Patents
Literature
1957 results about "Data filtering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data filtering in IT can refer to a wide range of strategies or solutions for refining data sets. This means the data sets are refined into simply what a user (or set of users) needs, without including other data that can be repetitive, irrelevant or even sensitive.
Data security system and method for separation of user communities
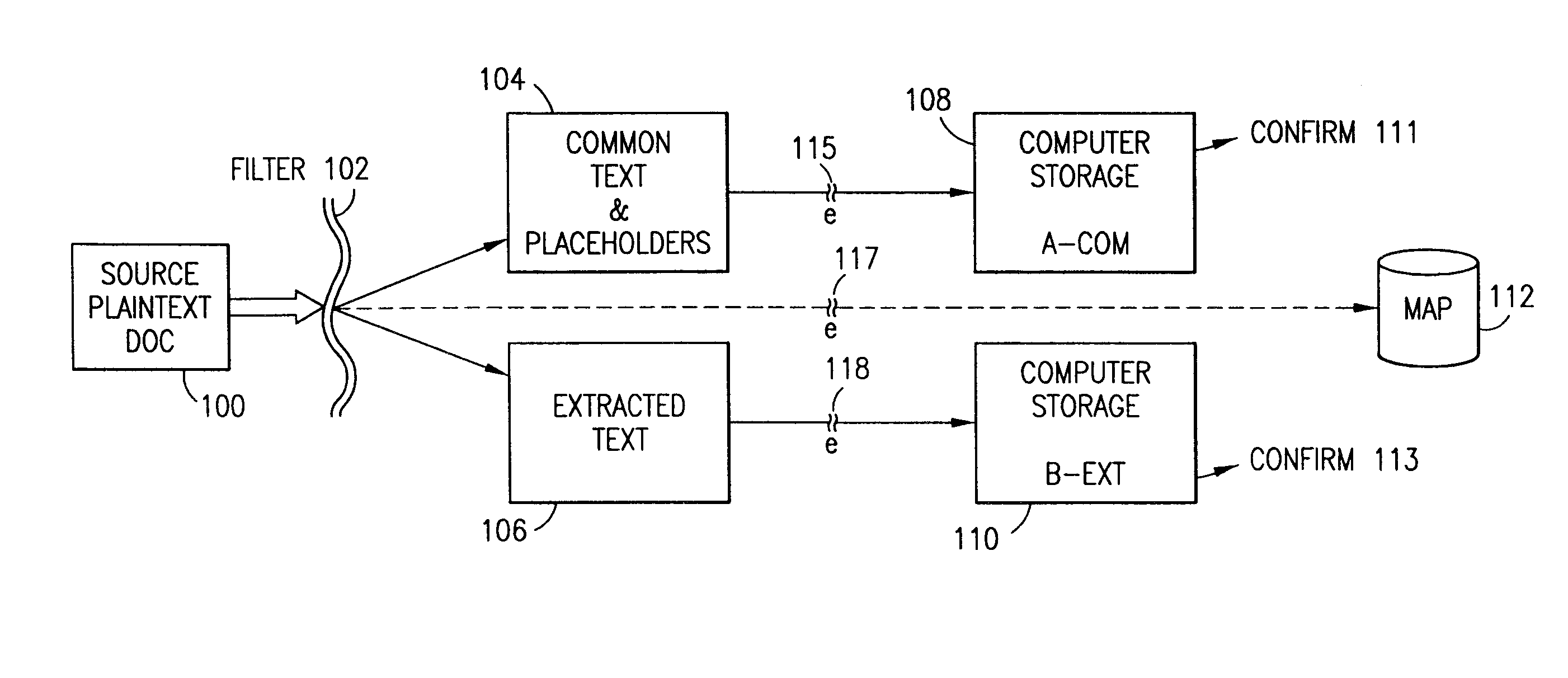
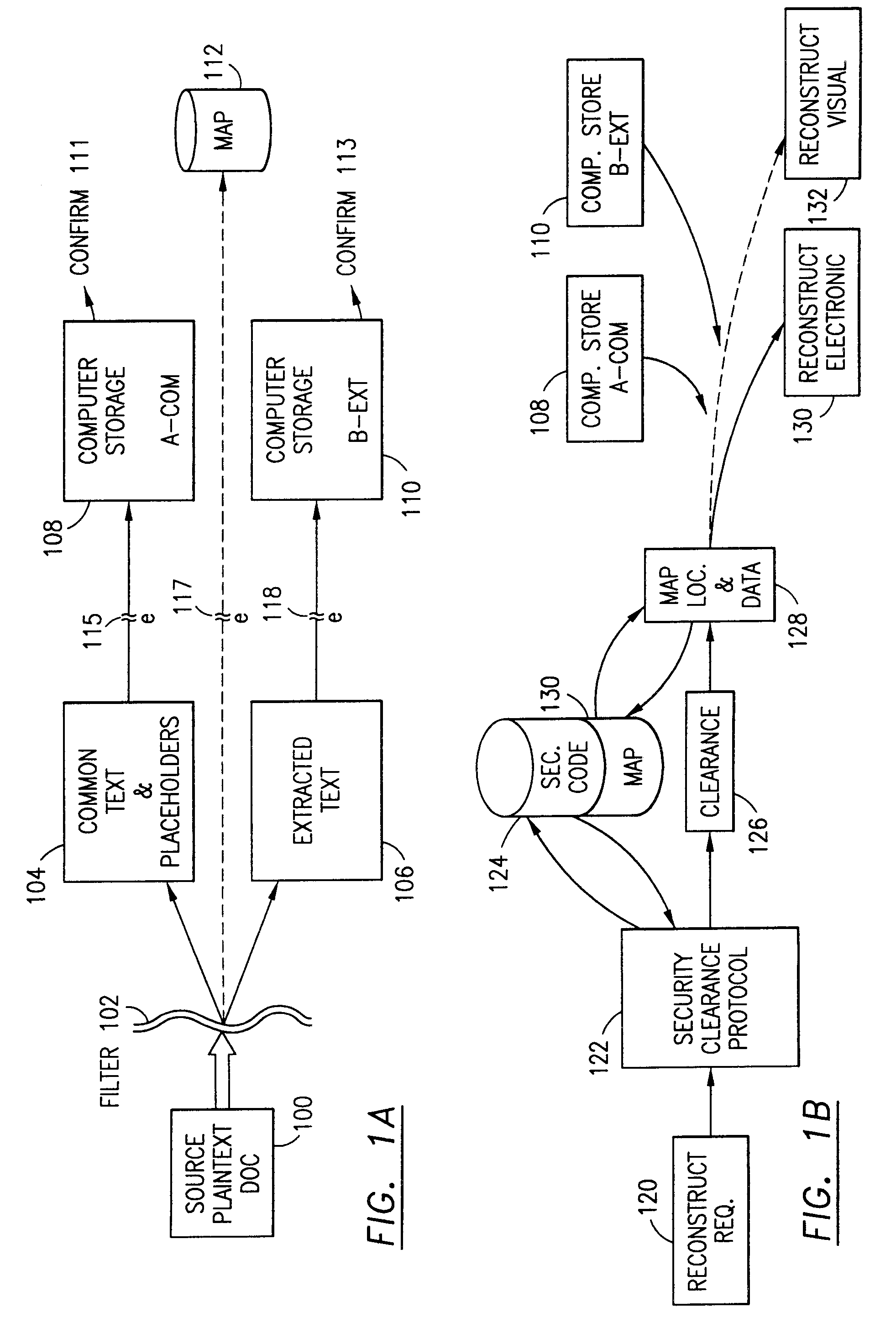
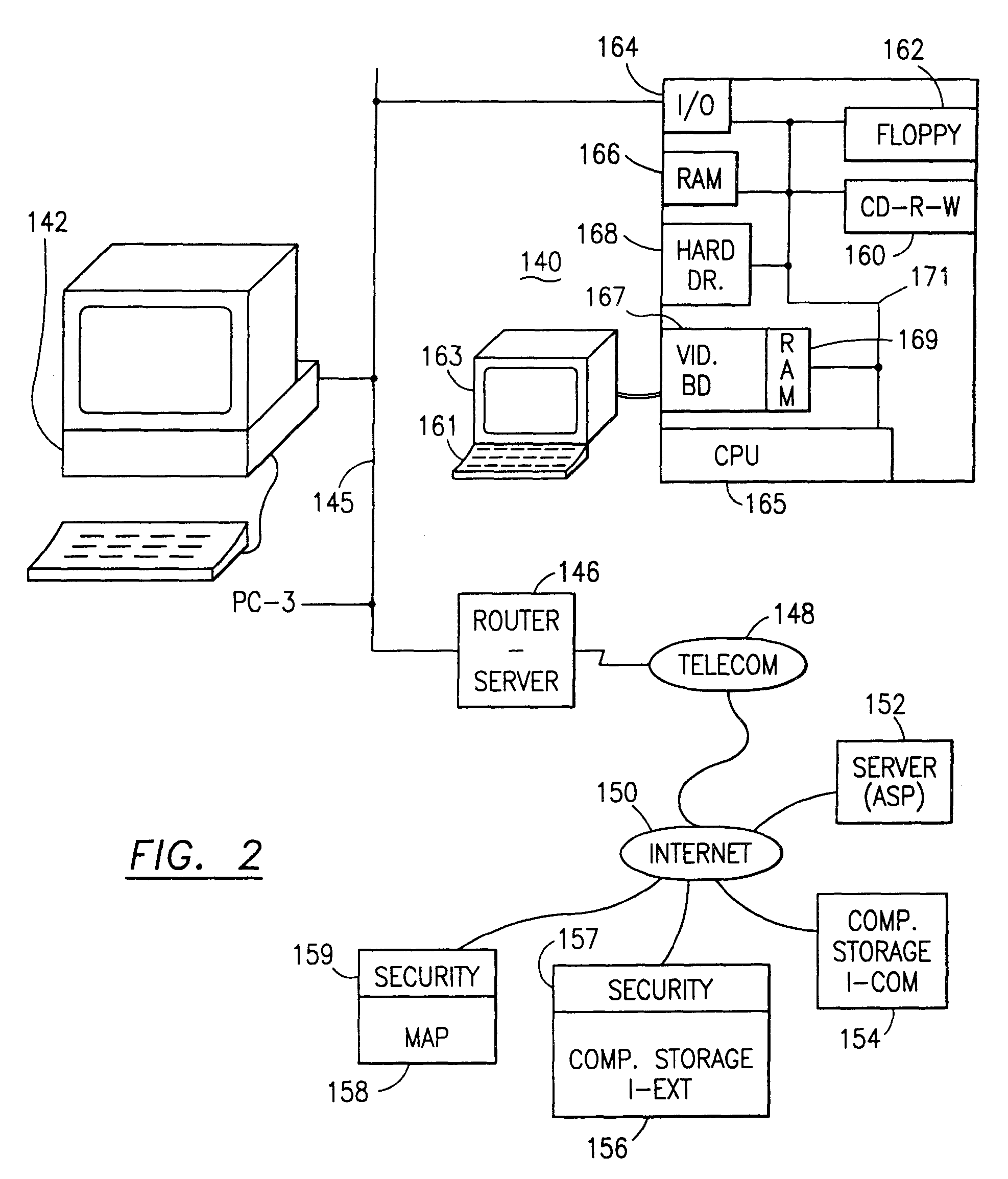
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
Process and method for data assurance management by applying data assurance metrics
InactiveUS8843487B2Digital data information retrievalDigital data processing detailsData sourceData quality
The present invention relates generally to methods, software and systems for measuring and valuing the quality of information and data, where such measurements and values are made and processed by implementing objectively defined, measurable, comparable and repeatable dimensions using software and complex computers. The embodiments include processes, systems and method for identifying optimal scores of the data dimension. The invention further includes processes, systems and method for data filtering to improve the overall data quality of a data source. Finally, the invention further includes processes, systems and method for data quality assurance of groups of rows of a database.
Owner:BLACK OAK PARTNERS
Methods for performing DAF data filtering and padding
InactiveUS6847737B1Reduce acquisition timeEnhance and improve imageImage enhancementImage analysisPattern recognitionData set
A method for padding, filtering, denoising, image enhancing and increased time-frequency acquisition is described for digitized data of a data set where unknown data is estimated using real data by adding unknown data points in a manner that the padding routine can estimate the interior data set including known and unknown data to a given accuracy on the known data points. The method also provides filtering using non-interpolating, well-tempered distributed approximating functional (NIDAF)-low-band-pass filters. The method also provides for symmetric and / or anti-symmetric extension of the data set so that the data set may be better refined and can be filtered by Fourier and other type of low frequency or harmonic filters.
Owner:IOWA STATE UNIVERSITY +1
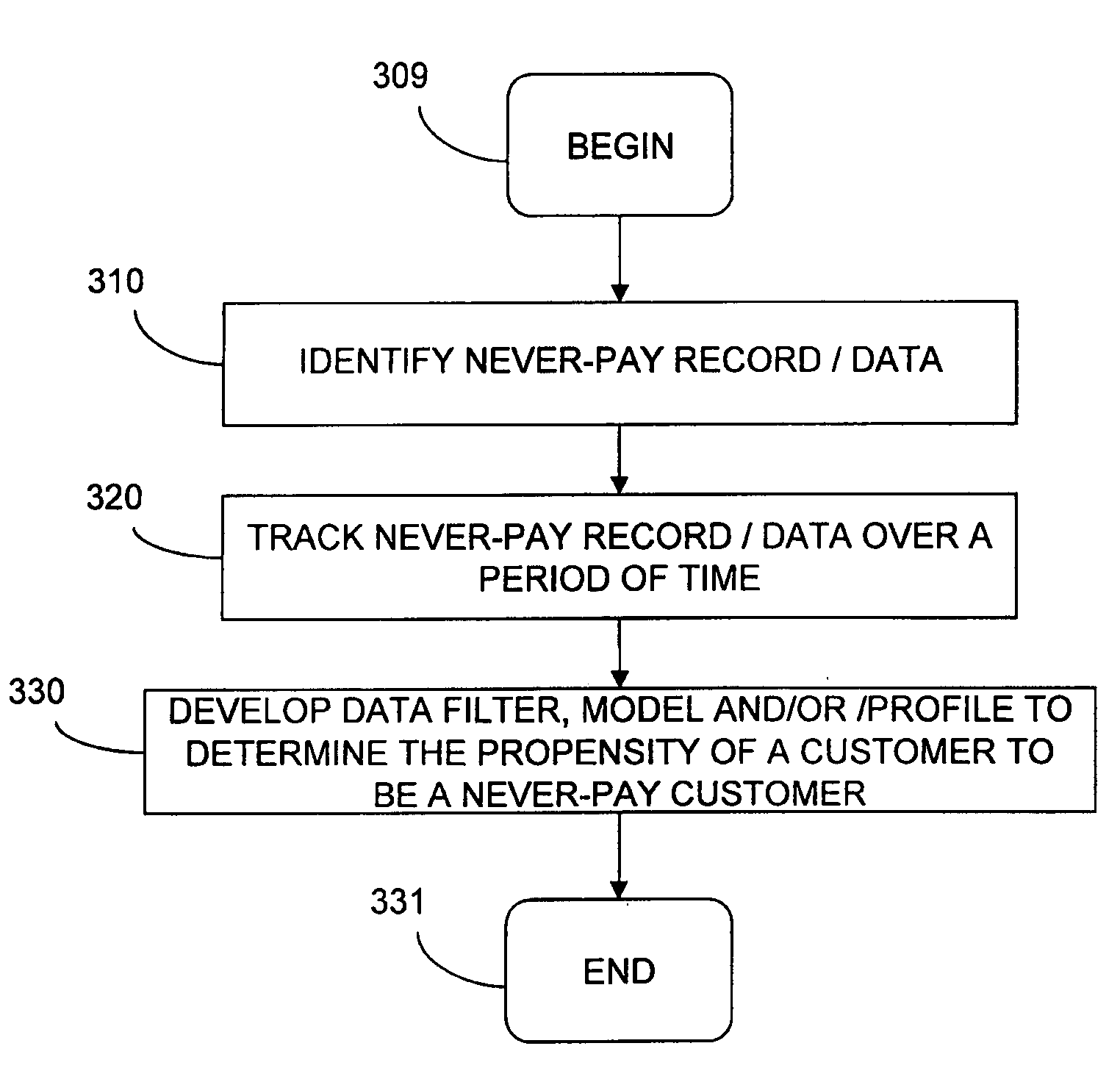
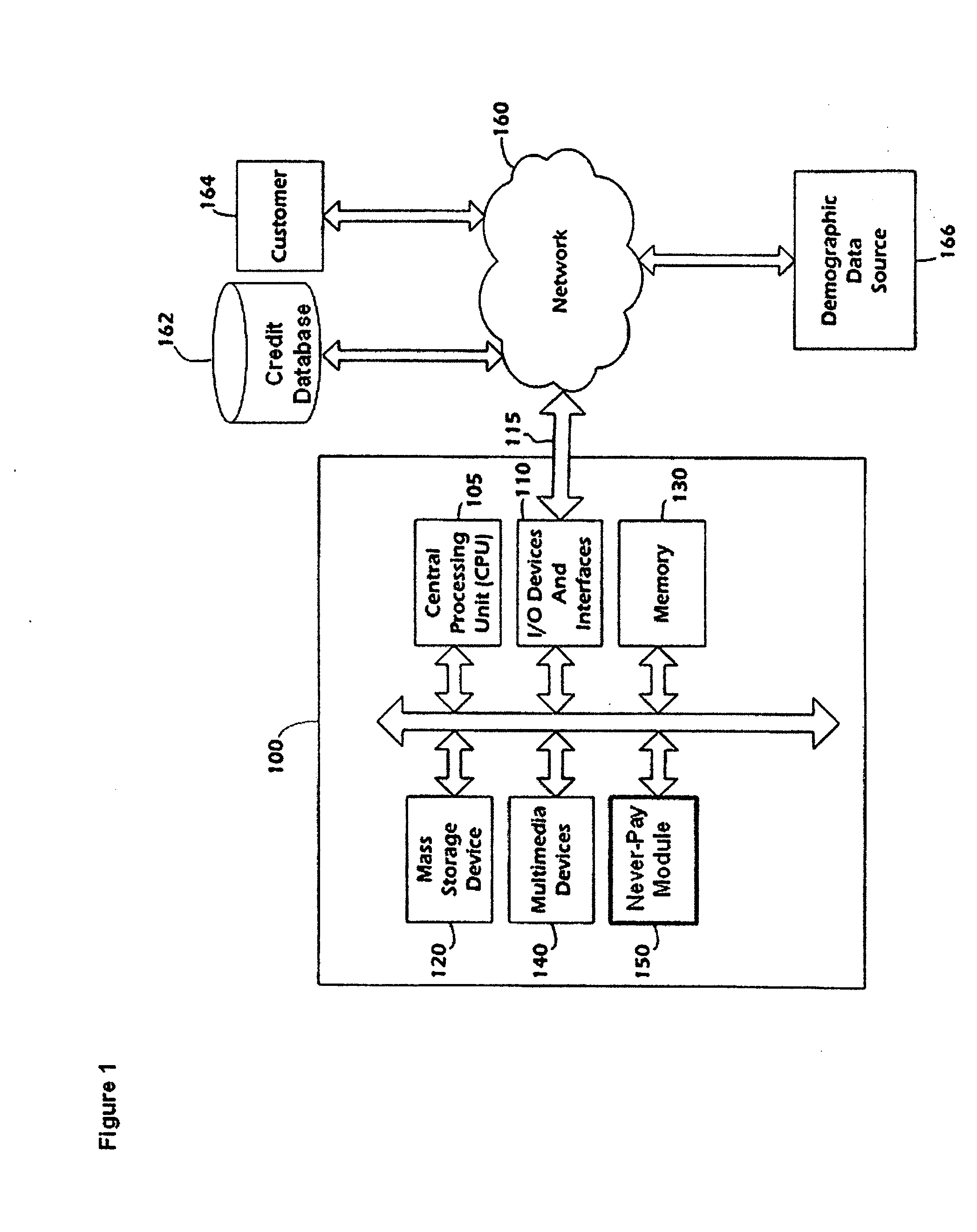
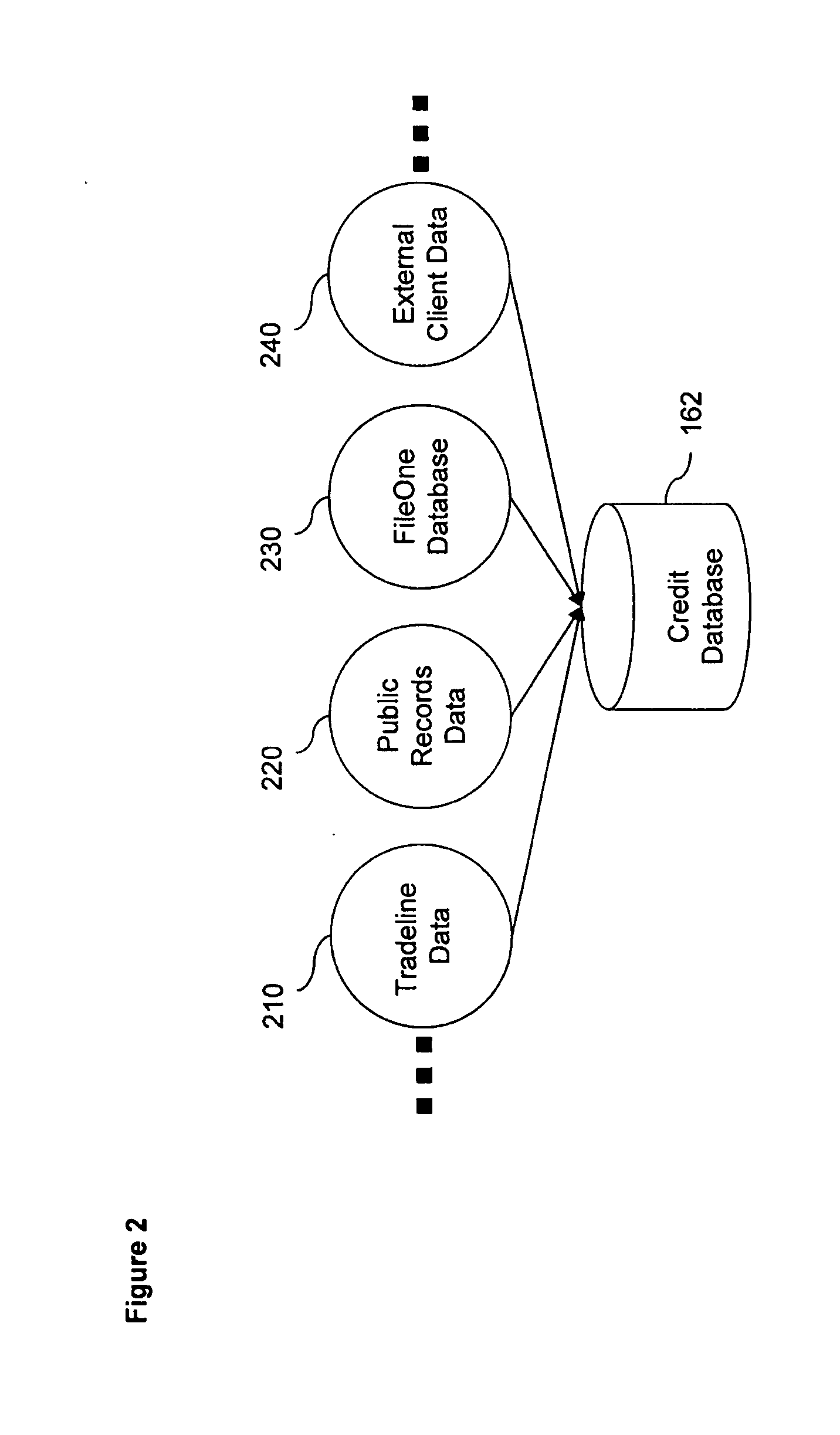
System and method for automated detection of never-pay data sets
Data filters, models, and / or profiles for identifying and / or predicting the never-pay population (for example, those customers that make a request for credit and obtain the credit instrument but over the life of the account, never make a payment) can be useful to various commercial entities, such as those issuing mortgages, home equity lines of credit, consumer or business lines of credit, automobile loans, credit card accounts, or those entities providing services, such as utility services, phone services, and the like.
Owner:EXPERIAN INFORMATION SOLUTIONS
Method and system for on-demand and scheduled services relating to travel and transportation
A system and a method for providing a user with an ability to manage an on-demand or scheduled service, the system including a mobile communicator configured to receive instructions from the user and to send user data; and a facilitator configured to receive the user data and to retrieve options data based on the user data, wherein the facilitator is further configured to: filter the options data based on an identification data, provide associated costs and relevant information for the filtered options data, and send the filtered options data and the associated costs to the mobile communicator.
Owner:RIDECHARGE
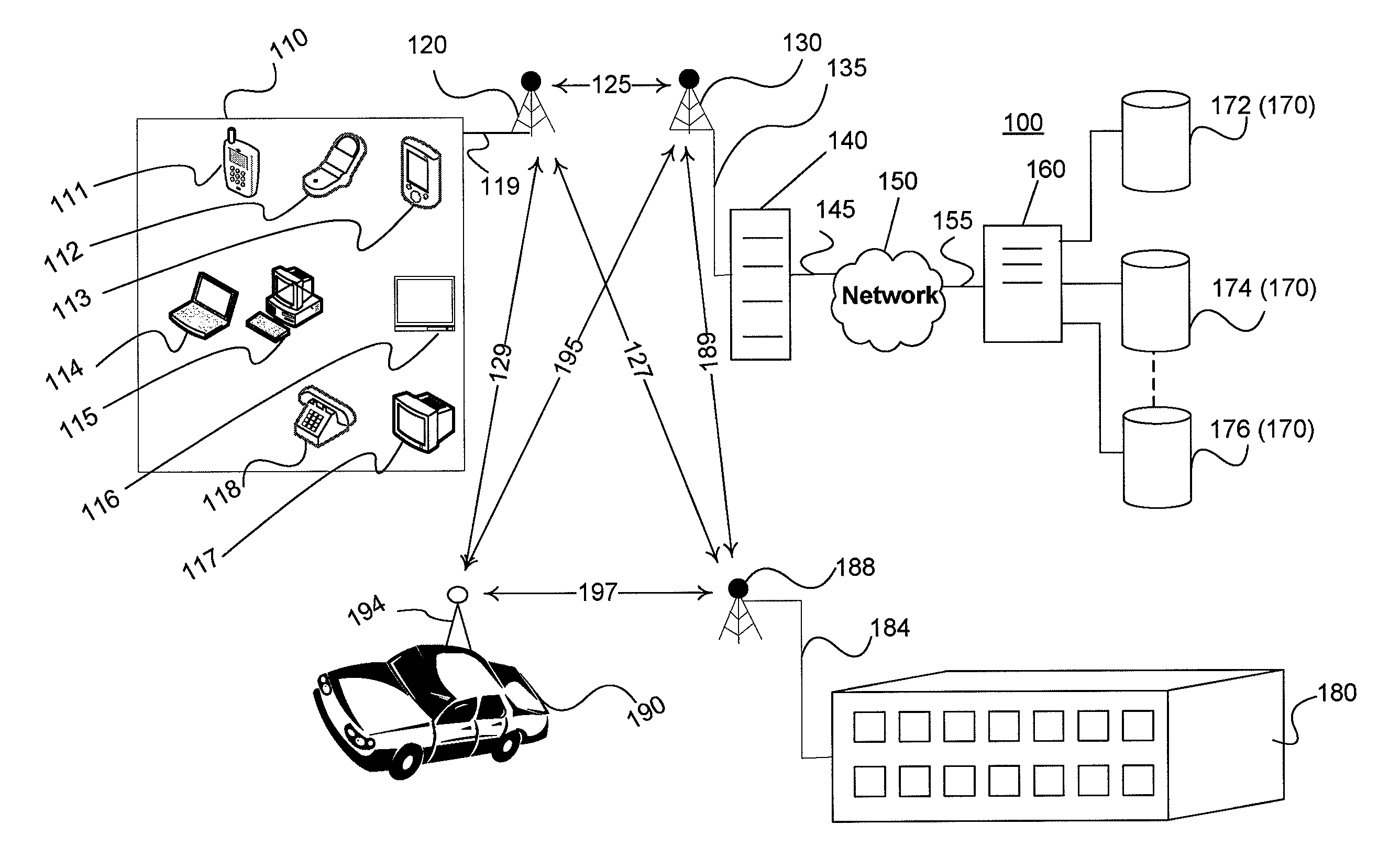
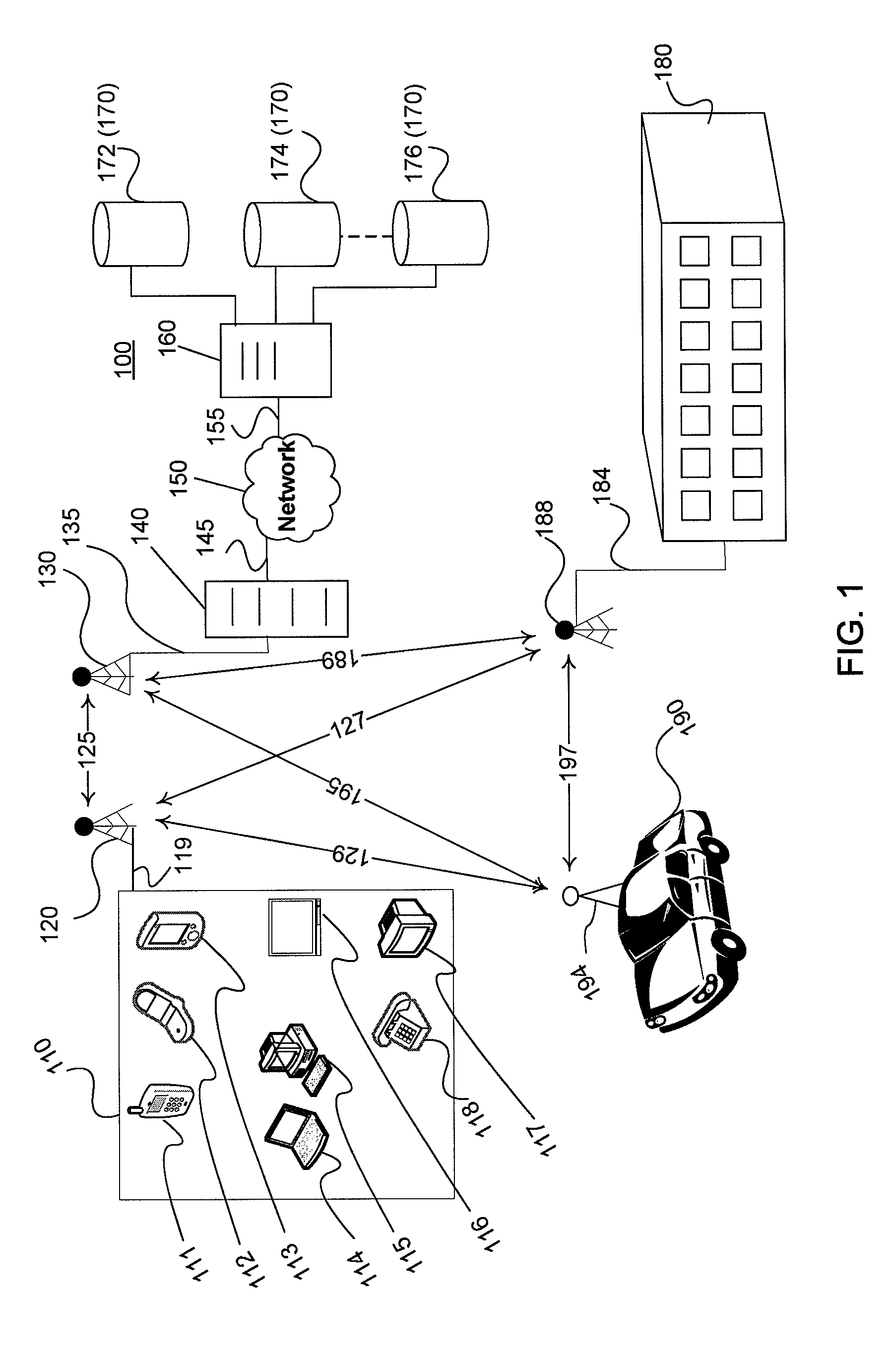
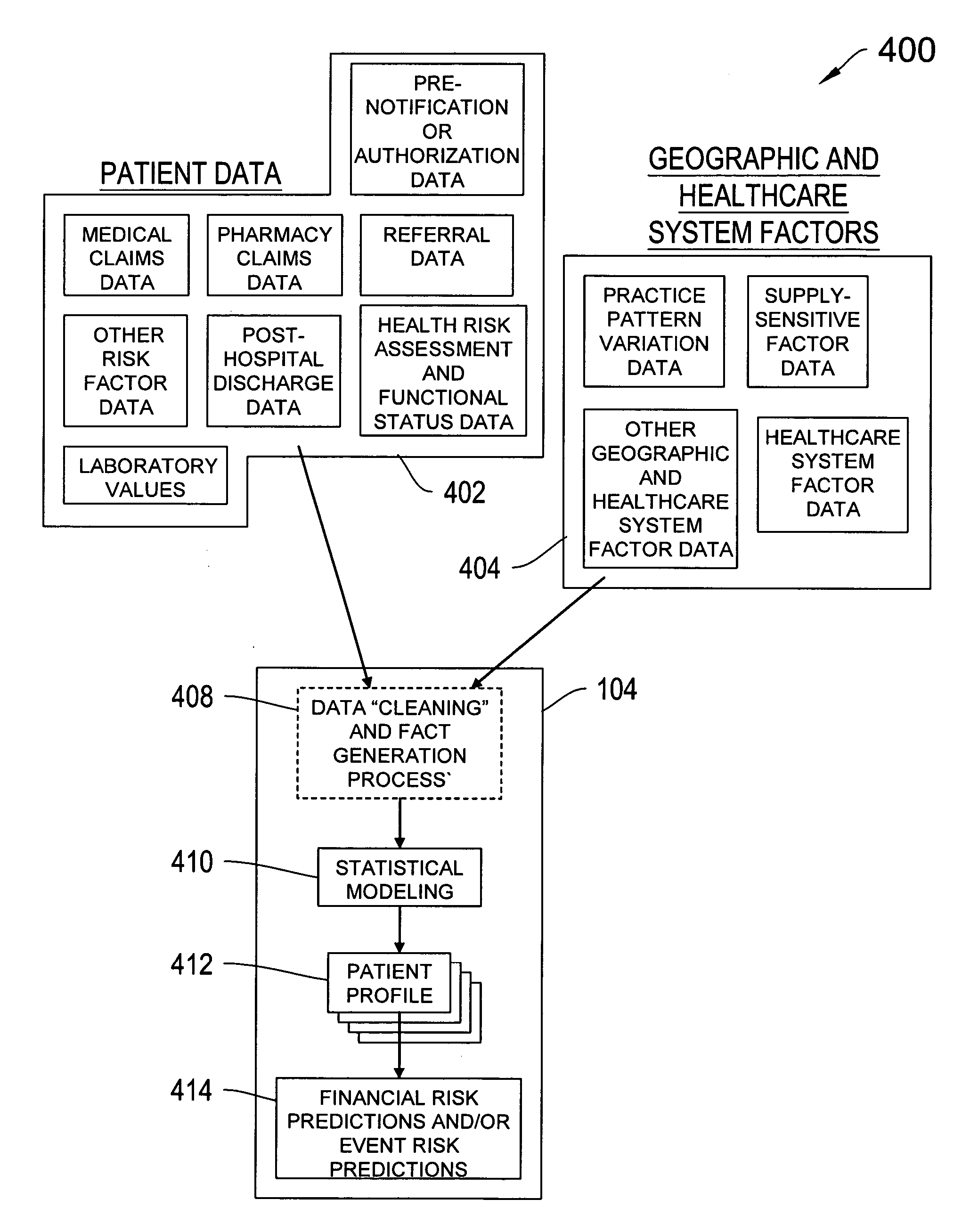
Systems and methods for predicting healthcare related financial risk
ActiveUS20060129428A1Reduce medical costsPrevent and mitigate occurrenceMedical simulationMedical data miningRisk levelRisk model
A system for predicting healthcare financial risk including the process of accessing patient data associated with one or more patents, accessing geographic and healthcare system data, filtering the patient data, geographic data, and healthcare system data into clean data, and applying a predictive risk model to the clean data to generate patient profile data and to identify a portion of the patients associated with a level of predicted financial risk.
Owner:HEALTH DIALOG SERVICES CORP
Methods for performing DAF data filtering and padding
InactiveUS7272265B2Reduce acquisition timeEnhance and improve imageImage enhancementImage analysisPattern recognitionData set
A method for padding, filtering, denoising, image enhancing and increased time-frequency acquisition is described for digitized data of a data set is described where unknown data is estimated using real data by adding unknown data points in a manner that the padding routine can estimate the interior data set including known and unknown data to a given accuracy on the known data points. The method also provides filtering using non-interpolating, well-tempered distributed approximating functional (NIDAF)-low-band-pass filters. The method also provides for symmetric and / or anti-symmetric extension of the data set so that the data set may be better refined and can be filtered by Fourier and other type of low frequency or harmonic filters.
Owner:IOWA STATE UNIV RES FOUND
System and method for filtering data
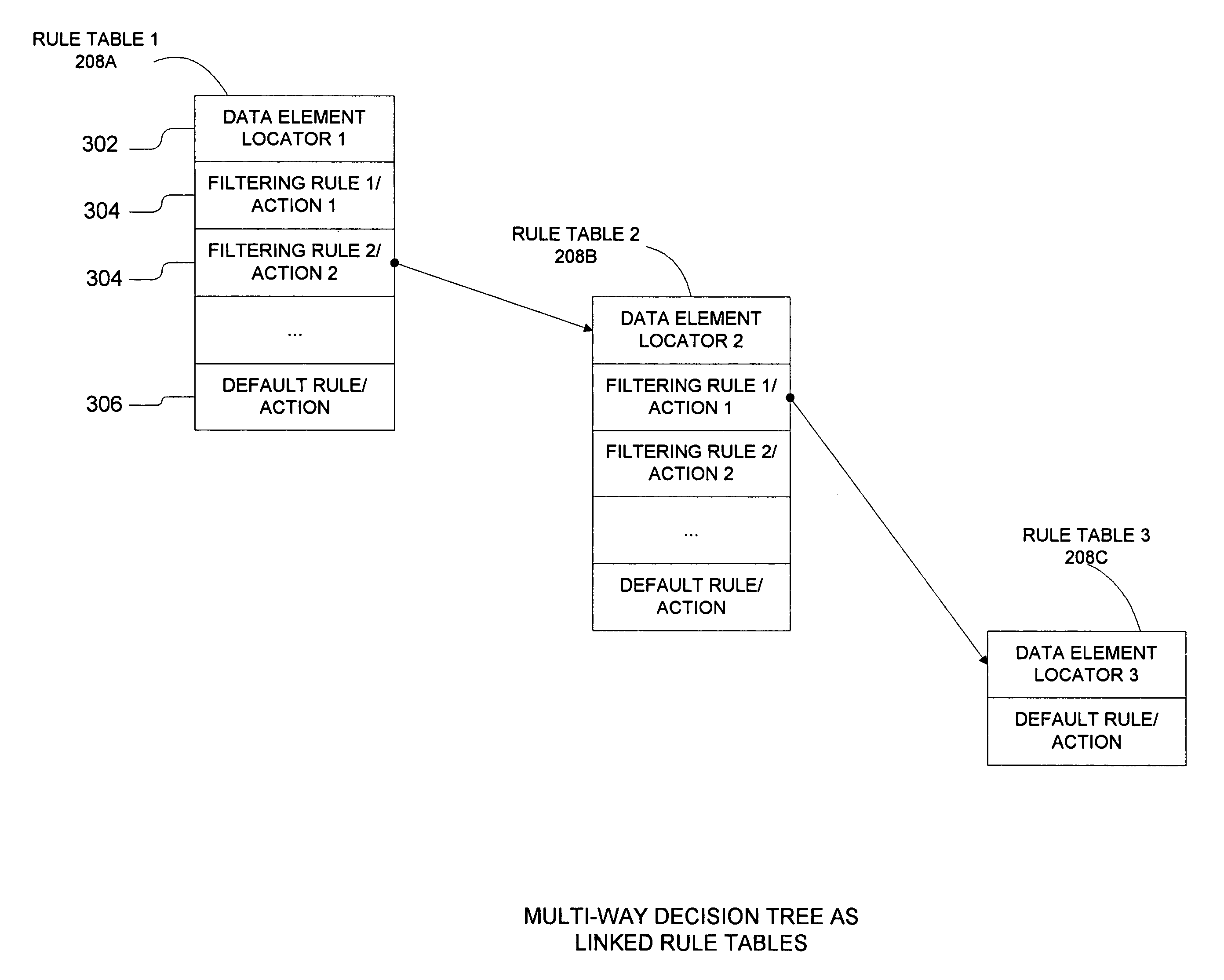
InactiveUS7133400B1Quickly and efficiently classifyQuickly and efficiently and filterDigital computer detailsData switching by path configurationFiltering rulesData element
A system for filtering data comprises a filtering database for storing layered rule tables and a data filtering engine coupled to the filtering database for filtering the input data using the layered rule tables. The data filtering engine filters or classifies input data using tests or rules performed on the data elements in the input data. The data elements are segments of data in the input data and are selected from the input data using a data element locator. Preferably, each rule table in the filtering database comprises a data element locator, a default rule, and zero or more filtering rules. The filtering rules comprise the tests or rules that are to be applied to the data elements. Each rule table corresponds to a single data element and each filtering rule in the rule table is to be applied to that data element.
Owner:INTEL CORP
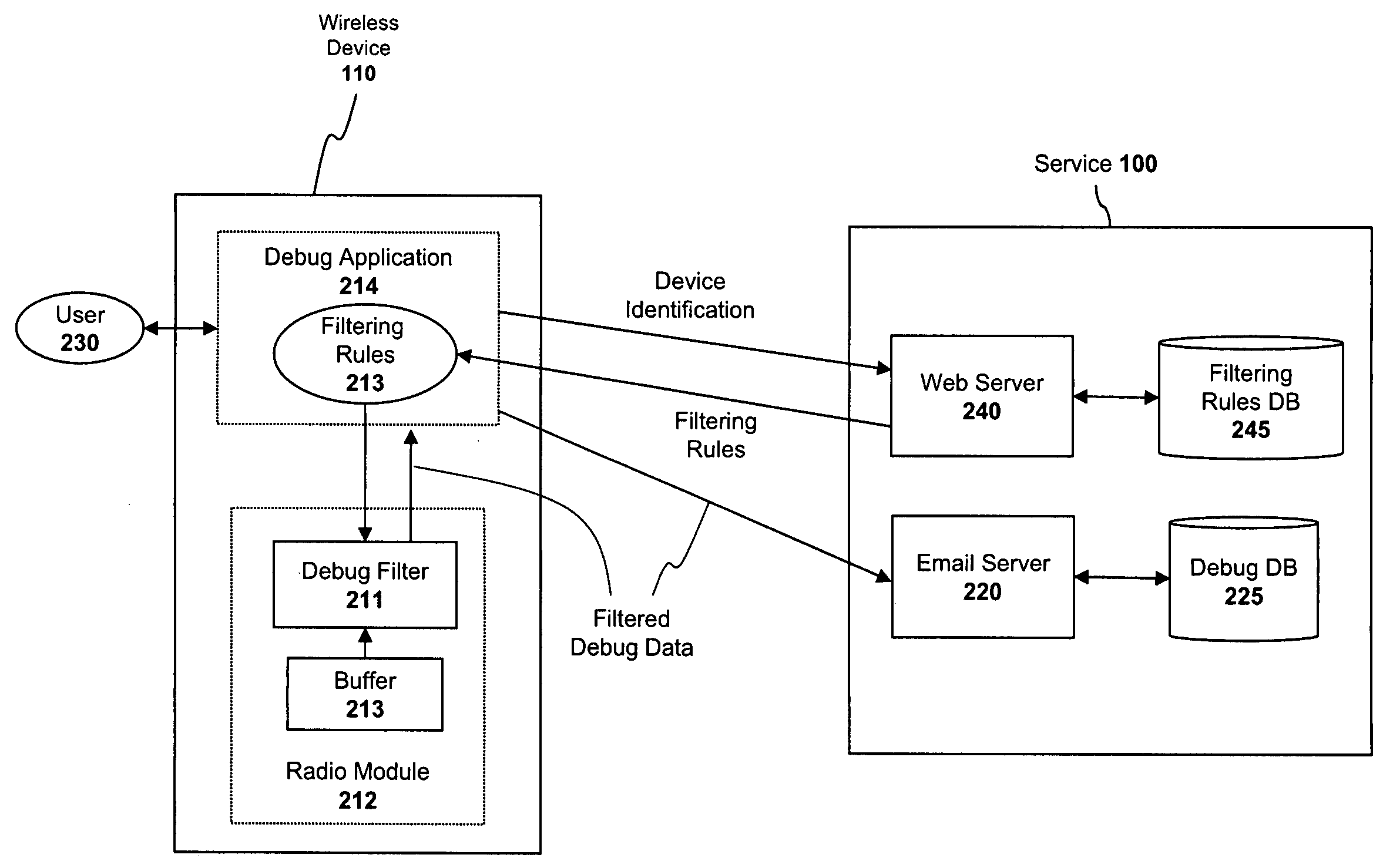
System and method for collecting debug data from a wireless device
ActiveUS20090138763A1Hardware monitoringMultiple digital computer combinationsComputer hardwareFiltering rules
A data processing apparatus having a memory for storing program code and a processor for processing the program code, the data processing apparatus comprising: a radio module to communicatively couple the data processing apparatus to a wireless network, the radio module generating a plurality of debug data in a plurality of signal classes; a set of debug data filtering rules specifying certain debug data within the plurality of signal classes to be collected from the radio module; and a debug application executed on the data processing apparatus, the debug application to apply the set of filtering rules, thereby causing only the specified set of debug data to be collected from the radio module.
Owner:MICROSOFT TECH LICENSING LLC
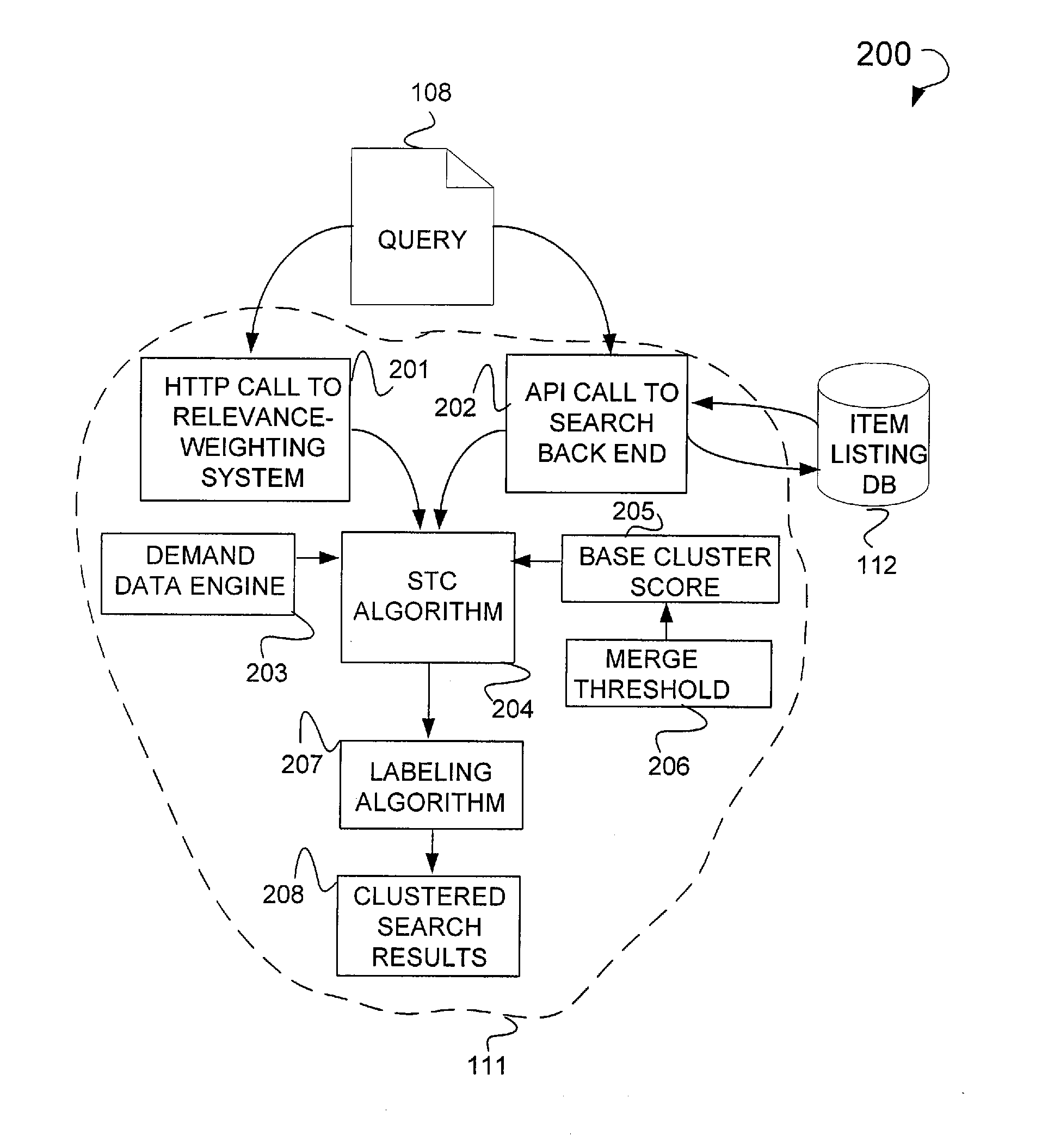
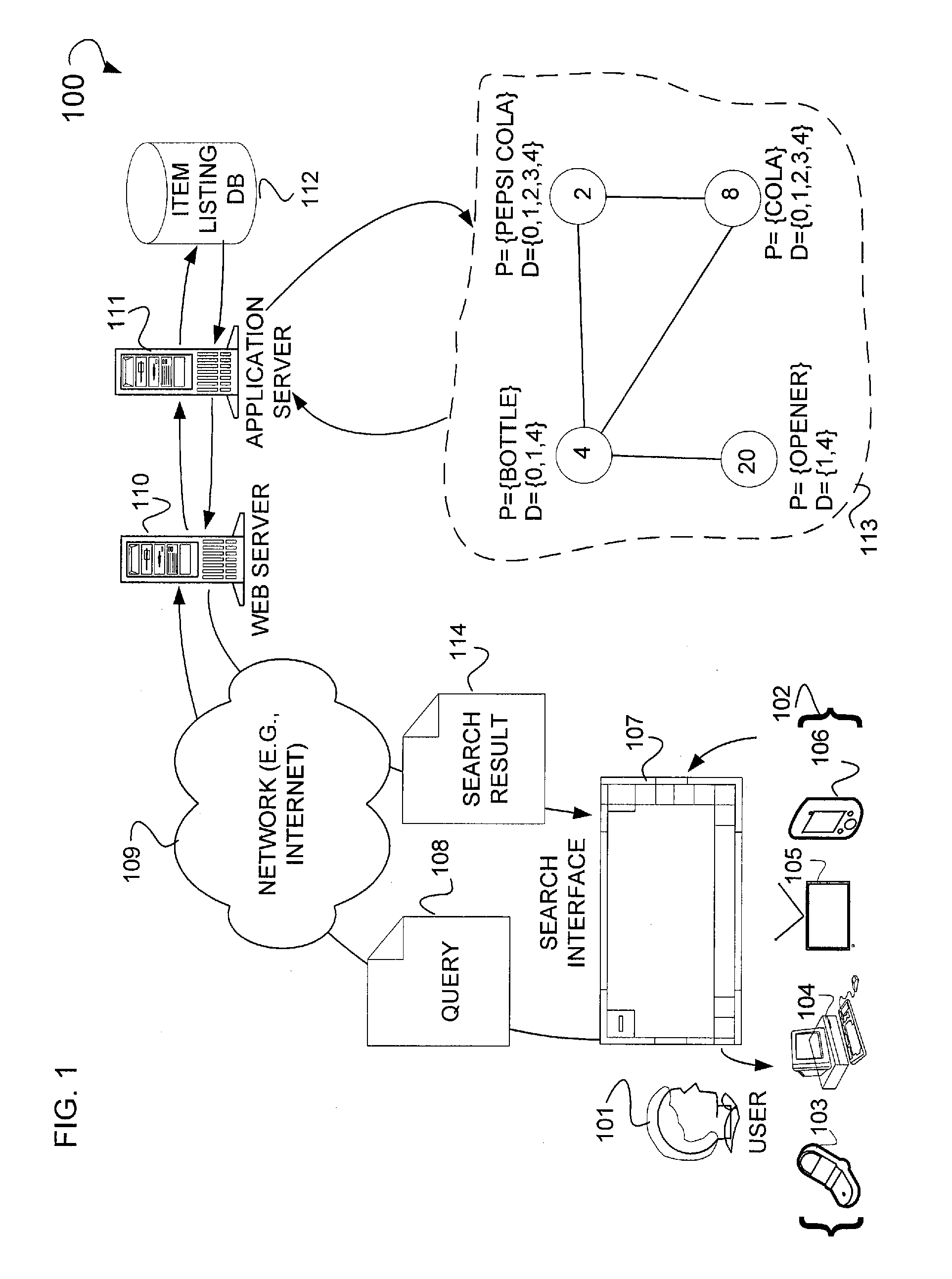
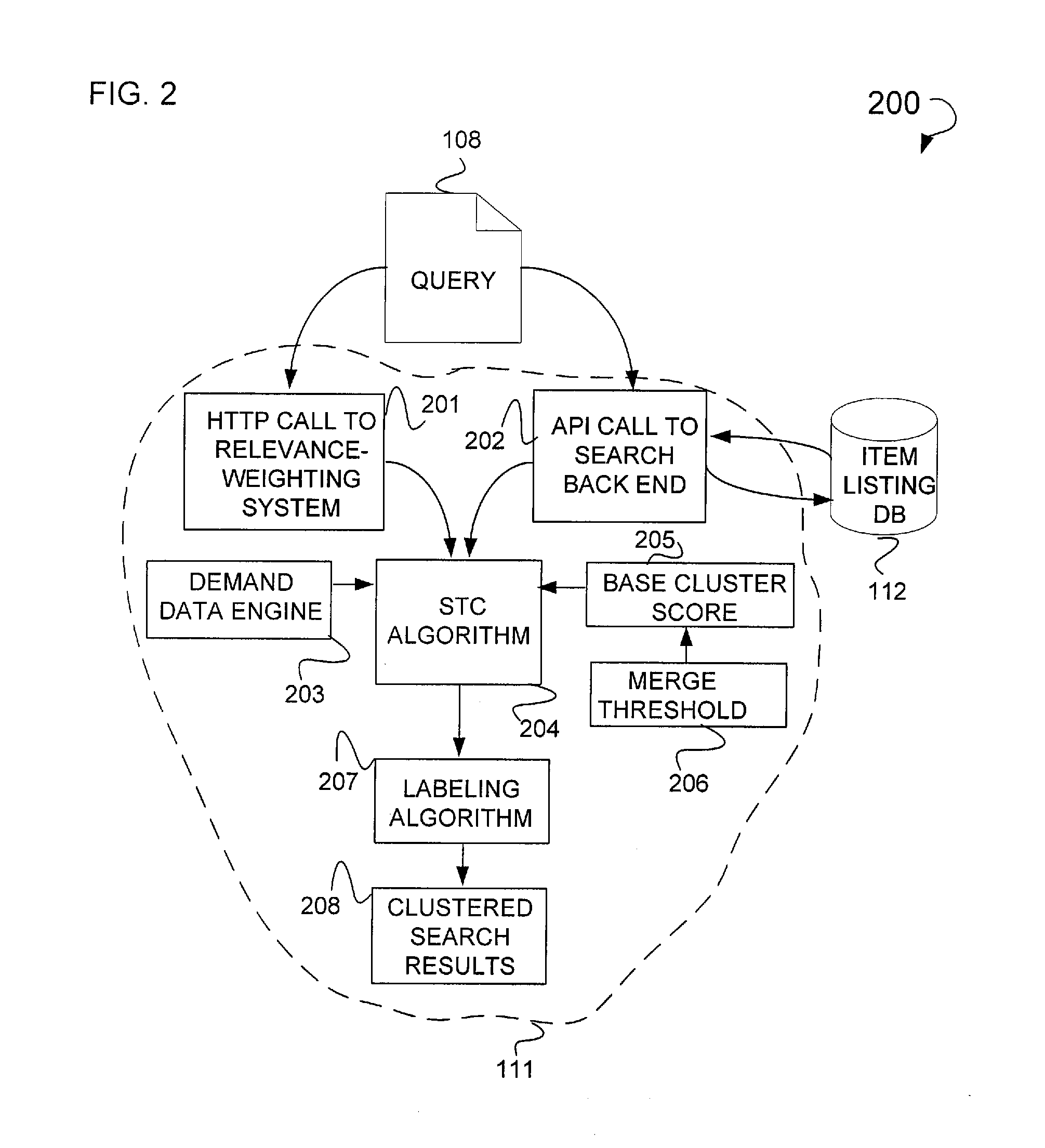
Search clustering
ActiveUS20080120292A1Web data indexingDigital data processing detailsSuffix sortingDocument preparation
In one example embodiment, a method is illustrated as including retrieving item data from a plurality of listings, the item data filtered from noise data, constructing at least one base cluster having at least one document with common item data stored in a suffix ordering, compacting the at least one base cluster to create a compacted cluster representation having a reduced duplicate suffix ordering amongst the clusters, and merging the compact cluster representation to generate a merged cluster, the merging based upon a first overlap value applied to the at least one document with common item data.
Owner:PAYPAL INC
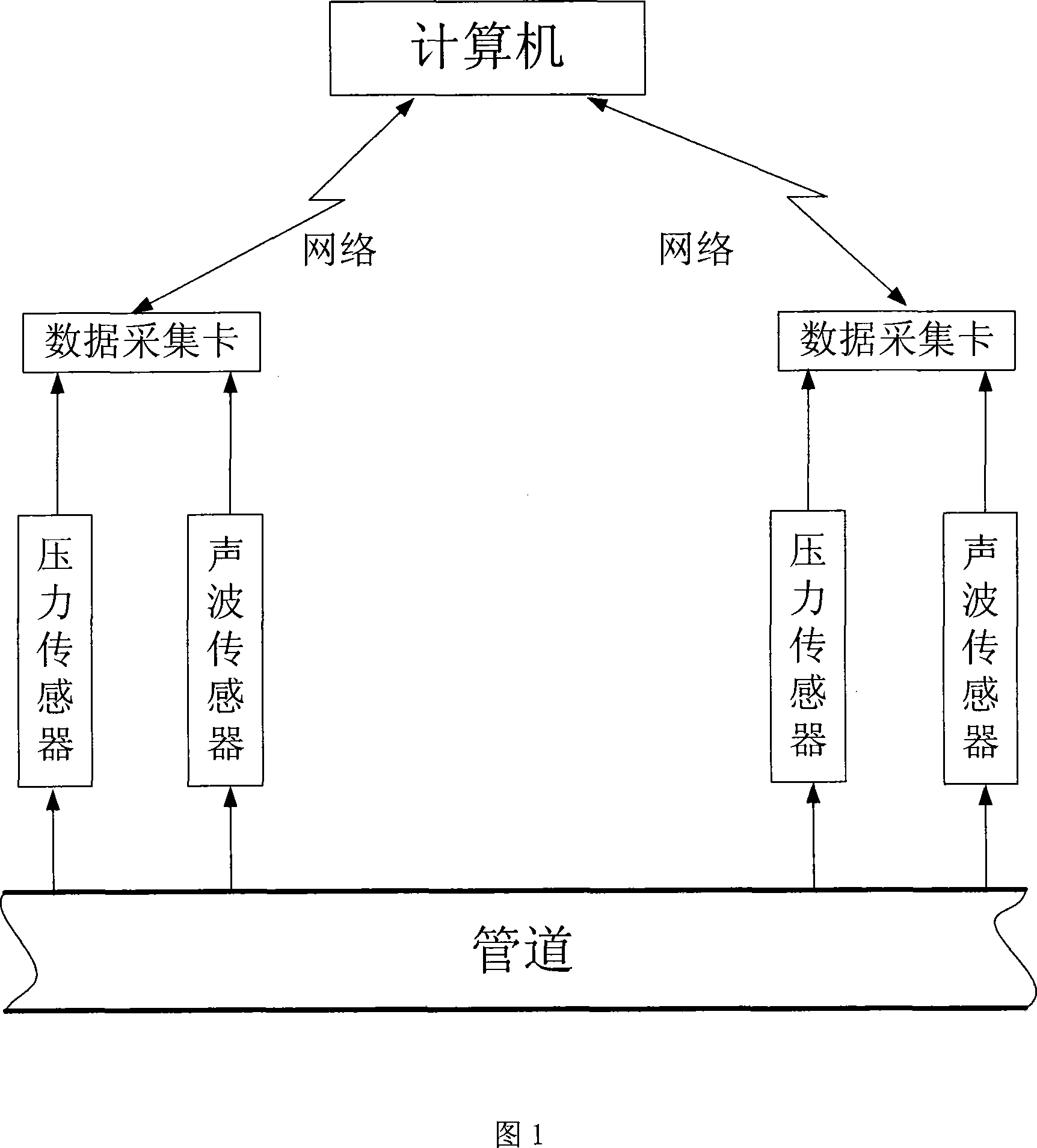
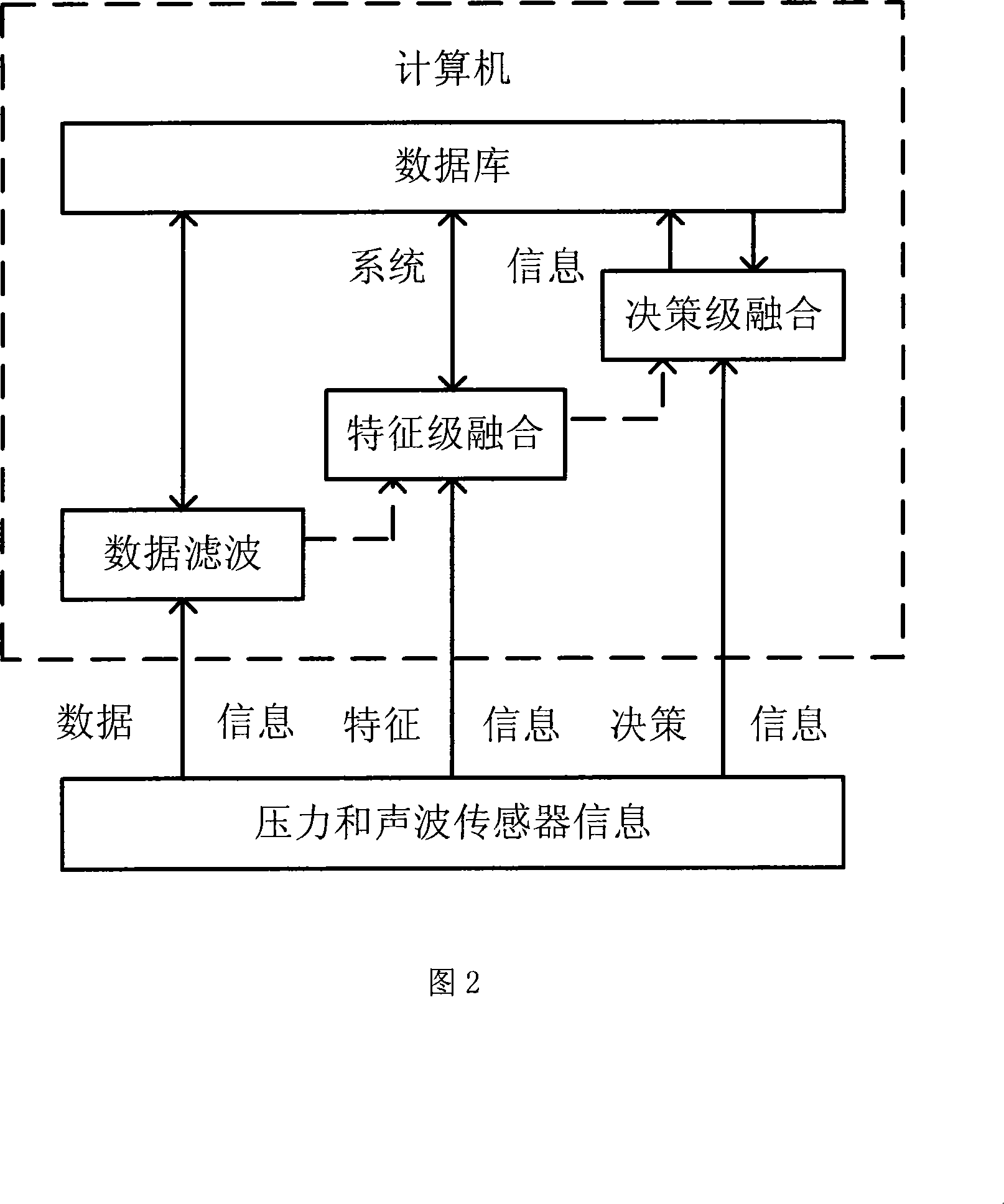
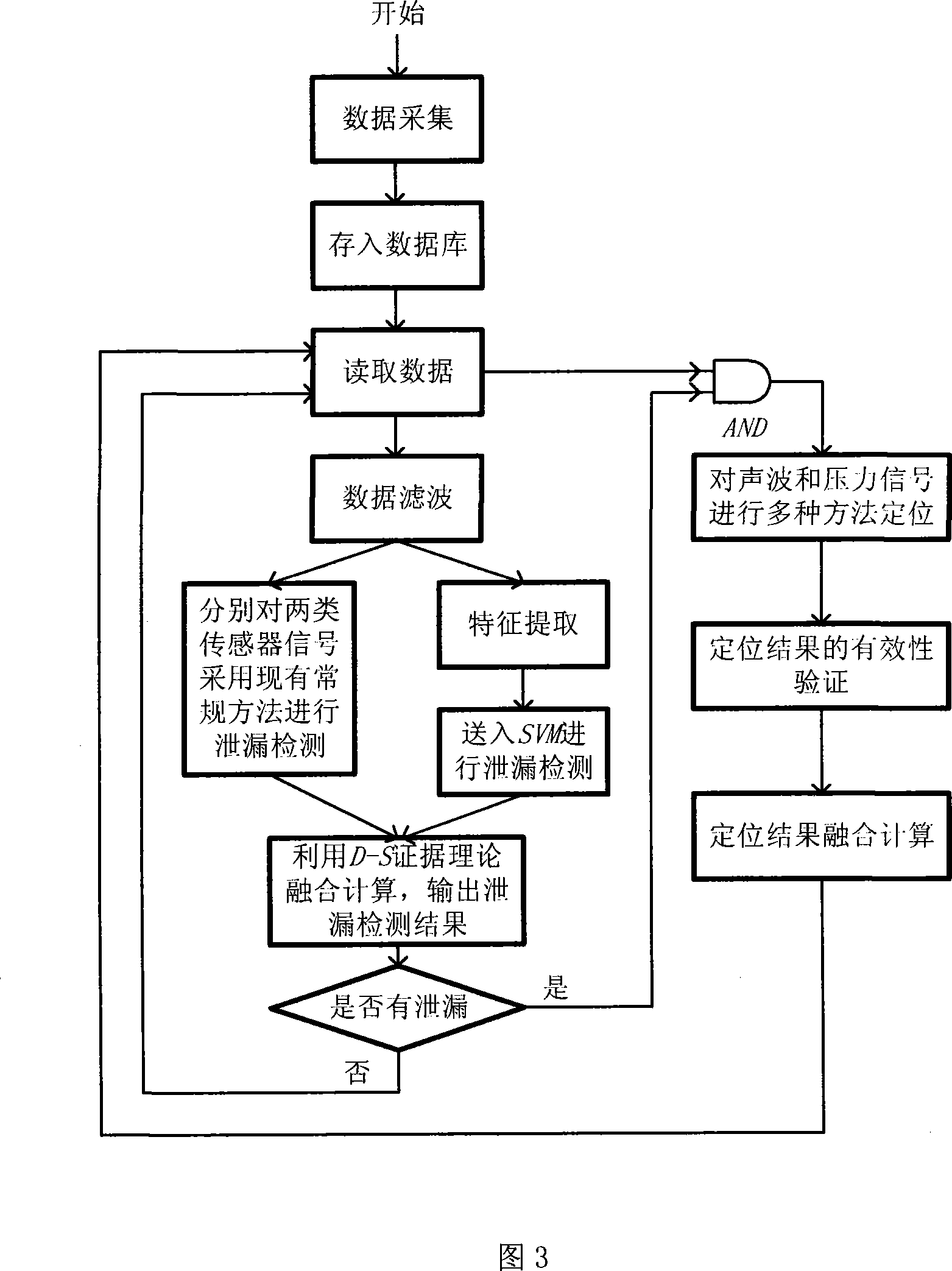
Leakage detecting and locating method based on pressure and sound wave information amalgamation
ActiveCN101196872AHigh precisionReduce false alarm ratePipeline systemsSpecial data processing applicationsThree levelAcoustic wave
A leakage detection location method based on pressure and sound information integration is provided, which belongs to the technology field of an oil (gas) pipeline fault diagnosis, and is characterized by leakage detection and leakage location based on information integration. The former comprises: separately acquiring the measurement data of the pressure on the upperstream end and downstream end of the pipeline and a sound wave sensor, sending the data to a computer and gaining final detection results through three levels processing including data filtering, characteristic level integration and decision level integration. If the detection result shows leakage, starting leakage location process based on information integration. The process first carries out leakage location by separately adopting the signals of two kinds of sensors and a plurality of different leakage location algorithms and finally gains the location results via integration of the location results based on the same sensor and different location methods and two levels processing based on the integration of the location results of two kinds of different sensors. The method can effectively reduce the false positive rate and false negative rate and improve the location precision.
Owner:TSINGHUA UNIV
Method, apparatus, and computer program product for collecting and displaying sporting event data based on real time data for proximity and movement of objects
A method, apparatus and computer program product are provided for collecting sporting event data based on real time data for proximity and movement of objects. In the context of a method, the method includes calculating a tag data filter parameter for a plurality of tag events based on received tag blink data and tag location data, wherein the tag data filter parameter comprises a blink period, distance span, or velocity, calculating a participant location data adjustment factor based on the tag data filter parameter, and calculating multidimensional player location information per unit time based on the plurality of tag events and the participant location adjustment factor.
Owner:ZEBRA TECH CORP
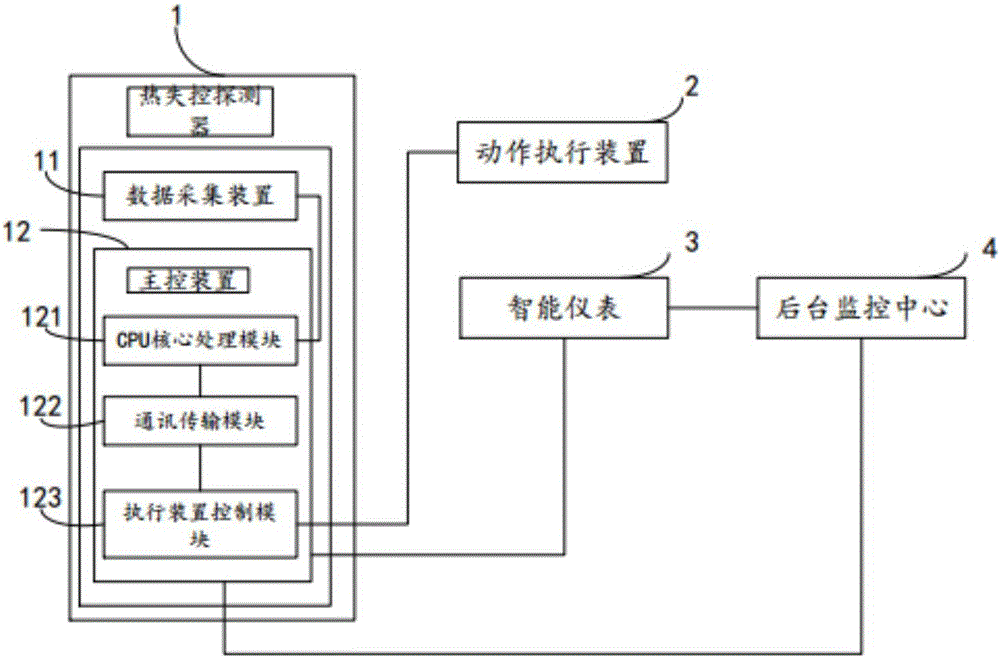
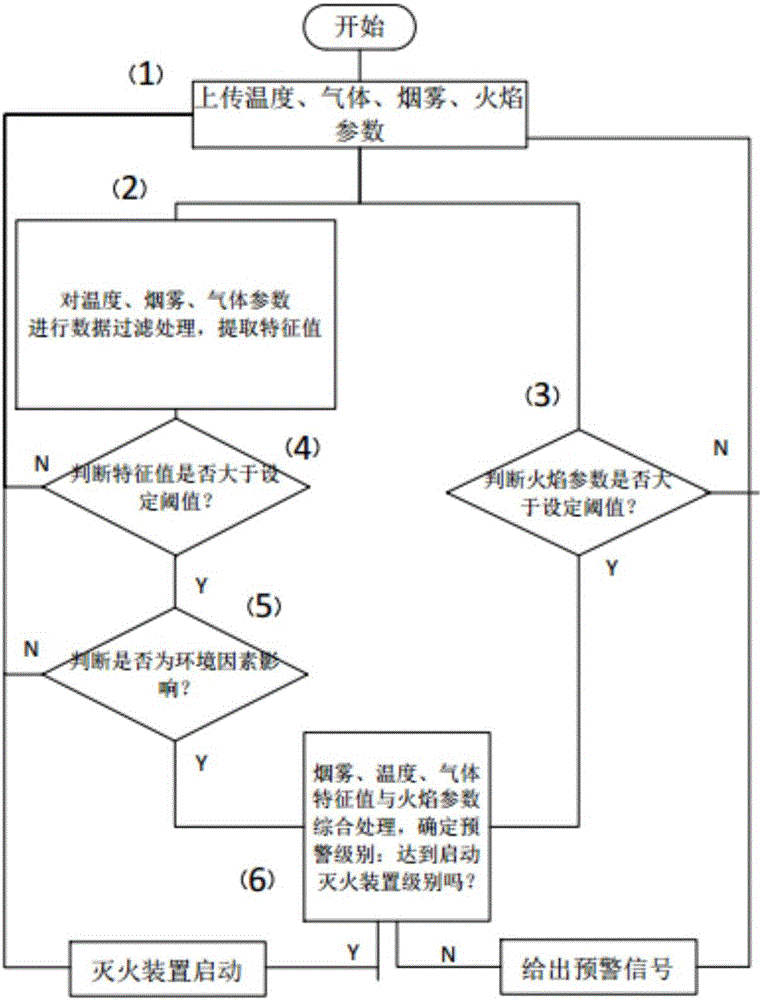
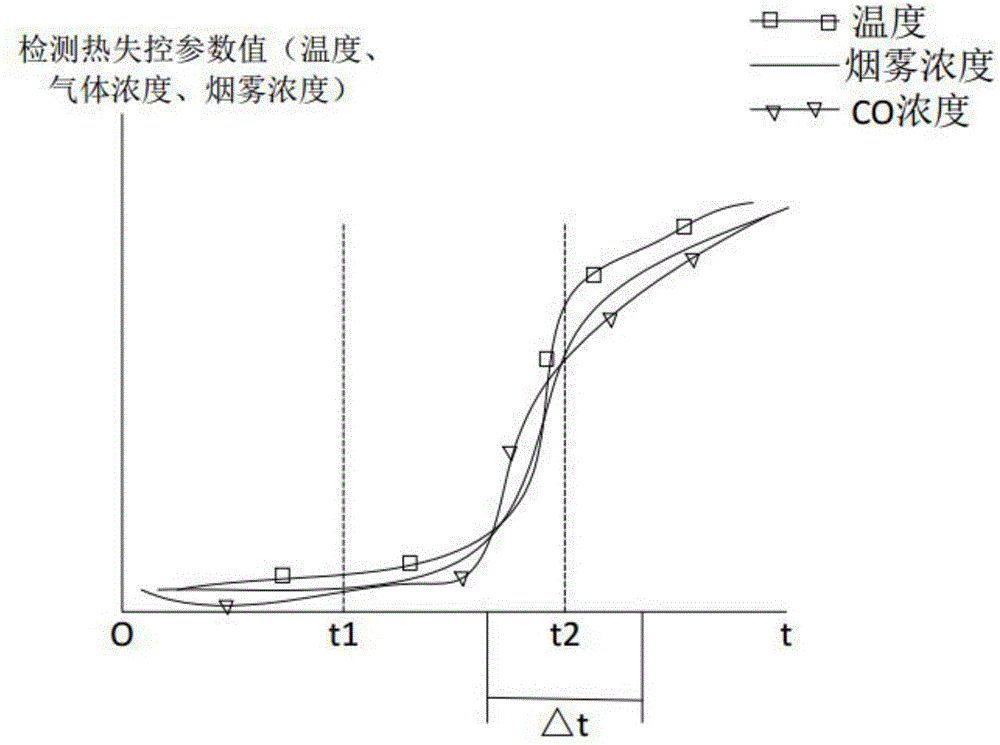
Battery thermal runaway detection system and detection method thereof
The invention relates to the technical field of new energy automobile battery safety monitoring, and particularly relates to a battery thermal runaway detection system. The battery thermal runaway detection system comprises an intelligent instrument, a background monitoring center and a thermal runaway detector arranged in a battery box. The battery thermal runaway detection system is characterized in that the thermal runaway detector comprises a data acquisition device and a master control device. The data acquisition device is used for acquiring the current thermal runaway parameters of all the detection nodes in the battery box and transmitting the current thermal runaway parameters to the master control device. The master control device comprises a CPU core processing module, a communication transmission module and a performing device control module. The invention also relates to a battery thermal runaway detection method comprising the steps that whether a flame value is greater than or equal to the preset flame threshold is judged; data filtering is performed on temperature, gas and smoke parameters so that characteristic values are extracted; and the parameters are comprehensively processed so that starting a fire-extinguishing device or giving a warning signal is determined. The beneficial effects are that the detection system is enabled to accurately grasp the fire extinguishing time so that the hidden trouble can be timely disposed.
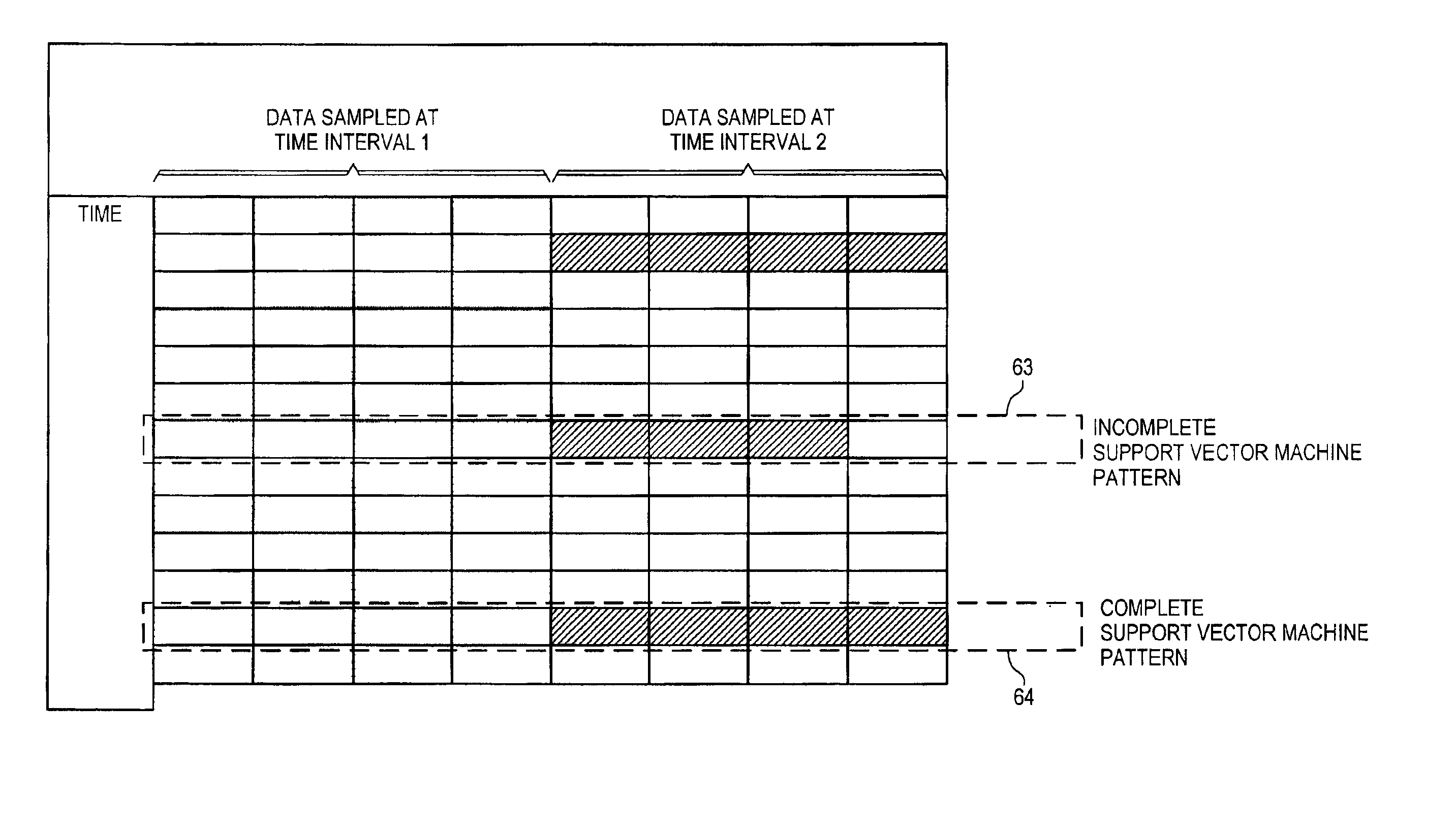
Owner:YANTAI INNOVATIVE NEW ENERGY TECH CO LTD
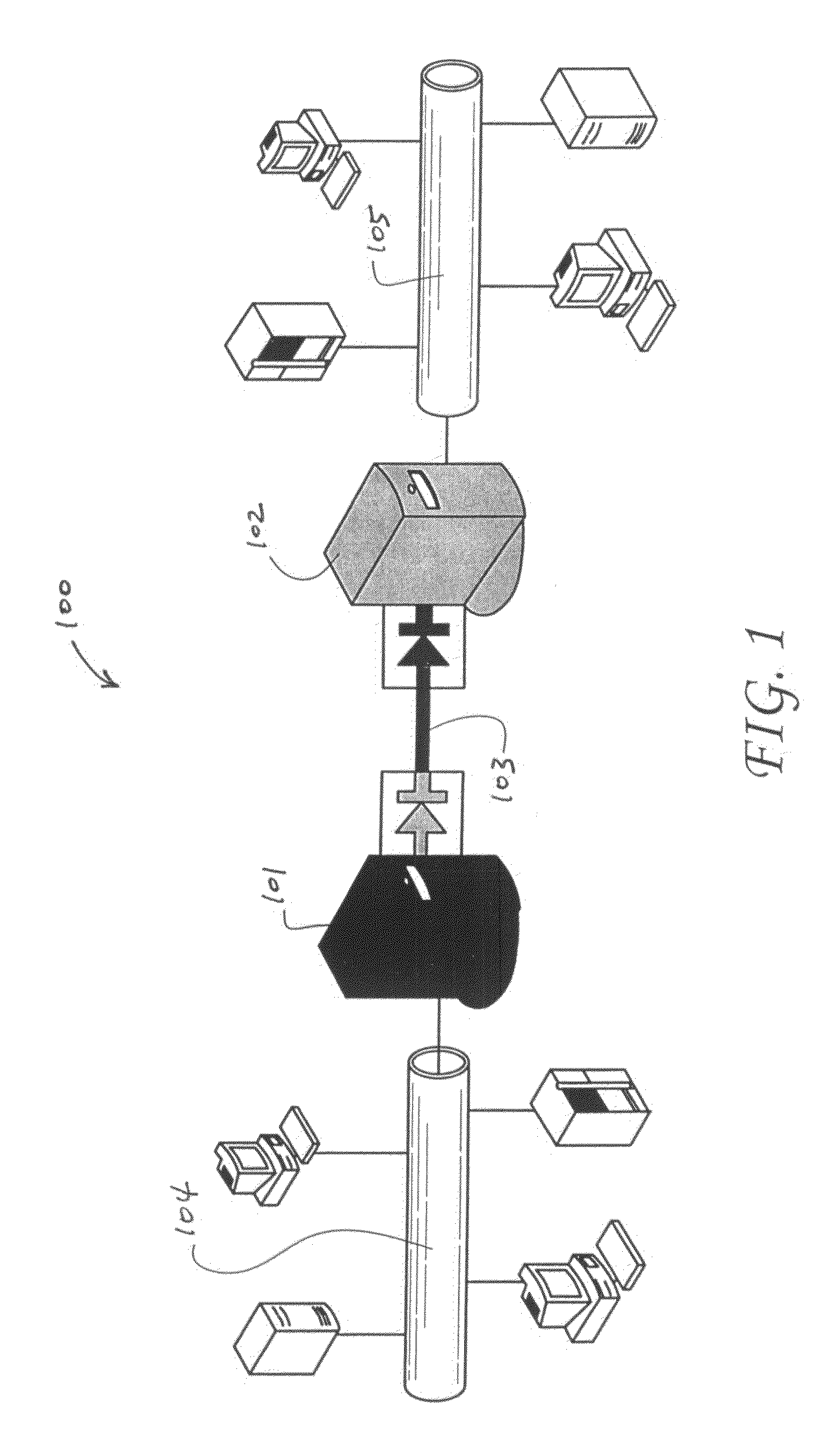
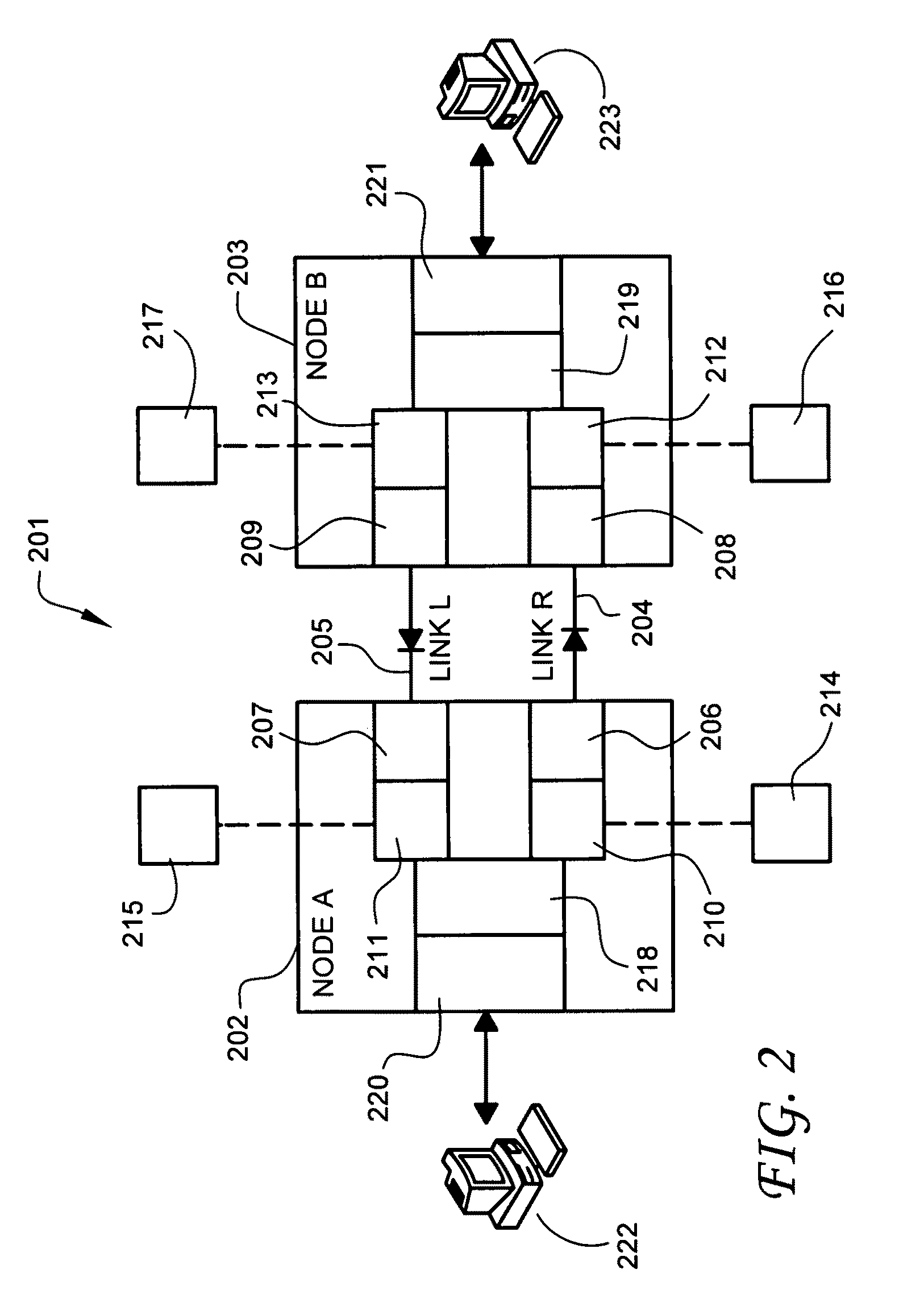
Bilateral communication using multiple one-way data links
ActiveUS7992209B1Digital data processing detailsUnauthorized memory use protectionTransfer systemComputer science
A bilateral data transfer system comprising a first node, a second node, a first one-way link for unidirectional transfer of first data from the first node to the second node, and a second one-way link for unidirectional transfer of second data from the second node to the first node, wherein the unidirectional transfer of the first data across the first one-way link and the unidirectional transfer of the second data across the second one-way link are independently administered by the bilateral data transfer system. Under such bilateral data transfer system, each of the one-way data links may be subject to separately administered security restrictions and data filtering processes. Hence, it enables secure bilateral communications across different network security domains.
Owner:OWL CYBER DEFENSE SOLUTIONS LLC
Data filtering in the internet of things
ActiveUS20130290305A1Increase speedEfficient data filteringDigital data information retrievalDigital data processing detailsProgramming languageThe Internet
This invention relates to the Internet of Things (IOT), and discloses a method and apparatus of data filtering in the IOT, where the IOT includes a plurality of sensor devices. The method includes: inputting an application deployed rule; converting the rule into at least one sub-predicate expression having static predicates and dynamic predicates; inputting data collected by the sensor devices; matching the collected data with the static predicates and the dynamic predicates of the sub-predicate expression in sequence; and distributing matched data to the application. In this invention, a rule is divided into static and dynamic predicates, and a match is performed on static predicates before dynamic predicates, so that the speed of predicate match can be improved and fast and efficient data filtering in the IOT can be achieved.
Owner:HCL TECH LTD
System and method for synchronizing data of wireless devices
InactiveUS7035879B2Data processing applicationsDatabase distribution/replicationApplication serverA domain
Owner:HON HAI PRECISION IND CO LTD
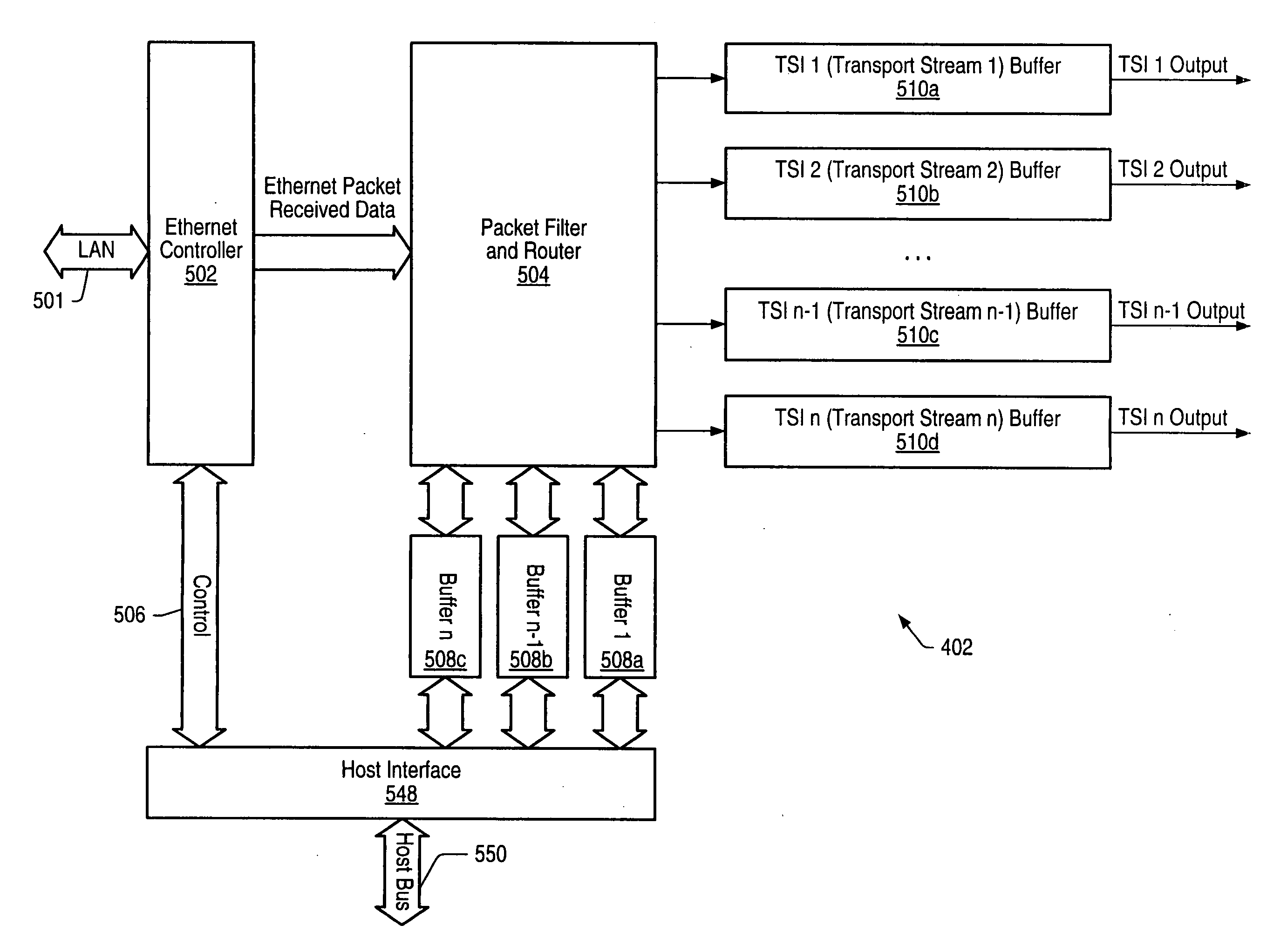
High speed ethernet MAC and PHY apparatus with a filter based ethernet packet router with priority queuing and single or multiple transport stream interfaces
ActiveUS20060174032A1Performance levelImprove efficiencySpecial service provision for substationDigital computer detailsData streamThe Internet
In one embodiment, an audio-visual content delivery system, such as a set-top box / personal video recorder system, is configured to interface with a local area network (LAN). A packet processing circuit comprised in the system may be configured to filter and route Ethernet packet data received from the LAN to specific ports and / or queues without host processor intervention. The packet processing circuit may utilize a set of filter and routing mechanisms configurable in hardware to interpret various Internet Engineering Task Force (IETF) networking transport protocols, and may transfer the packet data in a format recognized by a variety of consumer subsystems, each of which may be coupled to the decoder. The packet processing circuit may be implemented as a semiconductor device, and may allow encapsulated application data, (encapsulated using standardized encapsulation techniques), to be routed to a plurality of different types of application sinks or processors, forming a point-to-point or multi-point serial or parallel data stream over a standard transport covering numerous levels of the ISO data communications stack.
Owner:MICROCHIP TECH INC
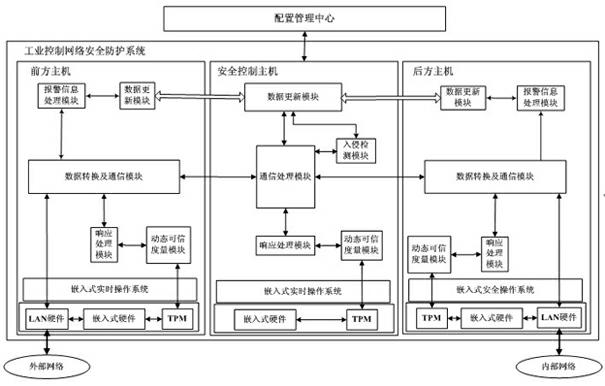
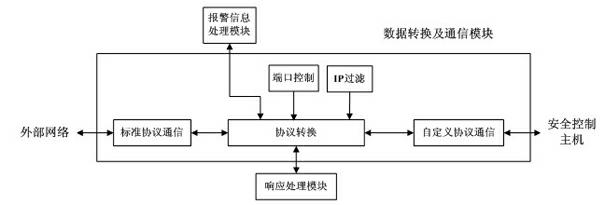
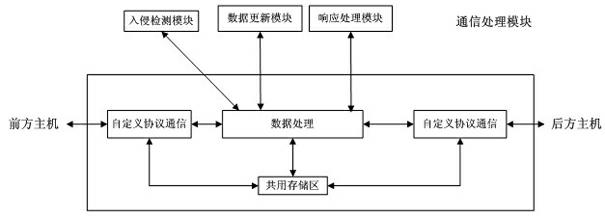
Industrial control network security protection method and system
InactiveCN102438026AImprove resistance to attackImprove securityUser identity/authority verificationData switching networksSystem transformationNetwork attack
The invention discloses an industrial control network security protection method and an industrial control network security protection system. The method comprises the following steps that: aiming at an external network attack, a front host performs first layer data filter and access control on external network data; a security control host caches data through a common storage region, performs intrusion detection on the data, timely alarms illegal data and informs hosts on two sides; a rear host performs deep filter and access control on the data and causes the legal data to enter an internal network; aiming at an internal network attack, the rear host performs the first data filter and access control on internal network data; the security control host caches the data through the common storage region, performs the intrusion detection on the data, timely alarms the illegal data and informs the hosts on the two sides; and the front host performs the deep filter and access control on the data and causes the legal data to enter an external network. By the method and the system, the network security level of an industrial control system is increased, and the cost on investment, system transformation and management is reduced.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
Markers for cached objects
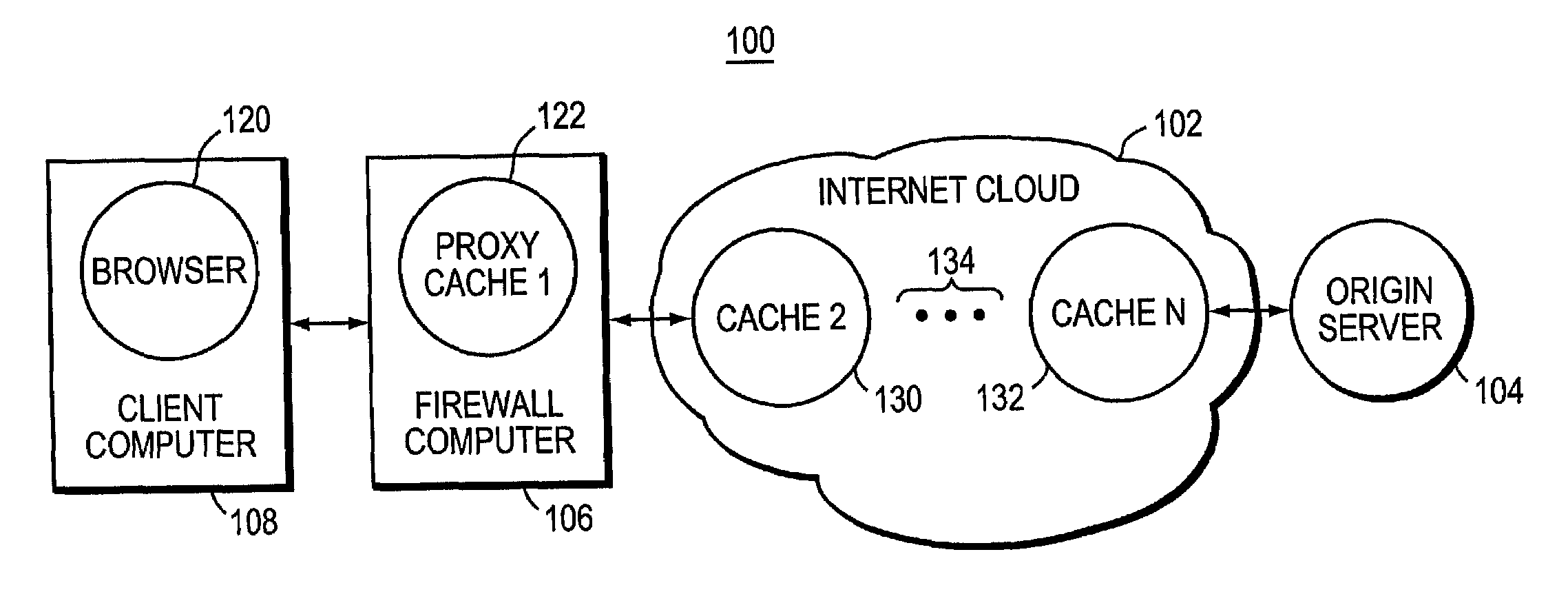
ActiveUS7680875B1Multiple digital computer combinationsWebsite content managementData streamClient-side
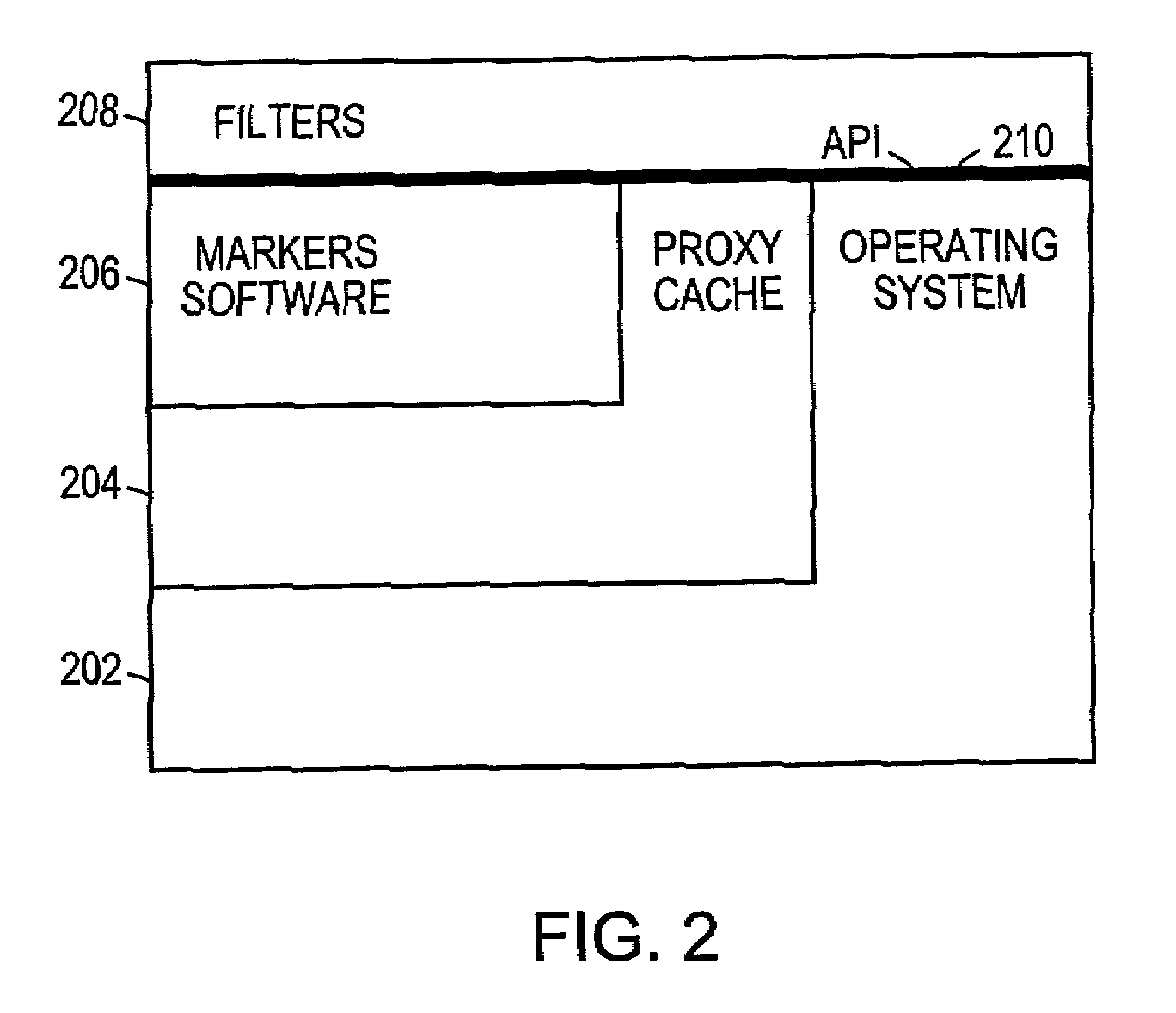
Markers are established in a data object to provide a means to refer to specified parts of the object. Each marker is established within the object by giving the location and length of the part of the object that is to be marked. The marker continues to mark that part of the object as changes are made elsewhere in the object. As data is received into the cache computer it is stored in a sequence of buffers. A plurality of filters, all executing concurrently, search for different interesting string in the object. Each filter finds its interesting strings and marks them using the markers. The result of filtering data of the object is a marker attribute table identifying each of the markers by the offset and length of the interesting strings located by the filters. Vend time is the time at which the object is streamed out of the cache to a client computer. Before the data is vended, a User Data Filter (UDF) executes a call function which sets up a string substitution table. The substitution table has entries for substitution, including the offset at which to make the substitution and the string to be substituted into the streaming object. A byte counter tracks the outgoing data stream of the object, and whenever the byte count matches an offset of a marker, the length entry in the marker attribute table determines the length of an omitted string, and the substitute string is placed in the outgoing data stream.
Owner:APPLE INC
Receiver and method
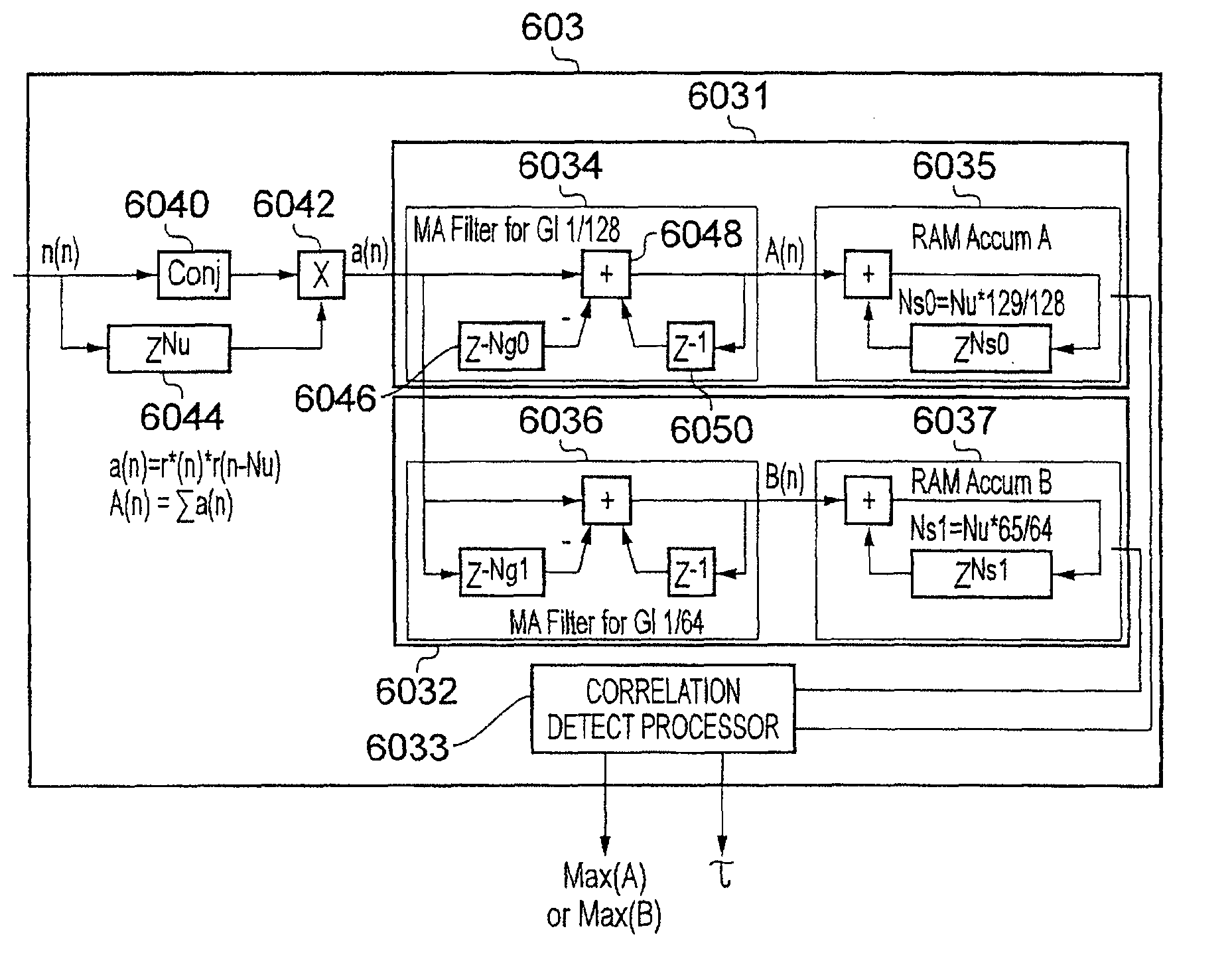
InactiveUS20110013732A1Improve integritySpeed up and improve accuracyAmplitude-modulated carrier systemsSecret communicationComputer scienceSymbol synchronization
A receiver for detecting and recovering data from Orthogonal Frequency Division Multiplexed (OFDM) symbols. The receiver comprises a demodulator, symbol synchronization unit, frequency transform processor, and coarse frequency offset detector. The demodulator generates sampled symbols. The symbol synchronisation unit has correlators, which receives the sampled symbols, and a correlation detection processor. Each correlator auto correlates each sampled symbol, and the correlation detection processor determines a start point of each symbol. The frequency transform processor receives the sampled symbols and performs a frequency transform on each symbol. The coarse frequency offset detector includes a pilot data filter, which includes taps corresponding to a value and spacing of the pilot pattern of the symbols and arranged to receive as an input the frequency domain symbols from the frequency transform processor, and a coarse frequency offset detect processor, which is arranged to detect a coarse frequency offset output from the pilot data filter.
Owner:SONY CORP
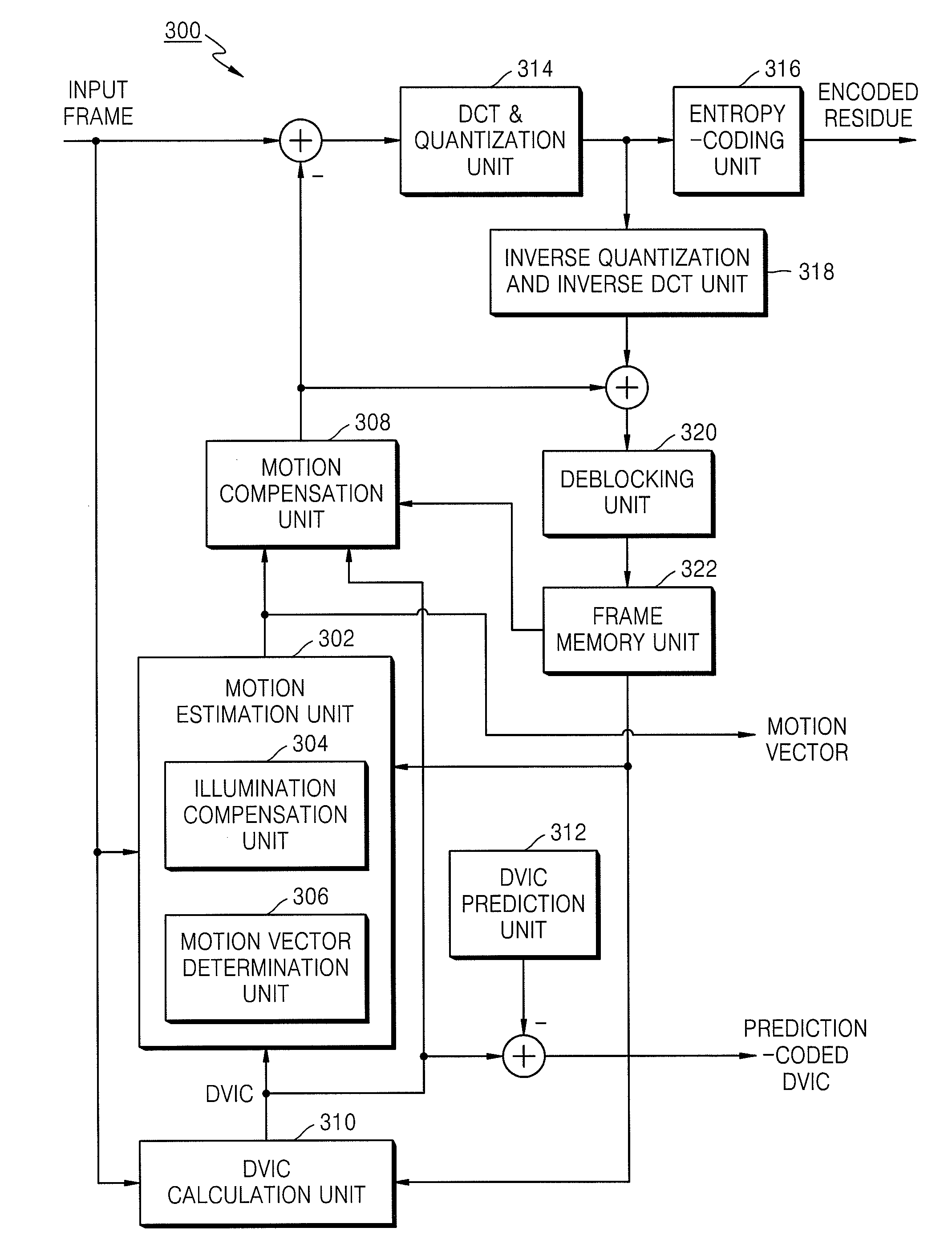
Method and apparatus for deblocking-filtering video data
InactiveUS20080170629A1Avoid problemsAvoid artifactsColor television with pulse code modulationPulse modulation television signal transmissionImaging processingDeblocking filter
Provided are a method and an apparatus for filtering video data. The method includes determining whether a difference value of illumination change (DVIC) of a current image processing unit containing a current block is different from a DVIC of an image processing unit that is adjacent to the current image processing unit and based on the determining, adjusting a filtering strength of a deblocking filter and performing deblocking filtering on a boundary of the current block using the filter with the adjusted filtering strength.
Owner:SAMSUNG ELECTRONICS CO LTD
Container-truck positioning system and method for container crane
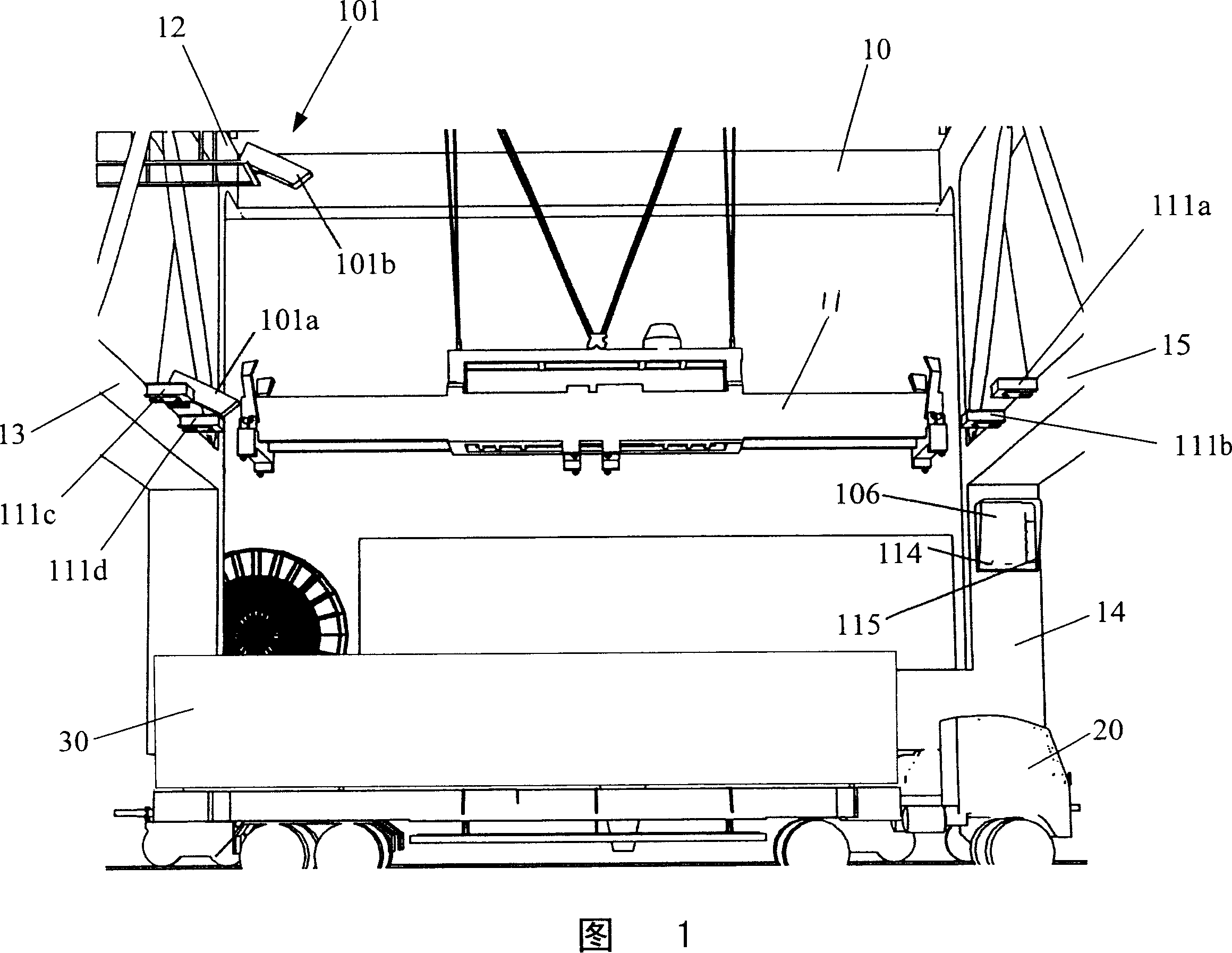
InactiveCN101096262AQuickly and accurately stop atQuick loading and unloadingLoad-engaging elementsImaging processingLaser scanning
The invention discloses a container-lorry alignment system of container crane and the method. Image pickup equipment set above the loading and unloading position of crane is used to shoot lorry image in real time and transfers the image to the image processing computer. The image processing computer combines pre-storing simulating lifting-tool profile into data image and transfers combined image to display controller by net in real time so as to control the display to display combined image set at the front of loading and unloading position of crane in visual field of lorry driver to help driver accomplish predetermining lorry. At least one suit of laser scanning equipment set on the front beam and back beam of crane is used to collect profile information of lorry or container on the lorry and transfer the information to computer system. The computer system carries out data filter to profile information and characteristic fitting. The information is contrasted with theoretical setting value and position error of lorry or container to the crane is analyzed and is transferred to the error display at the front of loading and unloading position of crane for displaying so as to help driver accomplish accurate position for lorry.
Owner:SHANGHAI ZHENHUA HEAVY IND
Method and system for filtering and suppression of telemetry data
ActiveUS20050273593A1Reduce in quantityReducing of unnecessary dataGalvano-magnetic hall-effect devicesData switching networksFiltering rulesEvent data
Embodiments of the invention are directed generally to data filtering methods, and combinations thereof, for reducing the quantity of non-actionable, redundant, or otherwise unnecessary data events reported to a network management system. According to an embodiment of the invention, a method for filtering event data in a network comprises: defining a plurality of discrete filtering rules, each of the plurality of rules performing at least one of a permit, deny, log, and rewrite function; assembling at least a first and second of the plurality of rules into an ordered sequence to form a first rule set; assembling at least a third and a fourth of the plurality of rules into an ordered sequence to form a second rule set; employing the first rule set in an appliance associated with a customer network; and employing the second rule set in a server associated with a network management system.
Owner:SUN MICROSYSTEMS INC
High speed filtering and stream dividing method for keeping connection features
InactiveCN1564547AReduce processing burdenGuaranteed wire-speed processing requirementsData switching networksTraffic capacityData stream
First, the invention sets up output port grouping rule and filtering tapping rule. Then, data filtering tapping process is carried out. IP data packets are picked up from original data packets received from network based on protocol analysis. Based on filtering tapping rule, data relevant to following processes are partitioned to group of each output port. Hash operation is carried out for address of data packet and port information in partitioned each group. Modular operation is carried our between the said Hash value and total number of port. The result is number of output port for the corresponding data packet in the group the data packet belongs to. Under high-speed backbone network, the invention meets need for clustering process and forwarding at high speed for mass data stream.
Owner:上海光华如新信息科技股份有限公司
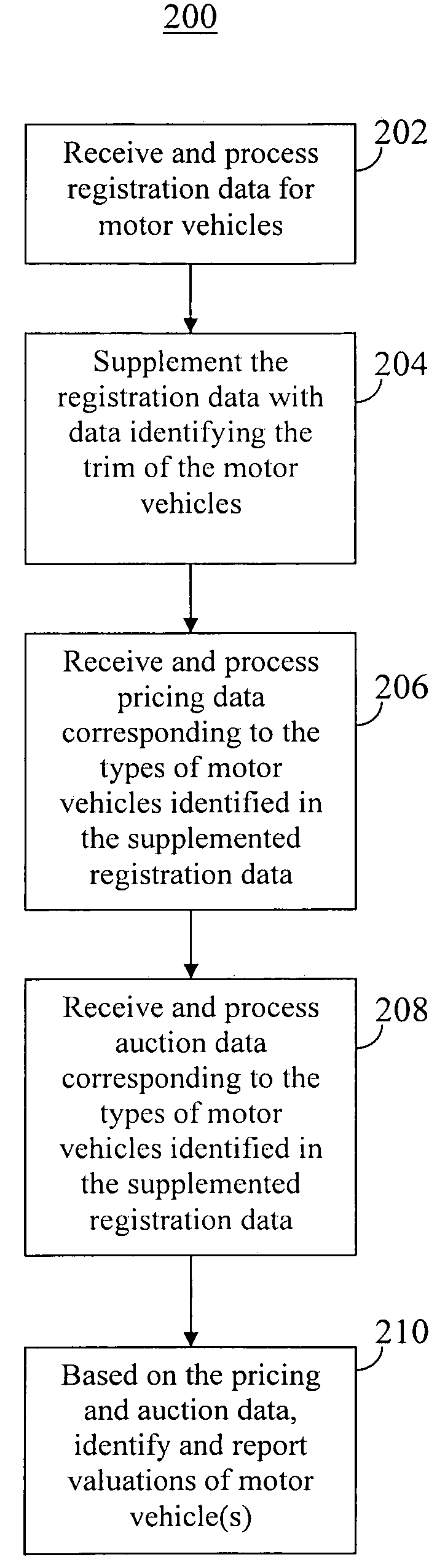
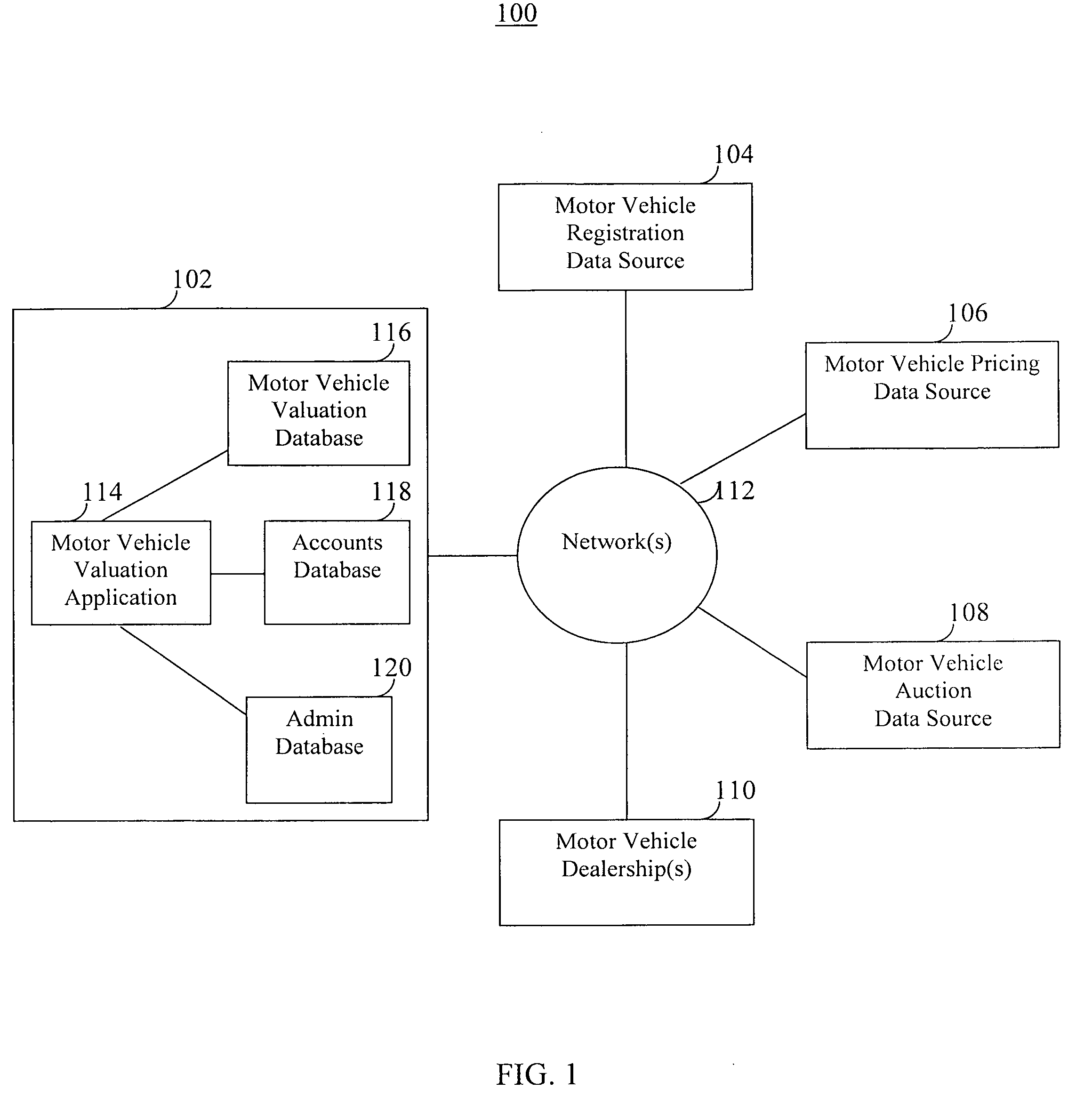
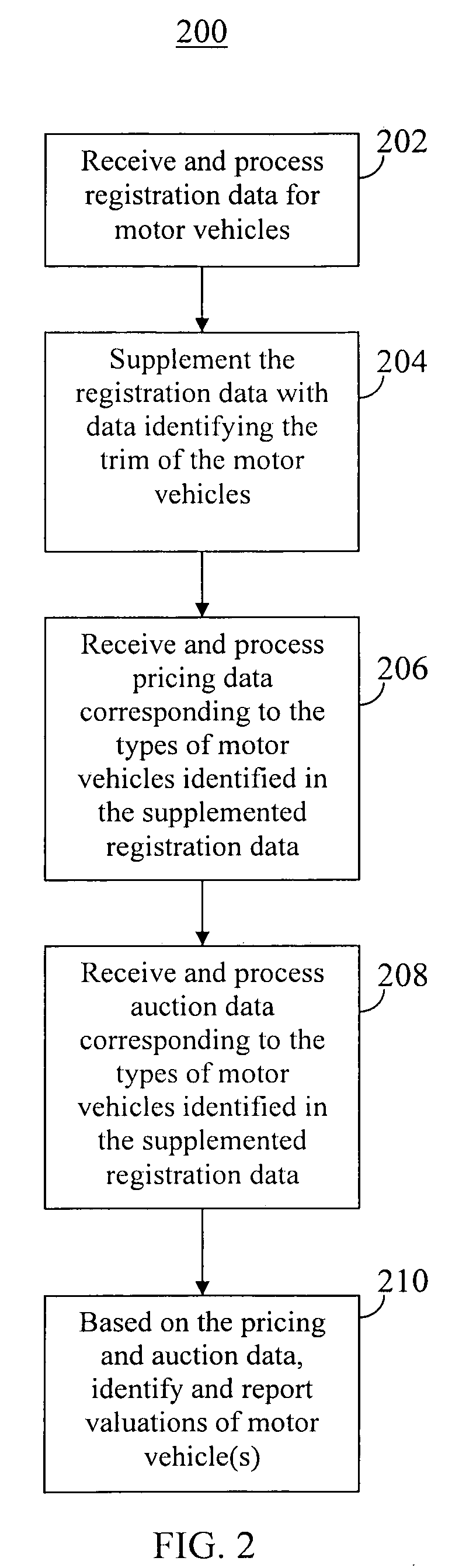
Motor vehicle valuation system and method with data filtering, analysis, and reporting capabilities
A motor vehicle valuation system and method with data filtering, analysis, and reporting capabilities is provided. For example, motor vehicle registration data, pricing data, and auction data may be processed in order to identify one or more types of motor vehicles (e.g., by make, model, year, and trim) for which a particular dealership is likely to generate a gross profit within that dealer's territory. The system may report this information to the dealership electronically, for example, within an interactive interface such as a web page.
Owner:VUENU MEDIA
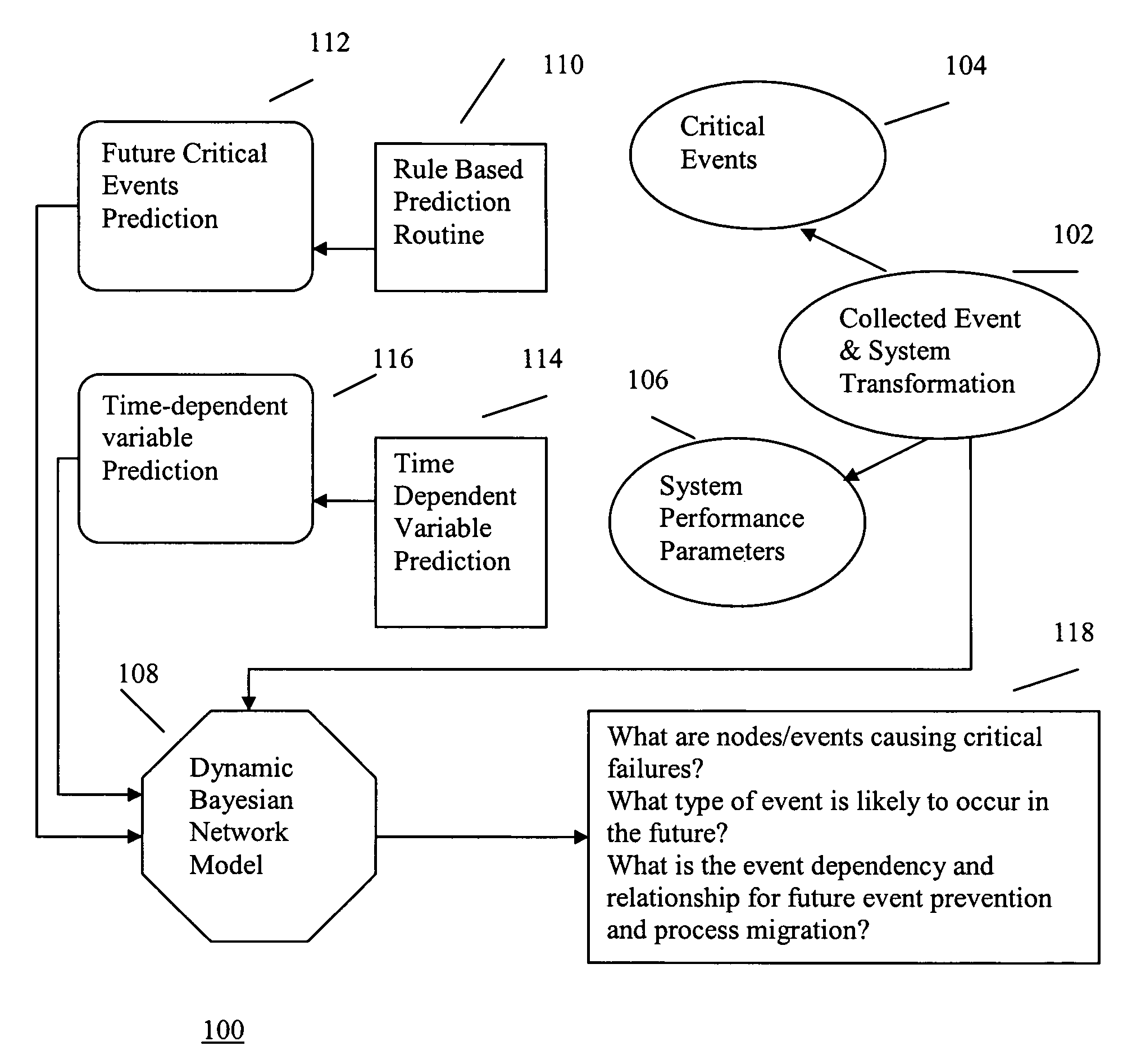
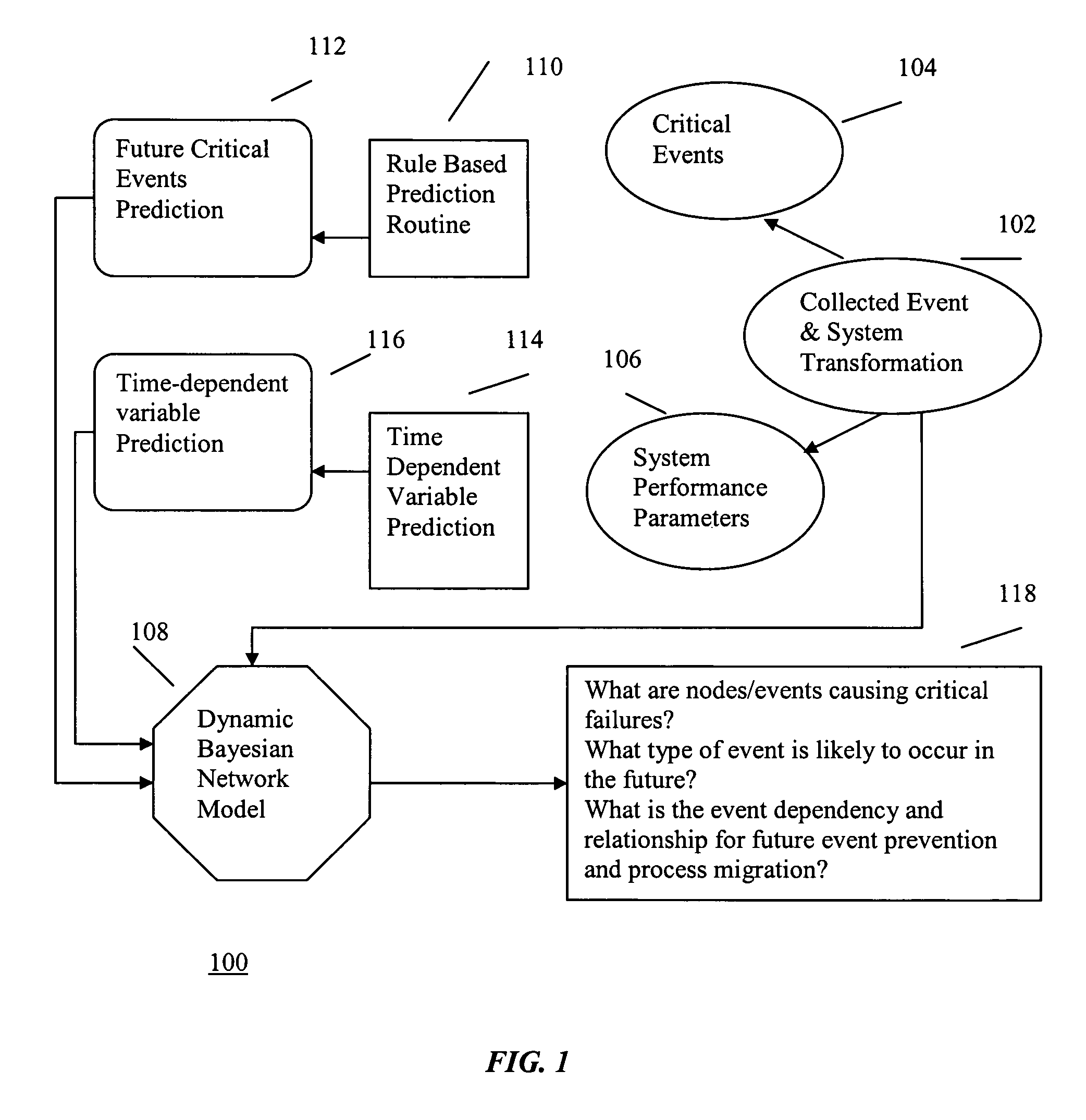
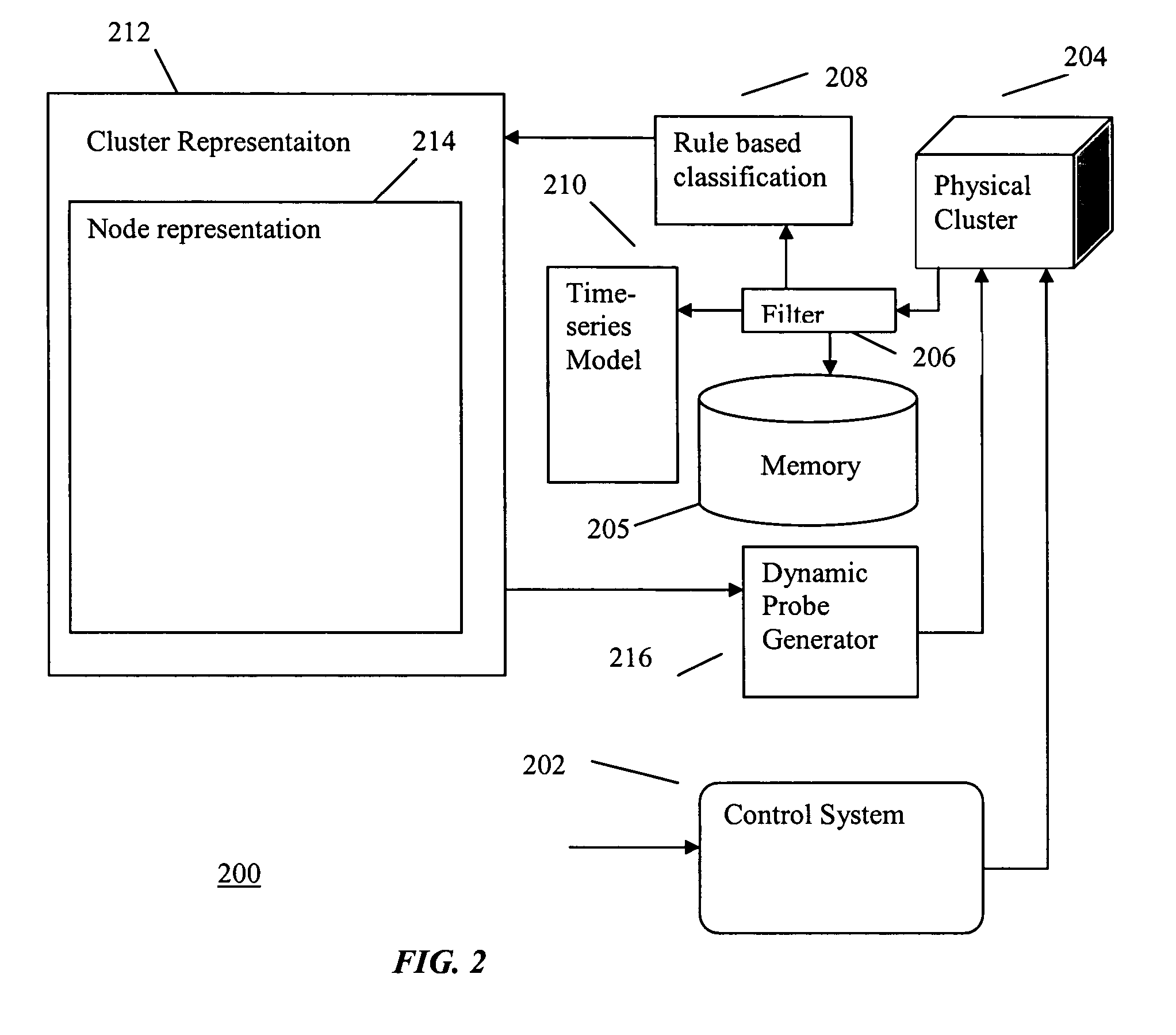
Hybrid method for event prediction and system control
InactiveUS7451210B2Data processing applicationsDigital computer detailsHybrid approachComputer cluster
Owner:GLOBALFOUNDRIES INC
Pre-processing input data with outlier values for a support vector machine
InactiveUS6941301B2Data processing applicationsDigital data processing detailsAlgorithmOutput device
A system and method for preprocessing input data to a support vector machine (SVM). The SVM is a system model having parameters that define the representation of the system being modeled, and operates in two modes: run-time and training. A data preprocessor preprocesses received data in accordance with predetermined preprocessing parameters, and outputs preprocessed data. The data preprocessor includes an input buffer for receiving and storing the input data. The input data may include one or more outlier values. A data filter detects and removes any outlier values in the input data, generating corrected input data. The filter may optionally replace the outlier values in the input data. An output device outputs the corrected data from the data filter as preprocessed data. The corrected data may be input to the SVM in training mode to train the SVM, and / or in run-time mode to generate control parameters and / or predictive output information.
Owner:ROCKWELL AUTOMATION TECH
Intrusion detection method for fusion of multiple neutral networks
InactiveCN101399672AImprove scalabilityImprove compatibilitySecuring communicationData setAnalysis data
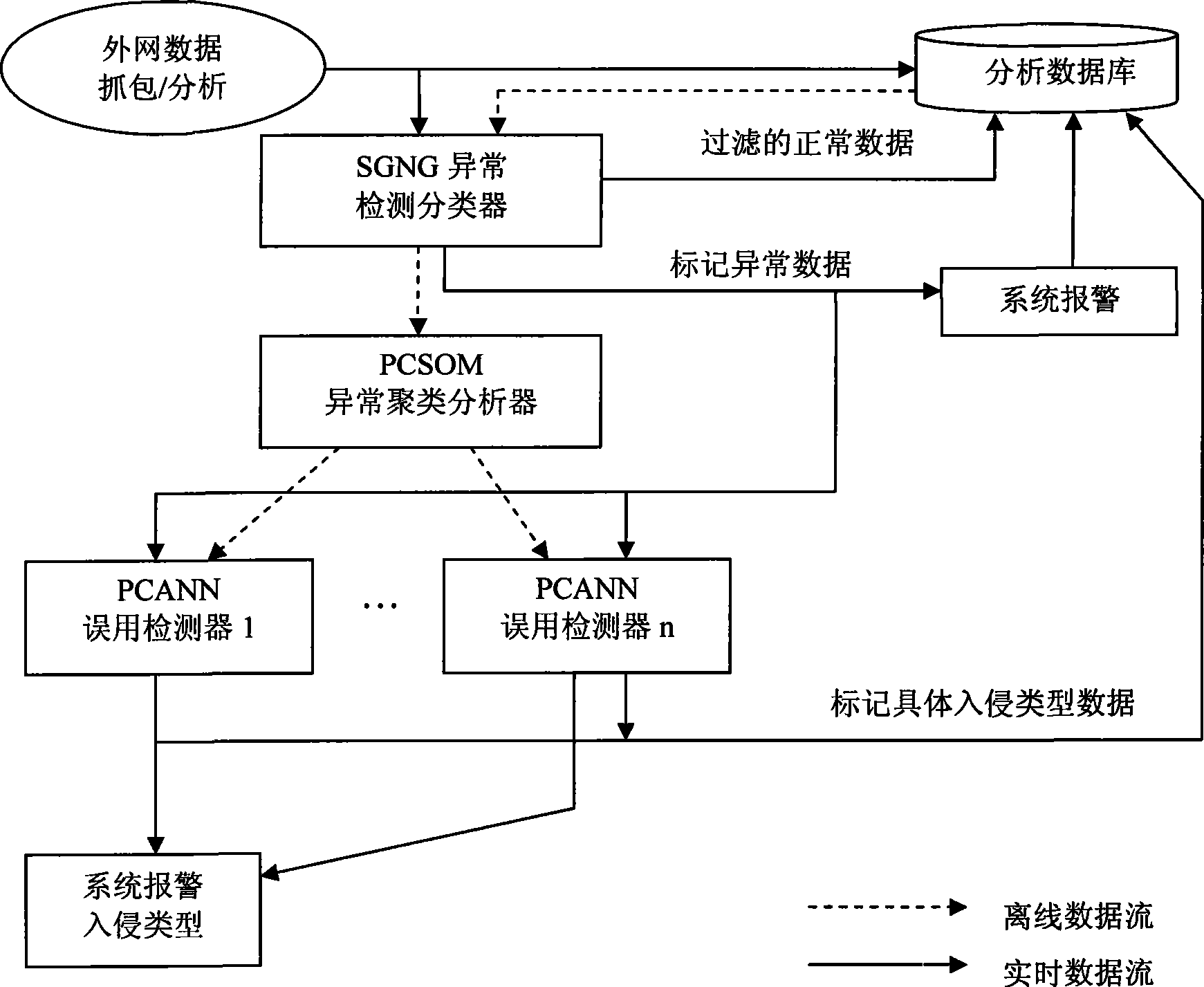
The invention provides a method for detecting intrusion by multiple neuronic network confusion, which comprises the following steps: data from external network is subject to packet sniffing and analyzing; the processed network data is simultaneously transmitted to an analytical database and a SGNG exception detection classifier, and the SGNG exception detection classifier is trained offline by normal categorical data acquired by a close network; the SGNG exception detection classifier identifies the detected exceptional data, carries out system alarm and stores the exceptional data into the analytical database; a data set which is identified as exception in the analytical database is provided for a PCSOM exception cluster analyzer for exceptional data cluster analysis; the exceptional data detected by the SGNG exception detection classifier is input to a plurality of parallel PCANN misuse detector respectively according to classifications; the PCANN misuse detector carries out concrete intrusion classification alarm on the detected exceptional data, simultaneously, all the exceptional data filtered by the PCANN misuse detector is identified and stored in the analytical database.
Owner:章毅 +1
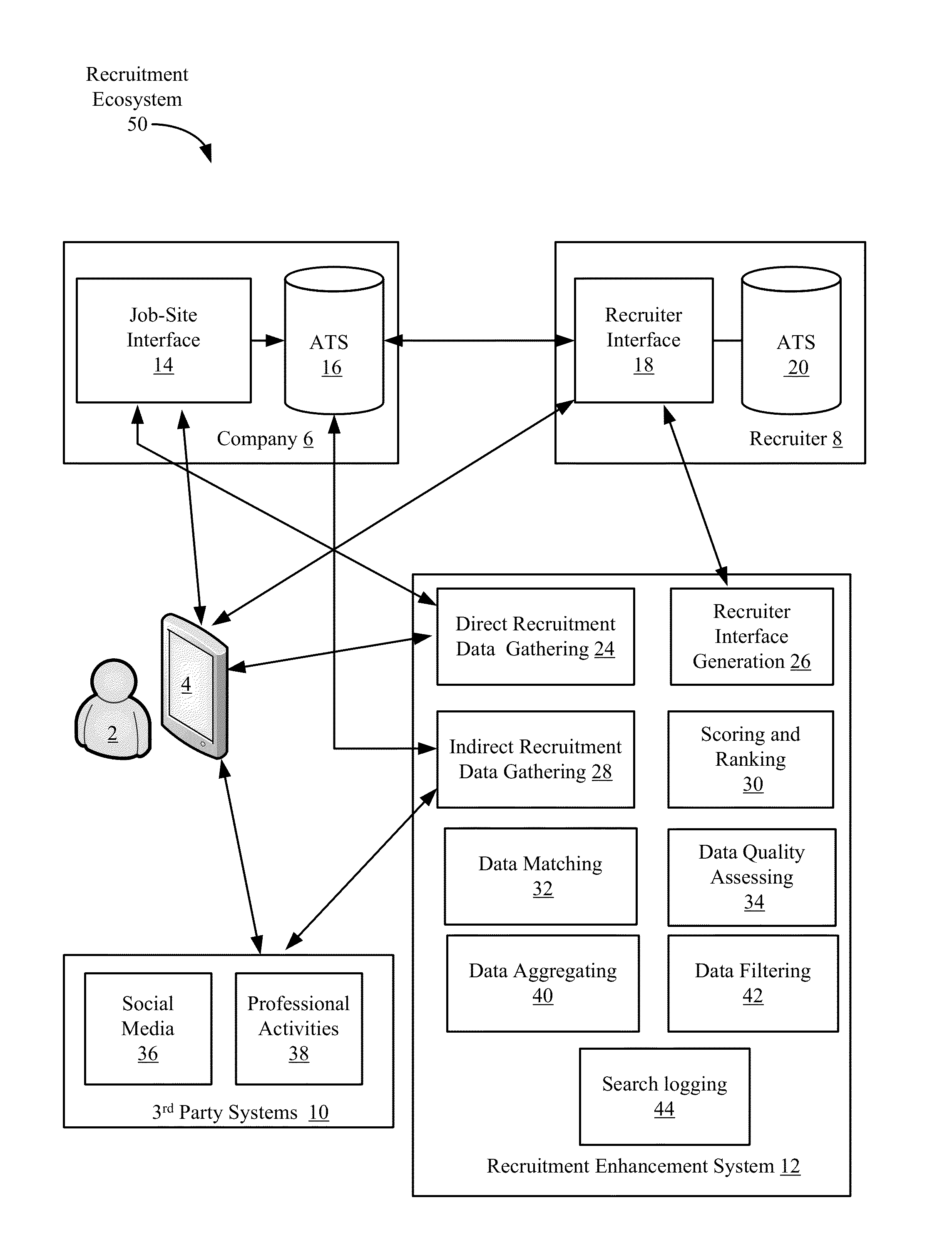
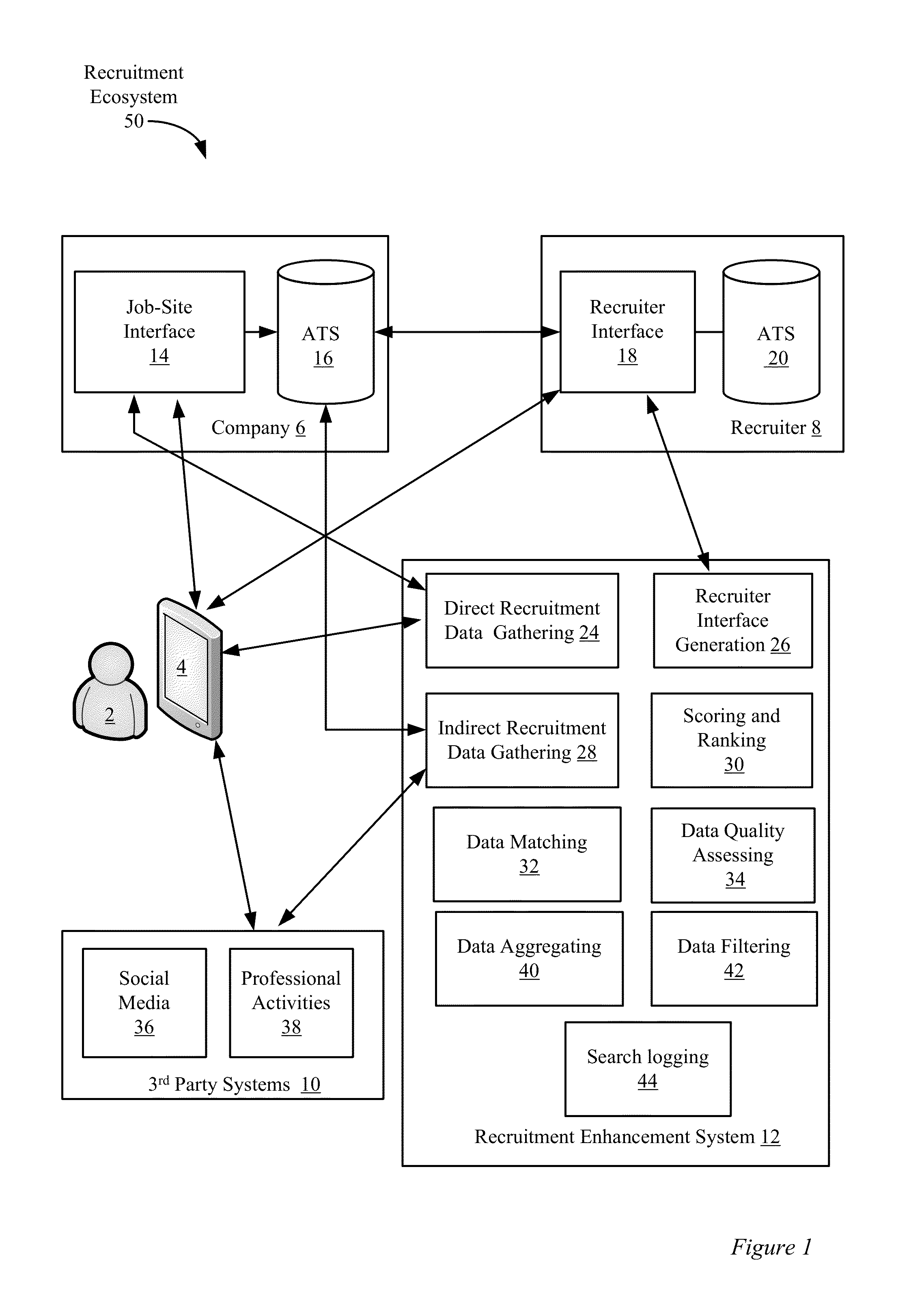
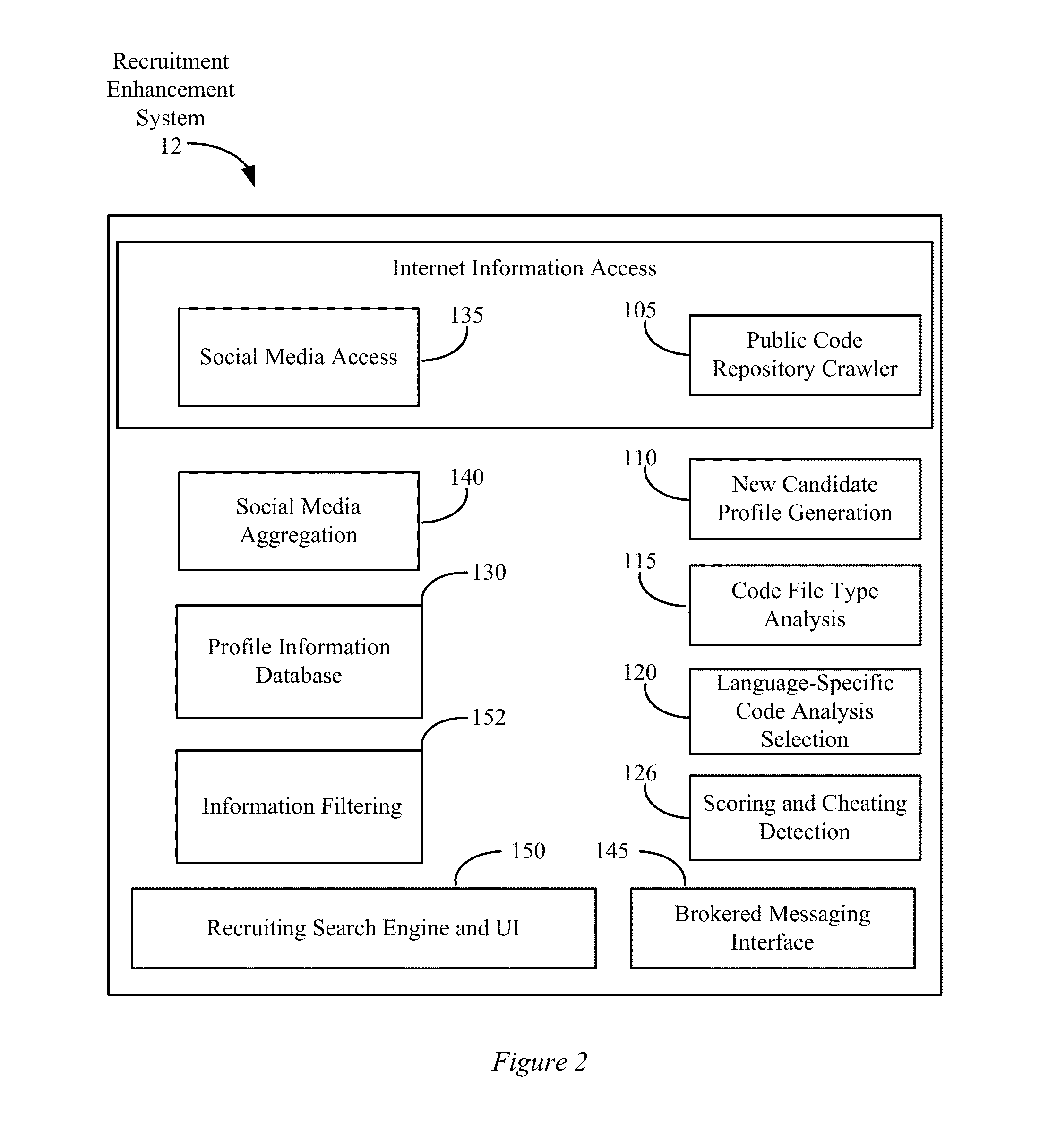
Social media data filtering for electronic job recruiting
A recruitment enhancement system is disclosed that can be used by job recruiters to assess job applicant's suitability for particular jobs. The recruitment enhancement system can maintain and regularly update a proprietary database including resume data and data gathered from social media sources for various individuals. The system can be configured to filter data before it is presented to a user. The filtering system can be configured such that only data “safe” for use in a hiring decision is presented about individuals. In one embodiment, the filtering can involve identifying protected class information for each individual and preventing its output via the system.
Owner:KCG IP HLDG
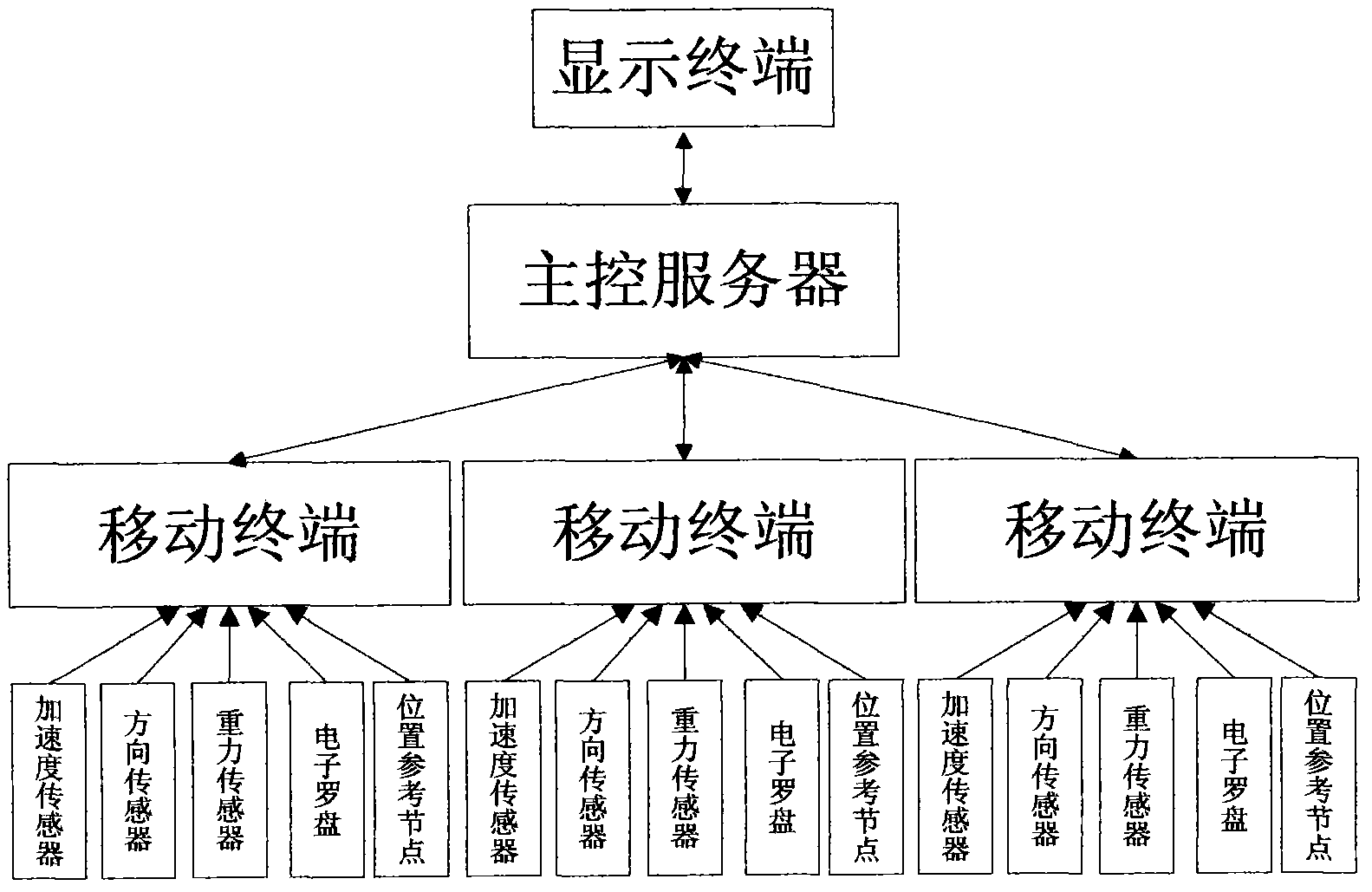
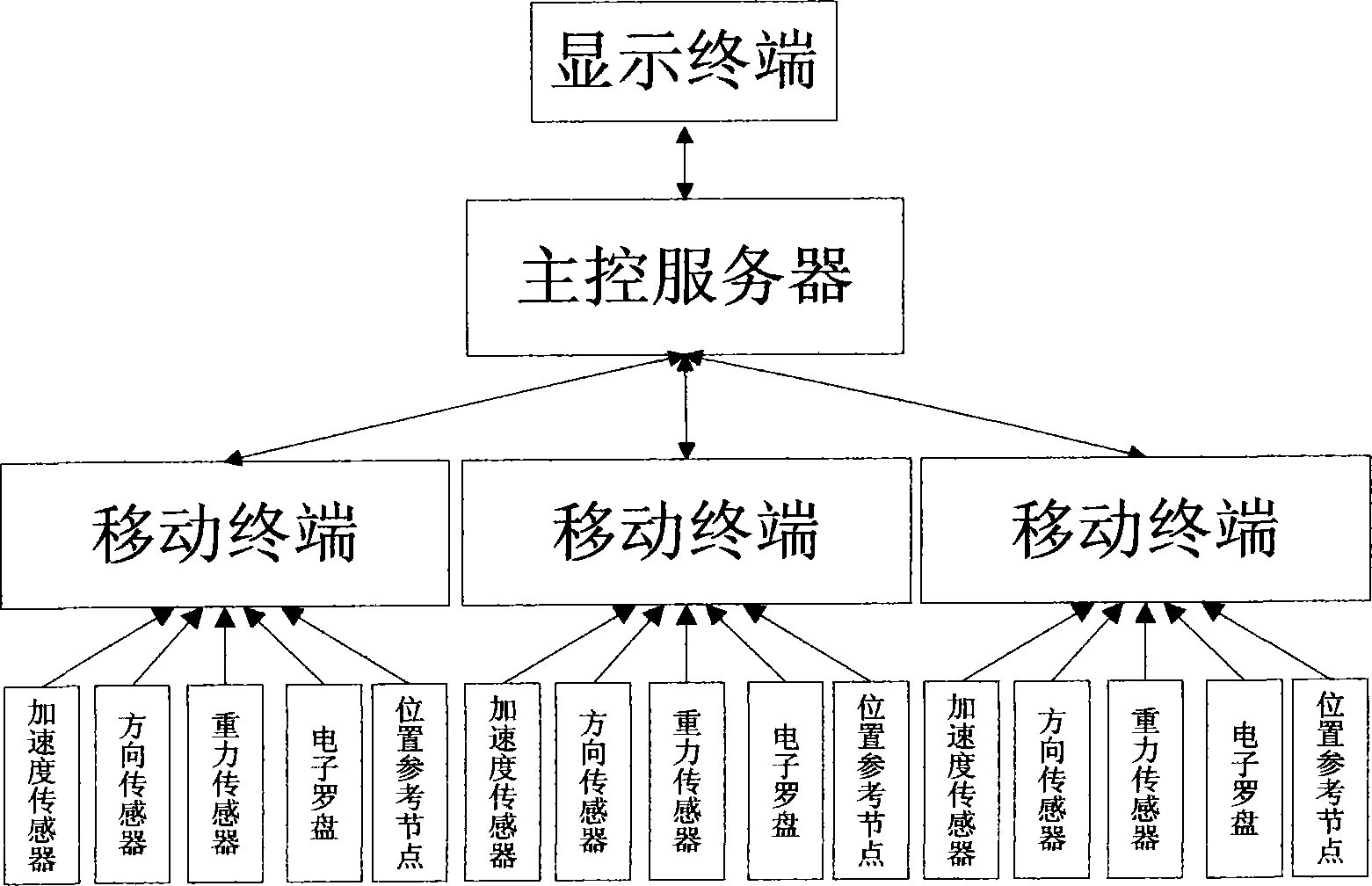
Indoor real-time locating system of mobile terminal
InactiveCN102710861AMake up for the lack of indoor positioning accuracyDifferent display effectSubstation equipmentComputer terminalData treatment
The invention relates to a real-time locating system, in particular to an indoor real-time locating system of a mobile terminal. A mobile terminal is firstly used for collecting data of sensors including data of an acceleration sensor, a directional sensor, a gravity sensor and an electronic compass, the position changing information of the mobile terminal is finally determined by comprehensively processing the data collected by the sensors, and then an initial position and comprehensive reference for a subsequent position are determined through the position information data transmitted by received position reference nodes. The data after being processed is transmitted to a main controller, after the received data is filtered and matched by the main controller, the specific position information of the mobile terminal is displayed on a display terminal.
Owner:北京六所新华科电子技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com