Patents
Literature
72 results about "Digital evidence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Digital evidence or electronic evidence is any probative information stored or transmitted in digital form that a party to a court case may use at trial. Before accepting digital evidence a court will determine if the evidence is relevant, whether it is authentic, if it is hearsay and whether a copy is acceptable or the original is required.
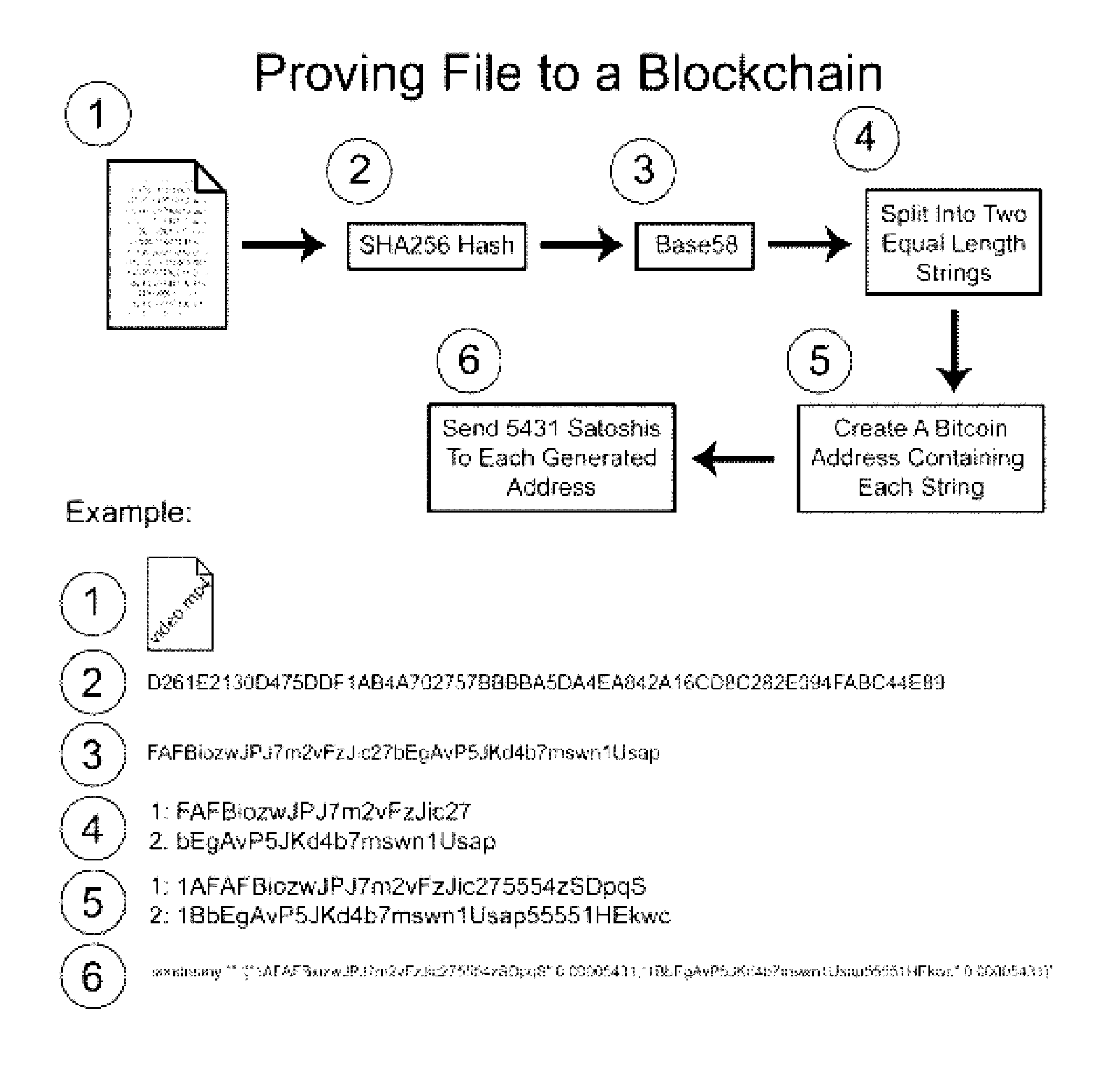
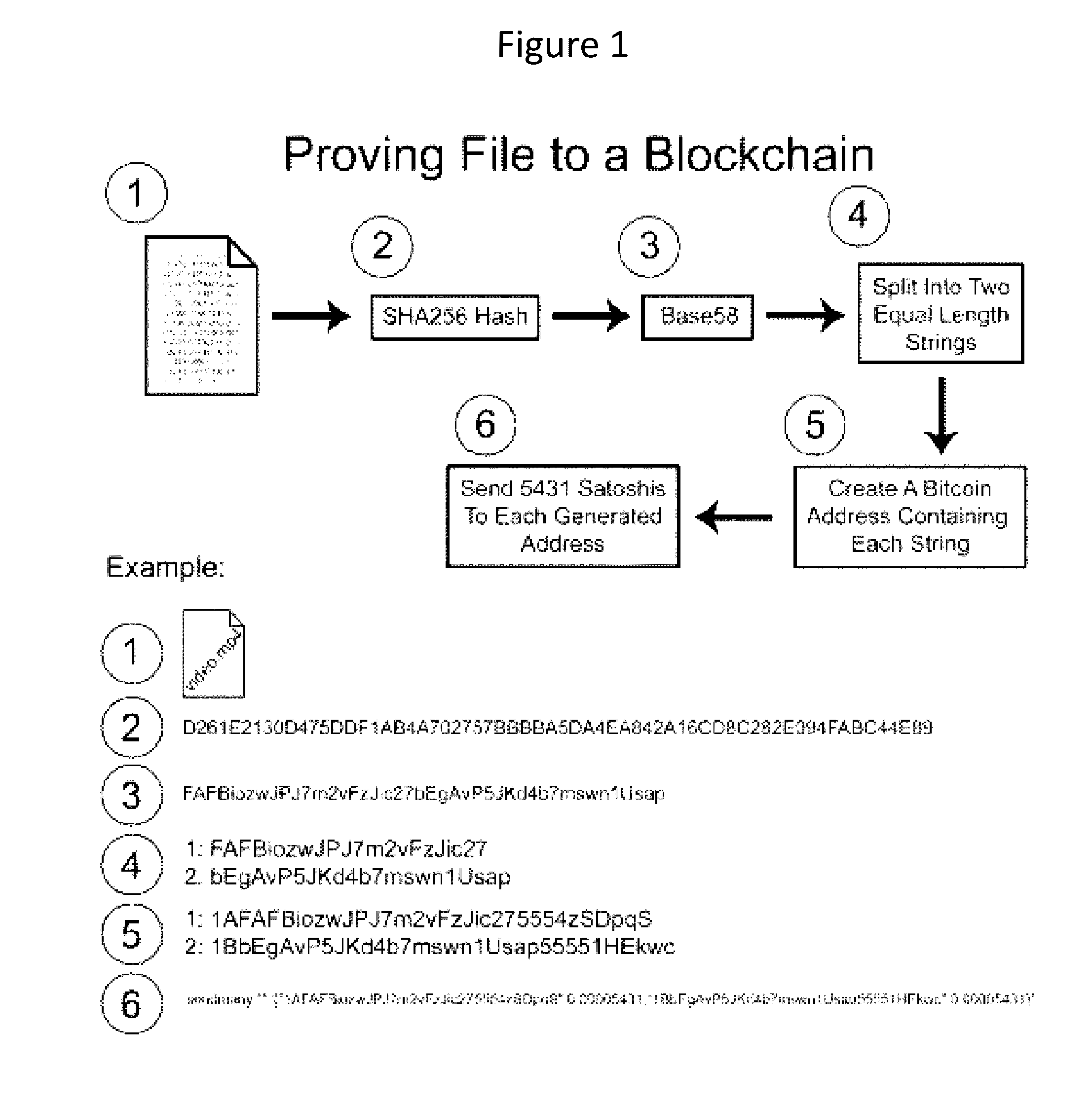
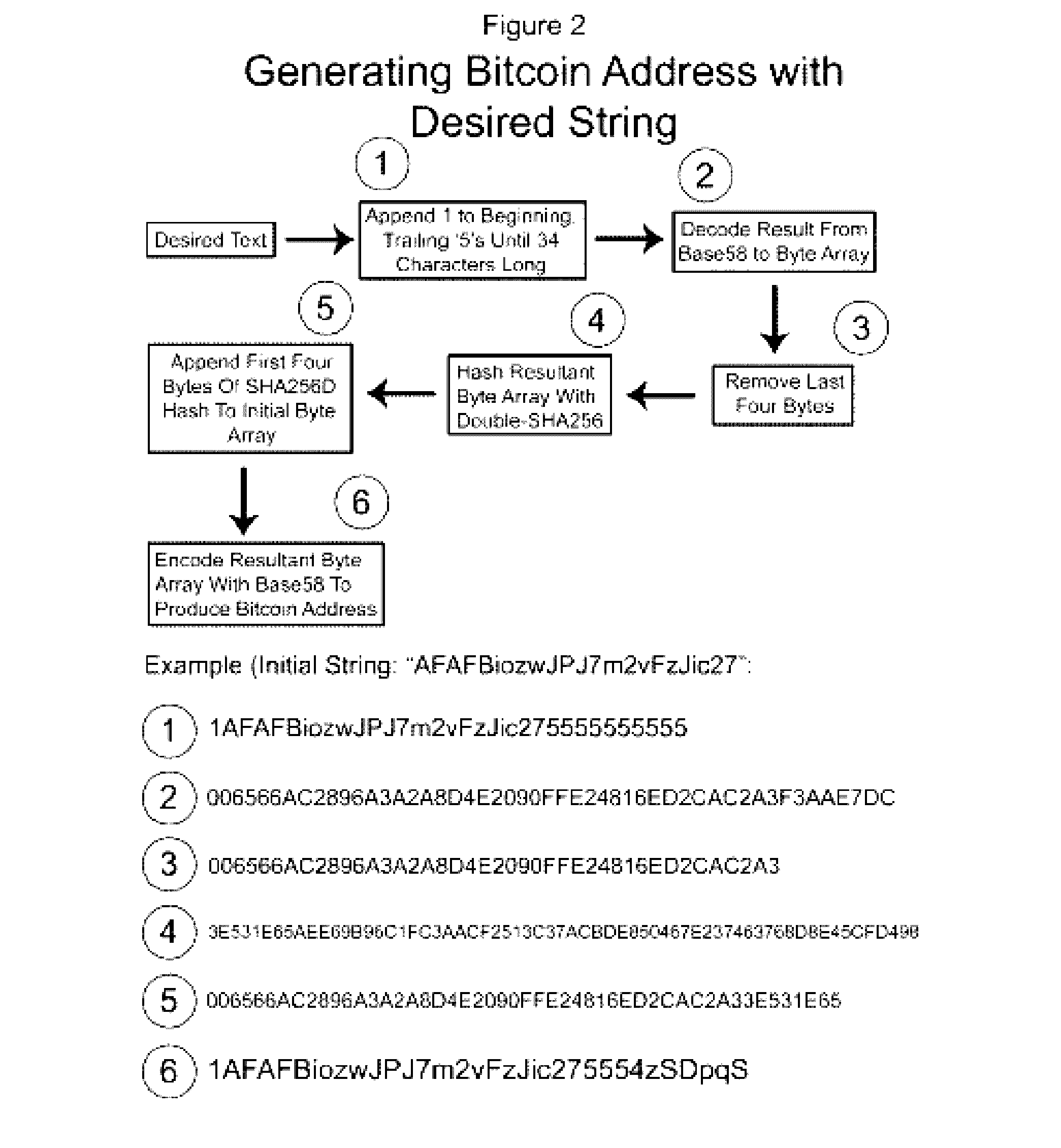
Authentication and verification of digital data utilizing blockchain technology
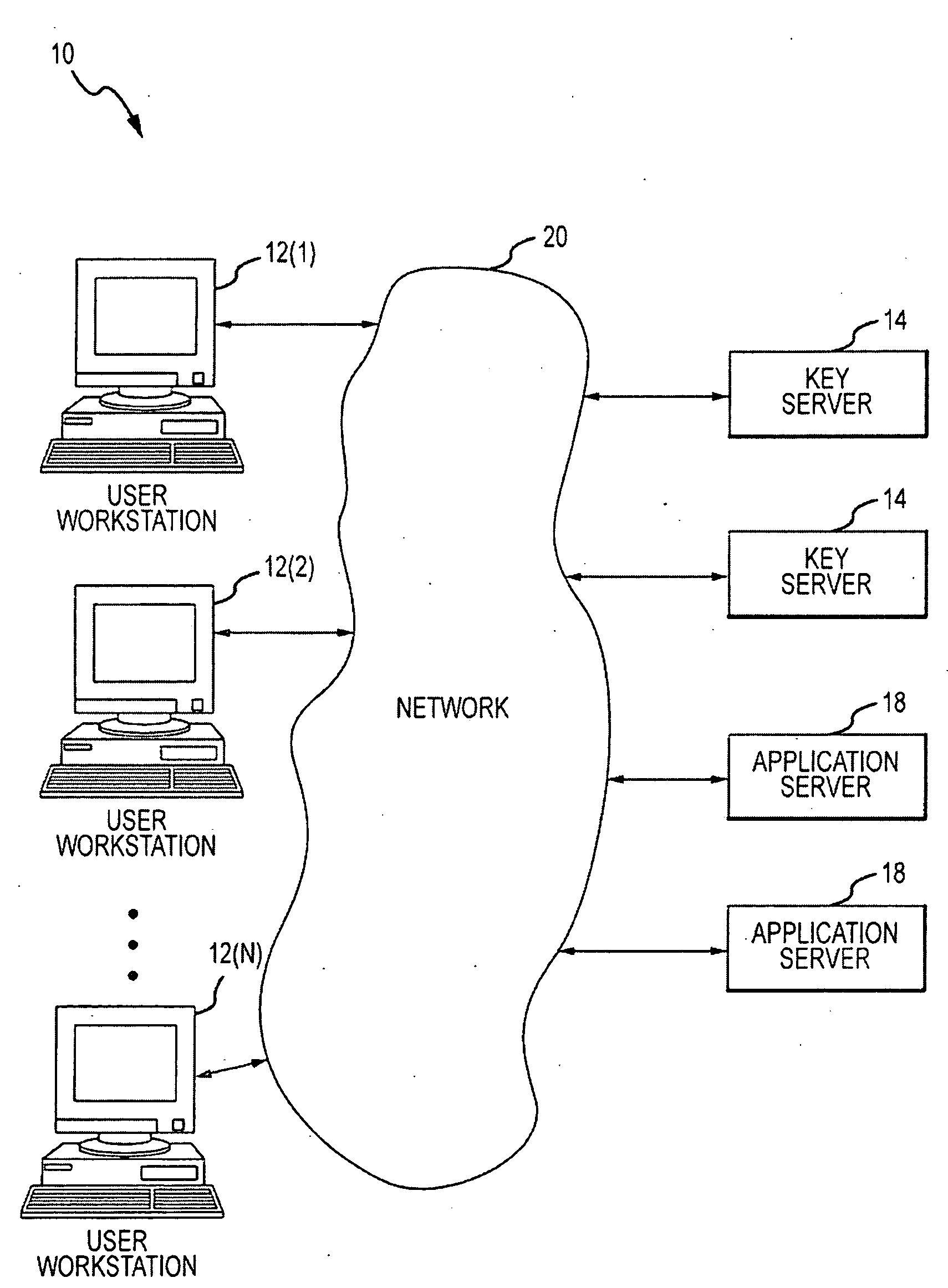
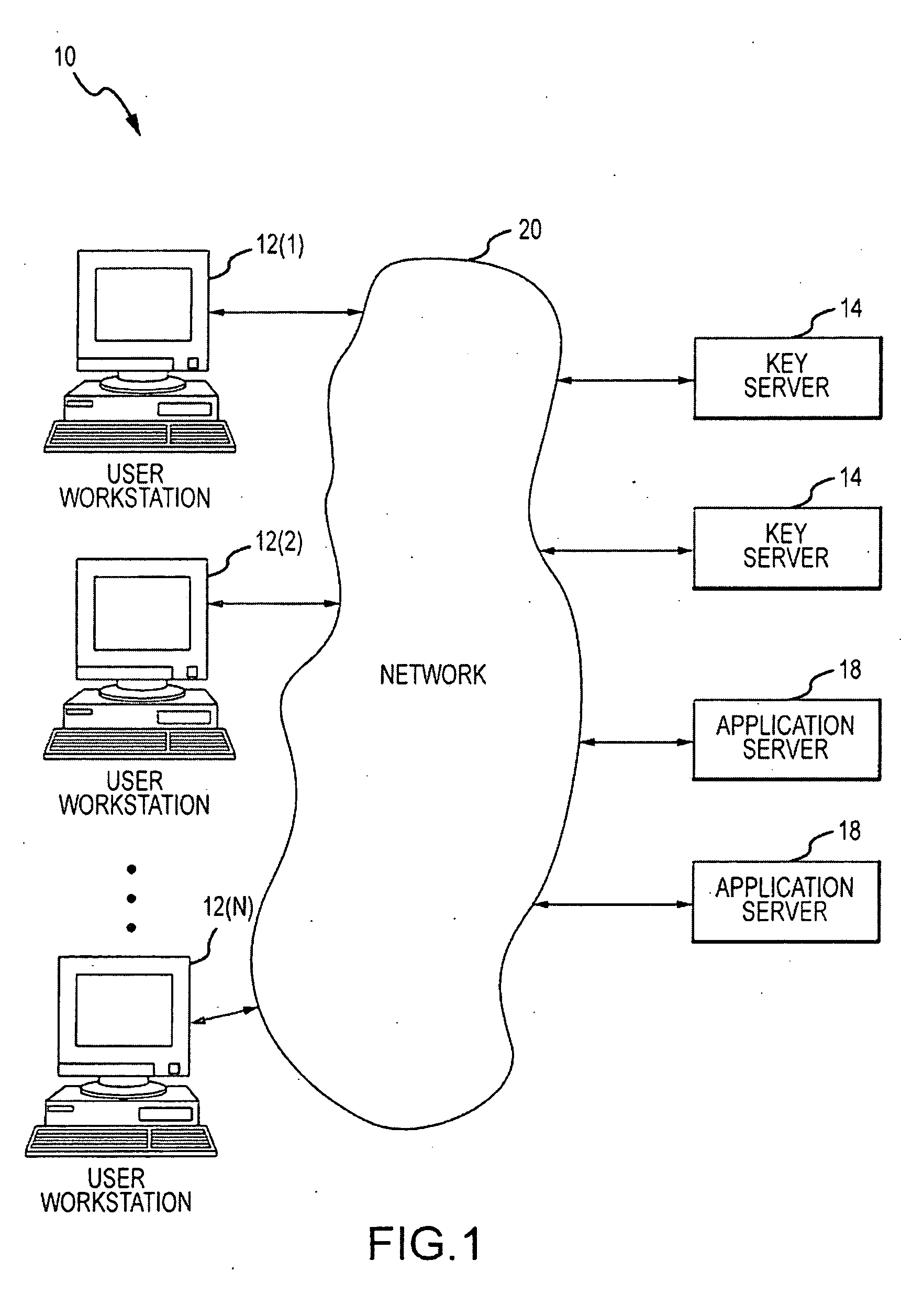
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
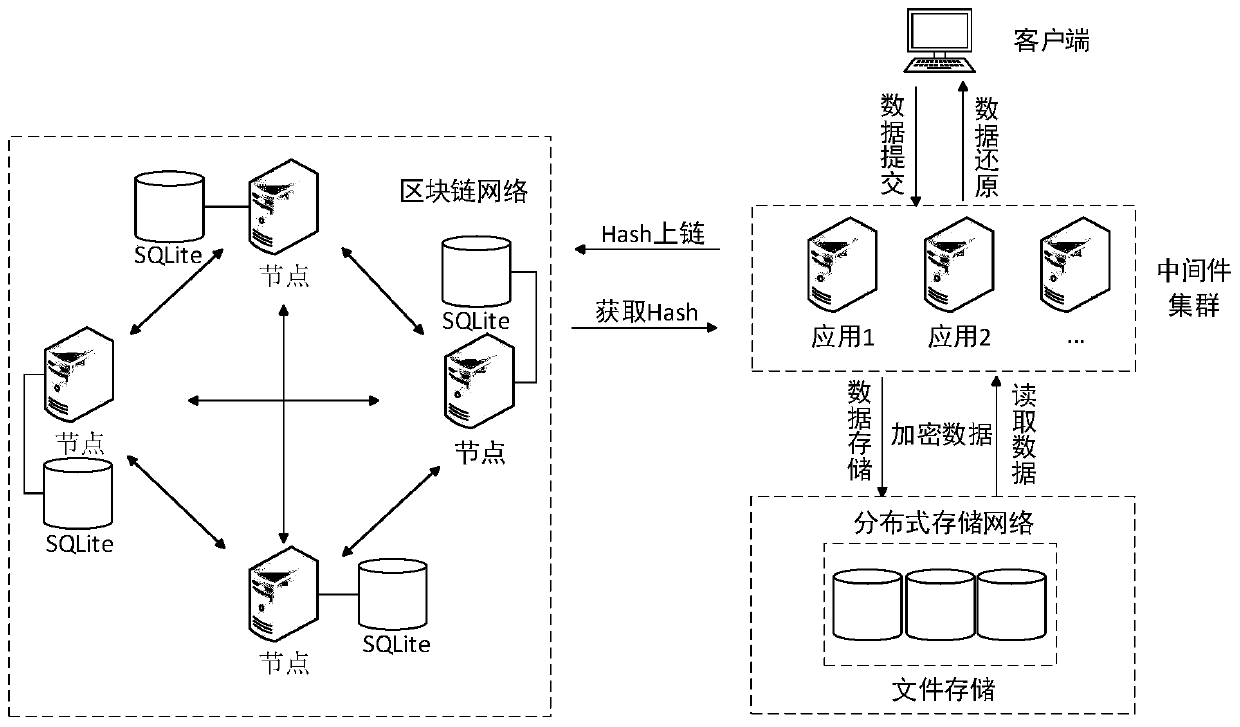
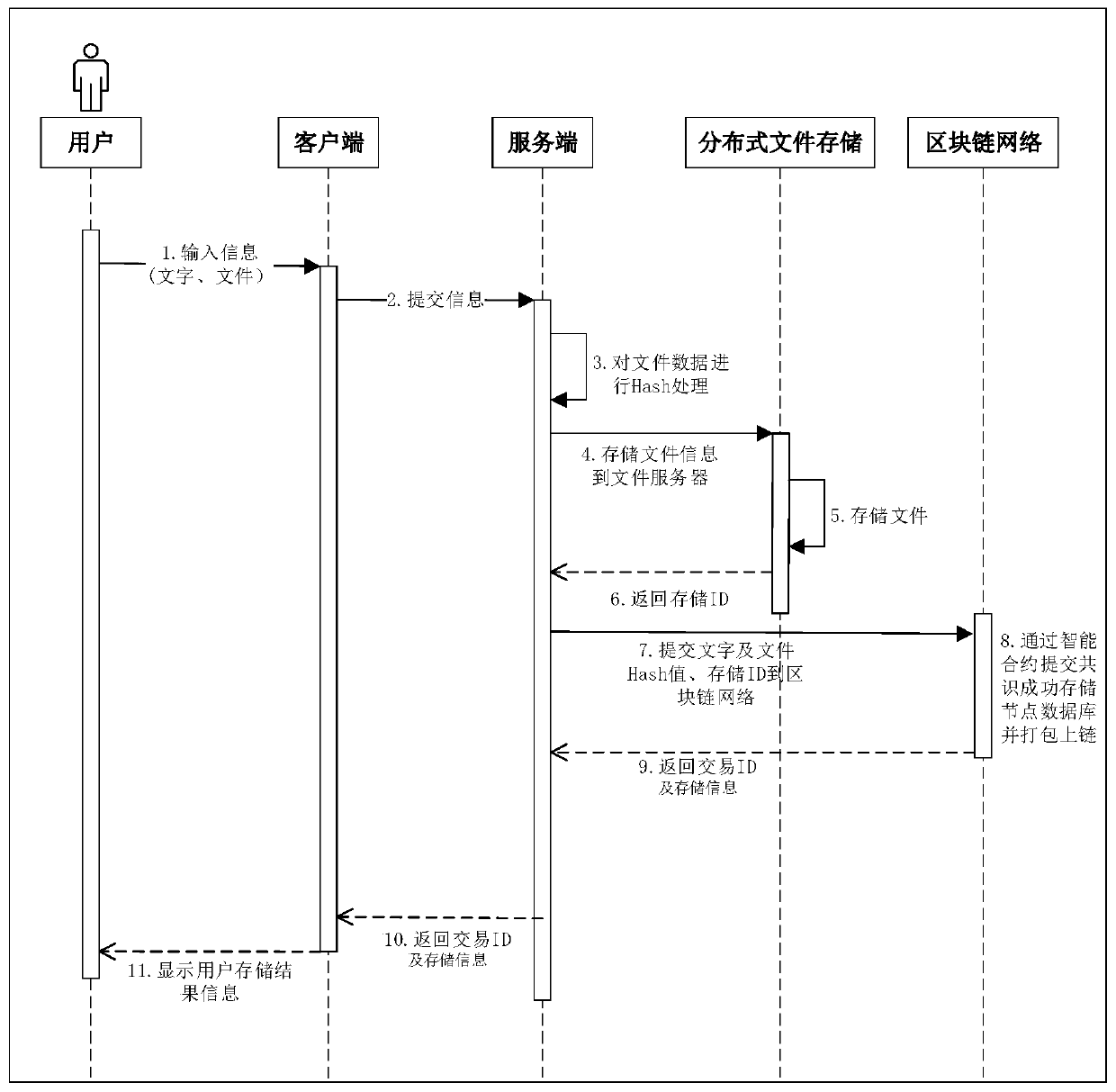
Digital evidence storage platform and evidence storage method based on block chain
ActiveCN110912937AAvoid single point of failure problemsSolve the problem of SQL syntax that does not support relational databasesUser identity/authority verificationDistributed File SystemSoftware engineering
The invention provides a digital evidence storage platform based on a block chain. In the platform, a server performs hash operation on a file in response to a request of submitting an electronic format file by a client to obtain a hash value corresponding to the file; the server performs information interaction with the distributed file system, names the file with a corresponding hash value, stores the file and acquires a storage ID of the file; the server performs information interaction with the blockchain network, and submits the hash value, the storage ID and the file creation informationcorresponding to the file to the blockchain network; the blockchain network successfully stores transaction data through the smart contract after consensus and packages the transaction data into blocks, and then returns successfully stored block transaction ID values to the server; and the server locally stores the submitted file and the hash value, the storage ID and the transaction ID corresponding to the file, and returns the storage state information of the file to the client. The authenticity and reliability of the data can be ensured.
Owner:HANGZHOU INST OF ADVANCED TECH CHINESE ACAD OF SCI
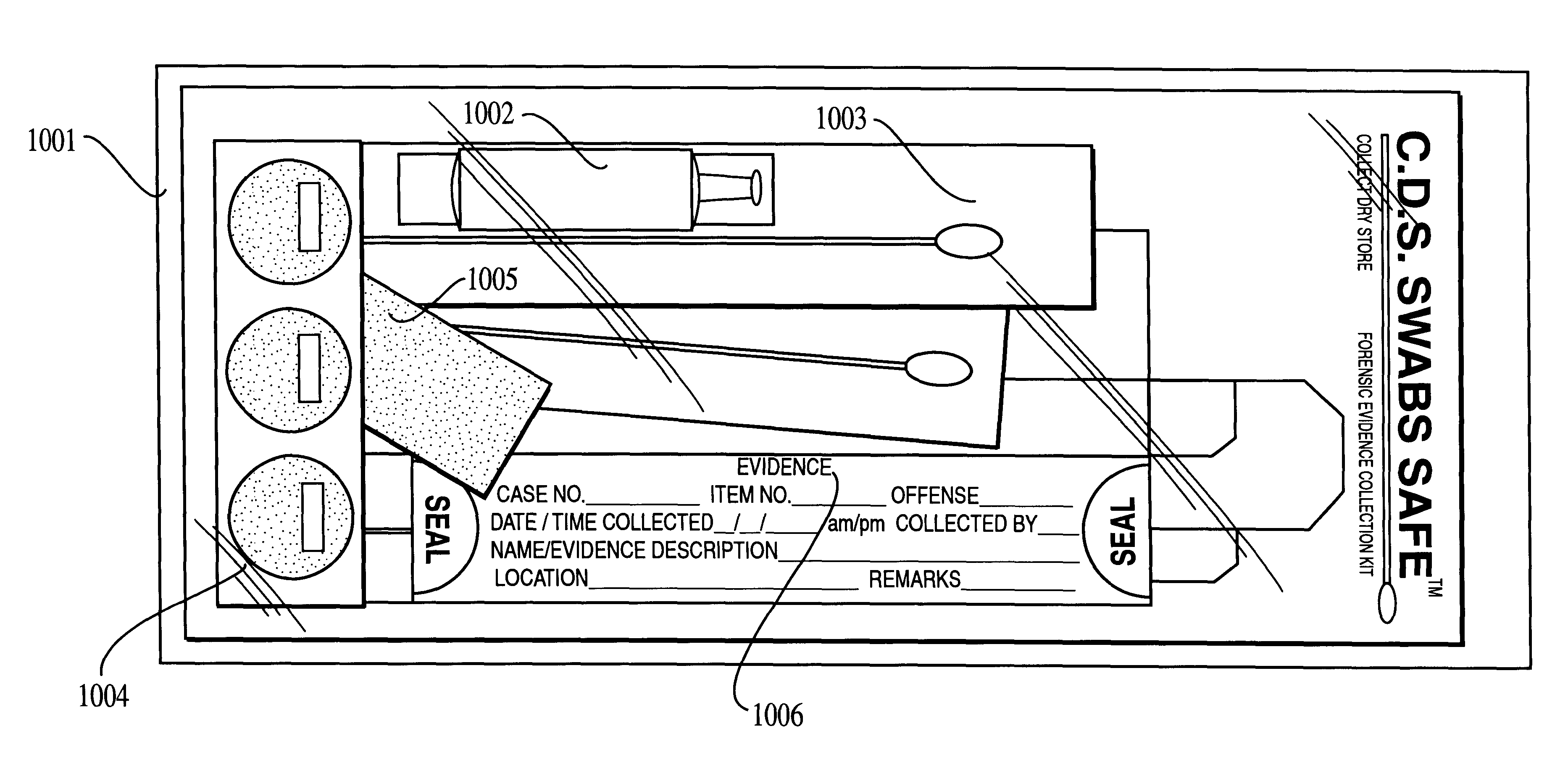
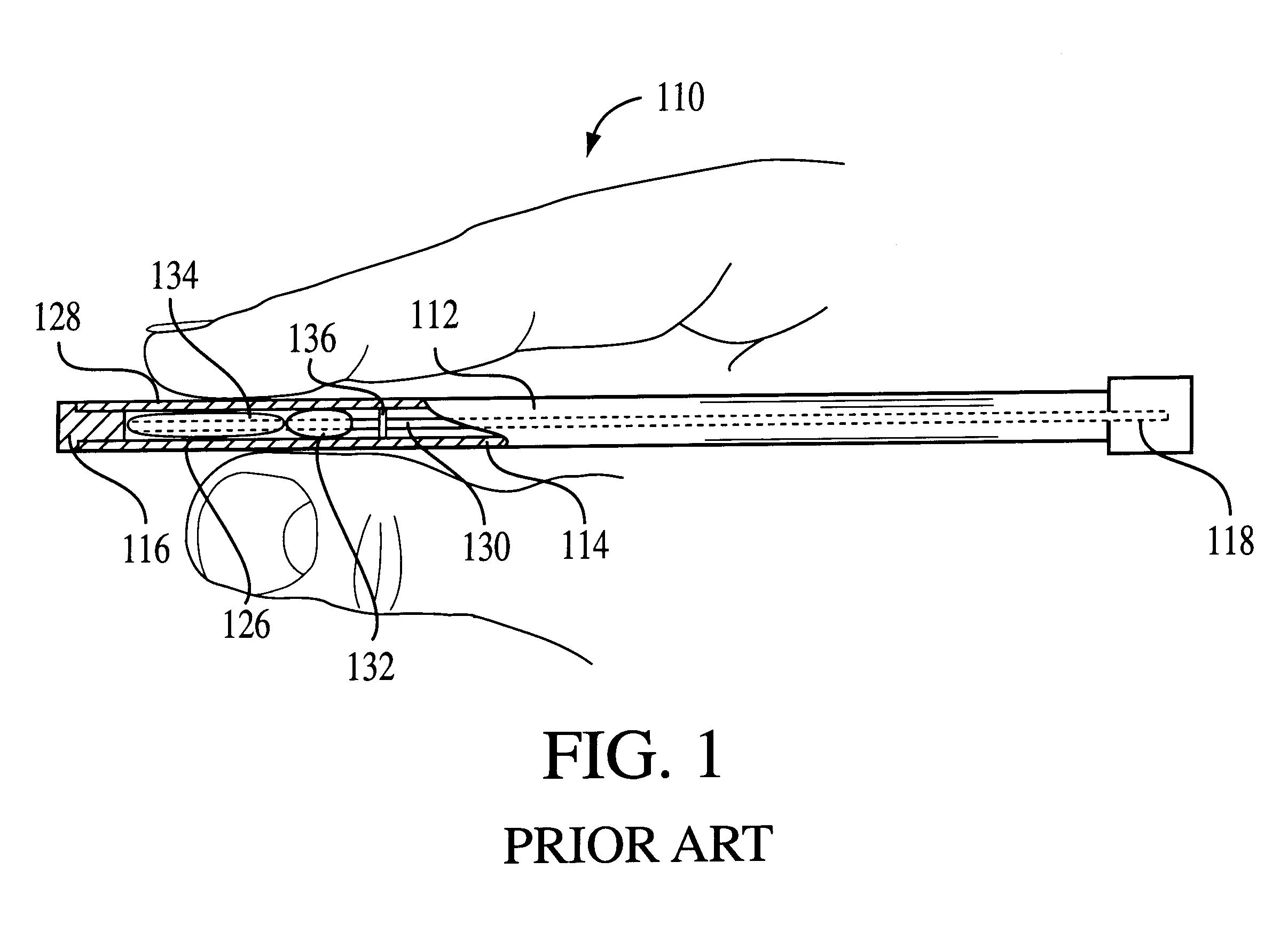
Foldable cardboard box for contact-free drying and long-term storage of biological evidence recovered on cotton swabs and forensic evidence collection kit including same
InactiveUS6085907APrevent tamperingDispensing apparatusVaccination/ovulation diagnosticsContact freeEngineering
A biological evidence collection apparatus provides contact-free drying, storage, identification, and protection against sample switch and contamination of collected biological samples. The apparatus may include the described forensic evidence collection kit which provides a set of tools for the collection and storage of biological evidence. The collection apparatus may also be used as part of a sexual assault evidence collection kit, or a kit for the collection of buccal swabs, and the like.
Owner:INST OF LEGAL MEDICINE OF THE UNIV OF BERNE
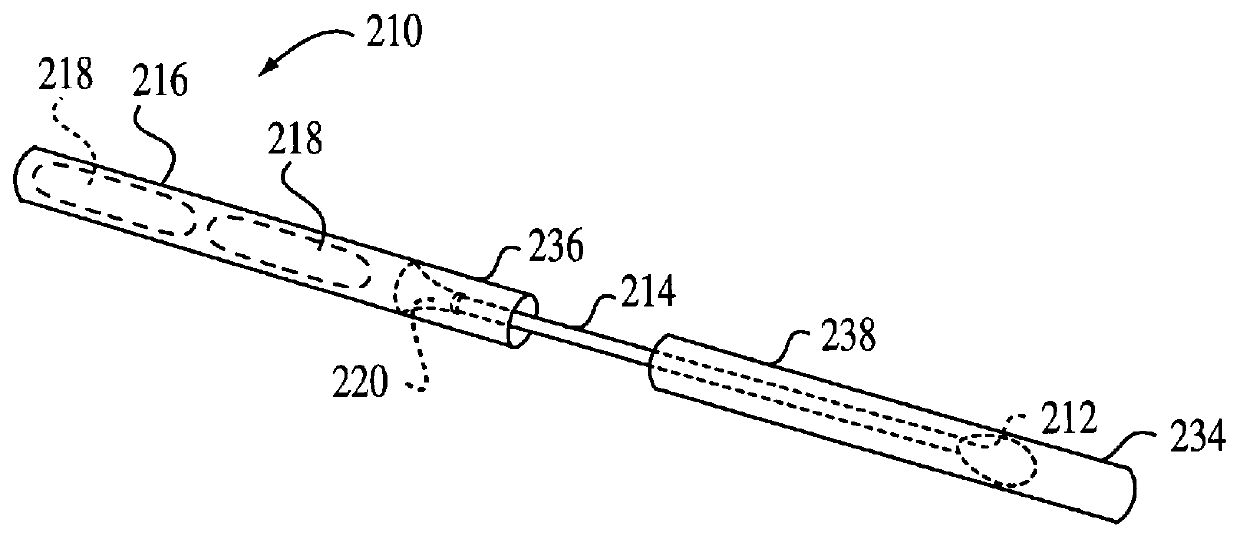
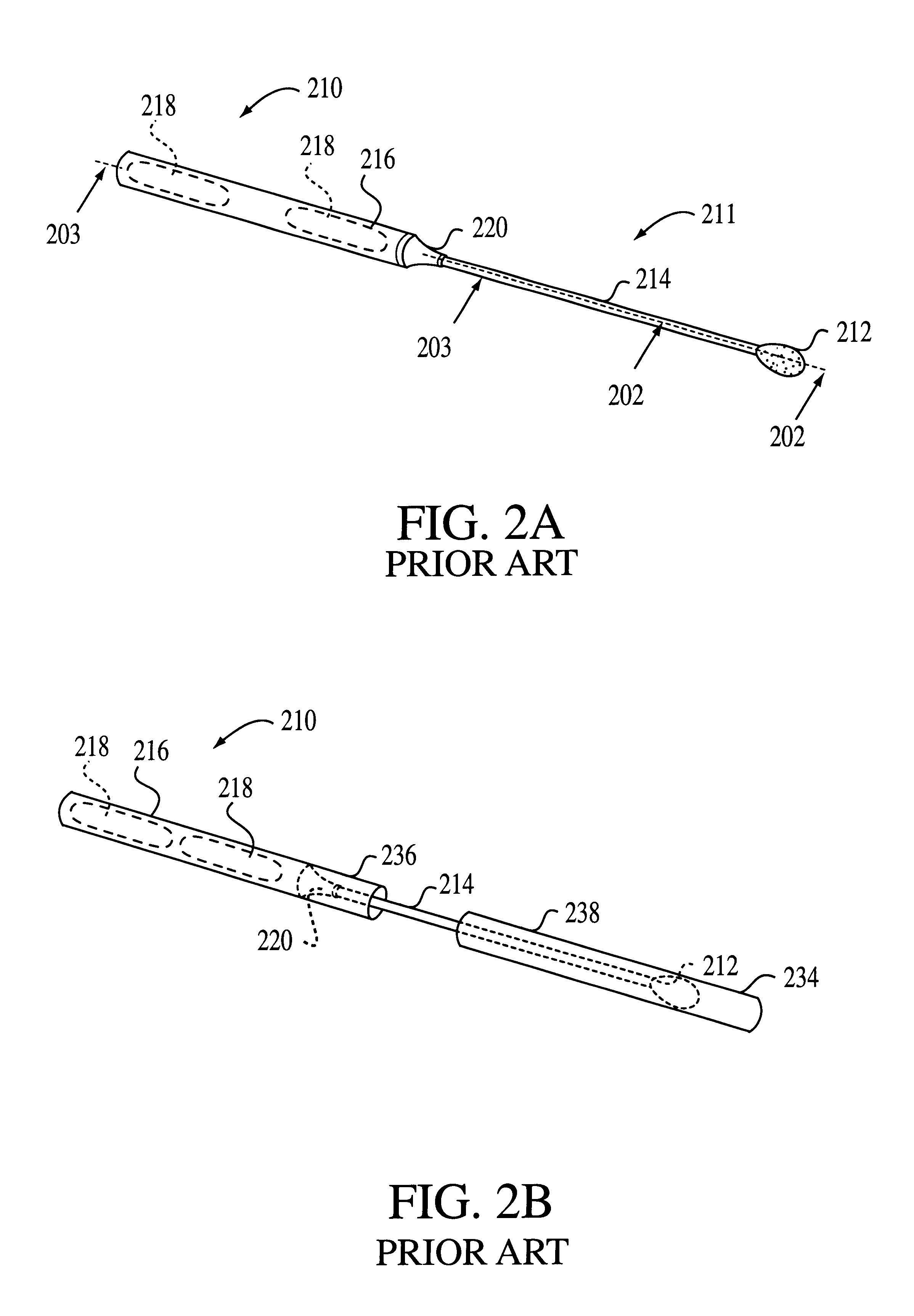
Foldable cardboard box for contact-free drying and long-term storage of biological evidence recovered on cotton swabs and forensic evidence collection kit including same
InactiveUS6171260B1Vaccination/ovulation diagnosticsDiagnostic recording/measuringContact freeEngineering
A biological evidence collection apparatus provides contact-free drying, storage, identification, and protection against sample switch and contamination of collected biological samples. The apparatus may include the described forensic evidence collection kit which provides a set of tools for the collection and storage of biological evidence. The collection apparatus may also be used as part of a sexual assault evidence collection kit, or a kit for the collection of buccal swabs, and the like.
Owner:INST OF LEGAL MEDICINE OF THE UNIV OF BERNE
Apparatus, method and system for collecting and utilizing digital evidence
InactiveUS20110058048A1Low billTelevision system detailsColor television detailsDigital evidenceBusiness process
Owner:PICOSMOS IL
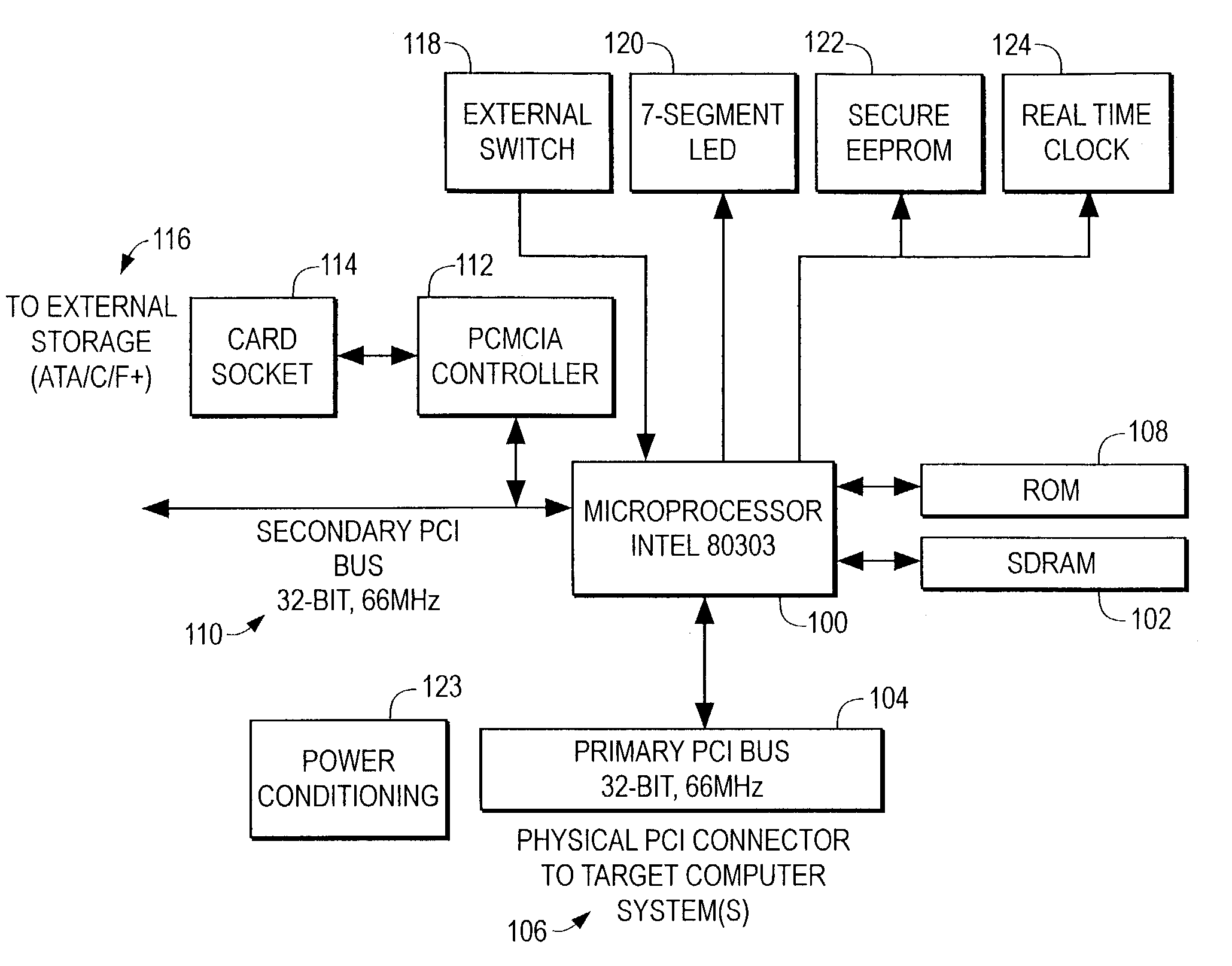
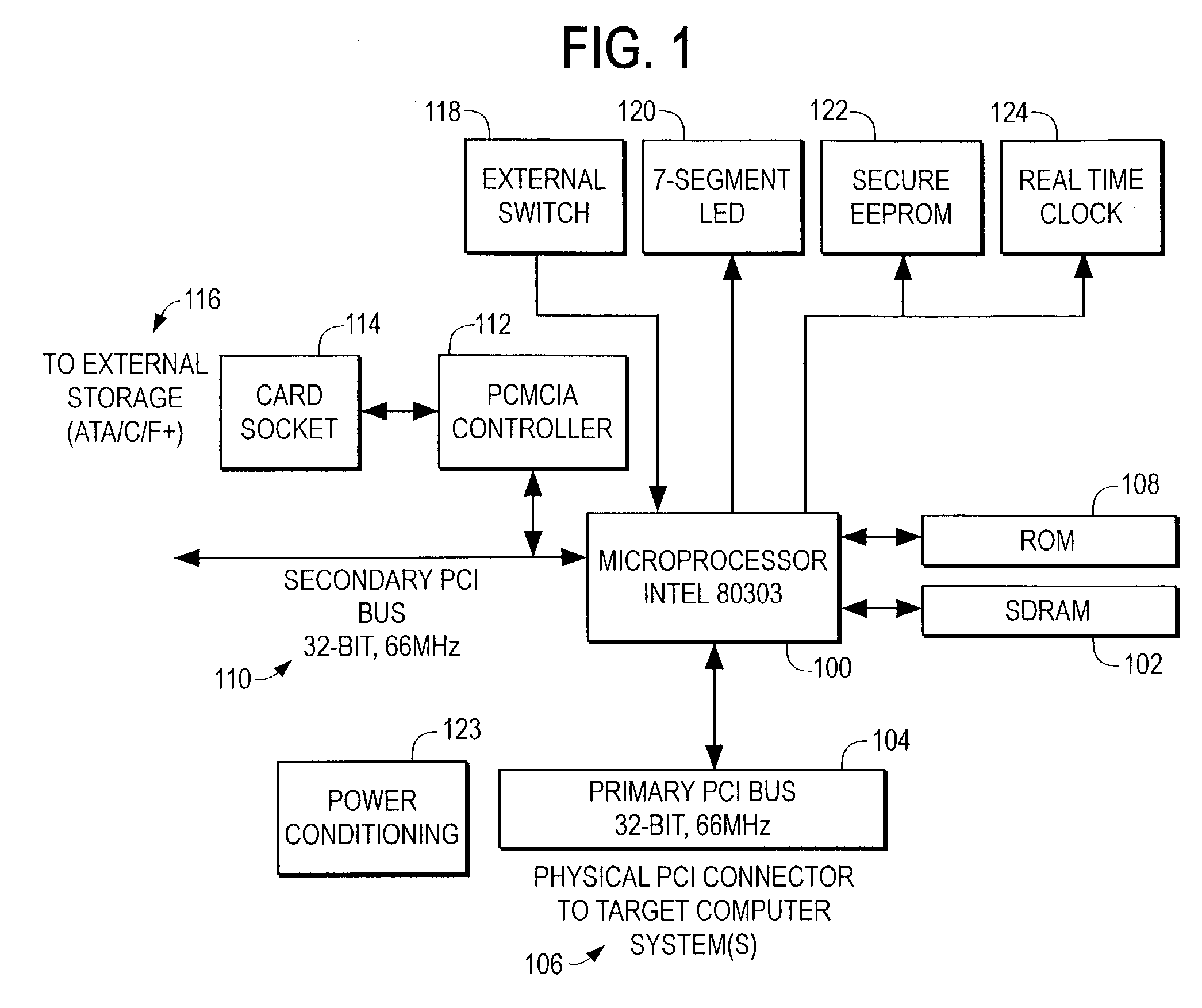
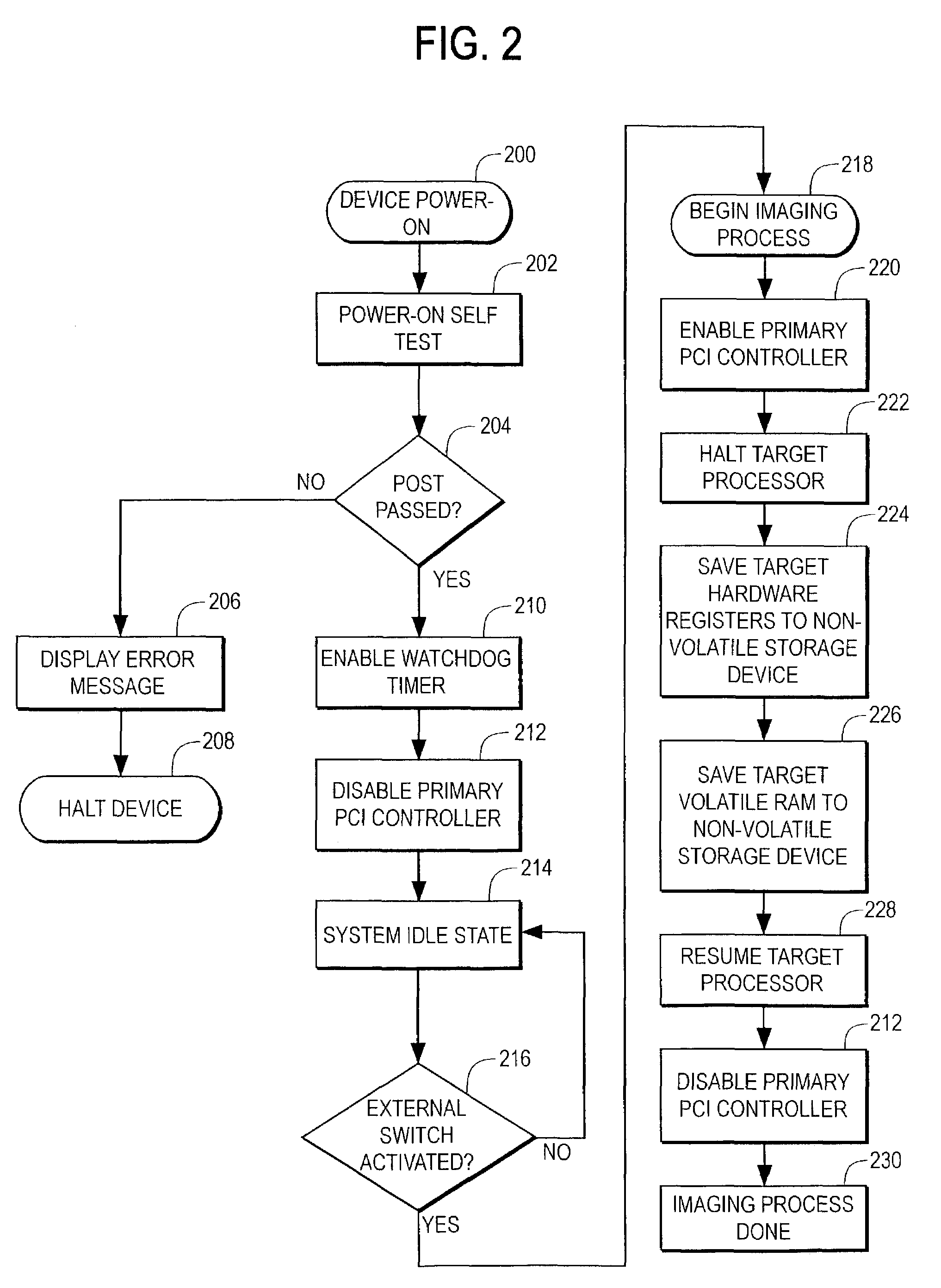
Method and apparatus for preserving computer memory using expansion card
InactiveUS7181560B1Maintain precisionSafe storageVolume/mass flow measurementUnauthorized memory use protectionExpansion cardProcessor register
A method for preserving digital evidence of a computer misconduct, the method including the steps of: prior to the misconduct, installing an expansion card capable of retrieving and storing a memory image and register information from a digital electrical computer in which the expansion card is installed; connecting a switch to regulate the expansion card from a location other than the computer; at the time of the misconduct, using the switch to trigger the retrieving and storing of the memory image and the register information into the expansion card; and subsequent to the misconduct, extracting the expansion card to preserve digital evidence of the computer misconduct. This method can be carried out further by subjecting the memory image and register information from the expansion card with another computer to forensic analysis.
Owner:GRAND JOSEPH +1
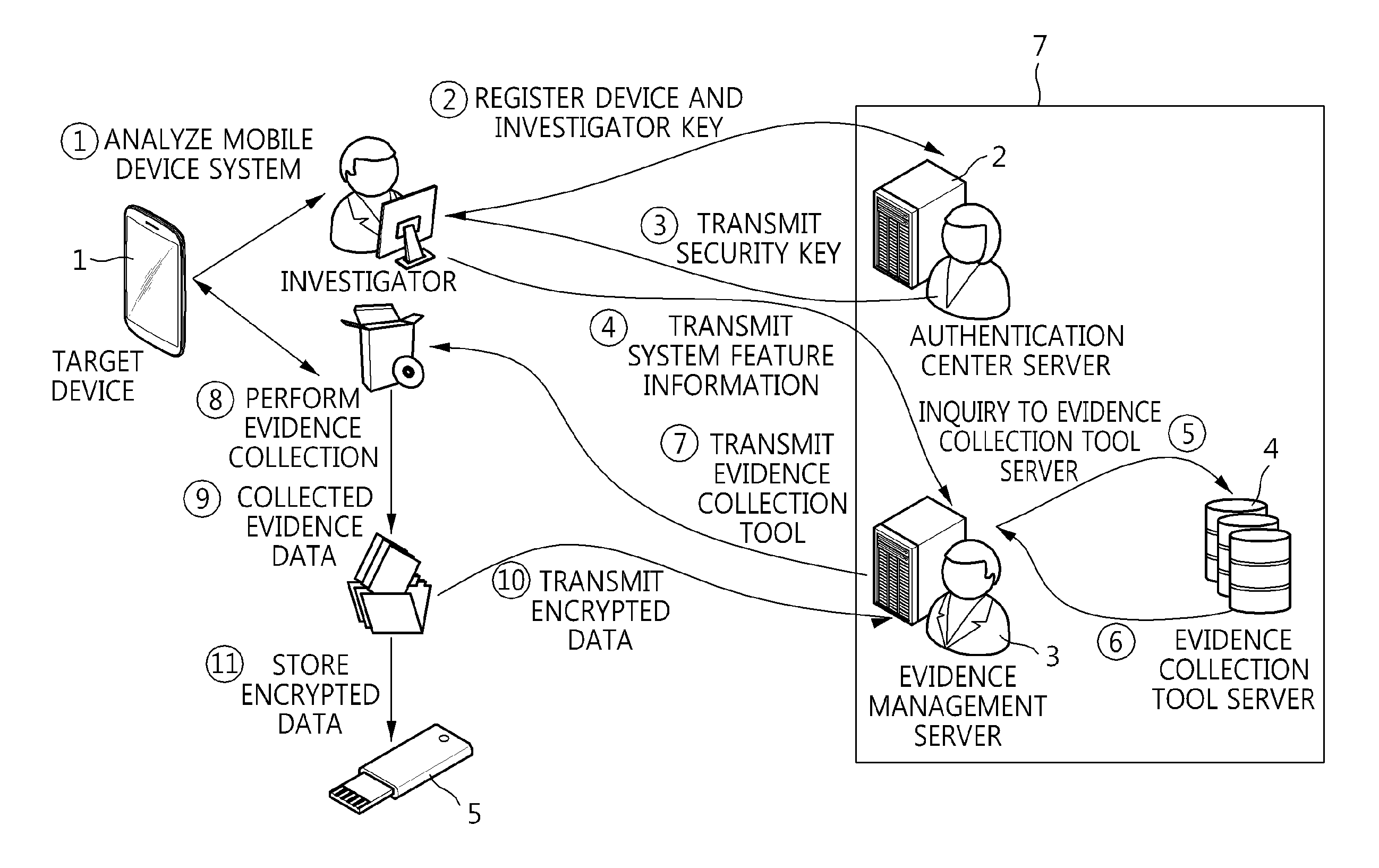
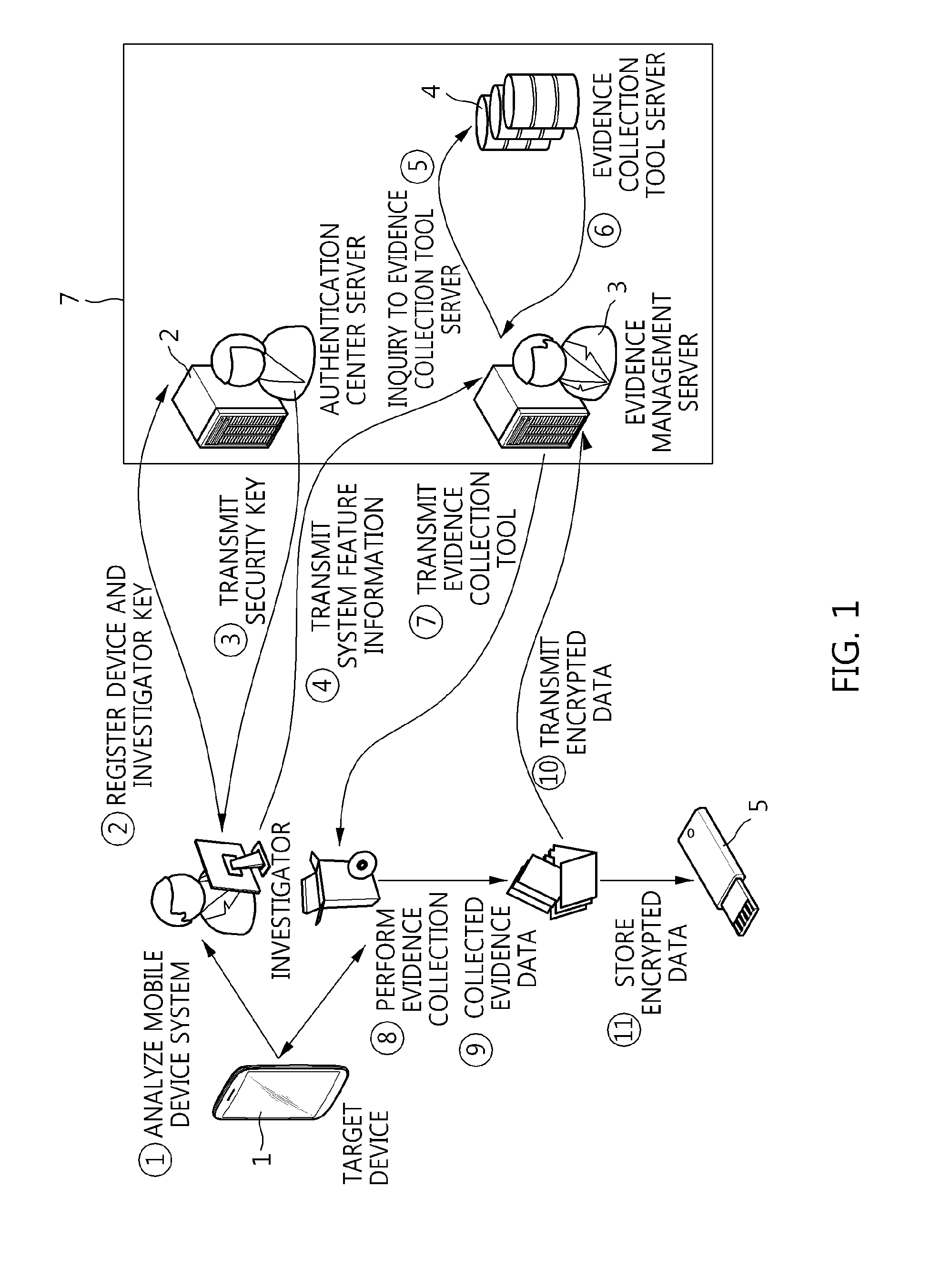
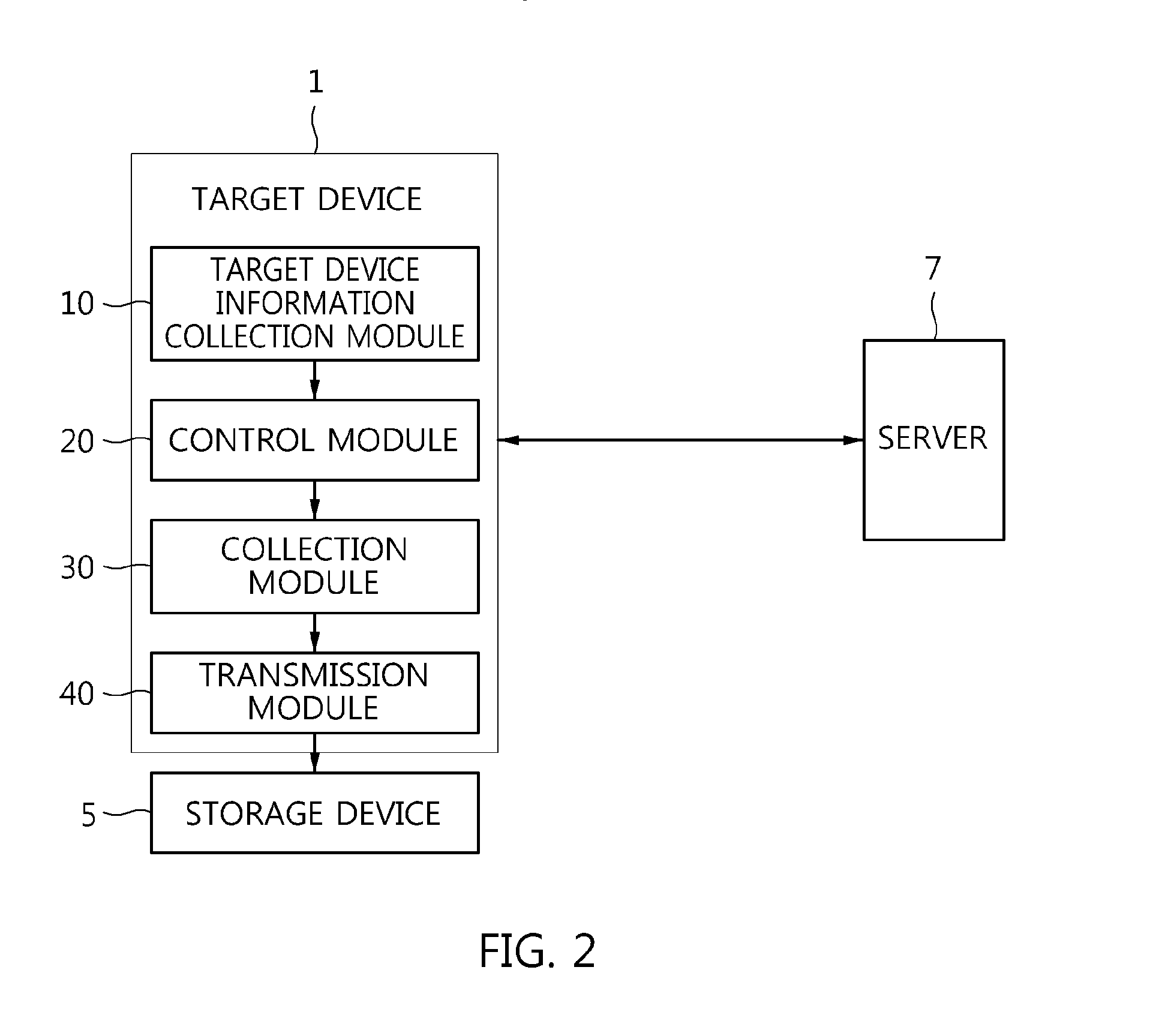
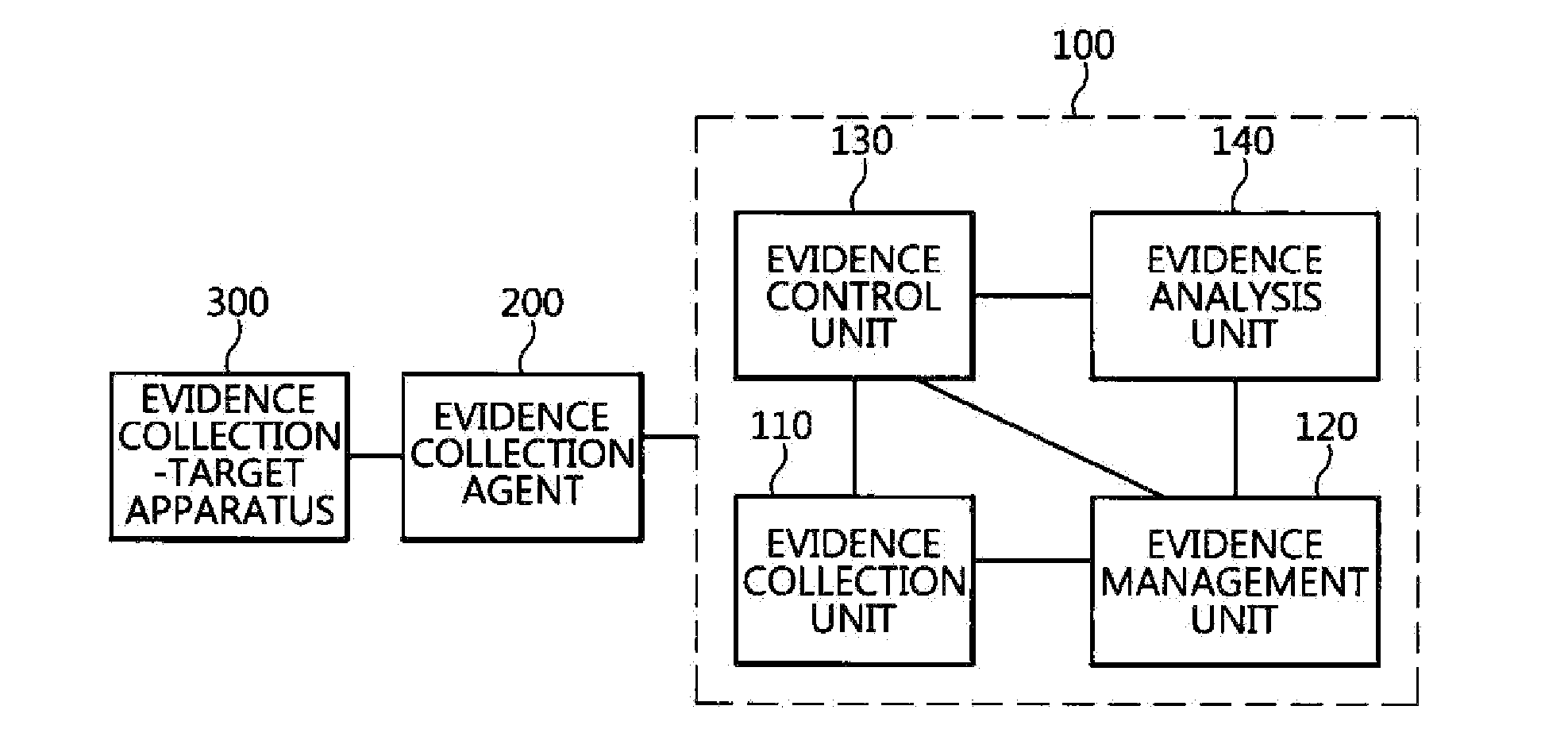
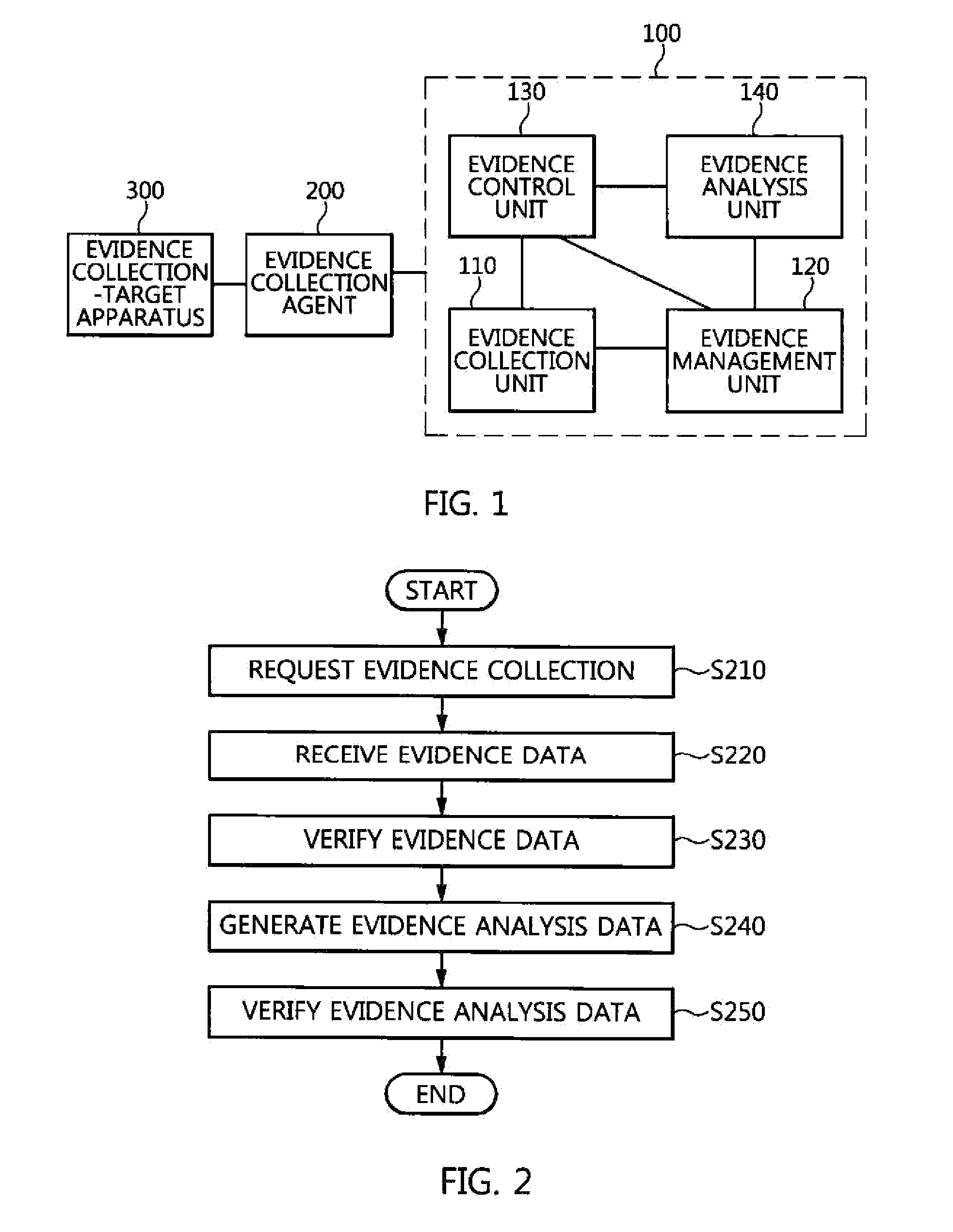
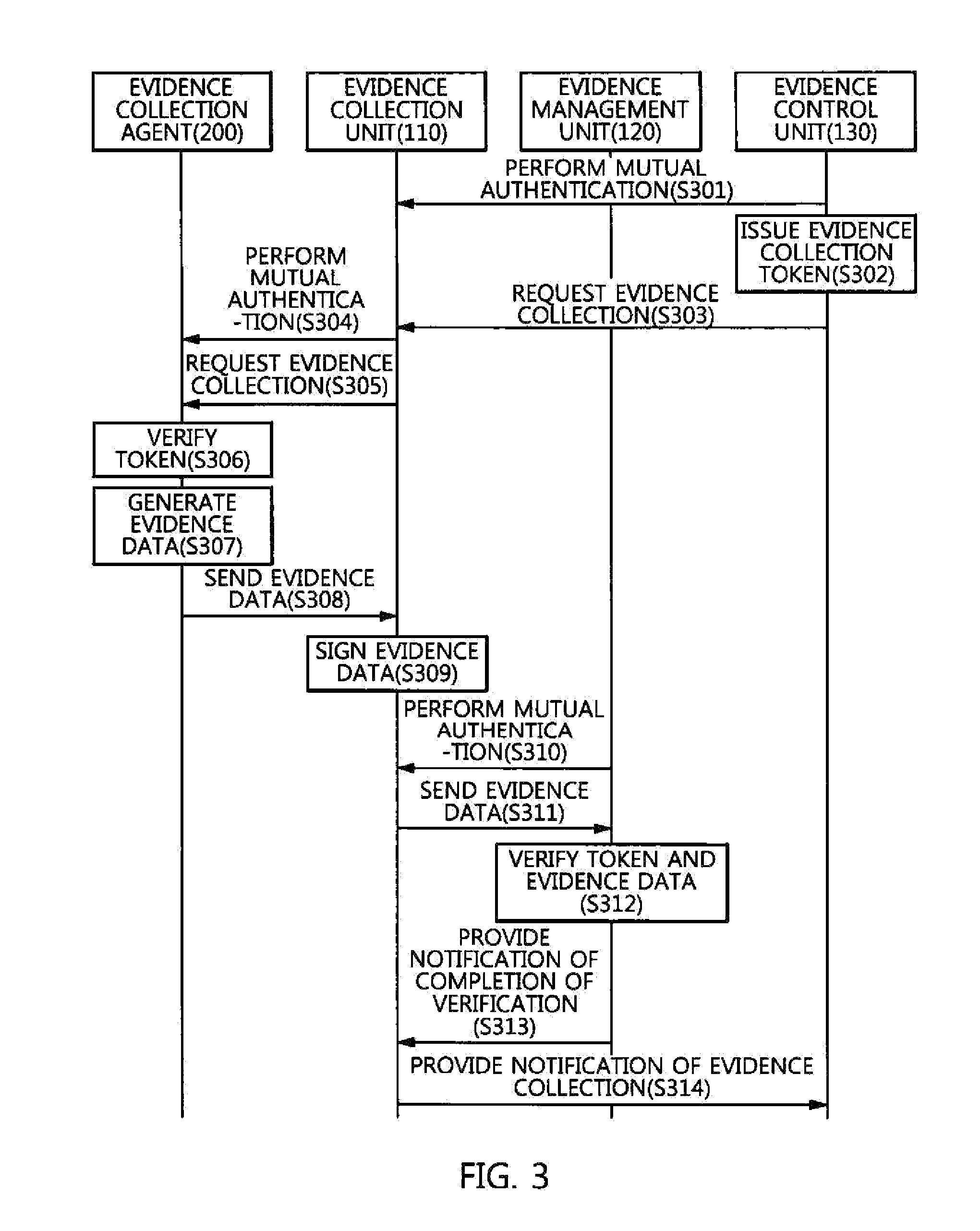
Method of providing evidence collection tool, and apparatus and method for collecting digital evidence in domain separation-based mobile device
InactiveUS20150326618A1Digital data processing detailsAnalogue secracy/subscription systemsDigital evidenceA domain
A method of providing an evidence collection tool, and an apparatus and method for collecting digital evidence in a domain separation-based mobile device are disclosed. The apparatus includes a target device information collection module, a collection module, a transmission module, and a control module. The target device information collection module collects the system feature information and user identification information of a domain separation-based mobile device. The collection module collects digital evidence using a received evidence collection tool. The control module transfers the user identification information and a previously inputted the investigator authentication key value to a server, transfers the security key from the server to the encryption unit of transmission module, the transmission module encrypts the digital evidence using a received security key and transmits the system feature information to the server, and transfers the evidence collection tool from the server to the collection module.
Owner:ELECTRONICS & TELECOMM RES INST
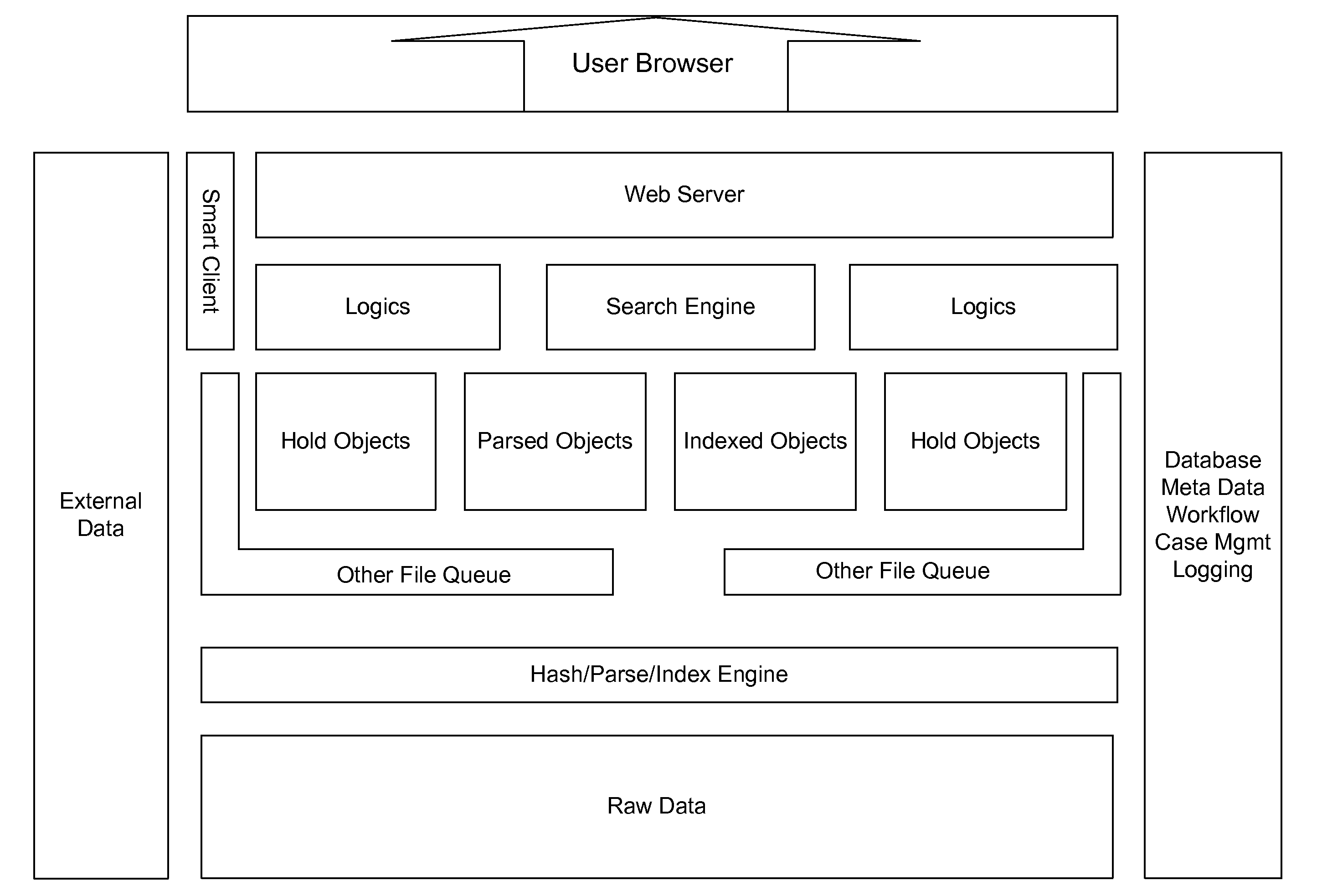
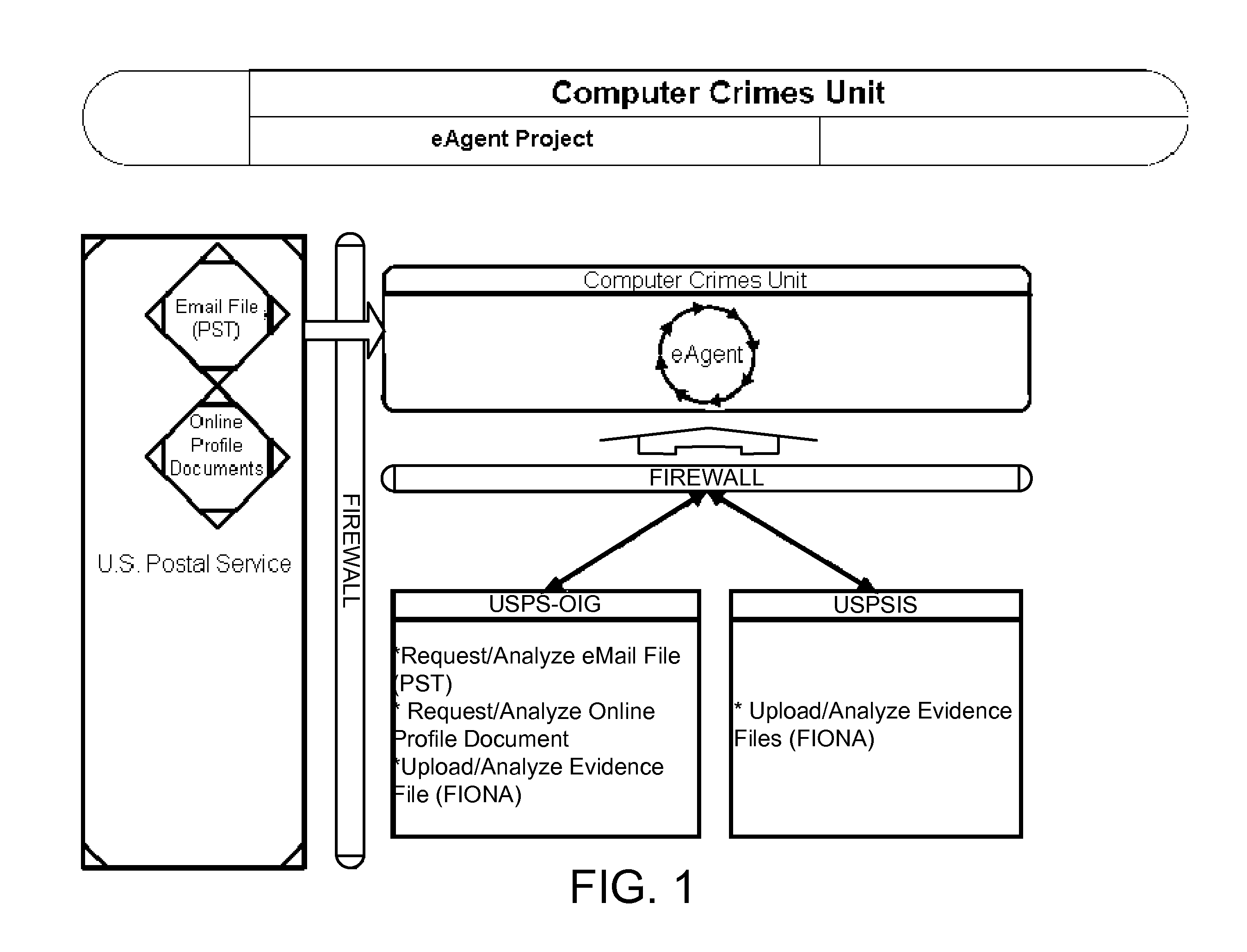
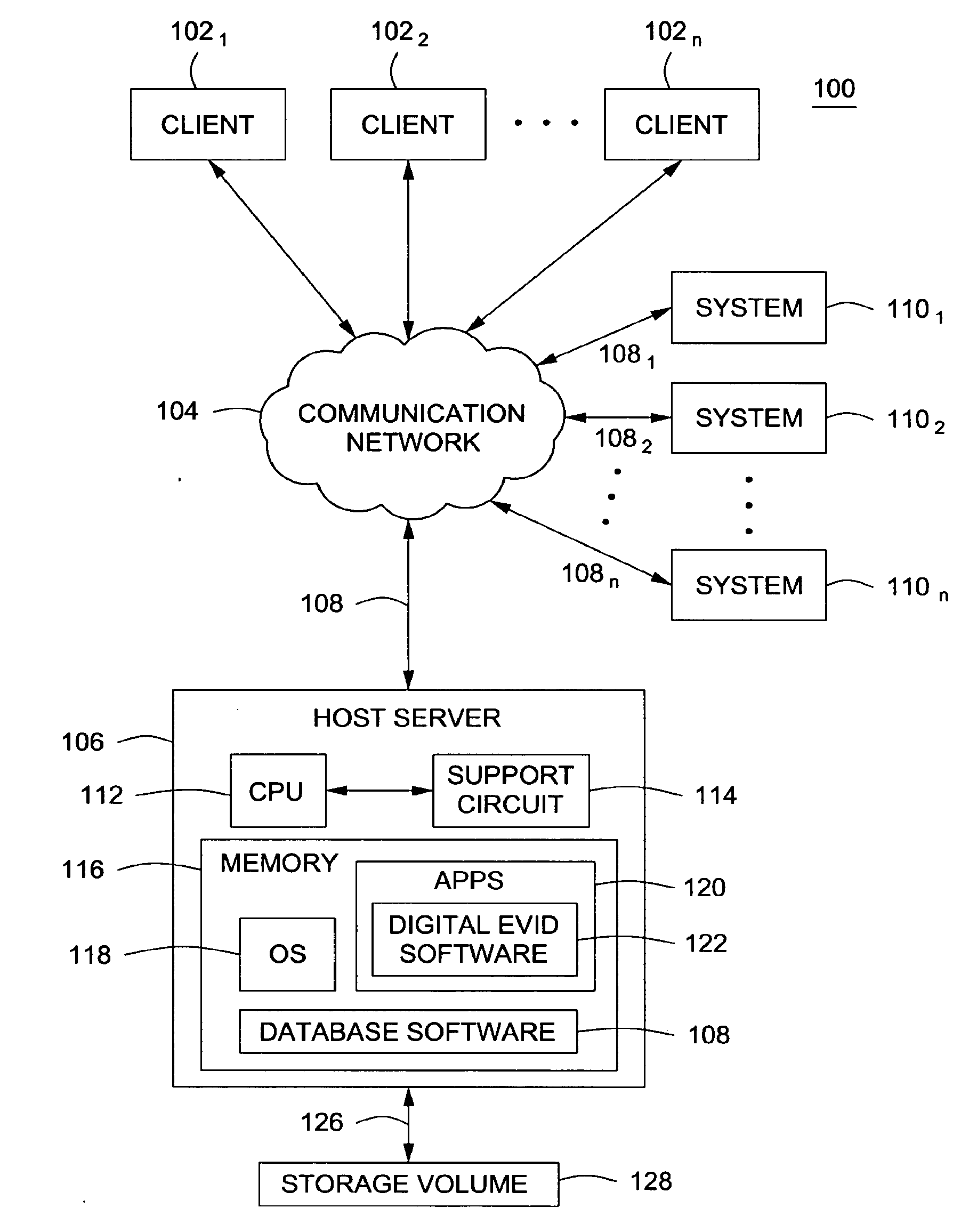
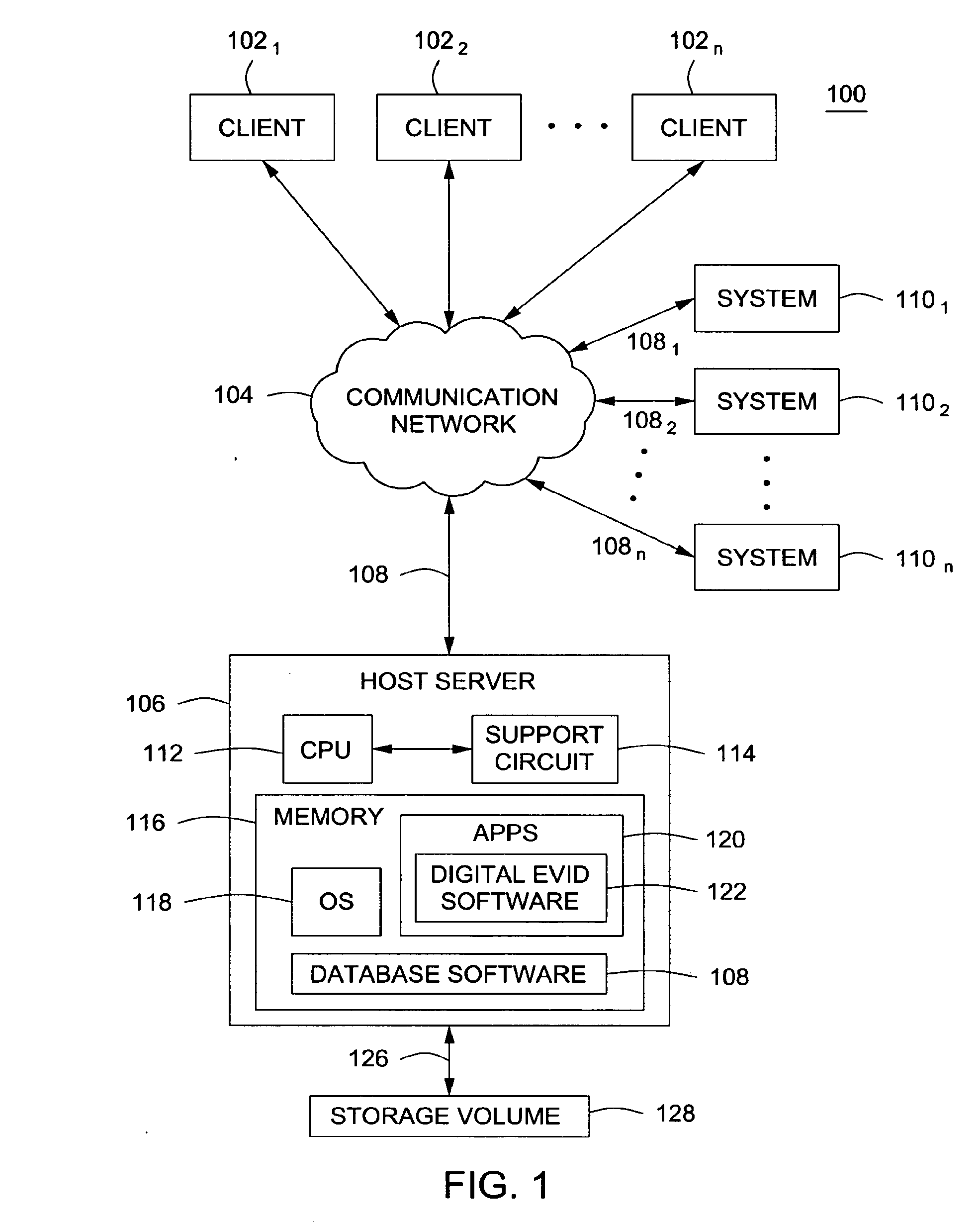
System and method for digital evidence analysis and authentication
ActiveUS20110264677A1Efficient mechanismDigital data processing detailsComputer security arrangementsRemote systemLabeled data
The system disclosed provides an efficient mechanism for acquiring email and other data from remote systems in a forensically sound manner. Email for users can be requested by investigators from email servers across the country. It is then be automatically acquired and made available to the examiner, subject to approval, and any others he deems have a need-to-know on a web based system. The data can be searched and bookmarked, and the bookmarks shared. Data can also be uploaded manually and combined with email data in the searching, bookmarking, and sharing.
Owner:US POSTAL SERVICE
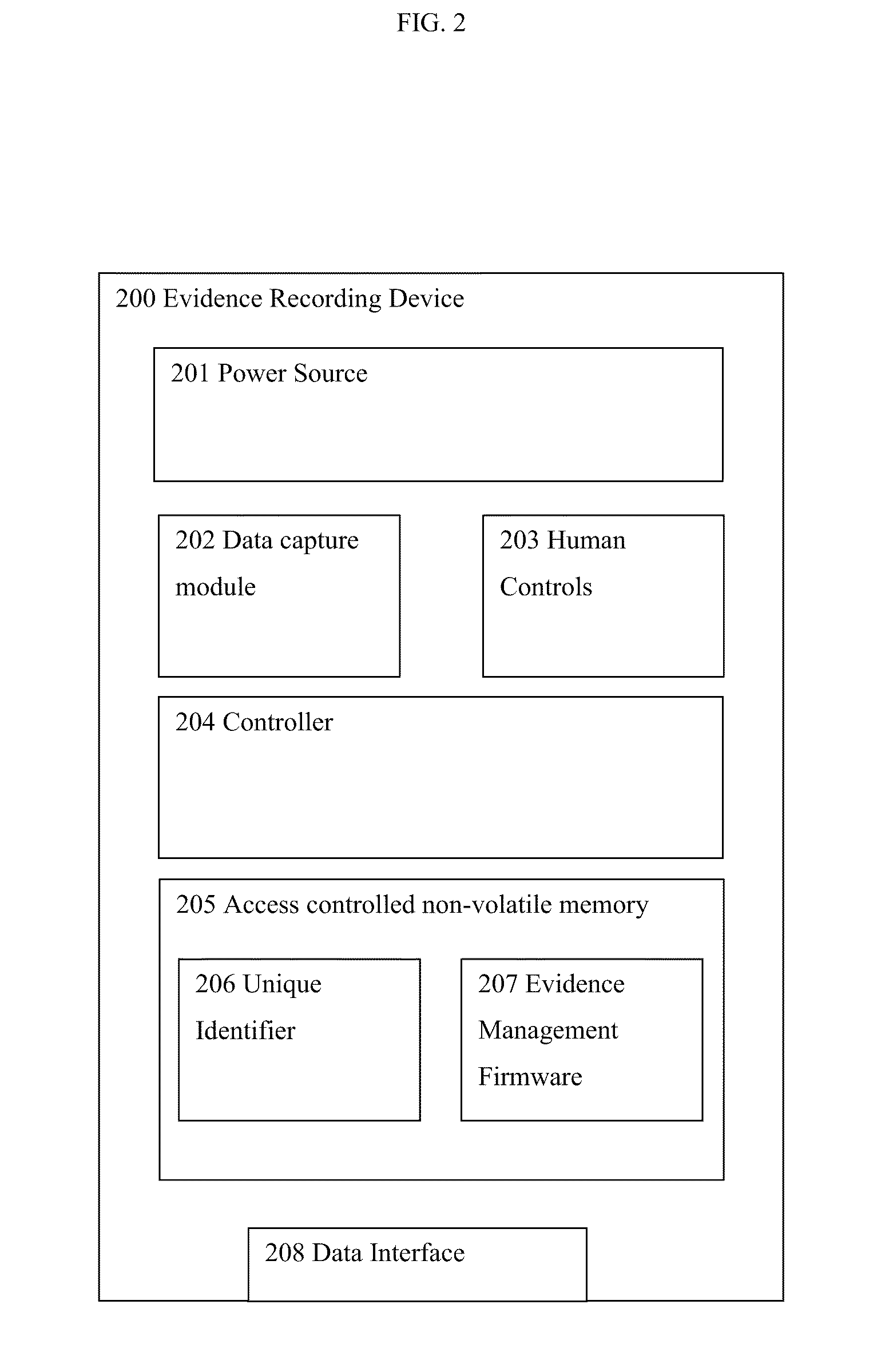
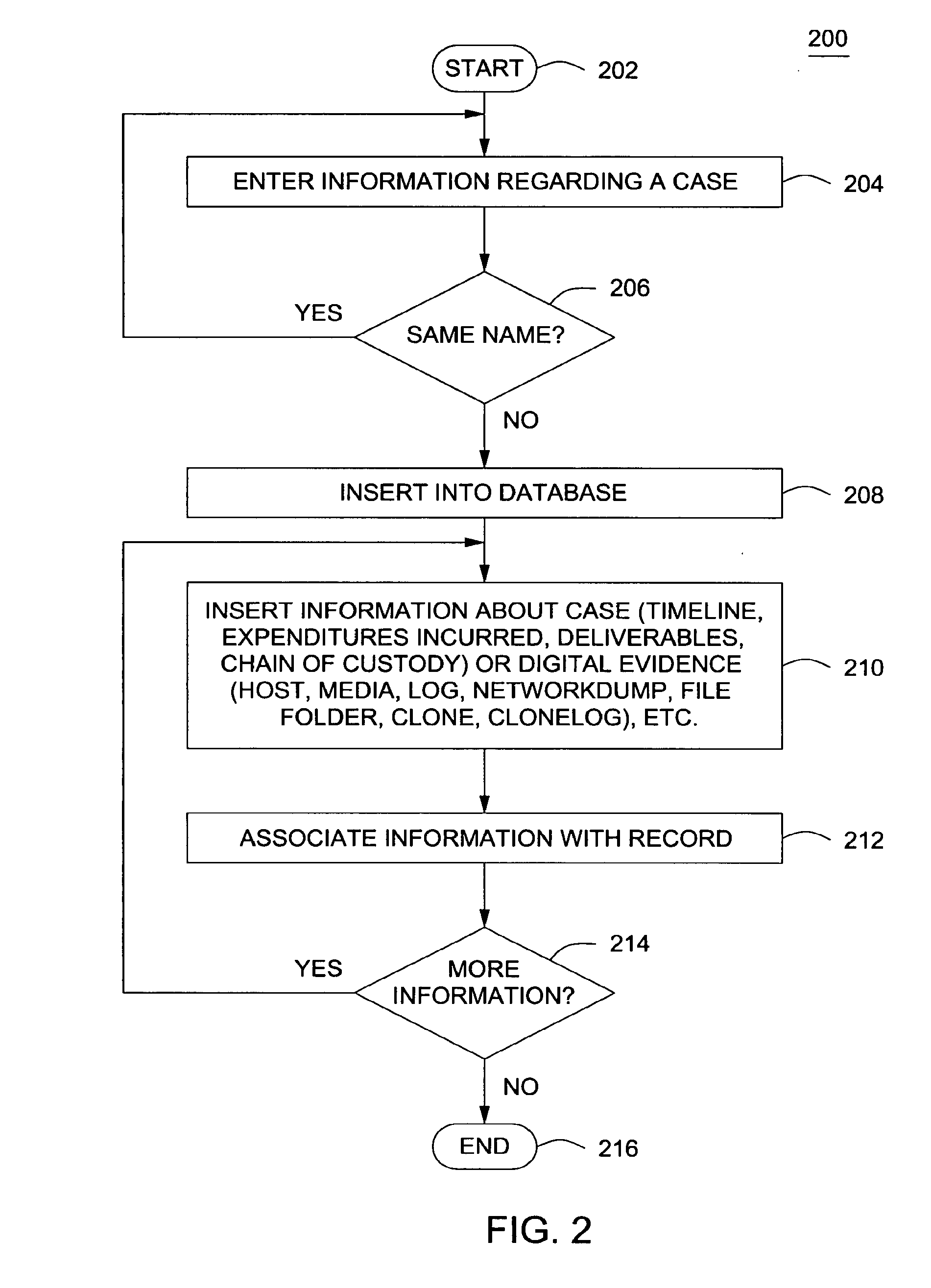
Method and apparatus for controlling digital evidence
InactiveUS20080098219A1Data processing applicationsUser identity/authority verificationDigital evidenceLibrary science
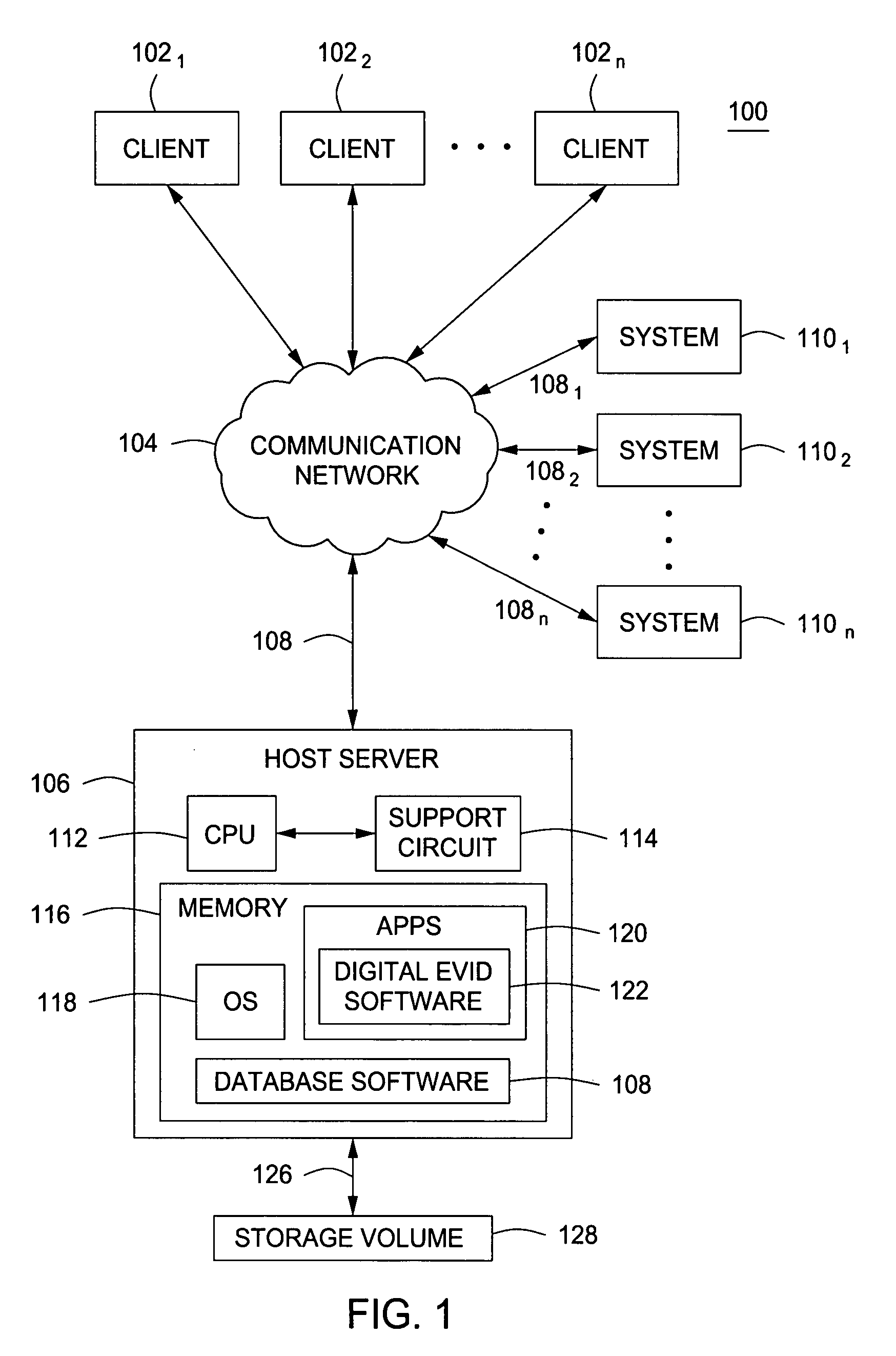
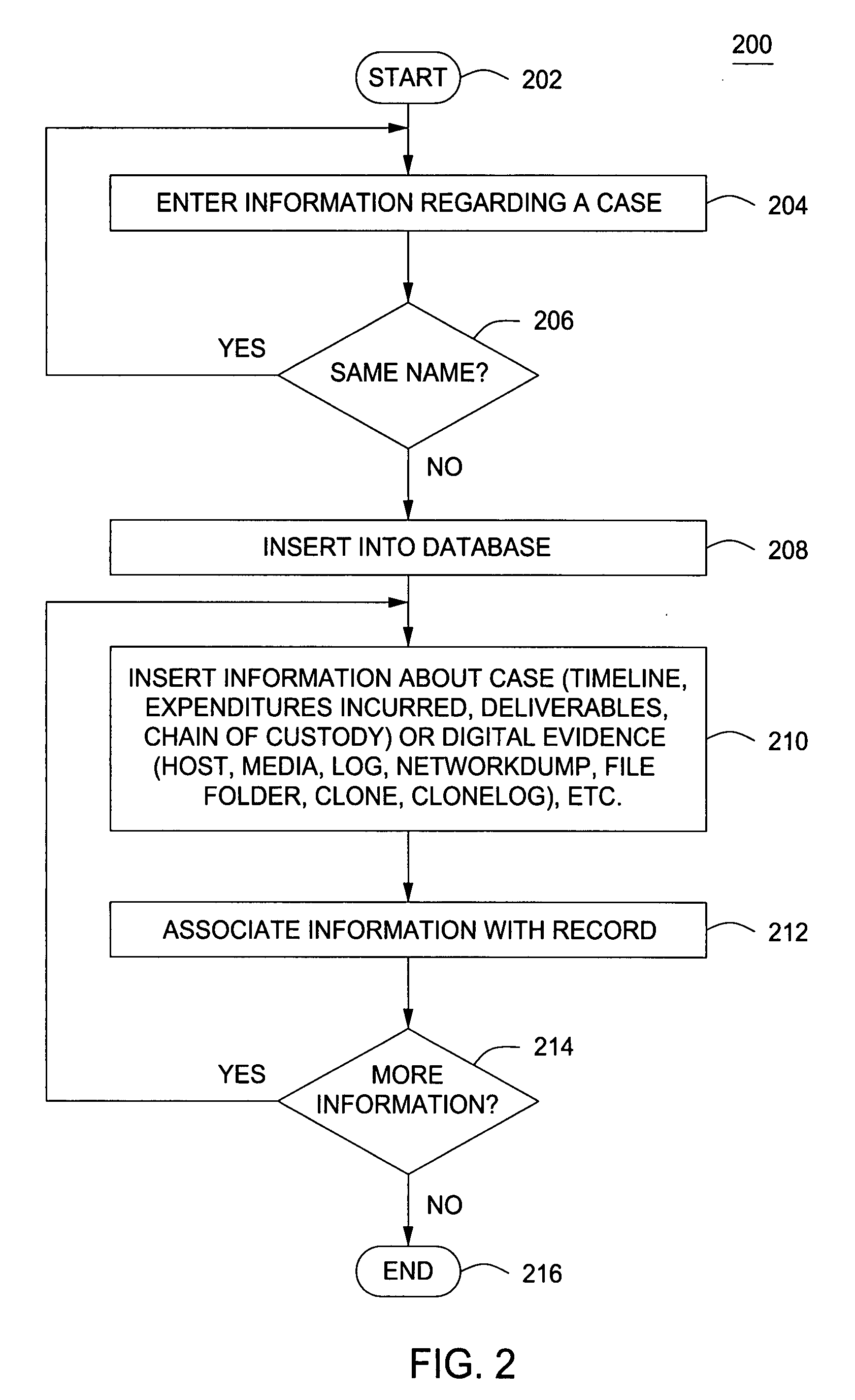
A method and apparatus for controlling digital evidence comprising creating a case record comprising information about an investigative case, electronically storing at least one piece of digital evidence into memory, and associating the stored at least one piece of evidence with the case record.
Owner:SUMO LOGIC INC
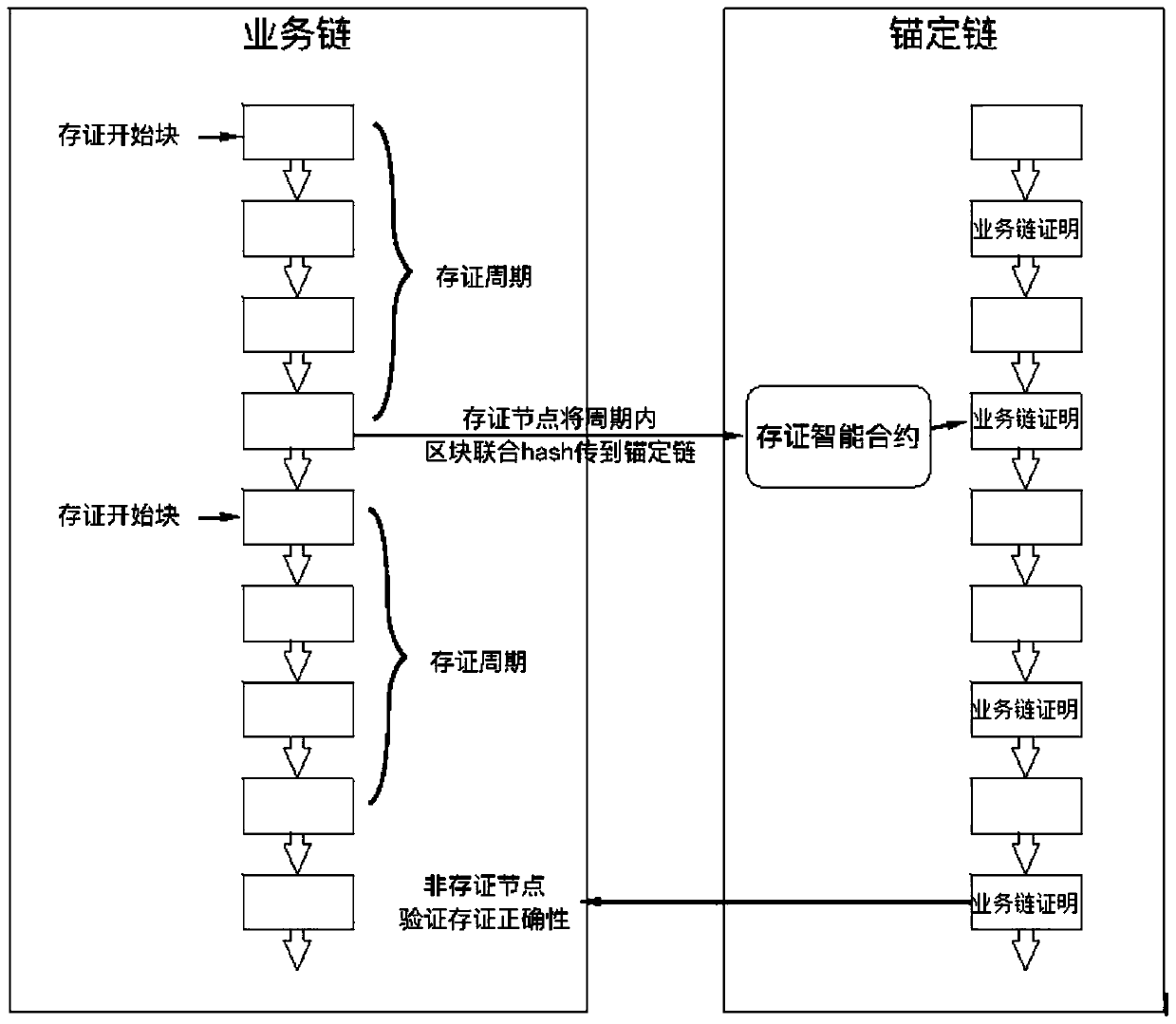
Method for implementing digital-forensics-oriented digital evidence supervision chain
ActiveCN103888241AImprove efficiencyEffective positioningUser identity/authority verificationDigital data authenticationThird partyTimestamp
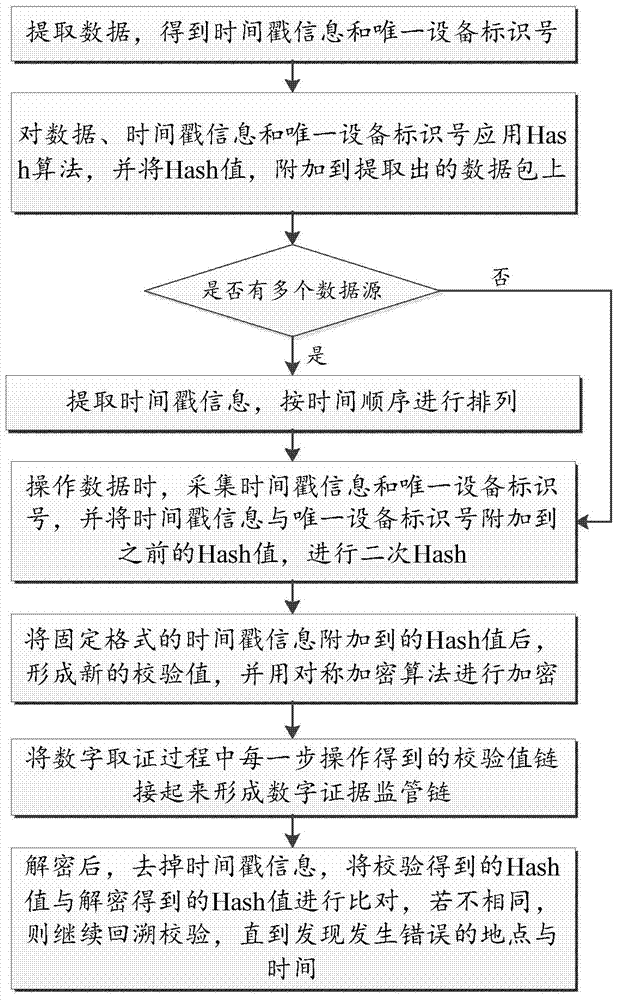
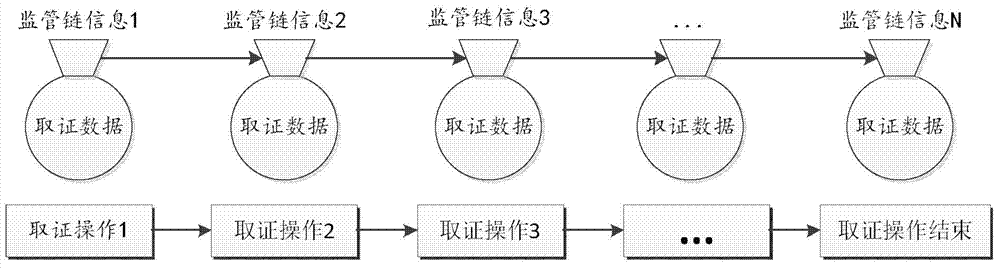
The invention relates to a method for implementing a digital-forensics-oriented digital evidence supervision chain. The method comprises the steps that first, timestamp information, a data package and an unique equipment identification number are extracted, then a Hash algorithm is used for encrypting to form calibration, so that data supervision chain information is formed, and when errors happen to digital evidence, backtracking is conducted according to the data supervision chain to find the time and place in which problems happen. According to the method, the timestamp information is added in the supervision chain information, the time of data changes is recorded, if a third party tampers or deletes the data and the like, the time can be recorded, meanwhile, the Hash algorithm is used for conducting signature validation on all the steps in the evidentiary process, and therefore the place where the errors happen to the digital evidence is effectively positioned. The problem that in the prior art, the time and the place in which the errors happen to the digital evidence can not be uniquely positioned is solved, and the efficiency of digital forensics work is improved.
Owner:临沂城投思索信息技术有限公司
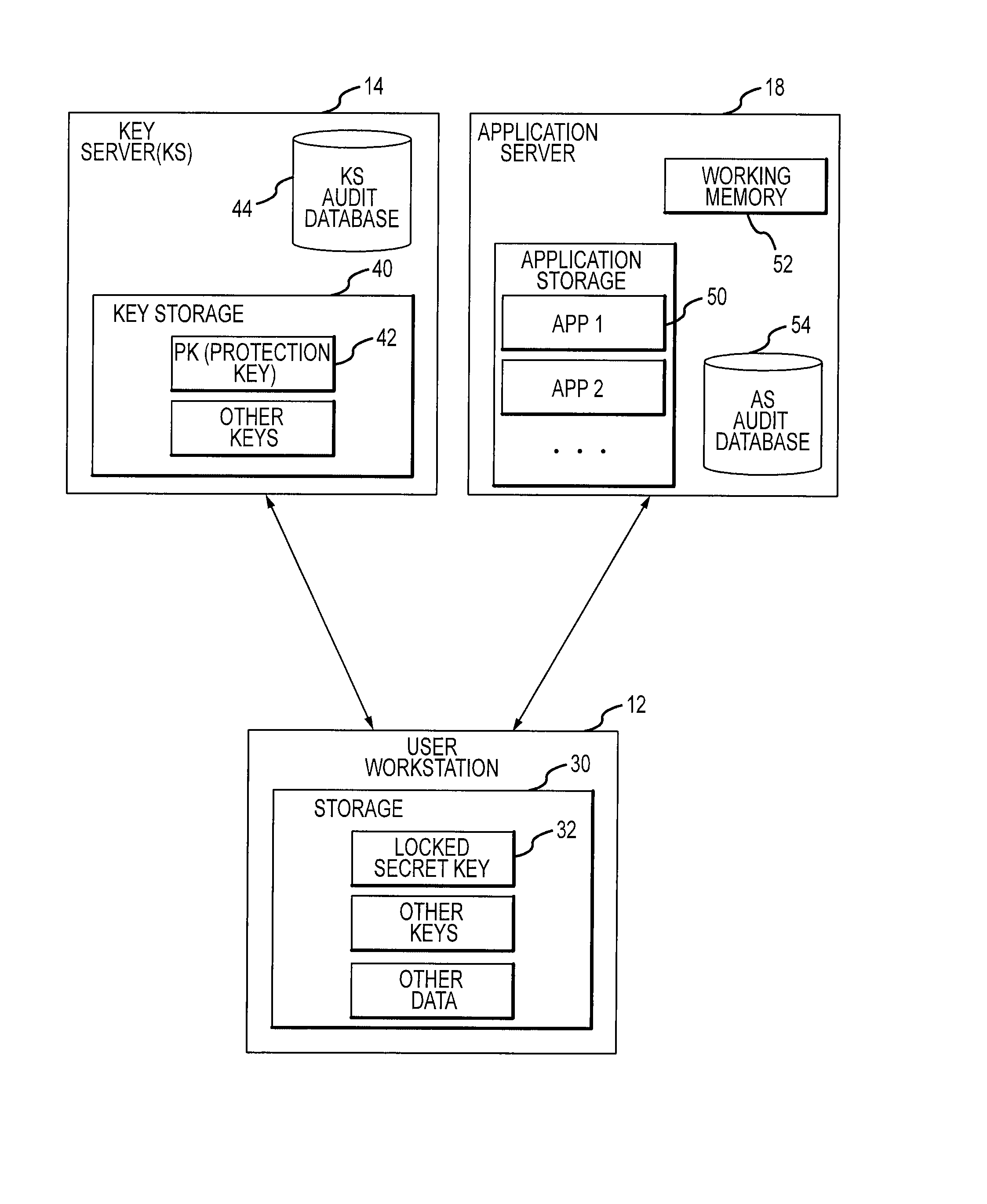
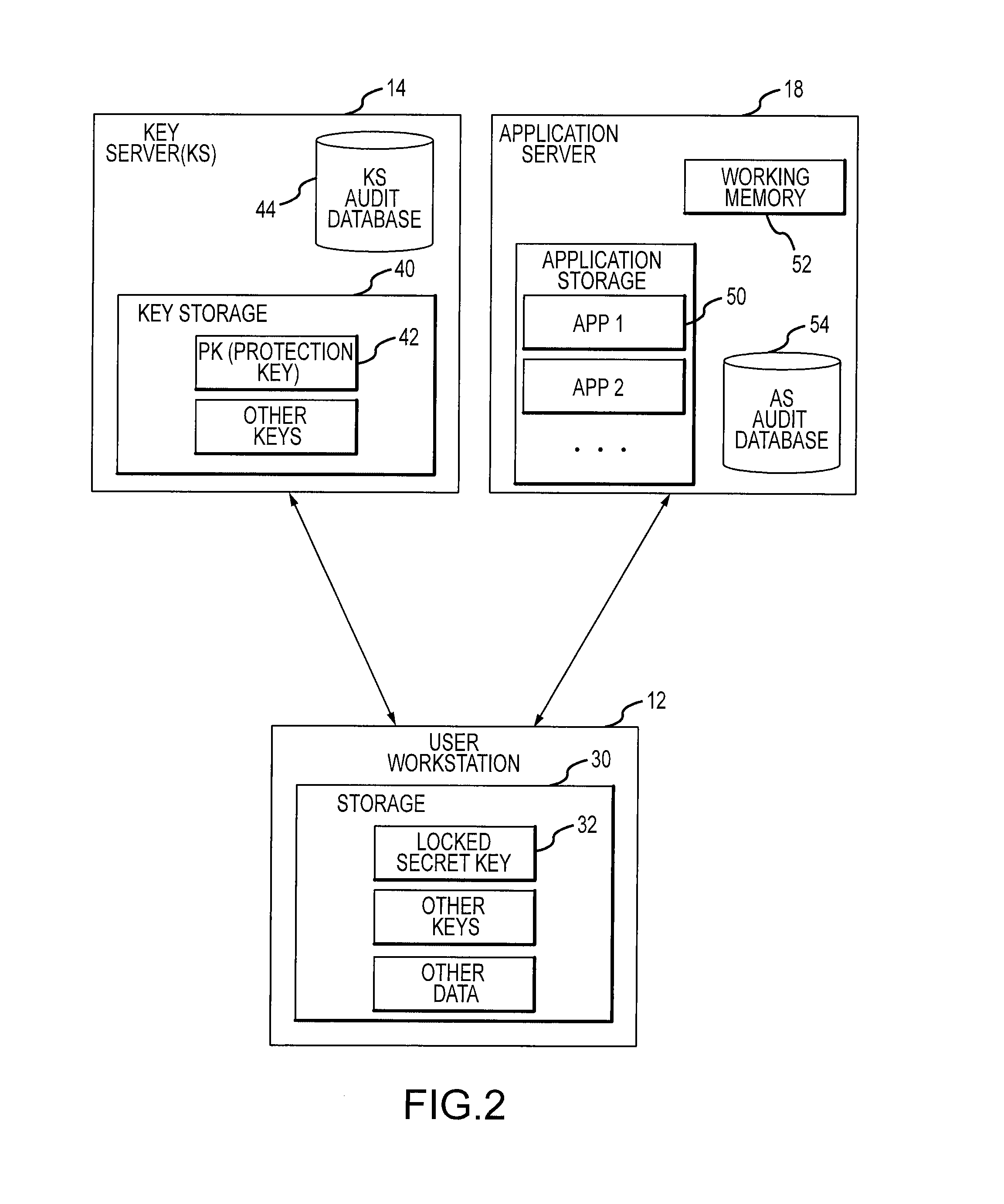
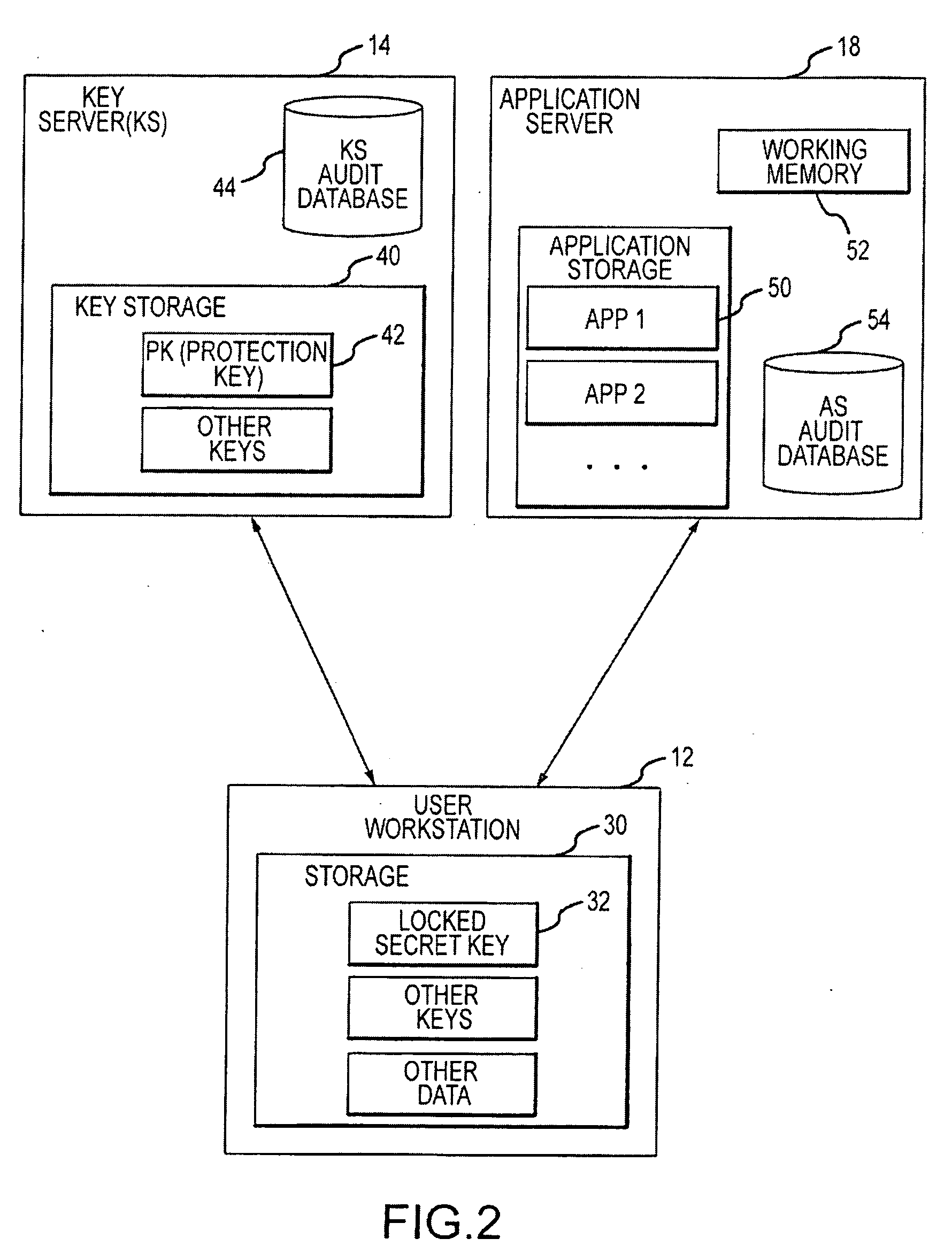
Auditing secret key cryptographic operations
InactiveUS7418728B2Key distribution for secure communicationDigital data processing detailsCryptographic protocolDigital evidence
In a cryptographic system, the unlocking of secret keys on a user system is audited and correlated with other events that typically occur after the secret key is used to perform a cryptographic operation. Audit evidence of secret key cryptographic operations is recorded for later review and / or analysis, for use as stored evidence of unauthorized activity and / or for use in refuting false claims of repudiation of authorized activity. Some systems might also provide users with user activity reports that can alert a user to suspicious or unauthorized activity using that user's access.
Owner:CA TECH INC
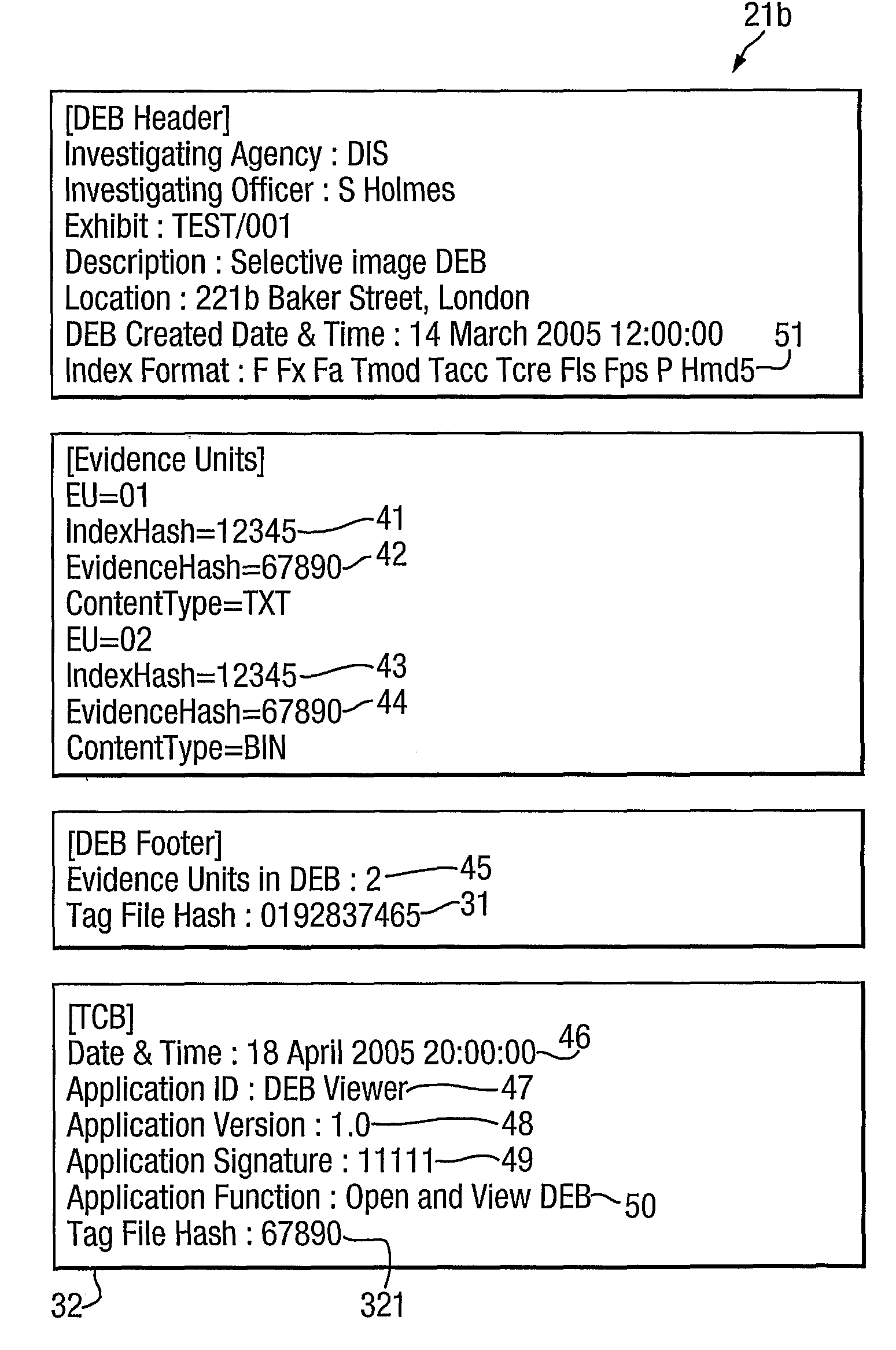
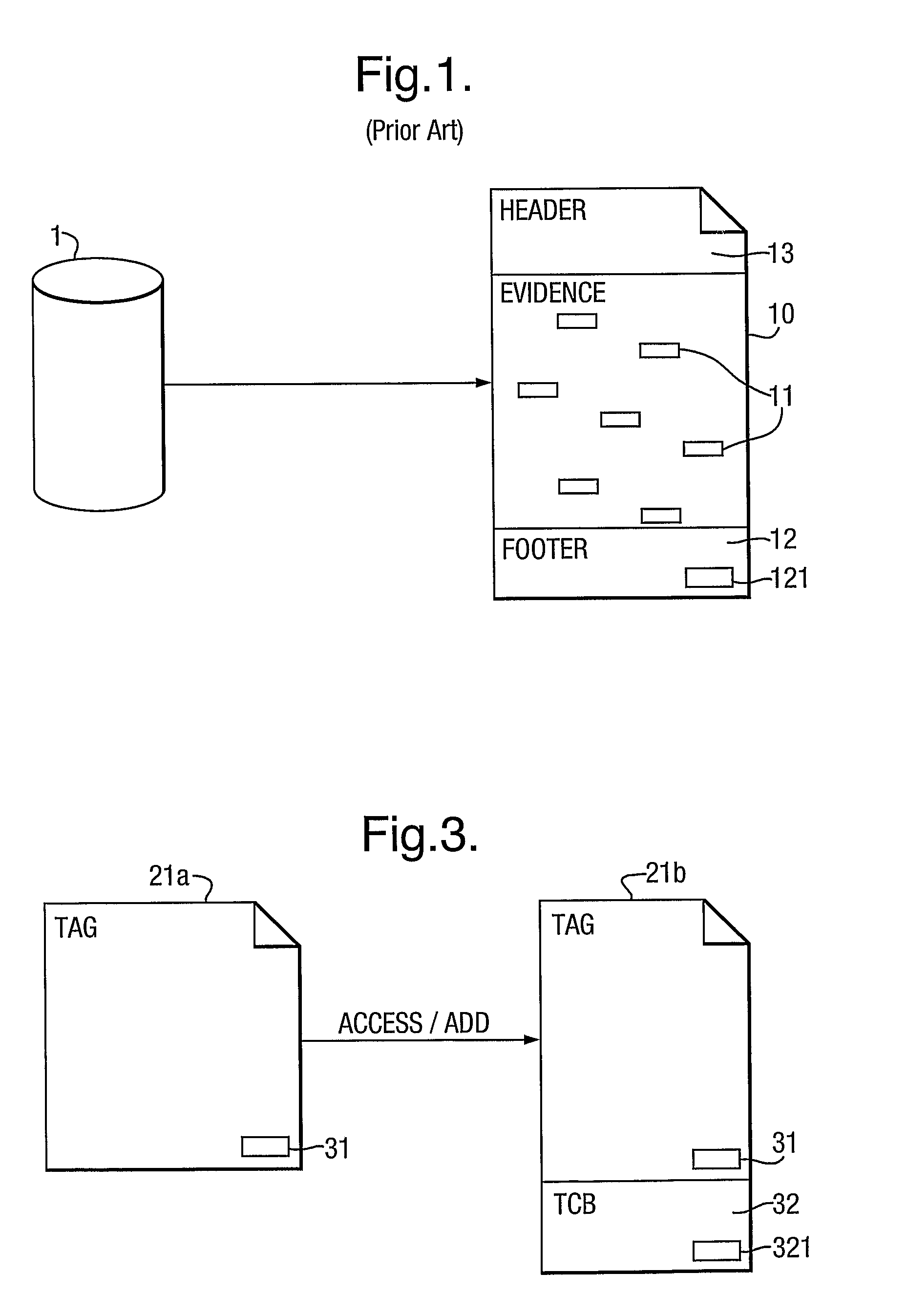
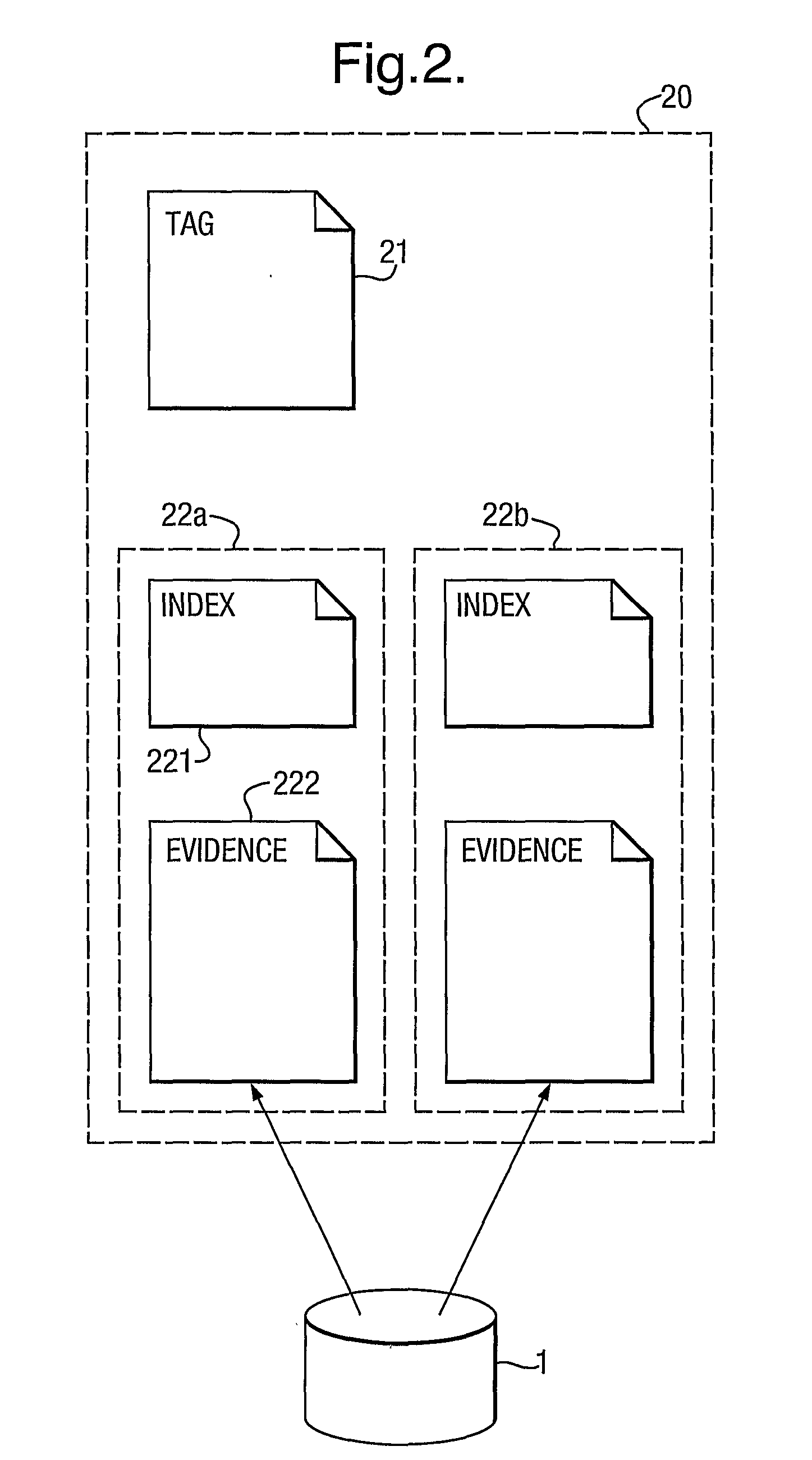
Digital Evidence Bag
InactiveUS20080195543A1Easy to trackEfficient analysisComputer security arrangementsOffice automationDigital dataDigital evidence
Data structures, methods, programs for computers, apparatus and systems for capturing, and analysing digital data, especially in the context of digital evidence gathering and analysis. Digital evidence is captured in digital evidence bags having an index file and one or more evidence units, the evidence units each comprising an index file and an evidence file. The evidence files contain copies of raw captured data whilst the associated index files contain text details of the contents and structure of the evidence files. The tag file contains data descriptive of the source and / or provenance of the evidence units and / or the digital evidence bag as a whole. Index information and evidence data may be in the same or distinct files.
Owner:QINETIQ LTD
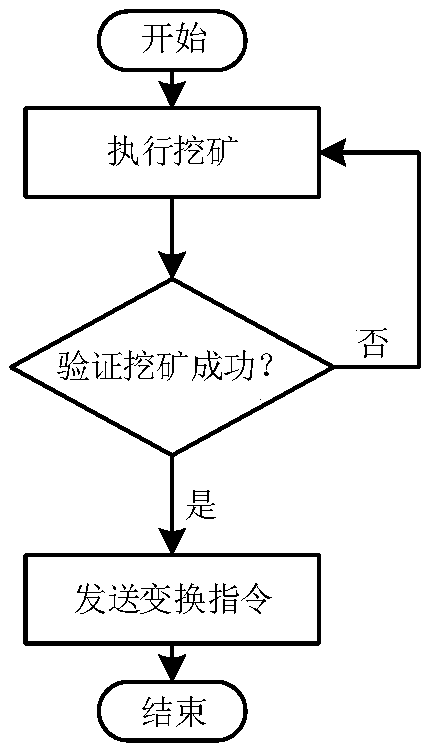
Array honey pot cooperative control method based on block chain
ActiveCN108521426AEffective defense against attacksResist attackPublic key for secure communicationTamper resistanceDigital evidence
The invention relates to an array honey pot cooperative control method based on a block chain. The method comprises the following steps: constructing a private chain by using an Ethereum platform, andrealizing de-centralized cooperative operation thought of a honey pot host cluster through a mining way; constructing a topological structure consistent with the Ethereum platform starting from a P2Pnetworking model, and realizing the communication through web3J. Each host in the array executes the mining, the host acquiring an accounting charging right can holds the post of a honey pot serviceconversion task at one periodic time, conversion information is sent through an encryption mechanism, and other host receives and executes the corresponding conversion instruction. Furthermore, external port request access data is stored in the block chain by using the tamper resistance of the block chain information, thereby obtaining the digital evidence for implementing the attack by an attacker. Through the method disclosed by the invention, the cooperative operation of the array honey pot host cluster is guaranteed, thereby trapping the attacker by using the true-false service in dynamicconversion, and the network security active defense aim is realized.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
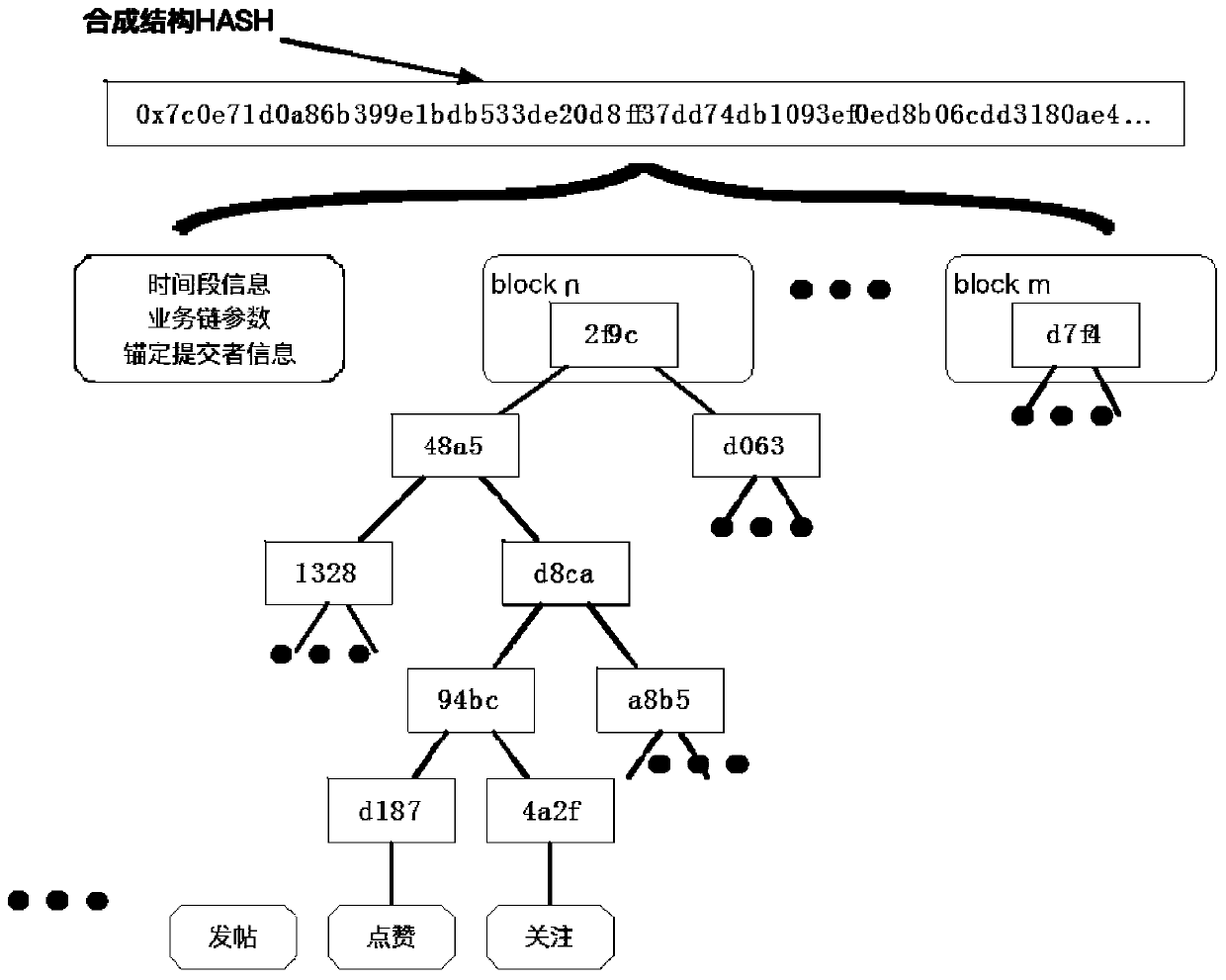
Cross-chain anchored block chain heterogeneous system
InactiveCN110717759AImprove operational efficiencyImprove business matching abilityDatabase distribution/replicationPayment protocolsFinancial transactionDigital evidence
The invention relates to the technical field of block chains, and discloses a cross-chain anchored block chain heterogeneous system. The system comprises a block chain anchoring chain and at least oneblock chain service chain, the blockchain service chain transmits and stores the evidence on a blockchain anchoring chain by creating a digital evidence for proving that the activity and data of theblockchain service chain cannot be tampered so as to complete evidence storage anchoring; wherein the blockchain anchoring chain uses a first consensus mechanism with high safety and high credibilityto perform consensus, and the consensus mechanism adopted by the blockchain service chain can be different from the first consensus mechanism. The consensus mechanism different from the anchoring chain is adopted in the blockchain service chain, so that each blockchain service chain selects a proper consensus mechanism according to own conditions, and the safety and credibility of the whole blockchain system are improved while each blockchain service chain maintains expandability and high operation efficiency. Evidence storage anchoring of credible evidences is completed, and meanwhile tampering invalidation of all transactions of a service chain is guaranteed.
Owner:成都九宽科技有限公司
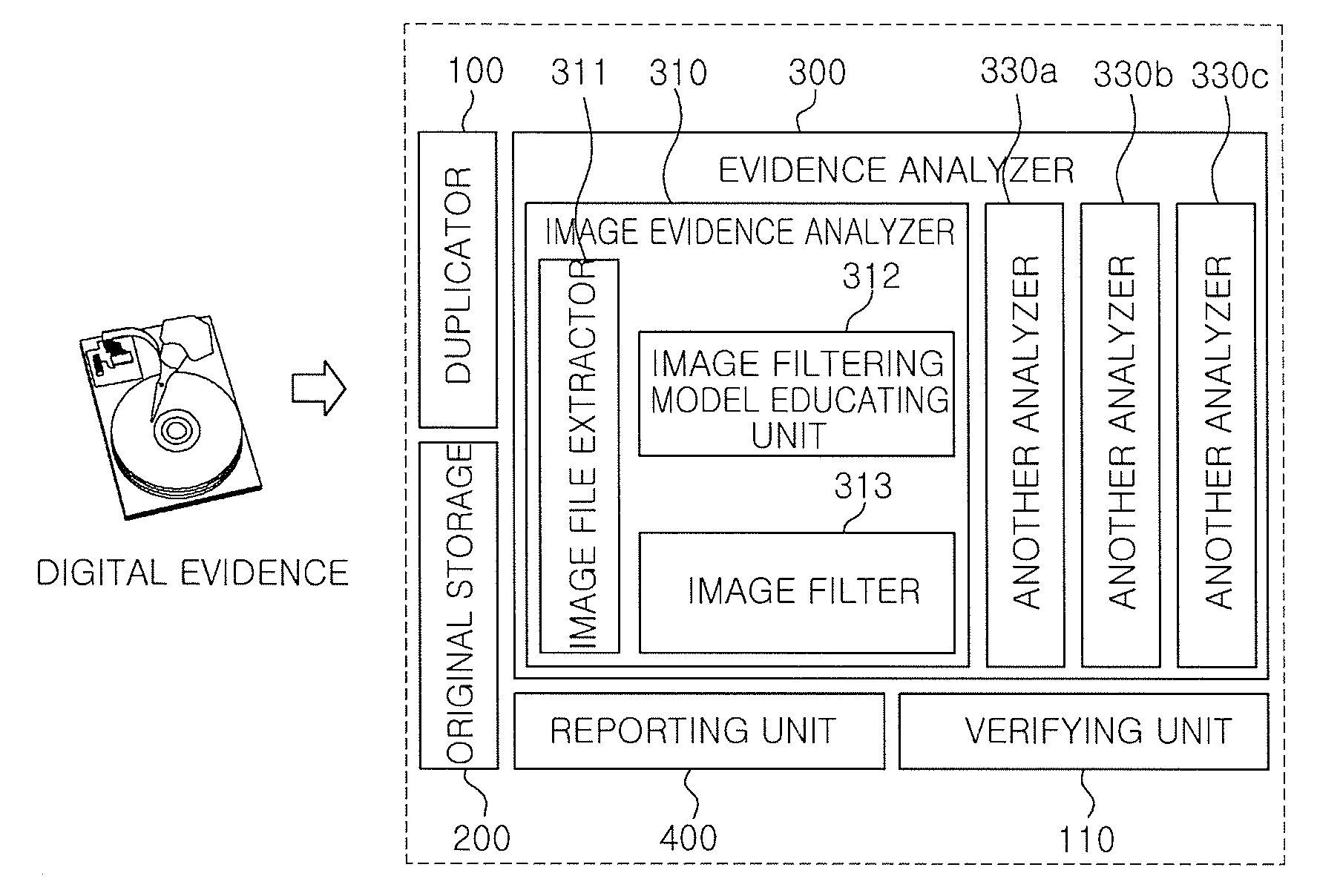
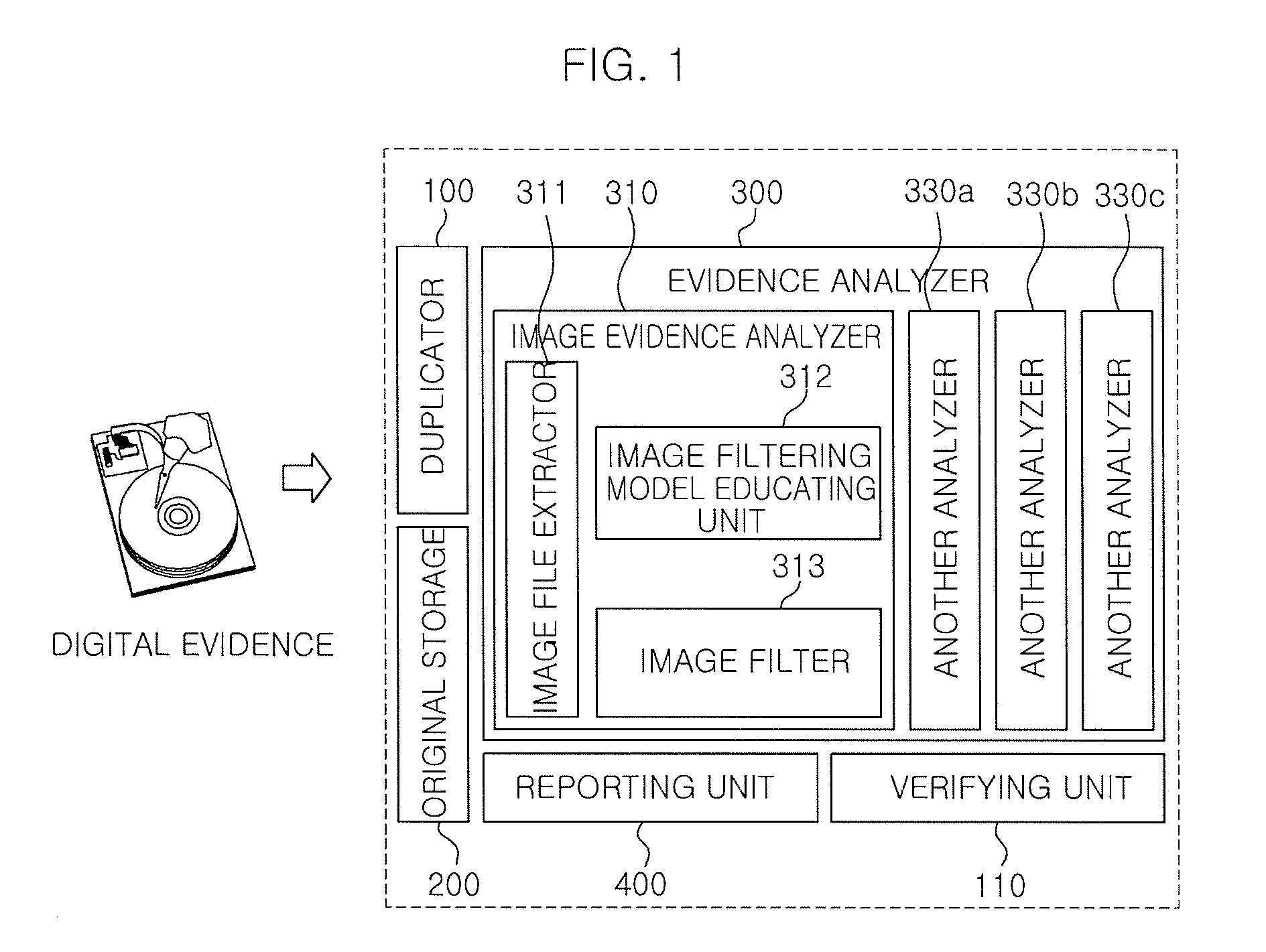
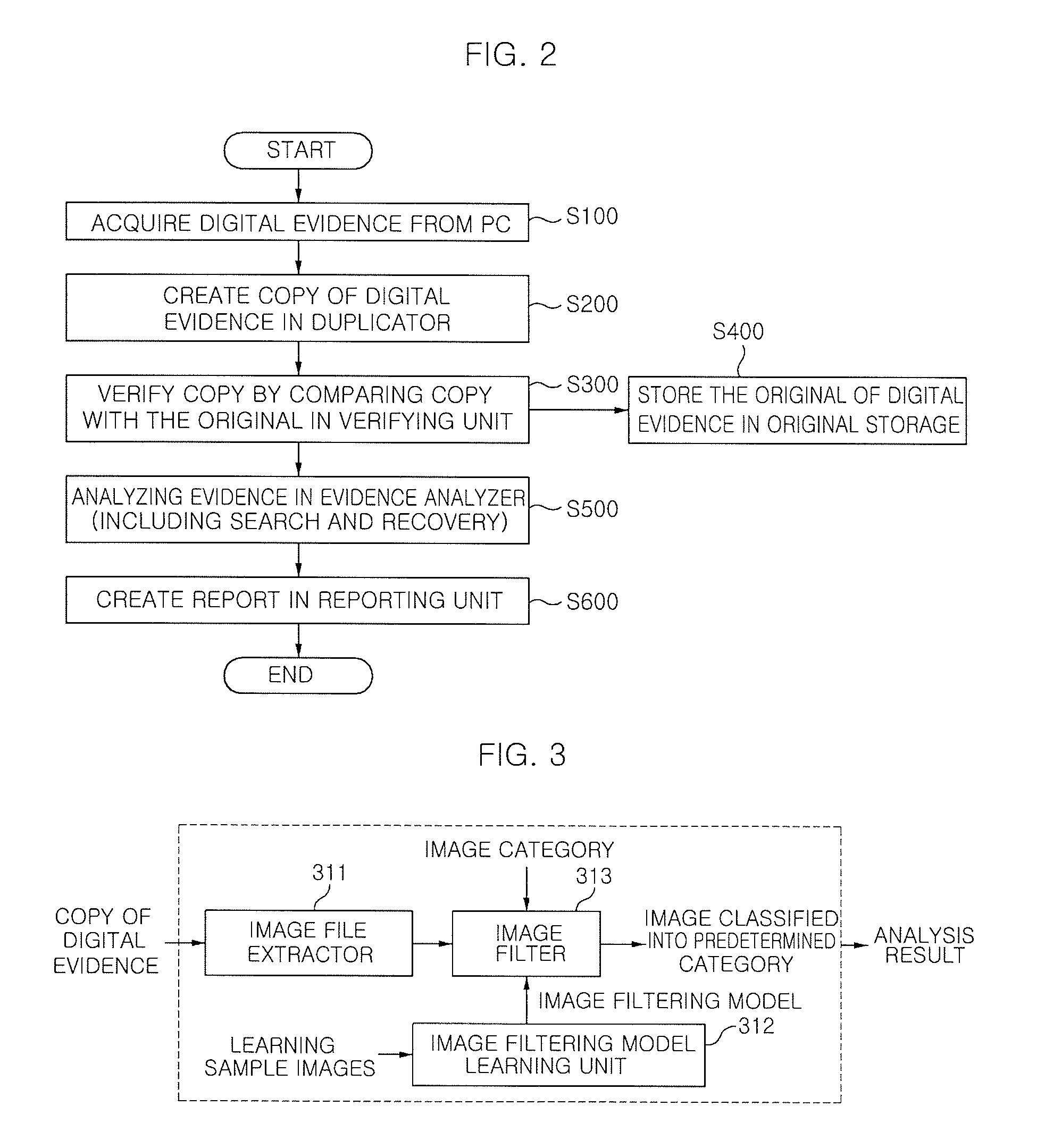
System for analyzing forensic evidence using image filter and method thereof
ActiveUS20090136140A1Simplify the analysis processEfficient executionProgram control using stored programsCharacter and pattern recognitionPattern recognitionLearning unit
The present invention provides a system for analyzing forensic digital evidence using an image filter and a method thereof. The system for analyzing forensic evidence using an image filter includes: a duplicator that creates a copy of digital evidence; a verifying unit that discriminates whether a copy and the original of the digital evidence are the same; an original storage that stores the original of the digital evidence; an evidence analyzer that classifies image files for the copy of the digital evidence stored in the original storage, on the basis of an image filtering model created by a learning model in accordance with predetermined categories, and then analyzes the evidence; and a reporting unit that creates a report about the result of evidence analysis. The image evidence analyzer includes an image file extractor, an image filtering model learning unit, an image filter, and a plurality of analyzers.
Owner:ELECTRONICS & TELECOMM RES INST
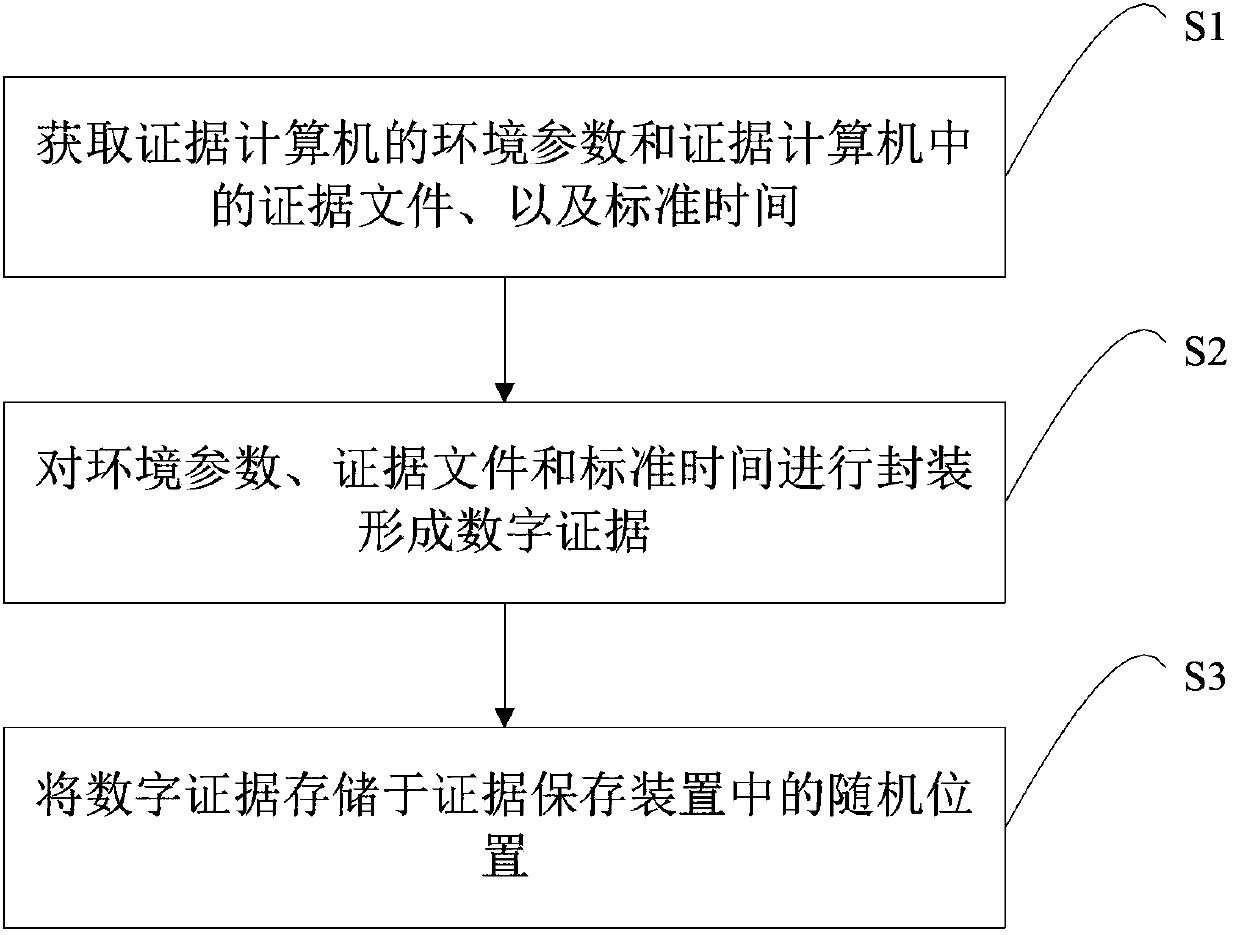
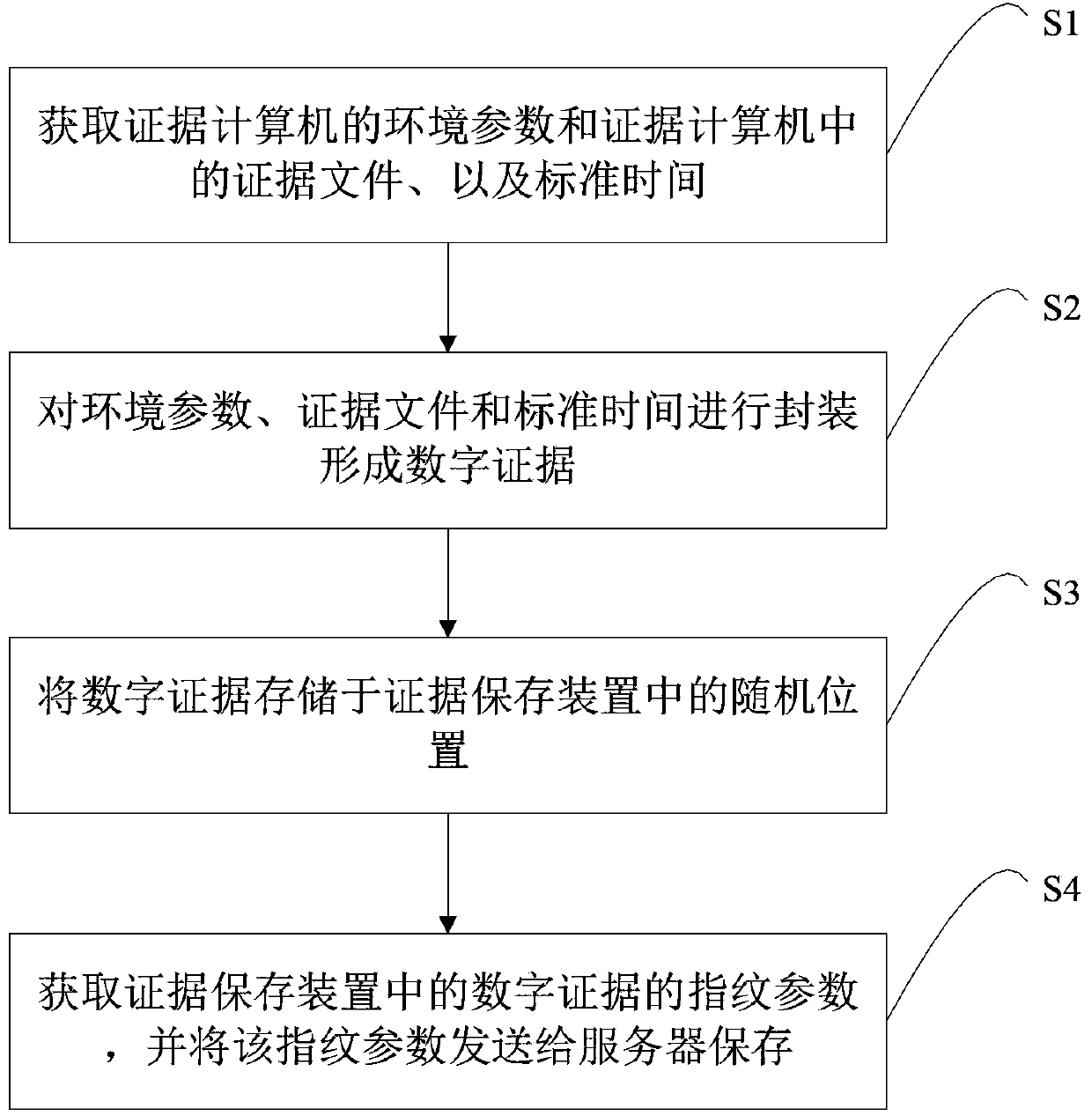
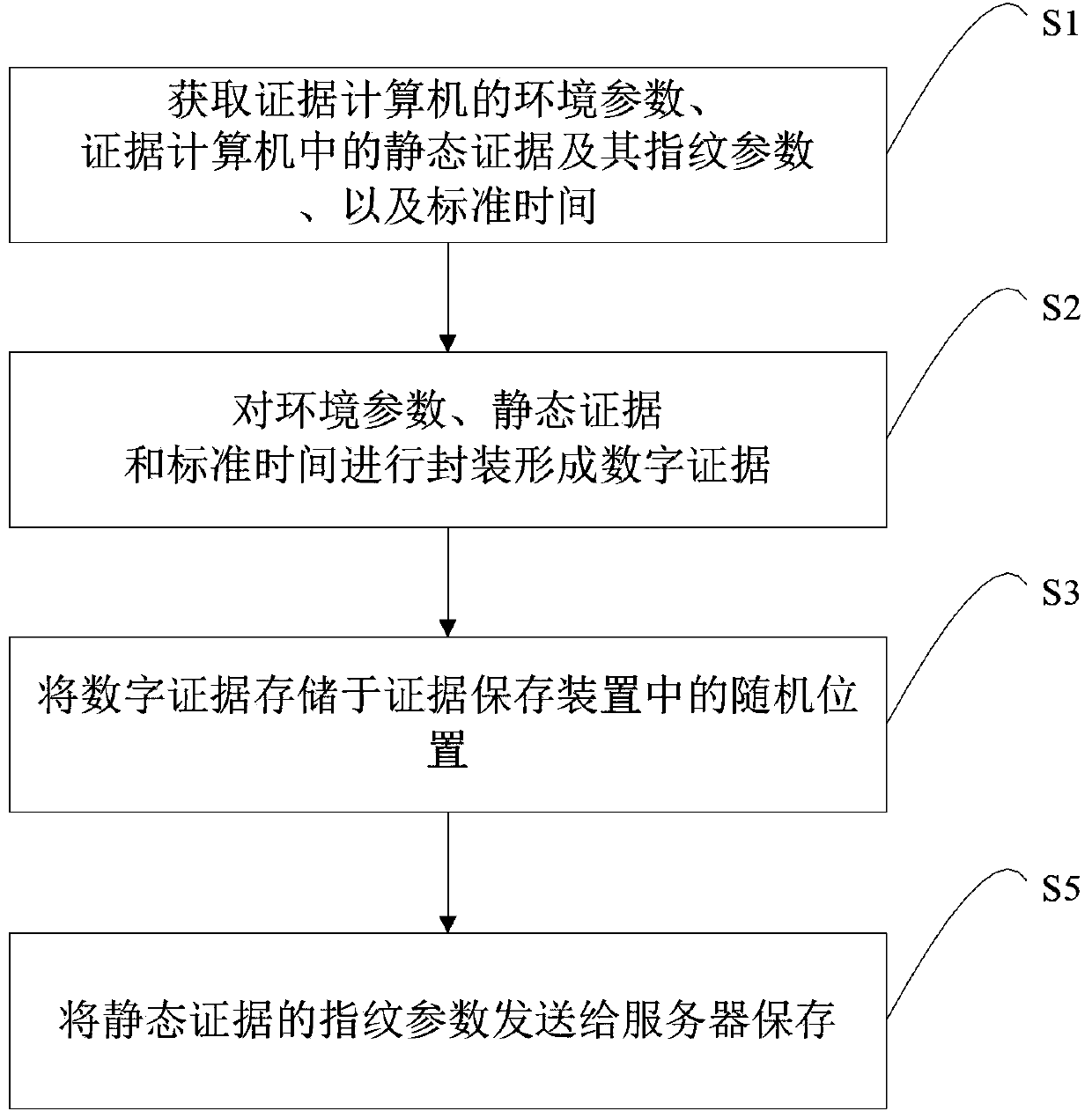
Method, device and system for protecting electronic evidence
InactiveCN103400083AAvoid the problem of inconvenient accessImprove objectivityDigital data protectionDigital data authenticationInternet privacyEngineering
The invention discloses a method, device and system for protecting electronic evidence. The method for protecting the electronic evidence comprises the following steps: acquiring the environment parameter of an evidence computer, evidence documents in the evidence computer and standard time; packaging the environment parameter, the data documents and the standard time so as to form digital evidence; and storing the digital evidence in random positions in an evidence storage device. According to the method for protecting the electronic evidence, primary evidence documents are not encrypted or recoded, and only the order of the evidence documents in the storage space in the evidence storage device is disturbed, so that the secret leakage preventing protection is conducted on the evidence documents, and the primitiveness of the evidence documents can be better ensured.
Owner:FUJIAN ETIM INFORMATION & TECH
Digital fingerprint system and method for piracy tracking and digital evidence obtaining
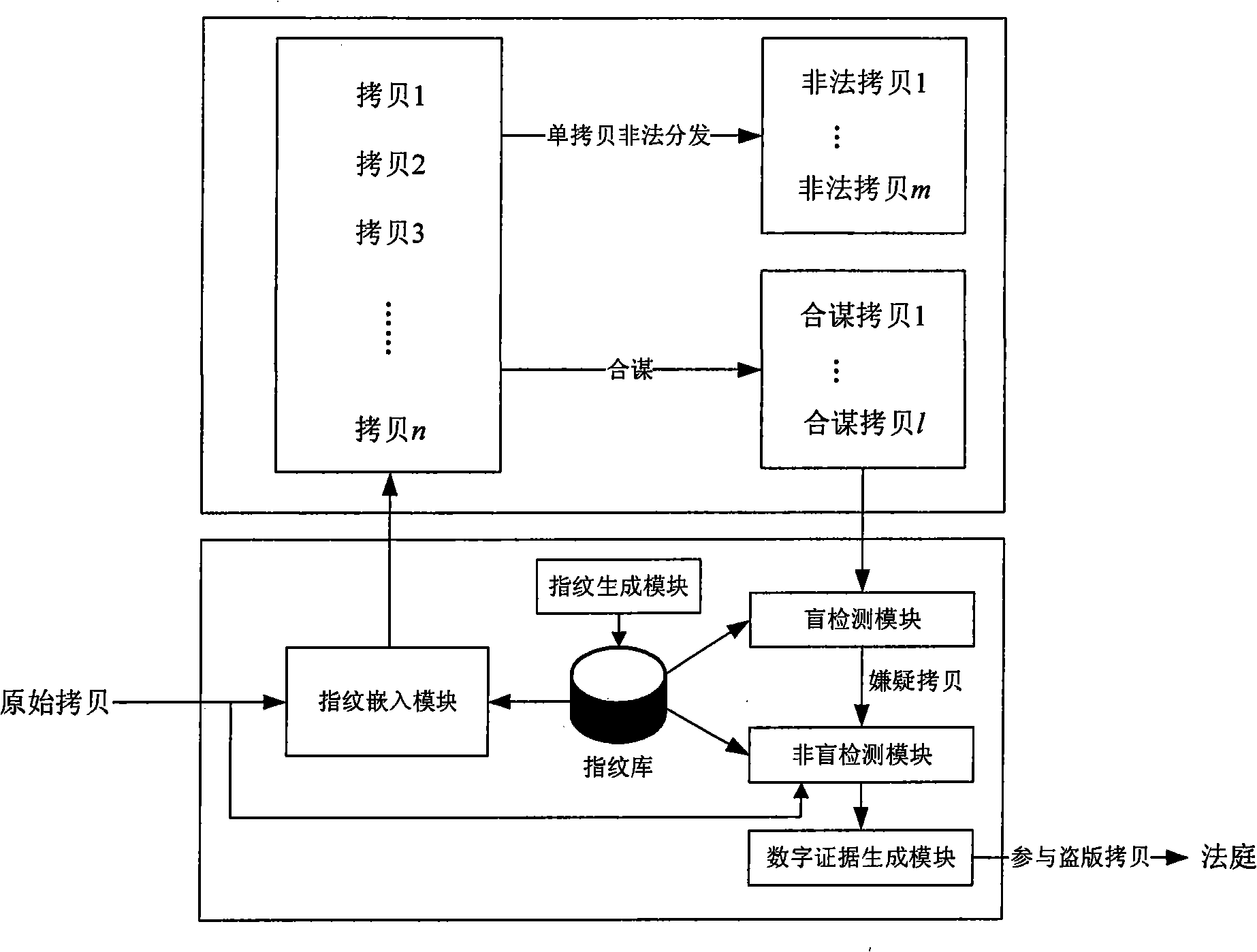
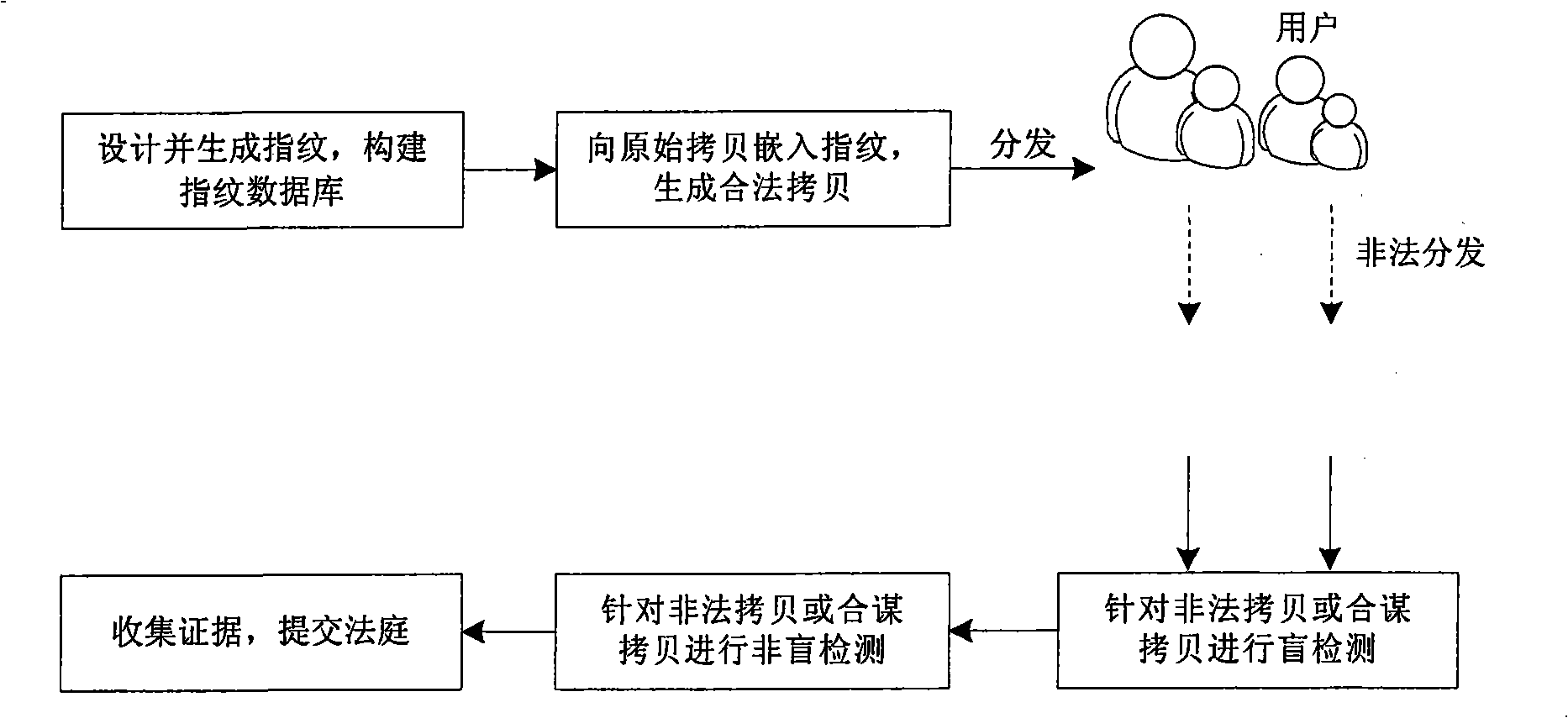
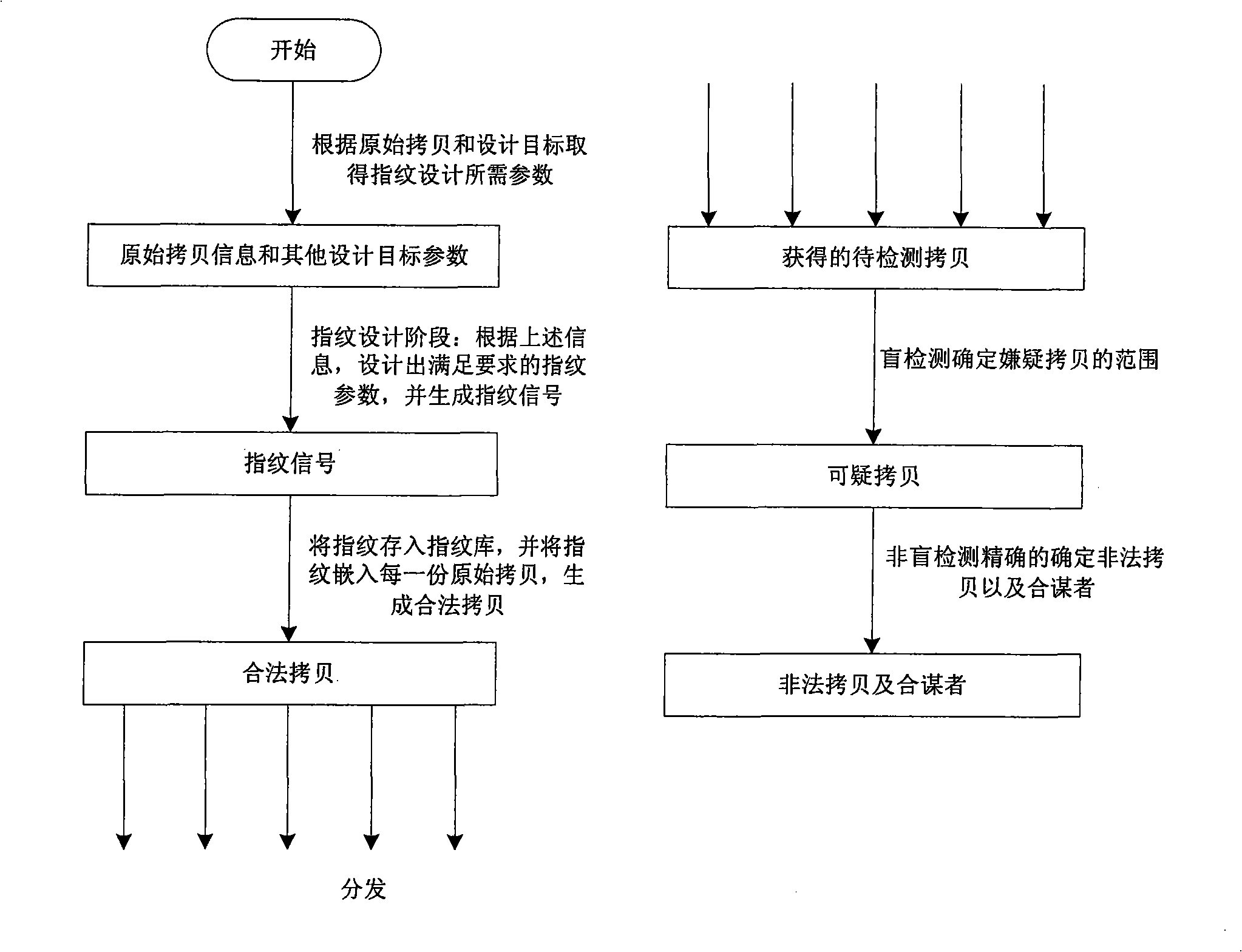
InactiveCN101339588AImprove detection efficiencyImprove detection accuracyImage data processing detailsProgram/content distribution protectionDigital evidenceDigital fingerprint
A digital fingerprint system used for piracy tracing and digital evidence-collecting comprises: a digital fingerprint generating module, a digital fingerprint storehouse, a digital fingerprint embedding module, a digital fingerprint blind-detection module, a digital fingerprint non-blind detection module and a digital evidence generating module; digital fingerprint method is that: (1) separately normally distributed Gauss signals are adopted as fingerprint signals to construct a digital fingerprint storehouse; (2) a spread spectrum embedding way is adopted to embed the fingerprints into an original copy, which generates a legal copy; (3) the legal copies are distributed and in the distribution process, the legal copies can experience a single copy illegal distribution or encounter a coalition attack, therefore a legal copy is formed; (4) the illegal copies are blindly detected to obtain a suspect copy in a lager scale; (5) the suspect copy obtained after being blindly detected is non-blindly detected; (6) the illegal copy and the original fingerprints obtained in procedure 3 and the coalition information obtained in procedure 5 are submitted as evidence to the court for trial. The digital fingerprint system has the advantages of higher detection efficiency and detection precision, thus can be widely applied in the tracing of multimedia content and piracy evidence-collecting.
Owner:BEIHANG UNIV
Digital processing and managing system of court exhibits
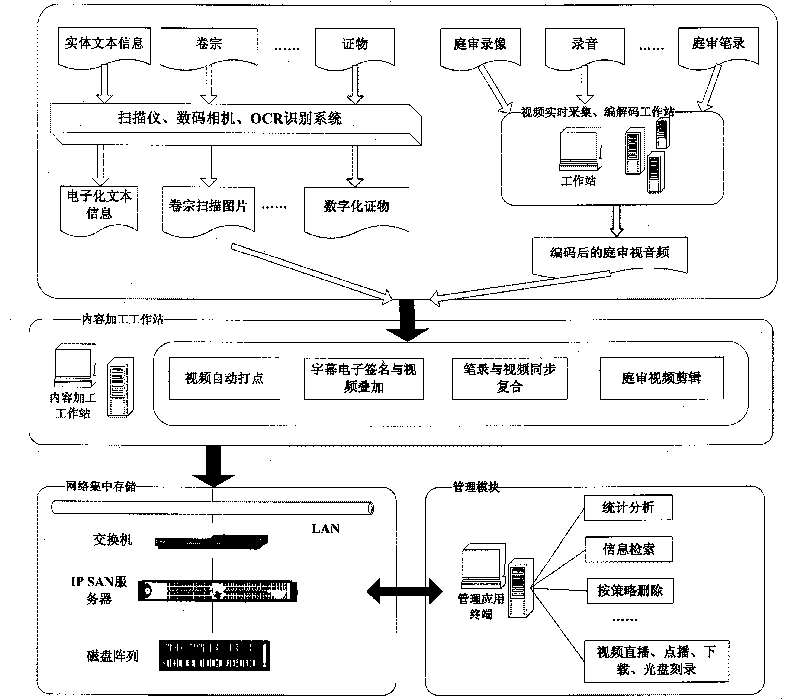
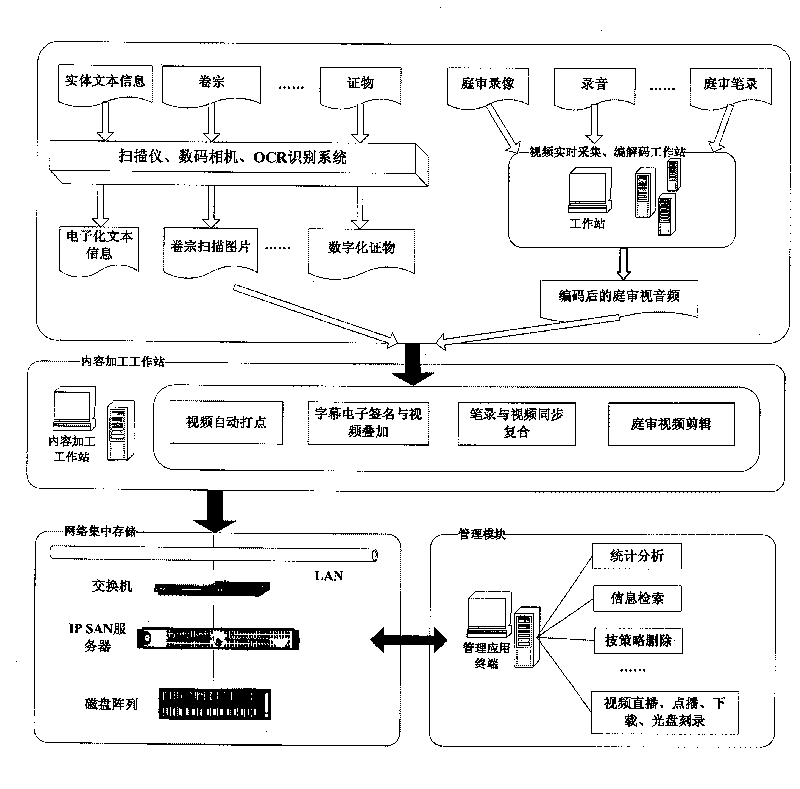
InactiveCN101739468AImprove trial efficiencyAvoid damageData acquisition and loggingInformation processingRelevant information
The invention relates to an information processing technology, in particular to a digital processing and managing system of court exhibits. The system carries out digital processing on the exhibits for court hearing through a corresponding processing device, thereby leading evidences and relevant information for court hearing to be easy to read, store, manage and retrieve; and information content after processing is stored through the network centralized storage form, thereby ensuring the reliability and the safety of data and facilitating the allocation of data resources. Digital evidences can be stored on a variety of media, thereby brining great convenience to filing and preservation of case files, preventing the damage of the exhibits caused by a variety of reasons, reducing the workload of staff and ensuring the science and the fairness of case trails.
Owner:NEWAUTO SILICON VALLEY VIDEO TECH
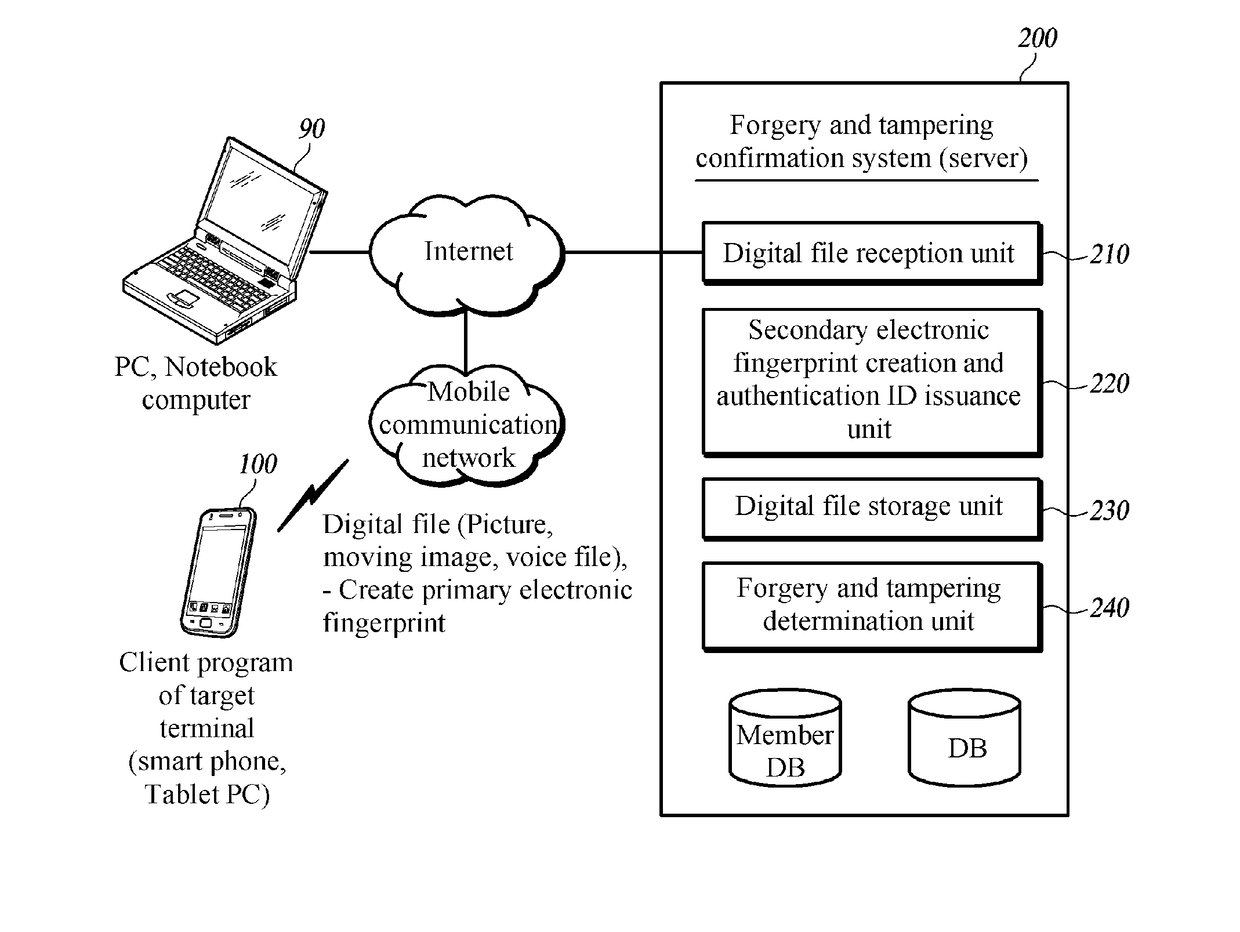
Evidence system and method to determine whether digital file is forged or falsified by using smart phone and smart phone having certification function of smart phone screen capture image and method thereof
InactiveUS20180026790A1Prevent forgeryPrevent tamperingMultiple keys/algorithms usageUser identity/authority verificationDigital dataDigital evidence
A system and method for proving forgery of digital file using a smart phone proves whether digital file recorded as digital evidence is tampered after the digital file is created, and is used in digital forensic and criminal investigation by proving that the digital file is not forged through the forgery confirmation system, and the digital file is used for substituting for notary fee, and used as data for proving a situation in an incident, data for proving foundation works after building construction, or evidence data for voice file in a threatening case. Since content transmitting information while using smart phone is stored as digital data through screen capture and a list of applications executed before the capture is converted and stored as hash value, the digital information authentication system through smart phone screen capture confirms actual facts thereafter by proving that the corresponding content is an original copy.
Owner:REPUBLIC OF KOREA (NTL FORENSIC SERVICE DIRECTOR MINIST OF PUBLIC ADMINISTRATION & SECURITY)
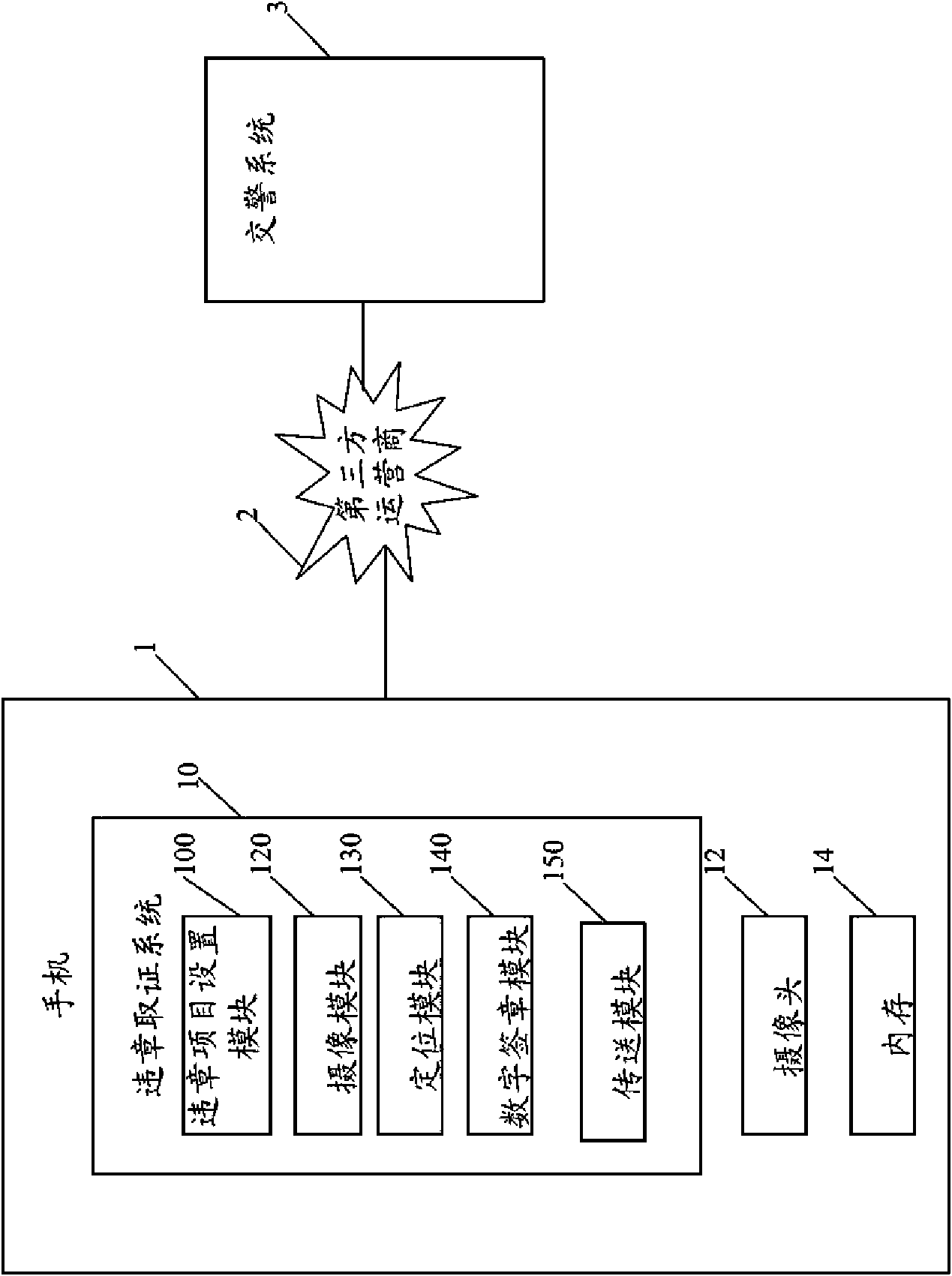
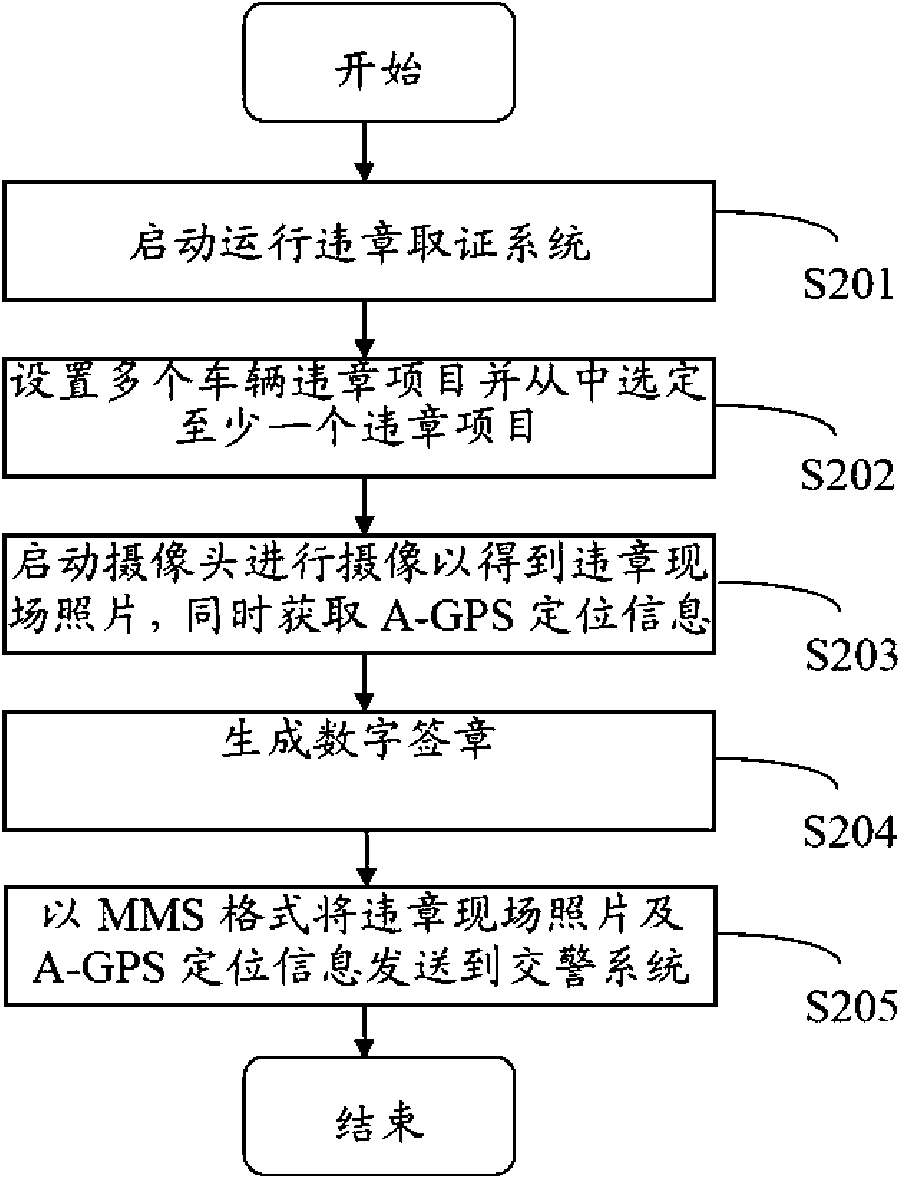
Regulation-violating behaviour evidence-obtaining system and method therefor
InactiveCN101620782AImprove work accuracyImprove work efficiencyRoad vehicles traffic controlDigital signatureDigital evidence
Owner:SHENZHEN FUTAIHONG PRECISION IND CO LTD +1
Method and apparatus for controlling digital evidence
ActiveUS20150066785A1Data processing applicationsDigital data protectionDigital evidenceLibrary science
A method and apparatus for controlling digital evidence comprising creating a case record comprising information about an investigative case, electronically storing at least one piece of digital evidence into memory, and associating the stored at least one piece of evidence with the case record.
Owner:SUMO LOGIC INC
Device and method for providing security in remote digital forensic environment
ActiveUS20160078240A1Digital data processing detailsAnalogue secracy/subscription systemsAnalysis dataGoal system
Owner:ELECTRONICS & TELECOMM RES INST
Evidence graph and vulnerability reasoning combined network evidence collection method and system
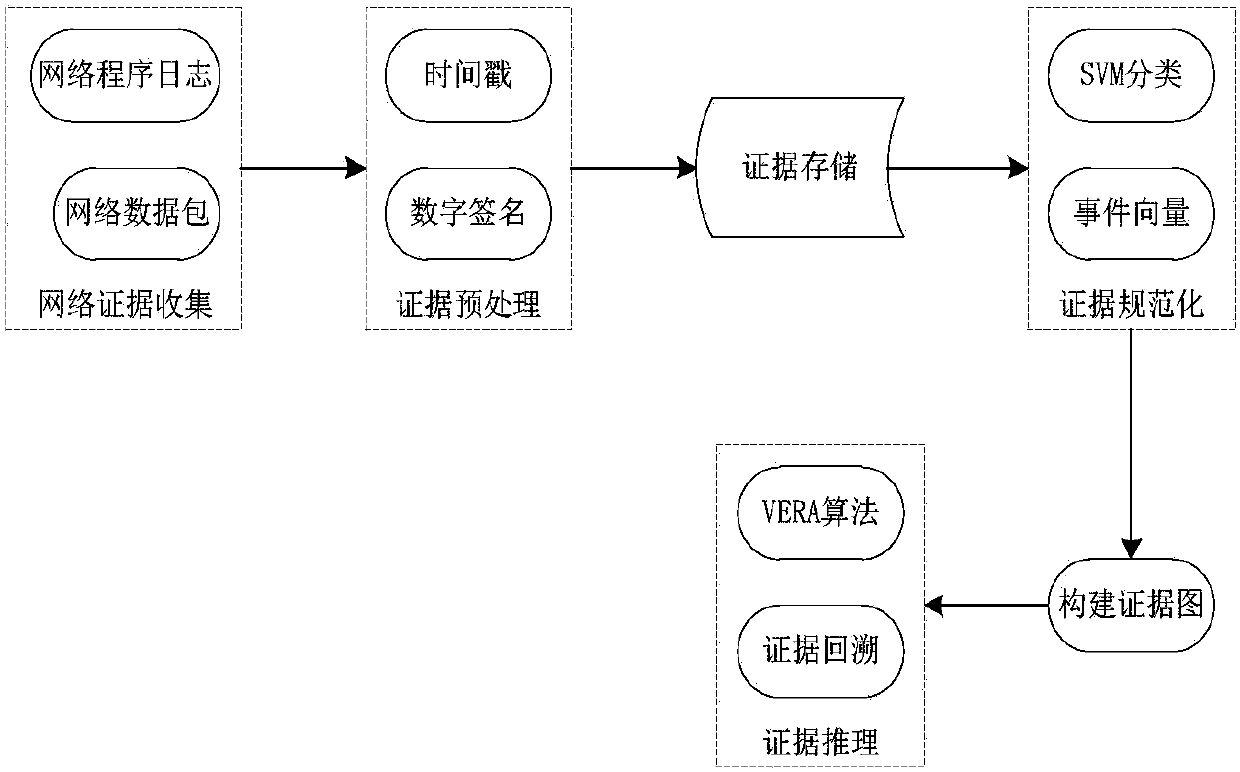
ActiveCN105959328ASolve problems that cannot be visualizedDiversity guaranteedTransmissionNODALData Origin
The invention relates to the field of digital evidence collection, and specifically relates to an evidence graph and vulnerability reasoning combined network evidence collection method and system. The method comprises the steps of collecting original data from heterogeneous data sources; storing the original data, thereby obtaining first storage data; separating evidence from the first storage data by use of a classification and recognition algorithm; marking the evidence, thereby obtaining event vectors of the evidence; establishing an evidence library according to the first storage data, the evidence and the event vectors; establishing an evidence graph according to the evidence library and an effective time sequence; and reasoning suspicious attack nodes through a VERA algorithm according to the evidence graph and simulating attack paths. Through adoption of the heterogeneous data sources, the comprehensiveness and integrity of the data sources can be ensured. The obtained evidence can be visually reflected by the VERA. According to the method, the problems that in the evidence collection process at the present stage, integrity and authenticity are poor and the obtained evidence cannot be reflected visually can be solved.
Owner:BEIJING UNIV OF TECH
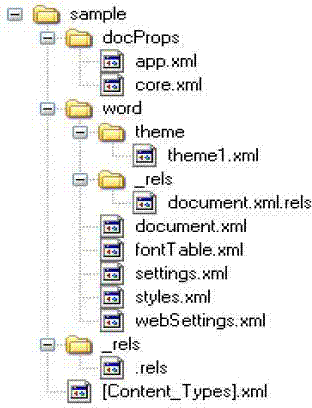
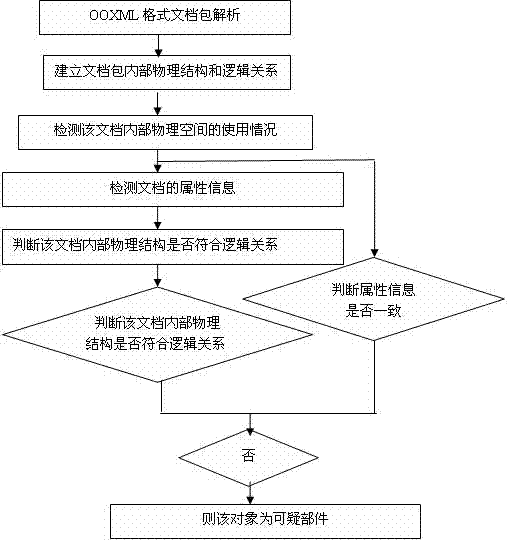
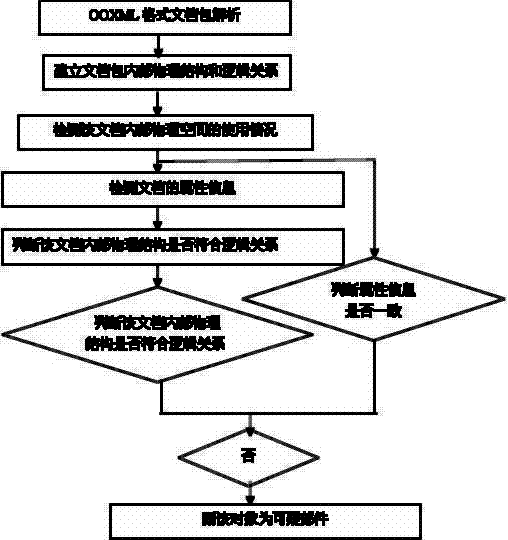
OOXML (office open extensible markup language)-based electronic document digital evidence collecting method and device thereof
InactiveCN102651057AImprove robustnessProgram/content distribution protectionSpecial data processing applicationsTime informationElectronic document
The invention relates to an OOXML (office open extensible markup language)-based electronic document digital evidence collecting method and a device thereof. The Office Open XML (OOXML) file format is a new file format adopted by Microsoft office 2007 and later versions. The method disclosed by the invention can collect relevant evidences from a suspected electronic file, such as author information, tampering time information, hidden secret file information and the like, so as to judge the copyright attribution of the electronic file and detect the confidential information and the like. The process of electronic file digital evidence collection does not alter any content of the electronic file, and the collected characteristics have strong robustness. Moreover, the method can resist attacks such as Save As, Delete, Edit, Copy and the like, and can be used for safety control of confidential information covering national defense, politics and commerce.
Owner:孙星明
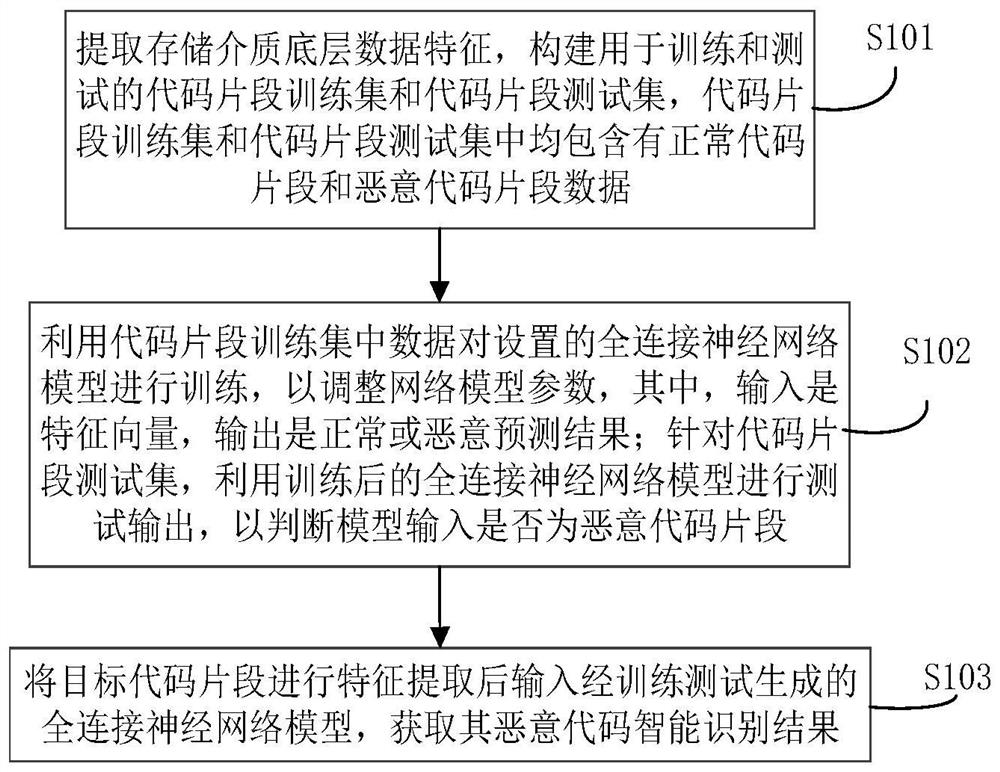
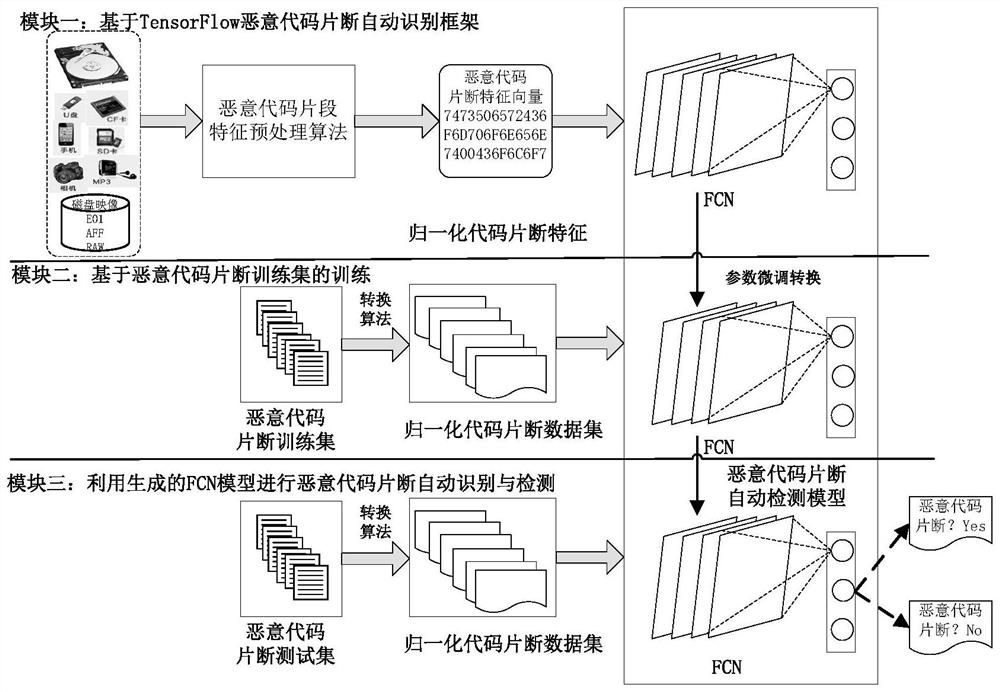
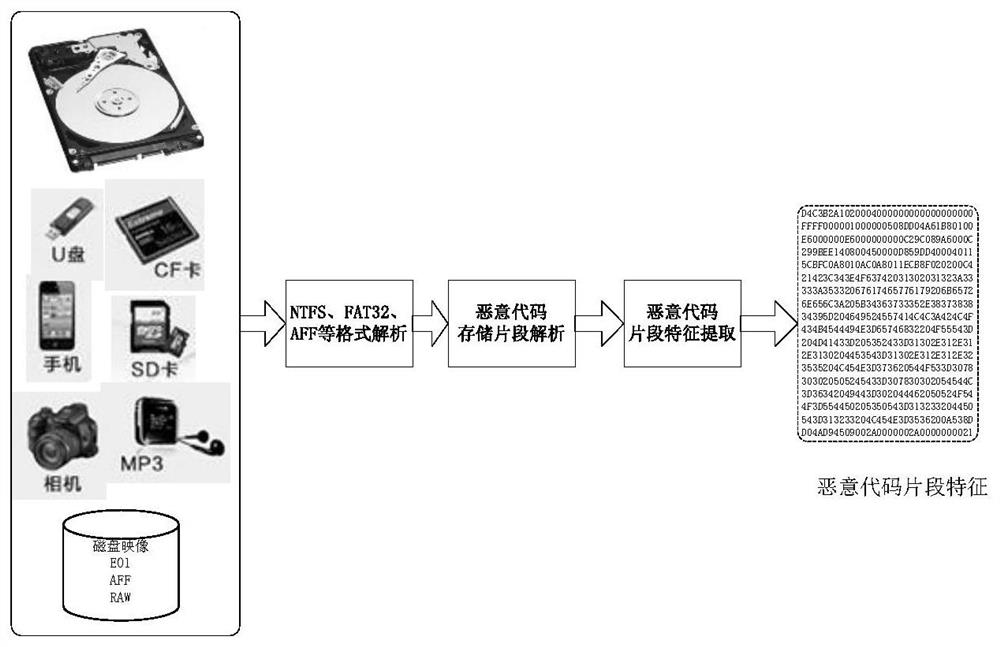
Intelligent malicious code fragment evidence obtaining method and system
ActiveCN111881447ACharacter and pattern recognitionPlatform integrity maintainanceFeature vectorFeature extraction
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
Auditing secret key cryptographic operations
InactiveUS20090034735A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesCryptographic protocolDigital evidence
In a cryptographic system, the unlocking of secret keys on a user system is audited and correlated with other events that typically occur after the secret key is used to perform a cryptographic operation. Audit evidence of secret key cryptographic operations is recorded for later review and / or analysis, for use as stored evidence of unauthorized activity and / or for use in refuting false claims of repudiation of authorized activity. Some systems might also provide users with user activity reports that can alert a user to suspicious or unauthorized activity using that user's access.
Owner:ARCOT SYSTEMS INC
Multimedia digital watermark evidence taking mobile phone
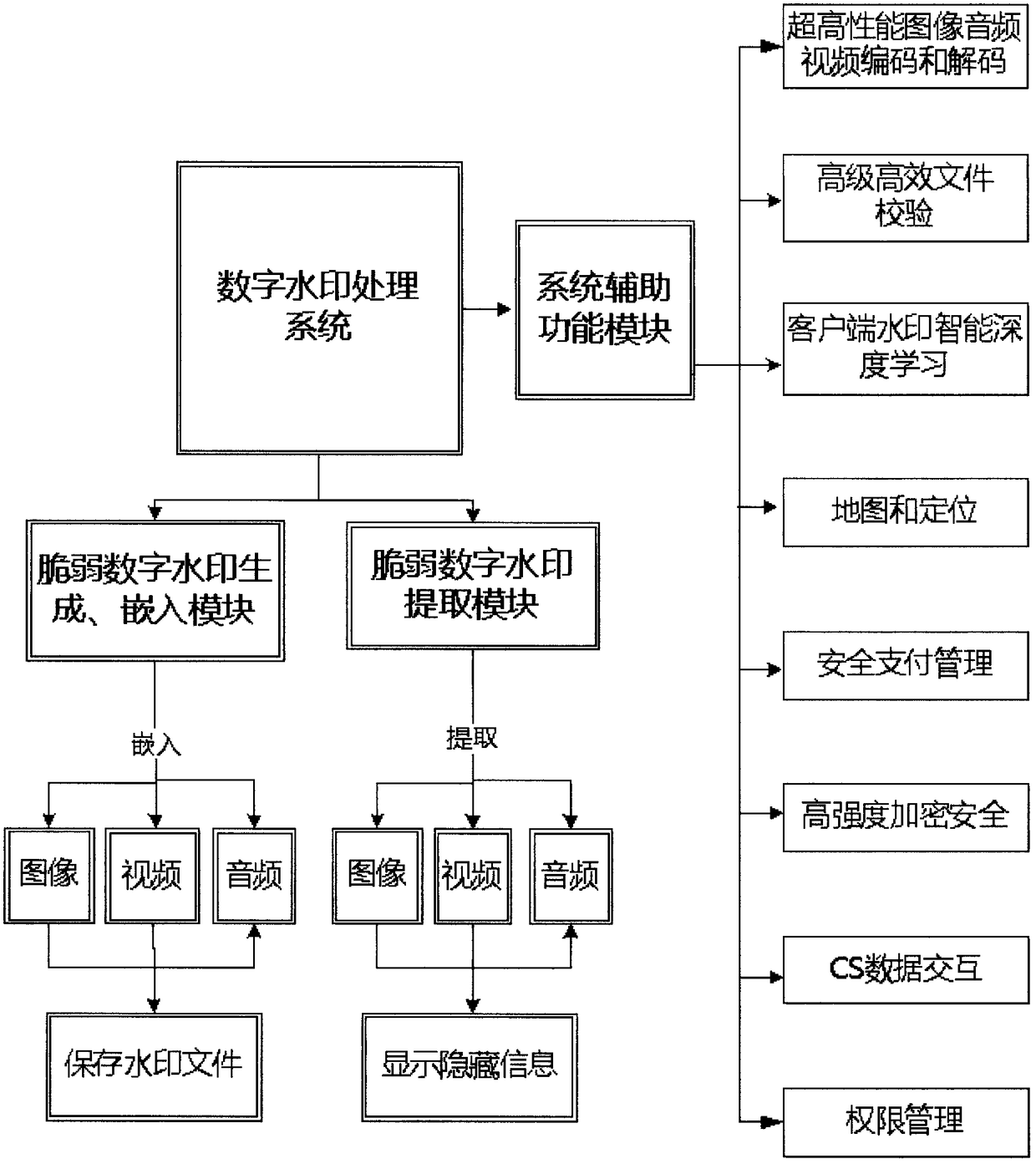
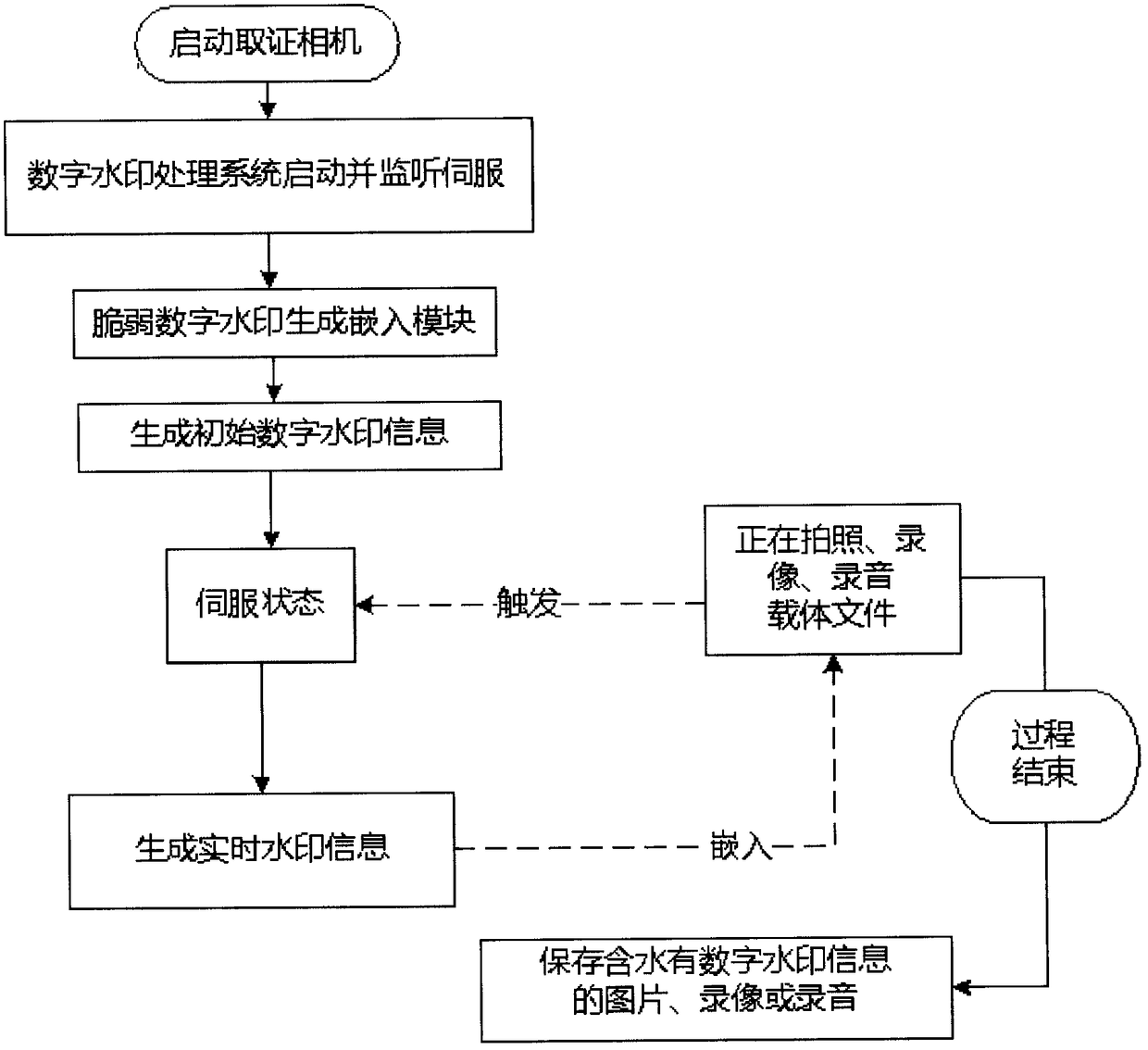
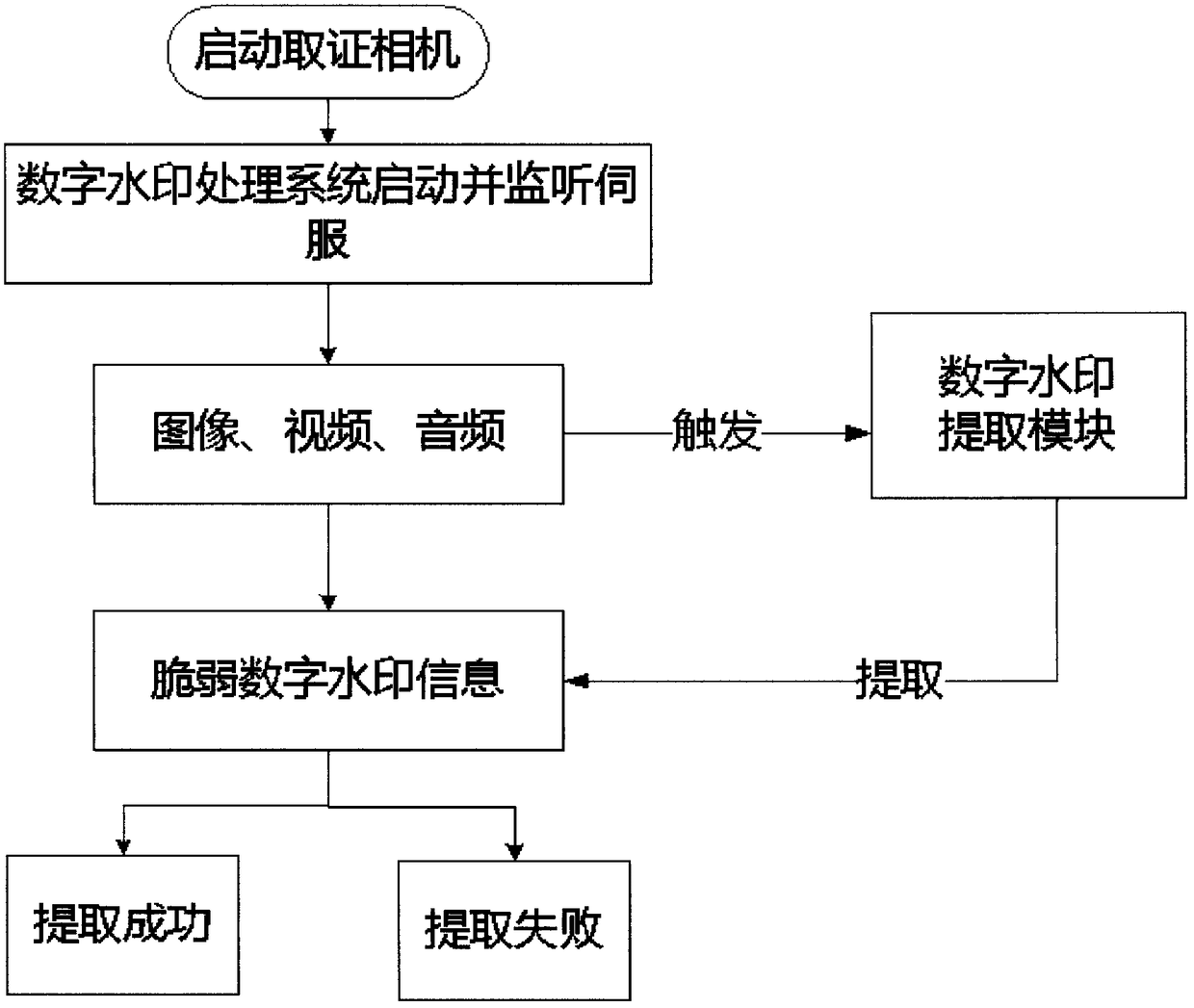
ActiveCN109151157AGain credibilityHave completeSubstation equipmentDigital video signal modificationFragilityDigital evidence
The invention discloses a multimedia digital watermark evidence taking mobile phone. The multimedia digital watermark evidence taking mobile phone is an intelligent evidence taking mobile phone whichuses the unique stability, concealment, security and fragility of a fragile digital watermark to ensure the integrity, the authenticity, the stability, the reliability and the authority of photographed and recorded multimedia data based on an image, audio and video fragile digital watermark embedding and extraction technology. When a user uses the mobile phone, imperceptible and unmodifiable fragile digital watermark information with unique identity confirmation is embedded in real time in a photographed image, audio and video. The image or the audio or the video with the fragile watermark canbe normally used and distributed but can not be modified manually. The authenticity of a file can be identified according to whether the photographed digital file contains the digital watermark information. The evidence taking process is quick, efficient, accurate, safe and convenient. The evidence taking content has the uniqueness of a digital evidence and the legal authority of evidence use, and the multimedia digital watermark evidence taking mobile phone disclosed in the invention can be used for evidence taking and recording in fields such as judicature, law enforcement and claim.
Owner:CHENGDU YUFEI INFORMATION ENG
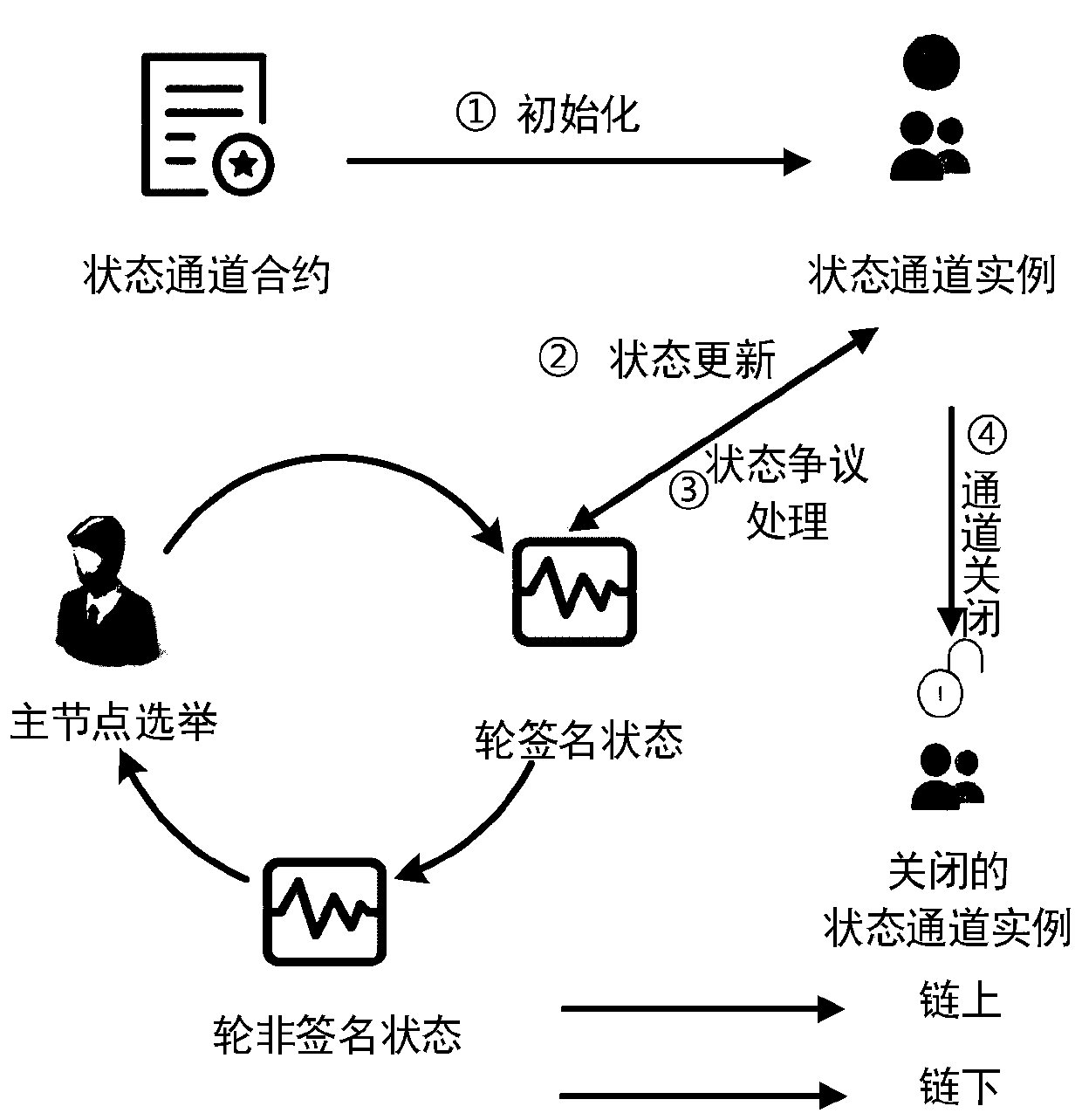
Distributed log auditing system and method based on state channel
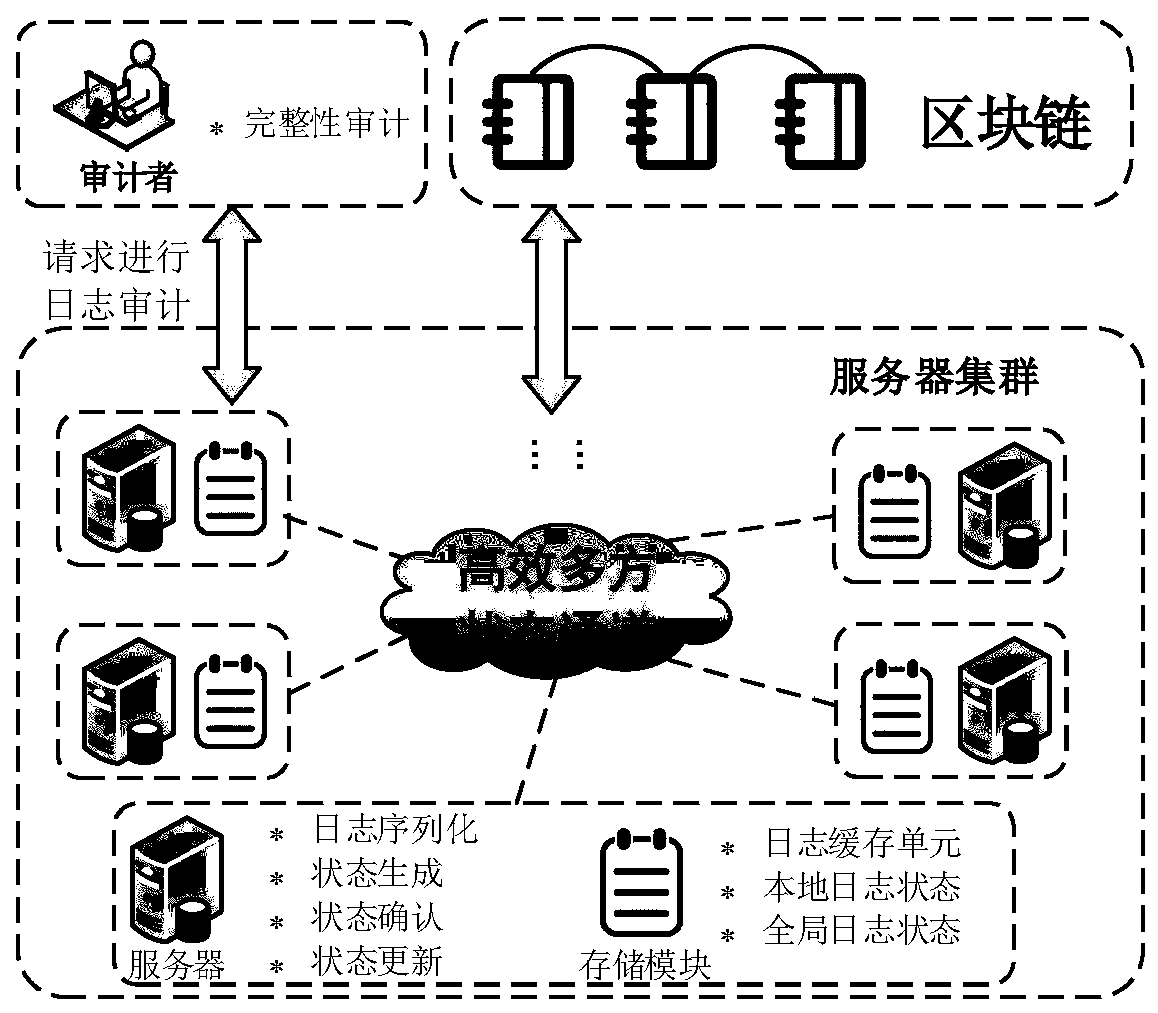
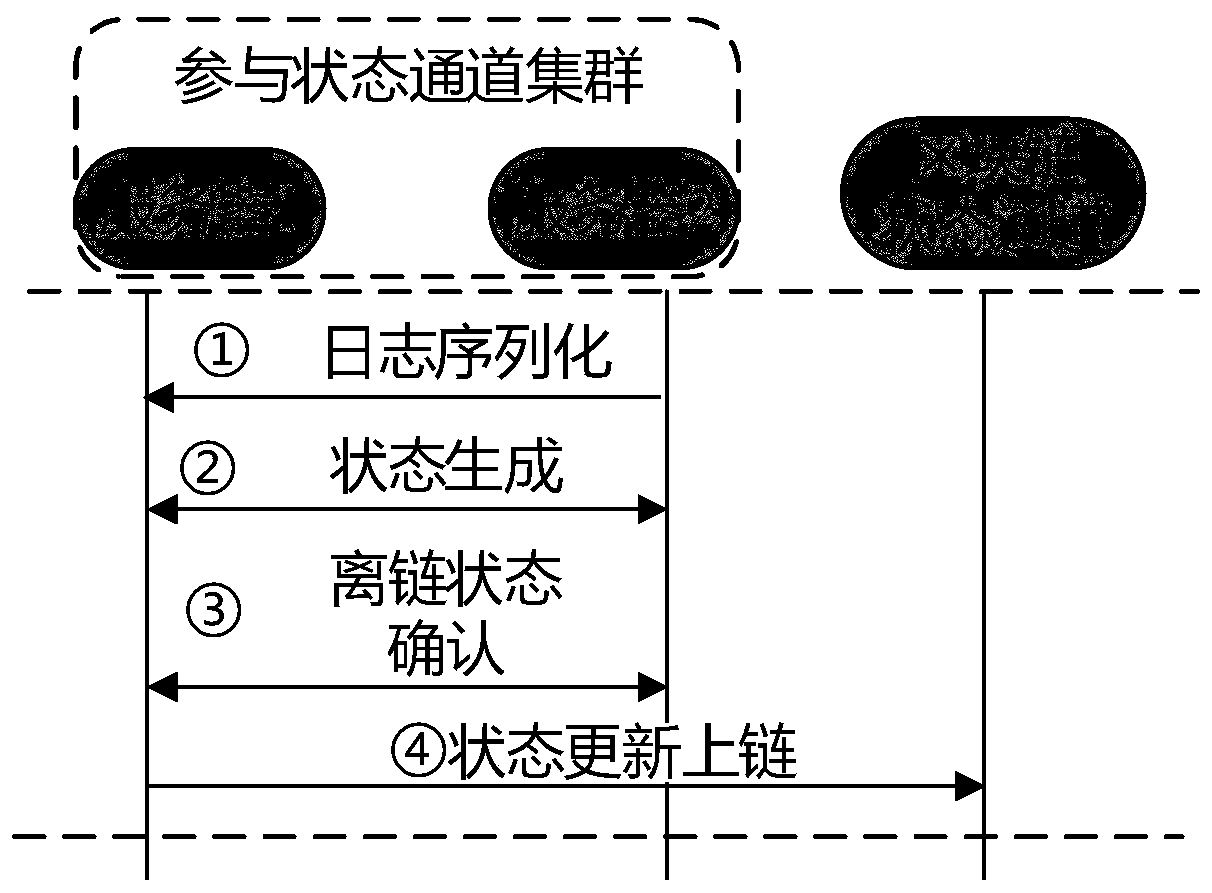
ActiveCN111490978AReduce on-chain storage overheadRapid positioningUser identity/authority verificationDigital data protectionServer logEngineering
The invention discloses a distributed log auditing system and method based on a state channel. The system comprises a state processing and storing unit in a log server, a block chain network containing a multi-party state channel contract and a log auditing unit of an external auditor. The state processing and storing unit in the log server is used for preprocessing logs, generating a local log state and a global log state and interacting with the block chain; the block chain network of the efficient multi-party state channel contract is used for protecting the security and integrity of the log state, and realizing the under-chain confirmation of the state through the state channel; and the log auditing unit of the external auditor is used for auditing the server log record and automatically obtaining an auditing result. The distributed log auditing system based on the state channel provided by the invention can provide a reliable and safe log integrity protection method for users in the fields of computer intrusion detection, digital evidence collection and the like.
Owner:WUHAN UNIV
Latency tolerant fault isolation
InactiveUS20150149024A1Vehicle testingRegistering/indicating working of vehiclesComputer accessDigital evidence
A method of latency tolerant fault isolation is provided. The method includes receiving, by a maintenance data computer, evidence associated with a test failure. The maintenance data computer accesses metadata to identify a system failure mode associated with the evidence and other potential evidence associated with the system failure mode. The maintenance data computer determines a maximum predicted latency to receive the potential evidence associated with the system failure mode based on the metadata. The method also includes waiting up to the maximum predicted latency to determine whether one or more instances of the potential evidence associated with the system failure mode are received as additional evidence. The maintenance data computer diagnoses the system failure mode as a fault based on the evidence and the additional evidence.
Owner:SIKORSKY AIRCRAFT CORP
Reading pen technology-based multimedia forensic evidence demonstration method and system
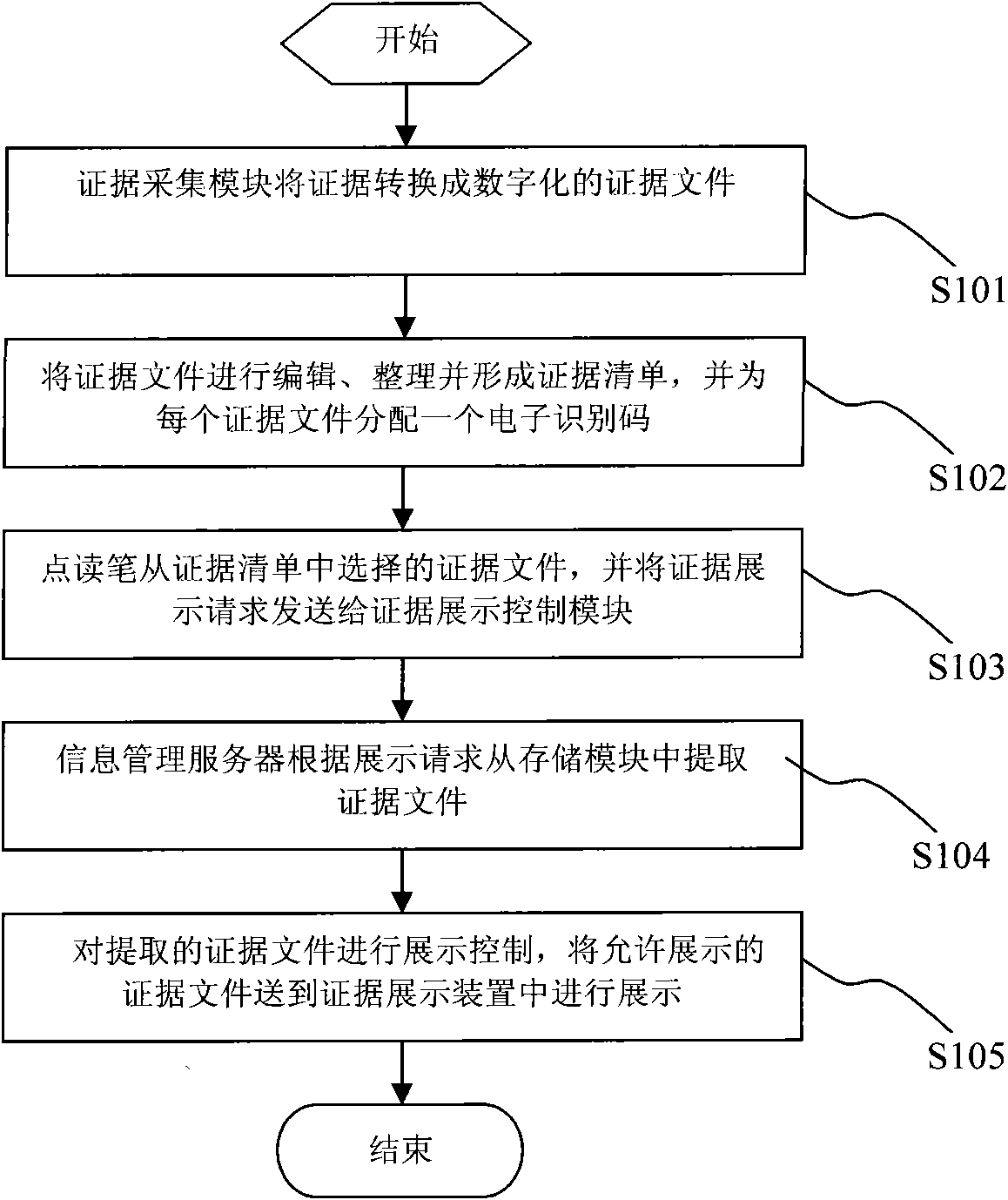
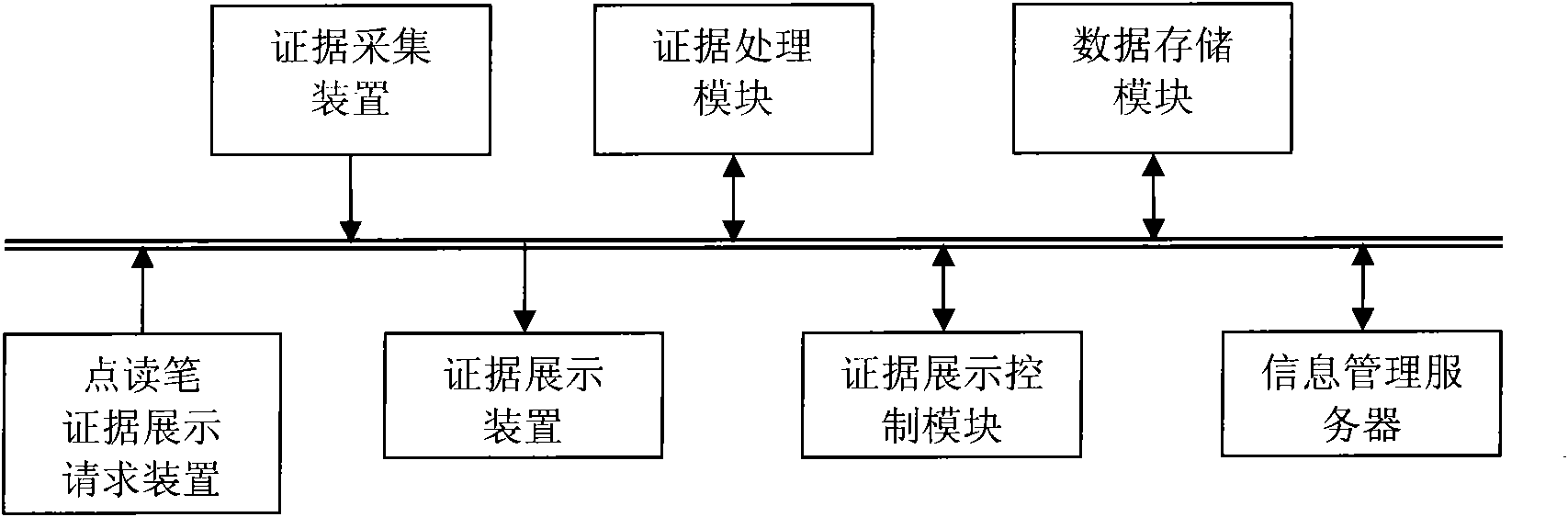
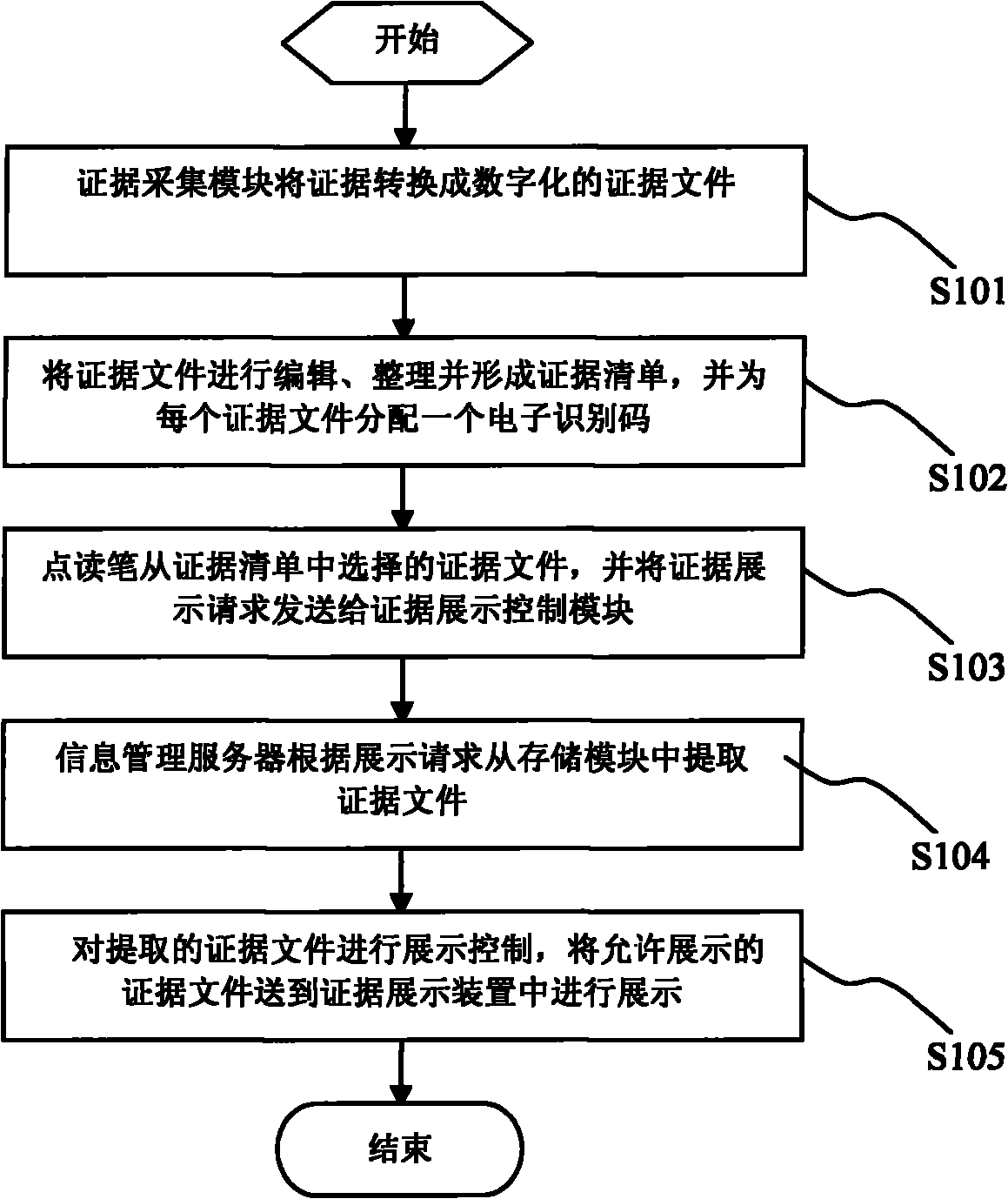
InactiveCN101826083AEvidence Shows SimpleEvidence display is intuitiveData processing applicationsSpecial data processing applicationsDigital evidenceLibrary science
The invention relates to a reading pen technology-based multimedia forensic evidence demonstration method and a reading pen technology-based multimedia forensic evidence demonstration system. The method comprises the following steps that: an evidence acquisition device converts acquired non-digital evidences into digital evidence files and transmits the digital evidence files to an evidence processing module for editing; an information management server lays out the edited evidence files to form an evidence list; a plaintiff or defendant selects the evidence file from the evidence list by using a reading pen and transmits evidence demonstration request information to an evidence demonstration control device; and finally a judge controls the evidence demonstration according to the details of a case. The method and device used by the method are simple and easy to operate, so that efficient and intuitive evidence demonstration is ensured in the court trial so as to save not only the trial time but also a large amount of expenditure.
Owner:NEWAUTO SILICON VALLEY VIDEO TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com