Proxy based adaptive two factor authentication having automated enrollment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
embodiment
PREFERRED EMBODIMENT
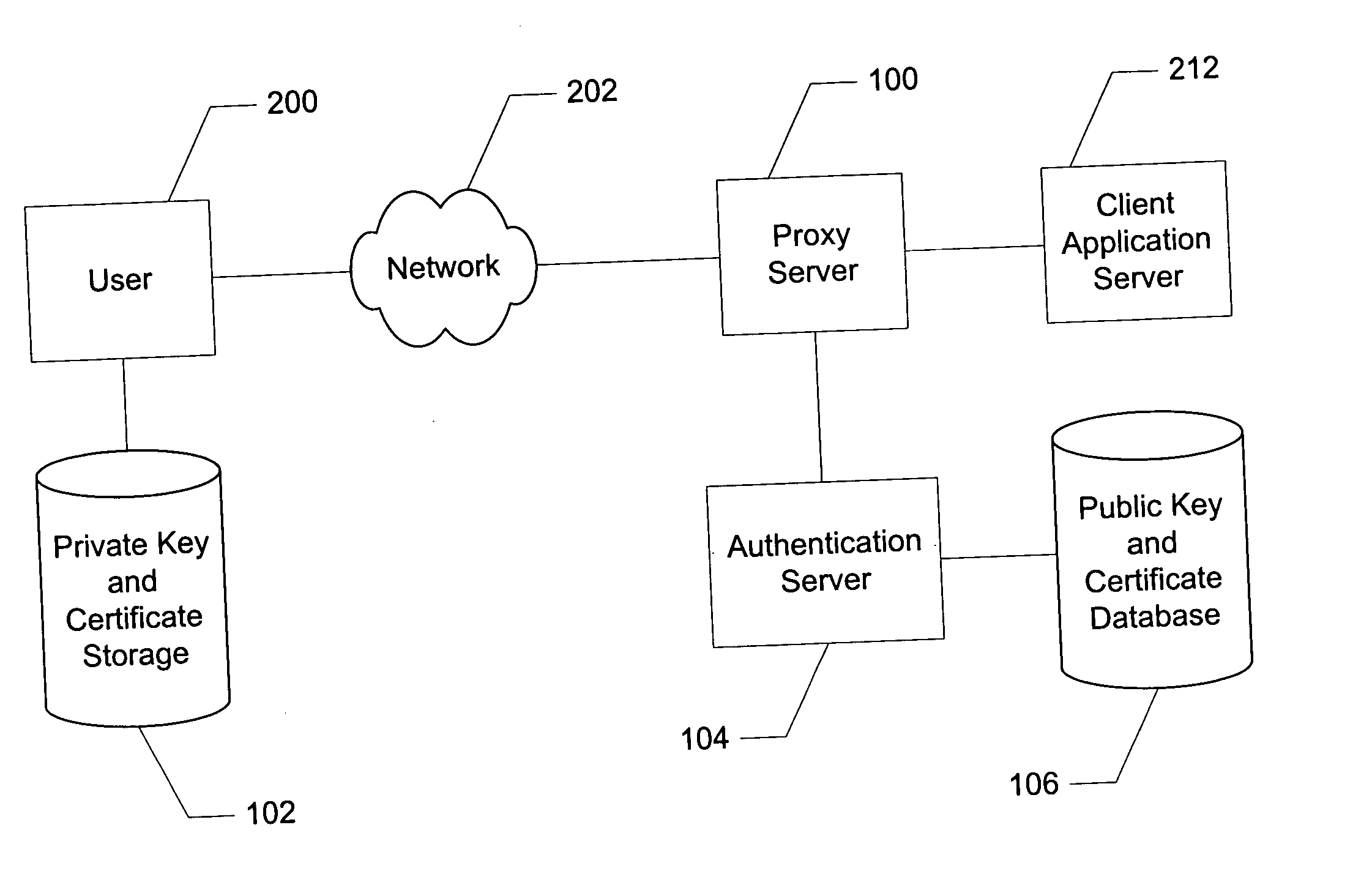
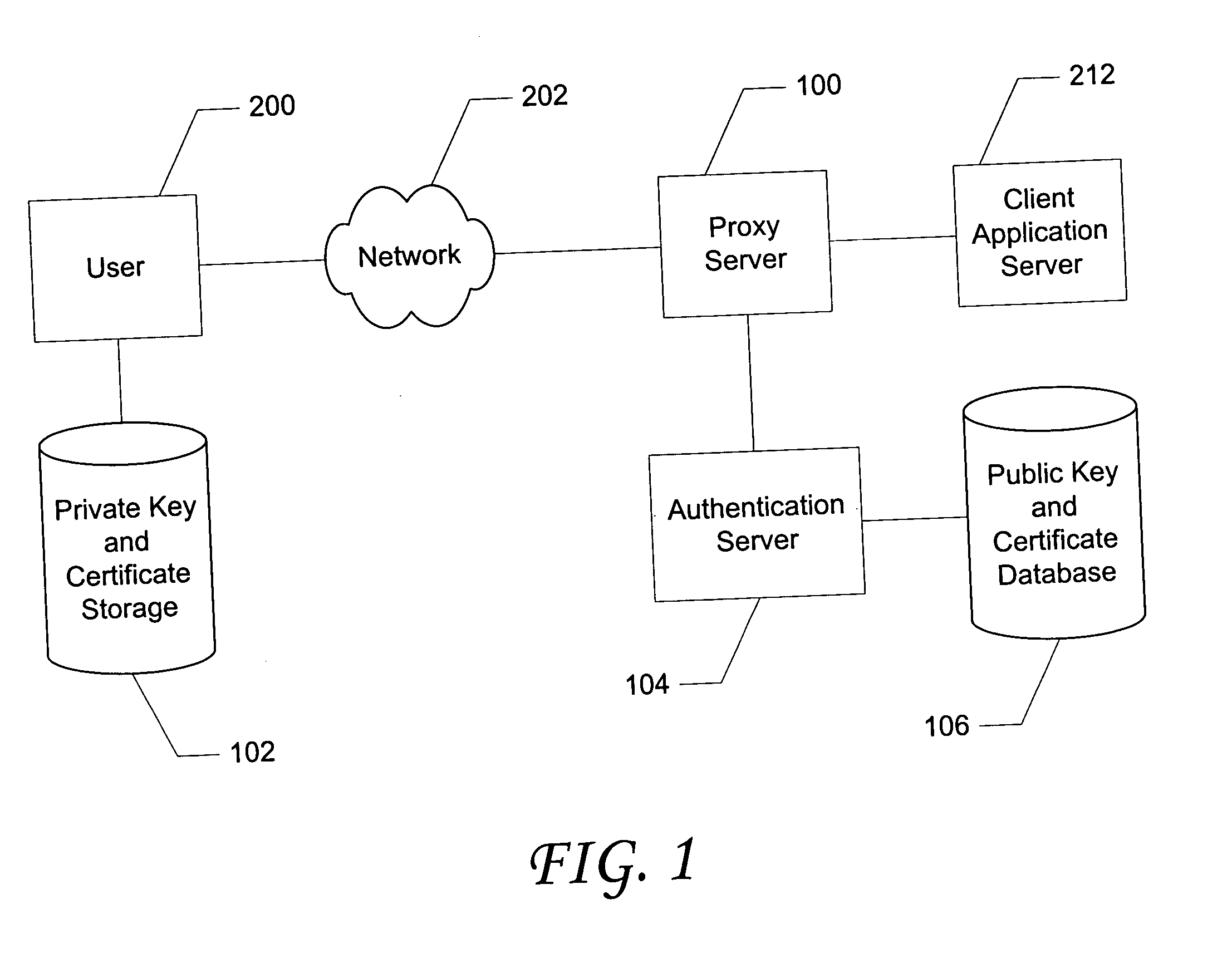
[0042] The disclosed invention is described below with reference to the accompanying figures in which like reference numbers designate like parts. Generally, numbers in the 200's refer to prior art elements or elements in the surrounding environment while numbers in the 100's refer to elements of the invention.
[0043] Overview
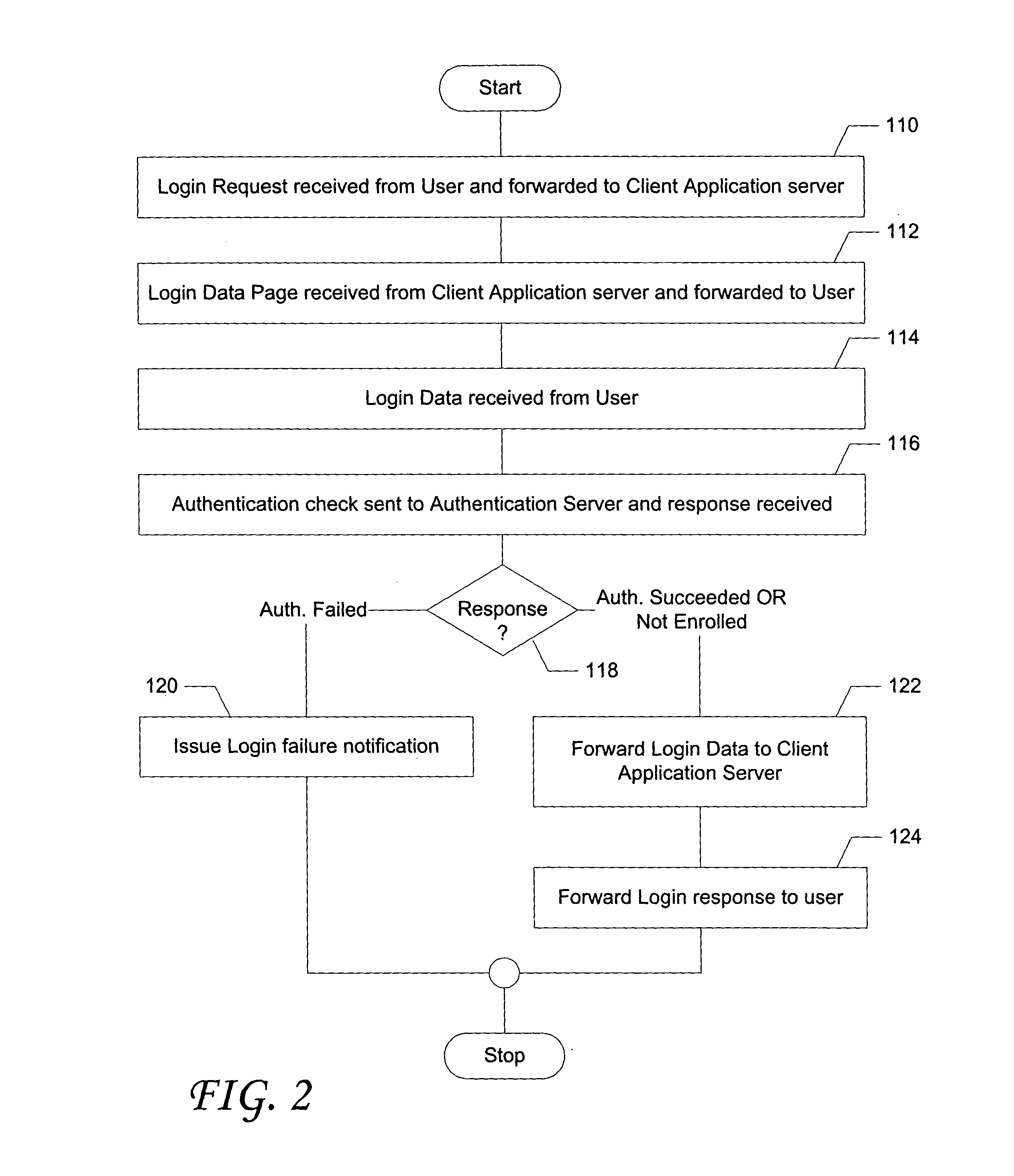
[0044] The inventive system presents a user friendly strong authentication system, and method of using, which is almost entirely transparent to the user. Activation of strong authentication is via one-click enrollment, after which authentication is performed by monitoring and intercepting messages used in the standard login sequence. User validation for purposes of enrollment is achieved by confirming successful logon to a client application. Encryption keys and a digital certificate are generated and stored through interaction between the user's browser and elements of the inventive system with no user involvement.
[0045] Until the user el...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com