Patents
Literature
93 results about "Signature detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
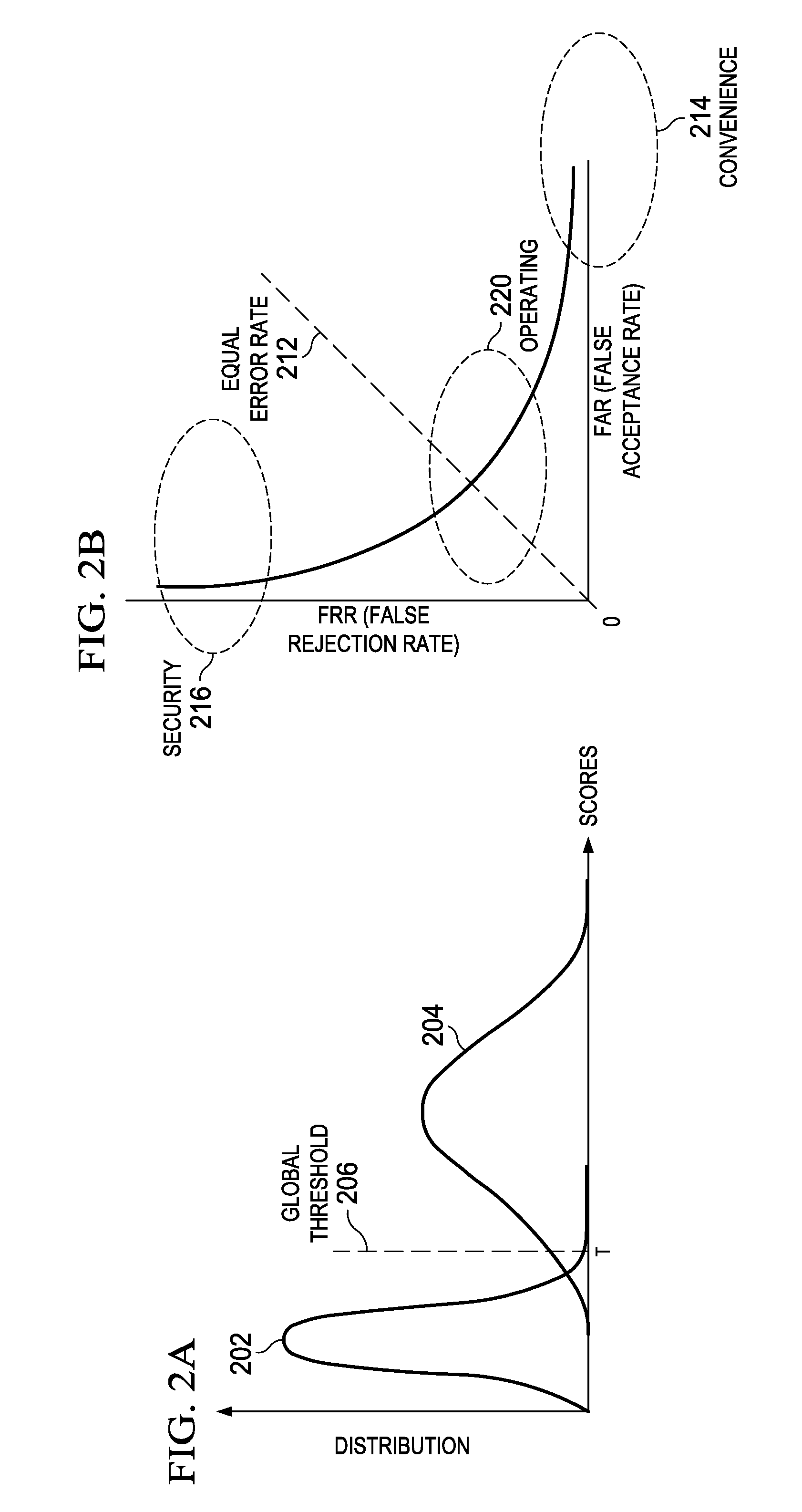
Signature Detection is the underlying technology behind Intrusion Detection, Intrusion Prevention (IDS/IPS), and Application Recognition systems. Signatures are patterns, which when matched, indicate the system should apply designated security or QoS policies.
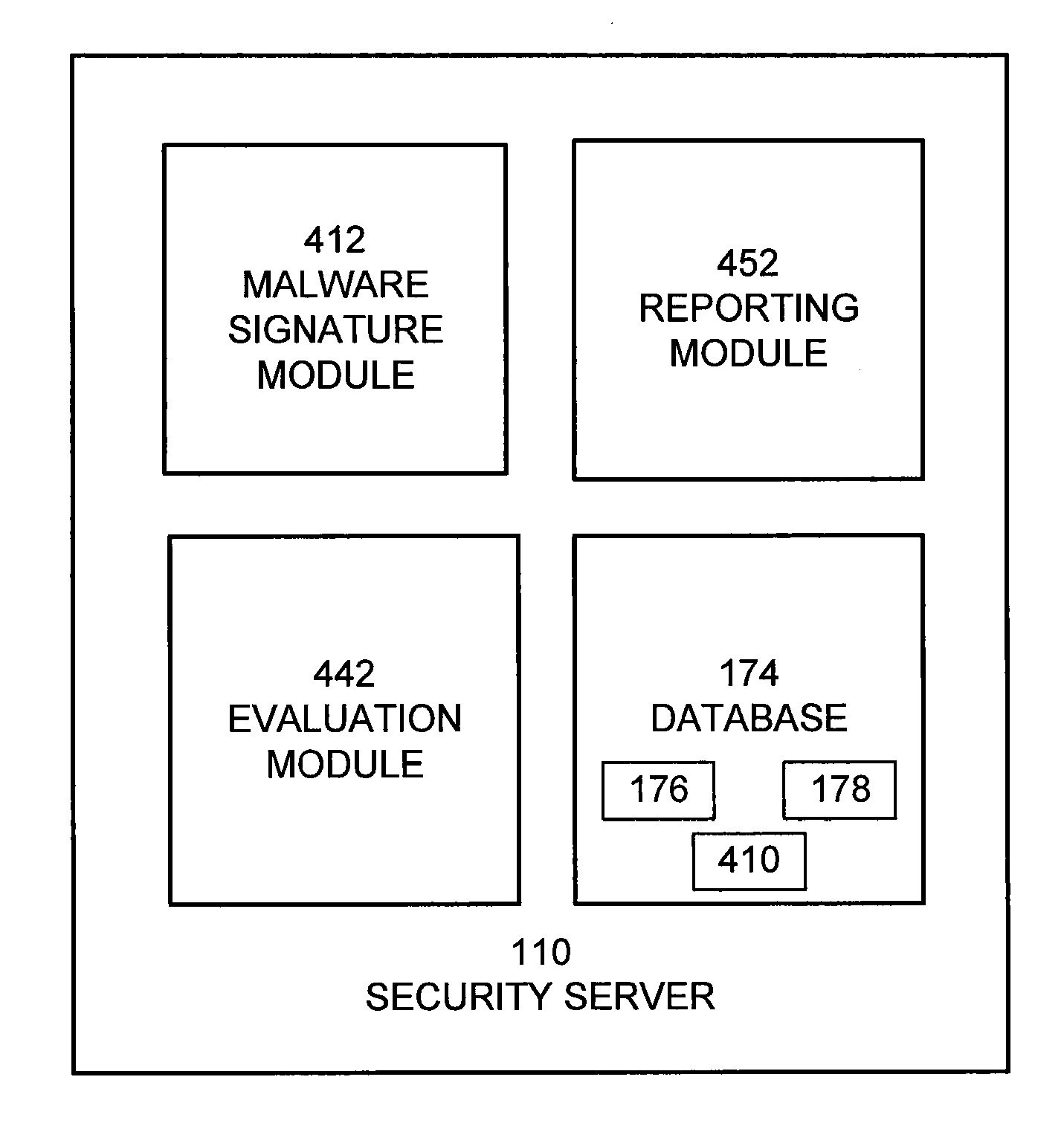
Reducing malware signature set size through server-side processing
A server provides a reduced set of malware signatures to clients. The reduced set of malware signatures has the same scope of coverage as a comprehensive set of malware signatures stored on the server, but with a higher rate of false positive detections. The server receives signature detection event reports from the clients. A signature detection event report identifies the signature in the reduced set that was detected, and includes information describing the suspicious entity in which the signature was detected. Upon receiving a signature detection event report from a client, the server evaluates the information describing the suspicious entity using one or more signatures in the comprehensive set to determine whether the signature detection event is a false positive or a legitimate malware detection. The security server provides the result of the evaluation to the client from which the report was received.
Owner:CA TECH INC
System and method for using signatures to detect computer intrusions
InactiveUS7032114B1Problem can be overcomeEnabling detectionMemory loss protectionUser identity/authority verificationIntrusion detection systemContinuation
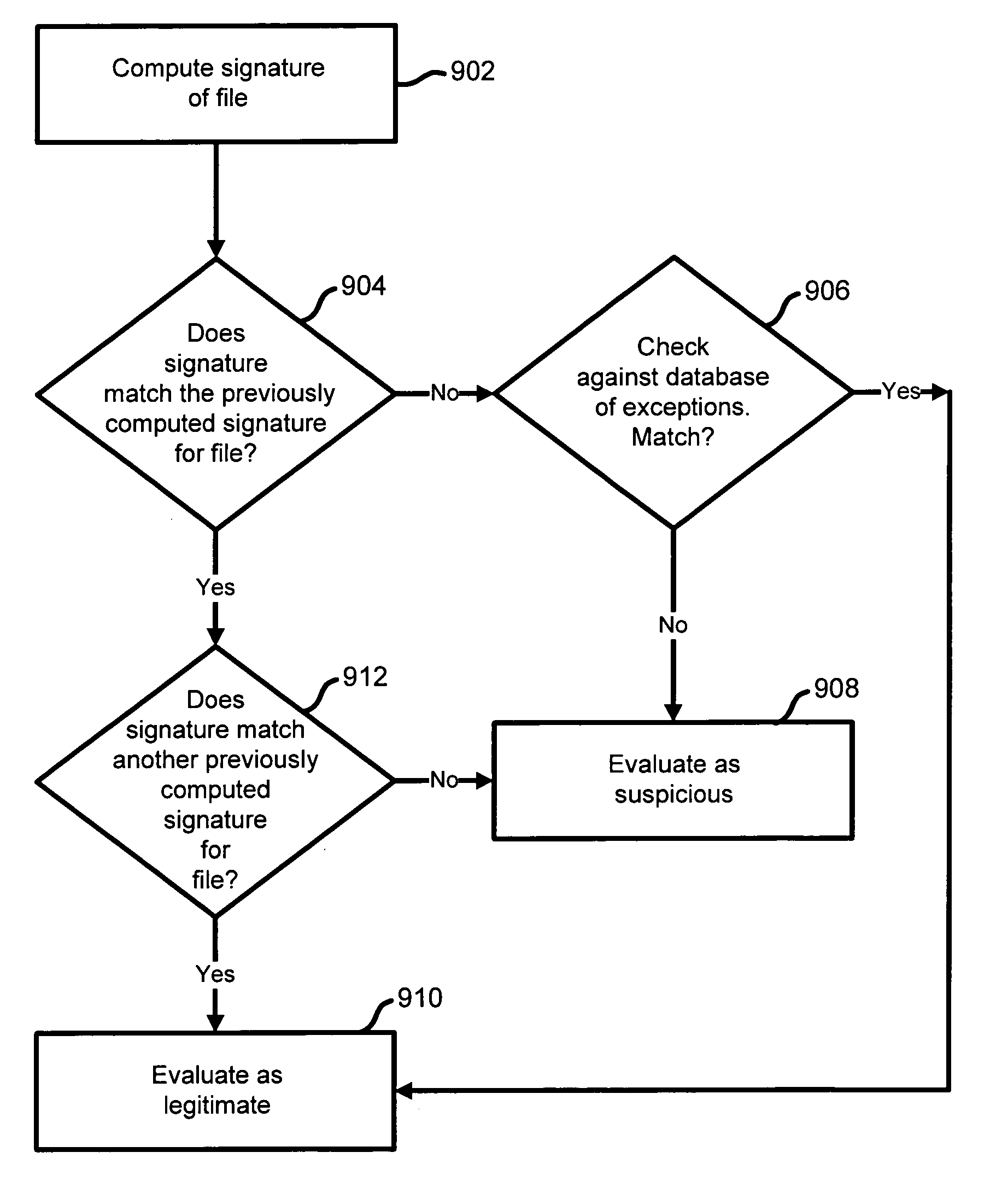
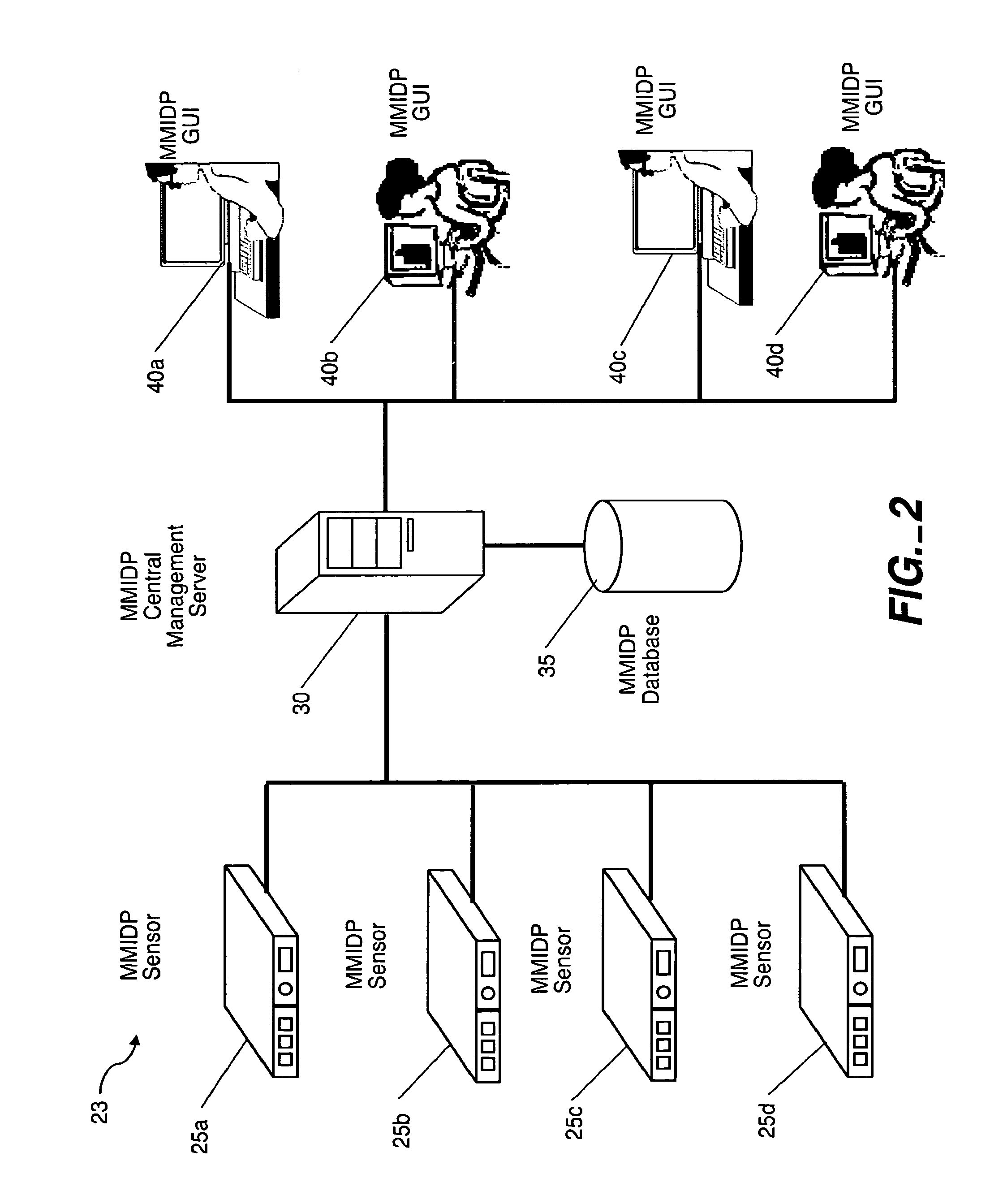
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
Detecting malicious behaviour on a computer network
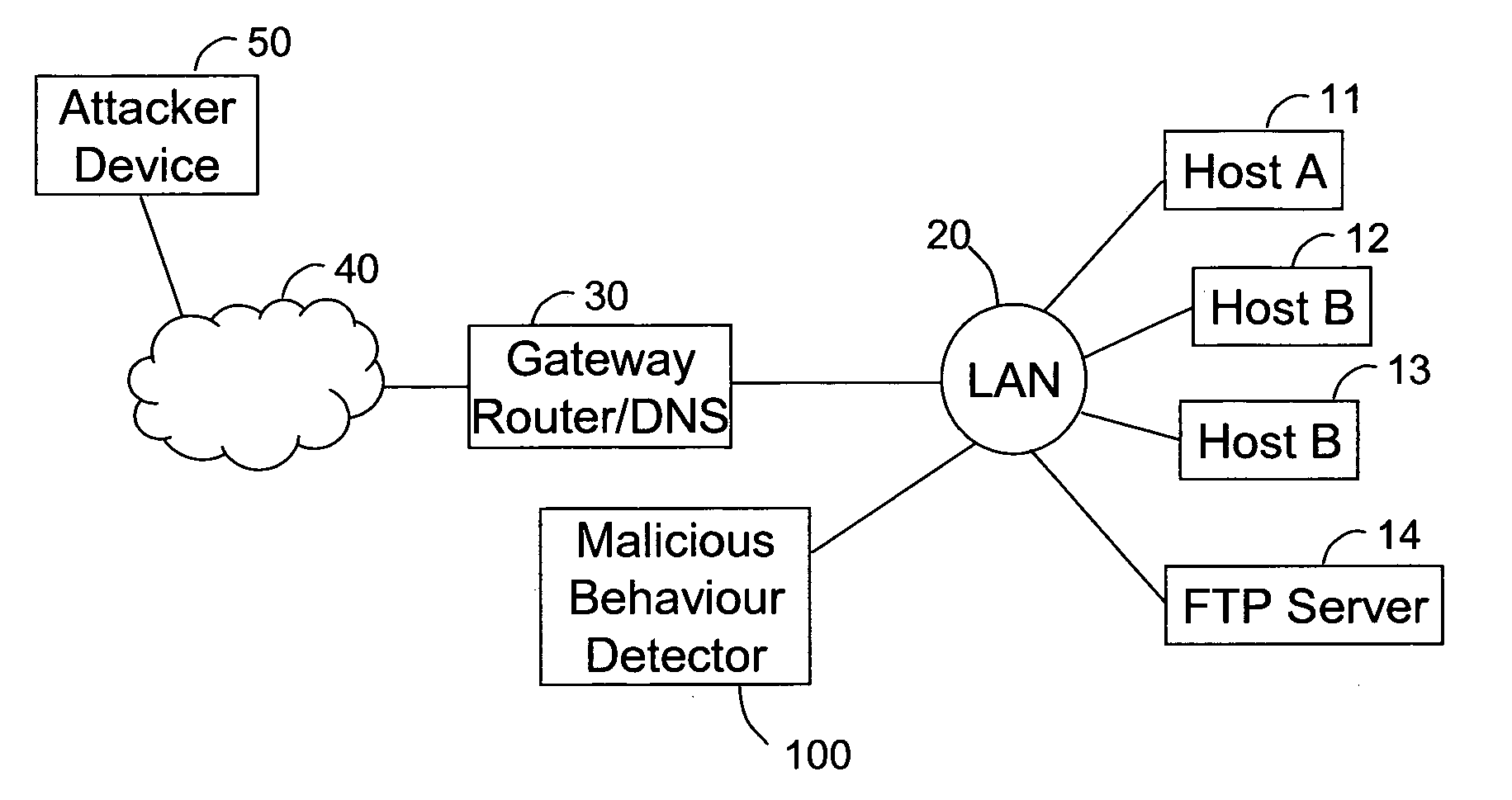
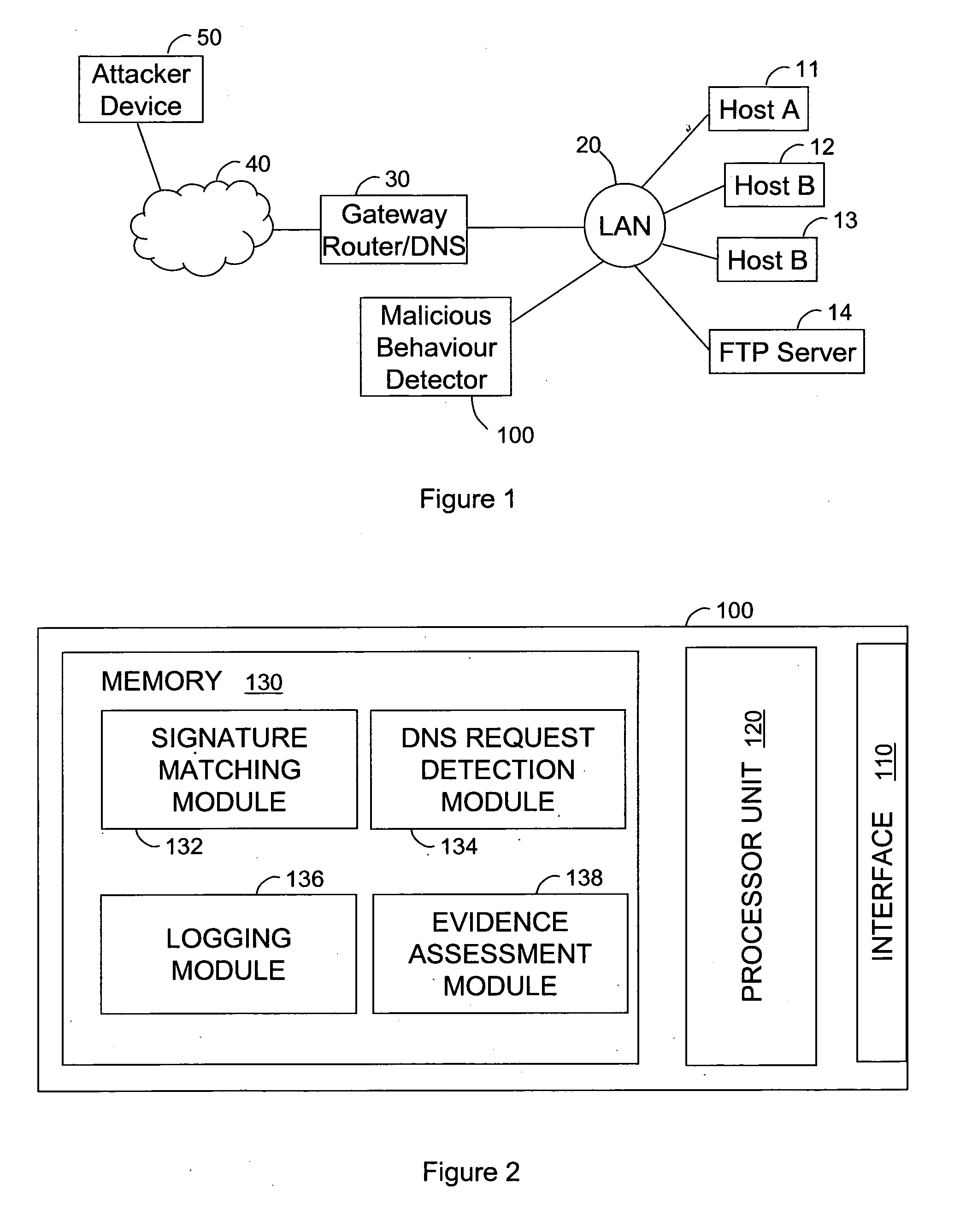
ActiveUS20110302656A1Increase opportunitiesReduce riskMemory loss protectionError detection/correctionDomain nameNetwork packet
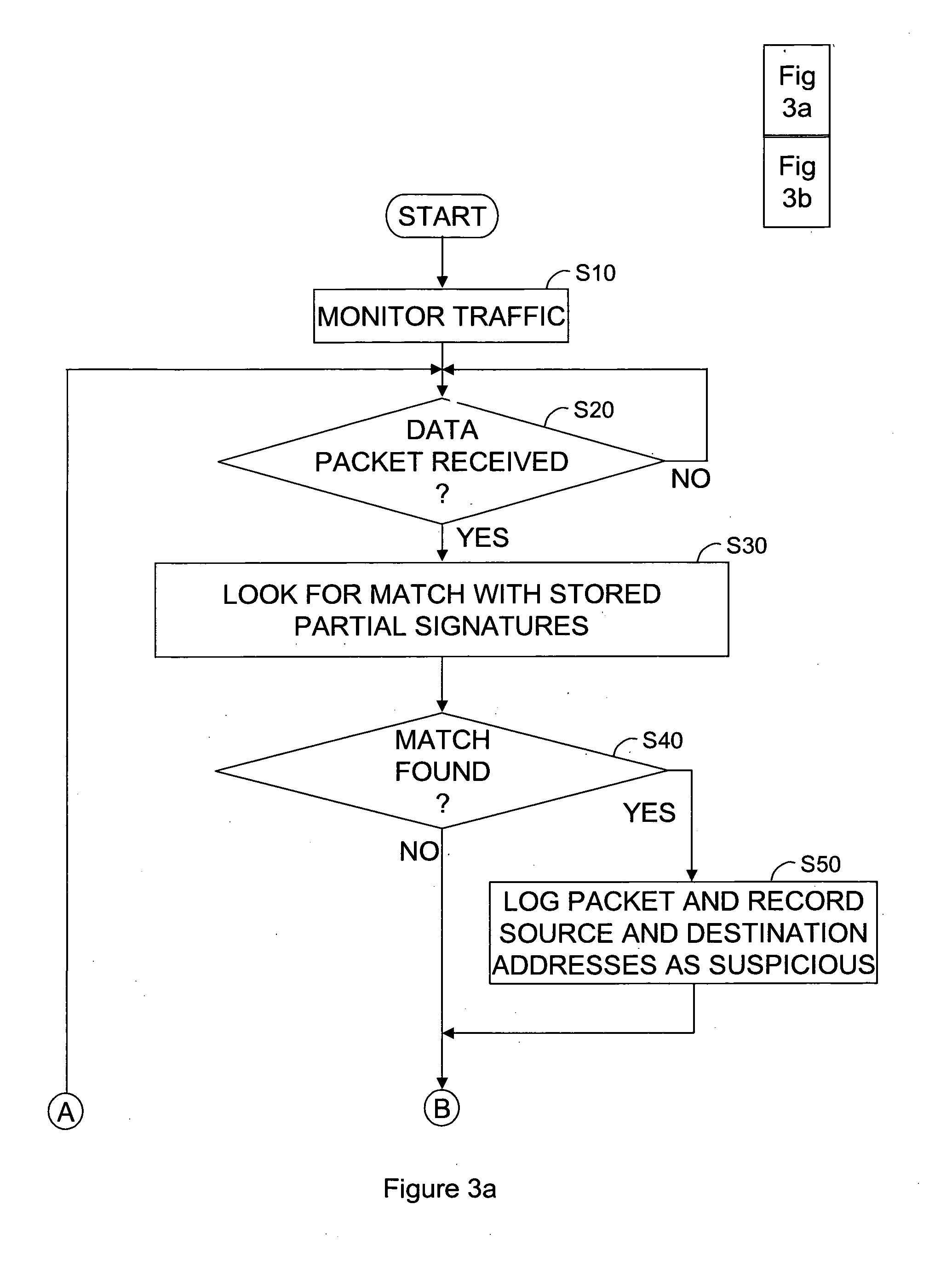
A malicious behaviour detector (100) for detecting malicious behaviour on a network, comprises a processor unit (120) and associated system memory (130) containing computer program code. The computer program code provides a signature matching module (132) to perform malicious partial signature detection by reading the contents of packets of data passing through the network to look for partial signatures associated with malicious programs; a Domain Name Service, DNS, request and / or response detection module (134) to monitor the requests made by hosts connected to the network and / or responses thereto; and an evidence assessment module (138) to analyse the results of the partial signature detection and the DNS monitoring make a determination of the suspected presence of malicious behaviour on the network based upon the analysis of the results of both the partial signature detection and the DNS monitoring.
Owner:BRITISH TELECOMM PLC
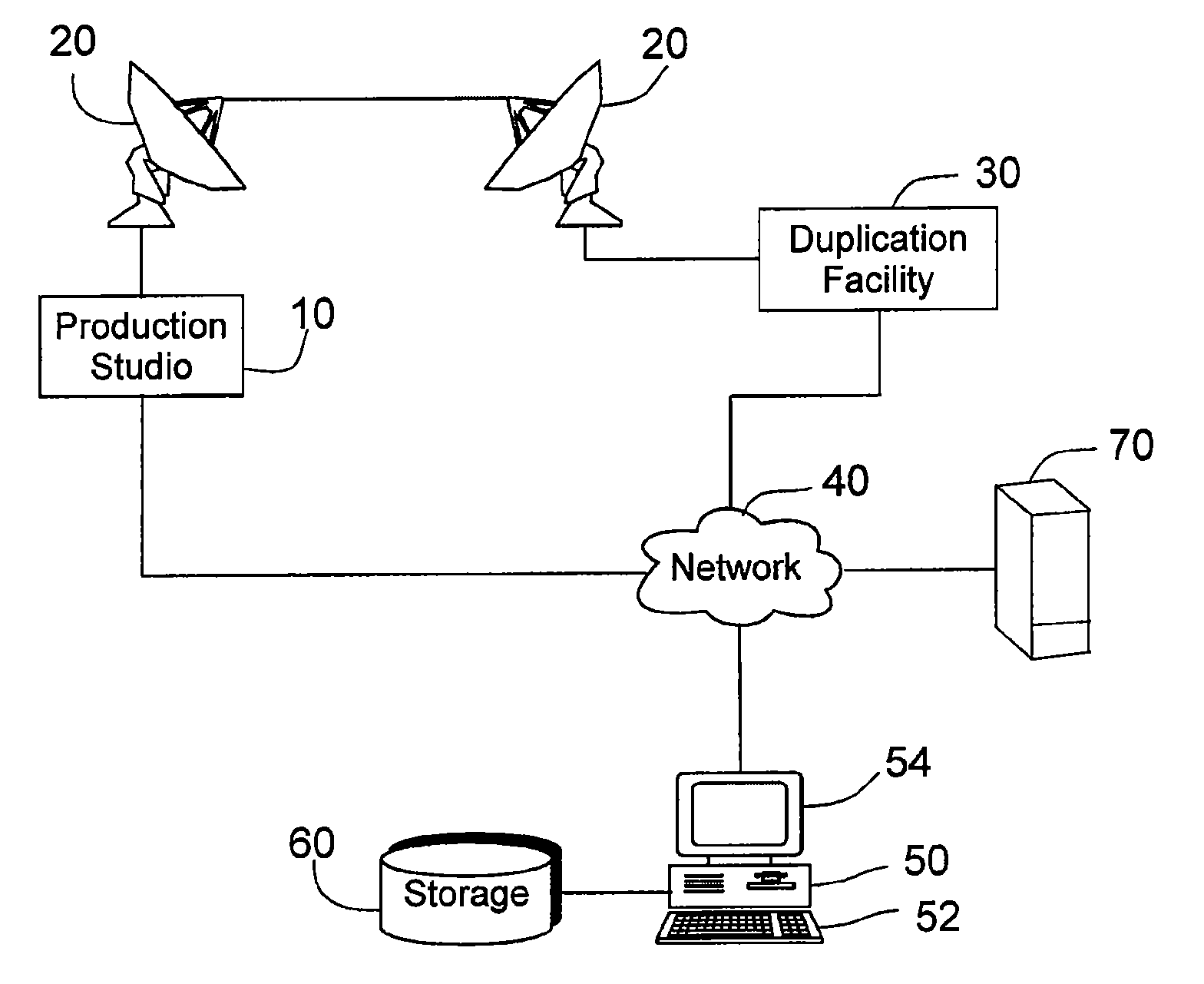
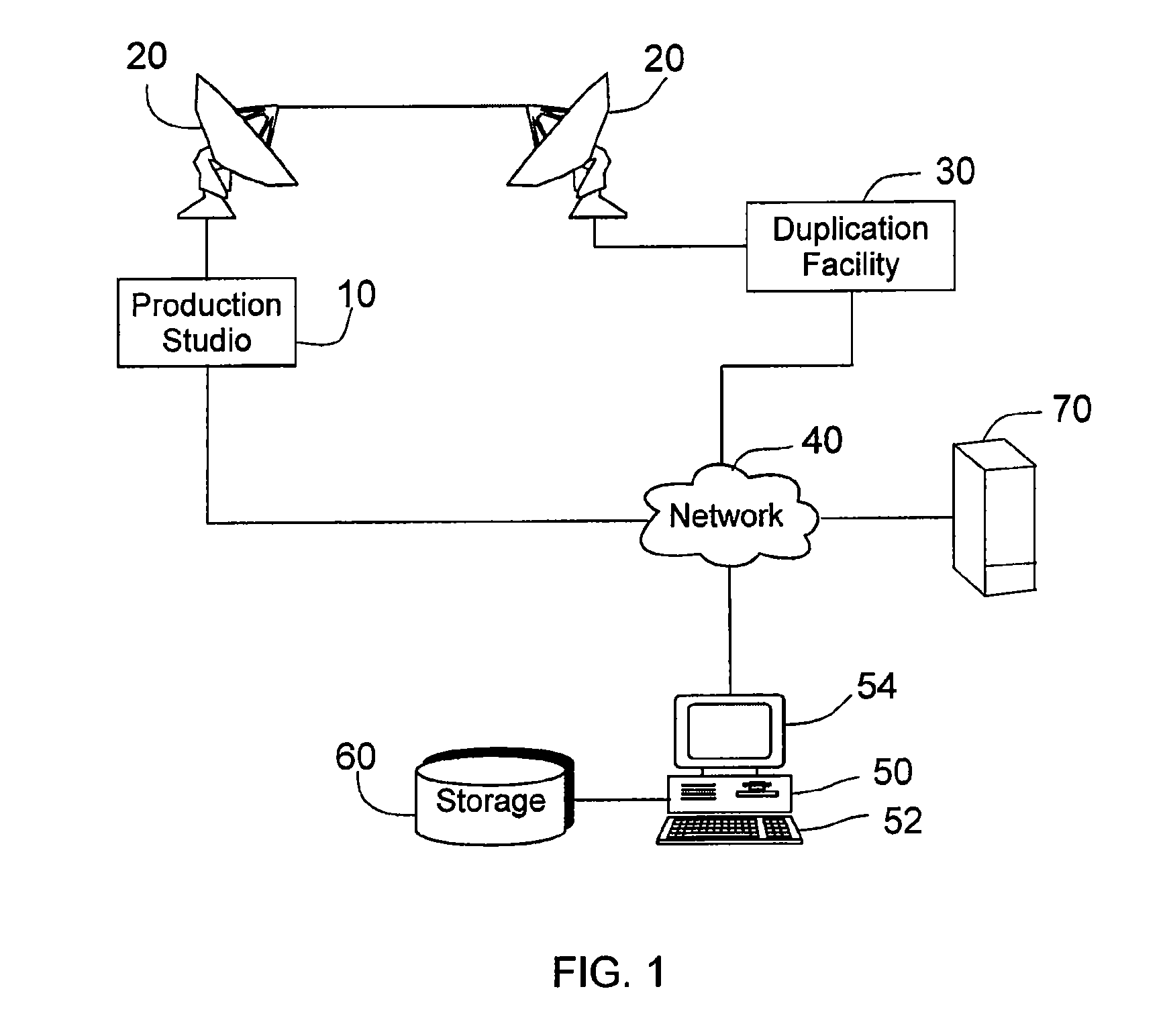
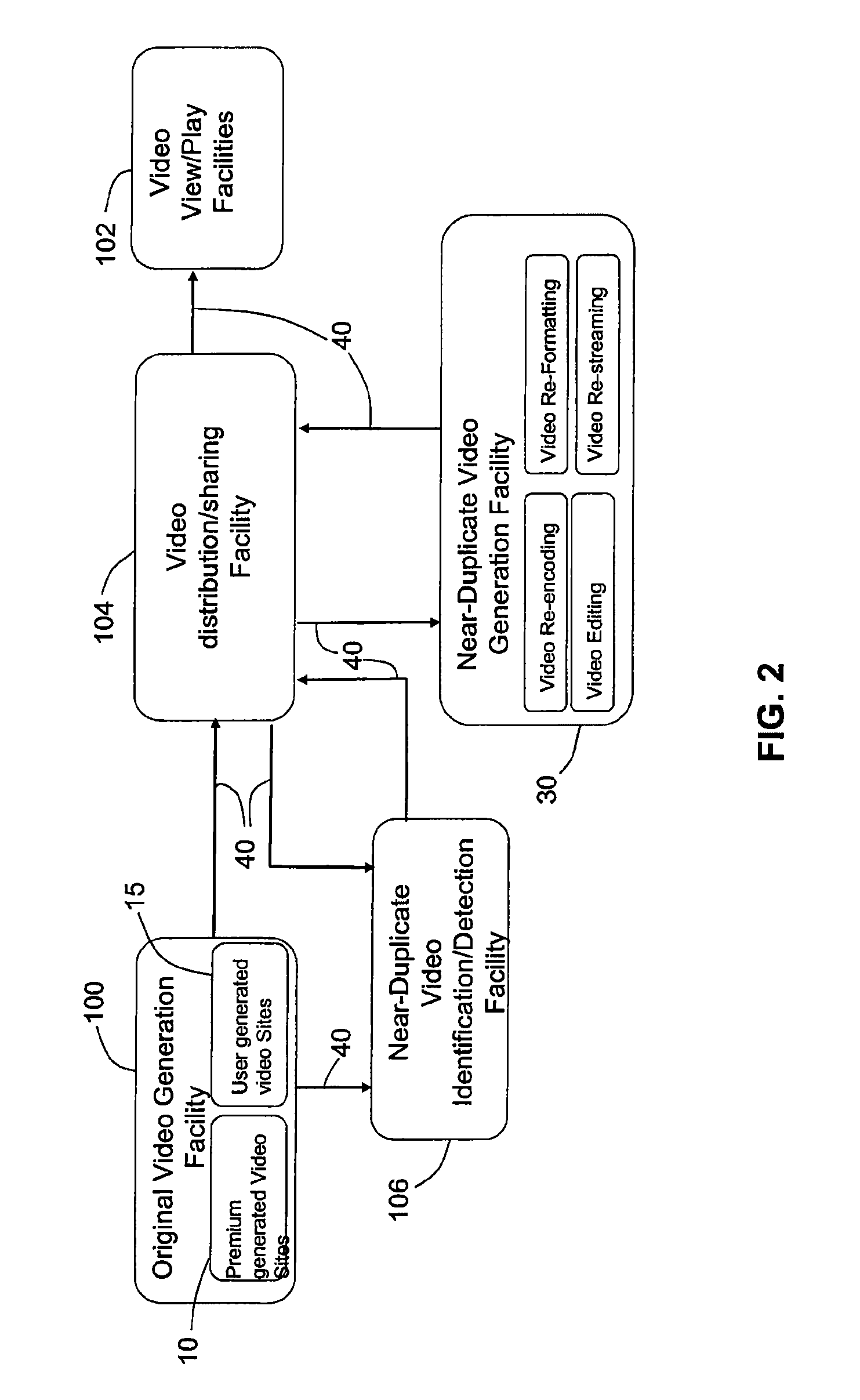
Method and apparatus for detecting near duplicate videos using perceptual video signatures
ActiveUS20110122255A1Television system detailsDigital data information retrievalThe InternetSignature detection
Methods and apparatus for detection and identification of duplicate or near-duplicate videos using a perceptual video signature are disclosed. The disclosed apparatus and methods (i) extract perceptual video features, (ii) identify unique and distinguishing perceptual features to generate a perceptual video signature, (iii) compute a perceptual video similarity measure based on the video edit distance, and (iv) search and detect duplicate and near-duplicate videos. A complete framework to detect unauthorized copying of videos on the Internet using the disclosed perceptual video signature is disclosed.
Owner:GOOGLE LLC
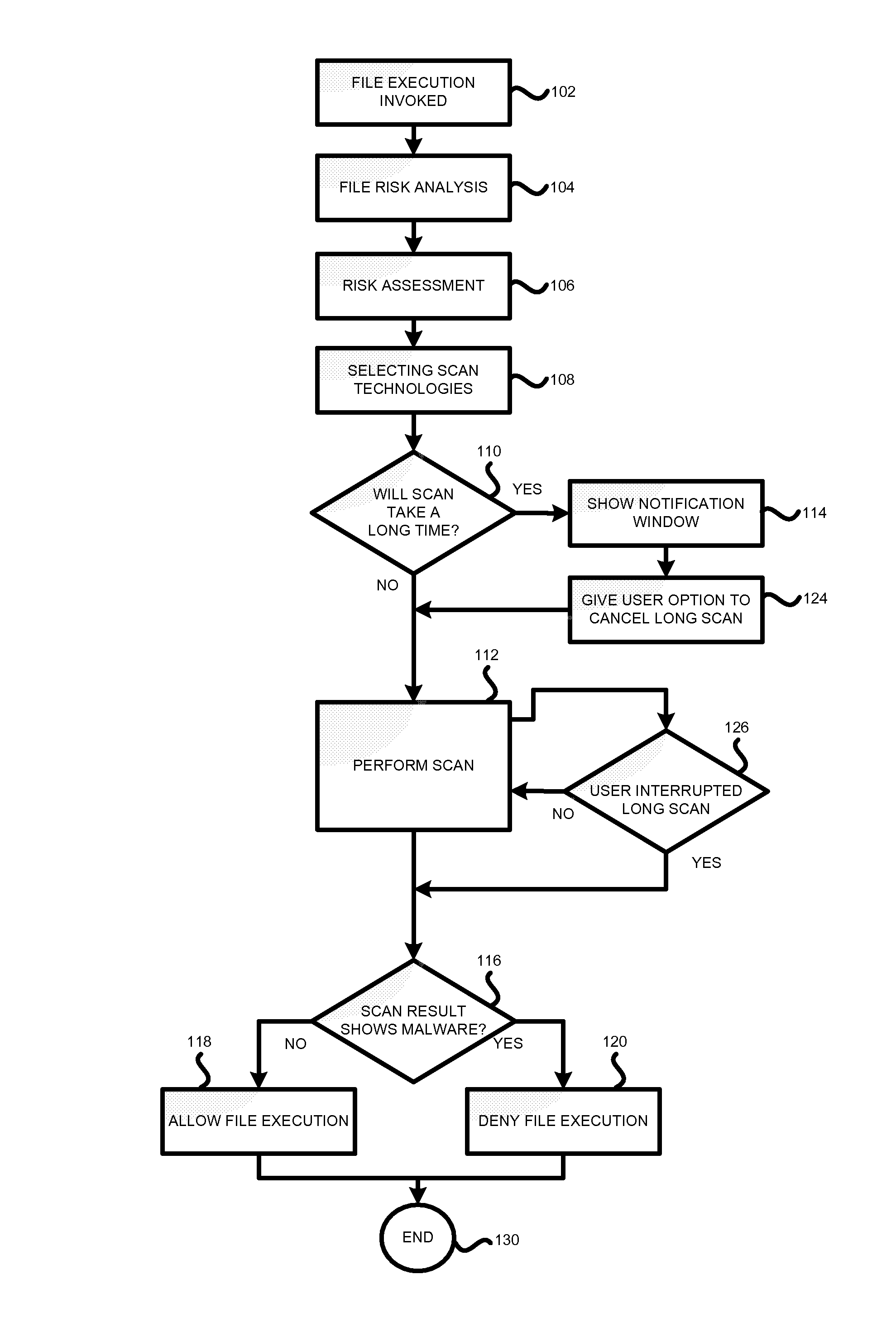
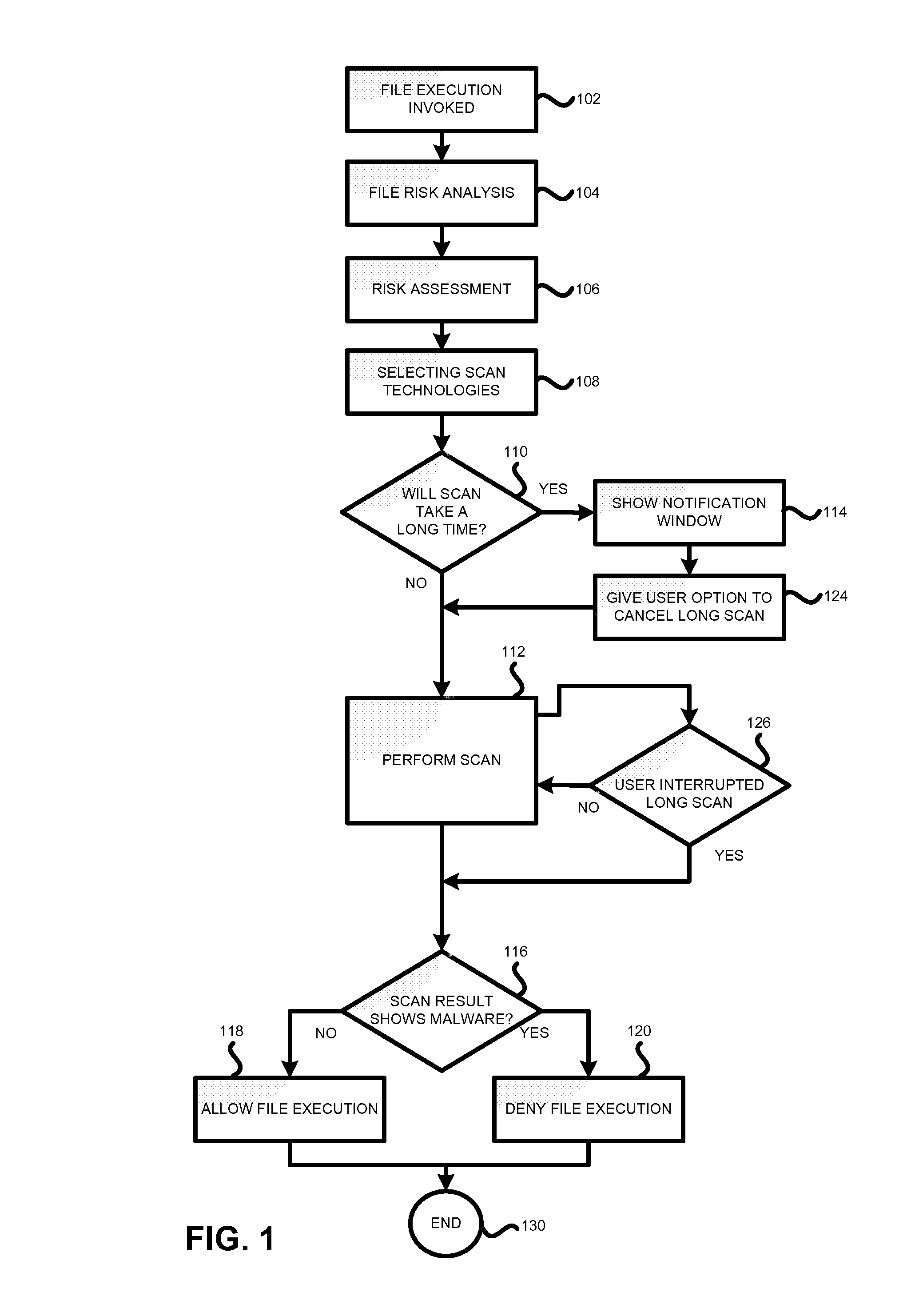
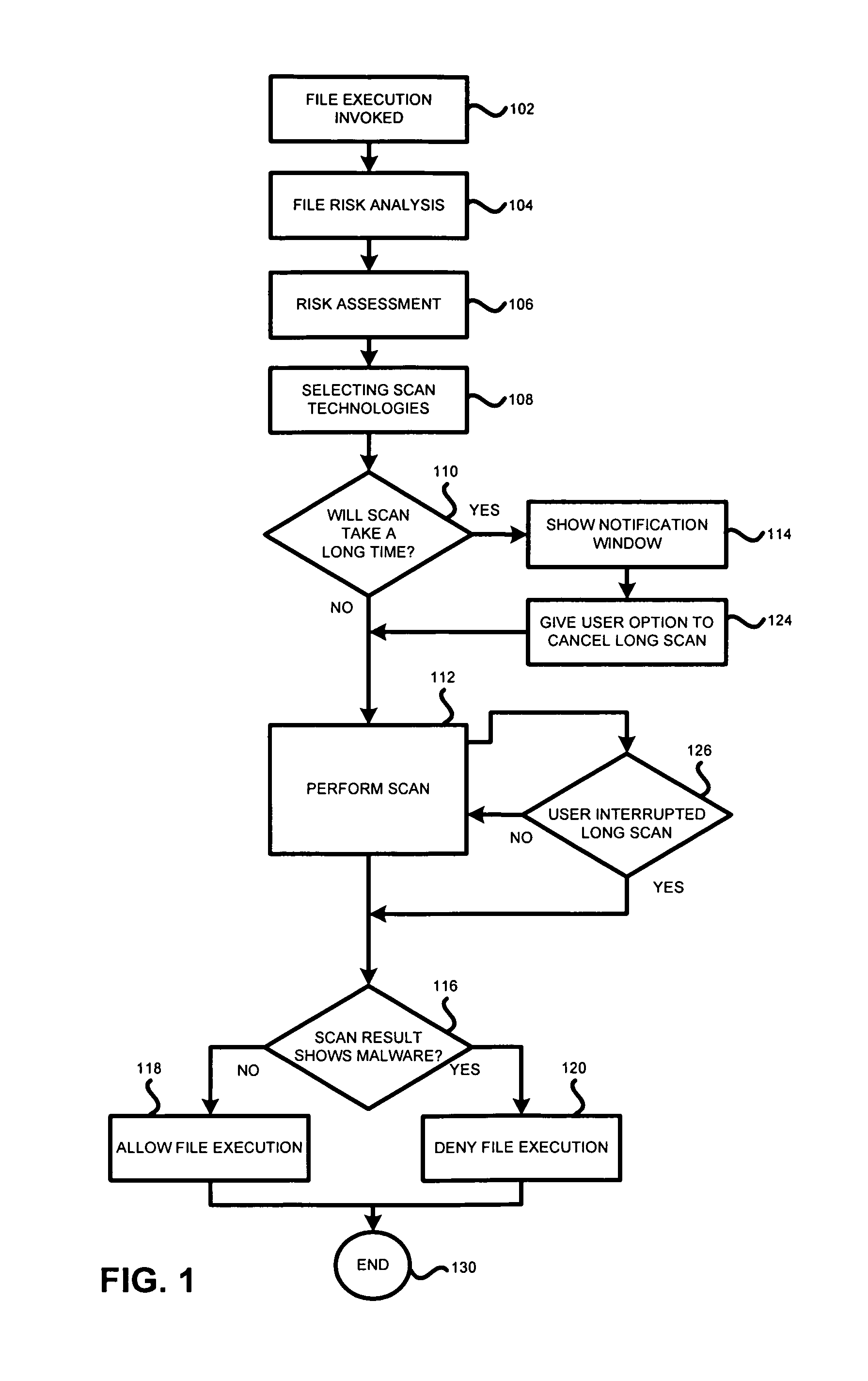
Method and system for anti-malware scanning with variable scan settings
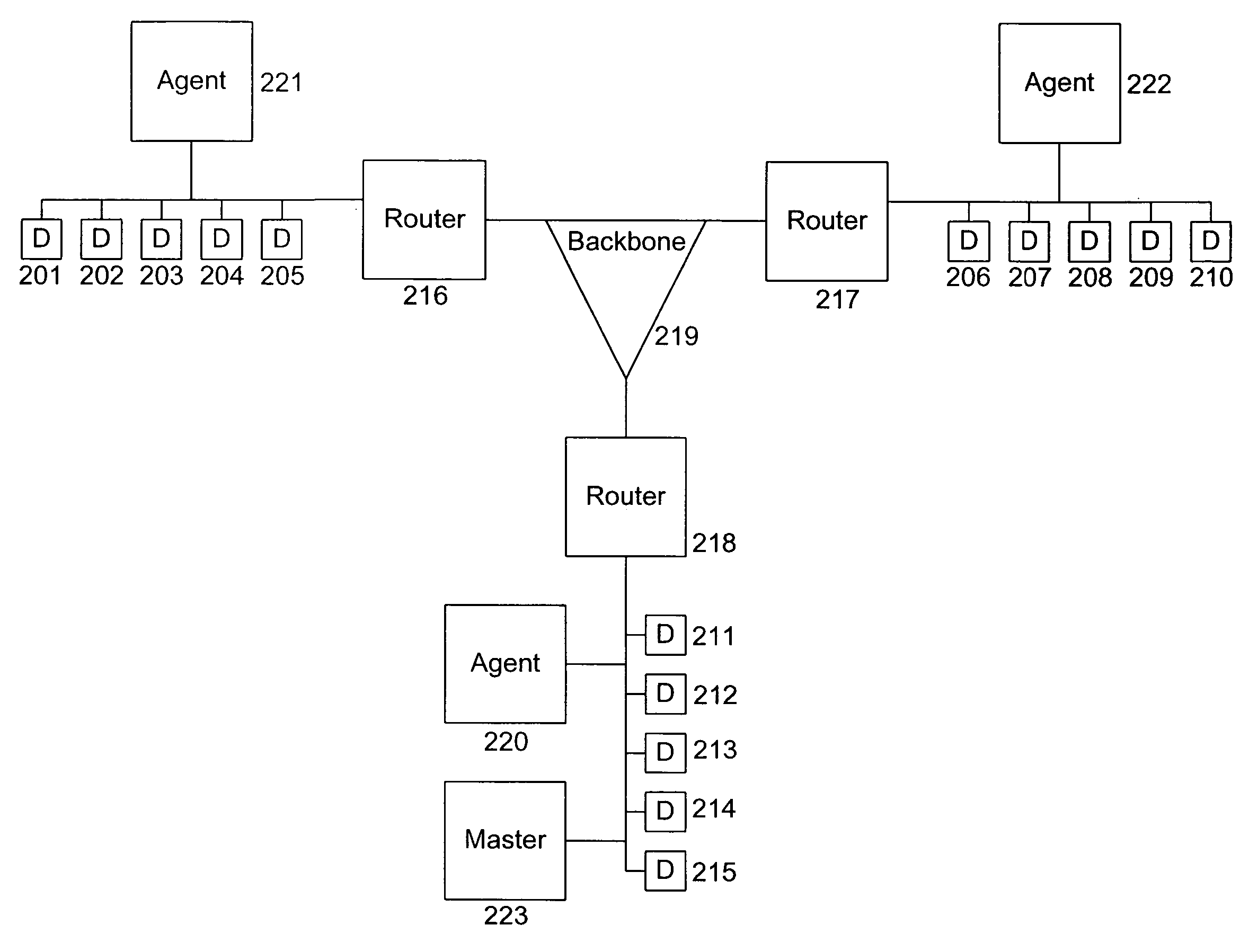
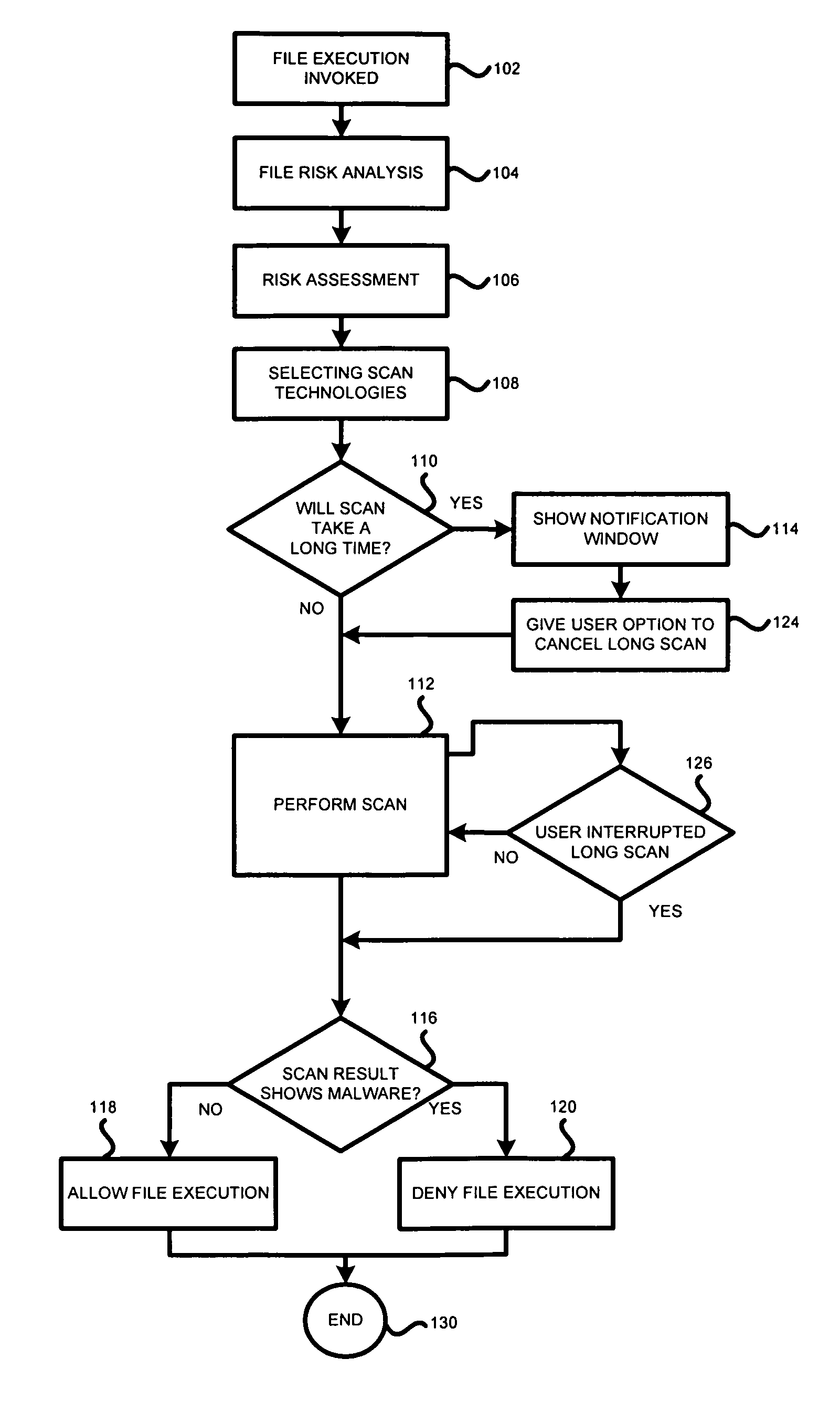
A system, method and computer program product for scanning an executable file for malware presence, the method comprising: (a) detecting an attempt to execute a file on a computer; (b) identifying whether the file is known or unknown; (c) if the file is a known file, performing a signature malware check; (d) if the file is an unknown file, performing risk analysis and risk assessment for the file; (e) based on the risk analysis and the risk assessment, identifying which malware detection algorithms need to be used for the file, in addition to signature detection; (f) performing the malware detection algorithms on the file; and (g) if no malware is detected, permitting execution of the file. The risk analysis is based on file source, file origin, file path, file size, whether the file is digitally signed, whether the file is a download utility, whether the file is packed, whether the file was received from a CDROM.
Owner:AO KASPERSKY LAB
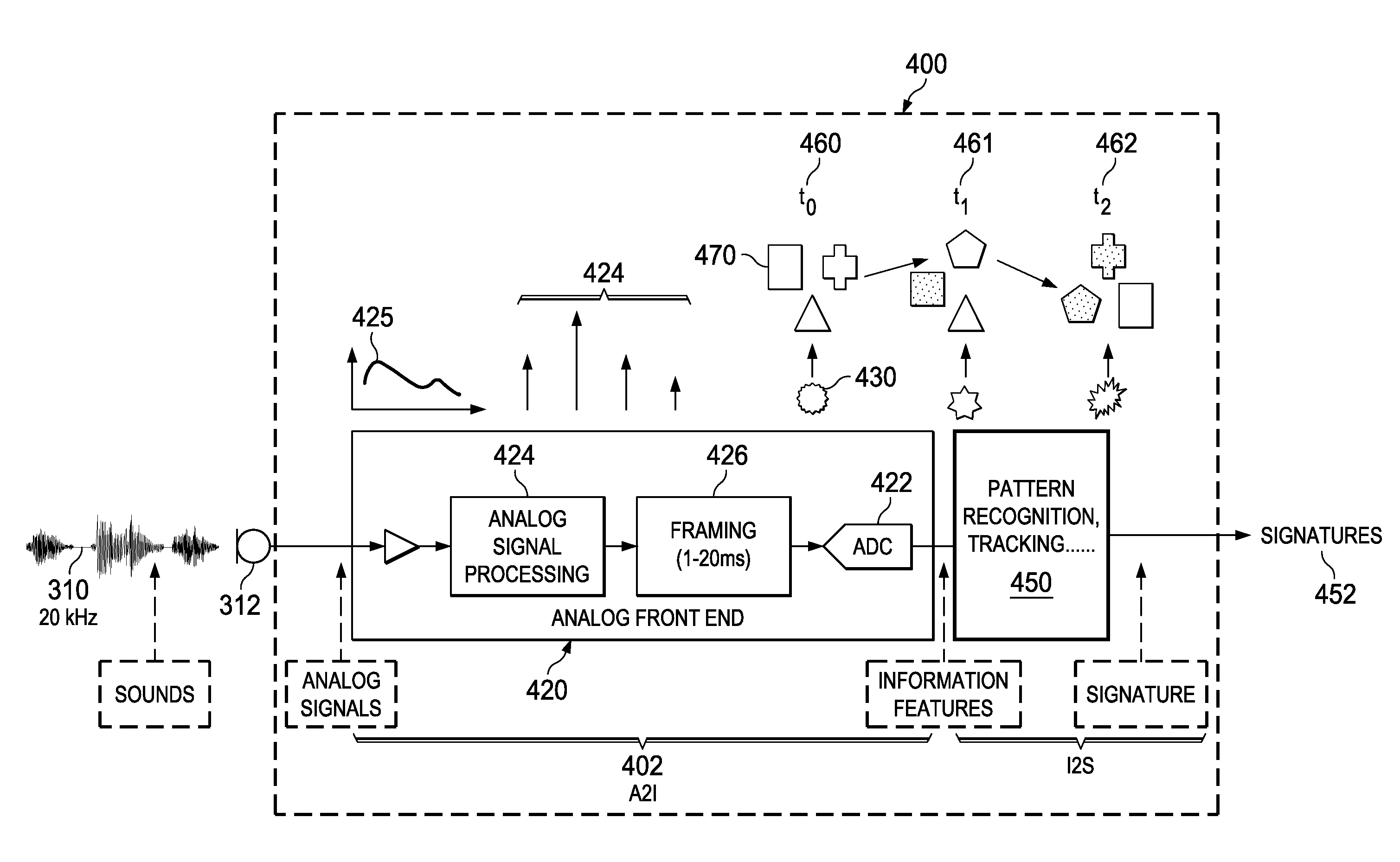
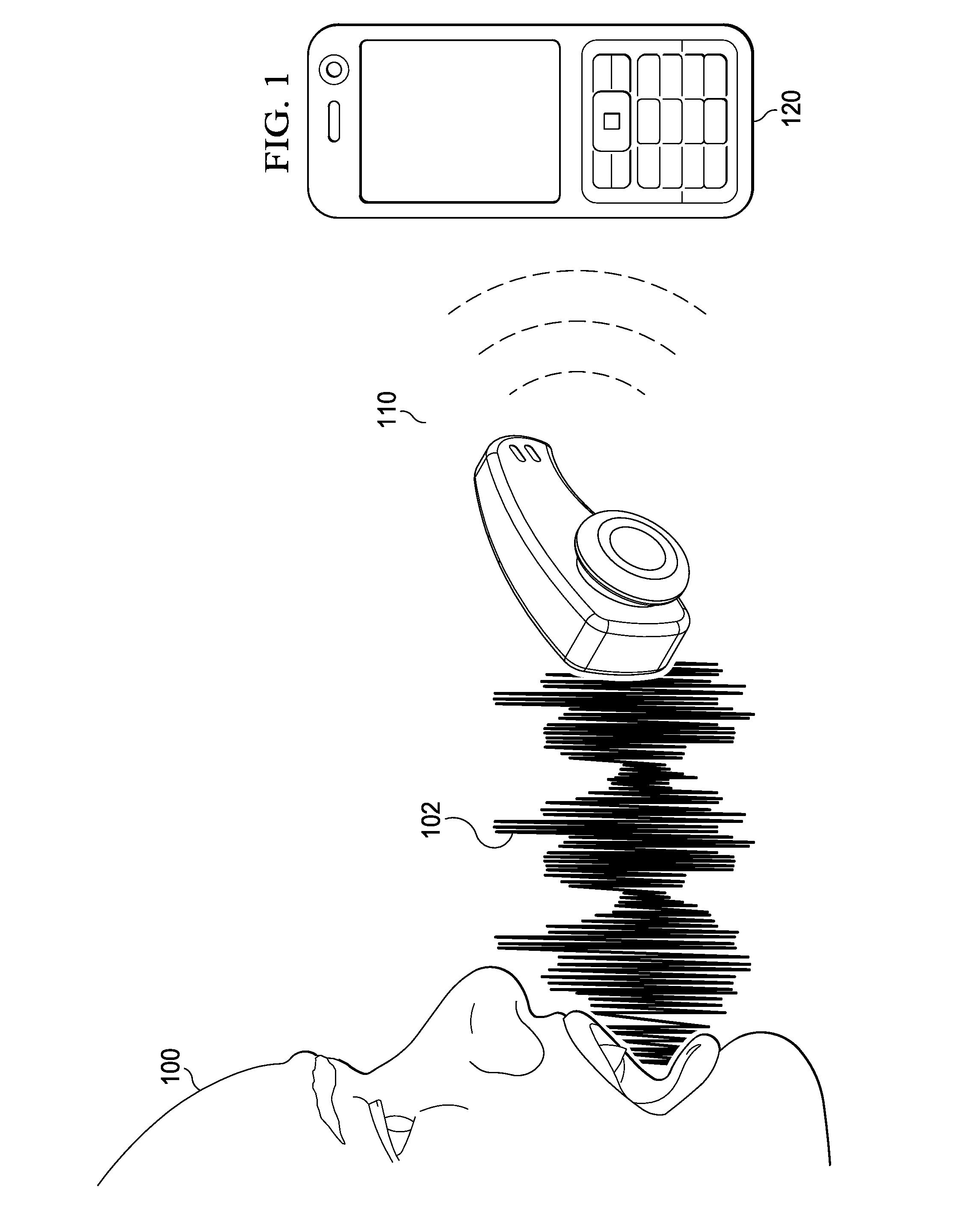
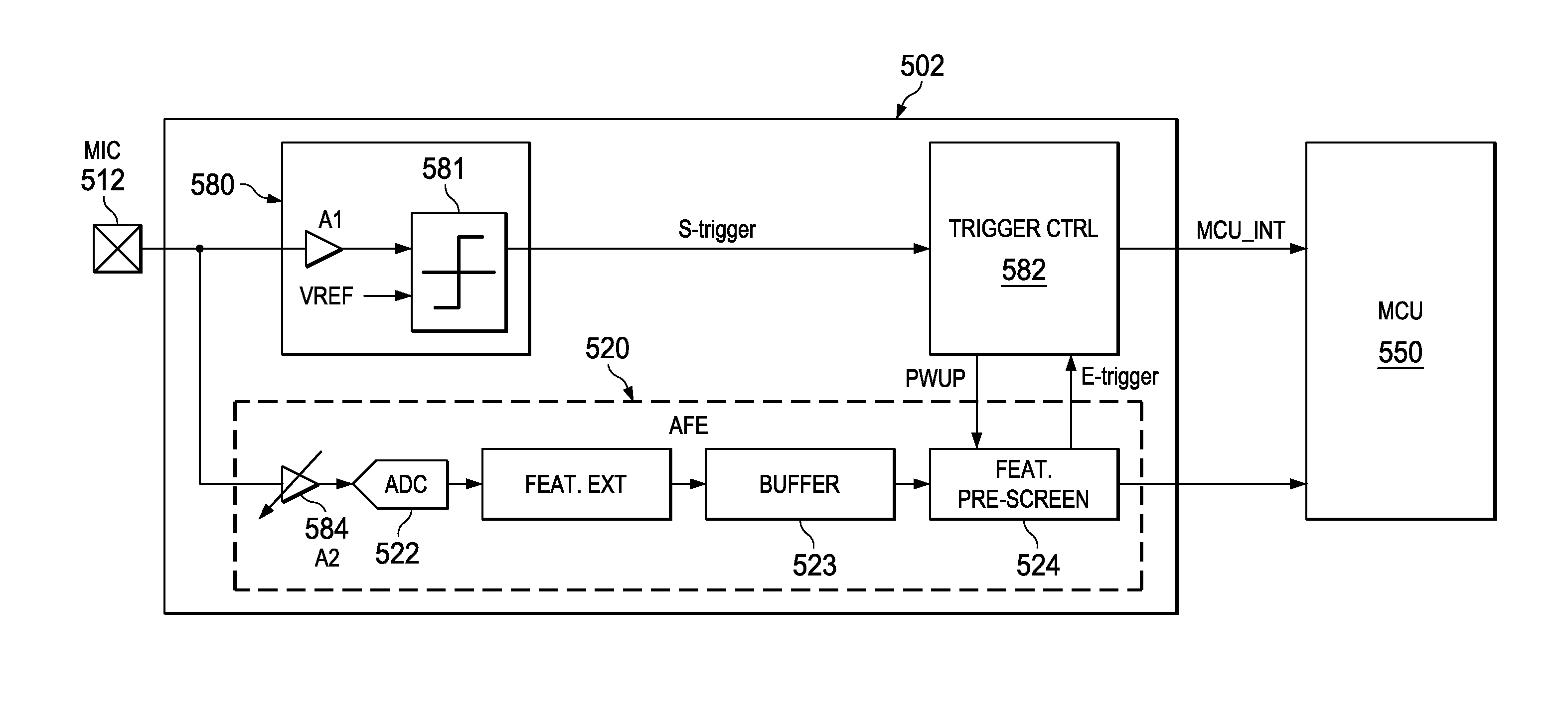
Acoustic Sound Signature Detection Based on Sparse Features
ActiveUS20150063575A1Digital data information retrievalElectrical apparatusSignature detectionAnalog signal
A low power sound recognition sensor is configured to receive an analog signal that may contain a signature sound. Sparse sound parameter information is extracted from the analog signal. The extracted sparse sound parameter information is processed using a sound signature database stored in the sound recognition sensor to identify sounds or speech contained in the analog signal, wherein the sound signature database comprises a plurality of sound signatures each representing an entire word or multiword phrase.
Owner:TEXAS INSTR INC
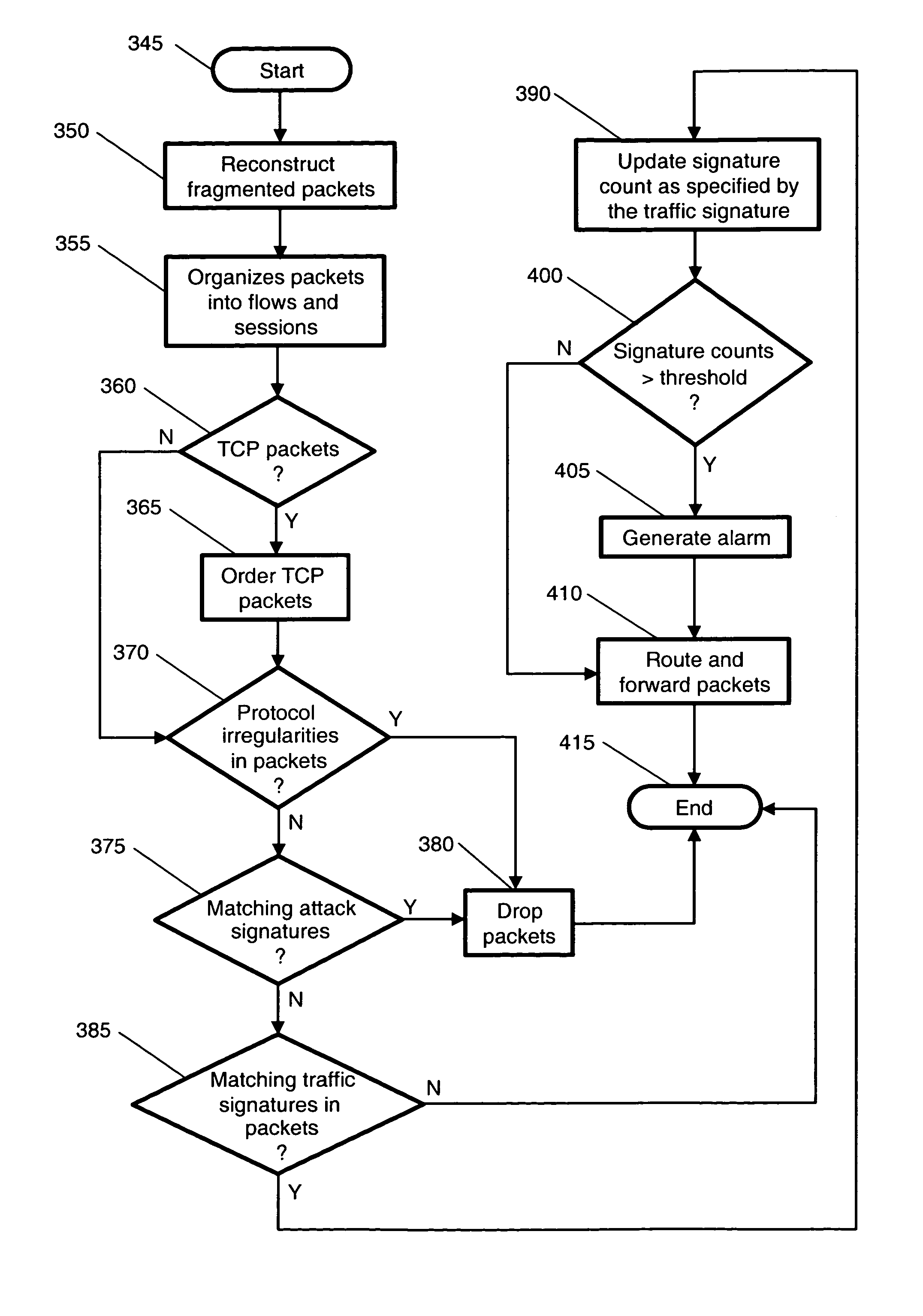
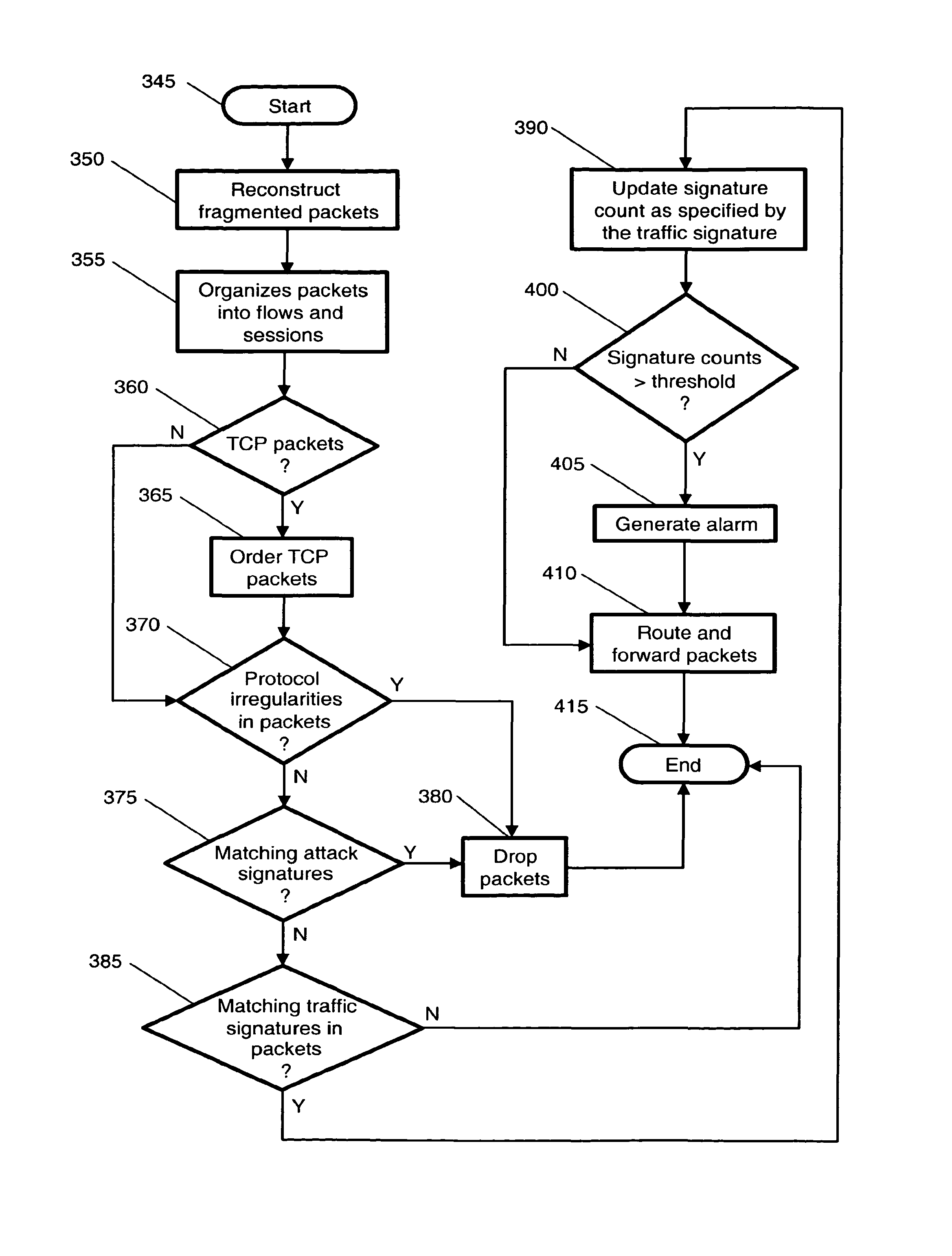
Multi-method gateway-based network security systems and methods
ActiveUS8370936B2Convenient and useful and cost-effective central managementSolve the high false alarm rateMemory loss protectionDigital data processing detailsTraffic capacityAnomaly detection
Systems and methods for detecting and preventing network security breaches are described. The systems and methods present a gateway-based packet-forwarding network security solution to not only detect security breaches but also prevent them by directly dropping suspicious packets and connections. The systems and methods employ multiple techniques to detect and prevent network security breaches, including stateful signature detection, traffic signature detection, and protocol anomaly detection.
Owner:JUMIPER NETWORKS INC
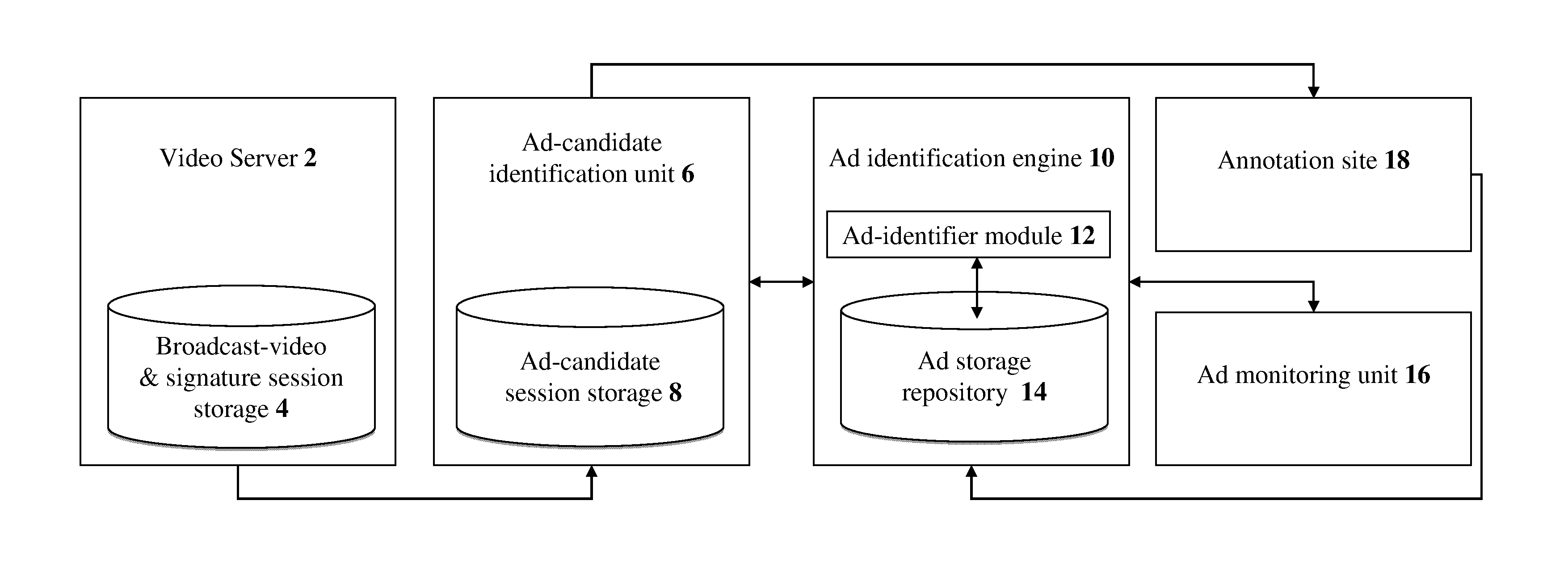
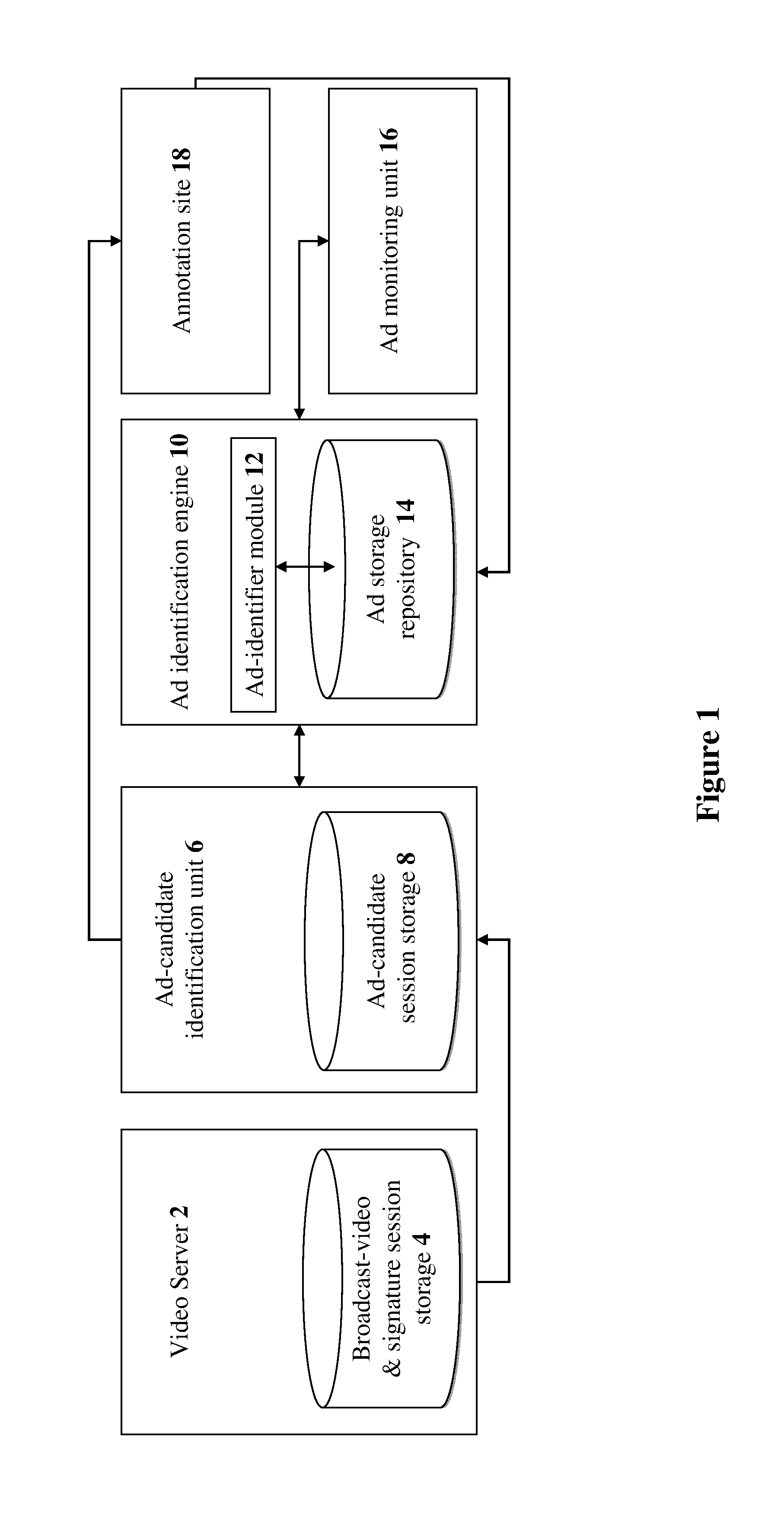
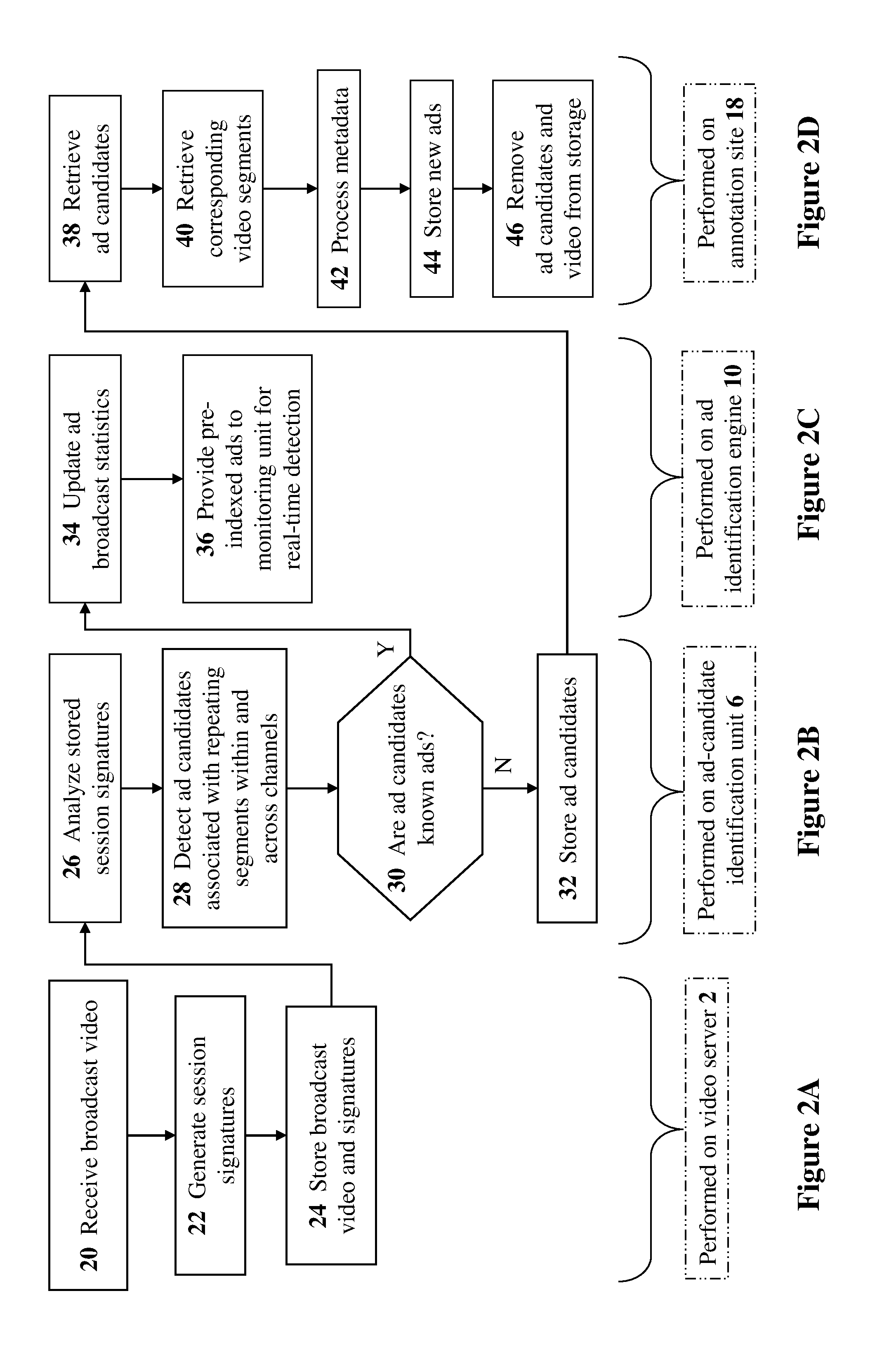
Methods and systems for providing broadcast ad identification
InactiveUS20140013352A1Enhanced B2BSelective content distributionElectrical cable transmission adaptationPattern recognitionSignature detection
The present invention discloses methods and systems for providing broadcast ad identification. Methods include the steps of: providing fingerprint signatures of each frame in a broadcast video; and designating at least two repeat fingerprint signatures upon detecting at least one fingerprint-signature match from the signatures. Preferably, methods further include: prior to the designating, determining whether the fingerprint signatures correspond to a known ad based upon detecting at least one fingerprint-signature match of the fingerprint signatures with pre-indexed fingerprint signatures of pre-indexed ads. Preferably, method further include: creating segments of the fingerprint signatures, ordered according to a timeline temporal proximity of the fingerprint signatures, by grouping at least two fingerprint signatures based on a repeat temporal proximity of at least two repeat fingerprint signatures respective of at least two fingerprint signatures. Preferably, methods further include detecting at least one ad candidate based on an occurrence of at least one repeat segment.
Owner:TVTAK
Intrusion detection with automatic signature generation
ActiveUS20050262560A1Memory loss protectionUser identity/authority verificationData packSignature detection
A method for detecting malicious programs within a computer network includes monitoring at least one first packet of data communicated over the network, analyzing the at least one first packet of data to detect the presence of a malicious program, generating a signature of the at least one first packet of data when a malicious program is detected, monitoring at least one second packet of data communicated over the network and detecting evidence of the malicious program in the at least one second packet of data utilizing the generated signature.
Owner:GOOGLE LLC
Method and system for antimalware scanning with variable scan settings
ActiveUS7725941B1Memory loss protectionUnauthorized memory use protectionDigital signatureSignature detection
A system, method and computer program product for scanning an executable file for malware presence, the method comprising: (a) detecting an attempt to execute a file on a computer; (b) identifying whether the file is known or unknown; (c) if the file is a known file, performing a signature malware check; (d) if the file is an unknown file, performing risk analysis and risk assessment for the file; (e) based on the risk analysis and the risk assessment, identifying which malware detection algorithms need to be used for the file, in addition to signature detection; (f) performing the malware detection algorithms on the file; and (g) if no malware is detected, permitting execution of the file. The risk analysis is based on file source, file origin, file path, file size, whether the file is digitally signed, whether the file is a download utility, whether the file is packed, whether the file was received from a CDROM.
Owner:AO KASPERSKY LAB
Analog to Information Sound Signature Detection
ActiveUS20150066498A1Position data use in hearing devicesSignal processingFeature extractionAnalog signal
A low power sound recognition sensor is configured to receive an analog signal that may contain a signature sound. The received analog signal is evaluated using a detection portion of the analog section to determine when background noise on the analog signal is exceeded. A feature extraction portion of the analog section is triggered to extract sparse sound parameter information from the analog signal when the background noise is exceeded. An initial truncated portion of the sound parameter information is compared to a truncated sound parameter database stored locally with the sound recognition sensor to detect when there is a likelihood that the expected sound is being received in the analog signal. A trigger signal is generated to trigger classification logic when the likelihood that the expected sound is being received exceeds a threshold value.
Owner:TEXAS INSTR INC
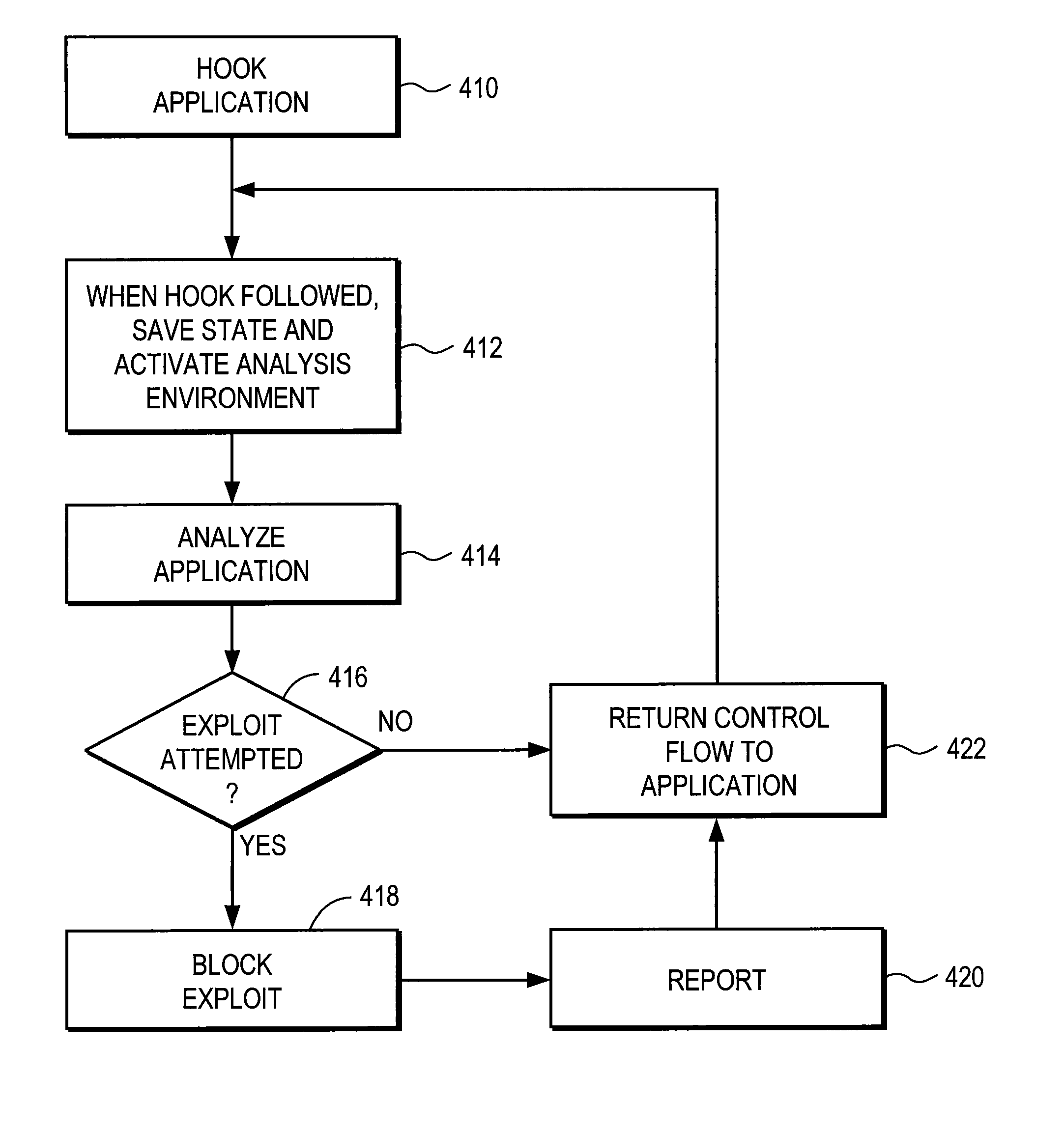
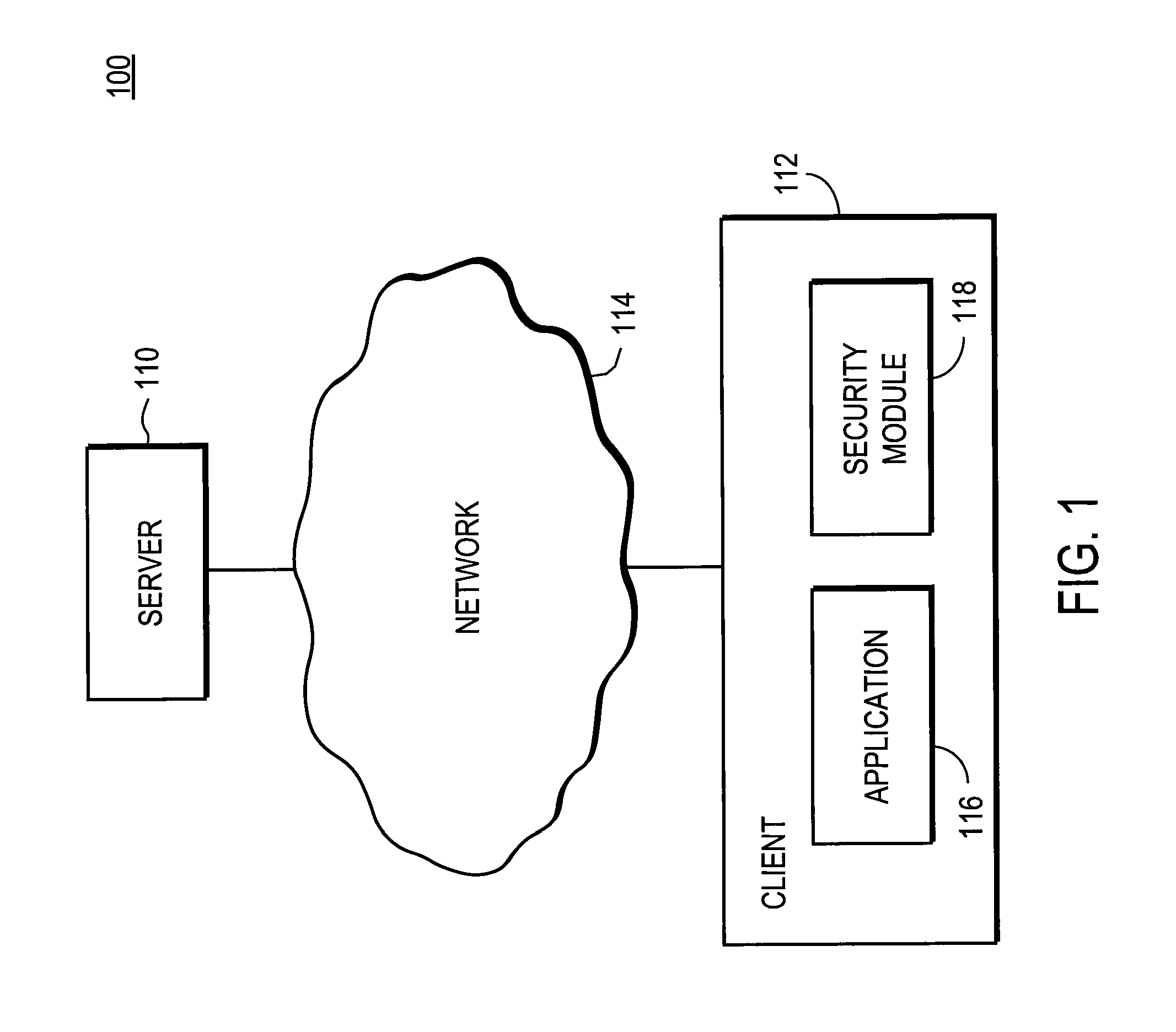
Control flow redirection and analysis for detecting vulnerability exploitation
A security module detects attempted exploitations of vulnerabilities of applications executing on a computer. The security module hooks an application on the computer. The hook transfers control flow to the security module if execution reaches a hooked location. When a hook is followed, the security module saves the state of the computer and activates an analysis environment. A virtual machine within the analysis environment executes signatures that programmatically analyze the state of the computer to determine whether a vulnerability in the application is being exploited. If a signature detects an exploit, the security module blocks the exploit by skipping over the one or more instructions that constitute the exploit, terminating the application, or performing a different action. The security module reports the detected exploit attempt to the user of the client. The security module returns control flow back to the application if it does not detect an exploit.
Owner:CA TECH INC
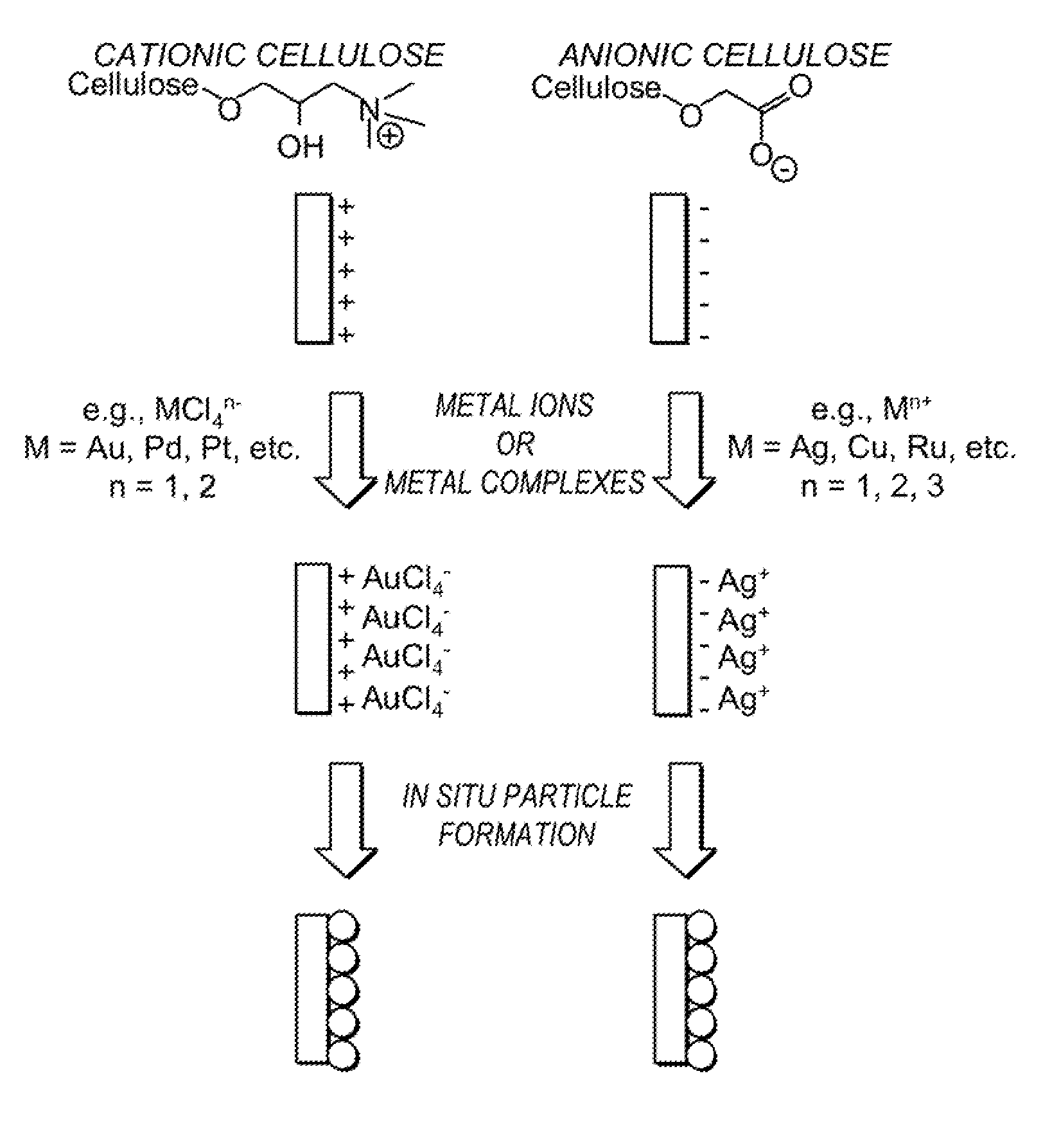
Conformal particle coatings on fiber materials for use in spectroscopic methods for detecting targets of interest and methods based thereon
InactiveUS20120058697A1Good spectral characteristicsMaterial nanotechnologyLayered productsTextile fiberFluorescence
Textile fibers and other fibrous substrates functionalized with particles are provided for use in the detection of targets of interest by spectroscopic methods. In one embodiment, a substrate is provided that comprises a conformal coating on its surface, wherein the coating comprises a plurality of chemically functional particles that are spectroscopically enhancing. Methods for producing such functionalized textile fibers are also provided. These textiles can be used as platforms for spectroscopic detection, including surface-enhanced Raman scattering (SERS), surface-enhanced infrared absorption (SEIRA), and surface-enhanced fluorescence (SEF). Functionalized textile fibers for use in the signature detection methods are produced by performing layer-by-layer self-assembly of particles on natural and synthetic textile substrates.
Owner:CORNELL UNIVERSITY
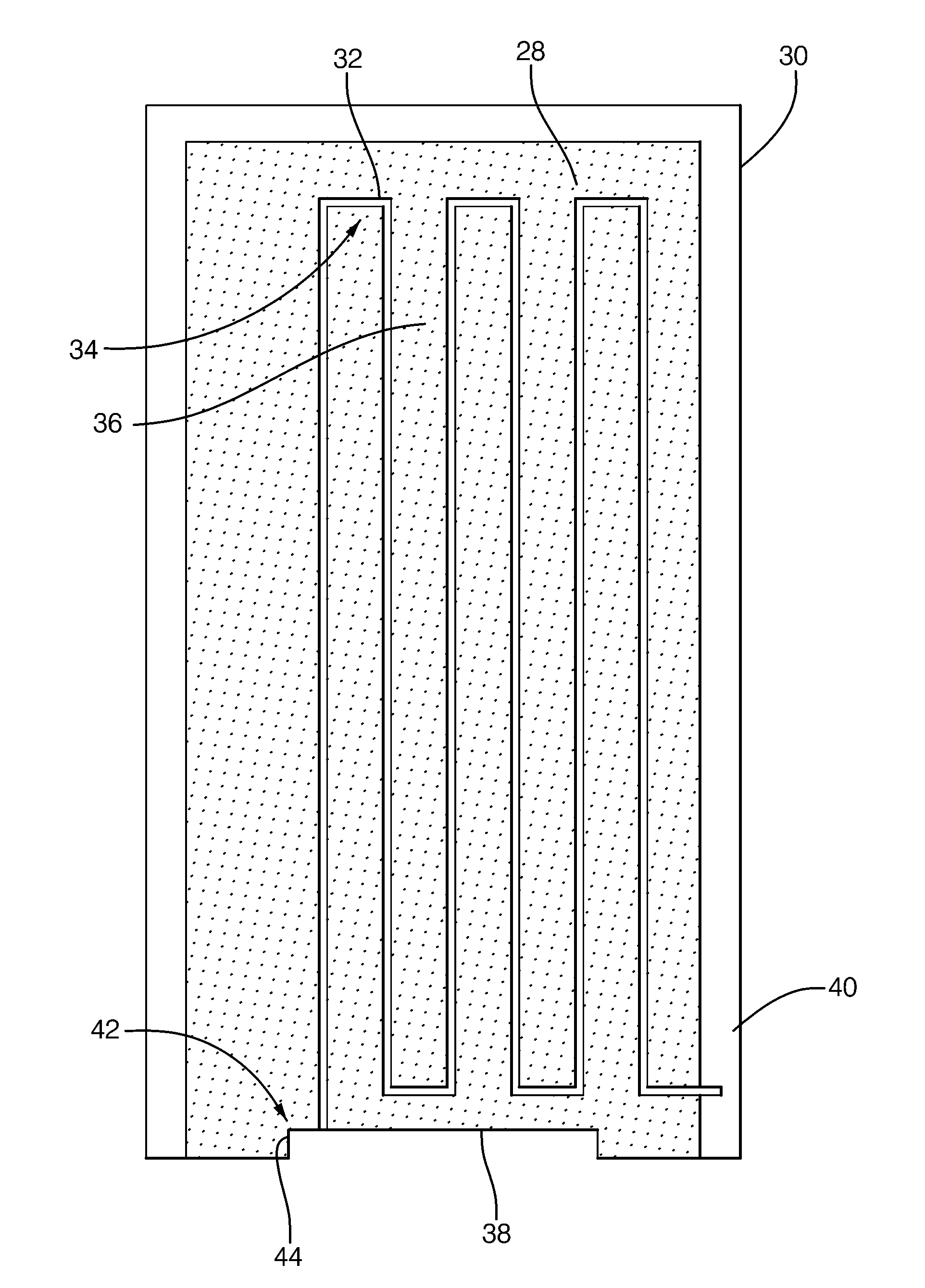
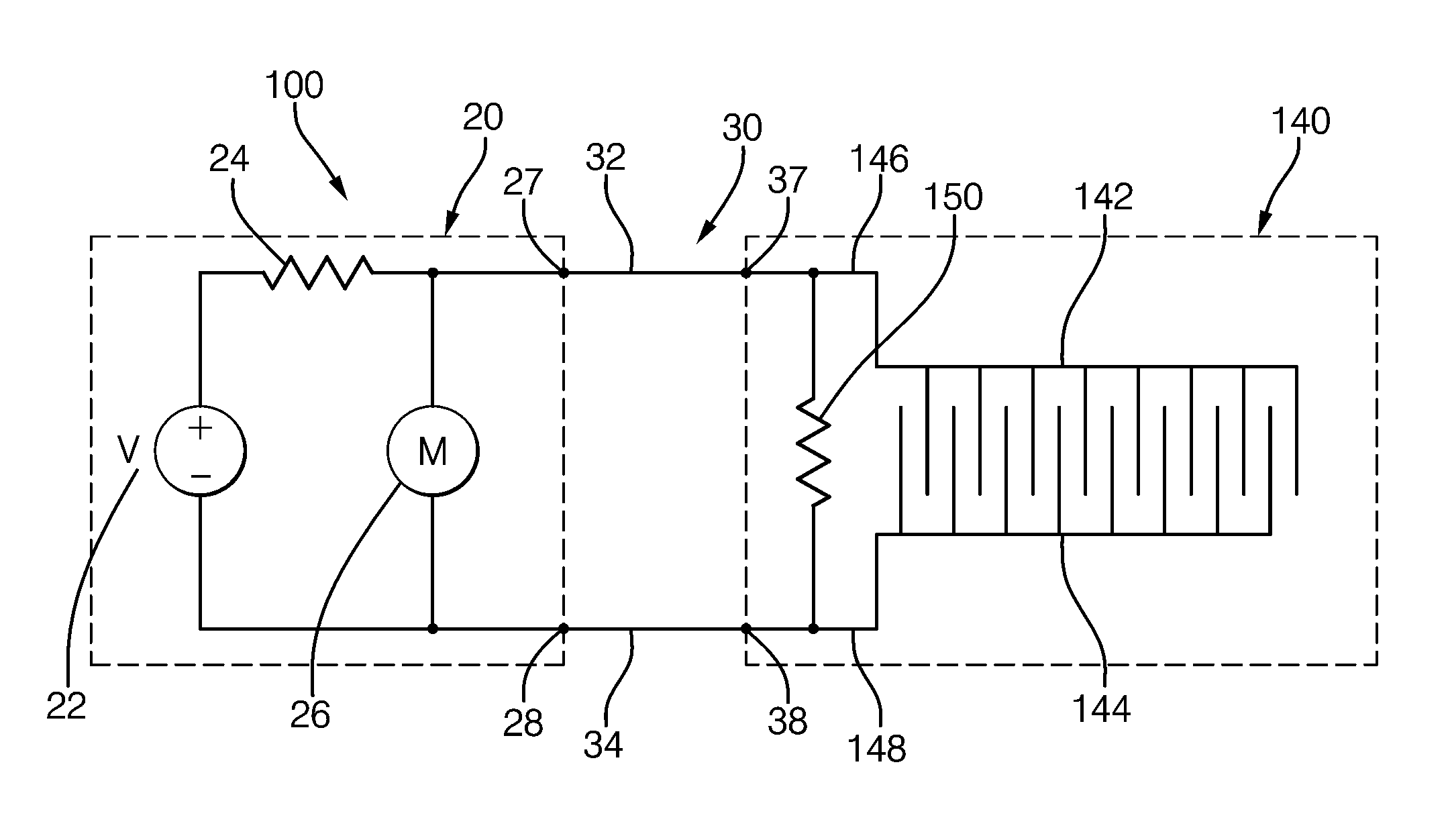
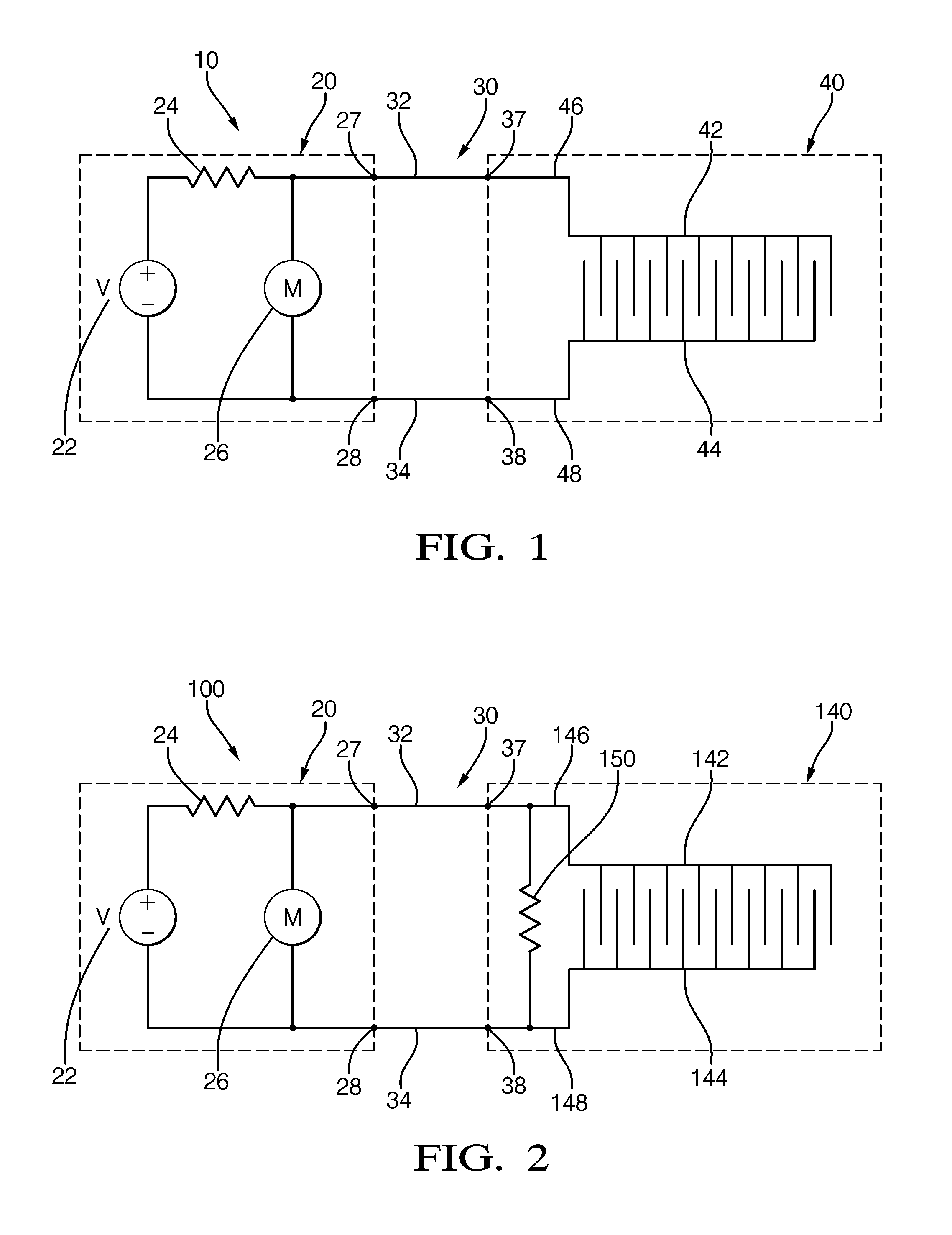
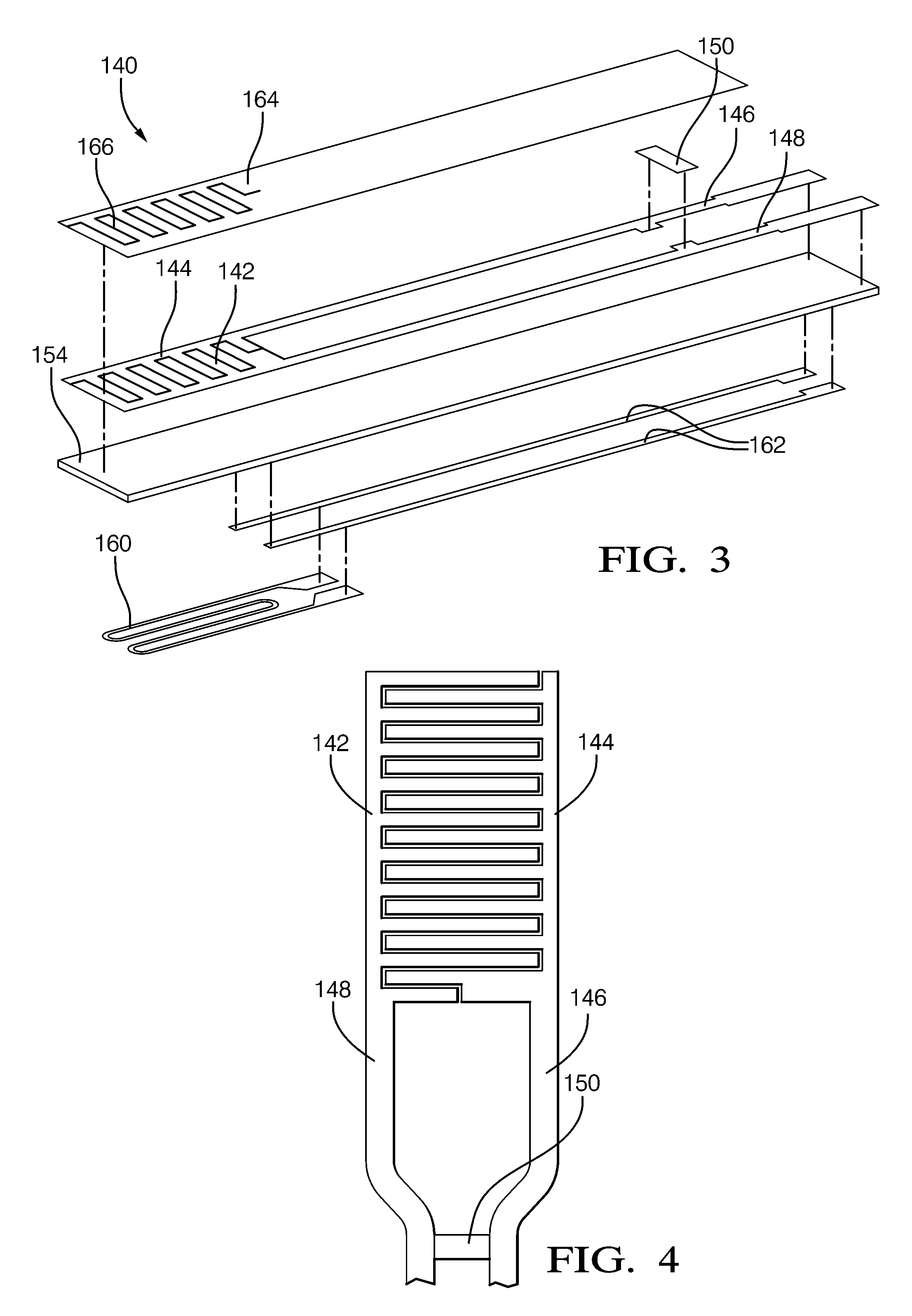
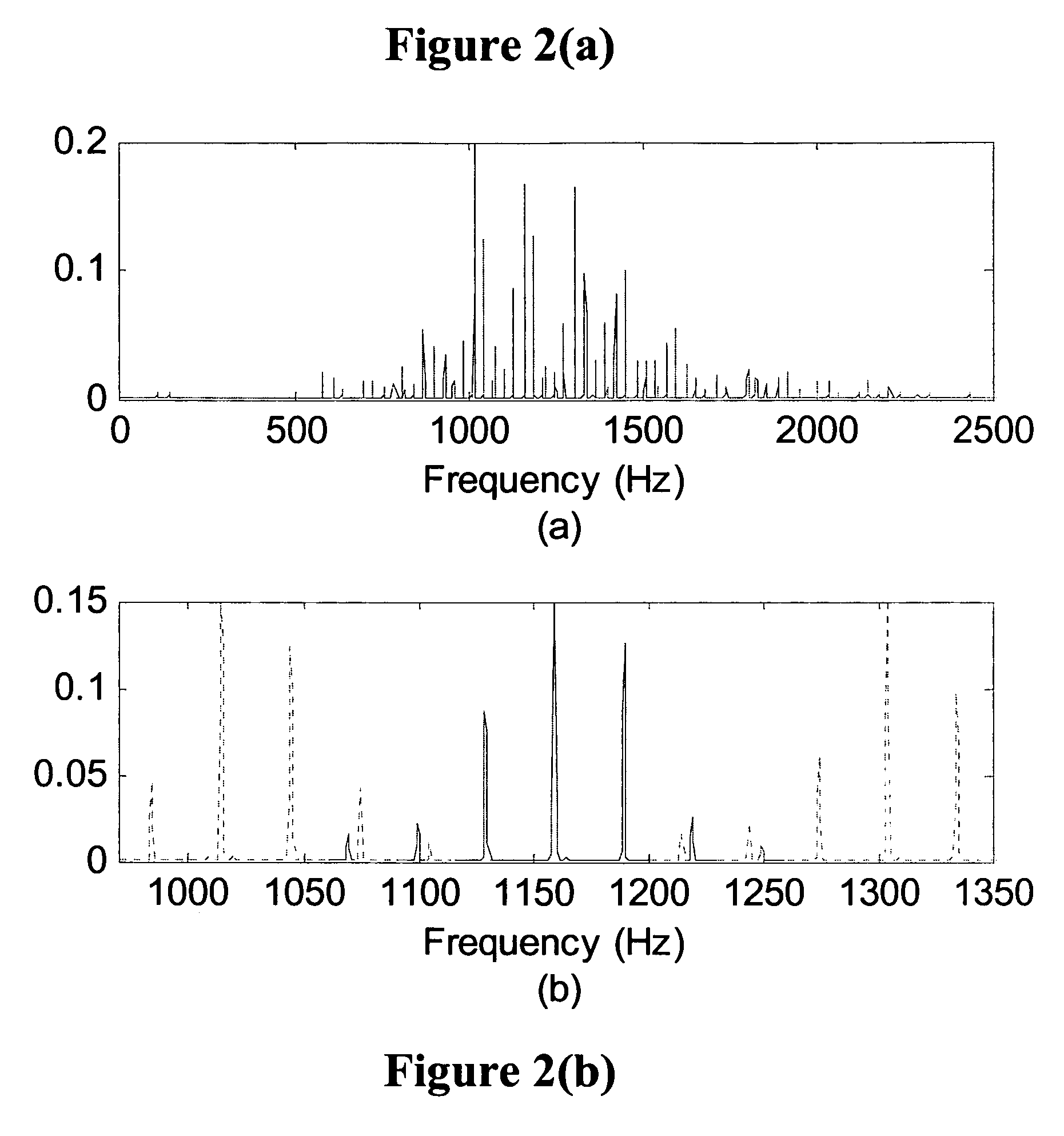
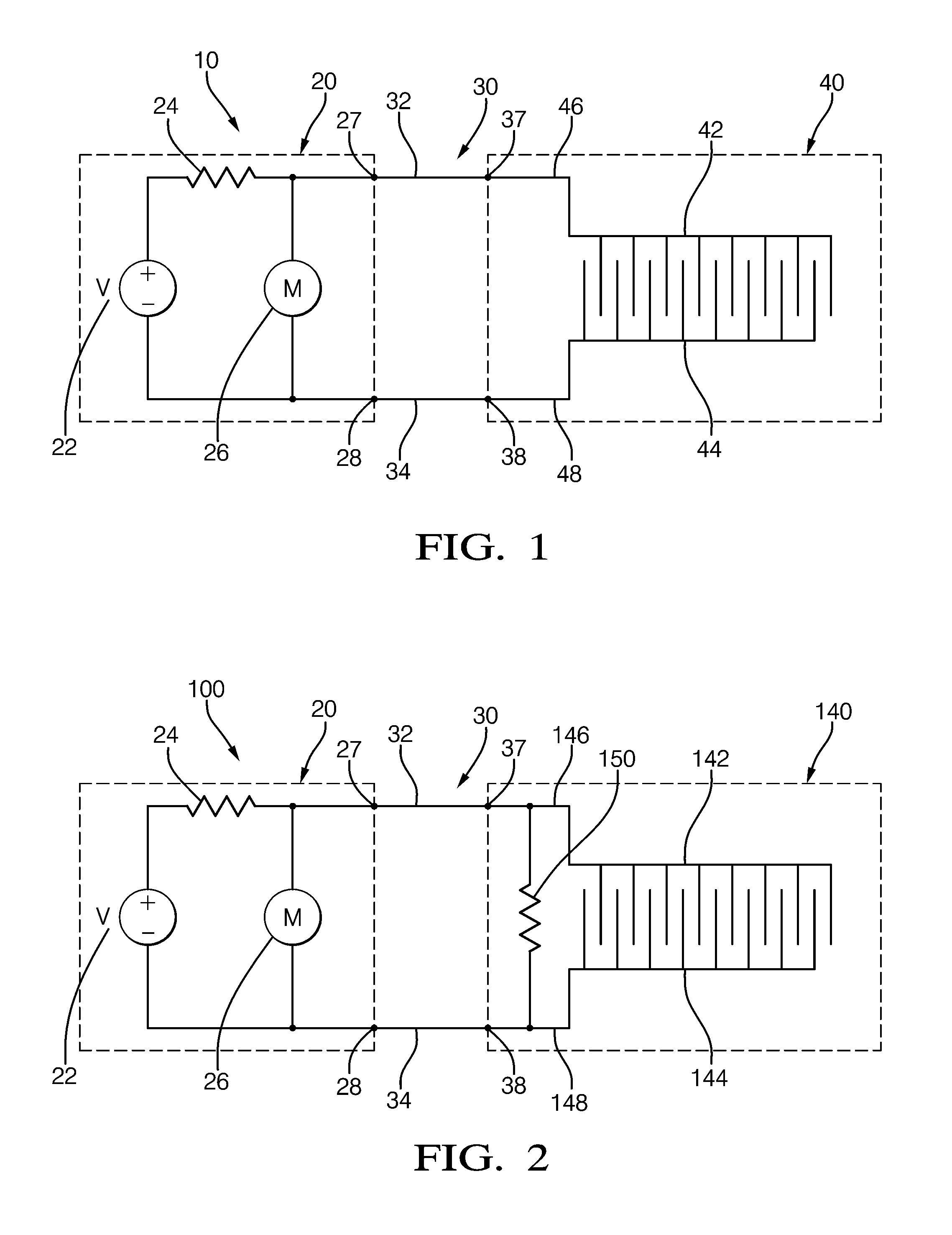
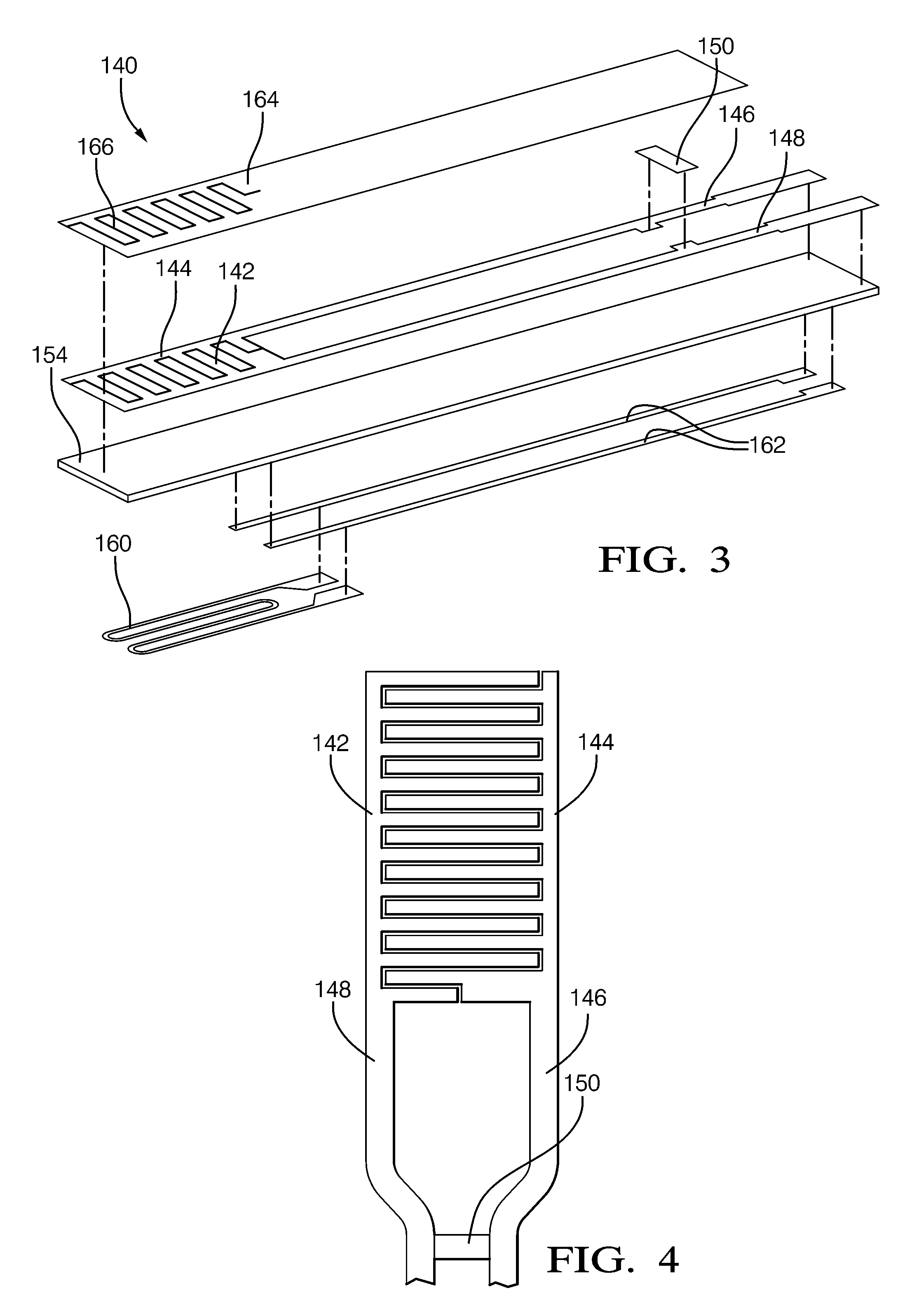
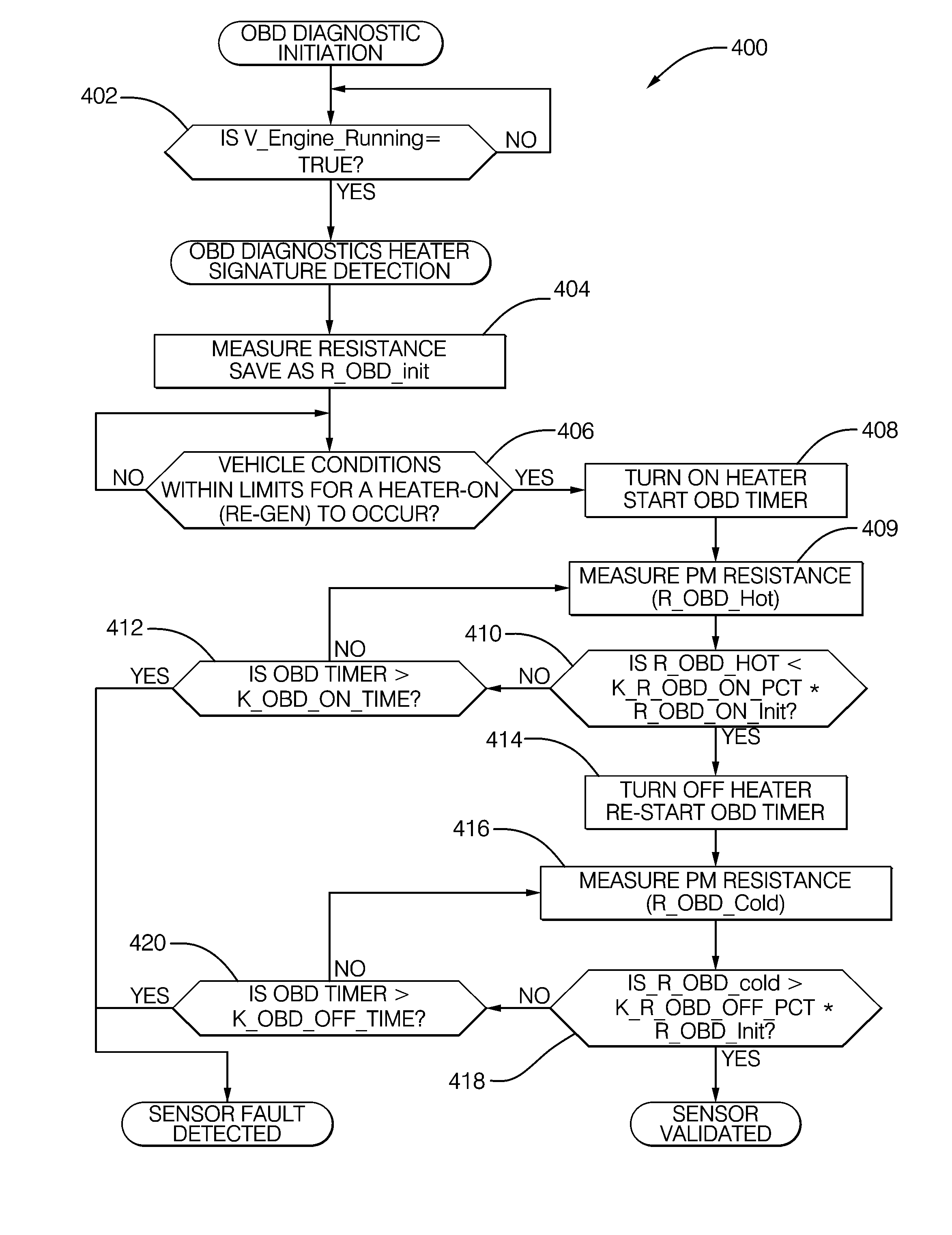
Method and System for Heater Signature Detection Diagnostics of a Particulate Matter Sensor
ActiveUS20110109331A1Electrical controlResistance/reactance/impedenceParticulatesElectrical resistance and conductance
A diagnostic method and system is described for diagnosing an operating condition of a conductive particulate matter sensor. The sensor has a substrate with electrical resistance that varies with temperature and two electrodes on the substrate adapted to collect particulate matter between the electrodes, thereby establishing an electrically conductive path through collected particulate matter between the electrodes that can be detected by measuring electrical resistance between the electrodes, Relect. The diagnosis is performed by heating the substrate in the area between the electrodes and detecting whether resistance varies with temperature as expected, and then cooling the substrate back down and detecting whether resistance varies with temperature as expected. If resistance varies as expected during both heating and cooling, then a validation is diagnosed that the sensor is in proper operating condition if resistance increases in a manner consistent with evaporation of condensate. If resistance does not vary as expected, then a failure condition is diagnosed.
Owner:DELPHI TECH IP LTD
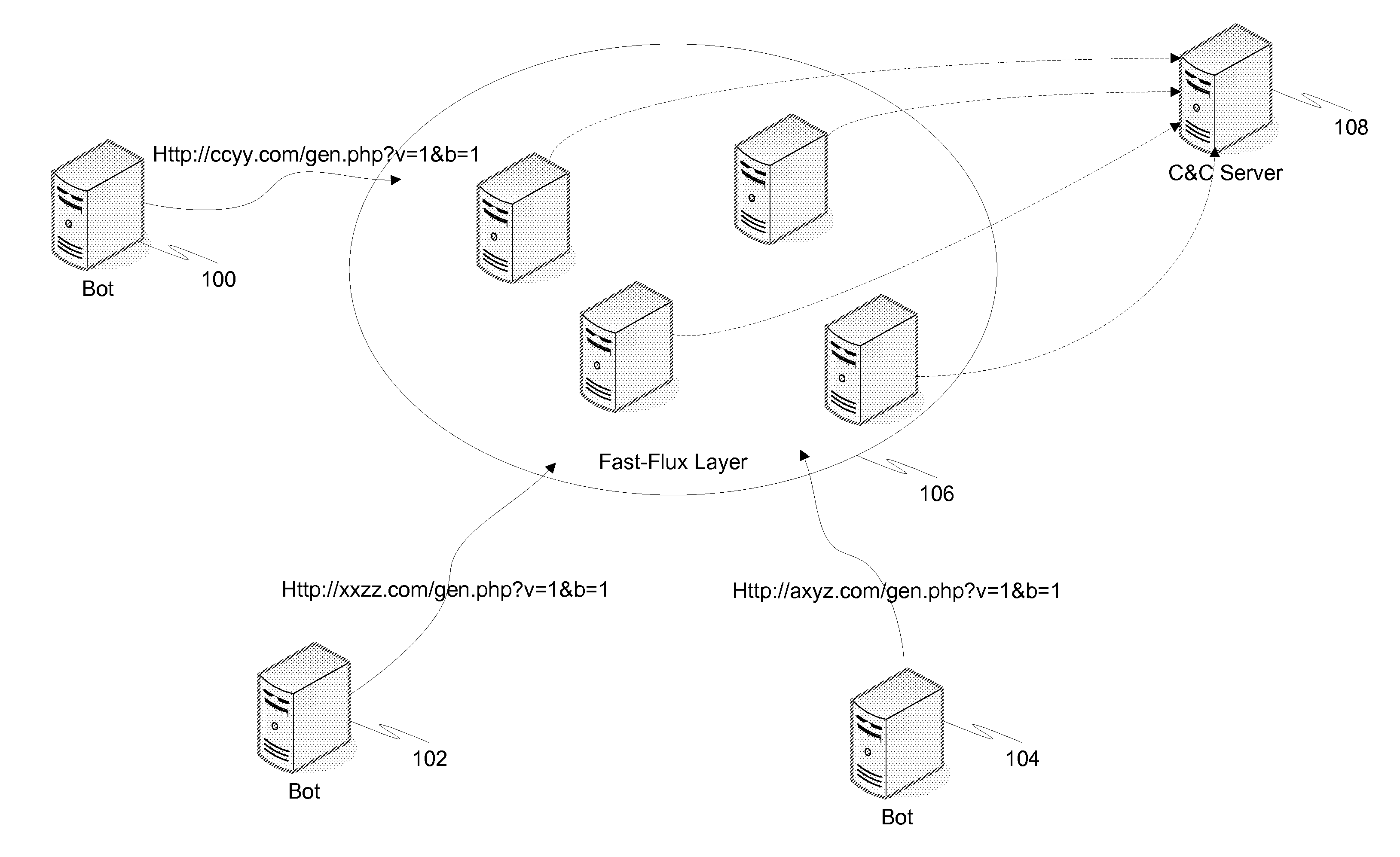
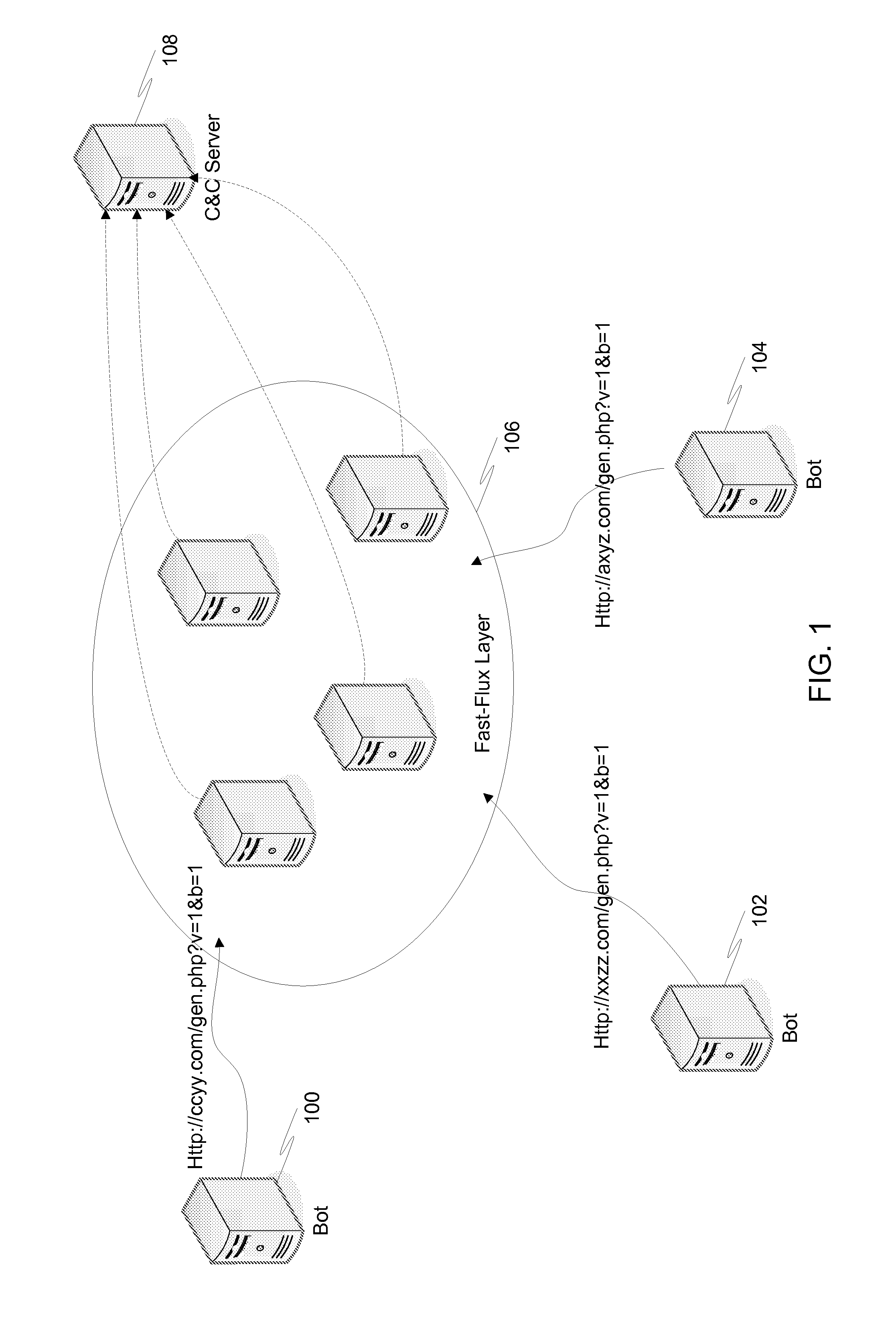
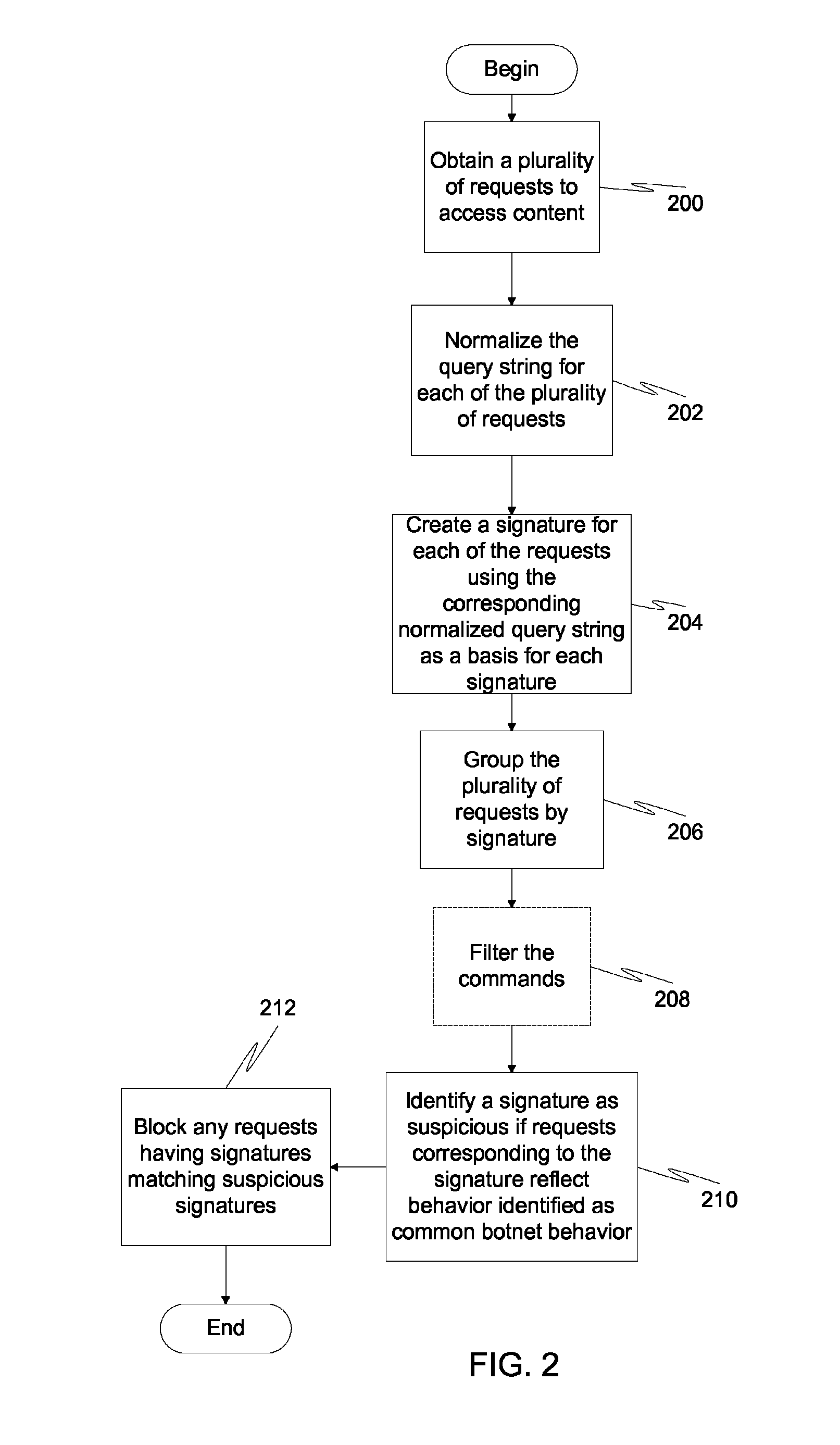
Command and control channel detection with query string signature
Detection and prevention of botnet behavior is accomplished by monitoring access request in a network. Each request includes a domain of content to access and a path of content to access, and each path includes a file name and query string. Once obtained, the query strings for each of these requests are normalized. A signature is then created for each of the normalized query strings. The obtained requests can then be grouped by signature. Once the requests have been grouped by signature, each grouping is examined to identify suspicious signatures based on common botnet behavior. Suspicious requests are used in back-end and front-end defenses against botnets.
Owner:TREND MICRO INC
Reputation based identification of false positive malware detections
A signature is identified in association with an entity at a client. A reputation score associated with the entity is identified, the reputation score indicating a likelihood that the entity will compromise the client. Whether the signature detection event is a false positive signature detection event is evaluated based on the reputation score and reported.
Owner:CA TECH INC
Context Aware Sound Signature Detection
A low power sound recognition sensor is configured to receive an analog signal that may contain a signature sound. Sparse sound parameter information is extracted from the analog signal. The extracted sound parameter information is sampled in a periodic manner and a context value is updated to indicate a current environmental condition. The sparse sound parameter information is compared to both the context value and a signature sound parameter database stored locally with the sound recognition sensor to identify sounds or speech contained in the analog signal, such that identification of sound or speech is adaptive to the current environmental condition.
Owner:TEXAS INSTR INC
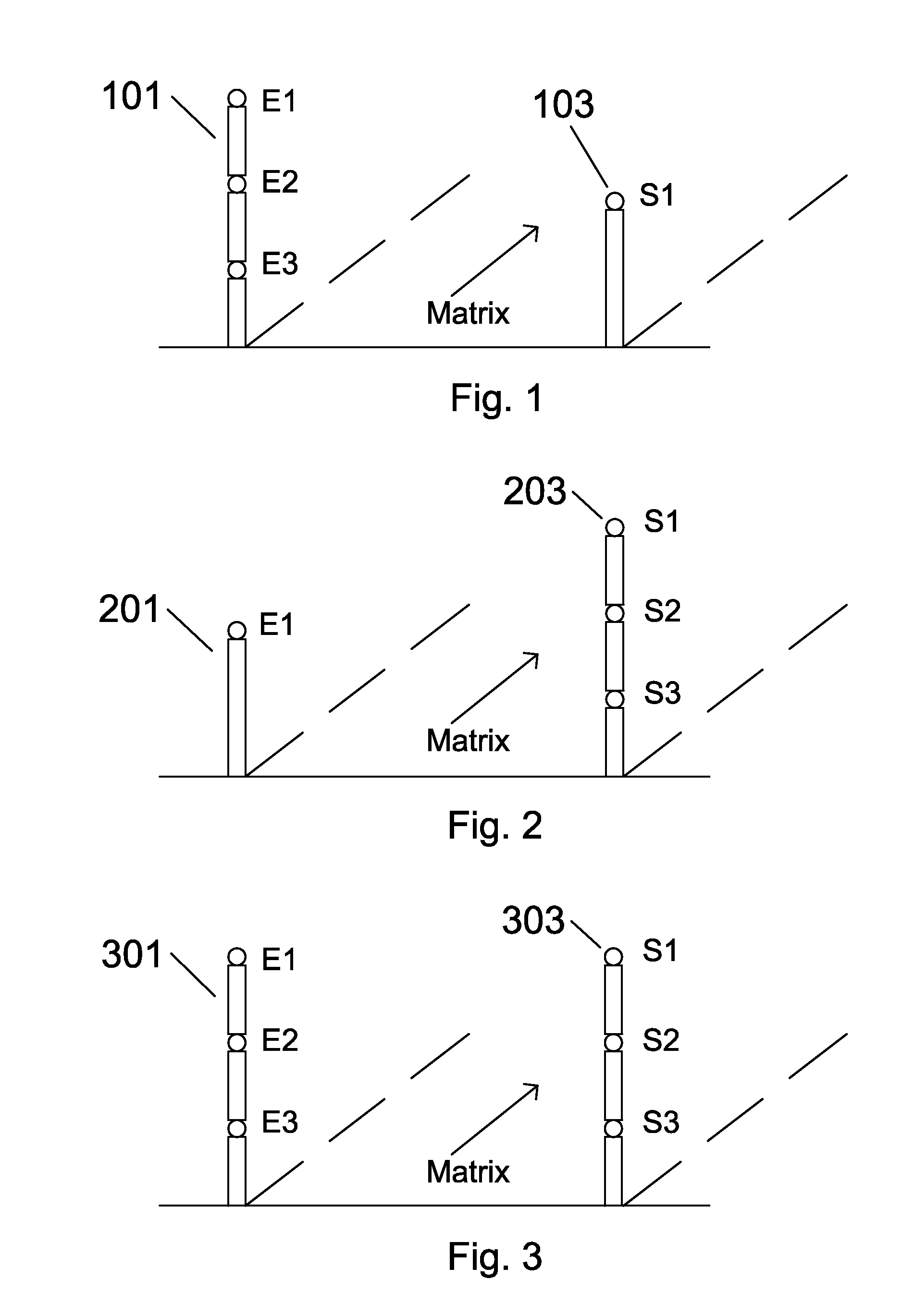
Electric Field Signature Detection Using Exciter-Sensor Arrays
An electric field signature detector for detecting and identifying objects that uses multiple electrostatic sensor nodes each having a passive sensing electrode whose free conduction electrons are displacement responsive to an externally applied or sensed electric field potential, and a transimpedance converter and amplifier exhibiting ultra-high input impedance for translating low level input displacement current from a sensing electrode into a useable output signal in response to a charge displacement signal induced on the passive sensing electrode by an external electric field. The electric field signature detector further includes an exciter for providing a reference electric field used in the retrieval and processing of an electric field signature representative of an object and class of object under investigation. The electric field signature detector having uses including military, security, anti-terrorist, and defense related.
Owner:RAMPART DETECTION SYST
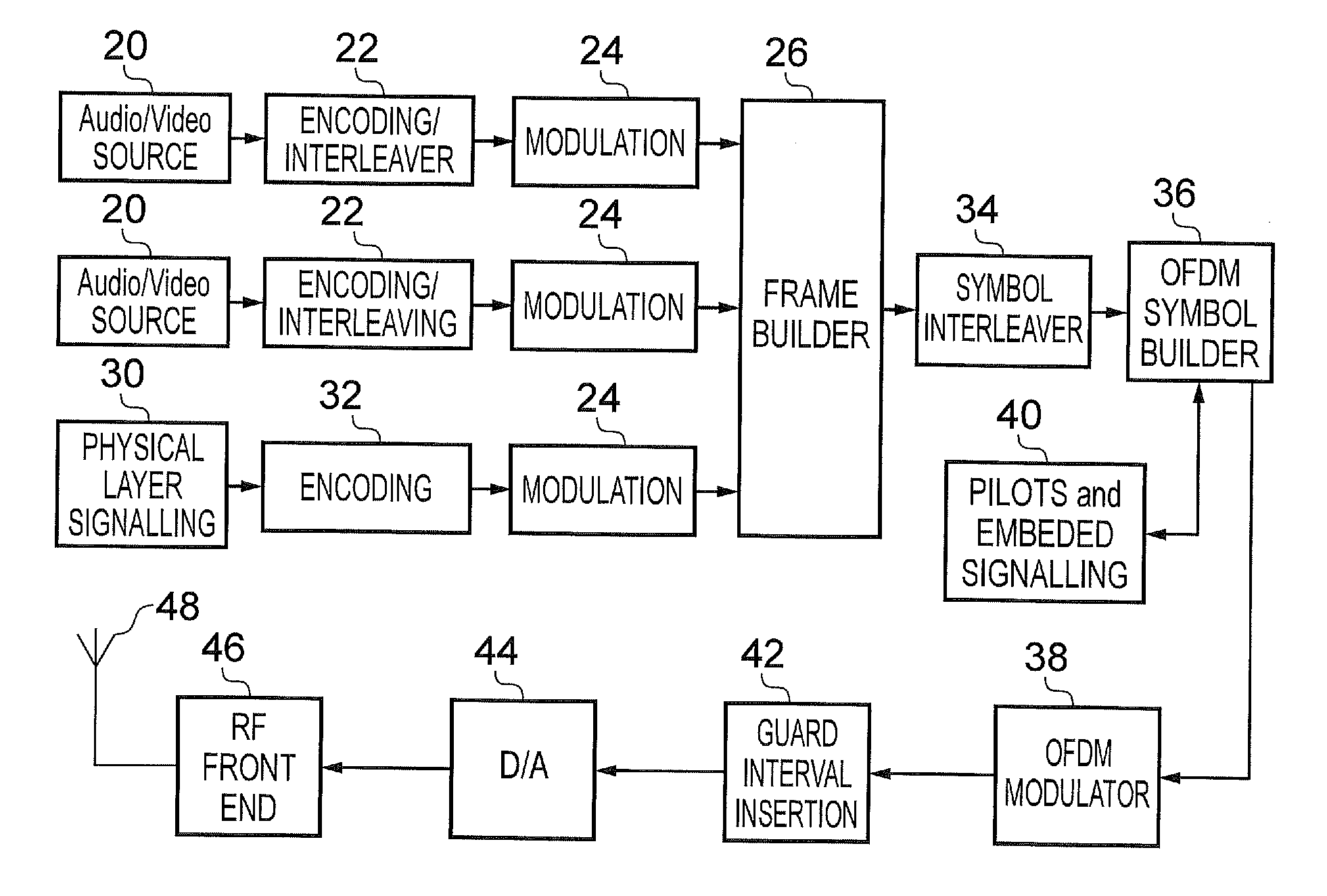
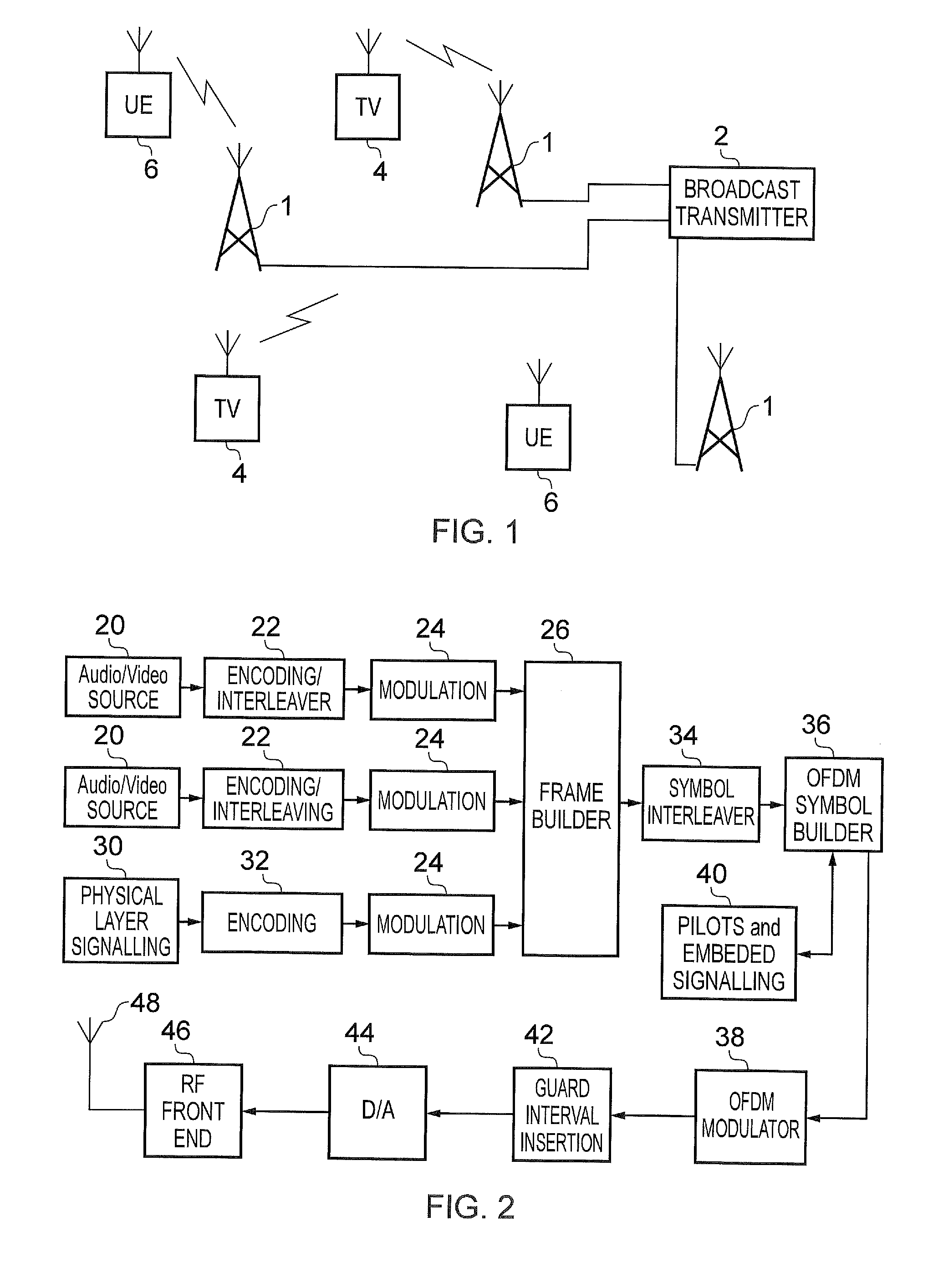
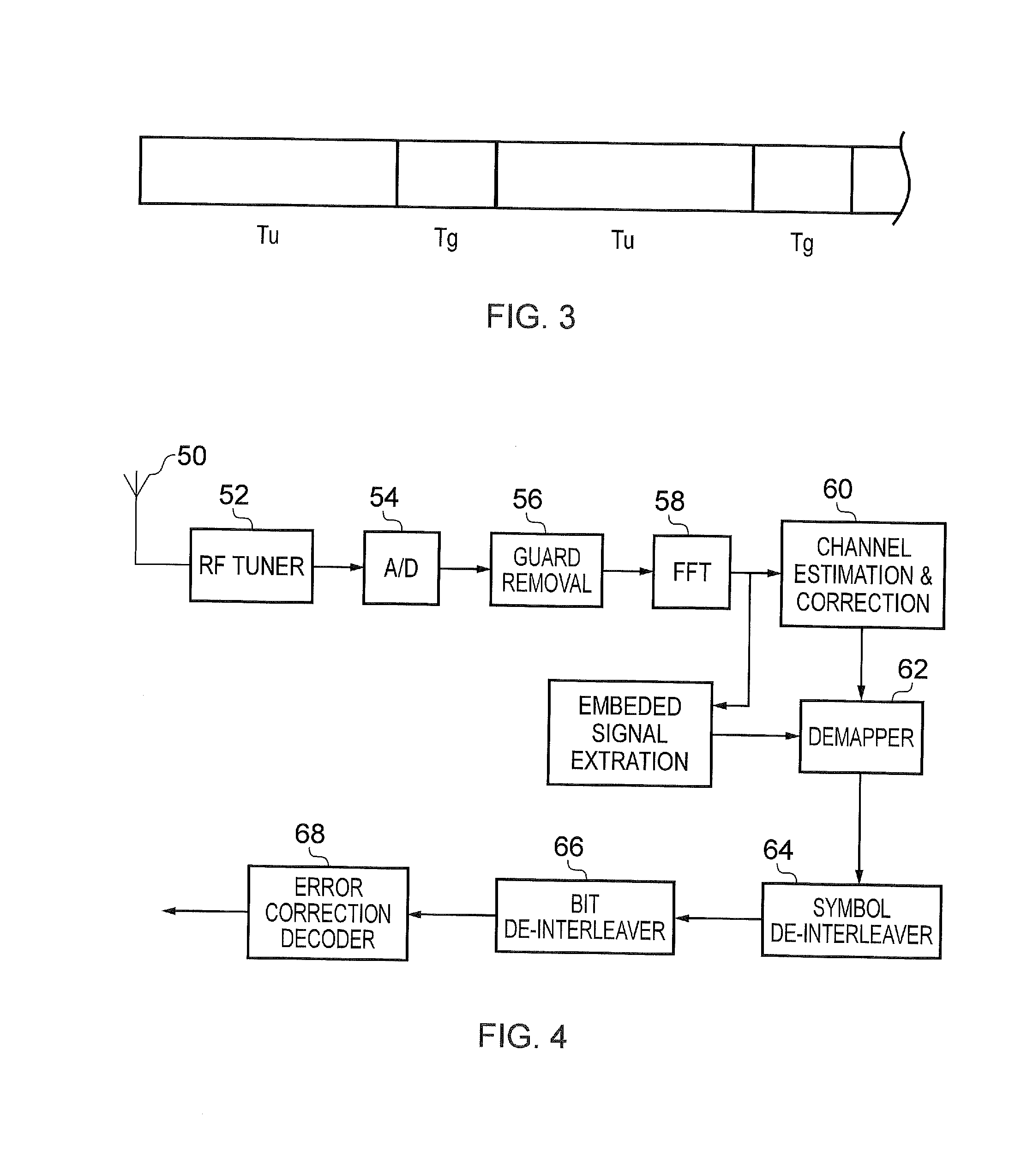
Implicit signalling in OFDM preamble with embedded signature sequence, and cyclic prefix and postfix aided signature detection
ActiveUS20160142237A1Reduce processReduce processing timeSecret communicationMulti-frequency code systemsTime domainCyclic prefix
A transmitter transmitting payload data using Orthogonal Frequency Division Multiplexed (OFDM) symbols, including: a frame builder configured to receive the payload data and to receive signalling data to use in detecting and recovering the payload data at a receiver, and to form the payload data with the signalling data into frames for transmission; a modulator configured to modulate a first OFDM symbol with the signalling data and to modulate one or more second OFDM symbols with the payload data; a signature sequence processor circuit providing a signature sequence; a combiner circuit combining the signature sequence with the first OFDM symbol; a prefixing circuit prefixing a guard interval to the first OFDM symbol to form a preamble; and a transmission circuit transmitting the preamble and the one or more second OFDM symbols. The guard interval is formed from time domain samples of a part of the signature sequence.
Owner:SATURN LICENSING LLC
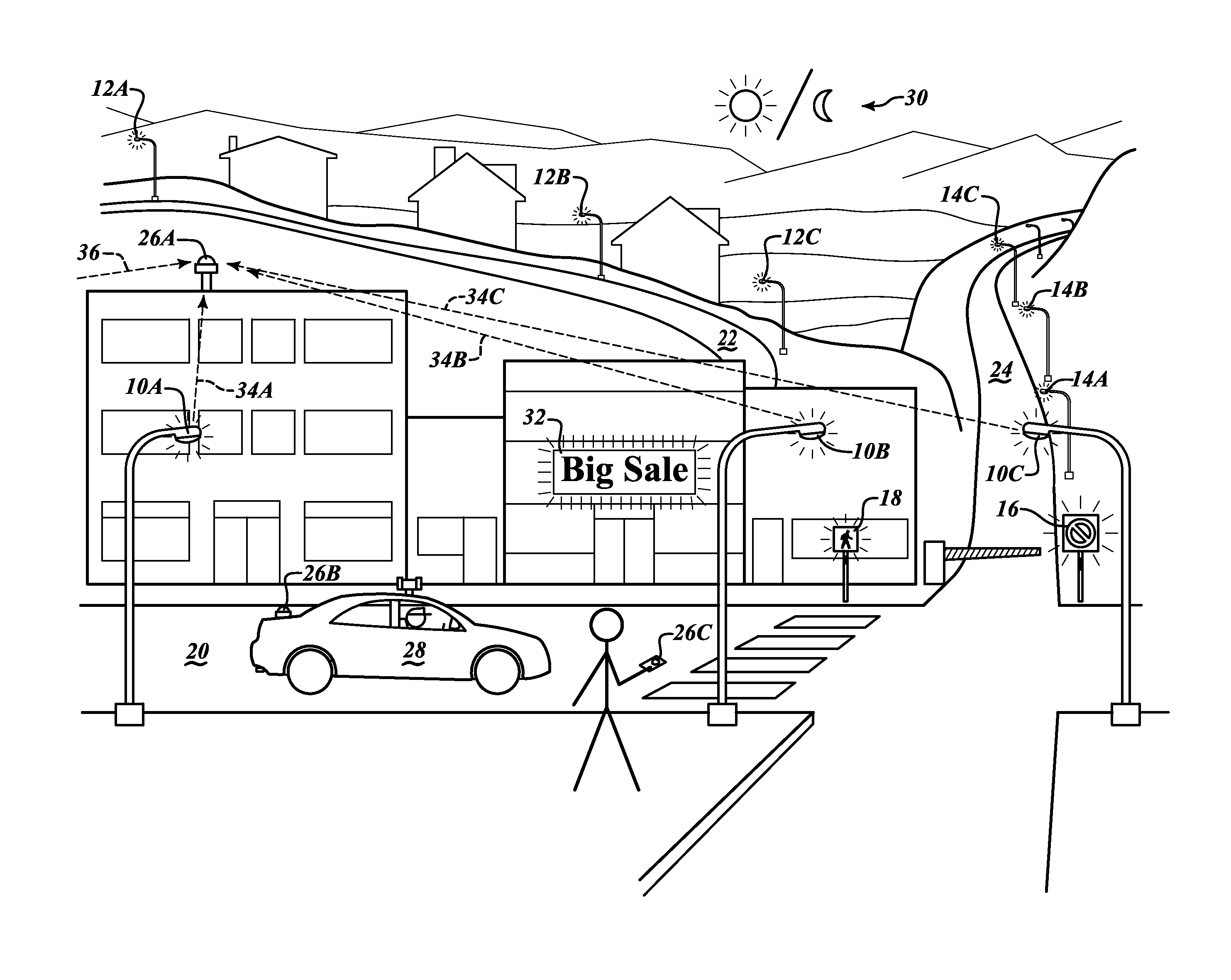
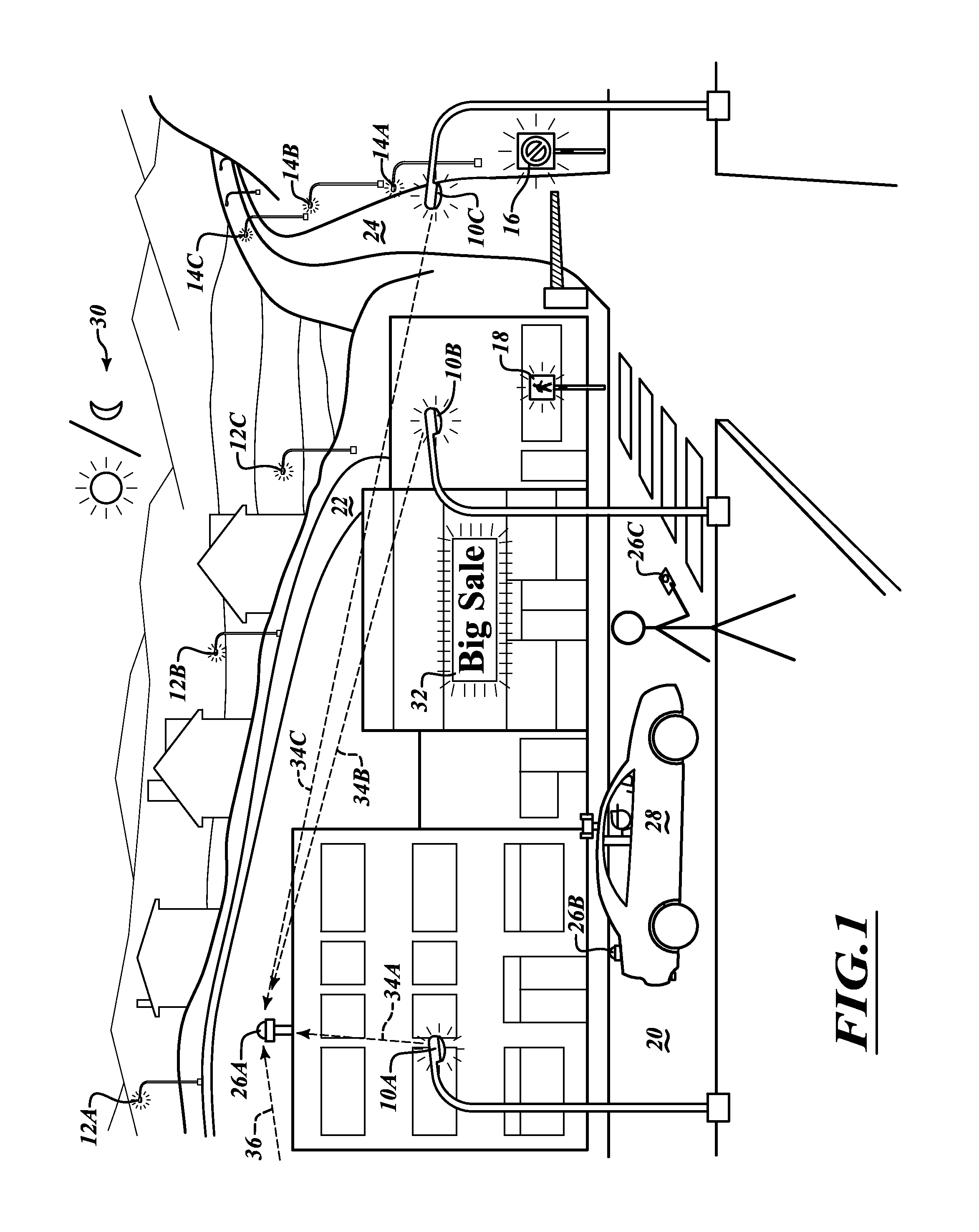
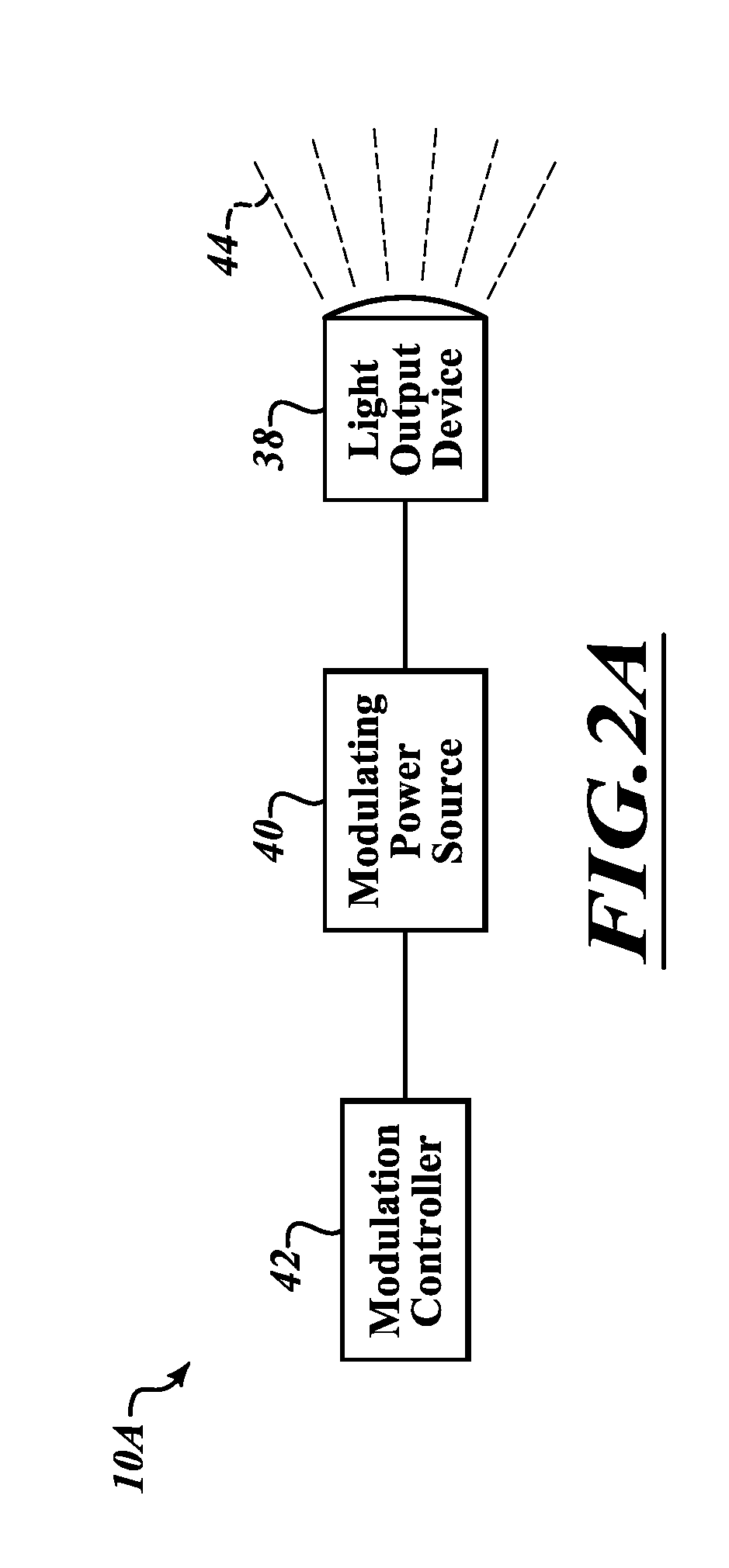
Devices and methods to produce and receive an encoded light signature
A signature encoded light system includes at least one light source. The at least one light source is configured to output a first encoded light signature embedded within light in the visible spectrum. A light signature detection device is configured to receive a composite light signal formed with light from the at least one light source and ambient light. The light signature detection device is configured to identify the first encoded light signature.
Owner:EOCYS
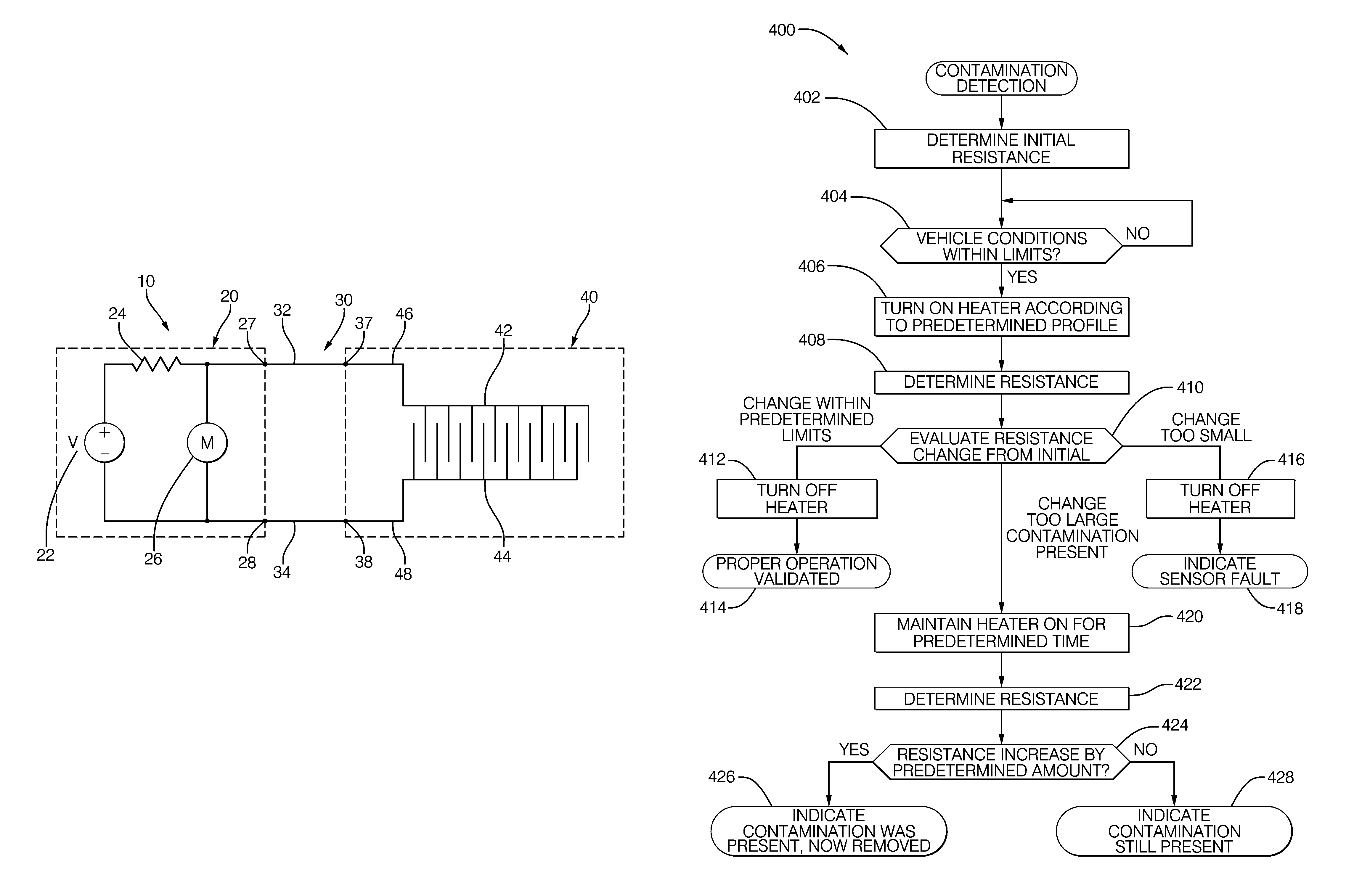
Method and system for contamination signature detection diagnostics of a particulate matter sensor
ActiveUS20130002271A1Electrical controlInternal combustion piston enginesElectrical resistance and conductanceParticulates
A diagnostic method and system is described for diagnosing an operating condition of a conductive particulate matter sensor. The sensor has a substrate with electrical resistance that varies with temperature and two electrodes on the substrate adapted to collect particulate matter between the electrodes, thereby establishing an electrically conductive path through collected particulate matter between the electrodes that can be detected by measuring electrical resistance between the electrodes, Relect. The diagnosis is performed by heating the substrate in the area between the electrodes and using the resistance between the electrodes to determine detecting whether contamination is present on the surface of the sensor. Heat may be maintained on the sensor to attempt to burn off a detected contaminant, and a subsequent resistance reading may be used to determine if the contaminant was successfully burned off.
Owner:DELPHI TECH IP LTD
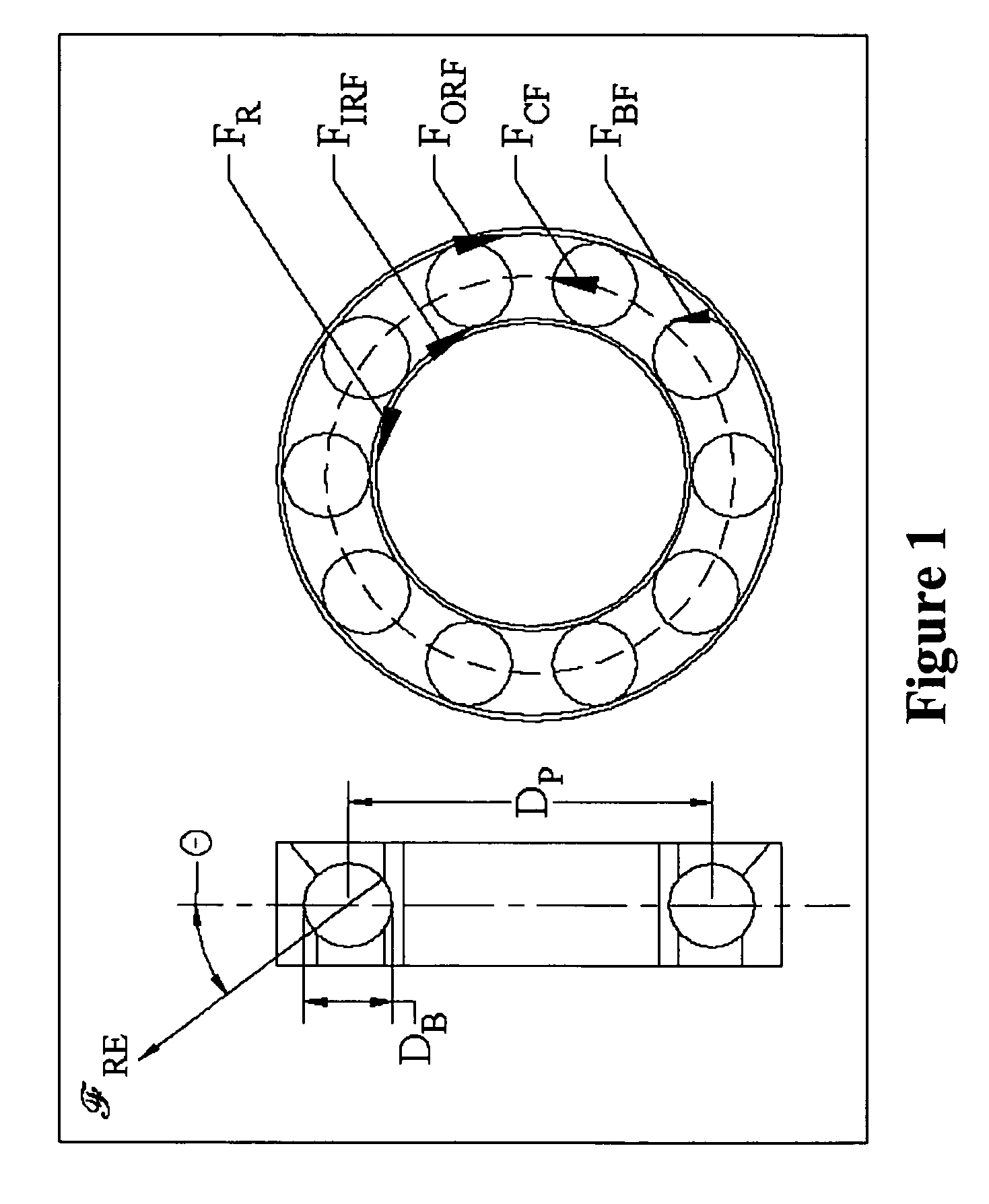
Bearing fault signature detection
InactiveUS7421349B1Vibration measurement in solidsMachine part testingRolling-element bearingEngineering
A device, and method, detects the presence of developing faults in rolling element bearings. Detection is accomplished by measuring the vibration of the apparatus in which the bearing is operating (motor, generator, engine, etc.) and searching for signatures unique to bearing faults. These signatures are predicted by a fault signature model and recognized by a detector, both of which are part of this invention.
Owner:USA AS REPRESENTED BY THE SEC OF THE NAVY THE
Method and system for contamination signature detection diagnostics of a particulate matter sensor
ActiveUS8823400B2Vehicle testingInternal combustion piston enginesElectrical resistance and conductanceParticulates
A diagnostic method and system is described for diagnosing an operating condition of a conductive particulate matter sensor. The sensor has a substrate with electrical resistance that varies with temperature and two electrodes on the substrate adapted to collect particulate matter between the electrodes, thereby establishing an electrically conductive path through collected particulate matter between the electrodes that can be detected by measuring electrical resistance between the electrodes, Relect. The diagnosis is performed by heating the substrate in the area between the electrodes and using the resistance between the electrodes to determine detecting whether contamination is present on the surface of the sensor. Heat may be maintained on the sensor to attempt to burn off a detected contaminant, and a subsequent resistance reading may be used to determine if the contaminant was successfully burned off.
Owner:DELPHI TECH IP LTD
Method and system for heater signature detection diagnostics of a particulate matter sensor
ActiveUS8249827B2Electrical controlResistance/reactance/impedenceParticulatesElectrical resistance and conductance
A diagnostic method and system is described for diagnosing an operating condition of a conductive particulate matter sensor. The sensor has a substrate with electrical resistance that varies with temperature and two electrodes on the substrate adapted to collect particulate matter between the electrodes, thereby establishing an electrically conductive path through collected particulate matter between the electrodes that can be detected by measuring electrical resistance between the electrodes, Relect. The diagnosis is performed by heating the substrate in the area between the electrodes and detecting whether resistance varies with temperature as expected, and then cooling the substrate back down and detecting whether resistance varies with temperature as expected. If resistance varies as expected during both heating and cooling, then a validation is diagnosed that the sensor is in proper operating condition if resistance increases in a manner consistent with evaporation of condensate. If resistance does not vary as expected, then a failure condition is diagnosed.
Owner:DELPHI TECH IP LTD
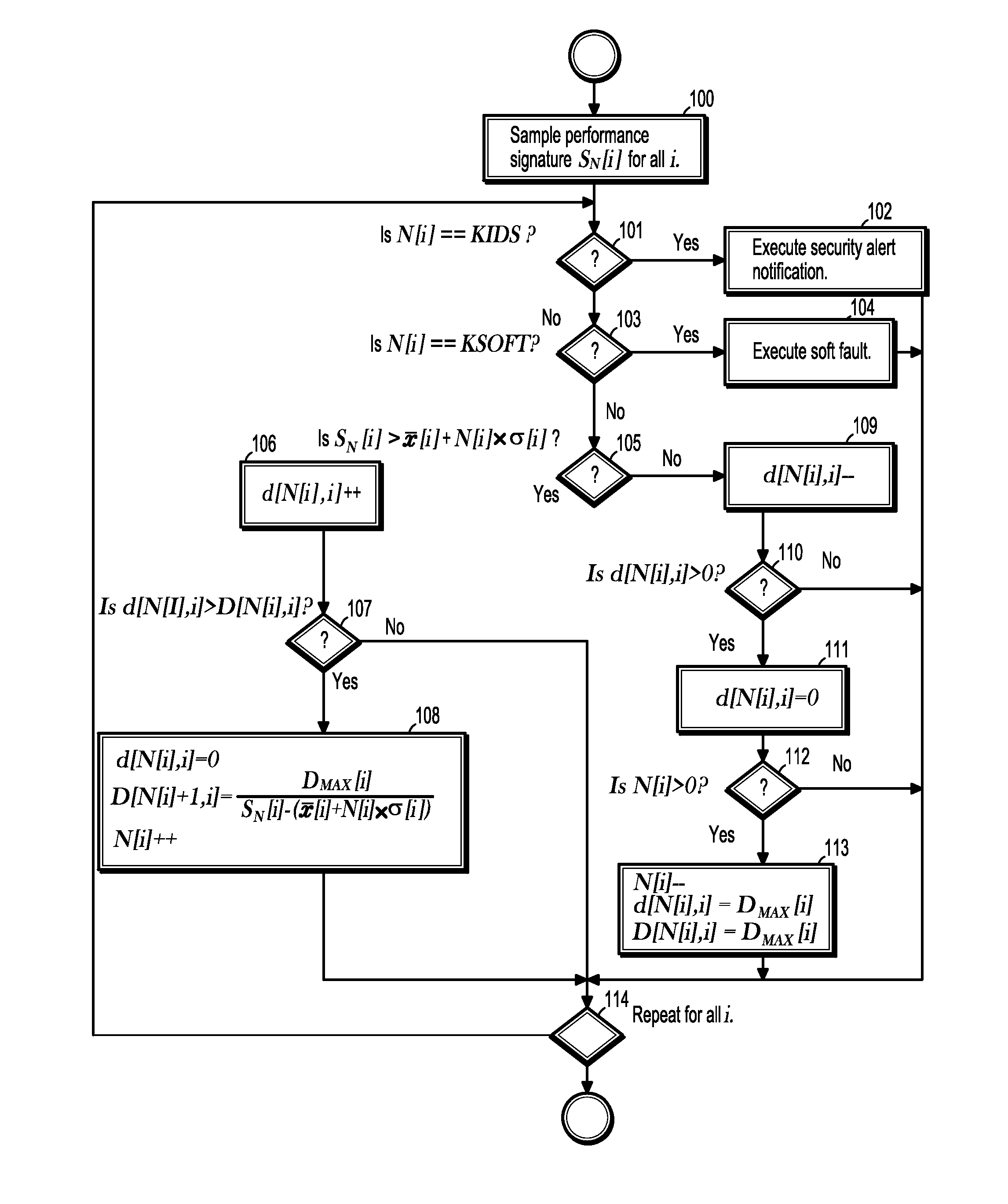
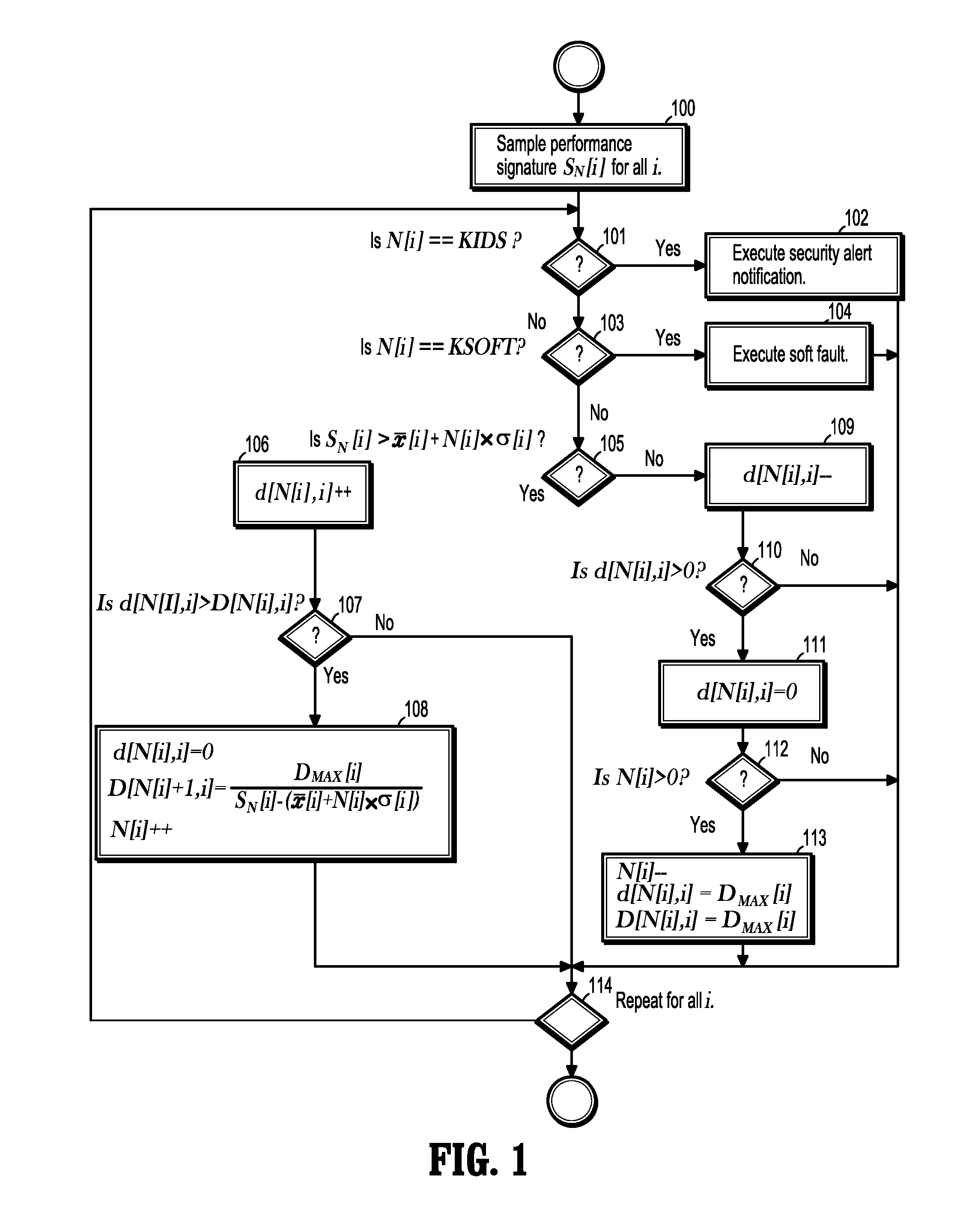
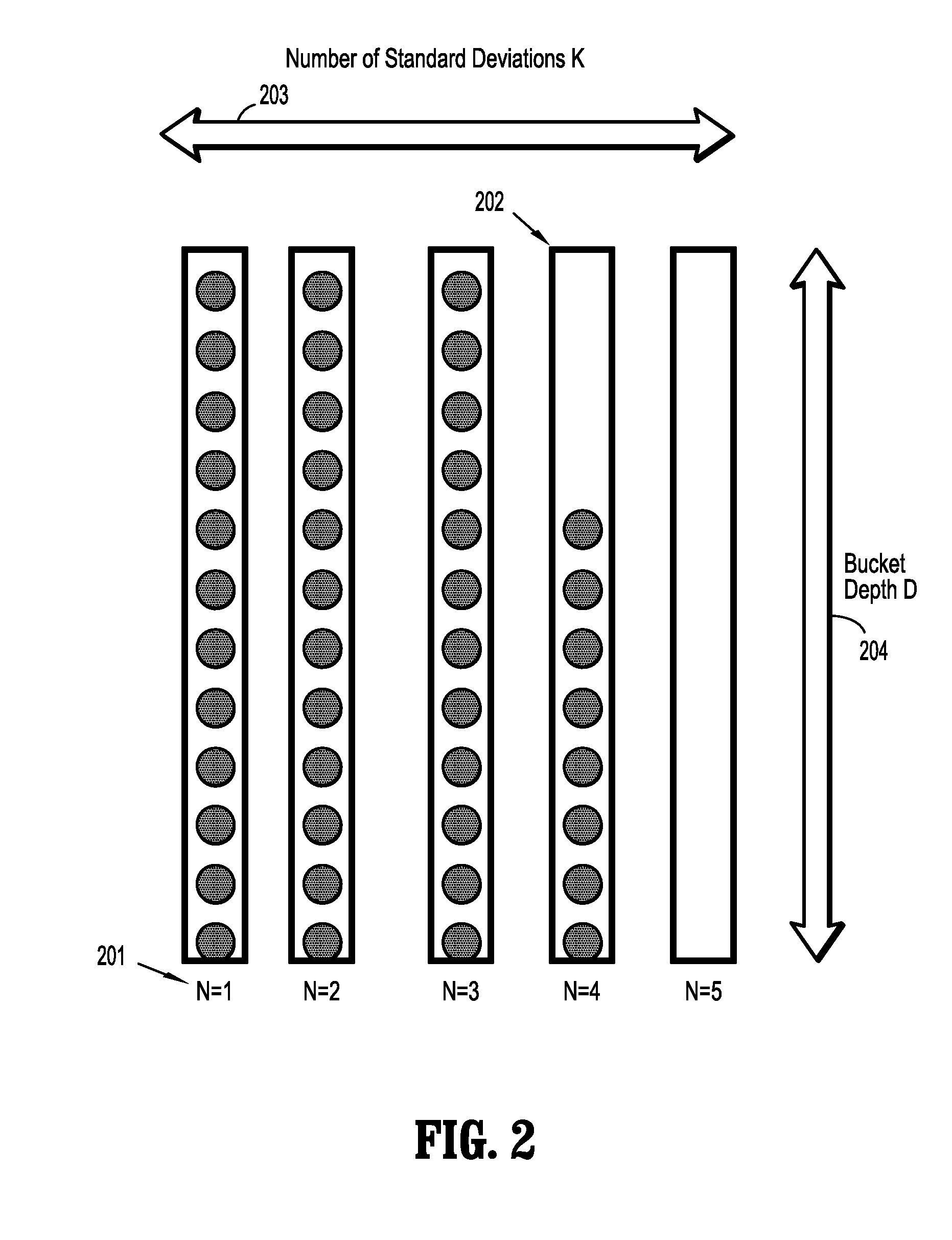
System and Method for Detecting Security Intrusions and Soft Faults Using Performance Signatures
ActiveUS20100241905A1Memory loss protectionUnauthorized memory use protectionOperational systemSoftware system
A method for detecting security intrusions and soft faults in a software system includes receiving a multi-dimensional performance signature built from operating system metrics sampled by a software system monitoring infrastructure, associating a plurality of buckets with each component of the performance signature, comparing a component of the sampled performance signature to an expected value for the performance signature component, where a bucket for the performance signature component is incremented if the sampled performance signature component exceeds the corresponding expected value, and the bucket for the performance signature component is decremented if the sampled performance signature component is less than the corresponding expected value, executing a security alert notification when the bucket for the performance signature component exceeds a first threshold, and executing a soft-fault notification when the bucket for the performance signature component exceeds a second threshold, where the first threshold is less than the second threshold.
Owner:SIEMENS CORP
Multi-method gateway-based network security systems and methods
InactiveUS8635695B2Accurately and comprehensively detecting and preventingSolve the high false alarm rateMemory loss protectionDigital data processing detailsTraffic capacityAnomaly detection
Systems and methods for detecting and preventing network security breaches are described. The systems and methods present a gateway-based packet-forwarding network security solution to not only detect security breaches but also prevent them by directly dropping suspicious packets and connections. The systems and methods employ multiple techniques to detect and prevent network security breaches, including stateful signature detection, traffic signature detection, and protocol anomaly detection.
Owner:JUMIPER NETWORKS INC
Sensory Stream Analysis Via Configurable Trigger Signature Detection
ActiveUS20140215235A1Optimum power conservationLow powerVolume/mass flow measurementBiological neural network modelsReconfigurable antennaGeneral purpose
The present inventors have recognized that proper utilization of reconfigurable event driven hardware may achieve optimum power conservation in energy constrained environments including a low power general purpose primary processor and one or more electronic sensors. Aspects of neurobiology and neuroscience, for example, may be utilized to provide such reconfigurable event driven hardware, thereby achieving energy-efficient continuous sensing and signature reporting in conjunction with the one or more electronic sensors while the primary processor enters a low power consumption mode. Such hardware is event driven and operates with extremely low energy requirements.
Owner:WISCONSIN ALUMNI RES FOUND
Method and apparatus for detecting near duplicate videos using perceptual video signatures
ActiveUS8587668B2Television system detailsDigital data information retrievalThe InternetSimilarity measure
Methods and apparatus for detection and identification of duplicate or near-duplicate videos using a perceptual video signature are disclosed. The disclosed apparatus and methods (i) extract perceptual video features, (ii) identify unique and distinguishing perceptual features to generate a perceptual video signature, (iii) compute a perceptual video similarity measure based on the video edit distance, and (iv) search and detect duplicate and near-duplicate videos. A complete framework to detect unauthorized copying of videos on the Internet using the disclosed perceptual video signature is disclosed.
Owner:GOOGLE LLC
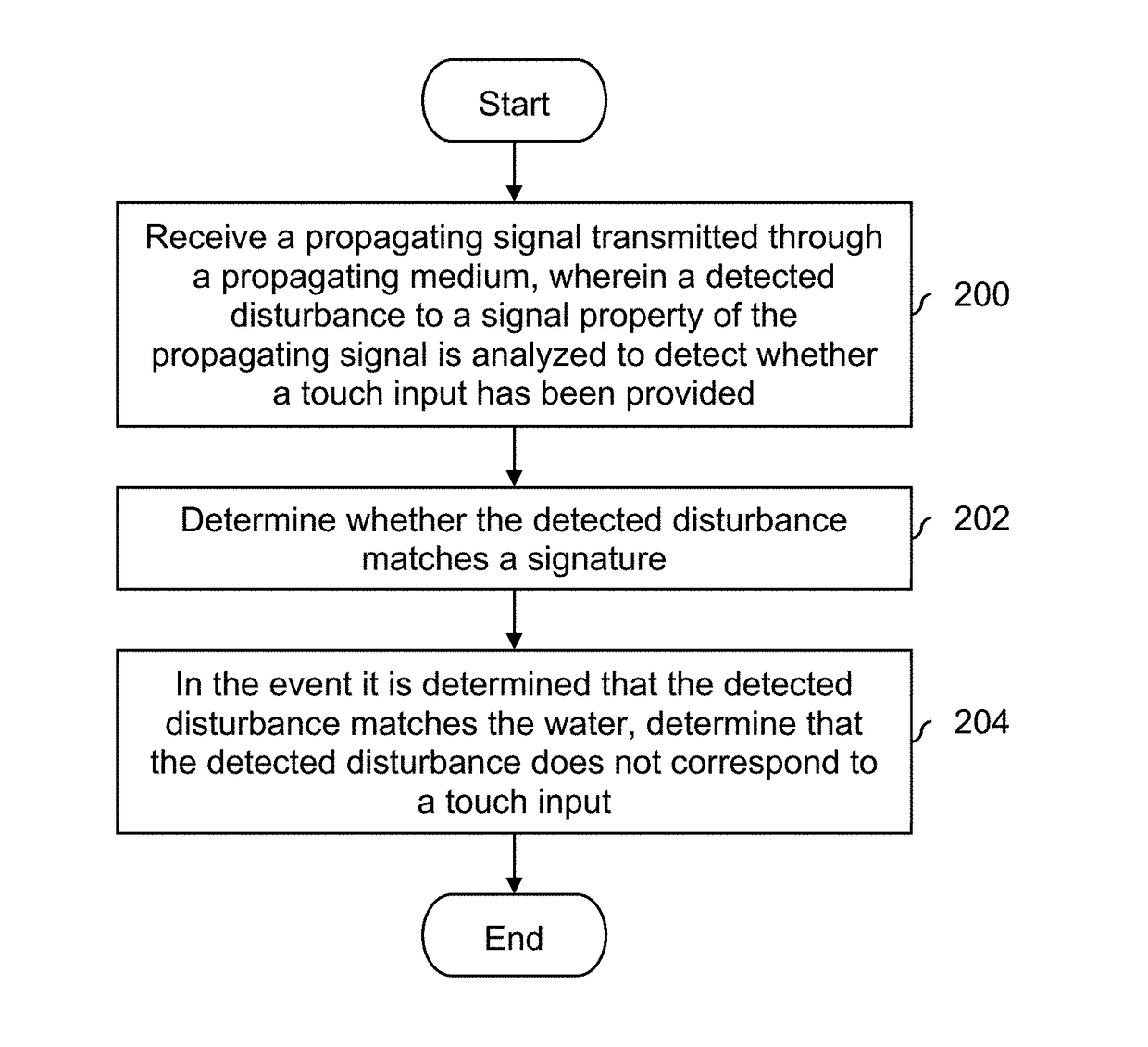
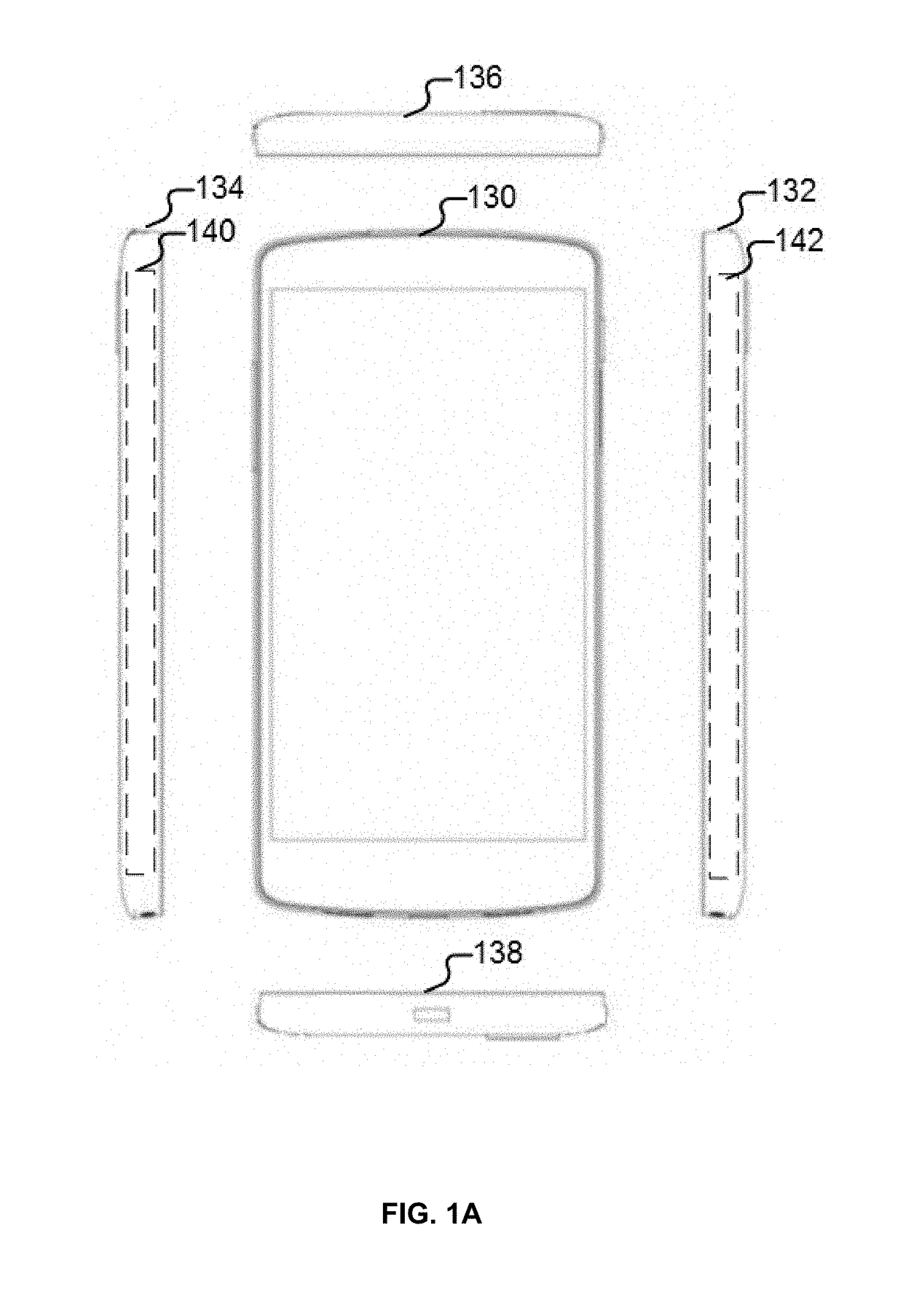
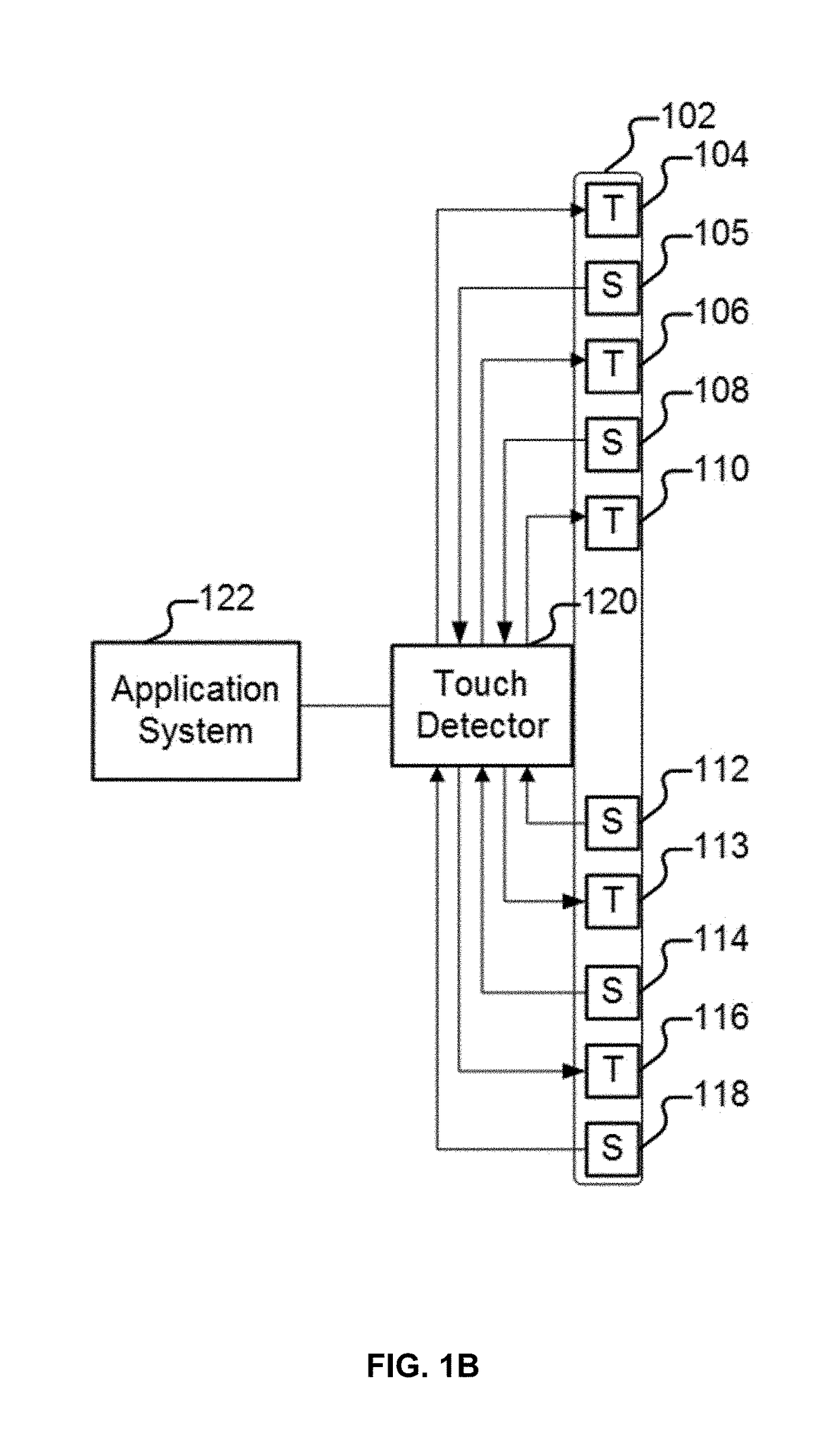
Detection of non-touch inputs using a signature
ActiveUS20180246612A1Input/output processes for data processingComputational physicsSignature detection
A propagating signal transmitted through a propagating medium is received where a detected disturbance to a signal property of the propagating signal is analyzed to detect whether a touch input has been provided. It is determined whether the detected disturbance matches a signature and in the event it is determined that the detected disturbance matches the signature, it is determined that the detected disturbance does not correspond to the touch input.
Owner:SENTONS
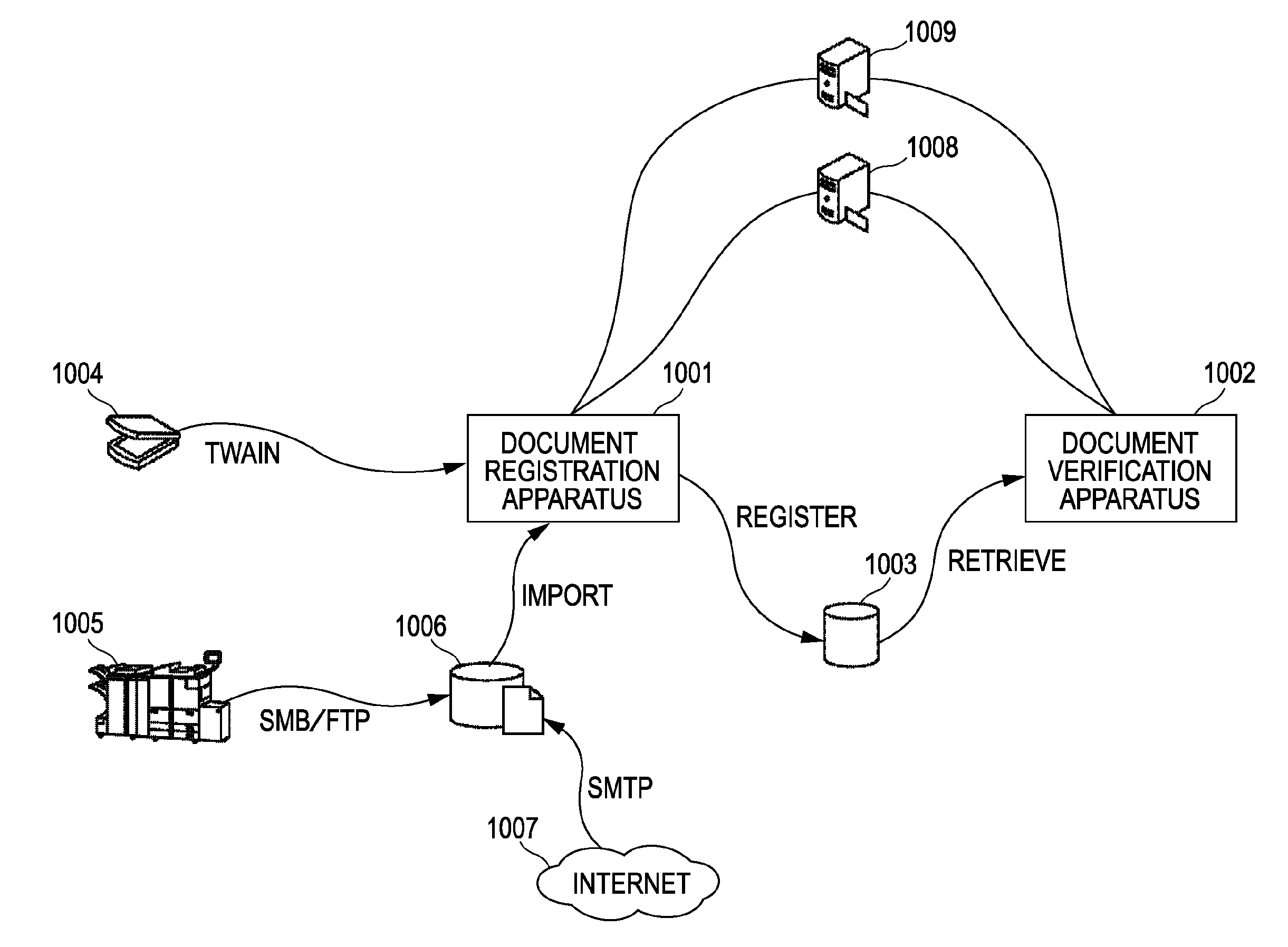
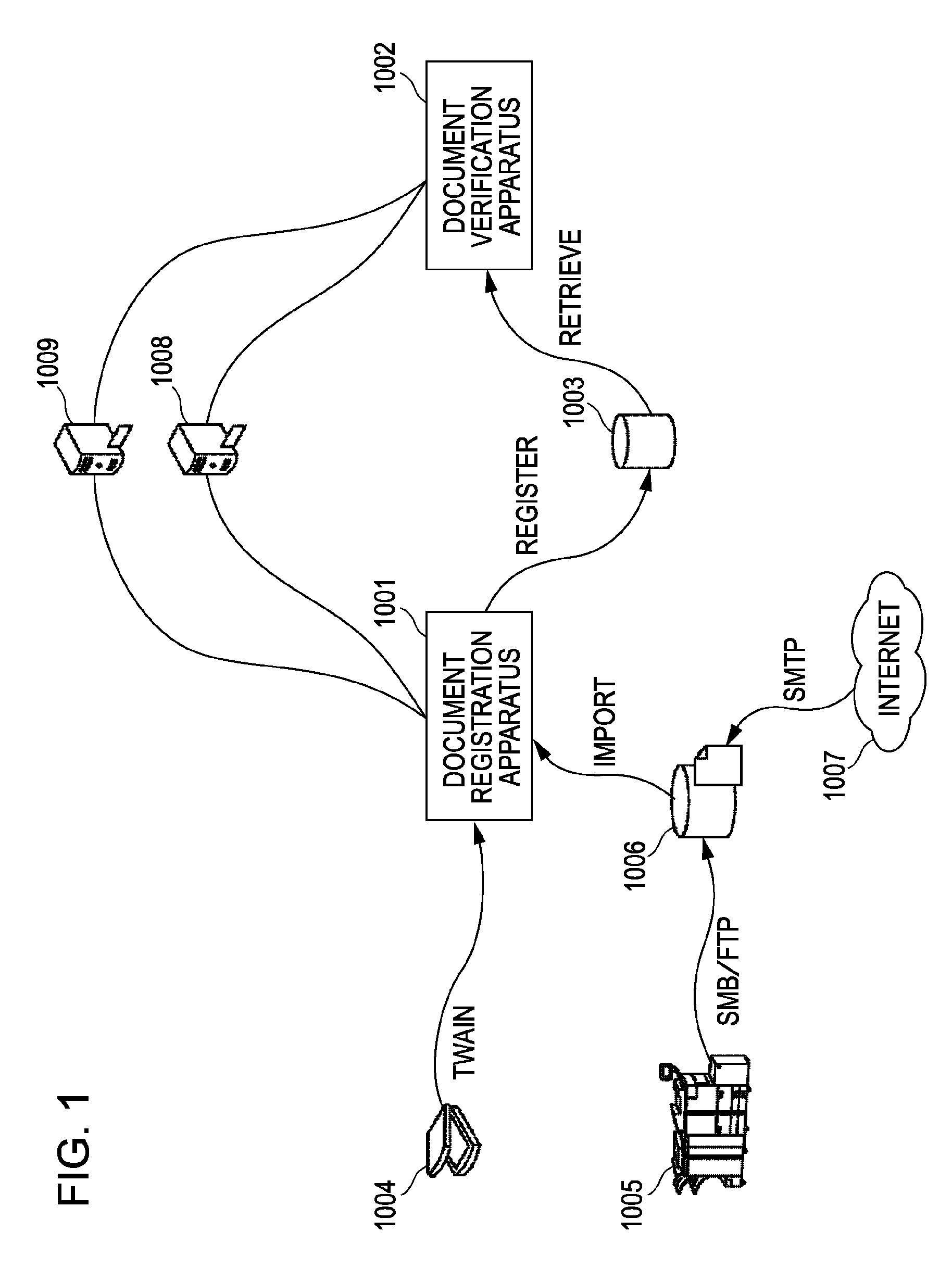
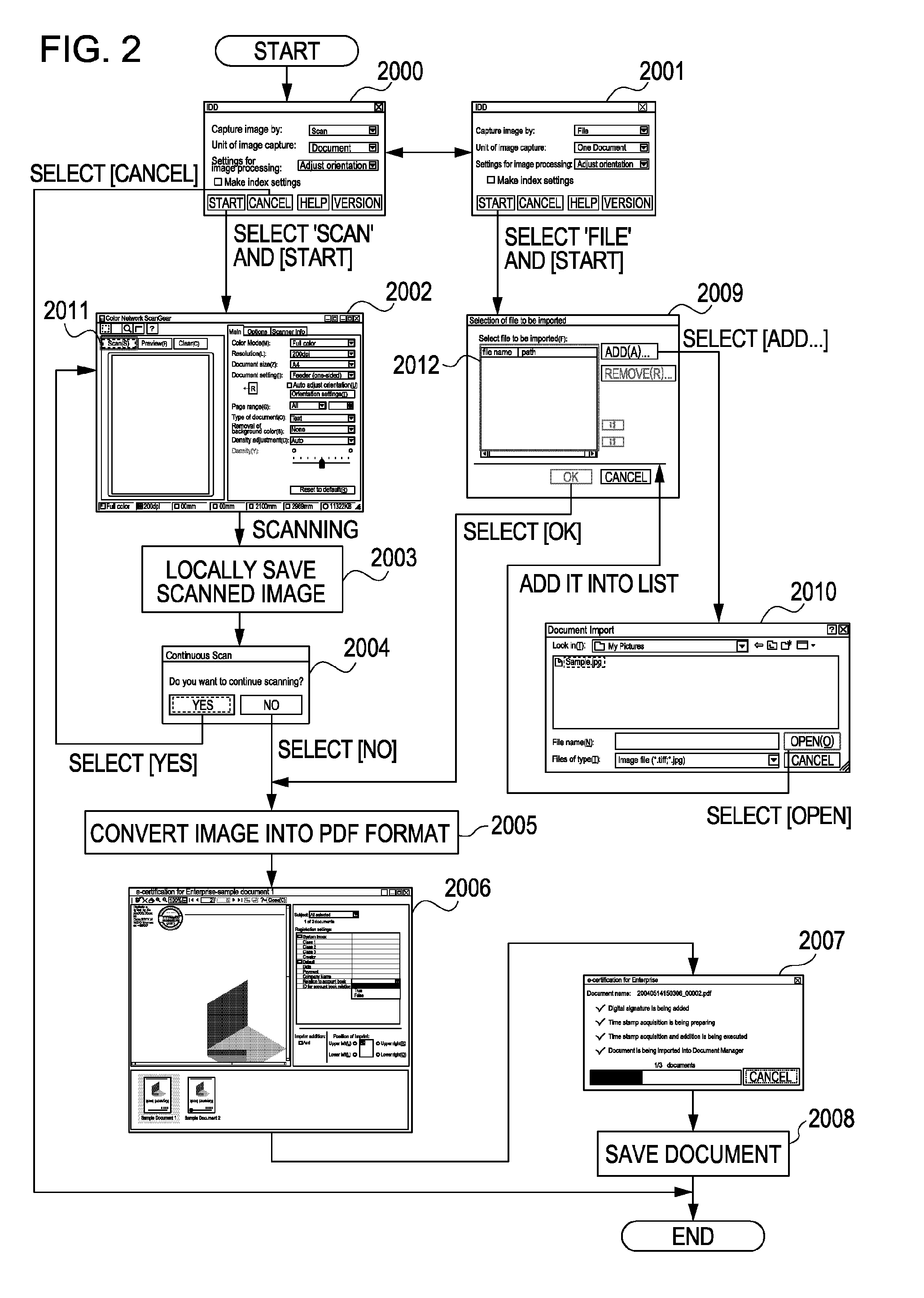
Signature verification apparatus, method for controlling signature verification apparatus, signing apparatus, method for controlling signing apparatus, program, and storage medium
InactiveUS20100023773A1User identity/authority verificationDigital data protectionSignature detectionDocumentation
A signature verification apparatus includes a determining unit configured to determine a type of a signature affixed to a document file, a first generating unit configured to, when the determining unit determines that the signature is of a first type, check the validity of a certificate contained in the signature, detect whether the document file has been tampered with based on the signature, and generate a first verification result indicating whether the signature is valid based on the check and the detection, and a second generating unit configured to, when the determining unit determines that the signature is of a second type, without checking the validity of a certificate contained in the signature, detect whether the document file has been tampered with based on the signature, and generate a second verification result indicating whether the signature is valid based on the detection.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com