Patents
Literature
49681 results about "Authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Authentication (from Greek: αὐθεντικός authentikos, "real, genuine", from αὐθέντης authentes, "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating personal identity documents, verifying the authenticity of a website with a digital certificate, determining the age of an artifact by carbon dating, or ensuring that a product or document is not counterfeit.
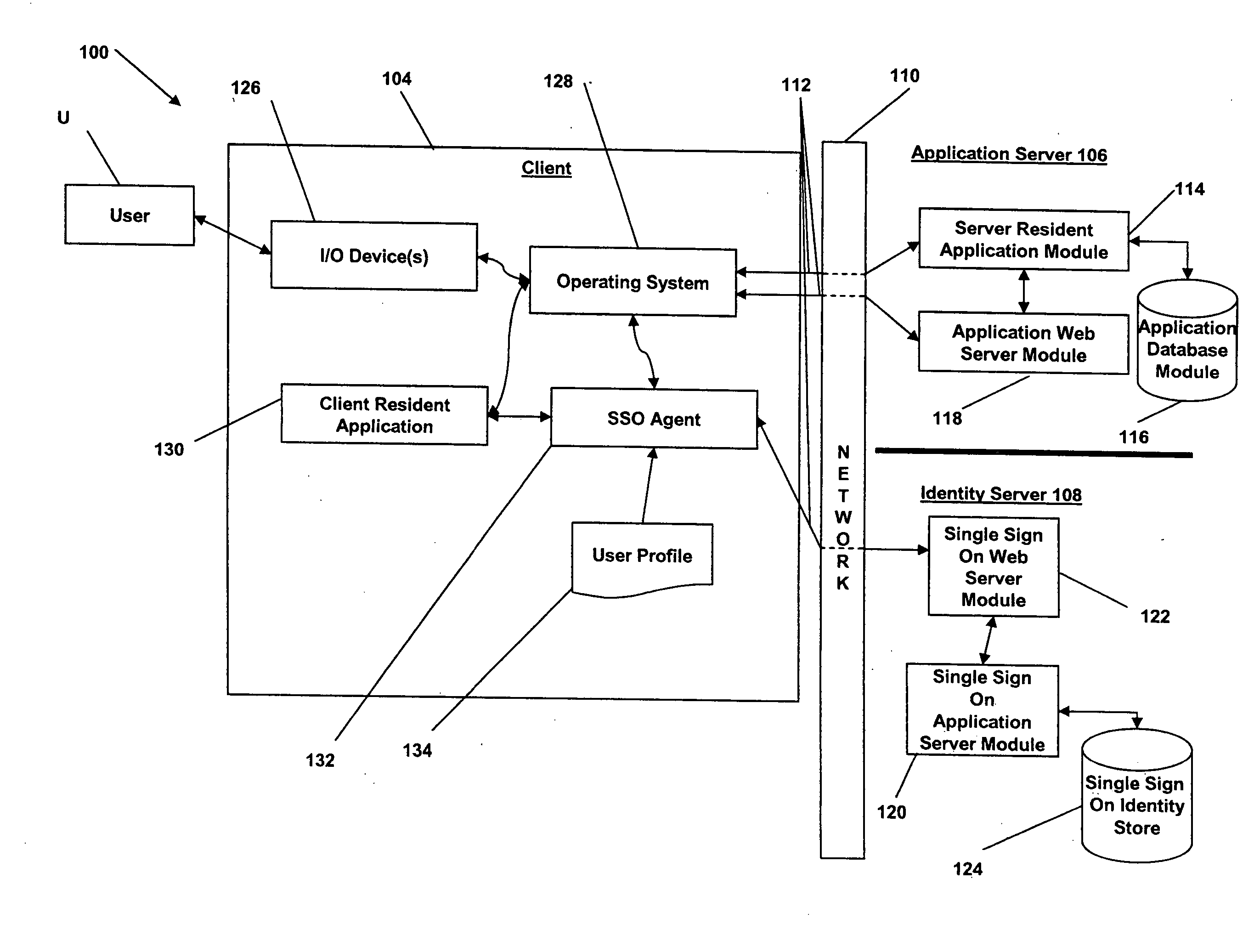
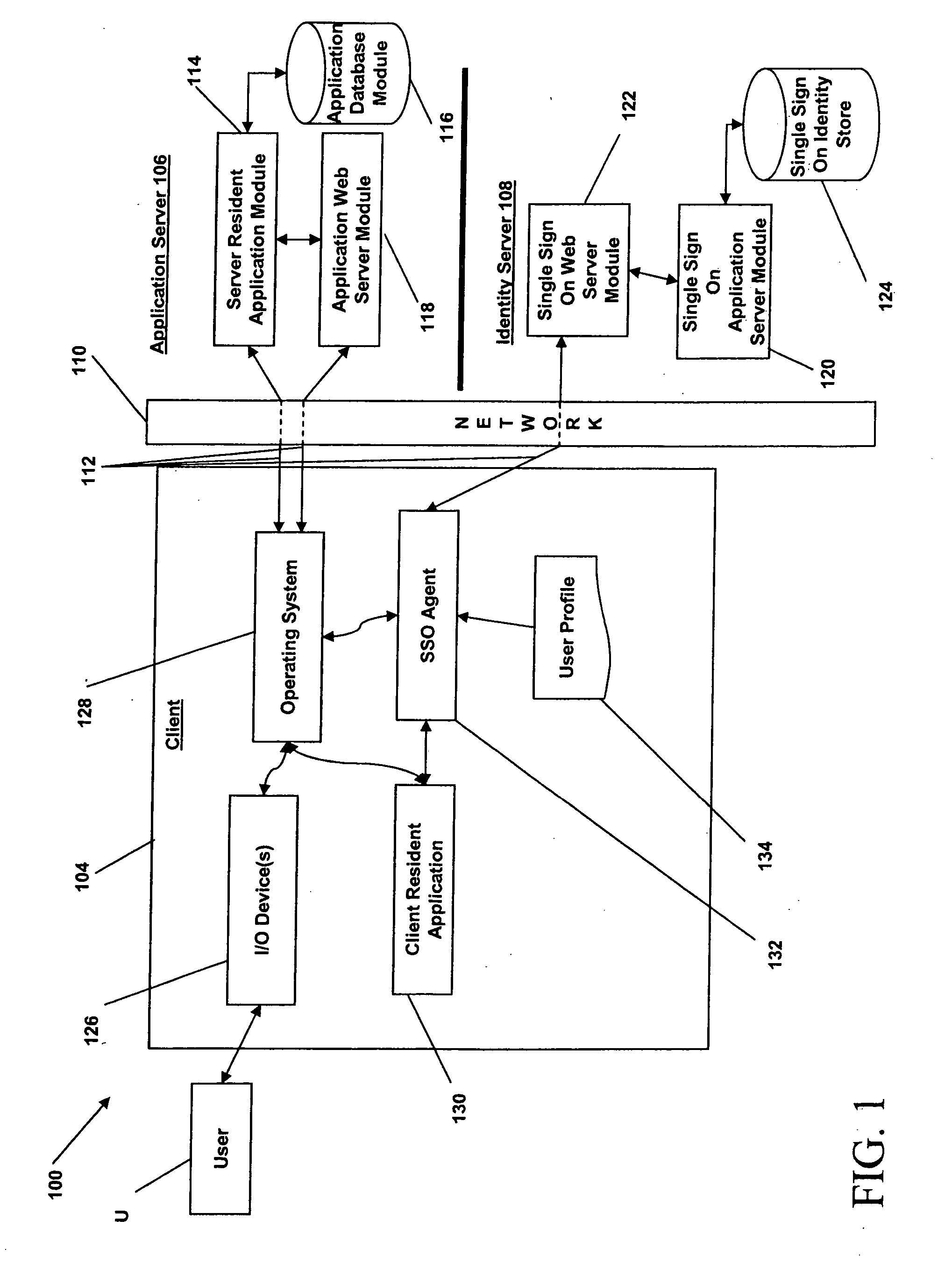
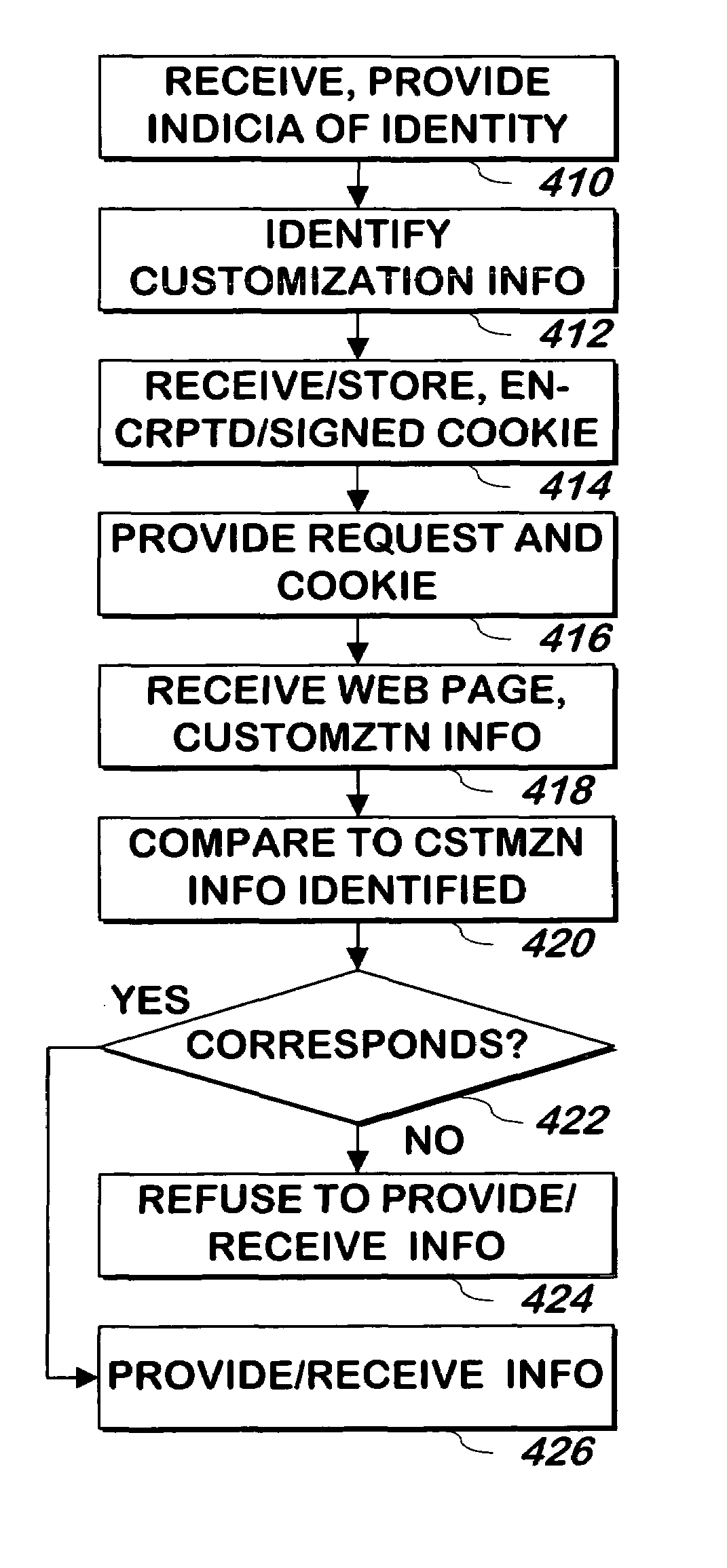
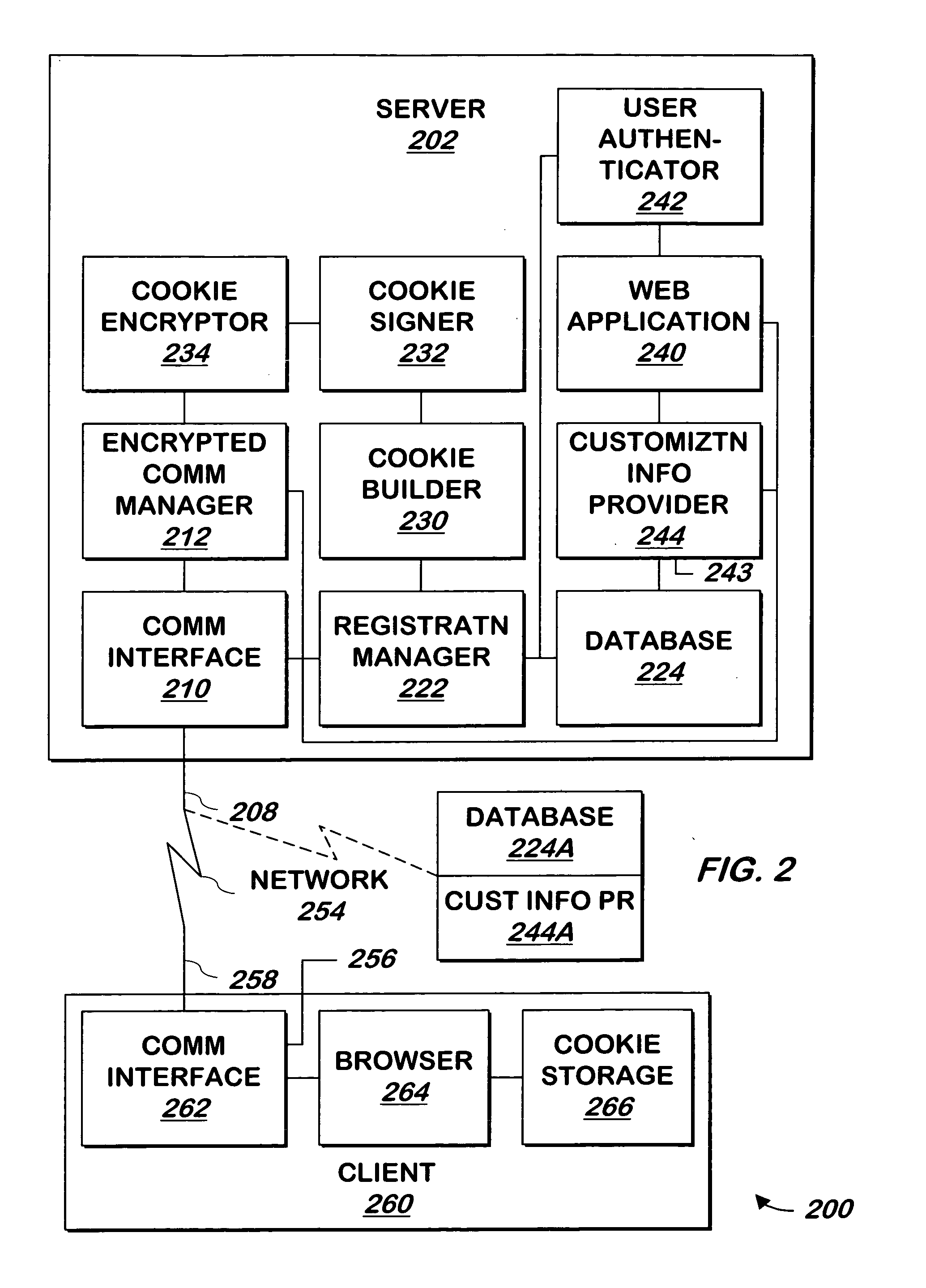
Managing user information on an e-commerce system
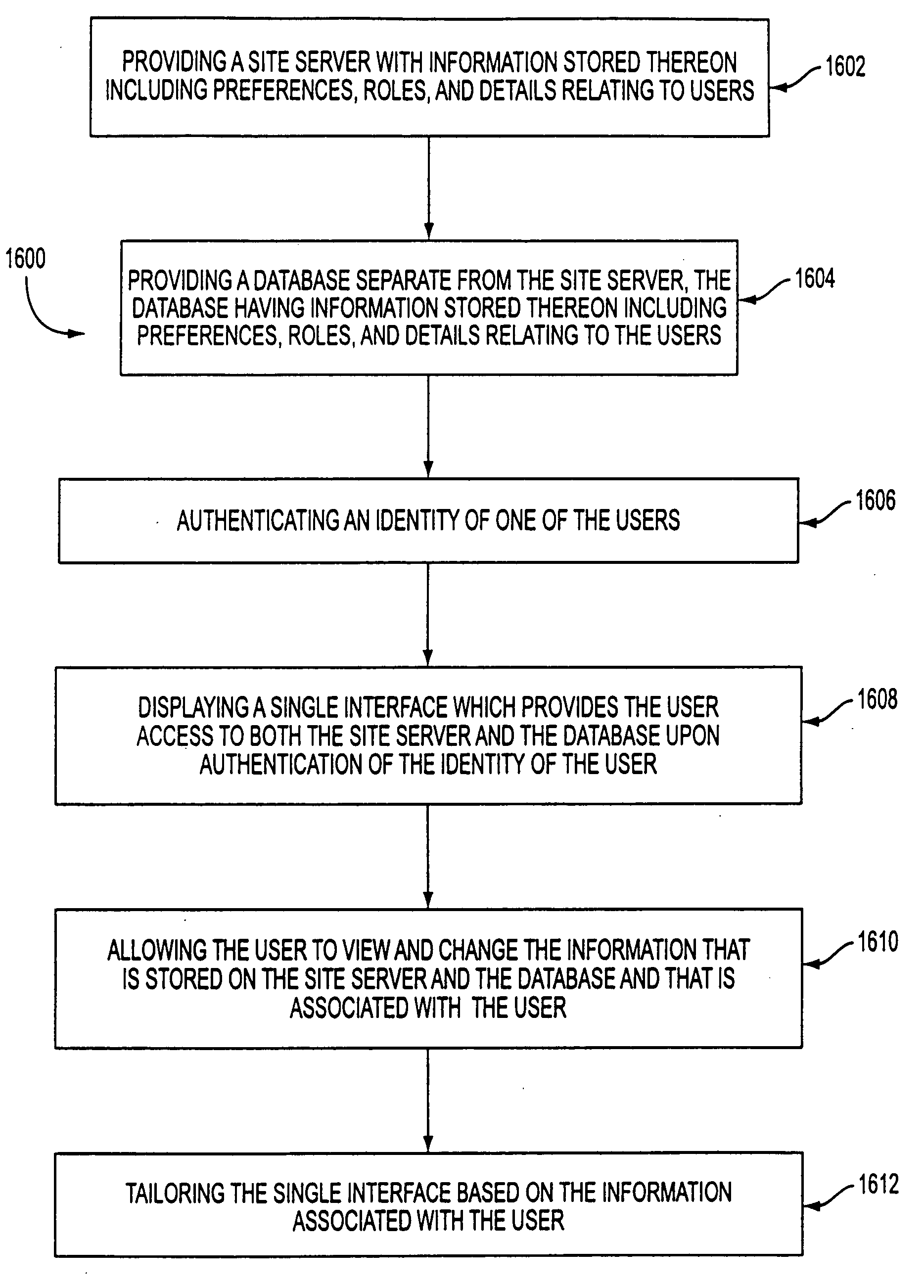
The present invention provides for the management of user information of both site server and regular web site users. A site server is provided with information stored thereon including preferences, roles, and details related to users. A database separate from the site server is also provided. The database has information stored thereon including preferences, roles, and details relating to the users. An identity of one of the users is authenticated. A single interface is displayed which provides the user access to both the site server and the database upon authentication of the identity of the user. The user is allowed to view and change the information that is stored on the site server and the database and that is associated with the user. The single interface is tailored based on the information associated with the user.
Owner:ACCENTURE GLOBAL SERVICES LTD
Enhanced syndication
InactiveUS20060173985A1Excellent ease of useRichly-functionedMechanical/radiation/invasive therapiesTechnology managementData feedData stream
A variety of tools and techniques are disclosed for managing, viewing, publishing, searching, clustering, and otherwise manipulating data streams. Data streams such as RSS data feeds may be searched, aggregated, and filtered into a processed feed. The processed feed, along with rules used to process the feed may be shared in a number of ways. A data feed management system may provide an integrated user interface through which a user may manage feeds, including searching for new feeds, managing and filtering current feeds, modifying a user profile, and sharing feeds and feed configuration data with other users. A server may provide a complementary search engine to locate new feeds and to store and / or index items or posts in known feeds. Together, these technologies may provide a richly-functioned feed management system and greater ease of use for individuals in managing large numbers of feeds and large amounts of data in feeds. Additional functional layers may provide for authentication, security, and privacy, metadata creation and management, and social networking features. Using the management tools and additional functionality, a syndicated data stream system may provide a platform for a wide array of useful consumer and business applications.
Owner:NEWSILIKE MEDIA GROUP
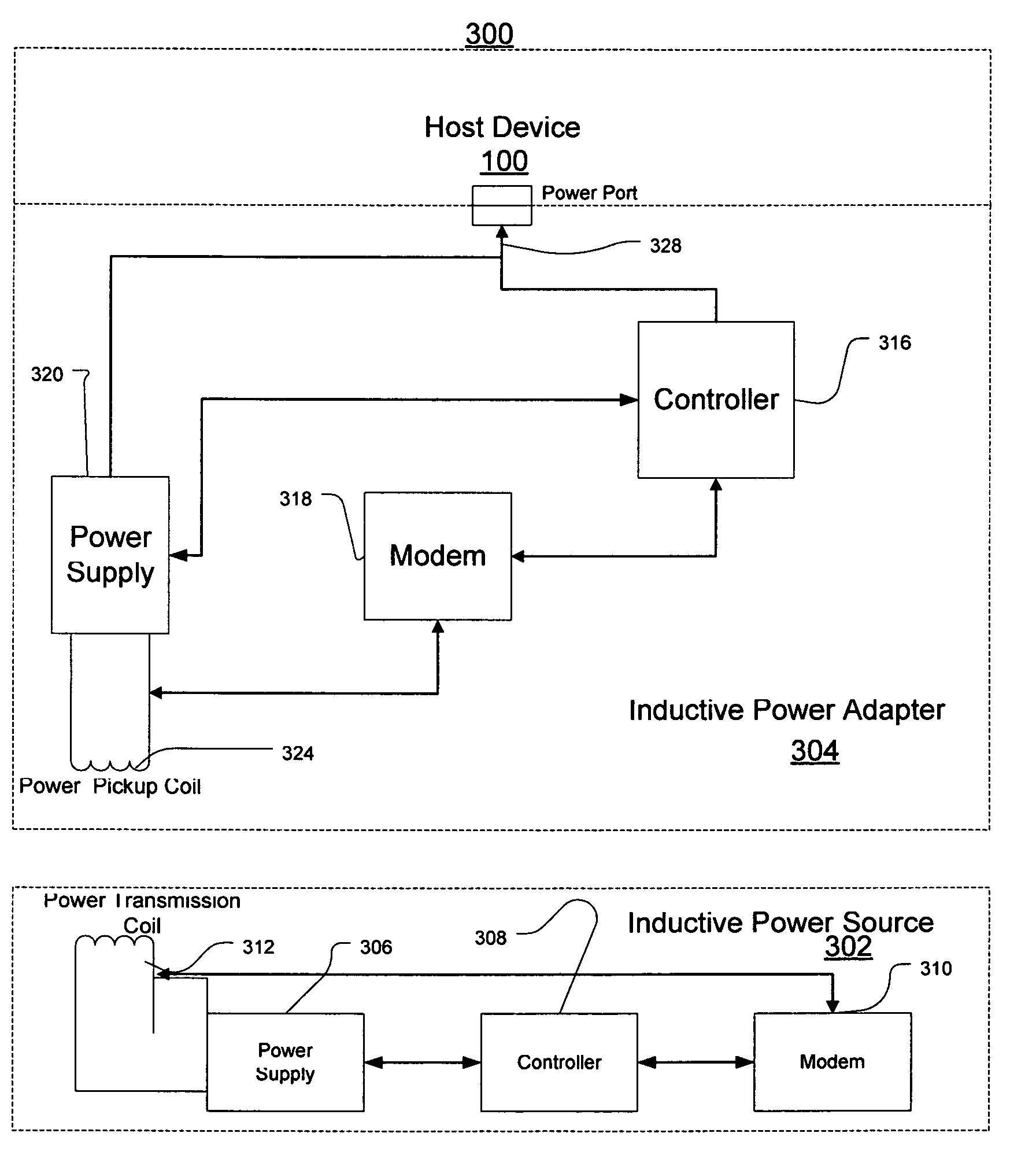
Inductive power adapter
ActiveUS7378817B2Enabling user convenienceMaximizes flexibility and efficiency and safetyVolume/mass flow measurementPower supply for data processingElectric power systemComputerized system
Owner:MICROSOFT TECH LICENSING LLC
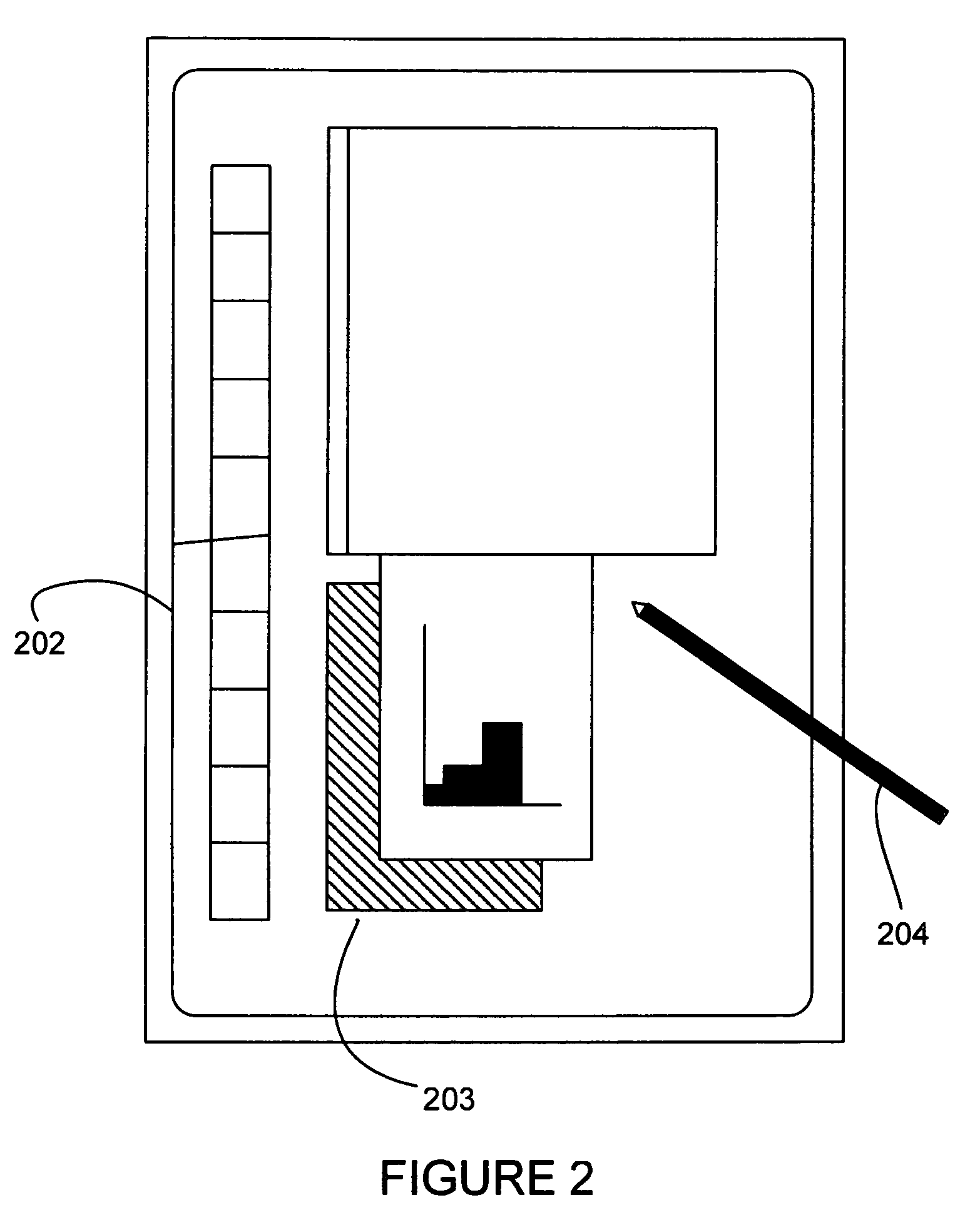
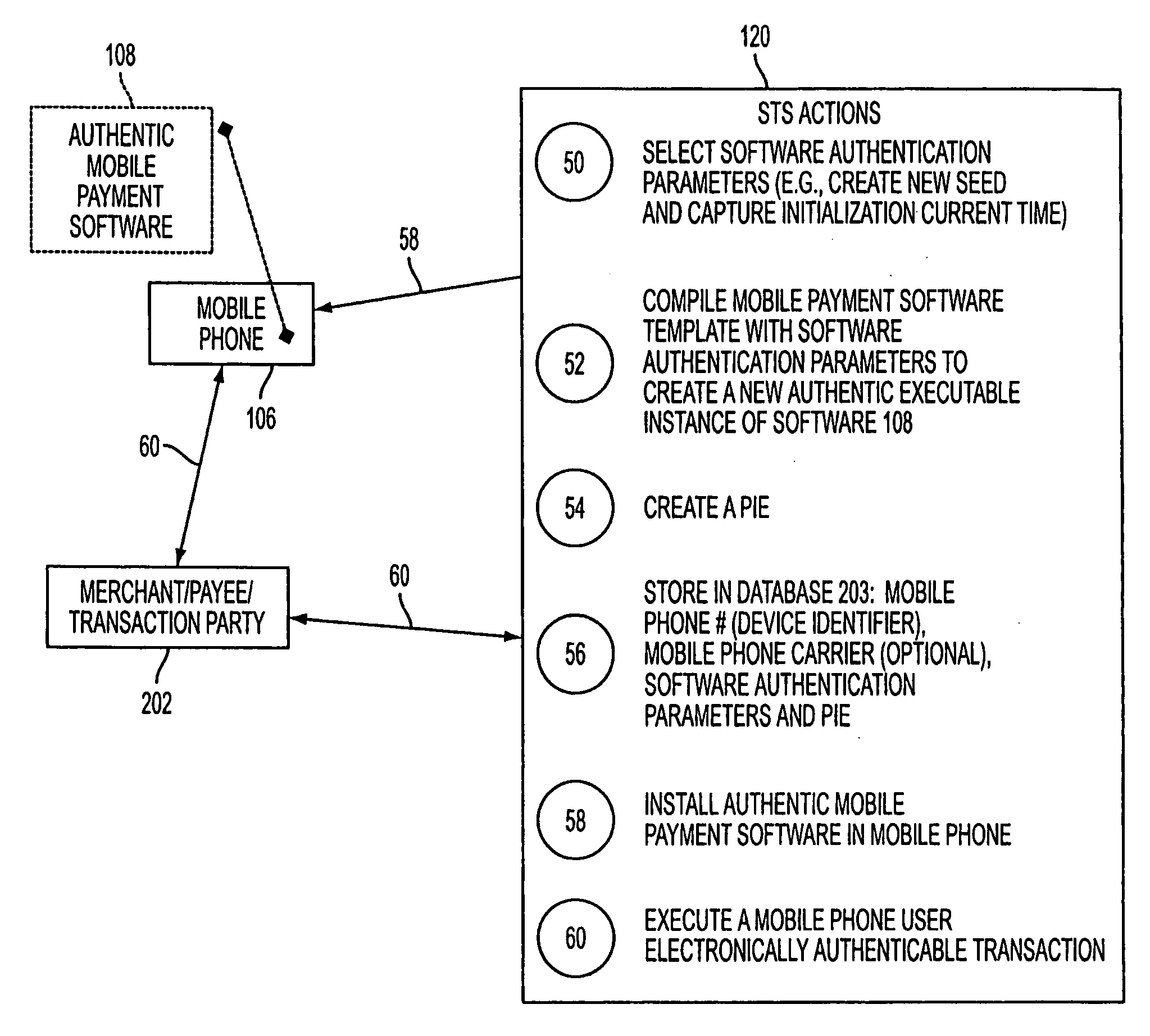
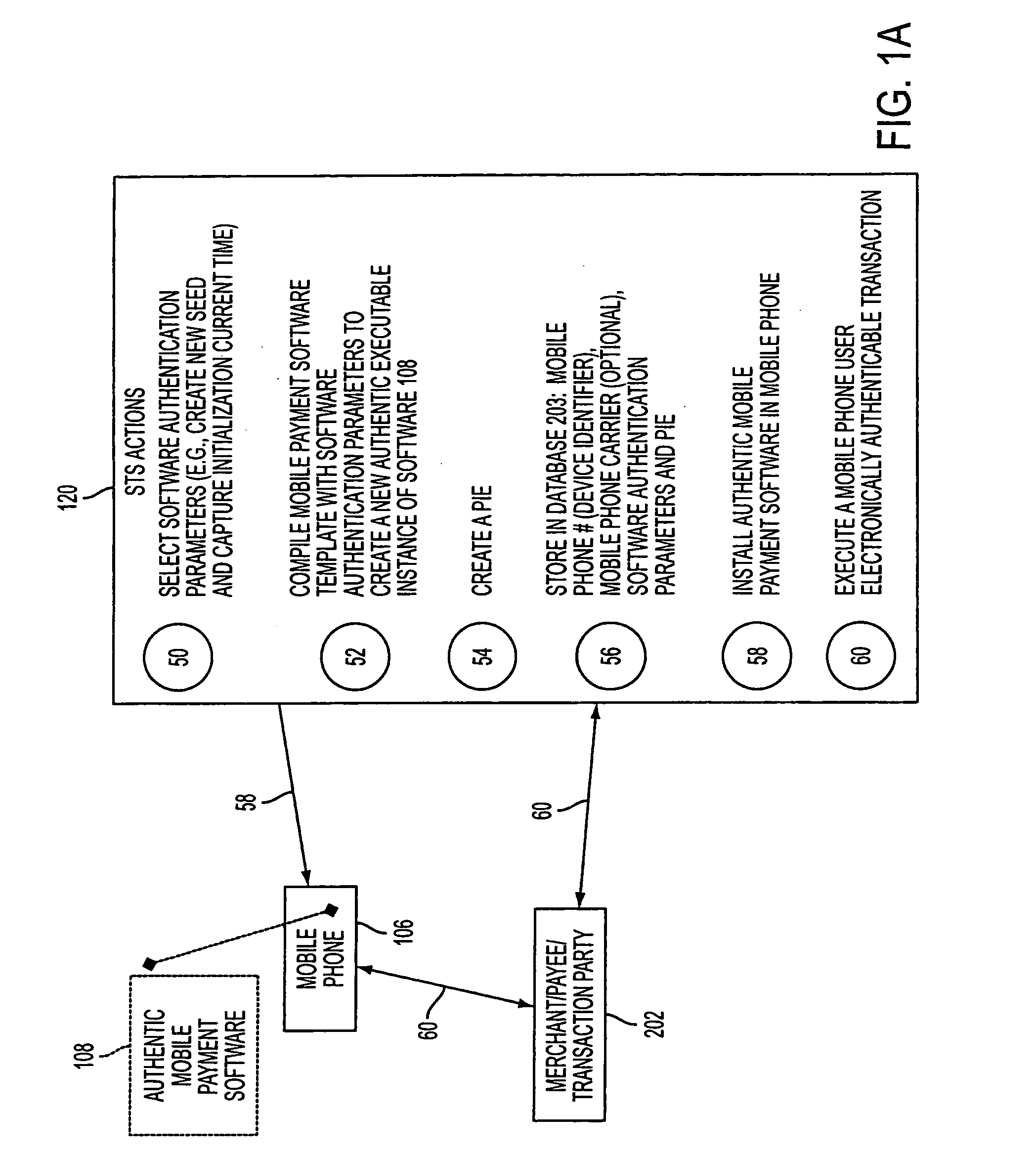
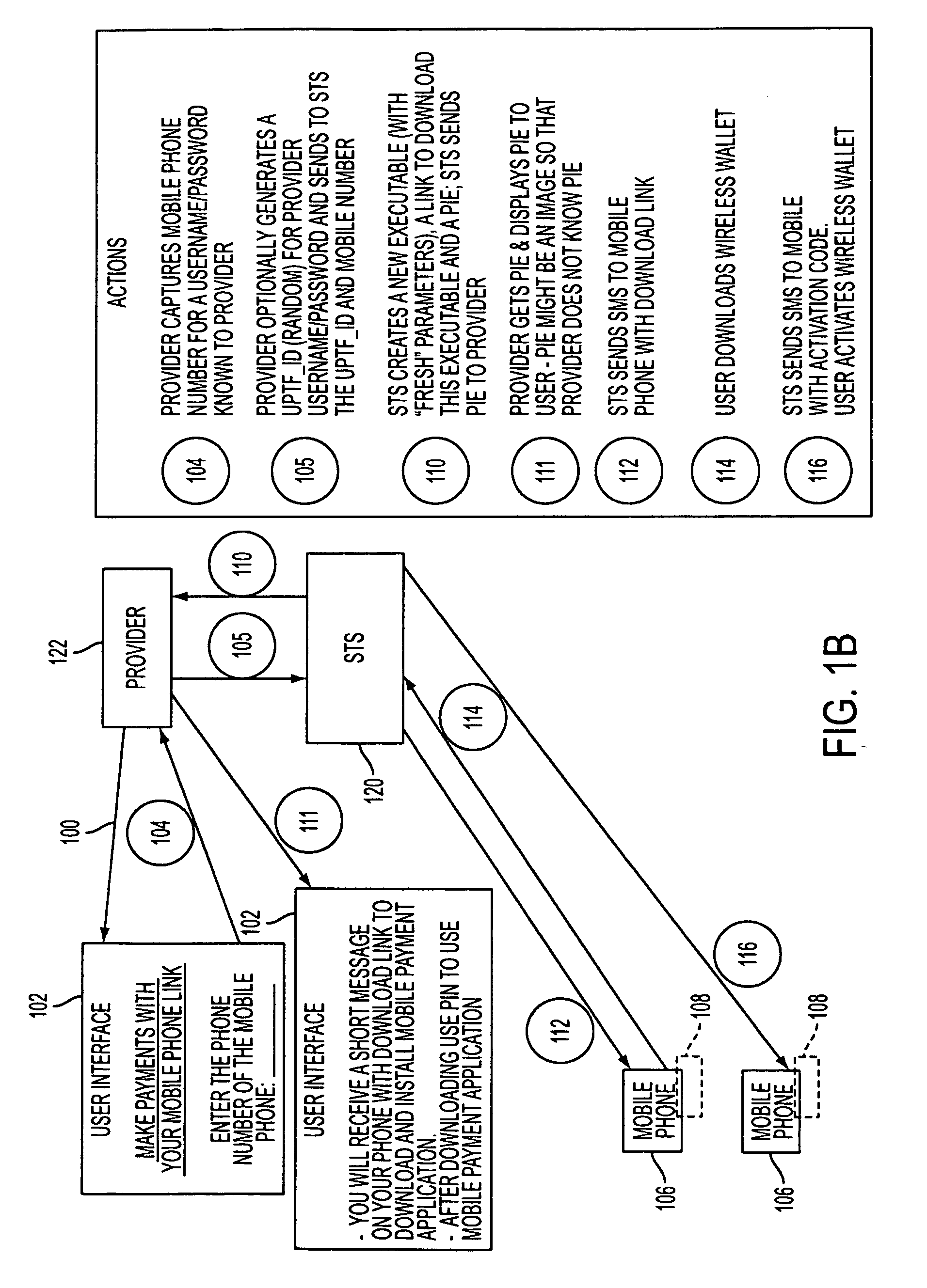
Wireless wallet
A mobile phone system and method of initializing, at a secure transaction server (STS), a mobile payment software with a software authentication parameter, as an authentic mobile payment software; providing an STS correlation between a personal identification entry (PIE) and the authentic mobile payment software; installing, in a mobile phone, the authentic mobile payment software; and inputting, by a user, the PIE to the installed authentic mobile payment software to generate according to the PIE and the software authentication parameter a transformed secure authenticable mobile phone cashless monetary transaction over the mobile phone network, as a mobile phone wireless wallet of the user of the mobile phone. The mobile phone authenticable cashless monetary transaction is performed according to an agreement view(s) protocol.
Owner:PCMS HOLDINGS INC
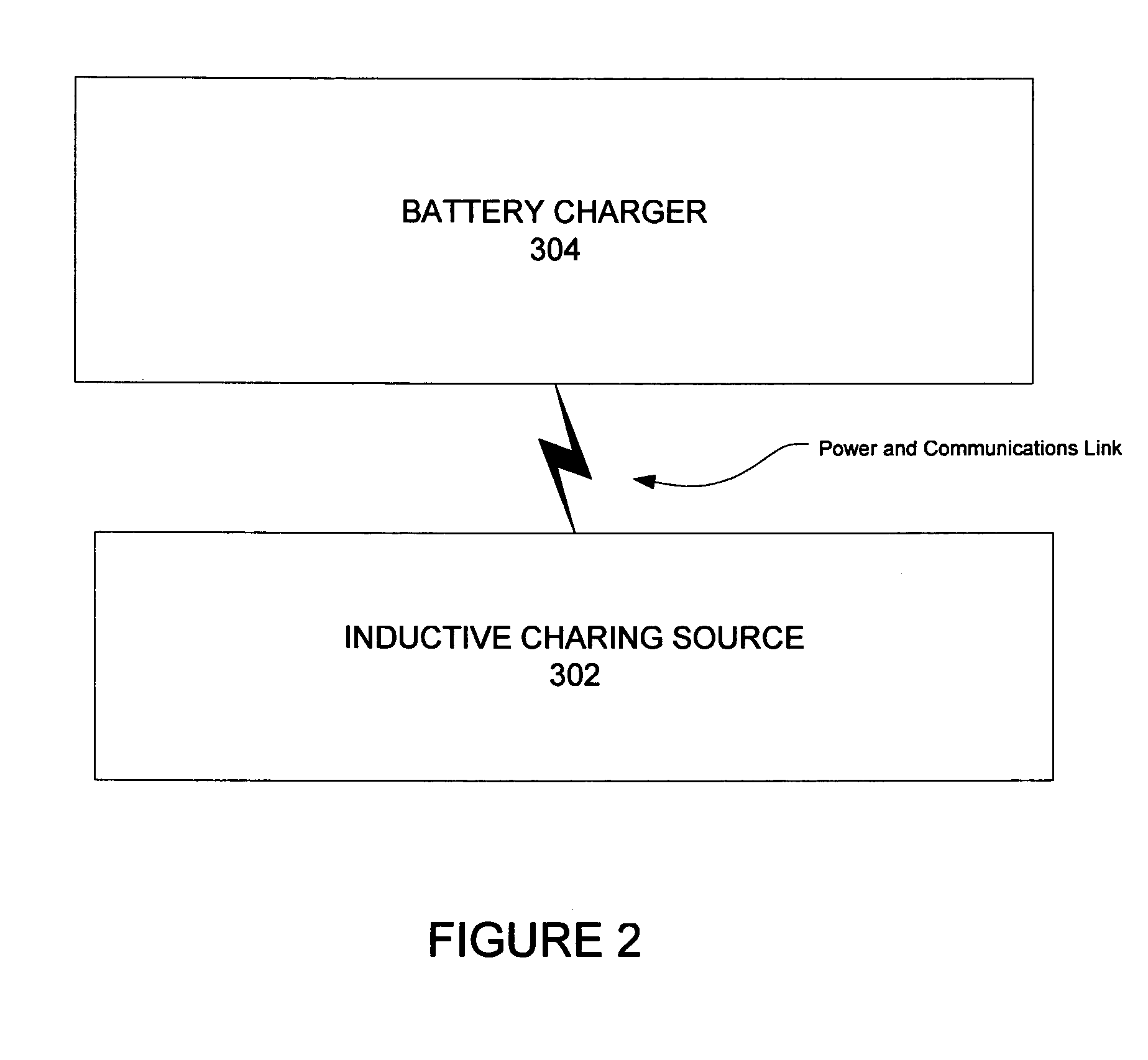
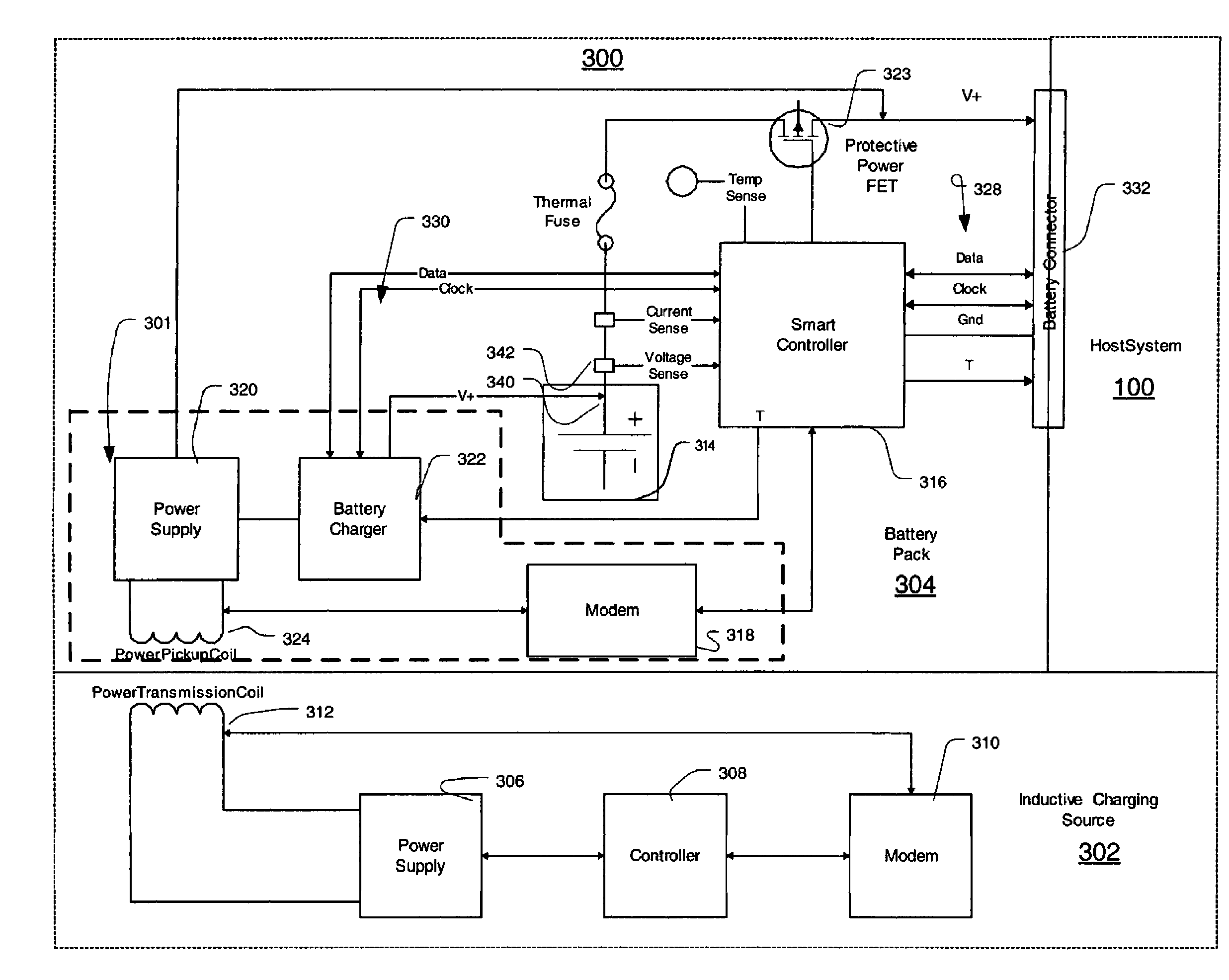
Inductive battery charger
InactiveUS7375493B2Circuit authenticationVolume/mass flow measurementElectrical batteryReceiver coil
An inductive charging system transfers energy by inductively coupling a source coil on a power source to a receiver coil for a battery charger. Source current may be received in the battery charger and converted for charging a battery pack. A wireless communication arrangement may also provide for authentication of devices that are allowed by the source to be powered or otherwise charged.
Owner:MICROSOFT TECH LICENSING LLC
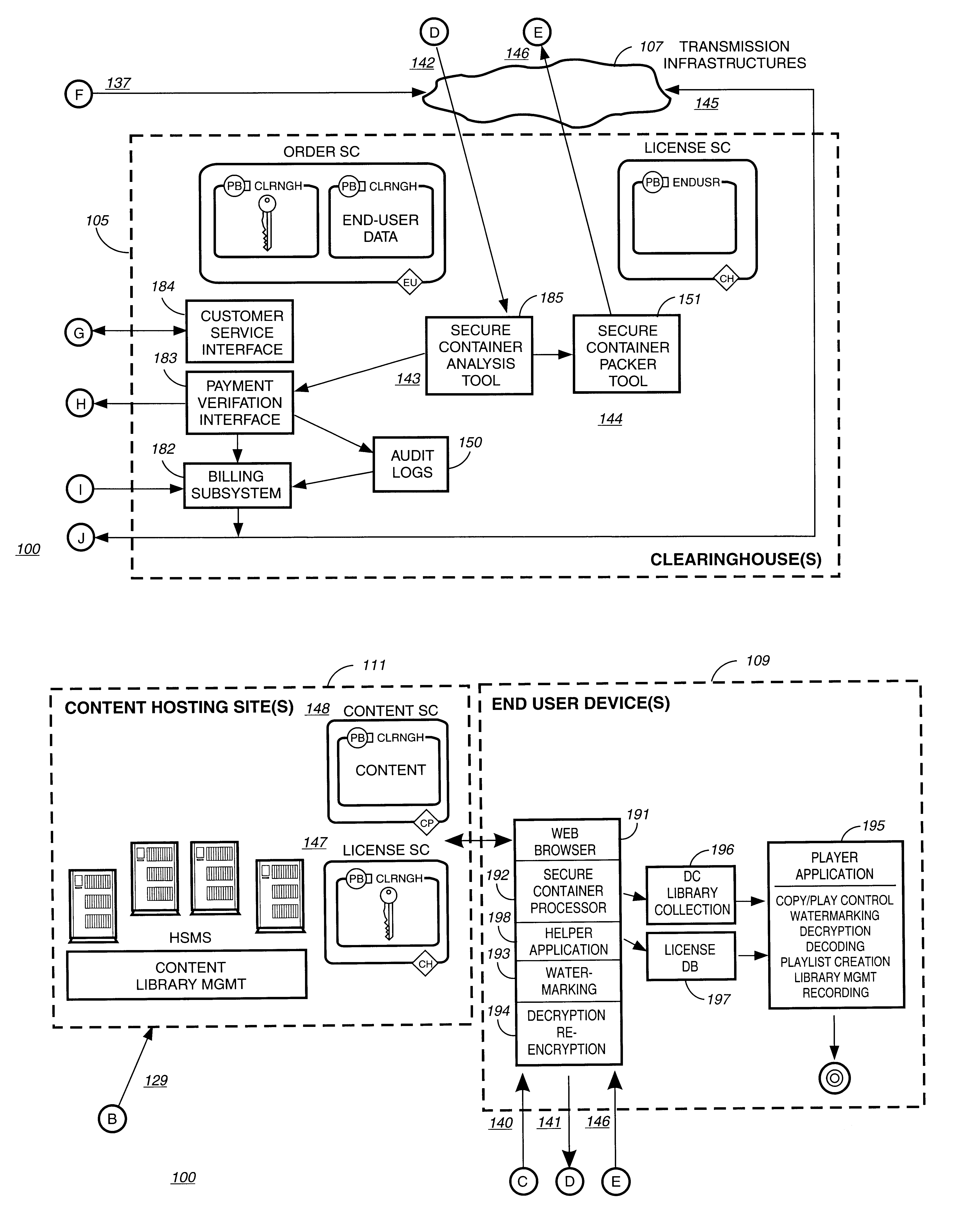
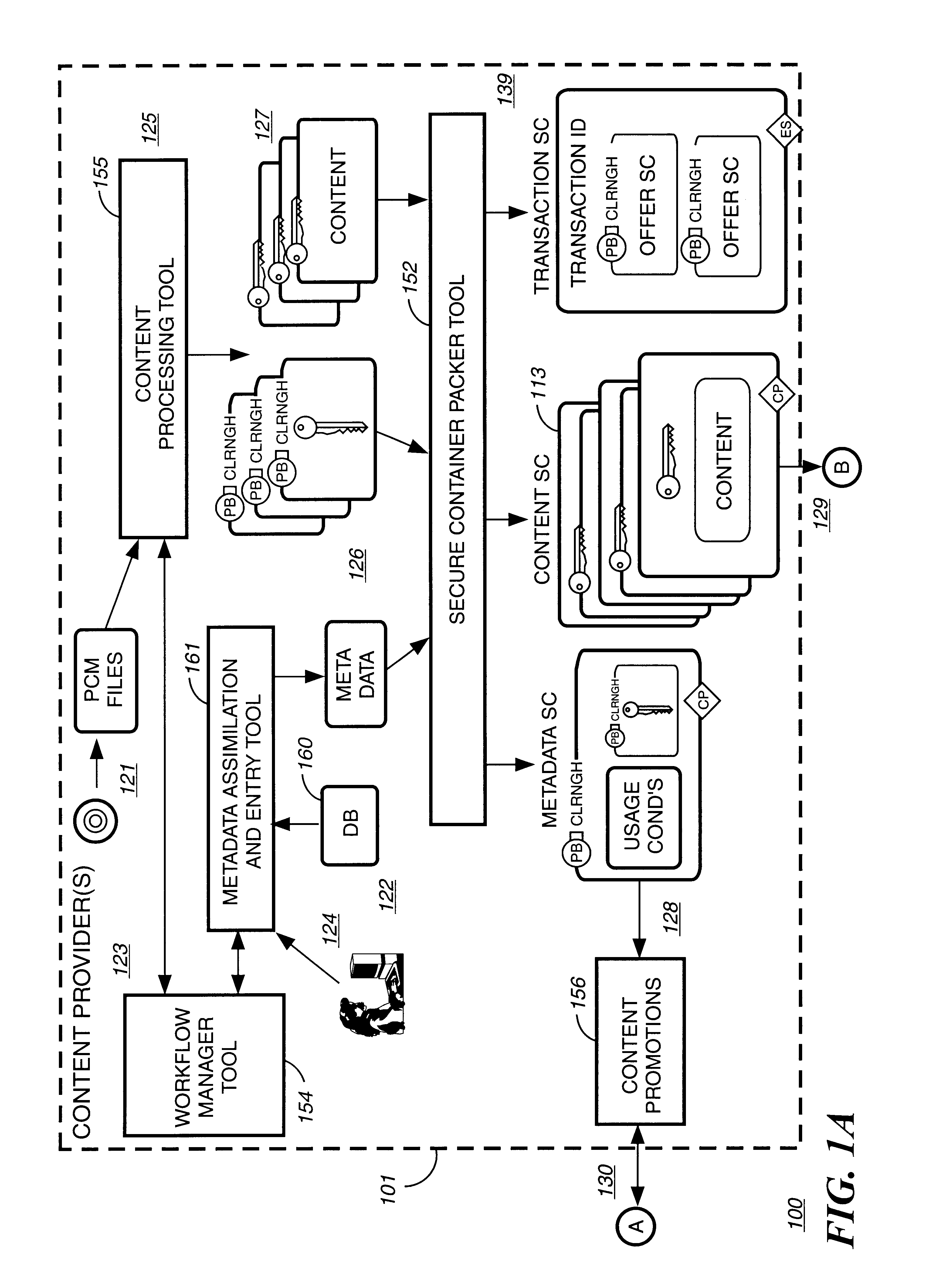
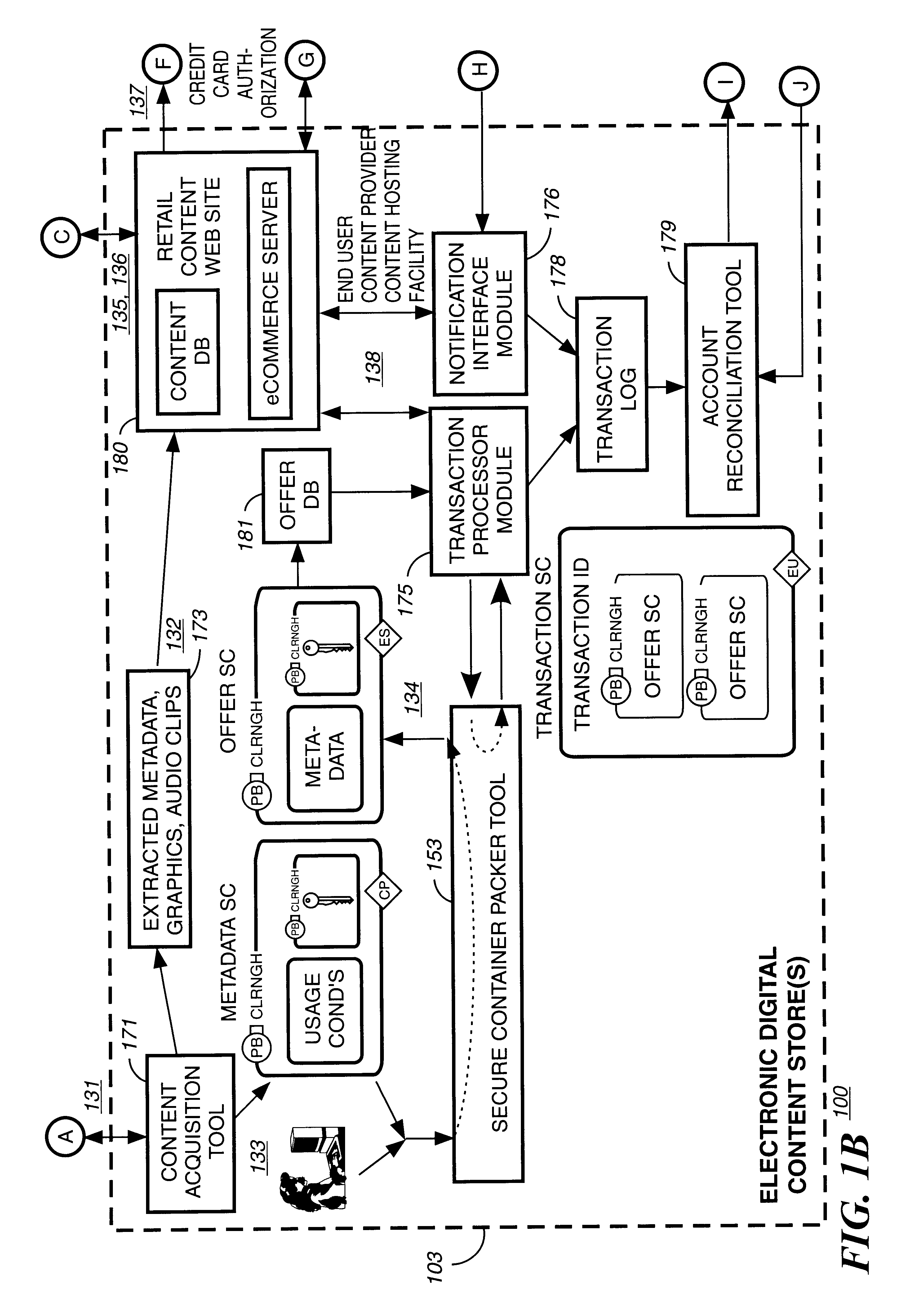
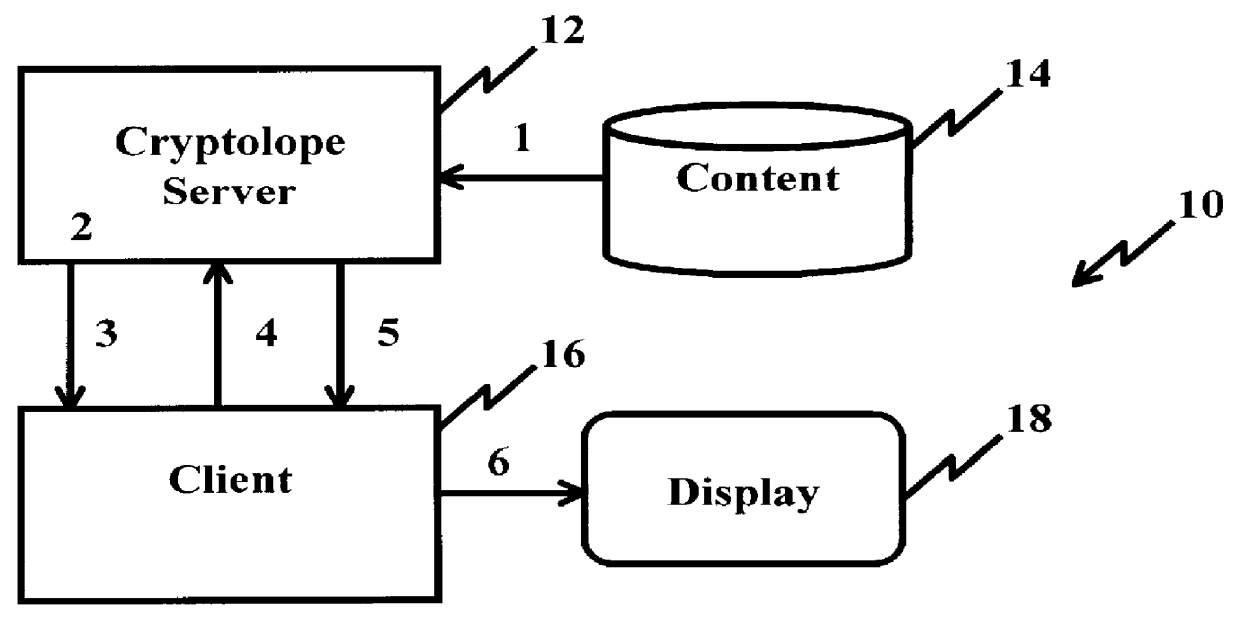
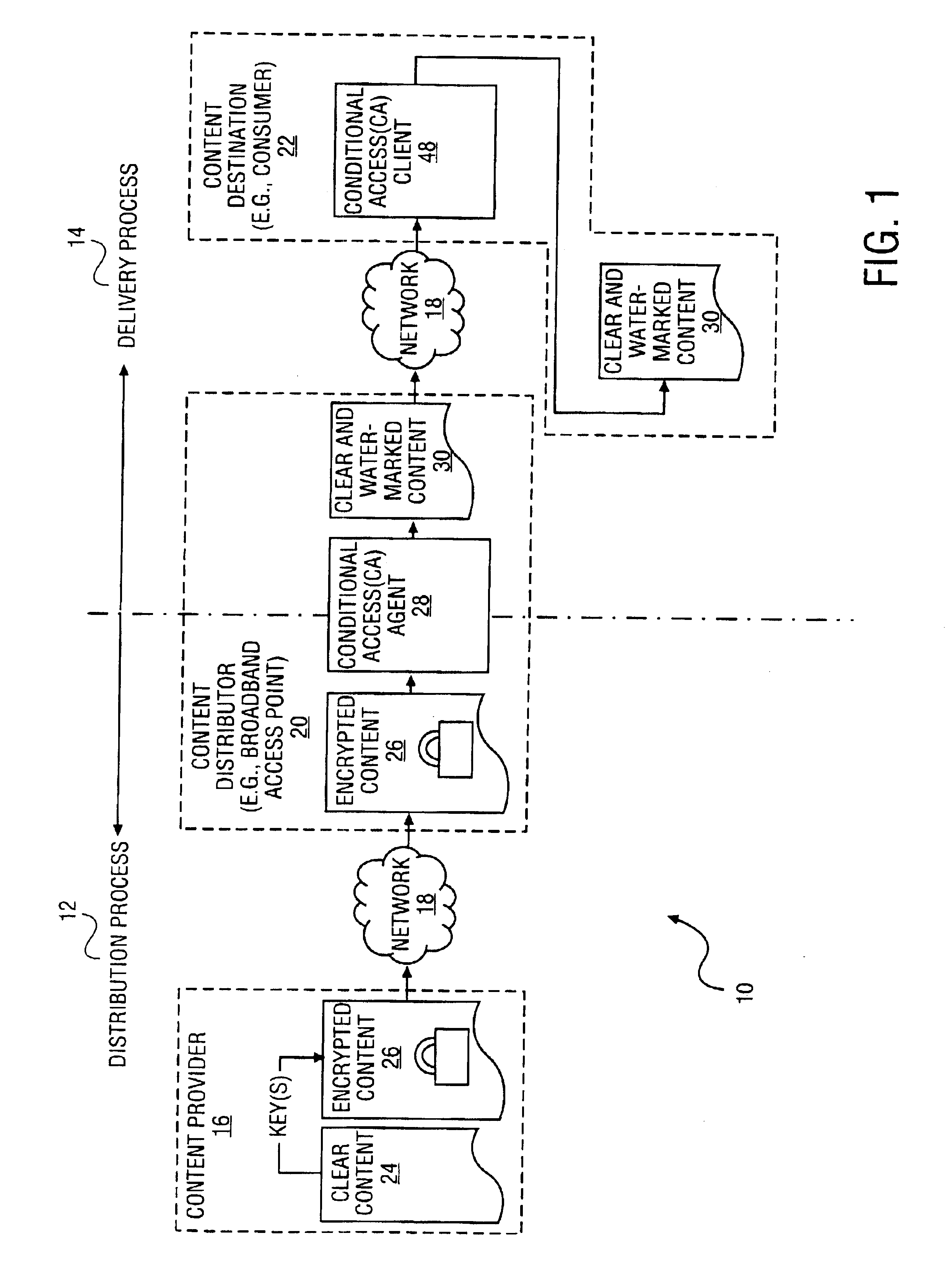
Secure electronic content distribution on CDS and DVDs
InactiveUS6611812B2Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
Wireless mesh point portable data terminal
ActiveUS8638806B2Power managementDigital data processing detailsMicrocontrollerWireless mesh network
A portable data terminal (PDT) adapted to participate in a wireless mesh network including a plurality of peer PDTs can comprise: a PDT module including an encoded information reading (EIR) device, and a mesh point (MP) module communicatively coupled to the PDT module. The MP module can include a microcontroller and at least one wireless communication interface and can be configured to perform IEEE 802.11-conformant wireless station services including authentication, de-authentication, privacy, and MAC service data unit delivery, and IEEE 802.11-conformant wireless distribution system services including association, disassociation, distribution, integration, and re-association. The MP module can be further configured, responsive to receiving a MAC frame addressed to a recipient inside the wireless mesh network, to deliver the MAC frame using the distribution service. The MP module can be further configured, responsive to receiving a MAC frame addressed to a recipient outside of the wireless mesh network, to deliver the MAC frame using the integration service. The MP module can be further configured to route an incoming MAC frame according to its destination address and the frame control field. The MP module can be further configured to cause the PDT module to exit said sleeping state responsive to receiving a mobile management software (MMS) wake-up command.
Owner:HAND HELD PRODS
Advanced authentication techniques and applications
ActiveUS20140289833A1Digital data processing detailsMultiple digital computer combinationsEngineeringDatabase
A system, apparatus, method, and machine readable medium are described for performing advanced authentication techniques and associated applications. For example, one embodiment of a method comprises: receiving a policy identifying a set of acceptable authentication capabilities; determining a set of client authentication capabilities; and filtering the set of acceptable authentication capabilities based on the determined set of client authentication capabilities to arrive at a filtered set of one or more authentication capabilities for authenticating a user of the client.
Owner:NOK NOK LABS
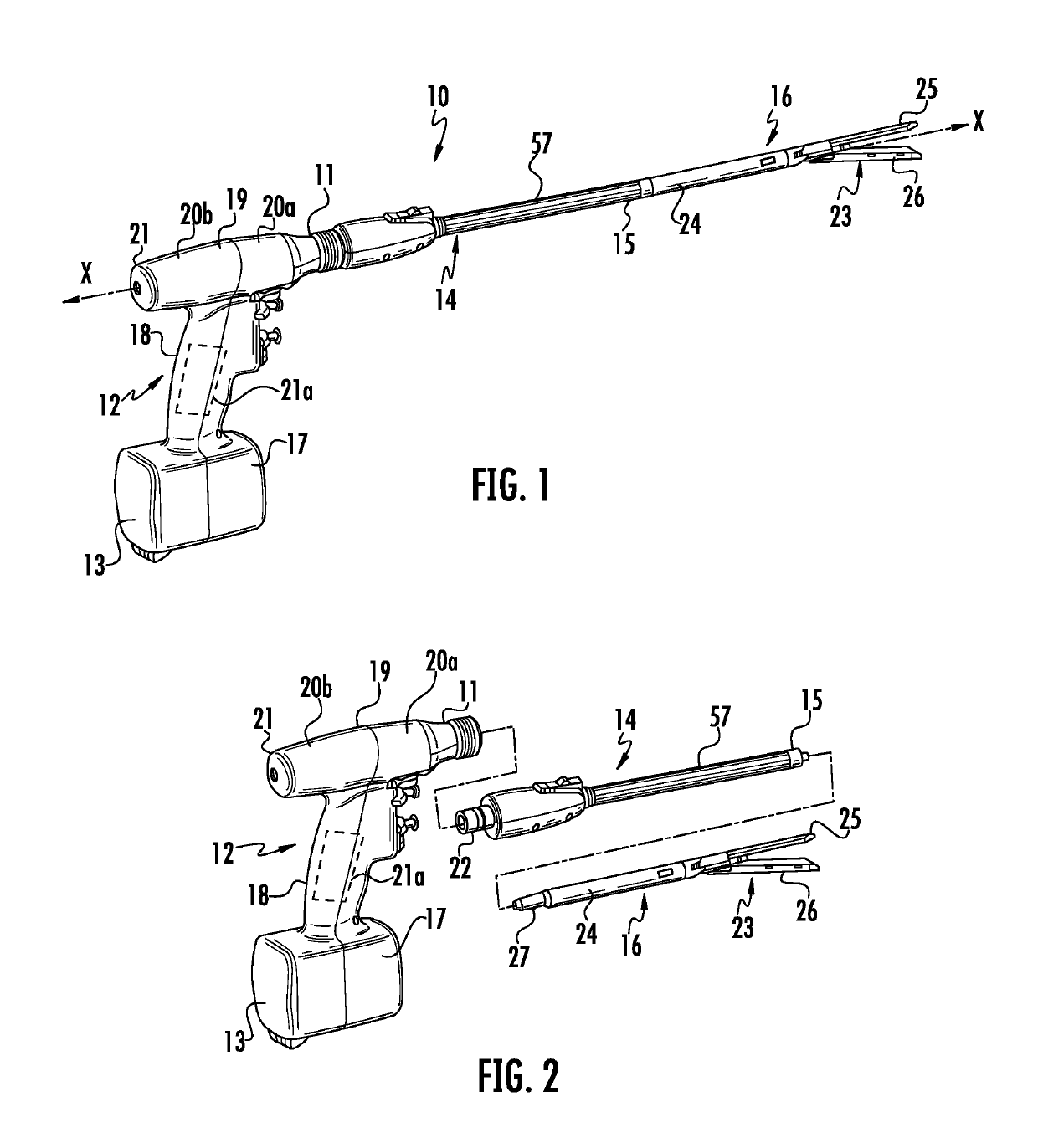
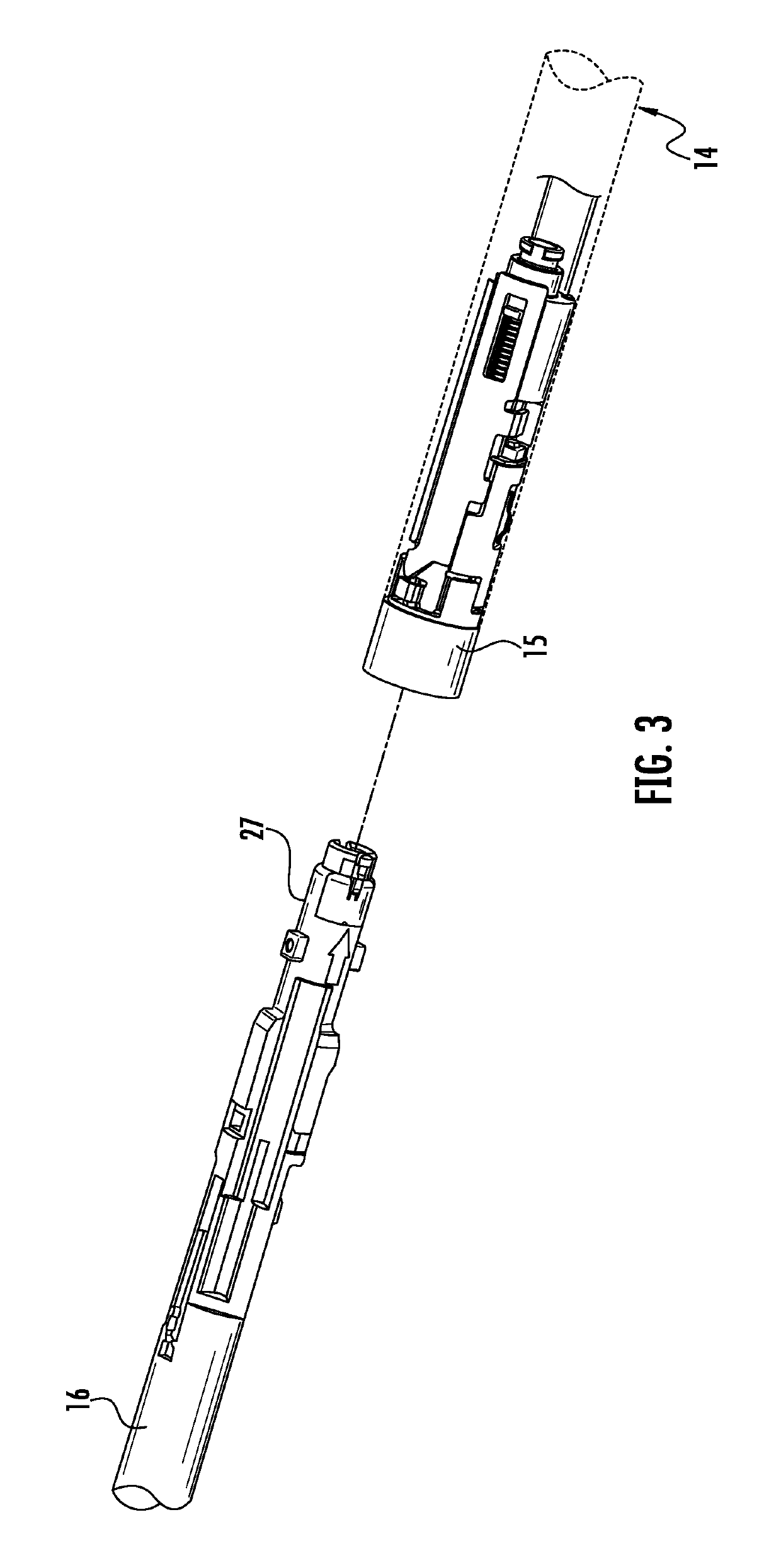
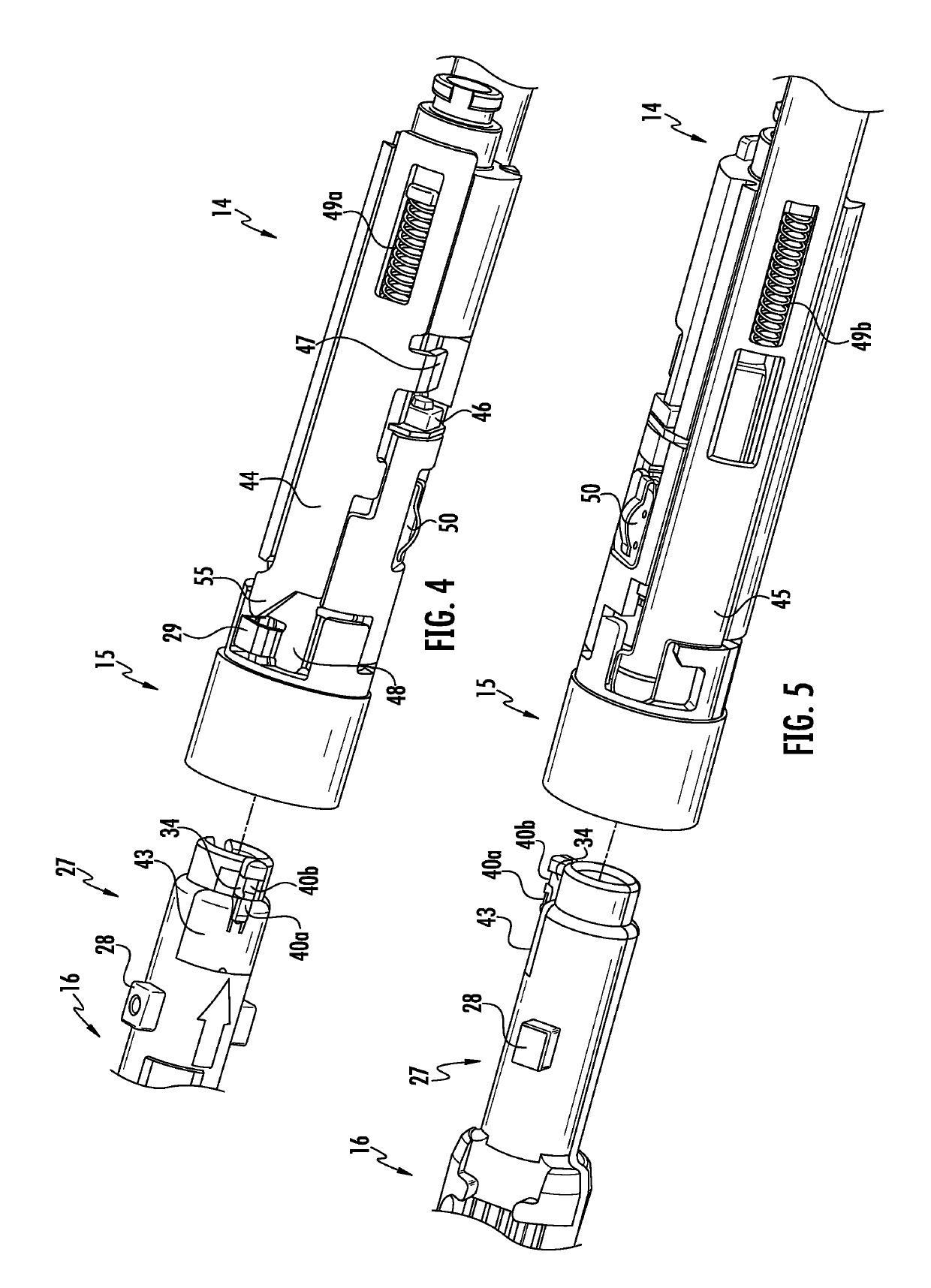
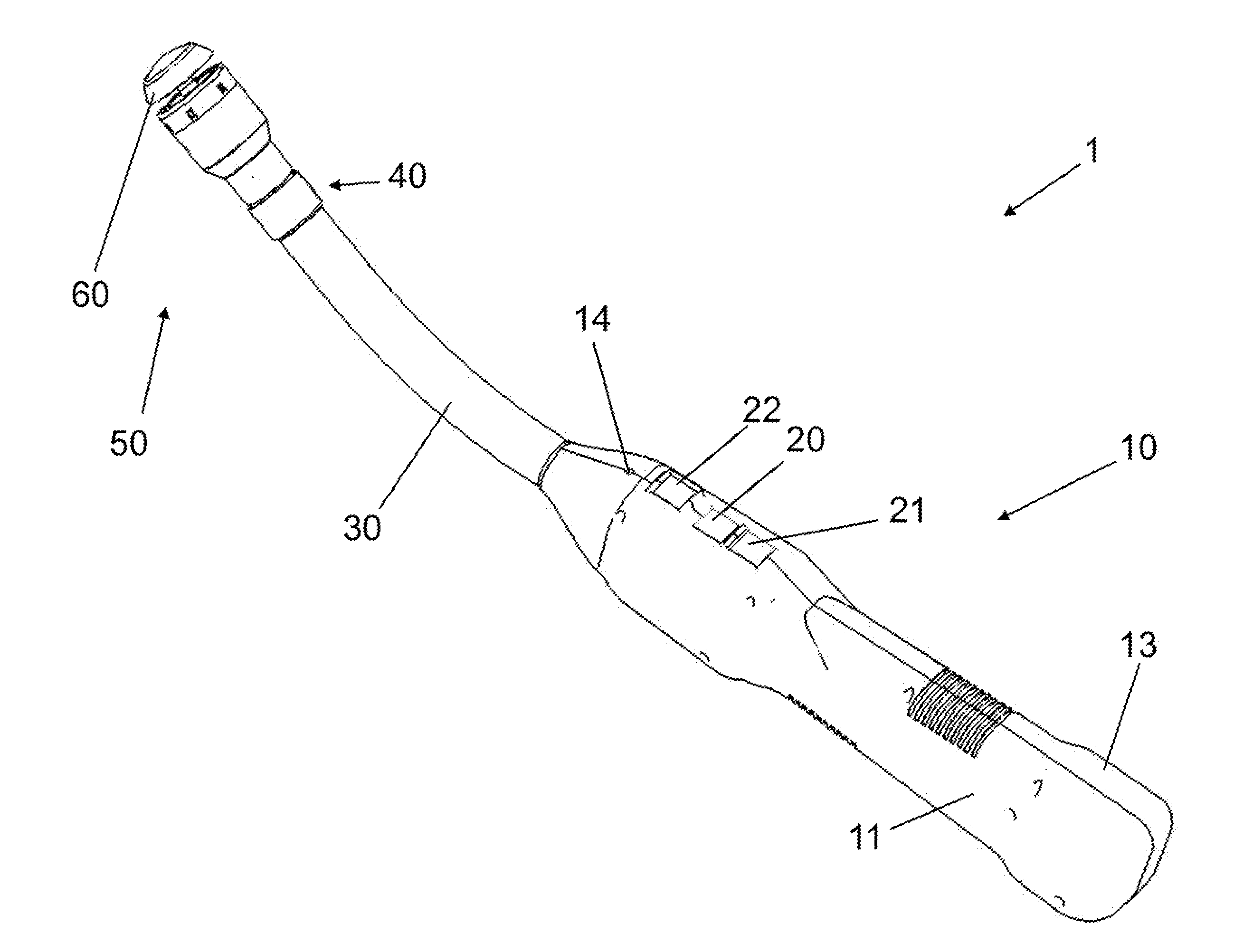
Authentication and information system for reusable surgical instruments
An authentication and information system for use in a surgical stapling device includes a handle assembly having a controller, the controller having at least one program and a memory, an adapter assembly, and a loading unit having a tool assembly mounted for articulation and a member for actuating articulation of the tool assembly, the loading unit having at least one chip assembly having a chip storing data indicating a position of the member when the tool assembly is in a fully articulated position.
Owner:TYCO HEALTHCARE GRP LP
Methods for Cryptographic Identification of Interchangeable Parts for Surgical Instruments
ActiveUS20100230465A1Comfortably fit into a user's handReduce manufacturing difficultySuture equipmentsStapling toolsEngineeringActuator
A method for encrypted authentication of interchangeable parts of a surgical instrument includes providing a surgical end effector at a distal end of a handle of the surgical instrument and electrically connecting an authentication controller within the handle to a receiving portion of the end effector. An interchangeable part is removably placed at the receiving portion. The interchangeable part is authenticated with the authentication controller when the interchangeable part is seated in the end effector.
Owner:CILAG GMBH INT
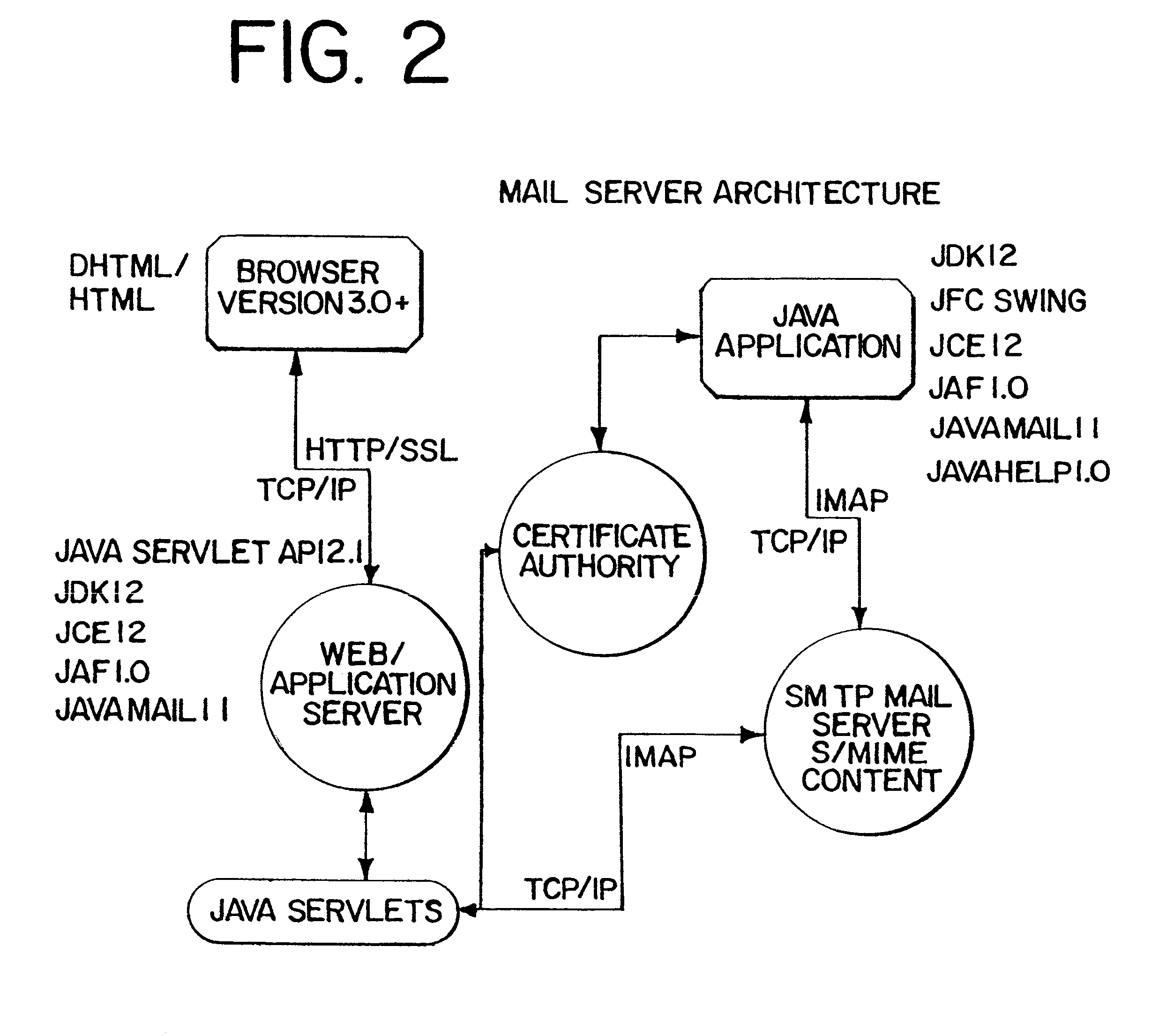
Interoperable full-featured web-based and client-side e-mail system
InactiveUS6356937B1More secure log-inMultiple digital computer combinationsOffice automationApplication softwareProprietary software
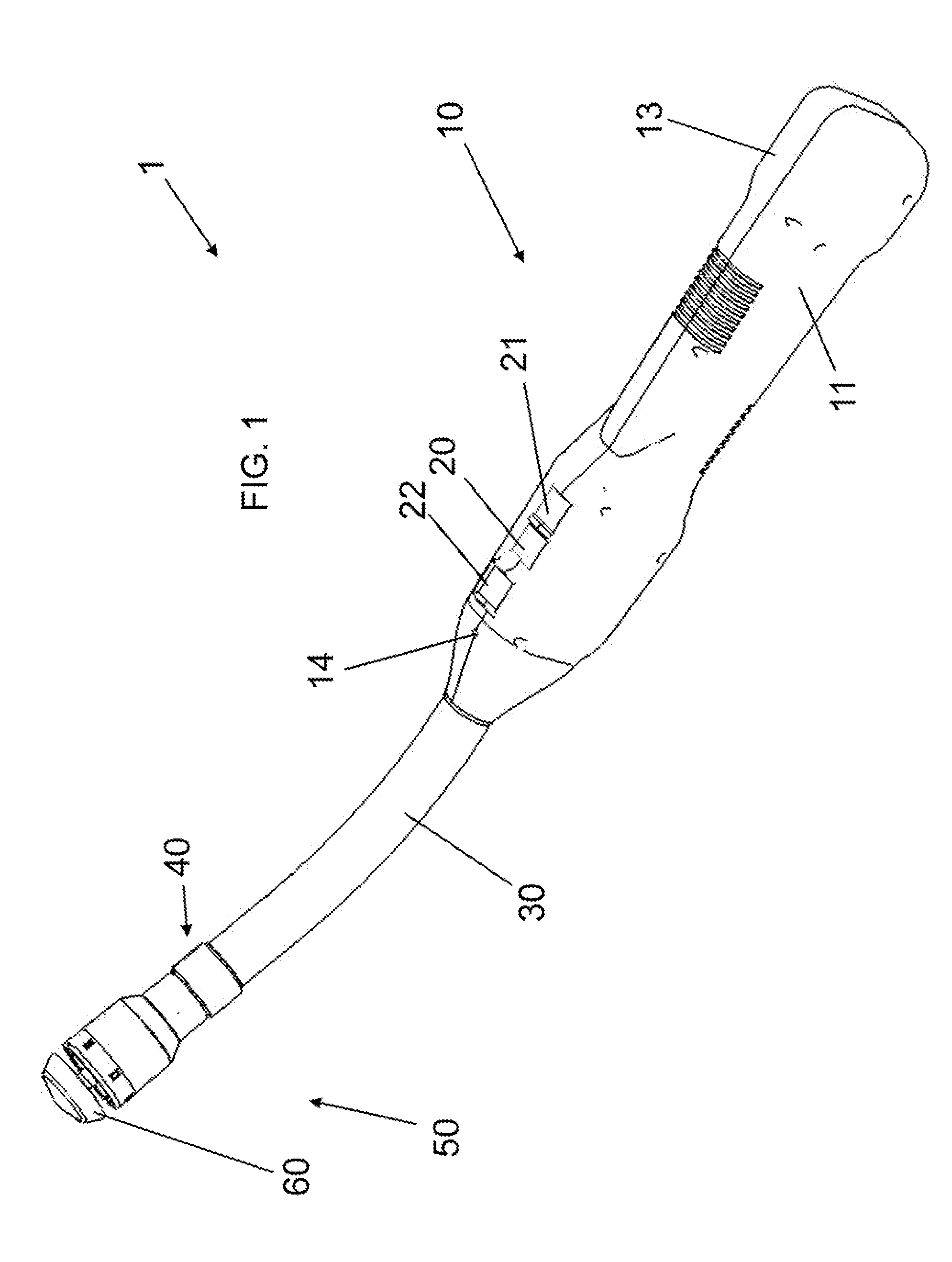
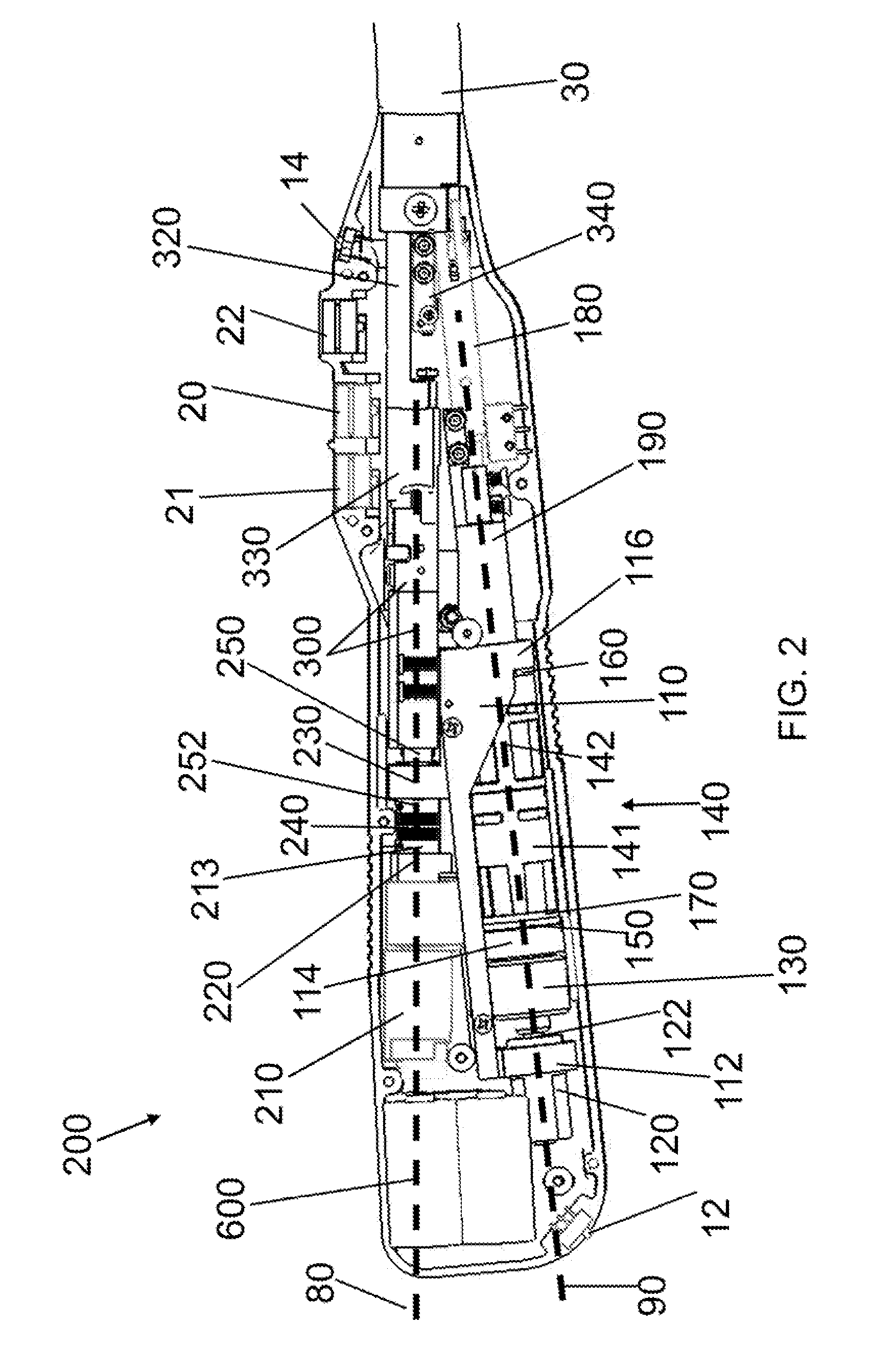
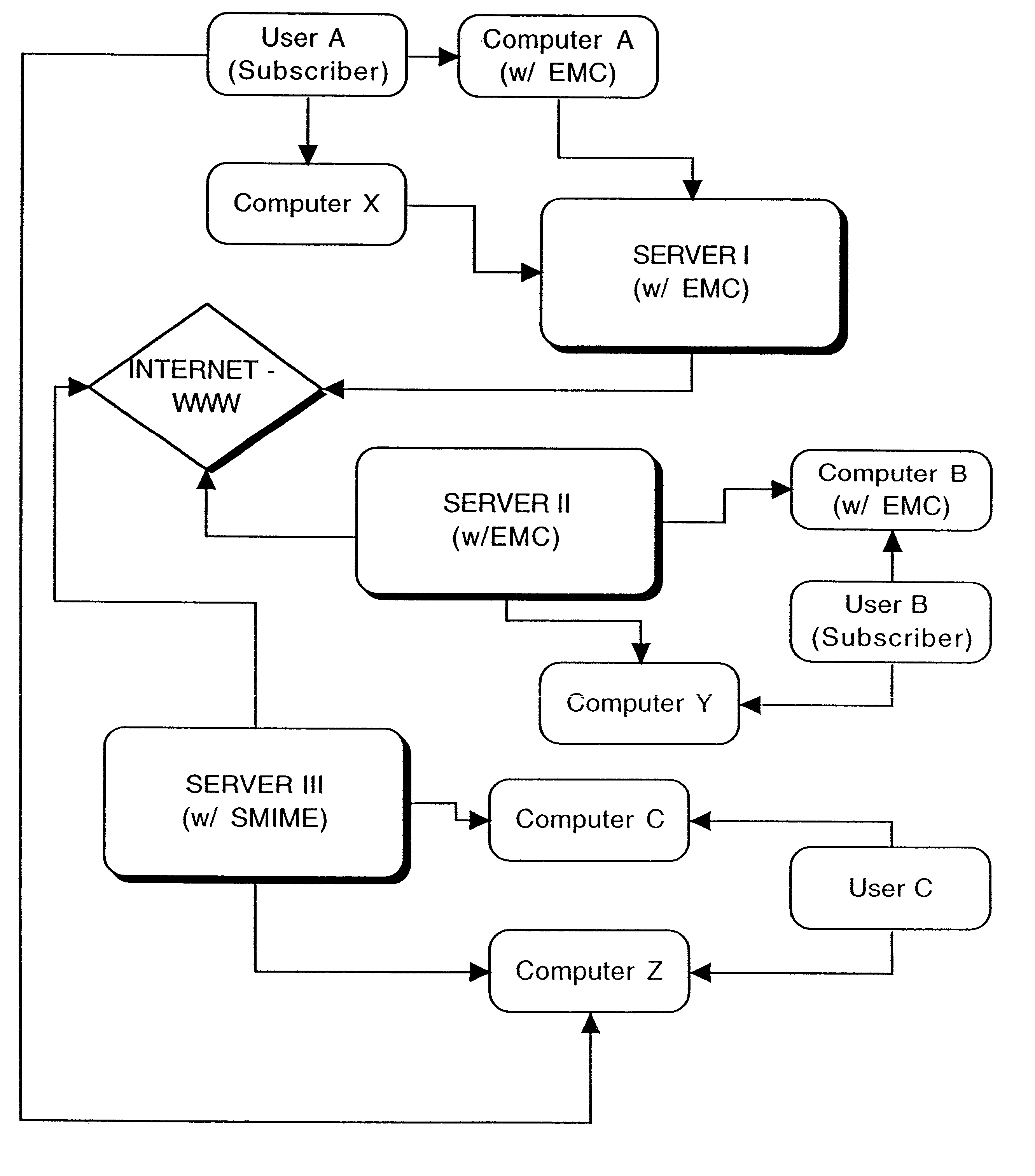
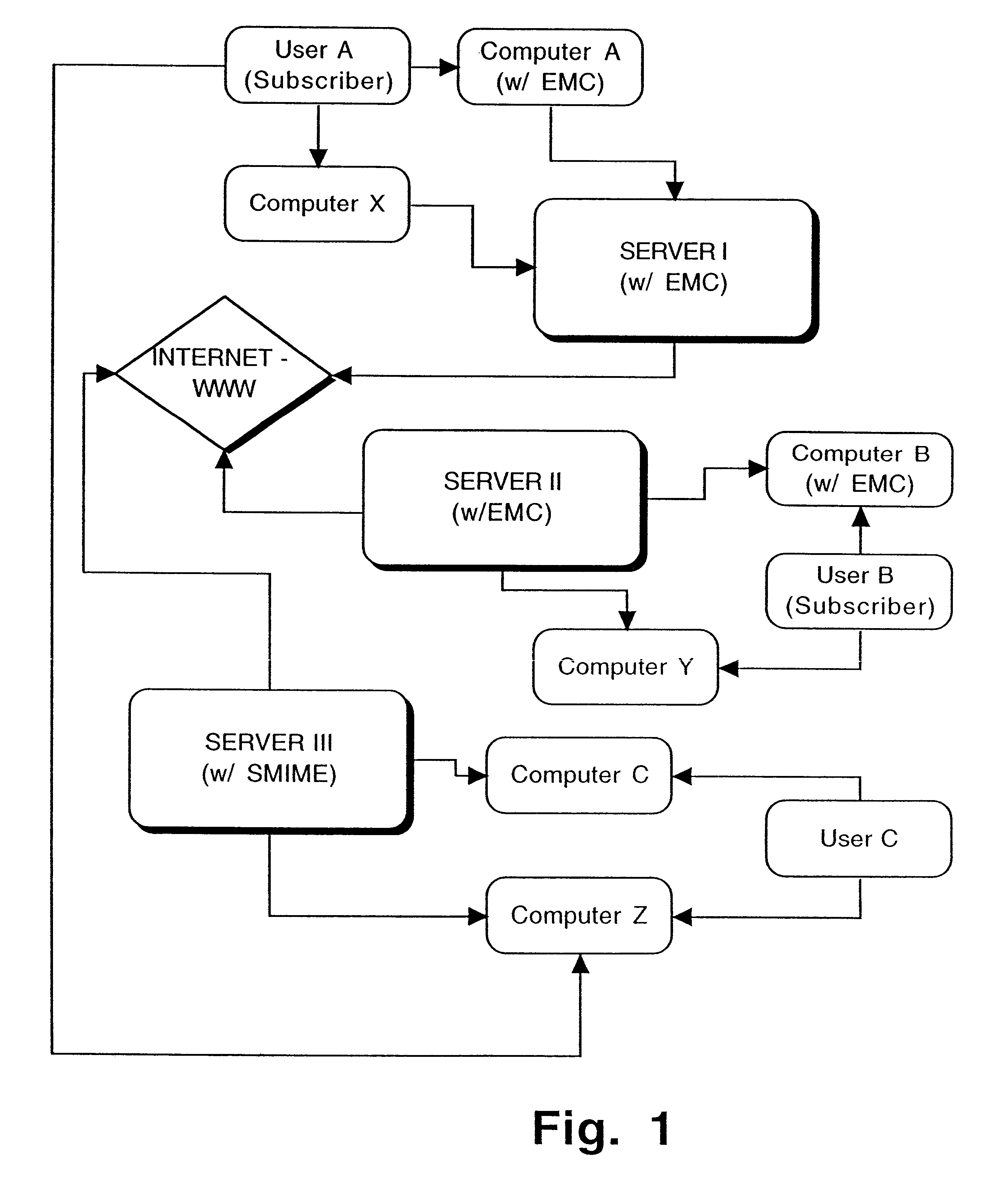
A full-featured e-mail system is used in both Internet-based and client-side (personal computer) forms. In each form, either basic e-mail service is provided to system subscribers or a secure, premium service with authentication, concealment, integrity, and non-repudiation functions for electronic messaging services is provided. In either form and at either level of service, subscribers can work off-line on their own computers with proprietary software loaded or, alternatively, on-line on any computer with an Internet connection. The system is interoperable, to preserve security, with all S / MIME compliant software applications, even for those users not subscribing to a service implementing the disclosed system. Digital certificates can be provided as a security service of the disclosed system, rather than requiring a second source with separate verification procedures. As additional optional features, the subscriber can control compression of outgoing attachment files, rather than having that function absent or operate in some automatic way. Decompression of such file attachments when received occurs automatically for subscribers, without having to invoke a different program or system. Interactive help features, book hierarchy uniformity for messages, accounts, certificates, virus warnings, and dual naming capability are also provided and available to subscribers in both the Web-based and the client-side application forms disclosed herein, and in both basic and premium service levels.
Owner:MEC MANAGEMENT LLC
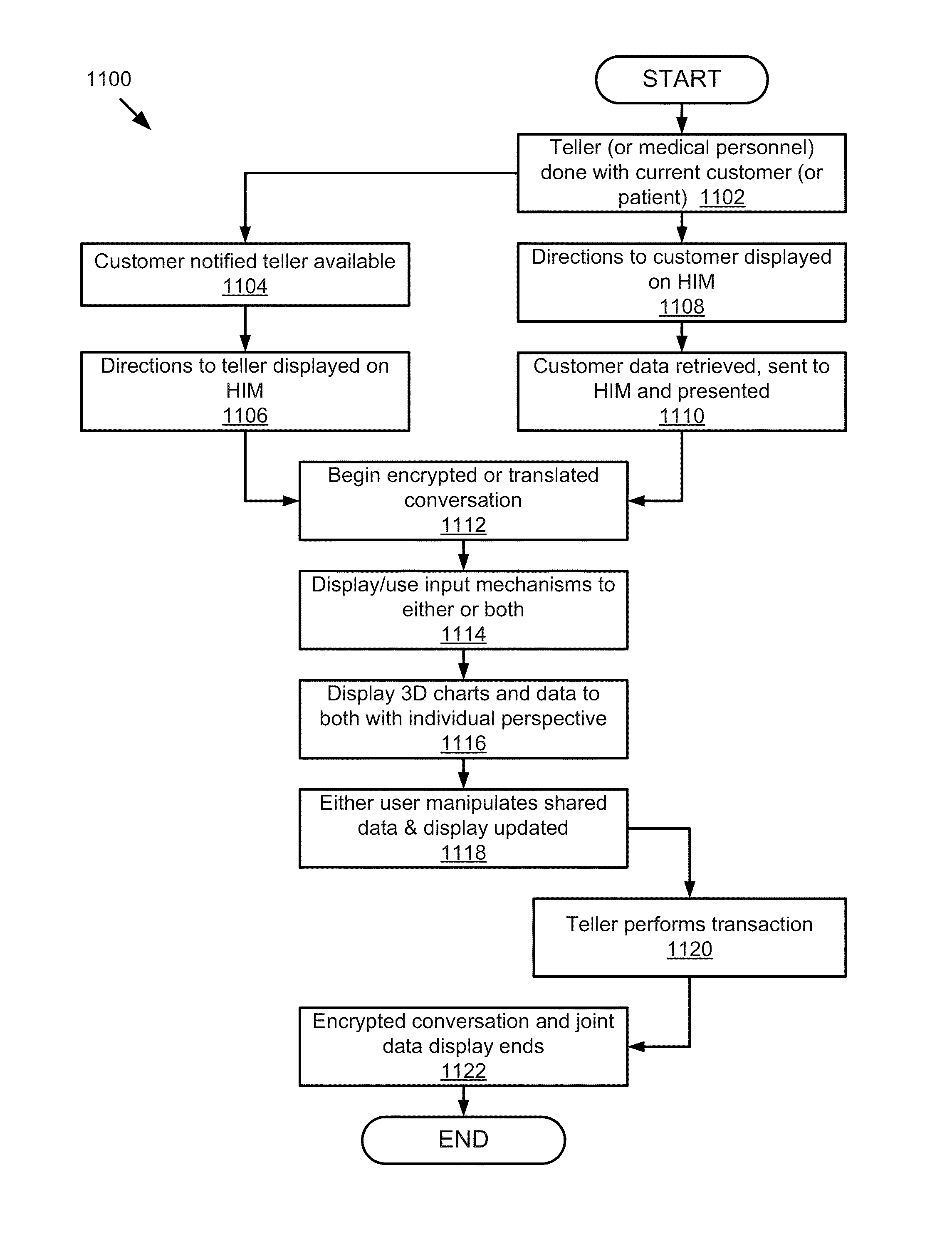
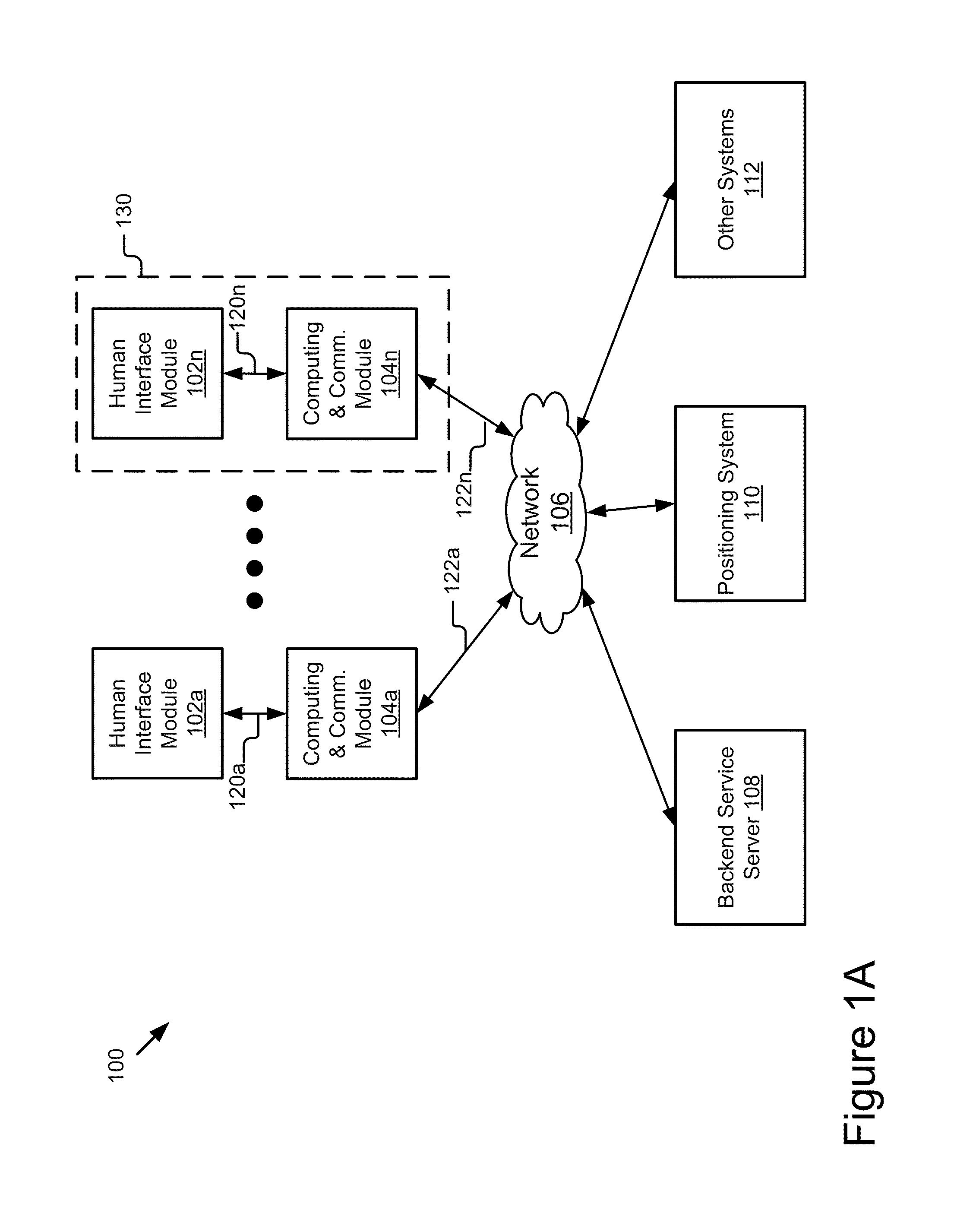
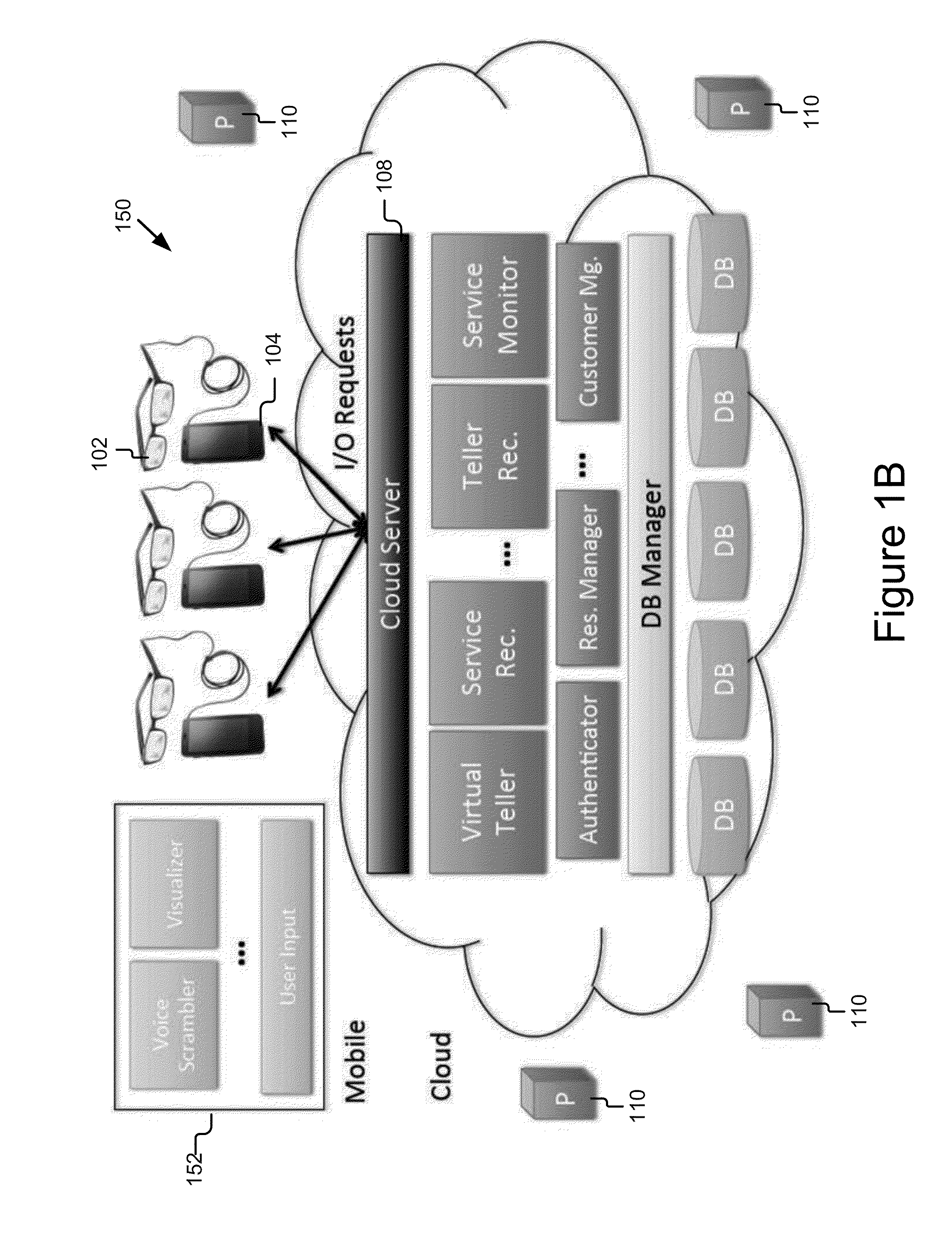
Mobile Information Gateway for Home Healthcare
A mobile information gateway comprises: a wearable human interface module having an image delivery and display mechanism for presenting information with a wide field of view and in three dimensions, a computing and communication module coupled for communication with the human interface module; and a backend service server coupled for communication with the computing and communication module, the backend service server for processing data for home healthcare. The present invention also includes a method for using the mobile information gateway for home healthcare comprises; capturing information with a wearable human interface module; processing the captured information to determine an identity of a user of the wearable human interface module; authenticating the identity of user; retrieving information using the captured information and the authenticated identity; and presenting the retrieved information using the wearable human interface module.
Owner:RICOH KK
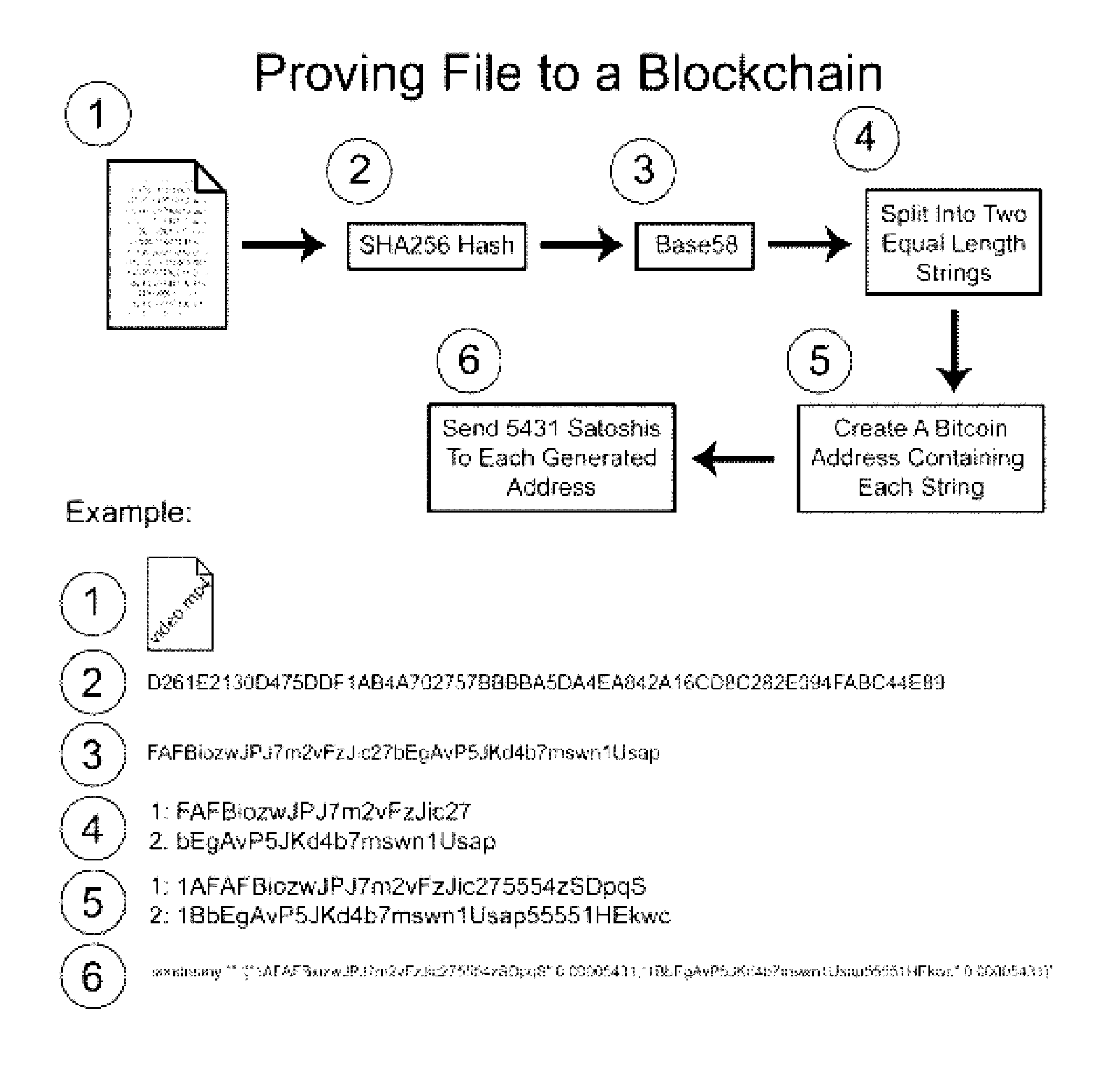
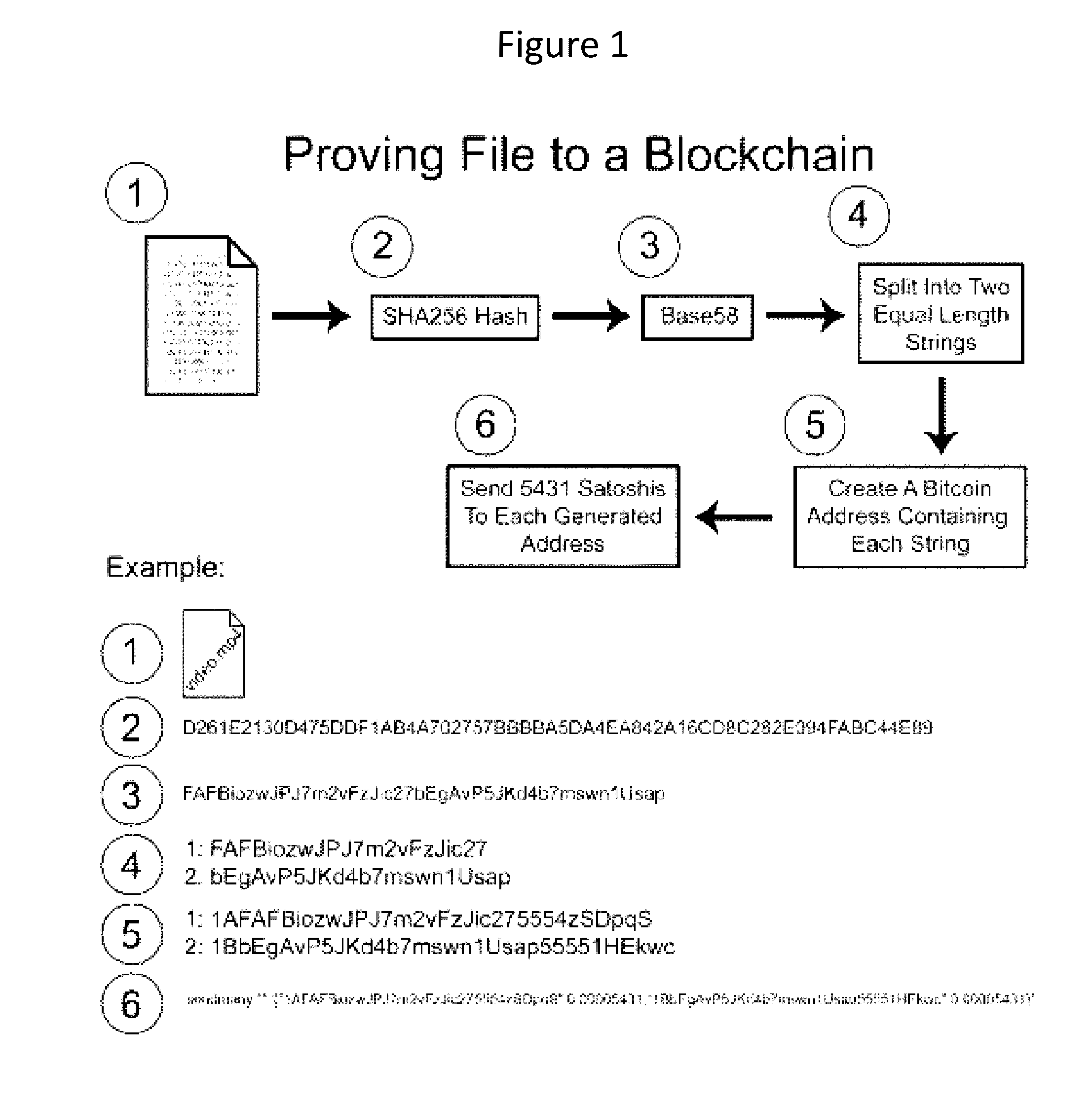
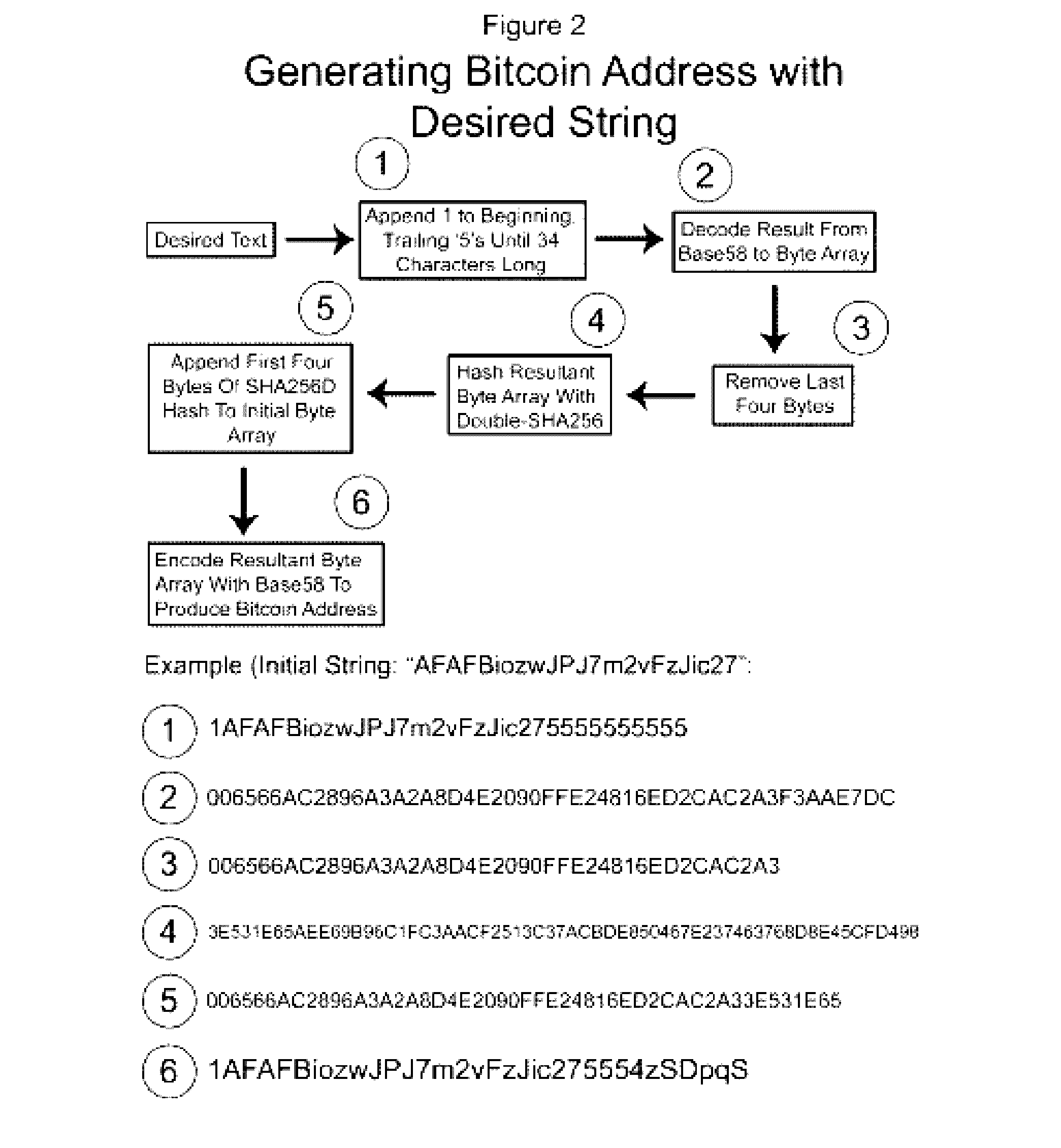
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
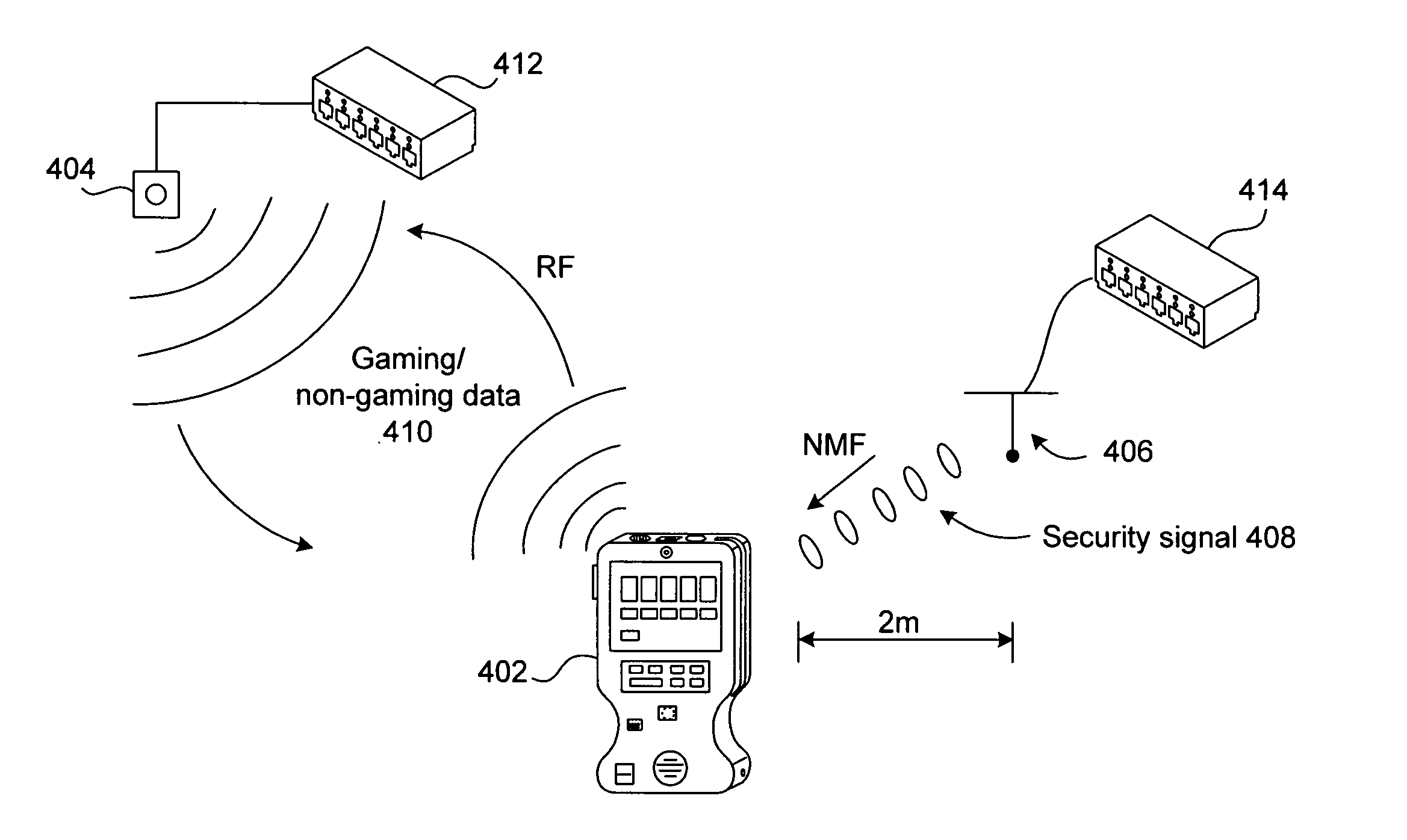
Mobile gaming devices for use in a gaming network having gaming and non-gaming zones
Novel gaming networks, devices, and systems for enabling game play on wireless, mobile gaming devices based on the location of the device are described. A mobile gaming device can be used for wagering game play when the device is physically present in an authorized game play zone in a gaming environment and is used by an authorized and verified user. A gaming environment is divided into zones wherein a zone either allows wagering game play on a device or does not. A zone has multiple transmitters that transmit security signals that are detectable by a mobile device at all times while the device is in the zone. An appropriate wireless communication standard can be used to transmit the security signal, such as near-field magnetic communication. The device has at least one user identification and authentication mechanism to ensure that only an authorized user is using the device.
Owner:IGT
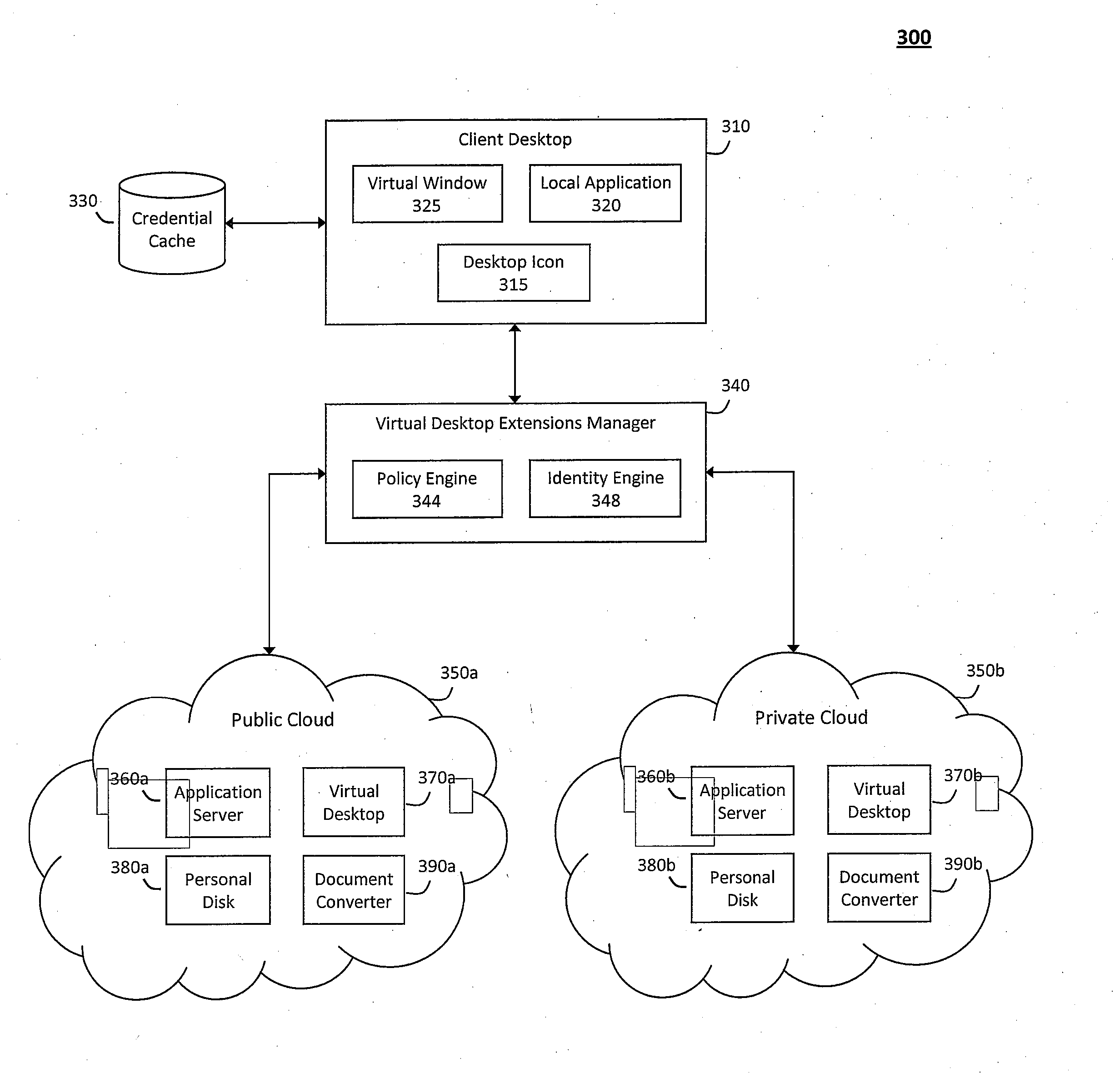
System and method for providing virtual desktop extensions on a client desktop
ActiveUS20110209064A1Simplify complexityProvide capabilityInput/output for user-computer interactionDigital data processing detailsClient-sideCloud computing
The system and method described herein may identify one or more virtual desktop extensions available in a cloud computing environment and launch virtual machine instances to host the available virtual desktop extensions in the cloud. For example, a virtual desktop extension manager may receive a virtual desktop extension request from a client desktop and determine whether authentication credentials for the client desktop indicate that the client desktop has access to the requested virtual desktop extension. In response to authenticating the client desktop, the virtual desktop extension manager may then launch a virtual machine instance to host the virtual desktop extension in the cloud and provide the client desktop with information for locally controlling the virtual desktop extension remotely hosted in the cloud.
Owner:MICRO FOCUS SOFTWARE INC
Systems and methods for multi-factor authentication
ActiveUS20070186106A1User identity/authority verificationElectric digital data processingInternet privacyControl system
Requests to gain access to secure resources are adjudicated according to authentication policies that include rules based on user-states derived from multiple heterogeneous access-control systems.
Owner:IMPRIVATA
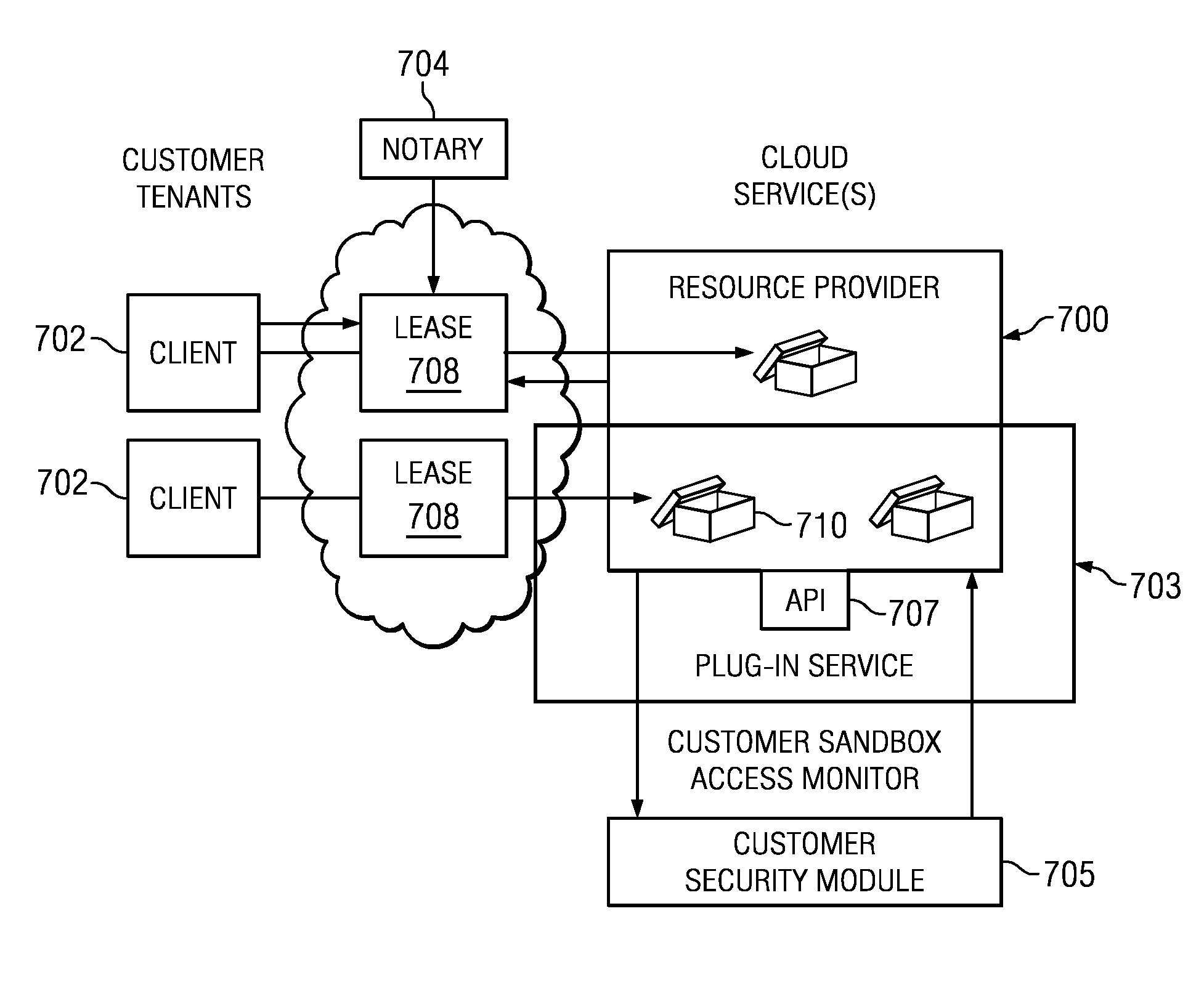
Authentication and authorization methods for cloud computing security
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
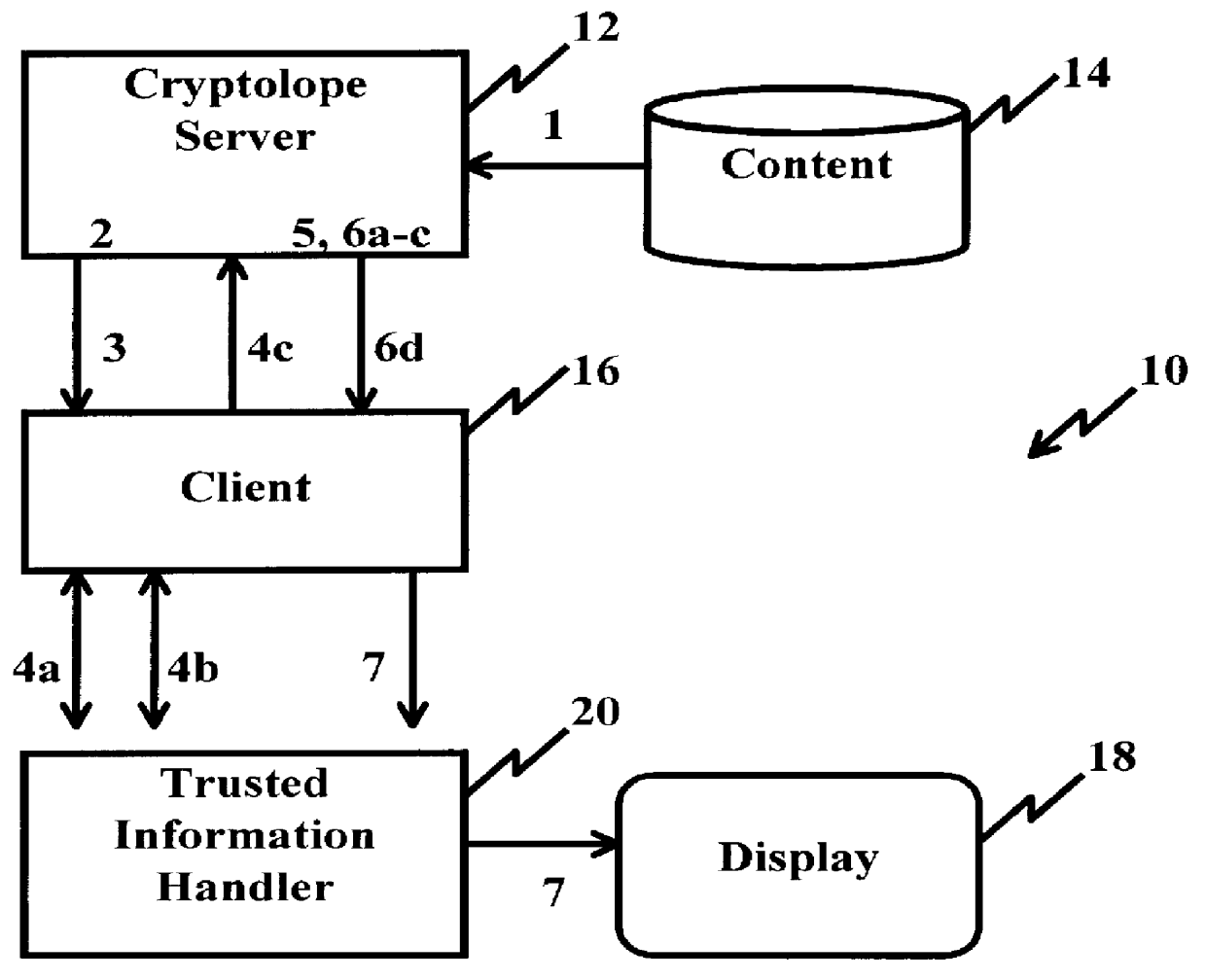
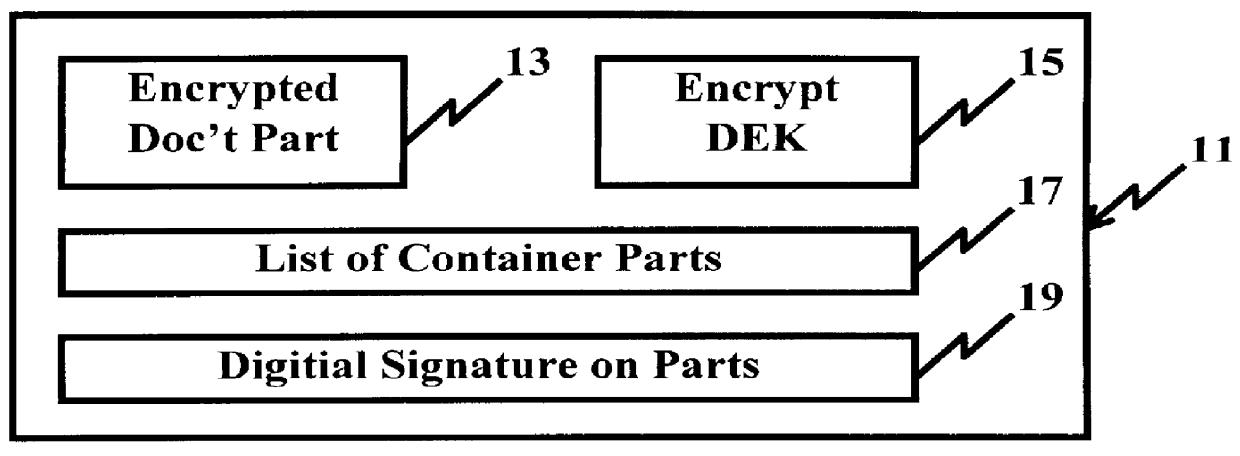
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
Systems and methods for communicating token attributes associated with a token vault
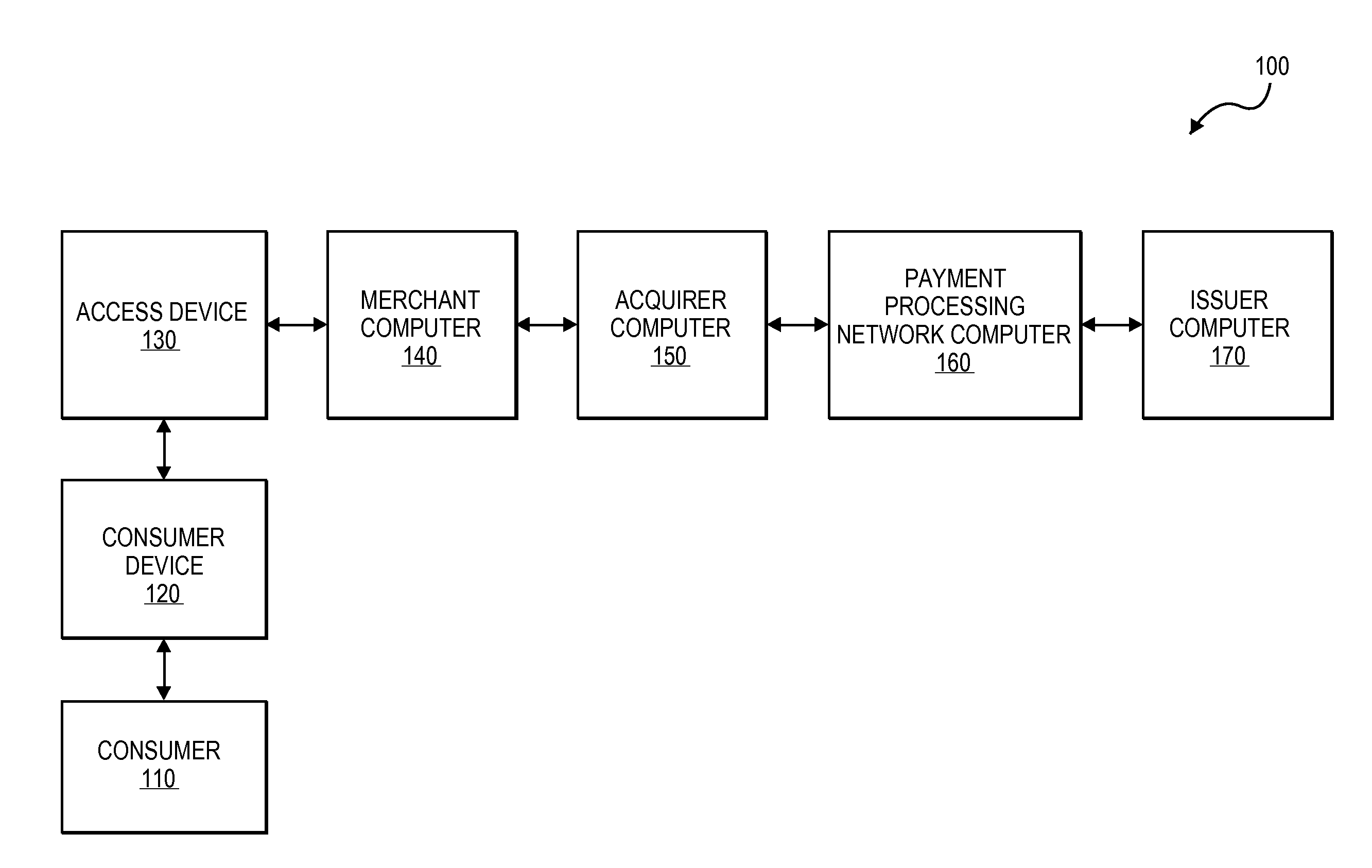
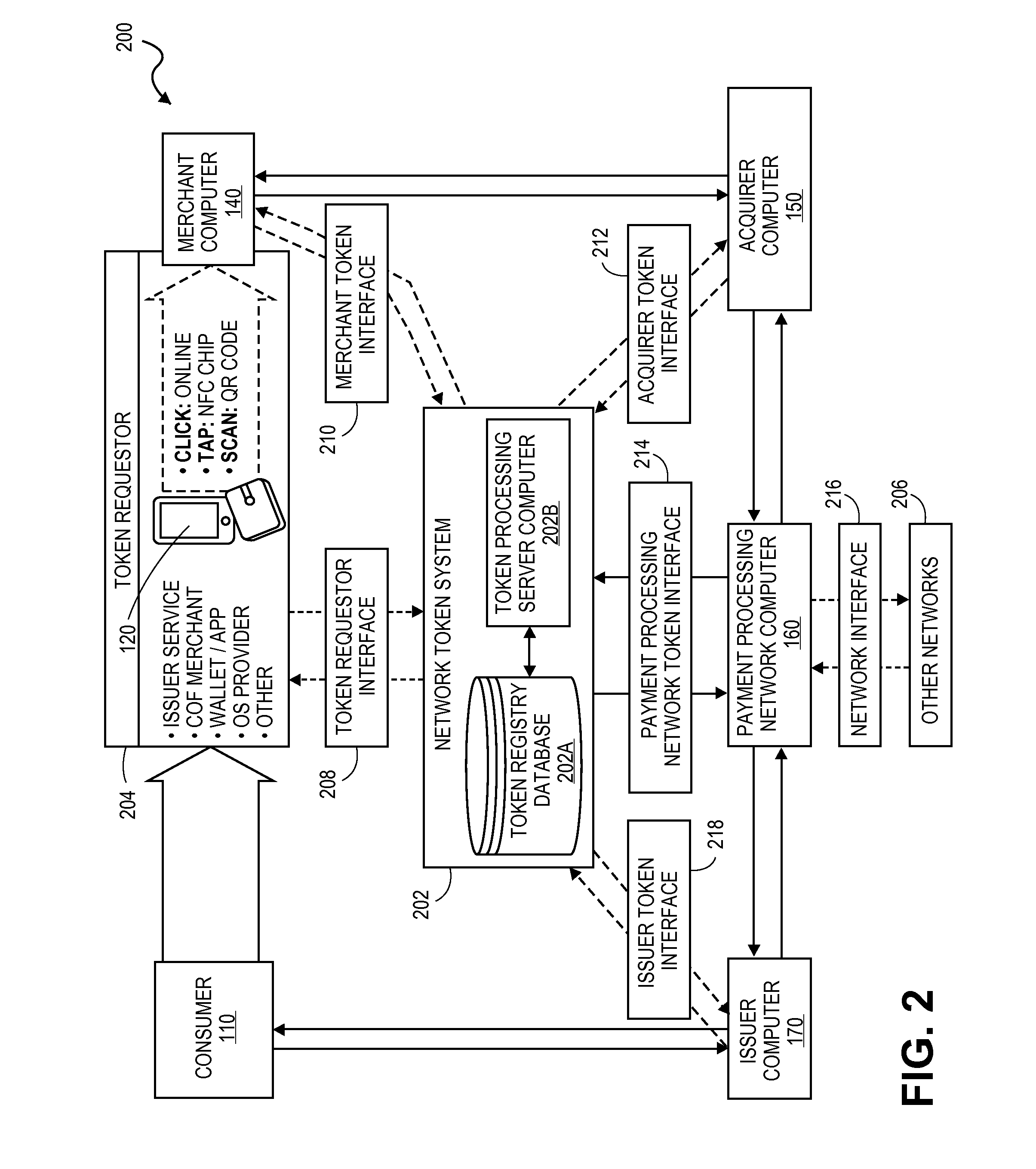
ActiveUS20150032627A1Convenient transactionSupported interoperabilityFinanceUser identity/authority verificationThird partyPayment transaction
Systems and methods for interoperable network token processing are provided. A network token system provides a platform that can be leveraged by external entities (e.g., third party wallets, e-commerce merchants, payment enablers / payment service providers, etc.) or internal payment processing network systems that have the need to use the tokens to facilitate payment transactions. A token registry vault can provide interfaces for various token requestors (e.g., mobile device, issuers, merchants, mobile wallet providers, etc.), merchants, acquirers, issuers, and payment processing network systems to request generation, use and management of tokens. The network token system further provides services such as card registration, token generation, token issuance, token authentication and activation, token exchange, and token life-cycle management.
Owner:VISA INT SERVICE ASSOC
Authentication and authorization methods for cloud computing security platform
ActiveUS20130007845A1Retain controlDigital data processing detailsUser identity/authority verificationThird partyResource pool
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
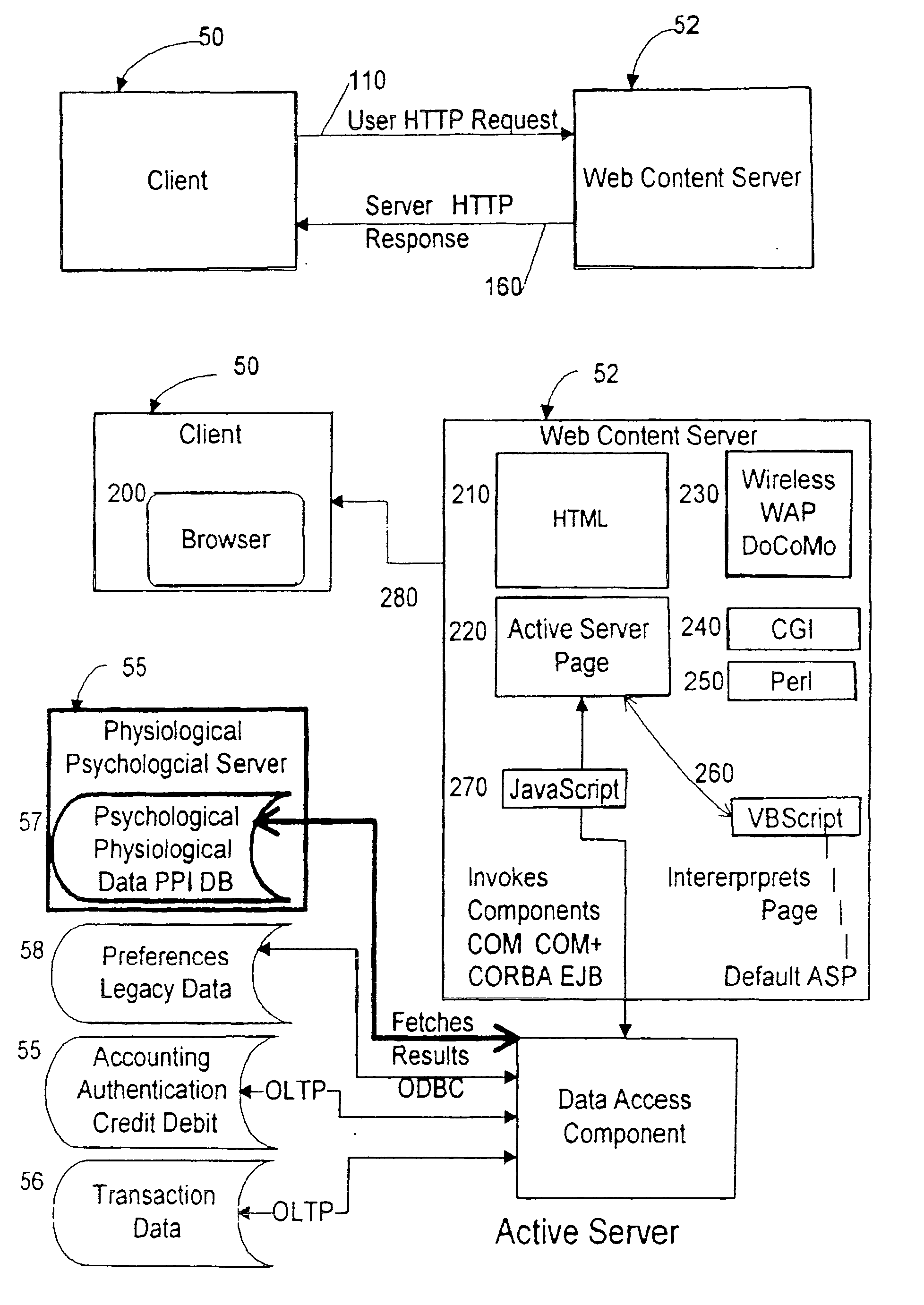
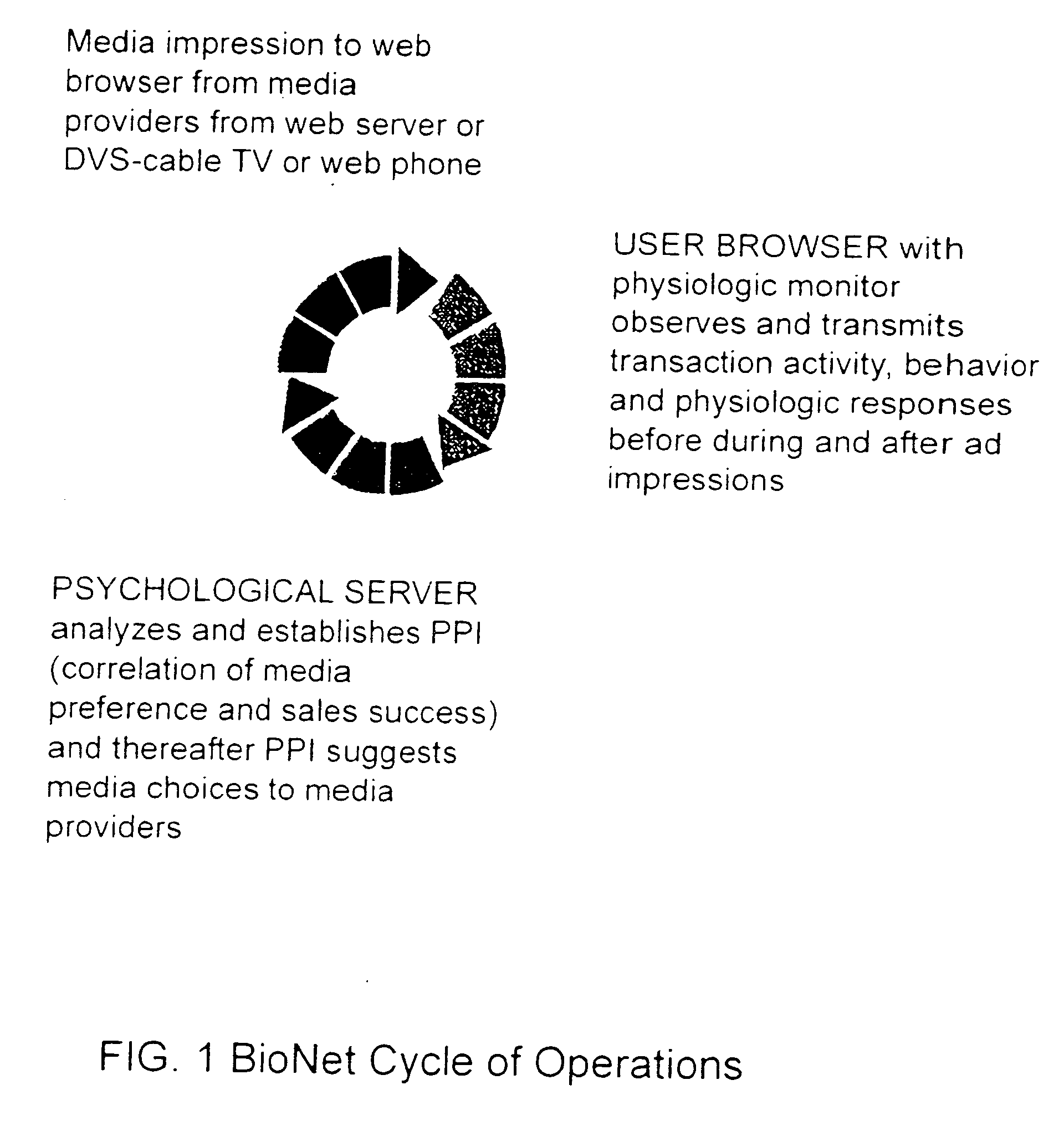
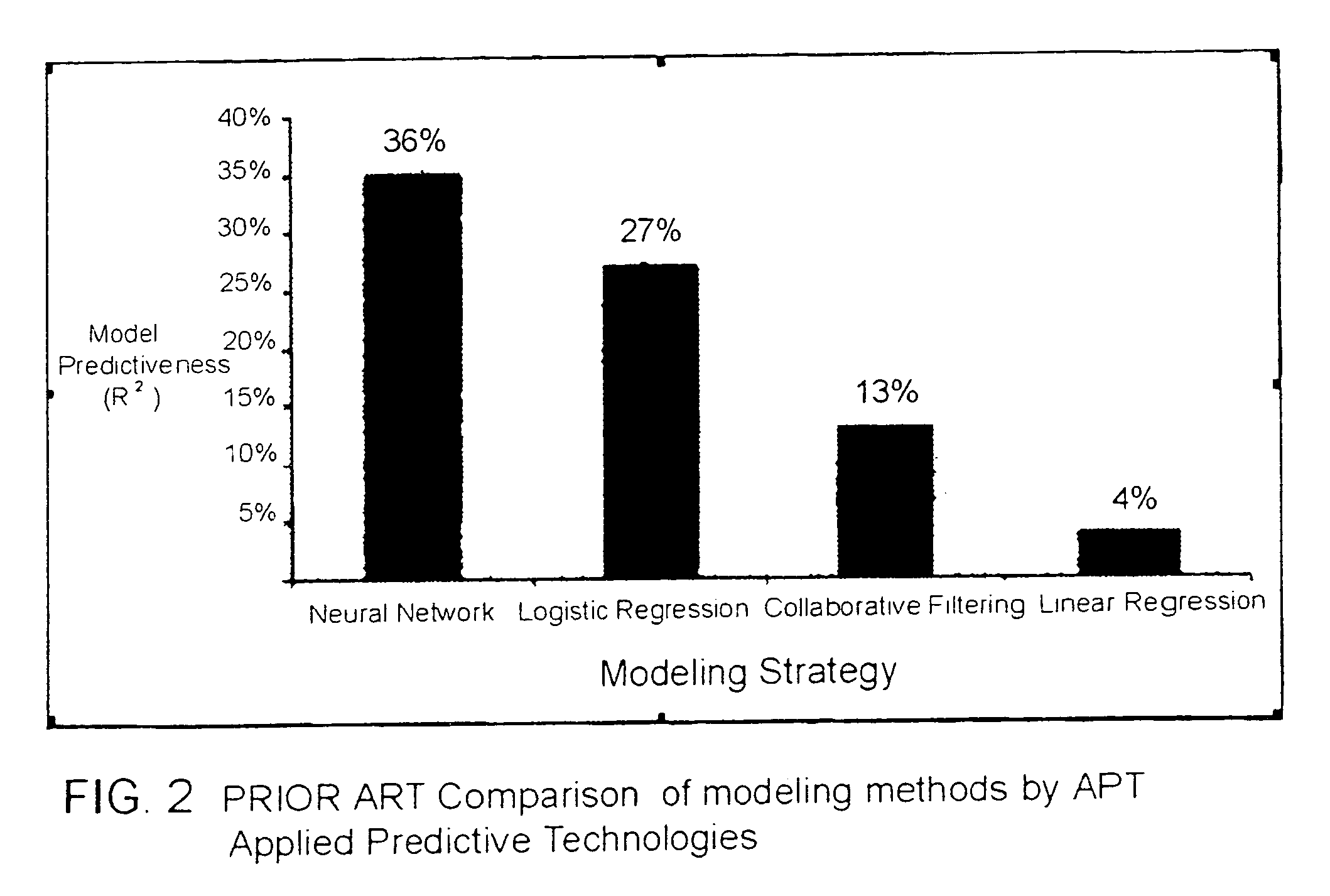
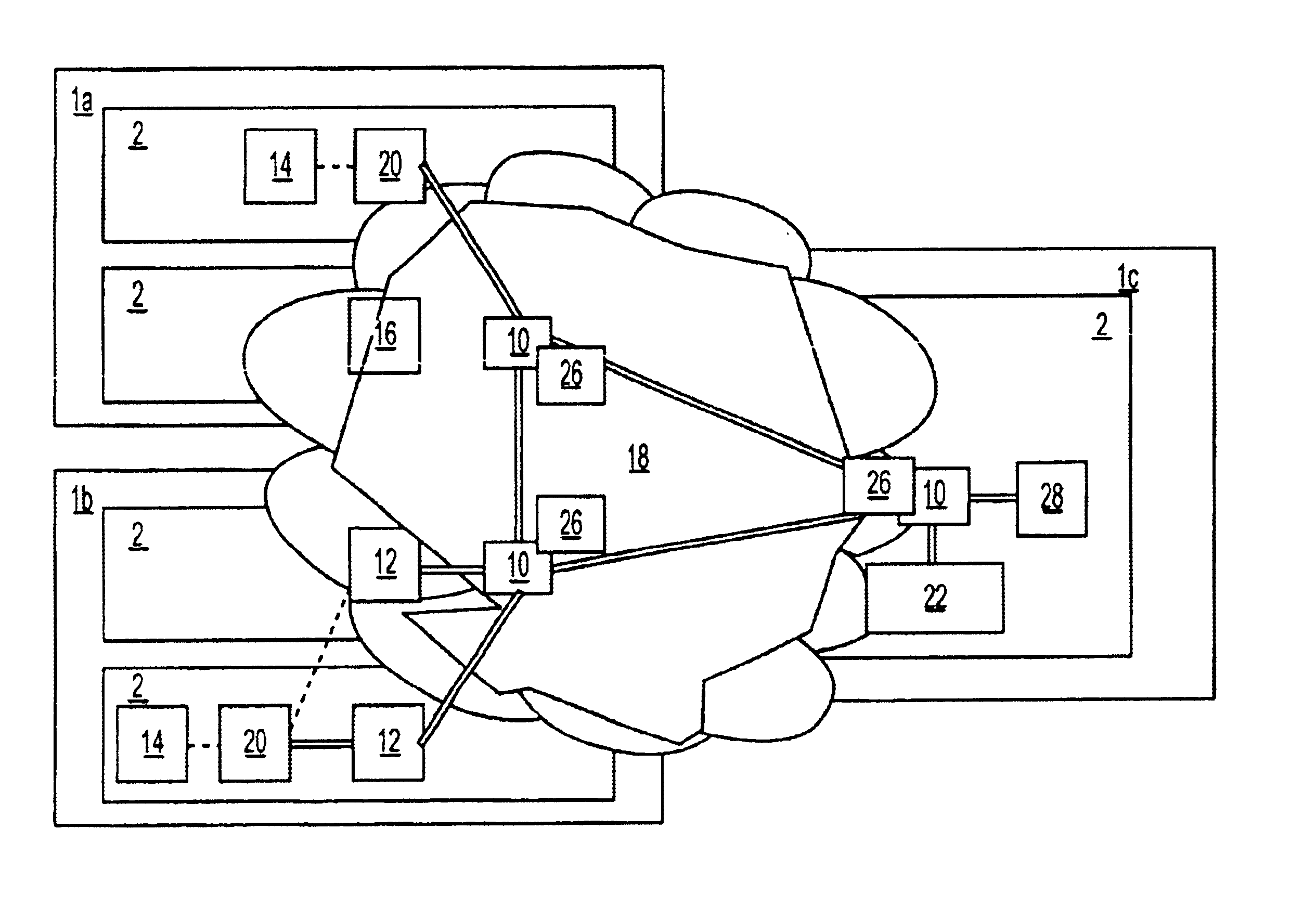
Input device for web content manager responsive to browser viewers' psychological preferences, behavioral responses and physiological stress indicators
InactiveUS20060293921A1Easy and efficient to manufactureLow costDiagnostic recording/measuringSensorsPulse oximetersBehavioral response
Owner:MCCARTHY JOHN +1
Network-based mobile workgroup system
InactiveUS6954790B2Multiple digital computer combinationsWireless network protocolsClient-sideAccess technology
A network-based mobile workgroup system has considerably wider appeal and application than normal virtual private networks in that it provides seamless mobility across a number of access technologies at the same time as it offers a granular security separation down to workgroup level. The mobile workgroup system is an access management system for mobile users with VPN and firewall functionality inbuilt. The mobile user can access the mobile workgroup system over a set of access technologies and select server resources and correspondent nodes to access pending their workgroup membership approvals. All workgroup policy rules are defined in a mobile service manager and pushed down to one or more mobile service routers for policy enforcement. The mobile service router closest to the mobile client, and being part of the mobile virtual private network, performs regular authentication checks of the mobile client during service execution. At the same time it performs traffic filtering based on the mobile user's workgroup memberships. Together, these two components constitute an unprecedented security lock, effectively isolating a distributed workgroup into a mobile virtual private network.
Owner:LONGHORN HD LLC
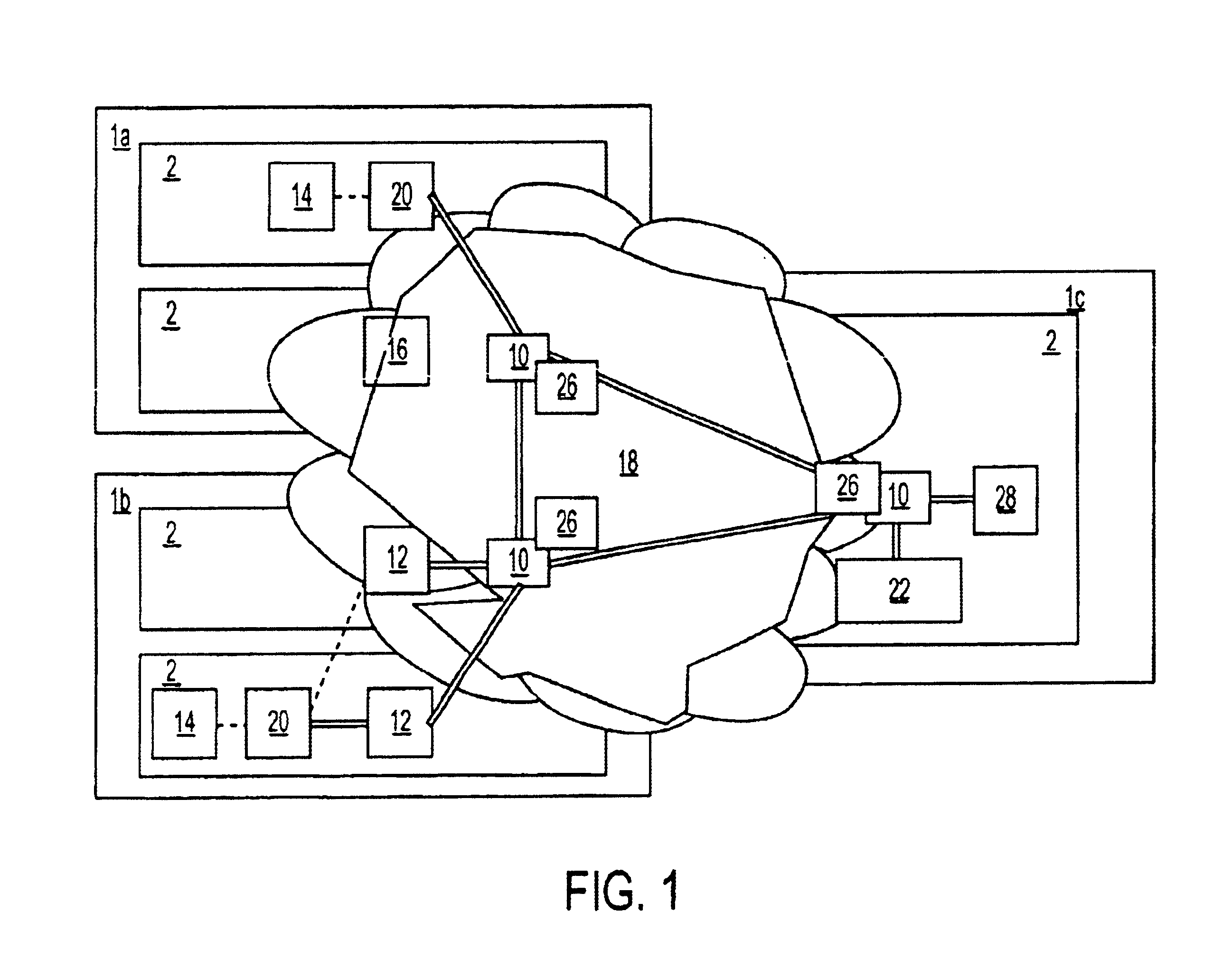
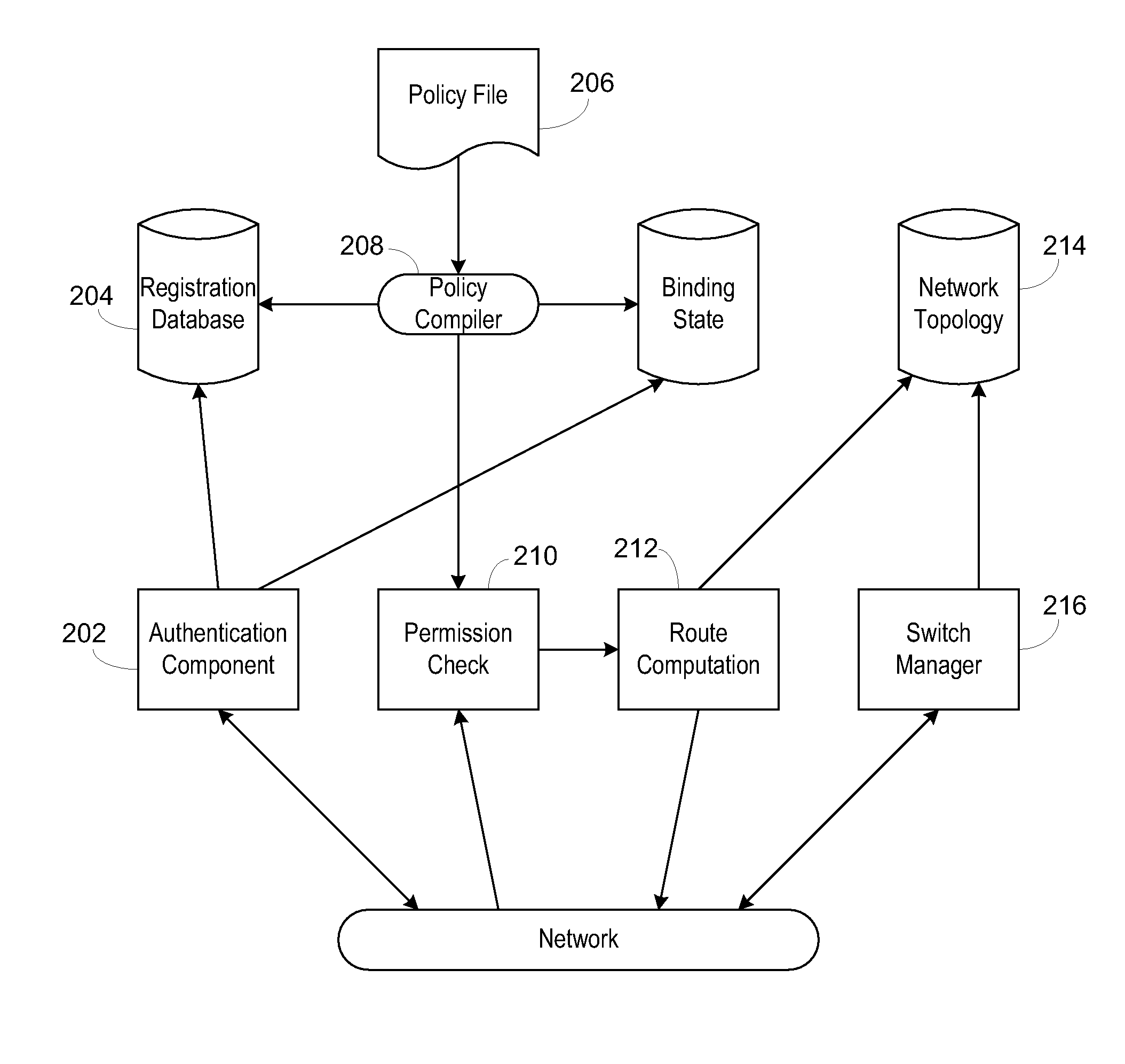
Secure network switching infrastructure
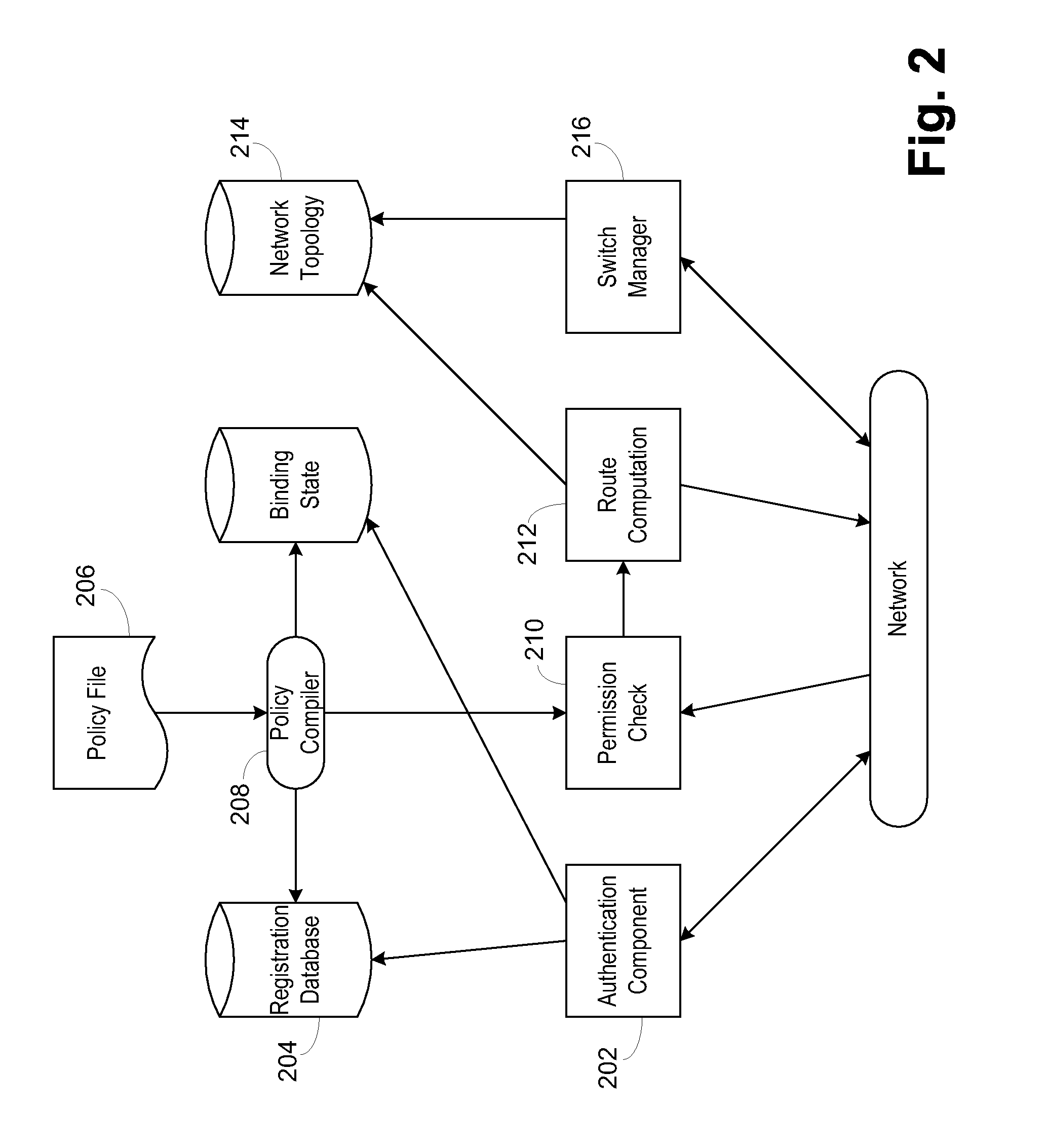
InactiveUS20080189769A1Reduces the trusted computing baseReduce overheadDigital data processing detailsUser identity/authority verificationNetwork packetNetwork control
Use of a centralized control architecture in a network. Policy declaration, routing computation, and permission checks are managed by a logically centralized controller. By default, hosts on the network can only route to the network controller. Hosts and users must first authenticate themselves with the controller before they can request access to the network resources. The controller uses the first packet of each flow for connection setup. When a packet arrives at the controller, the controller decides whether the flow represented by that packet should be allowed. The switches use a simple flow table to forward packets under the direction of the controller. When a packet arrives that is not in the flow table, it is forwarded to the controller, along with information about which port the packet arrived on. When a packet arrives that is in the flow table, it is forwarded according to the controller's directive.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Multi-access mode electronic personal assistant
InactiveUS6895558B1Digital data information retrievalMultiplex communicationVocal responseData access
A system enables communication between server resources and a wide spectrum of end-terminals to enable access to the resources of both converged and non-converged networks via voice and / or electronically generated commands. An electronic personal assistant (ePA) incorporates generalizing / abstracting communications channels, data and resources provided through a converged computer / telephony system interface such that the data and resources are readily accessed by a variety of interface formats including a voice interface or data interface. A set of applications provides dual interfaces for rendering services and data based upon the manner in which a user accesses the data. An electronic personal assistant in accordance with an embodiment of the invention provides voice / data access to web pages, email, file shares, etc. A voice-based resource server authenticates a user by receiving vocal responses to one or more requests variably selected and issued by a speaker recognition-based authentication facility. Thereafter an application proxy is created.
Owner:MICROSOFT TECH LICENSING LLC
Inductively charged battery pack
ActiveUS7375492B2Enabling user convenienceMaximizes flexibility and efficiency and safetyCircuit authenticationVolume/mass flow measurementElectrical batteryEngineering
An inductive charging systems transfers energy by inductively coupling a source coil on a charging source to a receiver coil on a charging portion of a battery pack. The source current is received in the battery pack and converted to direct current for storage in the battery pack cells. Communication between a charging source and the charging portion is provided. A wireless communication arrangement provides for authentication of devices that are allowed by a source to be charged.
Owner:MICROSOFT TECH LICENSING LLC
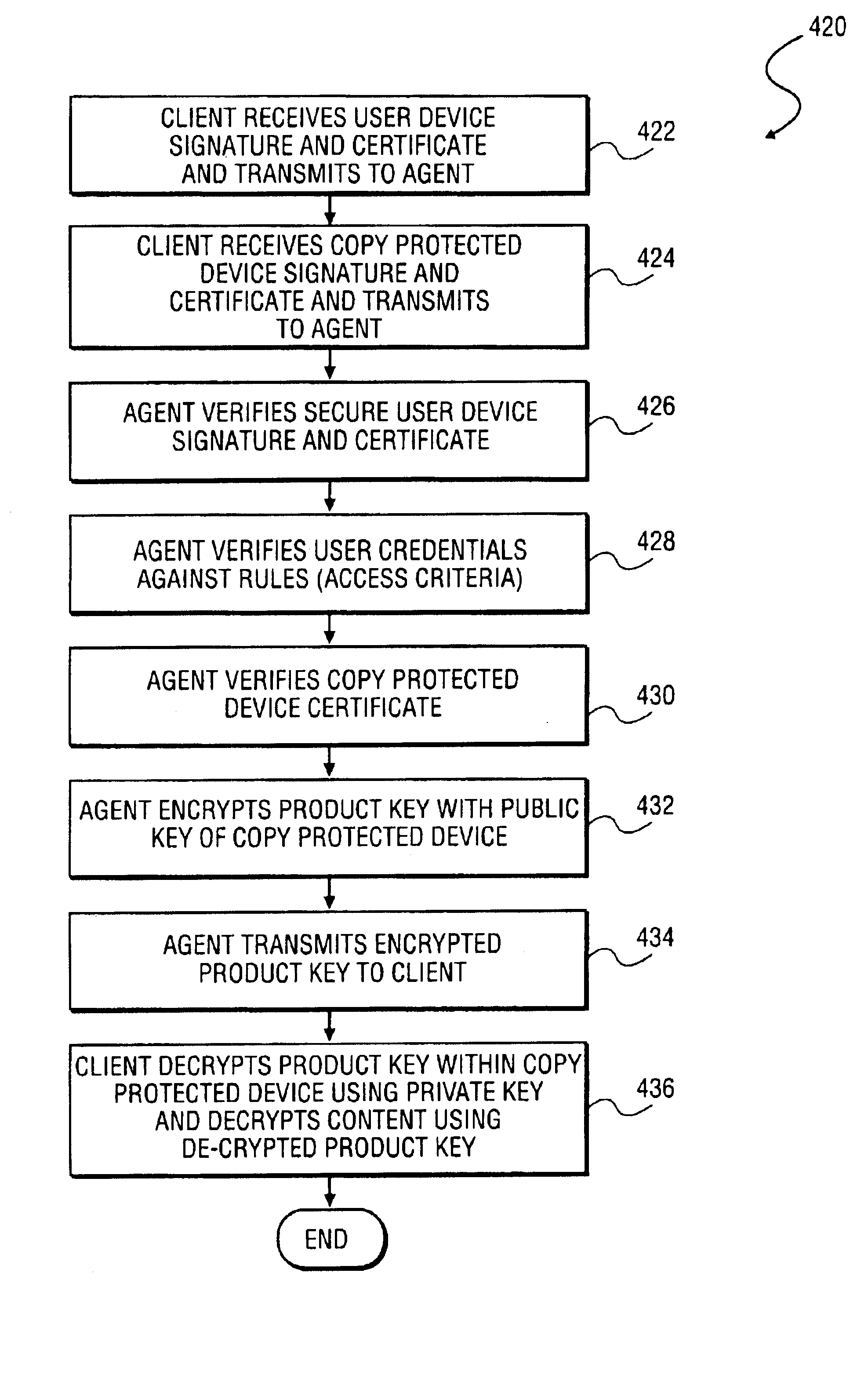
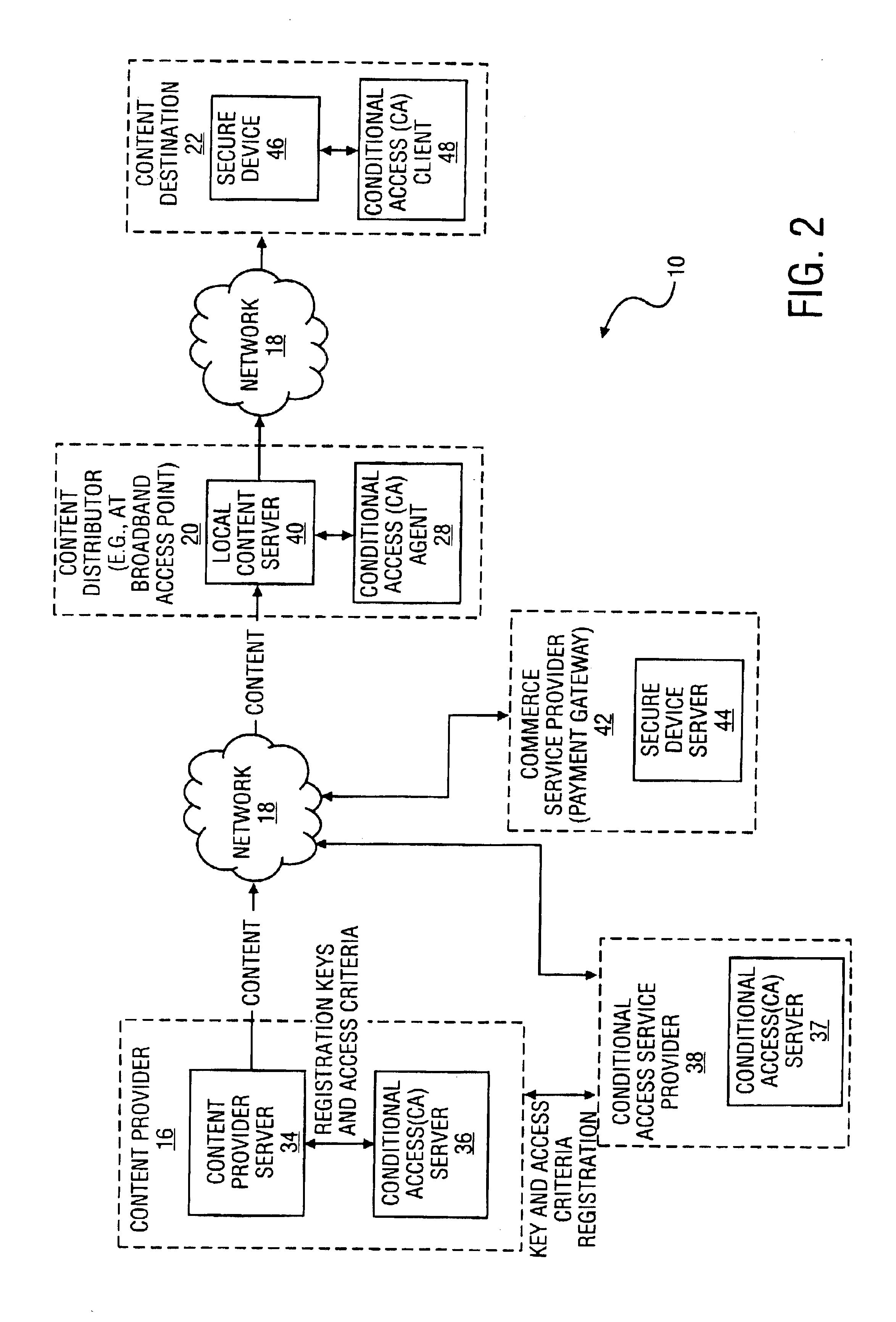
Method and system to secure content for distribution via a network
InactiveUS6961858B2Key distribution for secure communicationDigital data processing detailsUser deviceAuthentication
A method and system to secure content for distribution via a communications network commences when a user device authentication process is associated with content from a content provider. A copy-protected device authentication process is associated with the content. The user device authentication process and the copy-protected device authentication process are separate authentication processes to protect the content from unauthorized access.
Owner:MIH TECH HLDG BV
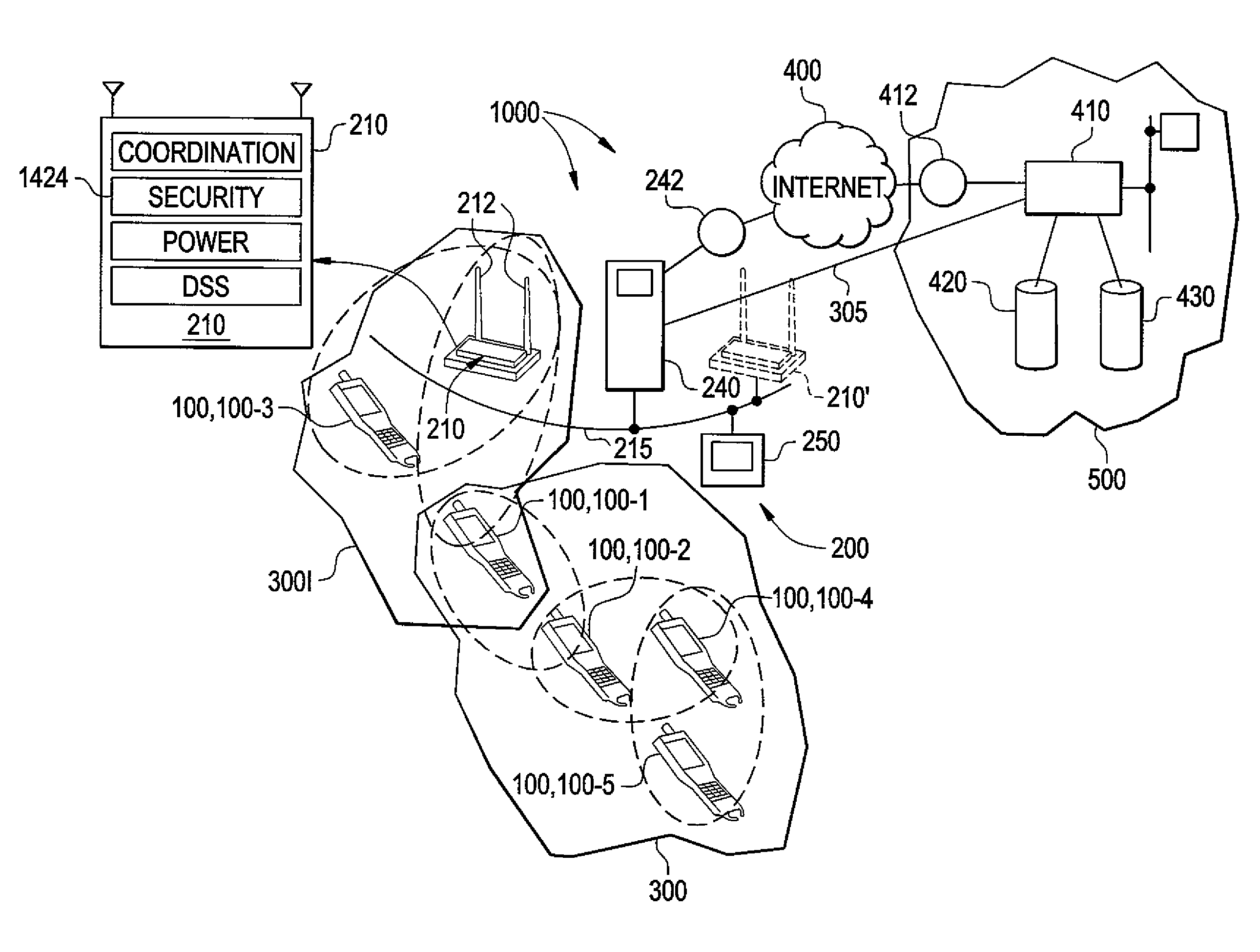
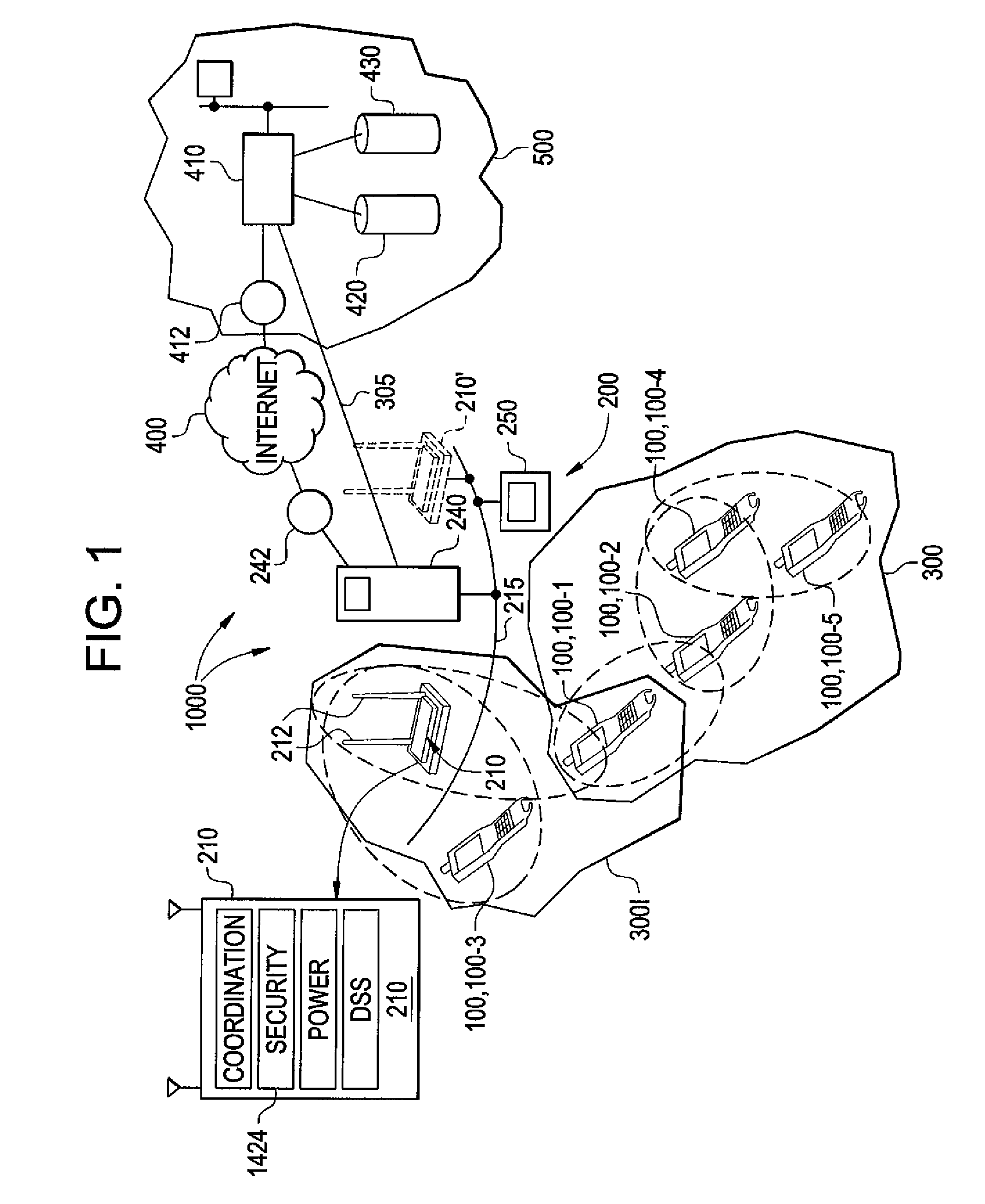
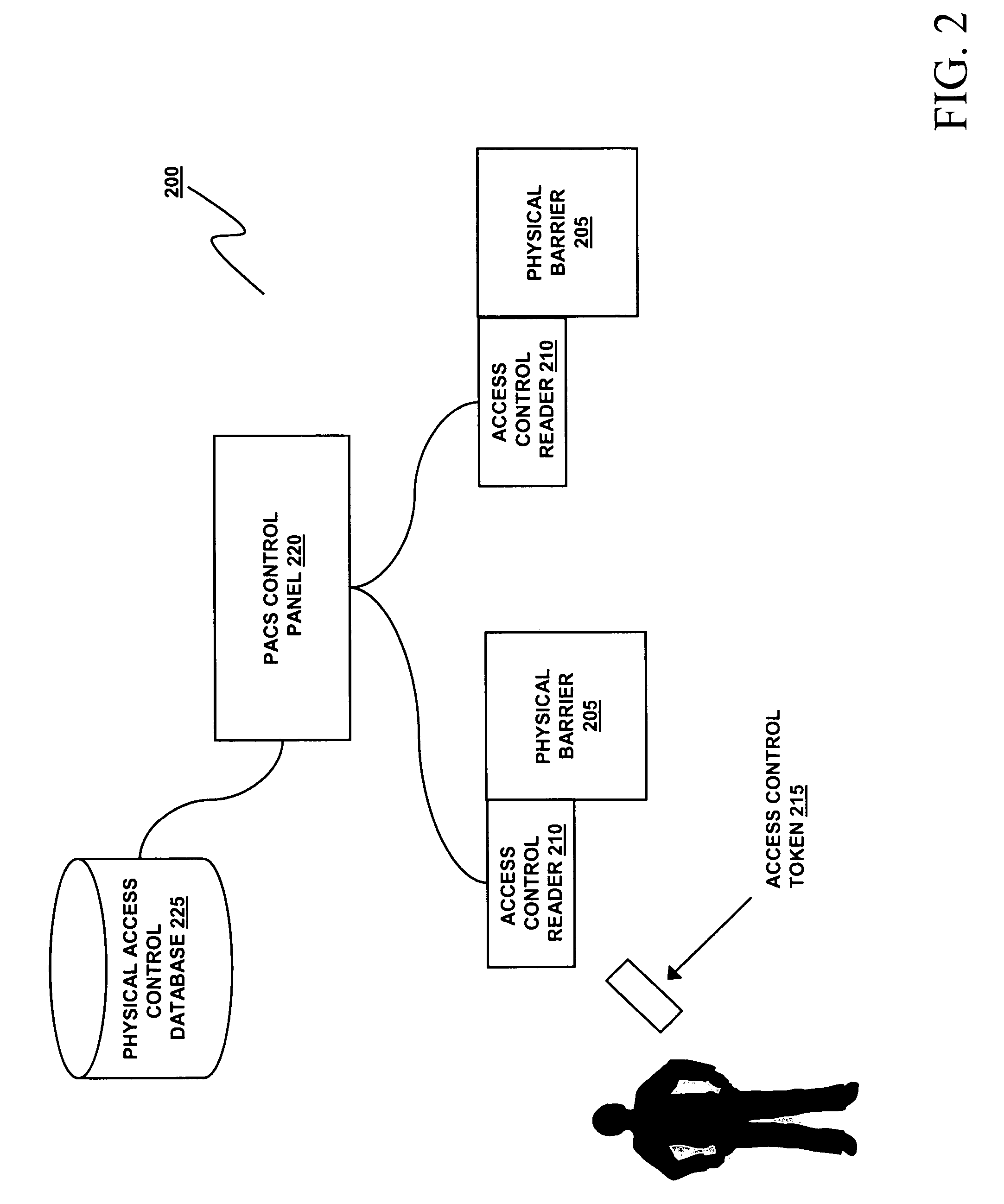
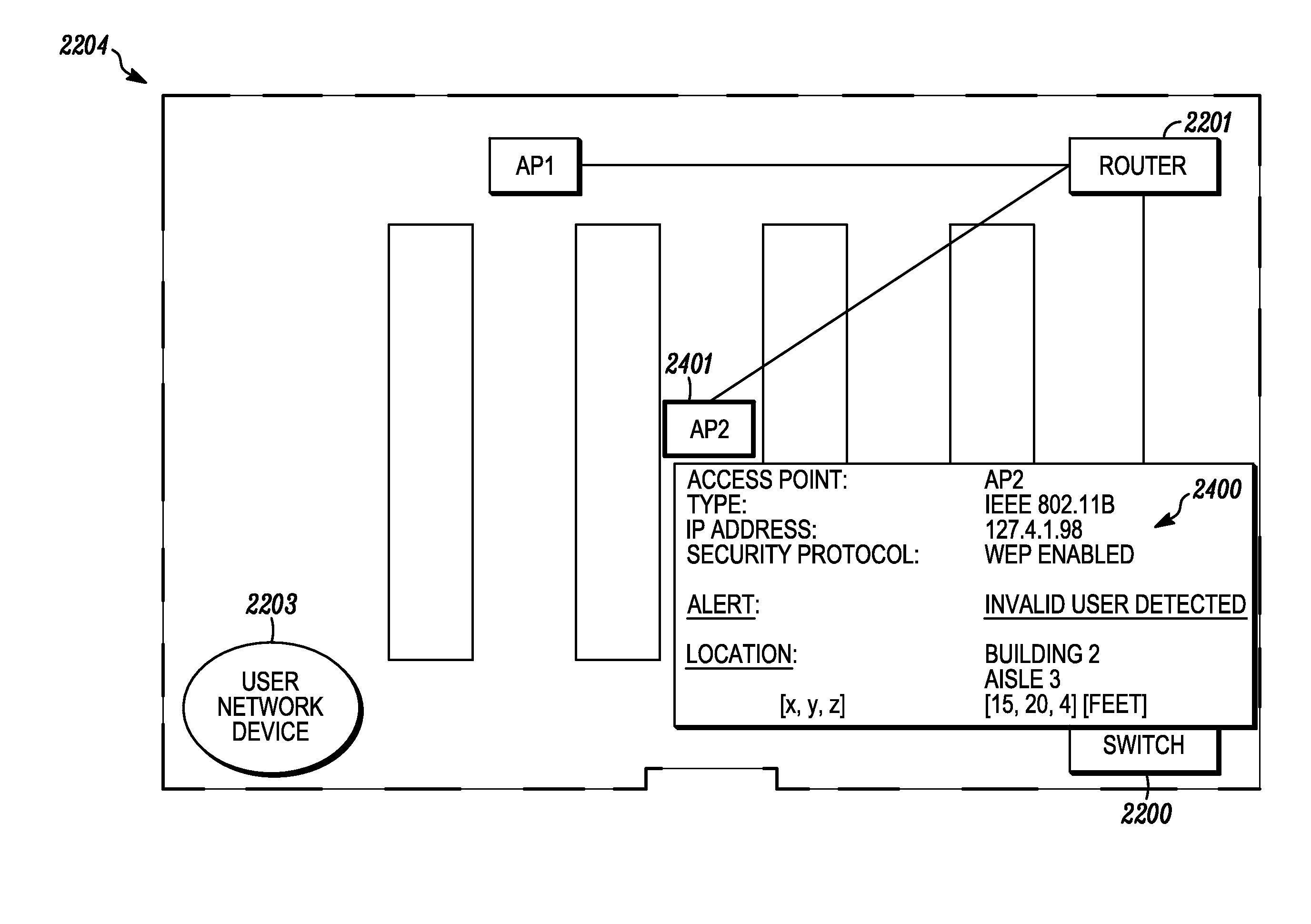
System and method for indicating the presence or physical location of persons or devices in a site specific representation of a physical environment
ActiveUS7295119B2Significant valueEasy to explainDigital data processing detailsBurglar alarm mechanical actuationCommunications systemDisplay device
A system and method for providing security to a wireless communication system having wireless communication components positioned at different locations within a physical environment are provided. The wireless communication components include an access point and a network device. A site-specific computerized representation of the physical environment displays the location of the wireless communication components including the access point and network device. The access point and network device identify the presence or a physical location of a possible intruder or intruder devices. An indicator is presented in the site-specific representation on the display when an erroneous authentication request or other undesired transmission is received by the network device or the access point.
Owner:EXTREME NETWORKS INC
Secure network commercial transactions
InactiveUS20060235795A1Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceBuying/selling/leasing transactionsPaymentSecure communication
Current embodiments provide for authorization and payment of an online commercial transaction between a purchaser and a merchant including verification of an identity of the purchaser and verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are often different network entities. Other embodiments also provide for protocols, computing systems, and other mechanisms that allow for identity and payment authentication using a mobile module, which establishes single or multilevel security over an untrusted network (e.g., the Internet). Still other embodiments also provide for a three-way secure communication between a merchant, consumer, and payment provider such that sensitive account information is opaque to the merchant, yet the merchant is sufficiently confident of the consumer's ability to pay for requested purchases. In yet another embodiment, electronic billing information is used for authorization, auditing, payment federation, and other purposes.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for authentication of users and web sites
InactiveUS7100049B2Digital data processing detailsUser identity/authority verificationWeb siteS system
Owner:EMC IP HLDG CO LLC
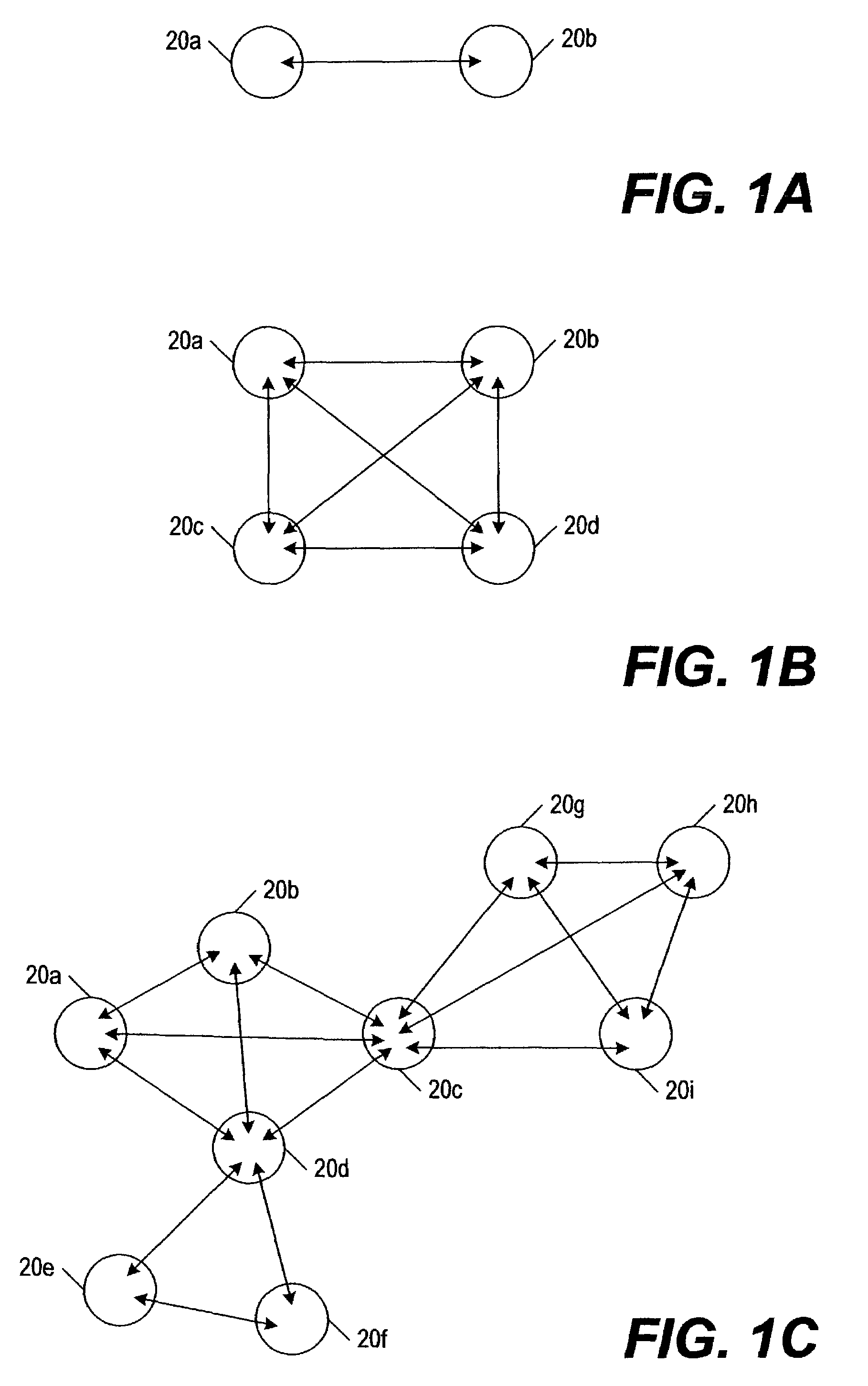
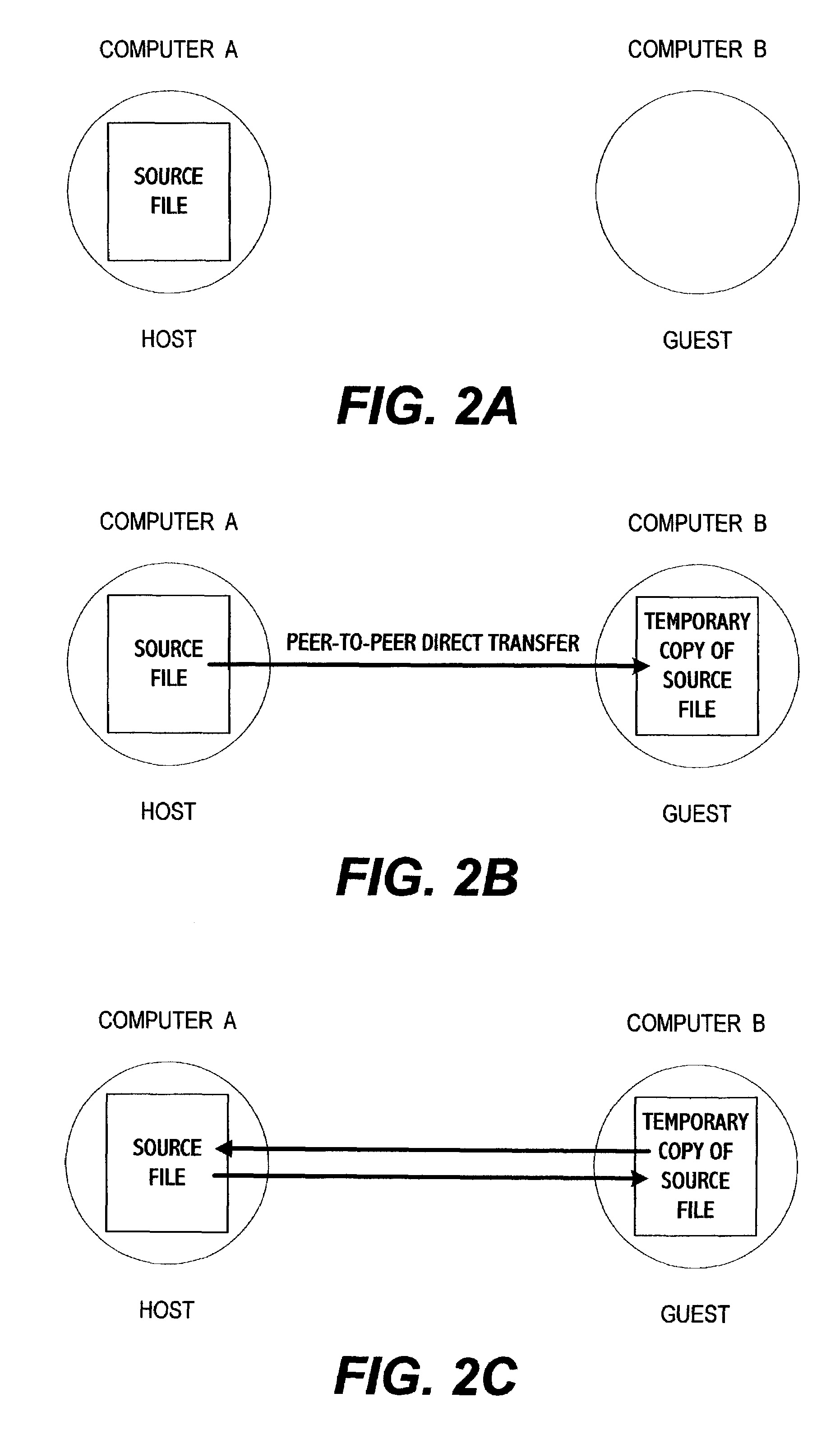
System for electronic file collaboration among multiple users using peer-to-peer network topology
InactiveUS7353252B1Avoid storage problemsMultiple digital computer combinationsOffice automationDocumentation procedurePrivate network
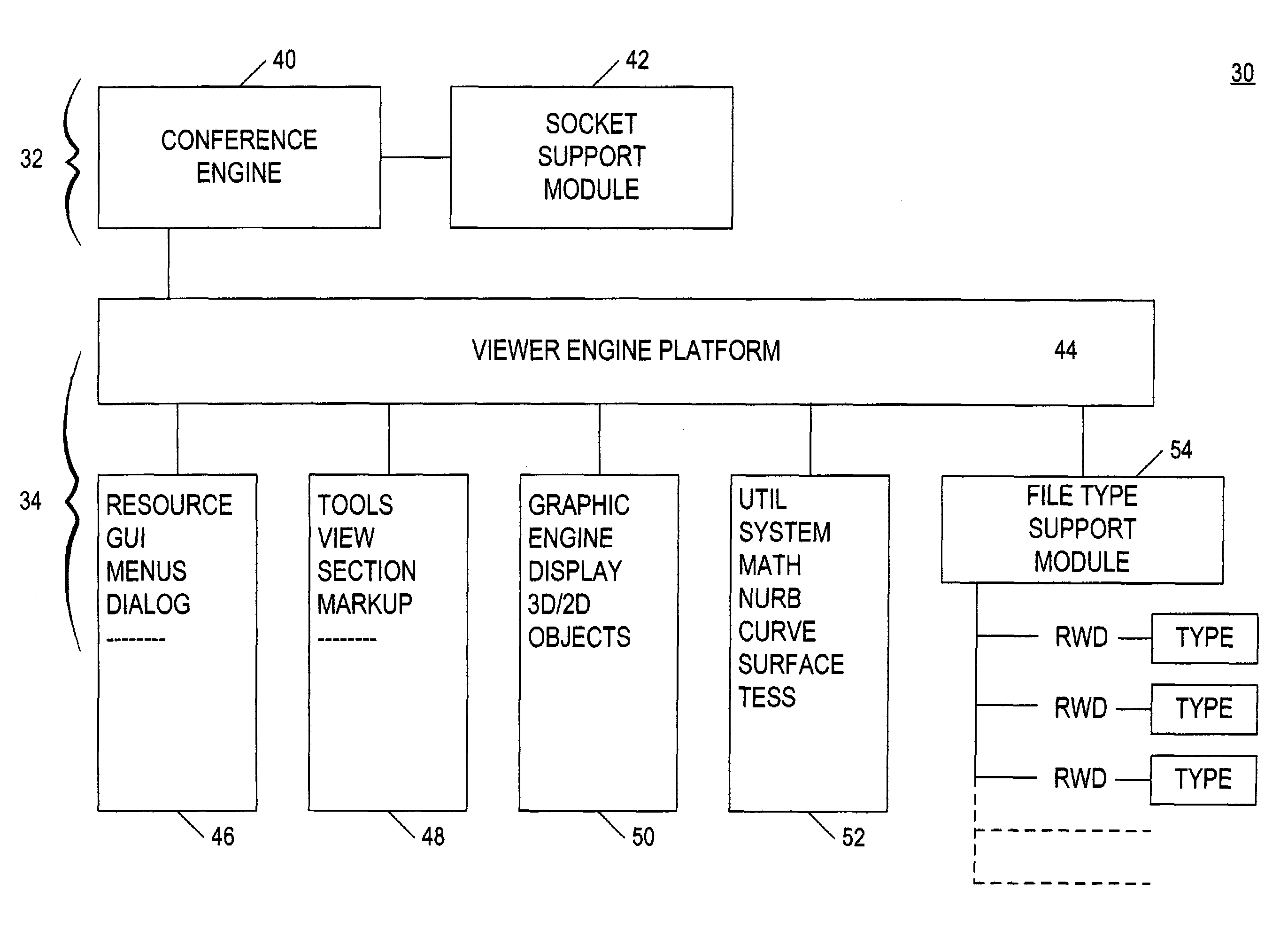
A system for electronic file collaboration among multiple users is implemented using command messages transmitted on dedicated network channels established between conference participants in a peer-to-peer architecture with total autonomy from a central server. The system employs owner-in-control methodology to allow direct transmission of copies of documents among participants by permission, and to prevent storage of copies of documents used in a conference by participants. Mark-ups, additions, and other actions occurring on a conference document can only be saved by the document owner. An advanced viewer engine is provided for reading, displaying and manipulating electronic data in texts, tables, vectors and 3D model formats, as well as common raster images. A proxy module allows data transmitted through IPFW routers or firewall devices with sufficient authentications and security measures.
Owner:SIGMA DESIGNS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com