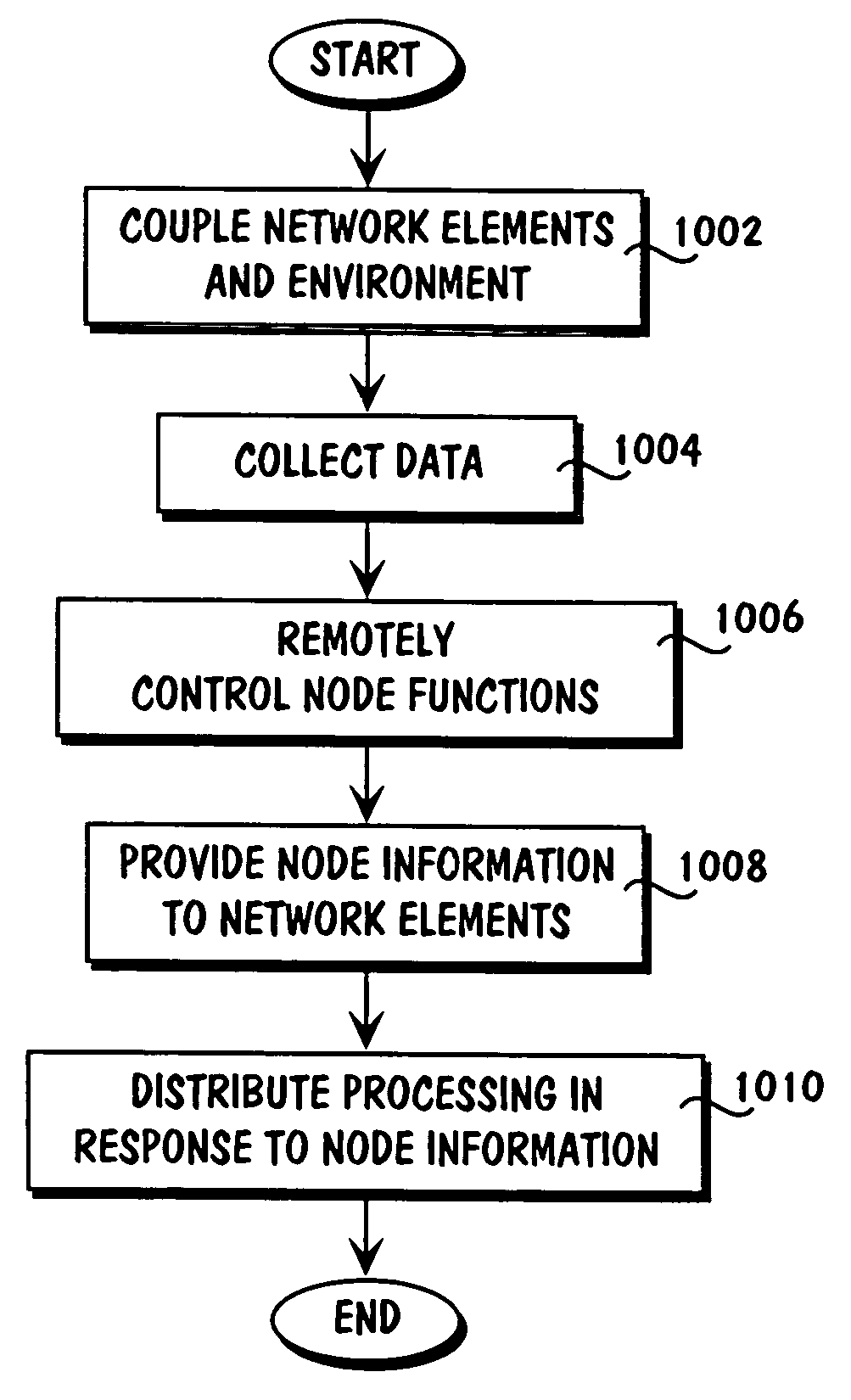
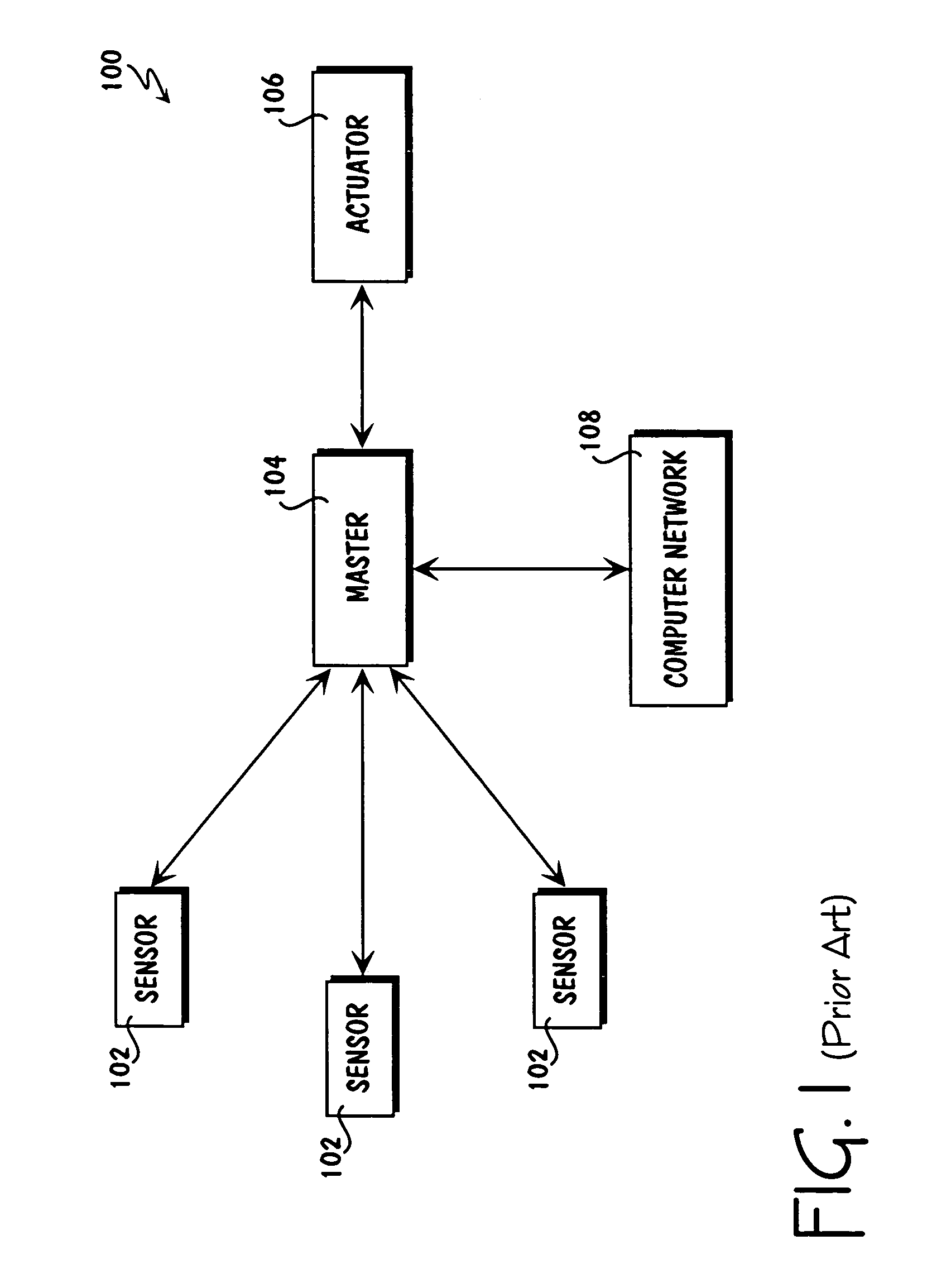
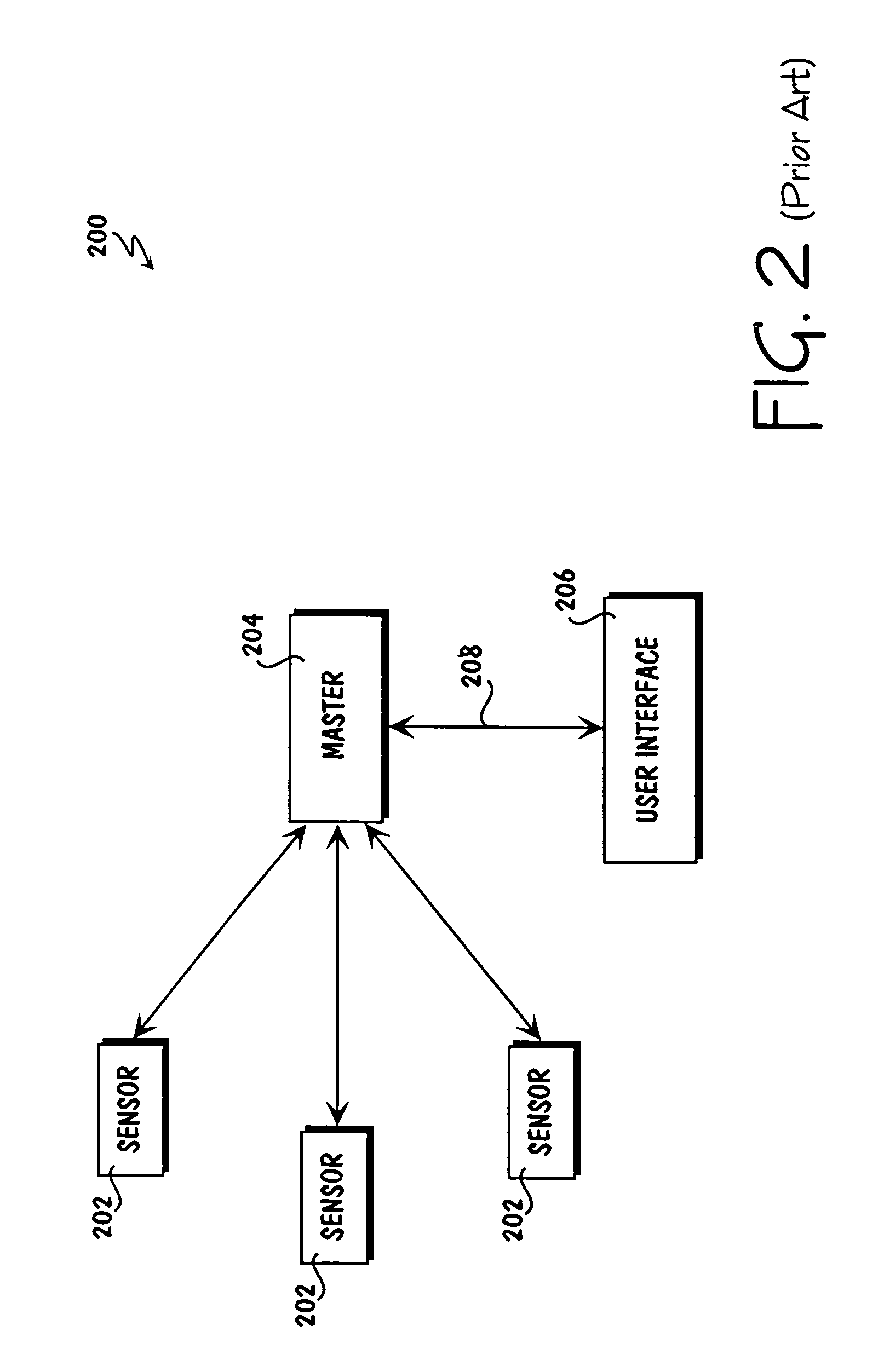
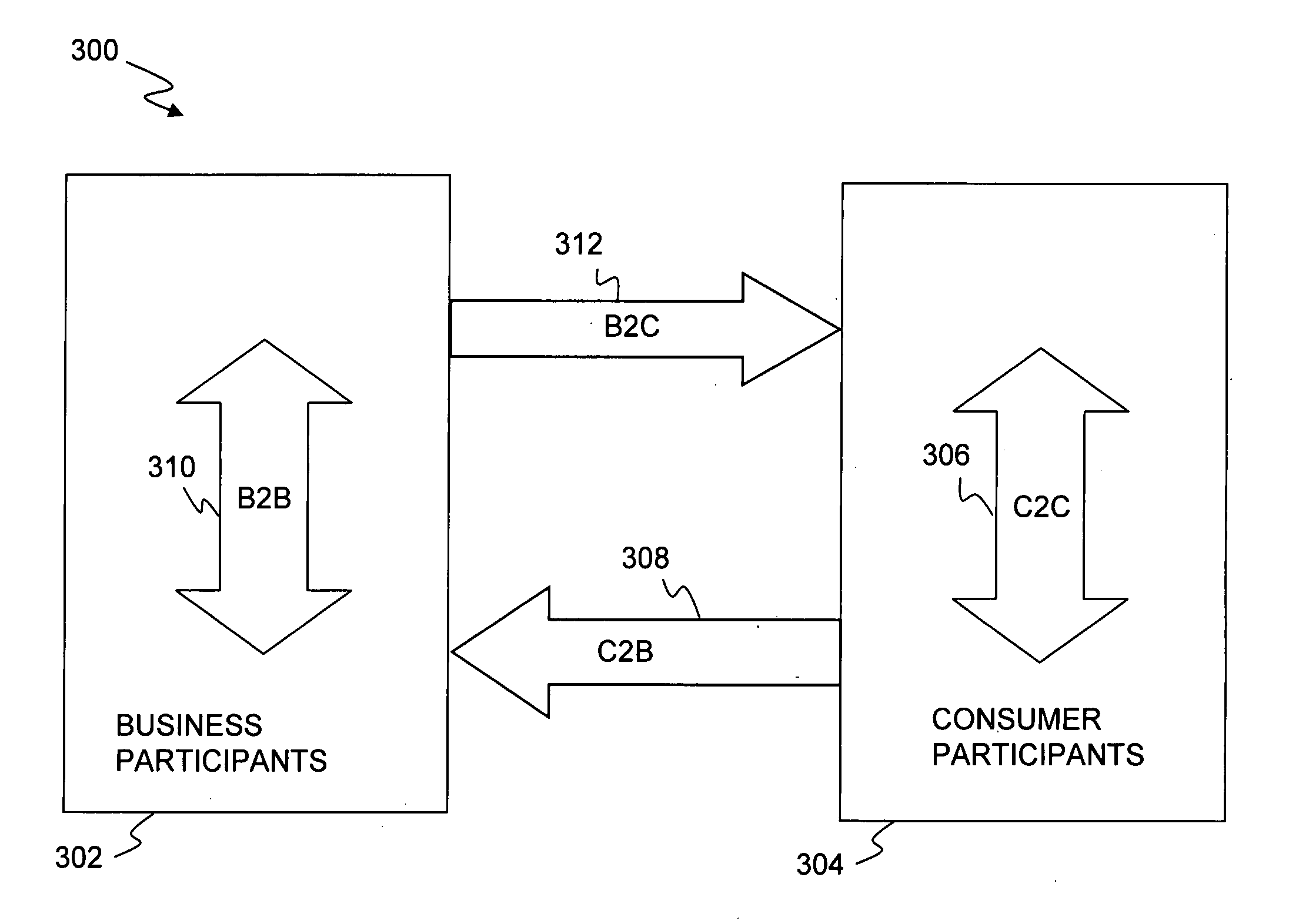
Patents
Literature
95491results about "Memory systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
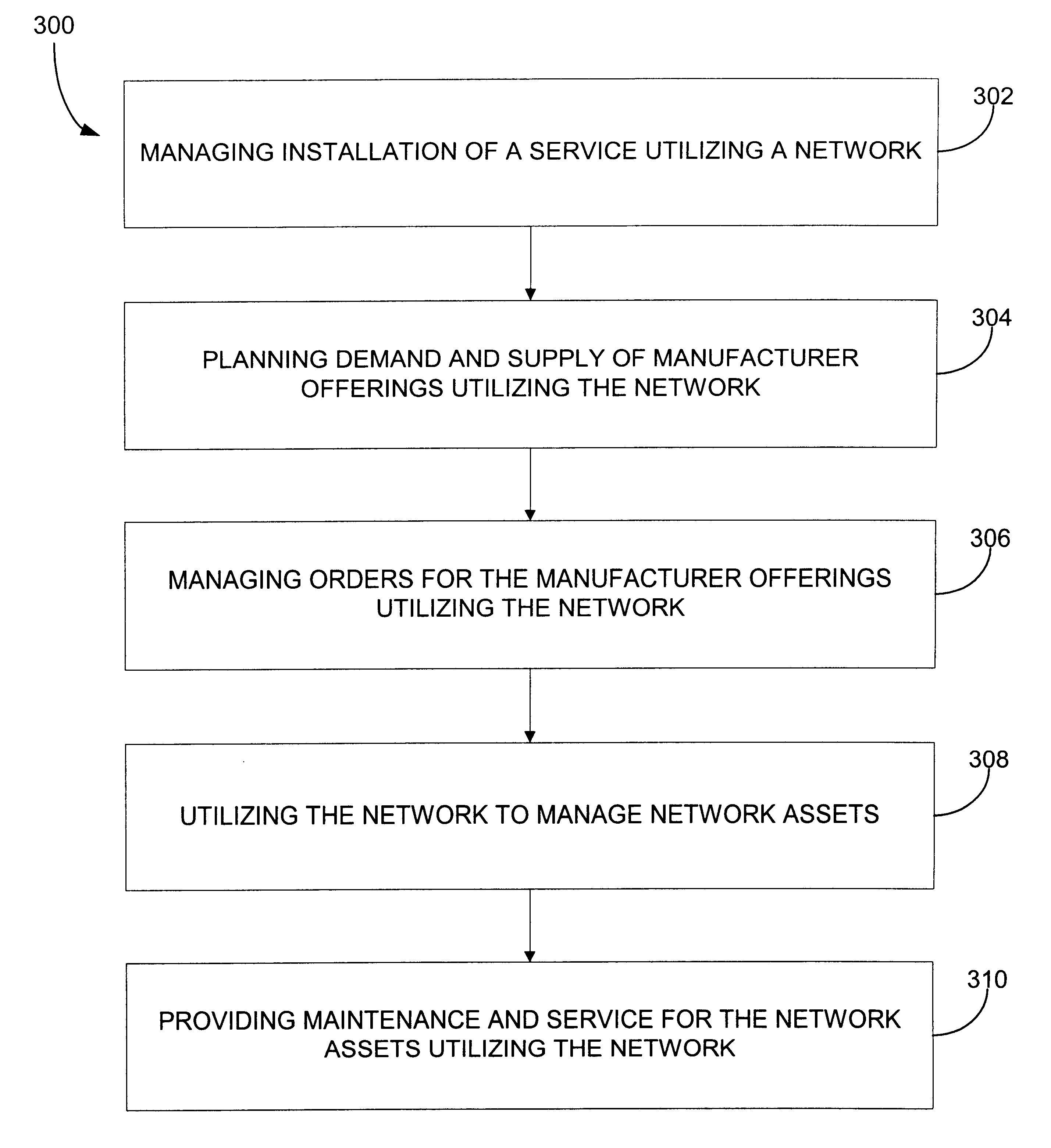
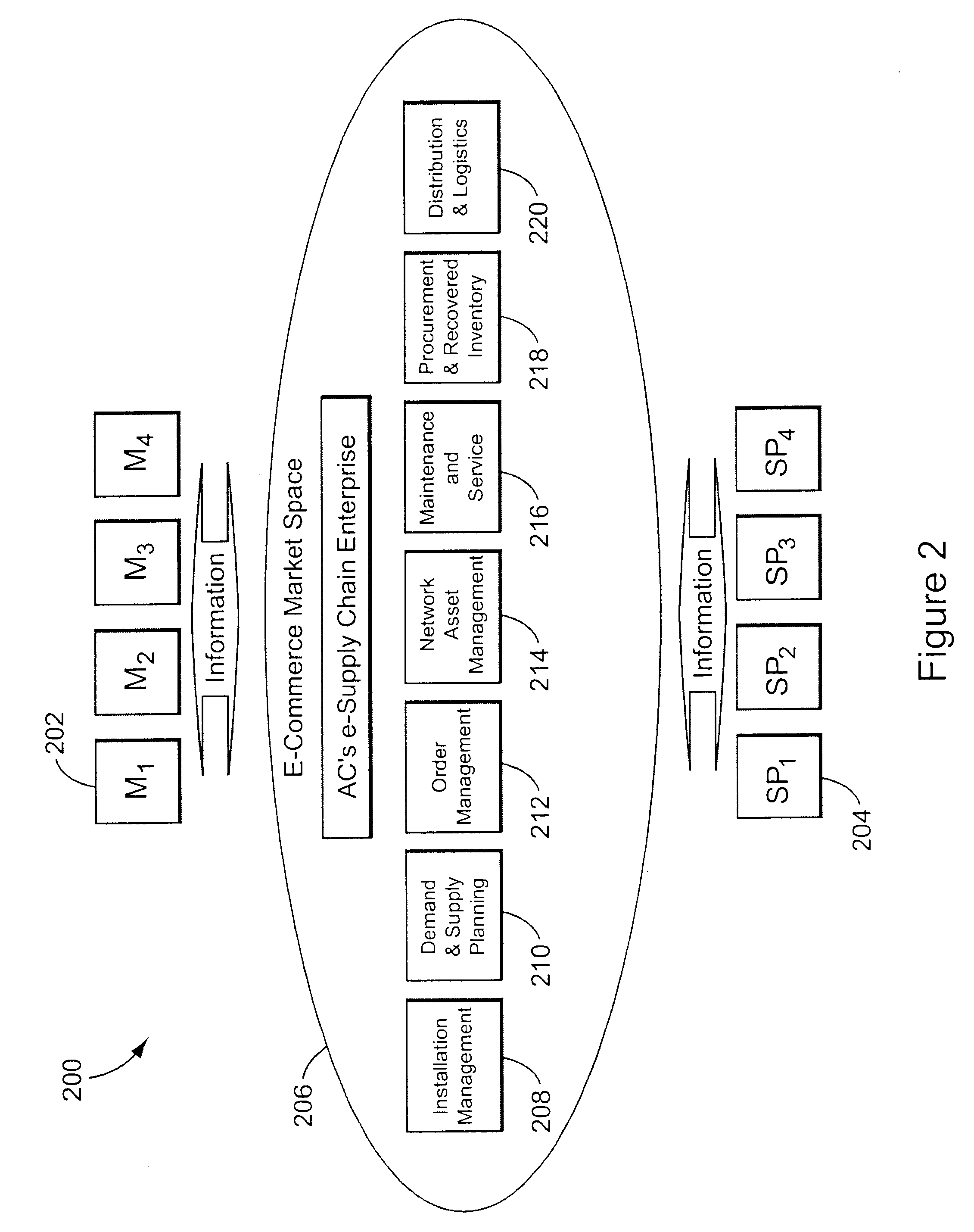
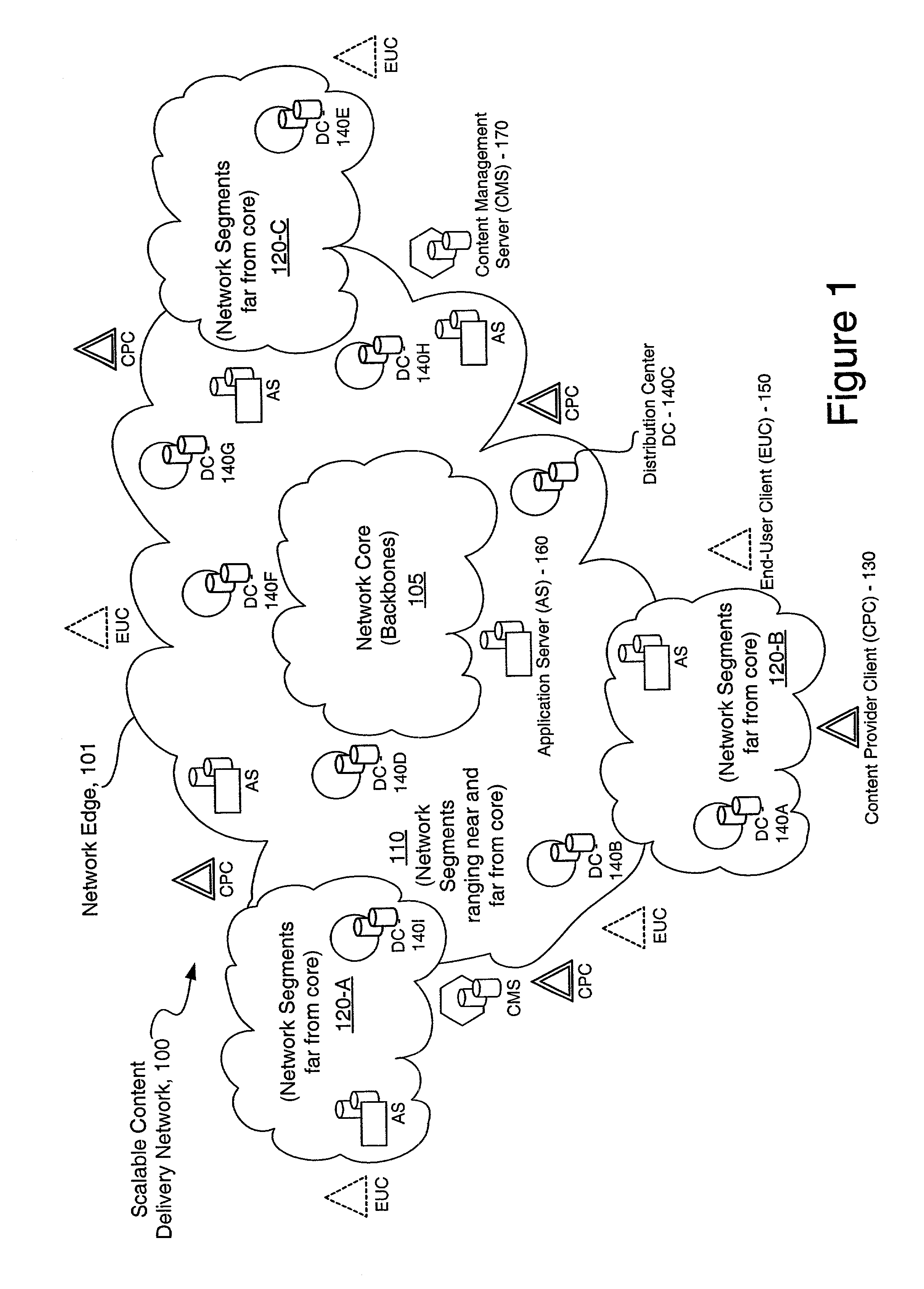
Providing collaborative installation management in a network-based supply chain environment
InactiveUS6606744B1Interconnection arrangementsSpecial service for subscribersWeb applicationService provision
A system, method and article of manufacture are provided for collaborative installation management in a network-based supply chain environment. According to an embodiment of the invention, telephone calls, data and other multimedia information are routed through a network system which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. The system includes integrated Internet Protocol (IP) telephony services allowing a user of a web application to communicate in an audio fashion in-band without having to pick up another telephone. Users can click a button and go to a call center through the network using IP telephony. The system invokes an IP telephony session simultaneously with the data session, and uses an active directory lookup whenever a user uses the system. Users include service providers and manufacturers utilizing the network-based supply chain environment.
Owner:ACCENTURE GLOBAL SERVICES LTD
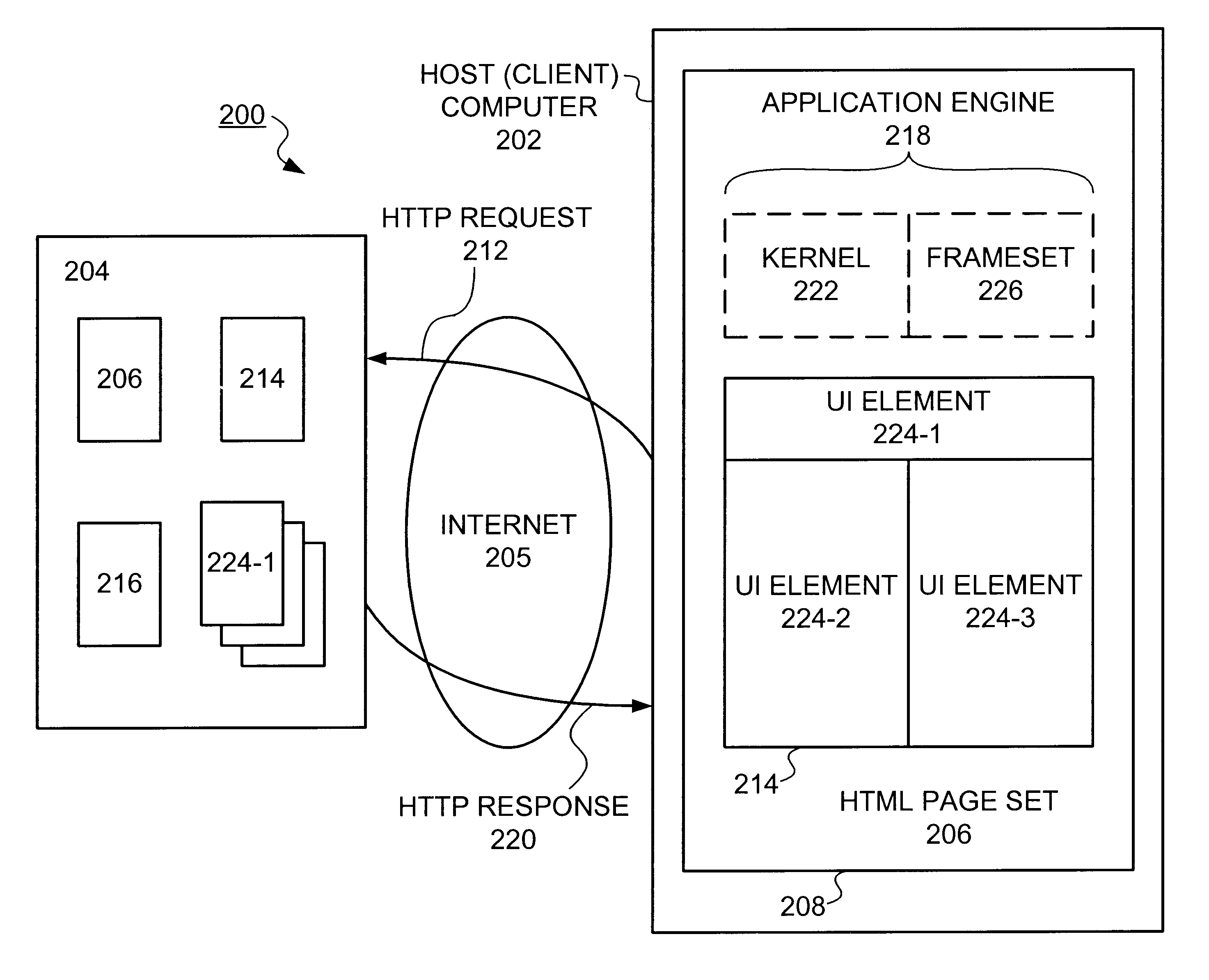
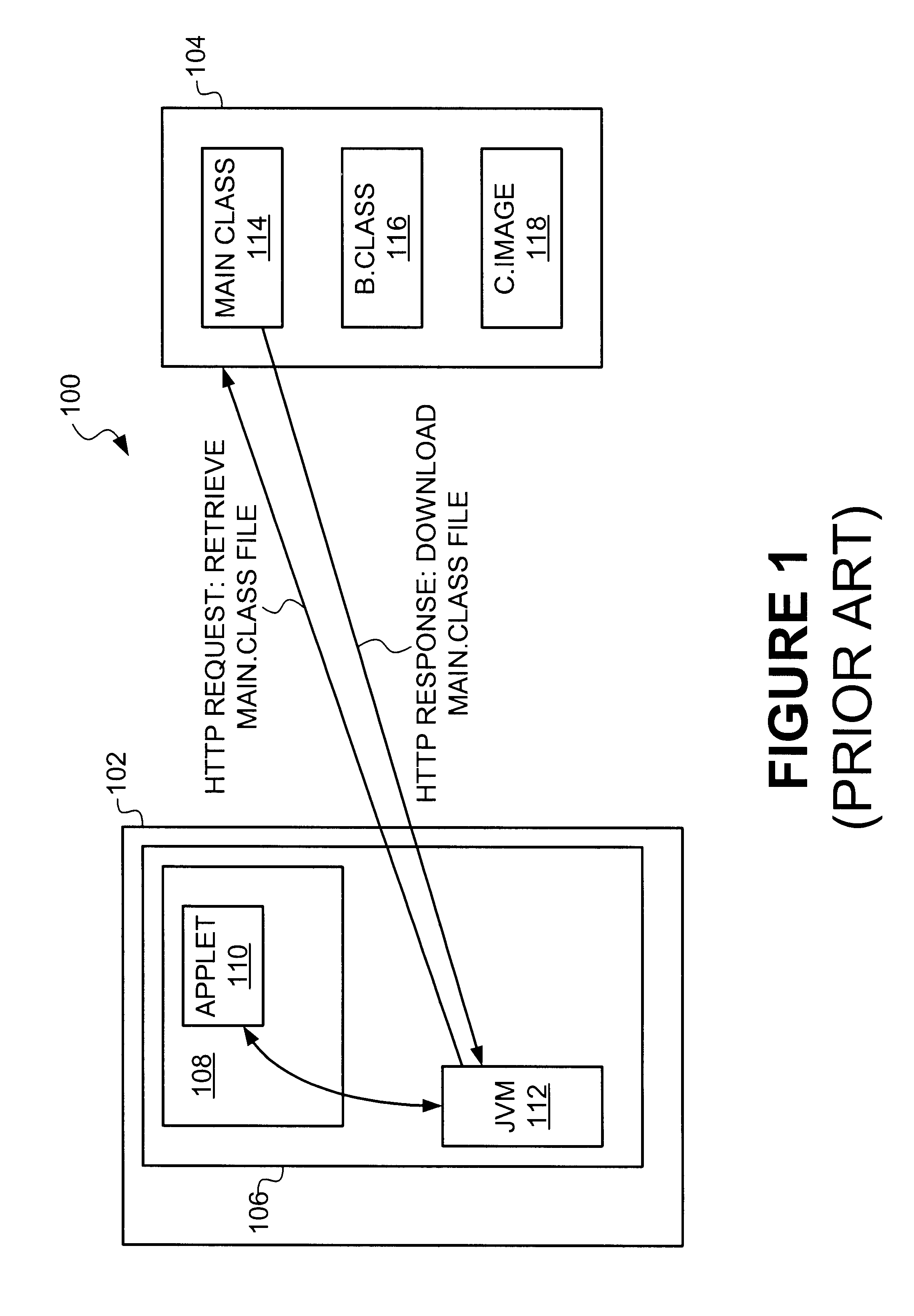
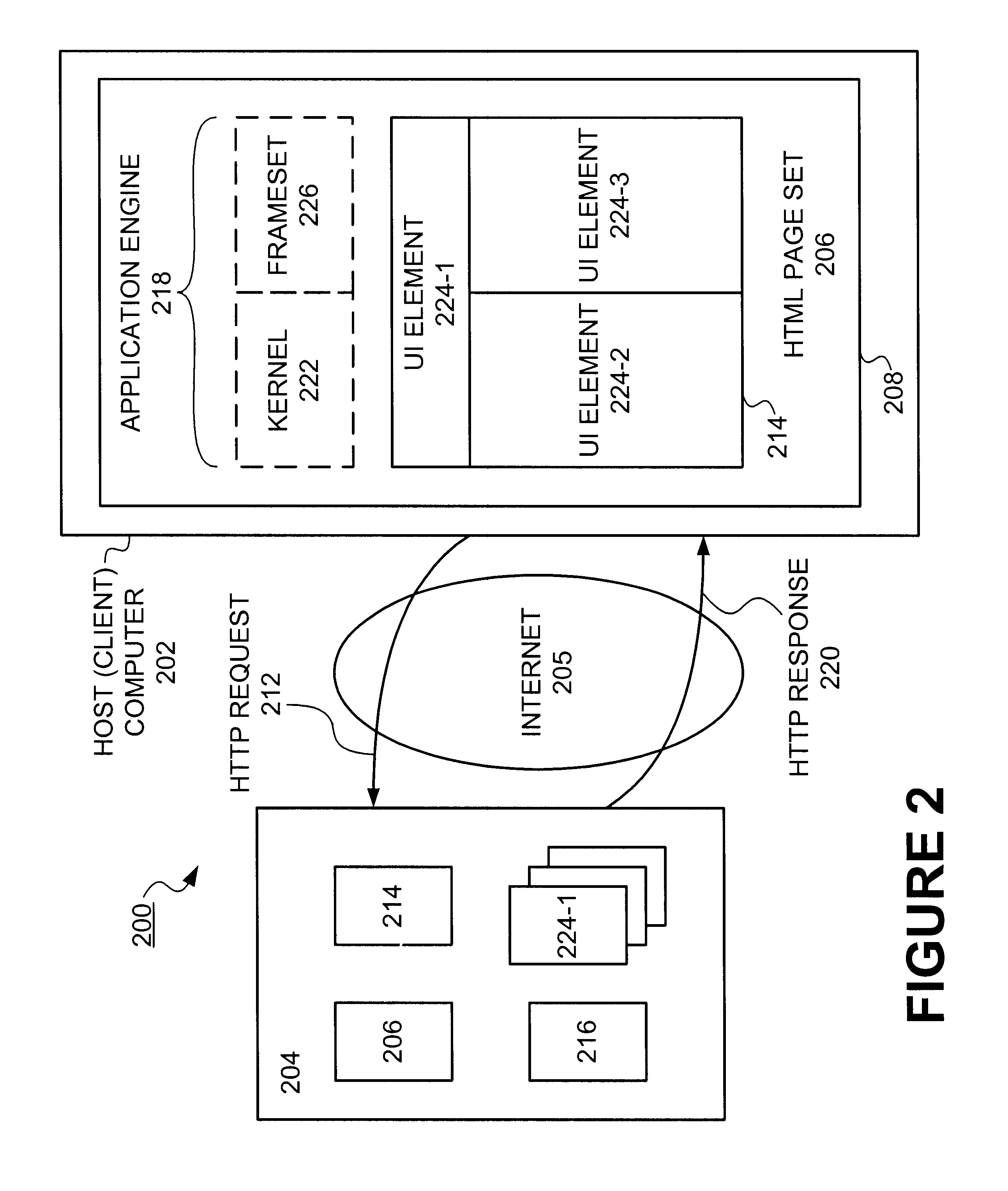
Apparatus and system for efficient delivery and deployment of an application
InactiveUS6393605B1Digital computer detailsMultiprogramming arrangementsClient-sideApplication software
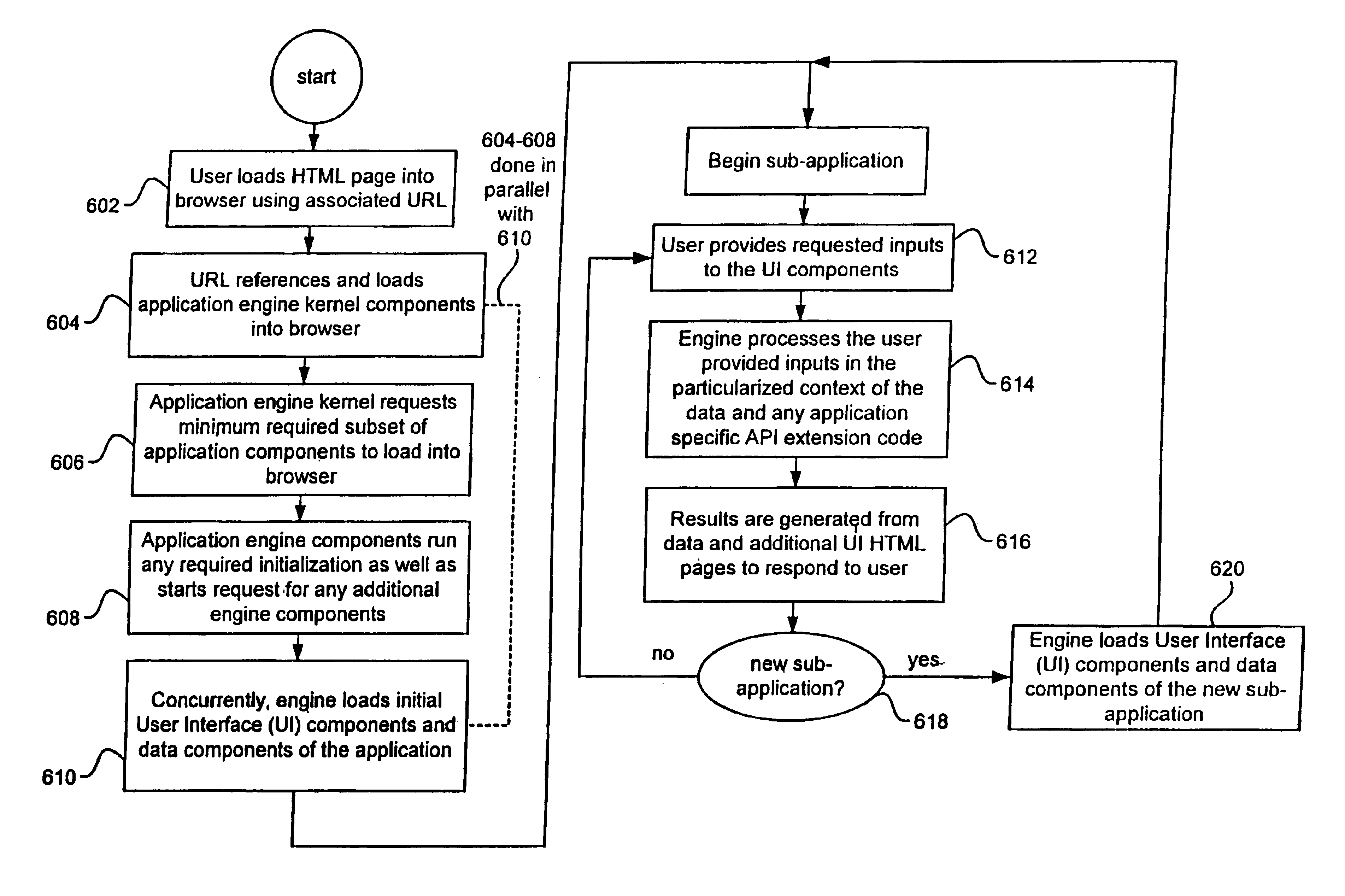
Methods and apparatus for deploying a generic application engine in a browser program executing on a client platform are described. As a method, an application engine kernel is formed in the browser program that is independent of the client platform and the browser program concurrently with loading user interface (UI) components and corresponding data components associated with the application engine. A minimum required subset of application engine components are then loaded by the kernel in order to process any initial user requests.
Owner:ORACLE INT CORP
Adaptive pattern recognition based control system and method
InactiveUS6400996B1Minimize timeEasy to implementError preventionFrequency-division multiplex detailsData streamSmart house
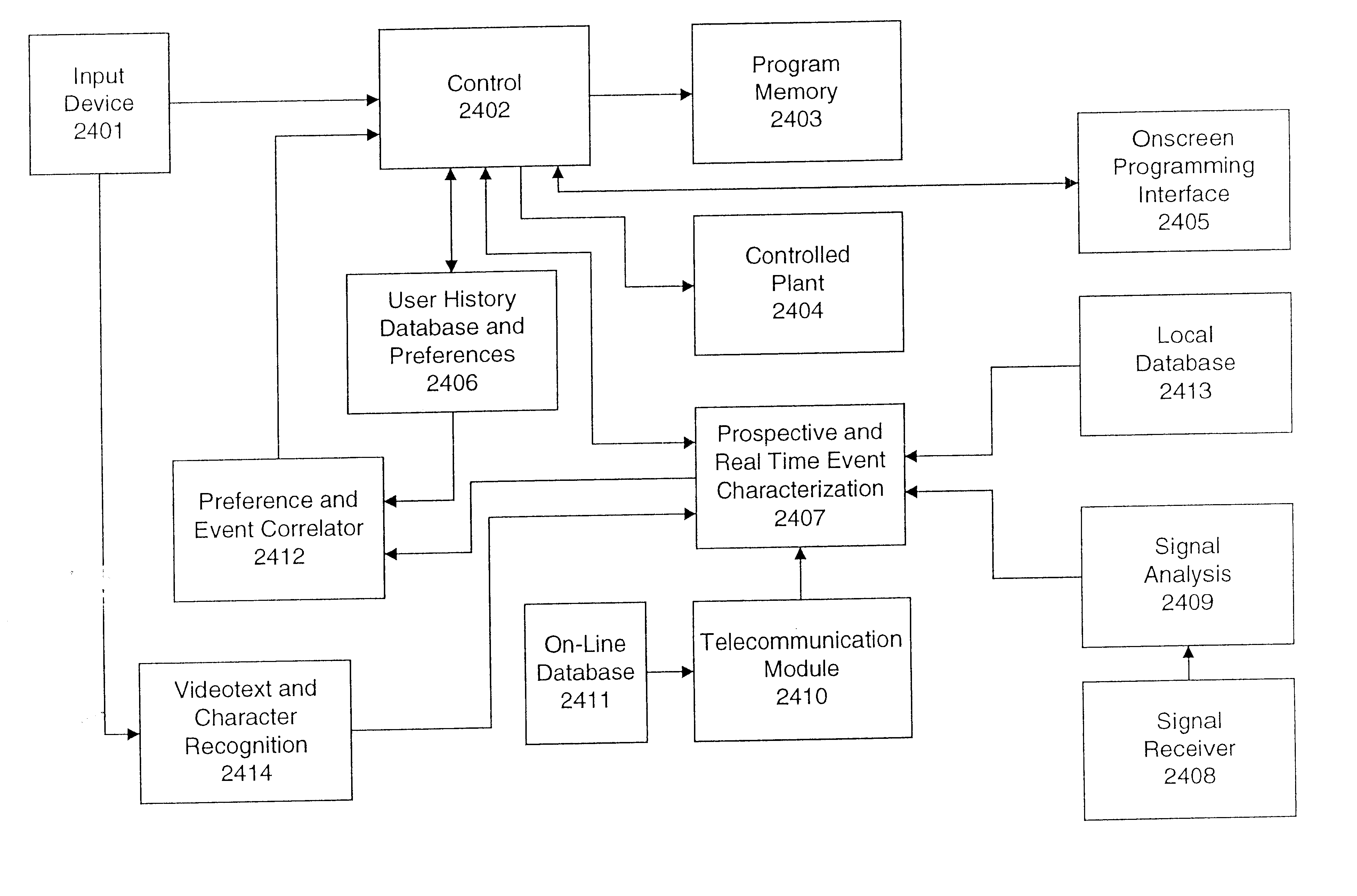
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation that may be efficiently processed to determine correspondence. Applications of the interface and system include a video cassette recorder (VCR), medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Techniques for managing multiple threads in a browser environment
Techniques for managing multiple threads in an asynchronous environment, such as a browser, are described. As a method, instantiating an event thread in response to a user event by a shell event handler block that provides shell functions for a user event. Once the event thread as been instantiated, managing the event thread by a generic thread manager block that provides a plurality of multithread management functions for the shell event handler. When required, blocking and unblocking the event thread by a blocking system that is arranged to block and unblock threads.
Owner:ORACLE INT CORP
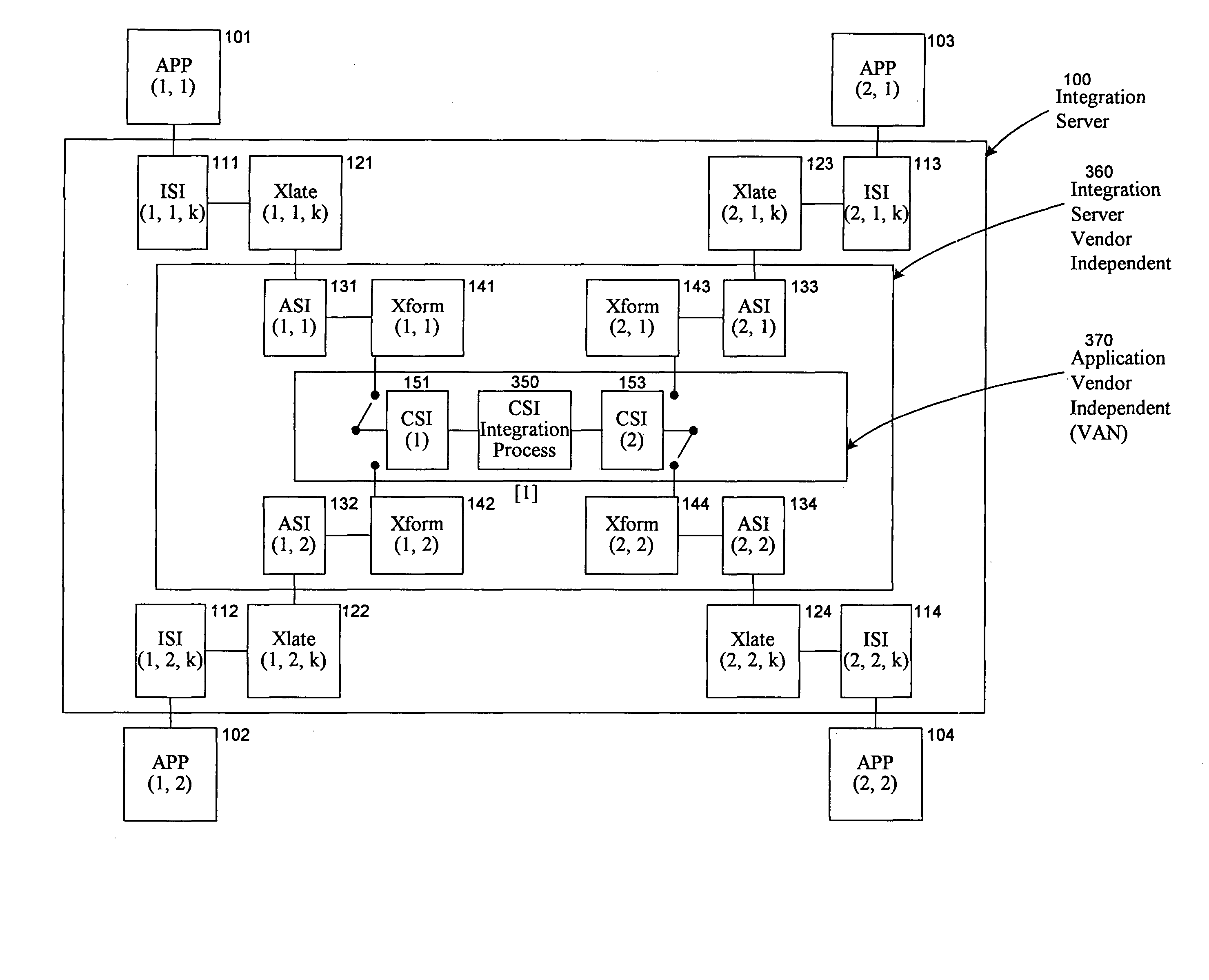
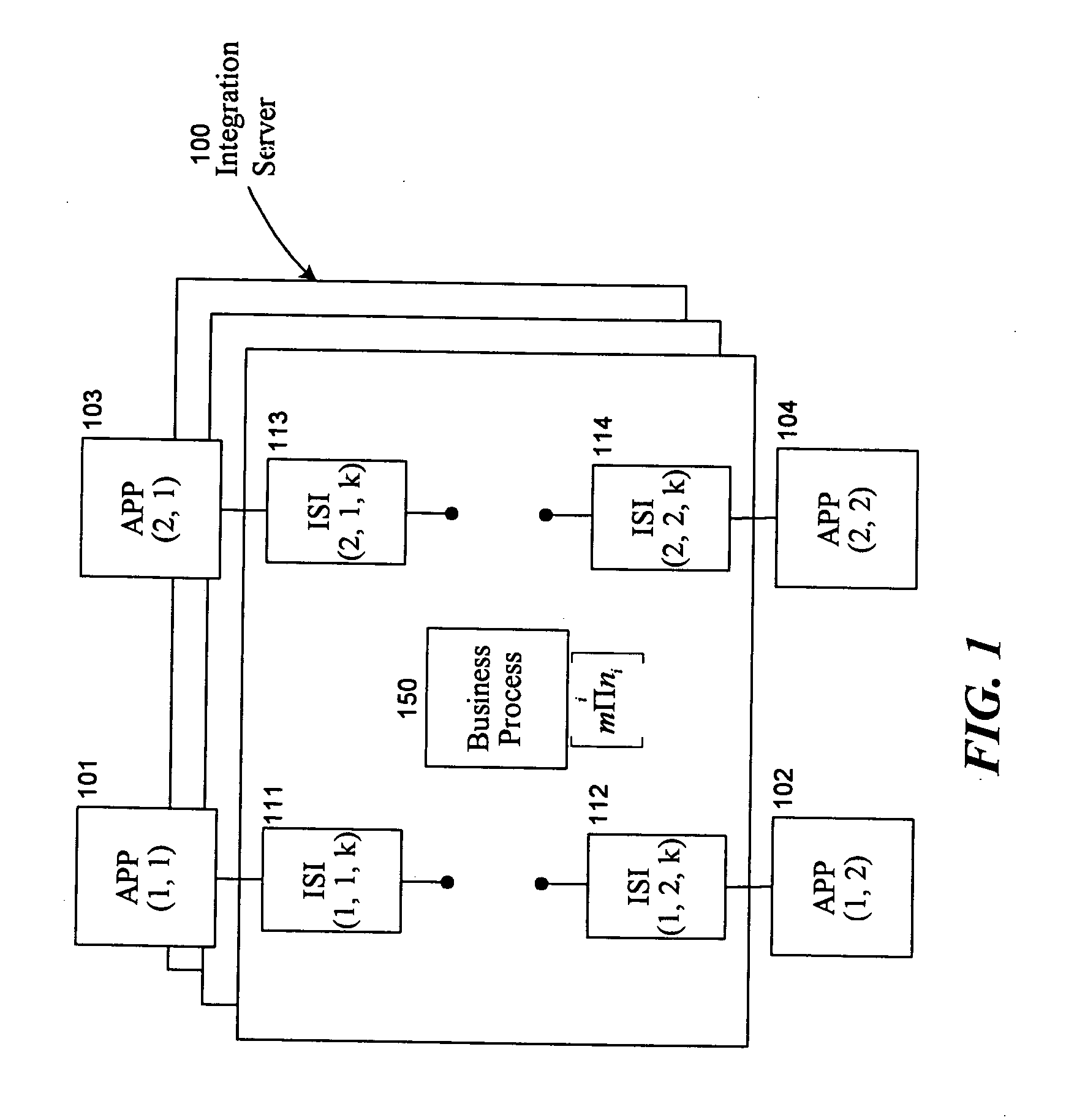
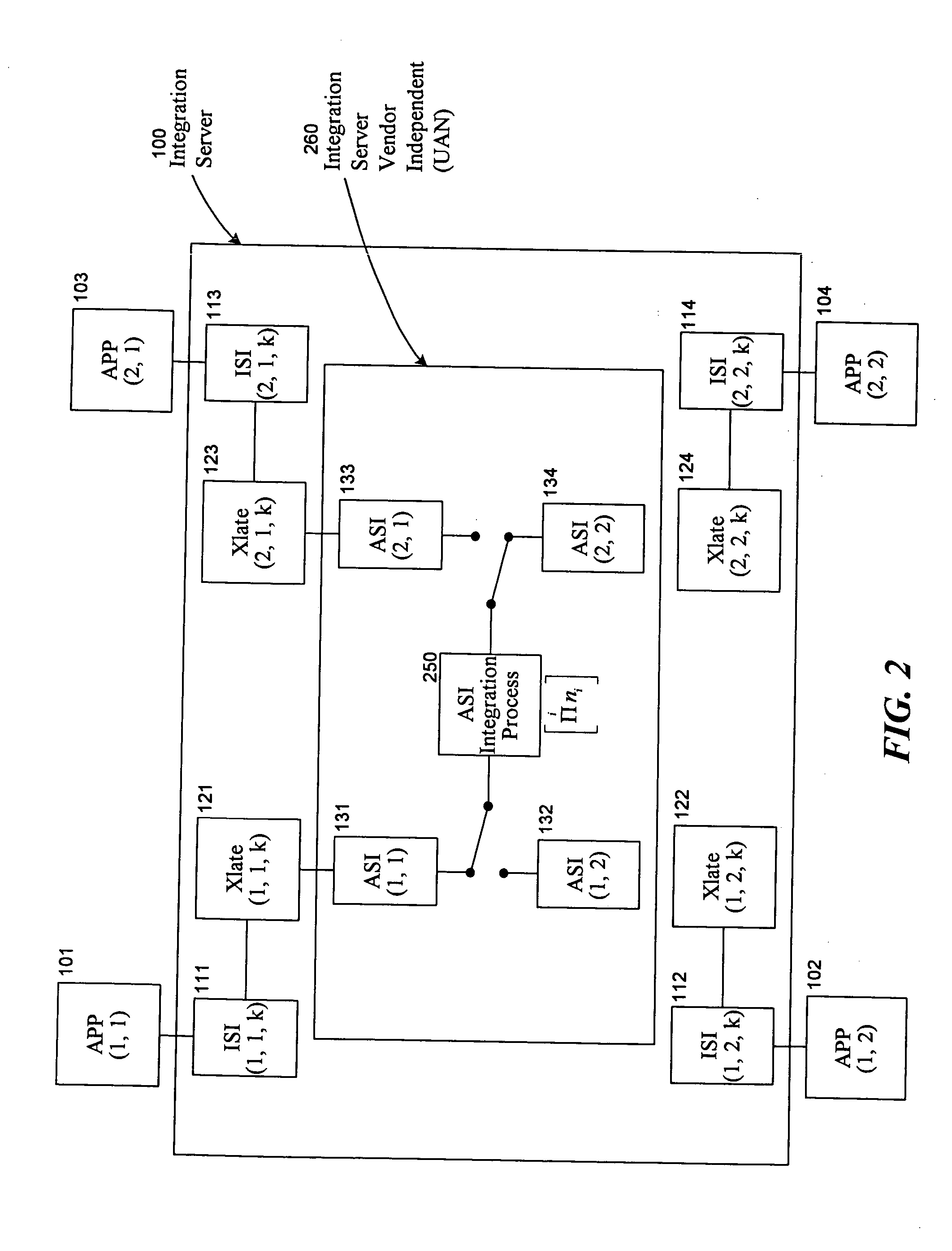
Universal application network architecture
A method and system for providing an integration environment in which integration processes can be developed independent of integration servers and applications. The integration environment provides an application service interface for each application that is independent of the integration servers. An integration process that is developed to use the application service interface is compatible with any integration server that supports the applications that the integration process accesses. The integration environment provides a common service interface for each type of application. The common service interface is independent of the application that is providing the service and is also independent of the integration server. Thus, an integration process developed to use the common service interface is compatible with any application of the appropriate type and any integration server.
Owner:ORACLE INT CORP
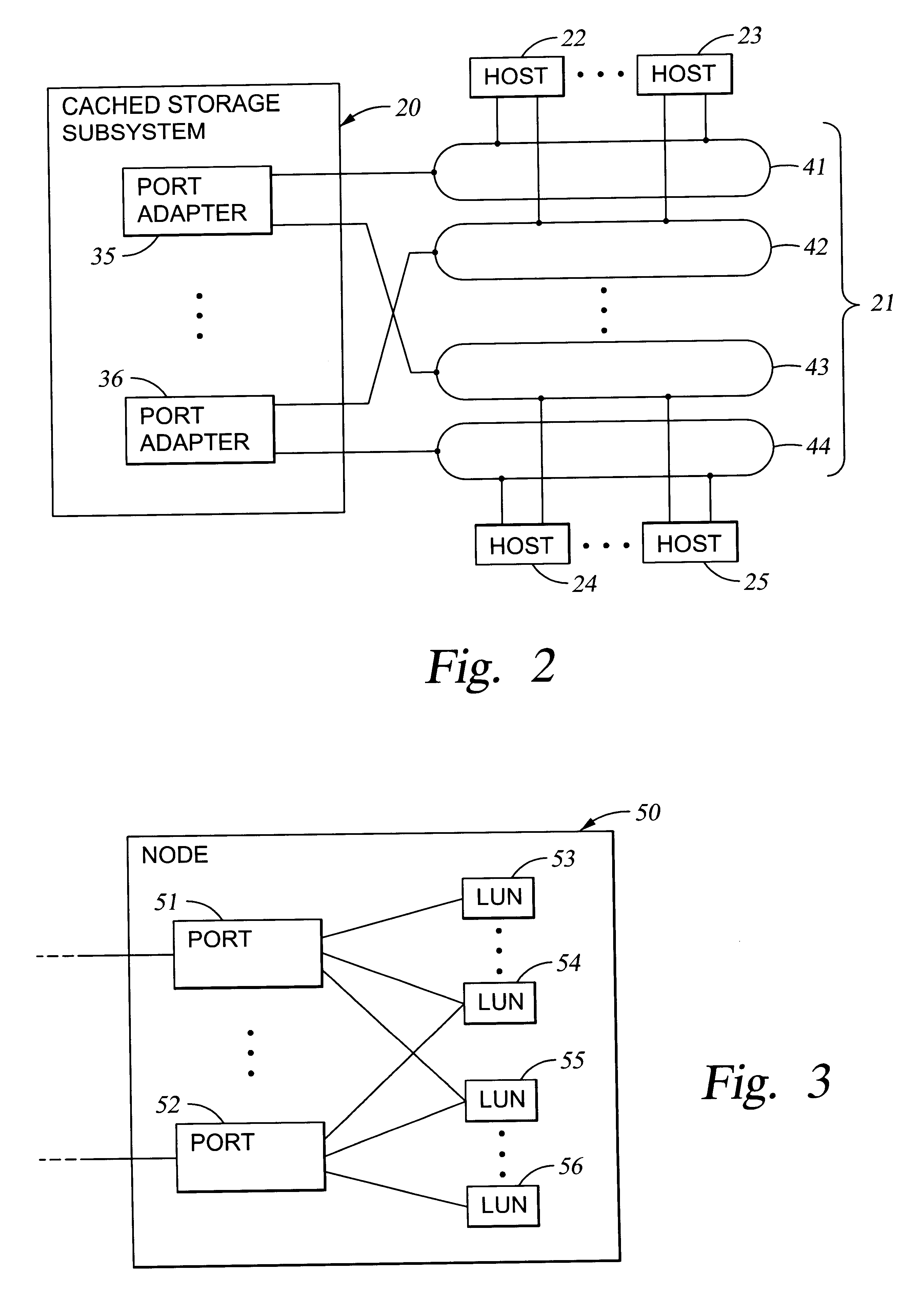
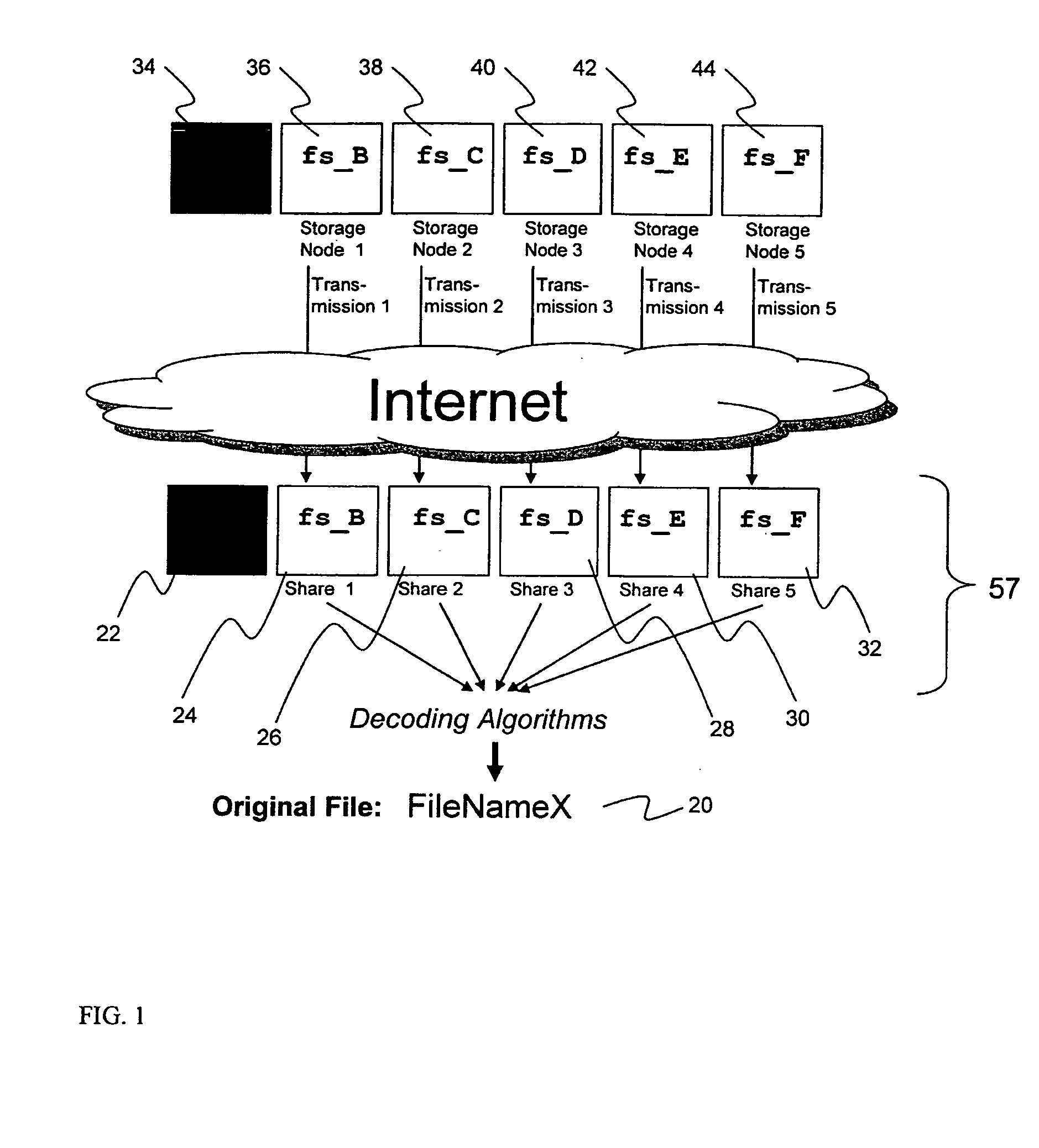
Method and system for managing distributed content and related metadata
InactiveUS7272613B2Reduce storage requirementsReduce amountData processing applicationsError detection/correctionControl systemFile system
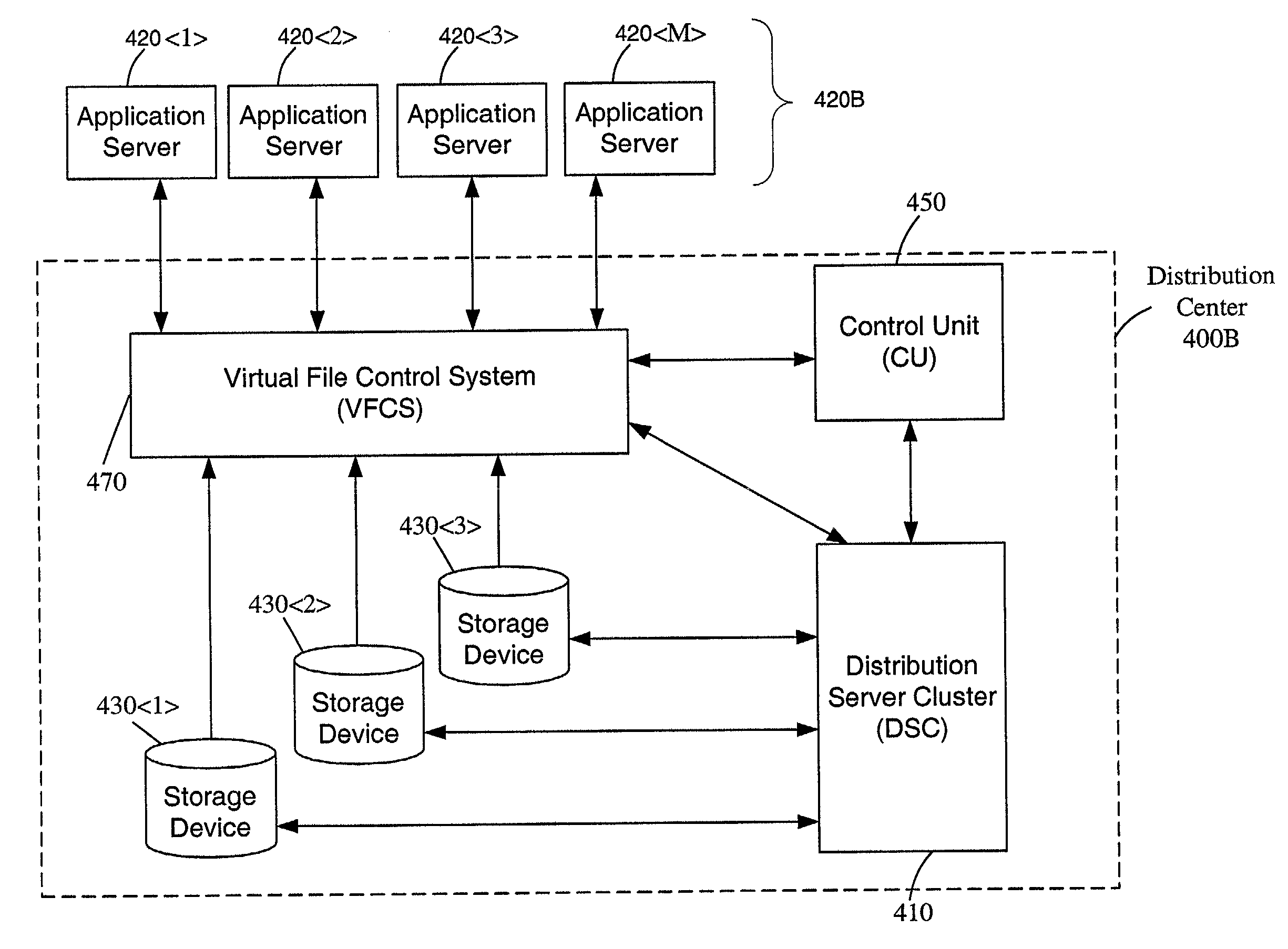
The invention provides a method and system for creating an innovative file system that separates its directory presentation from its data store. The method and system include processing, division, distribution, managing, synchronizing, and reassembling of file system objects that does not delay the presentation of the content to the user, but also uses a reduced amount of storage space. The invention includes the ability to manage and control the integrity of the files distributed across the network, and the ability to serve and reconstruct files in real time using a Virtual File Control System.
Owner:PRISMEDIA NETWORK +1
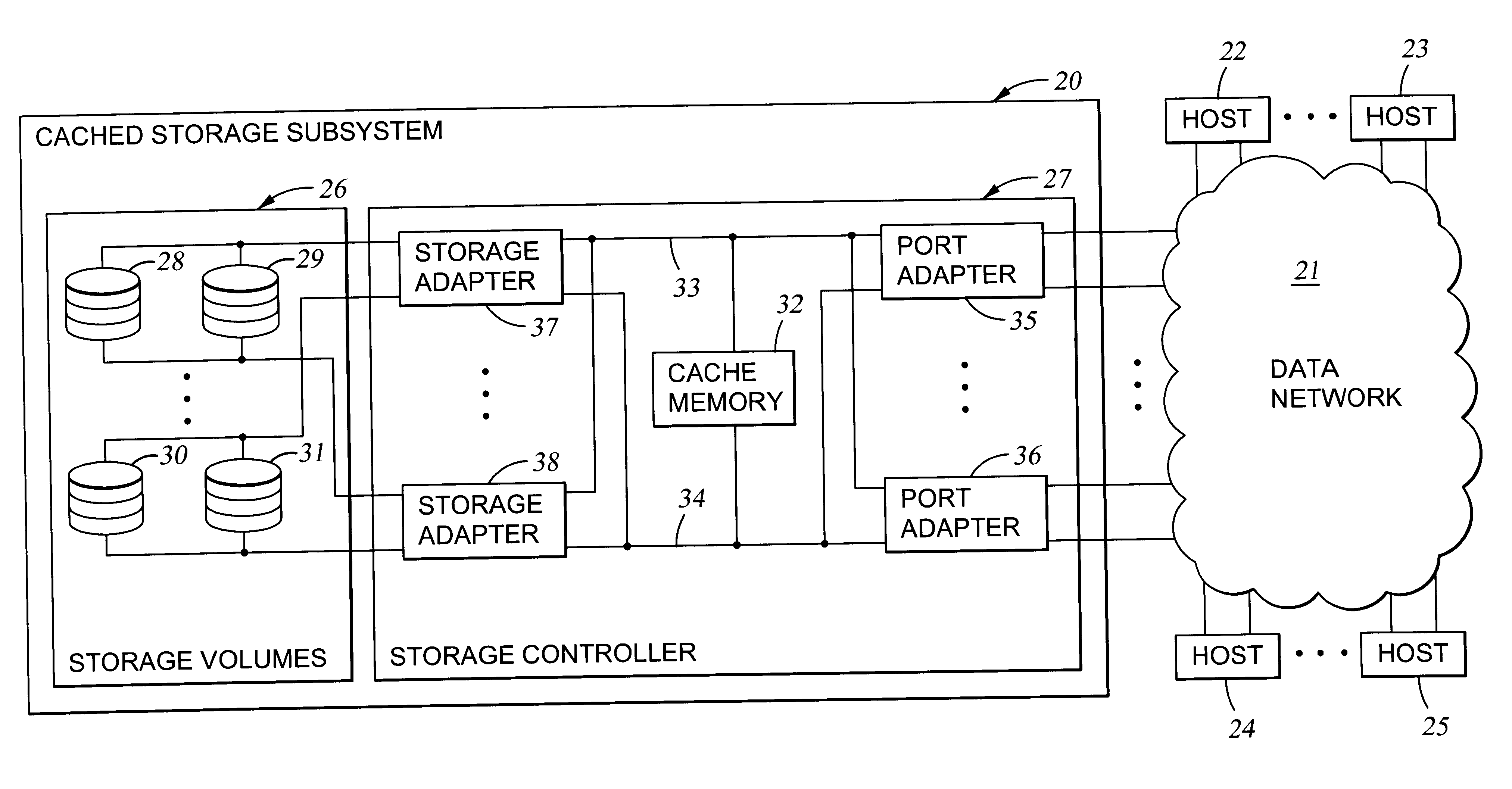
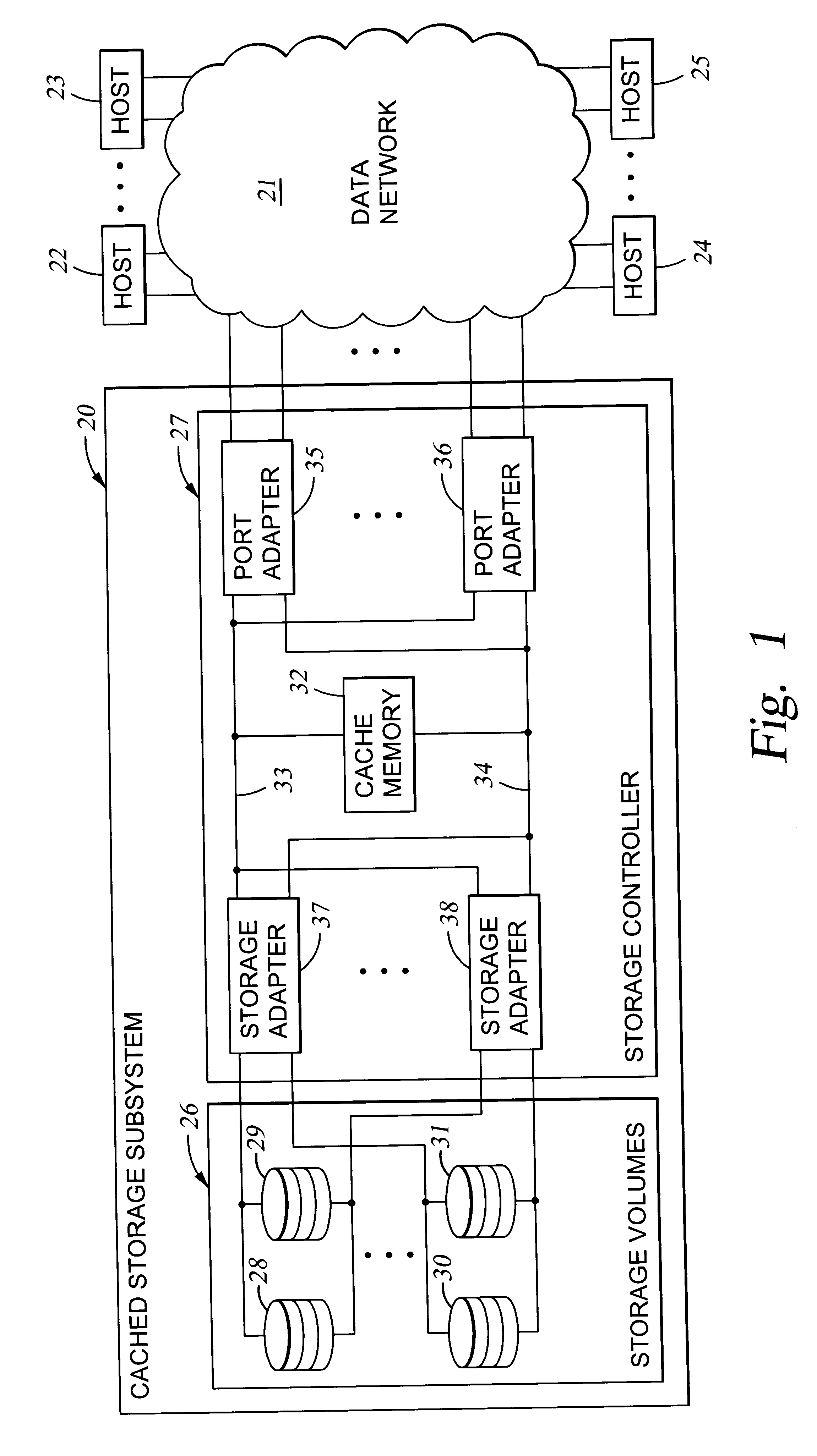
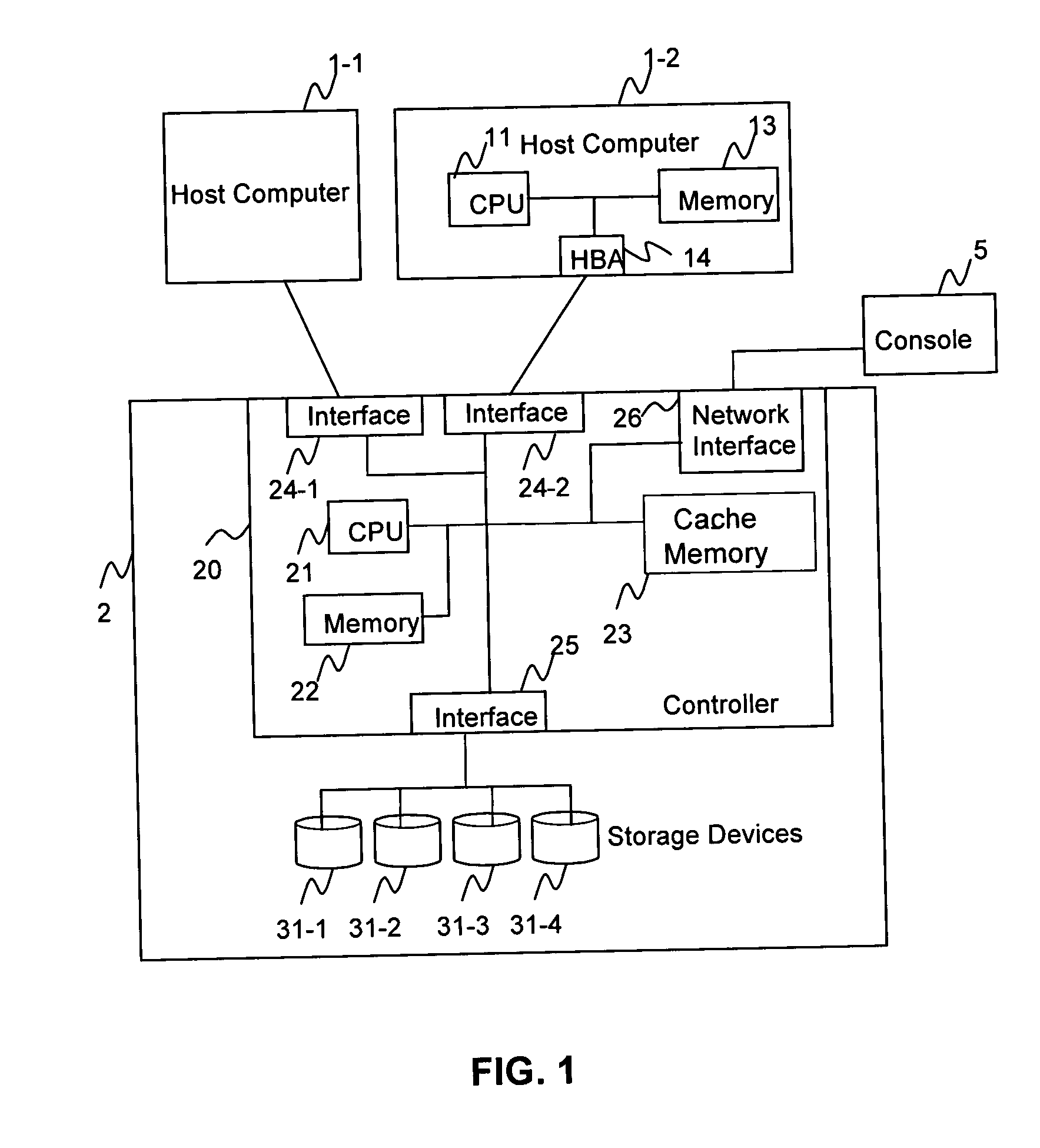
Virtual ports for data transferring of a data storage system
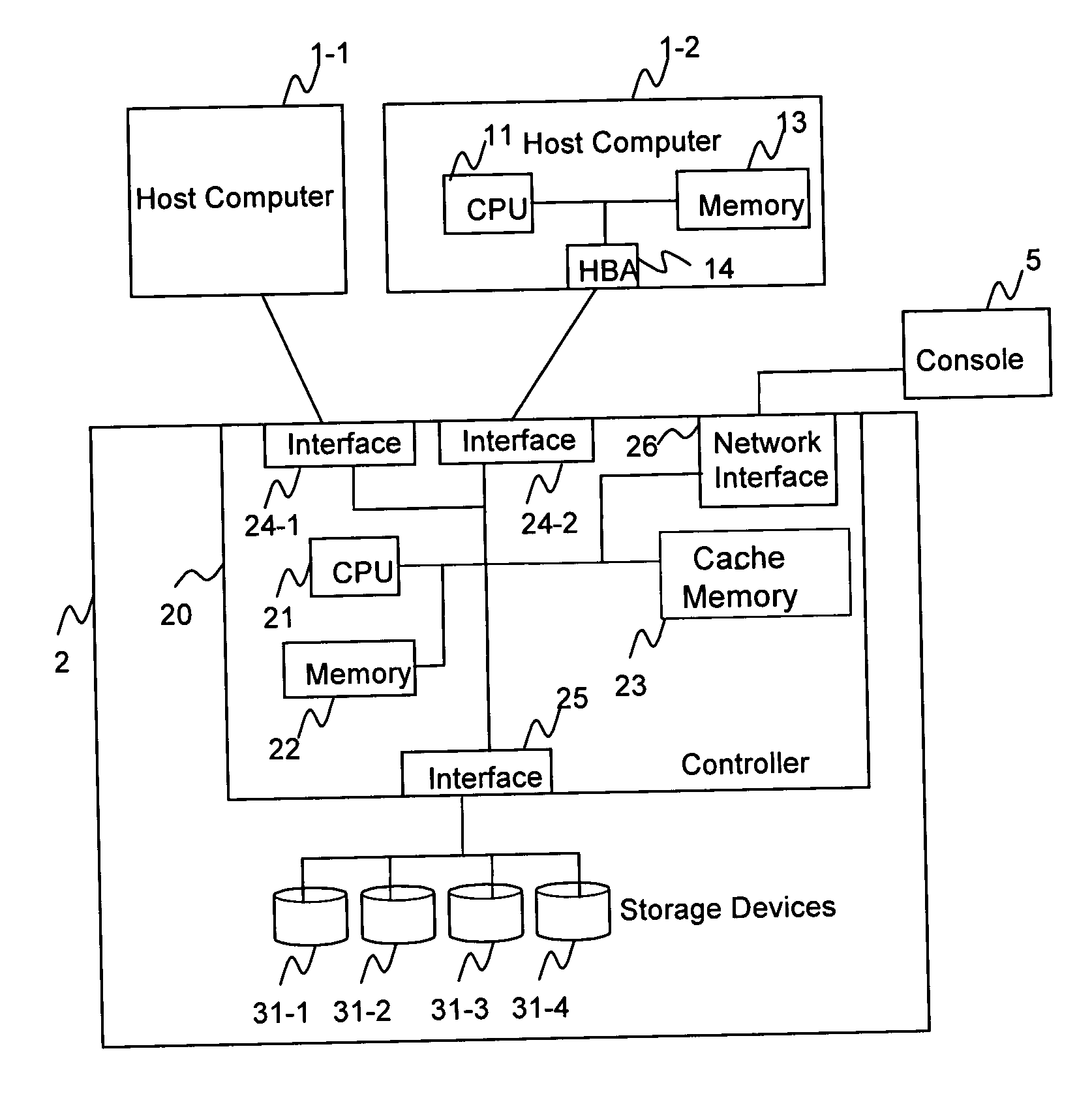
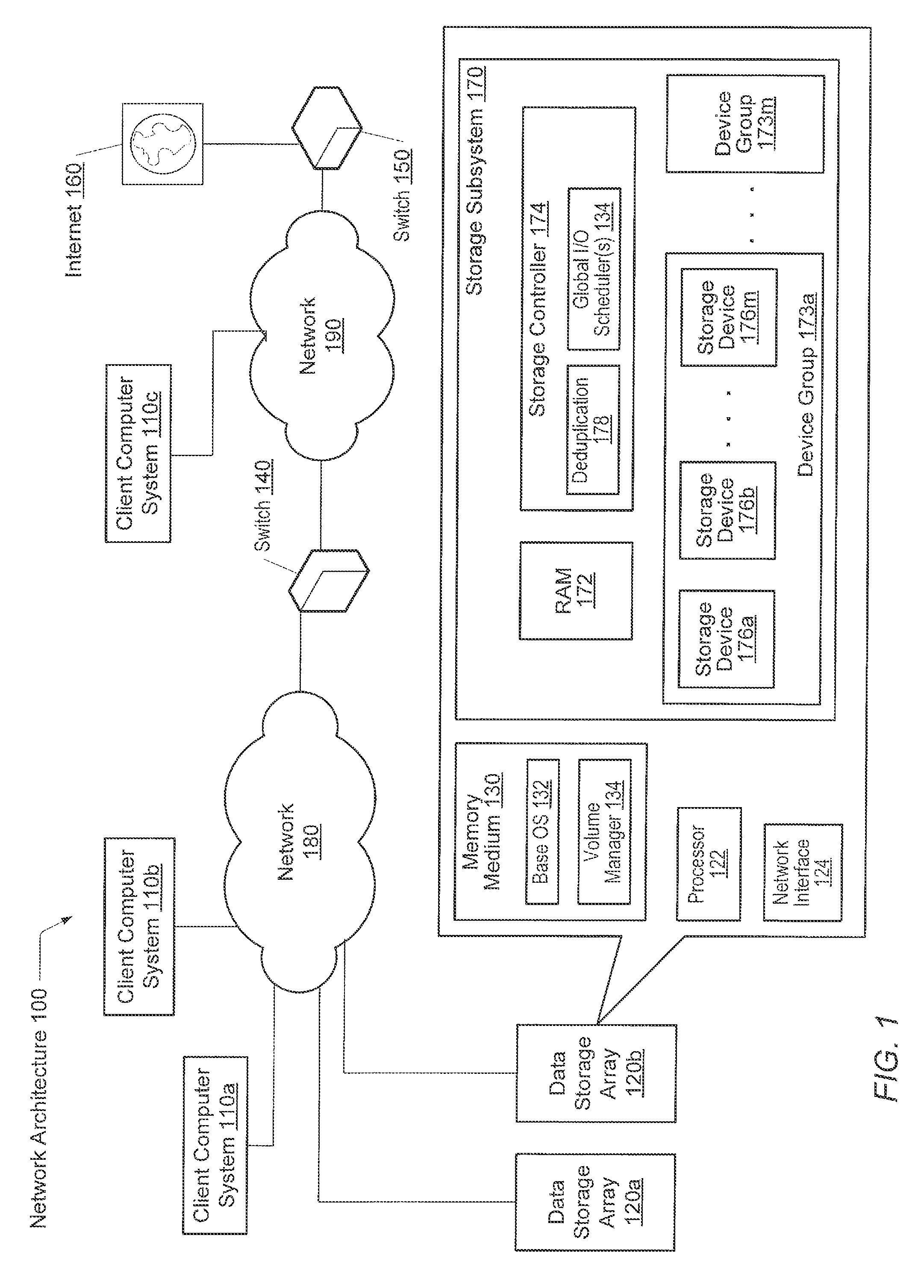
A storage controller has at least one physical data port for a data network including host processors. The storage controller is programmed to provide a plurality of virtual ports for access to storage, and a virtual switch for routing storage access requests from the physical port to the virtual ports. The virtual ports and the virtual switch are defined by software. The virtual ports appear to the hosts as physical ports in the data network. For example, in a Fiber-Channel network, the virtual ports have World Wide Names (WWNs) and are assigned temporary addresses (S_Ds), and the virtual switch provides a name server identifying the WWNs and S_IDs of the virtual ports. For convenient partitioning of storage among host processors, one or more virtual ports are assigned to each host, and a set of storage volumes are made accessible from each virtual port. A host can access storage at a virtual port only if the virtual port has been assigned to the host. Preferably, storage can be accessed through each virtual port by no more than one assigned host, although a shared volume may be accessible from more than one virtual port. The storage controller may provide a service for reporting to a host the virtual ports through which the host can access storage, and the storage volumes that are accessible to the host through each of the virtual ports.
Owner:EMC IP HLDG CO LLC
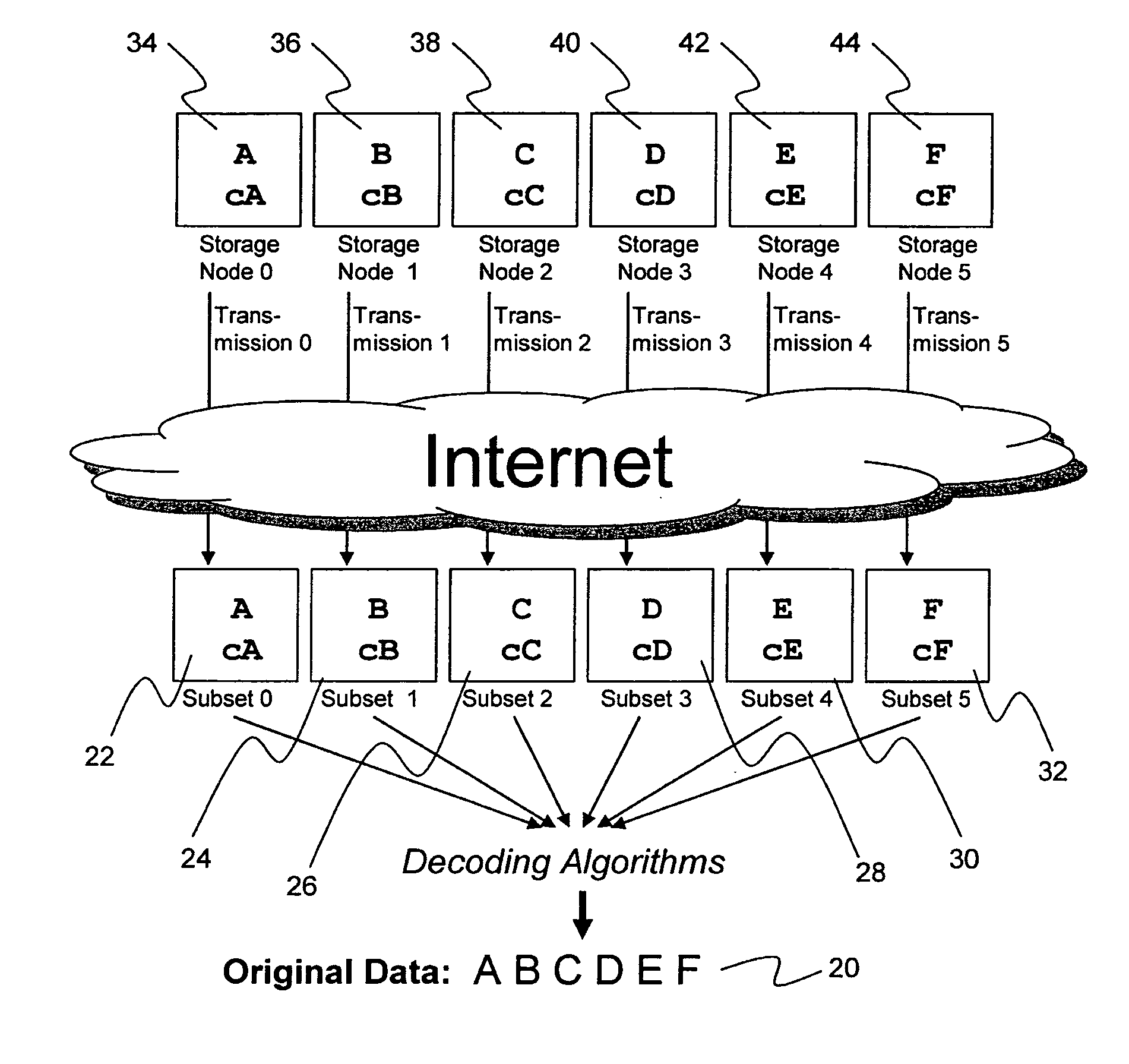
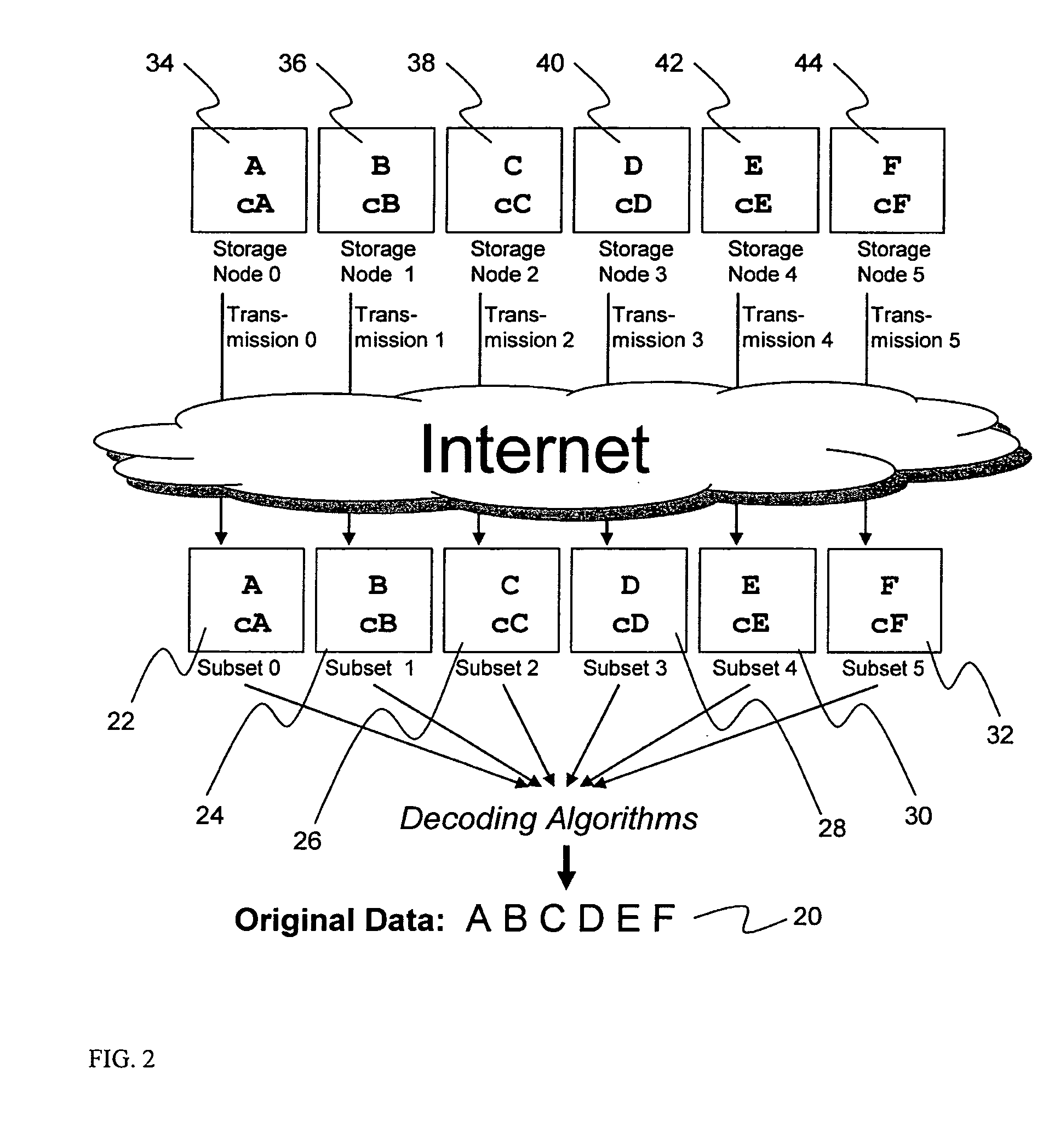
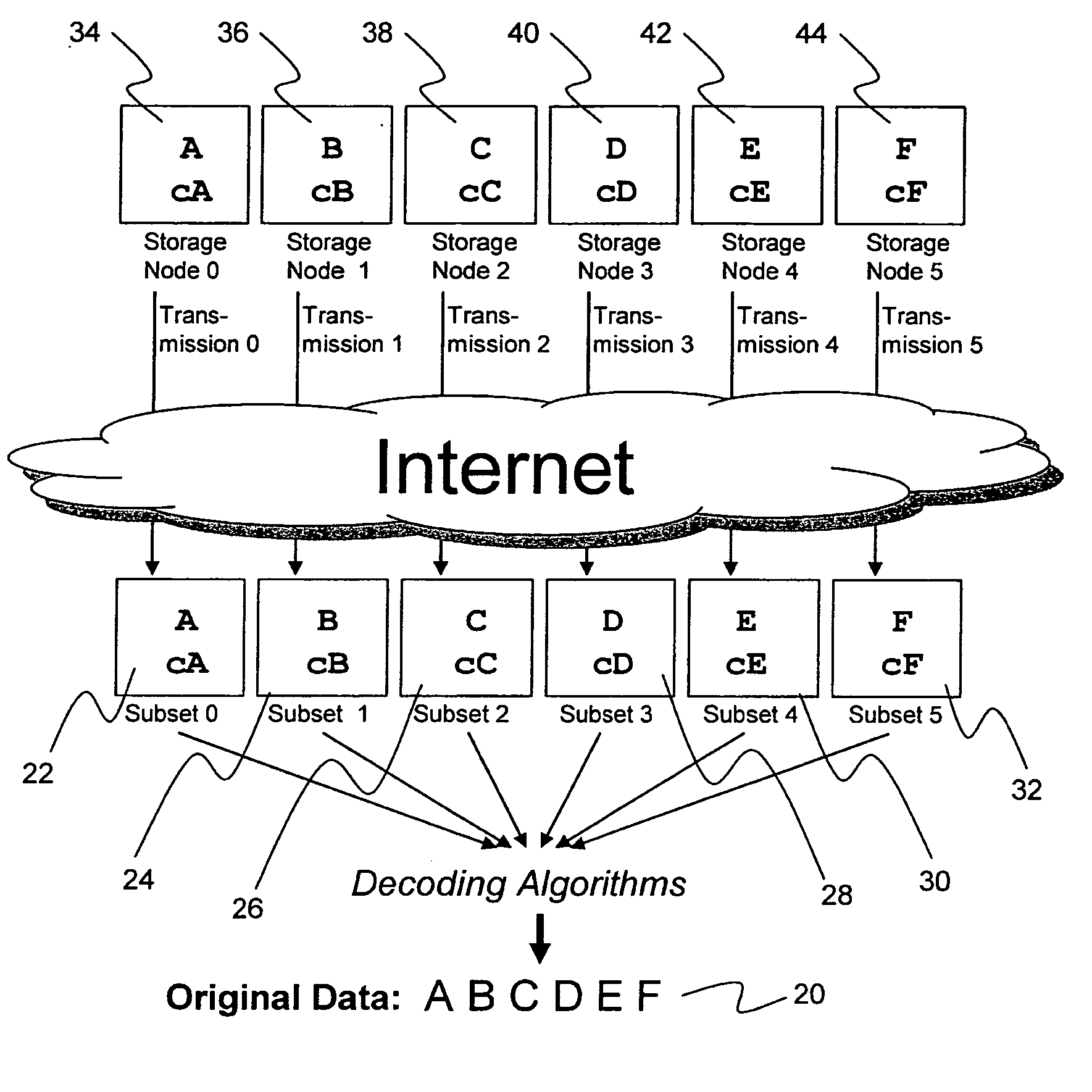
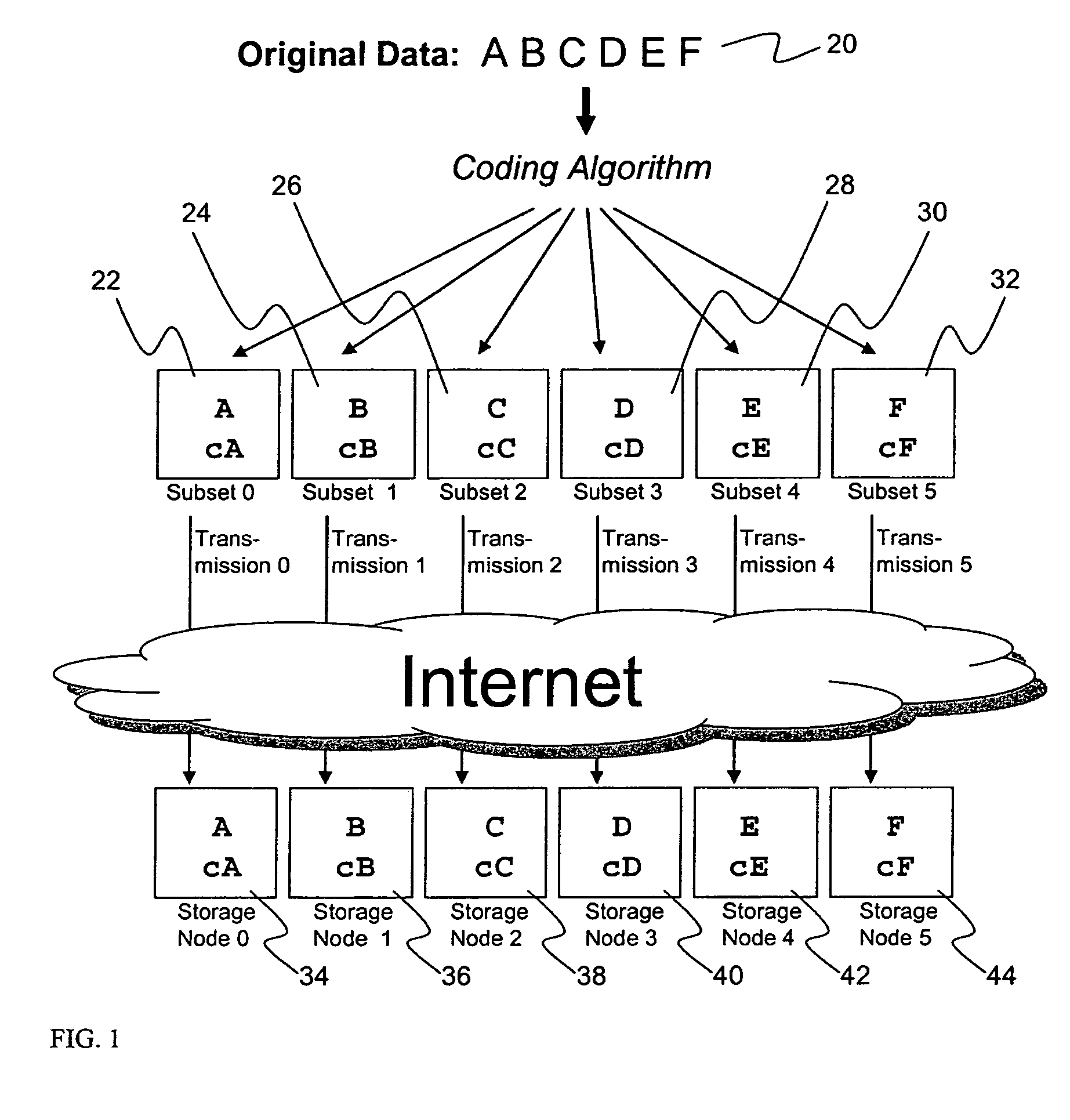
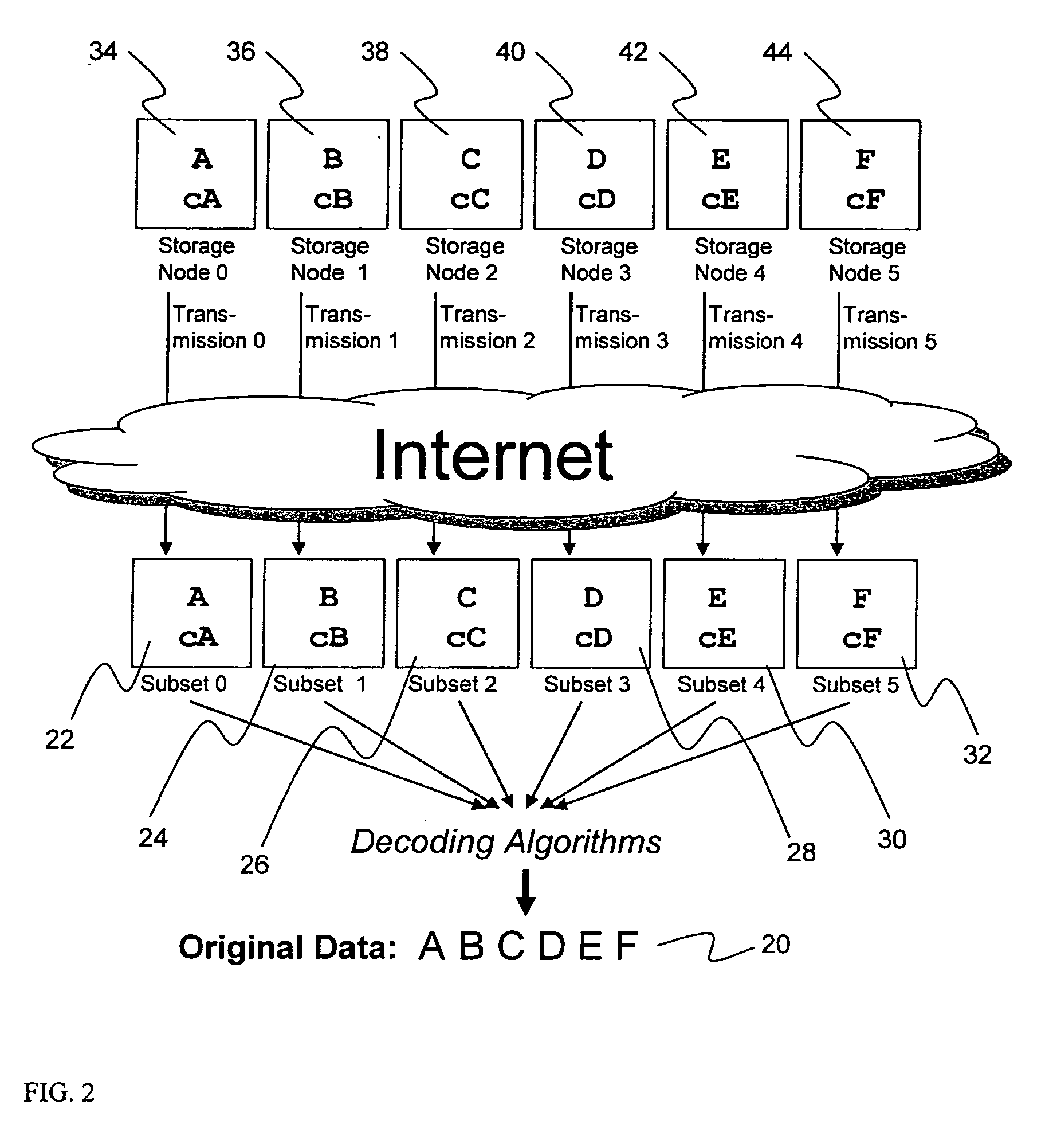
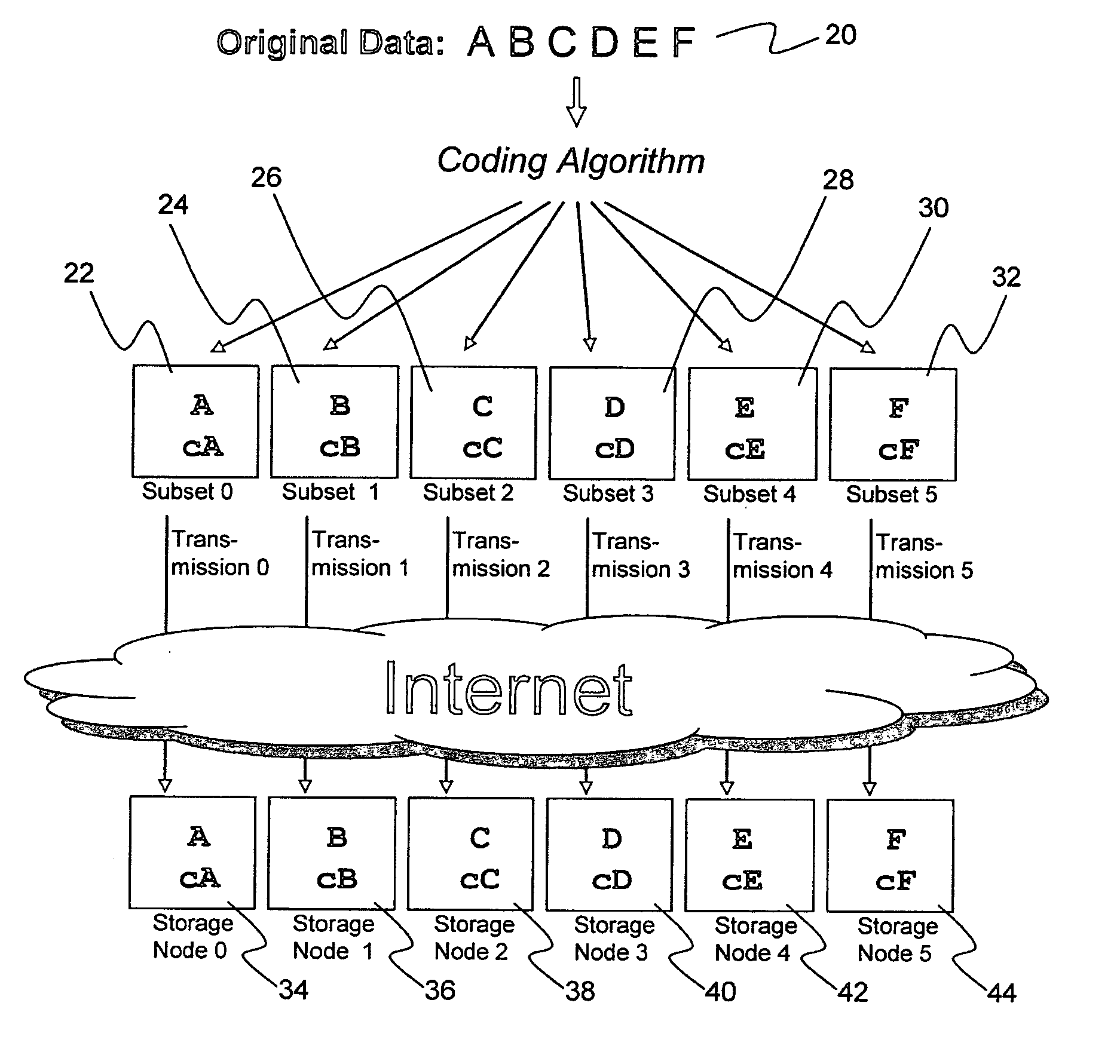
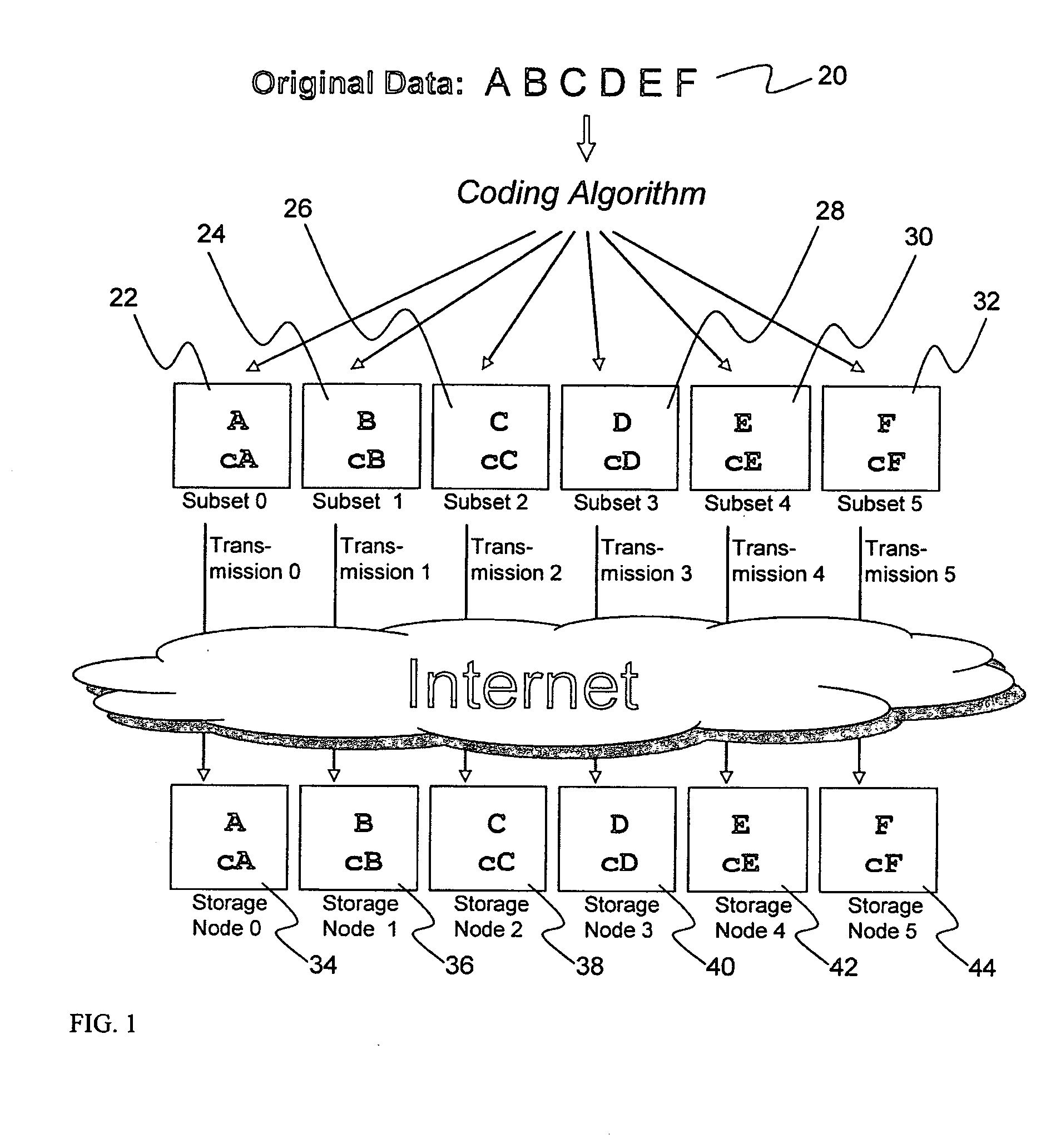
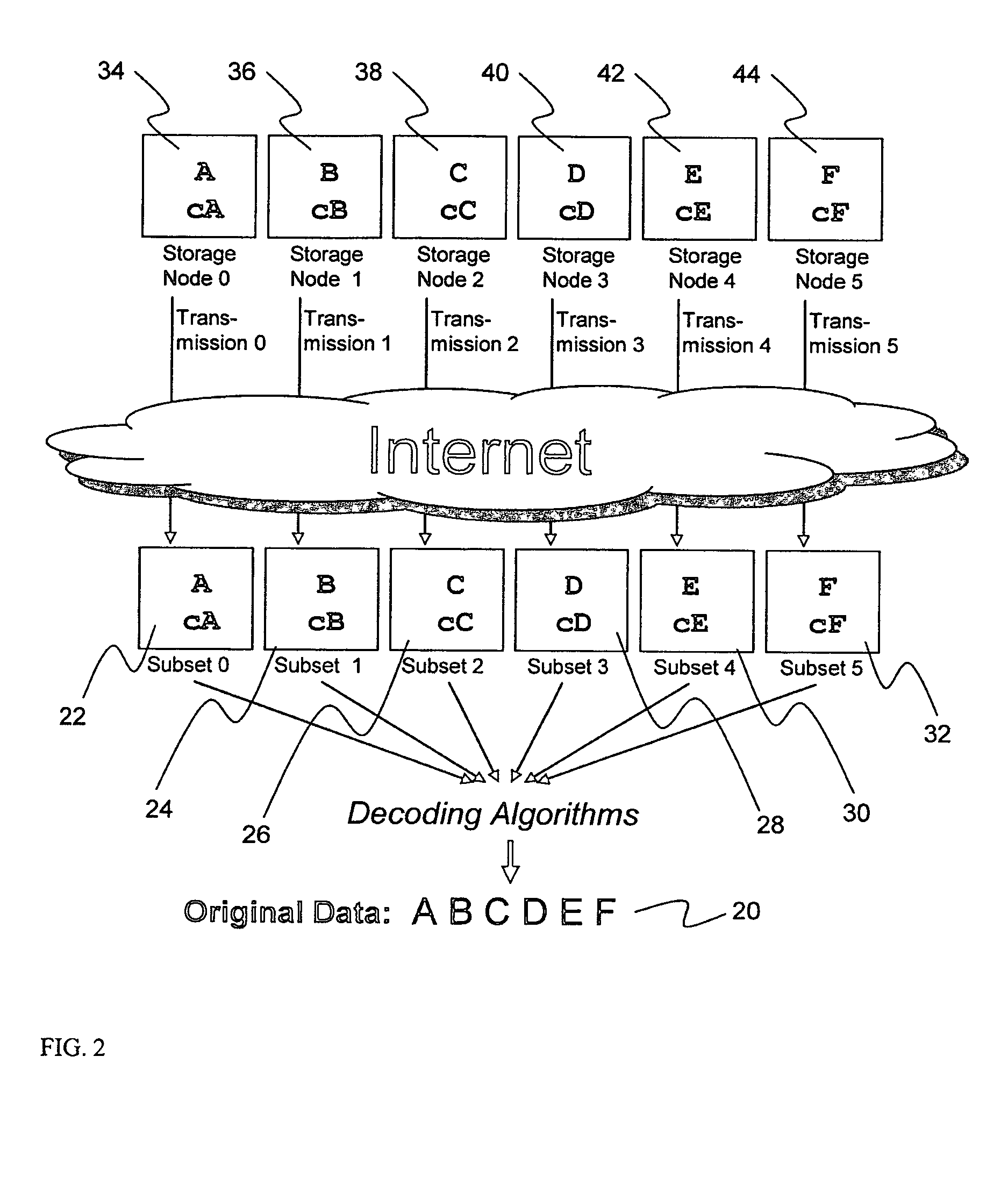
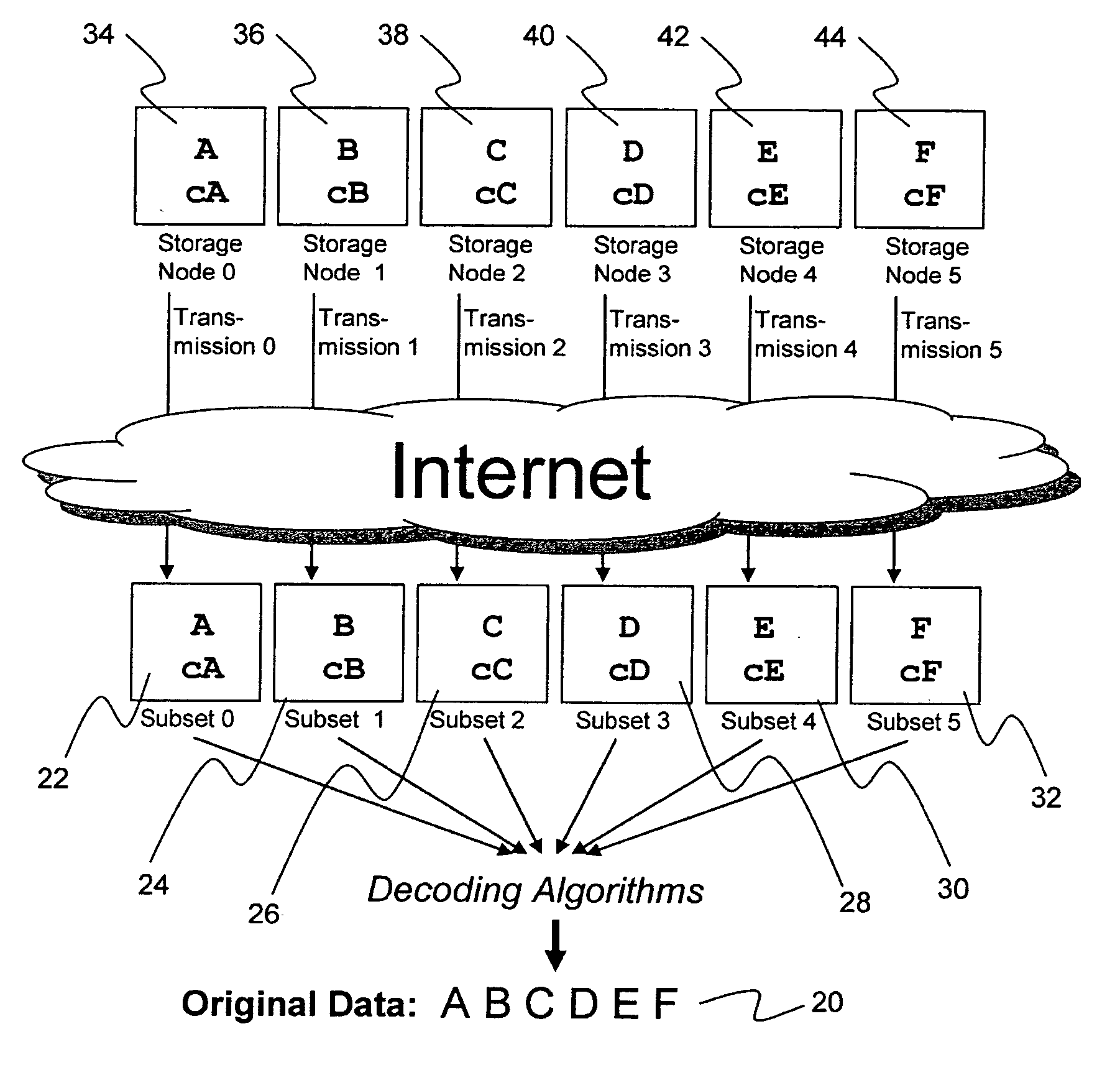
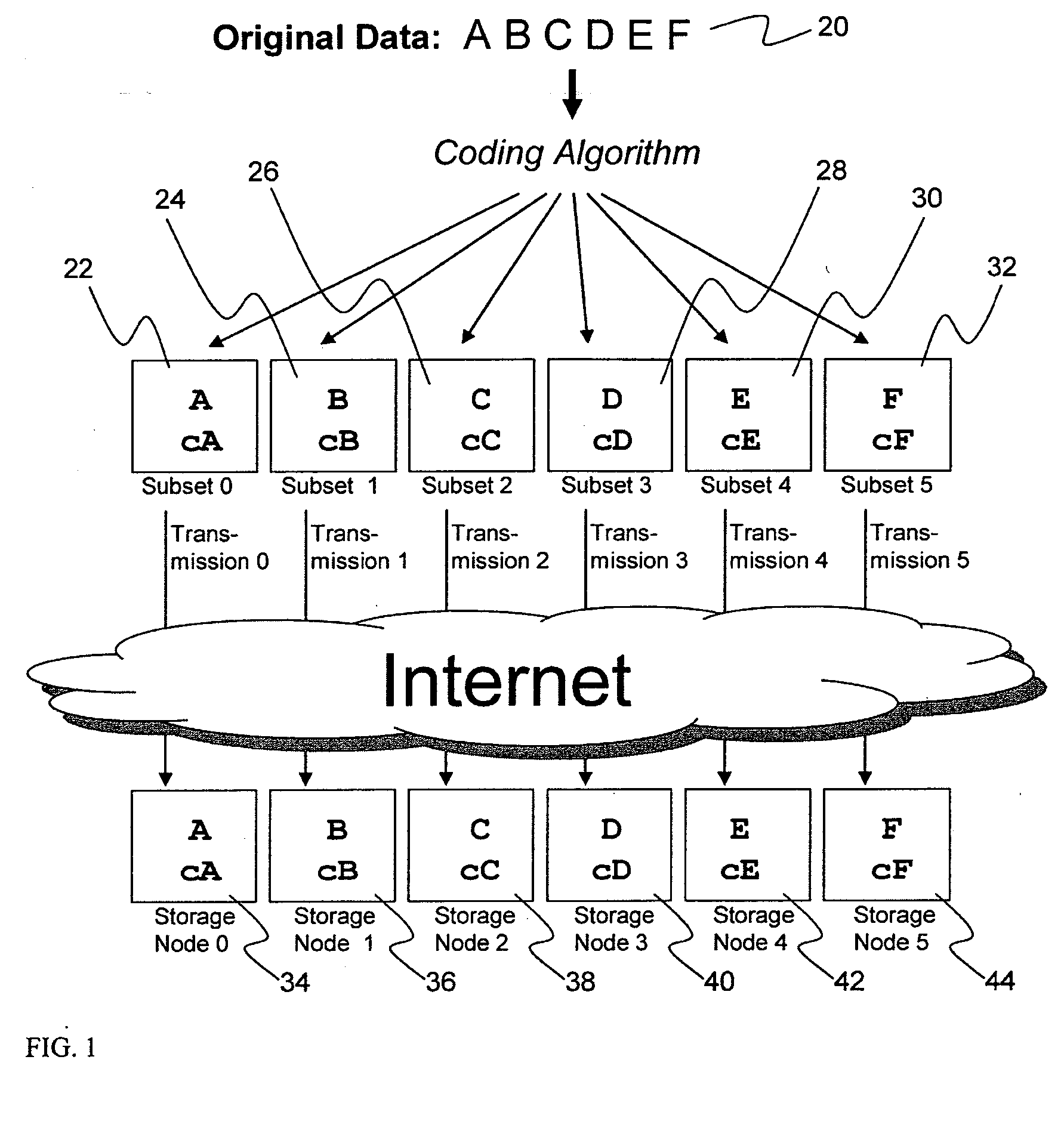
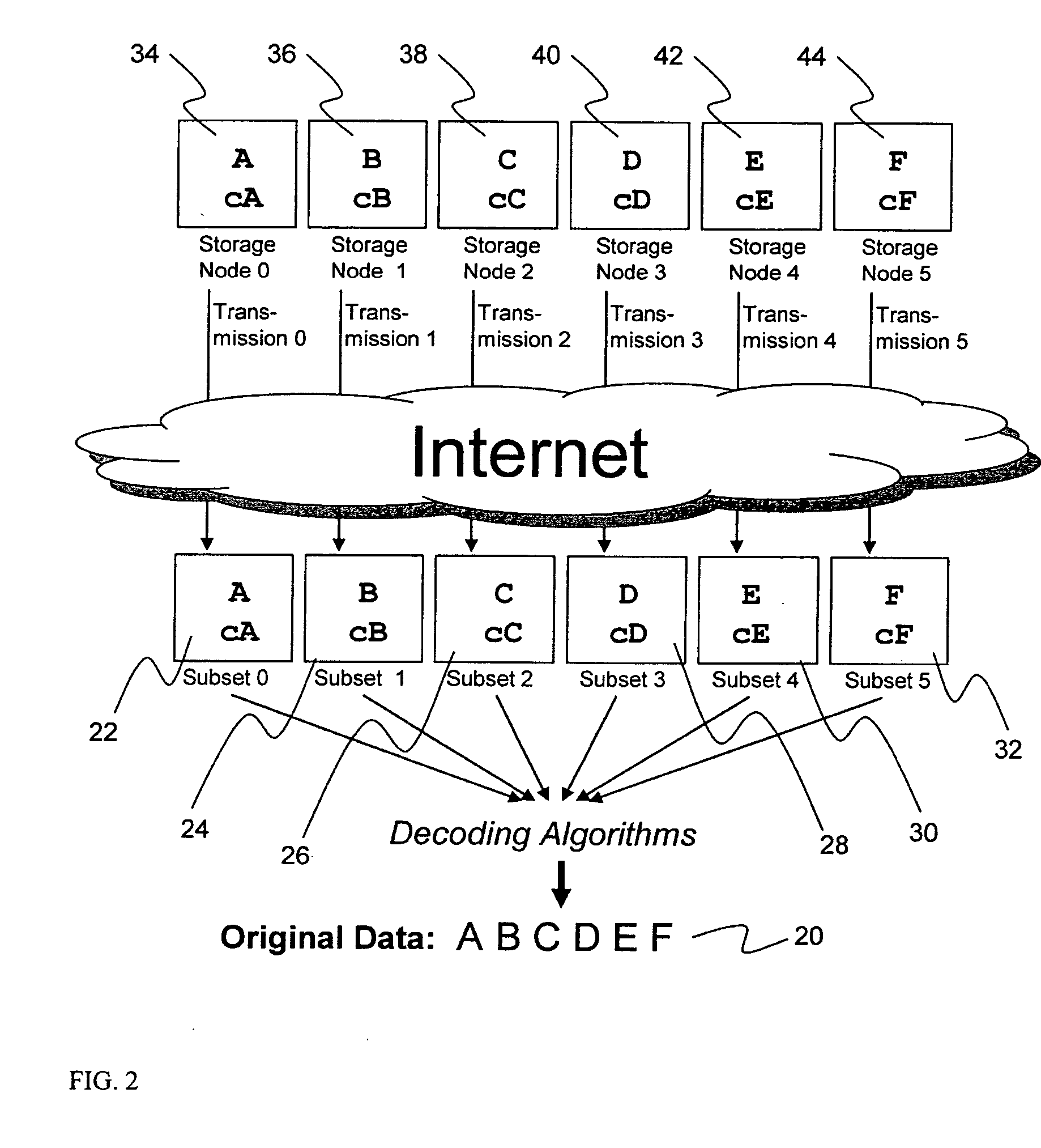
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
Metadata management system for an information dispersed storage system
ActiveUS20070079083A1Less usableImprove privacyComputer security arrangementsMemory systemsInformation dispersalMetadata management
Briefly, the present invention relates to an information dispersal sytem in which original data to be stored is separated into a number of data “slices” in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate storage devices as a way of increasing privacy and security. In accordance with an important aspect of the invention, a metadata management system stores and indexes user files across all of the storage nodes. A number of applications run on the servers supporting these storage nodes and are responsible for controlling the metadata. Metadata is the information about the data, the data slices or data subsets and the way in which these data subsets are dispersed among different storage nodes running over the network. As used herein, metadata includes data source names, their size, last modification date, authentication information etc. This information is required to keep track of dispersed data subsets among all the nodes in the system. Every time new data subsets are stored and old ones are removed from the storage nodes, the metadata is updated. In accordance with an important aspect of the invention, the metadata management system stores metadata for dispersed data where: The dispersed data is in several pieces. The metadata is in a separate dataspace from the dispersed data. Accordingly, the metadata management system is able to manage the metadata in a manner that is computationally efficient relative to known systems in order to enable broad use of the invention using the types of computers generally used by businesses, consumers and other organizations currently.
Owner:PURE STORAGE
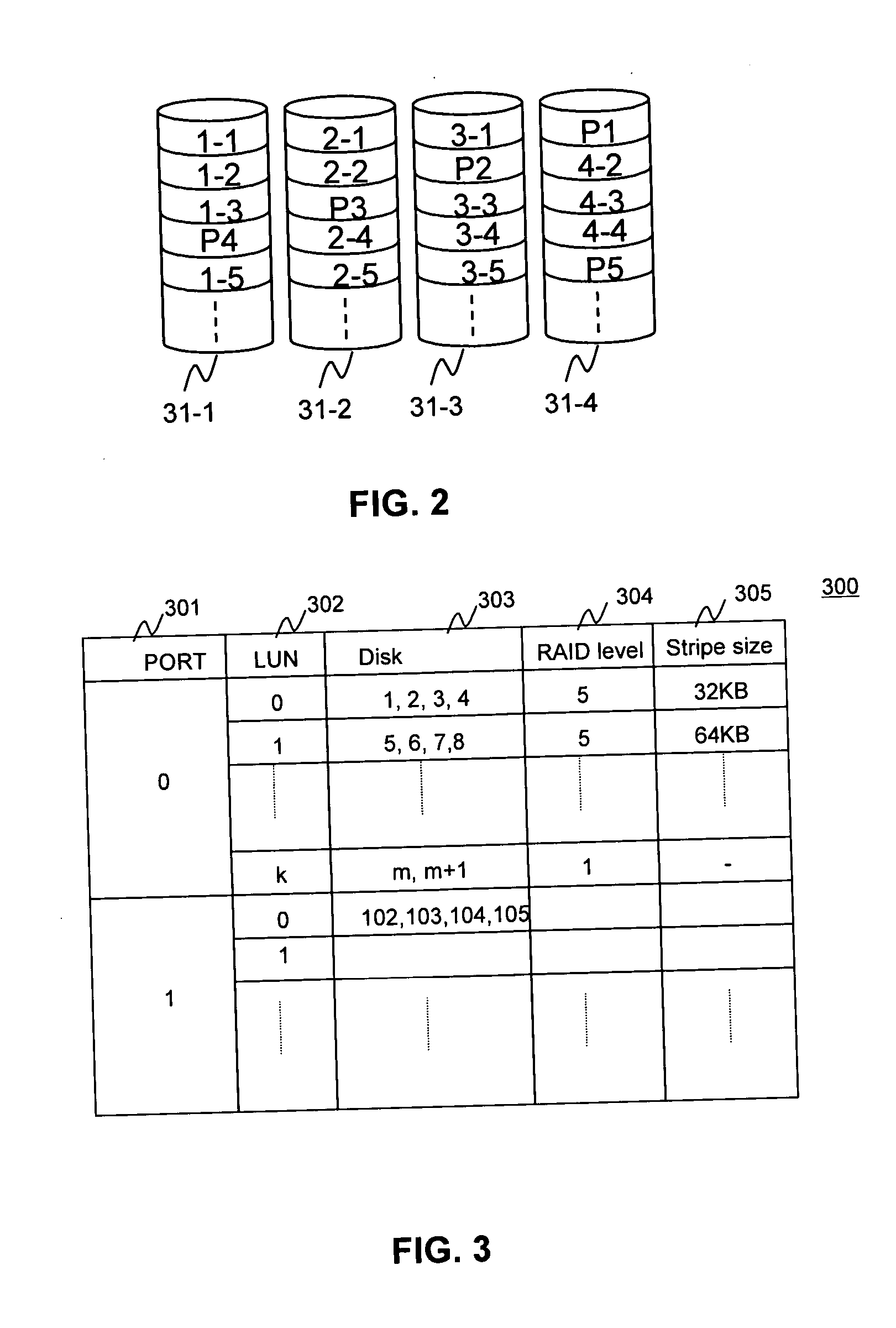
Method and apparatus for reconstructing data in object-based storage arrays
A method and apparatus for placing objects on a storage device of a storage system and reconstructing data of objects in the storage device. The storage system stores data as objects and implements a RAID architecture including a plurality of the storage devices, and a disk controller for processing Object-based Storage Device (OSD) commands. Each object includes data and attribute. Parity data is calculated for reconstructing an object upon occurrence of a storage device failure. Each storage device includes plural stripes each having a predetermined length. Each object is stored in a stripe wherein an attribute is stored in the head of the stripe and data is stored after the attribute. When the object size exceeds the stripe length, the remainder of the object is stored in the next stripe, and when another object is to be stored, an attribute is stored at a head of a further next stripe and data is stored just after the attribute.
Owner:GOOGLE LLC
Billing system for information dispersal system
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
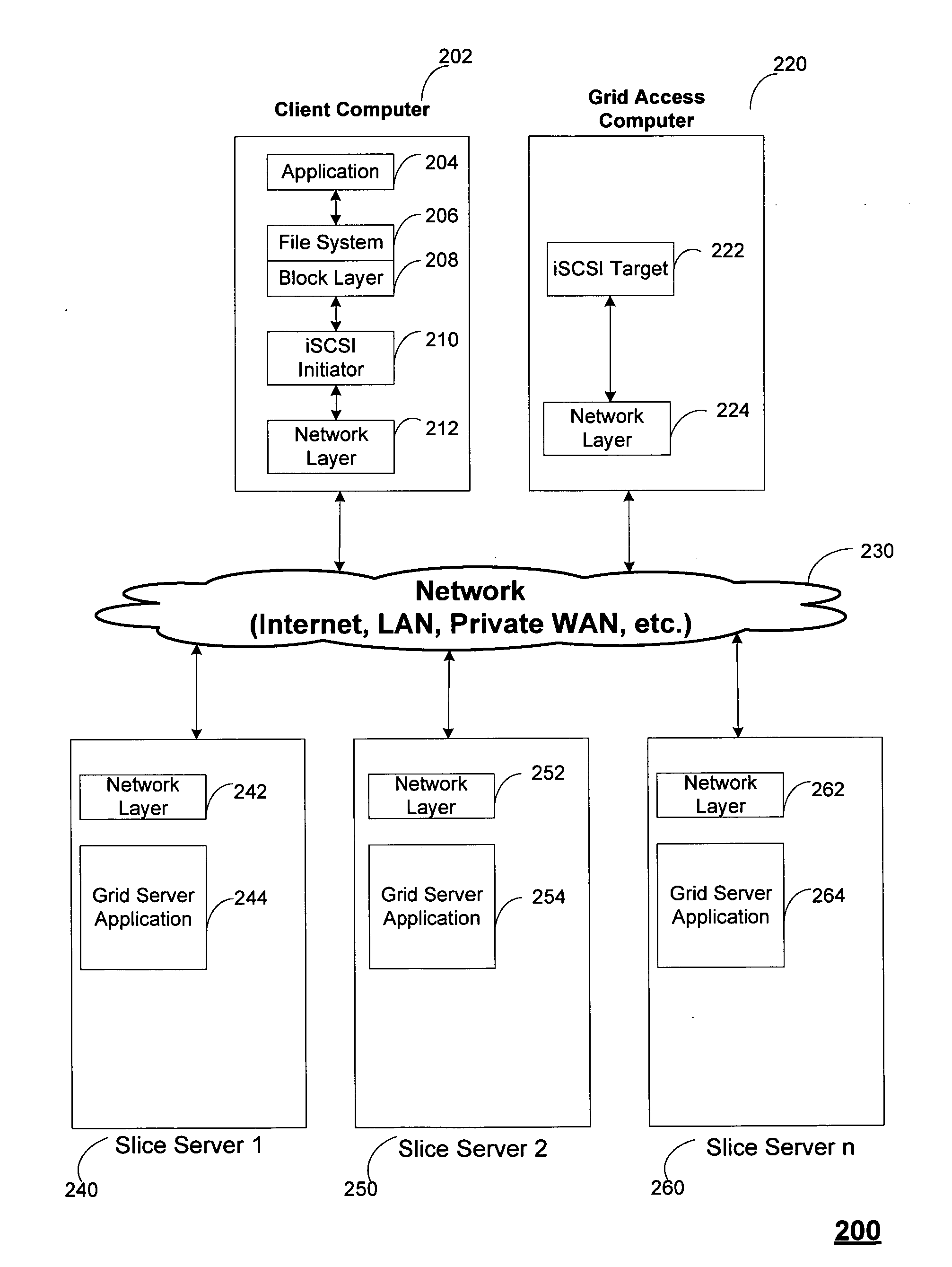
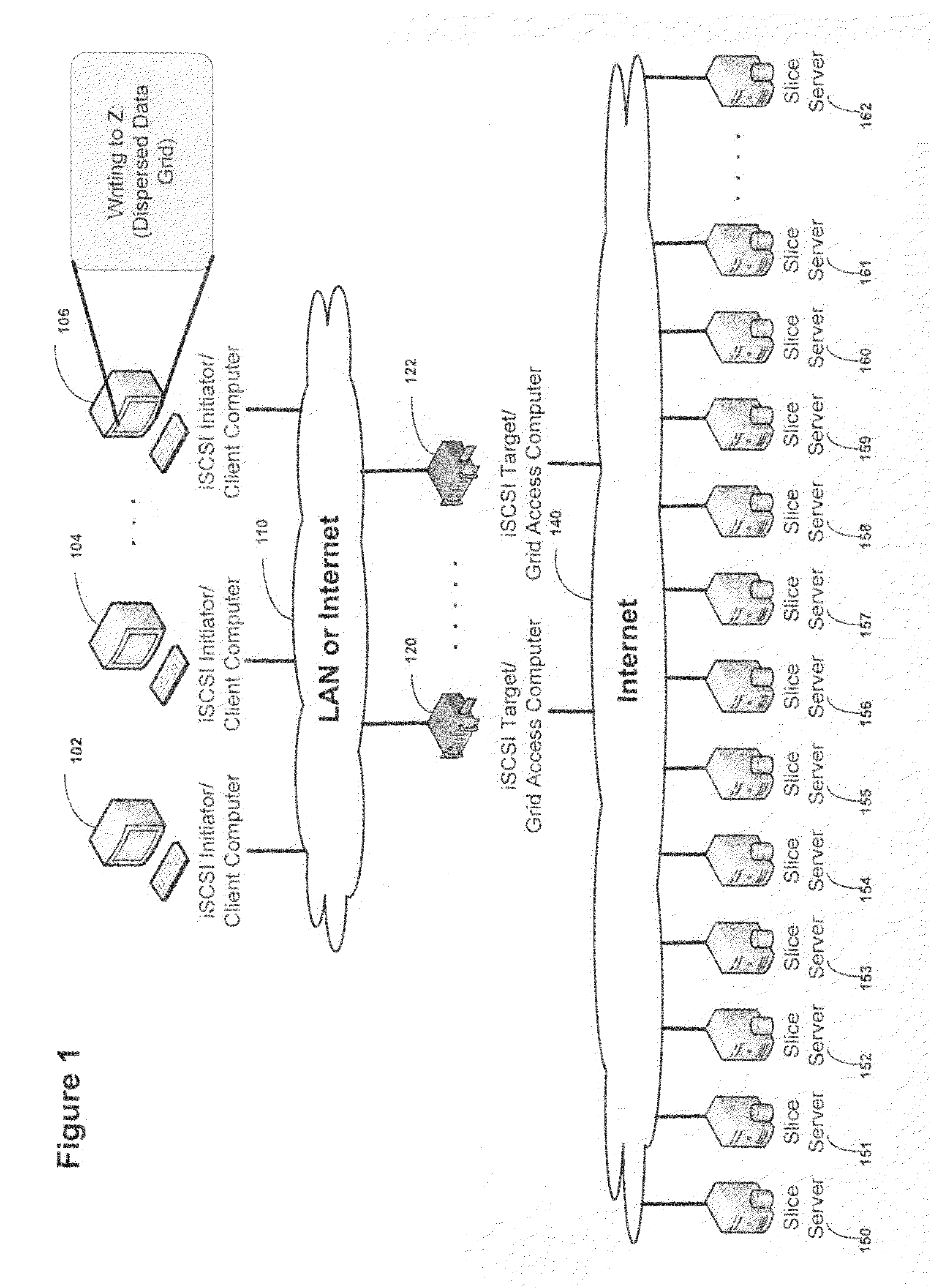
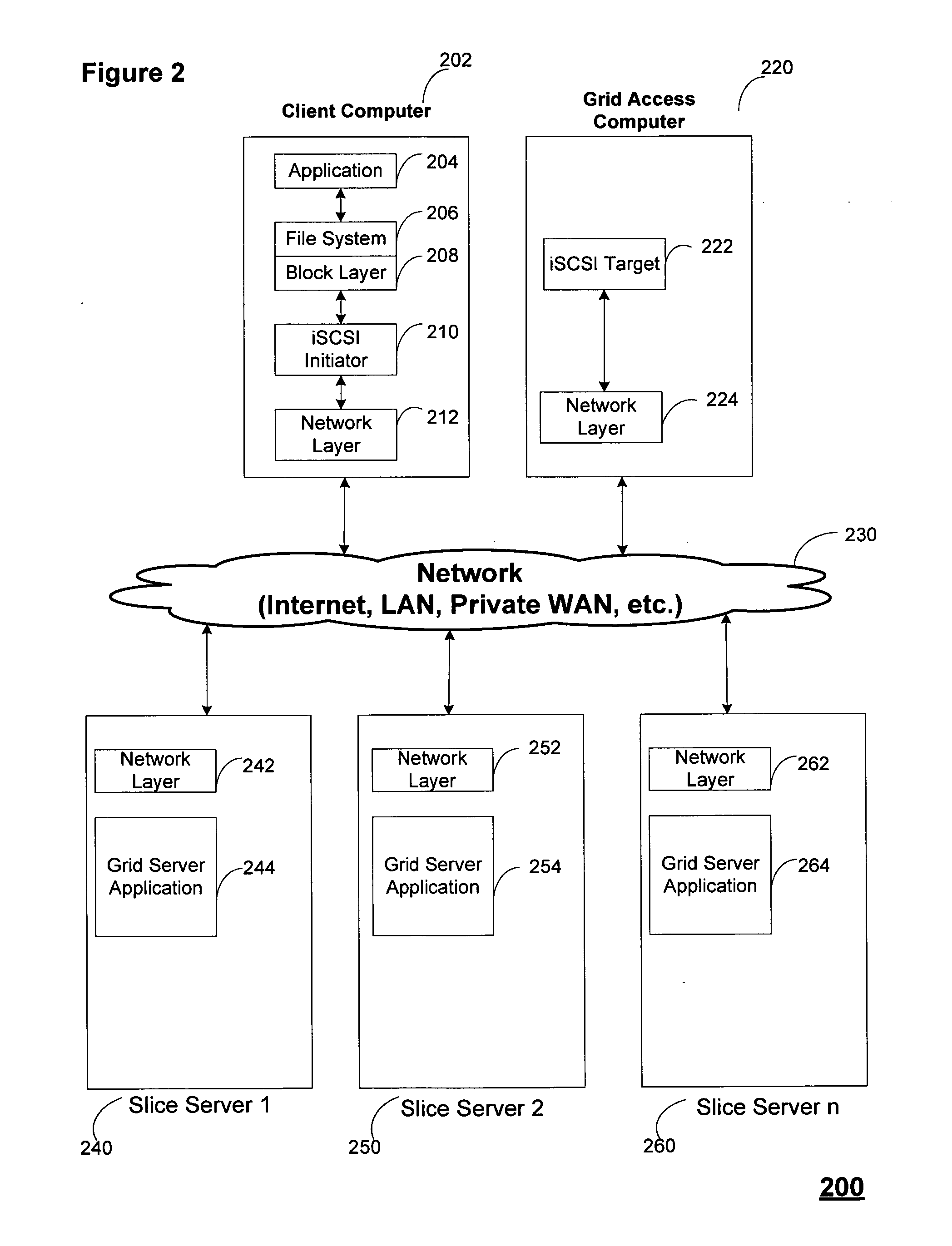
Block based access to a dispersed data storage network
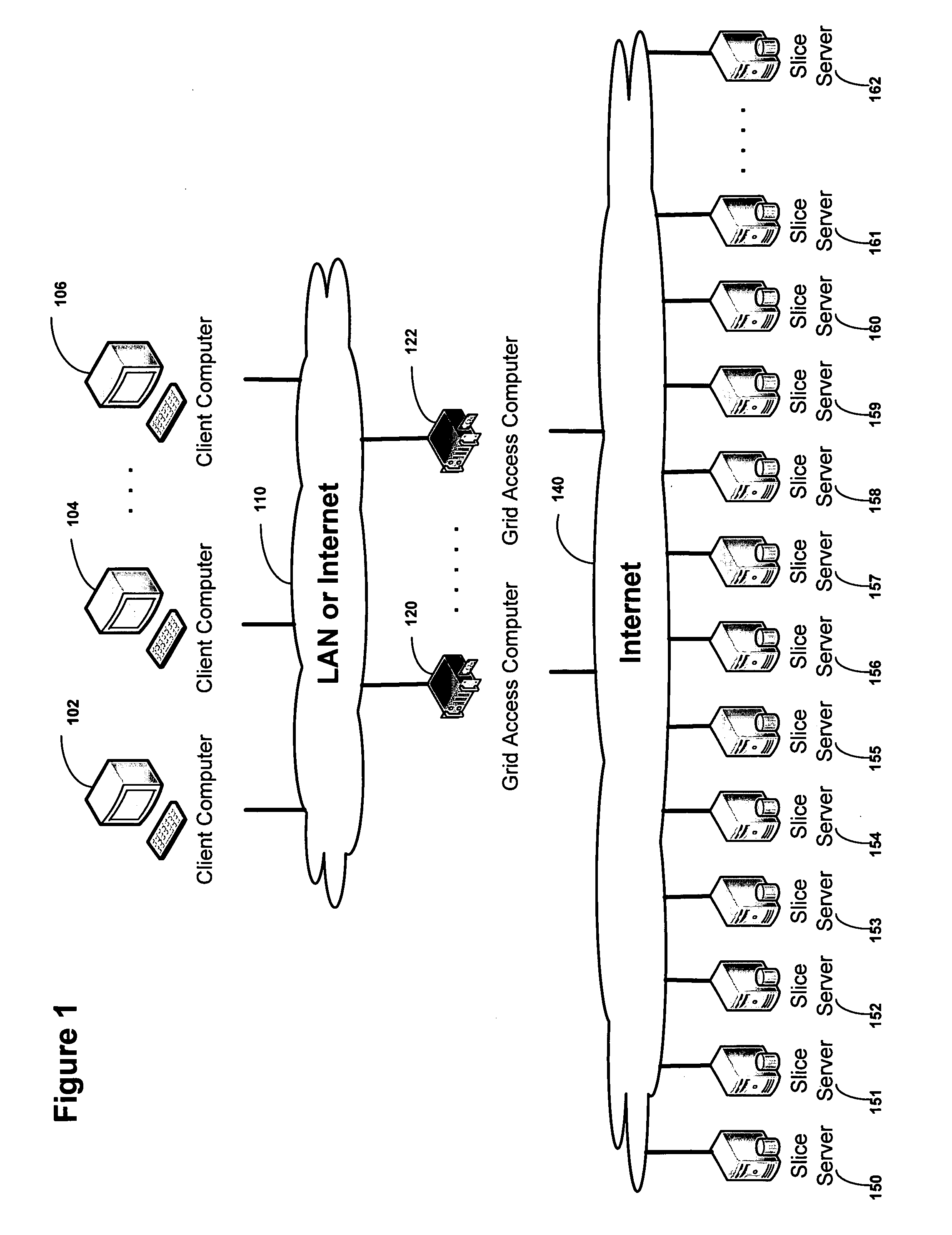
ActiveUS20100023524A1Simple methodDigital data processing detailsError detection/correctionFile systemData store
A block-based interface to a dispersed data storage network is disclosed. The disclosed interface accepts read and write commands from a file system resident on a user's computer and generates network commands that are forwarded to slice servers that form the storage component of the dispersed data storage network. The slice servers then fulfill the read and write commands.
Owner:PURE STORAGE
Digital data storage system
ActiveUS20070079081A1Less usableImprove privacyComputer security arrangementsMemory systemsOriginal dataSmall data
An efficient method for breaking source data into smaller data subsets and storing those subsets along with coded information about some of the other data subsets on different storage nodes such that the original data can be recreated from a portion of those data subsets in an efficient manner.
Owner:PURE STORAGE
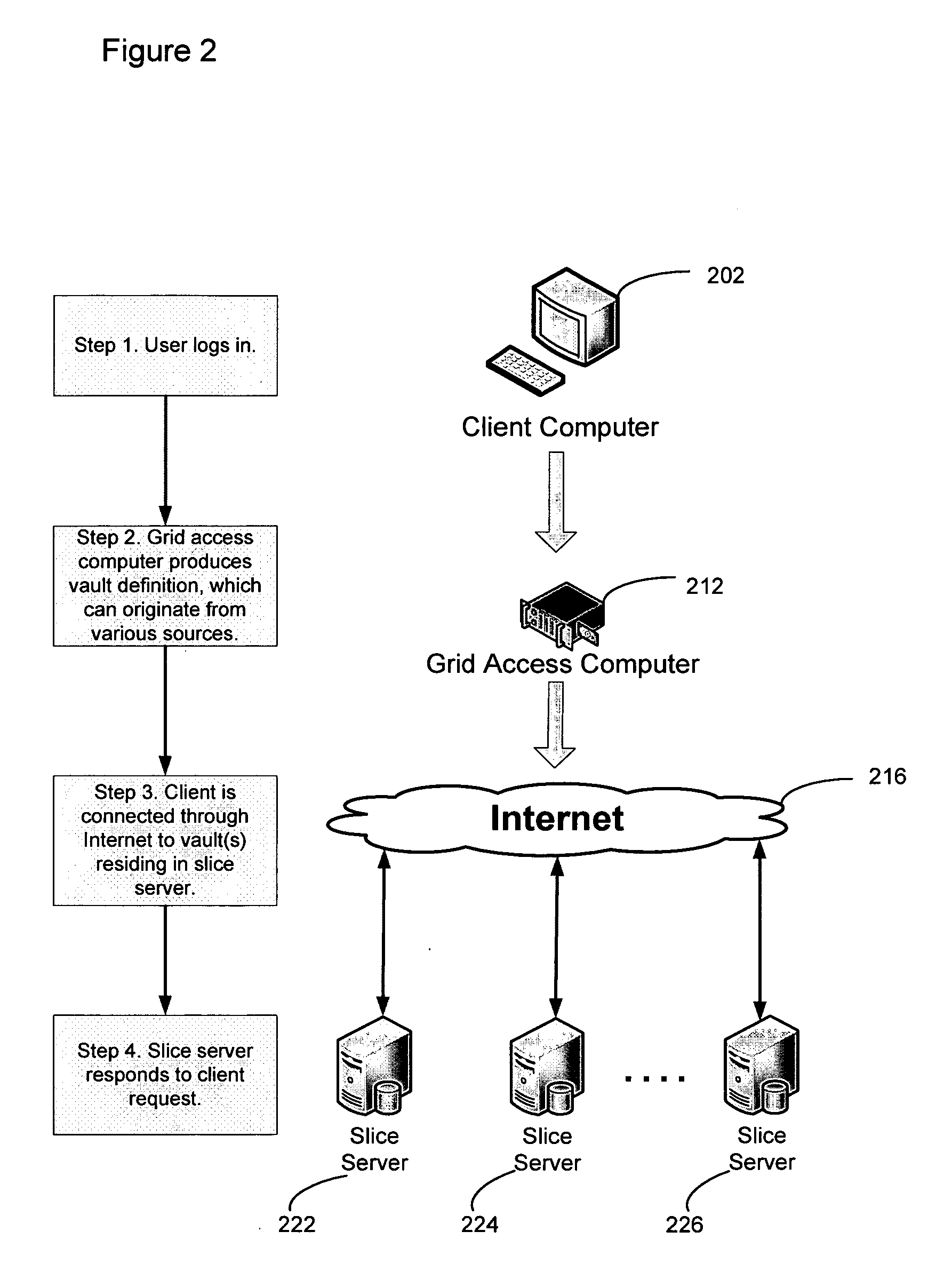
Virtualized data storage vaults on a dispersed data storage network
ActiveUS20090094251A1Efficient managementData processing applicationsDigital data processing detailsInformation dispersalVirtualization
A system, method, and apparatus for implementing a plurality of dispersed data storage networks using a set of slice servers are disclosed. A plurality of information records are maintained, with each information record corresponding to a dispersed data storage network. The information record maintains what slice servers are used to implement the dispersed data storage network, as well as other information needed to administer a DDSN, such as the information dispersal algorithm used, how data is stored, and whether data is compressed or encrypted.
Owner:PURE STORAGE
Method for reducing database recovery time
ActiveUS7222133B1Reduce database recovery timeShorten recovery timeData processing applicationsError detection/correctionComplete dataComputer science
Owner:UNISYS CORP
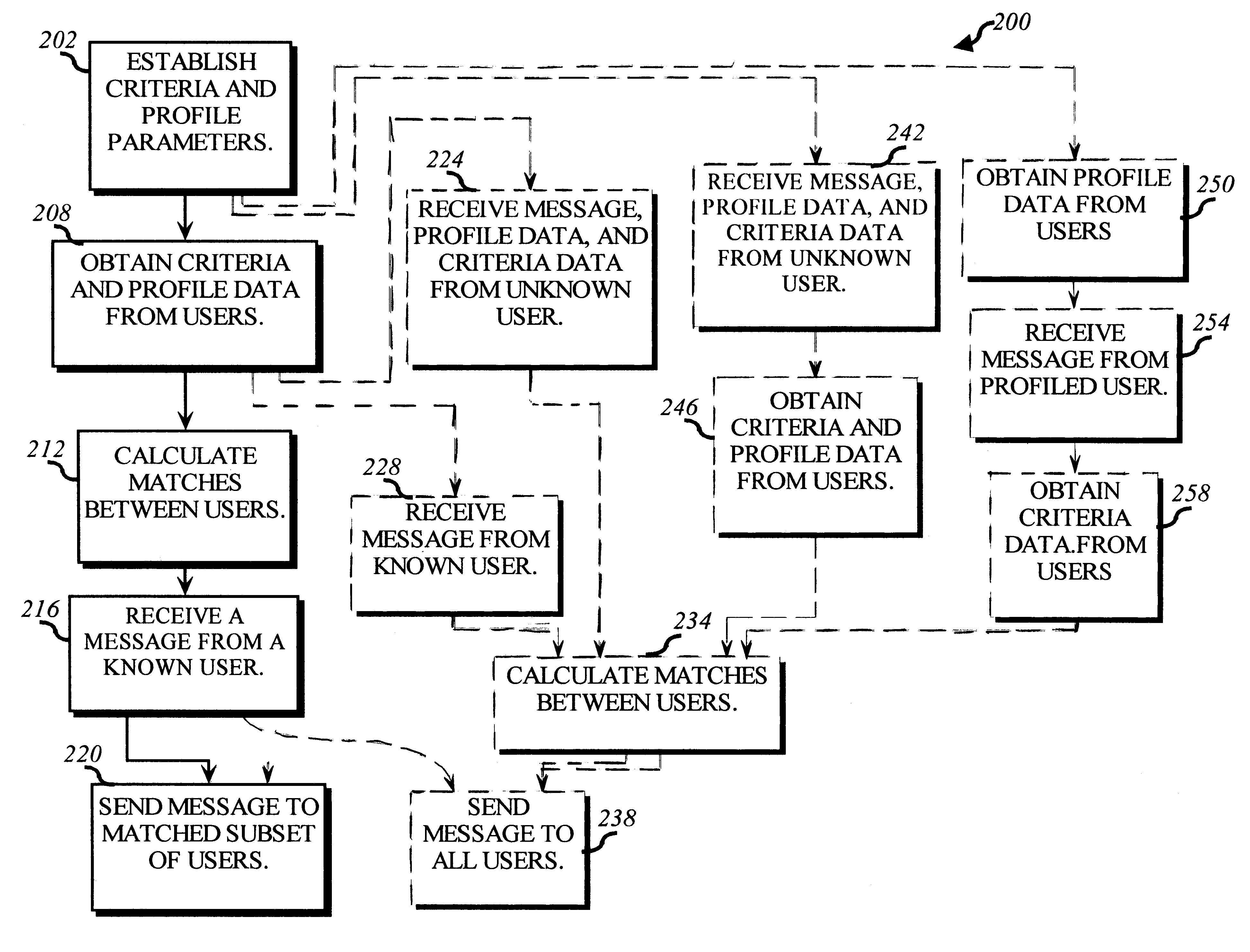
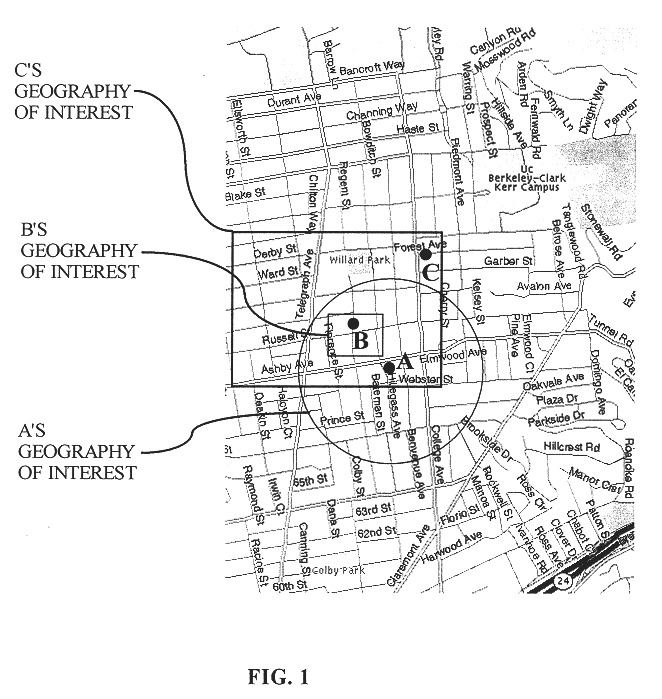
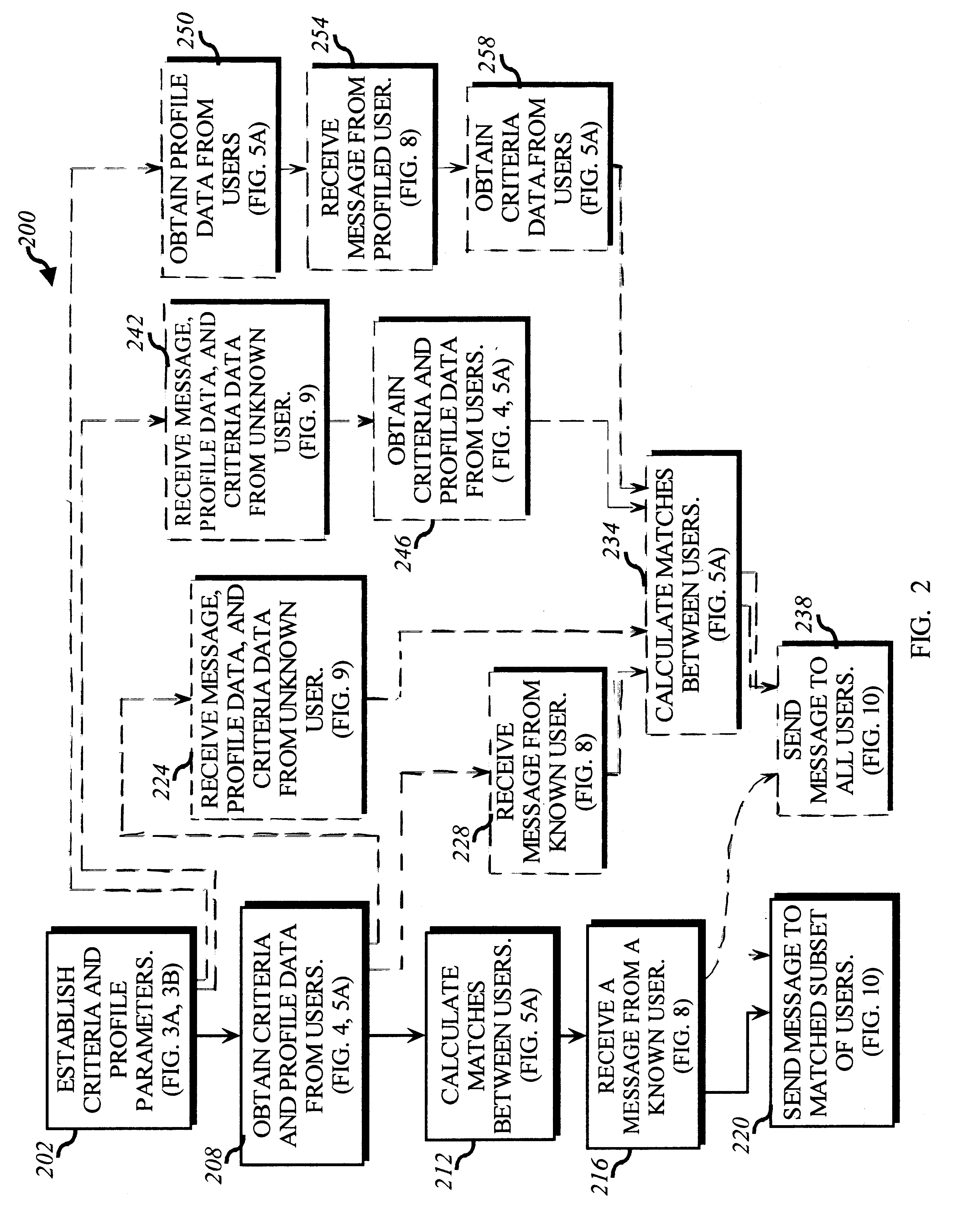
Dynamically matching users for group communications based on a threshold degree of matching of sender and recipient predetermined acceptance criteria
InactiveUS6480885B1Quality of communicationReduce in quantitySpecial service provision for substationMultiprogramming arrangementsPersonalizationWeb service
A method for enabling users to exchange group electronic mail by establishing individual profiles and criteria, for determining personalized subsets within a group. Users establish subscriptions to an electronic mailing list by specifying user profile data and acceptance criteria data to screen other users. When a user subscribes, a web server establishes and stores an individualized recipient list including each matching subscriber and their degree of one-way or mutual match with the user. When the user then sends a message to the mailing list, an email server retrieves 100% her matches and then optionally filters her recipient list down to a message distribution list using each recipient's message criteria. The message is then distributed to matching users. Additionally, email archives and information contributions from users are stored in a database. A web server creates an individualized set of web pages for a user from the database, containing contributions only from users in his recipient list. In other embodiments, users apply one-way or mutual criteria matching and message profile criteria to other group forums, such as web-based discussion boards, chat, online clubs, USENET newsgroups, voicemail, instant messaging, web browsing side channel communities, and online gaming rendezvous.
Owner:TUMBLEWEED HLDG LLC
Method for collecting and processing data using internetworked wireless integrated network sensors (WINS)
InactiveUS7020701B1High reliability accessEasy to operateEnergy efficient ICTPower managementReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
Systems and methods for use of structured and unstructured distributed data
InactiveUS20070061487A1Increase flexibilityDigital data processing detailsDatabase distribution/replicationDistributed databaseComputer science
The invention relates to hardware, software and electronic service components and systems to provide large-scale, reliable, and secure foundations for distributed databases and content management systems, combining unstructured and structured data, and allowing post-input reorganization to achieve a high degree of flexibility.
Owner:NEWSILIKE MEDIA GROUP
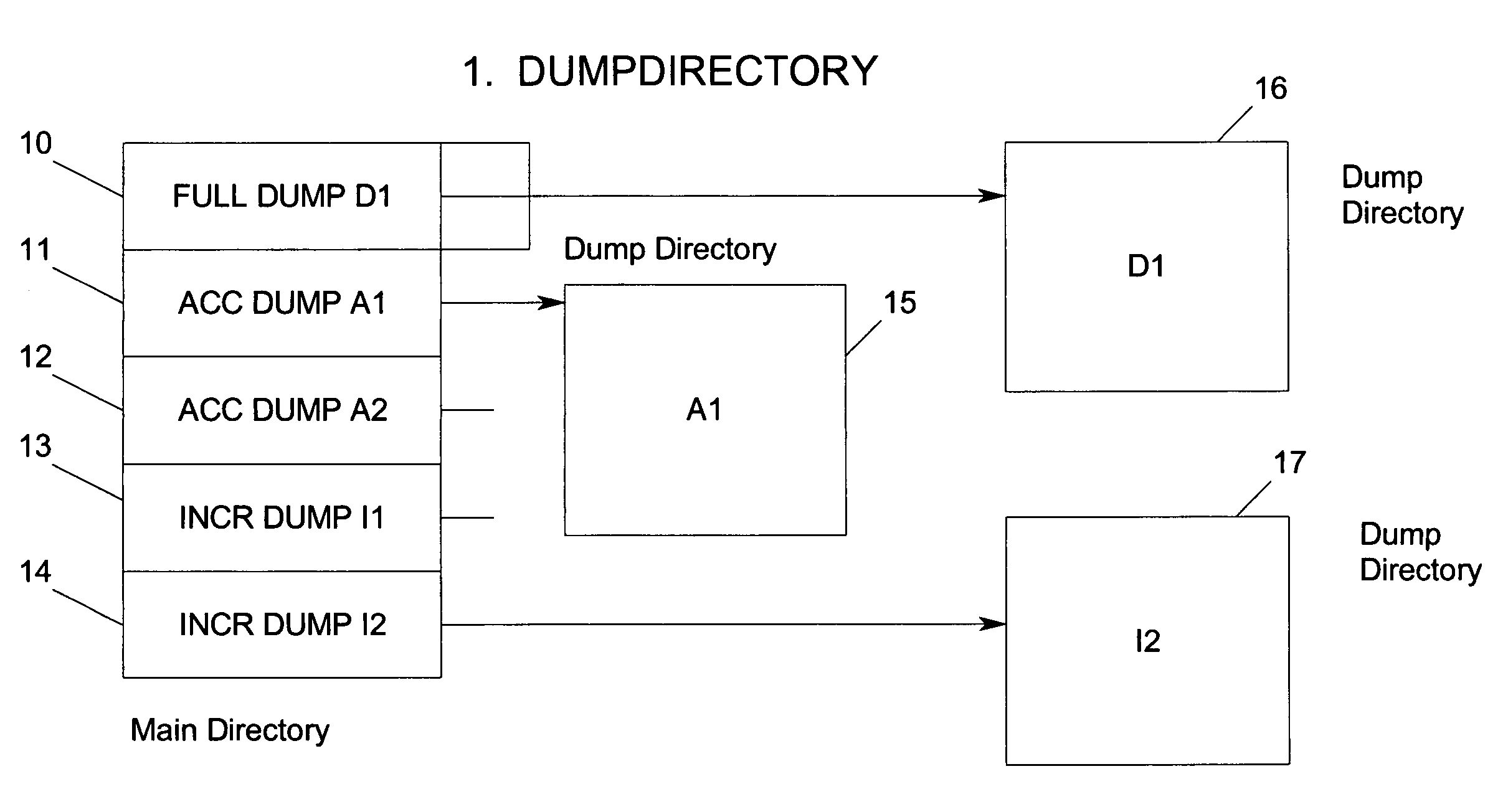
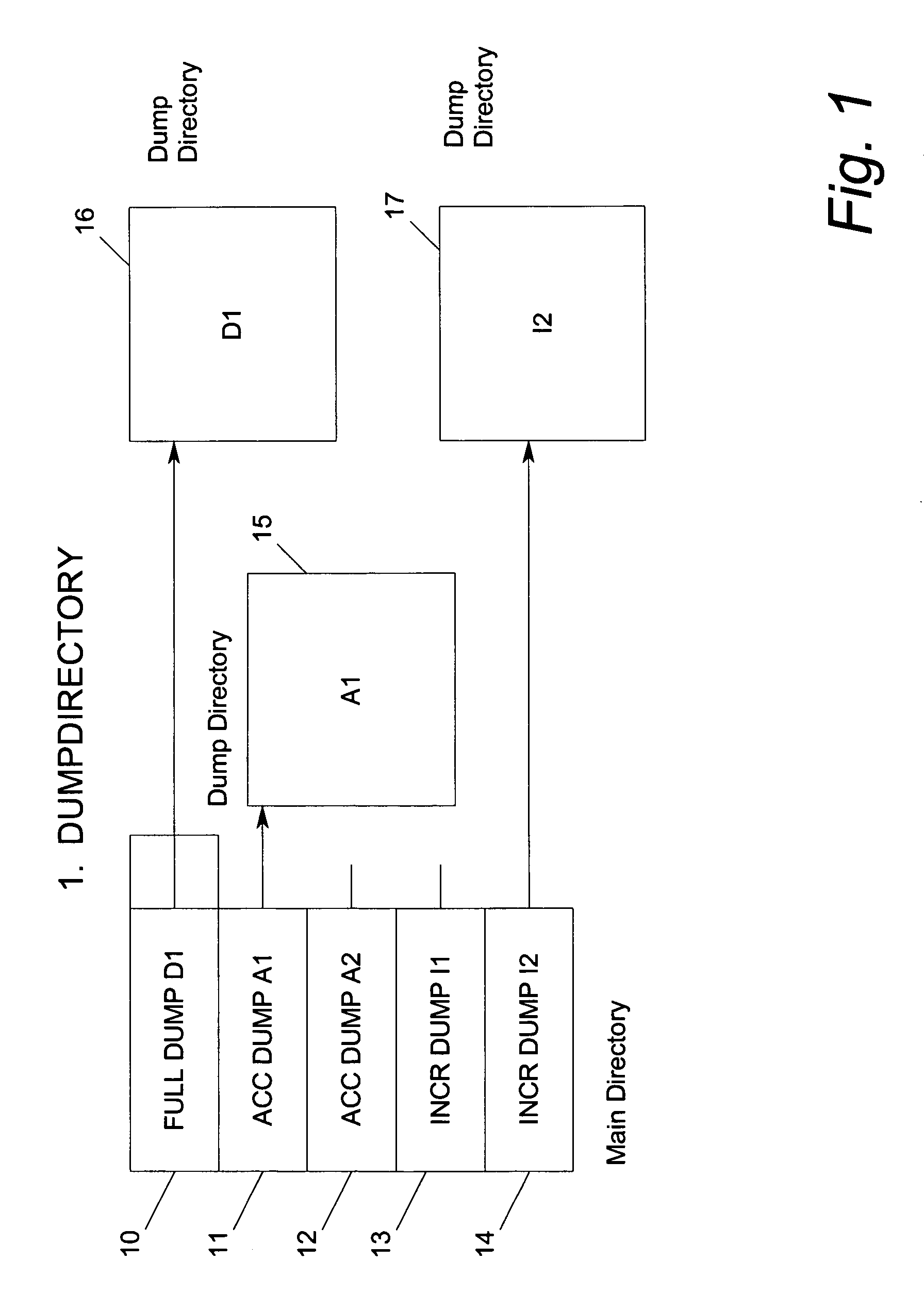
Method and system for incremental time zero backup copying of data
InactiveUSRE37601E1Maintaining continued availability of datasetsReduce suspensionRedundant operation error correctionMemory systemsData processing systemData set
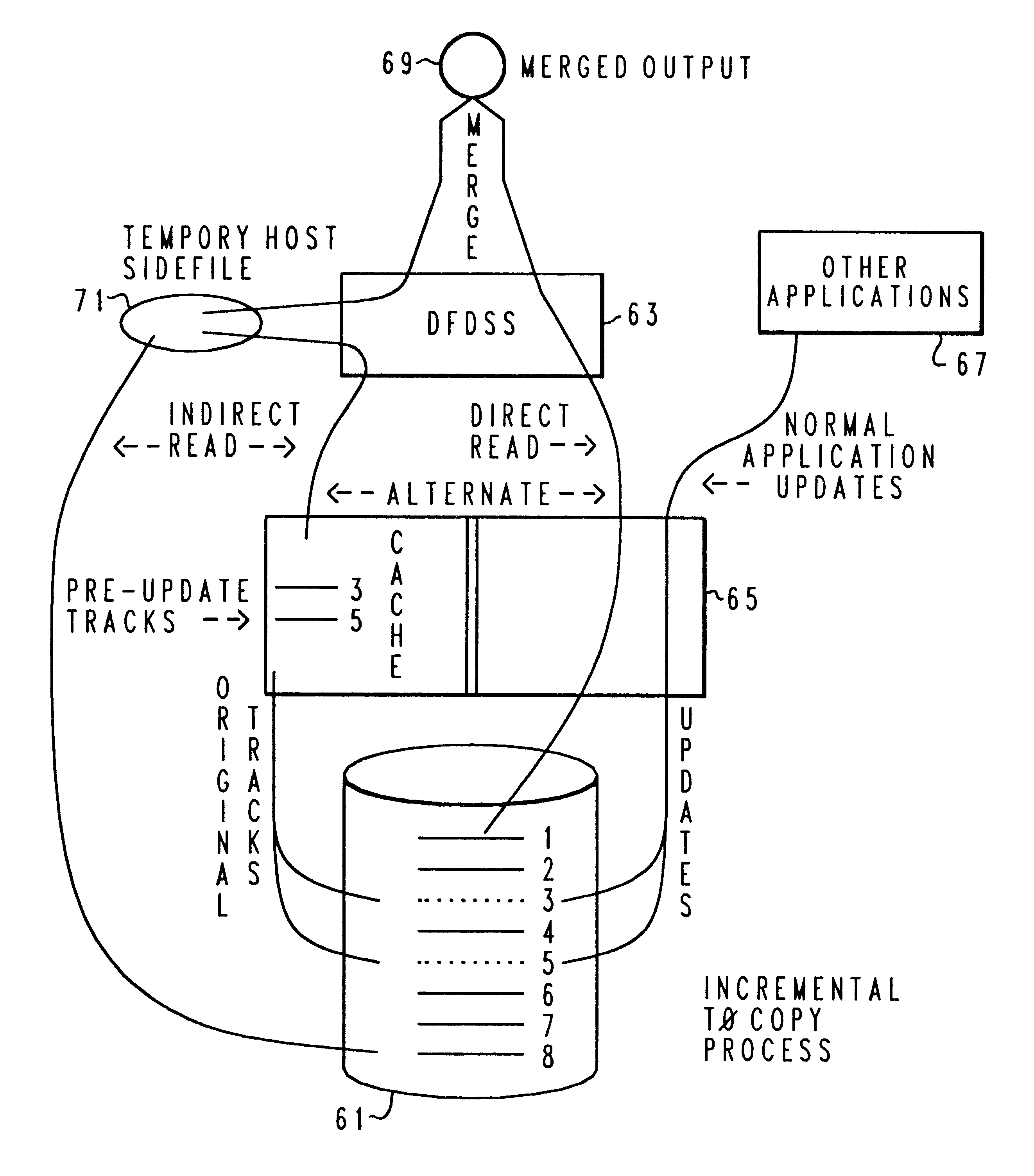
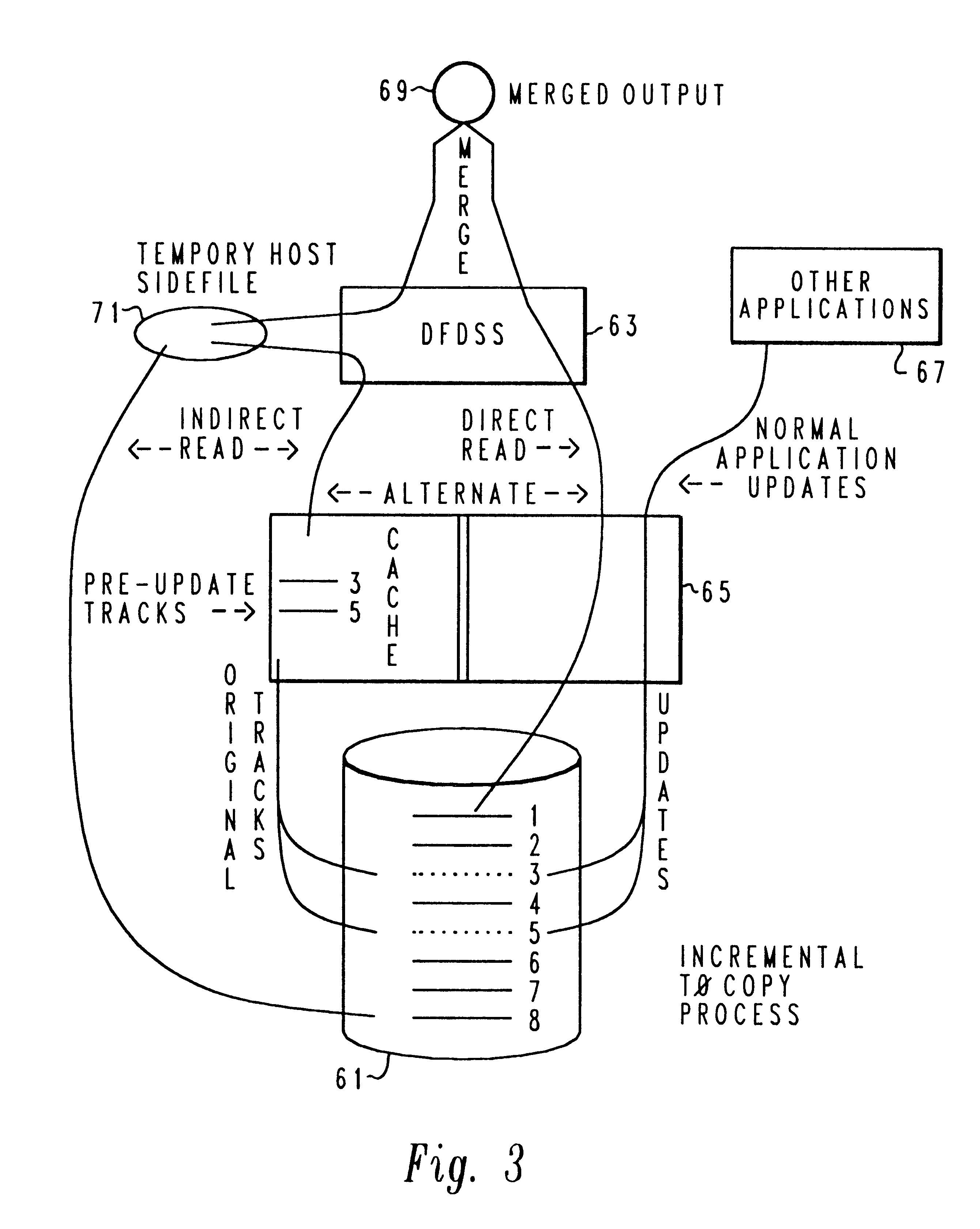
Backup copying of designated datasets representing a first selected point in time consistency may be performed in a data processing system on an attached storage subsystem concurrent with data processing system application execution by first suspending application execution only long enough to form a logical-to-physical address concordance, and thereafter physically backing up the datasets on the storage subsystem on a scheduled or opportunistic basis. An indication of each update to a selected portion of the designated datasets which occurs after the first selected point in time is stored and application initiated updates to uncopied designated datasets are first buffered. Thereafter, sidefiles are made of the affected datasets, or portions thereof, the updates are then written through to the storage subsystem, and the sidefiles written to an alternate storage location in backup copy order, as controlled by the address concordance. At a subsequent point in time only those portions of the designated datasets which have been updated after the first selected period and time are copied, utilizing an identical technique.
Owner:IBM CORP
Television chat system
InactiveUS20050262542A1Television conference systemsAnalogue secracy/subscription systemsInteractive televisionTelevision equipment
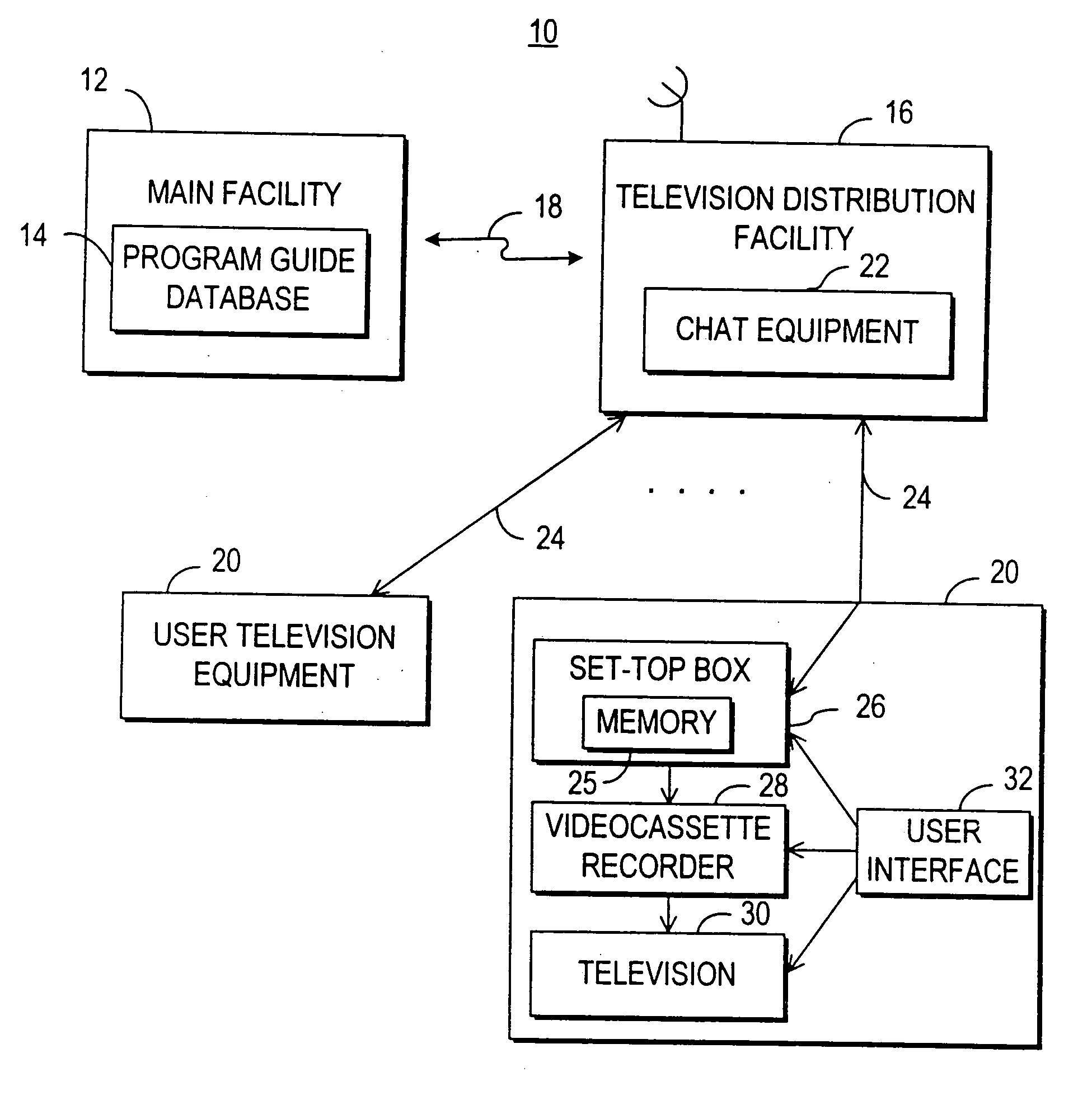
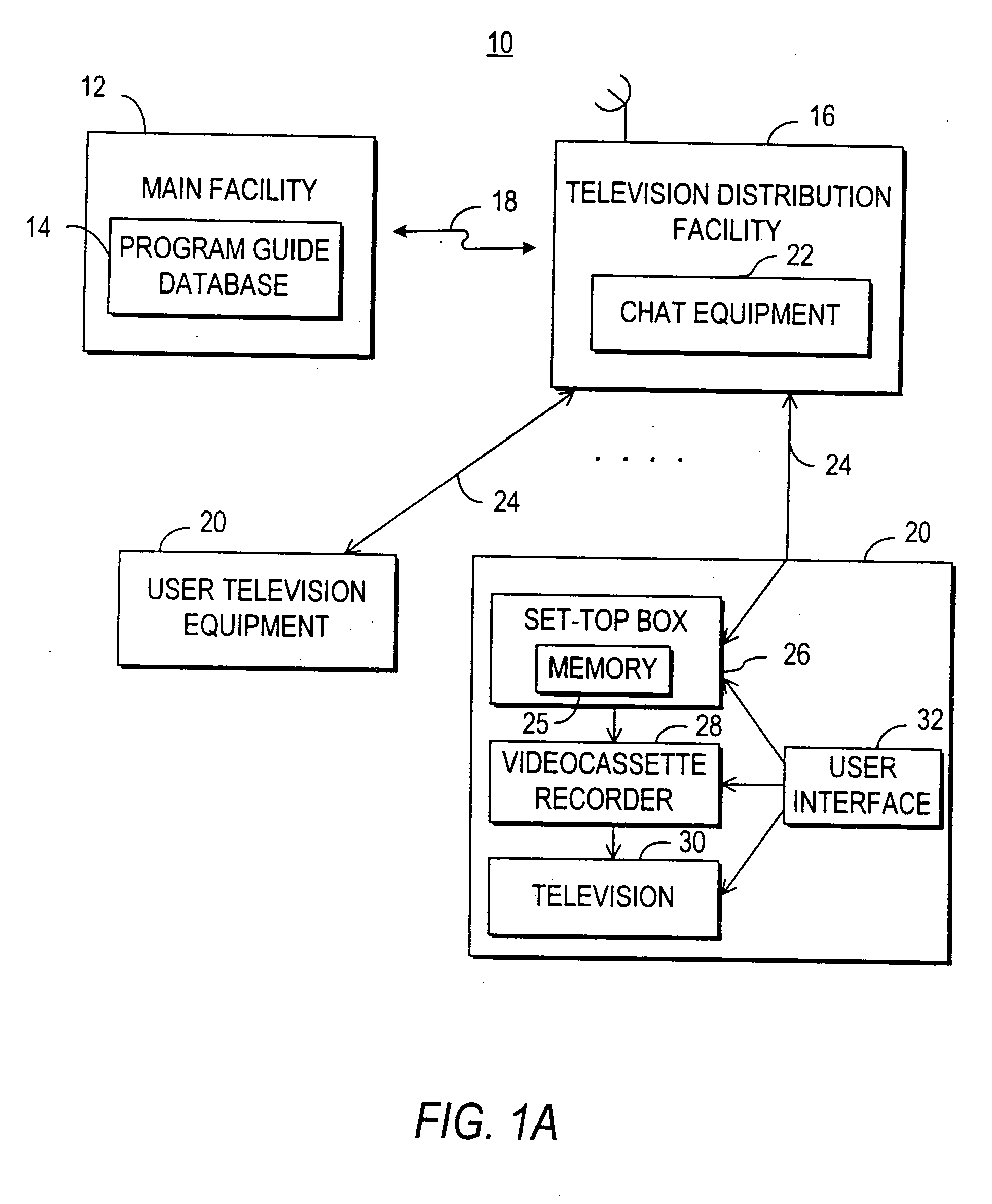
A television chat system is provided that allows television viewers to engage in real-time communications in chat groups with other television viewers while watching television. Users of the television chat system may engage in real-time communications with other users who are currently watching the same television program or channel. The system allows real-time communications in a chat group to be transmitted between users at user television equipment devices via a television distribution facility. The television chat system of the present invention permits users to join chat groups related to television programs, channels, or categories of programs that the user may be interested in. Real-time communications may be textual messages, audio communications, or video communications. The television chat system may also allow users to send chat requests to ask other users to enter a chat group. The system also permits users to establish chat groups that television viewers are permitted to join. The television chat system may be based on an interactive television program guide or set-top box application implemented on a set-top box.
Owner:ALL MEDIA GUIDE +10
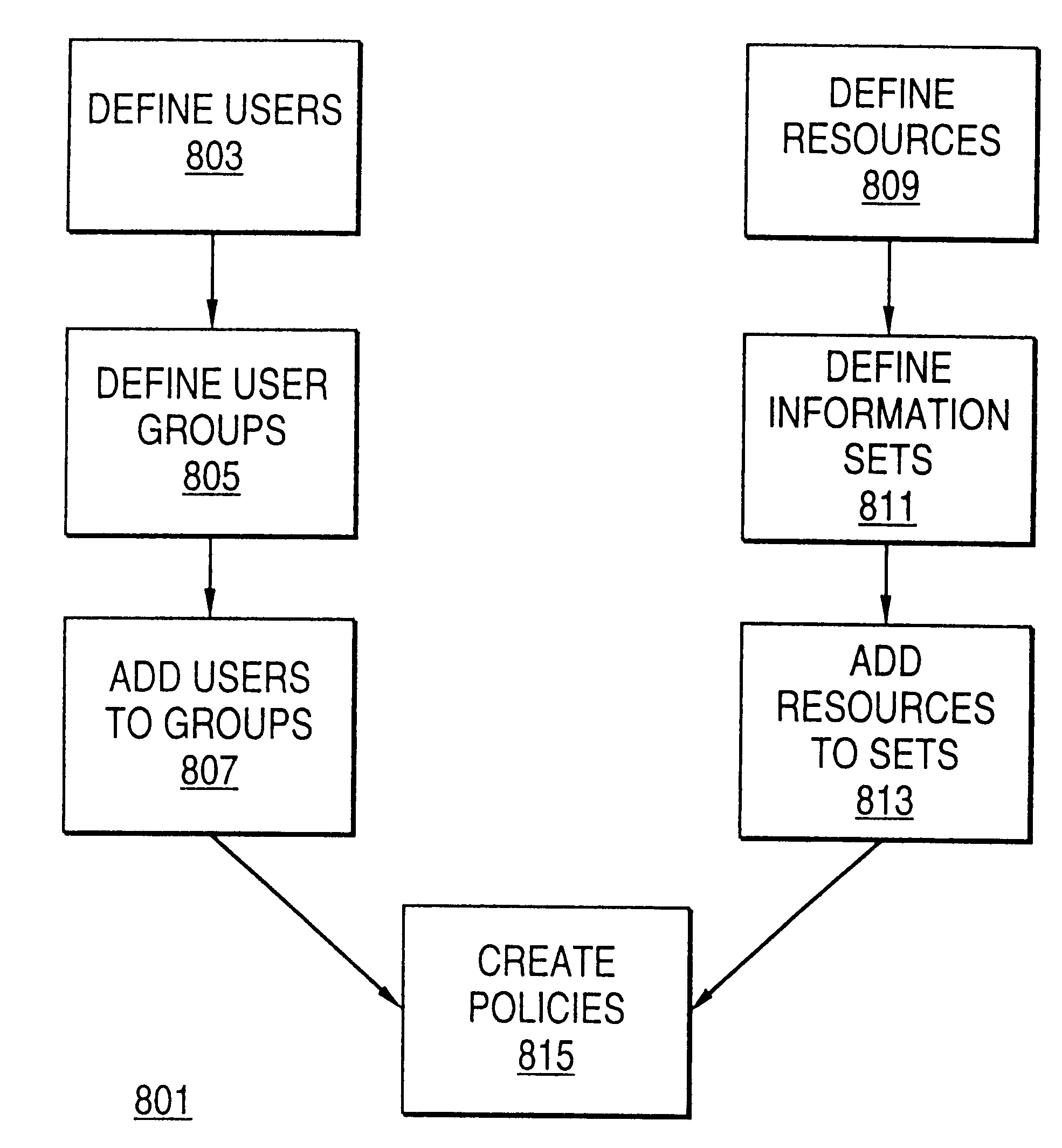
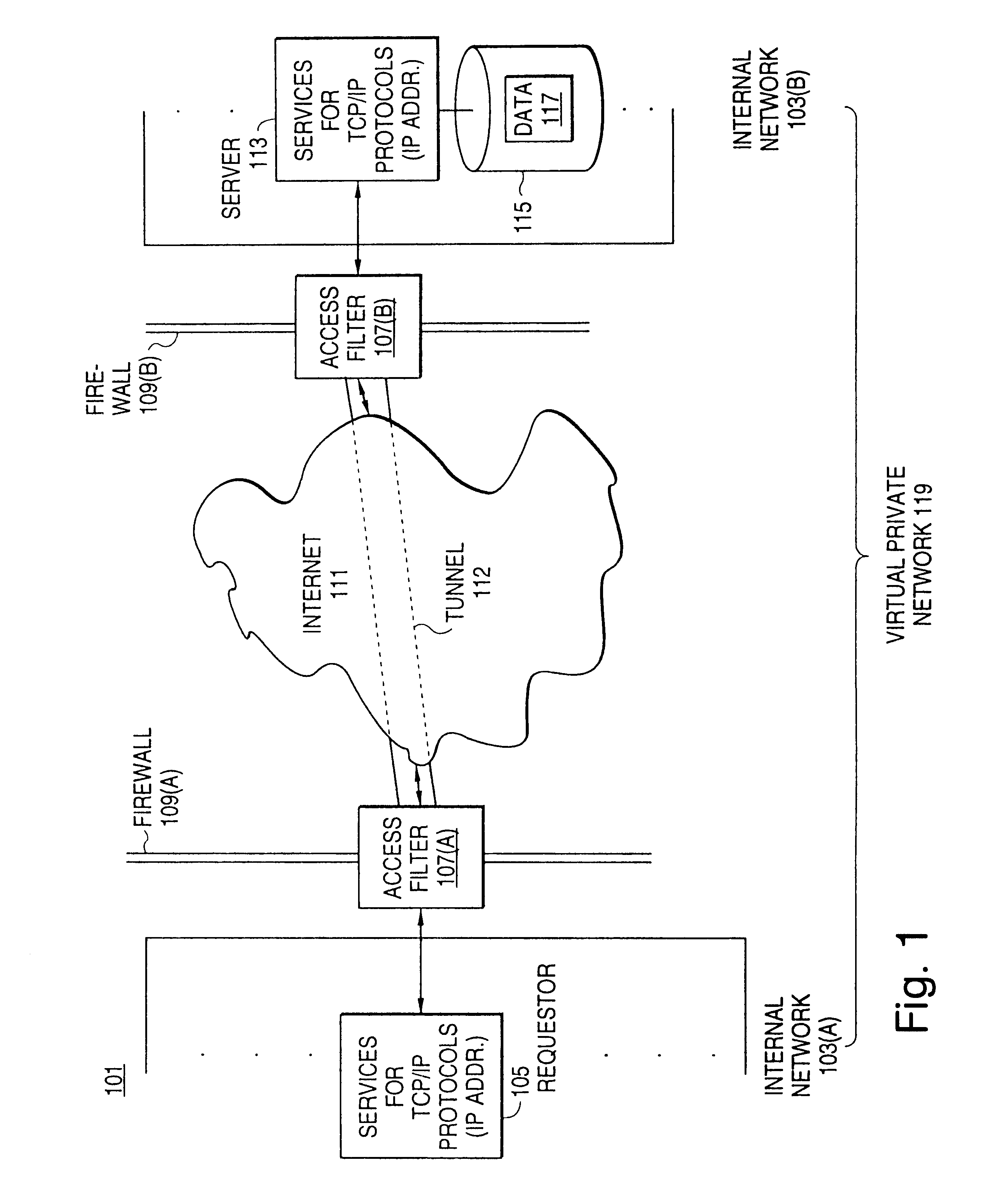
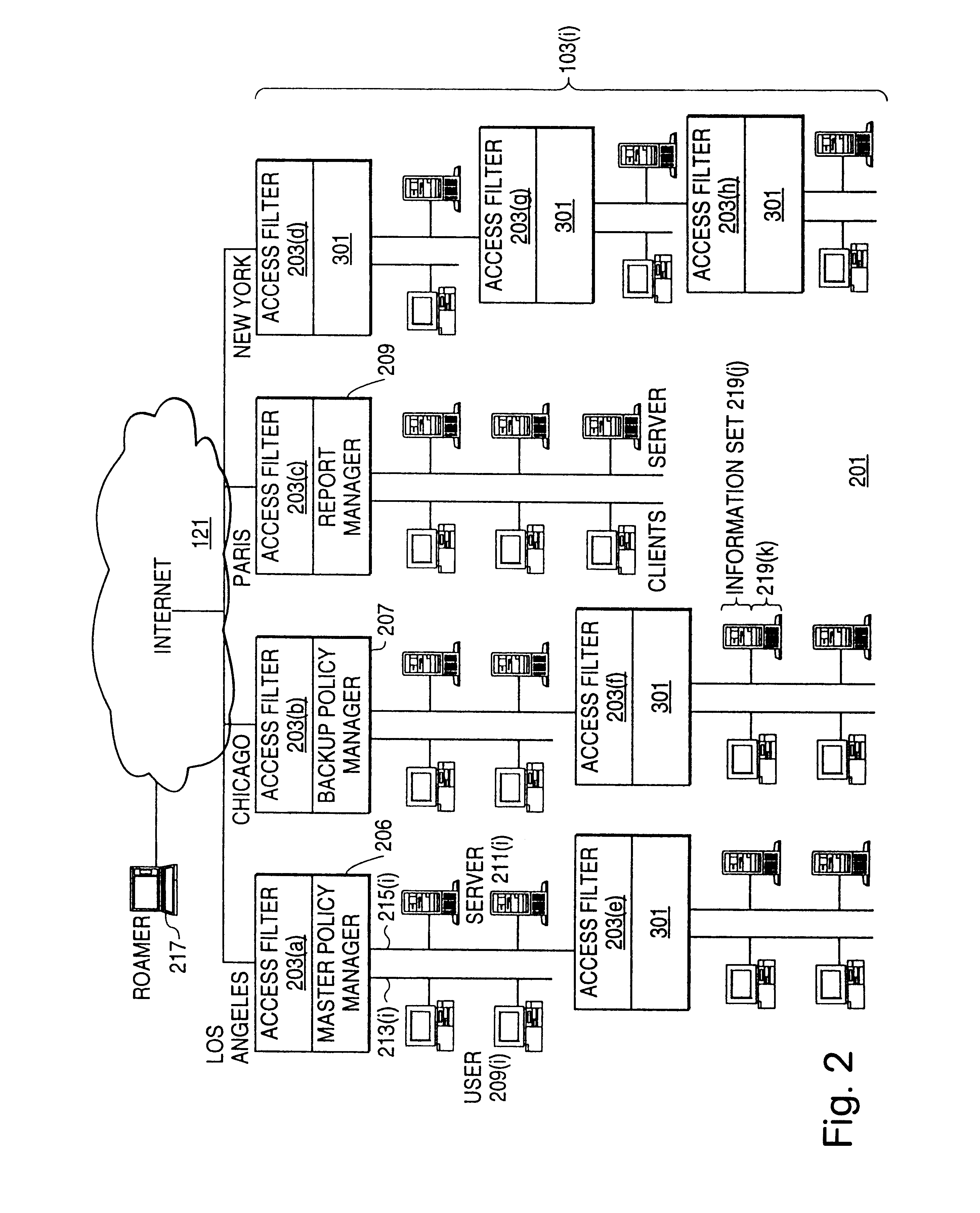
Distributed administration of access to information
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
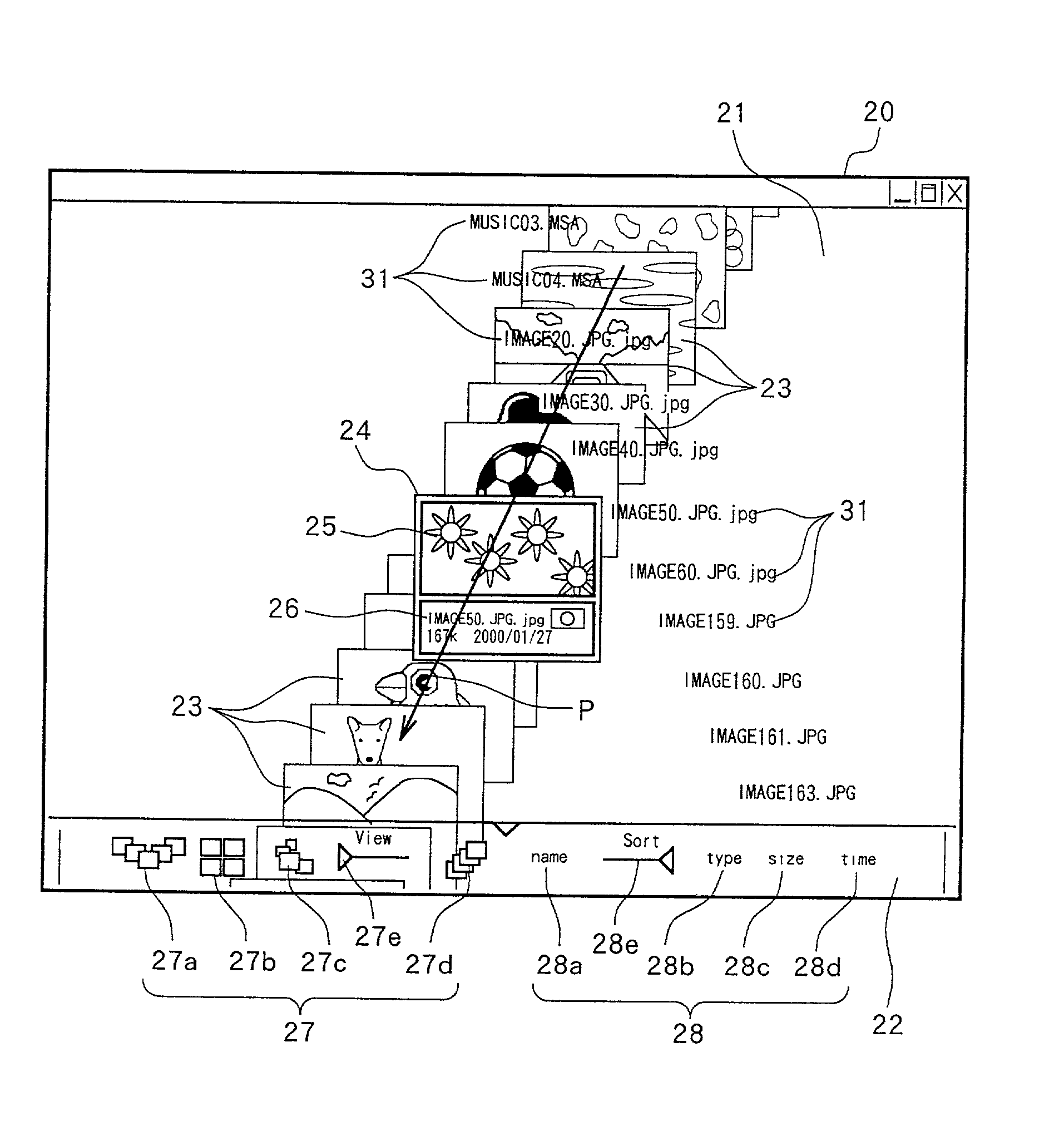
System for managing data objects
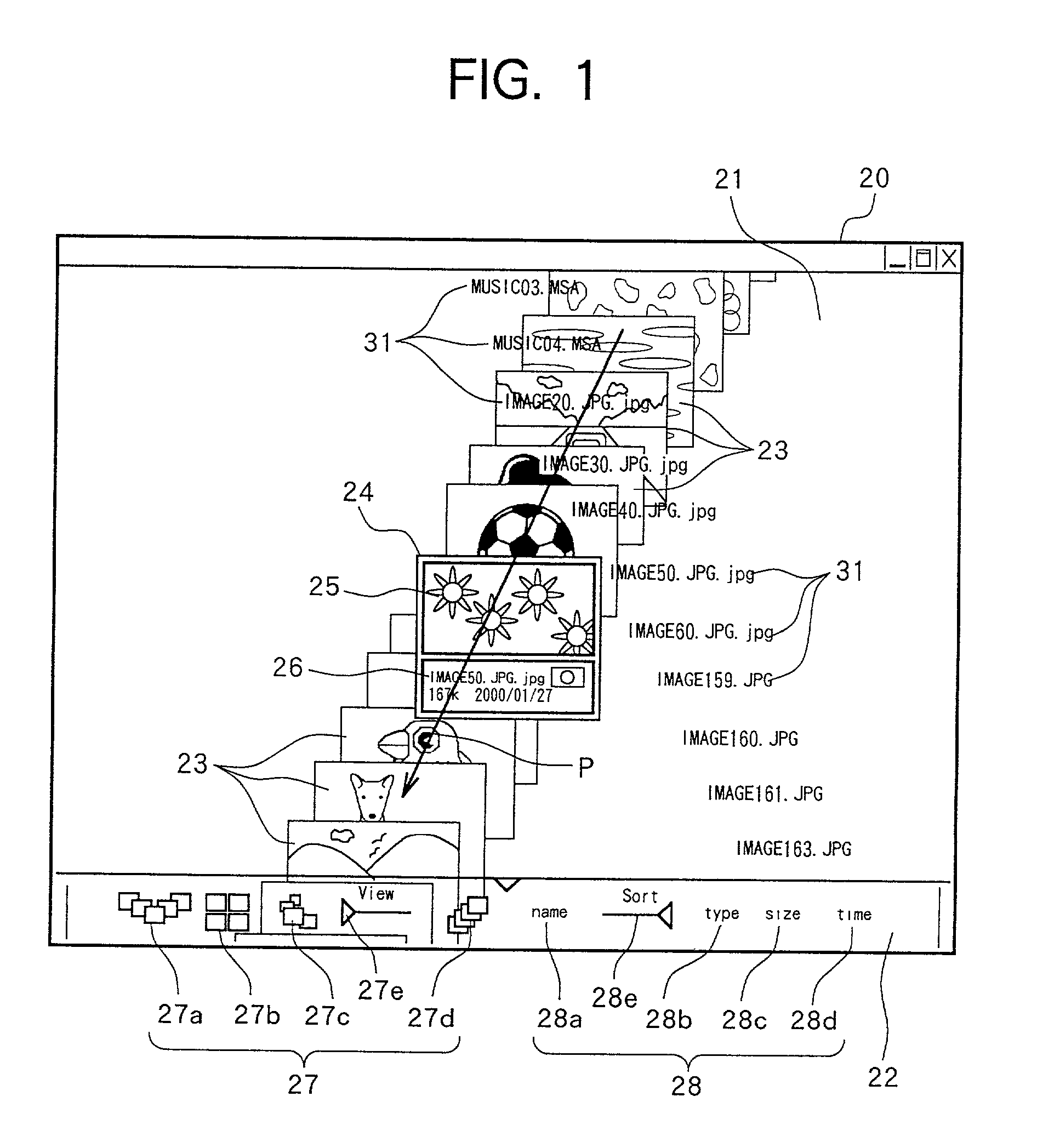
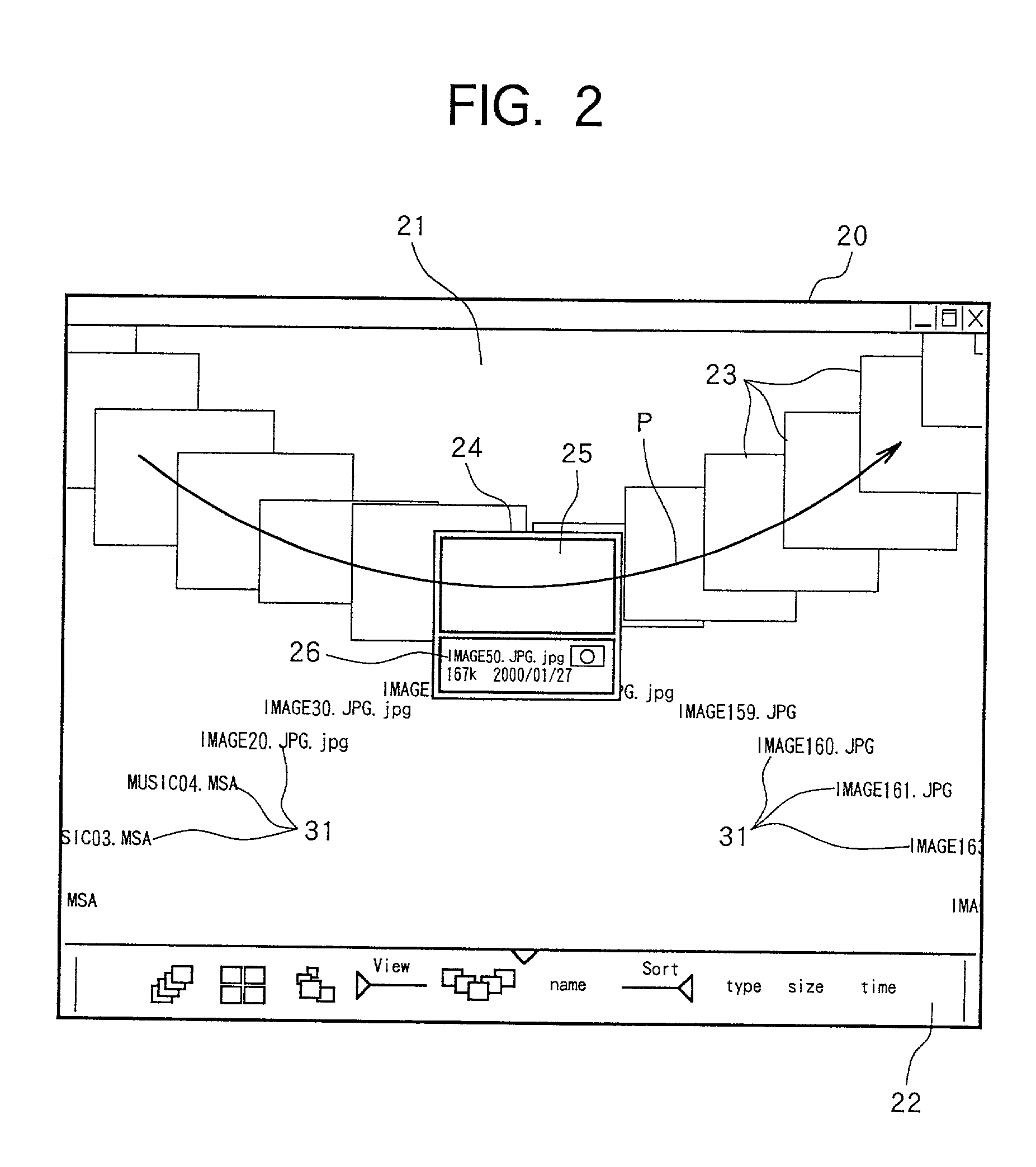
InactiveUS20020033848A1Television system detailsCo-operative working arrangementsUser inputThumbnail
A device for managing image and audio files displays thumbnails, which are representative of the files, on a screen in different arrangements, depending on the selected layout and order. When the user enters input to indicates that he or she wishes to browse through the thumbnails, the thumbnails move across the screen in sequence, following a path through a focus outline in the center of the screen. The path followed by the thumbnails depends on the selected layout.
Owner:TESSERA ADVANCED TECH
Systems and methods using cryptography to protect secure computing environments
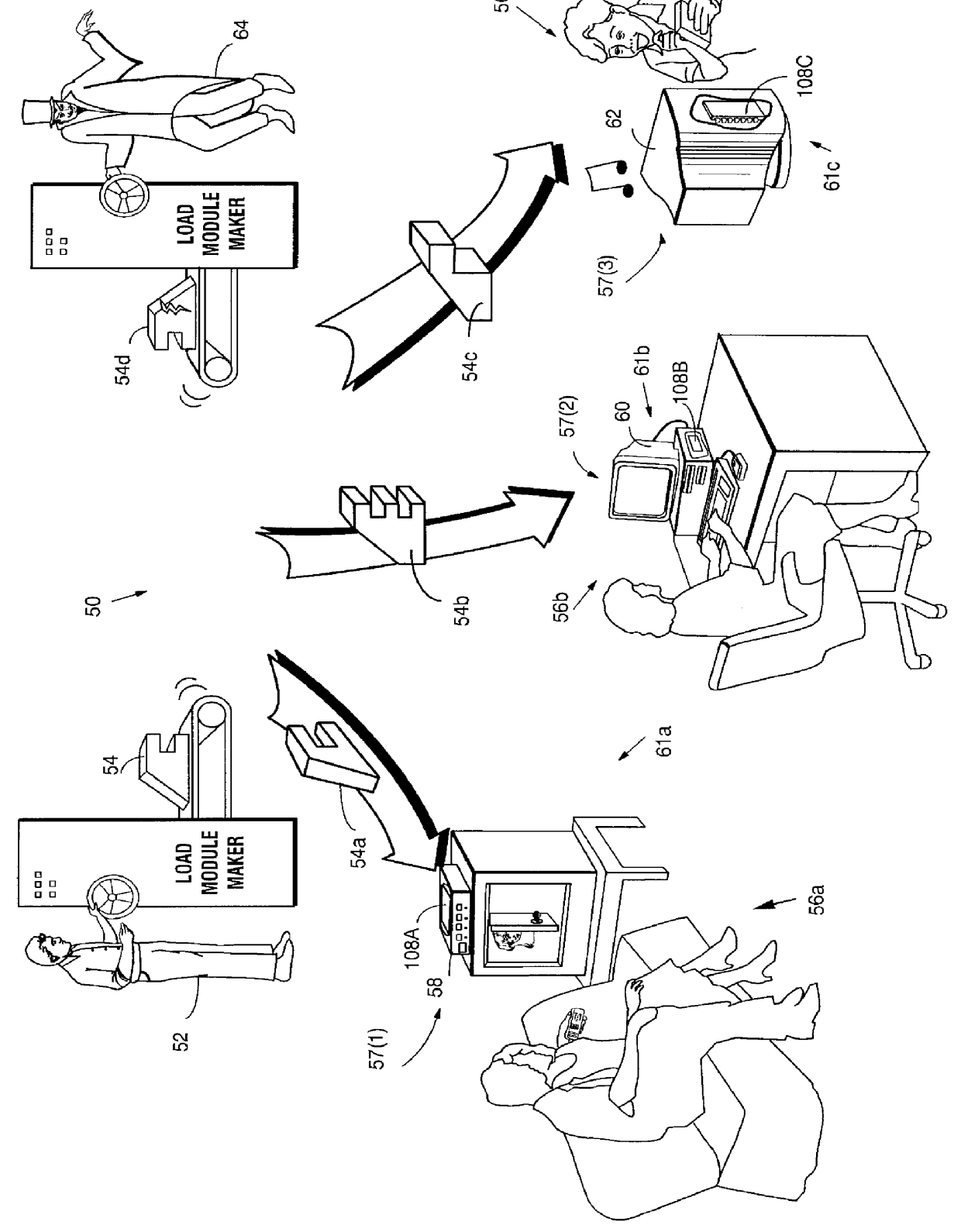
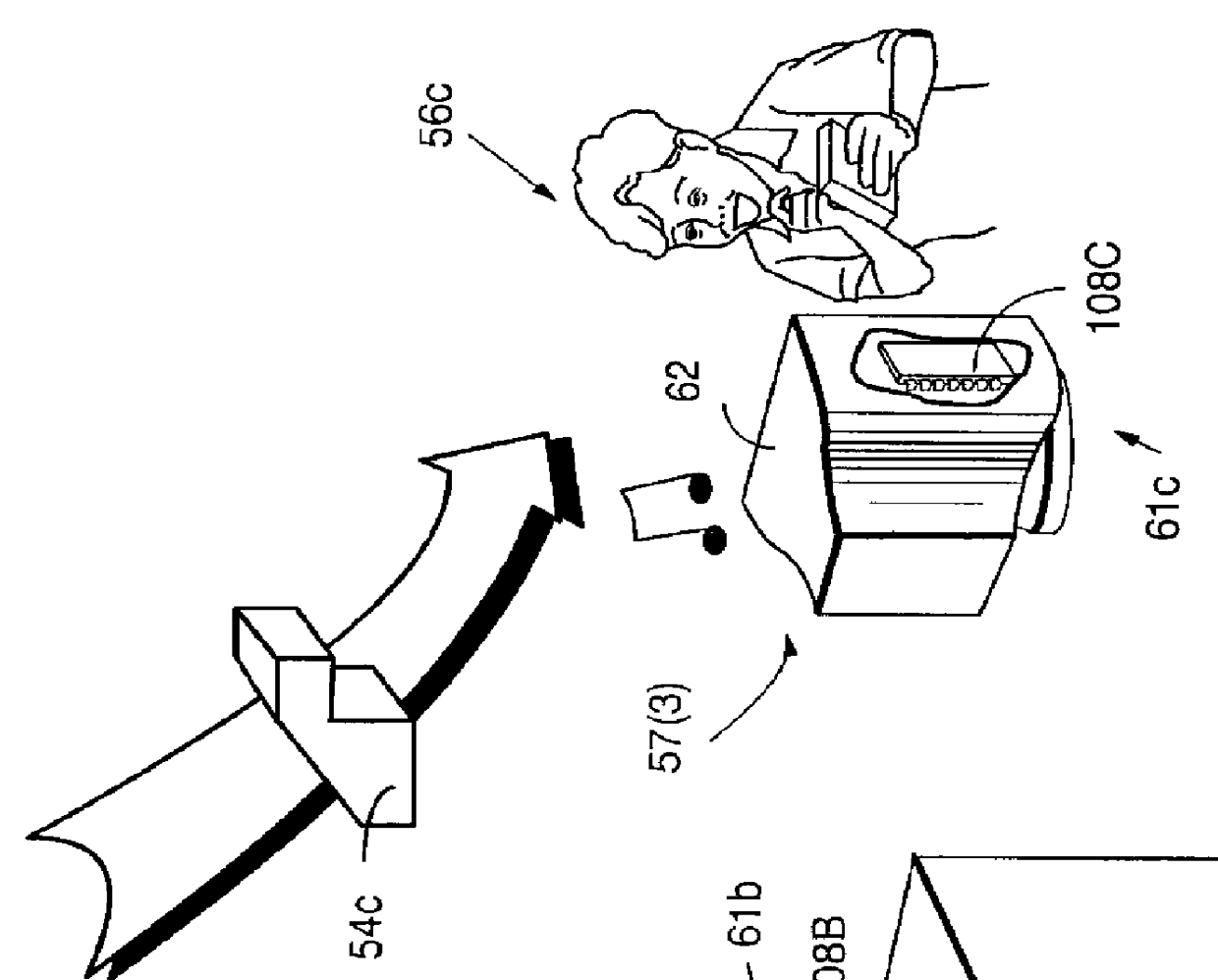
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
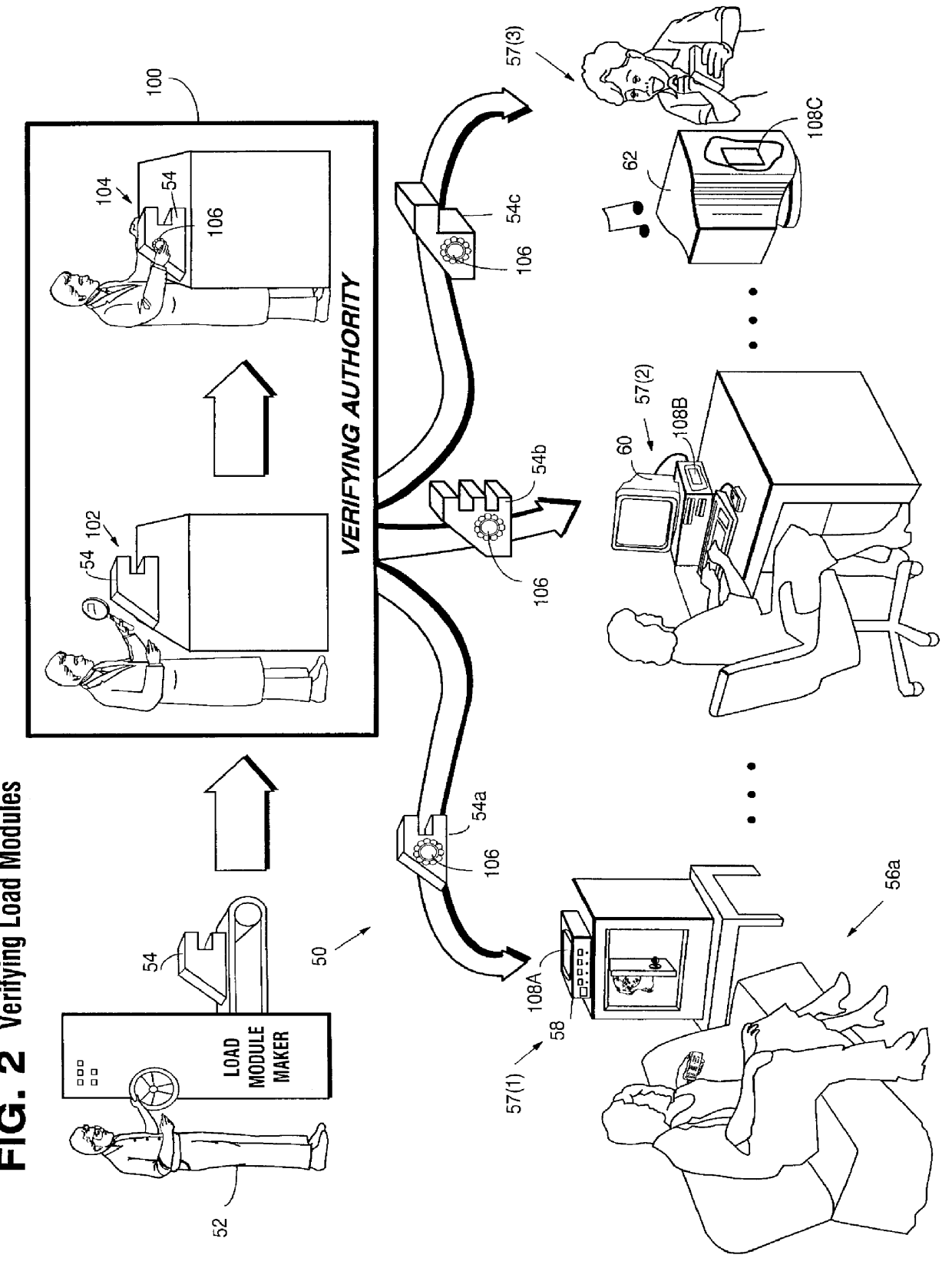
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
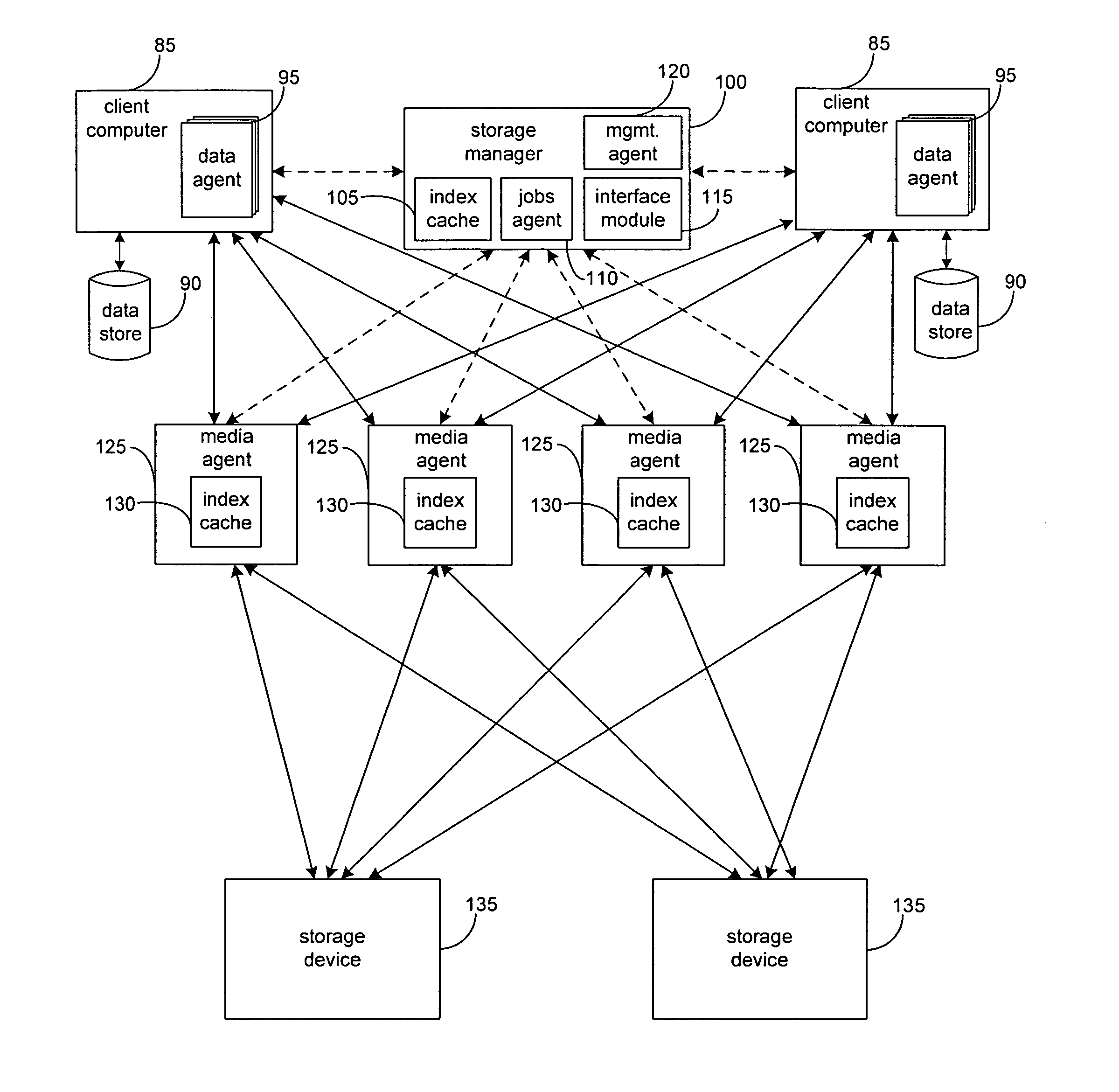
Systems and methods for monitoring application data in a data replication system
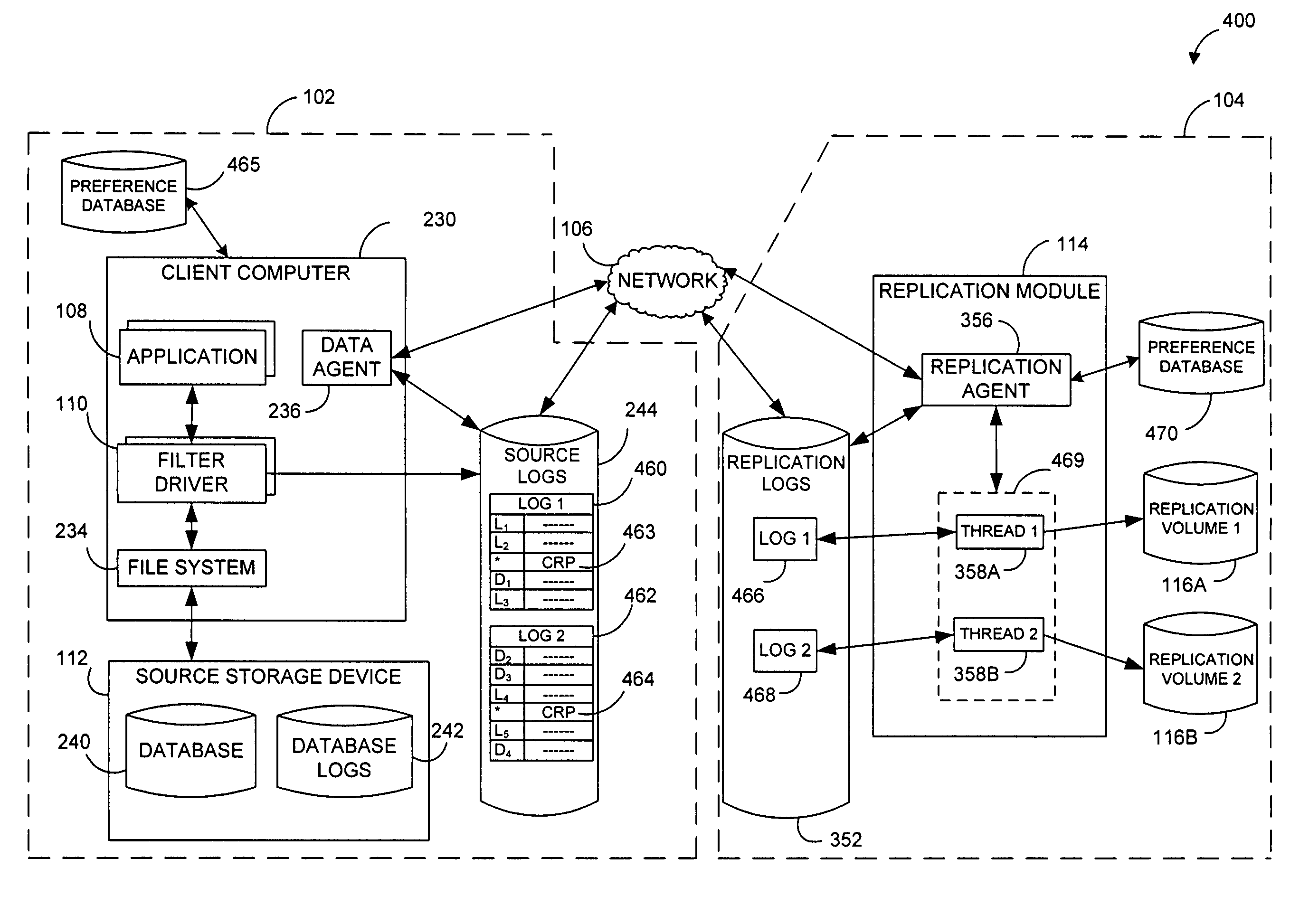
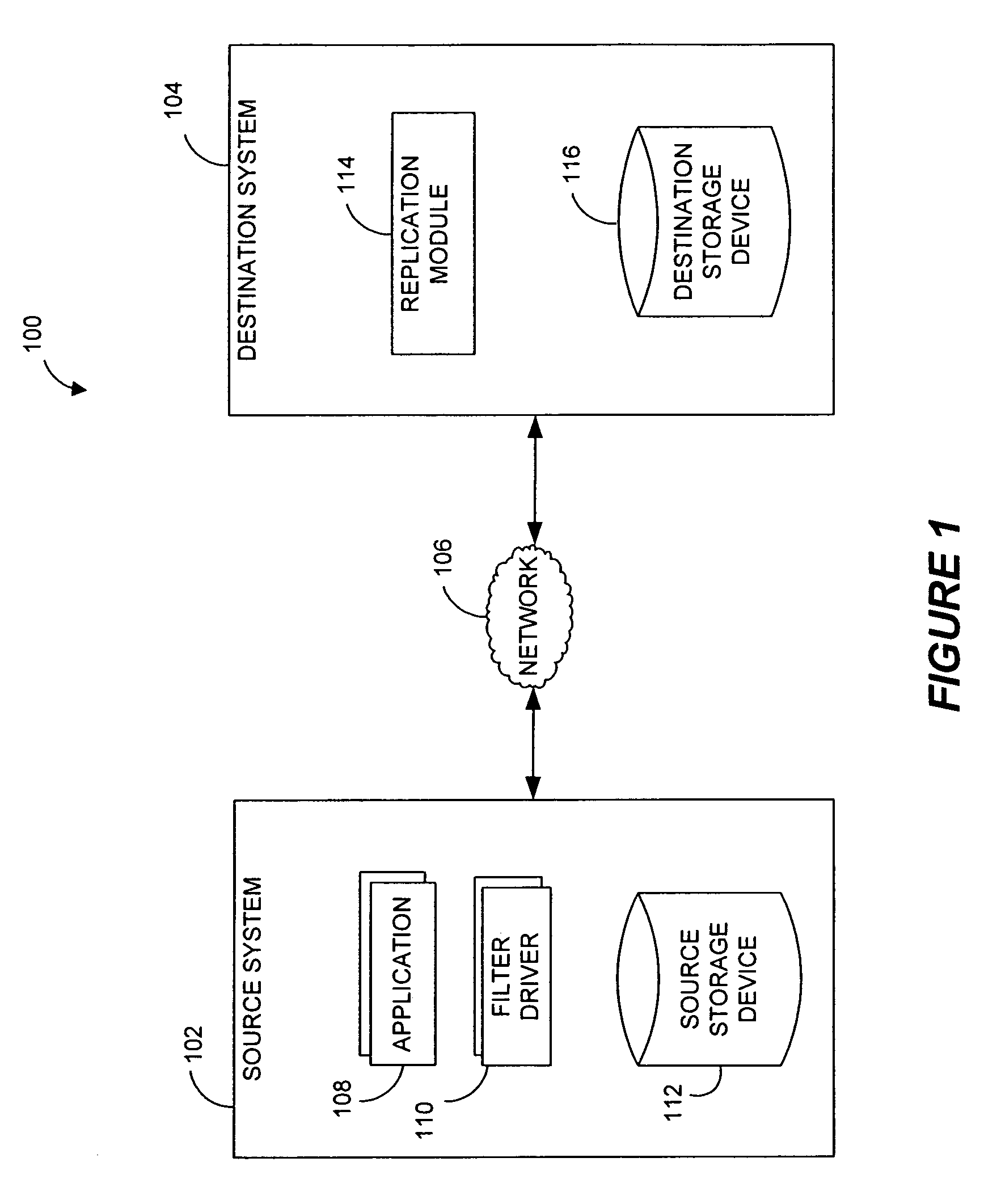
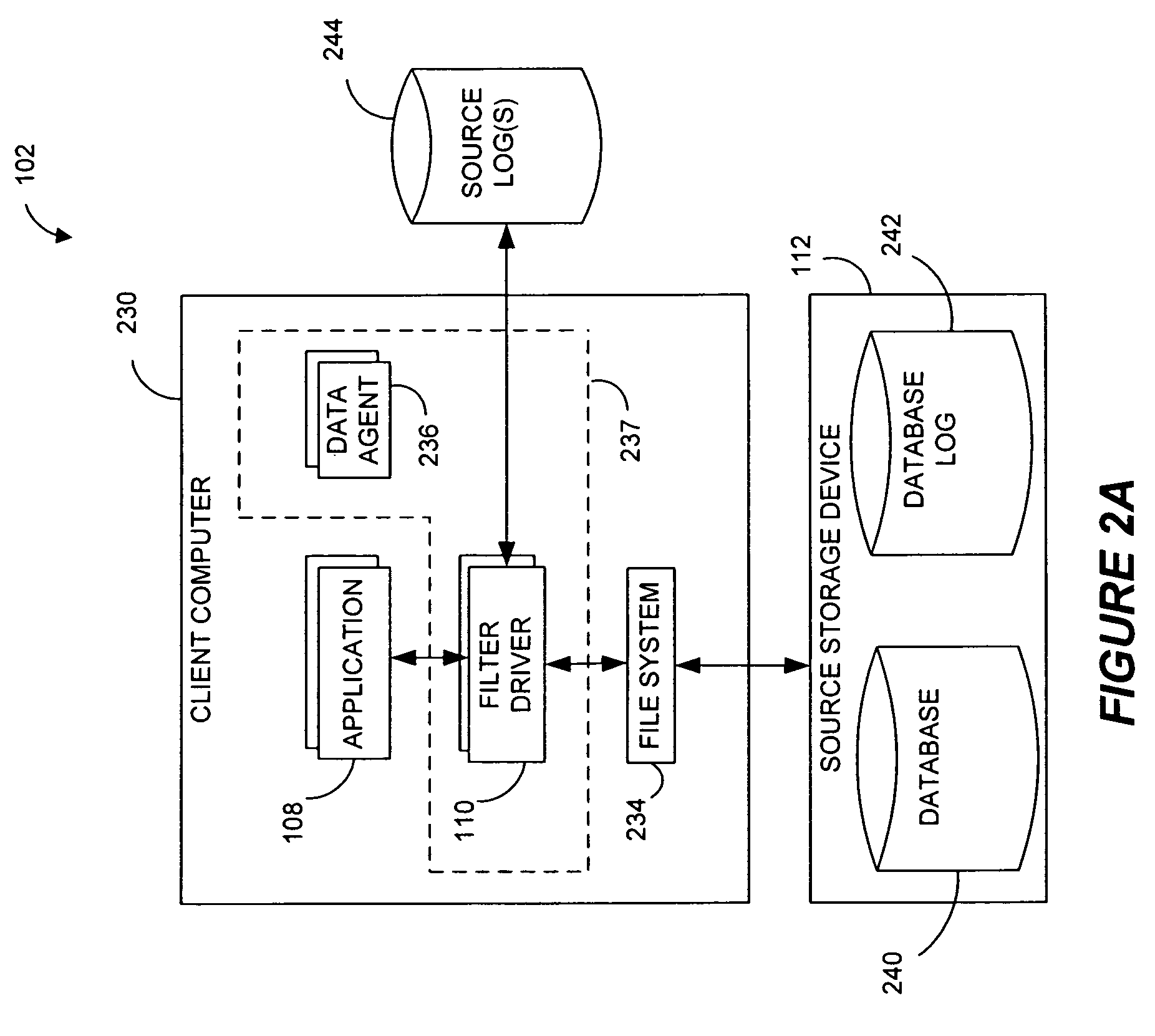
InactiveUS7617262B2Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS6418424B1Minimal costAvoid the needTelevision system detailsDigital data processing detailsHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
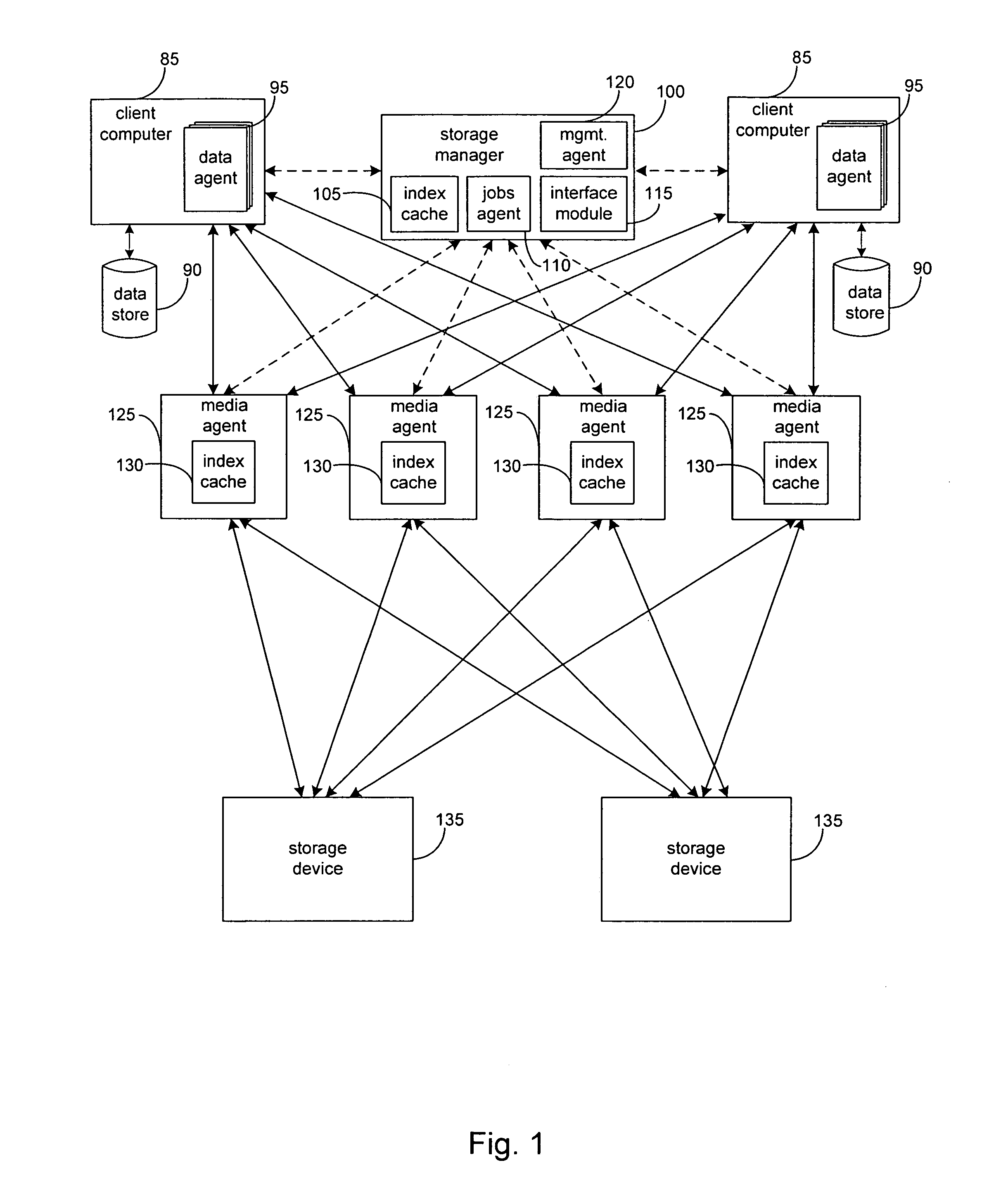
System and method to support simulated storage operations
ActiveUS7536291B1Error detection/correctionMultiple digital computer combinationsOperating systemSimulated data
The present invention includes a system for simulating the performing of data storage operations. The system may include a storage manager component, at least one media management component directed by the storage manager component to manage storage operations to at least one storage device, and a storage emulation module adapted to simulate the characteristics of the at least one storage device. Under the direction of the storage manager, the emulation module may be adapted to simulate storage operations to one or more storage devices performed by one or more of the media management components.
Owner:COMMVAULT SYST INC
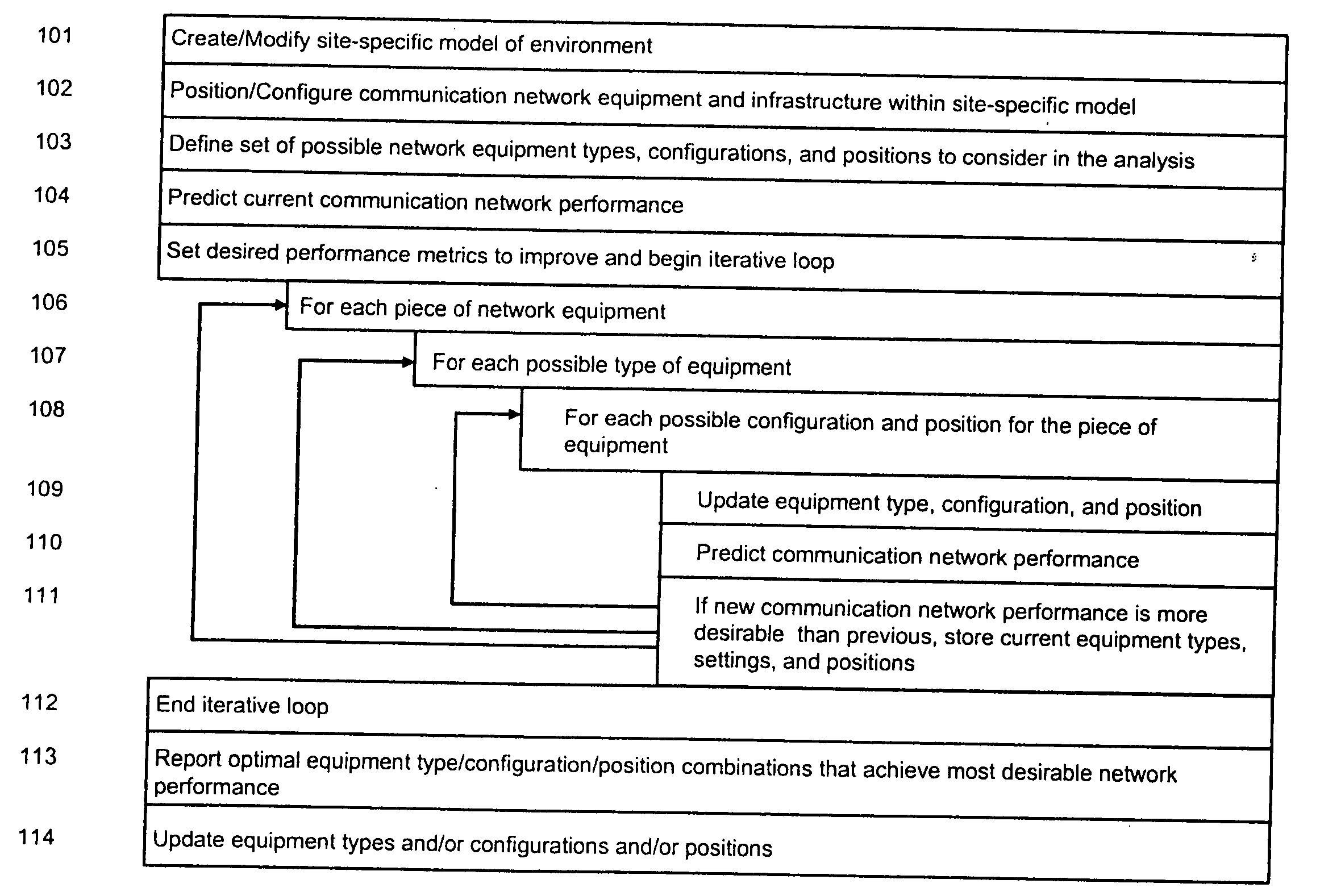
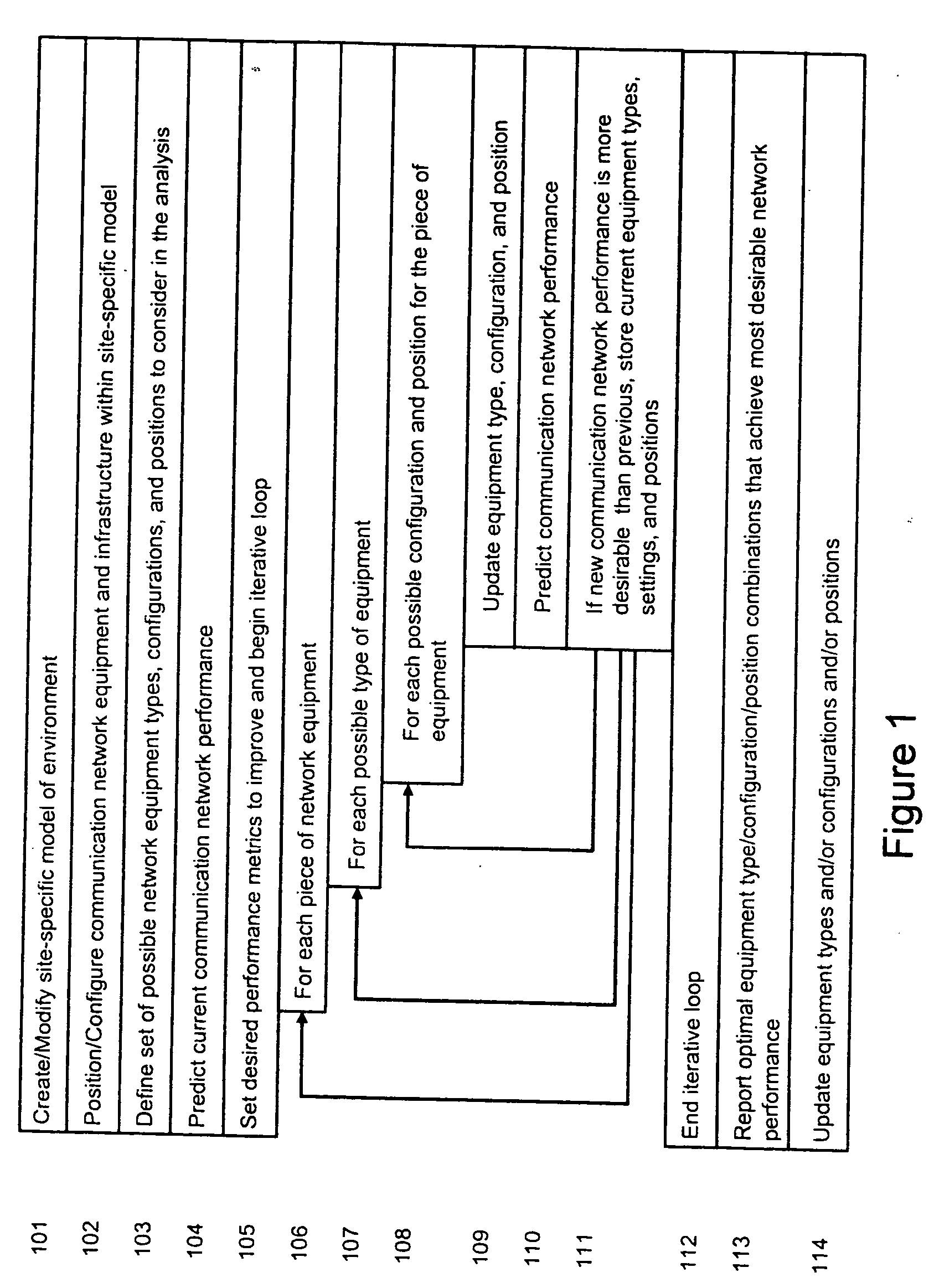
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
File system shell
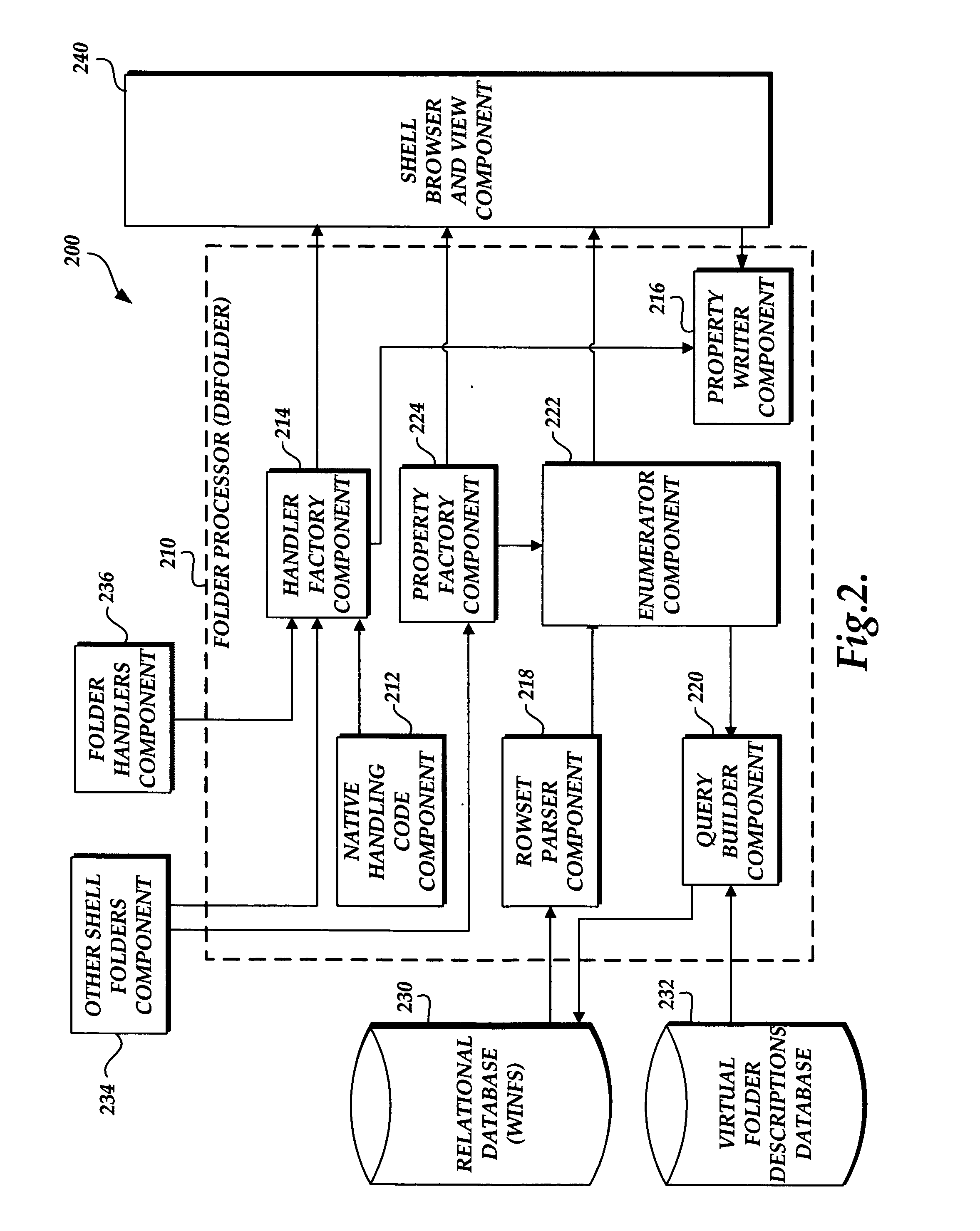
InactiveUS20060036568A1Adapt quicklyDigital data information retrievalSpecial data processing applicationsView basedProject type
A file system shell is provided. One aspect of the shell provides virtual folders which expose regular files and folders to users in different views based on their metadata instead of the actual physical underlying file system structure on the disk. Users are able to work with the virtual folders through direct manipulation (e.g., clicking and dragging, copying, pasting, etc.). Filters are provided for narrowing down sets of items. Quick links are provided which can be clicked on to generate useful views of the sets of items. Libraries are provided which consist of large groups of usable types of items that can be associated together, along with functions and tools related to the items. A virtual address bar is provided which comprises a plurality of segments, each segment corresponding to a filter for selecting content. A shell browser is provided with which users can readily identify an item based on the metadata associated with that item. An object previewer in a shell browser is provided which is configured to display a plurality of items representing multiple item types.
Owner:MICROSOFT TECH LICENSING LLC
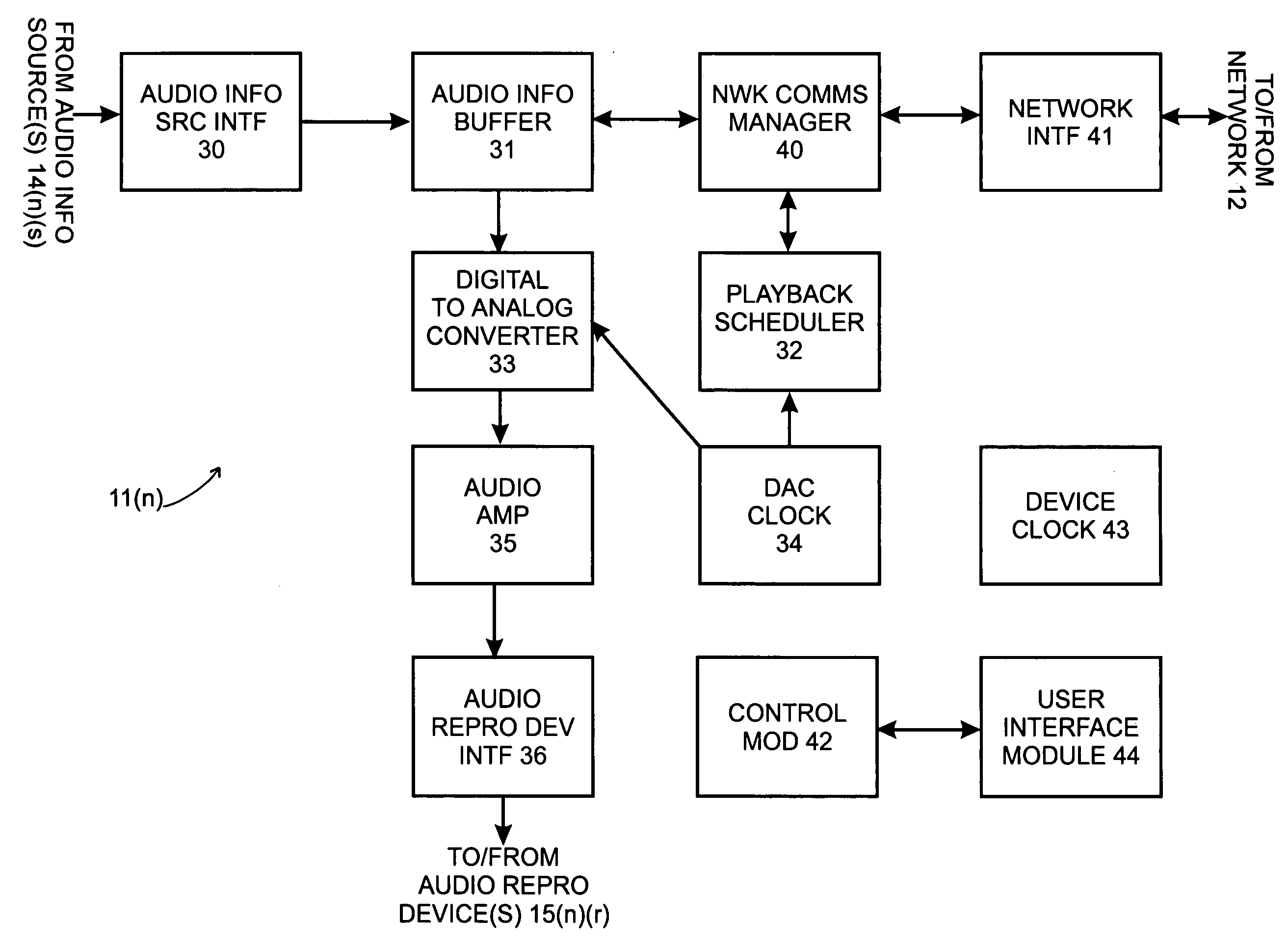
System and method for synchronizing operations among a plurality of independently clocked digital data processing devices
ActiveUS20070038999A1Maintenance operationTelevision system detailsGain controlElectronic data processingIndependent clock
A system is described for maintaining synchrony of operations among a plurality of devices that have independent clocking arrangements. The system includes a task distribution device that distributes tasks to a synchrony group comprising a plurality of devices that are to perform the tasks distributed by the task distribution device in synchrony. The task distribution device distributes each task to the members of the synchrony group over a network. Each task is associated with a time stamp that indicates a time, relative to a clock maintained by the task distribution device, at which the members of the synchrony group are to execute the task. Each member of the synchrony group periodically obtains from the task distribution device an indication of the current time indicated by its clock, determines a time differential between the task distribution device's clock and its respective clock and determines therefrom a time at which, according to its respective clock, the time stamp indicates that it is to execute the task.
Owner:SONOS
Garbage collection in a storage system
ActiveUS8527544B1Memory architecture accessing/allocationDigital data information retrievalRefuse collectionControl store
A system and method for performing garbage collection. A system includes a storage medium, a first table including entries which map a virtual address to locations in the storage medium, and a second table with entries which include a reverse mapping of a physical address in a data storage medium to one or more virtual addresses. A storage controller is configured to perform garbage collection. During garbage collection, the controller is configured to identify one or more entries in the second table which correspond to a segment to be garbage collected. In response to determining the first table includes a valid mapping for a virtual address included in an entry of the one of the one or more entries, the controller is configured to copy data from a first location identified in the entry to a second location in the data storage medium, and reclaim the first storage location.
Owner:PURE STORAGE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com