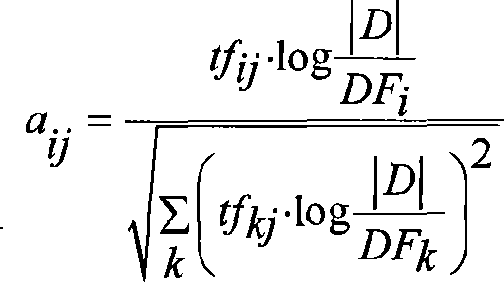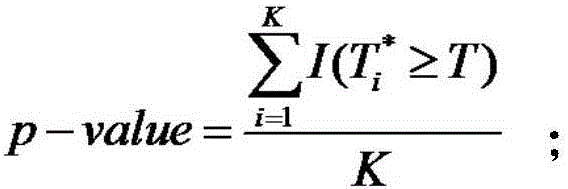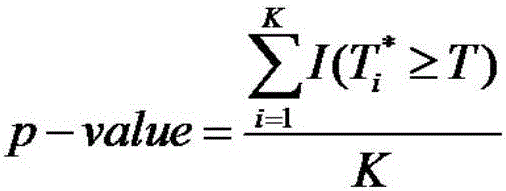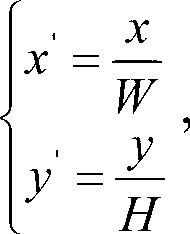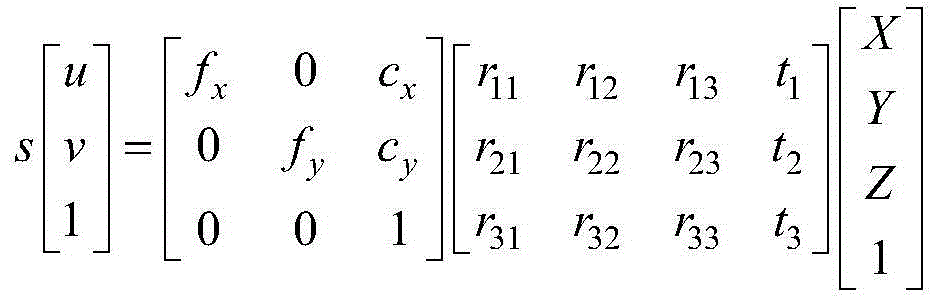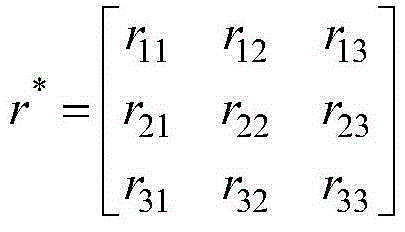Patents
Literature
641 results about "False positive rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In statistics, when performing multiple comparisons, a false positive ratio (or false alarm ratio) is the probability of falsely rejecting the null hypothesis for a particular test. The false positive rate is calculated as the ratio between the number of negative events wrongly categorized as positive (false positives) and the total number of actual negative events (regardless of classification).
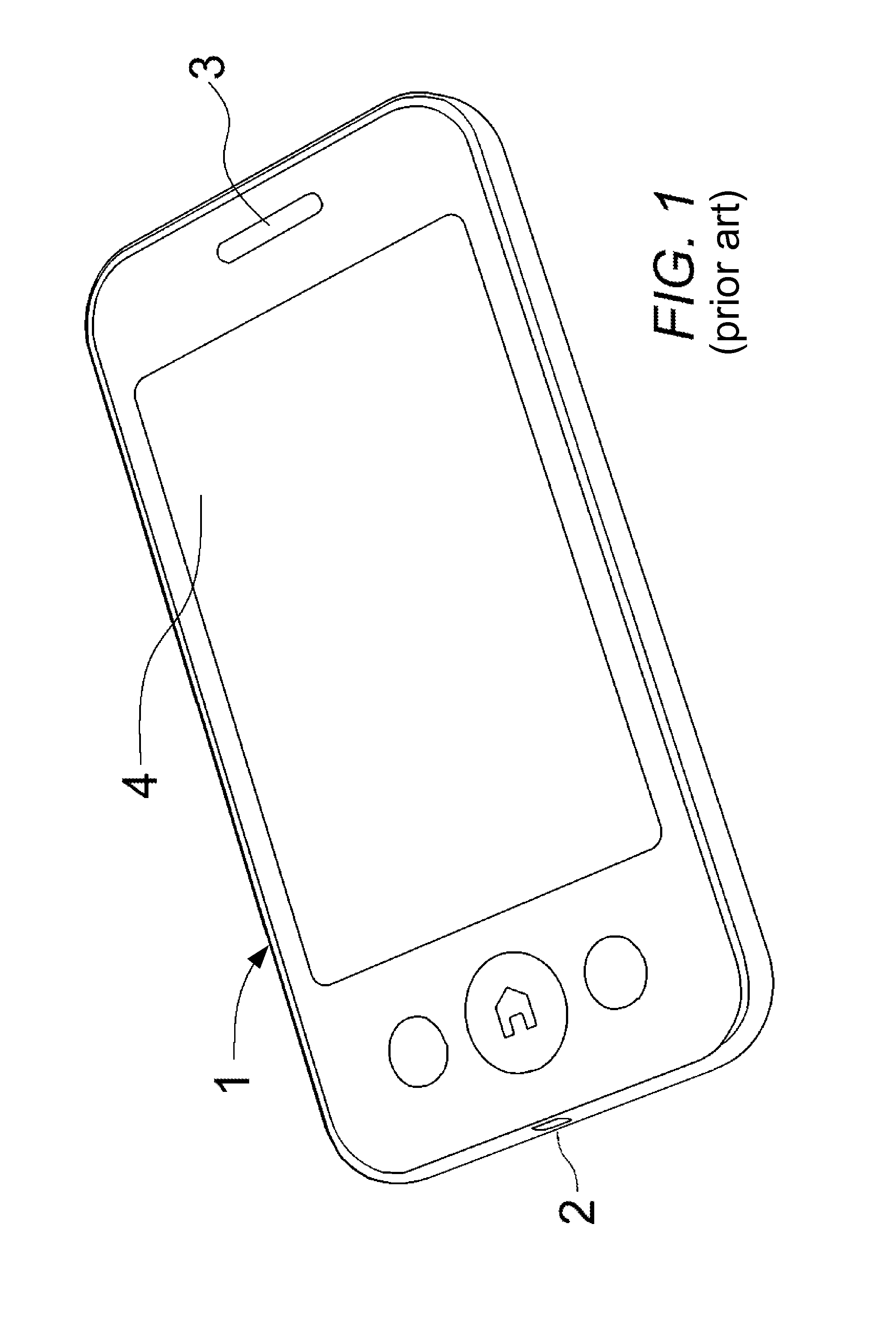
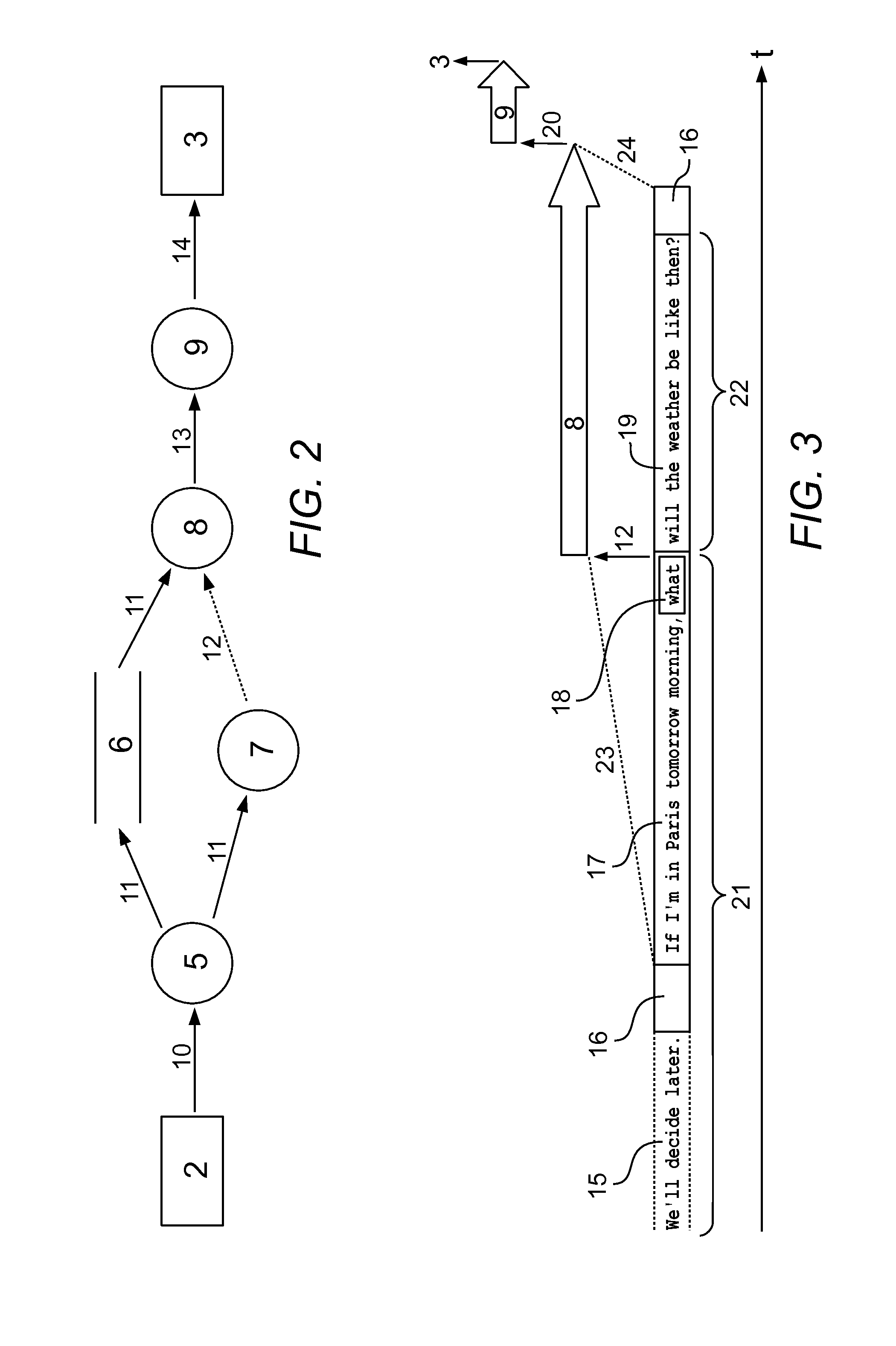
Method for Voice Activation of a Software Agent from Standby Mode
InactiveUS20140214429A1Save energyPower managementDigital data processing detailsDialog systemBiological activation
A method for voice activation of a software agent from a standby mode. In one embodiment, an audio recording (2) is buffered in an audio buffer (6) and at the same time, the audio recording is input to a secondary voice recognition process (7) which is economical in terms of energy and has an increased false positive rate. When a keyword is recognized, a primary voice recognition process (8) is activated from an inactive state, which converts the audio buffer to text and inputs it to a dialog system (9) which analyzes as to whether there is a relevant question made by the user. If this is the case, the user gets an acoustic reply (3), and if this is not the case, the dialog system and the primary voice recognition process immediately return to the inactive state and transfer the control to the secondary voice recognition process.
Owner:INODYN NEWMEDIA
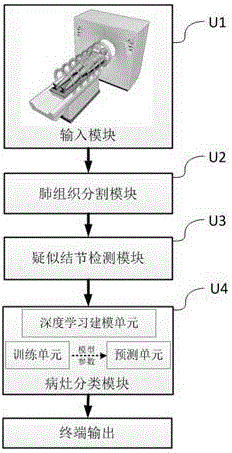
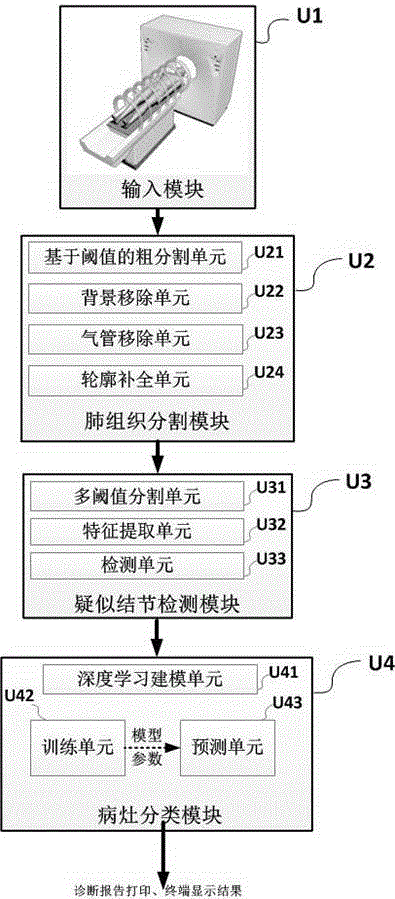
Automatic detection system for pulmonary nodule in chest CT (Computed Tomography) image
ActiveCN106780460AAvoid nodulesImplement classificationImage enhancementImage analysisPulmonary nodulePrediction probability
The invention relates to an automatic detection system for a pulmonary nodule in a chest CT (Computed Tomography) image. The system provides improvements for the problems of large calculated amount of computer aided software, inaccurate prediction and few prediction varieties. The improvement of the invention comprises the steps of acquiring a CT image; segmenting a pulmonary tissue; detecting a suspected nodular lesion area in the pulmonary tissue; classifying nidi based on a nidus classification model of deep learning; and outputting an image mark and a diagnosis report. The system has high nodule detection rate and relatively low false positive rate, acquires an accurate locating, quantitative and qualitative result of a nodular lesion and a prediction probability thereof. The end-to-end (from a CT machine end to a doctor end) nodular lesion screening is truly realized, the accuracy and operability demands of doctors are satisfied and the system has wide mar5ket application prospects.
Owner:杭州健培科技有限公司
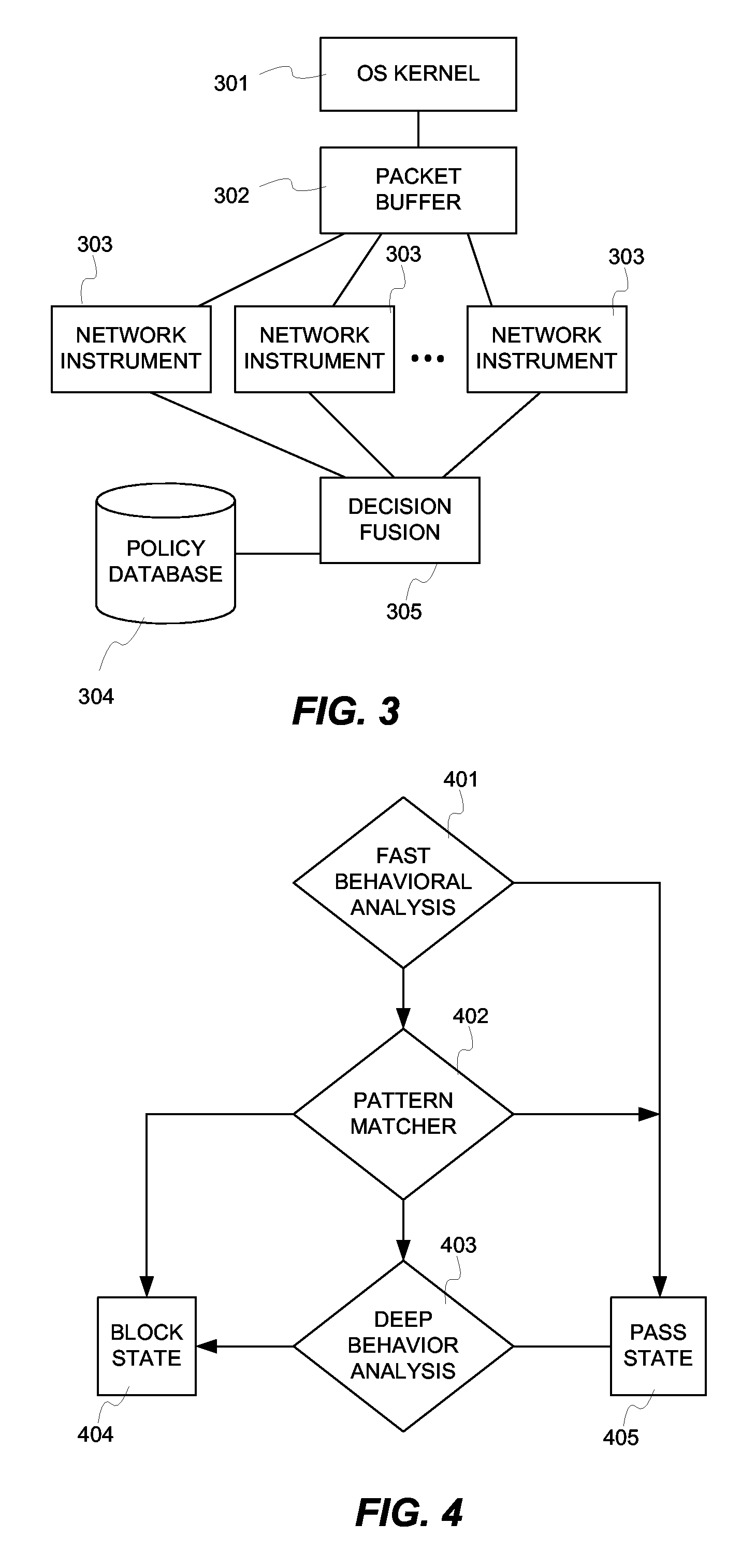
Fusion instrusion protection system
InactiveUS20070056038A1Solve the high false positive rateEfficient Anomaly DetectionMemory loss protectionError detection/correctionAnomaly detectionSensor fusion
An intrusion protection system that fuses a network instrumentation classification with a packet payload signature matching system. Each of these kinds of systems is independently capable of being effectively deployed as an anomaly detection system. By employing sensor fusion techniques to combine the instrumentation classification approach with the signature matching approach, the present invention provides an intrusion protection system that is uniquely capable of detecting both well known and newly developed threats while having an extremely low false positive rate.
Owner:LOK TECH
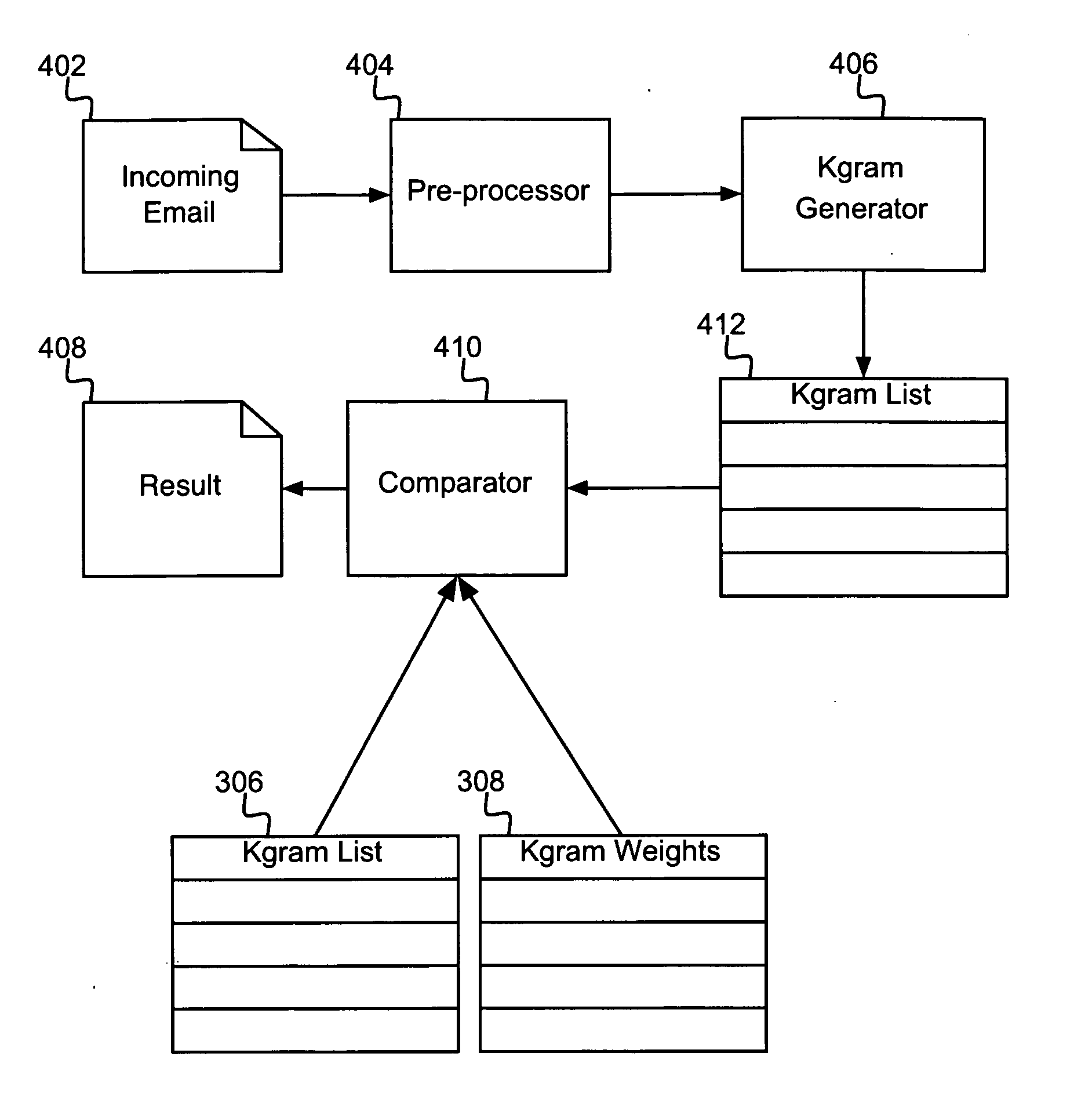
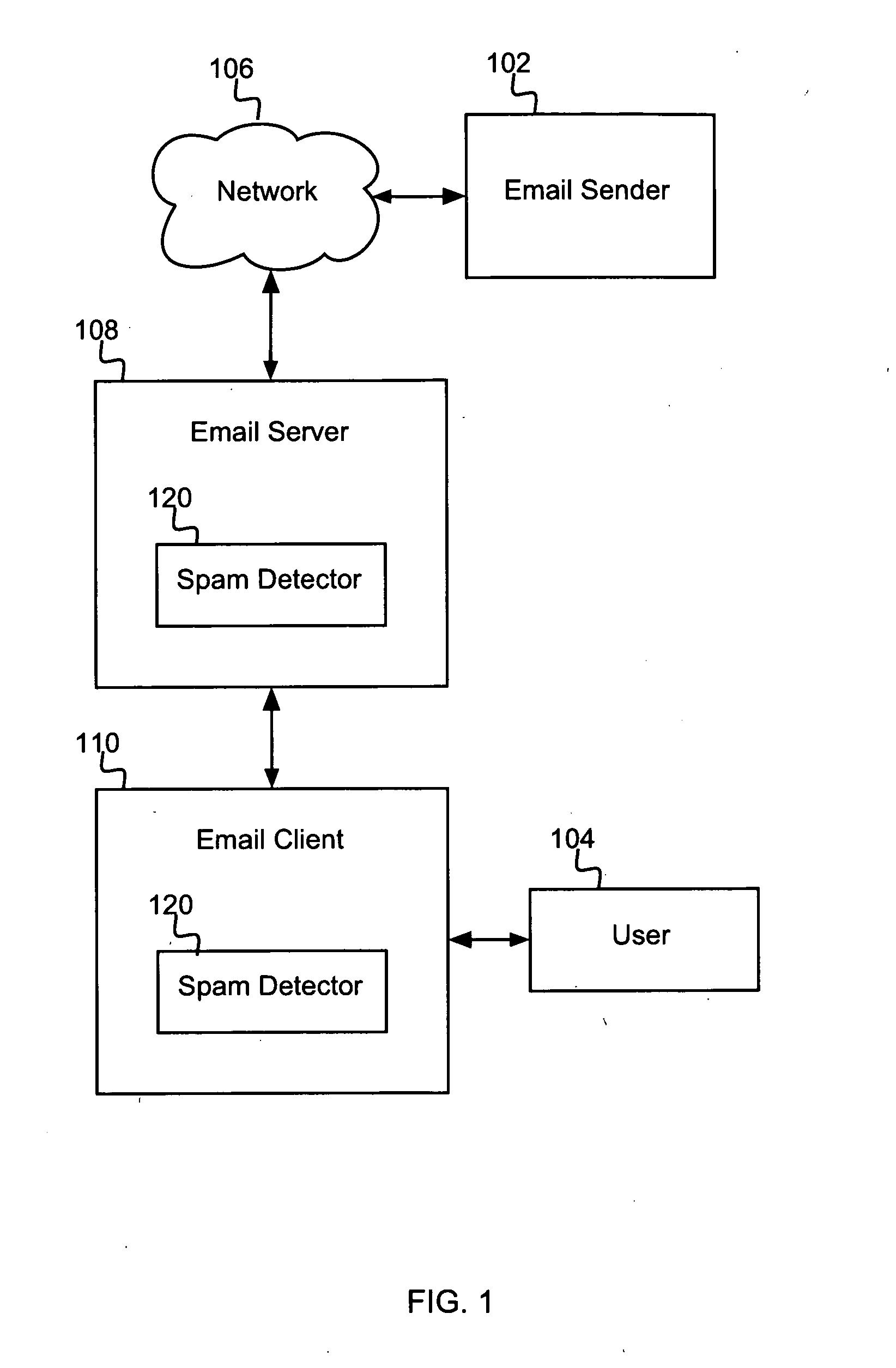
Detecting spam email using multiple spam classifiers
InactiveUS20060149821A1Multiple digital computer combinationsData switching networksSpammingData mining
A method for detecting undesirable emails is disclosed. The method combines input from two or more spam classifiers to provide improved classification effectiveness and robustness. The method's effectiveness is improved over that of any one constituent classifier in the sense that the detection rate is increased and / or the false positive rate is decreased. The method's robustness is improved in the sense that, if spammers temporarily elude any one constituent classifier, the other constituent classifiers will still be likely to catch the spam. The method includes obtaining a score from each of a plurality of constituent spam classifiers by applying them to a given input email. The method further includes obtaining a combined spam score from a combined spam classifier that takes as input the plurality of constituent spam classifier scores, the combined spam classifier being computed automatically in accordance with a specified false-positive vs. false-negative tradeoff. The method further includes identifying the given input email as an undesirable email if the combined spam score indicates that the input e-mail is undesirable.
Owner:IBM CORP
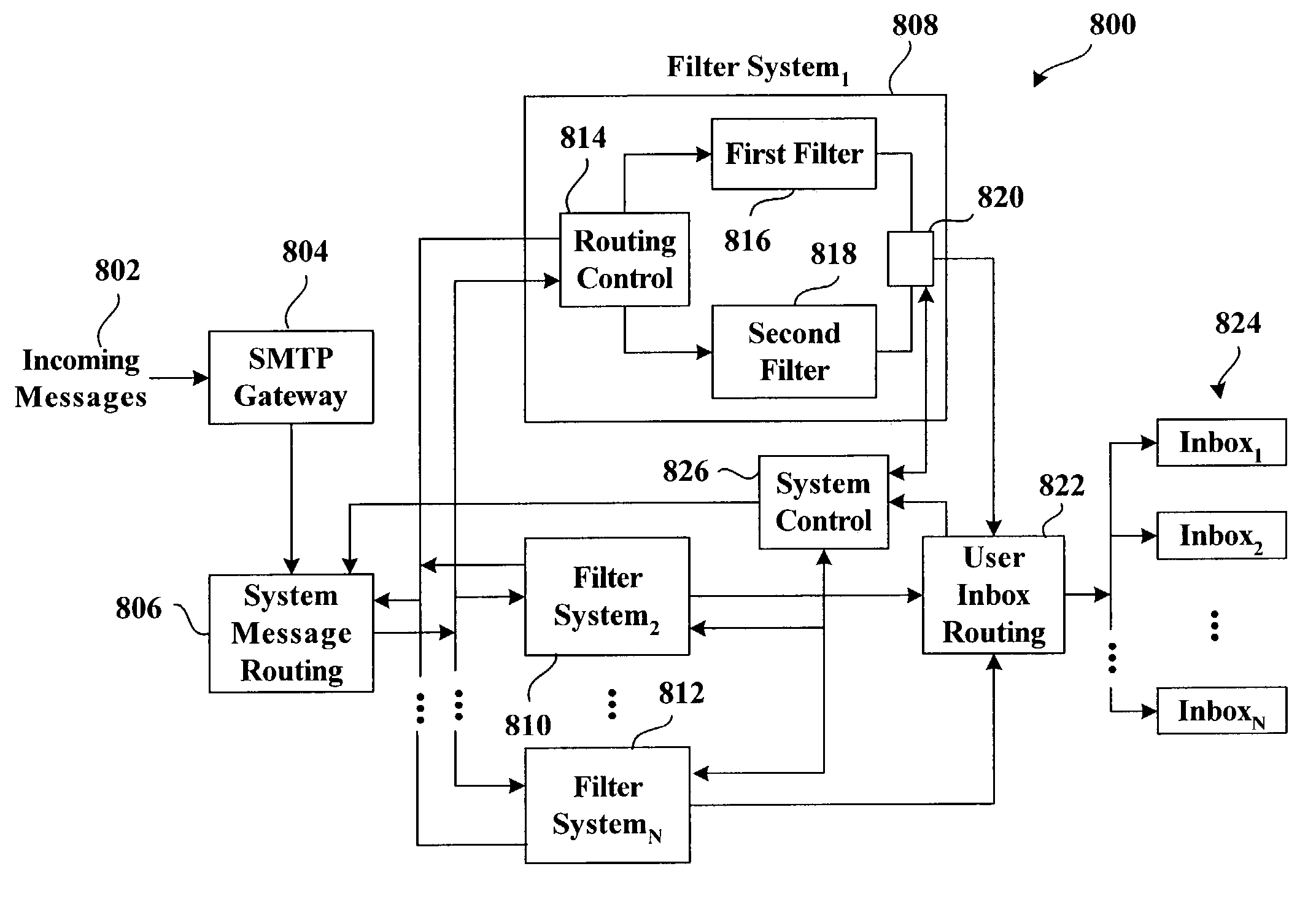
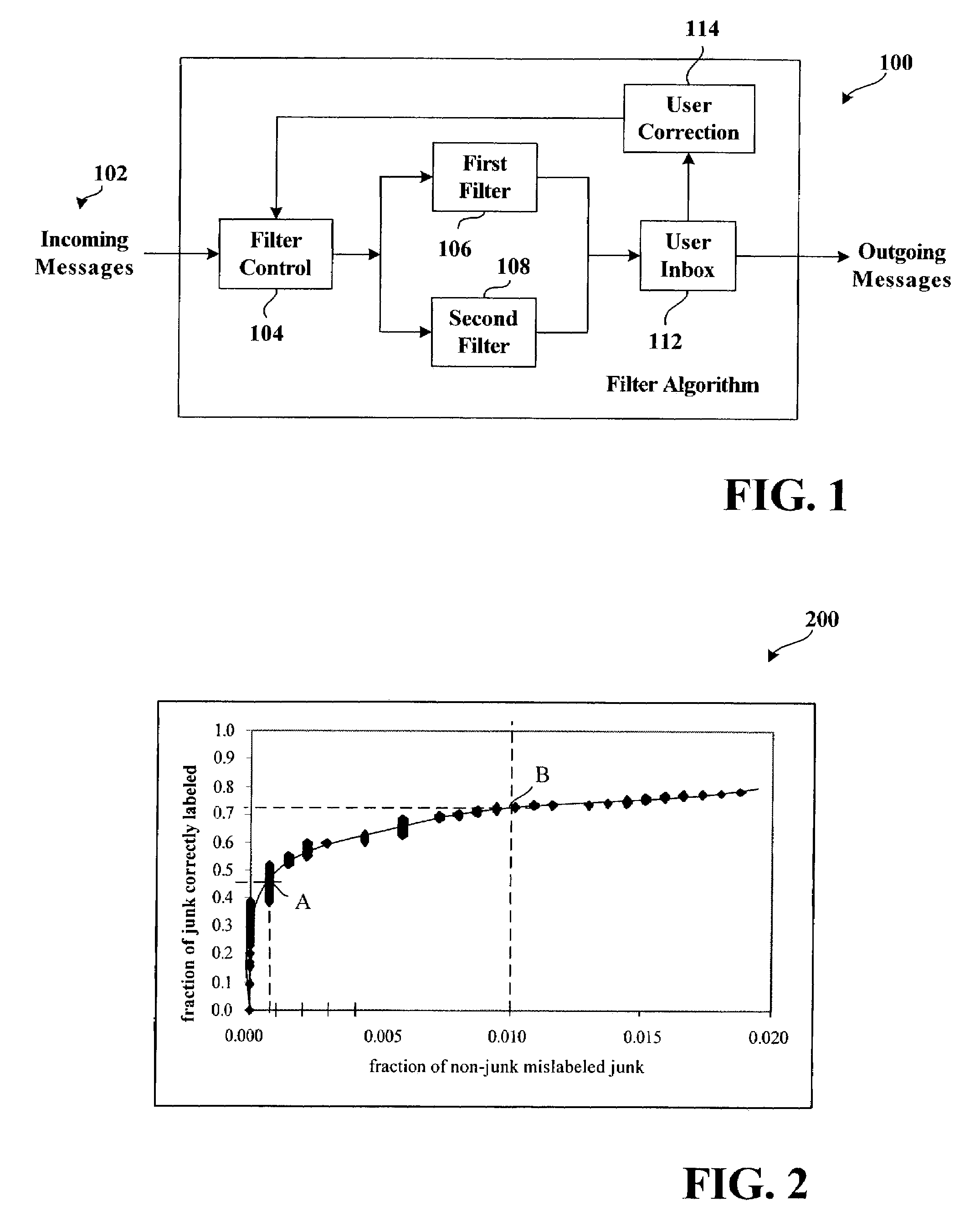
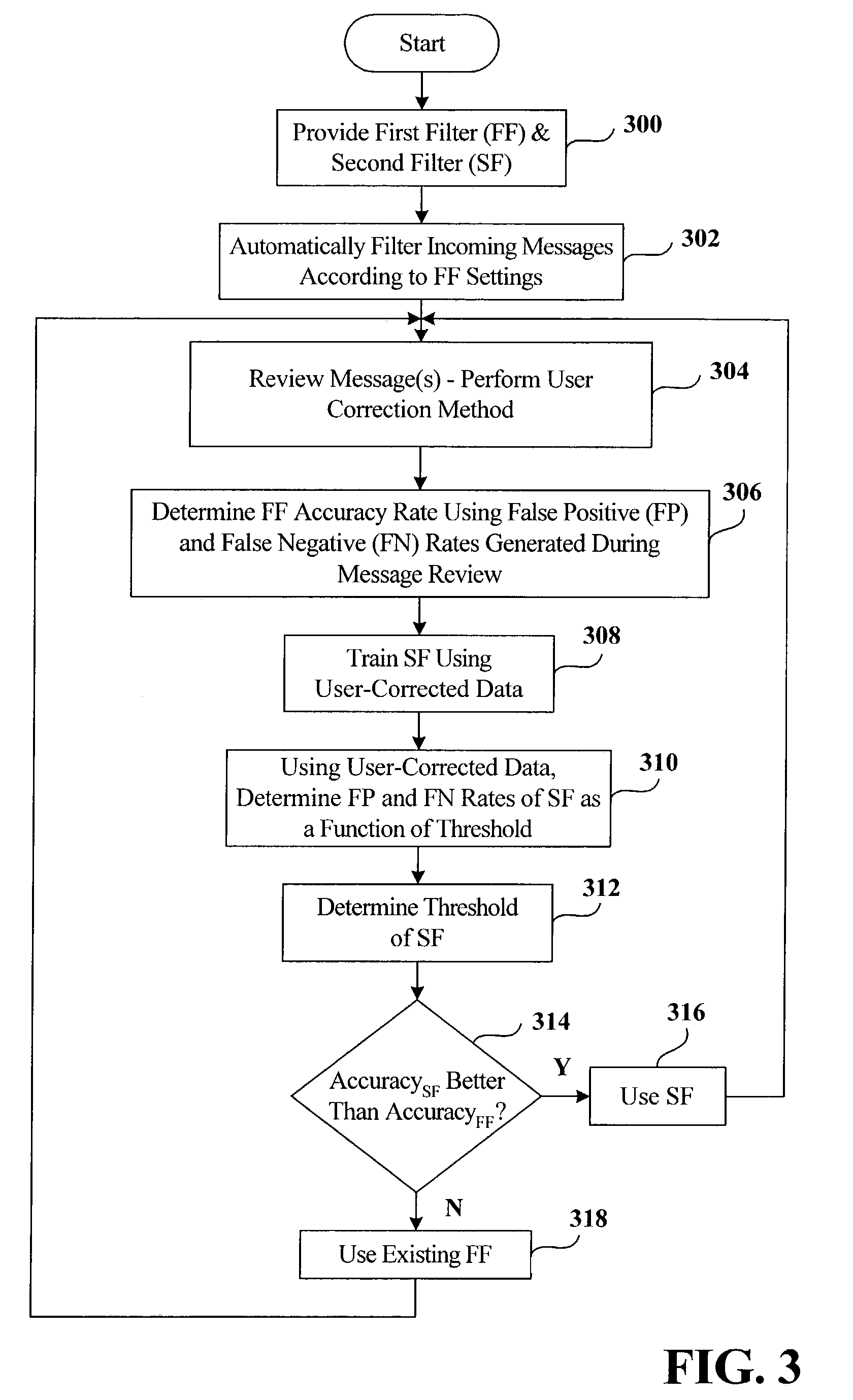
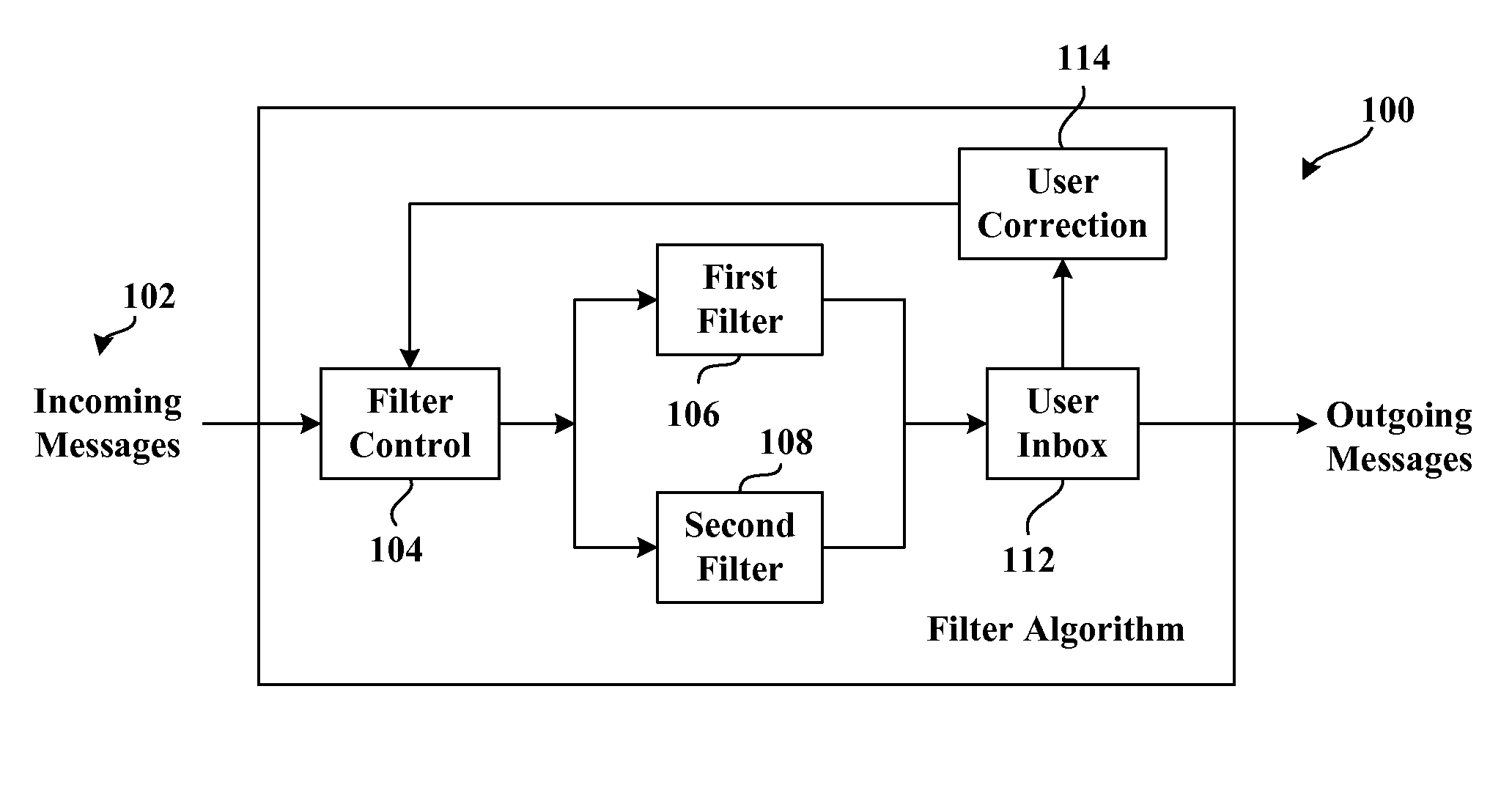
Adaptive junk message filtering system
InactiveUS7249162B2Well formedPromote employmentMultiple digital computer combinationsOffice automationFilter systemSelf adaptive
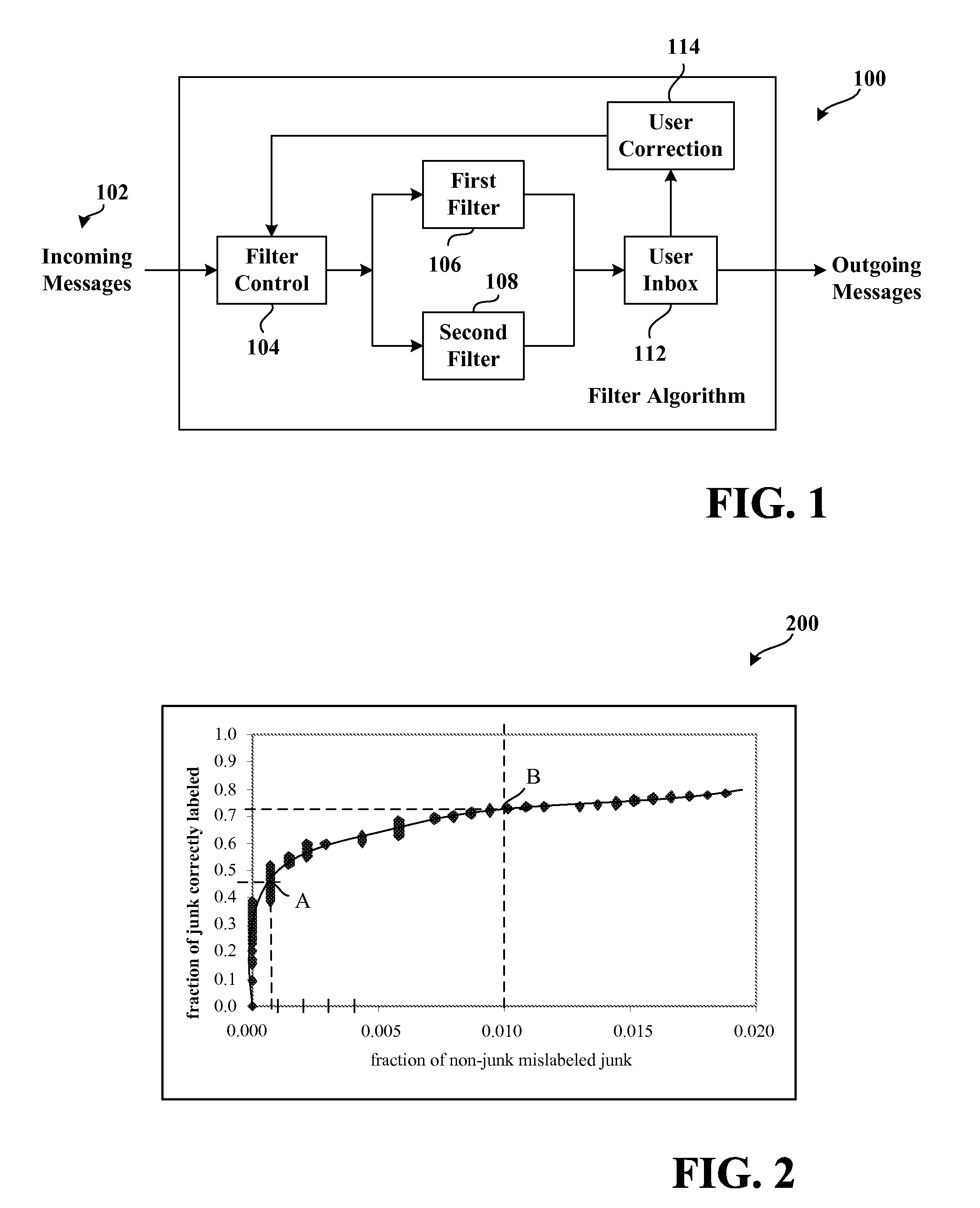
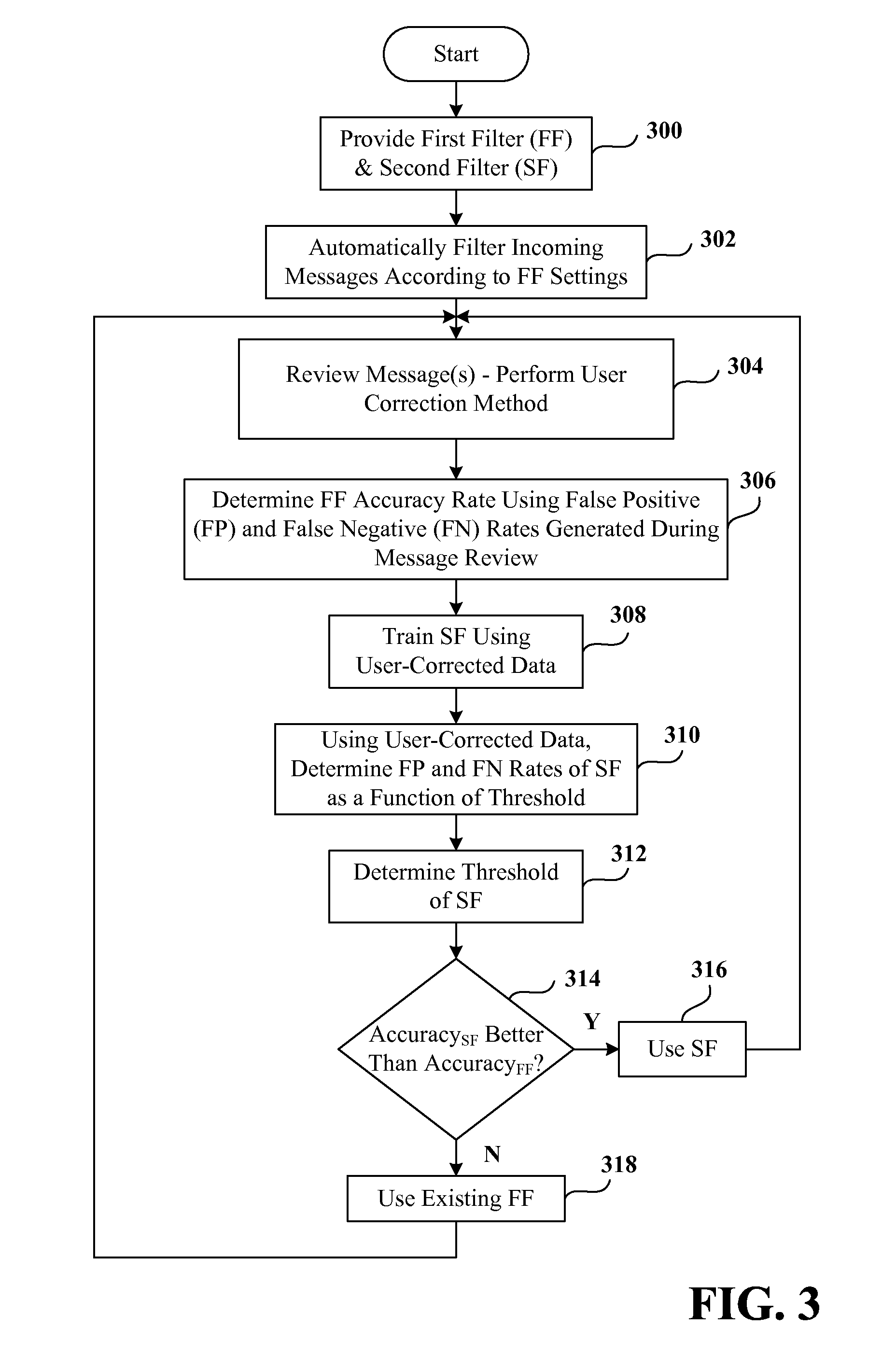
The invention relates to a system for filtering messages—the system includes a seed filter having associated therewith a false positive rate and a false negative rate. A new filter is also provided for filtering the messages, the new filter is evaluated according to the false positive rate and the false negative rate of the seed filter, the data used to determine the false positive rate and the false negative rate of the seed filter are utilized to determine a new false positive rate and a new false negative rate of the new filter as a function of threshold. The new filter is employed in lieu of the seed filter if a threshold exists for the new filter such that the new false positive rate and new false negative rate are together considered better than the false positive and the false negative rate of the seed filter.
Owner:MICROSOFT TECH LICENSING LLC
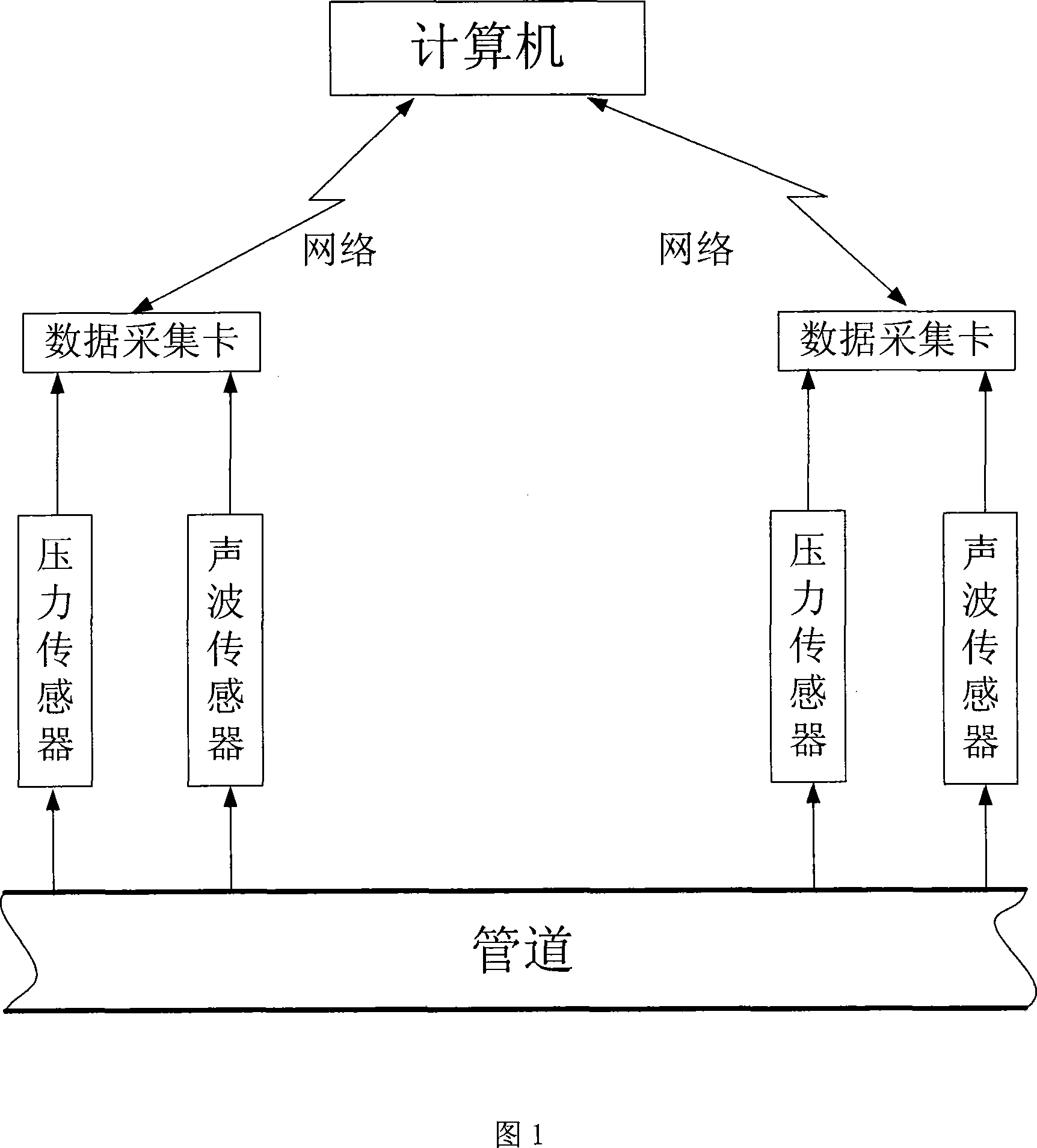
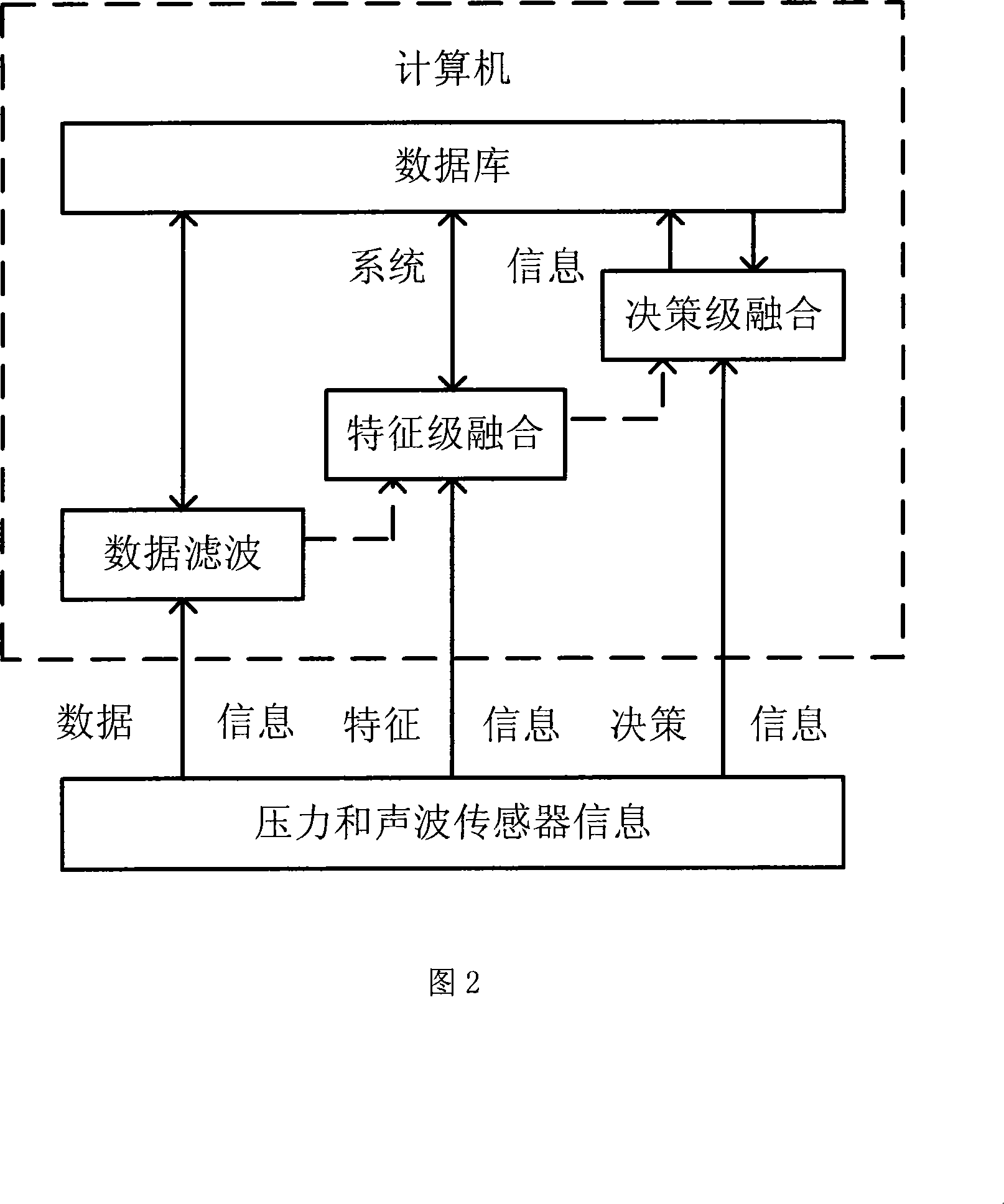
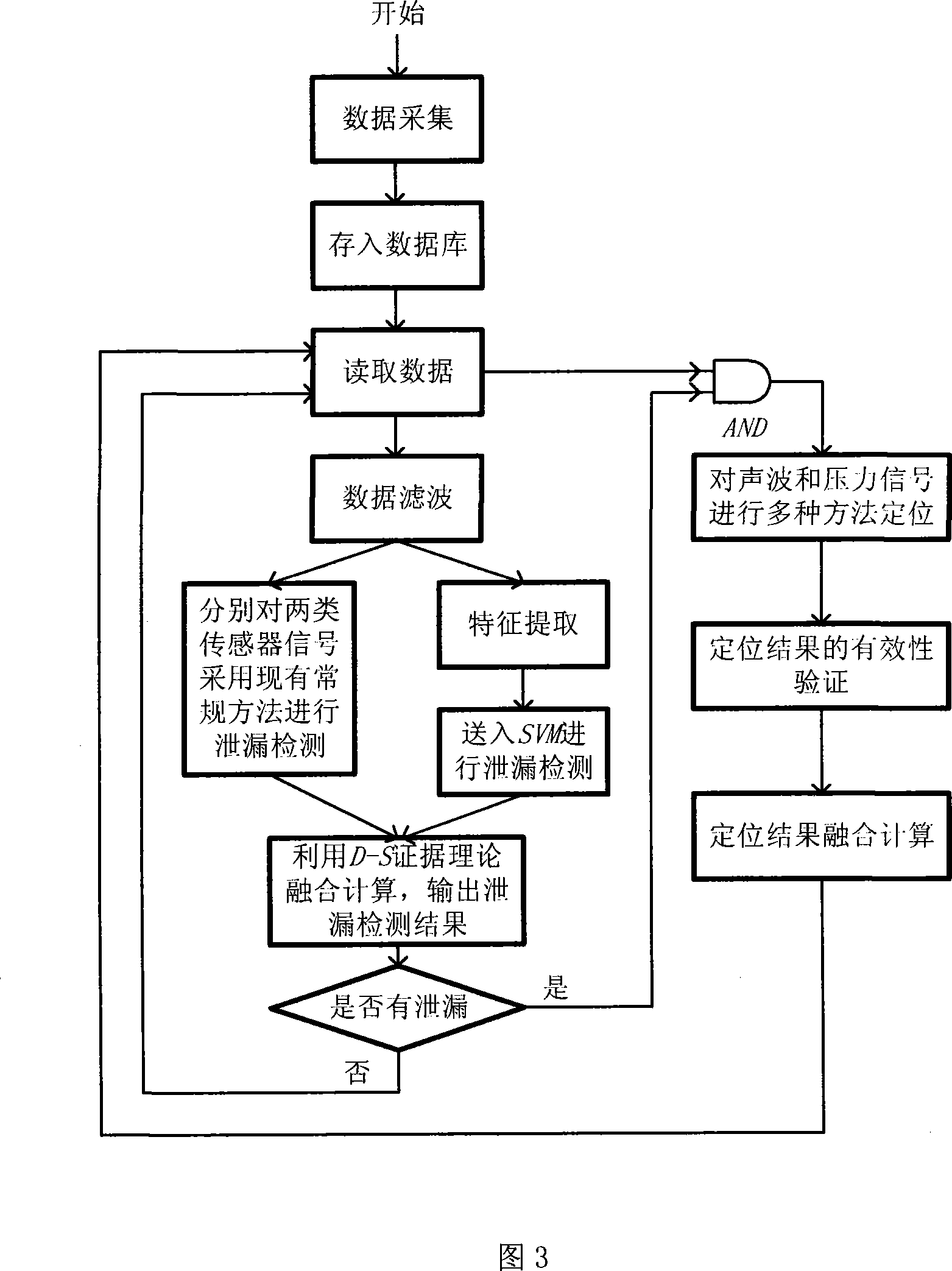
Leakage detecting and locating method based on pressure and sound wave information amalgamation
ActiveCN101196872AHigh precisionReduce false alarm ratePipeline systemsSpecial data processing applicationsThree levelAcoustic wave
A leakage detection location method based on pressure and sound information integration is provided, which belongs to the technology field of an oil (gas) pipeline fault diagnosis, and is characterized by leakage detection and leakage location based on information integration. The former comprises: separately acquiring the measurement data of the pressure on the upperstream end and downstream end of the pipeline and a sound wave sensor, sending the data to a computer and gaining final detection results through three levels processing including data filtering, characteristic level integration and decision level integration. If the detection result shows leakage, starting leakage location process based on information integration. The process first carries out leakage location by separately adopting the signals of two kinds of sensors and a plurality of different leakage location algorithms and finally gains the location results via integration of the location results based on the same sensor and different location methods and two levels processing based on the integration of the location results of two kinds of different sensors. The method can effectively reduce the false positive rate and false negative rate and improve the location precision.
Owner:TSINGHUA UNIV
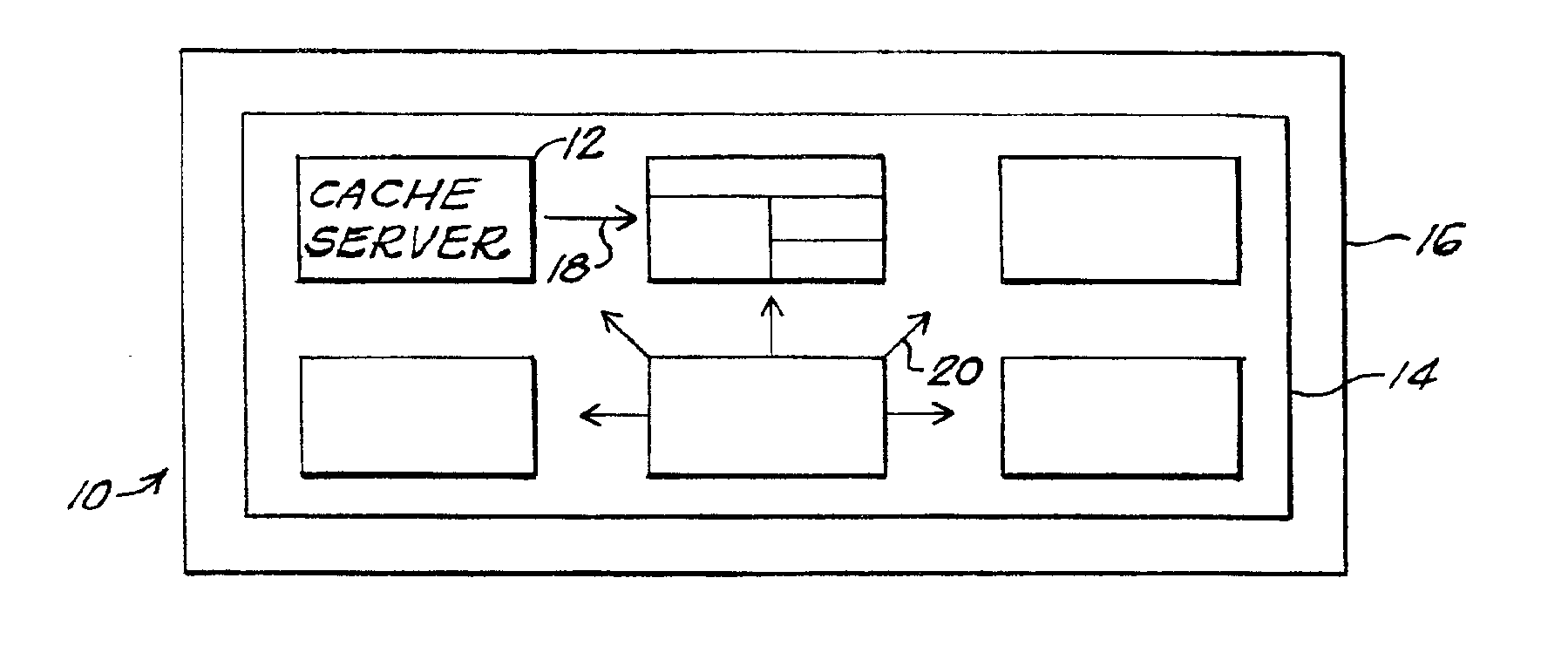
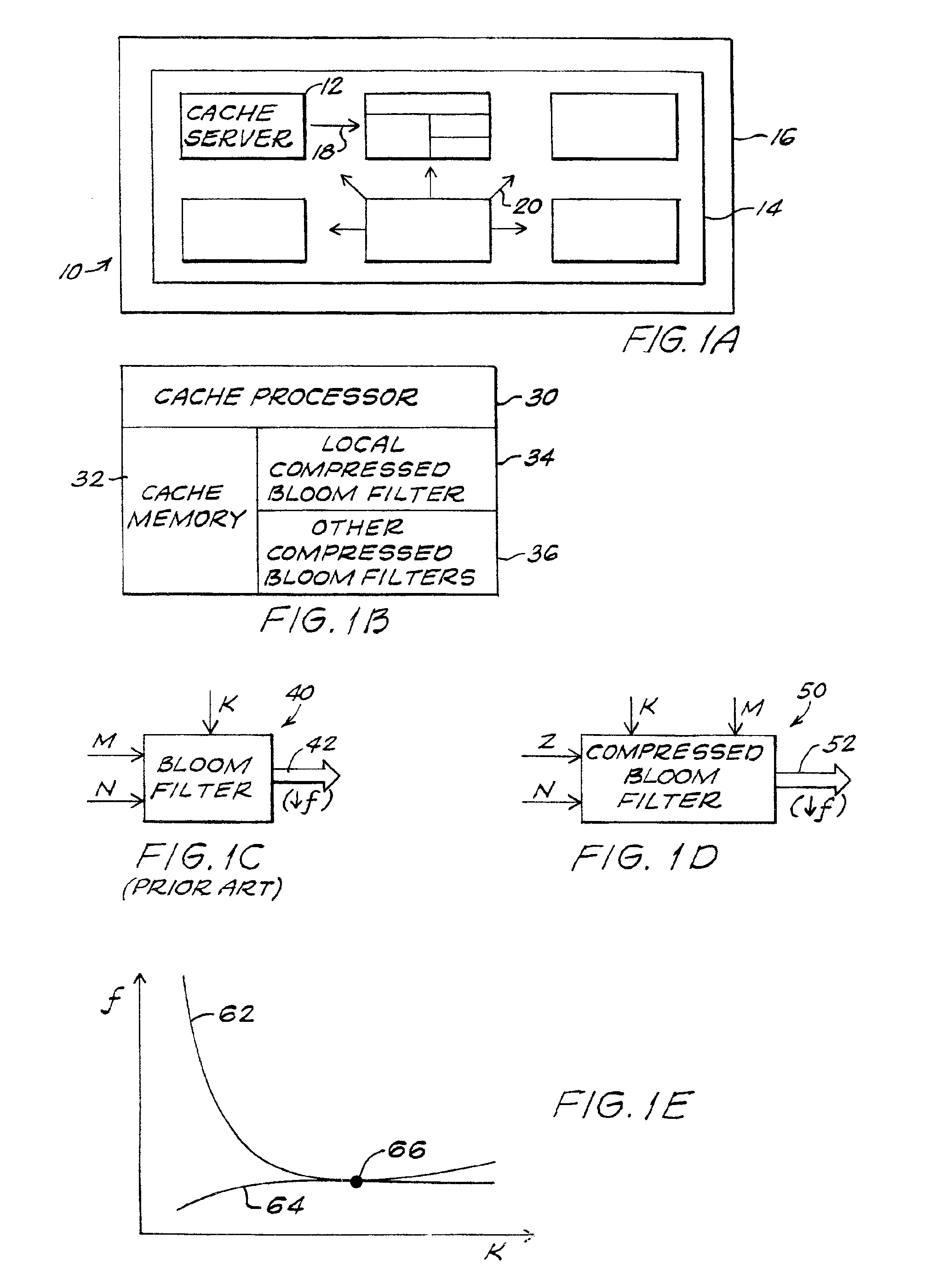
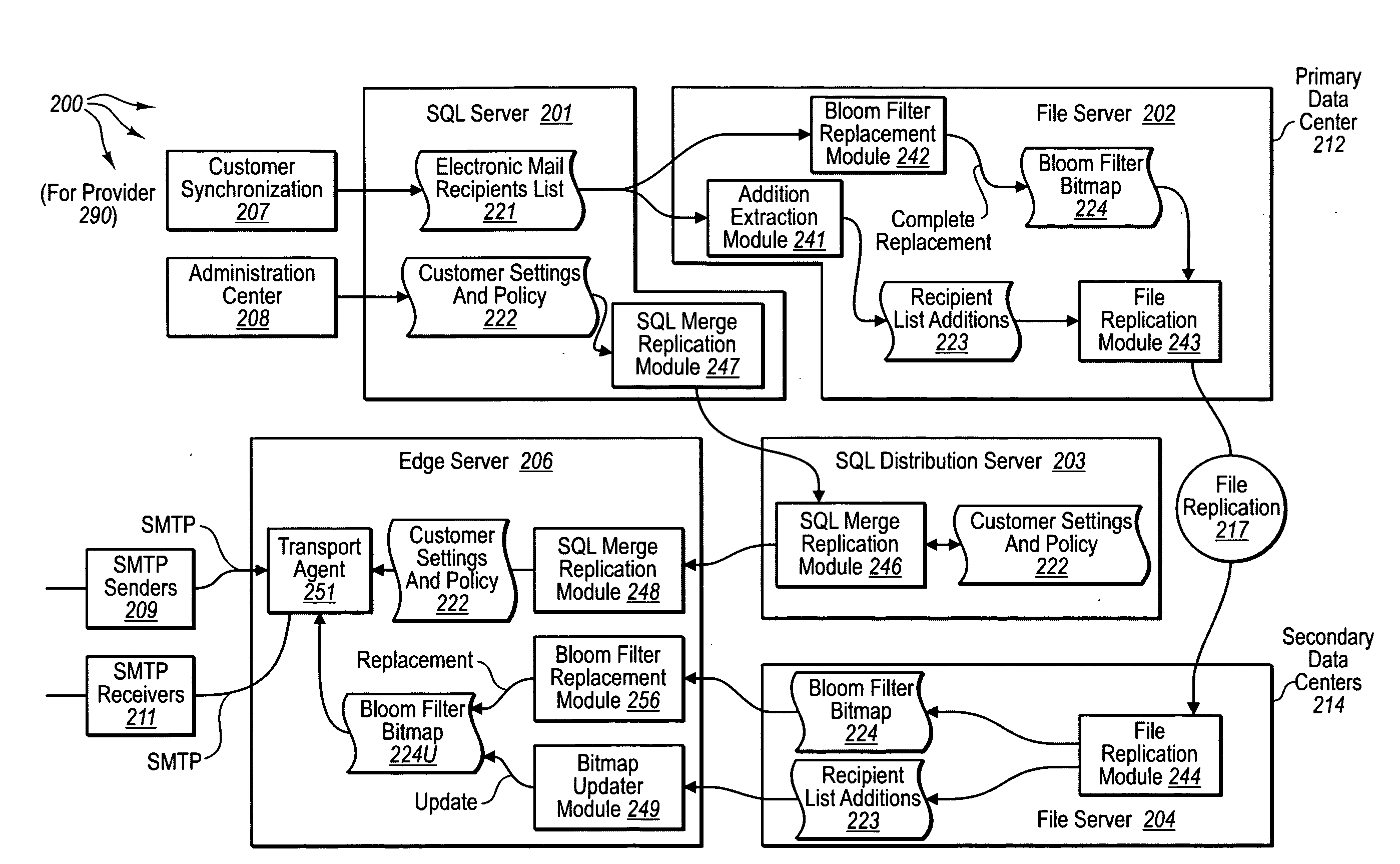
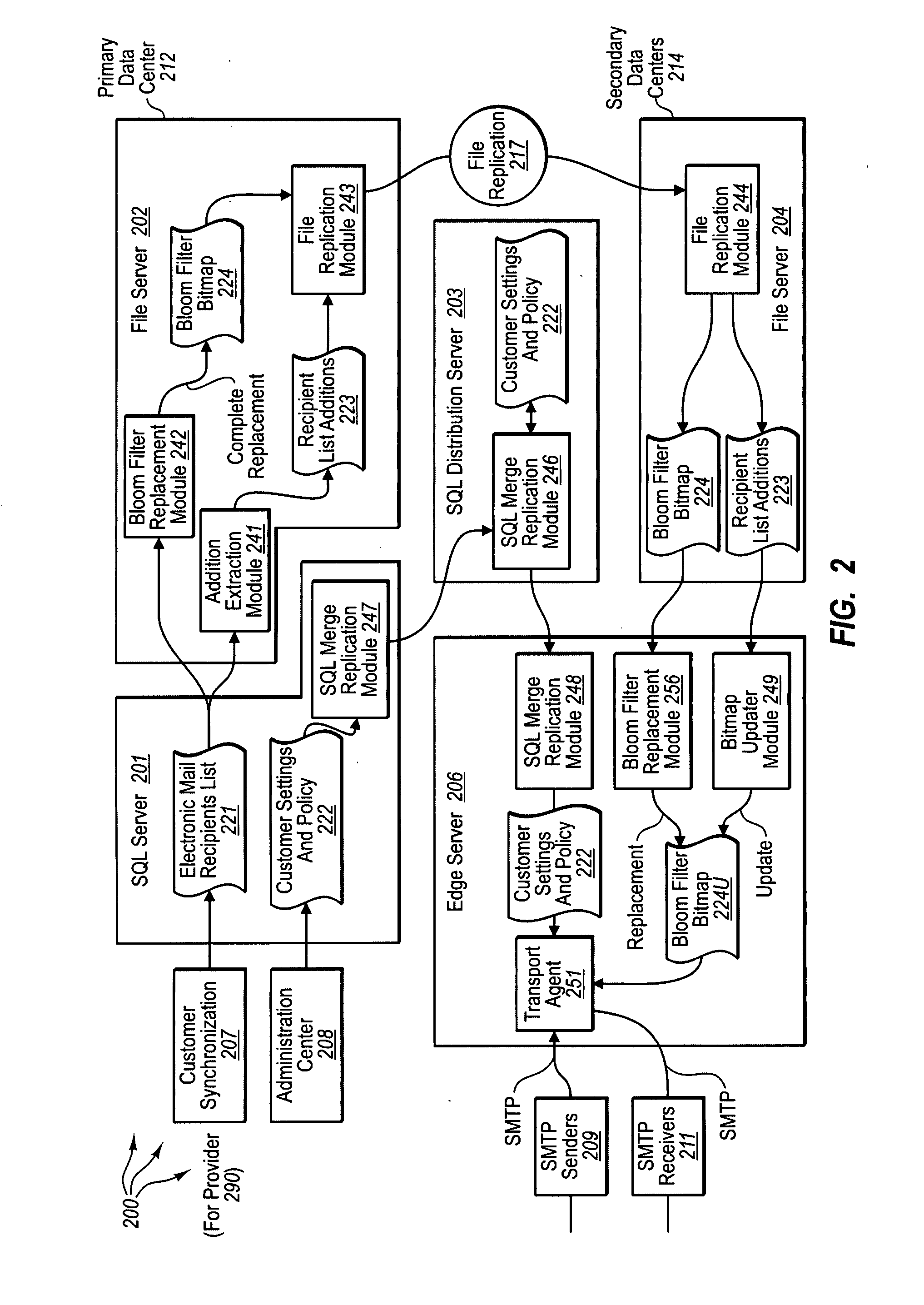
Distributed, compressed Bloom filter Web cache server
InactiveUS6920477B2Minimizing rateReduce false alarm rateData processing applicationsMultiple digital computer combinationsArray data structureWeb cache
Compressed Bloom filters that act as a message as well as a data structure provide smaller false positive rates, reduced bits broadcast and / or reduced computational overhead in distributed Web proxy servers and other distributed networks.
Owner:BREED AUTOMOTIVE TECH INC +1
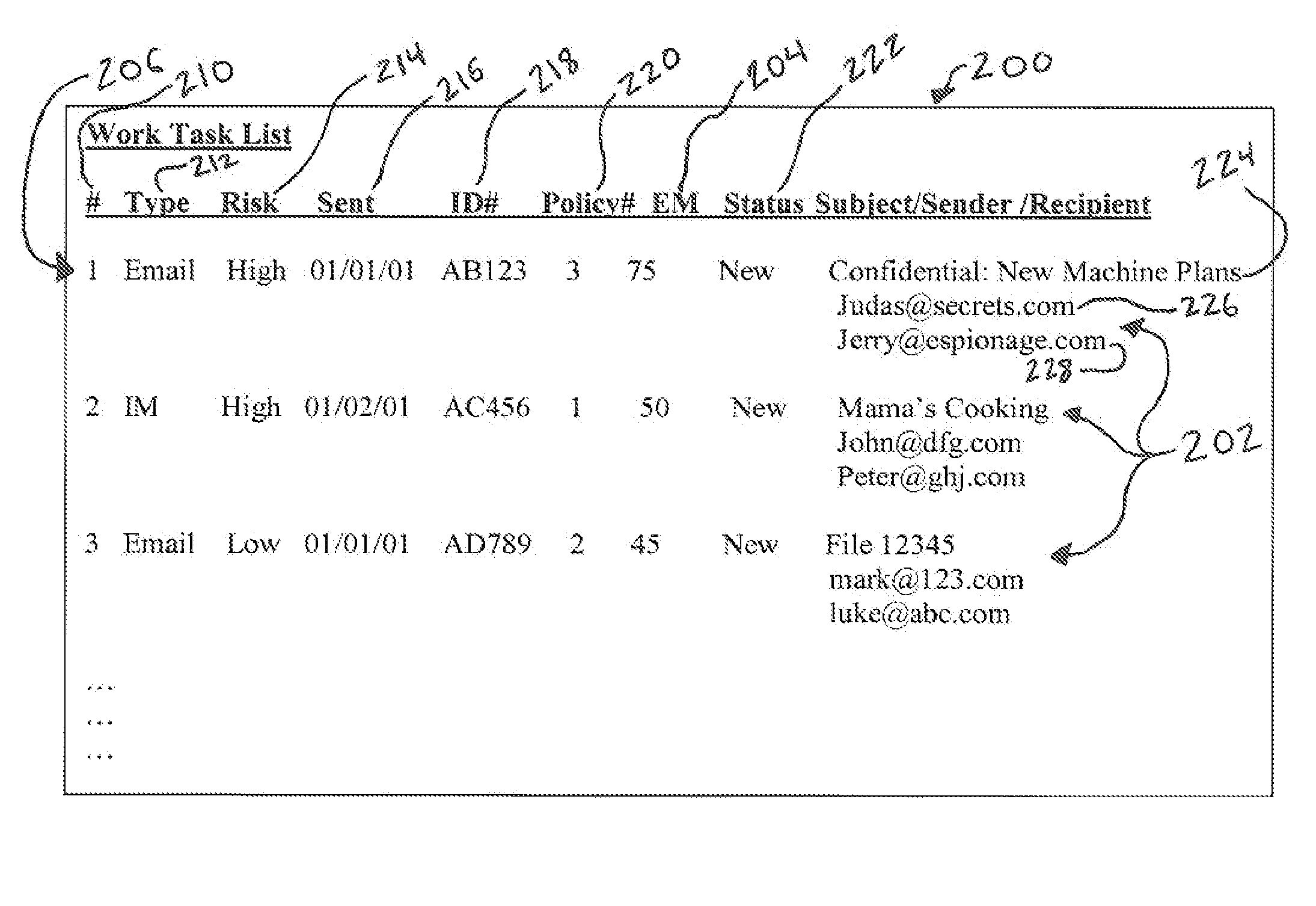
Work prioritization system and method
InactiveUS20080168453A1Multiprogramming arrangementsComputer security arrangementsWork taskComputer science
A work prioritization system and method that includes determining a task false positive rate for the work task. The work prioritization system and method may further include determining an event materiality score based on the task false positive rate and prioritizing the work task within the plurality of work tasks based on the event materiality score.
Owner:CATERPILLAR INC
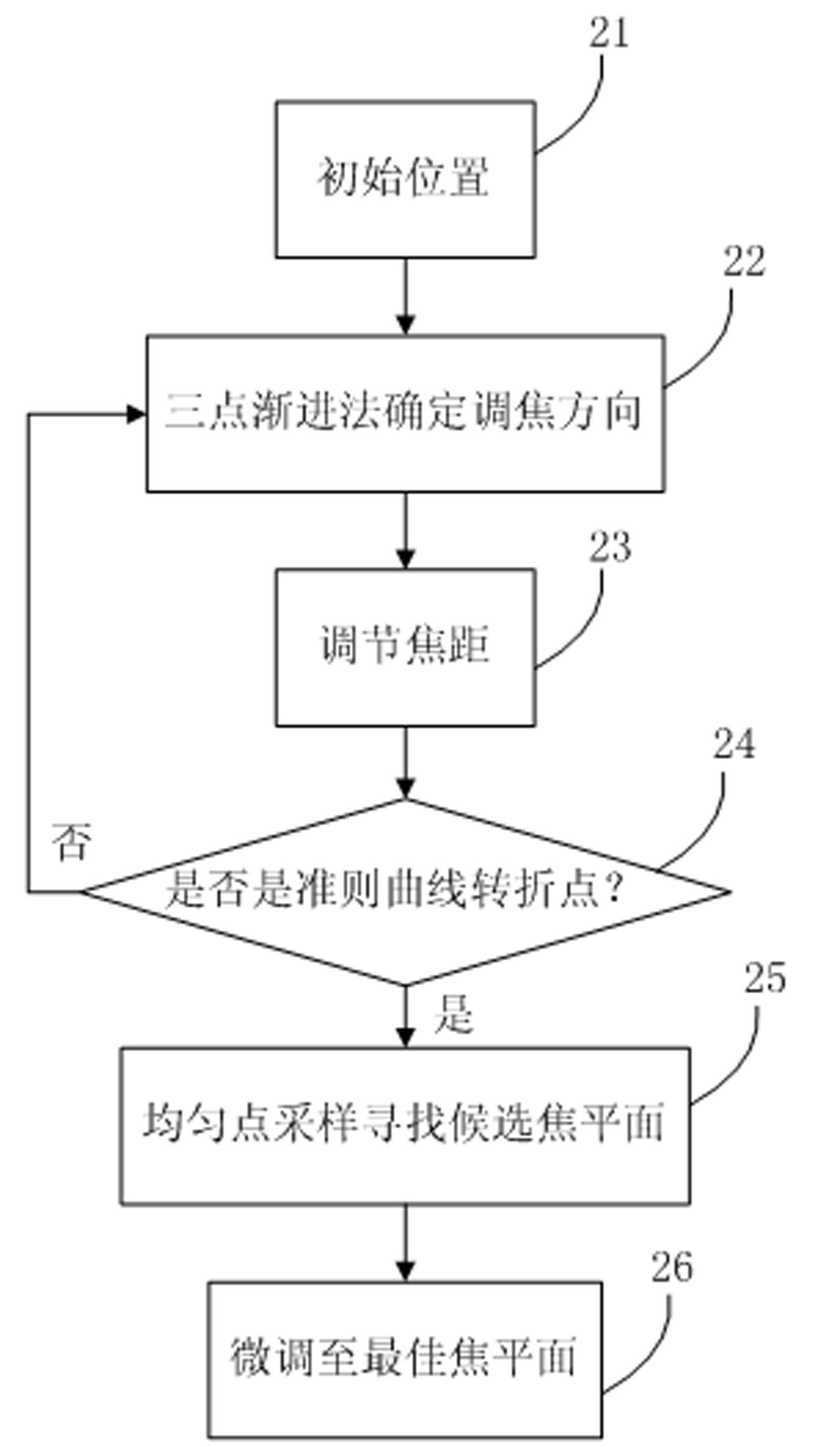
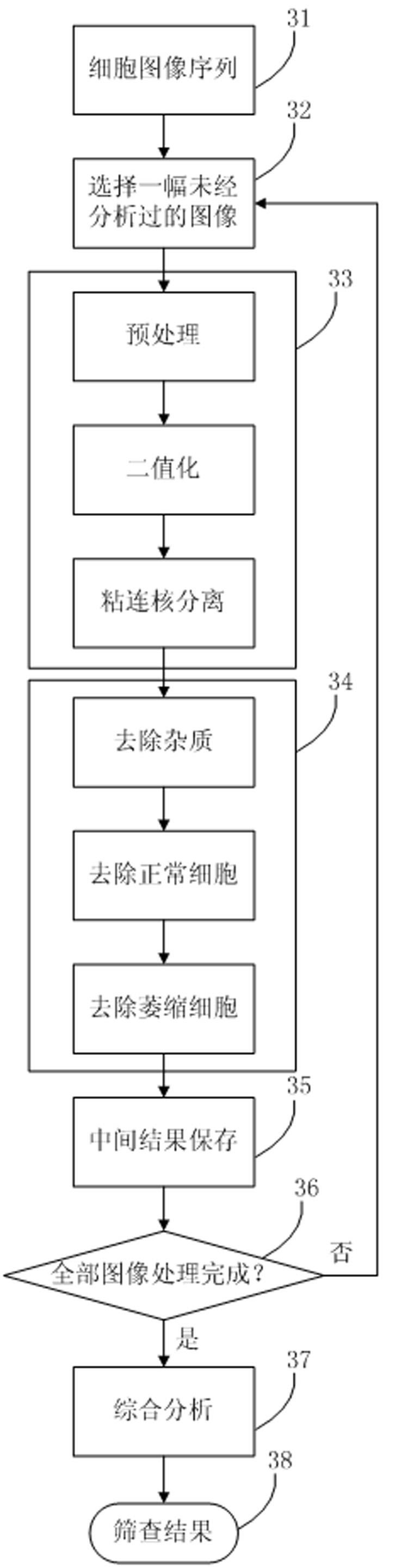
Automatic screening system and automatic screening method using thin-prep cytology test
ActiveCN102682305AIncreased sensitivityStrong specificityCharacter and pattern recognitionPattern recognitionScreening method
The invention discloses an automatic screening system and an automatic screening method using a thin-prep cytology test. The system comprises an image acquisition module, an image segmentation module, a target recognition module and a comprehensive analysis module. The method provided by the invention respectively adopts a three-point evolutionary uniform sampling method to guarantee the reliability of automatic focusing, the coarse-to-fine segmentation algorithm to improve the segmentation accuracy of pathological cell nucleuses, a series of filters to rapidly filter various impurities, and a cascade classifier training method to greatly reduce the false positive rate, and uses relative features to conduct comprehensive analysis. The method disclosed by the invention has the advantages of high sensitivity over pathological cells, high specificity over normal cells, high recognition speed and high automation degree, so that the diagnostic accuracy can be improved and the workload of a cytopathologist is reduced at the same time.
Owner:MAIKE SIBEI INTELLIGENT APP SHENZHEN
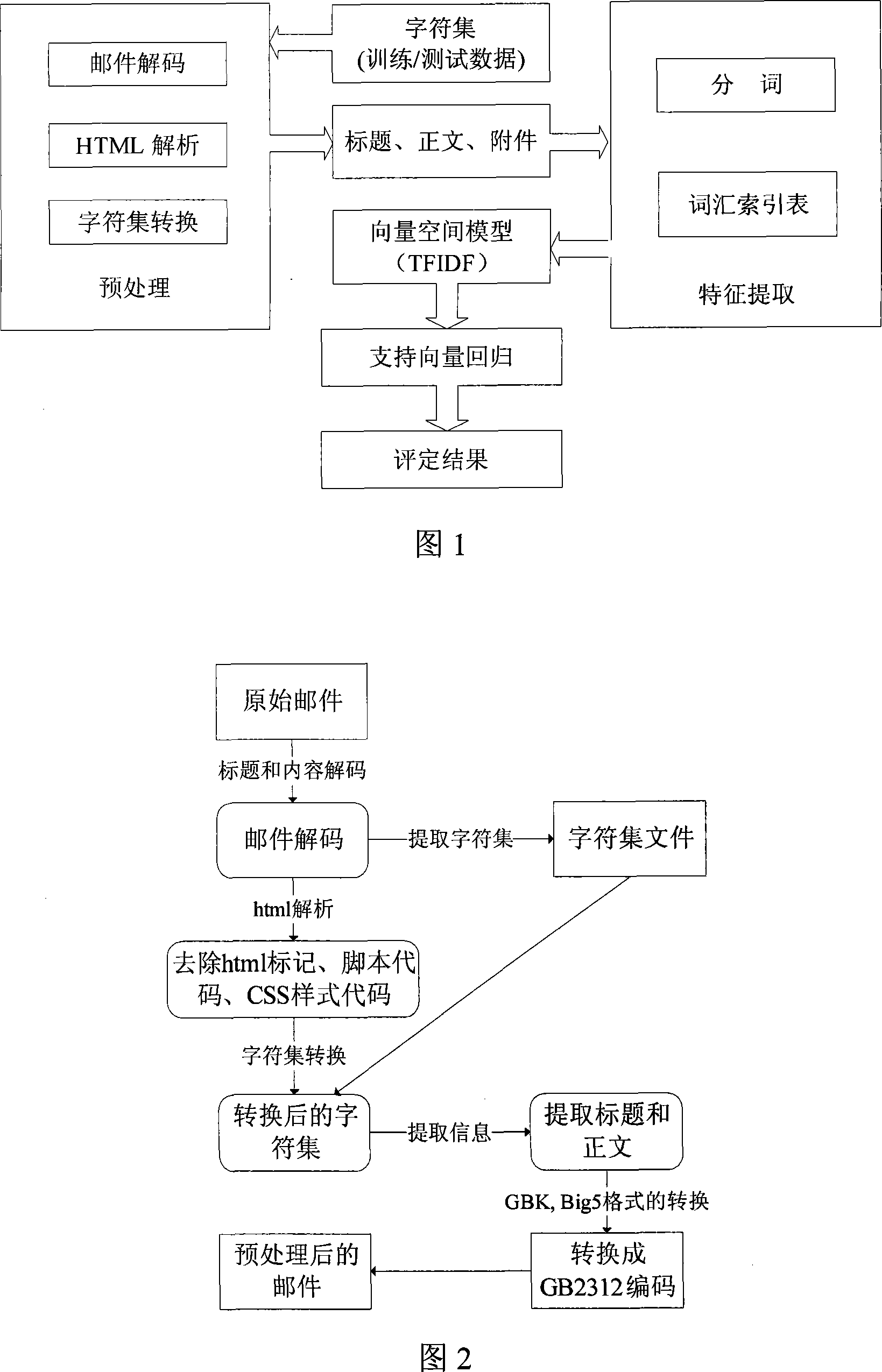
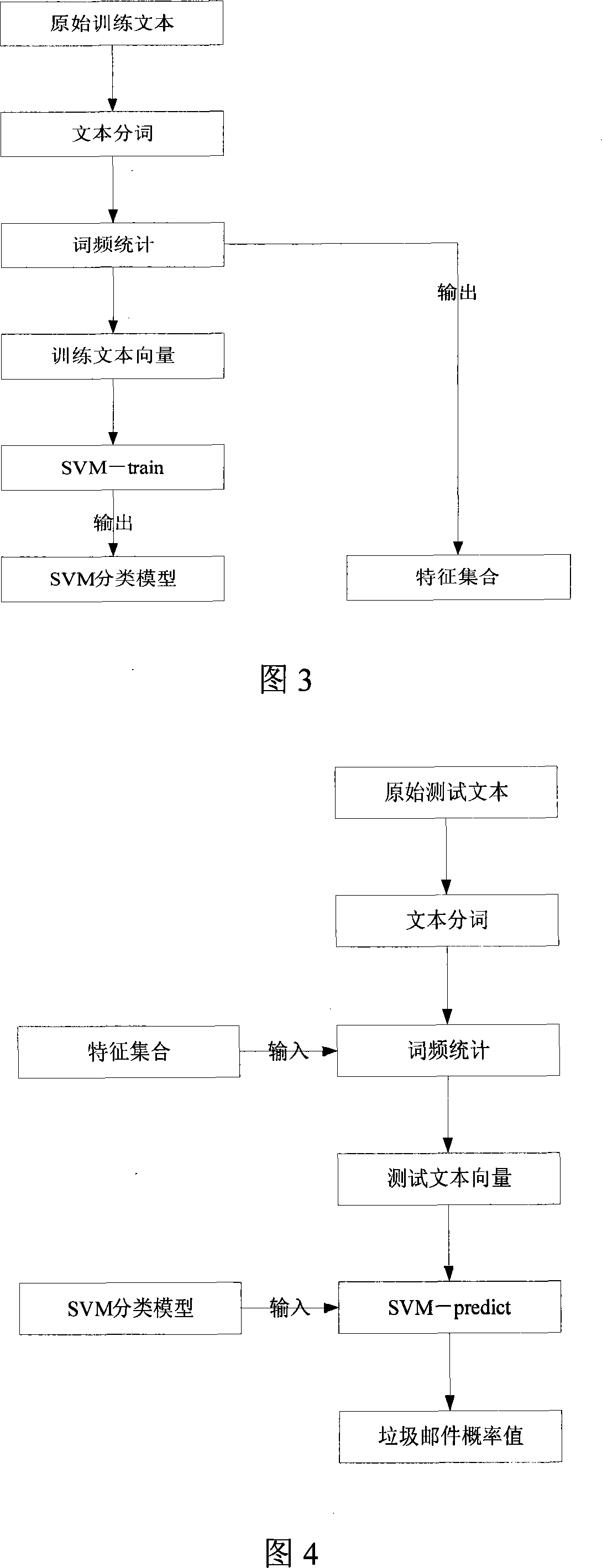
Filtering method for spam based on supporting vector machine
InactiveCN101106539ASolve the problem of unequal cost of misjudgmentIncrease the weight valueOffice automationData switching networksSupport vector machineRelevant information
The invention discloses a junk mail filtering method based on support vector machine (SVM). The steps are as following: 1) analyze the mail and extract the message relevant to title, text and character set; 2) carry out divided syncopation to the extracted text message content; 3) make statistics of word frequency in mail and utilize TF-IDF formula to map the mail text to vector; 4) utilize LibSVM to train the mail sample and obtain support vector machine model; 5) utilize support vector machine model to classify new mail and obtain the probability value of junk mails; 6) utilize threshold value adjustment to guarantee a lower level of false positive rate of normal mails to junk mails and ultimately judge whether mails are junk mails. The invention utilizes the advantage of highest single model classification accuracy of the support vector machine, improves the correctness of junk mail filtering, according to the text feature and activity feature and at the same time, also effectively solves the problem of unequal miscarriage cost in junk mail filtering.
Owner:ZHEJIANG UNIV
Neural network-based method for identifying and classifying visible components in urine
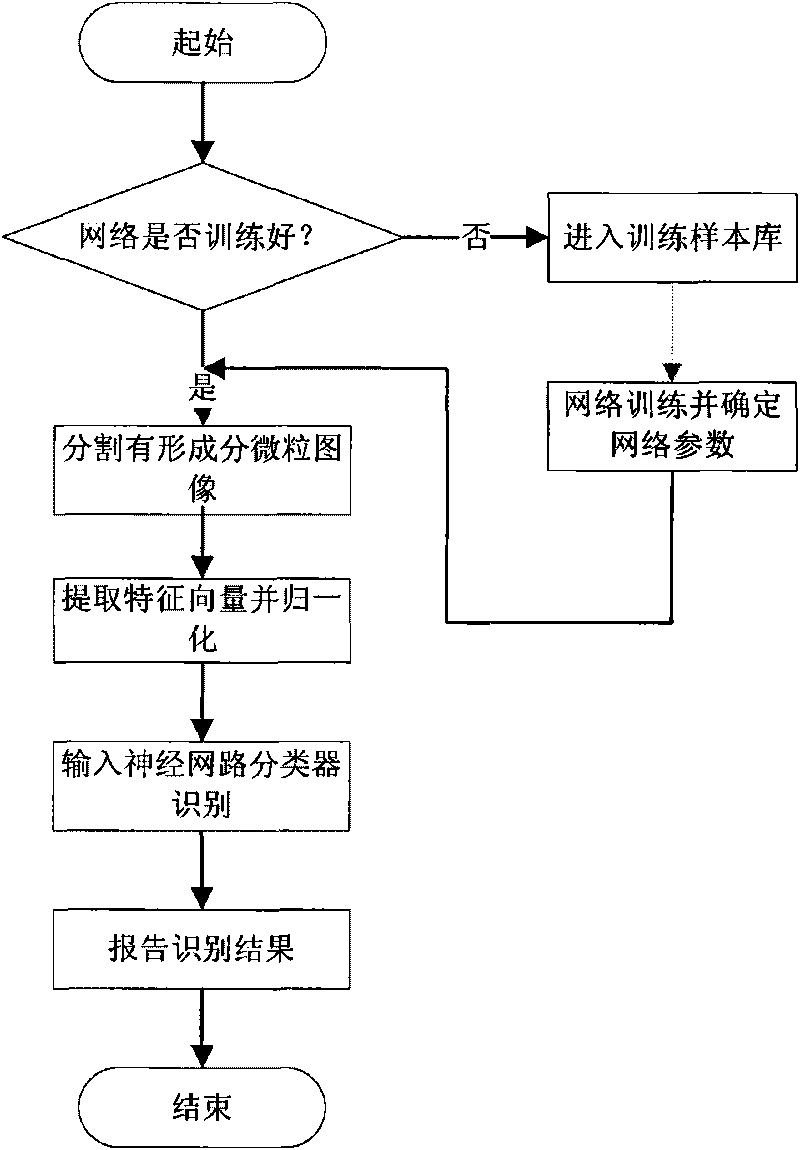
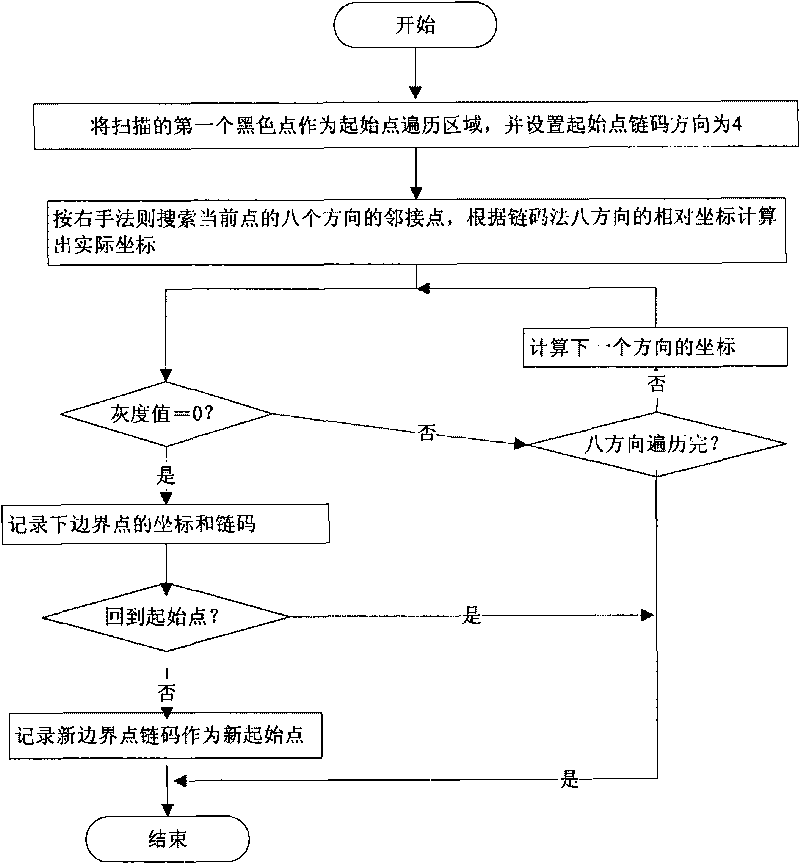
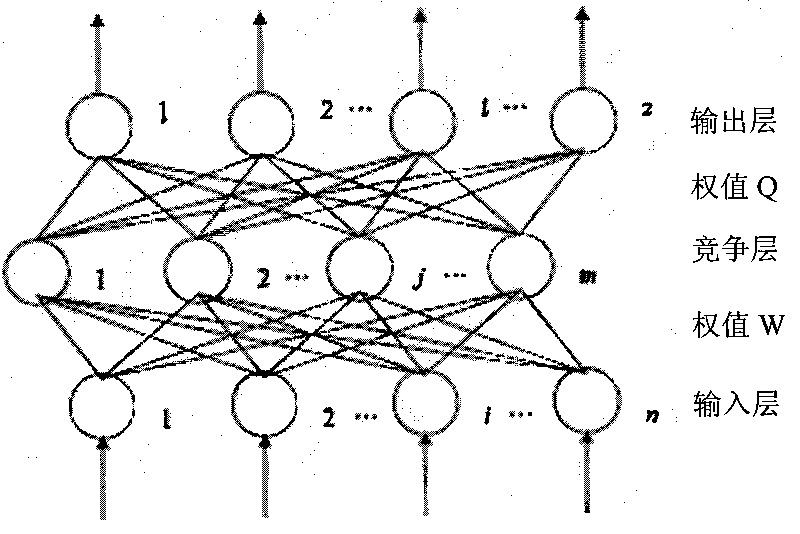
ActiveCN101713776AQuick Auto DetectHigh speedImage analysisNeural learning methodsNerve networkClassification methods
The invention relates to a neural network-based method for identifying and classifying visible components in urine, and belongs to a method for identifying and classifying the visible components in the urine. The method comprises the following steps: shooting an image of a urine sample with a flowing microscope system in urinary sediment detection equipment, and transmitting the image to a memoryof a urinary sediment image workstation; segmenting the shot image in the step 1 to form visible component particle images of the urine, calculating shape and texture feature vectors of the segmentedvisible component particle images in the step 2, and taking the vectors as input of an intelligent neural network; and receiving the feature vectors of the visible component particle images to be identified, normalizing to a range of [0,1], and inputting the trained intelligent neural network for identification. The method has high identification rate and low false positive rate, and greatly improves the accuracy and objectiveness of identifying the visible components in the clinical urine. Meanwhile, the workload of doctors is greatly lightened, and the standardization and automation of detecting the visible components in the urine are realized.
Owner:DIRUI MEDICAL TECH CO LTD
Copy number variation detection method based on next generation sequencing
ActiveCN105760712ASolving Detection ErrorsAvoid detection errorsBiostatisticsSequence analysisComputation complexitySlide window
The invention discloses a copy number variation detection method based on next generation sequencing. The method comprises the following steps: pre-processing copy number variation data, constructing a sliding window, calculating of statistics, implementing a replacement policy, constructing zero distribution, and carrying out performance evaluation of an algorithm. The performance evaluation of the algorithm comprises the steps of judging whether a relatively high correct positive rate can be acquired by the algorithm under the condition that a false positive rate is controllable, evaluating whether the algorithm can relatively accurately estimate a p value or not, detecting a boundary detection capability of copy number variation, and analyzing the calculation complexity of the algorithm. With the adoption of the copy number variation detection method, the problem of copy number variation detection errors, caused by the fact that sequencing platforms and sequencing levels are different, is solved, and a result is relatively accurate; data is normalized by utilizing characteristics of a multi-peak frequency histogram, so that a normal region and a copy number variation region are accurately divided; and a new model is established by a comprehensive effect of relevance between a variation reads number and a variation site, so that the inconsistency problem is solved, and the remarkable level of copy number variation is objectively estimated.
Owner:XIDIAN UNIV
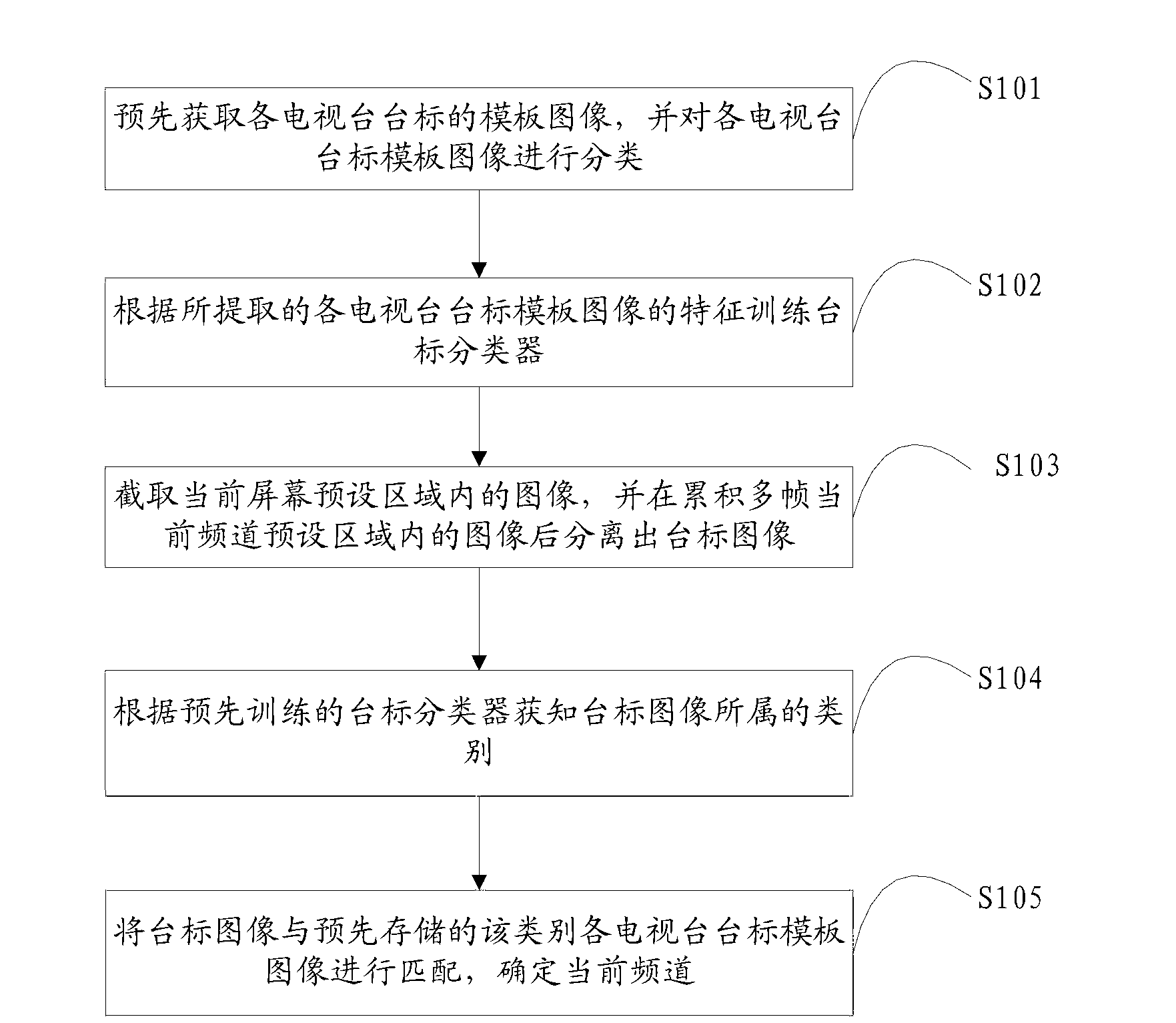
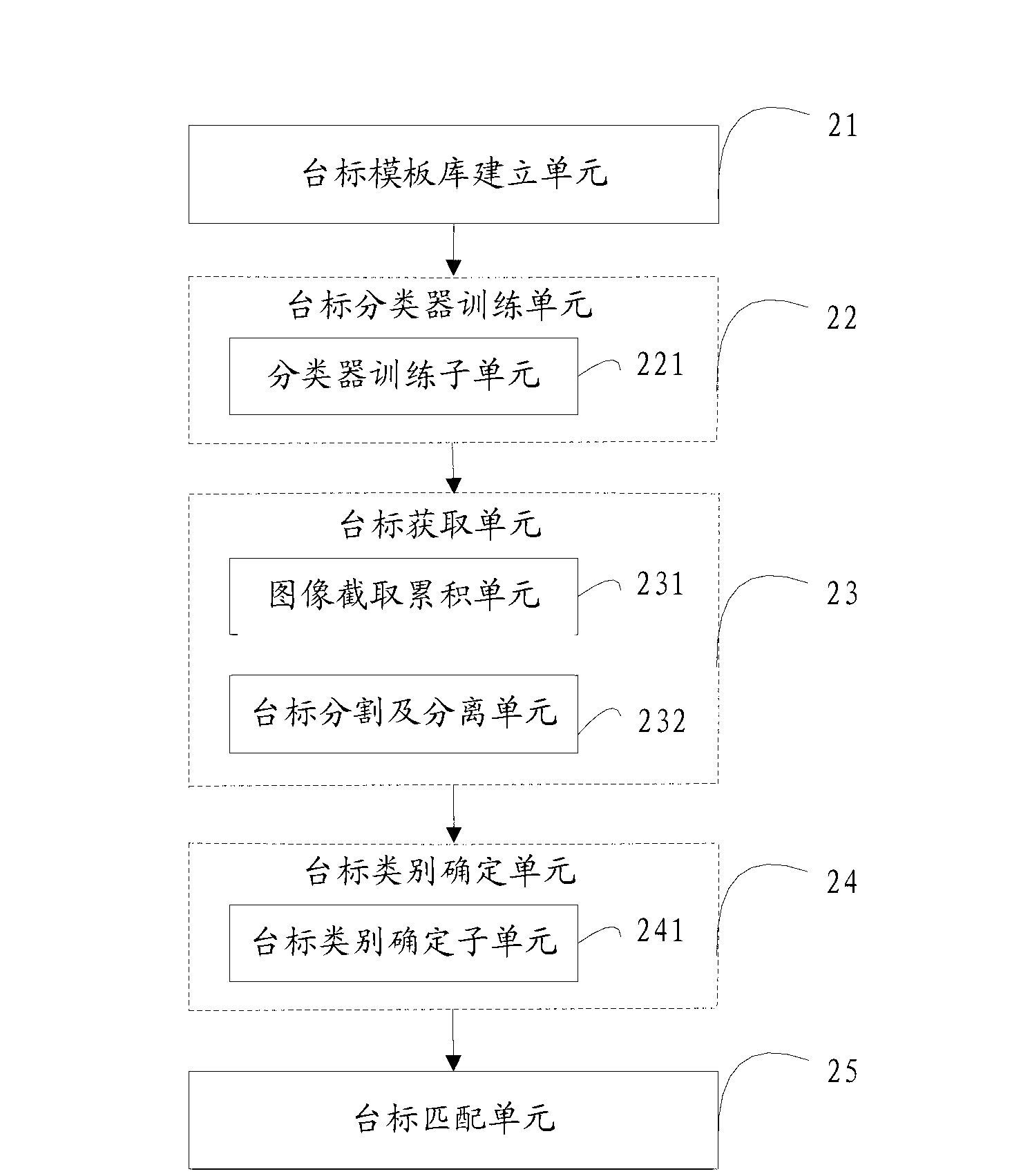
Station caption identifying method and device
ActiveCN103020650AEffective recognition speedEffective template matching method and pre-stored high-efficiency recognition speedCharacter and pattern recognitionTemplate matchingCurrent channel
The invention is applicable to the field of multimedia application, and provides a station caption identifying method and device. The station caption identifying method comprises steps of: intercepting an image in a predetermined area of the current screen, isolating the image of a station caption after multi-frame images in the predetermined area of the current channel are accumulated; obtaining the category of the station caption by a pre-trained station caption categorizer; and matching the station caption with each pre-stored station caption template image belonging to the category, so as to determine the current channel. According to the station caption identifying method and device, after being isolated, the station caption is matched with station captions which are pre-stored and are effectively categorized by using the effective template matching method, the identifying method based on the category and the identifying method based on the template matching are effectively combined, so that not only can the false positive rate be effectively reduced, but also the high-efficient identifying speed and the high rate of identification are provided.
Owner:TCL CORPORATION
Generic shellcode detection
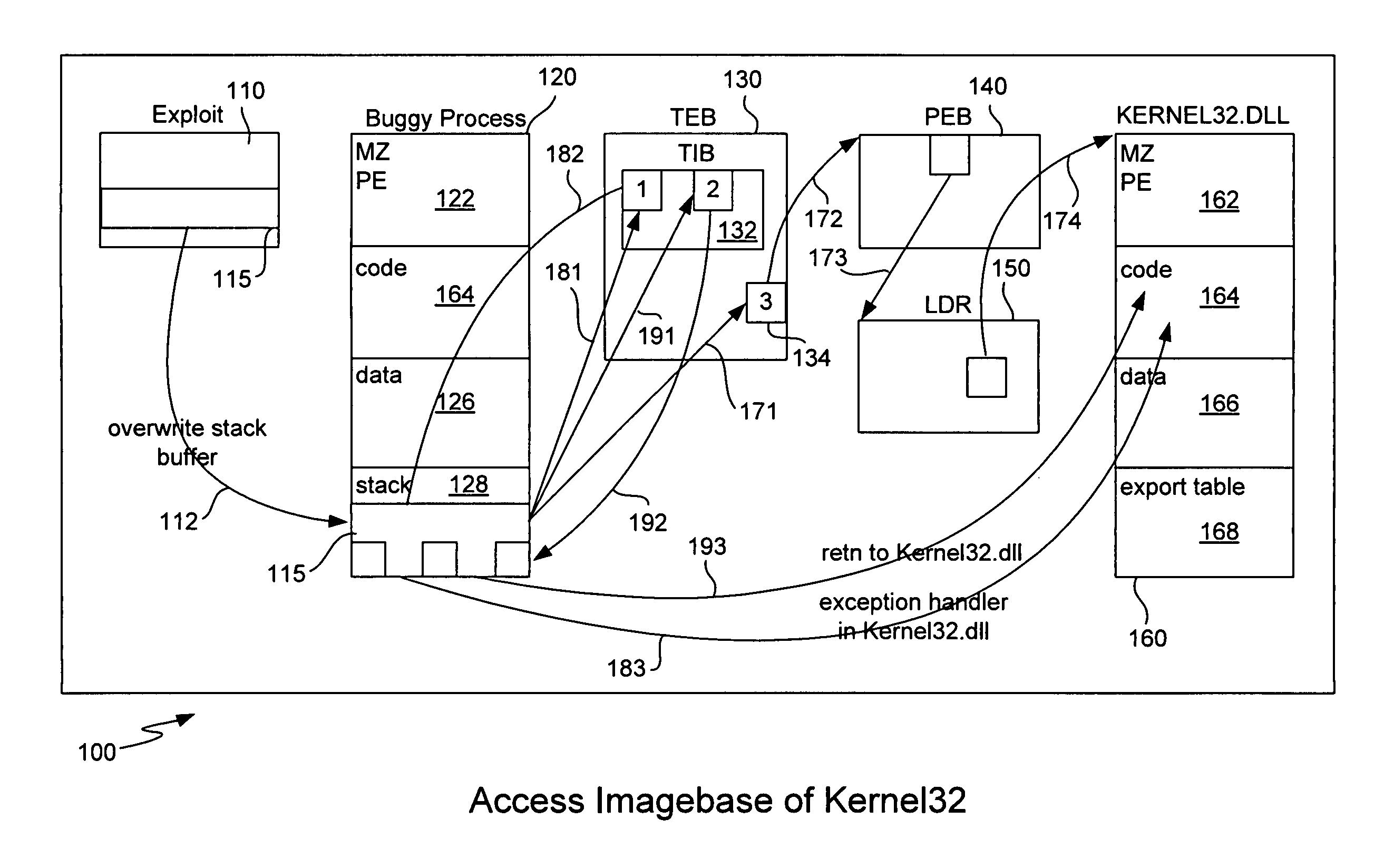
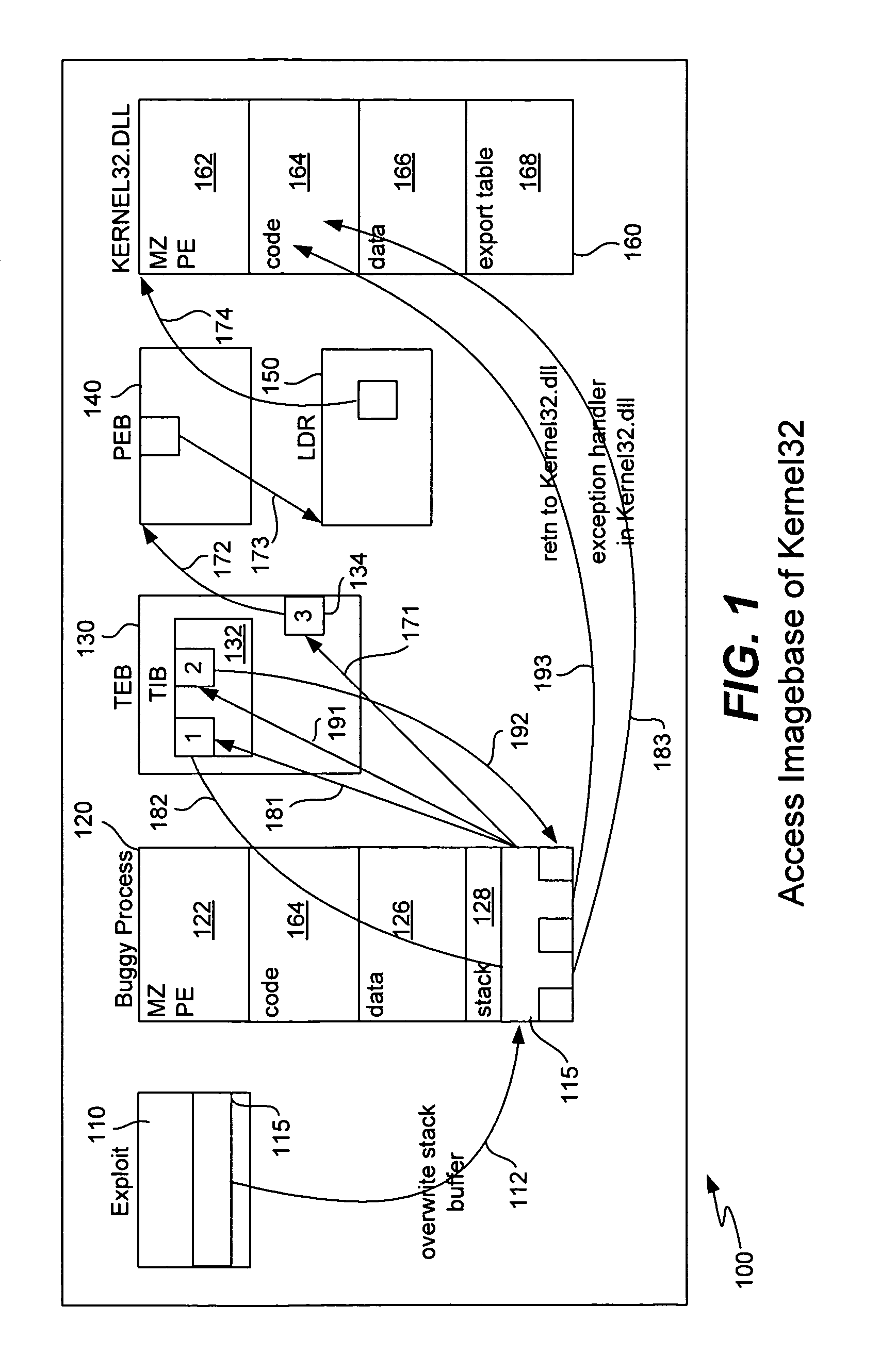
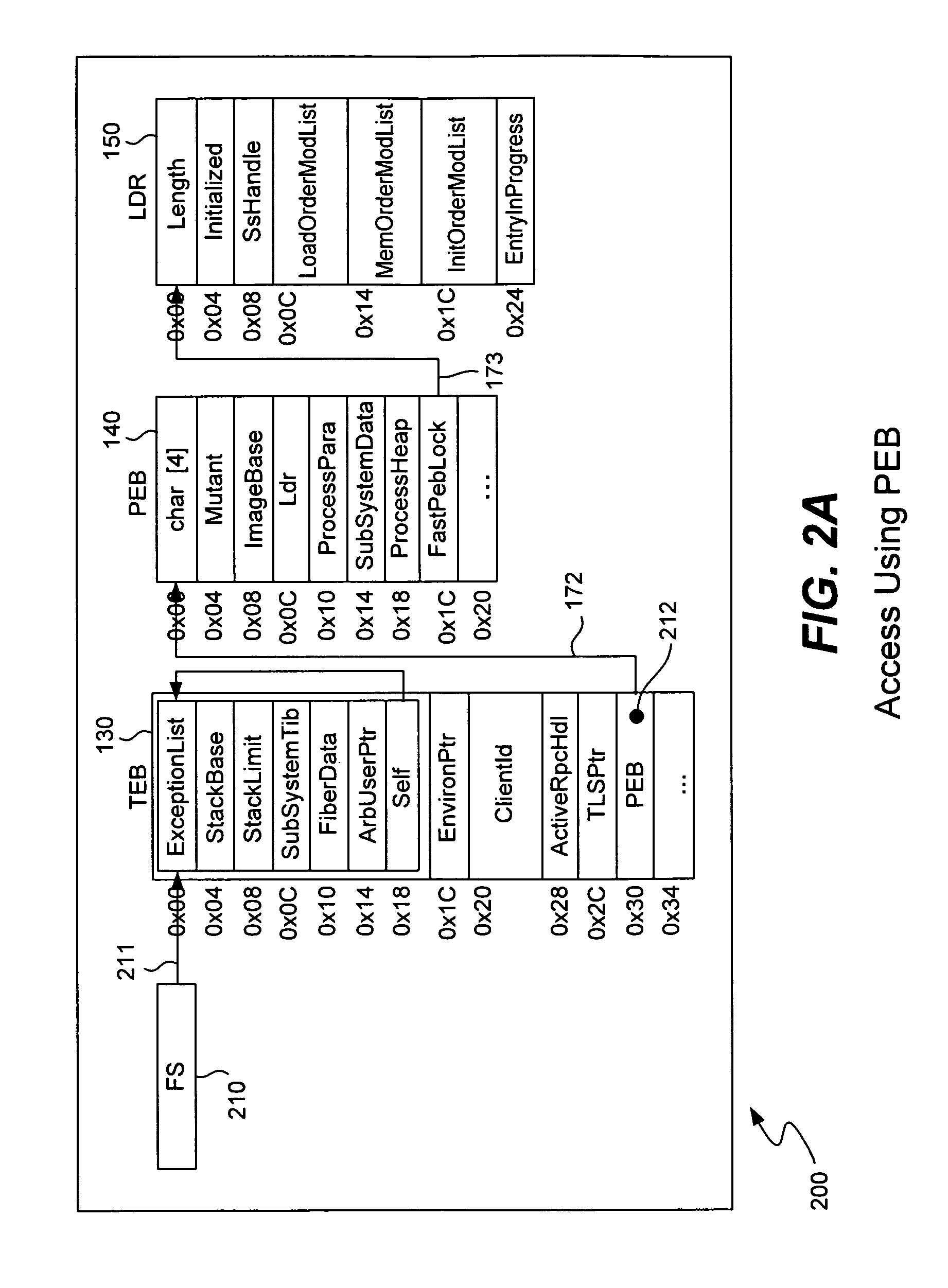
ActiveUS8307432B1Quick analysisImprove the detection rateMemory loss protectionError detection/correctionBuffer overflowShellcode
Detecting buffer-overflow exploits scans generically for shellcode without using virus signatures and maintains close to a zero false-positive rate. Shellcode is detected generically without determining specifically which buffer-overflow exploit is being used. Protection is offered against unknown buffer-overflow exploits. A file is scanned to determine if a vulnerable buffer in that file includes suspect code that has characteristics of shellcode. Next, it is determined if the suspect code contains a routine to find the imagebase of Kernel32.dll using any of the techniques of PEB, TOS or SEH (process environment block, top of stack or structured exception handling). It is next determined if the suspect code contains a routine to search for APIs in the export table of kernel32.dll. Techniques for analyzing the suspect code include static analysis and executing the code in an emulator. A high sensitivity setting determines that shellcode is present when any of the techniques of PEB, TOS or SEH are found.
Owner:TREND MICRO INC
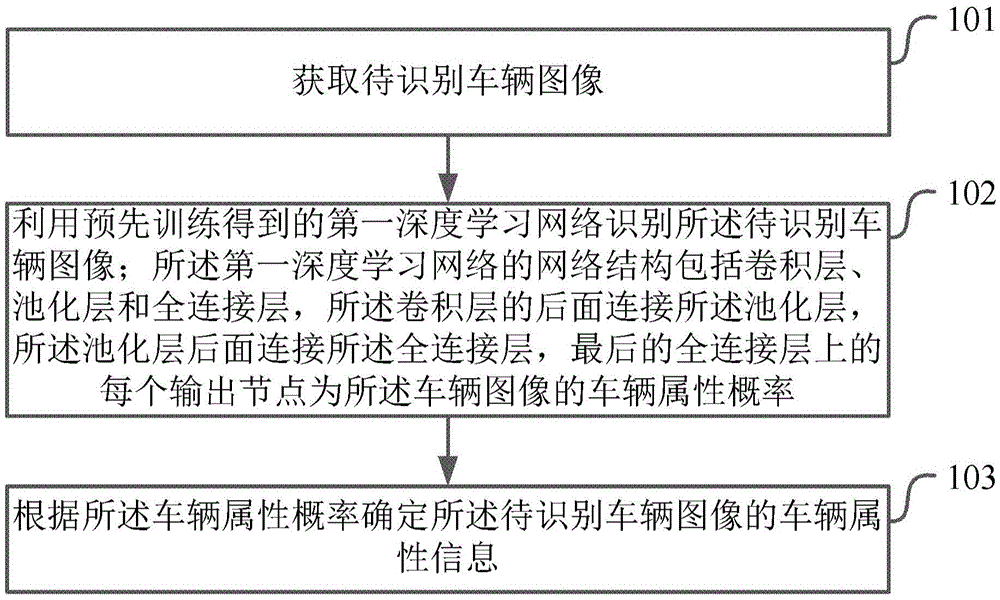
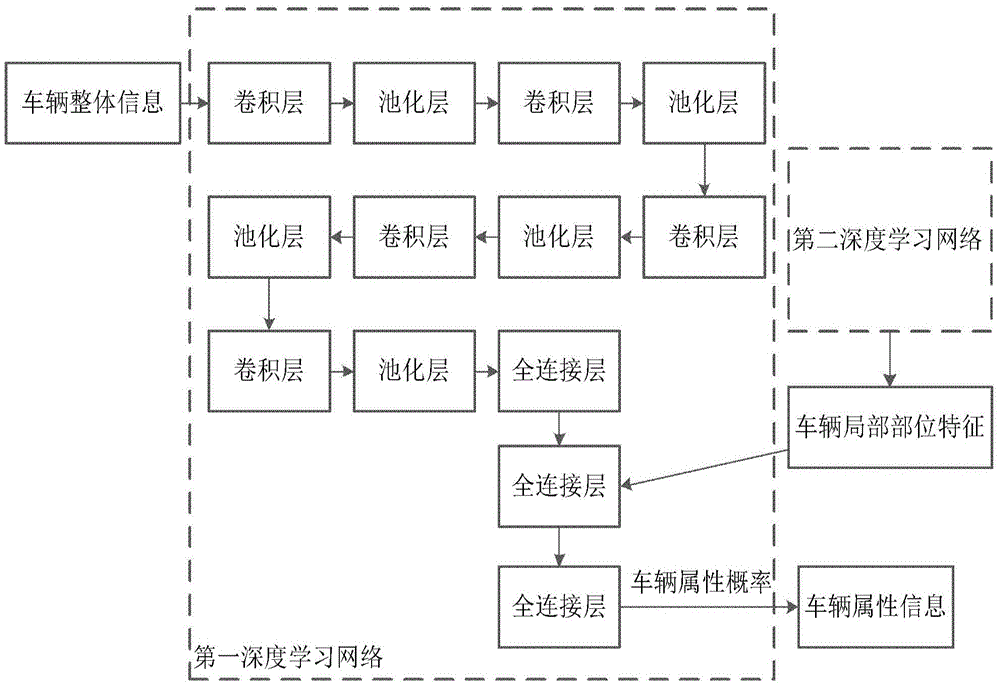
Vehicle identification method and device
ActiveCN105574550AImprove accuracyReduce false alarm rateBiological neural network modelsCharacter and pattern recognitionPattern recognitionNetwork structure
This application provides a vehicle identification method and device. The method includes the following steps that: a vehicle image to be identified is obtained; a first deep learning network which is obtained through pre-training is utilized to identify the vehicle image to be identified; the network structure of the first deep learning network includes convolutional layers, pooling layers and all-connection layers, the pooling layers are connected behind the convolutional layers, the all-connection layers are connected behind the pooling layers, and each output node on the all-connection layers is the vehicle attribute probability of the vehicle image; and the vehicle attribute information of the vehicle image to be identified is determined according to the vehicle attribute probability. According to the method provided by the technical schemes of the invention, since the deep learning network is utilized to identify a vehicle, the deep learning network is competent enough to describe and distinguish objects, and therefore, compared with a method according to which features are defined manually to carry out classification, the method of the invention has higher accuracy as well as lower false positive rate and false negative rate.
Owner:BEIJING DEEPGLINT INFORMATION TECH
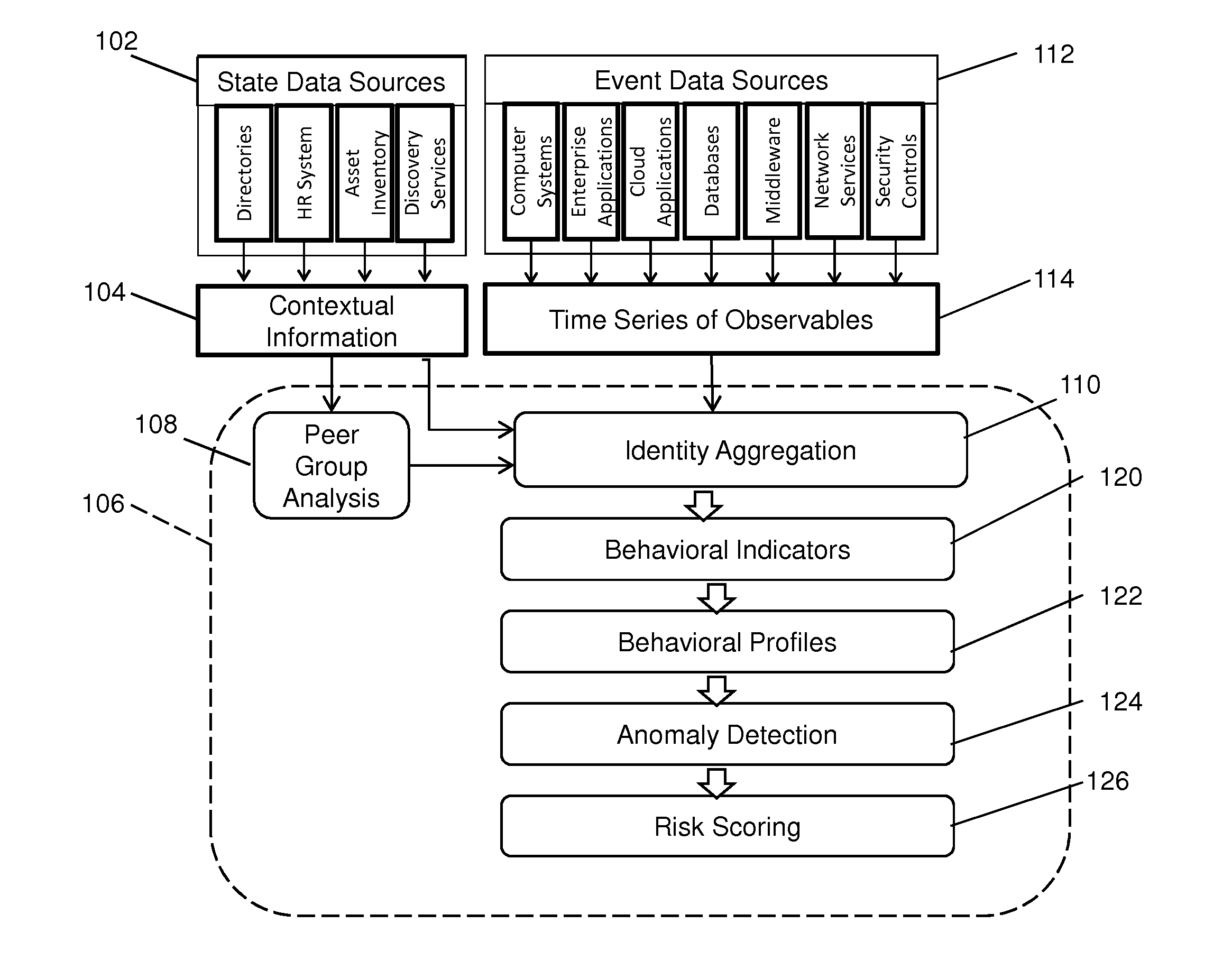
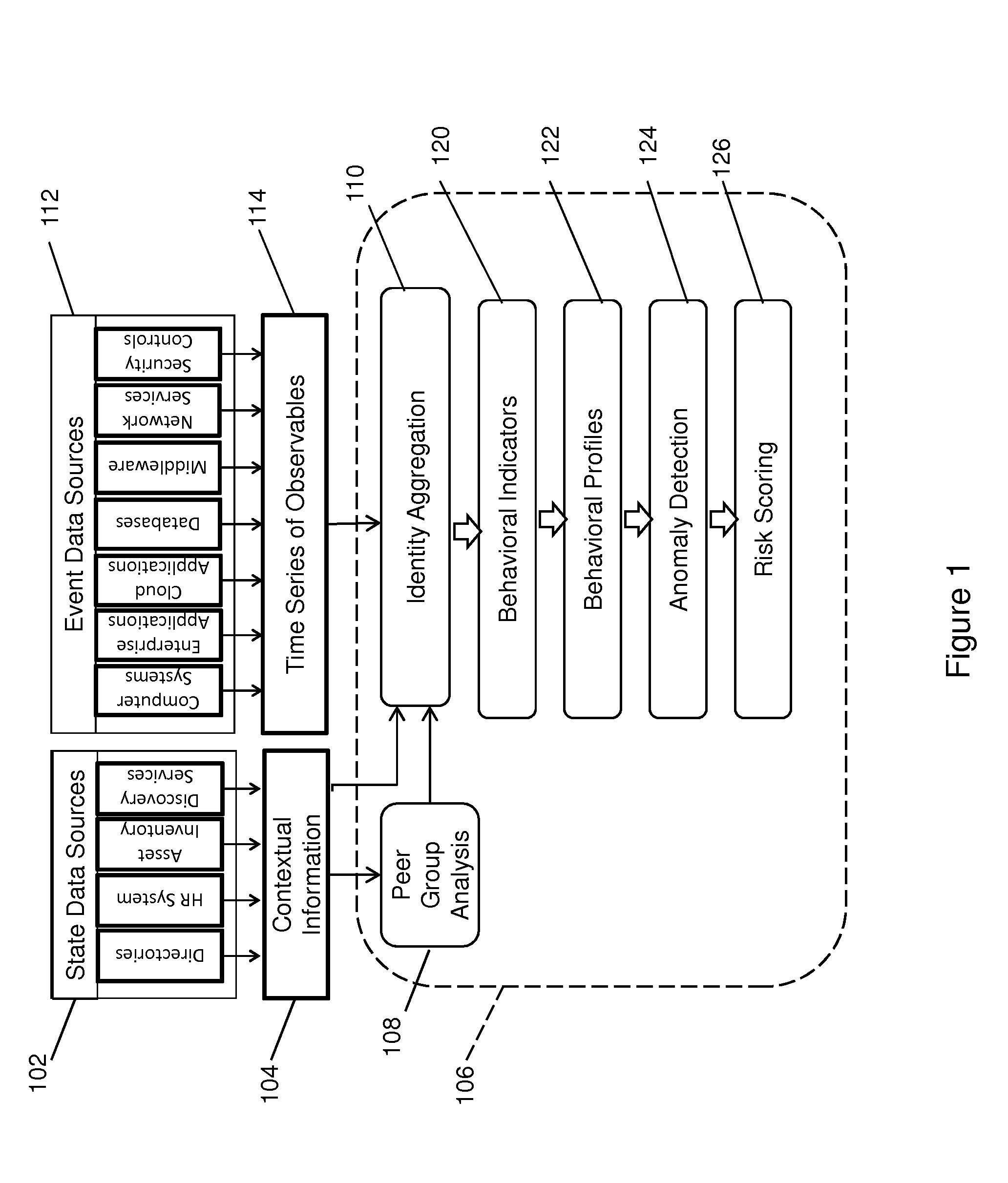
Anomaly Detection Using Adaptive Behavioral Profiles
Anomalous activities in a computer network are detected using adaptive behavioral profiles that are created by measuring at a plurality of points and over a period of time observables corresponding to behavioral indicators related to an activity. Normal kernel distributions are created about each point, and the behavioral profiles are created automatically by combining the distributions using the measured values and a Gaussian kernel density estimation process that estimates values between measurement points. Behavioral profiles are adapted periodically using data aging to de-emphasize older data in favor of current data. The process creates behavioral profiles without regard to the data distribution. An anomaly probability profile is created as a normalized inverse of the behavioral profile, and is used to determine the probability that a behavior indicator is indicative of a threat. The anomaly detection process has a low false positive rate.
Owner:SECURONIX INC
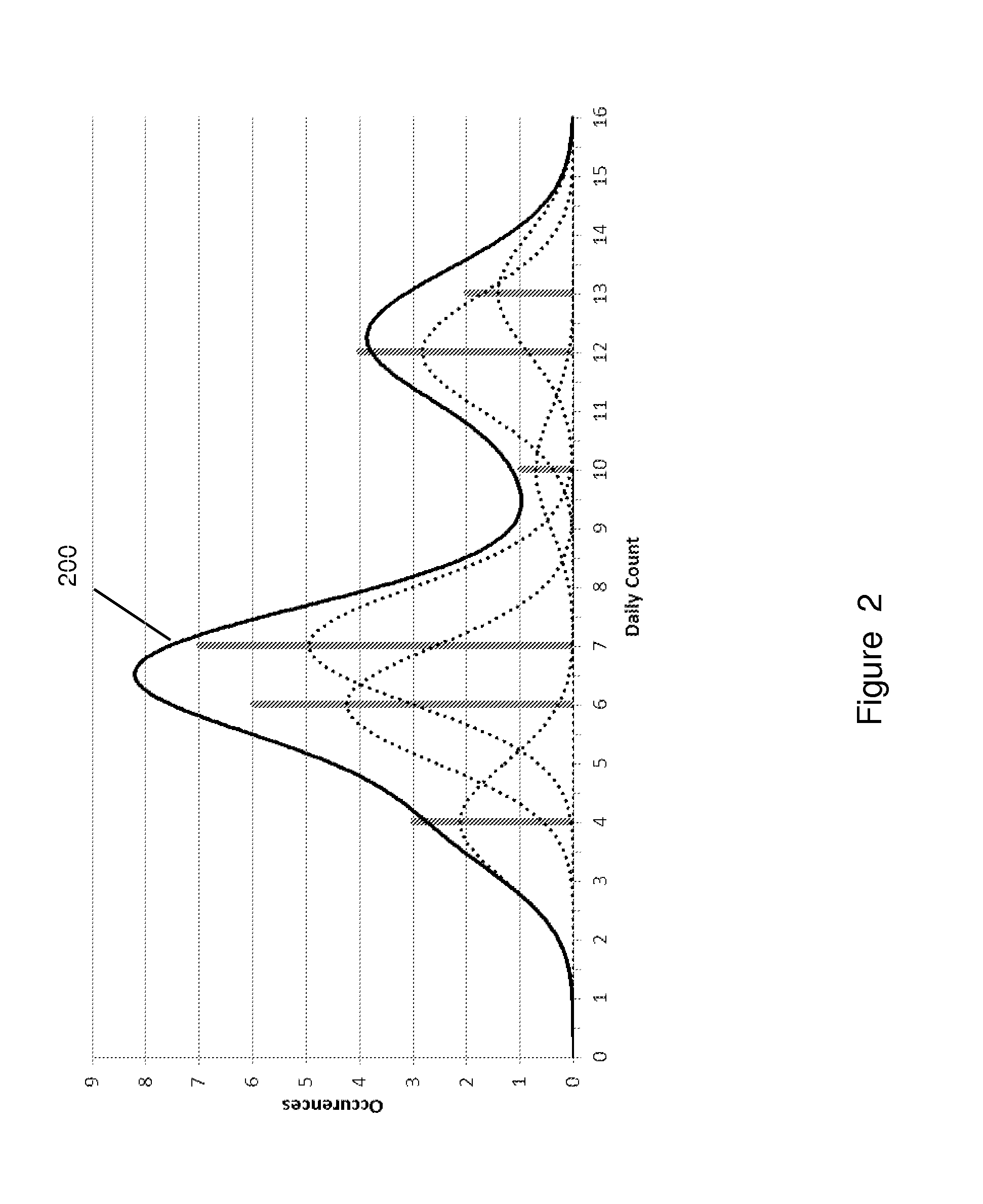
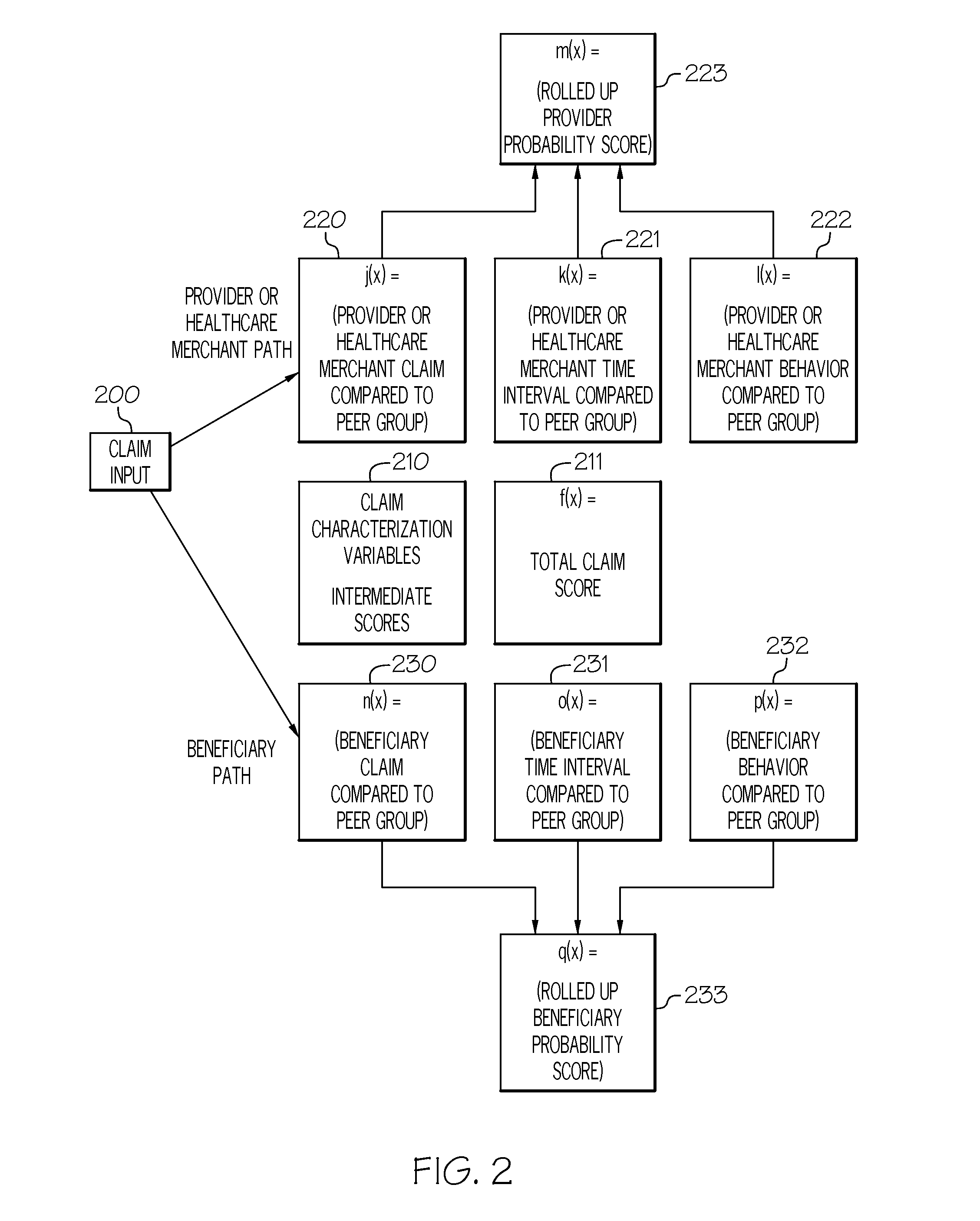
Characterizing healthcare provider, claim, beneficiary and healthcare merchant normal behavior using non-parametric statistical outlier detection scoring techniques
InactiveUS20130085769A1Predictive performanceHigh false positive rateOffice automationPatient-specific dataScalar ValueCrowds
This invention uses non-parametric statistical measures and probability mathematical techniques to calculate deviations of variable values, on both the high and low side of a data distribution, from the midpoint of the data distribution. It transforms the data values and then combines all of the individual variable values into a single scalar value that is a “good-ness” score. This “good-ness” behavior score model characterizes “normal” or typical behavior, rather than predicting fraudulent, abusive, or “bad”, behavior. The “good” score is a measure of how likely it is that the subject's behavior characteristics are from a population representing a “good” or “normal” provider, claim, beneficiary or healthcare merchant behavior. The “good” score can replace or compliment a score model that predicts “bad” behavior in order to reduce false positive rates. The optimal risk management prevention program should include both a “good” behavior score model and a “bad” behavior score model.
Owner:RISK MANAGEMENT SOLUTIONS
Method and System for Filtering False Positives
ActiveUS20100114877A1Reducing false positivesReduce morbidityData processing applicationsDigital data processing detailsData recordingData mining
Owner:INT BUSINESS MASCH CORP
Method and apparatus for defending distributed denial-of-service (DDOS) attack through abnormally terminated session
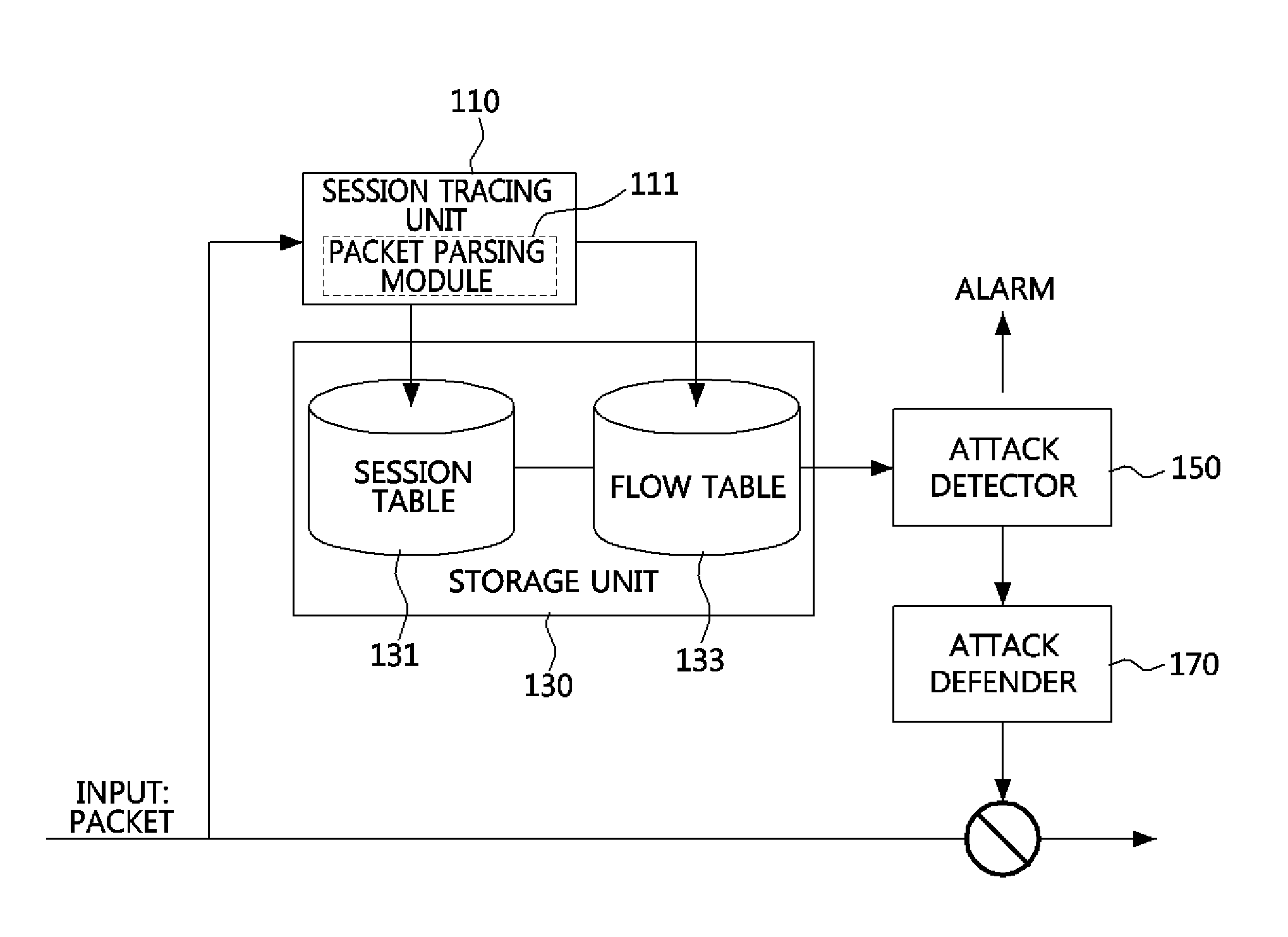
InactiveUS20130074183A1Reduce the amount requiredReduce rateMemory loss protectionData taking preventionFalse positive rateComputer security
There are provided a method and apparatus for defending a Distributed Denial-of-Service (DDoS) attack through abnormally terminated sessions. The DDoS attack defending apparatus includes: a session tracing unit configured to parse collected packets, to extract header information from the collected packets, to trace one or more abnormally terminated sessions corresponding to one of pre-defined abnormally terminated session cases, based on the header information, and then to count the number of the abnormally terminated sessions; and an attack detector configured to compare the number of the abnormally terminated sessions to a predetermined threshold value, and to determine whether a DDoS attack has occurred, according to the results of the comparison. Therefore, it is possible to significantly reduce a false-positive rate of detection of a DDoS attack and the amount of computation for detection of a DDoS attack.
Owner:ELECTRONICS & TELECOMM RES INST
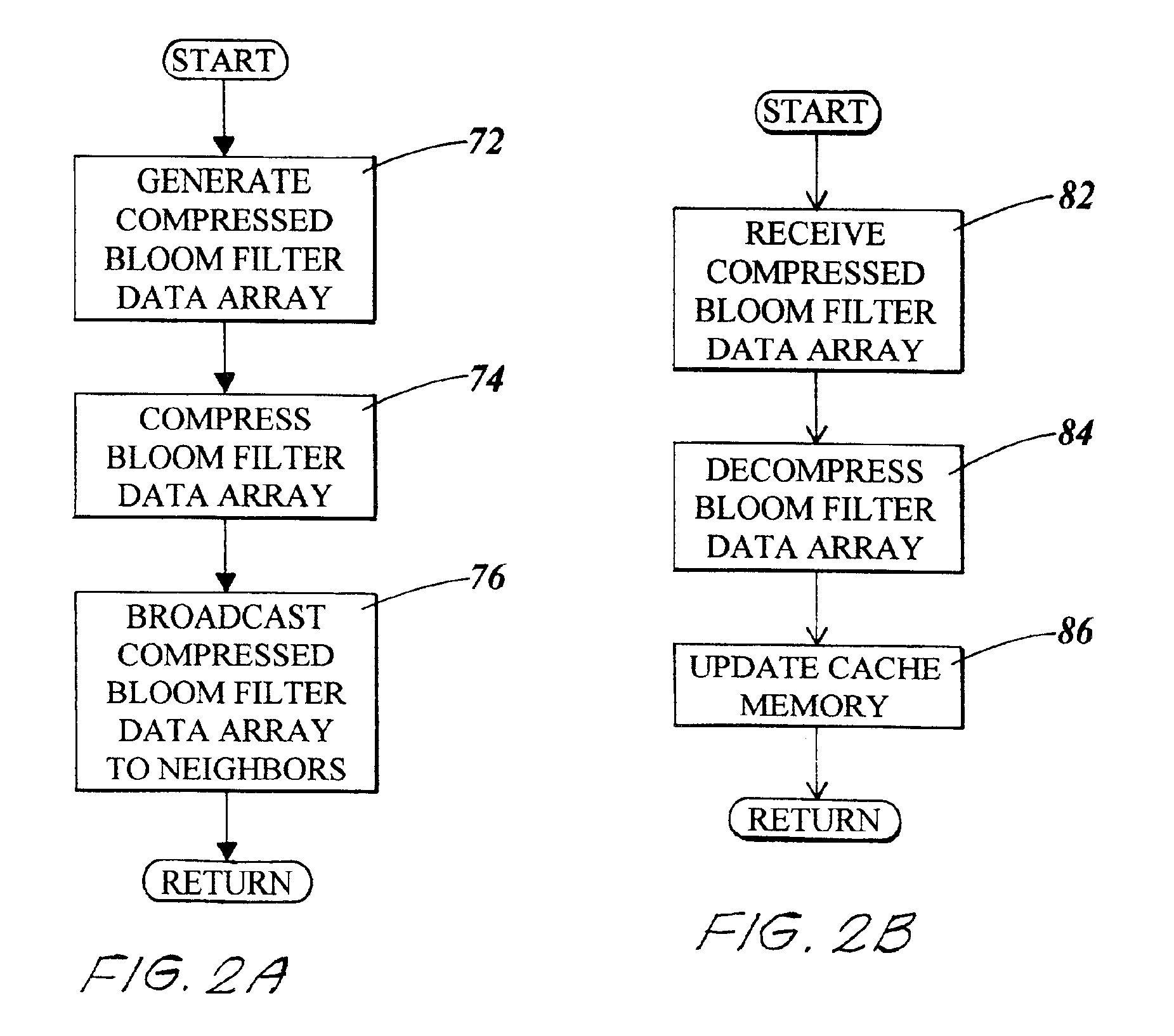
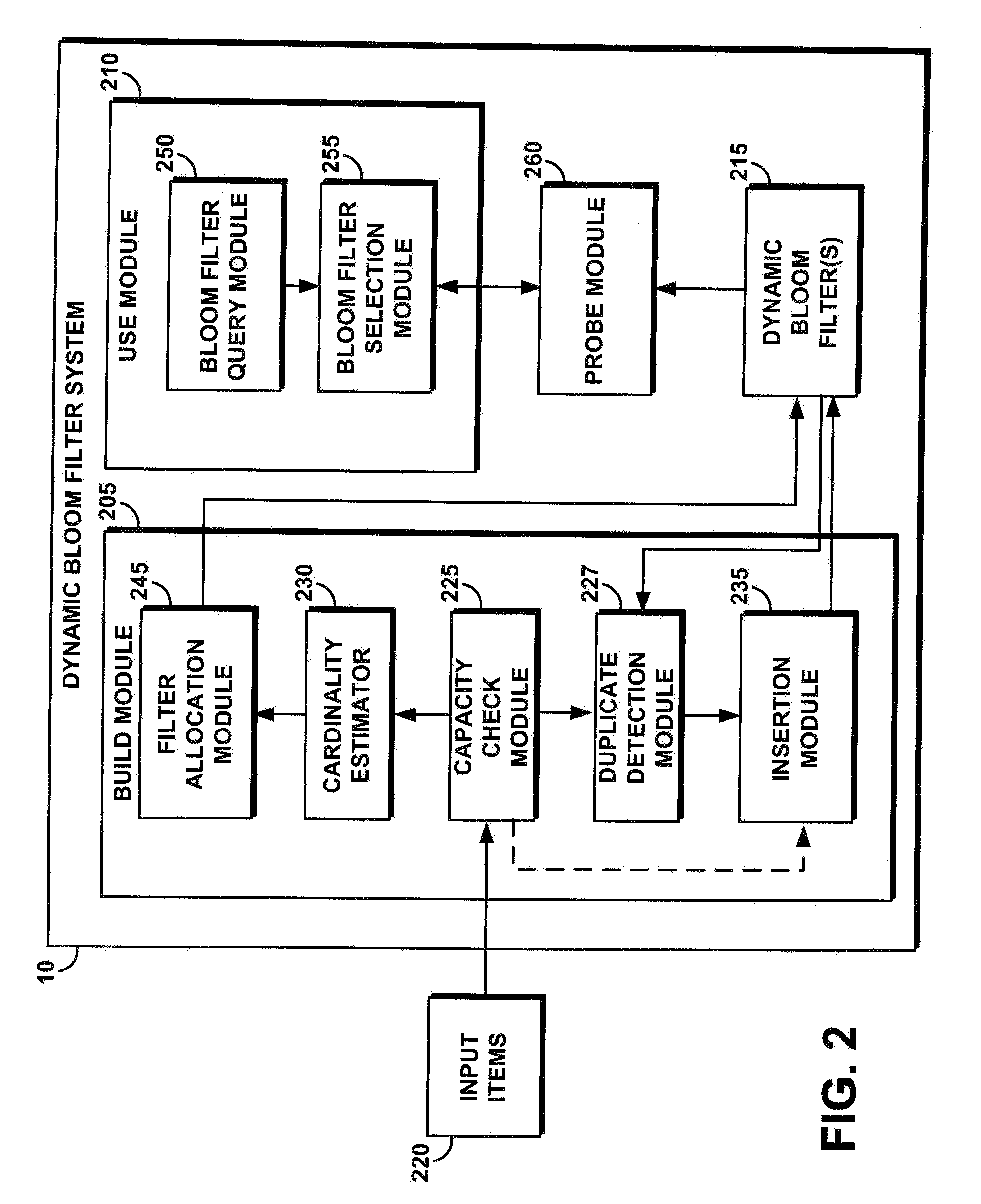
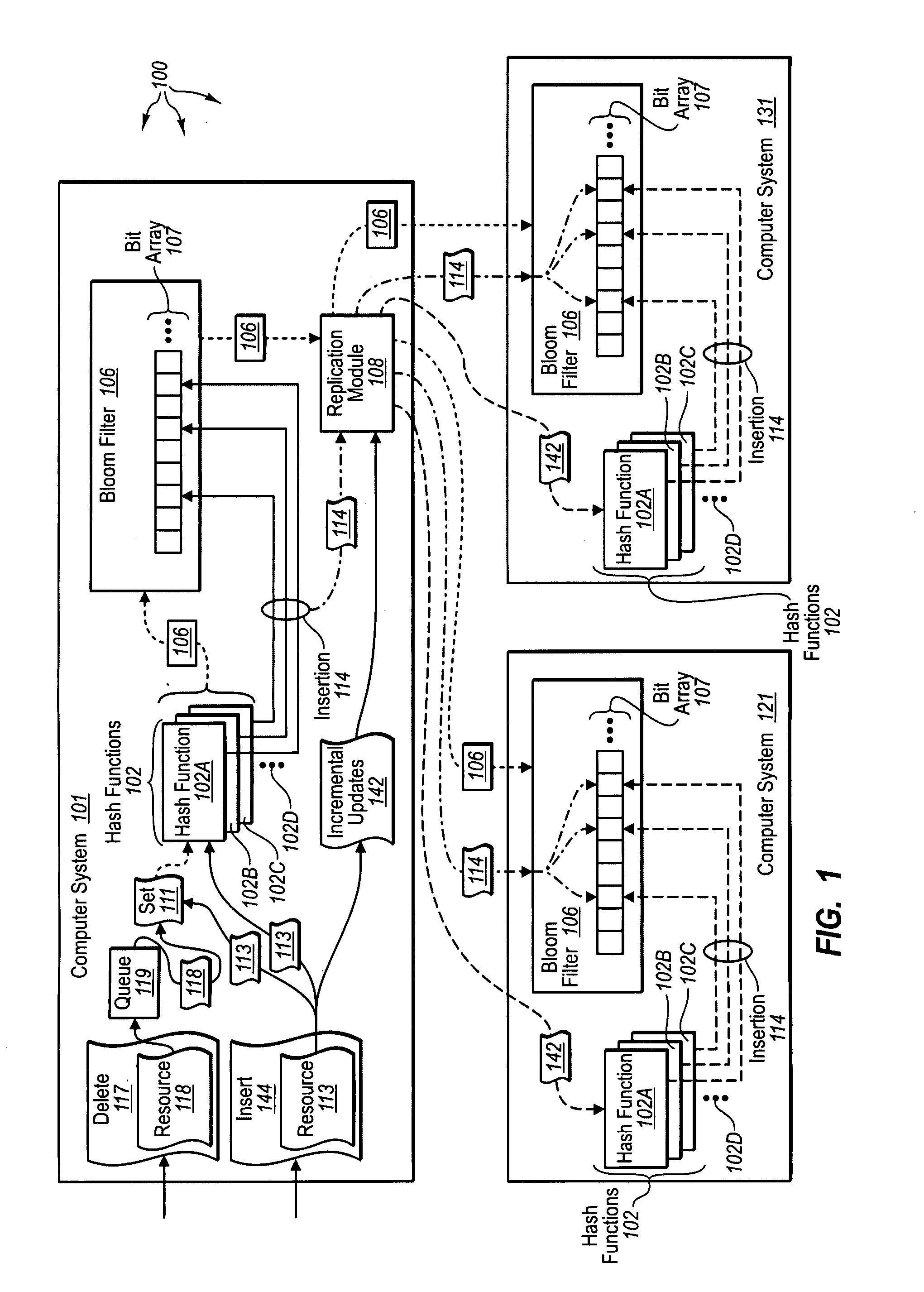
System and method for generating and using a dynamic bloom filter
InactiveUS20080154852A1Reduce the amount requiredTime can be spentMemory adressing/allocation/relocationComplex mathematical operationsHash functionBloom filter
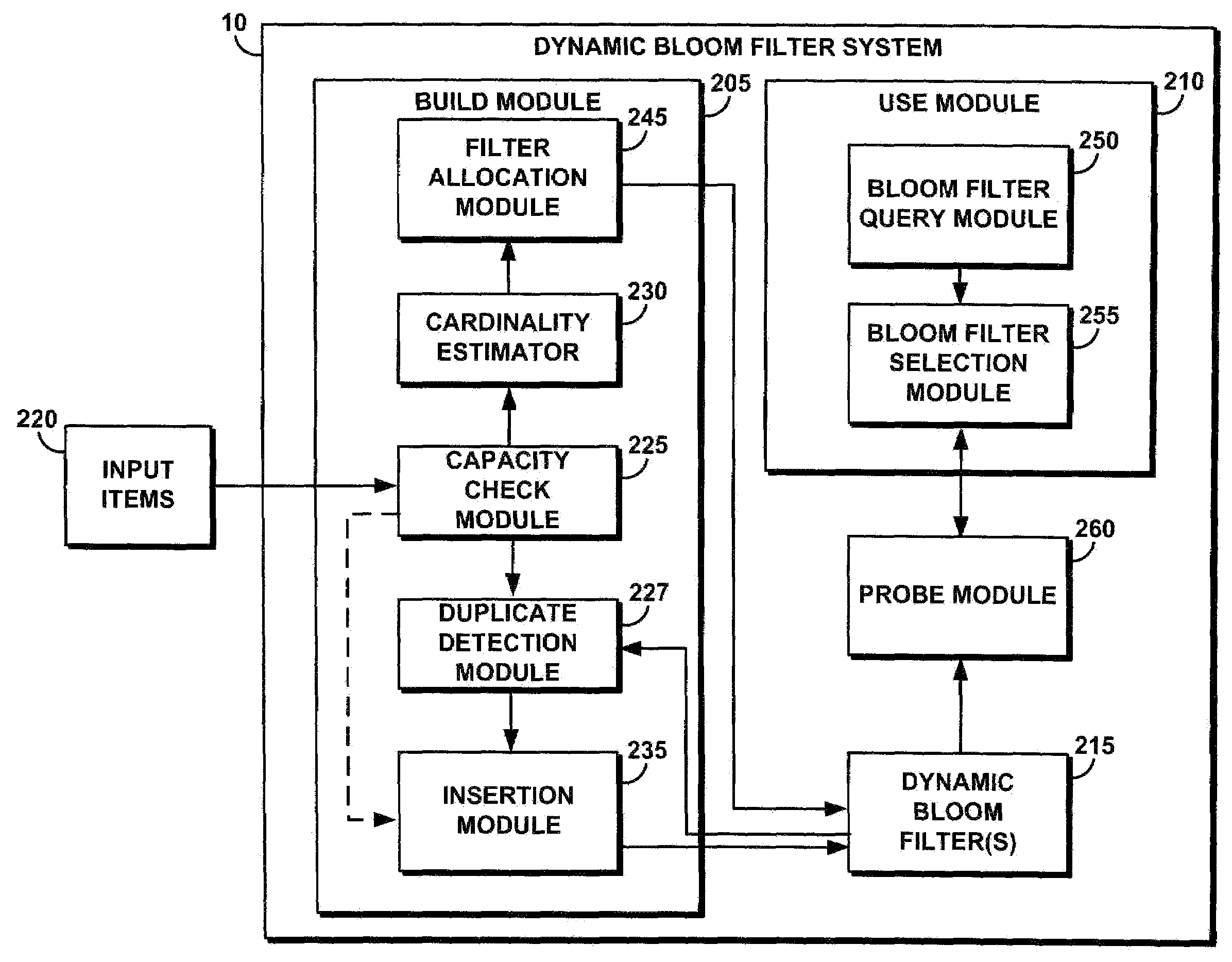
A dynamic Bloom filter comprises a cascaded set of Bloom filters. The system estimates or guesses a cardinality of input items, selects a number of hash functions based on the desired false positive rate, and allocates memory for an initial Bloom filter based on the estimated cardinality and desired false positive rate. The system inserts items into the initial Bloom filter and counts the bits set as they are inserted. If the number of bits set in the current Bloom filter reaches a predetermined target, the system declares the current Bloom filter full. The system recursively generates additional Bloom filters as needed for items remaining after the initial Bloom filter is filled; items are checked to eliminate duplicates. Each of the set of Bloom filters is individually queried to identify a positive or negative in response to a query. When the system is configured such that the false positive rate of each successive Bloom filter is decreased by one half, the system guarantees a false positive rate of at most twice the desired false positive rate.
Owner:IBM CORP
Method for rapidly obtaining CRISPR/Cas9 (clustered regularly interspersed short palindromic repeats/Cas9) gene knockout stable cell line through monoclonal cell sorting
InactiveCN107418974AImprove knockout productivitySave the trouble of screeningVectorsStable introduction of DNAFluorescenceHigh survival rate
The invention relates to a method for rapidly obtaining a CRISPR / Cas9 (clustered regularly interspersed short palindromic repeats / Cas9) gene knockout stable cell line through monoclonal cell sorting and belongs to the technical field of genetic engineering and genetic modification. According to the method, a CRISPR / Cas9 system, single-cell sorting by a flow cytometer and fluorescent protein screening on an expression vector are combined, positive monoclonal cells can be obtained in short time, and gene knockout work efficiency of the cell line is greatly improved. Compared with a traditional cell line gene knockout method, the flow cytometer is utilized for single-cell sorting, on one hand, tedious work of antibiotic screening is omitted, so that a large quantity of single cells can be obtained in quite short time, and on the other hand, the condition that cells in each culture hole are single cells can be guaranteed and false positive rate is reduced. Sorting is performed 40-80 h after cell transfection, at the time point, the highest survival rate of the cells after sorting can be guaranteed, and the screening efficiency is improved accordingly.
Owner:XINXIANG MEDICAL UNIV
Updating bloom filters
InactiveUS20100228701A1Digital data processing detailsMemory adressing/allocation/relocationEmail addressParallel computing
The present invention extends to methods, systems, and computer program products for updating Bloom filters. Embodiments of the invention facilitate more efficient use Bloom filters across multiple computers connected across a WAN (potentially having limited bandwidth and latency characteristics), such as, for example, computers located on different continents. The acceptability of false positives is leveraged by allowing the operation of removing items from a set to be batched and delayed. On the other hand, insert operations may be more latency sensitive as a delayed insert results in the semantic equivalent to a false negative. As such, additions to a set are processed in closer to real time to update Bloom filters. In some embodiments, Bloom filters are used to check set membership for electronic mail addresses.
Owner:MICROSOFT TECH LICENSING LLC
Adaptive junk message filtering system
InactiveUS20080010353A1Facilitates data filteringEasy to optimizeMultiple digital computer combinationsOffice automationPattern recognitionFilter system
Owner:MICROSOFT TECH LICENSING LLC
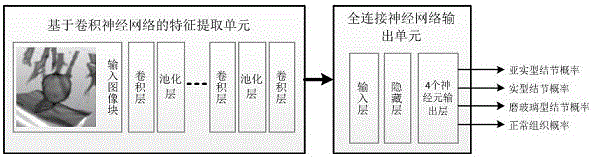
Deep learning method-based automatic pulmonary nodule detection method
ActiveCN108389190AEasy to implementSmall amount of calculationImage enhancementImage analysisPattern recognitionPulmonary nodule
The invention discloses a deep learning method-based automatic pulmonary nodule detection method. The method comprises the following steps of: a, preprocessing: acquiring CT files of a plurality of patients so as to form a data set, and making the CT file corresponding to each patient to a CT file comprising 100-600 slices, wherein a pixel separation distance of each slice is 1*1*1 mm, and the size of each slice is 512*512 pixel; b, lung area image extraction: carrying out pixel value binarization on the CT file of each patient on the basis of a Heinz unit value so as to obtain a mask map of alung area, and extracting a lung area image according to the mask map; c, pulmonary nodule detection: detecting a U-Net convolutional neural network to carrying out pulmonary nodule detection on thelung area image so as to obtain a U-Net training model; and d, false positive rate reduction: training a deep residual network to get rid of false positive points of pulmonary nodules in the U-Net training model so as to obtain a detection model, and carrying out automatic pulmonary nodule detection on the CT files of the patients by using the detection model. The method is high in automatic detection precision.
Owner:贵州联科卫信科技有限公司
Preventing attacks in a data processing system
InactiveUS7555777B2Improve protectionLower Level RequirementsMemory loss protectionUnauthorized memory use protectionData processing systemMonitoring system
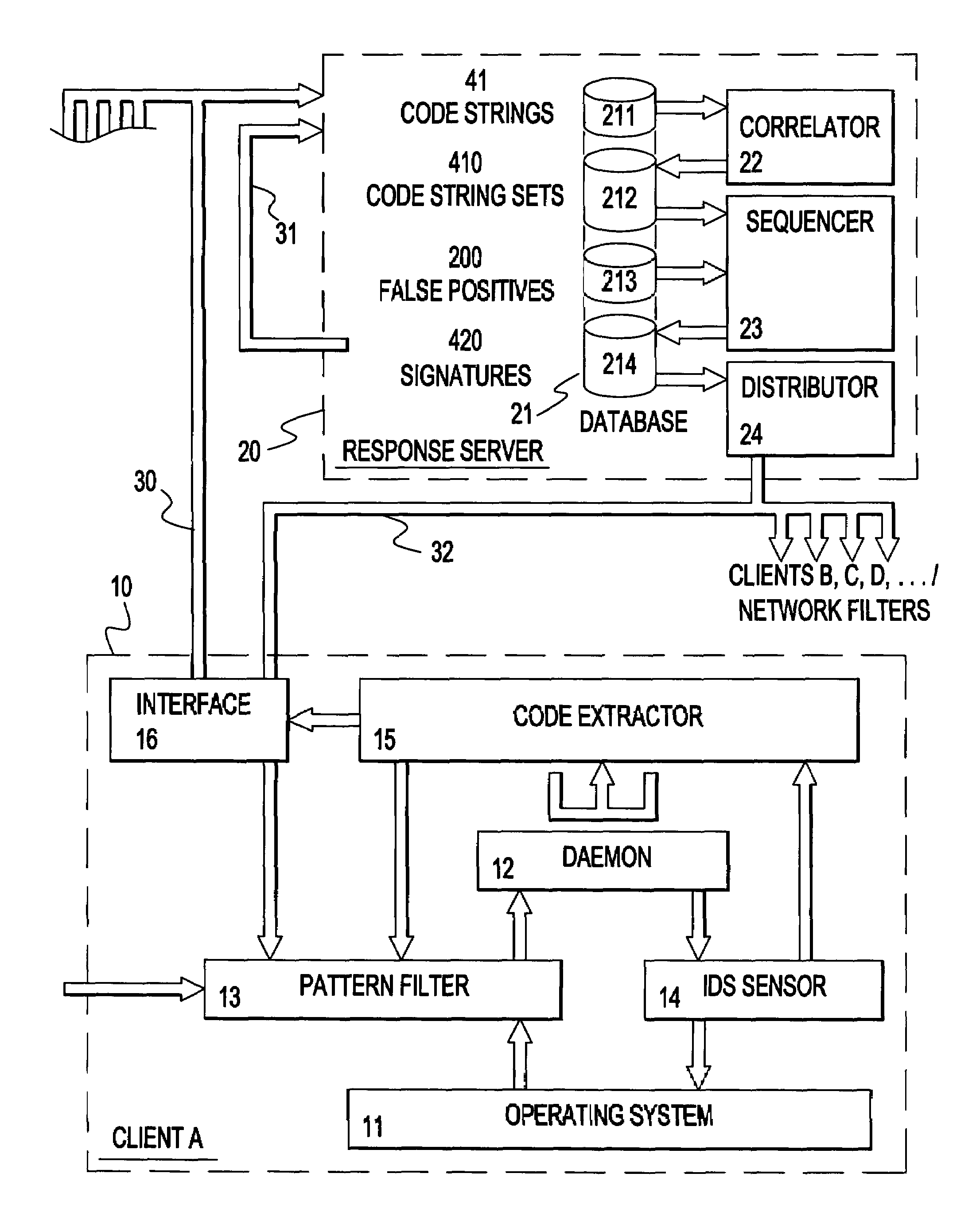
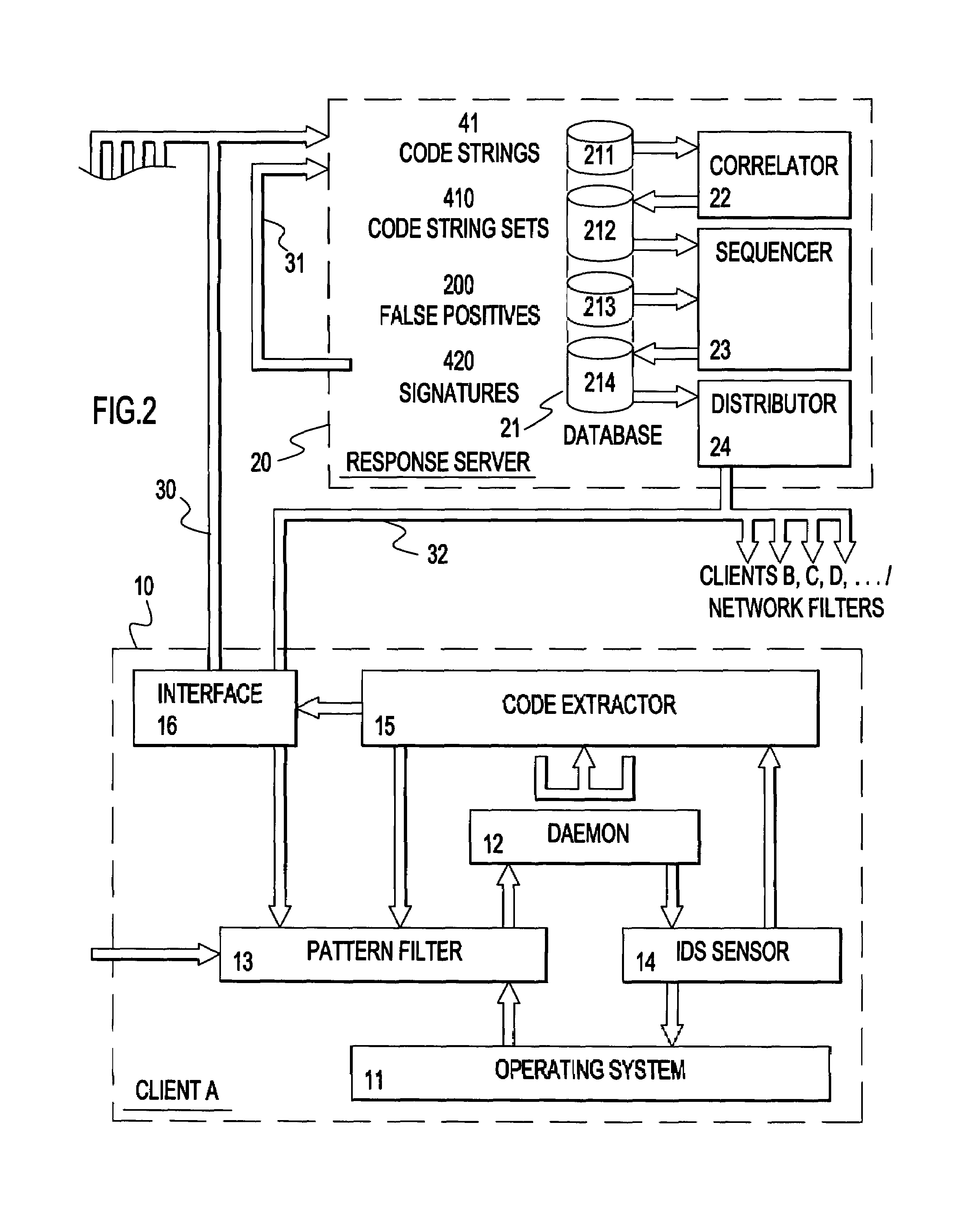
A method and apparatus for facilitating reduction in successful attacks on a monitored data processing system, such as a host computer. An intrusion detection system comprises a host or application based sensor for detecting code based intrusions with a relatively low false-positive rate. Malicious code strings related to a detected intrusion are identified, extracted and forwarded to a pattern filter located in the monitored data processing system to prevent further intrusions using said malicious code strings. The malicious code strings may be forwarded to a response server for assembling sets of similar malicious code strings for which signatures are generated to permit identification of all malicious code strings contained in a set. The generated signatures are then distributed to monitored and / or monitoring systems of a protected network to prevent further intrusions using the malicious code strings and variations thereof.
Owner:IBM CORP
Clean-free solder paste low in ICT (in circuit testing) false positive rate
InactiveCN104416297AImprove flow characteristicsAvoid stayingWelding/cutting media/materialsSoldering mediaZinc alloysSurface-active agents
The invention discloses clean-free solder paste low in ICT false positive rate. The clean-free solder paste low in ICT false positive rate comprises, by weight, 80%-91% of solder alloy powder and 9%-20% of flux. The key is that the flux is composed, by weight, of 10%-35% of rosin of the softening point below 110 DEG C, 40%-60% of composite solvent, 3%-10% of thixotropic agent of the melting point below 140 DEG C, 5%-15% of composition activator and 0.2%-1.5% of nonionic surface active agent. The solder alloy is a stannum-silver-copper alloy, a stannum-silver alloy, a stannum-copper alloy, a stannum-bismuth-copper alloy, a stannum-zinc alloy, a stannum-zinc-bismuth alloy, a stannum-plumbum alloy or a stannum-plumbum-silver alloy.
Owner:EUNOW ELECTRONICS TECH CO LTD SUZHOU
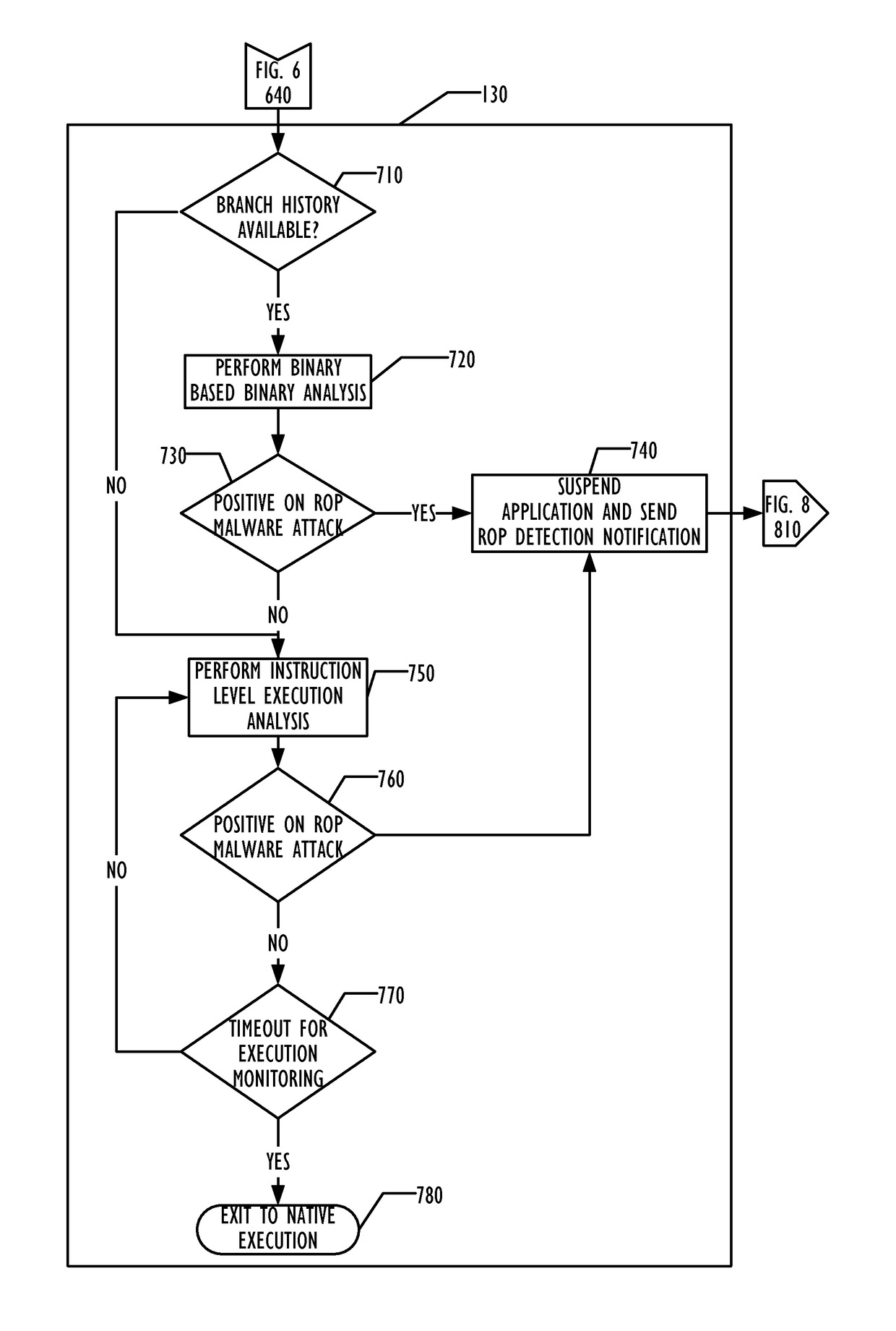
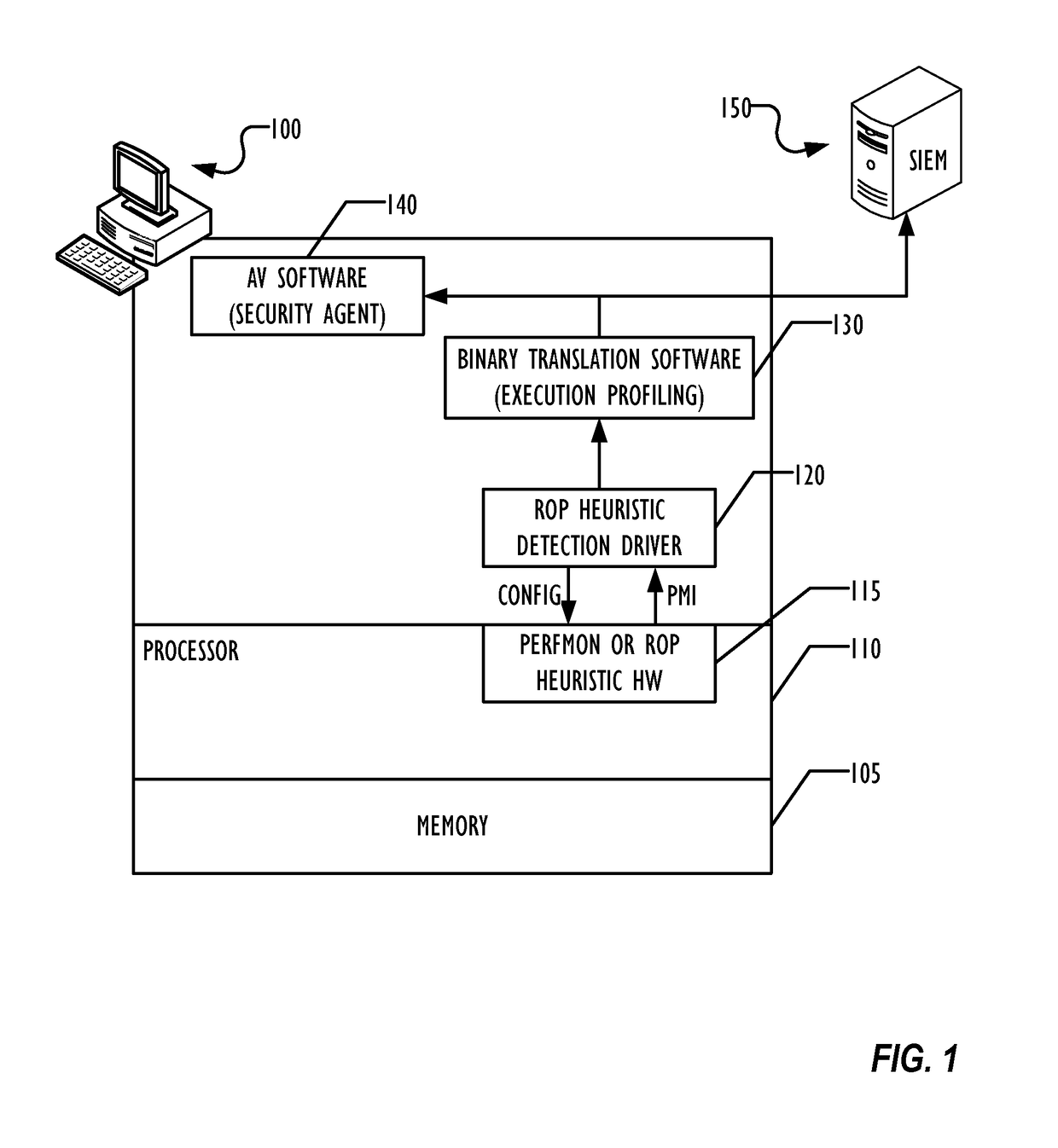
Hardware heuristic-driven binary translation-based execution analysis for return-oriented programming malware detection
A combination of hardware monitoring and binary translation software allow detection of return-oriented programming (ROP) exploits with low overhead and low false positive rates. Embodiments may use various forms of hardware to detect ROP exploits and indicate the presence of an anomaly to a device driver, which may collect data and pass the indication of the anomaly to the binary translation software to instrument the application code and determine whether an ROP exploit has been detected. Upon detection of the ROP exploit, the binary translation software may indicate the ROP exploit to an anti-malware software, which may take further remedial action as desired.
Owner:MCAFEE LLC
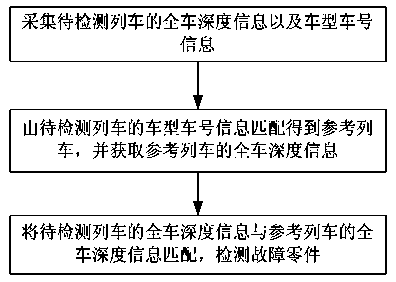
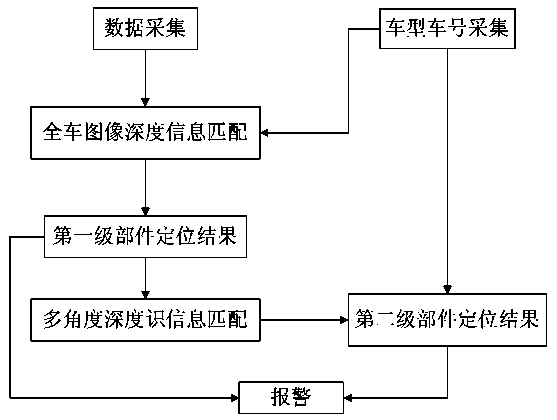
Train anomaly recognition detection method and system
ActiveCN104200464AReal-time abnormal state identificationImprove operational safety monitoring capabilitiesImage analysisVisual functionVisual perception
The invention discloses a train anomaly recognition detection method and system and belongs to the technical field of automatic image recognition. The recognition method includes the steps of collecting whole train depth information of a train to be detected and a reference train, matching a train model and a train number with the whole train depth information of the train to be detected and the reference train for recognizing faulty components, and matching depth information of the faulty components with that of reference parts for determining faulty parts. The recognition system comprises a collection module for collecting the whole train depth information of the train to be detected, a reference train information acquisition module and a faulty part detection module. A method of collecting three-dimensional image information of a running train with the depth information overcomes the visual function limitation of traditional two-dimensional image information so as to facilitate quick find of actual faulty points of a detection worker, reduce the false positive rate of the system and improve the maintenance efficiency of the detection worker.
Owner:SUZHOU NEW VISION SCI & TECH
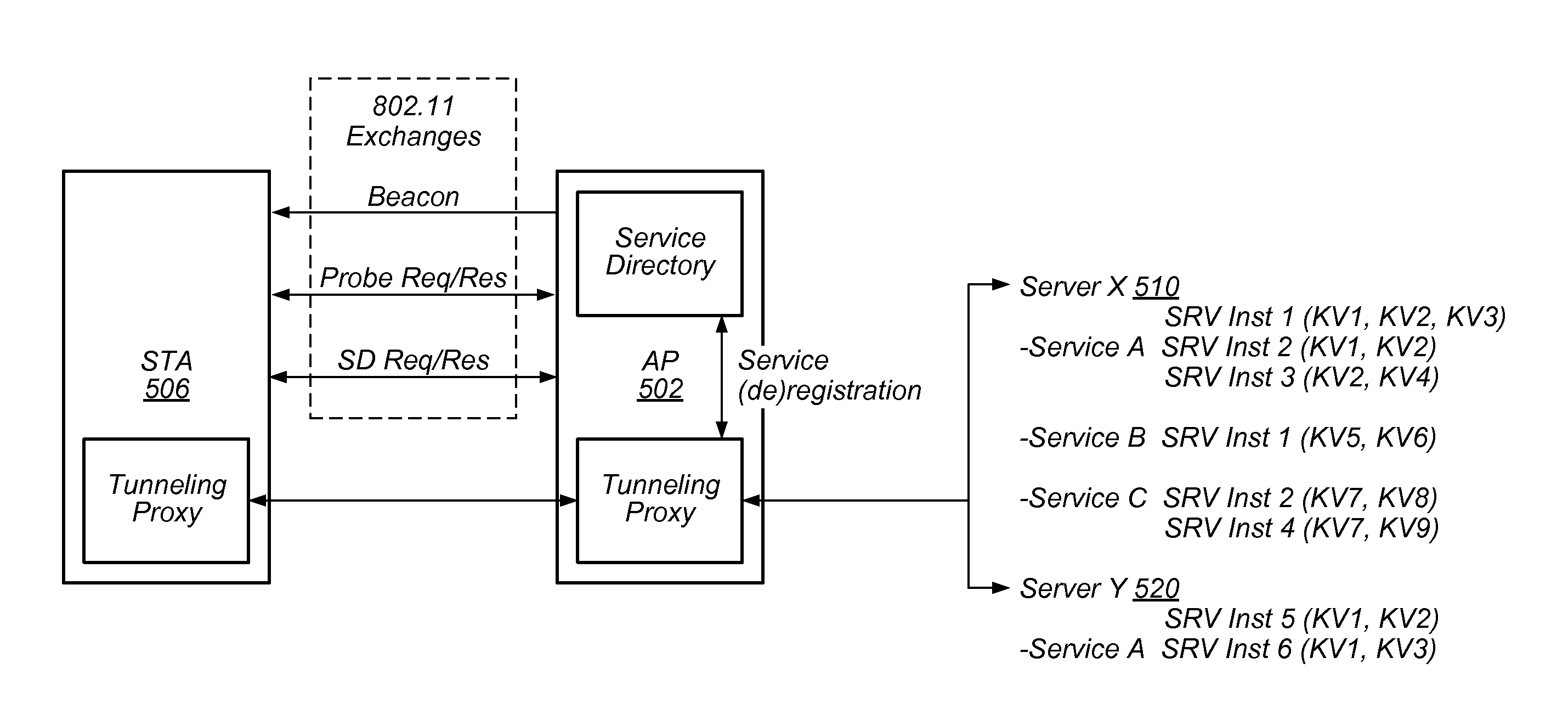
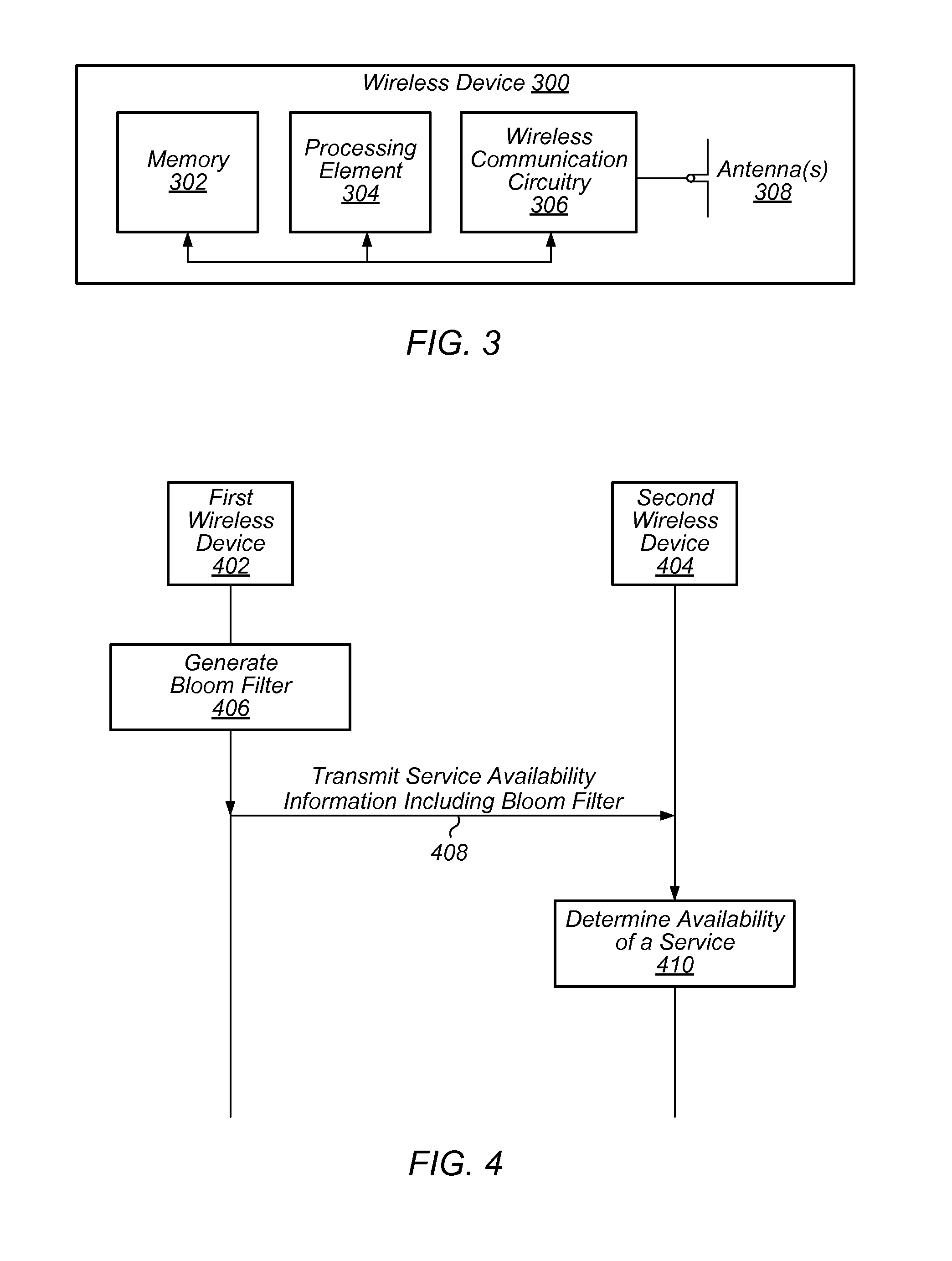
Dynamic Bloom Filter Operation for Service Discovery
ActiveUS20150363704A1Improve efficiencyImprove scalabilityService provisioningServices signallingHash functionFalse positive paradox
This disclosure relates to service discovery using a dynamically configurable Bloom filter. According to some embodiments, various parameters of the Bloom filter may be determined by a first wireless device. The parameters may include a number of services advertised using the Bloom filter, a false positive rate of the Bloom filter, a set of hash functions used with the Bloom filter, and / or a size of the Bloom filter. The Bloom filter may be generated according to the determined parameters. The Bloom filter, along with some or all of the parameters of the Bloom filter, may be transmitted by the first wireless device. A second wireless device may use the Bloom filter as part of a service discovery process to determine whether or not a desired service is available via the first wireless device.
Owner:APPLE INC
In-vivo detection method based on attitude information
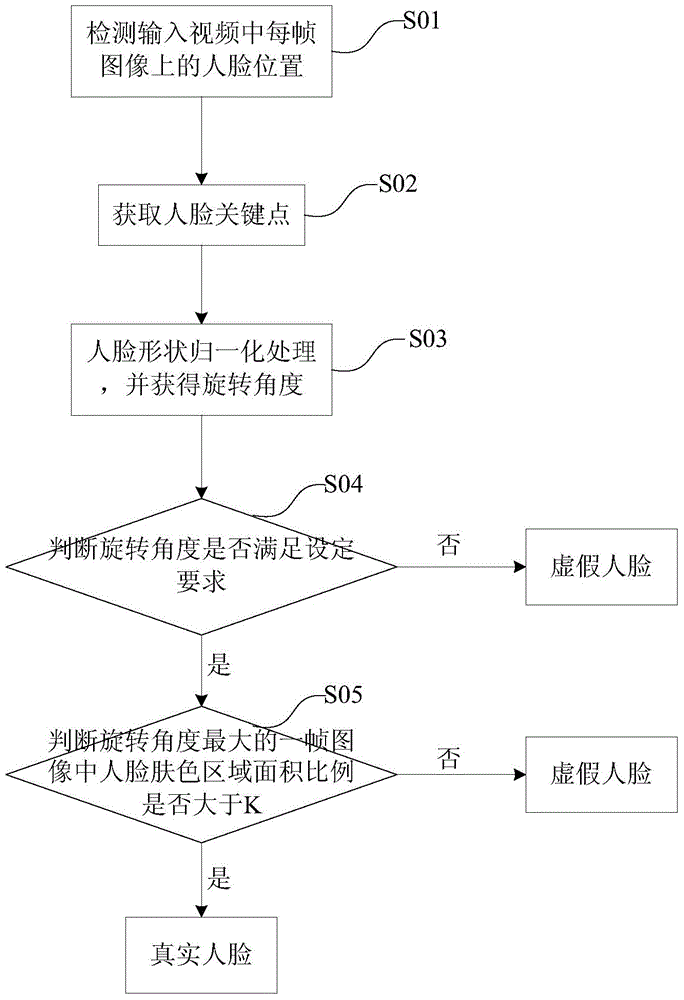
ActiveCN104794465ASatisfy the false positive rateHigh speedCharacter and pattern recognitionPattern recognitionSkin color
The invention relates to an in-vivo detection method based on attitude information. The method comprises the following steps: (1) detecting a face position on each frame image in an input video; (2) acquiring facial key points and a face shape formed by the key points; (3) performing normalization processing on the face shape based on a 3D face model, and acquiring a rotating angle of the face shape relative to the 3D face model; (4) connecting rotating angles of multiple continuous frame images to form a curve, judging whether the curve meets the set requirement, if so, executing a step (5), otherwise, judging that the face is a false face, and exiting; and (5) judging whether the area of a face color area in a frame image with the largest rotating angle is larger than K, if so, judging that the face is a real face, otherwise, the face is a false face. Compared with the prior art, the method disclosed by the invention has the advantages of low false positive rate, high speed and the like.
Owner:SHANGHAI YITU INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com