Patents
Literature
143 results about "Strong authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
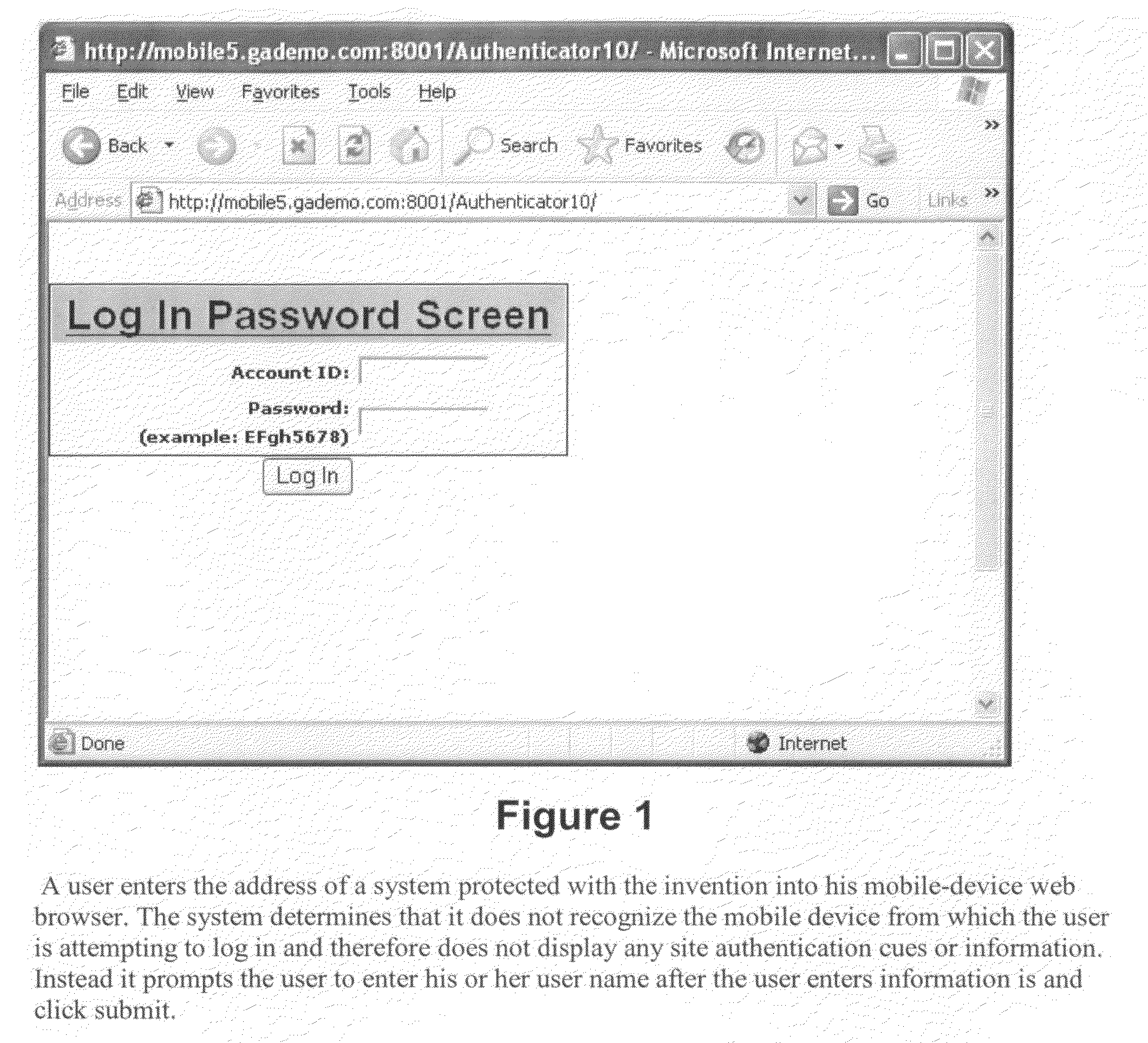
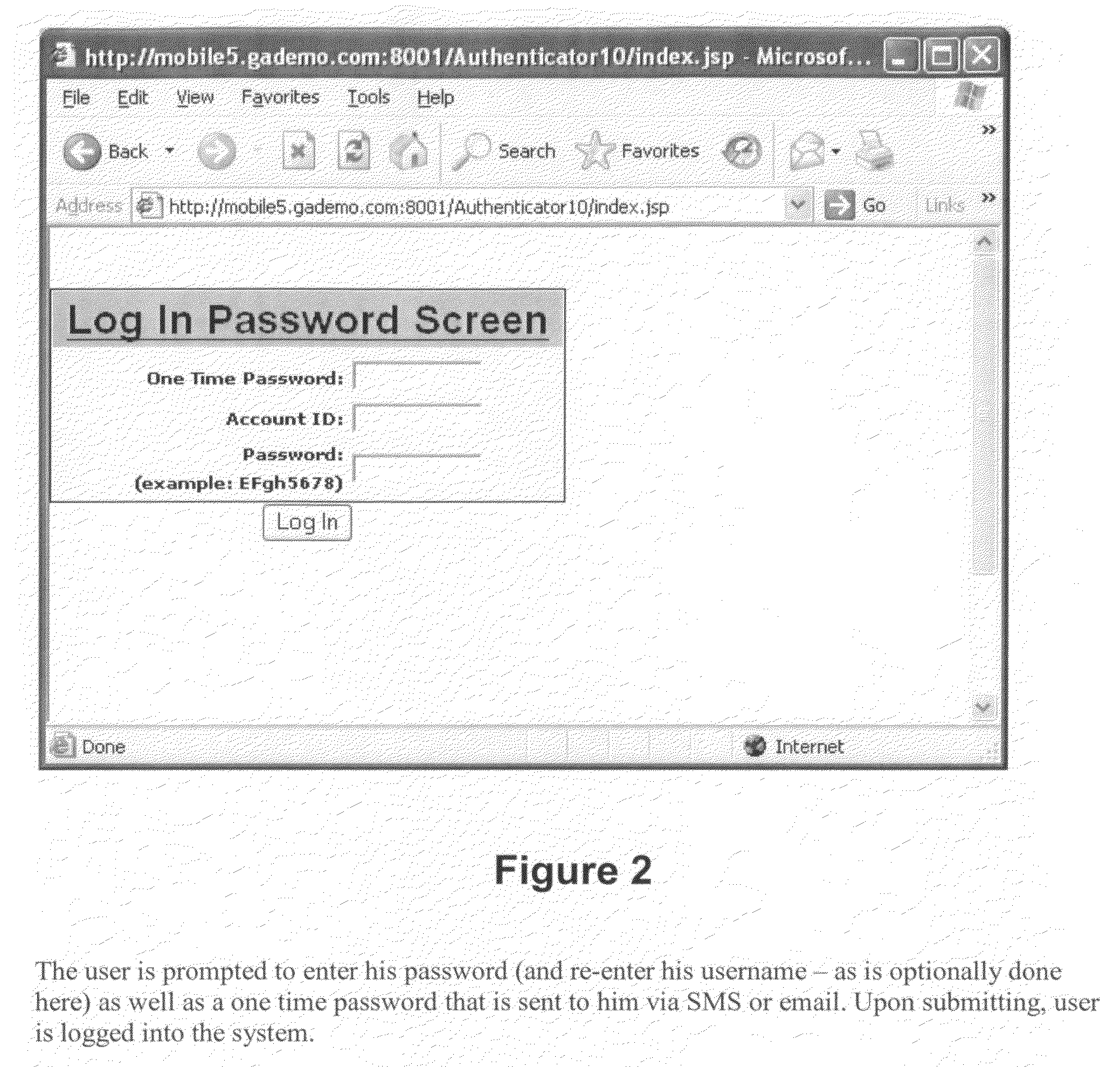
Strong authentication is a notion with several definitions.
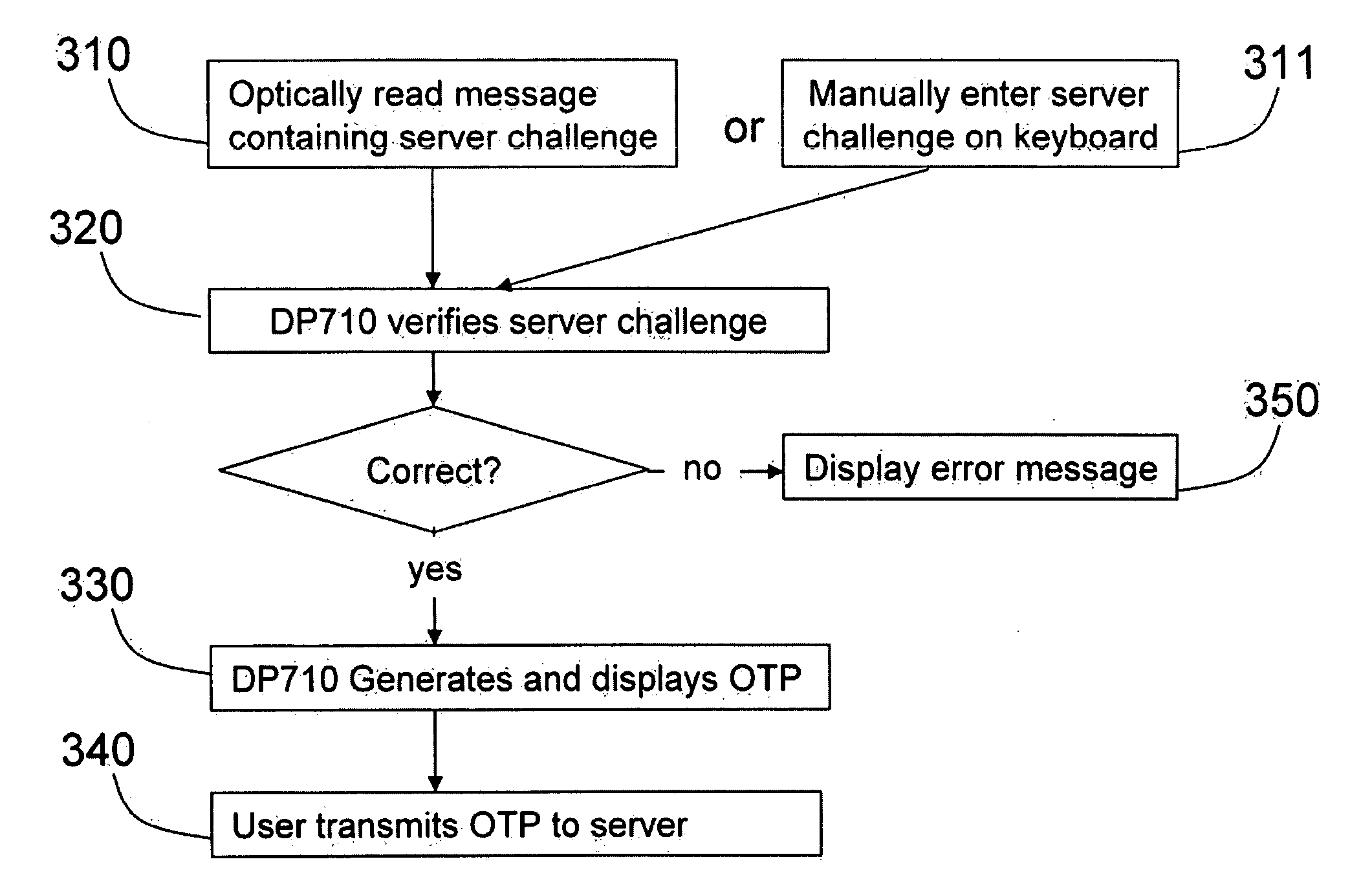
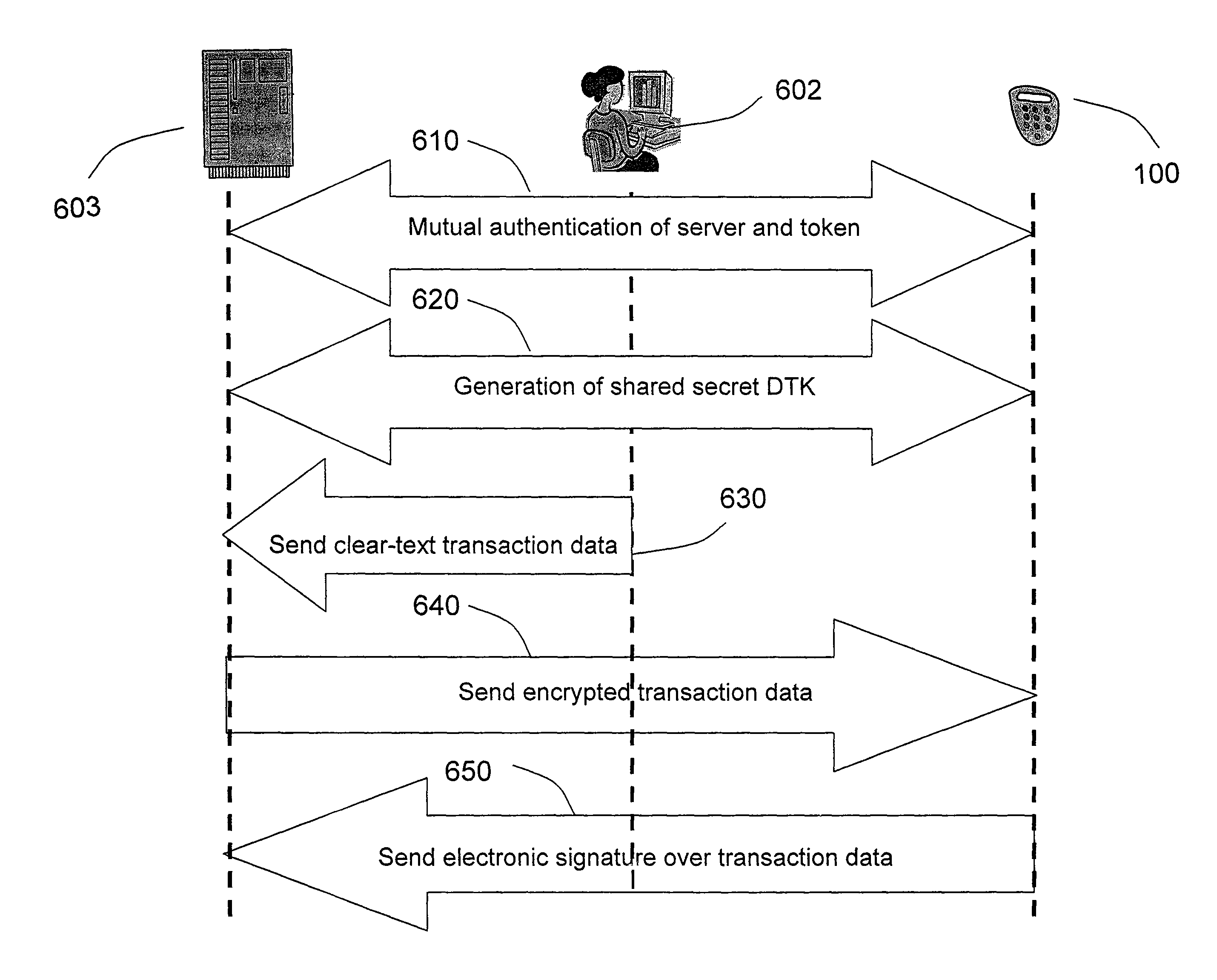
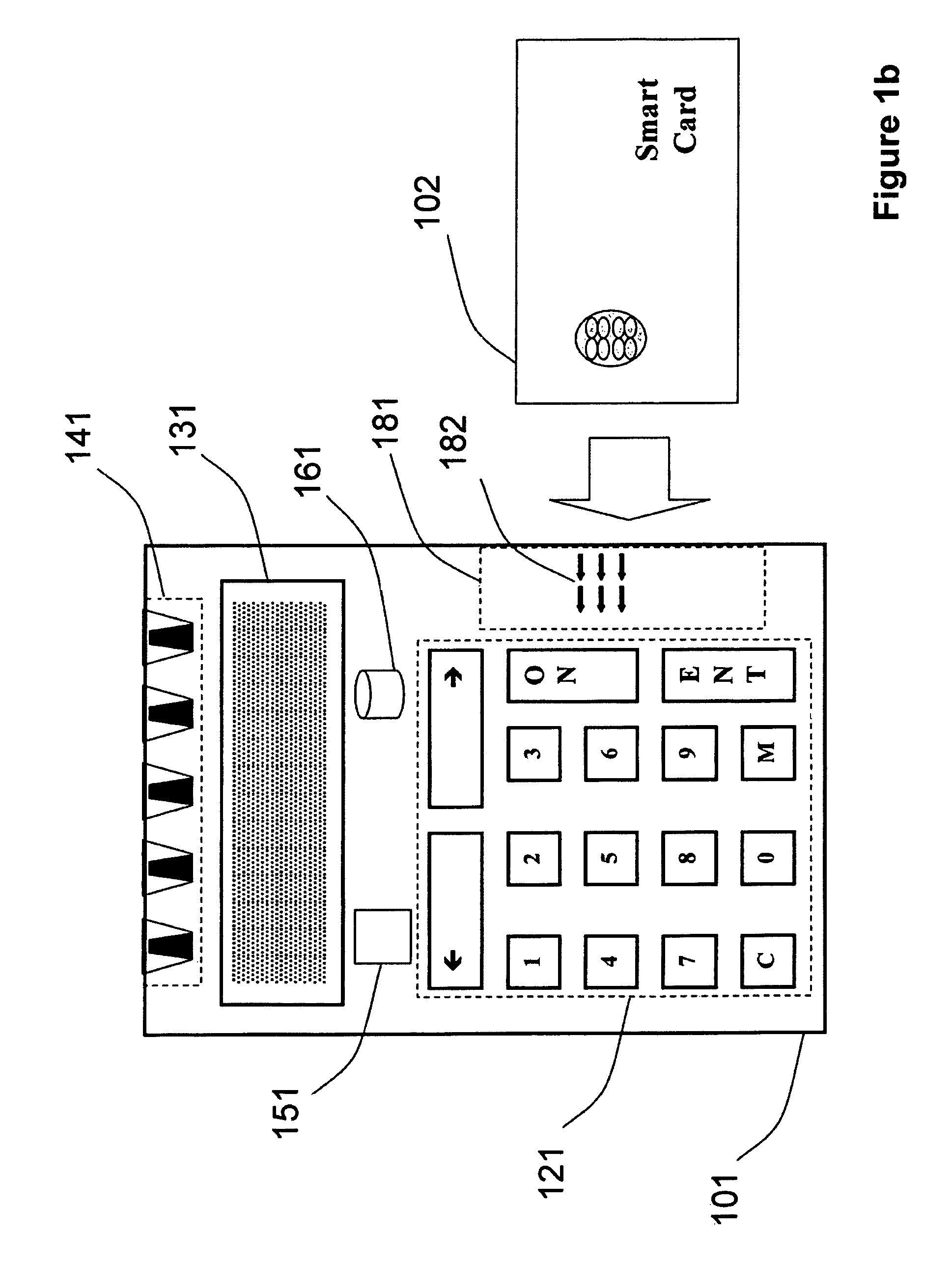
Strong authentication token generating one-time passwords and signatures upon server credential verification
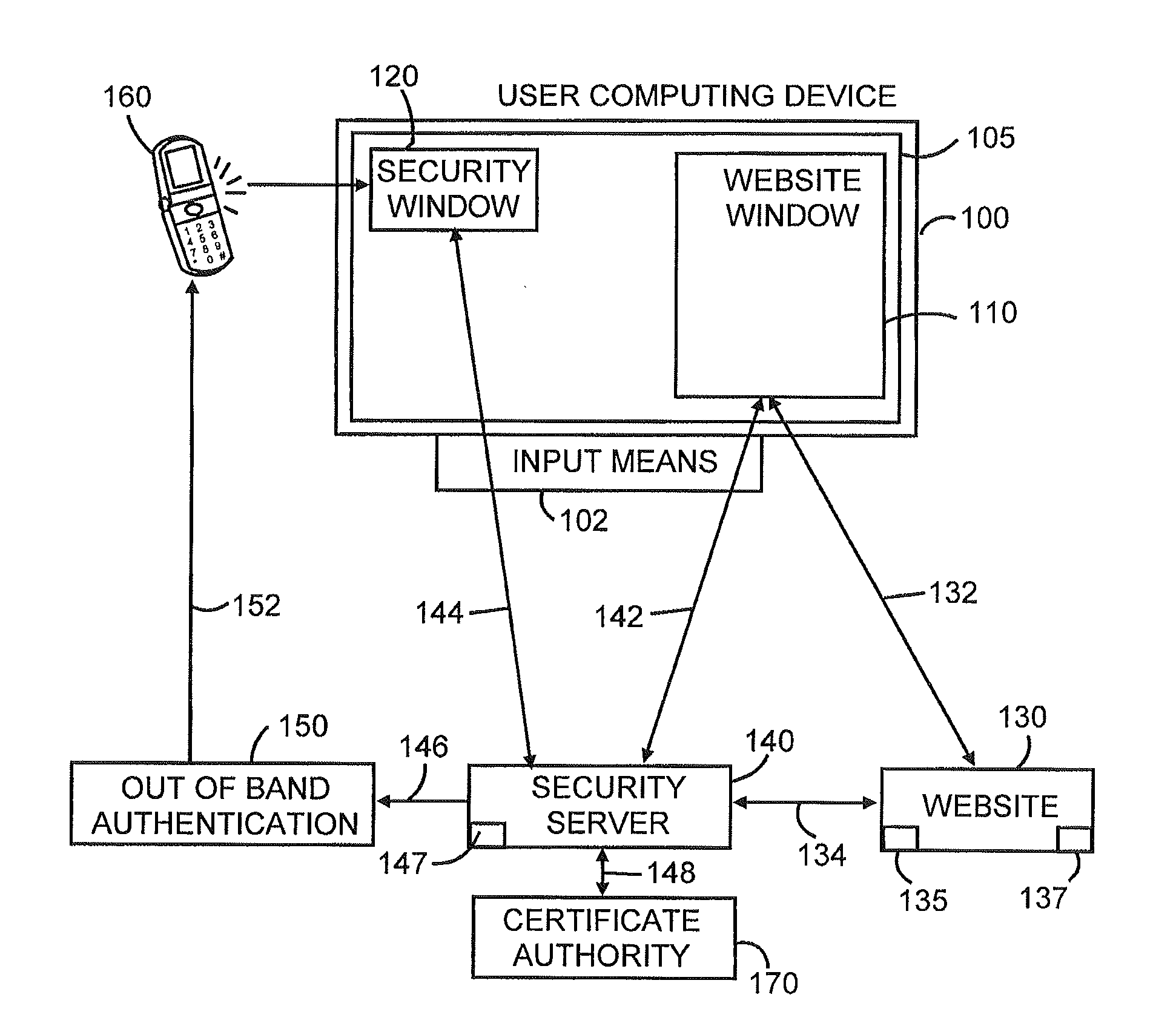
ActiveUS20090235339A1Transfer size reductionHighly secureDigital data processing detailsMultiple digital computer combinationsInternet privacyTransaction data
The invention defines a strong authentication token that remedies a vulnerability to a certain type of social engineering attacks, by authenticating the server or messages purporting to come from the server prior to generating a one-time password or transaction signature; and, in the case of the generation of a transaction signature, signing not only transaction values but also transaction context information and, prior to generating said transaction signature, presenting said transaction values and transaction context information to the user for the user to review and approve using trustworthy output and input means. It furthermore offers this authentication and review functionality without sacrificing user convenience or cost efficiency, by judiciously coding the transaction data to be signed, thus reducing the transmission size of information that has to be exchanged over the token's trustworthy interfaces
Owner:ONESPAN NORTH AMERICA INC
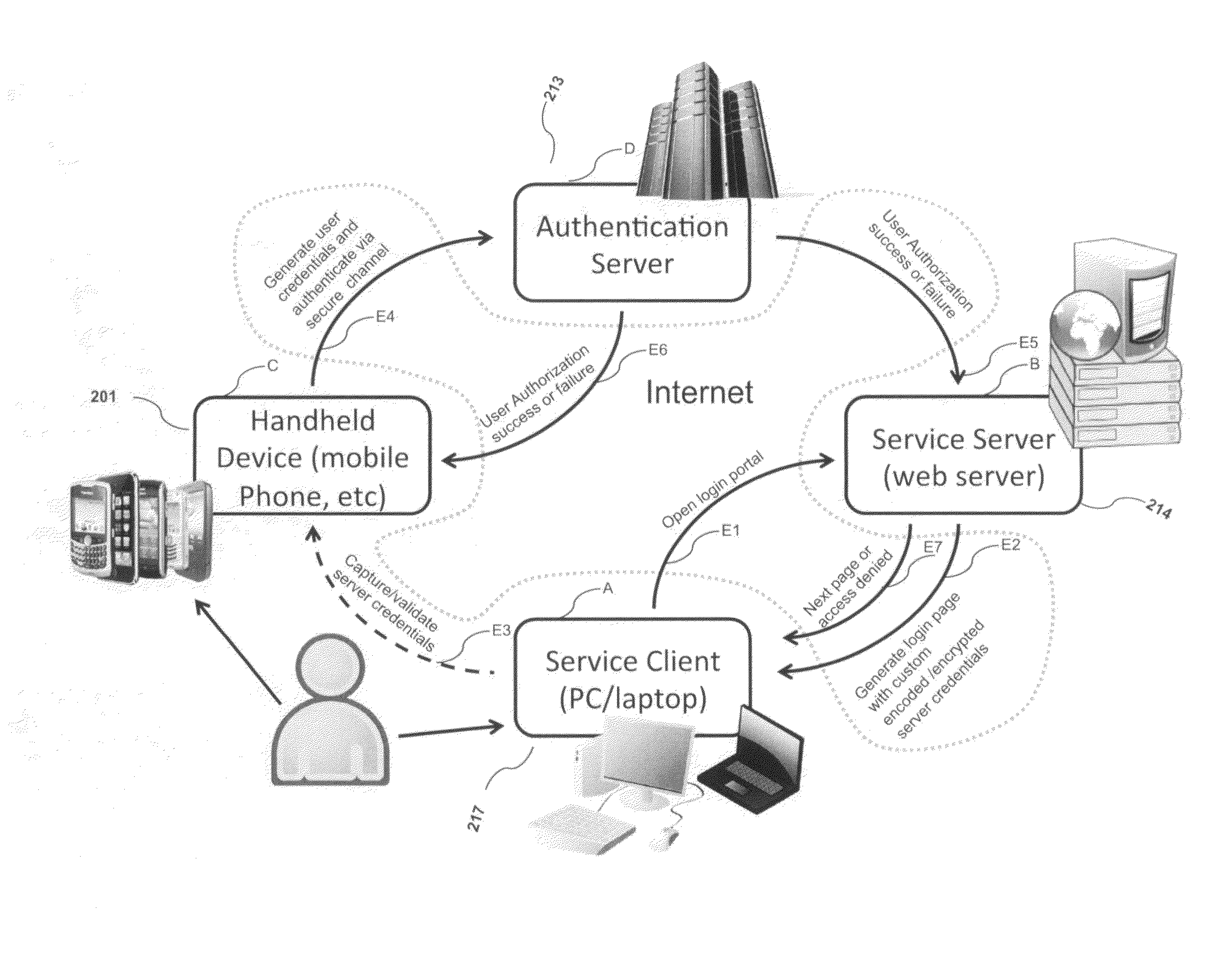
System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication
ActiveUS8763097B2Digital data information retrievalDigital data processing detailsOutbound communicationBarcode
Owner:GCOM IP LLC
Flexible end-point compliance and strong authentication for distributed hybrid enterprises
ActiveUS20110307947A1Digital data processing detailsMultiple digital computer combinationsUser authenticationClient-side
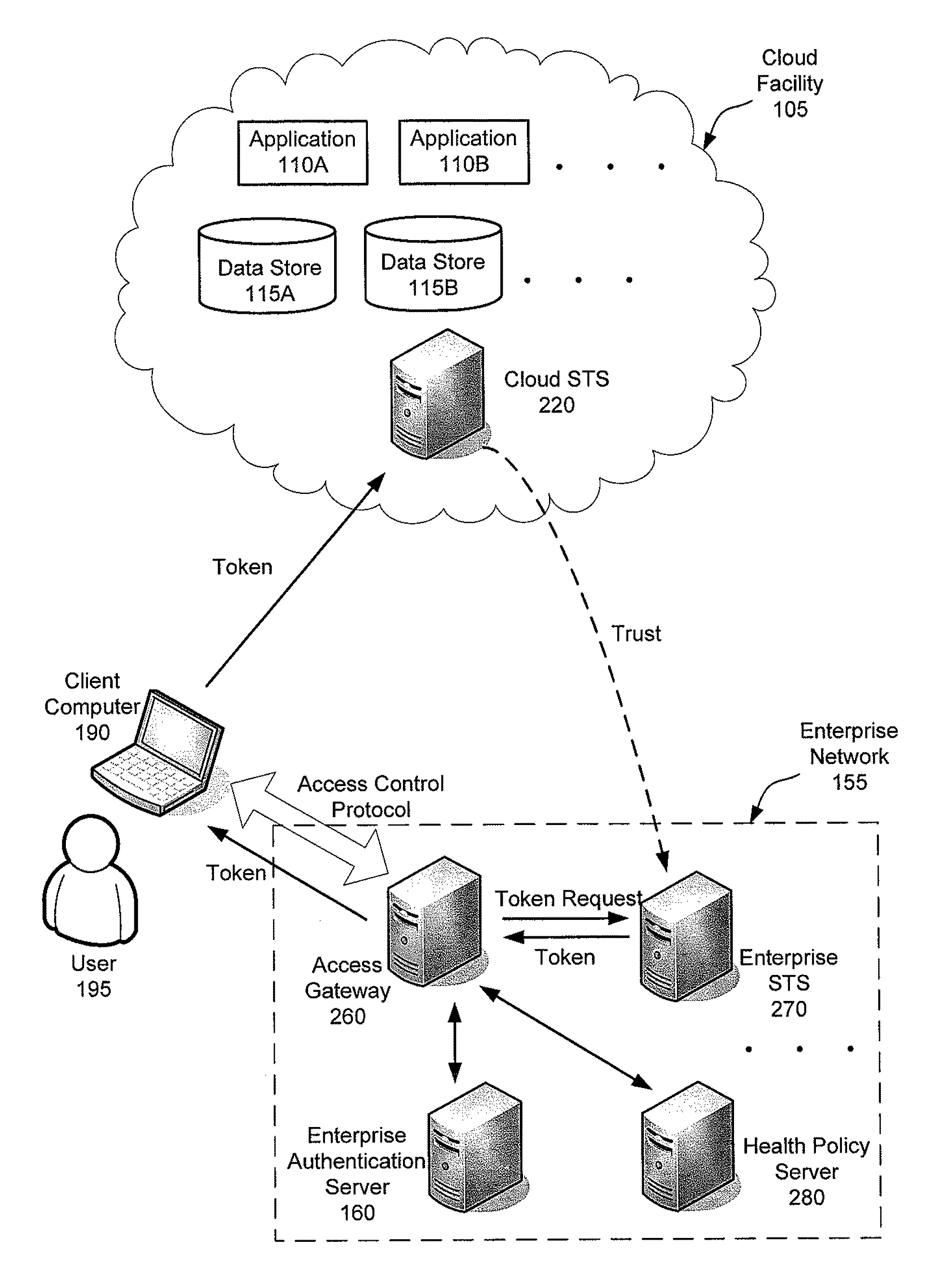
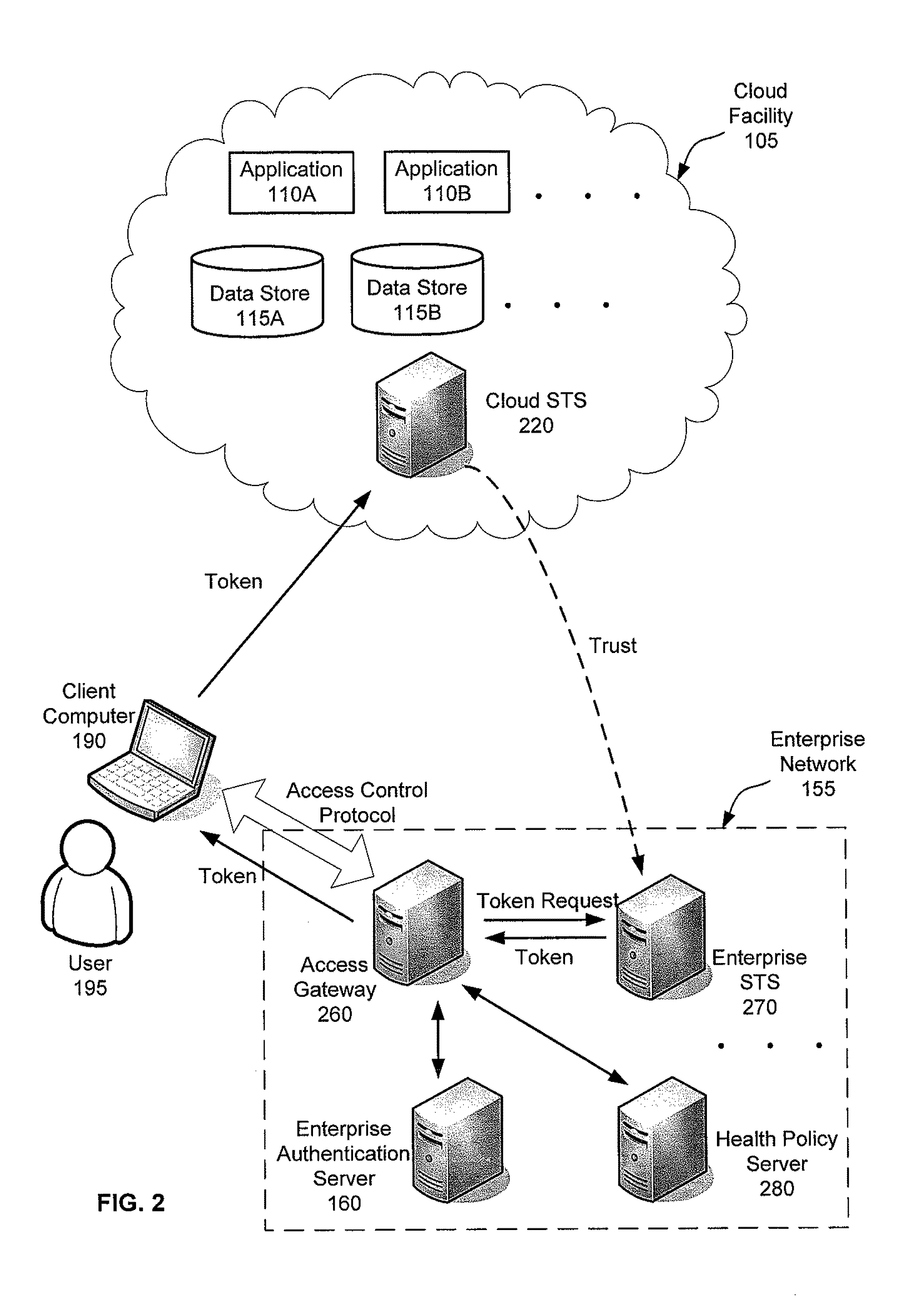
Systems, methods and apparatus for accessing at least one resource hosted by at least one server of a cloud service provider. In some embodiments, a client computer sends authentication information associated with a user of the client computer and a statement of health regarding the client computer to an access control gateway deployed in an enterprise's managed network. The access control gateway authenticates the user and determines whether the user is authorized to access the at least one resource hosted in the cloud. If the user authentication and authorization succeeds, the access control gateway requests a security token from a security token service trusted by an access control component in the cloud and forwards the security token to the client computer. The client computer sends the security token to the access component in the cloud to access the at least one resource from the at least one server.
Owner:MICROSOFT TECH LICENSING LLC
Secure and reliable document delivery
InactiveUS6988199B2Key distribution for secure communicationUser identity/authority verificationPrivate networkPaper document
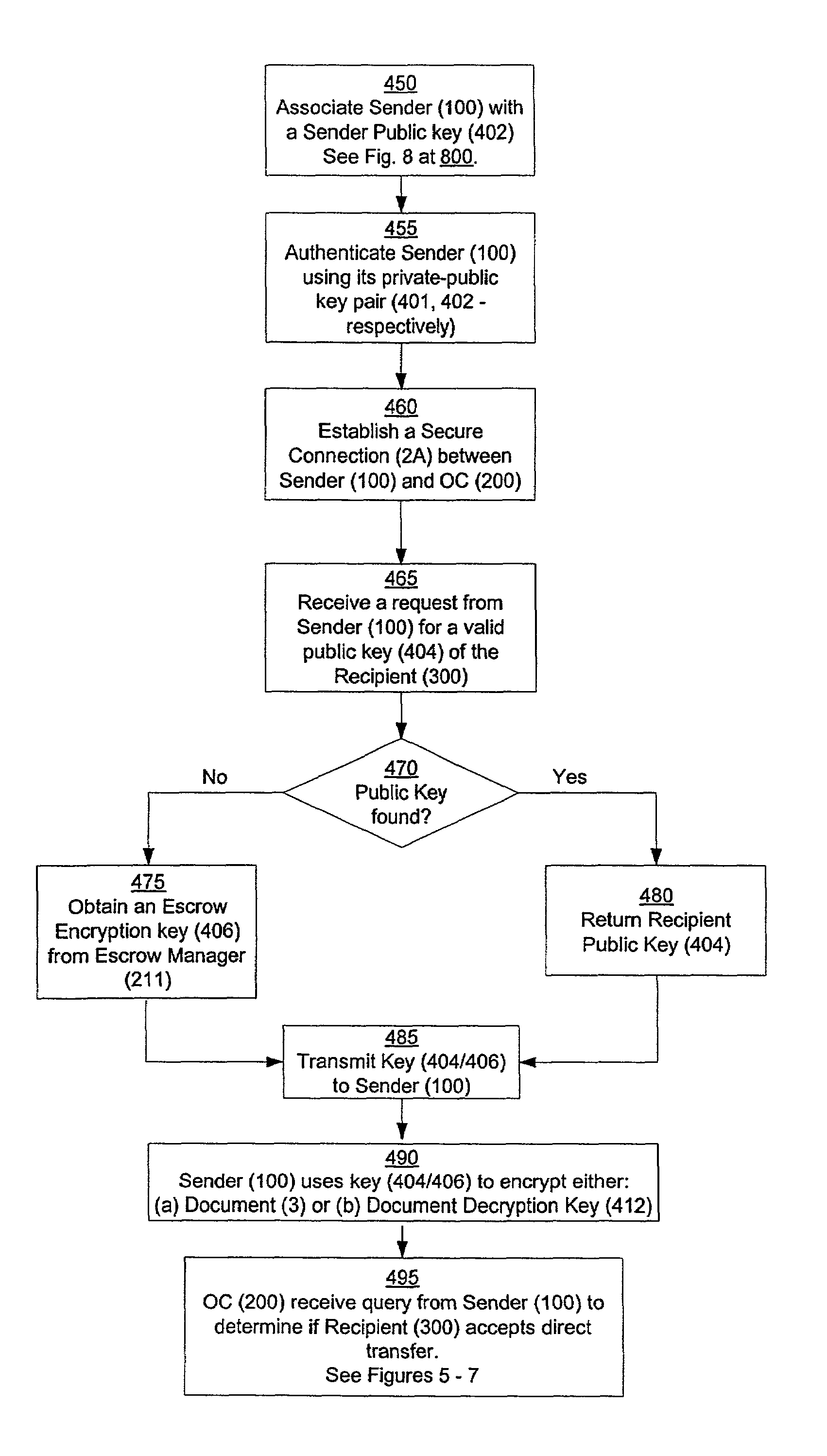
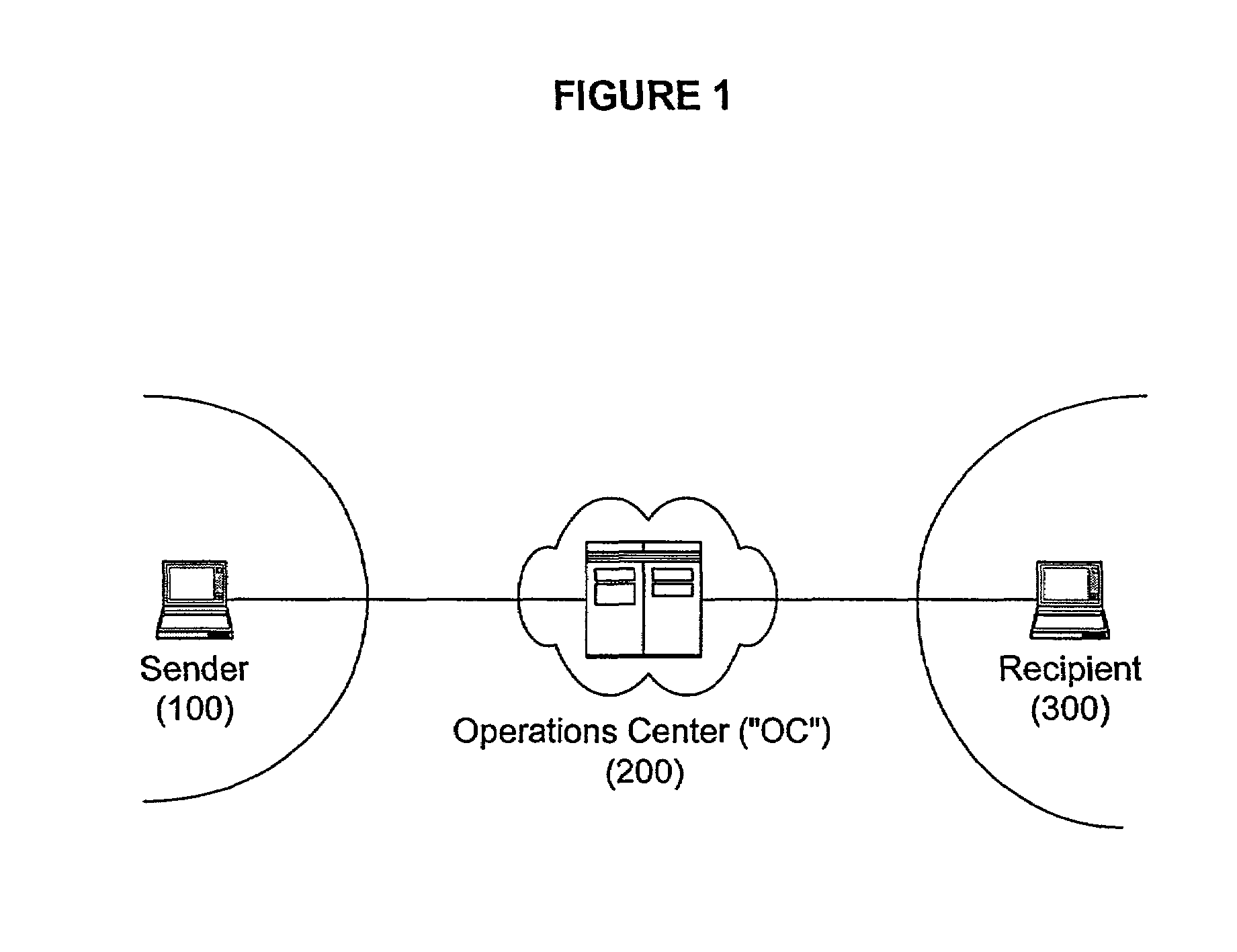
An Operations Center (OC) (200) acts as a central key manager and intermediary in securely, reliably and non-repudiably delivering a document (3) from a sender (100) to a recipient (300). The OC (200) acts as a key manager to facilitate the process of strong authentication of the sender (100) and the recipient (300), encryption of the delivery (510), and setup of reliable connections (2A, 2B, 2C). In a preferred embodiment, the reliable connections (2A, 2B, 2C) are virtual private network connections.
Owner:BAE SYST APPLIED INTELLIGENCE US
System, design and process for strong authentication using bidirectional OTP and out-of-band multichannel authentication
ActiveUS20120240204A1Digital data information retrievalDigital data processing detailsOutbound communicationBarcode
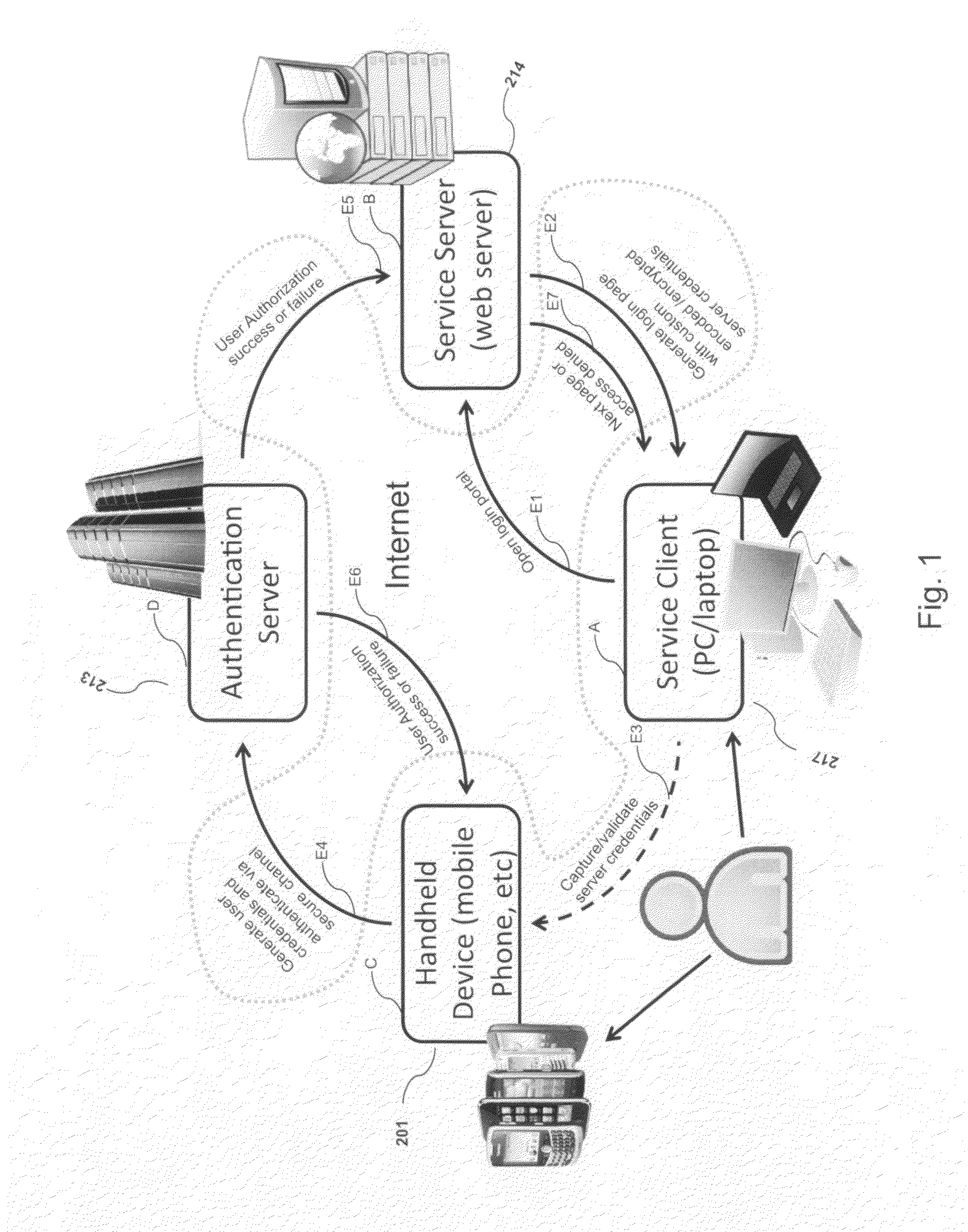
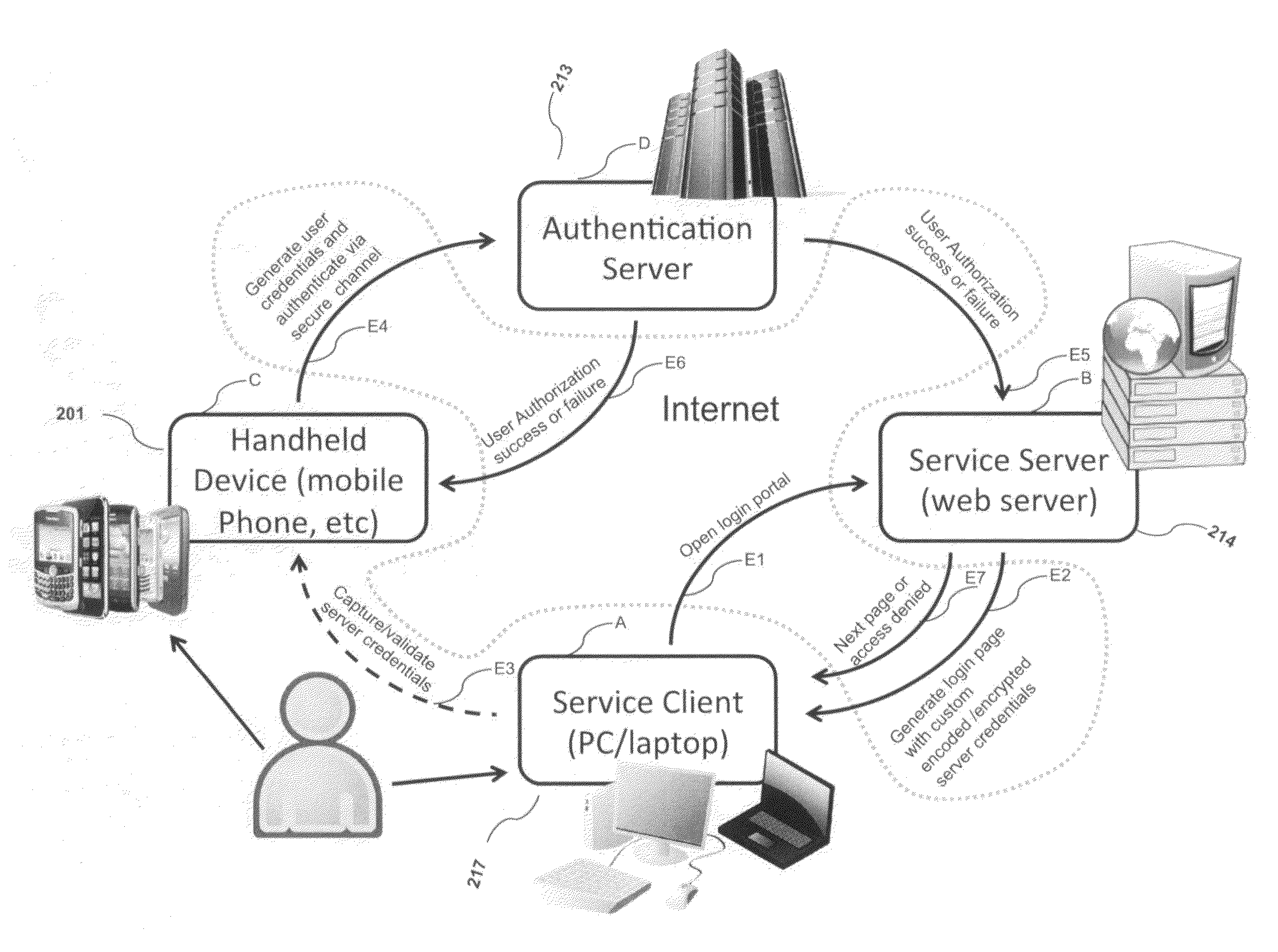
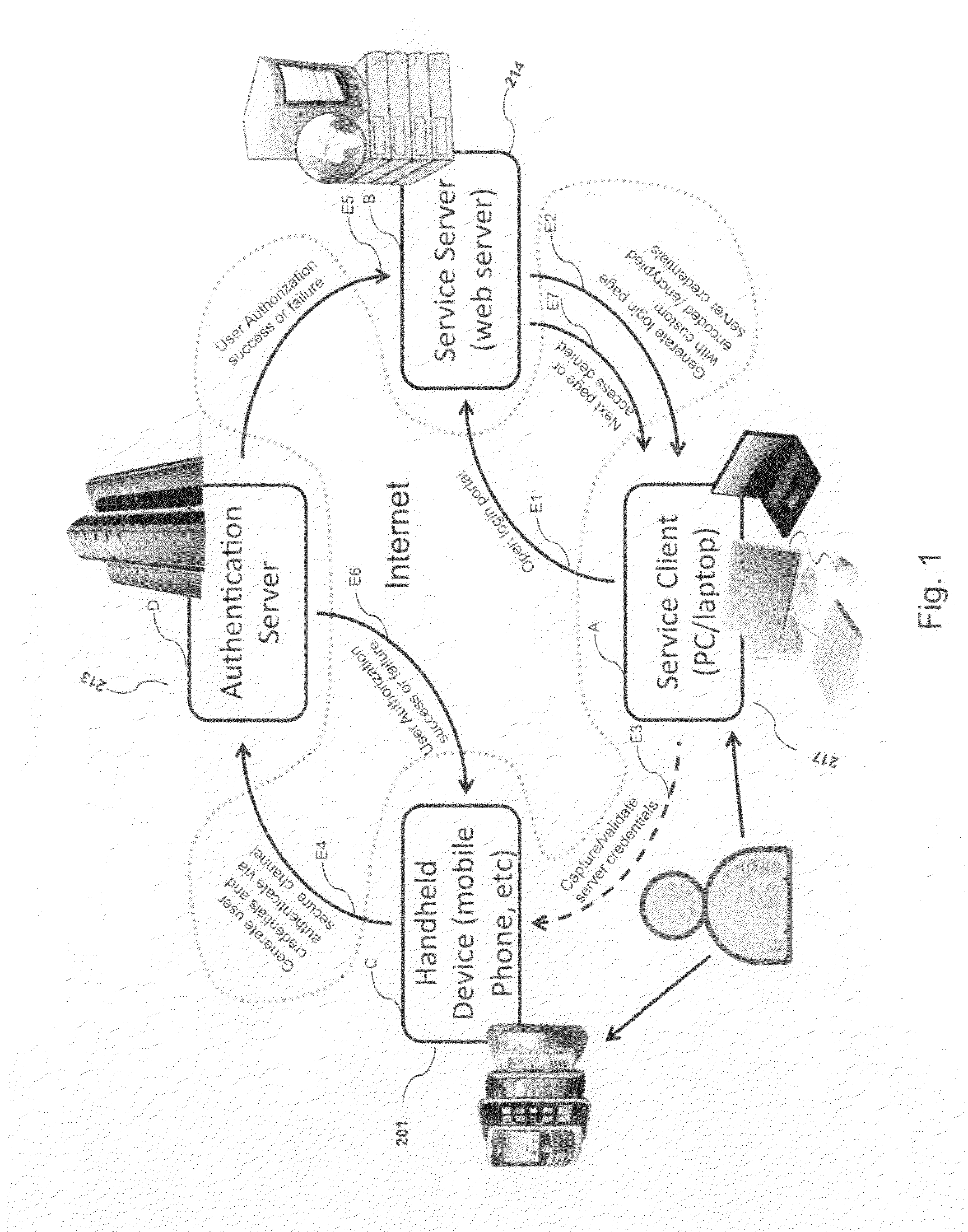
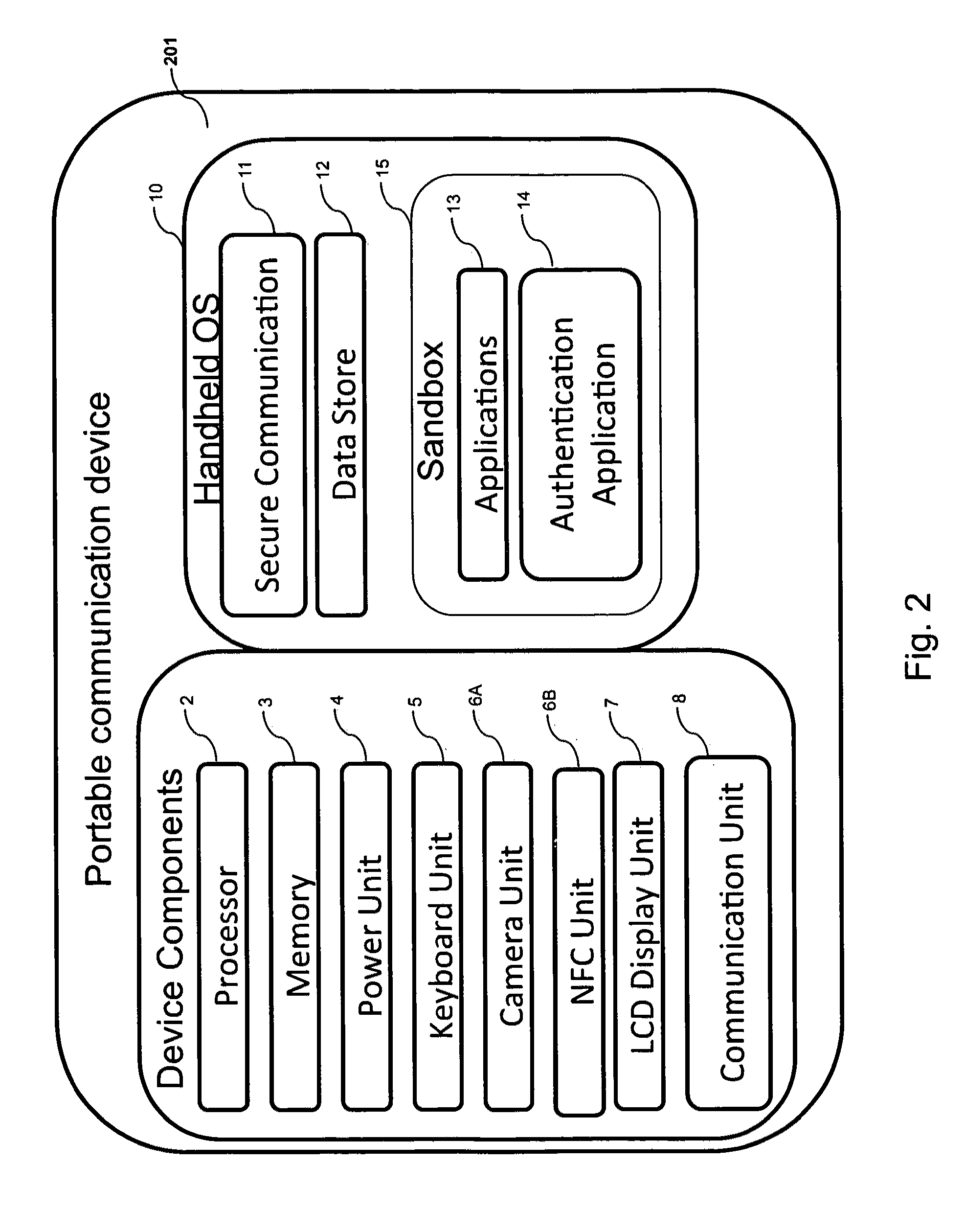
Systems and methods of authentication according to the invention are provided comprising a user, a service client, a service server, a portable communications device and an authentication server, wherein the method comprises use of one time passwords and out-of-band outbound communication channels. This system gives access to authentication seekers based on OTP out of band outbound authentication mechanism. The authentication seeker or system user scans a multi-dimensional barcode or another like encoding mechanism and validates the client and triggers the out of band outbound mechanism. The portable mobile device invokes the client server to request authentication. The client server authenticates the user based on a shared secret key and the user is automatically traversed to the next page.
Owner:GCOM IP LLC
Data Integrity and Non-Repudiation
ActiveUS20080045342A1Reduce boot timeImprove loading timeUnauthorized memory use protectionHardware monitoringComputer hardwareData integrity
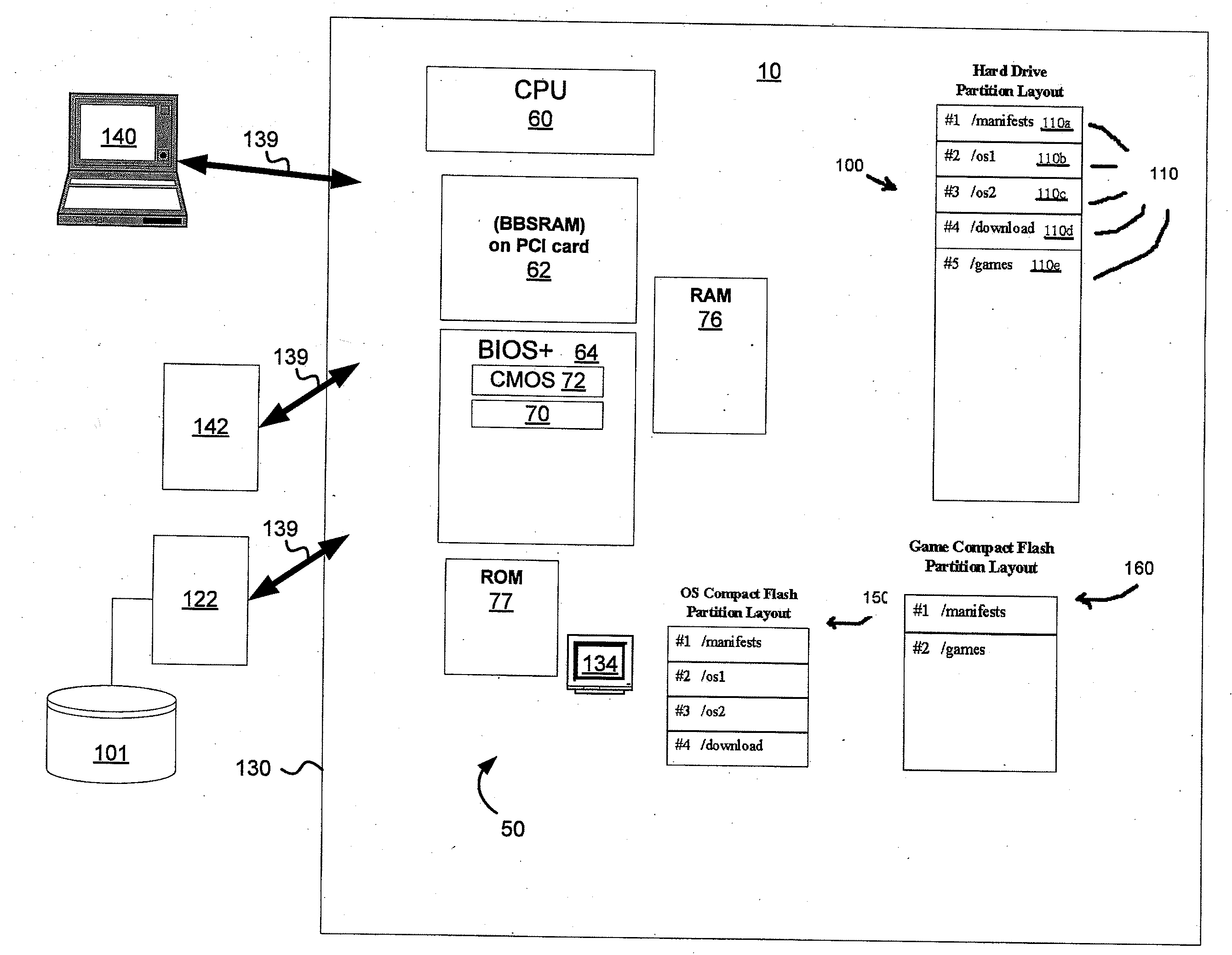
Disclosed is a system and method that uses digital signature technology to authenticate the contents of one or more manifests located on a storage device. Each manifest contains a list of file records, where each record contains the name of a file stored on the storage device, and a signature value derived from the contents of the file. At boot time, the gaming machine first authenticates the contents of the manifest and then authenticates the contents of the files using the signature value stored in the manifest. Files are verified using the signature, as they are needed, during the boot up of the operating system and throughout normal operation. This method reduces the boot time of the gaming machine and eliminates the need to check digital signatures for each individual file or over the entire contents of a non-secure media. Similarly, a method of adding authentication ability to legacy software components without necessarily altering the legacy software components is disclosed. Introduction of a stronger authentication algorithm, or when a private key has been compromised would normally require the software component to be re-built to support the new algorithm or private / public key pair; however, a method is disclosed where algorithms and key pairs may be changed and applied to legacy software without having to re-built, re-test, re-sign, or re-submit the component to regulatory agencies for approval. Also disclosed is a system and method of establishing a trusted environment containing a gaming operating system and associated authentication module, file system drivers, and / or network drivers that may be used to in the process of authenticating contents of one or more manifests located on a storage device.
Owner:LNW GAMING INC
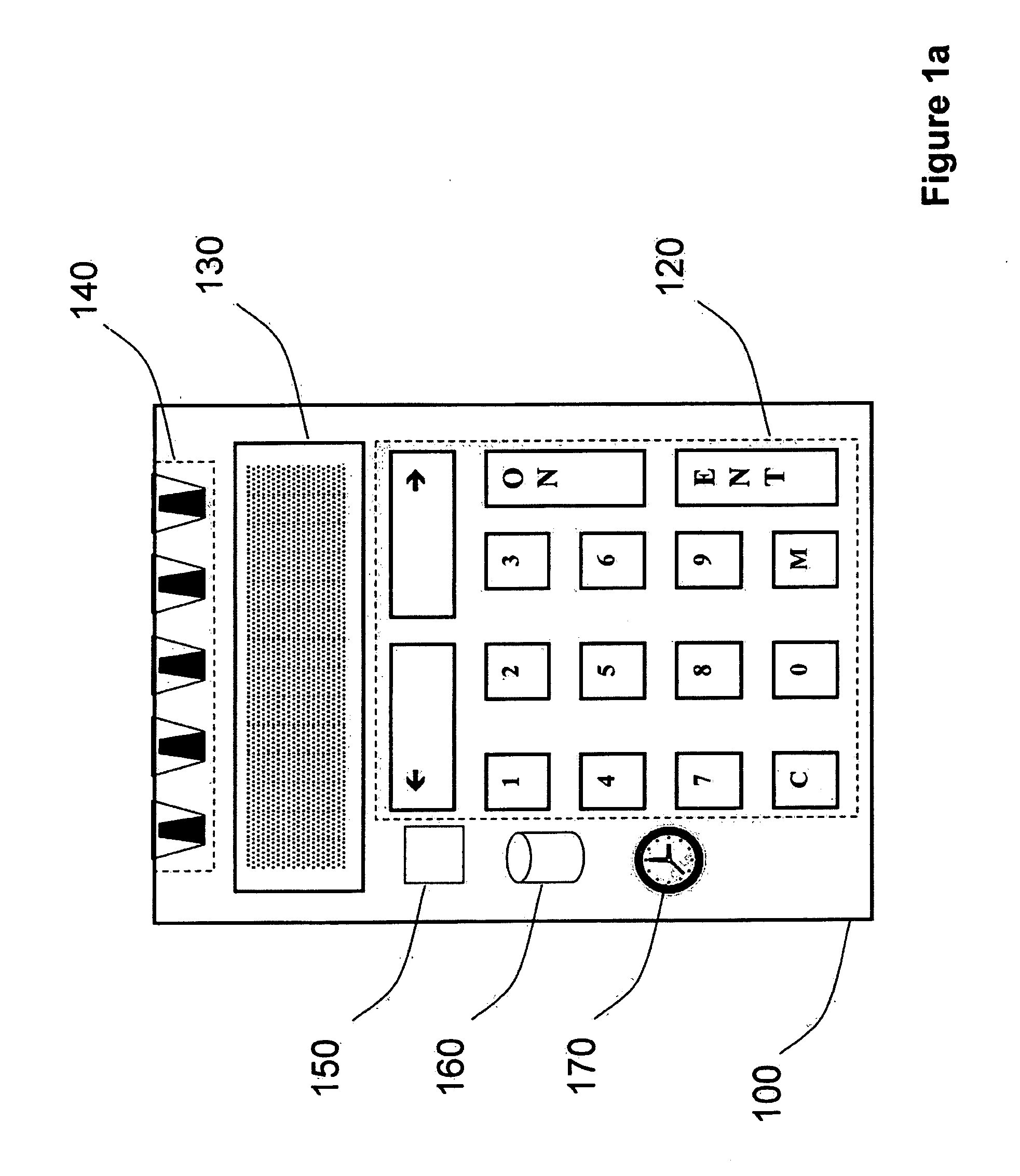
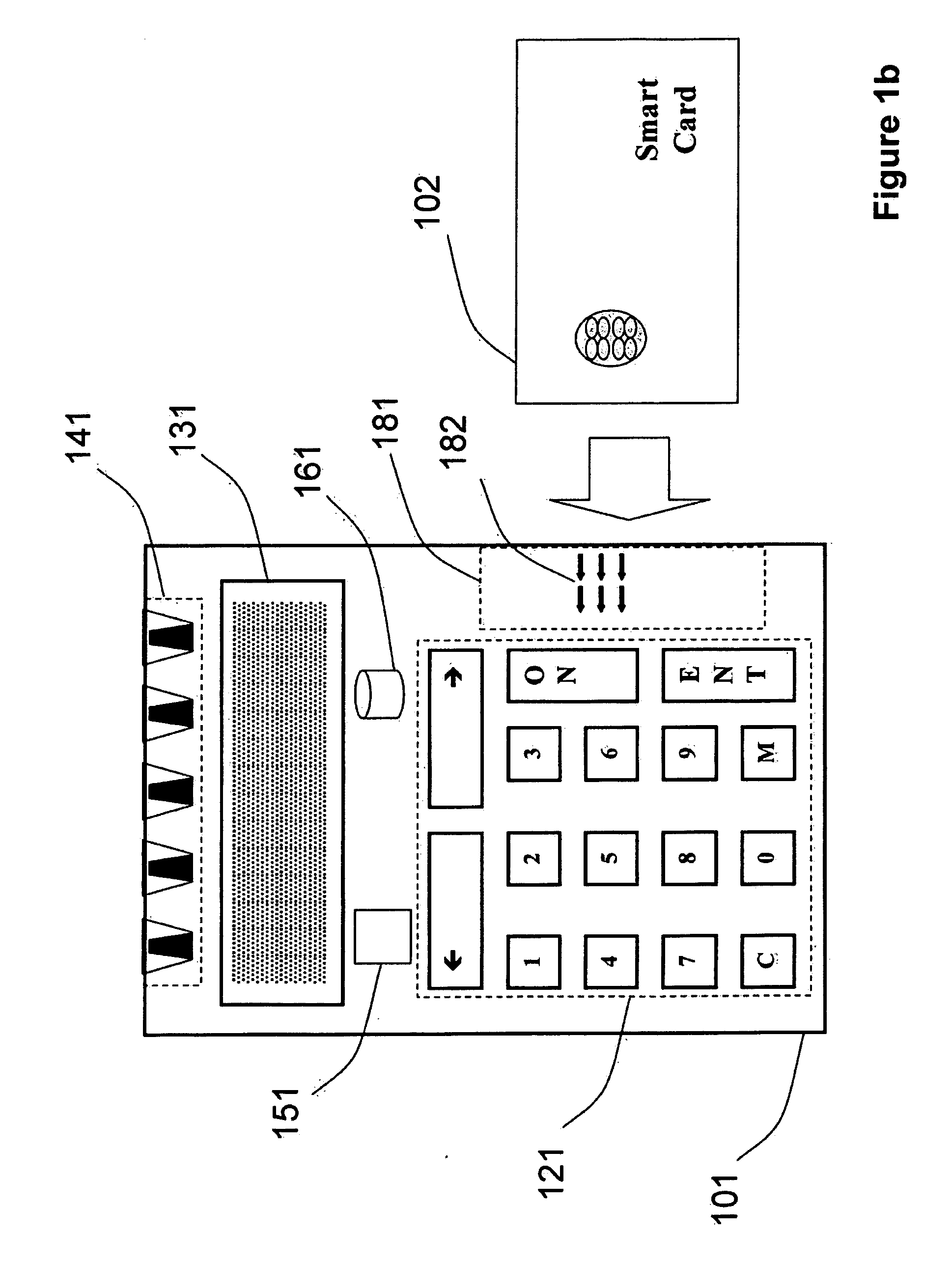
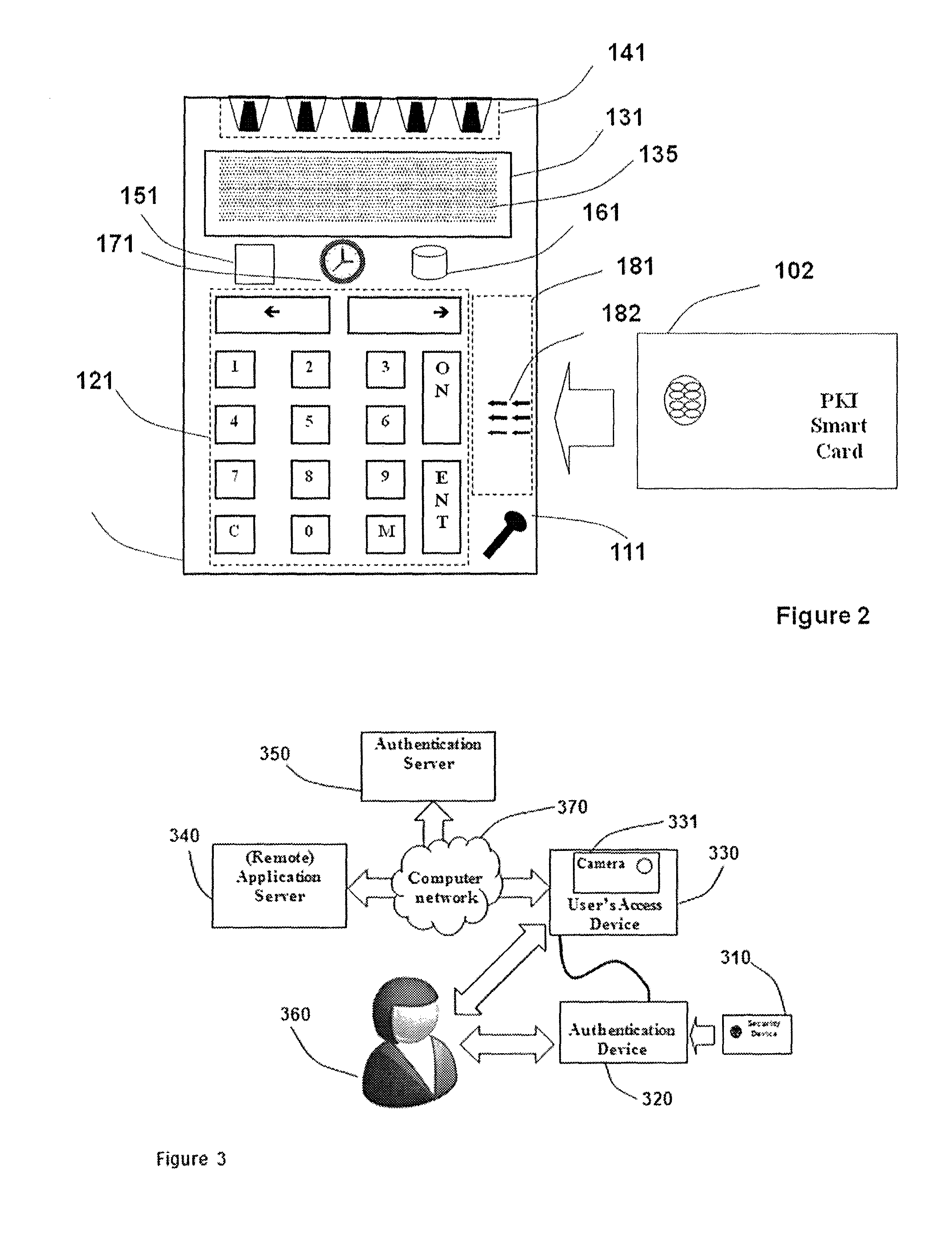
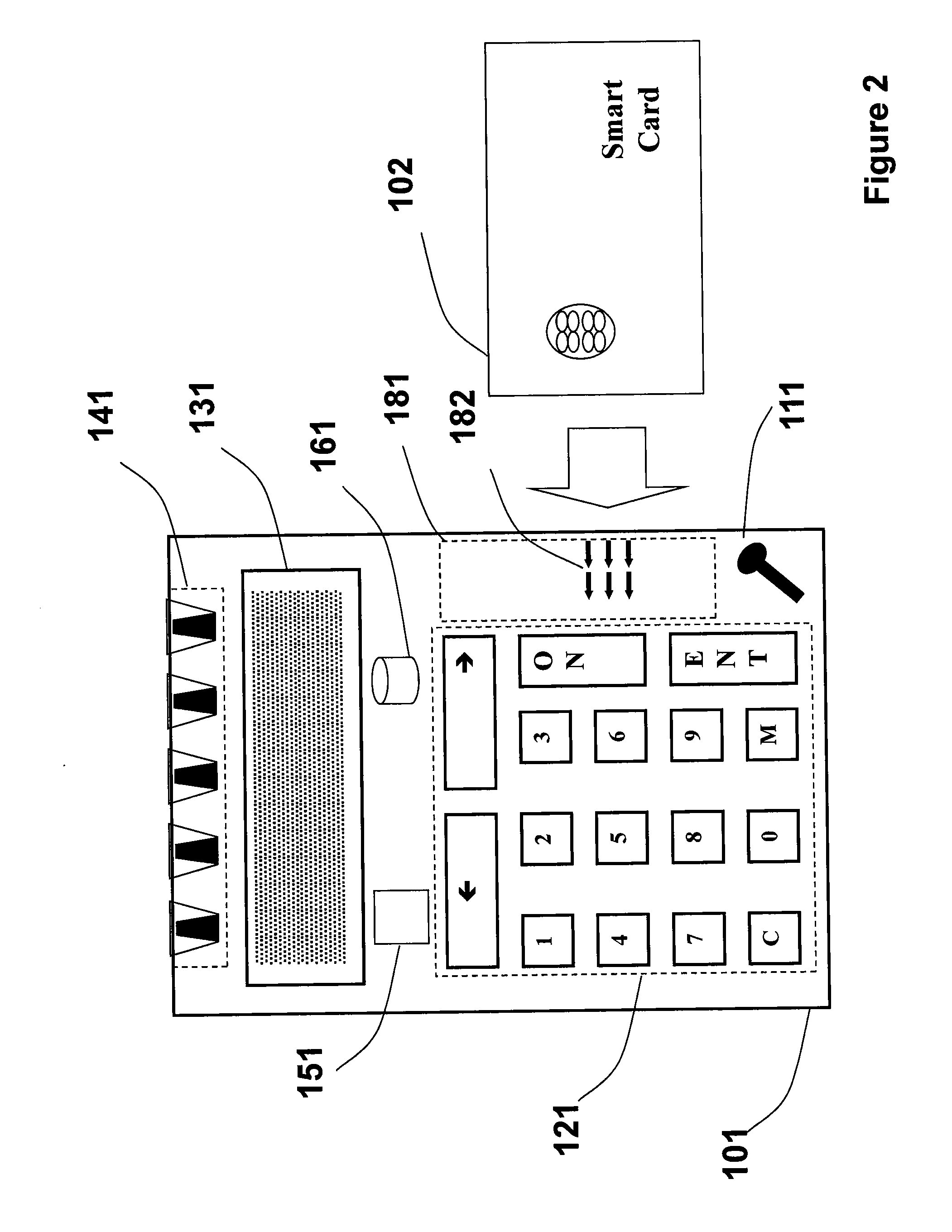
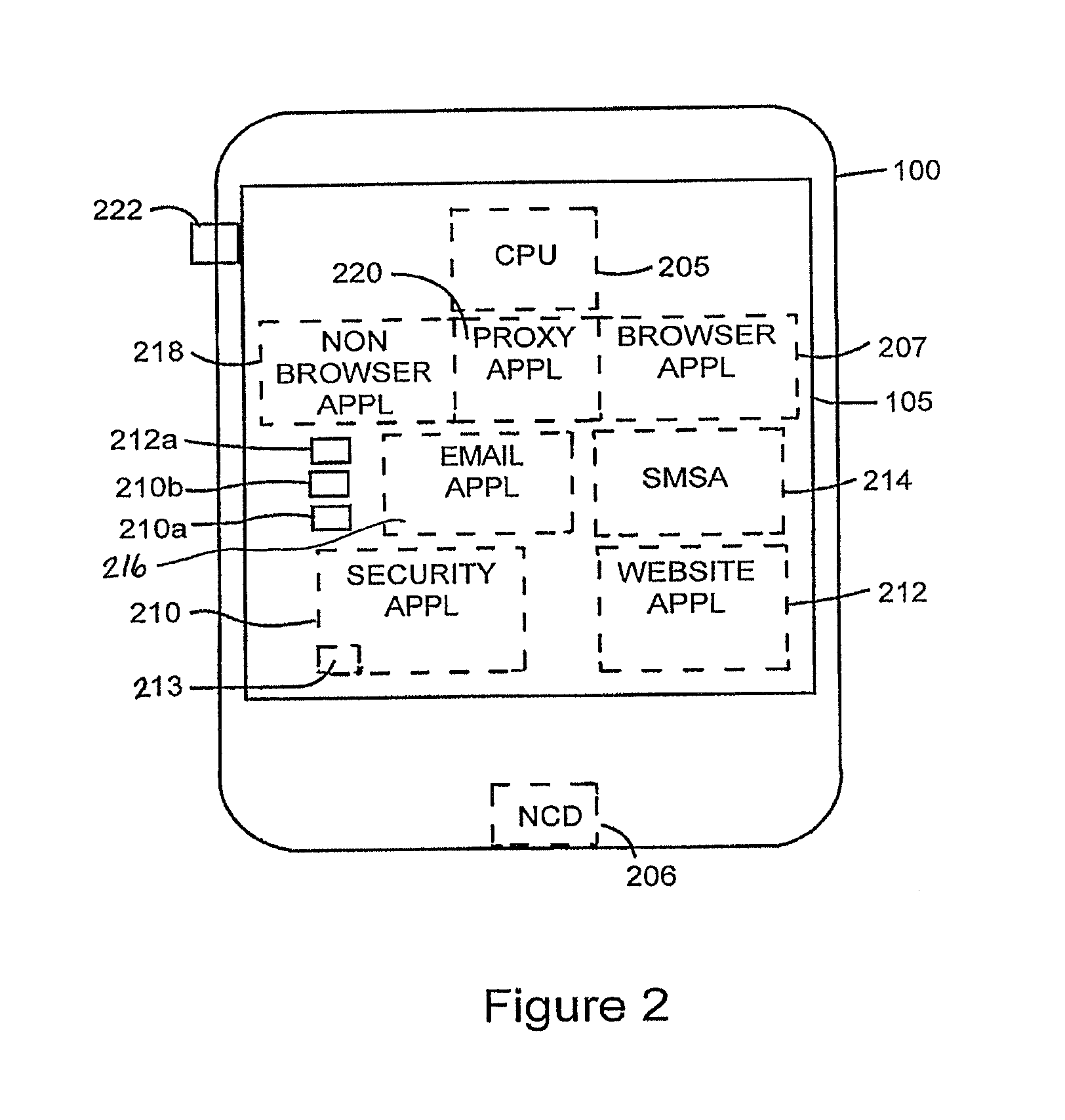
Strong authentication token with visual output of pki signatures
InactiveUS20130198519A1Improve securityUser identity/authority verificationDigital data authenticationDisplay deviceSecret code
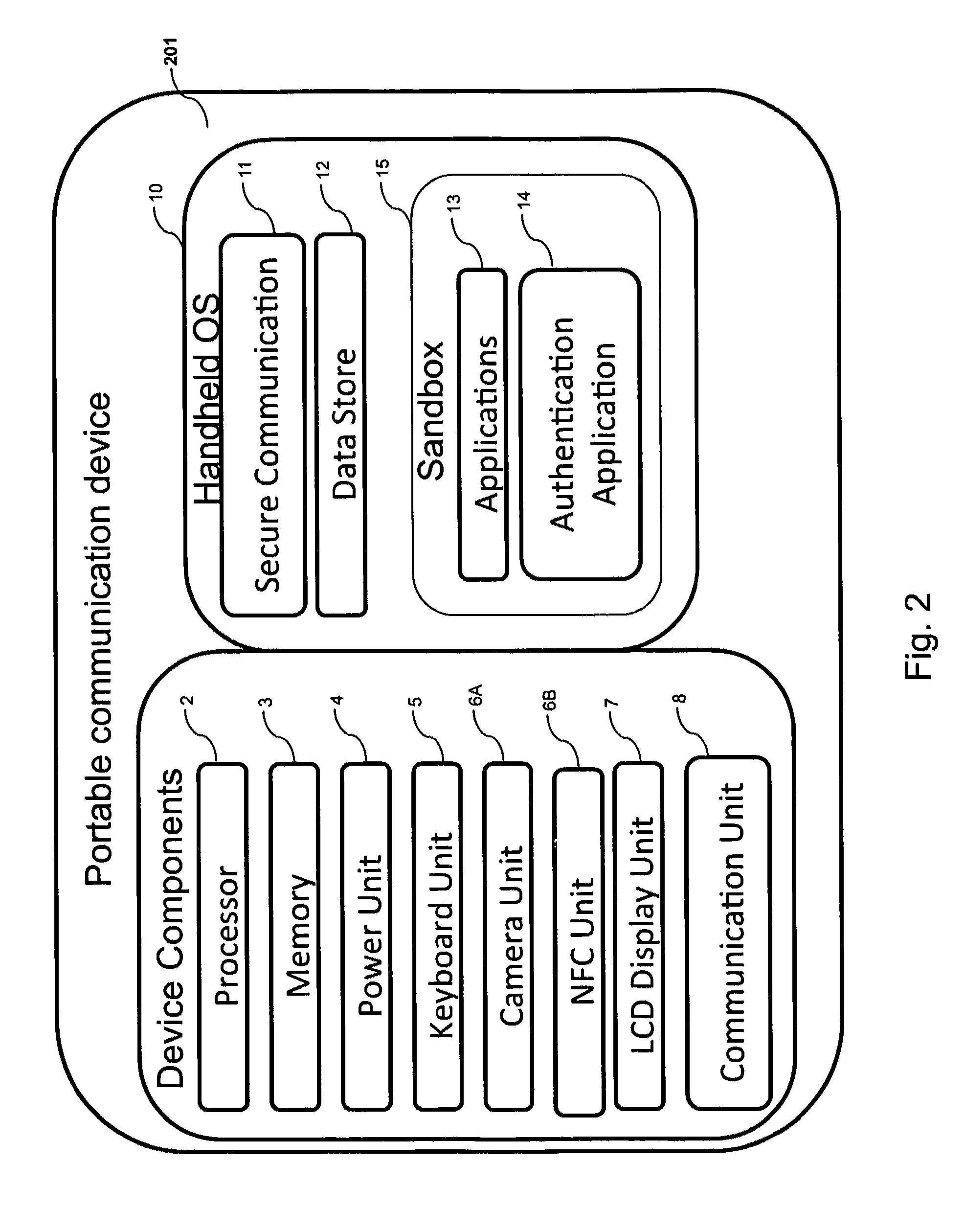
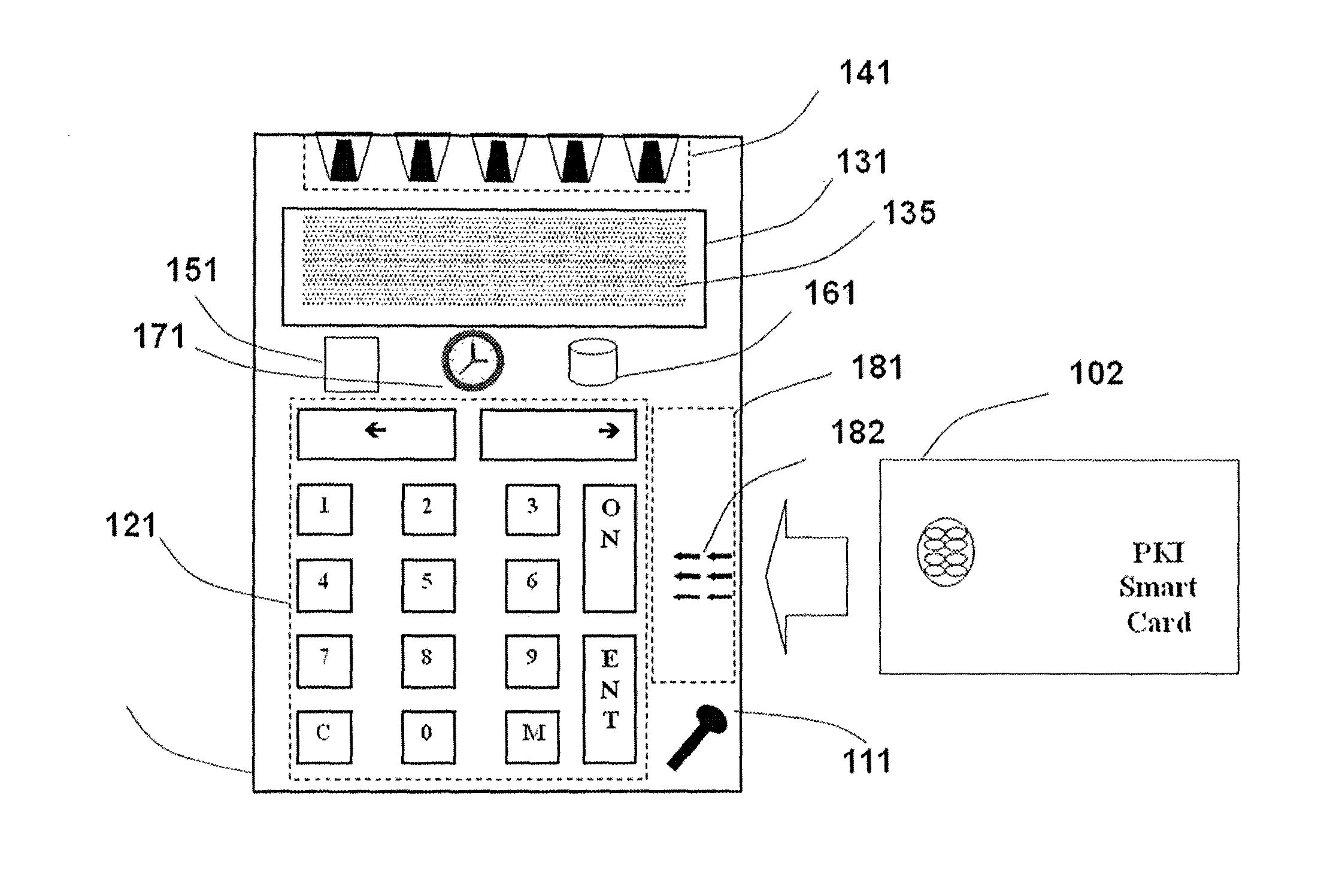
A handheld authentication device comprising a data processor and a display is adapted to: generate an input value; submit the input value to an asymmetric cryptographic operation; obtain the result of said asymmetric cryptographic operation; generate an authentication message substantially comprising the result of the asymmetric cryptographic operation; encode the authentication message into one or more images; and display these images on the display. A method for securing computer-based applications remotely accessed by a user comprises capturing images displayed on the display of an authentication device of the user whereby these images have been encoded with an authentication message generated by the authentication device and whereby the authentication message comprises the result of an asymmetric cryptographic operation on an input value; decoding the images to retrieve the authentication message; retrieving the result of the asymmetric cryptographic operation from the authentication message; verifying the authentication message.
Owner:ONESPAN NORTH AMERICA INC
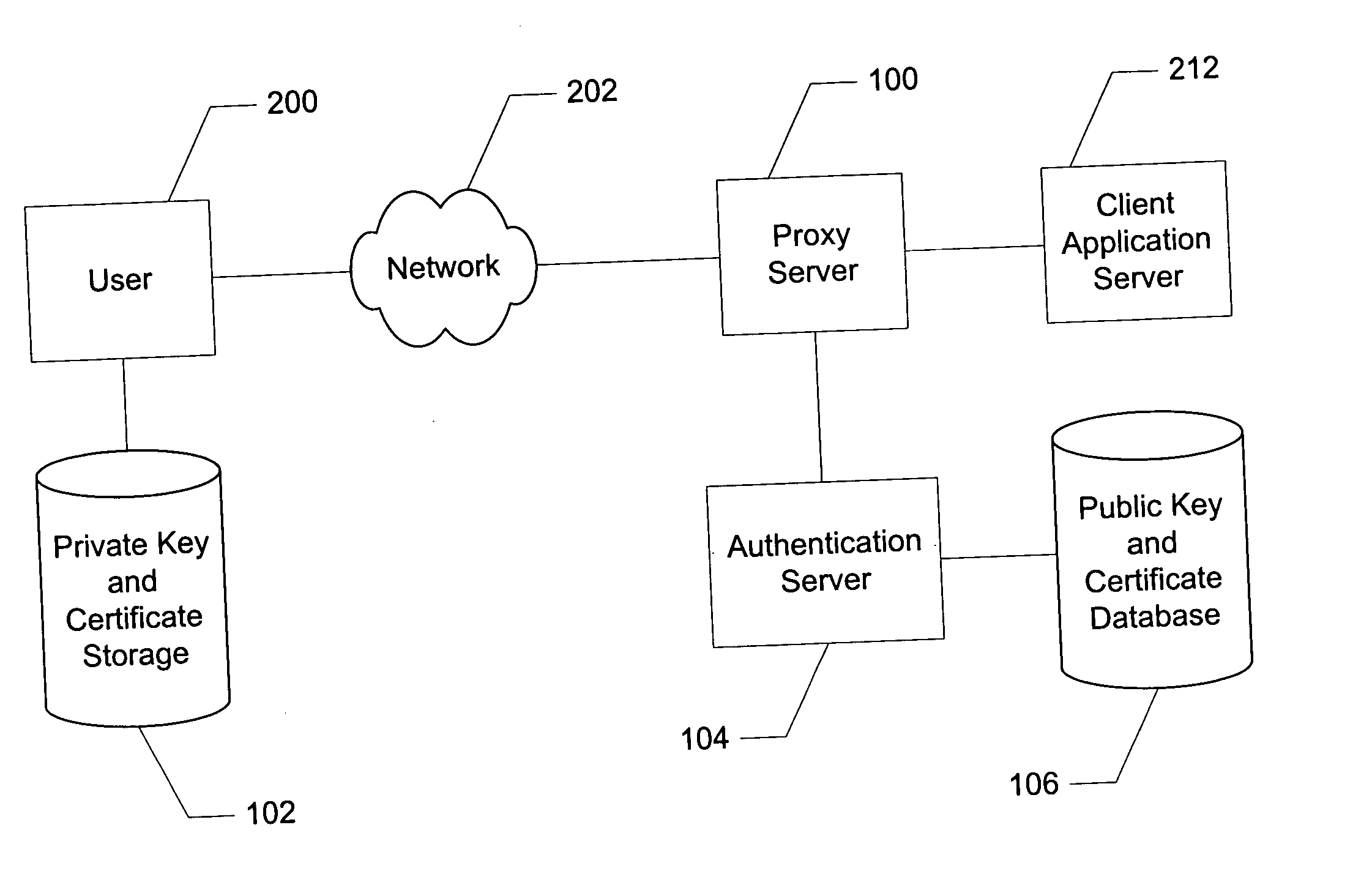
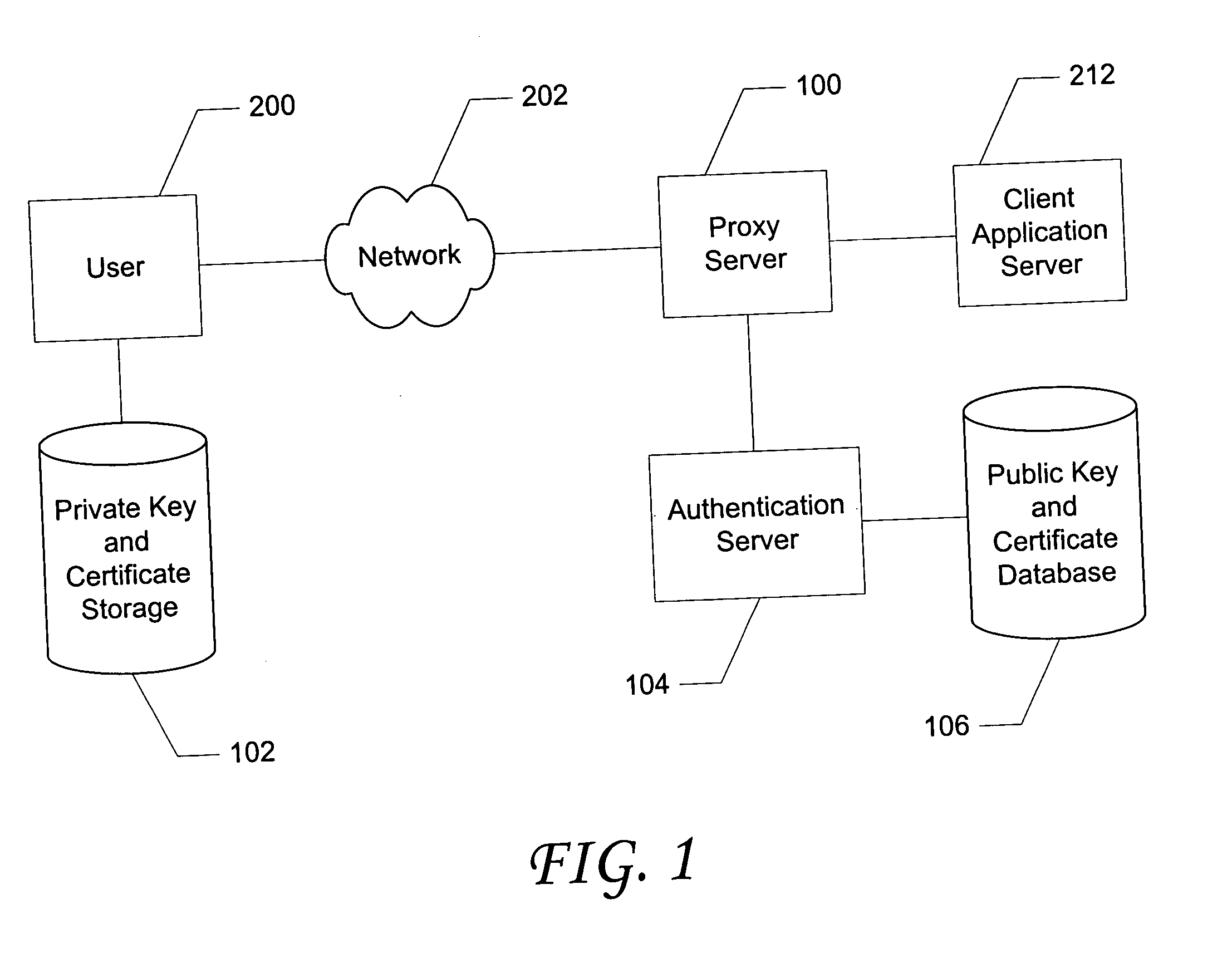
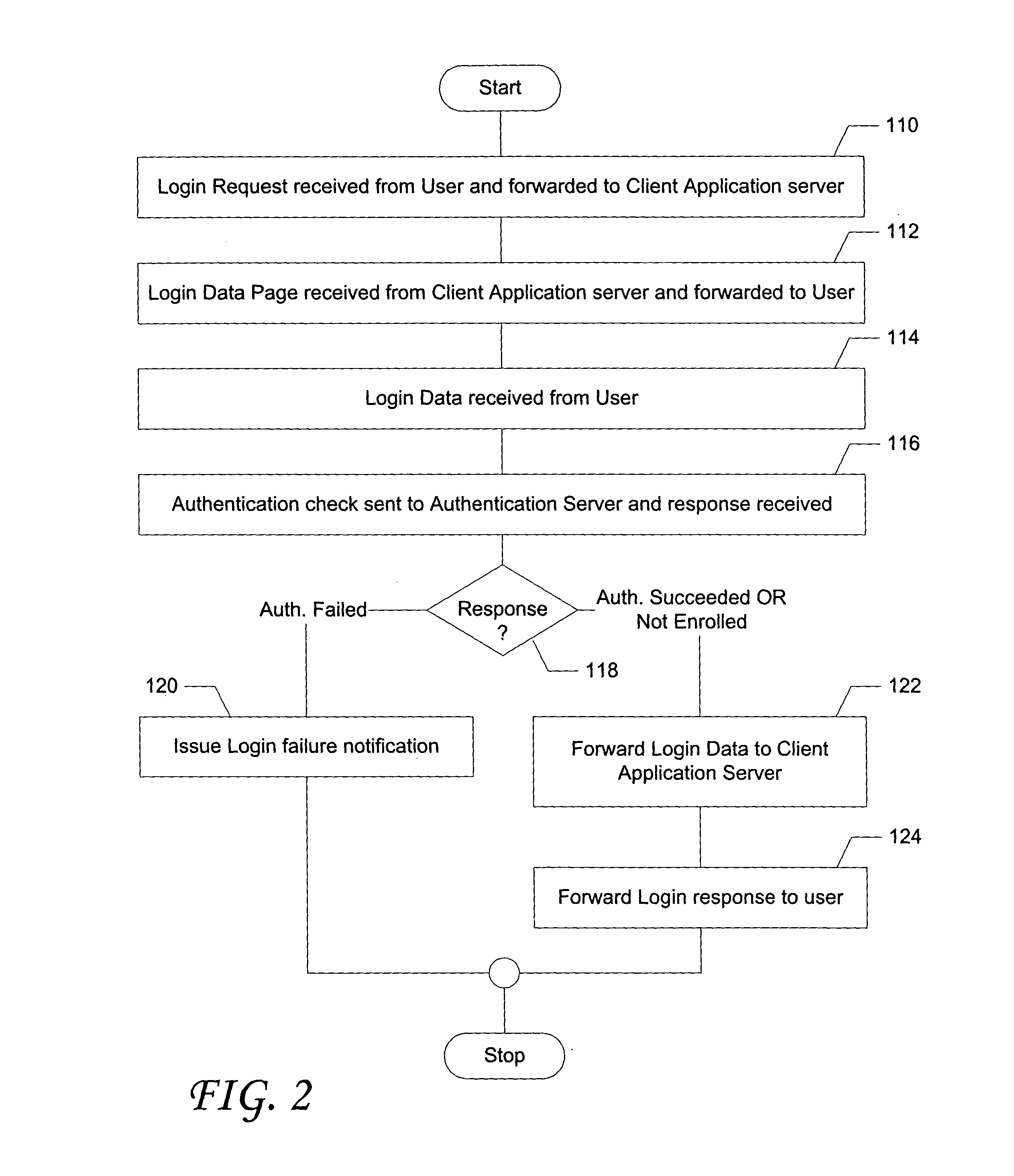
Proxy based adaptive two factor authentication having automated enrollment
InactiveUS20050021975A1Transparent authenticationImprove simplicityDigital data authenticationSecret communicationClient-sideStrong authentication
A method of and system for adding strong authentication to an existing network based application. A proxy based monitoring process screens data sent to and from a client application and intercepts login requests. These intercepted requests are redirected to an authentication process which first checks to see if the user logging in has enrolled in strong authentication. If not enrolled, the user is allowed to continue with a normal login. If enrolled, the user is authenticated by requesting digital identification data, such as a digital certificate, from the user's computer. If authentication succeeds, the user is allowed to proceed on to the normal login process. If authentication fails, the login attempt is blocked. User enrollment is automated, requiring no user interaction beyond the initial request. Verification for purposes of issuing a digital certificate, or other identifying data, is by means of confirming that the user being enrolled is currently logged in to the client application.
Owner:LIU GOUPING
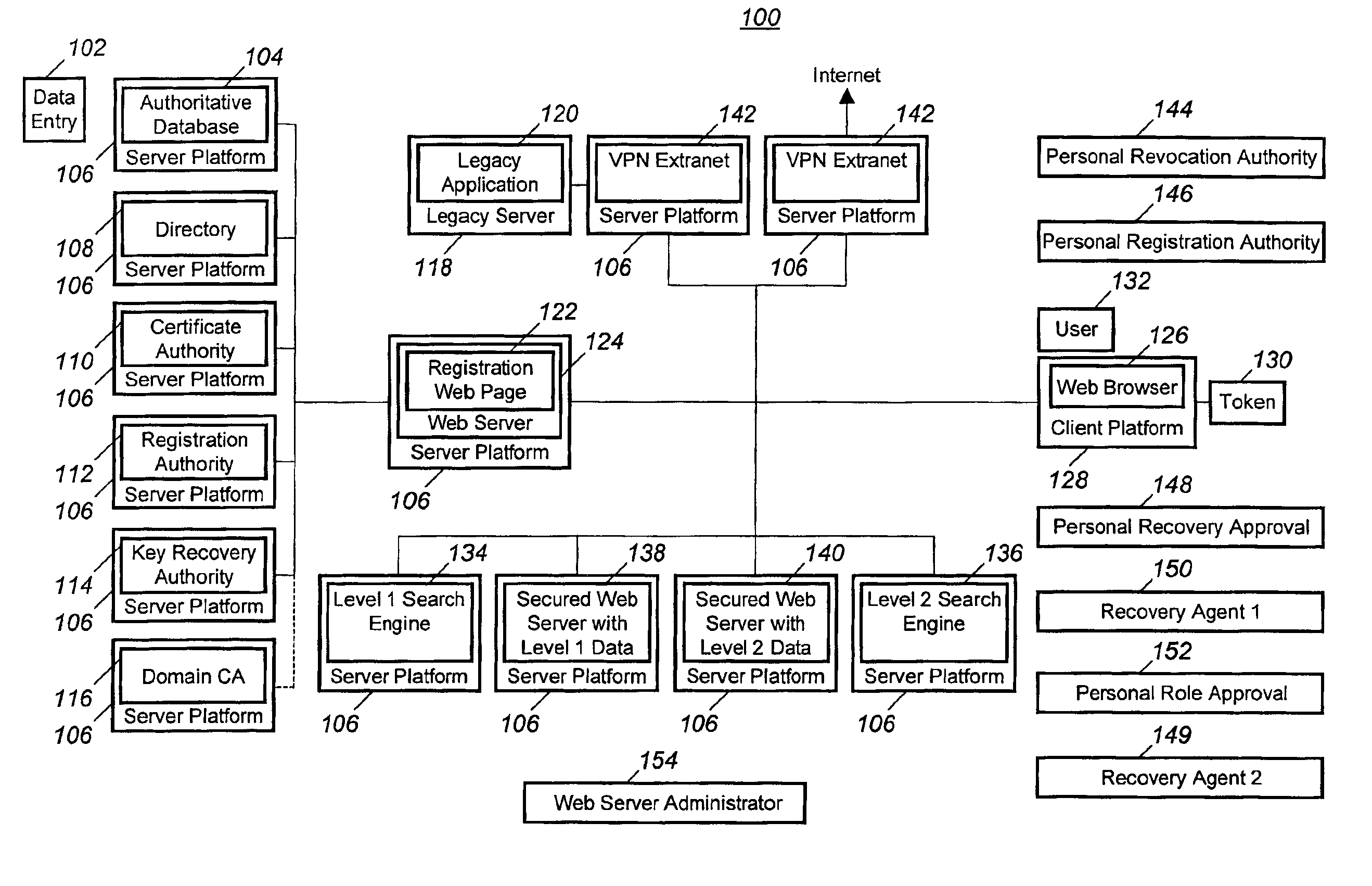
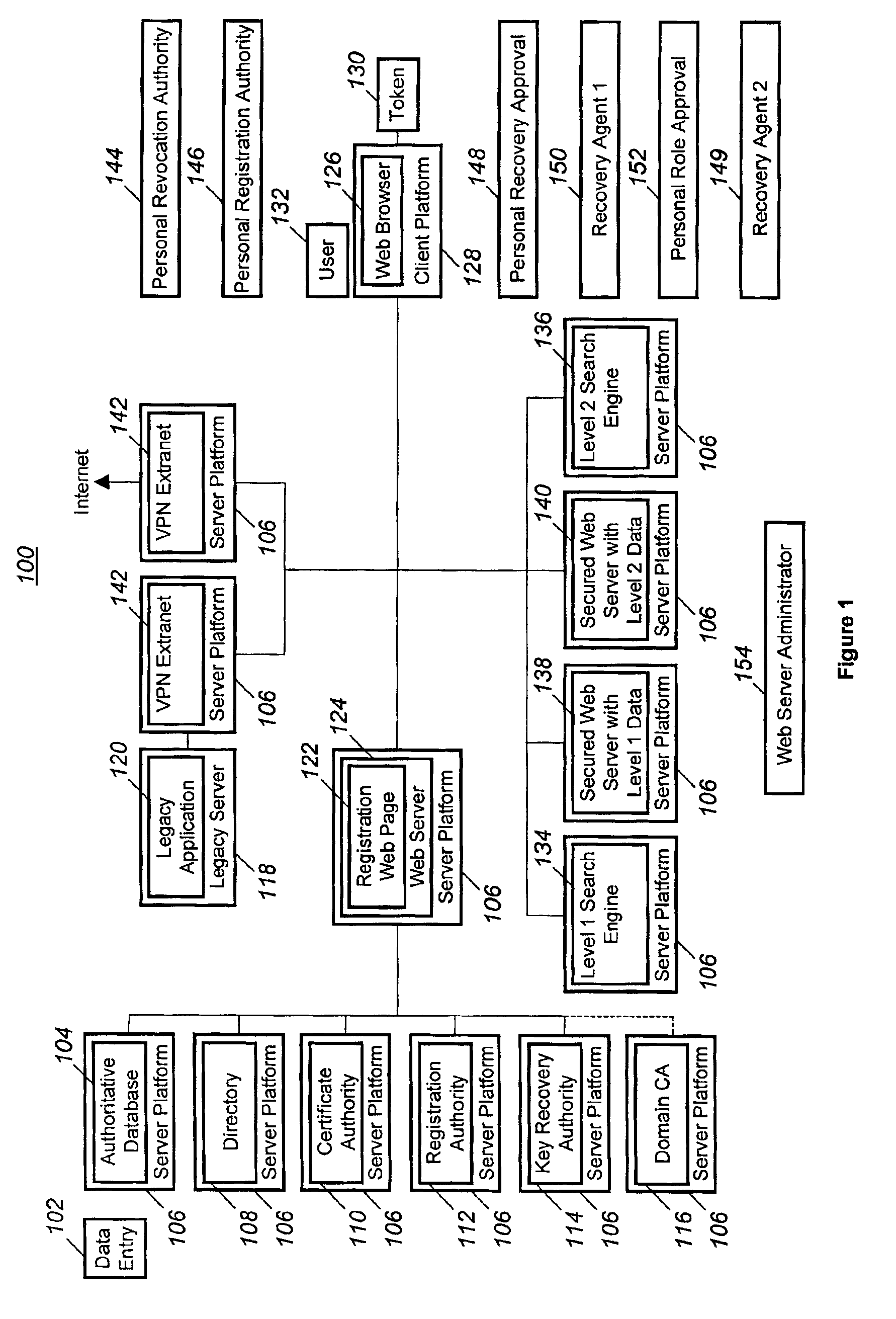
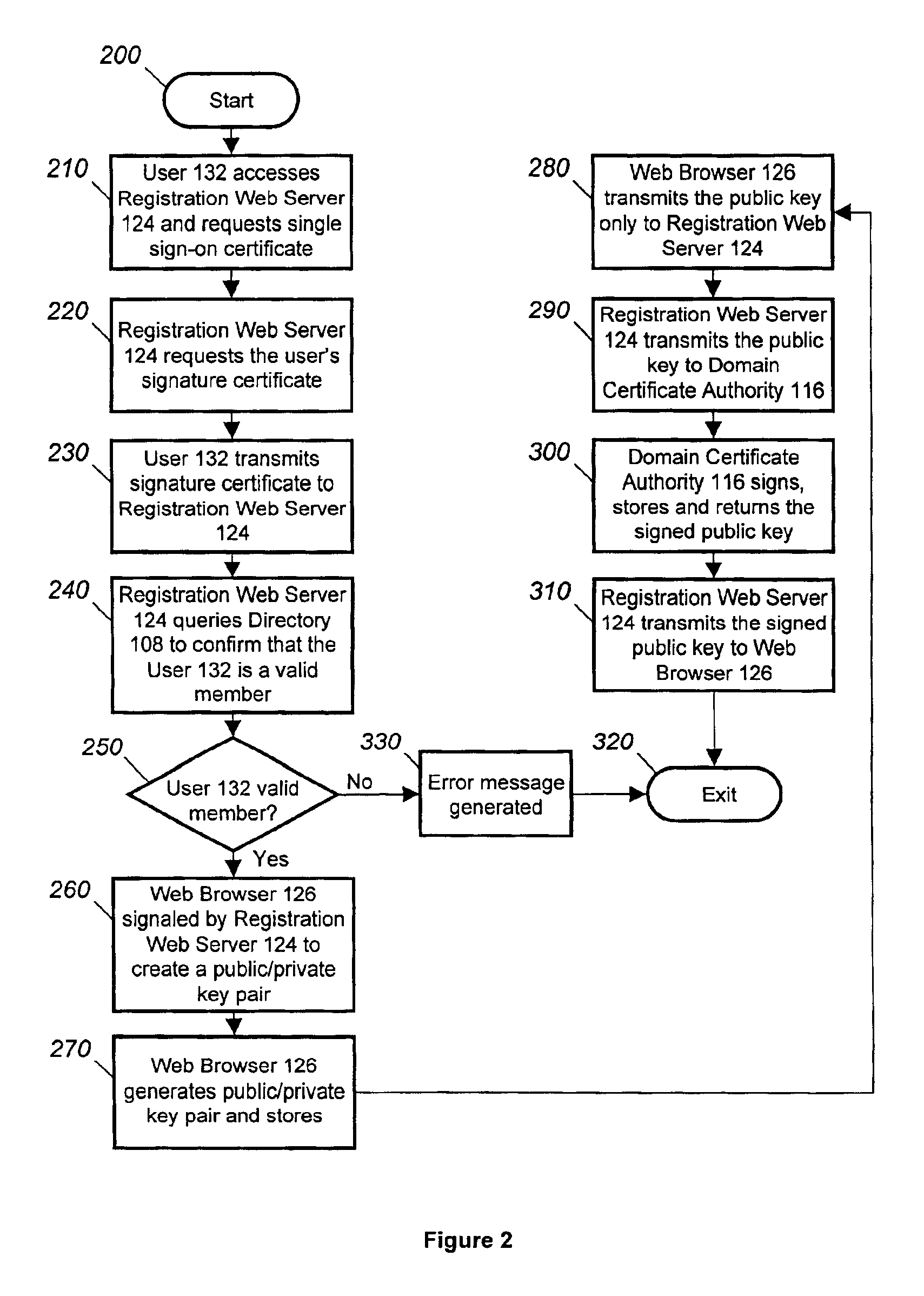
Technique for obtaining a single sign-on certificate from a foreign PKI system using an existing strong authentication PKI system
InactiveUS7069440B2Key distribution for secure communicationData processing applicationsNetwork generationStrong authentication
A method and computer program in which a user (132) may have a digital certificate created using a strong authentication technique. Once the user has the digital certificate he may then request the generation of a “single sign-on” certificate that will allow the user (132) access to a foreign computer networks. This is accomplished by the user (132) contacting a registration web server (124) and requesting the generation of “single sign-on” for the foreign computer network. Thereafter, the registration web server (124) may take a public key generated based on the digital certificate and request the creation of a “single sign-on” by simply creating a public key from the digital certificate.
Owner:NORTHROP GRUMMAN SYST CORP
Authentication methods and apparatus for vehicle rentals and other applications
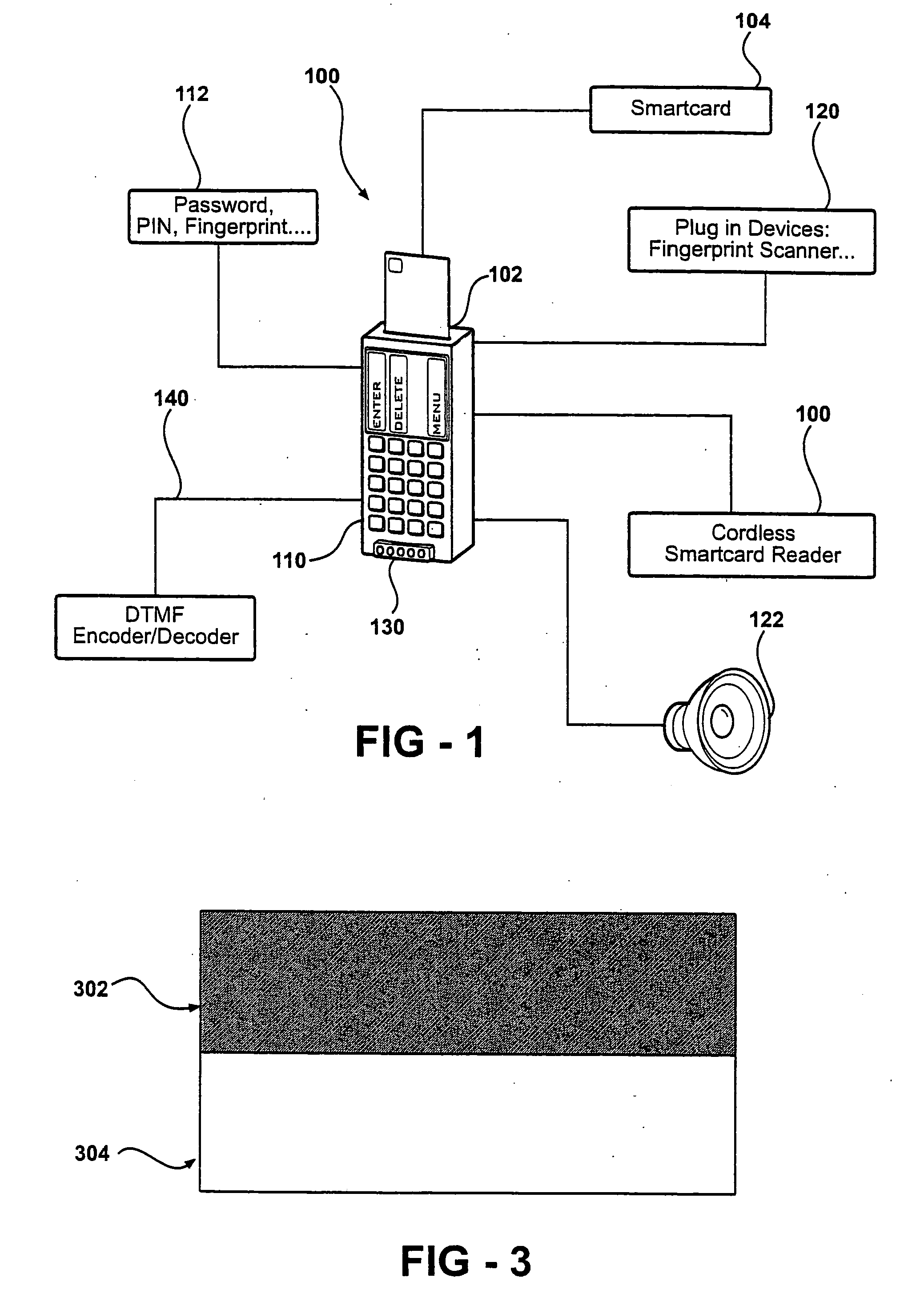
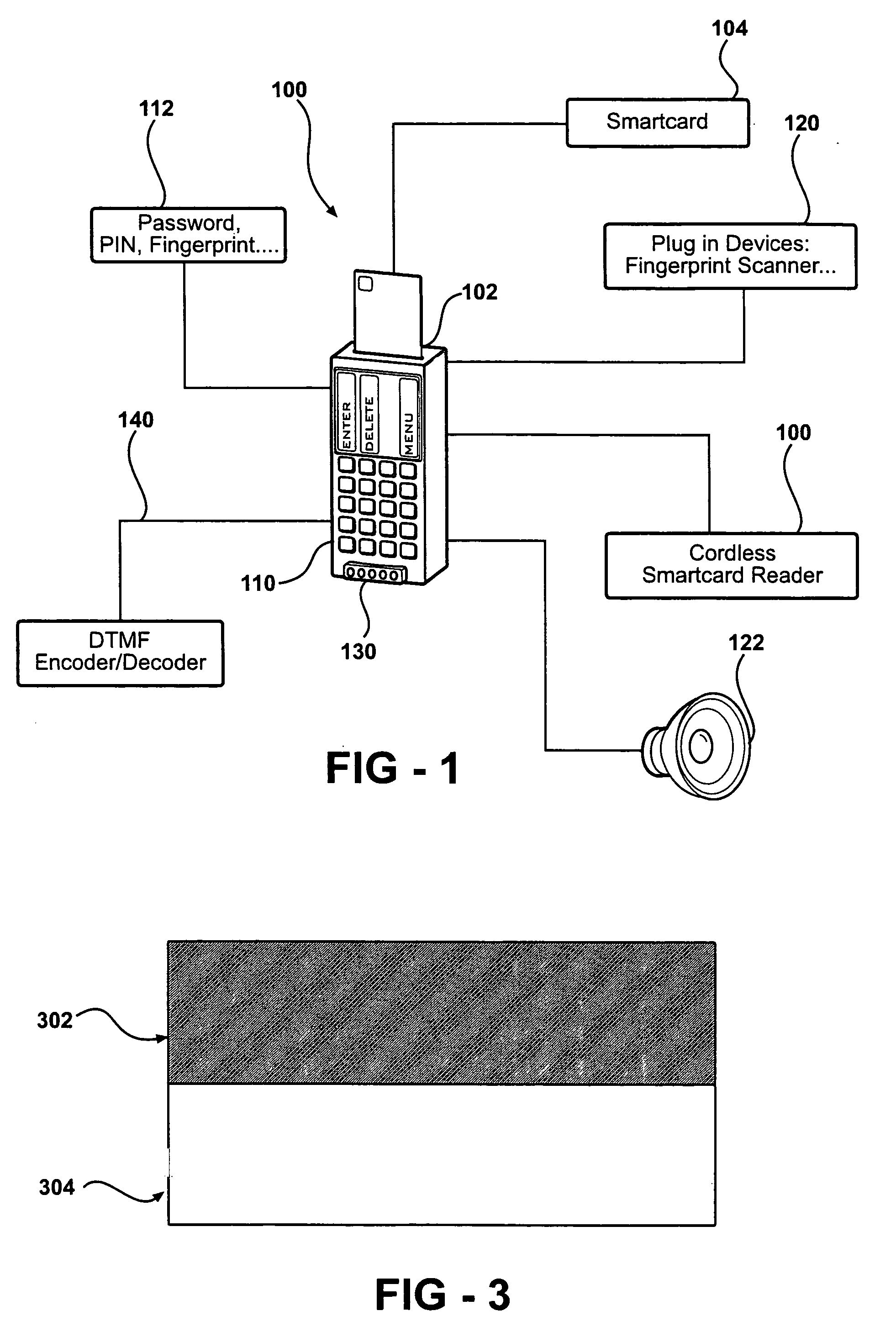
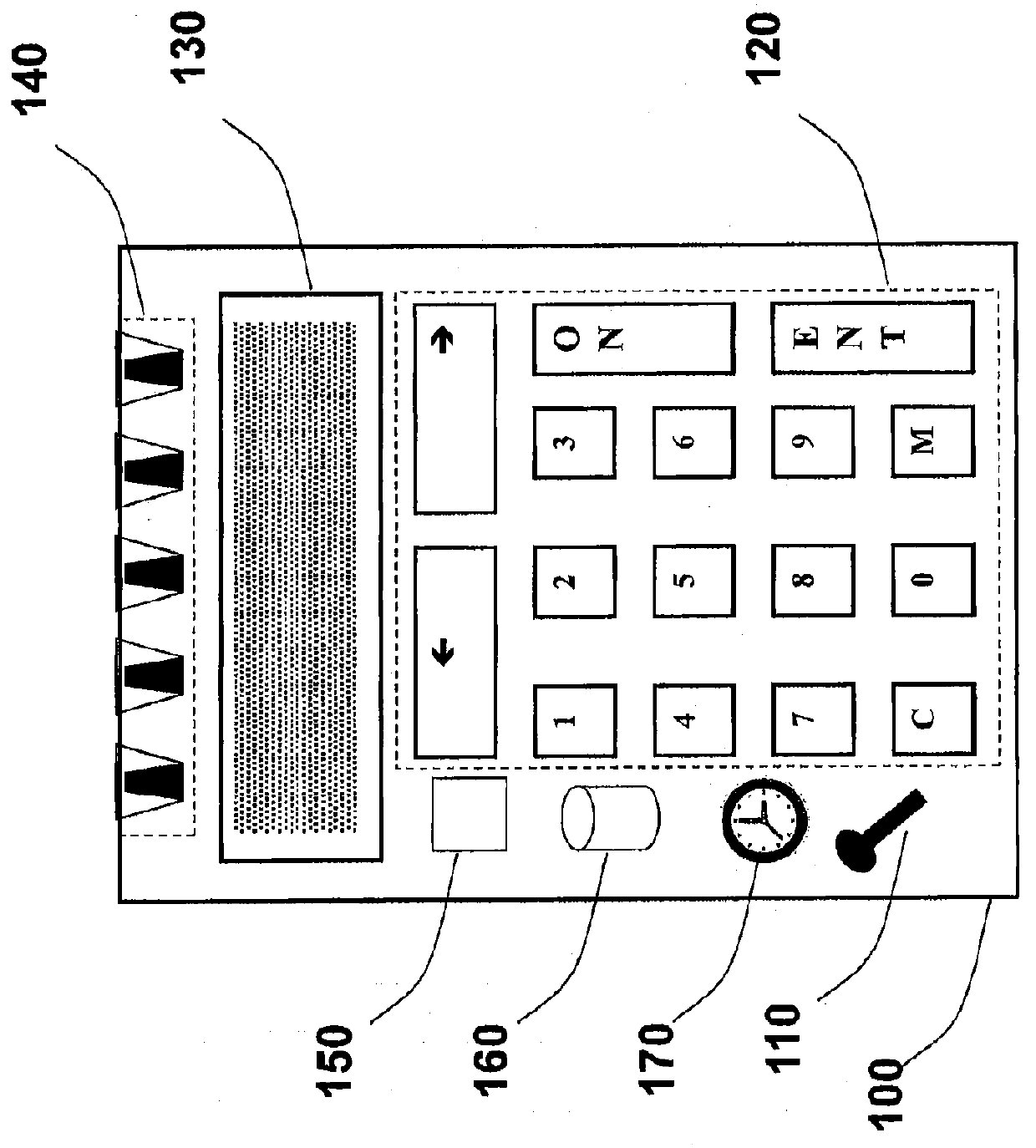
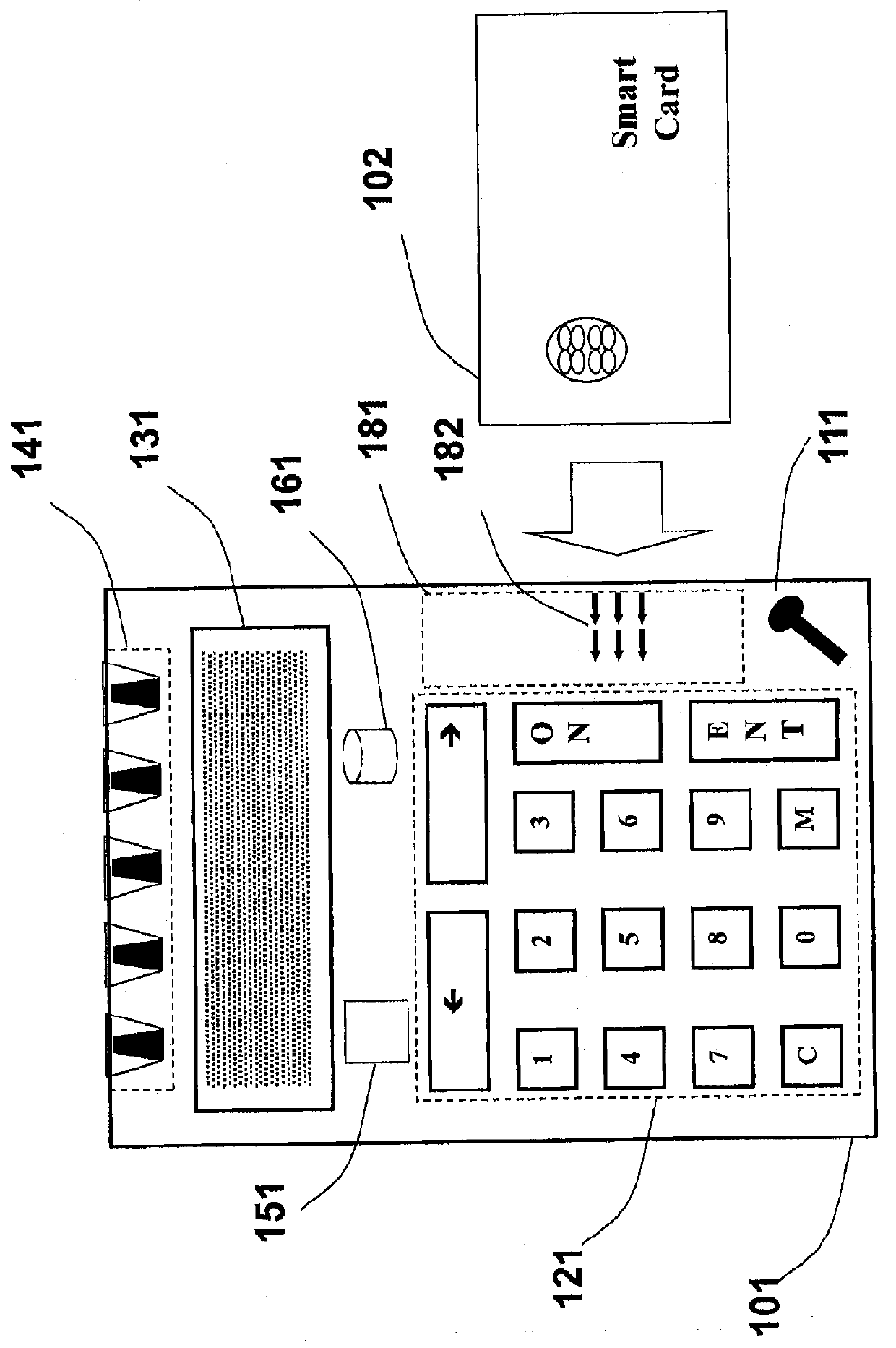
InactiveUS20050001028A1Strong authenticationTicket-issuing apparatusPayment architectureEmbedded securitySmart card
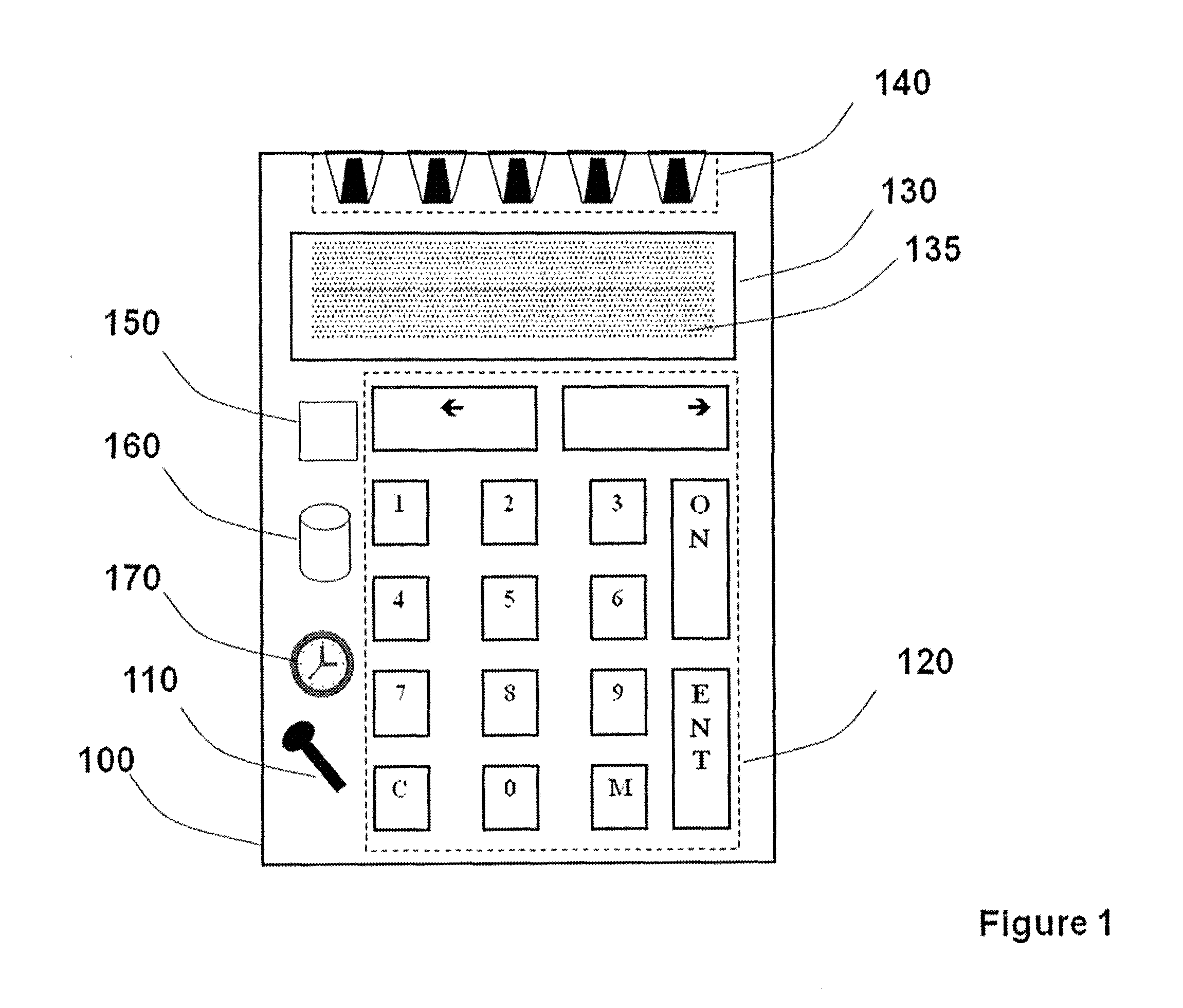
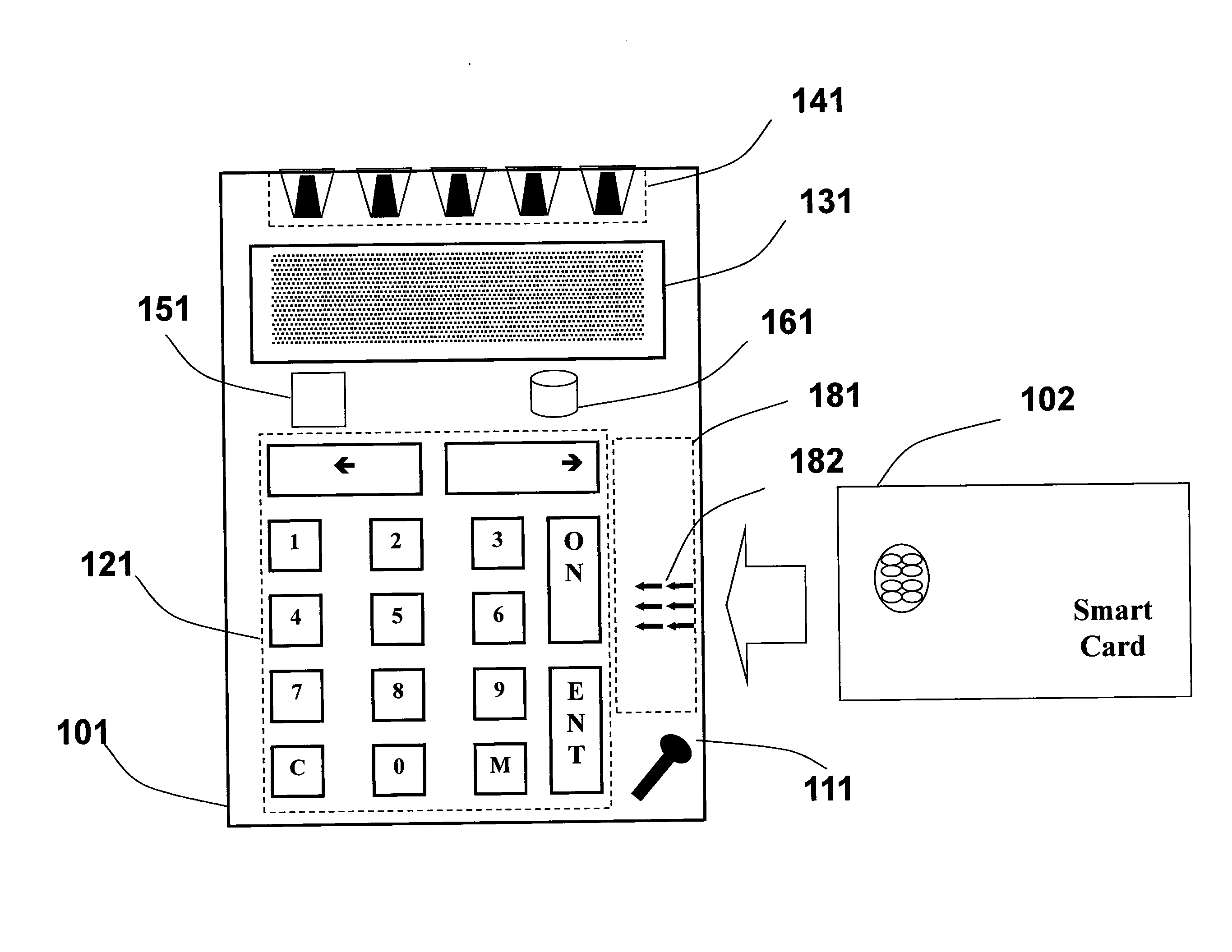
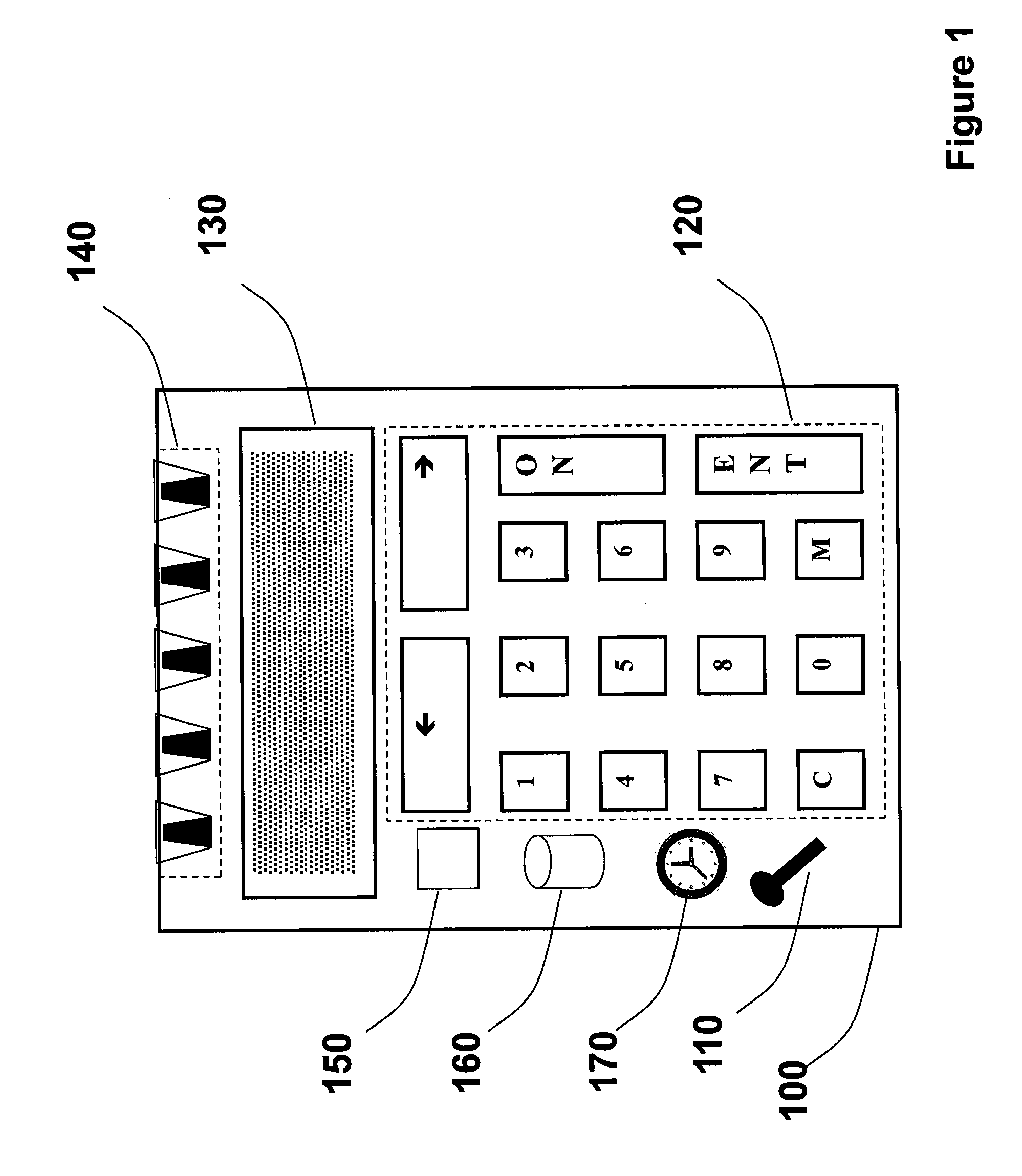
An autonomous and portable smartcard reader device incorporates a high level of embedded security countermeasures. Data transfers are encrypted with two specific input devices, namely a light sensor and PIN or other keyboard entry, and at the output through the use of a dual-tone encoder-decoder. The unit may be used alone or as a plug-in to another device such as a PDA, cell phone, or remote control. The reader may further be coupled to various biometric or plug-in devices to achieve at least five levels of authentication, namely, (1) the smartcard itself; (2) the smartcard reader; (2) the PIN; (3) private-key cryptography (PKI); and (5) the (optional) biometric device. These five levels account for an extremely strong authentication applicable to public networking on public / private computers, and even on TV (satellite, cable, DVD, CD AUDIO, software applications. Transactions including payments may be carried out without any risk of communication tampering, authentication misconduct or identity theft. The invention finds utility in a wide range of applications, including commercial transactions and security, including the generation of prepaid credit / debit card numbers, vehicle rental, and other uses.
Owner:BRITE SMART
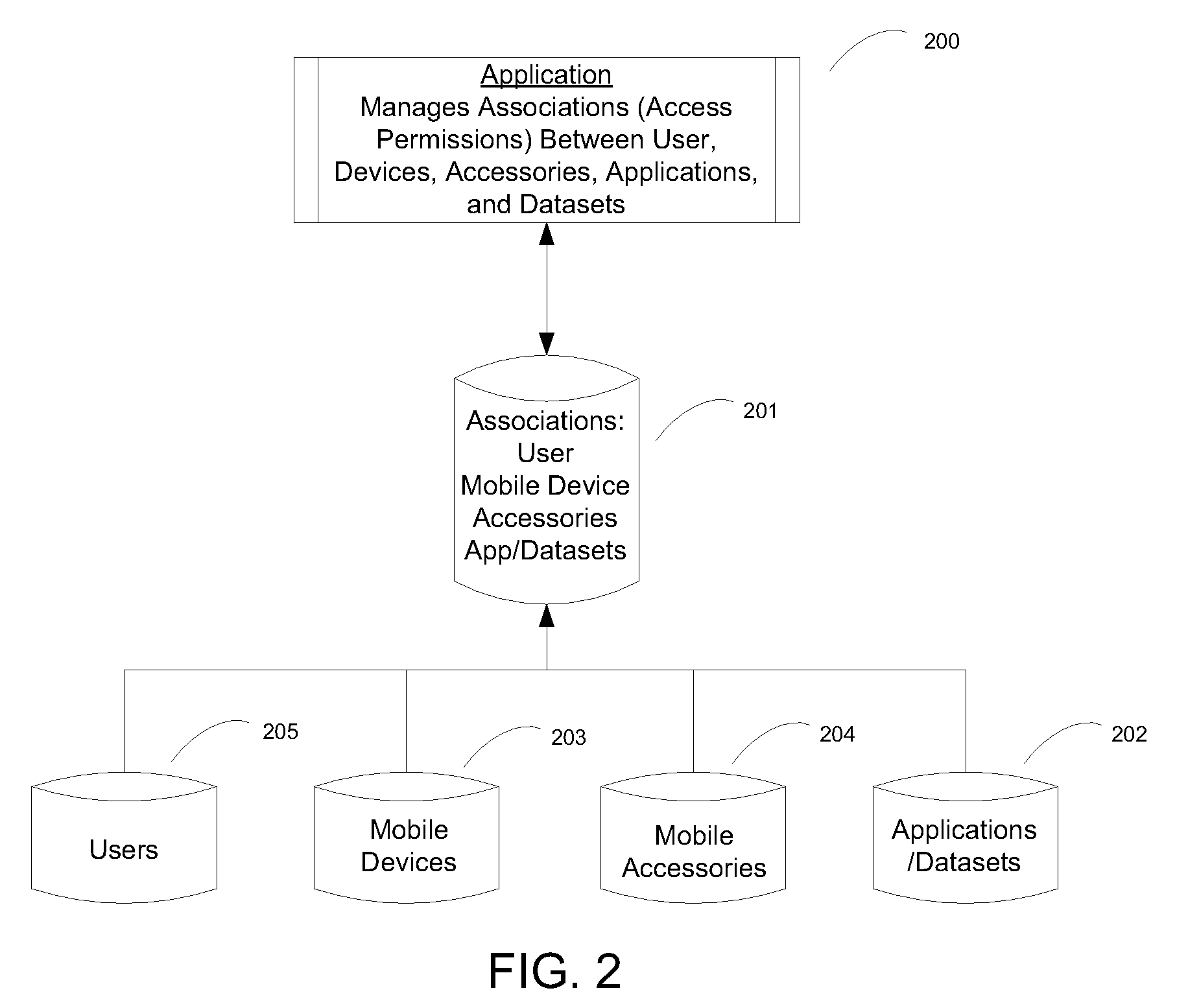
System and method for securely accessing mobile data
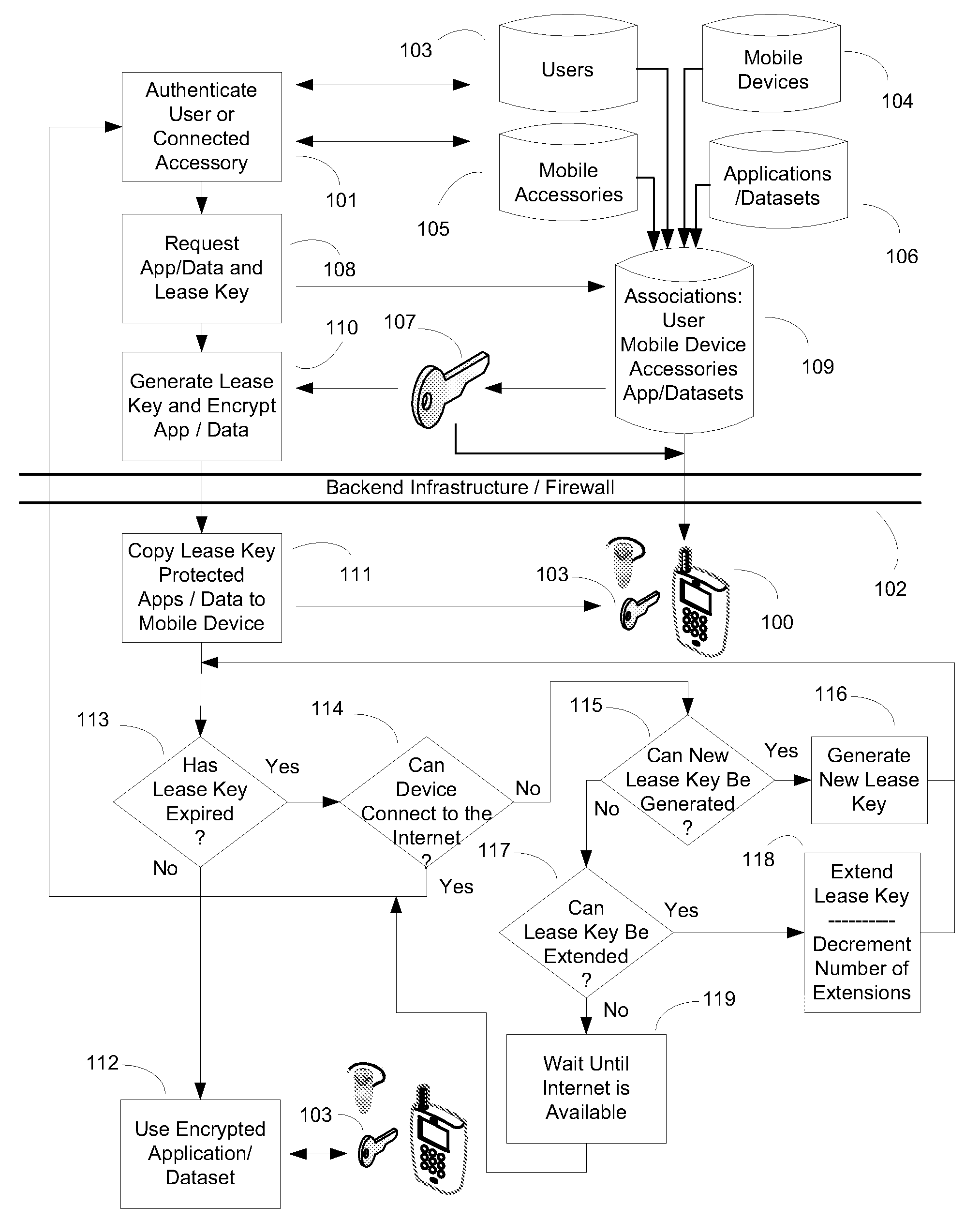
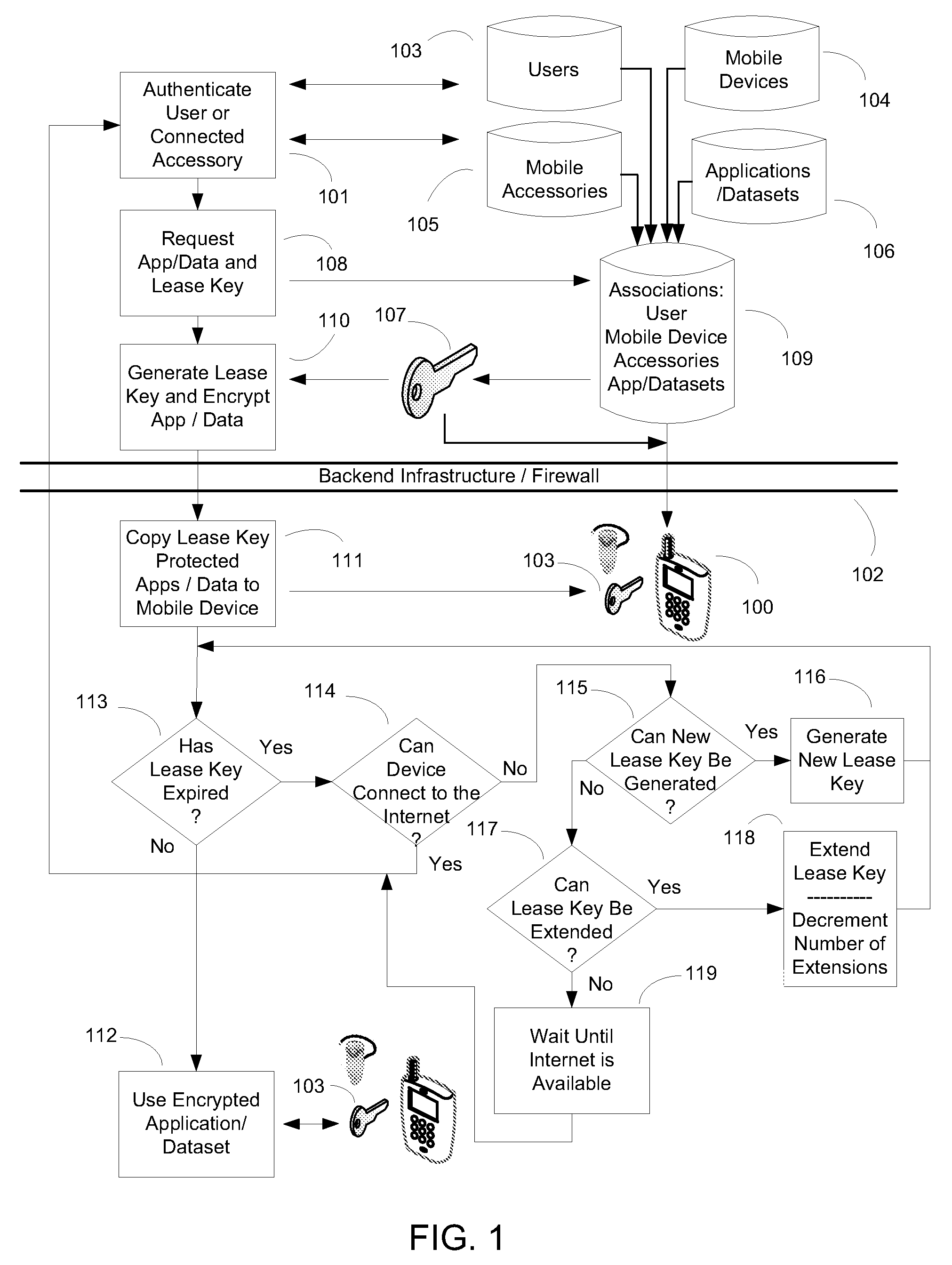
ActiveUS20090240947A1Sufficient evidenceEasy to implementDigital data processing detailsUser identity/authority verificationInternet privacyMobile data access
The present invention provides a system and method for maintaining secure information on mobile devices and that balances security and convenience in the provision of mobile data access. Security is maintained by extending the use of industry-accepted two-factor authentication methods, and convenience is enhanced by utilizing a user's existing mobile device accessories as an authentication factor. As a result, the present invention provides a strong authentication system and method without the cost or burden of requiring the user to acquire additional hardware for security purposes.
Owner:VAULTUS MOBILE TECH
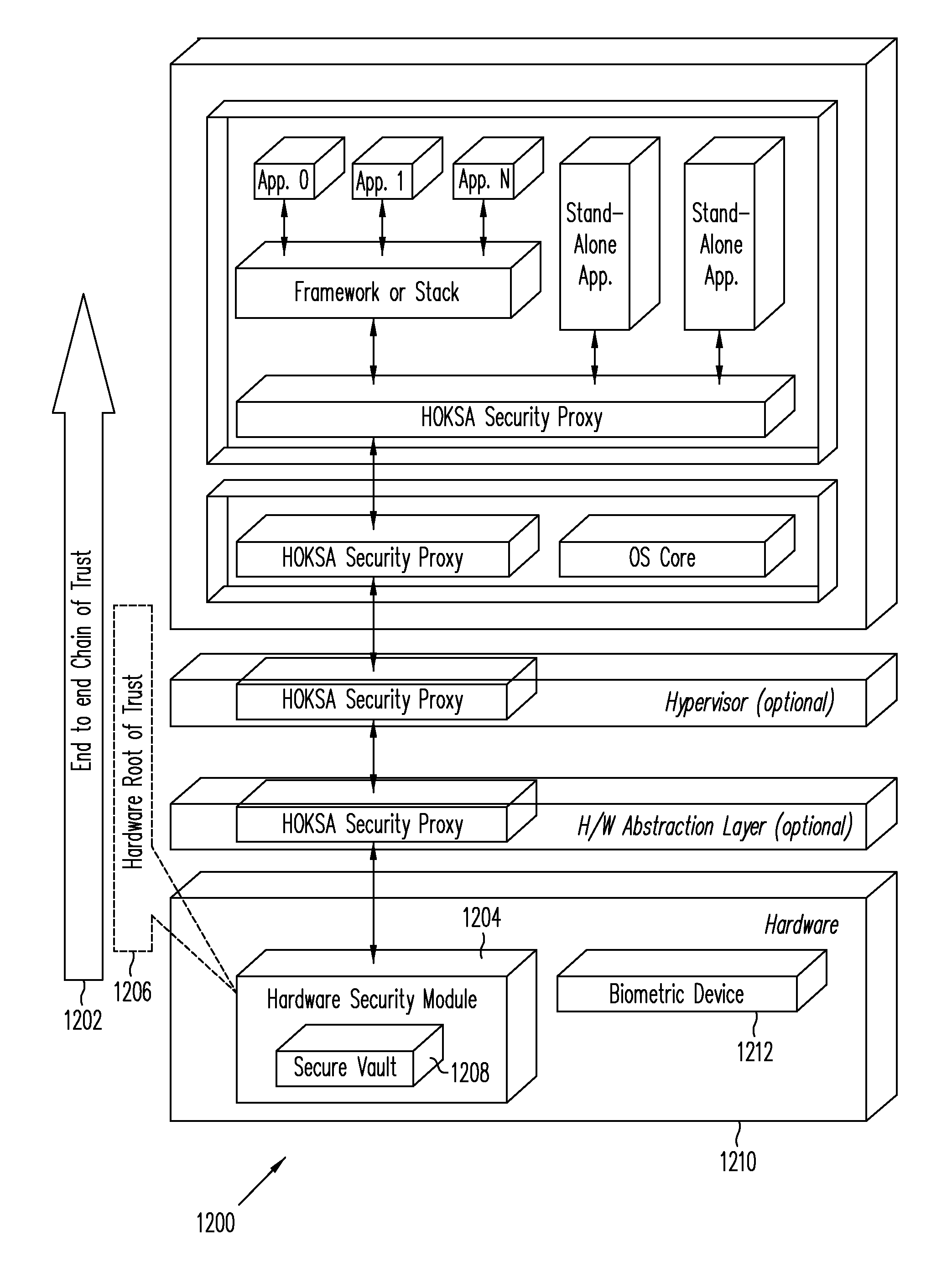
Hardware-Based Zero-Knowledge Strong Authentication (H0KSA)
InactiveUS20100306531A1Reduce riskUser identity/authority verificationDigital data authenticationHardware security moduleChain of trust
Systems and methods are provided for a device to engage in a zero-knowledge proof with an entity requiring authentication either of secret material or of the device itself. The device may provide protection of the secret material or its private key for device authentication using a hardware security module (HSM) of the device, which may include, for example, a read-only memory (ROM) accessible or programmable only by the device manufacturer. In the case of authenticating the device itself a zero-knowledge proof of knowledge may be used. The zero-knowledge proof or zero-knowledge proof of knowledge may be conducted via a communication channel on which an end-to-end (e.g., the device at one end and entity requiring authentication at the other end) unbroken chain of trust is established, unbroken chain of trust referring to a communication channel for which endpoints of each link in the communication channel mutually authenticate each other prior to conducting the zero-knowledge proof of knowledge and for which each link of the communication channel is protected by at least one of hardware protection and encryption.
Owner:PAYPAL INC
Common authentication service for network connected applications, devices, users, and web services
ActiveUS7546276B2User identity/authority verificationPayment architectureService protocolWeb service
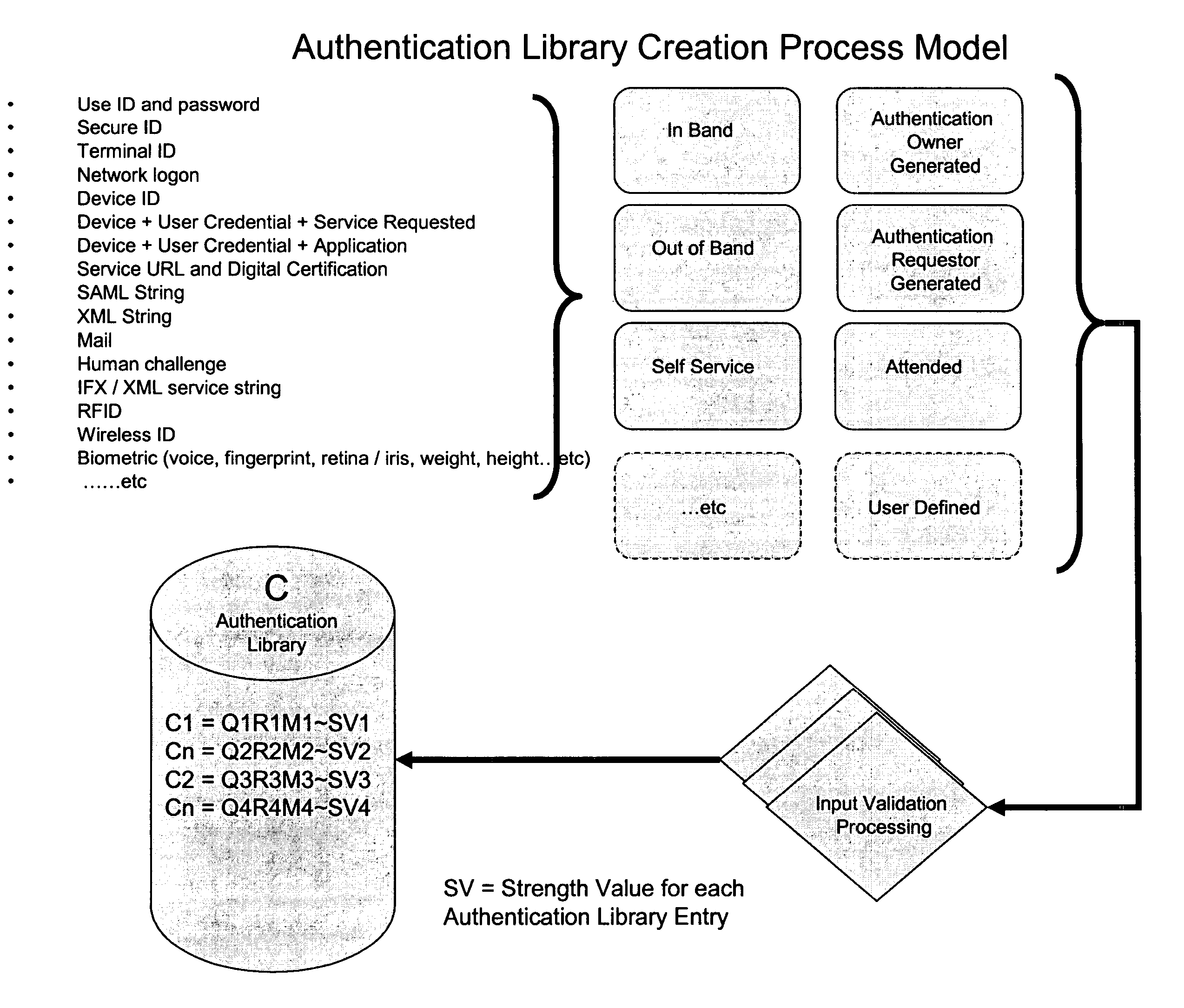
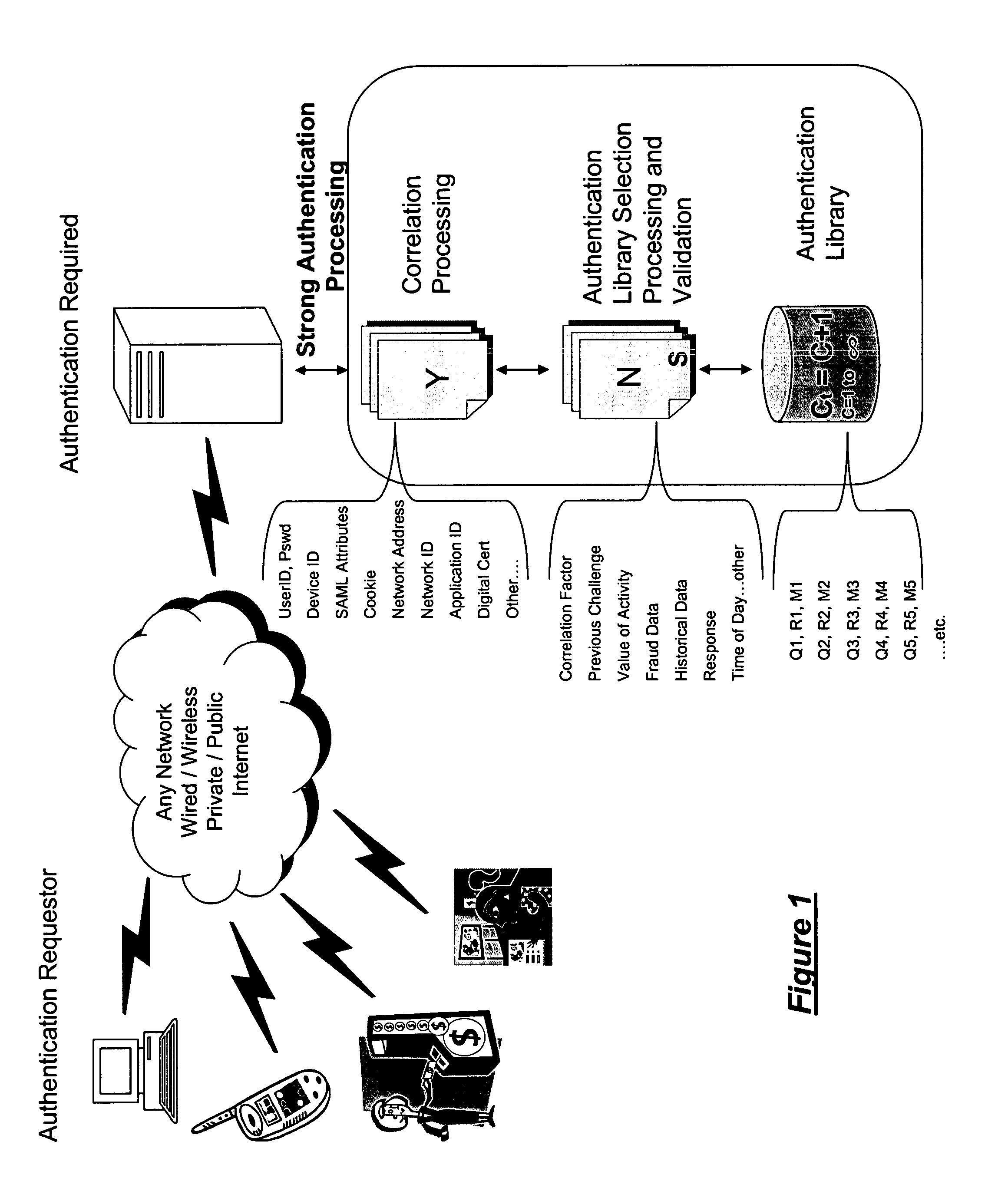
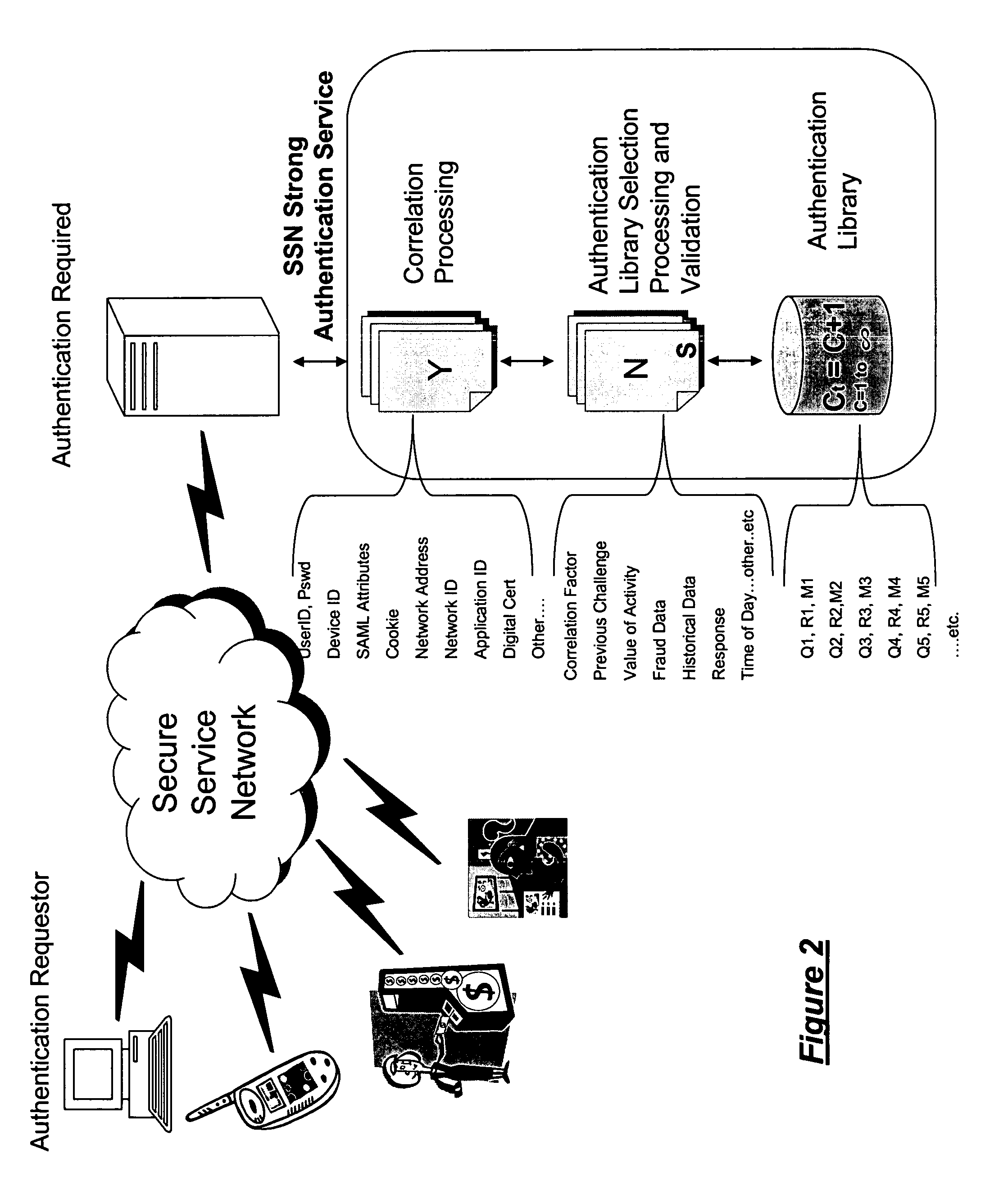
System architecture for network connected applications, devices, users, and web services providing security effected by means for managing interaction with an authentication library that effects a correlation between the use and creation of library entries having predetermined correlation indicia for effecting strong authentication of users and participants within the network. A common authentication service (CAS) based upon an XML or web services protocol is described.
Owner:RANDLE WILLIAM M +1
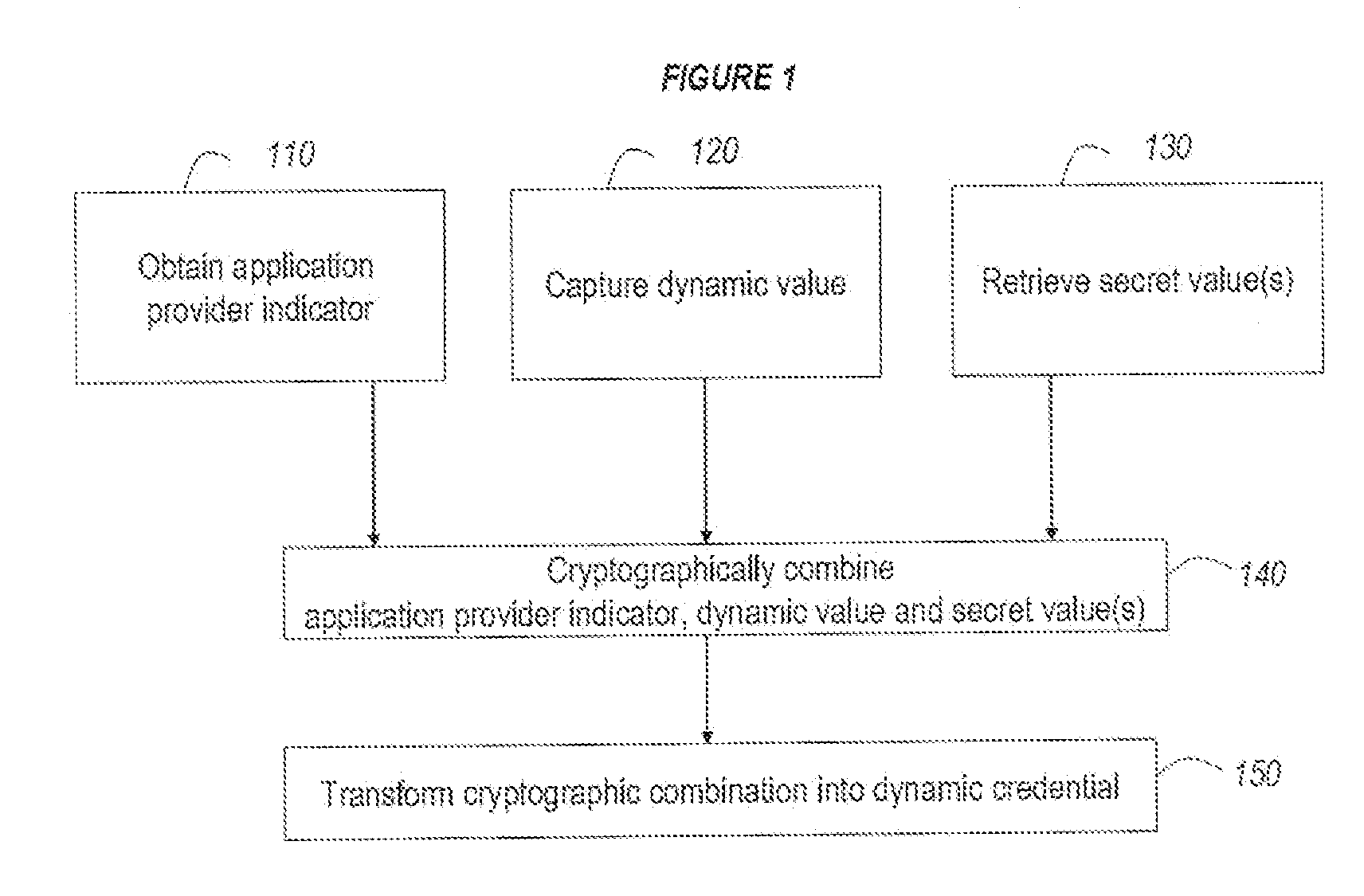
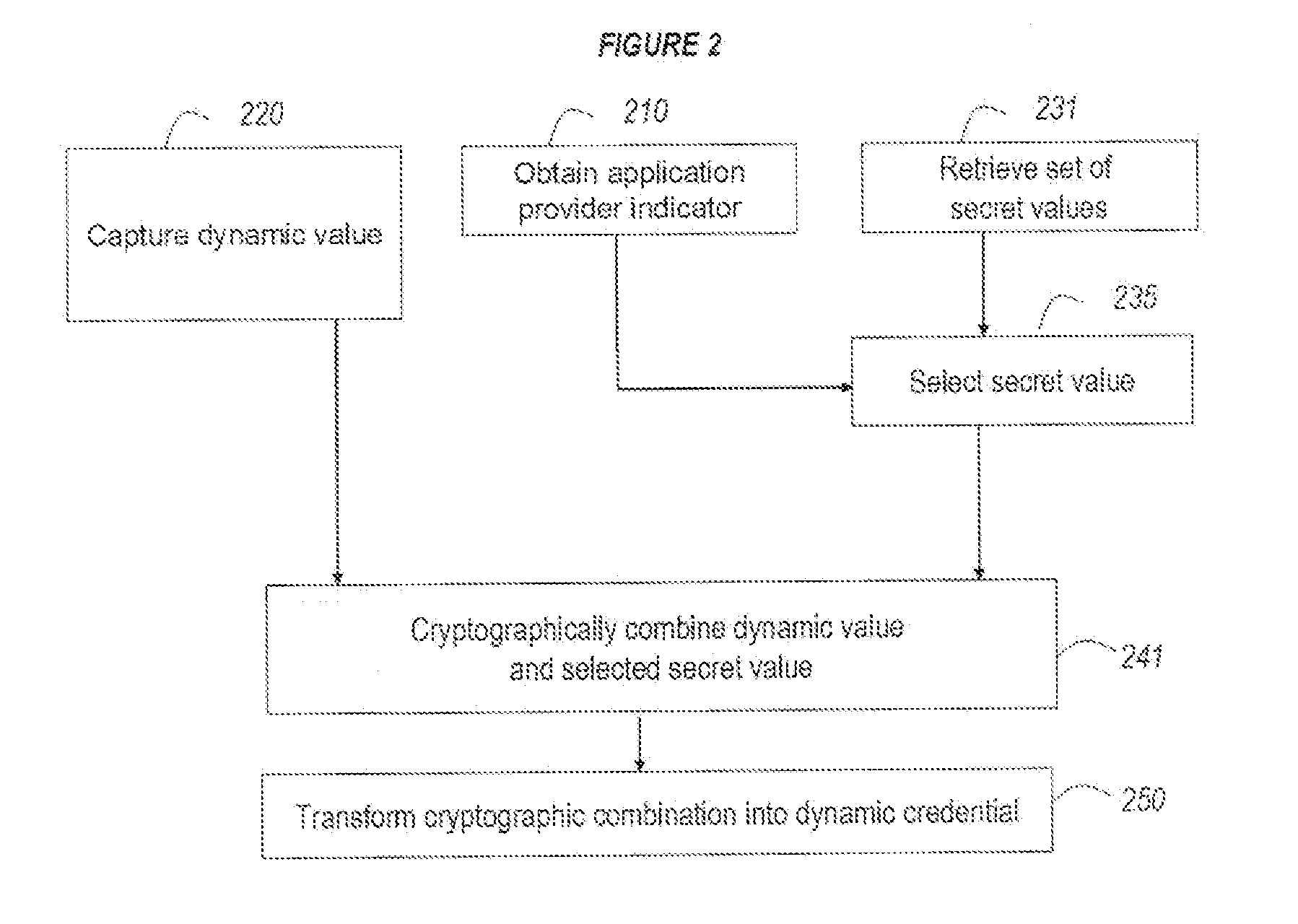
Strong authentication token usable with a plurality of independent application providers
ActiveUS20110099384A1Low costCost can be dividedMultiple keys/algorithms usageDigital data processing detailsPersonalizationUnique identifier
Owner:ONESPAN NORTH AMERICA INC
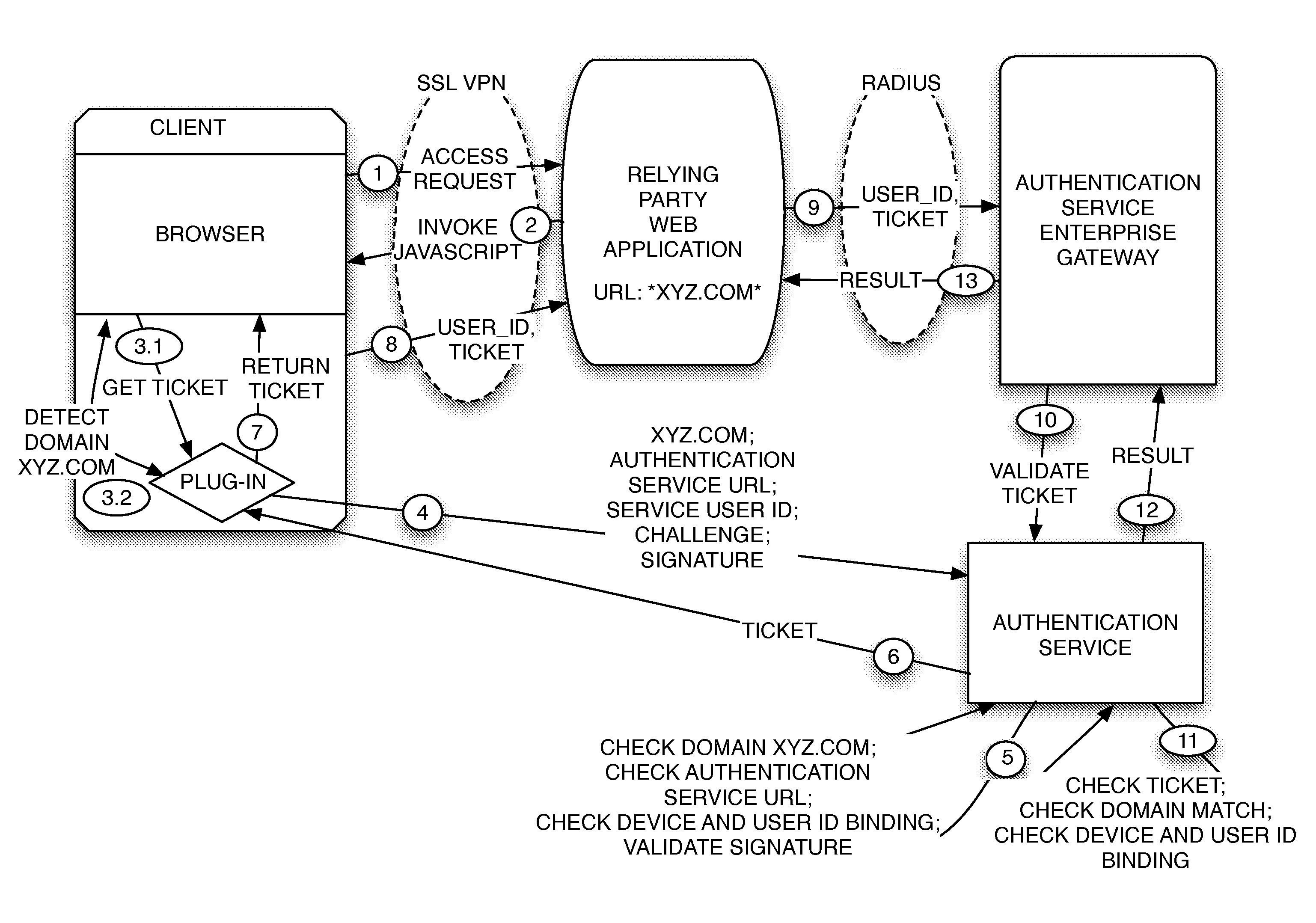
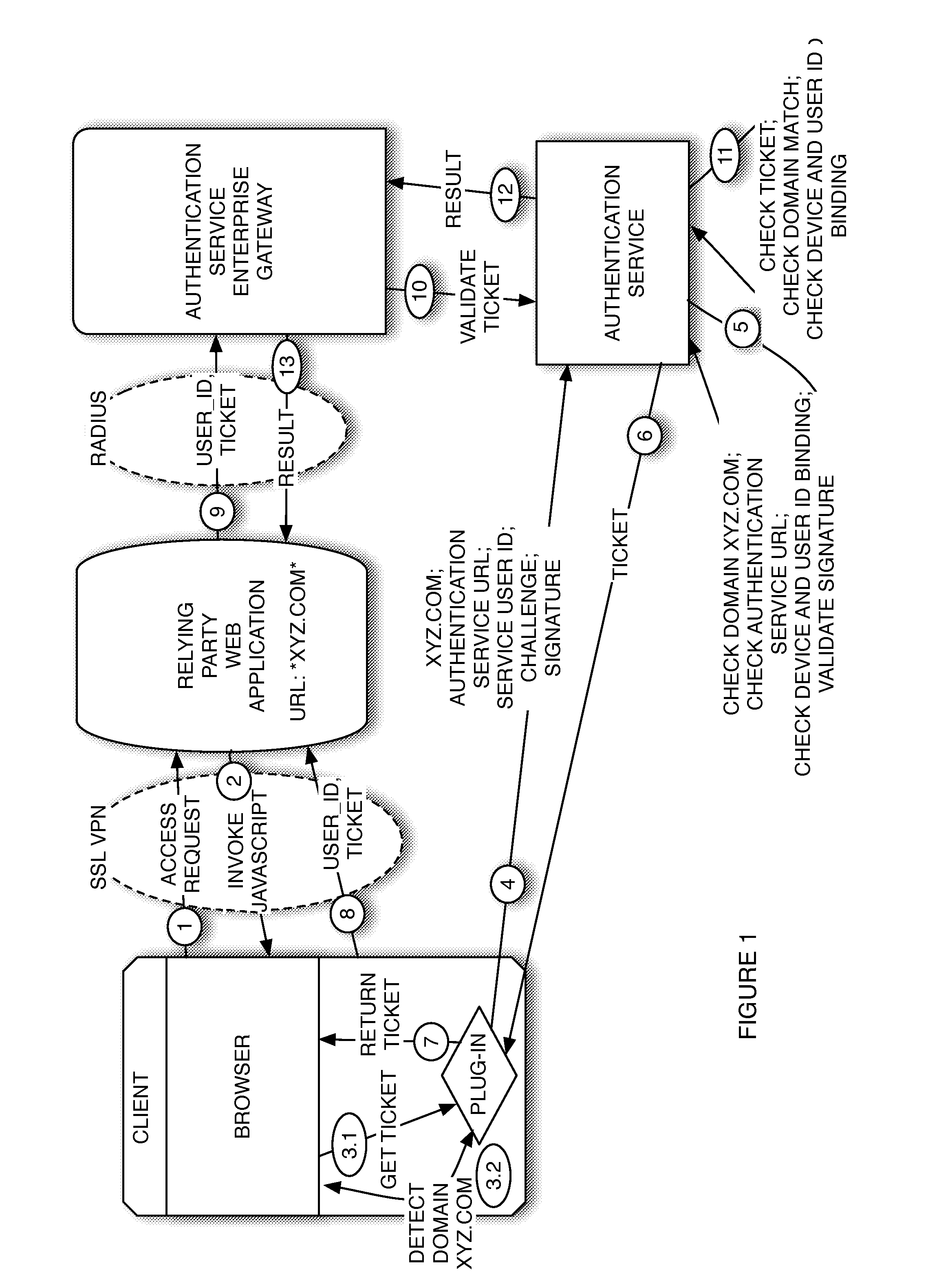
Ticket based strong authentication with web service
ActiveUS8584224B1Reduce the possibilityDigital data processing detailsUser identity/authority verificationWeb applicationWeb service
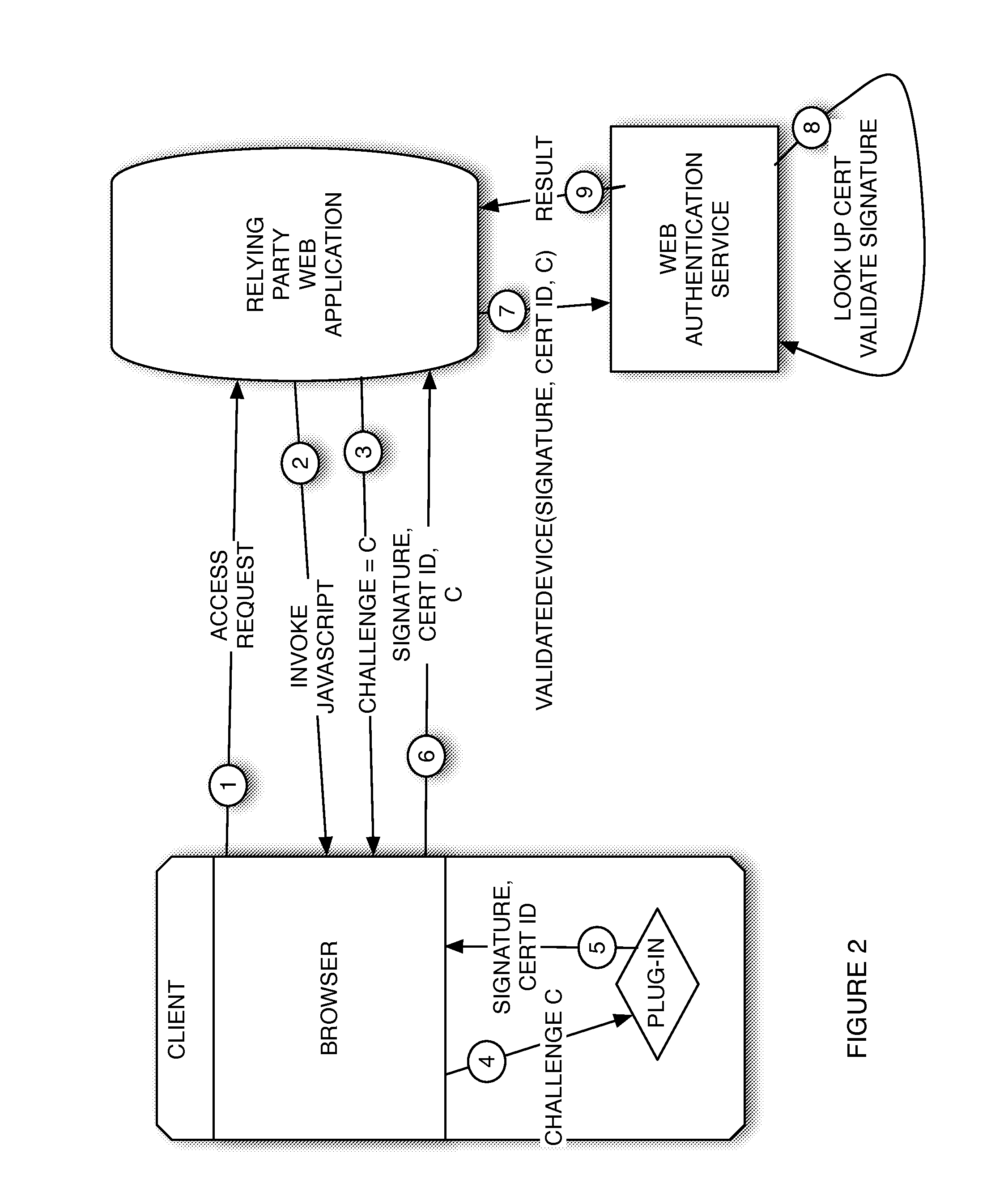
A system for authenticating a user to a relying party. A user sends an access request to a relying party web application. In response, the application sends a page with JavaScript that detects a plug-in at the user and detects the relying party domain. The plug-in uses its device certificate or other pre-established credentials to sign a challenge along with other site and user information including the site domain, the authentication service URL and user identifier, and send it, along with the data including the domain and the user identifier, to an authentication service. The service authenticates the information and sends back to the plug-in a short ticket that can be passed on to the relying party, which can validate it using the Radius protocol and an authentication service call, thereby authenticating the user.
Owner:CA TECH INC
Method and apparatus for authenticating a shipping transaction
InactiveUS6991174B2Strong authenticationTicket-issuing apparatusPayment architectureEmbedded securitySmart card
An autonomous and portable smartcard reader device incorporates a high level of embedded security countermeasures. Data transfers are encrypted with two specific input devices, namely a light sensor and PIN or other keyboard entry, and at the output through the use of a dual-tone encoder-decoder. The unit may be used alone or as a plug-in to another device such as a PDA, cell phone, or remote control. The reader may further be coupled to various biometric or plug-in devices to achieve at least five levels of authentication, namely, (1) the smartcard itself; (2) the smartcard reader; (2) the PIN; (3) private-key cryptography (PKI); and (5) the (optional) biometric device. These five levels account for an extremely strong authentication applicable to public networking on public / private computers, and even on TV (satellite, cable, DVD, CD AUDIO, software applications. Transactions including payments may be carried out without any risk of communication tampering, authentication misconduct or identity theft. In essence, the device is a closed box with only two communication ports. The emulation of the device is therefore extremely complex due to the fact that it involves PKI and or identity-based encryption (IBE), key pair, elliptic curves encryption scheme, hardware serialization for communication and software implementation, in conjunction with a specific hardware embodiment and service usage infrastructure component that returns a response necessary for each unique transaction.
Owner:BRITE SMART
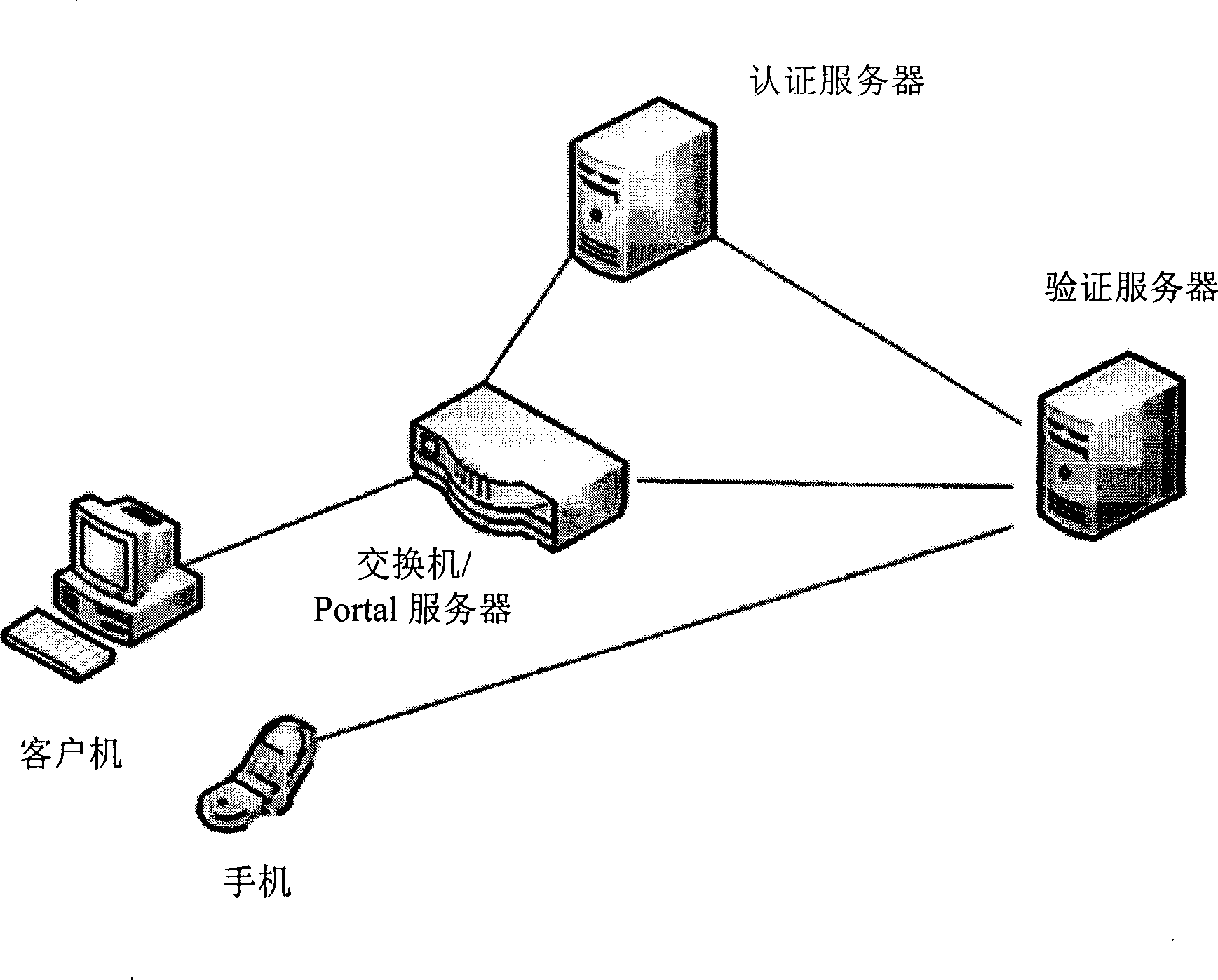
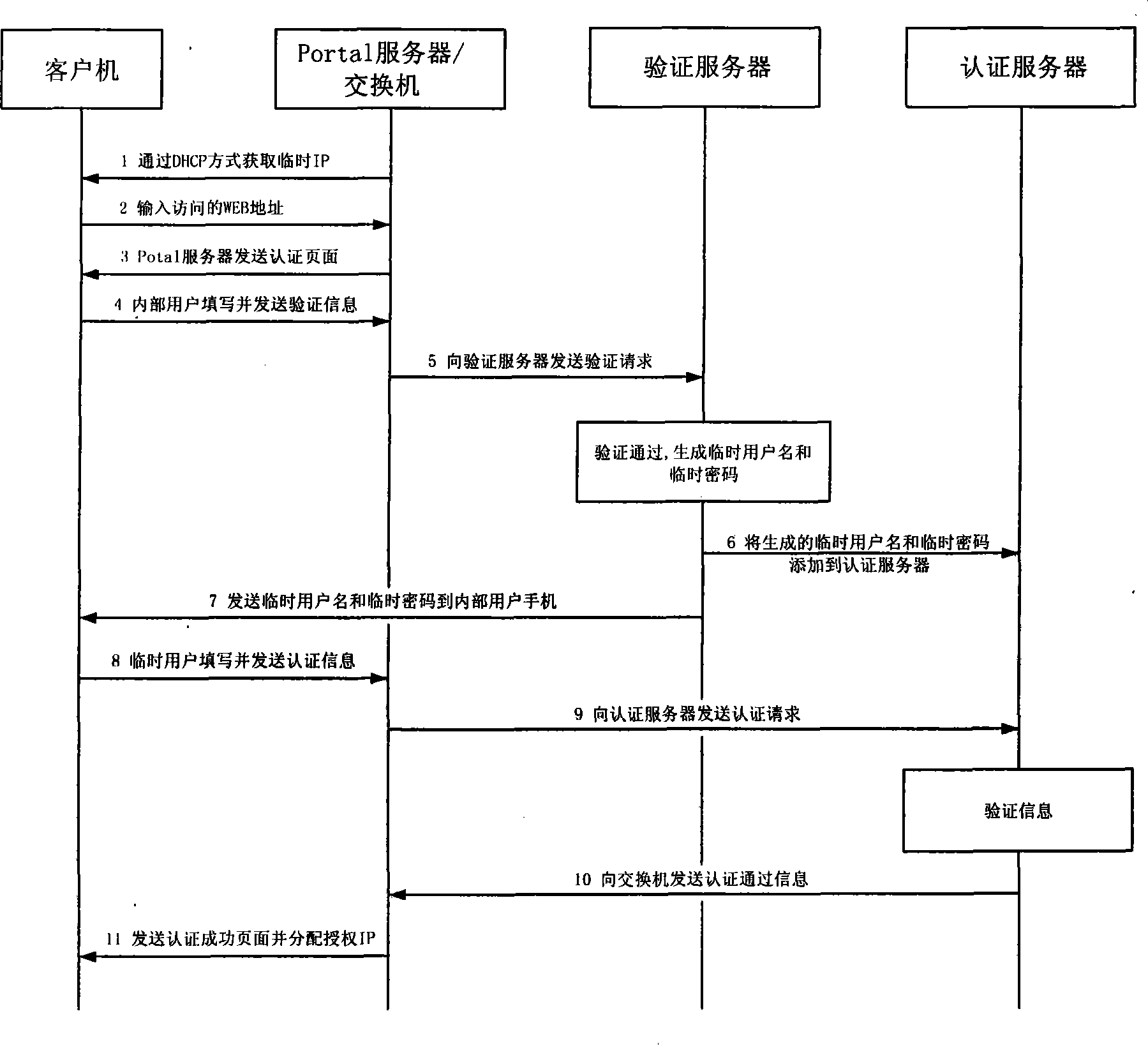
Method for local area network access authentication of casual user
ActiveCN101369893ASimple and standardized management processNot easy to be stolenUser identity/authority verificationData switching by path configurationManagement processAuthentication server
The invention relates to a method for implementing a user access authentication in a local area network, especially to a method for implementing a casual user access authentication in a public local area network. Firstly an internal user applies a casual user name and a key for the casual user through the authentication of a authentication server, the authentication server dynamically generates the casual user name and the key, then the casual user name and the key are stored in a user list of the authentication server, simultaneously the casual user name and the key are transmitted to a mobile phone of the internal user, the casual user uses the casual user name and the key for access authentication, and visits the authorized network resource after the authentication of the authentication server. The method of the invention adopts a double-factor and strong authentication system, the internal user is authenticated once, and the casual user is authenticated twice. The method can greatly improves the system safety, the casual user name and the key are all dynamically generated which are not easy to steal with high safety, and the management process for the casual user is simple and standard.
Owner:CHINA MOBILE GROUP DESIGN INST
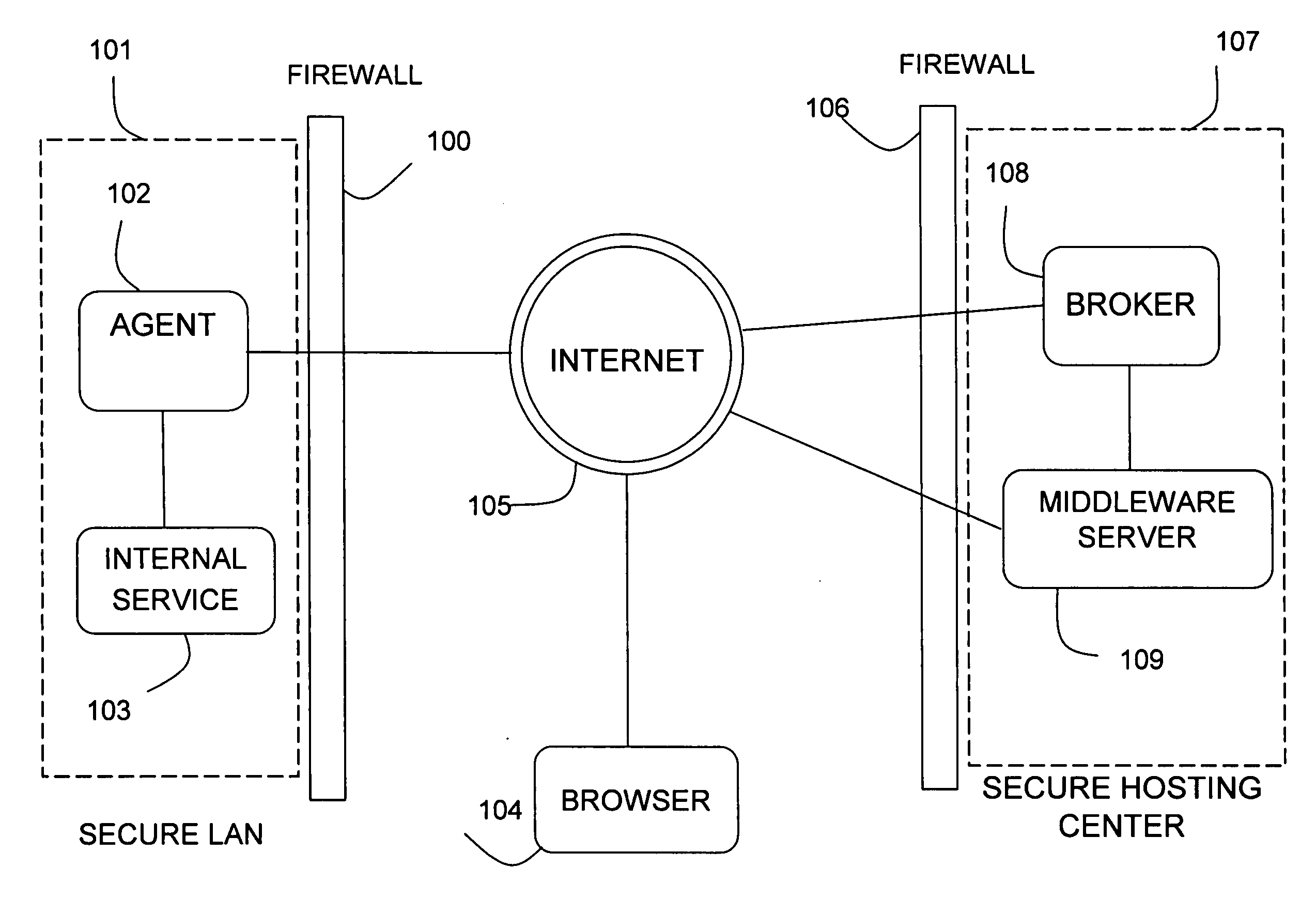
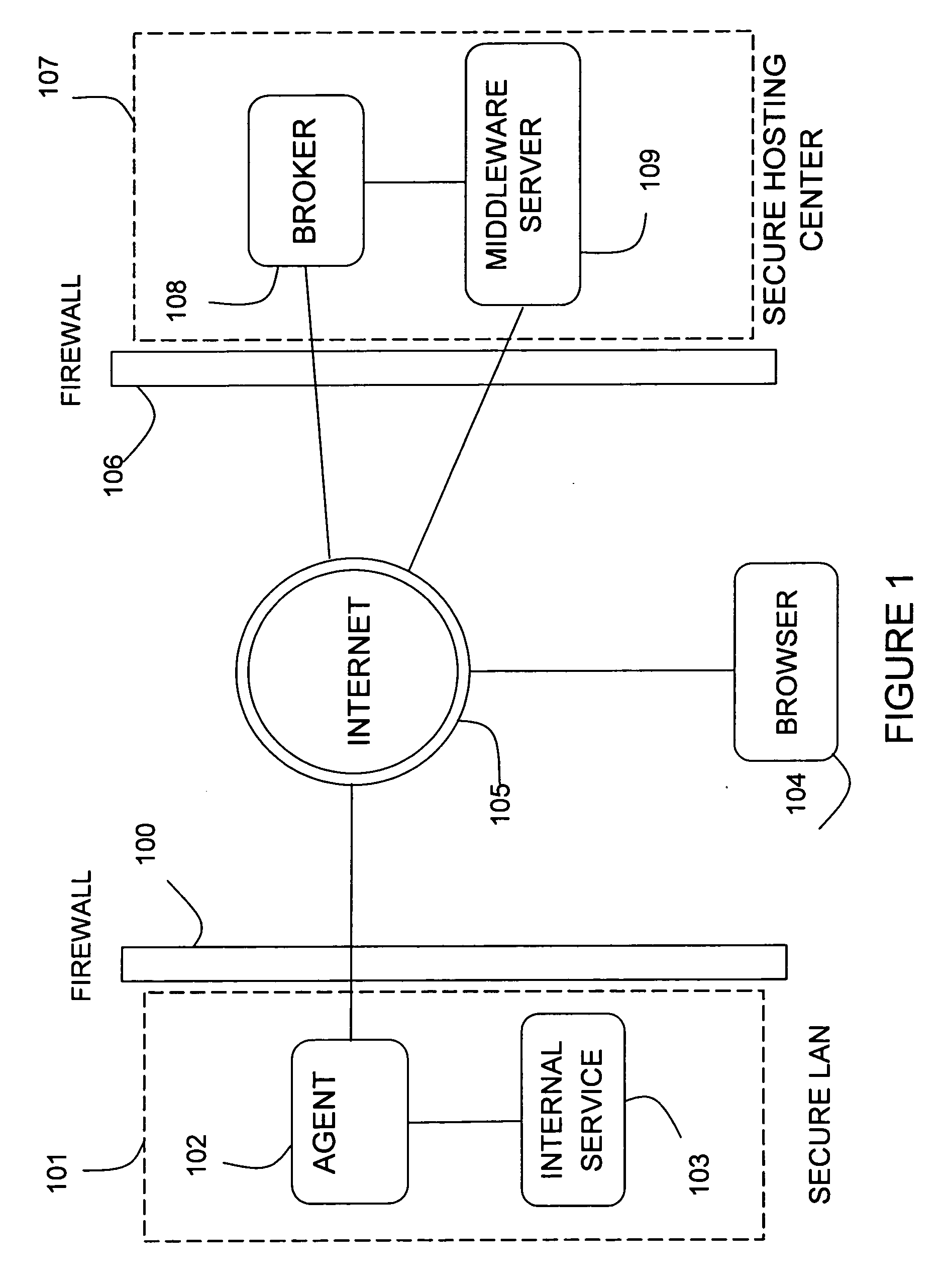
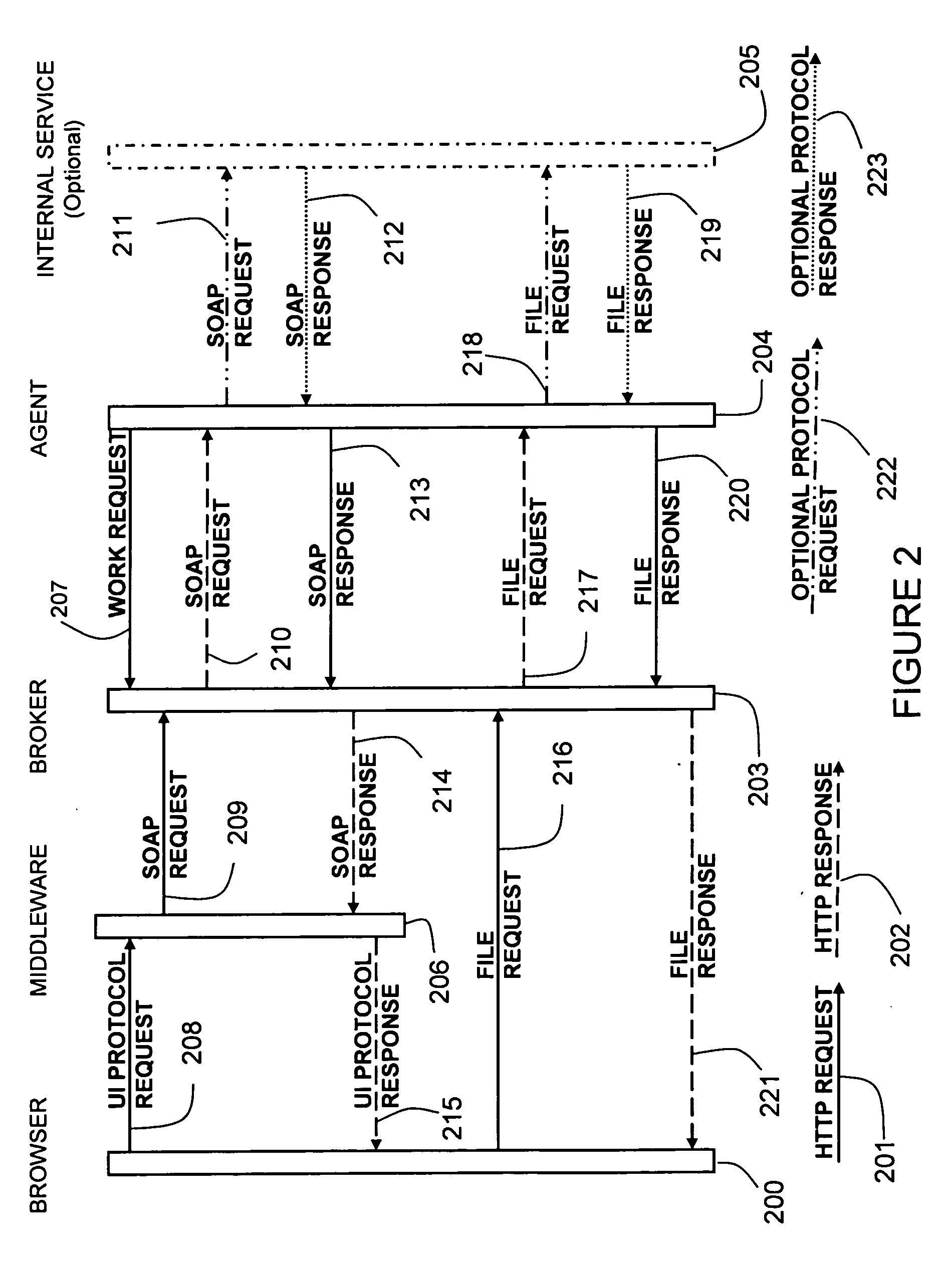
Method and apparatus for accessing Web services and URL resources for both primary and shared users over a reverse tunnel mechanism
A method and apparatus for accessing Web services and URL resources for both primary and shared users over a reverse tunnel mechanism are provided. Current limitations on accessing Web services and URL resources located behind firewalls or otherwise made secure and largely inaccessible are overcome through a novel use of a “reverse tunneling” mechanism. The mechanism uses an Agent to obfuscate physical address endpoints of Web services and other resources, as well as to package SOAP service requests in such a way that they can be passed through firewalls unimpeded. All of this data transfer is made secure through encryption, strong authentication, and by making use of the security environment on both a user's individual device and the LAN proper. In addition, a primary user may share data access rights within the secure LAN environment to a secondary user and, using the present invention, provide only those access rights to the shared user over the open Internet.
Owner:BUNGEE LABS INC
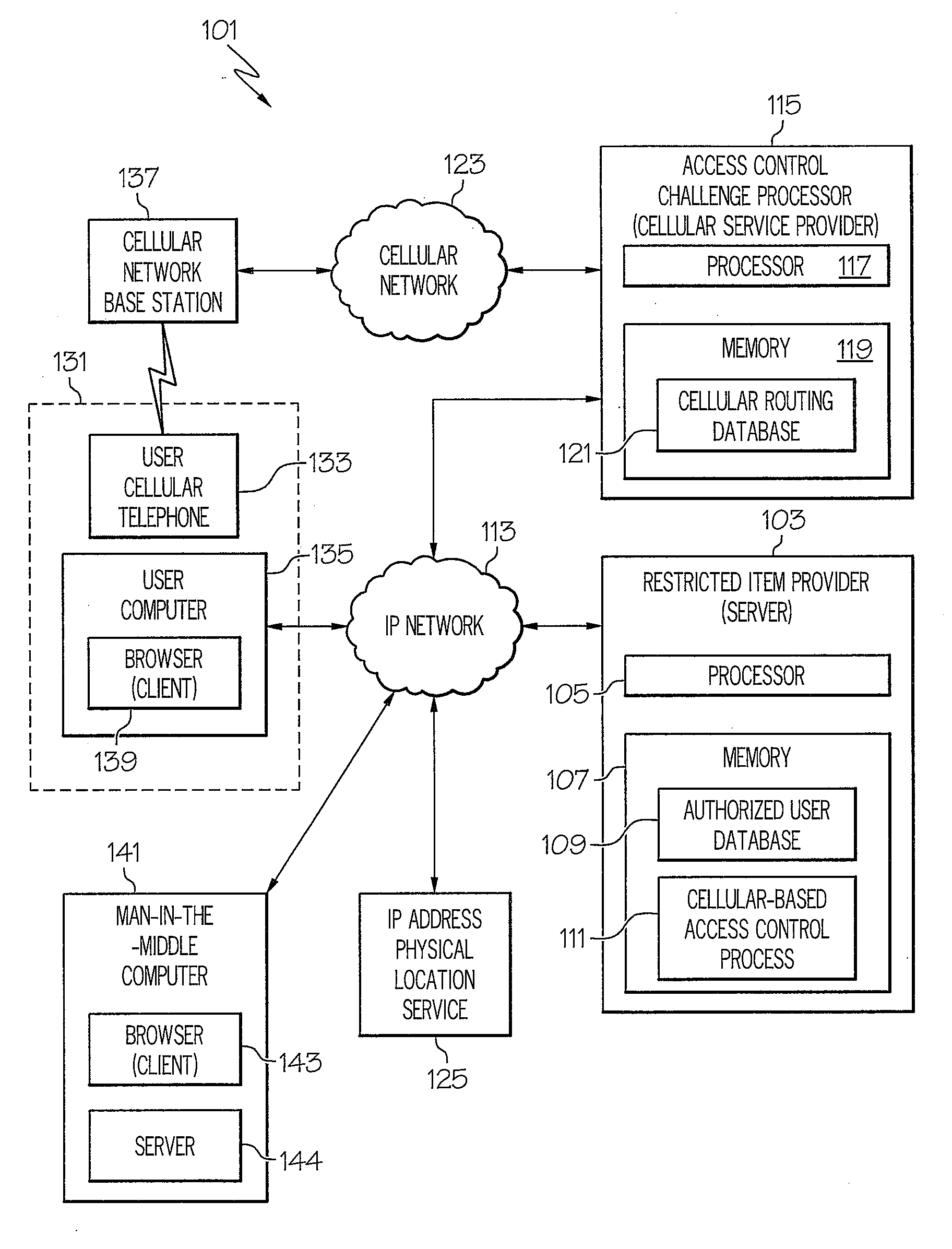
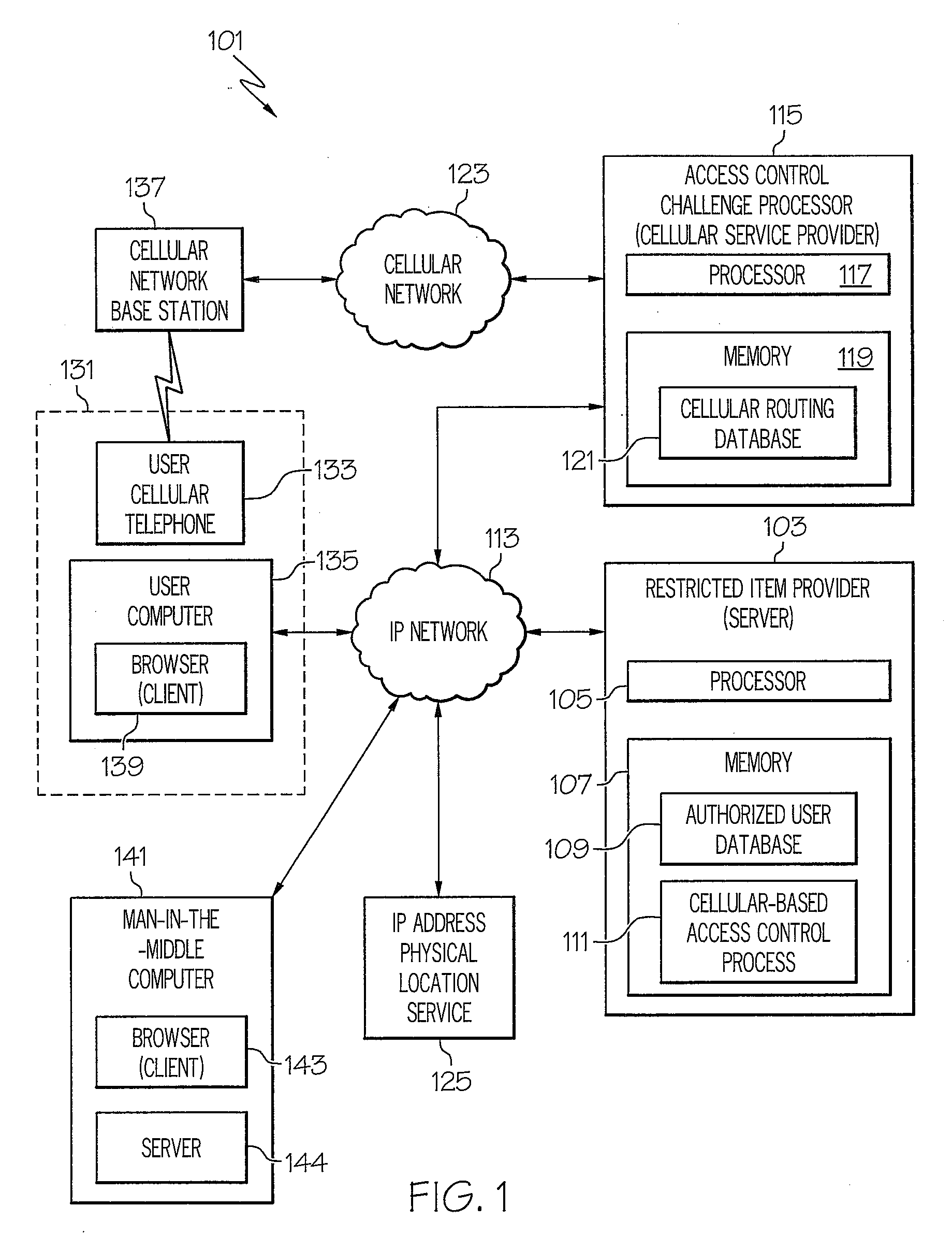
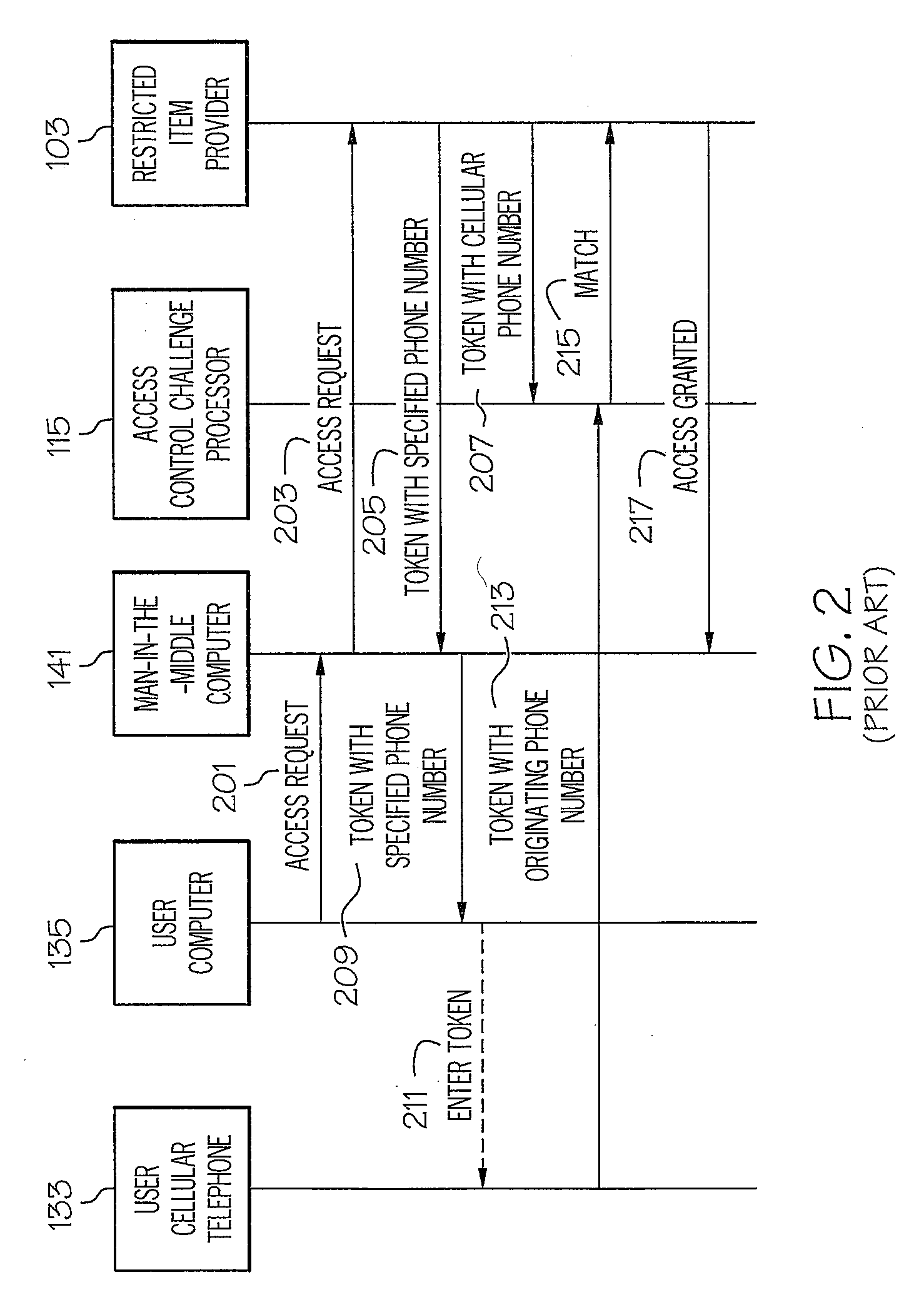
Method of and system for strong authentication and defense against man-in-the-middle attacks
InactiveUS20080318548A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMan-in-the-middle attackStrong authentication
A man-in-the-middle attack resistant method of and system for controlling access of a user to a restricted item receives a request from a user of a first device for access to a restricted item. The system determines the physical location of the first device. The system provides a token to the user and prompts the user to send the token to a recipient using a second device. The system denies the user access to the restricted item if the token is sent from a physical location not matching the physical location of the first device.
Owner:IBM CORP
Method and system for strong, convenient authentication of a web user
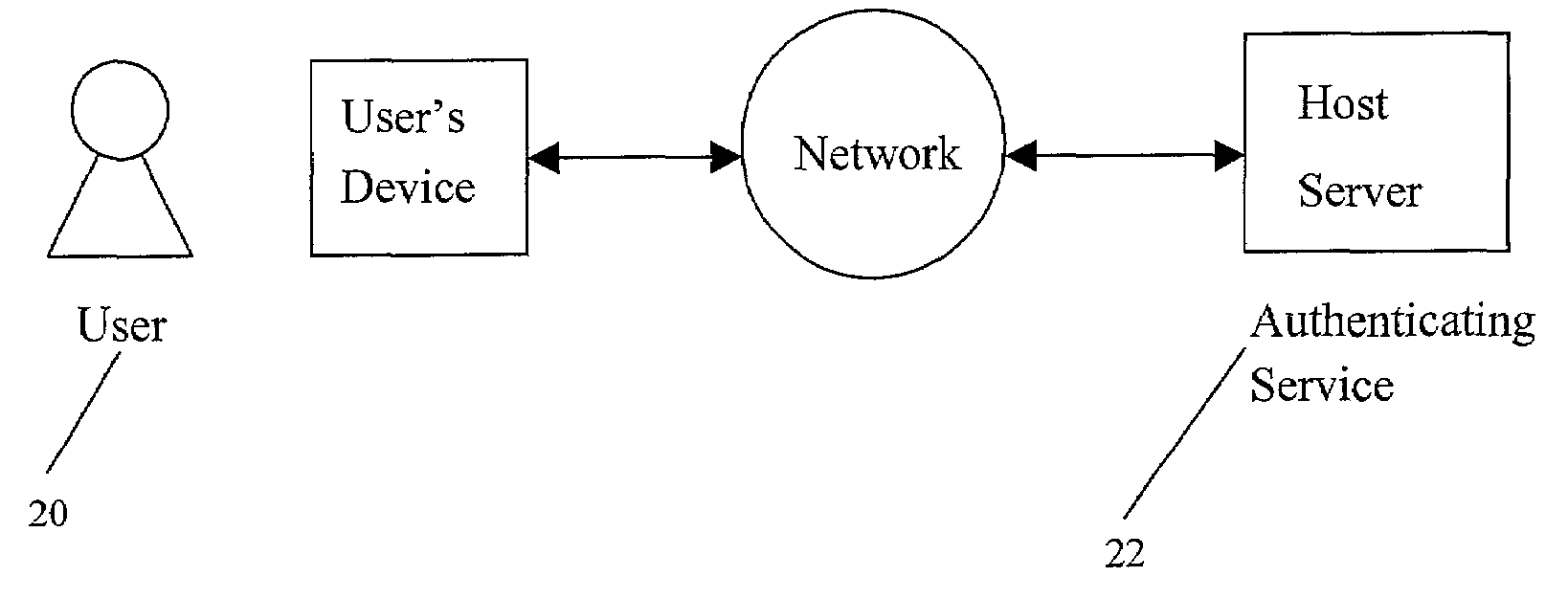
InactiveUS6970853B2Easy to useQuick updateDigital data processing detailsUser identity/authority verificationUser devicePassword
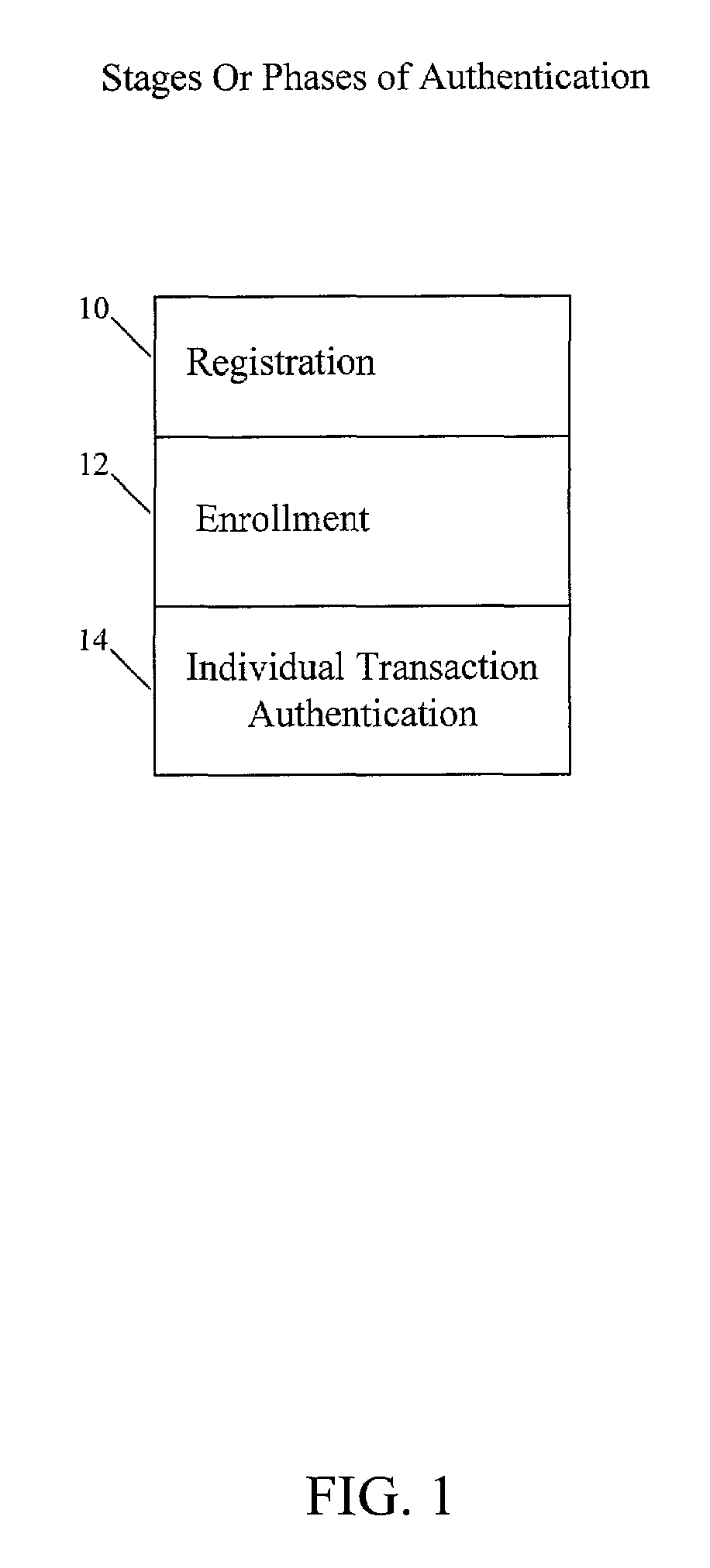
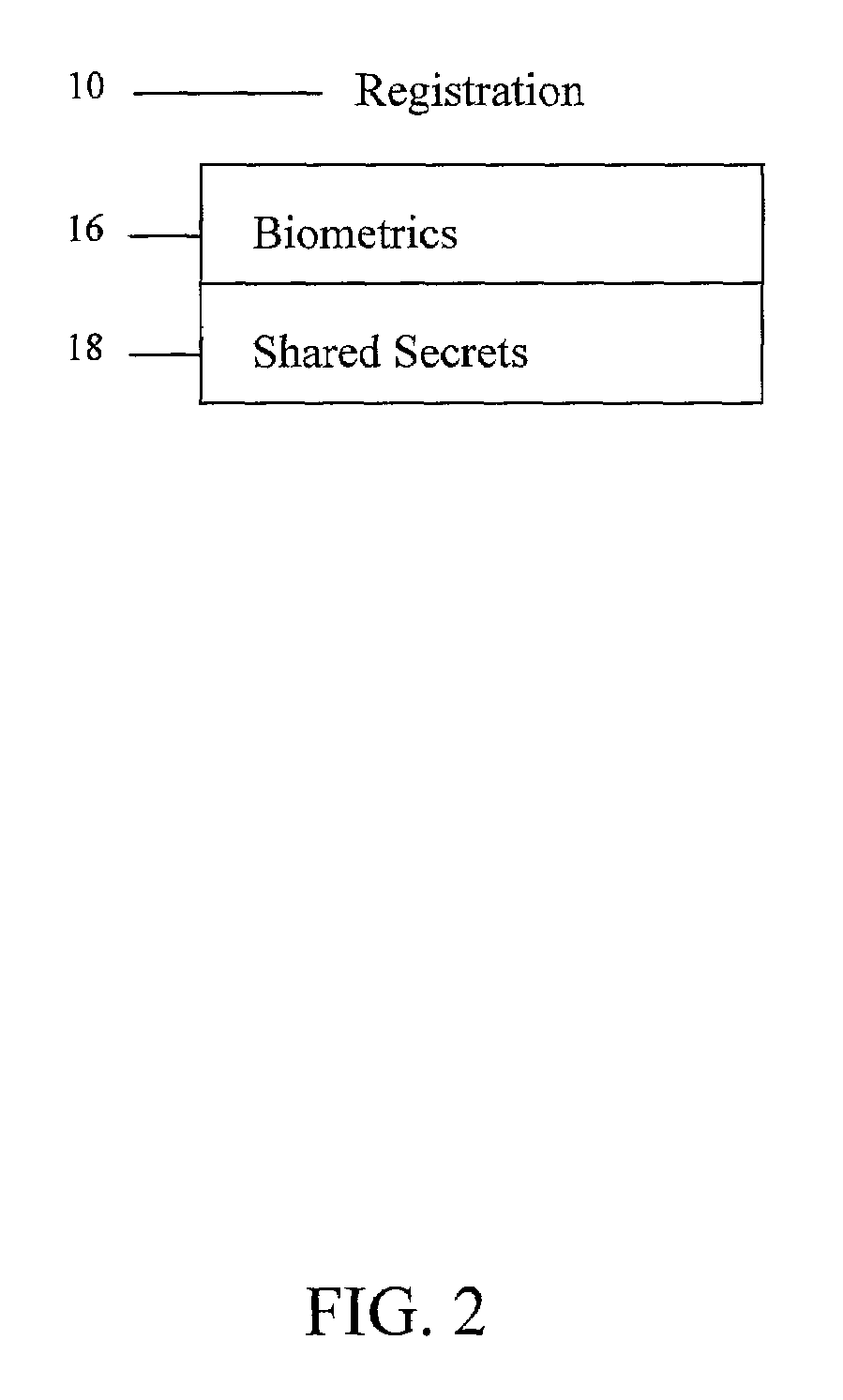
A method and system for strong, convenient authentication of a web user makes use, for example, of a computing device, such as a user's personal computer (PC), coupled over a network, such as the Internet, to one or more servers, such as the host server of an authenticating authority, as well as one or more databases of the authenticating authority. The authentication process is broken into three phases, namely a registration phase, an enrollment phase, and a transaction authentication phase, with each phase being less intrusive and less secure than the preceding phase. In the registration phase, an authenticating authority registers the user based upon identification of the user using a strong authentication technique and provides an authenticating token to the user, which can be used in the enrollment phase to enroll one or more user devices for the user. Thereafter, in the transaction authentication phase, the authenticating authority can authenticate the user for a transaction based on presentation by the user of a user password via the enrolled user device.
Owner:CITIBANK
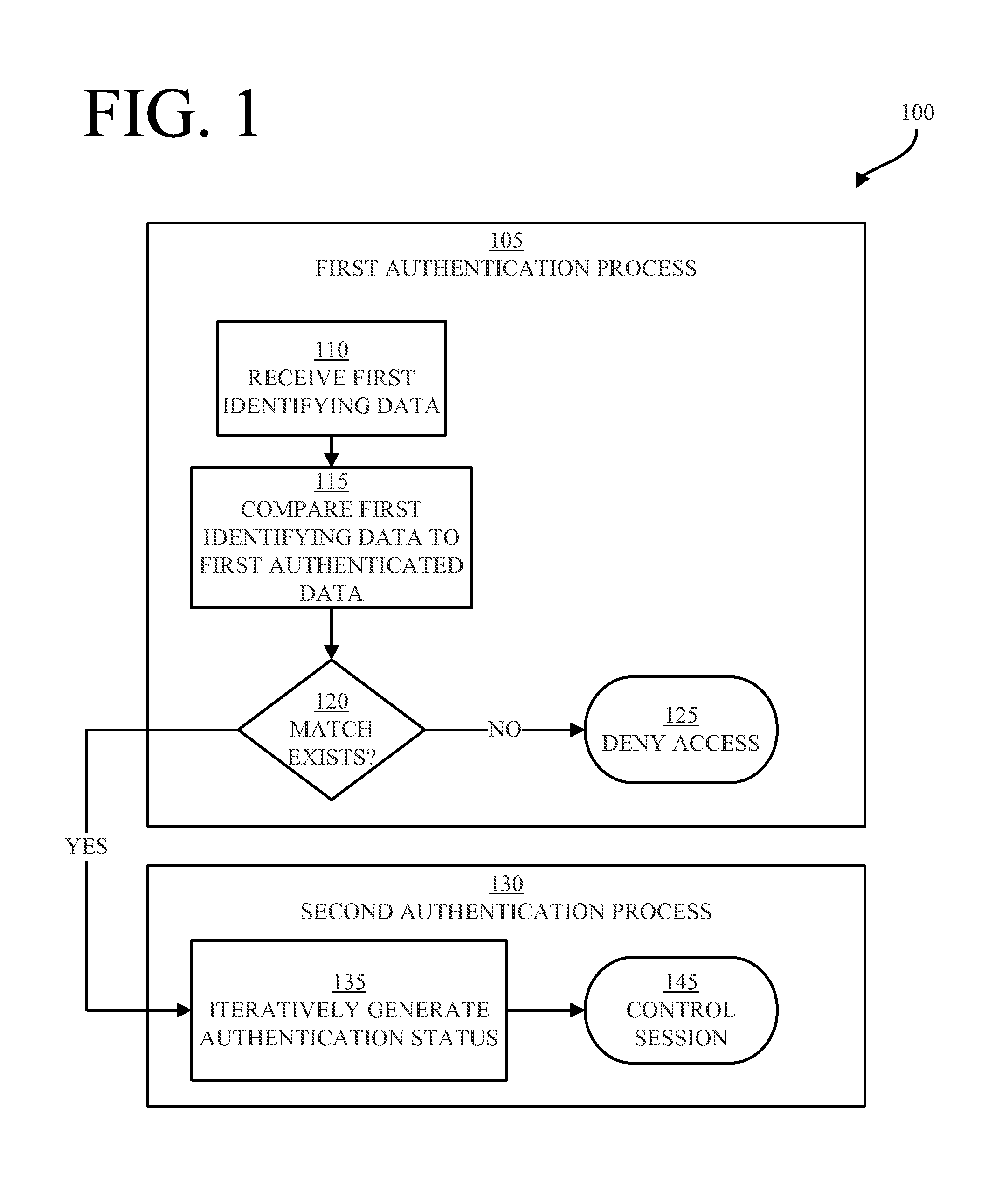
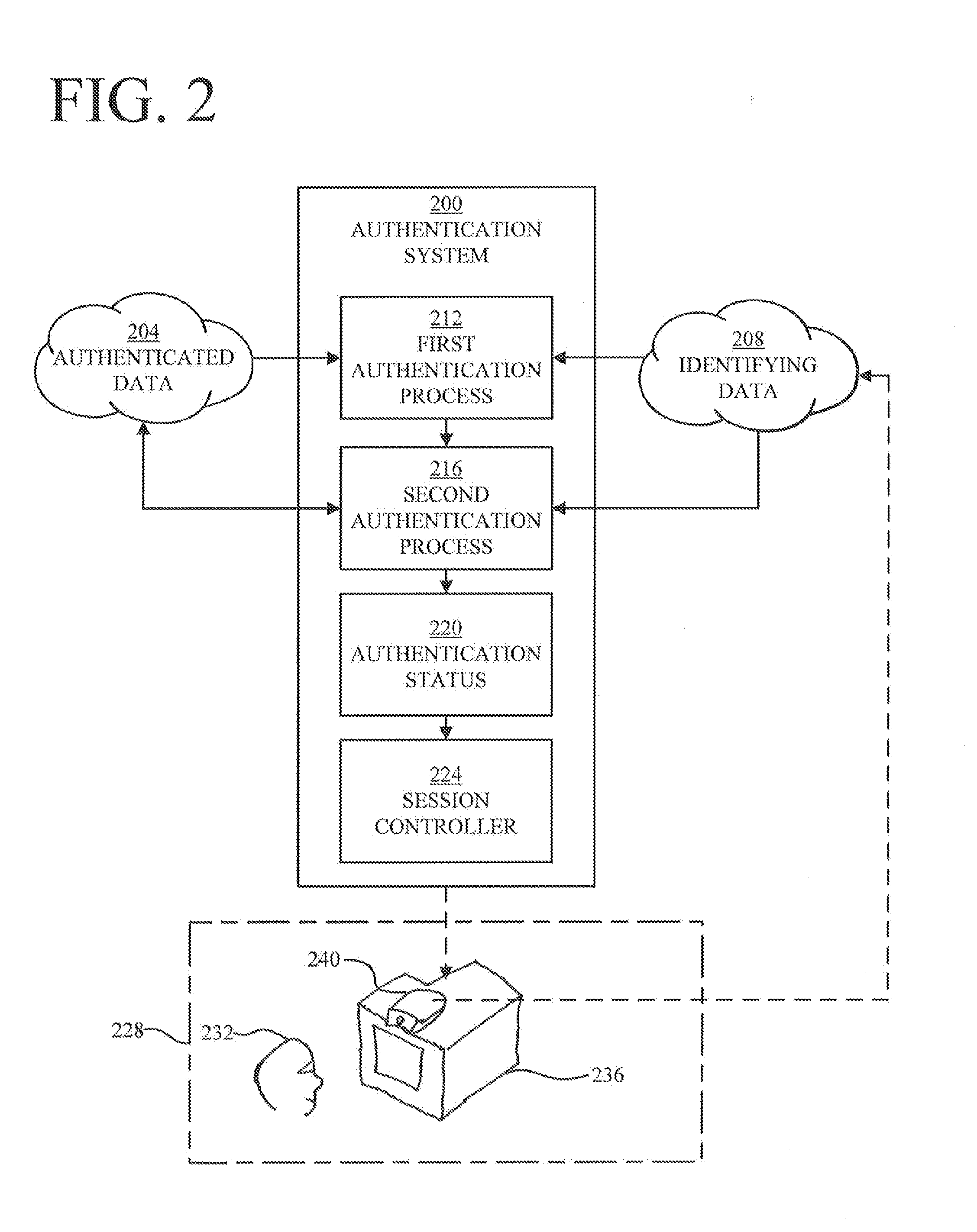
Continuous Authentication, and Methods, Systems, and Software Therefor
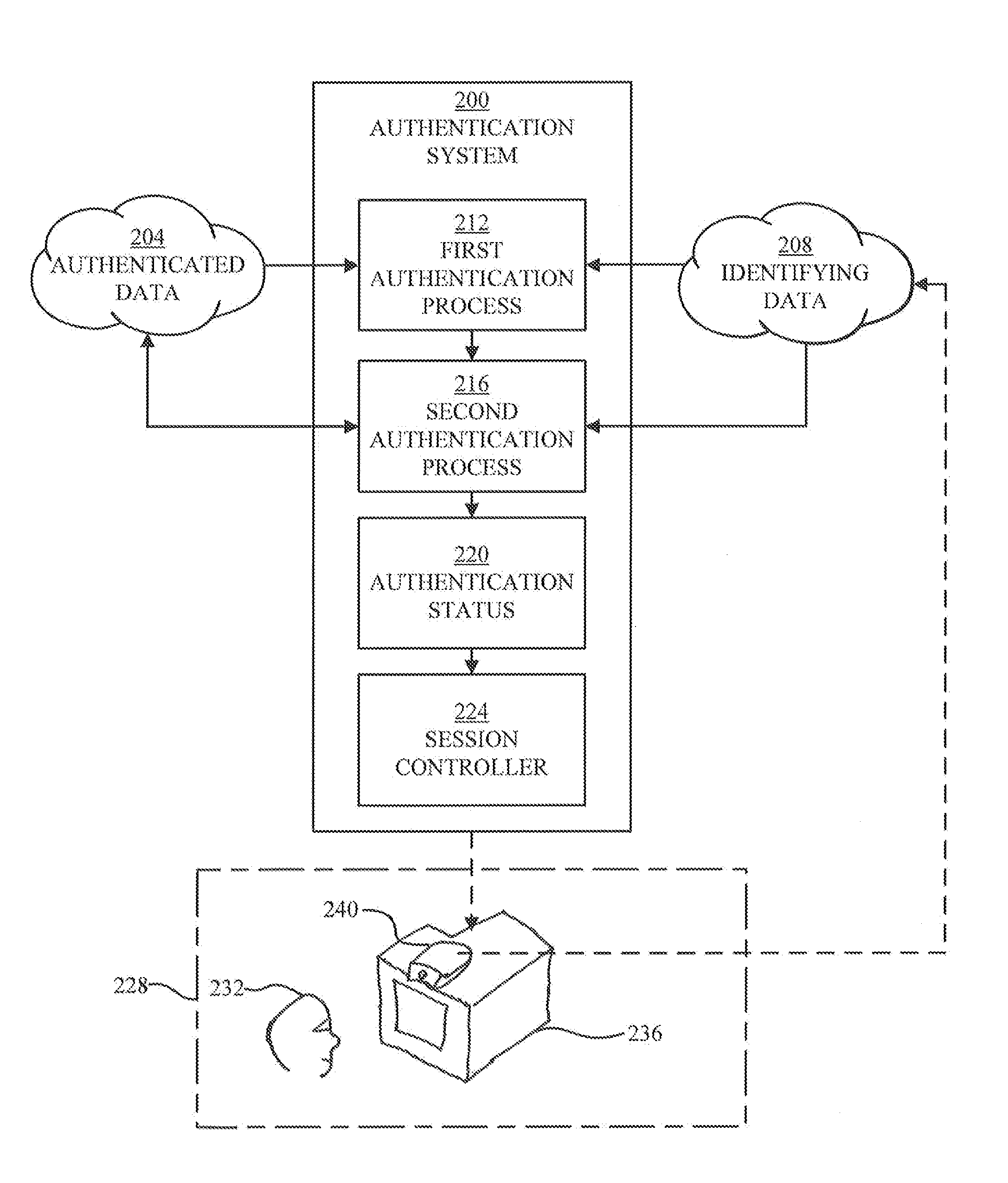
InactiveUS20140250523A1Digital data processing detailsUnauthorized memory use protectionStrong authenticationControl equipment
Controlling a registered-user session of a registered user on a device using first and second authentication processes and a handoff from the first process to the second process. In one embodiment, the first authentication process is a stronger process performed at the outset of a session, and the second authentication process is a weaker process iteratively performed during the session. The stronger authentication process may require cooperation from the user, while the weaker authentication process is preferably one that requires little or no user cooperation. In other embodiments, a strong authentication process may be iteratively performed during the session.
Owner:CARNEGIE MELLON UNIV
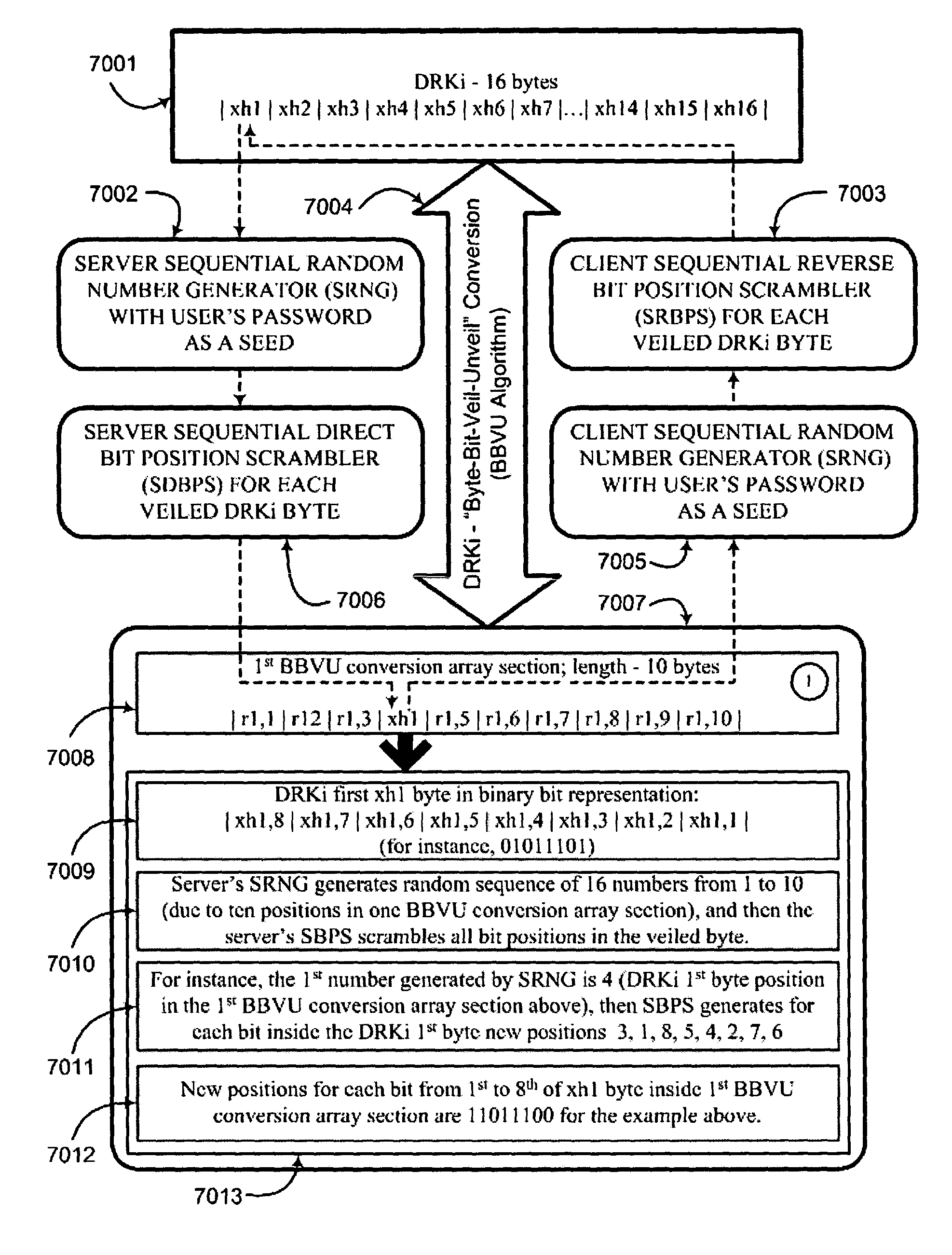
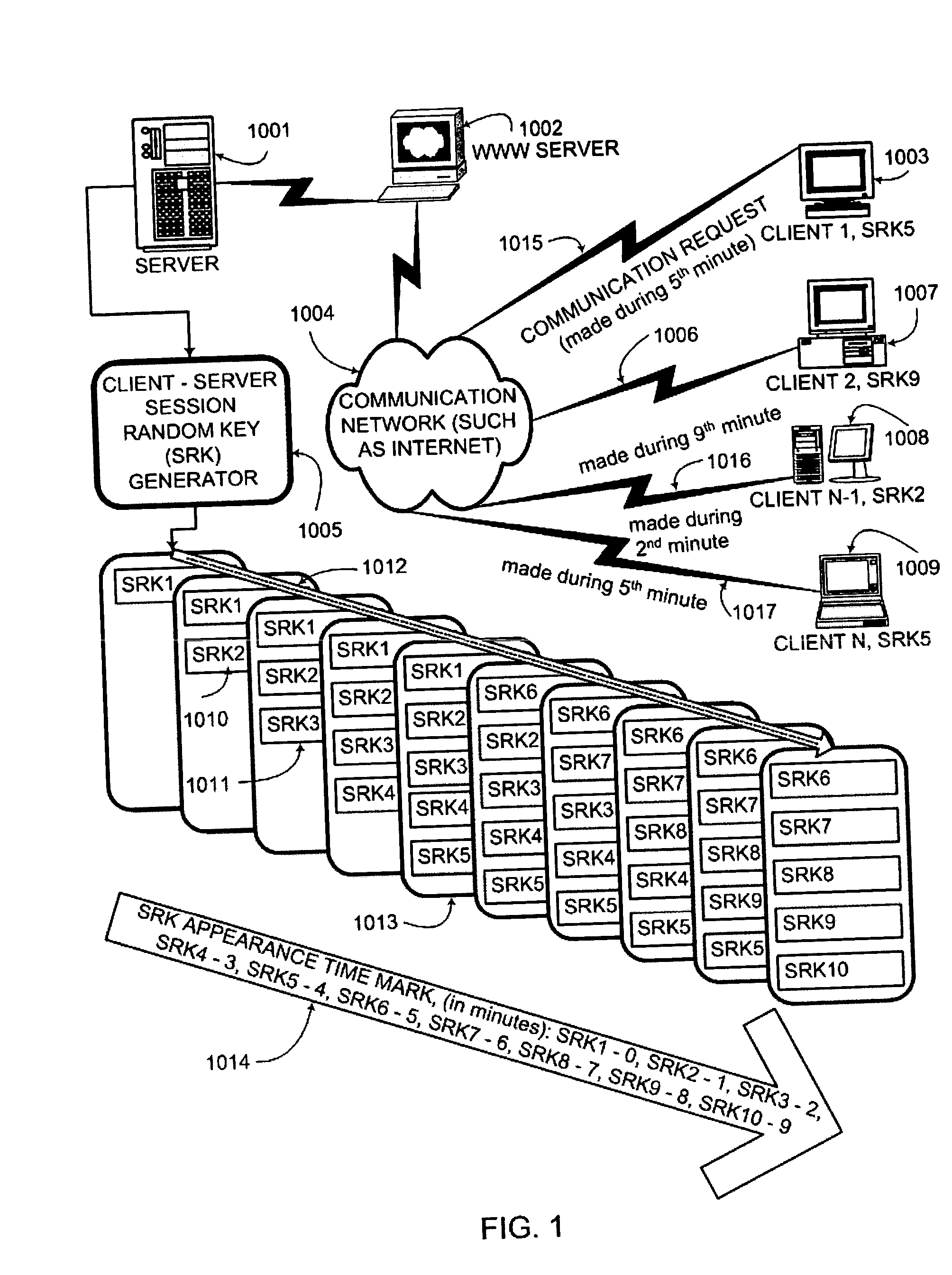
Key conversion method for communication session encryption and authentication system
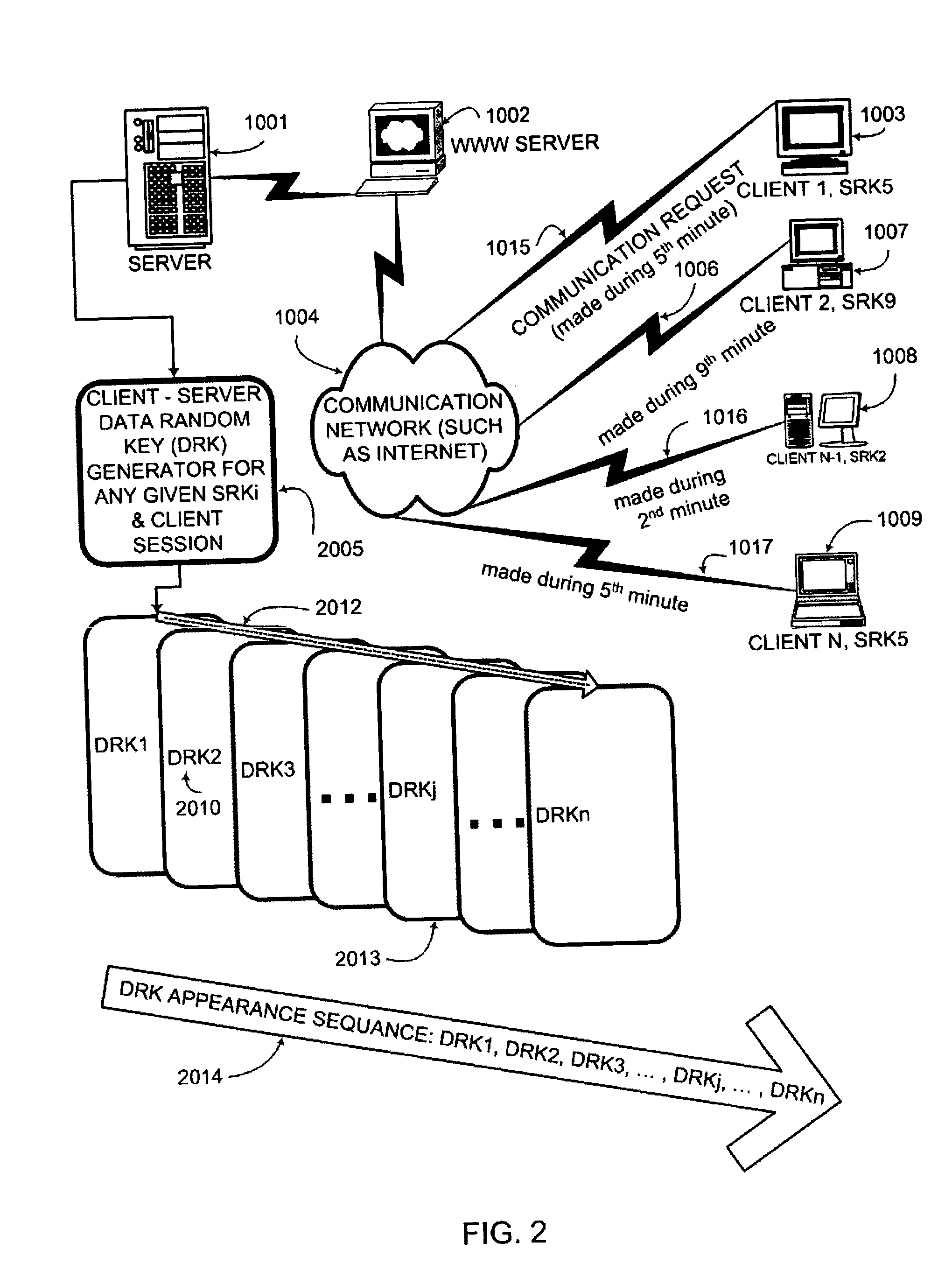
ActiveUS20050050322A1Secure EncryptionKey distribution for secure communicationUser identity/authority verificationAuthentication systemStrong authentication
An interactive mutual authentication protocol, which does not allow shared secrets to pass through untrusted communication media, integrates an encryption key management system into the authentication protocol. The server encrypts a particular data random key by first veiling the particular data random key using a first conversion array seeded by a shared secret, and then encrypting the veiled particular data random key. The client decrypts and unveils the particular data random key using the shared secret, and returns a similarly veiled version of the particular data random key using a second conversion array seeded by a shared secret. Access to the shared secret indicates authenticity of the stations. The procedure may be repeated for a second shared secret for strong authentication, without allowing shared secrets to pass via untrusted media.
Owner:AUTHERNATIVE INC
Preventing Unauthorized Account Access Using Compromised Login Credentials
ActiveUS20130254857A1Digital data processing detailsMultiple digital computer combinationsInternet privacyComputerized system
User login information submitted as part of an attempt to log into a computer system is evaluated for unauthorized or illegitimate use based on indicators of suspicious behavior. Example indicators of suspicious behavior include whether the login information is known to have been compromised, whether the login attempt originates from a network source or a physical source that has previously originated an attempt to log in using login information known to have been compromised, and whether multiple login attempts using the login information from multiple users has originated from the source. A suspicion index can be calculated based on the presence of the indicators of suspicious behavior. The system can require enhanced authentication based on the measurement of suspicious behavior.
Owner:META PLATFORMS INC
System and method for augmented user and site authentication from mobile devices
InactiveUS20090235346A1Strong authenticationMinimal inconvenienceDigital data processing detailsUser identity/authority verificationWeb browserInternet privacy
A system and method for augmented user and site authentication from mobile devices is disclosed herein. The system and method provides for the performing of strong authentication of users, whether human or otherwise, as well as of site authentication, which is optimized for use when such users access a system from a mobile device using a web browser or mini-web browser. In doing so the claimed invention utilizes multiple different heuristic algorithms and / or scoring values for device identification based on the type of mobile device, and may further identify the specific type of device attempting such access.
Owner:GREEN ARMOR SOLUTIONS
Strong authentication token with acoustic data input
InactiveUS20120221859A1Increase chanceSimilar costDigital data processing detailsUser identity/authority verificationCommon baseCommunication interface
Strong authentication tokens for generating dynamic security values having an acoustical input interface for acoustically receiving input data are disclosed. The tokens may also include an optical interface for receiving input data and may have a selection mechanism to select either the acoustical or the optical input interface to receive data. A communication interface may be provided to communicate with a removable security device such as a smart card and the token may be adapted to generate dynamic security values in cooperation with the removable security device. The acoustic signal received by the token may be modulated using a frequency shift keying modulation scheme using a plurality of coding frequencies to code the acoustical signal where each coding frequency may be an integer multiple of a common base frequency.
Owner:ONESPAN NORTH AMERICA INC
Strong authentication token generating one-time passwords and signatures upon server credential verification
ActiveUS8302167B2Transfer size reductionHighly secureDigital data processing detailsMultiple digital computer combinationsInternet privacyTransaction data
The invention defines a strong authentication token that remedies a vulnerability to a certain type of social engineering attacks, by authenticating the server or messages purporting to come from the server prior to generating a one-time password or transaction signature; and, in the case of the generation of a transaction signature, signing not only transaction values but also transaction context information and, prior to generating said transaction signature, presenting said transaction values and transaction context information to the user for the user to review and approve using trustworthy output and input means. It furthermore offers this authentication and review functionality without sacrificing user convenience or cost efficiency, by judiciously coding the transaction data to be signed, thus reducing the transmission size of information that has to be exchanged over the token's trustworthy interfaces.
Owner:ONESPAN NORTH AMERICA INC
Enhanced 2chk authentication security with query transactions
ActiveUS20130333008A1Increase flexibilityImprove protectionDigital data processing detailsMultiple digital computer combinationsBiological activationSecure communication channel
A security server receives a request of a user to activate a secure communications channel over the network and, in response, transmits an activation code for delivery to the user via another network. The security server receives an activation code from the user network device via the network, compares the received activation code with the transmitted activation code to validate the received activation code, and activates the secure communications channel based on the validation. The security server next receives a query including a question for the user from an enterprise represented on the network, transmits the received enterprise query to the user network device via the secure communications channel, and receives, from the user network device via the secure communications channel, a user answer to the transmitted enterprise query. The security server then transmits the received user answer to the enterprise to further authenticate the user to the enterprise.
Owner:PAYFONE
Method and apparatus for encoding and decoding data transmitted to an authentication token
ActiveUS20120221860A1Increase chanceSimilar costDigital data processing detailsUser identity/authority verificationCommunication interfaceSmart card
Methods and apparatus for encoding and decoding data transmitted acoustically and / or optically to strong authentication tokens to generate dynamic security values are disclosed. The tokens may also include a selection mechanism to select either an acoustical or an optical input interface to receive data. A communication interface may be provided to communicate with a removable security device such as a smart card and the token may be adapted to generate dynamic security values in cooperation with the removable security device.
Owner:ONESPAN NORTH AMERICA INC
Authentication scheme for ad hoc and sensor wireless networks
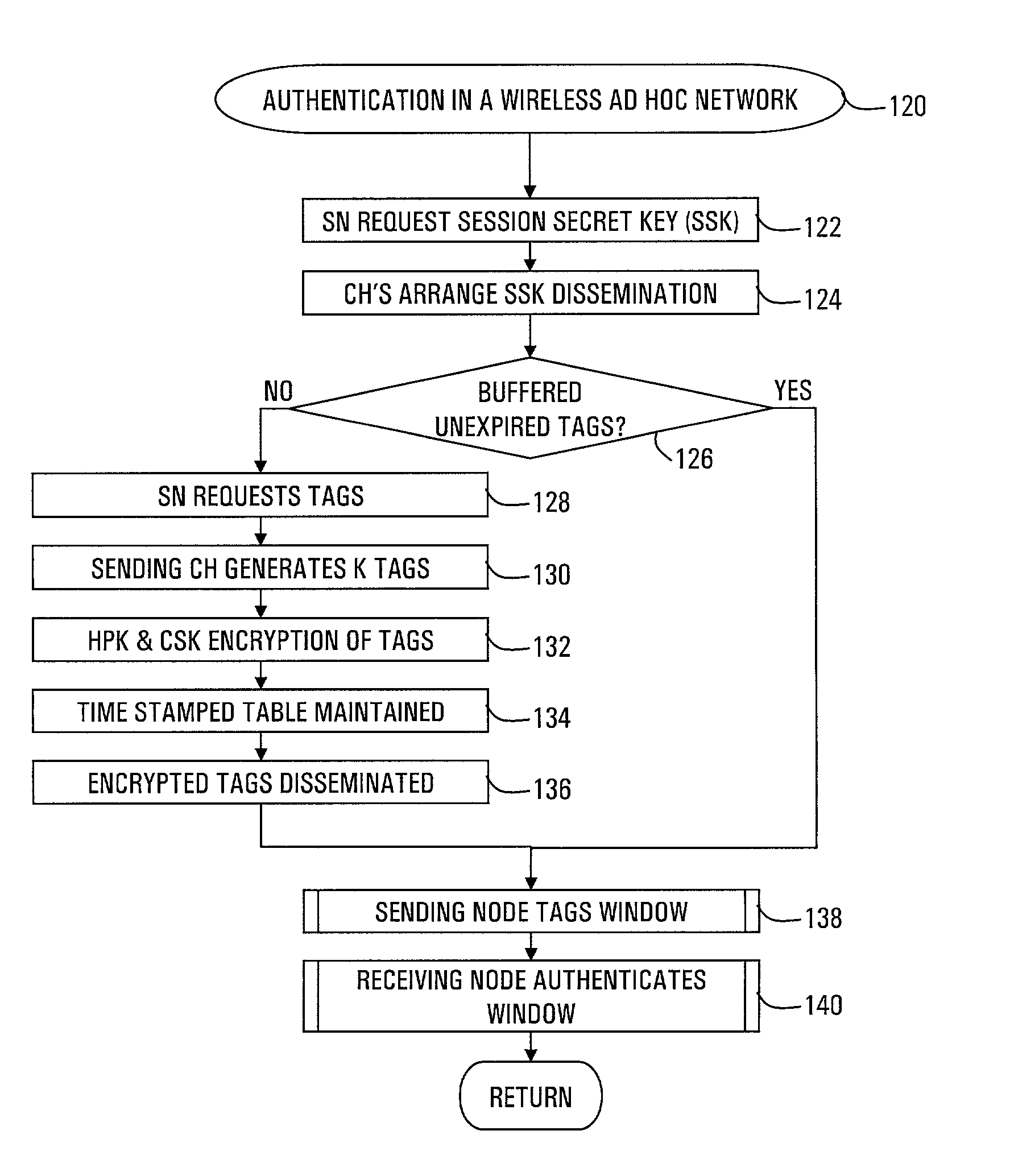
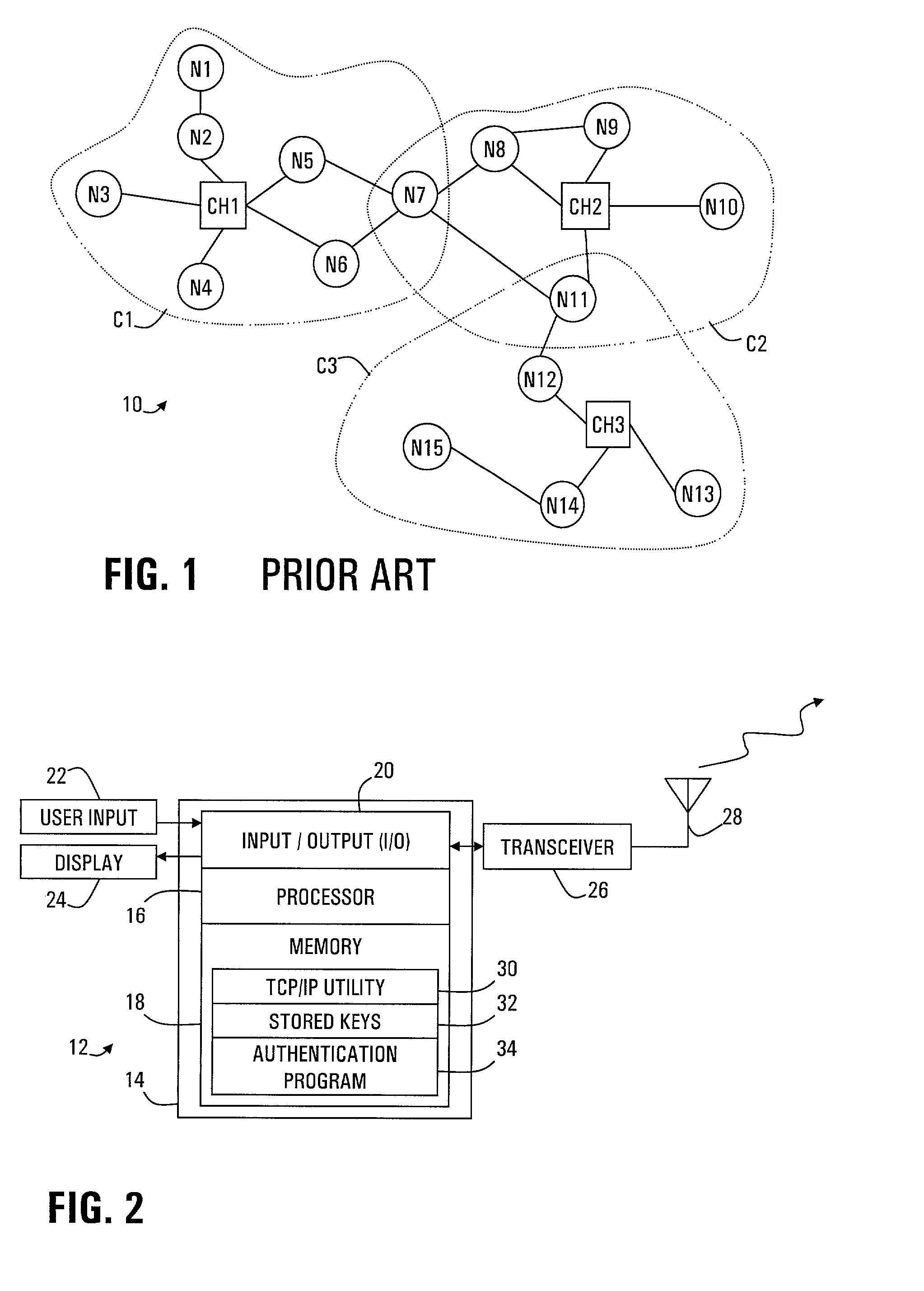
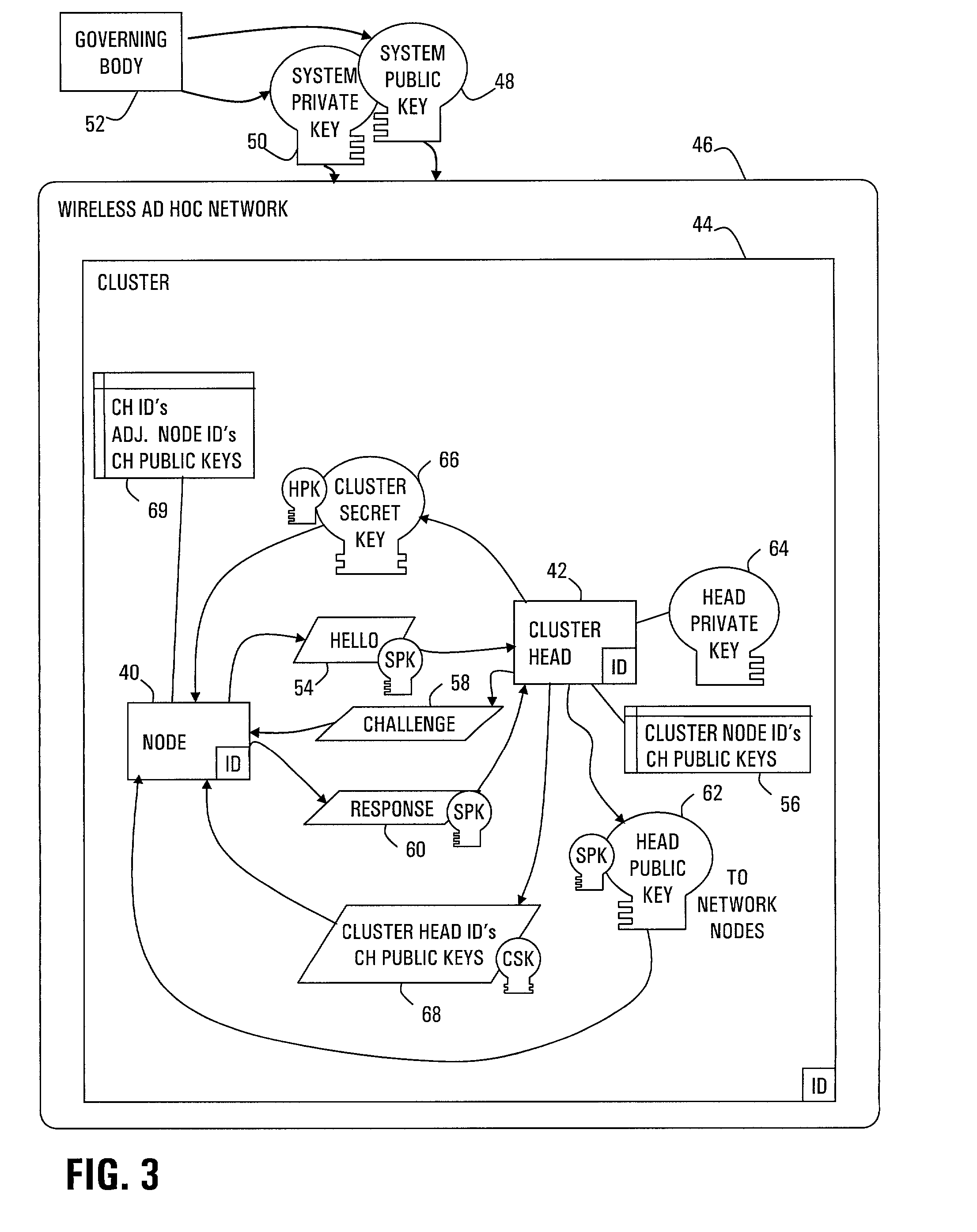
InactiveUS7096359B2Without excessive computational and power consuming overheadKey distribution for secure communicationUser identity/authority verificationDigital signatureChecksum
Strong authentication of packets sent between nodes of different clusters in a two-tier ad hoc network is provided by the cluster heads. Each cluster head authenticates nodes that enter the cluster. Thereafter, when a sending node requests a session from its cluster head with a receiving node in another cluster, the cluster head negotiates a session secret key (SSK) with the corresponding cluster head of the receiving node. Further, the cluster head provides authentication tags for the sending node to use with each packet. Each authentication tag is time-stamped, digitally signed by the cluster head, encrypted with the SSK, and includes indicators of message integrity, including a sequence number and TCP header field of checksum. The sending node further calculates a check result from a number of the authentication tags, encrypted with the SSK, so that the receiving node can authenticate the number of packets.
Owner:CINCINNATI UNIV OF
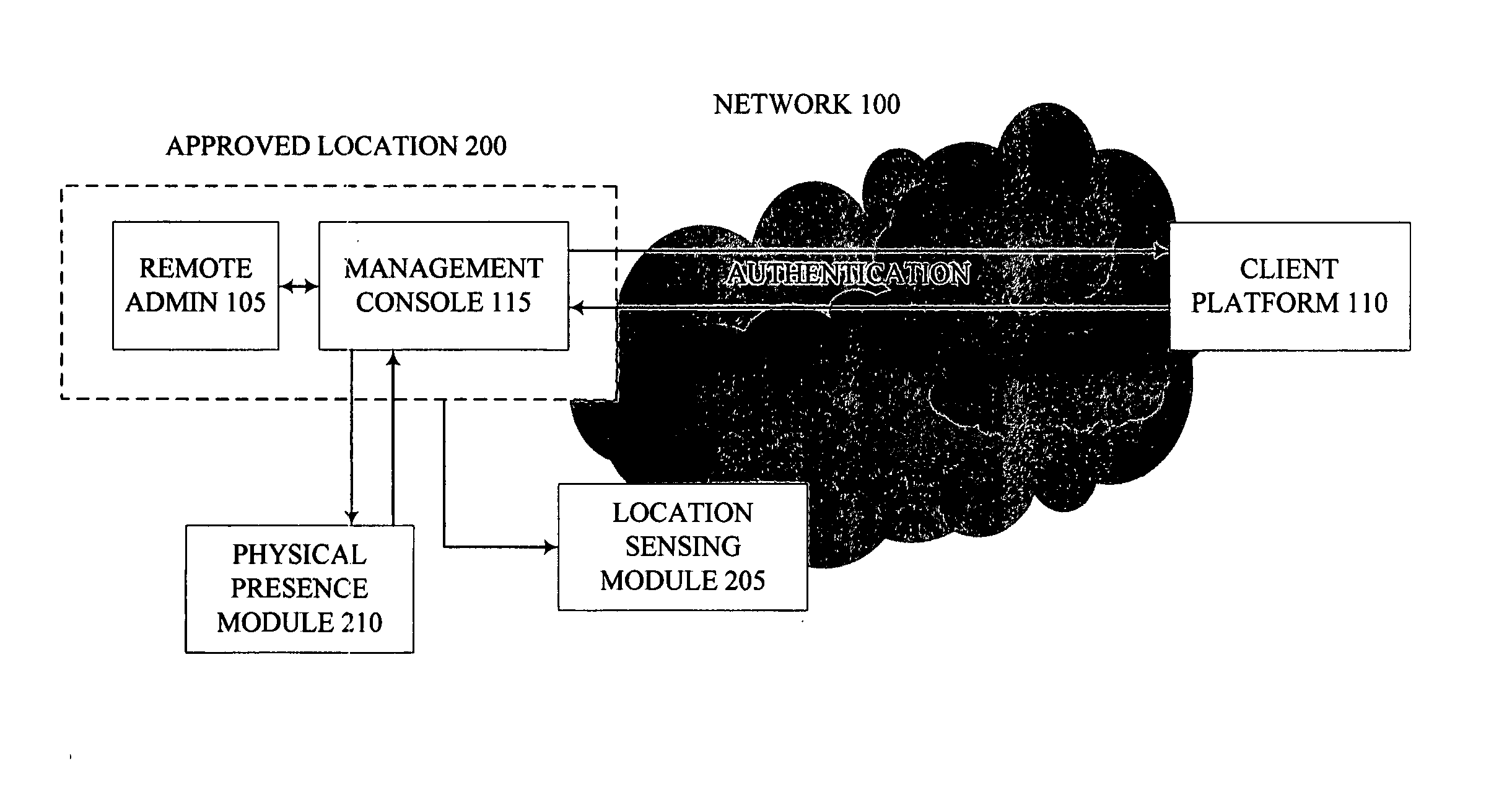
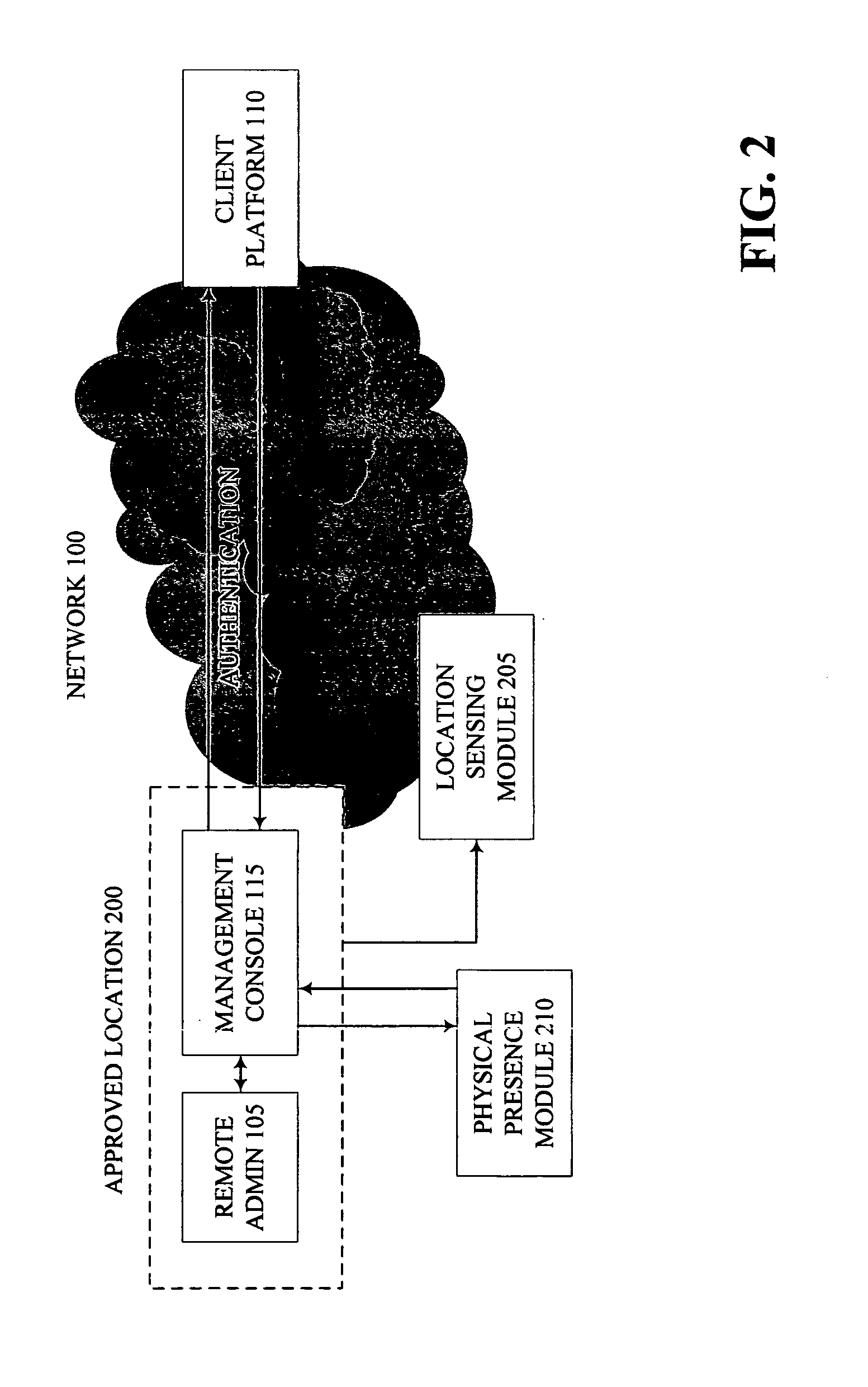
Method, apparatus and system for providing stronger authentication by extending physical presence to a remote entity
InactiveUS20070143826A1Digital data processing detailsUser identity/authority verificationStrong authenticationAuthentication
A method, apparatus and system enable secure remote authentication. According to embodiments of the present invention, a remote administrator may be authenticated by accessing an approved secure location, transmitting location information with an access request and providing proof of physical presence in the access request. Additionally, in one embodiment, the location information and / or proof of presence may be signed by a security key to further tamper-proof the remote administrator's identity.
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com