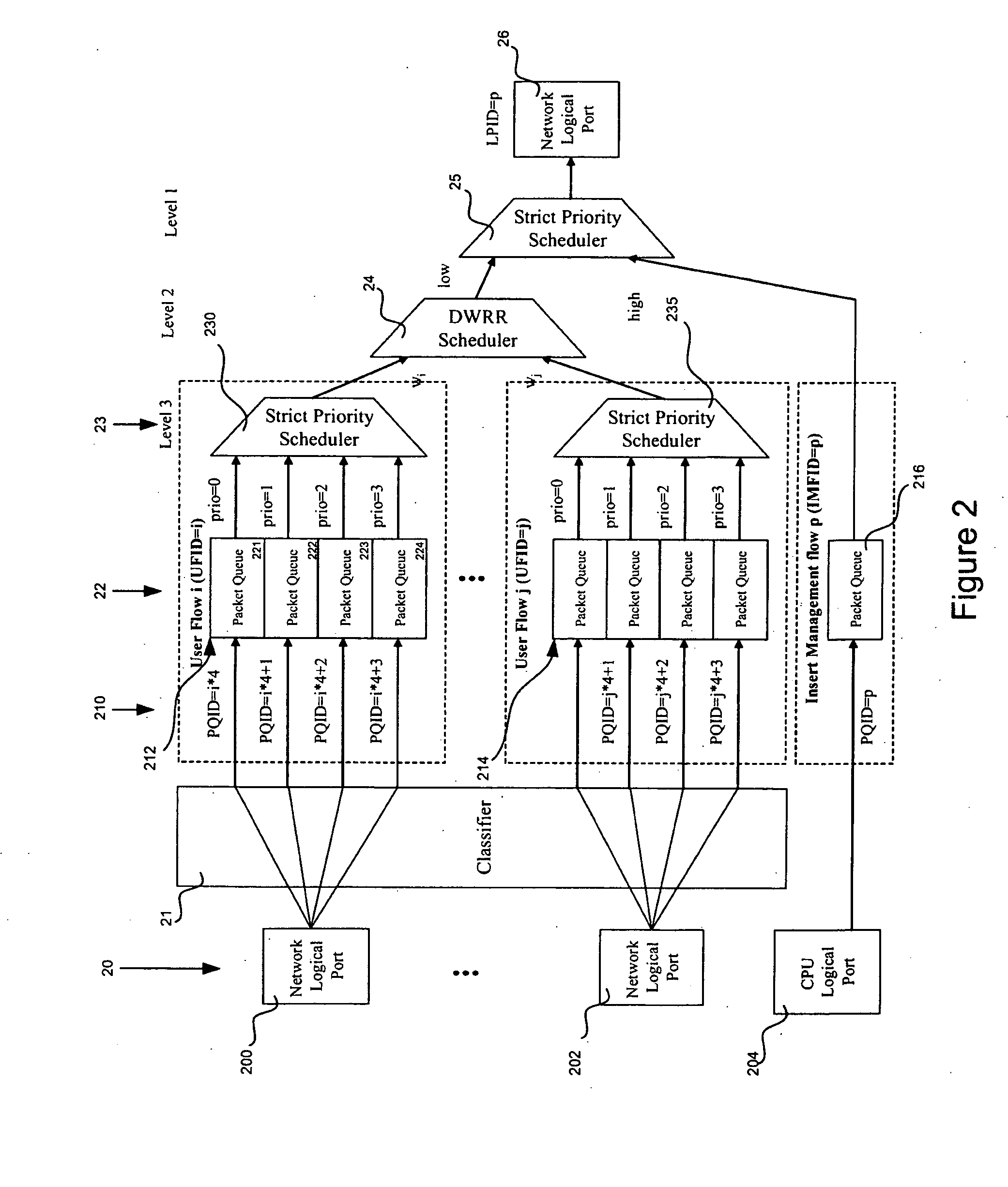
InactiveUS20070070895A1Reduce hardware complexityError preventionTransmission systemsThree levelData stream
A data flow egress scheduler and shaper provides multiple levels of scheduling for data packets exiting communications devices. A classifier separates data from multiple sources by data flow and by priority within a data flow. An output controller requests a data packet for transmission and the scheduler selects a next available highest priority packet from a next in sequence data flow or from a management data queue. The shaper can control the rates of classes of service to be scheduled by the device. The scheduler typically comprises three levels of scheduling. Large numbers of output ports can be implemented in a single device by a virtual scheduler that services each data flow, output port and data source as a shared component, maintain context for groups of schedulers and data flows.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Method and system for evaluating network safety situation
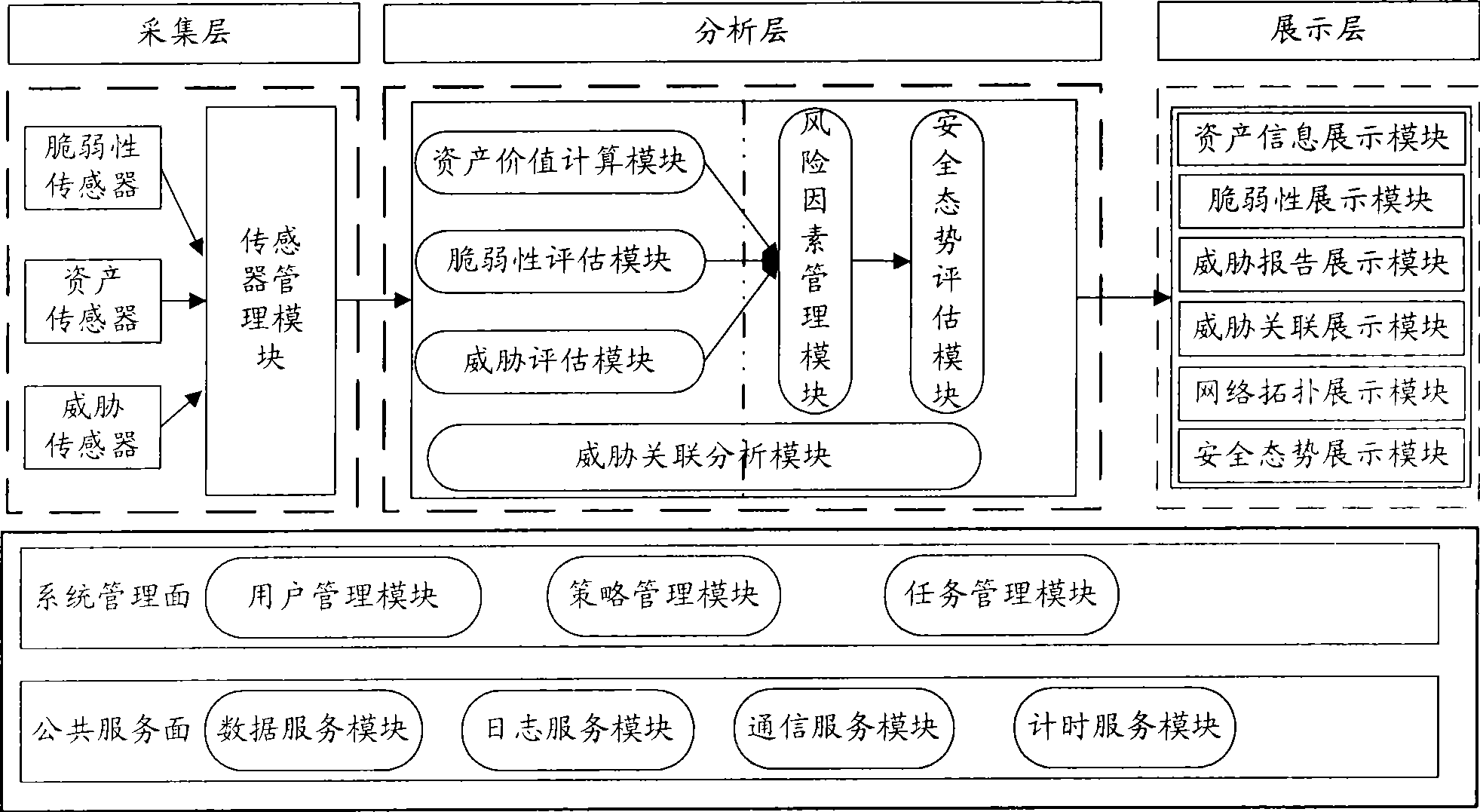
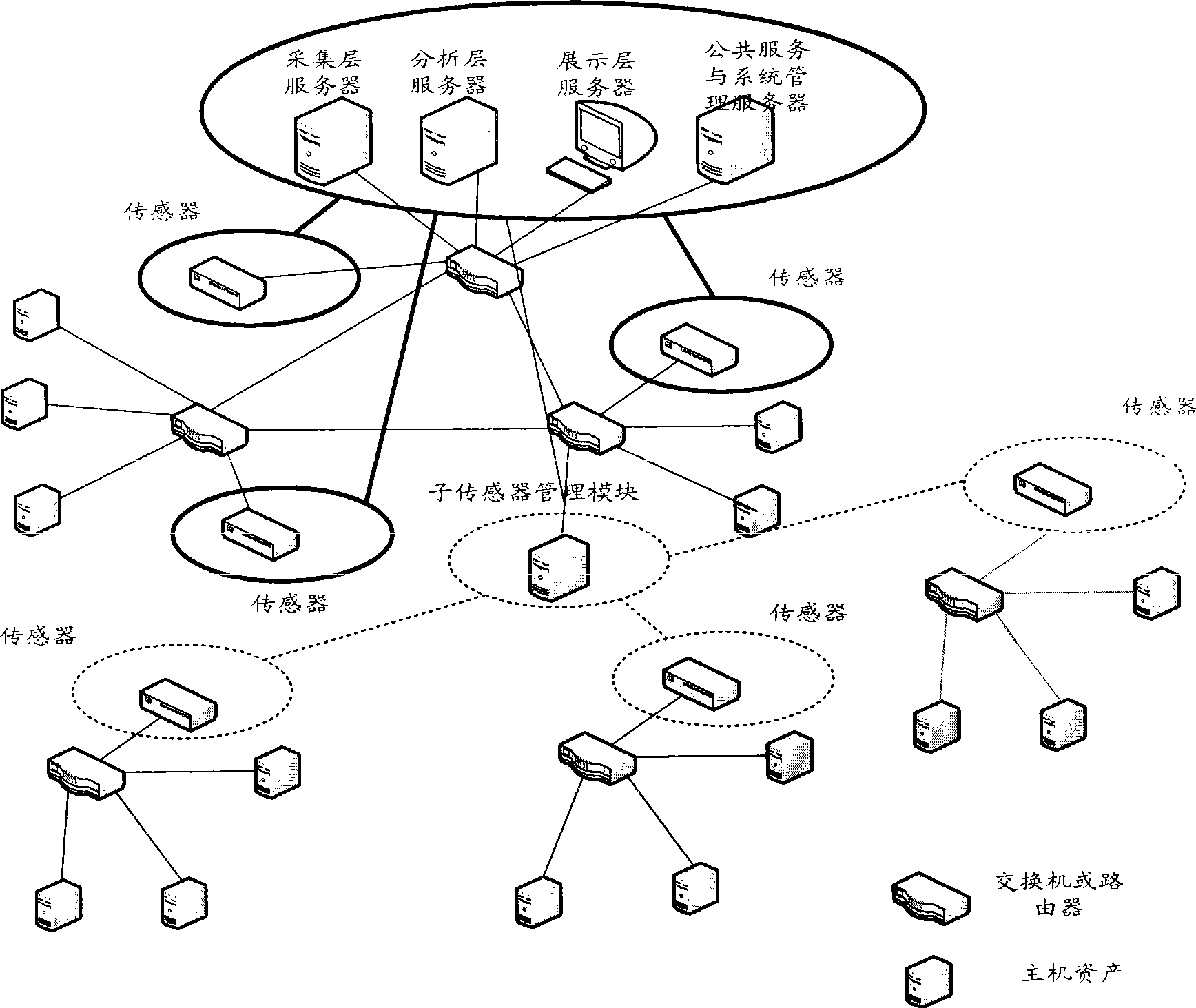
InactiveCN101436967AEasy to operateImprove securityData switching networksThree levelSecurity solution
The invention relates to a method for evaluating the security situation of a network and a system thereof. The system has a two-surface three-level framework and is provided with a public service surface and a service management surface for executing uniform coordinated management on each functional module of the system; according to a service logic processing flow, the system is divided into three levels: an acquisition level, an analysis level and an exhibition level for completing four evaluating operations of assets, frangibility, threat and security situation; the invention is based on the characteristic of service operation in the network, combines the prior risk evaluation method, the prior flow and the prior security detection tool and provides a set of a novel dynamic real-time evaluation method. The system can analyze the assets and service of the network and the risk of the whole network and carries out the evaluation of the security situation. The system can provide the security state of the whole network in macroscopy, can deepen to specific service and assets and know the specific security problem, thereby effectively helping network security personnel to analyze the root of the security problem and assisting to provide a security solution proposal and implement a defense measure.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Error coding in asynchronous transfer mode, internet and satellites
InactiveUS7190681B1Big impactEasily threshold decodableError detection/correctionTime-division multiplexThree levelSystems design
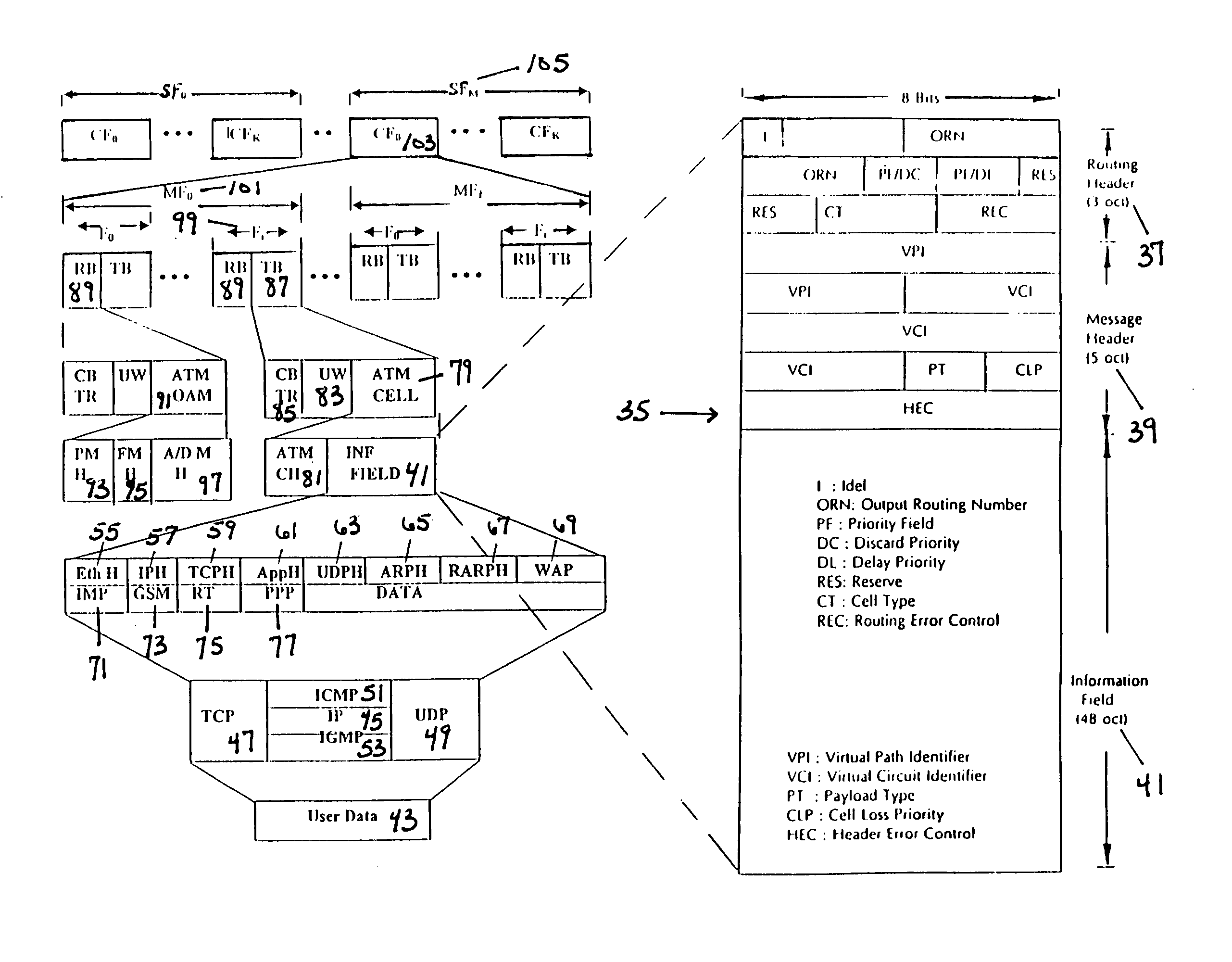
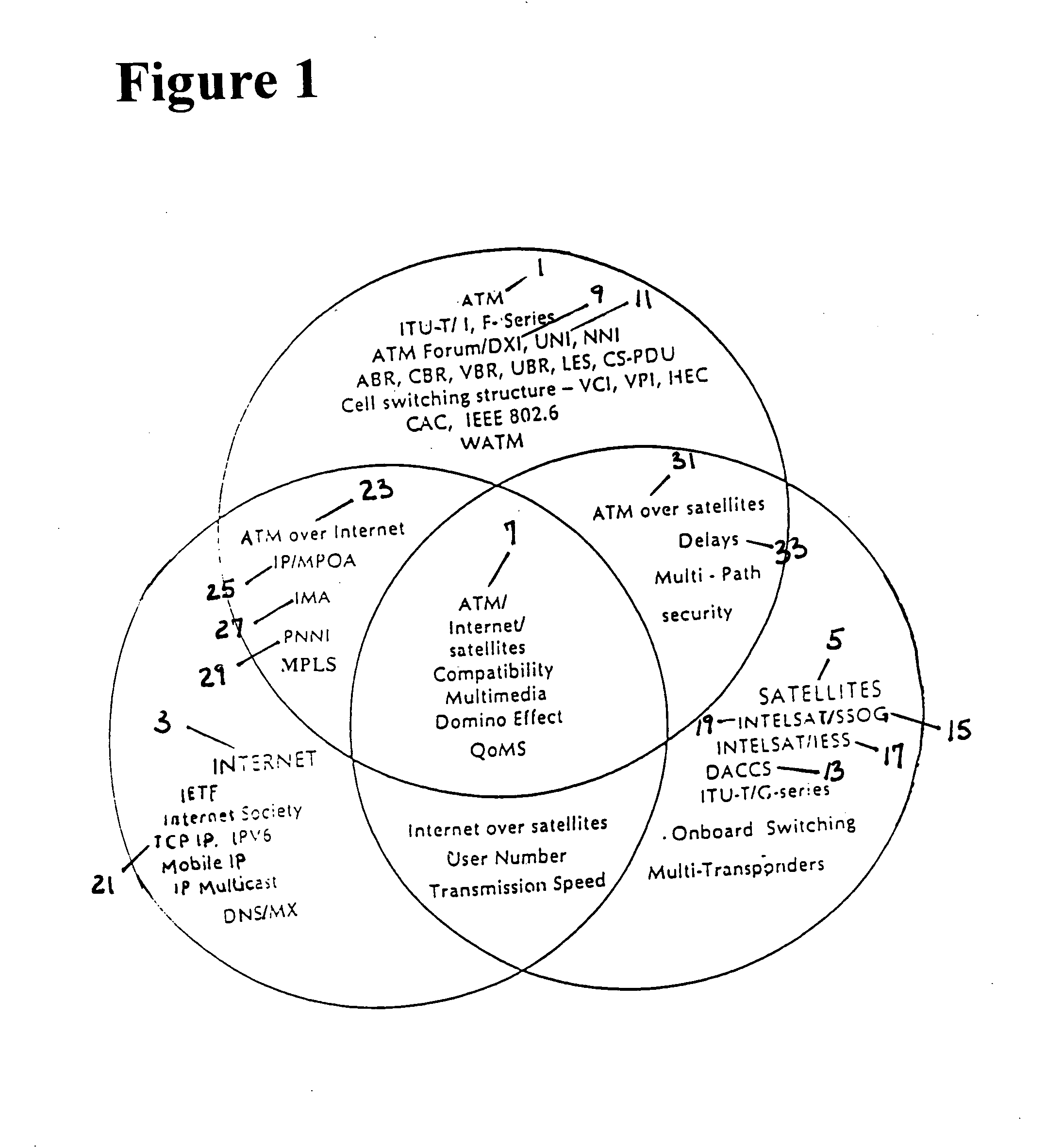
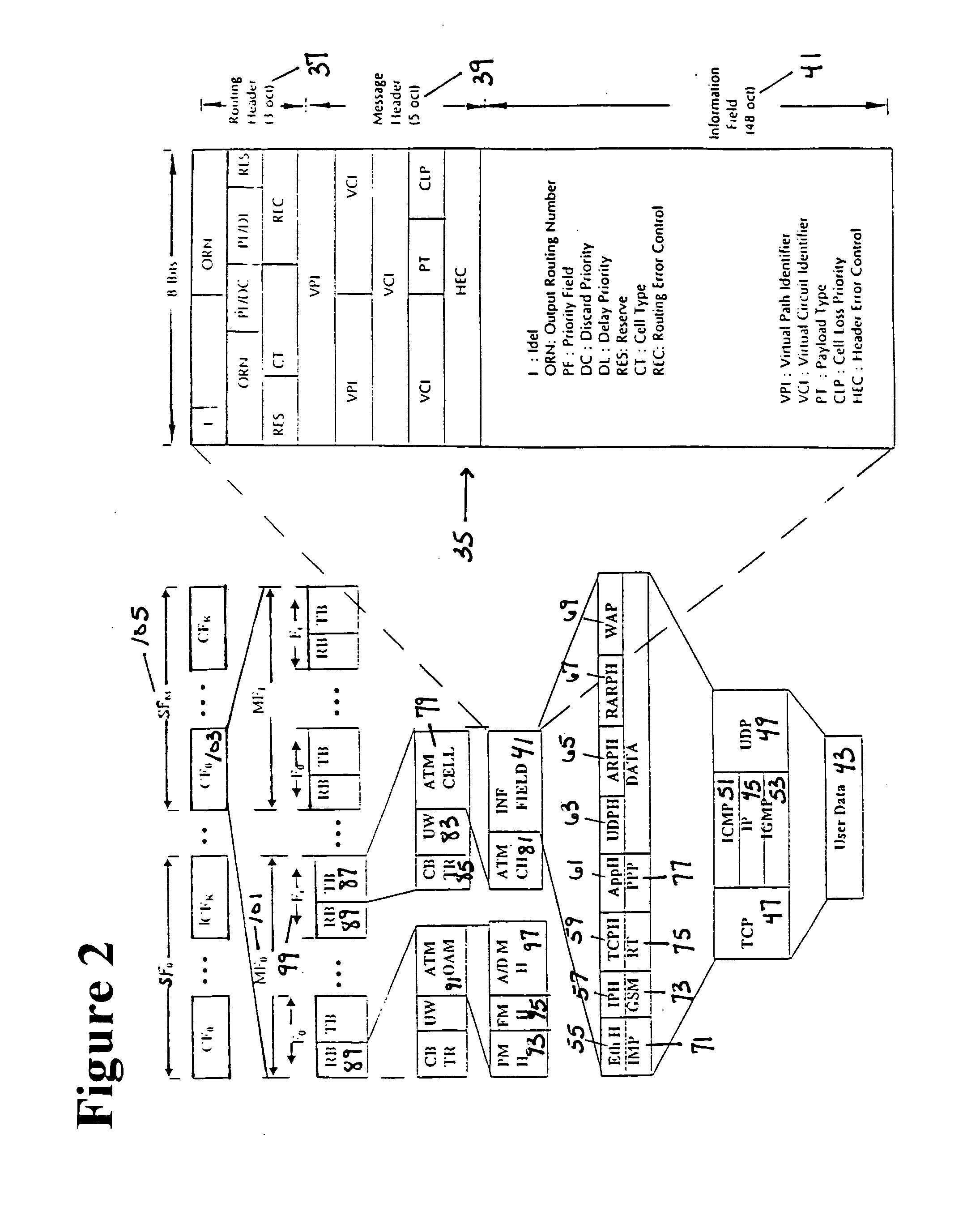
The transmission of ATM, Internet, and satellite communications is unified through international standardized protocol embedment. Global and Local performance optimization are achieved through the combination of combinatorial, dynamic, and probabilistic programming. A simultaneous domino effect of bandwidth conservation, efficiency enhancement, reliability improvement, traffic congestion prevention, delay minimization, and speed multiplication are realized for any digital communication system, particular in Internet. With three levels of error coding in ATM cells, the loss cell recovery and bit integrity are preserved. From its mathematical roots, new combinatorial sets are systematically generated, and applications of the sets are identified. Among the applications, optimal sequences can be produced for multi-user and multi-function communication system designs. Optimality is in terms of maximum possible number of sequences with given sequence length and sequence characteristics. The results are unique and theoretically proven. By serial and parallel concatenation of error codecs, reliability of multimedia transmission can be satisfied to any desirable level. As a part of the unified transmission scheme, the acquisition and synchronization method of cascading sequences exhibits significant improvement in correlation properties and detection probabilities. A method of using block designs is demonstrated to derive, to generate, and to construct low-density parity check block codes and threshold decodable convolutional codes. An efficiency evaluation method is formulated for the combination operation of ATM, Internet, and satellites.
Owner:WU WILLIAM W
Method and apparatus to manage network client logon scripts using a graphical management and administration tool
A GUI (Graphical User Interface) Manager is used by a network administrator to fill-in predefined templates. The administrator does not need to compile, debug or write a single line of scripting code. The GUI manager has a “select the box” and “point and click” and “fill-in the blank” approach for selecting computer settings. The predefined configuration and / or template(s) are used by a logon script program on a client system to manage the configuration of resources on at least one client. There are three levels of resources that can be managed. The first type of resource is an operating system. The second type of resource is an application resource. And the third type of resource is to redirect a resource on the client to a resource on a network such as a drive letter mapping. Resources include configurations from the group of configuration settings consisting of drive mappings, shell folders, printer deployment, proxy server access, application paths, service packs, anti-virus updates, policies and automatic mail profile creation. In another embodiment, validation logic is used on the clients' system during the execution of an application program that takes the template and applies the defined configuration settings in the template to the clients' system so as to automatically configure at least one configuration setting for a user if the combination of one or more predefined conditions for a selected group, a selected operating system and a selected connection method are met. In still another embodiment, an interpretive engine is used on the client's system to permit the administration of client resources with a template while also allowing network administrators to build their own custom logon scripts.
Owner:QUEST SOFTWARE INC
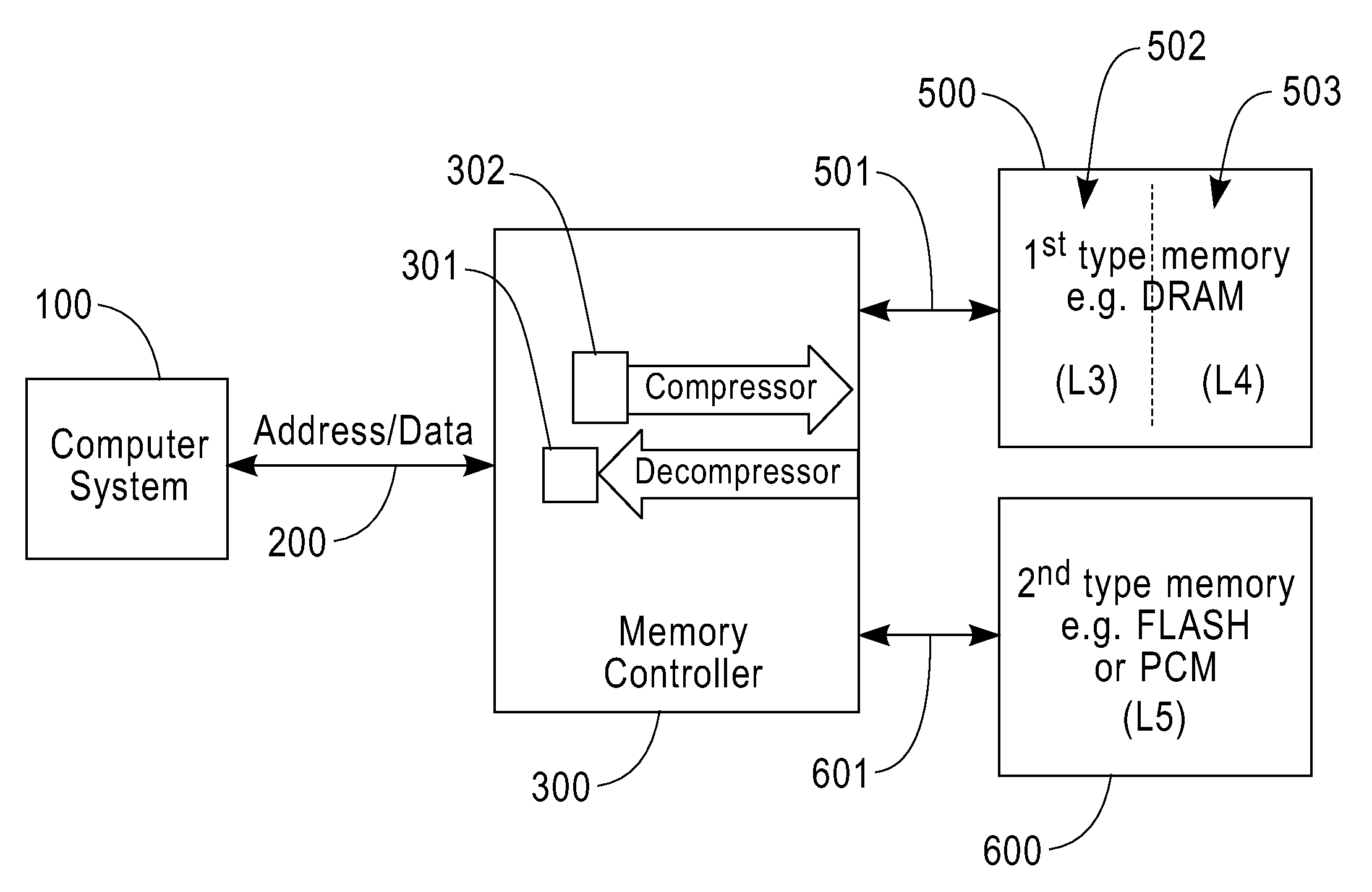
Bus attached compressed random access memory
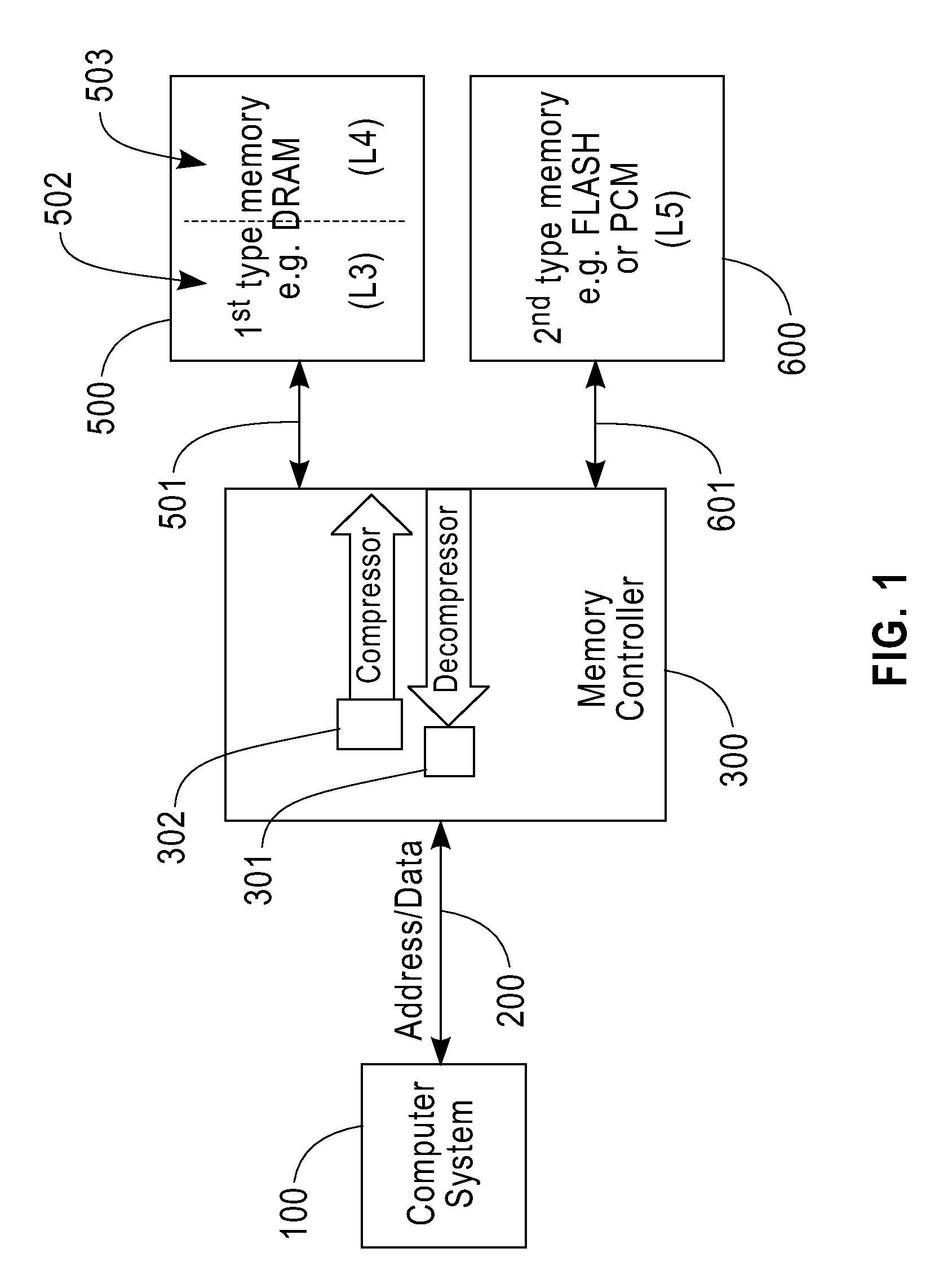
InactiveUS20090254705A1Eliminate the problemLow costMemory architecture accessing/allocationMemory adressing/allocation/relocationThree levelMemory hierarchy
A computer memory system having a three-level memory hierarchy structure is disclosed. The system includes a memory controller, a volatile memory, and a non-volatile memory. The volatile memory is divided into an uncompressed data region and a compressed data region.
Owner:IBM CORP
Method and system for knowledge-based filling and verification of complex forms
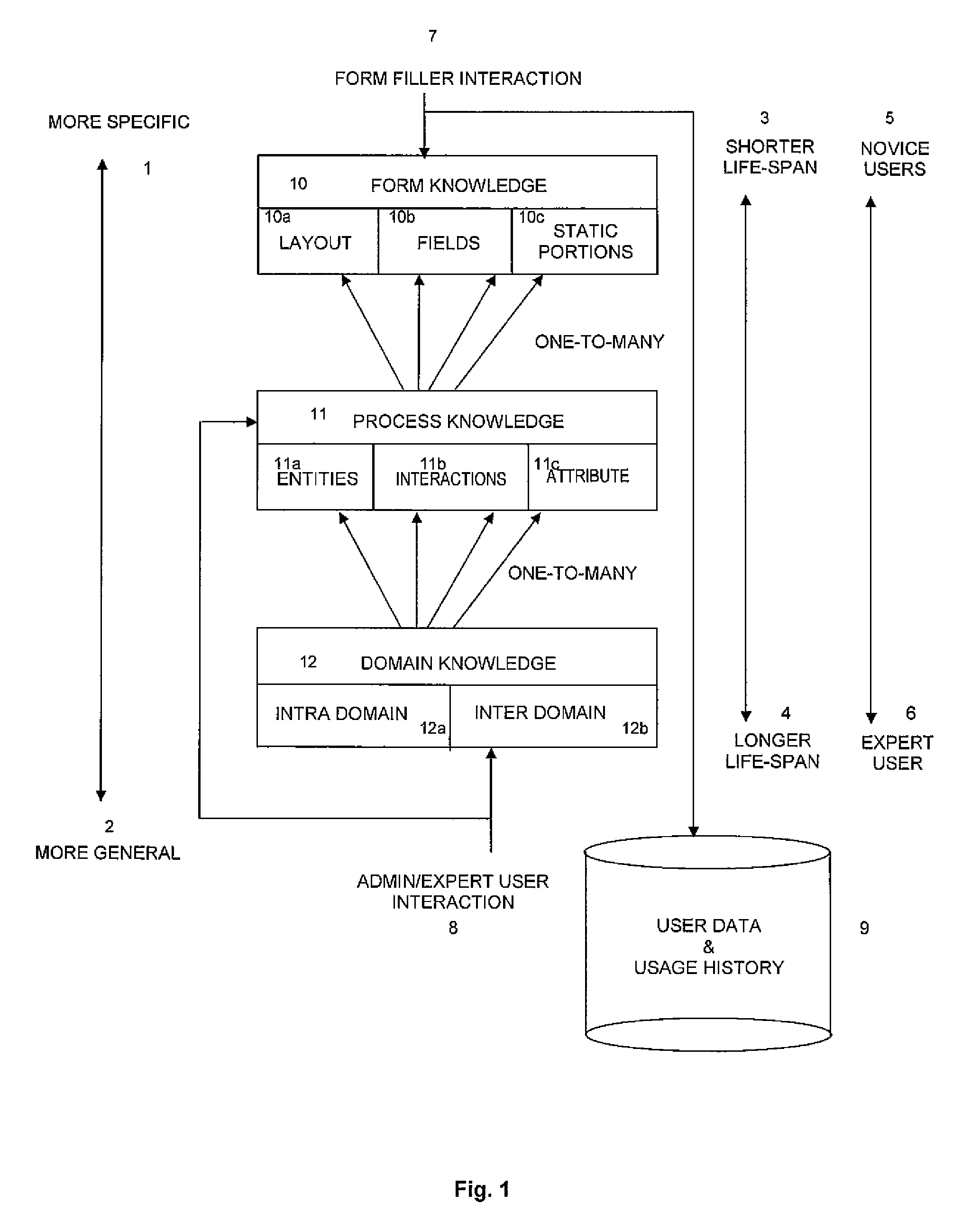
InactiveUS20090204881A1Natural language data processingSpecial data processing applicationsThree levelData mining
Filling forms is an activity, which finds its use in several day-to-day functions of any organization. The system of the present invention proposes the abstraction of the knowledge required to fill forms into a hierarchy containing three levels including form, process and domain knowledge. Such an abstraction caters to a variety of users with varying expertise, from the novice form-filling user to the expert. By encapsulating knowledge in this manner, the system of the present invention removes the complexity involved in the process of form-filling. Further, methods are proposed within the present invention to automatically fill and verify forms, used for a variety of end-uses.
Owner:MS SCMOOTH INDIA PRIVATE
Native lookup instruction for file-access processor searching a three-level lookup cache for variable-length keys
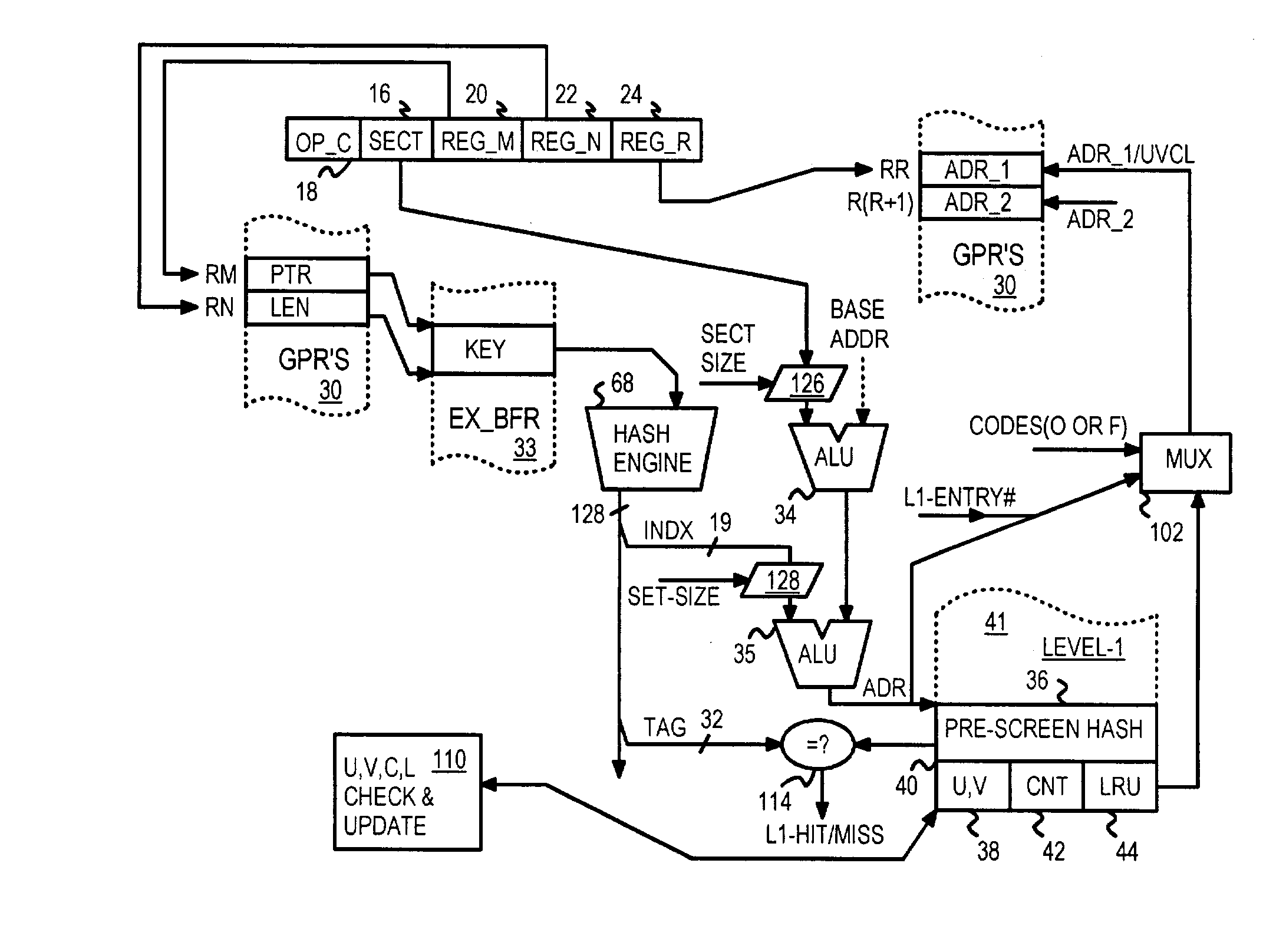
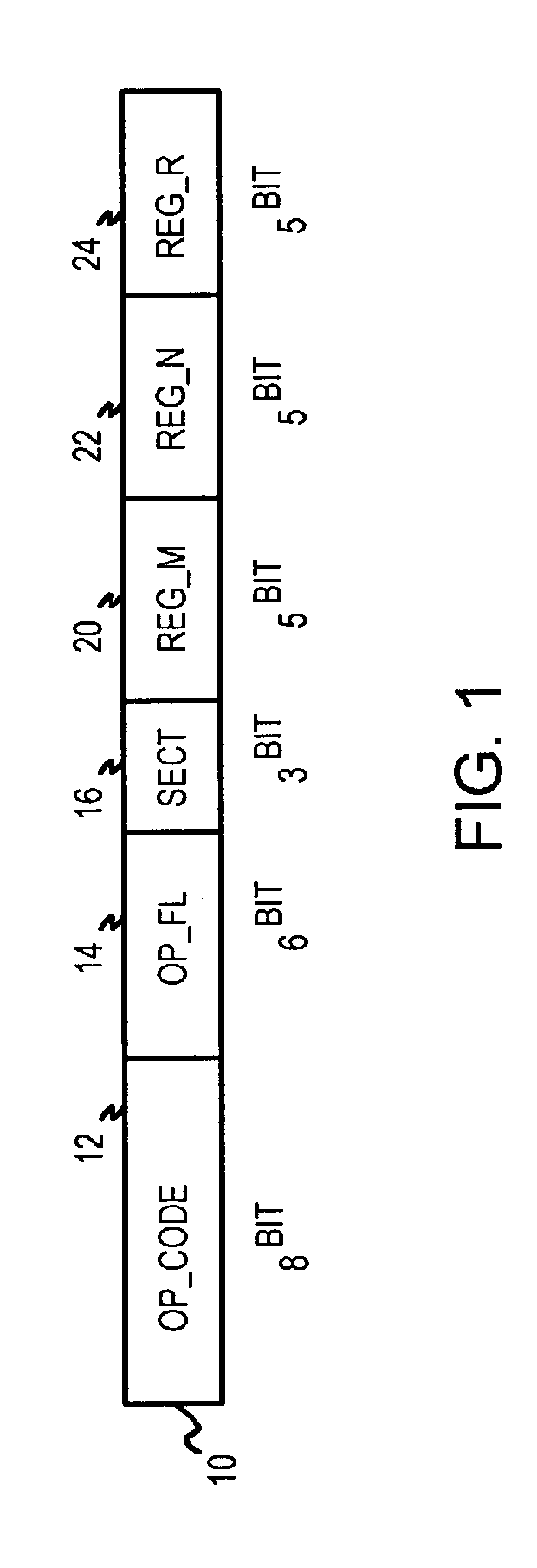
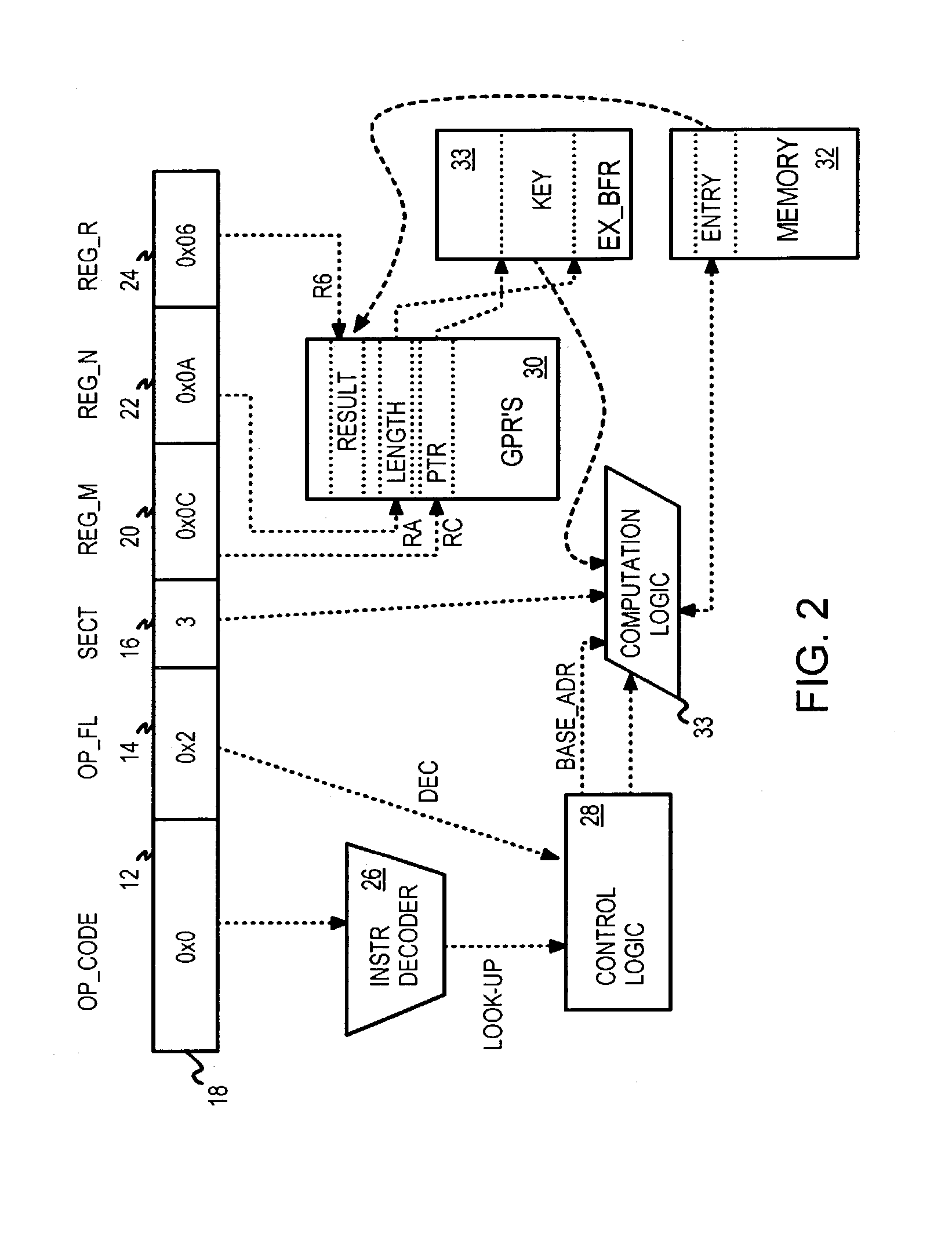
InactiveUS7093099B2Memory adressing/allocation/relocationDigital computer detailsThree levelGeneral purpose
A processor natively executes lookup instructions. The lookup instruction is decoded to determine which general-purpose register (GPR) contains a pointer to a lookup key in a buffer. A variable-length key is read from the buffer and hashed to generate an index into a first-level cache and a hashed tag. An address of a bucket of entries for the index is generated and tags from these entries are read and compared to the hashed tag. When an entry matches the hashed tag, a second-level entry is read. A stored key from the second-level entry is compared to the input key to determine a match. The addresses of the matching second-level and first-level entries are written to GPR's specified by operands decoded from the lookup instruction. When the key or entry data is long, the second-level entry also contains a pointer to a key extension or data extension in a third-level cache.
Owner:RPX CORP
Method and control circuitry for a three-phase three-level boost-type rectifier
InactiveUS20030128563A1Easy to analyzePoor waveform qualityAc-dc conversion without reversalEfficient power electronics conversionThree levelDynamic balance
A synchronized control method for a three-phase three-level boost-type rectifier with reduced input current ripple and balanced output voltages is disclosed. The proposed control allows simplifying the control circuit as much as possible without compromising the rectifier performance. In fact, besides simplicity, the control method featured synchronized command signals to de switching devices, minimized input current ripple, full controllability of the output voltage, dynamic balance of the output center point, constant switching frequency, simplified design of EMC filters, good transient and steady state performance, and low cost. The invention described first the most important configurations that the three-phase three-level boost-type rectifier may assume and studied the converter's operation. The concept involved for output voltage, input current, neutral point balance and control system design was presented.
Owner:VERTIV CORP
Nonvolatile semiconductor memory having three-level memory cells and program and read mapping circuits therefor
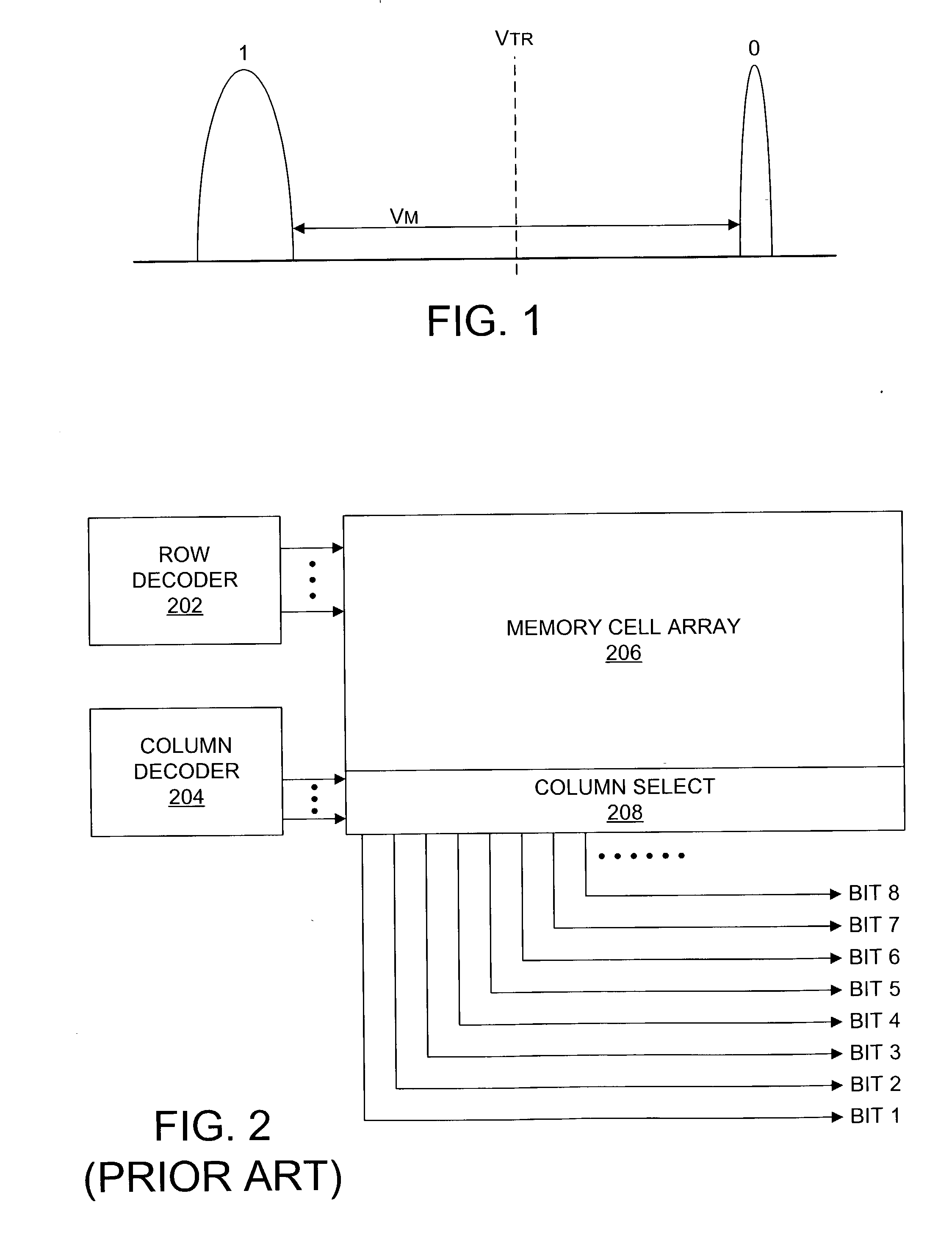
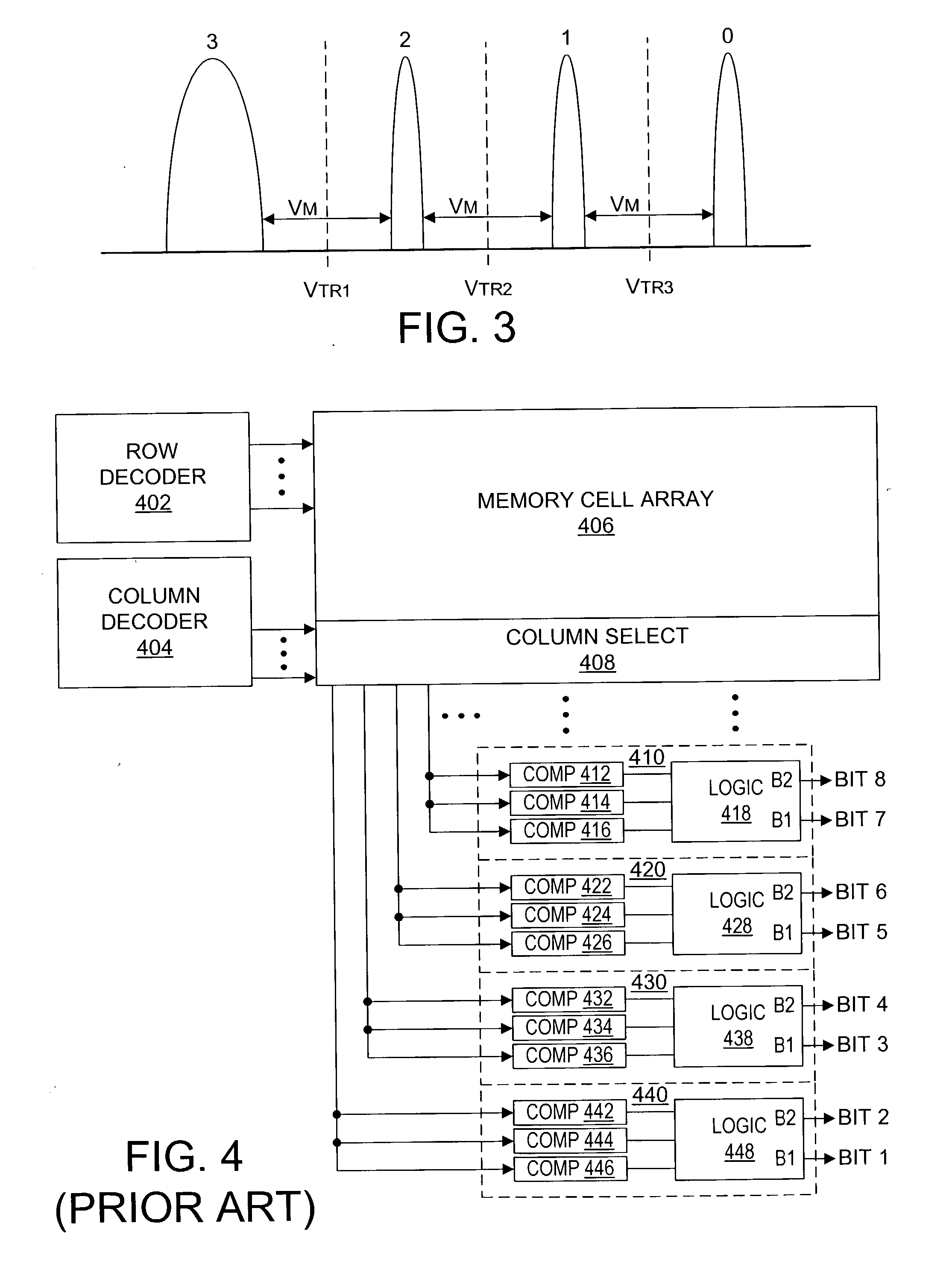
A memory uses multiple threshold levels in a memory cell that are not a power of two, and further uses a cell mapping technique wherein the read mapping is only a partial function The domain of read states for a single three-level memory cell, for example, has three states, but only two of them can be uniquely mapped to a bit. The domain of read states for two three-level memory cell, for example, has nine states, but only eight of them can be uniquely mapped to three bits. Although the read mapping is only partial, the voltage margin for the three-level memory cells is larger that the voltage margin available in the commonly used four-level memory cells. This increased voltage margin facilitates memory cell threshold voltage sensing, thereby increasing the reliability of the memory. Memory reliability may be further improved by increasing the voltage margin between the memory cell 0 state and the 1 state relative to the voltage margin between the 1 state and the 2 state, which more effectively accommodates charge loss from the 0 state through electron leakage. Asymmetrical read and program mapping may also be used to improve read reliability in the presence of ground noise or VCC noise.
Owner:WINBOND ELECTRONICS CORP
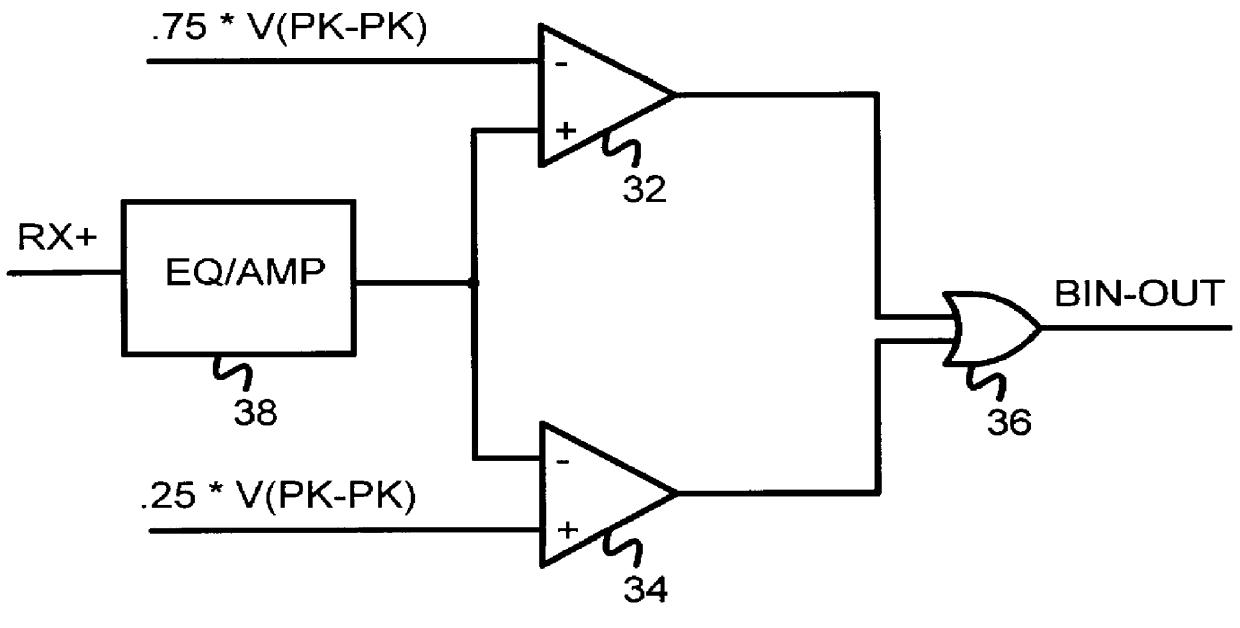
Self-biasing CMOS PECL receiver with wide common-mode range and multi-level-transmit to binary decoder
InactiveUS6049229AReduced Power RequirementsSimplify interconnect routingLogic circuits characterised by logic functionLogic circuits coupling/interface using field-effect transistorsThree levelEmitter-coupled logic
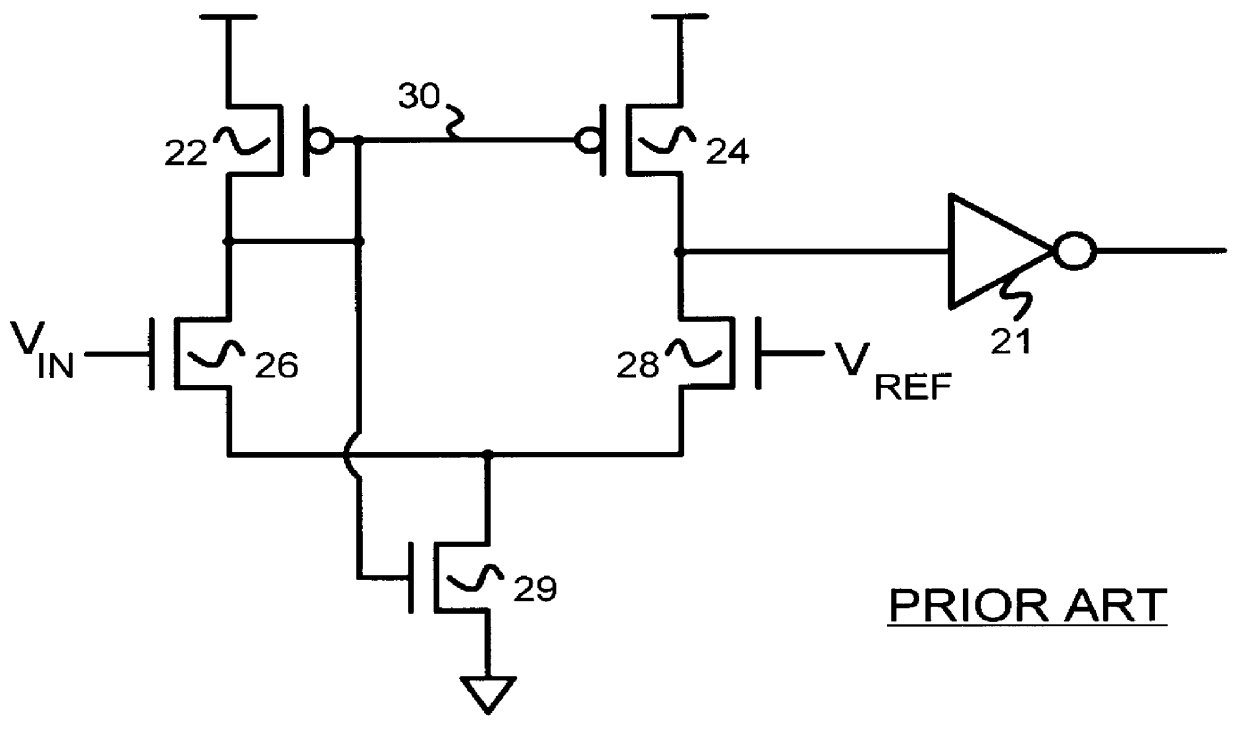
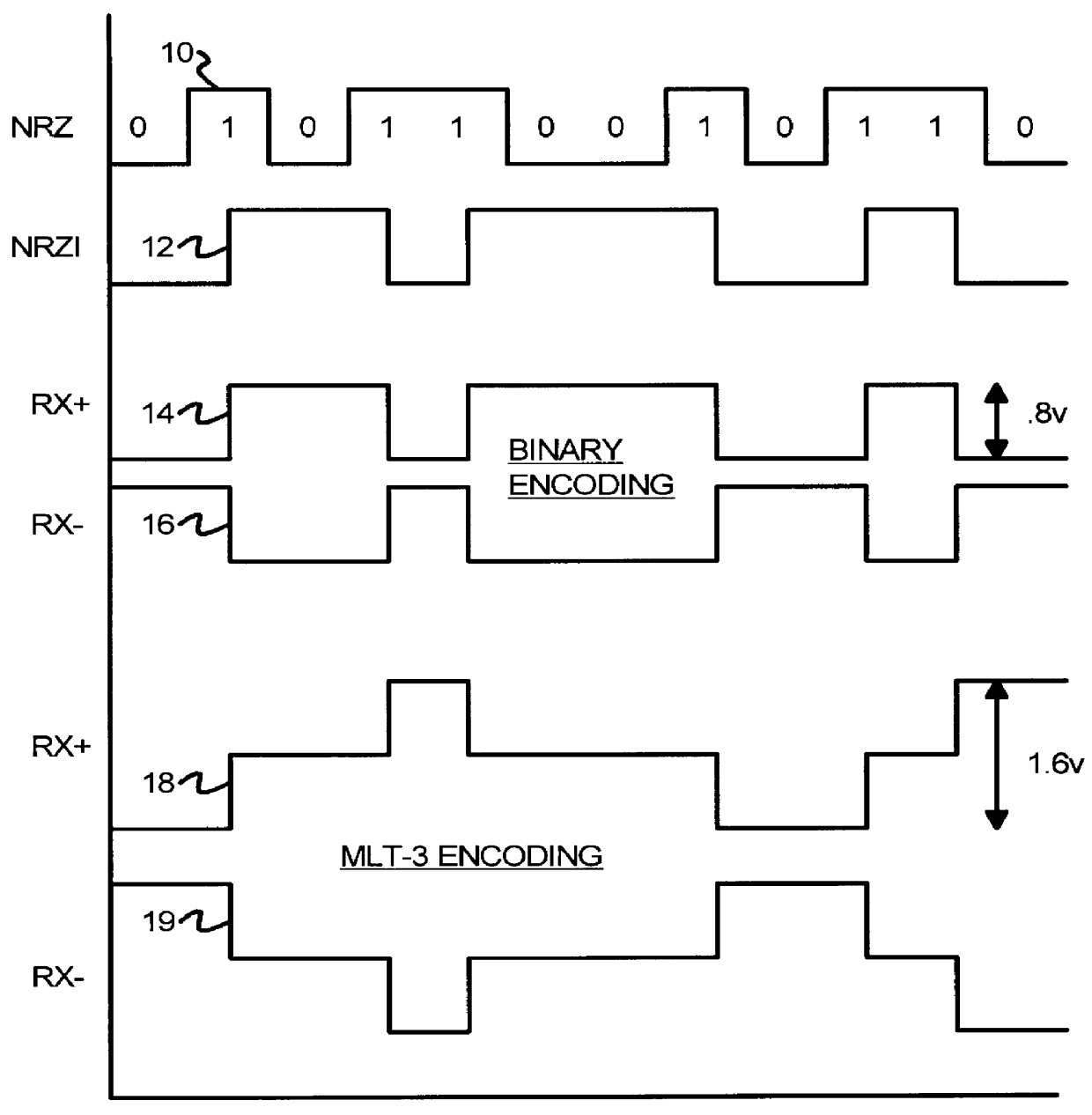
A pseudo-emitter-coupled-logic (PECL) receiver has a wide common-mode range. Two current-mirror CMOS differential amplifiers are used. One amplifier has n-channel differential transistors and a p-channel current mirror, while the second amplifier has p-channel differential transistors and an n-channel current mirror. When the input voltages approach power or ground, one type of differential transistor continues to operate even when the other type shuts off. The outputs of the two amplifiers are connected together and each amplifier receives the same differential input signals. The tail-current transistor is self-biased using the current-mirror's gate-bias. This self biasing of each amplifier eliminates the need for an additional voltage reference and allows each amplifier to adjust its biasing over a wide input-voltage range. Thus the common-mode input range is extended using self biasing and complementary amplifiers. The complementary self-biased comparators can be used for receiving binary or multi-level-transition (MLT) inputs by selecting different voltage references for threshold comparison. Using the same reference on both differential inputs eliminates a second reference for multi-level inputs having three levels. Thus binary and MLT inputs can be detected and decoded by the same decoder.
Owner:DIODES INC
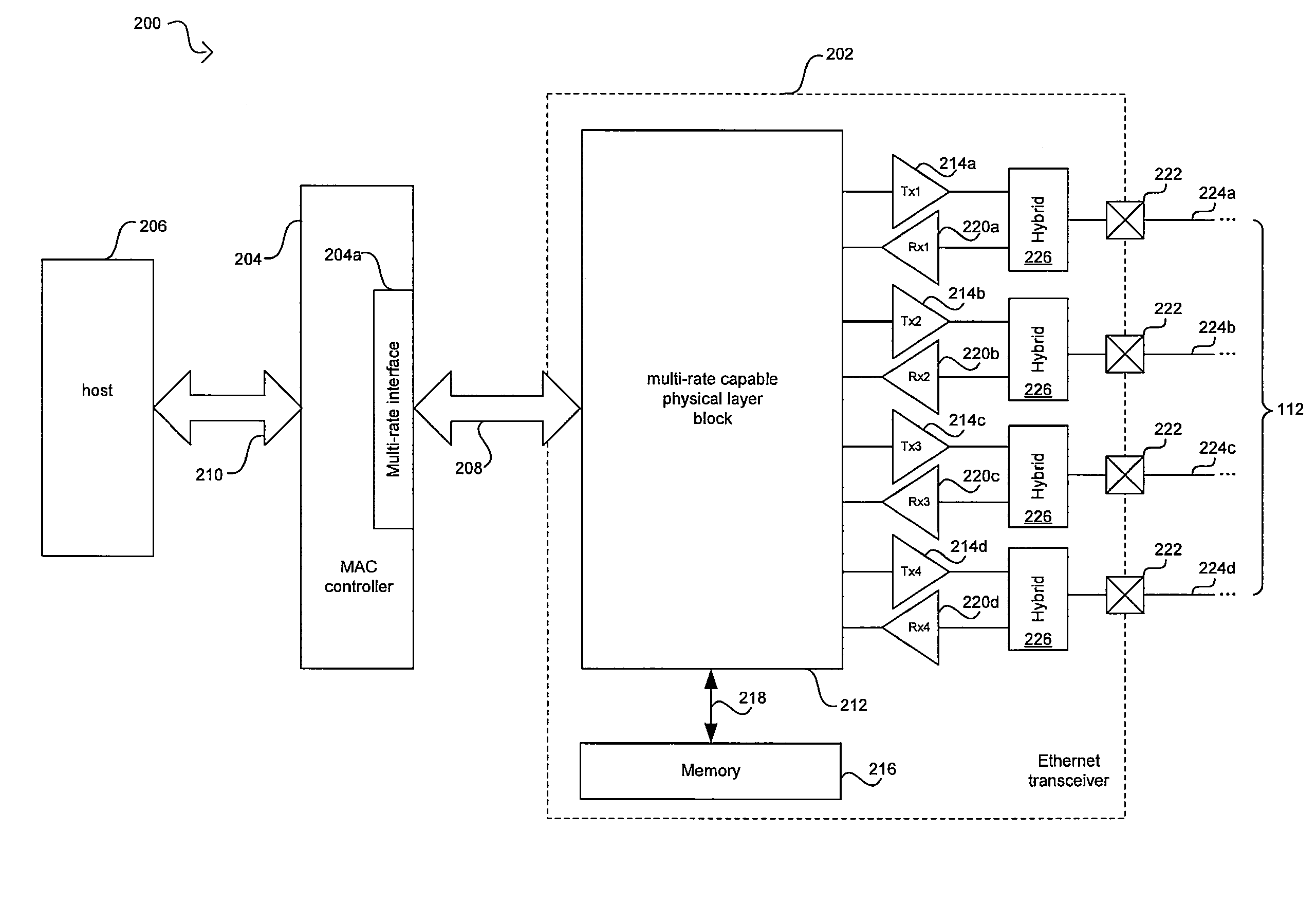
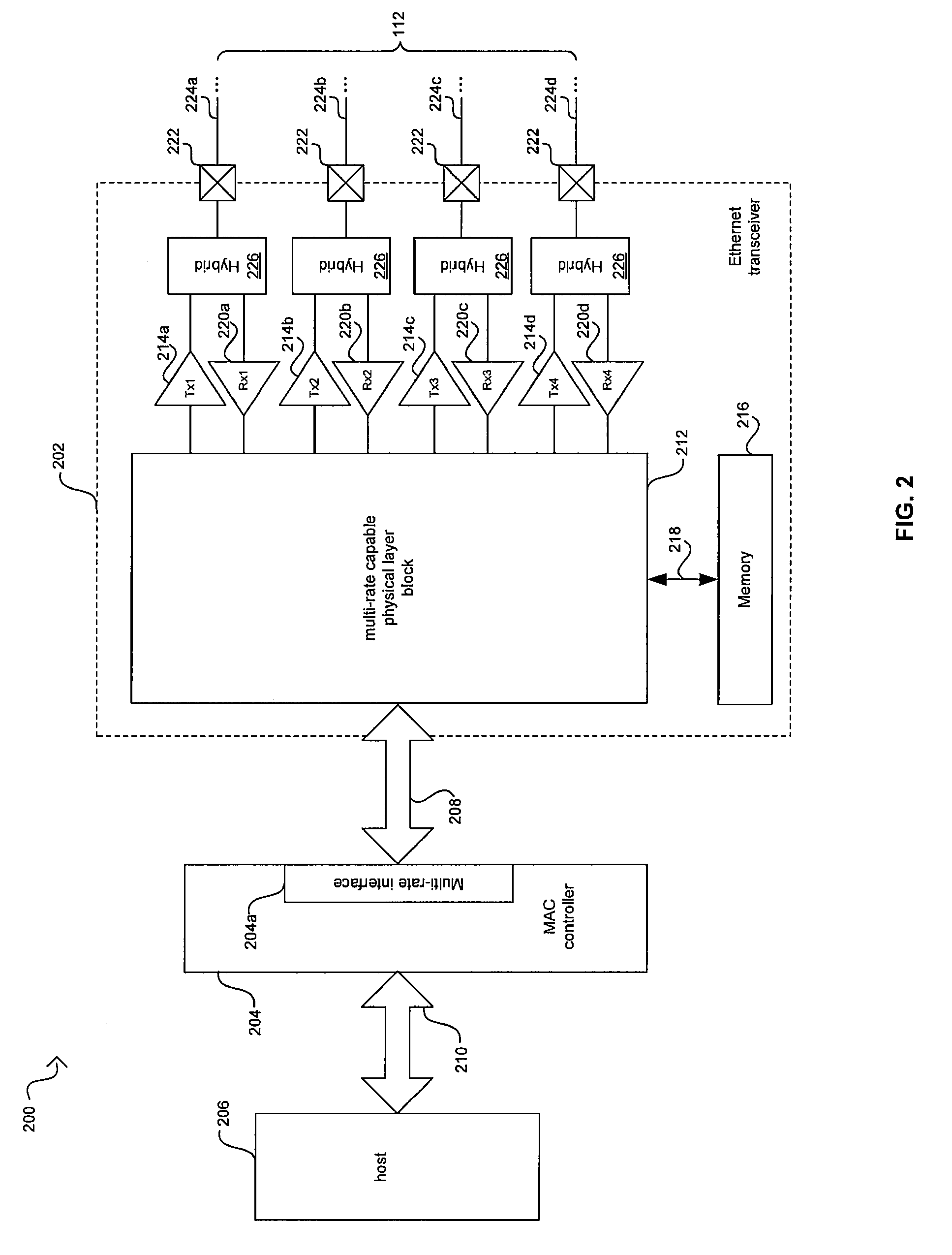
Method and system for energy efficient signaling for 100mbps Ethernet using a subset technique
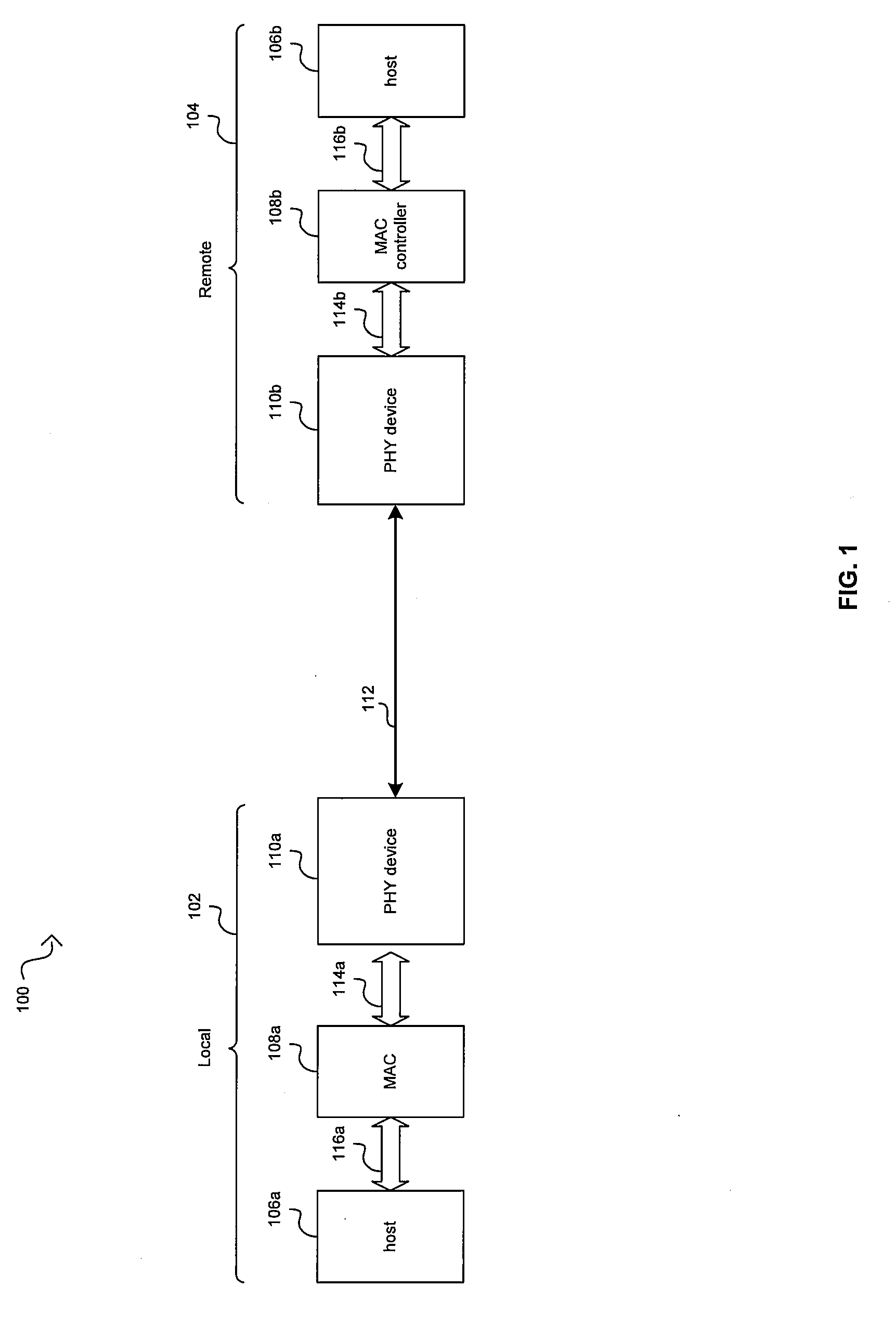
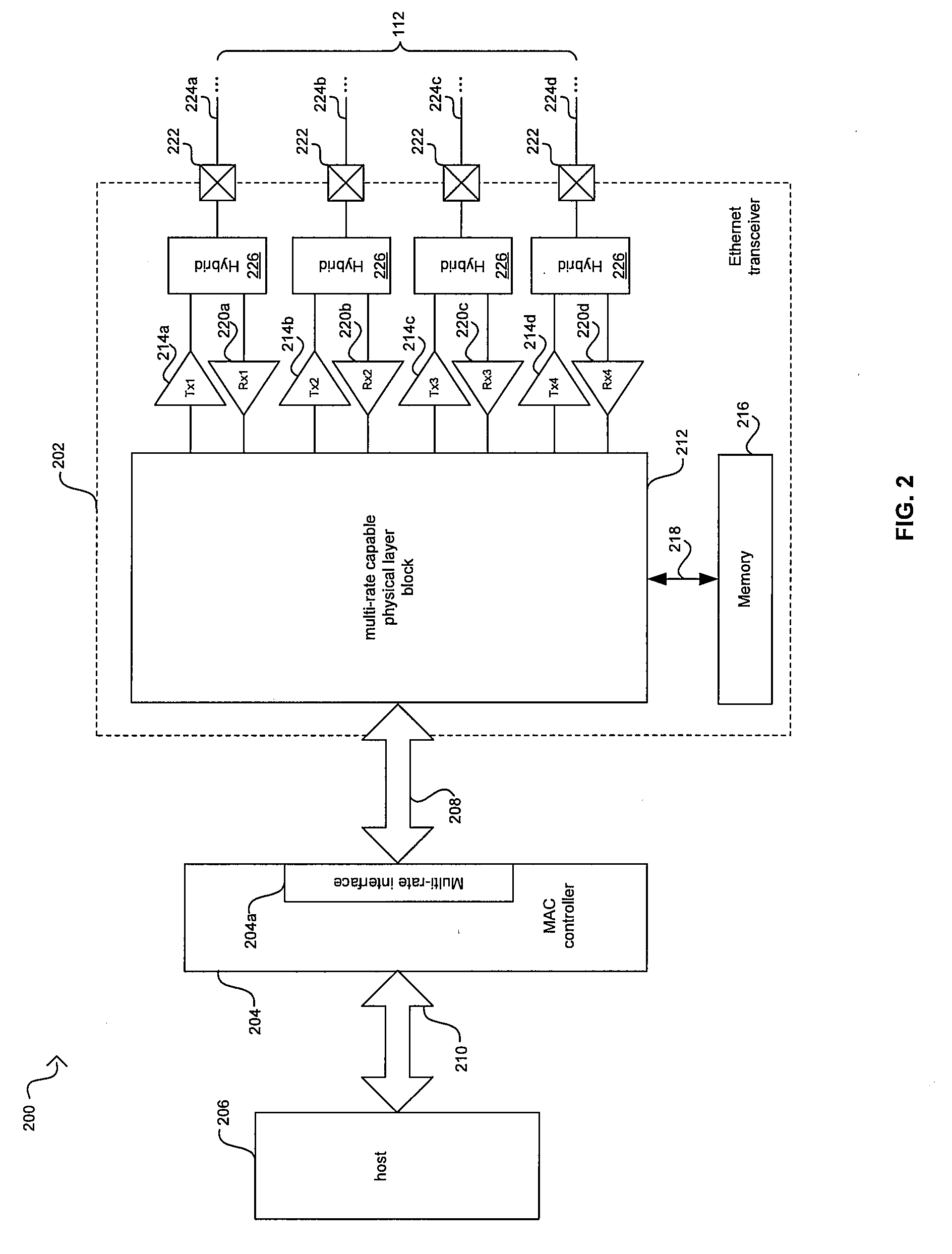
Aspects of a method and system for energy efficient signaling for 100 mbps Ethernet using a subset are provided. In this regard, a network device enabled to communicate over a network link at 1 Gbps or faster may be configured to communicate over the network link at, or approximately at, 100 Mbps by reducing a number of active channels over which the network device communicates and / or reducing a size of a signal constellation utilized by the network device to encode data. The device may communicate according to 1GBASE-T or 10GBASE-T standards. The number of active channels may be reduced to a single bidirectional channel or two unidirectional channels. The signal constellation may be reduced to two or three levels. One or more components of the network device may be unnecessary for recovering data when communicating at 100 Mbps and may thus be powered down, or placed into a lower power mode.
Owner:AVAGO TECH INT SALES PTE LTD
High efficiency driver for miniature loudspeakers
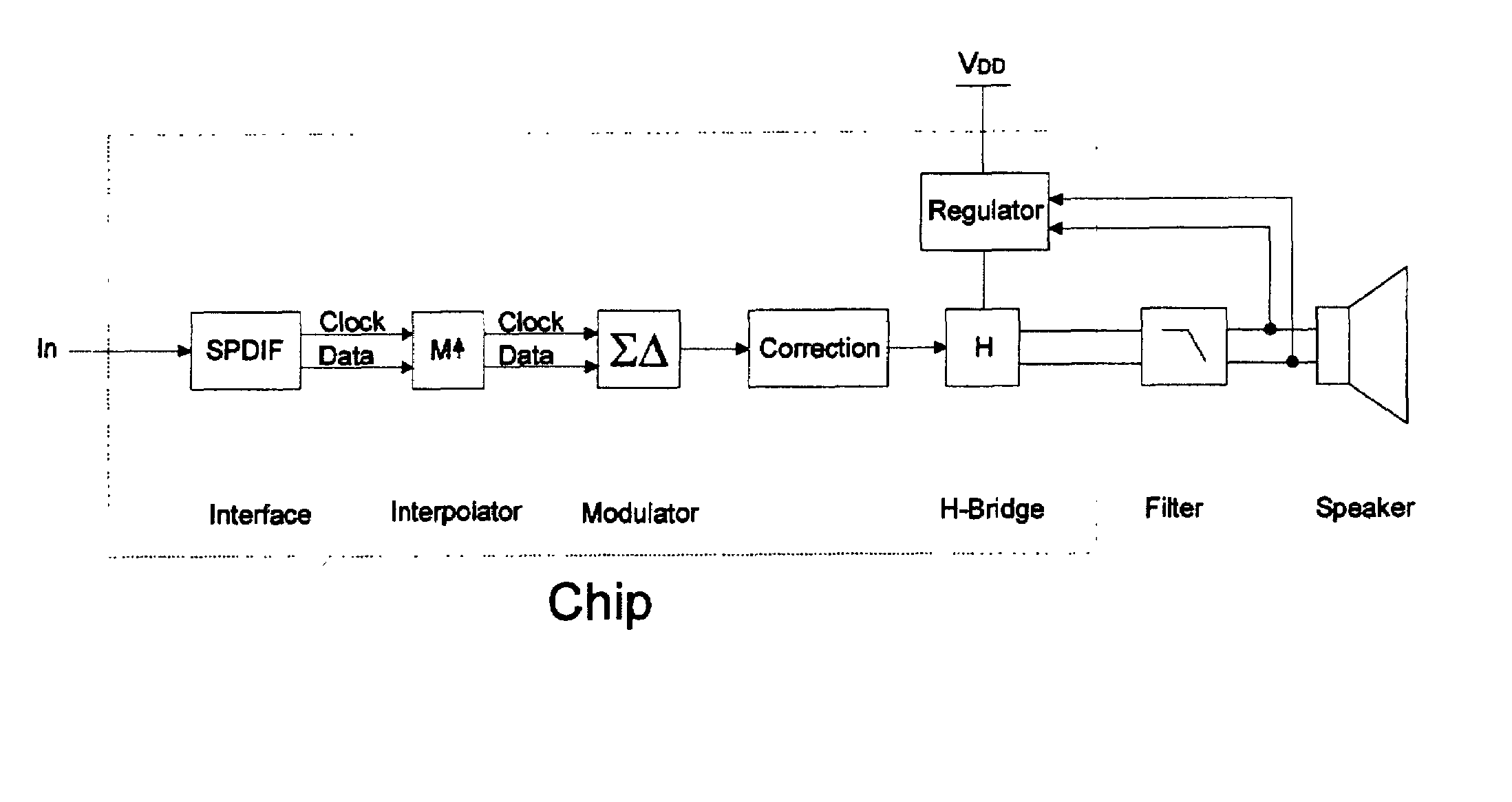
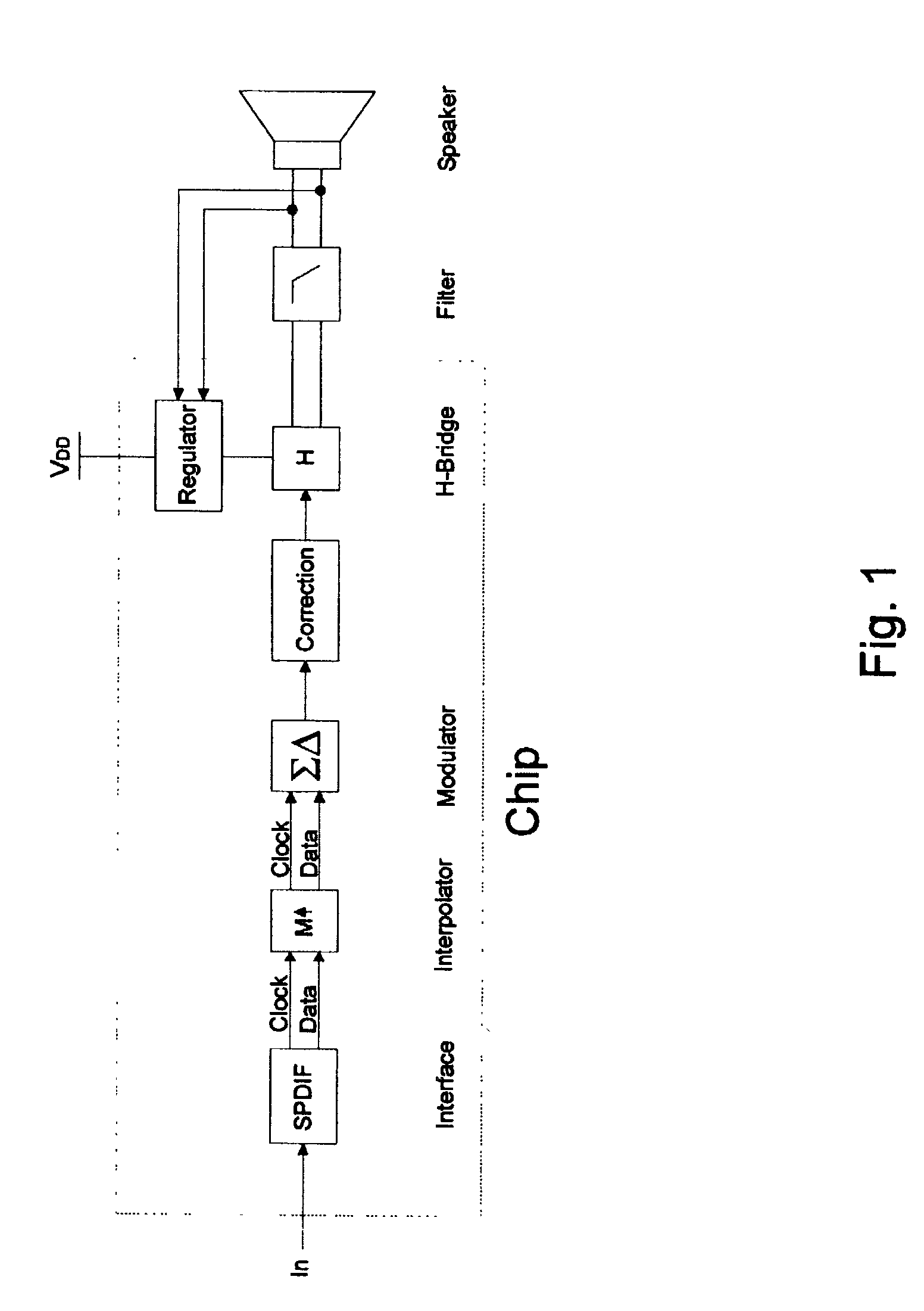
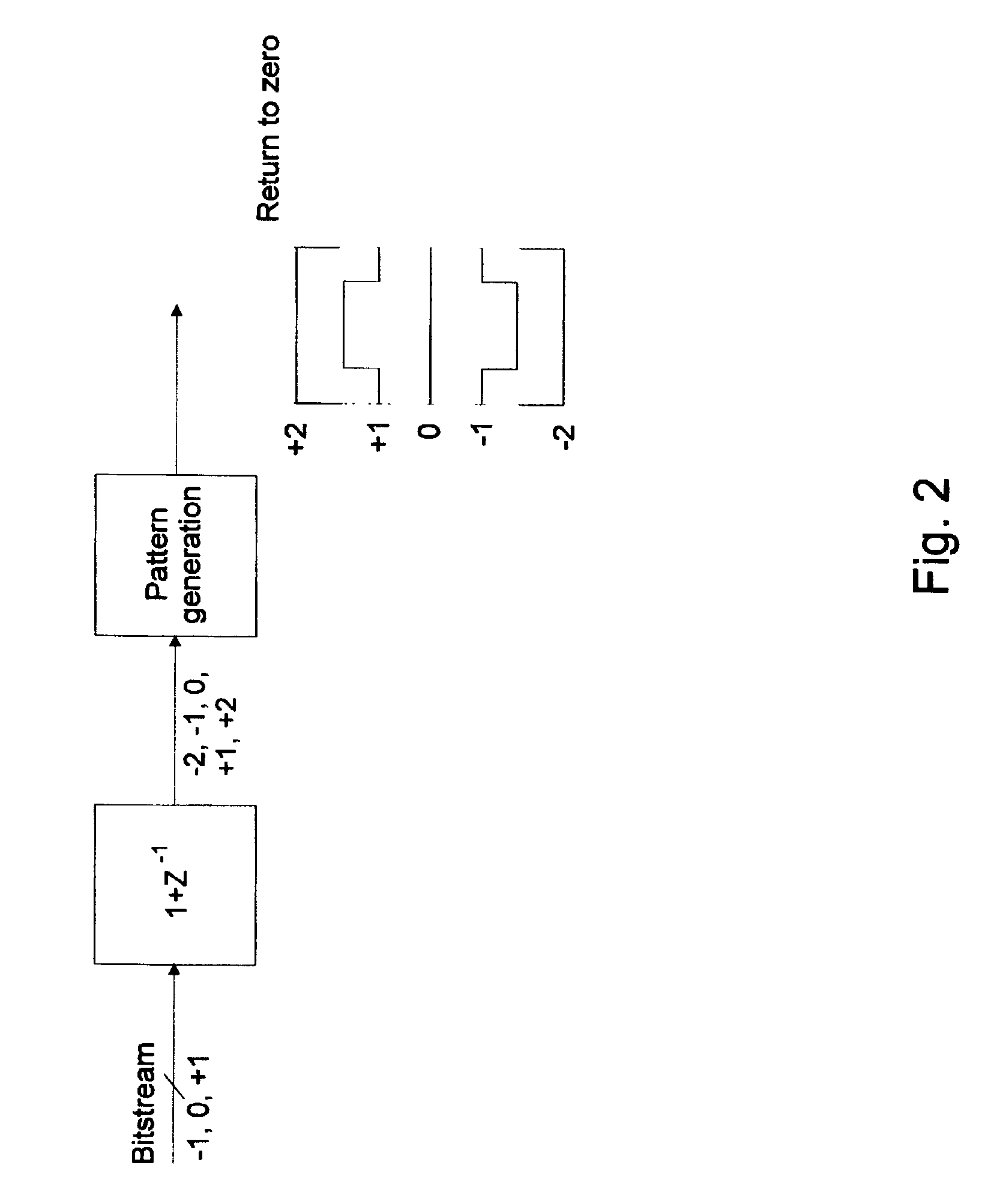
ActiveUS7336794B2Digitally weighted transducing elementsTransducer casings/cabinets/supportsThree levelReturn-to-zero
In a first aspect the present invention provides a compact high efficiency driver suitable for driving a loudspeaker, such as a miniature loudspeaker for mobile phones or hearing aids. The driver comprising an interface for receiving an input signal, a three-level modulator, and a three-level H-bridge. The interface may be adapted to receive a digital input signal. In a preferred embodiment of the driver the H-bridge is controlled by a correction circuit which is operated by a Return-To-Zero scheme. In a further preferred embodiment the driver comprises a supply voltage step-up circuit for increasing a voltage supplied to the H-bridge. In a second aspect the present invention provides a miniature loudspeaker assembly having a built-in driver. In a third aspect the present invention provides a mobile device with a built-in miniature loudspeaker assembly.
Owner:TDK CORPARATION
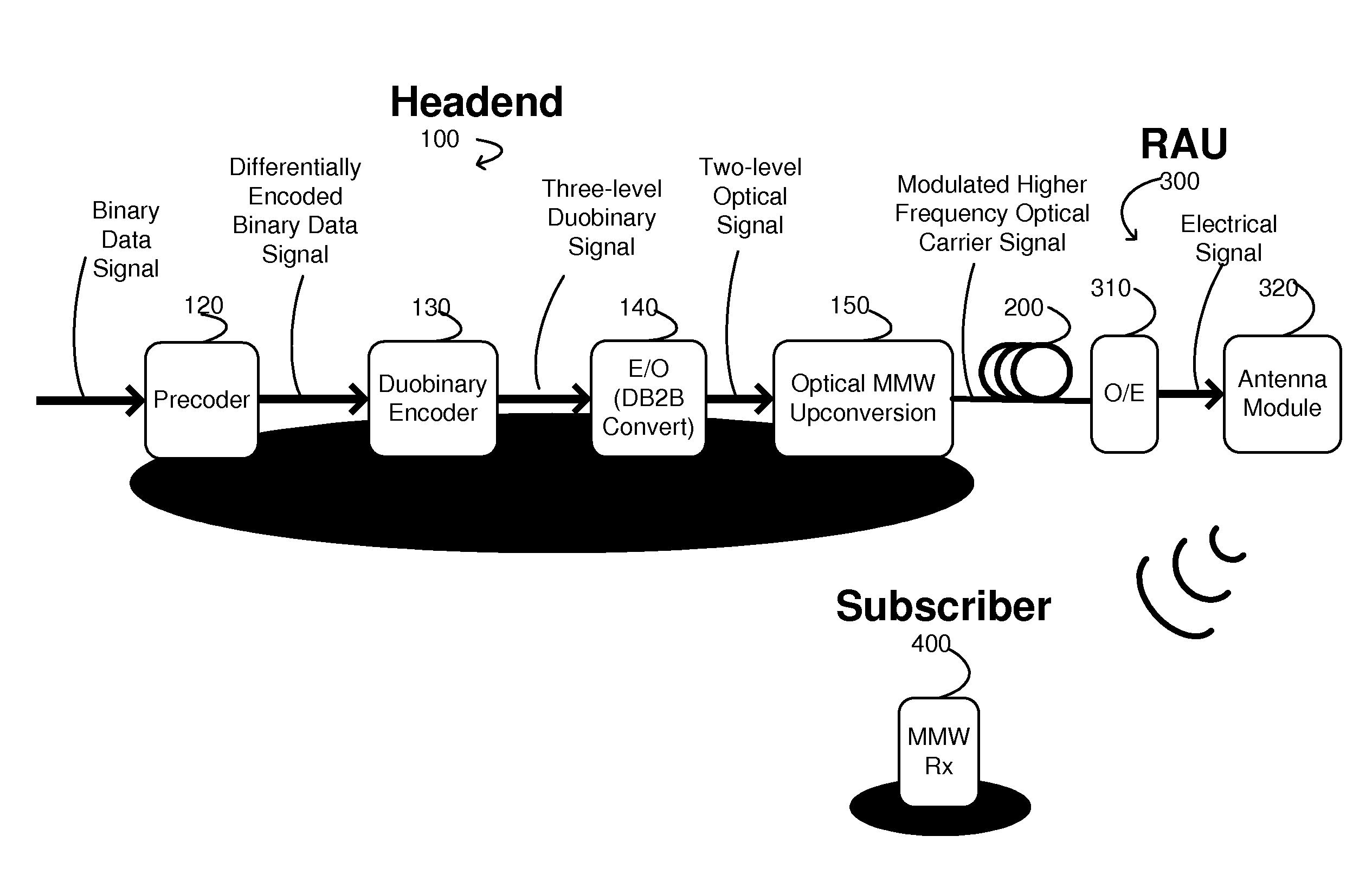
Systems and methods for providing an optical information transmission system
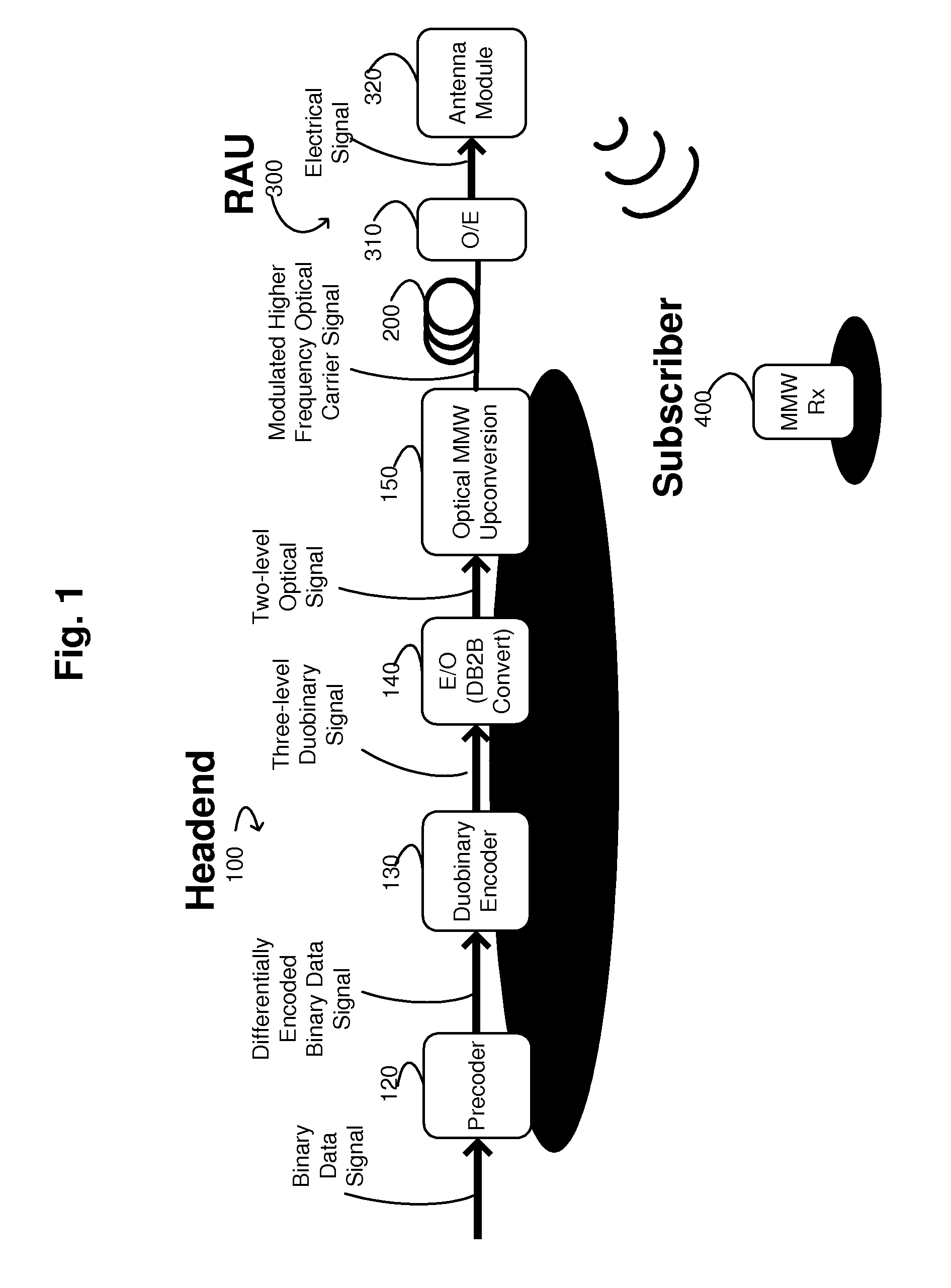
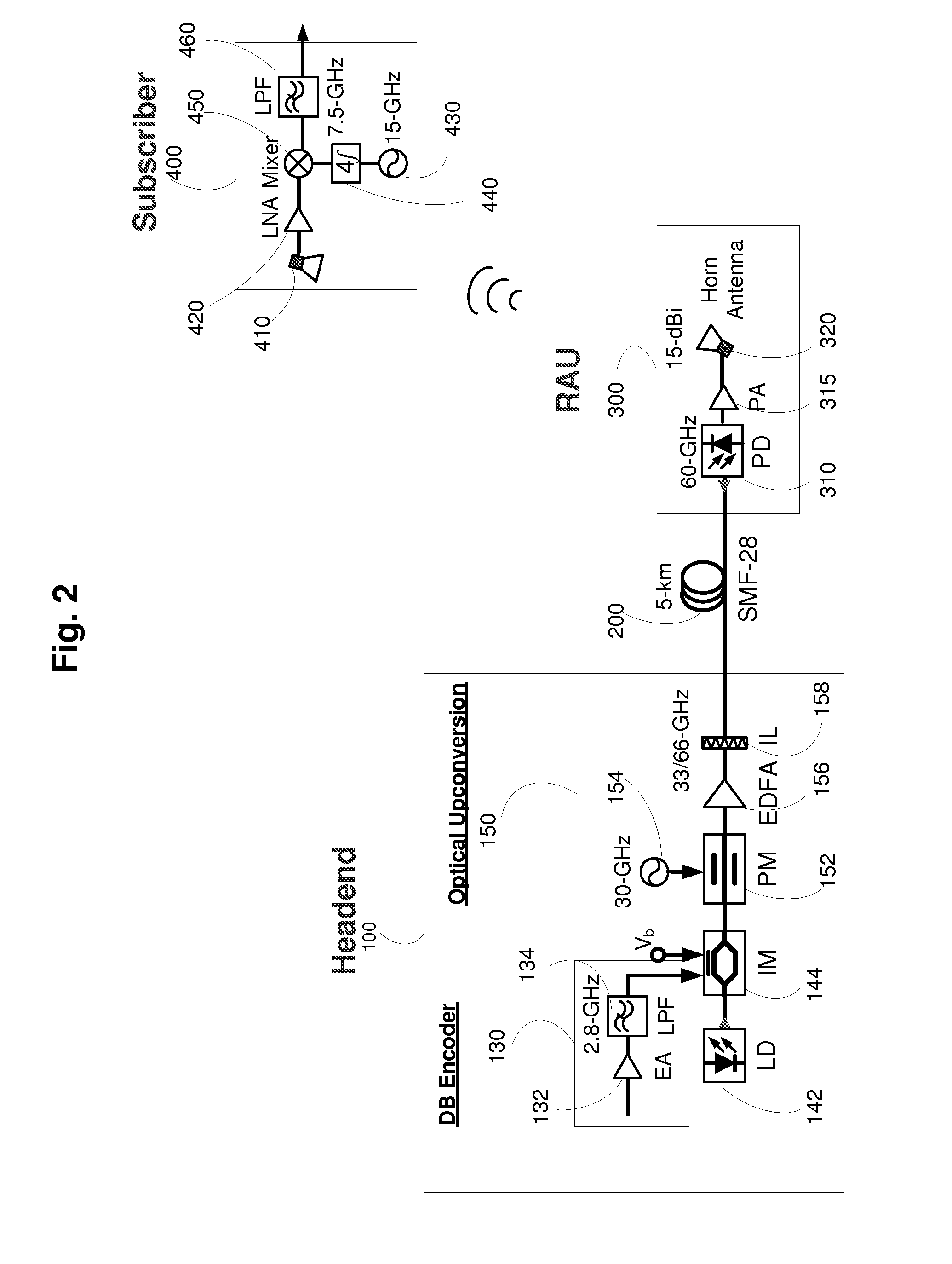
The present invention describes systems and methods of providing optical information transmission systems. An exemplary embodiment of the present invention includes a precoder configured to differentially encode a binary data signal, a duobinary encoder configured to encode the differentially encoded binary data signal as a three-level duobinary signal, an electrical-to-optical conversion unit configured to convert the three-level duobinary signal into a two-level optical signal, and an optical upconversion unit configured to modulate the two-level optical signal onto a higher frequency optical carrier signal and transmit the modulated higher frequency optical carrier signal onto an optical transmission medium.
Owner:GEORGIA TECH RES CORP
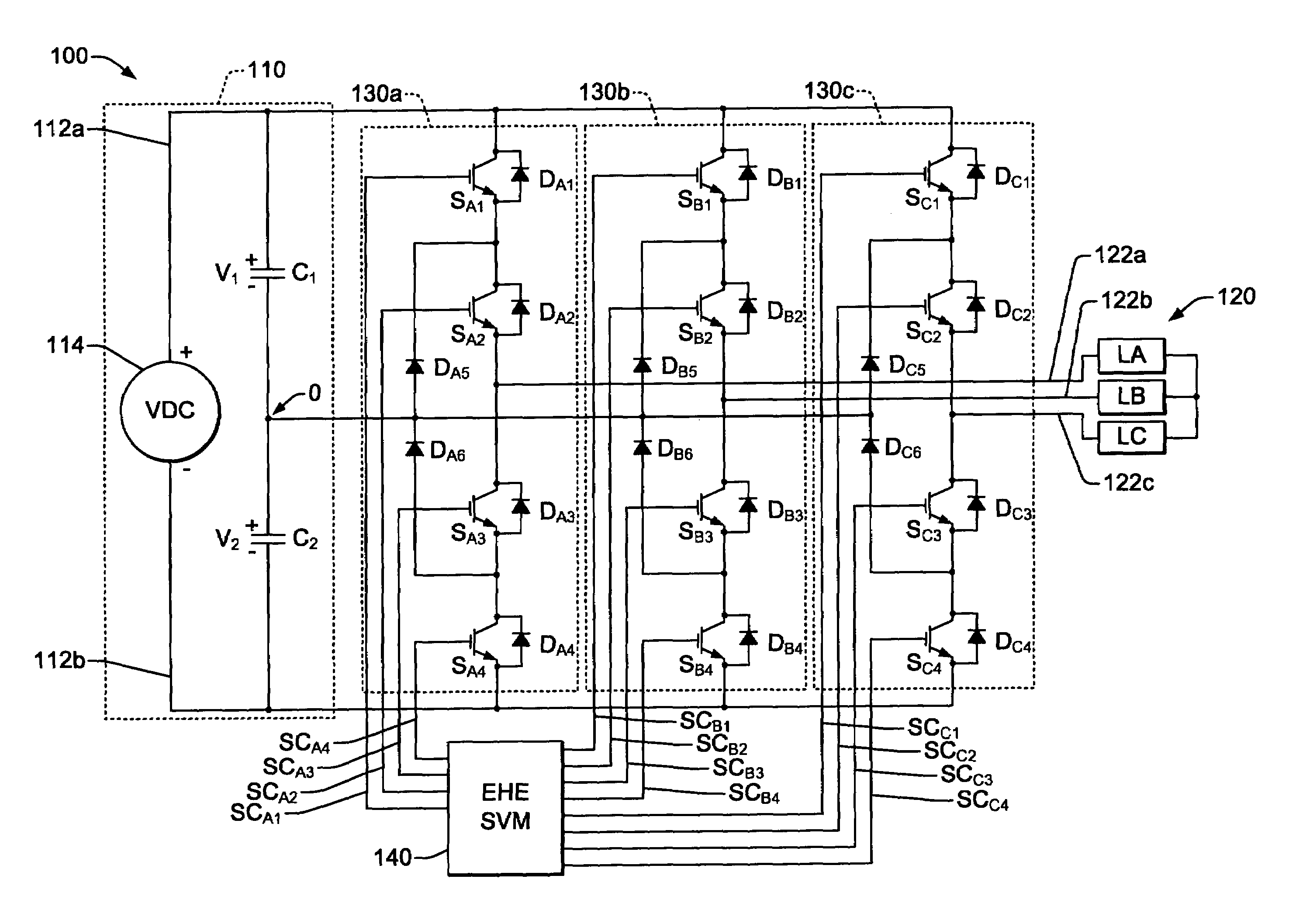
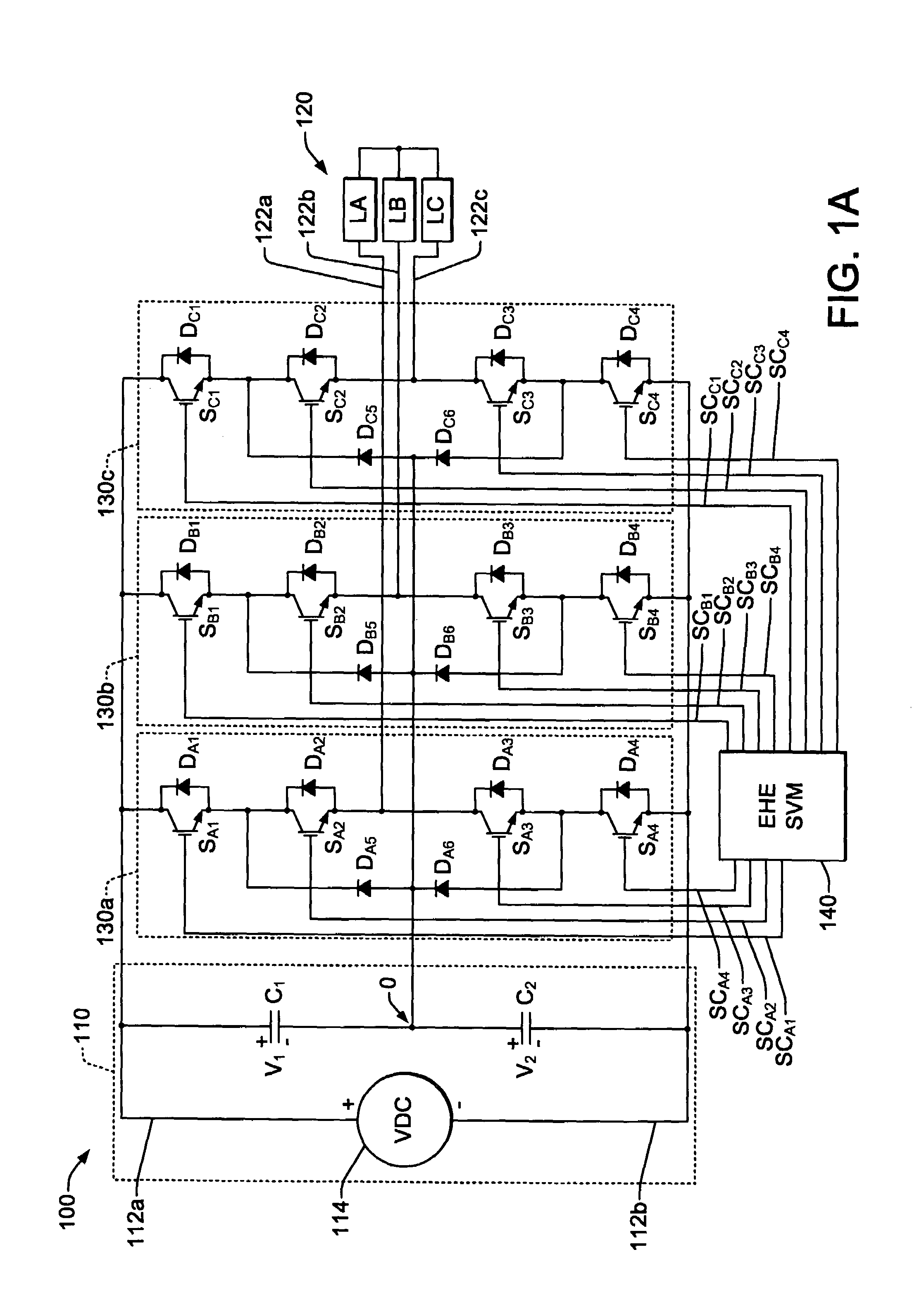
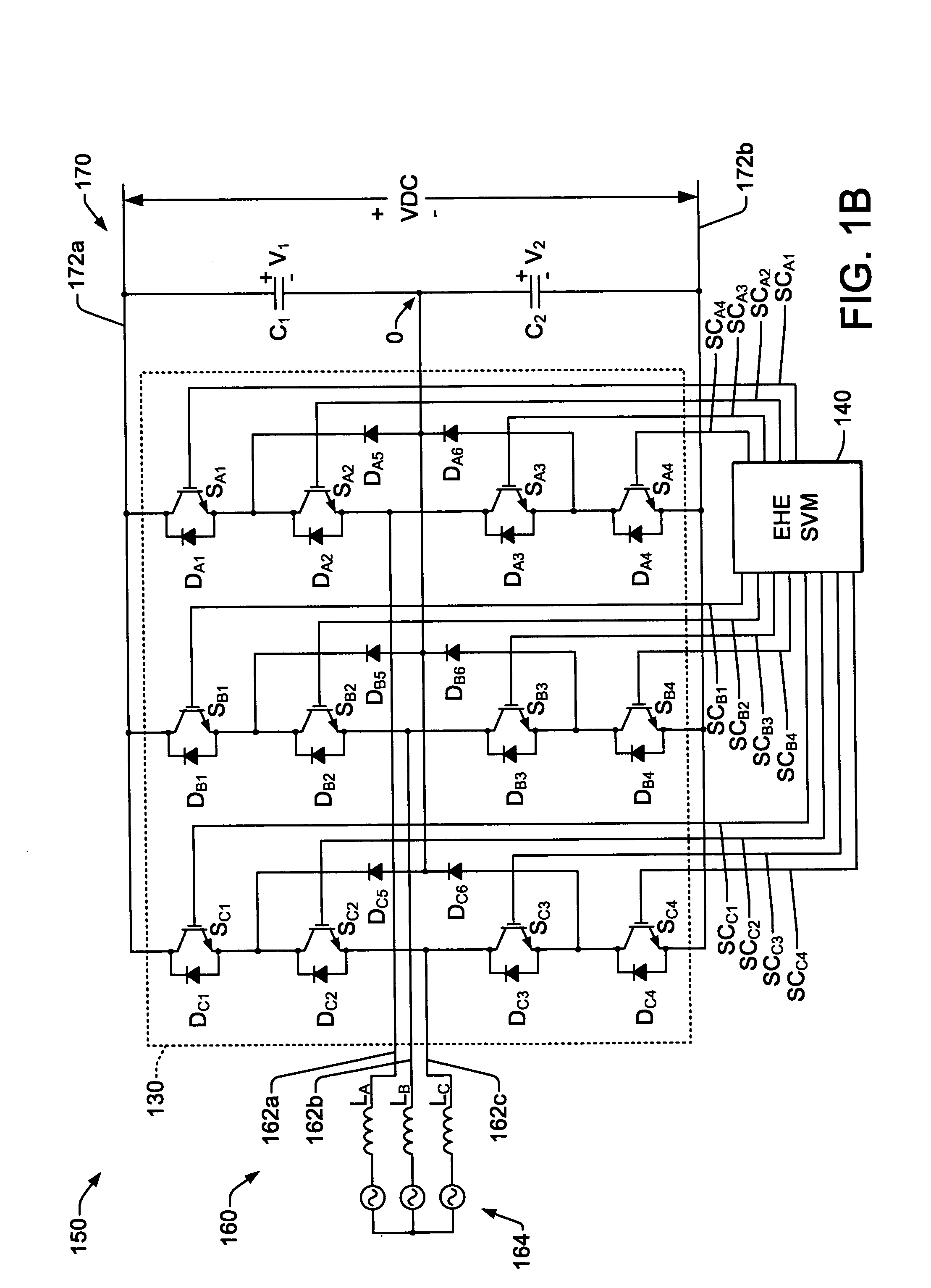
DC voltage balance control for three-level NPC power converters with even-order harmonic elimination scheme
Three-level inverter and rectifier power conversion systems and space vector modulation (SVM) controls having even-order harmonic elimination for neutral voltage balancing with a predefined vector switching sequences for half-wave symmetry in open loop system operation. The vector sequence listings for each SVM diagram segment includes switching state entries individually indicating one of three possible switching state levels positive (P), zero (0), or negative (N) for each of three or more switching groups of the power conversion system, with listings for each pair of first and second diametrically opposite diagram segments include symmetrically opposite switching states, with positive levels in the entries of the listing for the first segment corresponding to negative levels in the entries of the listing for the second segment and vice versa.
Owner:ROCKWELL AUTOMATION TECH
Software development method and system for executing model drive structure
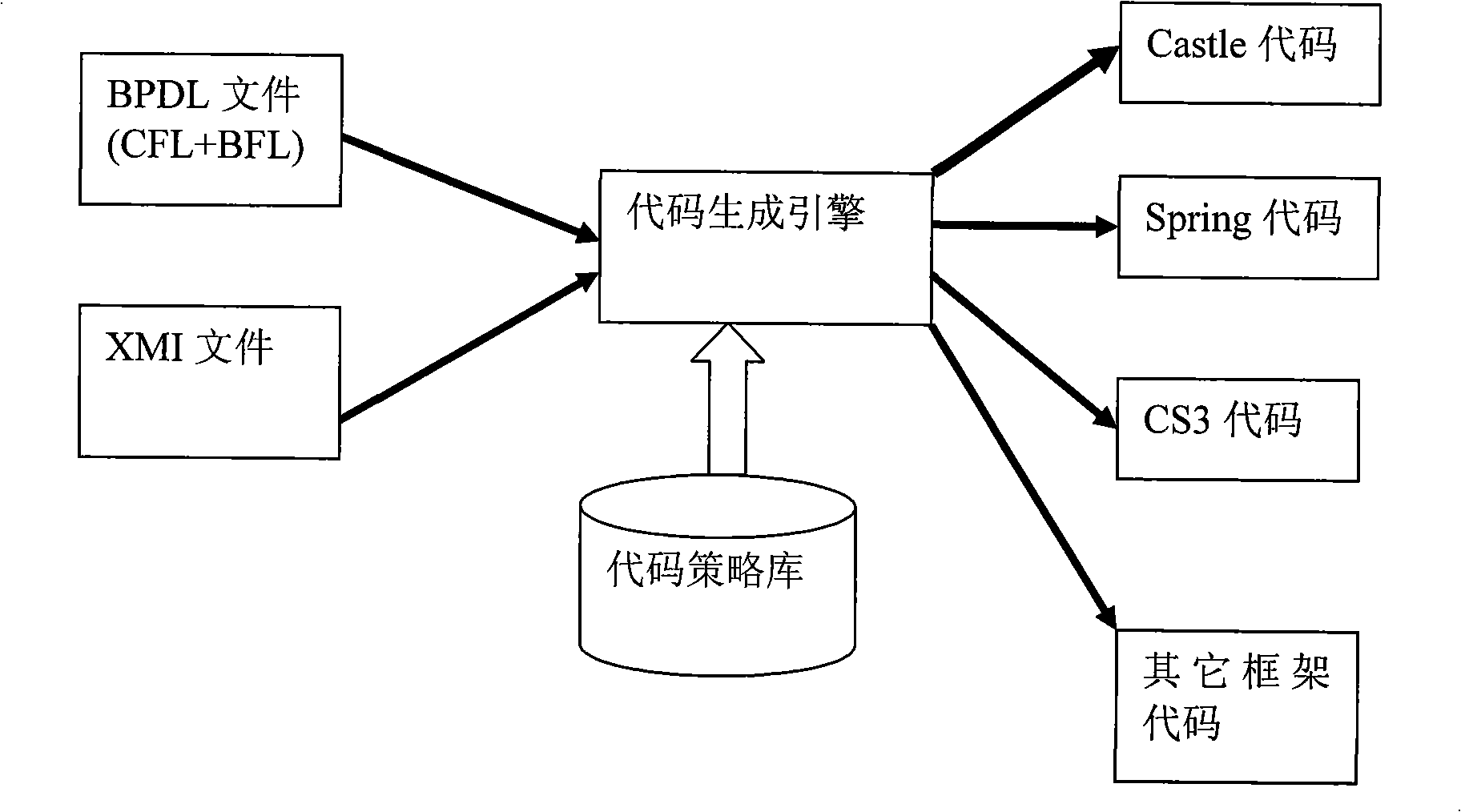
InactiveCN101256492ALow costImprove portabilityMultiprogramming arrangementsSpecific program execution arrangementsSoftware development processThree level
The invention discloses a software development method for performing model driven architecture and the system thereof, belonging to the field of computer software. The method comprising the following steps: abstracting a business flow process into node elements, customizing a node business flow description file from control flow, core business flow and page flow three levels, customizing a data model file, and inputting the business flow file and the data model file into a parser to generate target frame codes. The invention also provides an attribute file of business flow graphical layout for WYSIWYG customizing the attribute information of the node elements; the system consists of a microkernel, a plug-in, a tools integration, an application server integration and a knowledge library. The invention can quickly respond to business requirement change and technical change, support highly modularized and highly integrated software system, has wide application and provides a solid foundation for further development of computer software technology.
Owner:宋乃辉
Embedded user assistance for software applications
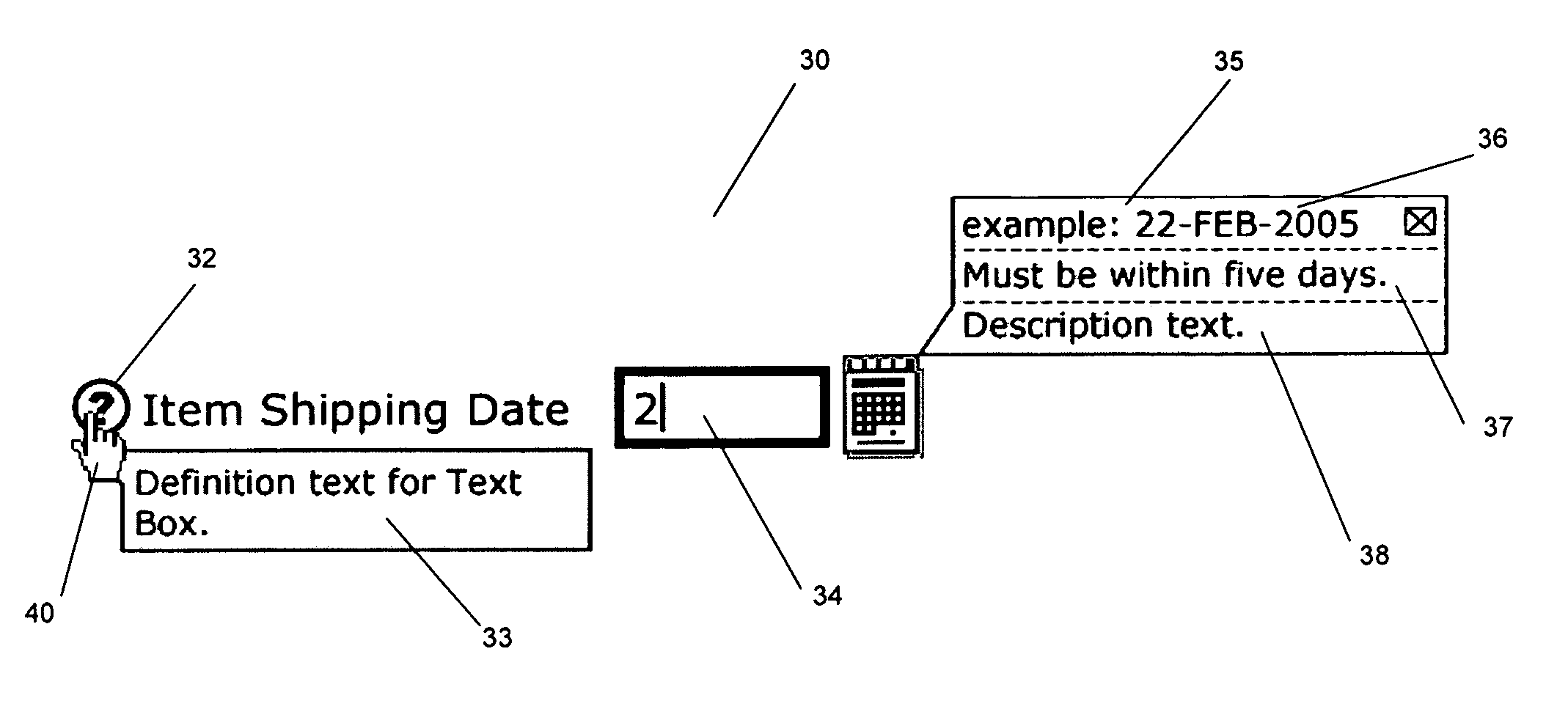
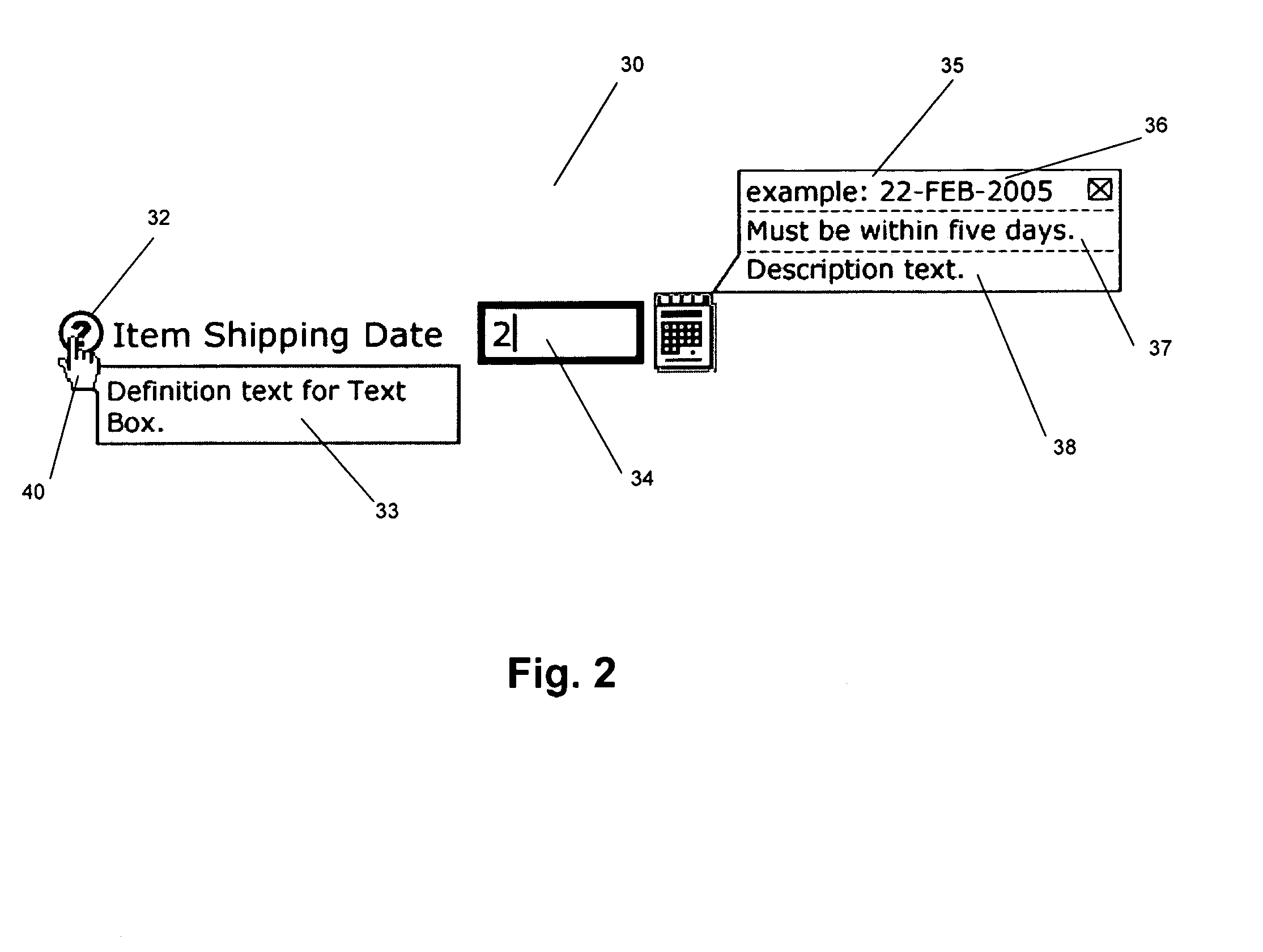
ActiveUS20090183072A1Execution for user interfacesInput/output processes for data processingThree levelApplication software
A system for providing user assistance receives a request for user assistance from a component on a user interface. The component includes a help identifier, and the request is generated by a type of user selection, such as the clicking of an icon. The system determines a level of user assistance based on the type of selection and retrieves user assistance content based on the help identifier and the determined level of user assistance. In one embodiment, the user interface includes three levels of user assistance.
Owner:ORACLE INT CORP
System for targeted advertisement, personal editing and parental control in a television network
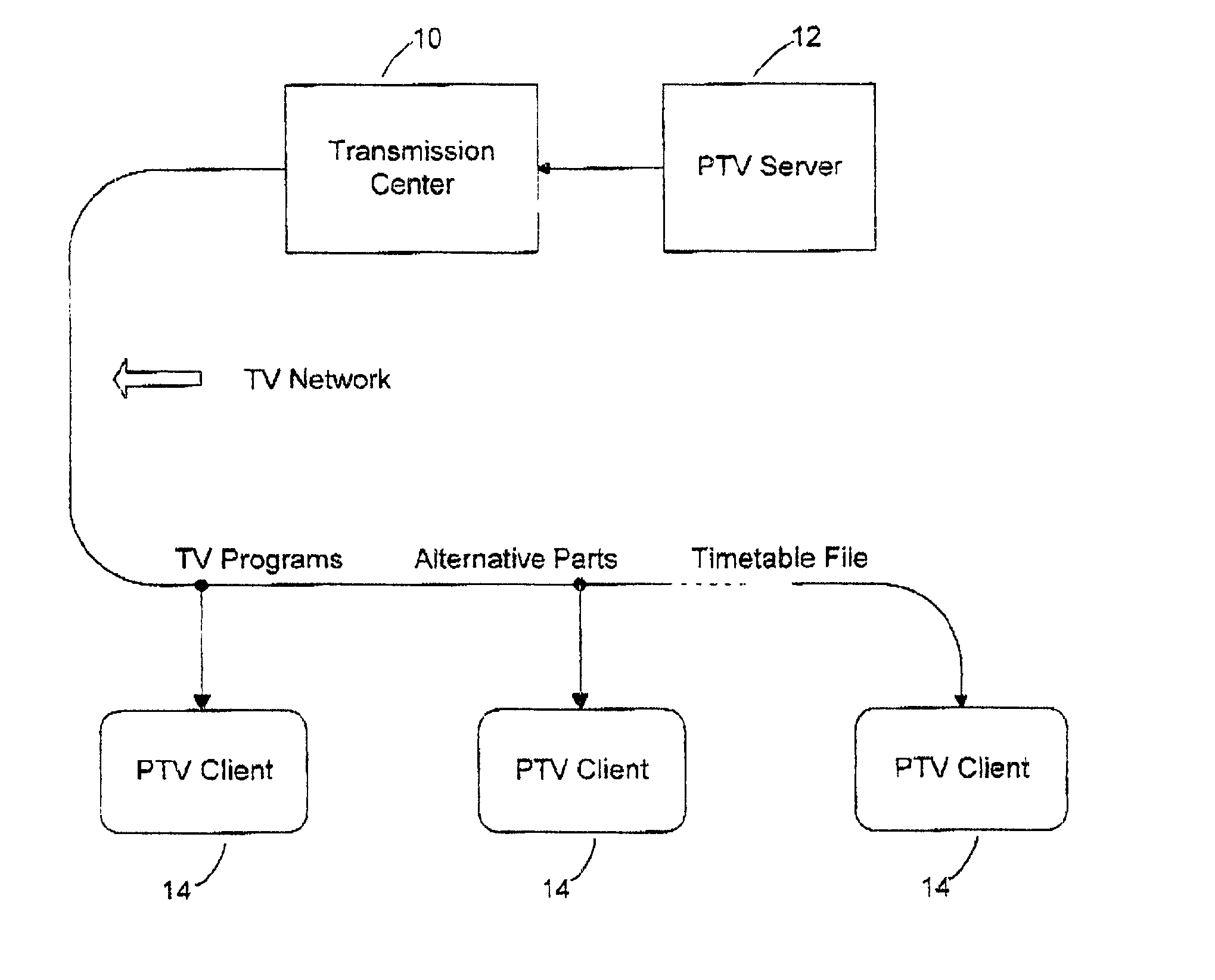
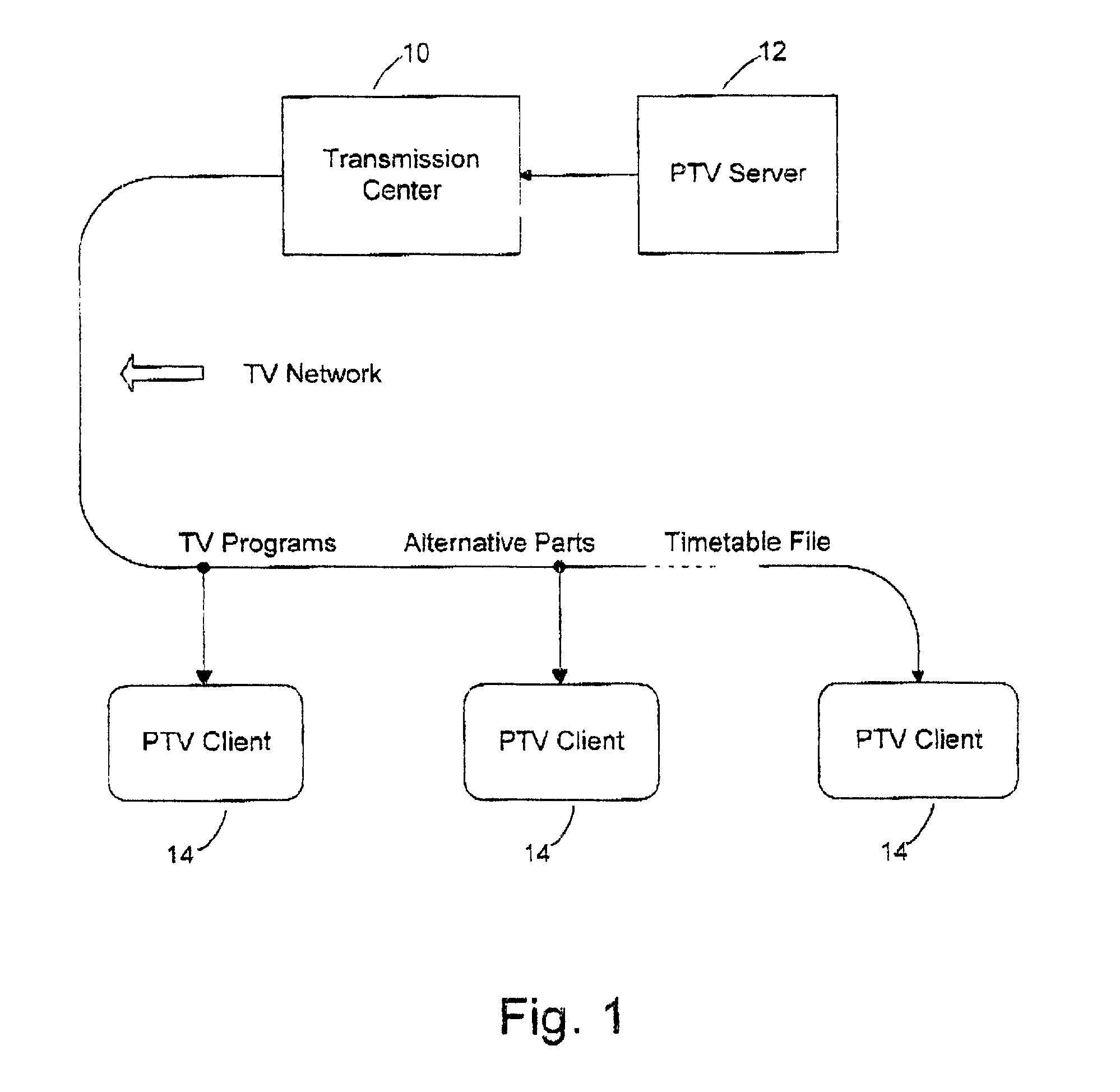
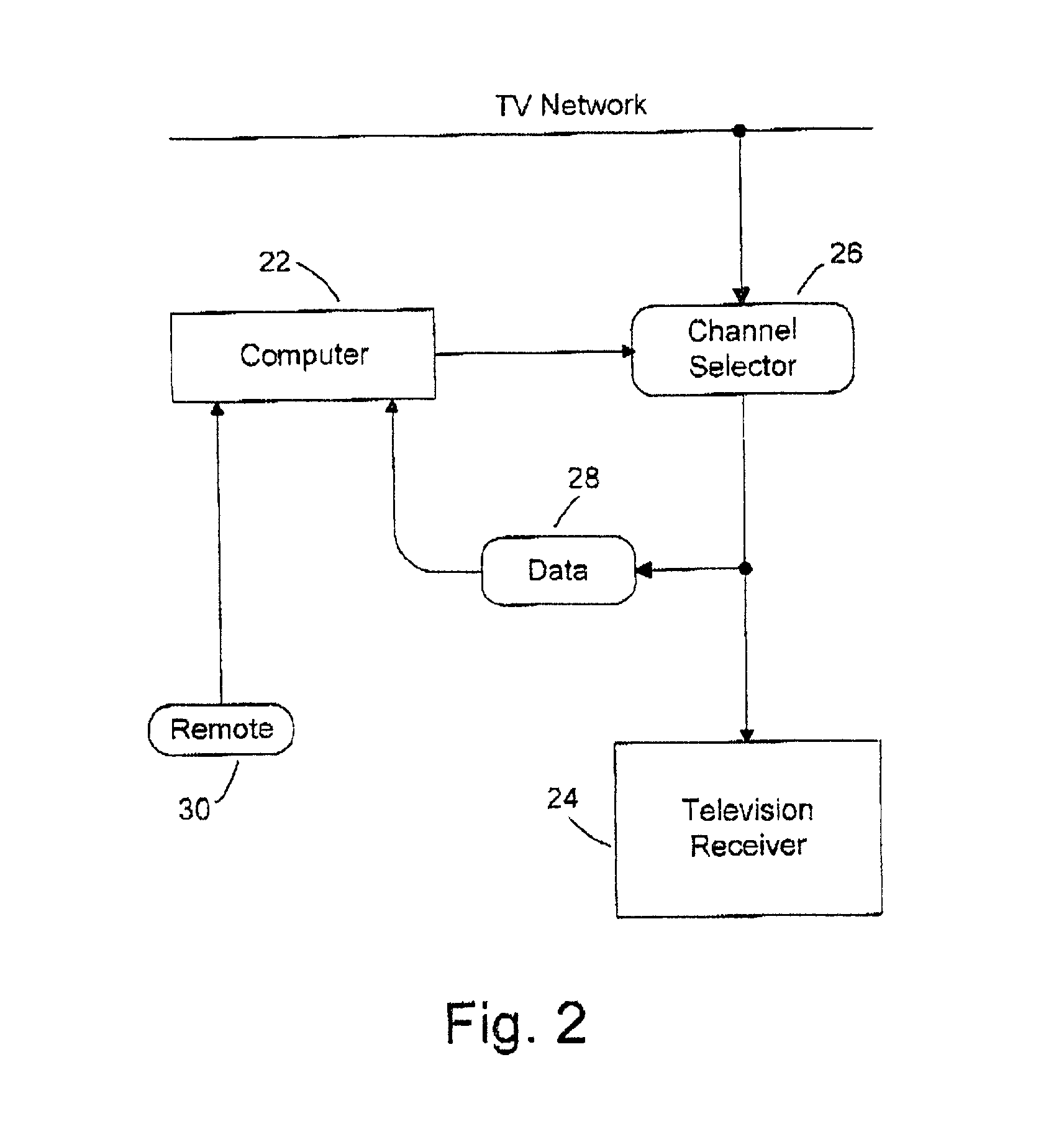
InactiveUS20020073421A1Easy to useAnalogue secracy/subscription systemsElectrical cable transmission adaptationThree levelTelevision receivers
A system for automatic personal editing of television programs based on viewer's information privately stored in viewer's computerized television receivers. The system, when activated, protects viewers, first of all children, filtering out everything that is unacceptable or useless. The filtering is carried out on three levels: blocking television programs, blocking some parts of the programs and replacing some parts by alternative video fragments. In particular, the system replaces a television commercial meaningless for a viewer by a commercial that may be of certain interest to the viewer. Another application is an improvement in management of controversial matter such as sex and violence. Depending on viewer's preferences the system replaces a certain scene by a commercial or restores such a scene if it has been replaced by a commercial in a program edited for broadcast television. The replacement technique uses basic channels for transmission of primary versions of television programs and auxiliary channels for transmission of alternative video fragments intended for replacement of some parts of the primary versions. A computerized receiver makes a decision on a replacement comparing viewer's information with information on the primary and alternative parts.
Owner:LEVITAN GUTMAN +1
Contour vector feature-based embedded real-time image matching method
ActiveCN102654902ASmall amount of calculationImprove matching speedCharacter and pattern recognitionThree levelTemplate matching
The invention provides a contour vector feature-based embedded real-time image matching method. The method uses the linear feature based on X and Y direction vectors, and has strong capability of resisting image distortion, noise, shading, illumination changes, polarity inversion and so on. An image pyramid search strategy is used, templates are quickly matched in a high-layer low-resolution image to be tested, and then, a target position is found out accurately by stepwise downward search, so that matching time is reduced greatly. According to the template image specific information, the best pyramid hierarchy number and the best rotation angle step size for the pyramid template matching of each layer are calculated automatically. An image pyramid highest-layer three-level screening matching strategy is provided, treatment is carried out according to the specific content of the image to be tested, and the first level of screening and the second level of screening are carried out; the non-target position is eliminated just by the addition and subtraction and the conditional statements, which is more efficient in the embedded system than using the multiplication and division; and the third level only processes fewer positions meeting the requirements of the above two levels, so that the matching speed is improved greatly. The overall method can realize the work of matching and locating the target at any angle and any coordinate.
Owner:JIANGNAN UNIV +1
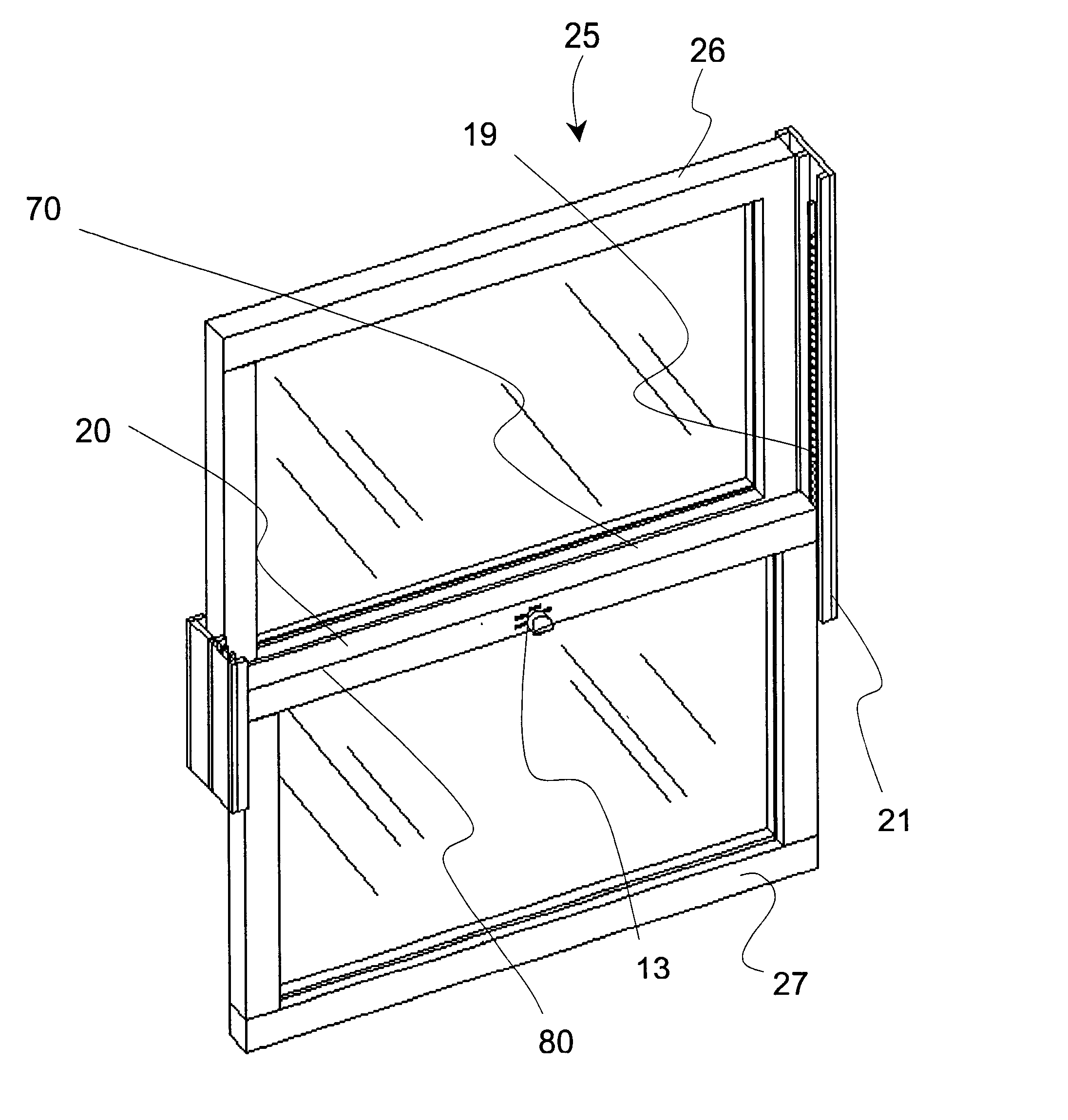
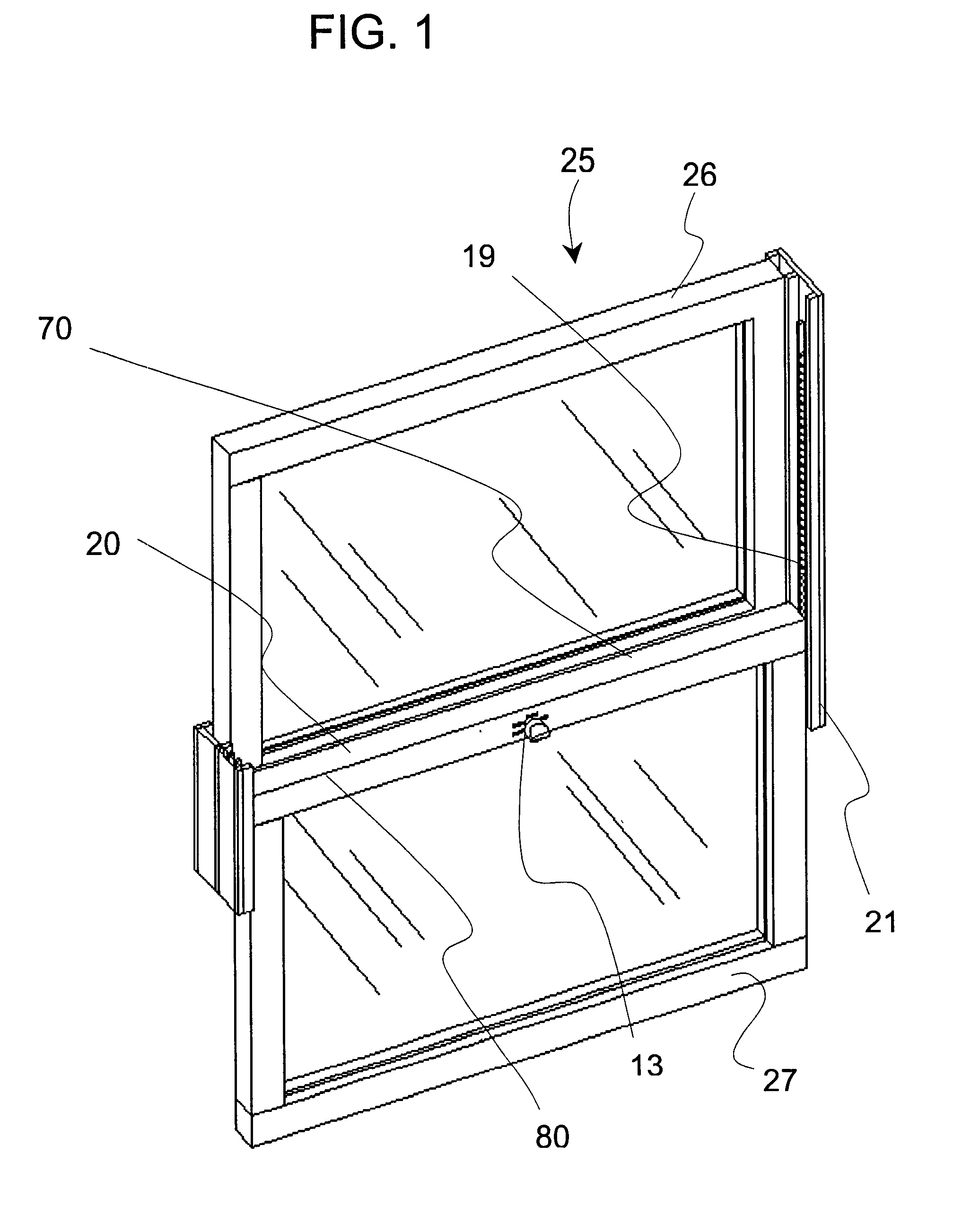
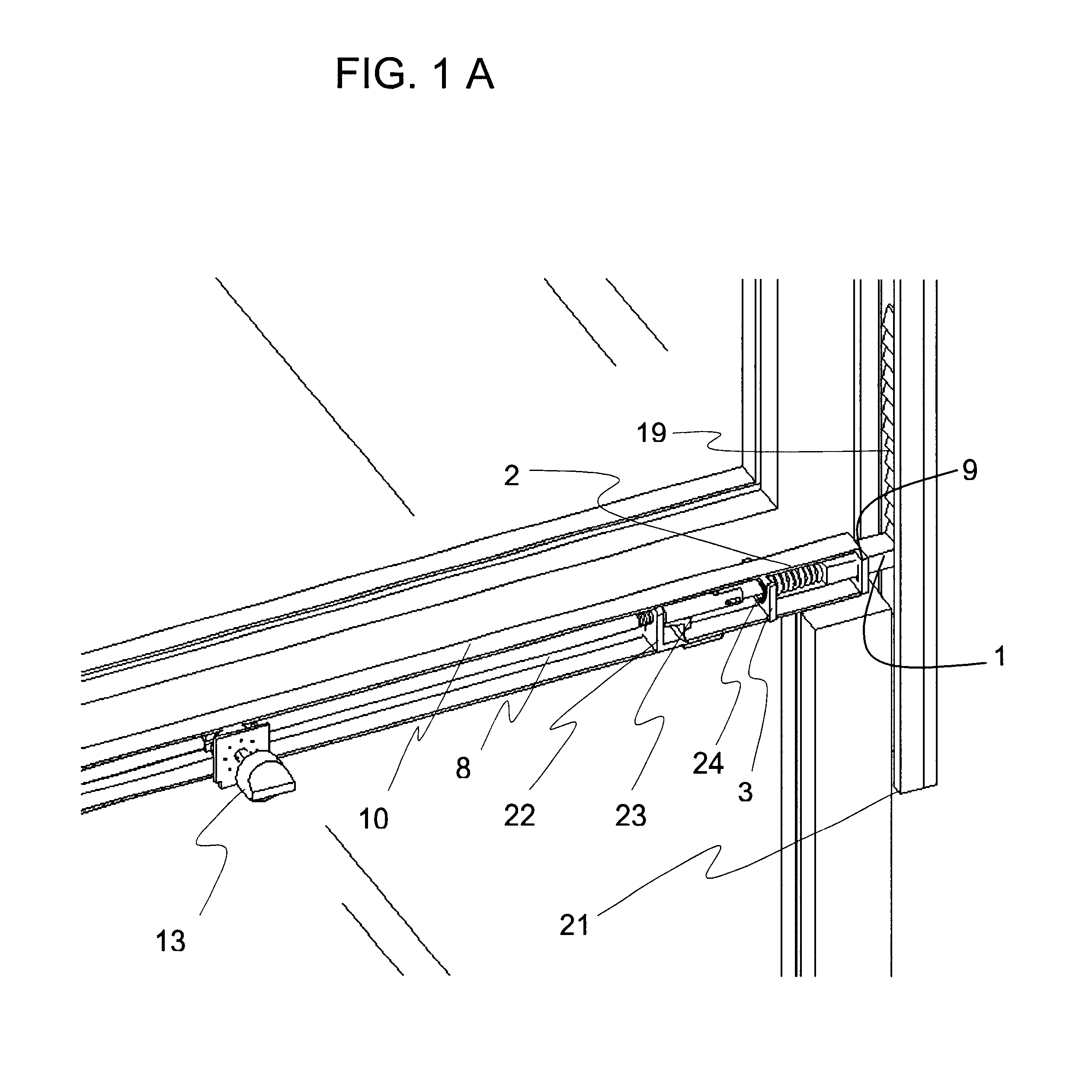
Window latch system
A sliding latch and locking mechanism, for windows and doors, whereby the latching mechanism provides a means for discrete position retention of a sliding window or door and provides an increased measure of security. The latching system combines four modes of operation i.e. lock, close only, raise (free sliding), and tilt to provide angular pivoting of window sash, that allow three levels of security, i.e. fully locked, close only with discrete positions maintained, and raise or lower without discrete positions maintained (free sliding). The latching system security levels are accomplished by means of a selector knob positioned to the desired mode of operation. Also, a mechanism is integrated to provide interlocking in the fully closed position with the upper or adjacent window or door sash.
Owner:ELLIOTT GORDON W
Communication system and method employing automatic repeat request
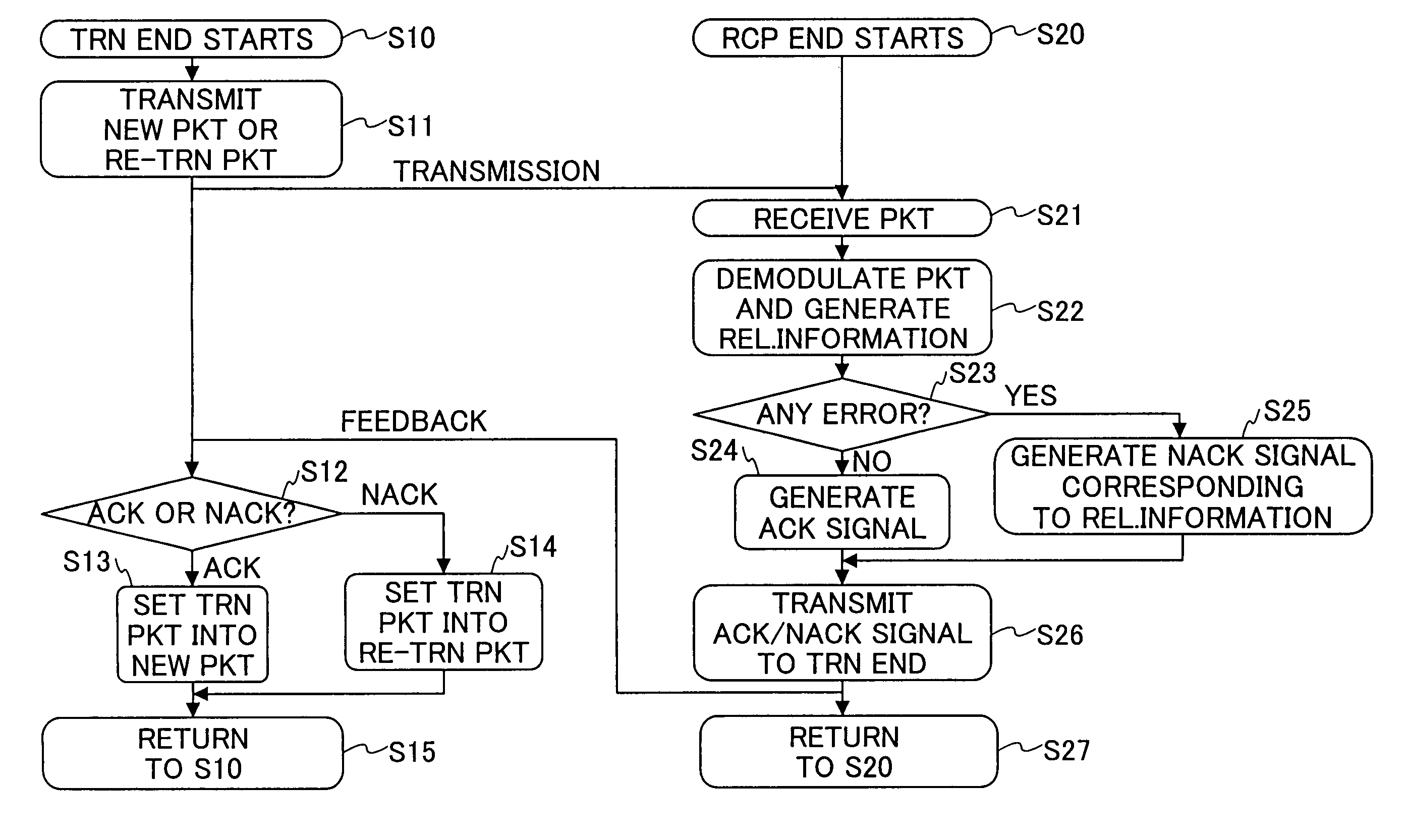
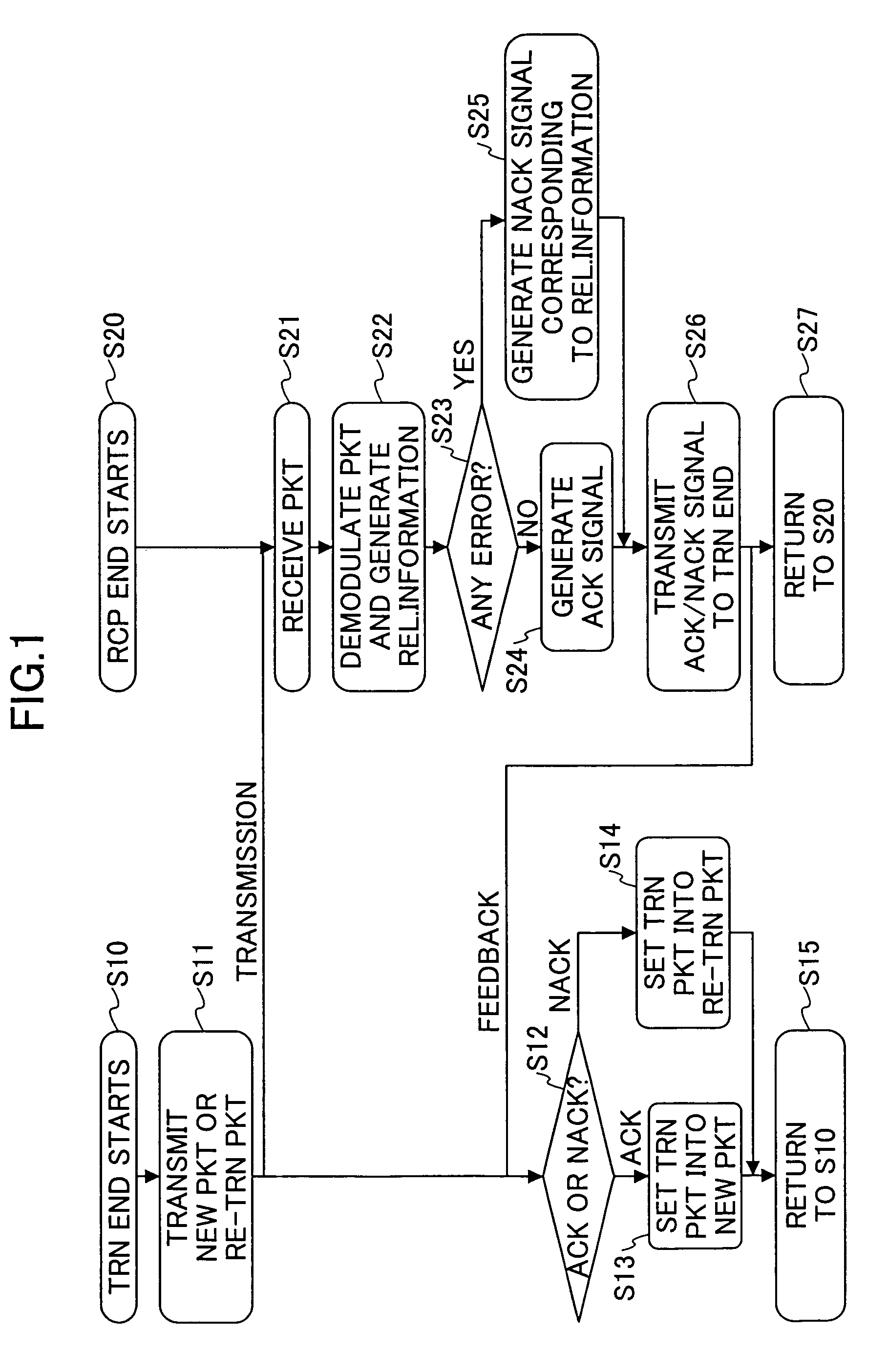
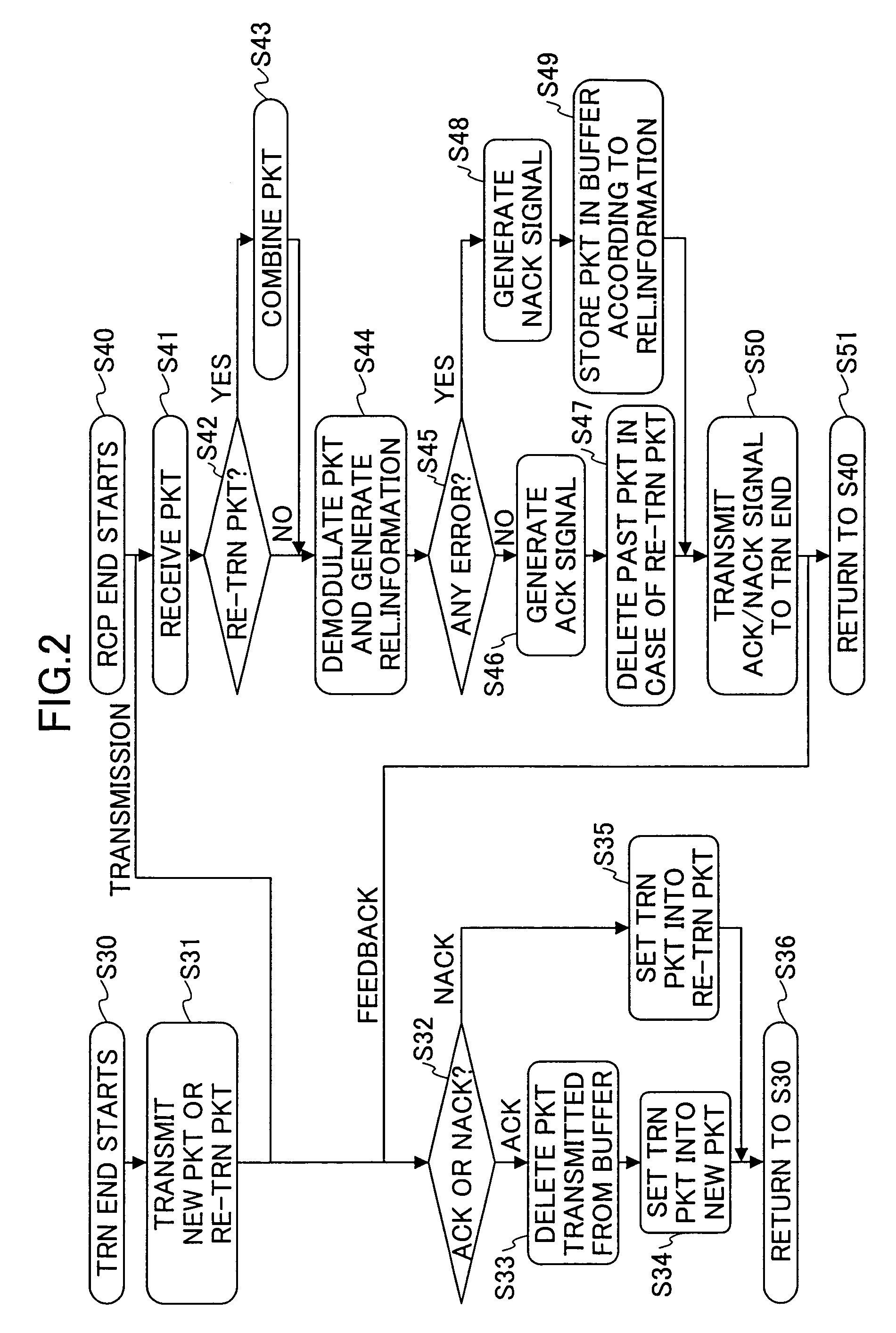
InactiveUS7185256B2Improve transmission performanceEfficiently signaledError prevention/detection by using return channelPower managementThree levelCommunications system
A communication system and method includes the steps of: a) transmitting an ACK signal indicating a received packet includes no error or a NACK signal indicating the received packet includes error from a reception end to a transmission end, and performing automatic repeat request; b) obtaining reliability of the received packet when demodulating it at the reception end; and c) reporting from the reception end to the transmission end the reliability of the received packet utilizing the ACK / NACK signal by using not less than three levels.
Owner:NTT DOCOMO INC
Method And System For Energy Efficient Signaling For 100MBPS Ethernet Using A Subset Technique
Aspects of a method and system for energy efficient signaling for 100 mbps Ethernet using a subset are provided. In this regard, a network device enabled to communicate over a network link at 1 Gbps or faster may be configured to communicate over the network link at, or approximately at, 100 Mbps by reducing a number of active channels over which the network device communicates and / or reducing a size of a signal constellation utilized by the network device to encode data. The device may communicate according to 1GBASE-T or 10GBASE-T standards. The number of active channels may be reduced to a single bidirectional channel or two unidirectional channels. The signal constellation may be reduced to two or three levels. One or more components of the network device may be unnecessary for recovering data when communicating at 100 Mbps and may thus be powered down, or placed into a lower power mode.
Owner:AVAGO TECH INT SALES PTE LTD
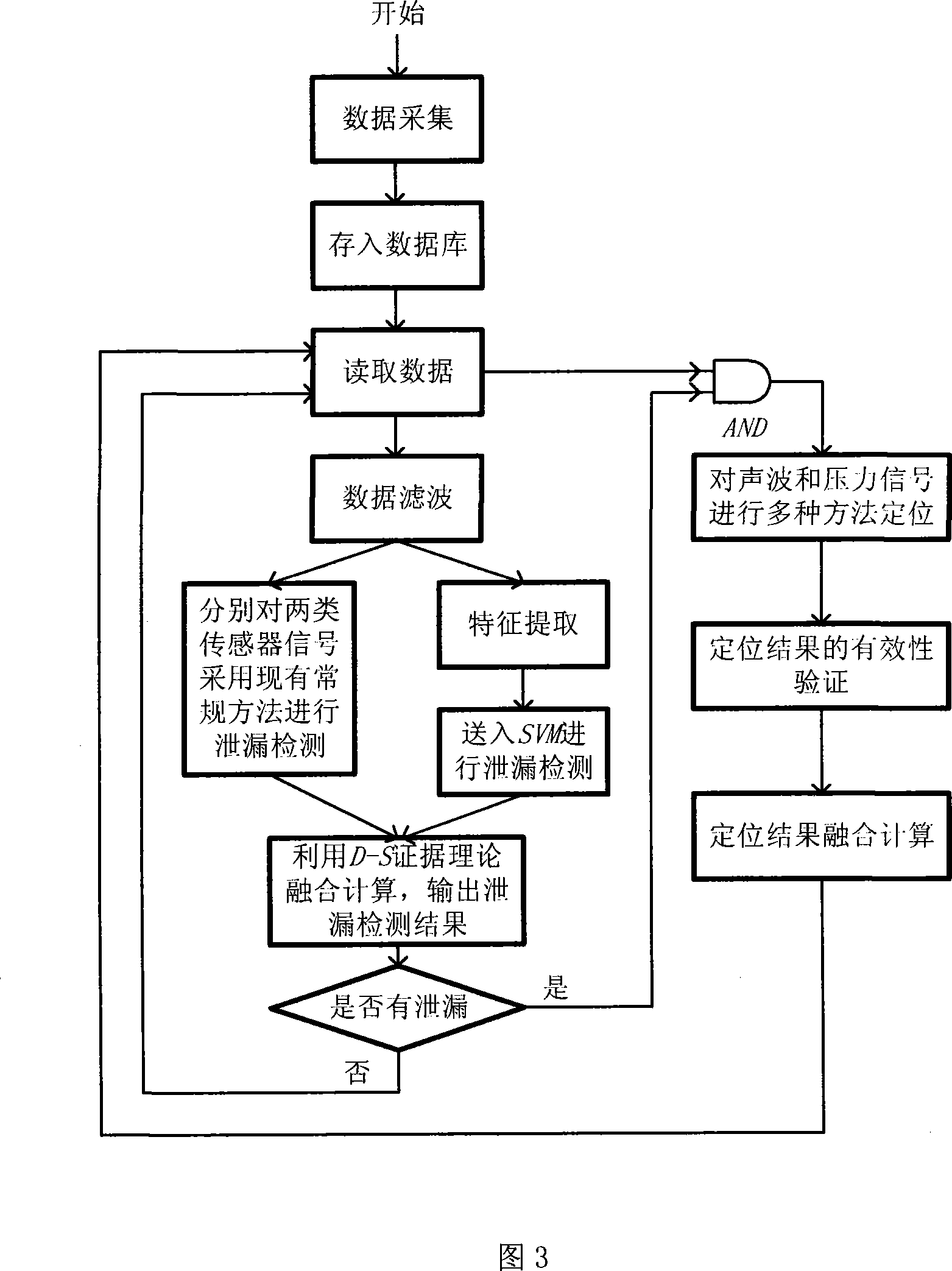
Leakage detecting and locating method based on pressure and sound wave information amalgamation
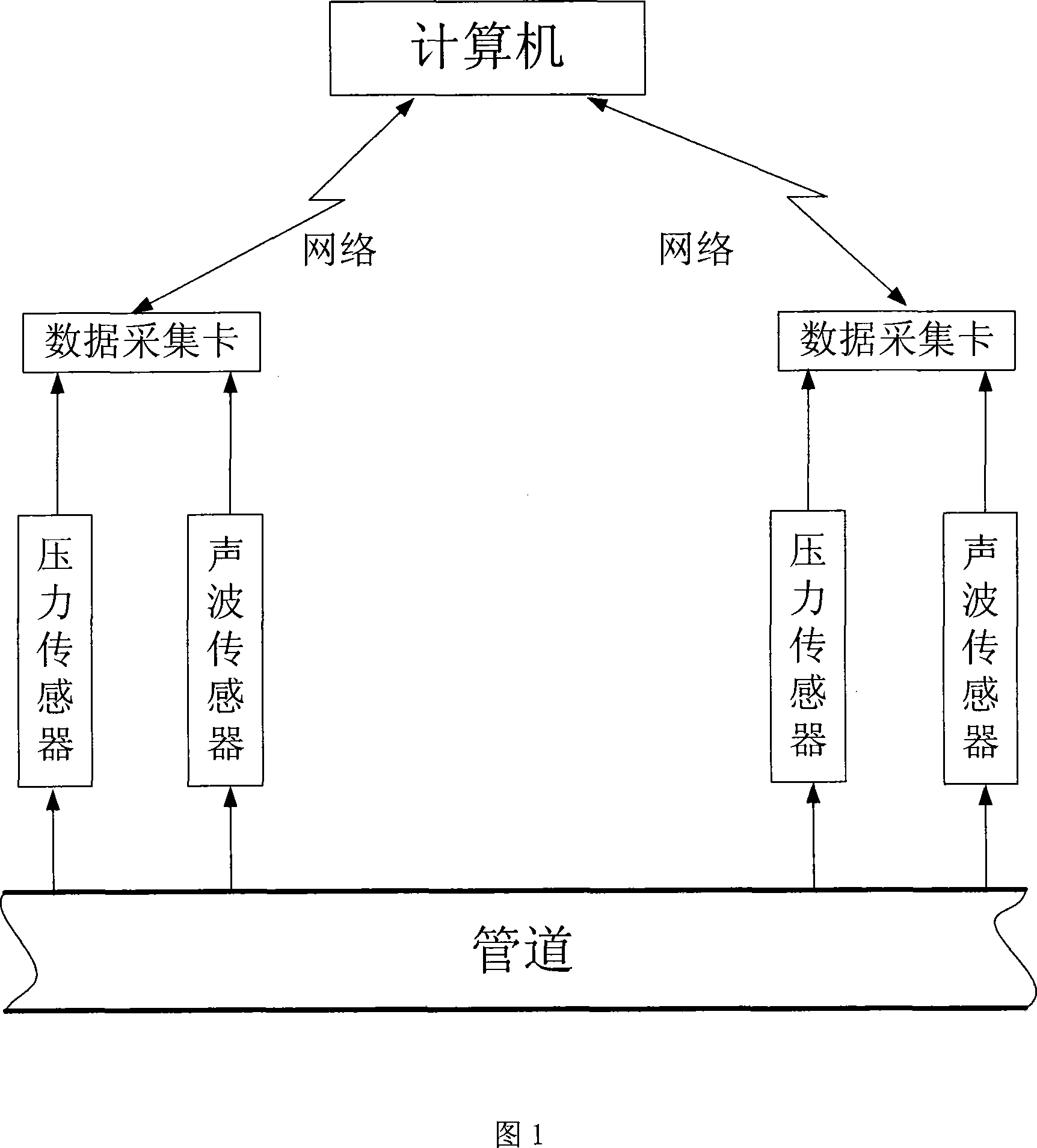
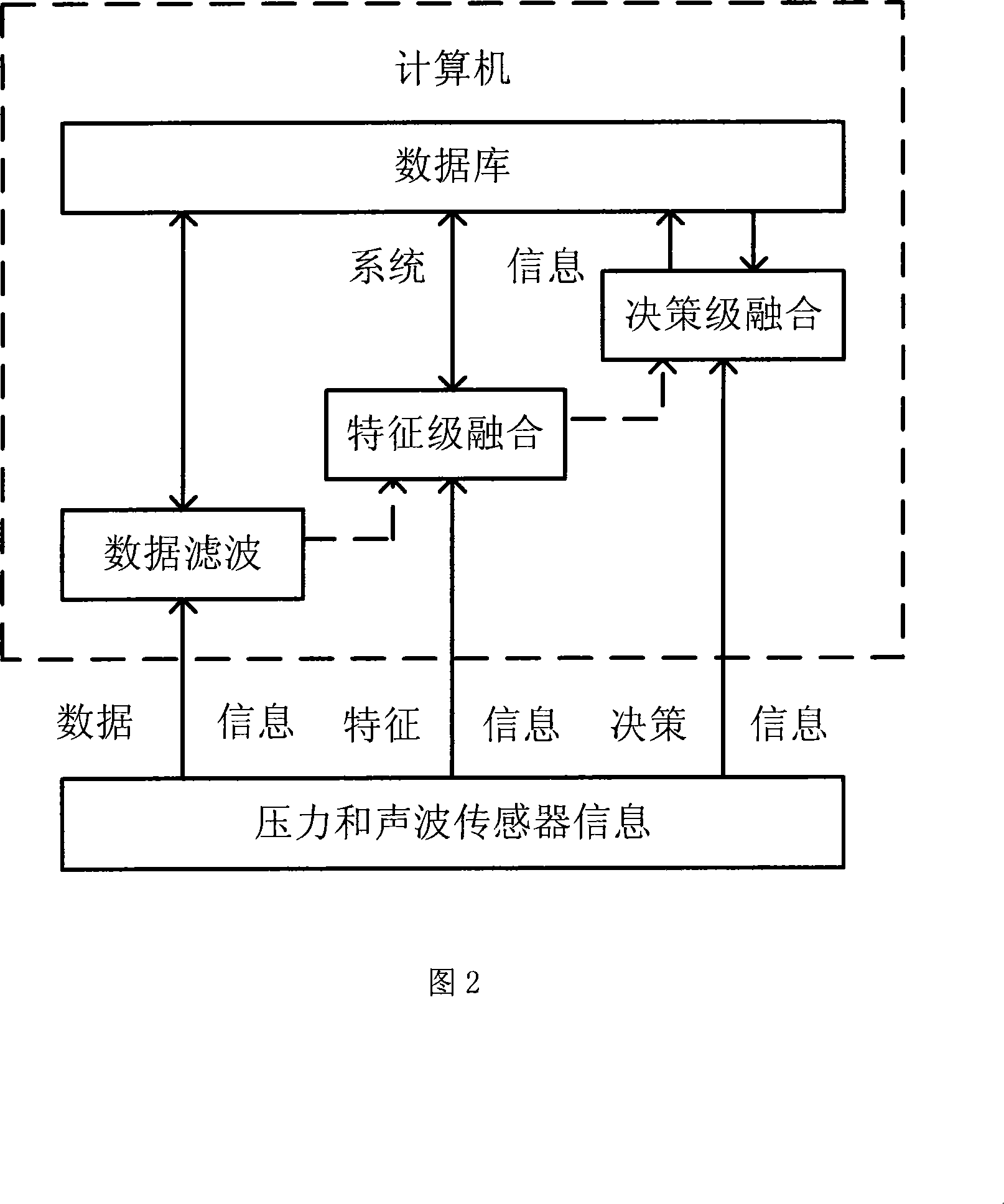
ActiveCN101196872AHigh precisionReduce false alarm ratePipeline systemsSpecial data processing applicationsThree levelAcoustic wave
A leakage detection location method based on pressure and sound information integration is provided, which belongs to the technology field of an oil (gas) pipeline fault diagnosis, and is characterized by leakage detection and leakage location based on information integration. The former comprises: separately acquiring the measurement data of the pressure on the upperstream end and downstream end of the pipeline and a sound wave sensor, sending the data to a computer and gaining final detection results through three levels processing including data filtering, characteristic level integration and decision level integration. If the detection result shows leakage, starting leakage location process based on information integration. The process first carries out leakage location by separately adopting the signals of two kinds of sensors and a plurality of different leakage location algorithms and finally gains the location results via integration of the location results based on the same sensor and different location methods and two levels processing based on the integration of the location results of two kinds of different sensors. The method can effectively reduce the false positive rate and false negative rate and improve the location precision.
Owner:TSINGHUA UNIV
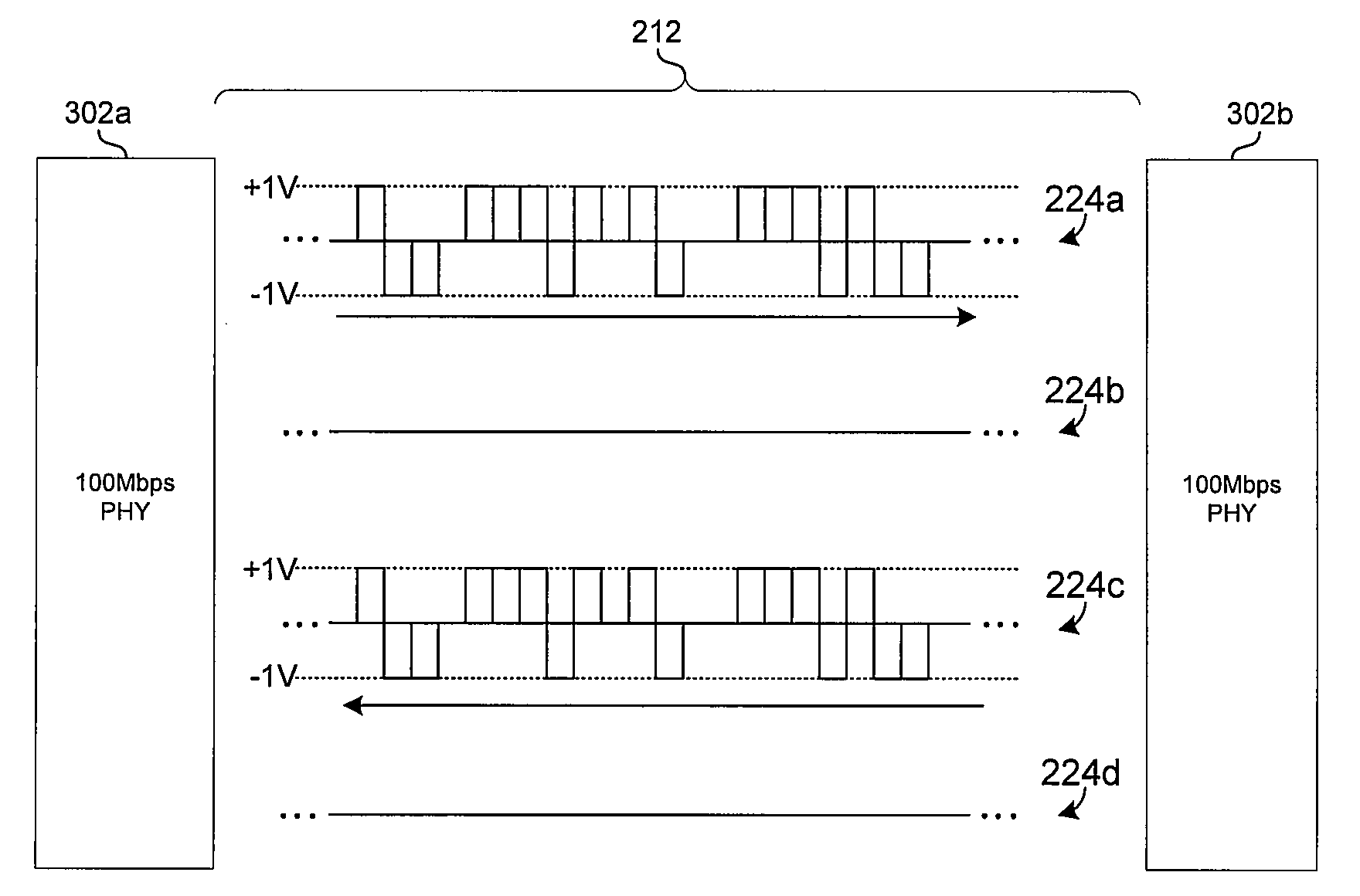
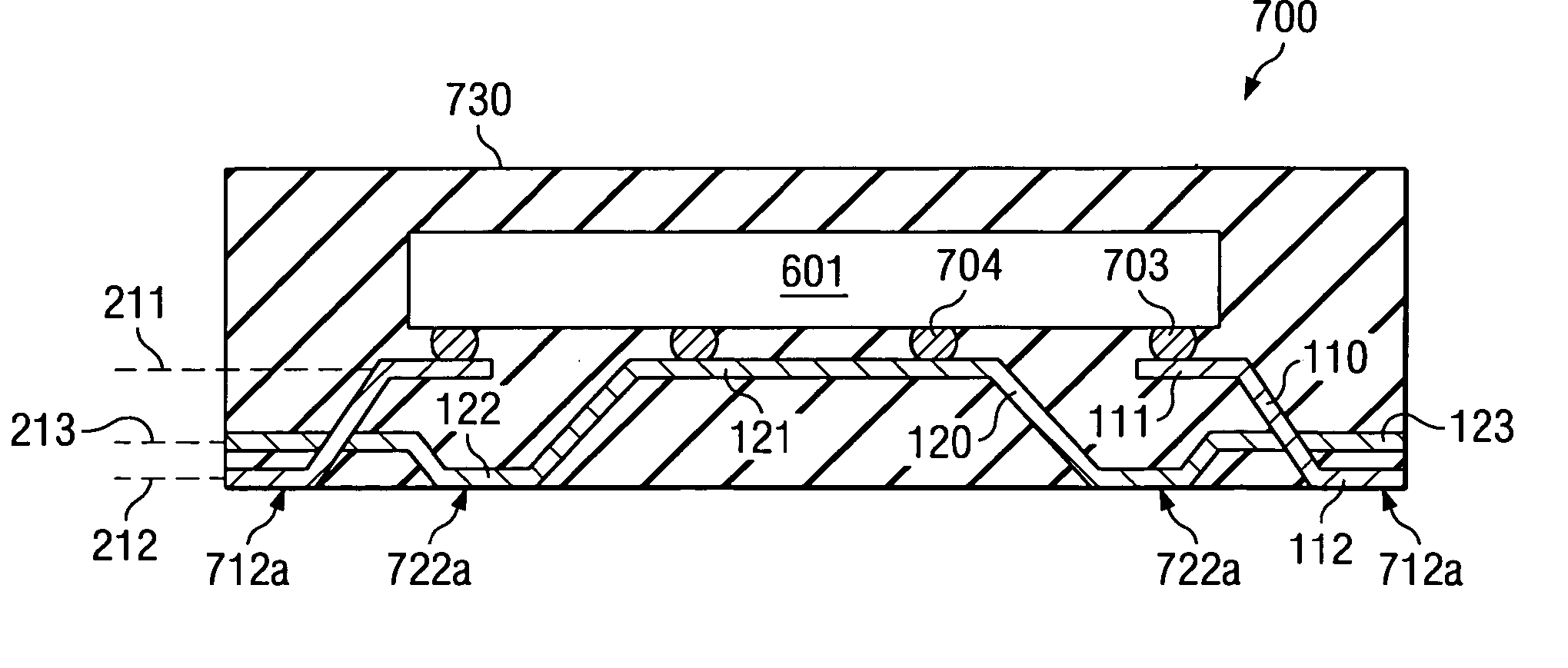
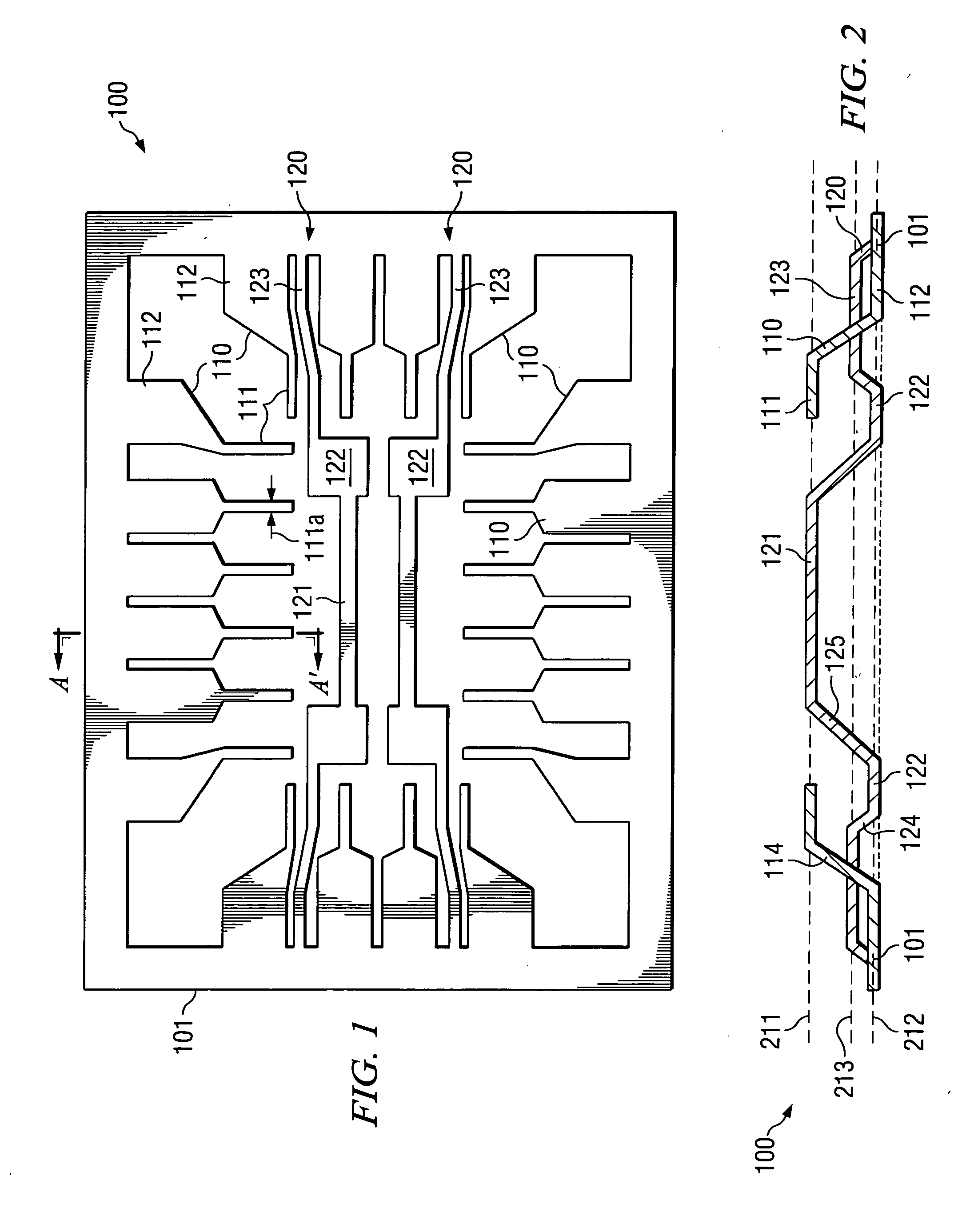
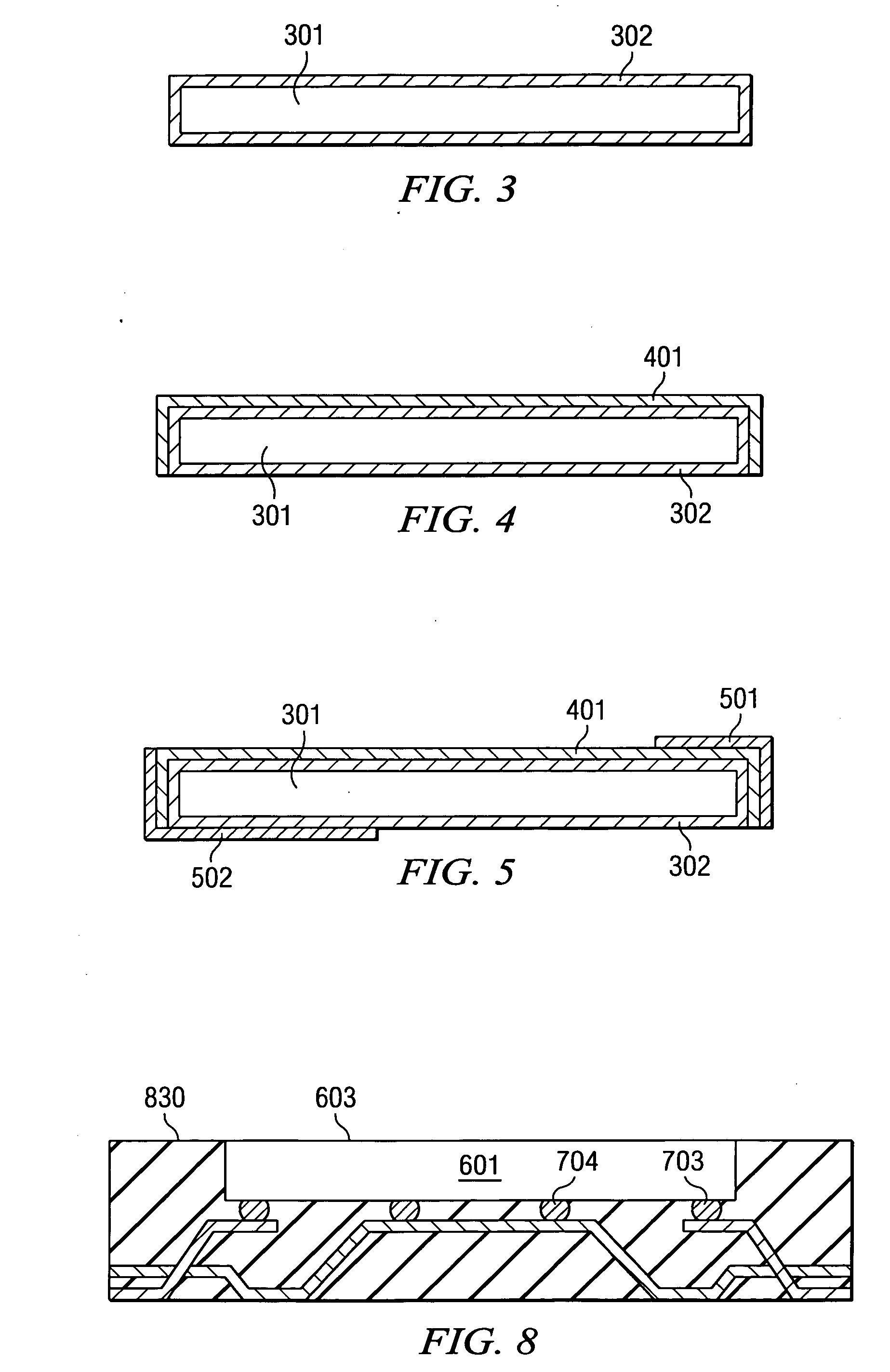
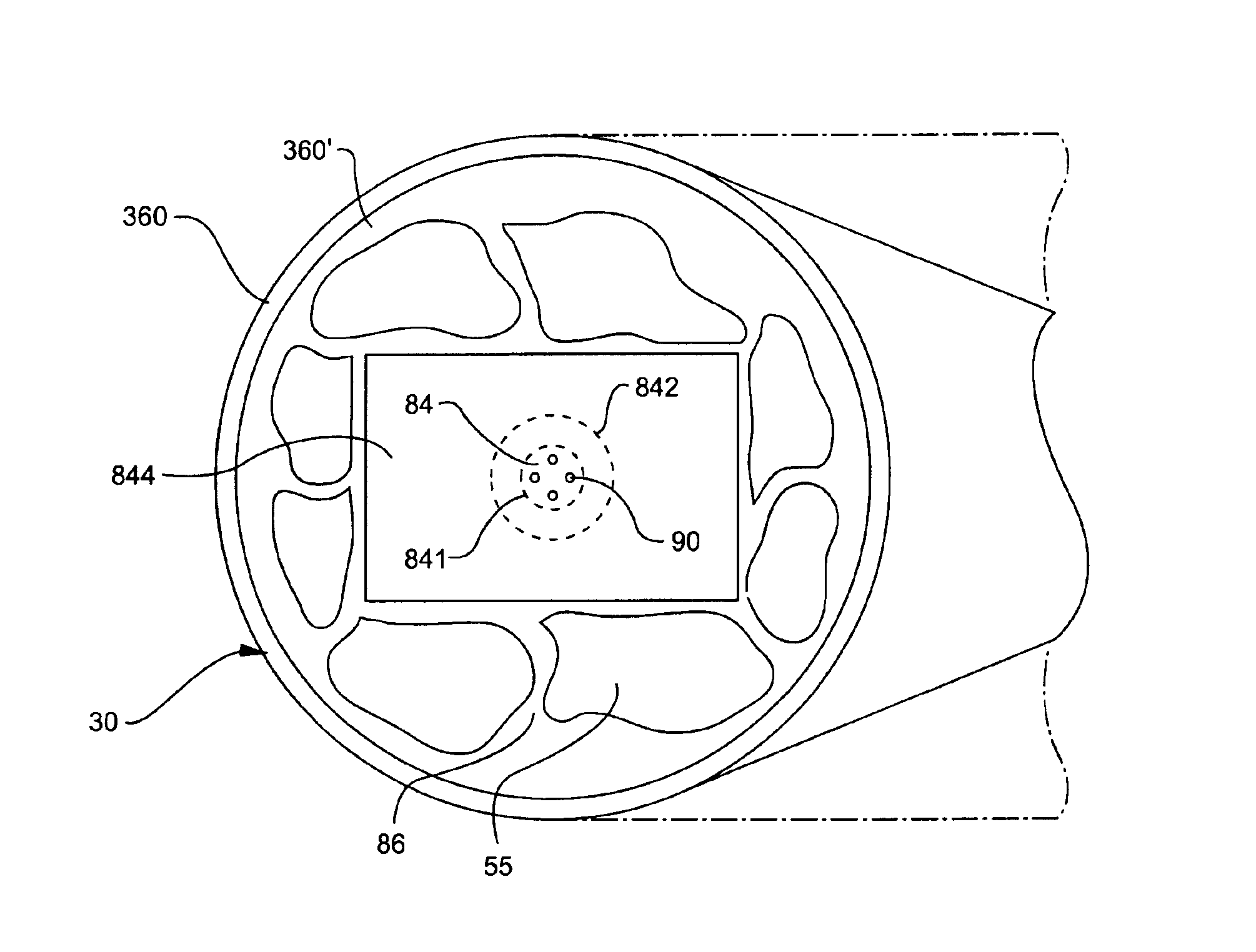
Three-level leadframe for no-lead packages
ActiveUS20050151238A1Tighter segment pitchSemiconductor/solid-state device detailsSolid-state devicesThree levelDevice material
A semiconductor device (700) having a leadframe with a first plurality of segments (110) having a narrow end portion (111) in a first horizontal plane (211) and a wide end portion (112) in a second horizontal plane (212). The leadframe further includes a second plurality of segments (120) having a narrow center portion (121) in the first horizontal plane, at least one wide center portion (122) in the second horizontal plane, and narrow end portions (123) in a third horizontal plane (213), which is located between the first and second planes.
Owner:TEXAS INSTR INC
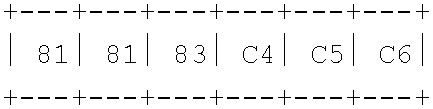
Data structure for creating, scoping, and converting to unicode data from single byte character sets, double byte character sets, or mixed character sets comprising both single byte and double byte character sets
InactiveUS6400287B1Creates delayIndividual digits conversionSpecial data processing applicationsThree levelMacro instruction
A data structure for specifying the types of constants whose character values are to be converted to Unicode; for specifying which code page or pages are used for specifying the character encodings used in the source program for writing the character strings to be converted to Unicode; and that can be used to perform conversions from SBCS, mixed SBCS / DBCS, and pure DBCS character strings to Unicode. A syntax suitable for specifying character data conversion from SBCS, mixed SBCS / DBCS, and pure DBCS representation to Unicode utilizes an extension to the conventional constant subtype notation. In converting the nominal value data to Unicode, currently relevant SBCS and DBCS code pages are used, as specified by three levels or scopes derived from either global options, from local AOPTIONS statement specifications, or from constant-specific modifiers. Global code page specifications apply to the entire source program. These global specifications allow a programmer to declare the source-program code page or code pages just once. These specifications then apply to all constants containing a request for conversion to Unicode. Local code page specifications apply to all subsequent source-program statements. These local specifications allow the programmer to create groups of statements containing Unicode conversion requests, all of which use the same code page or code pages for their source-character encodings. Code page specifications that apply to individual constants allow a detailed level of control over the source data encodings to be used for Unicode conversion. The conversion of source data to Unicode may be implemented inherently to the translator (assembler, compiler, or interpreter) wherein it recognizes and parses the complete syntax of the statement in which the constant or constants is specified, and performs the requested conversion. Alternatively, an external function may be invoked by a variety of source language syntaxes which parses as little or as much of the source statement as its implementation provides, and returns the converted value for inclusion in the generated machine language of the object program. Alternatively, the conversion may be provided by the translator's macro instruction definition facility.
Owner:IBM CORP
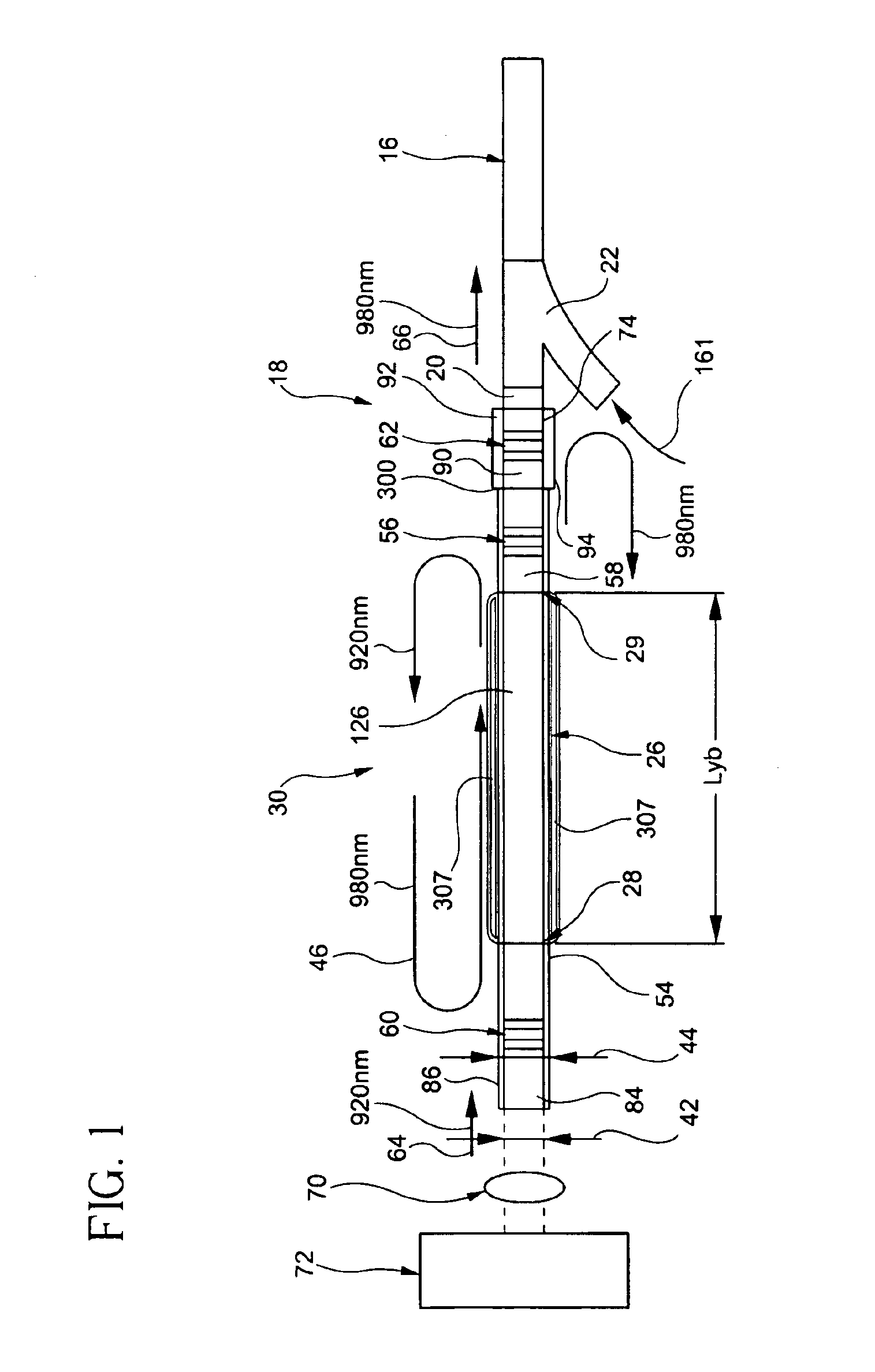
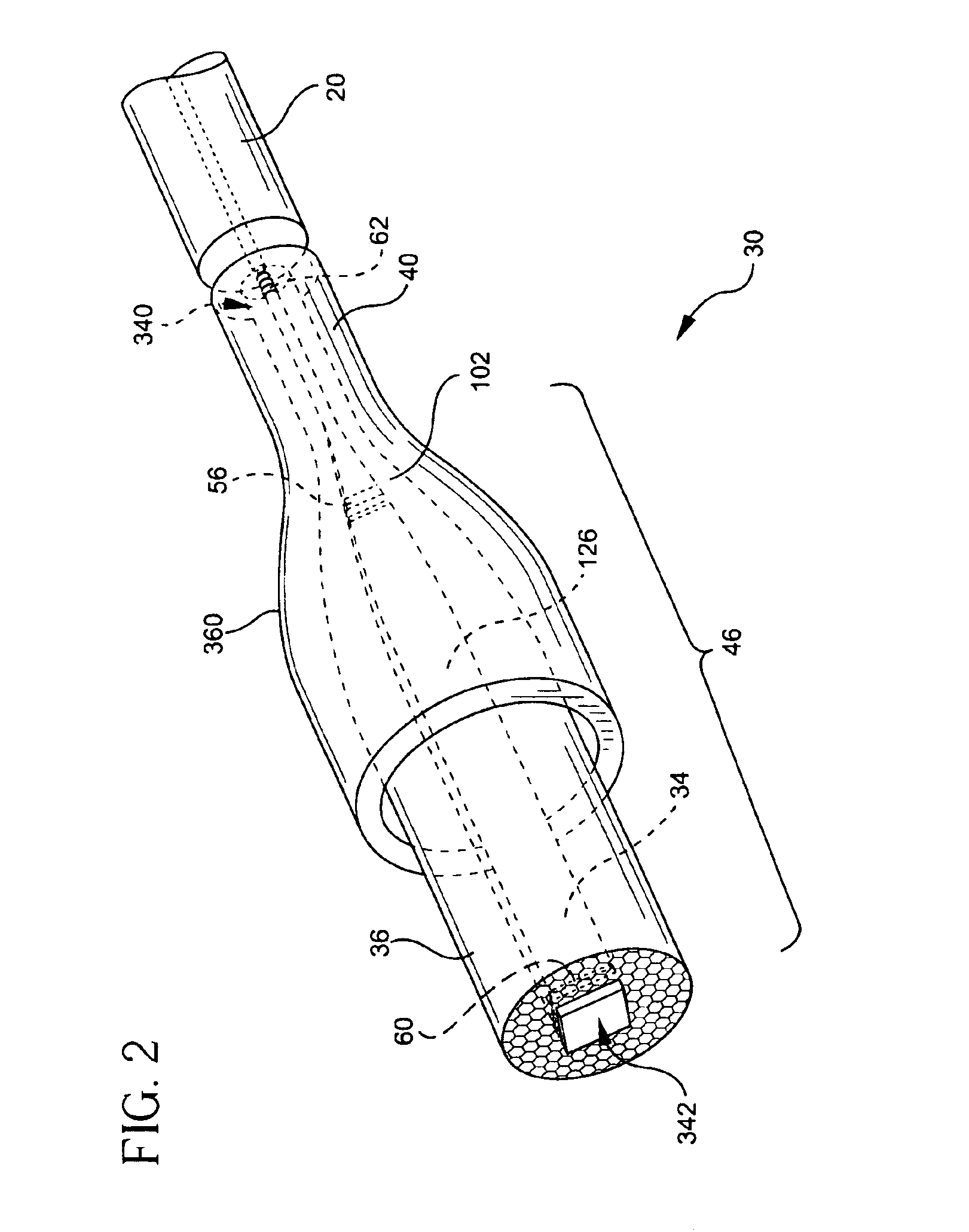
Three-level air-clad rare-earth doped fiber laser/amplifier
InactiveUS6987783B2Facilitates dopingLower effective refractive indexOptical wave guidanceLaser using scattering effectsThree levelAudio power amplifier
An optically-active air-clad fiber (30) includes a core (34, 84) that facilitates doping with an ion optically excitable and having a three-level optical transition when pumped at a first end (28) of an optical cavity (46) by a multimode pump source (72) at a pump wavelength (64) for lasing at a signal wavelength (66) different than the pump wavelength (64) at a second end (29) of the optical cavity (46), the core (34, 84) having a refractive index, wherein the core (34, 84) is transformed from the first end to proximate the second end (29) thereof such that the optically-active fiber (30) is multimode at the pump wavelength proximate to the first end (28), and is single-mode at the signal wavelength proximate to the second end (29). An air-clad (36, 86) surrounds at least one portion of the core (34, 84) and has a lower effective refractive index than the refractive index of the core (34, 84).
Owner:CORNING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com