Patents
Literature
505 results about "On-Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
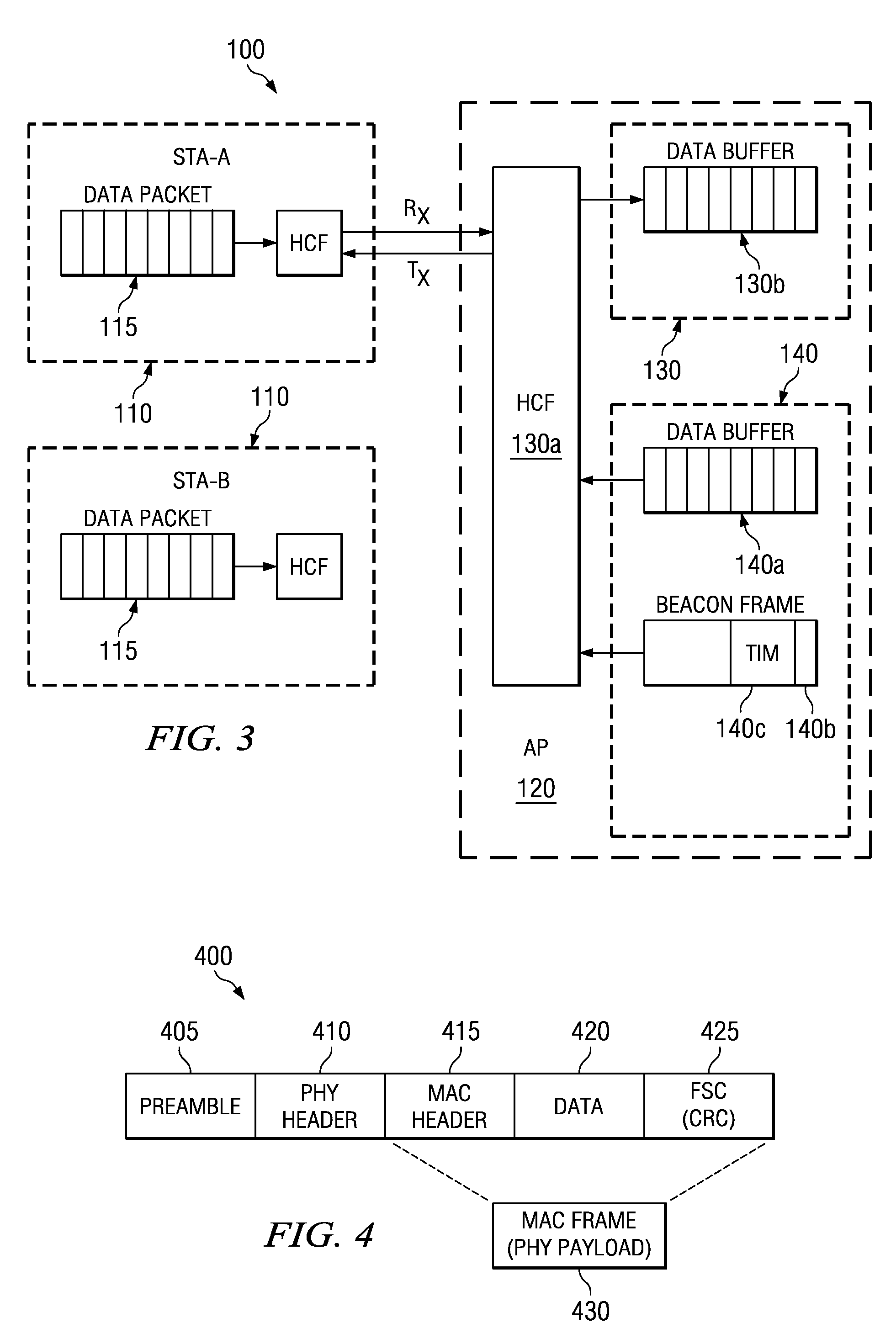
In information technology, a protocol is the special set of rules that end points in a telecommunication connection use when they communicate. Protocols specify interactions between the communicating entities.
Wireless wallet
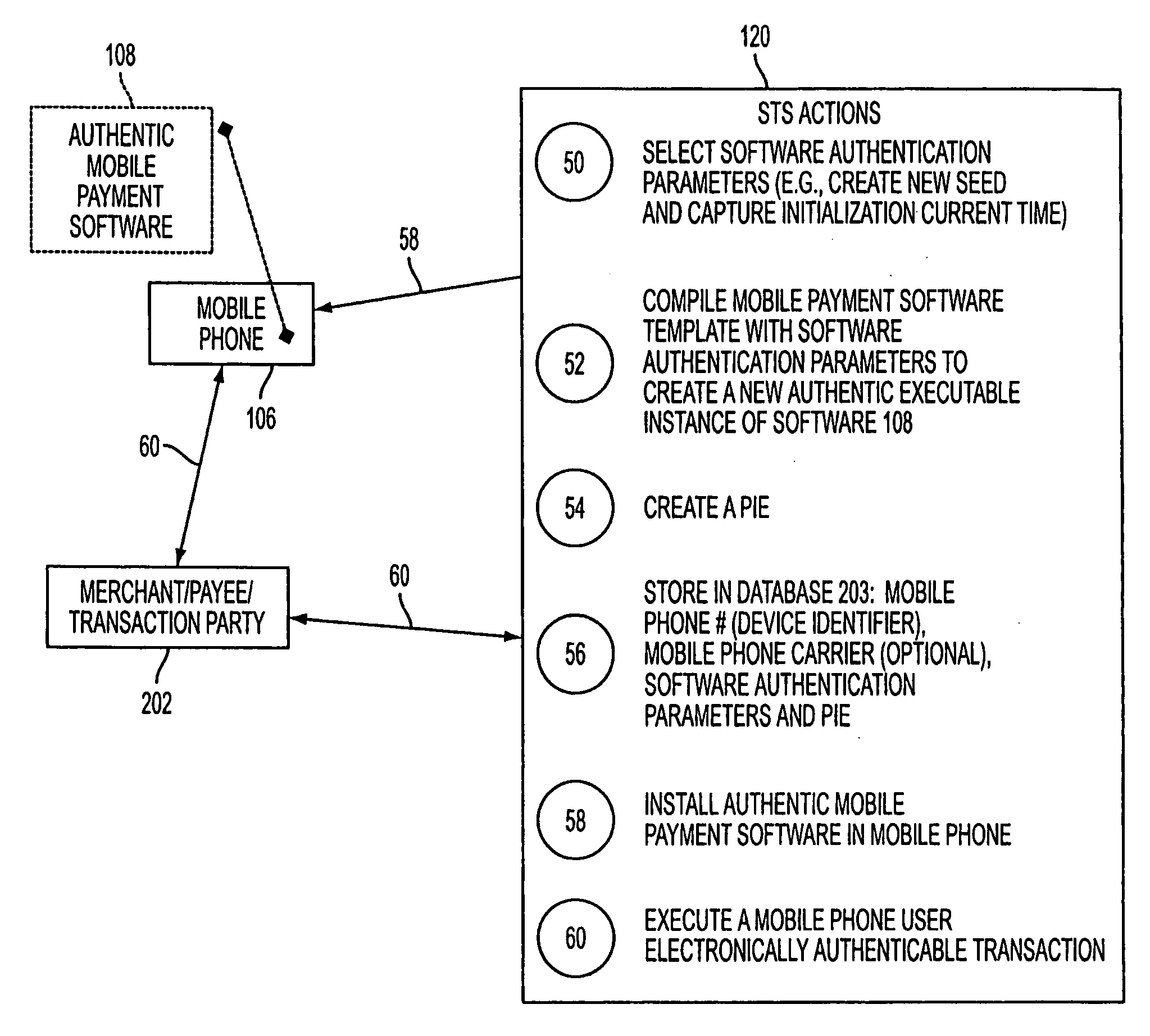
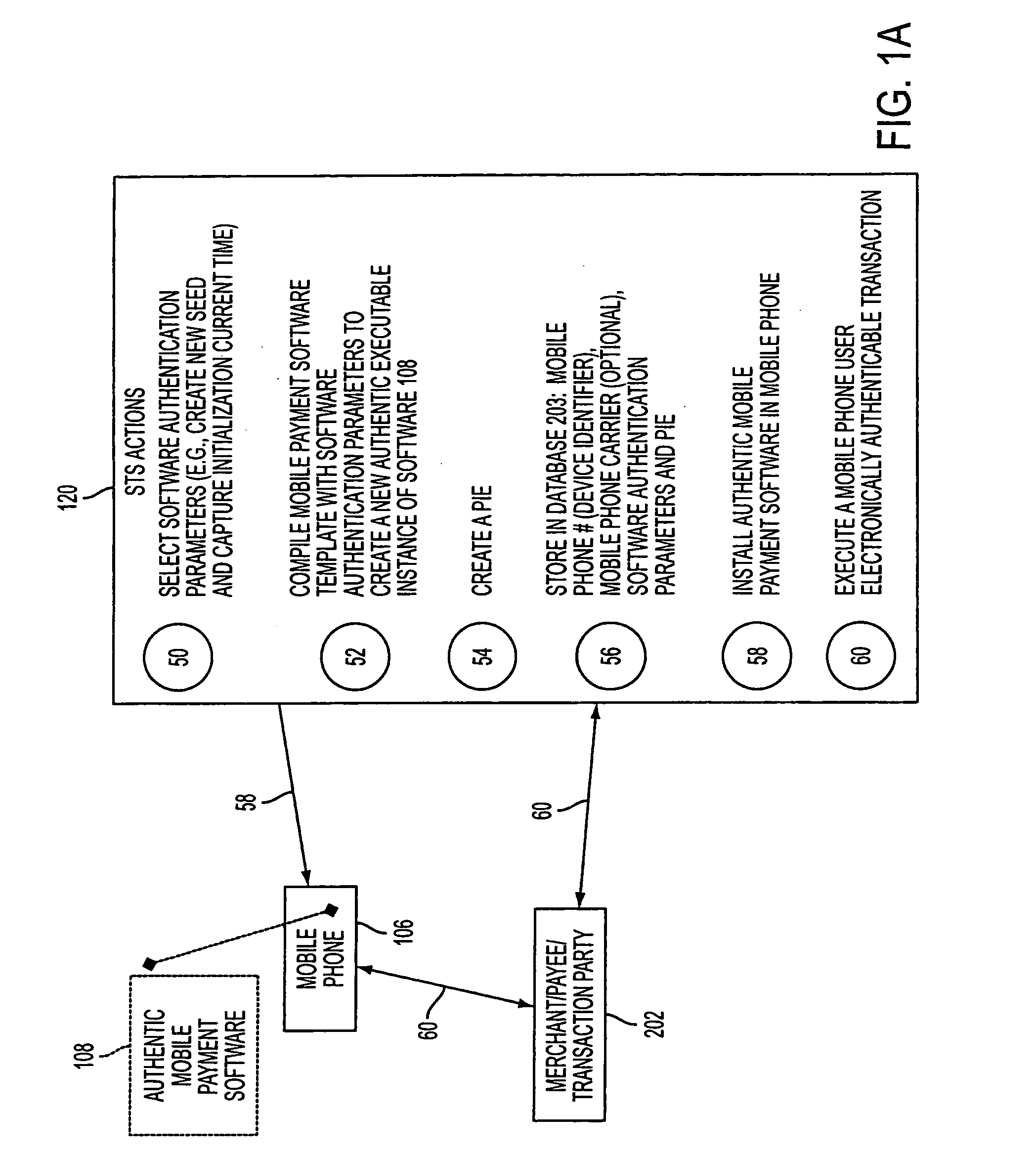
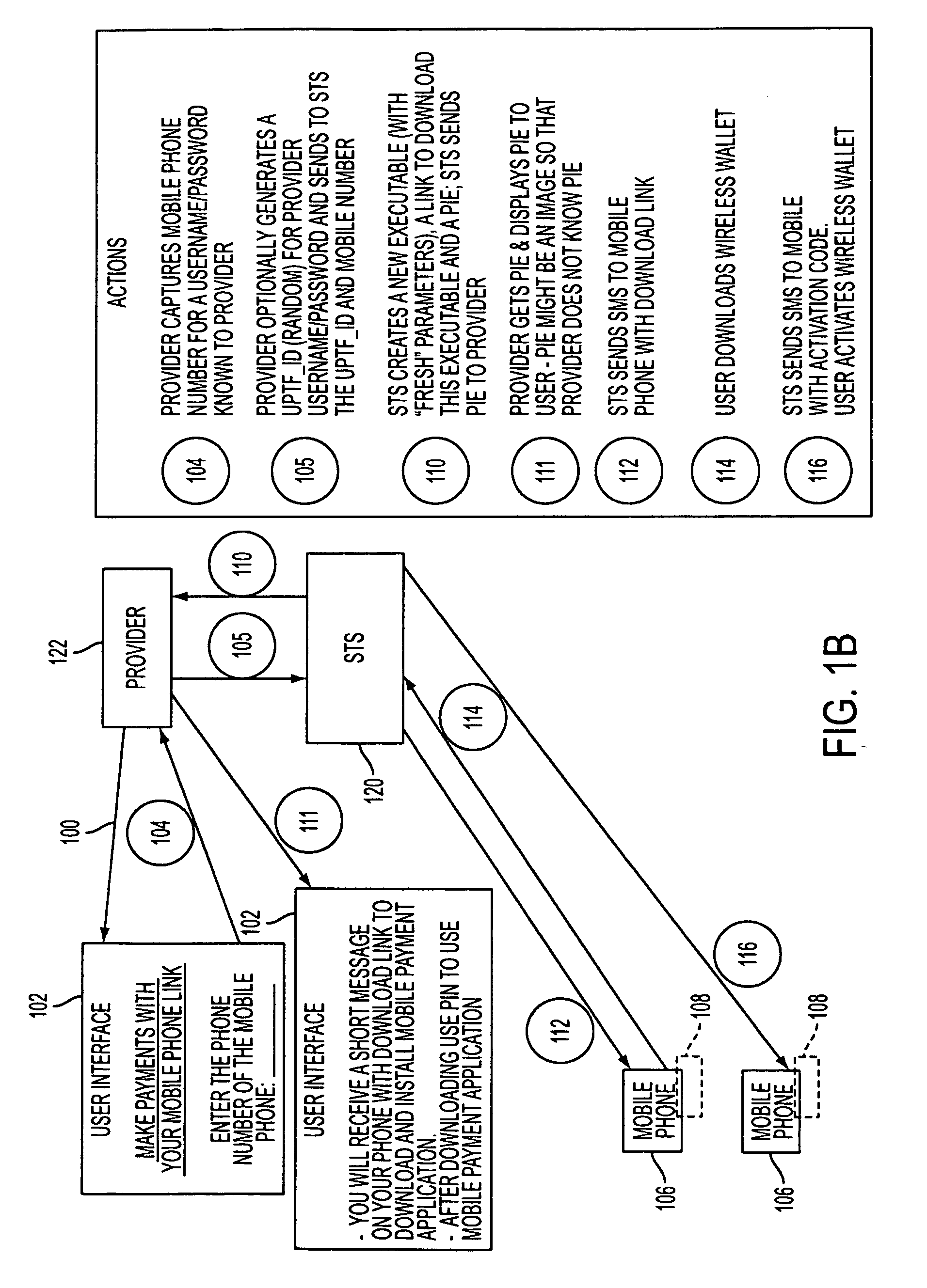
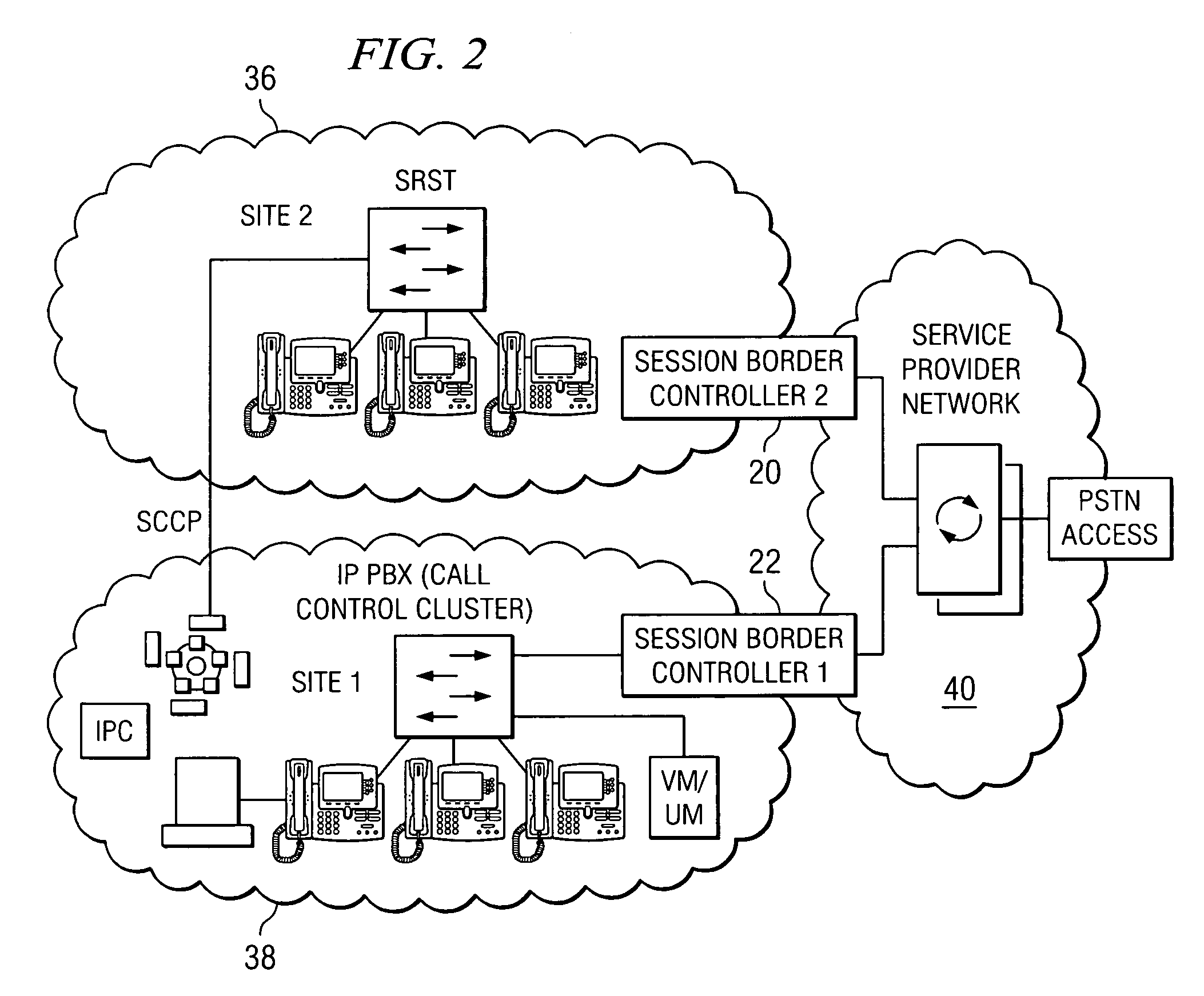
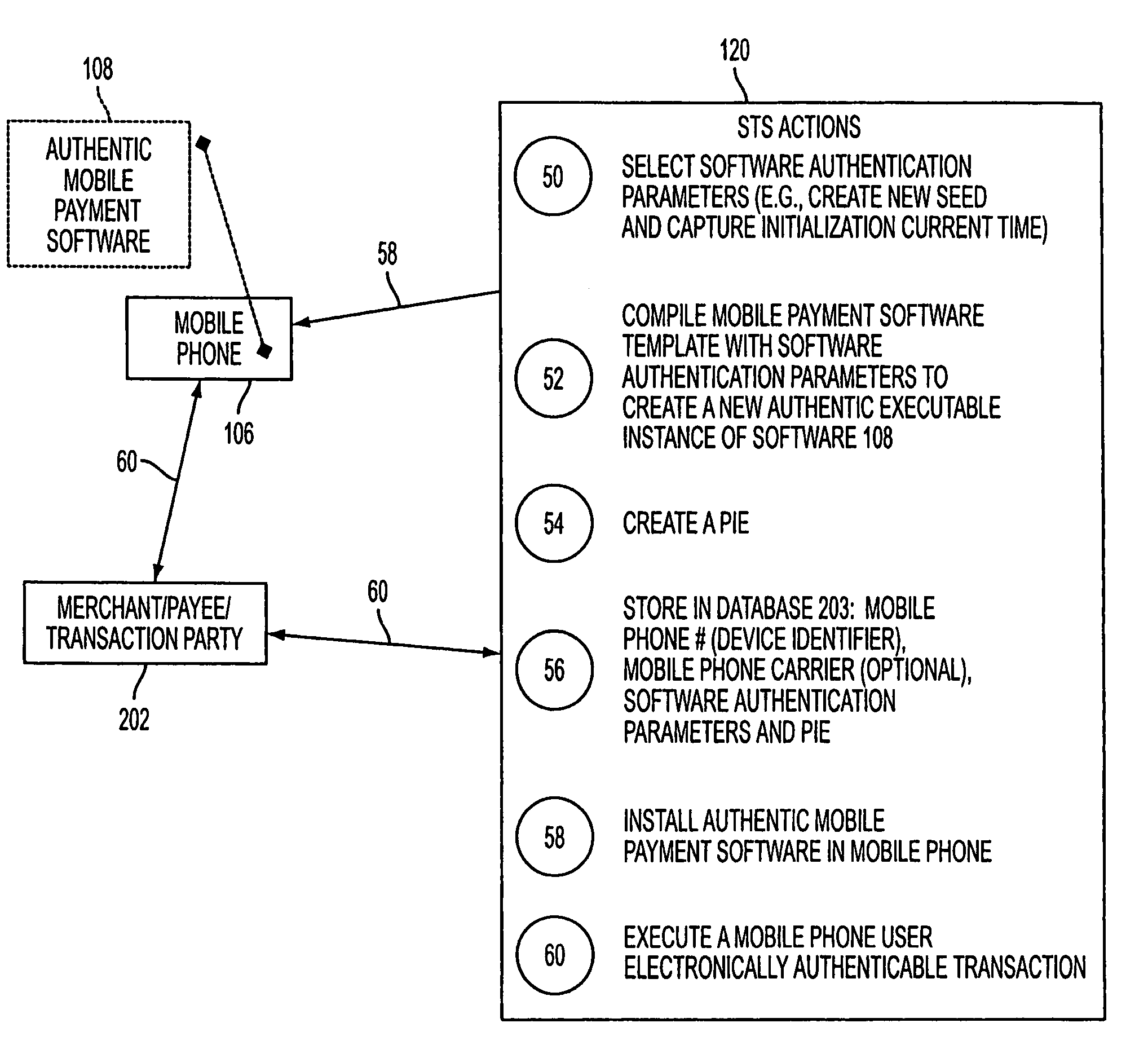
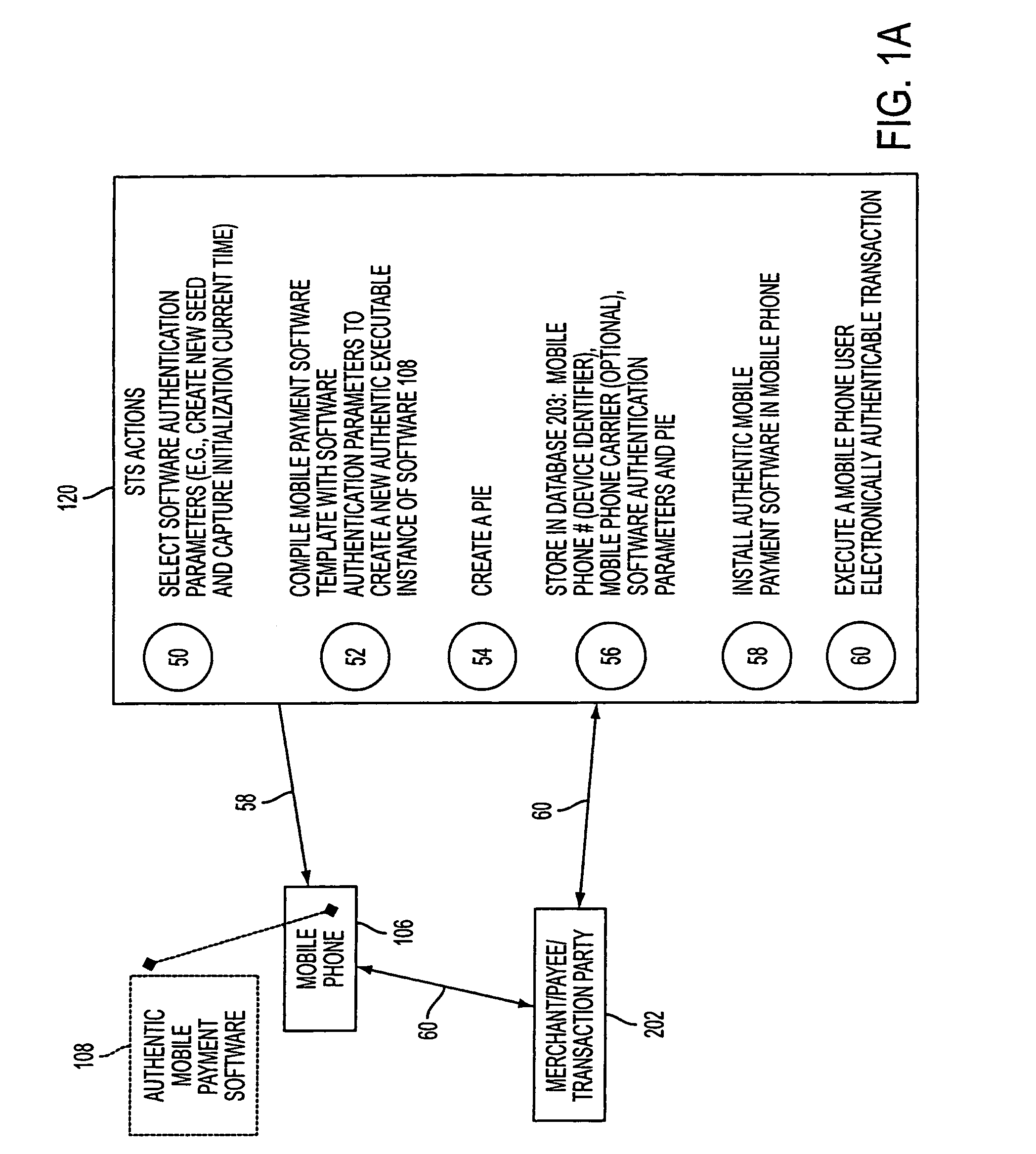
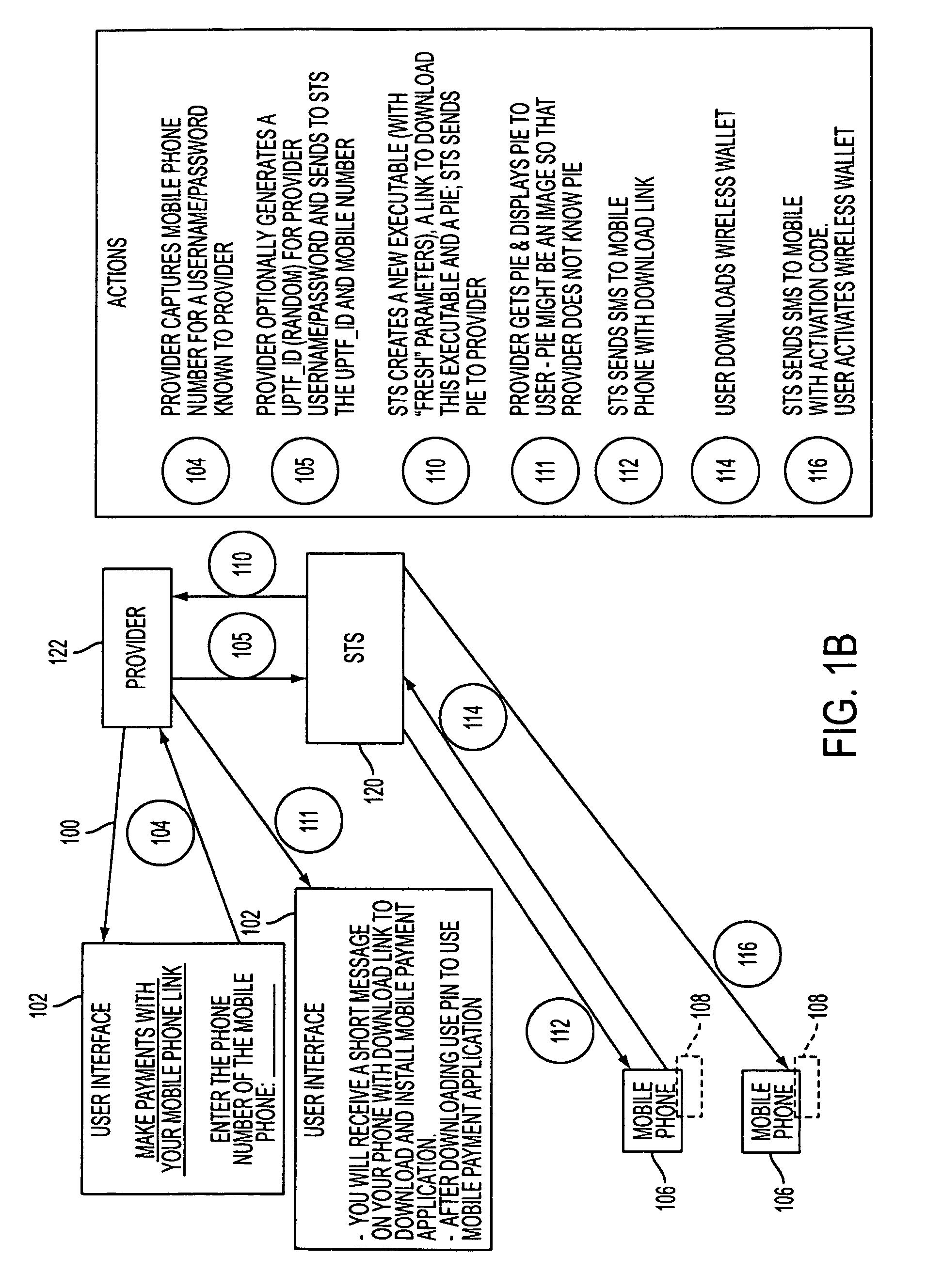
A mobile phone system and method of initializing, at a secure transaction server (STS), a mobile payment software with a software authentication parameter, as an authentic mobile payment software; providing an STS correlation between a personal identification entry (PIE) and the authentic mobile payment software; installing, in a mobile phone, the authentic mobile payment software; and inputting, by a user, the PIE to the installed authentic mobile payment software to generate according to the PIE and the software authentication parameter a transformed secure authenticable mobile phone cashless monetary transaction over the mobile phone network, as a mobile phone wireless wallet of the user of the mobile phone. The mobile phone authenticable cashless monetary transaction is performed according to an agreement view(s) protocol.
Owner:PCMS HOLDINGS INC
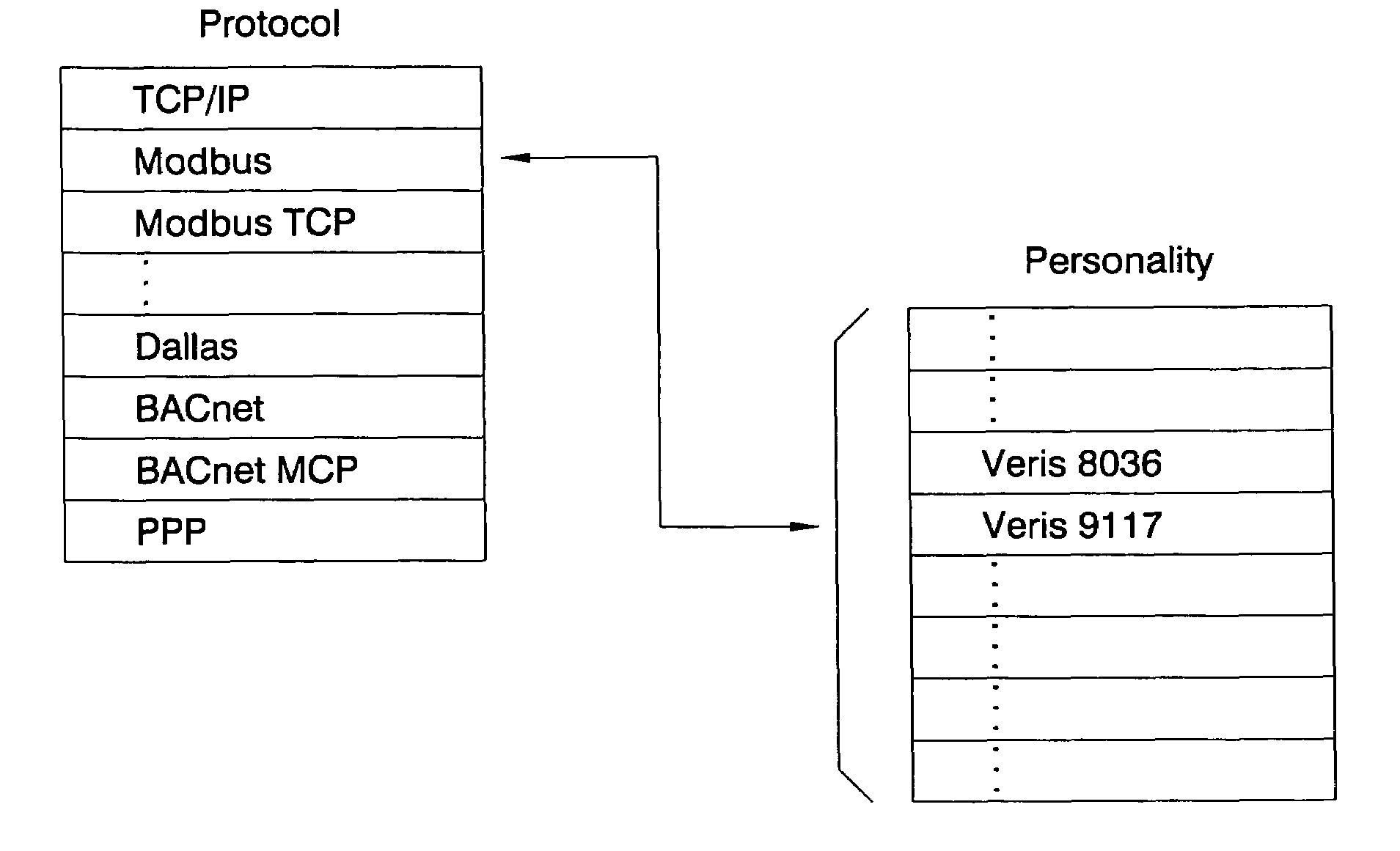
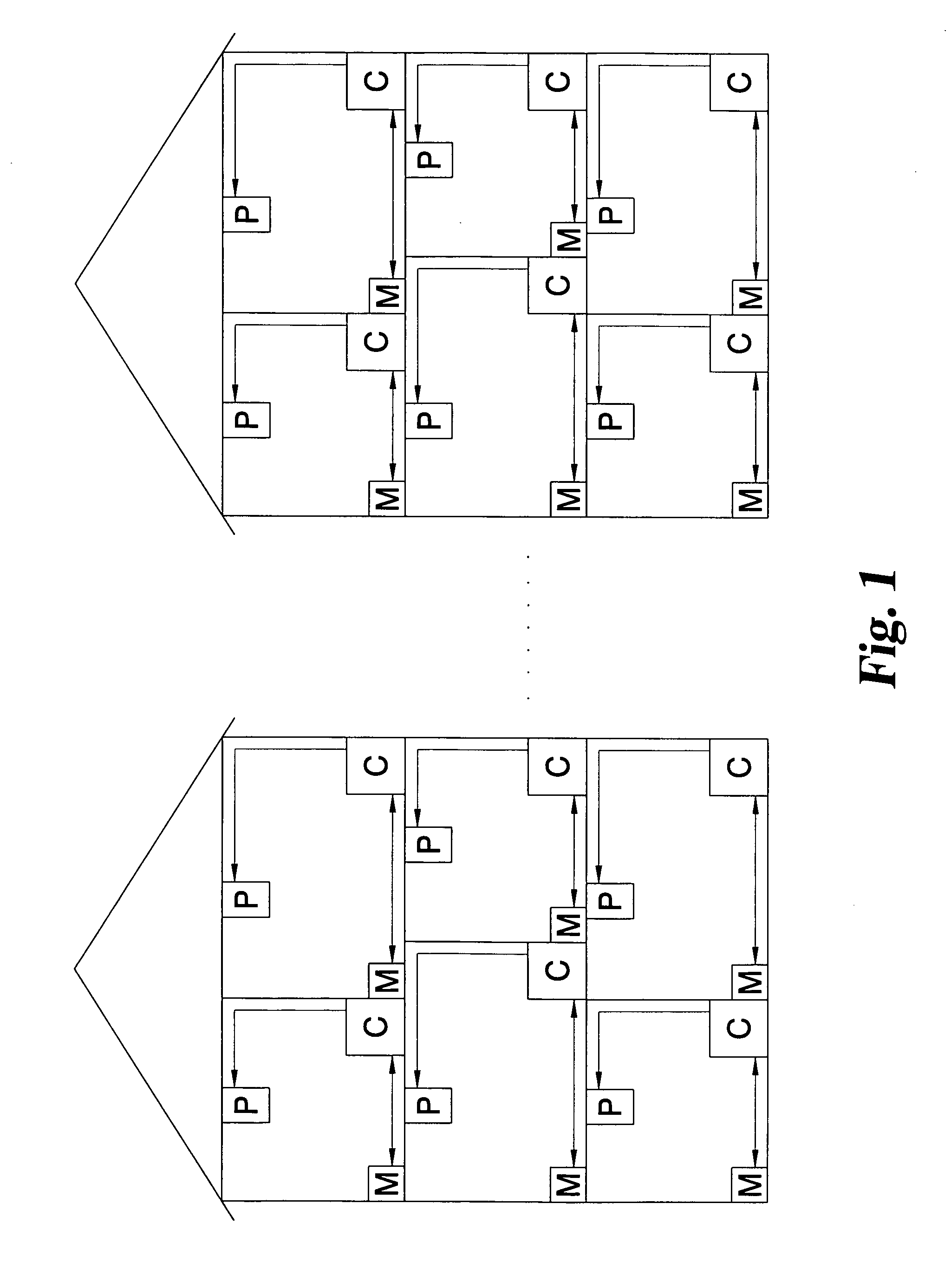
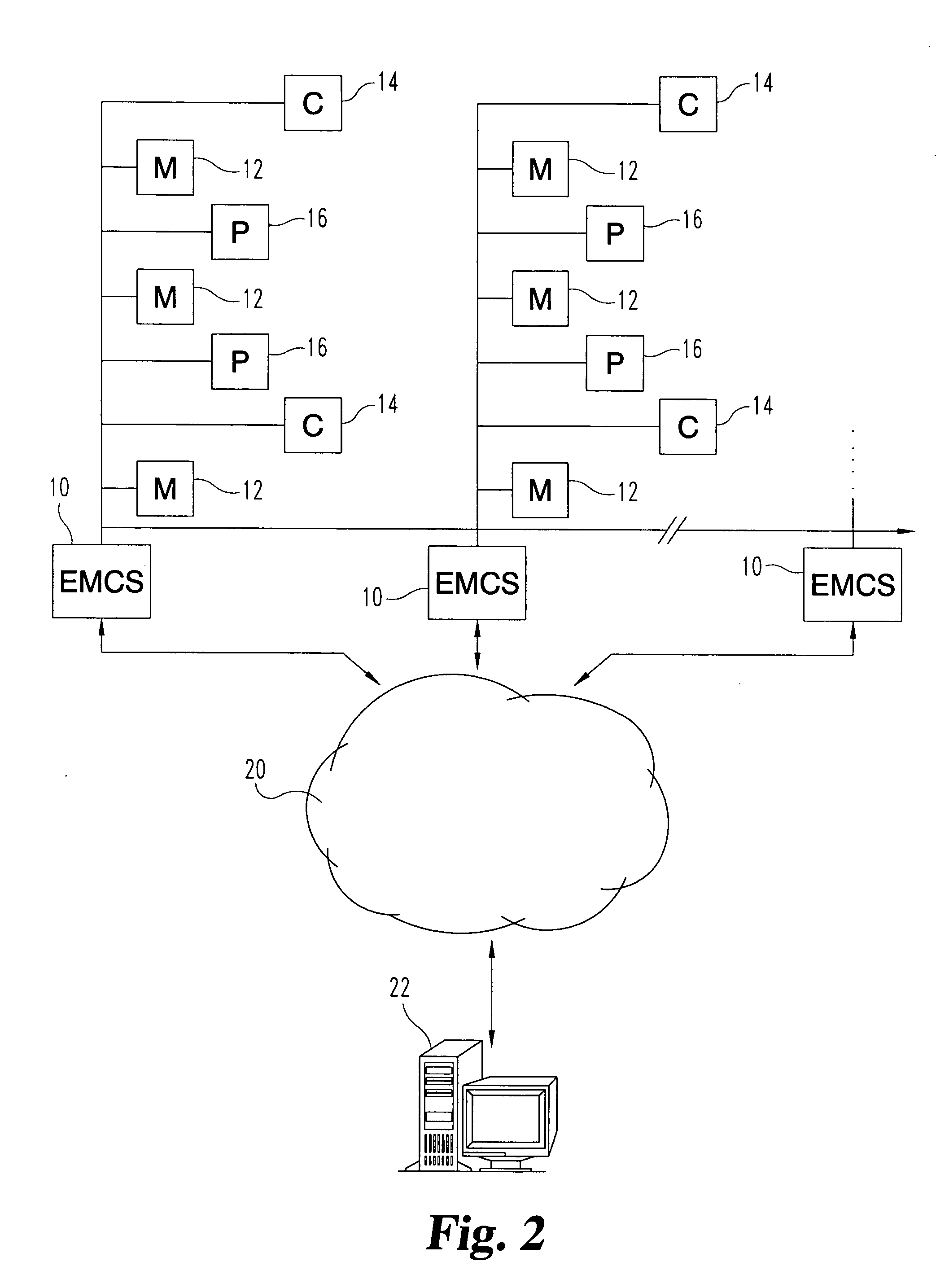
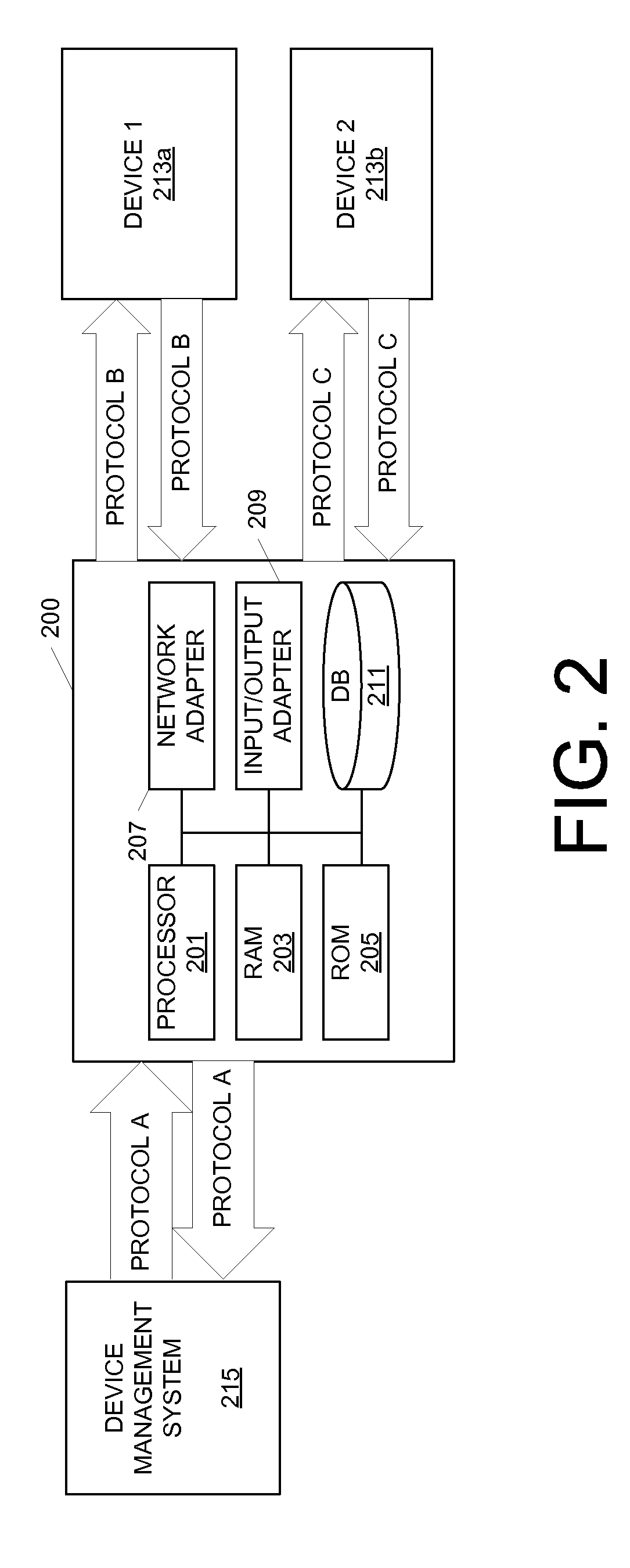
System and method for distributed facility management and operational control
ActiveUS7349761B1Programme controlSampled-variable control systemsControl systemEnvironmental control system
An environmental control system controls monitoring and operation of a multiplicity of disparate environmental control devices by determining an appropriate configuration for each control device and communicates corresponding monitoring and control commands to each device in accordance with its corresponding communication protocol over a selected I / O port. An operational instruction set includes a structural definition of an enterprise facility in which devices are defined by personality modules and communicate with a system host in accordance with a protocol defined in a protocol module. Facility implementation is defined by a node tree structure which collects suitable protocol nodes under a corresponding I / O interface port node. Device (personality) nodes are collected under corresponding protocol nodes, and data point nodes depend from their corresponding device nodes. Data points nodes are individually accessible by merely traversing the node tree using a URL-like notational structure, allowing off-site users to control and monitor environmental devices by issuing commands in the form of a URL.
Owner:CISCO TECH INC +1
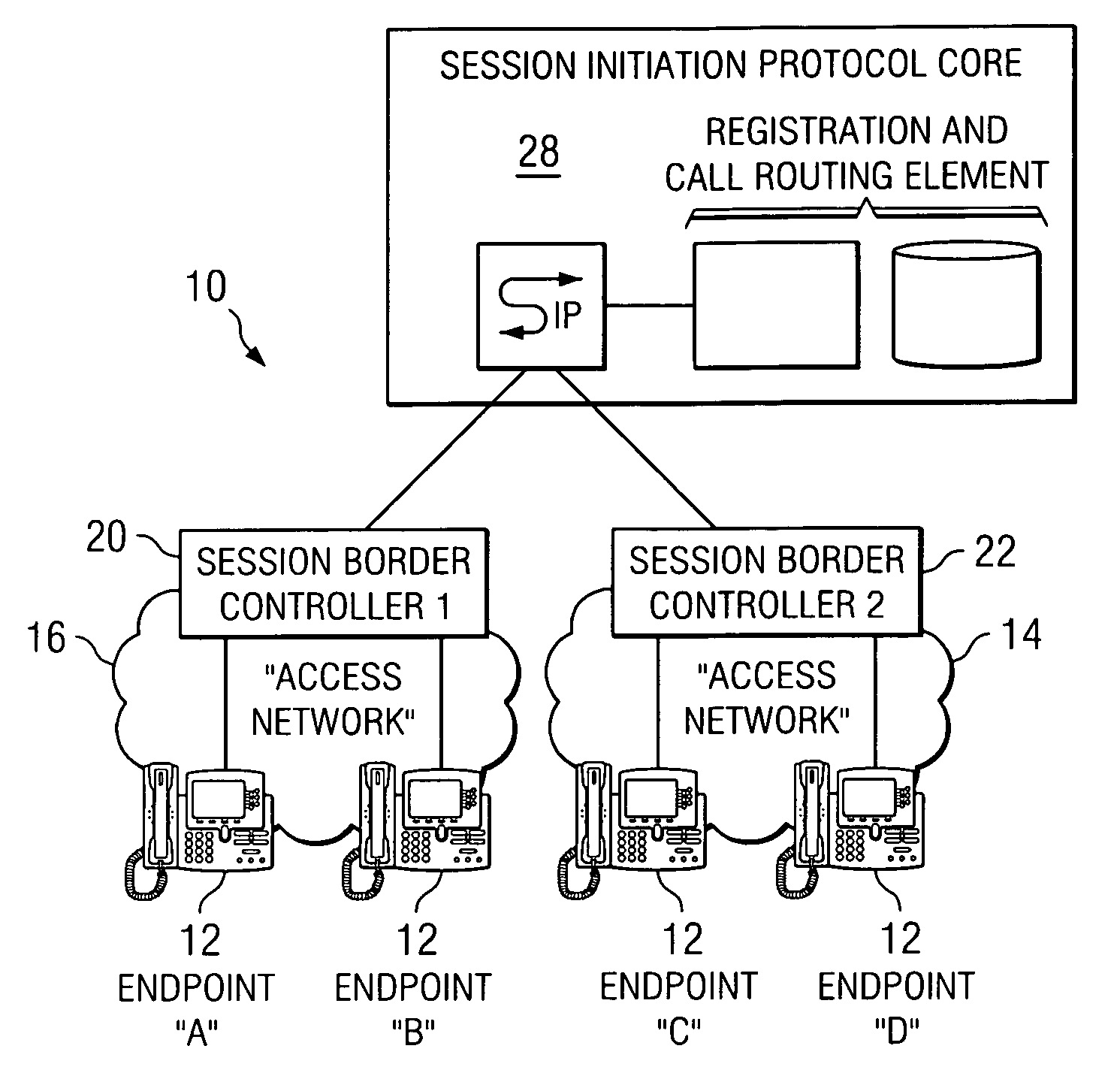
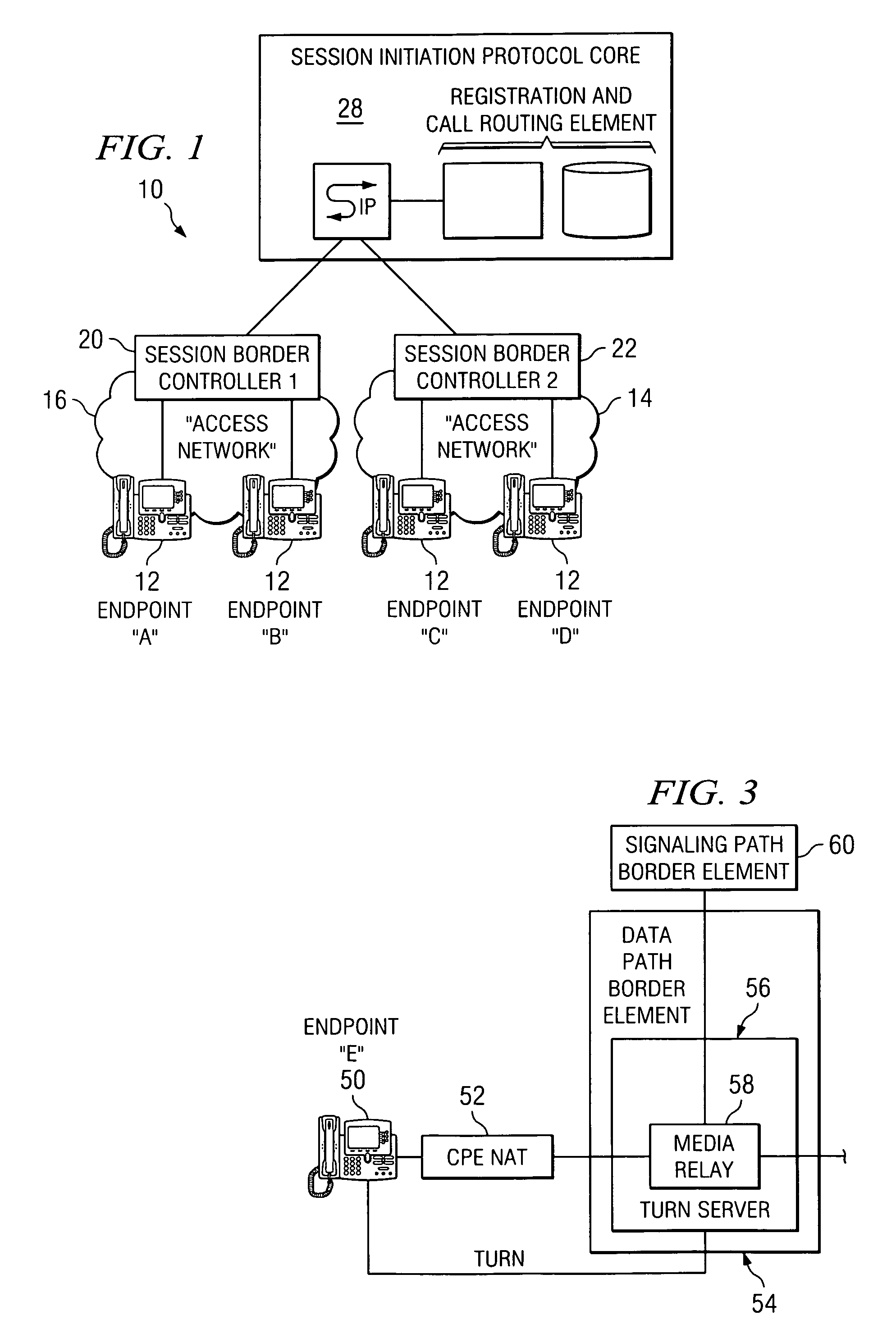
System and method for optimizing communications between session border controllers and enpoints in a network environment
ActiveUS20070019619A1Reduce disadvantagesReduce problemsMultiplex system selection arrangementsSpecial service provision for substationDatapathSession border controller
An apparatus for optimizing communications between session border controllers in a network environment is provided that includes a session border controller (SBC) operable to communicate with a first endpoint and a second endpoint. The SBC is also operable to communicate with a data path border element (DBE) and a signaling path border element (SBE). The DBE is operable to provide a media relay for a communication session involving the endpoints, the media relay being invoked by either of the endpoints using a traversal using relay network address translation (TURN) protocol, which allows the SBC to operate in either of two modes depending on protocol support present in the endpoints.
Owner:CISCO TECH INC
Wireless wallet
Owner:PCMS HOLDINGS INC
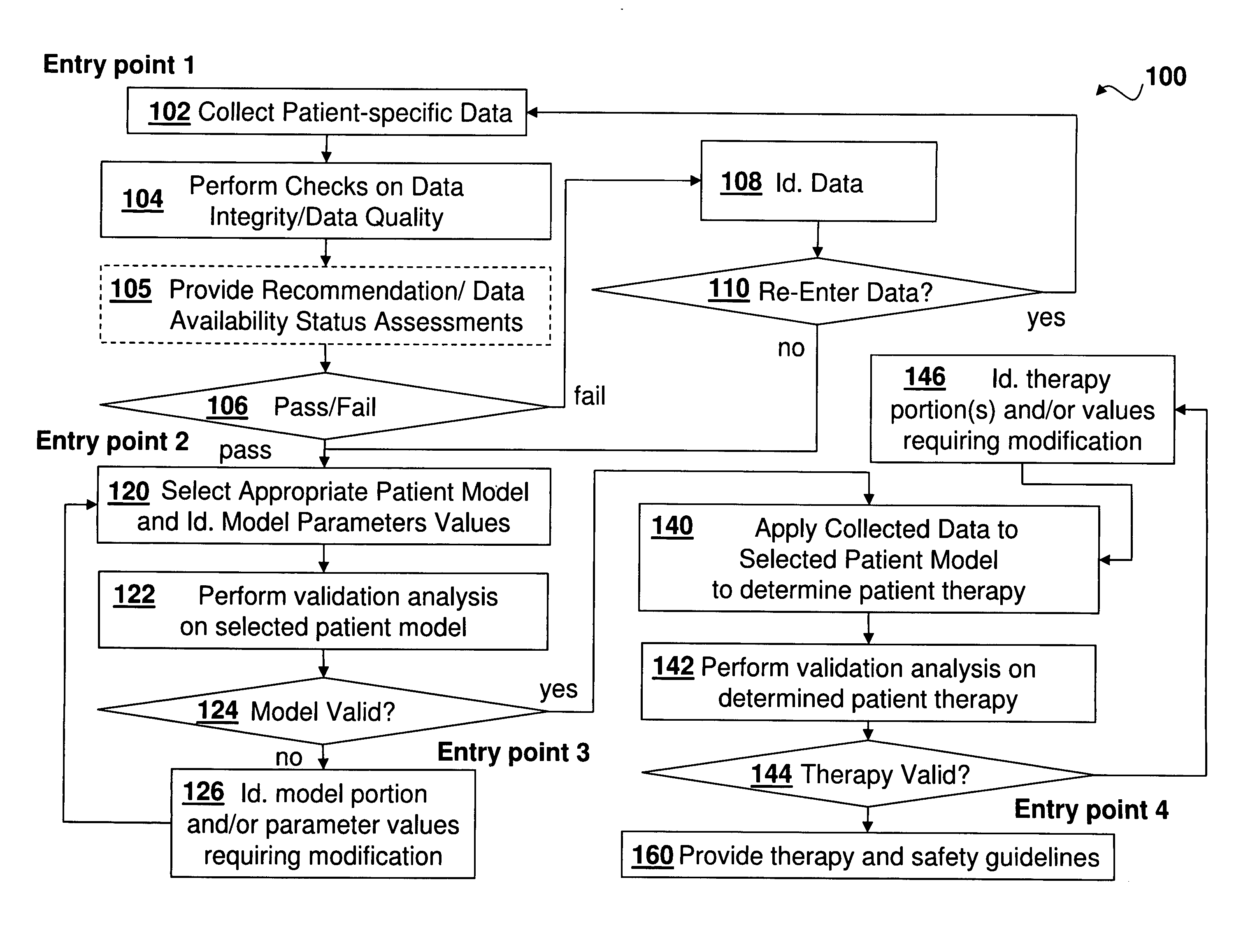
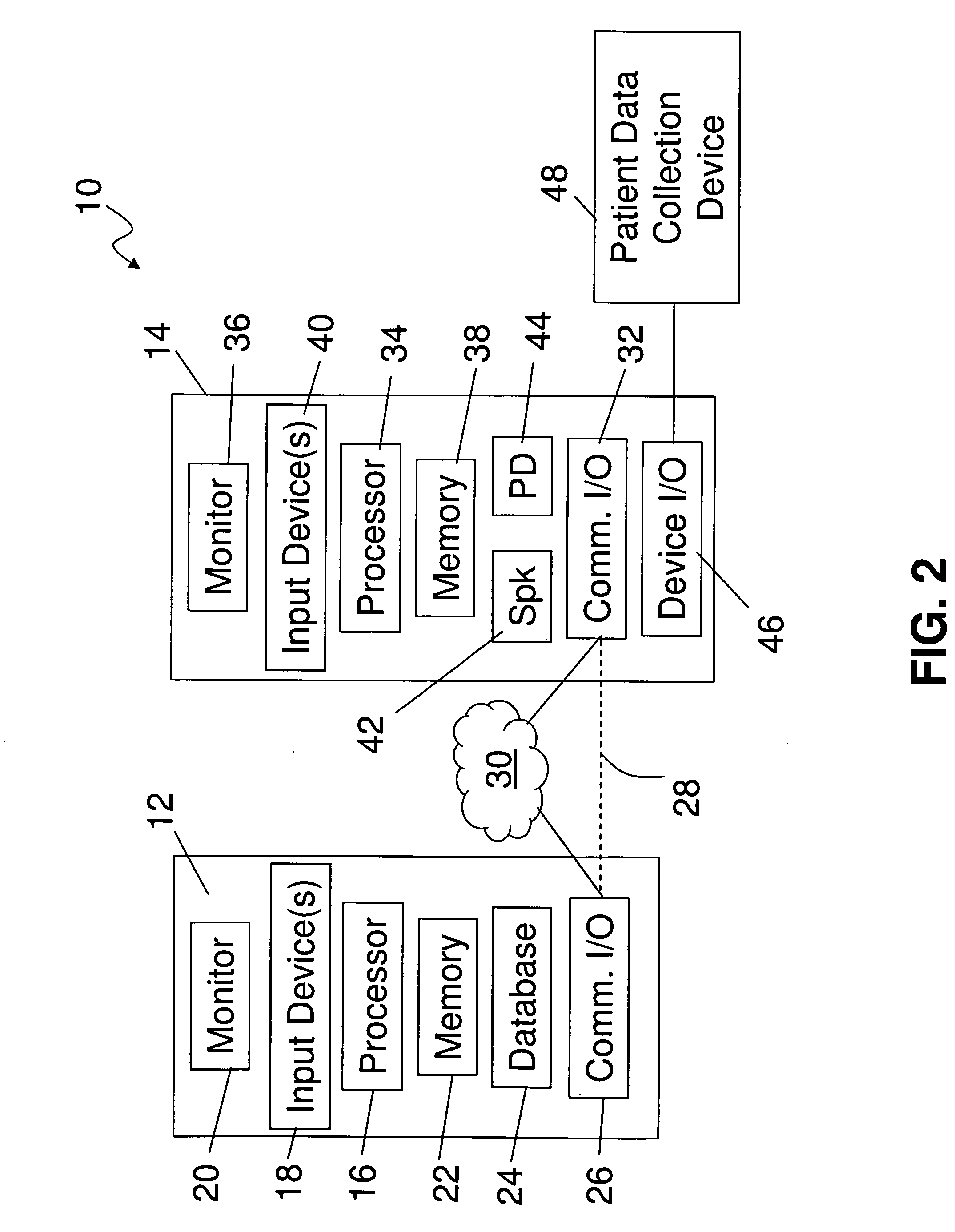
Medical Diagnosis, Therapy, And Prognosis System For Invoked Events And Methods Thereof
A diagnosis, therapy and prognosis system (DTPS) and method thereof to help either the healthcare provider or the patient in diagnosing, treating and interpreting data are disclosed. The apparatus provides data collection based on protocols, and mechanism for testing data integrity and accuracy. The data is then driven through an analysis engine to characterize in a quantitative sense the metabolic state of the patient's body. The characterization is then used in diagnosing the patient, determining therapy, evaluating algorithm strategies and offering prognosis of potential use case scenarios.
Owner:ROCHE DIABETES CARE INC
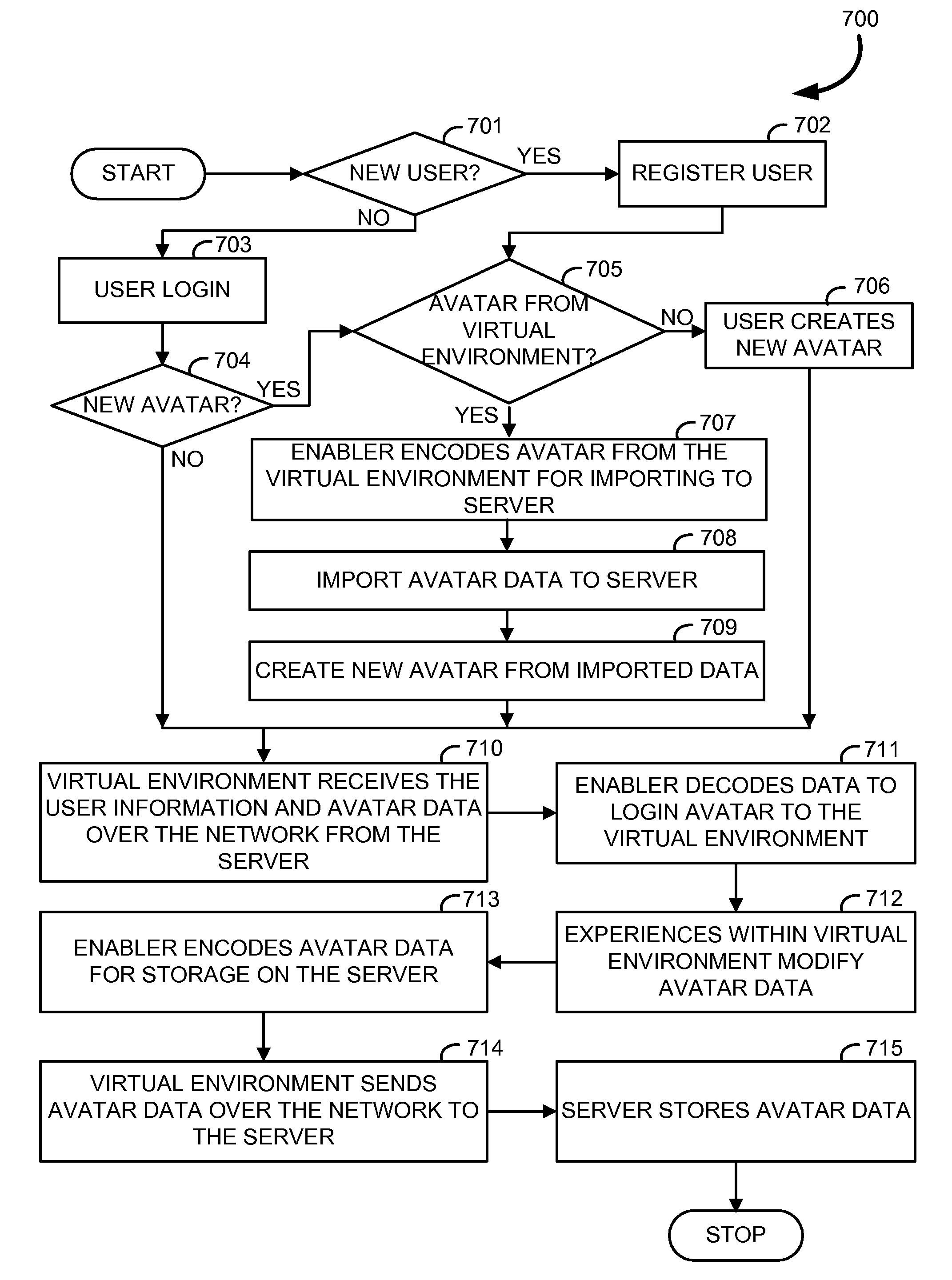
Systems and methods for managing a persistent virtual avatar with migrational ability
InactiveUS20080120558A1Seamless migratory abilityImprove durabilityVideo gamesTransmissionClient-sideOn-Protocol
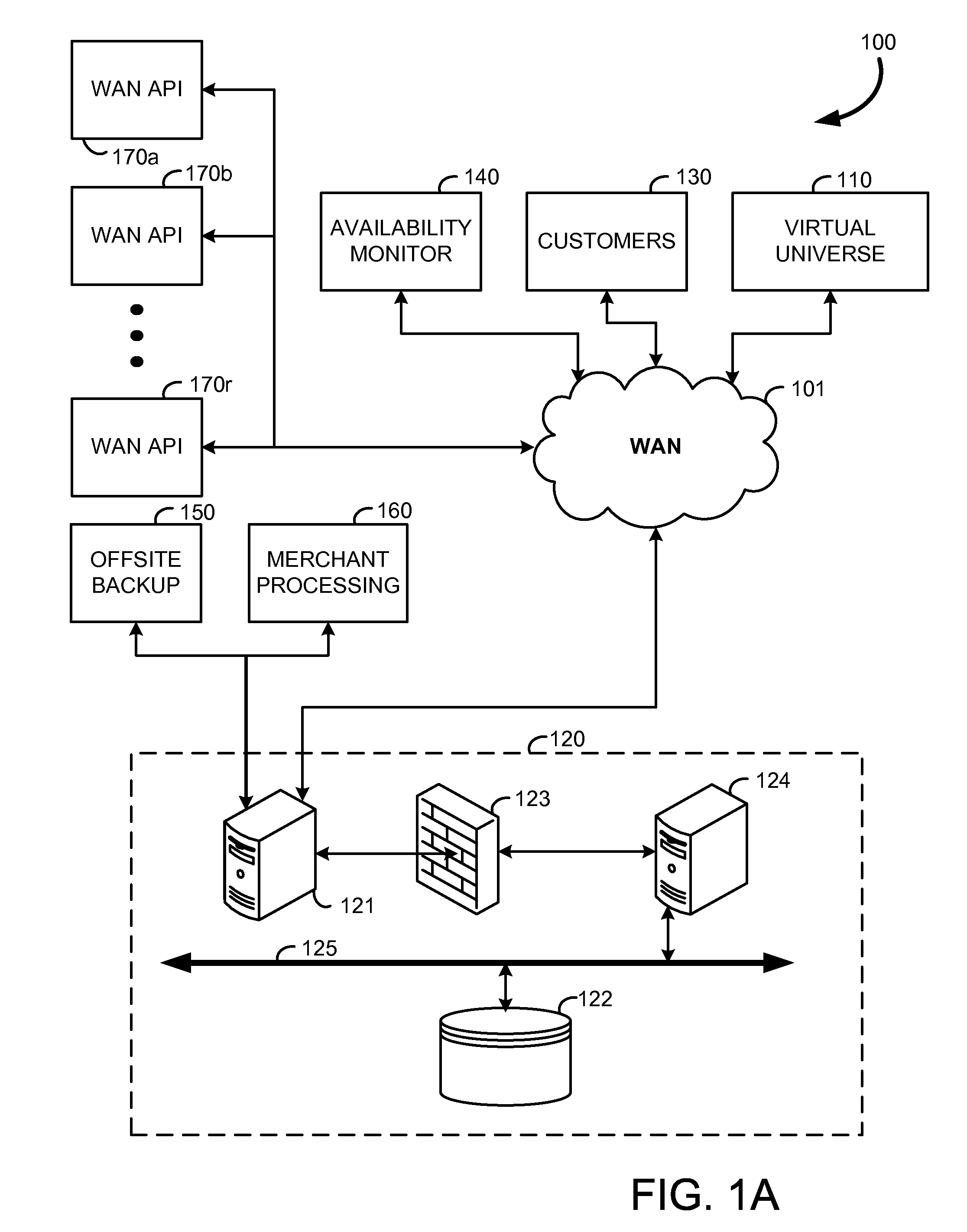
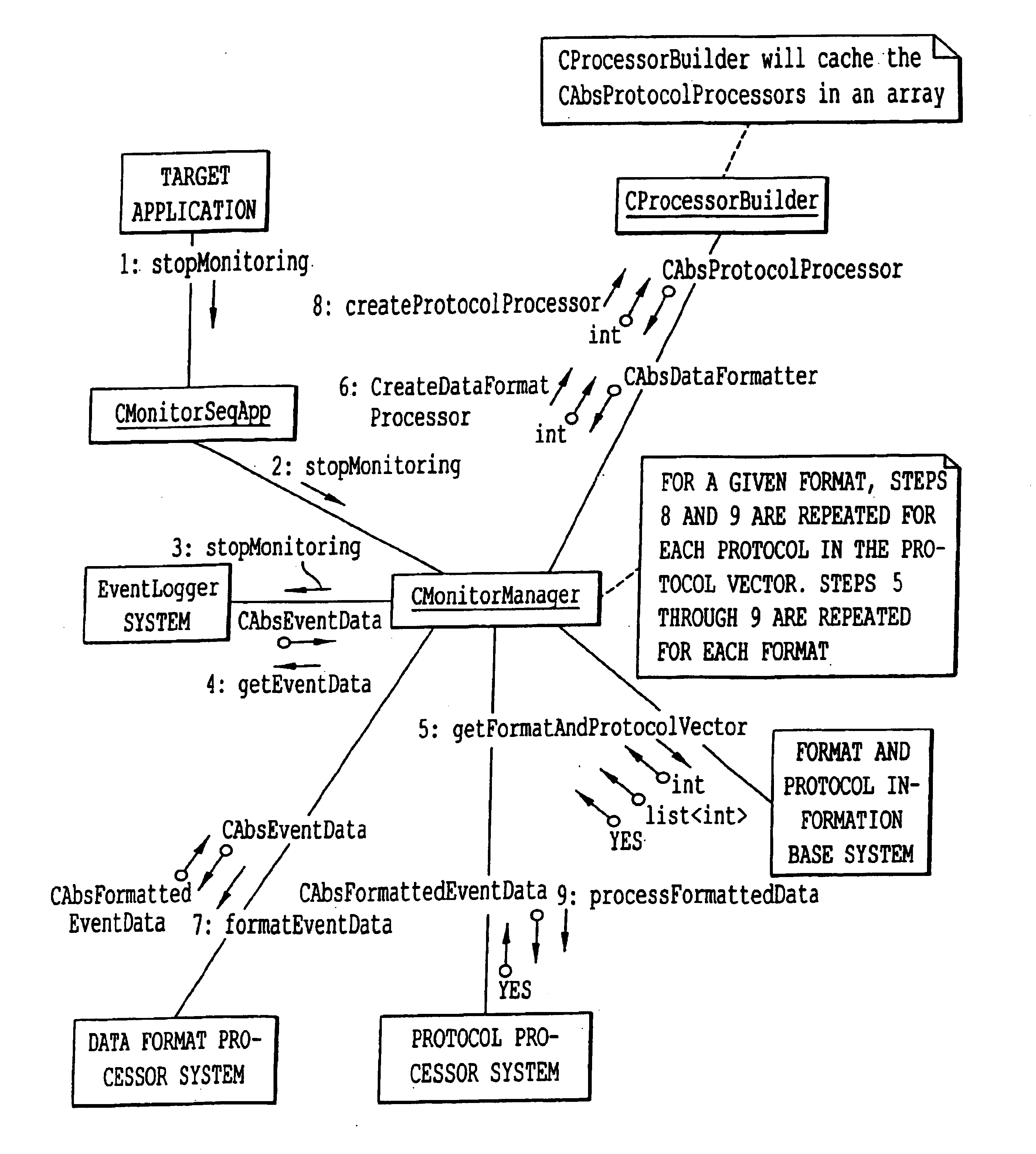
Systems and methods for managing a virtual avatar with migrational ability, and brokering information, are provided. The persistent avatar exists in a plurality of virtual environments and includes attributes generated by an attribute generator, an enabler for enabling virtual environments to access the stored attribute data, and a migrator for allowing the avatar to migrate from one virtual environment to another while the attributes of the persistent avatar remain substantially constant. The enabler utilizes at least one client based on protocol suite. Stored attribute data is modifiable by experiences in any virtual environment. User of the persistent avatar is notified when events occur in any virtual environment, or within real life, by monitoring for events with a monitor, assessing importance of the event with an assessor, and notifying the owner with an informer of the event if it exceeds a threshold of importance.
Owner:BOTANIC TECH INC
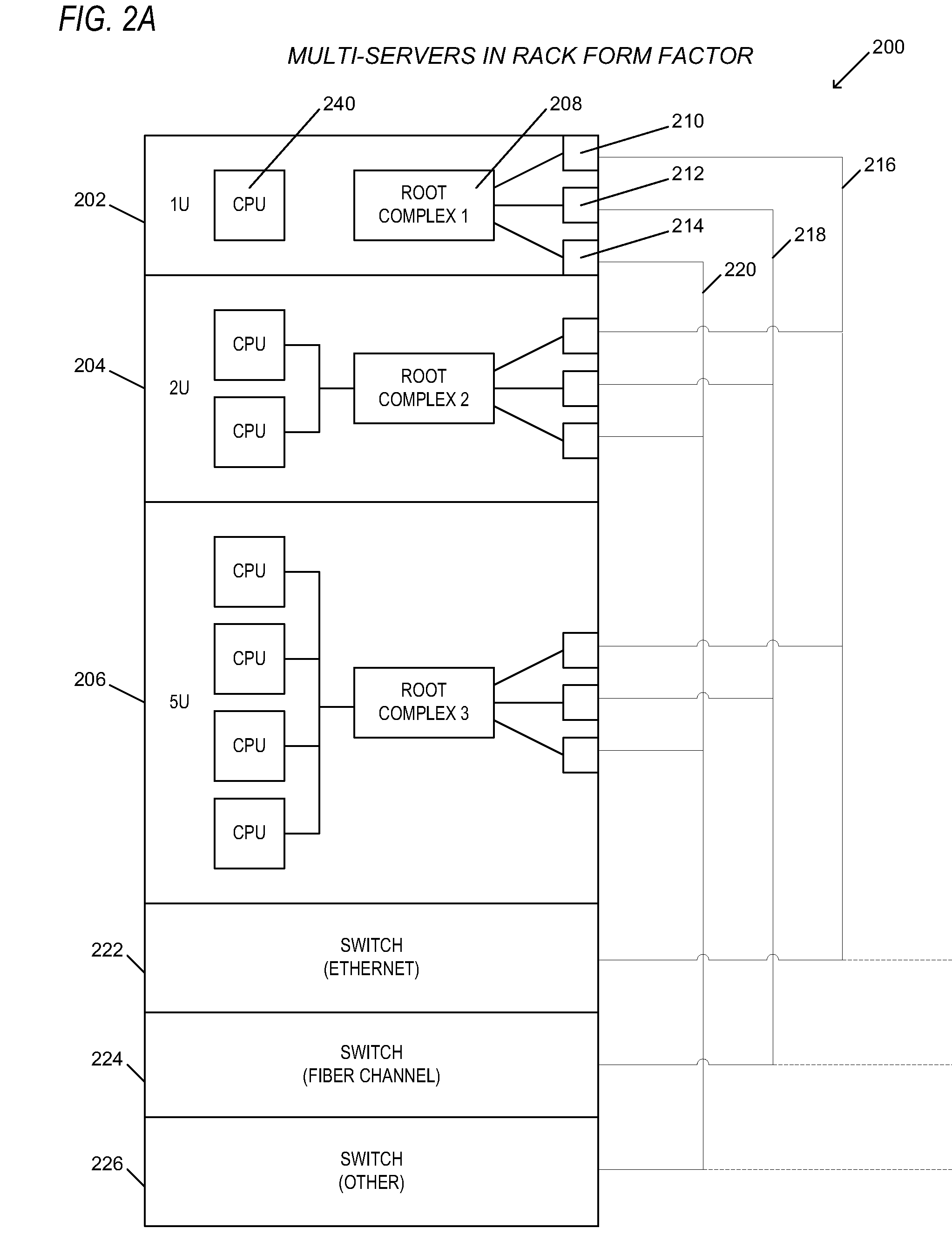
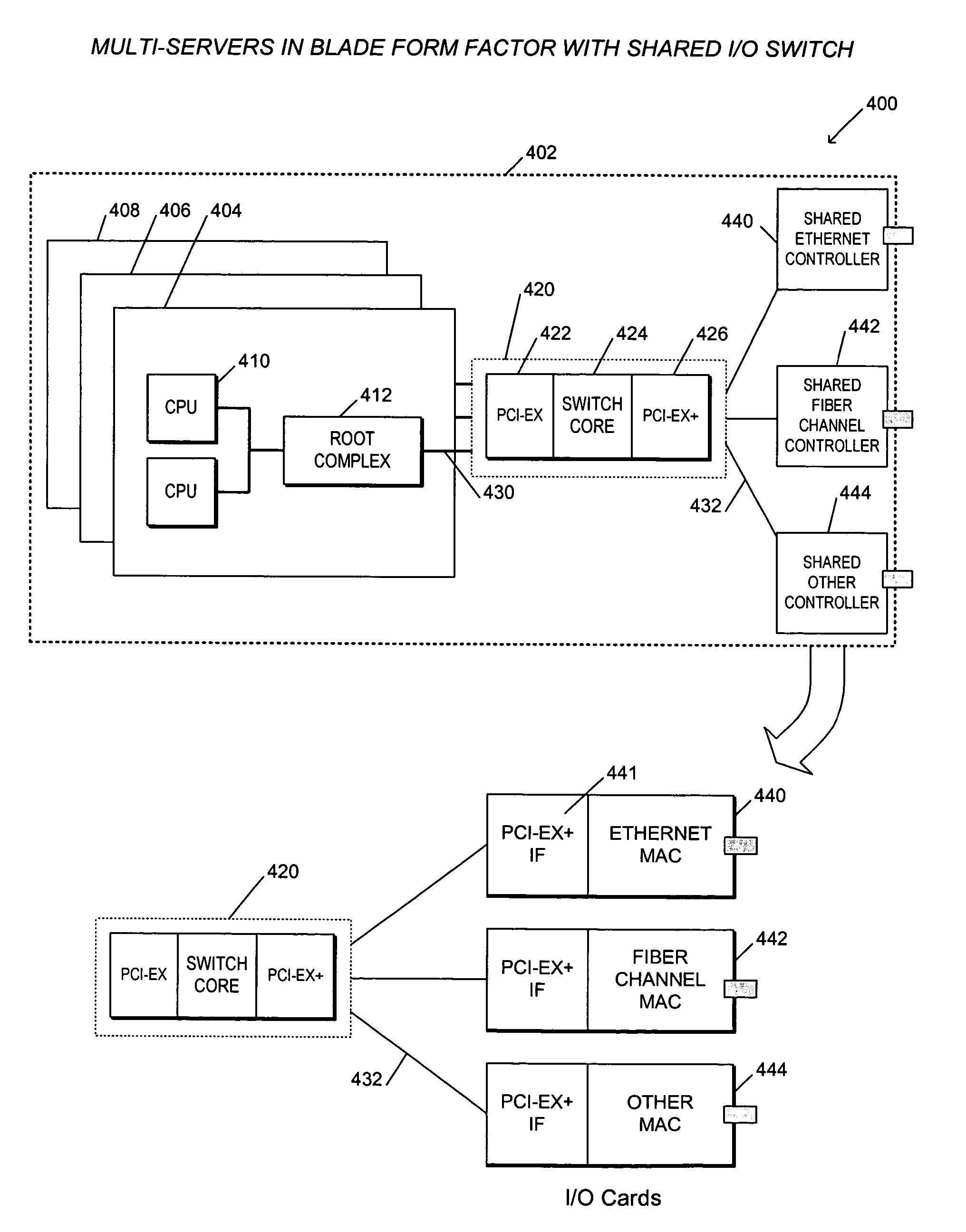
Switching apparatus and method for providing shared I/O within a load-store fabric
ActiveUS20060184711A1Multiplex system selection arrangementsData switching by path configurationOperational systemOn-Protocol
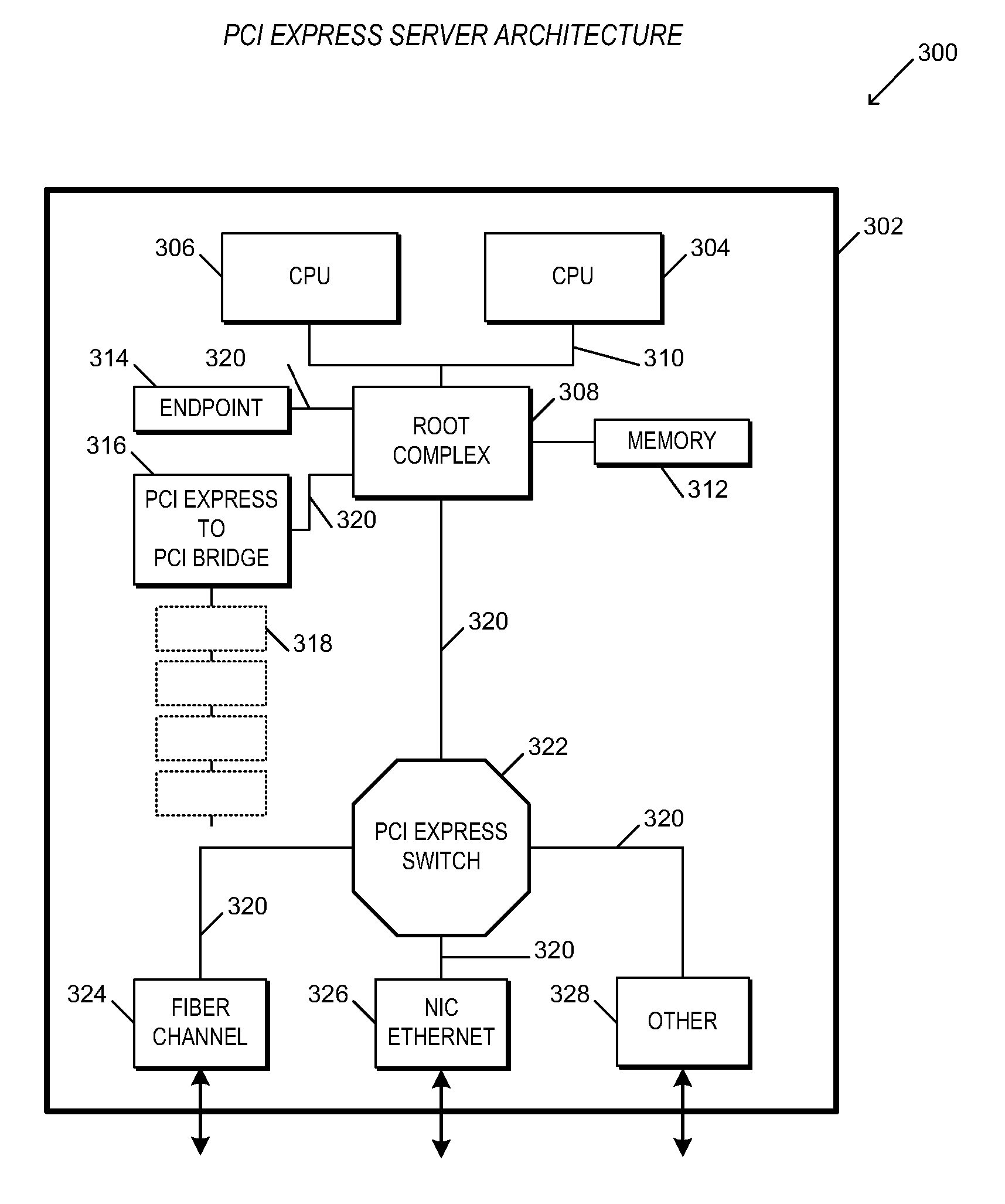
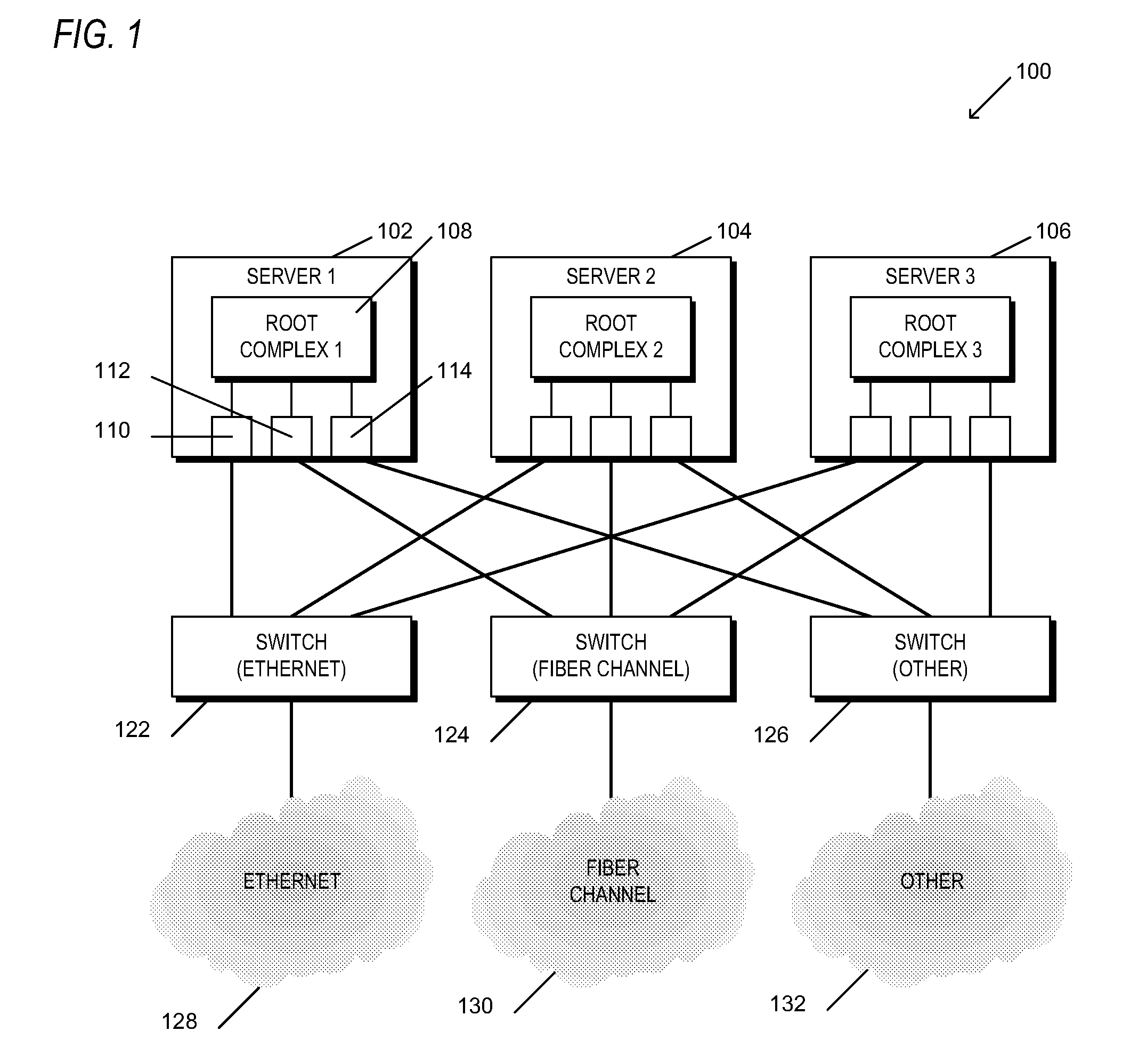
An apparatus and method are provided that enable I / O devices to be shared among multiple operating system domains. The apparatus has a first plurality of I / O ports, a second I / O port, and core logic. The first plurality of I / O ports is coupled to a plurality of operating system domains (OSDs) through a load-store fabric, each routing transactions between the plurality of OSDs and the switching apparatus. The second I / O port is coupled to a first shared input / output endpoint. The first shared input / output endpoint requests / completes the transactions for each of the plurality of OSDs. The core logic is coupled to the first plurality of I / O ports and the second I / O port. The core logic routes the transactions between the first plurality of I / O ports and the second I / O port. The core logic designates a corresponding one of the plurality of OSDs according to a variant of a protocol, where the protocol provides for routing of the transactions only for a single OSD.
Owner:AVAGO TECH INT SALES PTE LTD
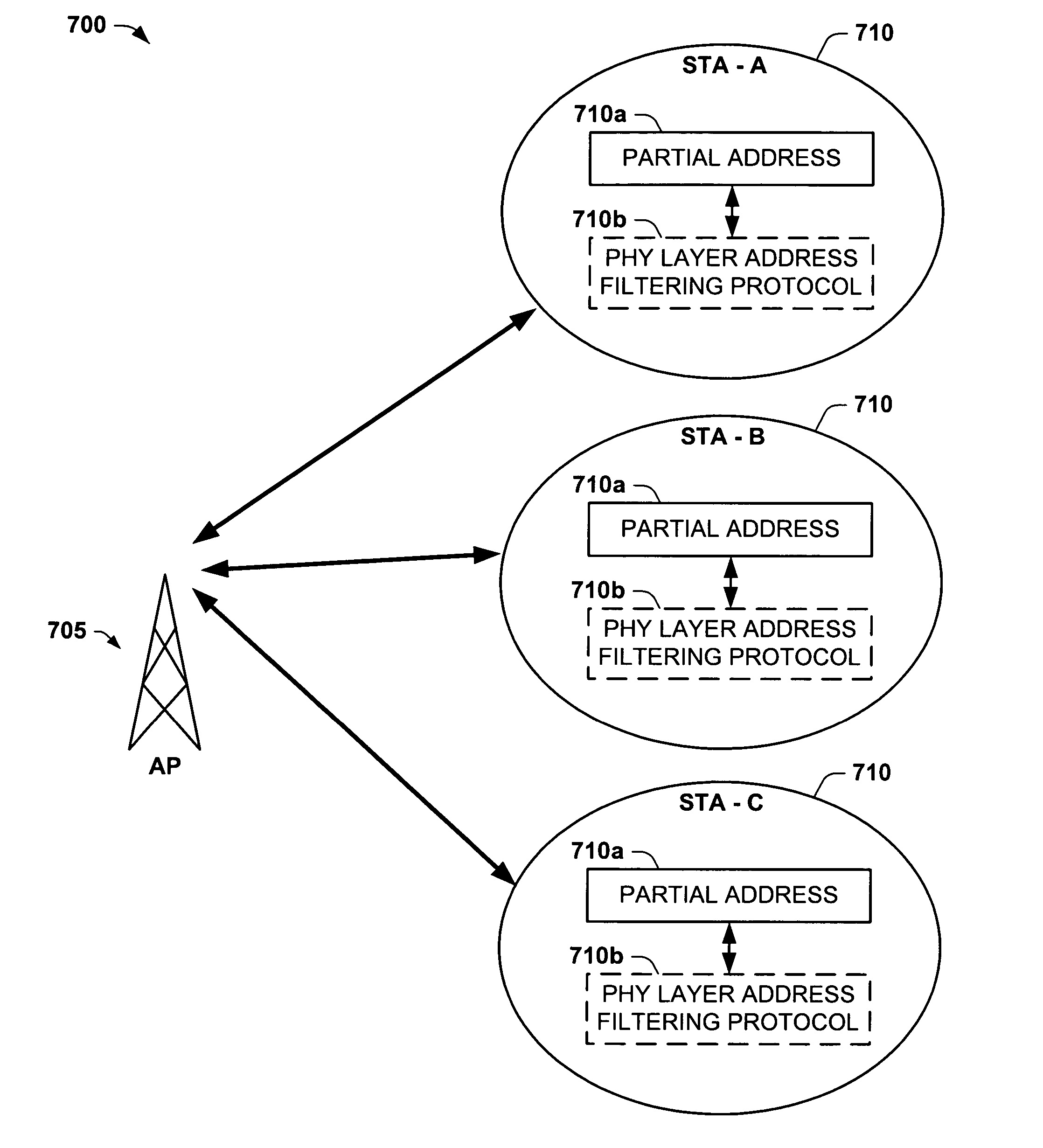
Power saving via physical layer address filtering in WLANs
ActiveUS20050025080A1Save powerSignificant wasted powerEnergy efficient ICTPower managementPhysical addressPhysical layer
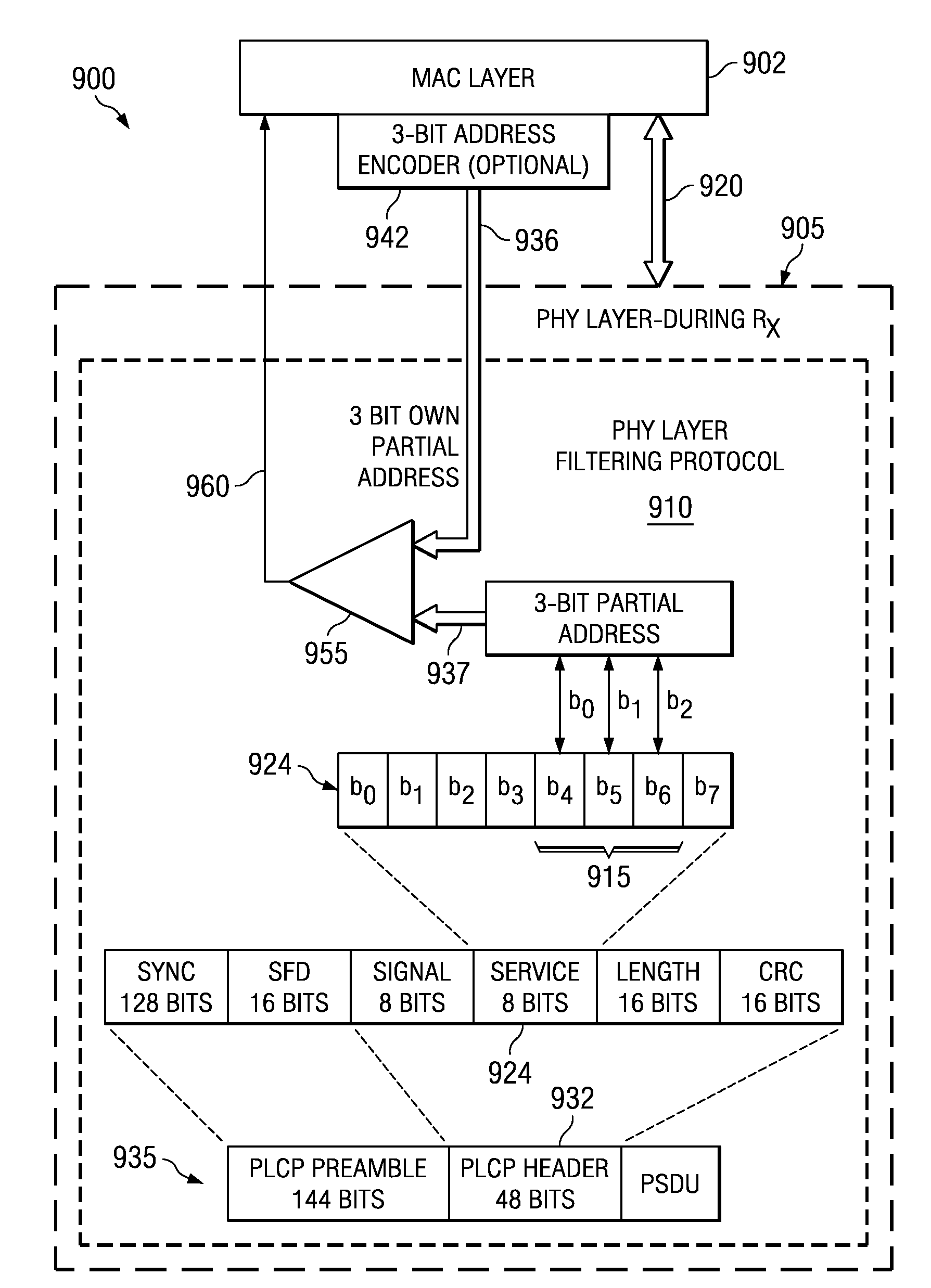
A system and method is described for saving power in a wireless network, using a physical layer address filtering protocol based on a partial address subset of the complete destination MAC address. The system comprises a PHY layer filtering protocol for generating the partial address and writing the partial address into a PHY layer header portion (e.g., PLCP header) of a sending station, or reading the partial address from the PHY layer header portion upon transmission of each frame. A receiving station receives and decodes these PHY layer header portion bits, in accordance with the protocol, and compares whether the subset of bits match that of the stations' own partial address. If a station finds a match, the station then continues further decoding the frame at PHY layer and send the complete frame to the MAC layer for further processing. The stations that do not have a match will not activate their MAC layer components. Thus, the stations of the network will avoid wasting power decoding a significant portion of the complete frame of other stations of the wireless local area networks and unnecessary MAC layer processing. When group addressed, control / management frames or other such frames are detected at the sending station, the address filtering protocol may be “disabled” using a partial address containing a predetermined value (e.g., all zeros).
Owner:TEXAS INSTR INC
Apparatus and method for sharing I/O endpoints within a load store fabric by encapsulation of domain information in transaction layer packets
ActiveUS7188209B2Multiplex system selection arrangementsData switching by path configurationComputer architectureOperational system
An apparatus having a first plurality of I / O ports, a second I / O port, and core logic. The first plurality of I / O ports is coupled to a plurality of operating system domains (OSDs) through a load-store fabric, each routing transactions between the plurality of OSDs and the switching apparatus. The second I / O port is coupled to a first shared input / output endpoint. The first shared input / output endpoint requests / completes the transactions for each of the plurality of OSDs. The core logic is coupled to the first plurality of I / O ports and the second I / O port. The core logic routes the transactions between the first plurality of I / O ports and the second I / O port. The core logic designates a corresponding one of the plurality of OSDs according to a variant of a protocol, where the protocol provides for routing of the transactions only for a single OSD.
Owner:AVAGO TECH INT SALES PTE LTD
Managing uplink resources in a cellular radio communications system
ActiveUS20090225709A1Increase data rateEasy to handleNetwork topologiesData switching by path configurationCellular radioCommunications system
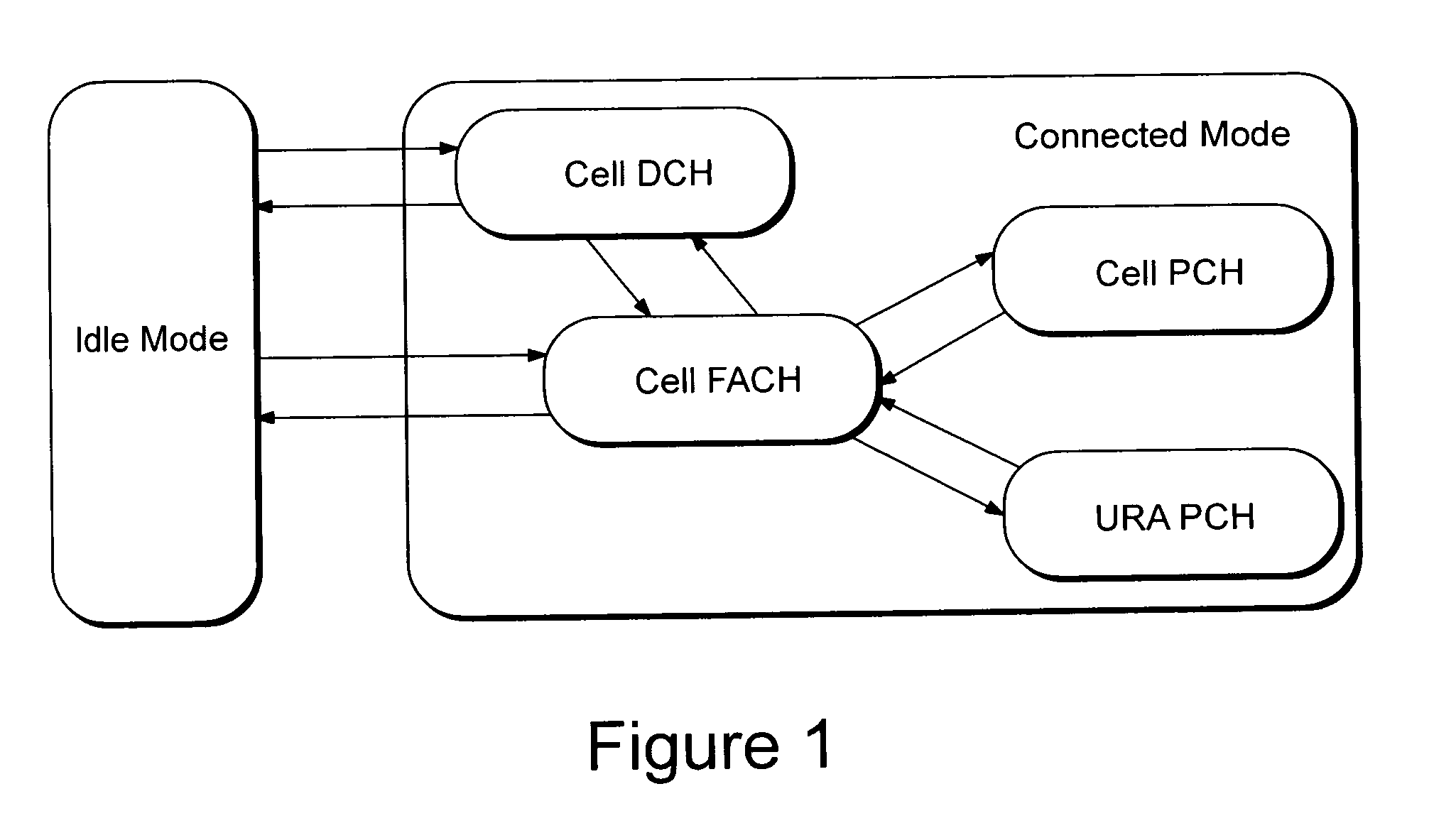
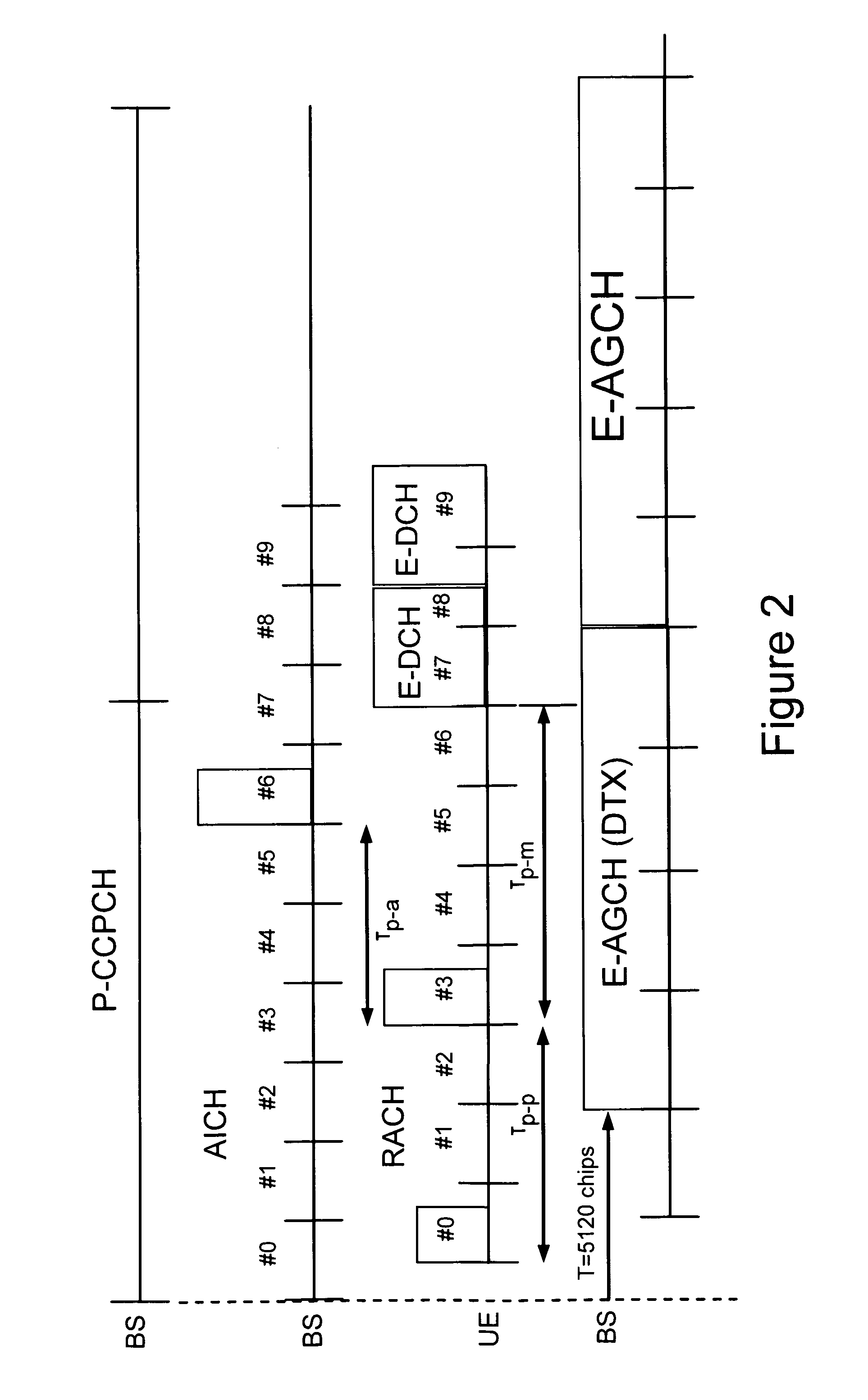
The technology in this application provides a method and apparatus for efficiently using common uplink radio resources, e.g. a common uplink enhanced-dedicated physical channel (E-DCH) resource. A UE releases a common E-DCH resource very quickly after a completed transmission. In addition or alternatively, a base station may release a common E-DCH resource configuration from the network side to free up common E-DCH resources for use by other UEs. A low overhead signaling scheme for quickly and effectively releasing of common E-DCH resources between a UE and a base station is also described. For example, existing signaling fields on protocol layer 2 (L2) or layer 1 (L1) may be used. In one preferred example embodiment, signaling fields already in use in a CELL_DCH service state are given a different meaning for UEs in a CELL_FACH service state so that common E-DCH resources are quickly and effectively released.
Owner:TELEFON AB LM ERICSSON (PUBL)
Power saving via physical layer address filtering in WLANs
ActiveUS7257095B2Save powerSolve the power is smallPower managementEnergy efficient ICTPhysical addressPhysical layer
A system and method is described for saving power in a wireless network, using a physical layer address filtering protocol based on a partial address subset of the complete destination MAC address. The system comprises a PHY layer filtering protocol for generating the partial address and writing the partial address into a PHY layer header portion (e.g., PLCP header) of a sending station, or reading the partial address from the PHY layer header portion upon transmission of each frame. A receiving station receives and decodes these PHY layer header portion bits, in accordance with the protocol, and compares whether the subset of bits match that of the stations' own partial address. If a station finds a match, the station then continues further decoding the frame at PHY layer and send the complete frame to the MAC layer for further processing. The stations that do not have a match will not activate their MAC layer components. Thus, the stations of the network will avoid wasting power decoding a significant portion of the complete frame of other stations of the wireless local area networks and unnecessary MAC layer processing. When group addressed, control / management frames or other such frames are detected at the sending station, the address filtering protocol may be “disabled” using a partial address containing a predetermined value (e.g., all zeros).
Owner:TEXAS INSTR INC
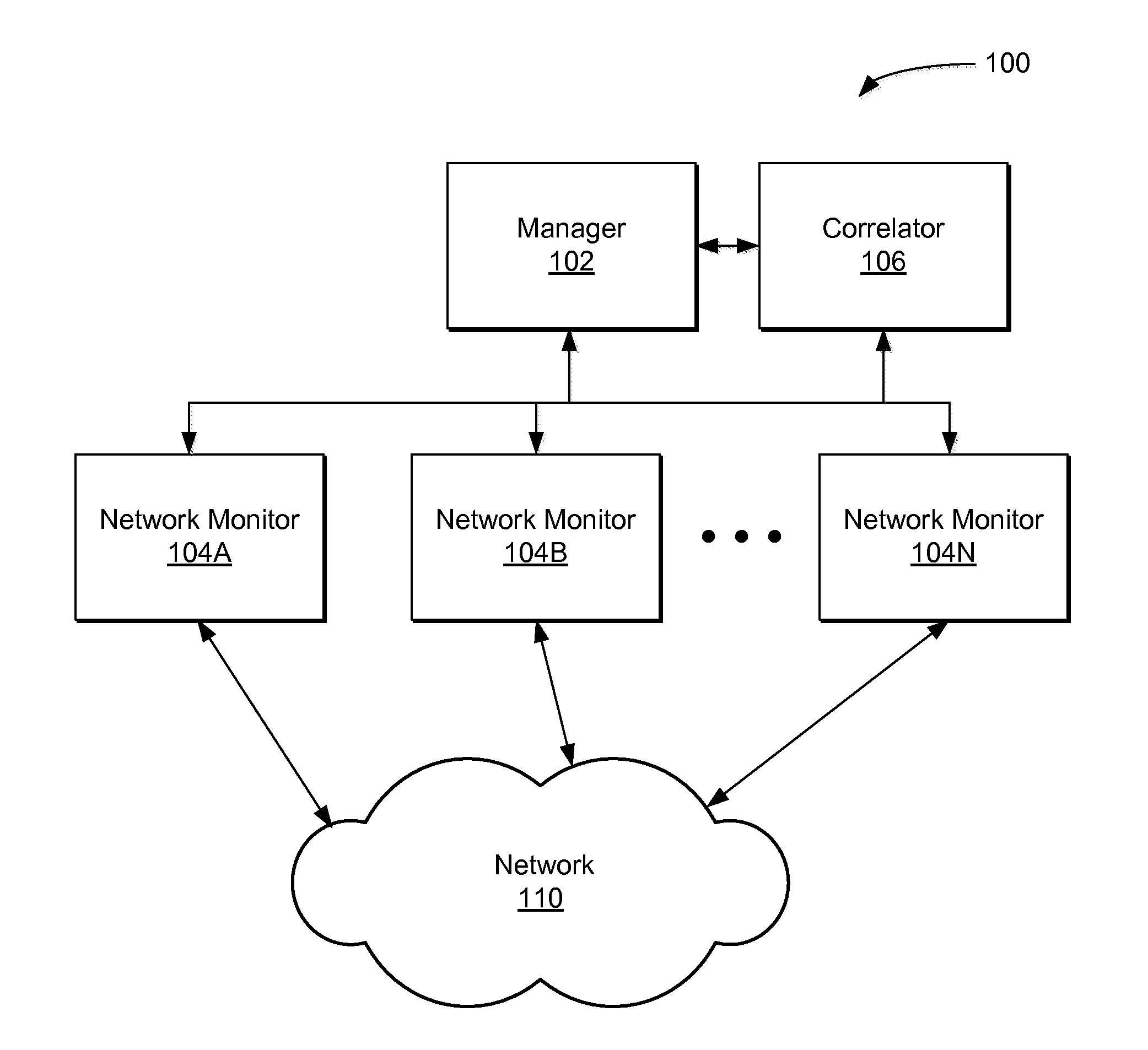
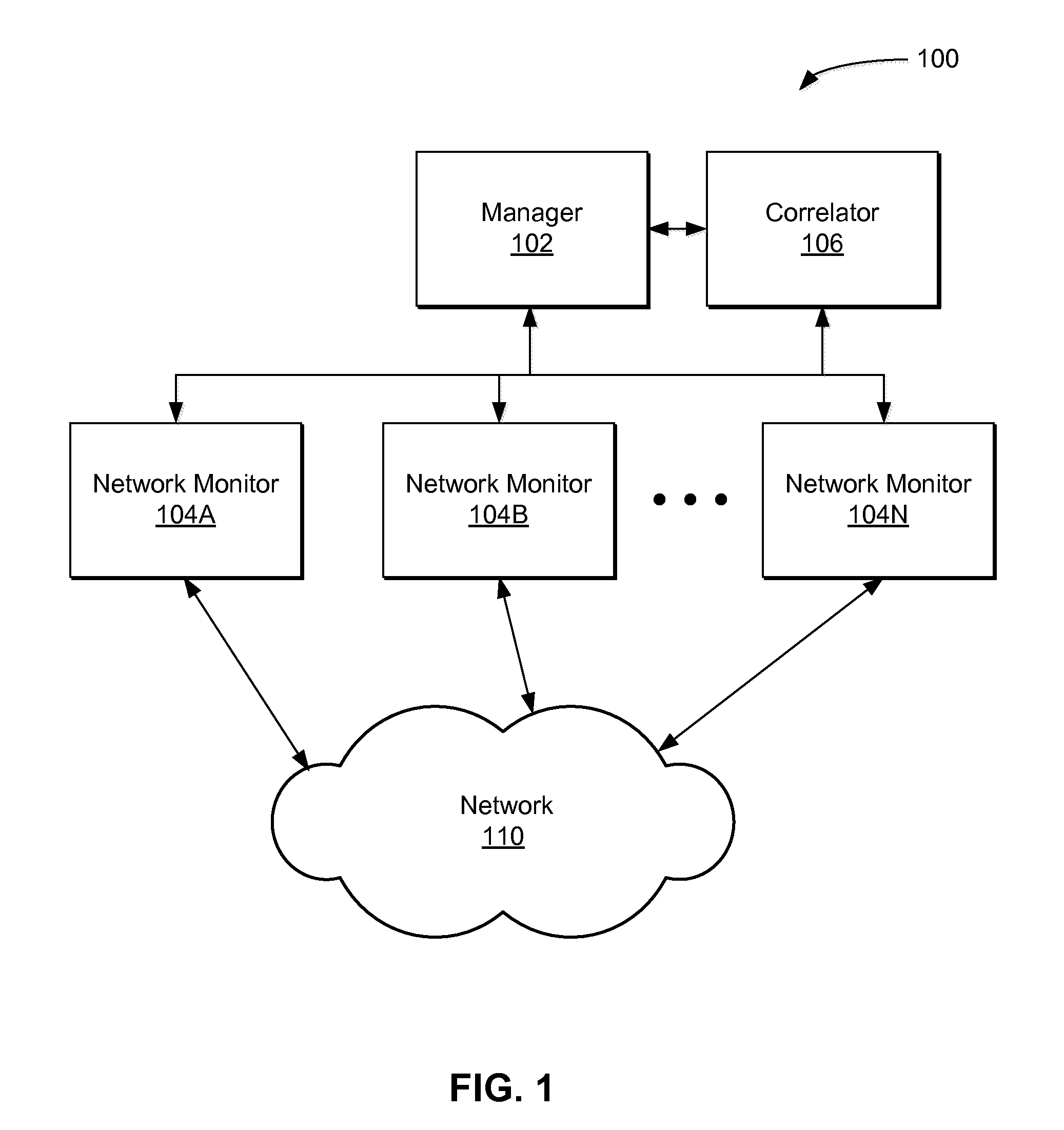
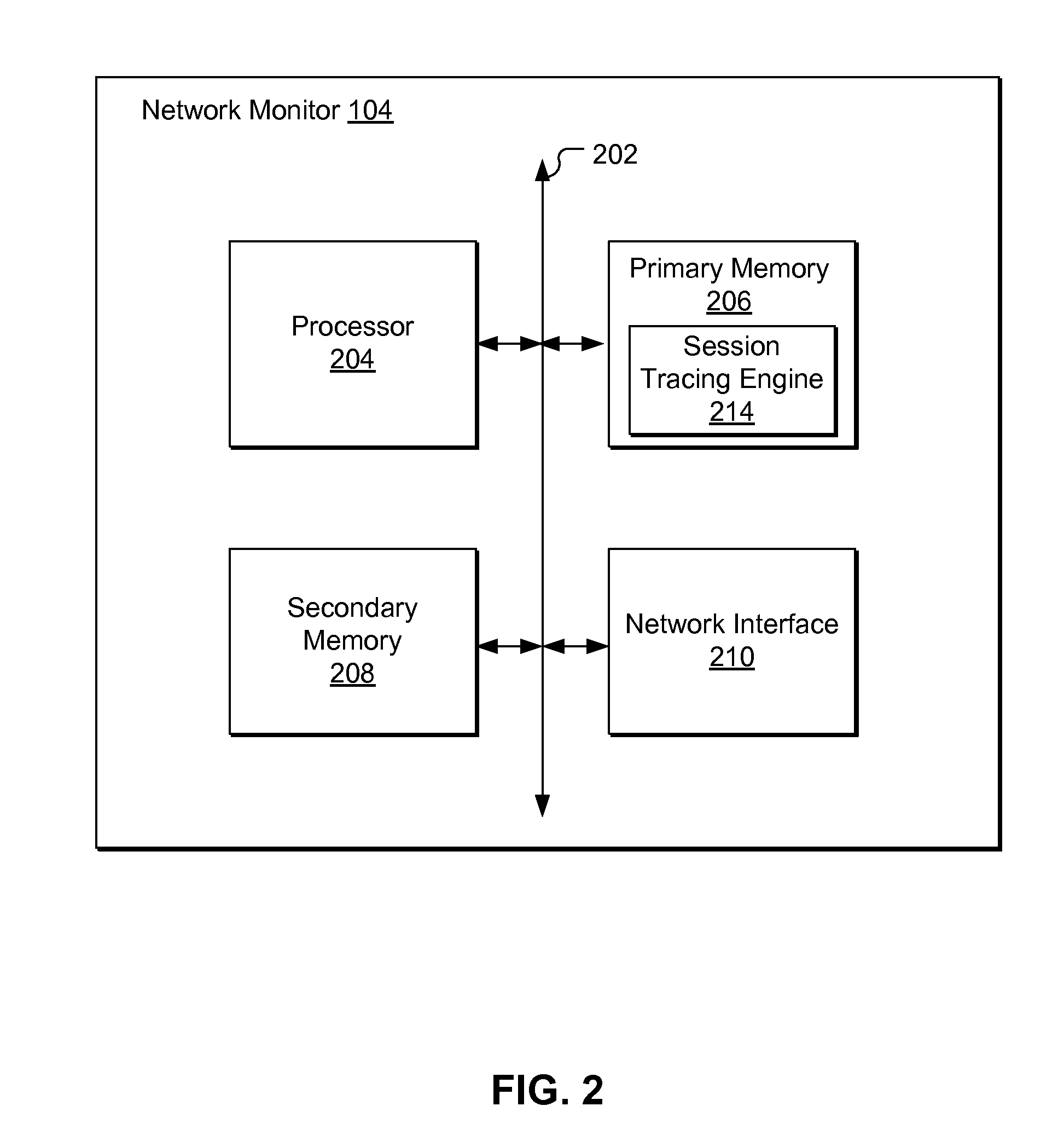
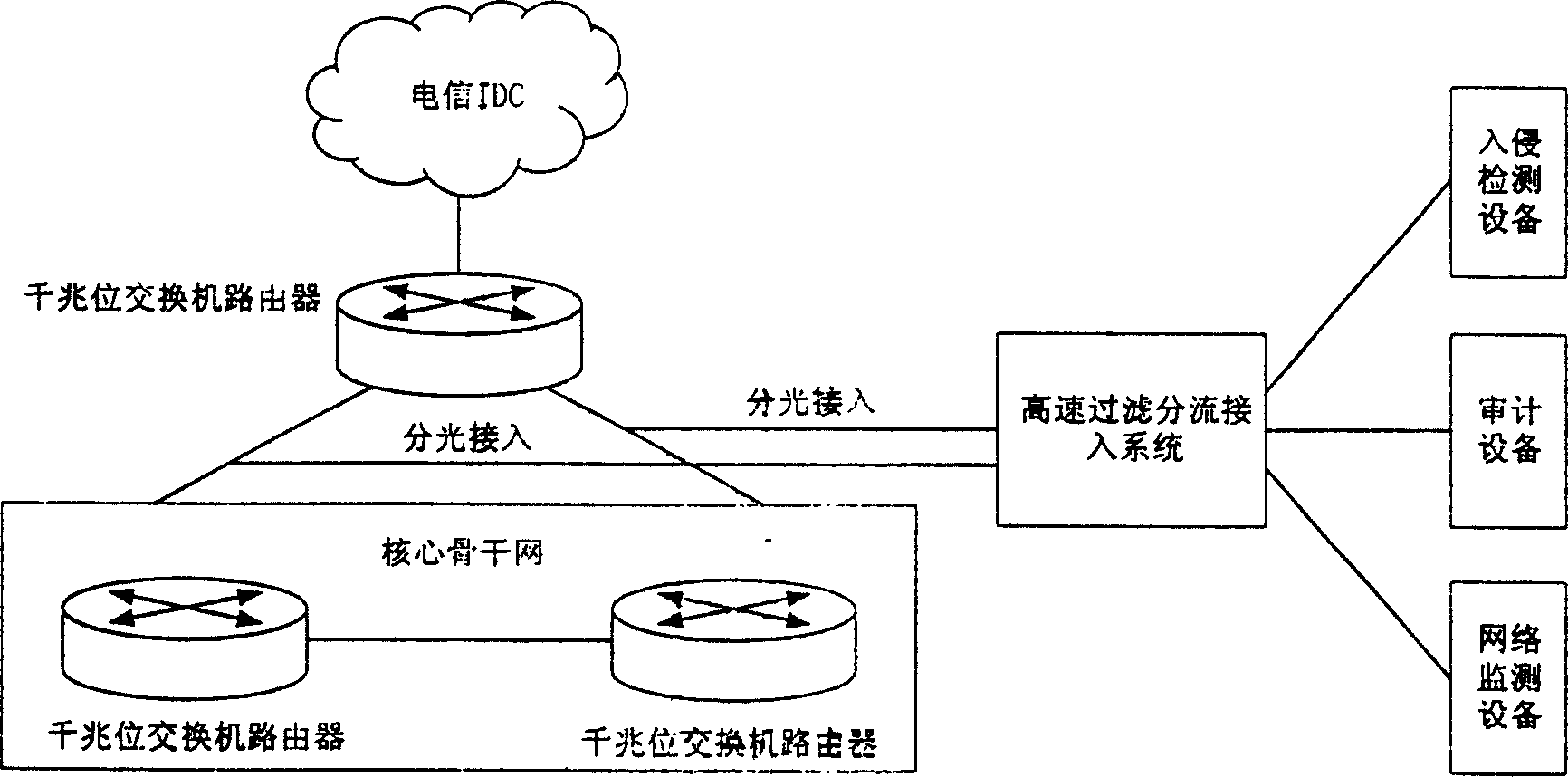
Real-Time Adaptive Processing of Network Data Packets for Analysis
ActiveUS20110249572A1Fast resultsSmall sizeError preventionFrequency-division multiplex detailsSingle sessionNetwork packet
A network monitoring system that summarizes a plurality of data packets of a session into a compact session record for storage and processing. Each session record may be produced in real-time and made available during the session and / or after the termination of the session. Depending on protocols, a network monitoring system extracts different sets of information, removes redundant information from the plurality of data packets, and adds performance information to produce the session record. The network monitoring system may retrieve and process a single session record or multiple session records for the same or different protocols to determine cause of events, resolve issues in a network or evaluate network performance or conditions. The session record enables analysis in the units of session instead of individual packets. Hence, the network monitoring system can analyze events, issues or performance of the network more efficiently and effectively.
Owner:NETSCOUT SYSTEMS
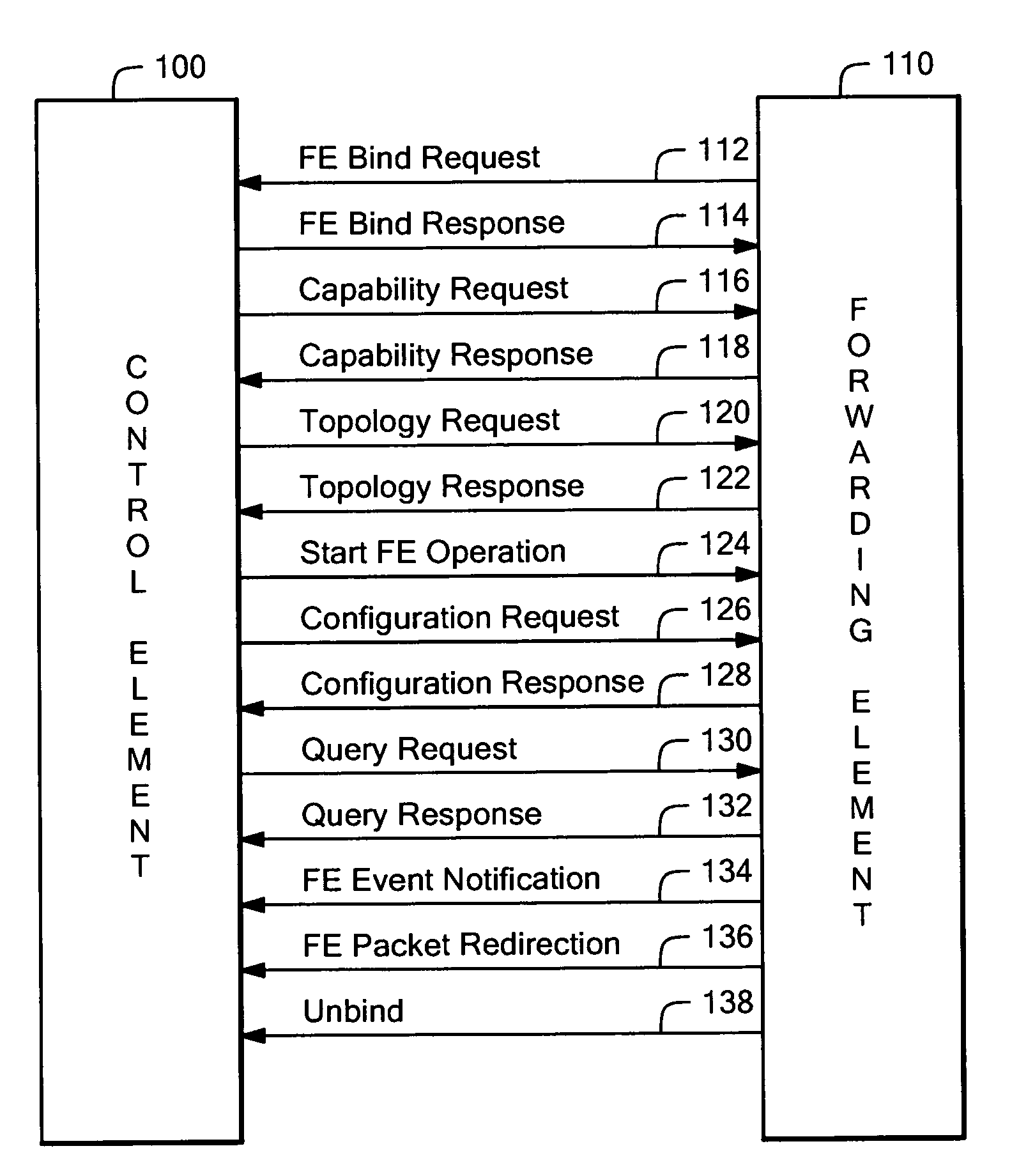
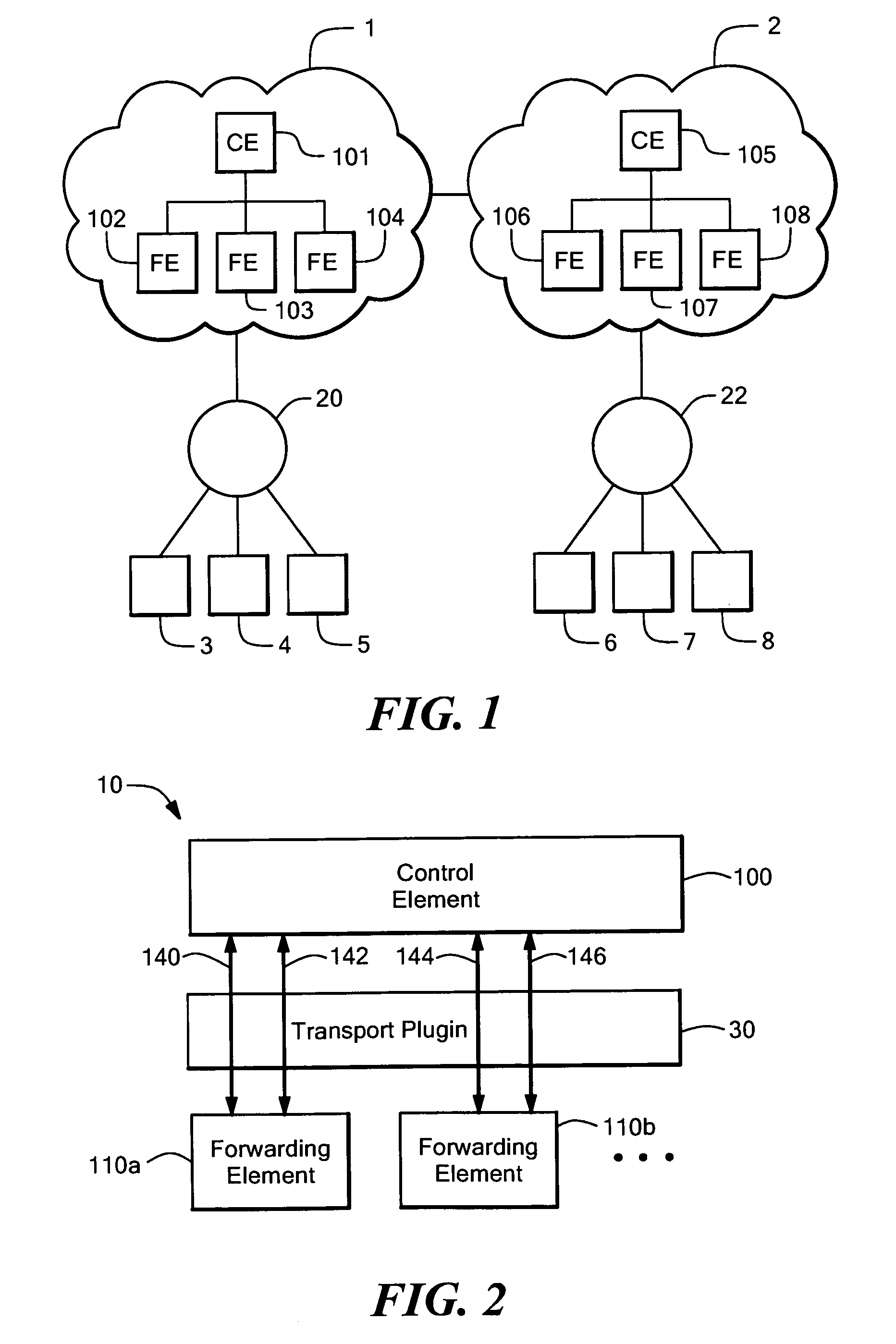
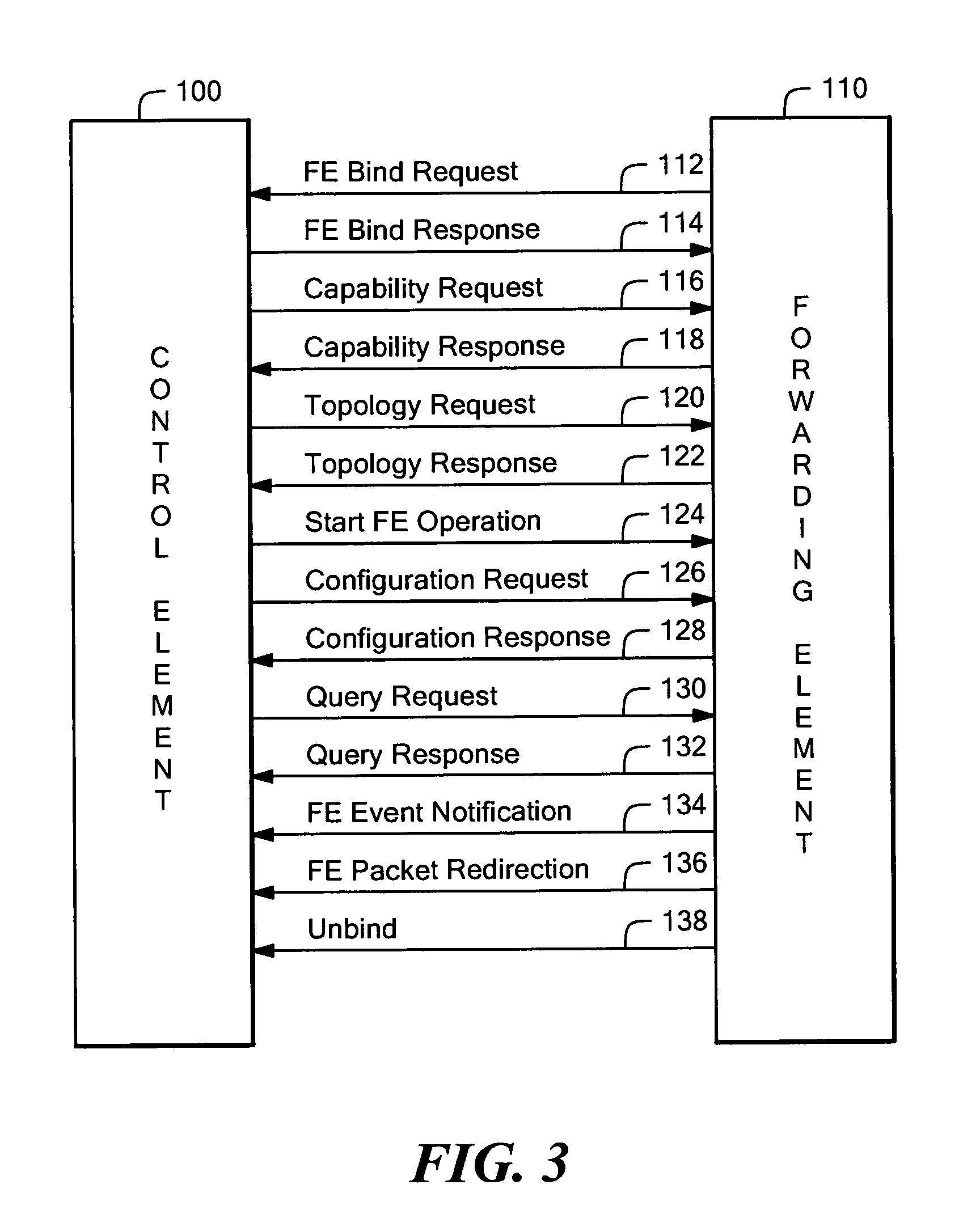
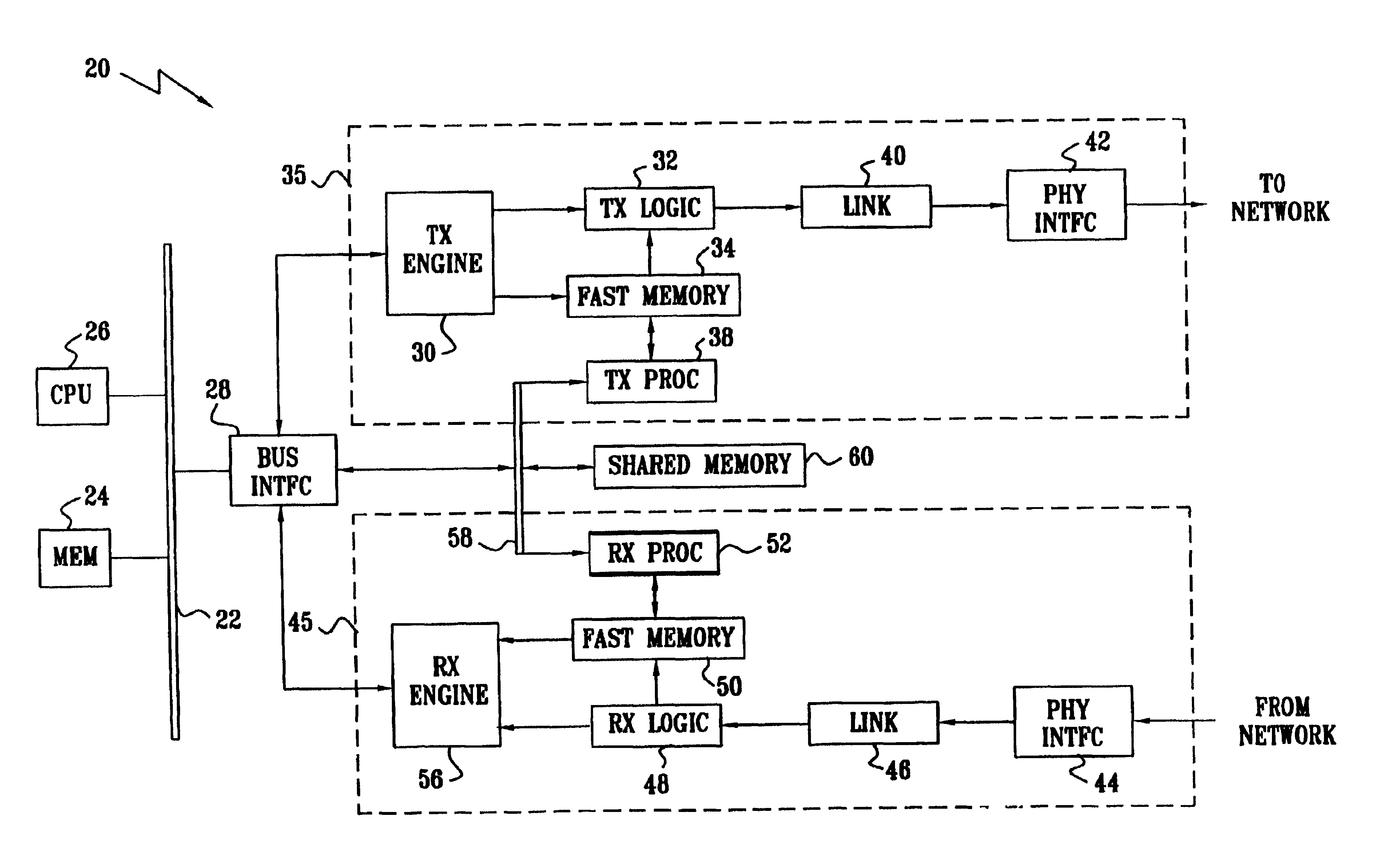
System and method to exchange information between a control element and forwarding elements in a network element architecture
A network element comprises a control element (CE), a plurality of forwarding element (FEs) and an interconnect in communication with said CE and at least one of said FEs. Communication across the interconnect between the CE and the plurality of FEs is done in accordance with a protocol that includes a binding phase used to provide a data channel between the CE and a first one of the FEs. The binding phase is further used to provide a control channel between the CE and the first one of the FEs, the control channel used to transport control and configuration messages. The control channel is separate from the data channel. The protocol also includes a capability discovery phase, a configuration operation phase and an unbind phase executed between the CE and the FE.
Owner:TAHOE RES LTD
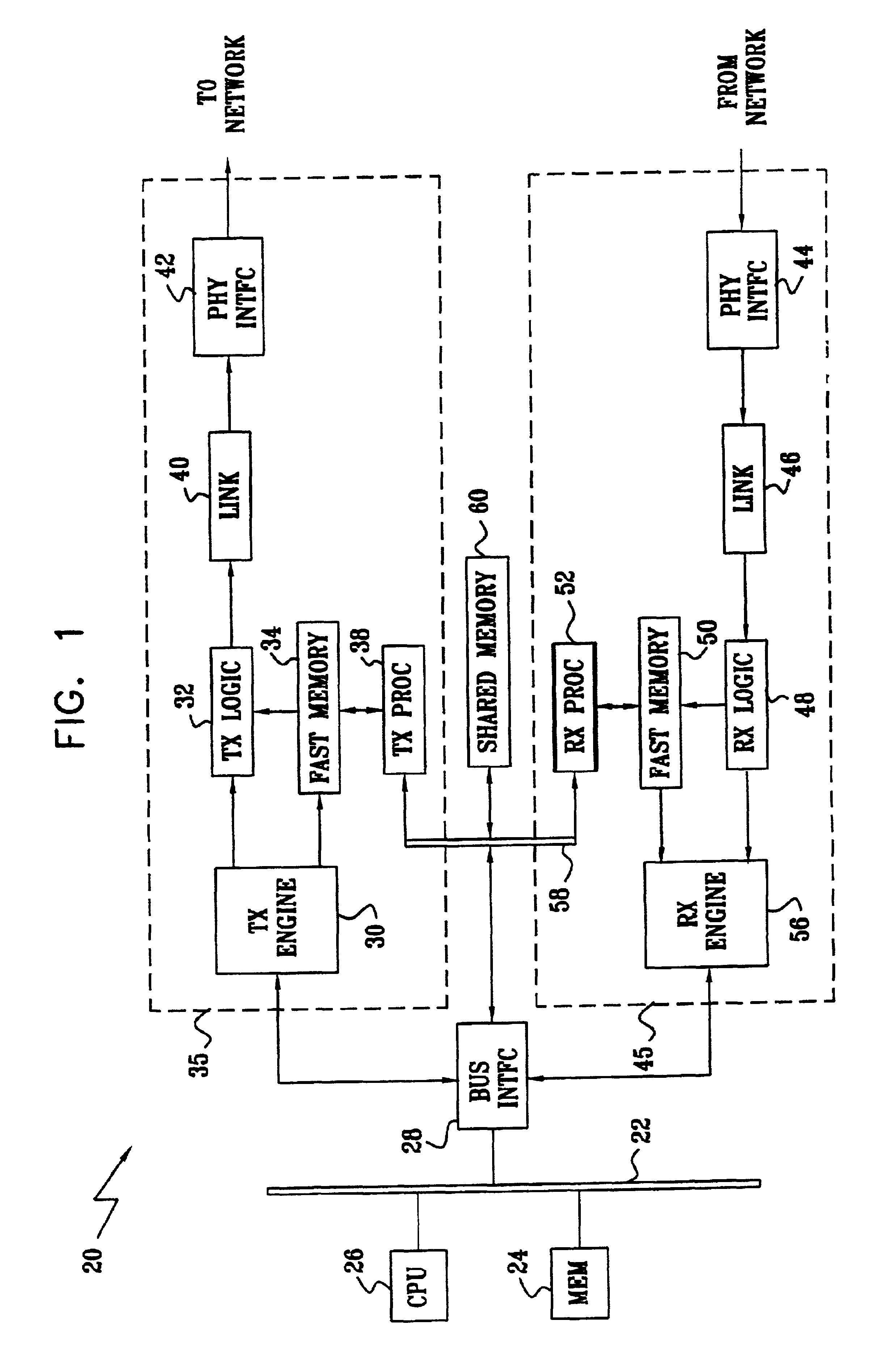
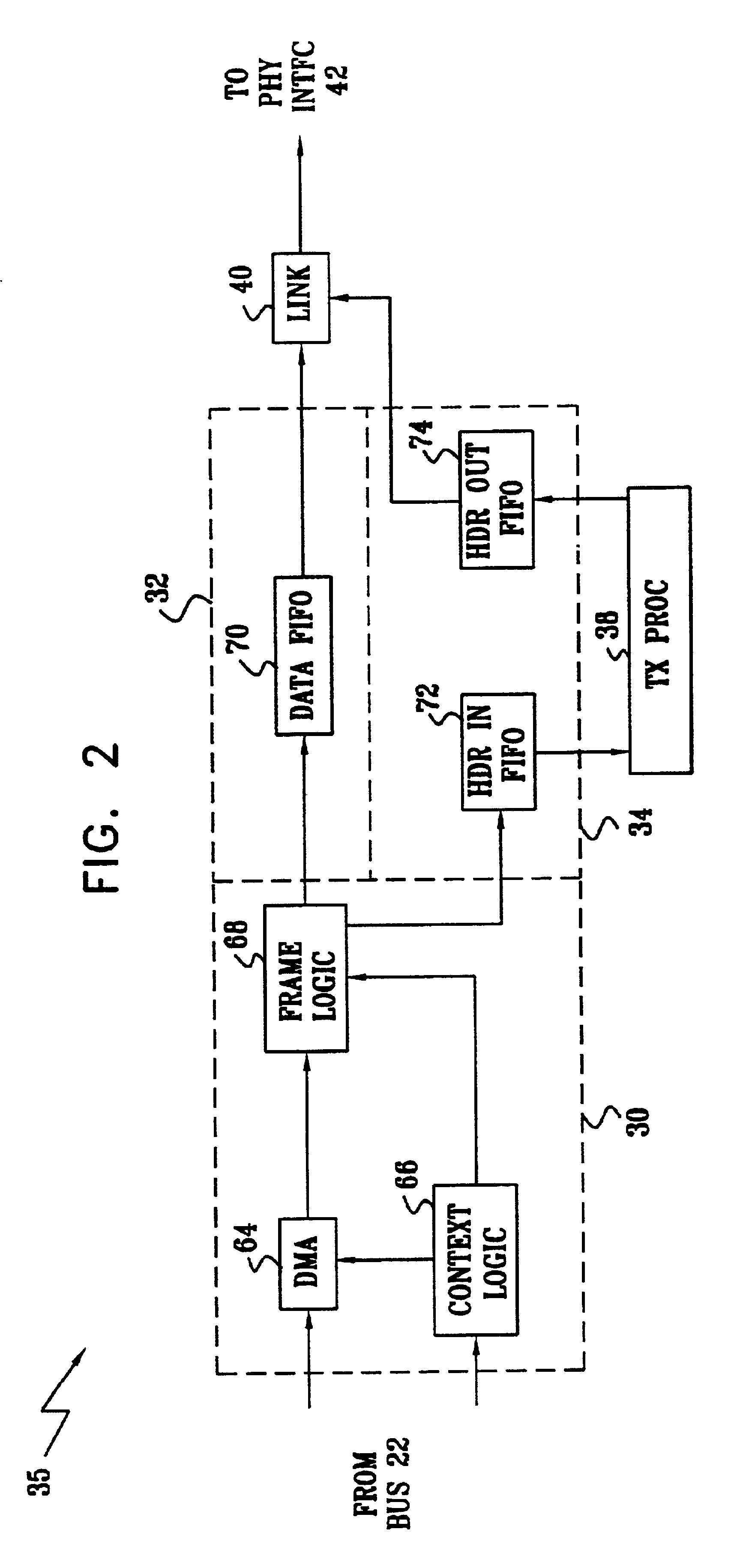
Network adapter with embedded deep packet processing
InactiveUS6947430B2Raise transfer toIncrease speedTime-division multiplexData switching by path configurationProtocol processingNetwork interface device
A network interface device includes host interface logic, arranged to receive from a host processor a frame of outgoing data that includes outgoing header information and outgoing payload data, and to separate the header information from the payload data. A transmit protocol processor is coupled to read and process the outgoing header information from the outgoing header memory so as to generate at least one outgoing packet header in accordance with a predetermined network protocol. Transmit logic is coupled to receive and associate the at least one outgoing packet header with the outgoing payload data from the outgoing data memory, so as to generate at least one outgoing data packet for transmission over a network in accordance with the protocol.
Owner:IBM CORP
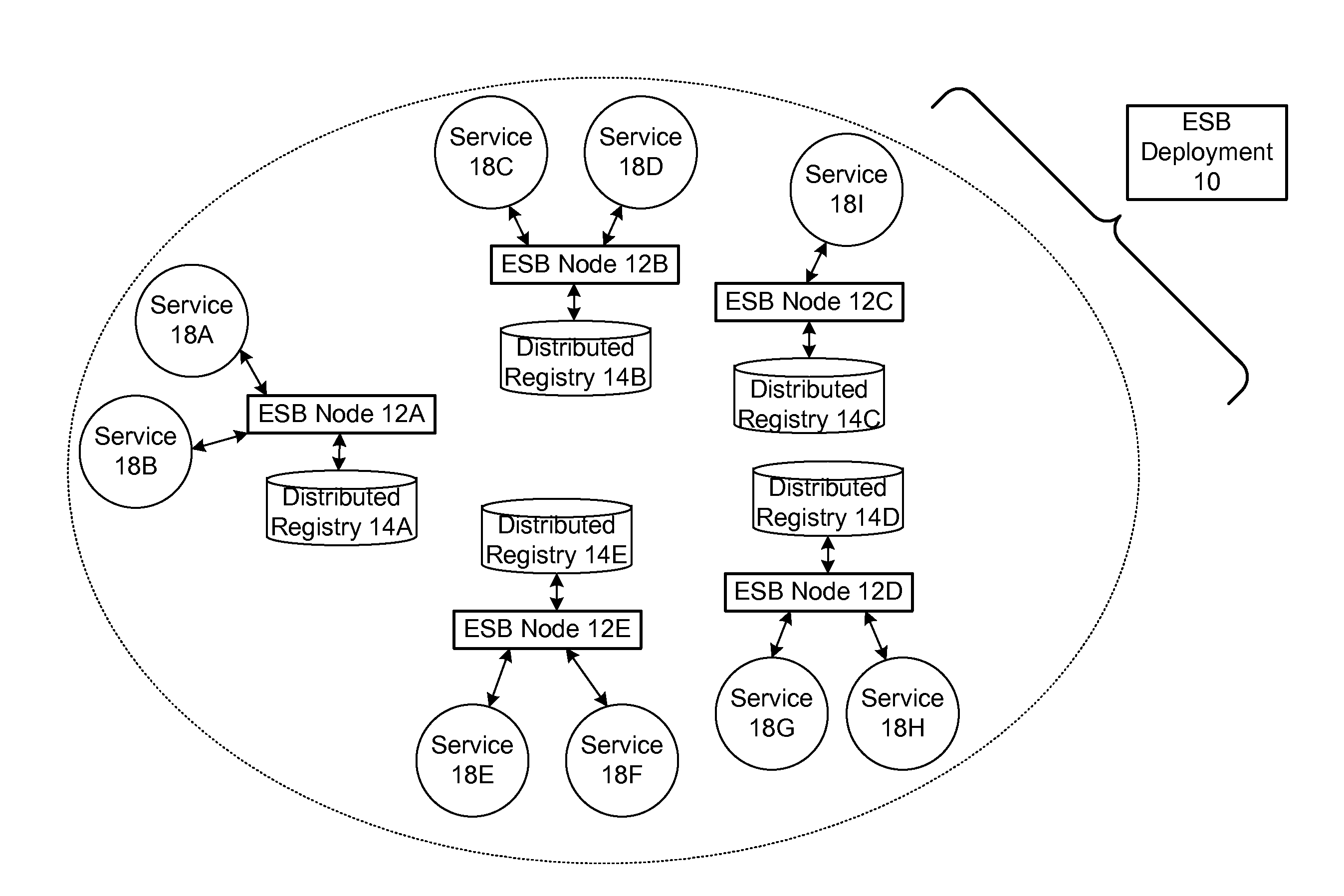
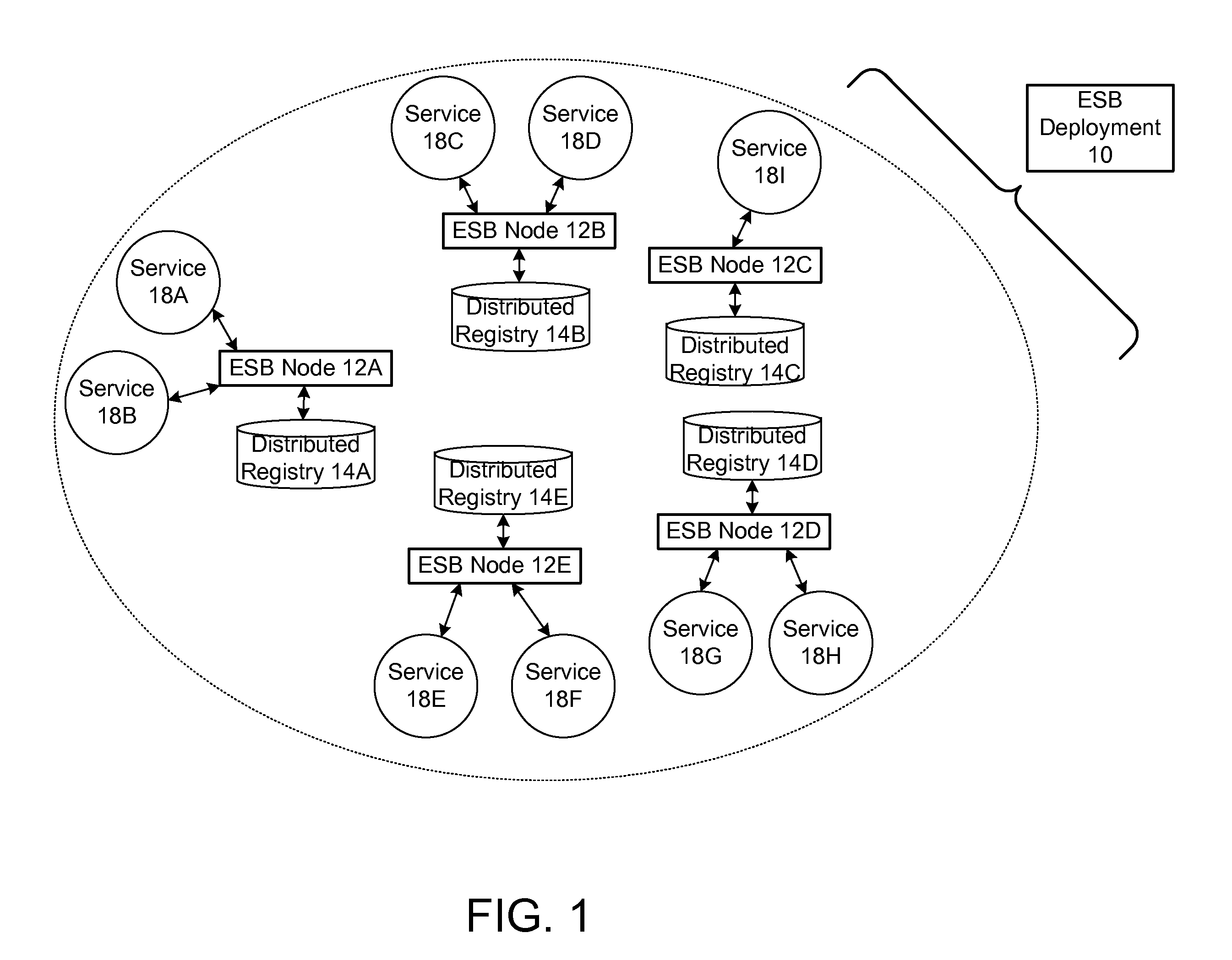
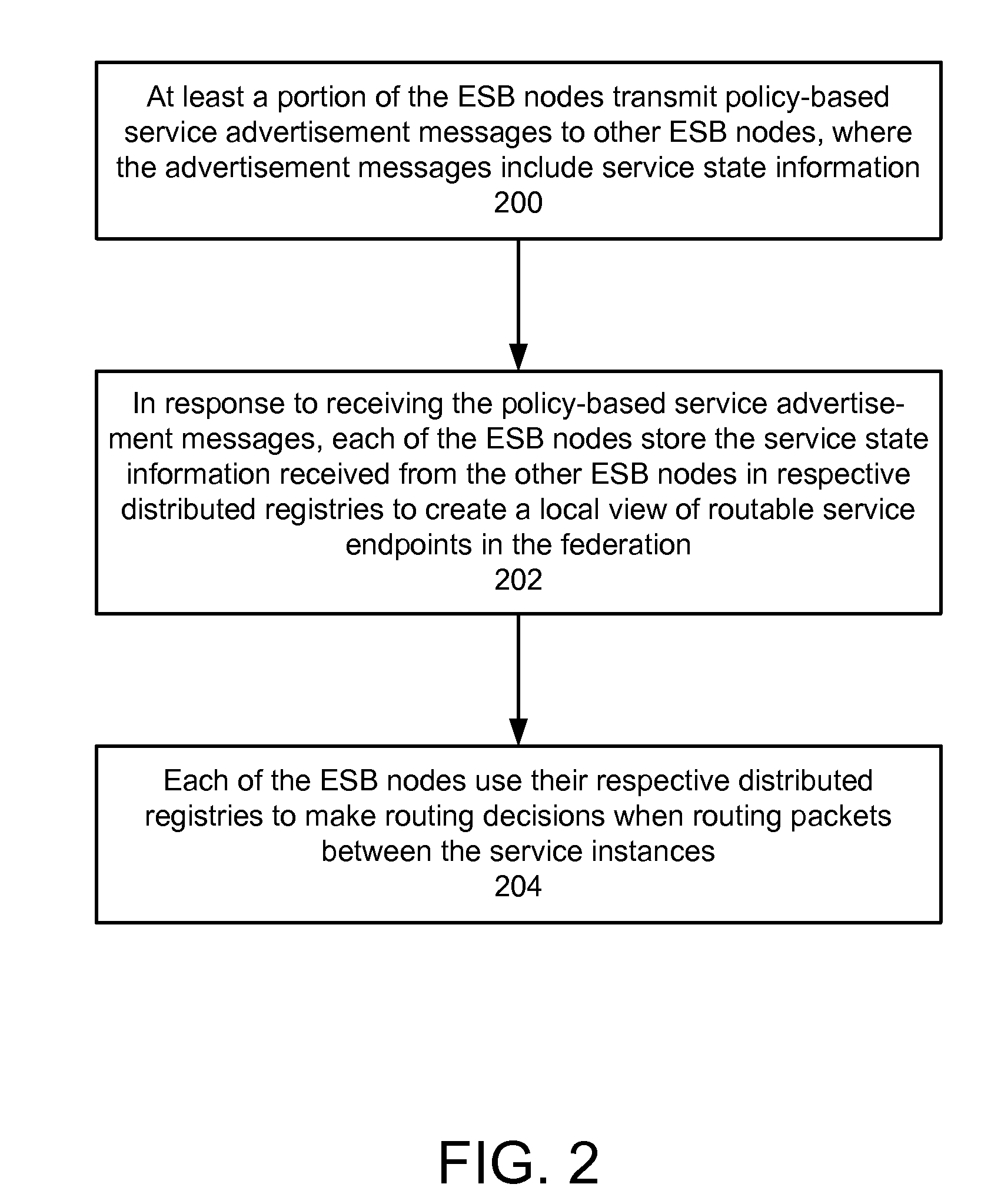
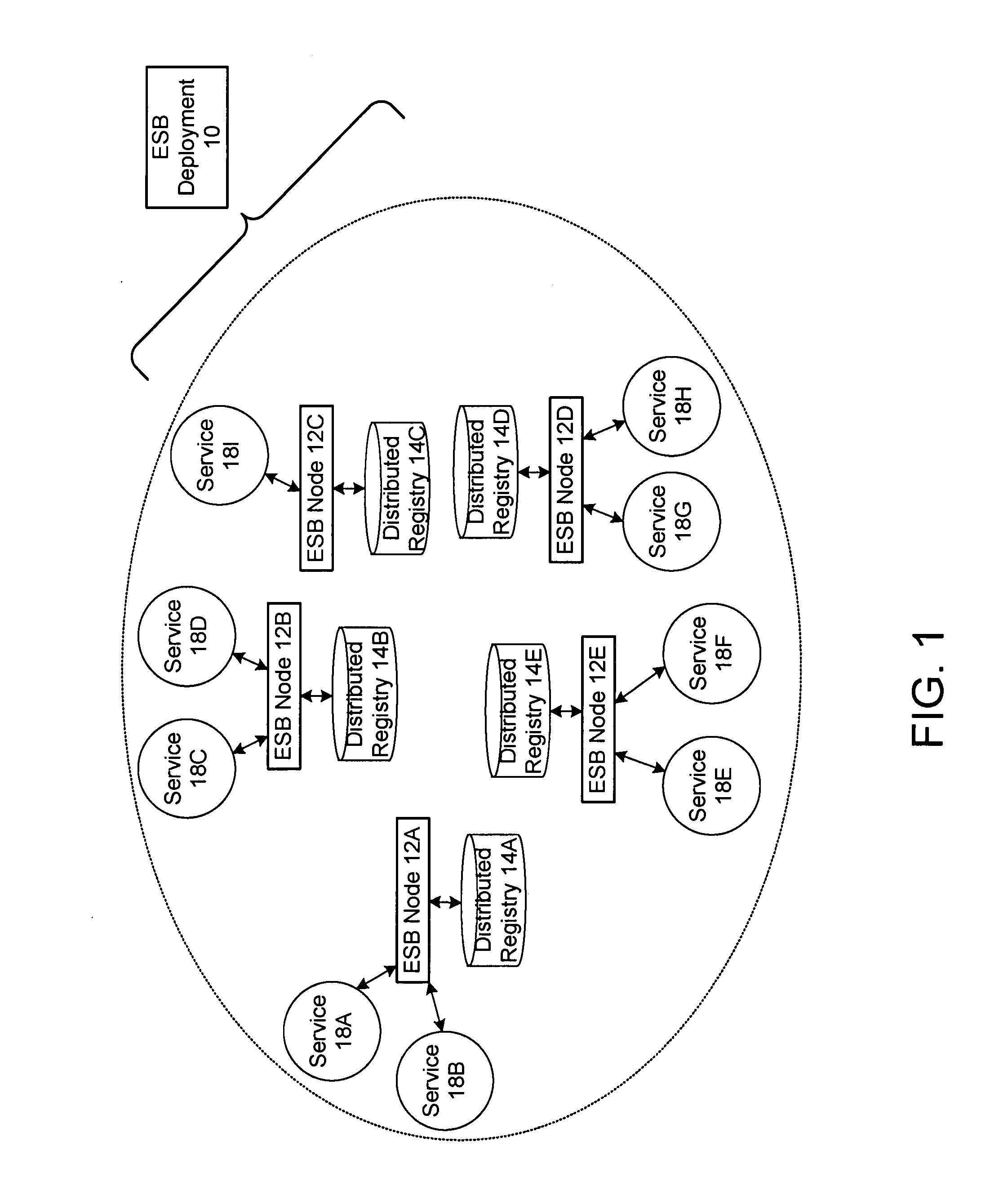
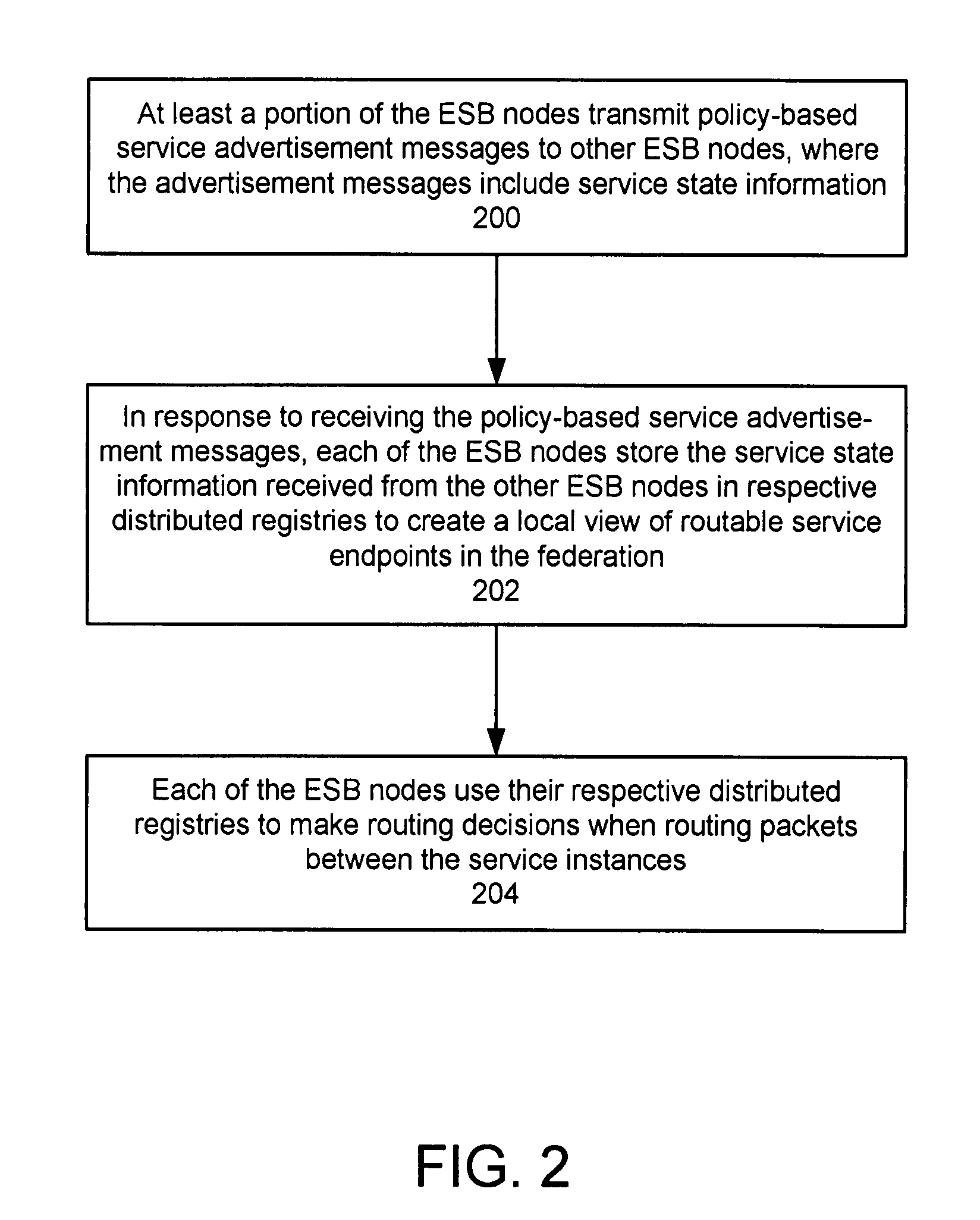
Protocol for enabling dynamic and scalable federation of enterprise service buses
ActiveUS20090070456A1Multiple digital computer combinationsMarketingRouting decisionEnterprise services
In a method and system for creating a federation of a plurality of enterprise service buses (ESBs), a plurality of ESB nodes provide connectivity to one or more services. According to a protocol, at least a portion of the ESB nodes transmit policy-based service advertisement messages to other ESB nodes, wherein the policy-based service advertisement messages include service state information. In response to receiving the policy-based service advertisement messages, each of the ESB nodes stores the service state information received from other ESB nodes in respective distributed registries to create a local view of routable service endpoints in the federation. Each of the ESB nodes then uses its respective distributed registry to make routing decisions when routing service requests.
Owner:SERVICENOW INC
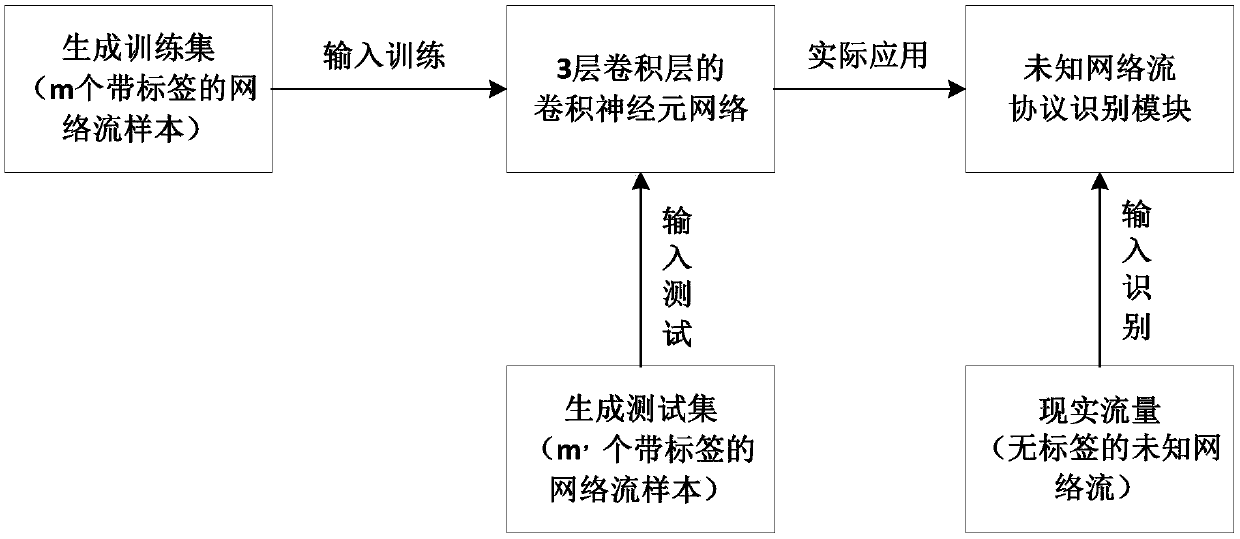
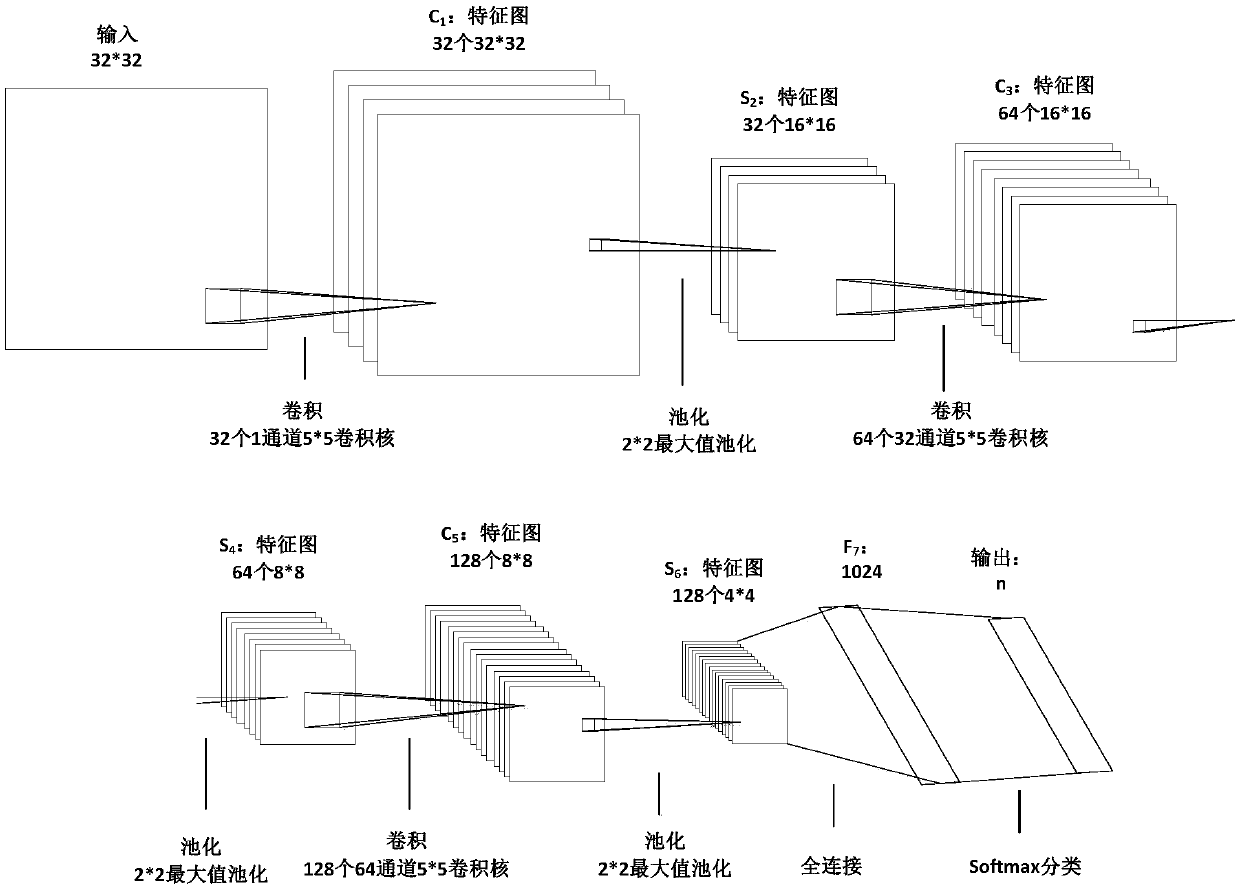
Network traffic protocol recognition method based on deep learning
ActiveCN107682216AFeatures that are good for classification tasksCapable of learningData switching networksTraffic capacityFeature extraction
The invention discloses a network traffic protocol recognition method based on deep learning. The similarity of network traffic data and images is utilized, the work of traffic feature value selectionand extraction is skipped and the network traffic data directly act as the input of a convolutional neural network to perform supervised learning and train a network traffic protocol recognition model so that the function of network traffic protocol recognition can be realized. According to the method, only a network traffic protocol sample to be recognized is provided for training of the convolutional neural network so that the features favorable for the classification task can be automatically extracted without spending energy on protocol feature extraction and selection; and the method haslearning and extending capacity and can be used for recognizing the new unknown protocol and can be extended to be applied to recognition of the network traffic including malicious codes and recognition of the corresponding program traffic.
Owner:NANJING NARI GROUP CORP +2
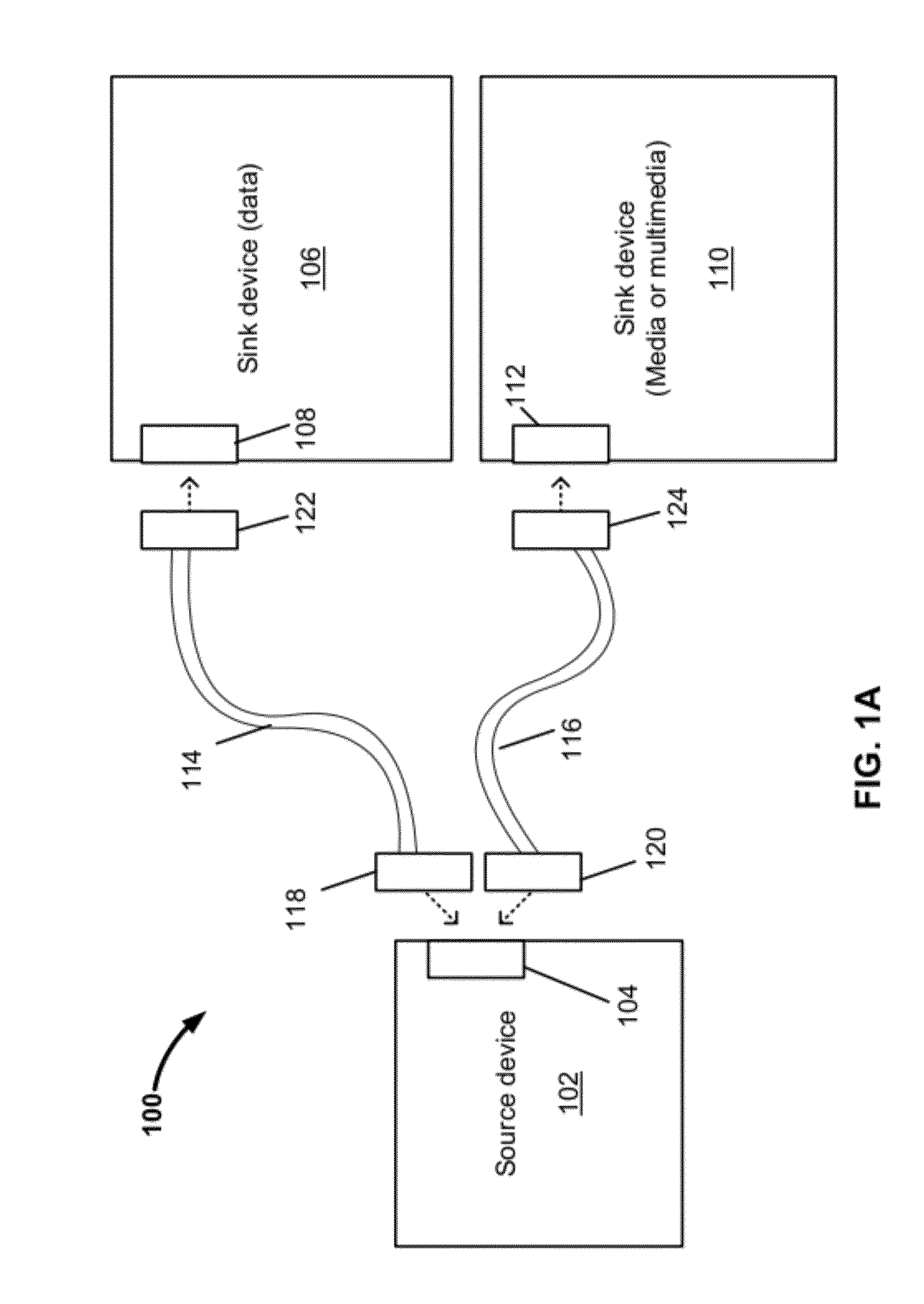
Transfer of Uncompressed Multimedia Contents or Data Communications
ActiveUS20120203937A1Input/output processes for data processingProtocol for Carrying Authentication for Network AccessUSB
A system and corresponding method for transferring data via an interface assembly. The data may be transferred between a USB port of a first device and a media port of a second device. Uncompressed high definition media data may be received from the USB port. The received uncompressed high definition media data may be supplied to a media connector in accordance with a first media standard, such that the supplied data can be transmitted in accordance with the first media standard via the media connector to the media port of the second device. The uncompressed high definition media data may include multimedia data and side-band communication data. A single signal may be encoded and decoded in accordance with a protocol that enables the single signal to communicate all side-band communication to and from the source device via a single pin of a USB connector.
Owner:ANALOGIX SEMICON
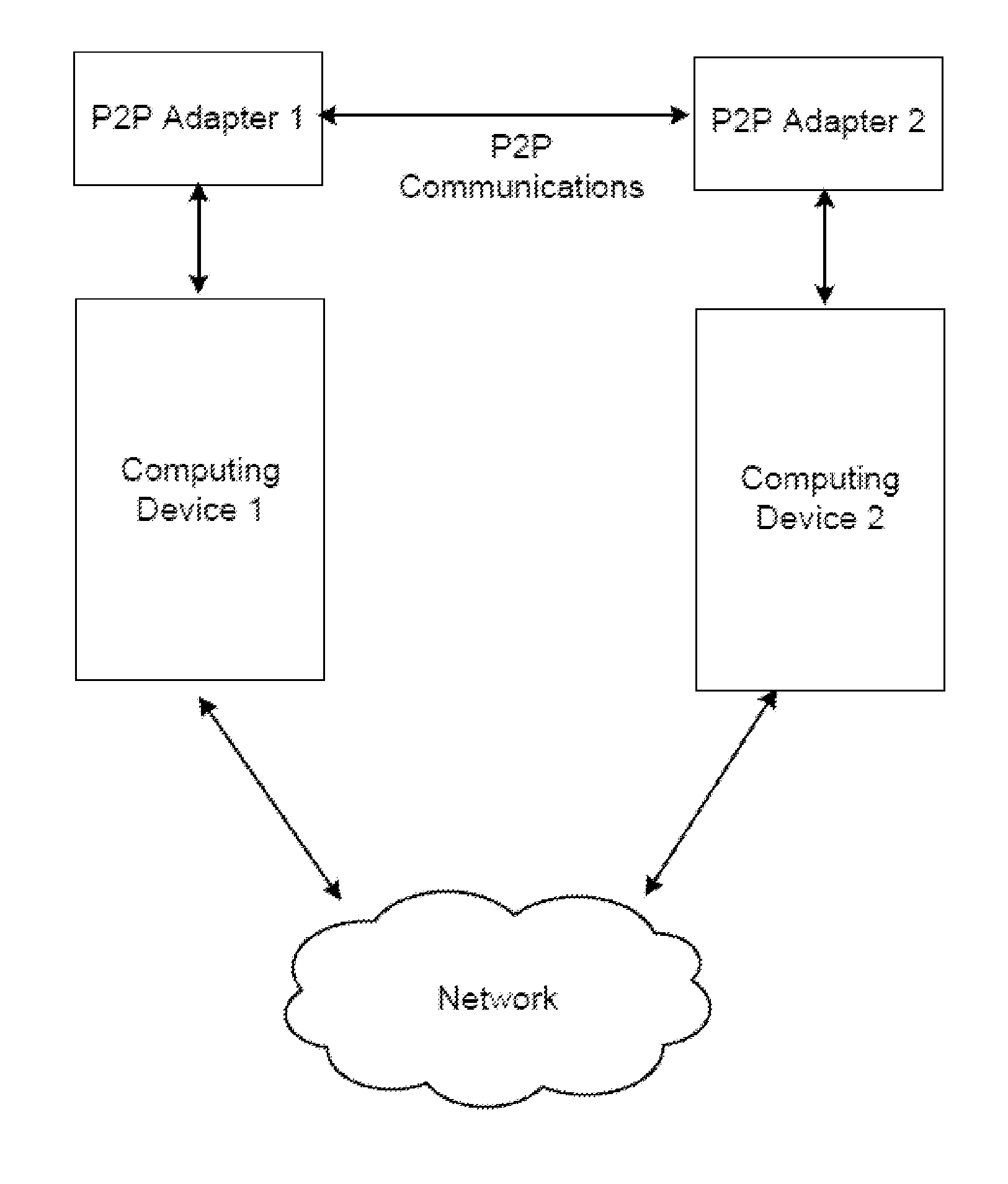
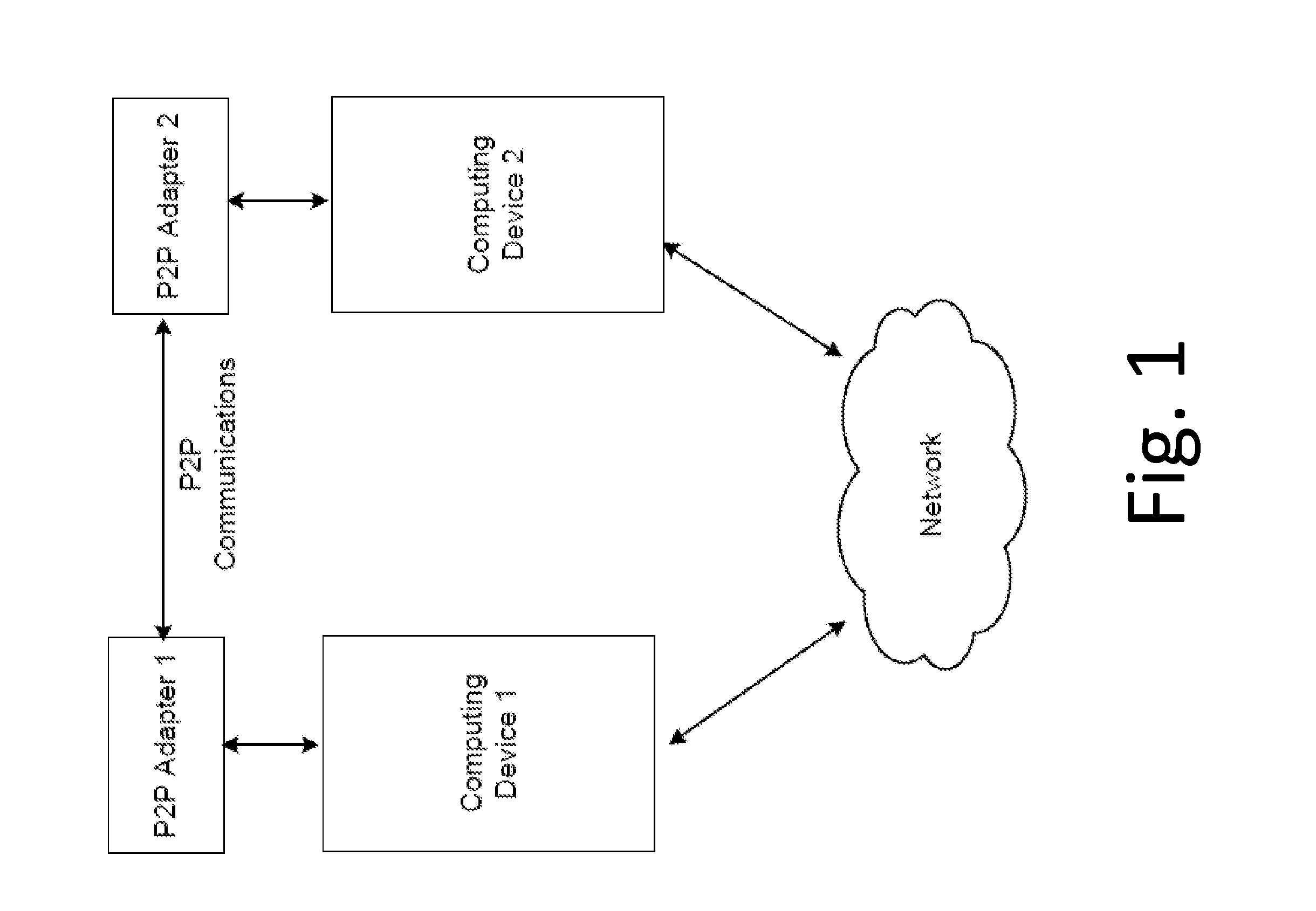
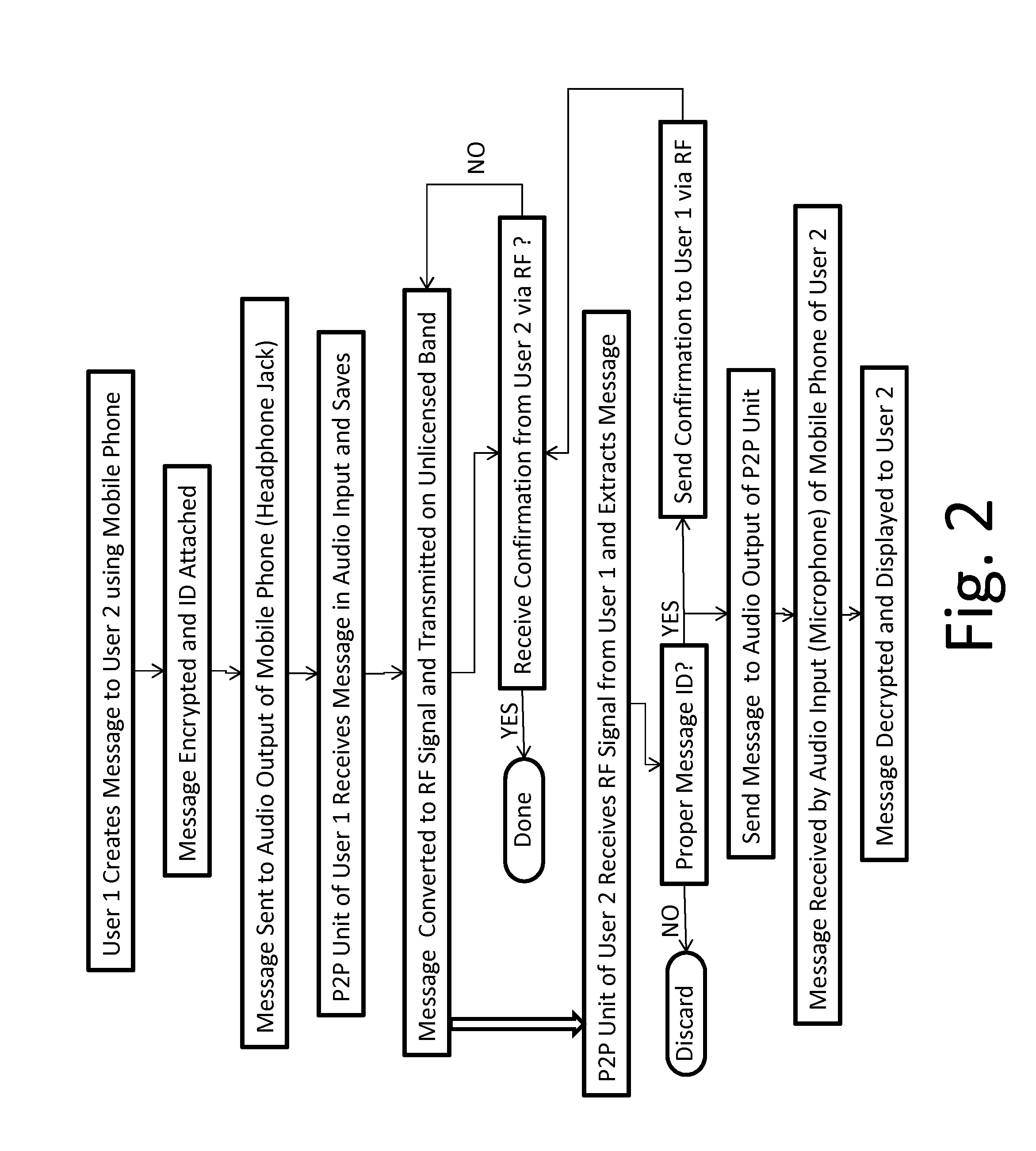
System and method for digital communication between computing devices
ActiveUS20150264626A1Optimization rangeError preventionTransmission systemsHuman–machine interfaceTransceiver
A wireless communication device, comprising radio frequency transceivers which transmit outbound messages to targeted receivers, and receive the inbound messages addressed to the respective transceiver; each having a processor which controls the transceiver to establish communication sessions according to a protocol, and processes targeting and address information. The transceiver communicates with a telephone device having a telephone address book containing information which defines the targets and address for a telephone network and perhaps other networks. The address book entries are human editable through a human machine user interface. The address book entries are intended for centrally controlled switch networks having hierarchically formatted address information, but since these are at least quasi-unique, they are used as address labels in an unswitched peer-to-peer network formed of the transceivers. This permits a common address scheme across the peer-to-peer network and switched network of the telephone device.
Owner:GOTENNA
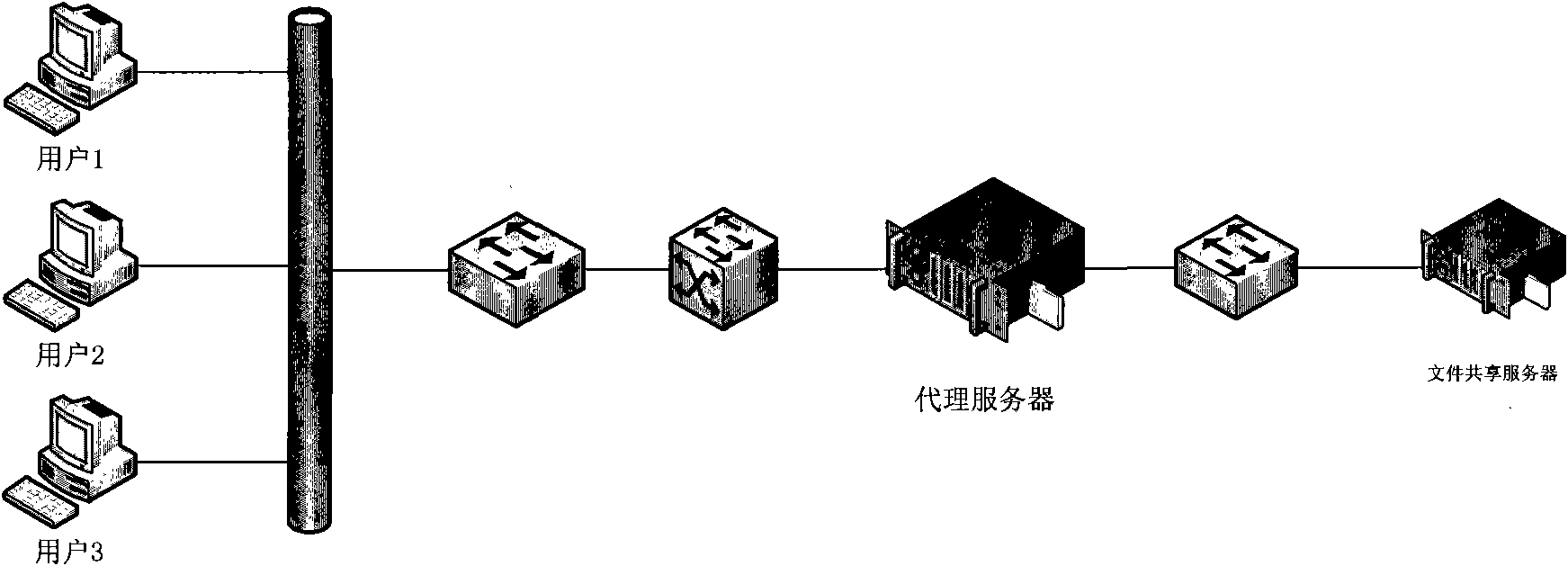
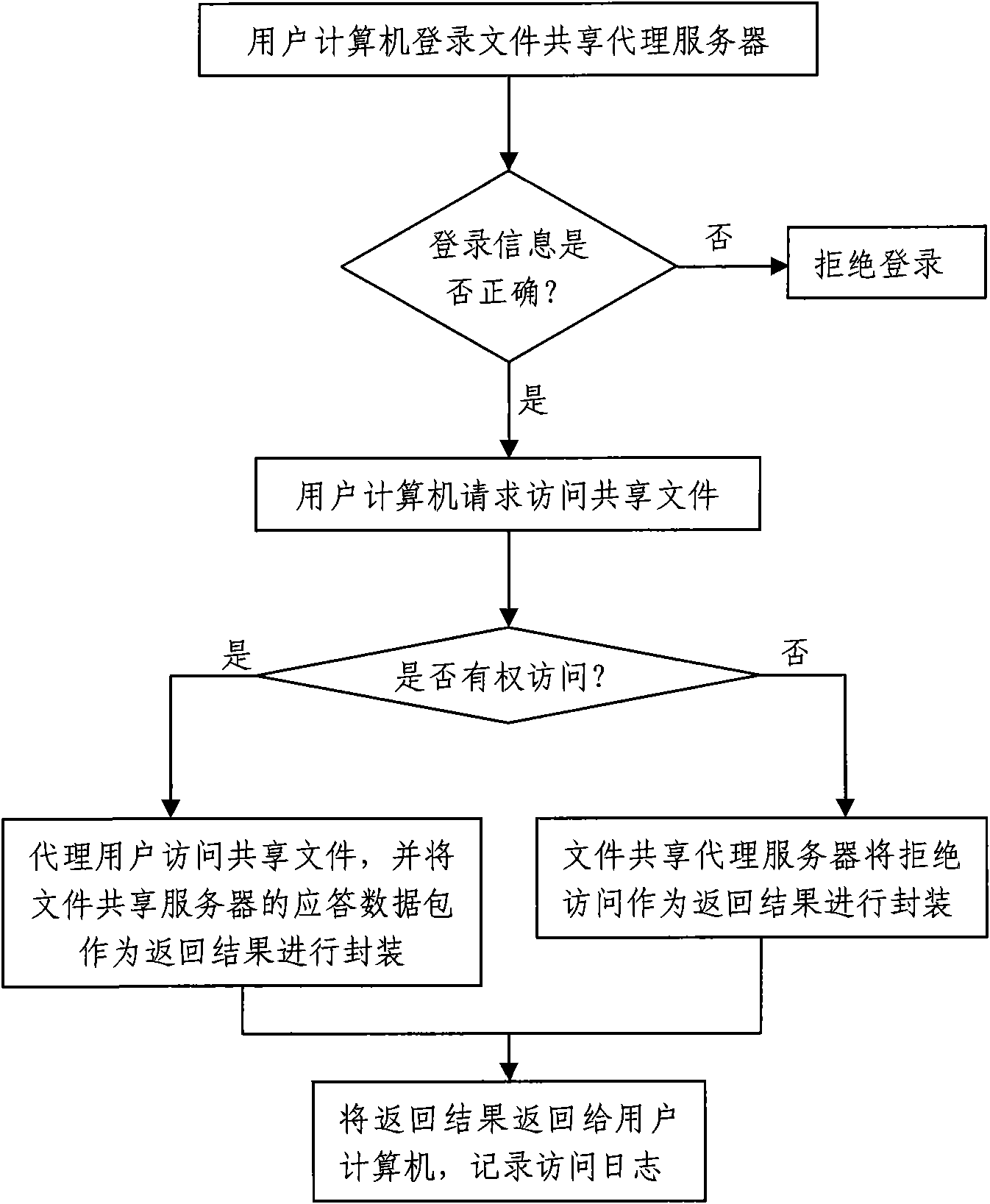
Method and system for realizing file sharing access control based on protocol proxy
The invention discloses a method for realizing file sharing access control based on protocol proxy. The method comprises that a subscriber computer inputs logon information to log on a file sharing proxy server; the logon information input by the subscriber computer is verified in the file sharing proxy serve; a response is made to a shared file access request initiated by the subscriber computerwhich passes the verification to judge whether the subscriber computer has access authority to a requested shared file A or not; if so, the subscriber computer accesses the shared file A by proxy andthe response data packet of the file sharing server is used as a return result and is encapsulated; and otherwise, an access refusal is used as the return result and is encapsulated, the return result is returned to the subscriber computer and an access log is recorded. The invention additionally discloses a system for realizing file sharing access control based on protocol proxy. The invention has the advantages that the shared file access is separated from the dependence on an ntfs file system and the use demands of flexible identity authentication and access behavior auditing can be satisfied.
Owner:北京时代亿信科技股份有限公司
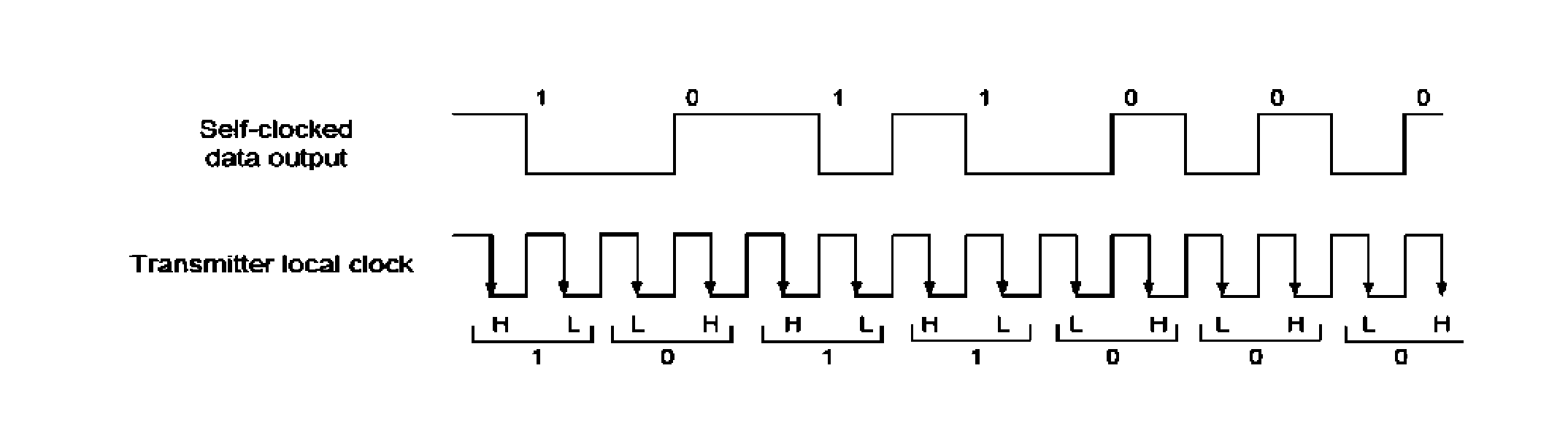
Method of data reliable transmission with user datagram protocol (UDP) in communication network
ActiveCN103036904AAdaptableReliable transmissionData switching networksReliable transmissionTransmission channel
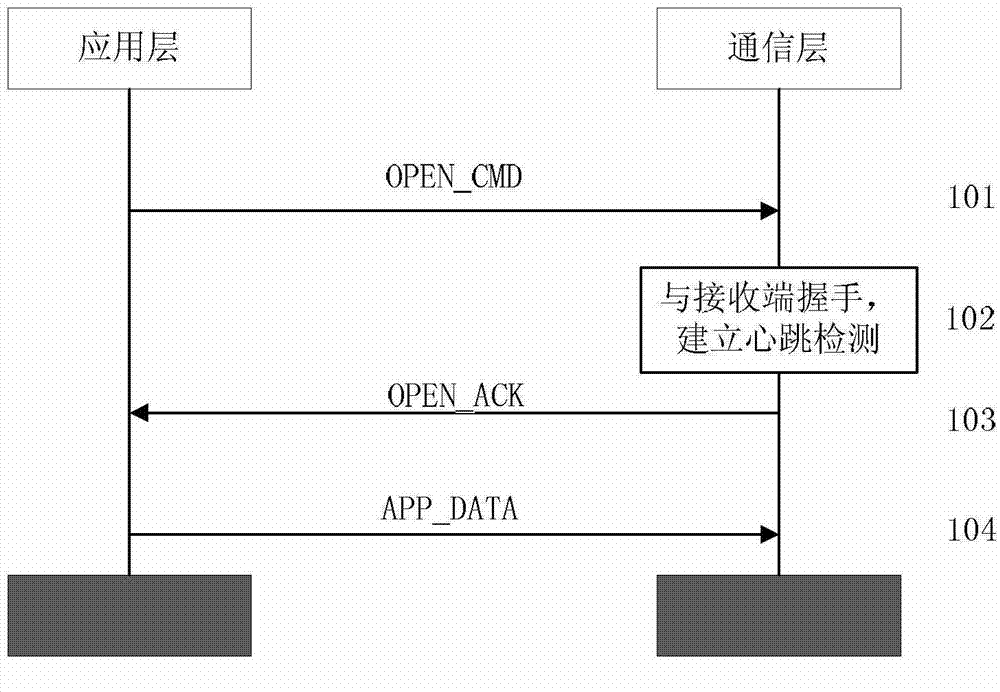
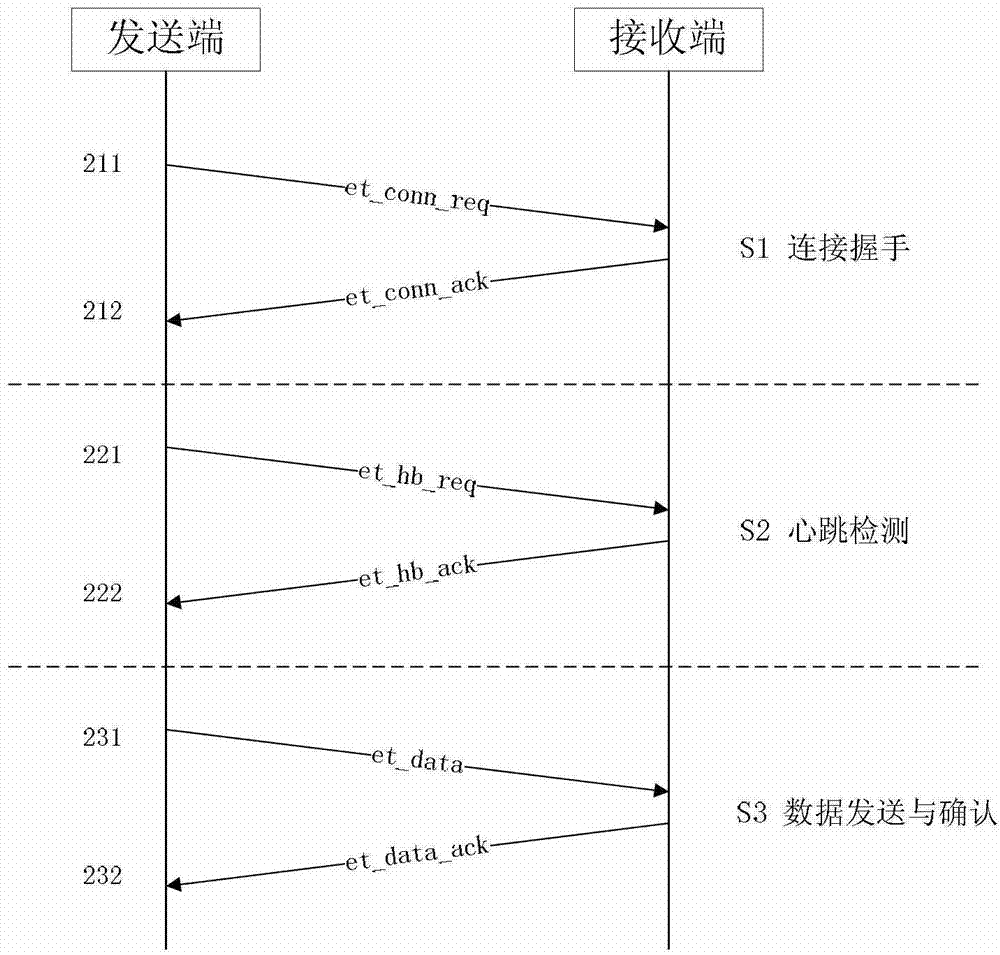
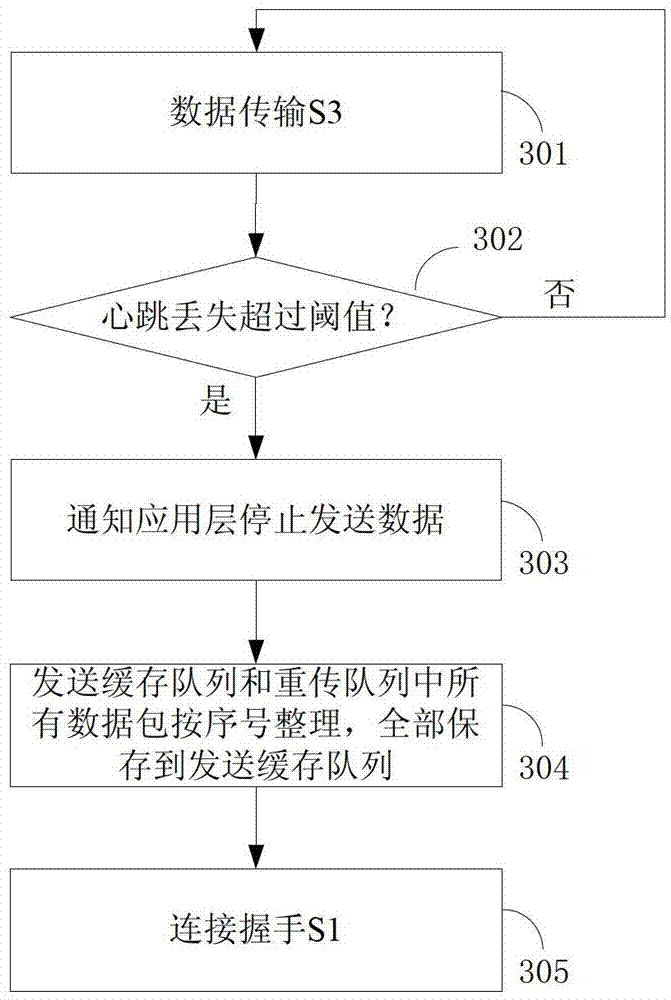
The invention provides a method of data reliable transmission with a user datagram protocol (UDP) in a communication network. The method comprises that firstly, connecting handshake is carried out between a data packet sending end and a data packet receiving end, a communication layer of the data packet sending end informs an application layer that a reliable transmission channel is built; in a data packet transmission process, the communication layer of the data packet sending end detects a channel state of the transmission channel through a heartbeat mechanism, and if the channel state changes, the application layer is informed. The method has strong adaptability and can be used for the communication network which is large in transmission delay difference. A mutual-informing mode is used between the application layer and the communication layer of the sending end, the application layer and the communication layer are in mutual independence and also a unified whole, data reliable transmission is achieved, and meanwhile the problem that when the transmission channel is in fault, the uninformed application layer sends data to the communication layer continuously and resources are consumed is avoided. According to the method, the communication layer of the receiving end transmits a data packet to the application layer directly according to protocol header information to activate task scheduling, and the method has more advantages than a polling scheduling strategy and a callback scheduling strategy.
Owner:EASTERN COMM
Method and system of remote diagnostic, control and information collection using a dynamic linked library of multiple formats and multiple protocols with restriction on protocol
InactiveUS6988141B1Facilitate configuration and received data analysisReduce analysisMultiple digital computer combinationsTransmissionApplication softwareRemote diagnostics
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality. Moreover, by supporting multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver.
Owner:RICOH KK
Method and arrangement for channel type switching
InactiveUS20050013287A1Short incubation periodImprove throughputNetwork traffic/resource managementData switching by path configurationRadio networksChannel parameter
The present invention relates to a method for improved and efficient usage of radio network resources with regard to the transmission properties of applied communication channel types and total network load by means of using early indications on the uplink or downlink of requests to establish new communication connection or adjust parameter settings of already existing connections regading the expectable amount of additional traffic due to such a connection. Early indications are, e.g., information on protocol type, the kind of requested communication service, the profile of the user equipment that has sent the request, or traffic history. In response to such indications the inventive method can forward, e.g., an uplink request and at the same time initiate a channel type switching providing appropriate channel parameter settings or adjustments. In case of congestion control it is another possibility to delay or even suppress uplink requests.
Owner:TELEFON AB LM ERICSSON (PUBL)
Simulation circuit switched fallback signaling connection monitoring method and monitoring system
ActiveCN105722106ASolve the problem that the failure point cannot be locatedWireless communicationVoice communicationNetwork packet
The invention provides a simulation circuit switched fallback signaling connection monitoring method and monitoring system. The monitoring method comprises the steps of generating protocol data packet information according to protocol stack configuration information; acquiring a voice call request in an analog first network; monitoring a signaling connection process of the voice call request processing when the first network falls back to a second network according to the protocol data packet information; and if a failure occurs to the signaling connection process, handling the failure. The above scheme achieves the signaling connection process of voice communication in an LTE network by means of simulation, meanwhile monitors the signaling connection process, timely acquires the failure in the communication, and solves the problems that the signaling connection process cannot be monitored in the course of LTE voice communication and that the point of failure cannot be positioned when the failure occurs in the network.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
Minimalist data collection for high-speed network data monitoring based on protocol trees
ActiveUS7543054B1Efficient retrievalTime-division multiplexMultiple digital computer combinationsNetwork architectureApplication software
According to one embodiment, a network architecture includes a plurality of application monitoring modules for monitoring network traffic data that store the data in meta-flow tuples with associated measures. The meta-flow tuples include a protocol dimension with a value corresponding to a leaf node in a protocol identifier array. The protocol identifier array represents a protocol tree structure based on a set of nodes with pointers to parent, sibling, and child nodes corresponding to the protocol tree. The pointers include protocol identifier values that correspond to memory offset values with respect to the array. For queried protocol dimensions, the protocol identifier array is used to traverse the protocol tree from the leaf node in the meta-flow to a matching node matching the queried protocol. If the queried protocol is found in the protocol lineage of the meta-flow, the measures for the meta-flow are used to satisfy the query.
Owner:NETSCOUT SYSTEMS
Device Communication, Monitoring and Control Architecture and Method
ActiveUS20120011233A1Facilitate communicationTransmission systemsDigital computer detailsCommunication interfaceControl system
A communication interface and a device control, management and monitoring system are provided to enable the networking of and communication between a multiple devices operating under different protocols. The communication interface may act as a translator or protocol converter that reformats transmissions from one protocol to another based on protocol compatibility between the recipient and transmitting devices. The device control and monitoring system may store predefined rules that are triggered when specified conditions associated with the networked devices are detected. The rules may specify an action to take such as transmitting a discount offer to a user or turning off a light. According to one or more arrangements, the communication interface may act as an intermediary between the networked devices and the device control system so that the device control system is not required to understand or be compatible with the various other protocols used by the networked devices.
Owner:COMCAST INTERACTIVE MEDIA
High speed filtering and stream dividing method for keeping connection features
InactiveCN1564547AReduce processing burdenGuaranteed wire-speed processing requirementsData switching networksTraffic capacityData stream
First, the invention sets up output port grouping rule and filtering tapping rule. Then, data filtering tapping process is carried out. IP data packets are picked up from original data packets received from network based on protocol analysis. Based on filtering tapping rule, data relevant to following processes are partitioned to group of each output port. Hash operation is carried out for address of data packet and port information in partitioned each group. Modular operation is carried our between the said Hash value and total number of port. The result is number of output port for the corresponding data packet in the group the data packet belongs to. Under high-speed backbone network, the invention meets need for clustering process and forwarding at high speed for mass data stream.
Owner:上海光华如新信息科技股份有限公司
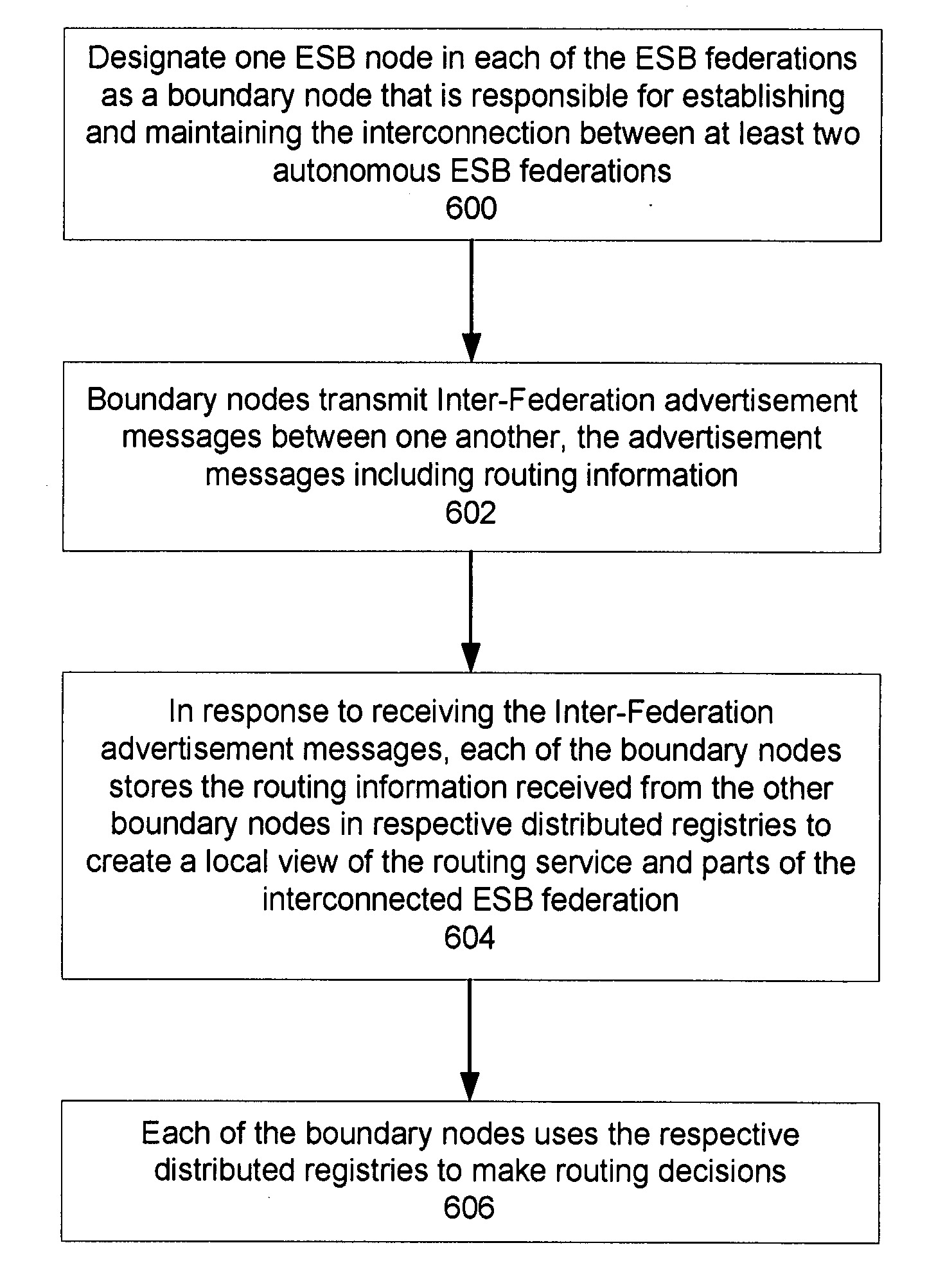
Protocol for enabling dynamic and hierarchical interconnection of autonomous federations of enterprise service buses
InactiveUS20090077251A1Multiple digital computer combinationsTransmissionRouting decisionInterconnection
In a method and system for creating an interconnection between autonomous enterprise service buses (ESB) federations, each one of the ESB federations comprise at least one ESB deployment, which further include a plurality of ESB nodes that provide connectivity to one or more services. According to a protocol, a first ESB node is designated in each of the ESB federations as a boundary node that is responsible for establishing and maintaining an interconnection between at least two of the ESB federations. Advertisement messages are transmitted between the boundary nodes that include routing information. In response to receiving the advertisement messages, each of the boundary nodes store the routing information received from other boundary nodes in respective distributed registries to create a local view of routable service endpoints in the federation. Each of the boundary nodes then use the respective distributed registries to make routing decisions when routing service requests.
Owner:IBM CORP
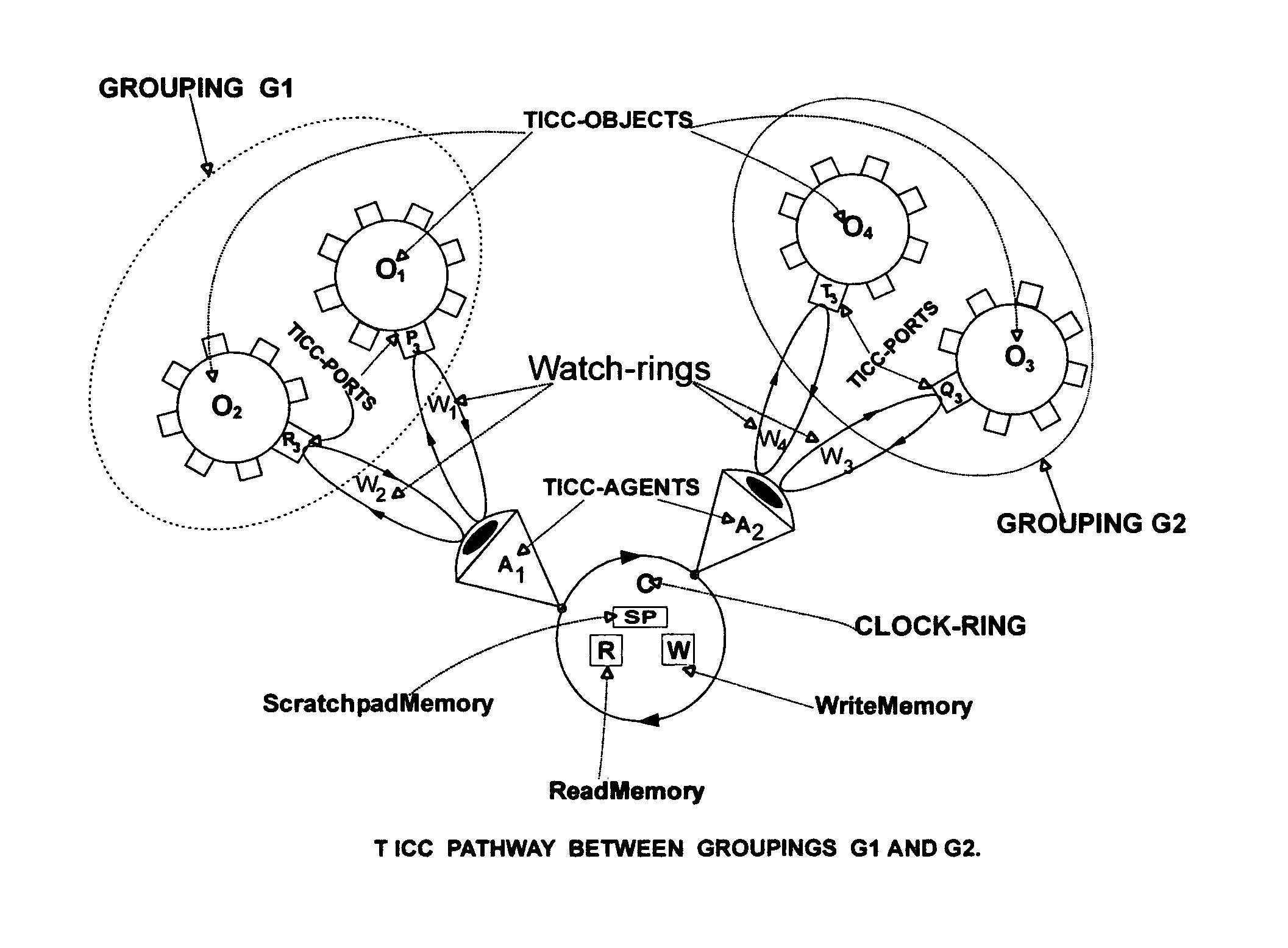
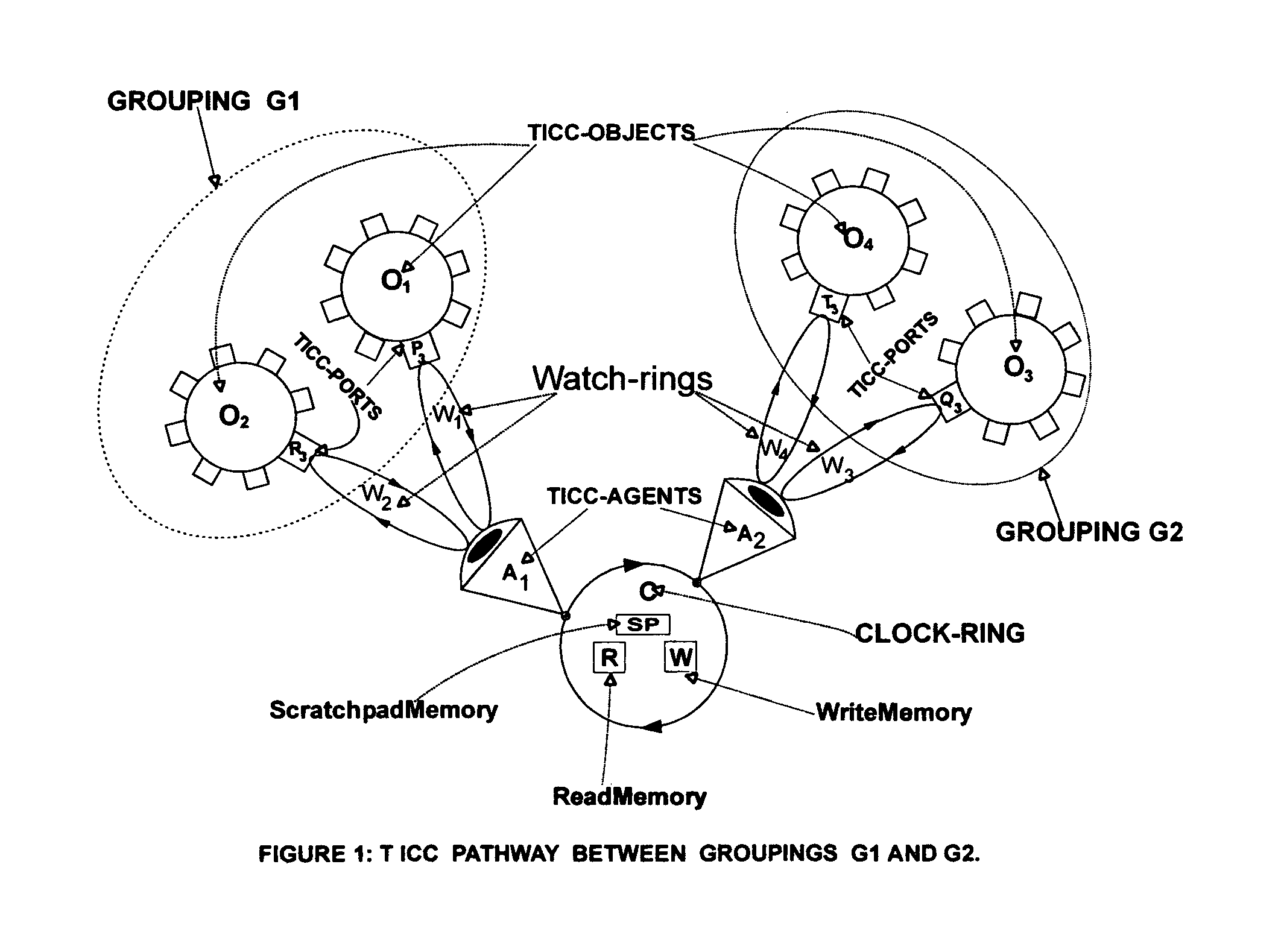
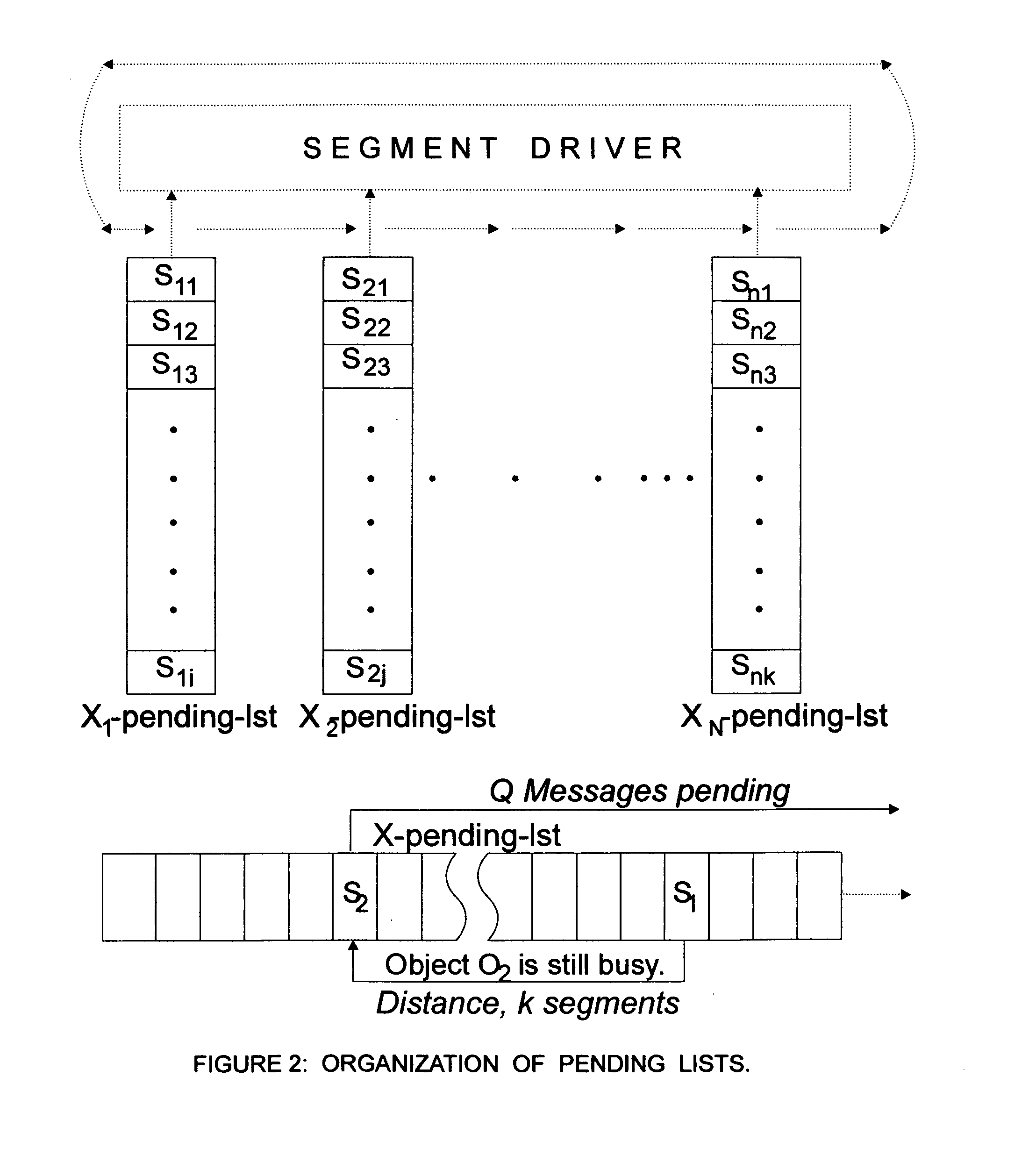
Technology for integrated computation and communication; TICC
InactiveUS7210145B2Eliminate needReduce communication costsProgram initiation/switchingInterprogram communicationMulti processorAsynchronous data
TICC manages asynchronous communications among groups of concurrent (parallel) processes (Objects) in multiprocessors. It dedicates one processor to function as Communications Processor, C. TICC defines a Causal Communication programming Language, called CCL, whose statements may appear intermixed with statements of any conventional programming language. TICC defines methods for compiling CCL statements in these mixed language programs into sequences of protocols which are executed by C, in parallel with on going computations guaranteeing (1) group-to-group loss less, buffer less, self-synchronizing asynchronous data transfers; (2) more than a hundred fold reduction in communication latencies; (3) Dynamic Flexibility to monitor, repair, reconfigure and update software objects without service interruption; and (4) protection and security of all data, distributed to or collected from communicating objects, based on an Agreement Protocol.
Owner:EDSS INC
Web-based enterprise management with multiple repository capability
InactiveUS6976262B1Data processing applicationsMultiple digital computer combinationsWeb-Based Enterprise ManagementResource information
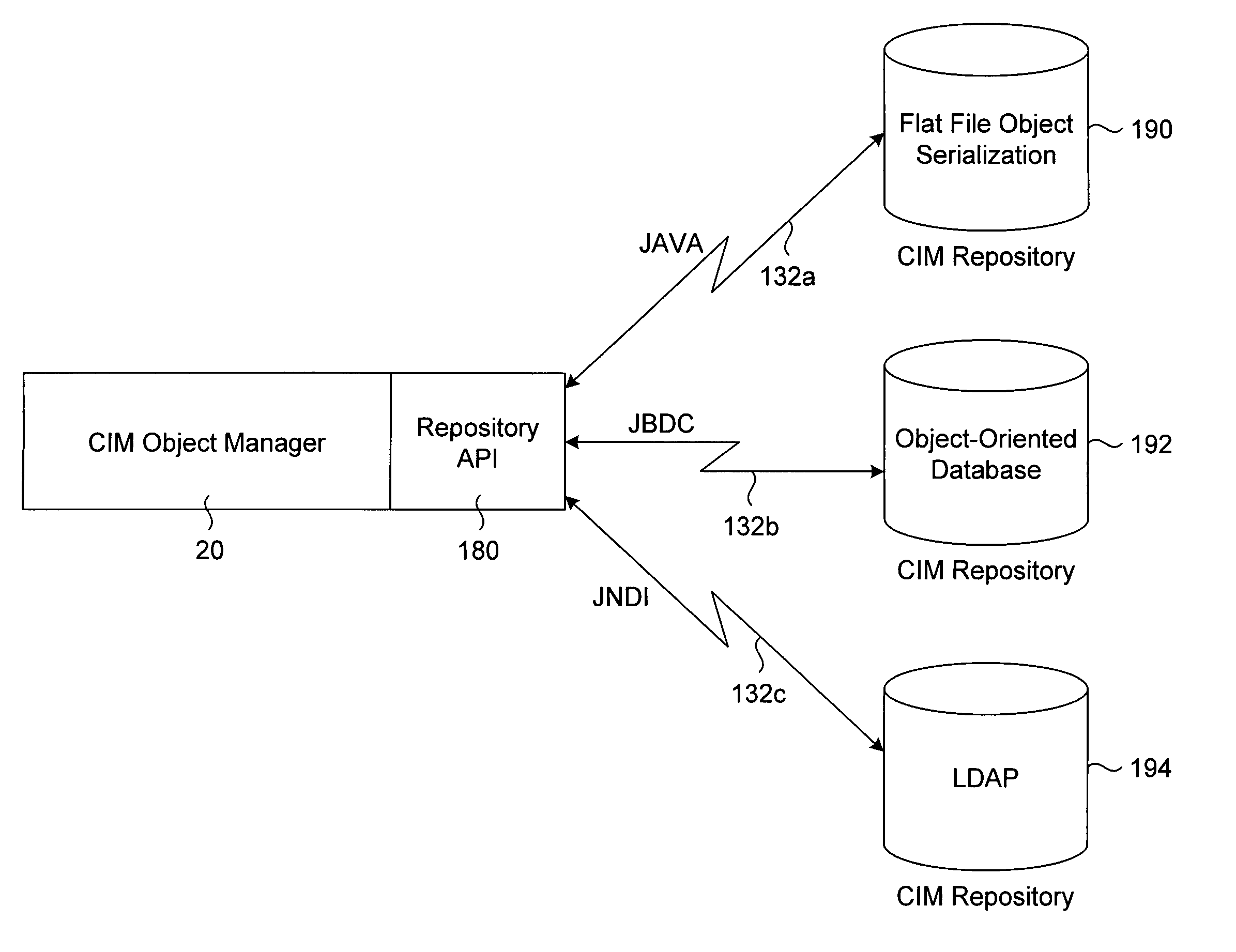
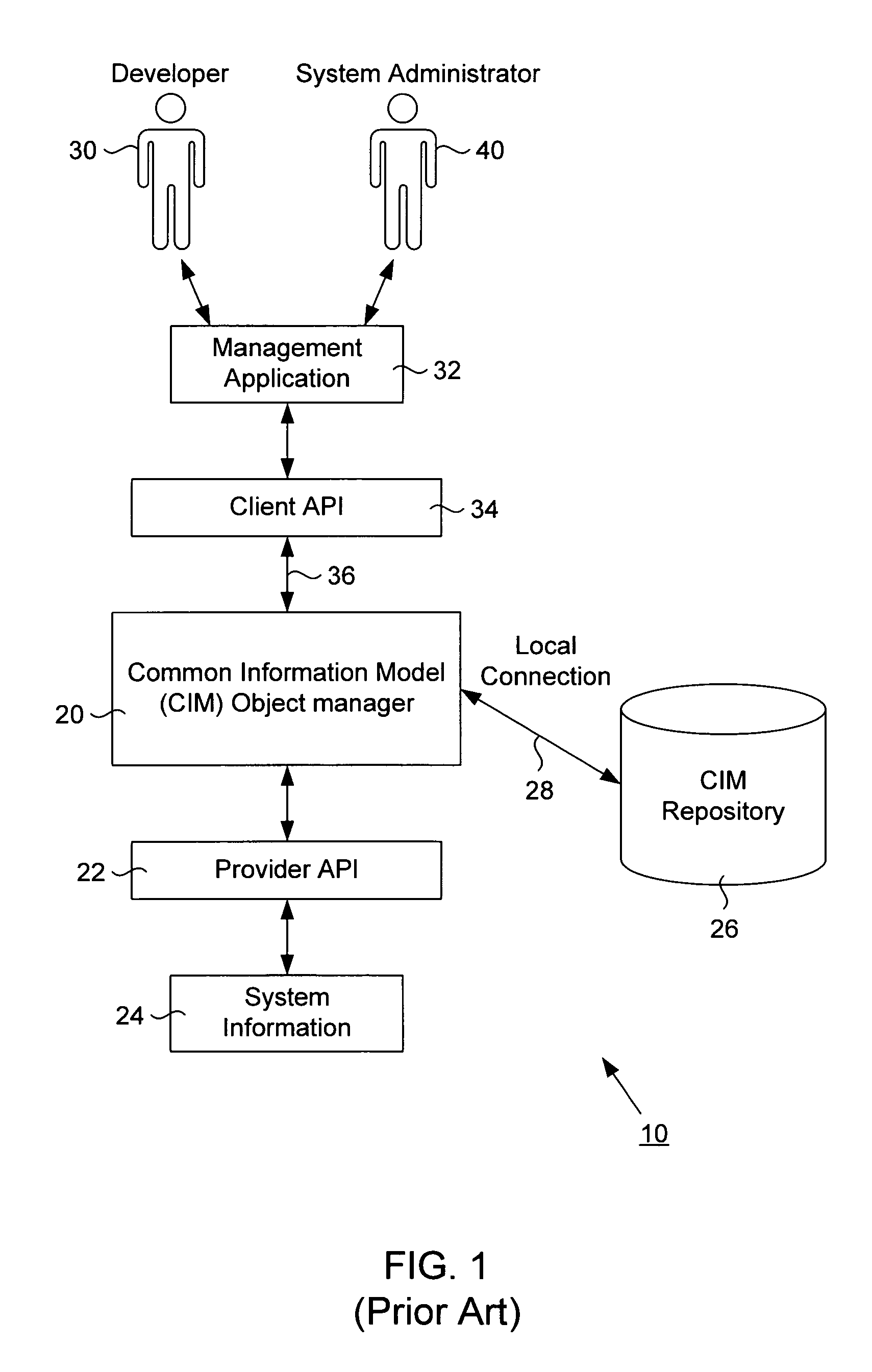
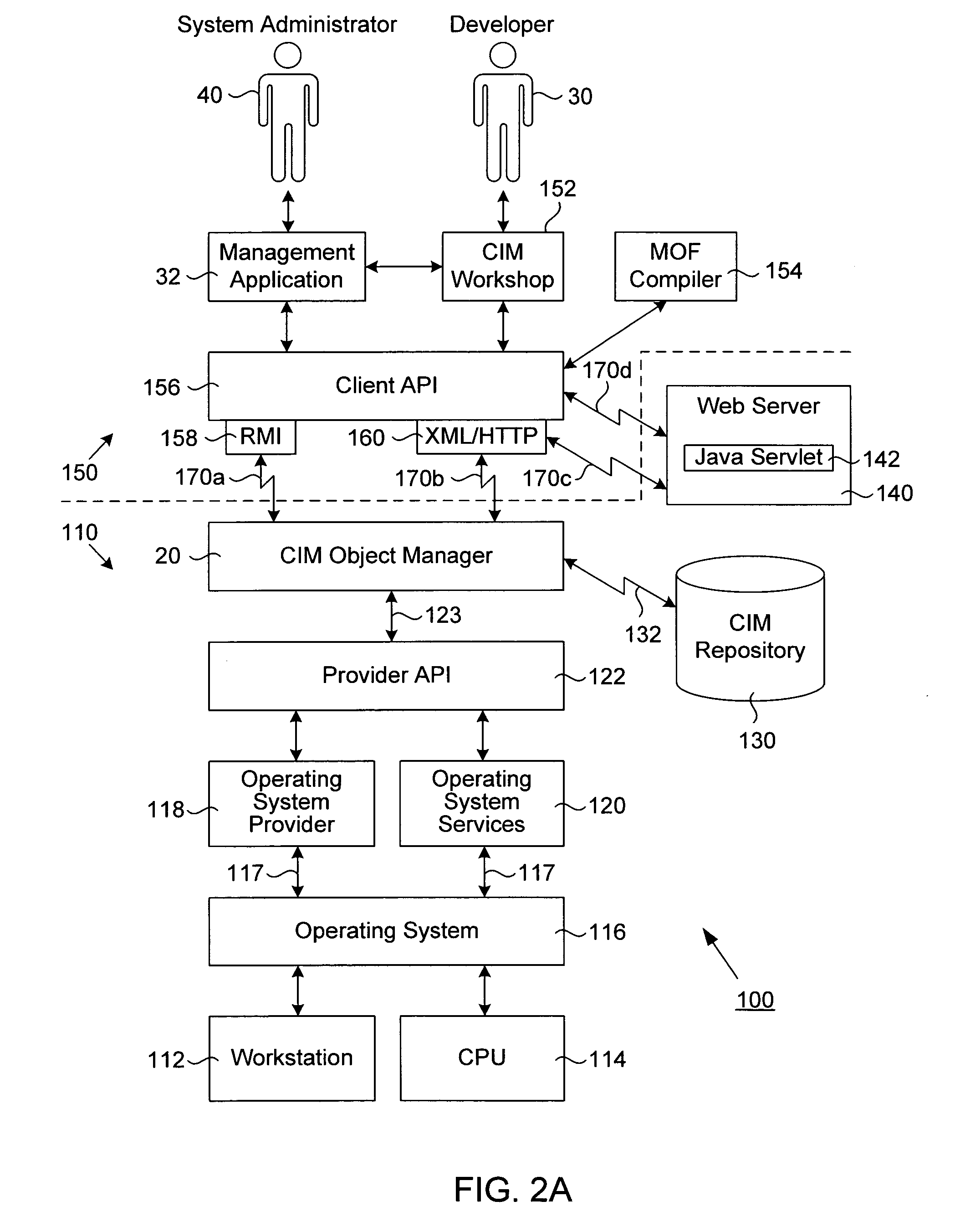
A transport neutral technique allows an object manager to communicate with a CIM repository using any of a variety of protocols. The object manager software is independent of the transport mechanism used and need not be changed if the transport mechanism changes. A computer system to be managed includes a CIM object manager and any number of provider APIs that provide resource information about the computer system. A CIM repository stores classes and instances used by the object manager. A remote application computer runs a software management application that communicates with the object manager of the computer system using a local client API. A Repository API of the object manager includes an interface definition defining all methods called by the object manager. Also included is a protocol-specific class that implements the interface definition; there is a protocol-specific class for each protocol desired to be supported. Each class implements methods using a specific protocol. A factory class is executed when the object manager invokes a method call passing in a desired protocol parameter. The factory class creates a protocol-specific object of one of the protocol-specific classes depending on the protocol parameter. The object is returned to the object manager which executes one of its protocol-specific methods thus allowing communication to a repository using a protocol independent of the object manager.
Owner:ORACLE INT CORP
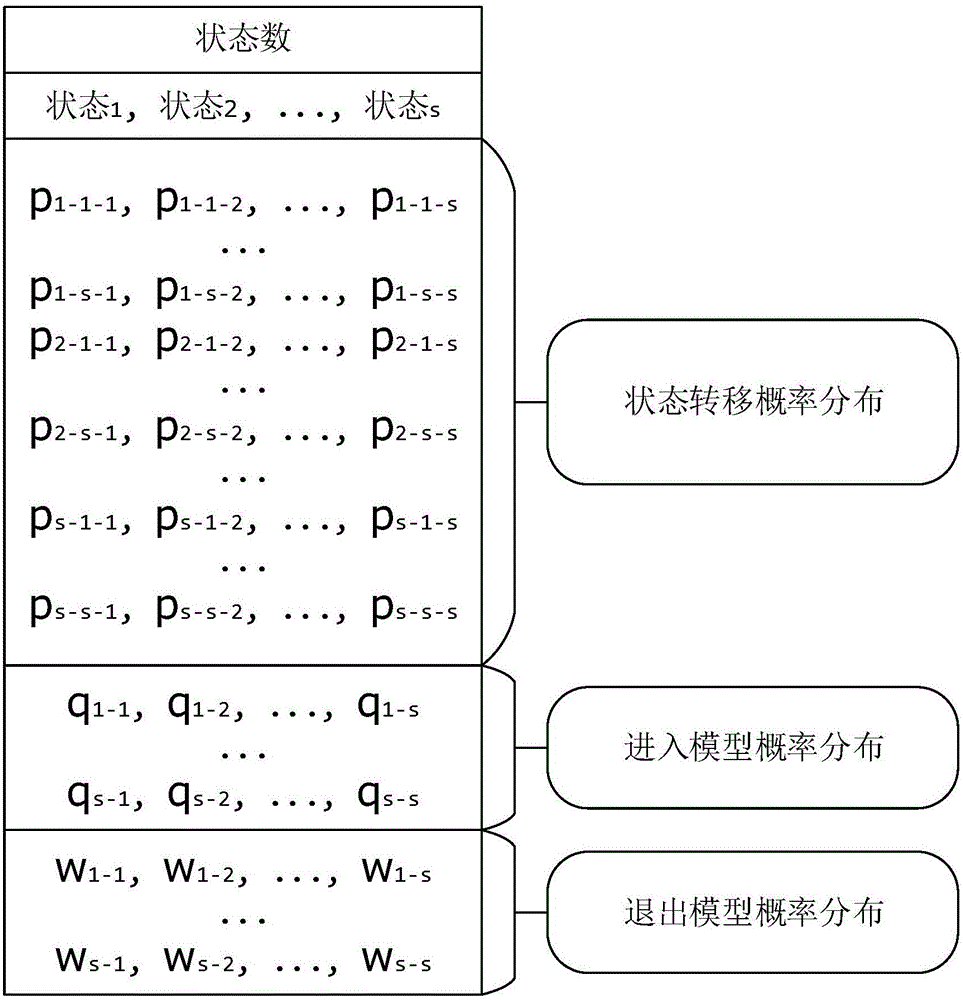
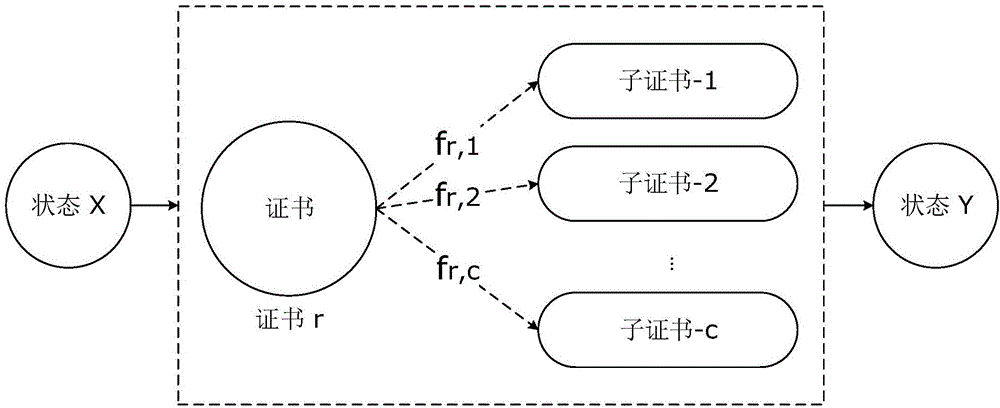
Network application encrypted traffic recognition method and device based on protocol attributes
The invention relates to a network application encrypted traffic recognition method and device based on protocol attributes, and belongs to the technical field of computer network service security. The device comprises an offline training module and an online identification module. The offline training module is composed of a data set obtaining module, a message type fingerprint establishment module based on a second order Markov chain and a certificate length clustering module. A training set is obtained through a data set obtaining module. Application fingerprints are obtained and stored according to the training set by the message type fingerprint establishment module based on the second order Markov chain; clustering results and application certificate cluster distribution probability are obtained and stored according to the training set by the certificate length clustering module. The offline training module is composed of a network traffic capturing module and a recognition module. The recognition module matches the network traffic obtained by the capturing module with a stored application fingerprint library one by one; moreover, the certificate clustering results are taken into consideration, thus obtaining a recognition probability; the recognition result is an application corresponding to the highest probability. Compared with the prior art, the method and the device have the advantage of improving the recognition accuracy and efficiency.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com