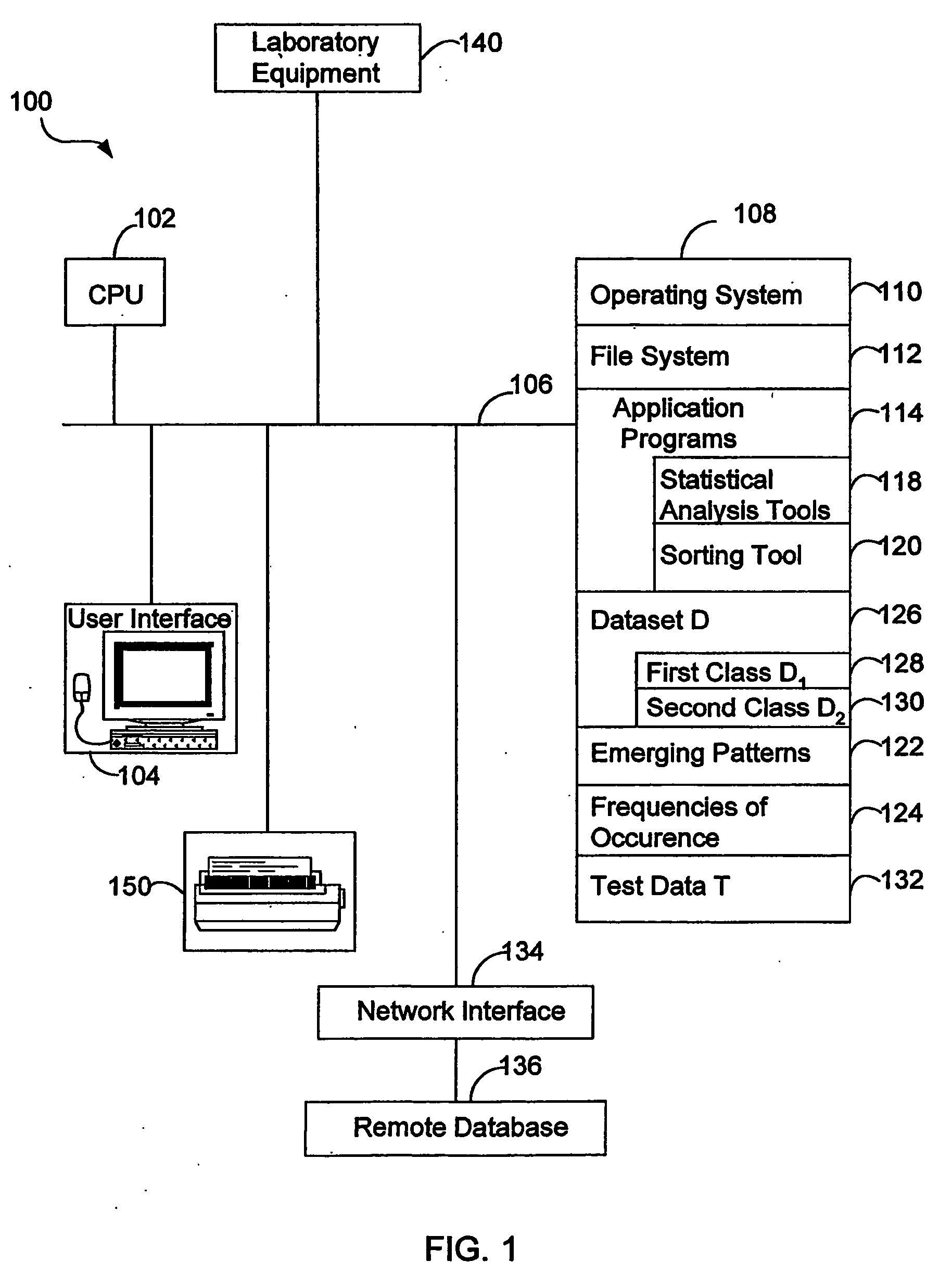
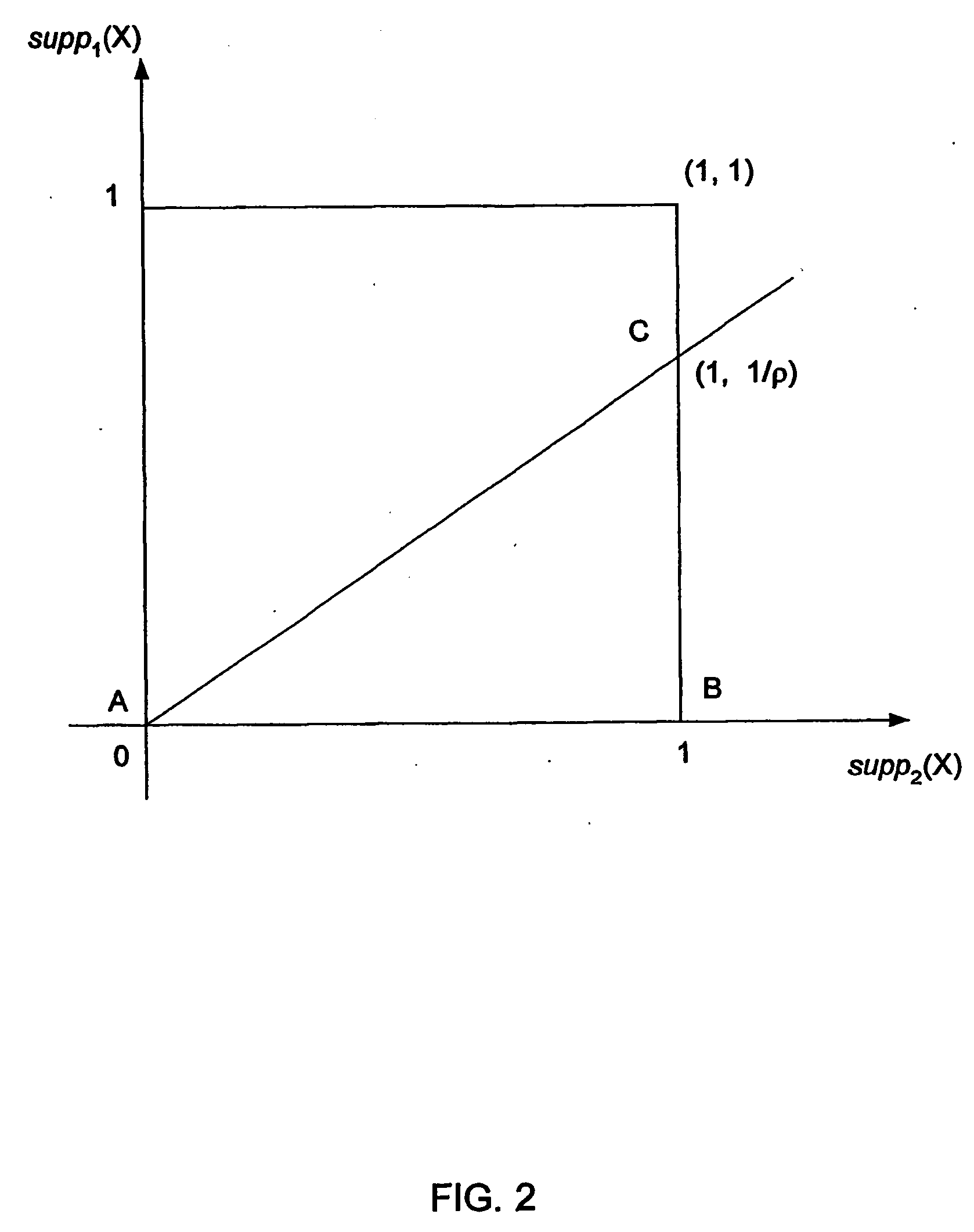Patents
Literature
2567results about How to "Cost efficient" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
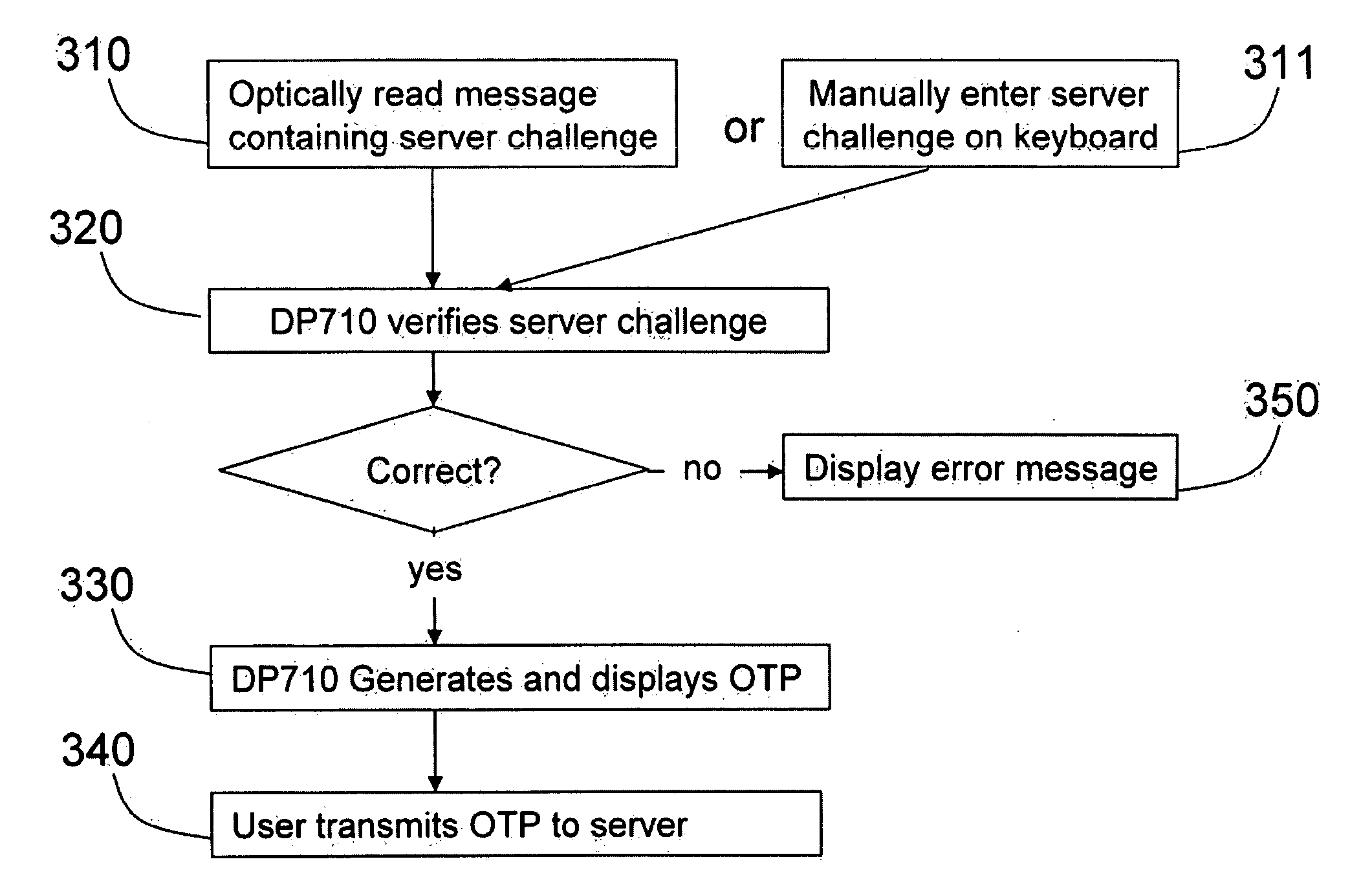
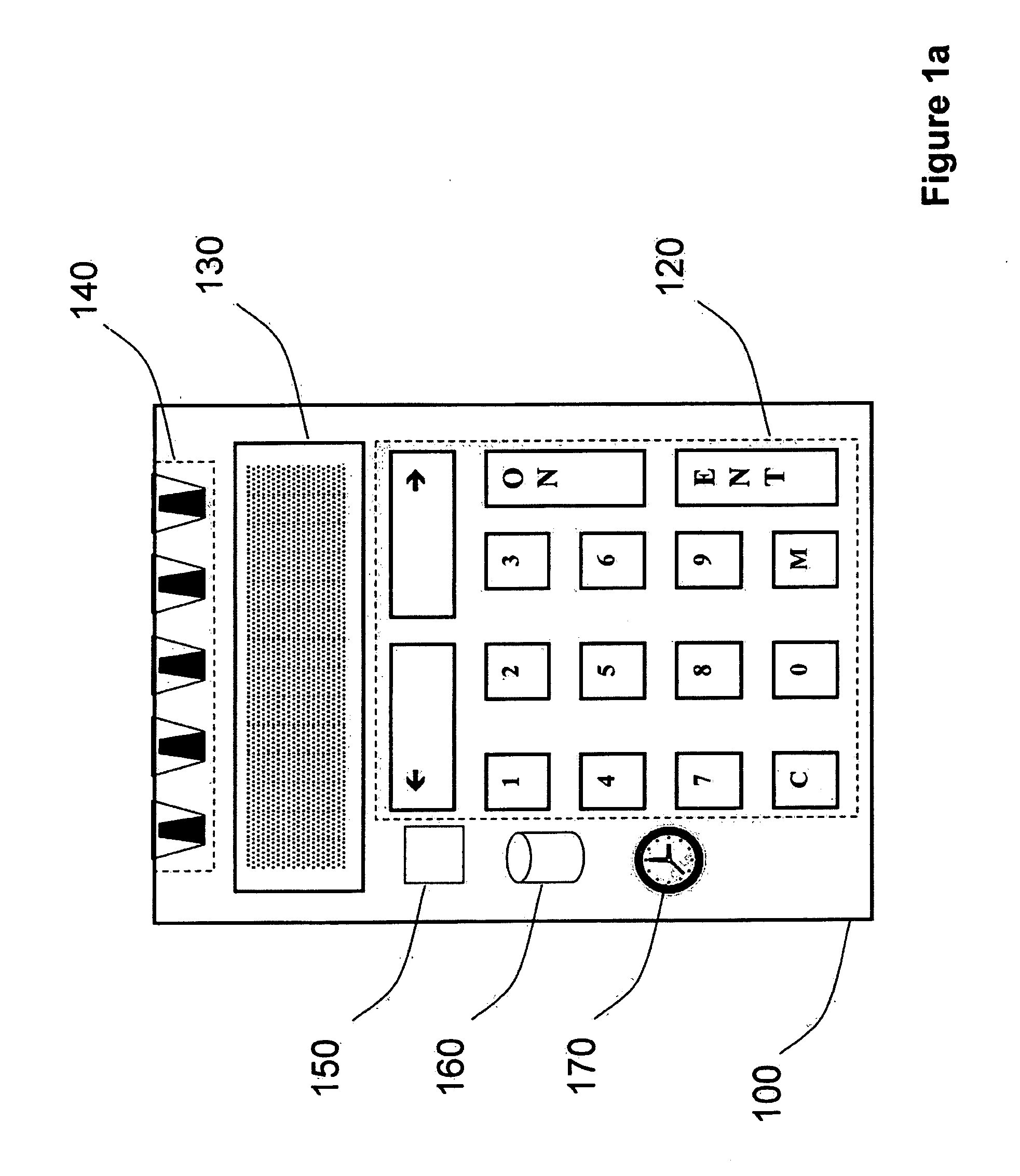
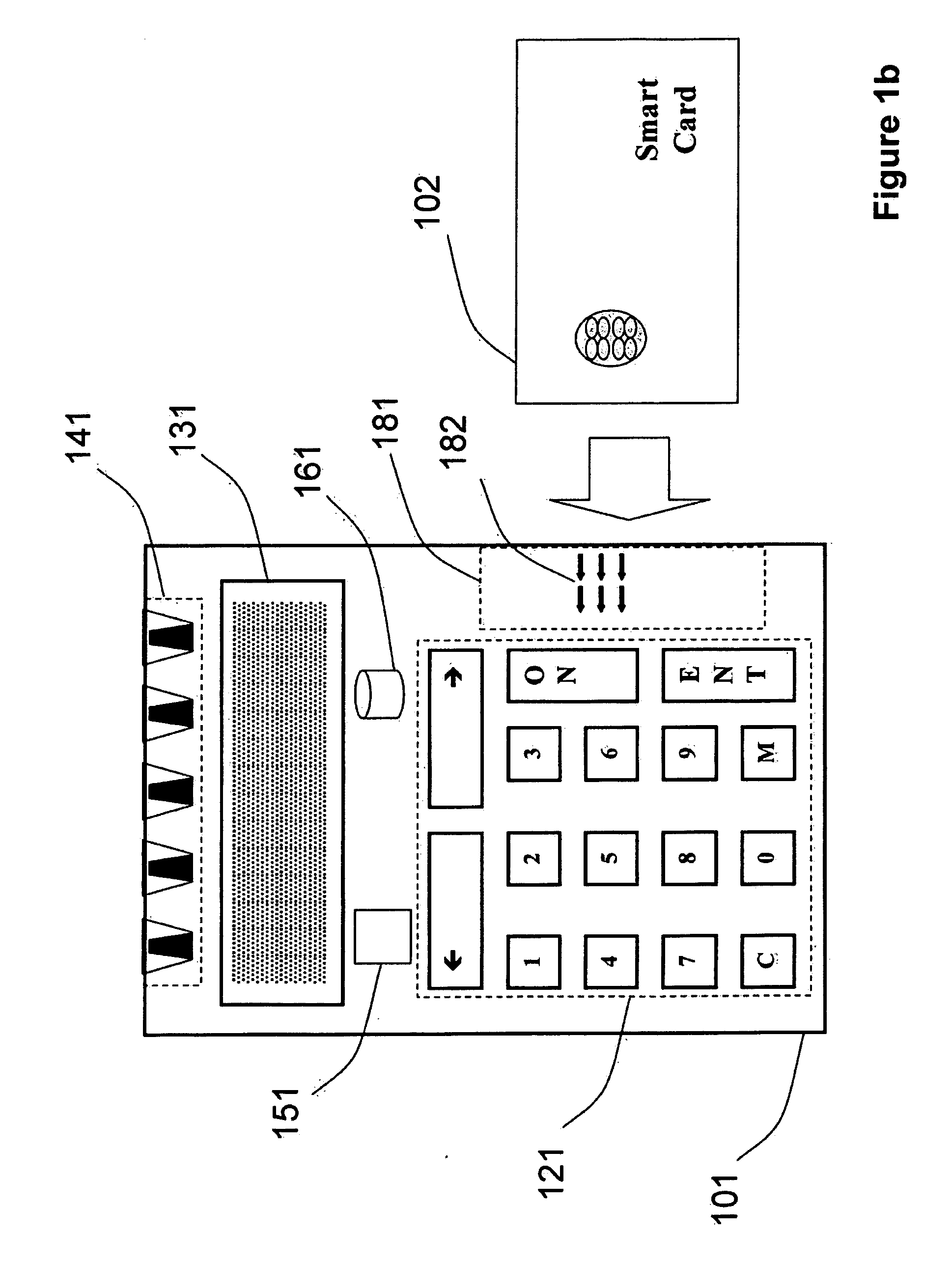
Strong authentication token generating one-time passwords and signatures upon server credential verification
ActiveUS20090235339A1Transfer size reductionHighly secureDigital data processing detailsMultiple digital computer combinationsInternet privacyTransaction data
The invention defines a strong authentication token that remedies a vulnerability to a certain type of social engineering attacks, by authenticating the server or messages purporting to come from the server prior to generating a one-time password or transaction signature; and, in the case of the generation of a transaction signature, signing not only transaction values but also transaction context information and, prior to generating said transaction signature, presenting said transaction values and transaction context information to the user for the user to review and approve using trustworthy output and input means. It furthermore offers this authentication and review functionality without sacrificing user convenience or cost efficiency, by judiciously coding the transaction data to be signed, thus reducing the transmission size of information that has to be exchanged over the token's trustworthy interfaces
Owner:ONESPAN NORTH AMERICA INC
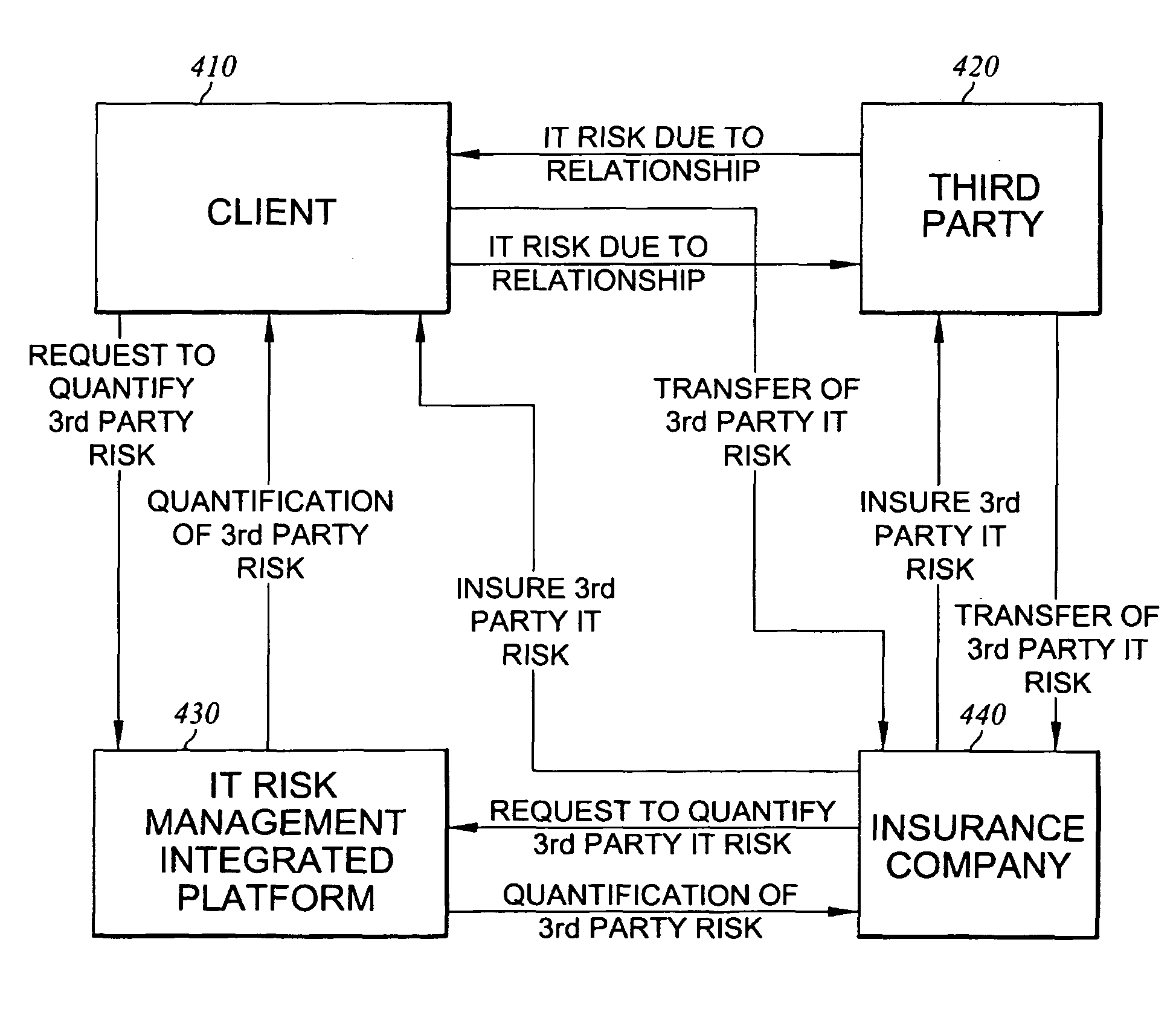
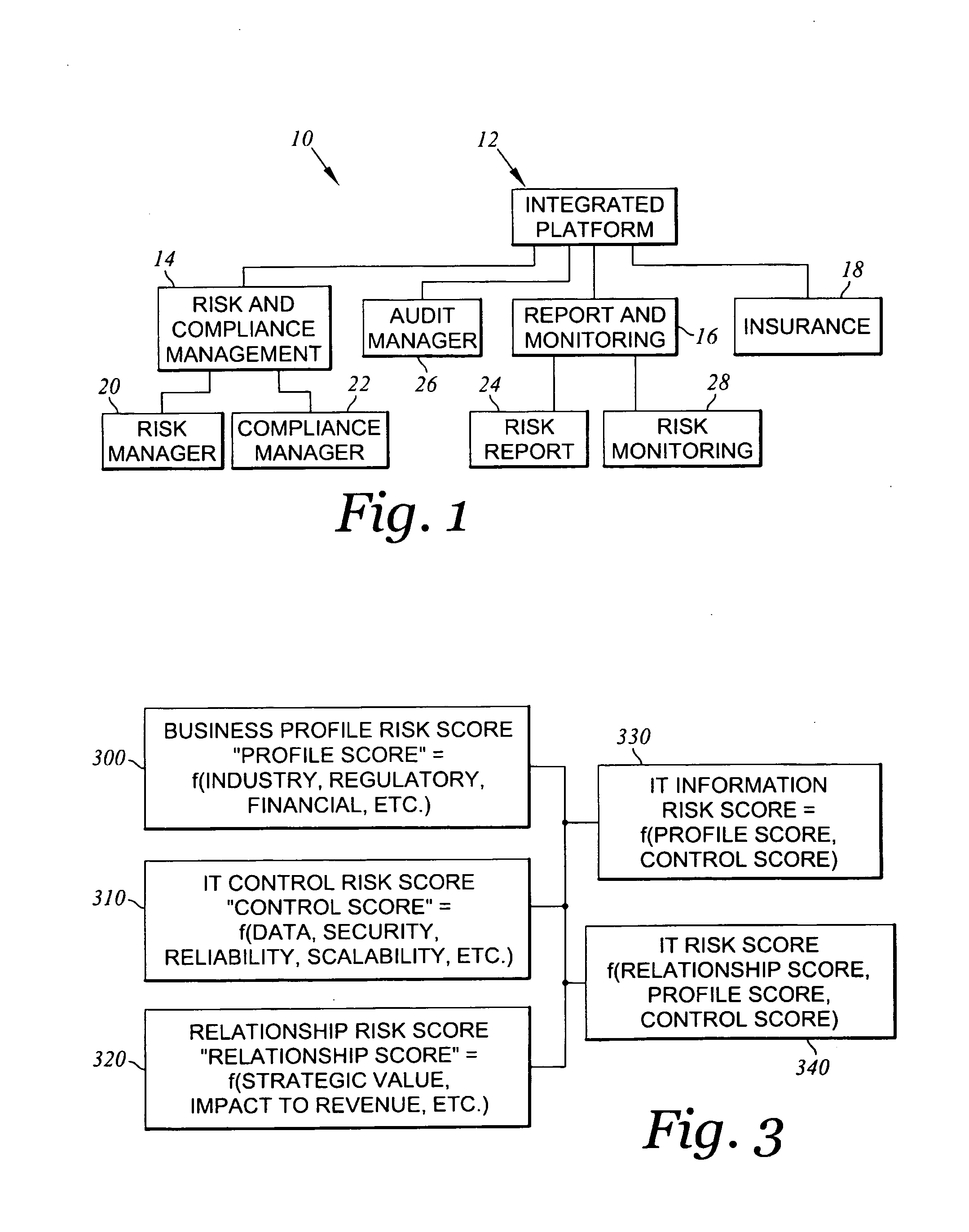
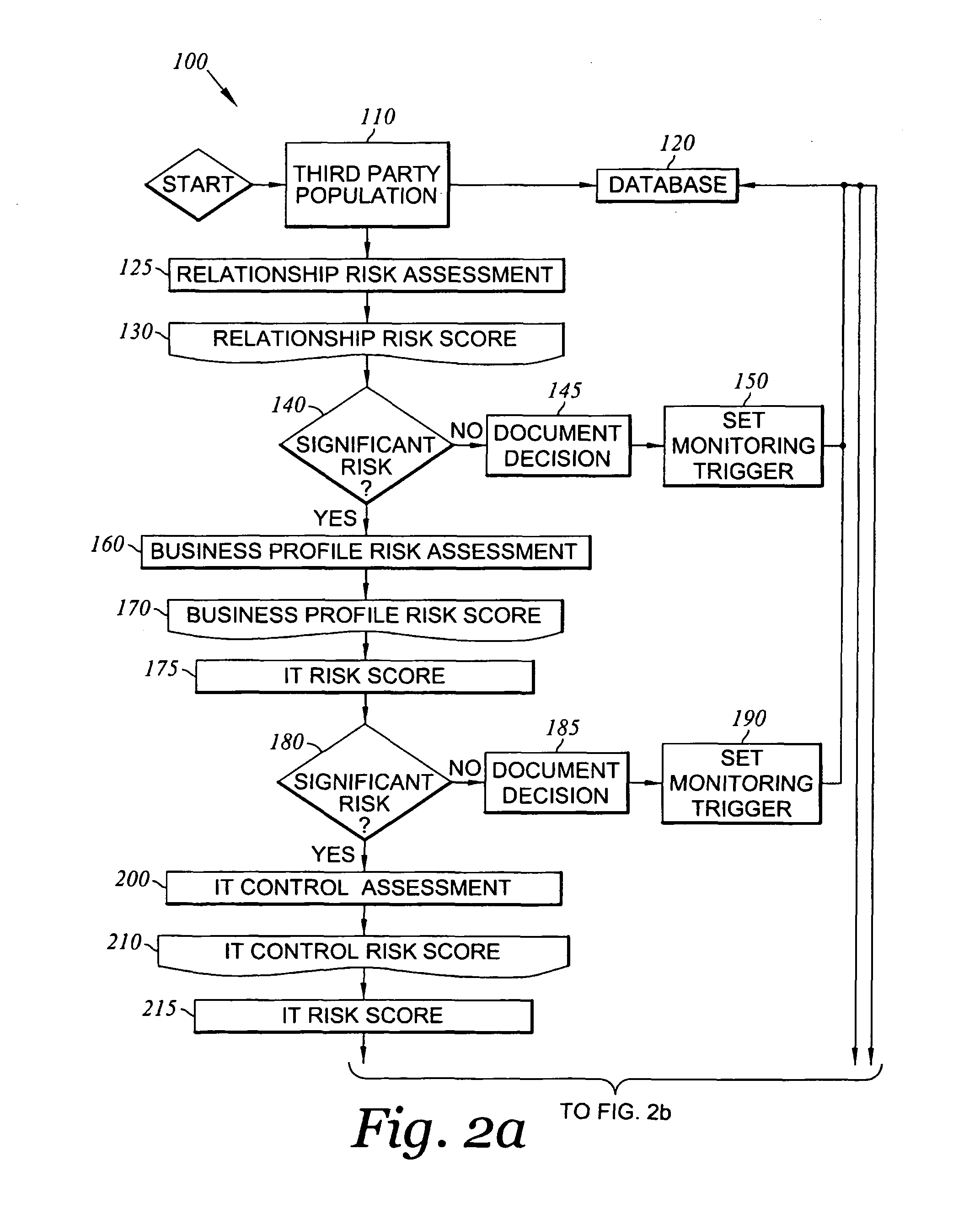
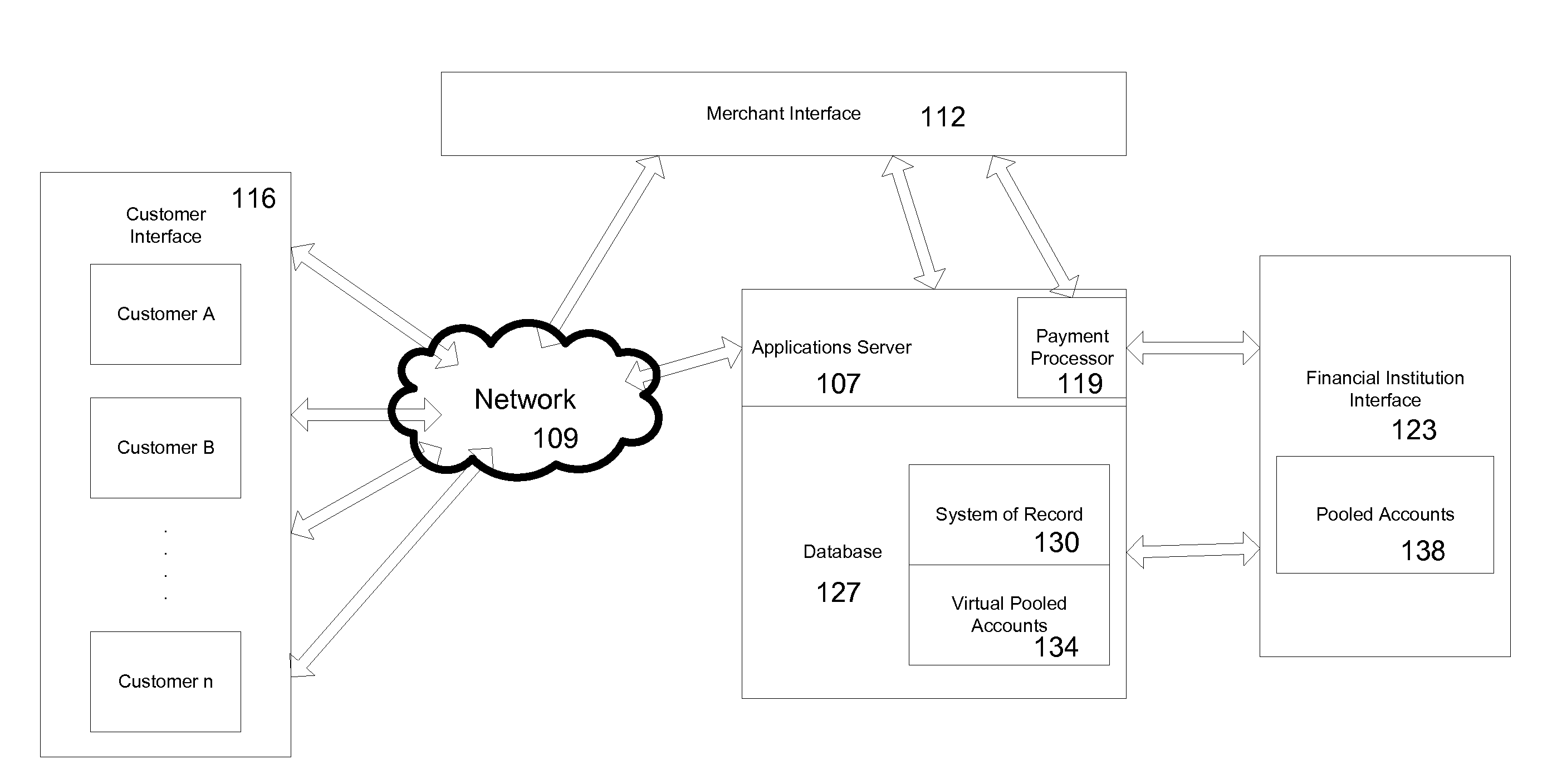
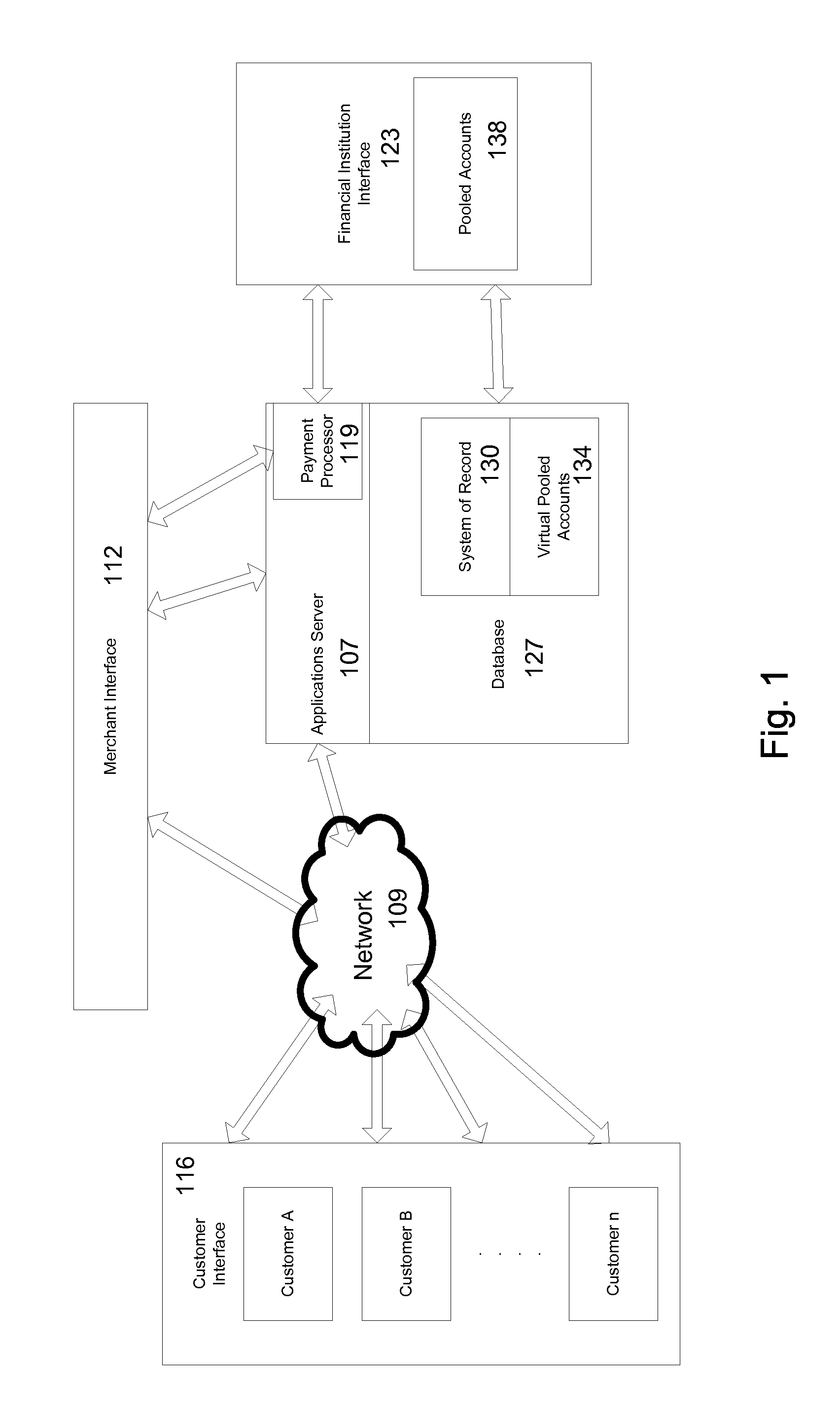
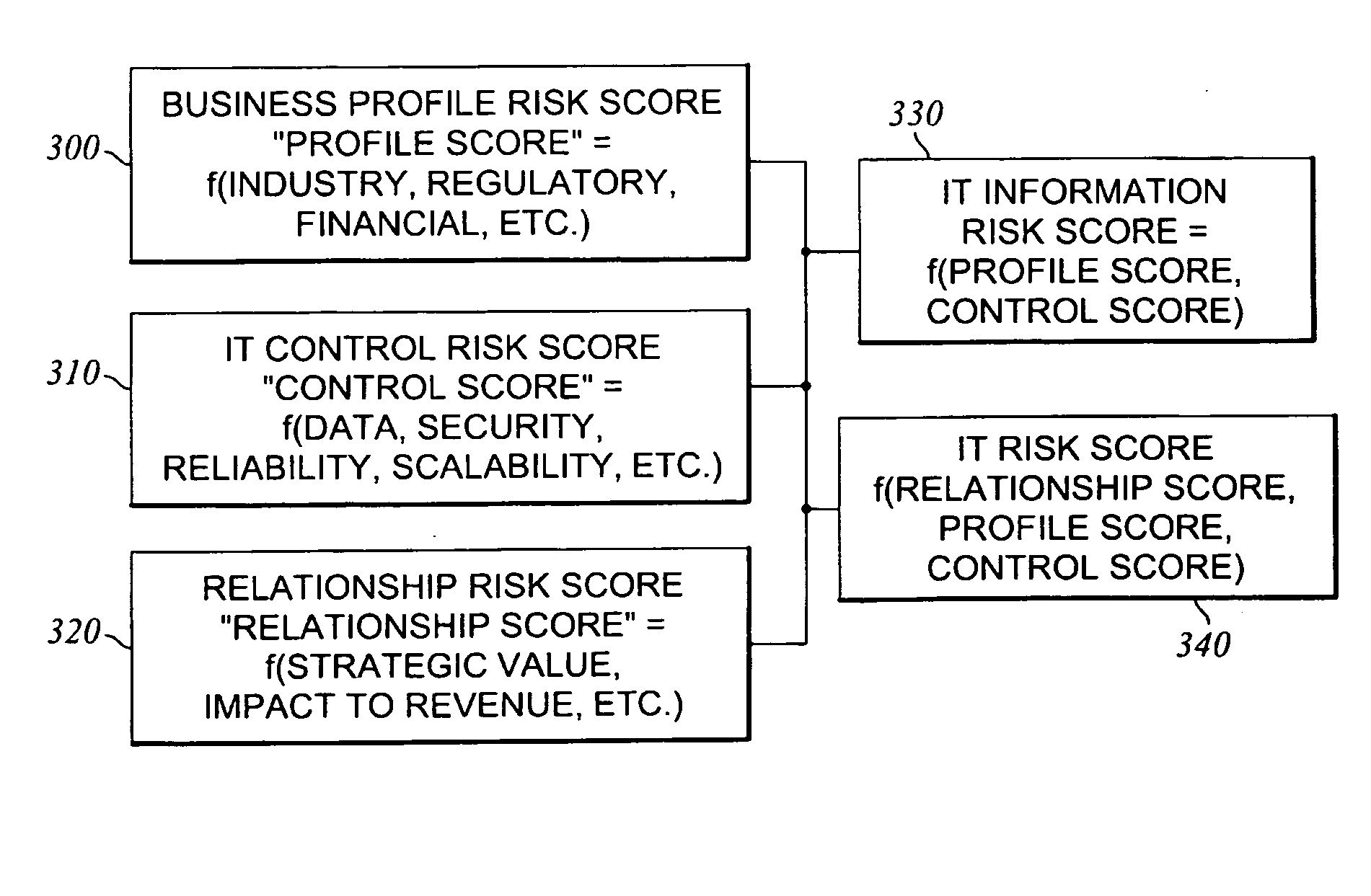
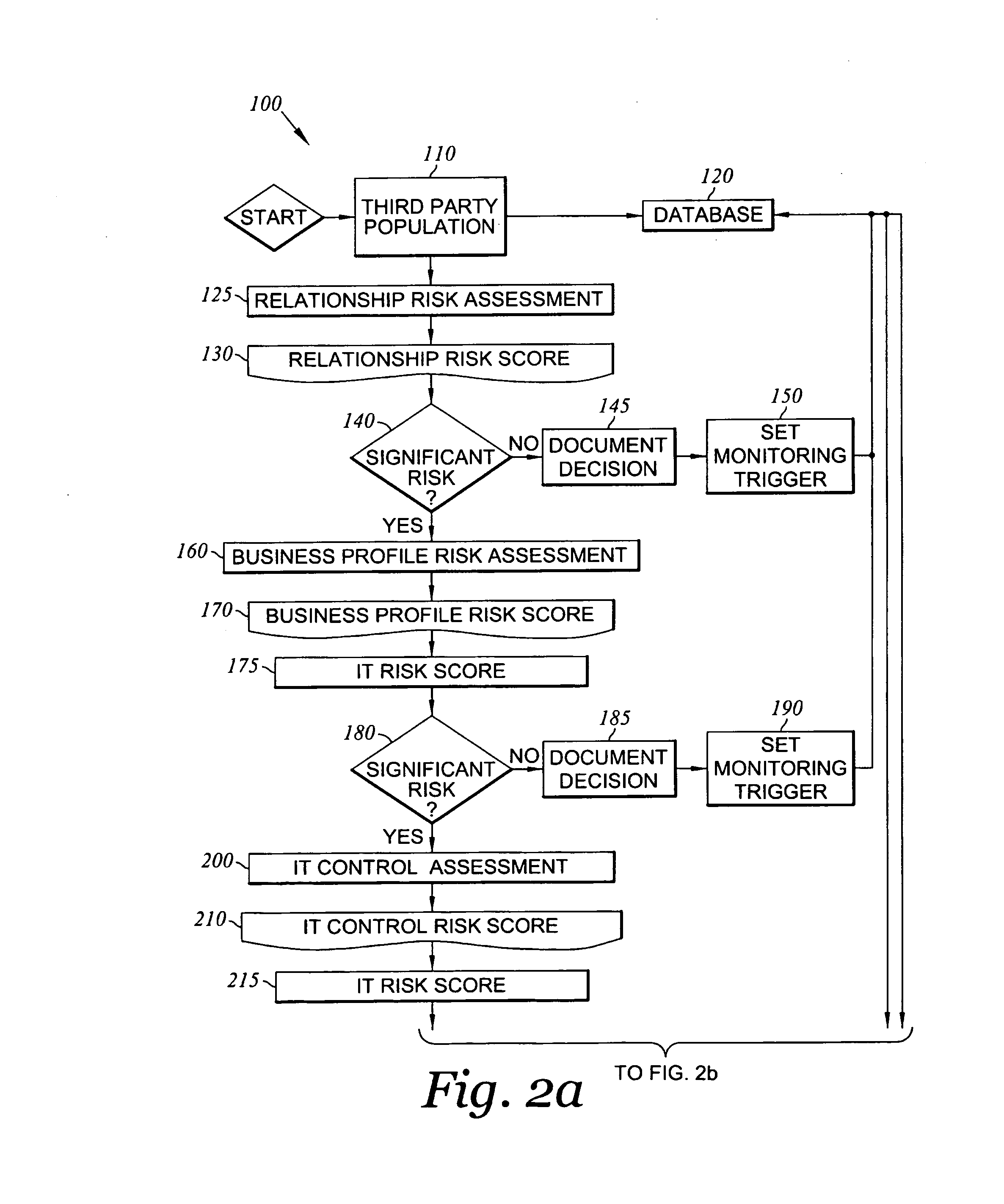
Method and system for assessing, managing, and monitoring information technology risk
A method for information technology (IT) and information asset risk assessment of a business relationship between a client and a third party. The method includes establishing a database. The database includes a plurality of IT information risk factors. The database is configured to receive IT risk information. The IT risk information is associated with the plurality of IT information risk factors. The plurality of IT information risk factors includes a subset of relationship risk factors. The subset of relationship risk factors are utilized for evaluating the business relationship risk between the client and the third party. The method also includes receiving IT risk information corresponding to the subset of relationship risk factors. The method continues with generating a relationship risk score. The relationship risk score is determined in response to evaluating the subset of relationship risk factors using the IT risk information corresponding to the subset of relationship risk factors.
Owner:OPTIV SECURITY INC
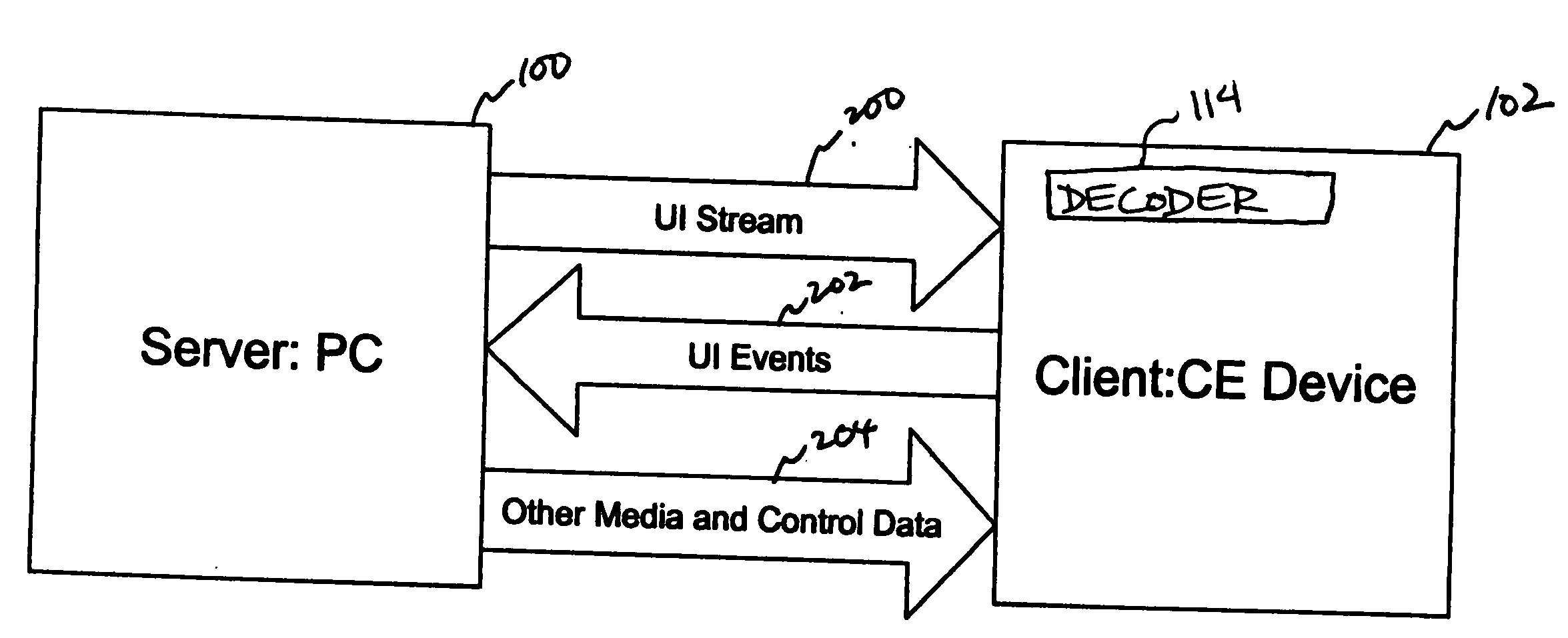
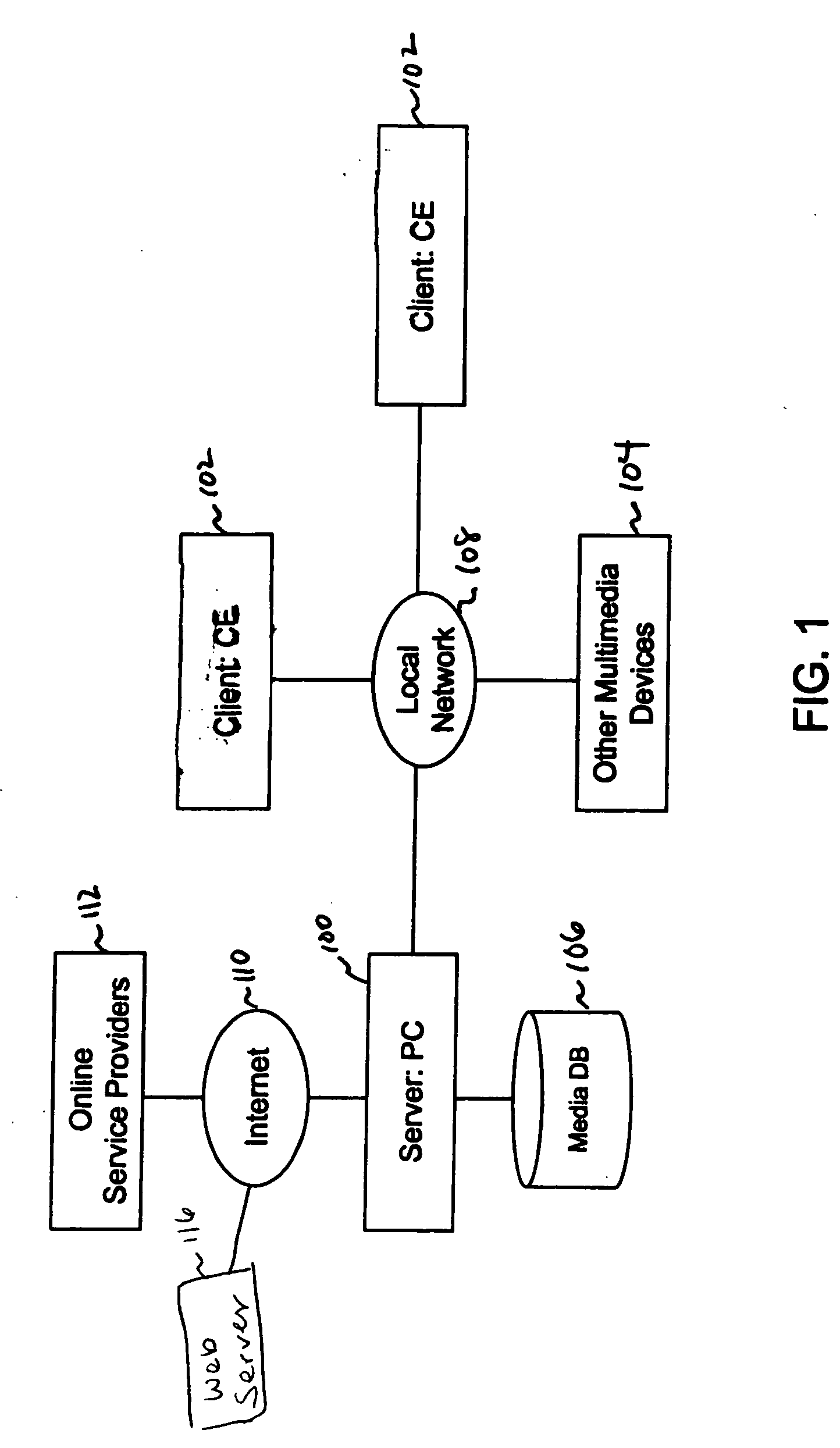
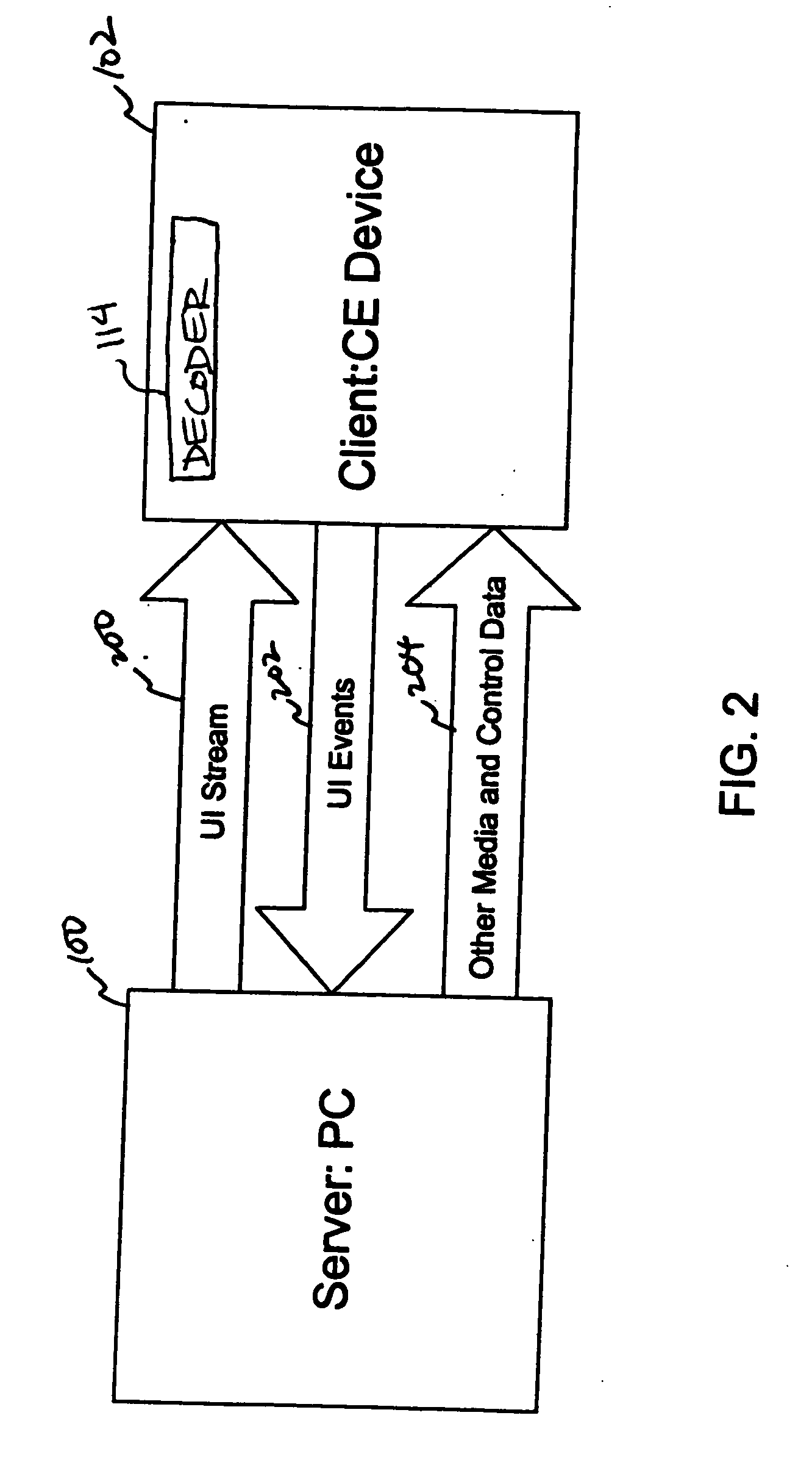
System and method for a remote user interface
InactiveUS20060174026A1Cost efficientCE device may be kept relatively simpleMultiple digital computer combinationsTelevision systemsUser inputMedia server
A remote user interface provides a full motion, full-color, dynamic interface with complex visuals without imposing heavy hardware requirements on a consumer electronics device. Instead, the hardware requirements are placed on another computer device that is designated as a media server. The media server generates the complex UI, encodes the UI into one or more compressed video frames, and transmits the compressed video frames to the CE device. The CE device plays the UI video as it would any other video. User inputs for interacting with the UI are transmitted and interpreted by the media server. The media server updates the UI images based on the interaction.
Owner:DIVX INC
Mobile Person-to-Person Payment System
InactiveUS20090319425A1The process is simple and fastEasy and fast accessFinancePayment architectureBarcodeFinancial transaction
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions can be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions can be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY INC
System and method for routing content
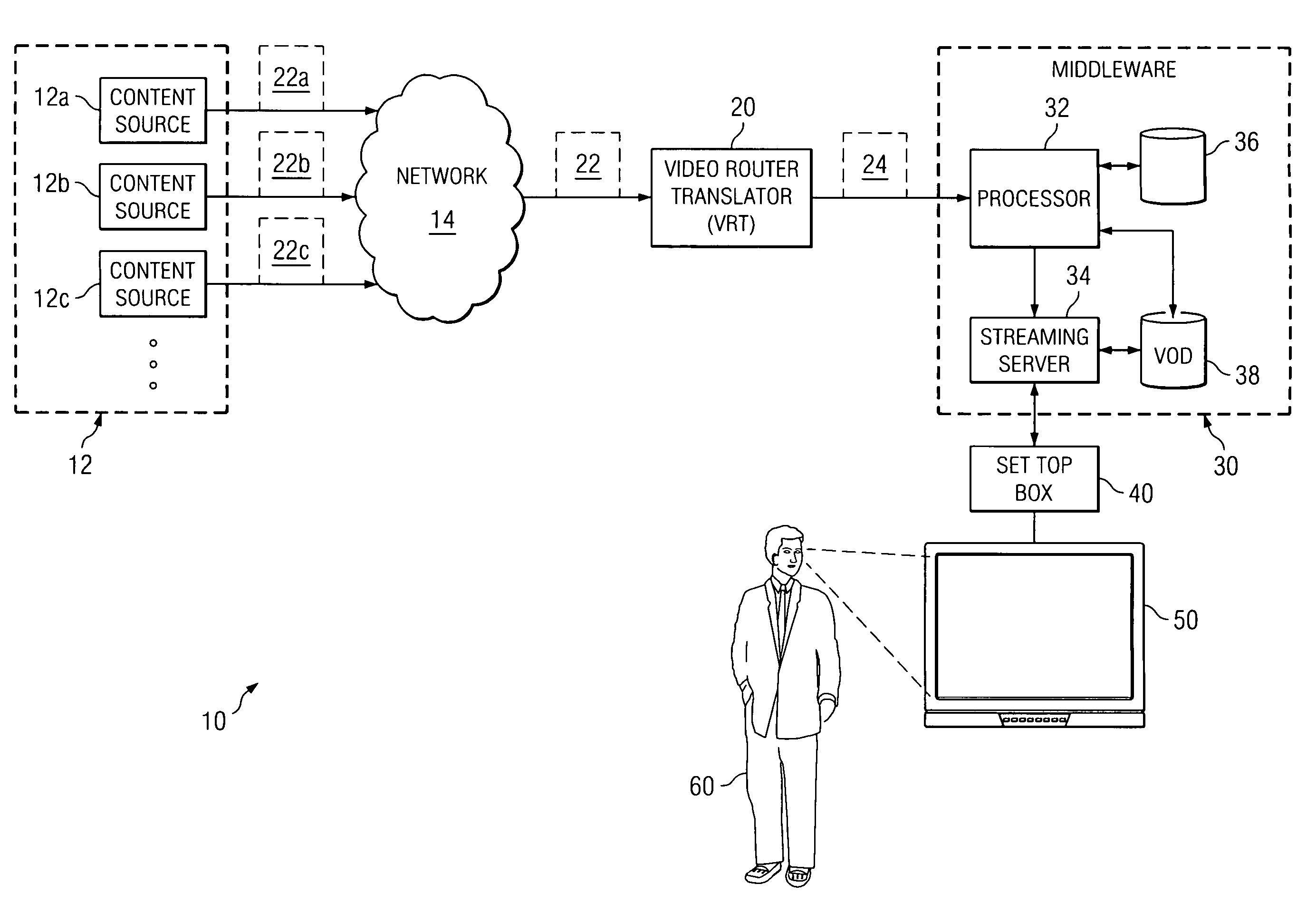
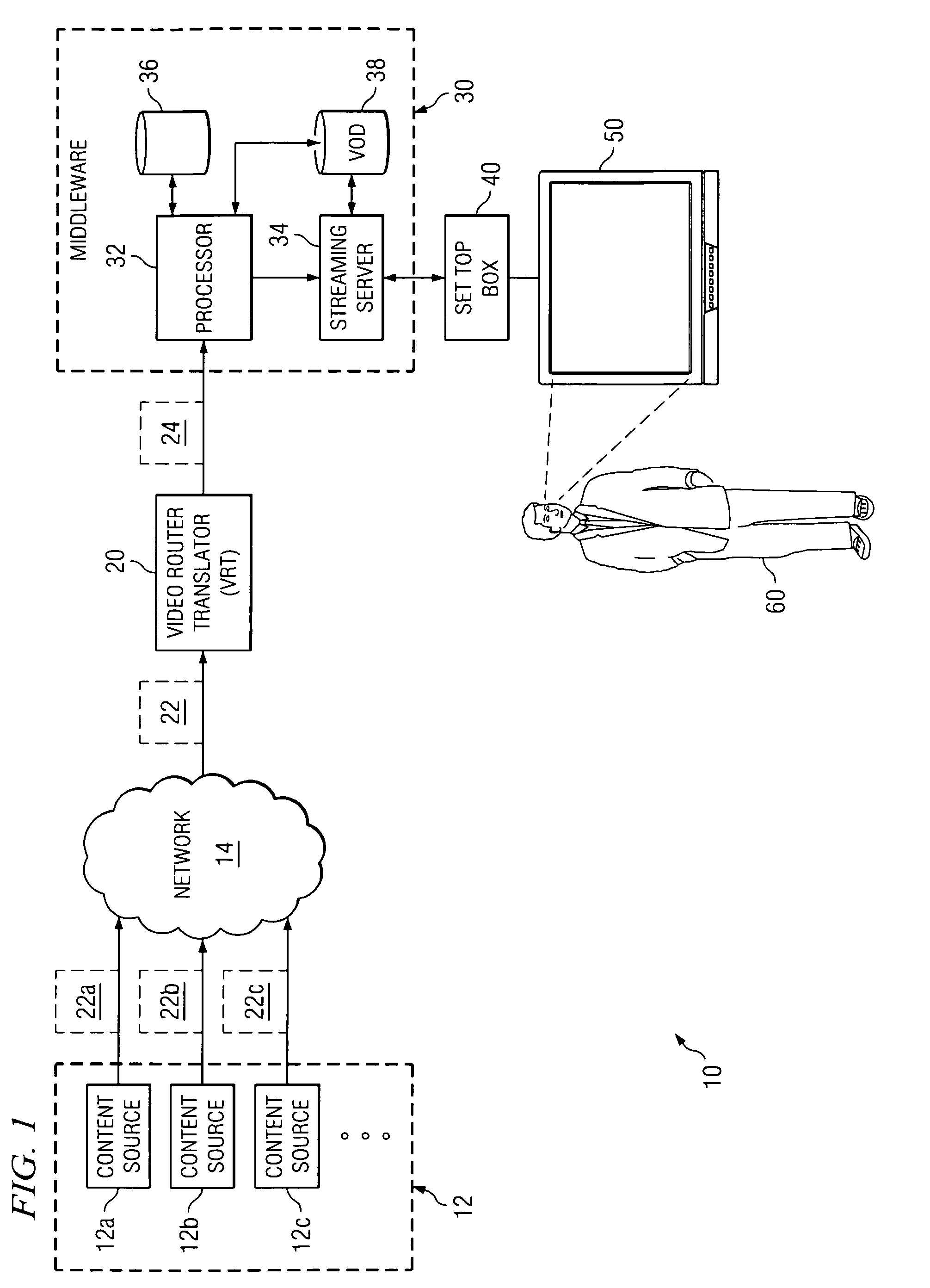
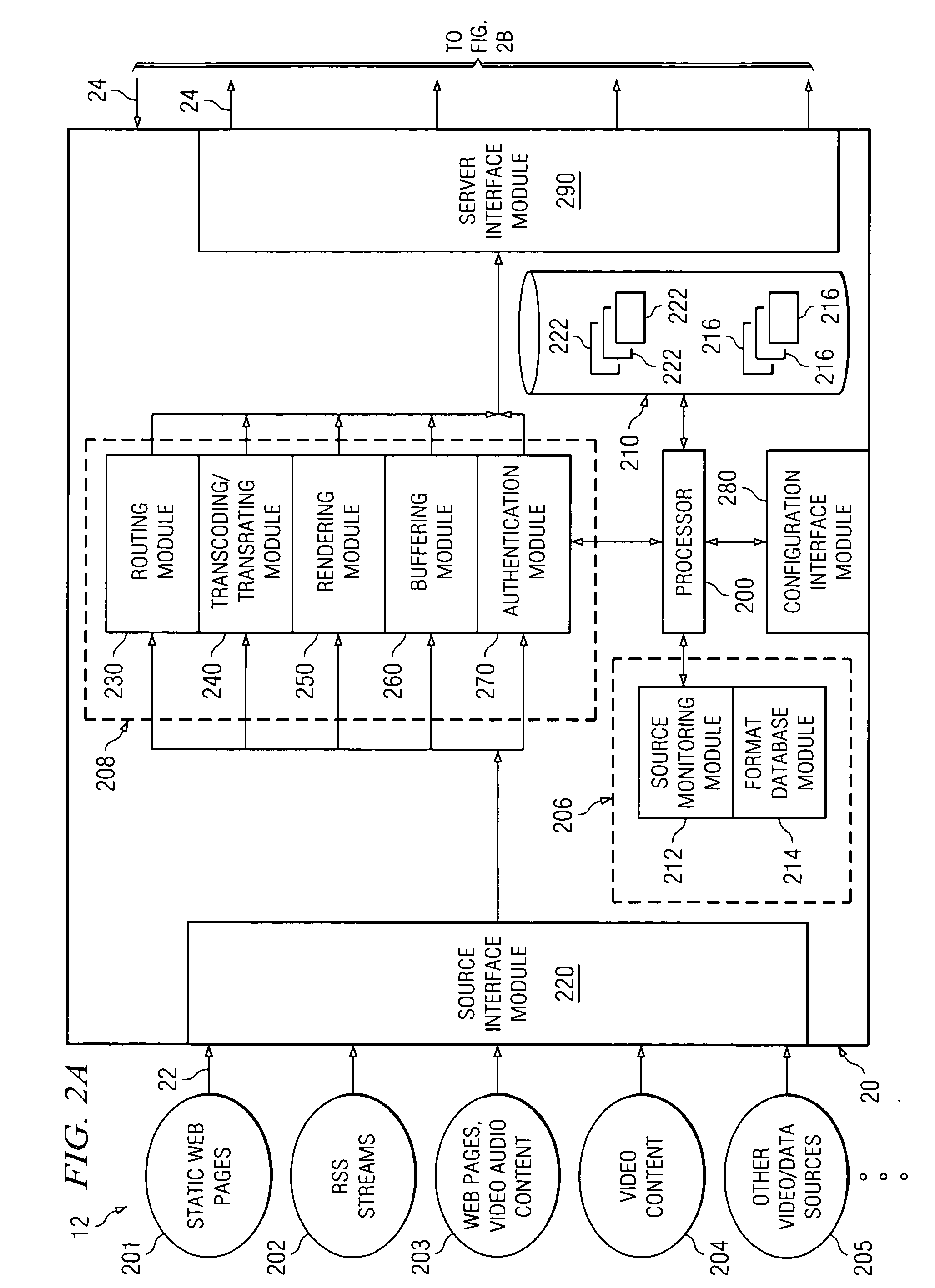
ActiveUS20070162945A1Delivery reduced eliminatedDisadvantages and reduced eliminatedAnalogue secracy/subscription systemsTwo-way working systemsDisplay deviceInformation transfer
A system for transmitting information to a display includes one or more content sources, a network, a content processor, and a display device. The content sources are each capable of transmitting content to a content router in first formats according to packet-based communication protocol. The network selectively couples content sources to the content processor. The content processor requests and receives content from a selected content source. The content processor then modifies the first formats and generates a video stream based on the received content and transmits the video stream to the display device. The display device then displays the video stream.
Owner:IMAGINE COMM
Method and system for identifying the identity of a user
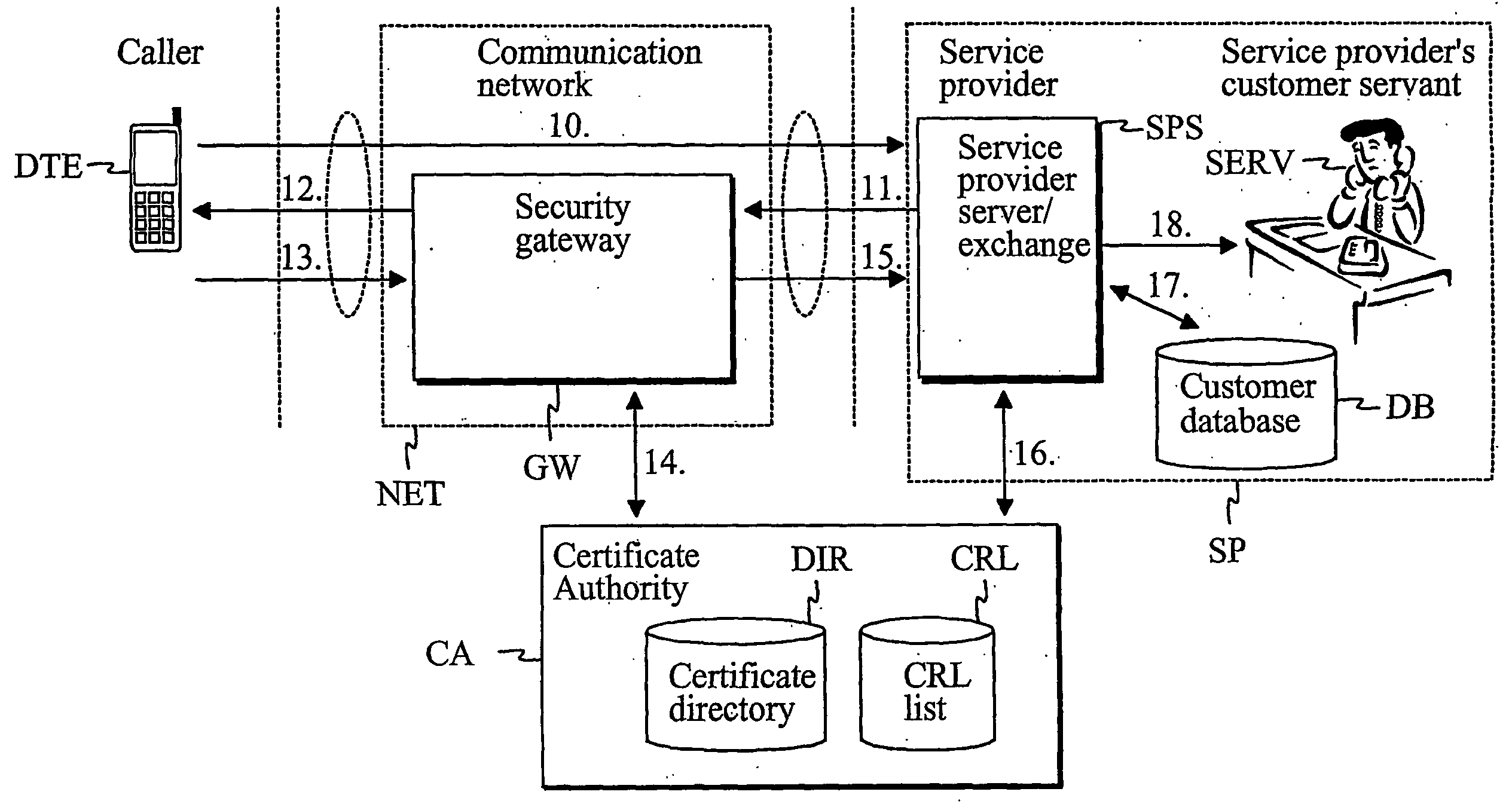
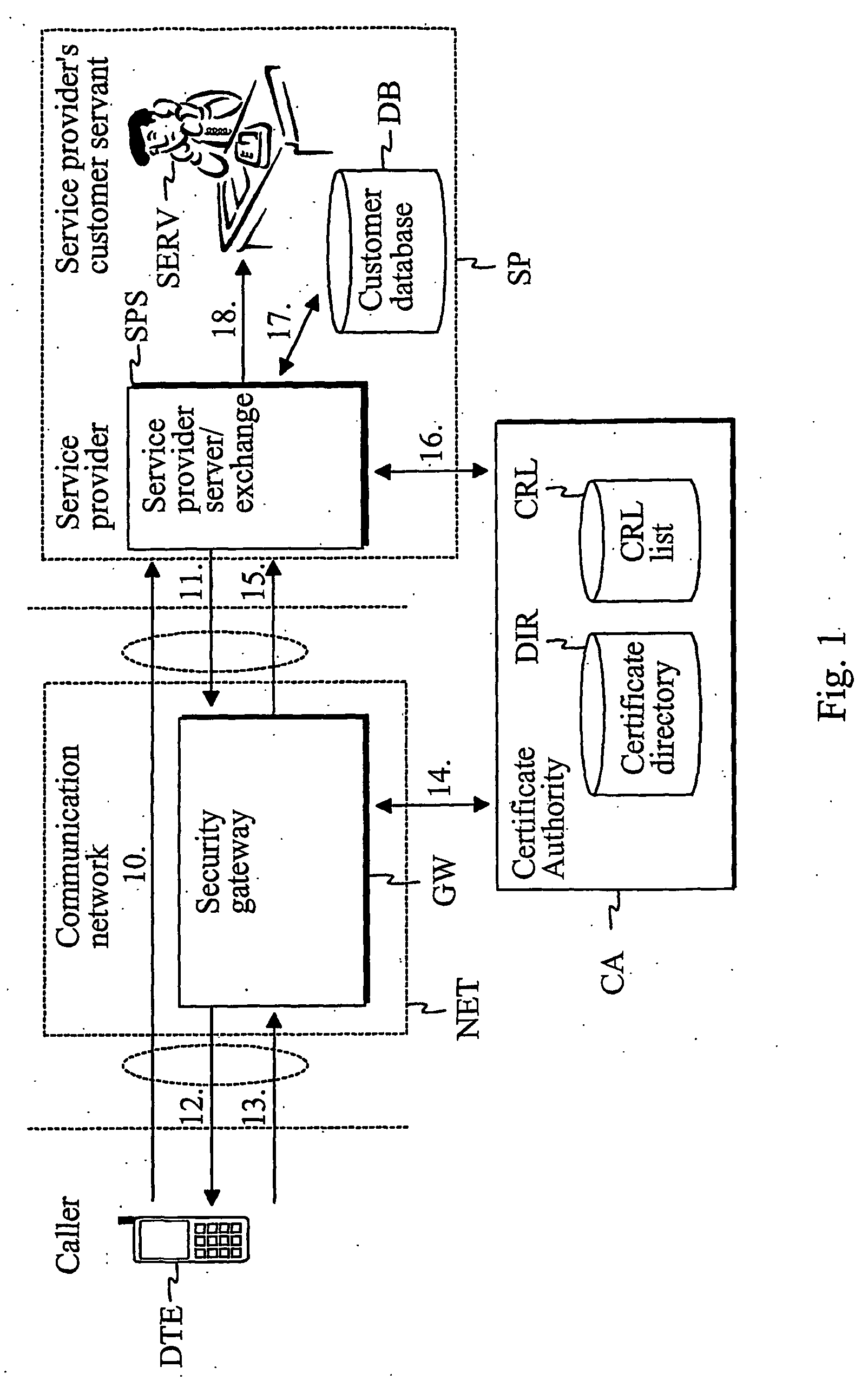
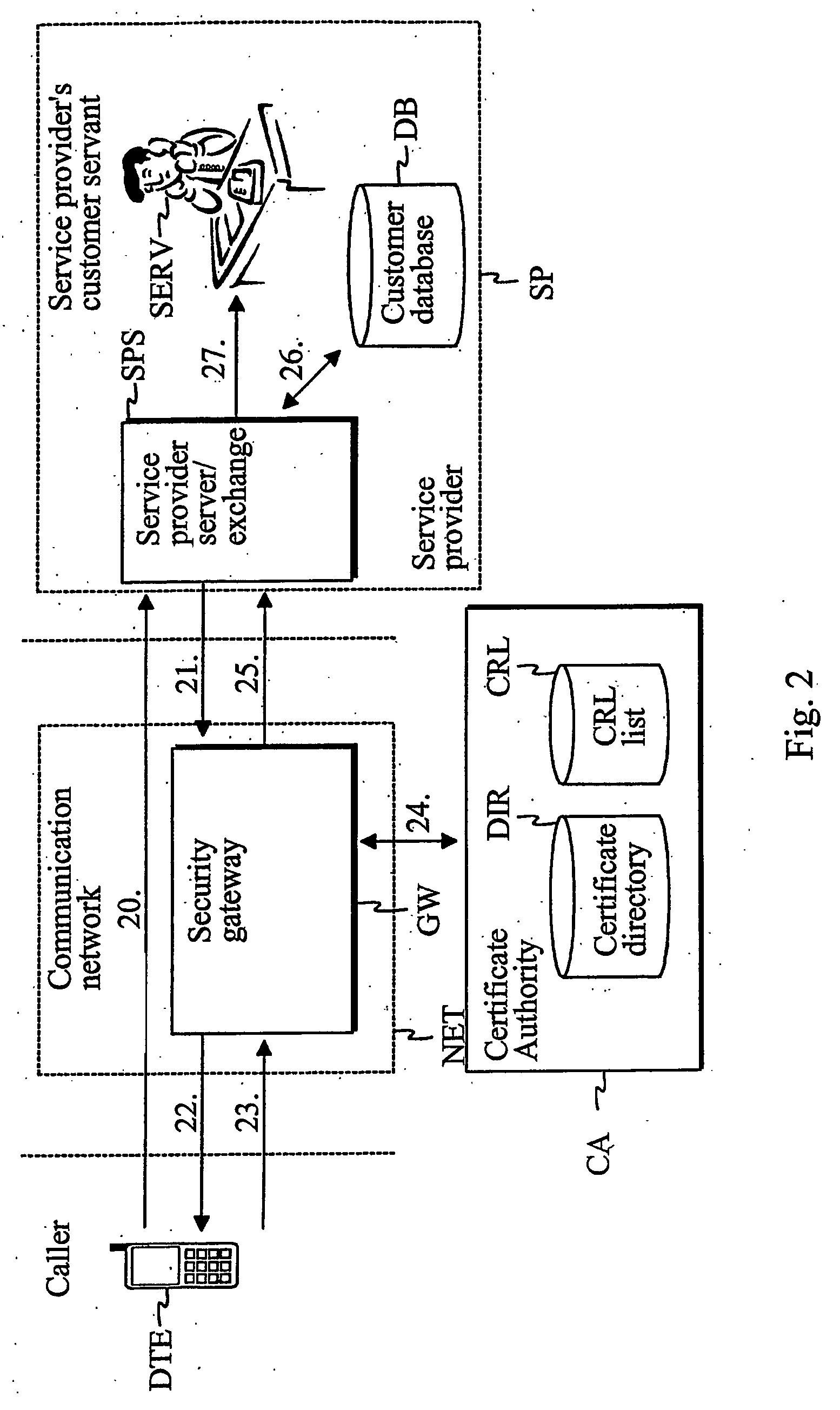
InactiveUS20060262929A1Easy to implementCost efficientSecret communicationTransmissionService providerService provision
The present invention describes a method and system for verifying the identity of a user of a first terminal in a communication system having at least a communication network (NET), a first terminal (DTE) associated with the communication network (NET) and a service provider (SP) associated with the communication network (NET). In the method, a first logical channel is set up via the communication network between the first terminal (DTE) and the service provider (SP). The user of the first terminal is identified after the first logical channel set up via a second logical channel other than the established first logical channel between the service provider and the first terminal prior to providing any services to the caller.
Owner:QITEC TECH GROUP
Reflector antenna radome with backlobe suppressor ring and method of manufacturing
ActiveUS7138958B2Reduce wind loadsCost efficientRadiating element housingsCollapsible/retractable loop antennasMetallic foilSuppressor
A radome adapted to reduce backlobes of an associated reflector antenna via application of a conductive ring with an inward facing edge about the periphery of the radome. The conductive ring may be applied extending around the radome periphery to an inside and or outside surface of the radome. The conductive ring may be formed upon the radome by metalising, electrodaging, over molding or the like. Further, the conductive ring may be a metal, metallic foil, conductive foam or the like which is coupled to the radome. An absorber in the form of a ring or a surface coating applied to the radome and or the distal end of the reflector may also be added between the radome and the reflector.
Owner:COMMSCOPE TECH LLC
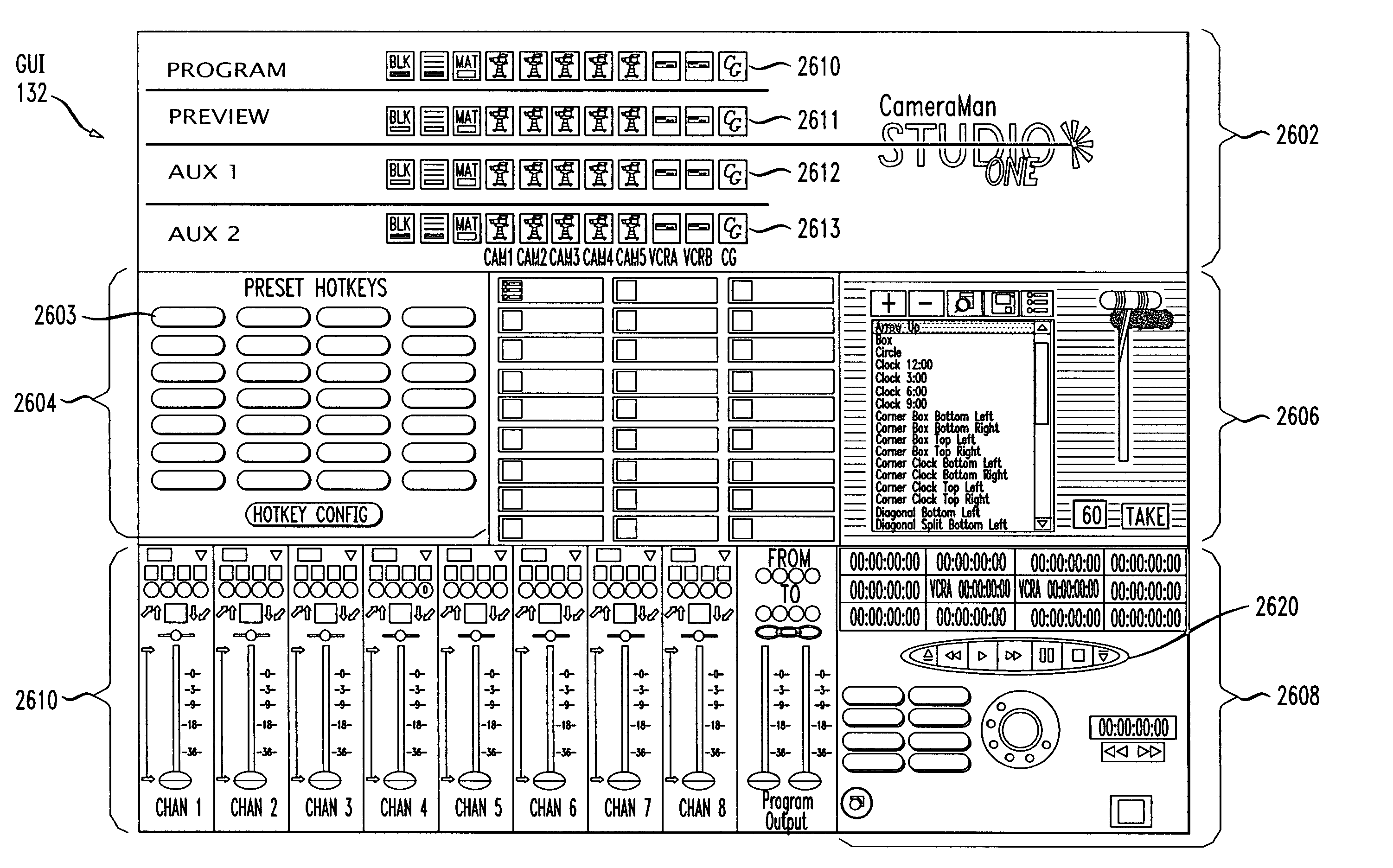
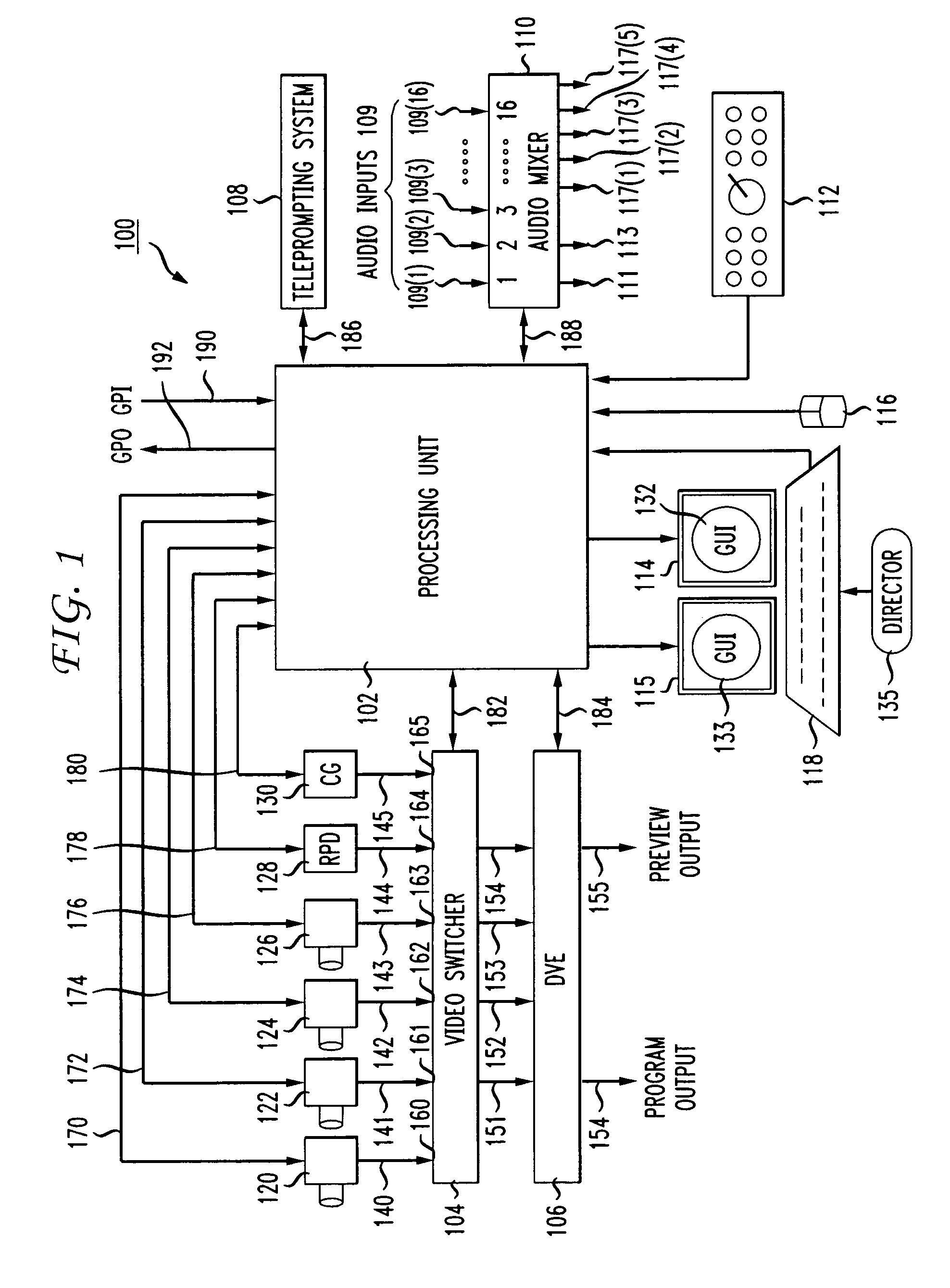
System and method for real time video production and multicasting
InactiveUS7024677B1Easy to controlCost efficientBroadcast information characterisationElectronic editing digitised analogue information signalsPersonalizationBroadcast time
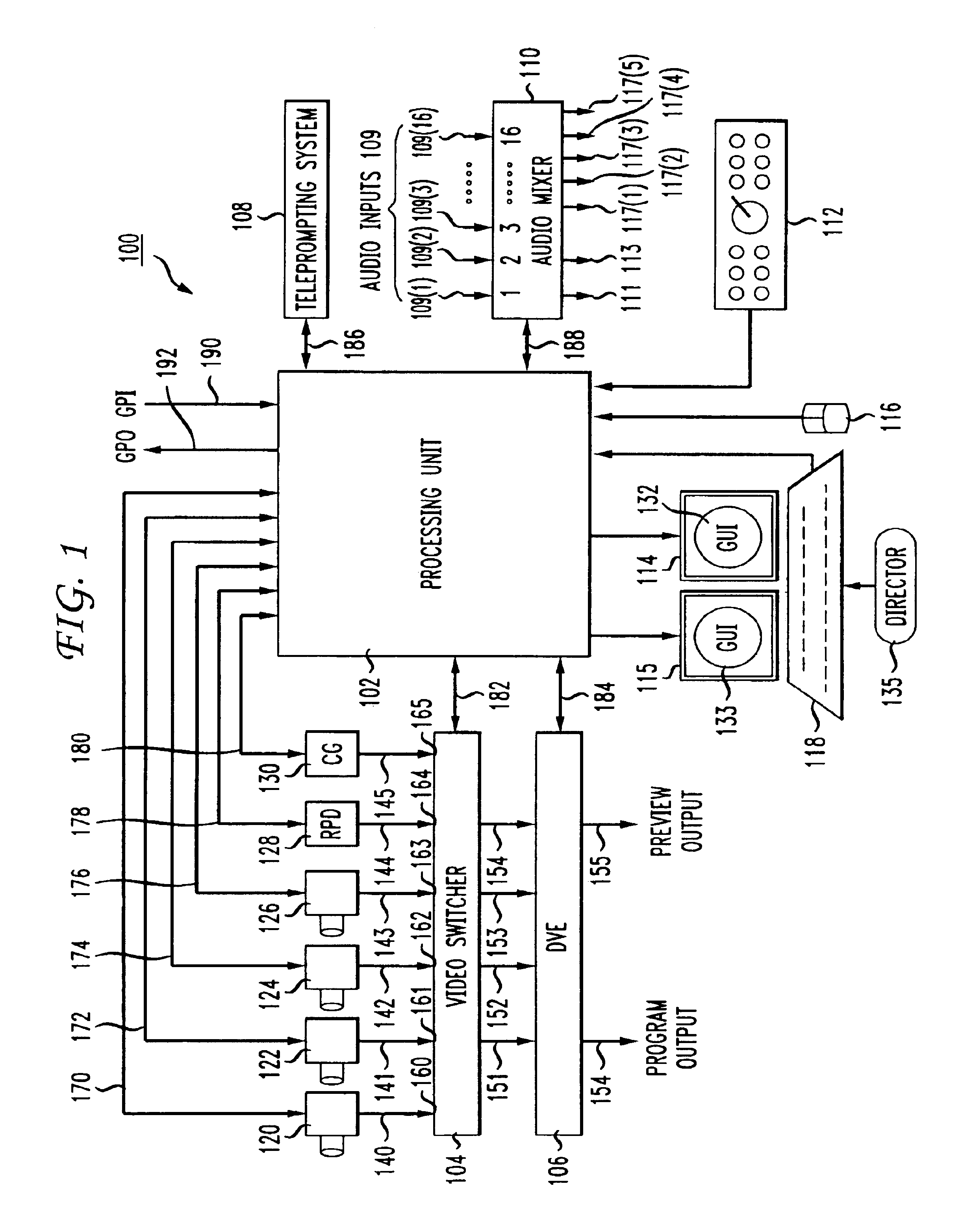
An integrated, fully automated video production system provides a video director with total control over all of the video production devices used to produce and broadcast a show. Such devices include, but are not limited to, cameras, robotic pan / tilt heads, video tape players and recorders (VTRs), video servers and virtual recorders, character generators, still stores, digital video disk players (DVDs), audio mixers, digital video effects (DVE), video switchers, and teleprompting systems. The video production system provides an automation capability that allows the video director to pre-produce a show, review the show in advance of “air time,” and then, with a touch of a button, produce the live show. In one embodiment, the invention provides a video production system having a processing unit in communication with one or more of the video production devices. The processing unit also records the show or elements from the show following its production. The show or elements can be recalled for subsequent broadcasts. An Internet interface supports live or on-demand requests for content from the video production. In an embodiment, an online user selects specific. elements and reorganizes the elements to personalize a broadcast. The processing unit receives and executes the online request to continuously stream or download the content to the user. In an embodiment, various supporting features enhance and extend the content of the video production, such as real time polling, hyperlinks to related web sites, video captions, and the like.
Owner:THOMSON LICENSING SA
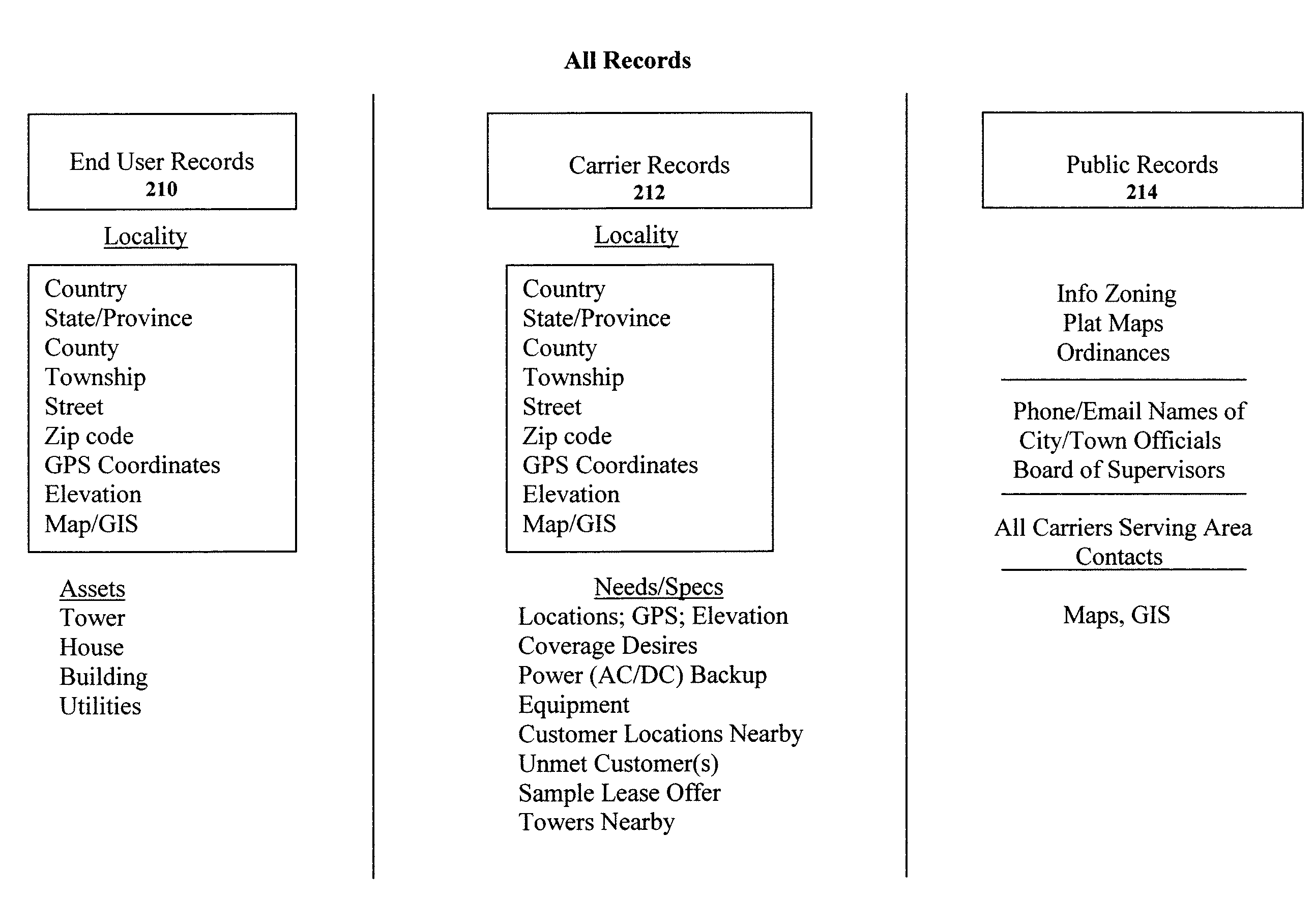
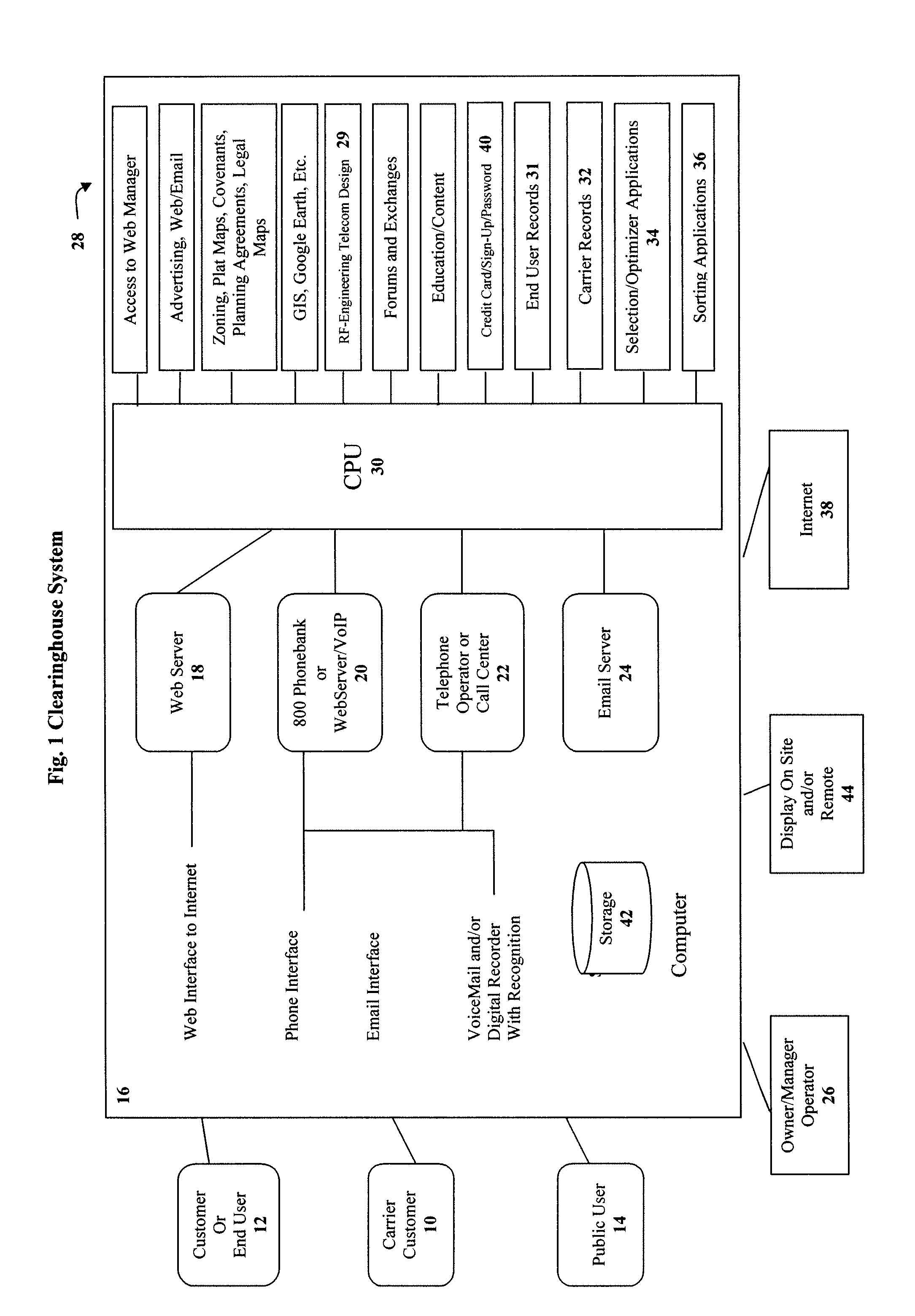
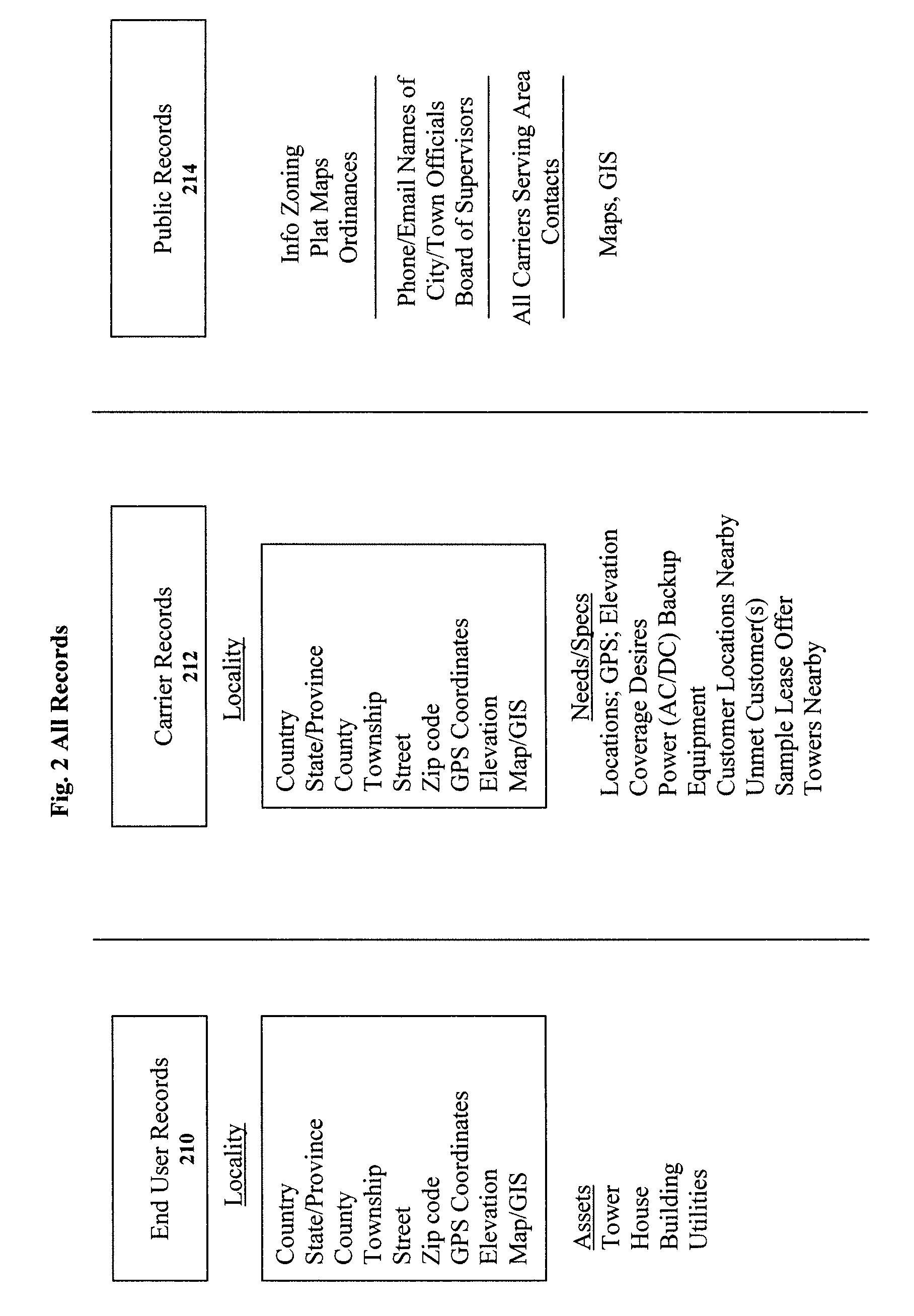
Clearinghouse system, method, and process for inventorying and acquiring infrastructure, monitoring and controlling network performance for enhancement, and providing localized content in communication networks
ActiveUS20090070379A1Broaden their knowledgeLow costError detection/correctionMultiple digital computer combinationsCommunications systemTelecom network
A computerized system, method and process allows telecommunications carriers to find, evaluate and select locations for equipment through direct access to end users, while providing citizens the opportunity to offer the use of their dwelling or other assets to carriers. The system and method further provides a computerized mechanism for (a) creating an inventory and marketplace for available properties for use in telecommunications networks, (b) providing quality and / or performance monitoring and control for wireless communication systems based on data in the clearinghouse, and (c) providing localized content over wireless networks using the clearinghouse.
Owner:RAPPAPORT THEODORE S
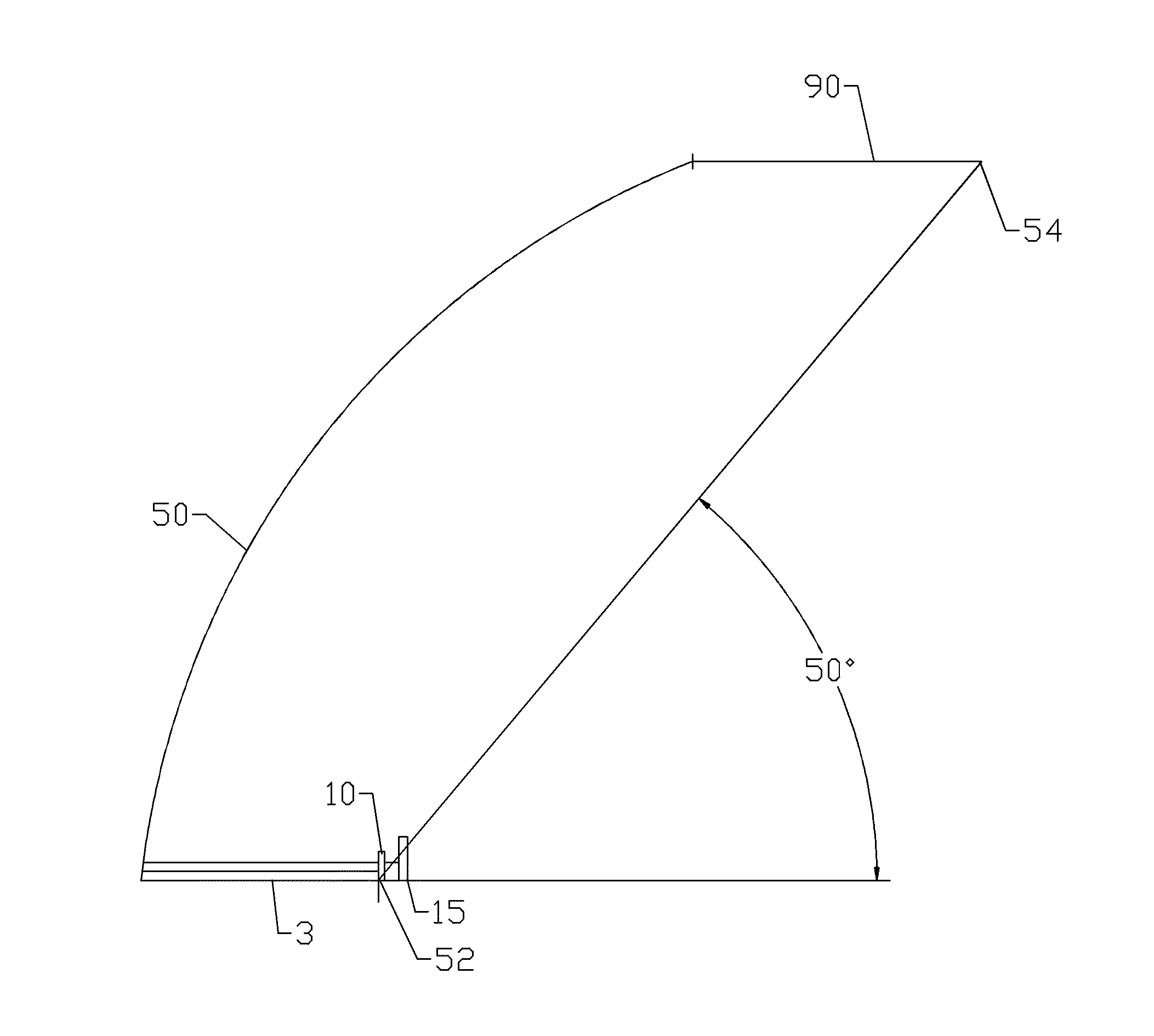
Low sidelobe reflector antenna with shield
ActiveUS9019164B2Area minimizationIncrease in sizeWaveguide hornsRadiating element housingsWaveguidePhysics
A front feed reflector antenna with a dish reflector has a wave guide is coupled to a proximal end of the dish reflector, projecting into the dish reflector along a longitudinal axis. A dielectric block may be coupled to a distal end of the waveguide and a sub-reflector coupled to a distal end of the dielectric block. A shield is coupled to the periphery of the dish reflector. A subtended angle between the longitudinal axis and a line between the focal point and a distal periphery of the shield is 50 degrees or less.
Owner:COMMSCOPE TECH LLC
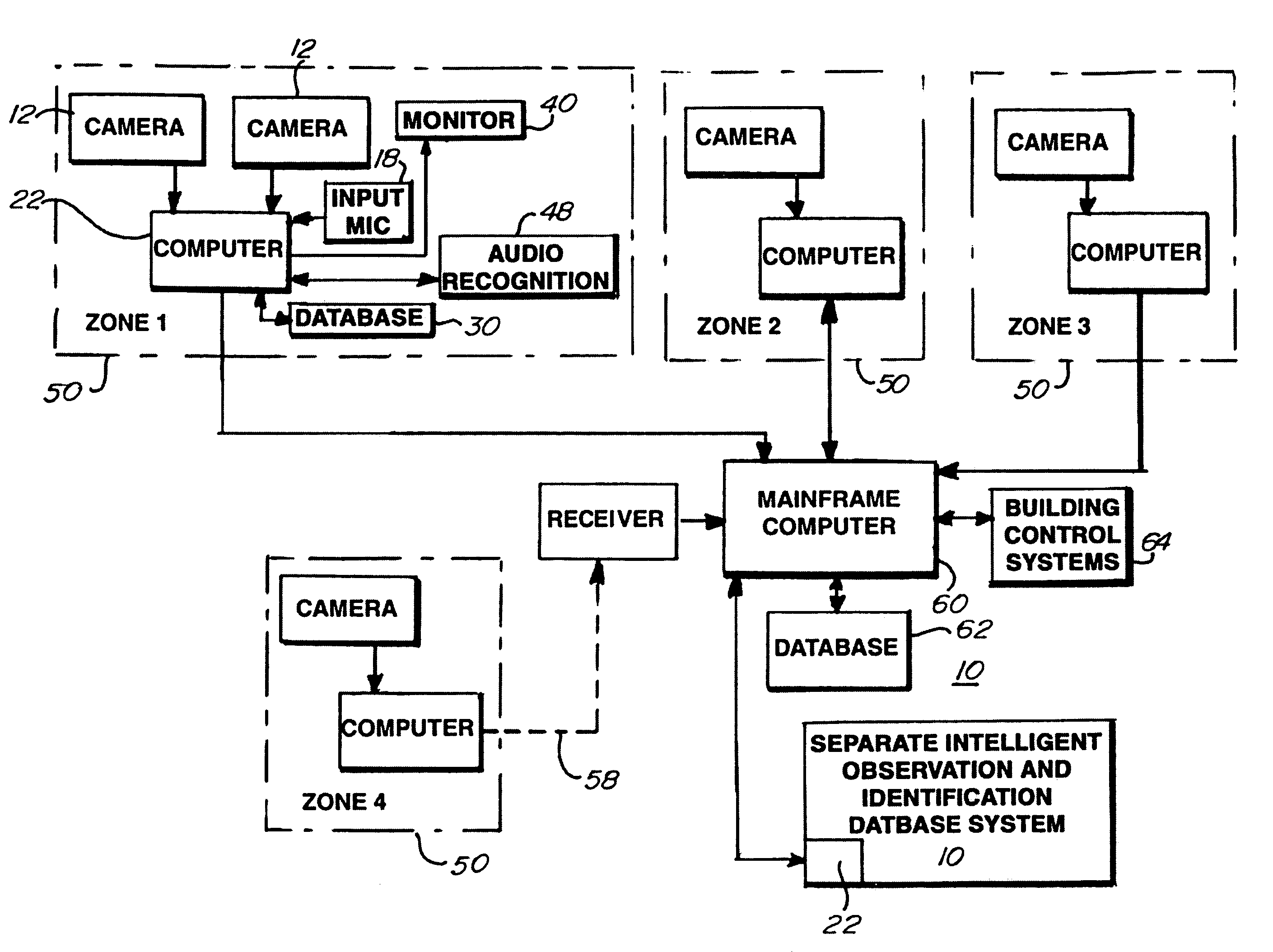
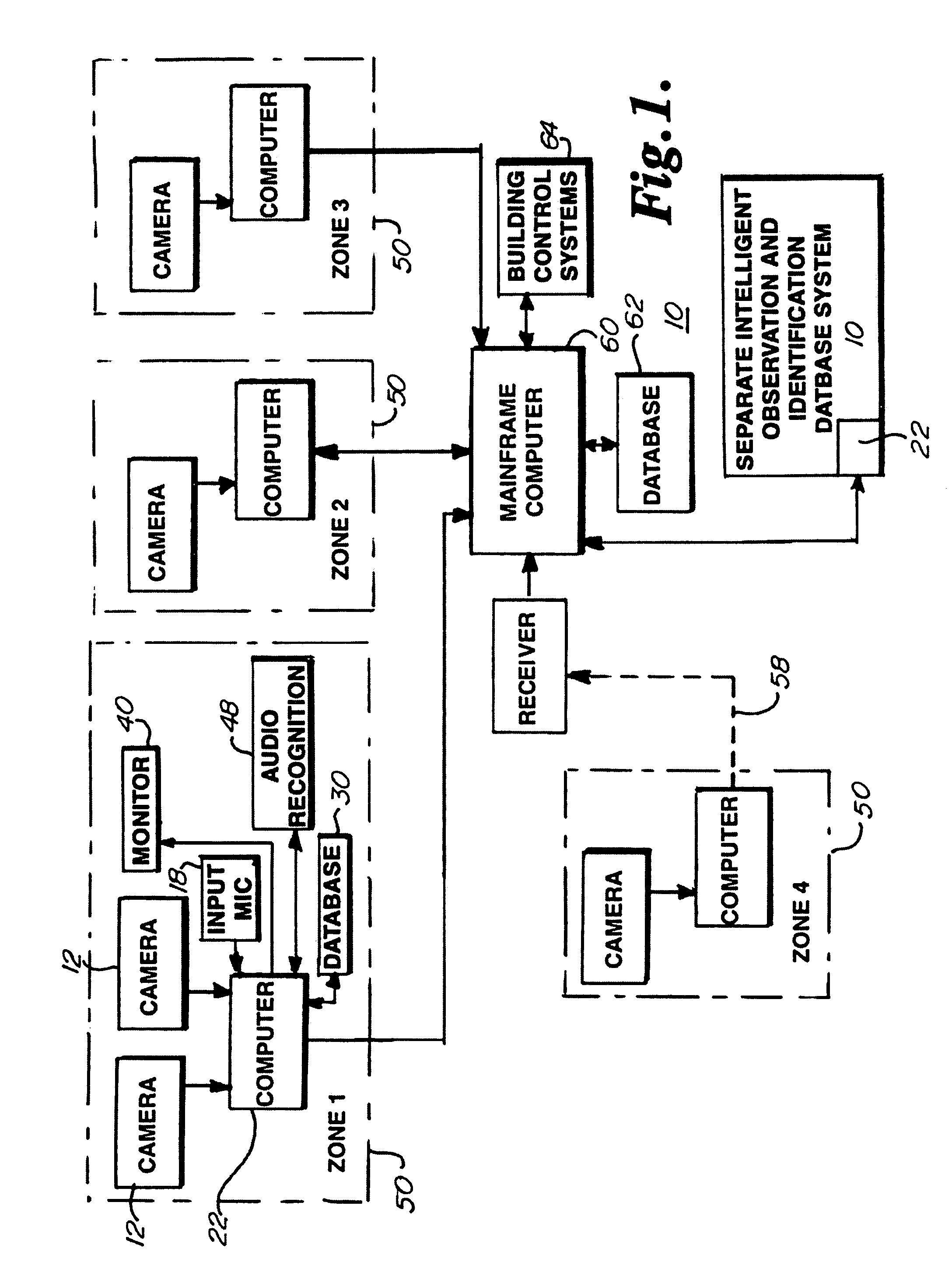
Intelligent observation and identification database system
ActiveUS7439847B2Inexpensive to maintainCheap manufacturingStill image data retrievalElectric signal transmission systemsForeign objectComputer science
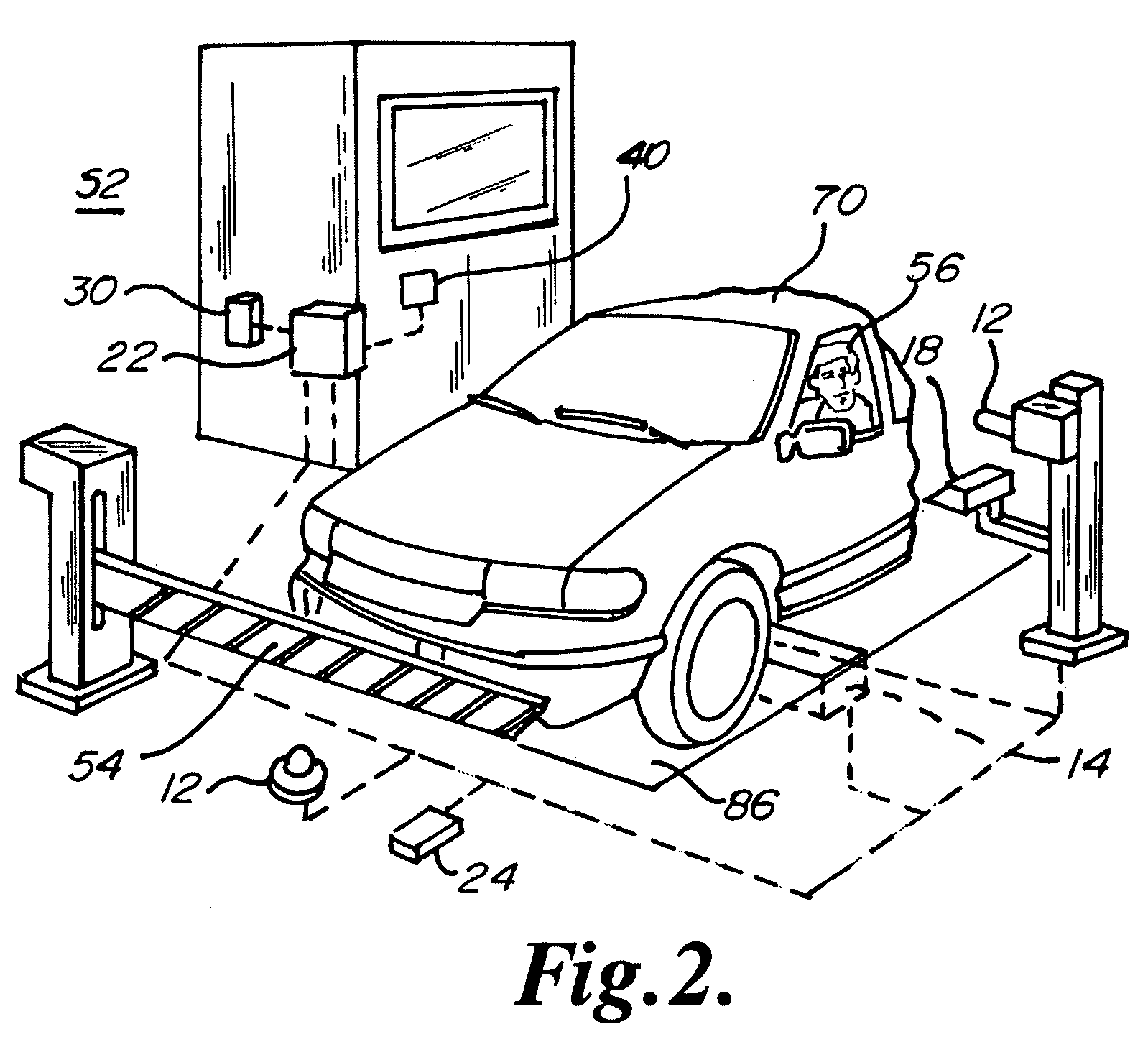
An intelligent video / audio observation and identification database system may define a security zone or group of zones. The system may identify vehicles and individuals entering or exiting the zone through image recognition of the vehicle or individual as compared to prerecorded information stored in a database. The system may alert security personnel as to warrants or other information discovered pertaining to the recognized vehicle or individual resulting from a database search. The system may compare images of a suspect vehicle, such as an undercarriage image, to standard vehicle images stored in the database and alert security personnel as to potential vehicle overloading or foreign objects detected, such as potential bombs. The system may track individuals or vehicles within a zone or between zones. The system may further learn the standard times and locations of vehicles or individuals tracked by the system and alert security personnel upon deviation from standard activity.
Owner:FEDERAL LAW ENFORCEMENT DEV SERVICES
Method for performing device security corrective actions based on loss of proximity to another device
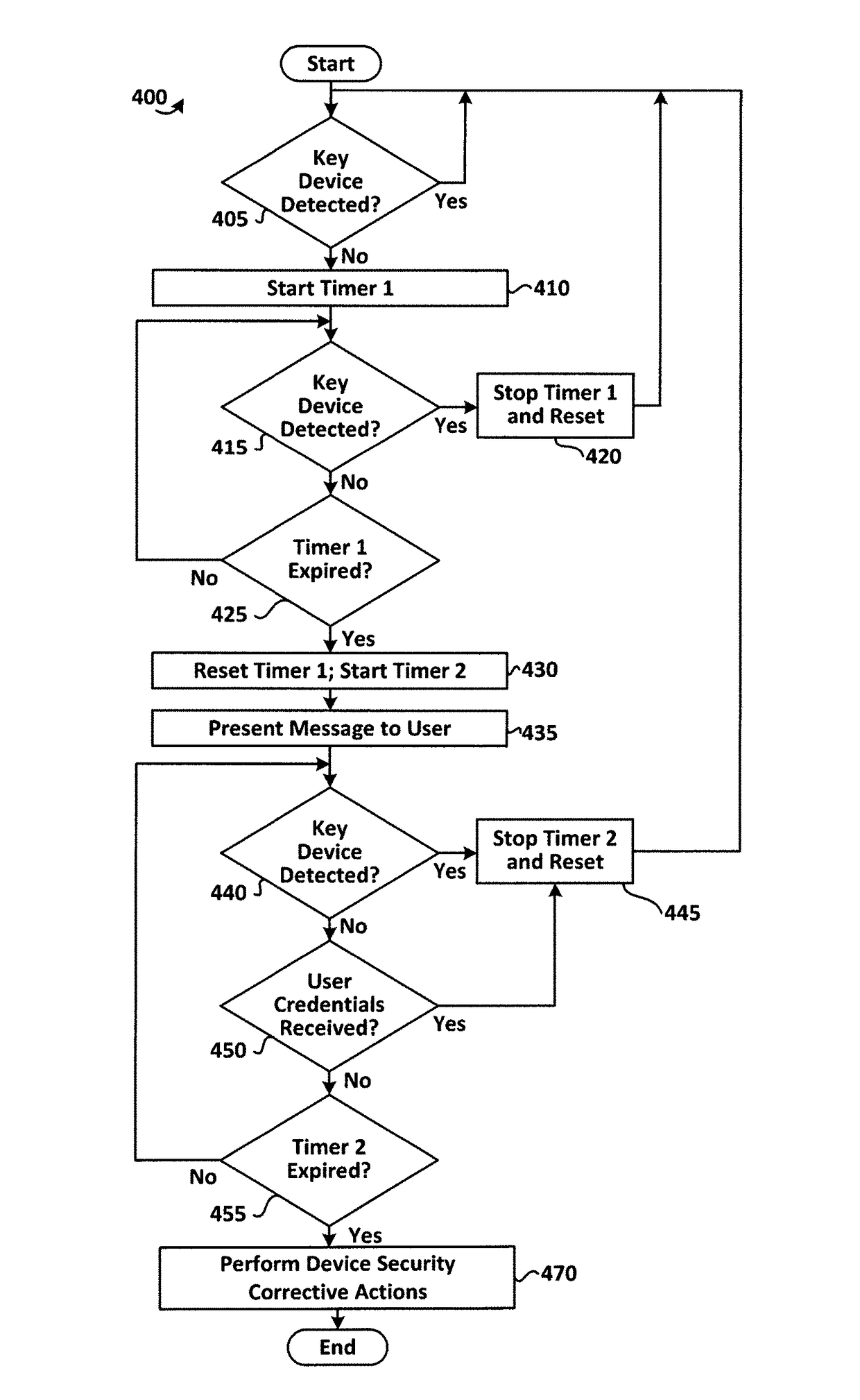
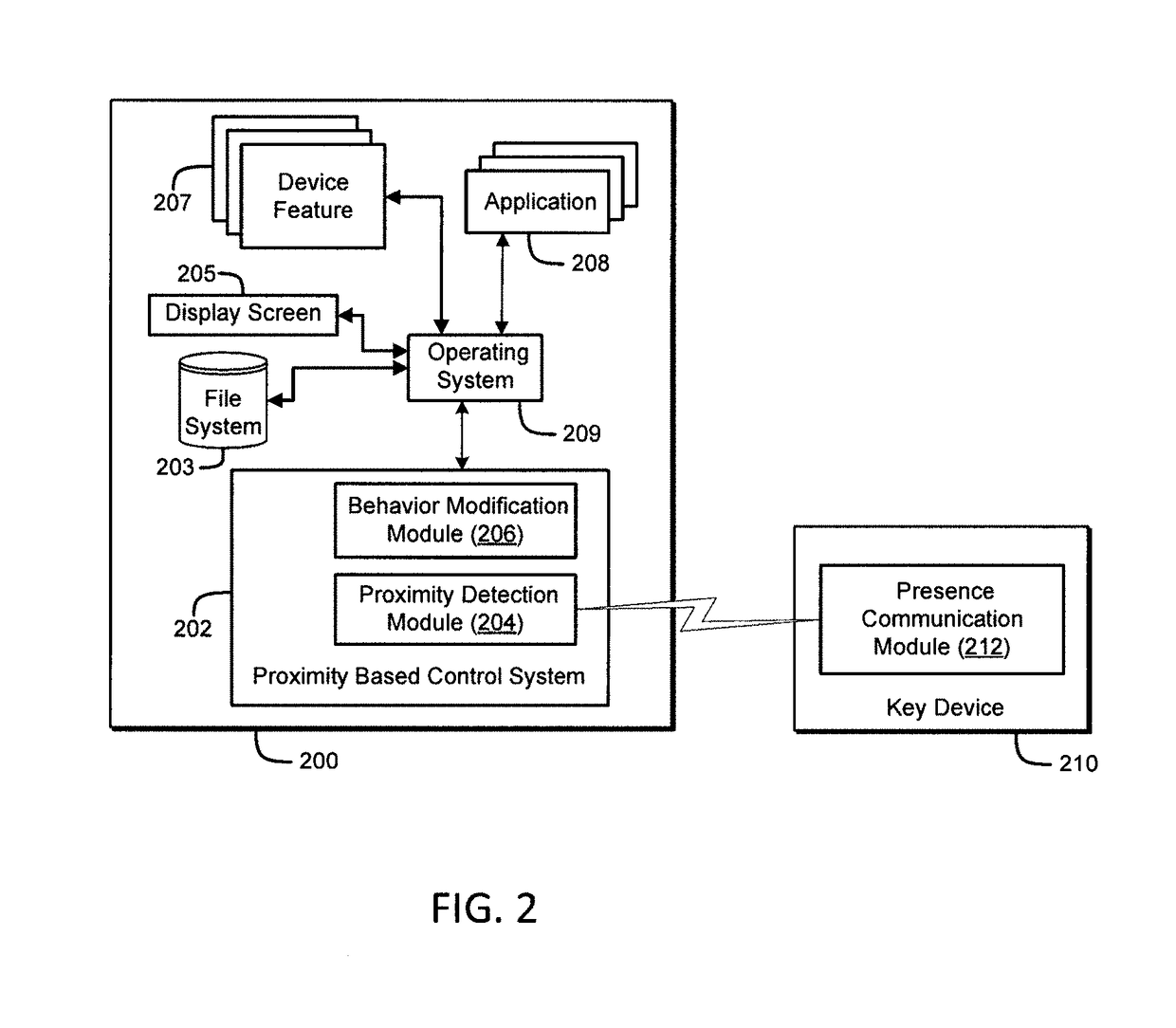
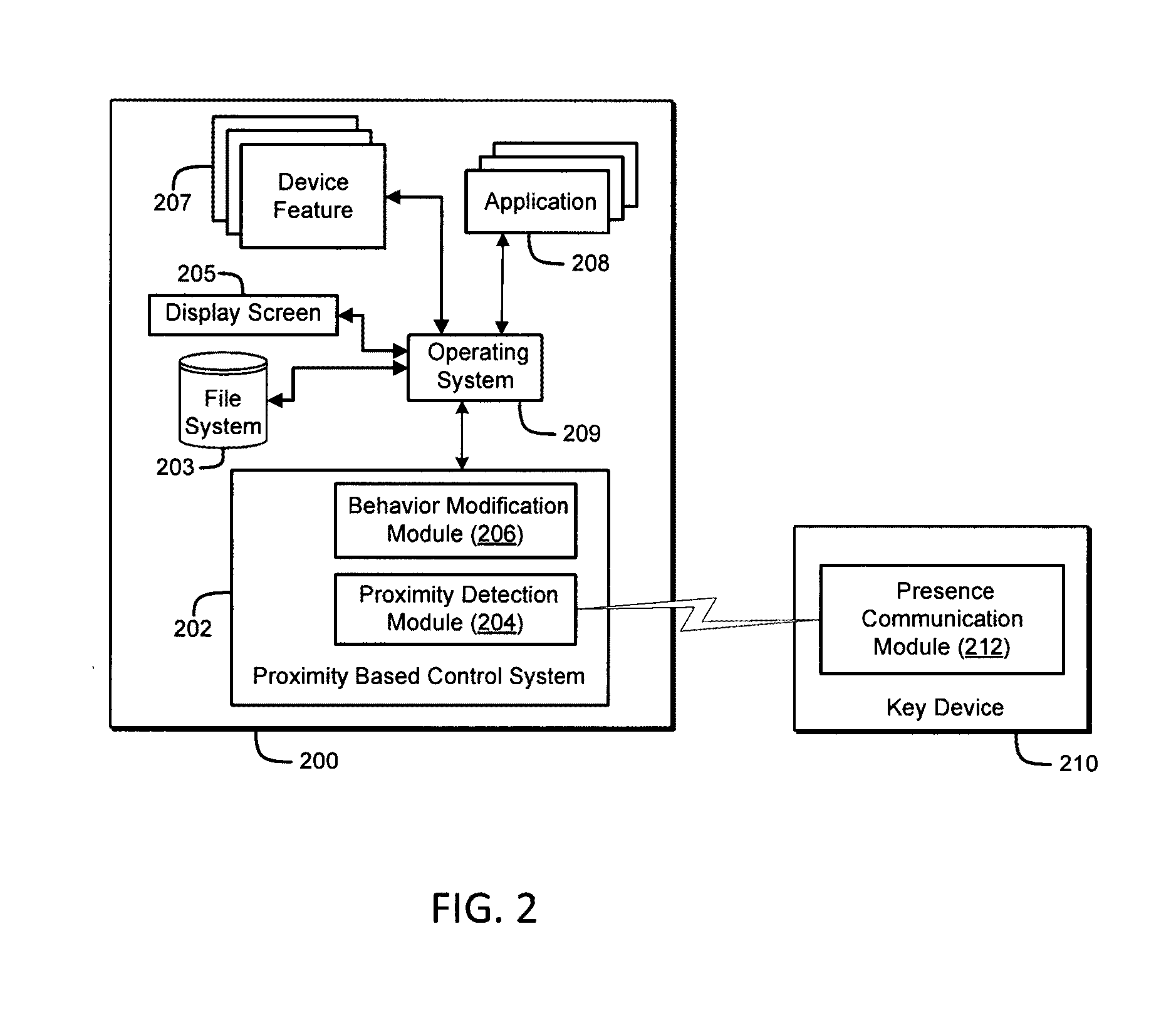
ActiveUS9763097B2Suppress lock mechanismImprove convenienceLocation information based serviceTransmissionComputer hardwareTime segment
The method disclosed herein provides for performing device security corrective action based on loss of proximity to another device, such as a key device. While a mobile communication device is locked, a mobile communication device determines whether or not a key device is within a specified distance. If the key device is not within the specified distance from the mobile communication device, a notification may be displayed on the mobile communication device. If a user responds to the notification, the user may prevent or alter the mobile communication device from performing at least one device security corrective action. If, however, the user does not respond to the notification within a specified time period, the at least one device security corrective action is performed on the mobile communication device.
Owner:LOOKOUT MOBILE SECURITY
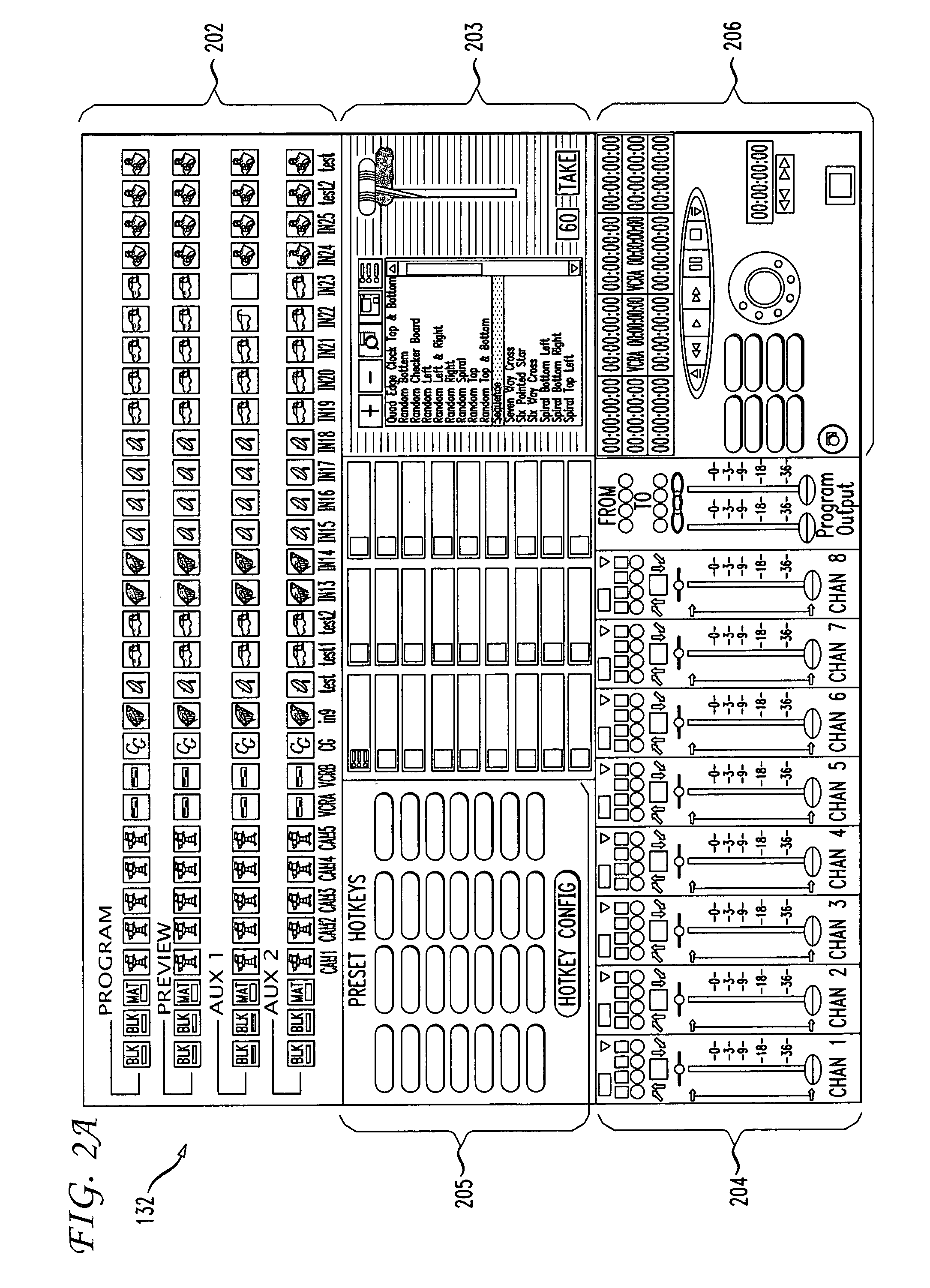
System and method for real time video production and distribution
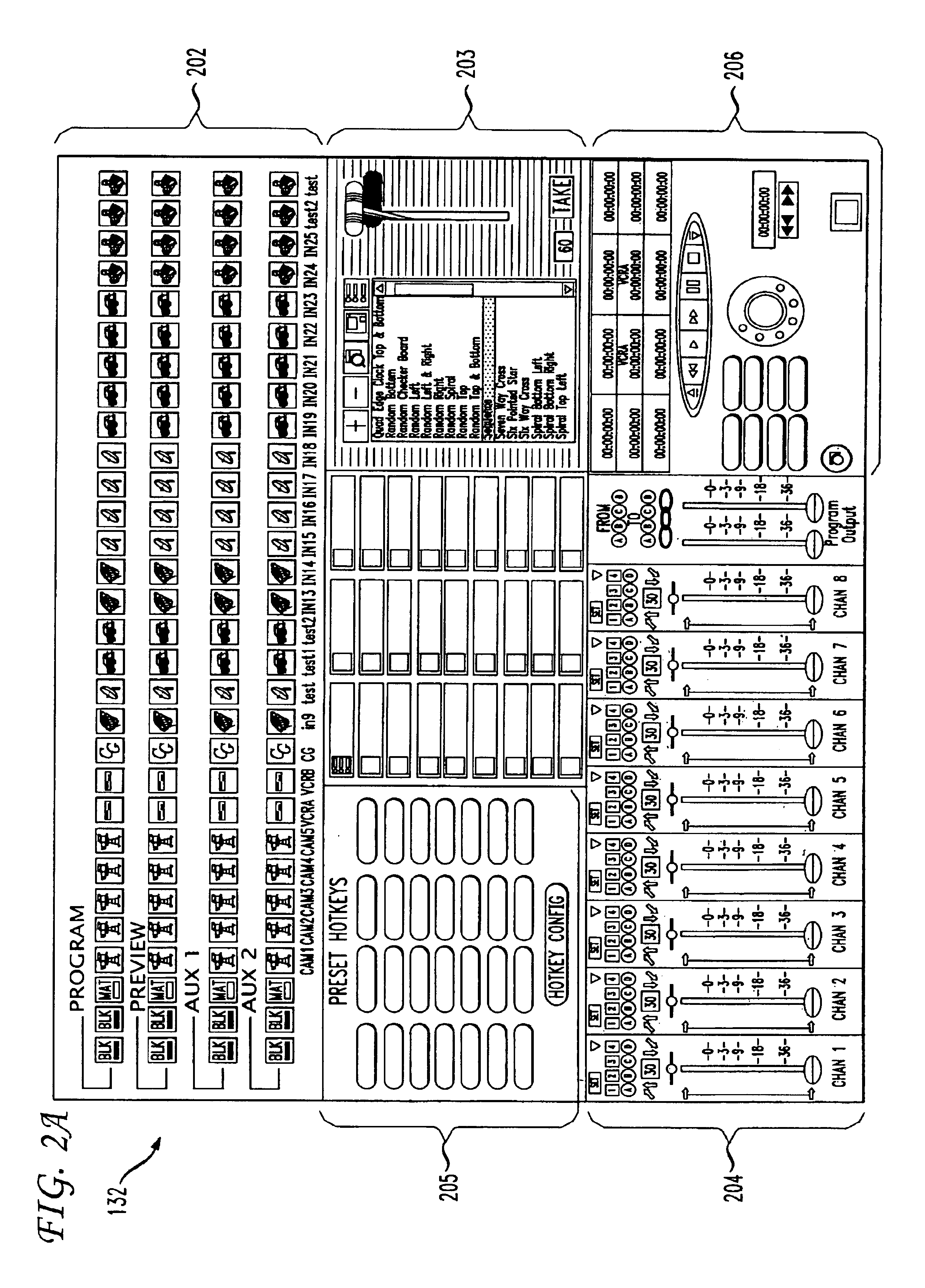
InactiveUS6952221B1Easy to produceQuality improvementElectronic editing digitised analogue information signalsCathode-ray tube indicatorsGraphicsThe Internet
A production system automates the control of production devices used to produce and broadcast a show. The system automation allows a video director to pre-produce, preview, and produce the live show from a single user interface. In an embodiment, a processing unit displays graphical controls for the production devices. A video director interacts with the graphical controls to thereby remotely control the production devices from one location. In an embodiment, a video director defines a set of production commands or instructions (i.e., “transition macro”). Upon execution, each production command directs the processing unit to transmit in series and / or parallel one or more control commands to one or more of the production devices. Production commands can be included to enable the show to be broadcast live or recorded for on-demand access. Live and / or on-demand productions are distributed over traditional television mediums and / or a computer network, including the Internet.
Owner:THOMSON LICENSING SA
Method for robust data collection schemes for large grid wireless networks
ActiveUS9202371B2Robust wireless communicationCost efficientElectric signal transmission systemsNetwork topologiesComputer networkData collector
If the number of rows in a matrix of wireless devices is greater than the number of columns, then vertical sweeping is performed including passing data along each of the columns of wireless devices to an end wireless device in each column. If the number of rows is less than the number of columns, then horizontal sweeping is performed including passing data along each of the rows of wireless devices to an end wireless device in each row. If the number of rows is equal to the number of columns, then diagonal sweeping is performed including passing data diagonally across each of the rows and columns of wireless devices to an end wireless device in each row and each column. The data is passed along the end wireless devices to a final destination data collector.
Owner:ROBERT BOSCH GMBH
Method and system for assessing, managing, and monitoring information technology risk
A method for information technology and information asset risk assessment of a business relationship between a client and a third party. The method includes establishing a database. The database includes a plurality of IT information risk factors stored in the database are associated with certain risks the client may be exposed to based on an action the client follows or based upon who the client uses as their third party provider. The database is configured to receive IT risk information. The IT risk information is associate with the plurality of IT information risk factors. The database is also configured to receive updated risk information for storage thereon. The method includes receiving risk information corresponding to the subset of relationship risk factors. The method continues with generating a relationship risk score. The relationship risk score is determined in response to evaluating the subset of relationship risk factors using the IT risk
Owner:OPTIV SECURITY INC
Intelligent virtual content distribution network system and method
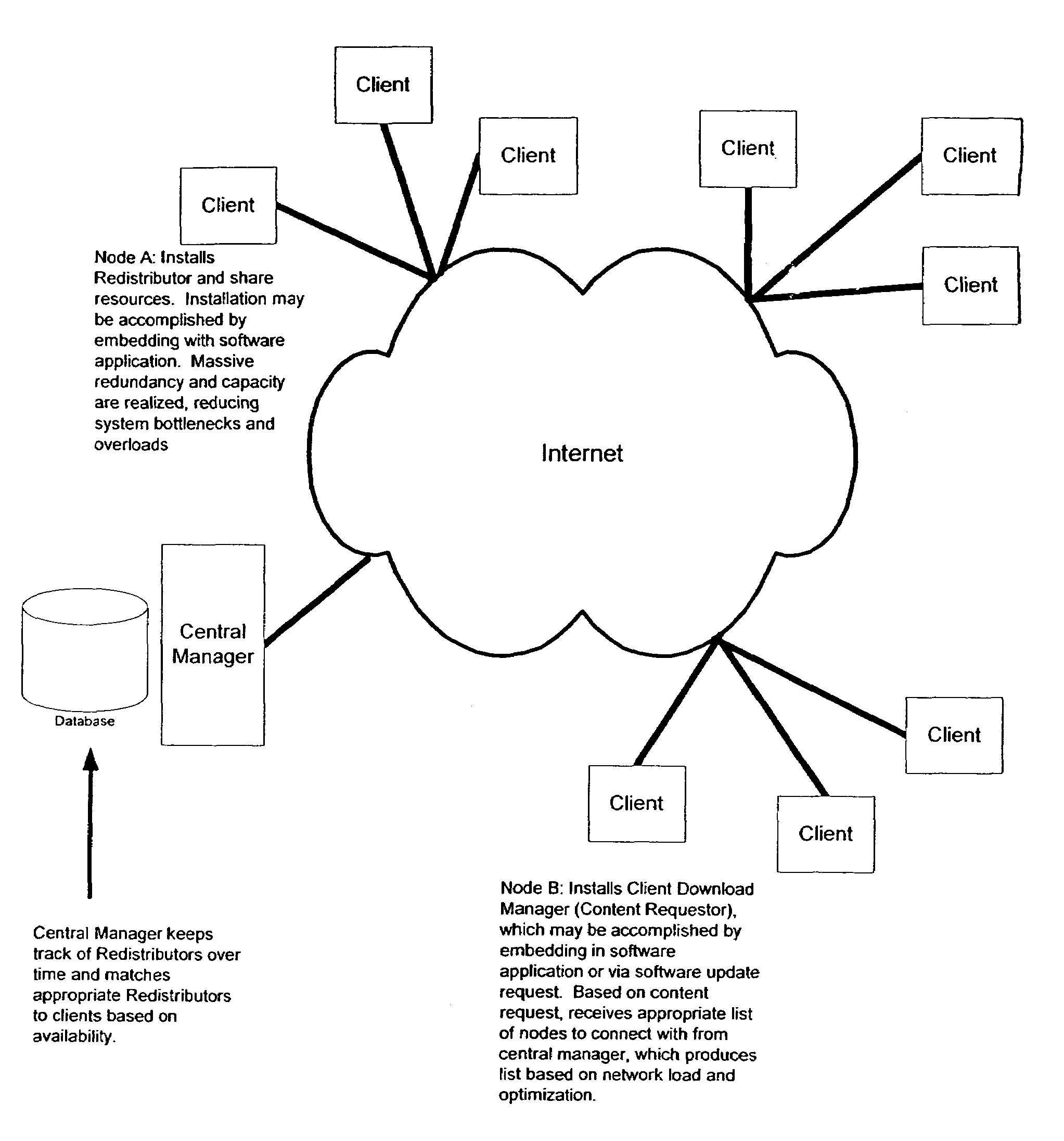
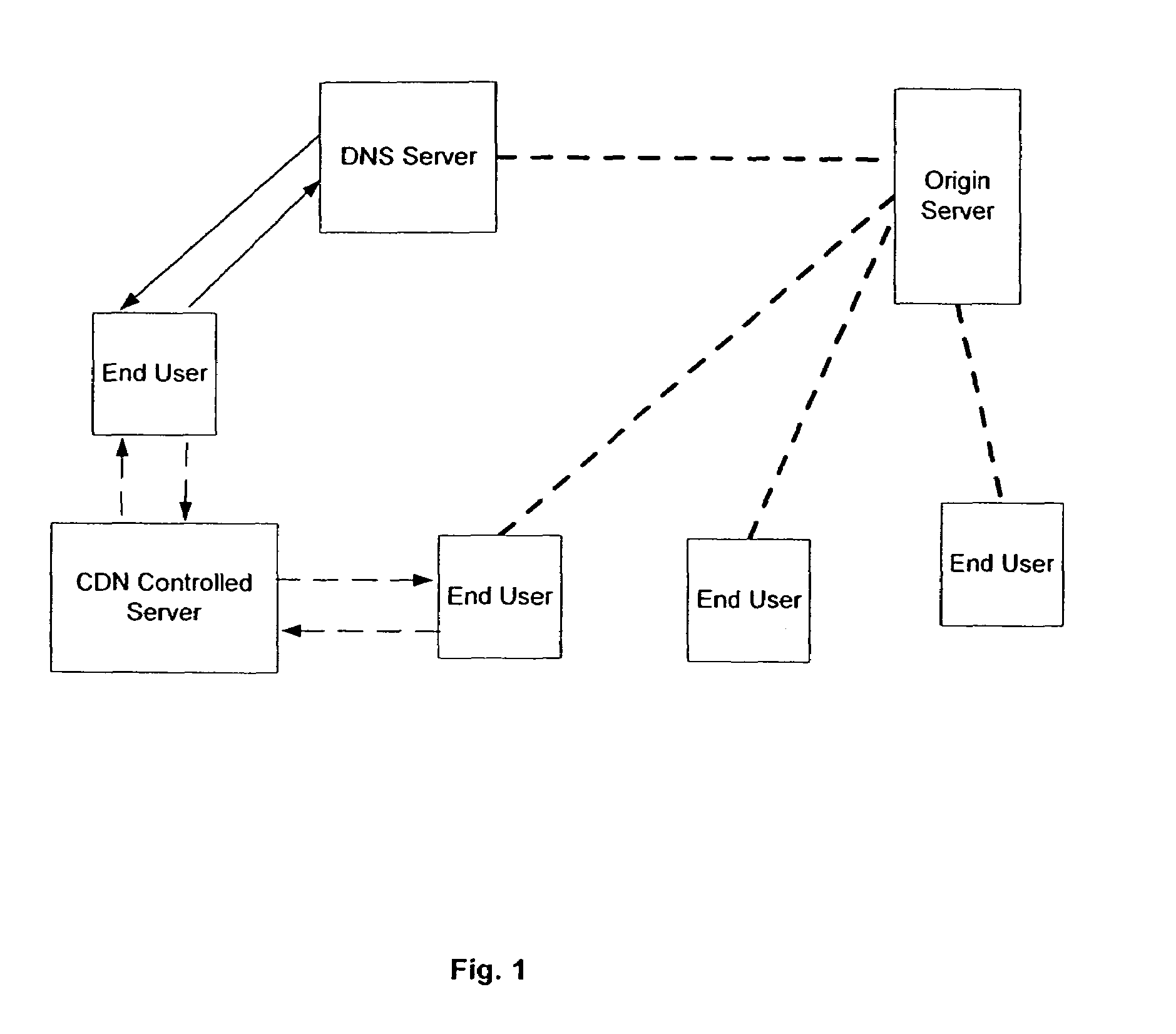
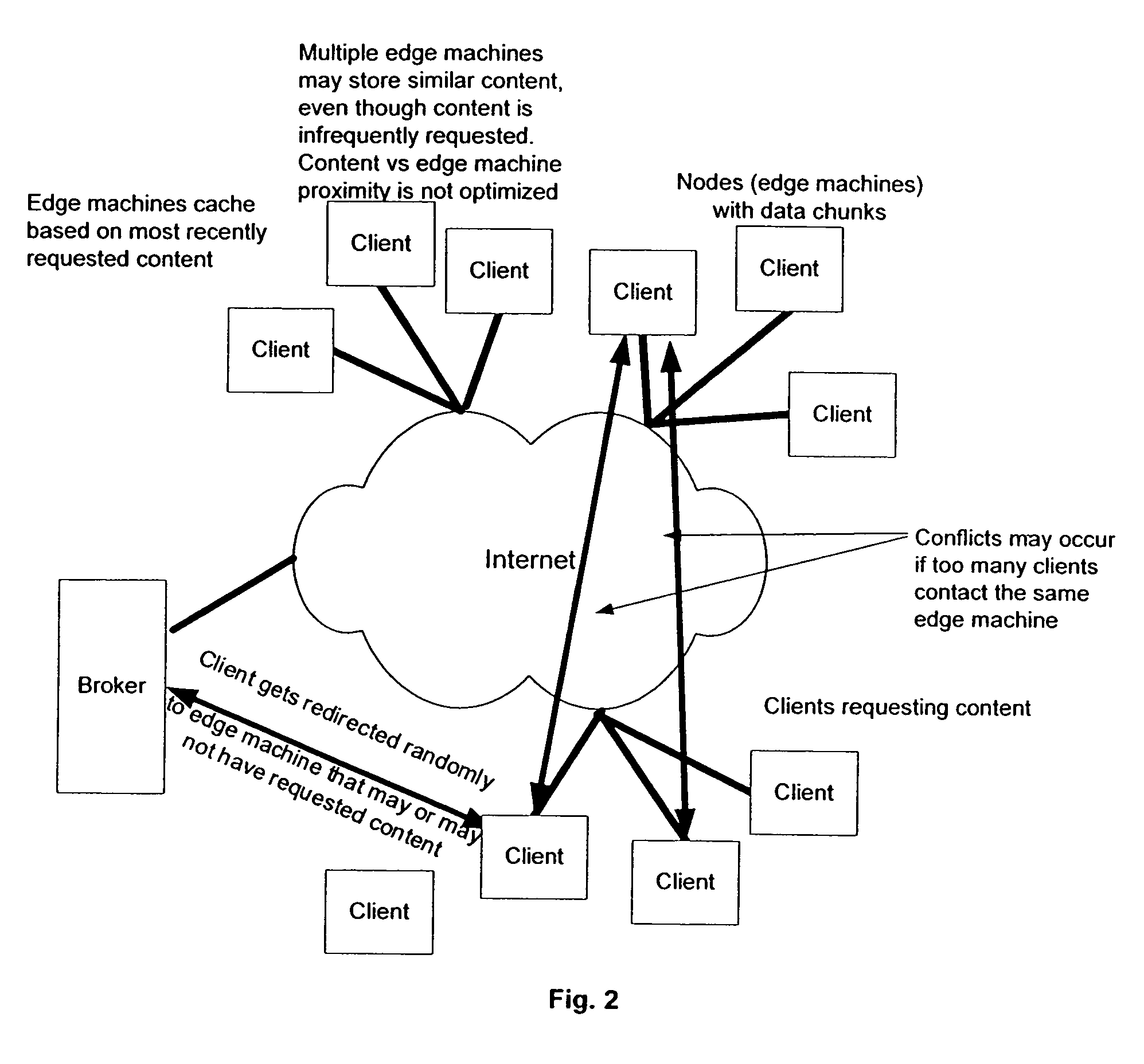
InactiveUS7653689B1Low costCost efficientMultiple digital computer combinationsTransmissionContent distributionClient-side
A method and system of use of a Content Distribution Network (CDN), wherein server functionality and client functionality are unbundled. Client software, which governs the accesses and request of the information from the CDN (i.e., server) is provided by a “thin” client architecture. The thin client software is capable of running on an as needed basis, therefore not allocating significant portions of available memory, except when being accessed. The server functionality retains the bulk of the software functionality to manage locally stored content, process content requests, and forward the requested data to content requesters running the client software.
Owner:ABACAST +2
Audio distribution and production system
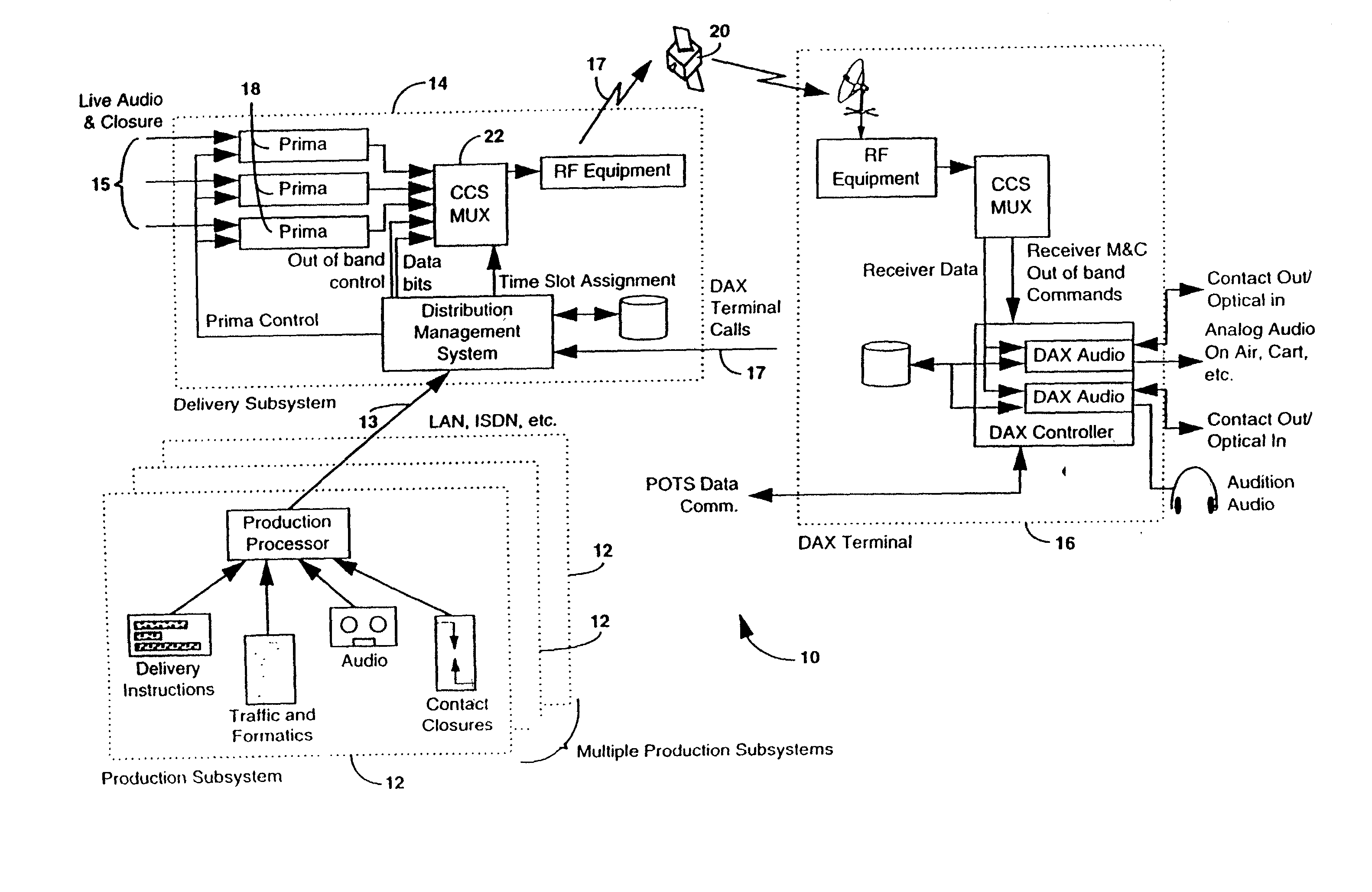
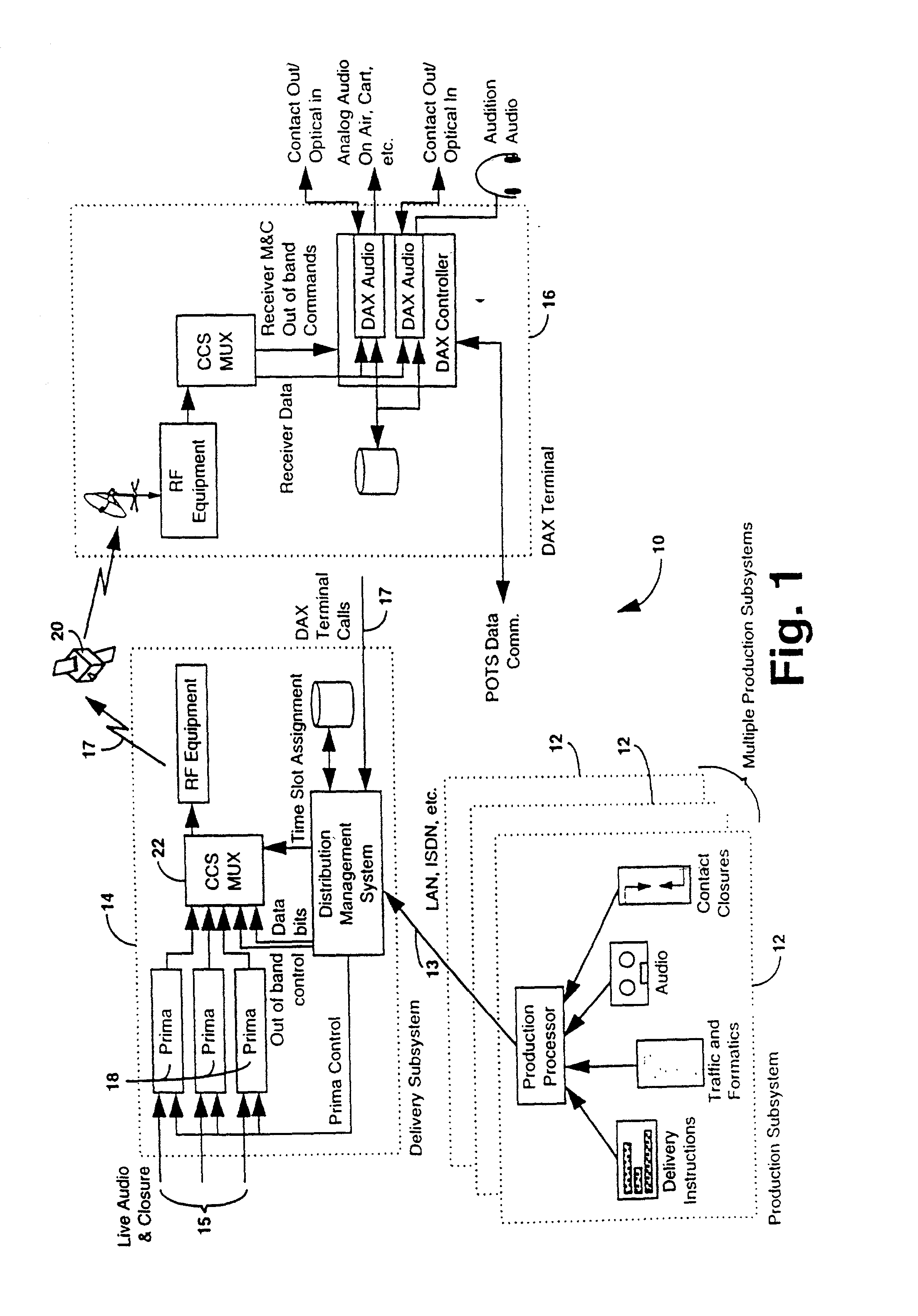
InactiveUS20020177914A1Economical to manufactureEasy and flexible programmabilityBroadcast systems characterised by addressed receiversModulated-carrier systemsData fileSatellite
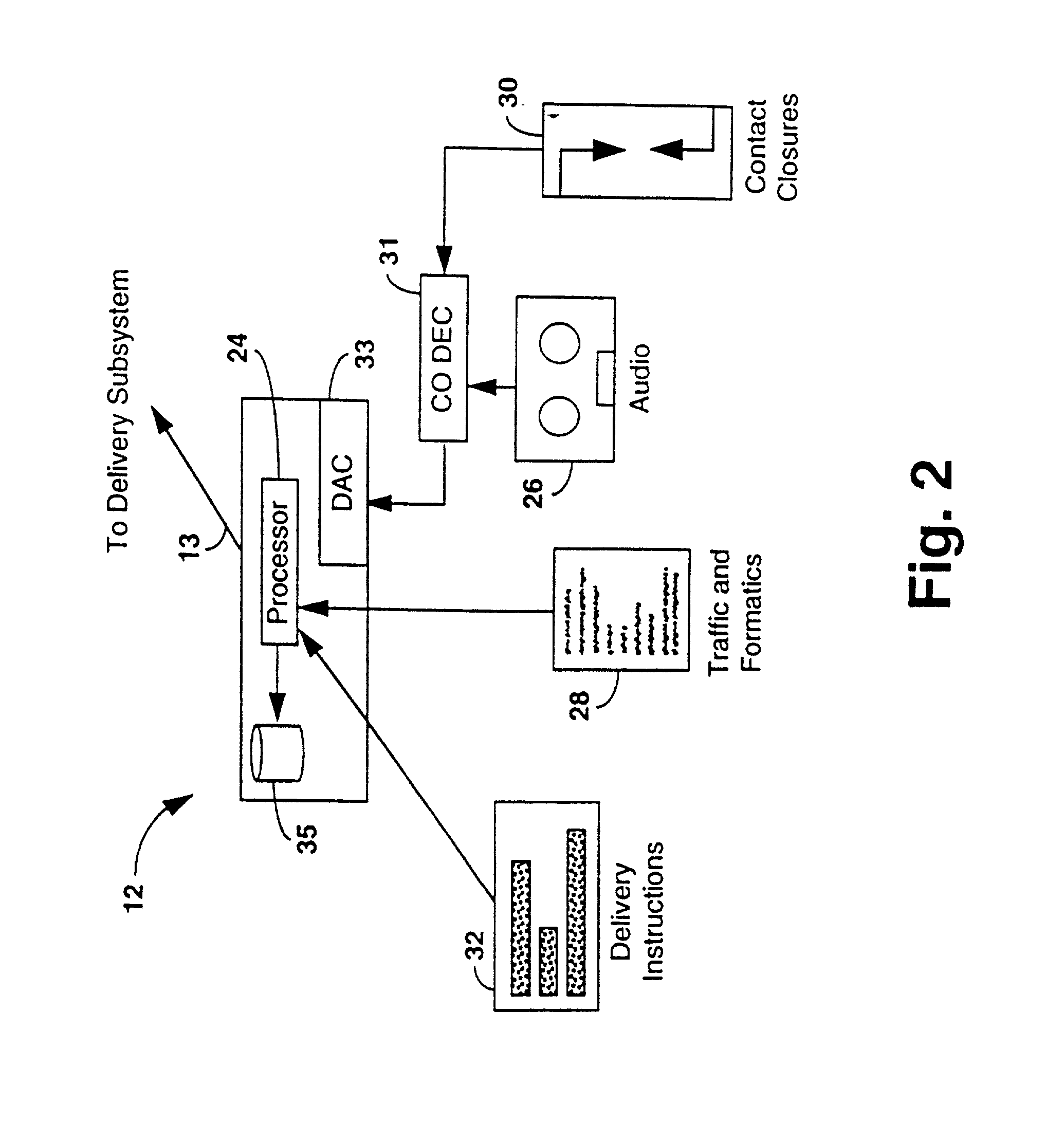
A data file delivery system is provided having, at a head end, a production subsystem which communicates with a delivery subsystem via a local area network, ISDN connection, and the like. The delivery subsystem communicates with an affiliate subsystem, at a tail end, via a satellite link, ISDN link and the like. The production subsystem enables a producer to create audio events which represent sequences of audio which are played to completion before another audio event occurs. Audio events are stored as audio files. Each audio event may include one or more of an audio sequence, text information, delivery instructions, and an attribute list having contact closure information and the like. Optionally, multiple audio events may be assembled at the production subsystem to form a play list. The audio files are transferred to the delivery subsystem. The delivery subsystem places the audio files in delivery envelopes and transmits the envelopes to the affiliate terminals. In addition, the delivery subsystem may transmit live audio and related contact closure information to the affiliate terminals. The affiliate terminal may be located at a user site. The affiliate terminals may store these events on the hard drive, play the events in real time or pass events to other affiliate terminals. The affiliate terminal may later play stored audio events.
Owner:CHASE TIM
Method for performing device security corrective actions based on loss of proximity to another device
ActiveUS20160337863A1Reduce user inconvenienceCost efficientLocation information based serviceTransmissionComputer hardwareCommunication device
The method disclosed herein provides for performing device security corrective action based on loss of proximity to another device, such as a key device. While a mobile communication device is locked, a mobile communication device determines whether or not a key device is within a specified distance. If the key device is not within the specified distance from the mobile communication device, a notification may be displayed on the mobile communication device. If a user responds to the notification, the user may prevent or alter the mobile communication device from performing at least one device security corrective action. If, however, the user does not respond to the notification within a specified time period, the at least one device security corrective action is performed on the mobile communication device.
Owner:LOOKOUT MOBILE SECURITY
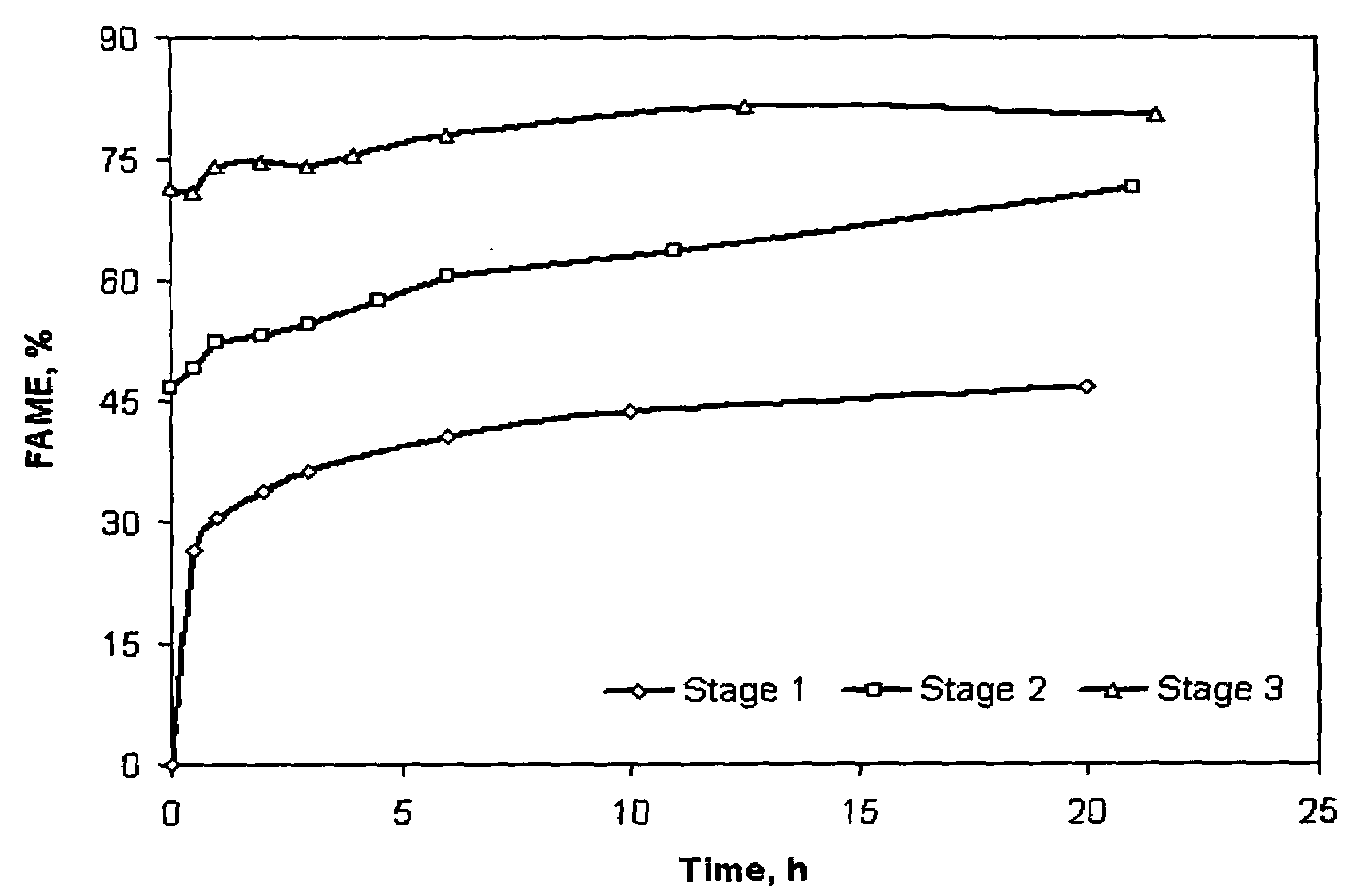
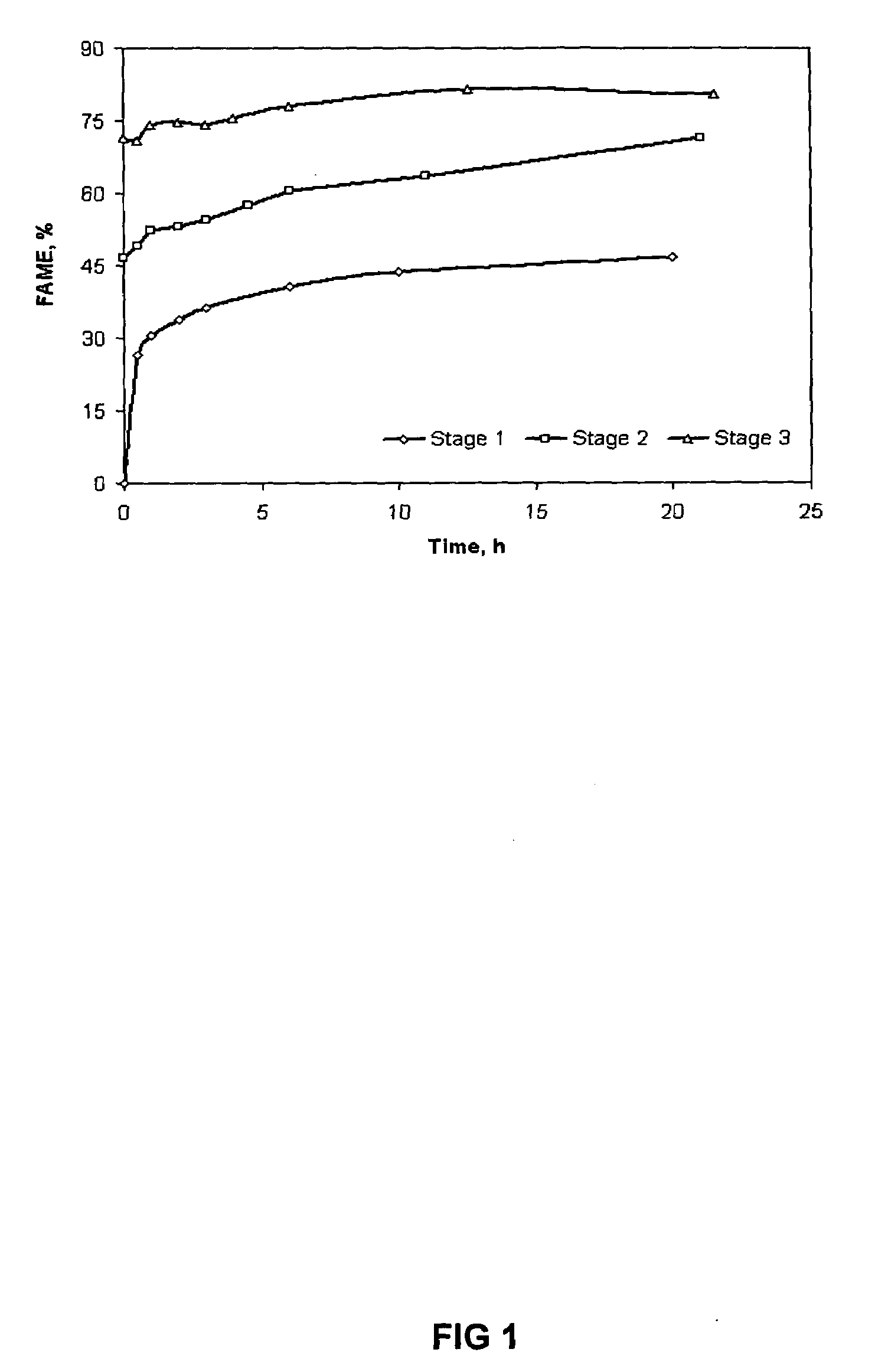
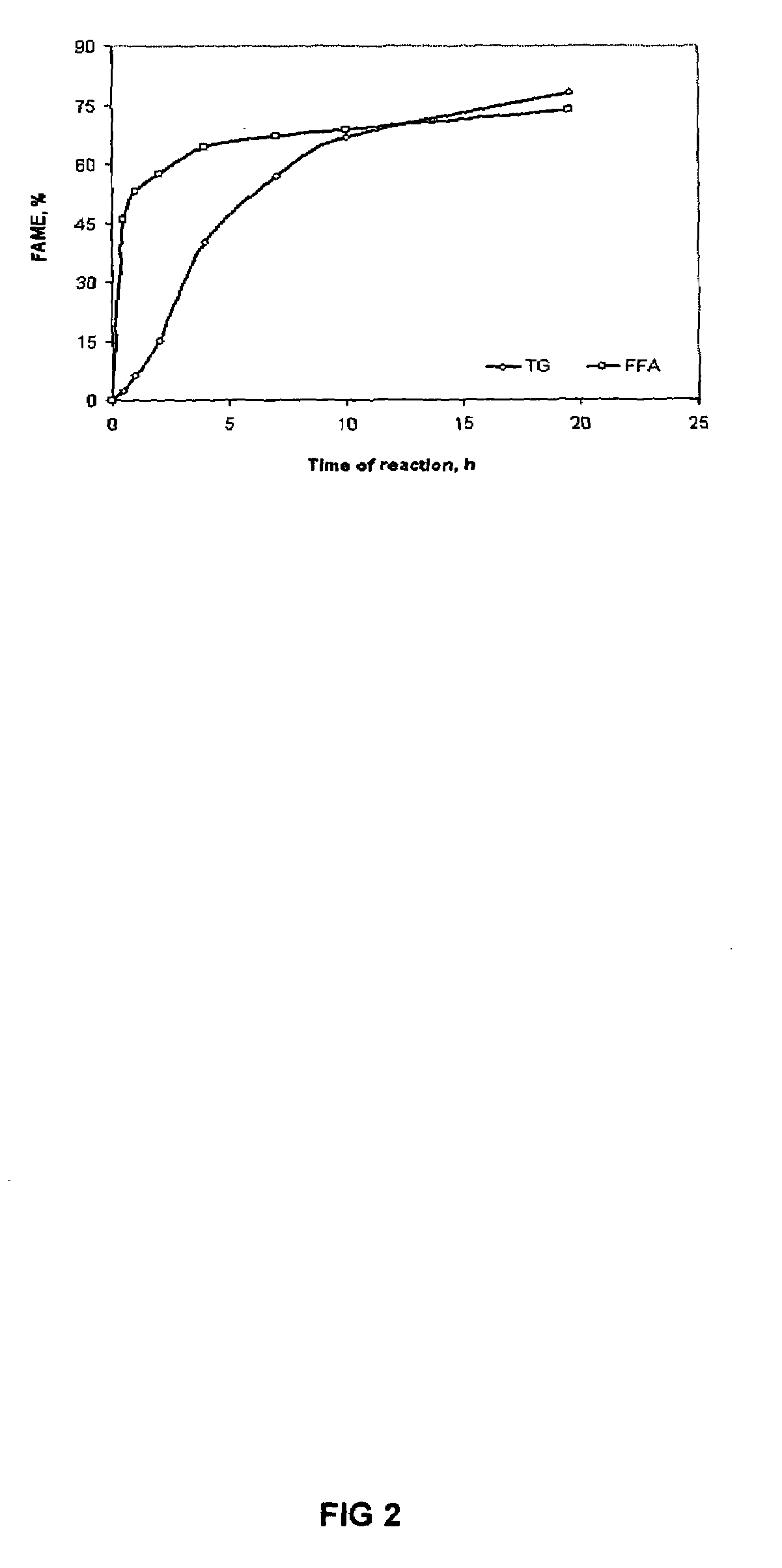
Method of converting free fatty acids to fatty acid methyl esters with small excess of methanol
InactiveUS6965044B1Cost efficientEasily separateFatty acid esterificationFatty acids production/refiningFatty acid esterFatty acid methyl ester
A method for converting free fatty acids in acid oil or acid fat into fatty acid methyl esters is disclosed. The method involves adding a small amount of methanol and an acid catalyst to the acid oil or acid fat and subjecting the mixture to conditions that allow the fatty acid methyl esters to form. A lipid phase containing the fatty acid methyl esters and triglycerides can from and be separated from the rest of the reaction mixture. The lipid phase can then be subjected to conditions suitable for converting the triglycerides into fatty acid methyl esters. The method of present invention is especially useful for a process of generating biodiesel using a starting material of vegetable and animal oils and fats that contain a relatively high level of free fatty acids.
Owner:IOWA STATE UNIV RES FOUND
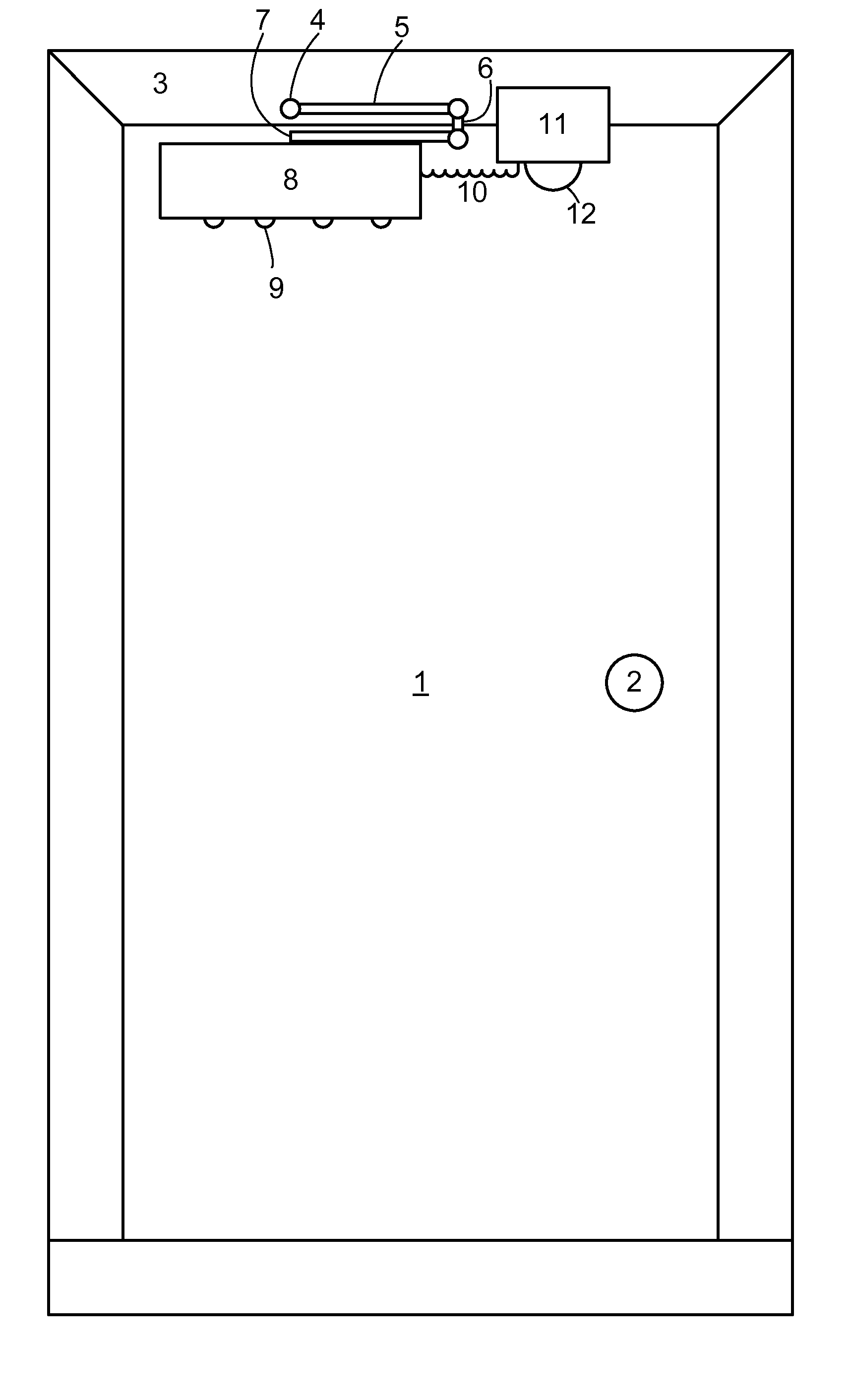
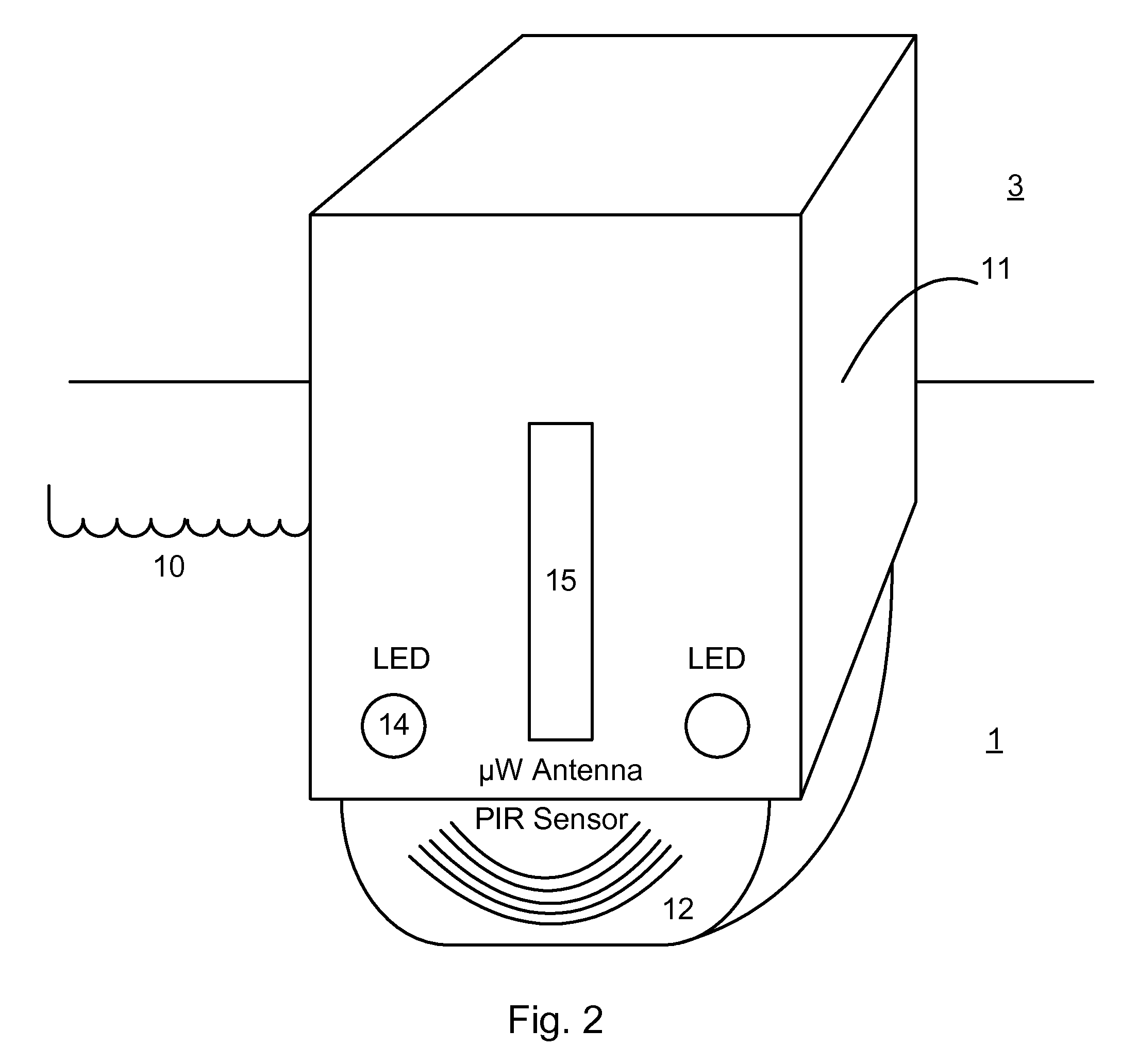
Intelligent door restraint
ActiveUS8225458B1Low costEasy to installProgramme-controlled manipulatorBuilding braking devicesStored energyElectronic controller
A method for controlling a door, comprising the steps of storing energy during a manual opening of a door, sensing an object within a doorway, selectively applying a force derived from the stored energy, to close the door, based on the sensing of an object in the doorway. The closure is preferably controlled by an electronic control. A door closing device comprising an energy storage device for storing energy during door opening and releasing the stored energy to subsequently close the door, a damping system for damping a closure of the door, a sensor for detecting an object within a doorway, having an output, a controllable device for selectively restraining the energy storage device from closing the door, and a control system for controlling the controllable device based on the output.
Owner:HOFFBERG STEVEN M
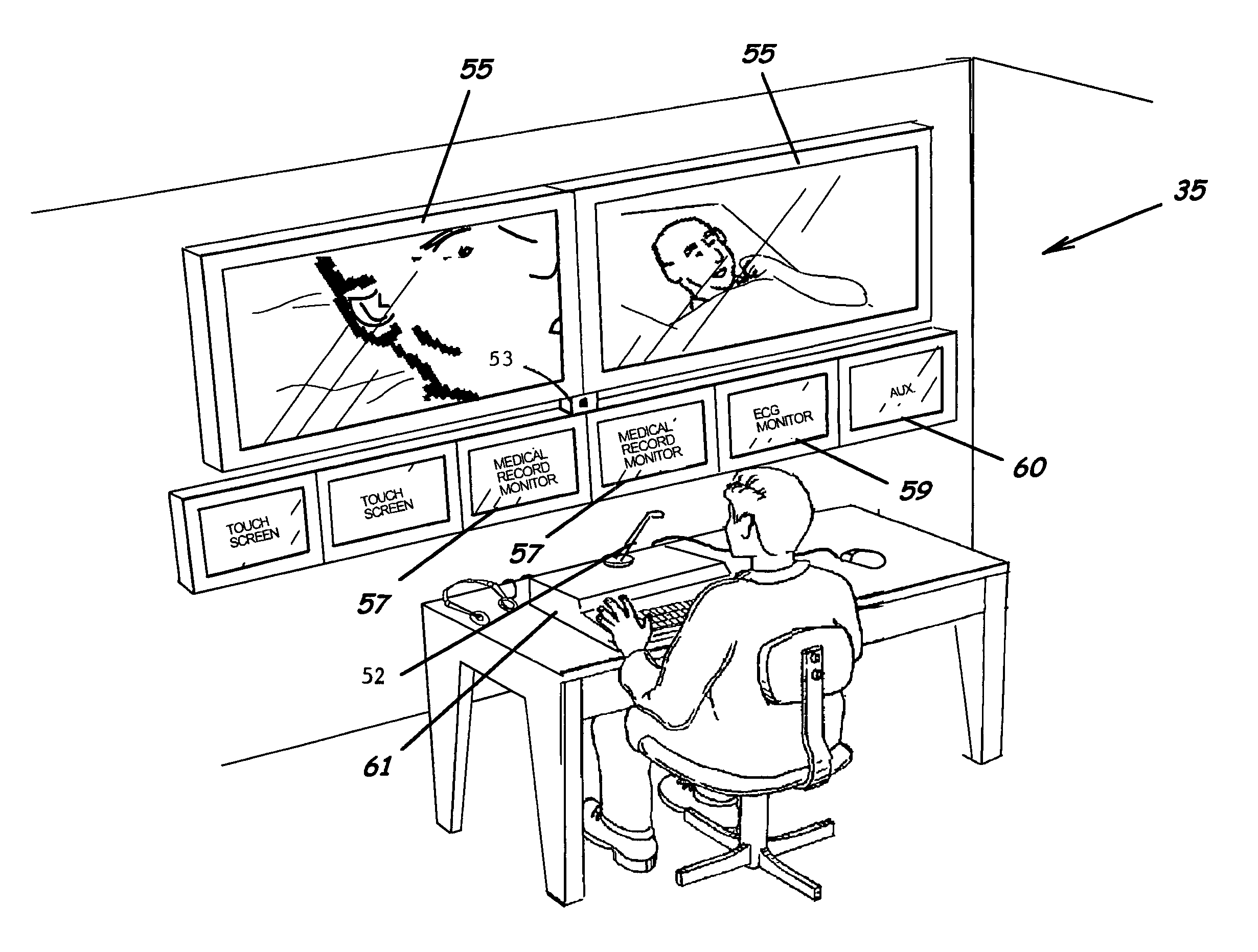
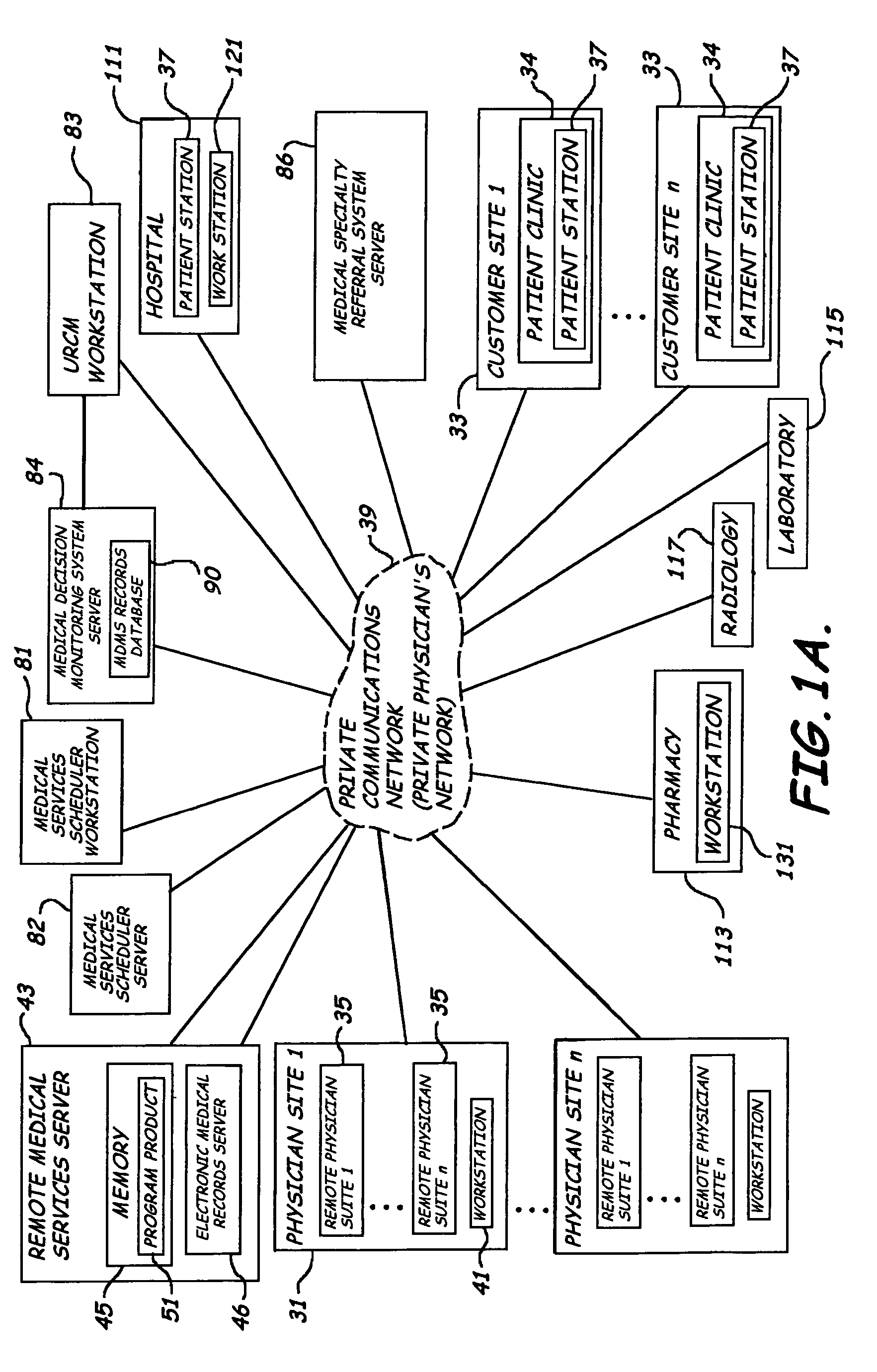
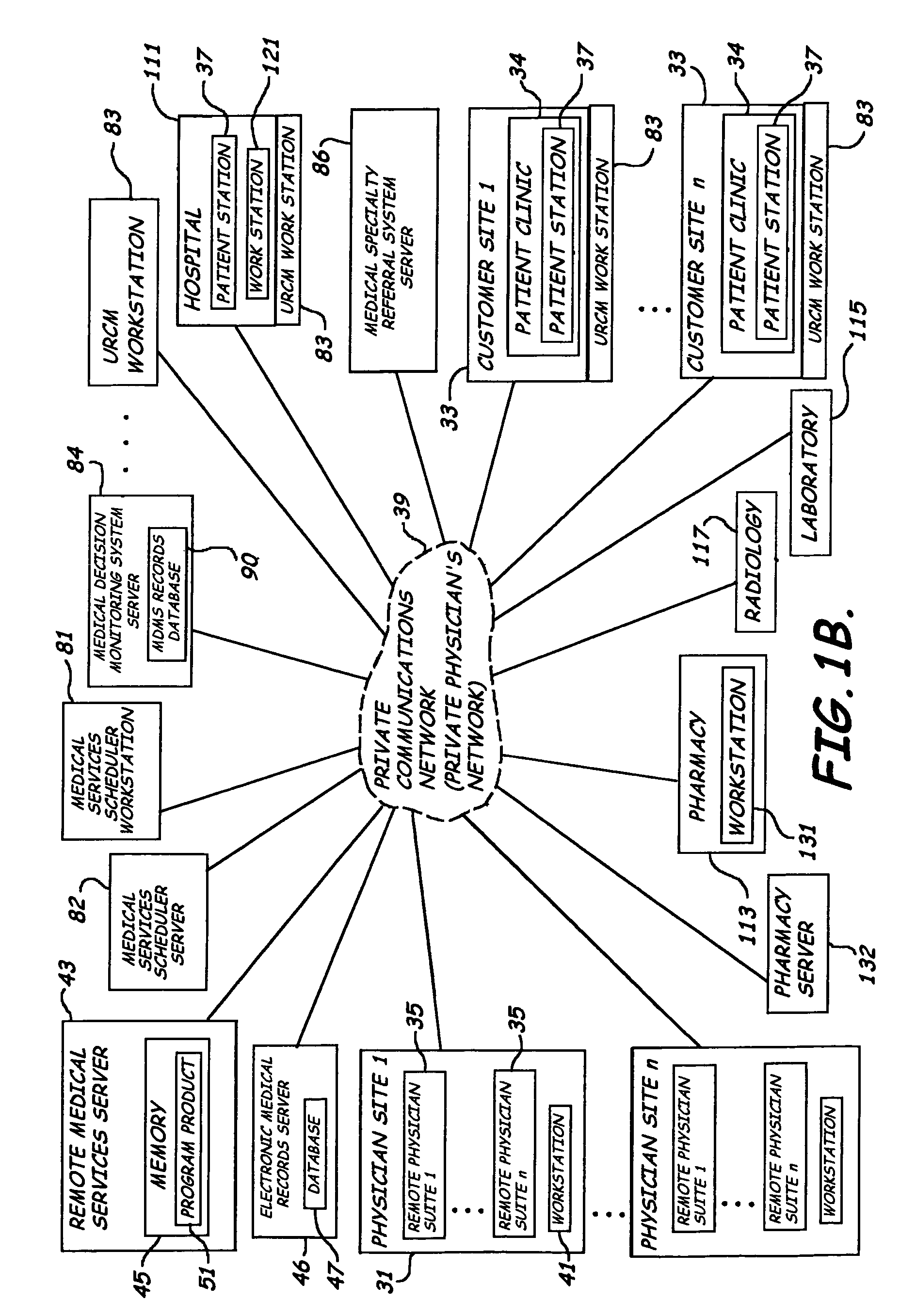
System, method and program product for delivering medical services from a remote location
ActiveUS7912733B2Enhanced medical service deliveryEffective resourcesMedical communicationData processing applicationsMedical recordDelivery suite
A system, program product, and methods related to enhanced medical services delivery to geographically distributed patient populations by remotely located physicians are provided. An embodiment of the system includes a remote medical services server, a plurality of patient electronic medical records stored in the memory of the remote medical services server, and a remote medical services program product stored in the memory of the remote medical services server adapted to access the plurality of patient electronic medical records to thereby allow display of and data entry in a selected patient electronic medical record. A patient medical service delivery station captures patient video images and displays remote physician video images. A remote physician medical service delivery suite in communication with the patient medical service delivery station through the communications network captures remote physician video images and displays patient video images and patient electronic medical records, to allow the remote physician to perform remote patient medical service delivery.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Dielectric lens cone radiator sub-reflector assembly
ActiveUS9105981B2Reduction of sub-reflector spill-overIncrease widthOptical articlesCoupling light guidesWaveguidePhysics
A dielectric cone radiator sub-reflector assembly for a reflector antenna with a waveguide supported sub-reflector is provided as a unitary dielectric block with a sub-reflector at a distal end. A waveguide transition portion of the dielectric block is dimensioned for insertion coupling into an end of the waveguide. A dielectric radiator portion is provided between the waveguide transition portion and a sub-reflector support portion. An outer diameter of the dielectric radiator portion is provided with a plurality of radially inward grooves extending radially inward to a diameter less than an inner diameter of the end of the waveguide and a lens bore extends from a proximal end of the dielectric block towards the distal end of the dielectric block at least to the sub-reflector support portion. The unitary dielectric block may be manufactured as a single contiguous monolithic portion of dielectric material via injection molding.
Owner:COMMSCOPE TECH LLC
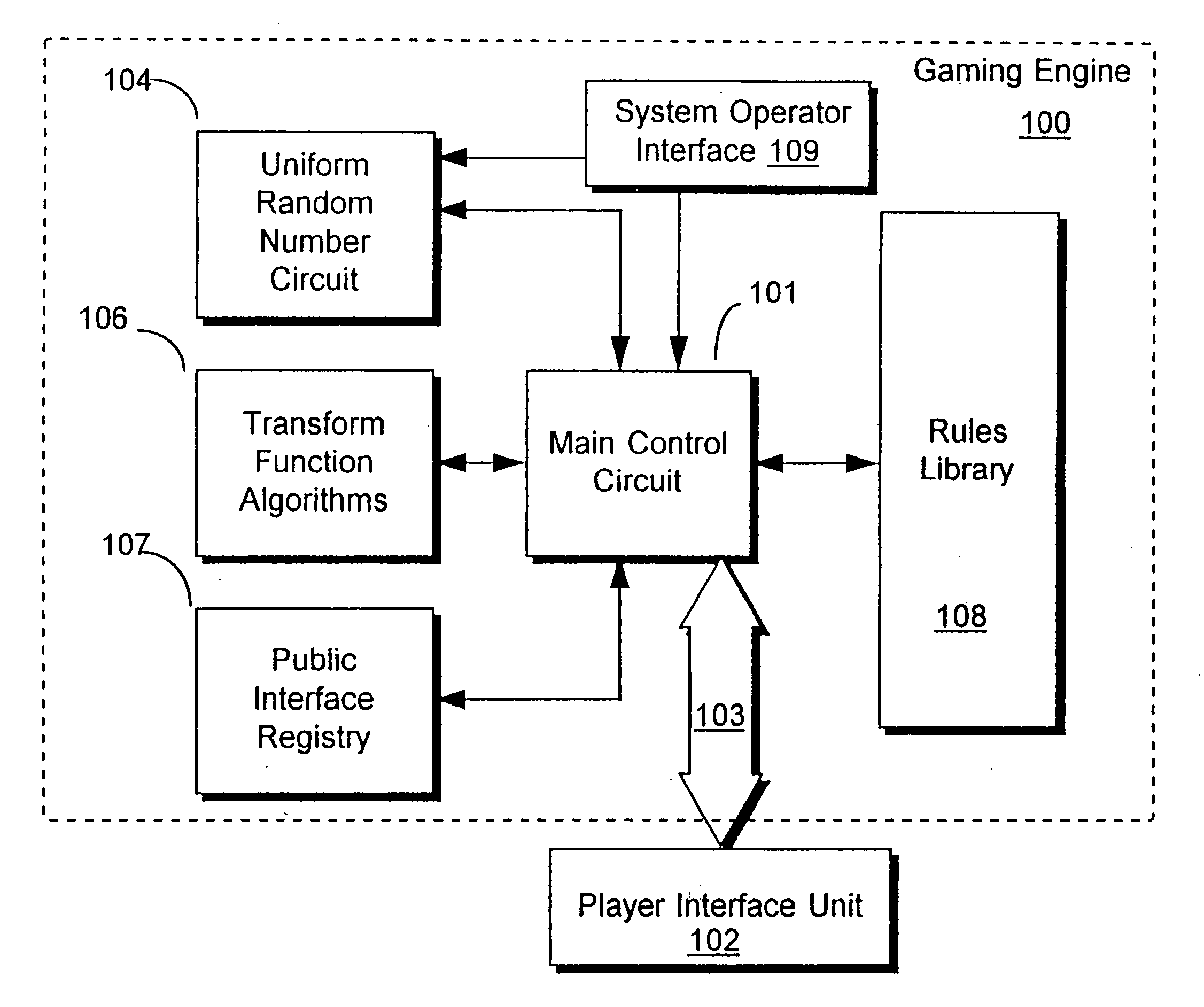
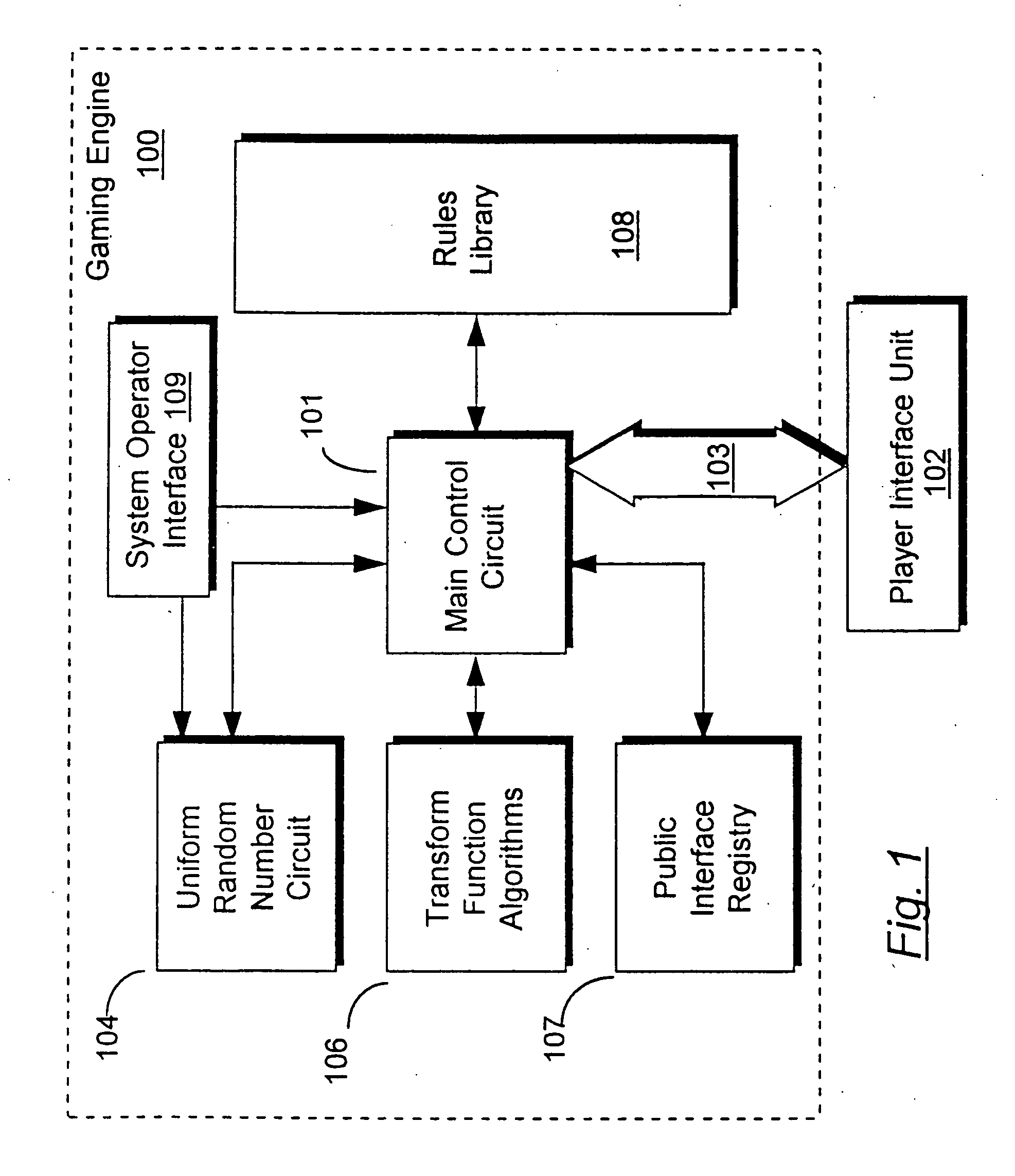
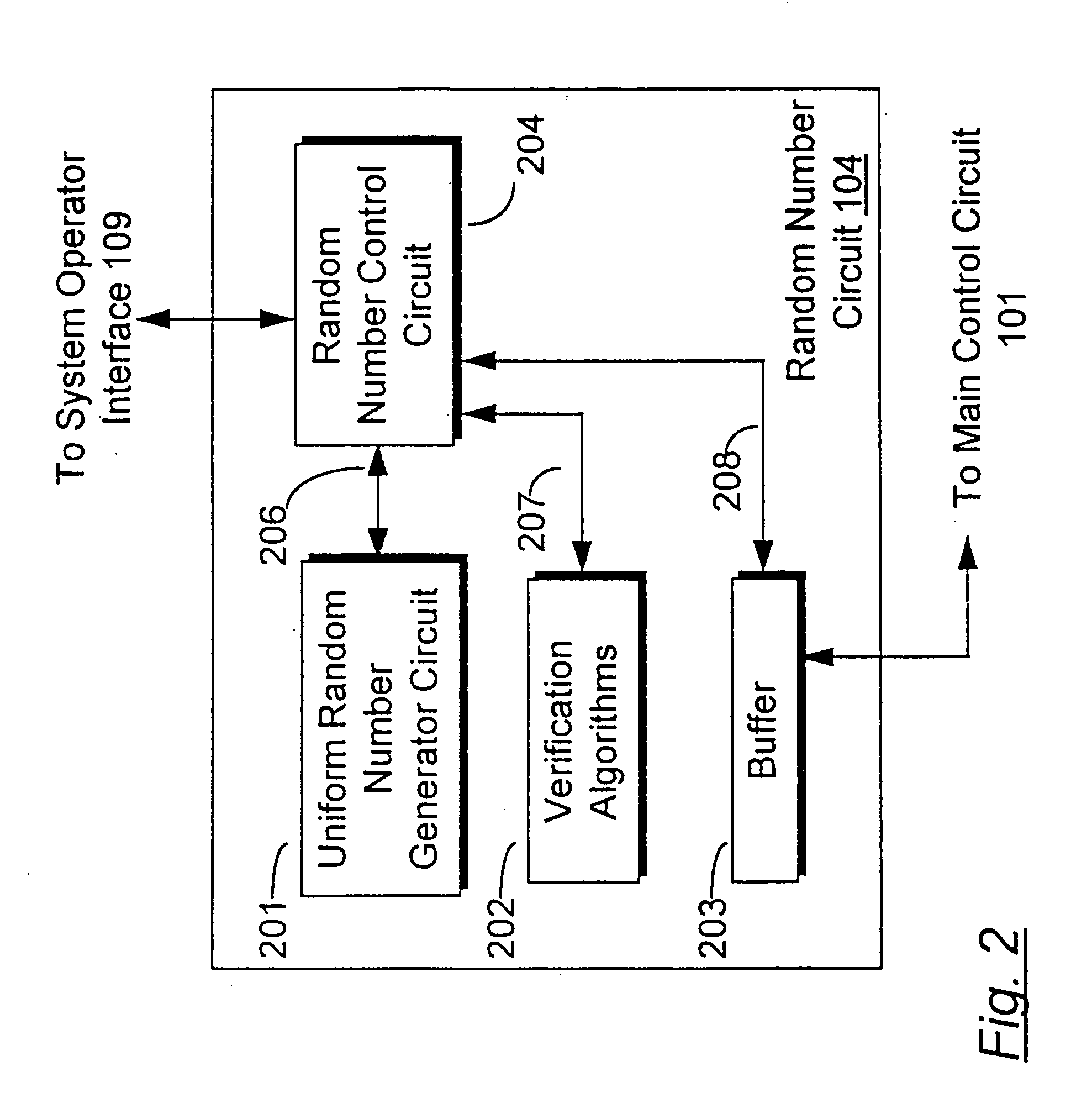
Method for control of gaming systems and for generating random numbers
InactiveUS20060165235A1Convenient timeImprove efficiencyRandom number generatorsMultiple digital computer combinationsArray data structureNumber generator
An apparatus for implementing a game having a deterministic component and a non-deterministic component wherein a player uses the game through at least one player interface unit. Each player interface unit generates a player record indicating player-initiated events. A random number generator provides a series of pseudo-random numbers and a rules library stores indexed rules for one or more games. An interface registry stores mapping records where the mapping records are used to associate the player-initiated events to pre-selected rules in the rules library. A control means is coupled to the player interface to receive the output of the player interface unit, coupled to the interface registry, the rules library, and the random number generator. The control means processes the player record and returns an output record to the player interface unit where the output record is determined by executing the game's rules with reference to the pseudo-random numbers and predefined combinatorial algorithms for selecting sets of the pseudo-random numbers.
Owner:ZYNGA
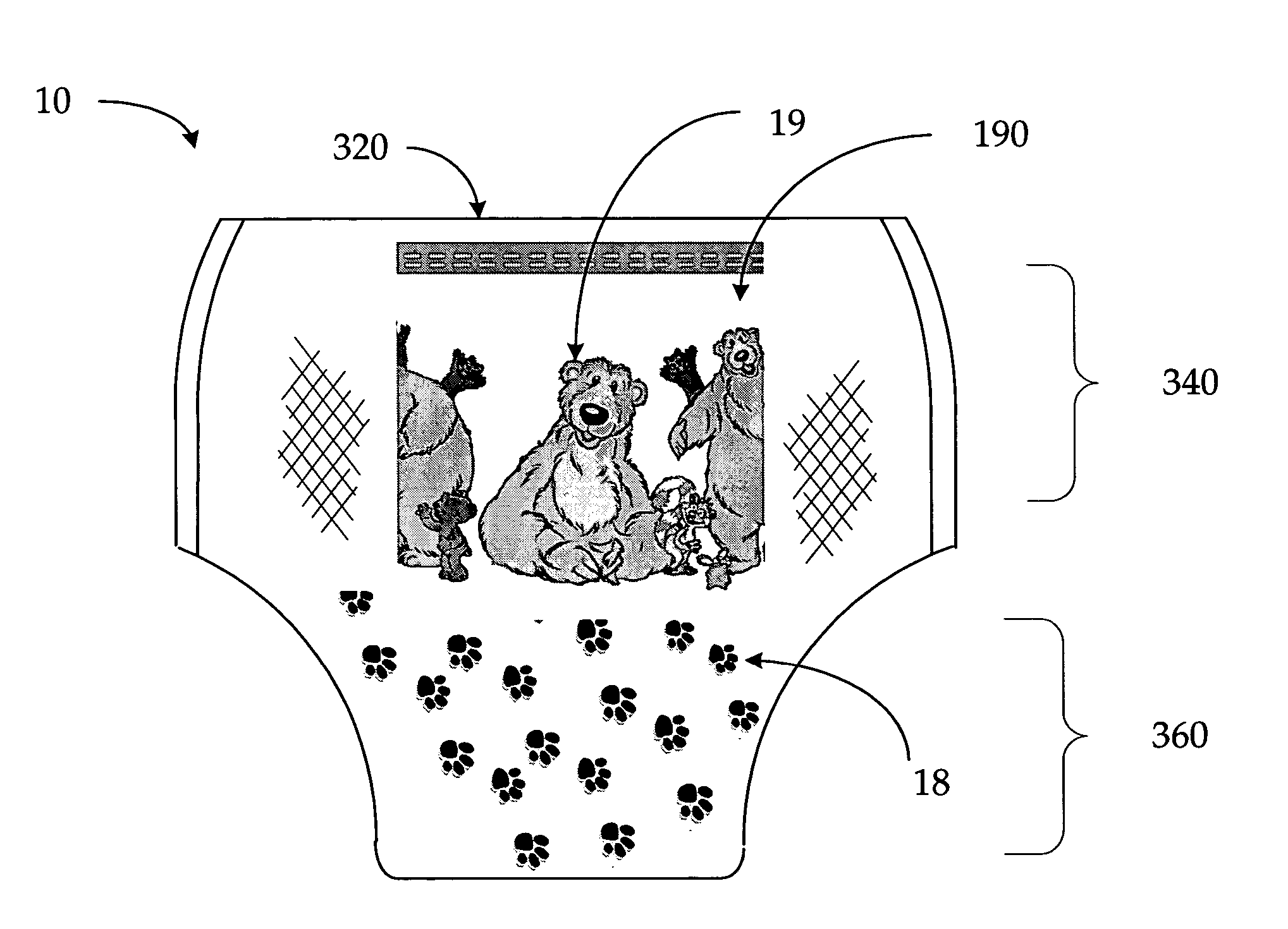
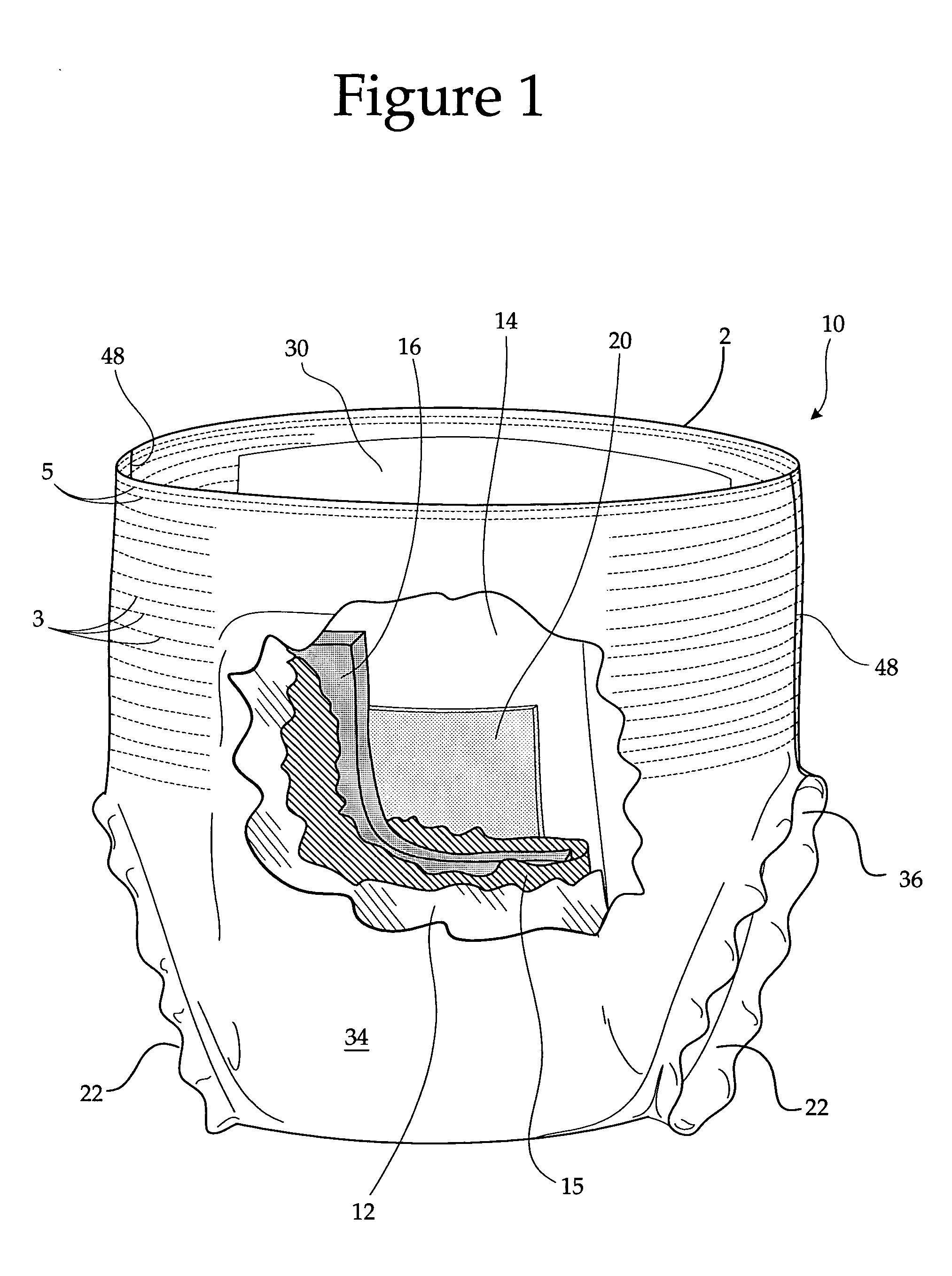
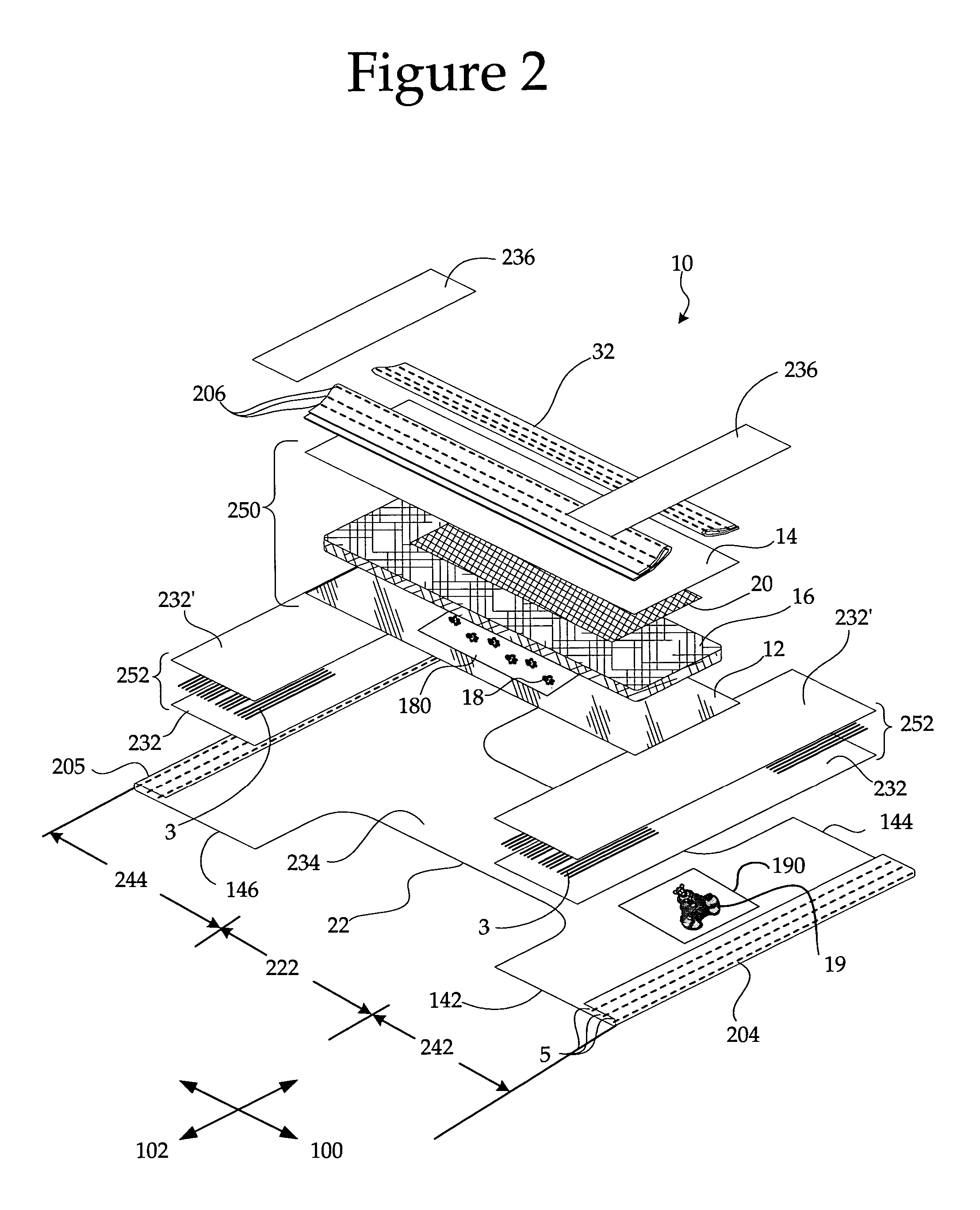
Disposable Absorbent Artcle with Wetness Indicator
InactiveUS20050065489A1Positive reinforcementCost efficientBaby linensTamponsPotty trainingEngineering
Absorbent articles that have wetness indicator graphics positioned thereon are disclosed, whereby the articles preferably include diapers, training pants, and adult incontinence products. The article includes a character graphic positioned in a waist region of the article, and a wetness indicator graphic that may be positioned in a crotch region. The character graphic is related to the wetness indicator graphic. The arrangement of the respective graphics preferably allow a caregiver to interact with a child to promote toilet training.
Owner:FIRST QUALITY RETAIL SERVICES
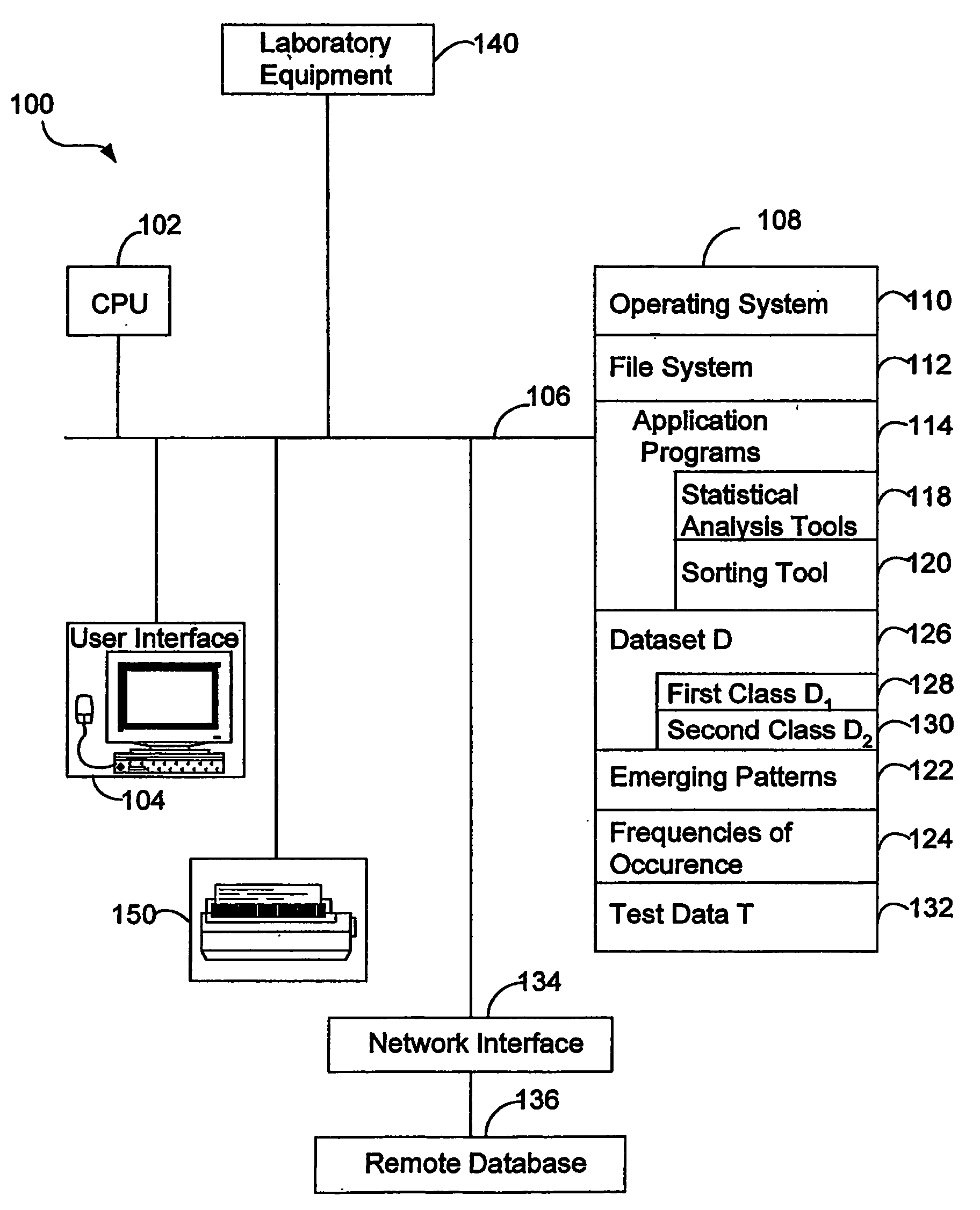
Prediction by collective likelihood from emerging patterns
InactiveUS20060074824A1Low costCost efficientBiostatisticsCharacter and pattern recognitionTraining data setsTest sample
A system, method and computer program product for determining whether a test sample is in a first or a second class of data (for example: cancerous or normal), comprising: extracting a plurality of emerging patterns from a training data set, creating a first and second list containing respectively, a frequency of occurrence of each emerging pattern that has a non-zero occurrence in the first and in the second class of data; using a fixed number of emerging patterns, calculating a first and second score derived respectively from the frequencies of emerging patterns in the first list that also occur in the test data, and from the frequencies of emerging patterns in the second list that also occur in the test data; and deducing whether the test sample is categorized in the first or the second class of data by selecting the higher of the first and the second score.
Owner:AGENCY FOR SCI TECH & RES
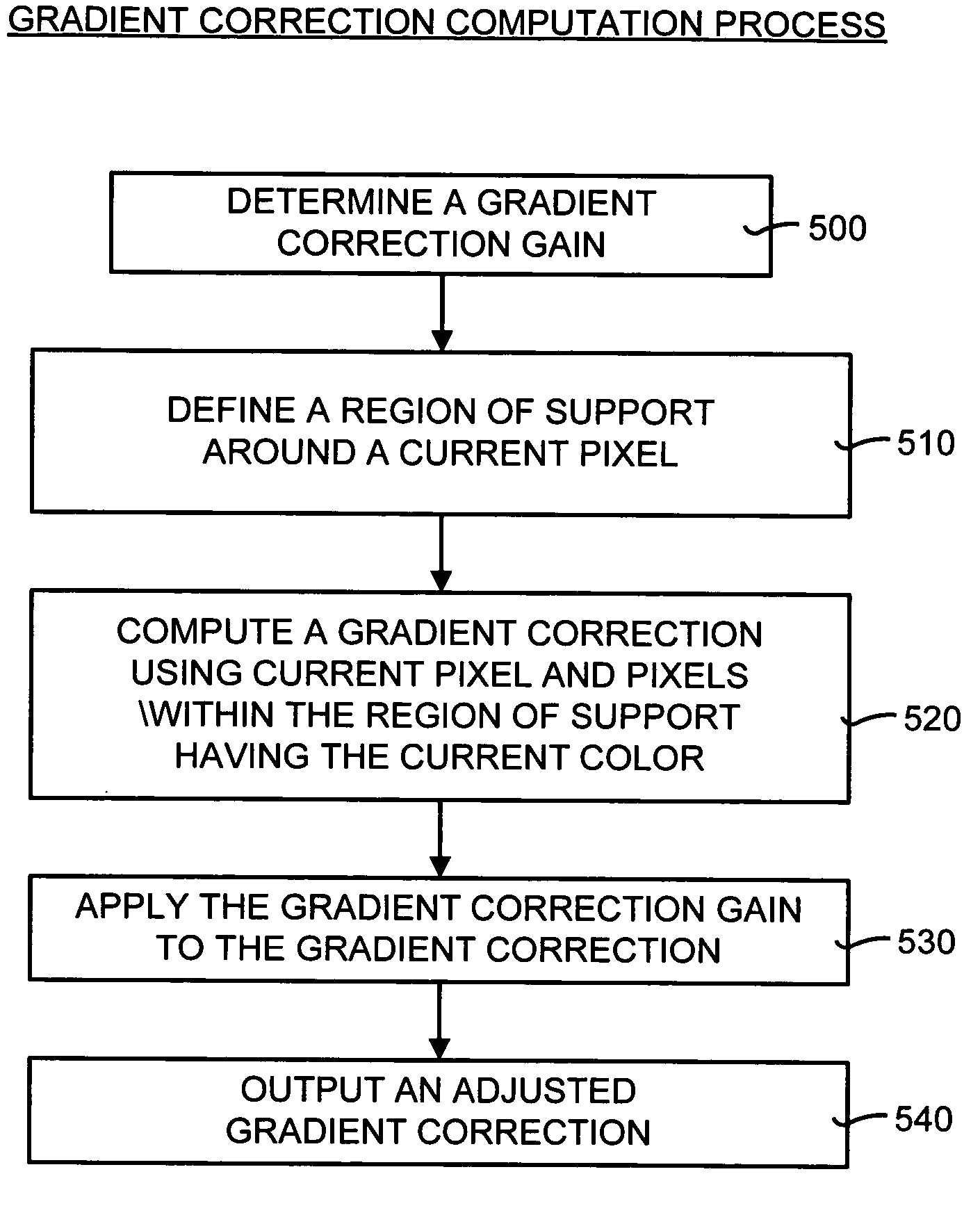
High-quality gradient-corrected linear interpolation for demosaicing of color images
ActiveUS7502505B2Improve performanceReduce complexityGeometric image transformationCharacter and pattern recognitionColor imageAlgorithm
A gradient-corrected linear interpolation method and system for the demosaicing of color images. The method and system compute an interpolation using some a current technique (preferably a bilinear interpolation technique to reduce computational complexity), compute a correction term (such as a gradient of a desired color at a given pixel), and linearly combine the interpolation and the correction term to produce a corrected, high-quality interpolation of a missing color value at a pixel. The correction term may be a gradient correction term computed from the current color of the current pixel. This gradient is directly used to affect and correct the estimated color value produced by the prior art interpolation technique. The gradient-corrected linear interpolation method and system may also apply a gradient-correction gain to the gradient correction term. This gradient-correction gain affects the amount of gradient correction that is applied to the interpolation.
Owner:MICROSOFT TECH LICENSING LLC
Fluid pump/generator with integrated motor and related stator and rotor and method of pumping fluid
InactiveUS7021905B2Small sizeReduce the number of partsGas turbine plantsRotary piston pumpsImpellerElectric machine
Owner:ADVANCED ENERGY CONVERSION
Mobile Networked Payment System
InactiveUS20110320347A1Easy and fast accessLow costFinancePayment architectureFinancial transactionApplication software
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions can be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions can be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
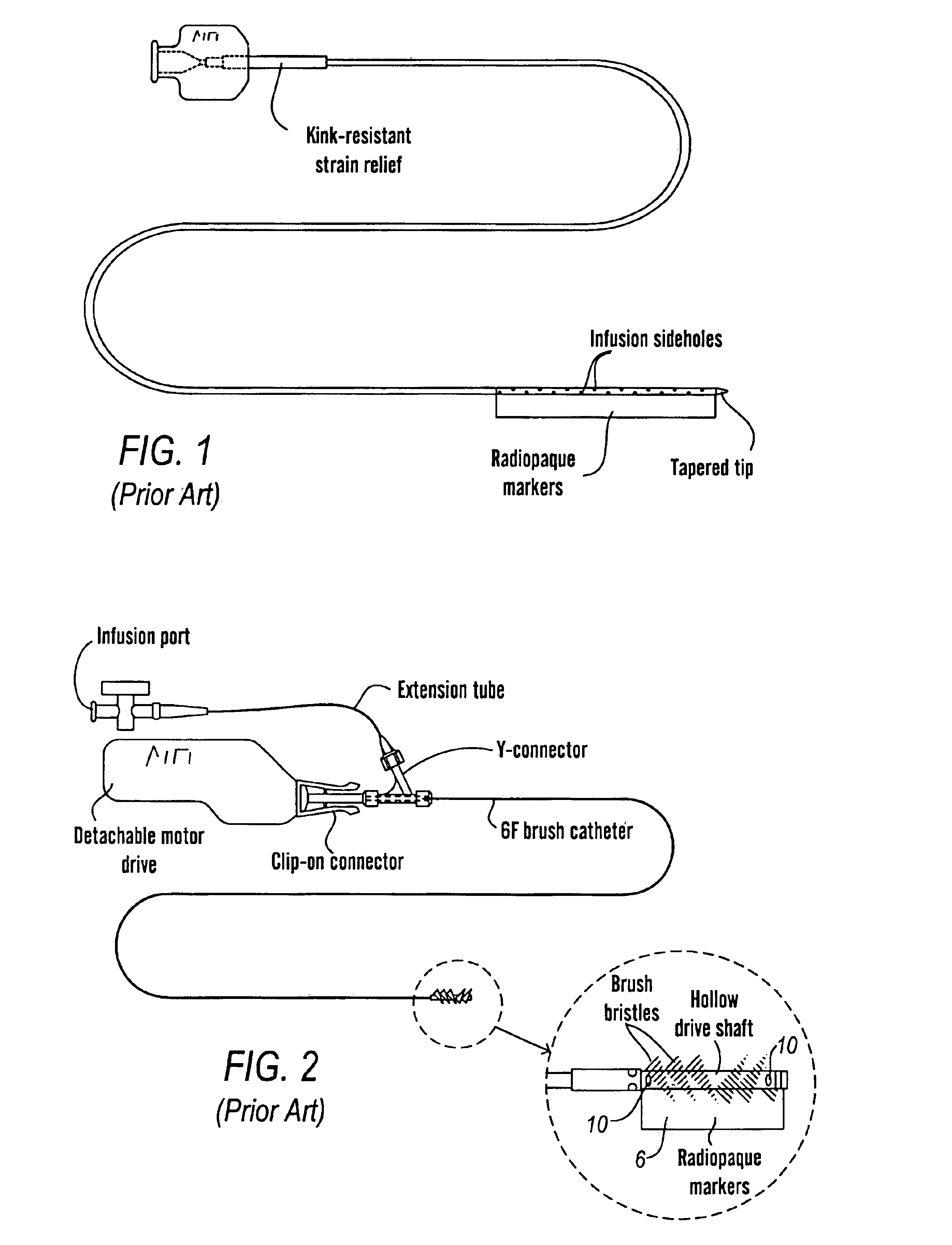
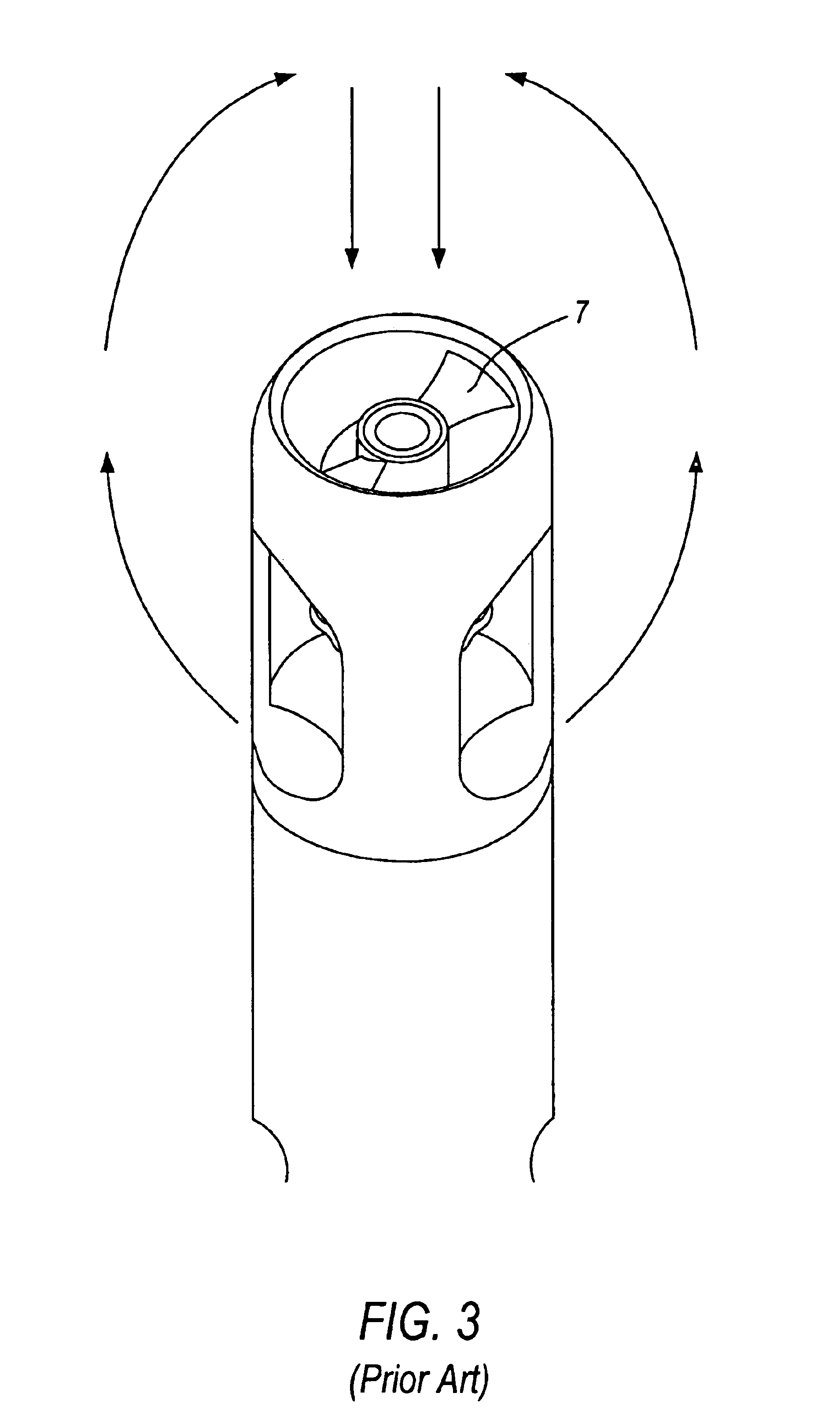
Mechanically active infusion catheter
A device and method to dissolve or eliminate blood clots from a patient relies upon a non-rapid moving mechanism to physically dissolve clots without damaging endothelium of the arteries and veins of a patient. In one embodiment, in addition to mechanical agitation of a clot, a thrombolytic agent is administered simultaneously with such agitation. Preferably, intermittent agitation is utilized over a prolonged period of time to effectuate clot removal.
Owner:COOK MEDICAL TECH LLC
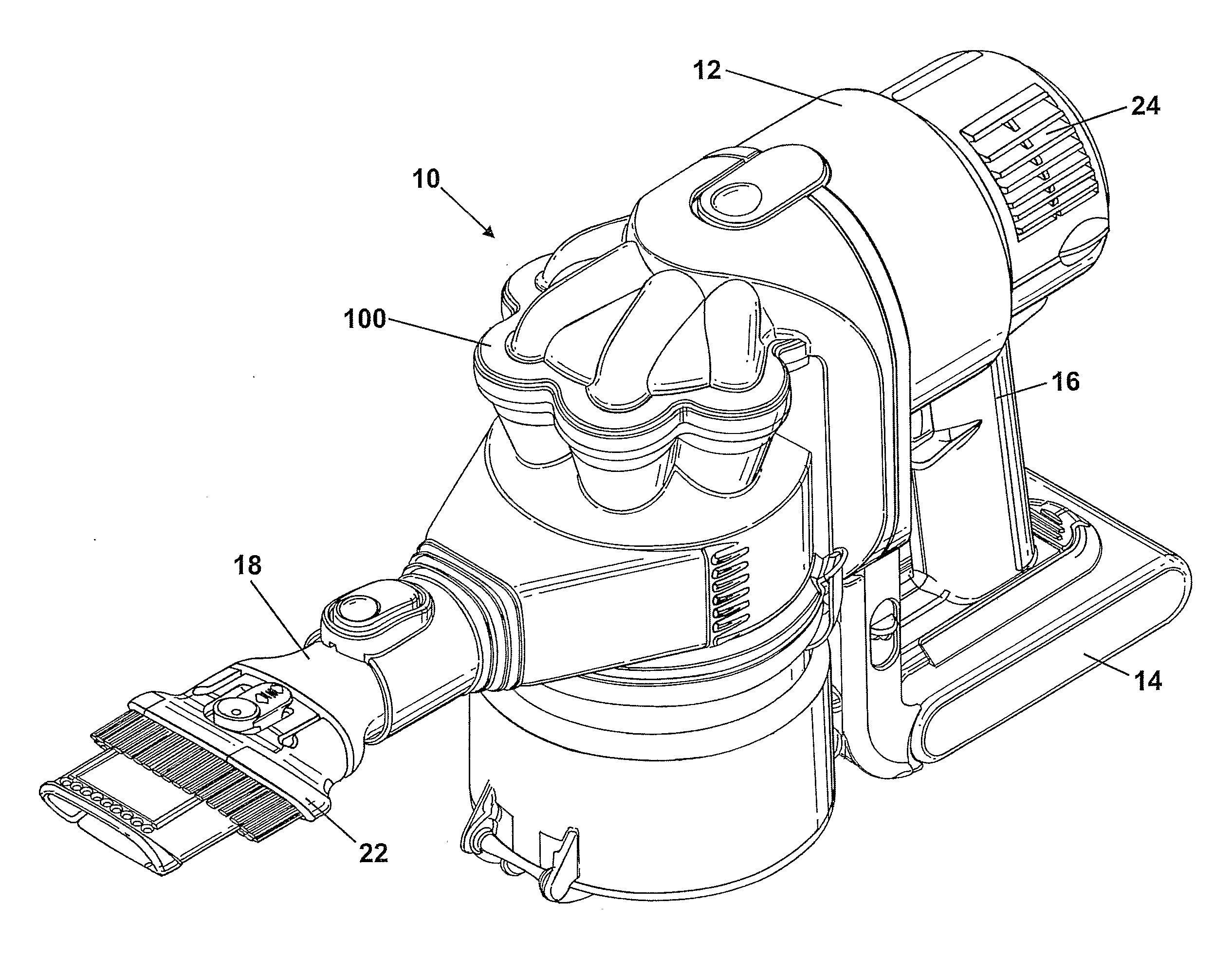
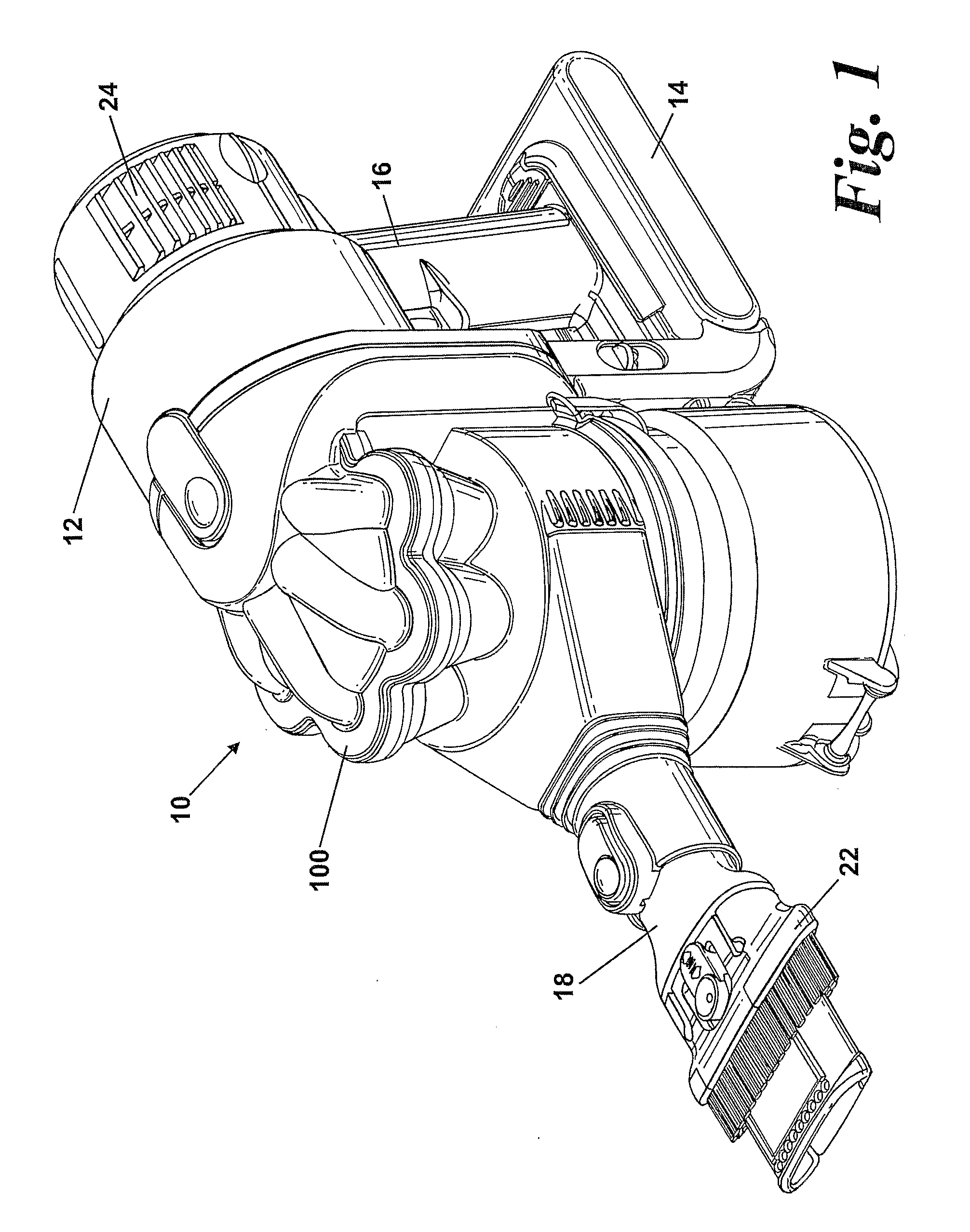
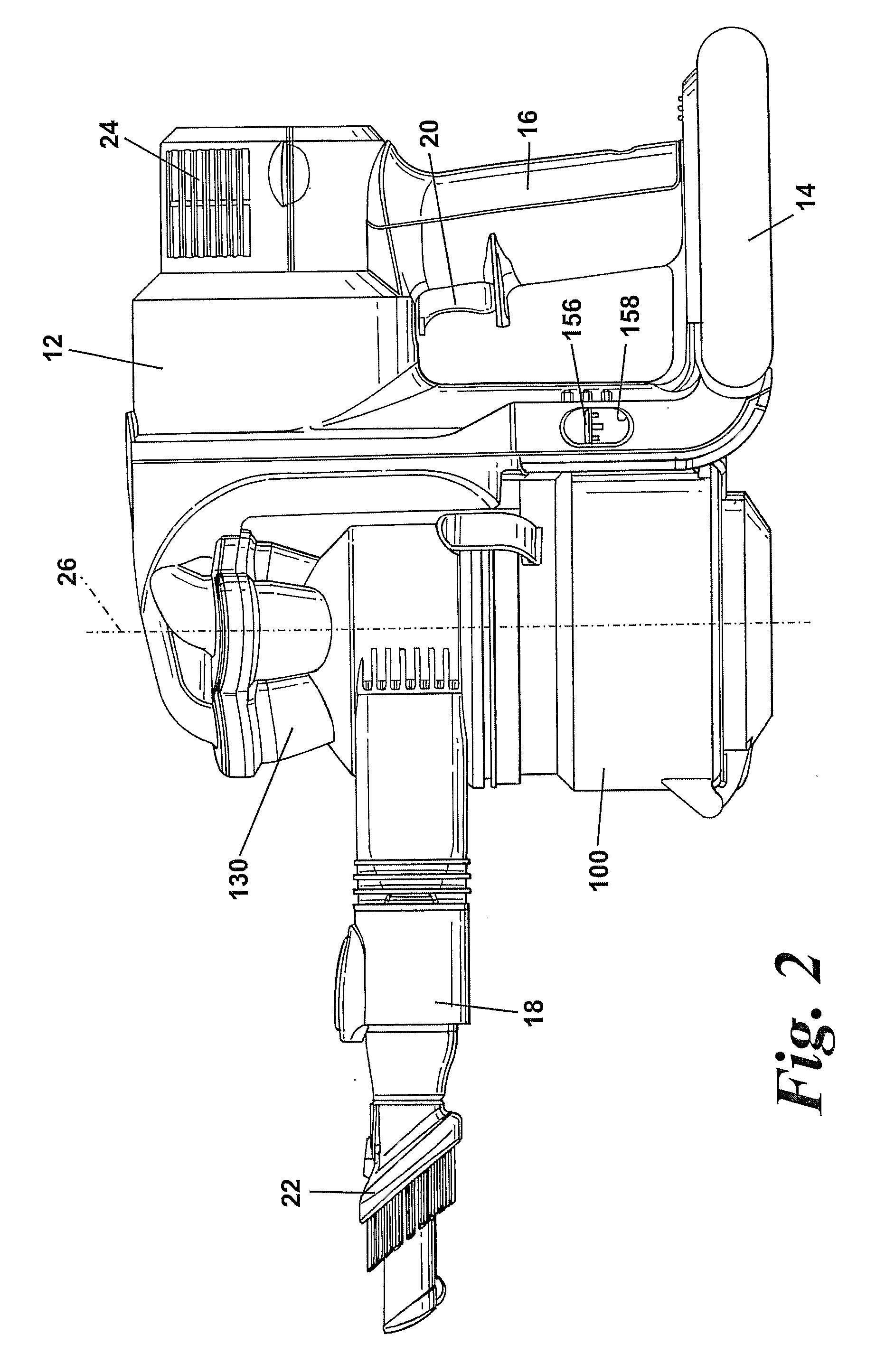
Handheld cleaning appliance
A handheld cleaning appliance includes a dirty air inlet, a clean air outlet and separating apparatus for separating dirt and dust from an airflow in an airflow path leading from the air inlet to the air outlet. The separating apparatus includes a cyclonic separator having at least one cyclone and a collector having a wall and a base member, the base member being held in a closed position by a catch and being pivotably connected to the wall. The appliance further includes a main body which incorporates an actuator for operating the catch. The actuator has a slidably mounted rod which is movable between an inoperative position and an actuating position in which the rod contacts part of the catch so as to allow the collector to be opened for emptying purposes. This arrangement allows the catch to be released without the user actually touching the collector.
Owner:DYSON TECH LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com