Patents
Literature
1046 results about "File size" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
File size is a measure of how much data a computer file contains or, alternately, how much storage it consumes. Typically, file size is expressed in units of measurement based on the byte. By convention, file size units use either a metric prefix (as in megabyte and gigabyte) or a binary prefix (as in mebibyte and gibibyte).
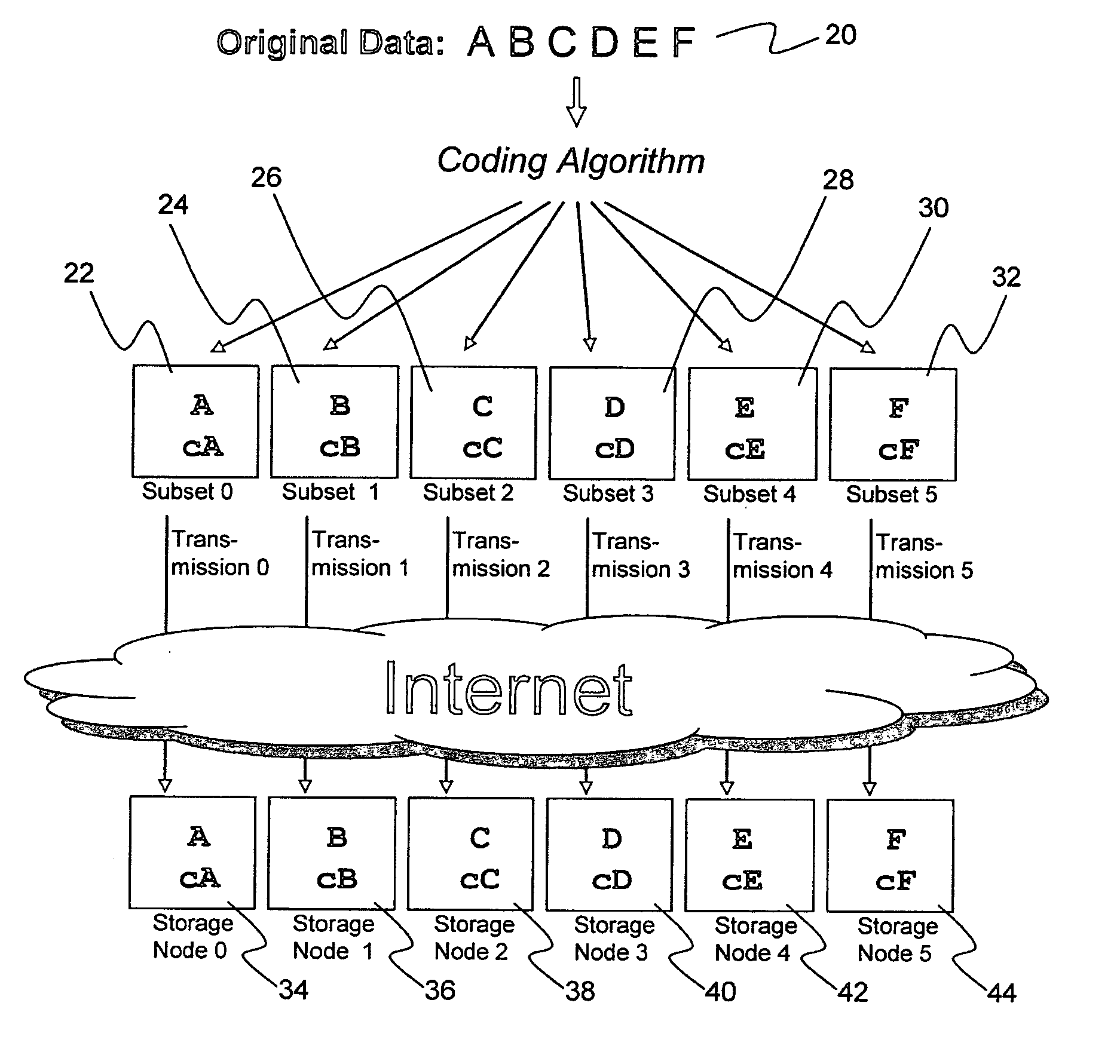
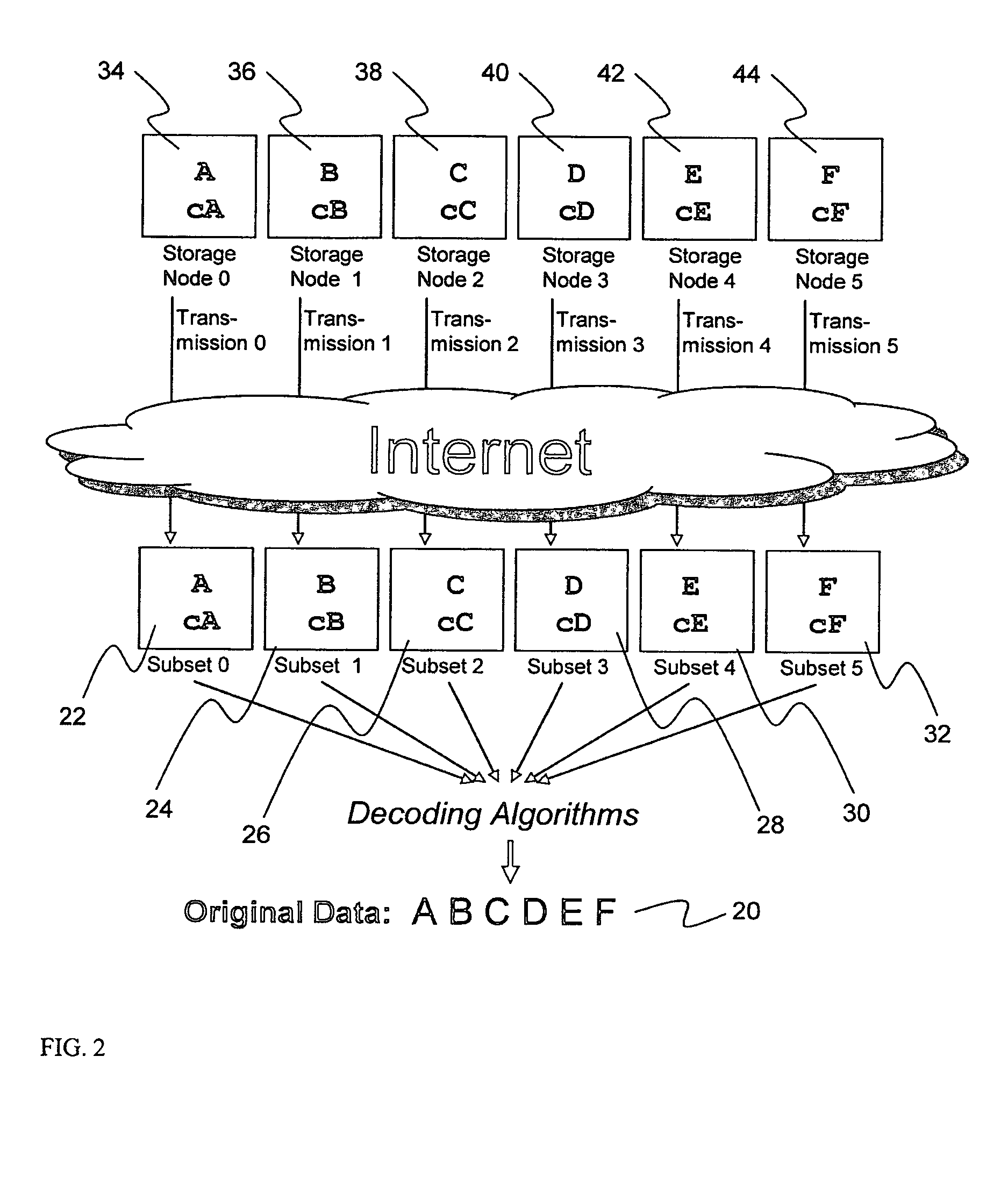
Billing system for information dispersal system
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
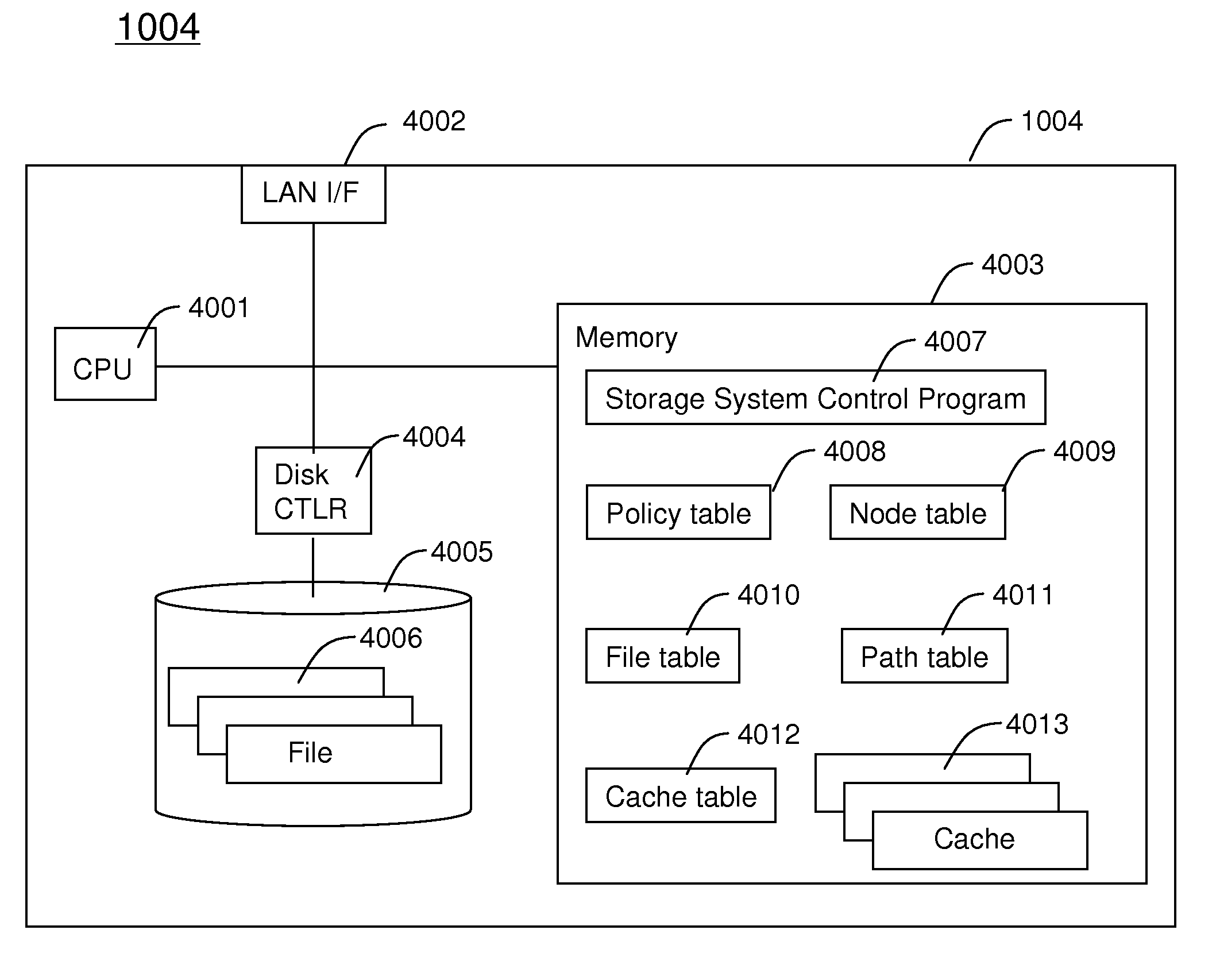
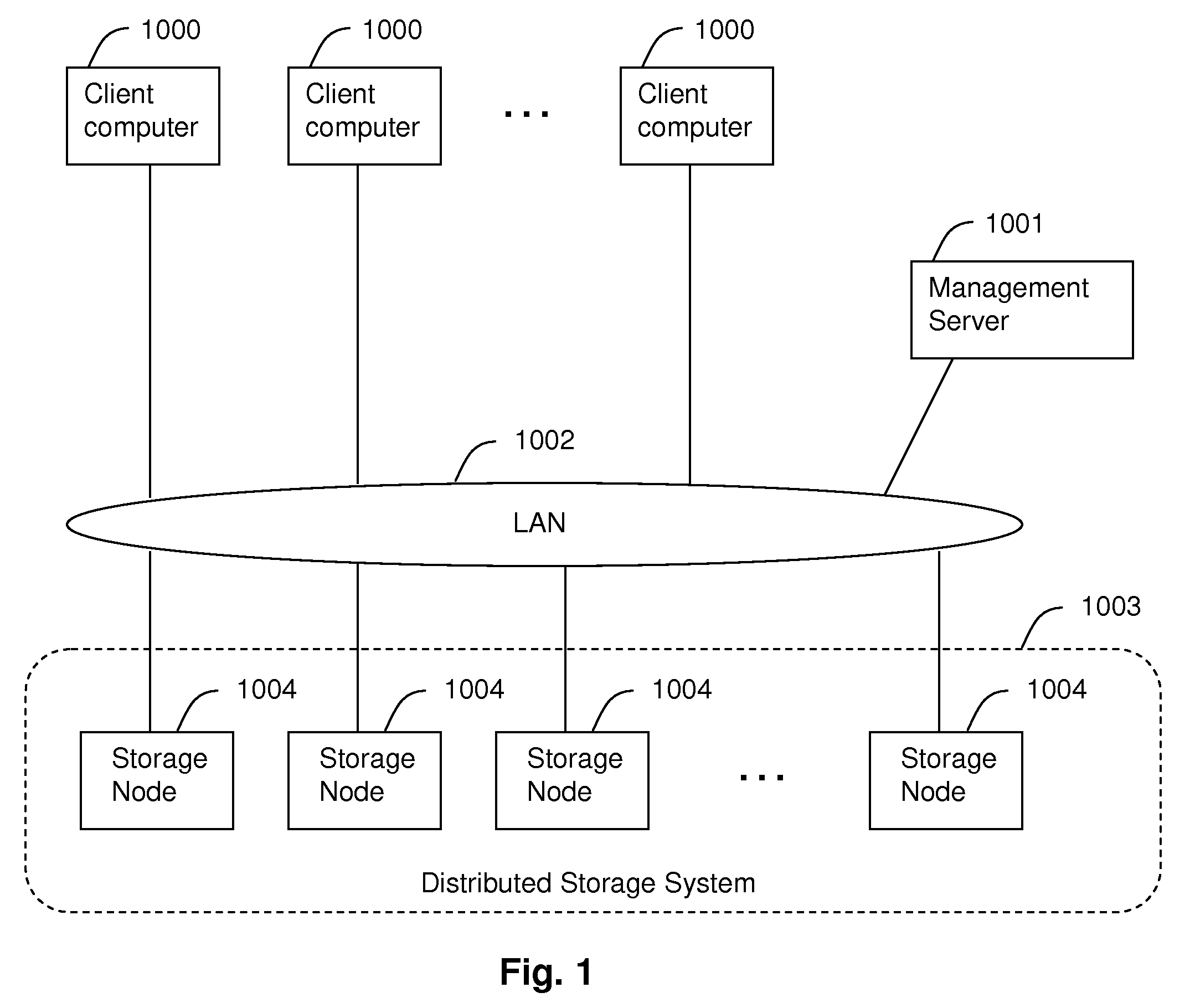
Method and apparatus for improving file access performance of distributed storage system
InactiveUS8086634B2Improve performanceReduce overheadDigital data information retrievalDigital data processing detailsNetwork connectivityDistributed memory systems
Embodiments of the invention provide methods and apparatus for improving the performance of file transfer to a client from a distributed storage system which provides single name space to clients. In one embodiment, a system for providing access to files in a distributed storage system comprises a plurality of storage nodes and at least one computer device connected via a network. Each storage node is configured, upon receiving a file access request for a file from one of the at least one computer device as a receiver storage node, to determine whether or not to inform the computer device making the file access request to redirect the file access request to an owner storage node of the file according to a preset policy. The preset policy defines conditions for whether to redirect the file access request based on at least one of file type or file size of the file.
Owner:HITACHI LTD
Circuit layout methodology using a shape processing application
InactiveUS7188322B2Low costSmall sizeCAD circuit designSpecial data processing applicationsManufacturing technologySoftware engineering
Owner:INT BUSINESS MASCH CORP
Method and system for creating and distributing collaborative multi-user three-dimensional websites for a computer system (3D Net Architecture)
InactiveUS7107549B2Easy accessImage data processingWeb data navigationHuman–machine interfaceFile size
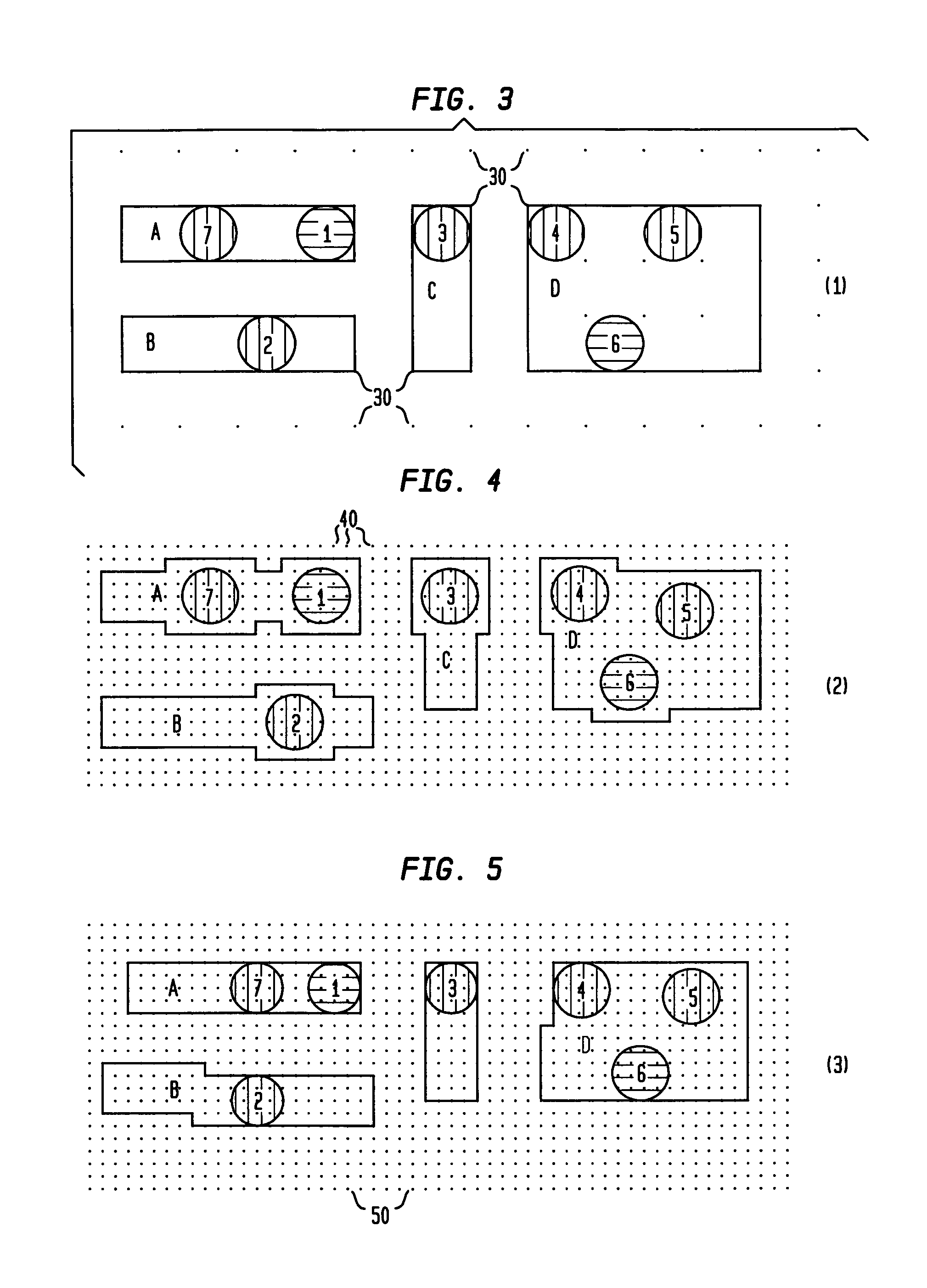
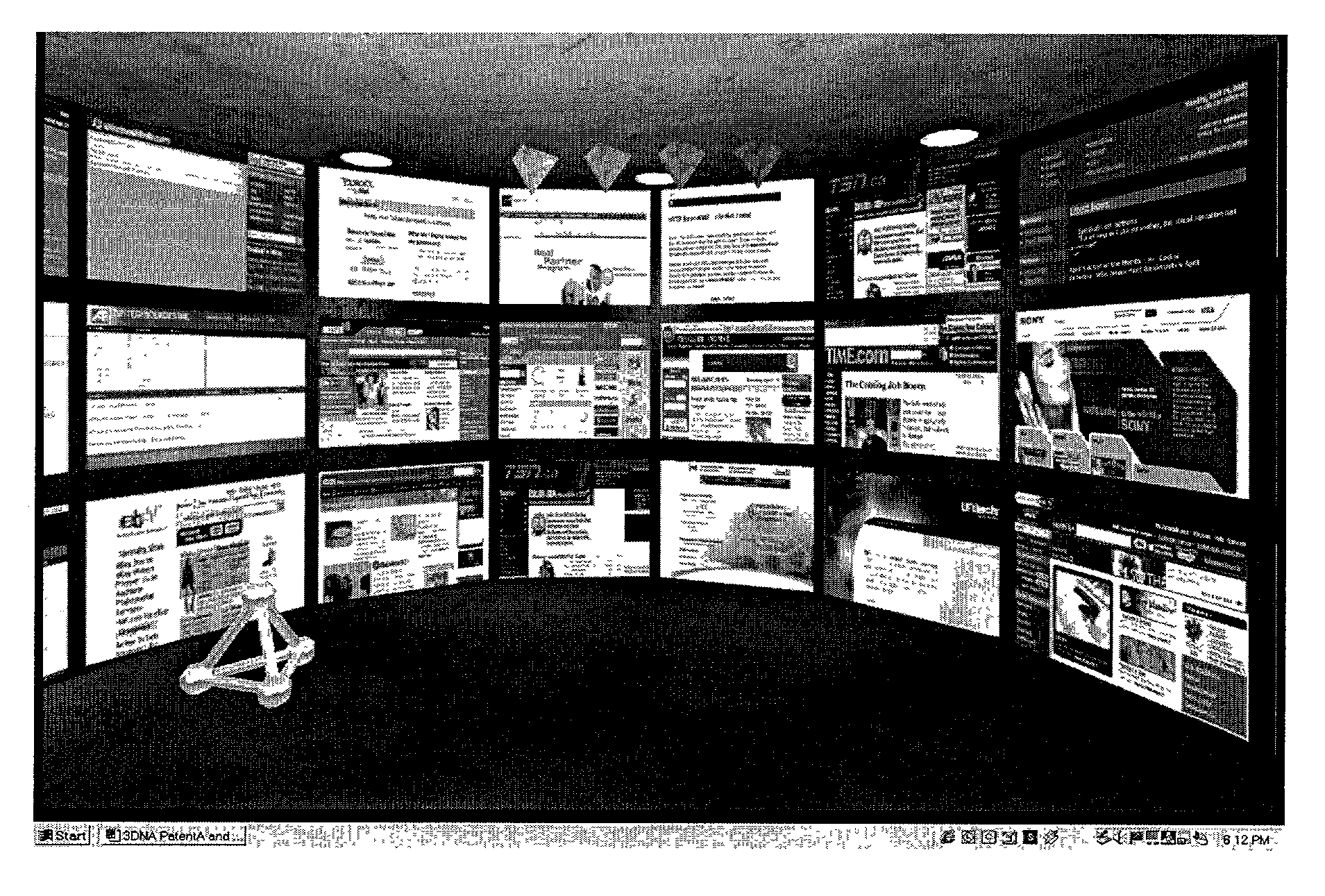
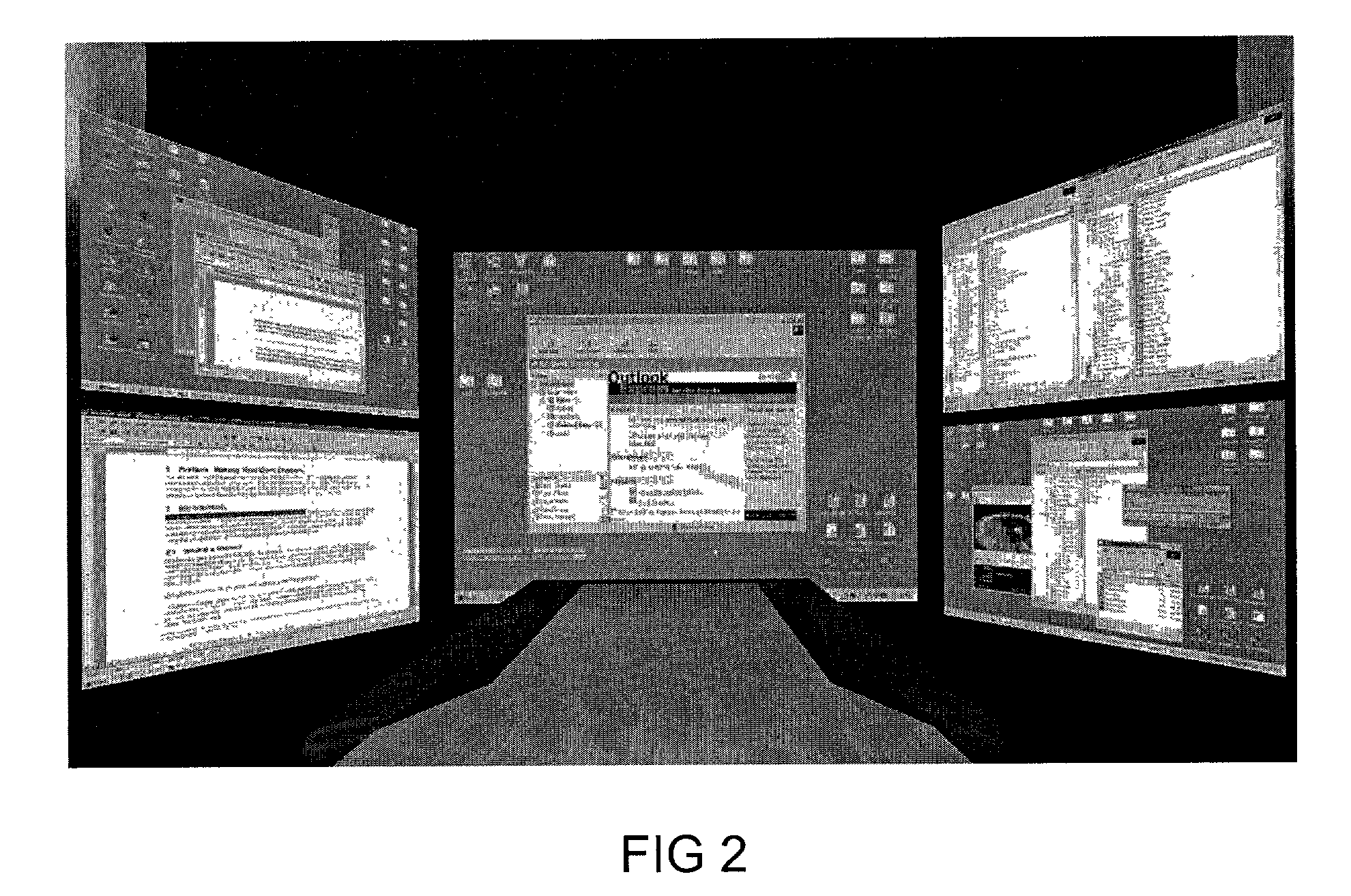
The present invention is a new 3D graphical user interface (3D GUI) technology that seamlessly integrates personal computer (PC) desktop, web portal, and data visualization functions in an intuitive 3D environment. This new paradigm in human computer interfaces provides a seamless and intuitive ability to create a 3D website, “walk” or navigate from one 3D website to another, and allows multiple users to collaborate and interact with each other and the website. The invention dynamically creates a customized 3D environment that allows intuitive access to complicated websites as well as seamless multi-user collaboration and interaction. —In a preferred embodiment of the invention—The 3D GUI installs as the active desktop on a PC, replacing the user's “wallpaper” with the 3D GUI. —In another embodiment—The 3D GUI is accessed via a standard web browser window (i.e. using Netscape Navigator or Internet Explorer). —In either of these embodiments—, The user can simply “walk” from one 3D website to another, see and communicate with other users that are also at that website, access website information and share information with other users currently visiting the website. The invention also provides a method for reducing the file size normally associated with transmitting all the content in a 3D website.
Owner:MIND FUSION LLC
Method and systems for efficient delivery of previously stored content
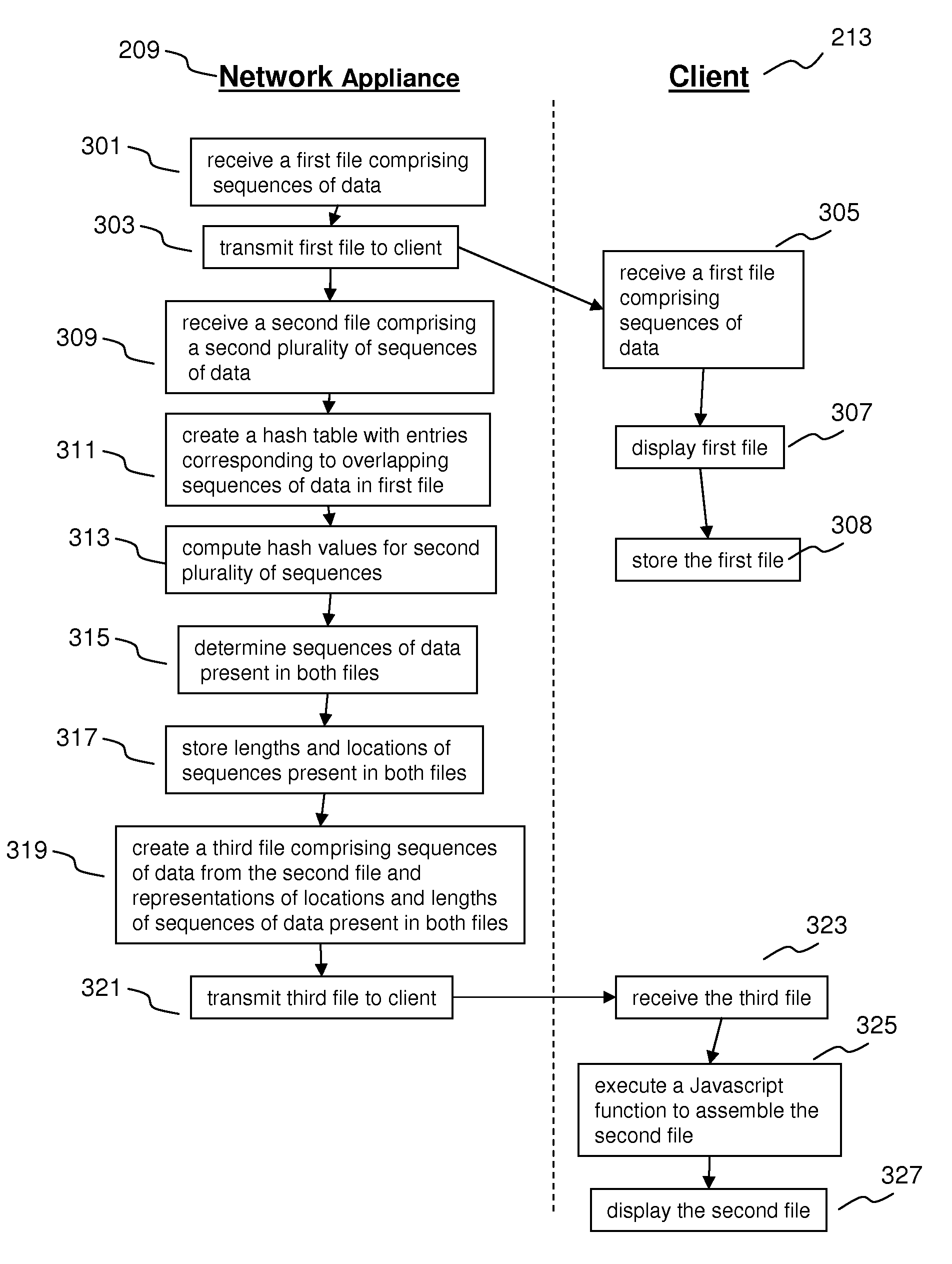
ActiveUS7756826B2Reduce file sizeData processing applicationsDigital data processing detailsFile sizeHash table
Systems and methods for reducing file sizes for files delivered over a network are disclosed. A method comprises receiving a first file comprising sequences of data; creating a hash table having entries corresponding to overlapping sequences of data; receiving a second file comprising sequences of data; comparing each of the sequences of data in the second file to the sequences of data in the hash table to determine sequences of data present in both the first and second files; and creating a third file comprising sequences of data from the second file and representations of locations and lengths of said sequences of data present in both the first and second files.
Owner:CITRIX SYST INC
Pre-approval of computer files during a malware detection
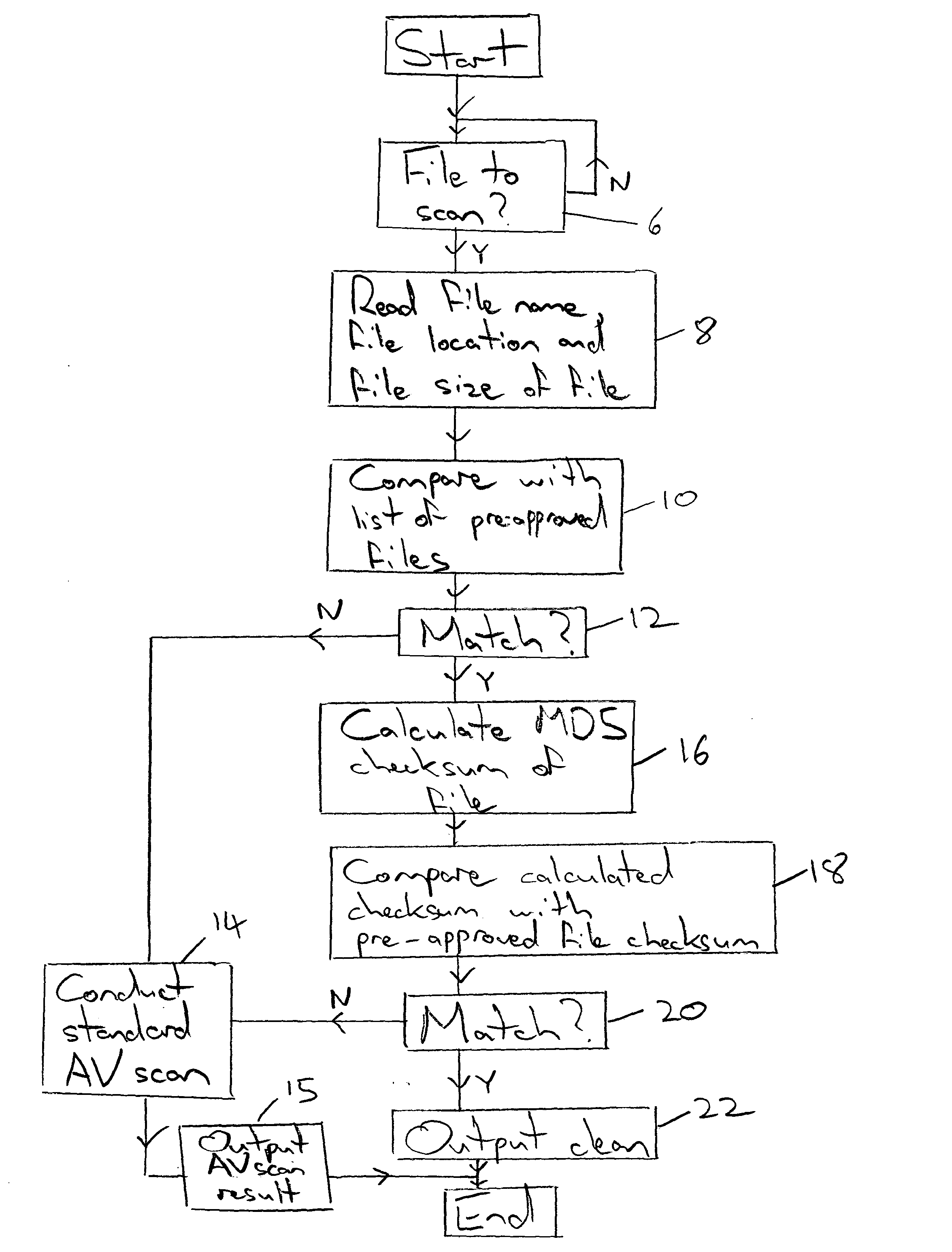
InactiveUS20050021994A1Addressing slow performanceEffectively ensureMemory loss protectionDigital data processing detailsChecksumFile size
A malware detection system seeking to identify computer viruses, worms, Trojans, banned files and the like acts to determine from the file name, file size and storage location of a computer file being tested, whether that computer file potentially matches a specific known malware free computer file stored within a list of such specific known malware free computer files. If a match occurs indicating that the candidate computer file is potentially the specific known malware free computer file, then this is confirmed by calculating a checksum of the candidate computer file and comparing this against a stored corresponding checksum of the specific known malware free computer file. If these checksums match, then the candidate computer file can be passed as clean without requiring further time consuming malware detection scanning.
Owner:MCAFEE INC
Method for storing information in DNA
InactiveUS20050053968A1Microbiological testing/measurementNanoinformaticsHuman DNA sequencingPresent method
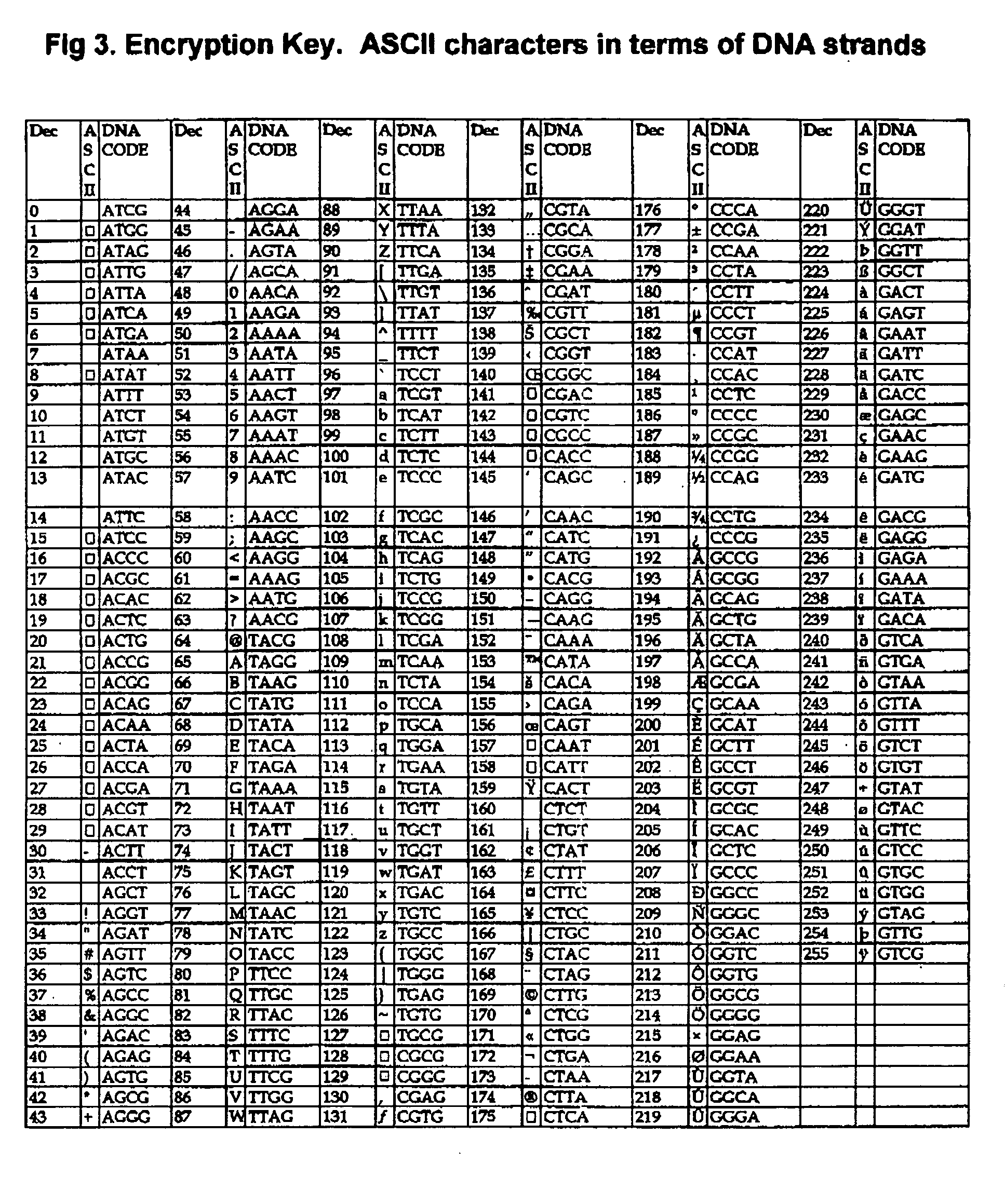
DNA is a natural molecular level storage device. Molecular storage devices use each molecule or part of it for storing a character. Thus it is possible to store information million of times than presently used storage devices. For example a JPEG image (i.e. flag of India) having file size of 1981 Bytes can be encrypted using 7924 DNA bases which occupies about 2694.16 nanometers In other words flag of India can be encrypted 8.07×105 times in human genome which comprises 6.4×109 DNA bases and occupy a tiny volume of about 0.02 μm3. A method for storing information in DNA has been developed which includes software and a set of schemes to encrypt, store and decrypt information in terms of DNA bases. The main advantages of the present method over exiting art is that it addresses complete set of extended ASCII characters set and thereby, encryption of all kind of digital information (text, image, audio etc.). First of all, information is, encrypted along with carefully designed sequences known as header and tail primers at both the ends of actual encrypted information. This encrypted sequence is then synthesized and mixed up with the enormous complex denatured DNA strands of genomic DNA of human or other organism.
Owner:COUNCIL OF SCI & IND RES
Circuit layout methodology
InactiveUS20060195809A1Simplifies design/layout ruleReduce data volumeCAD circuit designSpecial data processing applicationsManufacturing technologyData preparation
A circuit layout methology is provided for eliminating the extra processing time and file-space requirements associated with the optical proximity correction (OPC) of a VLSI design. The methodology starts with the design rules for a given manufacturing technology and establishes a new set of layer-specific grid values. A layout obeying these new grid requirements leads to a significant reduction in data preparation time, cost, and file size. A layout-migration tool can be used to modify an existing layout in order to enforce the new grid requirements.
Owner:IBM CORP
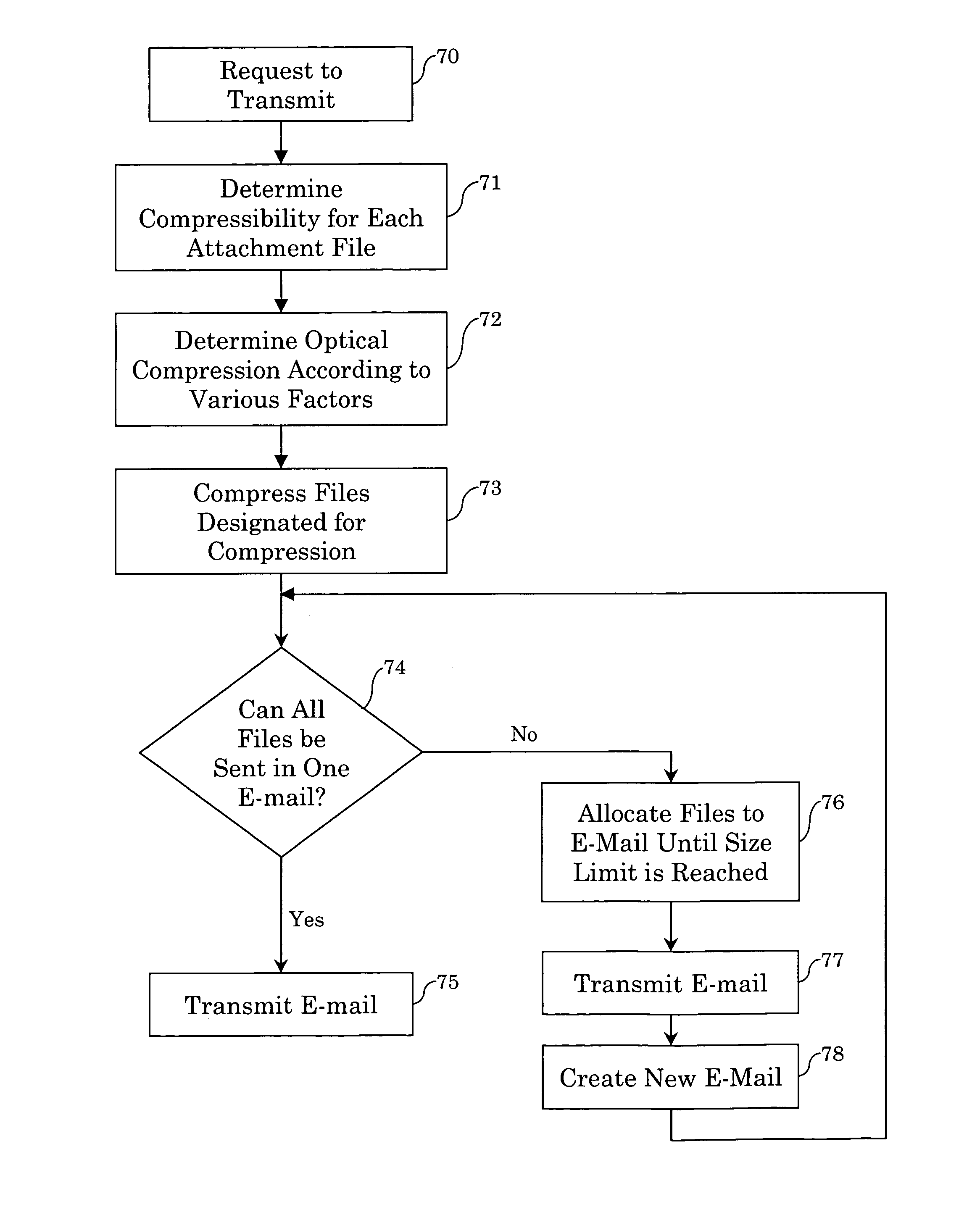
Method and apparatus for compressing attachments to electronic mail communications for transmission
InactiveUS7089286B1Compression is selectiveMaximize sizeMultiple digital computer combinationsData switching networksCommunications systemEmail attachment
The present invention is directed to a method and system for compressing attachments to electronic mail communications for transmission. In an e-mail communications system, a table stores, for each of a plurality of different types of files, a compressibility value corresponding to a percentage by which the file can be compressed in size. An e-mail attachment configuration module is configured to compress each attachment file of a type having a compressibility value greater than a threshold value in an e-mail communication. In another embodiment, the e-mail attachment configuration module compresses a number of the plurality of attachment files according to file size and the corresponding compressibility value, such that the total size of the e-mail communication after compression is maximized and is less than a threshold size. The attachment configuration module can be incorporated into a system for configuring packages of application files, designated from within user applications, to be sent as e-mail attachments in e-mail communications.
Owner:BELLSOUTH INTPROP COR
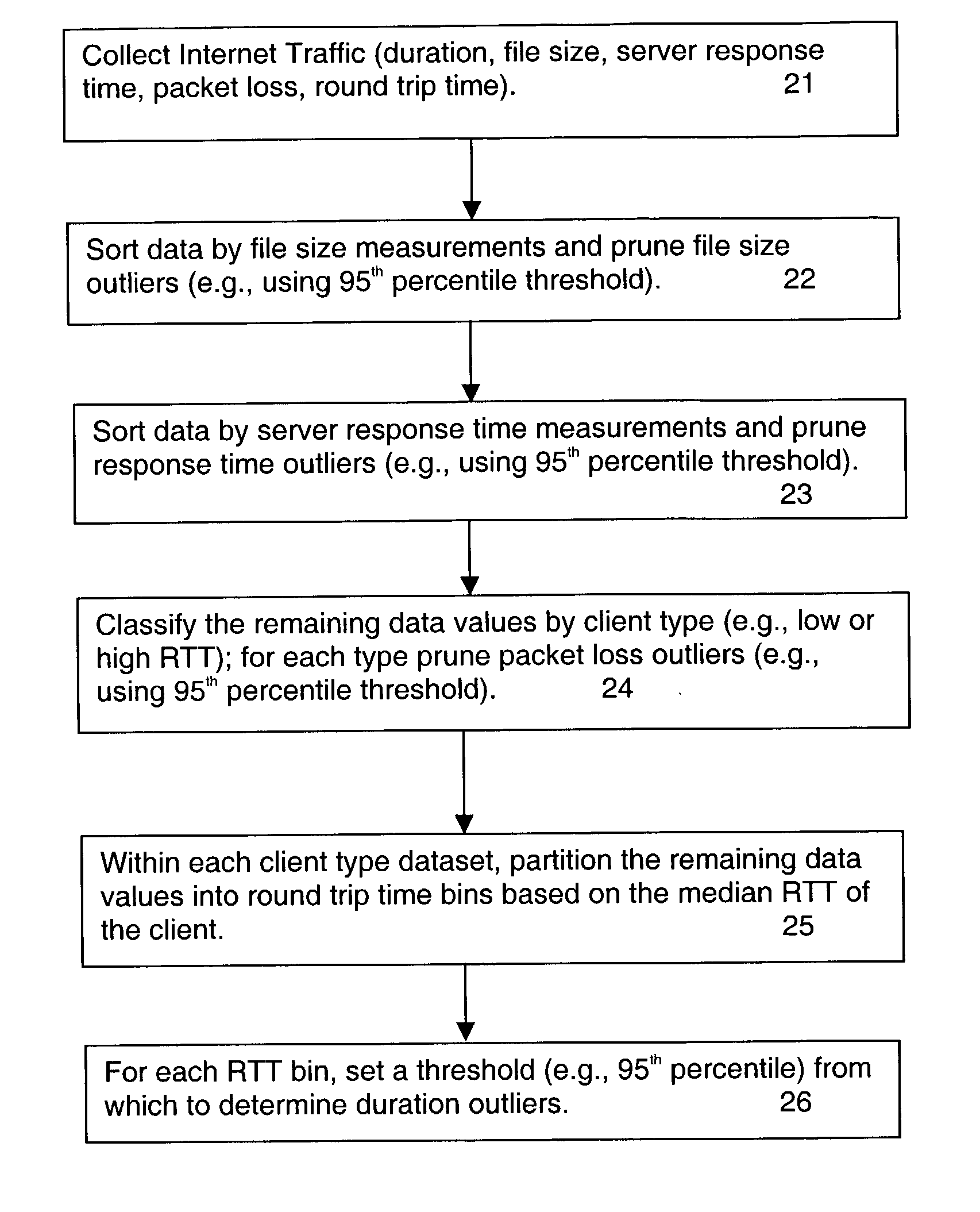
Method for detecting congestion in internet traffic
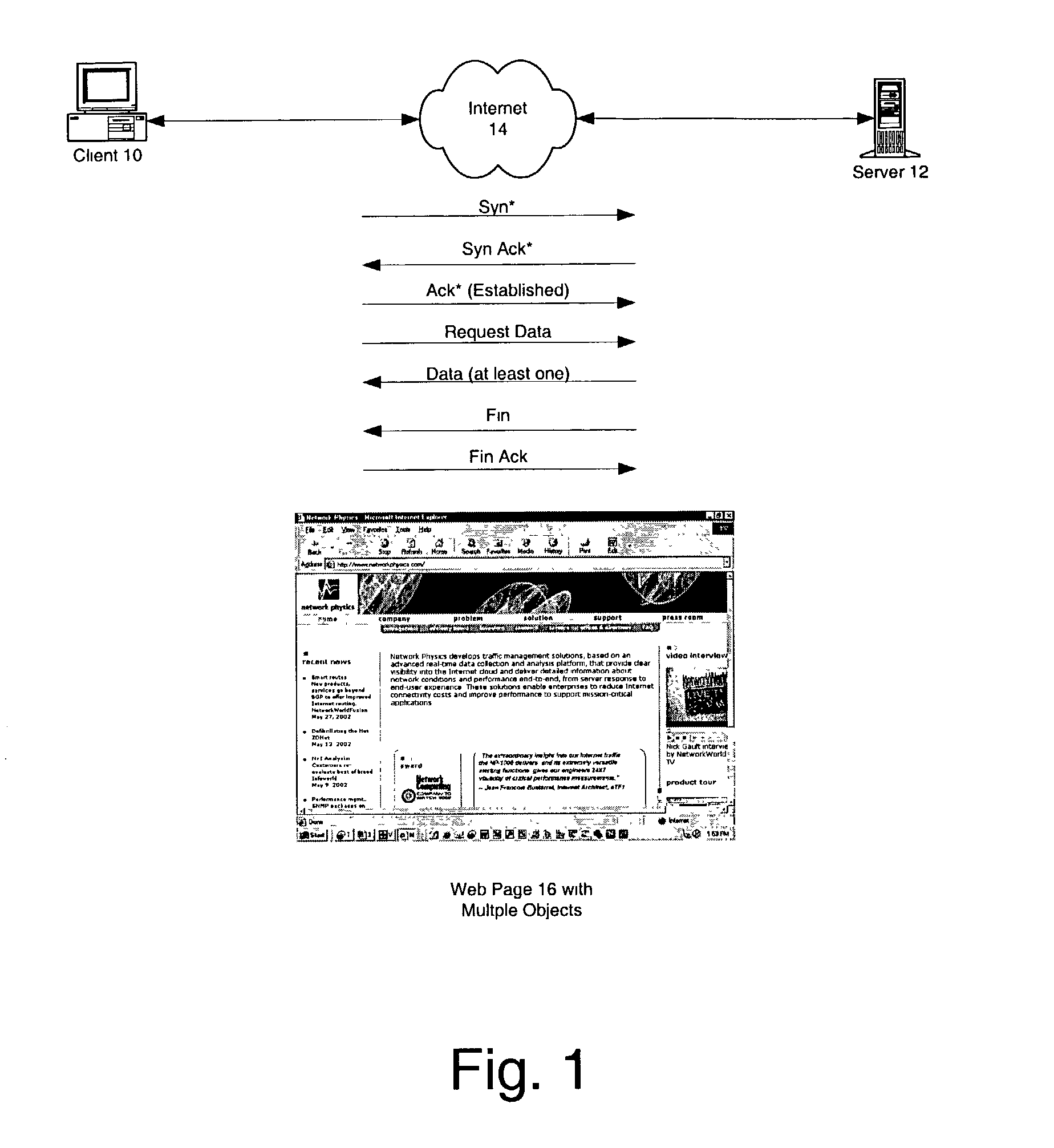
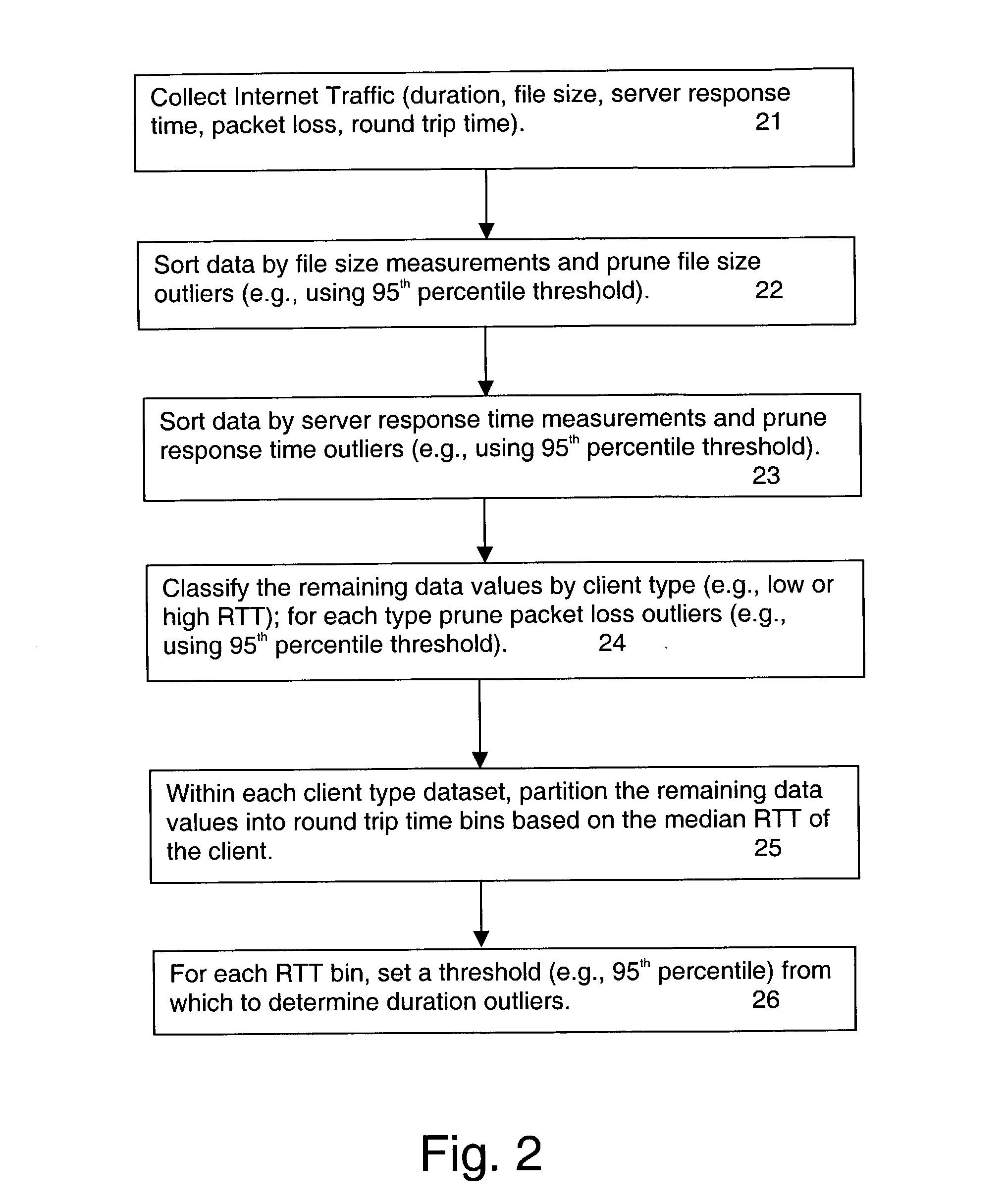
A baseline for internet traffic duration is established by (i) collecting internet traffic data regarding file size, server response time, packet loss and round trip time, (ii) removing from this data outliers associated with file size, server response time and packet loss per client type, and (iii) organizing any remaining data into round trip time bins according to median values of round trip time per client type. Thereafter, historical or newly collected Internet traffic data is compared against threshold values for each round trip time bin to locate duration outliers. These duration outliers are indicators of congestion and congestion episodes may be identified by the continued presence of such outliers over successive time intervals.
Owner:RIVERBED TECH LLC
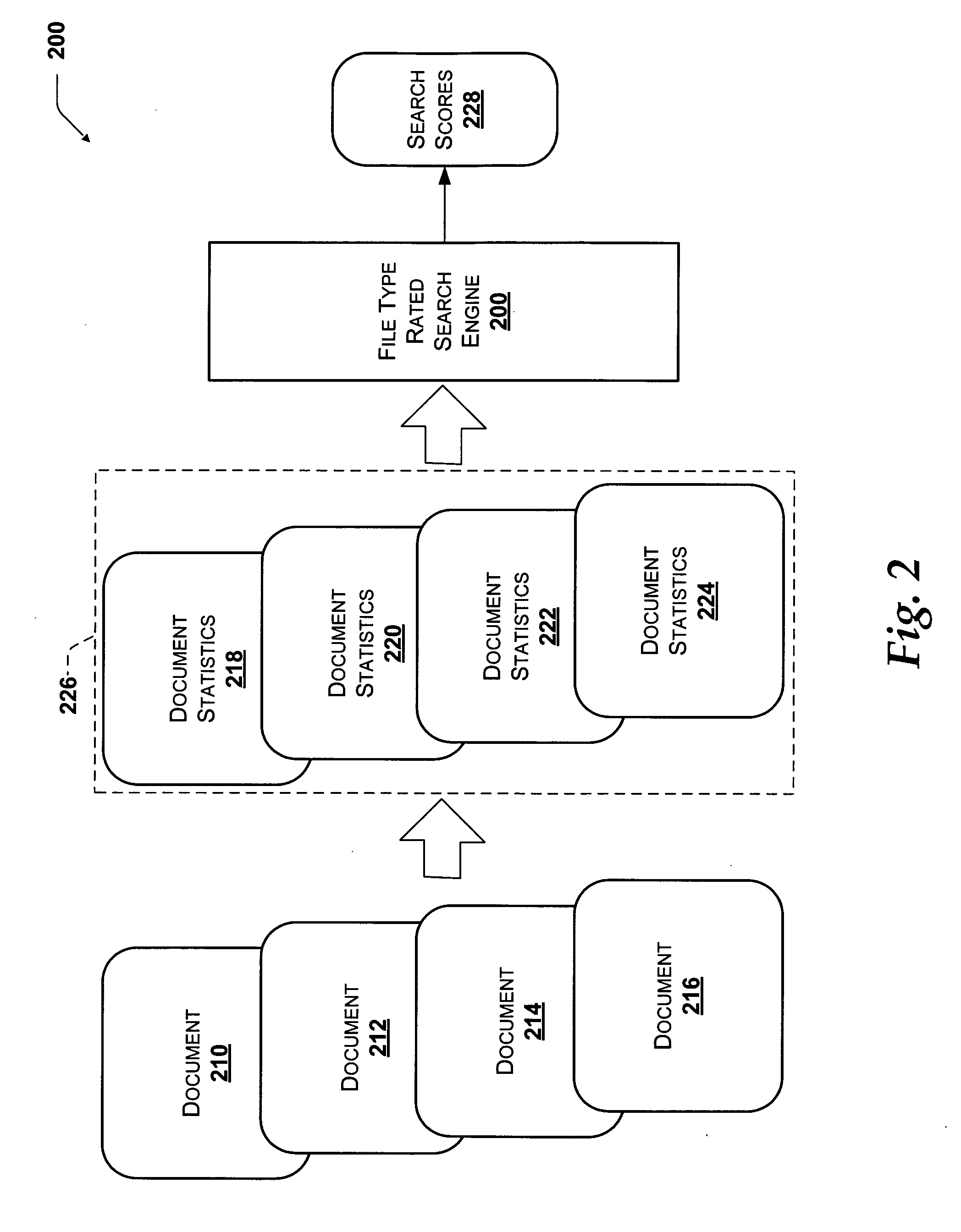
System and method for ranking search results using file types
InactiveUS20060200460A1High precisionImprove rankingDigital data information retrievalSpecial data processing applicationsFile sizeDocument preparation
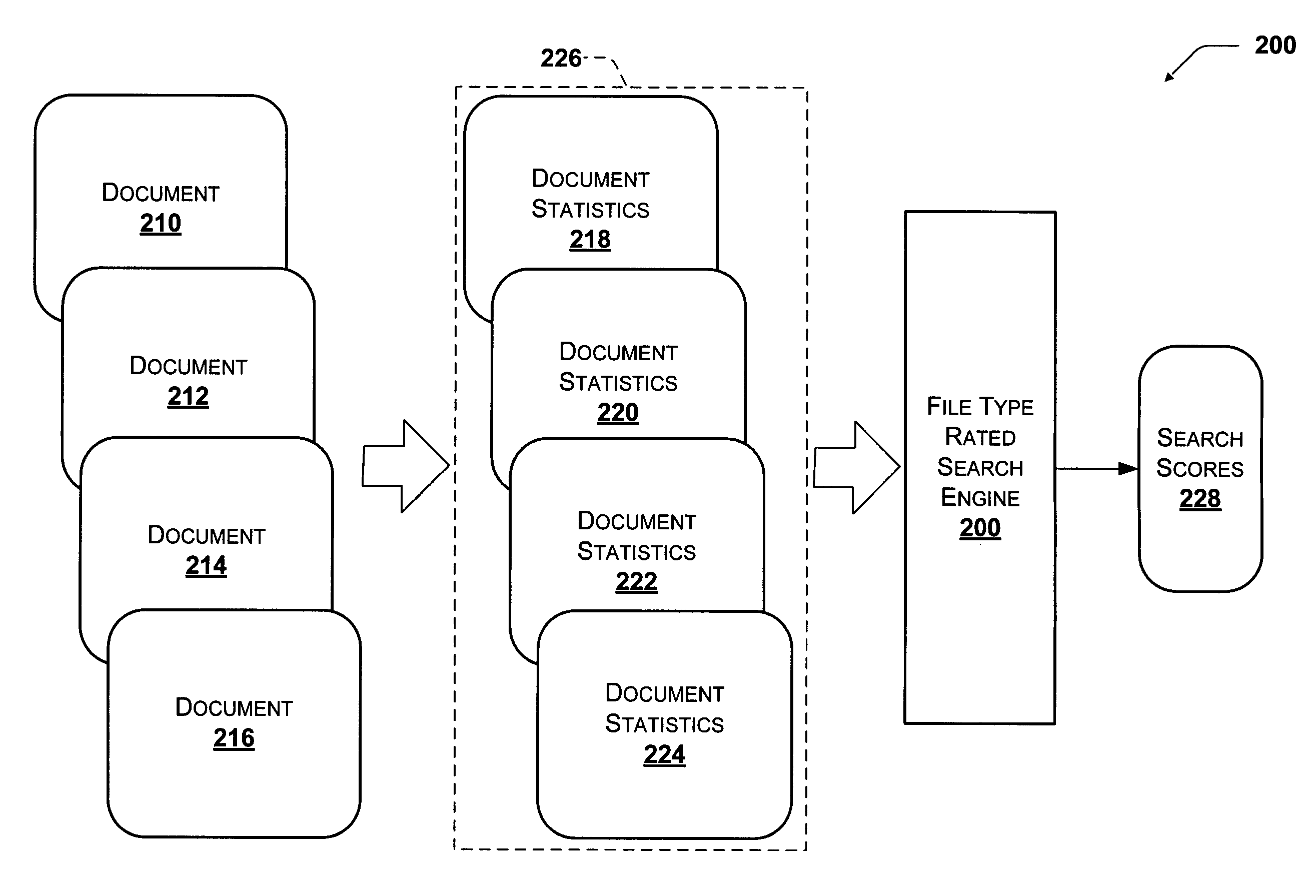
Search results of a search query on a network are ranked according to an additional ranking function for the prior probability of relevance of a document based on document property. The document property may be the document's file type, the file size, the document language, or another query-independent property of the document. The query-independent values for each document property may be weighted according to relevance measurements of the document based on the document property. As more relevance measurements of the documents may be obtained, the query-independent values for each document property may be updated to reflect the new measurements.
Owner:MICROSOFT TECH LICENSING LLC
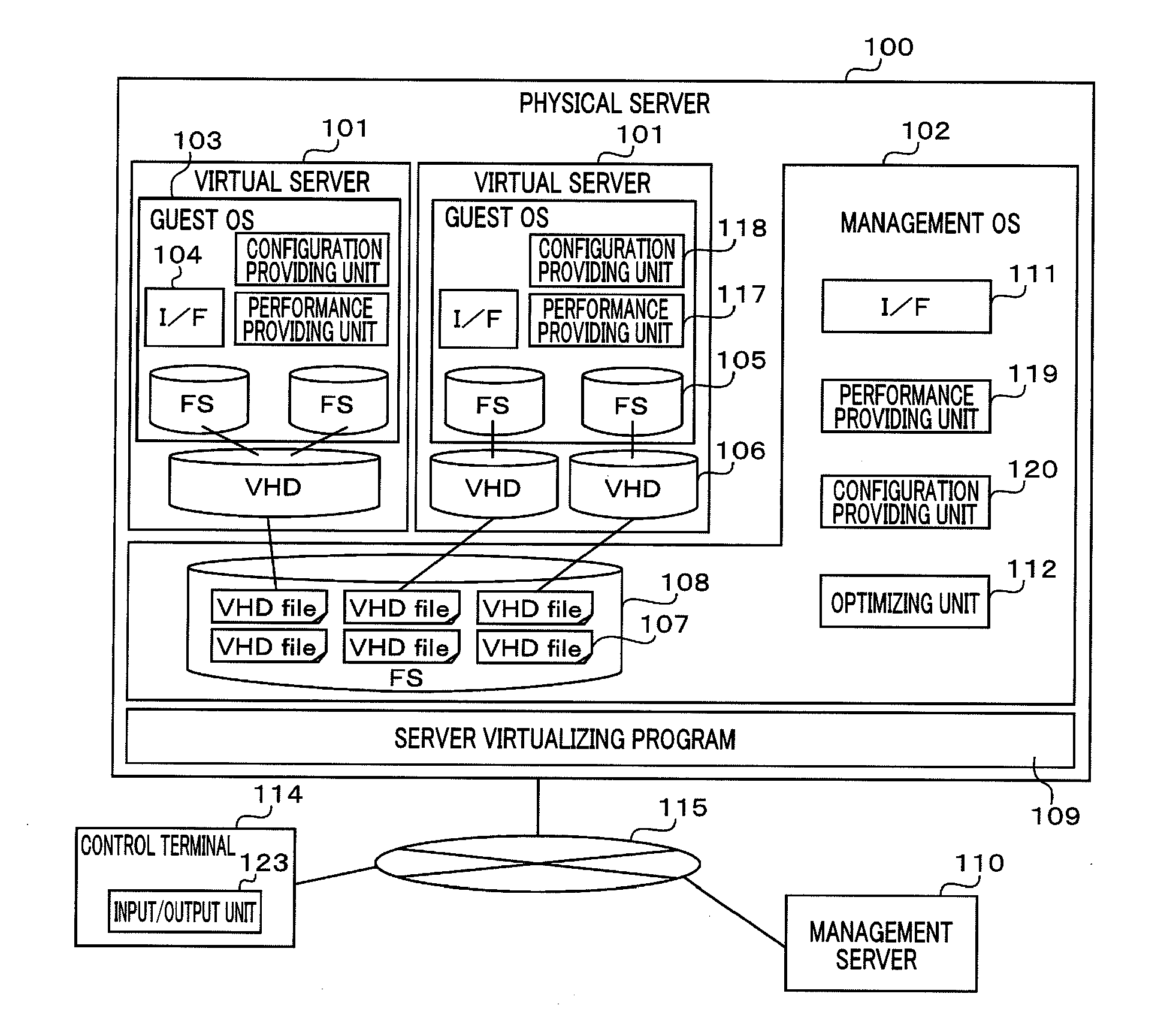
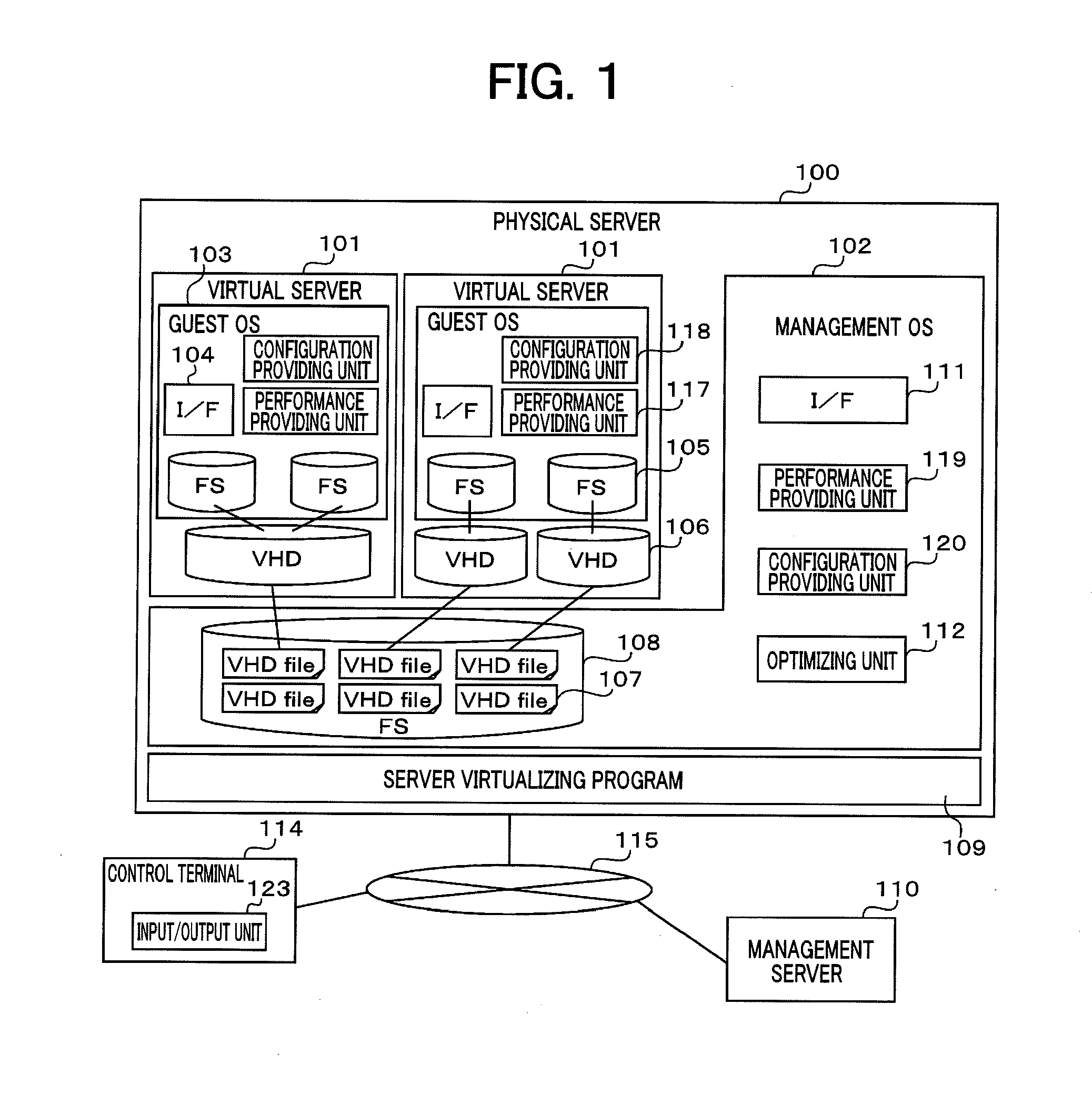
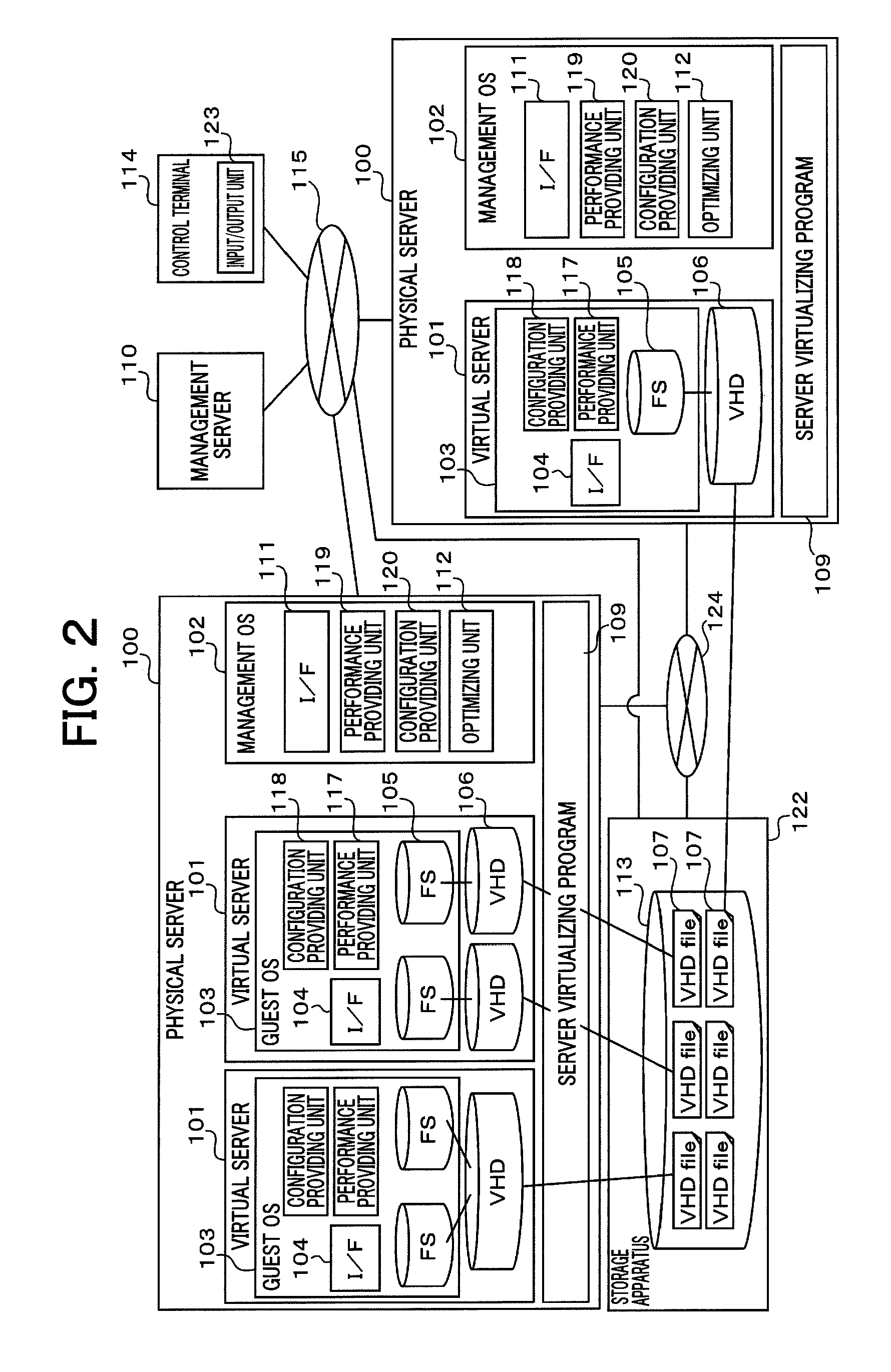
Management server, management method, and management program for virtual hard disk
InactiveUS20120221611A1Easy to manageSpecial data processing applicationsMemory systemsFile systemFile size
A file system corresponding to virtual hard disk files is identified, and a file size of the virtual hard disk files after optimization is calculated from the size of the volume in use of the file system so that a volume size can be ensured by the optimization is calculated. Specifically, a management server performs the above-described processing, and has the following structure. The management server is connected to a physical server that is virtually composed of virtual servers including virtual had disks. The management server comprises a volume acquiring unit that acquires the volume in use of a first file system on the virtual hard disks; a file size acquiring unit that acquires the file size of virtual hard disk files corresponding to the first file system; and a calculating unit that calculates an optimized file size of the virtual hard disk files on the basis of a difference between the acquired volume in use and the file size.
Owner:HITACHI LTD
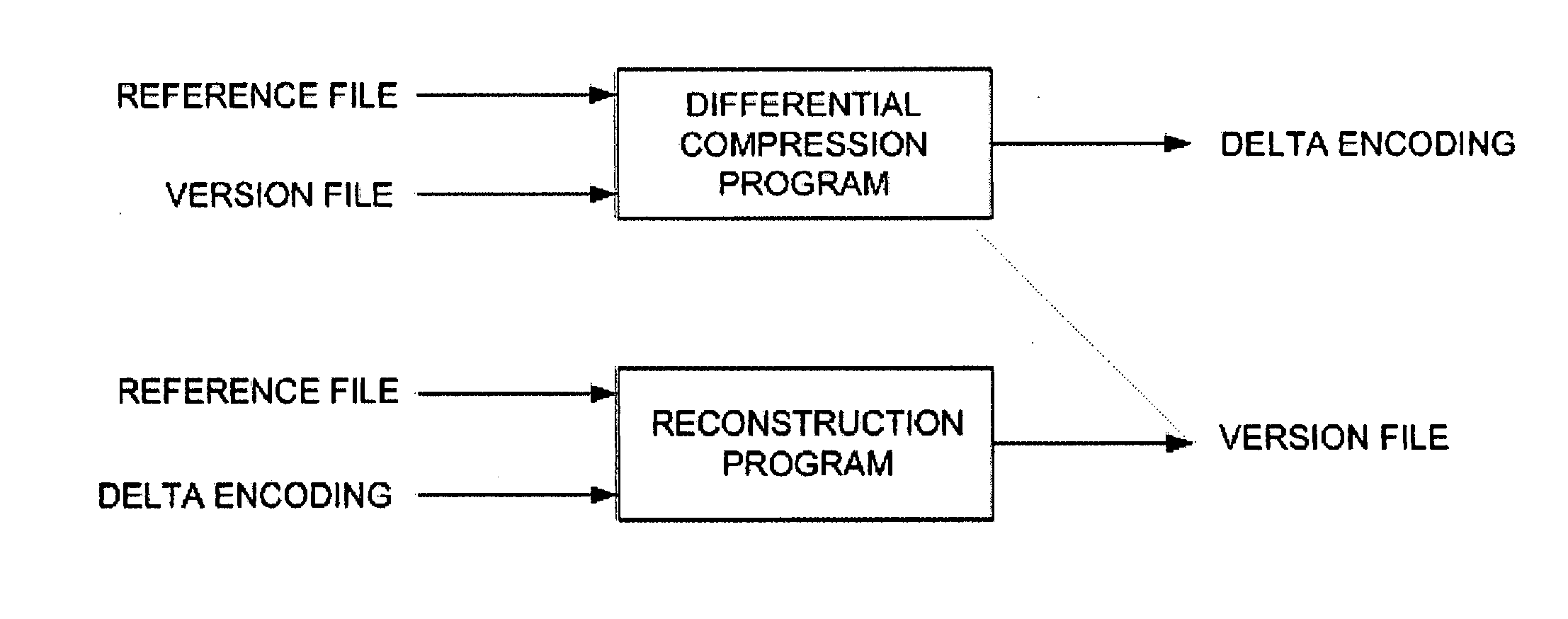
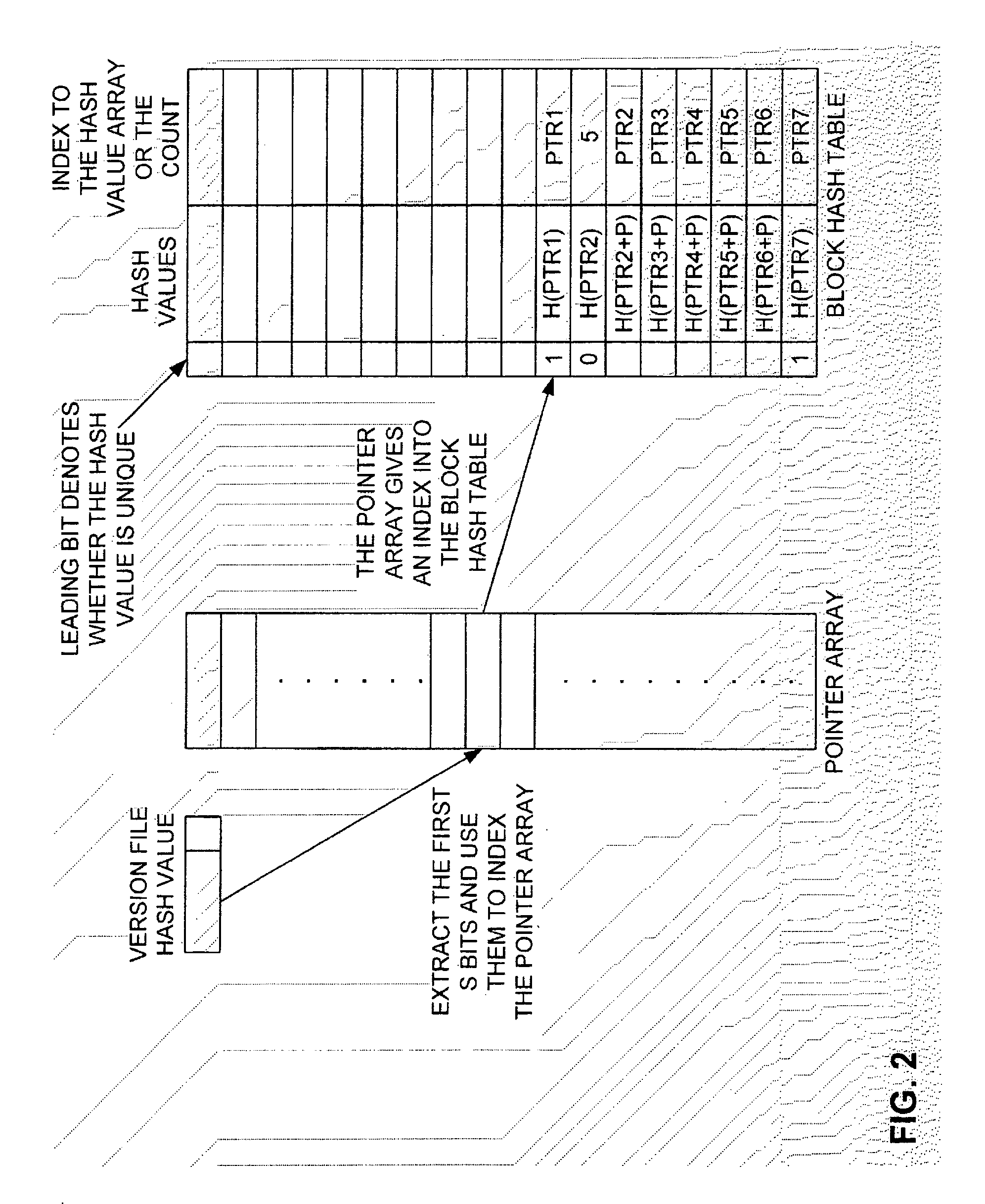
Method and Computer Program Product for Finding the Longest Common Subsequences Between Files with Applications to Differential Compression
InactiveUS20060112264A1Improve I/O performanceLow costCode conversionSecuring communicationLongest common subsequence problemGreedy algorithm
A differential compression method and computer program product combines hash value techniques and suffix array techniques. The invention finds the best matches for every offset of the version file, with respect to a certain granularity and above a certain length threshold. The invention has two variations depending on block size choice. If the block size is kept fixed, the compression performance of the invention is similar to that of the greedy algorithm, without the expensive space and time requirements. If the block size is varied linearly with the reference file size, the invention can run in linear-time and constant-space. It has been shown empirically that the invention performs better than certain known differential compression algorithms in terms of compression and speed.
Owner:IBM CORP
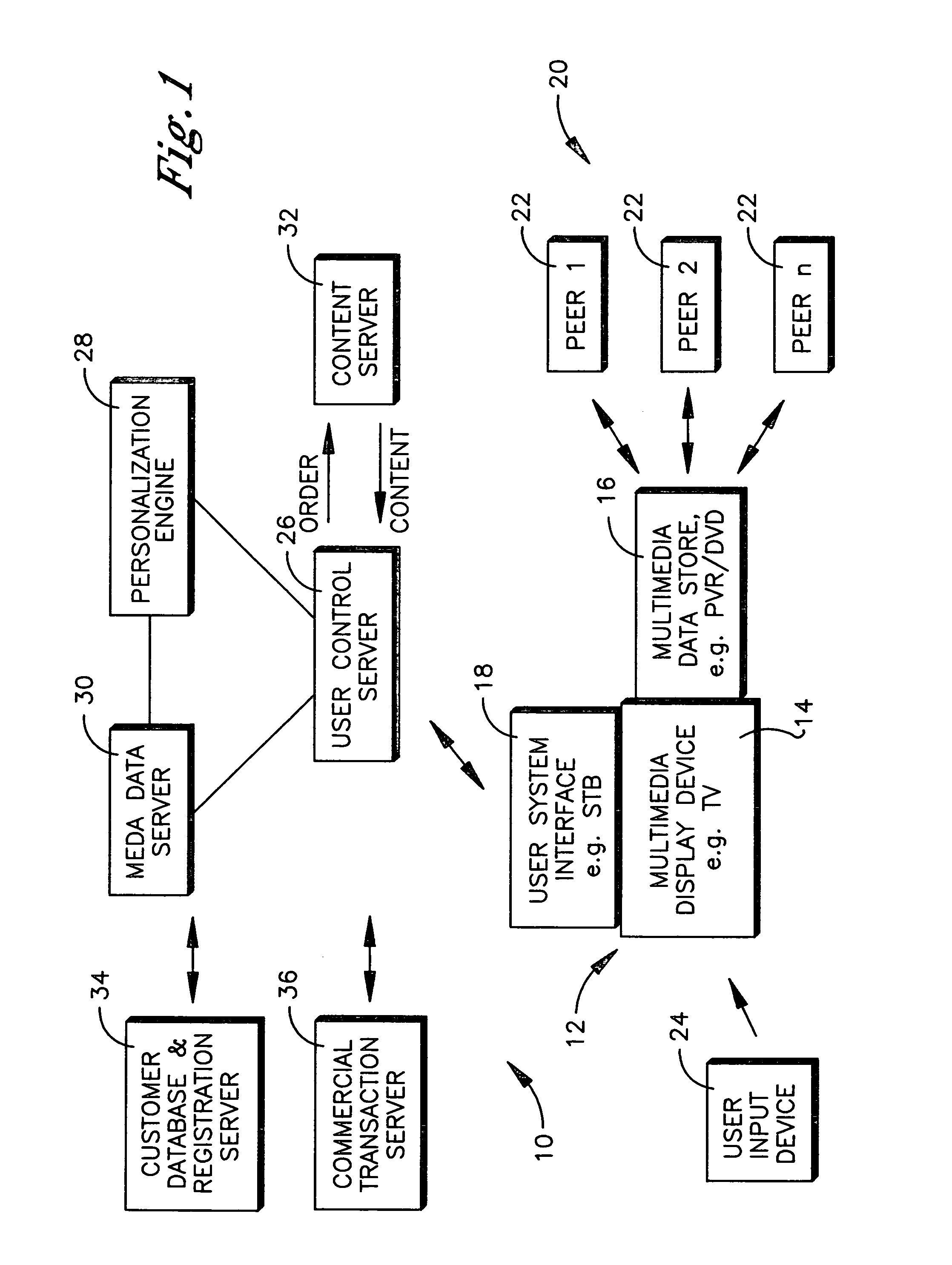
System and method for content delivery
InactiveUS20070277202A1Television system detailsResource management arrangementsFile sizeUser profile
Based on a user profile, content that is predicted to be desired by the user, including past episodes of a series that may have been missed by the user, is downloaded to the user's home system during periods of low bandwidth usage in the home system. A determination is made dynamically as to whether to provide the content from a server or a peer-to-peer network based on network attributes, file size, etc.
Owner:SONY CORP +1
Quota management in client side data storage back-up
InactiveUS20020147733A1Easily understandable back-upEasy to useRedundant operation error correctionMemory systemsFile sizeClient-side
There is disclosed a method of managing backed up data storage region of a plurality of client computers, enforced by a client side agent, and based upon a total of files stored within a client back up data storage region A total file size of current files stored at the client computer is compared to a first soft back up quota limit, at which a warning message is displayed, and a second, hard back up limit, at which back up of client files to a back up computer is prohibited. Quota limits can be set centrally from a back up computer, and deployed to each of the plurality of client computers served by a back up computer. Elimination of backed up file duplication is made at the back up computer, by use of a database and pointers to common files for a plurality of computers.
Owner:HEWLETT PACKARD DEV CO LP
Method and device for reconstructing torrent content metadata
A method for reconstructing torrent content metadata, i.e. a torrent identifier, a segment length and an amount of segments of a torrent content file, without access to the torrent content metafile, comprises the steps of: A. obtaining the torrent content identifier from torrent signaling from a client; B. obtaining a torrent content file size from said torrent signaling from said client; C. obtaining a tracker address from said torrent signaling from said client: D. obtaining a peer address from a tracker; E. contacting a peer via the peer address; F. downloading sequential minimum size blocks of a full size segment from the peer in order to determine the segment length; G. calculating the amount of segments from the torrent content file size and the segment length.
Owner:PIECE FUTURE PTE LTD
Method and system for file-system based caching
InactiveUS7024452B1Improve efficiencyImprove securityDigital data information retrievalMemory adressing/allocation/relocationFile systemFile size
A method and system for file-system based caching can be used to improve efficiency and security at network sites. In one set of embodiments, the delivery of content and storing content component(s) formed during generation of the content may be performed by different software components. Content that changes at a relatively high frequency or is likely to be regenerated between requests may not have some or all of its corresponding files cached. Additionally, extra white space may be removed before storing to reduce the file size. File mapping may be performed to ensure that a directory within the cache will have an optimal number of files. Security at the network site may be increased by using an internally generated filename that is not used or seen by the client computer. Many variations may be used is achieving any one or more of the advantages described herein.
Owner:OPEN TEXT SA ULC
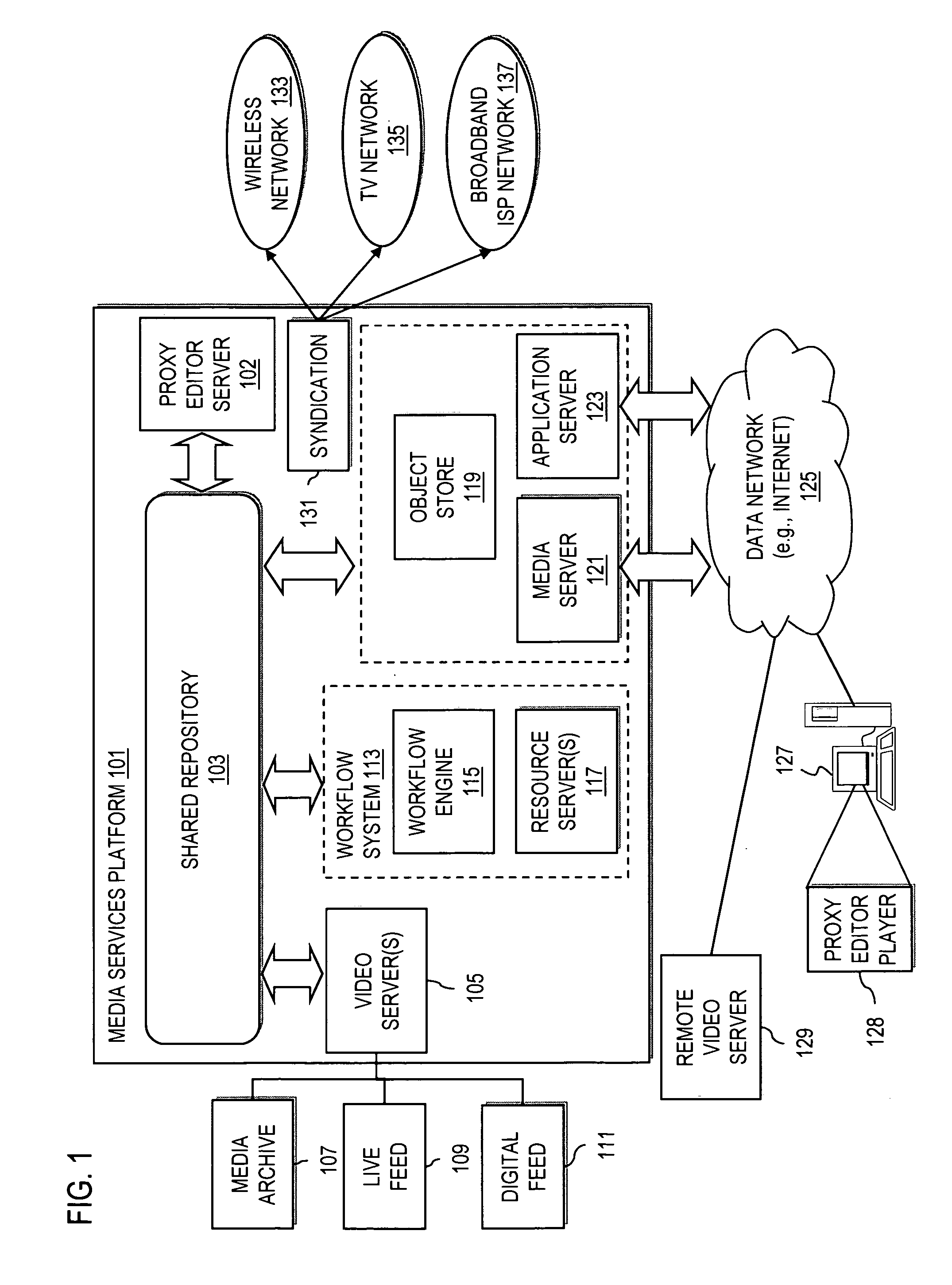
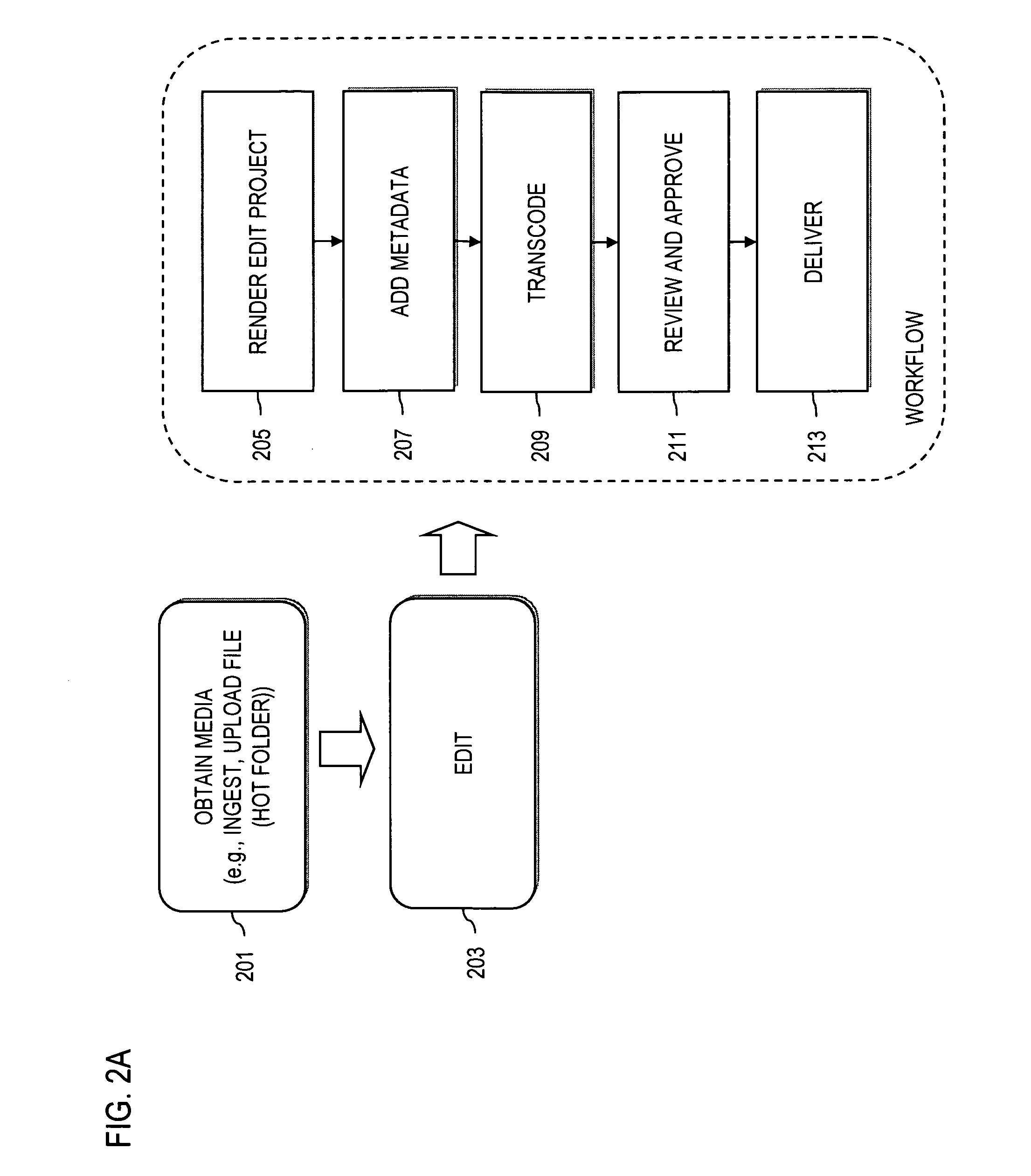
Method and system for providing remote digital media ingest with centralized editorial control
ActiveUS20070113184A1Electronic editing digitised analogue information signalsRecord information storageFile sizeCentral repository
An approach provides for remote digital media ingest with centralized editorial. A remote ingest process is initiated over a data network to create a media file from a feed (such as a live broadcast feed). The media file is stored at a central repository. A device is configured to edit the media file by using a proxy file of the media file, wherein the proxy file represents a reduced file size of the media file.
Owner:VERIZON PATENT & LICENSING INC +2
Extended Intelligent Video Streaming System
InactiveUS20080189752A1Shorten the timeStatic indicating devicesDigital data processing detailsVideo playerView based
A method for playing back video files optimizes display viewing while minimizing file size. On of a plurality of video files representing the same video production is automatically selected for viewing based on multiple criteria, such as network bandwidth, the type of video players available to display the video file, the format of the video file and the platform used to display the file. The width and height of the image displayed from the selected video file is adjusted to match the resolution of a display screen, or a user specified image size. A system for transmitting and displaying large media files uses an online streaming service to upload full-length movies and other video and audio files to a wide array of viewers. The system includes a robust, scalable, and fat upload technique that allows files of any size to be uploaded to customers' accounts by the customers. It is specifically tuned to handle hundreds of uploads per second of files which are typically several hundred mega bytes large. Increased scalability is achieved by clustering servers behind a front-end server than gives customers a relative level of distribution transparency.
Owner:G-4 INC
Method and system for graphical file management
Owner:BONADIO ALLAN R
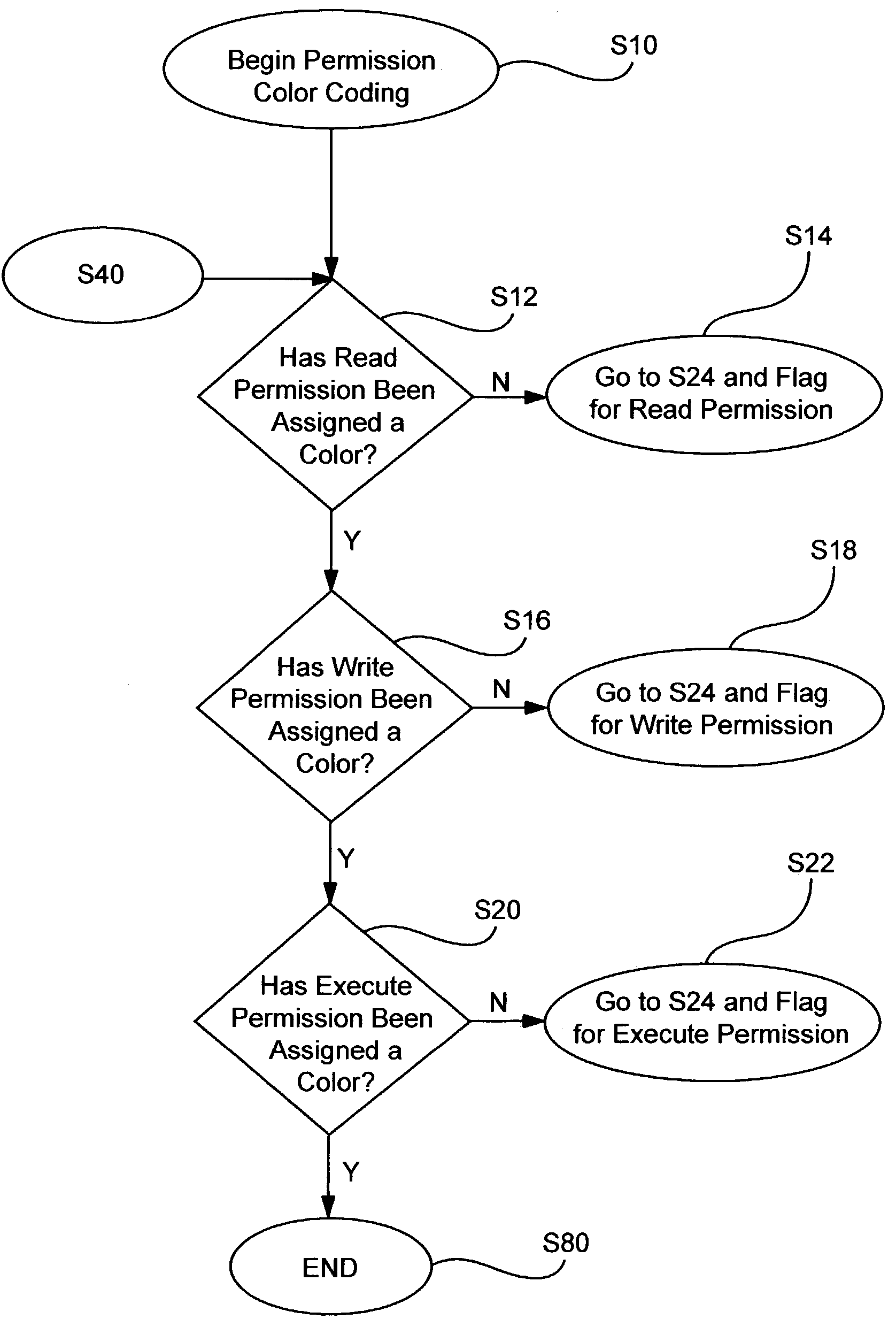
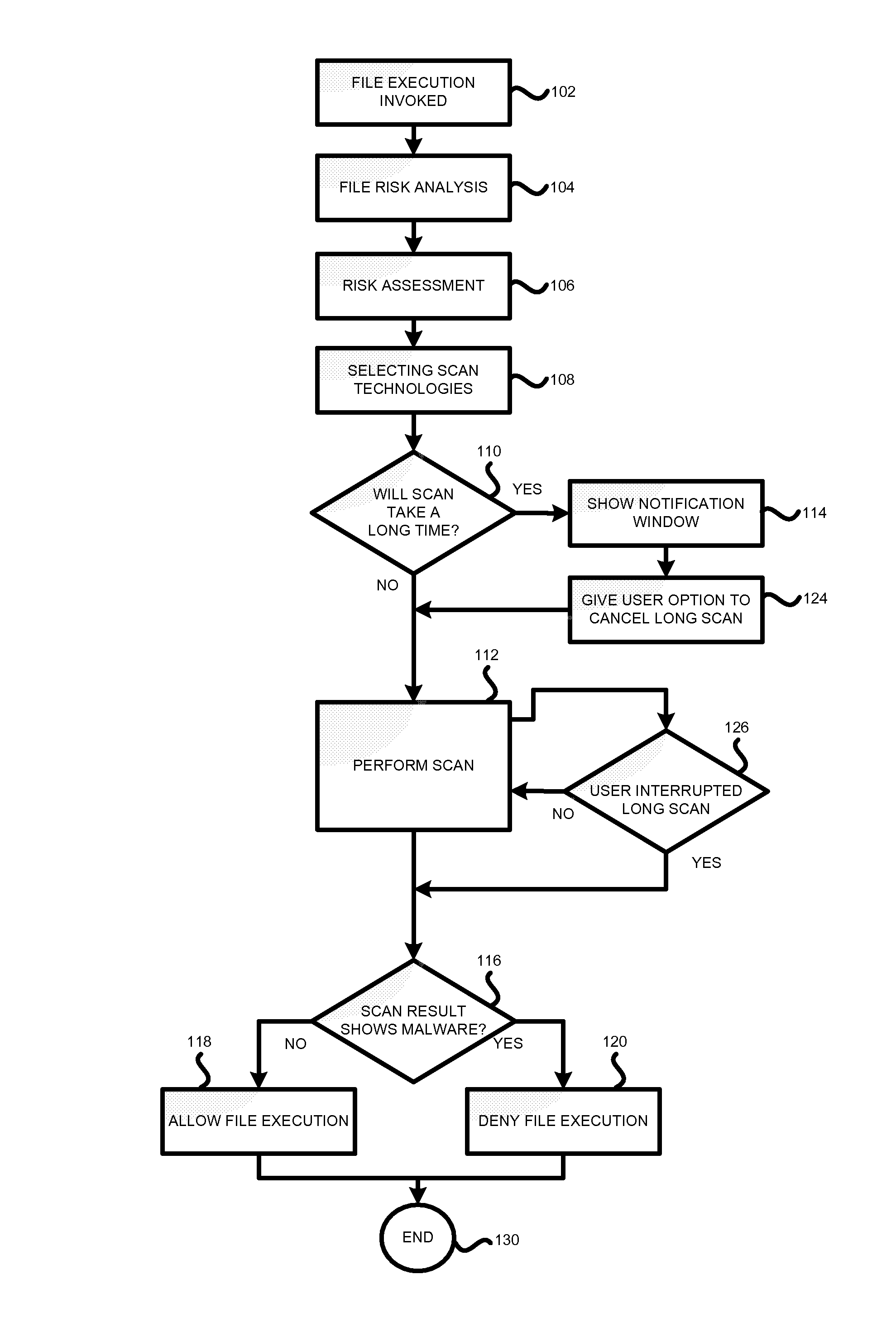
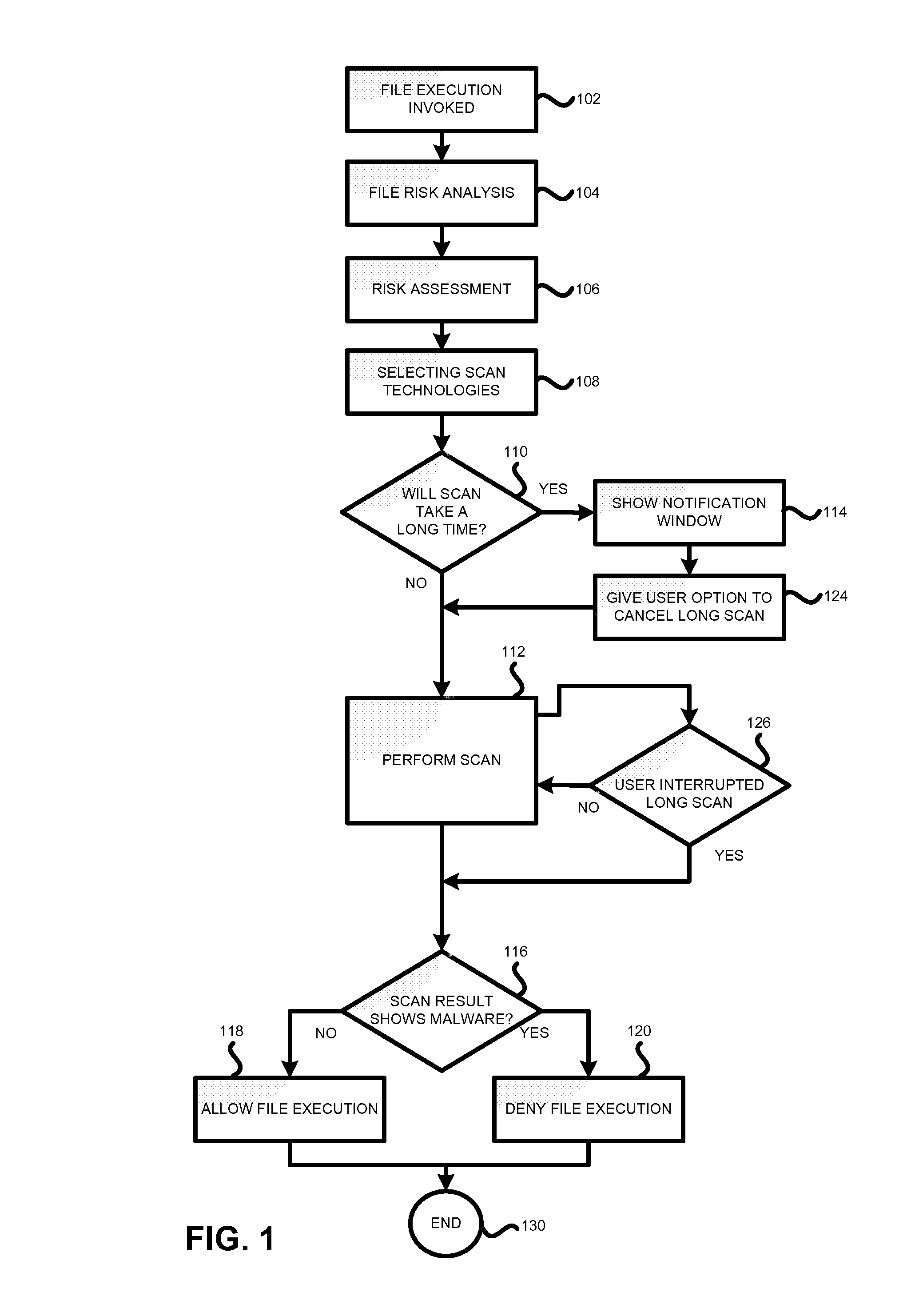
Method and system for anti-malware scanning with variable scan settings
A system, method and computer program product for scanning an executable file for malware presence, the method comprising: (a) detecting an attempt to execute a file on a computer; (b) identifying whether the file is known or unknown; (c) if the file is a known file, performing a signature malware check; (d) if the file is an unknown file, performing risk analysis and risk assessment for the file; (e) based on the risk analysis and the risk assessment, identifying which malware detection algorithms need to be used for the file, in addition to signature detection; (f) performing the malware detection algorithms on the file; and (g) if no malware is detected, permitting execution of the file. The risk analysis is based on file source, file origin, file path, file size, whether the file is digitally signed, whether the file is a download utility, whether the file is packed, whether the file was received from a CDROM.
Owner:AO KASPERSKY LAB
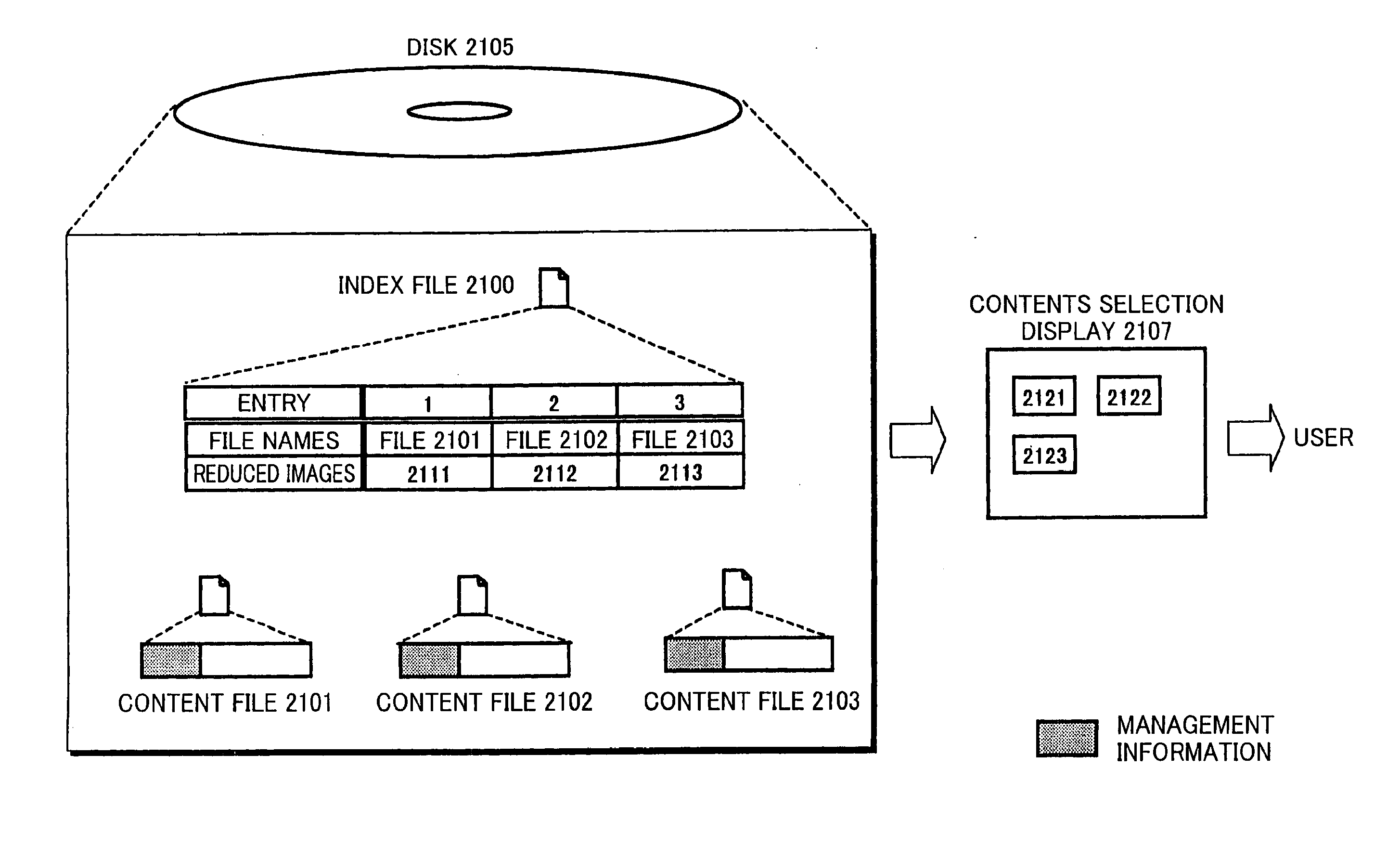
Data recording method, data erasure method, data display method, storage device, storage medium, and program
The objective of the present invention is to manage reference movies using an index file, without causing the user to be perplexed. The reference movies are generated because of, for instance, the upper limit of the file size. The index file manages sets of information regarding the files being managed. Examples of these sets of information are information for determining whether or not a file is presented to the user, information for determining whether or not a file is original, and information indicating whether or not nondestructive editing has been done. Based on such information, the erasure, displaying a list, and so on are carried out. Thus, it is possible to manage the reference movies using the index file, without causing the user to be perplexed.
Owner:SHARP KK
Multi-pass variable bitrate media encoding
InactiveUS20050015246A1Enhance listening experienceQuality improvementSpeech analysisFile sizeComputer science
An encoder uses multi-pass VBR control strategies to provide constant or relatively constant quality for VBR output while guaranteeing (within tolerance) either compressed file size or, equivalently, overall average bitrate. The control strategies include various techniques and tools, which can be used in combination or independently. For example, in a first pass, an audio encoder encodes a sequence of audio data partitioned into variable-size chunks. In a second pass, the encoder encodes the sequence according to control parameters to produce output of relatively constant quality. The encoder sets checkpoints in the second pass to adjust the control parameters and / or subsequent checkpoints. The encoder selectively considers a peak bitrate constraint to limit peak bitrate. The encoder stores auxiliary information from the first pass for use in the second pass, which increases the speed of the second pass. Finally, the encoder compares signatures for the input data to check consistency between passes.
Owner:MICROSOFT TECH LICENSING LLC
Image data management method and system using network
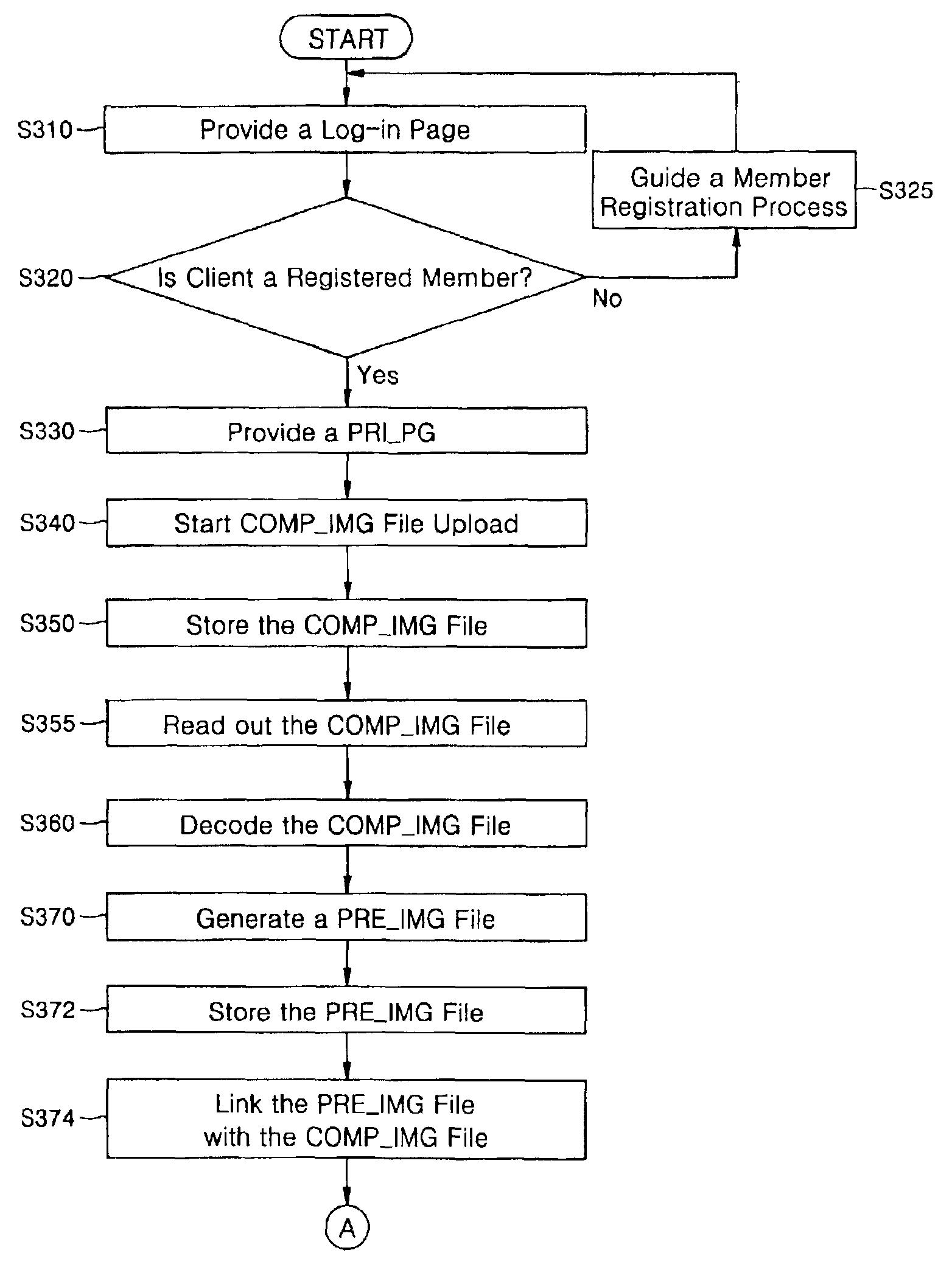
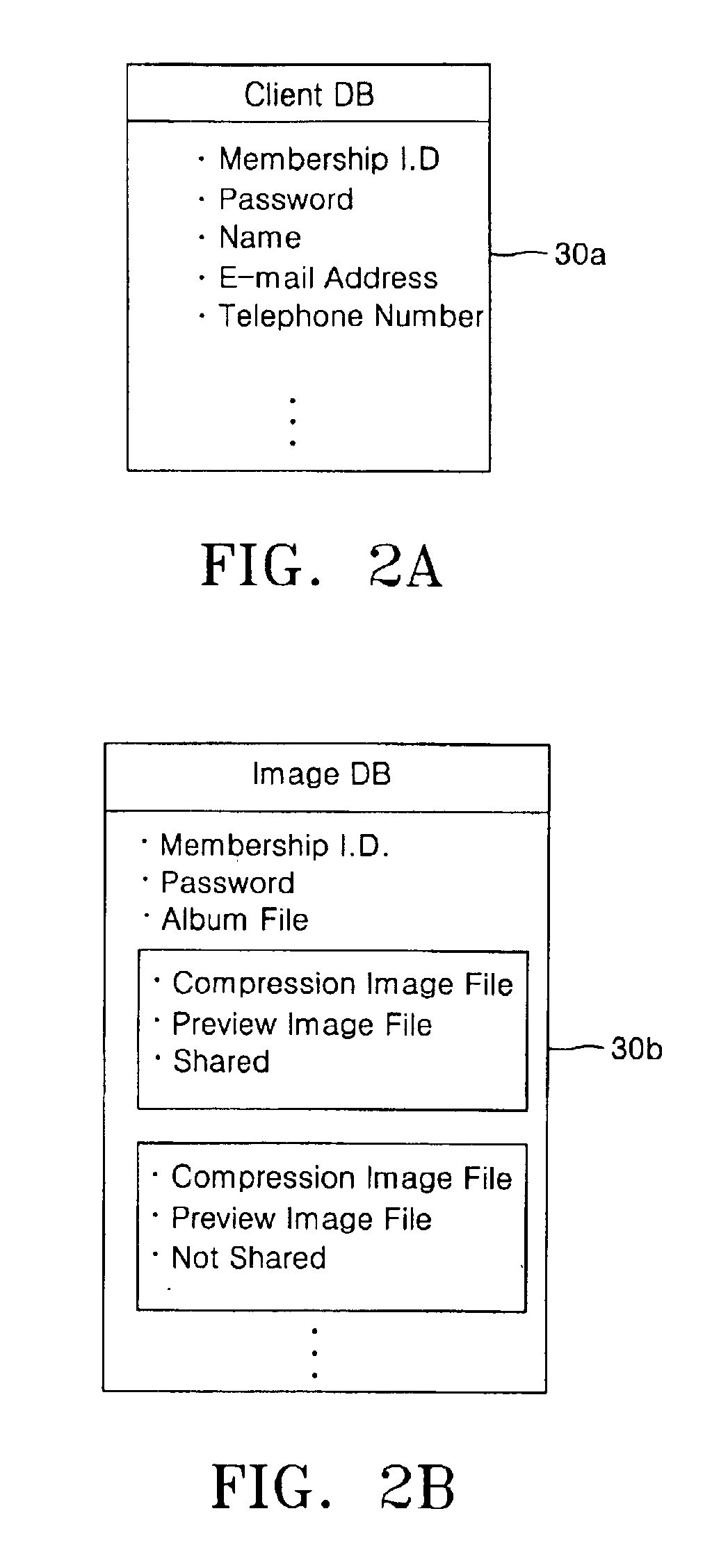
ActiveUS6883009B2Shorten the time periodDigitally marking record carriersCharacter and pattern recognitionComputer graphics (images)Data file
A method for managing an original image data file uploaded from a terminal of a client and a system for materializing the method. The method includes storing the original image data file in a database; generating a preview image data file by using the original image data file, wherein the preview image data file has a predetermined file size smaller than that of the original image data file; storing the preview image data file in the database; and linking the preview image data file with the original image data file. The system includes a storage device a storage device, an image management device, a retrieval device and an image process device. The storage device stores information of a client, original image data files and preview image data files each linked with corresponding one of the original image data files. The image management device generates a preview image data file by using a corresponding original image data file. The retrieval device reads out an original image data file from the storage device, on the basis of search data externally provided. The image process device provides an image selection page to the client terminal and generates the search data for the preview image data file selected by the client.
Owner:PHILIPS NORTH AMERICA LLC
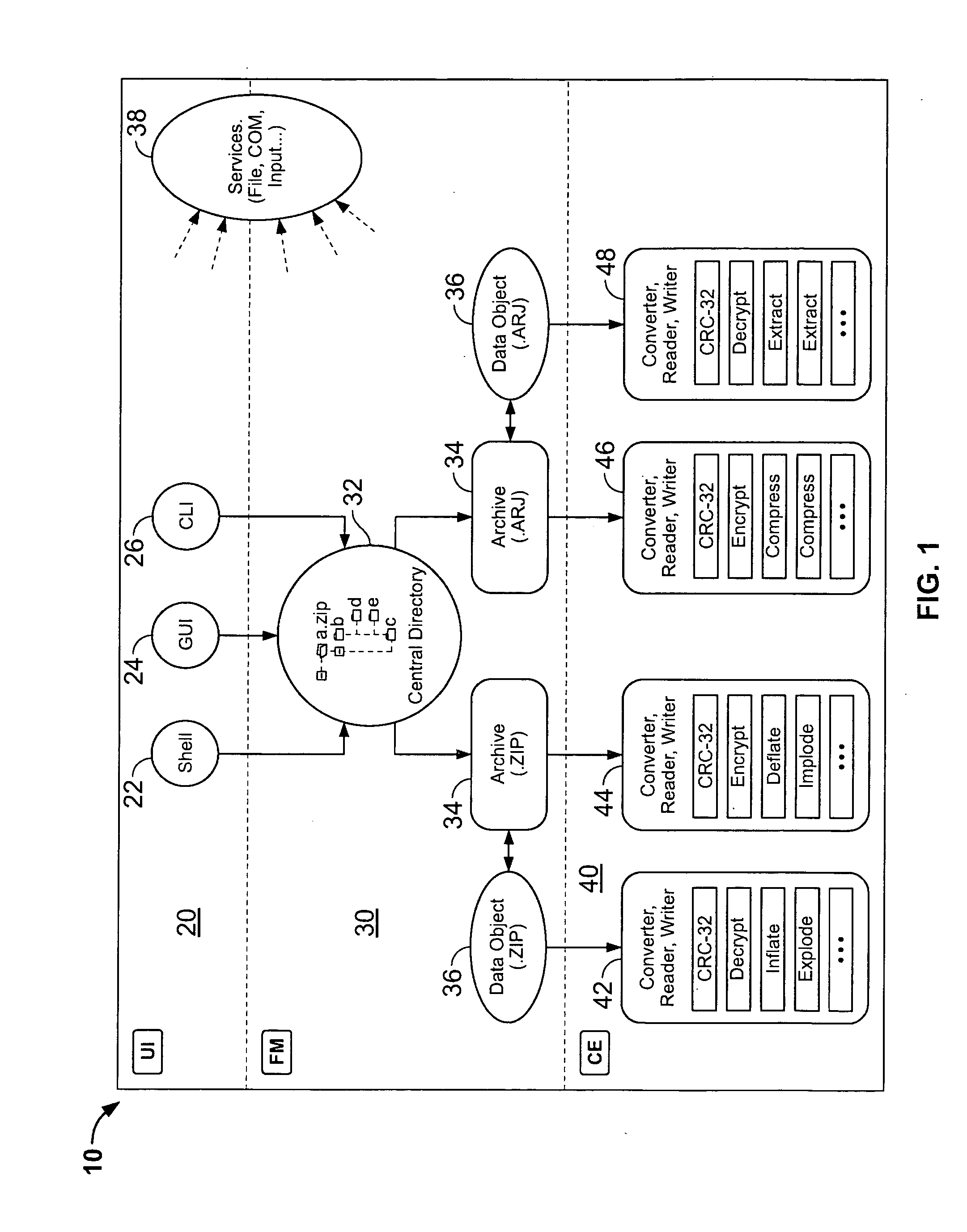
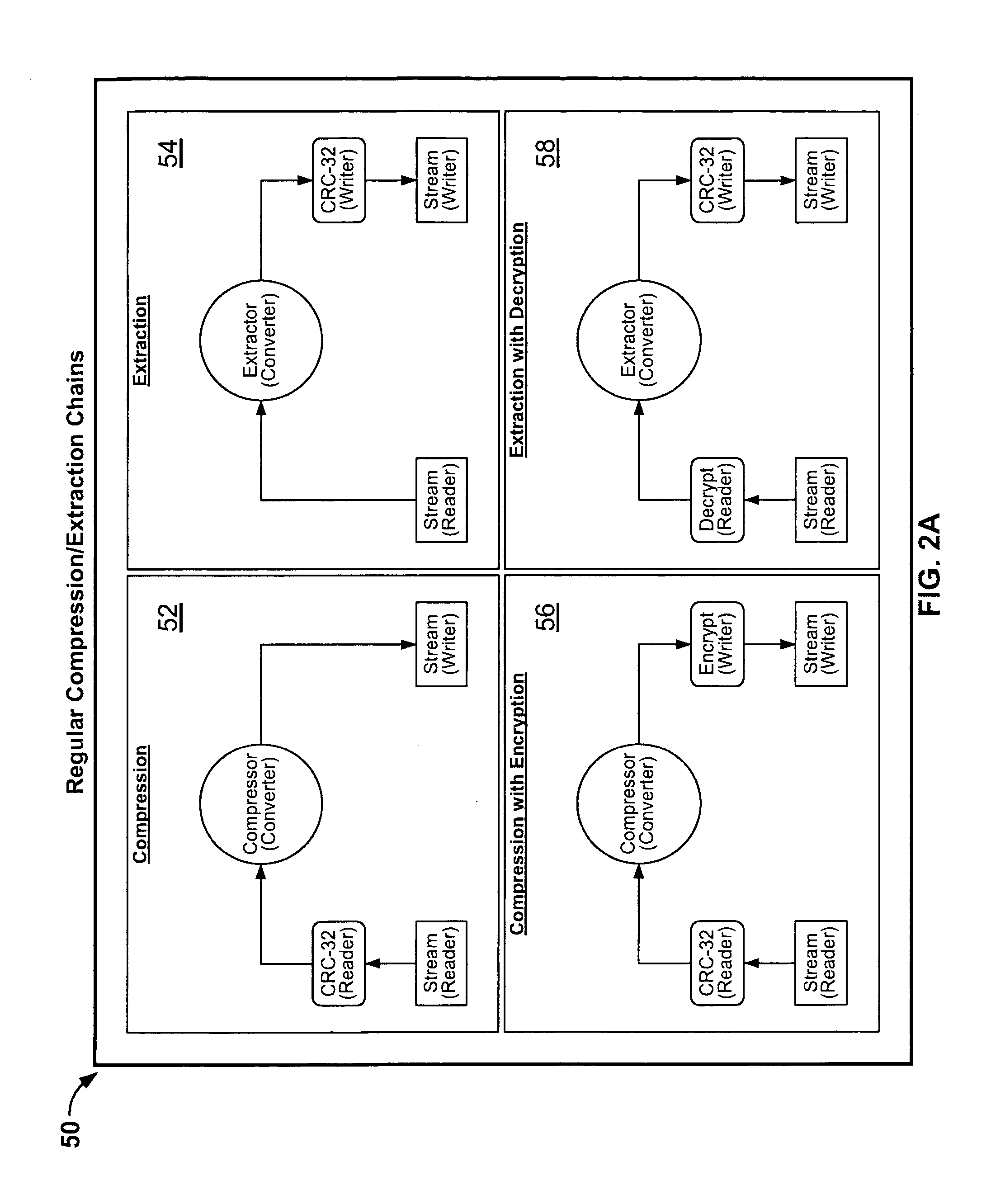
System and method for manipulating and managing computer archive files
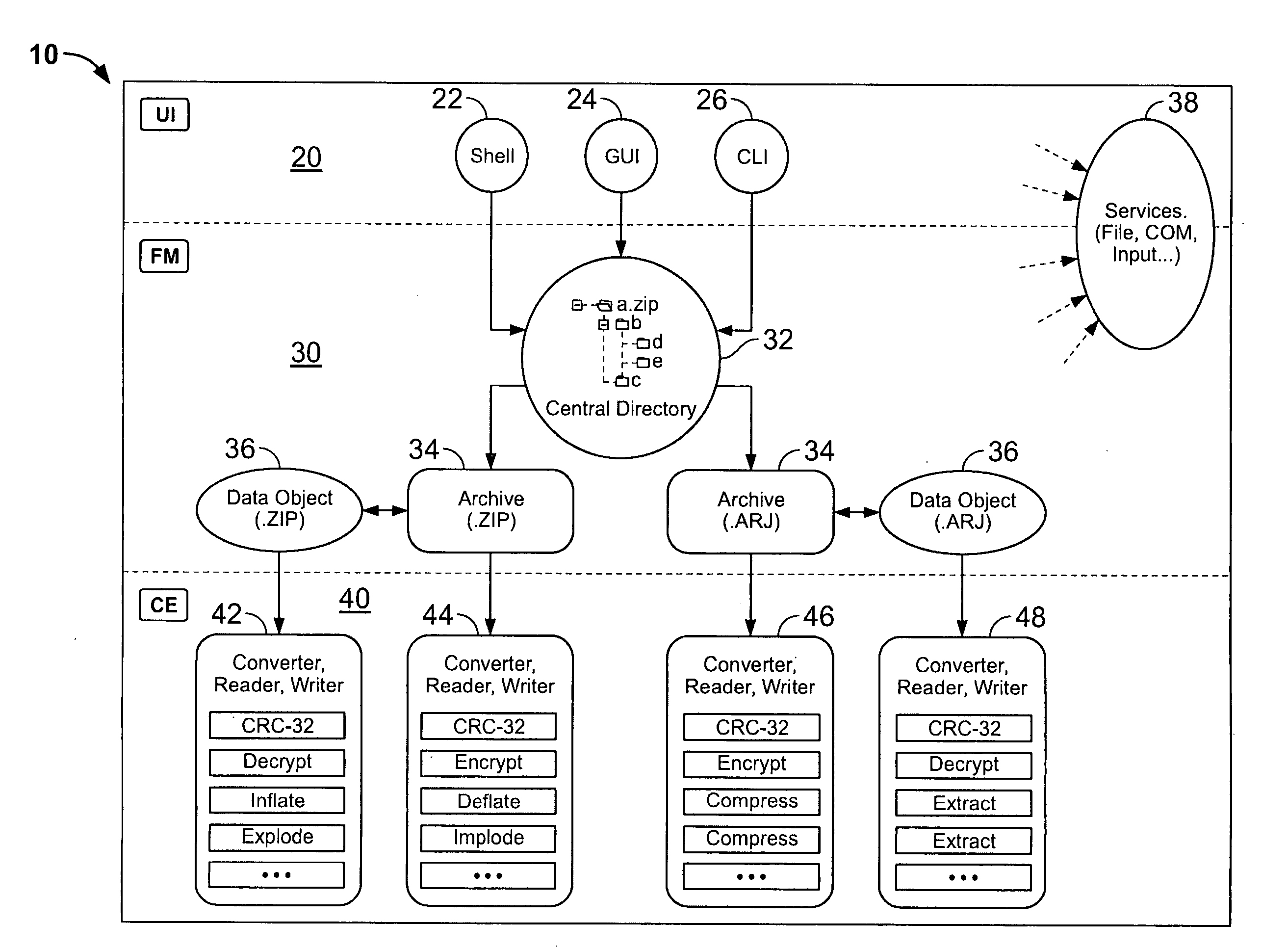
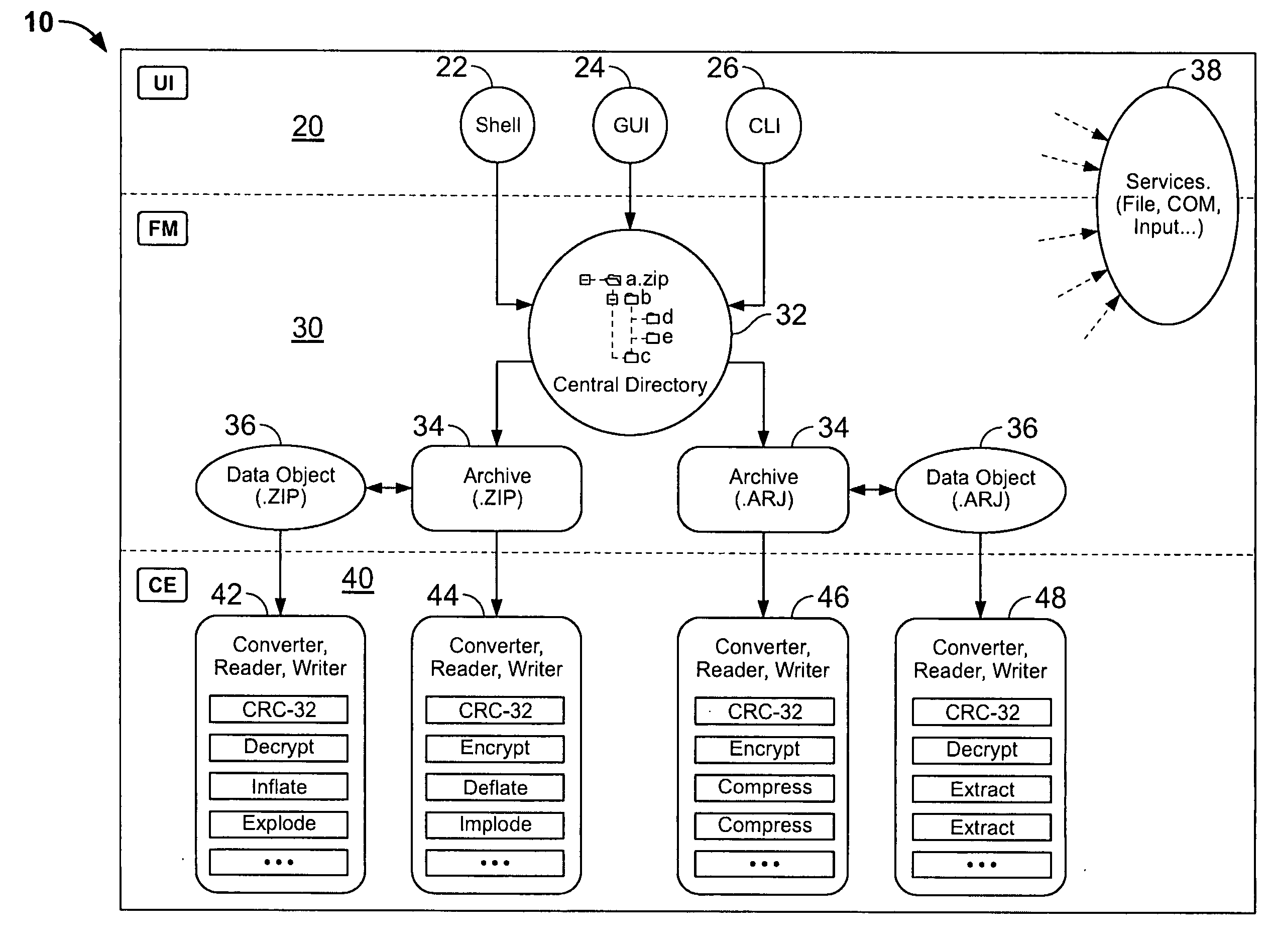
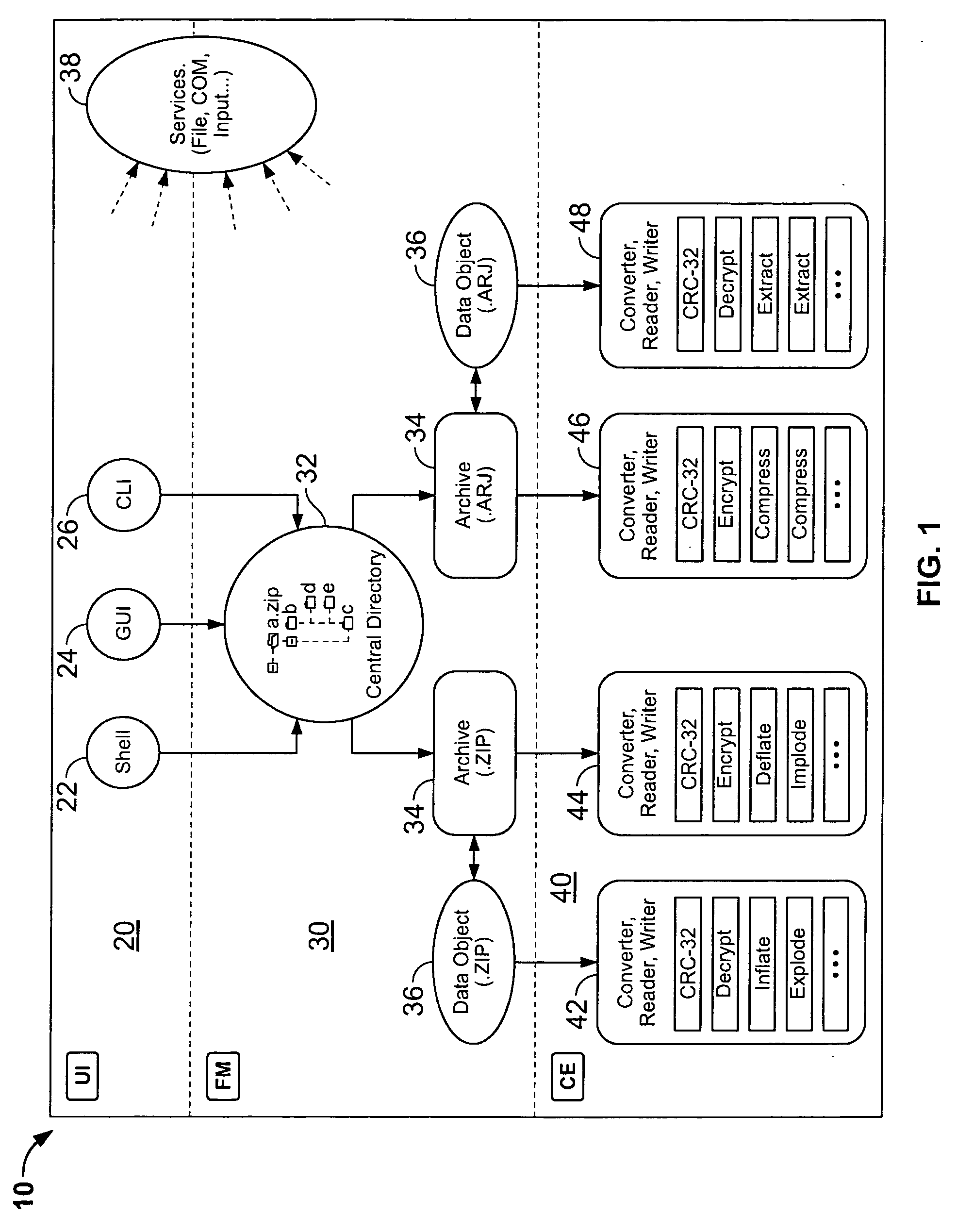
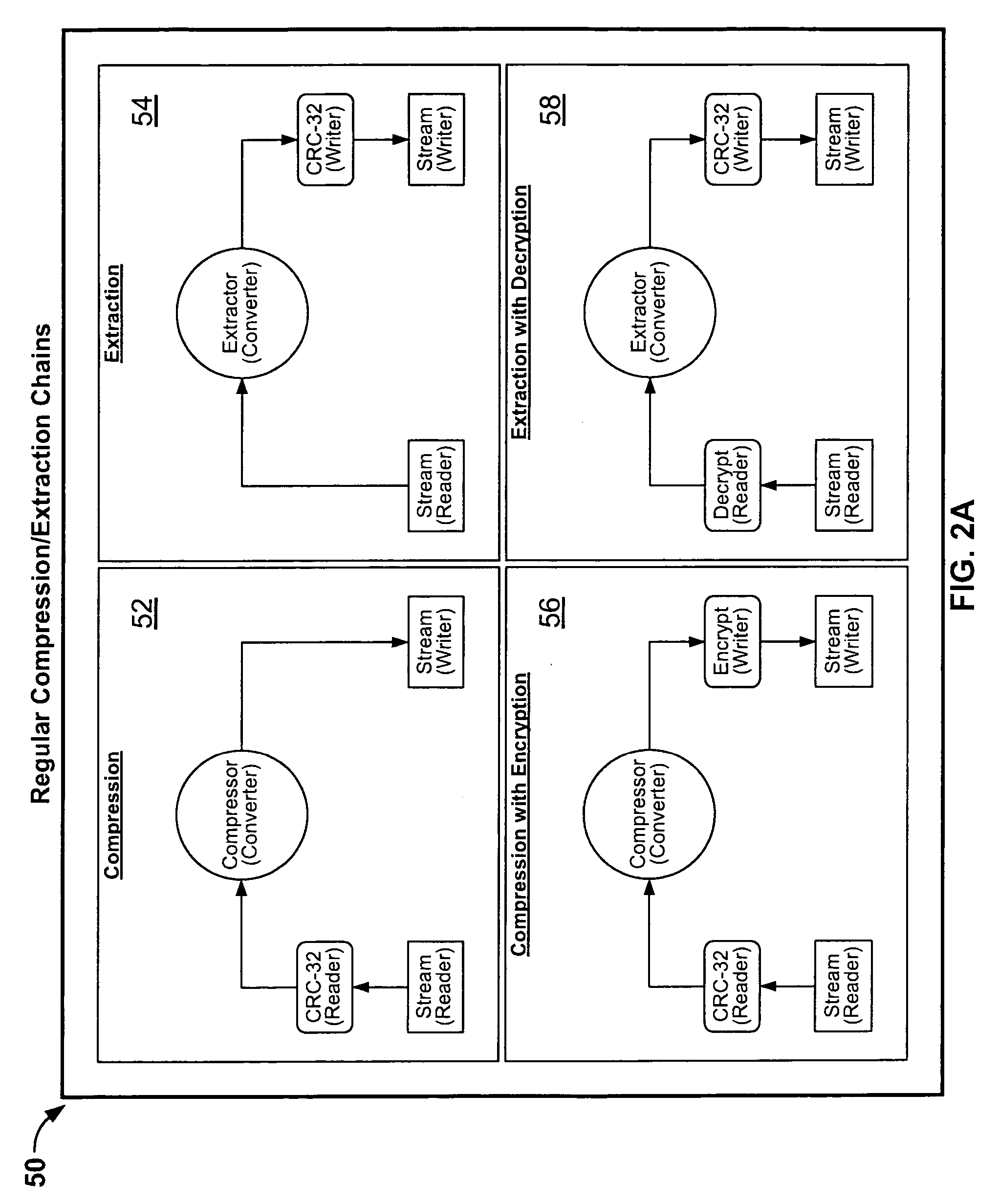
InactiveUS20060143714A1Digital data information retrievalDigital data processing detailsDigital signatureFile size
Certain embodiments of the present invention provide an archive management application that operates within a host application to provide access to an archive and / or allow access to and / or modification of files in an archive using the host application's interface, instead of operating as a separate standalone archive management application. In an embodiment of the present invention, a file archiving system may include a user interface component, a file management component and a compression / extraction engine component. The user interface component may include an enhanced user interface of a host application that provides an interface for a user. The file management component may include a central directory that provides a representation of the contents of an archive. The compression / extraction engine component may include a file size module and / or a security module. The file size module may be used to compress and / or decompress a file in an archive. The security module may be used to encrypt, decrypt, digitally sign and / or authenticate a file in an archive.
Owner:PKWARE
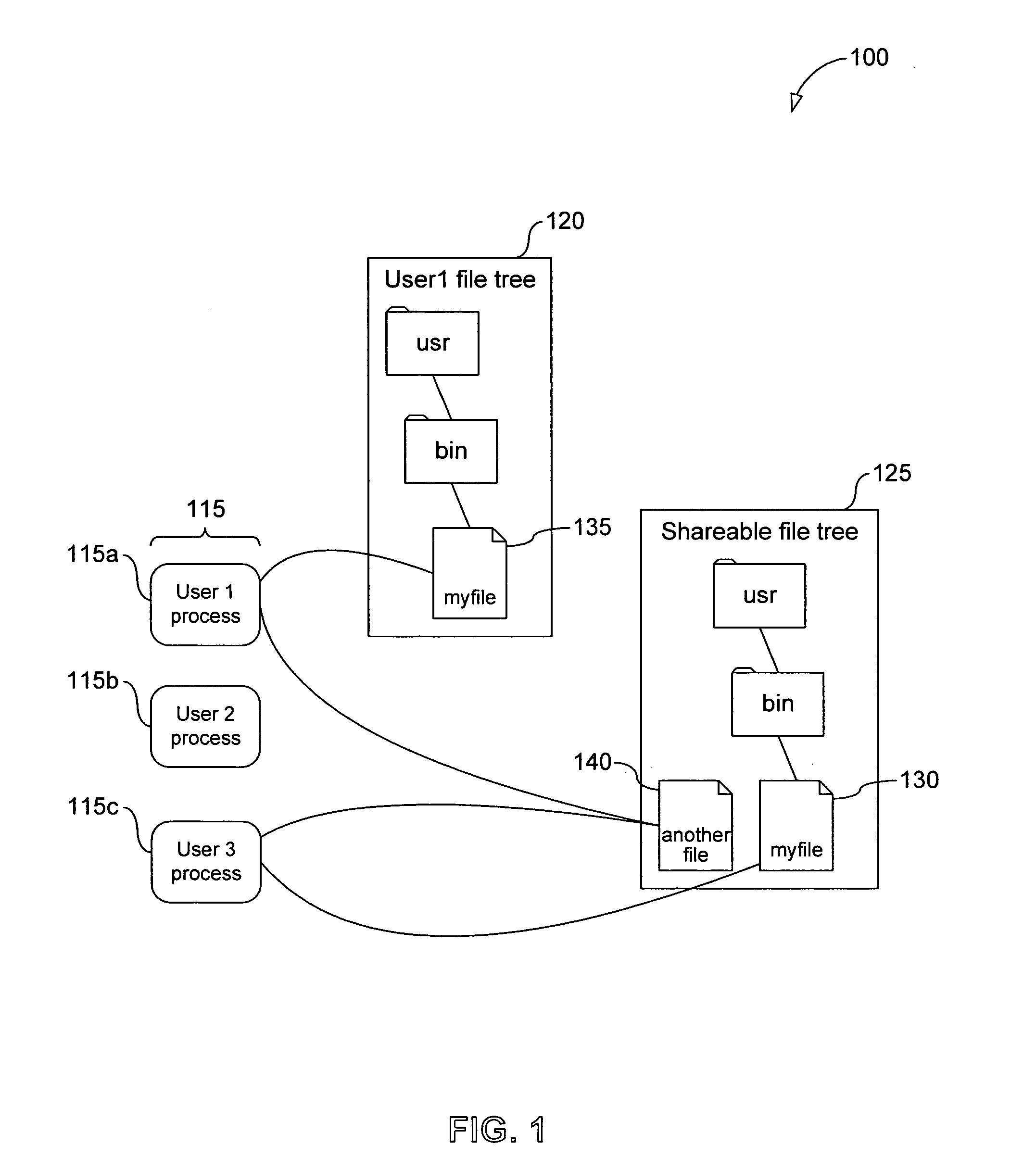
System, method and computer program product for multi-level file-sharing by concurrent users
ActiveUS7328225B1Efficient multi-user accessEfficient file sharingData processing applicationsSpecial data processing applicationsOperational systemFile size
A method of accessing a shareable computer file includes receiving a request to access the shareable computer file, retrieving a file ID from a stub file corresponding to the shareable computer file, retrieving a file name from a database corresponding to the file ID, accessing the shareable computer file if a user has not modified the shareable computer file, and accessing a modified copy of the shareable file stored in the stub file if the user has modified the shareable computer file. A database is generated in operating system space or accessed using the operating system, and includes file IDs and their corresponding file names for shareable computer files. The stub file is generated locally to correspond to the shareable computer file, and includes a modified copy of the shareable computer file if the shareable computer file has been modified, and a link to the shareable computer file if the shareable computer file has not been modified. If the shareable computer file has not been modified, a read-only operation retrieves any of file contents, file position and file size from the shareable computer file. File attributes relating to the shareable computer file can be retrieved from the stub file. The database is provided by the operating system for use by a Virtual Private Server.
Owner:VIRTUOZZO INT GMBH
Data processing method for information processing system, information processing system, storage medium, and program
ActiveUS20060044601A1Avoid problemsEasy to operateDigitally marking record carriersDigital computer detailsInformation processingFile size
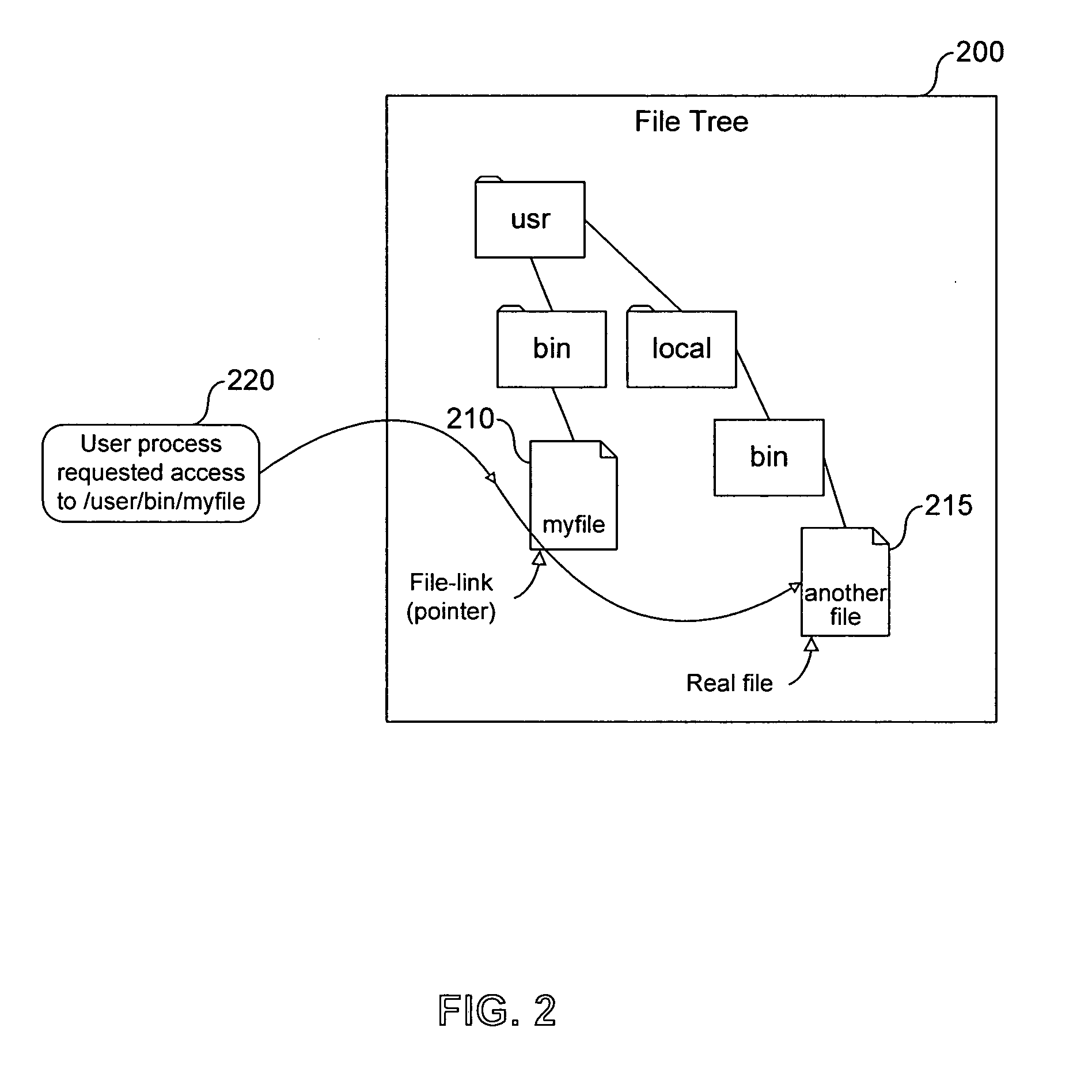
In a system in which a host computer and MFP are connected via a communication medium such as a network or the like, upon transmitting image data stored in a box of the MFP to the host computer, the transmission data size (file size) is displayed before transmission. The user can transmit image data with a desired file size. When the amount of transmission data is large, the load on resources such as a memory, CPU, and the like of a device as a destination of transmission can be reduced.
Owner:CANON KK
System and method for manipulating and managing computer archive files
Certain embodiments of the present invention provide an archive management application that operates within a host application to provide access to an archive and / or allow access to and / or modification of files in an archive using the host application's interface, instead of operating as a separate standalone archive management application. In an embodiment of the present invention, a file archiving system may include a user interface component, a file management component and a compression / extraction engine component. The user interface component may include an enhanced user interface of a host application that provides an interface for a user. The file management component may include a central directory that provides a representation of the contents of an archive. The compression / extraction engine component may include a file size module and / or a security module. The file size module may be used to compress and / or decompress a file in an archive. The security module may be used to encrypt, decrypt, digitally sign and / or authenticate a file in an archive.
Owner:PKWARE
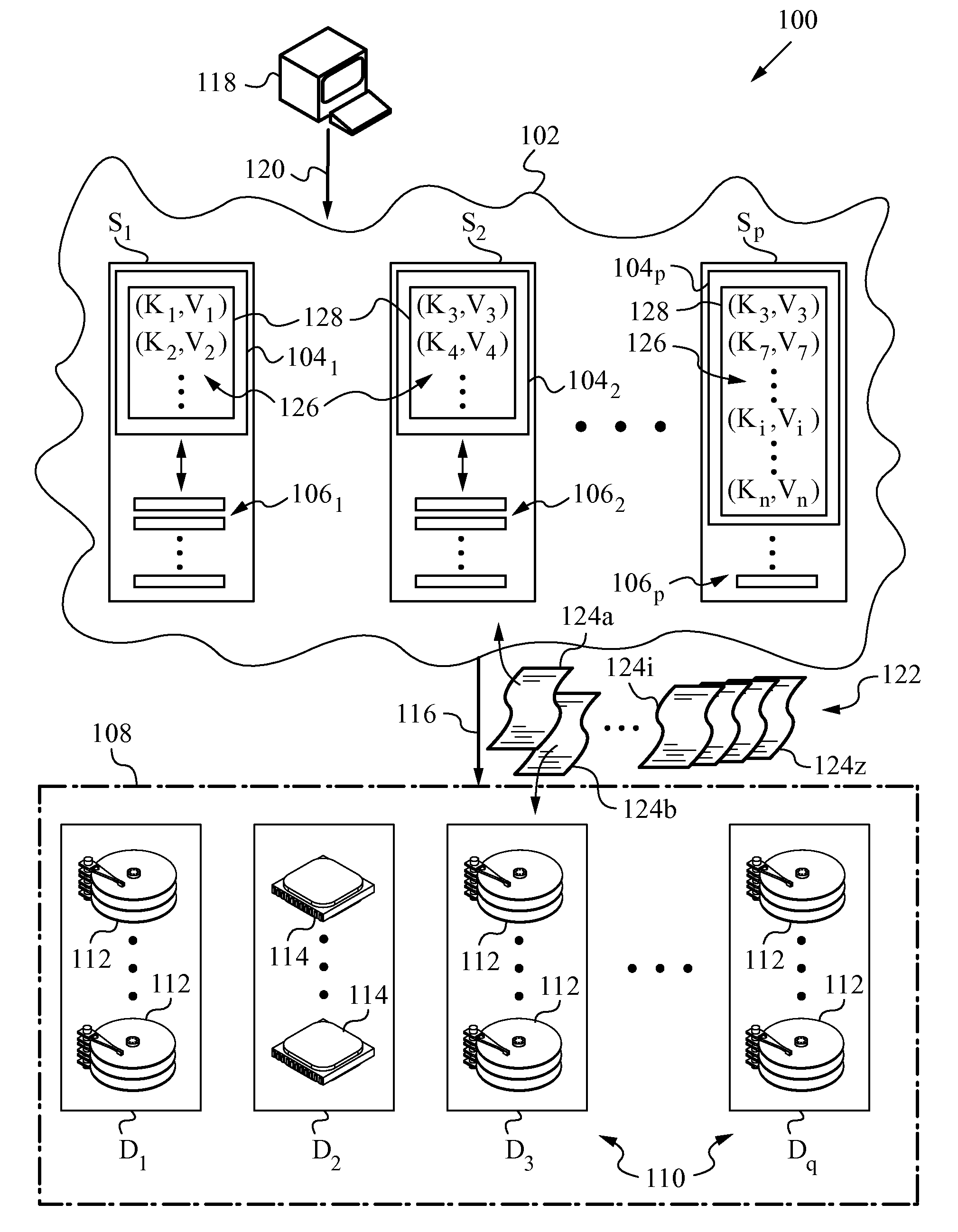
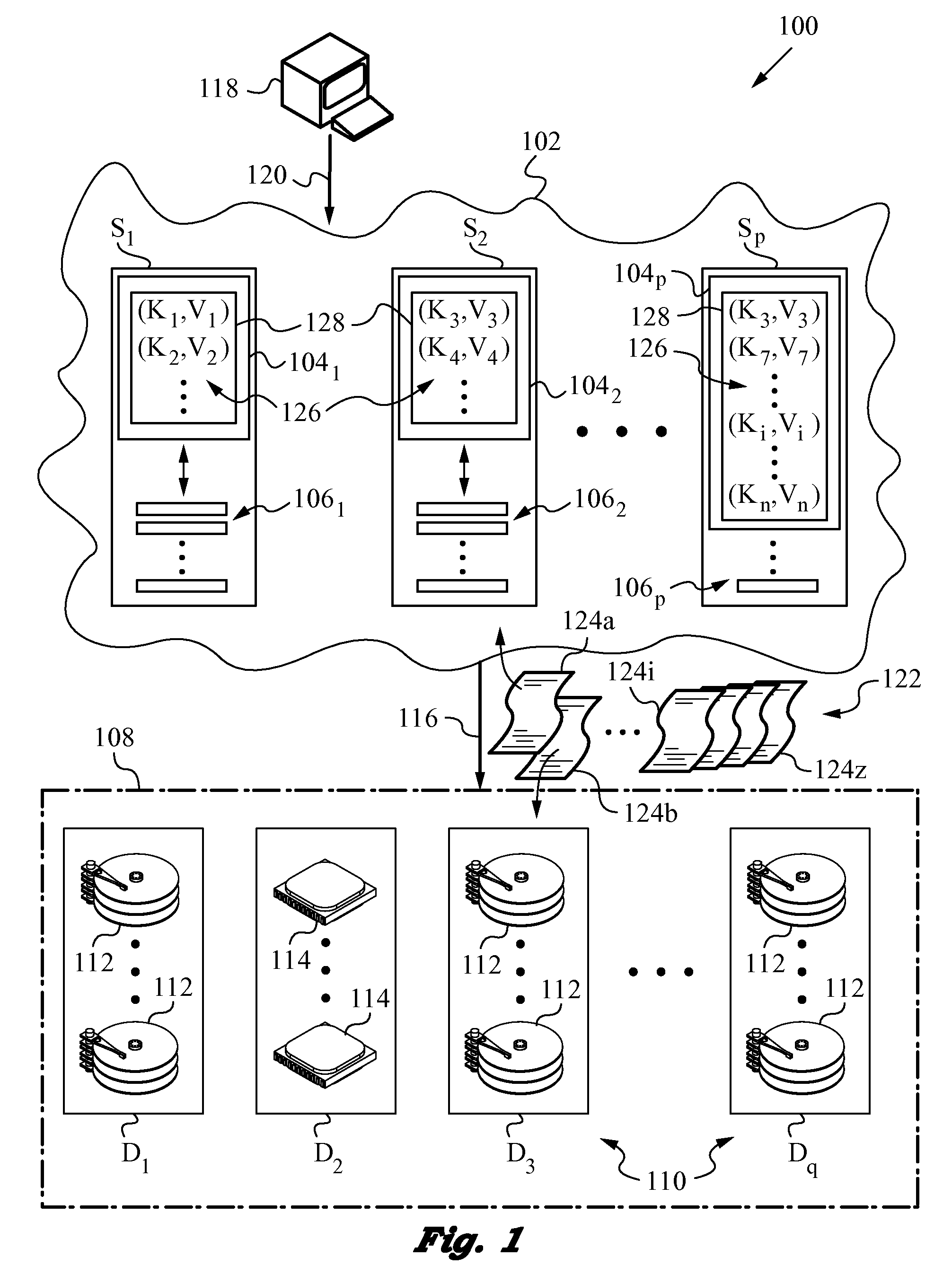
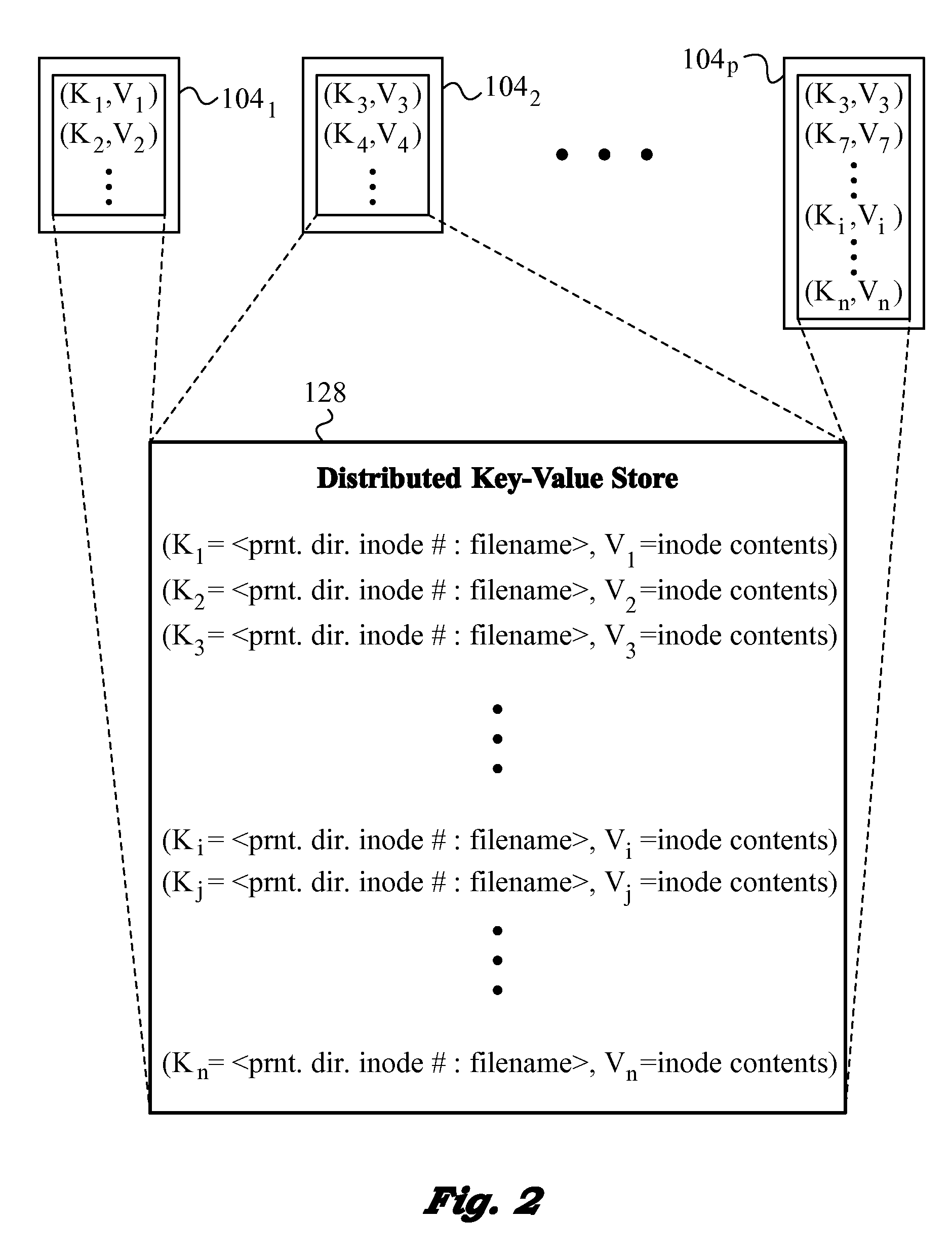
Scalable Distributed Metadata File System using Key-Value Stores
InactiveUS20120284317A1High-performance and more scalableEnsure fitFile access structuresFile metadata searchingDistributed File SystemFile system
A computer-implemented method and a distributed file system in a distributed data network in which file metadata related to data files is distributed. A unique and non-reusable mode number is assigned to each data file that belongs to the data files and a directory of that data file. A key-value store built up in rows is created for the distributed file metadata. Each of the rows has a composite row key and a row value (key-value pair) where the composite row key for each data file includes the mode number and a name of the data file. When present in the directory, the data file is treated differently depending on size. For data files below the maximum file size the entire file or portion thereof is encoded in the corresponding row value of the key-value pair. Data files above maximum file size are stored in large-scale storage.
Owner:ZETTASET
Forensics tool for examination and recovery and computer data
InactiveUS20070226170A1Avoid modificationAvoid creatingData processing applicationsError detection/correctionElectronic discoveryFile size
The present invention concerns an electronic forensic tool for conducting electronic discovery and computer forensic analysis. The present invention allows a non-technical person such as a non-forensic expert to conduct electronic discovery and thereby obviate the need for an expert in many situations. The present invention allows for electronic discovery in a forensically sound manner. The present invention also concerns a business method for electronic discovery involving a software program and a command server for generating expanded functionality. The client software may be distributed at minimal or no cost, preferably as a CD. Using the client software, a user boots a target machine to determine whether a target machine contains data of interest. The client software will, however, only display limited data such as file information, date, last modified, and file size. To access and examine the actual underlying data, the user must obtain additional functionality, e.g. by purchasing a command block from the control server. The additional functionality will allow the client program to extract the data of interest or the entire contents of the target machine to an external device for further analysis.
Owner:SUN DAVID
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com