Patents
Literature
197759 results about "Computer hardware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer hardware includes the physical, tangible parts or components of a computer, such as the cabinet, central processing unit, monitor, keyboard, computer data storage, graphics card, sound card, speakers and motherboard. By contrast, software is instructions that can be stored and run by hardware. Hardware is so-termed because it is "hard" or rigid with respect to changes or modifications; whereas software is "soft" because it is easy to update or change. Intermediate between software and hardware is "firmware", which is software that is strongly coupled to the particular hardware of a computer system and thus the most difficult to change but also among the most stable with respect to consistency of interface. The progression from levels of "hardness" to "softness" in computer systems parallels a progression of layers of abstraction in computing.
Watermark embedder and reader
InactiveUS6614914B1Mitigates effect of printingEasy to detectCoin-freed apparatusRecord information storageGraphicsComputer hardware
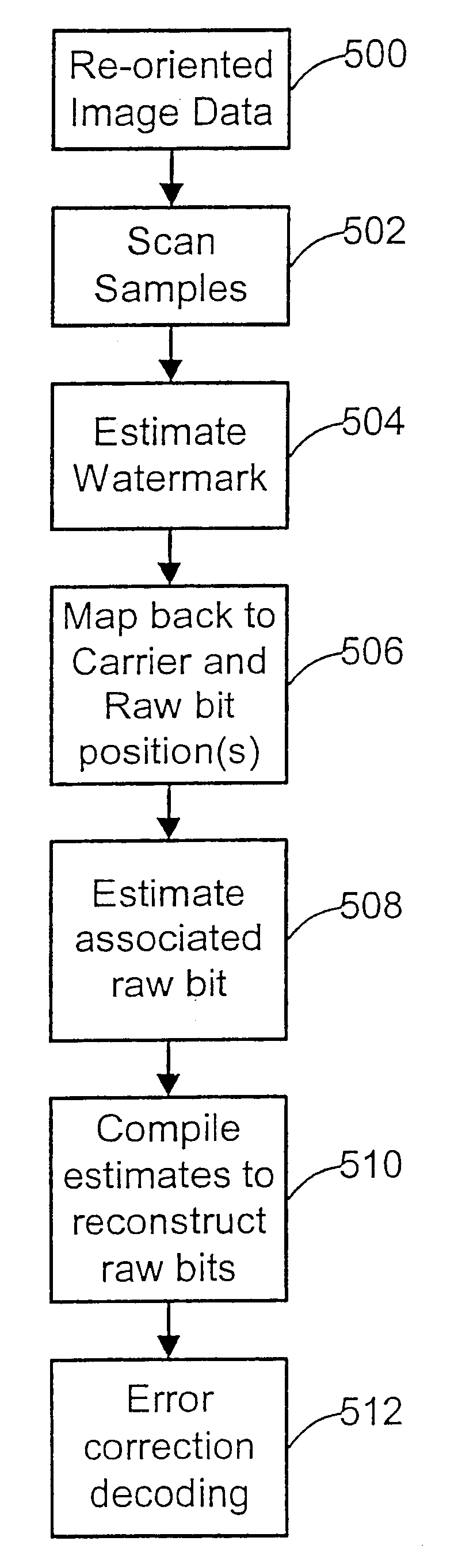
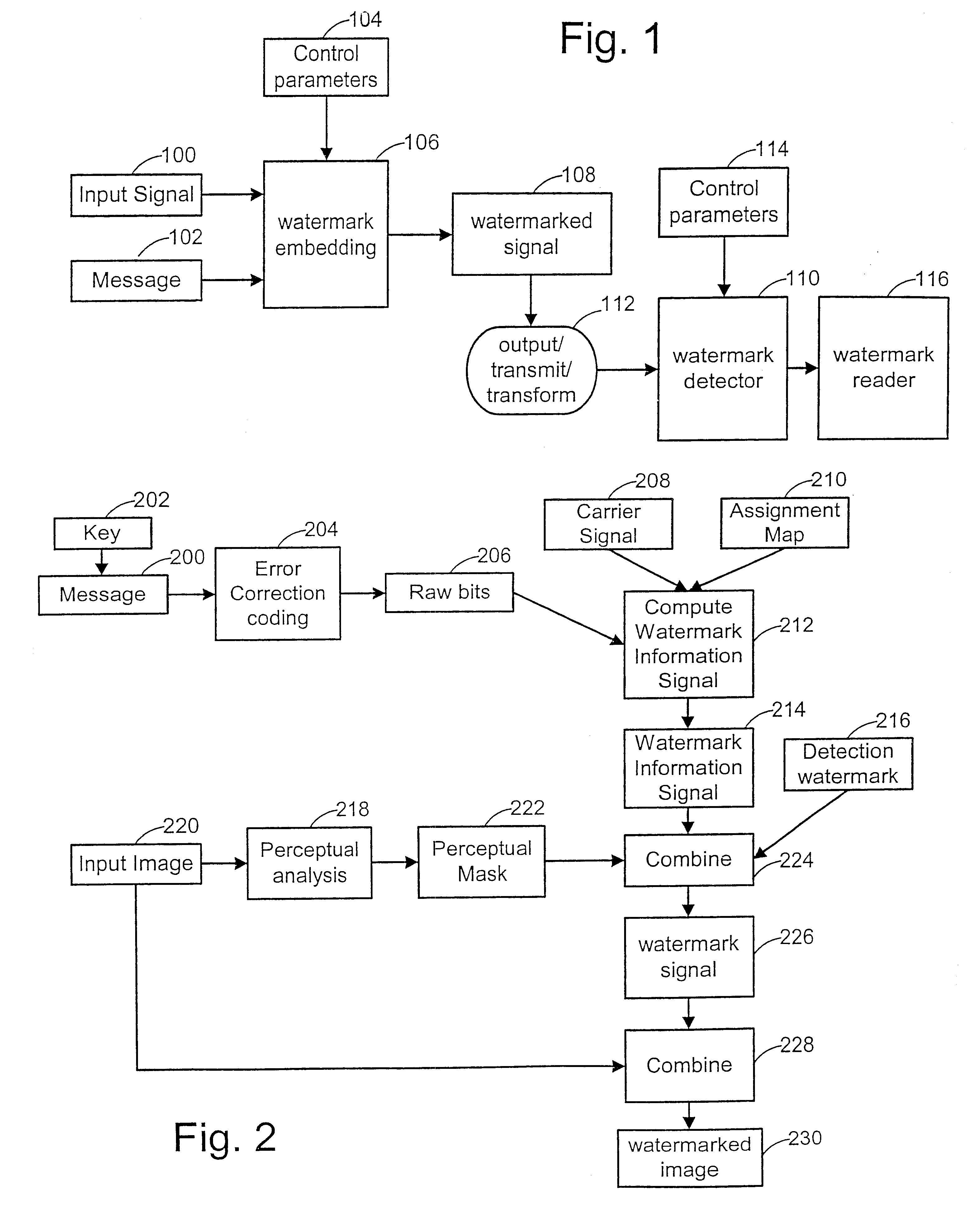
A watermark system includes an embedder, detector, and reader. The watermark embedder encodes a watermark signal in a host signal to create a combined signal. The detector looks for the watermark signal in a potentially corrupted version of the combined signal, and computes its orientation. Finally, a reader extracts a message in the watermark signal from the combined signal using the orientation to approximate the original state of the combined signal. While adapted for images, video and audio, the watermark system applies to other electronic and physical media. For example, it can be applied to mark graphical models, blank paper, film and other substrates, texturing objects for ID purposes, etc.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
Delivering service to a client via a locally addressable interface
InactiveUS6438594B1Multiple digital computer combinationsSpecific program execution arrangementsComputer hardwareClient-side
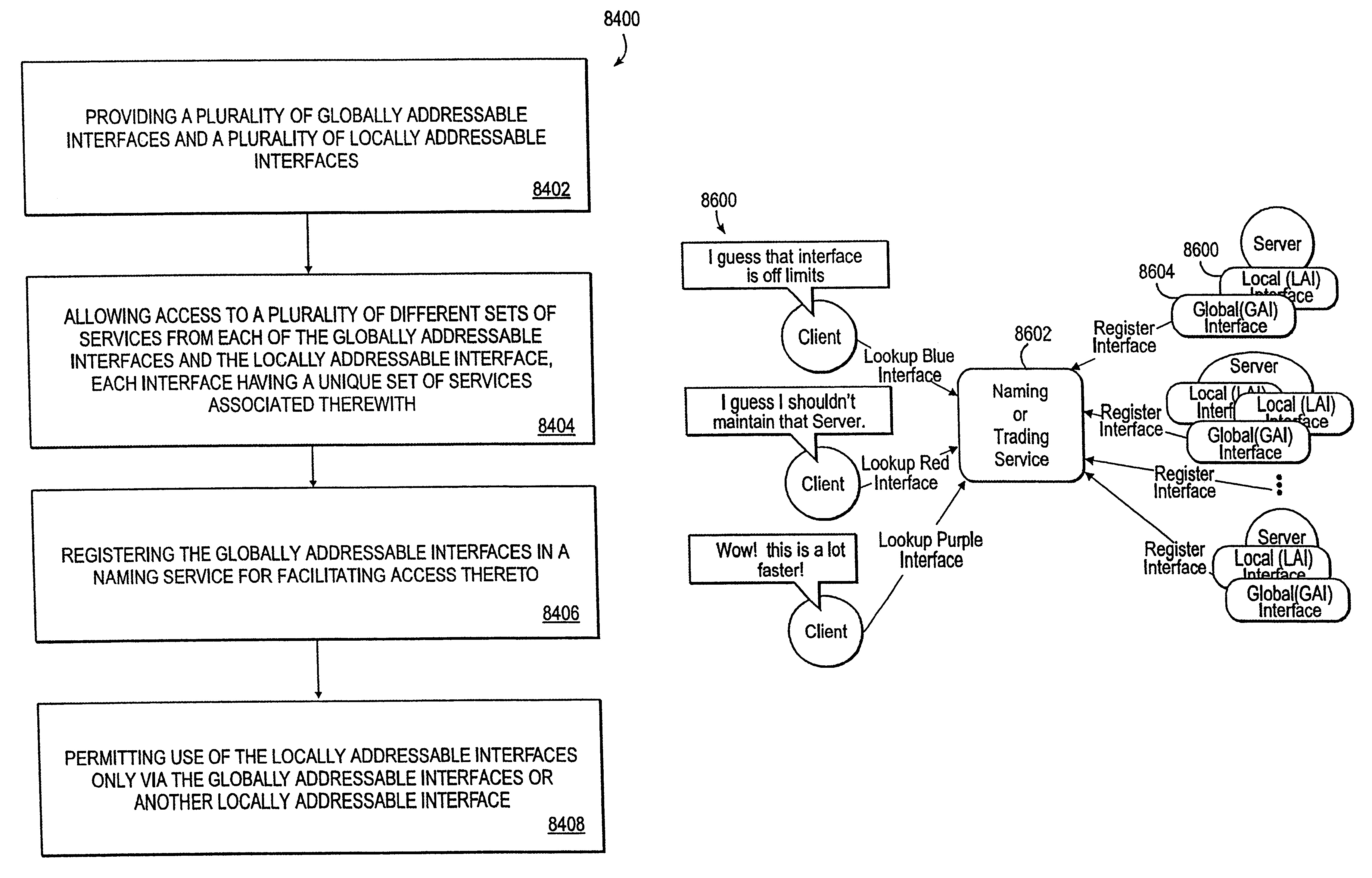
A system, method, and article of manufacture are provided for delivering service via a locally addressable interface. A plurality of globally addressable interfaces and a plurality of locally addressable interfaces are provided. Access is allowed to a plurality of different sets of services from each of the globally addressable interfaces and the locally addressable interface. Each interface has a unique set of services associated therewith. The globally addressable interfaces are registered in a naming service for facilitating access thereto. Use of the locally addressable interfaces is permitted only via the globally addressable interfaces or another locally addressable interface.
Owner:ACCENTURE GLOBAL SERVICES LTD
Wireless communication
ActiveUS8102278B2Low costReduce power consumptionProgramme controlElectric signal transmission systemsComputer hardwareConverters
Described is a sensor unit having a measured signal receiver, which registers a measured signal, an A / D converter for digitizing the measured signal, a transceiver device for wireless data communication to an environmental device, and a processor. The processor is a control processor for activating the measured signal receiver, the A / D converter, and the transceiver device. The digitized measured signal is transmitted directly via the transceiver device to the environmental device, without the complex and performance-intensive and therefore costly analysis occurring in the sensor unit.
Owner:VEGA GRIESHABER GMBH & CO
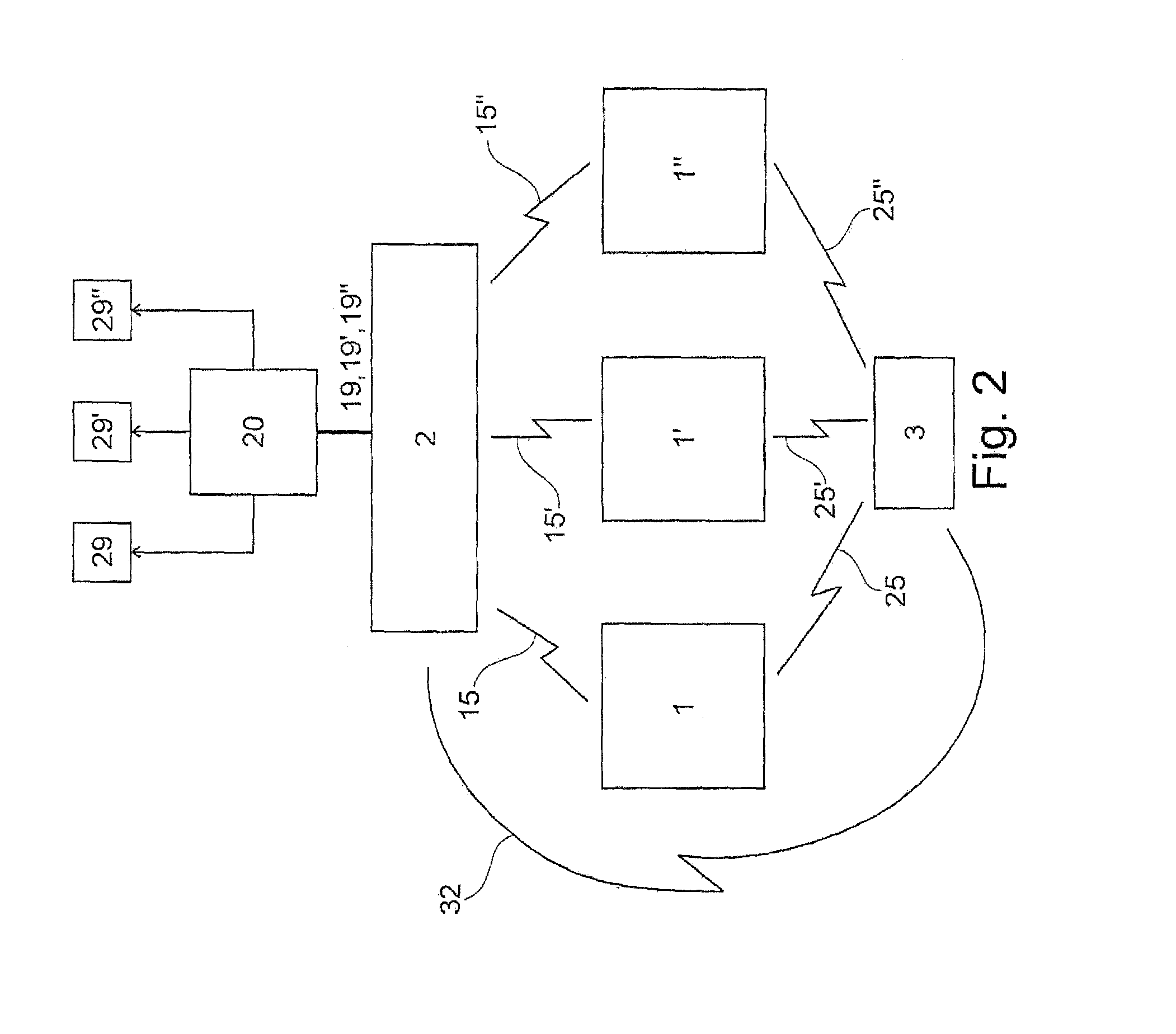
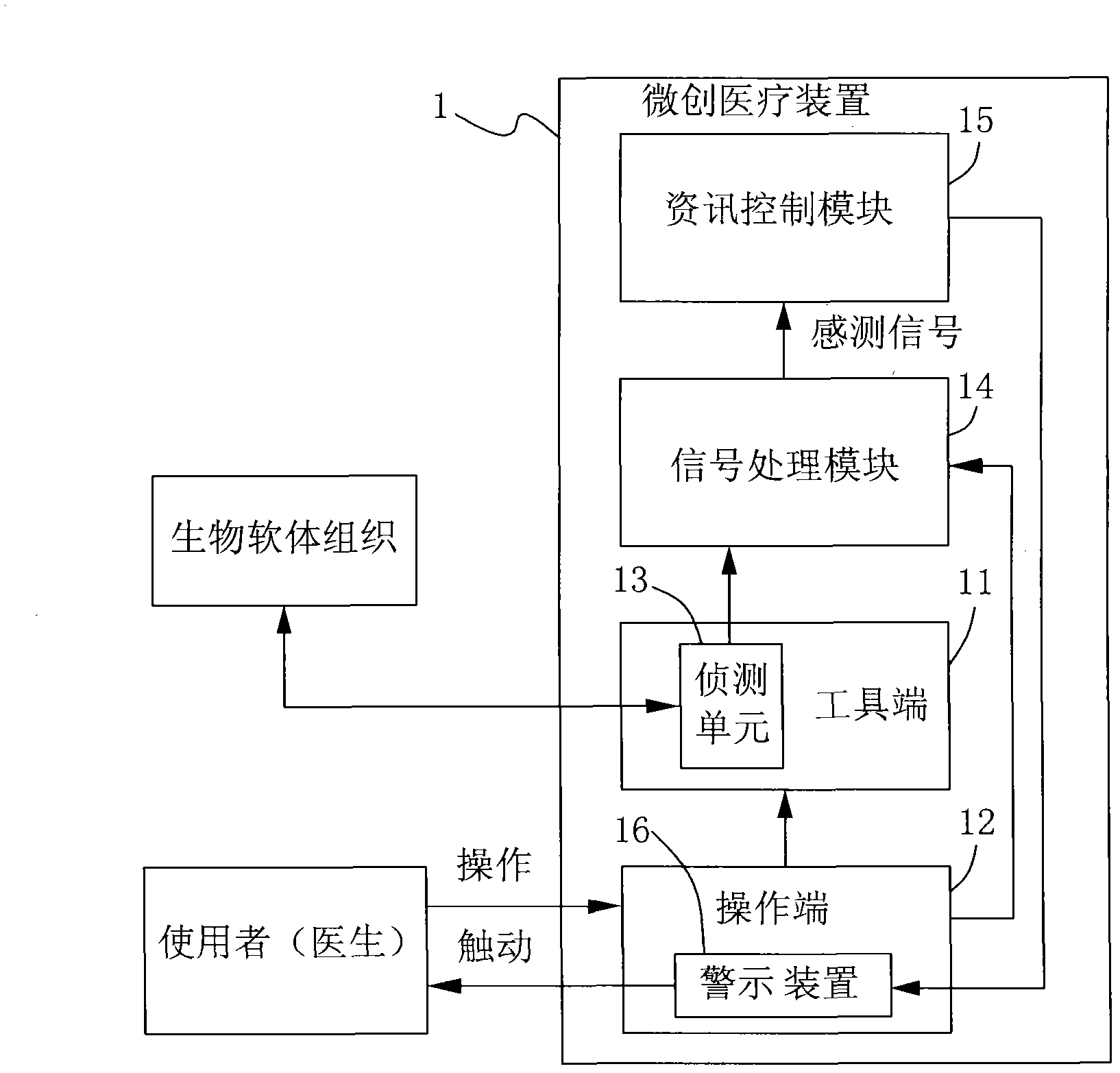
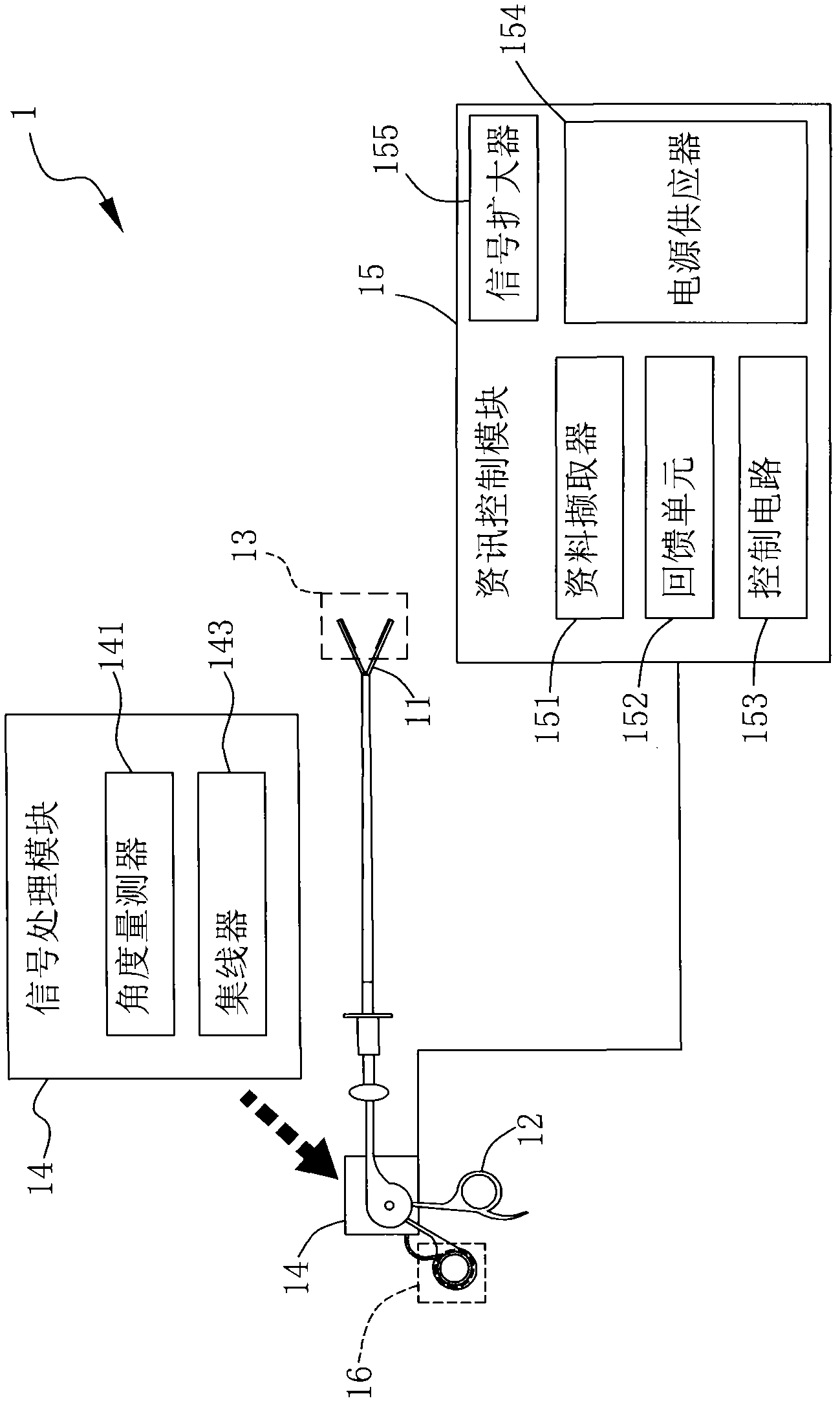
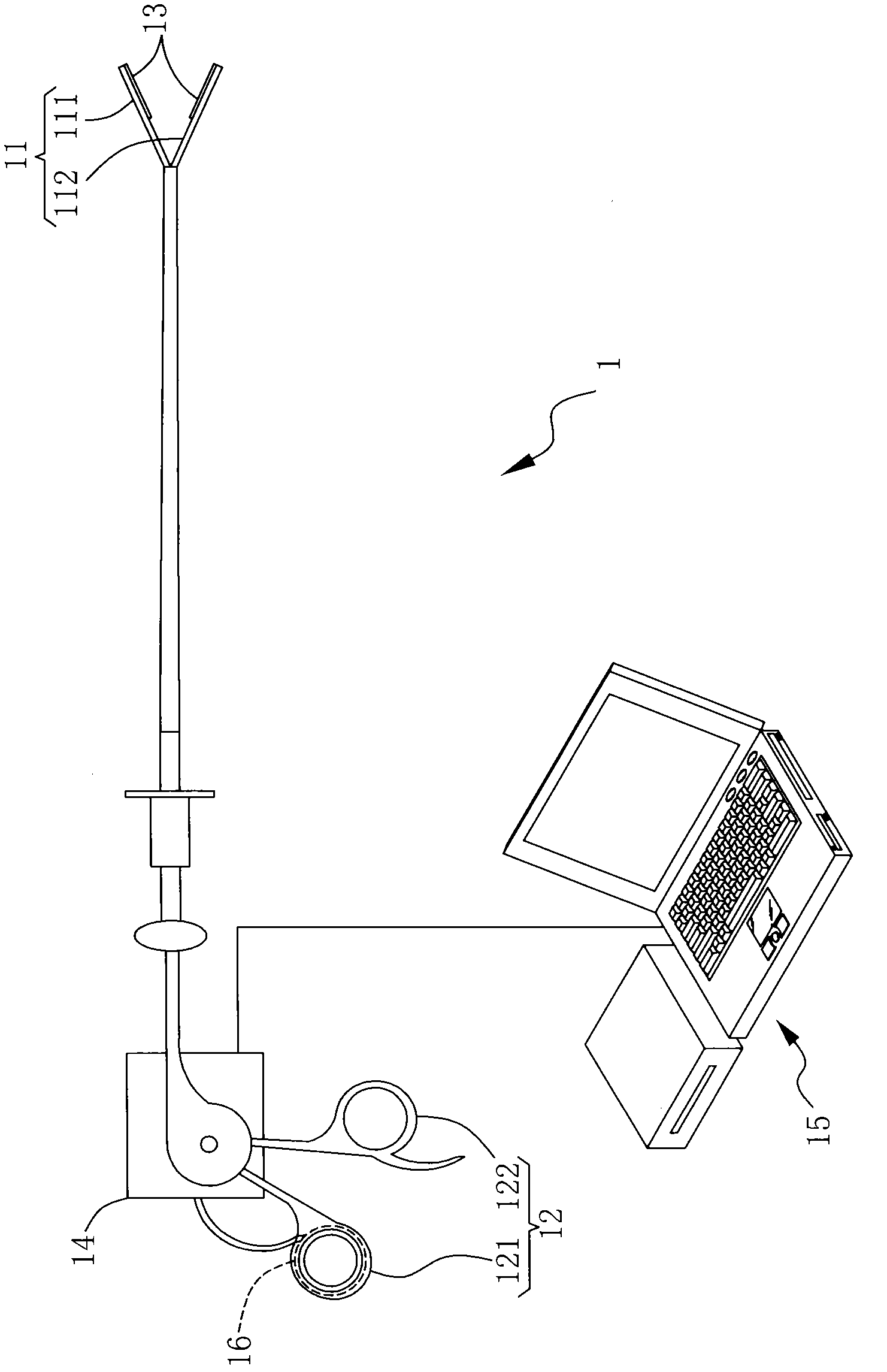
Minimal invasion medical device
The invention discloses a minimal invasion medical device. The minimal invasion medical device comprises a tool end, an operating end, a sensing end, a signal processing module, an information control module and a warning device, wherein the operating end controls the tool end to act; the sensing unit is arranged above the tool end; the signal processing module is electrically connected with the sensing unit; the information control module is electrically connected with the signal processing module; and the warning device is arranged above the operating end. Data contacted with the tool end is transformed into an electronic signal by the sensing unit on the tool end, the electronic signal is transmitted by the signal processing module and the information control module judges whether to drive the warning device to generate warning to inform a user on the operating end.
Owner:DAFAR INT
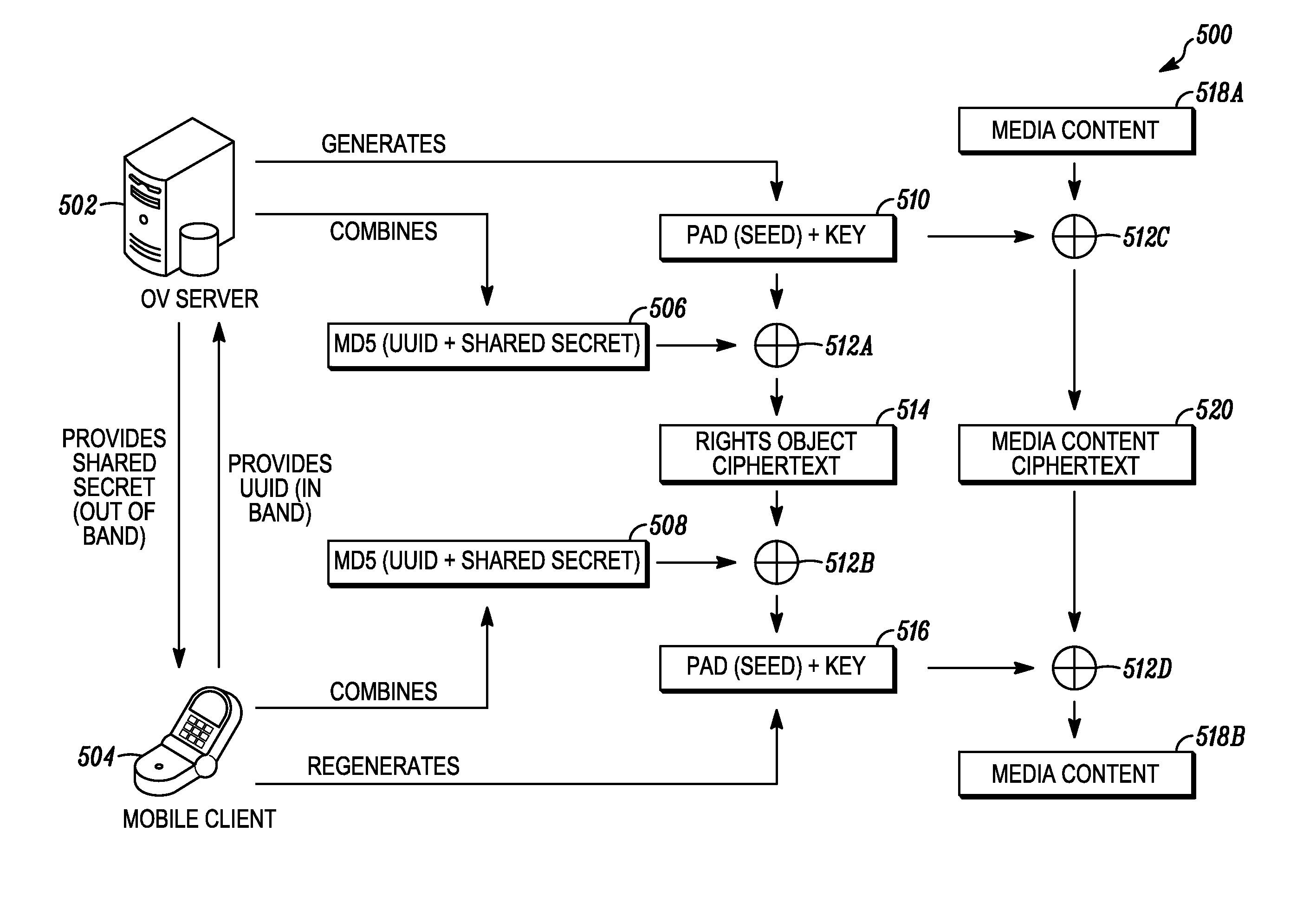
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
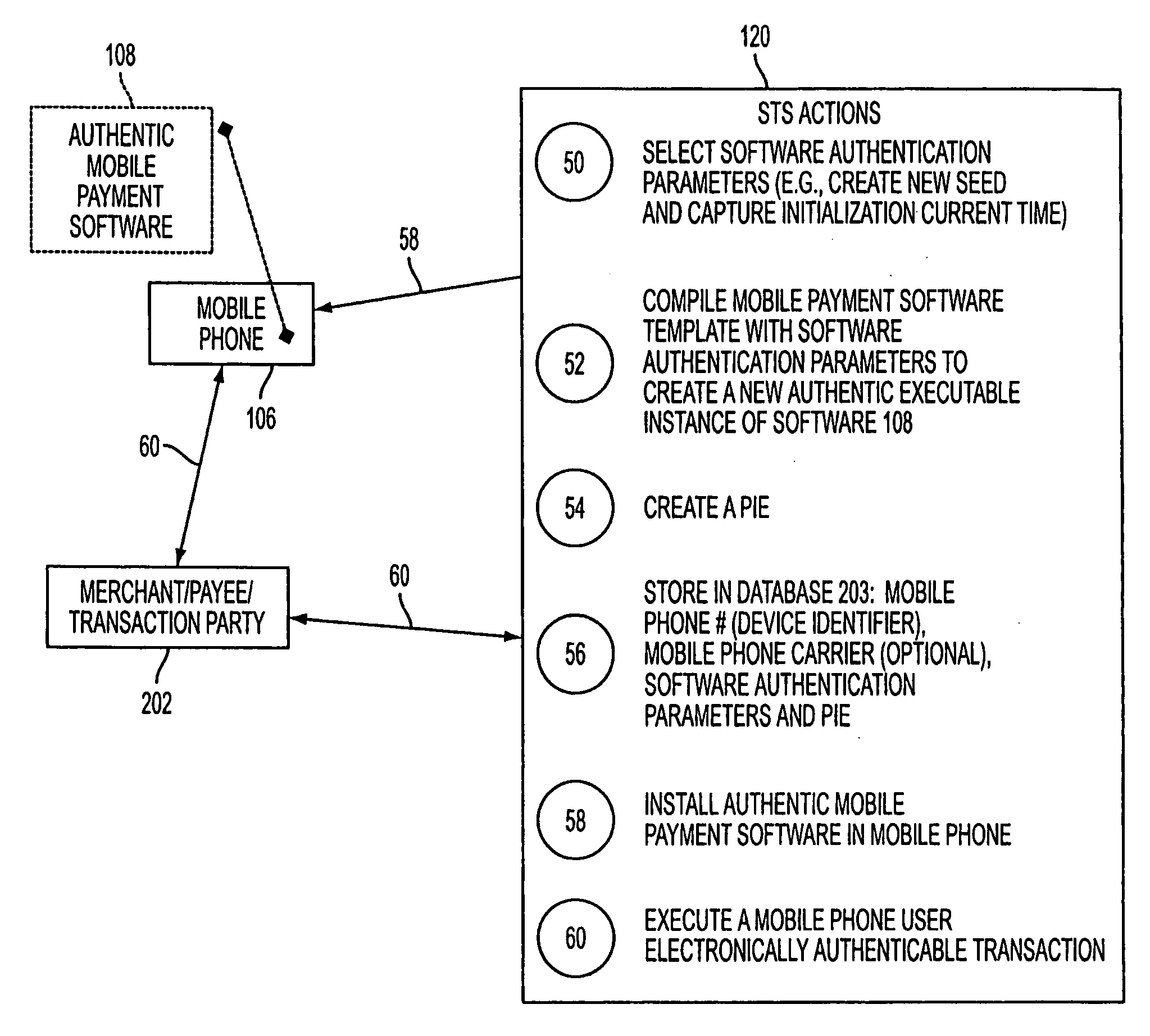
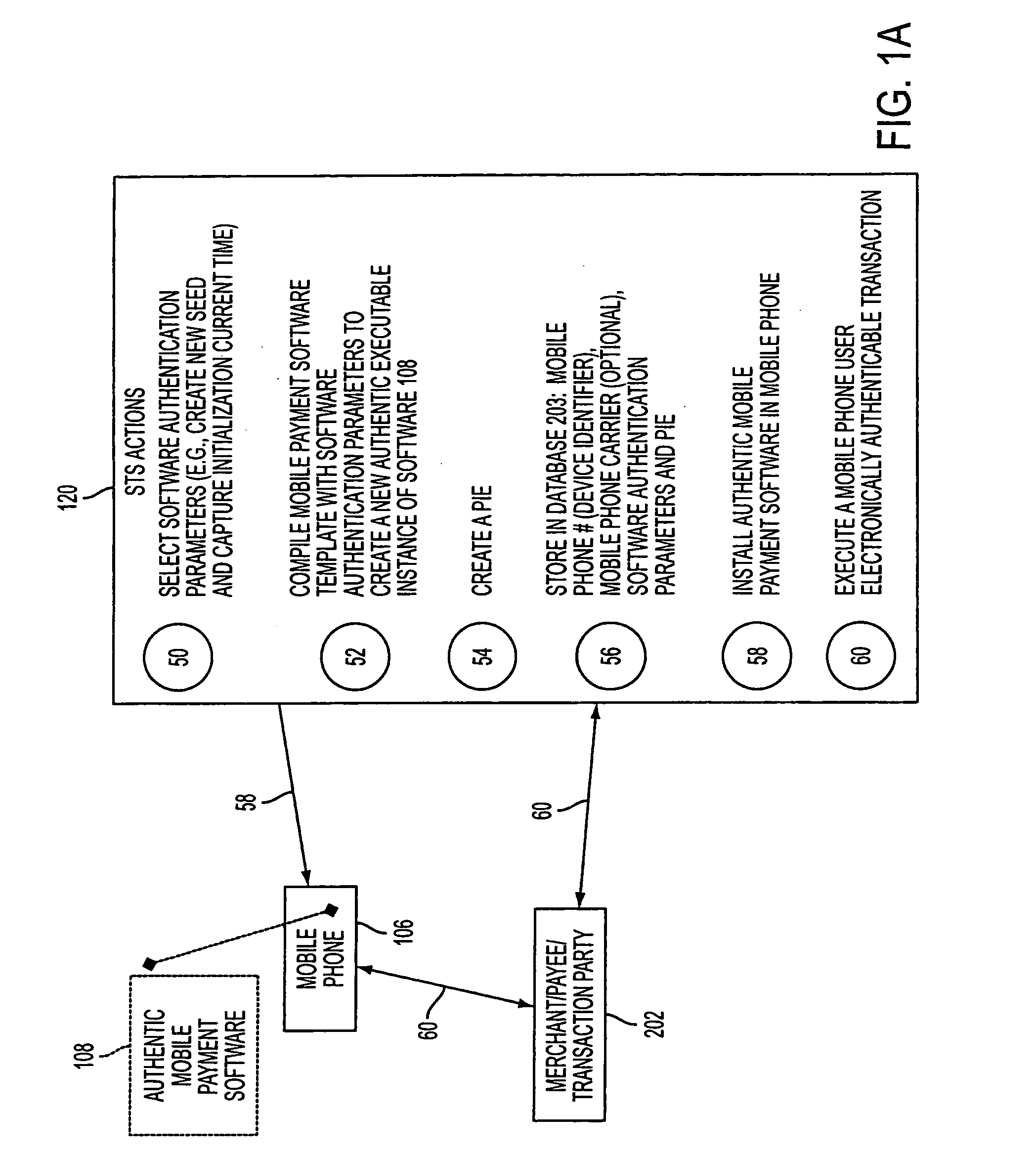
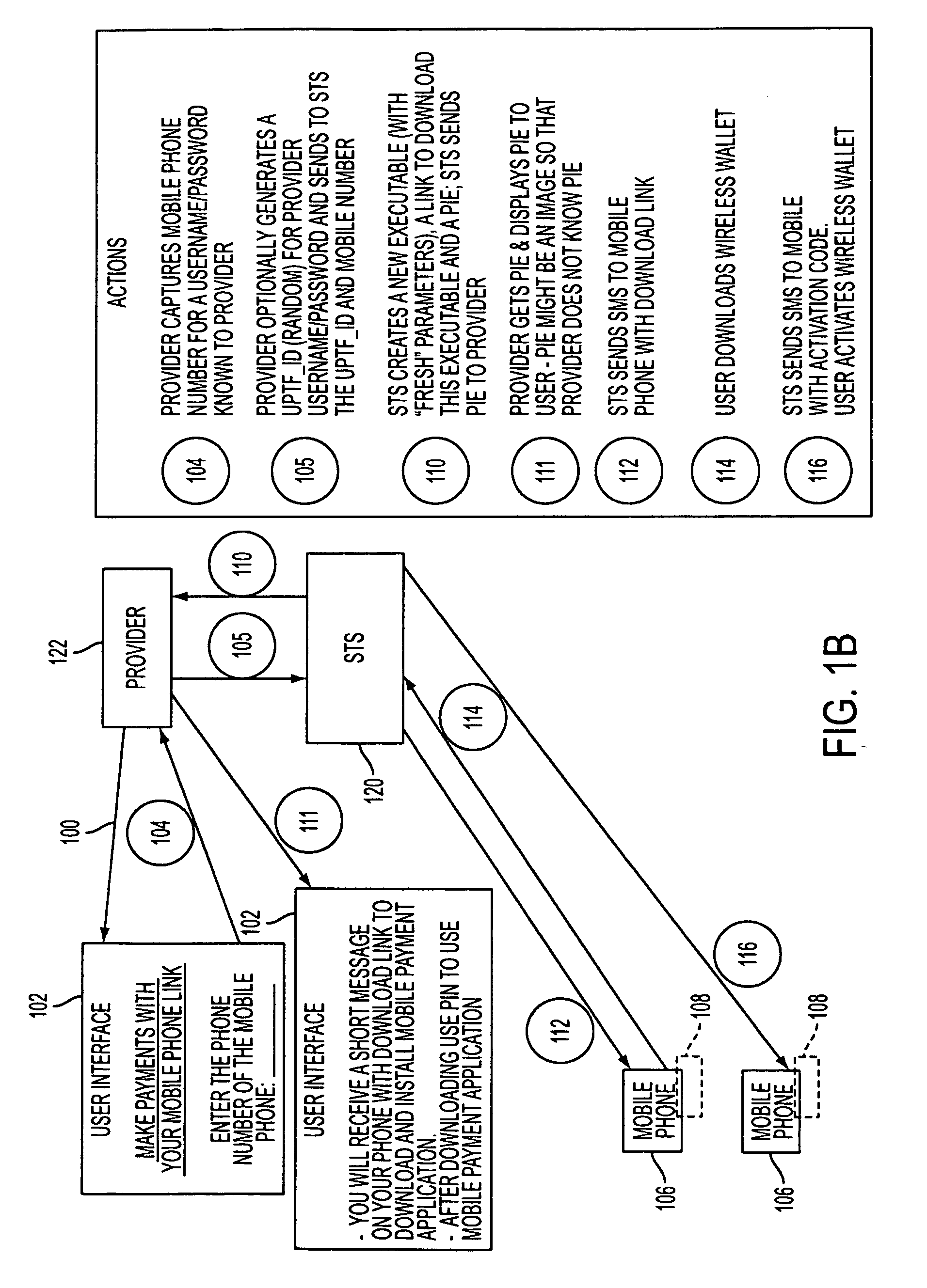
Wireless wallet
A mobile phone system and method of initializing, at a secure transaction server (STS), a mobile payment software with a software authentication parameter, as an authentic mobile payment software; providing an STS correlation between a personal identification entry (PIE) and the authentic mobile payment software; installing, in a mobile phone, the authentic mobile payment software; and inputting, by a user, the PIE to the installed authentic mobile payment software to generate according to the PIE and the software authentication parameter a transformed secure authenticable mobile phone cashless monetary transaction over the mobile phone network, as a mobile phone wireless wallet of the user of the mobile phone. The mobile phone authenticable cashless monetary transaction is performed according to an agreement view(s) protocol.
Owner:PCMS HOLDINGS INC
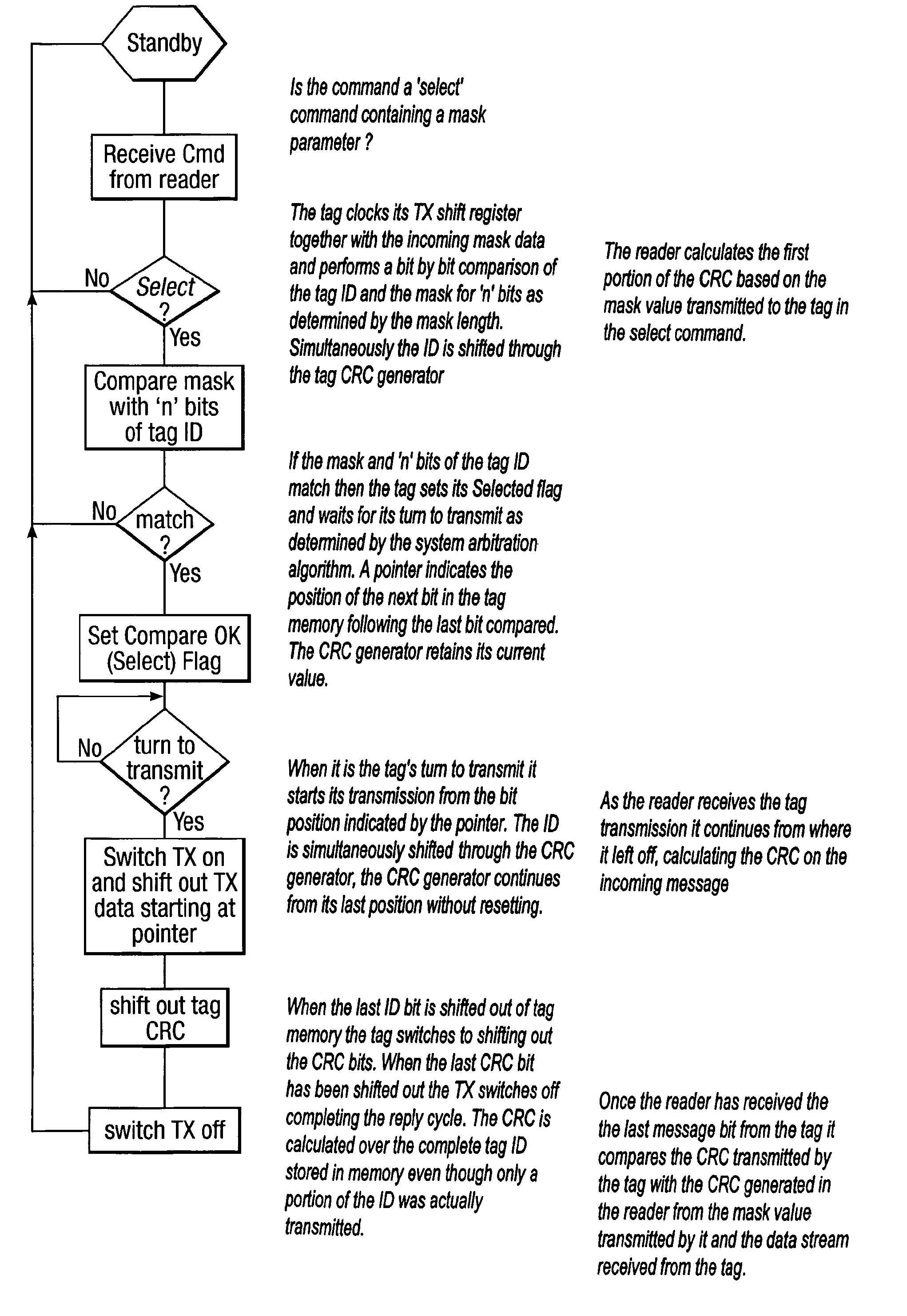
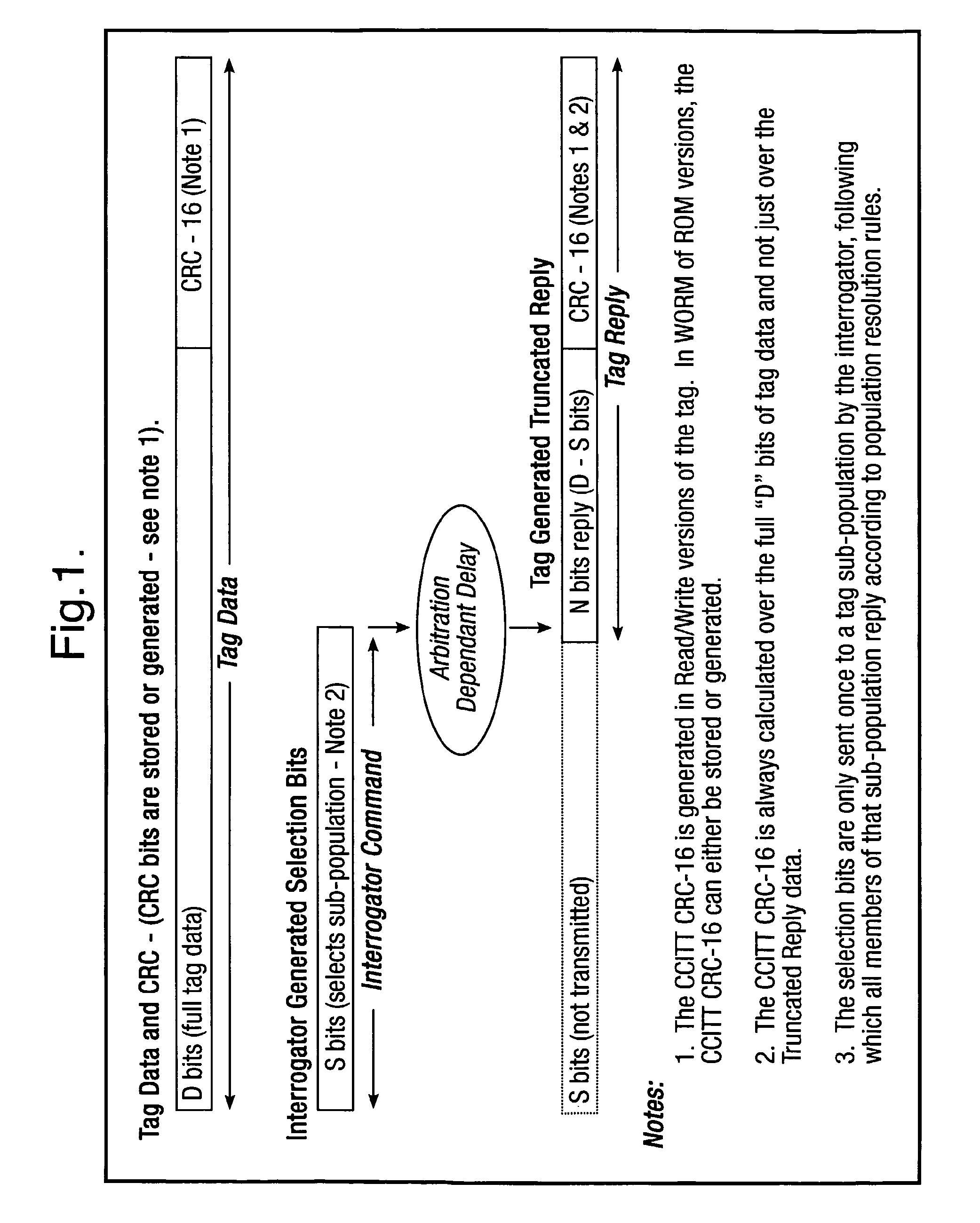
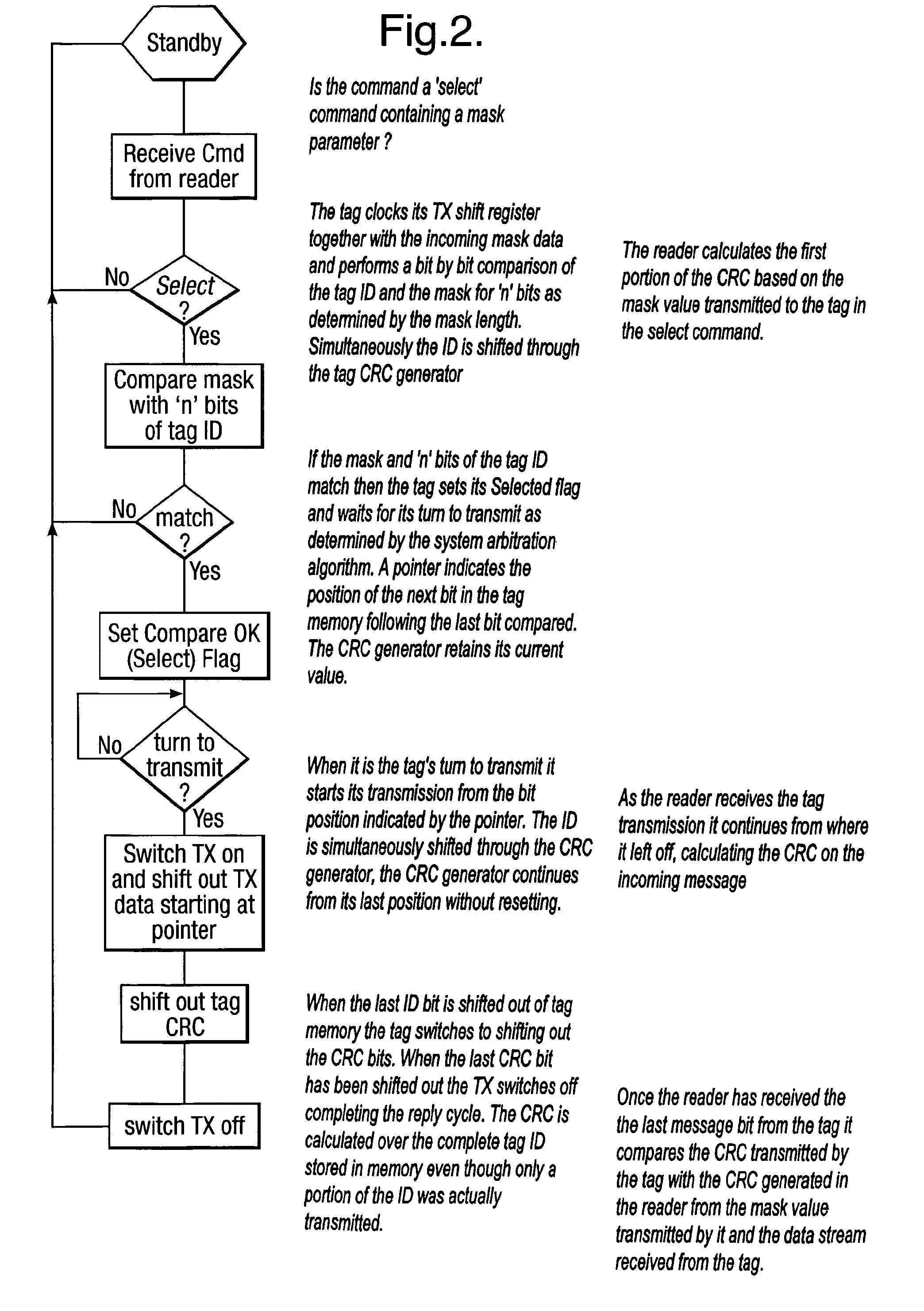
Method and system for calculating and verifying the integrity of data in a data transmission system
ActiveUS7987405B2Not having capability to accuratelyStay flexibleError preventionMemory record carrier reading problemsComputer hardwareData integrity
A method is described of calculating and verifying the integrity of data in a data communication system. The system comprises a base station and one or more remote stations, such as in an RFID system. The method includes transmitting a select instruction from the base station to the one or more remote stations, the select instruction containing a data field which matches a portion of an identity or other data field in one or more of the remote stations; transmitting from a selected remote station or stations a truncated reply containing identity data or other data of the remote station but omitting the portion transmitted by the base station; calculating in the base station a check sum or CRC from the data field originally sent and the truncated reply data received and comparing the calculated check sum or CRC with the check sum or CRC sent by the remote station.
Owner:ZEBRA TECH CORP
Debugging site errors by an admin as a guest user in a multi-tenant database environment
An approach for debugging site errors in a multi-tenant database system is disclosed. An example method can include receiving a request from a site administrator to access an enhanced error message and determining if the site administrator is approved for viewing the enhanced error message by evaluating exceptions associated with the enhanced error message, the request, and the site administrator. The example method further includes modifying a detailed error message related to the request for generating the enhanced error message, and providing the enhanced error message to the site administrator based on the approval determination.
Owner:SALESFORCE COM INC
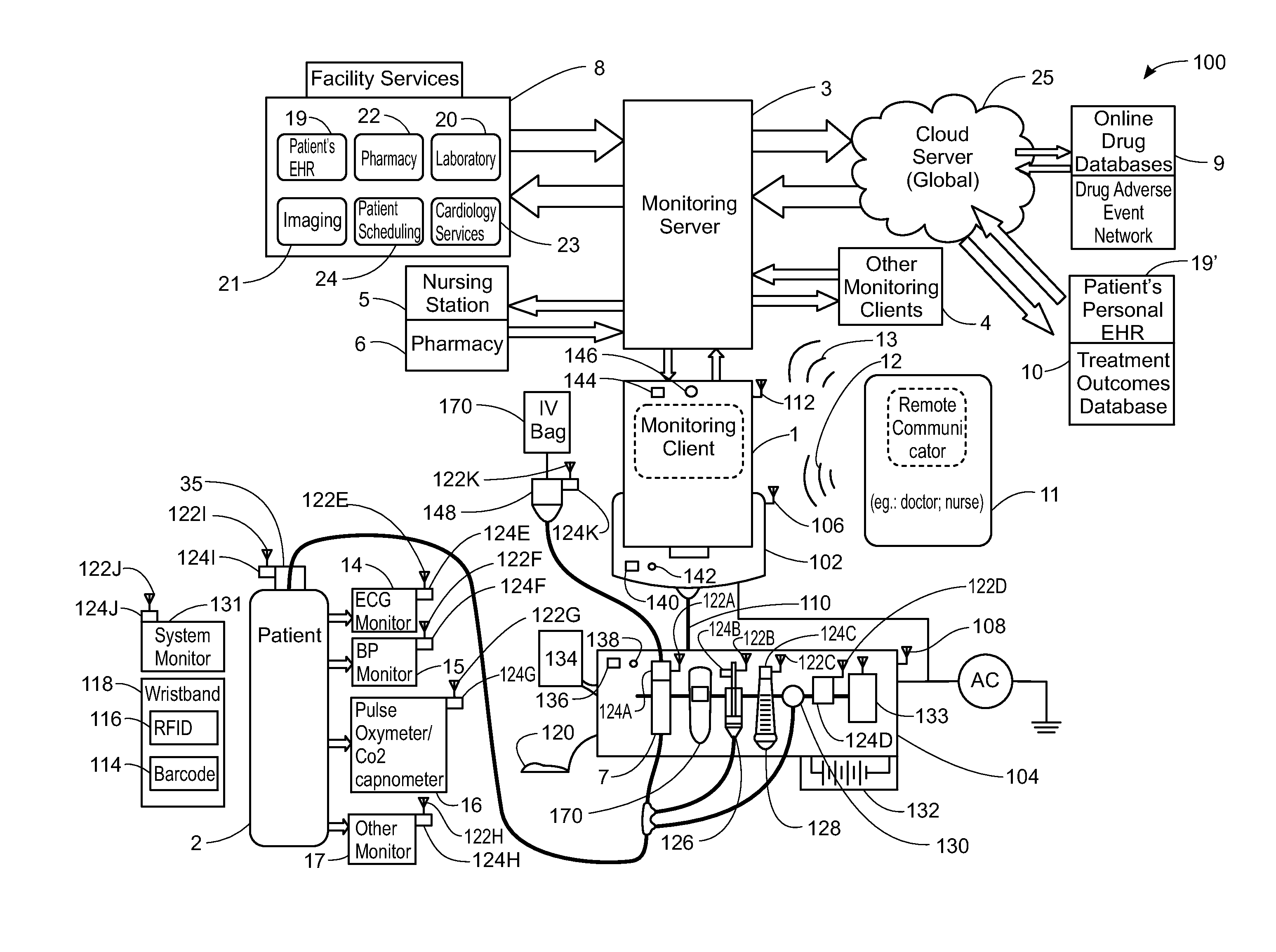
System, Method, and Apparatus for Electronic Patient Care
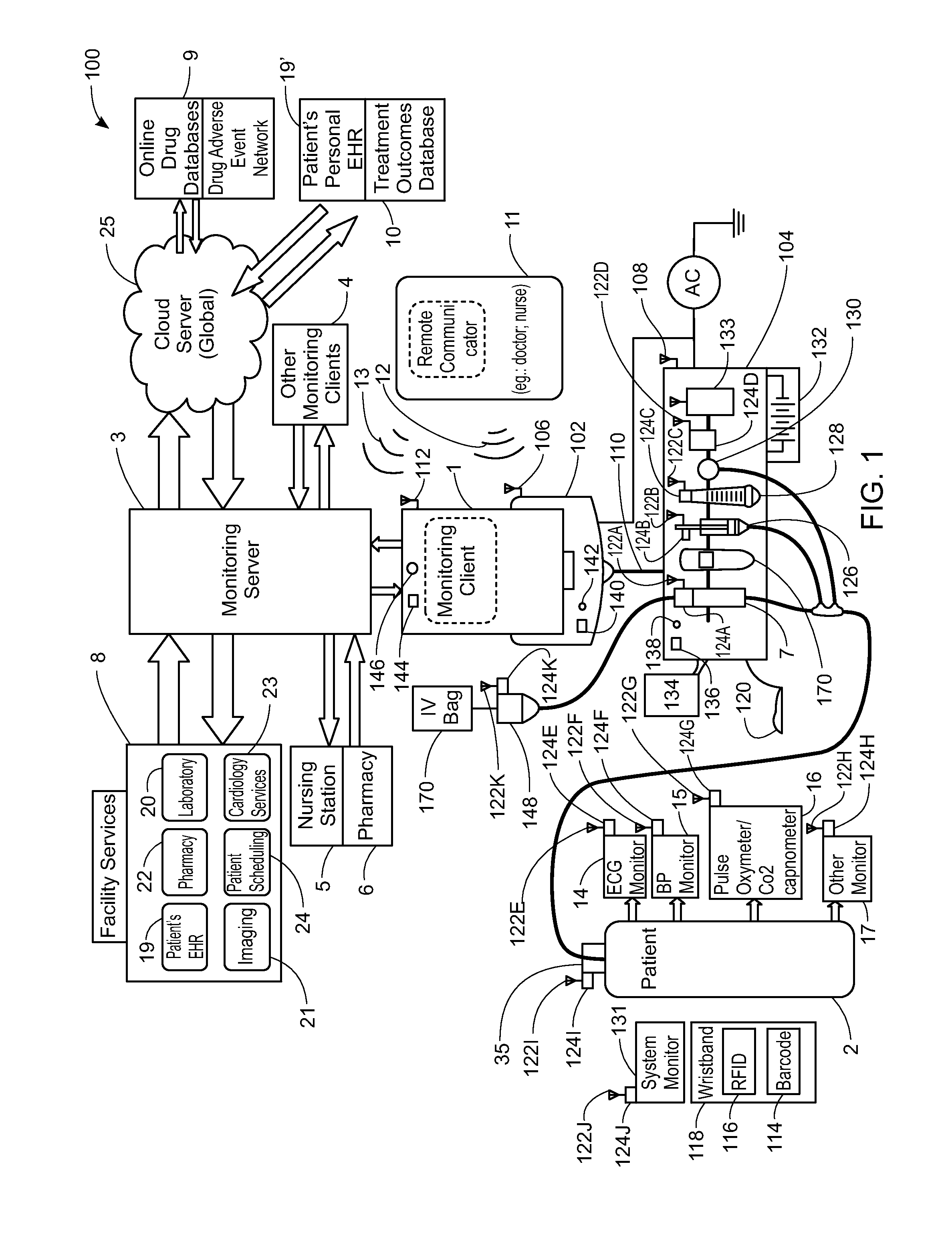
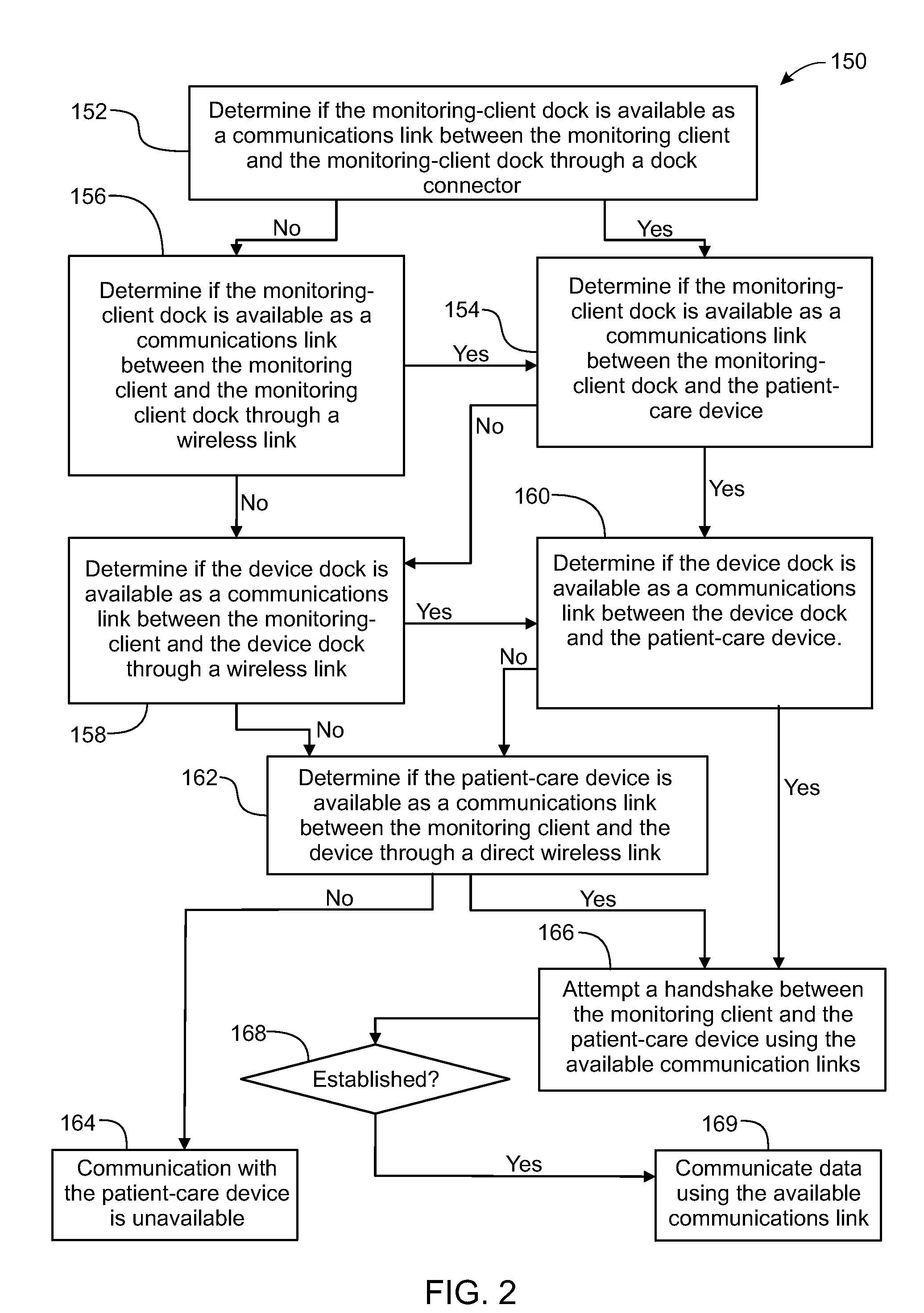
ActiveUS20130317753A1Quantity minimizationPerson identificationDigital computer detailsComputer hardwareCommunication link
A method implemented by an operative set of processor executable instructions configured for execution by a processor includes: determining if a monitoring client is connected to a base through a physical connection; establishing a first communications link between the monitoring client and the base through the physical connection; updating, if necessary, the interface program on the monitoring client and the base through the first communications link; establishing a second communications link between the monitoring client and the base using the first communications link; and communicating data from the base to the monitoring client using the second communications link.
Owner:DEKA PROD LLP
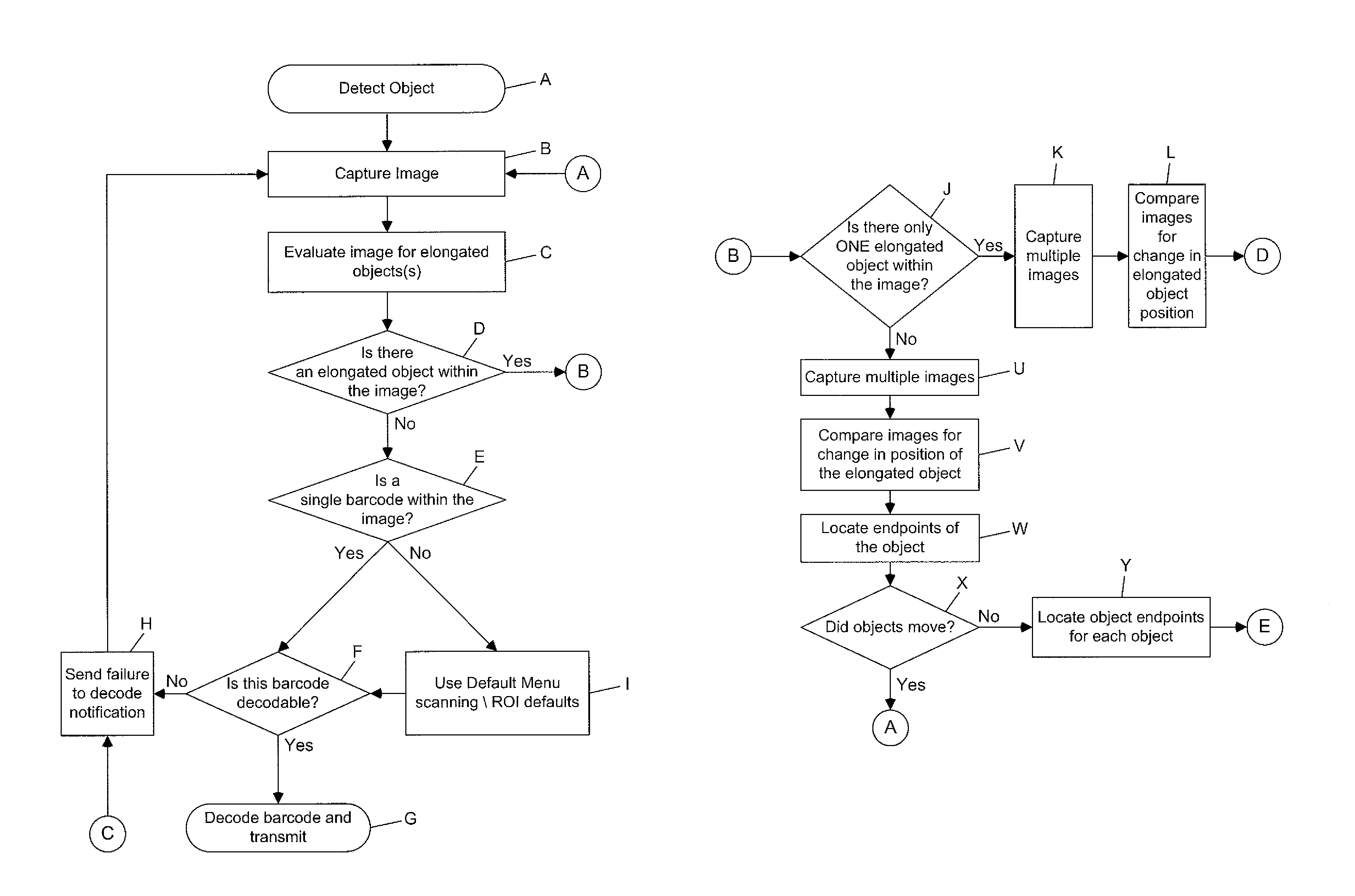
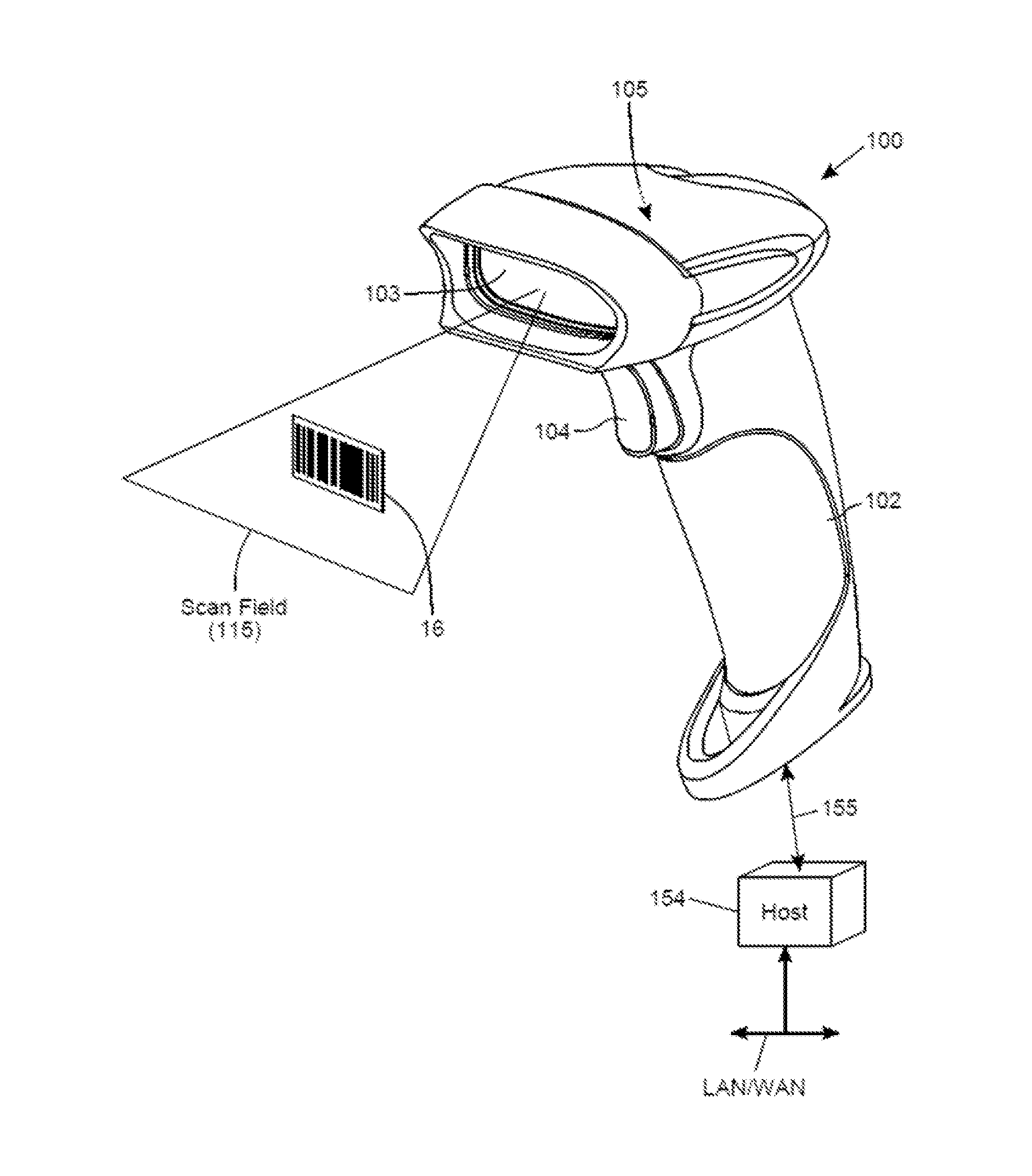
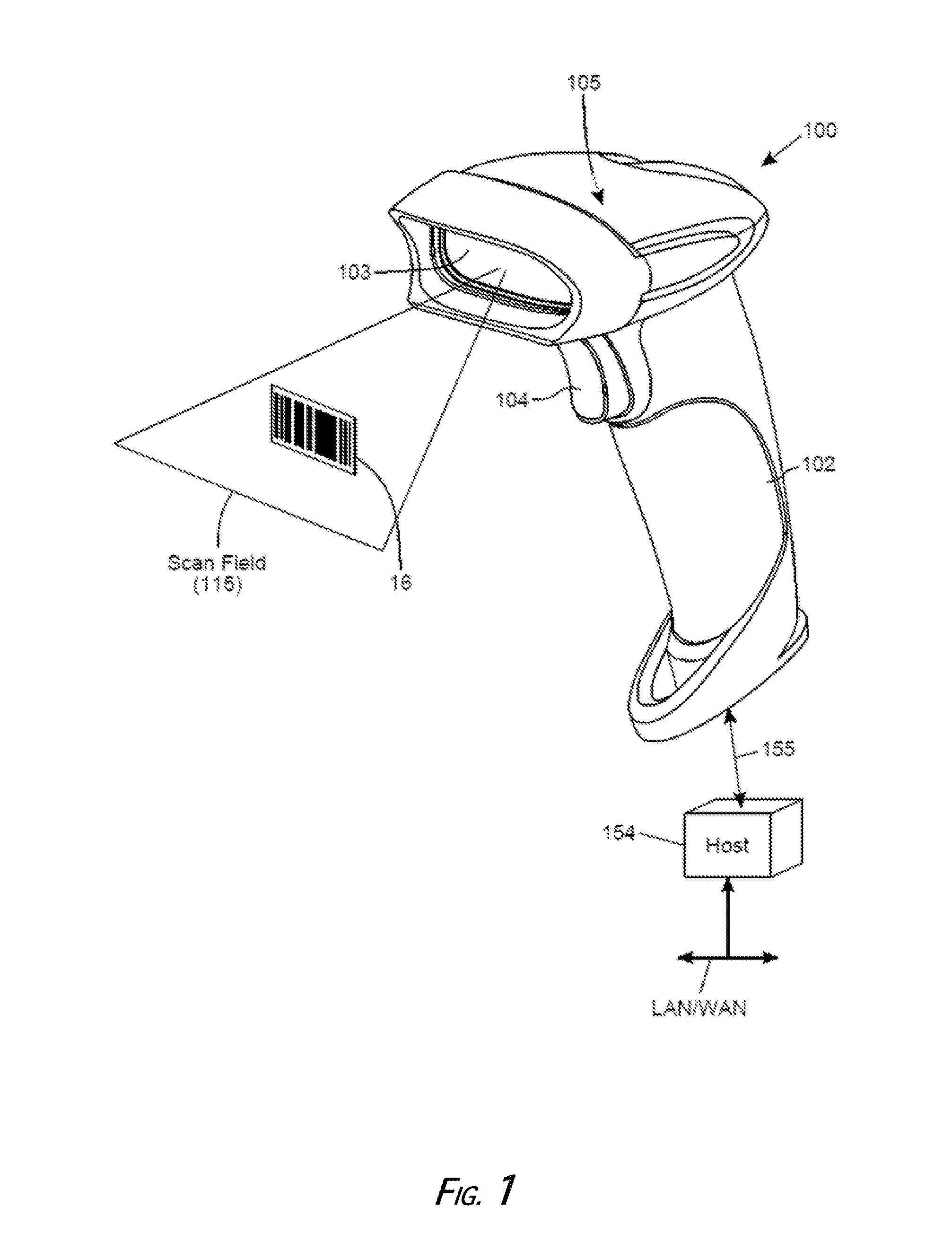
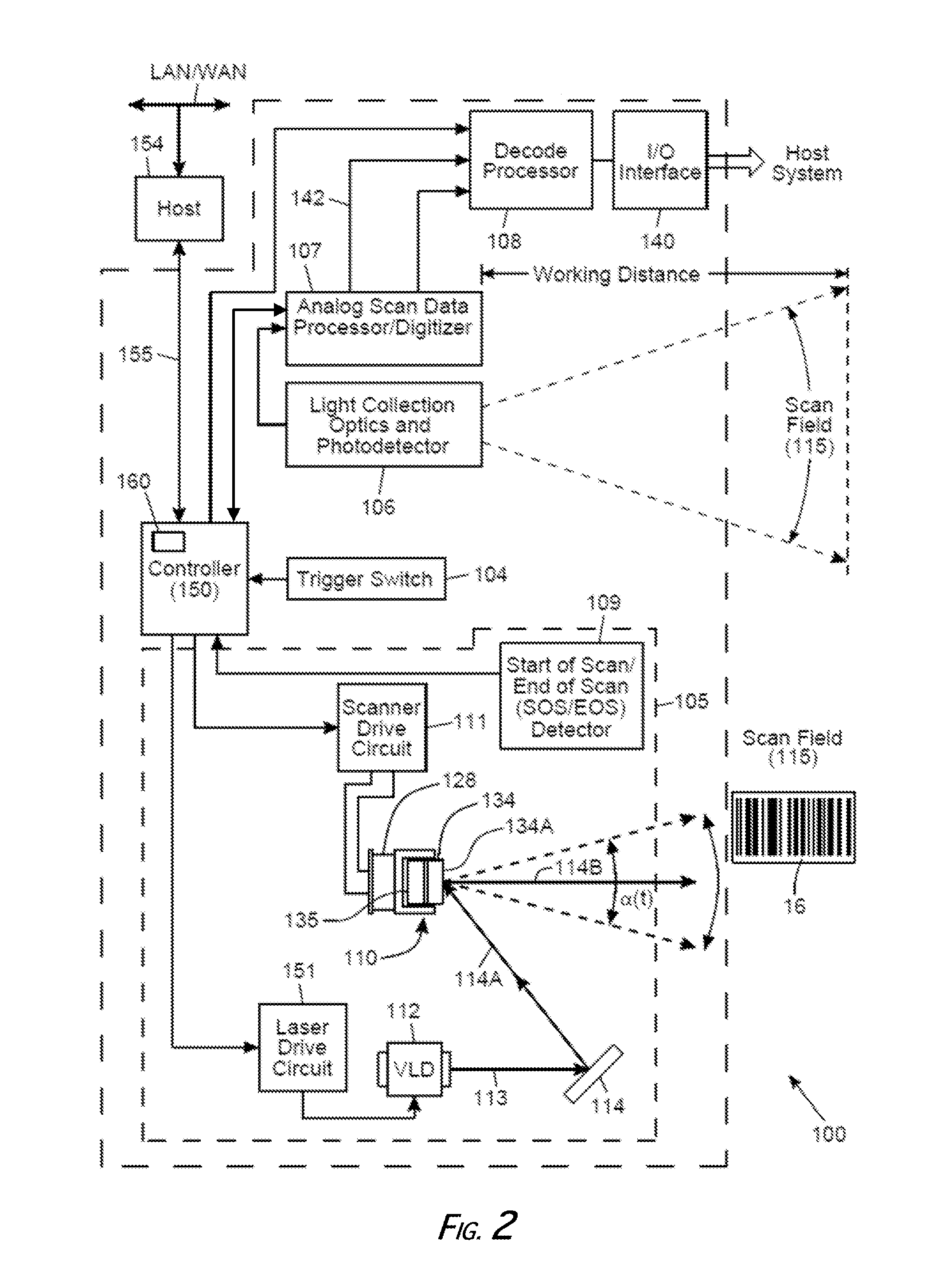
Digital-imaging based code symbol reading system having finger-pointing triggered mode of operation
ActiveUS8490877B2Character and pattern recognitionSensing by electromagnetic radiationComputer hardwareProgramming language
A digital-imaging based system for and method of reading graphical indicia, including code symbols, on objects such as, but not limited to, code symbol menus by the user simply pointing his or her finger at the particular code symbol on the code symbol menu to be read, while digital images of the code symbol menu and the pointing finger are automatically captured, buffered and processed.
Owner:METROLOGIC INSTR
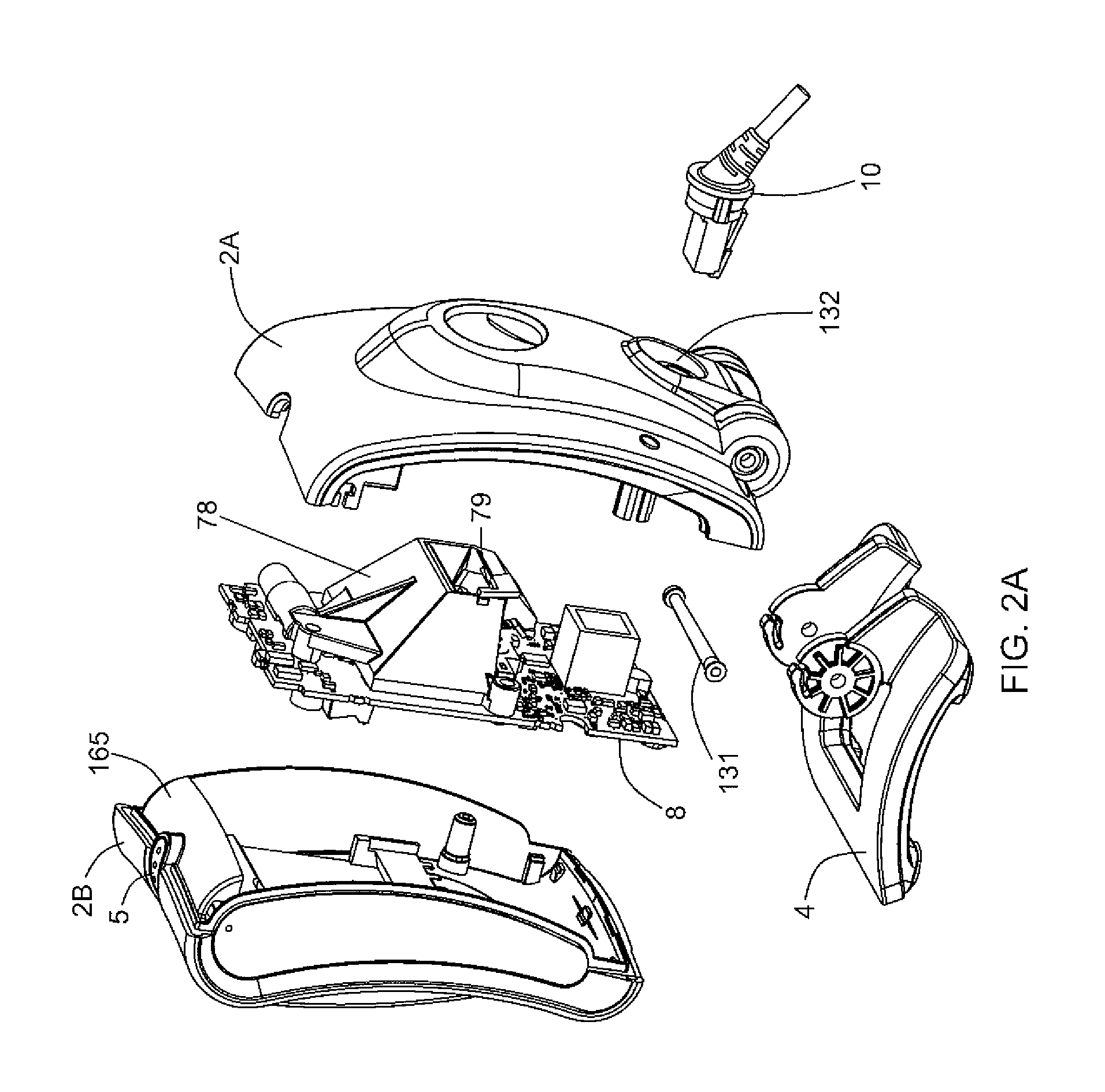
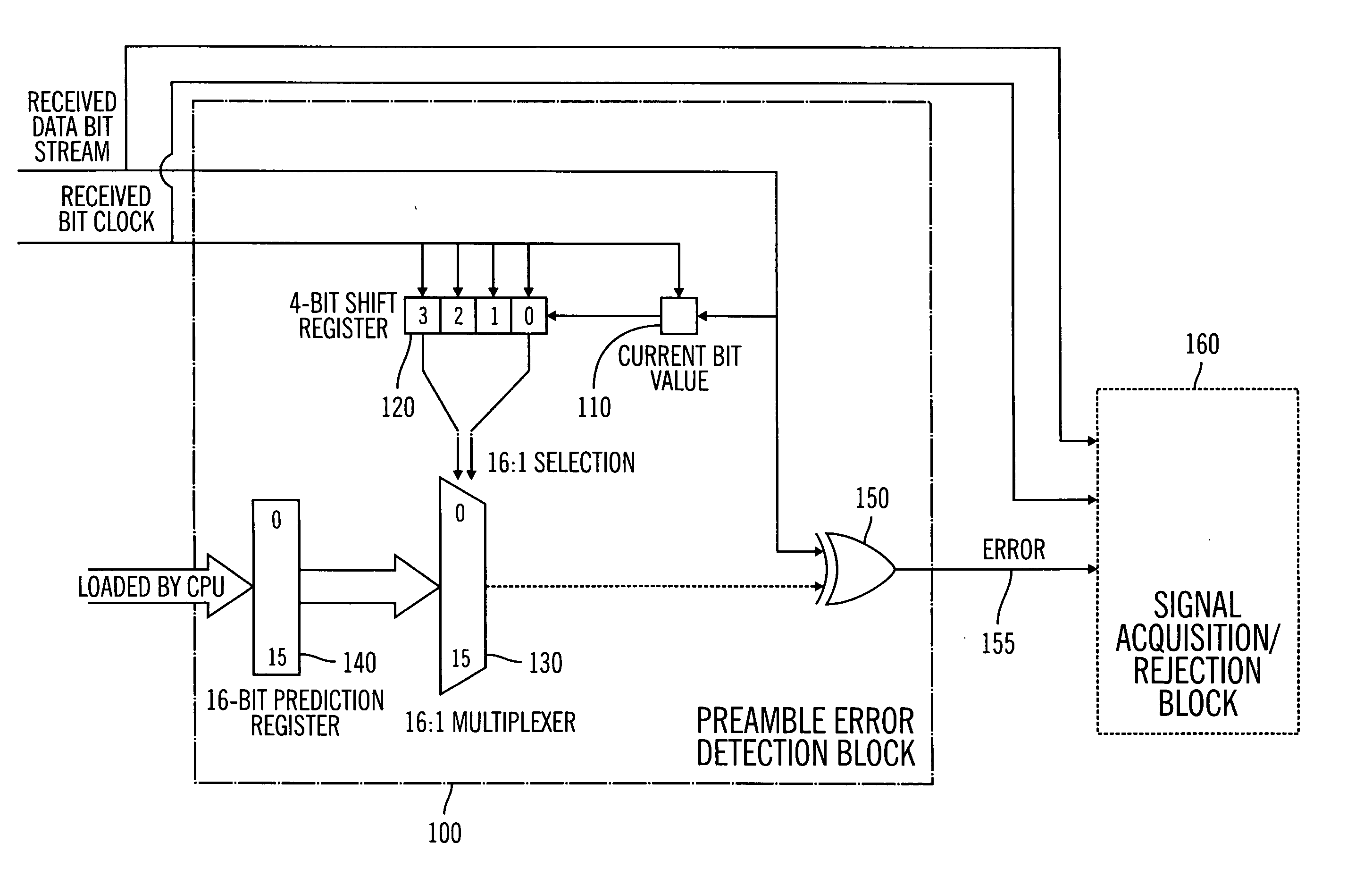
Rapid discrimination preambles and methods for using the same
InactiveUS20050195930A1Sync fastLess power consumptionEnergy efficient ICTElectrotherapyComputer hardwareSystems approaches
A system, method and program are disclosed for achieving rapid bit synchronization in low power medical device systems. Messages are transmitted via telemetry between a medical device and a communication device. The synchronization scheme uses a portion of a unique preamble bit pattern to identify the communication device allowing for economical communications with a minimum expenditure of energy. A special set of preamble bit patterns are utilized for their unique synchronization properties making them particularly suited for rapid bit synchronization. These unique preamble bit patterns further provide simplification to the preamble error detection logic.
Owner:MEDTRONIC MIMIMED INC
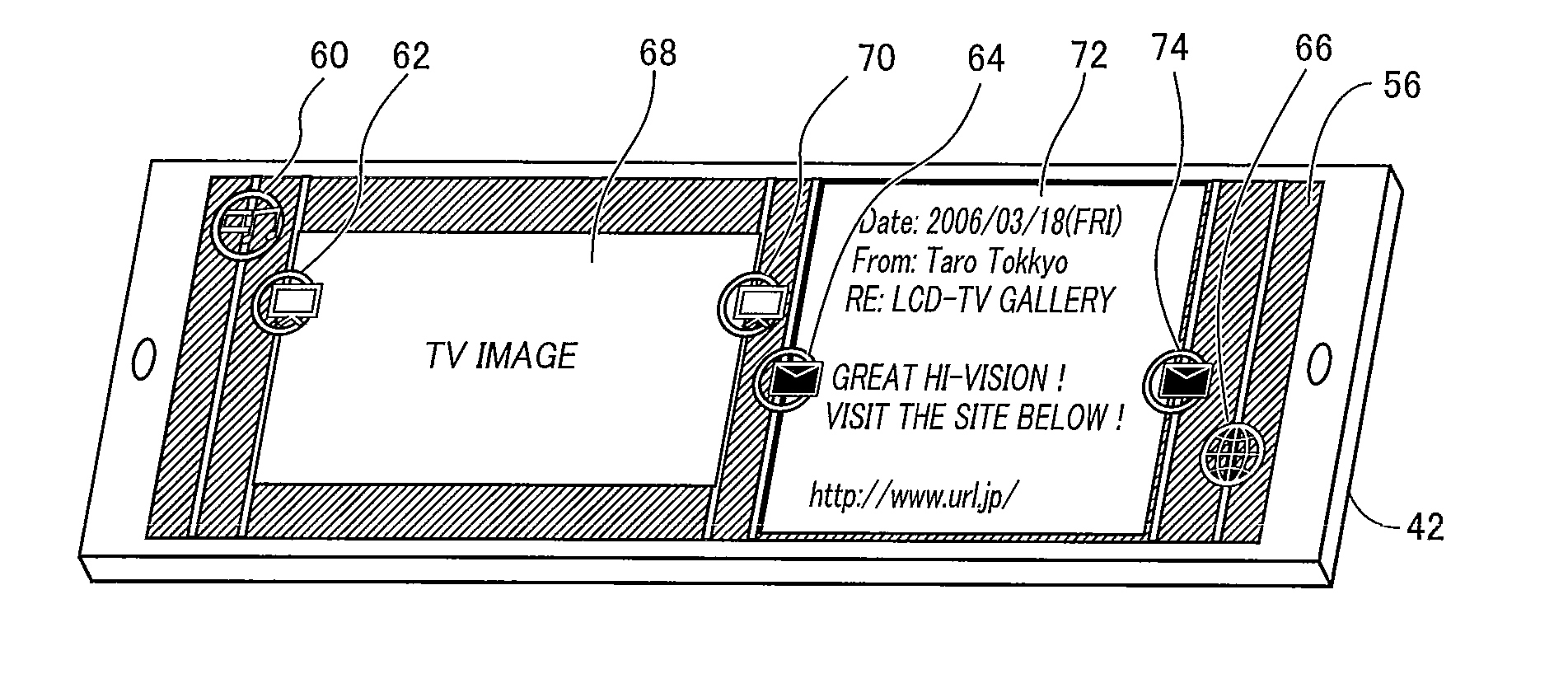
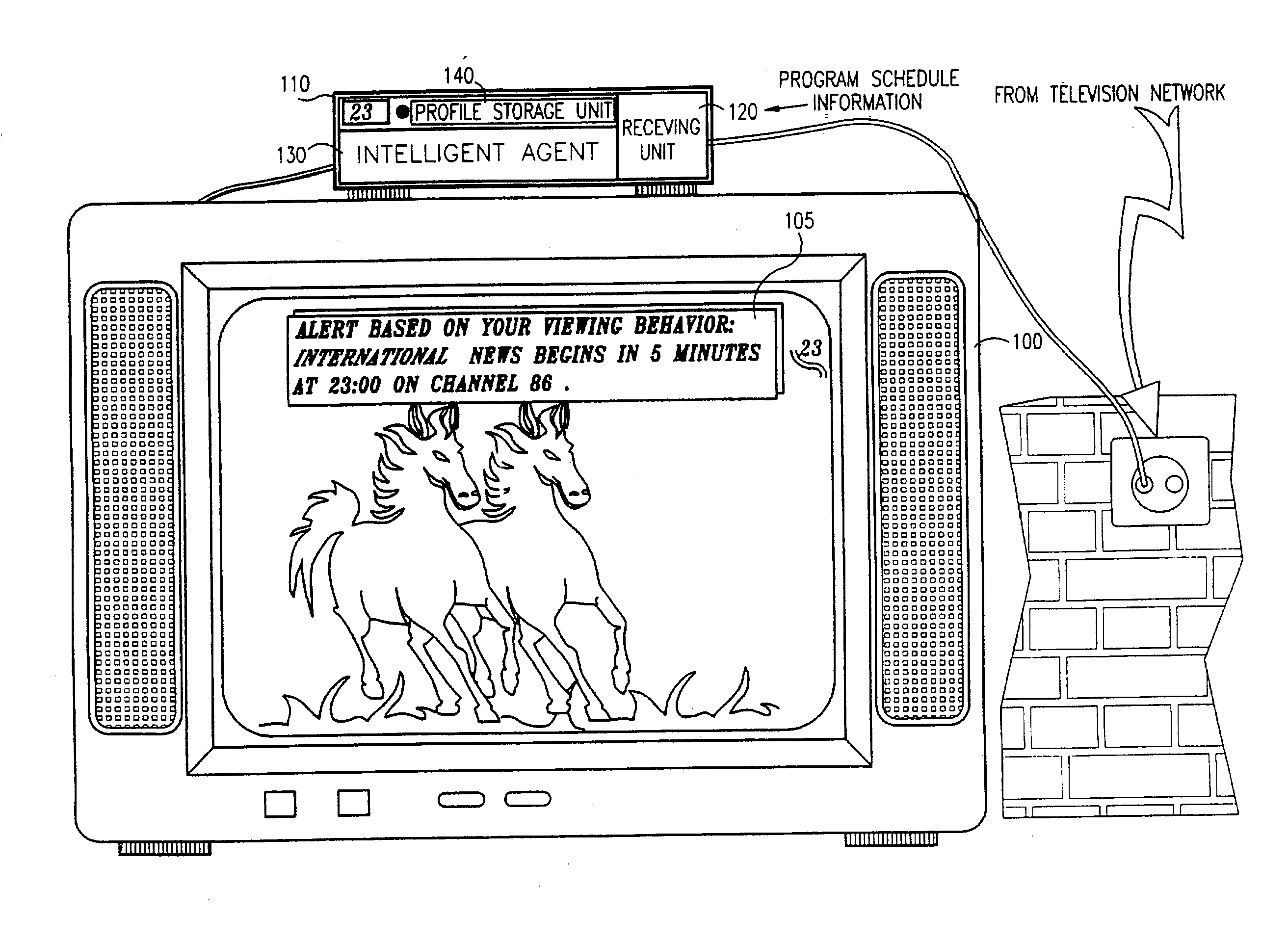
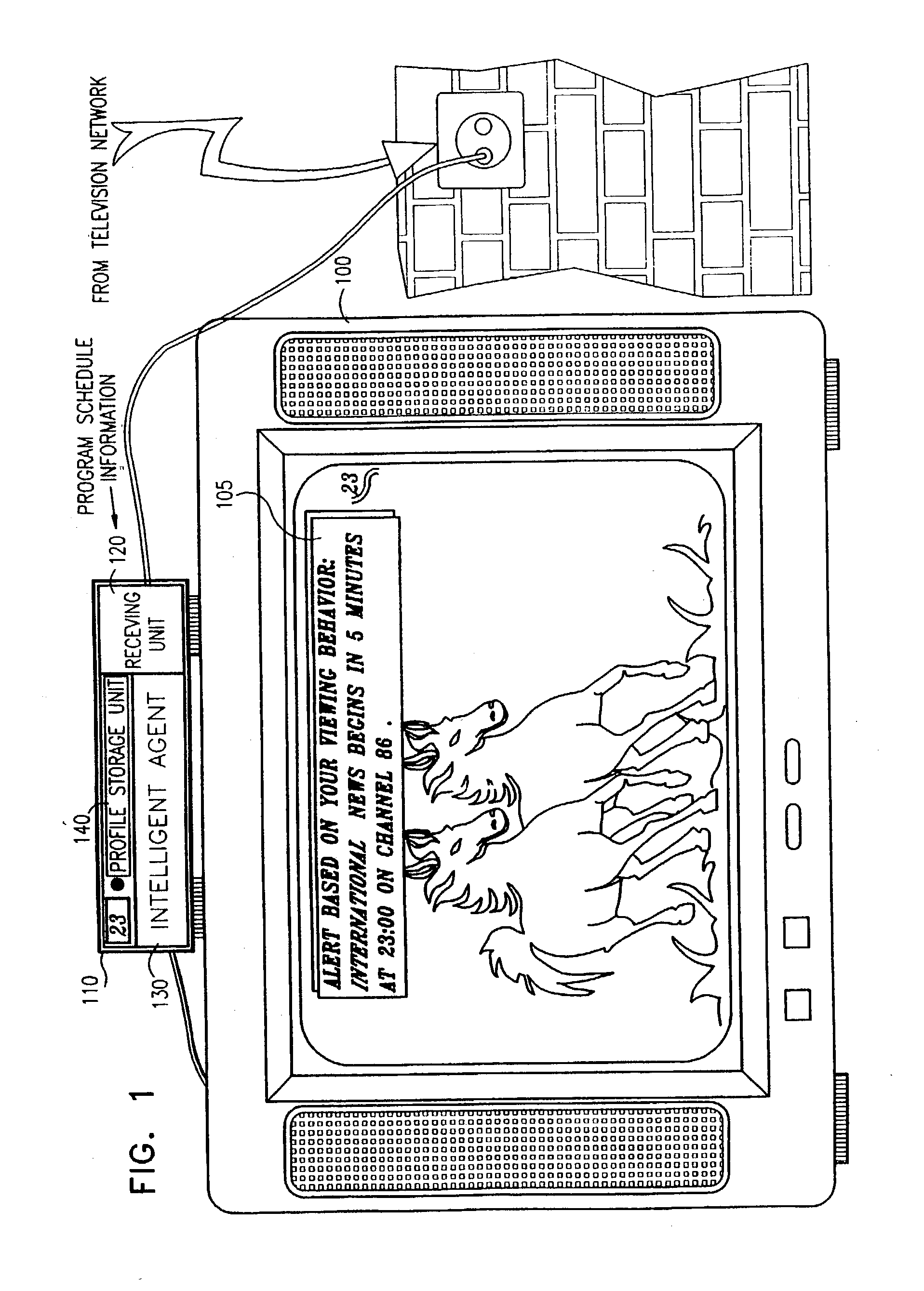
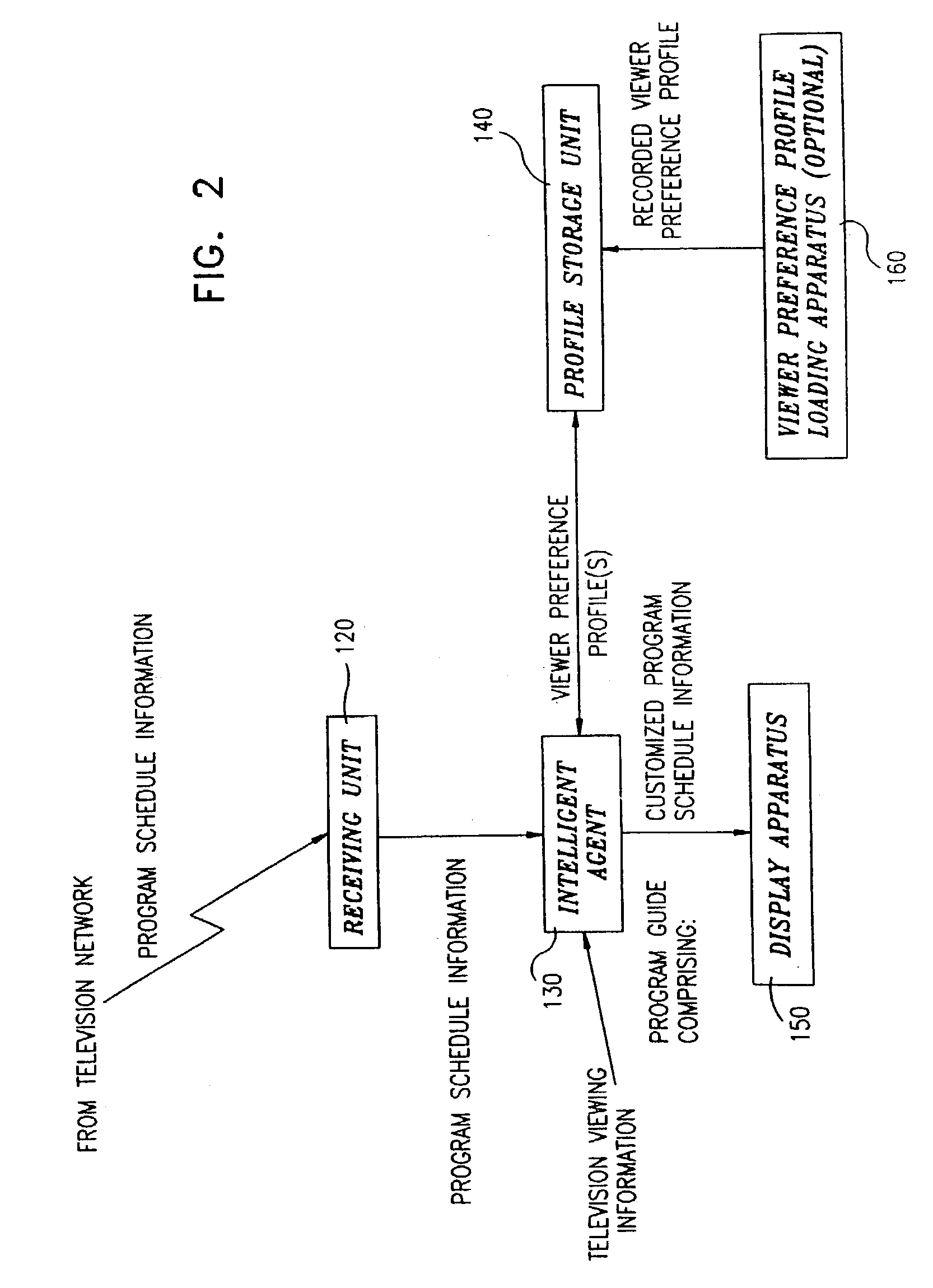
Graphical tuning bar for a multi-program data stream
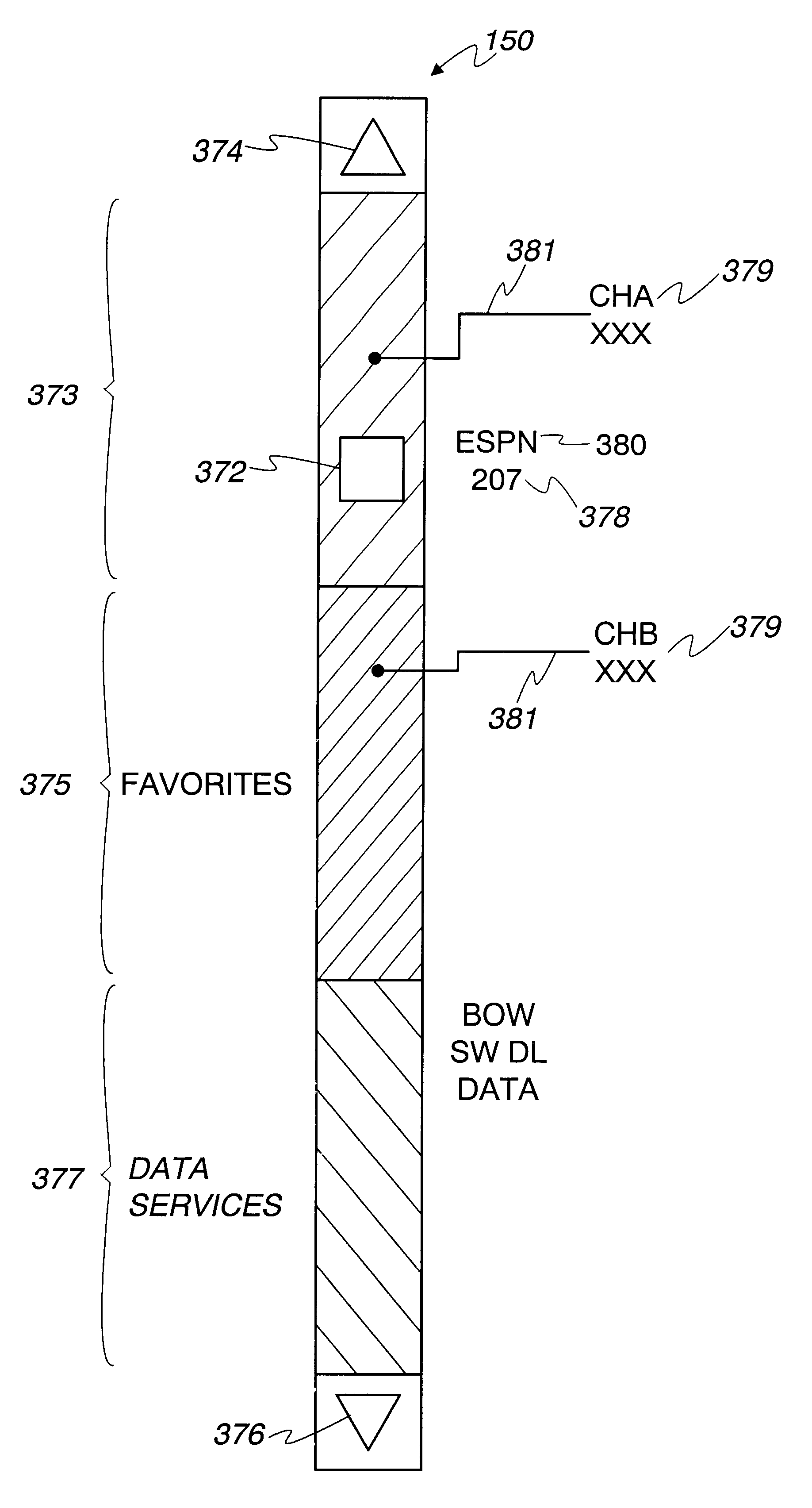
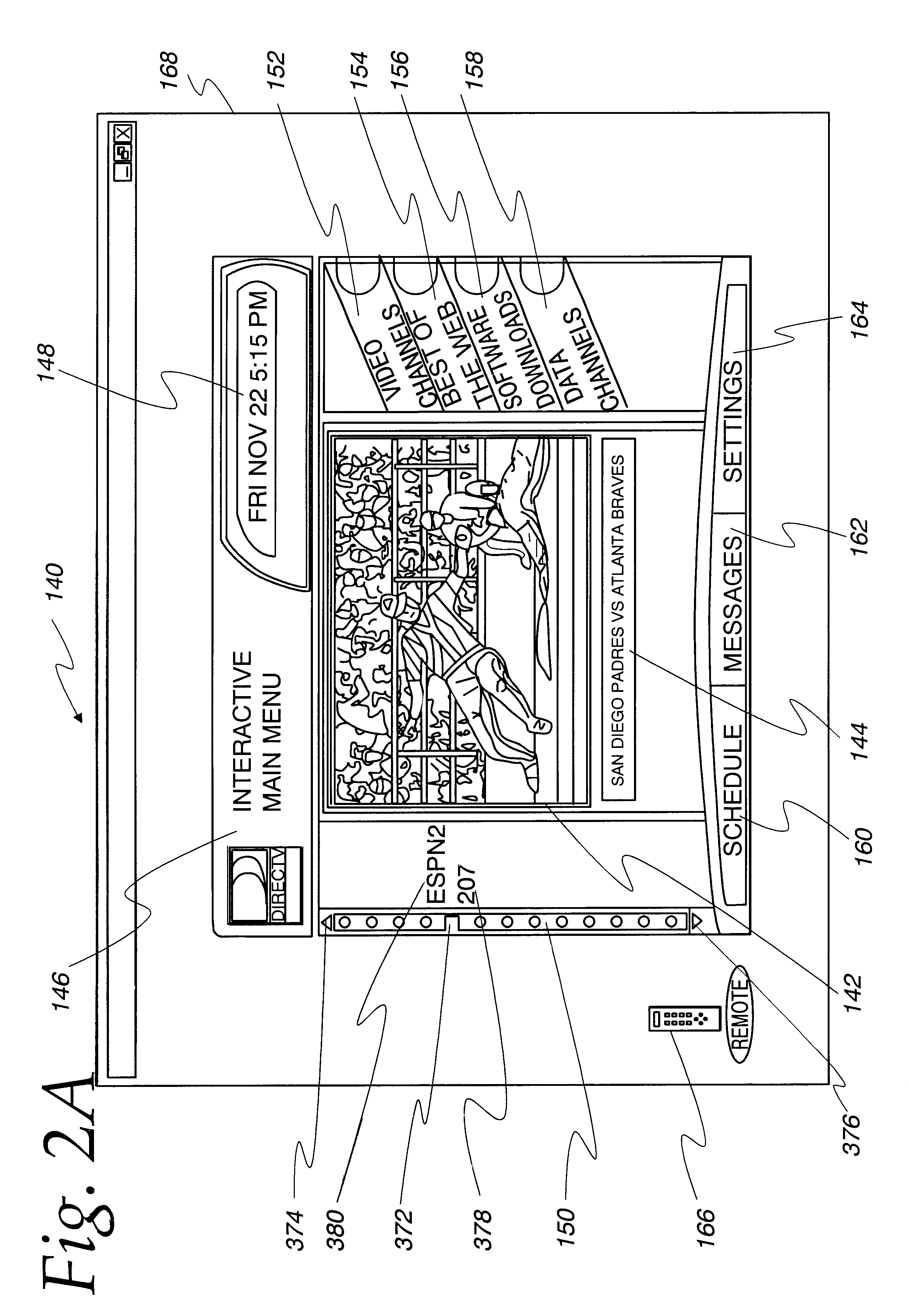
InactiveUS6522342B1Improve displayFacilitate selectionTelevision system detailsData processing applicationsComputer basedGraphical user interface
A computer based graphical user interface for facilitating the selection and display of transmitted audio, video and data includes a main menu state with a first multi-segment display having an active video / audio segment and a tuning segment. The active video segment displays a currently tuned program and the tuning segment includes an elongated graphic bar. The elongated graphic bar is dynamically sub-divided into a plurality of contiguous regions so that each of the regions uniquely corresponds to a program parsed from a multi-program data stream. The tuning segment also includes a graphic slider that overlays the graphic bar and that is movable along the length of the graphic bar so that the currently tuned program corresponds to the portion of the graphic bar underlying the current position of the graphic slider.
Owner:HUGHES ELECTRONICS
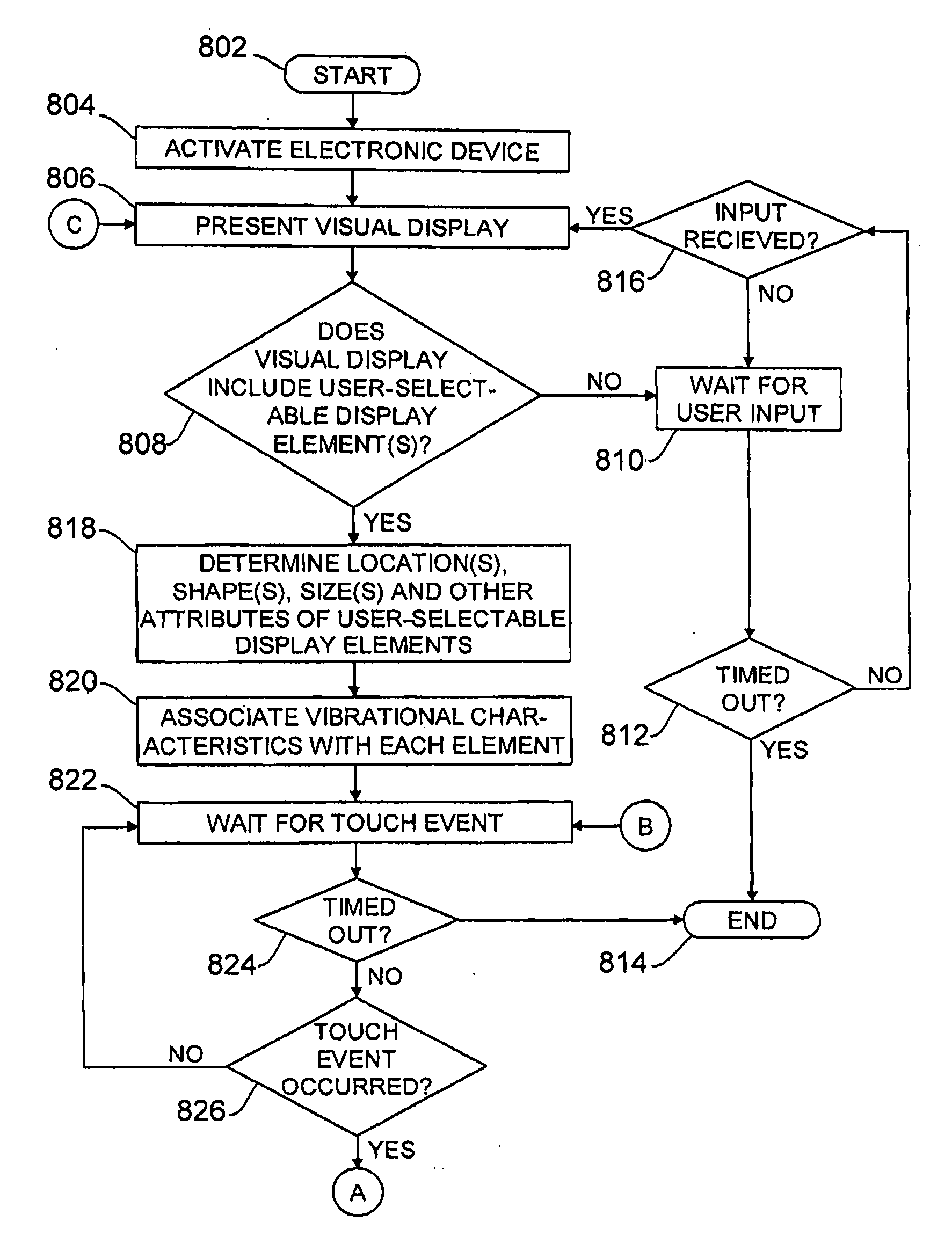
Multi-touch display screen with localized tactile feedback
Systems, methods, computer-readable media, and other means are described for utilizing touch-based input components that provide localized haptic feedback to a user. The touch-based input components can be used and / or integrated into any type of electronic device, including laptop computers, cellular telephones, and portable media devices. The touch-based input components can use, for example, a grid of piezoelectric actuators to provide vibrational feedback to a user, while the user scrolls around a click wheel, slides across a trackpad, or touches a multi-touch display screen.
Owner:APPLE INC
Video data recorder with integrated channel guides
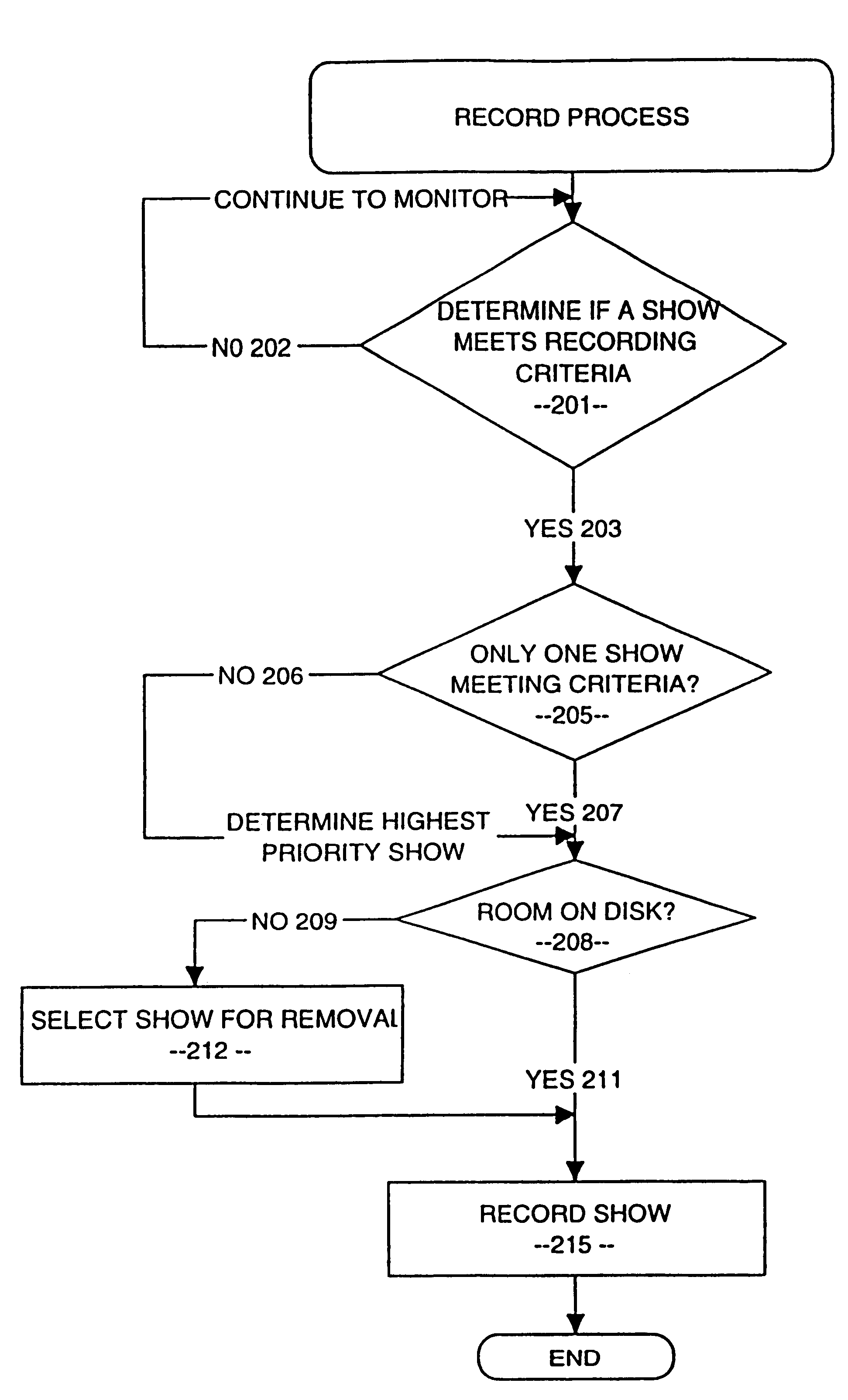
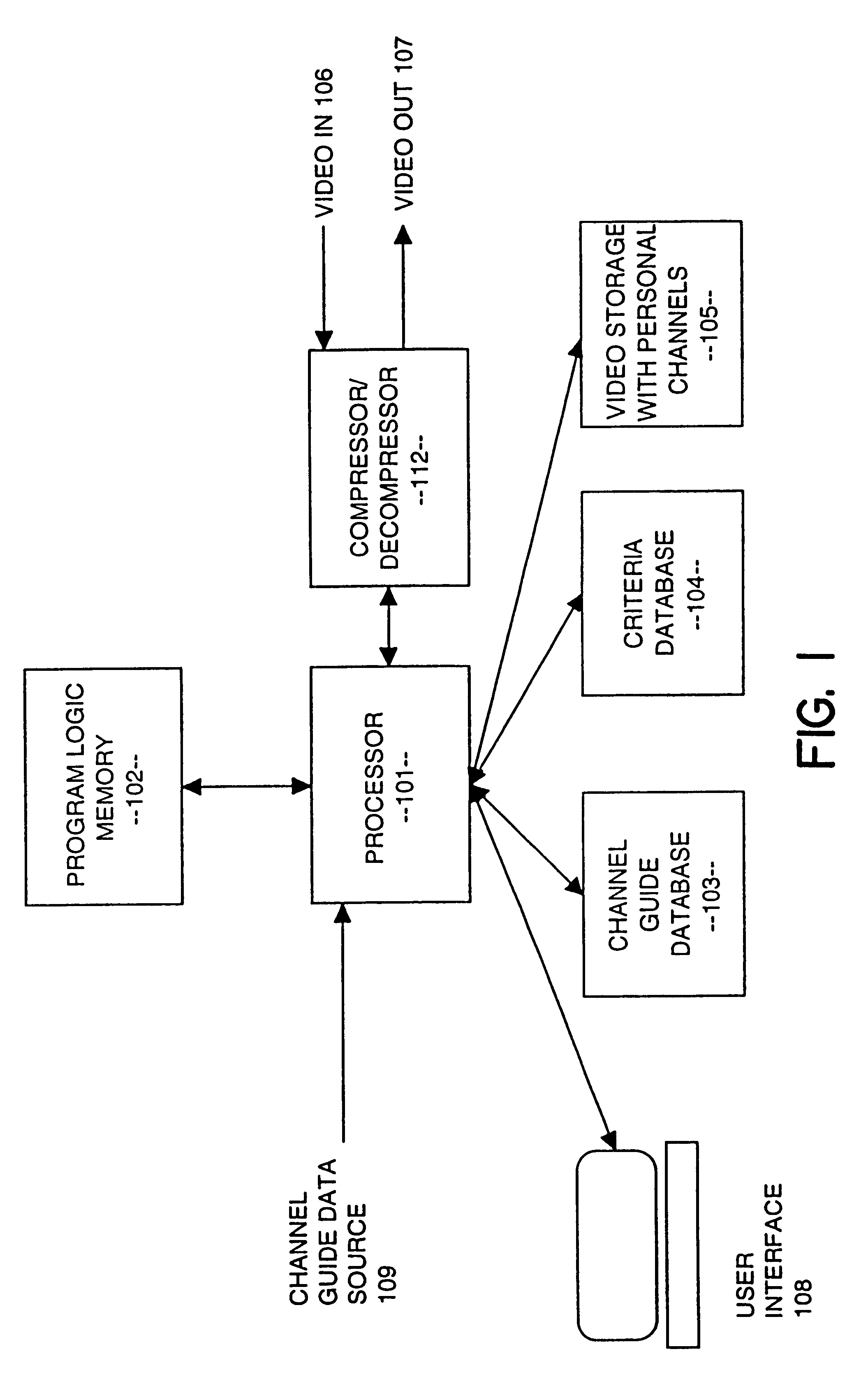
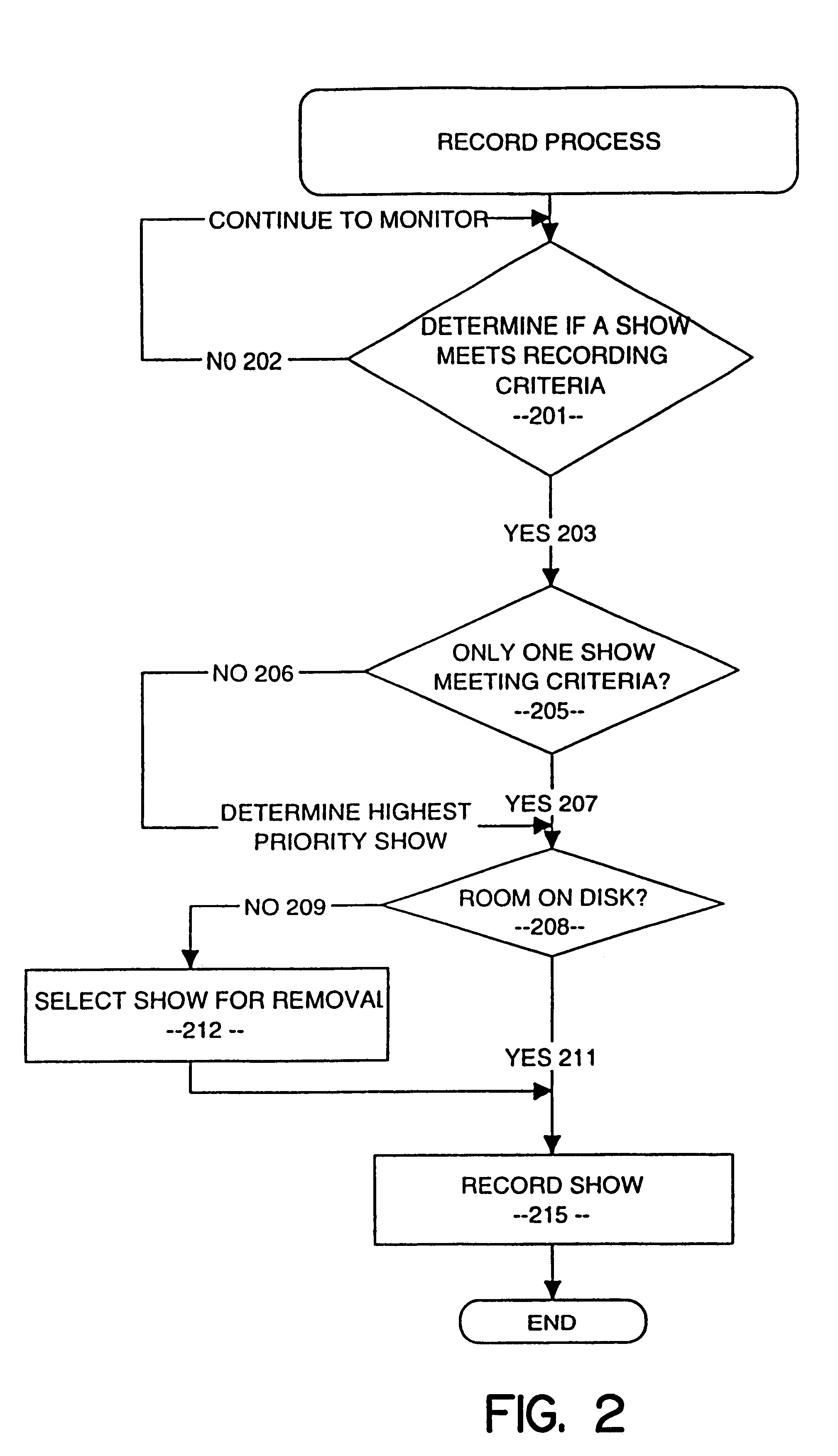
InactiveUS6324338B1Television system detailsDisc-shaped record carriersComputer hardwareVideo Tape Recording
A video data recordable having integrated channel guides allowing a user to control recording and storage of television signals into personal channels for later playback and viewing. In the described embodiment, the user may specify criteria for recording of shows from an input source such as a broadcast signal and shows are then selected based on the user specified criteria and recorded for later playback. Storage of the shows may be organized into personal channels in order to facilitate later playback, e.g., the user may specify a channel of action movies, a channel of nature programming, a channel for sports, etc. The shows to be recorded may also have a predefined format which may be used to ease playback of recorded programming by allowing the user to easily locate and playback sections of programming of interest.
Owner:THE DIRECTV GROUP
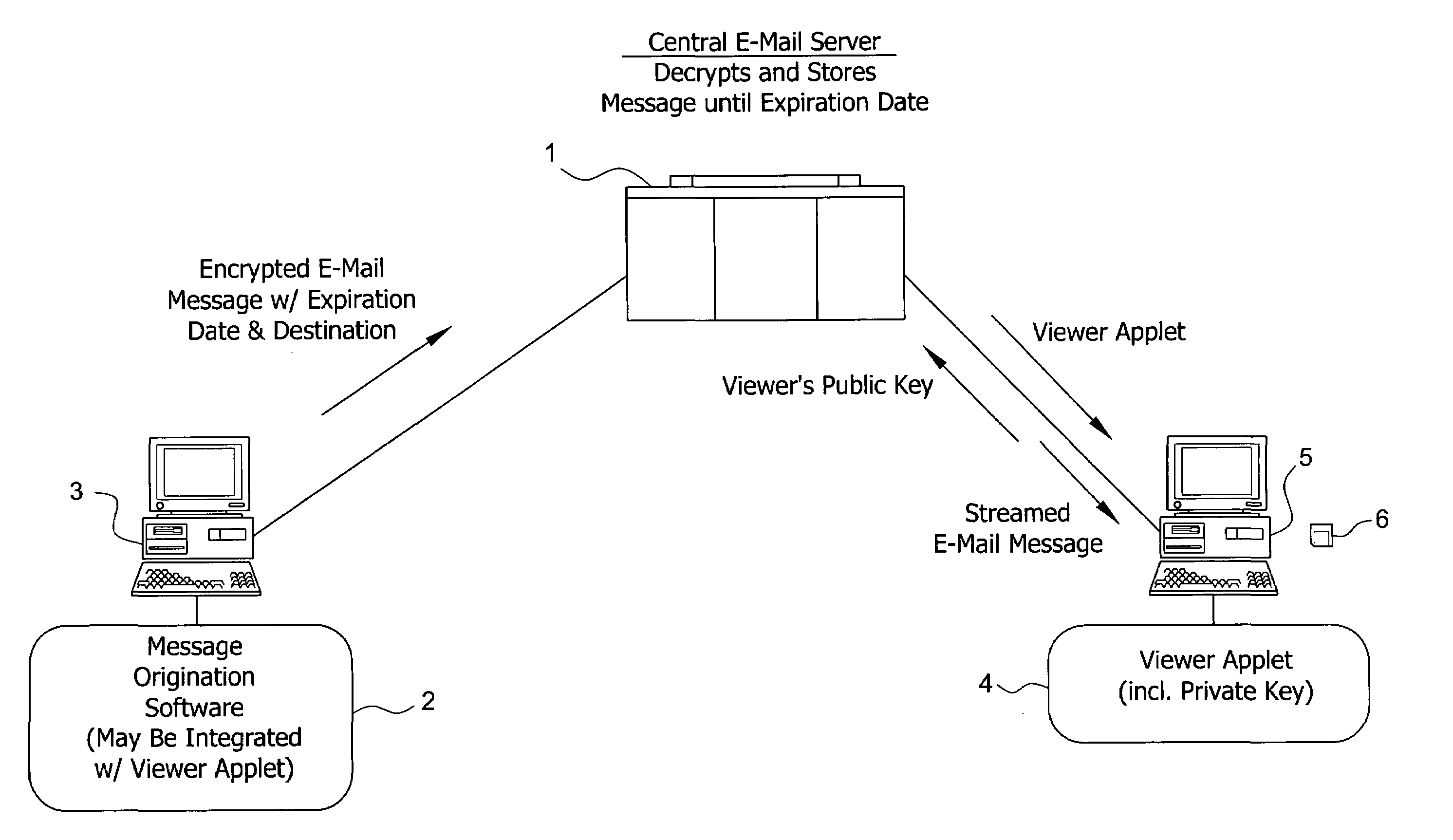
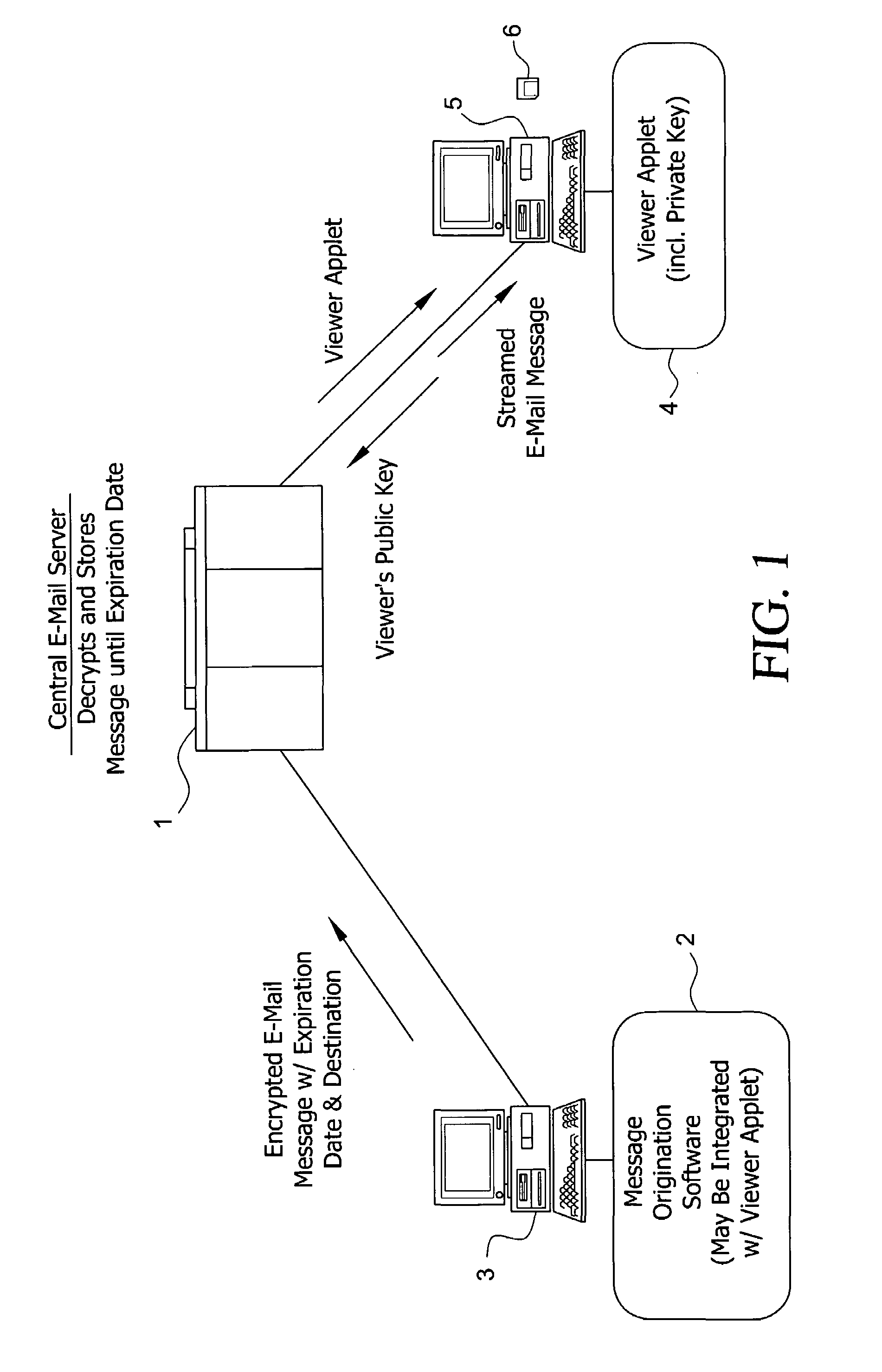
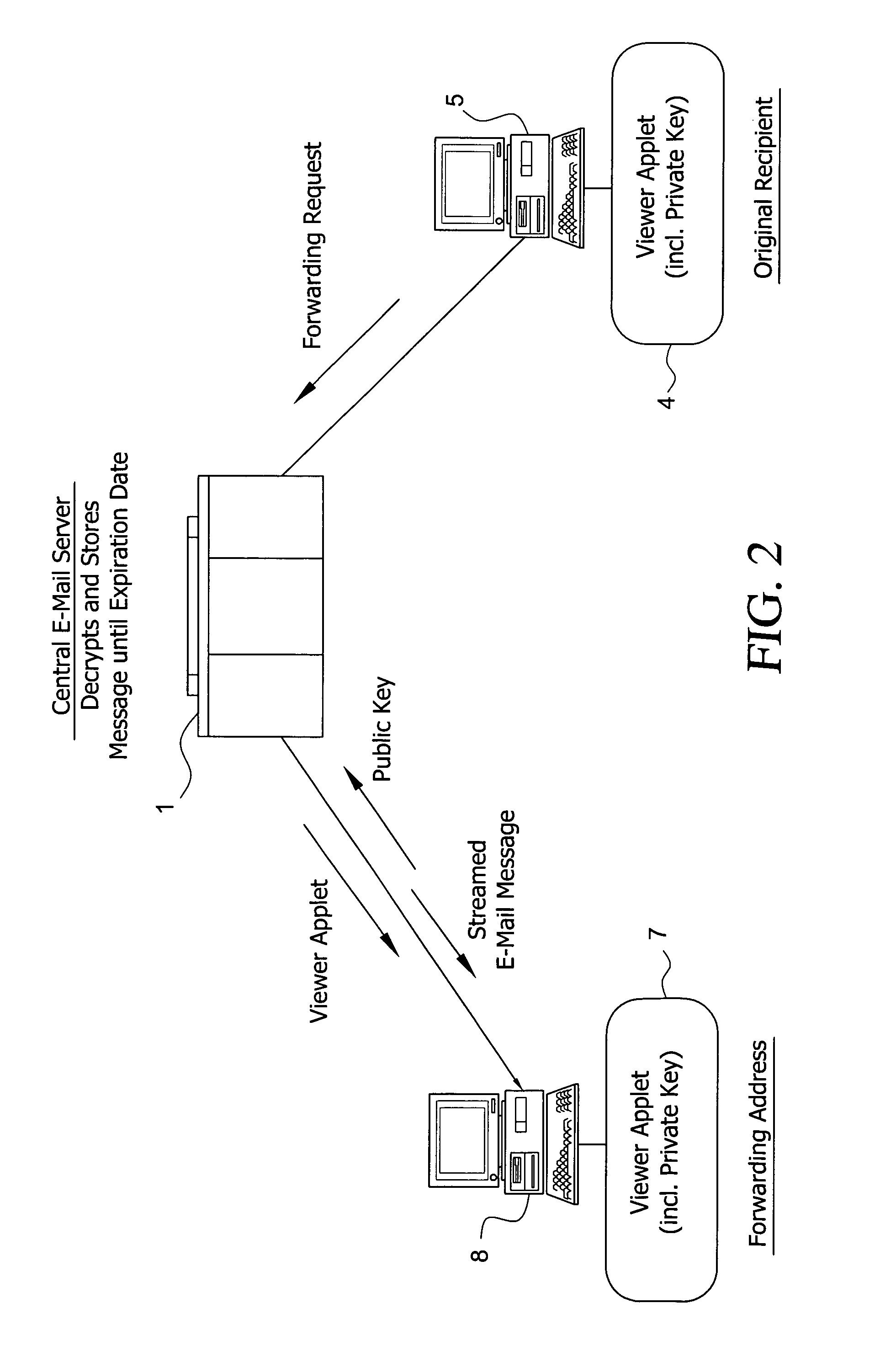
System and method for enabling the originator of an electronic mail message to preset an expiration time, date, and/or event, and to control processing or handling by a recipient
InactiveUS7149893B1Limited lifespanRapid and efficient mannerDigital data processing detailsAnalogue secracy/subscription systemsExpiration TimeComputer hardware
An electronic mail system and method enables the originator of a message sent by electronic mail to select a date, time, or event at which the message and all incarnations of the message to self-destruct, regardless of the number and types of computers or software systems that may have interacted with the message. The system and message also permits the originator to include processing and handling limitations. The necessary control over the message is achieved by encrypting the message and enabling viewing only through a viewer applet arranged to facilitate destruction of the message upon the occurrence of the selected expiration time, date, or event, and to implemented the handling and processing limitations. A central server can be used to exercise additional control over the message by serving as a proxy destination, and by streaming the encrypted message to the viewer applet. The viewer applet can be transmitted to new recipients with the message so that the system and method can direct mail to any electronic mail user.
Owner:RESOURCE CONSORTIUM LTD LLC
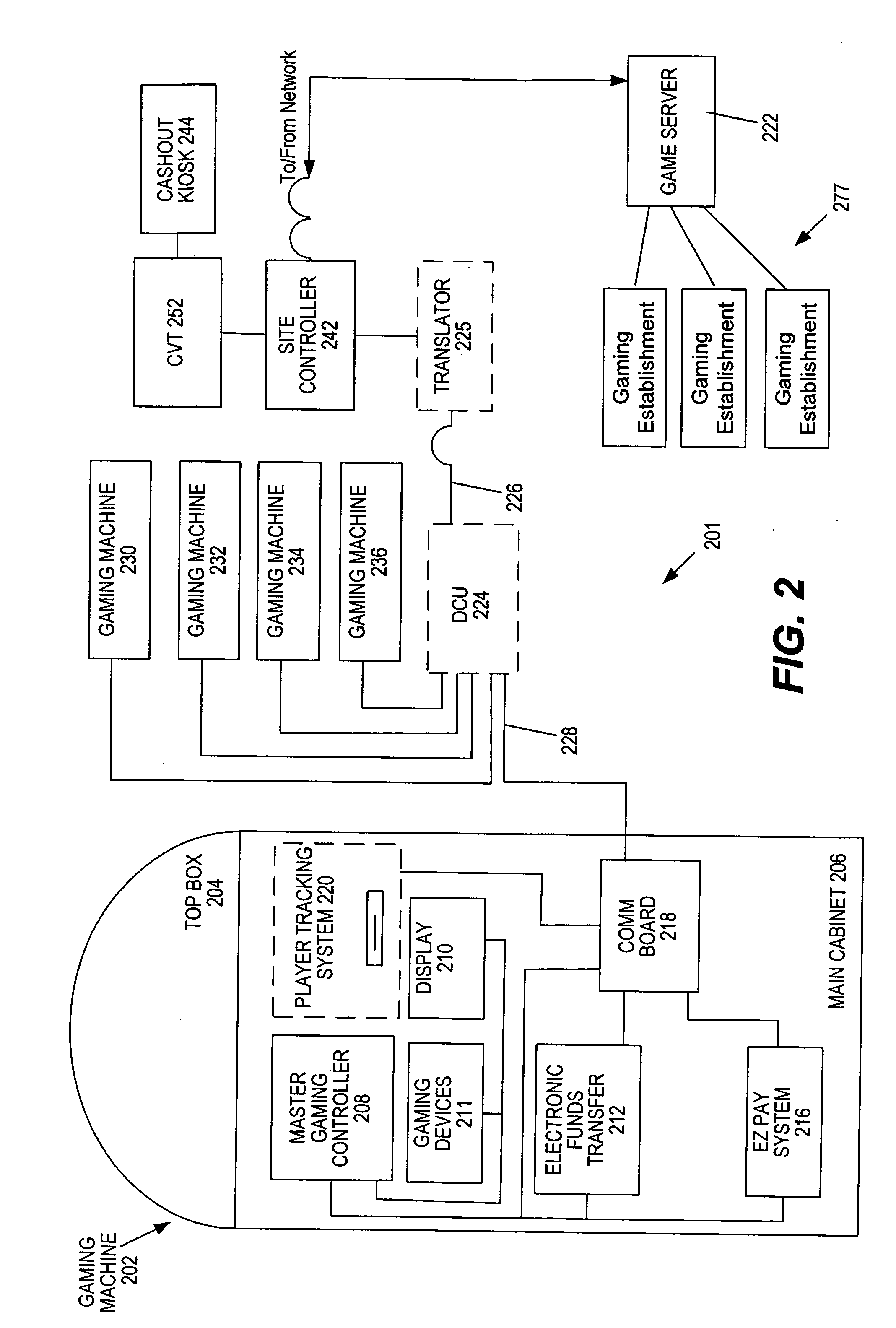
Method and apparatus for registering a mobile device with a gaming machine
InactiveUS20060189382A1User identity/authority verificationCard gamesComputer hardwareCommunications system
Disclosed are methods, apparatus, and systems, including computer program products, implementing techniques for securing a gaming machine for a player of the gaming machine using a mobile device such as a cell phone associated with the player. A player input requests securing of the gaming machine. Responsive to the player input, an access code and a security code are retrieved. The access code defines an access point of a communication system. The security code is specific to a game play session for the player at the gaming machine. The retrieved access code and security code are provided for the player. When the mobile device accesses the communications system and submits the security code, a secure signal is sent to the gaming machine, instructing the gaming machine to enter a remote game play state. The gaming machine can be released from the remote game play state responsive to a releasing event. In one implementation, a wireless interface enables communication between the mobile device and gaming machine according to a wireless protocol such as Bluetooth.
Owner:IGT
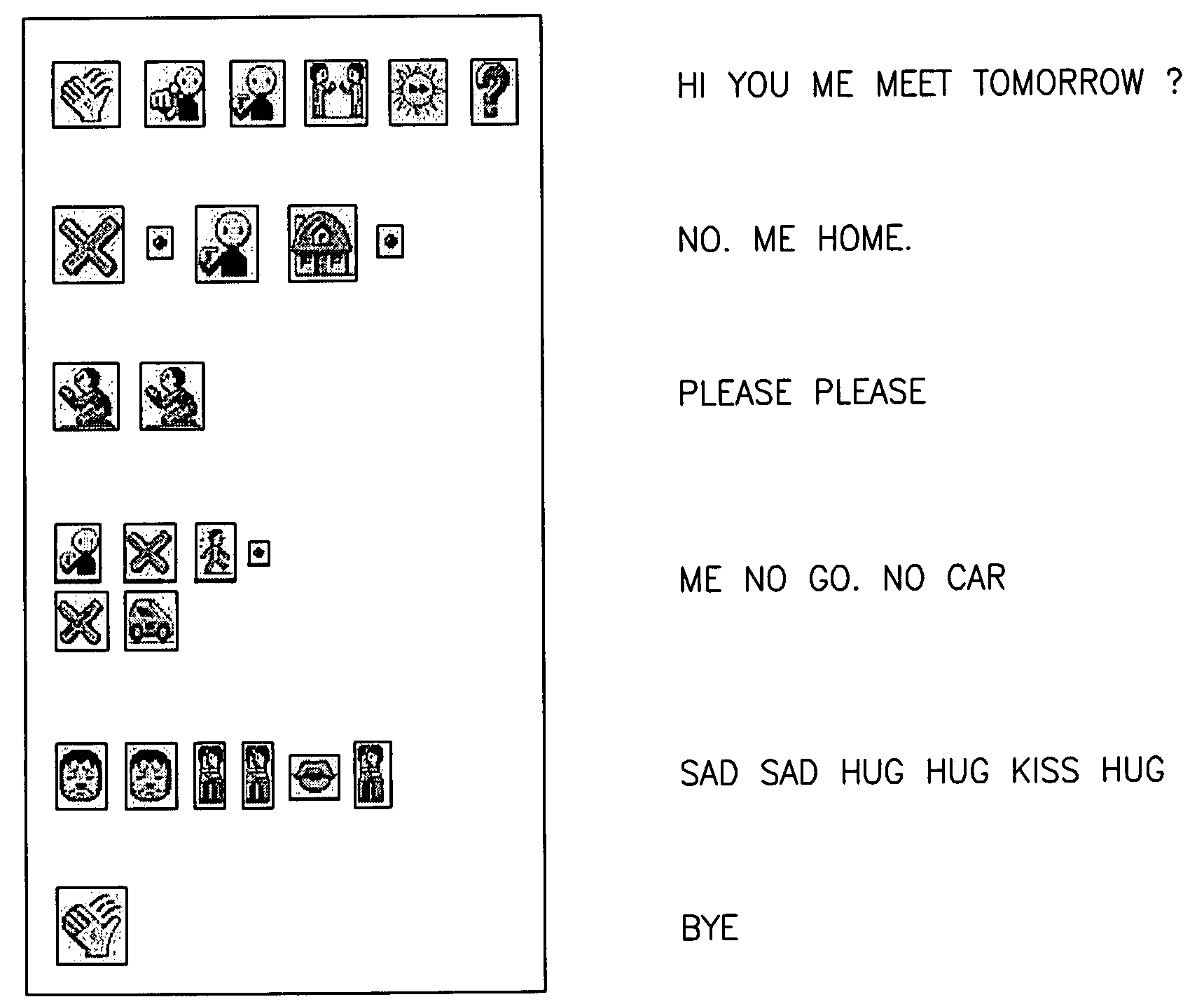
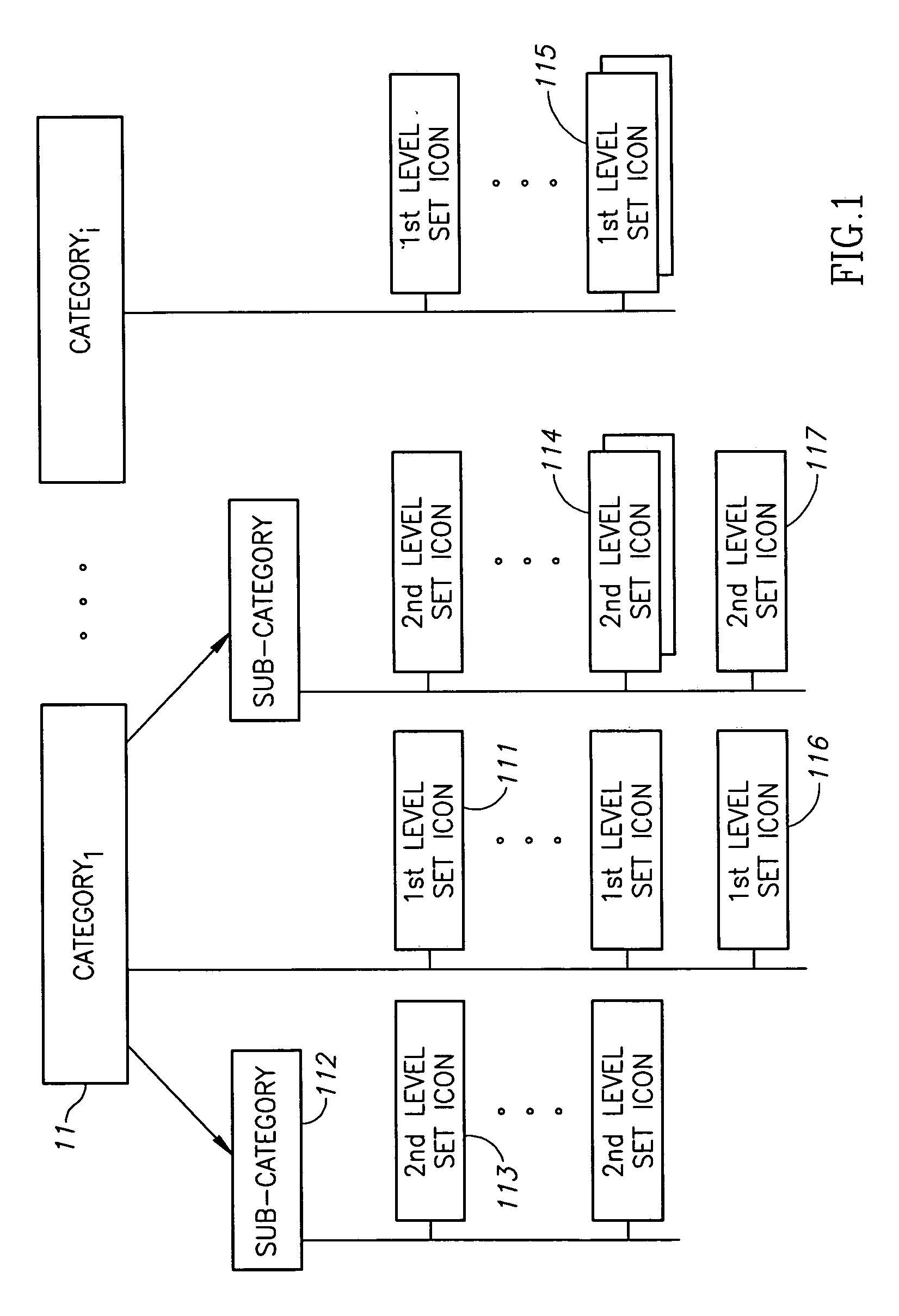
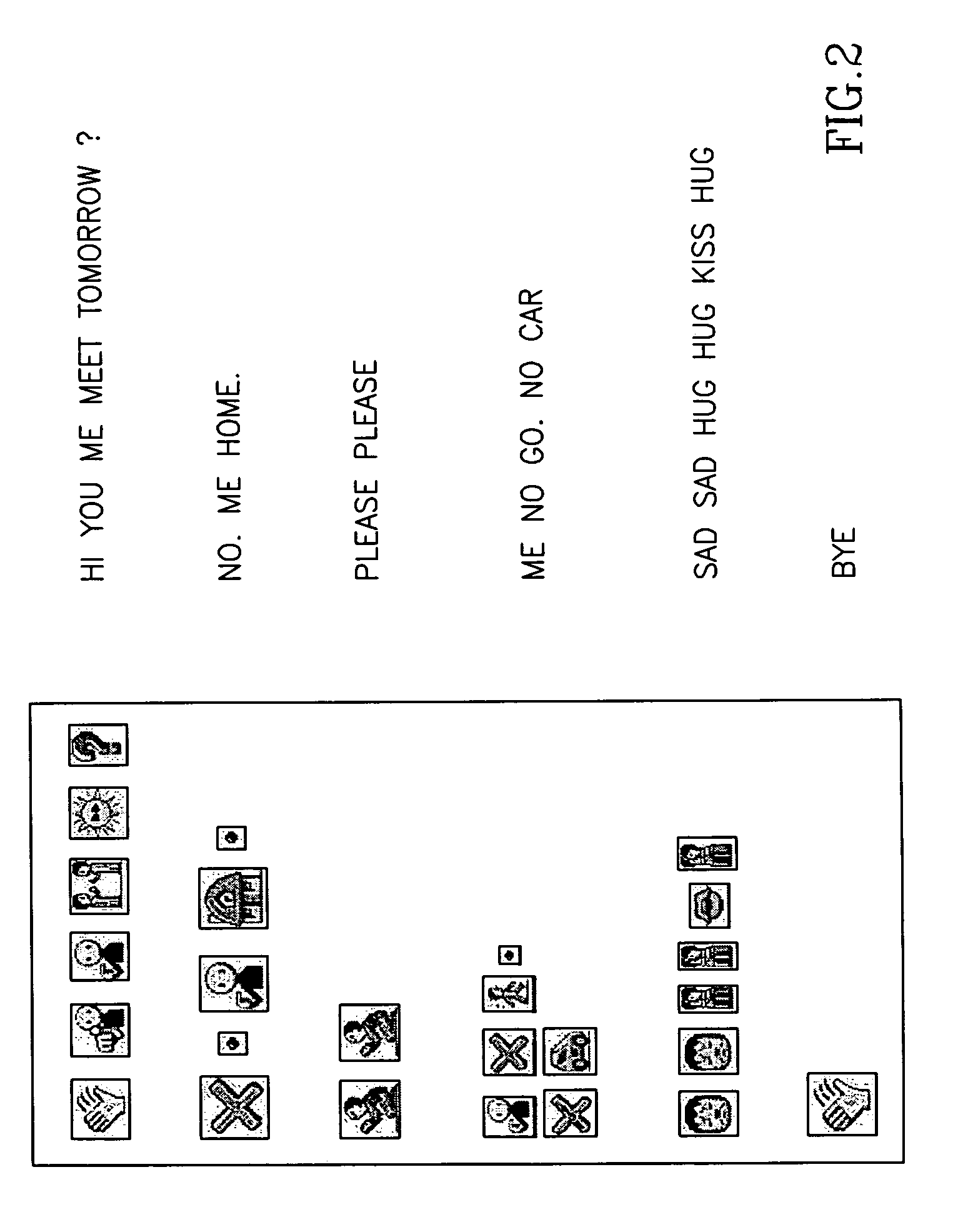
Iconic Communication
ActiveUS20100179991A1Reduce possible complexityDevices with multiple display unitsConnection managementComputer hardwareDisplay device
A method of controlling an external display using a personal communication device, comprising:providing an external display;processing an iconic message on a personal communication device to generate at least one instruction for said display;transmitting said at least one instruction from said personal communication device to said external display responsive to said processing; anddisplaying on external display in response to said at least one instruction.
Owner:KNAPP INVESTMENT
System and Method for Reading Code Symbols at Long Range Using Source Power Control
A system and method are presented for improving the performance of code scanners in the extended and far ranges. At these distances, the intensity of the laser beam reflected off the code symbol can be markedly decreased, thereby decreasing the likelihood of a successful reading of the code symbol by the code scanner. The system provides for dynamic power increases to the laser source to generate a greater dynamic range.
Owner:HAND HELD PRODS
Multi-window management apparatus and program, storage medium and information processing apparatus
InactiveUS20100088634A1Easy to understandFacilitates user operationCathode-ray tube indicatorsInput/output processes for data processingInformation processingComputer hardware
Owner:SHARP KK
Transaction apparatus and method
InactiveUS6315195B1Low production costEasy to operateHybrid readersPoint-of-sale network systemsComputer hardwareBarcode
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
Electronic display with photo-addressing means
InactiveUS7023420B2Static indicating devicesNon-linear opticsComputer hardwareComputer graphics (images)
Owner:E INK CORPORATION
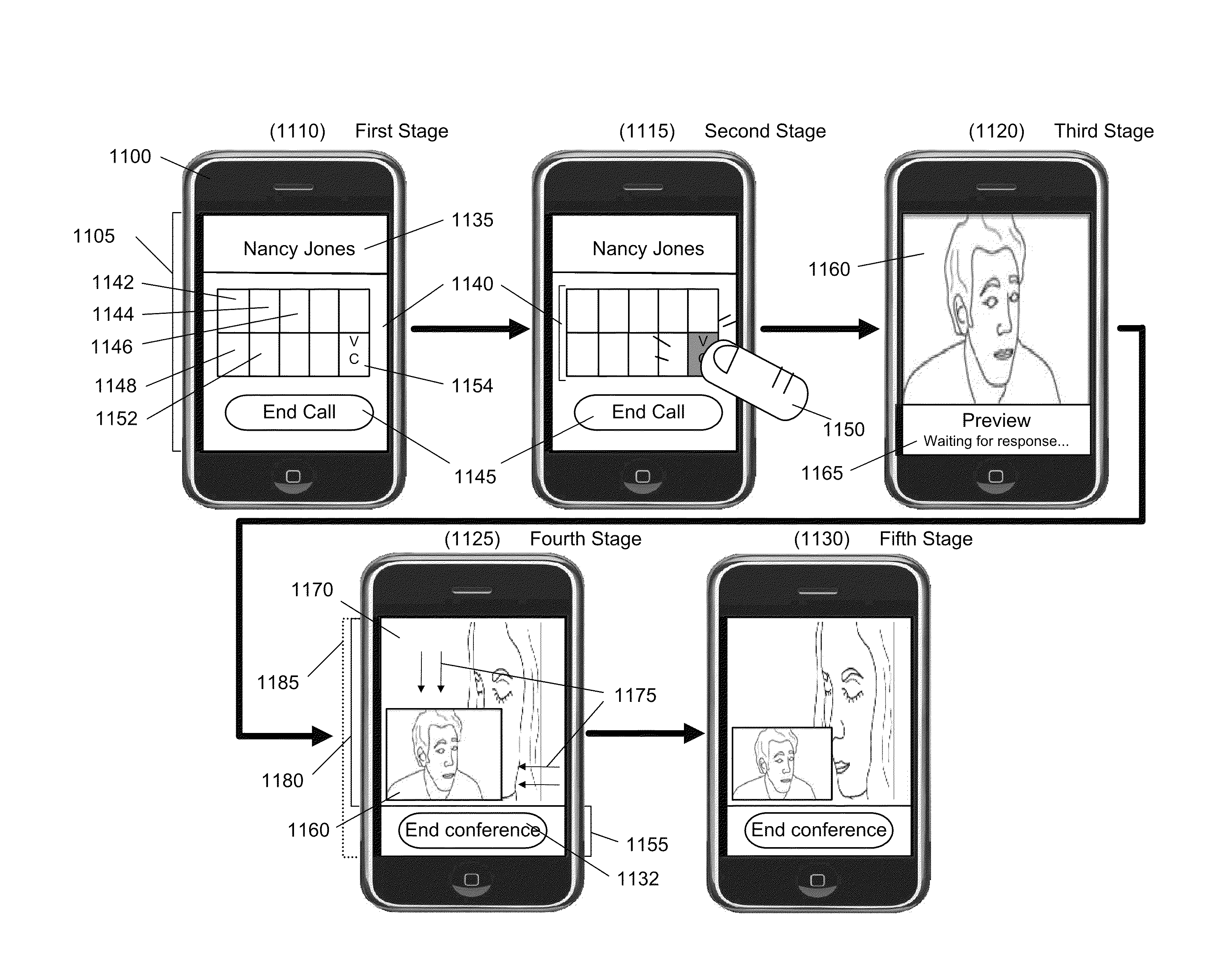
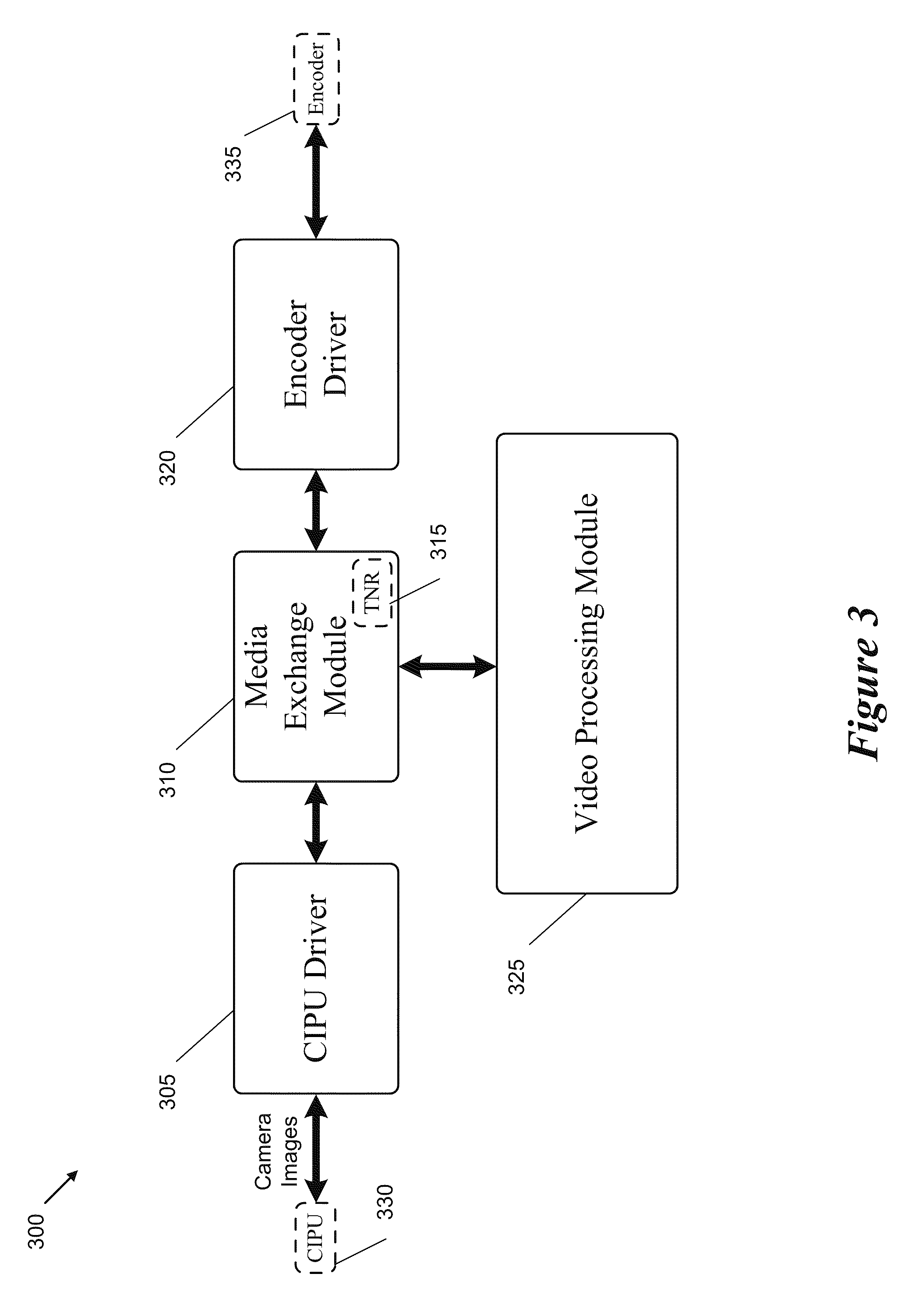
Establishing a Video Conference During a Phone Call
ActiveUS20110249073A1Smooth transitionTelevision system detailsTelevision conference systemsComputer hardwareMobile device
Some embodiments provide a method for initiating a video conference using a first mobile device. The method presents, during an audio call through a wireless communication network with a second device, a selectable user-interface (UI) item on the first mobile device for switching from the audio call to the video conference. The method receives a selection of the selectable UI item. The method initiates the video conference without terminating the audio call. The method terminates the audio call before allowing the first and second devices to present audio and video data exchanged through the video conference.
Owner:APPLE INC
Advanced television system
InactiveUS20030088872A1Easy to switchSimplified user interfaceTelevision system detailsAnalogue secracy/subscription systemsTelevision systemComputer hardware
In a digital television recording method, programs are selected for recording based on analysis of program schedule information, user preferences, and the priority of previously recorded programs if there is insufficient memory.
Owner:CISCO TECH INC
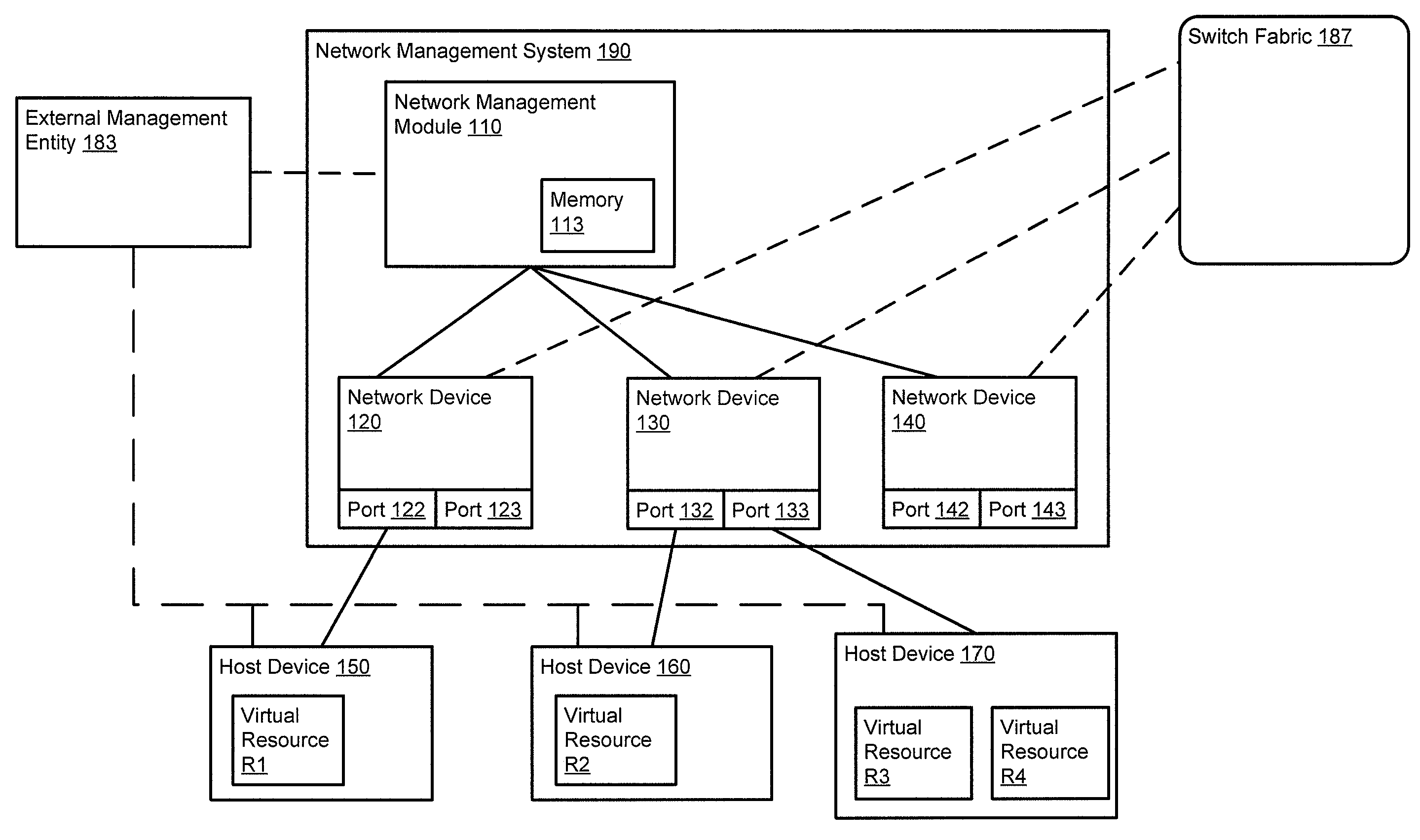
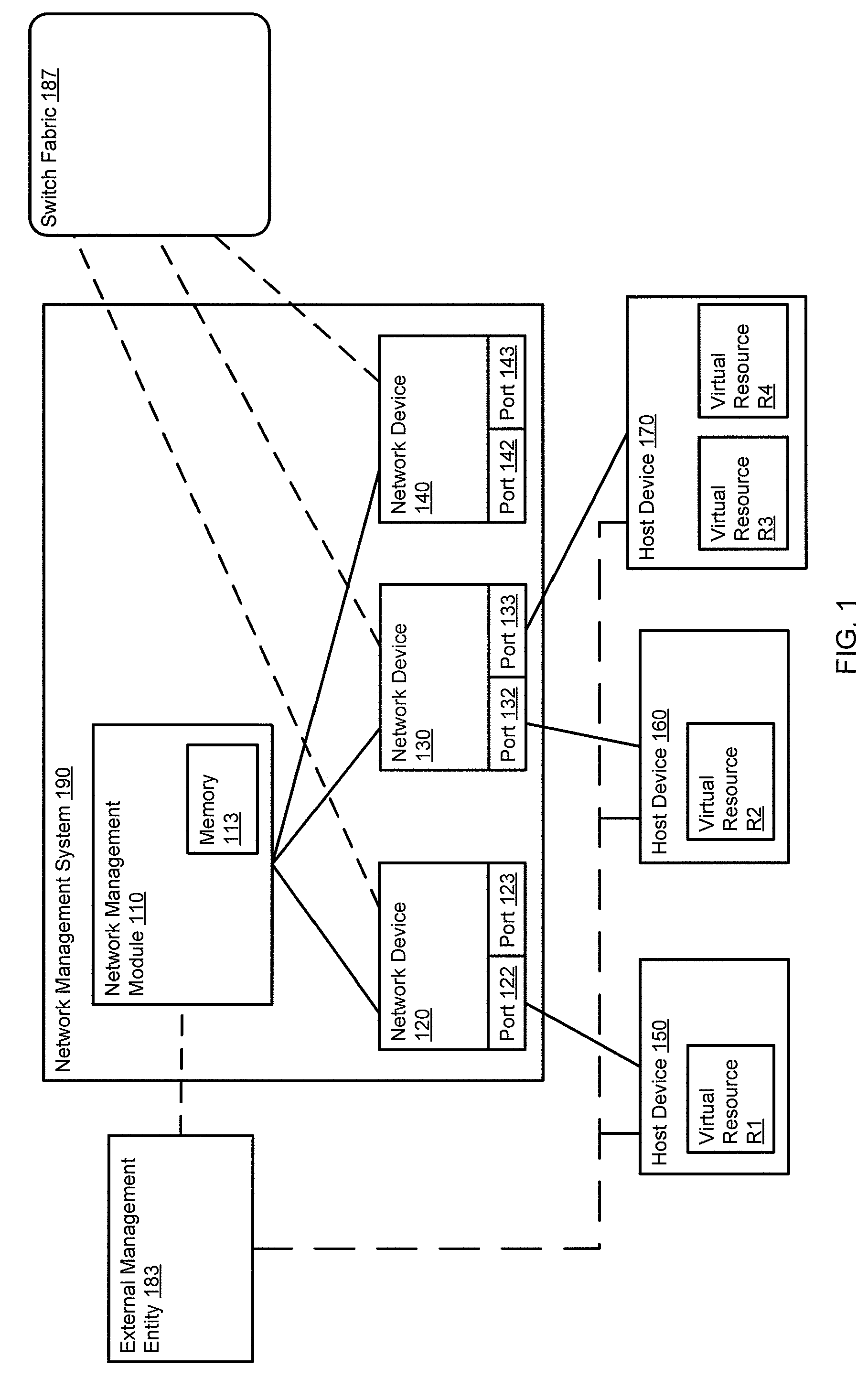
Method and apparatus for determining a network topology during network provisioning
Owner:JUMIPER NETWORKS INC
System and method for securely transmiting sensitive information
InactiveUS20130194301A1Inhibitory contentSecure transmissionCathode-ray tube indicatorsDigital data protectionComputer hardwareClient-side
A system and method for securely transmitting information over a communications network comprises receiving a message notification that a recipient has a message on a recipient's client device from a processor based server upon receipt of the message from a sender's client device. The message from the sender's client device is stored in a storage device by the server. The recipient accesses the server to view the message using the recipient's client device. The message is rendered and displayed on the screen by the recipient's client device in accordance with a display method selected by the sender of the message to present only a portion of the message at any given time to the recipient. The prevents the message from being recorded or captured.
Owner:BURN NOTE
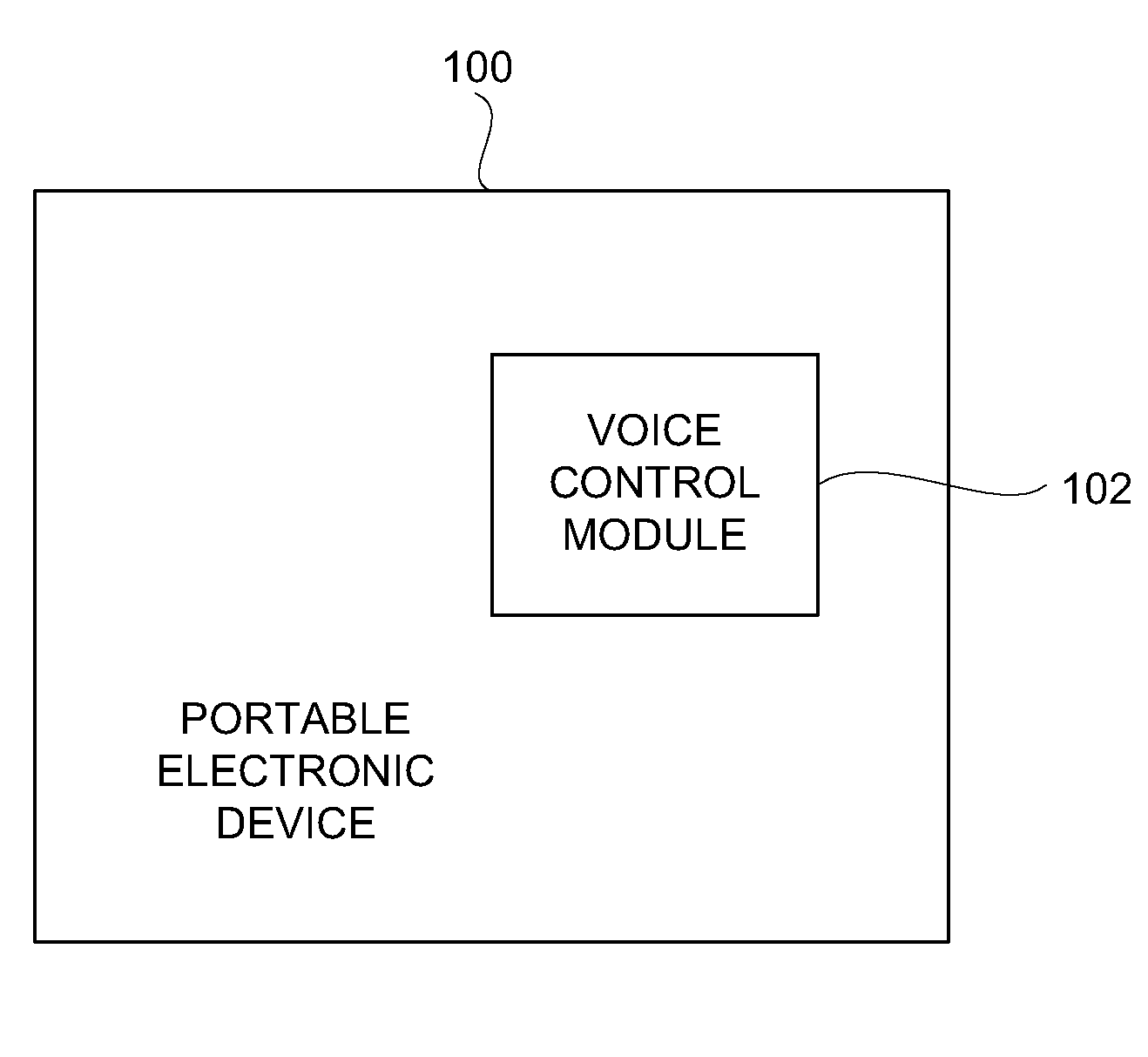
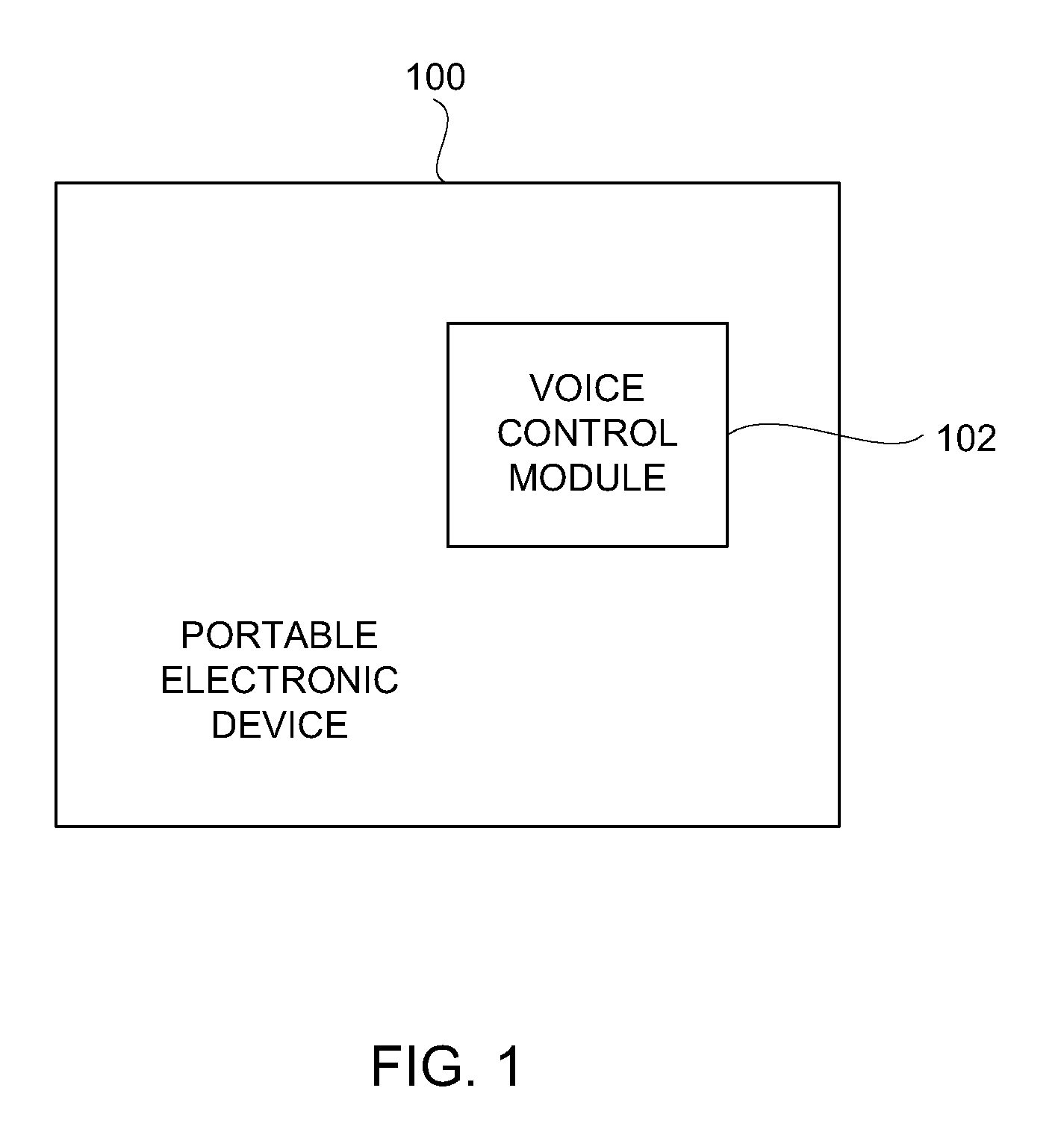
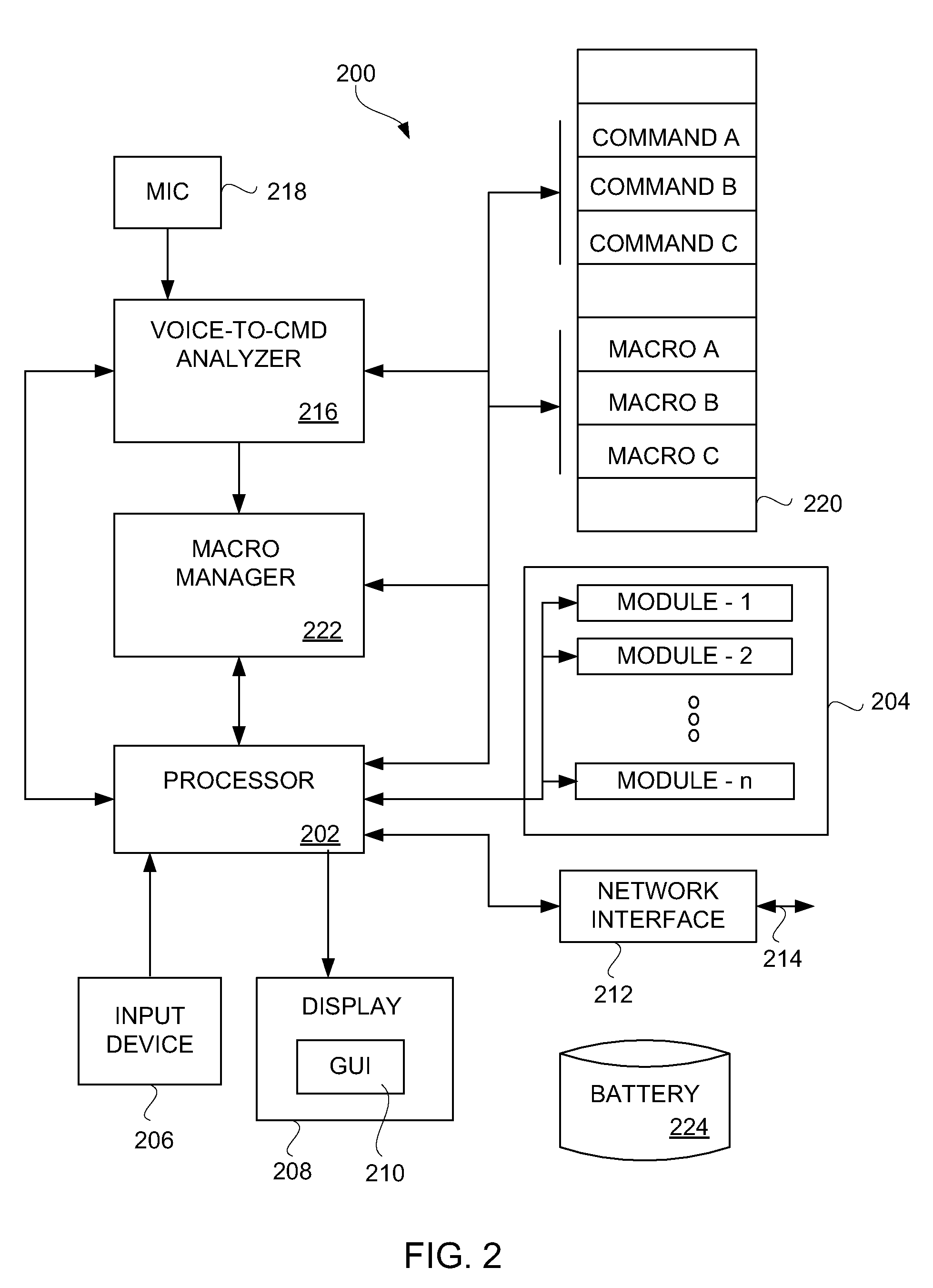
Method and System for Operating a Multi-Function Portable Electronic Device Using Voice-Activation
ActiveUS20080248797A1Lower the volumePower managementDevices with voice recognitionActivation methodComputer hardware
Methods and systems in which a portable electronic device can be voice activated are disclosed. The portable electronic device can be a multi-function electronic device. The voice activation can be robust and context sensitive. The voice activation can also be utilized without any preparatory user action with respect to the portable electronic device. The portable electronic device can also interact with a media system.
Owner:APPLE INC
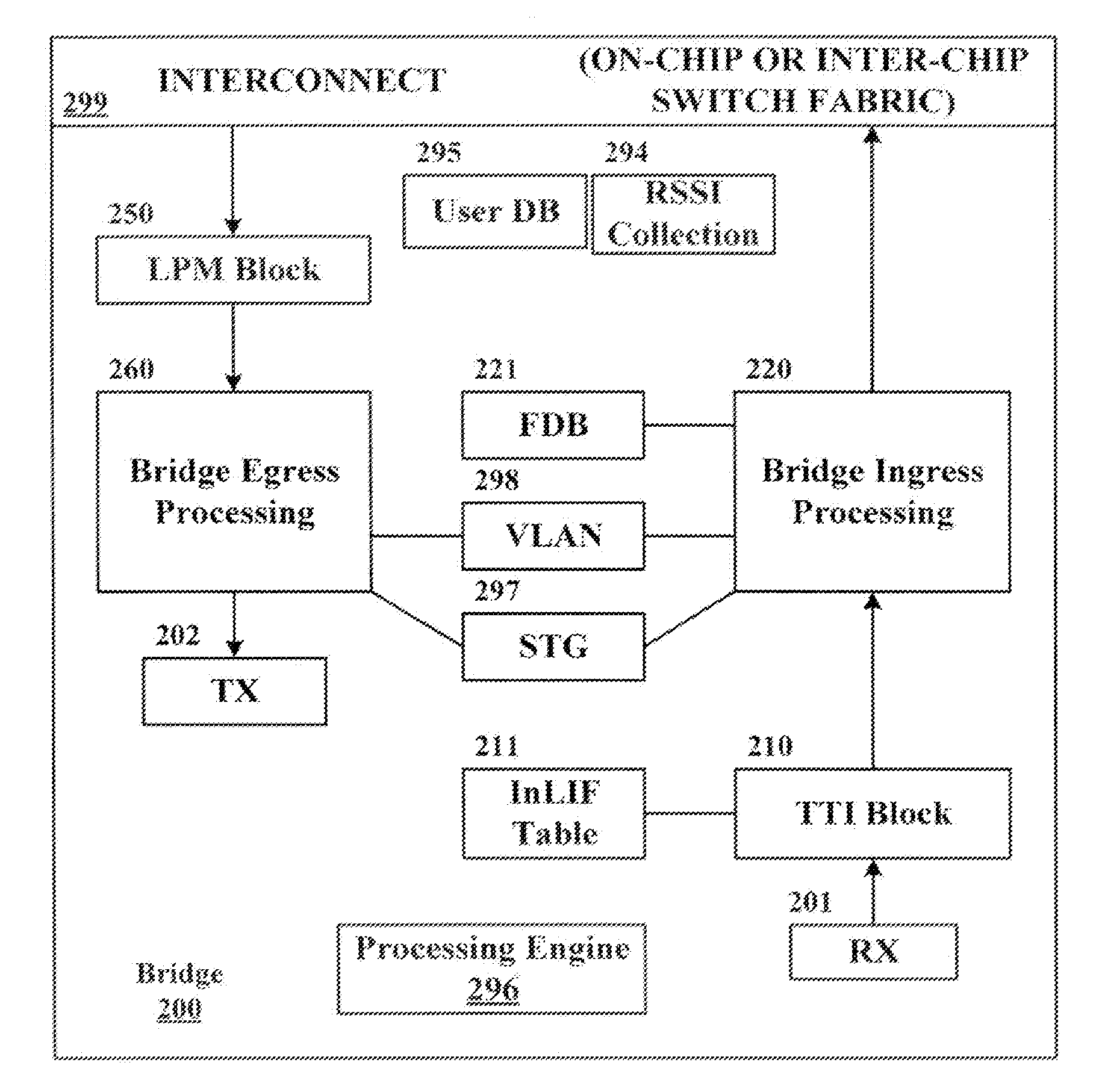
Logical bridging system and method
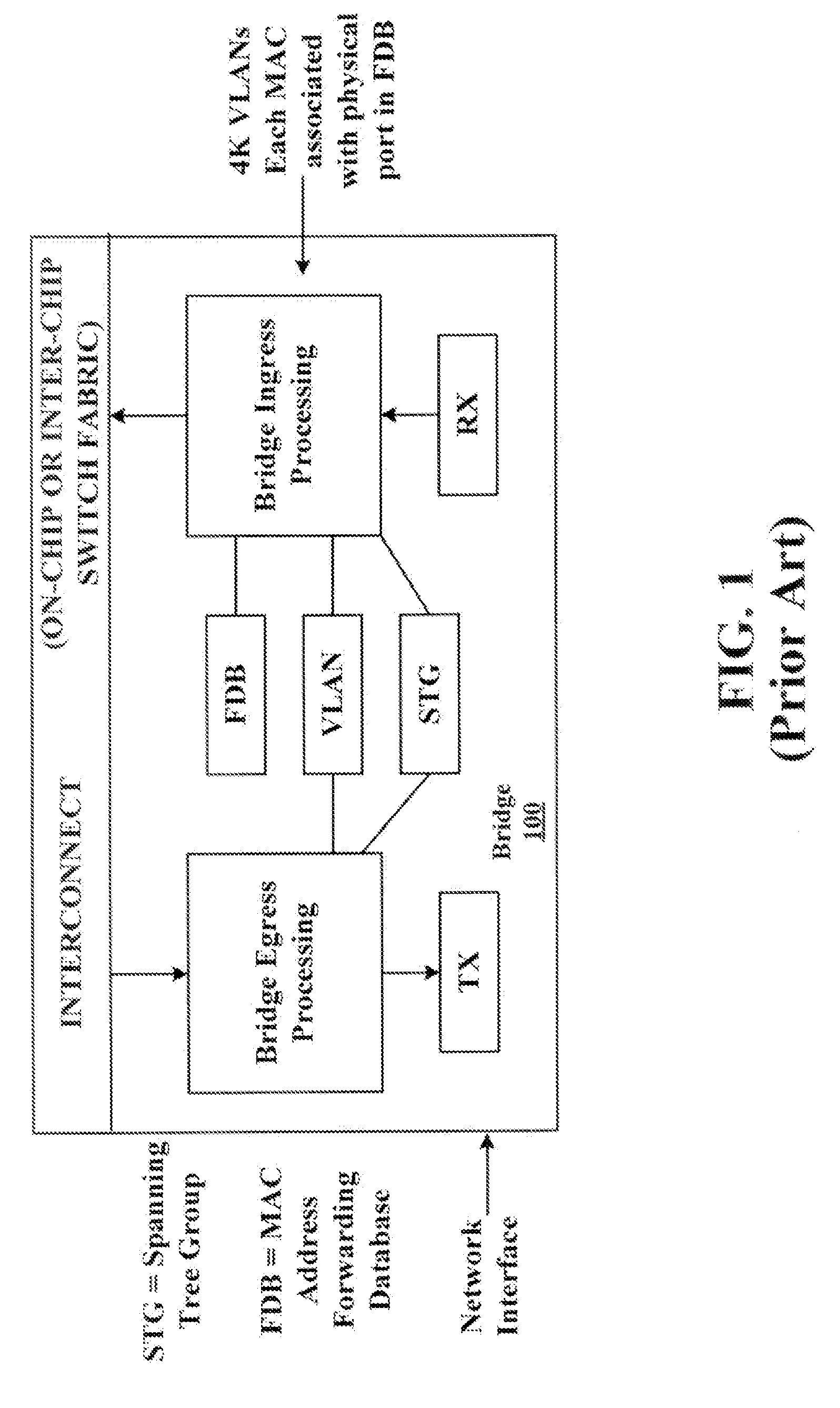
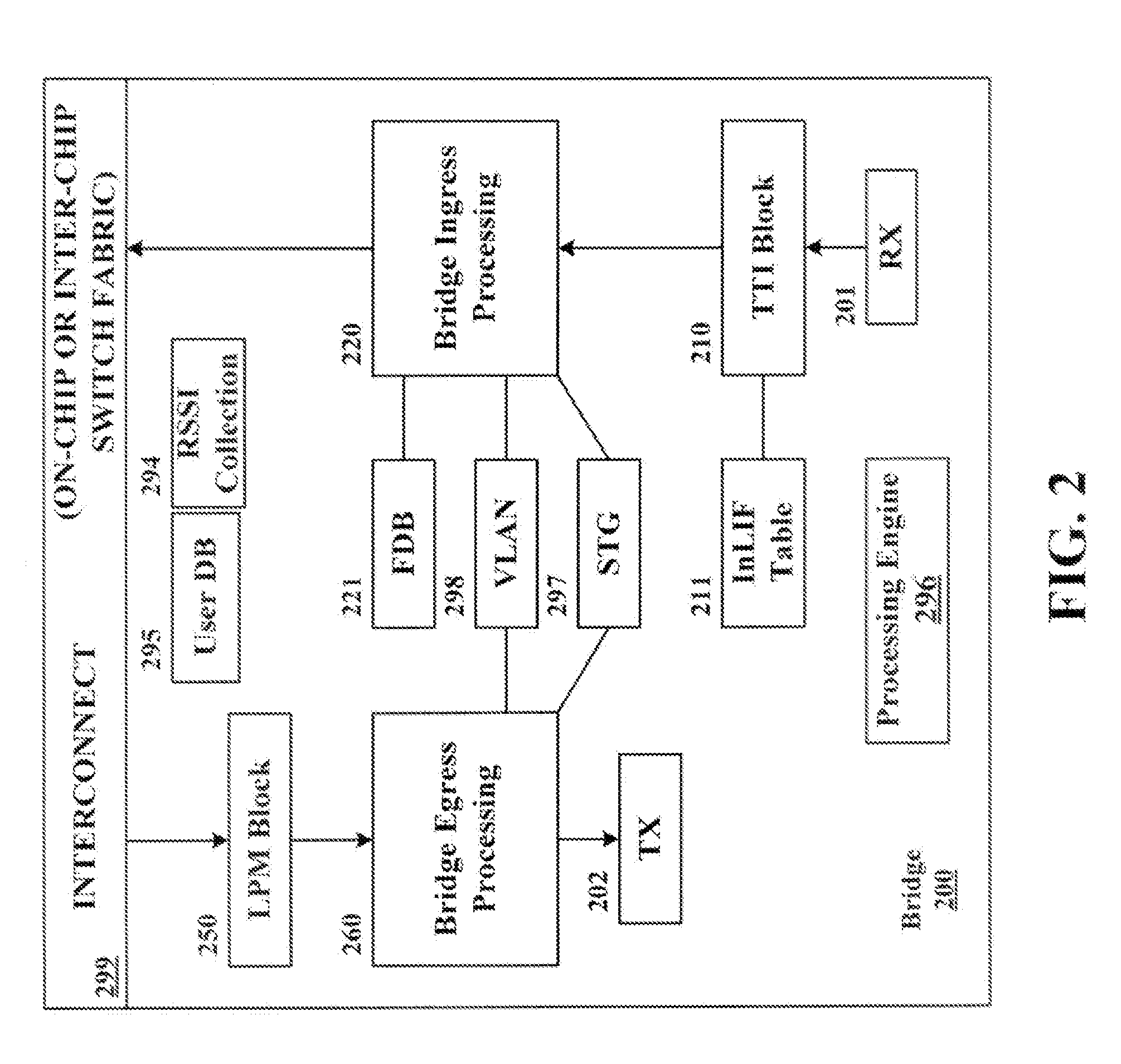
A system and method of extending a standard bridge to enable execution of logical bridging functionality are disclosed. In some implementations, a logical bridge may assign source logical port information to a data packet based on characteristics of the data packet, employ the source logical port information to learn the source address and to forward the data packet to a logical egress port, and map the logical egress port to a physical egress port at which the data packet is to be egressed. A tunnel interface may optionally be applied to a data packet upon egress.
Owner:MARVELL ISRAEL MISL
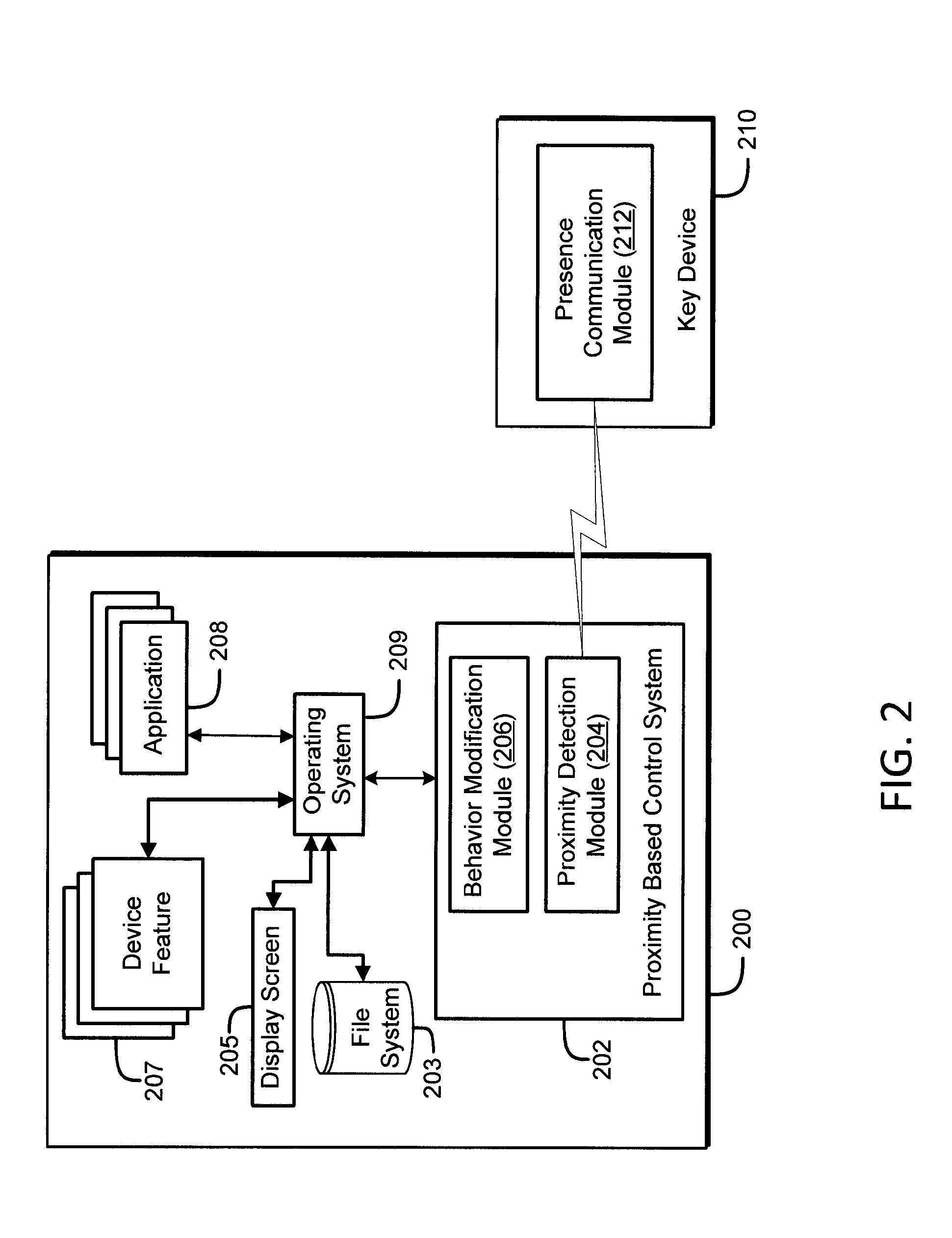
System and method for changing security behavior of a device based on proximity to another device
ActiveUS20140282877A1Reduce user inconvenienceCost efficientDigital data processing detailsNetwork topologiesComputer hardwareUser input
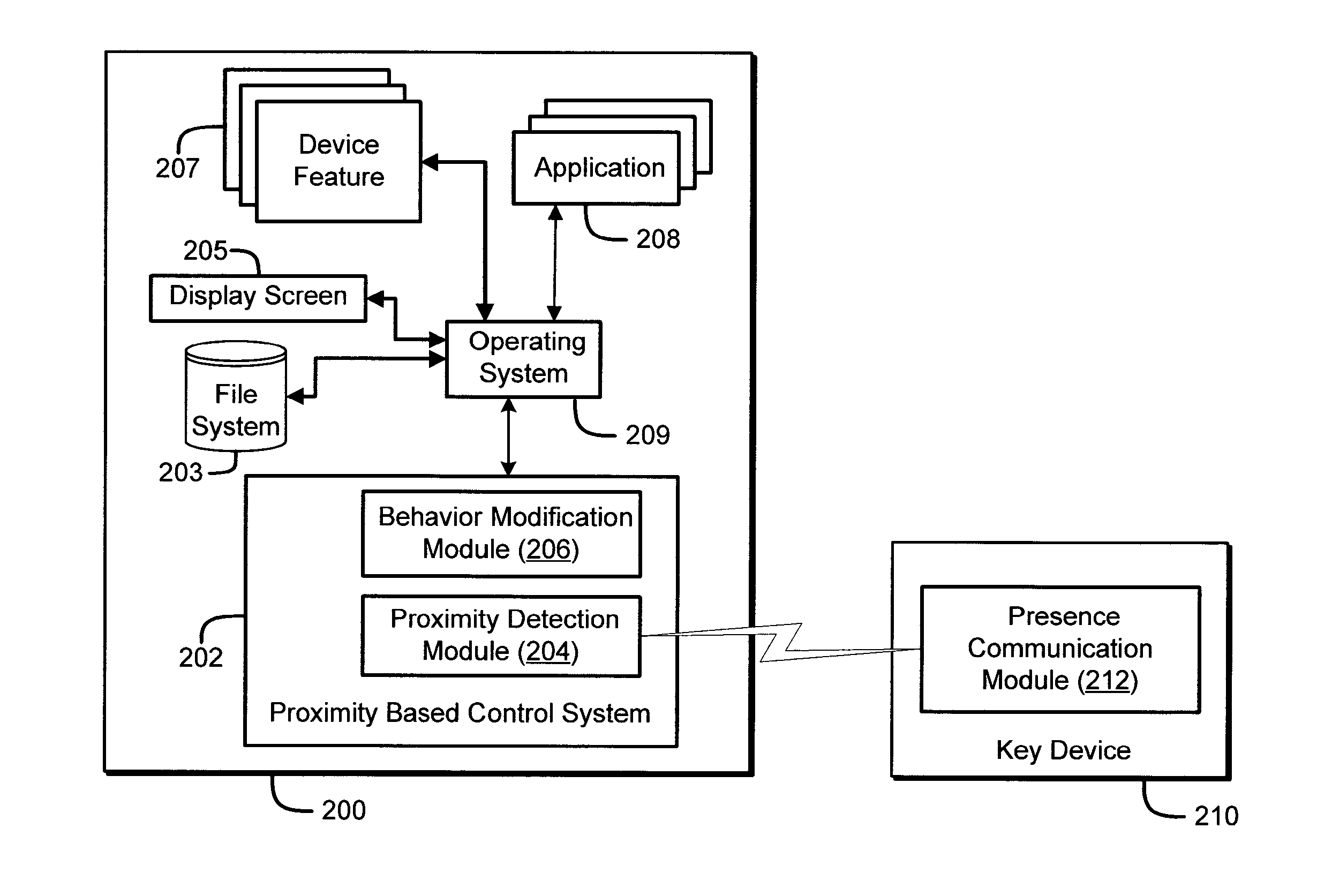
The security and convenience of a mobile communication device is enhanced based on a separate key device. If the key device is near the mobile communication device, the mobile communication device may be automatically unlocked without the user having to input an unlock code. The mobile communication device may be automatically unlocked into a first mode having a first level of functionality. If the user inputs a correct unlock code, the mobile communication device may be unlocked into a second mode having a second level of functionality, greater than the first level of functionality.
Owner:LOOKOUT MOBILE SECURITY
Hash-based systems and methods for detecting and preventing transmission of unwanted e-mail
InactiveUS20040073617A1Digital computer detailsComputer security arrangementsComputer hardwareElectronic mail
A system (120) detects transmission of potentially unwanted e-mail messages. The system (120) may receive e-mail messages and generate hash values based on one or more portions of the e-mail messages. The system (120) may then determine whether the generated hash values match hash values associated with prior e-mail messages. The system (120) may determine that one of the e-mail messages is a potentially unwanted e-mail message when one or more of the generated hash values associated with the e-mail message match one or more of the hash values associated with the prior e-mail messages.
Owner:STRAGENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com