Patents
Literature
155 results about "Session border controller" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
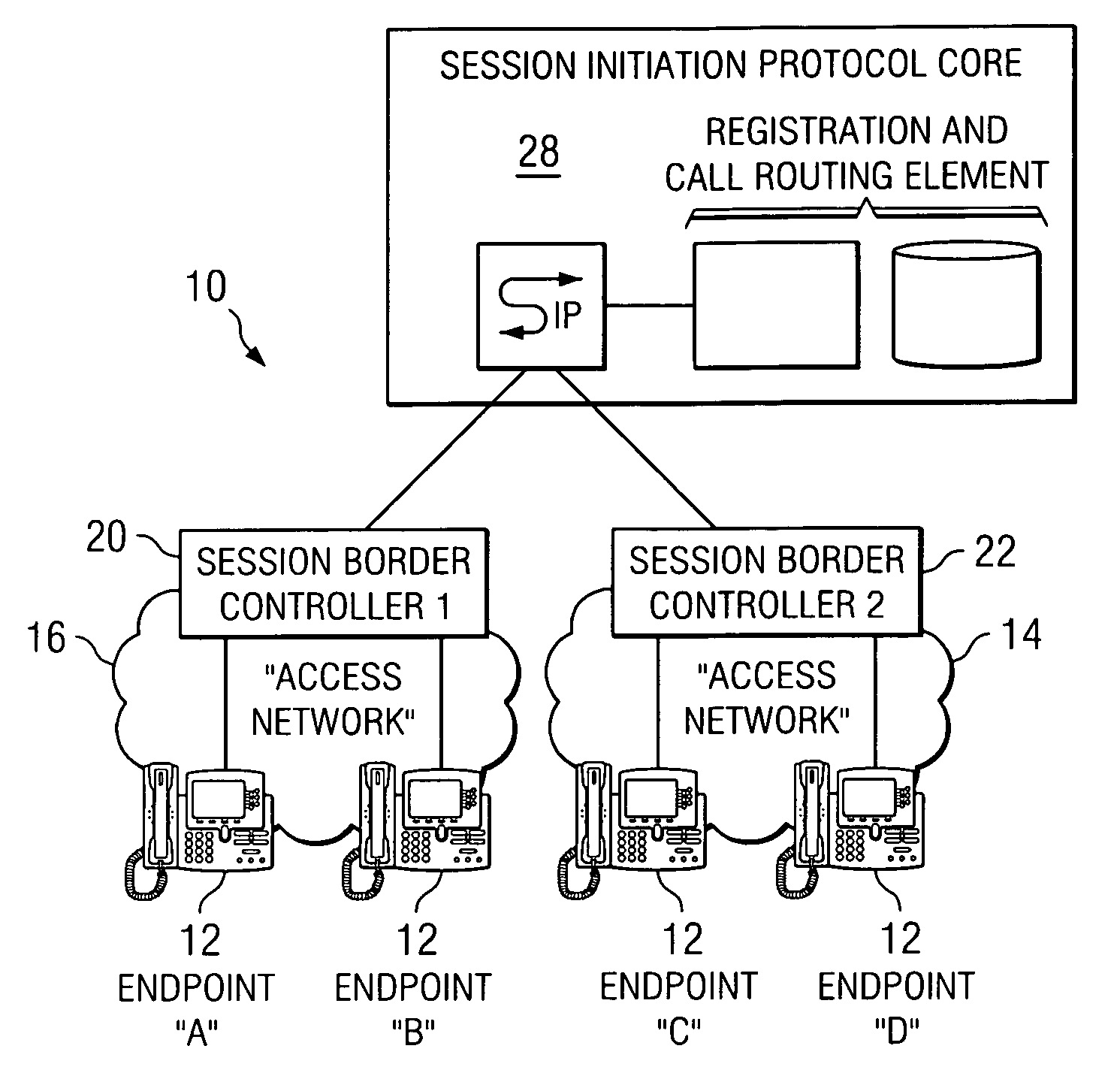
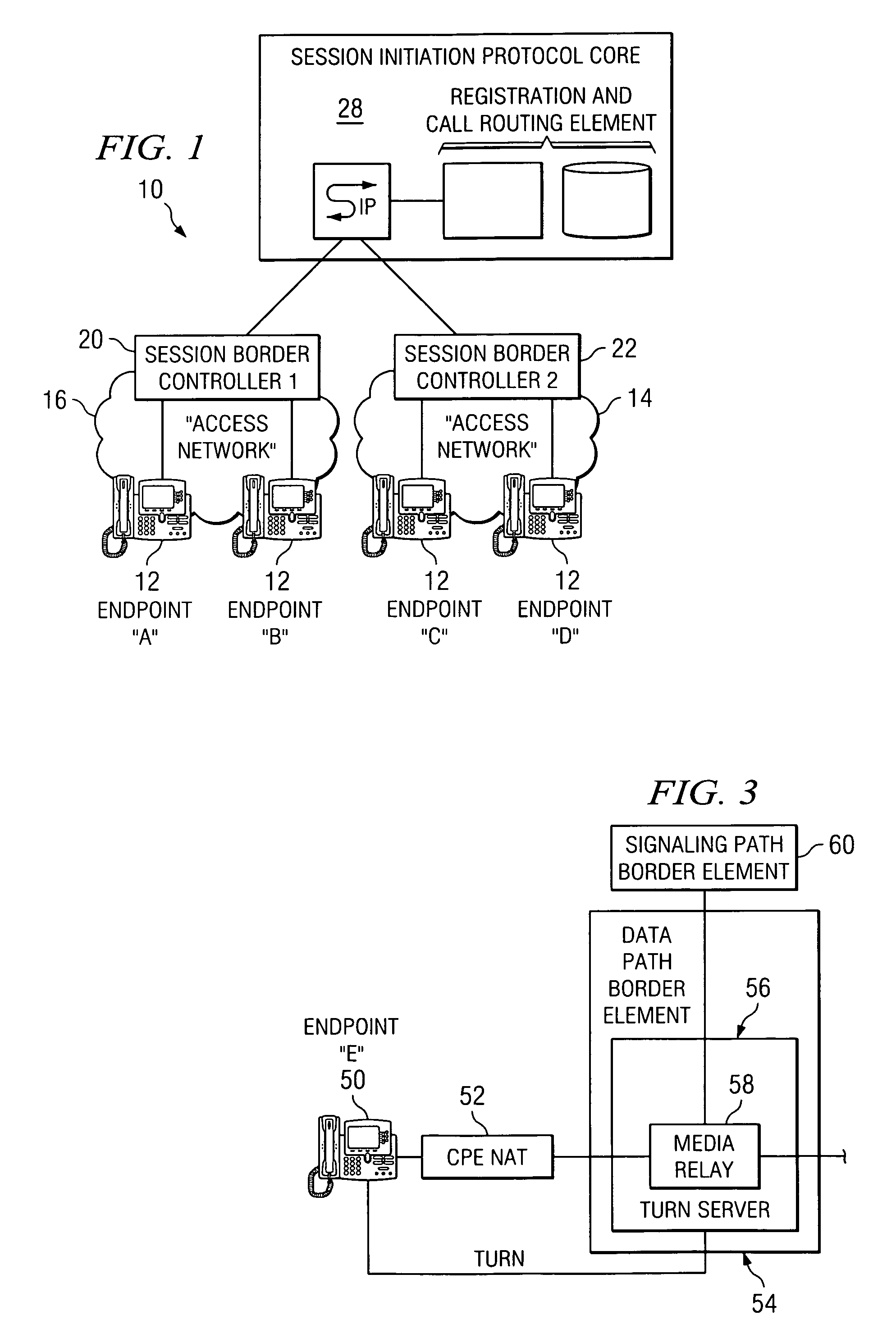
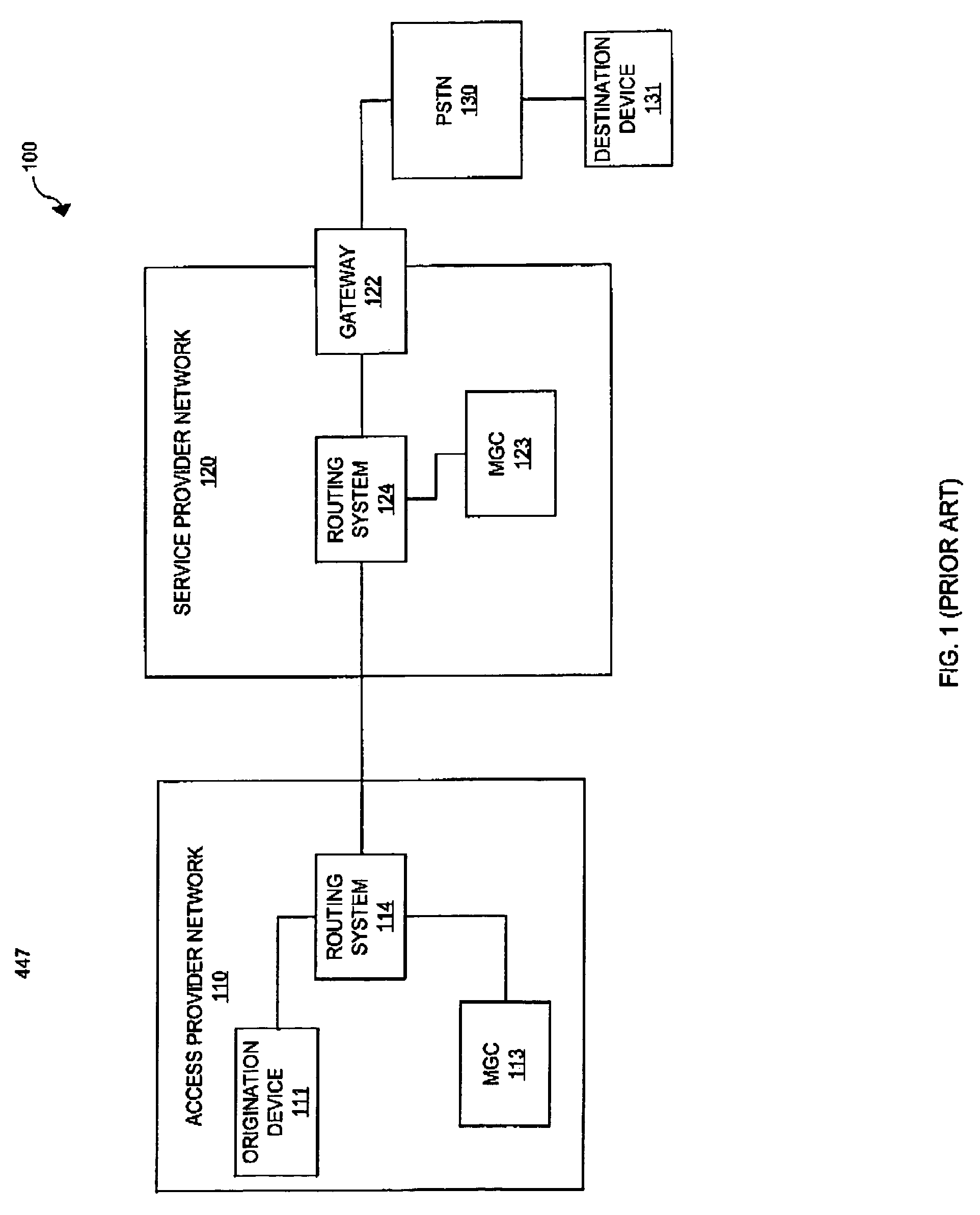
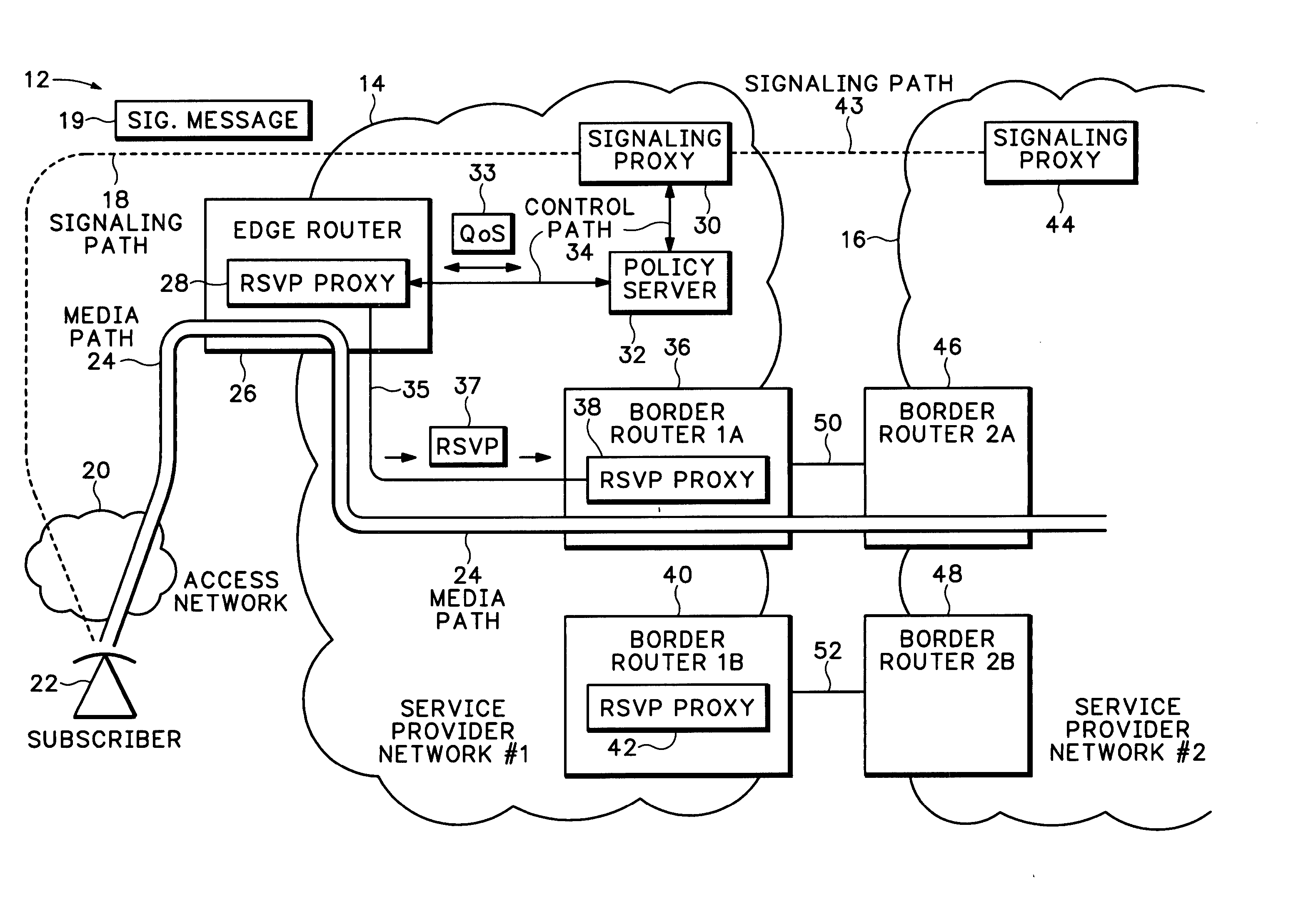
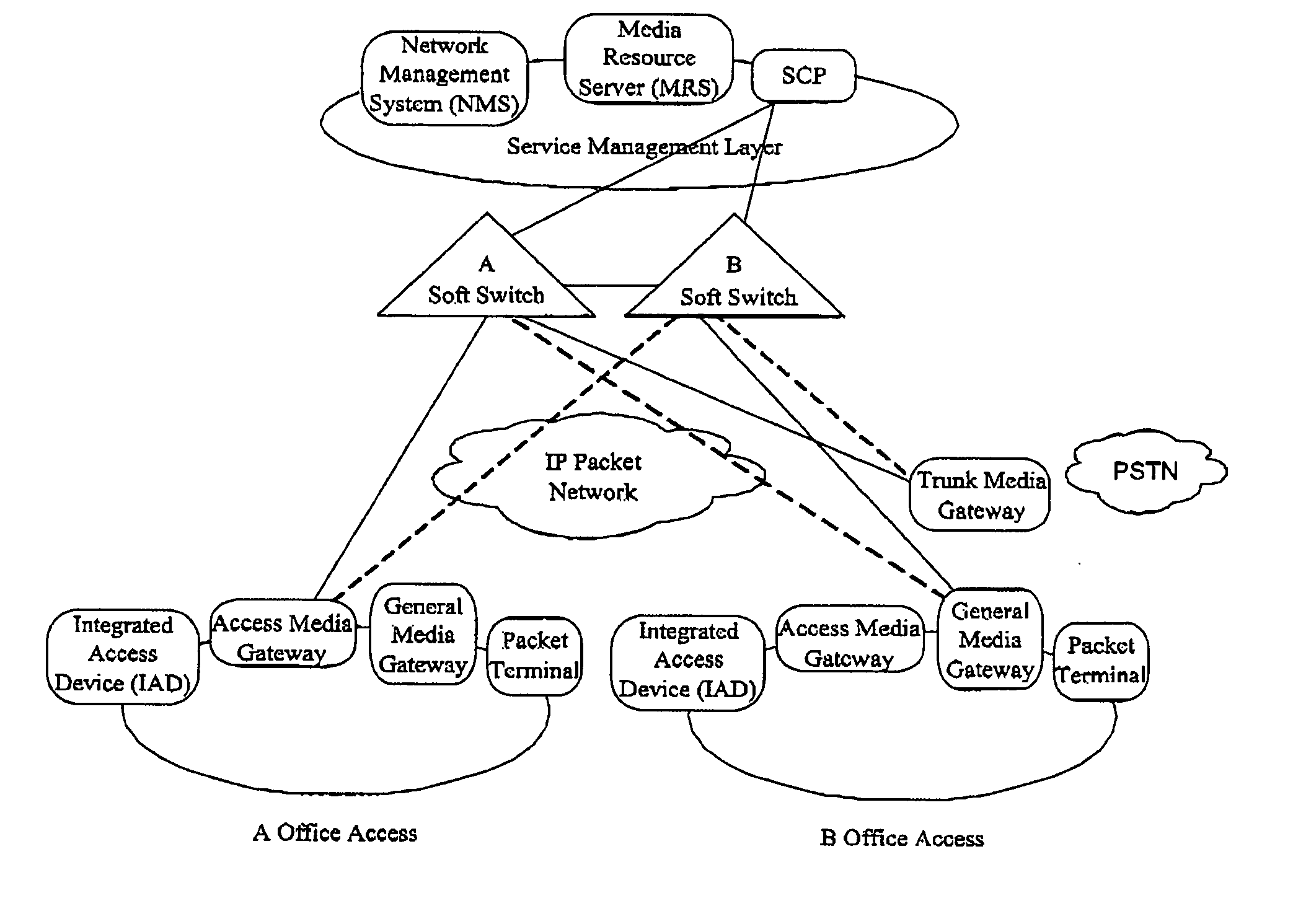
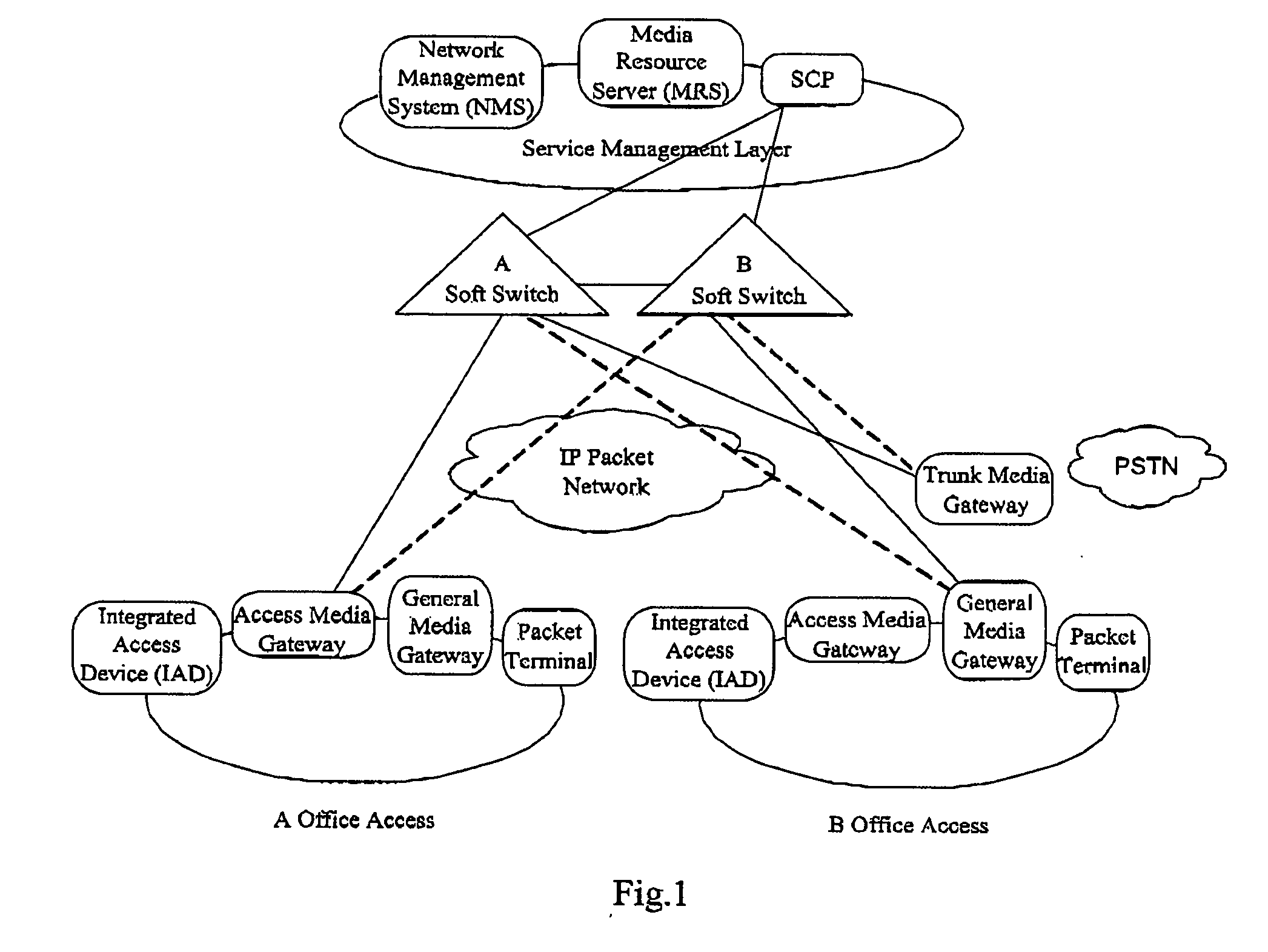
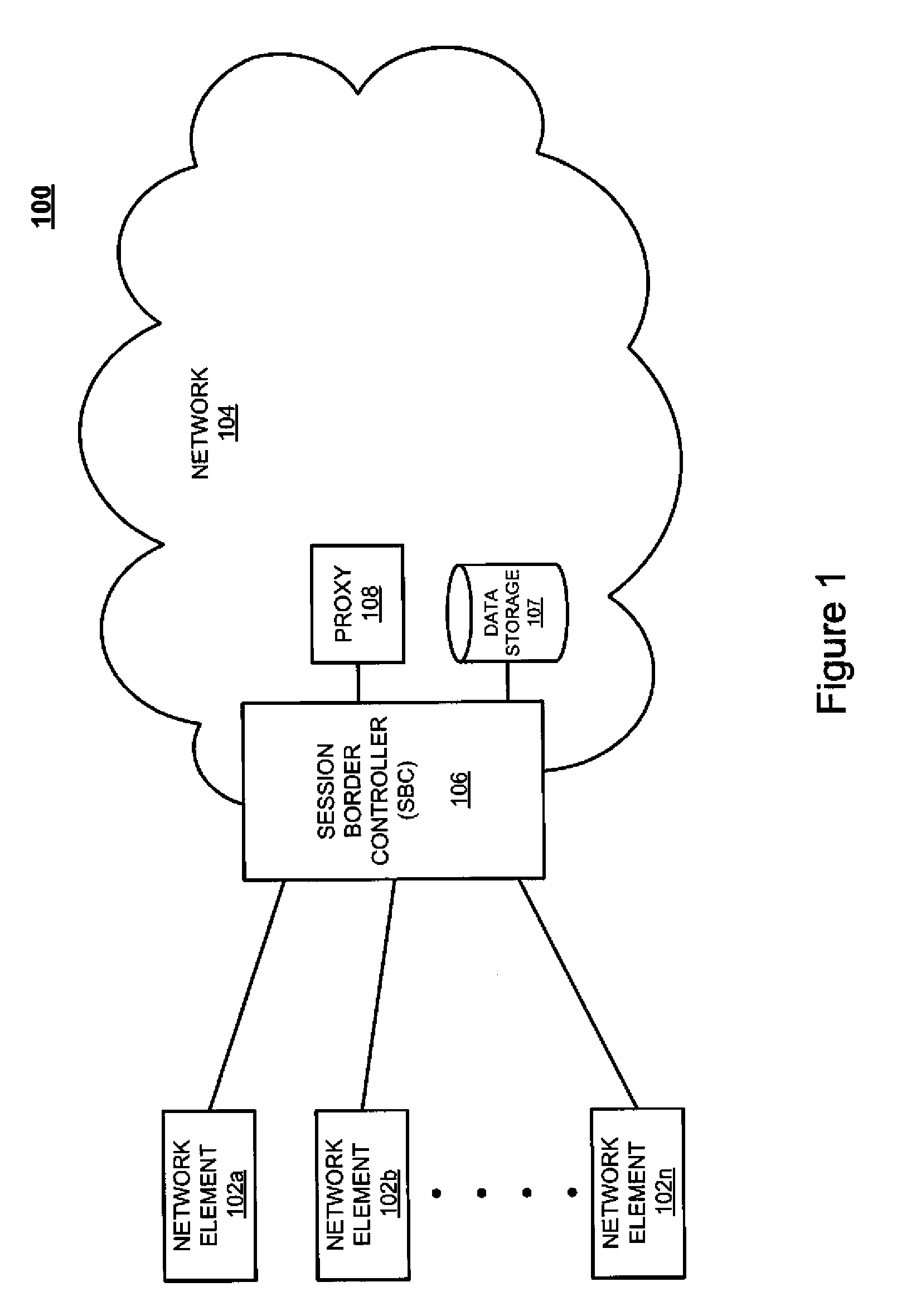
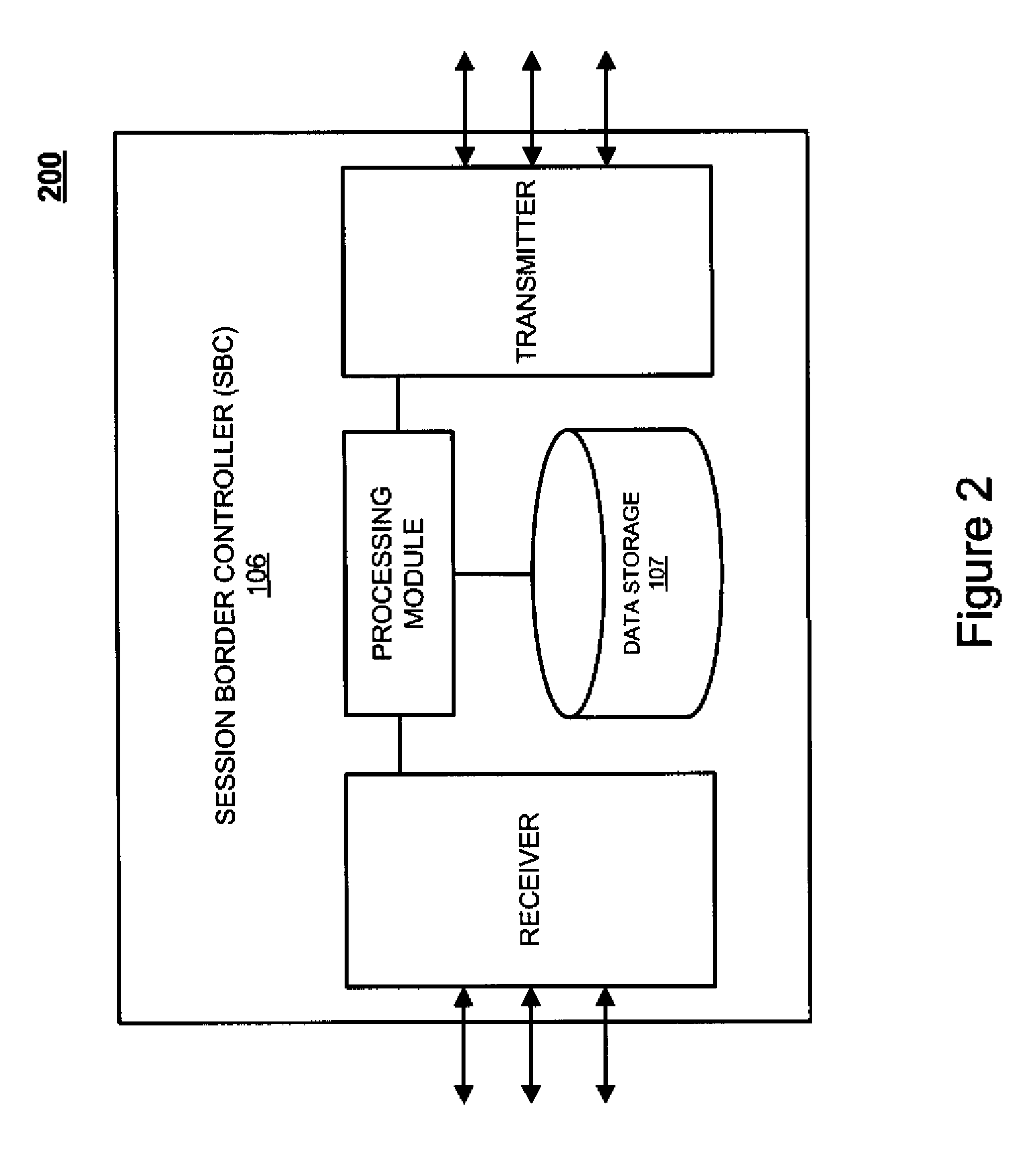
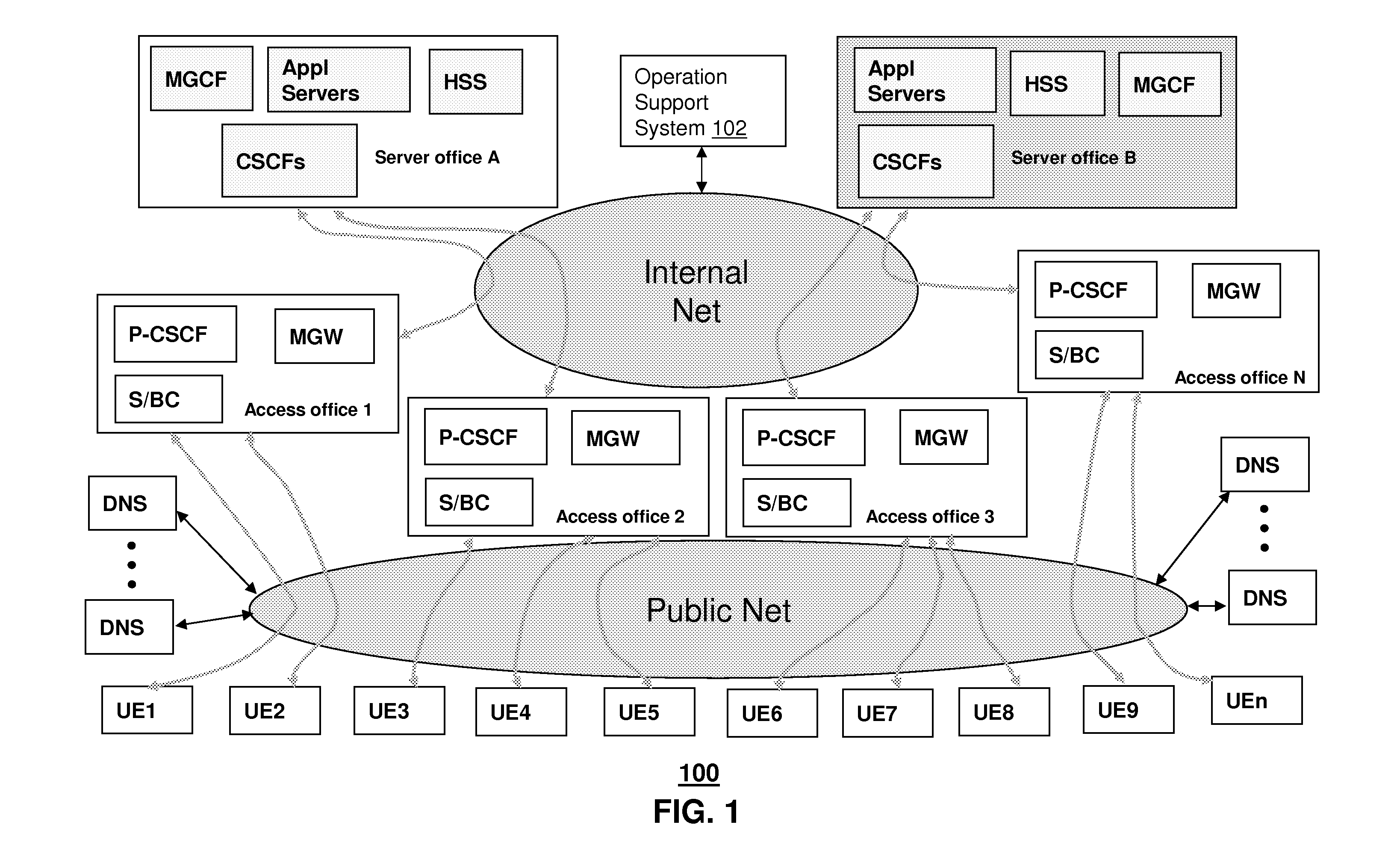
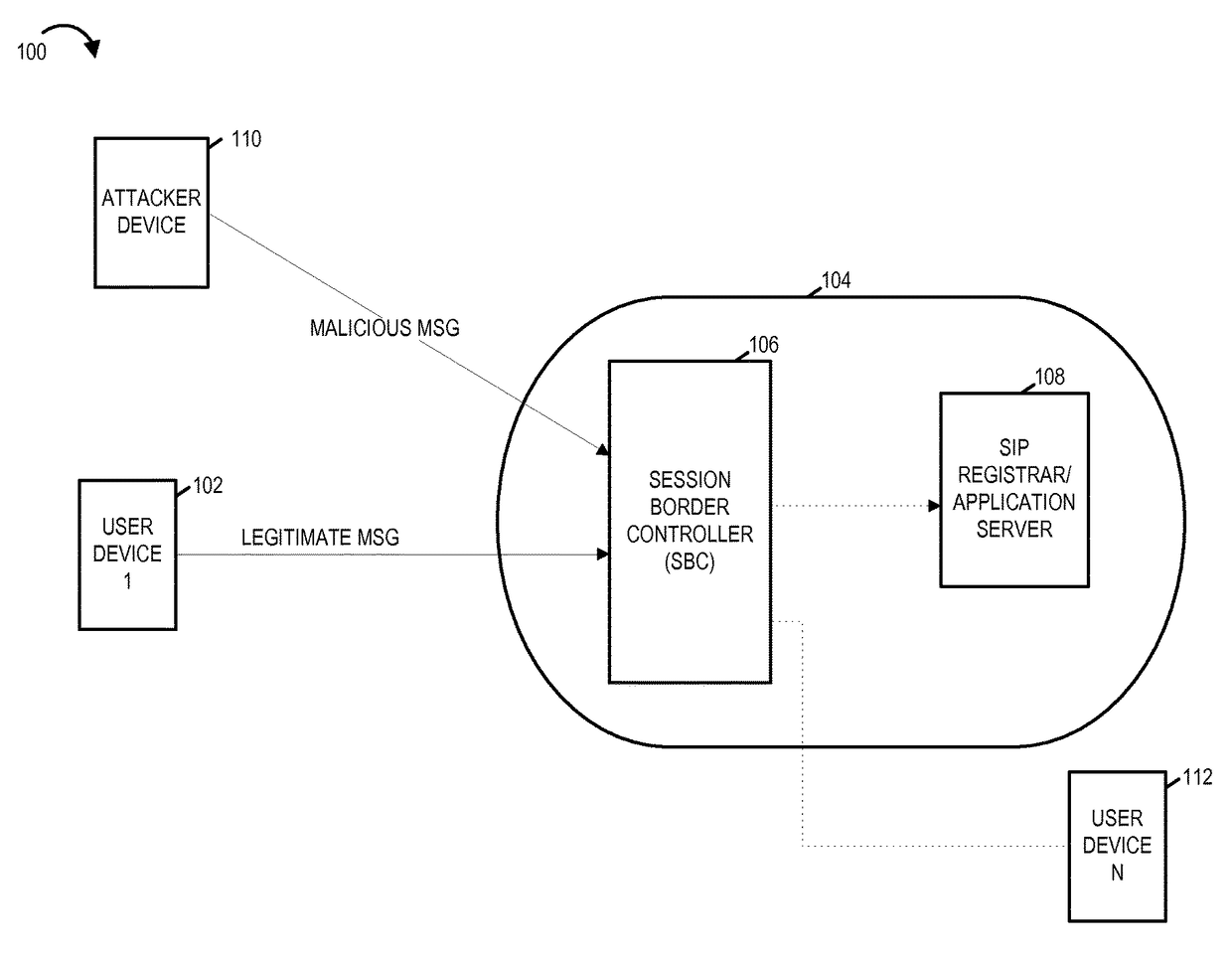
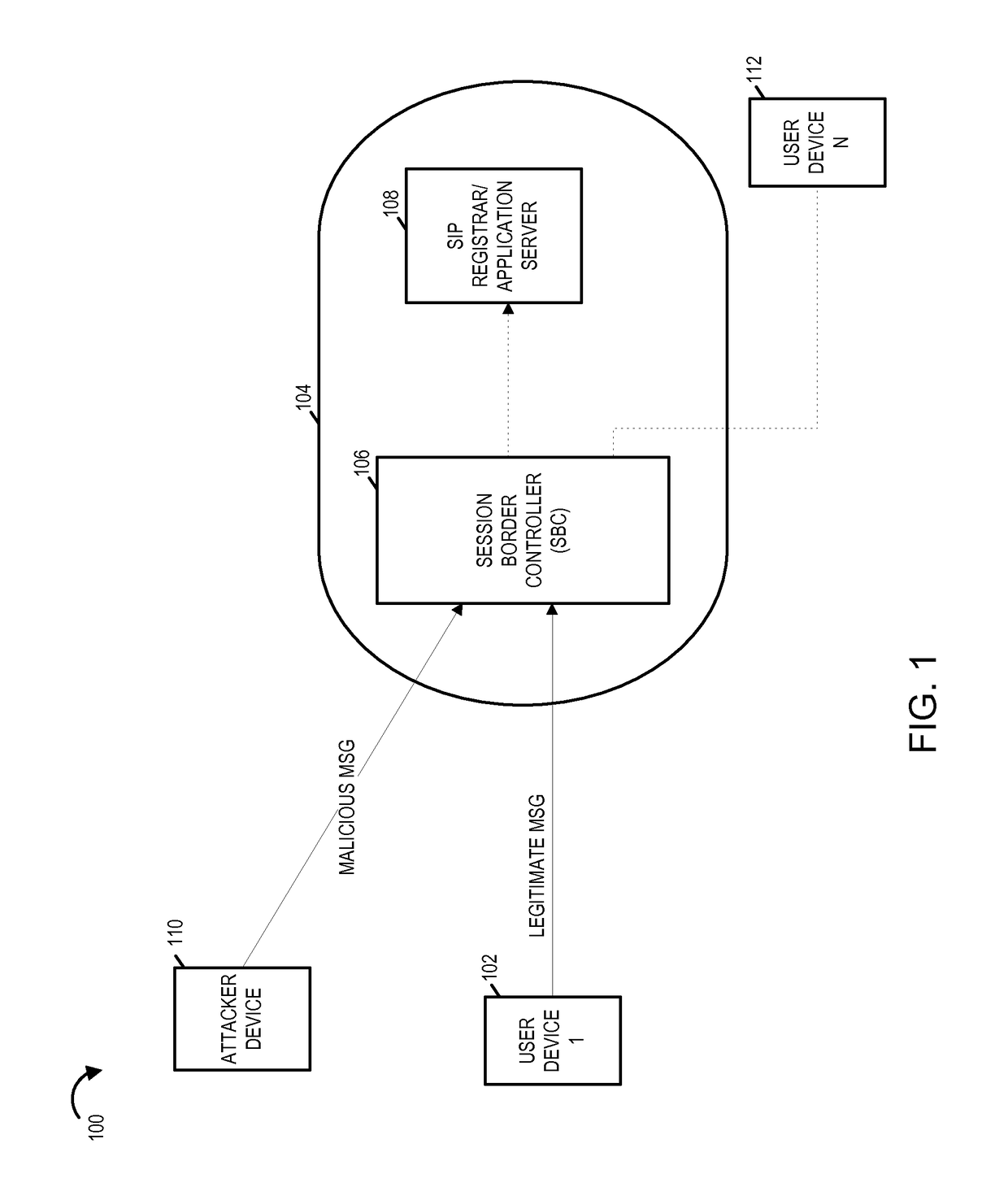
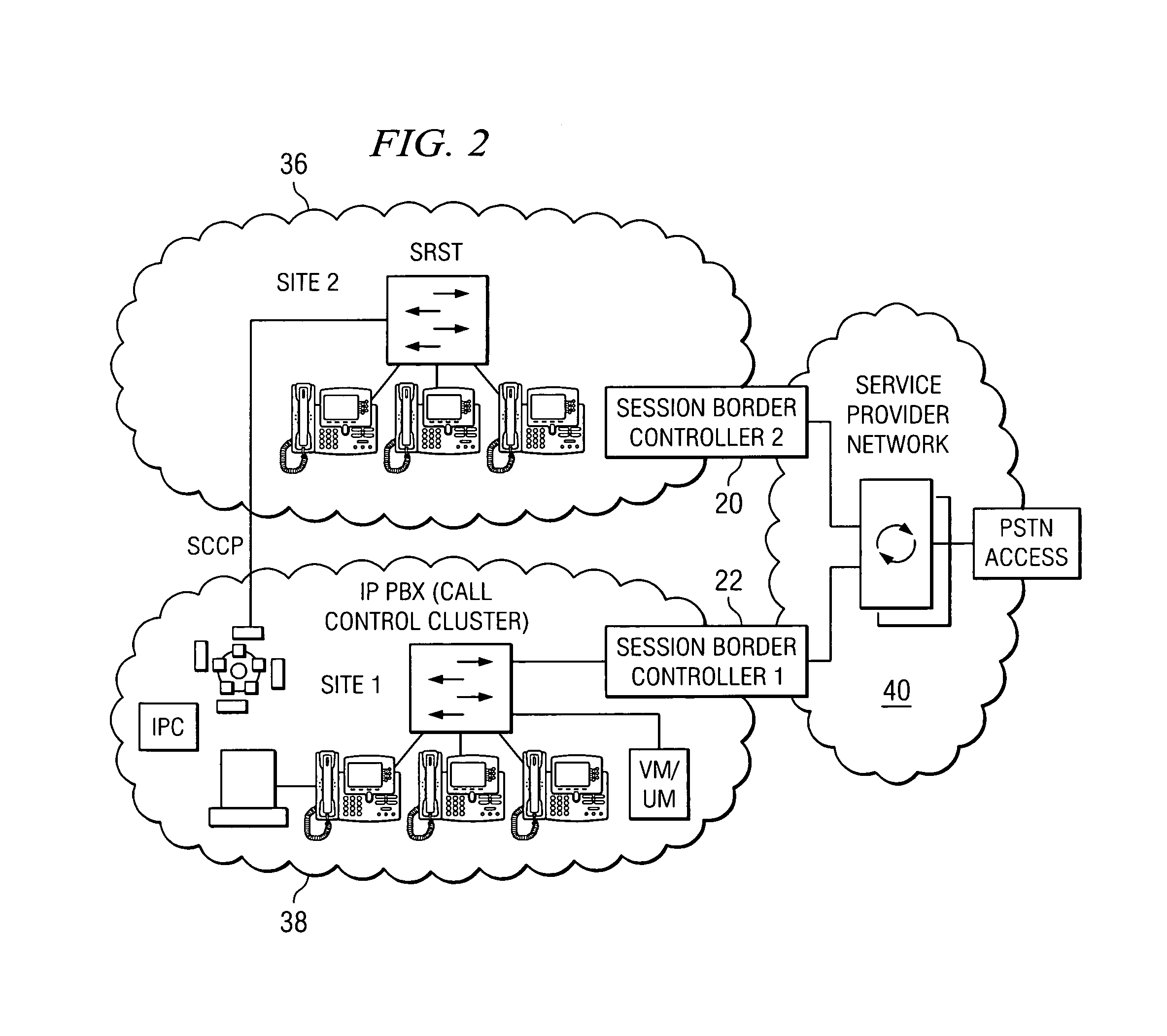
A session border controller (SBC) is a network element deployed to protect SIP based voice over Internet Protocol (VoIP) networks. Early deployments of SBCs were focused on the borders between two service provider networks in a peering environment. This role has now expanded to include significant deployments between a service provider's access network and a backbone network to provide service to residential and/or enterprise customers.
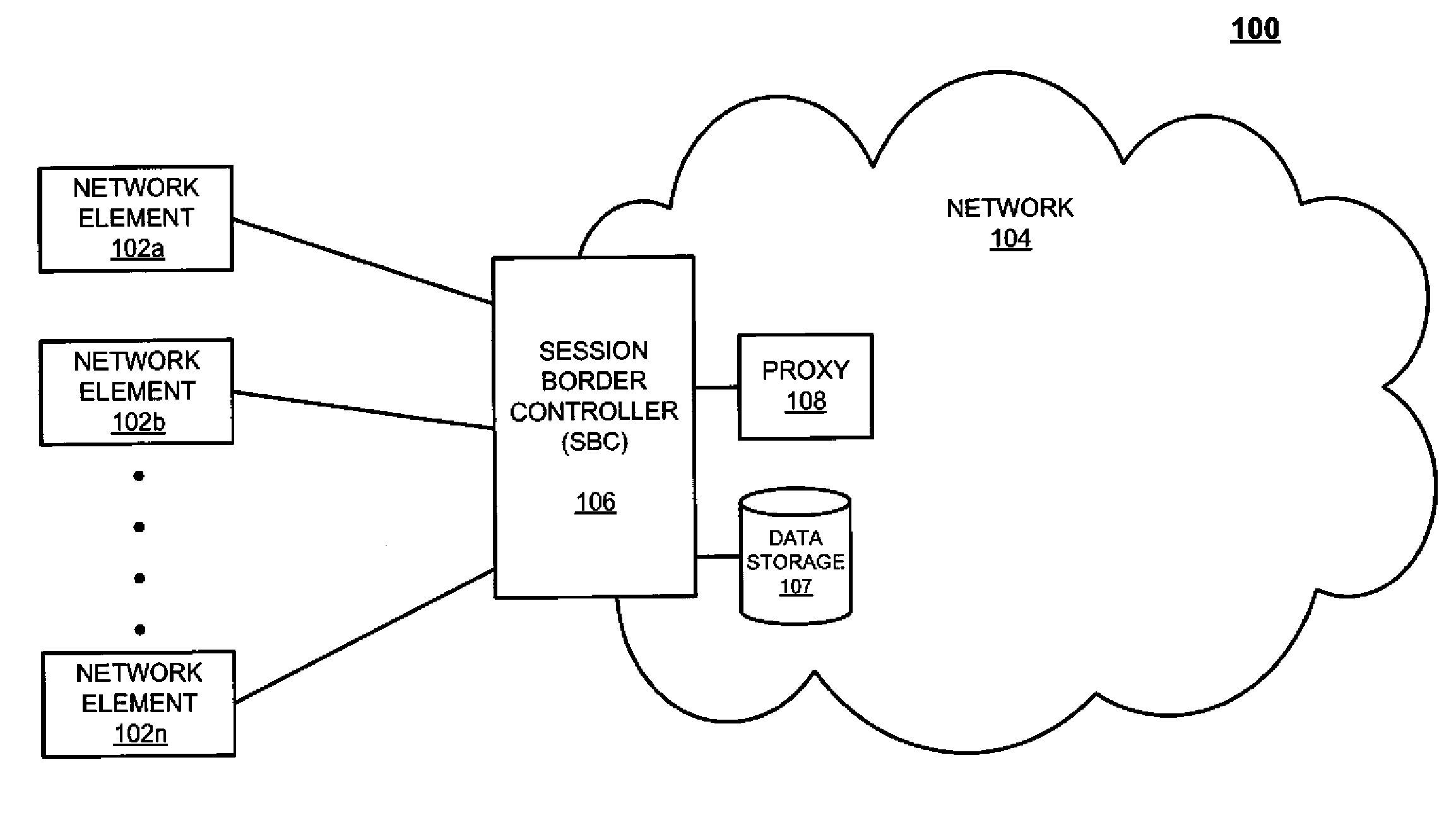
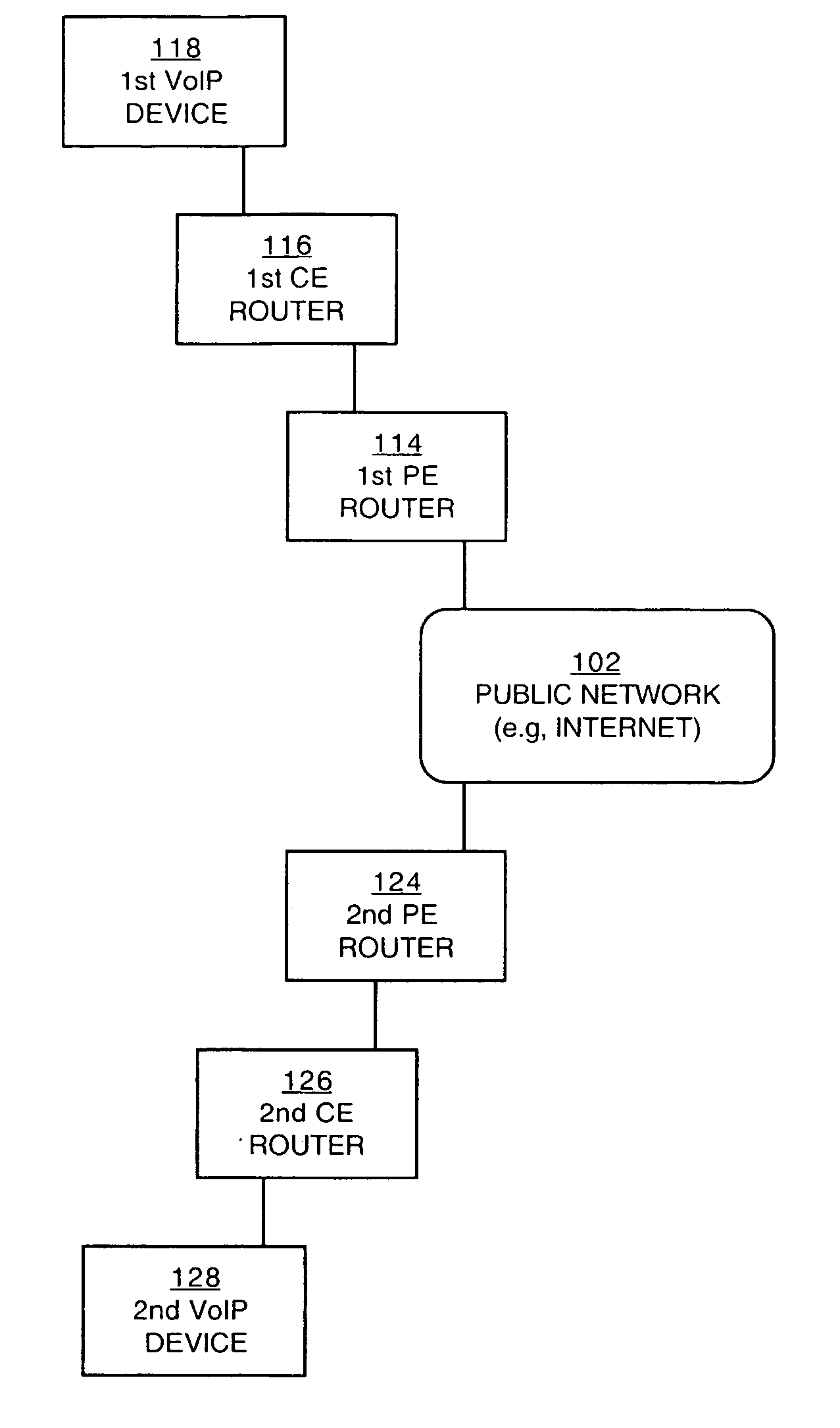
System and method for optimizing communications between session border controllers and enpoints in a network environment
ActiveUS20070019619A1Reduce disadvantagesReduce problemsMultiplex system selection arrangementsSpecial service provision for substationDatapathSession border controller
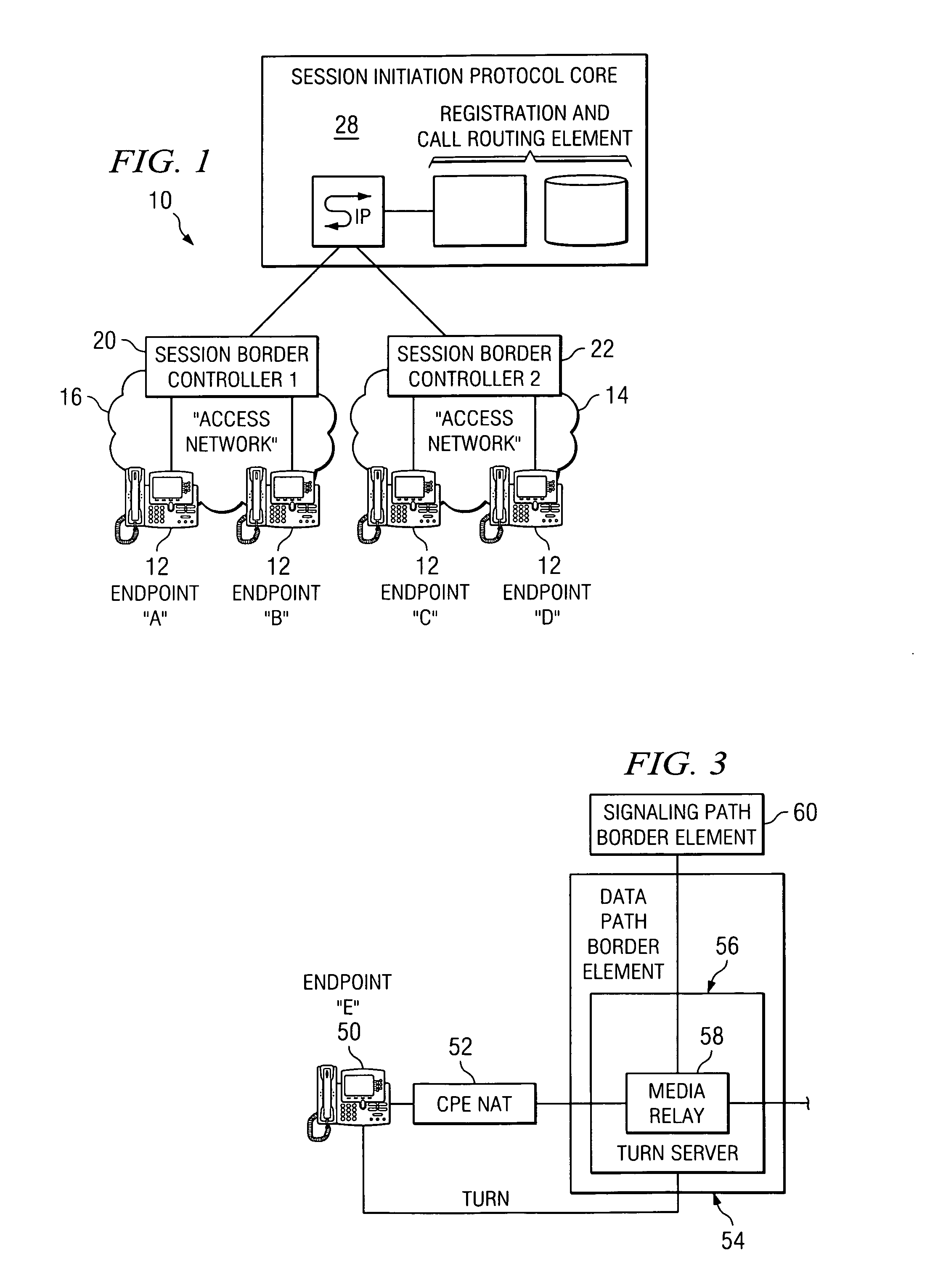
An apparatus for optimizing communications between session border controllers in a network environment is provided that includes a session border controller (SBC) operable to communicate with a first endpoint and a second endpoint. The SBC is also operable to communicate with a data path border element (DBE) and a signaling path border element (SBE). The DBE is operable to provide a media relay for a communication session involving the endpoints, the media relay being invoked by either of the endpoints using a traversal using relay network address translation (TURN) protocol, which allows the SBC to operate in either of two modes depending on protocol support present in the endpoints.
Owner:CISCO TECH INC
Mobility management entity for high data rate wireless communication networks
ActiveUS7457265B2Reduce amountEasy to manageTime-division multiplexData switching by path configurationSession controlGranularity
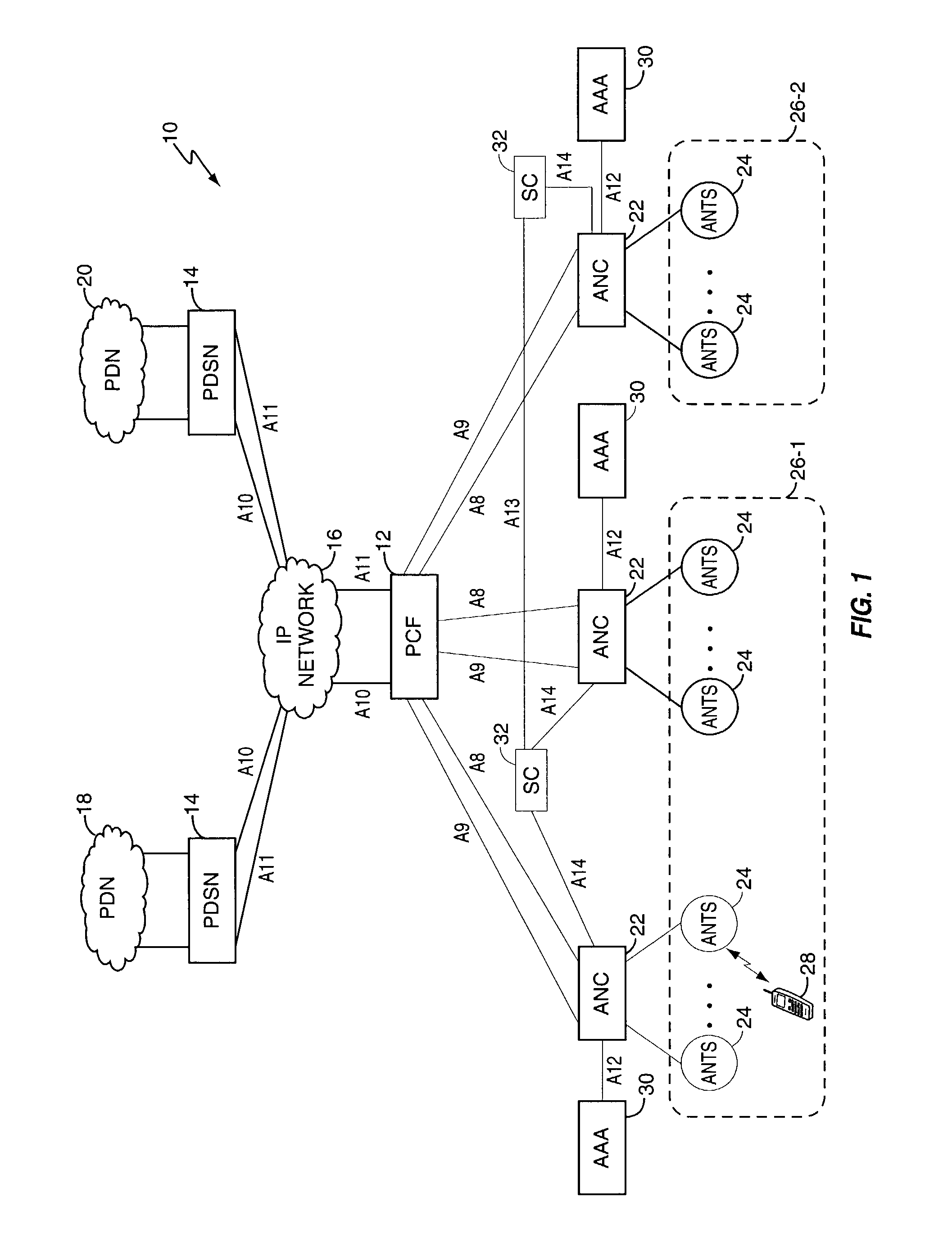
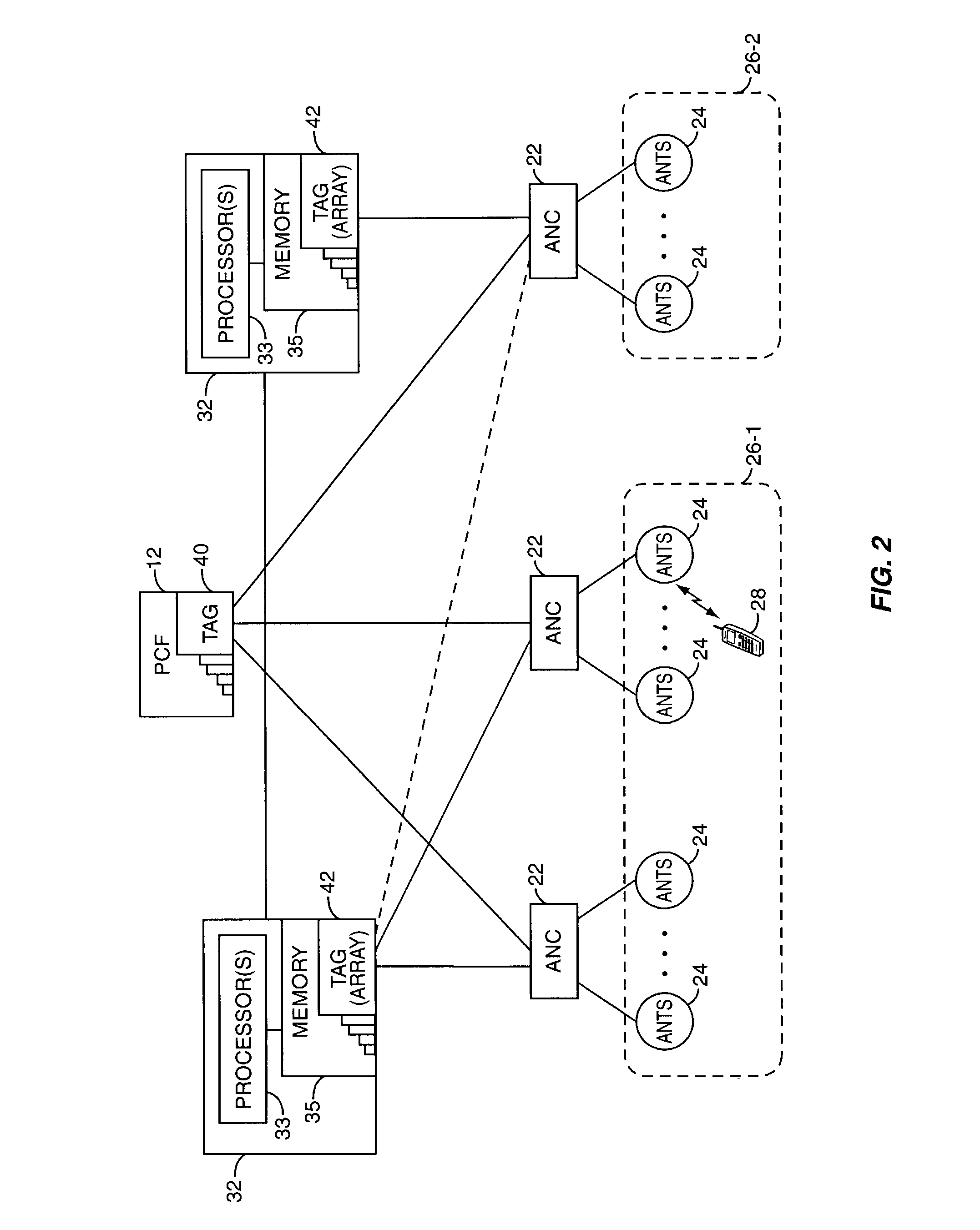
A session controller provides mobility management support in a 1xEVDO wireless communication network, such as one configured in accordance with the TIA / EIA / IS-856 standard. Operating as a logical network entity, the SC maintains location (e.g., a pointing tag) and session information at an access network controller (ANC) granularity, thus allowing it to track access terminal (AT) transfer between ANCs but within subnet boundaries, where a network subnet comprises one or more ANCs. This allows a packet control function (PCF) to maintain location information at a packet zone granularity, thereby reducing mobility management overhead at the PCF. The SC provides updated tag and session information to PCFs, ANCs, and other SCs as needed. Information exchange with other SCs arises, for example, when two or more SCs cooperate to maintain or transfer routing and session information across subnets.
Owner:TELEFON AB LM ERICSSON (PUBL)
Dynamic facsimile transcoding in a unified messaging platform
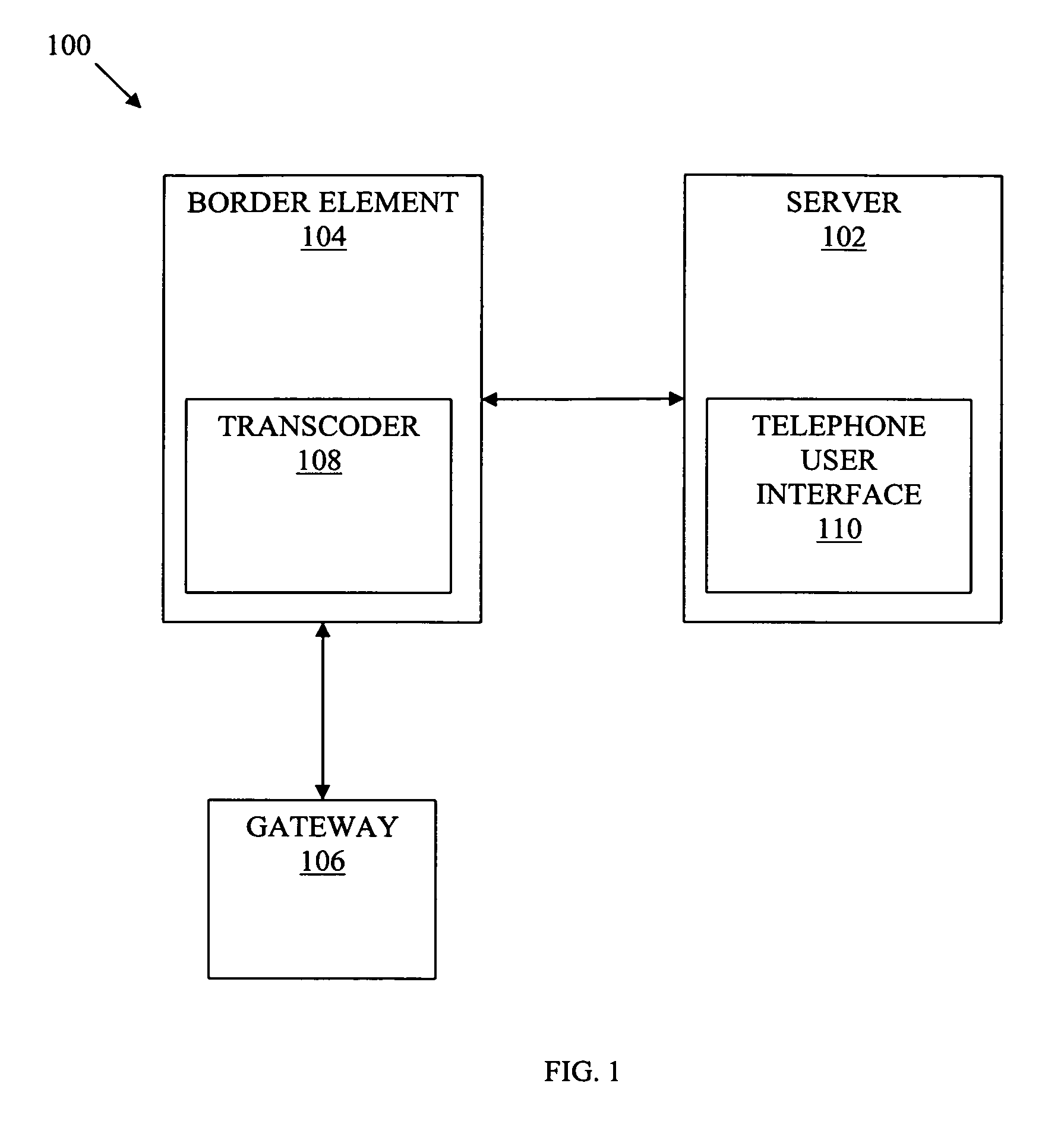
Facsimile transcoding is dynamically invoked for devices that do not support T.38 fax protocol. In this way, a unified messaging platform can process facsimiles from endpoints that are not T.38 capable without using without digital signal processor resources. Dynamic fax transcoding can be performed at a session border controller, allowing transcoding resources to be engaged only for non-T.38 endpoints rather than for all calls on an interface.
Owner:AT&T INTPROP I L P
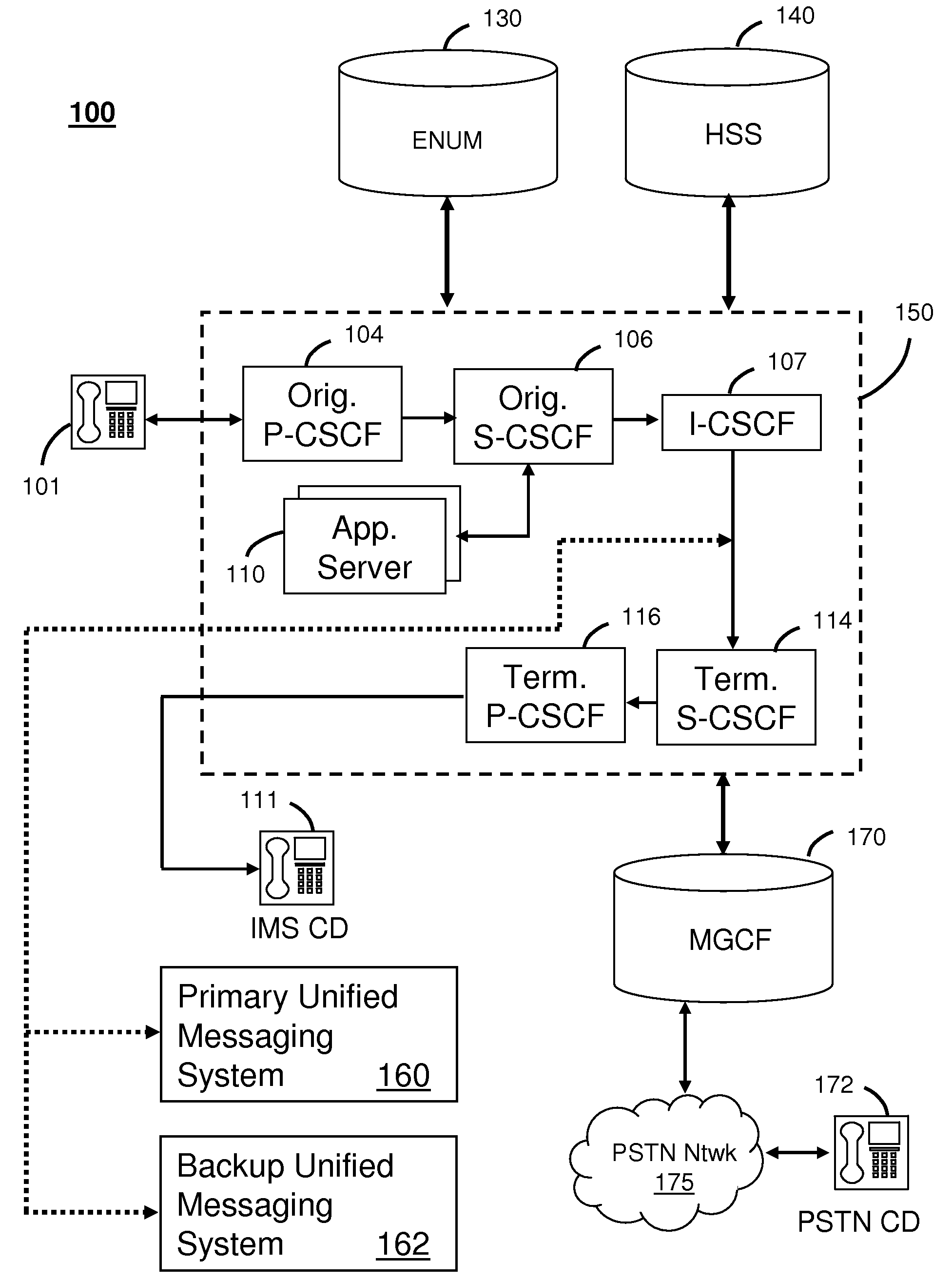
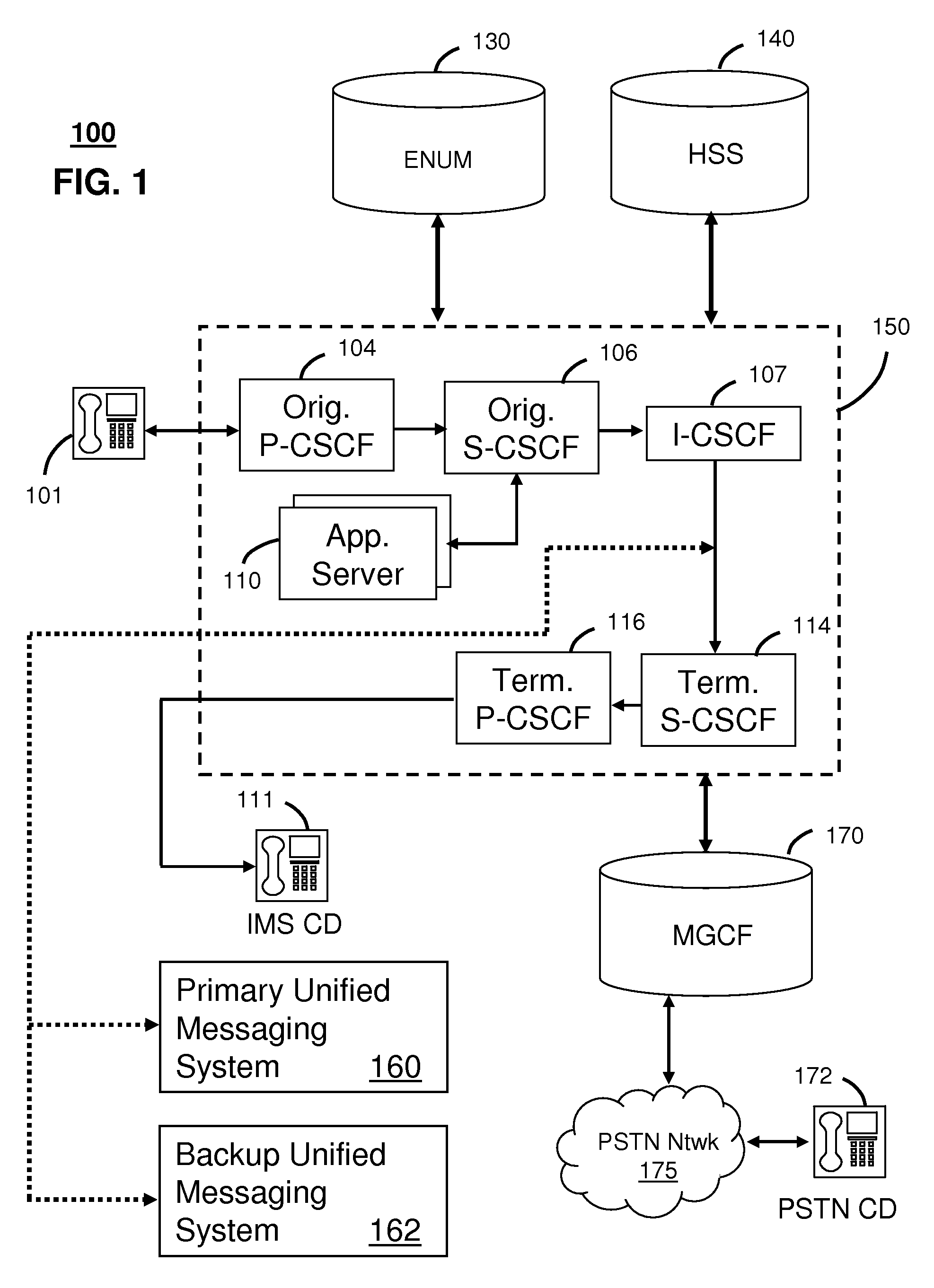
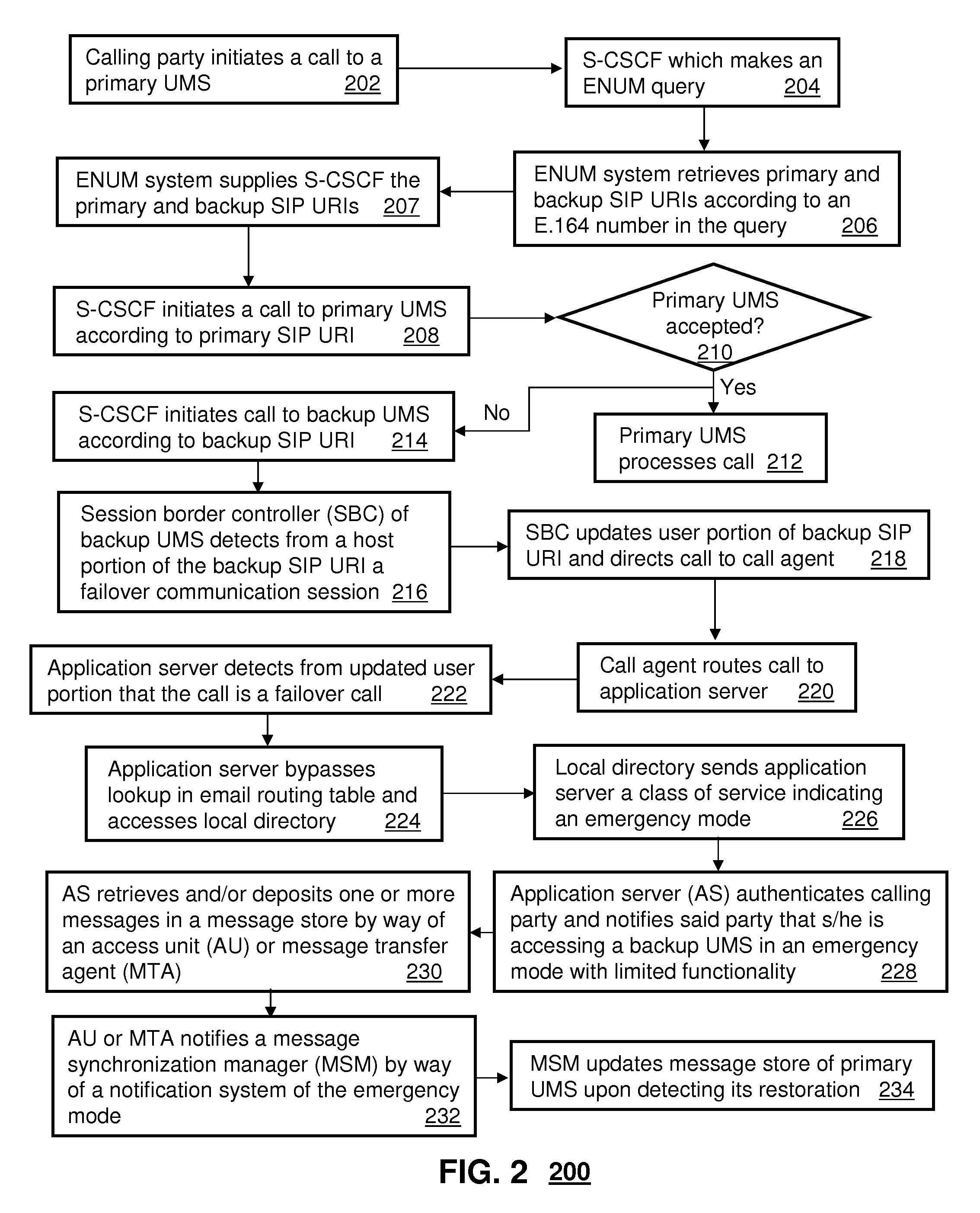
System for alternate communications in an internet protocol multimedia subsystem network
InactiveUS20090093250A1Error preventionAutomatic call-answering/message-recording/conversation-recordingFailoverSession Initiation Protocol
A system that incorporates teachings of the present disclosure may include, for example, a Unified Messaging System (UMS) having a Session Border Controller (SBC) to receive a Session Initiation Protocol Uniform Resource Identifier (SIP URI), detect from a host portion of the SIP URI that the SIP URI is associated with a failover communication session, update a user portion of the SIP URI to indicate a failure disposition, and route the updated SIP URI to a call agent of the UMS. Additional embodiments are disclosed.
Owner:AT&T INTPROP I L P
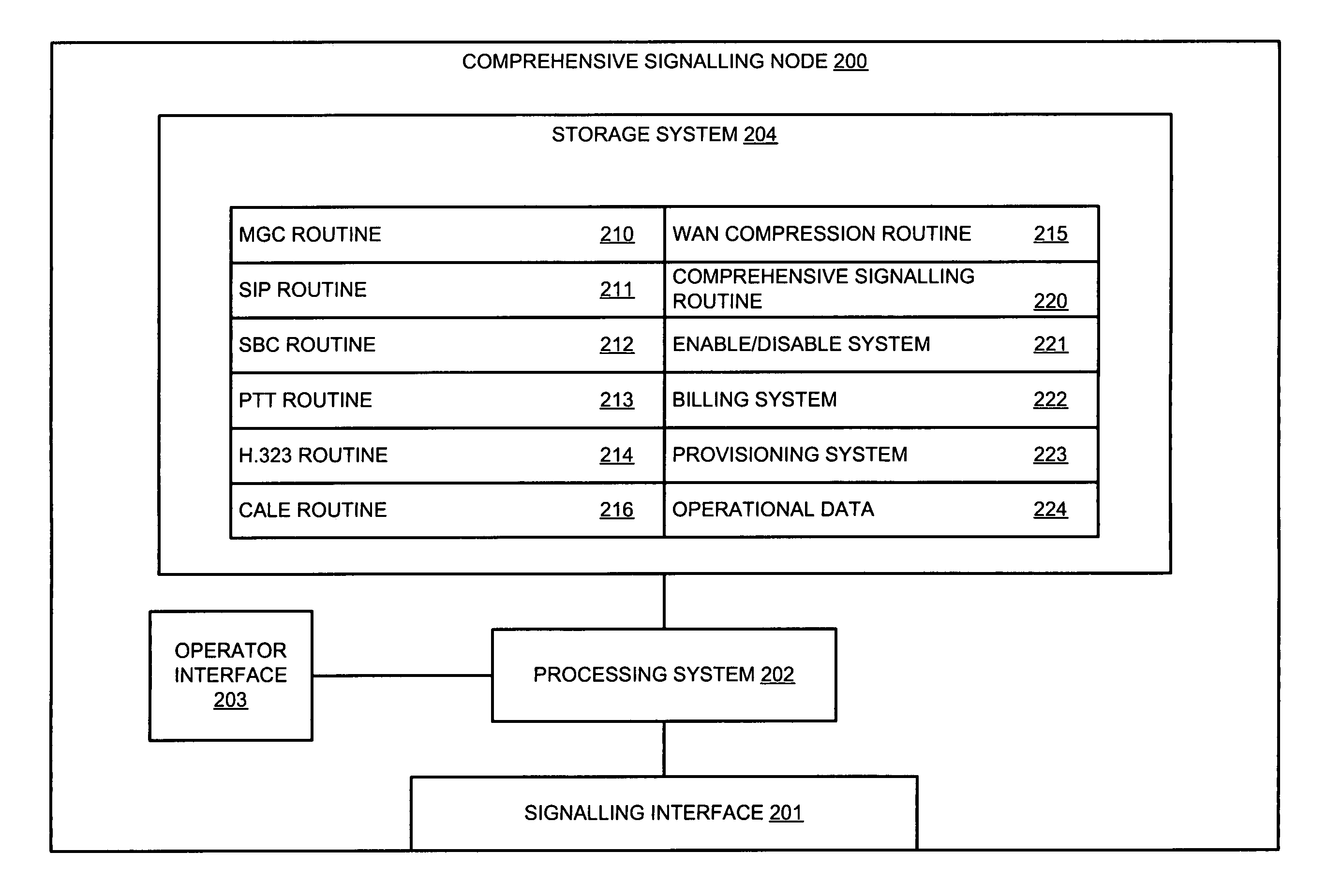
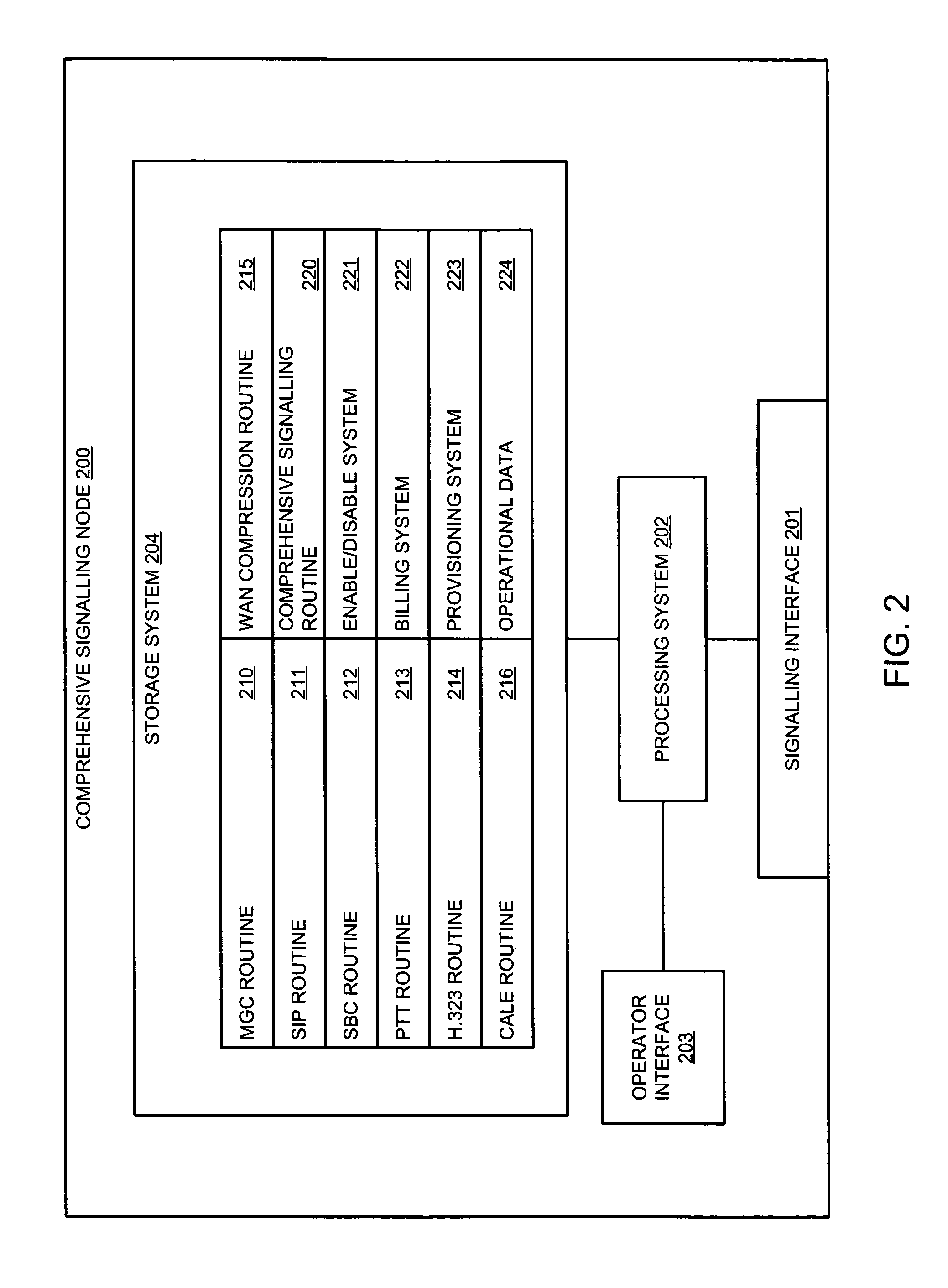
Comprehensive signaling node and method, including a plurality of signaling routines
InactiveUS7564855B1Interconnection arrangementsDigital data processing detailsSession Initiation ProtocolPush-to-talk
Owner:SPRINT CORPORATION
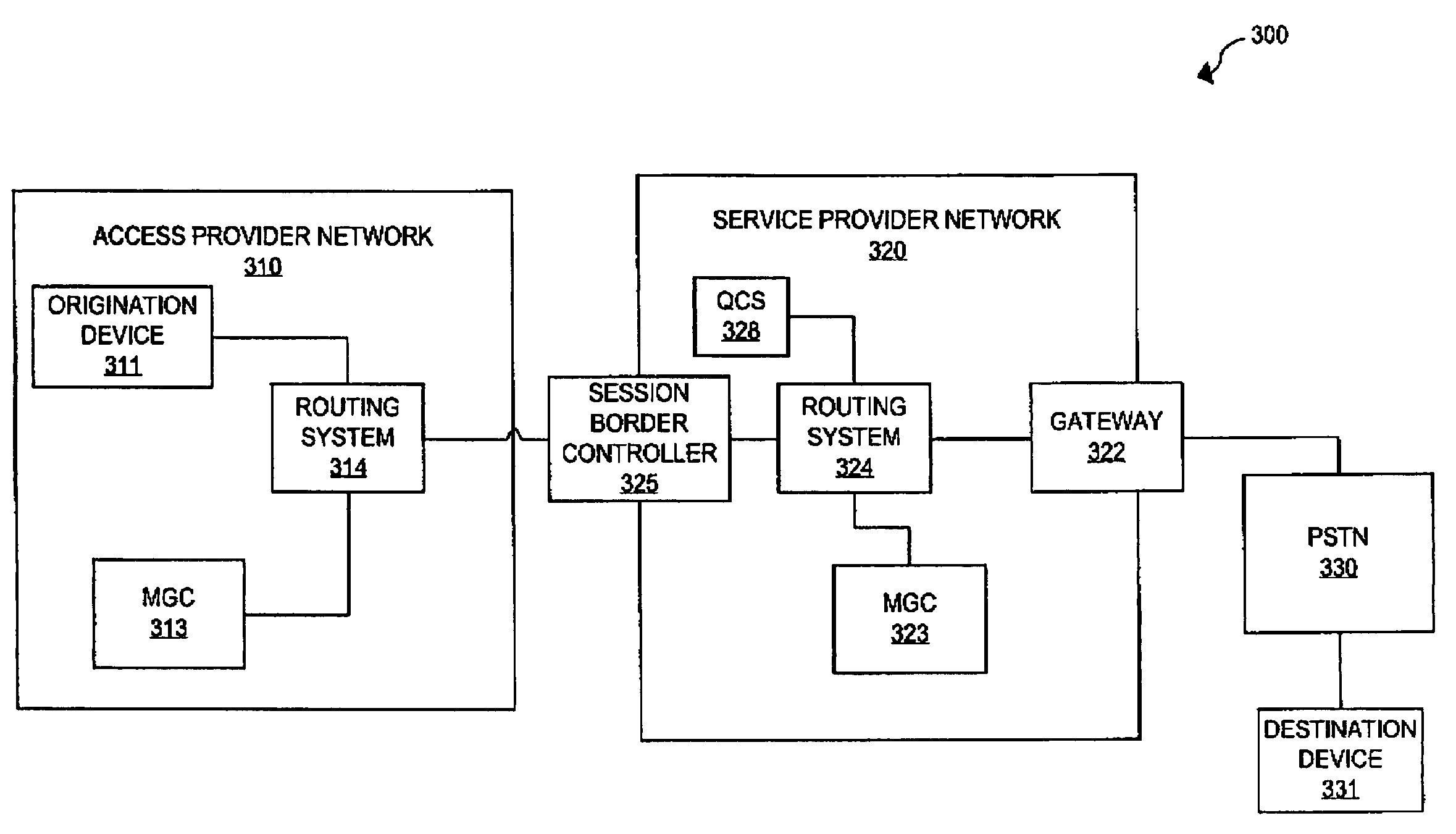
Quality correlation testing
ActiveUS7463634B1Effectively and efficiently ensureData switching by path configurationMultiple digital computer combinationsService provisionClient-side
A session border controller is configured to receive a first session quality message for a session transferred from an origination device in an access provider network to a gateway in the service provider network, receive a second session quality message for the session transferred from the gateway to the origination device, and transfer the first session quality message and the second session quality message to a quality correlation system. The quality correlation system is configured to receive the first session quality message and the second session quality message from the session border controller, receive signaling information for the session, process the signaling information with the first session quality message and the second session quality message to determine a session status message for the session, and transfer the session status message to a client device. The client device is configured to receive and display the session status message.
Owner:T MOBILE INNOVATIONS LLC
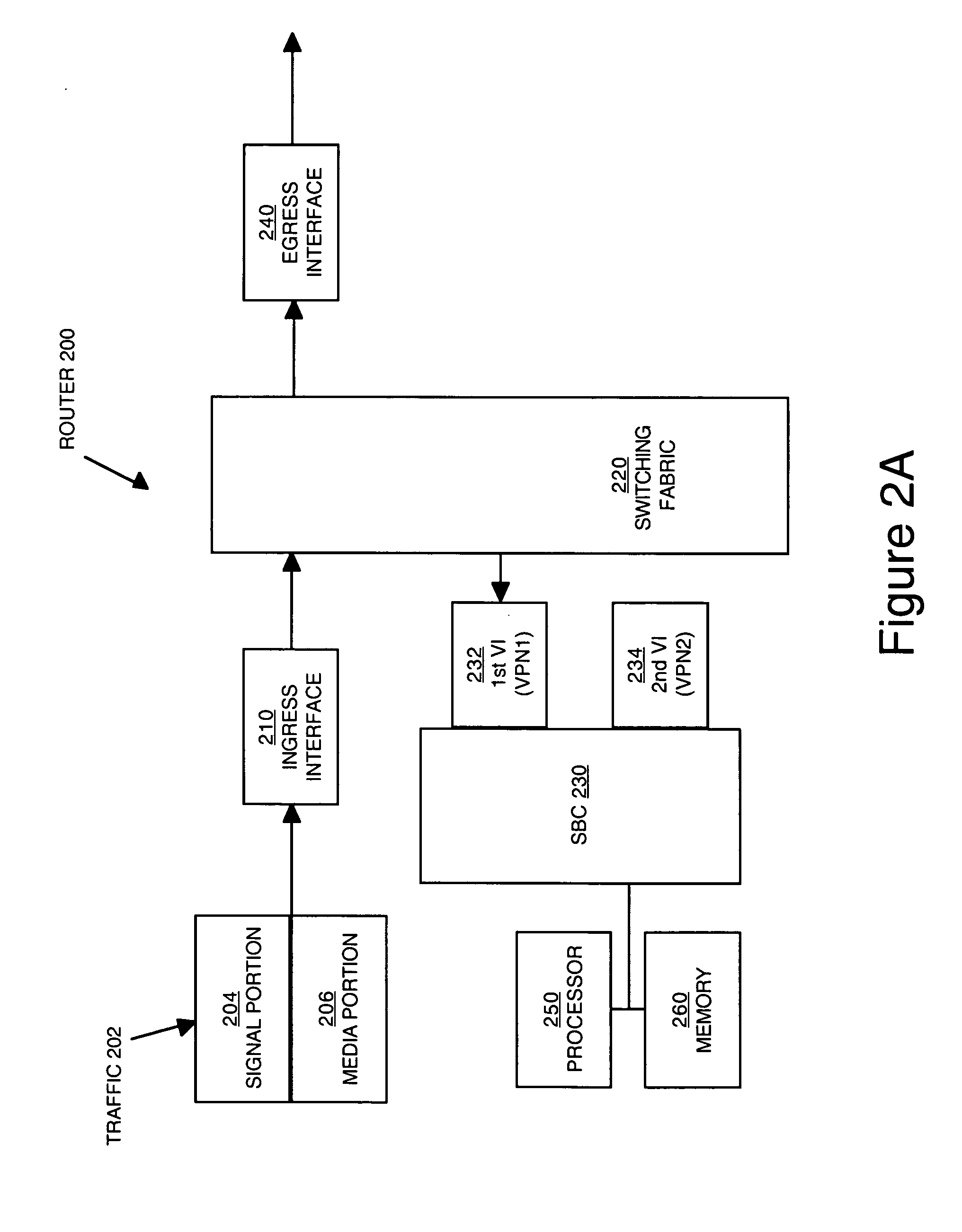
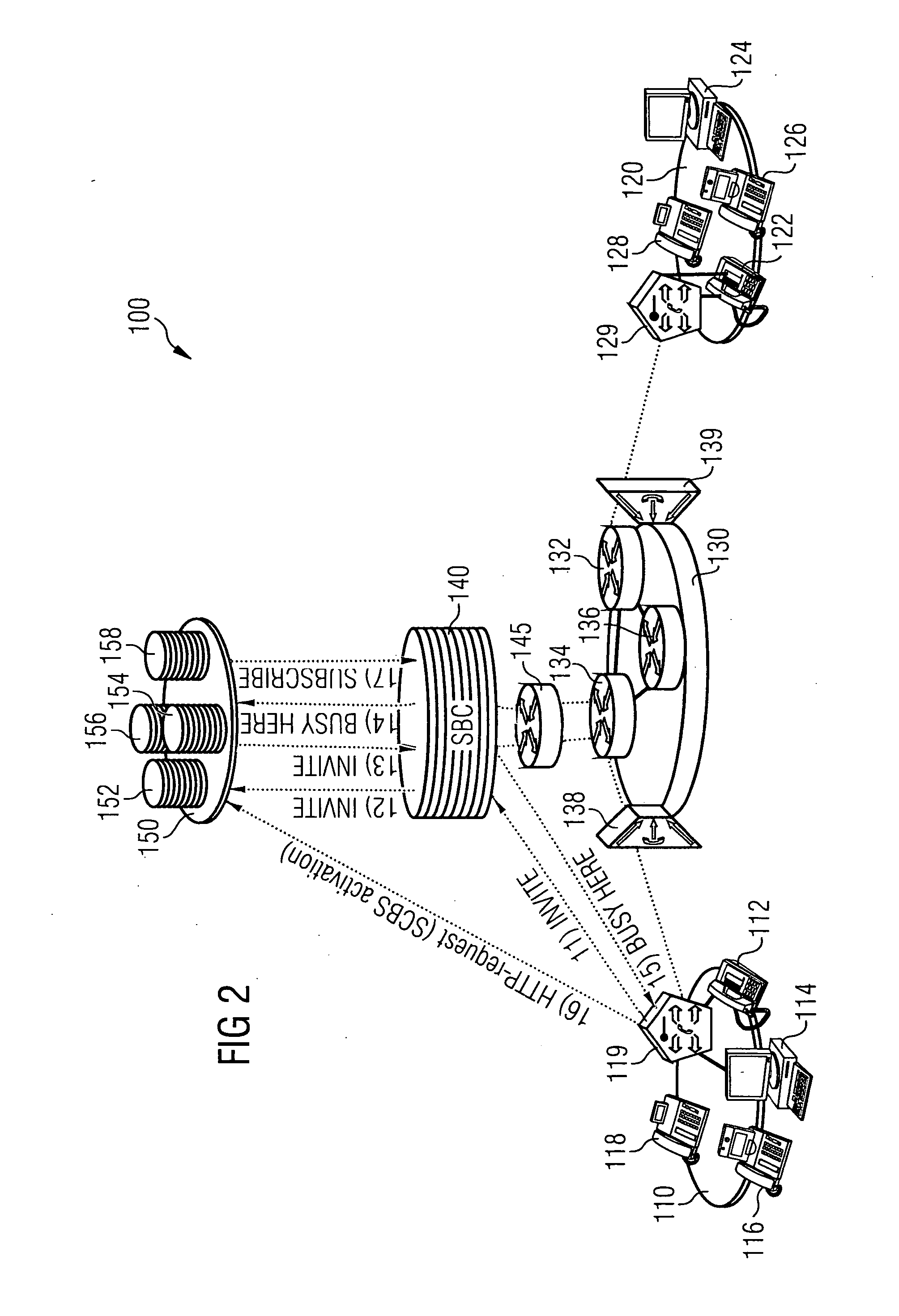
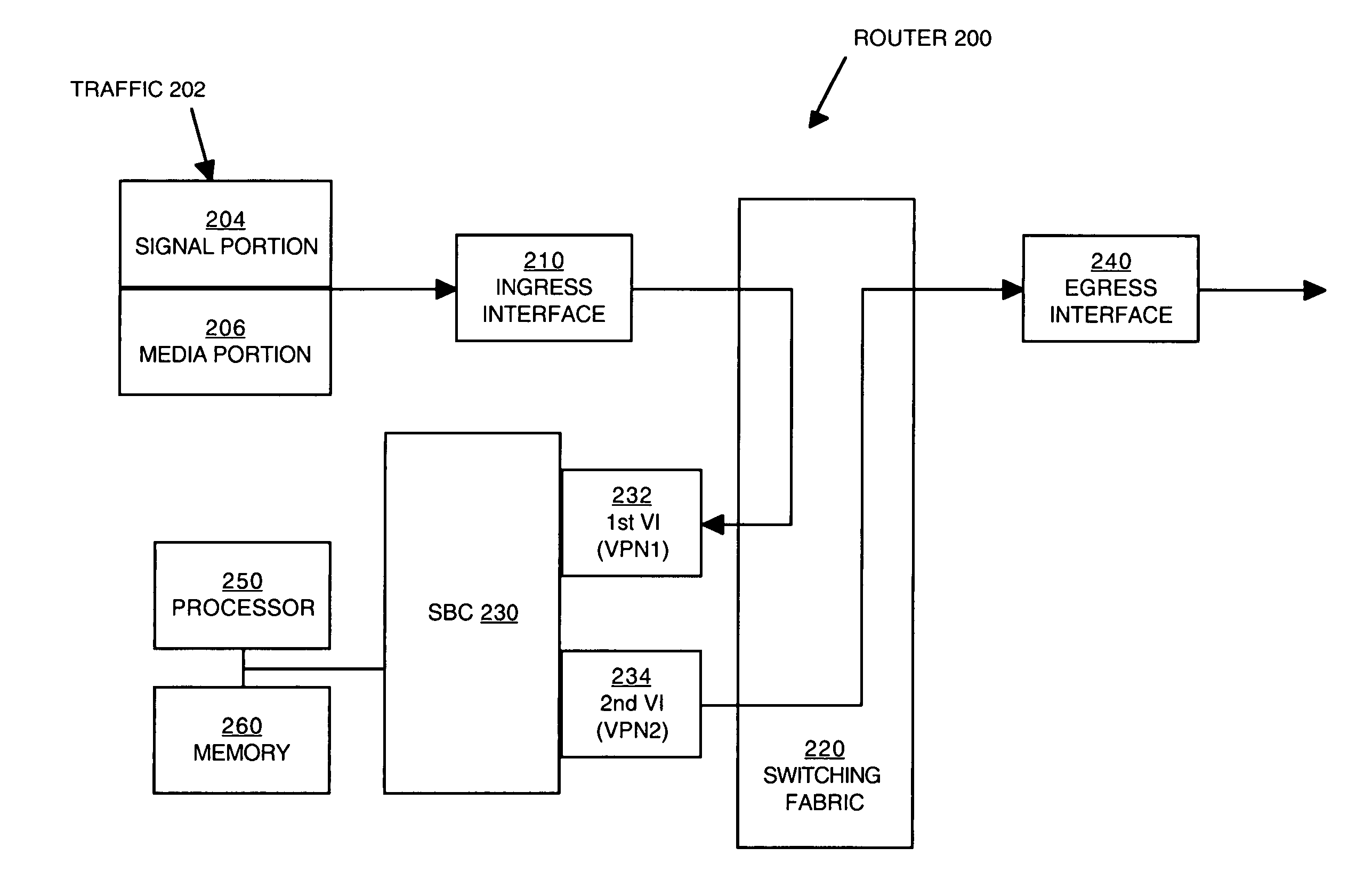
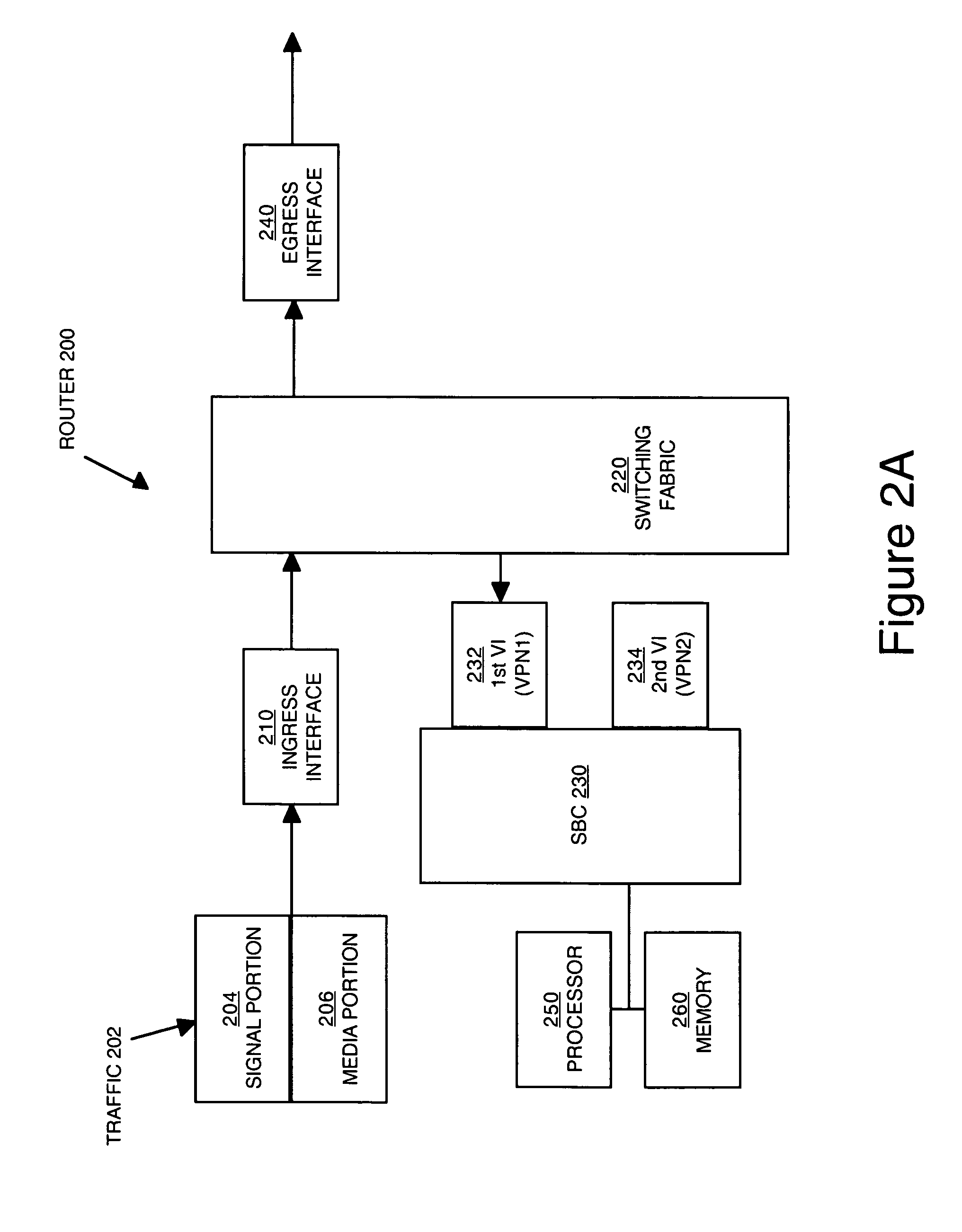
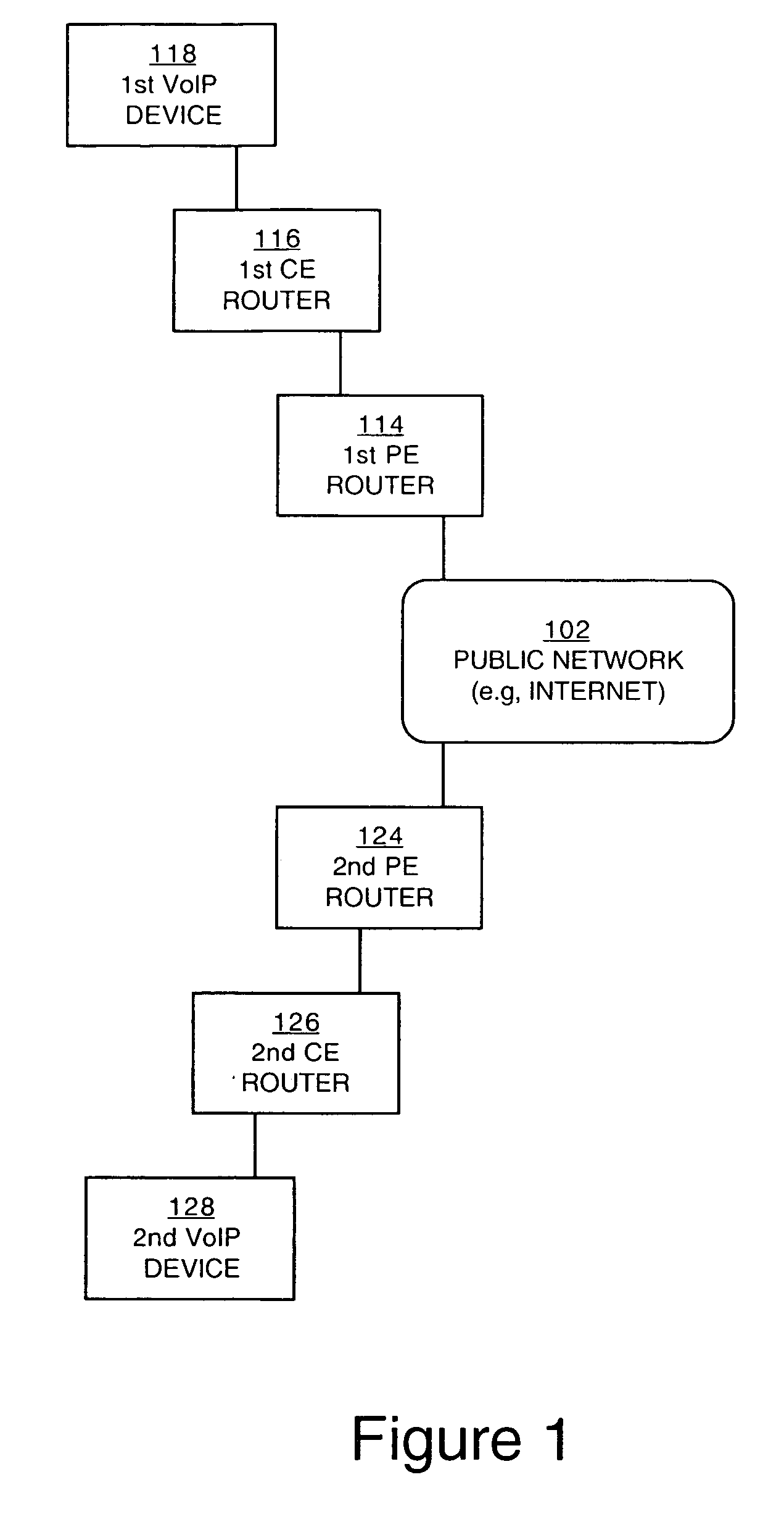
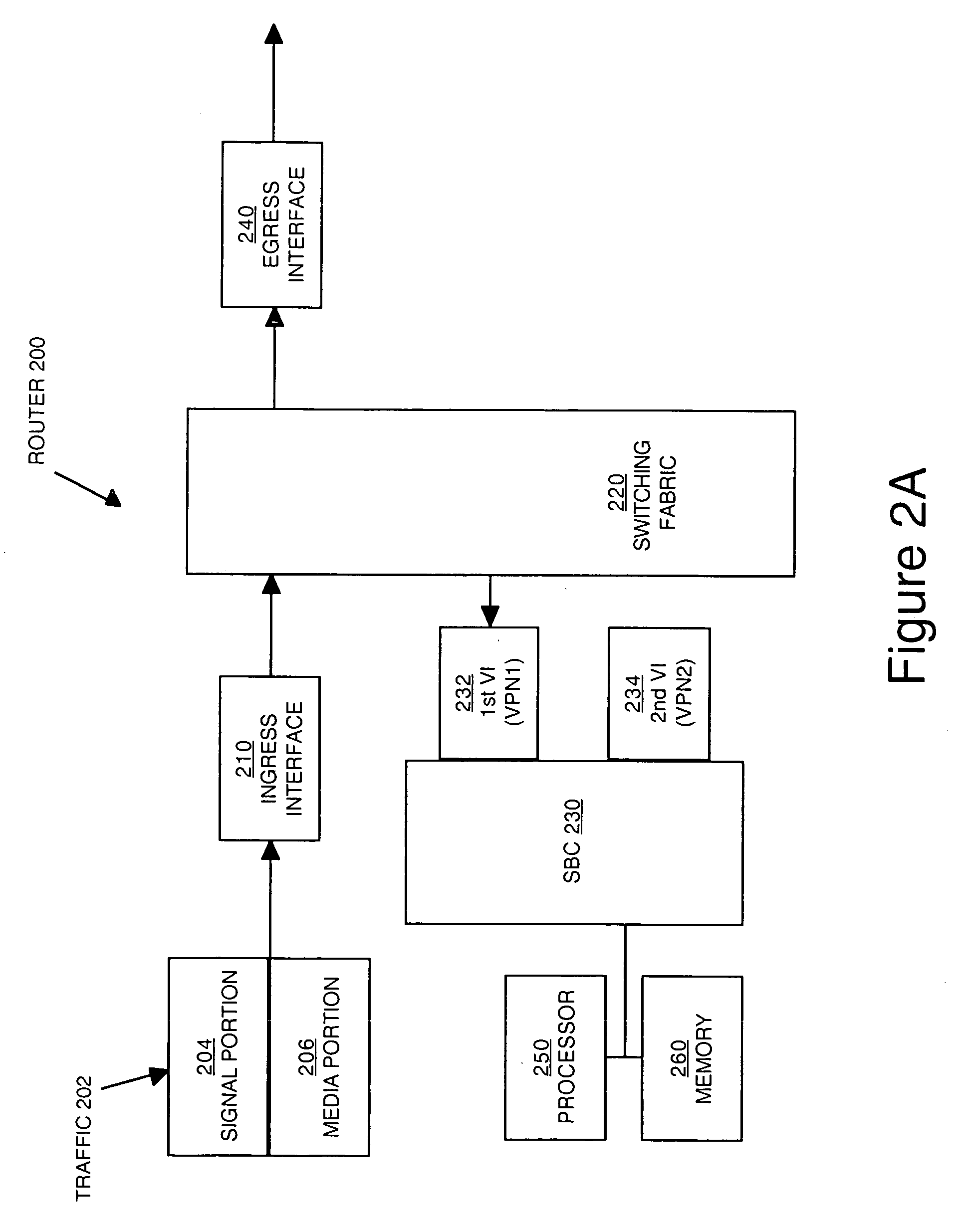
Managing traffic within and between virtual private networks when using a session border controller
Methods and devices for managing traffic are described. Traffic from a source in a virtual private network (VPN) is received. The traffic is directed to a virtual interface that is designated to receive traffic from the VPN. The virtual interface is configured to associate the traffic with an identifier that uniquely identifies the VPN to a session border controller (SBC). The SBC can use the identifier to determine whether the source and the destination of the traffic are in the same VPN.
Owner:CISCO TECH INC
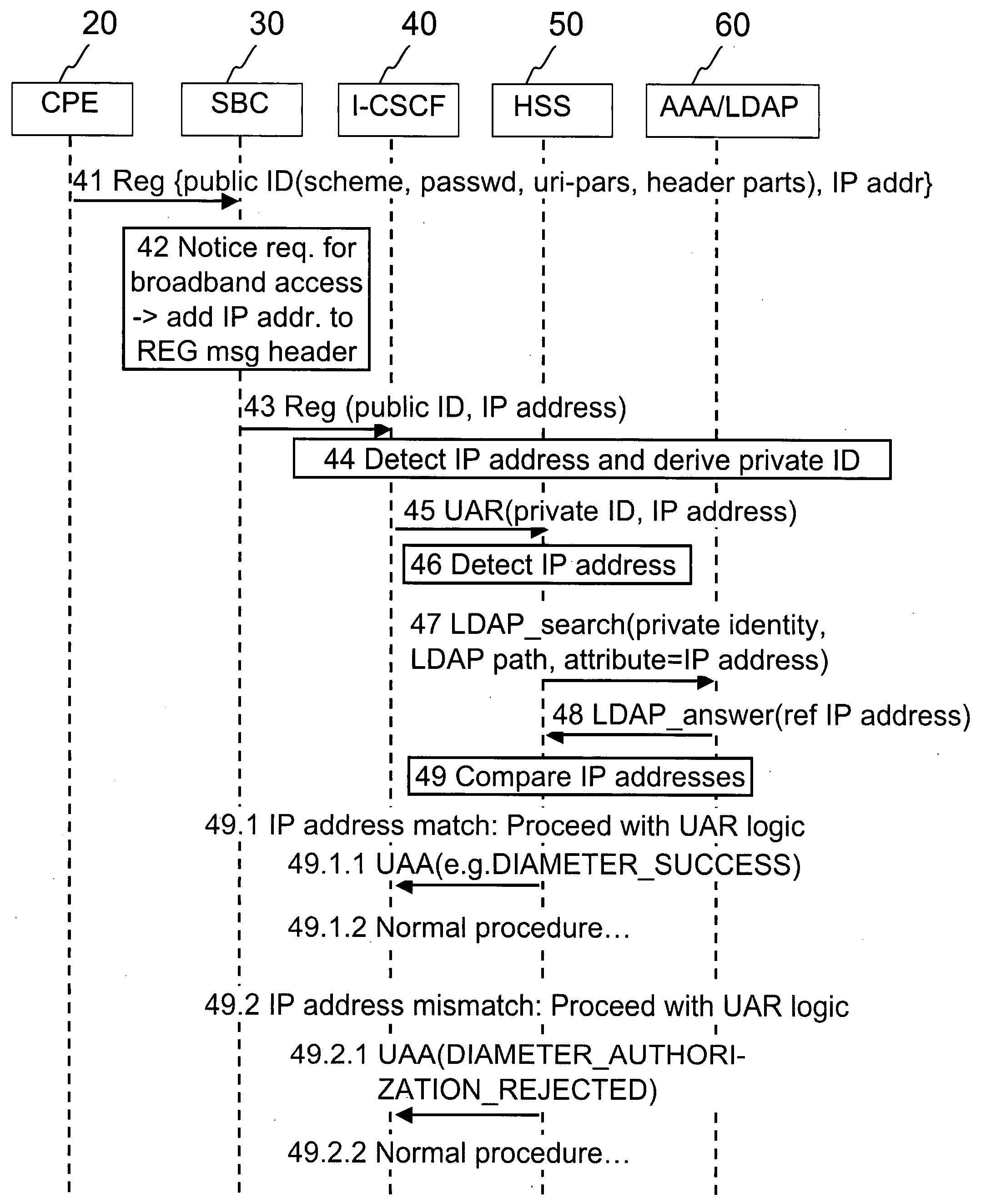
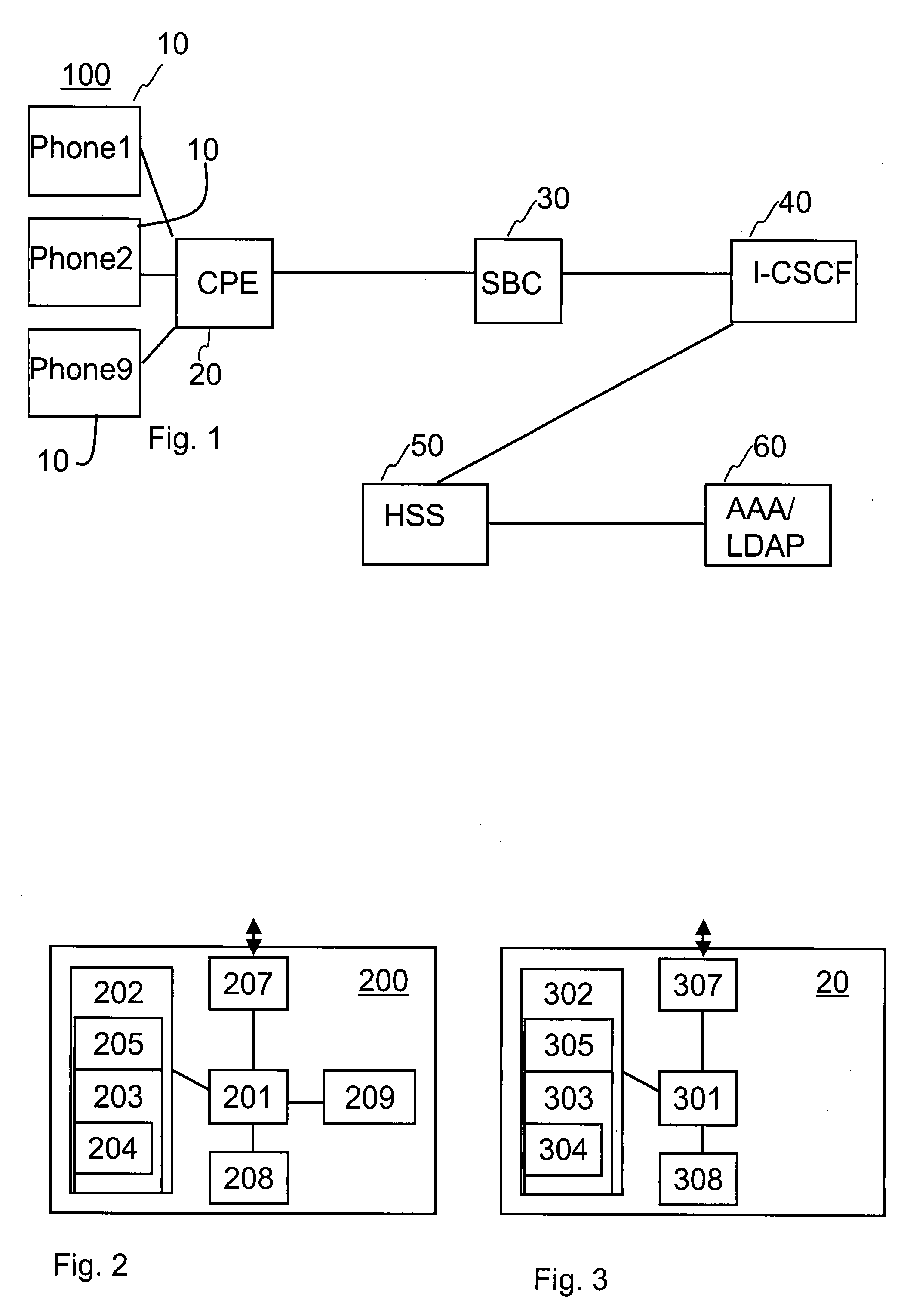
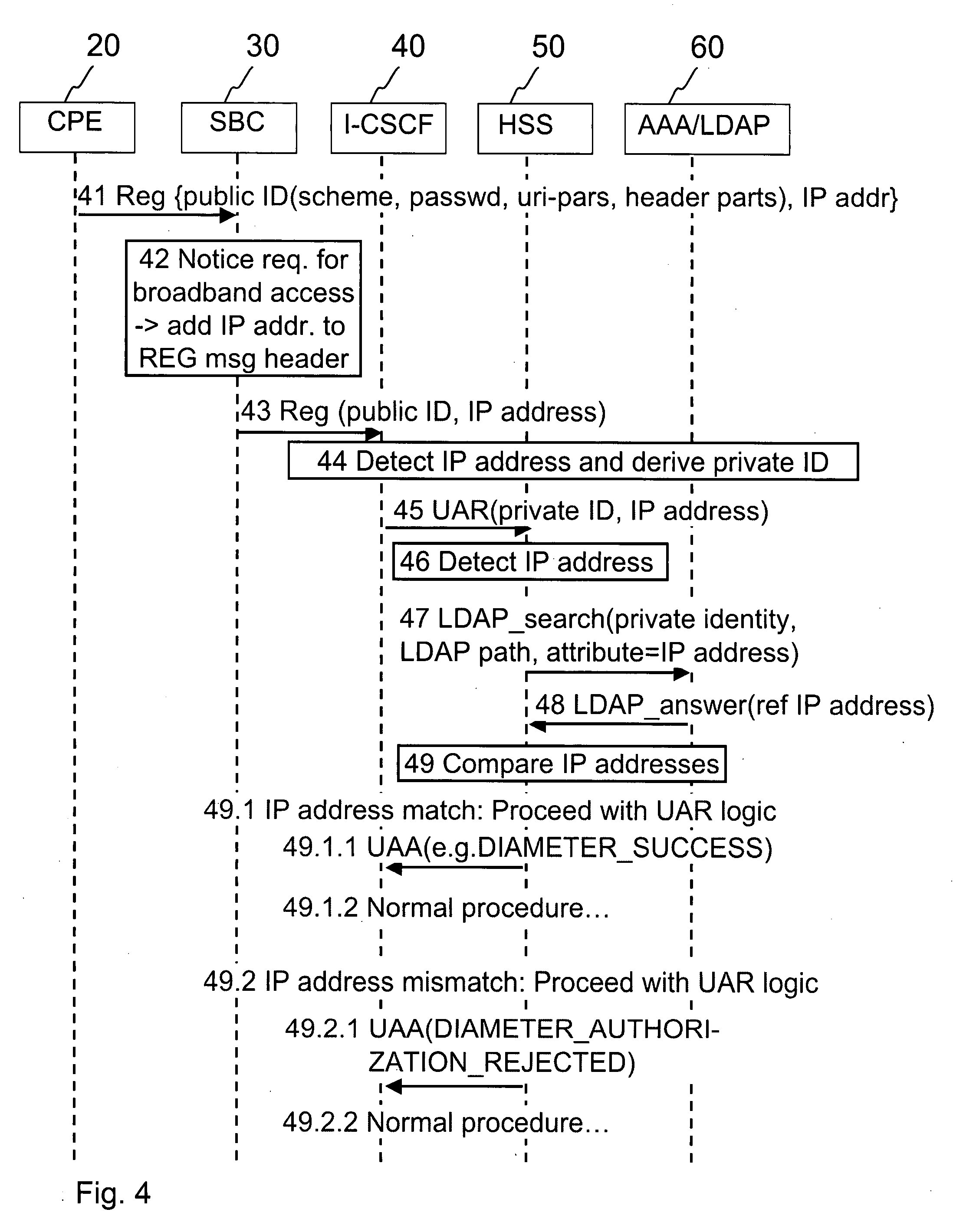
Subscriber access authorization
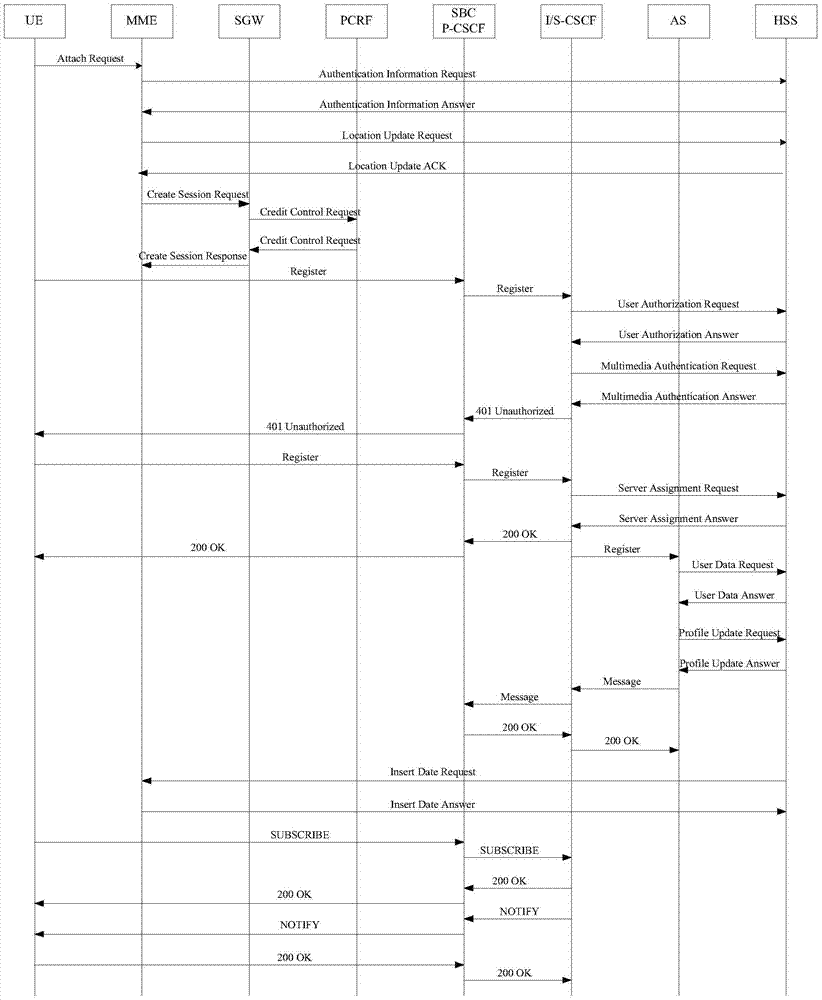
A method for registering a session initiation protocol (SIP) client to an internet protocol multimedia subsystem (IMS), in which a SIP client having a given IP address, public identity and private identity sends a registration request to a session border controller (SBC) for registering the public identity to the IMS, the SBC responsively causes an authorization request to be sent to another network entity in the IMS, the authorization request indicating the IP address of the SIP client and a private identity, the another network entity obtaining from an LDAP / AAA server a reference address based on the private identity and deciding whether to allow the authorization of the public identity to the IMS based on the correspondence between the reference address and the IP address of the SIP client.
Owner:NOKIA TECHNOLOGLES OY
Method and apparatus for network-based admission control using path-coupled quality of service signaling
ActiveUS20070008882A1Improved admission controlImproved of medium path routingError preventionTransmission systemsAccess networkNetwork control
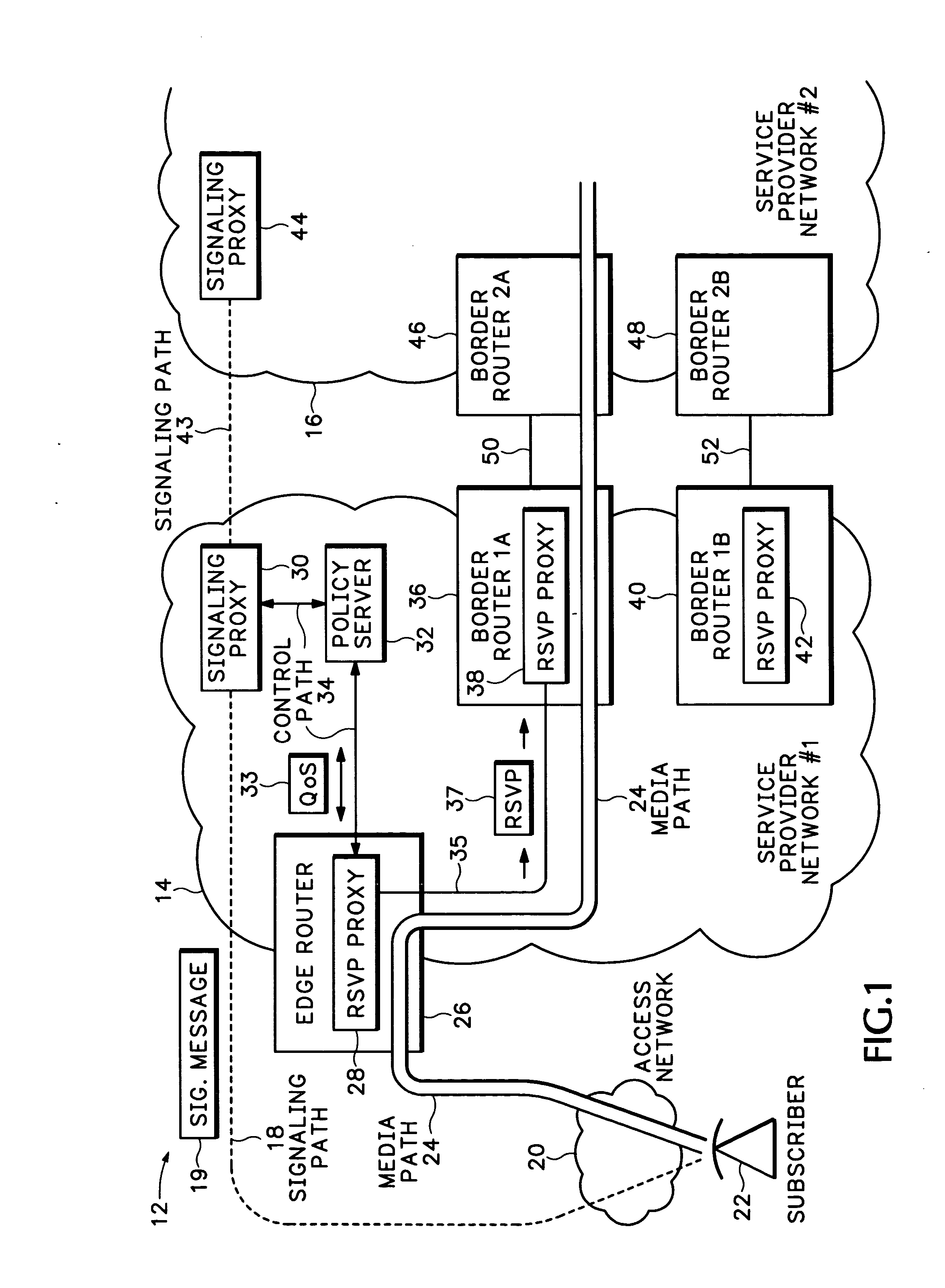
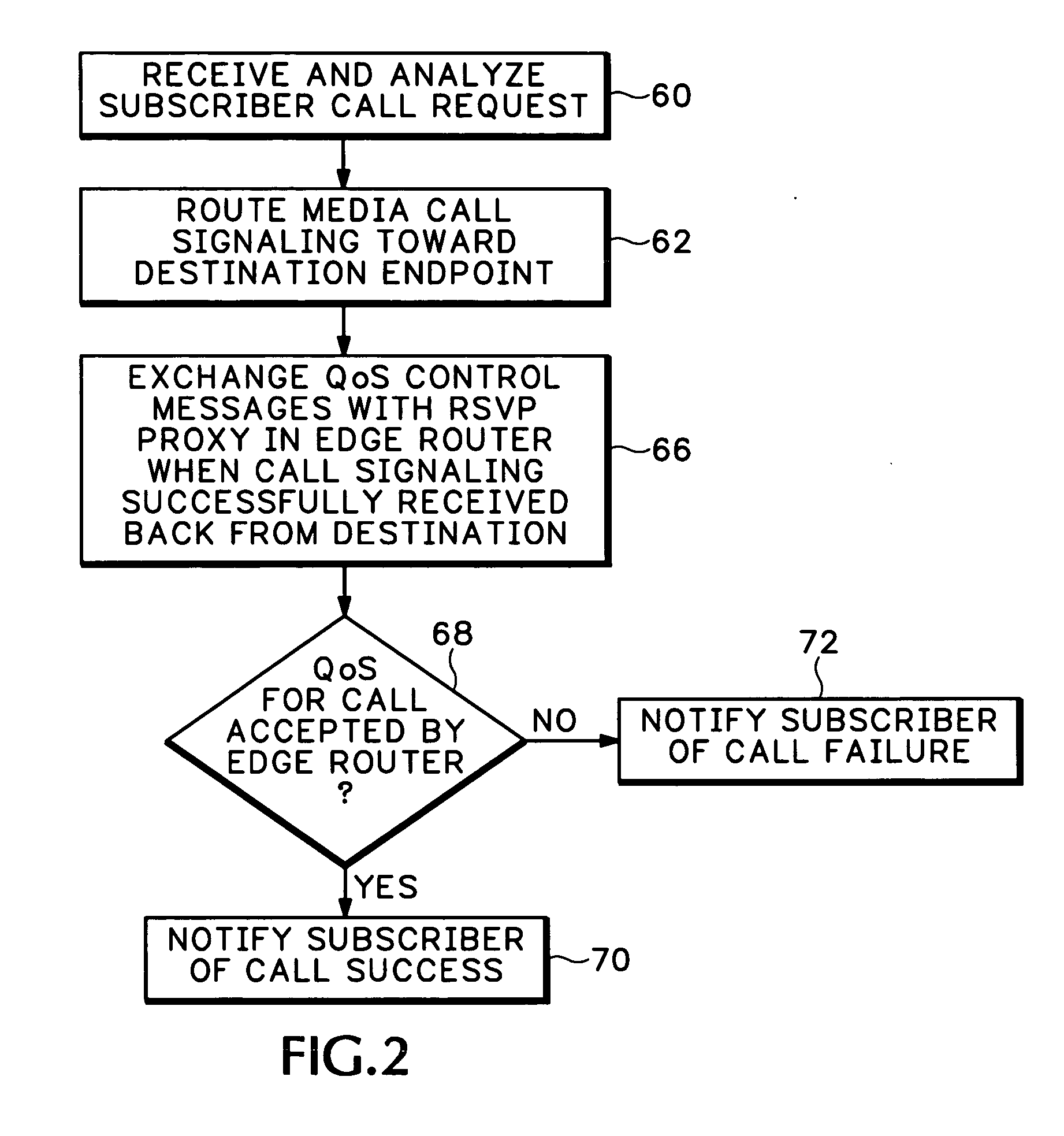
A Resource ReSerVation Protocol (RSVP) proxy is used in combination with a signaling proxy to provide improved admission control, Quality of Service (QoS) reservation, and media path routing. This avoids entangling call signaling with media plane functions as required with Session Border Controllers (SBCs). A QoS access network control scheme, such as Packet Cable Multi-Media (PCMM) and / or Dynamic Quality of Service (DQoS), is conventionally used to set up QoS and other flow states on an access network. However, the gate parameters established during this access operation are also provided to an RSVP proxy in an edge router. The gate parameters trigger the RSVP proxy to attempt to establish a QoS reservation over the packet network toward a media flow destination. If admission control for the QoS reservation is successful, the edge router permits the signaling proxy to complete the media call.
Owner:CISCO TECH INC
Method of Providing Session Mobility
ActiveUS20070189220A1Improved session mobilityKeep it privateMultiplex communicationConnection managementSession Initiation ProtocolTelecommunications network
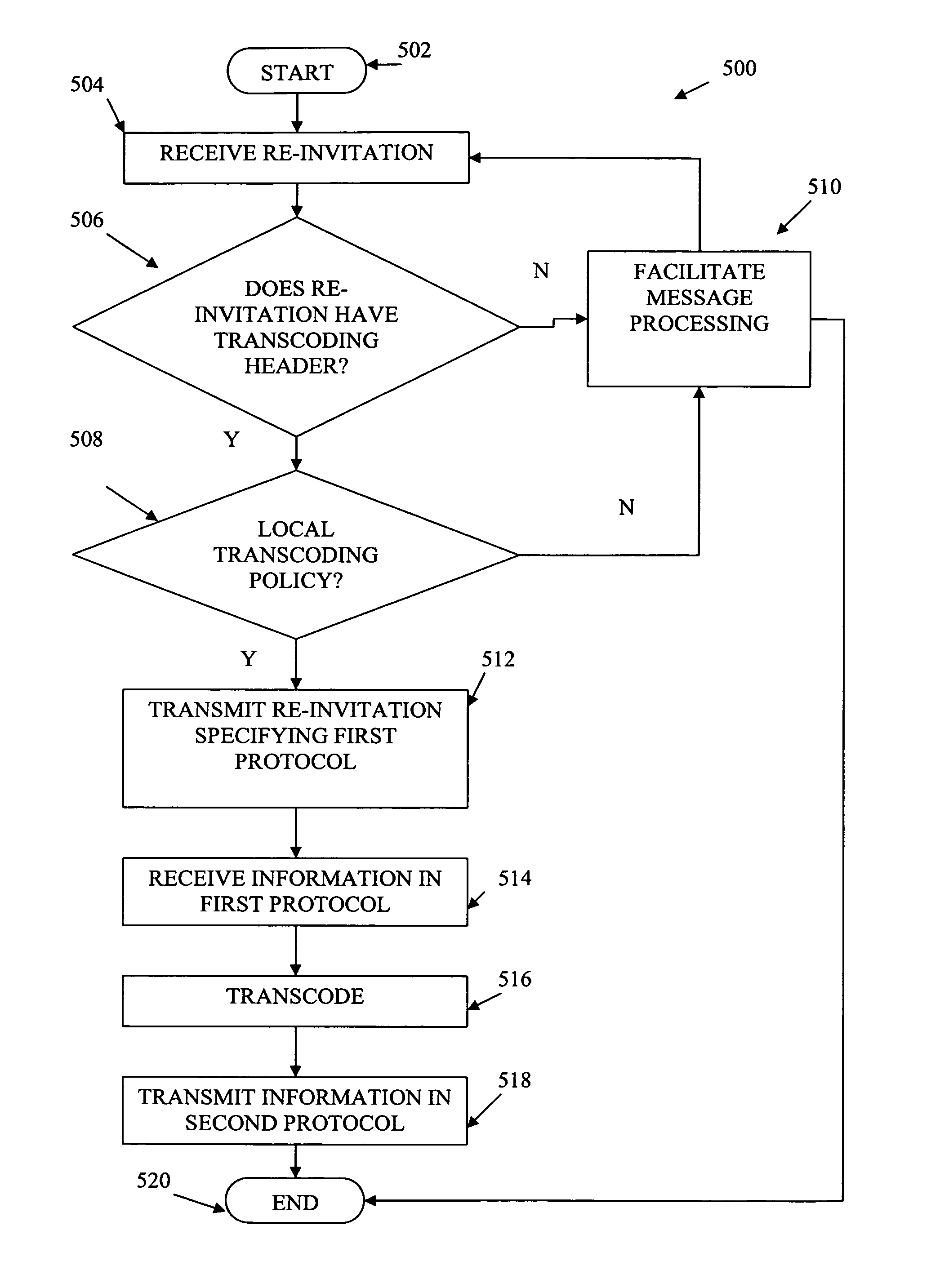
The invention concerns a method of providing session mobility to an IP based real-time session in a telecommunications network whereby the telecommunications network uses the session initiation protocol for the setup and control of the session. The session comprises a media stream between a first terminal associated to a first network access point of the telecommunications network and a second terminal associated to a second network access point of the telecommunications network. A re-invite session initiation protocol signalling message related to session mobility of said session is intercepted at a session-related session border controller of the telecommunications network. Said session border controller initiates a corresponding session hand-over of said session. In said session hand-over, the media stream of said session is redirected to a new network access point of the first terminal and / or a new terminal.
Owner:ALCATEL LUCENT SAS
System and method for enabling communication sessions in a network environment
ActiveUS20100082557A1Digital data processing detailsMultiple digital computer combinationsSession Initiation ProtocolPrivate network
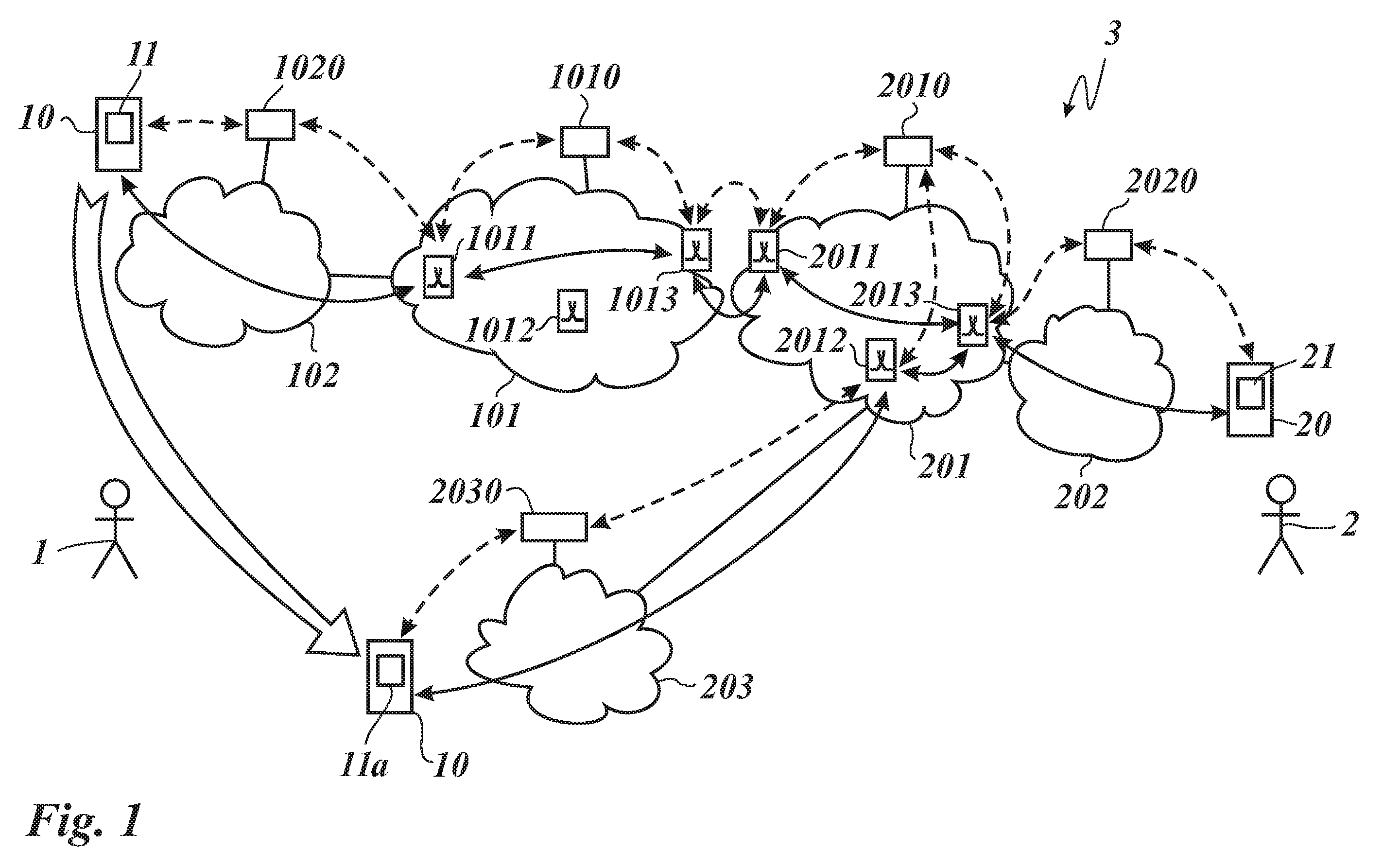
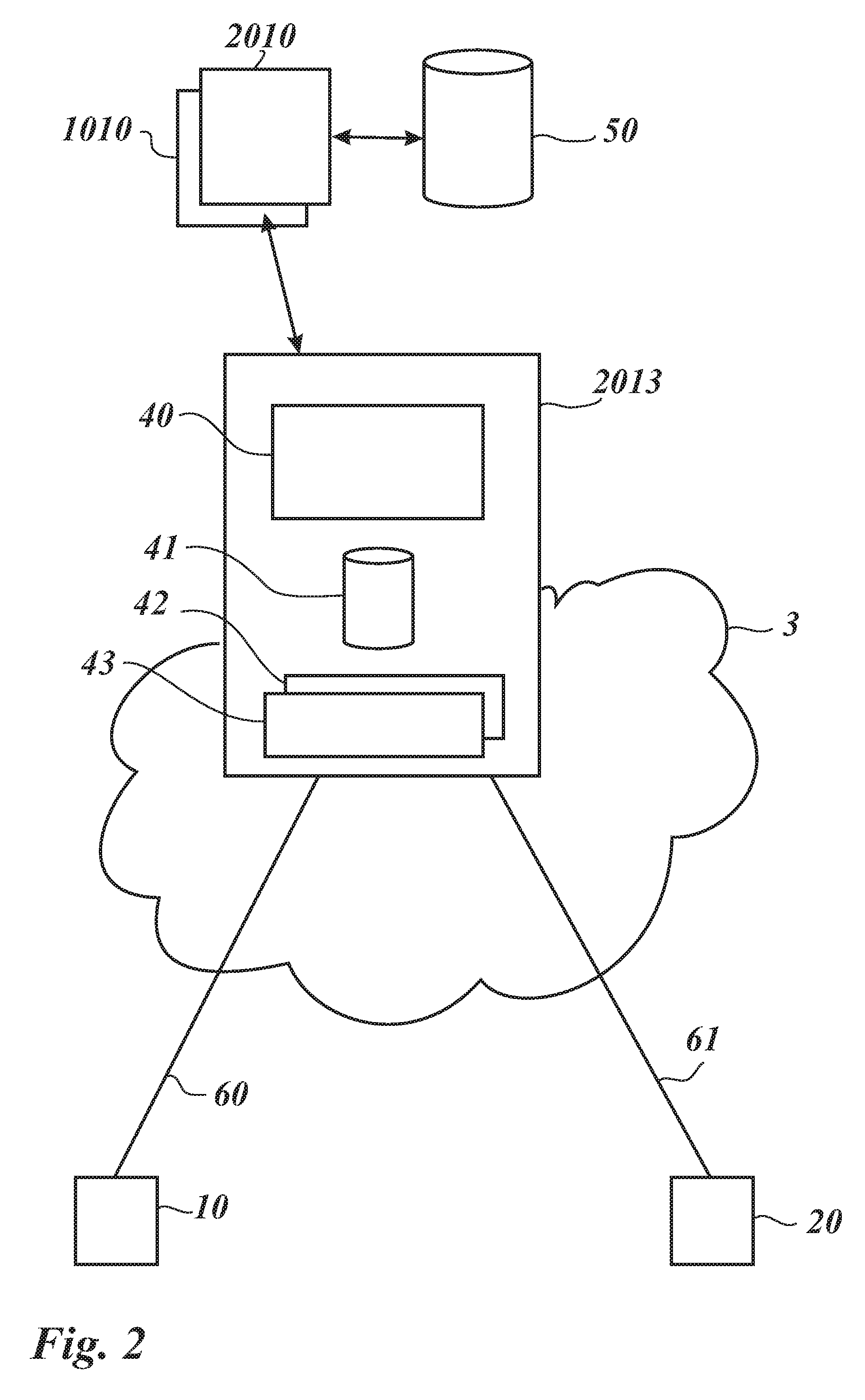
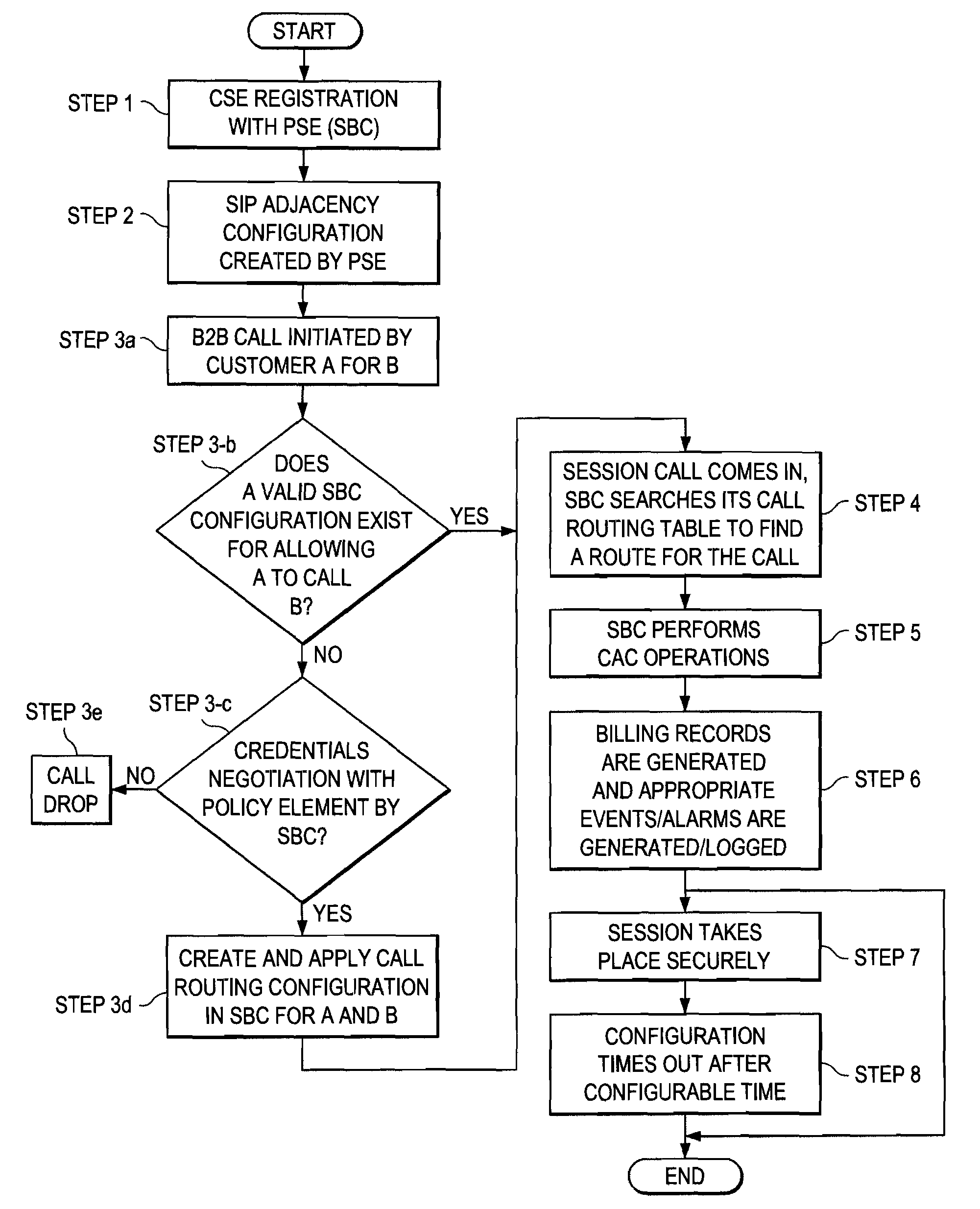
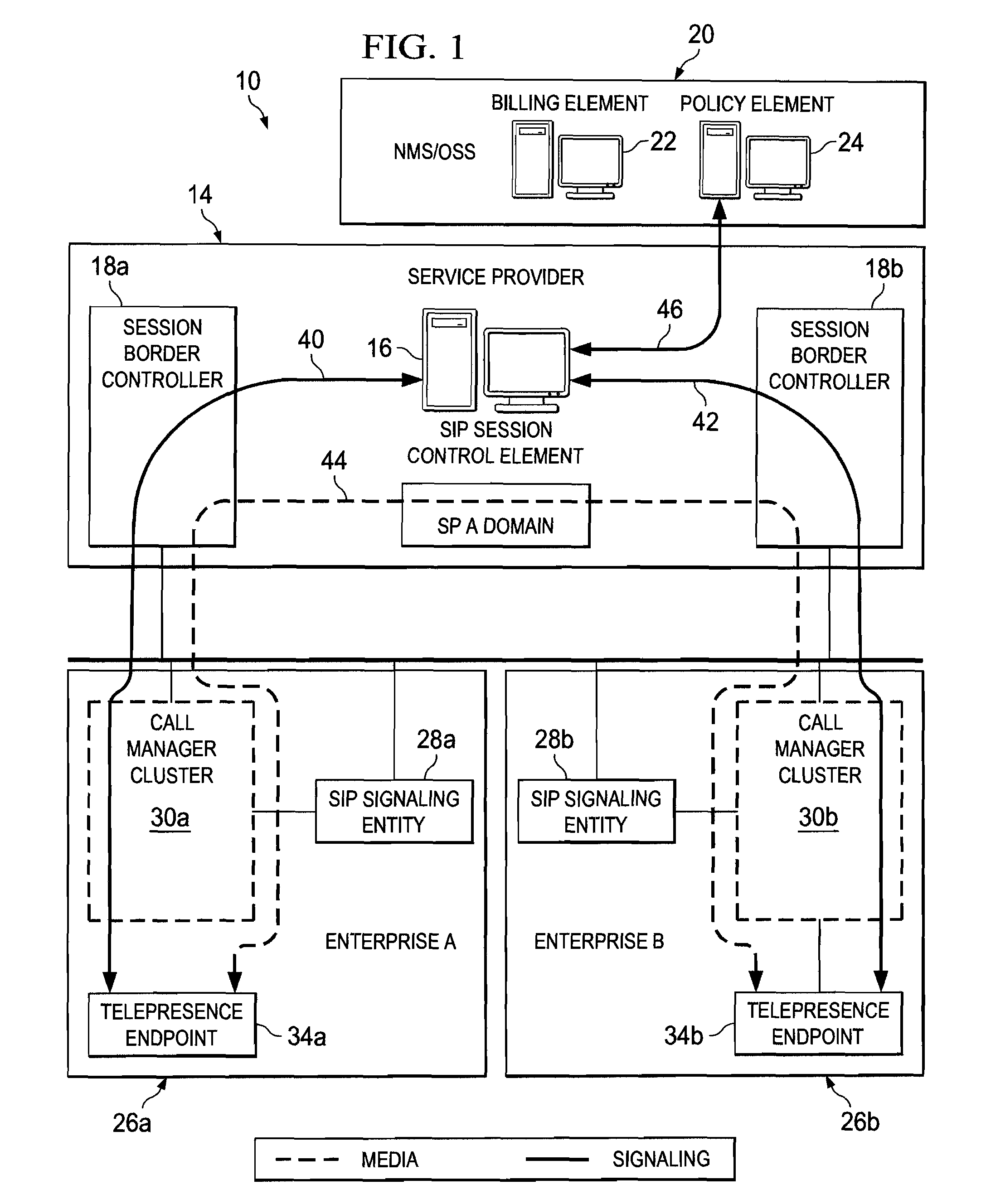
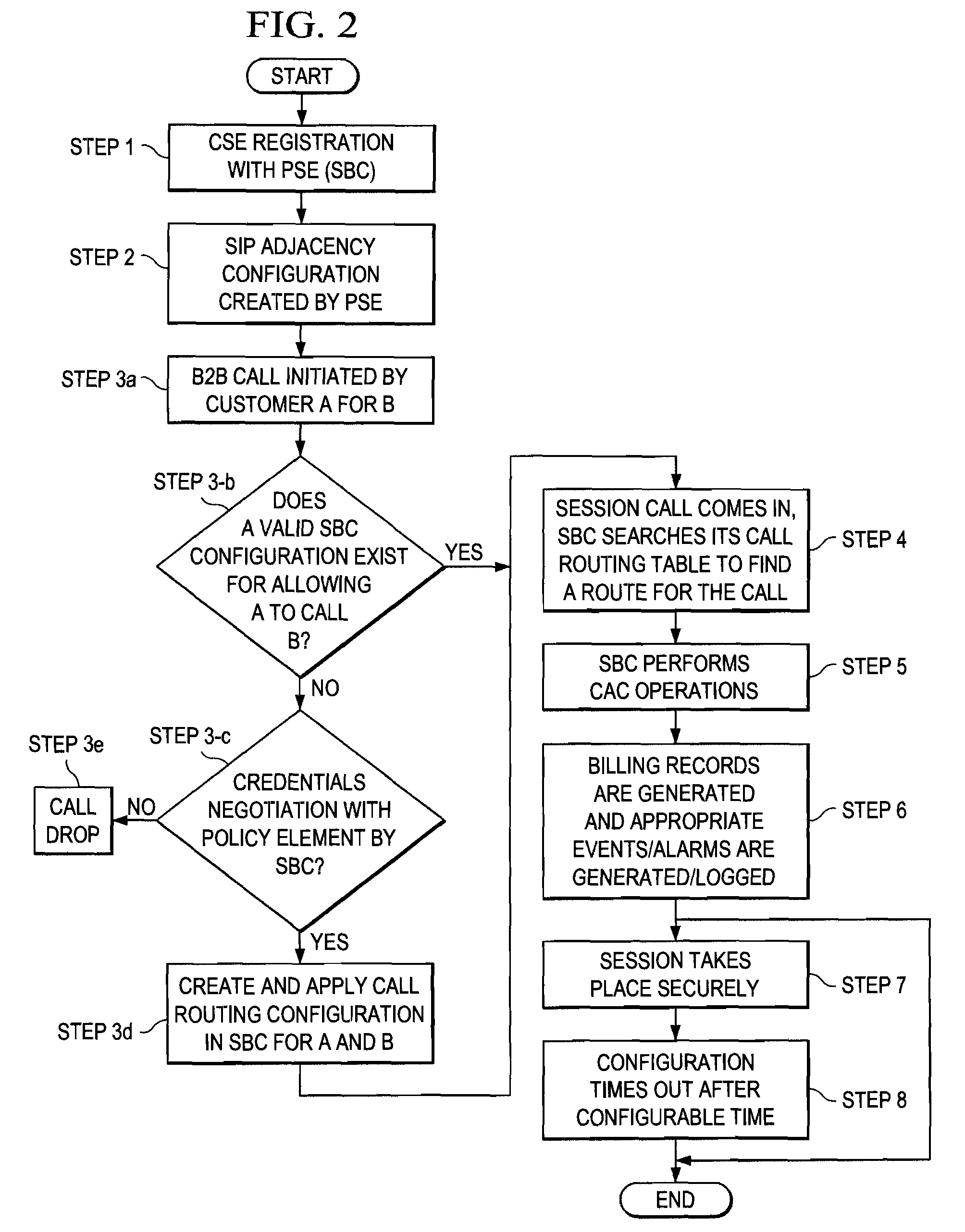
A method is provided in one example implementation and the method includes receiving a query for a policy (e.g., a multi-media session) that pertains to a selected one of first and second endpoints. Each endpoint interfaces with their respective session initiation protocol entity, which interacts with a session border controller (SBC). The method further includes negotiating credentials via a policy element and a selected SBC and determining, via a selected policy within the policy element, whether a requested communication session is prohibited or conducted between the endpoints. In more specific embodiments, each SBC makes a mapping between signaling entity information and pre-configured SBC virtual private network (VPN) information used for dynamic configuration of the communication session, and wherein a SIP [or other communication protocol] adjacency configuration is created, where adjacency characteristics are defined for each enterprise in which the endpoints reside.
Owner:CISCO TECH INC
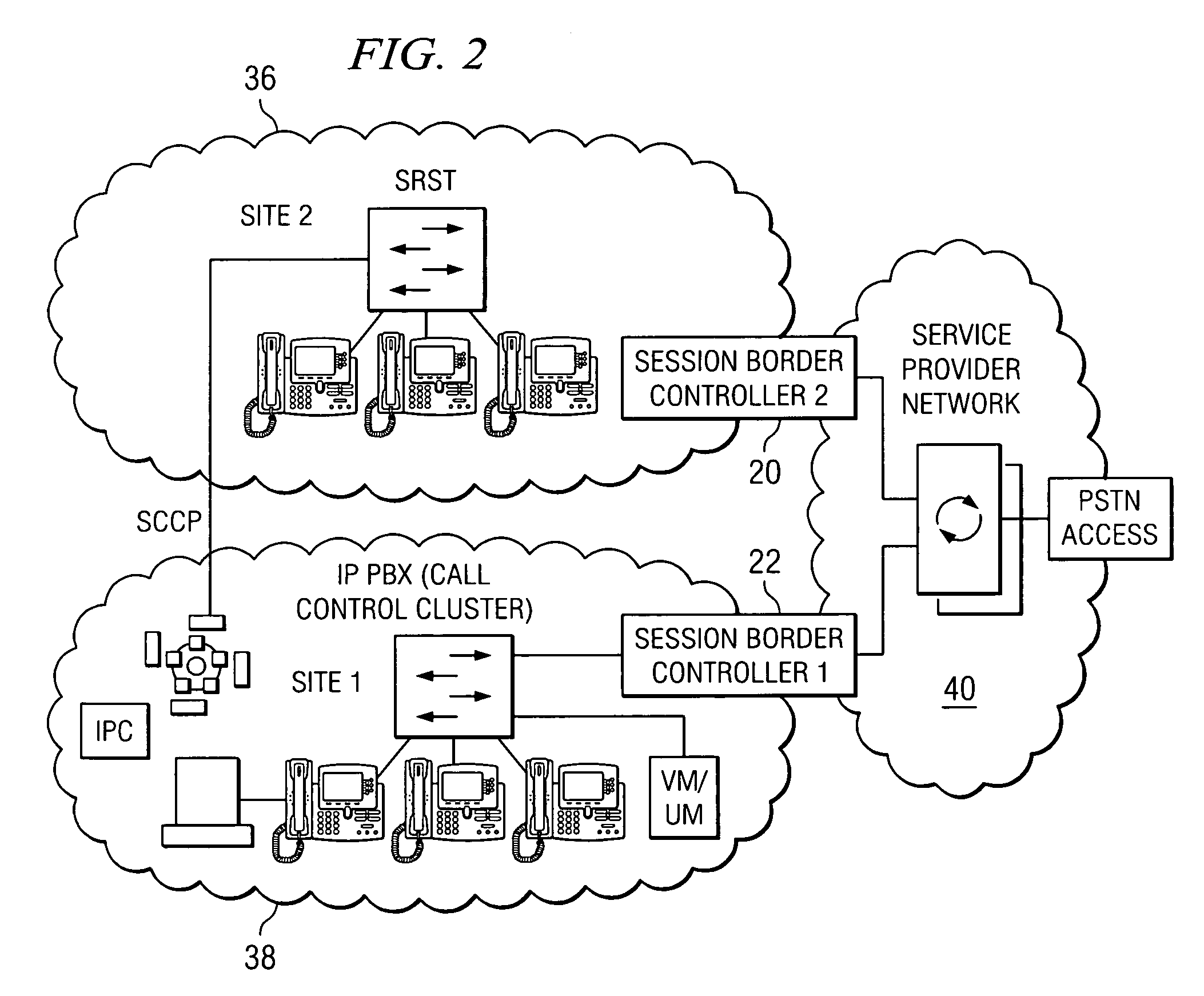
Method and system for implementing backup based on session border controllers
ActiveUS20070160058A1Improve communication reliabilityImprove securityData switching by path configurationTerminal equipmentSoft switch
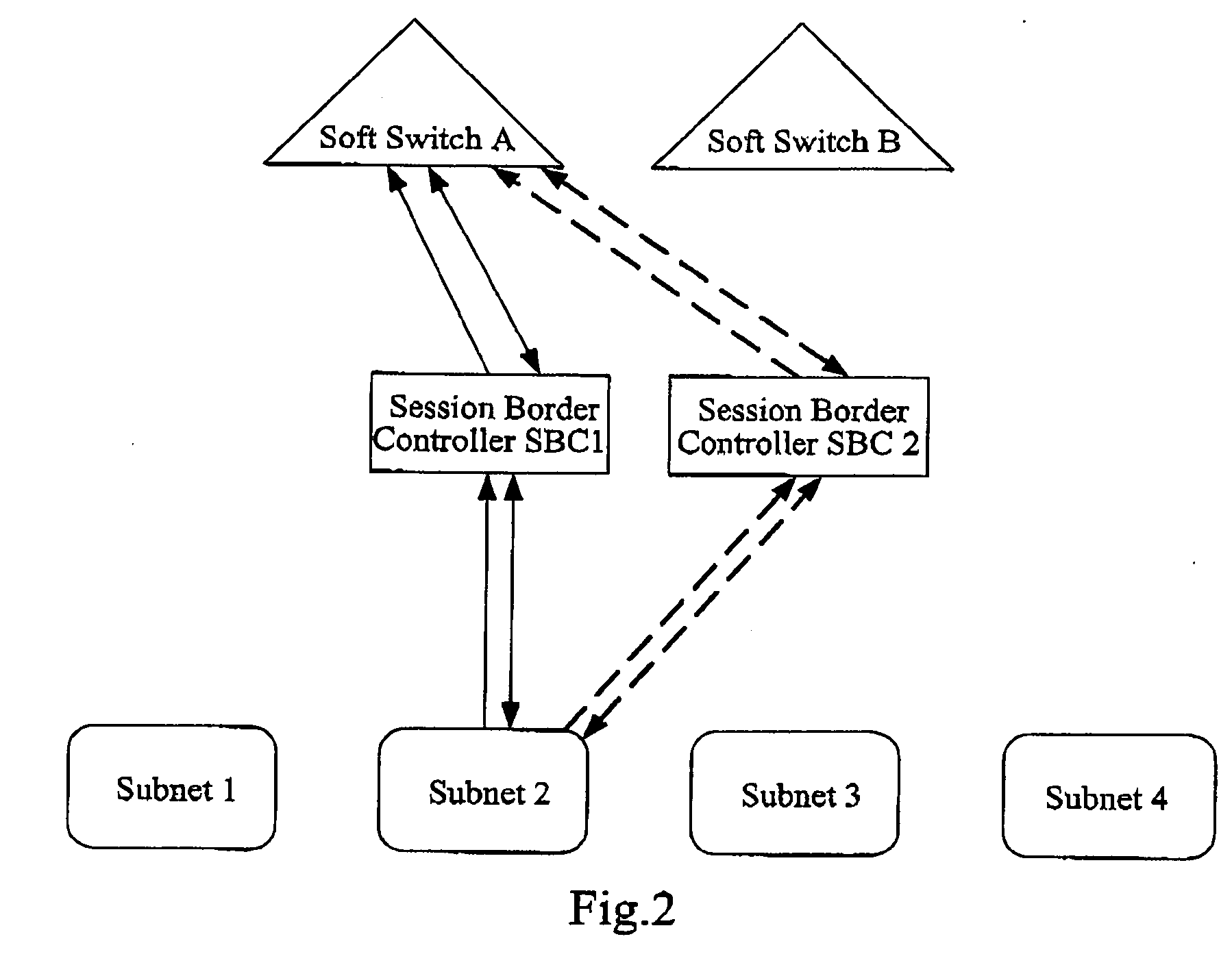
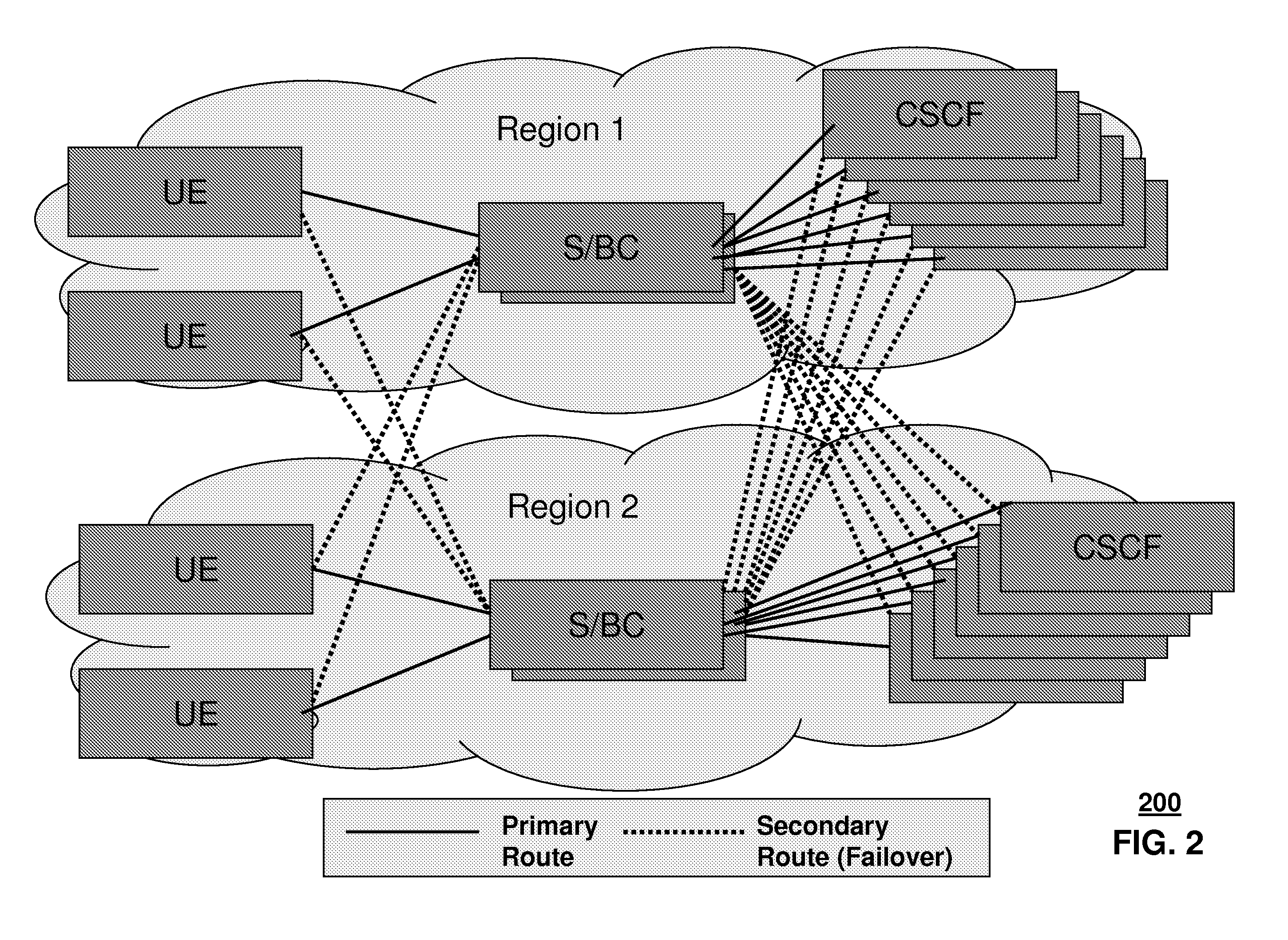
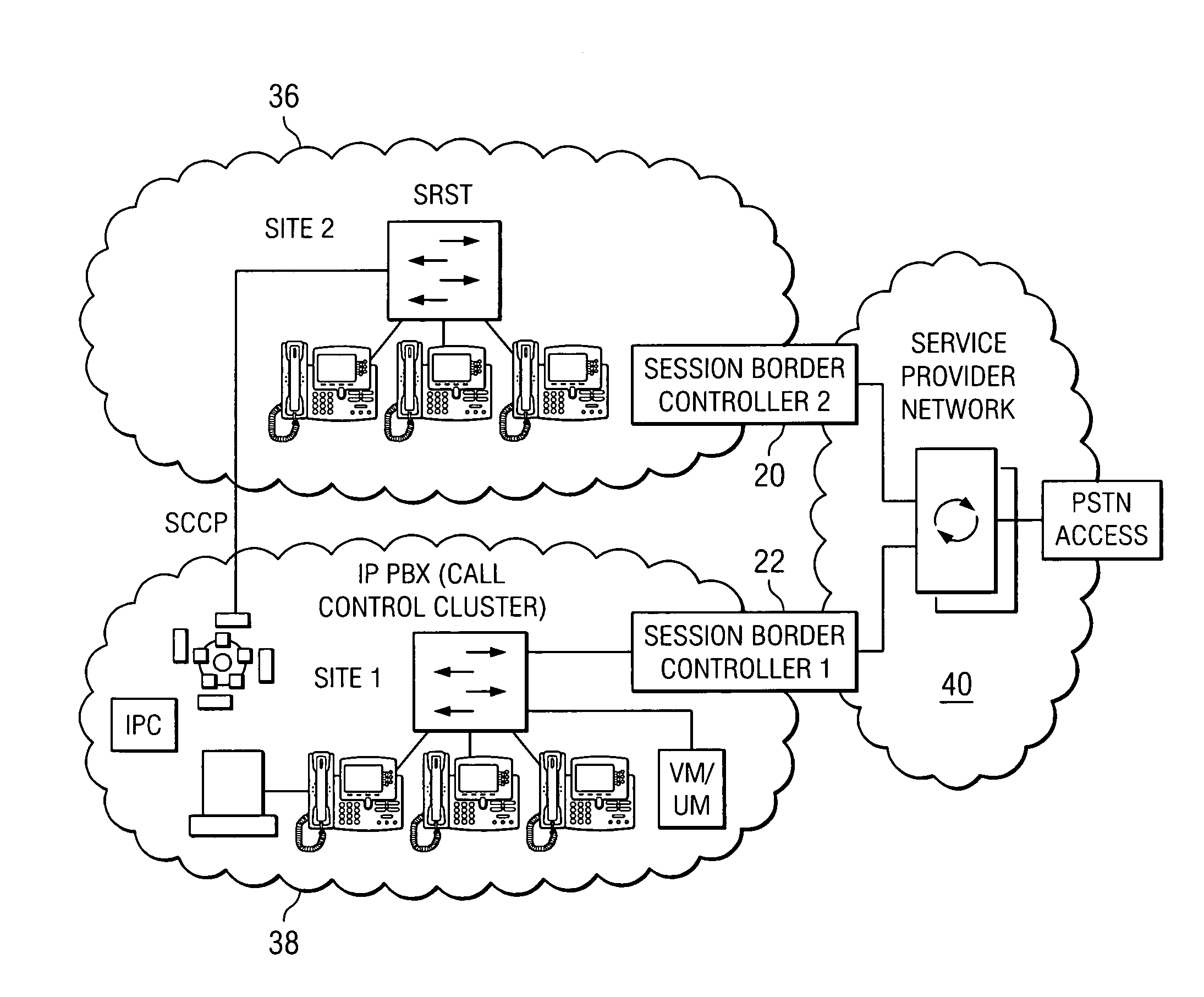
A method and a system for implementing backup based on session border controllers, including: a terminal device registers to a first soft switch via a first session border controller; the terminal device detects whether a failure concerning the first session border controller occurs. If a failure occurs, the terminal device registers to the first soft switch via a second session border controller; the first or the second session border controller detects whether a failure concerning the first soft switch occurs. If a failure occurs, the terminal device registers to the second soft switch. In addition, the invention further provides a corresponding system. With the present invention, media stream can pass through the NAT and firewall on the basis of adding session border controllers in the NGN network, and by implementing dual homing of the session border controller, paralyzing of the soft switches can be prevented, or a disaster tolerance mechanism for emergency communication can be provided, when burst disaster
Owner:HUAWEI TECH CO LTD
Methodology, Measurements and Analysis of Performance and Scalability of Stateful Border Gateways
ActiveUS20100058457A1Improve efficiencyEffective isolationMultiple digital computer combinationsProgram controlGraphicsExtensibility
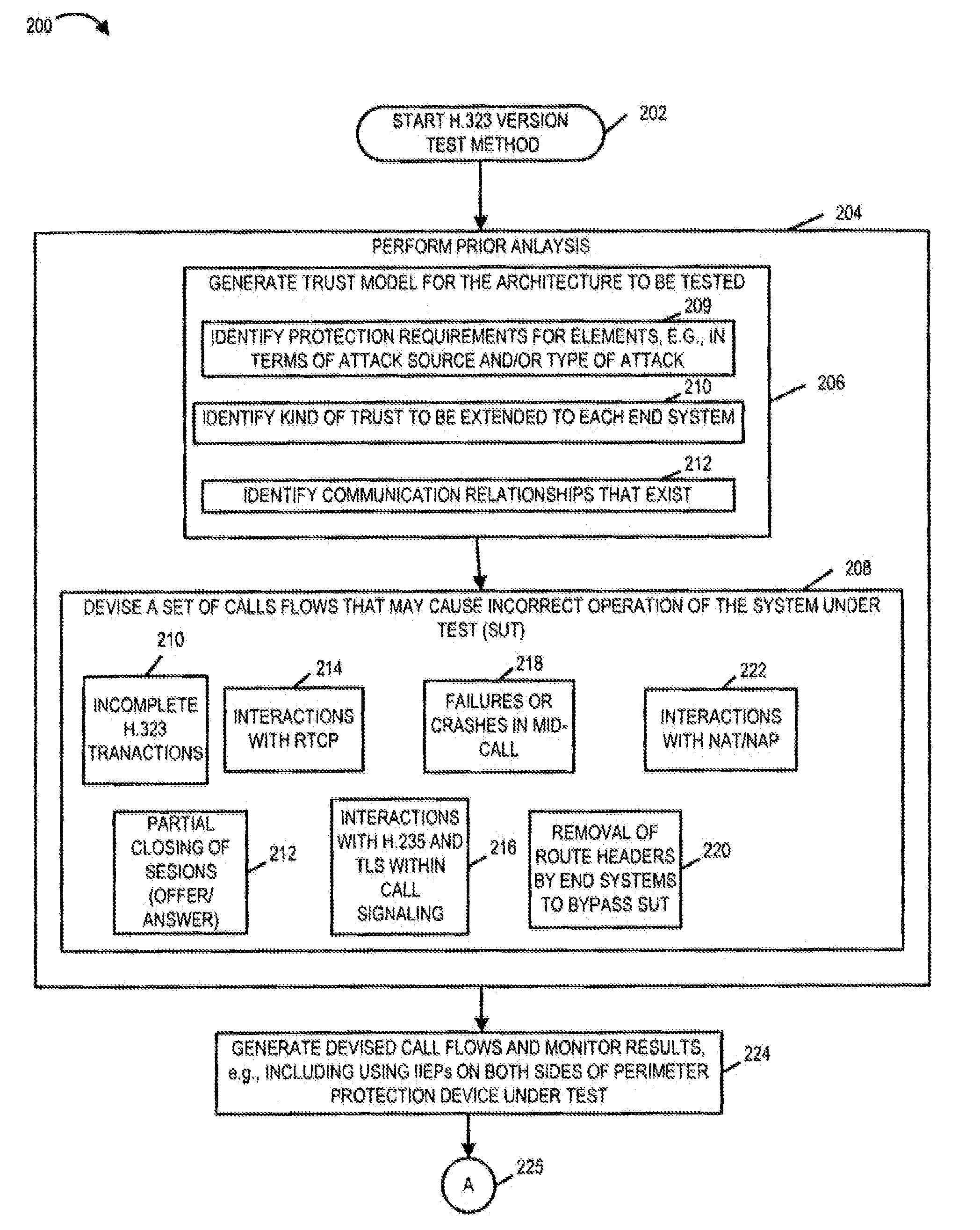
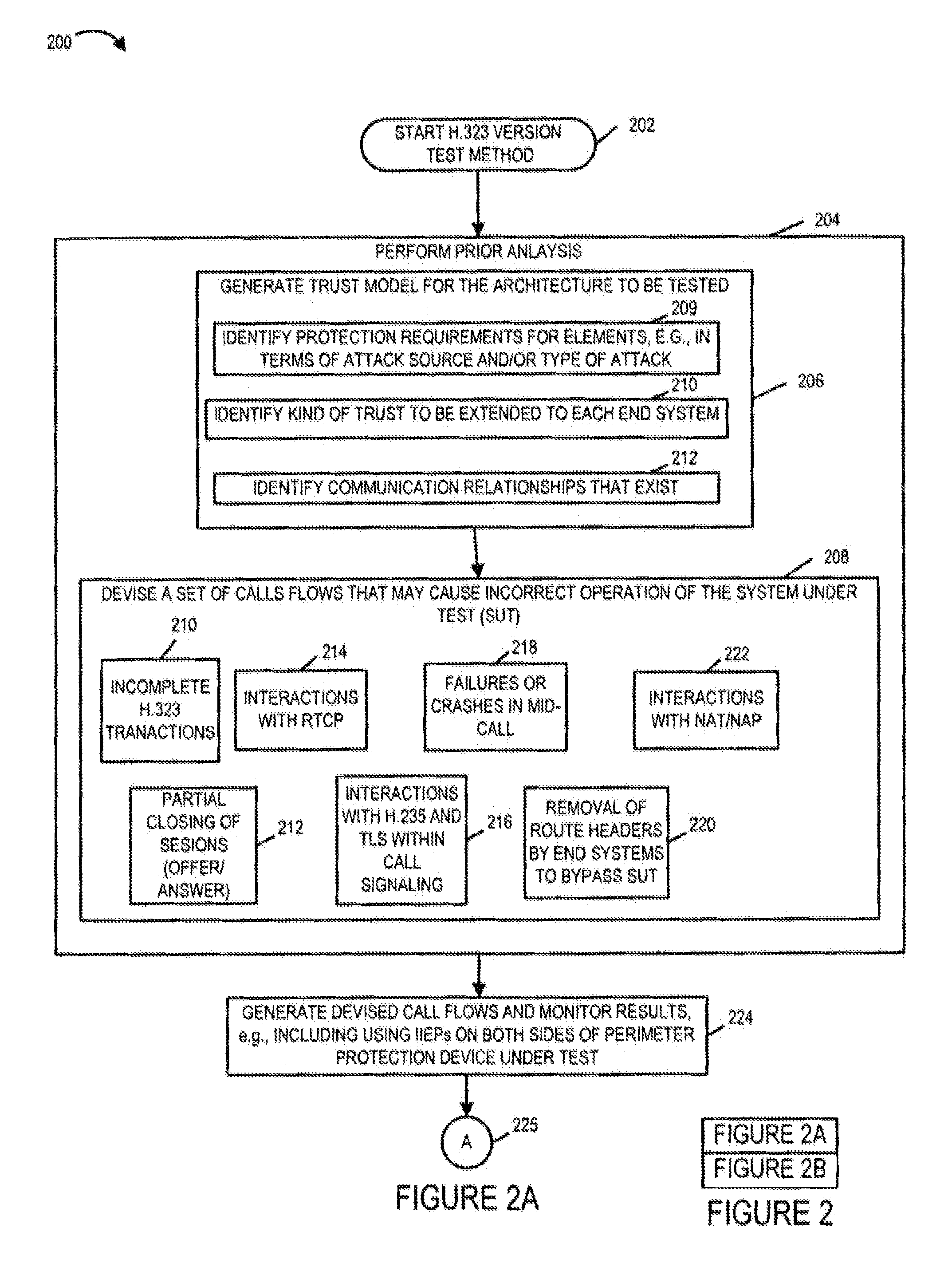
Methods and apparatus for testing of Internet-Protocol packet network perimeter protection devices, e.g., Border Gateways such as Session Border Controllers, including 5 dynamic pinhole capable firewalls are discussed. Analysis and testing of these network perimeter protection devices is performed to evaluate the ability of such device to perform at carrier class levels. The efficiency of state look table functions as well as call signaling processing capacity, implemented in a particular perimeter protection device, are determined and evaluated. Proper performance and efficiency of such perimeter protection devices are evaluated as a function of incoming call rate and as a function of total pre-existing active calls. Various different network perimeter protection devices, e.g., of different types and / or from different manufactures, can be benchmarked for suitability to carrier class environments and comparatively evaluated. Test equipment devices, e.g., enhanced Integrated Intelligent End Points (IIEPs), for fault testing, 15 evaluating and stressing the network perimeter protection devices in a system environment are described. Typically these specialized test devices are used in pairs, one on each side of the firewall under test. These test equipment devices include a heavy duty traffic generator module, monitoring and analysis capability including a utilization analysis module, and a graphical output capability.
Owner:PALO ALTO NETWORKS INC
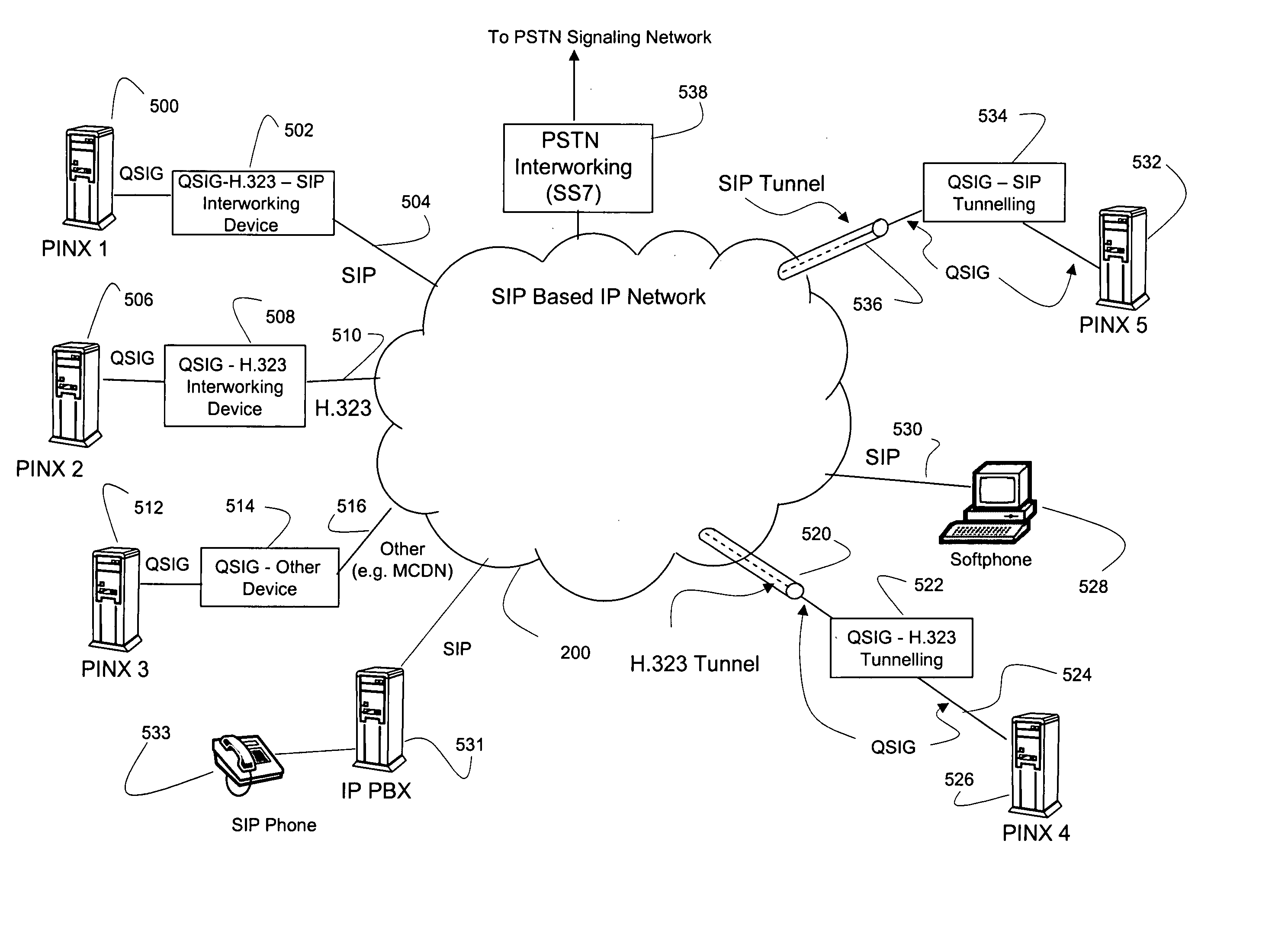
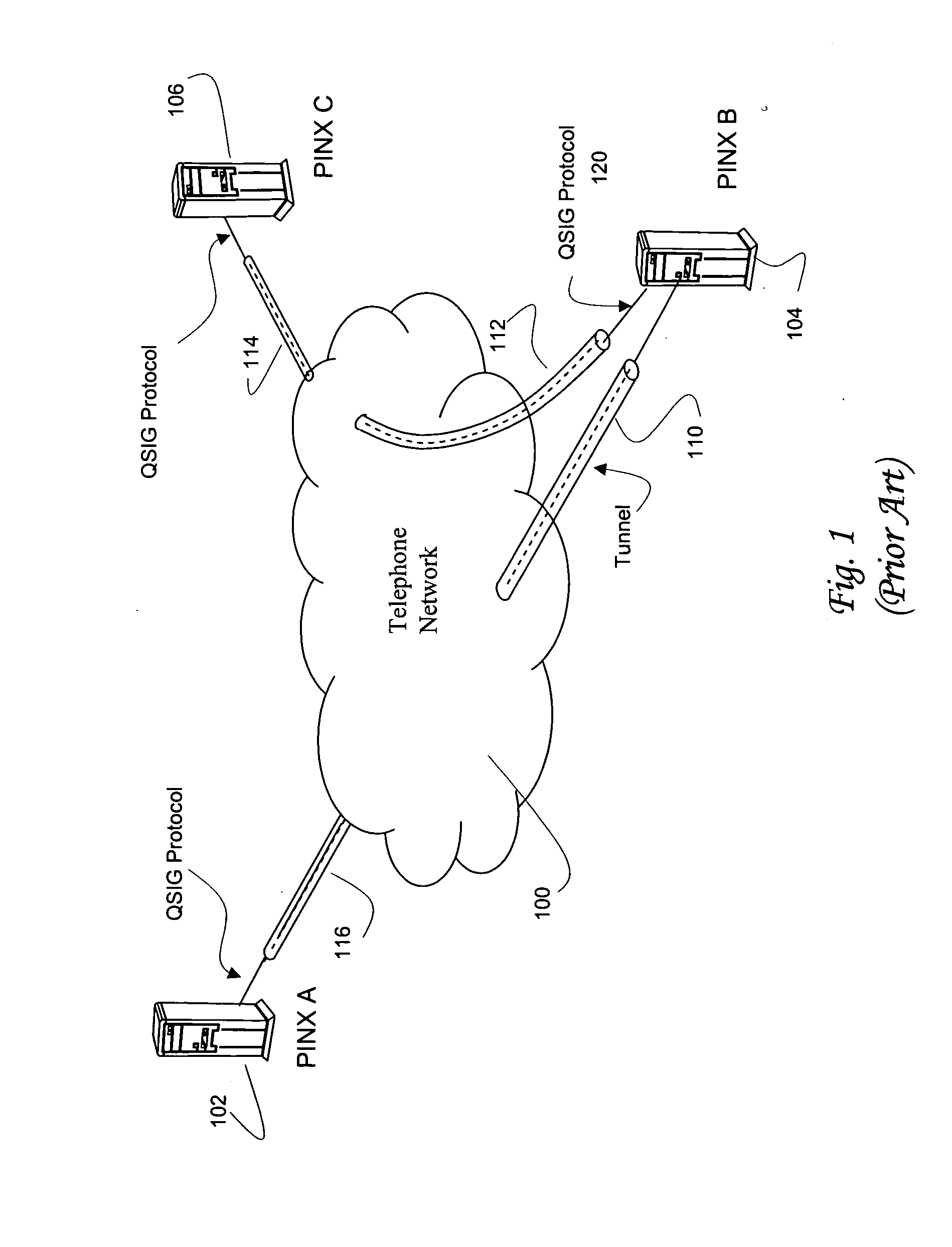
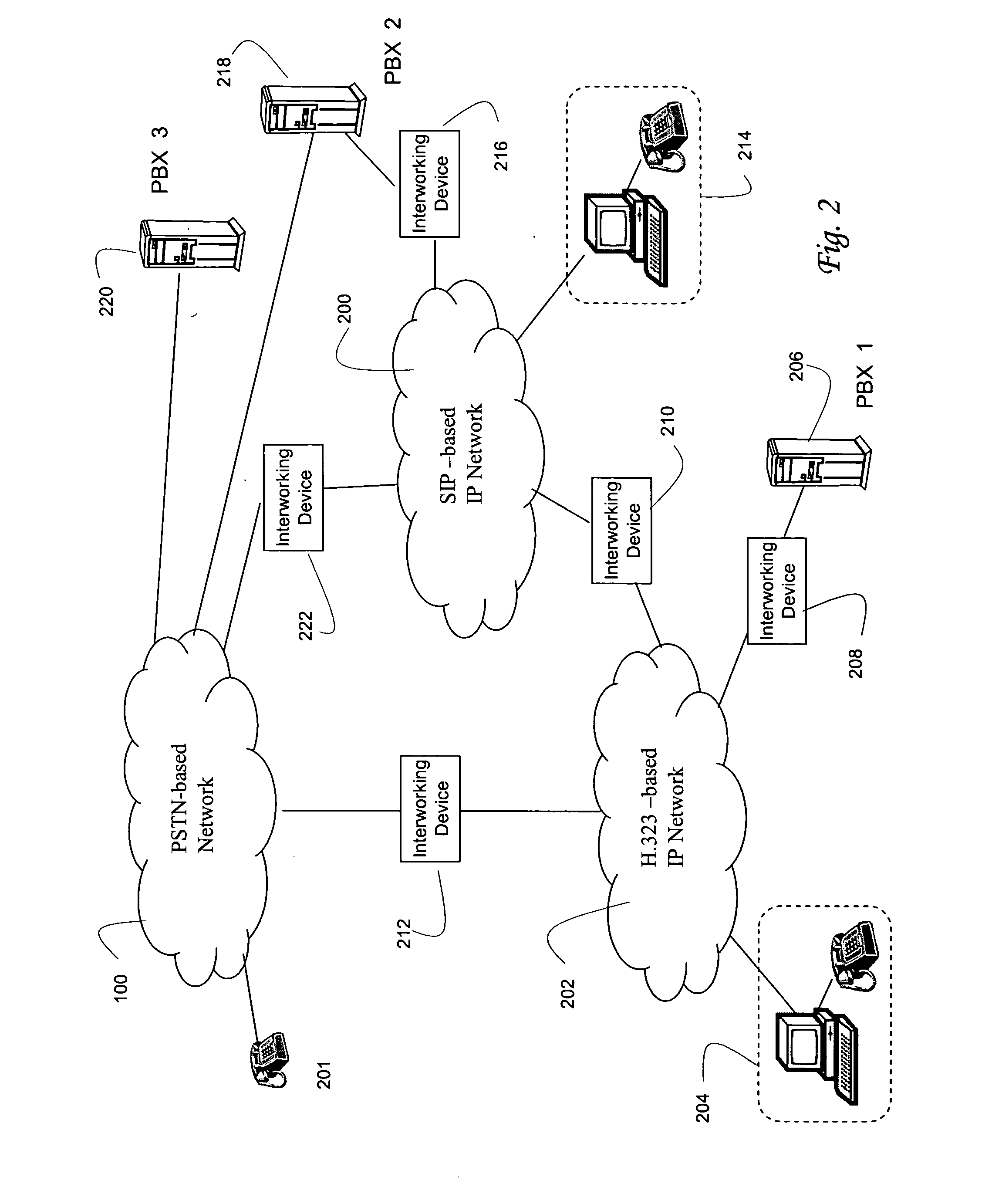
Systems and methods for interworking QSIG and H.323 signaling in a SIP-based network
A SIP-based network architecture is defined allowing a variety of access methods for interfacing QSIG-based signaling devices. The QSIG-based signaling devices are typically enterprise-based PBXs that either interface directly via QSIG, or adapt QSIG signaling to related signaling protocols via gateways, which can be customer premise or network based. The gateways can either interwork QSIG signaling or tunnel QSIG signaling over H.323, SIP, or other protocols. Upon reaching the SIP-based network, Session Border Controllers process the signaling. The Session Border Controllers terminate the tunnel (if used) and extracts the QSIG signaling for interworking to SIP, thereby facilitating a homogeneous SIP-based core network. In addition to interworking QSIG signaling, the Session Border Controllers perform other signaling related functions for the SIP-based network that are performed at a point as near as possible to the network's edge.
Owner:VERIZON PATENT & LICENSING INC
Method and system for implementing aggregate endpoints on IMS networks
ActiveUS20120219127A1Reliable registrationInterconnection arrangementsDigital data processing detailsSession controlSession border controller
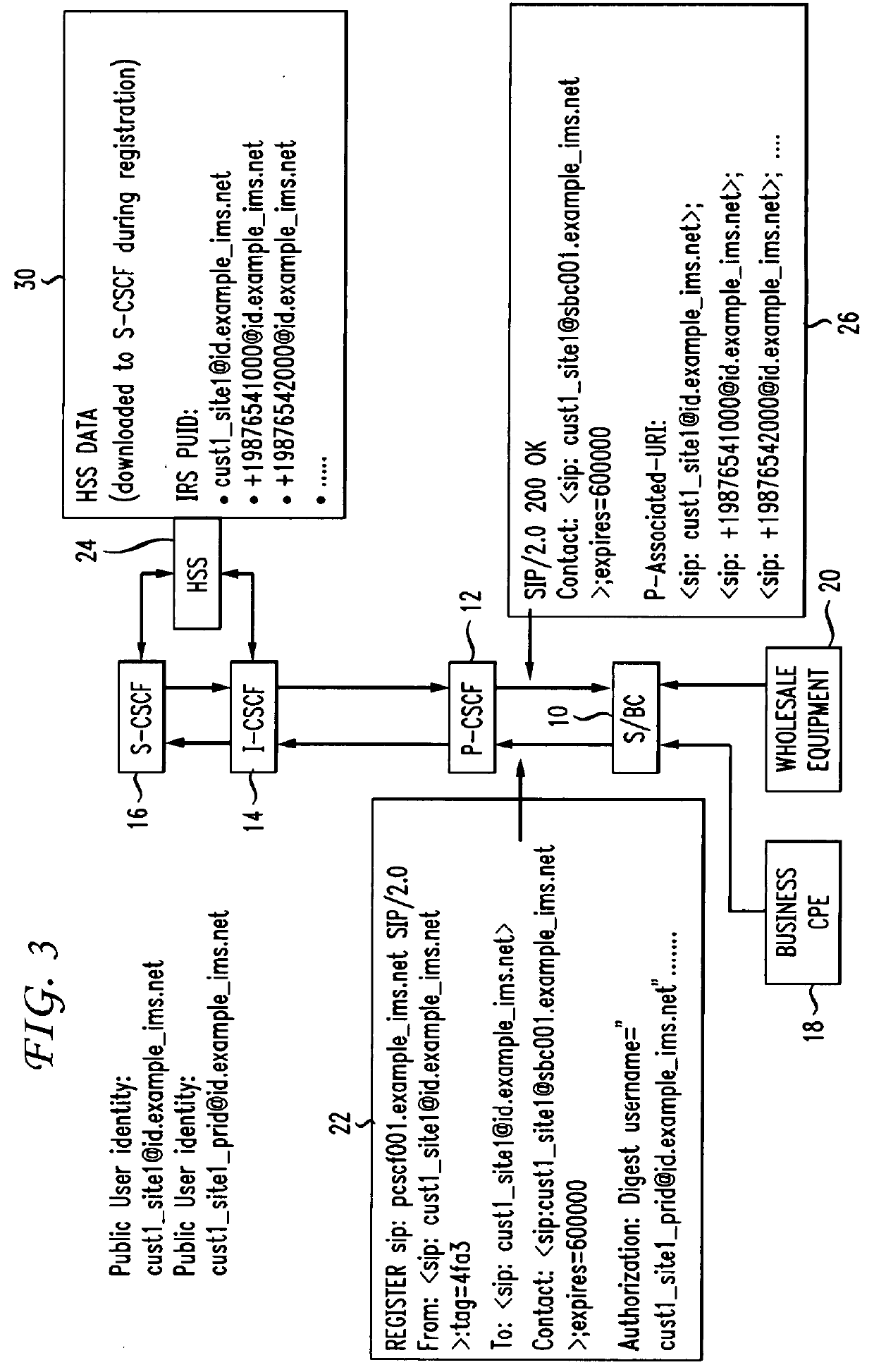
A method and system are adapted to provide telephony services to aggregate endpoints on an Internet Protocol Multimedia Subsystem (IMS) network. The method includes assigning one or multiple PUIDs for surrogate registration purposes during the provisioning of the aggregate endpoint, performing reliable surrogate registration on behalf of the aggregate endpoint, allowing multiple SBCs to perform surrogate registrations independently for the same aggregate endpoint to achieve reliability, and providing reliable connection from an IMS core to the aggregate endpoints via multiple S / BCs. The system includes one or more Session Border Controllers (S / BC), at least one set of Call / Session Control Functions (CSCF), and an HSS operatively coupled together.
Owner:ACME PACKET +1
Device initiated multiple grants per interval system and method
ActiveUS20120047273A1Broadband local area networksTime-division multiplexService flowQuality of service
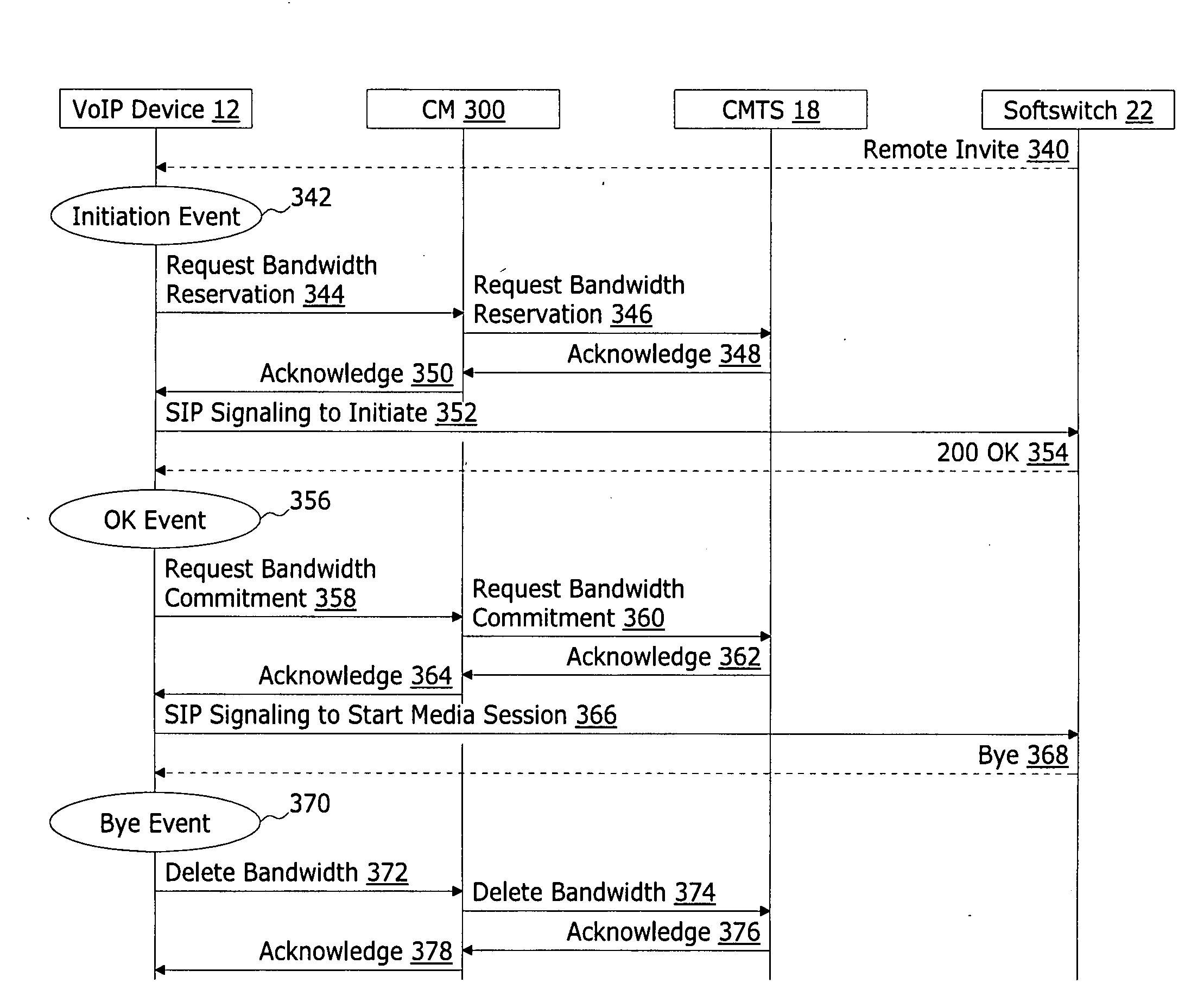
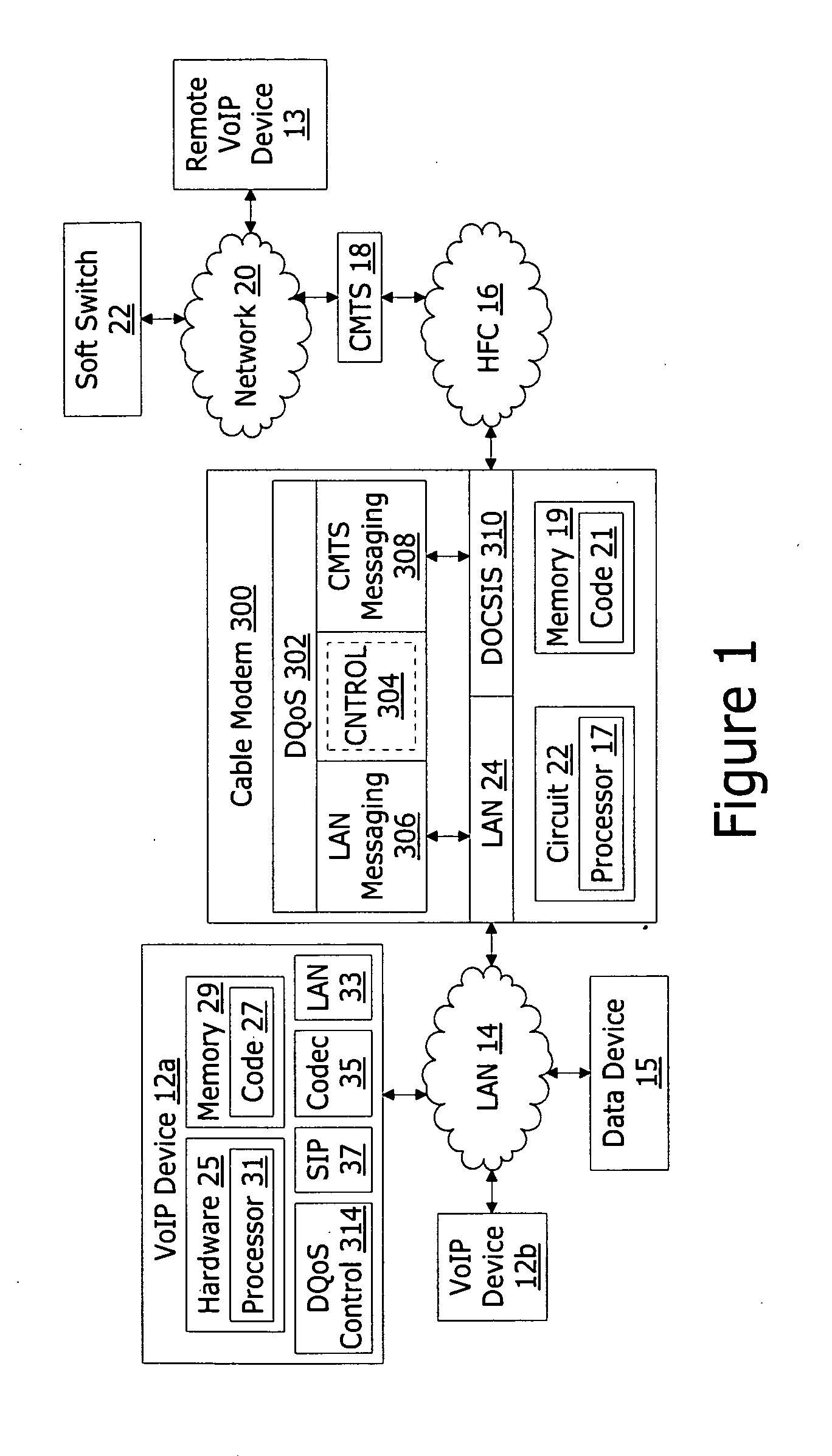
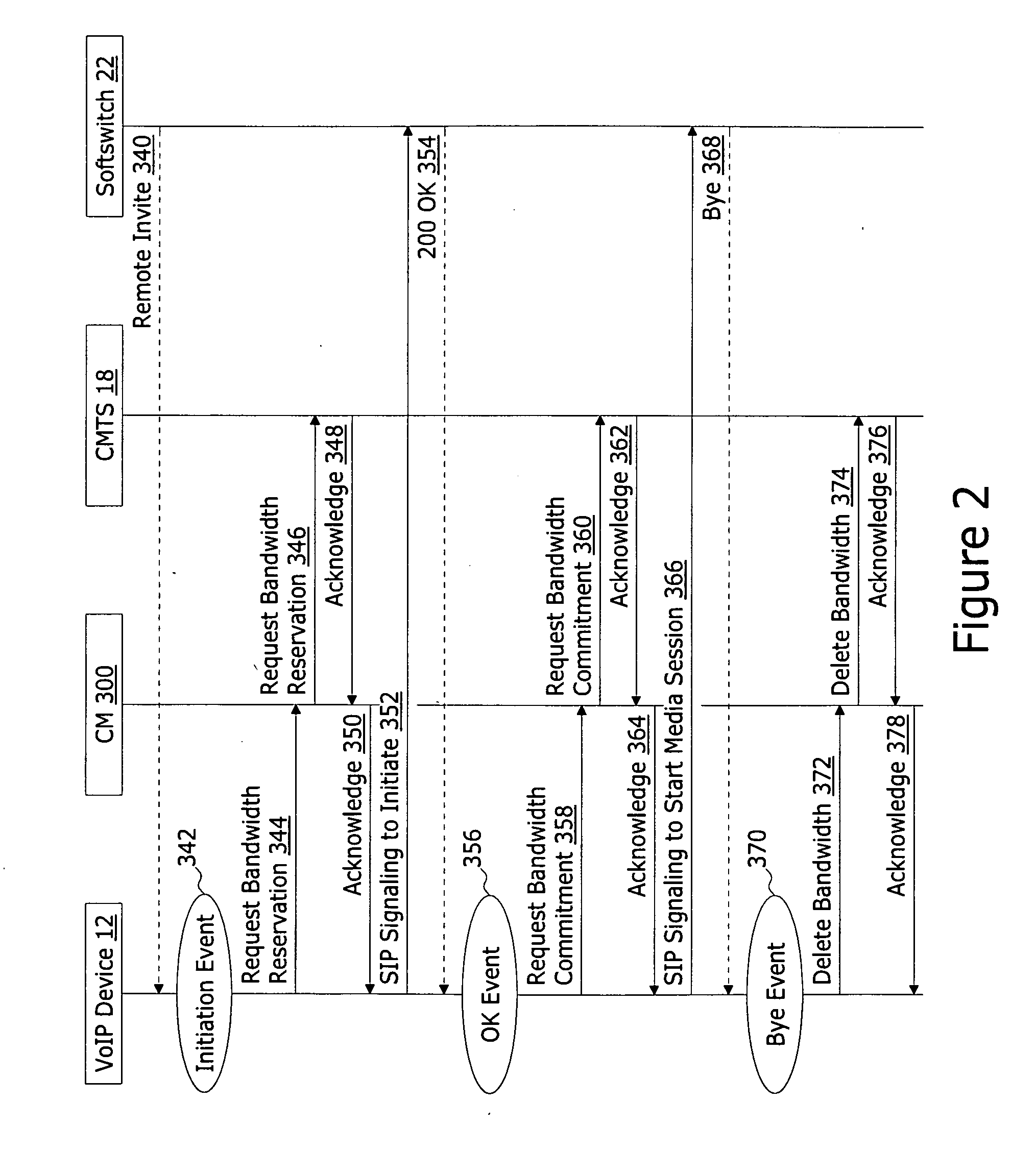
A cable modem integrated session border control circuit operates as a point of demarcation between a local area network (LAN) and a DOCSIS network and, in response to receiving a Session Initiation Protocol (SIP) message, which includes Session Description Protocol (SDP), from a VoIP device coupled to the LAN, communicates with a Cable Modem Termination System (CMTS) to take advantage of DOCSIS Dynamic Quality of Service (DQoS) if a VoIP session between the VoIP device and a remote endpoint includes use of the DOCSIS network. The cable modem integrated session border controller further determines required service flow attributes. If required service flow attributes, as determined from the SDP of the SIP message, matches service flow attributes of an existing UGS service flow with a CMTS, a DOCSIS Dynamic Service Chance (DSC) request is used to add an additional sub flow to the existing UGS service flow. If attributes fail to match attributes of all existing UGS service flows, a DOCSIS Dynamic Service Change (DSC) request is used to initiate an additional UGS service flow with the required service flow attributes.
Owner:INNOMEDIA PTE
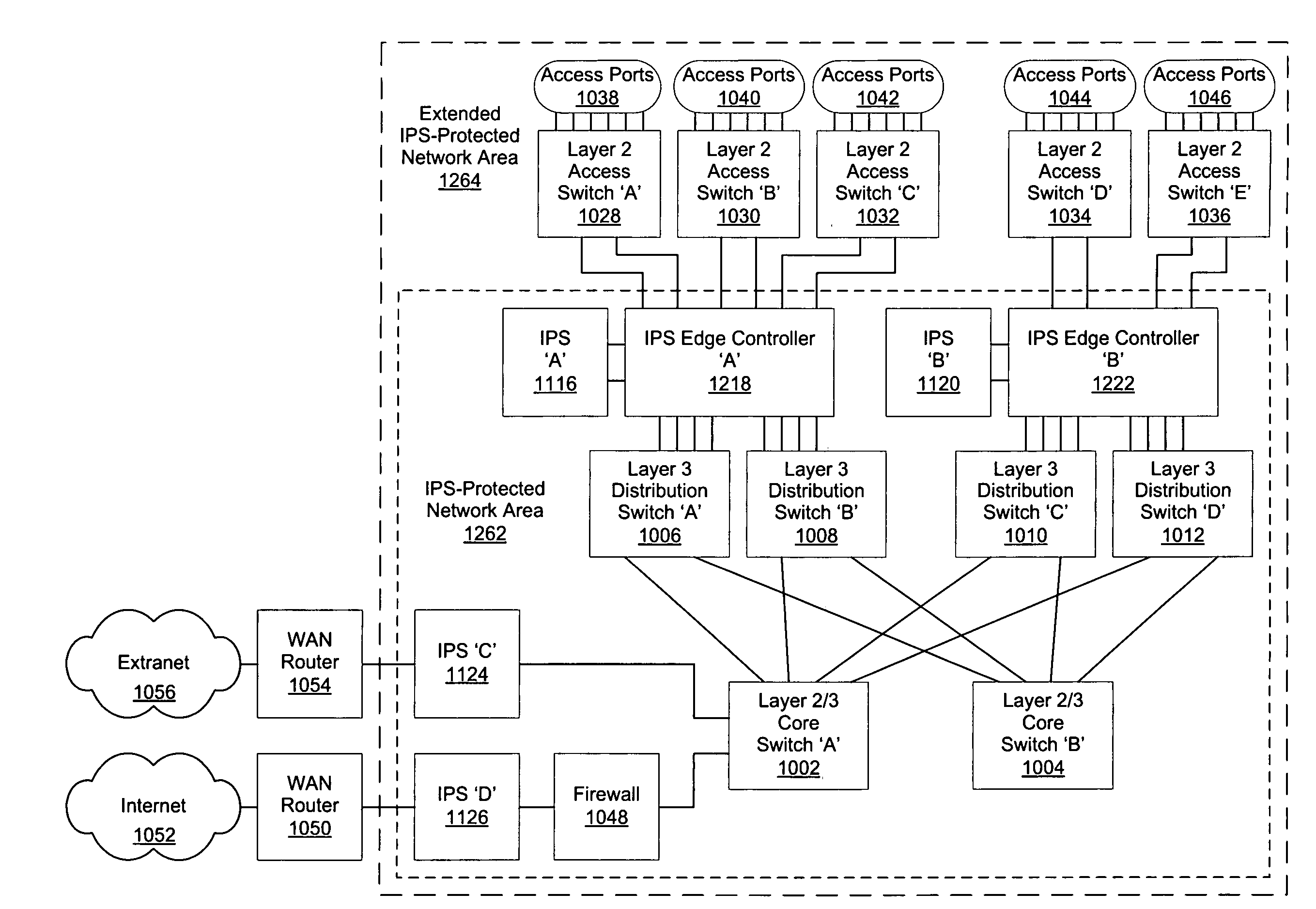
Intrusion prevention system edge controller
ActiveUS20070280222A1High network connection speedImprove usabilityMultiplex system selection arrangementsCircuit switching systemsNetwork connectionPrivate network
A system and method for extending the implementation of one or more Intrusion Prevention Systems (IPSs) such that each user can be placed in the IPS traffic path to create secure containment areas at a granular level, port types and port counts are increased, and higher network connection speeds are supported. In different embodiments of the invention, traffic load is balanced across two or more IPSs, enabling enhanced availability during system failures, replacements or updates. IPS performance is improved by enhancing traffic management of “trusted” (e.g., pass-through) and “known bad” (e.g., discarded) traffic flows and decreasing configuration task workloads. Other embodiments of the invention include, but are not limited to, extending the implementation of proxy devices, virtual private networks (VPNs), session border controllers (SBCs), firewalls, protocol gateways and other bump-in-the-wire systems.
Owner:TREND MICRO INC
System and method for preventing header spoofing
InactiveUS20100175122A1User identity/authority verificationMultiple digital computer combinationsService provisionSession border controller
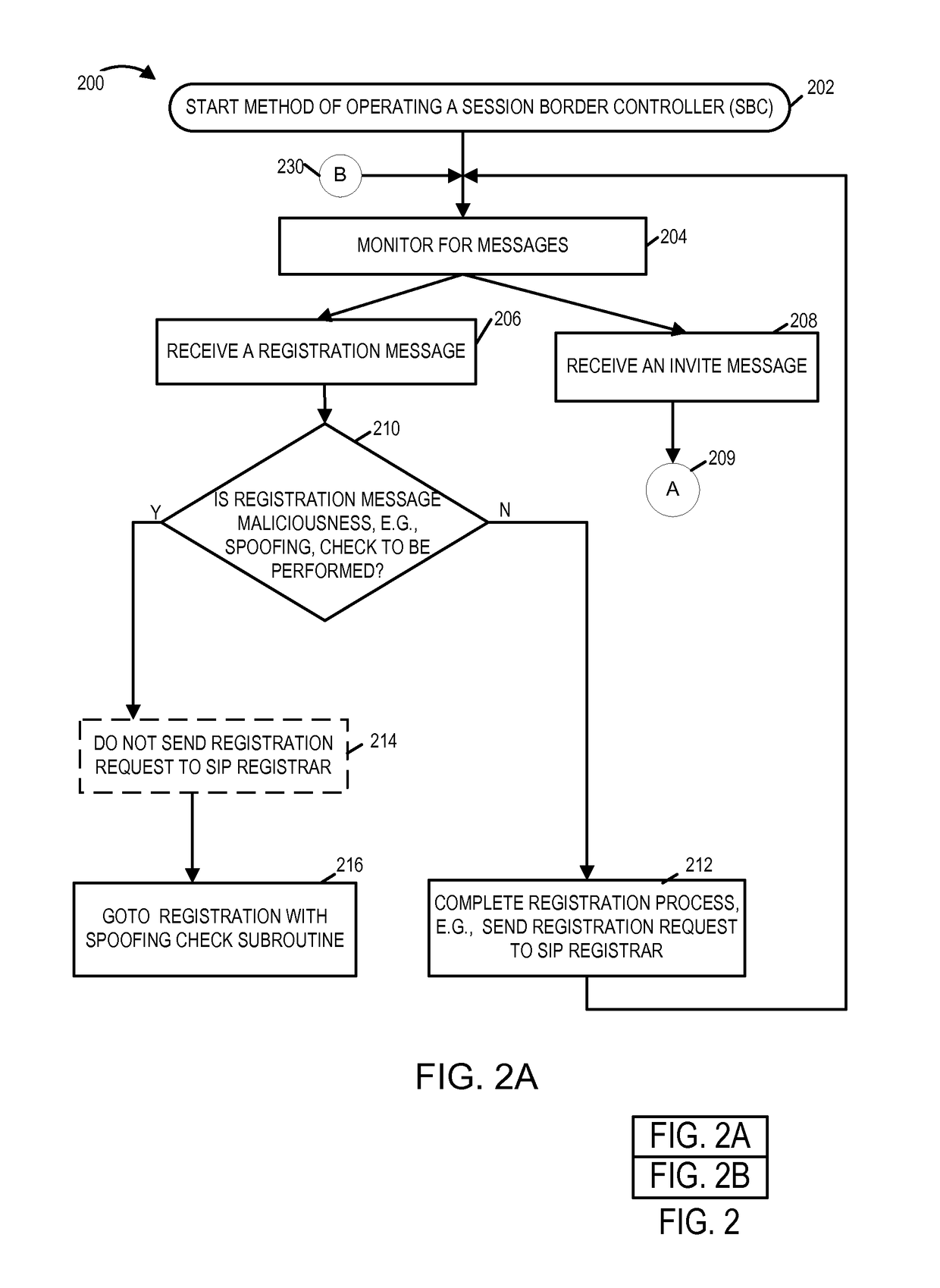
A system and method for preventing spoofing including a receiver at a session border controller (SBC) configured to receive a message from a network element, wherein the message is a request for network access and the message comprises a first source information. The system and method may also include one or more processors at the session border controller (SBC) configured to identify an identifier associated with the network element, wherein the identifier corresponds to a second source information, and to replace the first source information in the message received from the network element with the second source information corresponding to the identifier of the network element. The system and method may also include one or more databases configured to store the second source information. The system and method may also include a transmitter at the session border controller (SBC) configured to transmit the message with the second source information to a service provider proxy for granting network access. In another embodiment, network access may be denied in the event it is determined that the first source information in the message received from the network element with the second source information corresponding to the identifier of the network element are different.
Owner:VERIZON PATENT & LICENSING INC
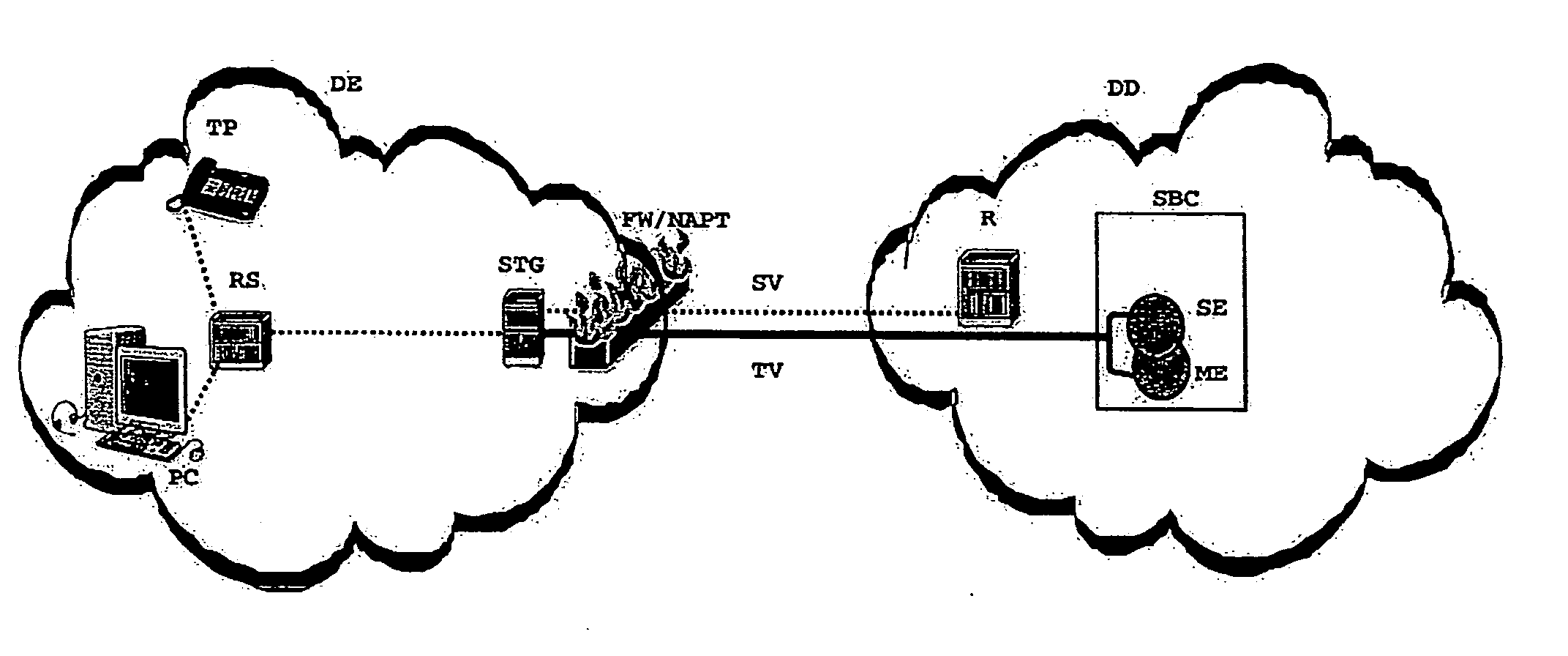
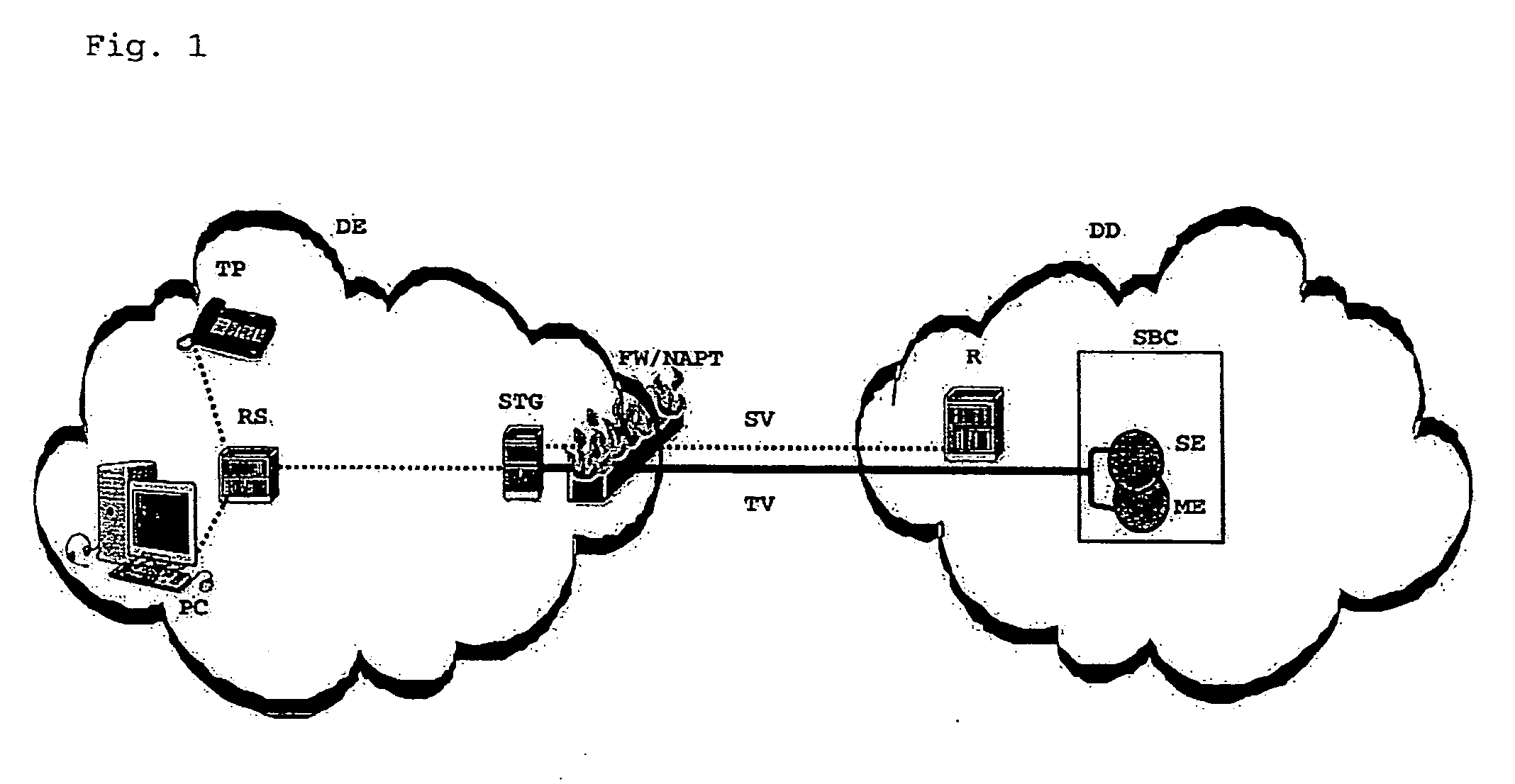
Method for routing bi-directional connections in a telecommunication network by means of a signalling protocol via an interposed firewall with address transformation device and also a telecommunication network and security and tunnel device for this
ActiveUS20060075483A1Multiple digital computer combinationsProgram controlTelecommunications networkService provision
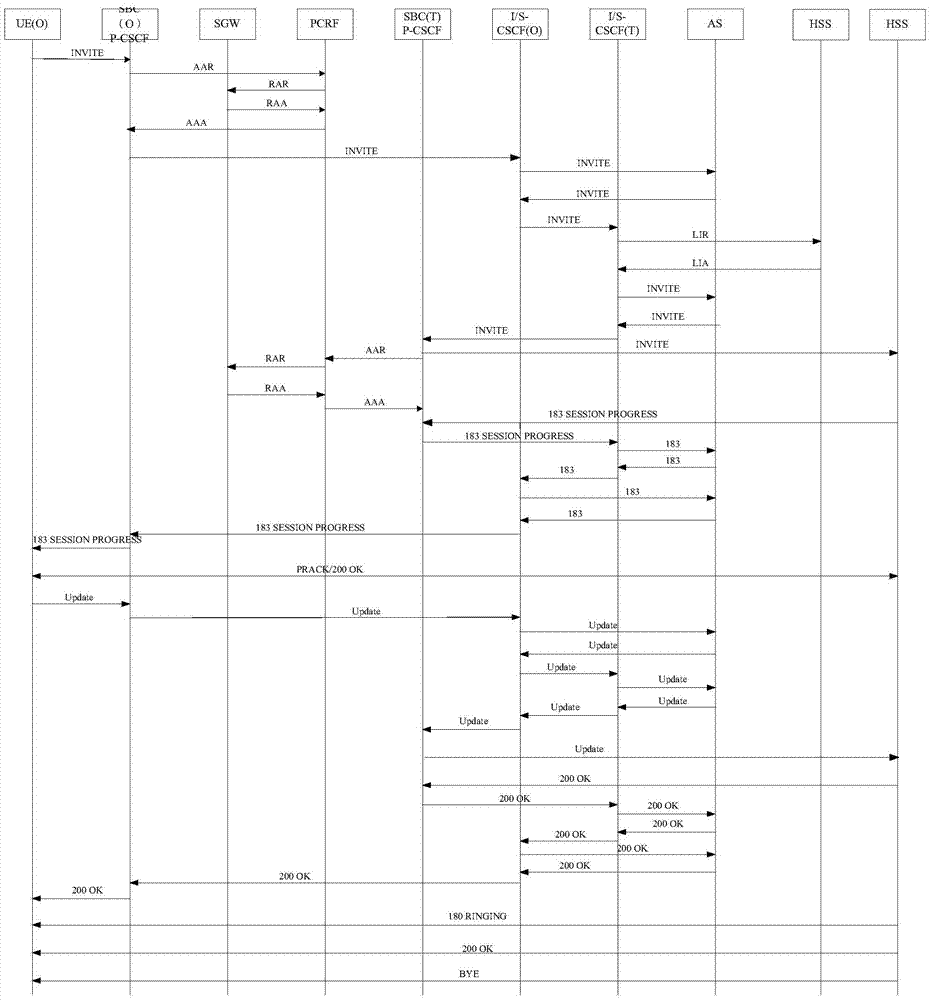
The invention relates to a method for routing a bi-directional end-to-end connection between an end subscriber and the domain of a service provider by means of a signalling protocol via an interposed firewall with address transformation device, wherein by means of a security and tunnel device, located in the end-to-end connection between the end subscriber and the firewall with address transformation device in the domain of the end subscriber, and a session border controller, located in the end-to-end connection in the domain of the service provider, a tunnel is set up between the security and tunnel device and the session border controller and a bi-directional data exchange takes place via the tunnel between the end subscriber and the domain of the service provider in the area between the security and tunnel device and the session border controller by means of a tunnel protocol, and also a telecommunication network and a security and tunnel device for this.
Owner:ALCATEL LUCENT SAS
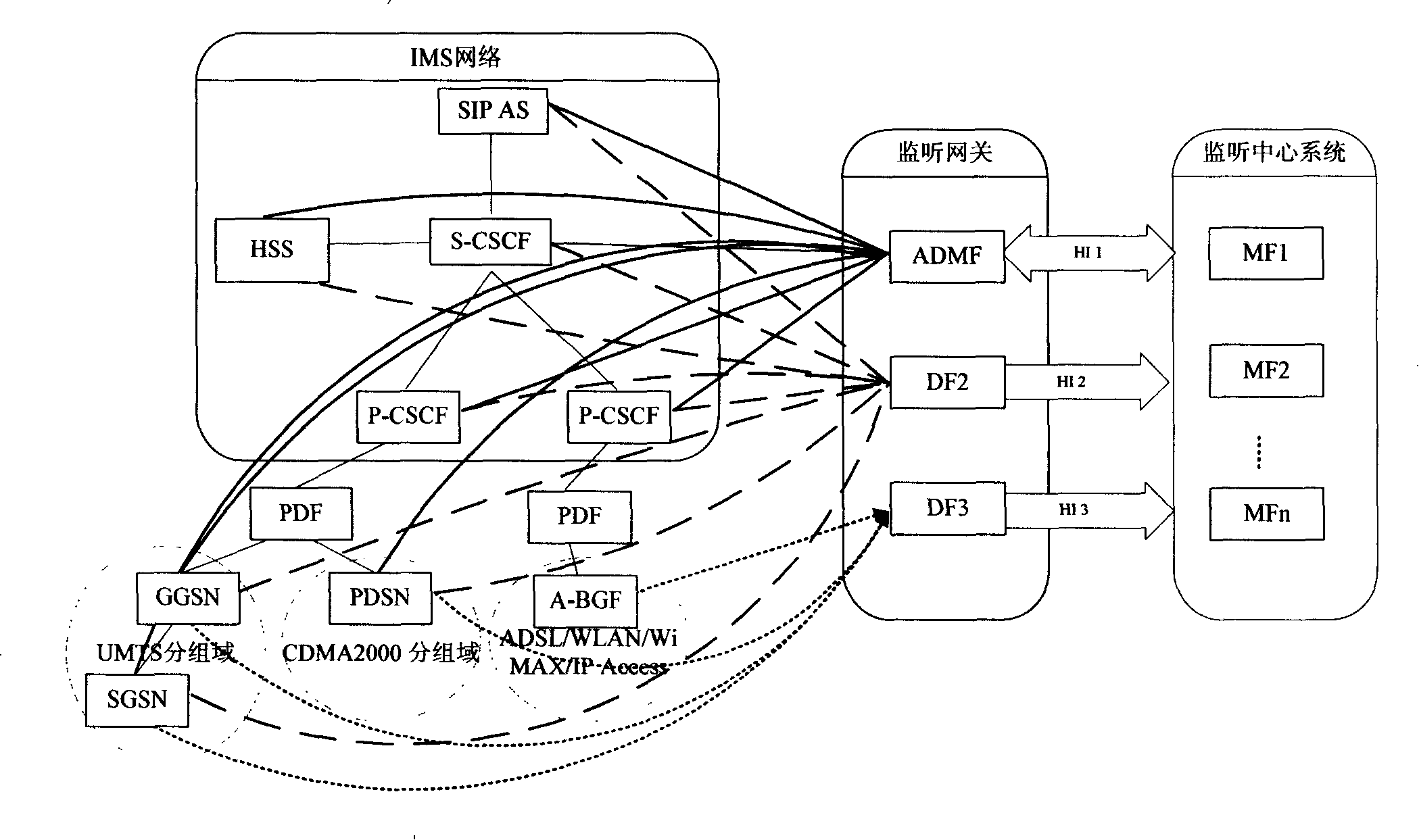
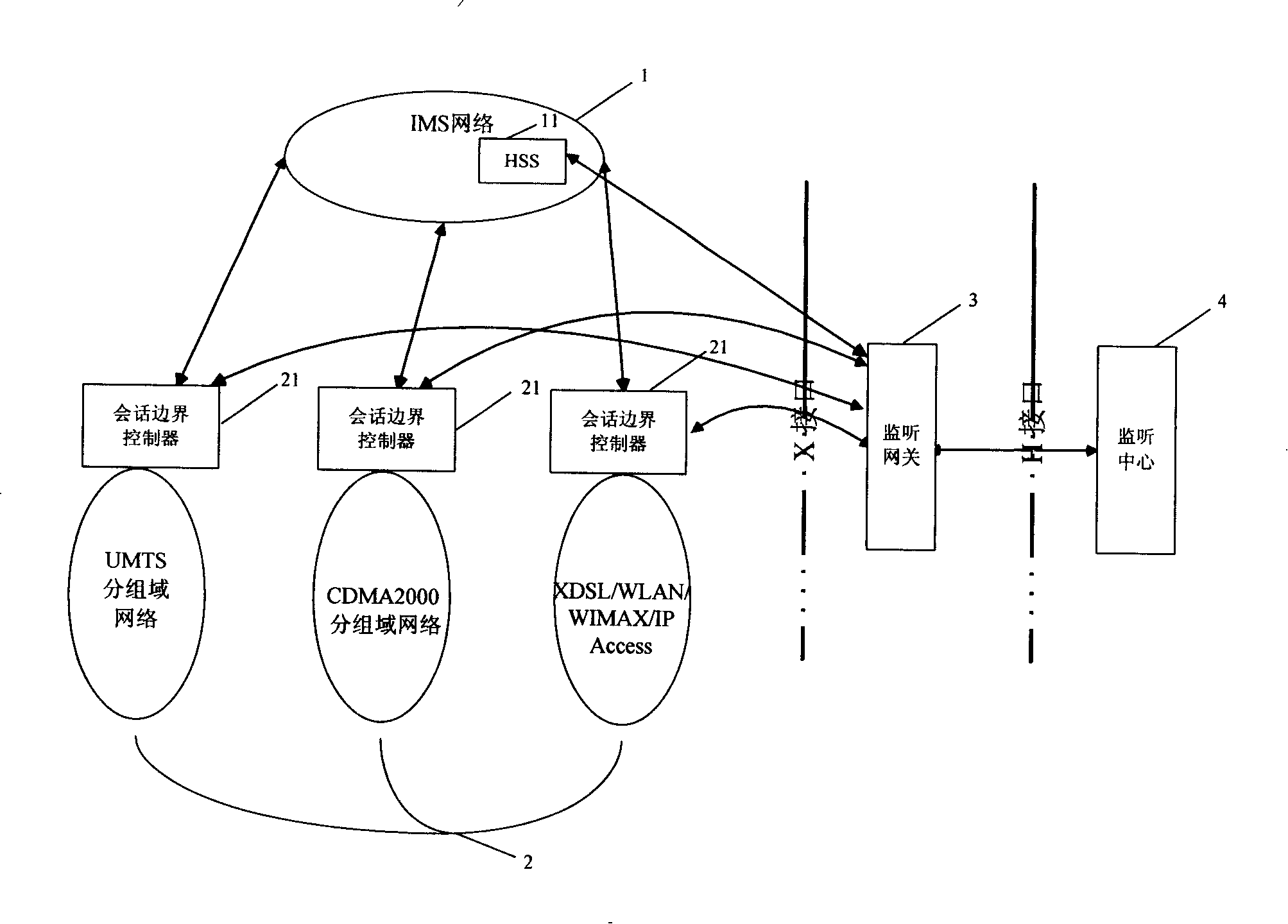
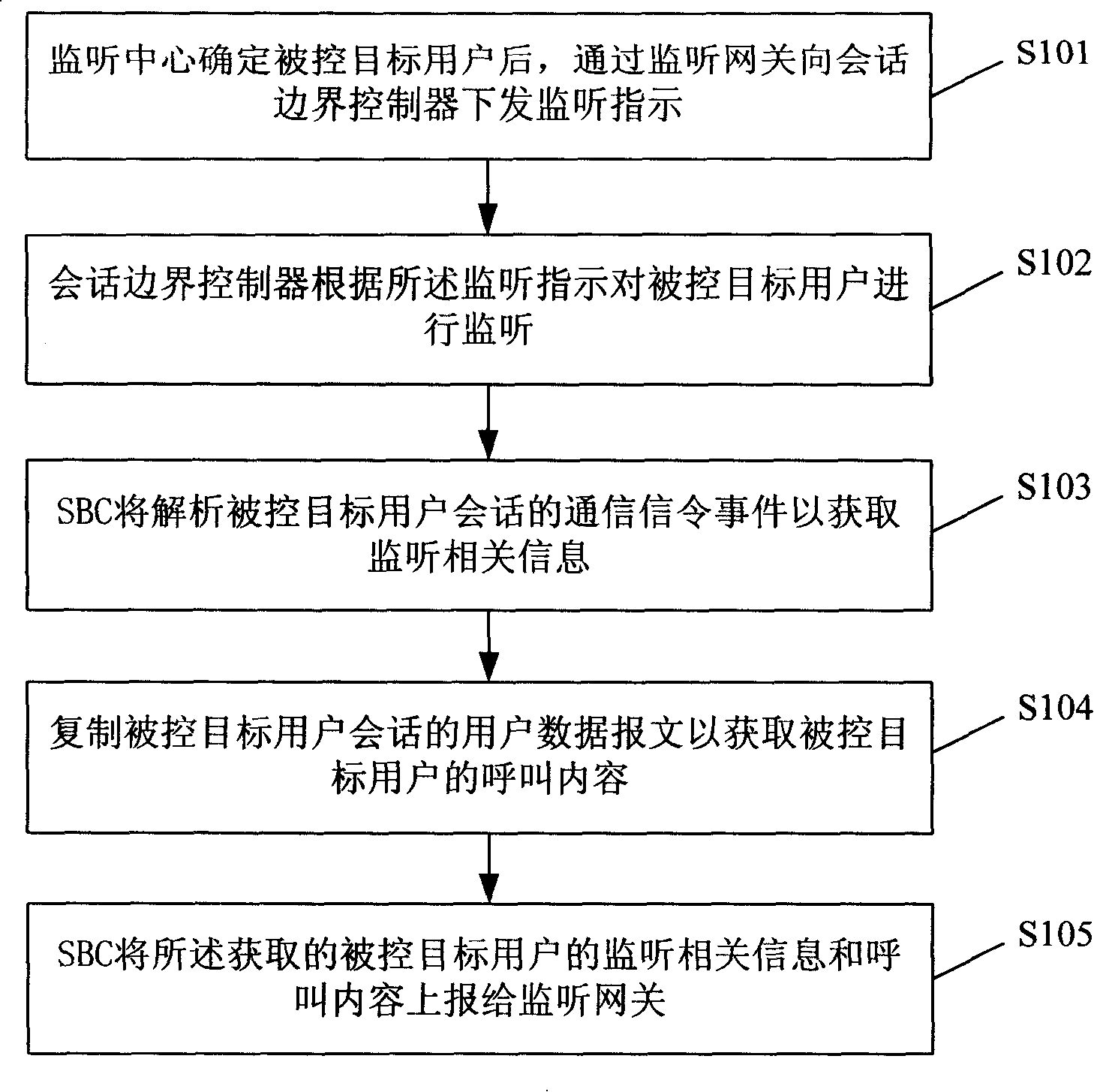
Session border controller, home user server, communication system and listening method
InactiveCN101212356ALower requirementReduce development costsData switching networksRelevant informationCommunications system
The invention provides a communication system and a monitoring method of a session border controller (SBC) and an assignment user server, which mainly comprises the following processes: a grouping domain network is accessed uniformly in an IP multimedia subsystem network to realize mutual communication through the SBC and is connected with a monitoring gateway through the SBC; when the monitoring is started, the monitoring gateway delivers monitoring indication to the SBC; the controlled object user is monitored by the SBC according to the monitoring indication; the relative monitoring information and the calling content of the controlled object users are obtained and reported to the monitoring gateway. Due to that only the SBC is required to be connected to the monitoring gateway to realize monitoring and the core network element of the IP multimedia subsystem network is not required to realize the monitoring function, the invention has low requirement to the monitoring gateway, small development cost for realizing the monitoring, low cost for developing, relatively simple networking and does not need cross products association.
Owner:HUAWEI TECH CO LTD
Method and apparatus for managing user endpoint devices in a communication network
ActiveUS20110078229A1Multiple digital computer combinationsTransmissionSession border controllerDomain name
A system that incorporates teachings of the present disclosure may include, for example, a user endpoint device having a controller to submit a query to a Domain Name System (DNS) for information associated with a Fully Qualified Domain Name (FQDN) assigned to at least one of a Local Access Transport Area (LATA) or rate center of the user endpoint device, and receive from the DNS one or more descriptors of one or more session border controllers, wherein the one or more descriptors are associated with the FQDN of the user endpoint device. Additional embodiments are disclosed.
Owner:AT&T INTPROP I L P
Network arrangement and method for handling sessions in a telecommunications network
InactiveUS20070002764A1Error preventionTransmission systemsApplication serverTelecommunications network
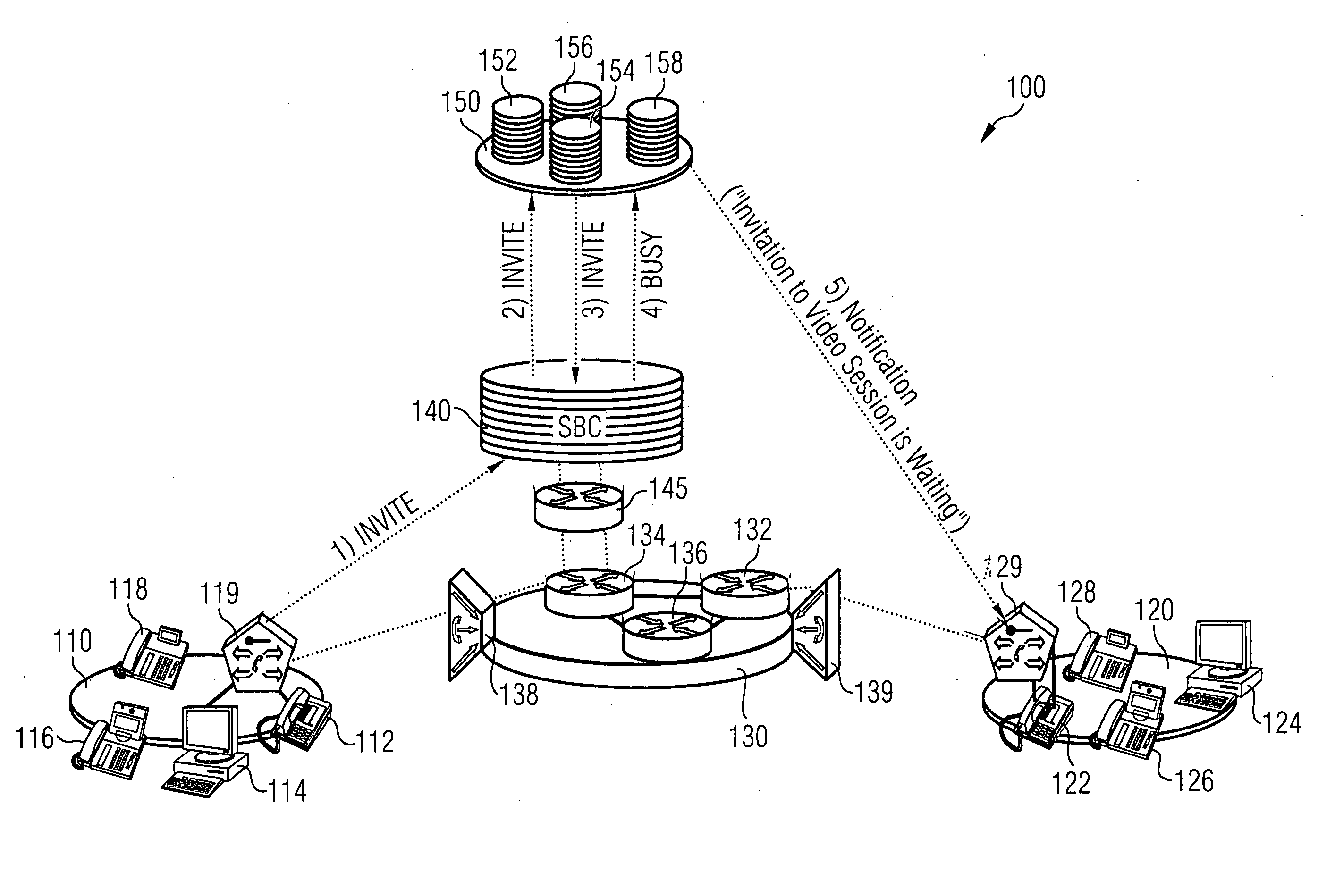
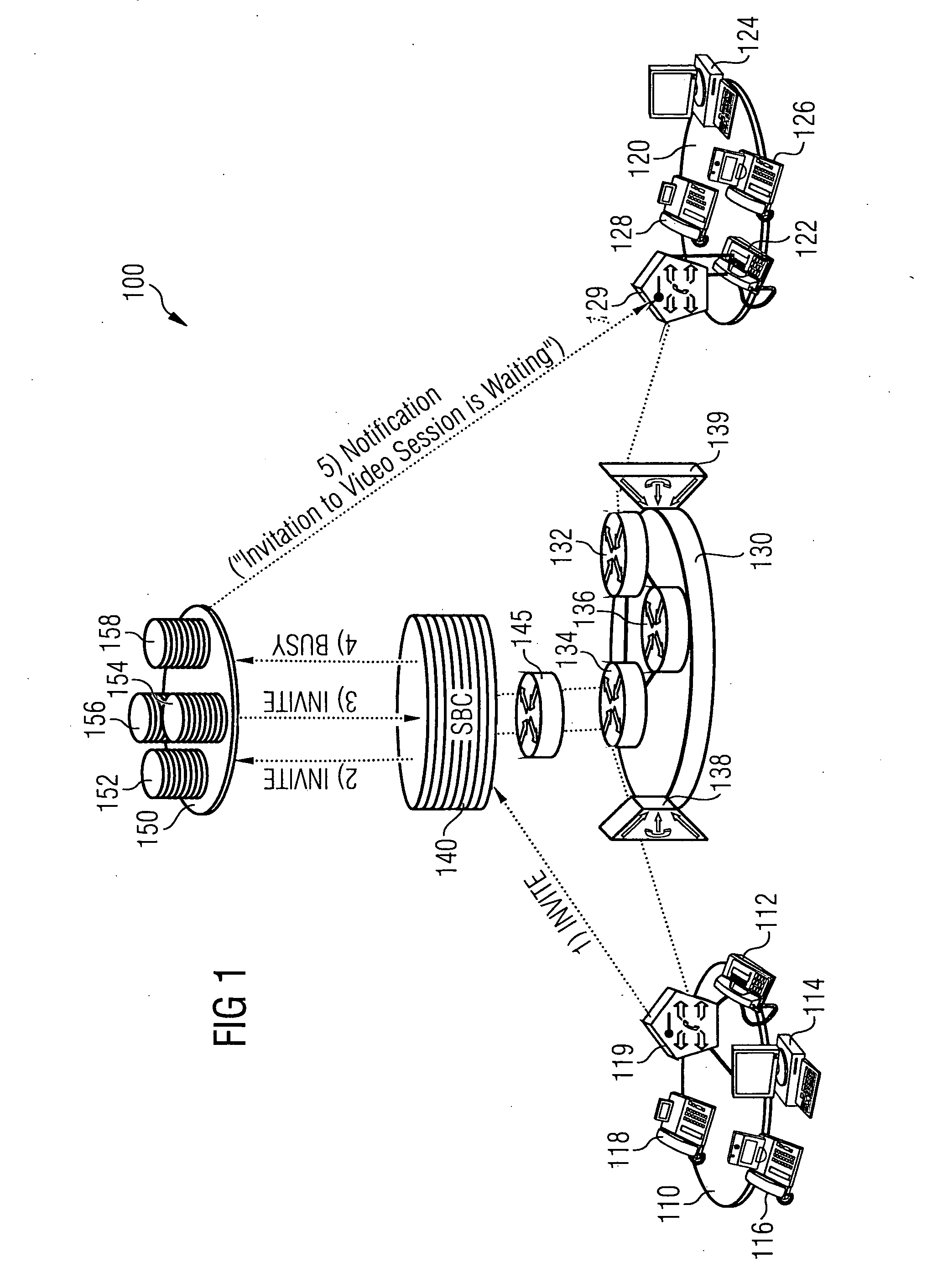
A novel network arrangement and method for handling sessions or calls in a communications network is provided. More particularly, a novel network arrangement and method for avoiding “ghost calls” in IP based communications networks for achieving higher session completion rates is provided. An inventive network arrangement comprises at least the following: a session border controller for monitoring and / or controlling available resources for sessions involving a user terminal and for determining a busy condition if a new session's resource requirements are in excess of the available resources; and an application server for intercepting a busy notification generated towards the new session's origination in response to a busy condition, the application server further configured to either generate a notification towards the new session's destination or redirect the new session to a different destination.
Owner:SIEMENS AG
Managing traffic within and between virtual private networks when using a session border controller
ActiveUS8169903B2Error preventionFrequency-division multiplex detailsTraffic capacityPrivate network
Methods and devices for managing traffic are described. Traffic from a source in a virtual private network (VPN) is received. The traffic is directed to a virtual interface that is designated to receive traffic from the VPN. The virtual interface is configured to associate the traffic with an identifier that uniquely identifies the VPN to a session border controller (SBC). The SBC can use the identifier to determine whether the source and the destination of the traffic are in the same VPN.
Owner:CISCO TECH INC
Methods and apparatus for detecting malicious attacks
Methods and apparatus for detecting VOIP spoofing attacks in systems that provide communication services over IP networks, for gathering information that can be used for preventing or mitigating future malicious attacks, are described. The methods and apparatus send various signals and check for expected responses. Actual responses and / or lack of responses to signals, e.g., messages, are detected, logged and used for making decisions as well as generating a record for informational purposes and analysis which can facilitate identification of common features of malicious packets and / or messages. The methods are well suited for use in a session border controller.
Owner:RIBBON COMM OPERATING CO INC
Long-term evolution voice signaling acquisition and service correlation method and apparatus
InactiveCN106961321AQuality assuranceRealize the whole process analysisSignal allocationWireless communicationSession controlData acquisition
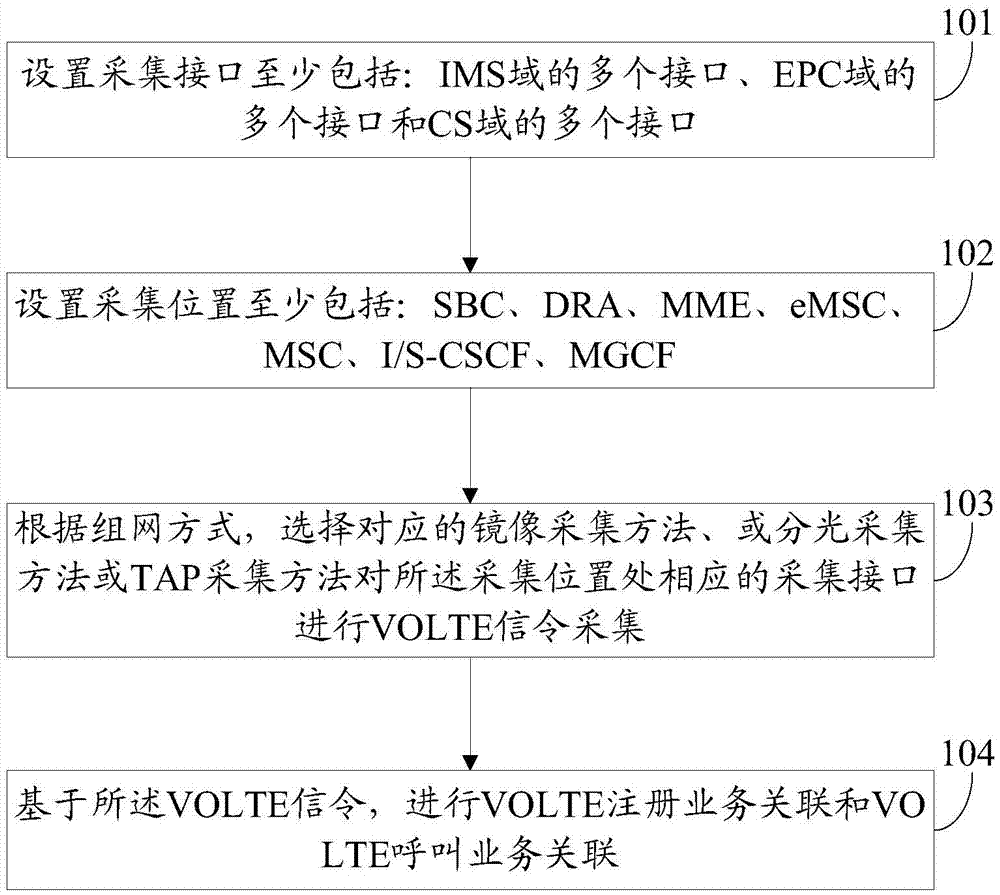
The invention discloses a VOLTE (Voice Over LTE) signaling acquisition and service correlation method and apparatus. The VOLTE signaling acquisition and service correlation method includes the steps: setting acquisition interfaces which at least include a plurality of interfaces of an IMS (IP Multimedia Subsystem) domain, a plurality of interfaces of an EPC (Evolved Packet Core) domain and a plurality of interfaces of a CS (Circuit Switch) domain; setting acquisition positions which at least include an SBC (Session Border Controller), a DRA (Diameter Routing Agent), an MME (Mobile Management Entity), a eMSC (evolved Mobile Switching Center), an MSC (Mobile Switching Center), I / S-CSCF (Interrogating / Serving Call Session Control Function) and MGCF (Media Gateway Control Function); according to the networking mode, selecting a corresponding mirror image method or a light splitting acquisition method or a TAP (Testing Access Point) acquisition method to perform VOLTE signaling acquisition on the corresponding acquisition interface at the acquisition position; and based on the VOLTE signaling, performing VOLTE registration service association and VOLTE call service association.
Owner:CHINA MOBILE GROUP ZHEJIANG
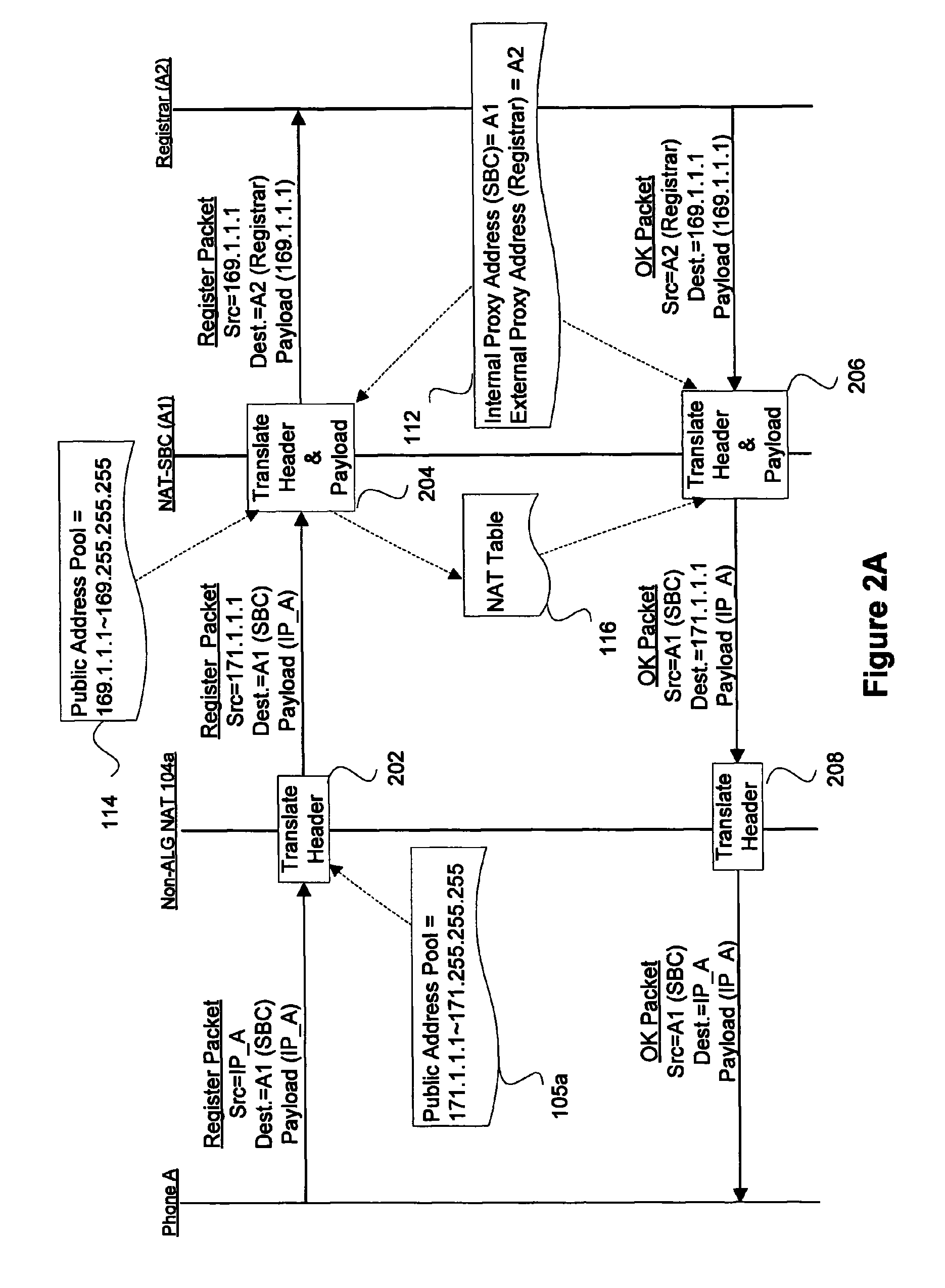
Mechanisms for using NAT at a session border controller
InactiveUS7860098B1Data switching by path configurationMultiple digital computer combinationsExpiration TimePrivate address
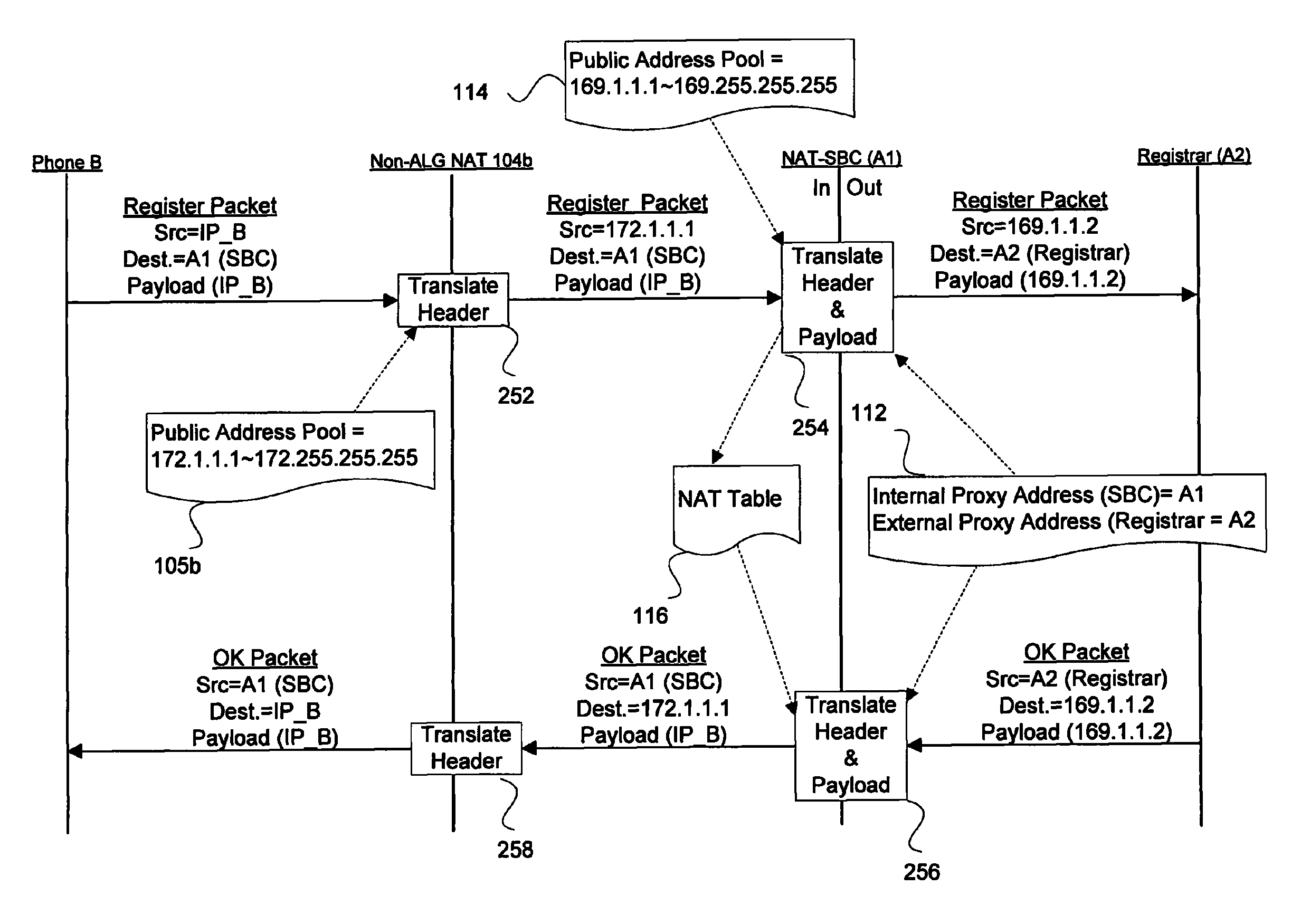
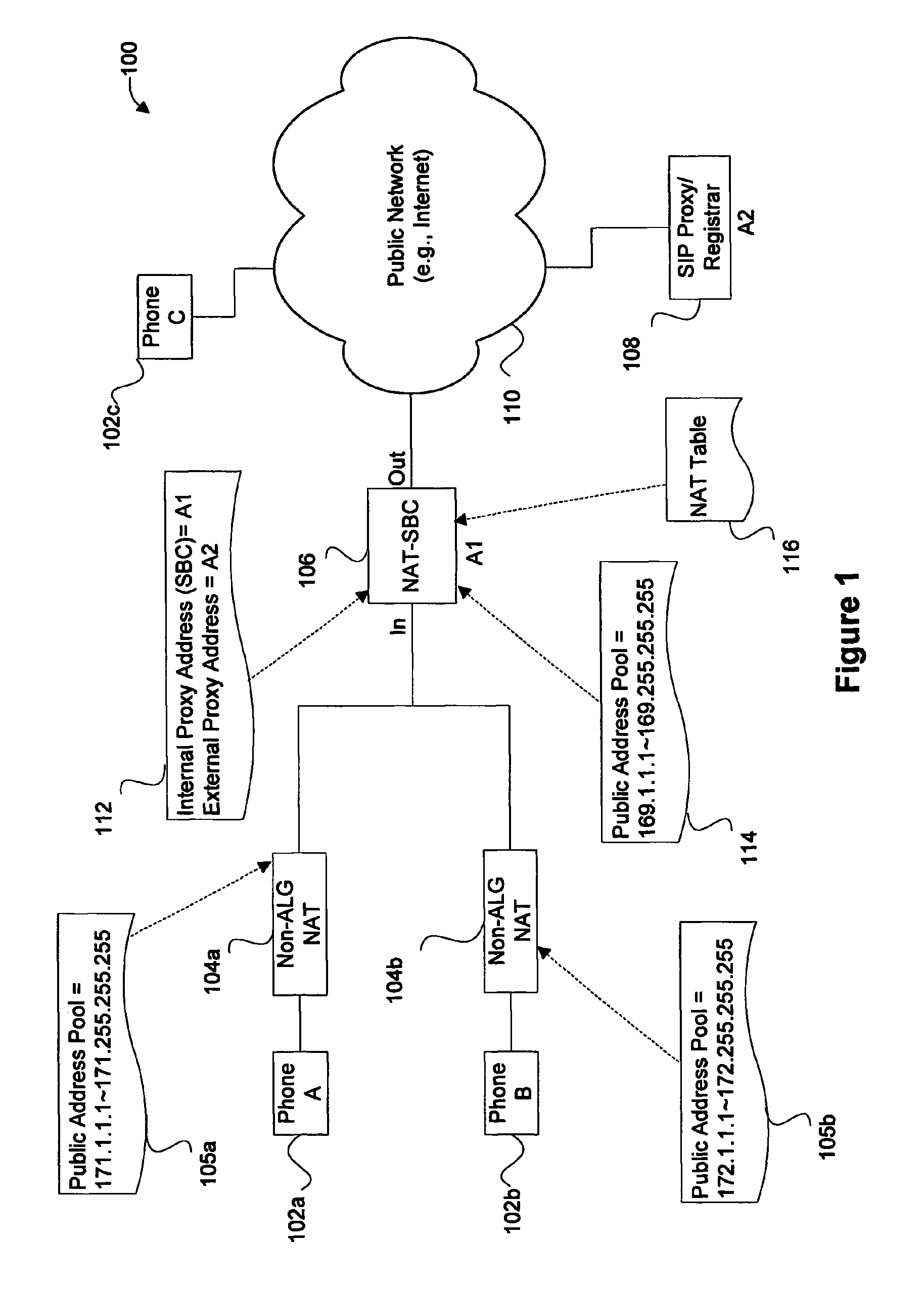
Disclosed are apparatus and methods for managing session data in a session border controller (SBC), where the session data is sent from a first node, such as a first phone, to a second node, such as a registrar or second phone. In general, embodiments of the present invention support SBC functionality by managing sessions through the SBC without implementing a terminate and regenerate of the sessions, but rather by intercepting packets destined to the second node and efficiently handling such functionality in the forwarding-path. Also in deployments where the endnodes require NAT (network address translation), mechanisms are provided in the SBC to perform NAT on the addresses embedded in the payload of the session data. In other aspects, mechanisms for keeping the sessions or NAT entries alive are facilitated at the SBC, even when an endnode has a expiration time that differs an expiration time of another device, such as a registar device. Other embodiments allow the actual media packets to flow through the SBC (e.g., for security, accounting, etc) while allowing two endnodes to utilize a same private address or domain.
Owner:CISCO TECH INC
Wireless isomer network vertical switch control method based on conversation edge control equipment SBC
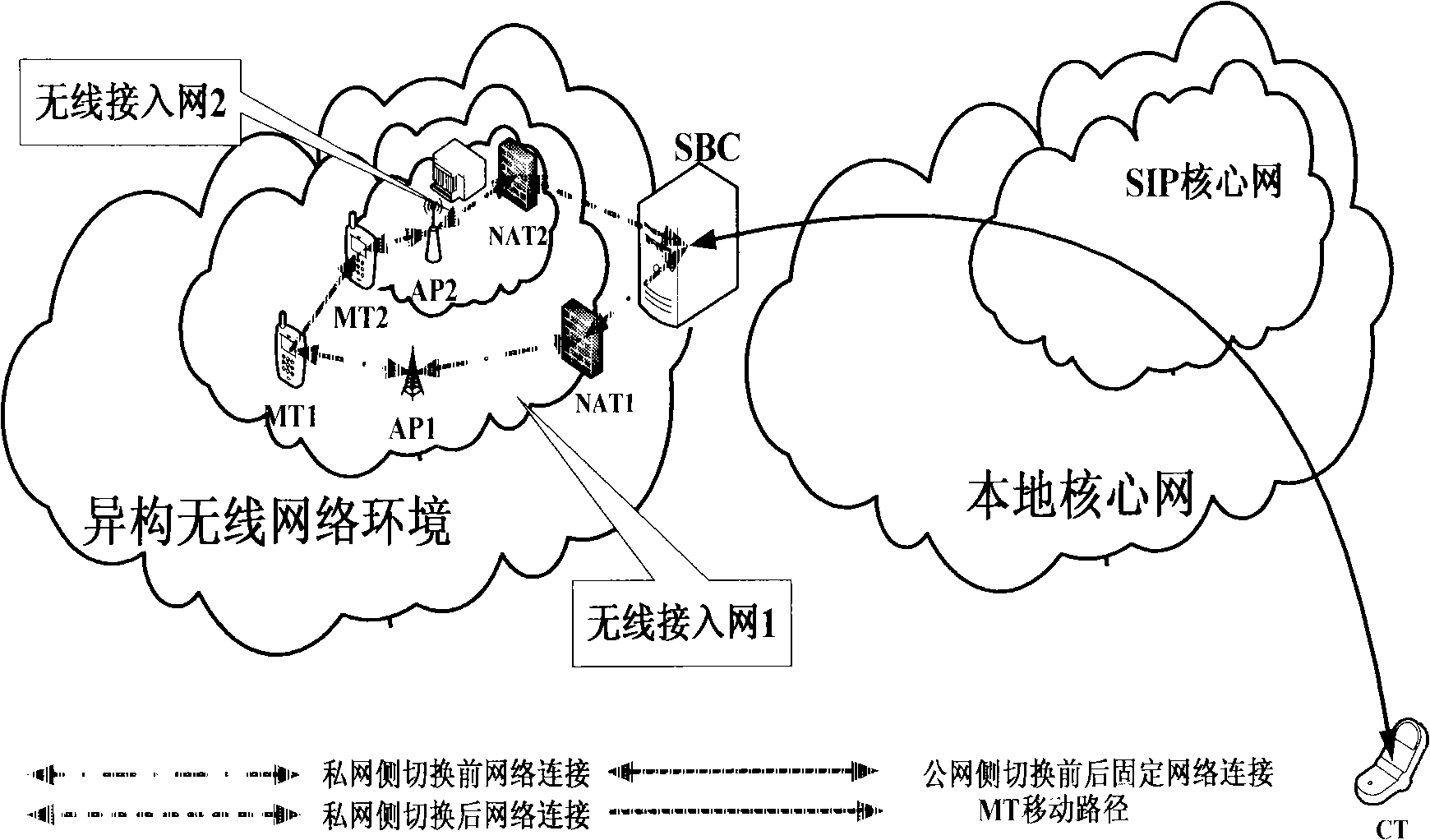
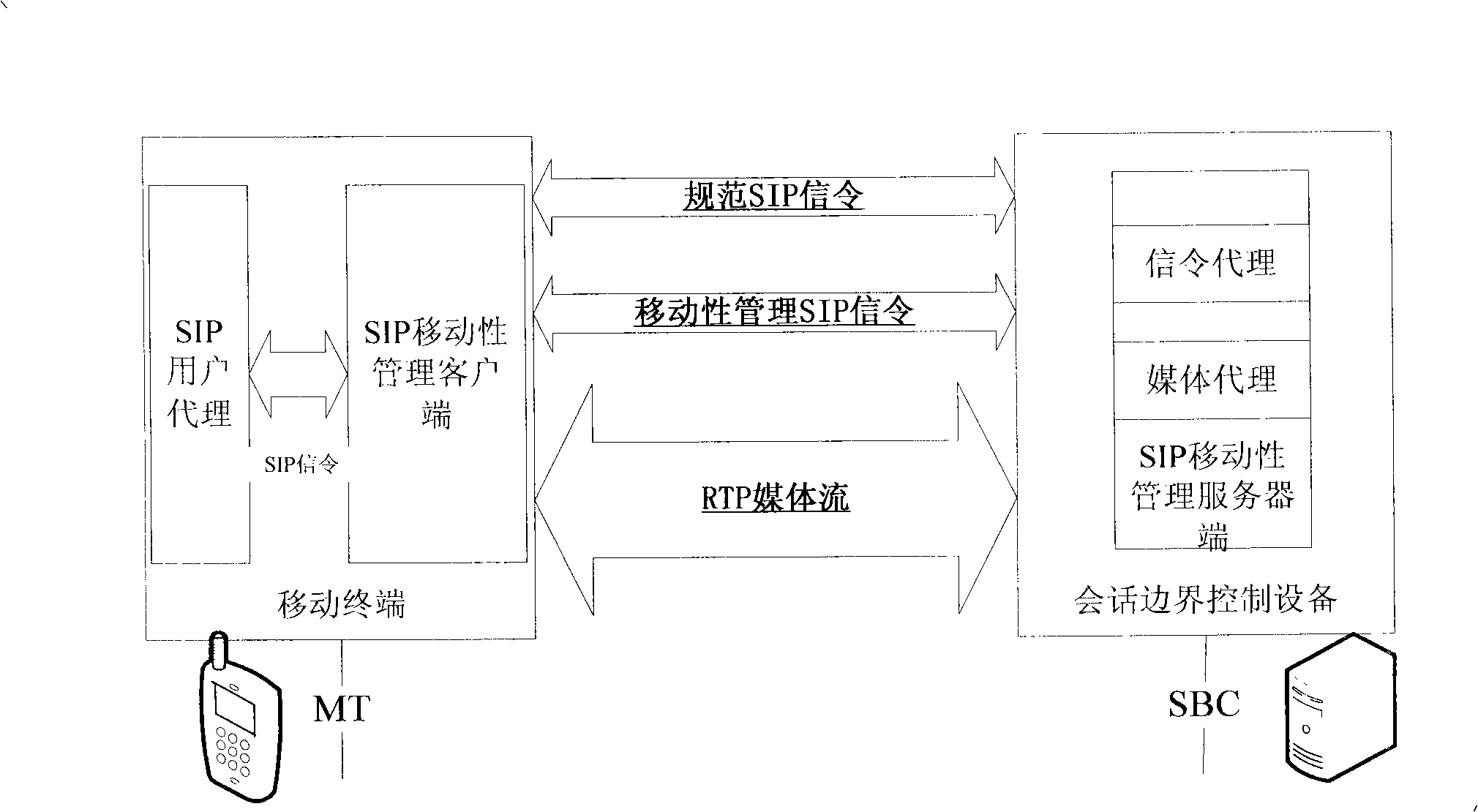
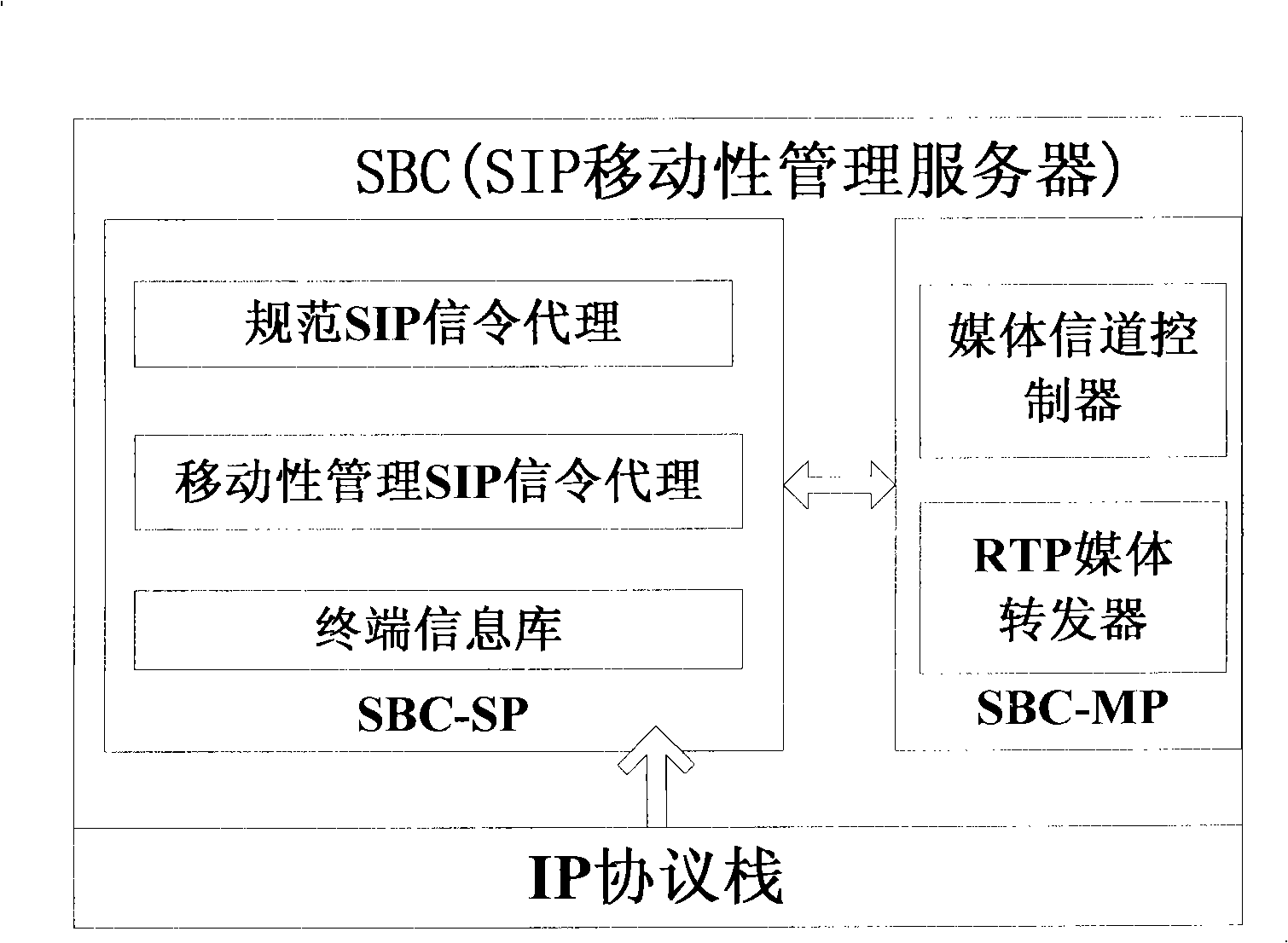
InactiveCN101296511ASolve the crossing problemAchieve smooth transitionRadio/inductive link selection arrangementsData switching networksSession controlThird generation
The invention relates to the mobile communication field, in particular to a method for controlling the vertical switch of a wireless heterogeneous network based on a session border controller (SBC) in an application layer mobility management technology. The method aims at the application of a multi-model mobile terminal in the multimedia services of the heterogeneous network, the SBC is utilized as a fixed mobile anchor point, an SIP protocol is adopted as a mobility management protocol, then the rapid vertical switch of the multimedia services of the multi-model mobile terminal among wireless heterogeneous networks such as GSM, WLAN and 3G, etc. is realized by the alternation of standardized and extended SIP signaling between two SIP function entities, namely, mobility management client terminal disposed in the multi-model terminal and the mobility management server disposed in session boarder controller, thereby reducing micro-mobile vertical switch delay and packet loss rate.
Owner:HUAZHONG UNIV OF SCI & TECH
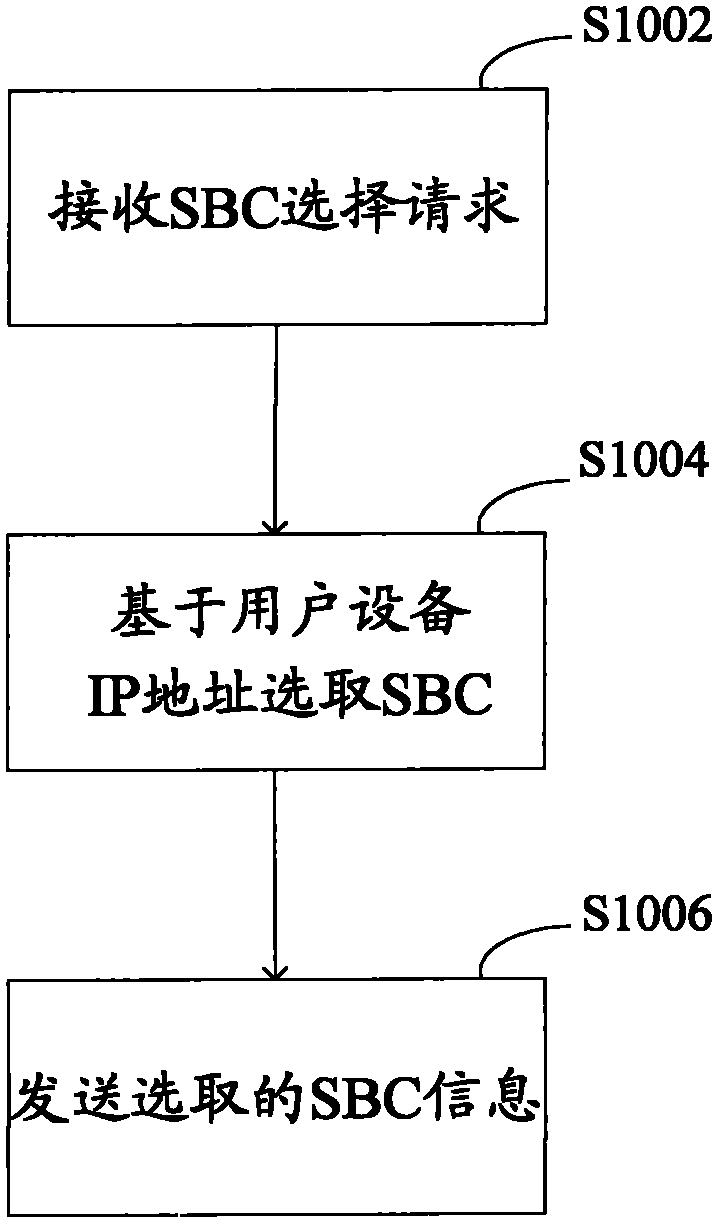
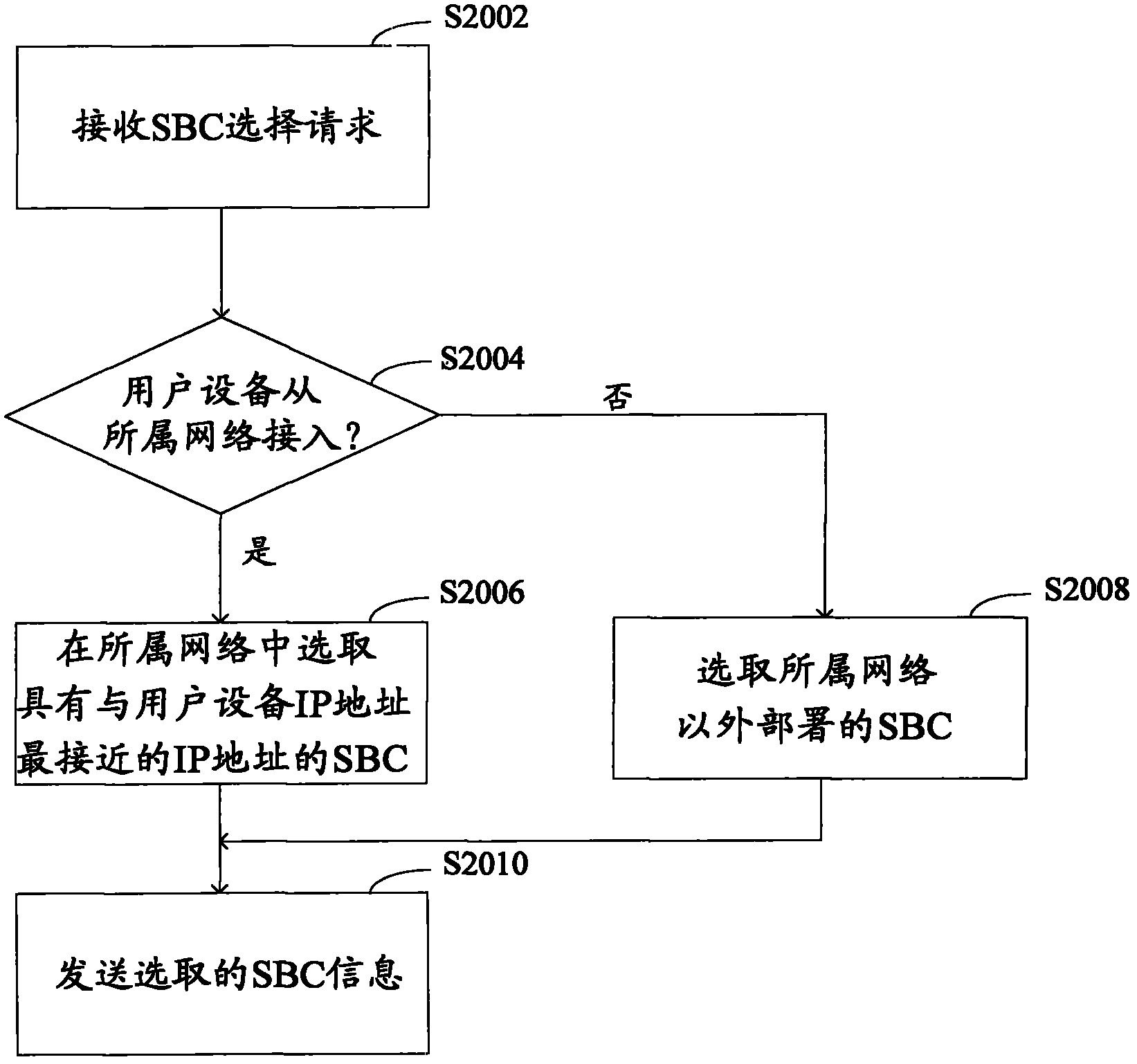
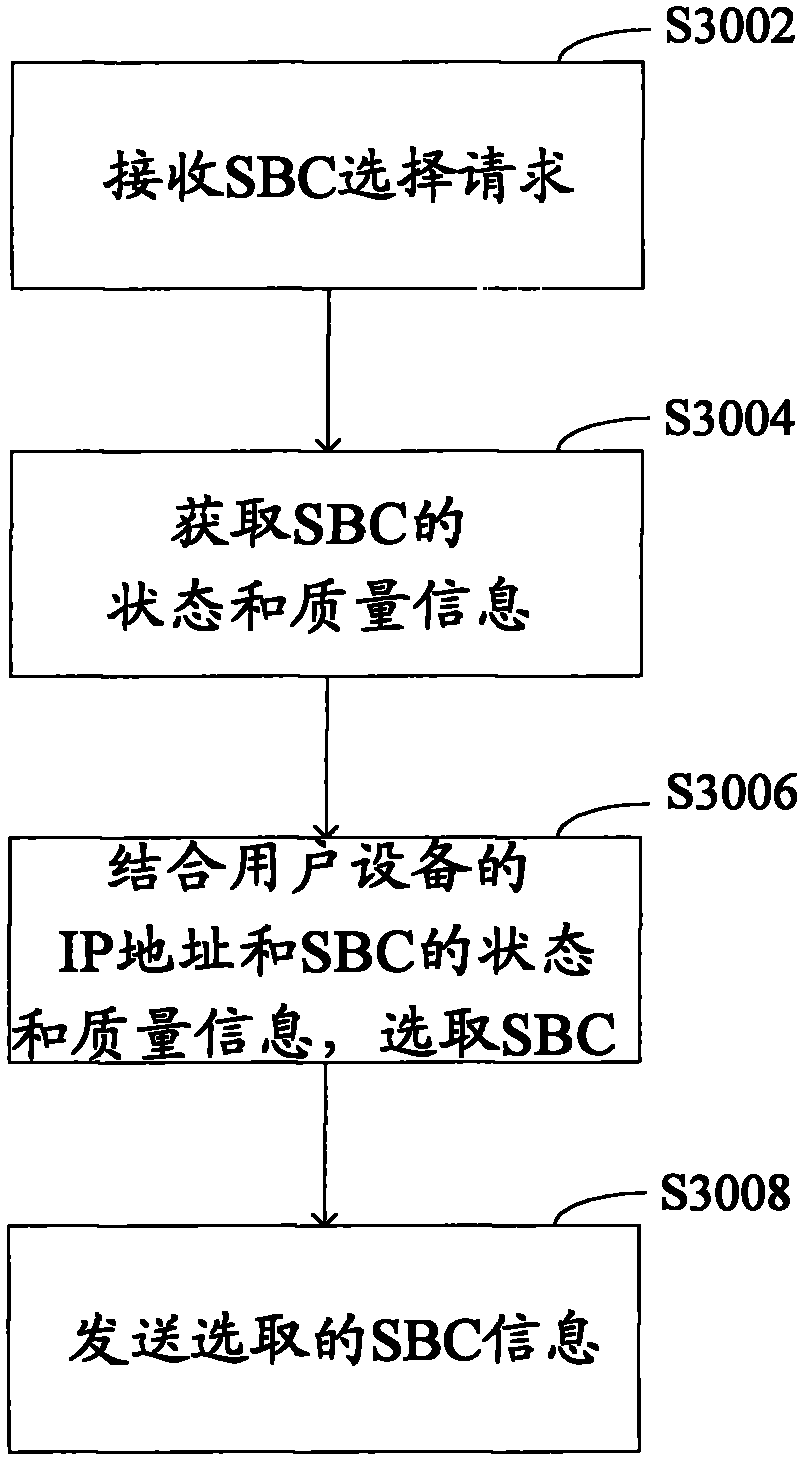
SBC selection method, SBC selection device, user equipment and SBC equipment
ActiveCN103188217AGood choiceImprove business qualityTransmissionIp addressSession border controller
The invention discloses an SBC (session border controller) selection method, an SBC selection device, user equipment and SBC equipment. The SBC selection method can comprise the steps that an SBC selection request of the user equipment is received; an SBC is selected, wherein the selection of the SBC is based on an IP (Internet Protocol) address of the user equipment; and information of the selected SBC is sent to the user equipment. According to the method and the device, the selection of the SBC can be optimized, so that the service quality is improved.
Owner:CHINA MOBILE COMM GRP CO LTD
Managing traffic within and between virtual private networks when using a session border controller
Methods and devices for managing traffic at a session border controller (SBC) are described. A signal portion of traffic en route from a source in a virtual private network (VPN) to a destination is received. The signal portion has embedded therein an identifier that uniquely identifies the VPN. The identifier is accessed to determine whether the destination is also in the VPN. A decision whether to direct a media portion of the traffic to an SBC is made depending on whether or not the destination is outside of the VPN.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com