Patents
Literature
6892 results about "Data connection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
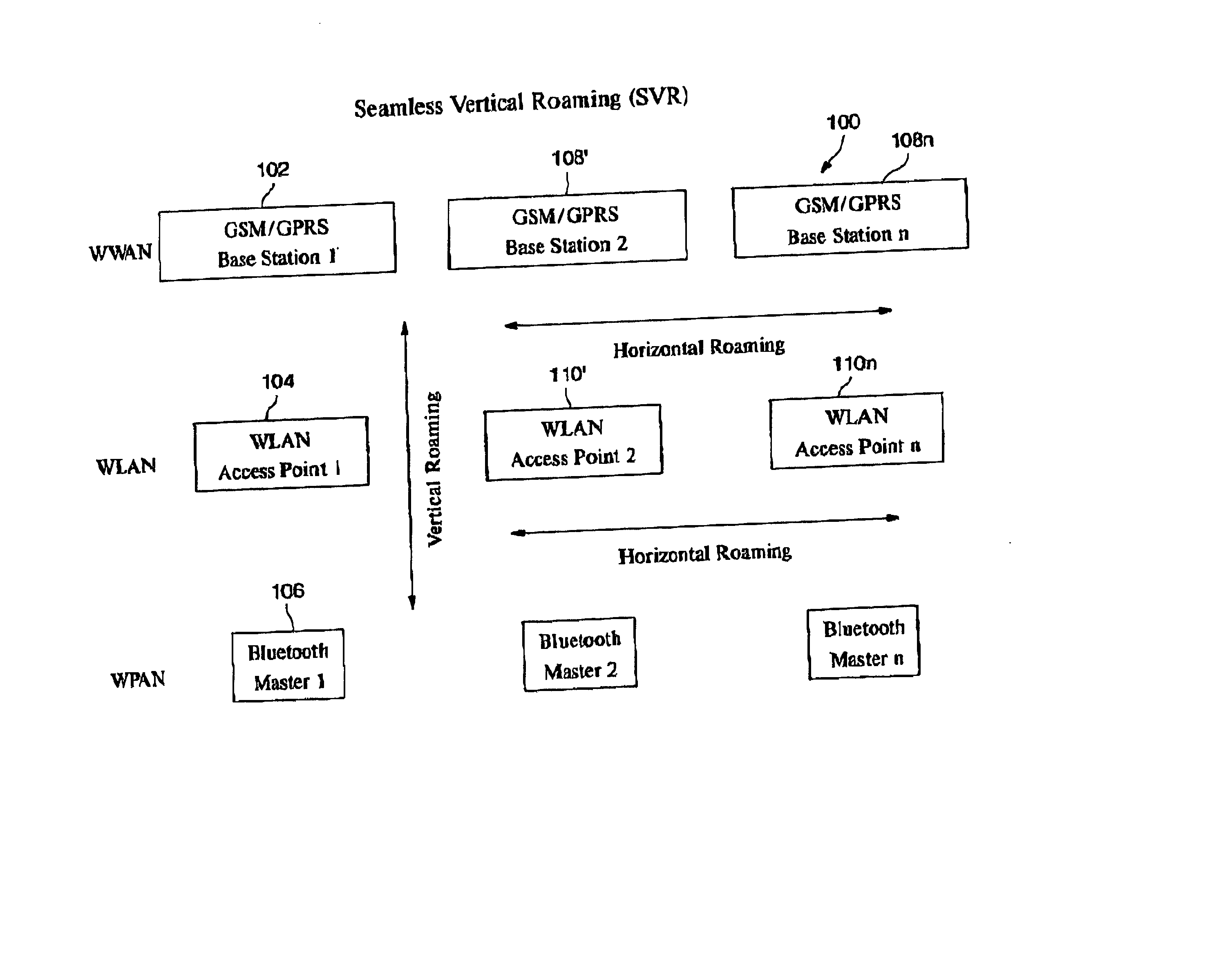
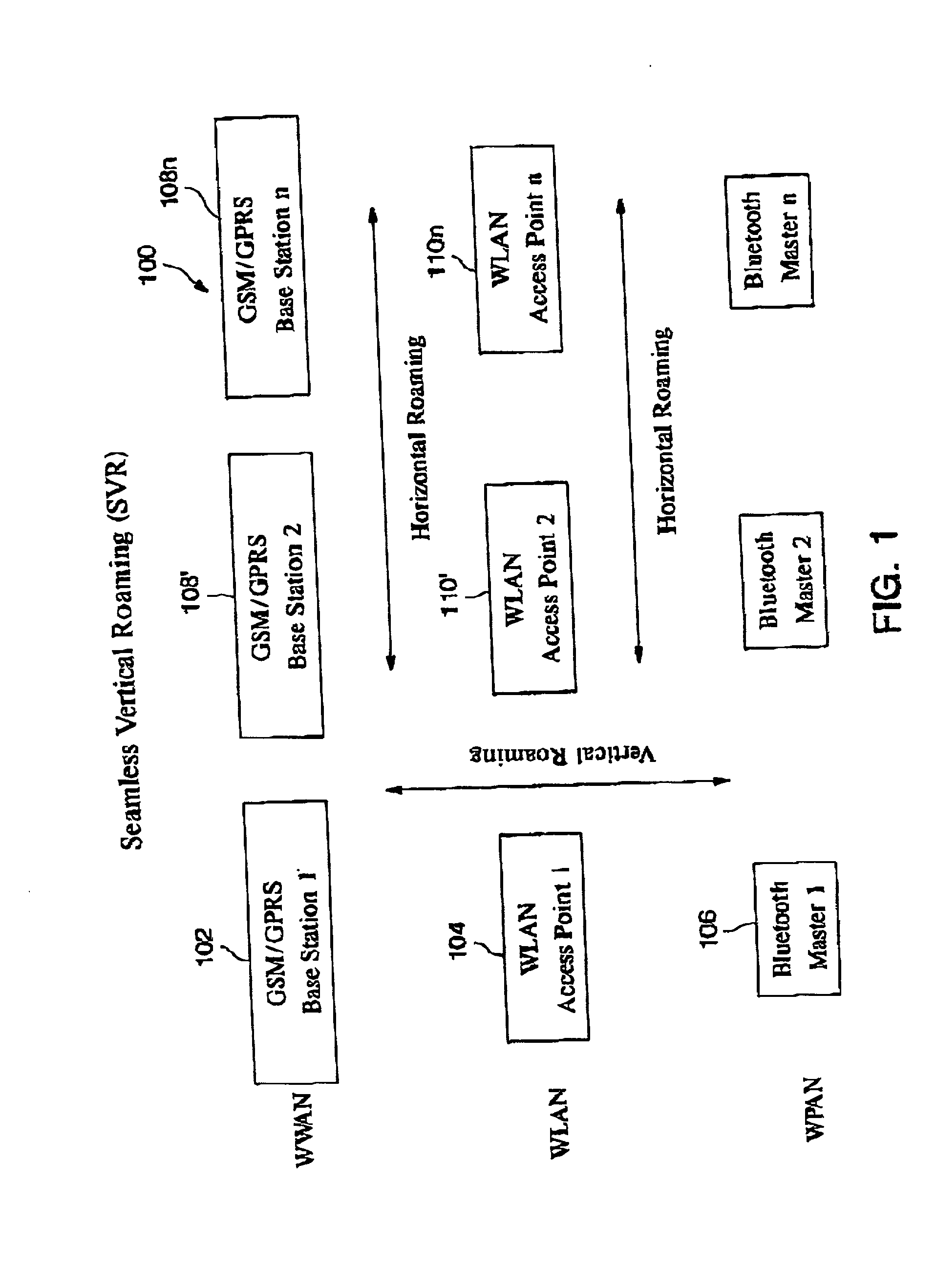
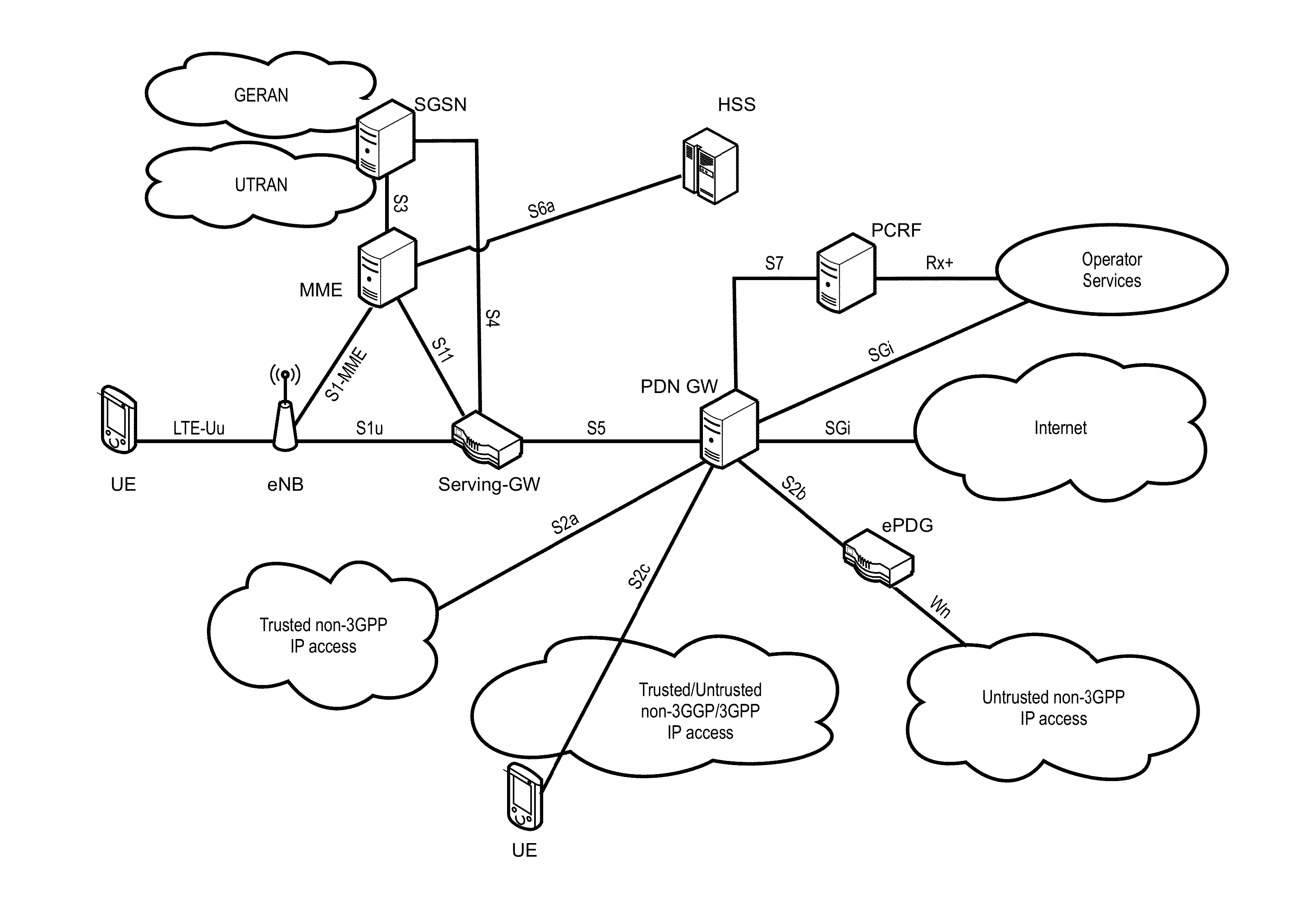
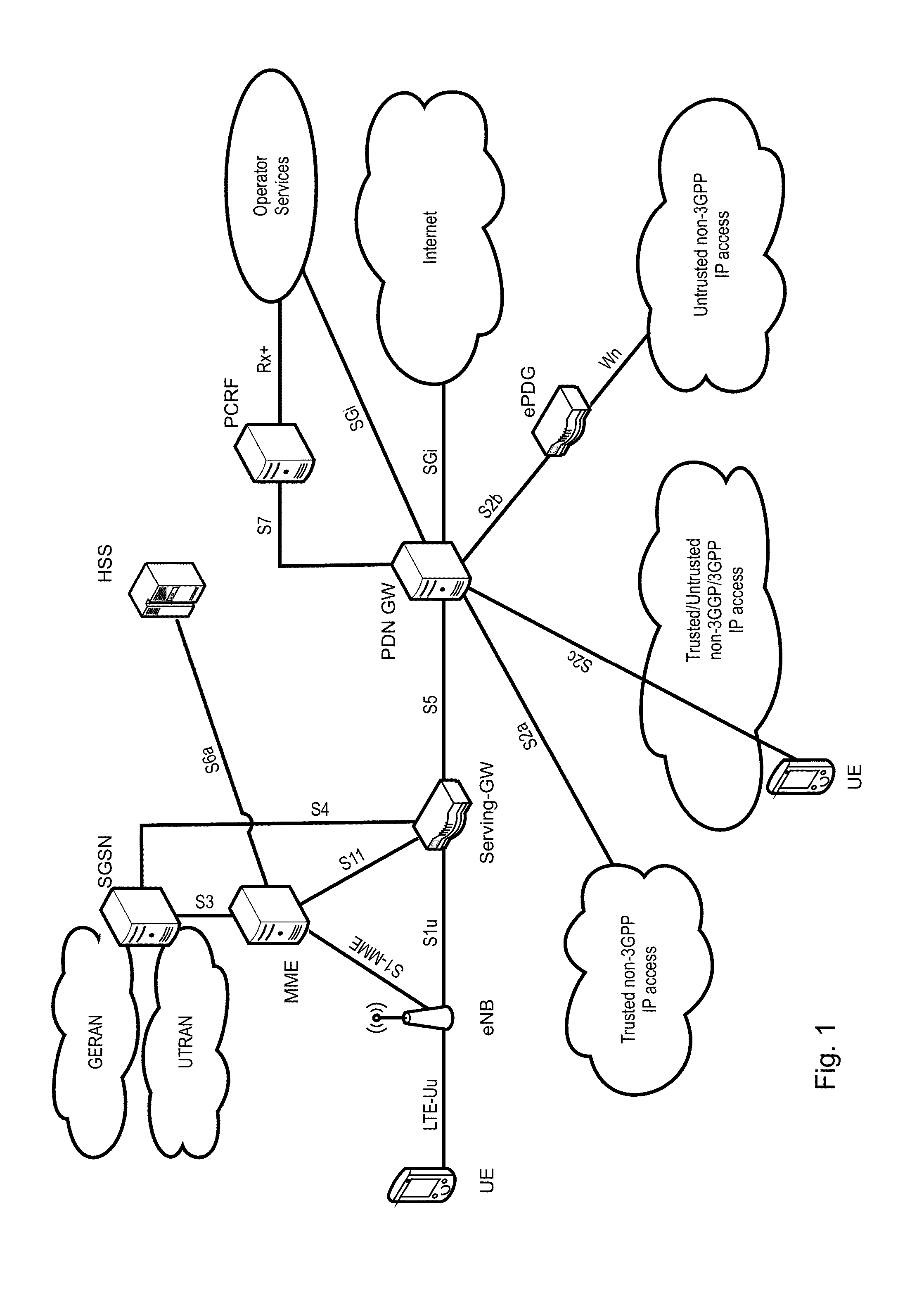
Automatic and seamless vertical roaming between wireless local area network (WLAN) and wireless wide area network (WWAN) while maintaining an active voice or streaming data connection: systems, methods and program products
ActiveUS20020085516A1Data switching by path configurationRadio/inductive link selection arrangementsData connectionUser verification
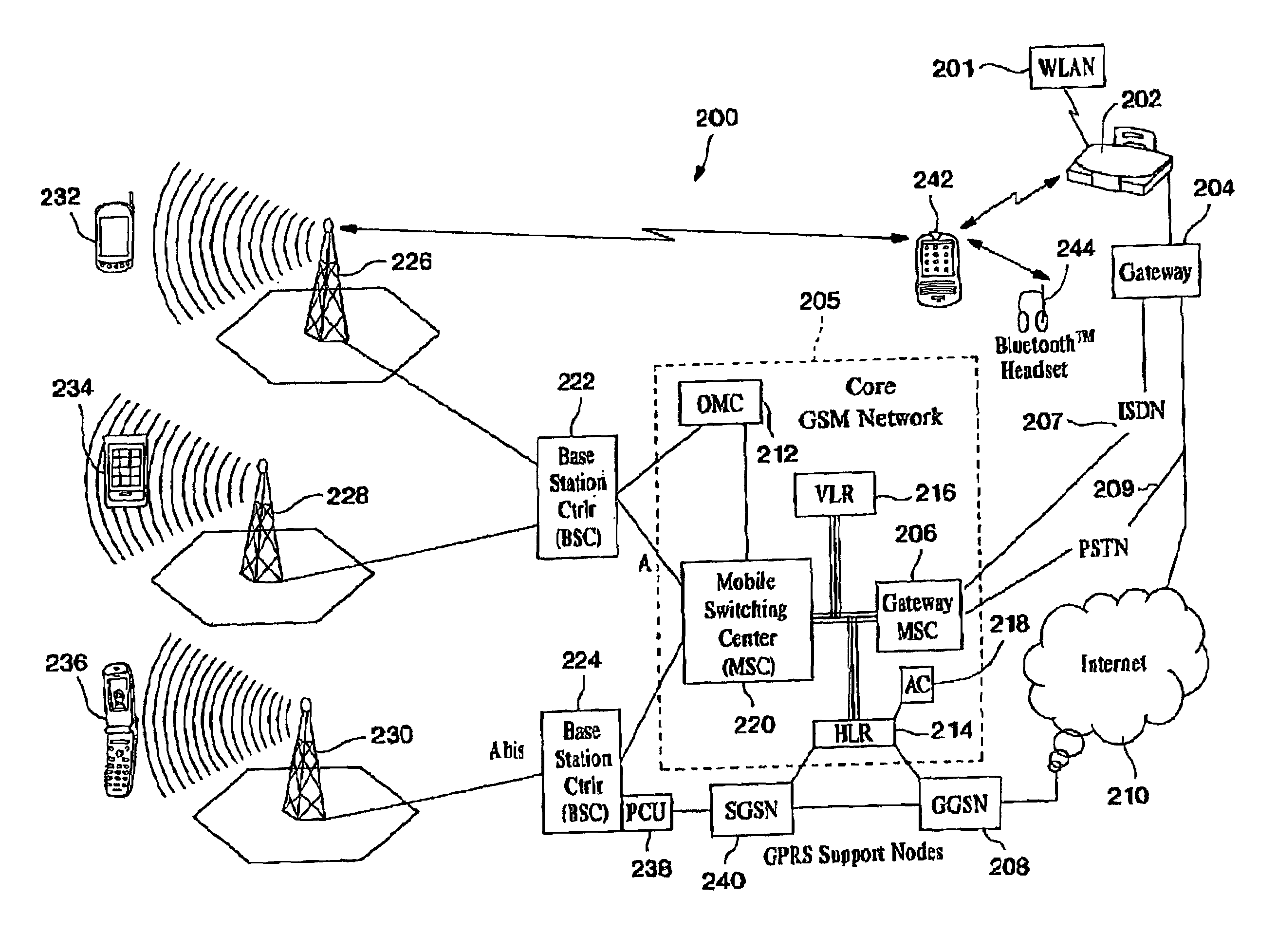
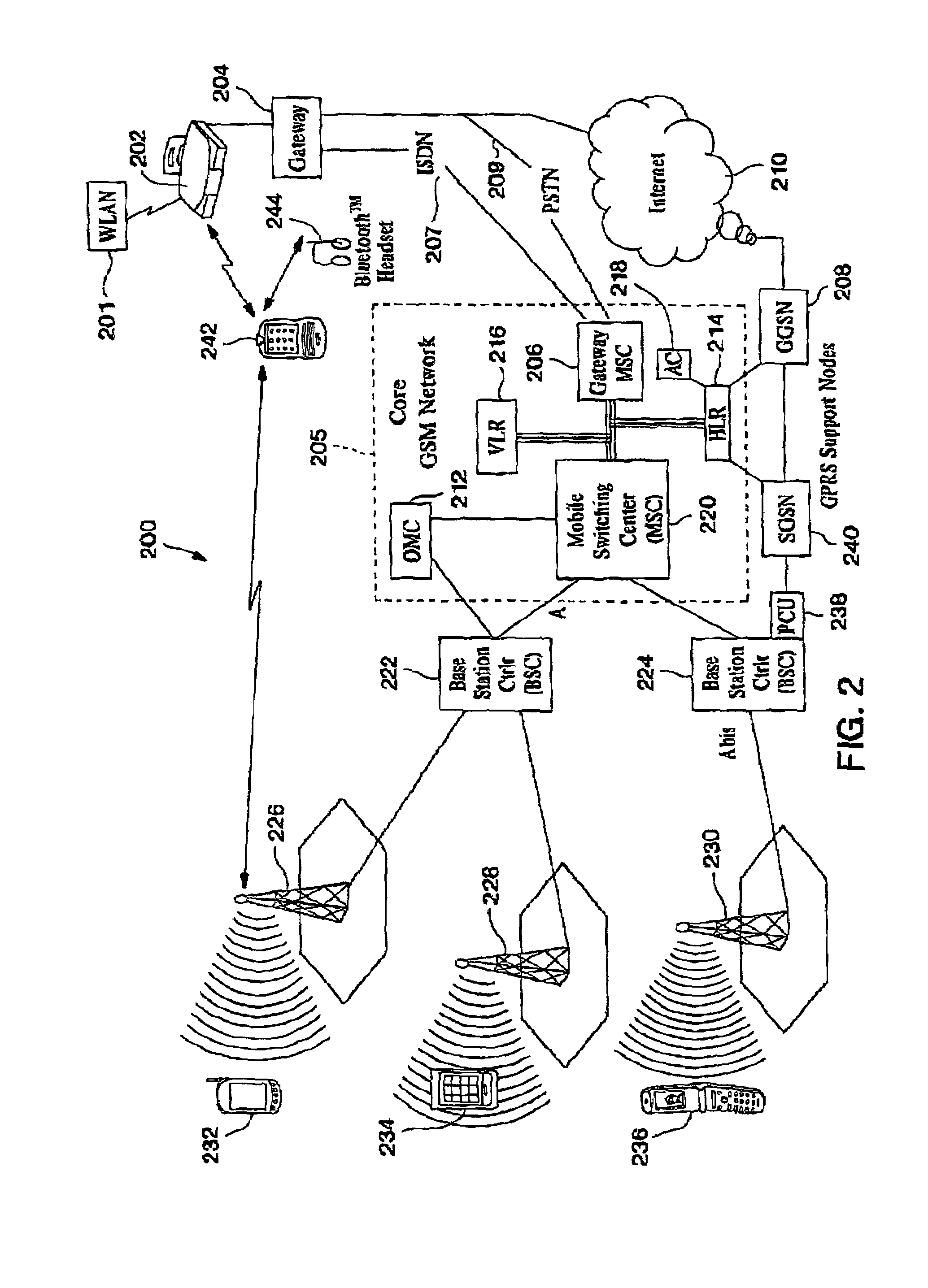
A Mobile Station (MS) is able to vertically roam in either direction between two different network, i.e. WWAN and WLAN. The MS is equipped with a dual mode Radio for WWAN and WLAN transmissions. The WLAN Radio is linked to a WLAN Enterprise Gateway Controller (EGC) via a first air link and the WWAN Radio is linked to a WWAN Base Transceiver Station (BTS) via a second air link. The EGC is connected to a Mobile Switching Center (MSC) which is in turn connected to the BTS. An outgoing VoIP call from the WLAN Radio to a remote party on the WWAN will transition or seamlessly switch over to a WWAN connection when the MS detects packet error rates, frequent scale back or consistent signal degradation. Upon such conditions, the WLAN Radio requests the EGC to request an Explicit Call Transfer via the MSC to the MS integrated WWAN Radio portion which automatically accepts the call based on referenced information stored in the user's subscriber identification module (SIM). Once the WWAN Radio is confirmed connected to the remote party on the WWAN, the WLAN Radio drops the WLAN connection. An incoming call between the MS and a remote user via the WWAN will transition to the WLAN Radio when the MS enters WLAN coverage. The MS issues an ECT to the WLAN. After user verification by the WLAN Radio and the EGC signals acceptance of the call, the WWAN Radio connection is dropped and the call is now established between the WLAN Radio and the remote party on the WWAN.
Owner:SYMBOL TECH LLC
Power receptacle wireless access point devices for networked living and work spaces
Owner:UBIQUITI INC
Systems and methods for mobile and online payment systems for purchases related to mobile and online promotions or offers provided using impressions tracking and analysis, location information, 2d and 3D mapping, mobile mapping, social media, and user behavior and information for generating mobile and internet posted promotions or offers for, and/or sales of, products and/or services in a social network, online or via a mobile device
A method, apparatus, computer readable medium, computer system, network, or system is provided for mobile and online payment systems for mobile and online promotions or offers or daily deal coupons or daily deal coupons aggregation provided using impressions tracking and analysis, location information, 2D and 3D mapping, social media, and user behavior and information for generating mobile and internet posted promotions or offers or daily deal coupons or daily deal coupons aggregation for, and / or sales of, products and / or services in a social network, online or via a mobile device-for mobile and web based promotions or offers that connect information and user behavior data to a user or related demographic location or user specified or predicted demographic location(s) for targeted promotions or offers for products and / or services in a social network, online or via a mobile device.
Owner:HEATH STEPHAN
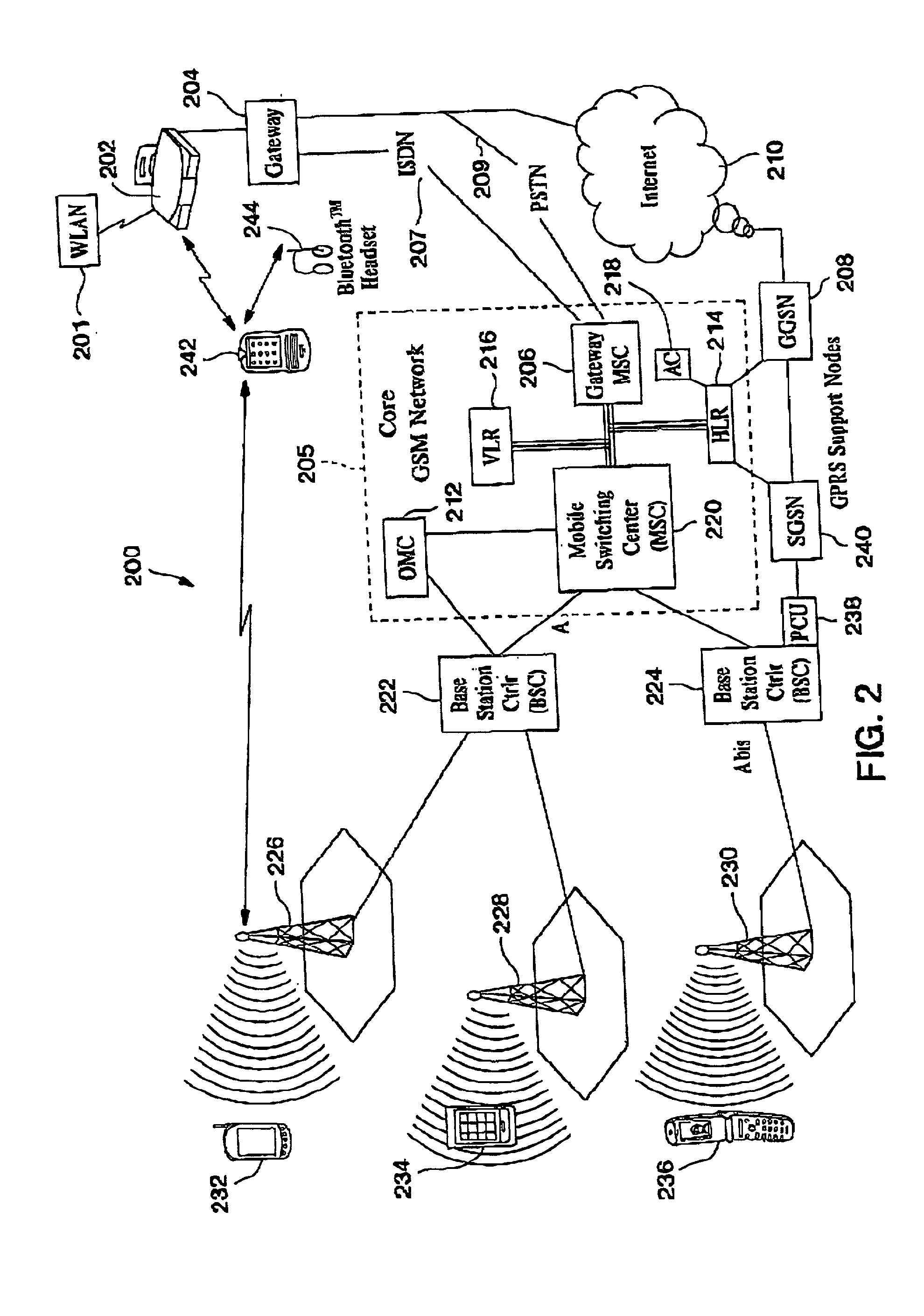
Automatic and seamless vertical roaming between wireless local area network (WLAN) and wireless wide area network (WWAN) while maintaining an active voice or streaming data connection: systems, methods and program products
ActiveUS7039027B2Data switching by path configurationRadio/inductive link selection arrangementsData connectionStreaming data
A Mobile Station (MS) is able to vertically roam in either direction between two different nerworks, i.e, WWAN and WLAN. The MS is equipped with a dual mode Radio for WWAN and WLAN transmissions. The WLAN Radio is linked to a WLAN Enterprise Gateway Controller (EGC) via a first air link and the WWAN Radio is linked to a WWAN Base Transceiver Station (BTS) via a second air link. An outgoing VoIP call from the WLAN Radio to a remote party on the WWAN will transition or seamlessly switch over to a WWAN connection when the MS detects packet error rates, frequent scale back or consistent signal degradation.
Owner:SYMBOL TECH LLC
System, method and article of manufacture for demonstrating E-commerce capabilities via a simulation on a network
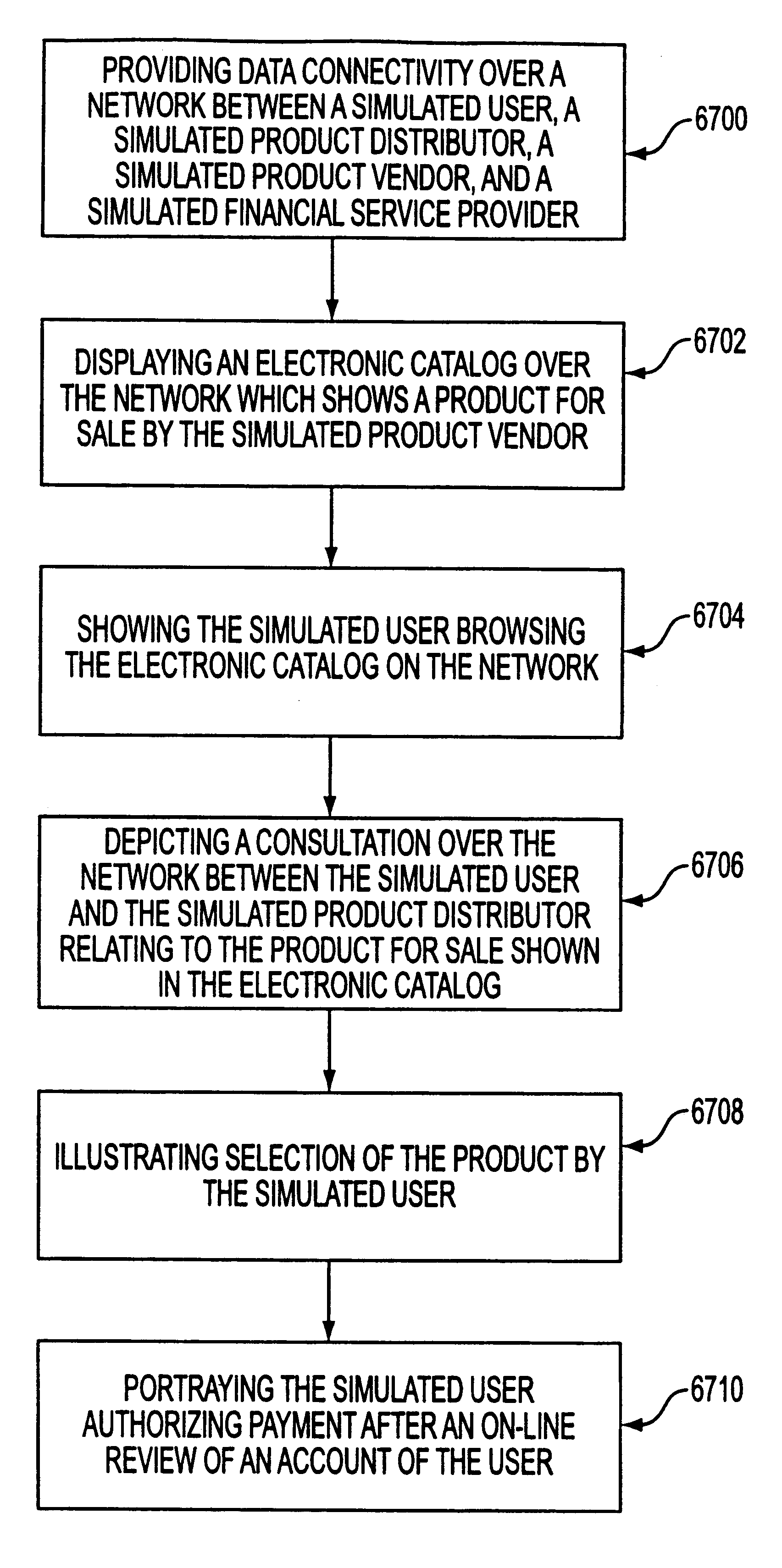
A system, method and article of manufacture are provided for demonstrating e-commerce capabilities on a network via a simulation. Data connectivity is provided over a network between a simulated user, a simulated product distributor, a simulated product vendor, and a simulated financial service provider. An electronic catalog is displayed over a network that shows a product for sale by the simulated product vendor. The simulated user is shown browsing the electronic catalog on the network. Further, a consultation over the network, relating to the product for sale shown in the electronic catalog, is depicted between the simulated user and the simulated product distributor. Selection of the product by the simulated user is illustrated. The simulated user is portrayed to authorize payment alter an on-line review of an account of the user.
Owner:ACCENTURE GLOBAL SERVICES LTD
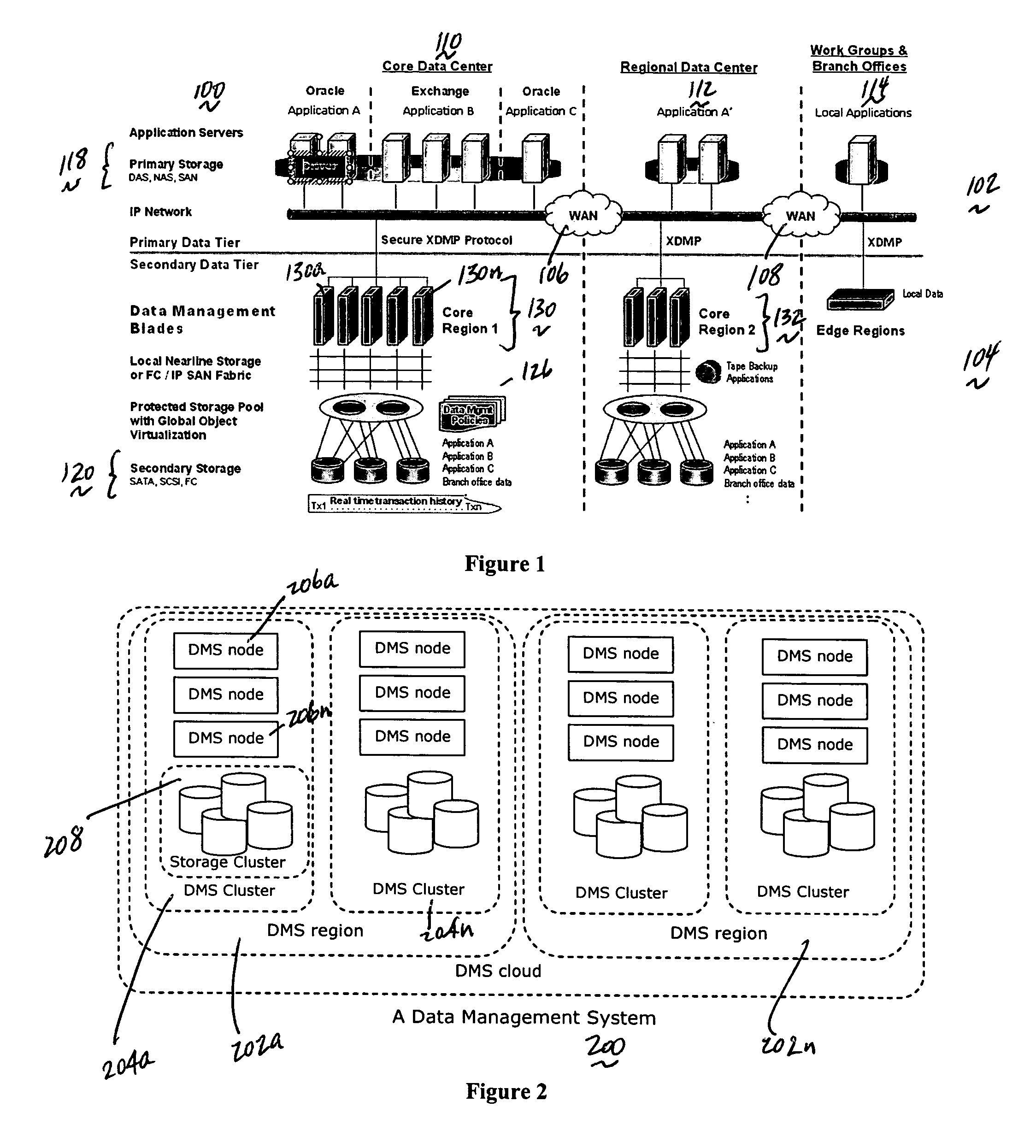
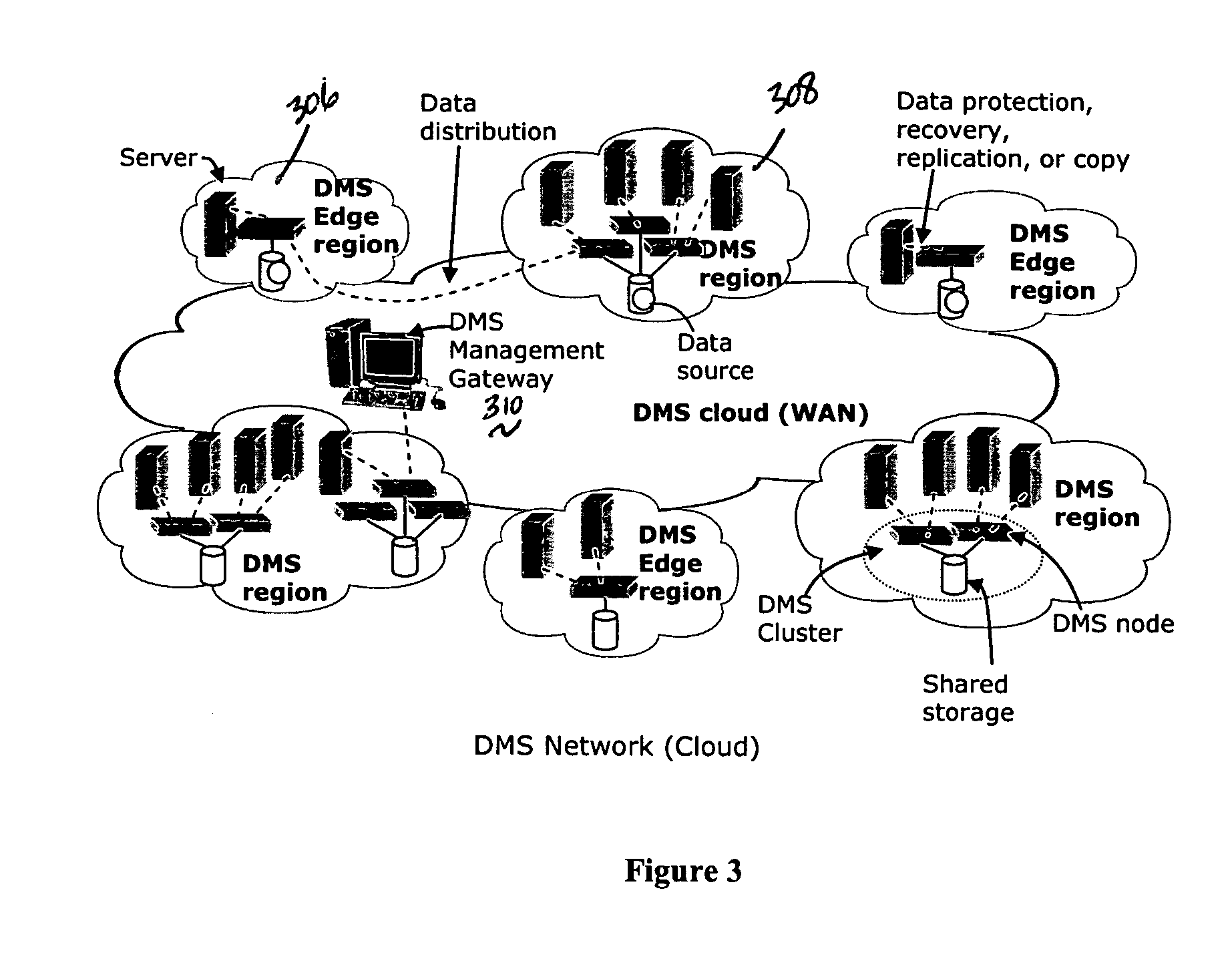
System for moving real-time data events across a plurality of devices in a network for simultaneous data protection, replication, and access services
ActiveUS20050262097A1Efficiently parallel processEfficiently route application-aware data changeDigital data information retrievalDigital data processing detailsData connectionData stream
A data management system or “DMS” provides a wide range of data services to data sources associated with a set of application host servers. The data management system typically comprises one or more regions, with each region having one or more clusters. A given cluster has one or more nodes that share storage. To facilitate the data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver provides a method and apparatus for capturing real-time data transactions in the form of an event journal that is provided to the data management system. The driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. Using the streams generated in this manner, the DMS offers a wide range of data services that include, by way of example only: data protection (and recovery), disaster recovery (data distribution and data replication), data copy, and data query and access.
Owner:QUEST SOFTWARE INC
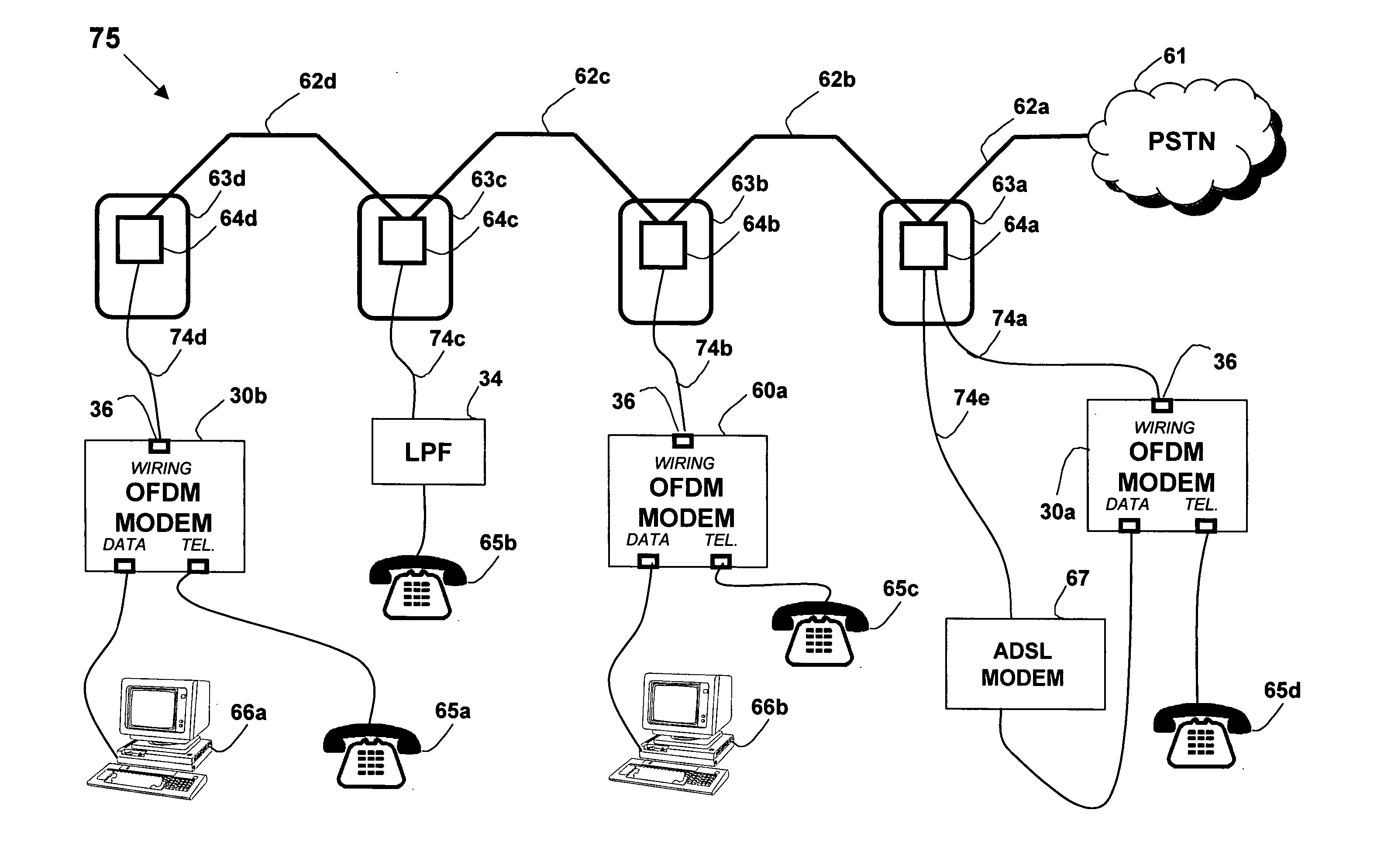
System and method for carrying a wireless based signal over wiring
InactiveUS20050249245A1Power distribution line transmissionFrequency-division multiplexData connectionModem device
A device, network and method wherein a standard wireless modem is coupled to wiring for carrying a wireless baseband signal that may be OFDM based, and may be directly generated by the wireless IF modem, or extracted from the modem RF signal. The wiring may be a building utility wiring, such as telephone, AC power or CATV wiring. The baseband signal is carried simultaneously with the utility service signal over the utility wiring using Frequency Division Multiplexing. The device may be enclosed with a data unit, a standalone dedicated enclosure, within an outlet or as a plug-in outlet adapter. Data units may couple the device by a wiring port such as standard data connector, or via wireless connection. The device may be locally powered or via a power signal carried over the wiring. This abstract is not intended to limit or construe the scope of the claims.
Owner:CORNING OPTICAL COMM WIRELESS
Tablet computing device with three-dimensional docking support
InactiveUS6856506B2Improved expansion baseImproved docking stationInput/output for user-computer interactionCoupling device connectionsTablet computerData connection
The present invention provides a tablet computer and a docking station assembly. This docking station comprises a docking assembly for positioning with three degrees of freedom and having a data connector for mechanically supporting and interfacing with the tablet computer. A support member couples the docking assembly to an expansion base. The base includes a number of ports for interfacing with a variety of peripheral devices or power supplies. These varieties of ports mount to a printed circuit board contained within the expansion base. A flexible printed circuit (FPC) combines the signal pathways for the variety of ports, allowing the signal pathways to travel from the printed circuit board and to the data connector. The tablet computing device has a plurality of contact or touch points positioned on the right and left edges of the tablet to facilitate aligning the tablet to the docking assembly in either a landscape or portrait mode.
Owner:ZEBRA TECH CORP
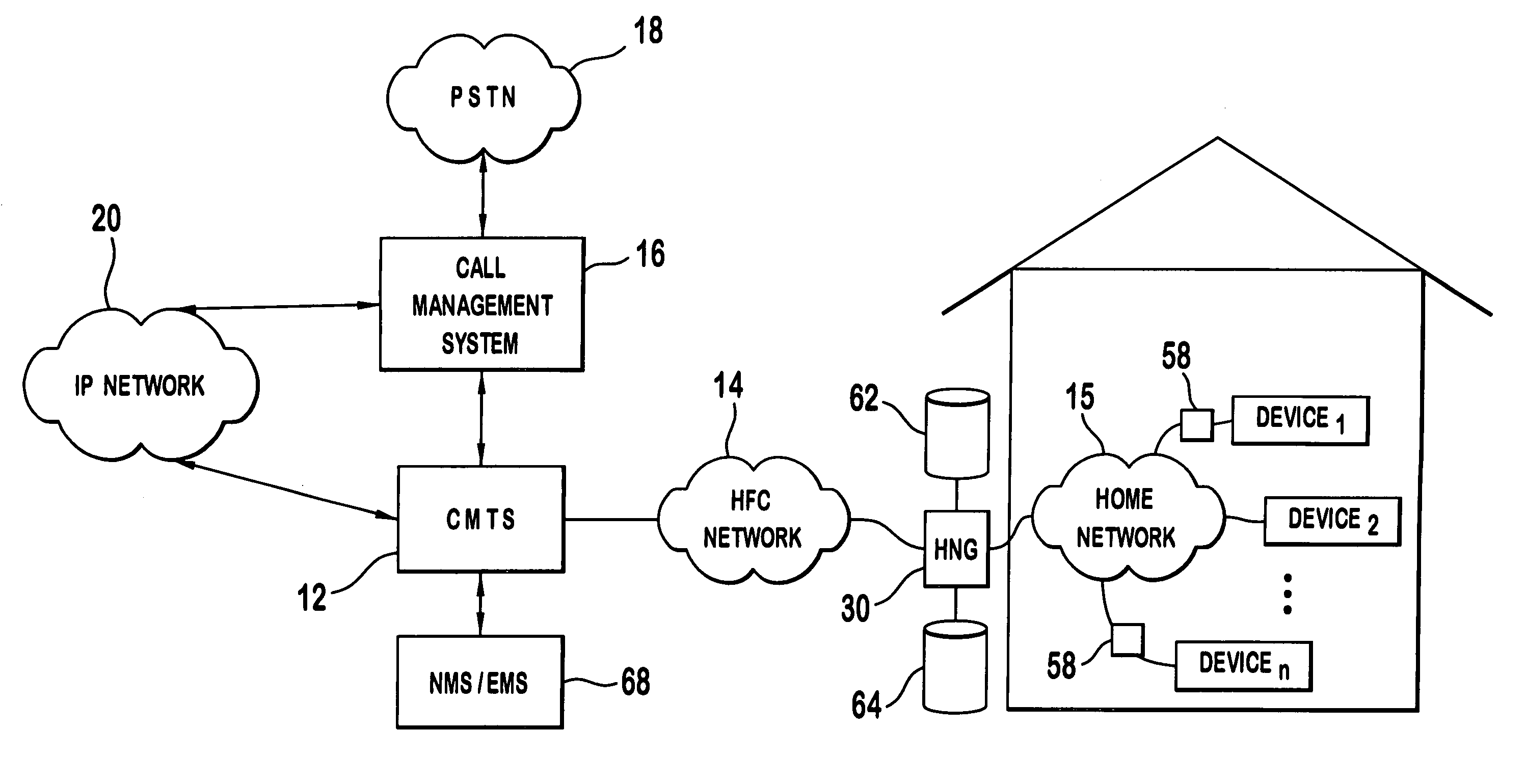
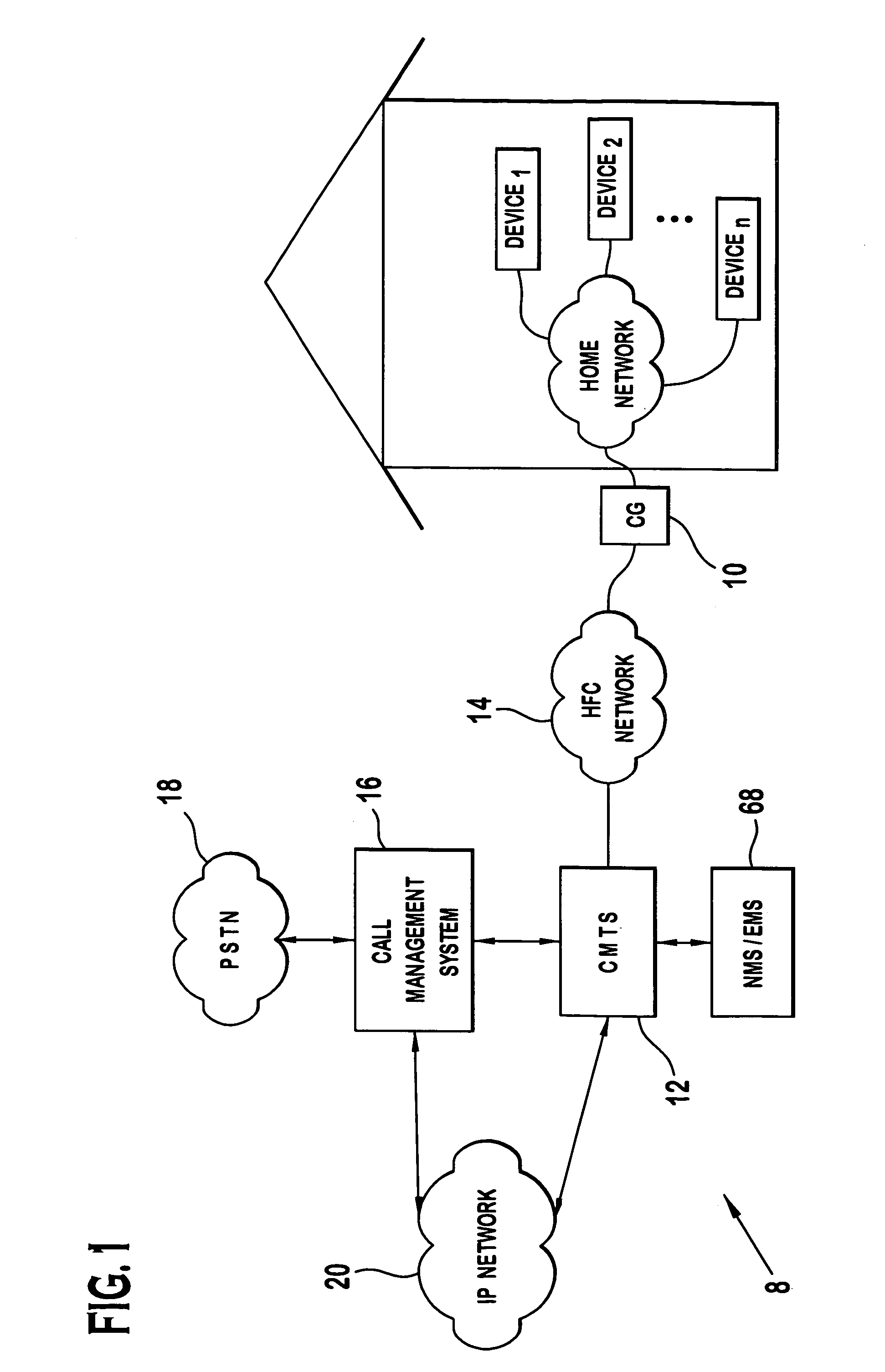
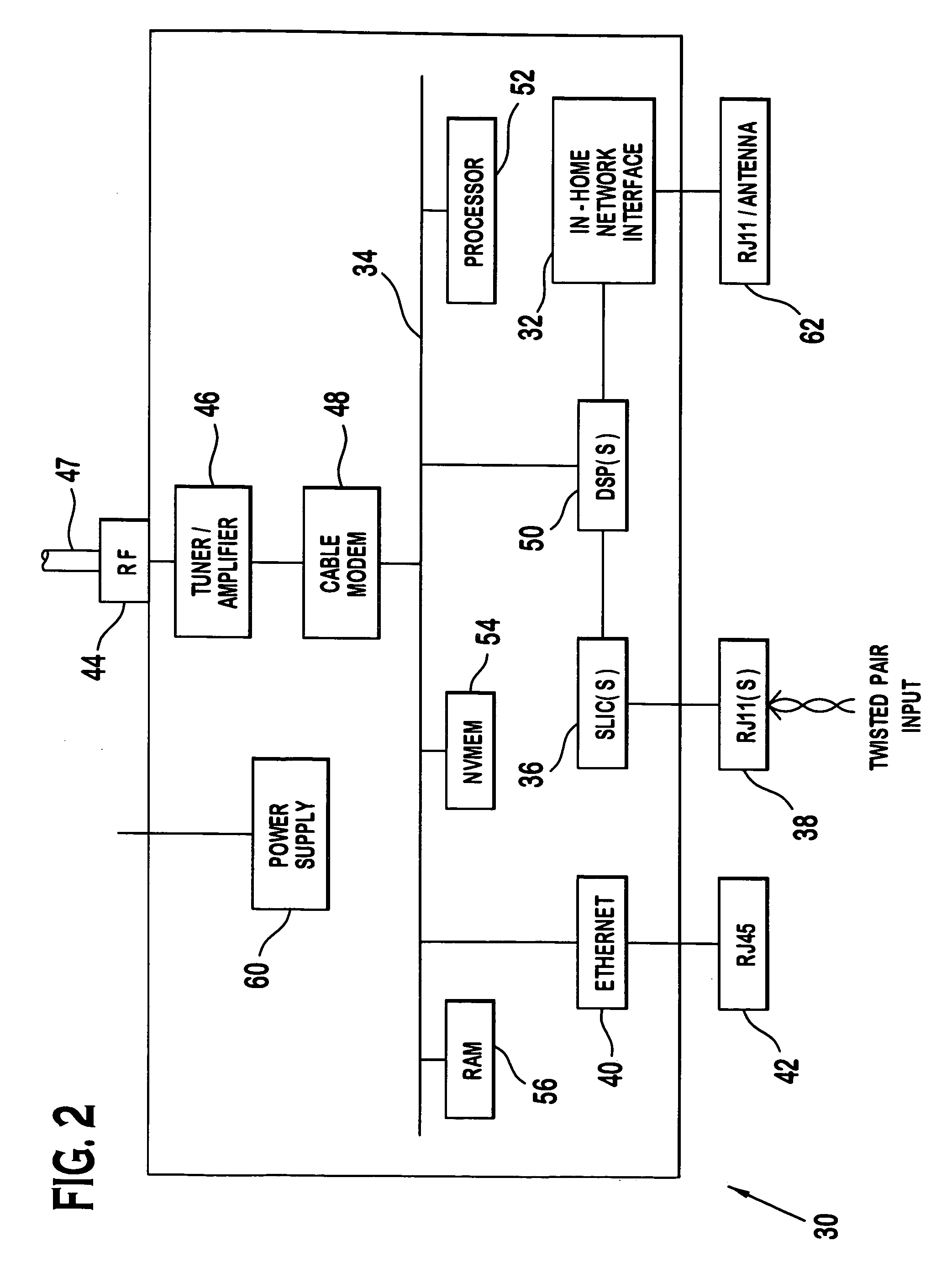
Home networking gateway
InactiveUS7035270B2Information formatOptical transmission adaptationsData connectionNetwork Communication Protocols
A home networking gateway provides an interface between an HFC network and an in-home network. Full voice and data connection between the HFC network and each device in the in-home network is provided through the interface. A translator included in the home networking gateway is utilized to provide a mapping between the communication protocols used in the in-home network and the protocols used in the HFC network, eliminating the need for the in-home network to be dependent upon the HFC-specific protocols.
Owner:GOOGLE TECH HLDG LLC
Multichip Packages
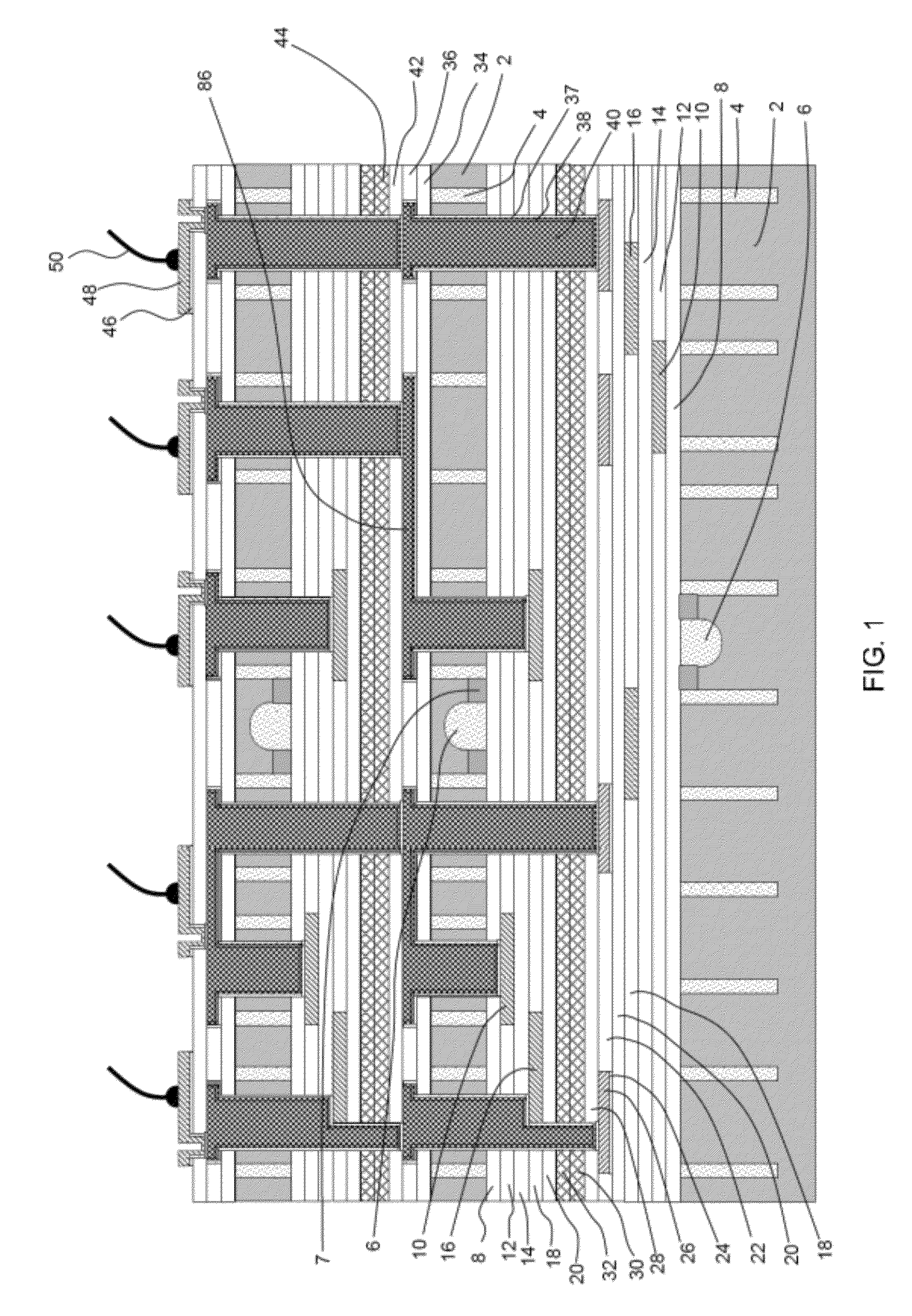
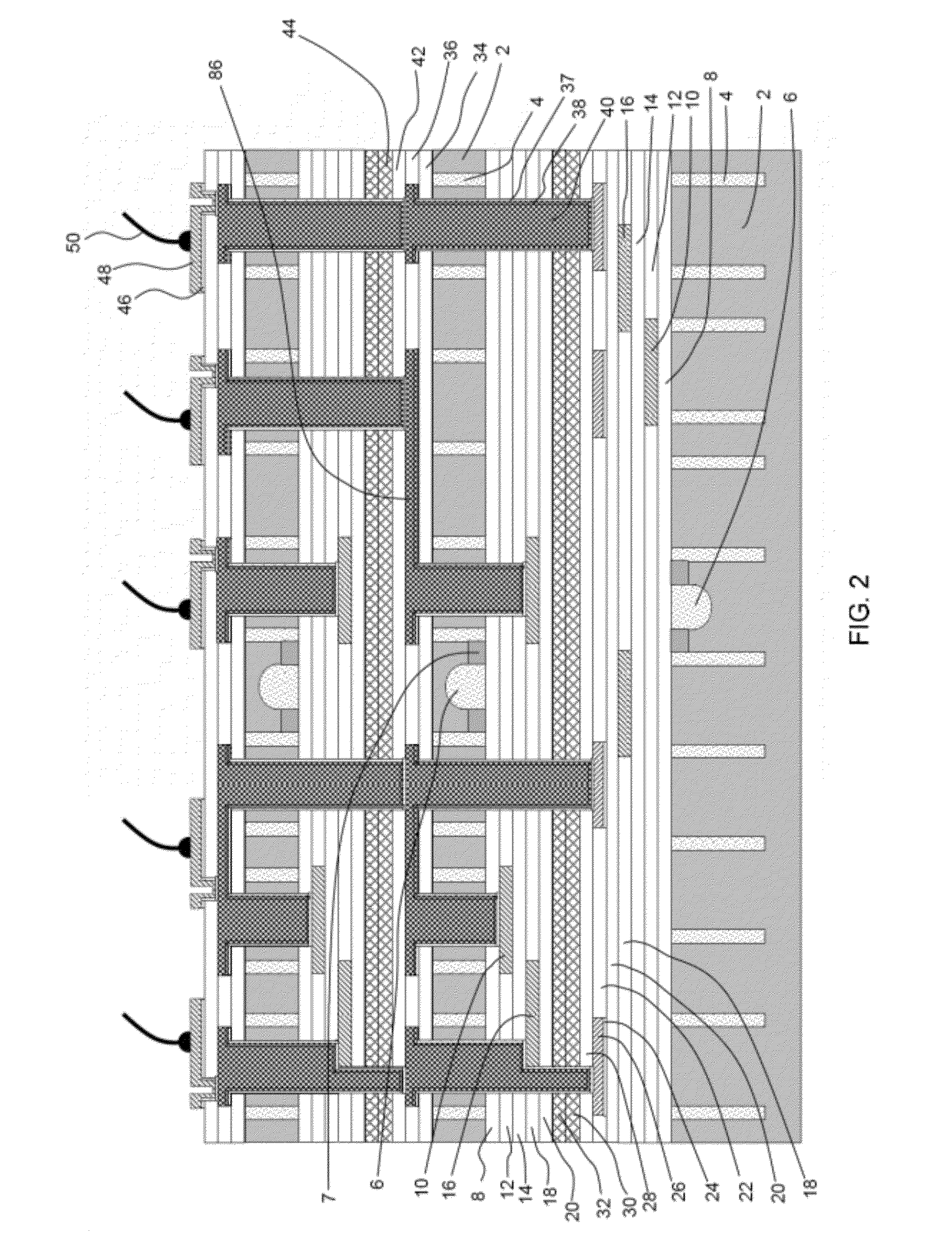
InactiveUS20120193785A1Semiconductor/solid-state device detailsSolid-state devicesData connectionEngineering
Multichip packages or multichip modules may include stacked chips and through silicon / substrate vias (TSVs) formed using enclosure-first technology. Enclosure-first technology may include forming an isolation enclosure associated with a TSV early in the fabrication process, without actually forming the associated TSV. The TSV associated with the isolation enclosure is formed later in the fabrication process. The enclosure-first technology allows the isolation enclosures to be used as alignment marks for stacking additional chips. The stacked chips can be connected to each other or to an external circuit such that data input is provided through the bottom-most (or topmost) chip, data is output from the bottom-most (or topmost) chip. The multichip package may provide a serial data connection, and a parallel connection, to each of the stacked chips.
Owner:MEGIT ACQUISITION
Short message transmission and handover procedures
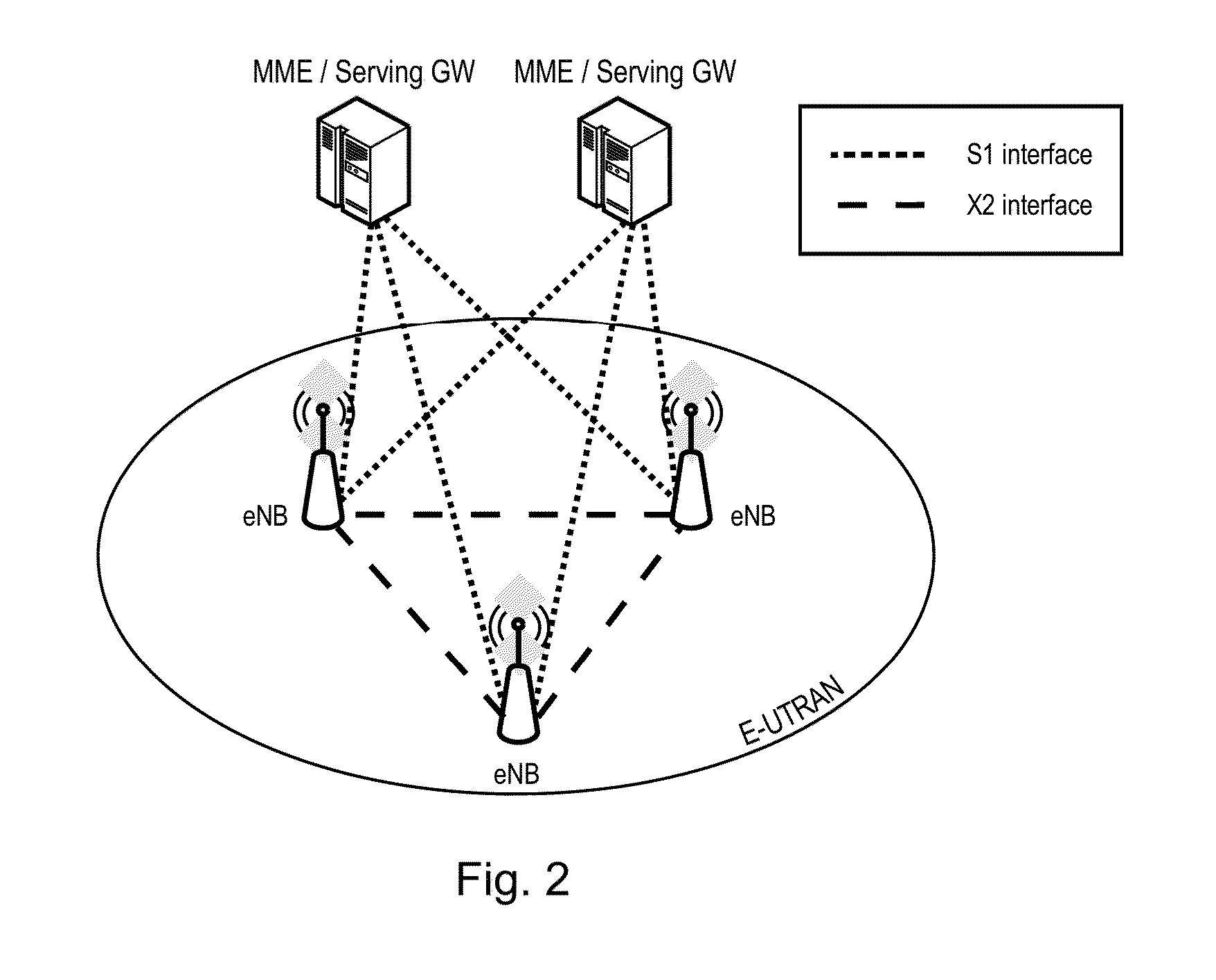
ActiveUS20140016614A1Improvement in handover procedureService provisioningConnection managementData connectionHandover procedure
The present invention relates to an improved method for handover of a mobile node from E-UTRAN to UTRAN in a scenario where SMS is the only service of the mobile node. The improved handover method allows saving radio resources by establishing the signalling connection for SMS exchange in the target network, and avoiding the data connection in the target network, since it is not used. The MME takes the decision to establish or not the data connection in the target UTRAN, and accordingly instructs the SGSN and UE to set the corresponding PDP contexts for the data connection to a “preserved” state, so as to avoid the establishment of same. Embodiments further relate to improved SMS delivery for IDLE mode UEs that activate ISR so as to avoid the involvement of the MSC server. Instead, packet-switched domain nodes are to be involved only.
Owner:SUN PATENT TRUST
Pointing interface for person-to-person information exchange
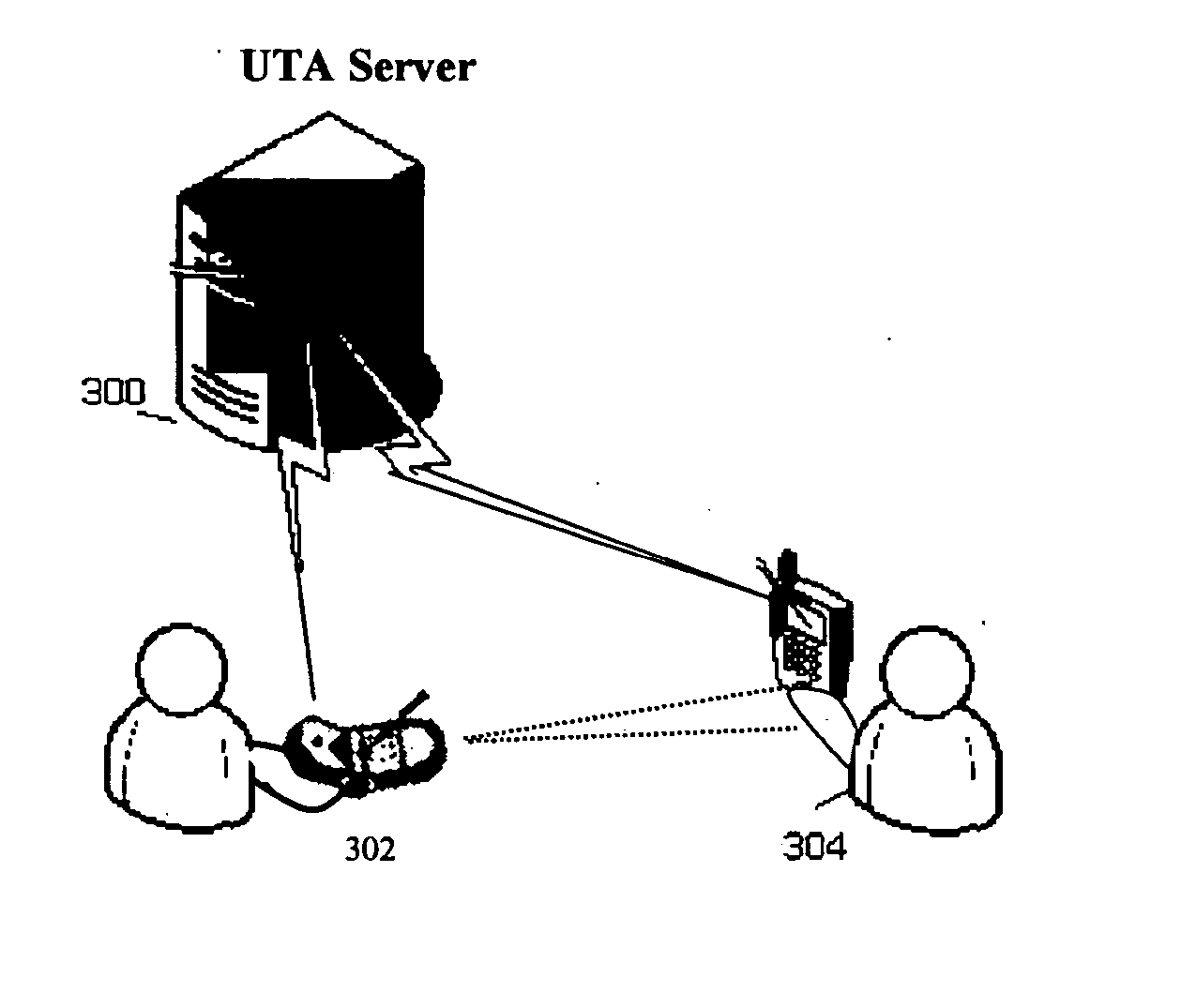
A system for enabling a person to person communication from one portable computing device to one or more other portable computing devices based upon physically pointing a portion of one portable computing device in the direction of other portable computing devices. The portable computing devices consist of a CPU, a locative sensor system, an orientation system, and an interface to a distributed network. The distributed network sends and receives data to the portable computing devices. Connected to the distributed network is a User Tracking Application (“UTA”). The User Tracking Application receives location and orientation information from each of the portable computing devices. Based on the location and orientation of the portable computing devices and via control of the users, messages and data may be sent between the devices. The User Tracking Application also allows filtering of groups of users based on particular attributes, such as, age, gender, profession, organizational affiliation, income, etc. The system also allows for the electronic retrieval of crowd demographics. A person with a portable computing device is able to point to a crowd of individuals and information about those individuals with portable computing devices may be retrieved and compiled.
Owner:OUTLAND RES
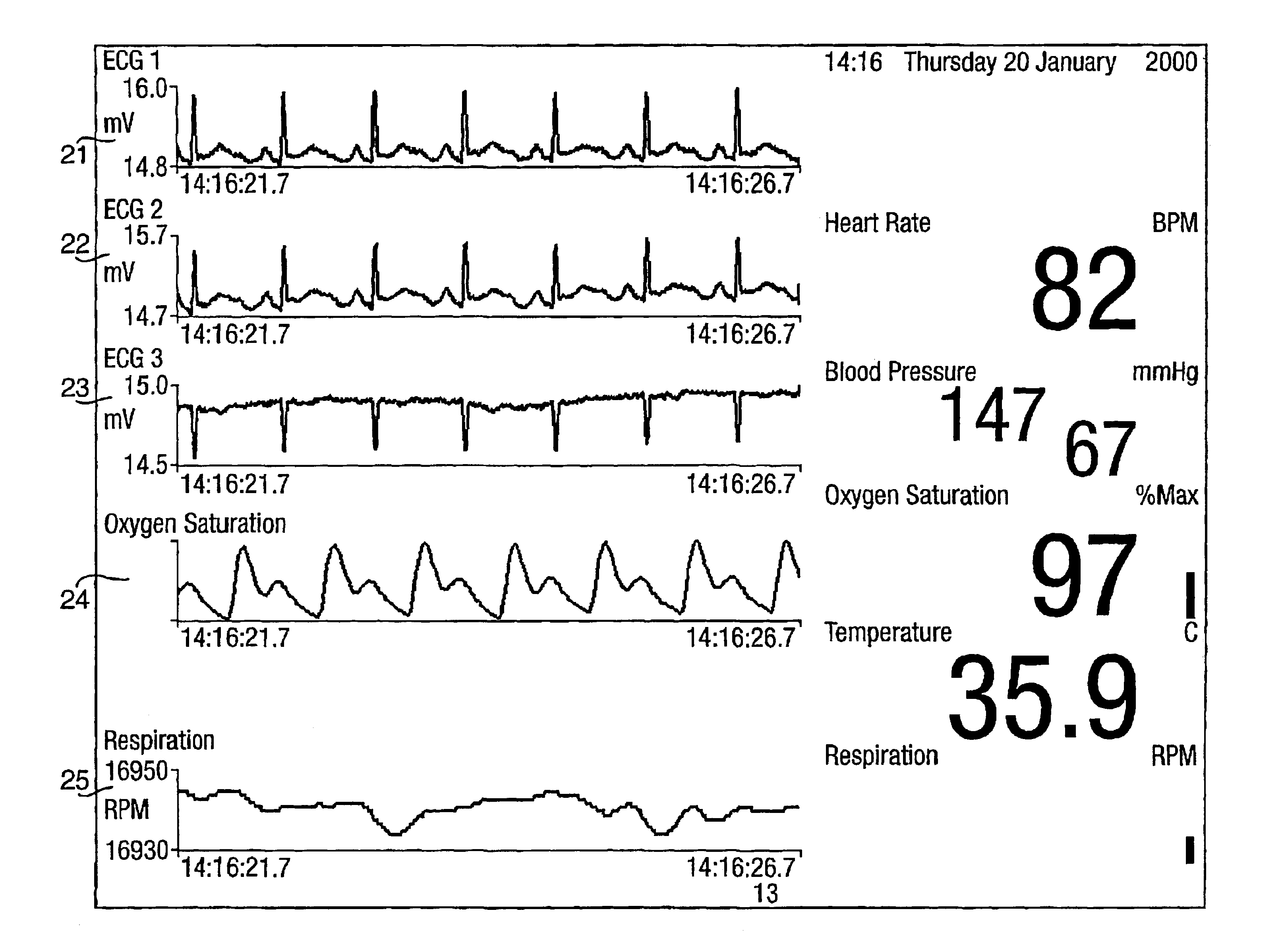
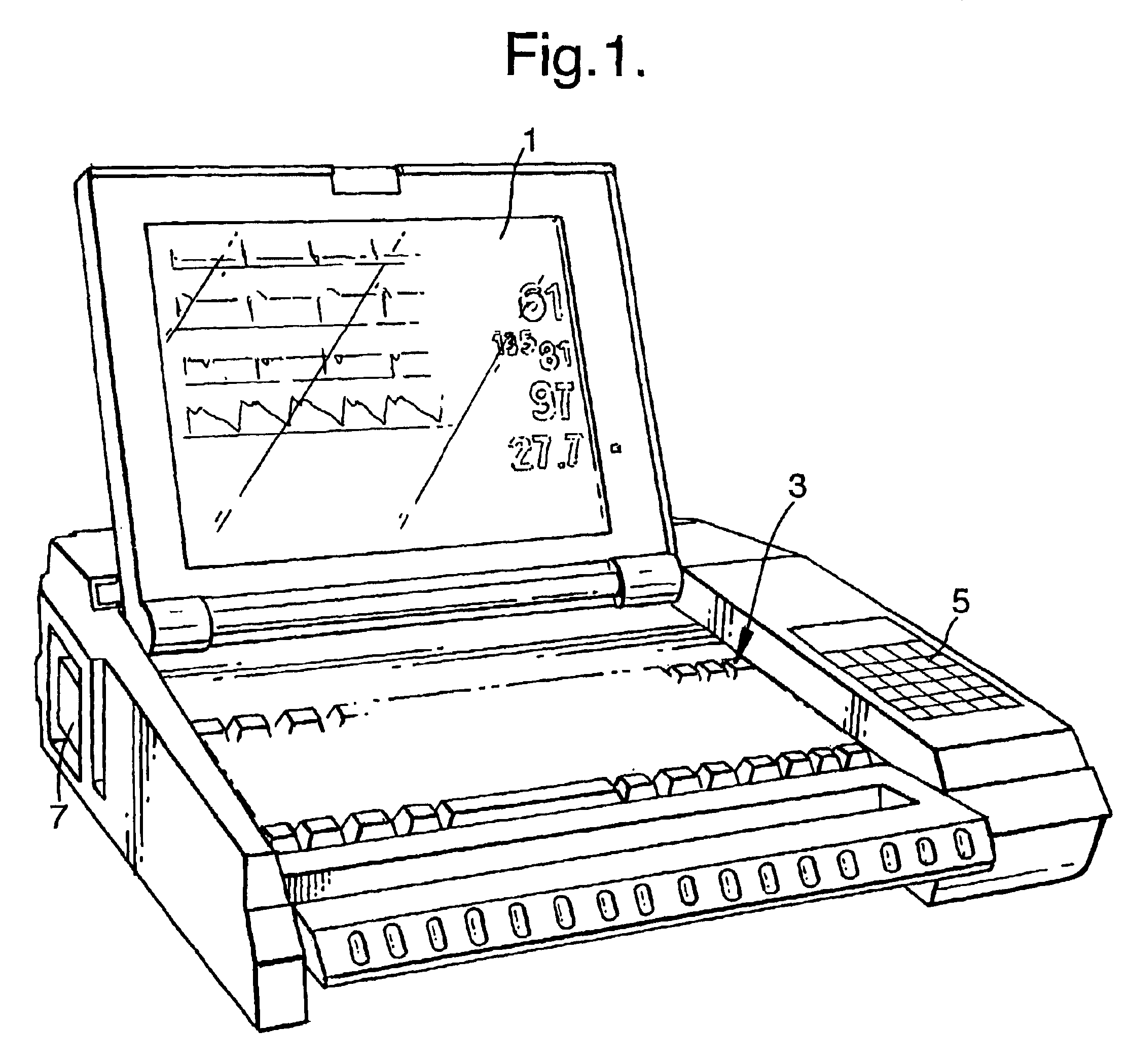
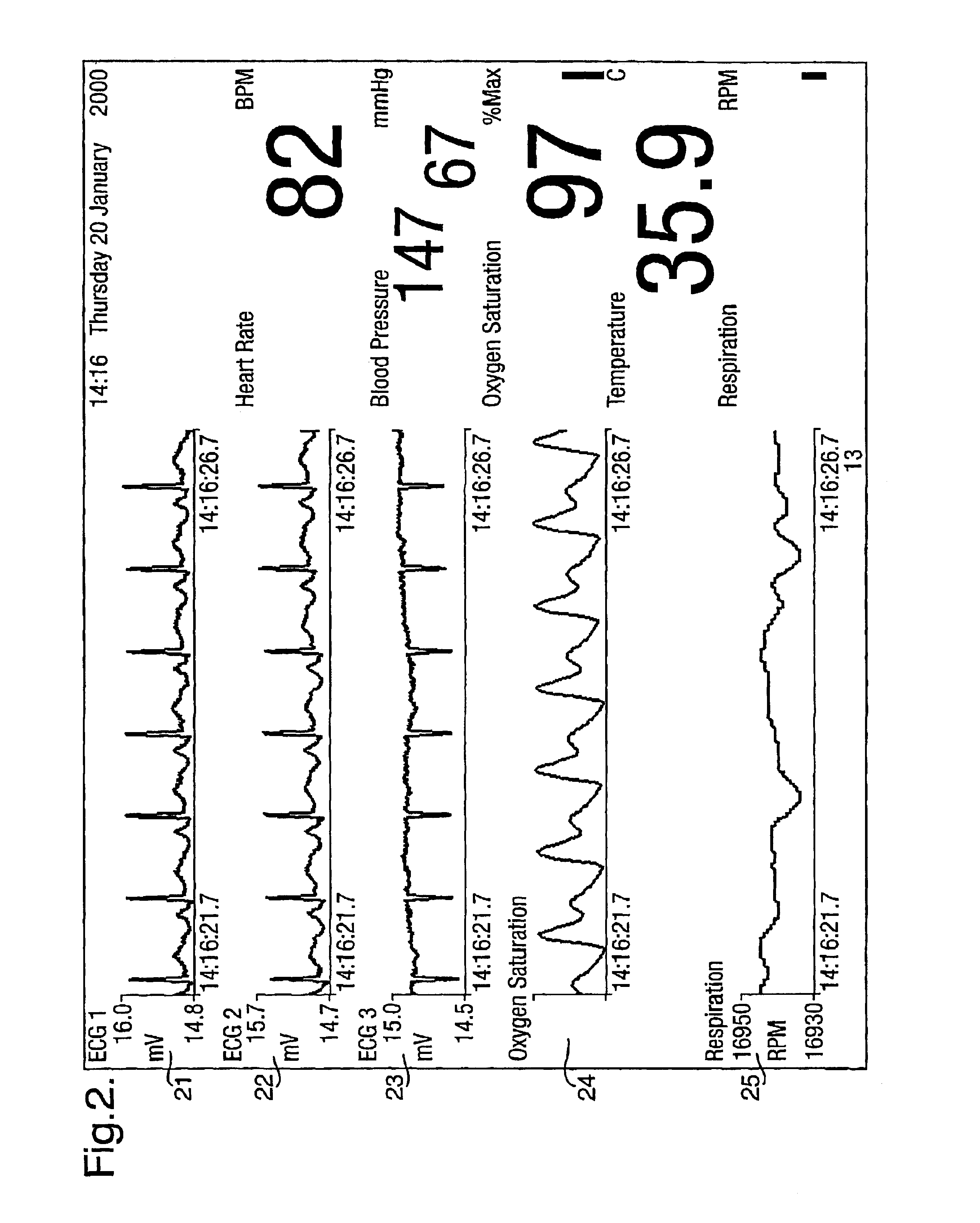
System and method for acquiring data
InactiveUS6839659B2Easy to carryImprove clarityAngiographyData acquisition and loggingData connectionHigh rate
A system for acquiring, and displaying, data such as physiological data, from a plurality of data connection devices, each of which monitor one or more different parameters and output data at different sampling frequencies based on their own system clocks. The system receives the data signals at different sampling frequencies and associates each sample of each signal with a time stamp derived from a single master clock. Low rate and high rate data are treated differently. Low rate data is associated with the current value of the master clock, where as high rate data is time stamped by giving the first sample a time stamp equal to the current value of the current master clock, subsequent samples being given an estimated time stamp based on the expected interval between samples derived from the sampling frequency of the data collection device, and the timescale given to the first example. The estimated time stamp may be periodically corrected, and the estimation calculation can be improved by correcting the value used for the interval between samples. The different signals can be displayed together on a display aligned with respect to a time axis. The system can display, the data in two different timescales, one showing a few seconds of data and one showing a few hours of data. The data traces are scrolled across the time axis, new data being added to one end of the trace.
Owner:ISIS INNOVATION LTD
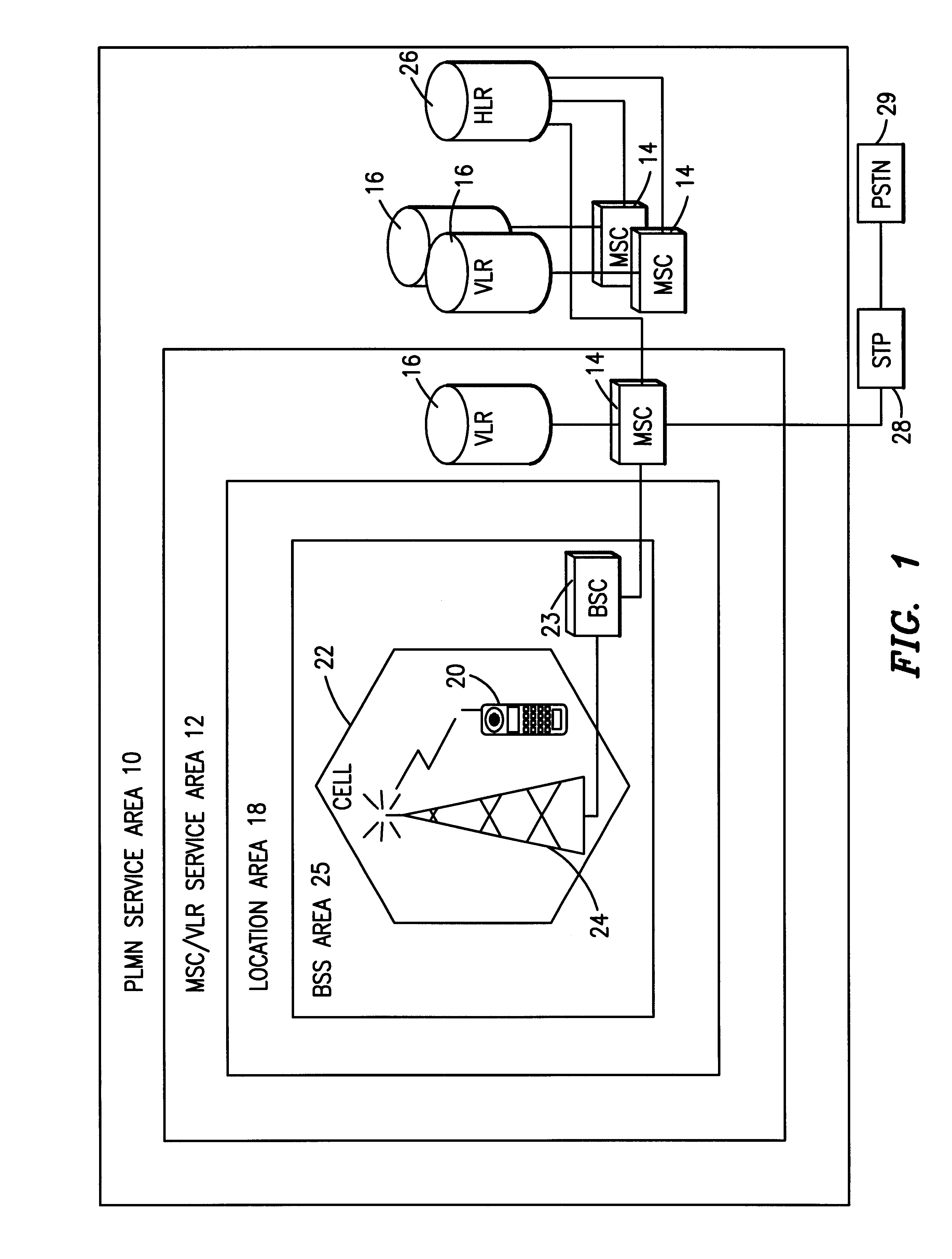
Application access control in a mobile environment
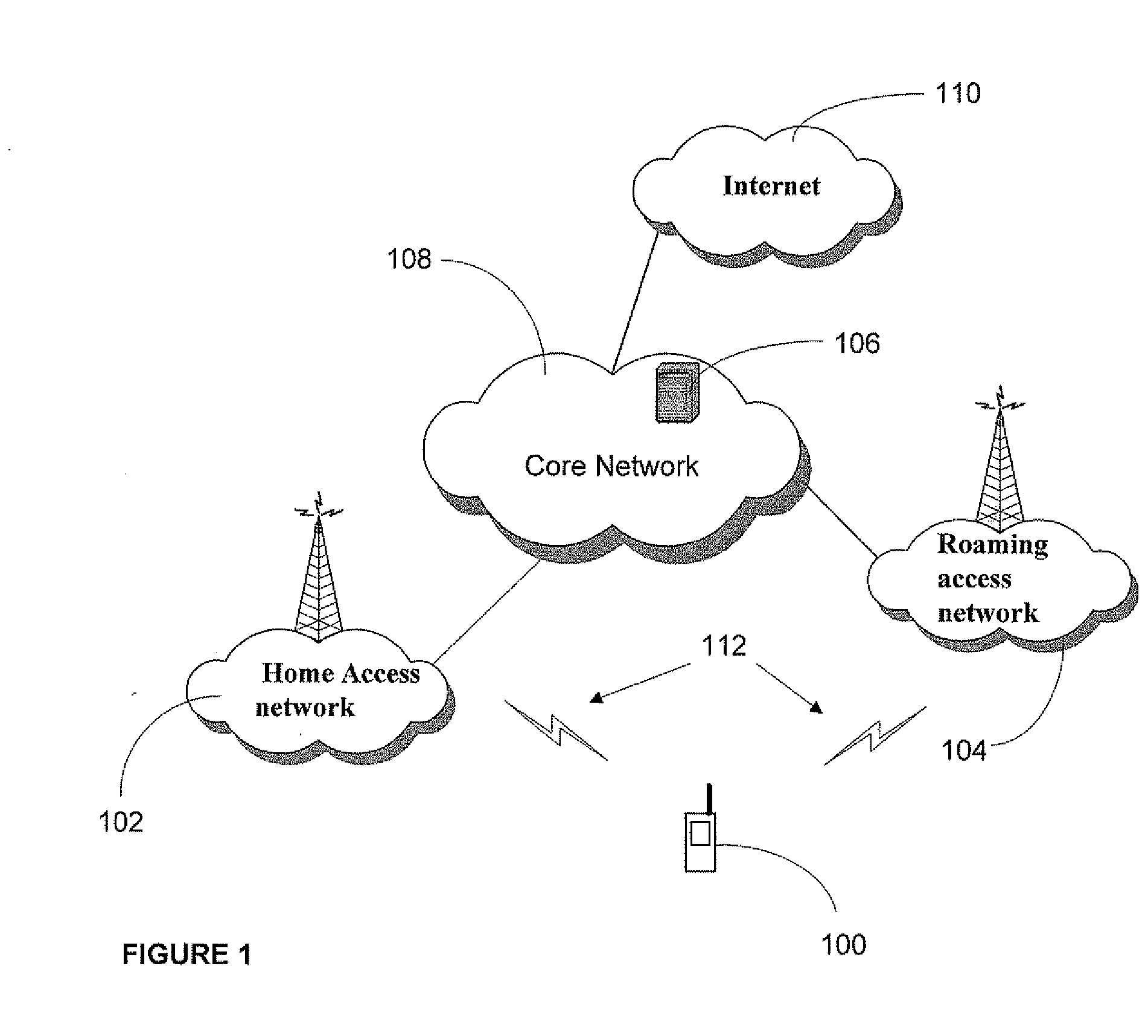
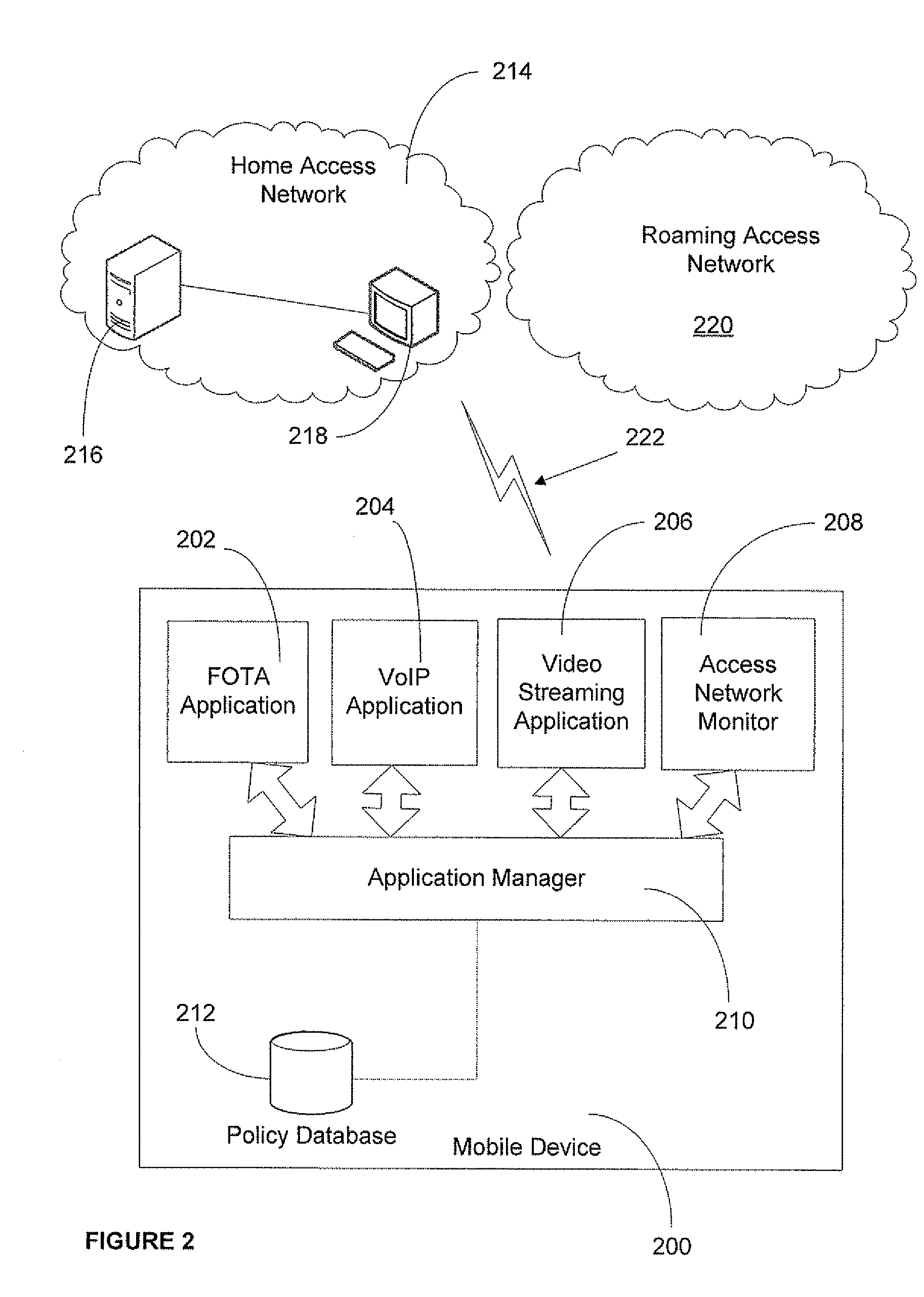
ActiveUS20080160958A1Avoid unwanted roaming chargeAvoid runningUnauthorised/fraudulent call preventionEavesdropping prevention circuitsData connectionAccess network
A system and method are described whereby a mobile device controls access to mobile applications based on access conditions associated with a current access network. To prevent mobile applications from running when the access conditions are not suitable, the mobile device includes a policy database used to store a list of access conditions that are inappropriate for launching the installed applications. The access conditions are based on the type of the current access network used by the mobile device for launching or maintaining the requested application session. The access conditions indicate whether the mobile device is currently accessing its home network or roaming on another provider's network. Similarly, the access conditions indicate the type of network access interface used by the current network to provide the data connection necessary to run the requested application. The policy database correlates predetermined actions with the access conditions associated with a given application session.
Owner:U S CELLULAR
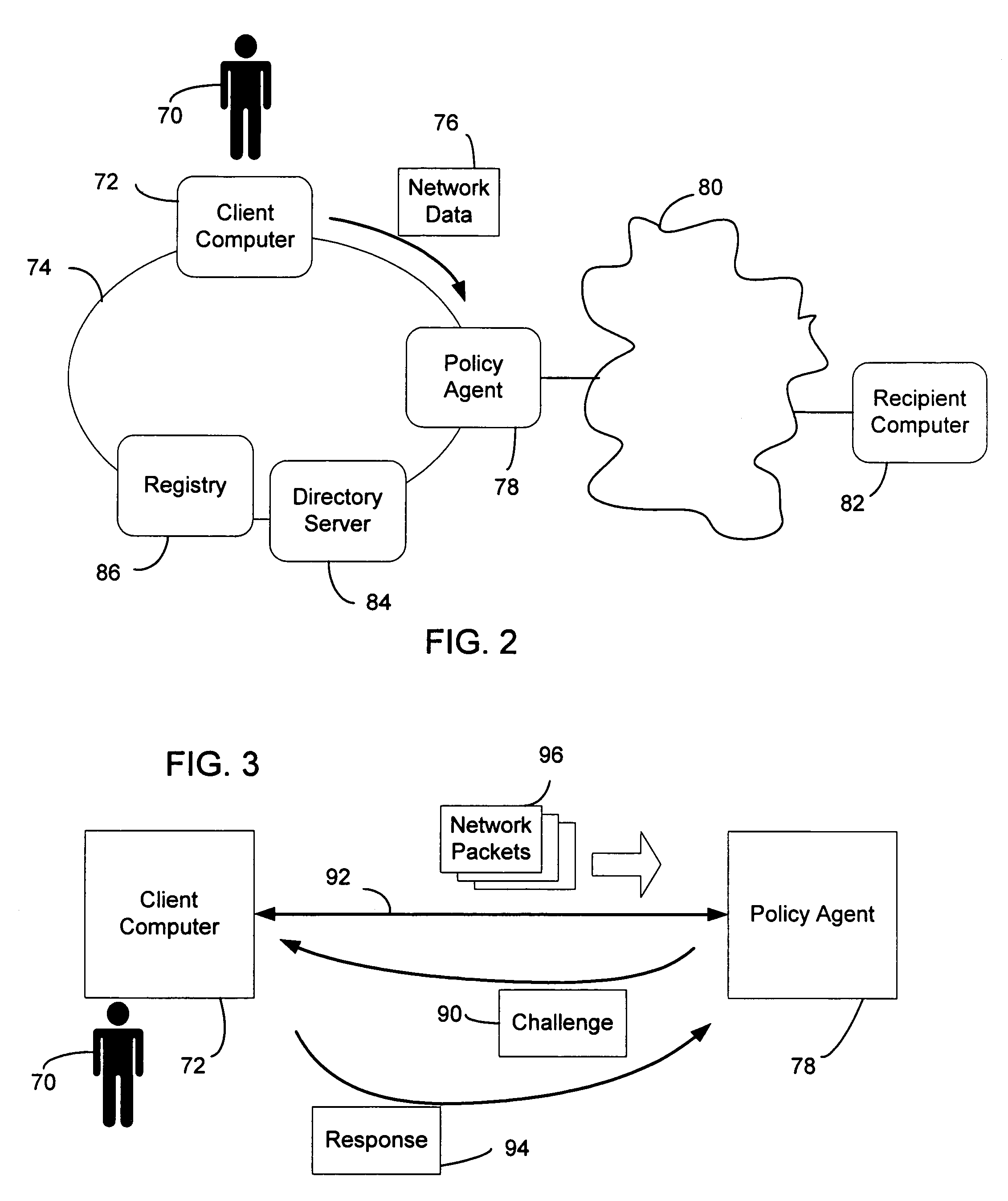
System and method of user authentication for network communication through a policy agent
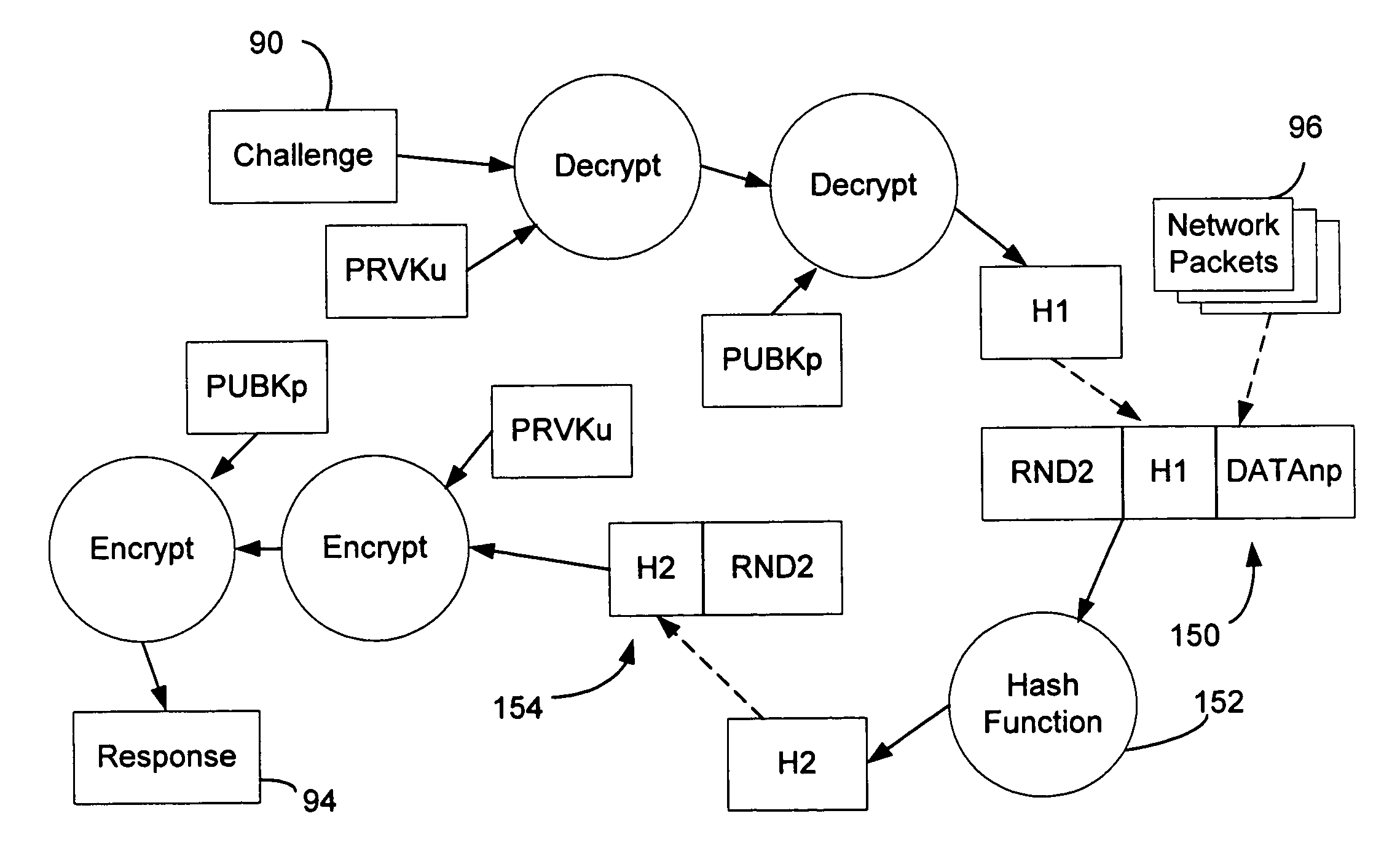
InactiveUS7039713B1Digital data processing detailsComputer security arrangementsData connectionUser authentication
A policy agent of a network performs an out-of-band user authentication process to verify the identity of a user of a client computer and associates the network data received from the client computer with the user. When the client computer initiates a network data connection to or through the policy agent, the policy agent sends an encrypted challenge to the client computer. The challenge is encrypted with a private key of the policy agent. When the client computer receives the challenge, it decrypts the challenge and prepares a message digest value based on the challenge and the network data sent by the user. The message digest value is then encrypted with the private key of the user to form a response, and the response is sent to the policy agent. The policy agent decrypts the response with the public key of the user to obtain the message digest value and calculates a digest value based on the challenge and the received network data. The policy agent then compares the calculated digest value with the decrypted digest value. A match between the two digest values indicates that the user is successfully authenticated and that the received network data are associated with the user. The policy agent may then apply network policies based on the credentials of the authenticated user.
Owner:MICROSOFT TECH LICENSING LLC
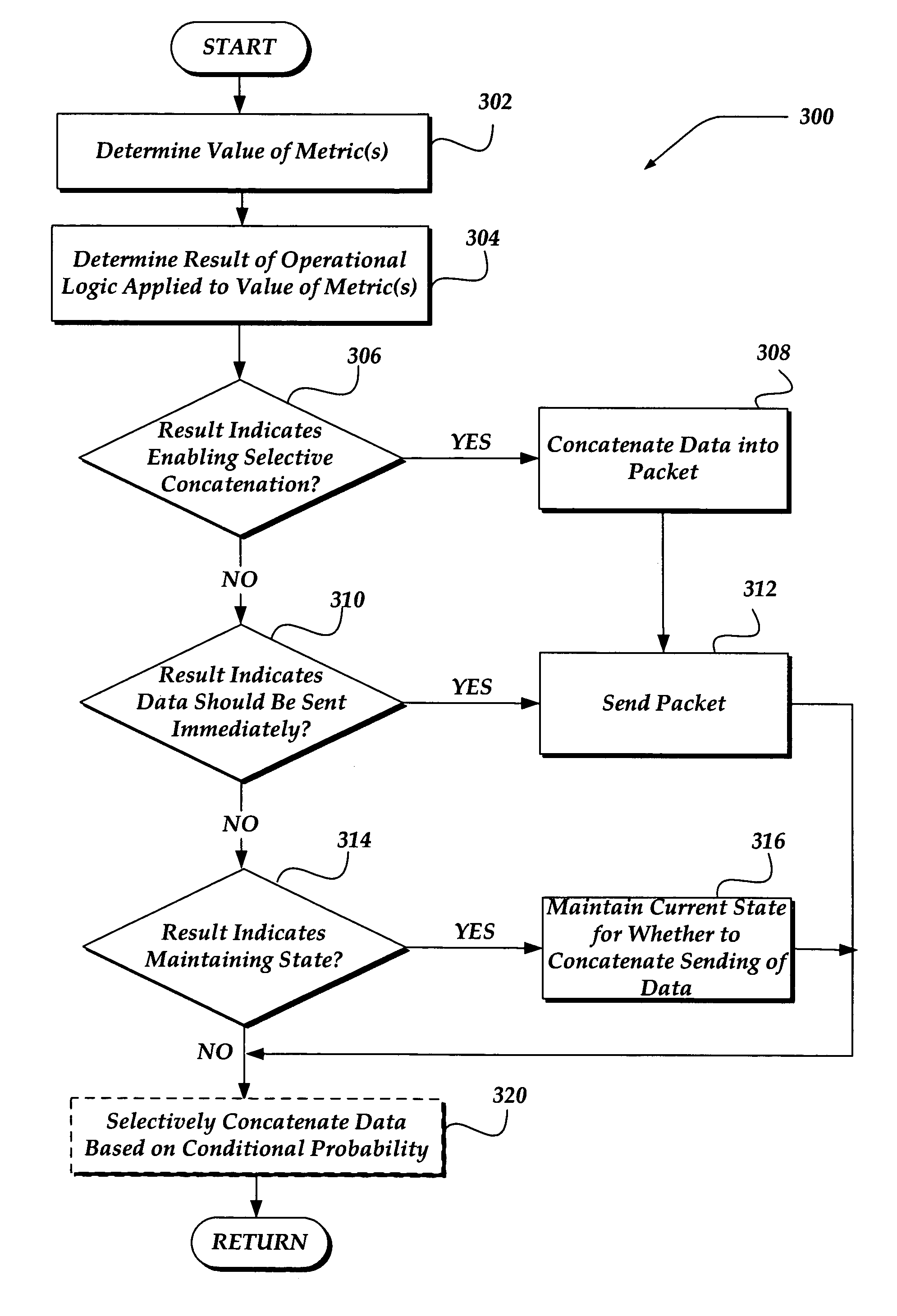
Selectively enabling network packet concatenation based on metrics
InactiveUS7873065B1Data switching by path configurationStore-and-forward switching systemsData connectionNetwork packet
A method, system, and apparatus are directed towards selectively concatenating data into a packet to modify a number of packets transmitted over a network based on a combination of network and / or send-queue metrics. In one embodiment, Nagle's algorithm is used for concatenating data into a packet. The concatenation may be selectively enabled based on heuristics applied to the combination of metrics. In one embodiment, the result may indicate that there should be a concatenation, or that data should be sent immediately, or that a current state for whether to concatenate or not should be maintained. The heuristics may include an expert system, decision tree, truth table, function, or the like. The heuristics may be provided by a user, or another computing device. In another embodiment, the concatenation may be enabled based on a conditional probability determined from the combination of metrics.
Owner:F5 NETWORKS INC
Methods and apparatus for monitoring local network traffic on local network segments and resolving detected security and network management problems occurring on those segments
InactiveUS20050060535A1Small sizeImprove search capabilitiesSecuring communicationElectric digital data processingData connectionData pack
A system for providing network security through manipulating data connections and connection attempts over a data-packet-network between at least two network nodes is provided. The system includes a system host machine, a first software application residing on the host machine for detecting and monitoring connection activity, a data store for storing connection related data, and a second software application for emulating one or more end nodes of the connections or connection attempts. In a preferred embodiment the system uses the detection software to detect one or more pre-defined states associated with a particular connection or connection attempt including states associated with data content transferred there over and performs at least one packet generation and insertion action triggered by the detected state or states, the packet or packets emulating one or more end nodes of the connection or connection attempt to cause preemption or resolution of the detected state or states.
Owner:PRAEMIO TECH
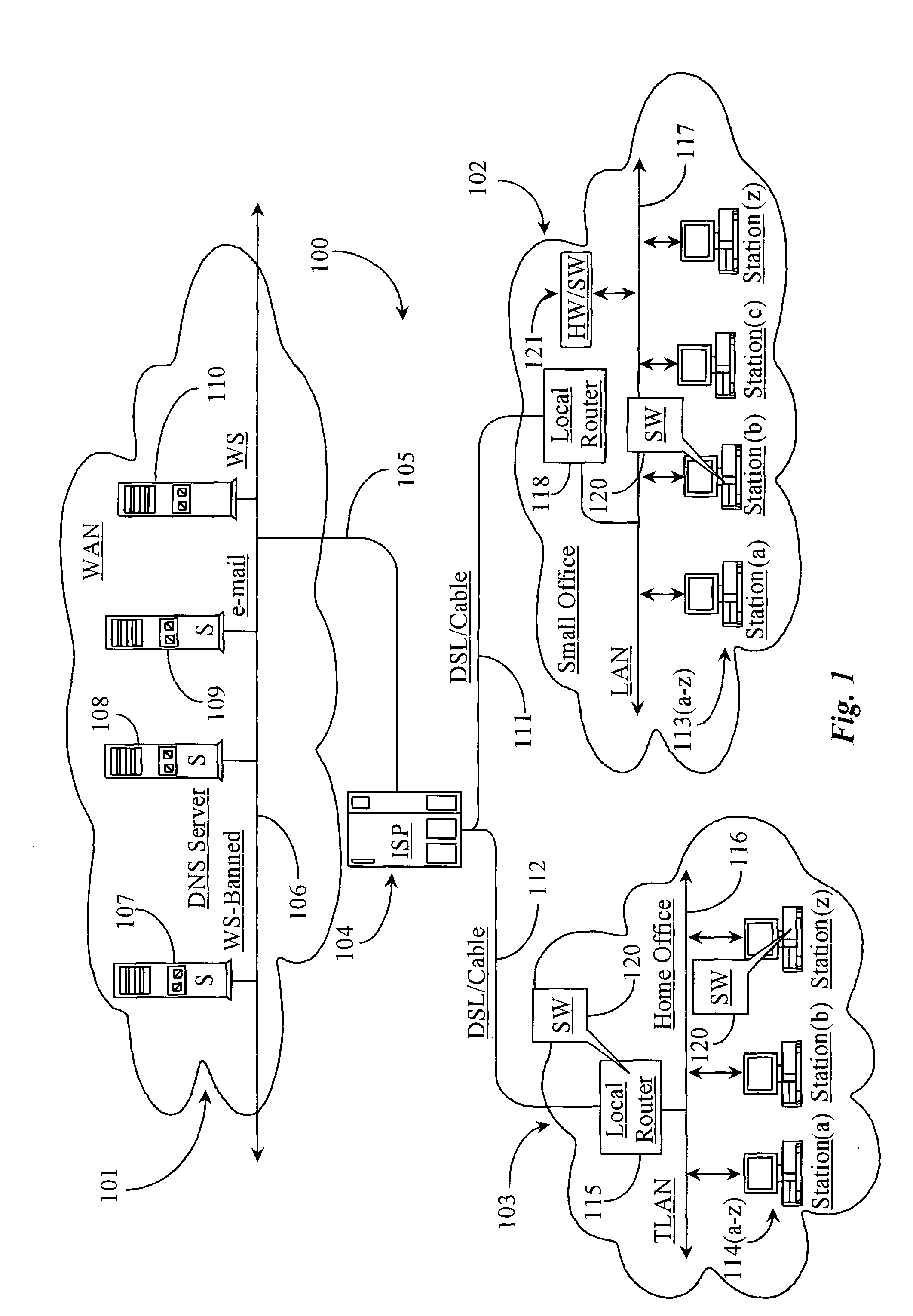
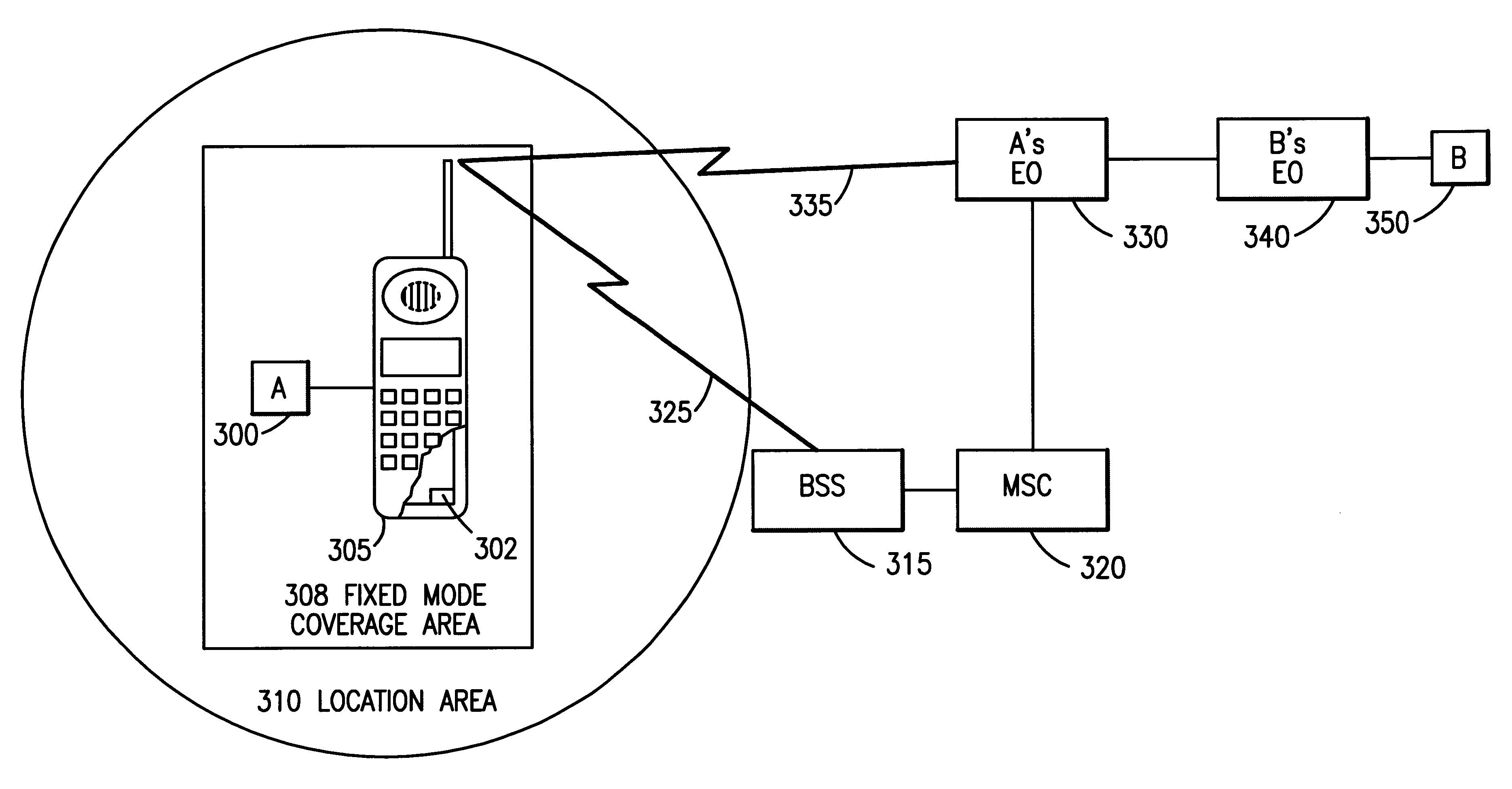
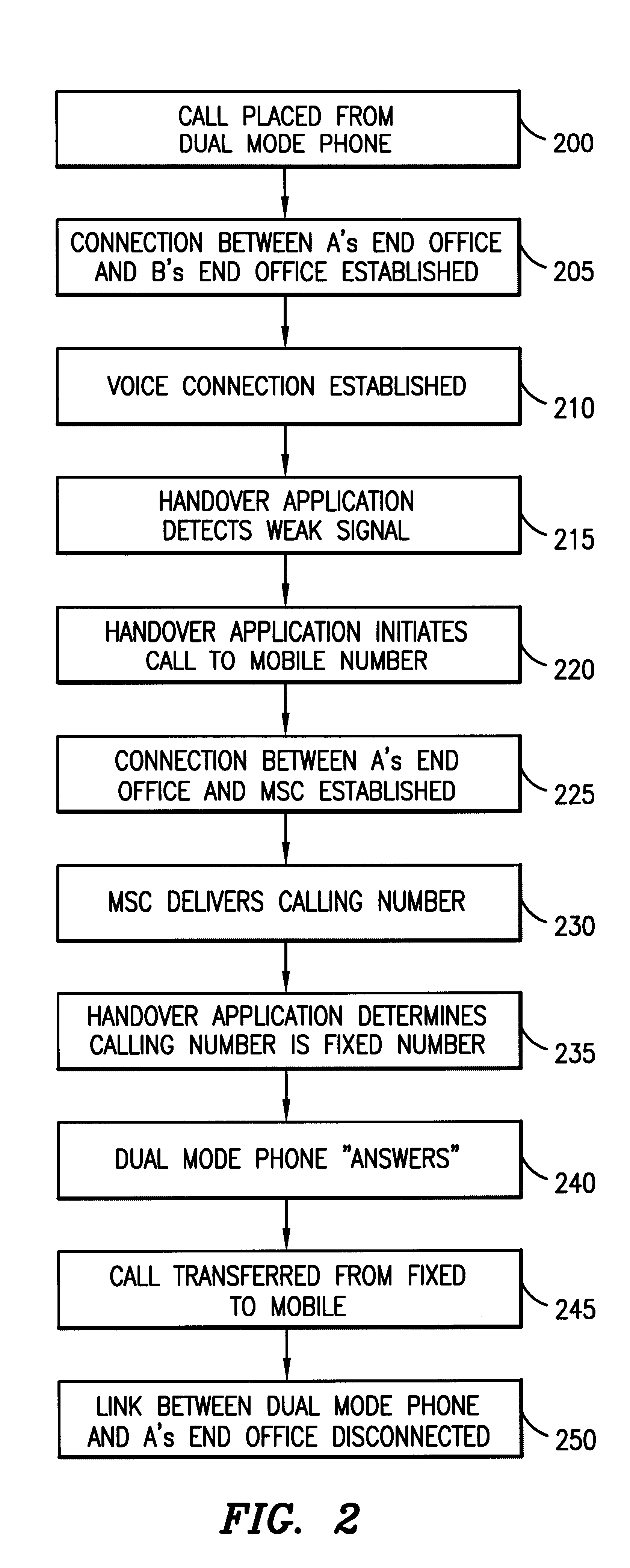
Handover between fixed and mobile networks for dual mode phones
InactiveUS6327470B1Radio/inductive link selection arrangementsWireless commuication servicesData connectionCall forwarding
A telecommunications system and method for performing a handover between the fixed (wireline) network and a mobile network during a call placed to or from a dual mode device, without any interruption in the voice or data connection. Therefore, for calls initiated in the fixed network, once the subscriber leaves the coverage area for the fixed mode of the dual mode device, the call continues as normal by transferring the call to the mobile network. Similarly, for calls initiated in the mobile network, once the subscriber moves back into the fixed mode coverage area, the call can be transferred to the fixed network in order to provide a lower rate to the subscriber, without any service interruption.
Owner:ERICSSON INC
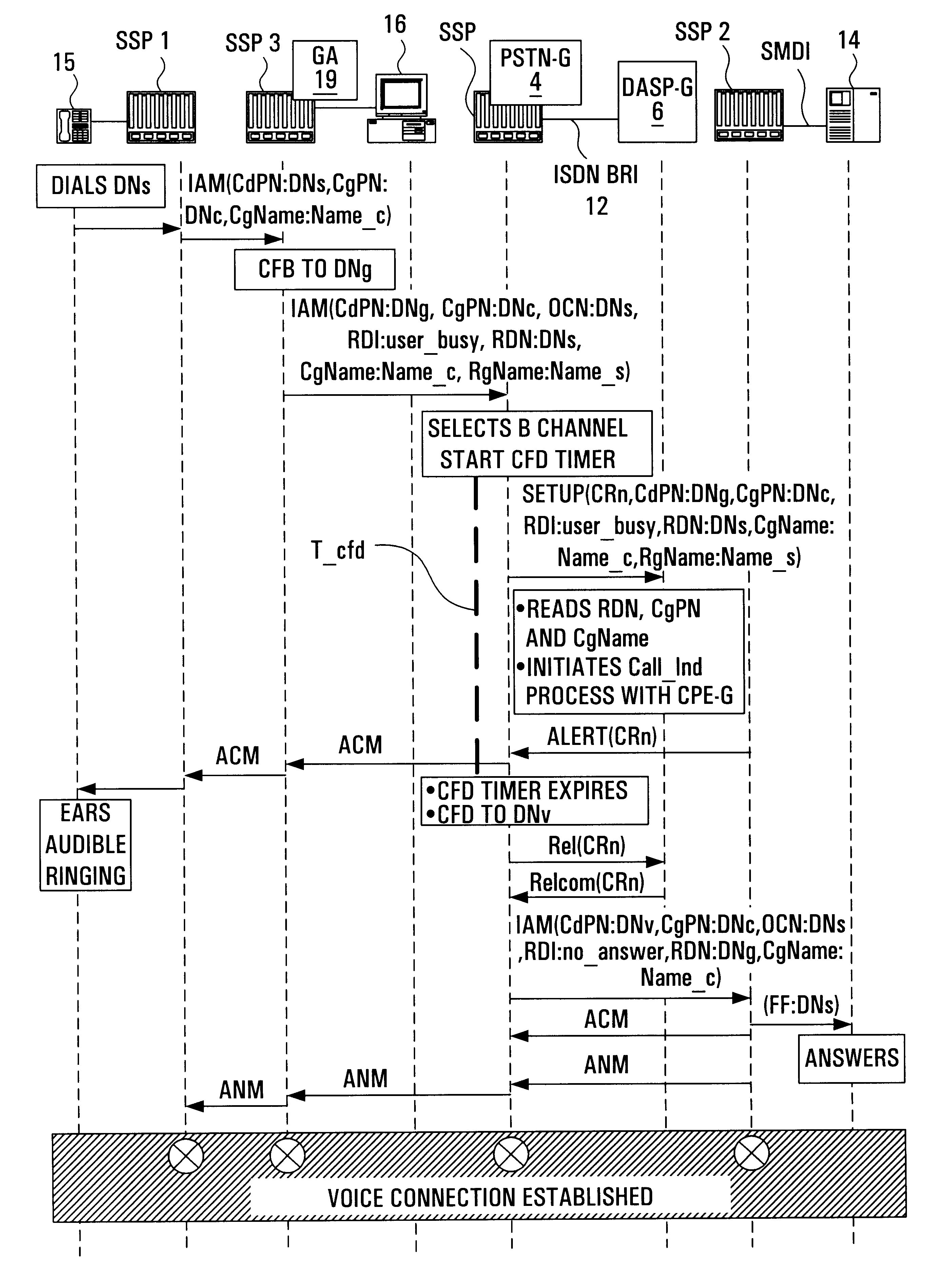
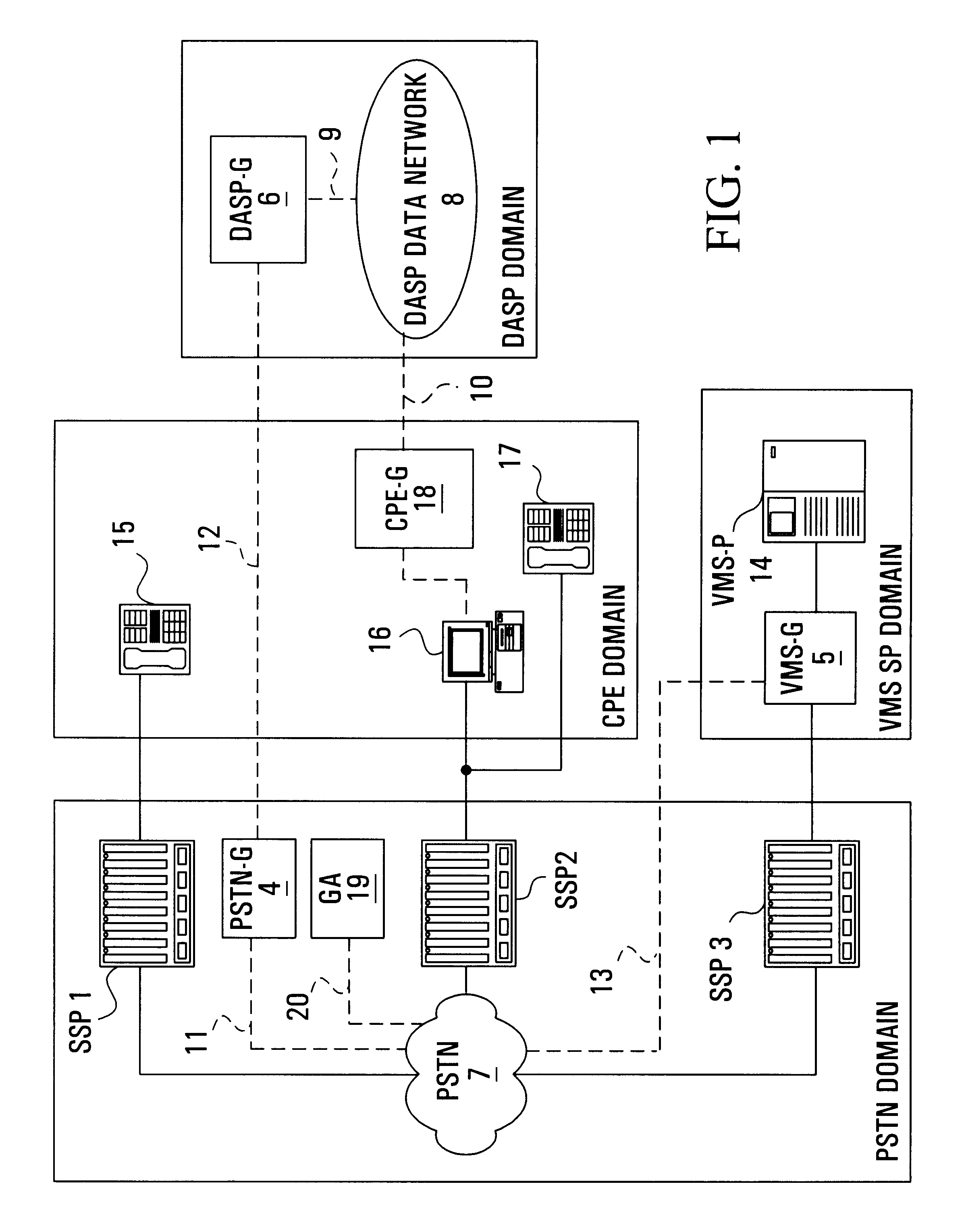
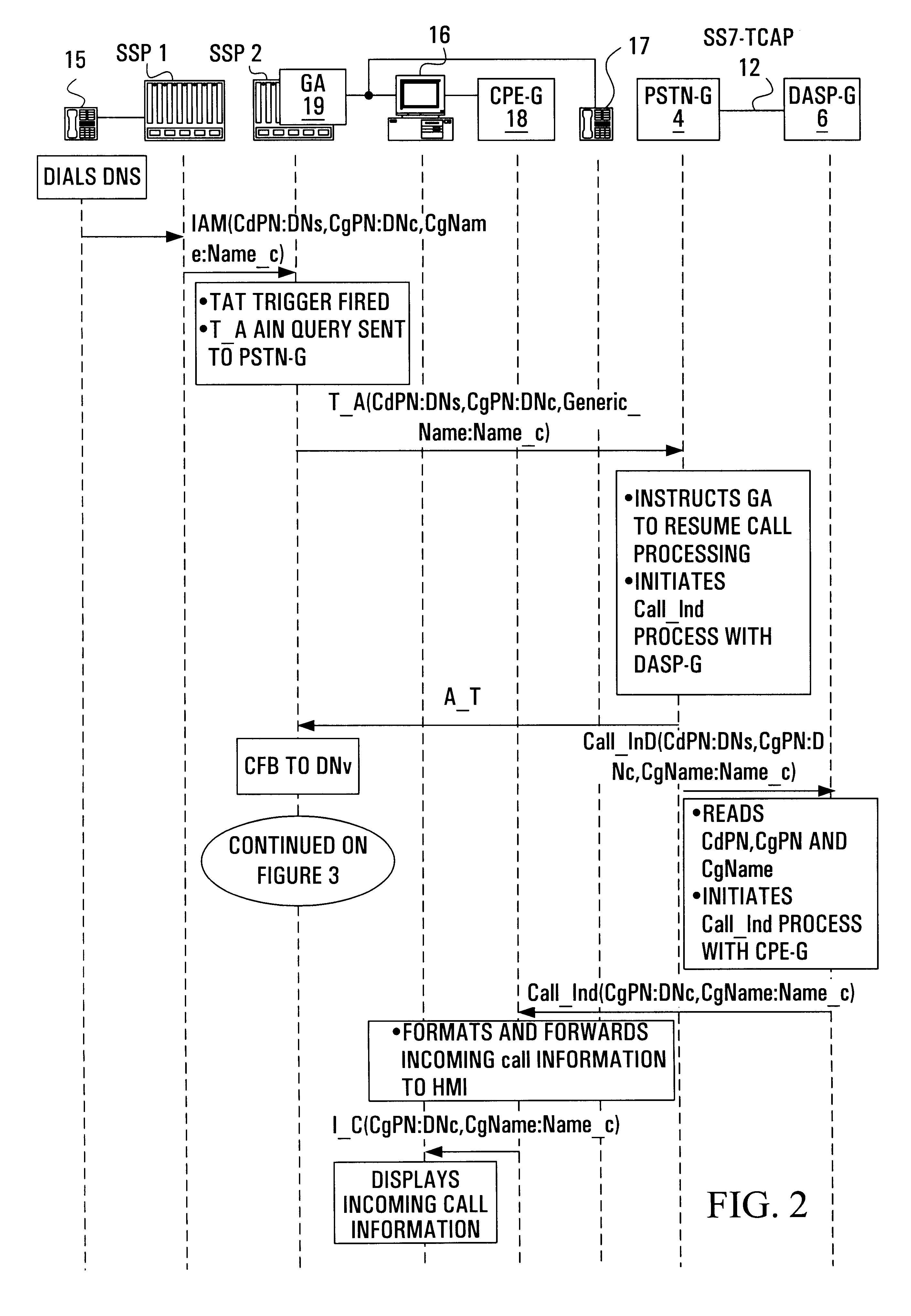
Internet-based telephone call manager
InactiveUS6212261B1Improve handlingImprove abilitiesInterconnection arrangementsSpecial service for subscribersData connectionData information
A method is provided that allows data access service provider subscribers to manage their telephone service through a data connection. The subscriber is enabled to obtain call data information and is provided real time control. During a data call, a visual incoming call indicator informs the subscriber, through a popup window, connected to the data access service provider that there is a call attempt. A visual message waiting indicator allows a subscriber, connected to the data access service provider to be notified of a pending message on the voice message system. A visual call disposition allows the subscriber, through the data connection, to dispose of calls. The call disposition options include forwarding a call to voice mail, playing an announcement to the calling party, forwarding the call to another line, sending a text message which could be converted to speech using text to speech technology, answering the call using voice over data call or terminating the data connection in order to accept the call.
Owner:RPX CLEARINGHOUSE
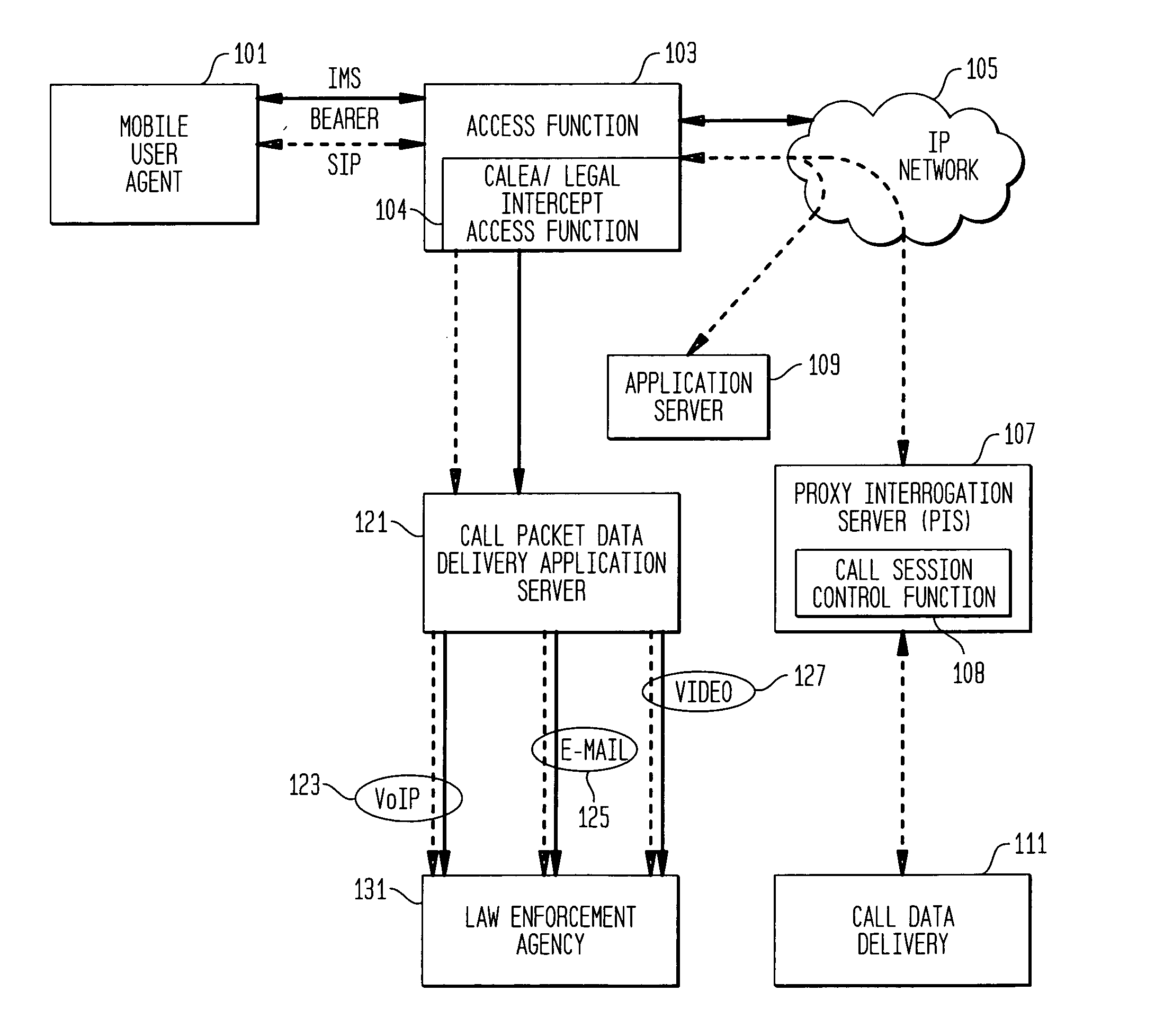
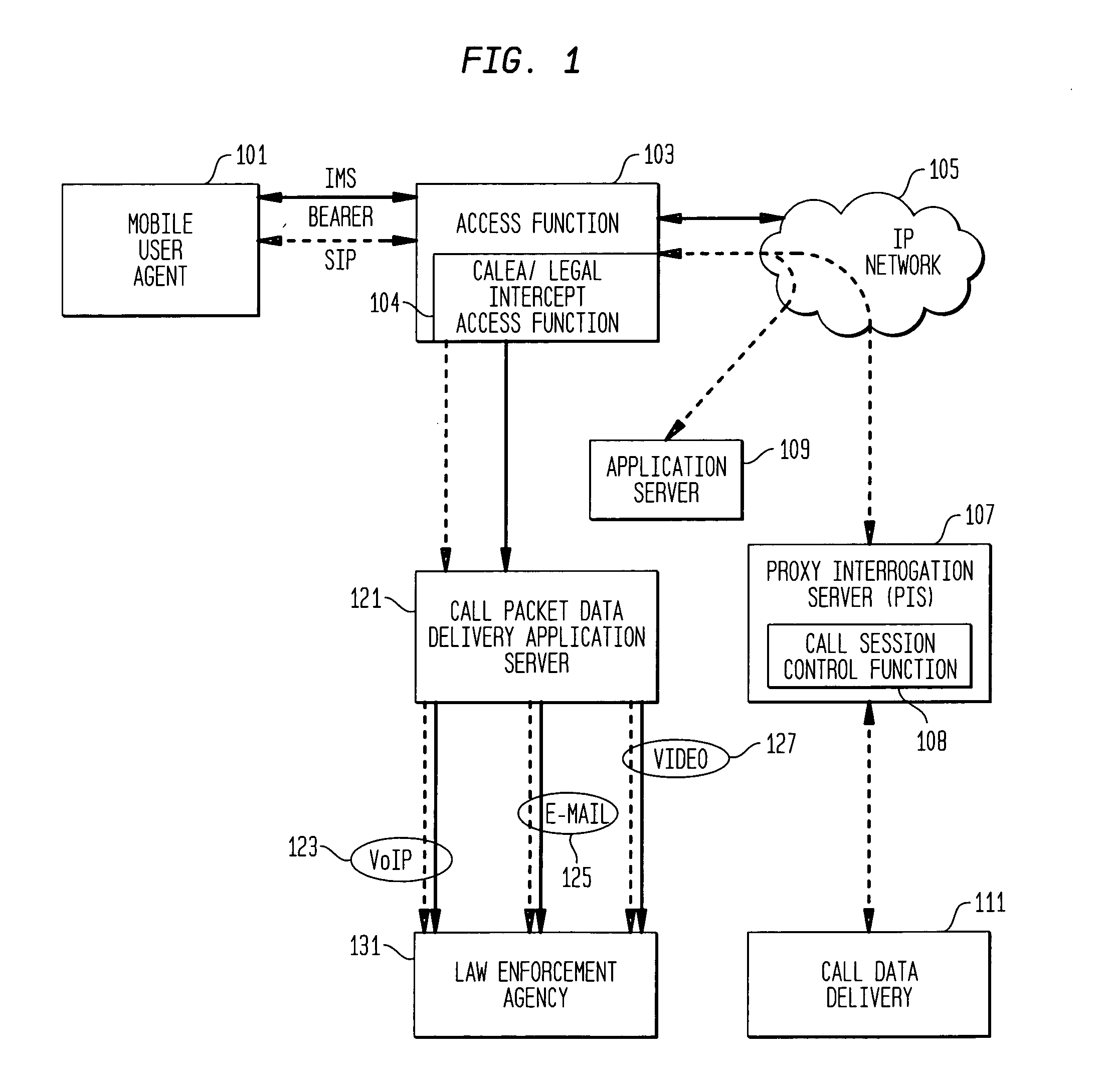
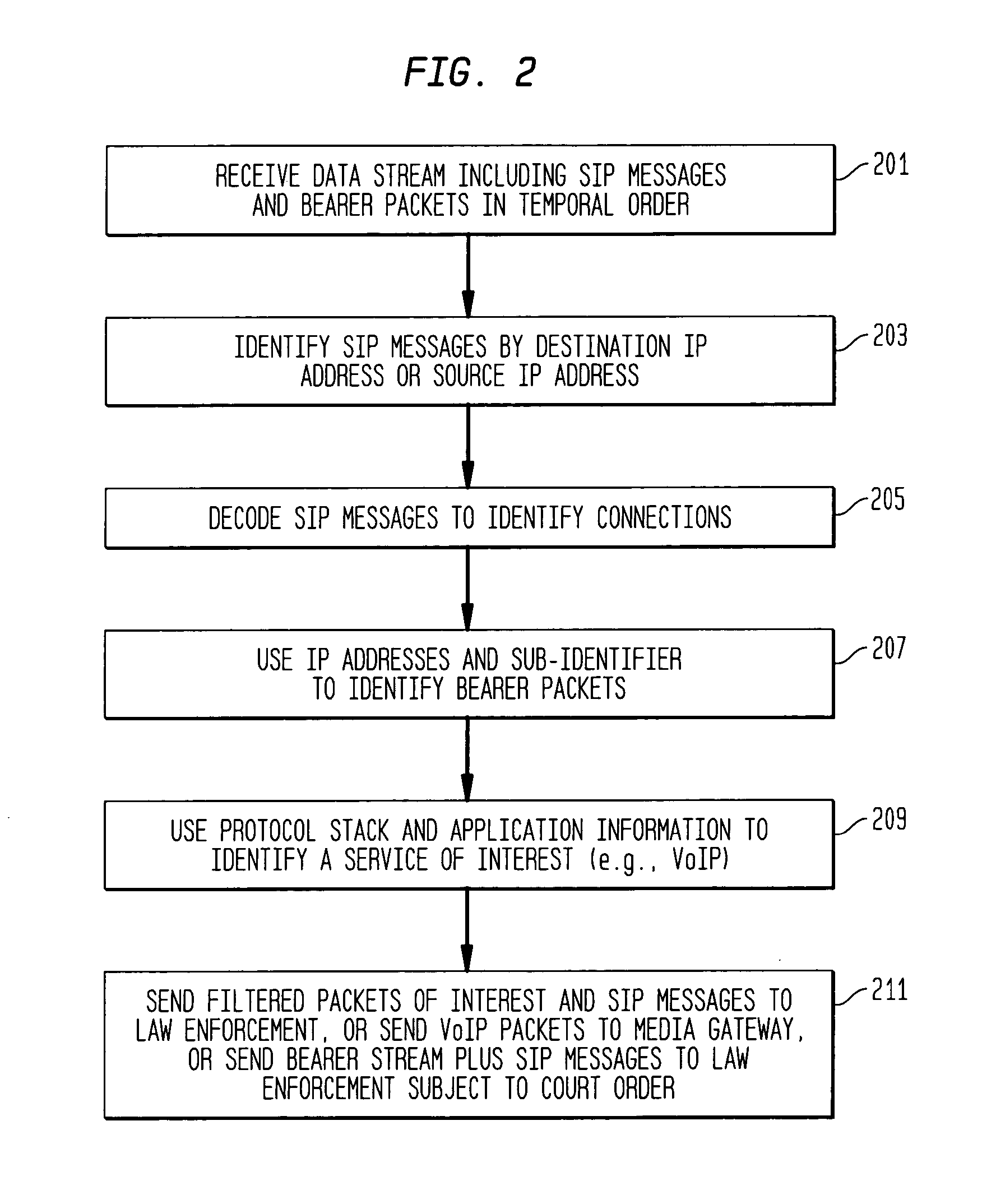
Providing CALEA/LegaI Intercept information to law enforcement agencies for internet protocol multimedia subsystems (IMS)
ActiveUS20060072550A1Supervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsData connectionApplication server
A method and apparatus for providing useful packet data to a CALEA / Legal Intercept collection function. At an access point to a network such as the Internet, sources and destinations of data connections are examined to determine whether any of the bearer messages should also be routed to a CALEA / Legal Intercept monitoring system. If this condition is recognized, the bearer messages and corresponding signaling control messages are correlated in a call packet delivery application server and then delivered to a CALEA / Legal Intercept monitoring system. Advantageously, the monitoring receives as a bundled message set the bearer message and the control messages used to route and otherwise process these bearer messages.
Owner:ALCATEL-LUCENT USA INC
Voice-over-IP enabled chat
InactiveUS7039040B1Avoid the needSpecial service provision for substationMultiplex system selection arrangementsCredit cardData connection
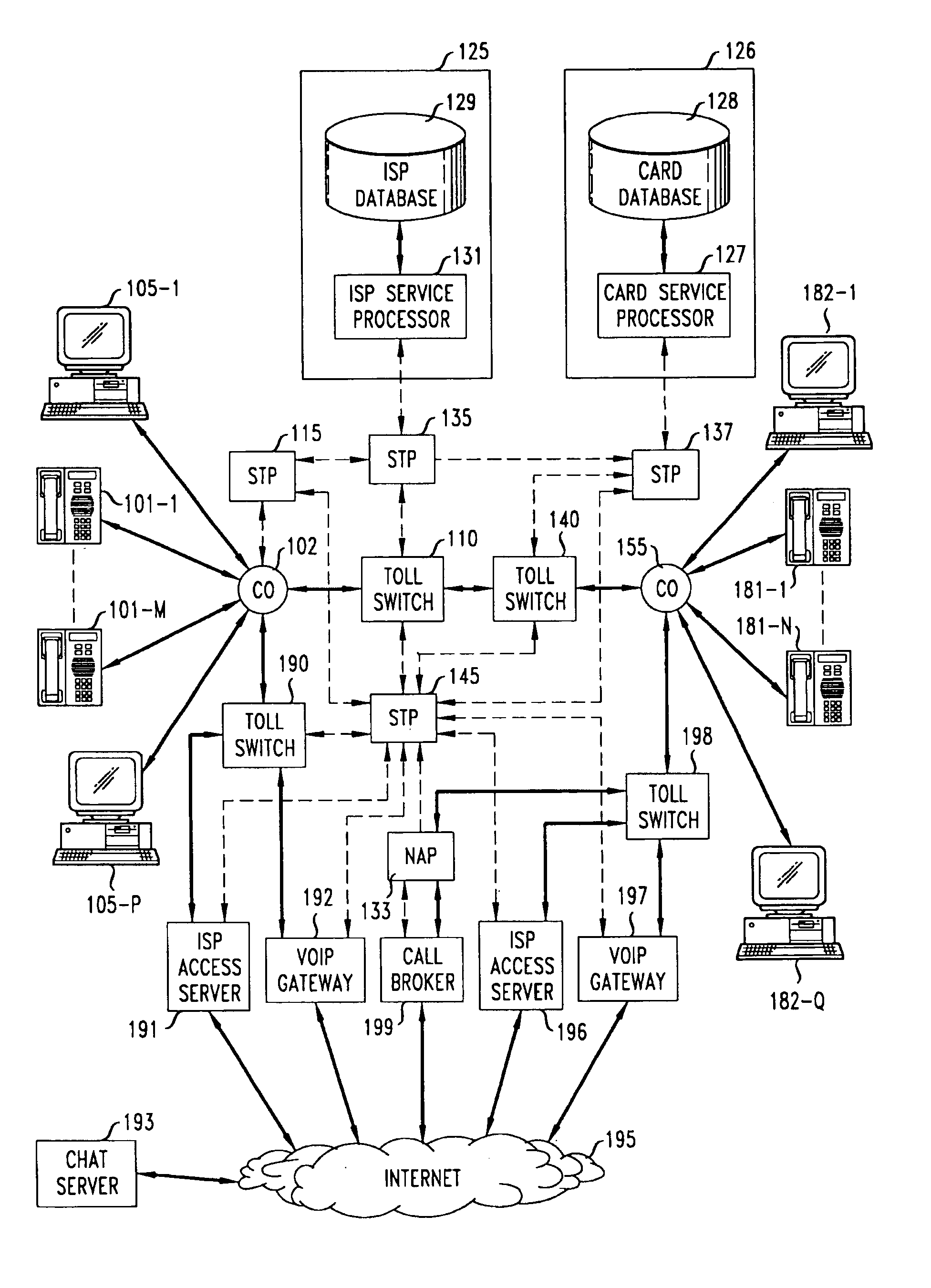
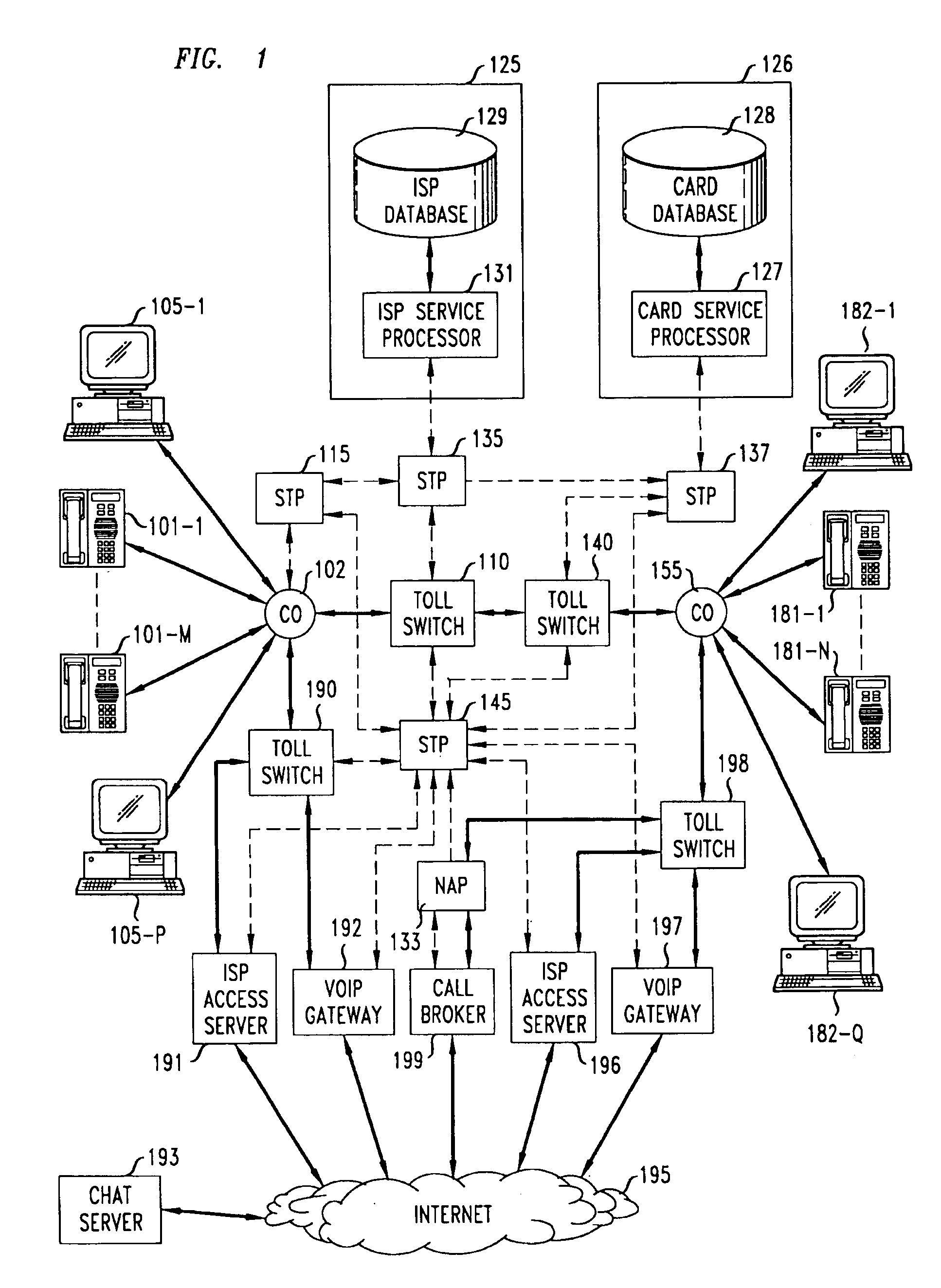
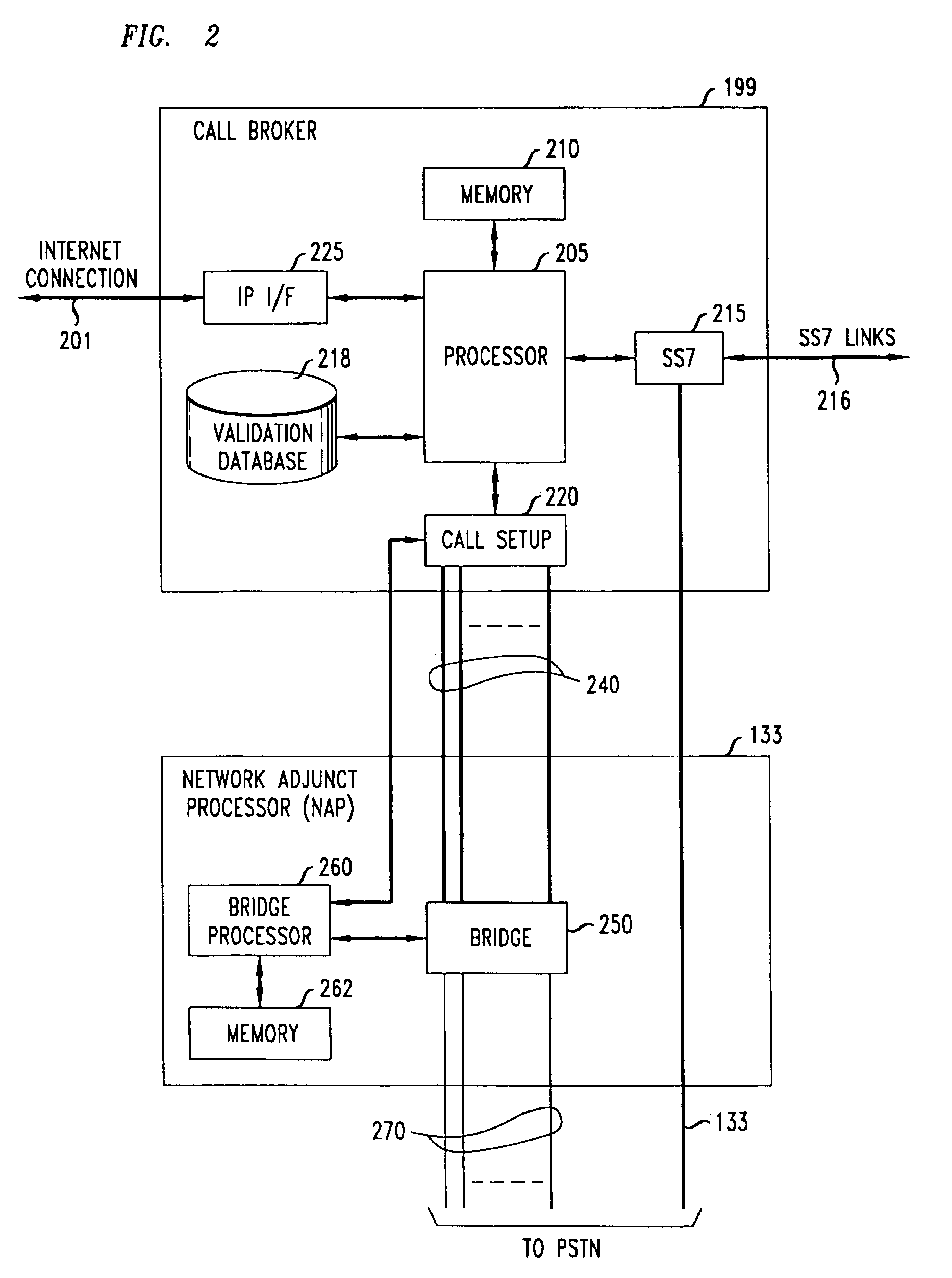
A network-based system and method for providing anonymous voice communications using the telephone network and data communications links under the direction of a Call Broker and associated network elements. A user (the call initiator) present in a text chat room session establishes a data connection to Call Broker and, after qualifying for access (e.g., using credit card information) and providing a callback number, receives voice session information and participant access codes for each desired participant in a voice call. The initiator causes session information and participant codes to be passed to one or more selected chat participants in the current text chat room. When a selected participant uses the received session information, and enters the received participant code and a callback number, the Call Broker in cooperation with a Network Adjunct Processor (NAP) completes voice links to the initiator and the selected participant(s). The need for each party to have a second subscriber line is advantageously avoided by having the Call Broker arrange to have one or more voice links completed through a VoIP link, and further reduces the need for second lines for participants by forwarding a Call Broker—placed call to a busy participant line to the participant's Internet Service Provider (ISP), which then sends a message to the participant announcing one or more options for receiving the incoming call, including receiving the incoming call through a VoIP link.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Transmission of packet data over a network with a security protocol
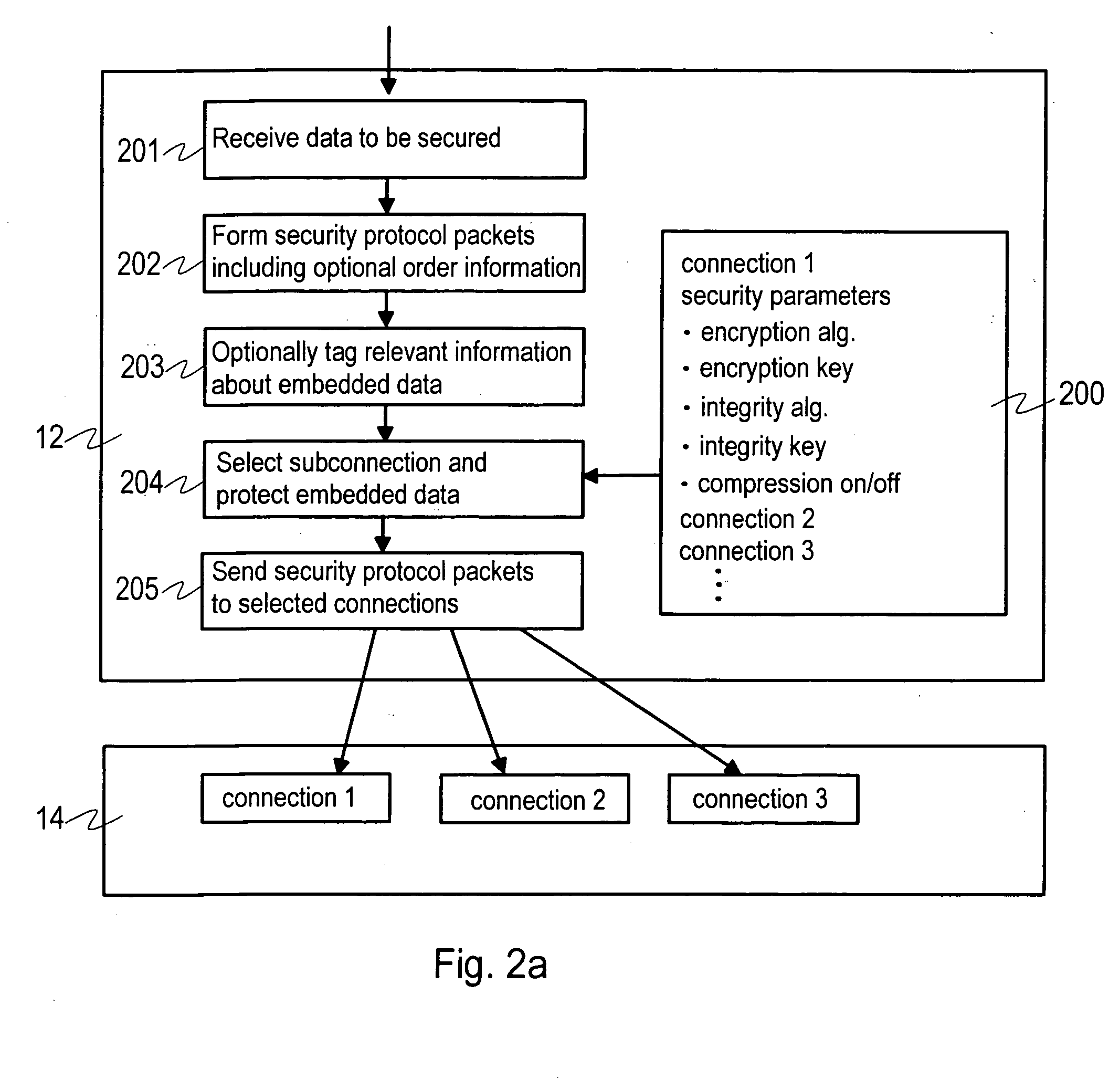
InactiveUS20070022475A1User identity/authority verificationMultiple digital computer combinationsData connectionData pack
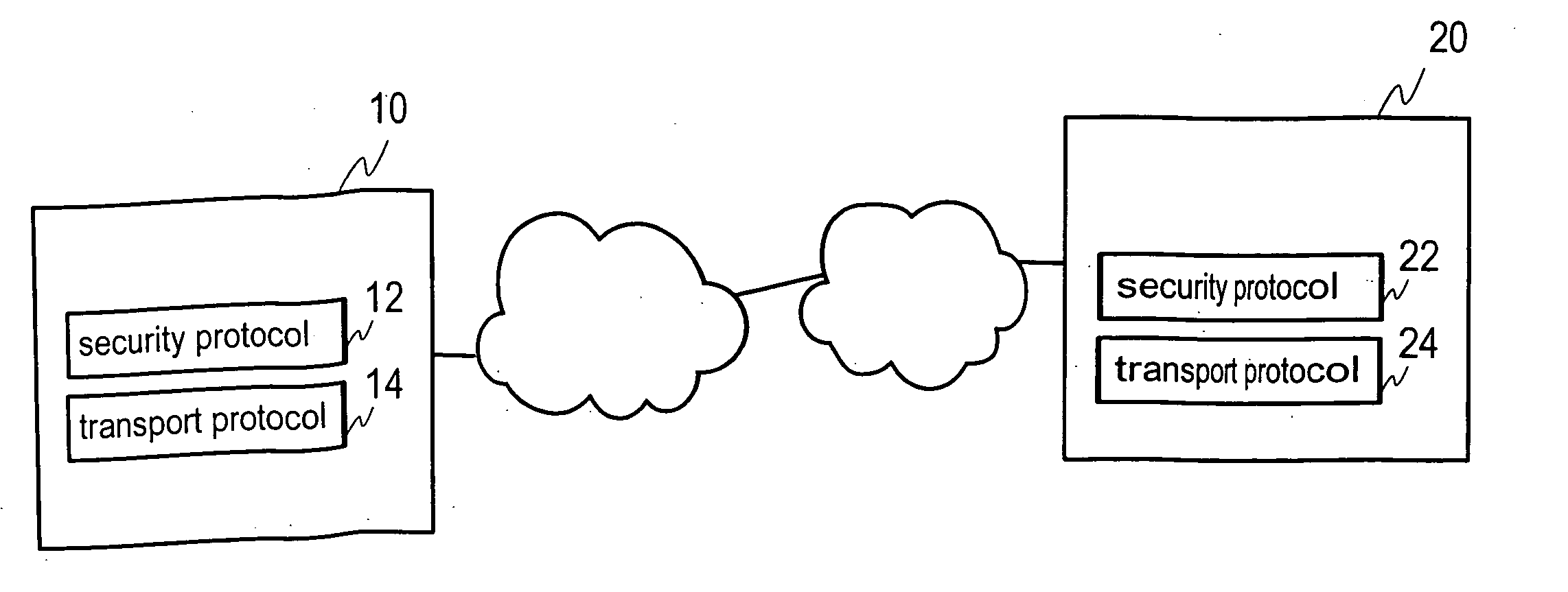
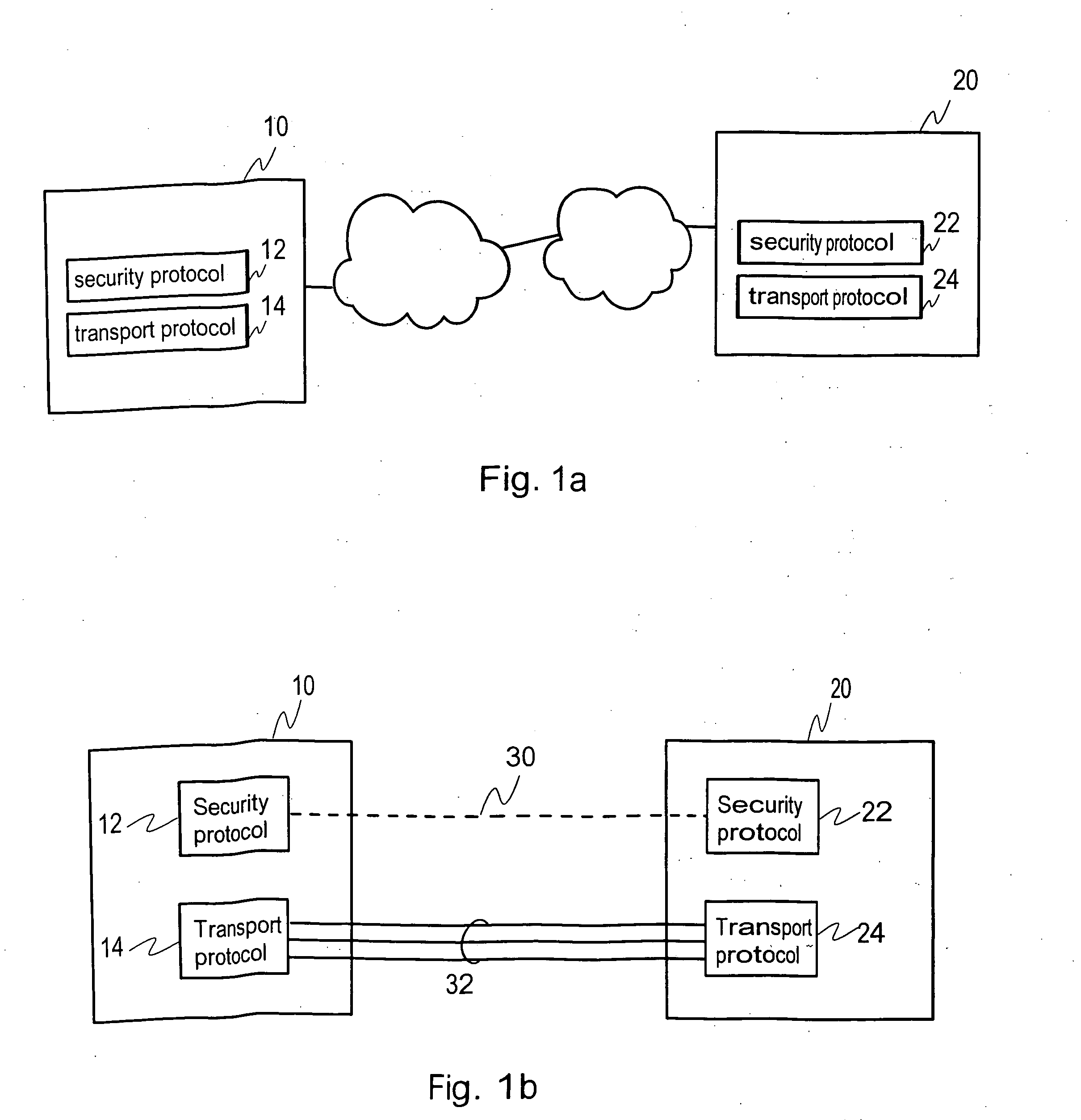
A method, device, system and computer program for providing a transport distribution scheme for a security protocol are disclosed. A first packet data connection is established to a remote node for transmitting packet data over a network with a security protocol. An authentication procedure is performed with the remote node via the first packet data connection for establishing a security protocol session with the remote node. At least one security parameter is negotiated with the remote node for transmitting packets through the first packet data connection. A second packet data connection is established to the remote node, and at least one security parameter is negotiated with the remote node for use with the second packet data connection. The first and second packet data connections are handled as packet data subconnections associated with the security protocol session.
Owner:TECTIA
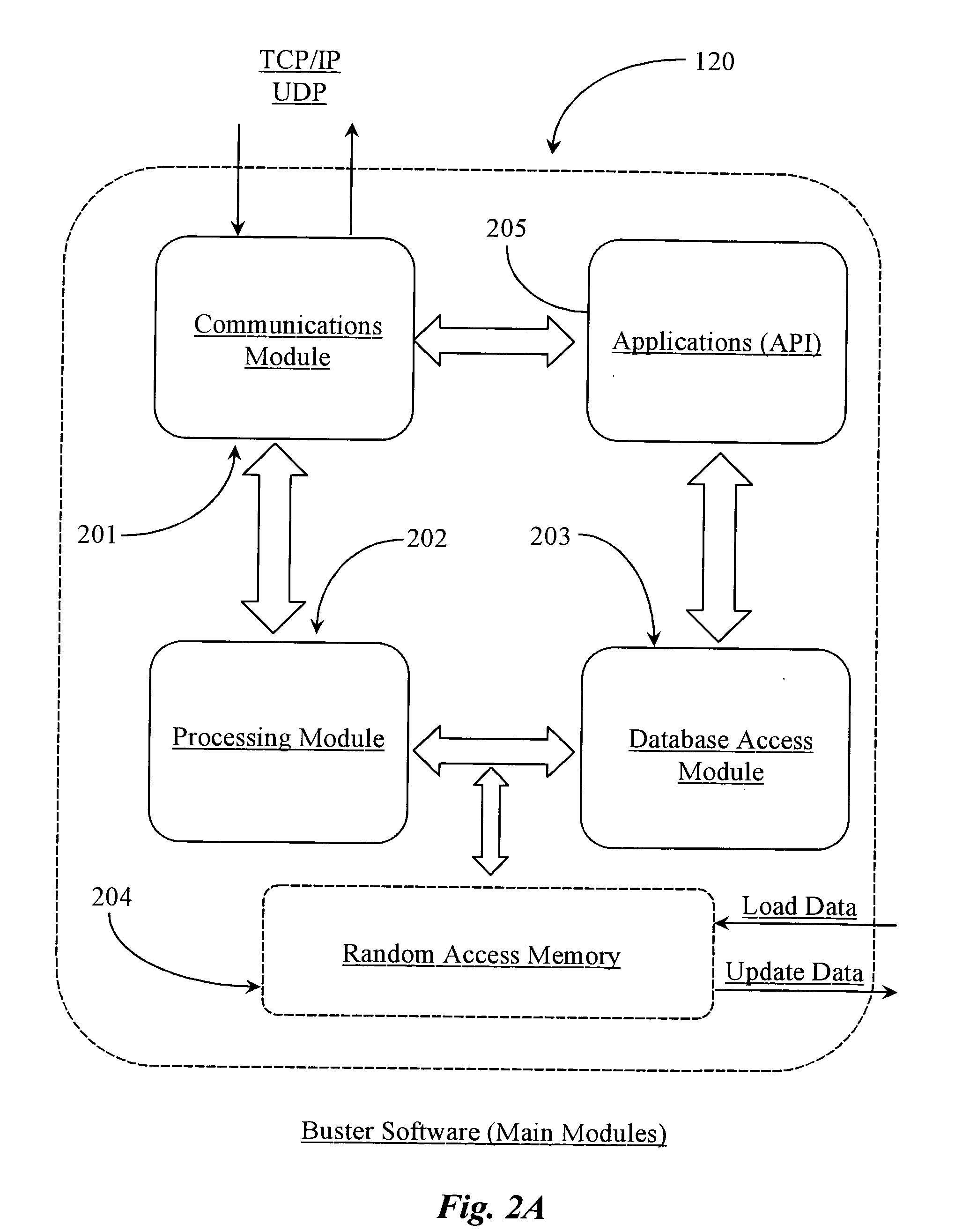
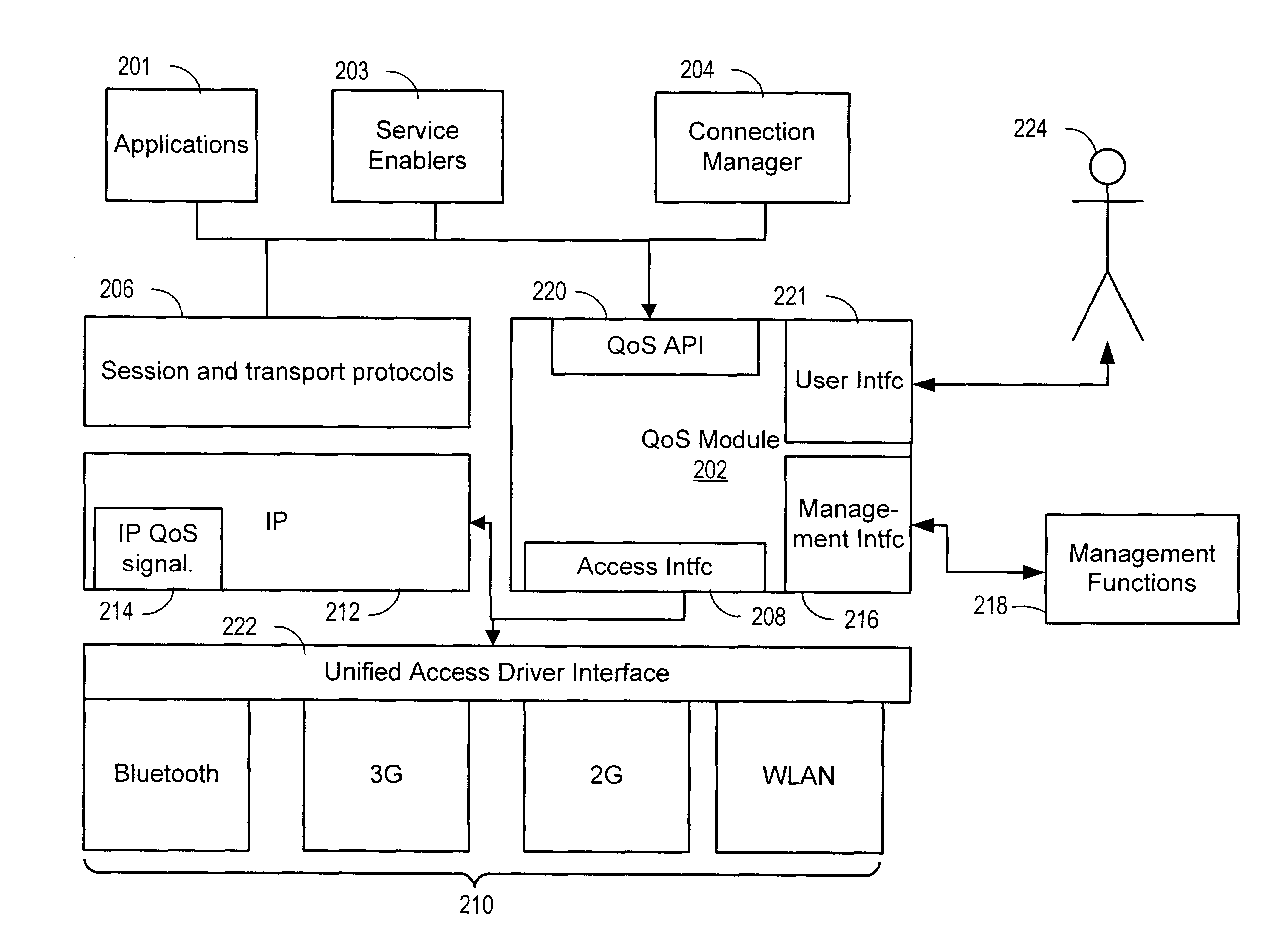
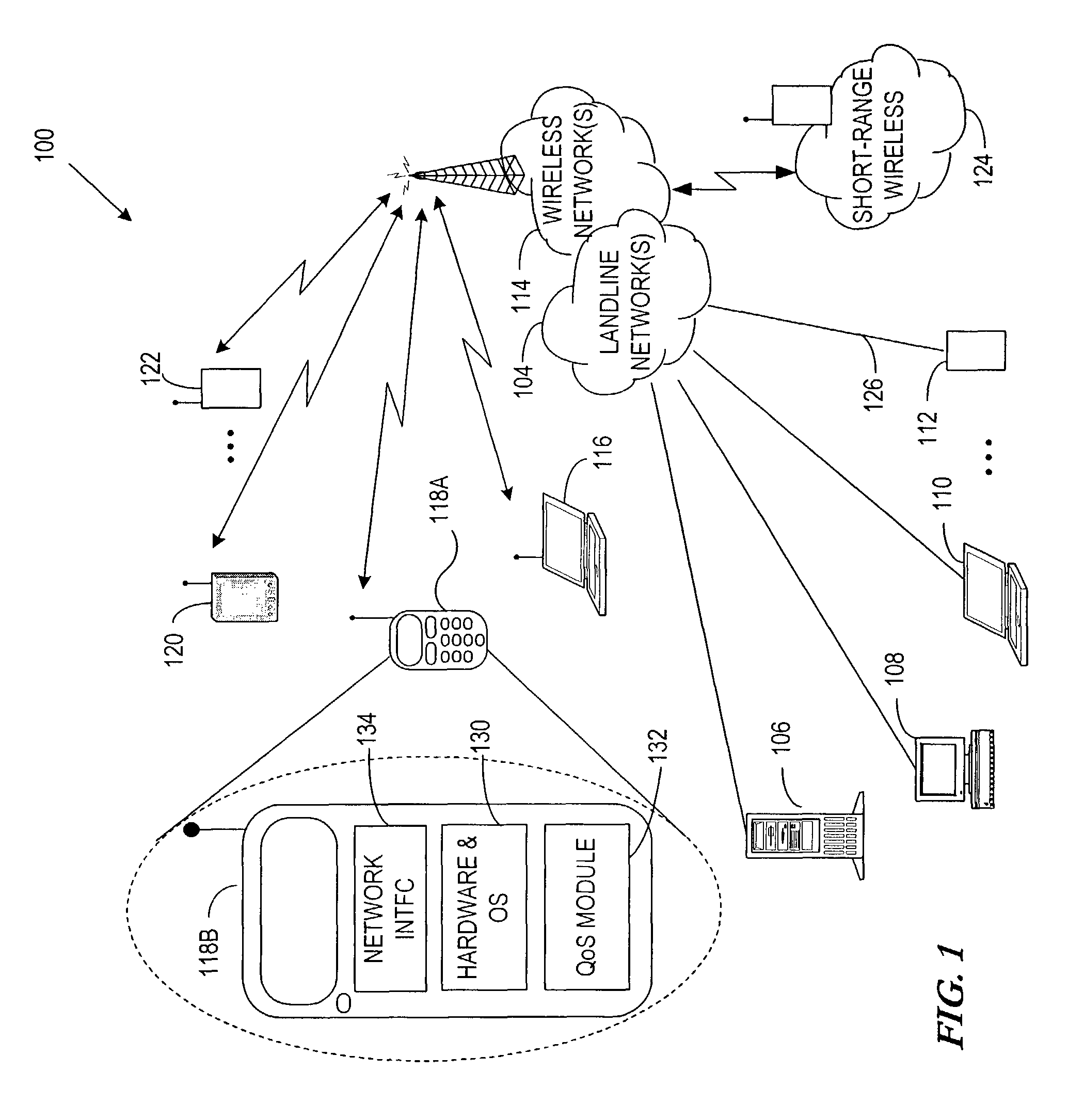
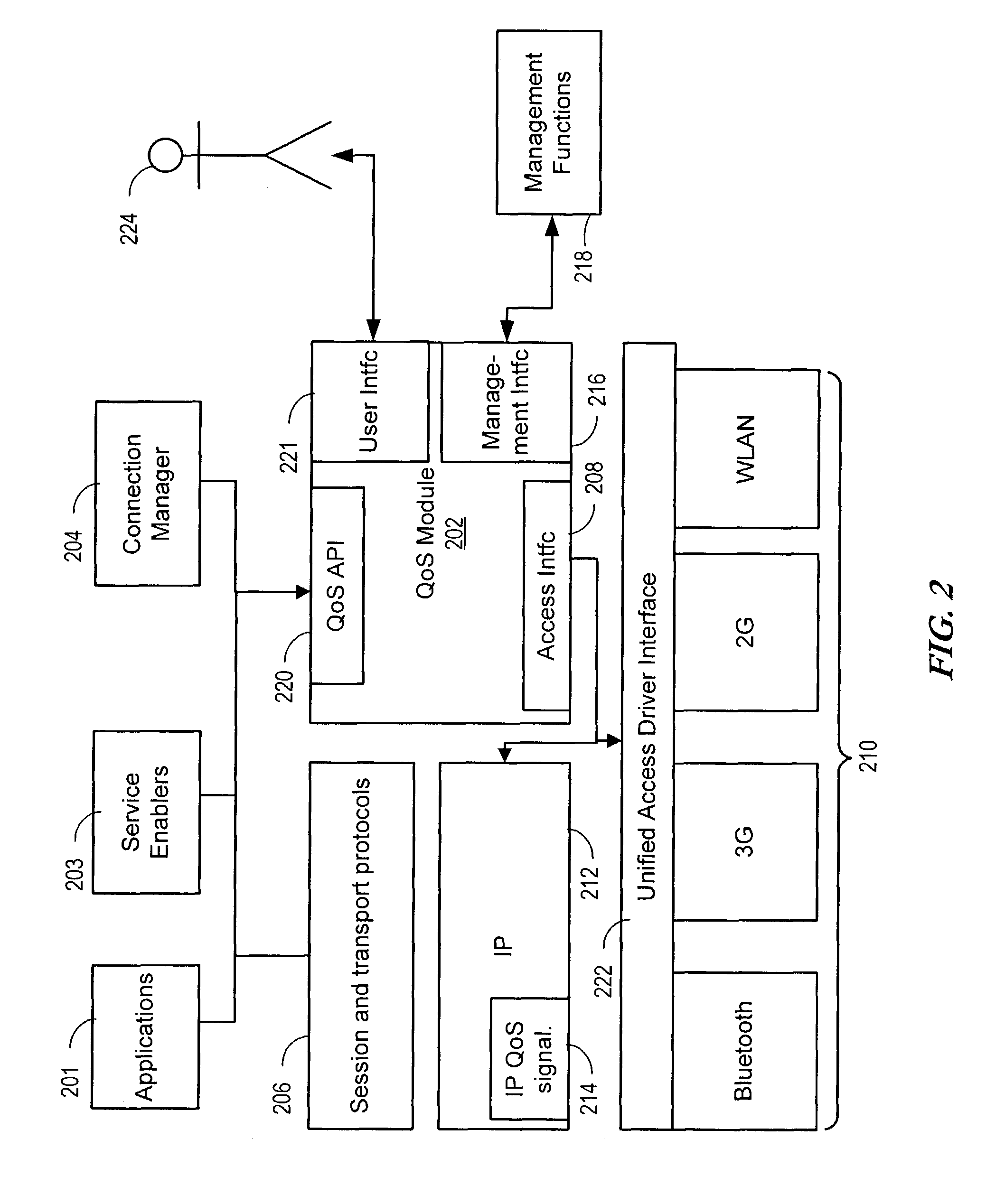
Apparatus and method for providing quality of service for a network data connection
ActiveUS8108520B2Providing serviceNetwork traffic/resource managementData switching by path configurationQuality of serviceData connection
A system, apparatus, and method are disclosed for providing quality of service (QoS) for a network data connection. The network data connection uses a network protocol selectable from a plurality of network protocols. A QoS module can receive a request for a generic QoS and apply this to the network protocol using a specific QoS associated with the protocol. The QoS module may include features for automatic management of QoS and a user interface for changing data connection parameters.
Owner:WSOU INVESTMENTS LLC
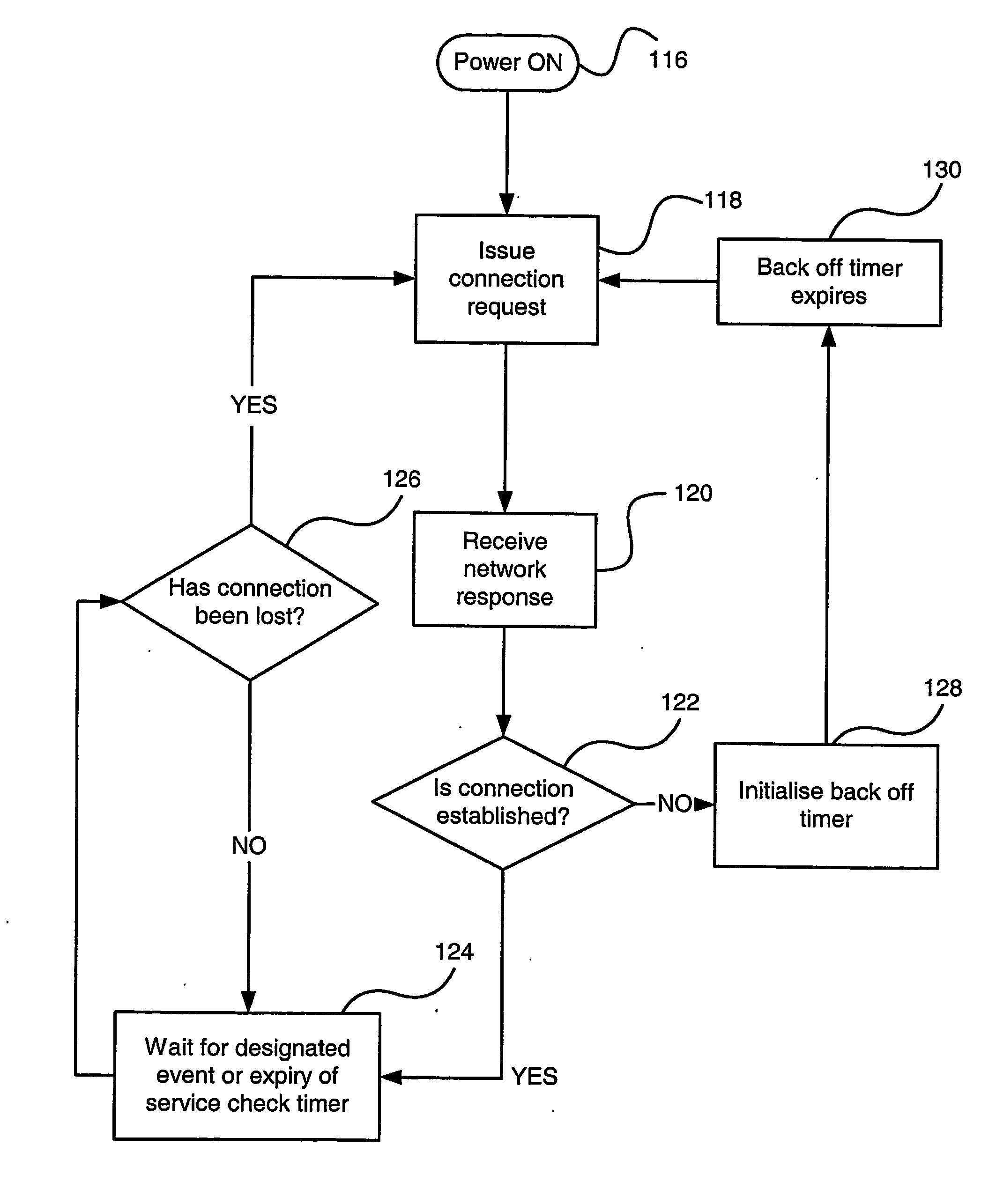
Method and system for maintaining a wireless data connection
ActiveUS20060063544A1Special service for subscribersConnection managementData connectionTelecommunications
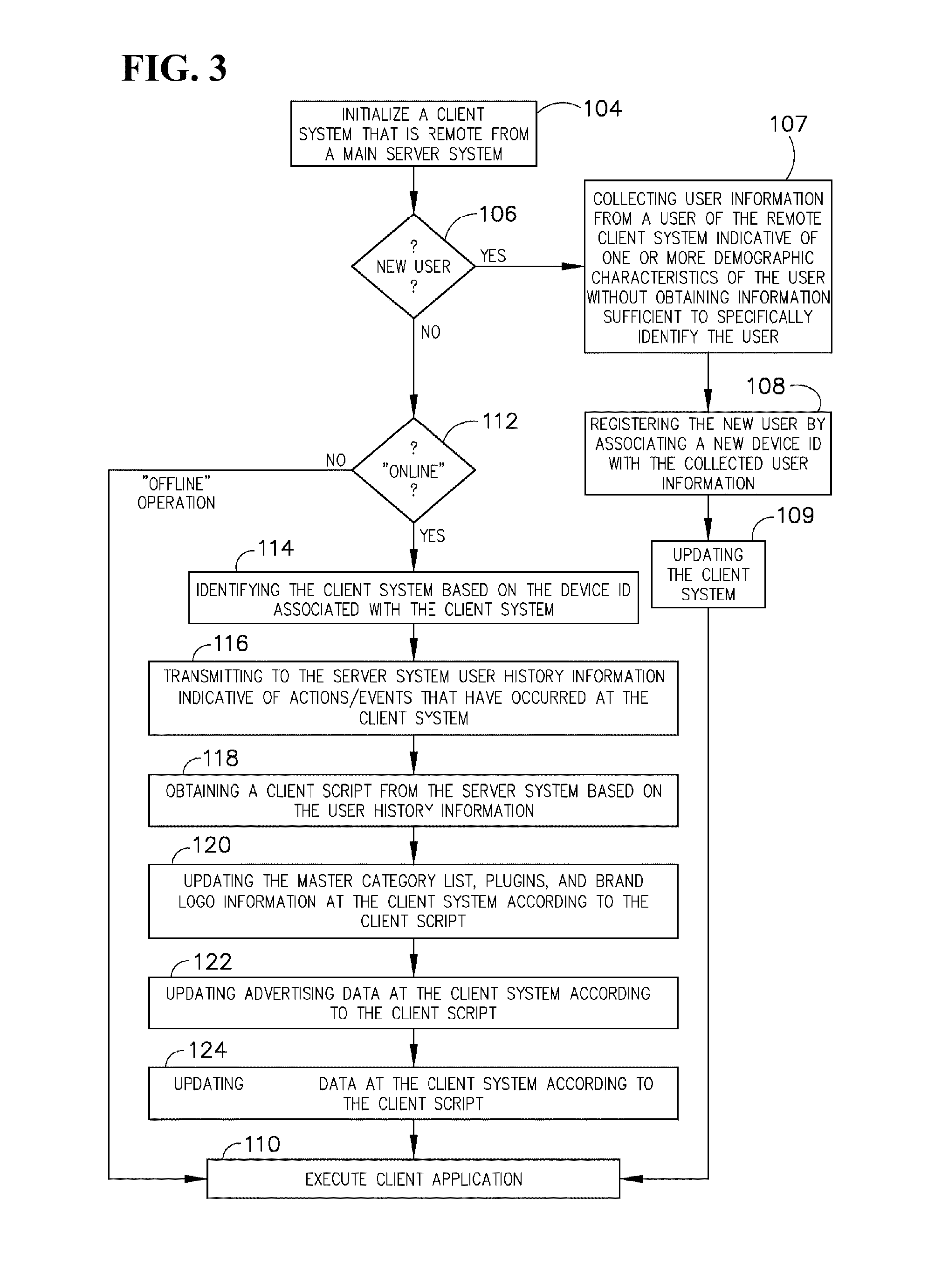
A system and method for establishing and maintaining an "always-on" data connection to a wireless network through the use of a back off timer and a service check timer is disclosed. The back off timer is initialized to a determined value when a connection is not established. When the timer expires, a connection attempt is made. As further connection attempts are made, the back off timer is set to ever-increasing values. When the data connection is established, the service check timer is initialized. The data connection status is determined at the expiry of the service check timer. When, at the expiry of the service check timer, the data connection is determined to be lost, the connection method is employed.
Owner:BLACKBERRY LTD
Method and apparatus for transmitting data over a network using a docking device
InactiveUS20020091796A1Telephonic communicationMultiple digital computer combinationsData connectionNetworked Transport of RTCM via Internet Protocol
A method and system for transmitting data over a network are described. In one embodiment, the system comprises a cradle to transmit data to a network server and an electronic device coupled to the cradle. The electronic device includes a sensor to trigger a data connection between the electronic device and the cradle. The electronic device also includes a transmitter to download the data to the cradle.
Owner:SPORTBRAIN
Removable disk storage array emulating tape library having backup and archive capability
InactiveUS6957291B2Enhance system functionsLow costInput/output to record carriersError detection/correctionData connectionHard disc drive
A hard disk drive based data archive system emulating a tape archive system includes a hot pluggable multi-drive magazine having a housing for holding a plurality of hard disk drives, each drive connected to receive power and data from the magazine in a controlled fashion, and at least one magazine receiving system for physically receiving the magazine and for thereupon providing power, data and control connections to the magazine, such that when the magazine is received within the magazine receiving system, the hard disk drives selectively receive power and data connections via the magazine and receiving system from a host computer. The magazine may be hot-disconnected from an active computing system environment and removed to an archive rack wherein each disk drive is periodically checked to ensure functionality and to provide some limited-bandwidth data retrieval functions via a network connection to the archive rack. A file mark structure enables a disk drive in the magazine to emulate functionality of a tape cartridge.
Owner:QUANTUM CORP
Wireless control of a field device in an industrial process
InactiveUS7010294B1Short response timeQuality improvementElectric testing/monitoringBroadcast transmission systemsData connectionWireless control
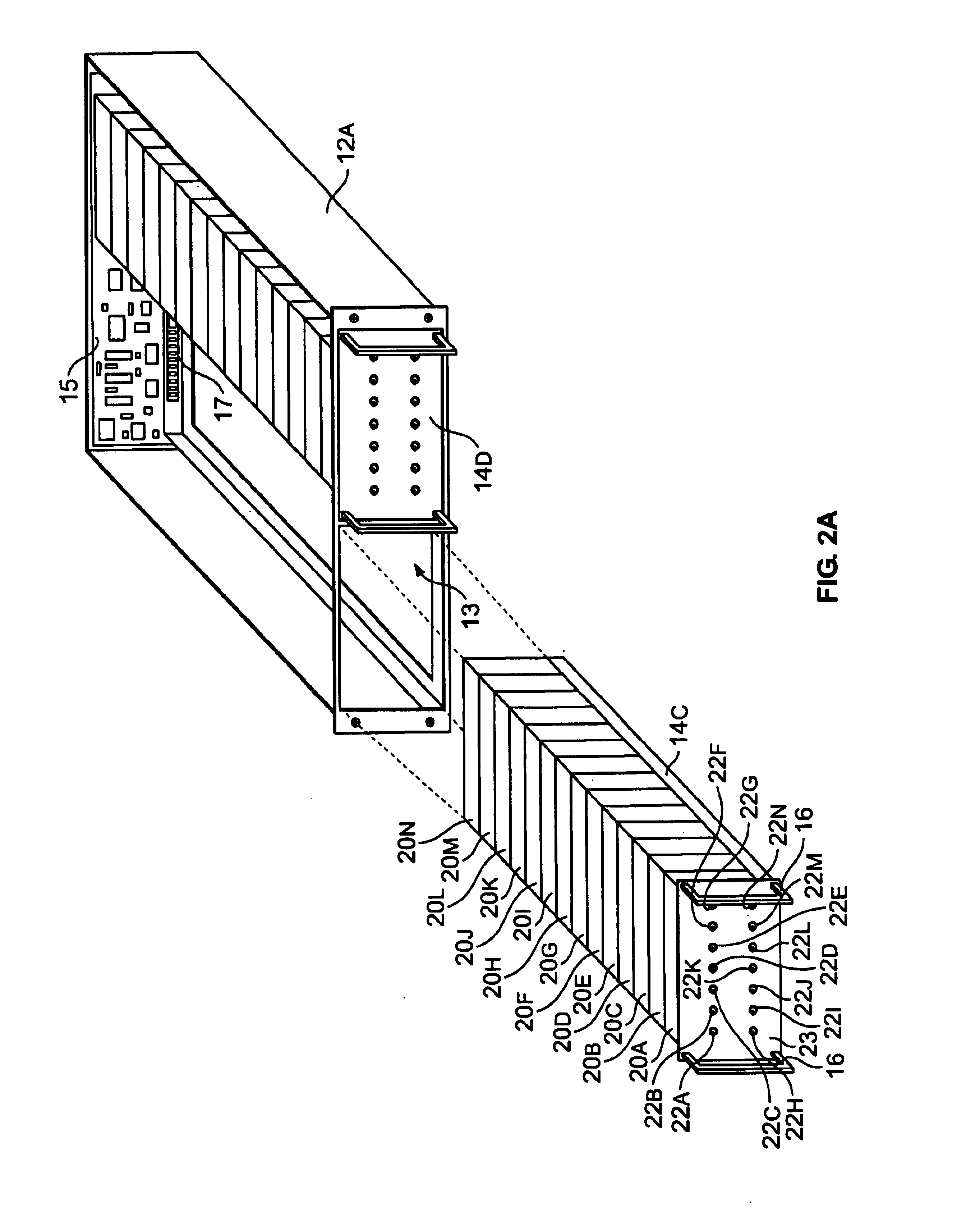
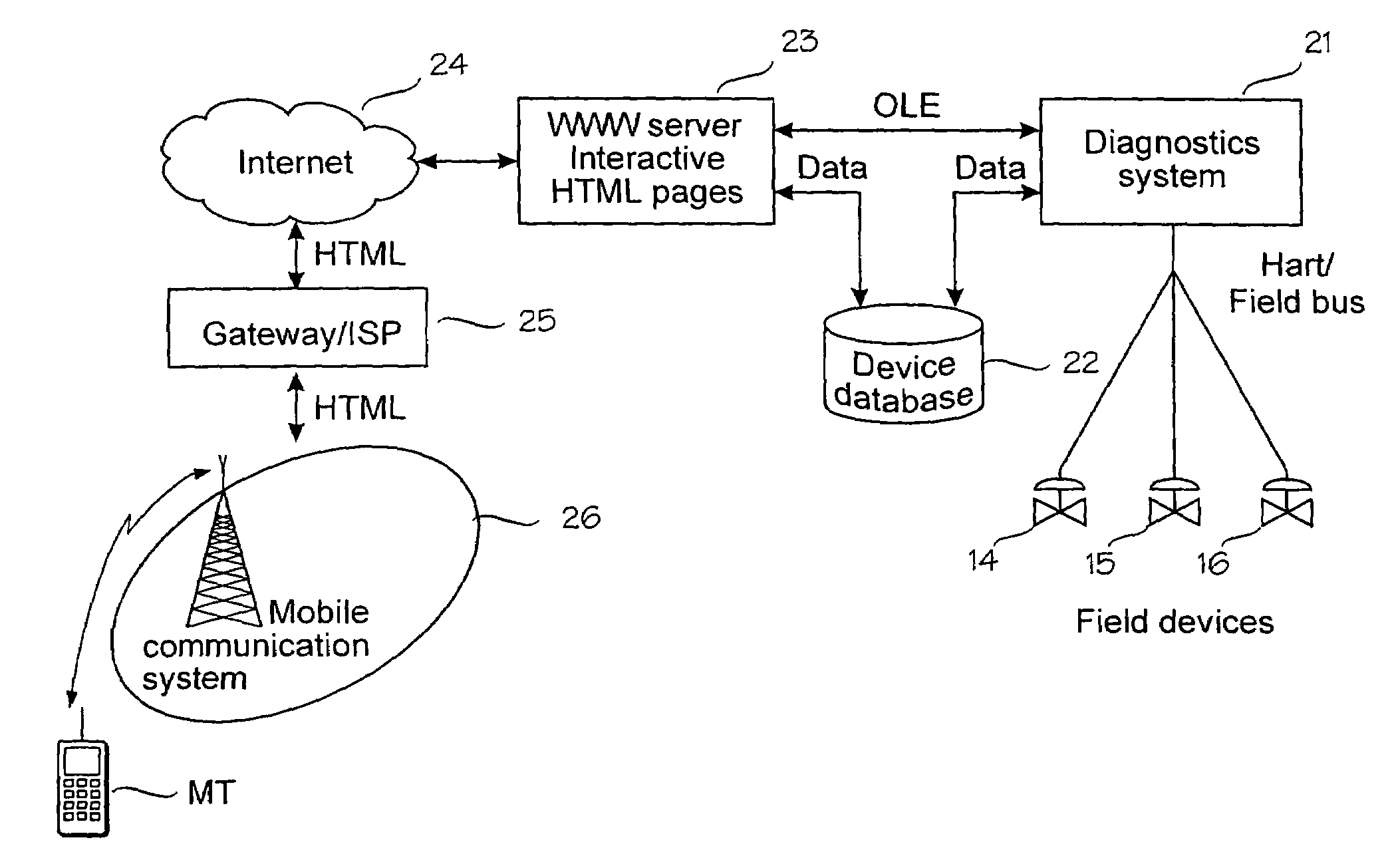
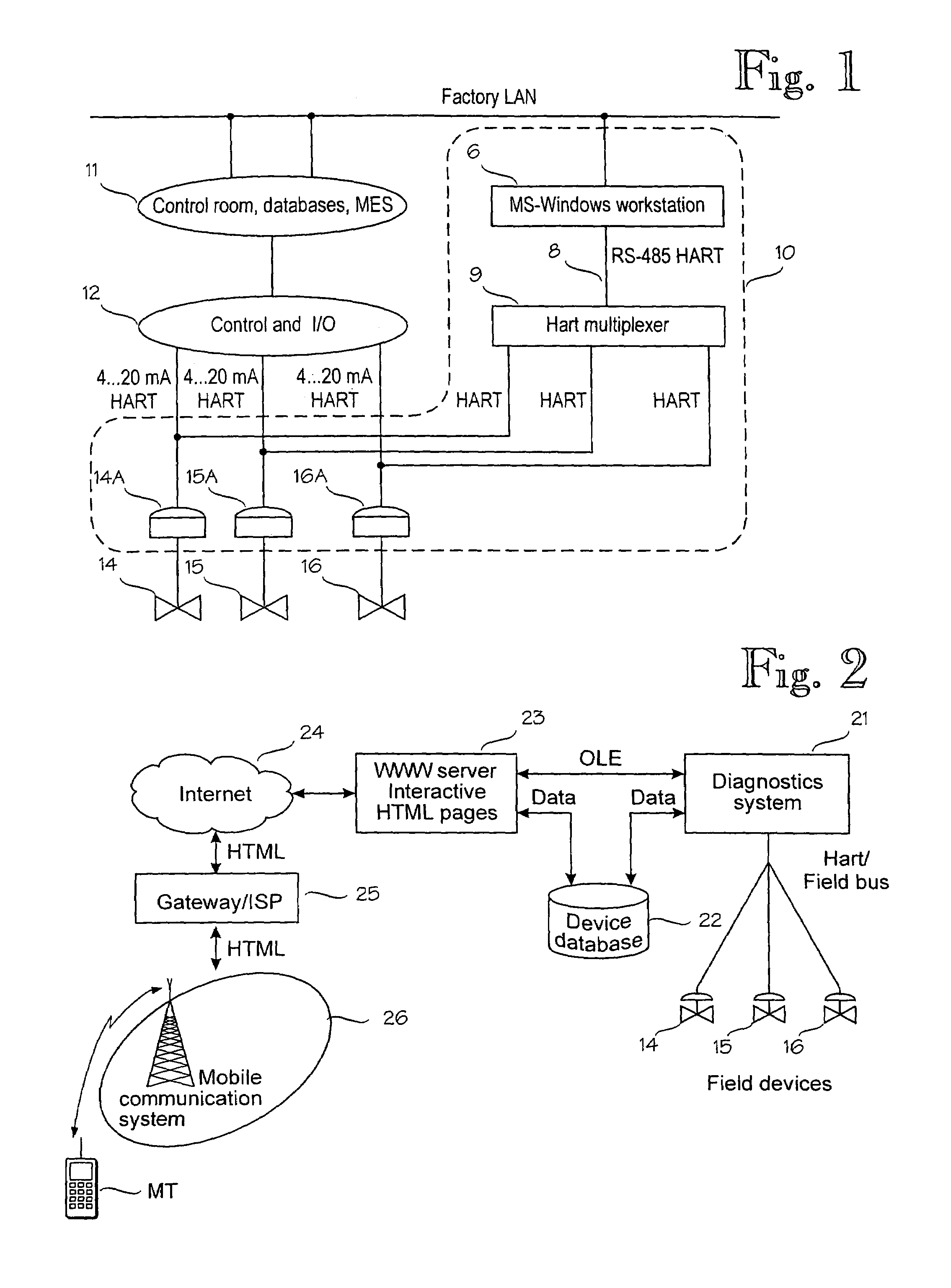
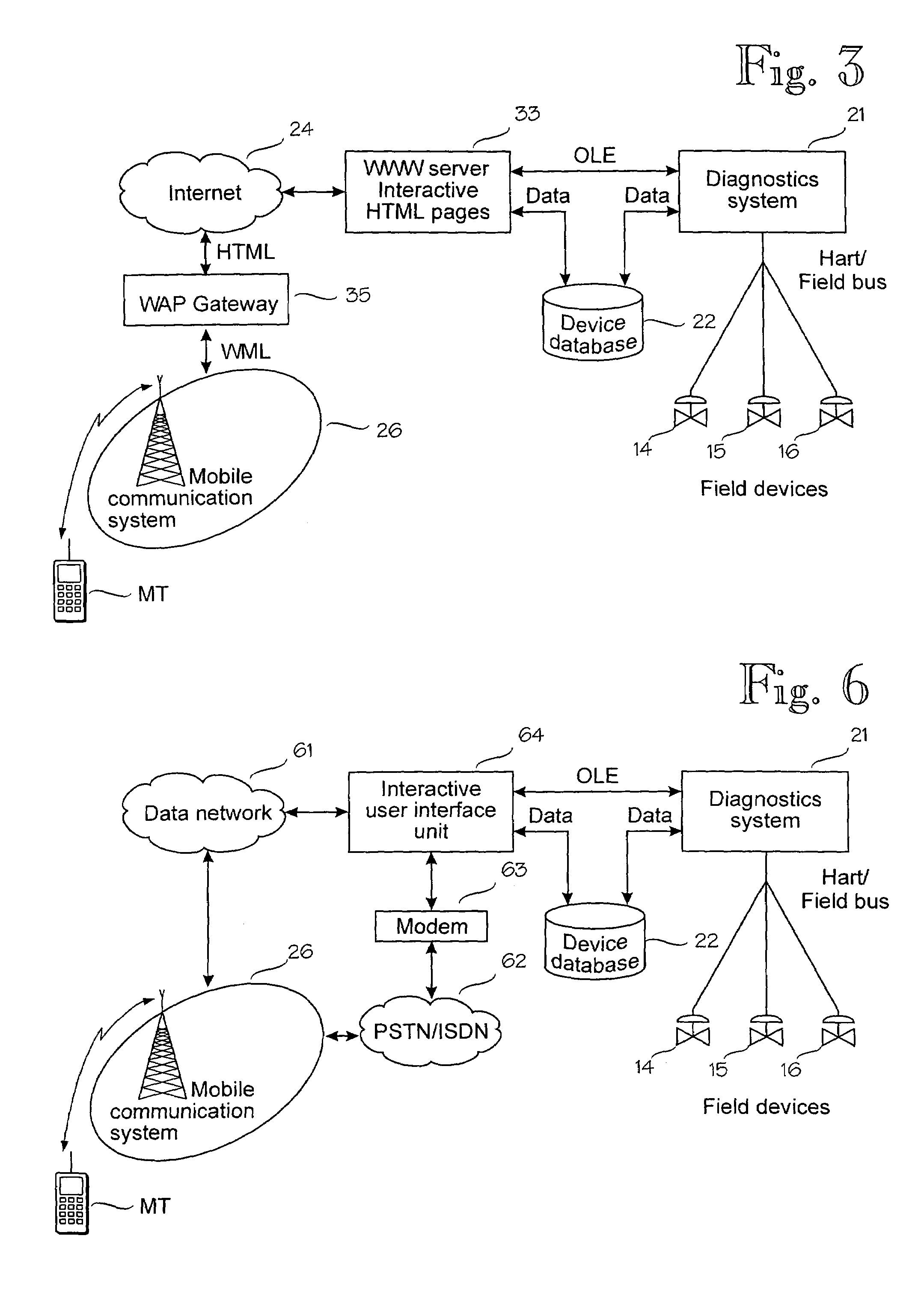
A mobile terminal is arranged to communicate over a cellular communication system with a control system connected to a plurality of field devices in an industrial process, in order to remote control, configure or monitor the field devices. The mobile terminal accesses through a dedicated data connection established over the cellular communication system an interactive user interface associated with the control system and arranged to utilize the configuration, control and management data of the control system. In the preferred embodiment, the interactive user interface is provided by a World Wide Web server.
Owner:METSO AUTOMATION OY
Methods and apparatus for establishing a computerized device tunnel connection
InactiveUS7673048B1Minimize bandwidth utilizationIncrease costError preventionTransmission systemsData connectionTelecommunications
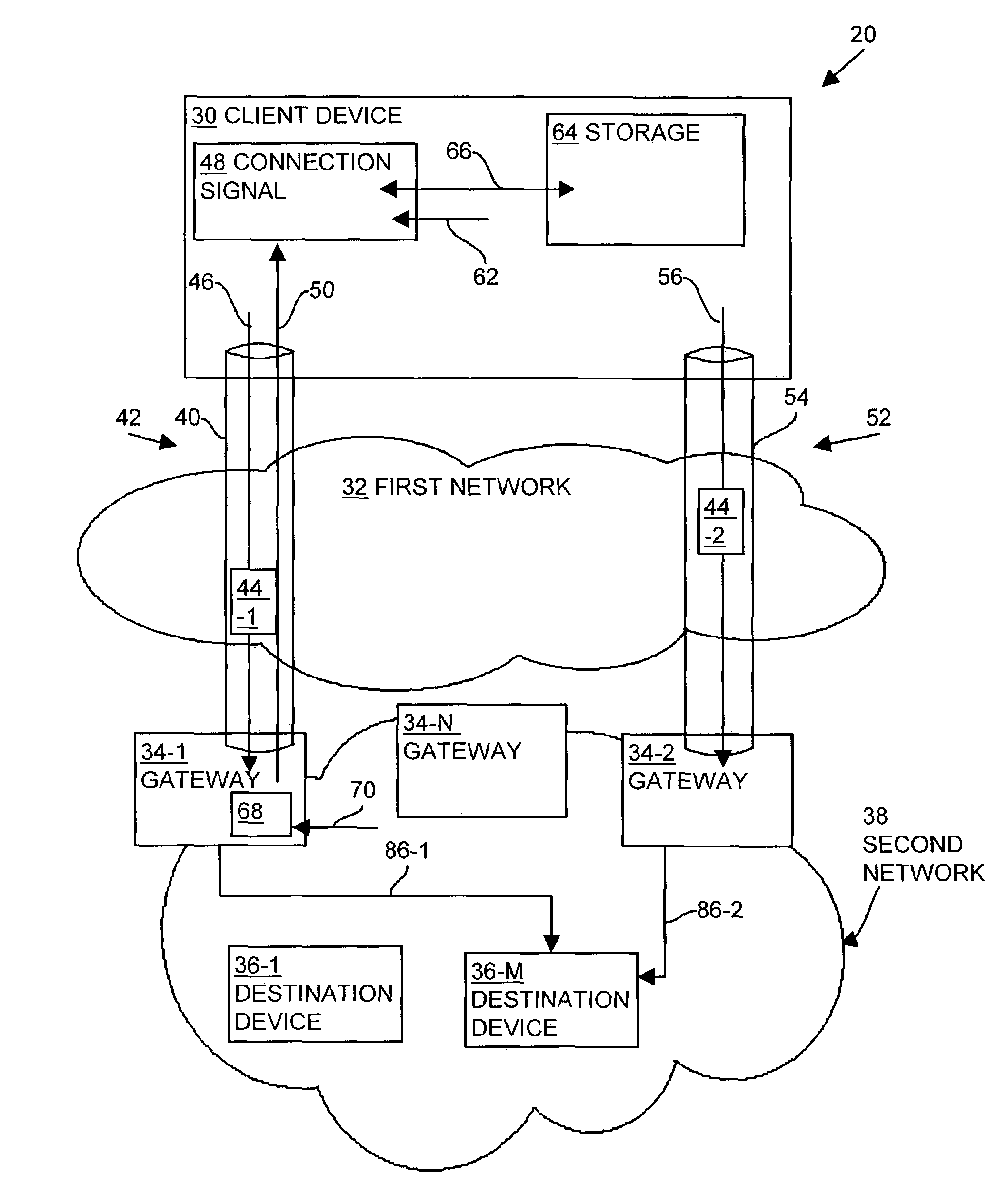
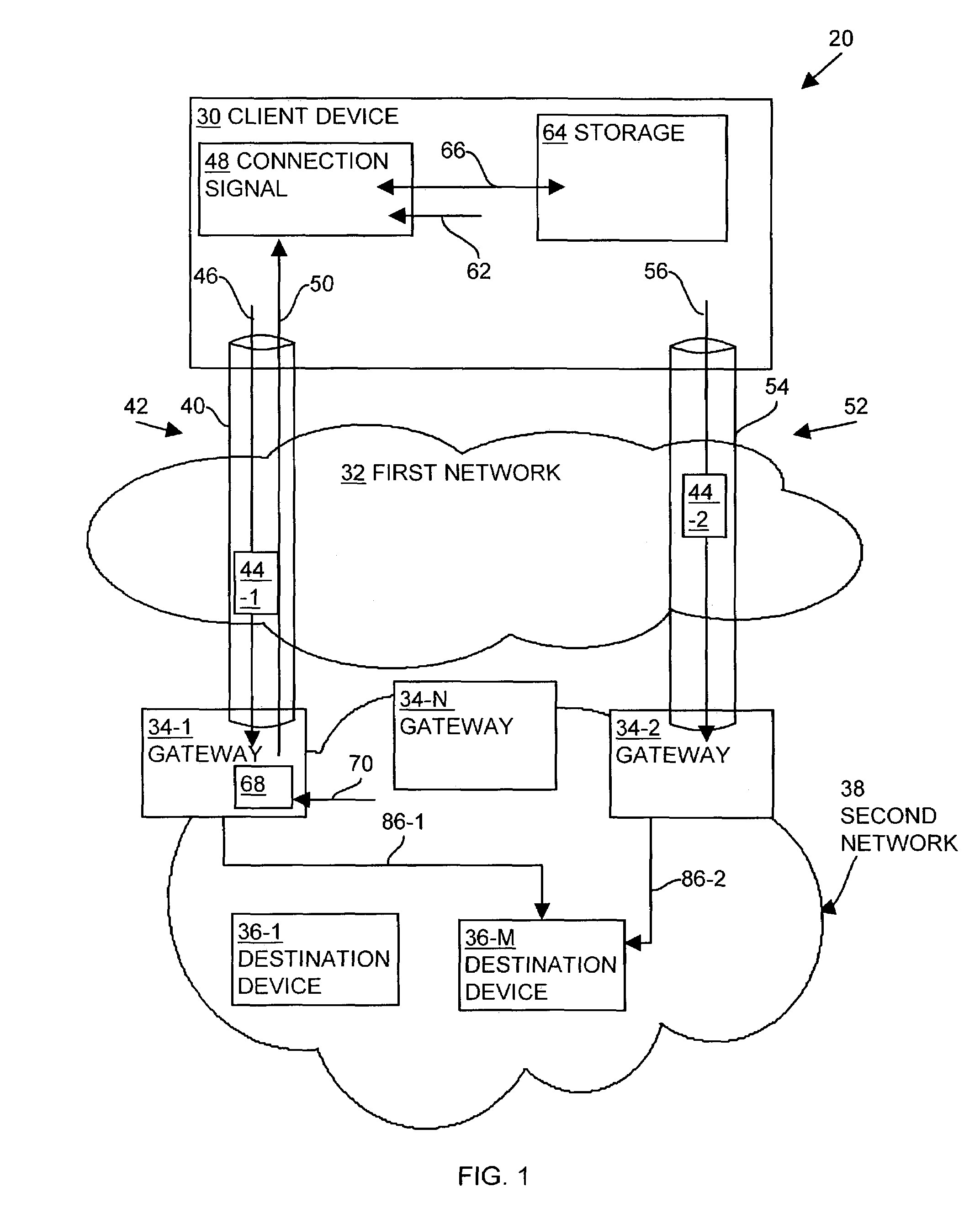
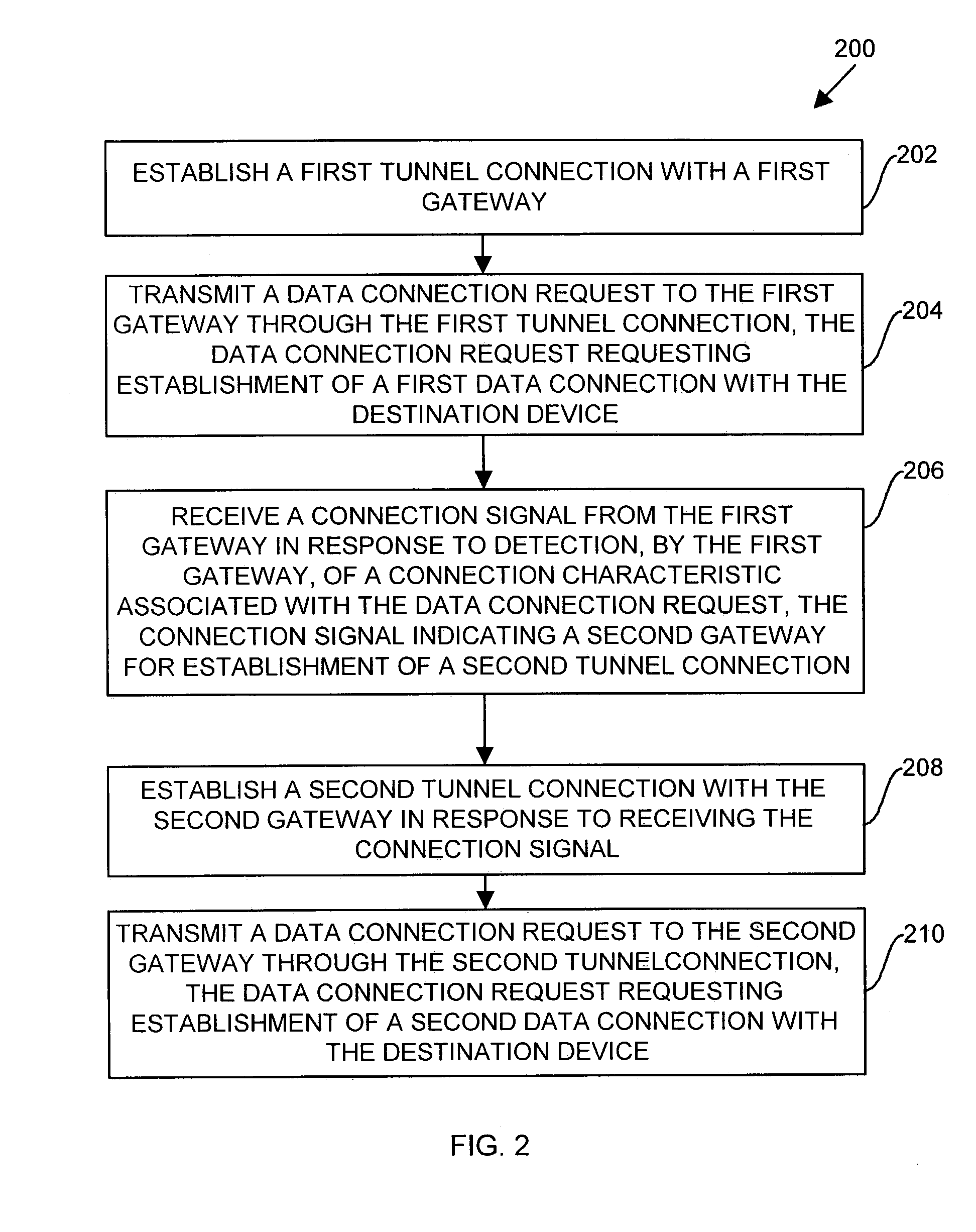
A client device establishes a first tunnel connection or tunnel, through a public network, with a first gateway of a private network and establishes, through the tunnel connection, a data connection with a destination device within the private network. The first gateway monitors or analyzes the geographic locations of the gateways associated with the private network relative to geographic location of the destination device associated with the data connection. Based upon such the monitoring, the first gateway transmits information to the client device relating to establishment of a second tunnel connection or tunnel with a second gateway of the private network. The client device establishes the second tunnel connection with the second gateway and establishes a data connection with the destination device through the second gateway. By establishing the second tunnel connection with the second gateway, the client device utilizes the bandwidth of the public network to exchange data with the destination device, thereby decreasing data transmission costs to the private network and decreasing private network latency.
Owner:CISCO TECH INC
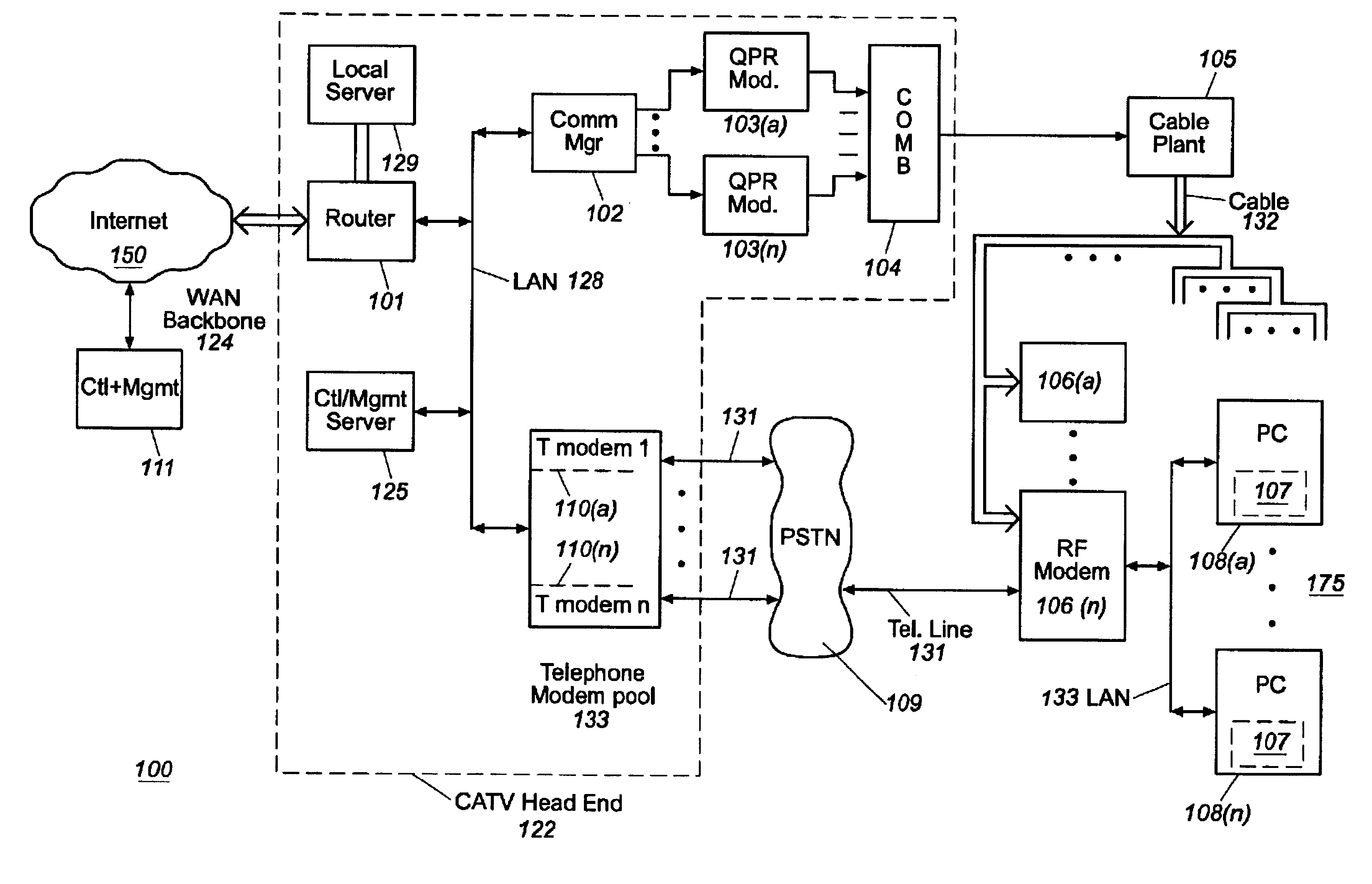
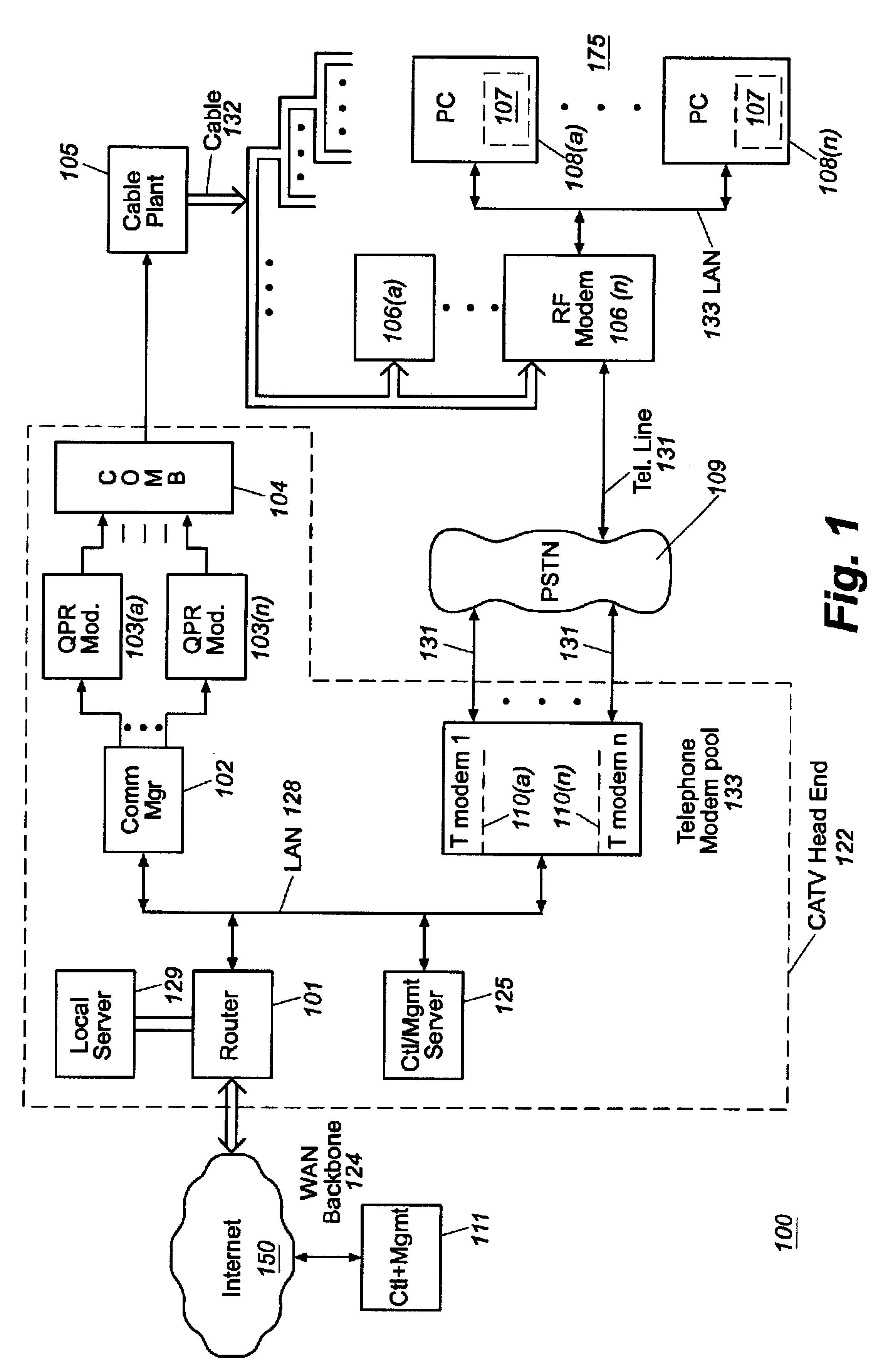
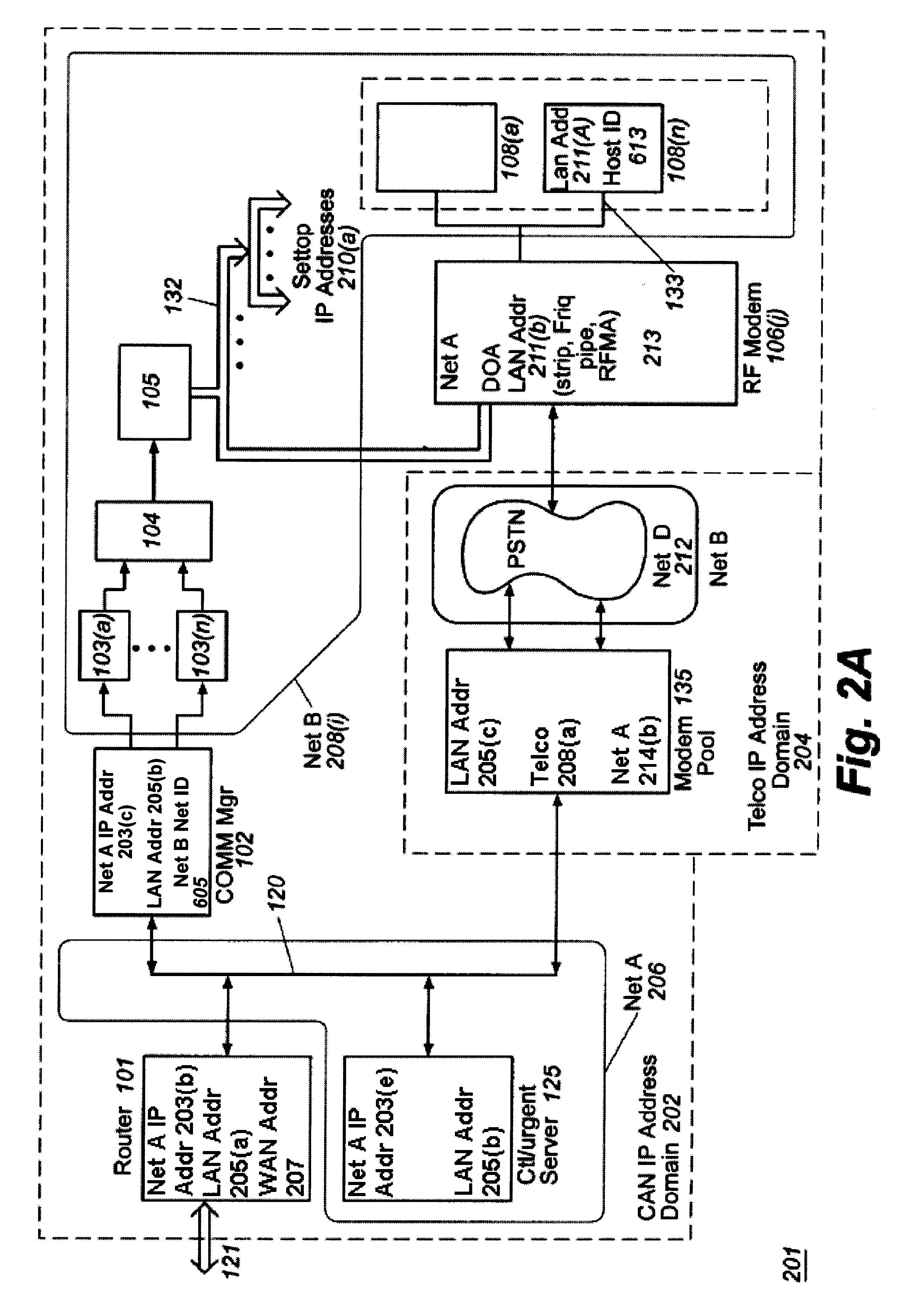
Usage statistics collection for a cable data delivery system
InactiveUS6308328B1Broadband local area networksBroadcast transmission systemsData connectionNetwork management
Apparatus for recording and collecting usage and other statistical data from components of a cable data network comprises a network manager for maintaining and collecting the statistics. Internet protocol addresses are associated with components of the network. The component maintains a software agent that manages a statistics database. Responsive to a manager request generated at a service provider defined time interval, the component software agent provides the usage statistics to the network manager in real-time during an Internet session with a host. When the host to Internet or other data connection is torn down due to failure, disconnect or inactivity time-out, remaining usage statistics data is collected and the session duration updated with the time of tear down. Usage statistics collected include the amount of data transferred to / from a host, the amount of data that is discarded due to insufficient resource capacity and amount of data that cannot be corrected despite forward error correction used in a downstream high capacity channel to the host. Data traps may be defined and downloaded to components of the network for implementation. As a result, billing of users of the cable data network can be usage sensitive and determined based on actual data transferred (including credit given for errored data) and / or time sensitive based on session duration.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com