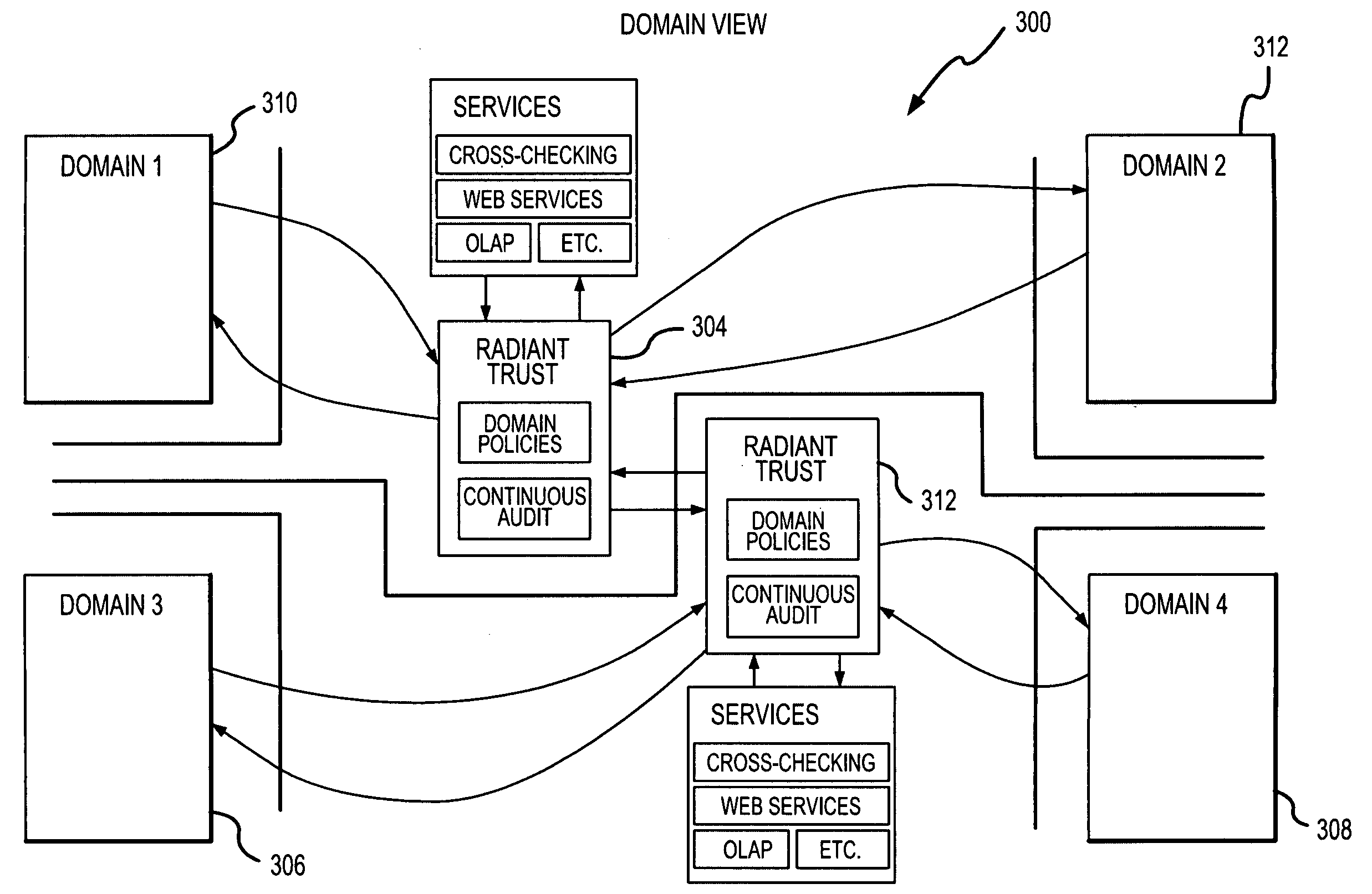
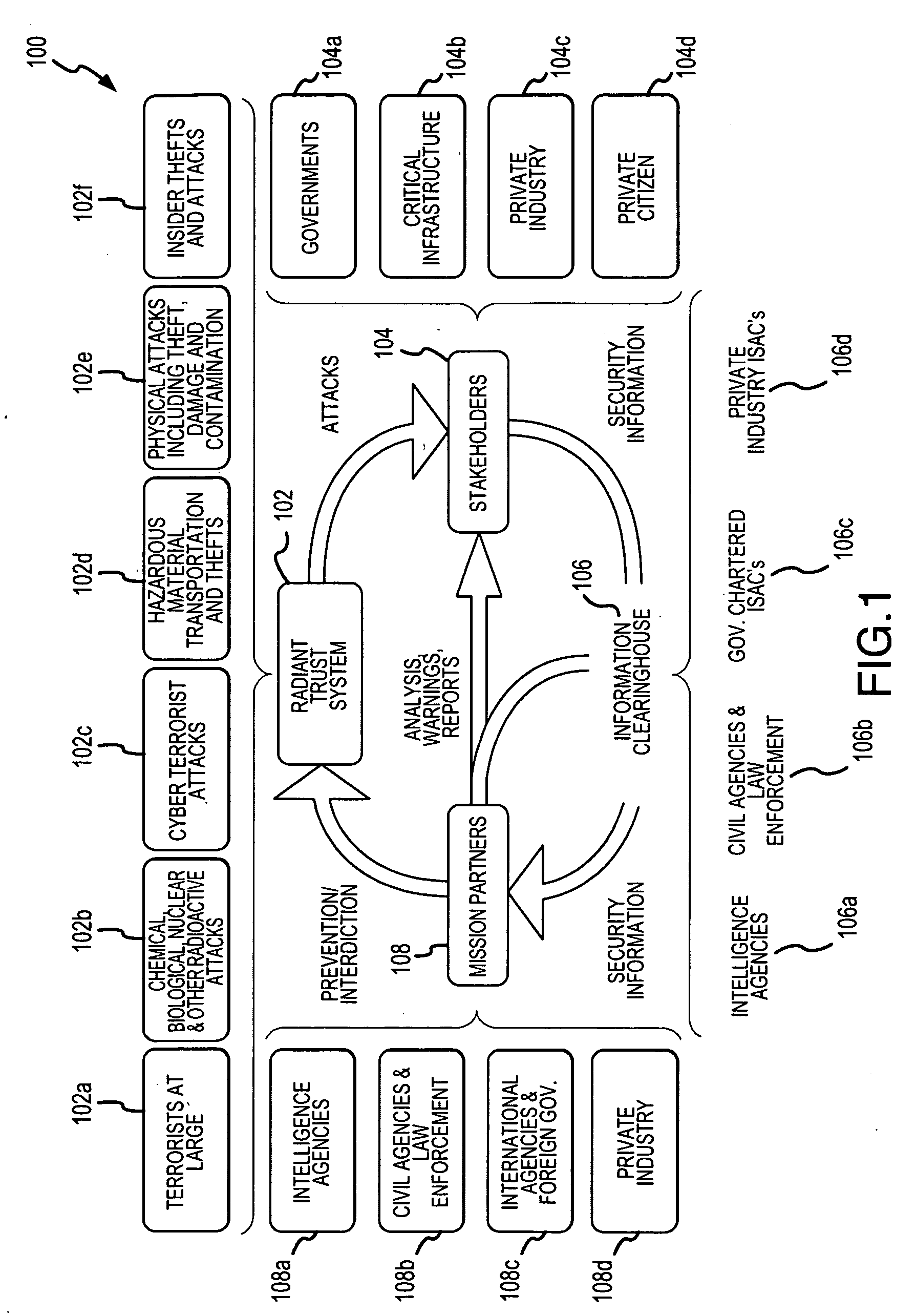
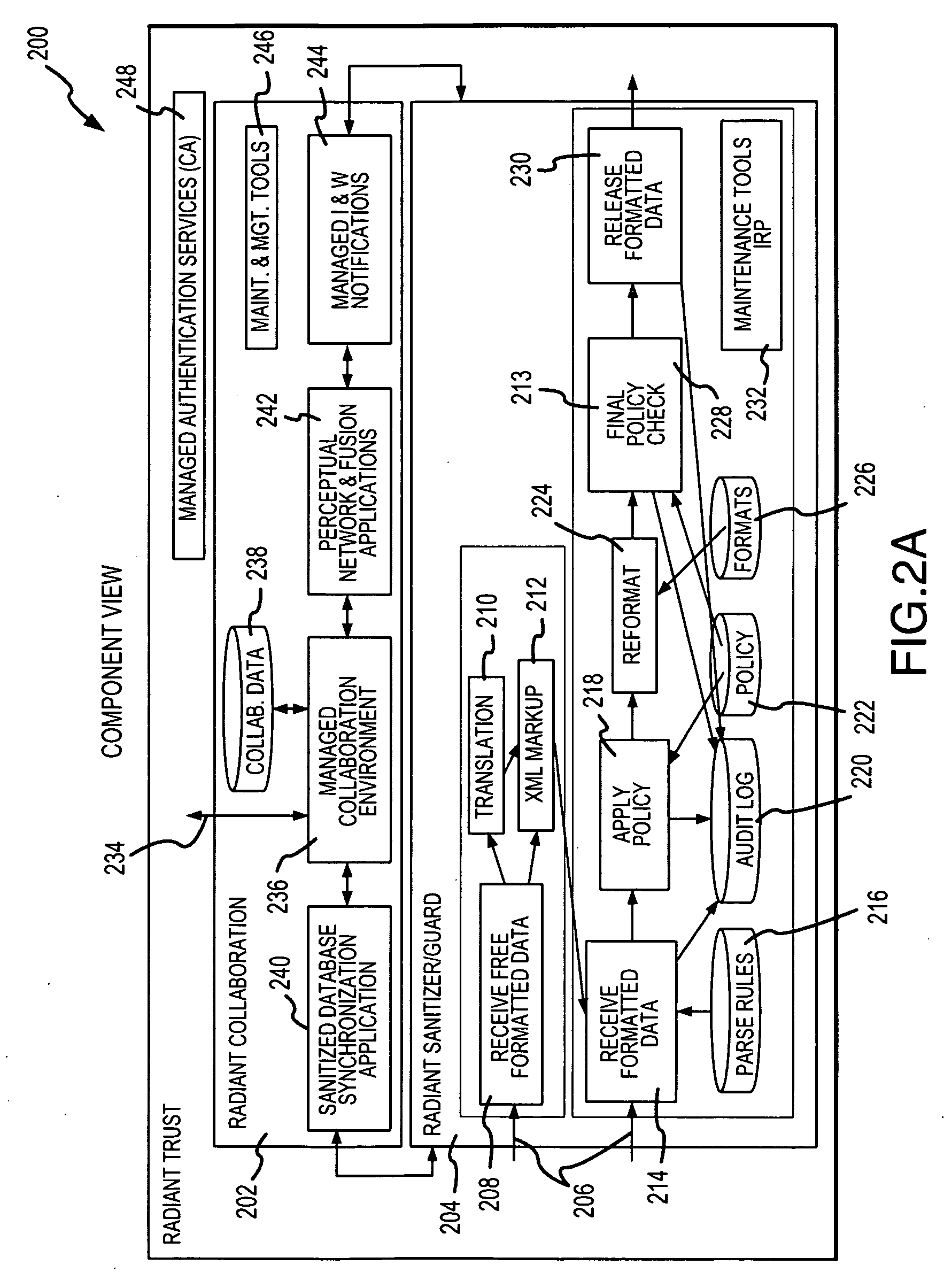
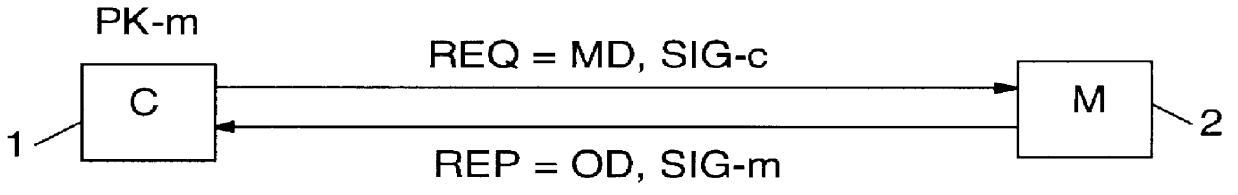Patents
Literature
5830 results about "Information exchange" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information exchange or information sharing is the act of certain entities (e.g. people) passing information from one to another. This could be done electronically or through certain systems. These are terms that can either refer to bidirectional information transfer in telecommunications and computer science or communication seen from a system-theoretic or information-theoretic point of view. As, "information," in this context invariably refers to (electronic) data that encodes and represents the information at hand, a broader treatment can be found under data exchange.
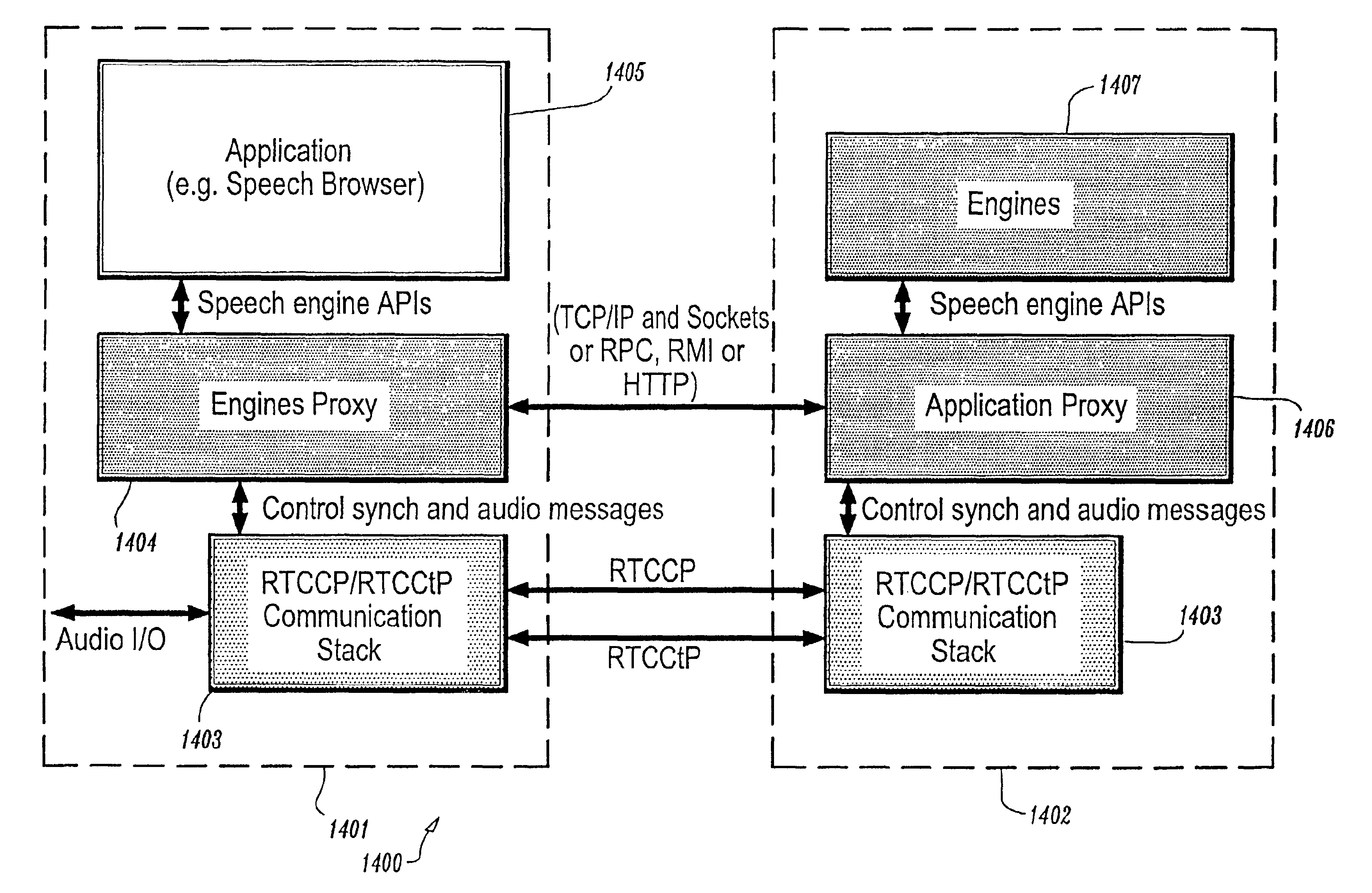
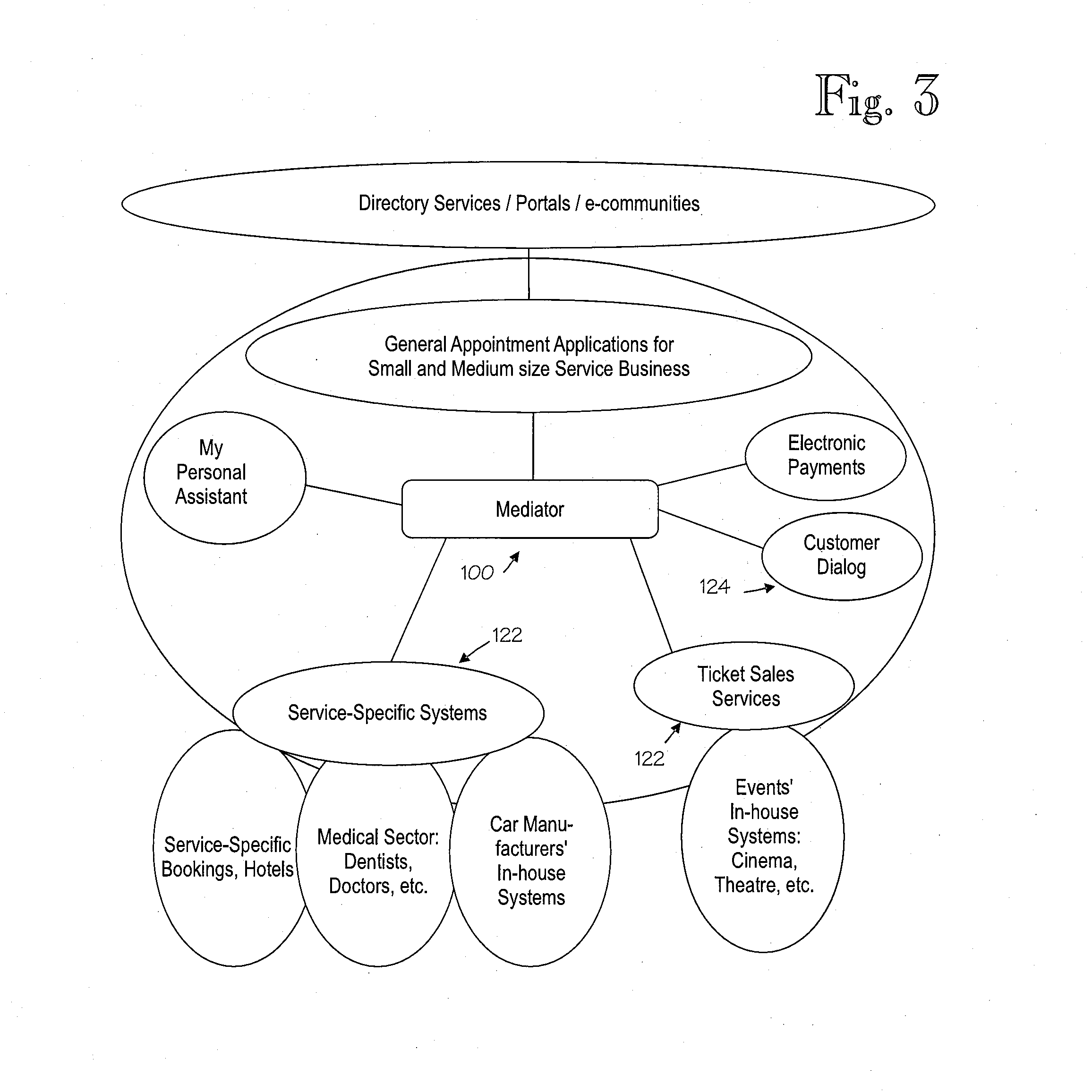
Conversational networking via transport, coding and control conversational protocols
InactiveUS6934756B2Broadcast transmission systemsMultiple digital computer combinationsSession controlRemote control
A system and method for implementing conversational protocols for distributed conversational networking architectures and / or distributed conversational applications, as well as real-time conversational computing between network-connected pervasive computing devices and / or servers over a computer network. The implementation of distributed conversational systems / applications according to the present invention is based, in part, on a suitably defined conversational coding, transport and control protocols. The control protocols include session control protocols, protocols for exchanging of speech meta-information, and speech engine remote control protocols.
Owner:IBM CORP
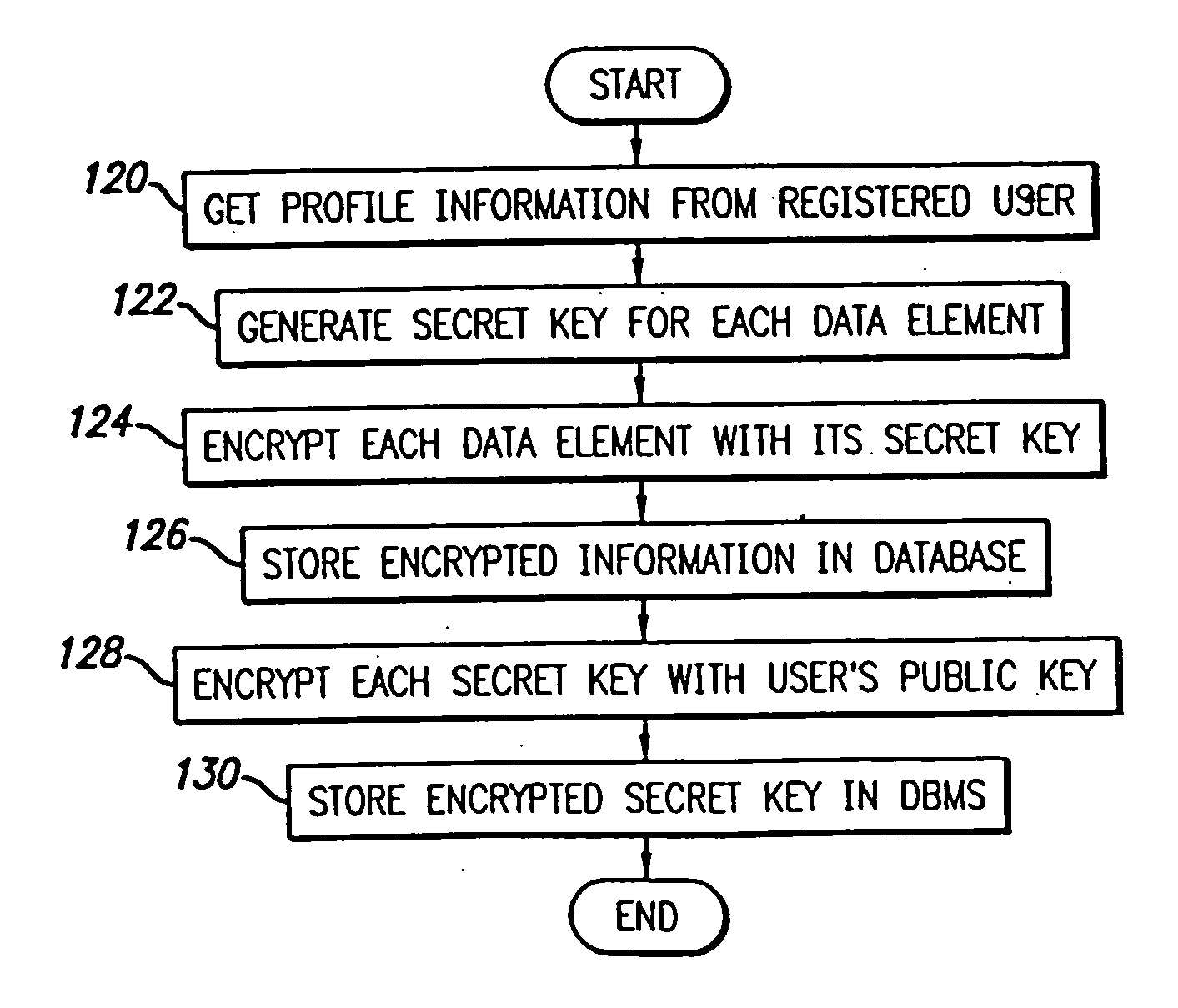
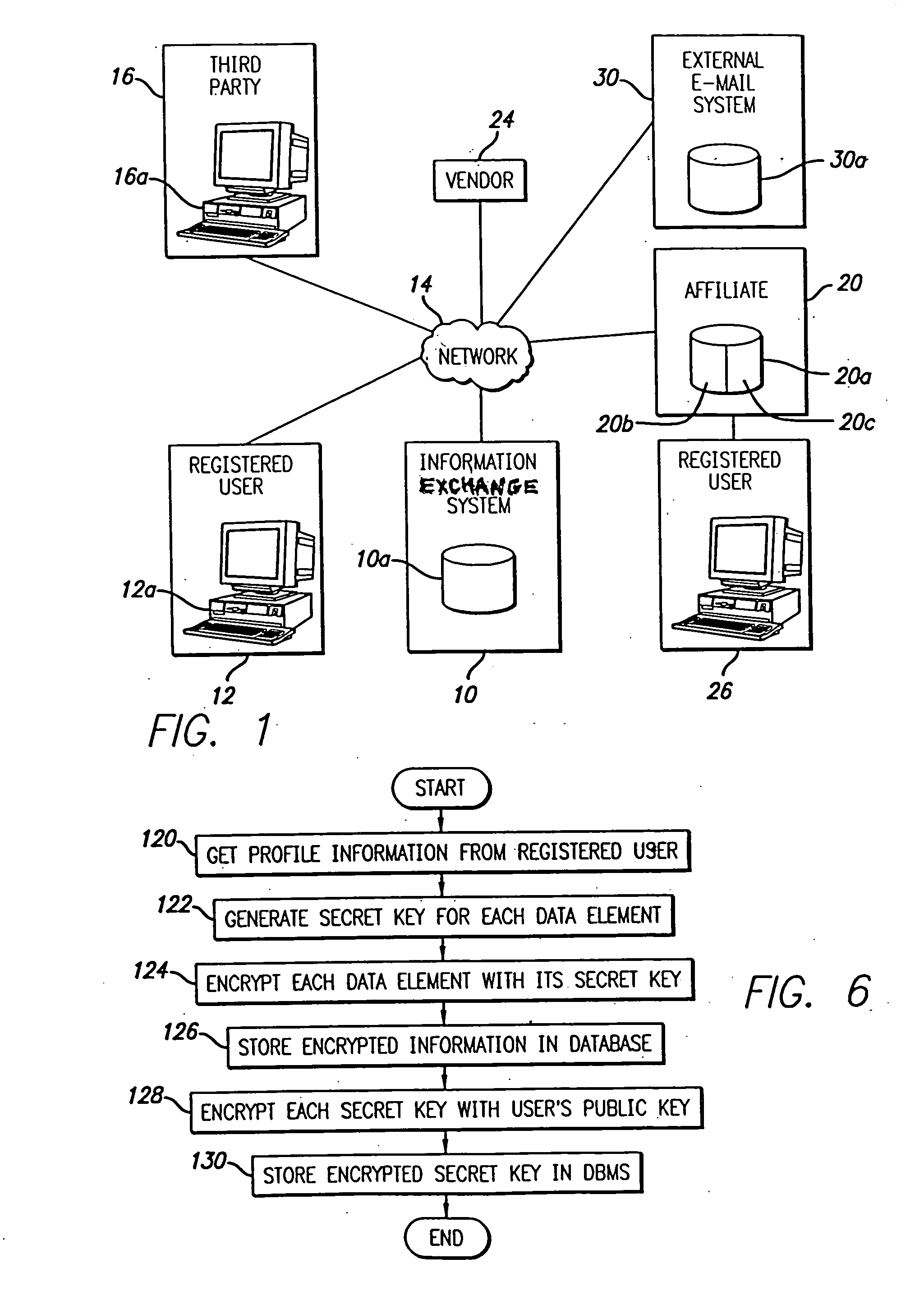
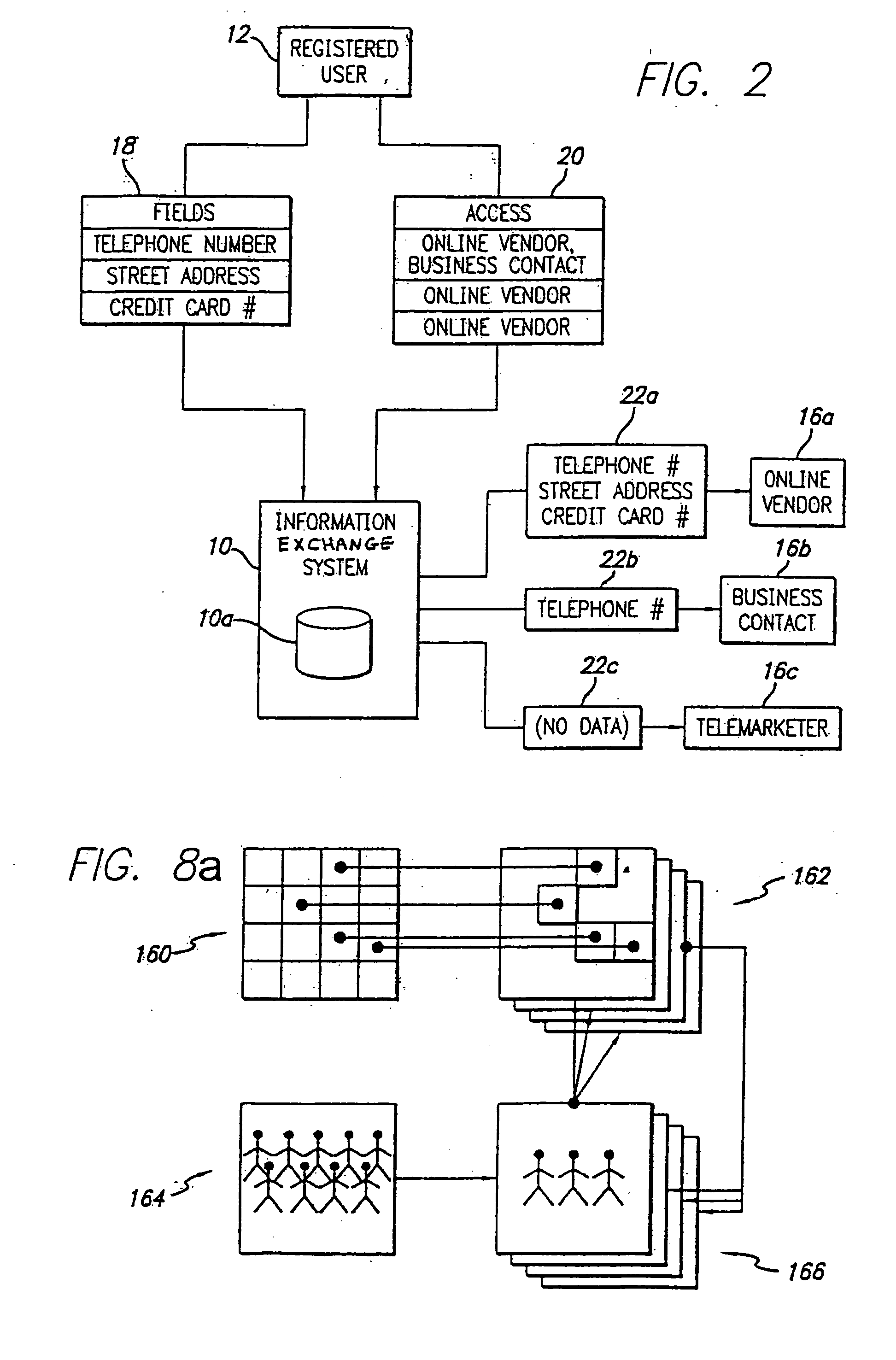
System and method for selective information exchange
InactiveUS20050192008A1Avoid accessComputer security arrangementsRadio/inductive link selection arrangementsTime informationThe Internet
A system and method for providing users with granular control over arbitrary information that allows for selective, real-time information sharing in a communications network such as the Internet is provided. In a network including a plurality of network devices operated by a plurality of users, a real-time information exchange system for sharing user profile information between respective users includes a database management system connected to the network. The database management system, which may be distributed across the network, stores the user profile information for a plurality of registered users of the information exchange system The user profile information includes a plurality of data elements, each data element having an associated one of the plurality of registered users. Each data element has an associated group of users to whom access to the data element has been granted, and users not included in the associated group of users are denied access to the data element. Each registered user may selectively control the granting and denying of access to each of its associated data elements by other respective user, on an element-by-element, and user-by-user basis. Further, each registered user may dynamically create its own data fields.
Owner:DESAI NIMESH +5
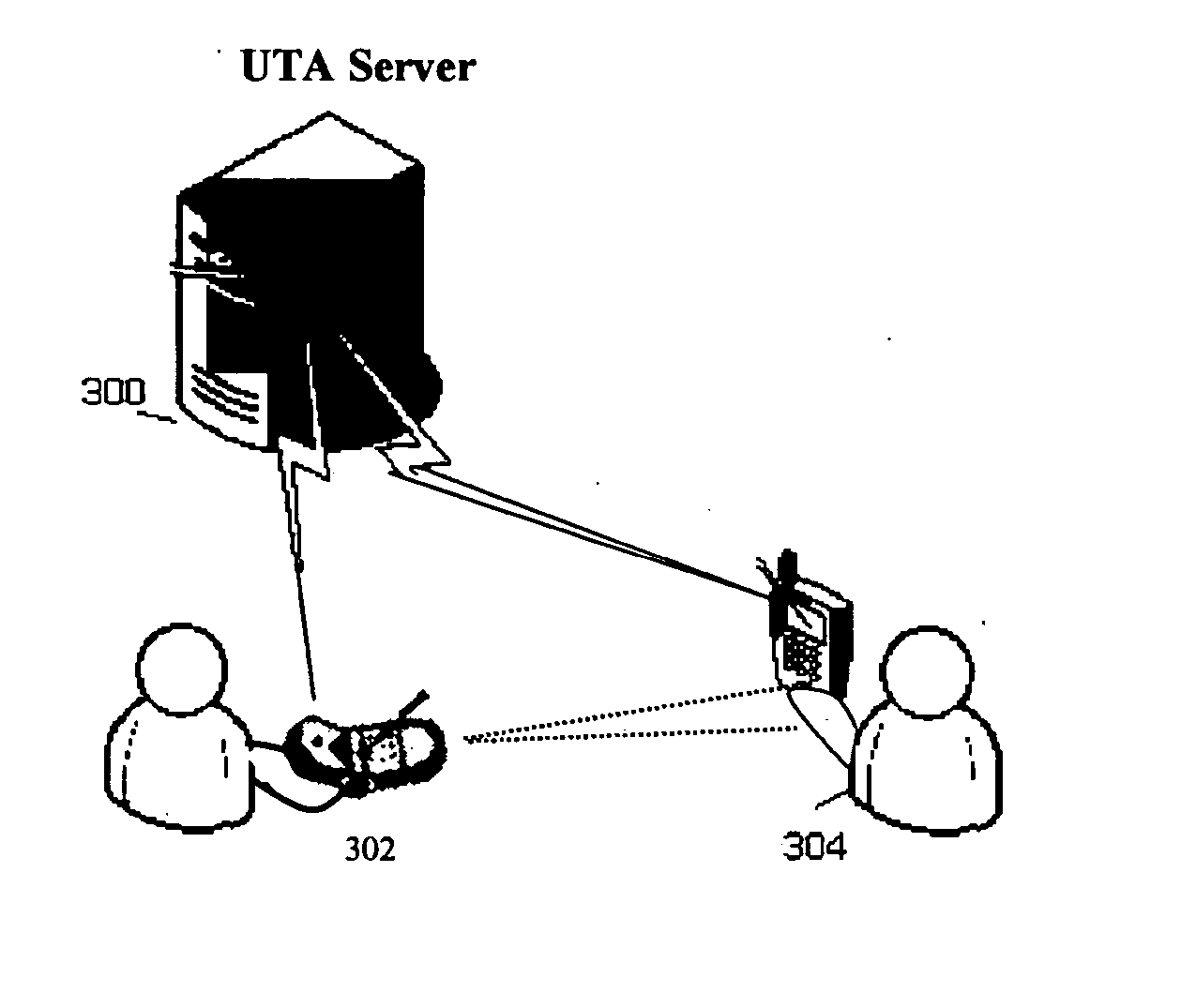
Pointing interface for person-to-person information exchange
A system for enabling a person to person communication from one portable computing device to one or more other portable computing devices based upon physically pointing a portion of one portable computing device in the direction of other portable computing devices. The portable computing devices consist of a CPU, a locative sensor system, an orientation system, and an interface to a distributed network. The distributed network sends and receives data to the portable computing devices. Connected to the distributed network is a User Tracking Application (“UTA”). The User Tracking Application receives location and orientation information from each of the portable computing devices. Based on the location and orientation of the portable computing devices and via control of the users, messages and data may be sent between the devices. The User Tracking Application also allows filtering of groups of users based on particular attributes, such as, age, gender, profession, organizational affiliation, income, etc. The system also allows for the electronic retrieval of crowd demographics. A person with a portable computing device is able to point to a crowd of individuals and information about those individuals with portable computing devices may be retrieved and compiled.
Owner:OUTLAND RES
Method and system for remote delivery of retail banking services
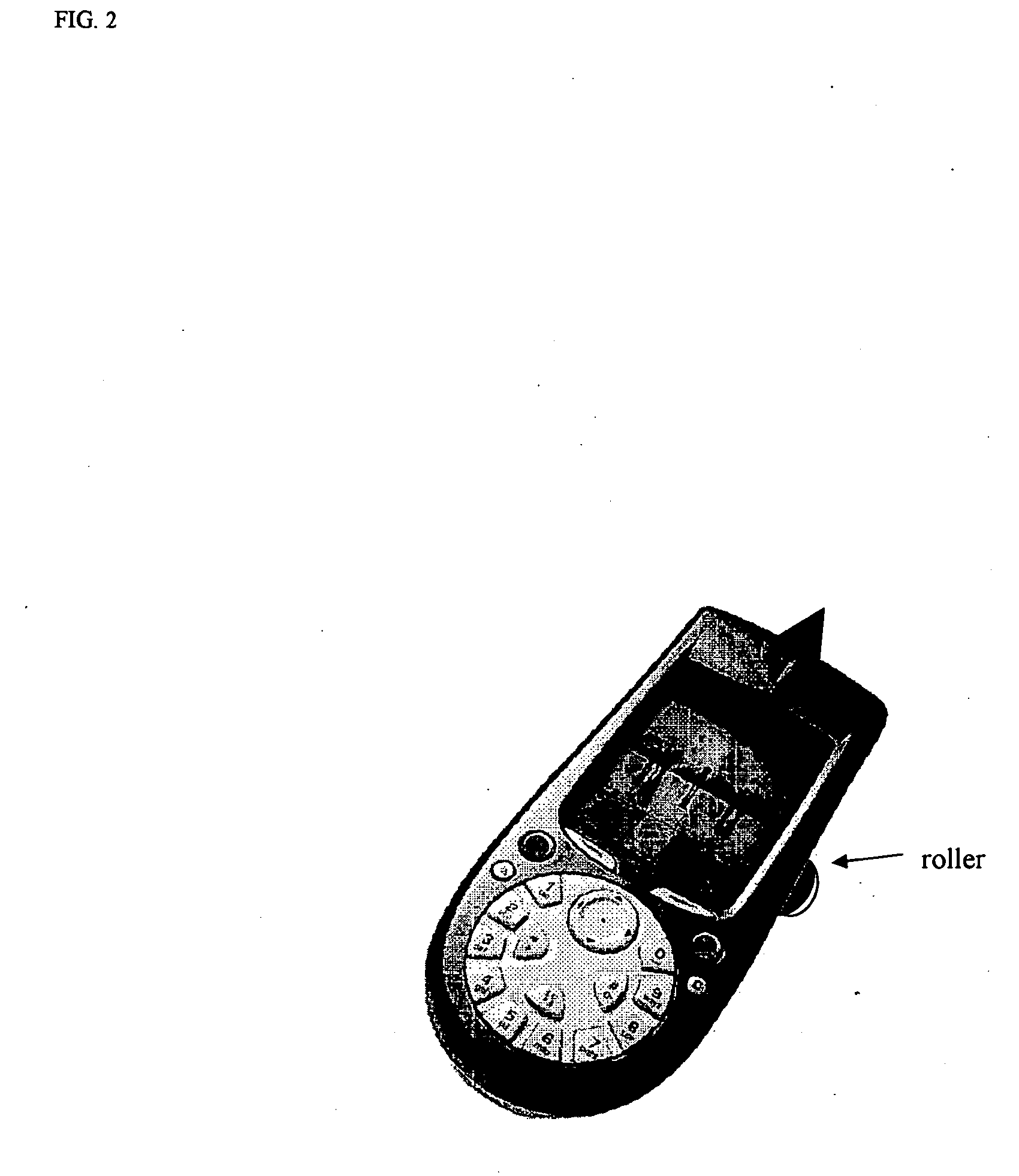
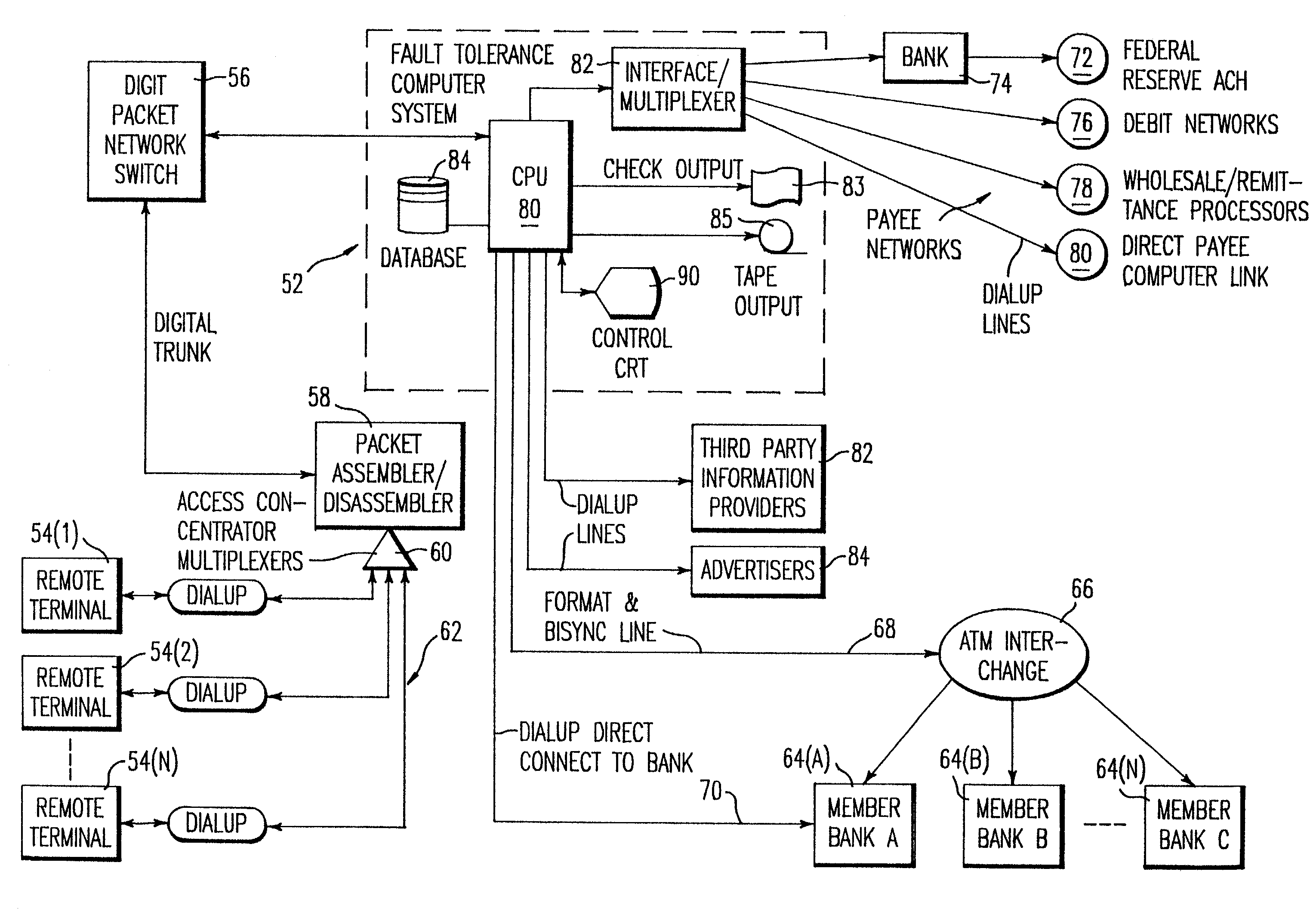
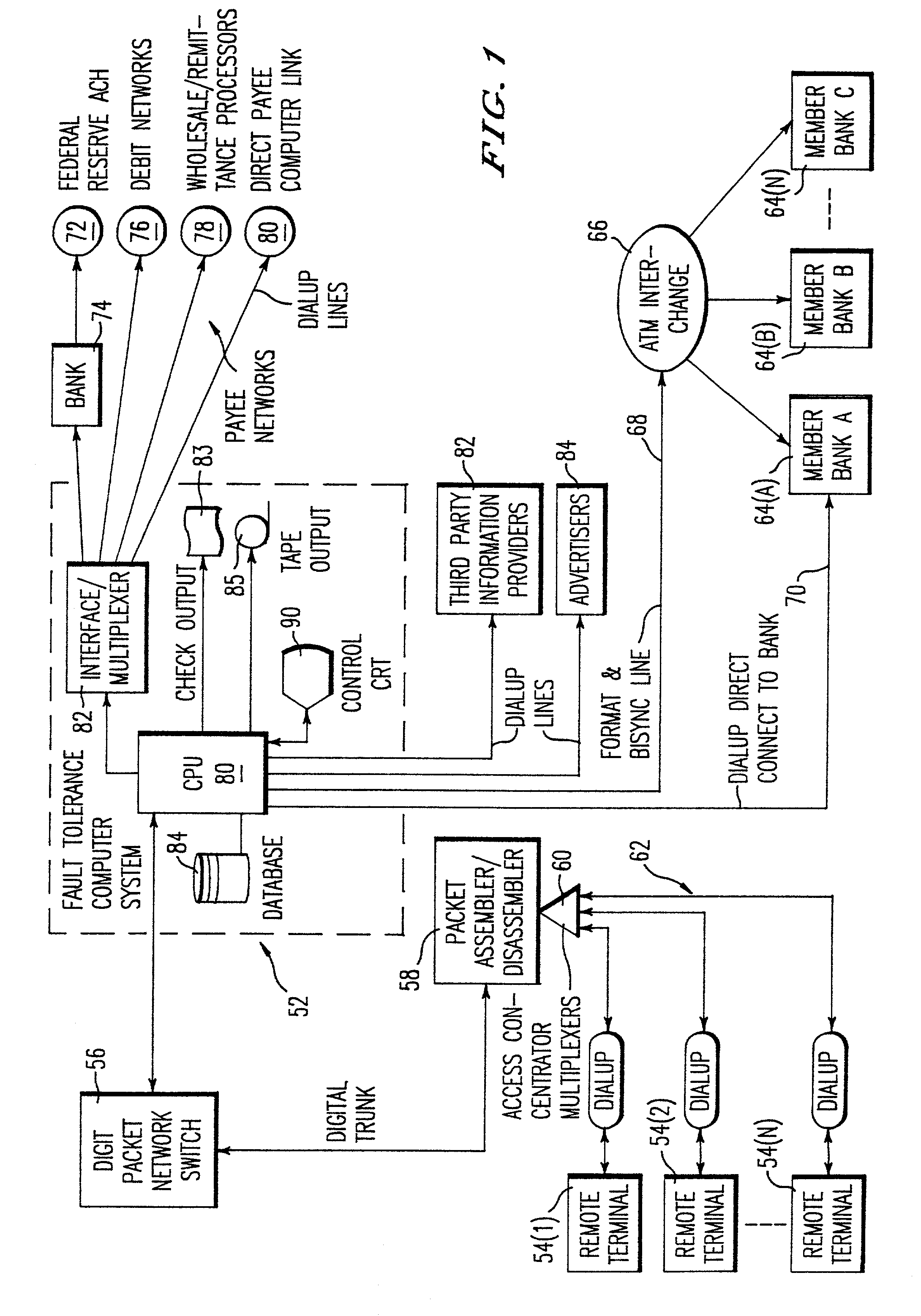
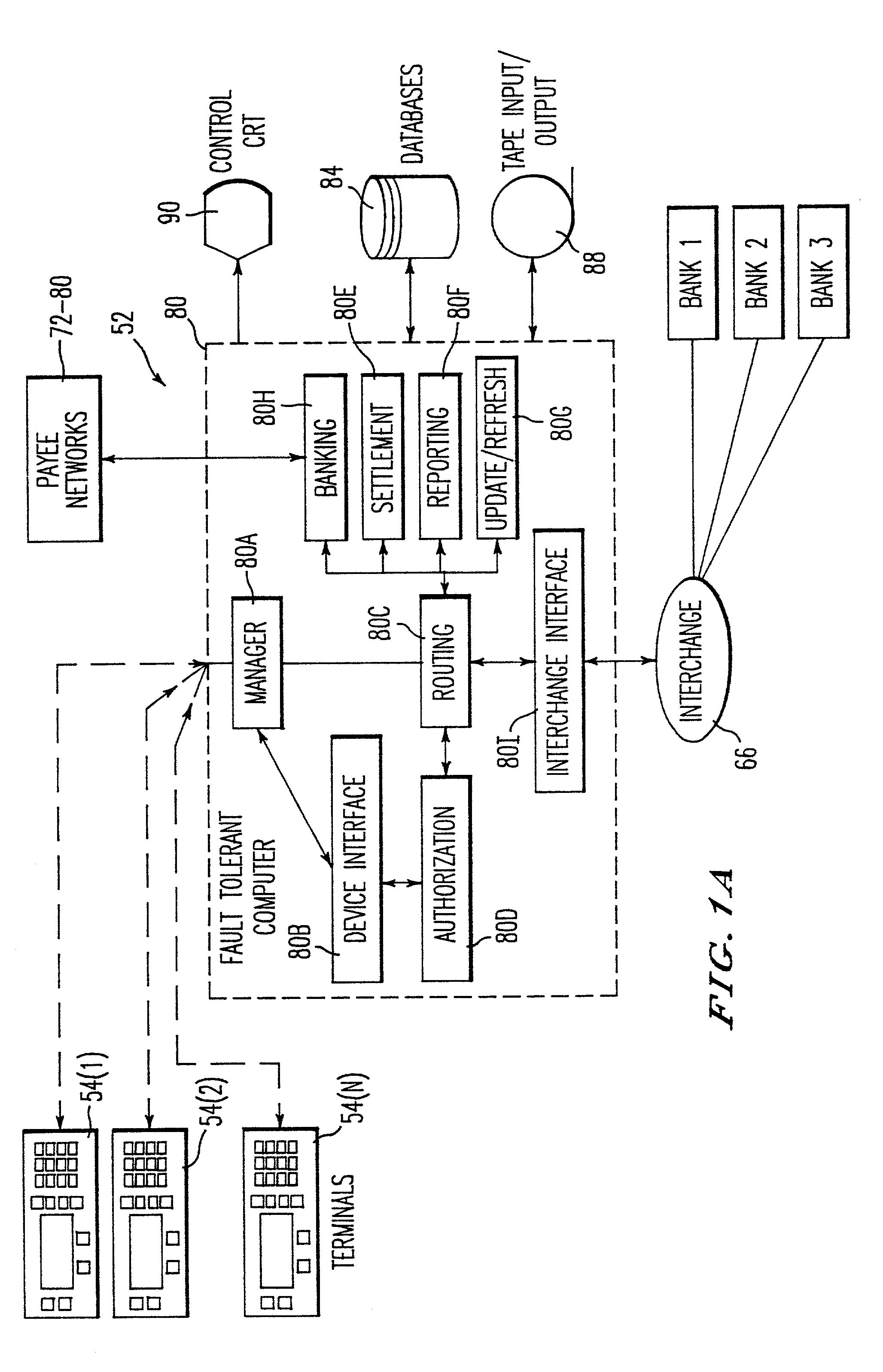
A practical system and method for the remote distribution of financial services (e.g., home banking and bill-paying) involves distributing portable terminals to a user base. The terminals include a multi-line display, keys “pointing to” lines on the display, and additional keys. Contact is established between the terminals and a central computer operated by a service provider, preferably over a dial-up telephone line and a packet data network. Information exchange between the central computer and the terminal solicits information from the terminal user related to requested financial services (e.g., for billpaying, the user provides payee selection and amount and his bank account PIN number). The central computer then transmits a message over a conventional ATM network debiting the user's bank account in real time, and may pay the specified payees the specified amount electronically or in other ways as appropriate. Payments and transfers may be scheduled in advance or on a periodic basis. Because the central computer interacts with the user's bank as a standard POS or ATM network node, no significant software changes are required at the banks' computers. The terminal interface is extremely user-friendly and incorporates some features of standard ATM user interfaces so as to reduce new user anxiety.
Owner:OFFICIAL PAYMENTS
Integrated system for network layer security and fine-grained identity-based access control
ActiveUS6986061B1Simple technologyUser identity/authority verificationDigital computer detailsKey exchangeMedia access control
Owner:TREND MICRO INC
Processes systems and networks for secure exchange of information and quality of service maintenance using computer hardware
InactiveUS20020040439A1Digital data processing detailsUser identity/authority verificationQuality of serviceData transformation
A system and method for providing external data-signal isolation, and signal-level information-preserving-data-transformations, to enable safe, operationally efficient, information sharing between protected information systems and networks and external, potentially hostile, information systems and networks which neutralizes any imbedded hostile executable codes such as viruses that may be in data-signals incoming from the external systems and networks. The system and method prevent untransformed external data-signals from entering protected systems and / or networks using an intermediate screen which is a computer hardware device. The intermediate screen (which may be implemented as a network of systems) is deployed between the protected systems and external systems and is used to process all incoming signals from the external system to obtain transformed data sets from which information is extracted before it is passed to the protected system. The incoming signals all remain confined in the intermediate screen.
Owner:KELLUM CHARLES W
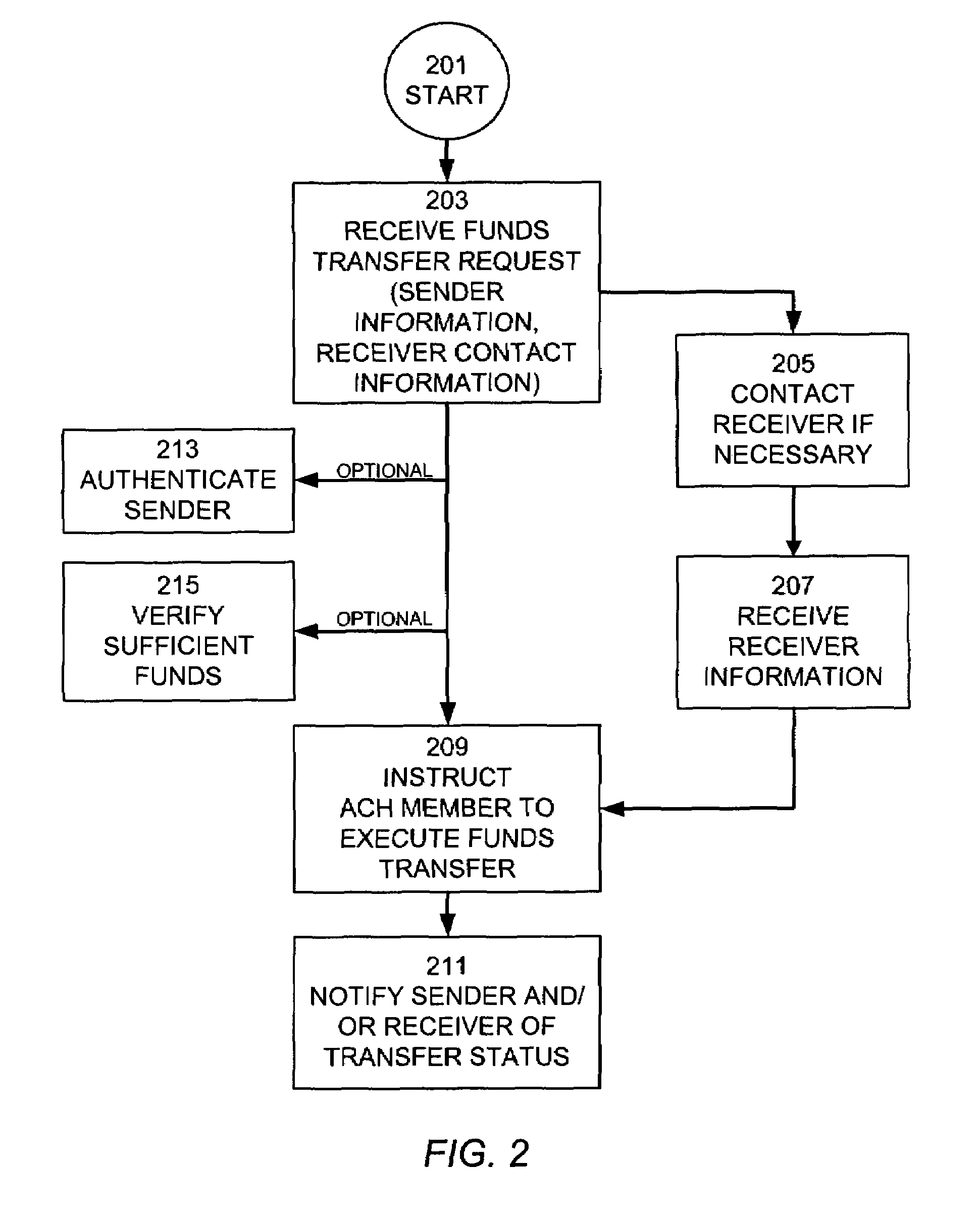
Consumer-directed financial transfers using automated clearinghouse networks
InactiveUS7395241B1Allocation is accurateEliminate contactComplete banking machinesFinanceThe InternetCheque
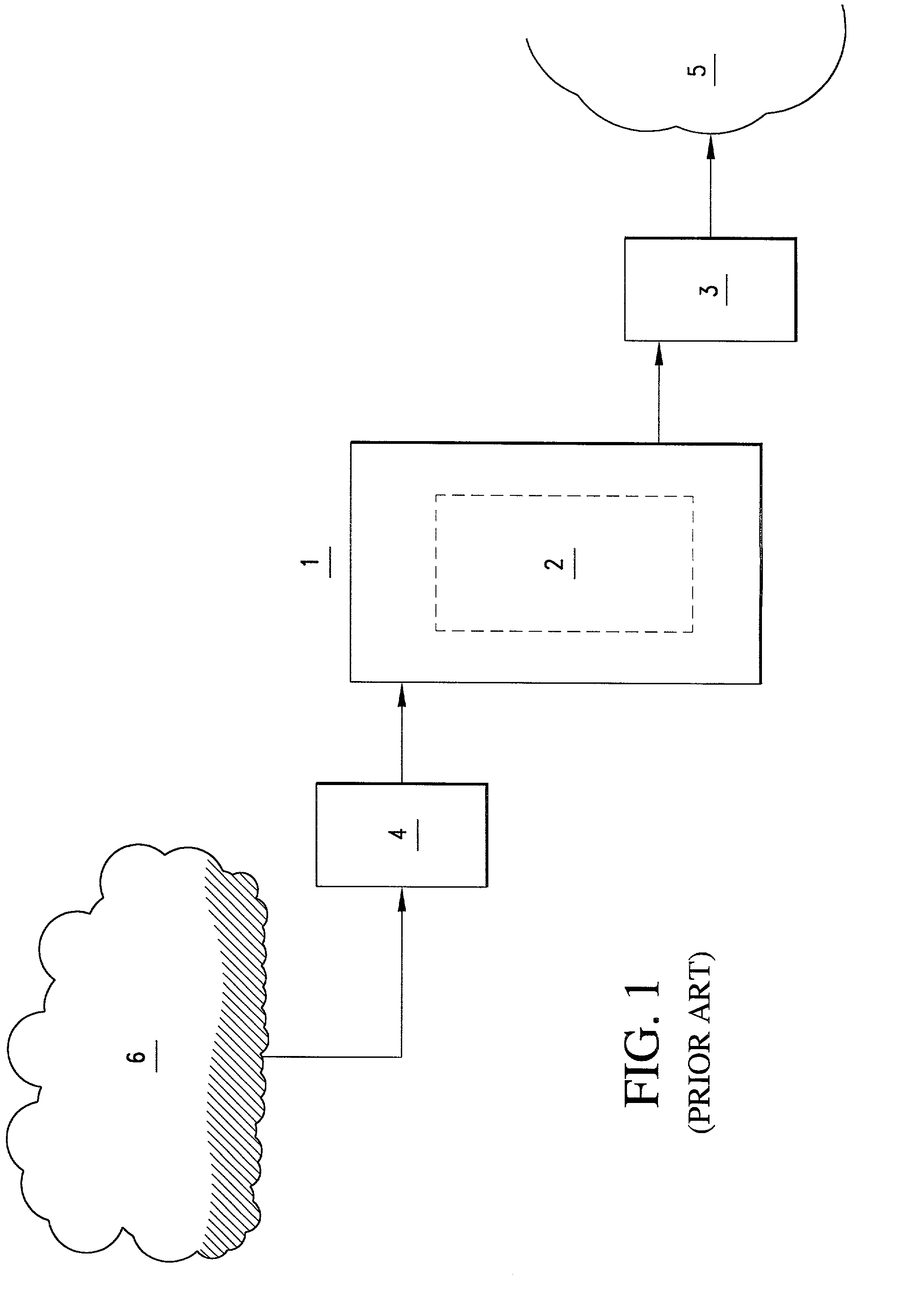
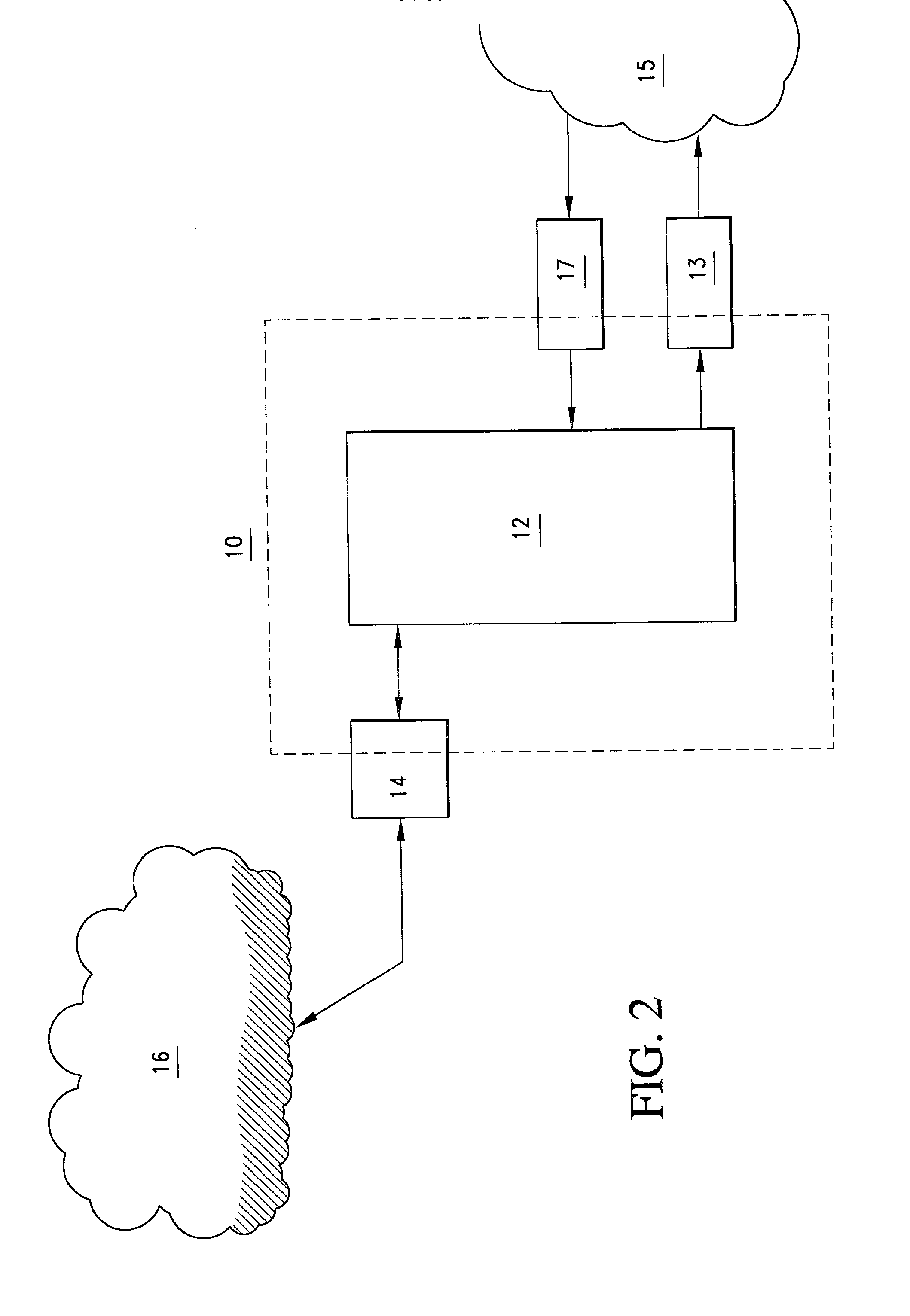
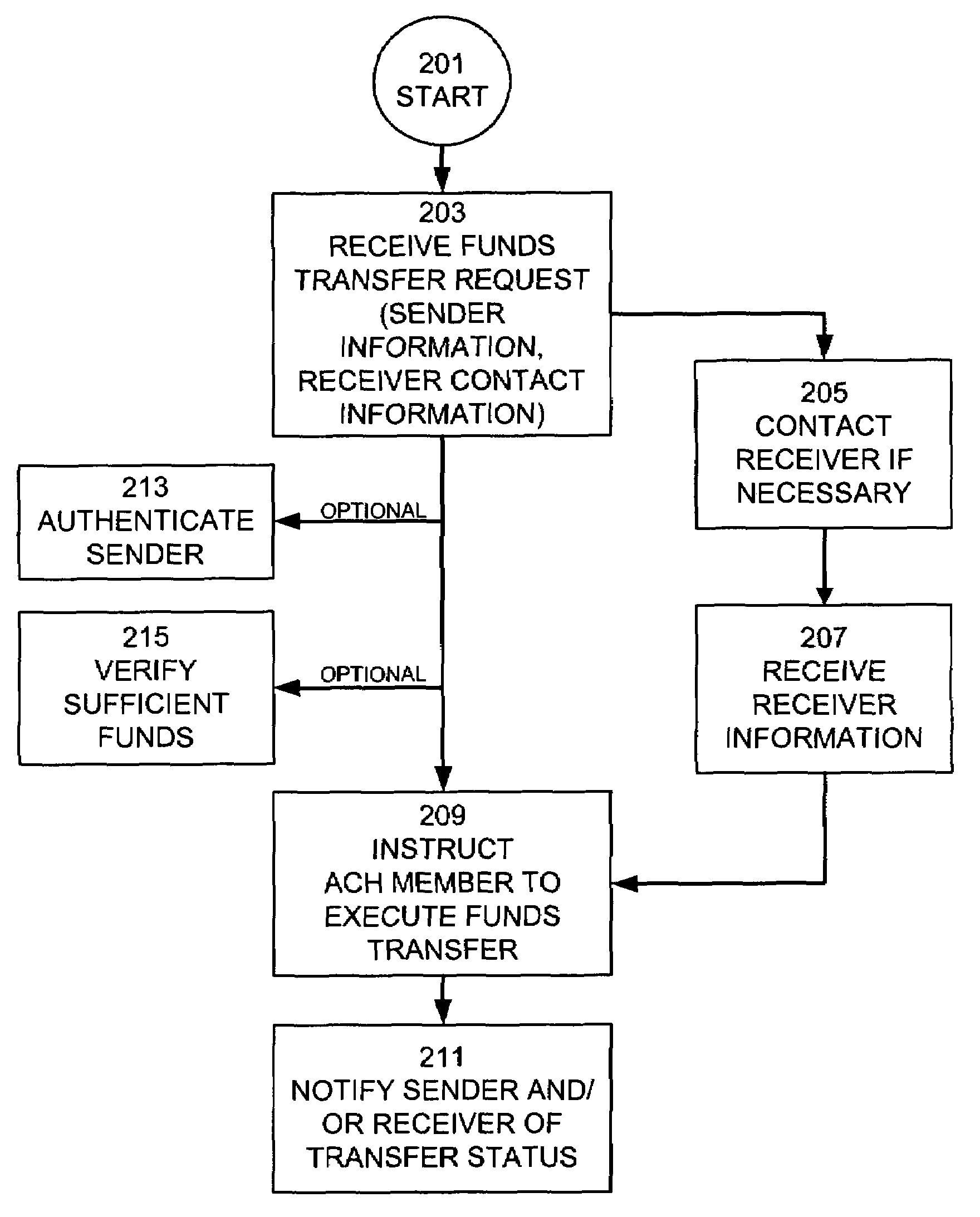
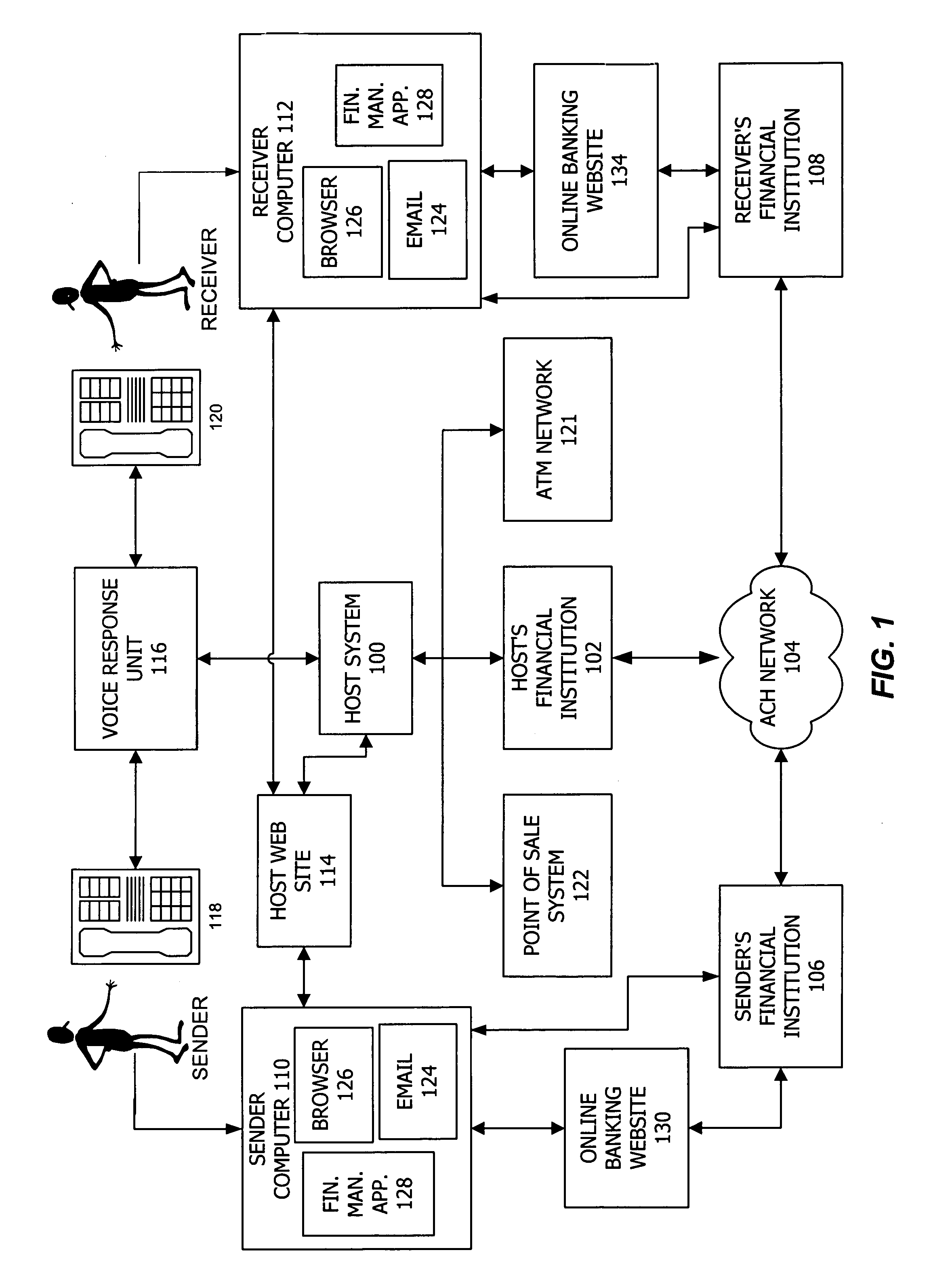
Consumer directed transfers of funds over the Internet are provided by a combination of systems and networks, including the Internet, email, and the Automated Clearinghouse system (ACH). A host system provided by a funds transfer service manages requests of senders to transfer funds and further manages responses of receivers to claim funds. The host system allows the sender to initiate the funds transfer by specifying the amount of the transfer and information for contacting the receiver, without the need to specify the account of the receiver for receiving the funds. Instead, the host system contacts the receiver and informs the receiver of the available funds; the receiver can then provide the necessary target account information for completing the funds transfer. The ACH is used to effect the transfer of funds, with the host system providing instructions for ACH entries to its financial institution using account information separately received from the sender and receiver. The credit risk associated with originating ACH entries is reduced by use of the Point of Sale system to verify sufficient funds in the sender's account by comparing the closing balance of the day the funds transfer is requested with the transfer amount. Sender fraud is reduced by comparing a sender provided balance (or check number / amounts) with an account balance acquired through automated means such as the POS system or ATM network.
Owner:INTUIT INC
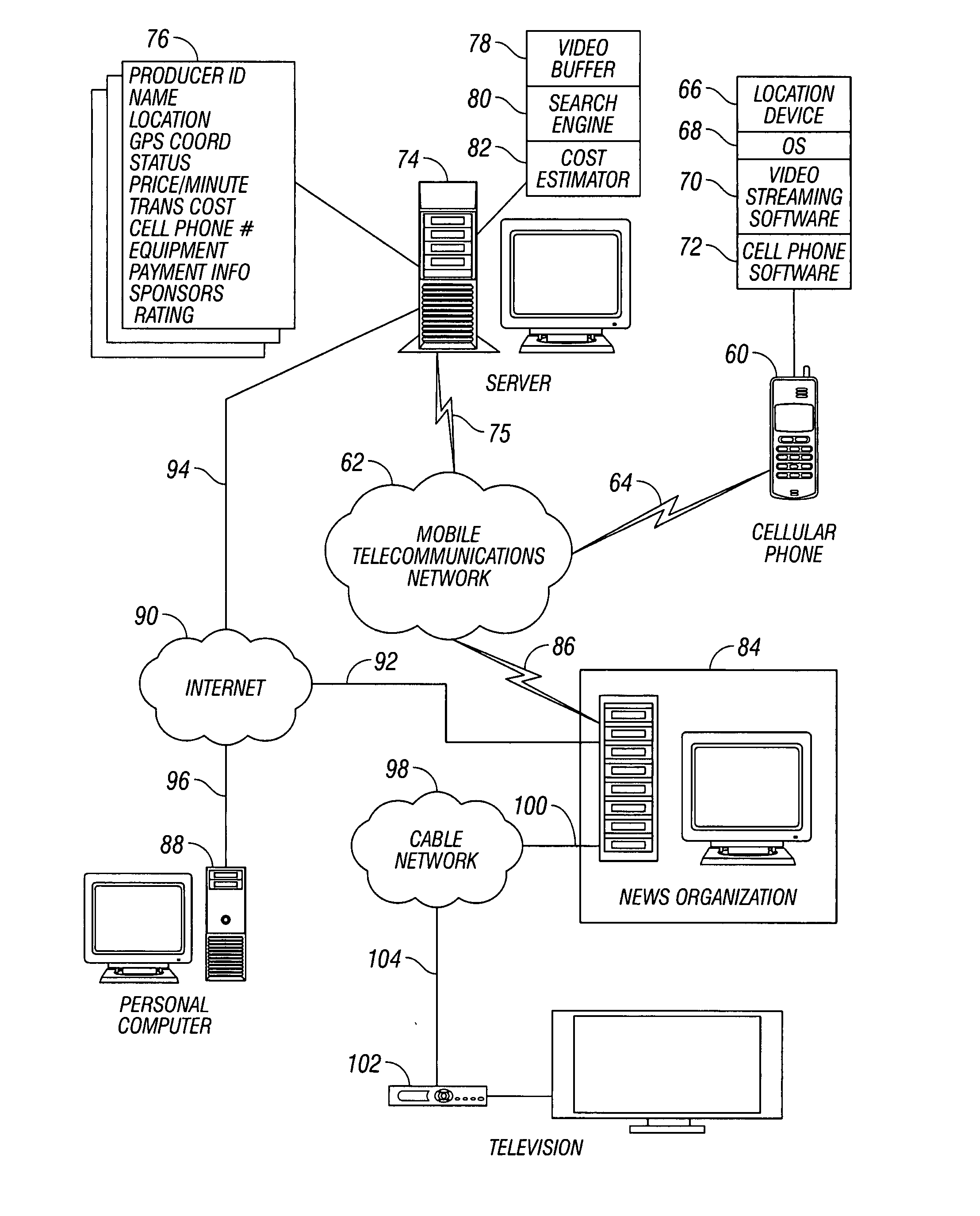
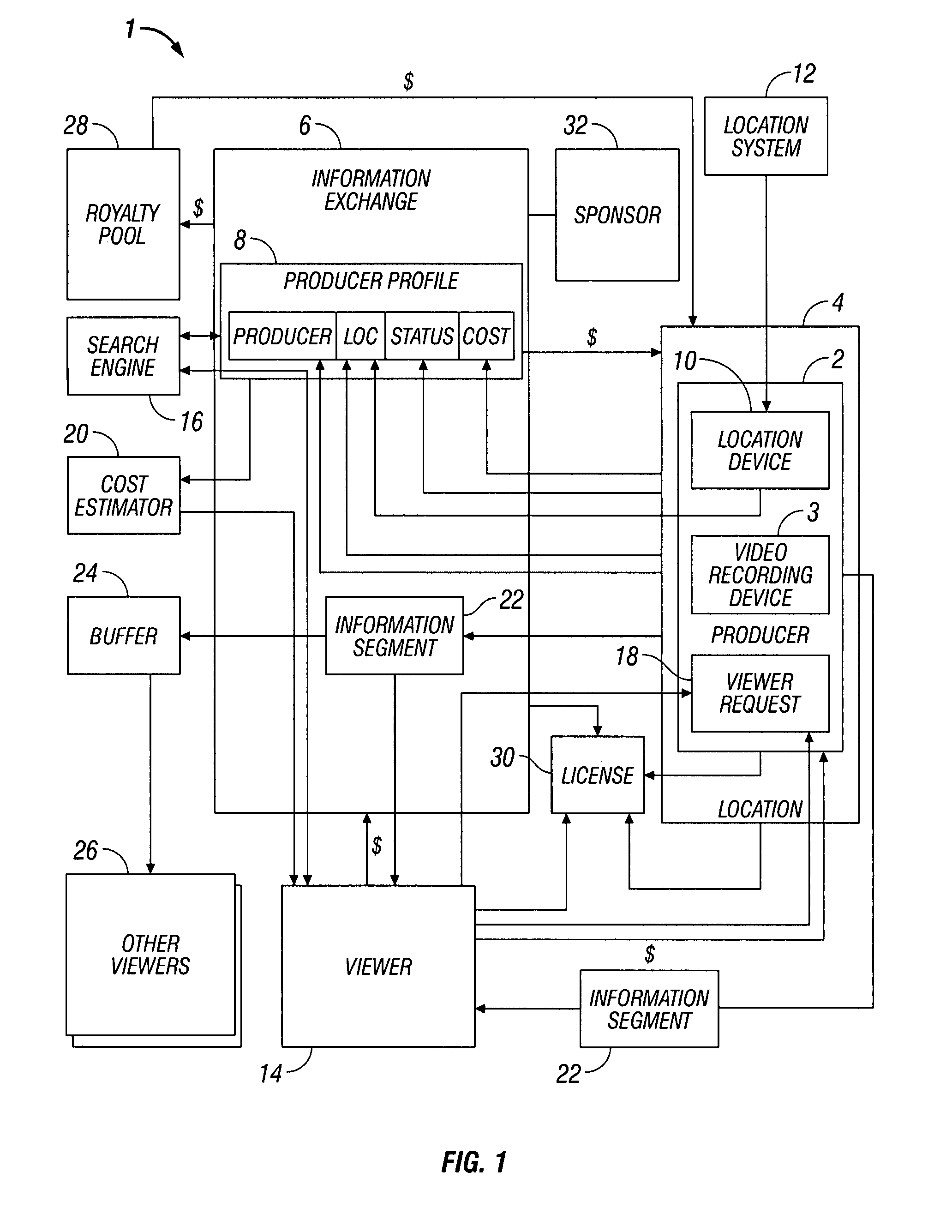
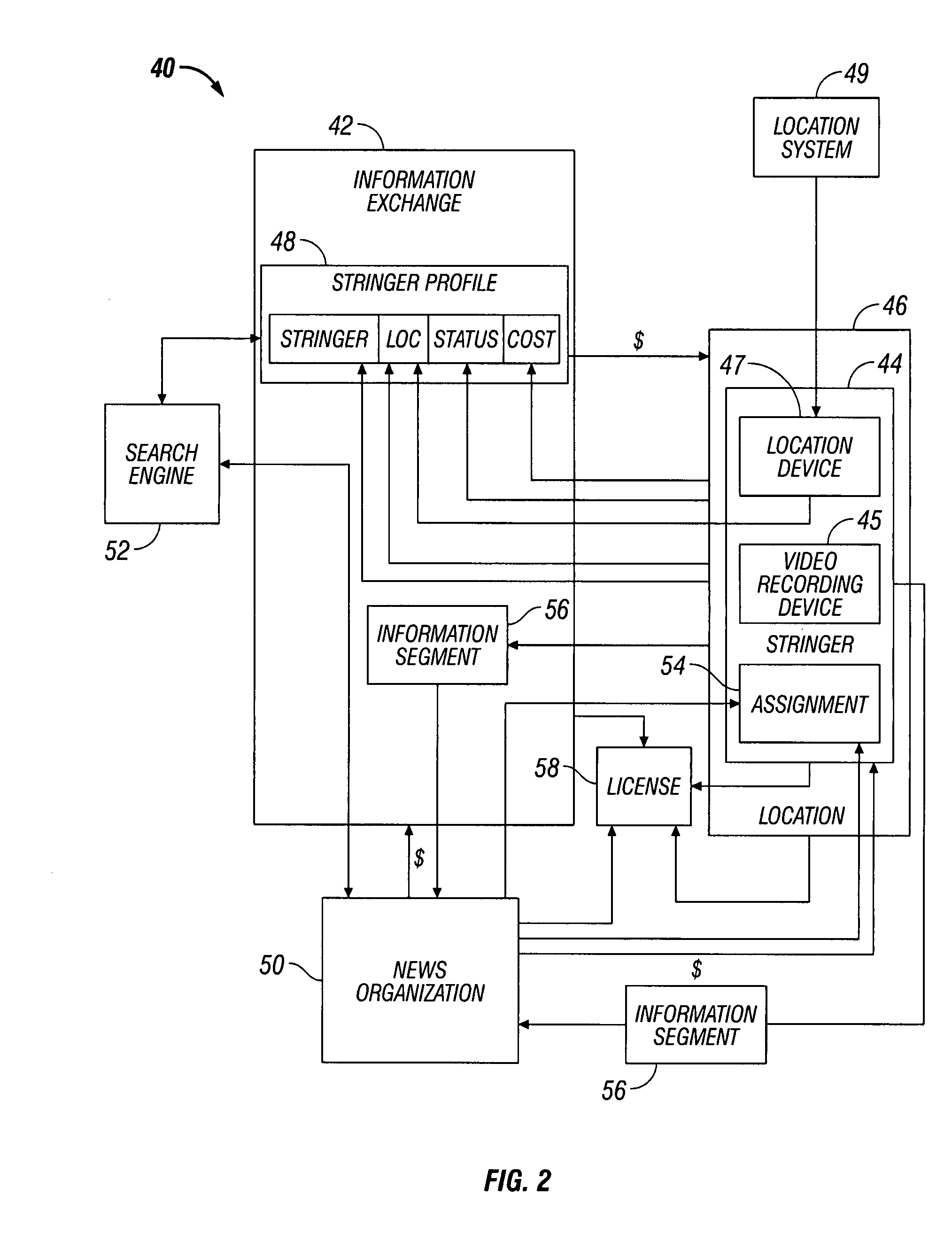
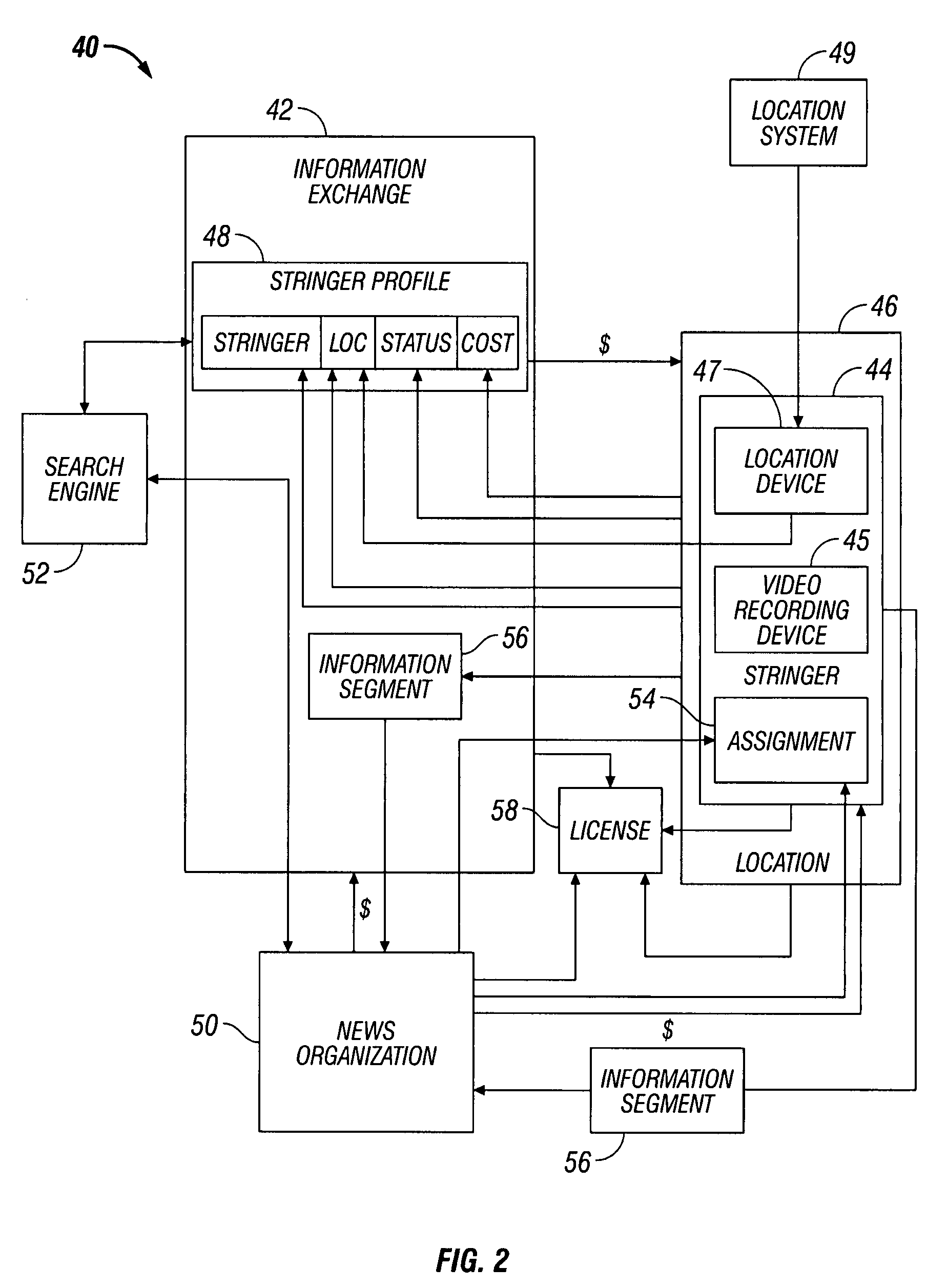
System and method for video on request
ActiveUS20080022329A1Digital data processing detailsAnalogue secracy/subscription systemsVideo recordVideo recording
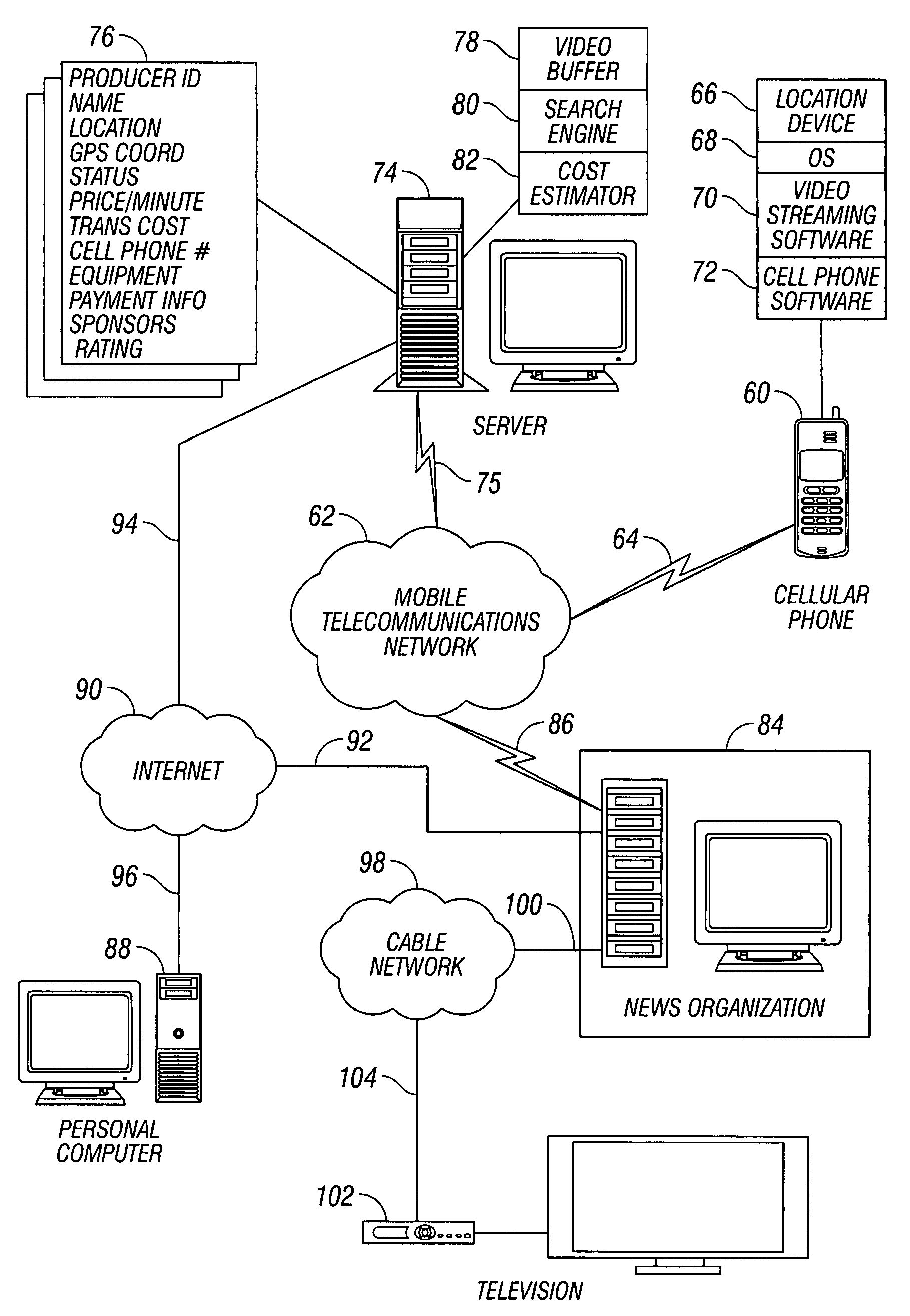
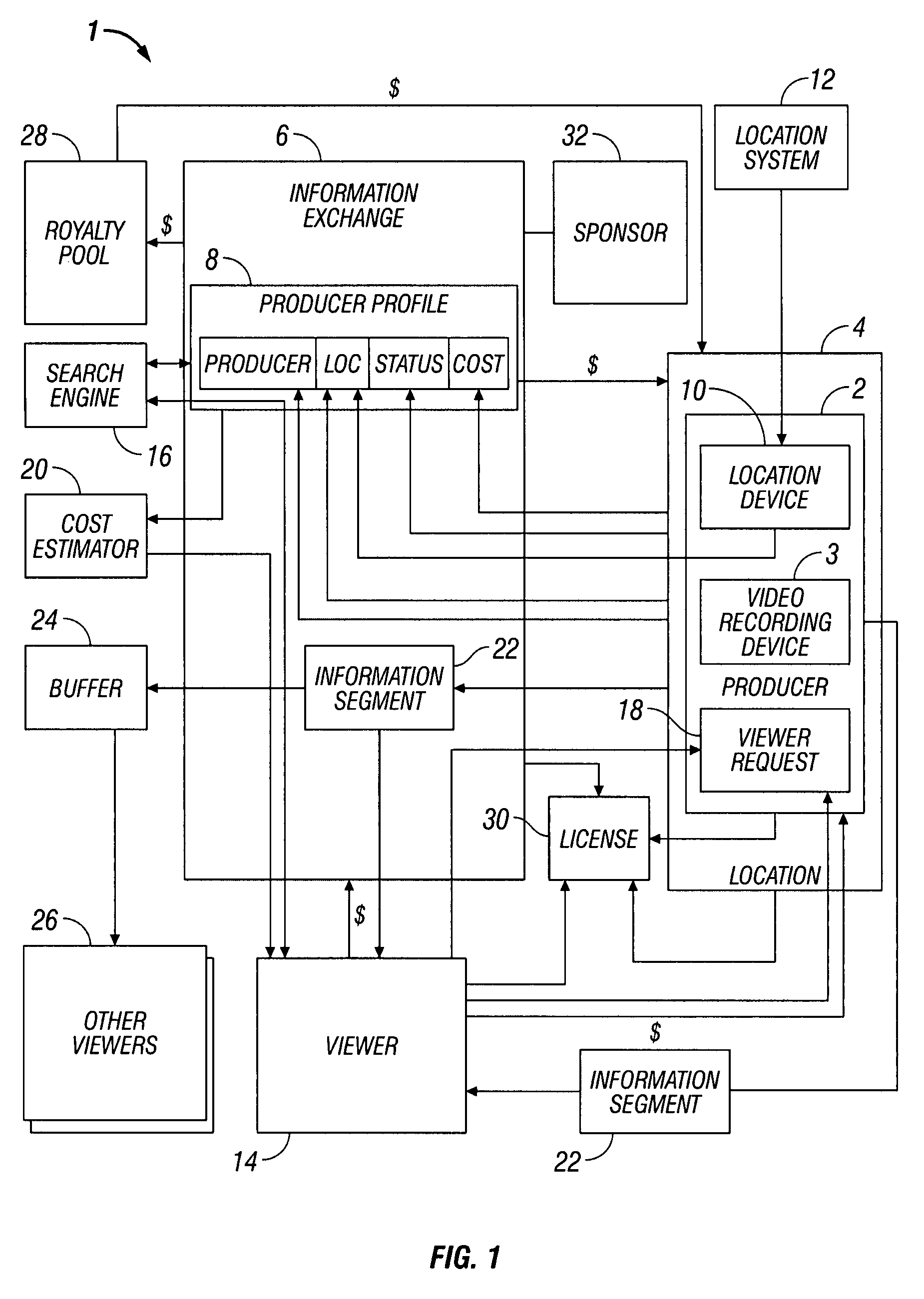
A video on request (“VOR”) system is disclosed. The VOR system includes a producer having a location device for providing location data and a video recording device. The VOR system also includes an information exchange having a producer database configured to store a producer profile having current location and status of the producer. The current location and status are continually updated based on the location data. The VOR system also includes a viewer having access to the information exchange to search the producer database for available producers within a predetermined range of a desired location. Upon finding the available producer at the desired location, the viewer requests an information segment to be produced by the producer from the desired location. The producer thereafter records the information segment and transmits the information segment to the viewer.
Owner:WM GLAD ENTERPRISES
Method and system for configuring wireless routers and networks
InactiveUS7031266B1Easy to deployAutomatically configurablePower managementNetwork traffic/resource managementWireless routerComputer network
A method and system for configuring a wireless router and a wireless communications network includes establishing connectivity between a wireless router and at least one wireline router. Connectivity between the wireless router and a plurality of neighboring wireless routers is established through the wireline router. The wireless router is configured based on information exchanged with the neighboring wireless routers through the wireline router.
Owner:CISCO TECH INC
Secure anonymous information exchange in a network
InactiveUS6061789AMinimize additional effort and expenditureUser identity/authority verificationDigital data protectionSystems designData set
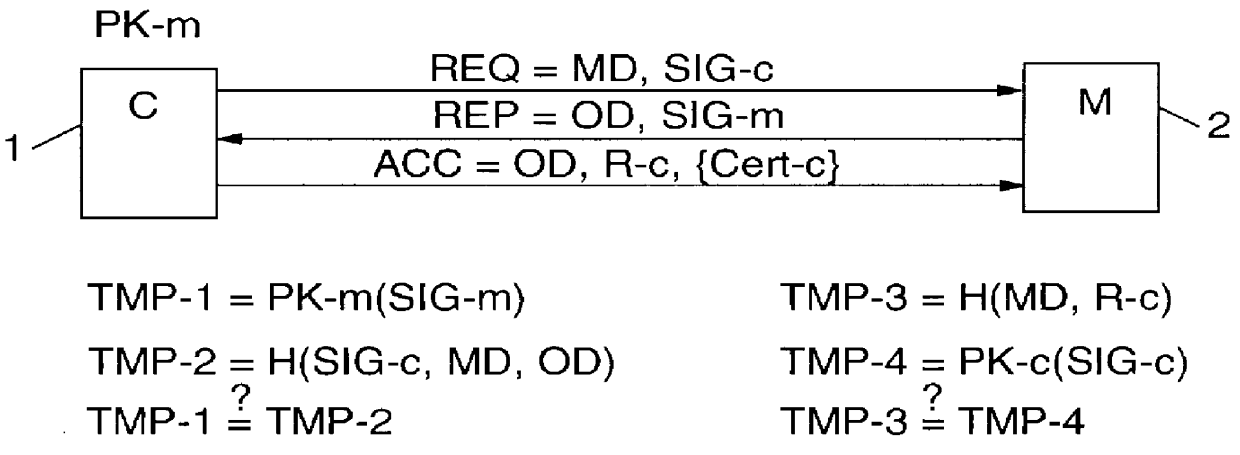
PCT No. PCT / IB96 / 00025 Sec. 371 Date Jul. 2, 1998 Sec. 102(e) Date Jul. 2, 1998 PCT Filed Jan. 12, 1996 PCT Pub. No. WO97 / 25801 PCT Pub. Date Jul. 17, 1997Computer network management for electronic commerce requires technical implementations of business processes. The process addressed here is a technical method for a communication in which two or more parties legitimately want to communicate anonymously, often before discussing a deal or closing a business, e.g. for anonymous bidding or auctioning in electronic commerce. Essentially, the invention is a method, described by a protocol, for safely exchanging data in a network that provides a public key infrastructure and an anonymous communication possibility between network users. It consists of a sequence of steps in which both sender (e.g. customer) and addressee (e.g. merchant) compose data sets (i.e., requests and replies) that are based on received data and / or prior knowledge. The data sets are enciphered to provide anonymity, and digitally signed to provide proof of the partner. The invention is also a system designed to implement the invented method.
Owner:GOOGLE LLC
System and method for video on request
ActiveUS7779444B2Digital data processing detailsAnalogue secracy/subscription systemsVideo recordVideo recording
A video on request (“VOR”) system is disclosed. The VOR system includes a producer having a location device for providing location data and a video recording device. The VOR system also includes an information exchange having a producer database configured to store a producer profile having current location and status of the producer. The current location and status are continually updated based on the location data. The VOR system also includes a viewer having access to the information exchange to search the producer database for available producers within a predetermined range of a desired location. Upon finding the available producer at the desired location, the viewer requests an information segment to be produced by the producer from the desired location. The producer thereafter records the information segment and transmits the information segment to the viewer.
Owner:WM GLAD ENTERPRISES
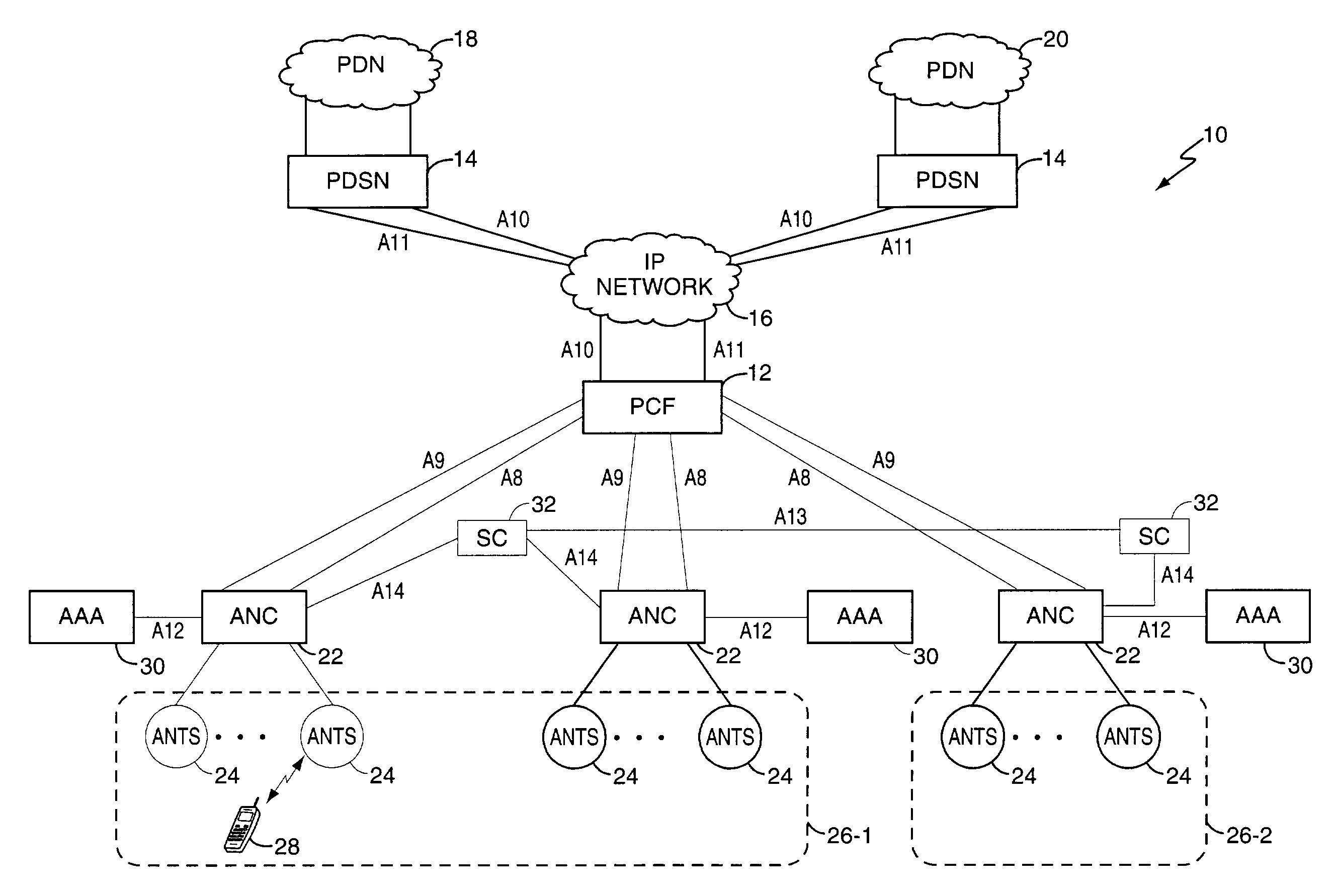
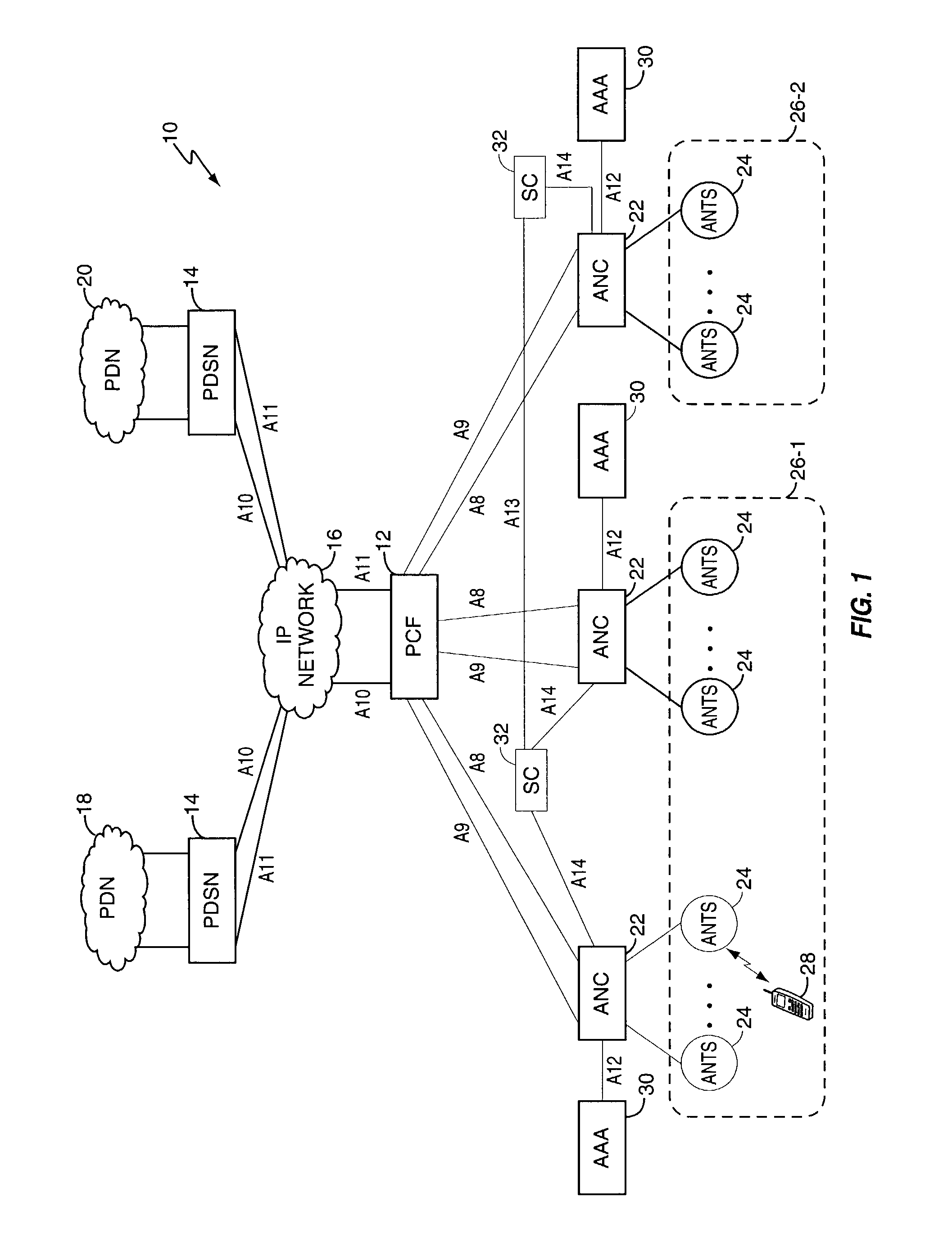
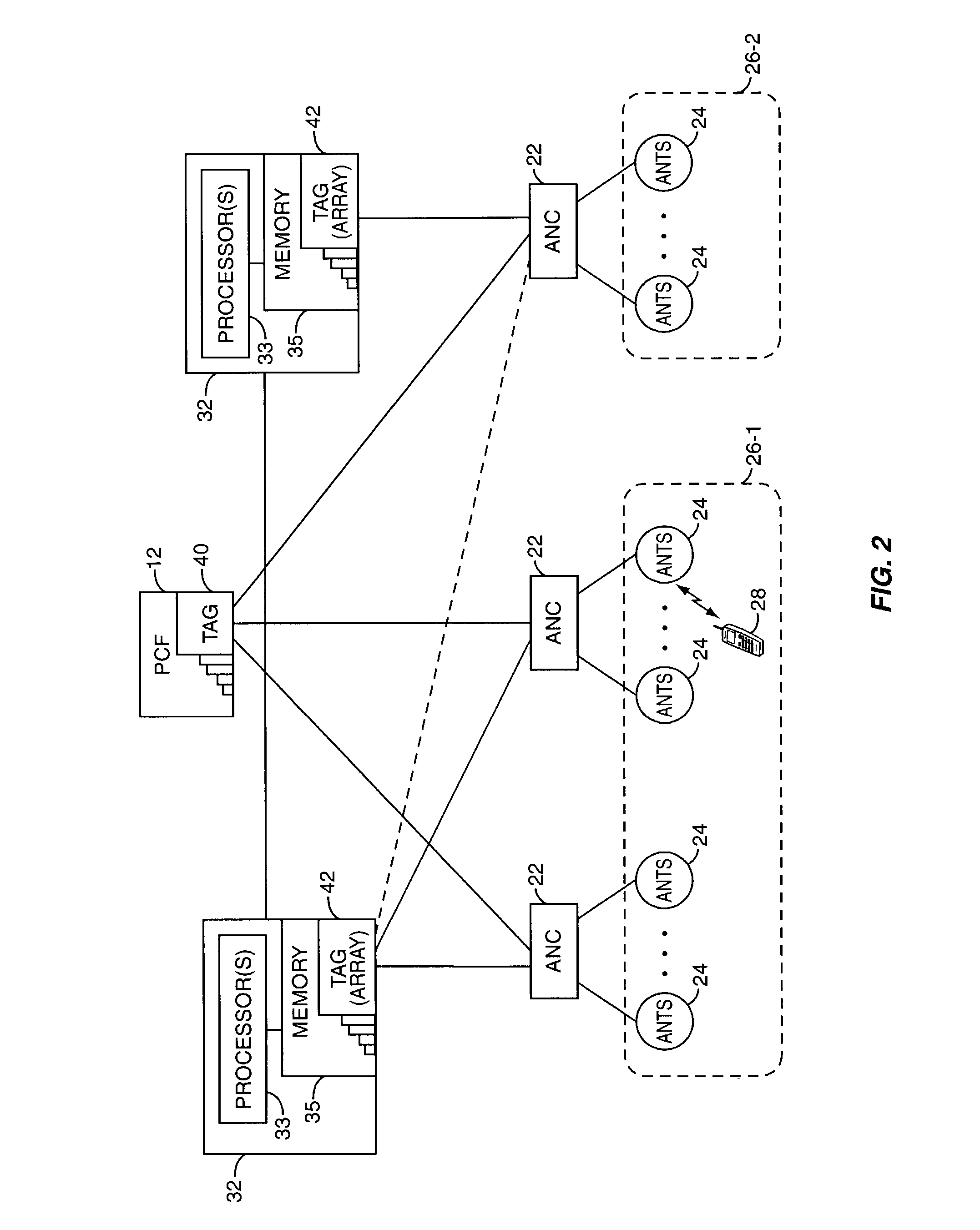
Mobility management entity for high data rate wireless communication networks
ActiveUS7457265B2Reduce amountEasy to manageTime-division multiplexData switching by path configurationSession controlGranularity
A session controller provides mobility management support in a 1xEVDO wireless communication network, such as one configured in accordance with the TIA / EIA / IS-856 standard. Operating as a logical network entity, the SC maintains location (e.g., a pointing tag) and session information at an access network controller (ANC) granularity, thus allowing it to track access terminal (AT) transfer between ANCs but within subnet boundaries, where a network subnet comprises one or more ANCs. This allows a packet control function (PCF) to maintain location information at a packet zone granularity, thereby reducing mobility management overhead at the PCF. The SC provides updated tag and session information to PCFs, ANCs, and other SCs as needed. Information exchange with other SCs arises, for example, when two or more SCs cooperate to maintain or transfer routing and session information across subnets.
Owner:TELEFON AB LM ERICSSON (PUBL)
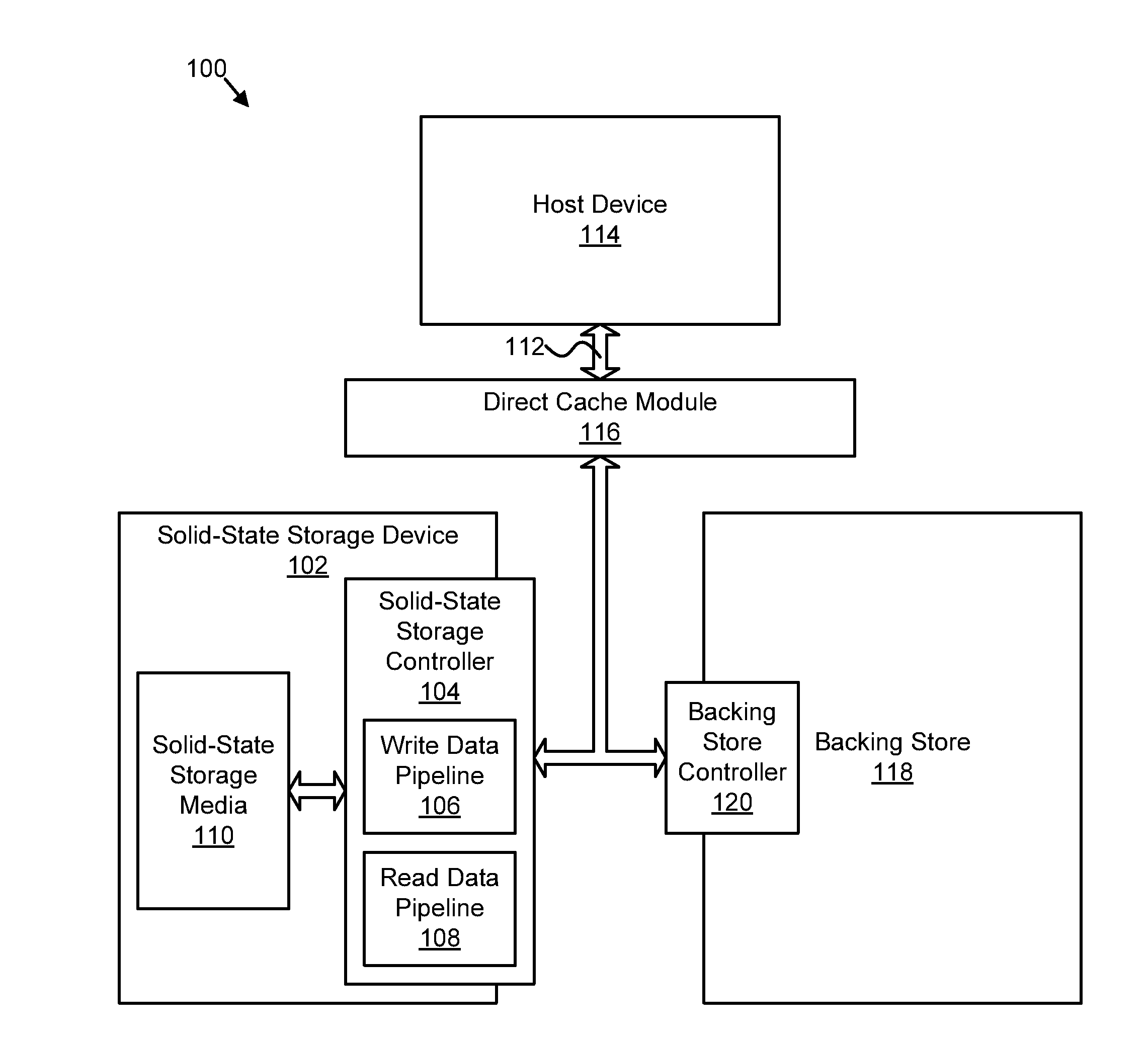
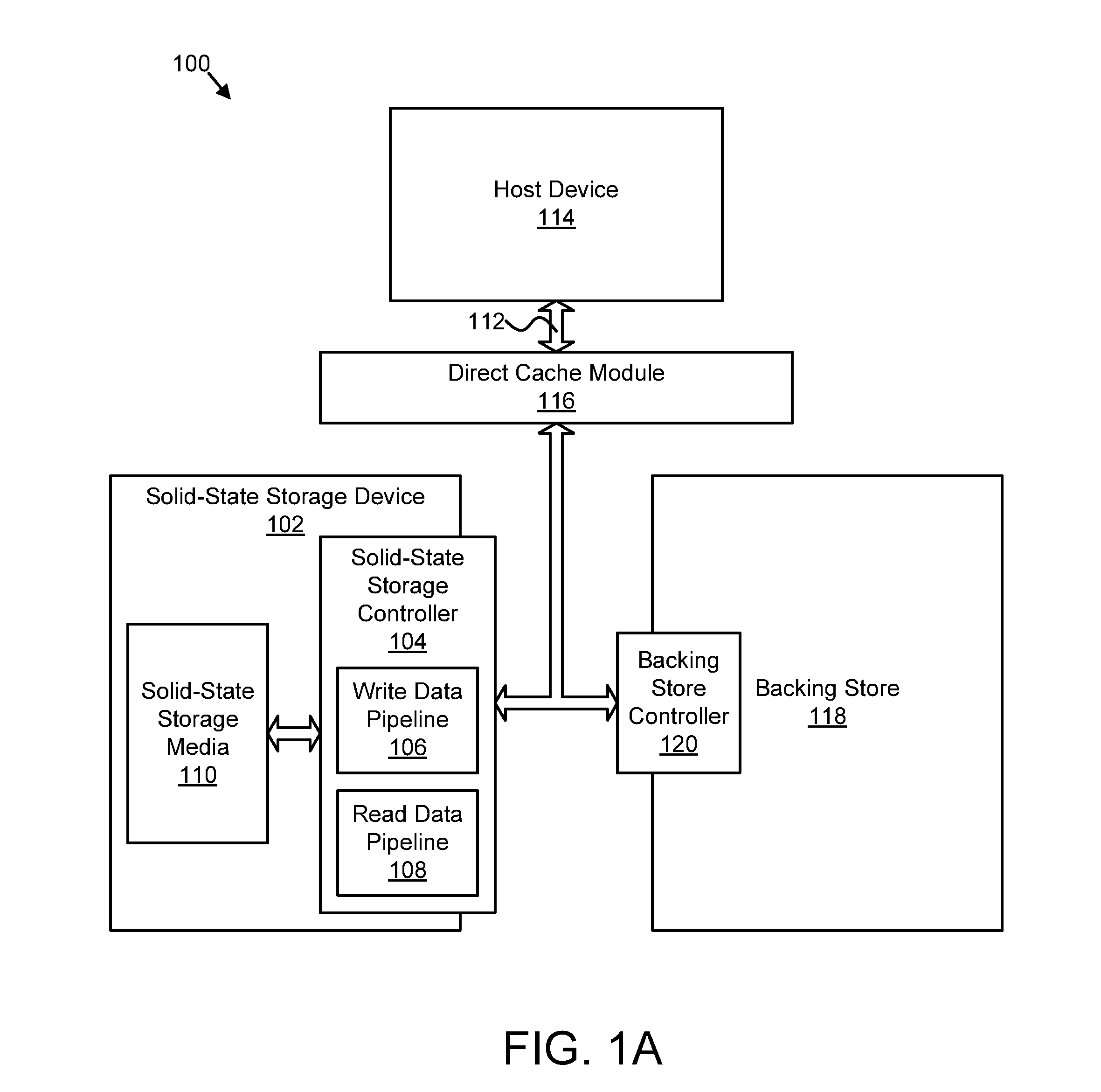
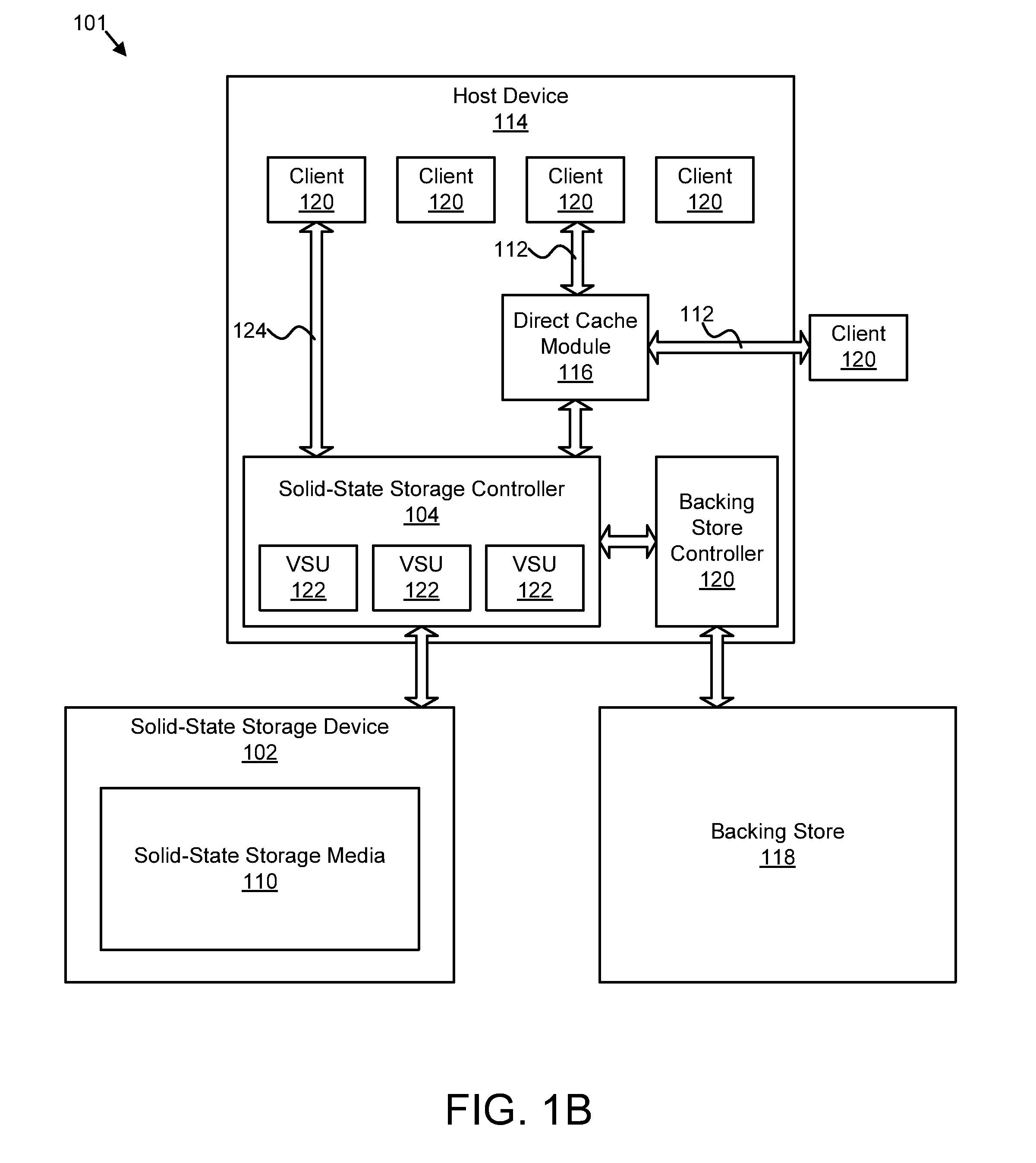
Apparatus, system, and method for managing a cache
ActiveUS20130191601A1Effective cachingMemory adressing/allocation/relocationSolid-state storageParallel computing
An apparatus, system, and method are disclosed for managing a cache. A cache interface module provides access to a plurality of virtual storage units of a solid-state storage device over a cache interface. At least one of the virtual storage units comprises a cache unit. A cache command module exchanges cache management information for the at least one cache unit with one or more cache clients over the cache interface. A cache management module manages the at least one cache unit based on the cache management information exchanged with the one or more cache clients.
Owner:SANDISK TECH LLC
Publishing layout wizard
InactiveUS6931591B1Expensive to maintainExpensive to updateCathode-ray tube indicatorsNatural language data processingGraphicsWeb browser
The present invention facilitates the specification and distribution of templated content materials by a content provider over an information exchange network such as the Internet. The present invention incorporates a system for managing inventories of graphical elements and their relationships to pre-defined page templates. A database capable of keeping track of users and their corresponding access privileges within the system is employed to monitor user activity. Ultimately, through the use of a software component delivered over the Internet for use within standard web browsers, end-users are able to populate templates under the constraints imposed by the rules of the manufacturers at the time of template design. These population elements which “fill in the blanks” of the pre-defined templates may be either of type IMAGE or TEXT. Image regions are populated by choosing from a subset of the entire image inventory, while TEXT types can be completely free form, with specific rules guiding justification, point size, font, and leading, or “fill in the blank” form with the same constraint rules as free form. Once the end user has met all of the criteria for a fully populated template, the system provides sophisticated means for downloading a high resolution file (such as a print-ready file or other file representation of the composed publication) which encapsulates all resources needed (layout, images, fonts, and constraint geometries) to fulfill the requirements of the publication. The downloaded file may be printed or published by electronic transfer, e.g., to a publisher for printing of the actual publication.
Owner:SAEPIO TECH
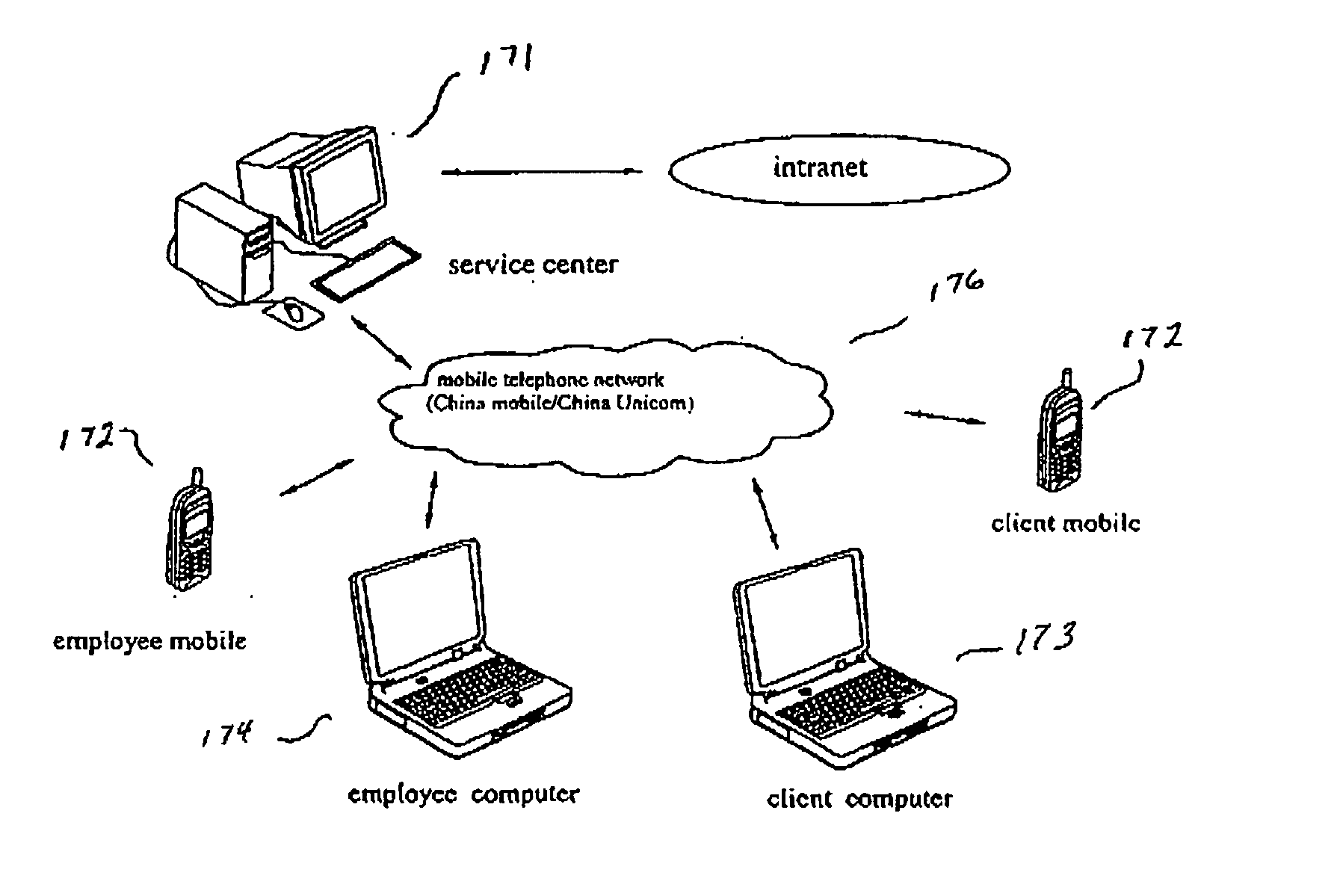
Managing recurring payments from mobile terminals
ActiveUS20120215696A1Smooth serviceConvenient introductionAccounting/billing servicesFinanceTerminal equipmentComputer terminal
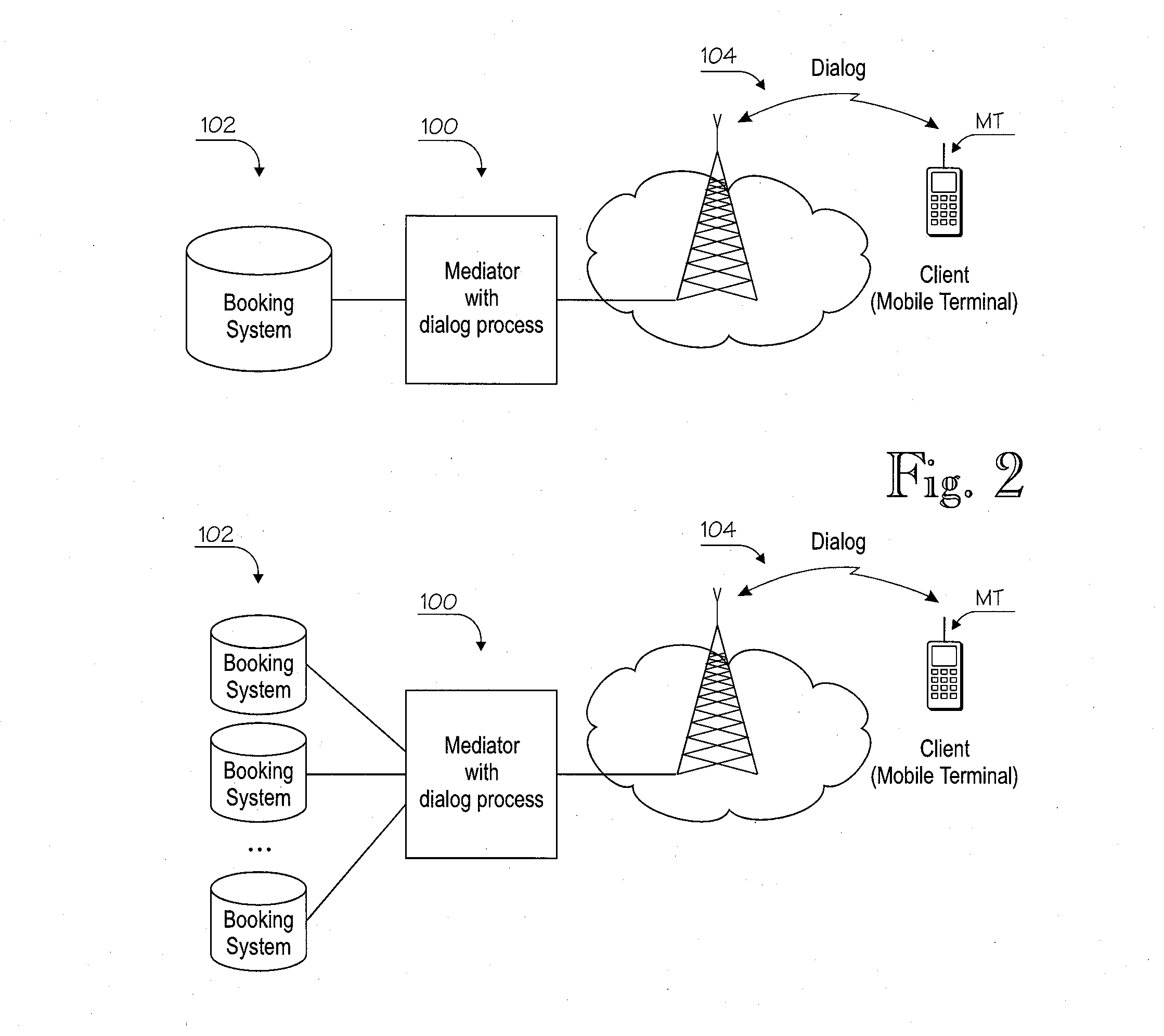
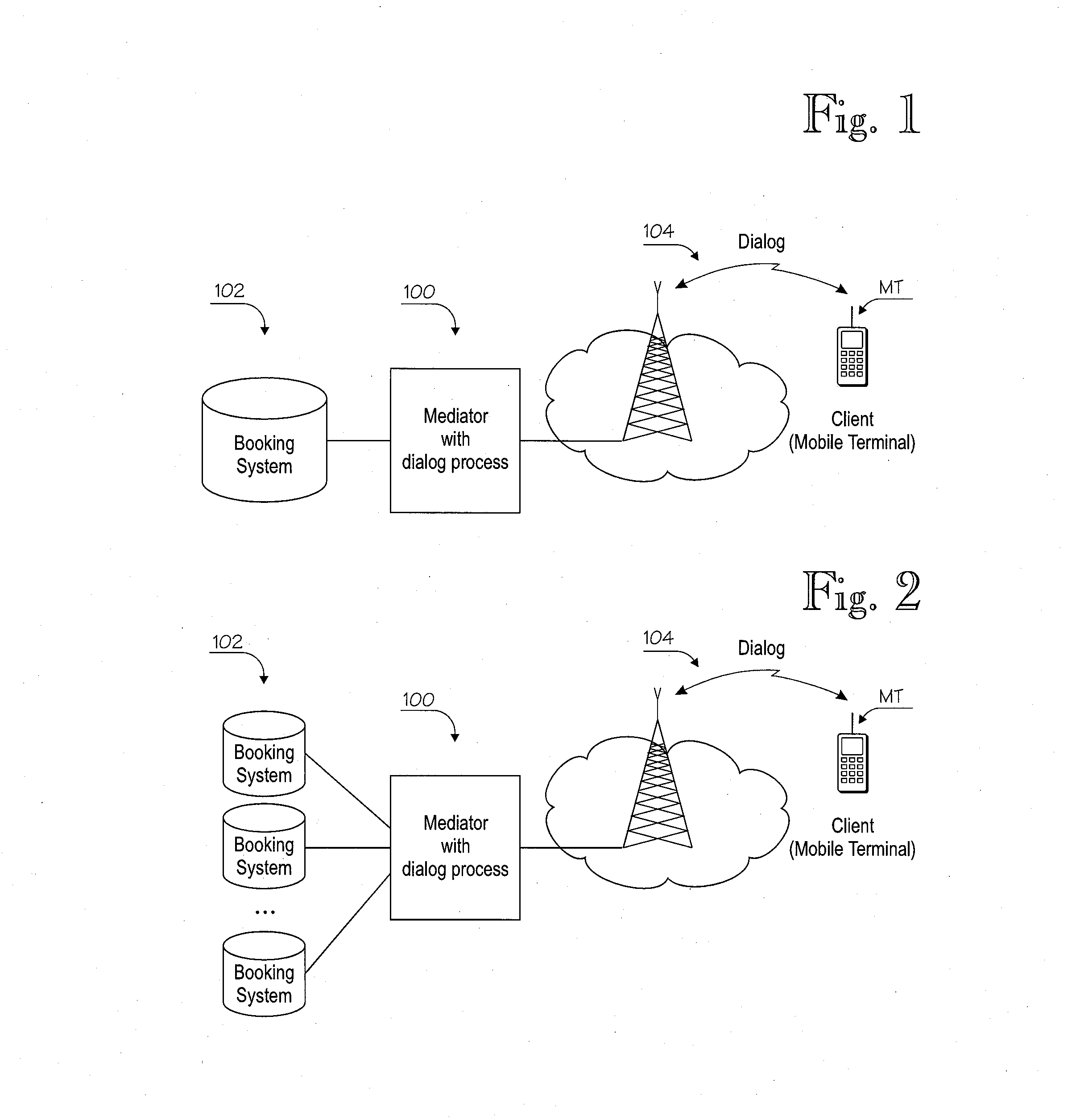
Equipment and methods for facilitating service provisioning in a system that includes a payment processor, a number of service providers and a mediator that mediates information exchange between the payment processor and service providers, and a mobile terminal operated by payment card holder. In some disclosed embodiments, service provisioning can be facilitated in cases wherein the payment processor must reside in a strictly regulated Payment Card Industry (PCI) compliant environment and the service providers operate servers that are not PCI-compliant.
Owner:SMARTCOM LABS OY
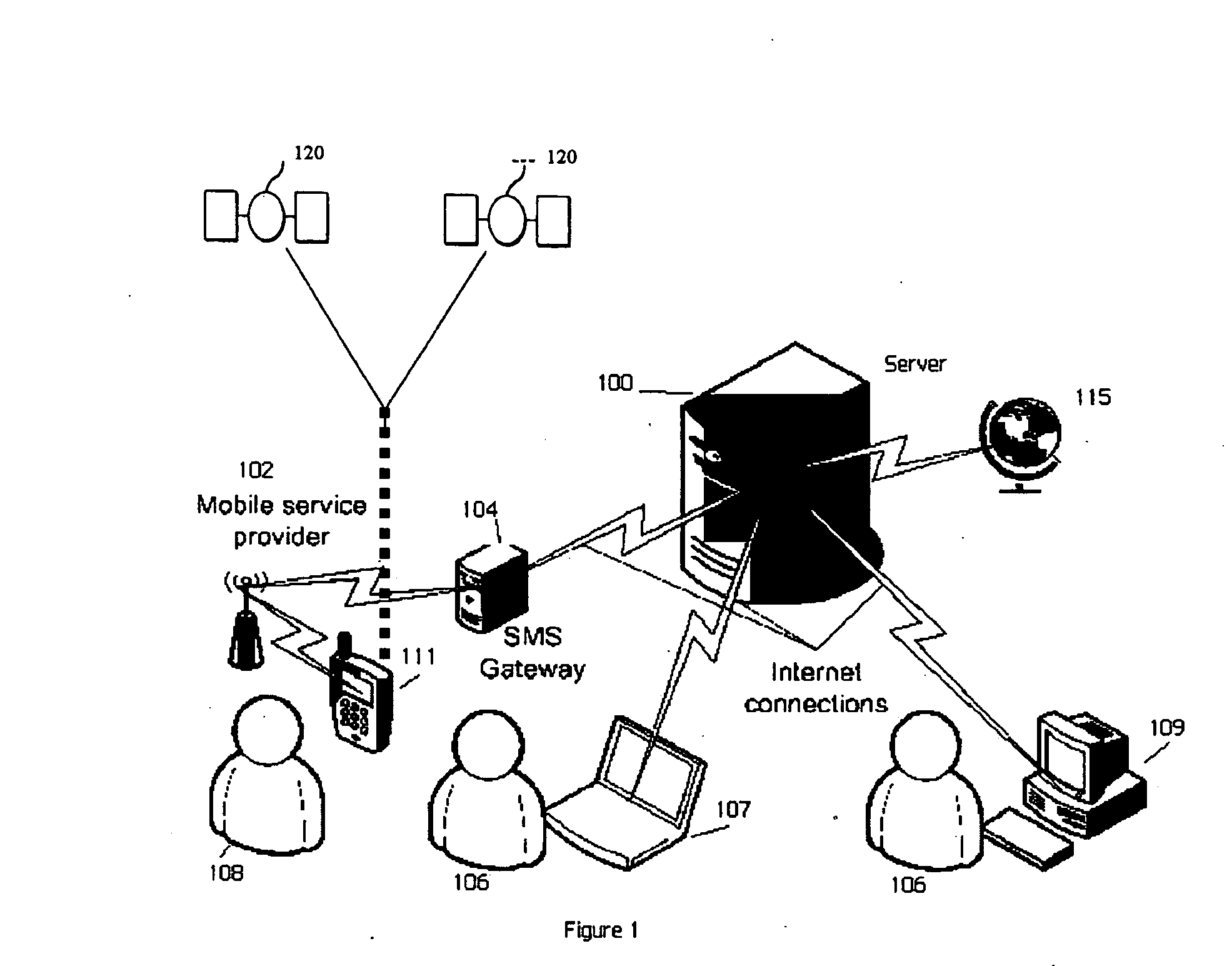
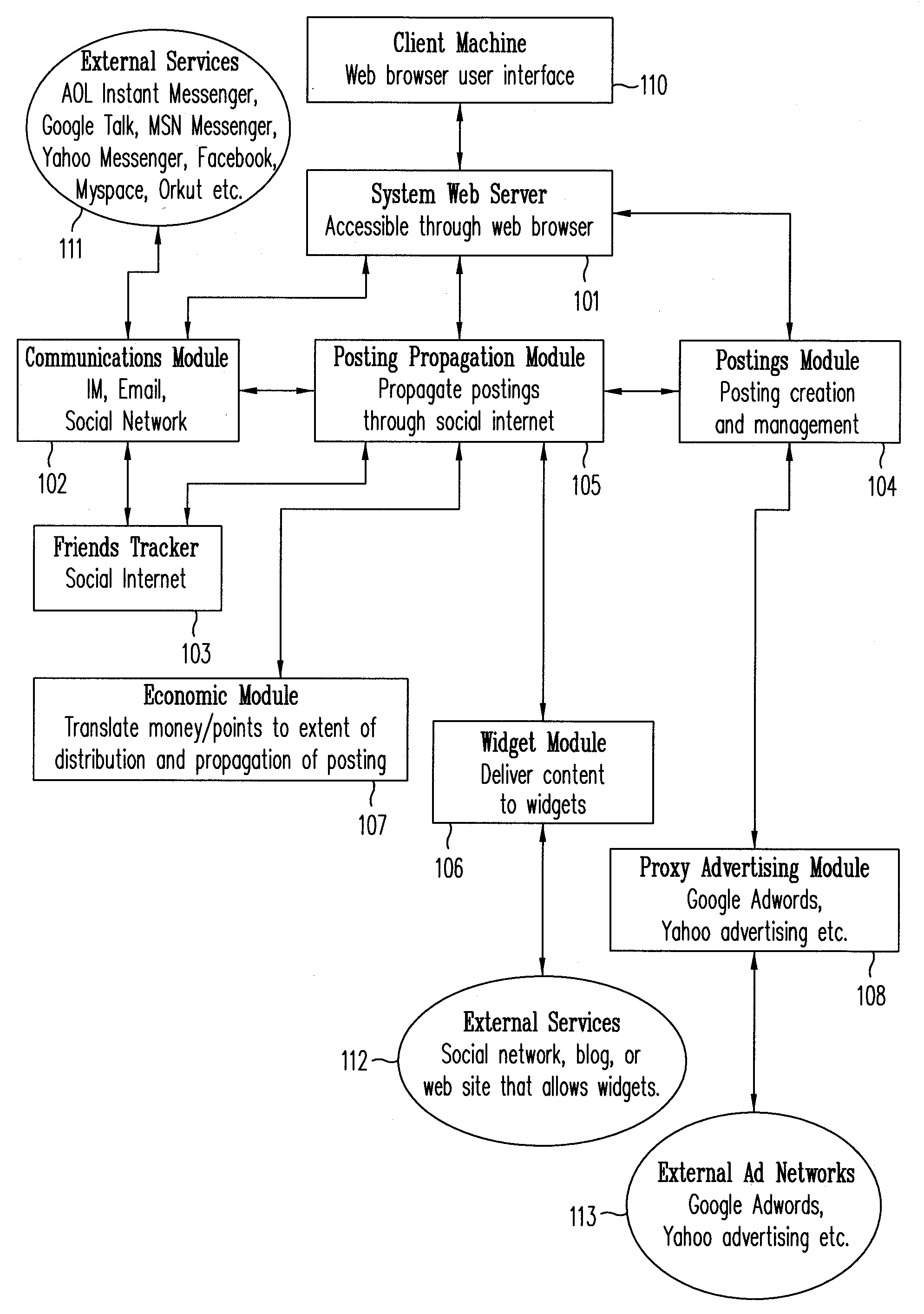
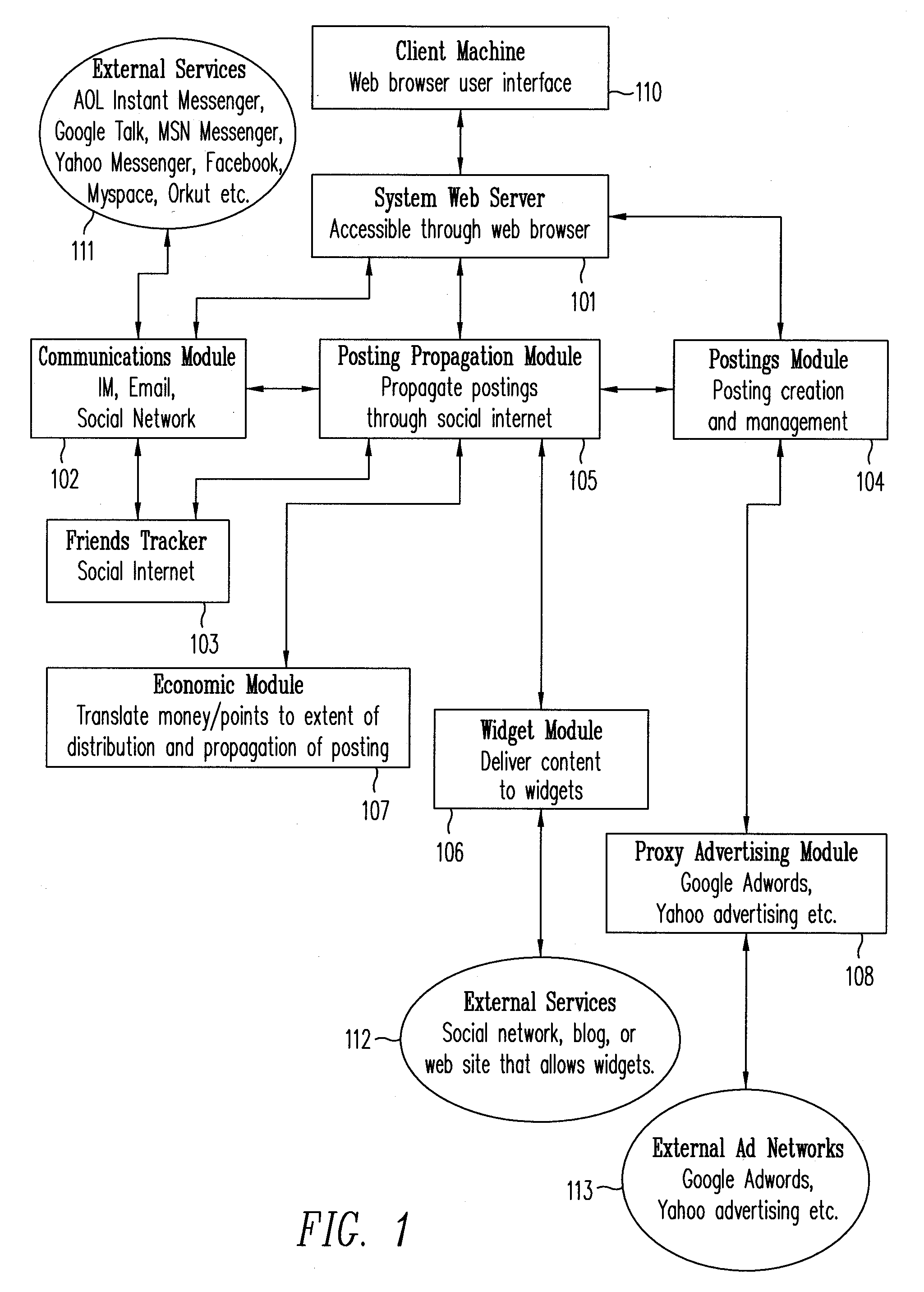
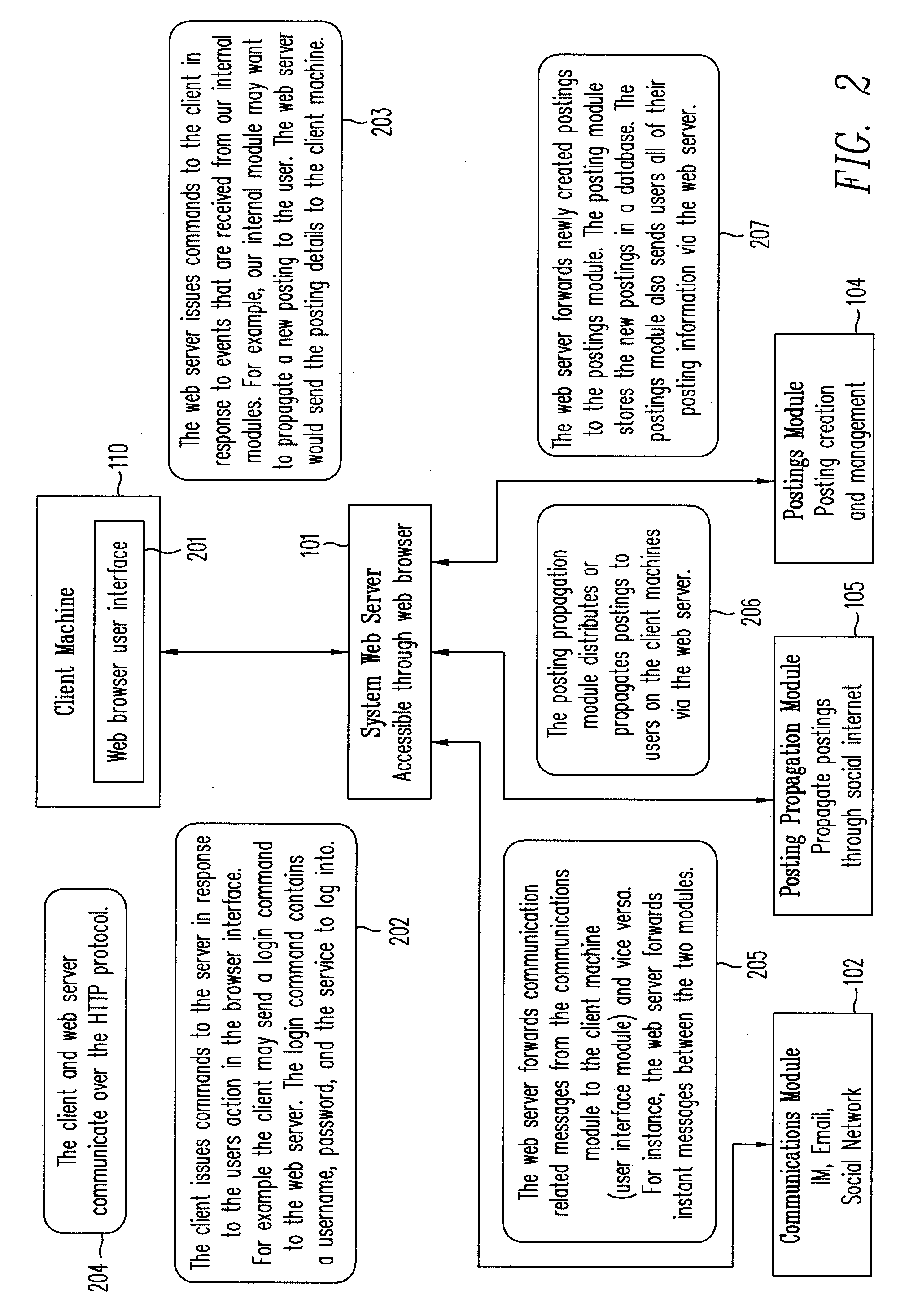
Method for information gathering and dissemination in a social network
InactiveUS20070266097A1Automatically and efficiently propagatingMultiple digital computer combinationsData switching networksWeb siteShort Message Service
A method is provided for automatically and efficiently propagating information using previously established social methods of communication (e.g., email, instant messaging (IM), social network message posting, and short message services). In conjunction with the method, a system for collecting and disseminating information on a social network is provided, which includes: (a) a server for providing a user interface (e.g., a user facing web site) which allows a user to exchange information with one or more external services, wherein the information exchange includes receiving a message from the user that the user intends to disseminate through the external services; (b) a message module which prepares the message received from the user for dissemination; and (c) a communication module coupled to the user interface, the message module and the external services to mediate the information exchange between the user and the external services.
Owner:PAGEBRITES
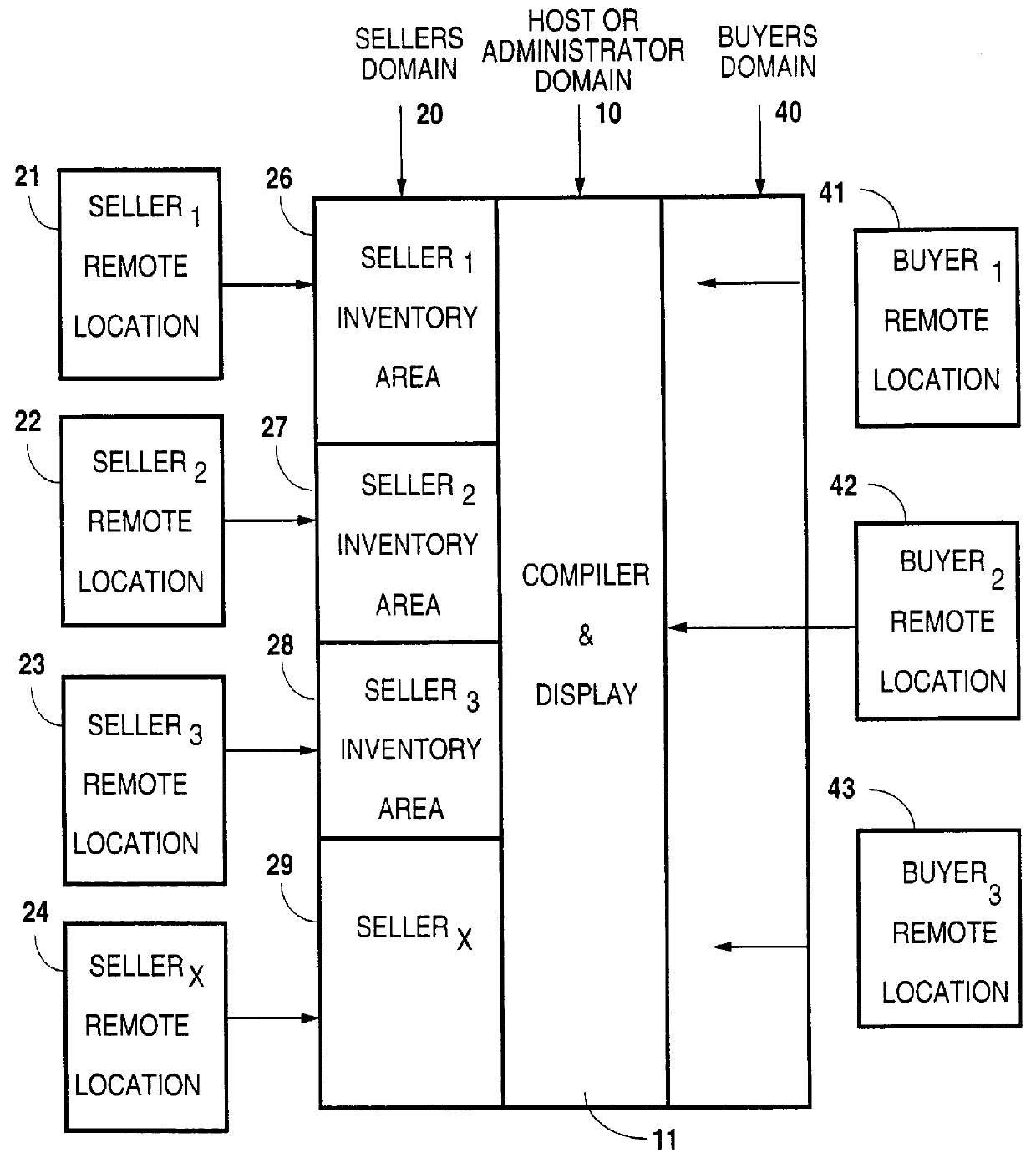
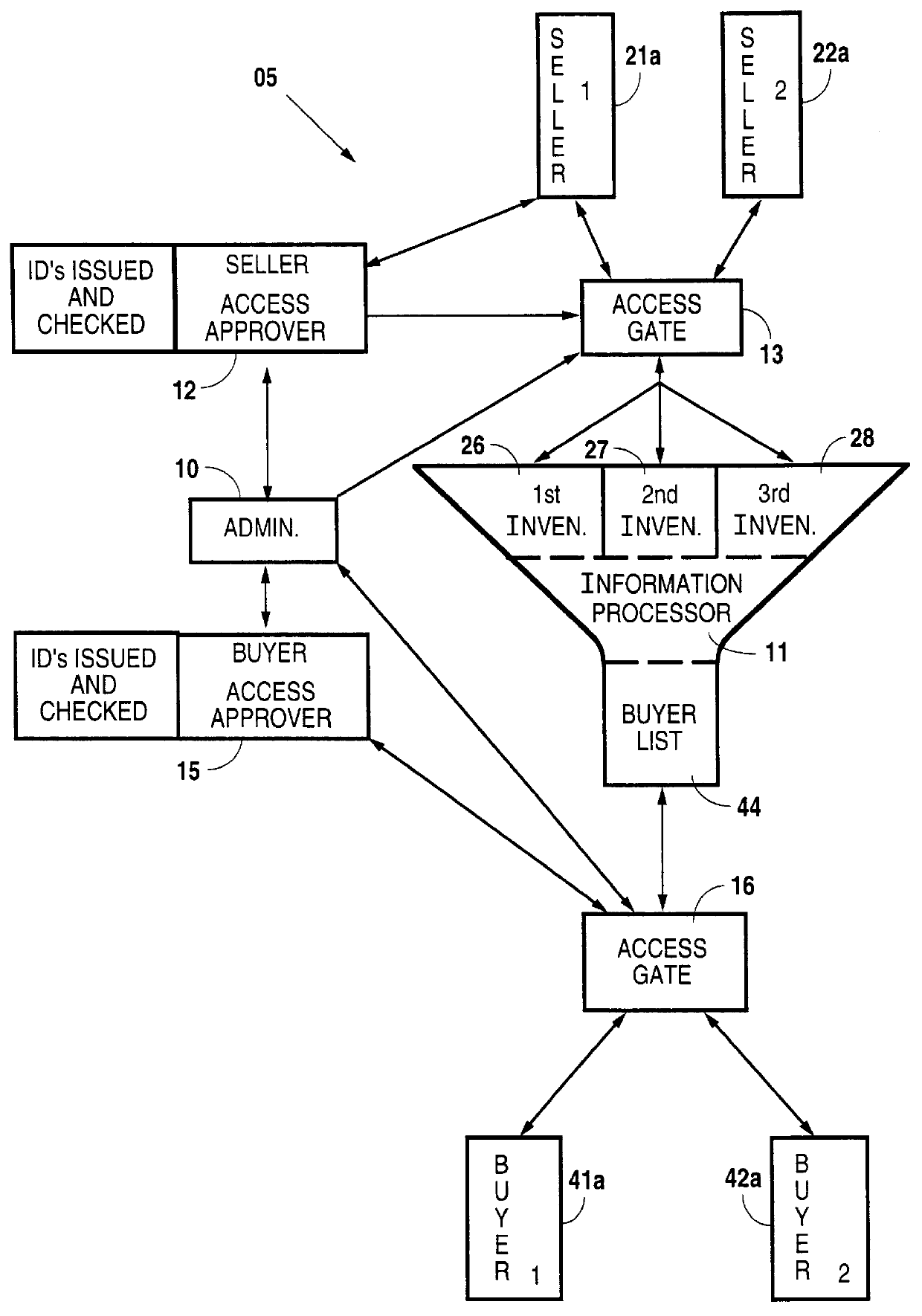
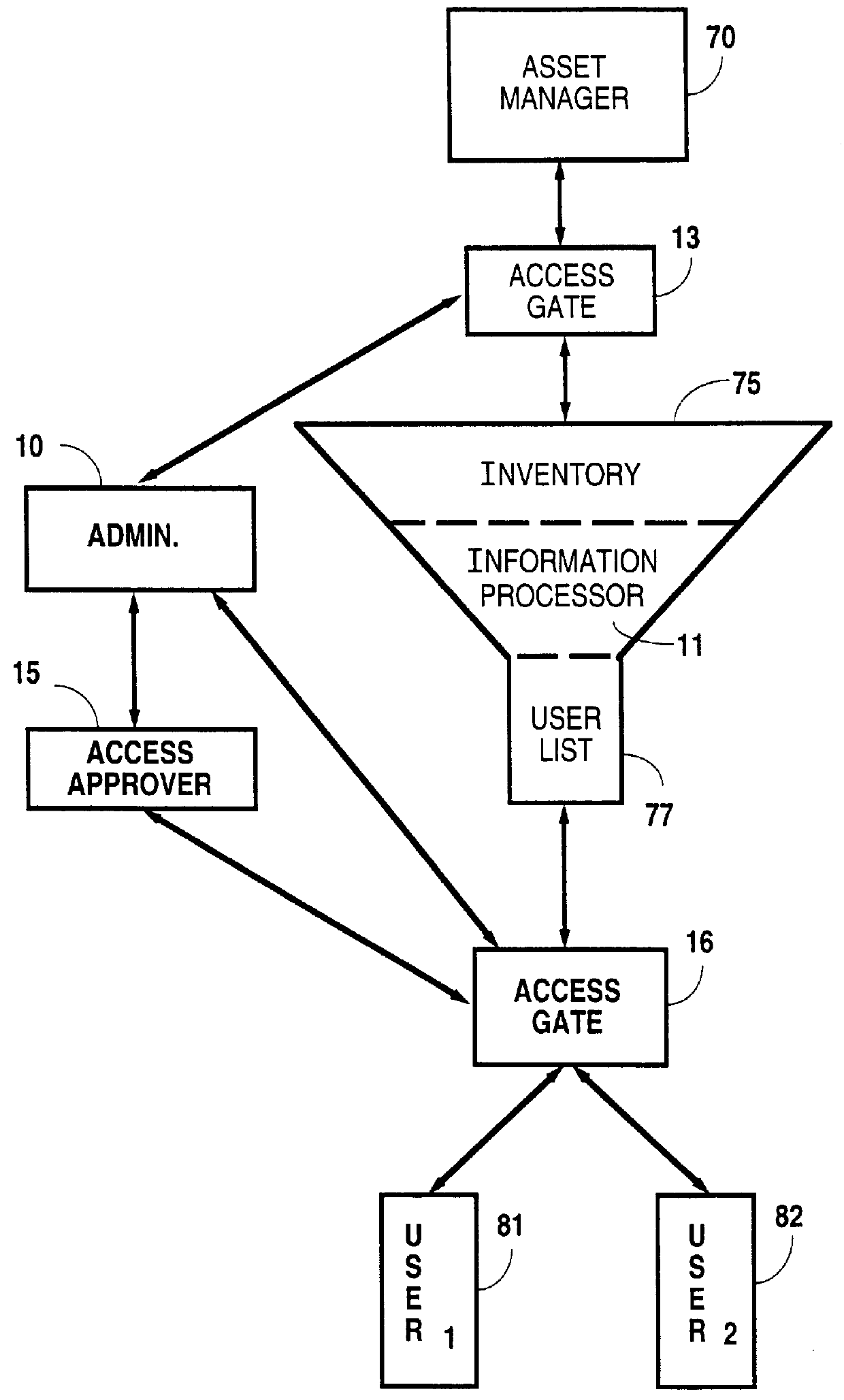
Automated and independently accessible inventory information exchange system
A method for exchanging information between providers and users of products and services in which an information management system is established that is computer based and has information processing and storage capabilities. The system also has electronic communication connections that permit buyers and sellers to electronically connect with the information management system for information exchange. Limited electronic access to the information management system is granted to approved sellers of products and services. After approval, each such seller is enabled to access inventory information of that seller for amendment purposes. Similarly, limited electronic access to the information management system is granted to approved buyers of products and services and are provided a searching capability to search a compilation of a plurality of seller's inventory information using criteria specified by that approved buyer. Last, a buyer's listing of products and services is compiled from the compilation of the seller's inventory information for that buyer based on that buyer's search criteria and in which duplicate inventory items are removed therefrom.
Owner:CXT SYST INC
Group key distribution
InactiveUS6038322AEfficient additionLow costKey distribution for secure communicationPublic key for secure communicationTimestampNetwork addressing
A method for distributing a secret key from a key holder H to intended group members M. The method assumes that during the distribution process each party, a group member M and the key holder H, can decrypt and encrypt exchanged information such that the encrypter knows that the decrypter will be the intended party. The method preferably uses a public key / private key encryption technique in which, for example, a trusted Certificate Authority in a public key infrastructure signs the certificates to provide the public keys involved in the encryption. Alternatively, the method, together with a symmetric cipher, uses a shared secret, established in an authenticated mechanism that is outside the information exchanges of the invention. Additionally, the method uses a strong mixing function that takes several items of data as input and produces a pseudo-random authentication (or digest). Inputs to the mixing function include identity stamps that are generated by each member M and key holder H. These inputs can be the identity of the stamp generator, such as a network address, port, or protocol, a timestamp, and / or a secret value that is known only to the stamp generator. The stamps include information to bind member M if generated by key holder H, and to bind key holder H if generated by member M. Consequently, the invention authenticates each communication exchange between member M and key holder H.
Owner:CISCO TECH INC
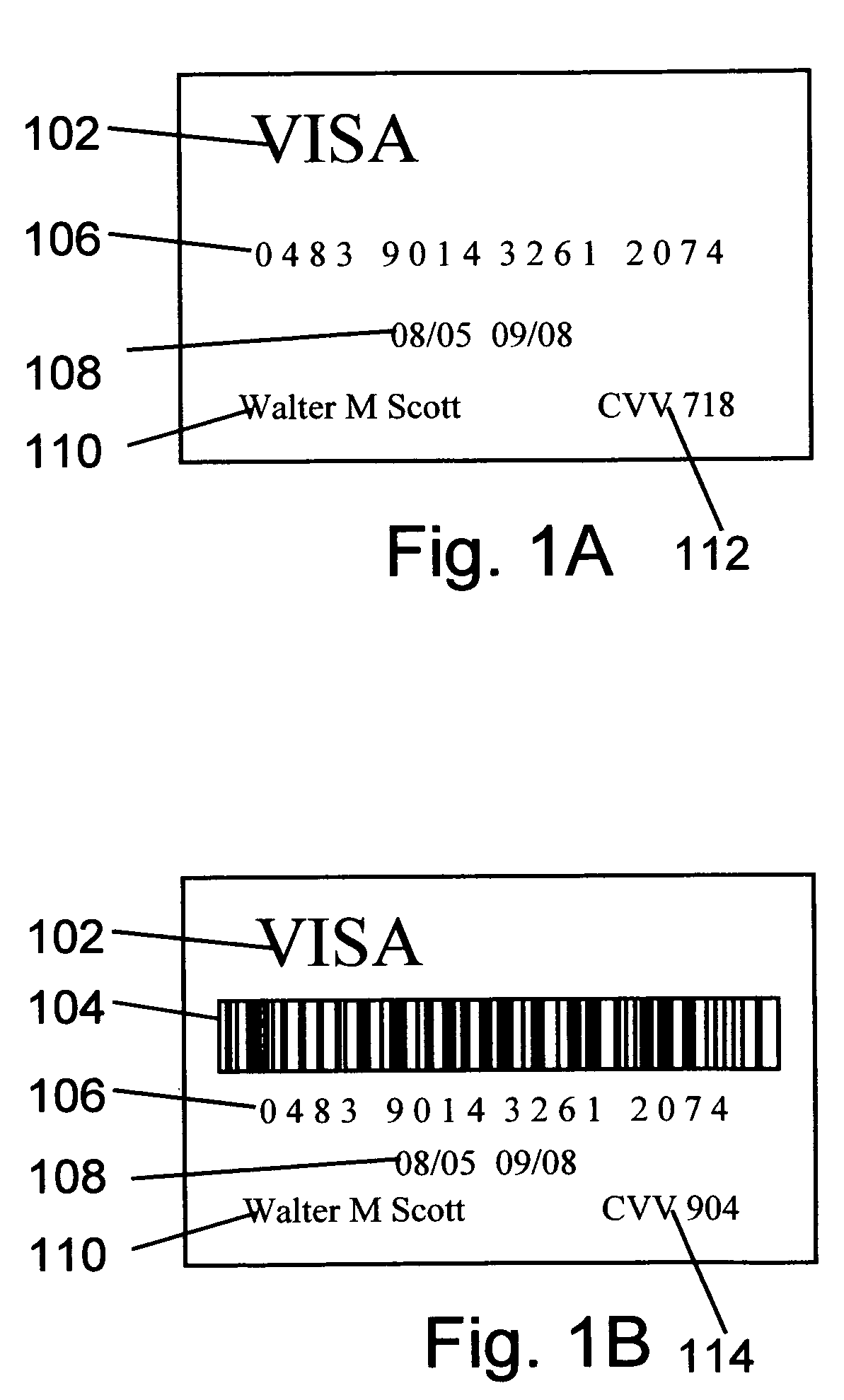
Account payment using barcode information exchange
A system for effecting transactions, typically retail transactions, by using account information stored on a computing device, such as a cell phone, wherein the computing device is placed on an optical reader at the merchant's establishment. The computing device generates a pattern, such as a bar code, on a visual display, which can be read by the merchant's optical reader. The display encodes account number and other information for the transaction. The merchant's optical reader also includes a display, which can be read by the computing device by using the cell phone camera. The merchant's display includes transaction amount and other information allowing updating of account information in the computing device. The computing device may include security codes and / or a fingerprint reader to allow access to the account information. The use of the fingerprint reader can provide positive identification of the individual, which may be used for restricted items such as age restricted items such as beer, cigarettes, and senior discounts.
Owner:LOVETT ROBERT
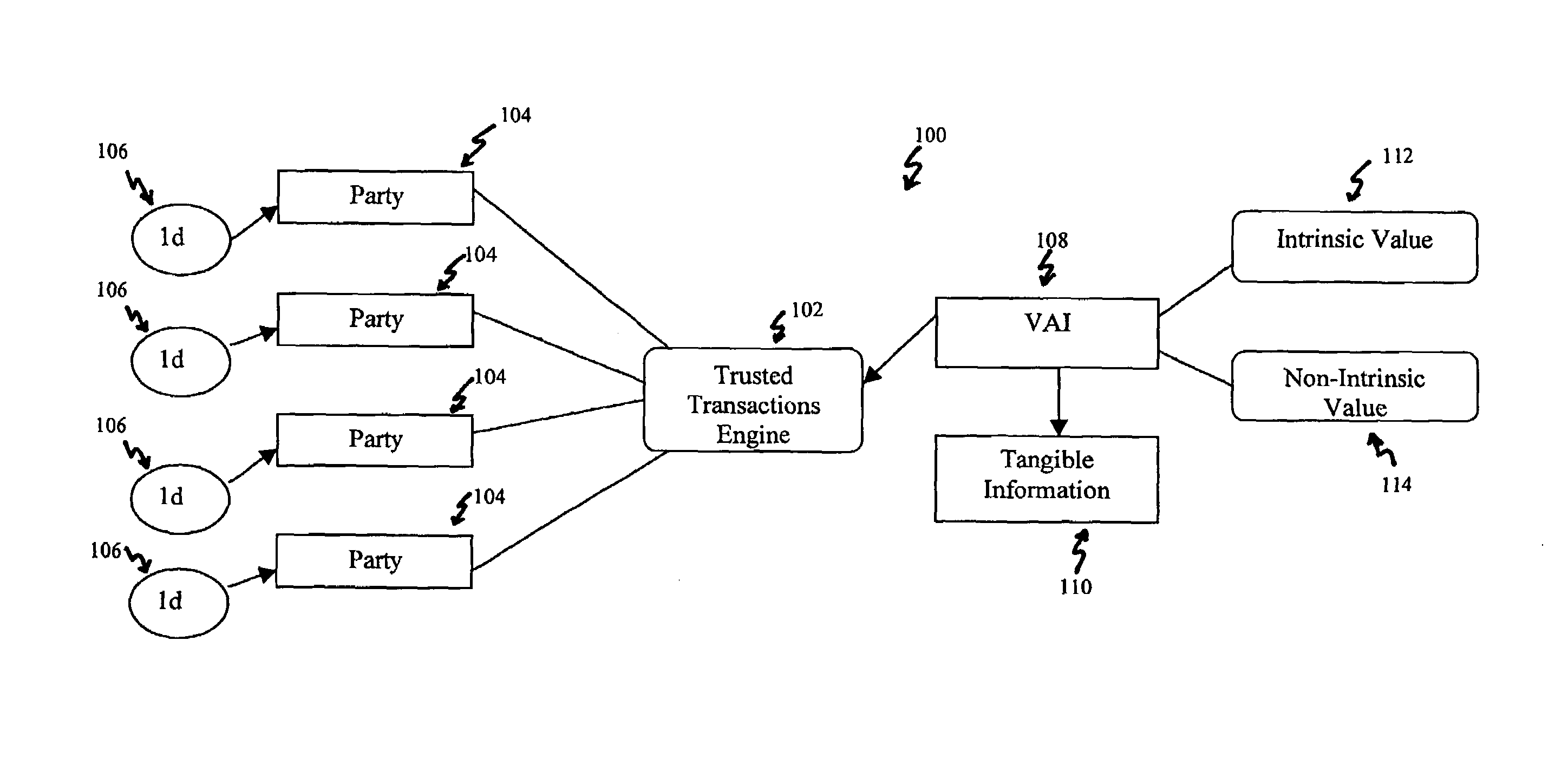
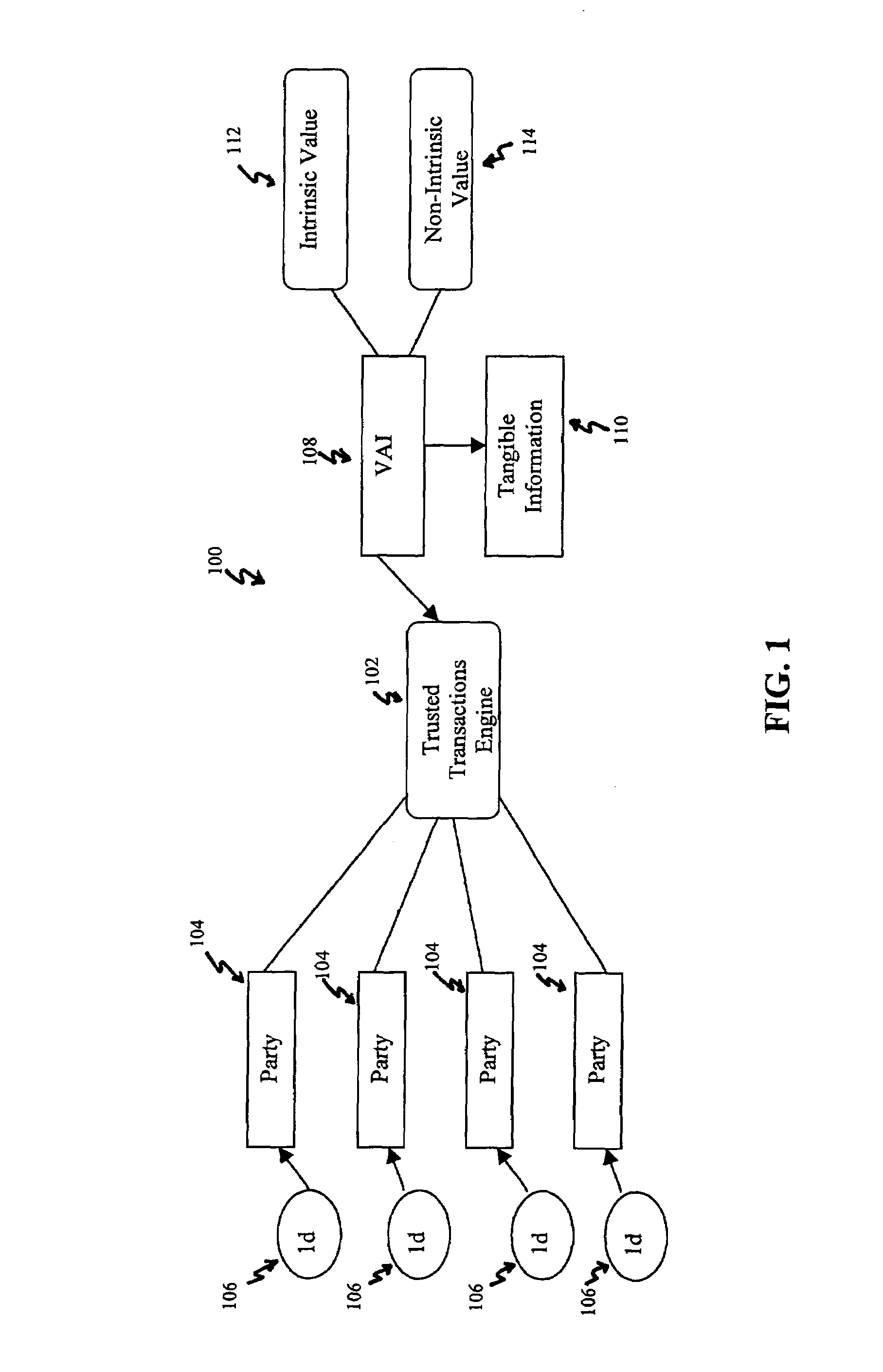
Systems, methods and devices for trusted transactions
InactiveUS7159116B2Convenient transactionLittle processing resourceMultiple keys/algorithms usagePublic key for secure communicationThe InternetSubject matter
The invention discloses a system for enhancing trust in transactions, most particularly in remote transactions between a plurality of transactional parties, for instance a seller and buyer(s) of goods and / or services over a public computer network such as the internet. Trust is disclosed to be a multivalent commodity, in that the trust that is to be enhanced relates to information about the subject matter of the transactions (e.g., the suitability of the goods and services sold), the bona fides of the supplier of the goods and services, the appropriateness of a pricing structure for a particular transaction or series of transactions, a quantum of additional transactional value that may be imparted to the transactional relationship, security of information exchange, etc. An important contributor to trust for such aspects of the transaction is disclosed to be the use of highly-secure steganographic computer processing means for data identification, authentication, and transmission, such that confidence in the transaction components is enhanced. By providing an integrated multivalent system for enhancing trust across a variety of categories (for a variety of transaction species, including those in which the need for trust is greater on the part of one party than of another, as well as those in which both require substantial trust enhancement), the invention reduces barriers to forming and optimizing transactional relationships.
Owner:WISTARIA TRADING INC
Interactive computer program for measuring and analyzing mental ability
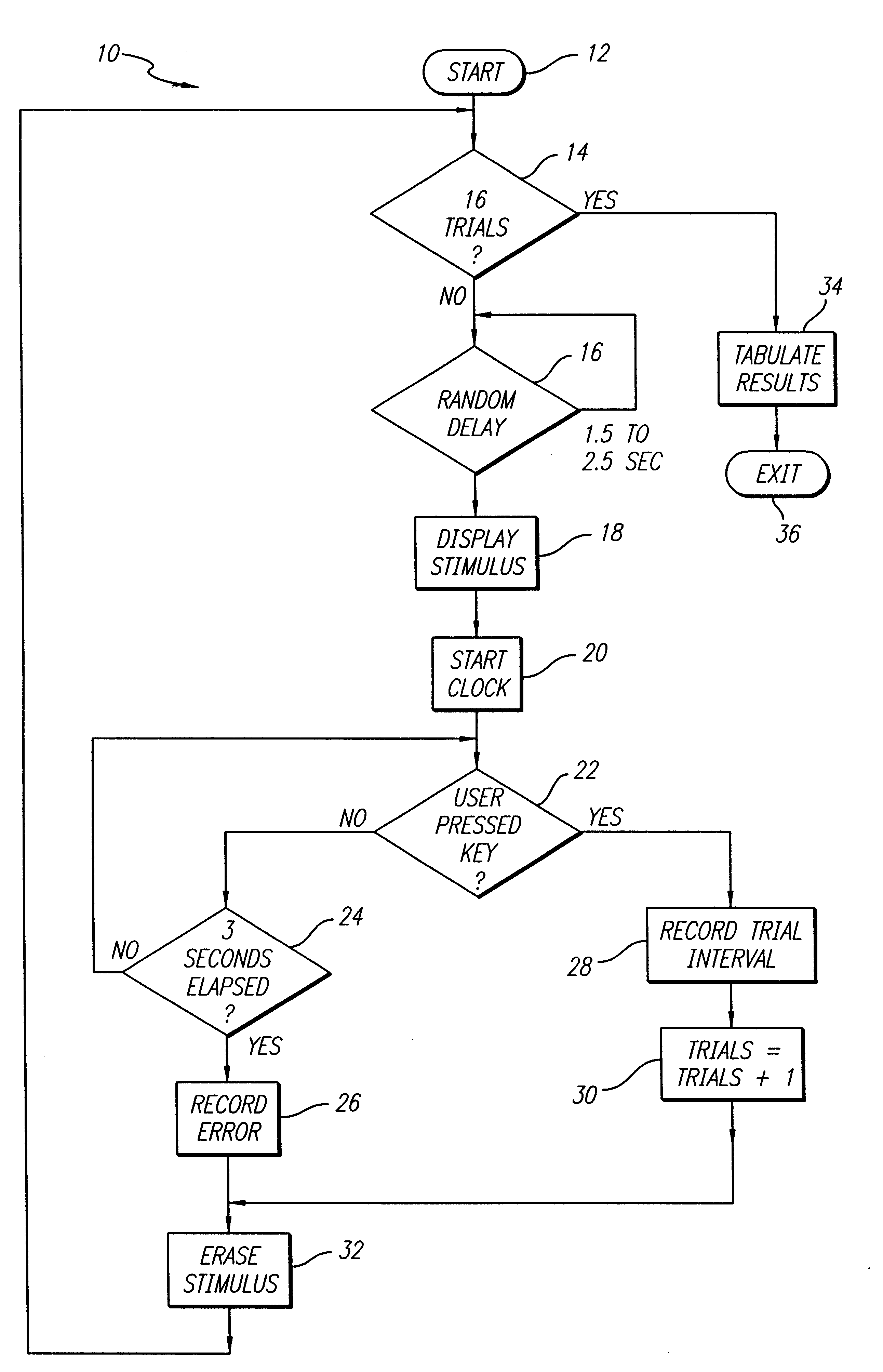
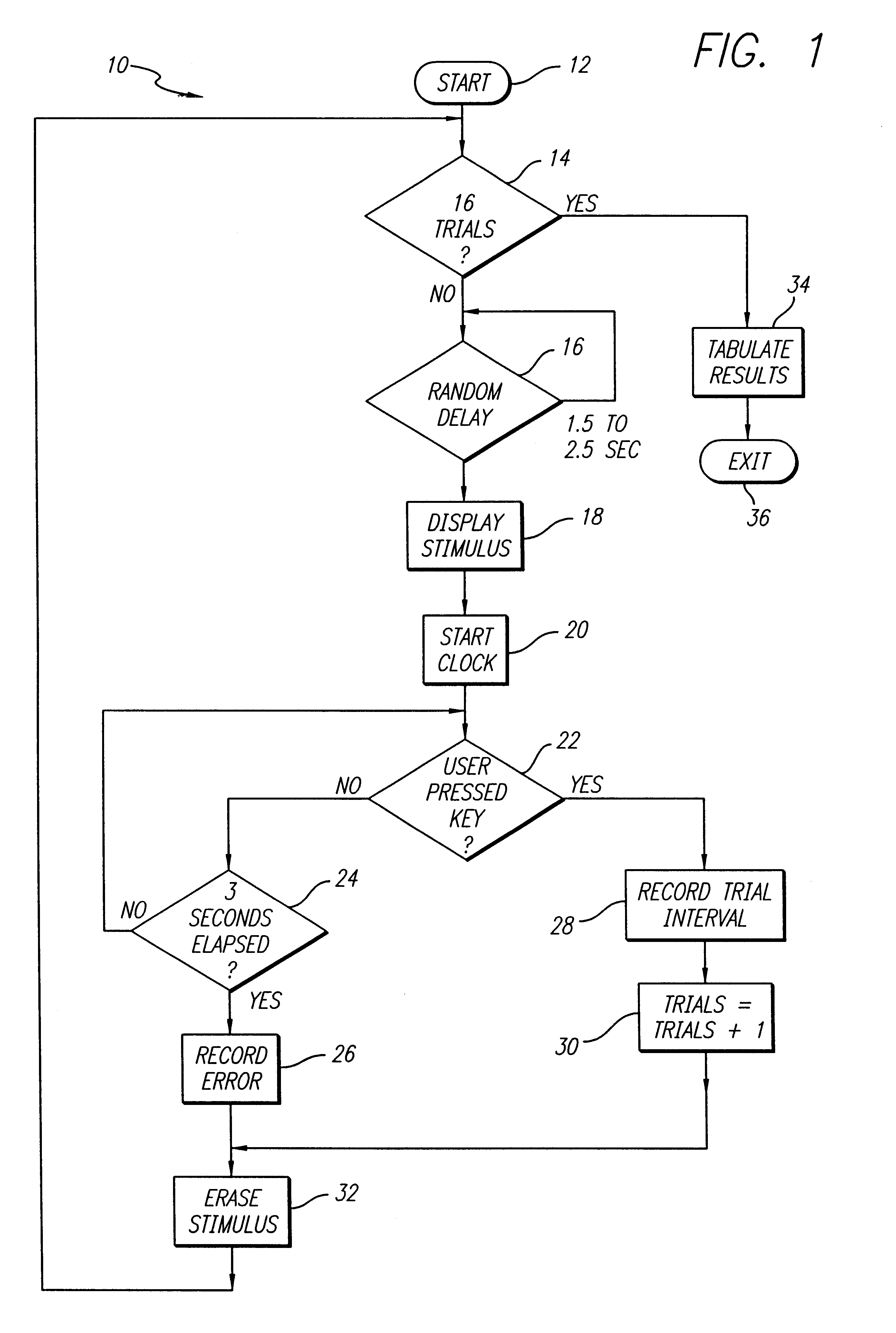
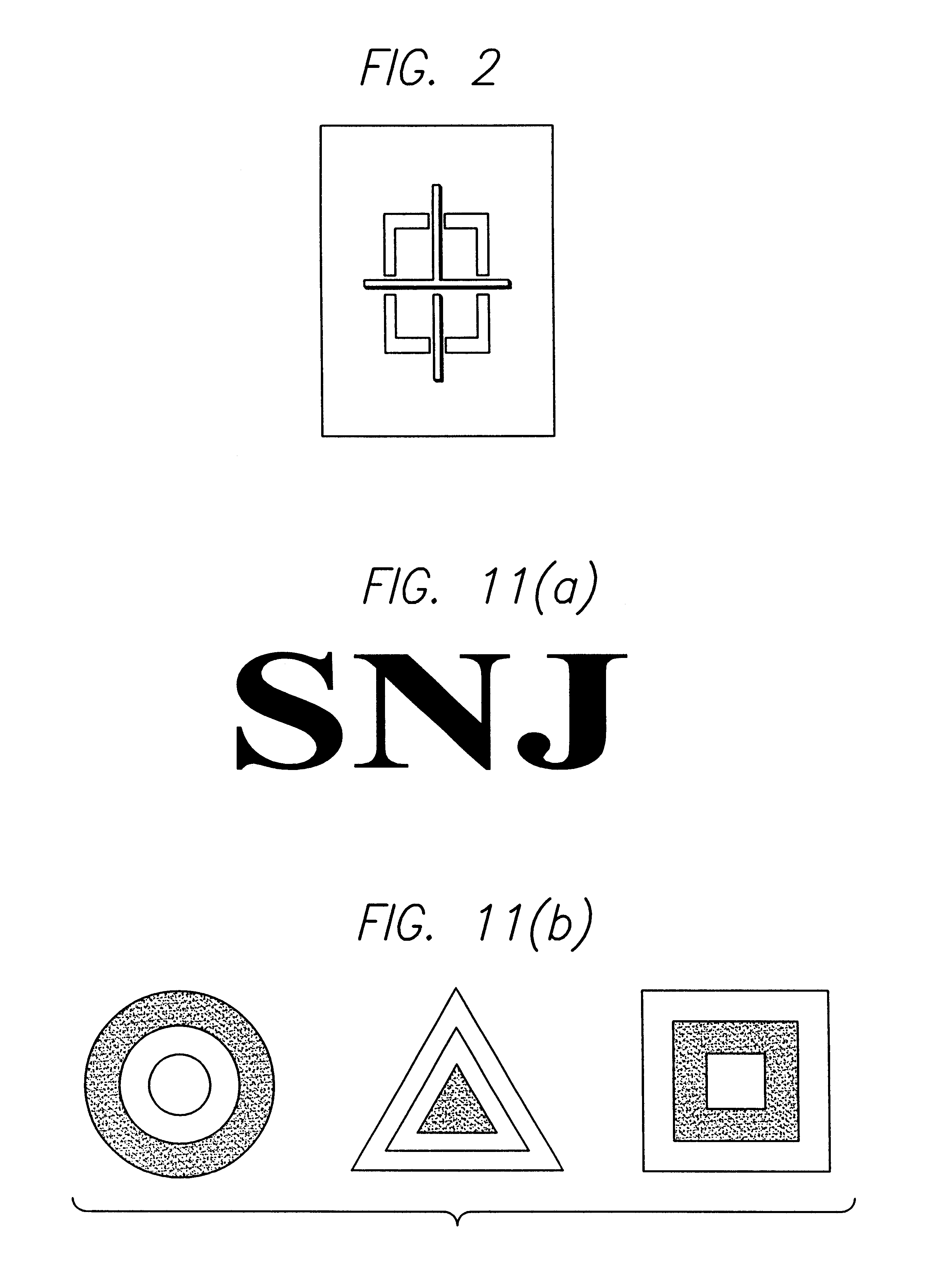
An interactive automatic system and technique for measuring and training of mental ability. In the illustrative embodiment, the invention is implemented on a computer which automatically presents a variety of visual and auditory stimuli. The system then measures reaction to the stimuli, adjusts certain stimulus parameters, and provides scores in response thereto. The scores are tabulated and displayed for analysis. In particular embodiments, the invention tests for physical reaction time, perceptual awareness thresholds, attention level, speed, efficiency and capacity of information processing by the brain and elementary cognitive processes, including memory, memory access and decision-making speed. The invention measures, identifies and quantifies noise in the subject's brain and elementary cognitive processing system, and the information exchange rate between the subject's left and right brain hemispheres. The inventive system compiles a history of the test scores, renders an overall performance rating, and delivers comments based on the subject scores. The complexity of the tests are adjusted based on the scores to optimally challenge cognitive capacities, thereby rendering more accurate evaluations of cognitive capacity, and optimizing learning of desired improvements in perceptual, physical and mental response speeds and efficiencies.
Owner:BCI
Information aggregation, processing and distribution system
InactiveUS20090094674A1Convenient and accurateEasy to useUser identity/authority verificationUnauthorized memory use protectionThird partyDistribution system
A utility is provided for managing exchanges of information within a context involving multiple users, for example, multi-user network collaboration. The invention enables automatic enforcement of a policy regarding sensitive information. The policy may be negotiated among the users and expressed as multiple rule sets that govern access to a use of sensitive information. The utility also logs activities involving sensitive information to ensure compliance with the policy. These logs can be audited by a third party or automatically processed for audit compliance by the utility. In this manner, an environment of trust is created which encourages fruitful collaboration.
Owner:LOCKHEED MARTIN CORP
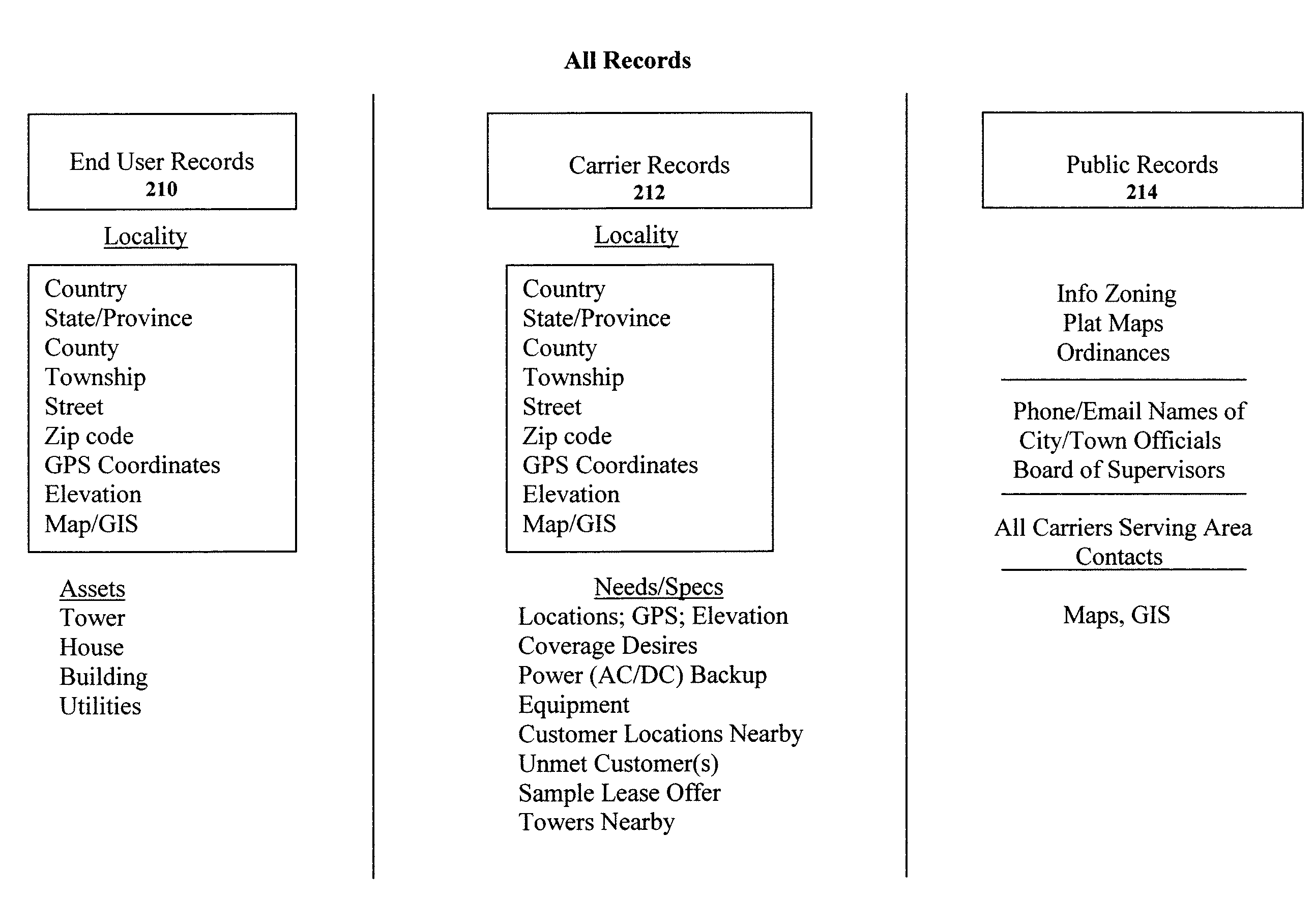
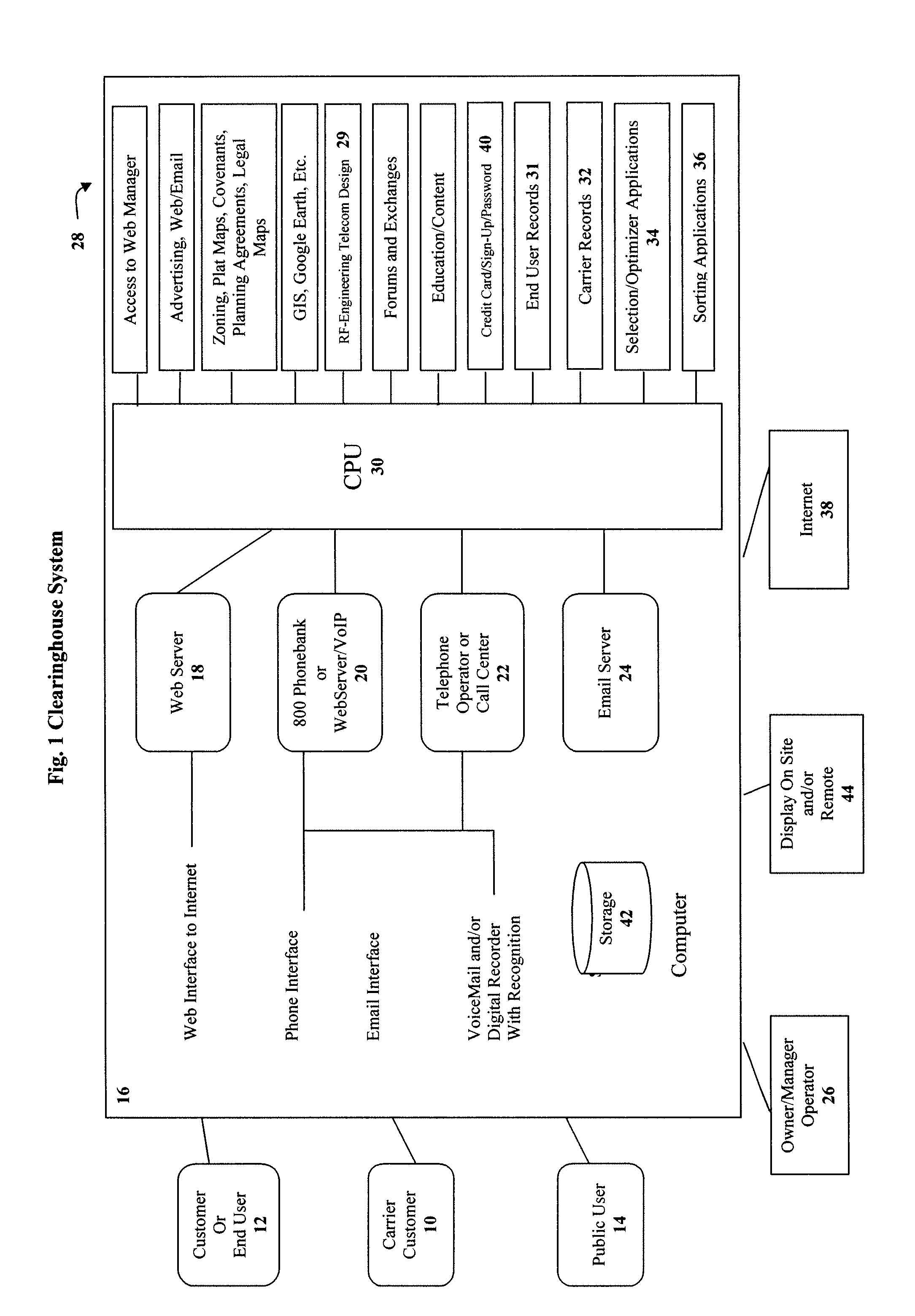
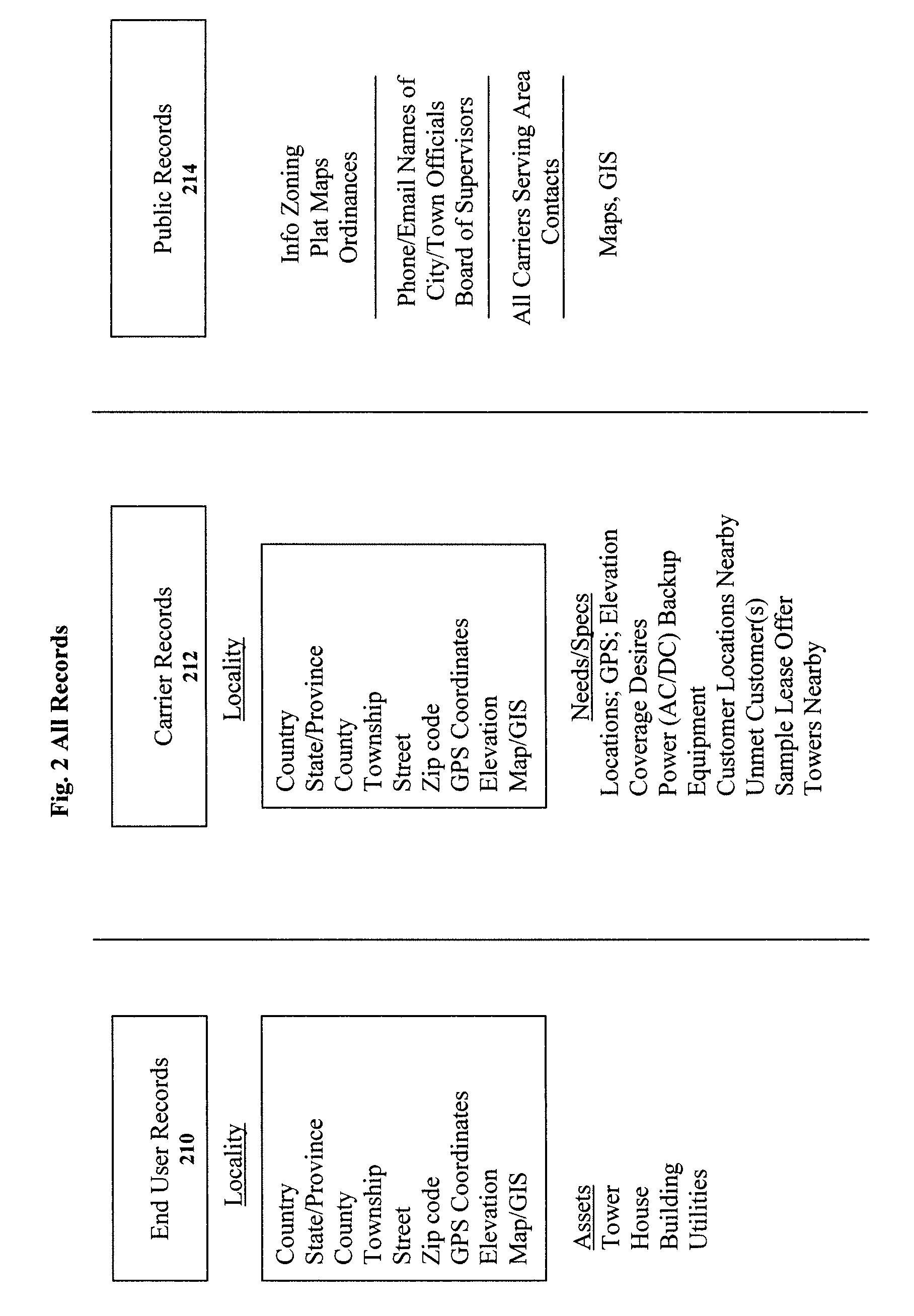
Clearinghouse system, method, and process for inventorying and acquiring infrastructure, monitoring and controlling network performance for enhancement, and providing localized content in communication networks
ActiveUS20090070379A1Broaden their knowledgeLow costError detection/correctionMultiple digital computer combinationsCommunications systemTelecom network
A computerized system, method and process allows telecommunications carriers to find, evaluate and select locations for equipment through direct access to end users, while providing citizens the opportunity to offer the use of their dwelling or other assets to carriers. The system and method further provides a computerized mechanism for (a) creating an inventory and marketplace for available properties for use in telecommunications networks, (b) providing quality and / or performance monitoring and control for wireless communication systems based on data in the clearinghouse, and (c) providing localized content over wireless networks using the clearinghouse.
Owner:RAPPAPORT THEODORE S
System and Methods to Store, Retrieve, Manage, Augment and Monitor Applications on Appliances
ActiveUS20110082900A1Reduce usageComputer security arrangementsMultiple digital computer combinationsDevice typeAuthentication
Systems and methods for managing applications on an appliance are provided. A server is in communication with appliances. The server is also coupled to databases which include appliance information, as well as application data. A user may authenticate using the appliance. A set of permissions may be associated with the user. The server then supervises information exchanged between the appliance and the server, as well as application functionality upon the appliance, by supplementing the applications downloaded to the appliance with supplemental code, referred to hereafter as an AppGuard. The AppGuard is tailored, using information related to the appliance, to the appliance type in order to ensure proper functionality. The AppGuard is executed upon installation, and collects device information for validation. After validation, the application may be run. Additionally, management of the applications may include augmenting, deleting, disabling or authorizing the application.
Owner:MALIKIE INNOVATIONS LTD
Enforcing policies in wireless communication using exchanged identities
ActiveUS20100061294A1Facilitating exchange of information and transactionShort capabilityDiscounts/incentivesServices signallingWi-FiComputer network
Techniques for facilitating the exchange of information and transactions between two entities associated with two wireless devices when the devices are in close proximity to each other. A first device uses a first short range wireless capability to detect an identifier transmitted from a second device in proximity, ideally using existing radio capabilities such as Bluetooth (IEEE802.15.1-2002) or Wi-Fi (IEEE802.11). The detected identifier, being associated with the device, is also associated with an entity. Rather than directly exchanging application data flow between the two devices using the short range wireless capability, a second wireless capability allows for one or more of the devices to communicate with a central server via the internet, and perform the exchange of application data flow. By using a central server to draw on stored information and content associated with the entities the server can broker the exchange of information between the entities and the devices.
Owner:PROXICOM WIRELESS
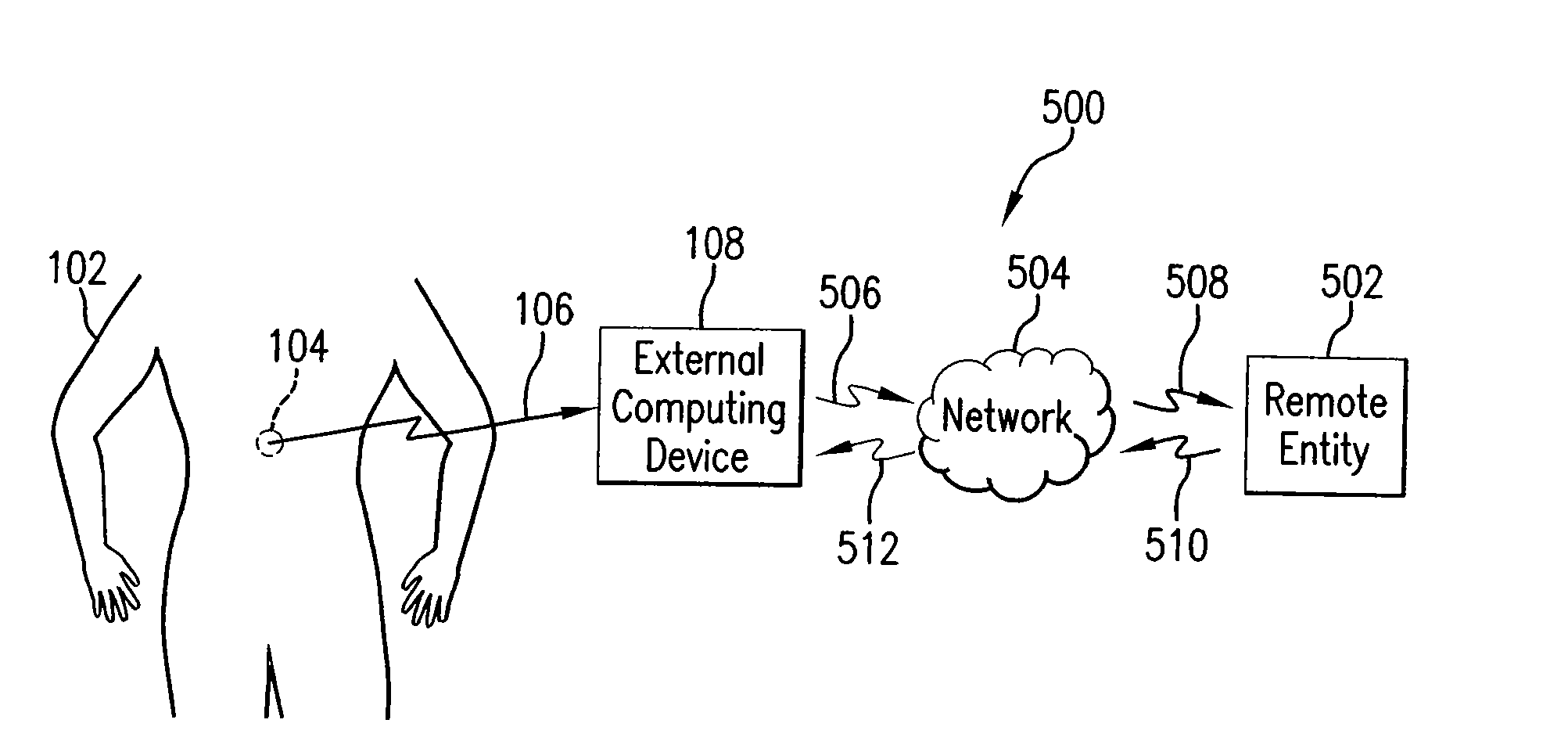
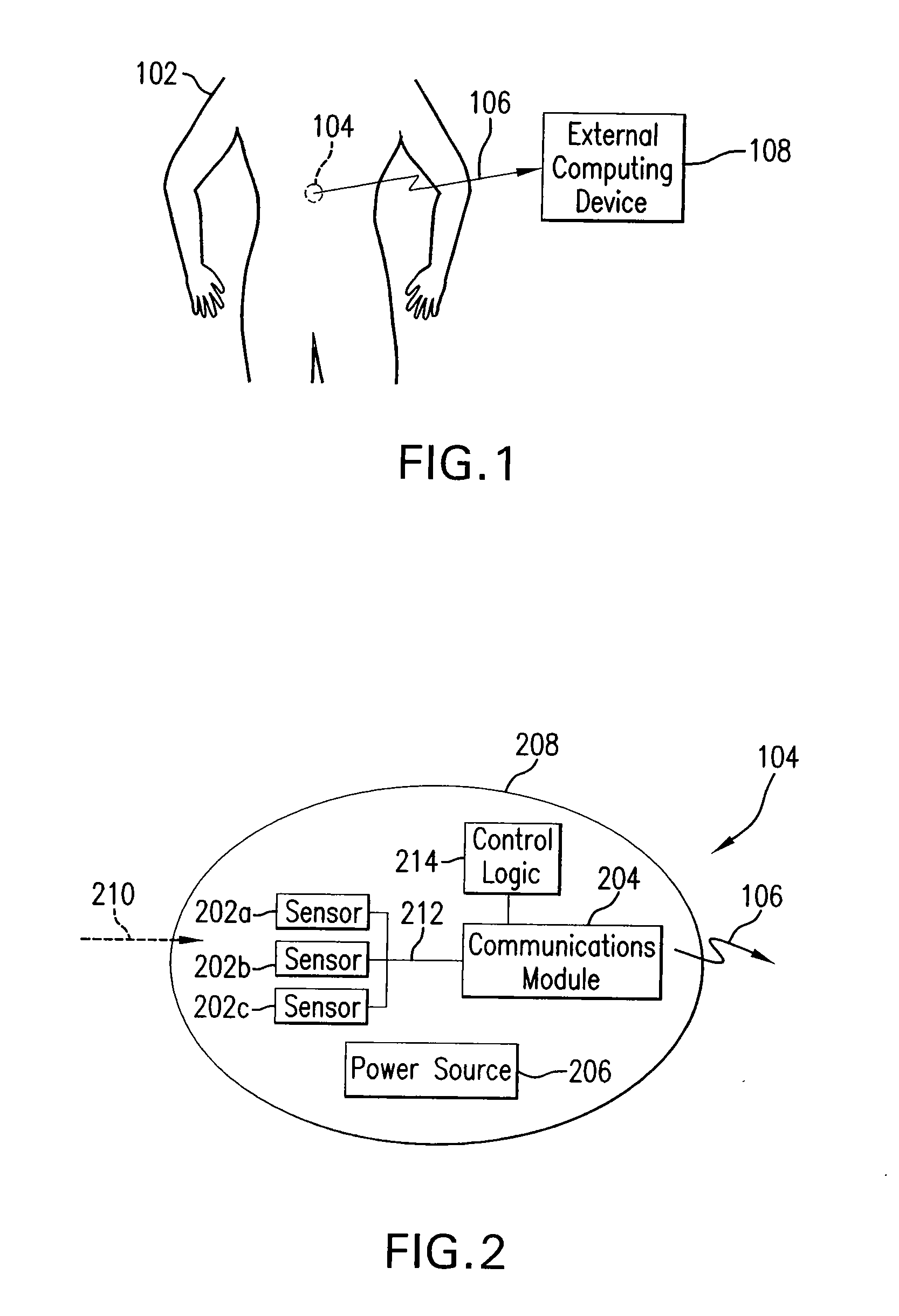
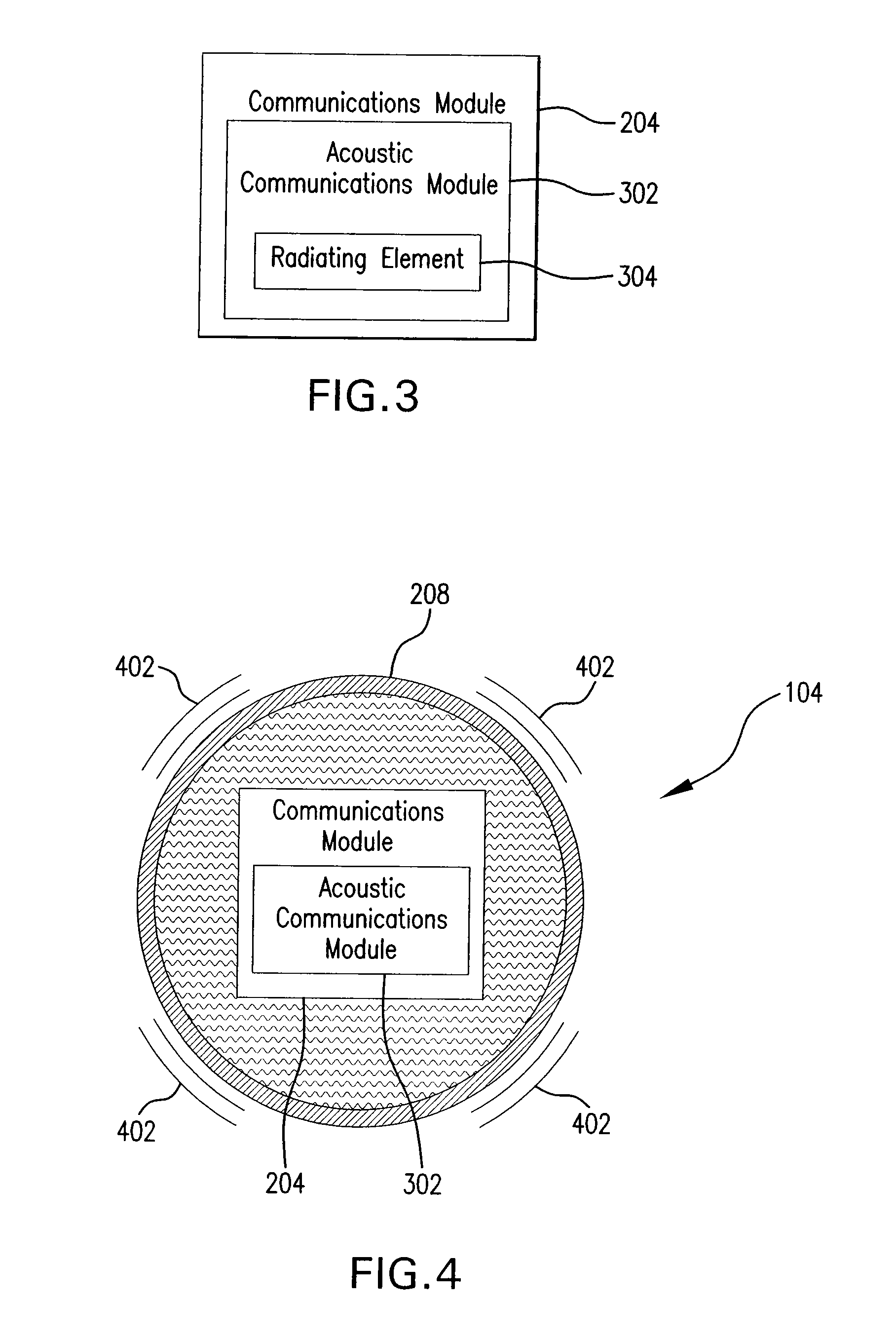
Methods and systems for acoustic data transmission
Owner:INNURVATION
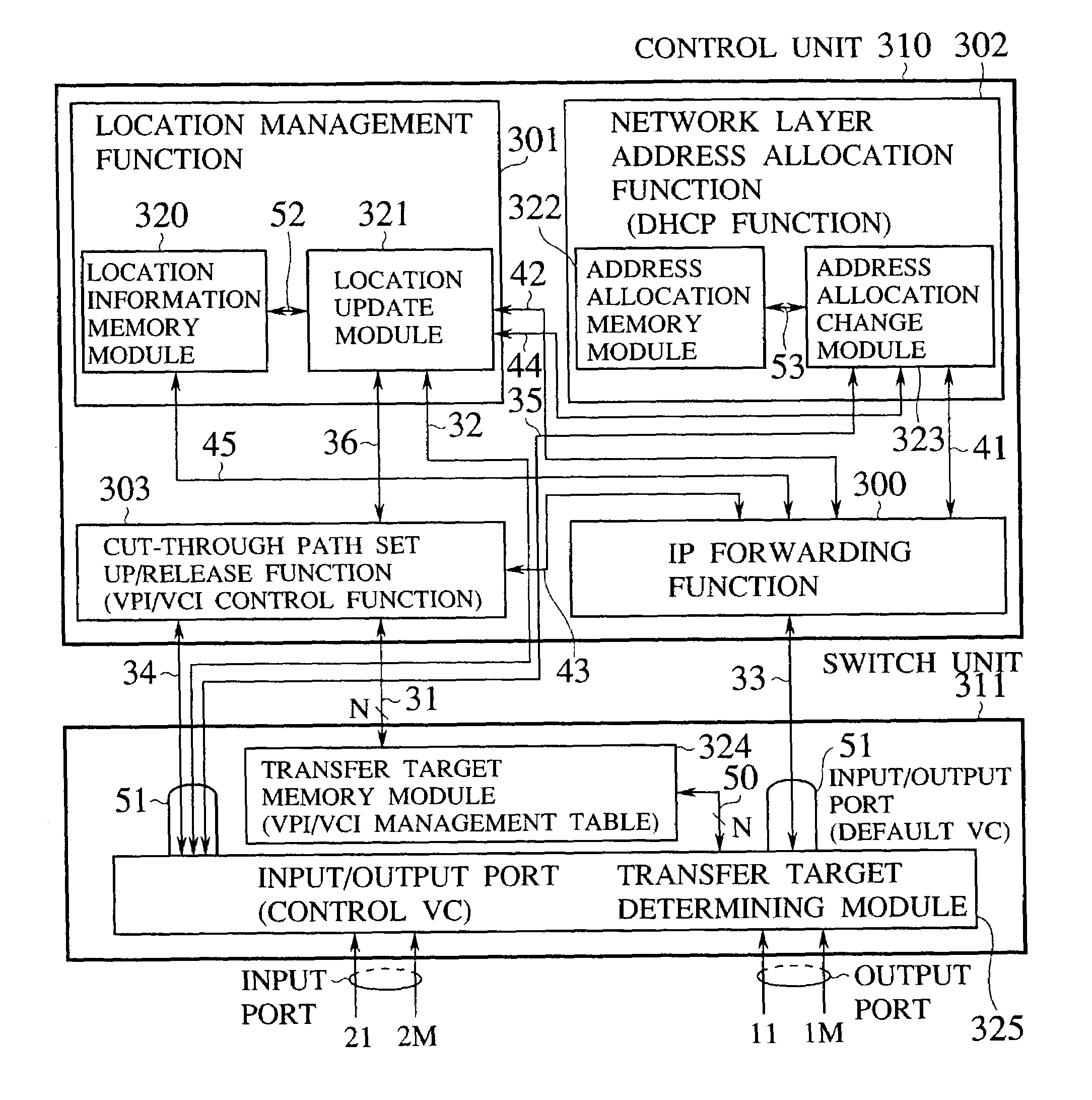
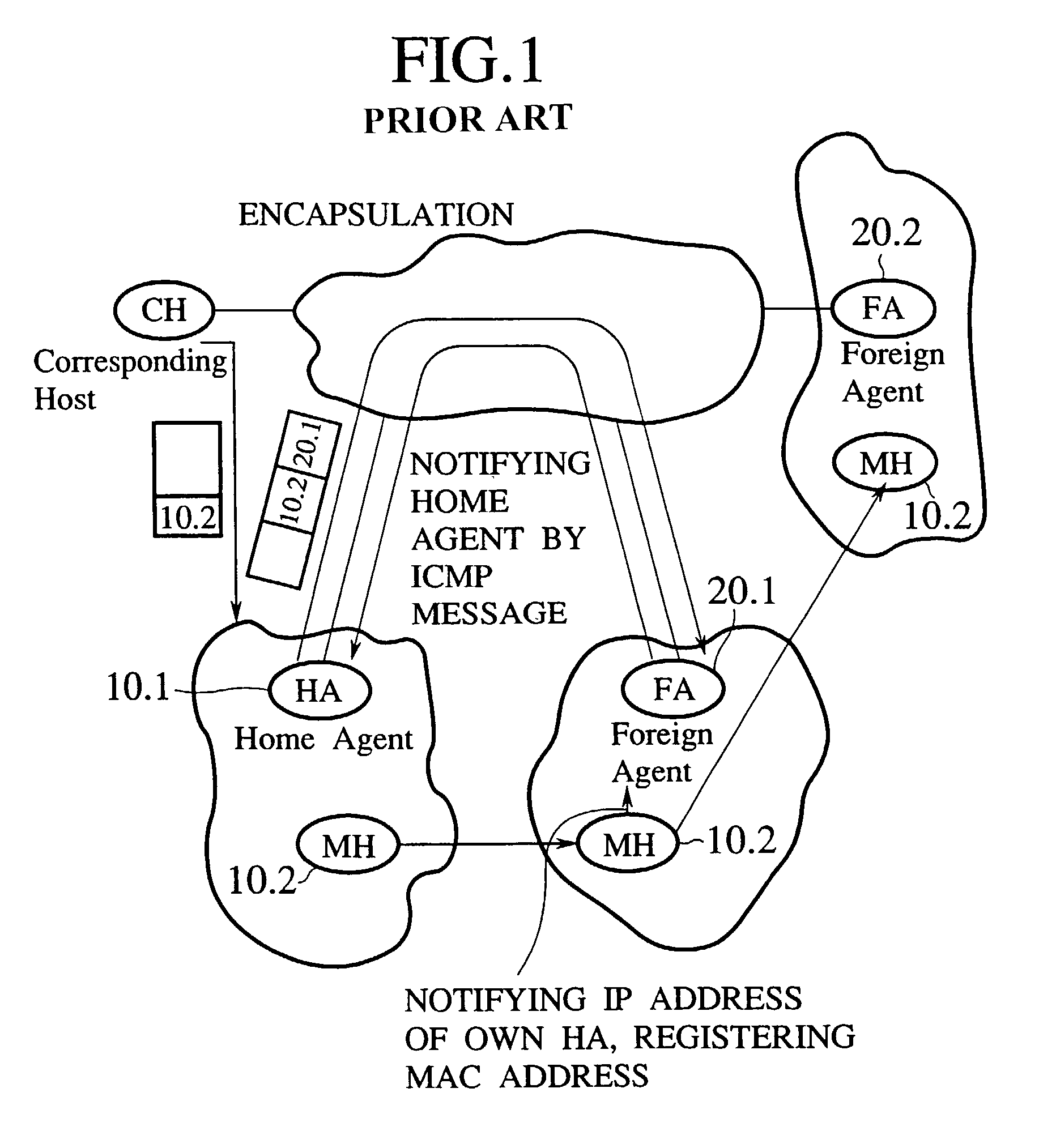
Router device, datagram transfer method and communication system realizing handoff control for mobile terminals
InactiveUS7151758B2Increase speedEasy to controlData switching by path configurationWireless network protocolsCommunications systemHandoff control
A mobile supporting router device for realizing the handoff control associated with the moving in high speed is forms by at least one first interface connected with radio base stations, each capable of accommodating at least one mobile terminal; at least one second interface connected with a wire network; an information exchanging unit for exchanging a routing protocol on a network layer, through the second interface; a memory unit for storing information regarding a routing on the network layer based on the routing protocol exchanged by the information exchanging unit; a transfer unit for transferring datagram through the first interface according to the information regarding the routing on the network layer stored in the memory unit; a moving detection unit for detecting a moving of the mobile terminal among the radio base stations; and an information updating unit for updating the information regarding the routing on the network layer stored in the memory unit when the moving of the mobile terminal is detected by the moving detection unit.
Owner:KK TOSHIBA
Method and system for wireless data communication in data processing system
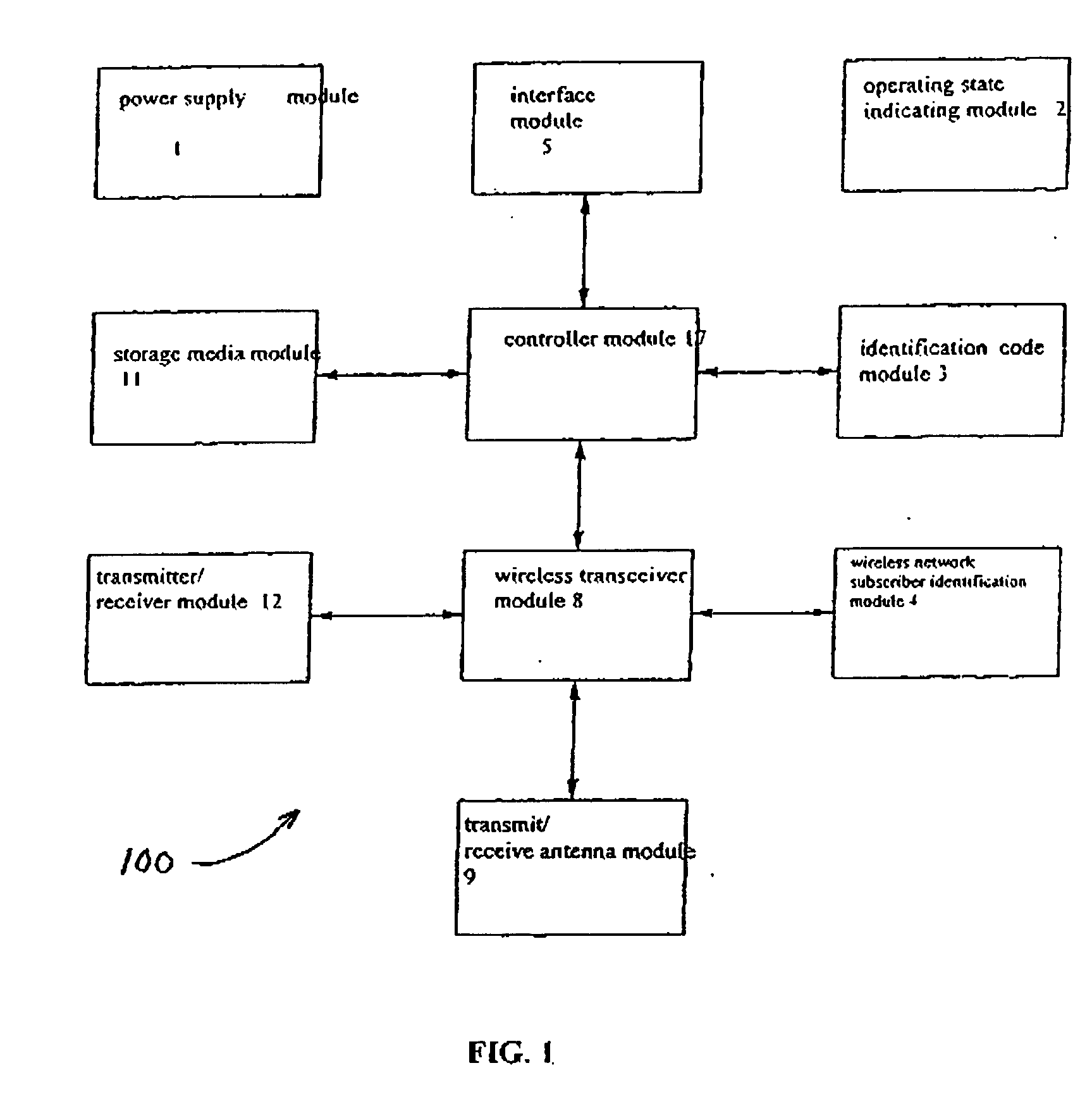
InactiveUS20050250536A1Wide coverageLow costConnection managementSubstation equipmentData processing systemCommunication interface
A method of wireless data communication in a data processing system comprise the steps of providing a wireless data communication device, in which installed are a wireless transceiver module for receiving and transmitting data information, and a controller and an interface module for controlling the wireless data communication device; establishing an information exchange channel between the device and the data processing system based on a serial or parallel connection or wireless communication interface; wherein the wireless data communication device transmits or receives the data information through the wireless transceiver module via a public wireless network. The device is connected with a variety of data processing equipments, such as, a computer host through a variety of interfaces, and has a wireless transceiver module which can receive or transmit information through a mobile telephone network, uses directly communication services provided by the mobile telephone network company, and thus has the advantages of being online at any time but at low cost. It can also connect to the Internet for transmitting and receiving information so as to realize wireless access to the Internet.
Owner:NETAK TECH KO LTD
Information Exchange Among Members of a Group of Communication Device Users
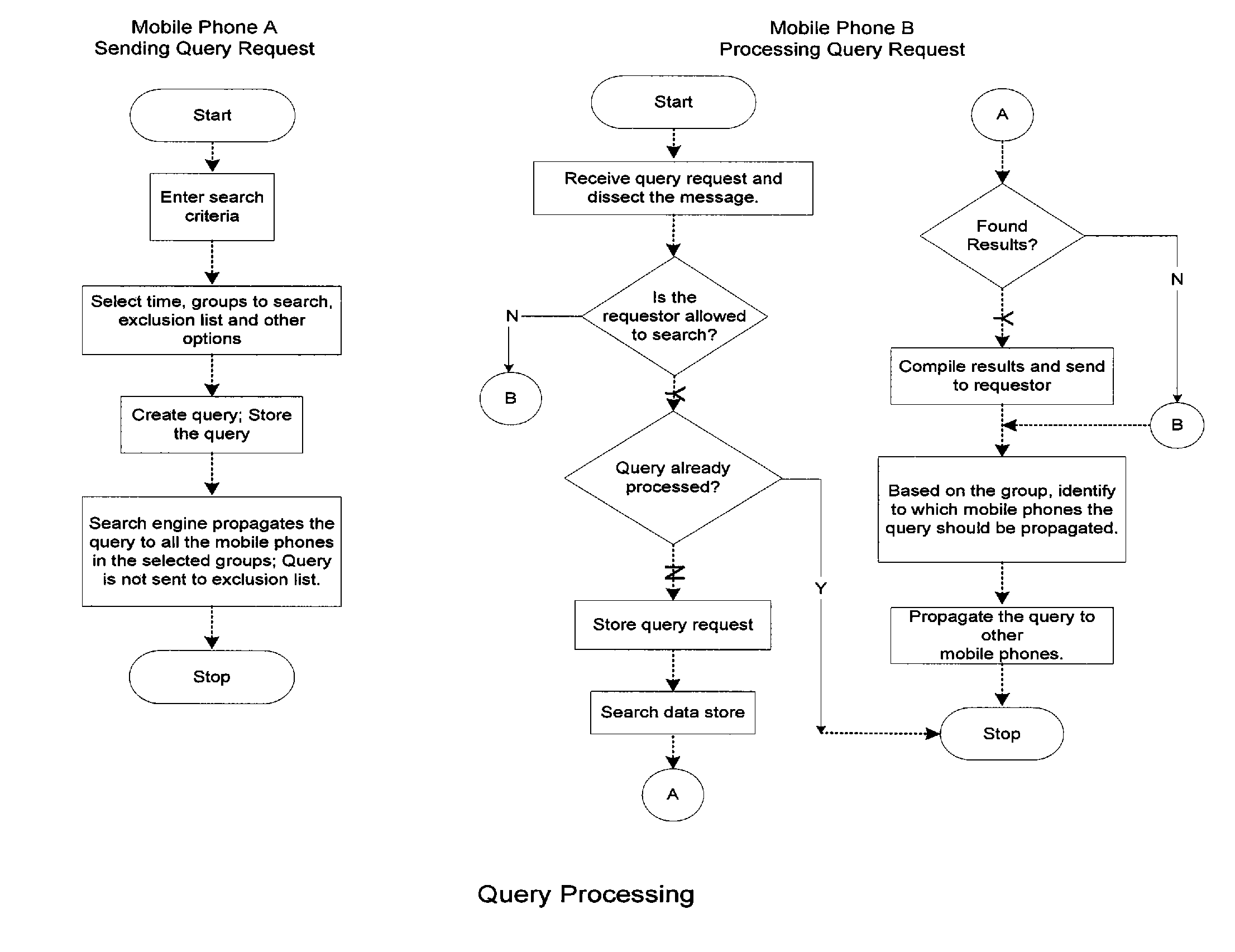
InactiveUS20070271234A1More dataFacilitate transmission and receptionDigital data information retrievalSpecial data processing applicationsLogical networkCommunication device
A method, system, and apparatus for controlling transmission and reception of communications between a plurality of telecommunication devices in a group to allow searching of stored resources is provided. The invention includes a group management module for creating and maintaining association links for each of the plurality of telecommunication devices representing a logical network of devices. The invention also includes a search engine for transmission and reception of communications between the devices in a group, the search engine configured to route a search query from an originating device along the association links to all devices in the group, search stored resources in all devices in the group, and return results of the search query to the originating device, thereby allowing searching of stored resources on all the plurality of telecommunication devices without relying on a centralized server or physical network or wireless network for storing resources.
Owner:RAVIKIRAN CHICKMANGALORE N
Vehicle collision prewarning method and apparatus
InactiveCN101407199AAvoid changeHigh precisionPedestrian/occupant safety arrangementAnti-collision systemsEarly warning systemDriver/operator
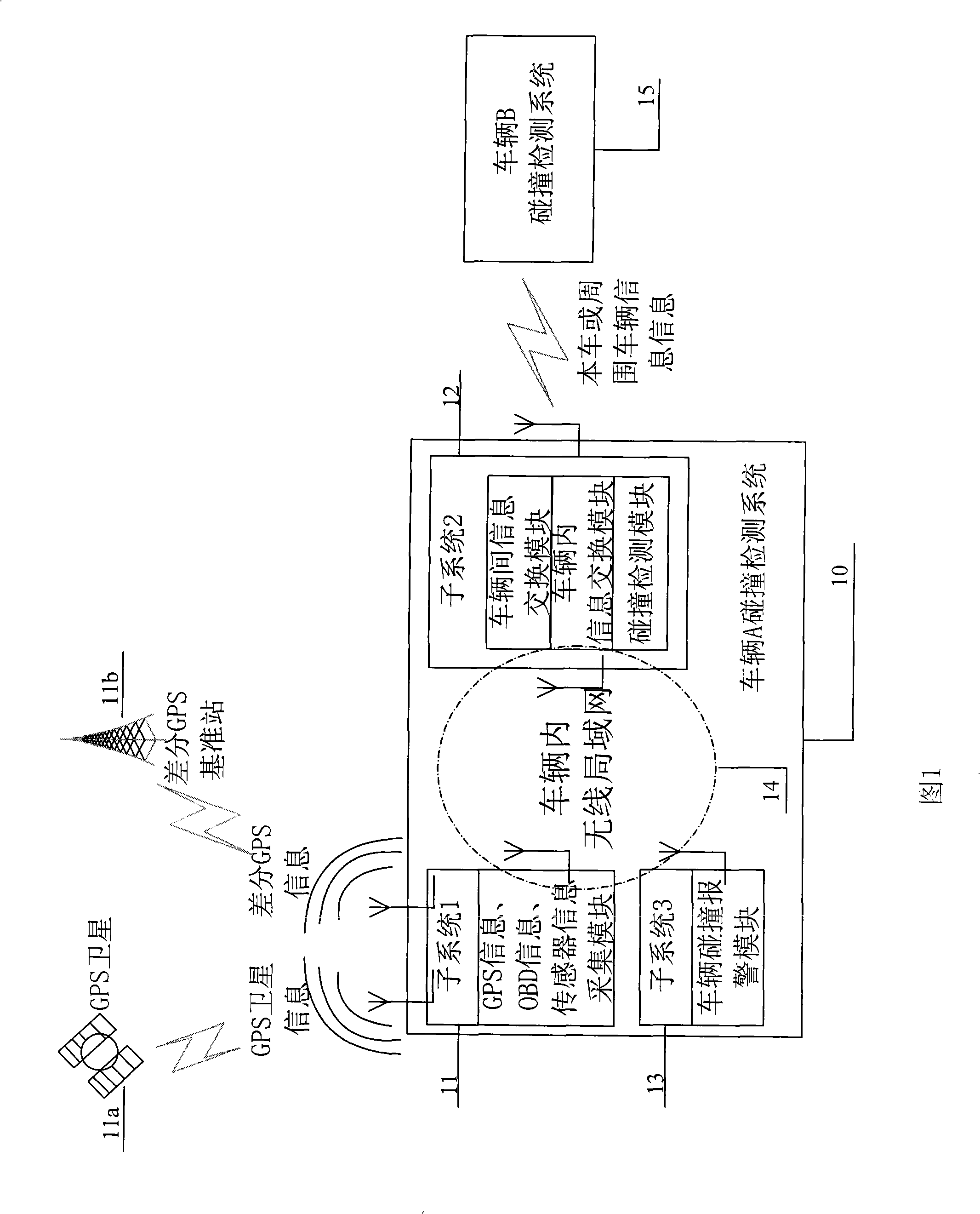
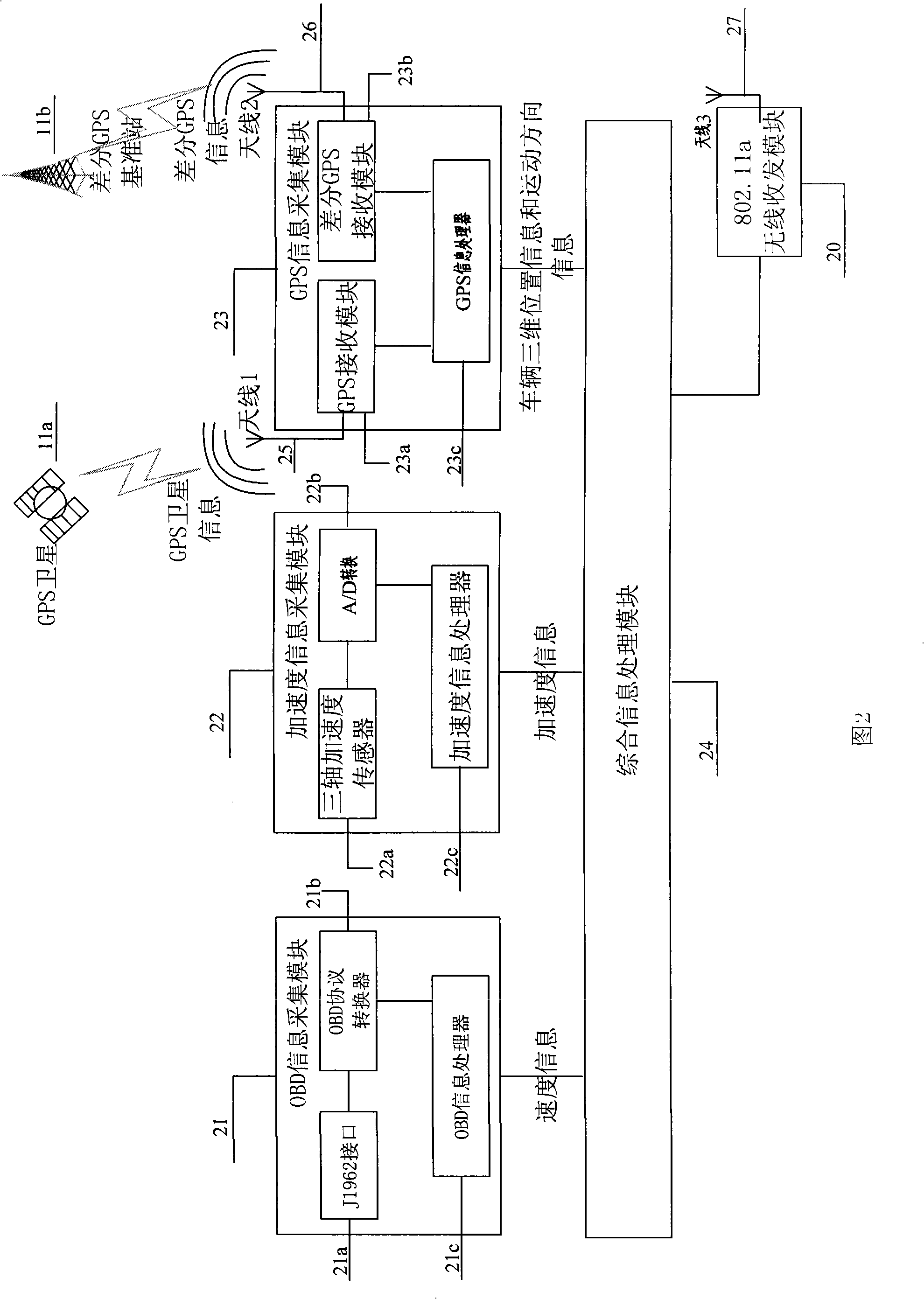
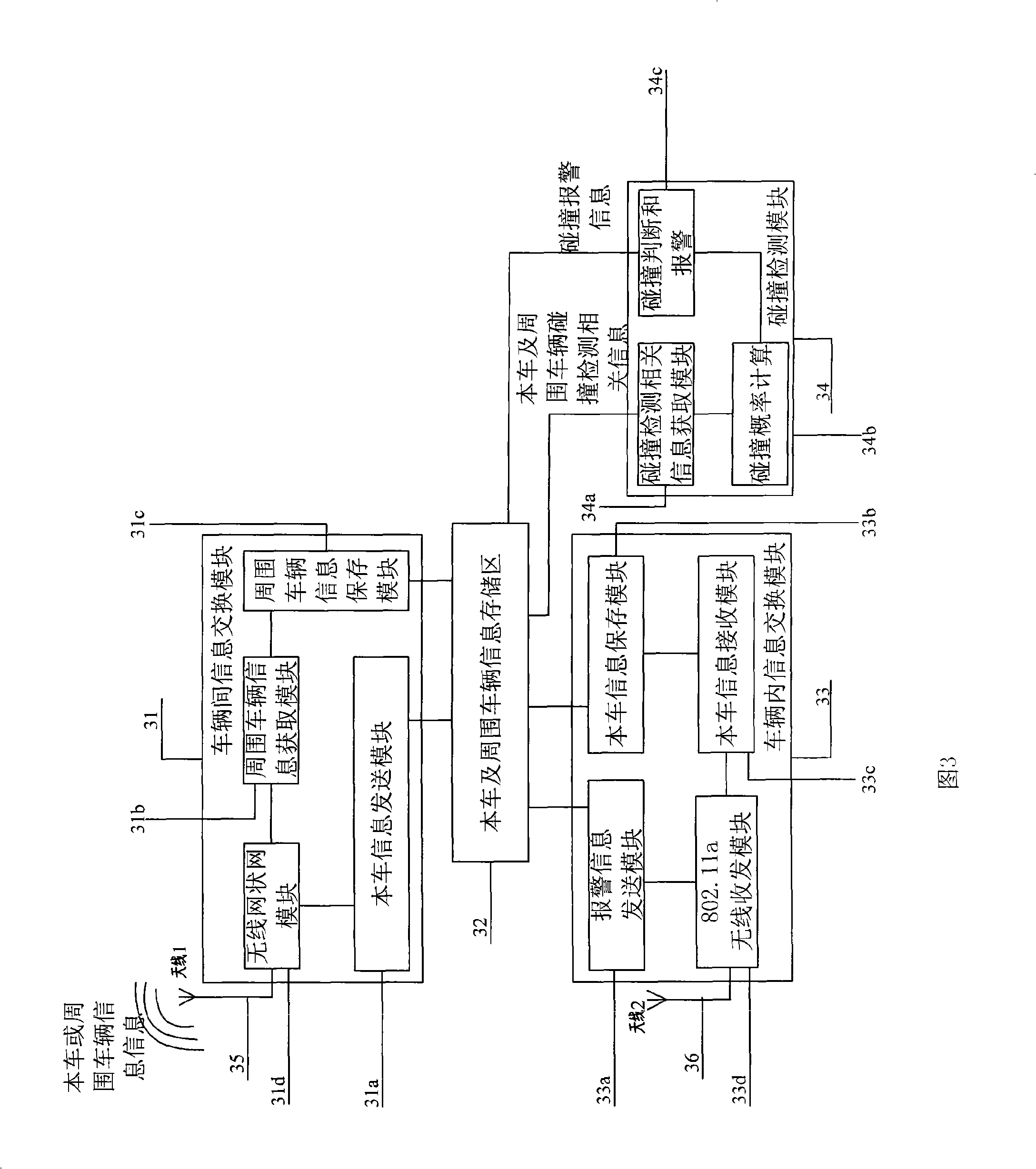
The invention discloses an early warning method and a device for vehicle collision. The early warning method is characterized in that the method comprises the following steps: after a vehicle is fired, colliding an early warning system to begin initializing each parameter, using an OBD information collection module, a sensor information collection module and a GPS information collection module to collect information of the vehicle, using an inter-vehicle information exchange module to collect peripheral vehicle information, sending the information of the vehicle to the peripheral vehicles, calculating individualized collision probability according to self state of a driver, and warning the driver; and the device consists of the OBD information collection module, the sensor information collection module, the GPS information collection module, the inter-vehicle information exchange module, an information exchange module in the vehicles, a collision detection module and a vehicle collision warning module. Each module exchanges information in the vehicle through a wireless local area network in the vehicle, does not change an electric line of the vehicle and does not increase wire harness inside the vehicle, and can effectively reduce occurrence of traffic accidents, so as to reduce casualties.
Owner:HUBEI UNIV OF AUTOMOTIVE TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com