Transmission of packet data over a network with a security protocol
a security protocol and packet data technology, applied in the field of transmission of packet data over a network, can solve the problems of low throughput of secure shell protocol, viruses on ip-based networks, malicious crackers and eavesdroppers,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
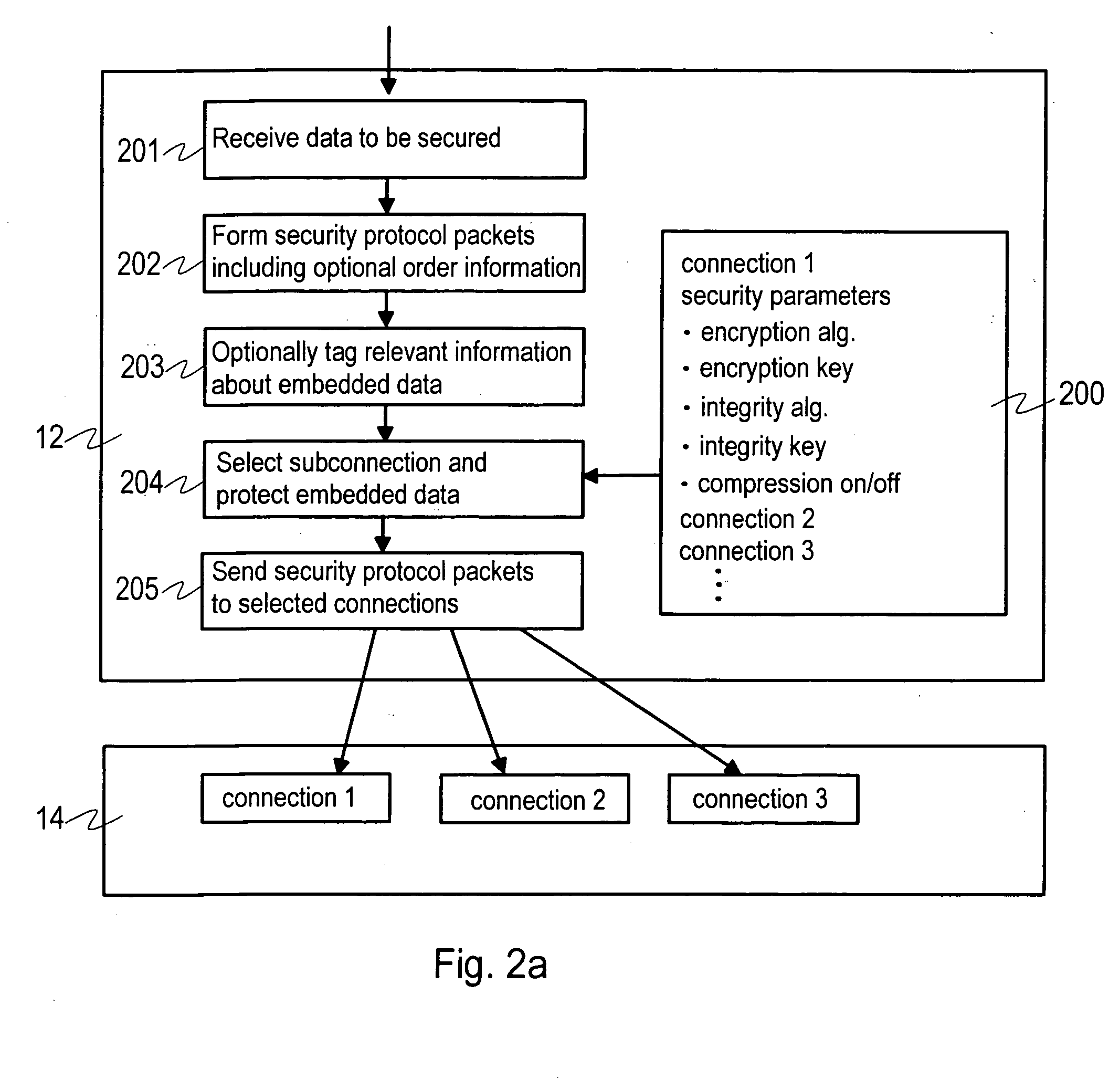
[0030] In the following, embodiments of the invention are often discussed in detail with reference to the Secure Shell protocol, but it is appreciated that embodiments of the invention may be applicable in connection with any security protocol using a reliable data transport protocol.
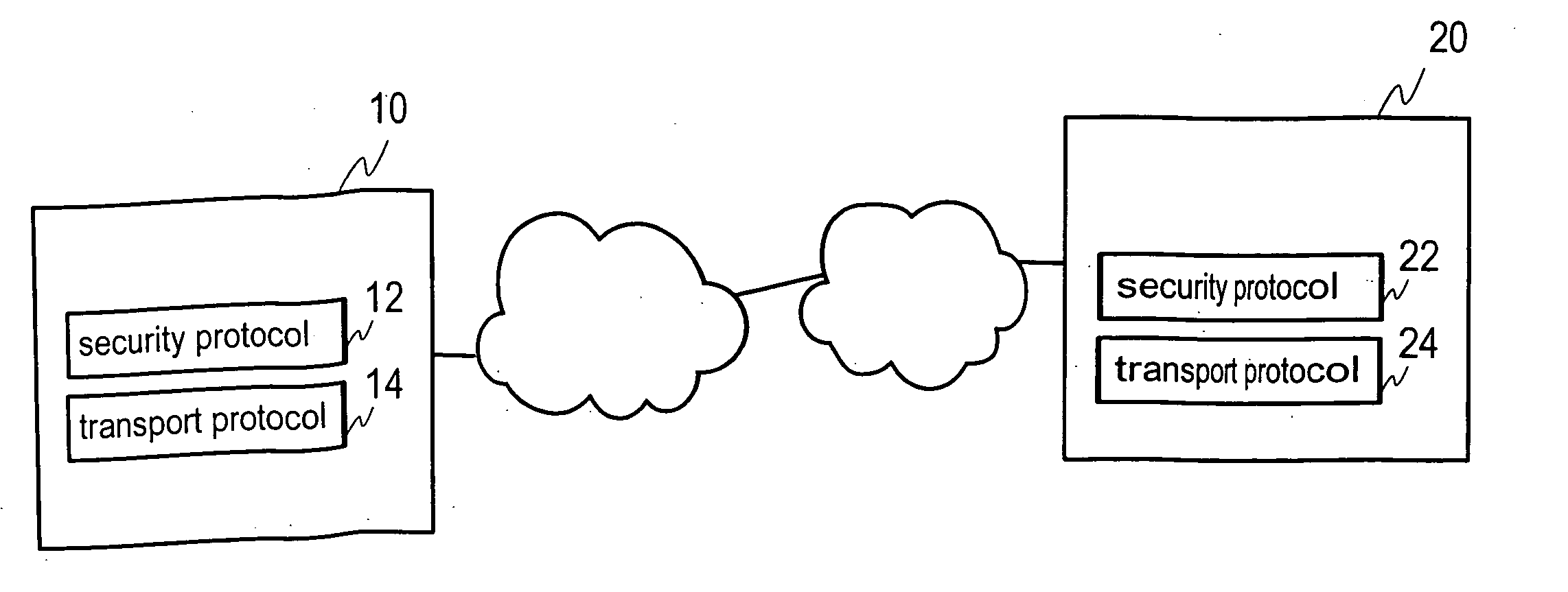
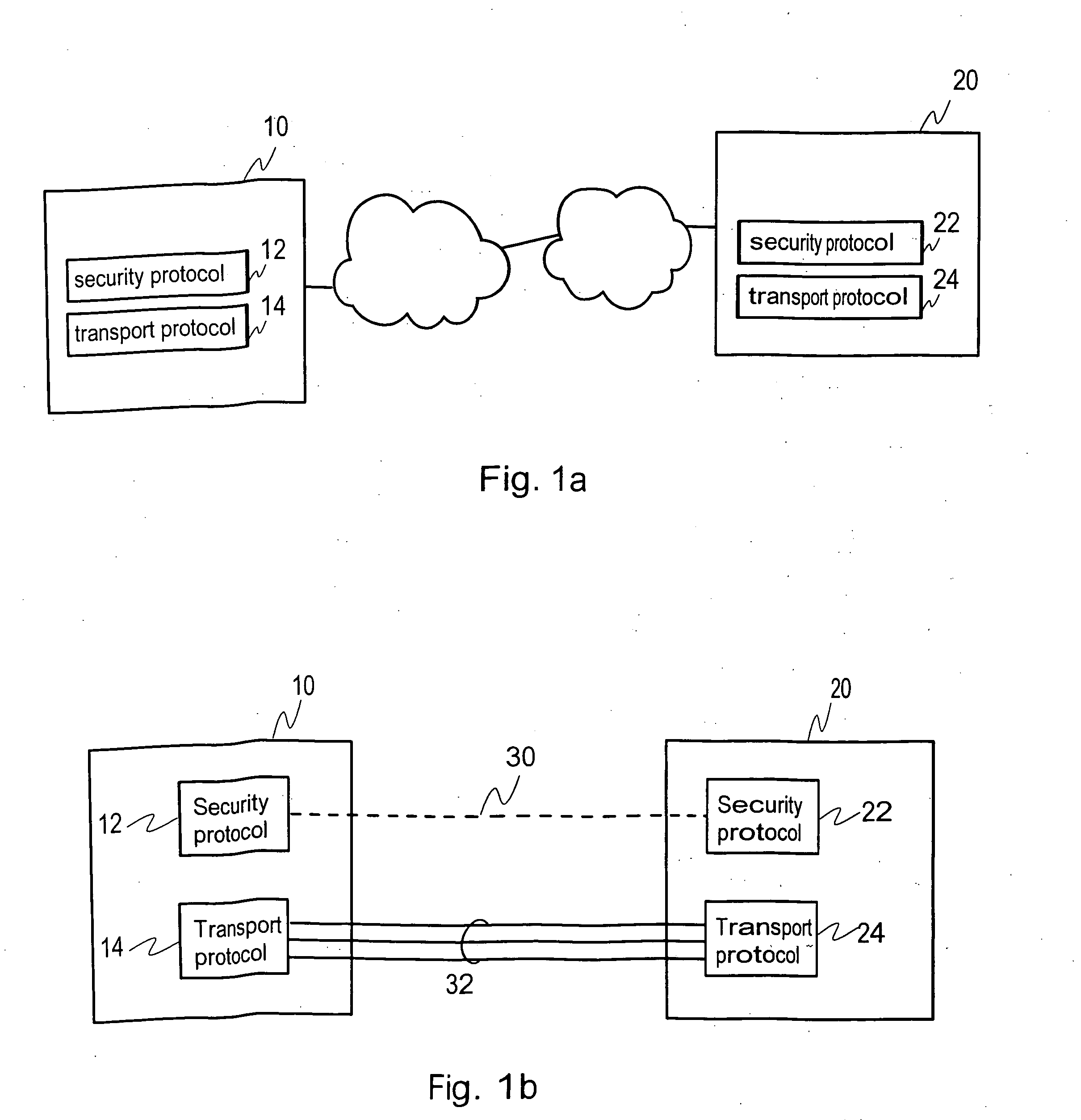
[0031]FIG. 1a shows schematically a communication network and two nodes 10, 20 communicating via the communication network, for example via the Internet. The communication network may include various subnetworks, as shown in FIG. 1a. A security protocol is used to provide secure data transport between the nodes 10 and 20 over the communication network. One of the nodes is typically a server and the other node is a client. The client contacts the server for forming a secure connection between the nodes.
[0032]FIG. 1b shows schematically, as an example, a security protocol session (or a security-protocol connection) 30 between two nodes 10, 20 in accordance with an embodiment of the present invention. Ea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com