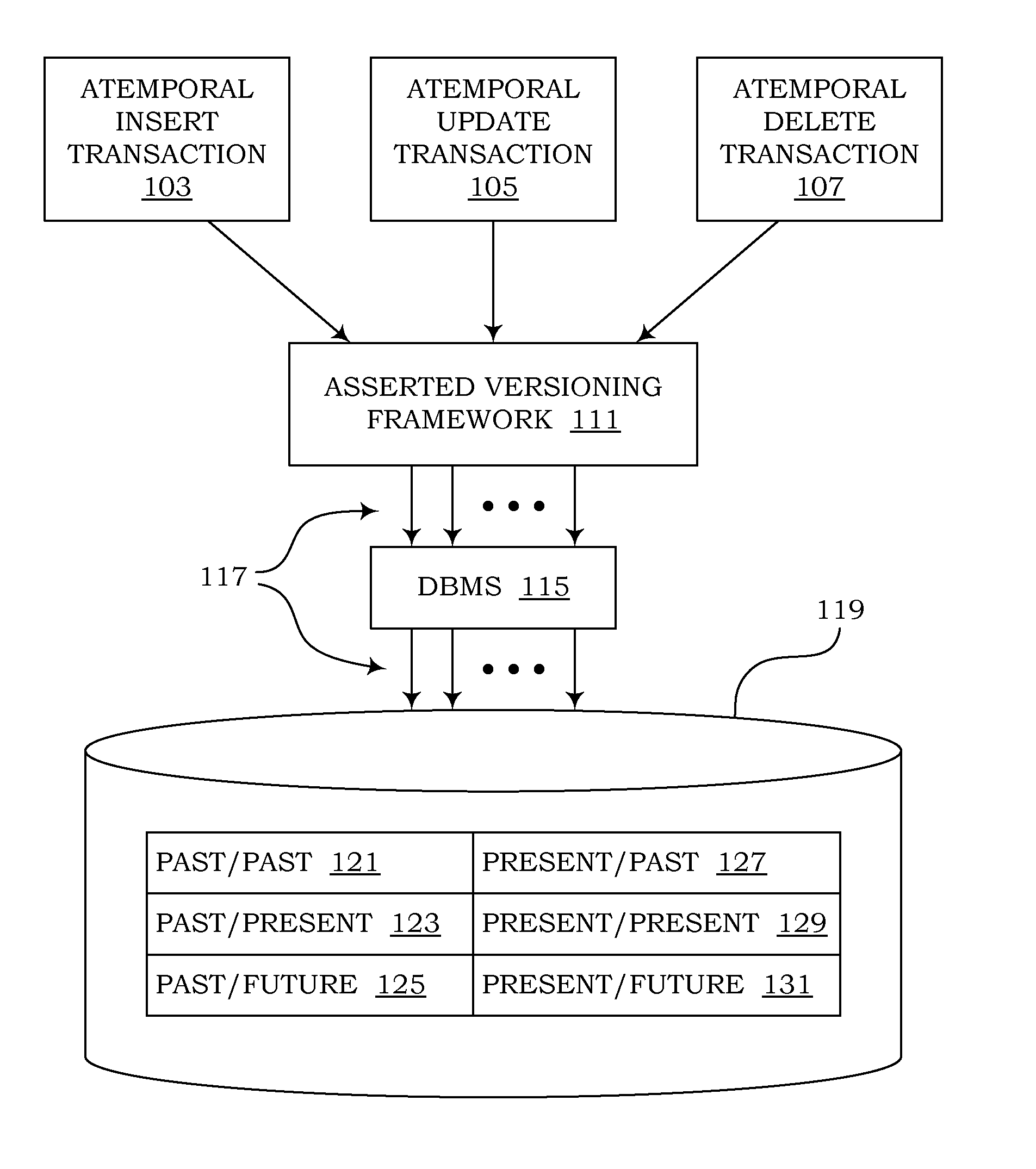
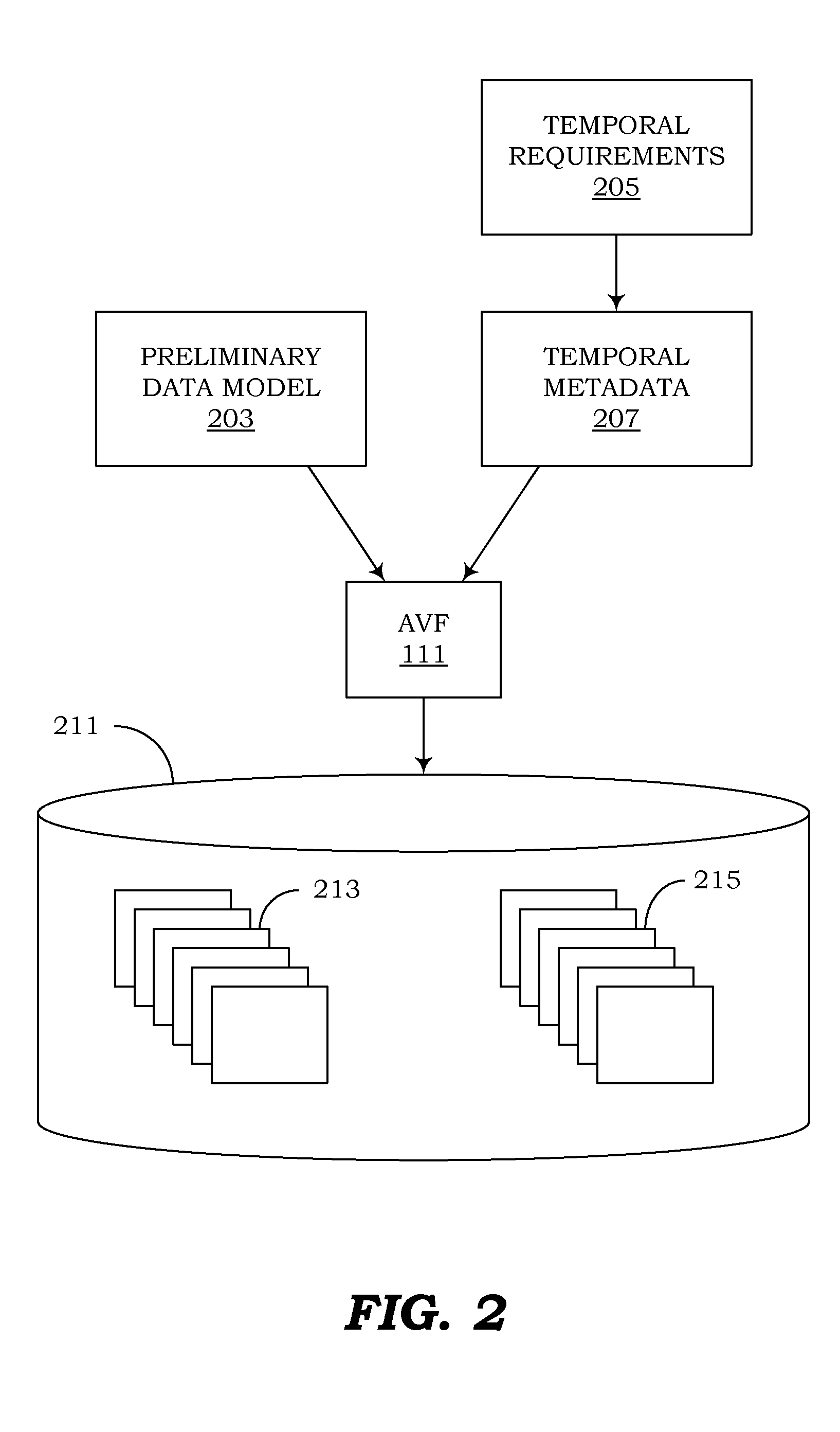
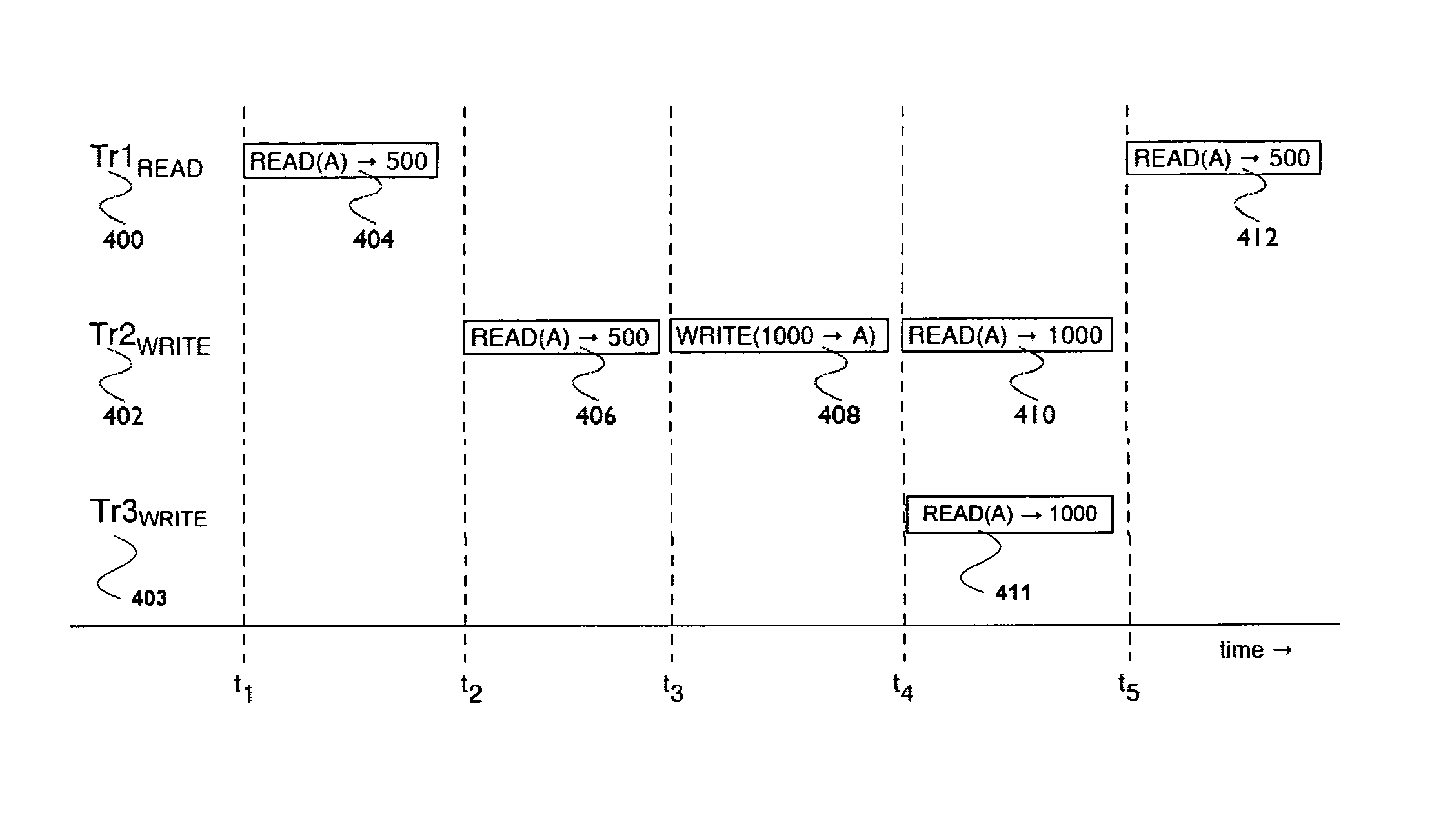
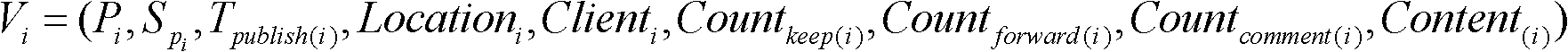Patents
Literature
1384 results about "Effective time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Effective Time means the time at which the Distribution occurs on the Distribution Date. Effective Time means 12:01 a.m. on the Effective Date; Effective Time means 12:01 a.m. Eastern Time on the Closing Date. Effective Time means the time at which the Distribution is effective on the Distribution Date.
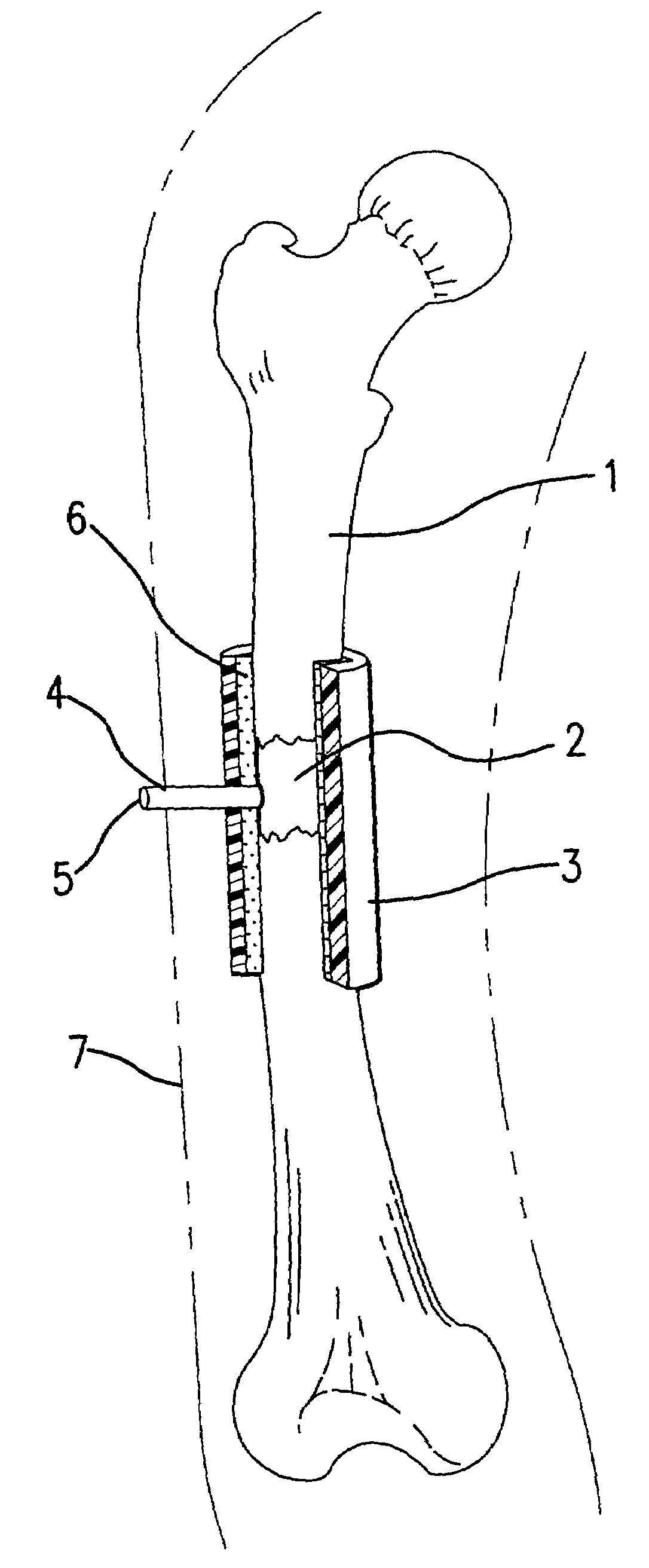
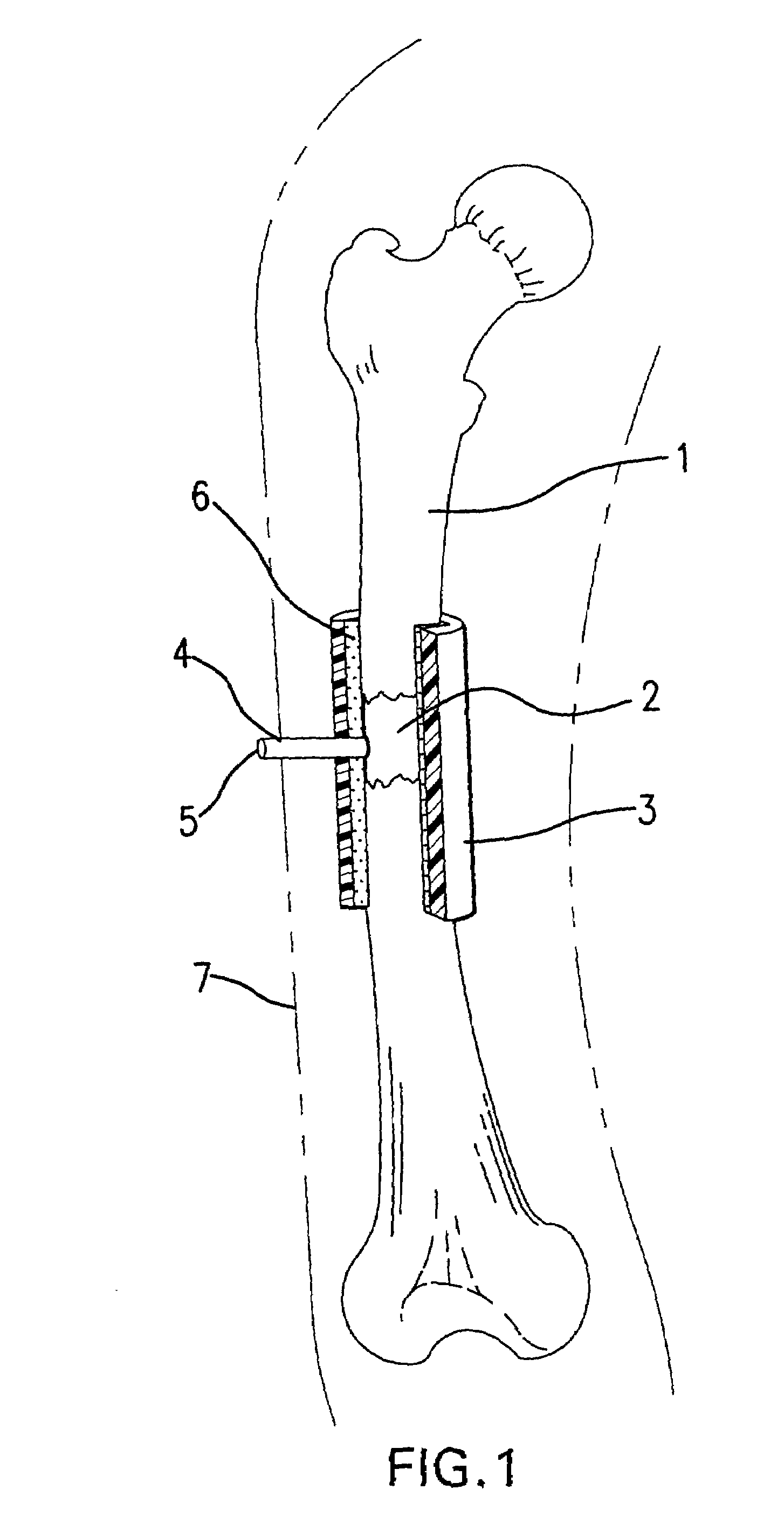
Bone regeneration device for long bones, and method of use
A method of stimulating bone regeneration in a discontinuous section of a long bone in a subject requiring same, comprising the step of applying to said discontinuous section of the bone an effective vacuum for an effective length of time. A device for carrying out the method consisting of a sealable tubular-shaped sleeve or cuff that fits snugly and sealably around the bone section to be treated and that can be evacuated via a port that is integral to the sleeve or port.
Owner:KCI LICENSING INC
Formula of wheel-rack solid lubrication additive for railway traffic
The invention discloses a prescription of a wheeltrack lubricant additive, which is characterized by strong bearing capacity, high temperature resistance and long effective time upon one time coating, thereby solving the defect that factigue crack expansion of the wheeltrack is accelerated by traditional grease for the generation of oil wedge effect. The prescription comprises 1 percent-30 percent of metal powder, 3 percent-50 percent of high temperature solid lubricant material and 5 percent-50 percent of fatty acid by weight. The strip solid materials can be produced in virtue of other accessories by the prescription.
Owner:张念
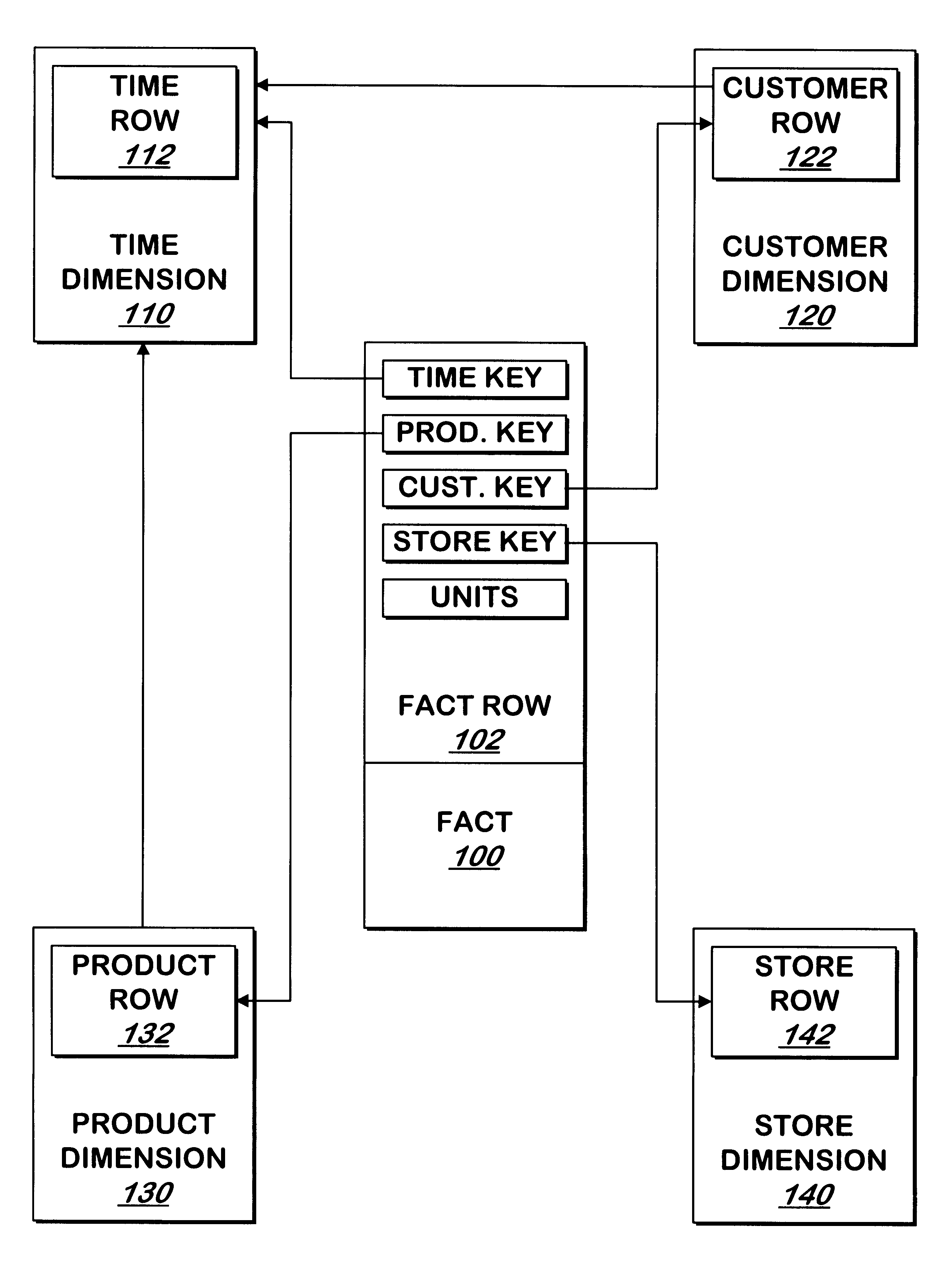
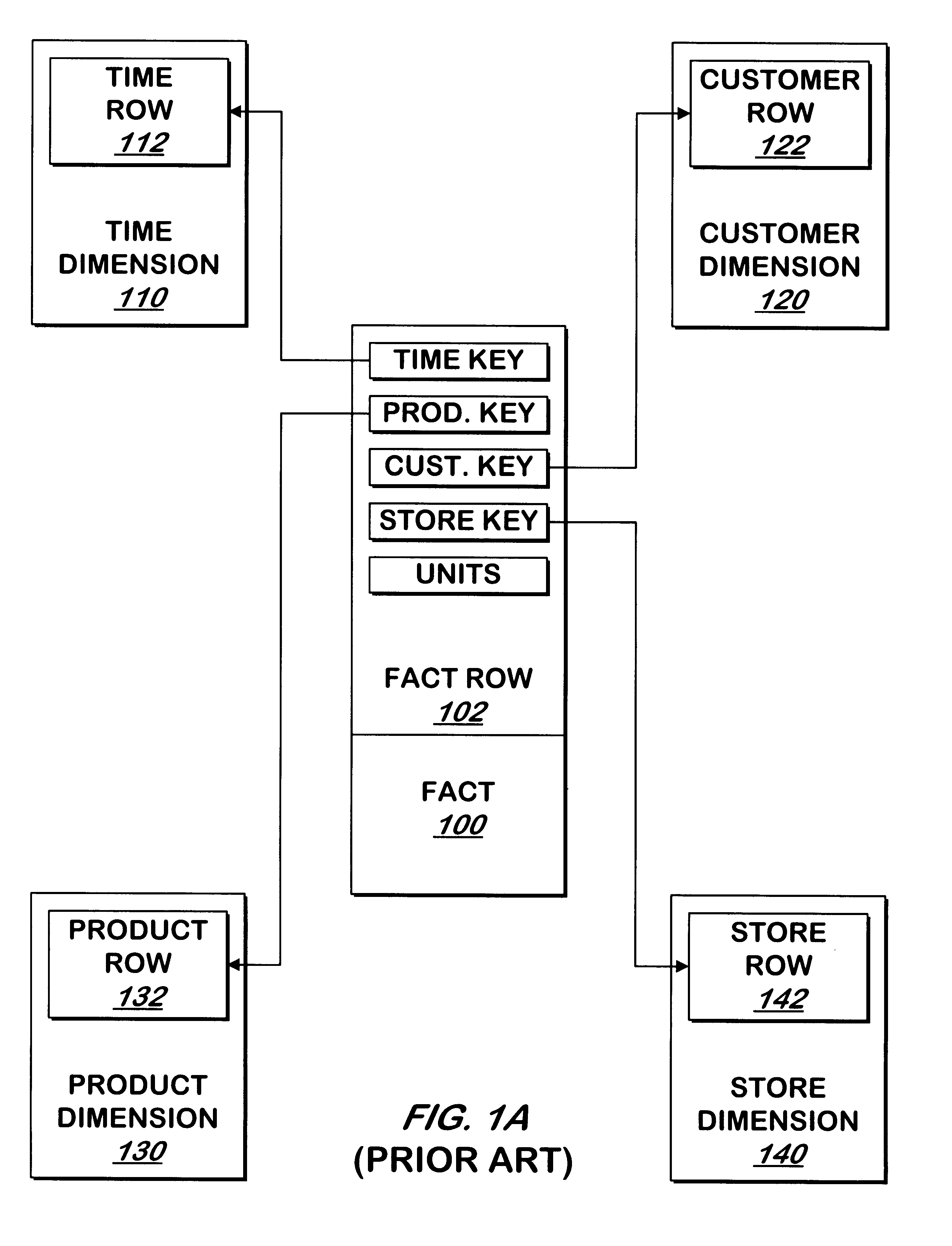
System and method for selecting rows from dimensional databases having temporal dimention
InactiveUS6233573B1Data processing applicationsDigital data information retrievalEffective timeDimension table
A system and method selects rows from a fact table in a dimensional database containing a fact table, a time dimension table and other dimension tables. The other dimension tables each contain rows containing a time invariant attribute to identify an item described by the row, an effective time attribute for the row, and other attributes. If an attribute for an item changes, a new row is added to the dimension table containing the time-invariant attribute for the item and current attributes for the item, without deleting or overwriting any existing rows for that item. Such dimension tables can be selected or used to create other tables using one or more time attributes of the dimension tables. The tables created can be selected or used to create still other tables using one or more time attributes of those tables. One or more of the resulting tables or one or more tables created from a resulting table are then joined to a table in the dimensional database or a table created from a table in the dimensional database.
Owner:AMAZON TECH INC
Method and system for cataloging news video
InactiveCN101616264AAutomatic catalog implementationSolve the problem of automatic semantic information annotationTelevision system detailsCharacter and pattern recognitionComputer moduleCataloging
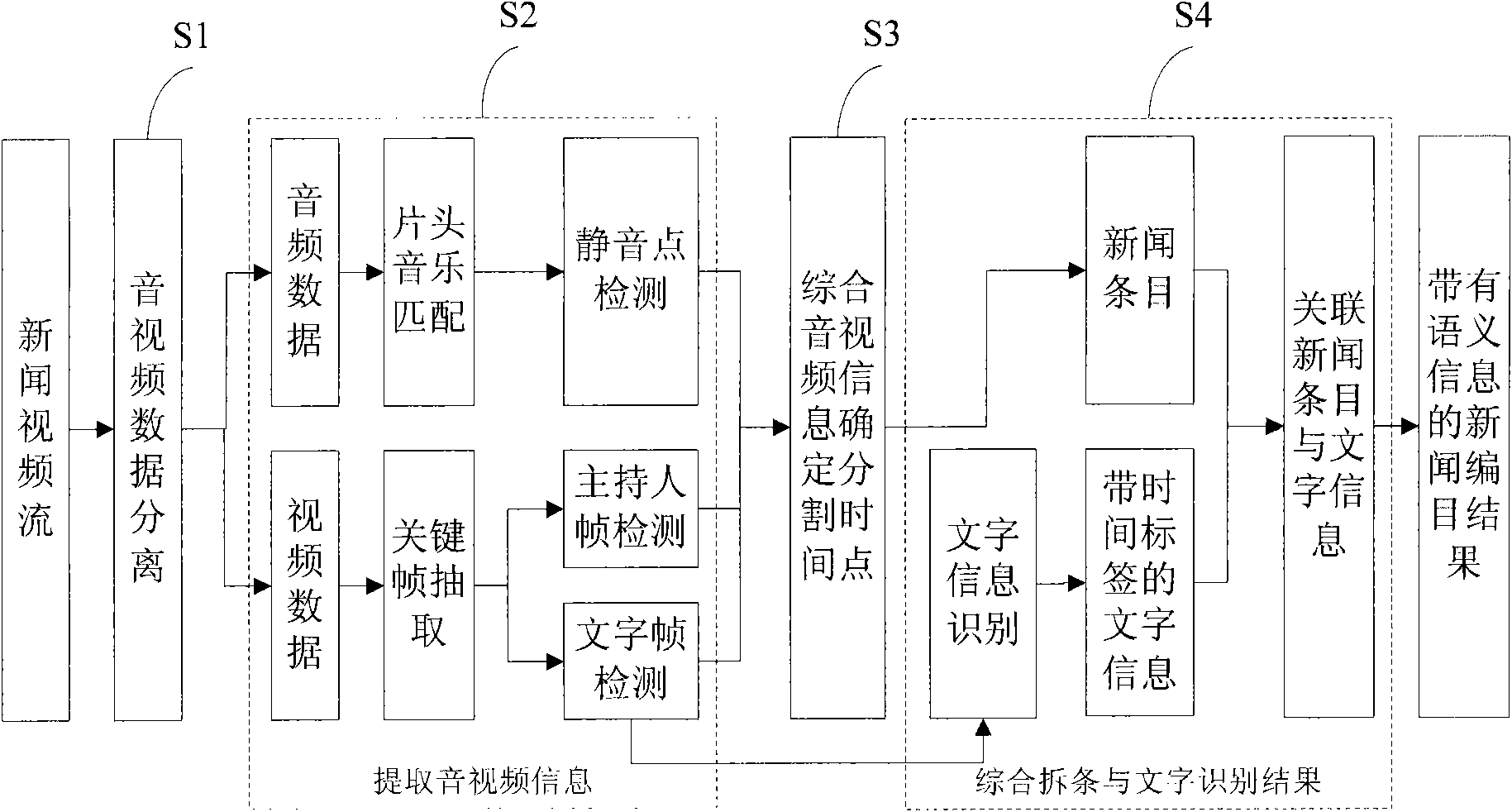
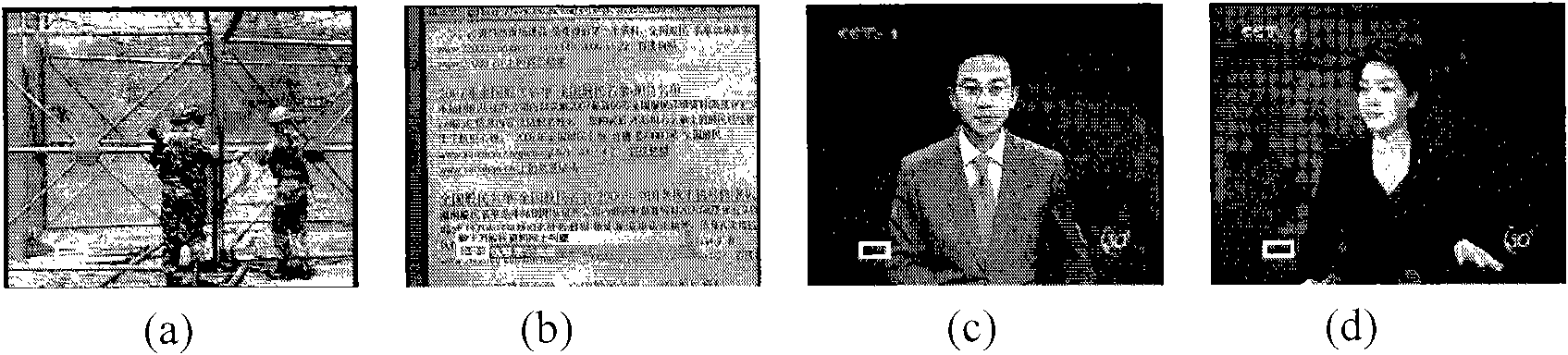
The invention relates to a method and a system for cataloging news video. The method realizes automatic cataloging of the news video based on caption bars, anchorman and audio mute point information in a news program, and comprises the following steps: carrying out audio-video separation of news video stream and head leader music matching of audio data to determine the effective time range of a news program in a file; determining an audio mute point, an anchorman frame and the emerging time of a caption frame within the effective time range, and carrying out comprehensive analysis processing to determine the division time point of news items; and identifying video caption information, associating the caption information with a division result, and taking the caption information after association as cataloging semantic information. The system comprises a bar removing module and an educing module connected with a news video bar-removing result database as well as a browse module, a play module and a correction module connected in parallel between a client and the news video bar-removing result database. The method and the system solve the problems of news automatic bar removing and news item automatic semantic information labeling and realize automatic cataloging of news programs, thereby having the advantages of high efficiency and low cost.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
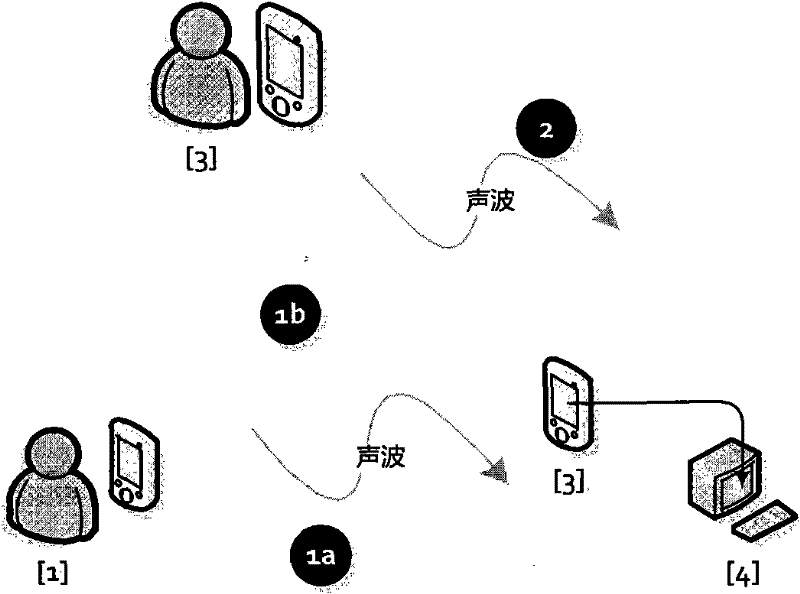
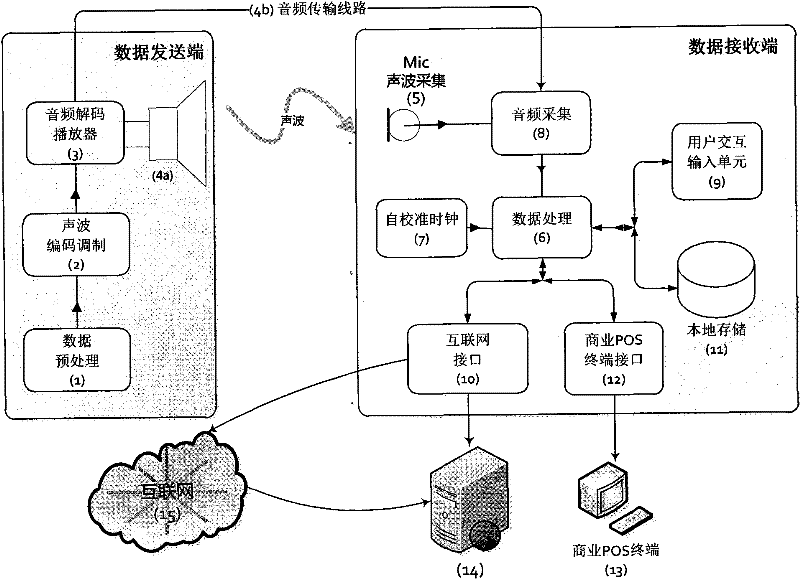
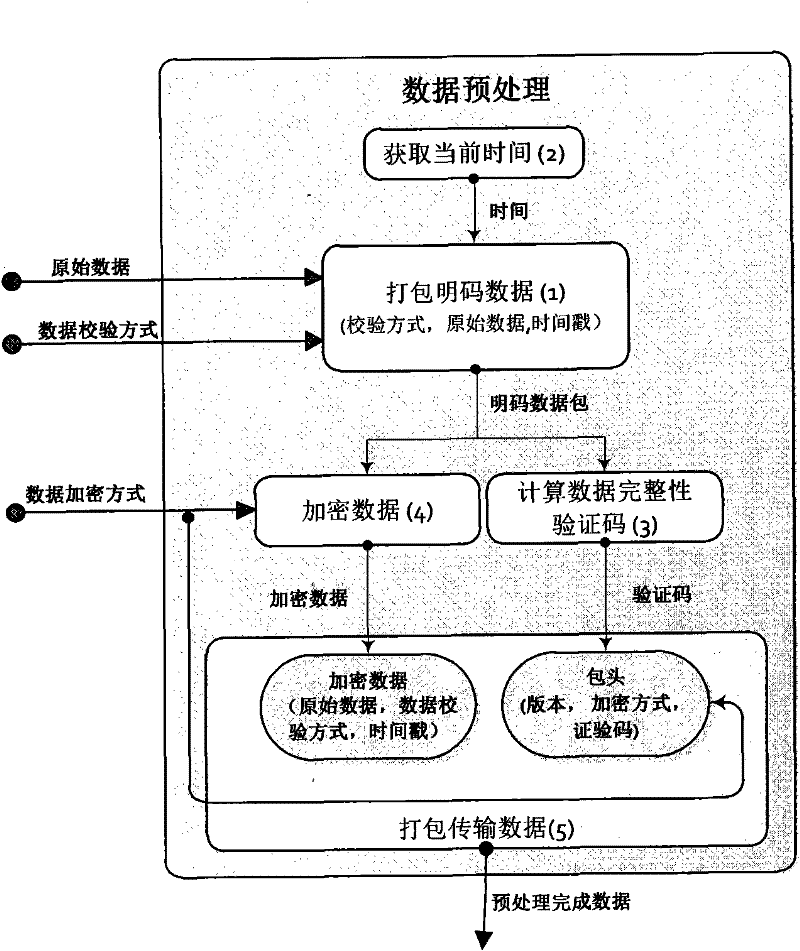
Device system and method for secure data communication based on sound waves
InactiveCN102299747AQuick collectionLow costNear-field transmissionSonic/ultrasonic/infrasonic transmissionComputer hardwareData integrity
The present invention discloses an apparatus, a system and a method for short-range sound wave communication. The system realizes non-contact secure transmission by using the sound wave as the data transmission medium, and also can realize a reliable and secure data link directly through an audio connection. The invention systematically constructs multiple end-to-end transmission verification mechanisms for the process of data transmission: transmission data integrity verification, valid time verification, password verification, service data verification and data encryption; and according to the security level of the data, the sending end specifies the requirements for encryption and data verification in the transmission data so as to notify the reception end which verifications should be performed to the data packets, how to perform the verifications, etc. By using the same verification processing manner, operations can be performed to the data (e.g. the payment and settlement function of an account). With lower cost, the present invention can realize the reliable communication of a small data volume using sound wave, and has certain security.
Owner:SHANGHAI CLOUDWAY INFORMATION TECH +1
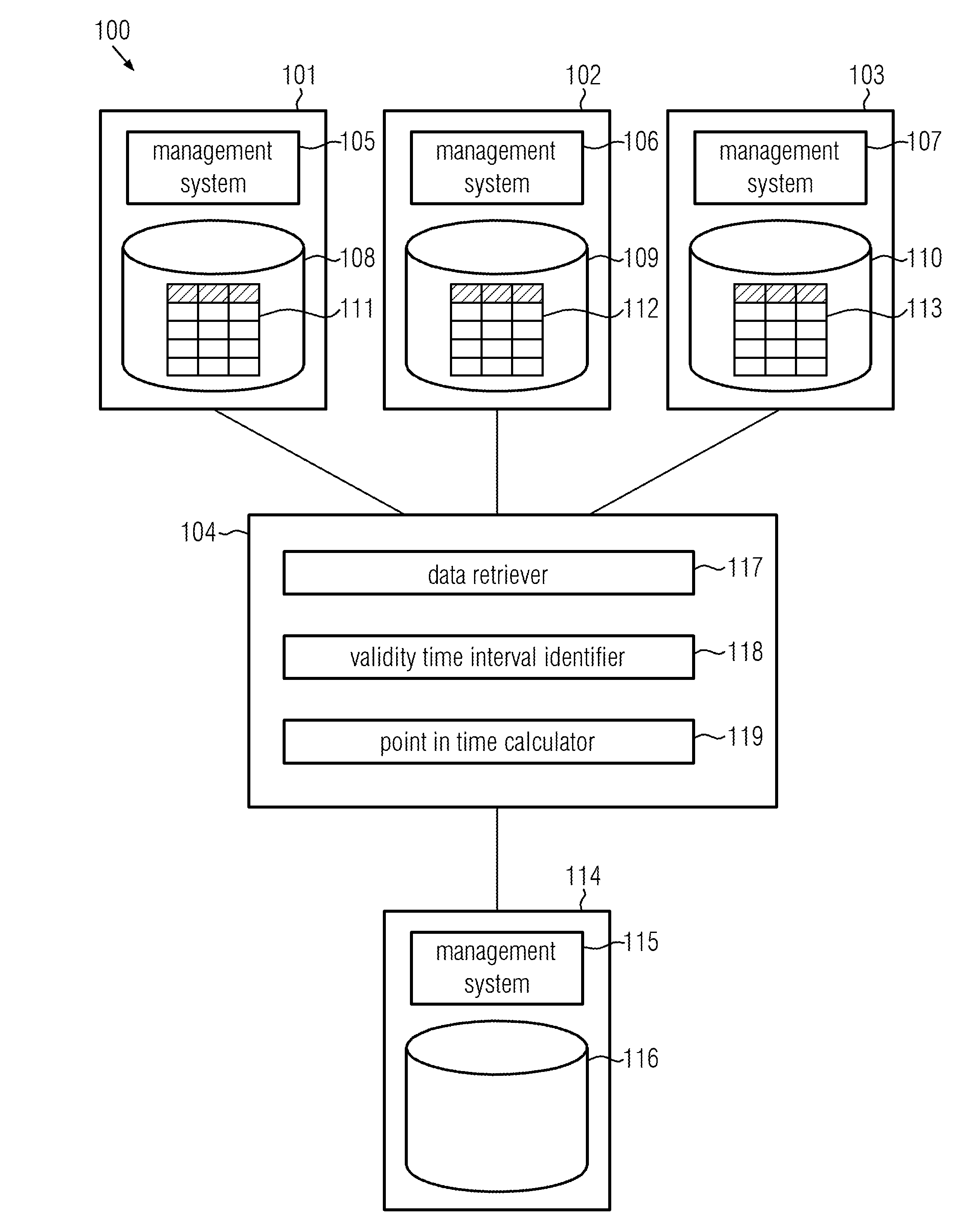
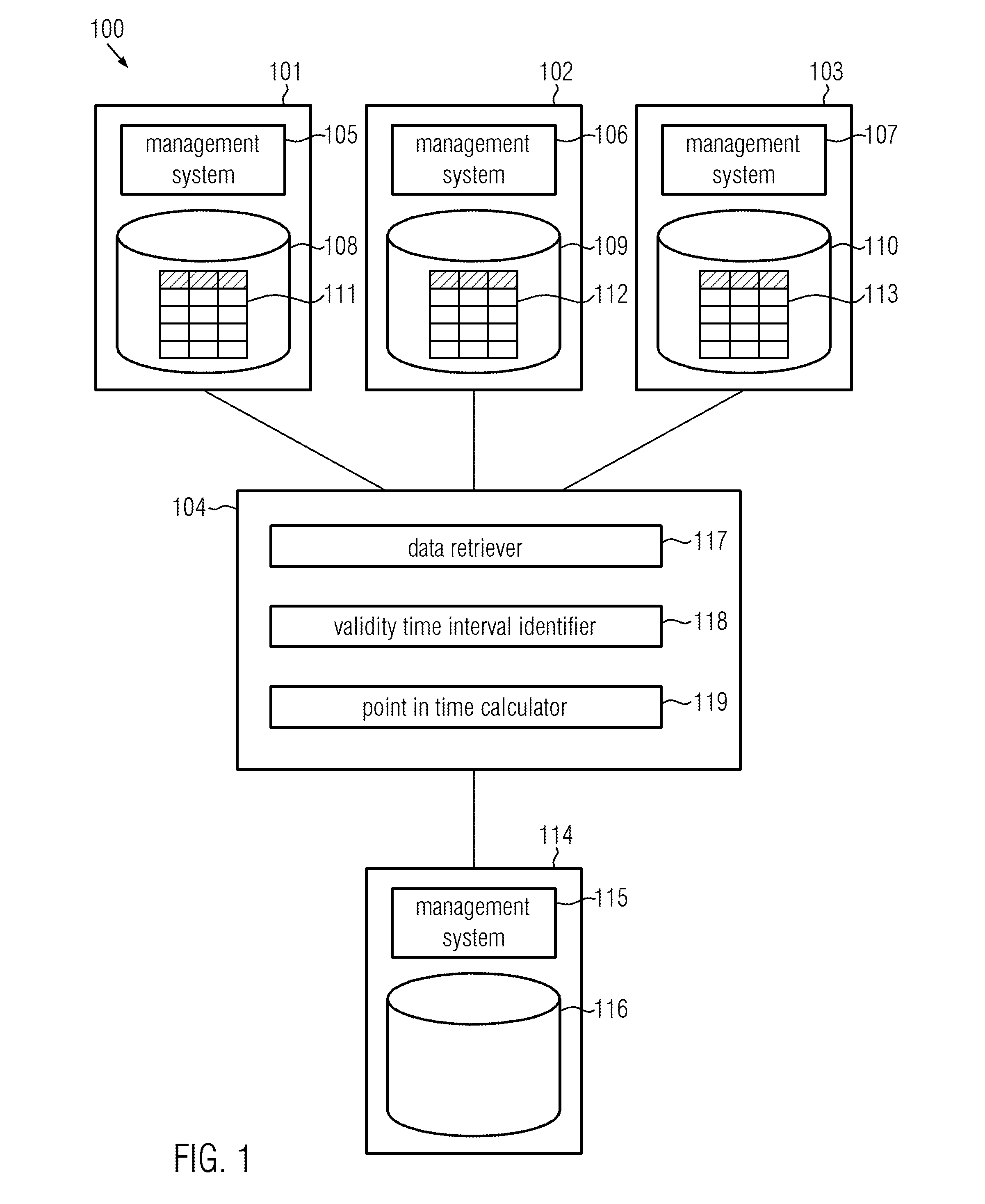
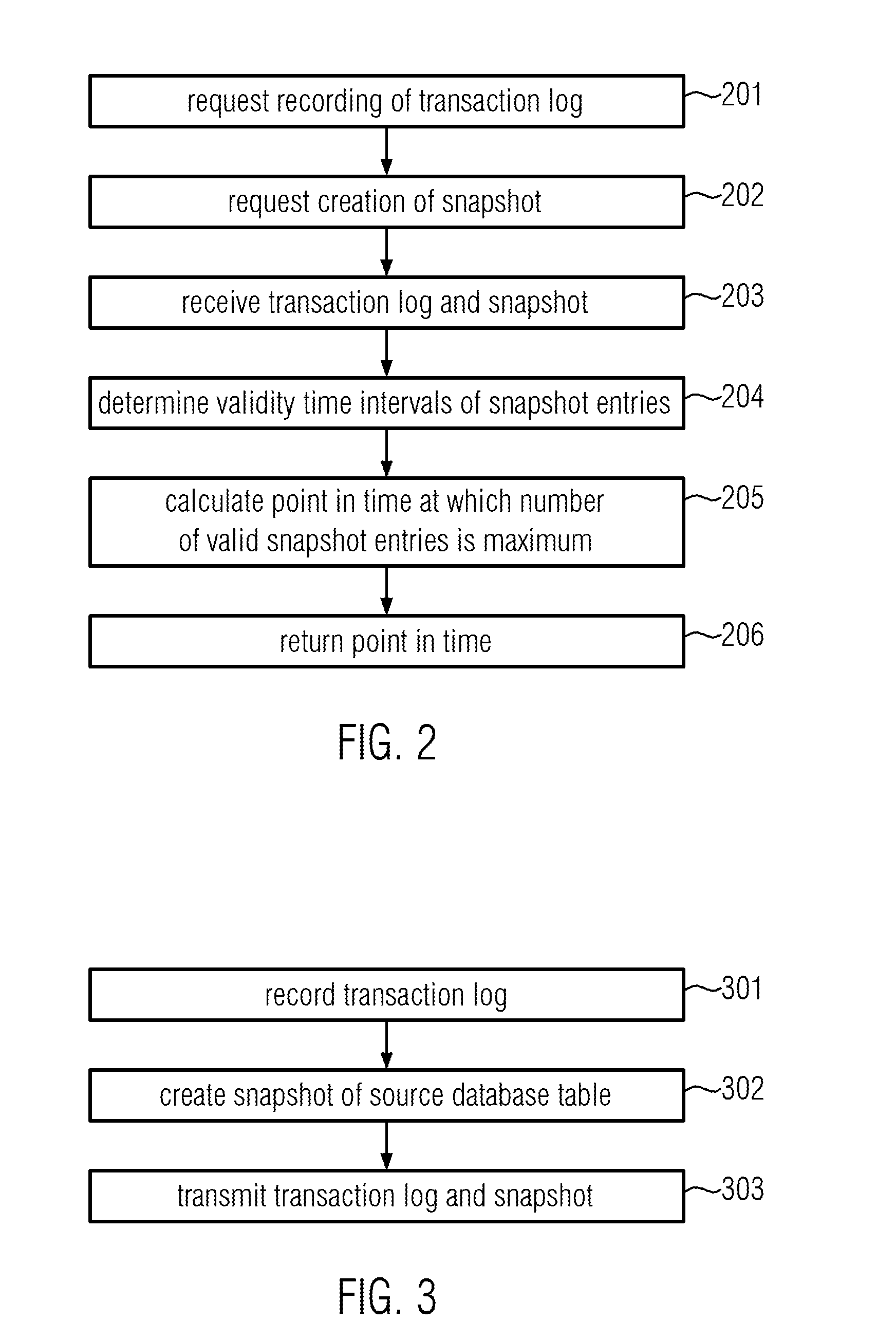
Method, computer readable storage medium and computer system for obtaining snapshots of data
InactiveUS20150052108A1Digital data processing detailsSpecial data processing applicationsTransaction logComputerized system
A method includes requesting a source database system including a source database table to record a transaction log including a plurality of transaction log entries that are representative of transactions including modifications of the source database table and to create a snapshot of the source database table during the recording of the transaction log. For each of a plurality of snapshot entries in the snapshot, one or more validity time intervals during which the snapshot entry is valid are determined on the basis of the transaction log. The snapshot entry is valid as long as it matches a corresponding entry in the source database table. A point in time at which a number of valid ones among the plurality of snapshot entries is maximum is determined. The calculated point in time is returned as an approximate value of a point in time at which the snapshot was created.
Owner:GLOBALFOUNDRIES INC
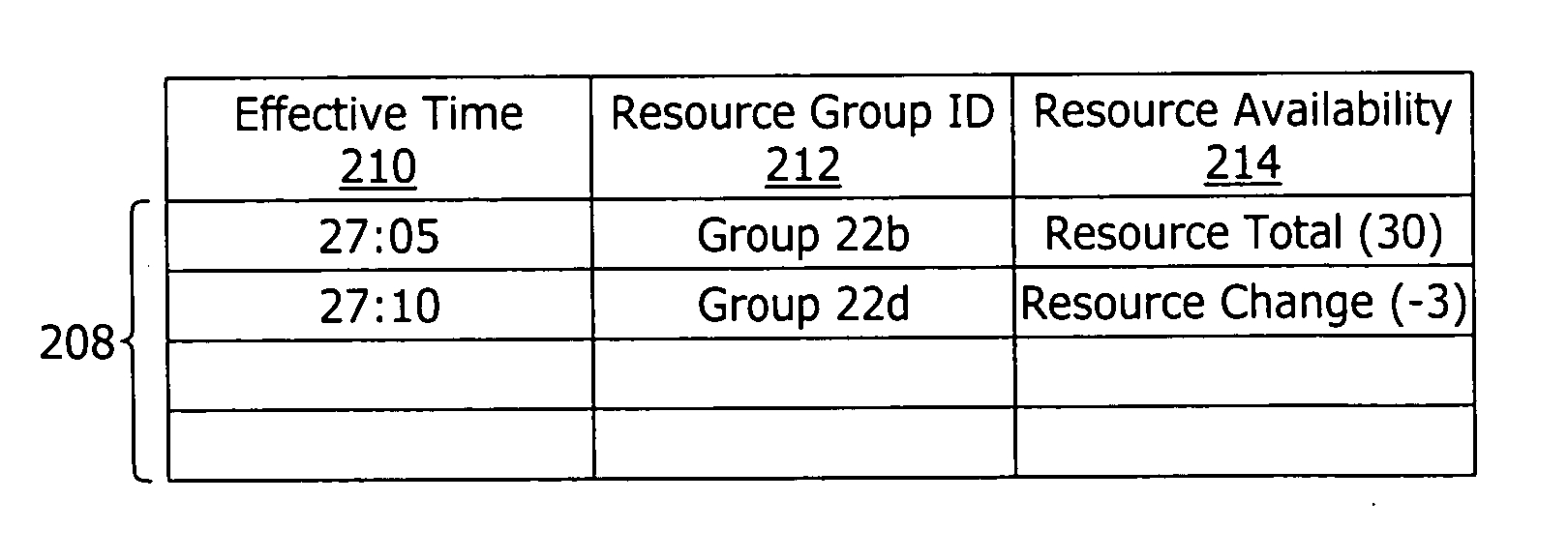
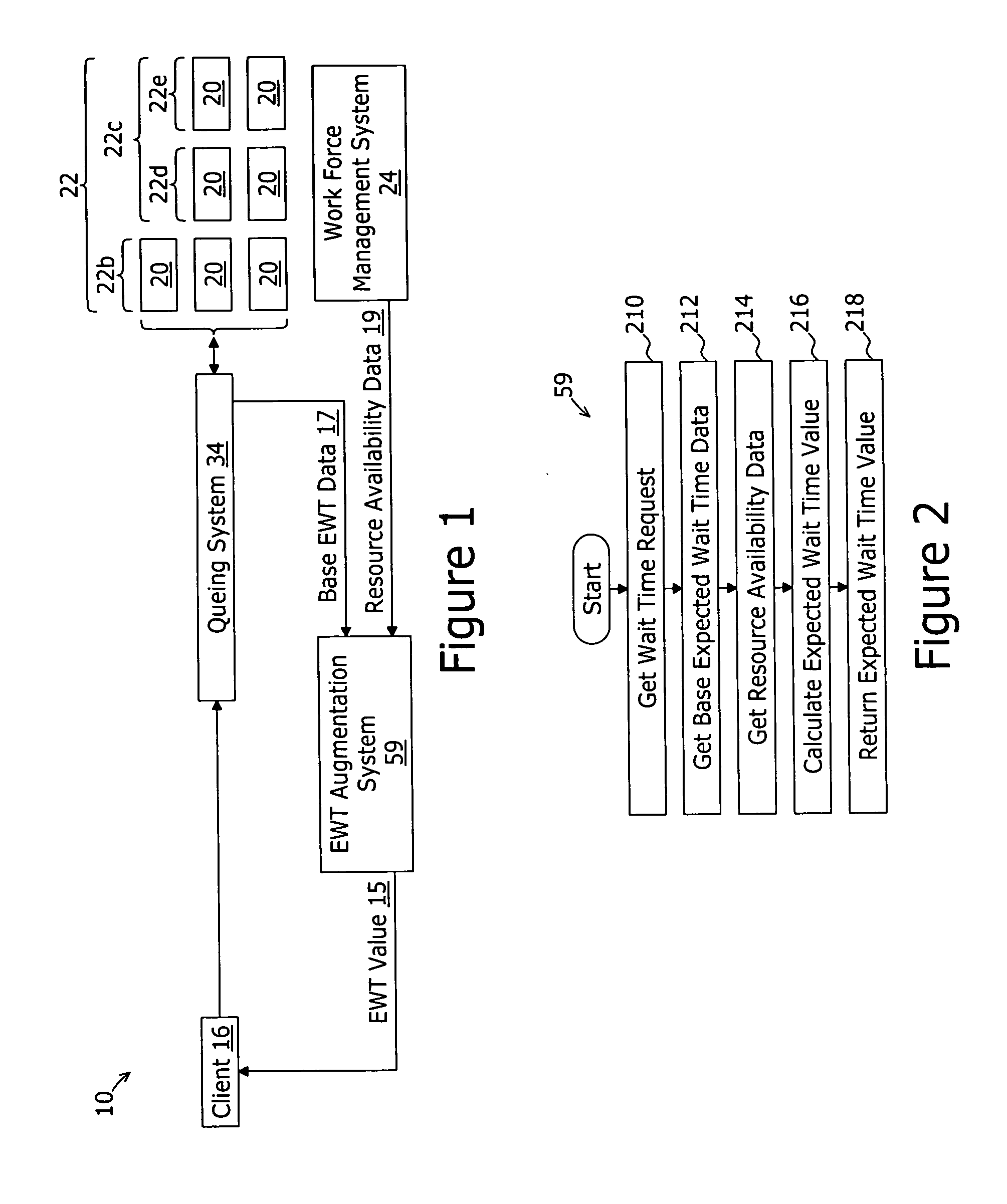
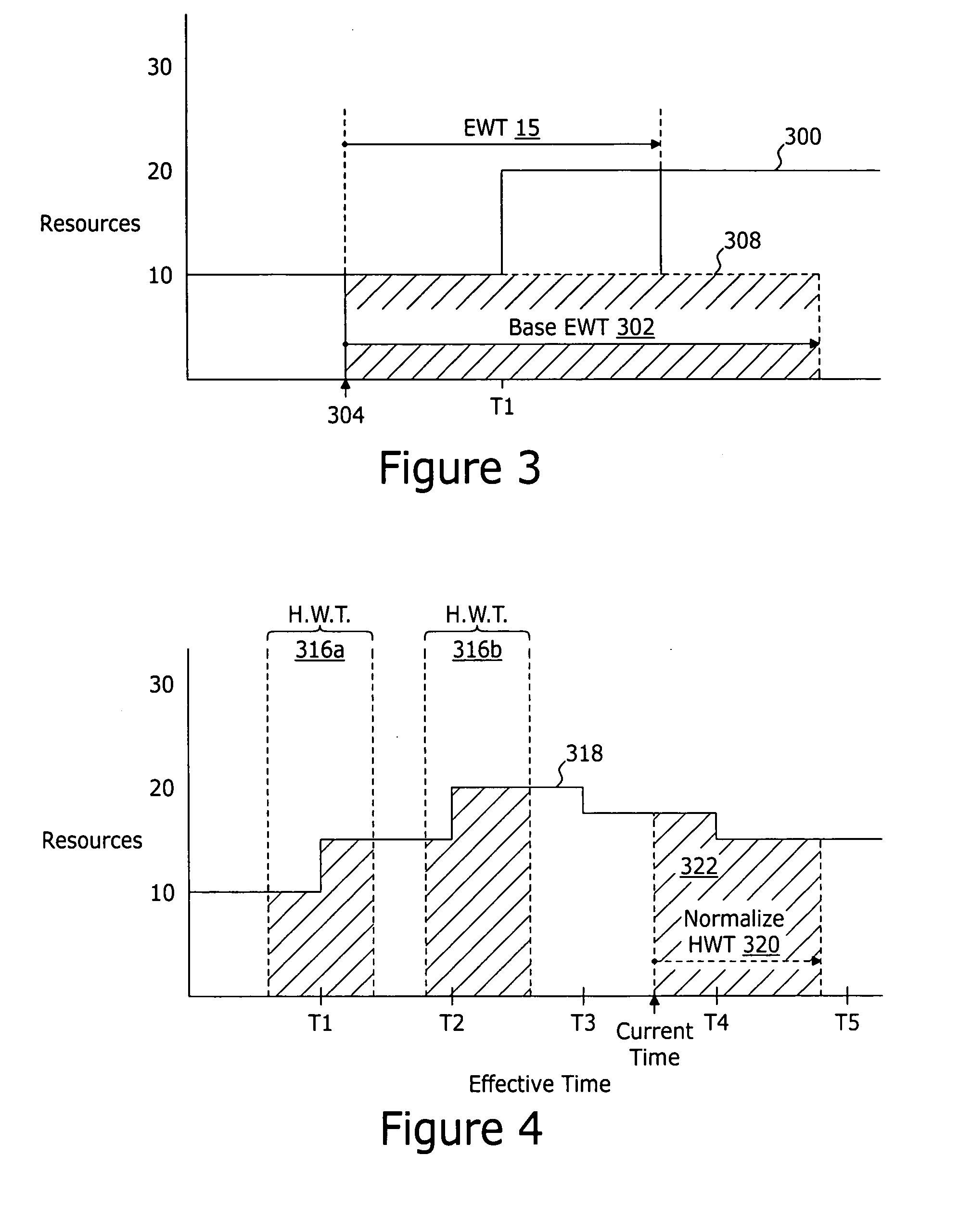
Expected wait time augmentation system and method
An expected wait time augmentation system generates an expected wait value representing a time duration expected to elapse before a subject client is connected to a resource for servicing. The expected wait time augmentation system comprises an interface to a work force management system for obtaining resource availability data and a wait time augmentation model for calculating an expected wait time value as a function of base expected wait time data and the resource availably data. The estimated wait time value is provided to the subject client. The resource availability data includes, but is not limited to, for a period of time: i) availability of resources; and ii) a scheduled change in the availability of resources. The scheduled change in the availability of resources may comprise a combination of data representing an effective time and a quantity of resources scheduled to be available at the effective time.
Owner:VIRTUAL HOLD TECH
Construction verification method and device capable of verifying security two-dimensional code offline
ActiveCN106452756AEasy to useCannot be tampered withKey distribution for secure communicationUser identity/authority verificationInformation analysisEffective time
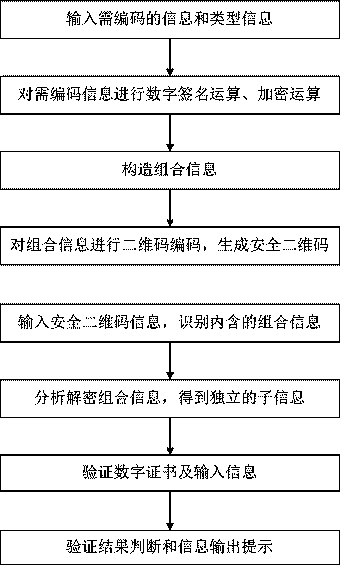
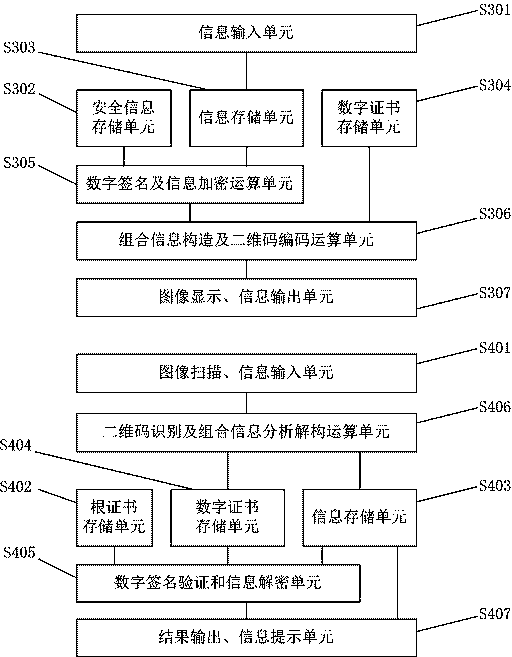
Embodiments of the invention provide a construction verification method and device capable of verifying a security two-dimensional code offline. The method comprises the following steps of inputting information that needs coding and type information, carrying out digital signature operation and encryption operation on the input information according to an information release type, constructing combination information, and encoding to generate a security two-dimensional code which can be verified off-line according to a two-dimensional code coding rule; inputting the information of the security two-dimensional code and identifying included combination information and type information, analyzing and decoding the combination information to obtain independent sub-information according to the type information of the two-dimensional code, and verifying digital certificate effectiveness information, a digital signature of the input information and an effective time limit of the input information; and if all verifications pass, showing that the offline verification of the security two-dimensional code is correct and the coding information source of the security two-dimensional code is credible, otherwise showing that the information release source of the security two-dimensional code is incredible. The method and the device have the beneficial effects that the security two-dimensional code cannot be tampered, counterfeited and denied, the public or private information can be released, and the integrity of the information of the security two-dimensional code and the authenticity of the source can be verified offline without a network connection.
Owner:王栋
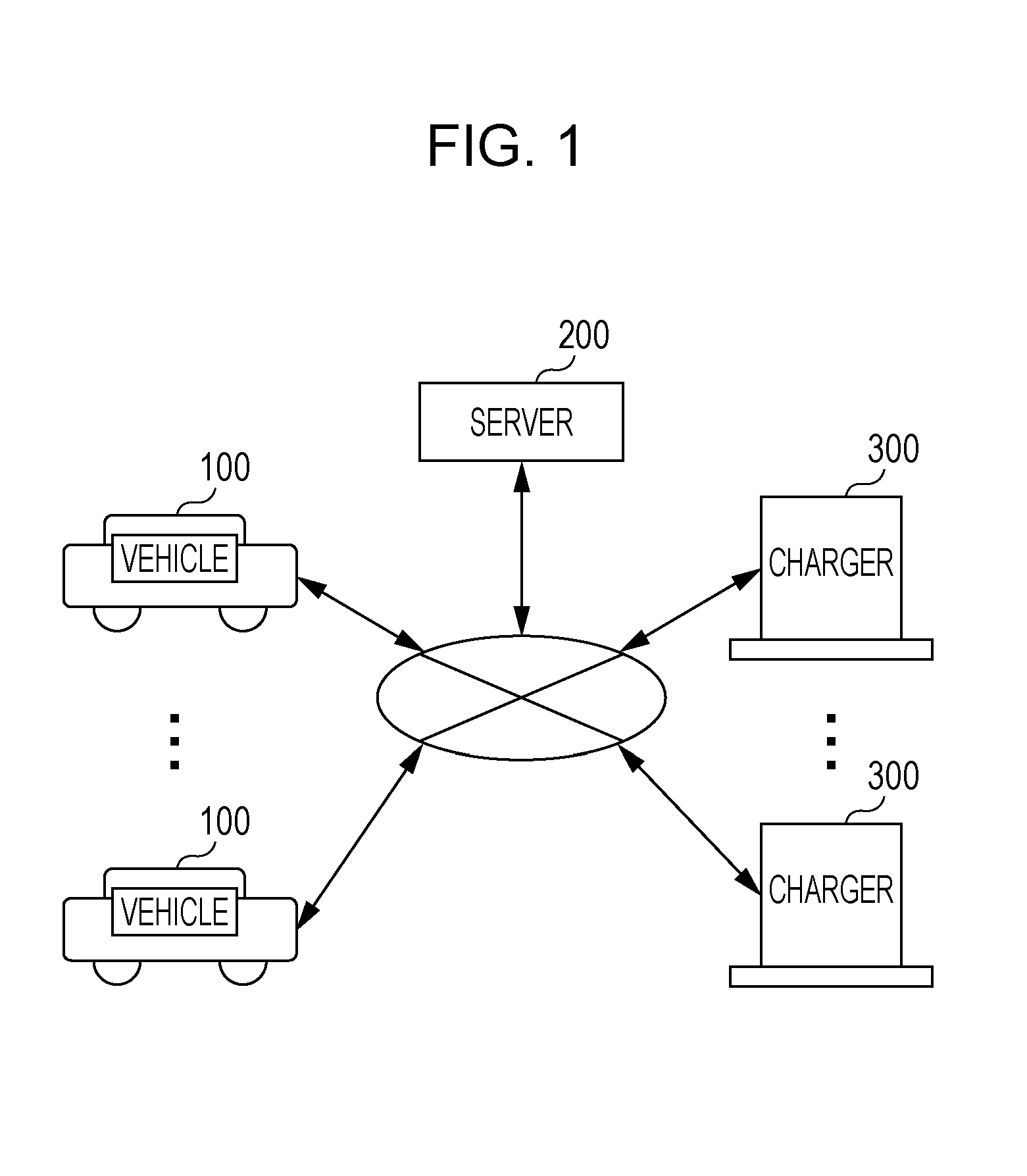
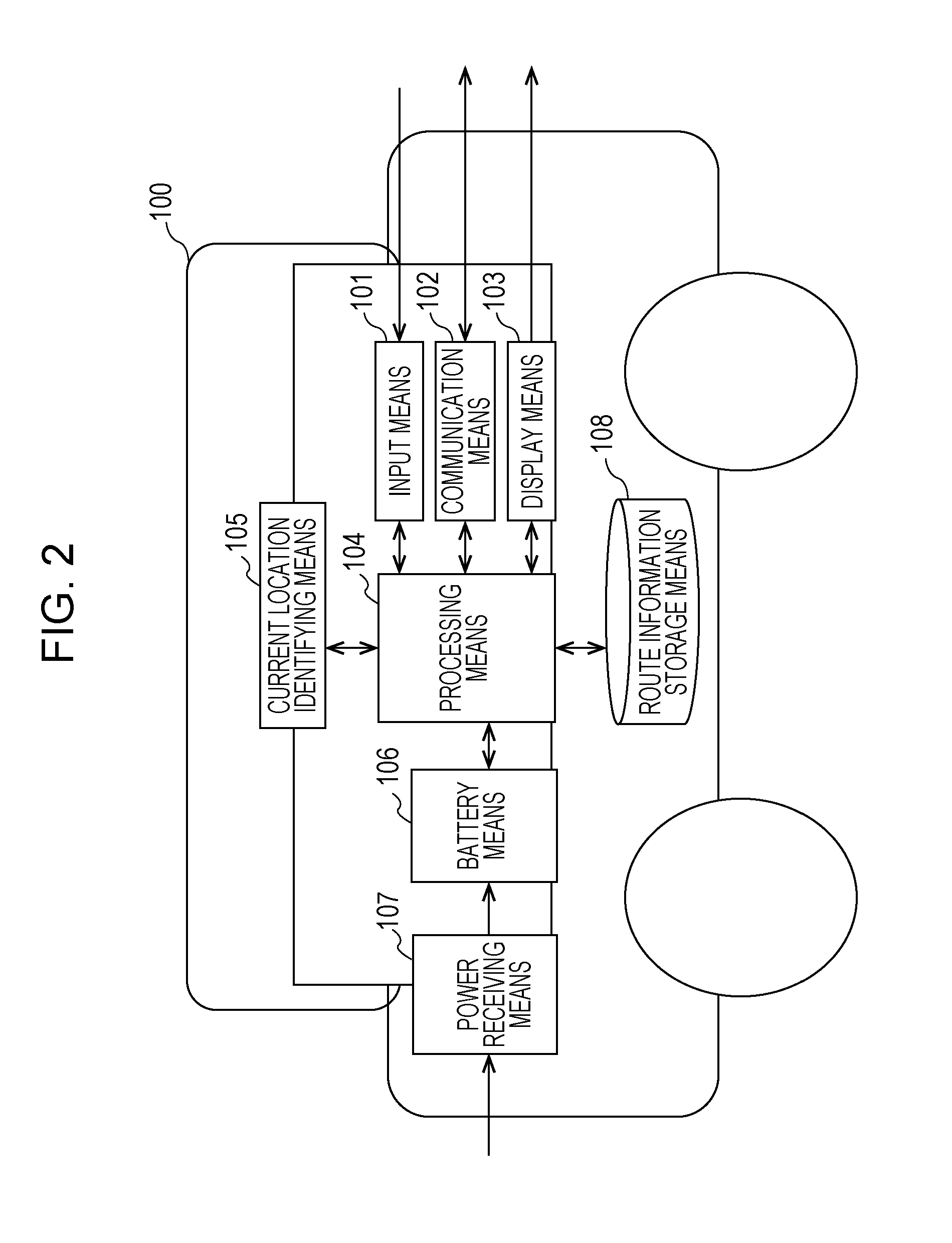
Control method, non-transitory computer-readable recording medium storing a program, information processing device, and reservation system
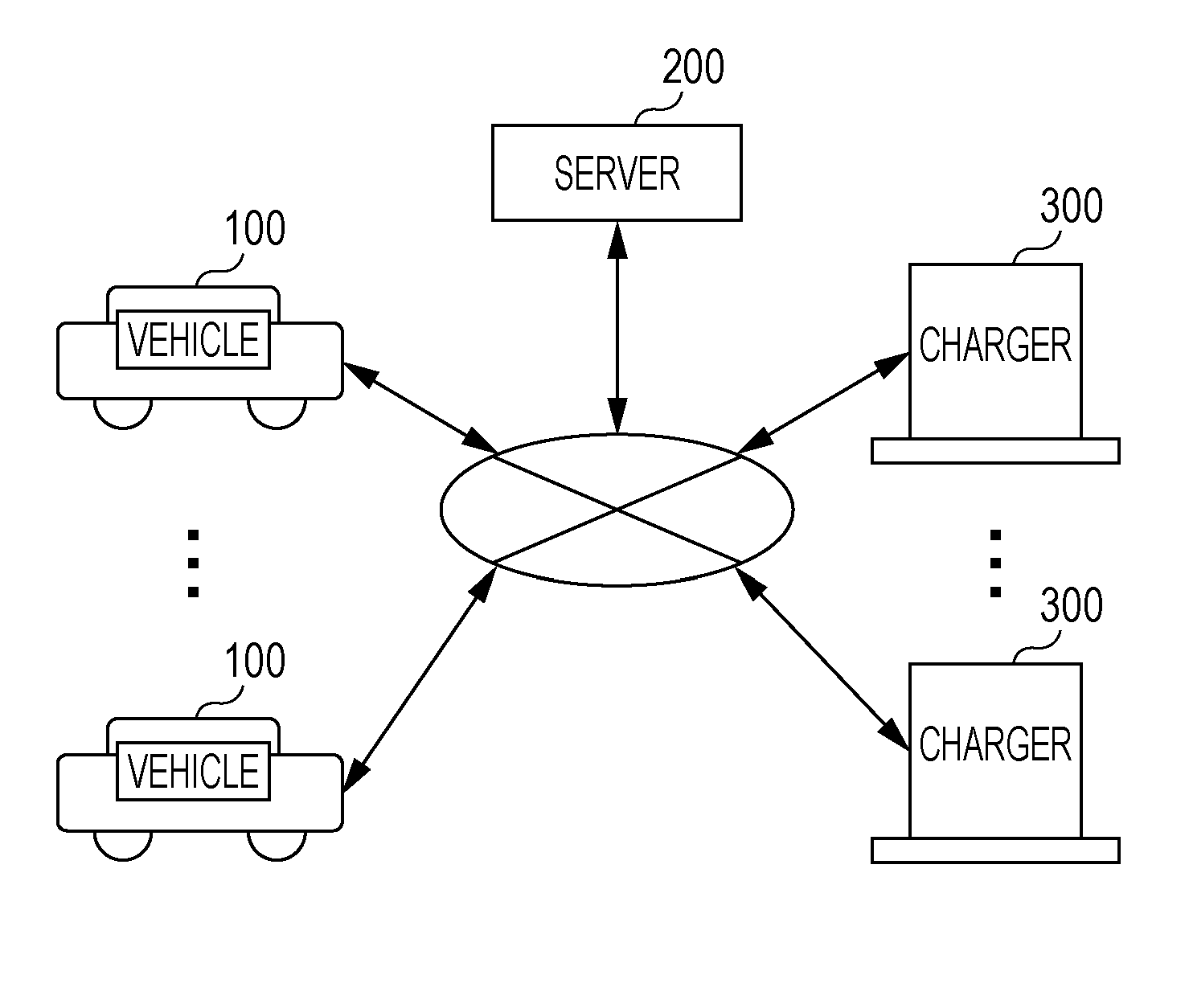
A reservation system reserves a charger to charge a power source of an electric automobile. A control method of an information processing device enables a charger to be reserved while taking into consideration arriving at a destination earlier. The information processing device searches for a charger within a predetermined range from a current location if the battery level has fallen below a first threshold value, and if a destination has been set and a plurality of searched chargers exist, calculates a predicted charging end point-in-time at each charger, based on a predicted arrival point-in-time to each charger and the availability state and charging capability of each charger. With the calculated predicted charging end point-in-time for each charger as the departure point-in-time from each charger, a charger of which the predicted destination arrival point-in-time is the earliest of the calculated predicted destination arrival point-in-times for each charger, is reserved.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Data interaction method, client and server
ActiveCN102624740APrevent tamperingAvoid the danger of vandalismUser identity/authority verificationTimestampHypertext Transfer Protocol over Secure Socket Layer
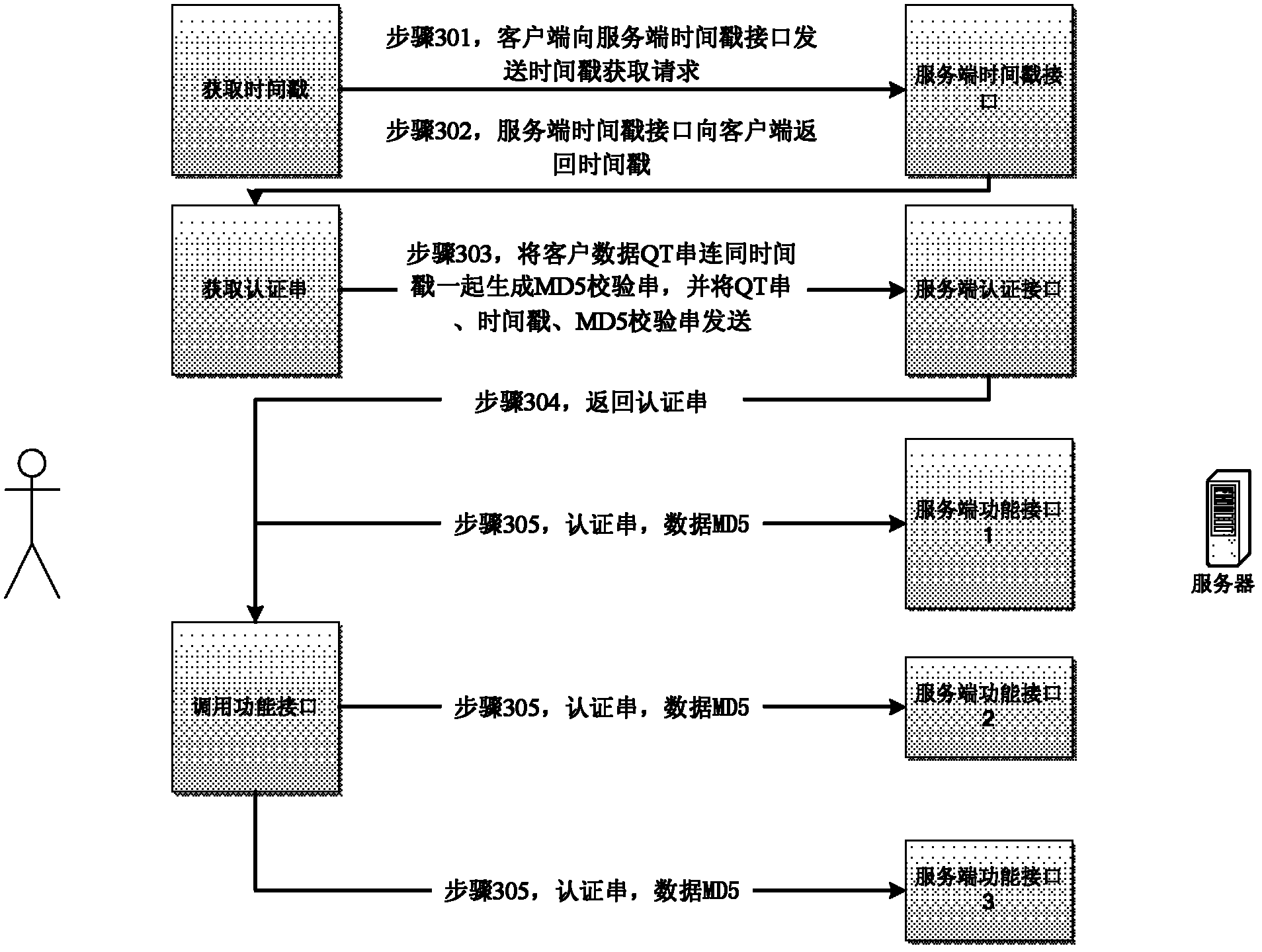
The invention provides a data interaction method, a client and a server, so as to solve the problems of requested replaying and client computer safety that cannot be solved by adopting HTTPS (Hyper Text Transfer Protocol Secure) technique. The method comprises the following steps: obtaining a timestamp from a service terminal; sending the first identifying information of a user, the timestamp and verifying data generated according to the first identifying information of the user and the timestamp to the service terminal; obtaining certified data encrypted by the service terminal, wherein the certified data comprises the encrypted data generated for the timestamp and second identifying information of the user; and using the certified data to access the service terminal. According to the method provided by the invention, HTTPS encryption and improved MD5 are used together while the encryptions at the client and service terminal are adopted, so that the possibility of distorting and falsifying data at 'end' and 'path' is efficiently avoided. Besides, the timeliness control is performed on interface calling by using effective time through the timestamp, so that the data damage risk caused by recording and largely replaying a user request is efficiently avoided.
Owner:BEIJING QIHOO TECH CO LTD
Constant current controller
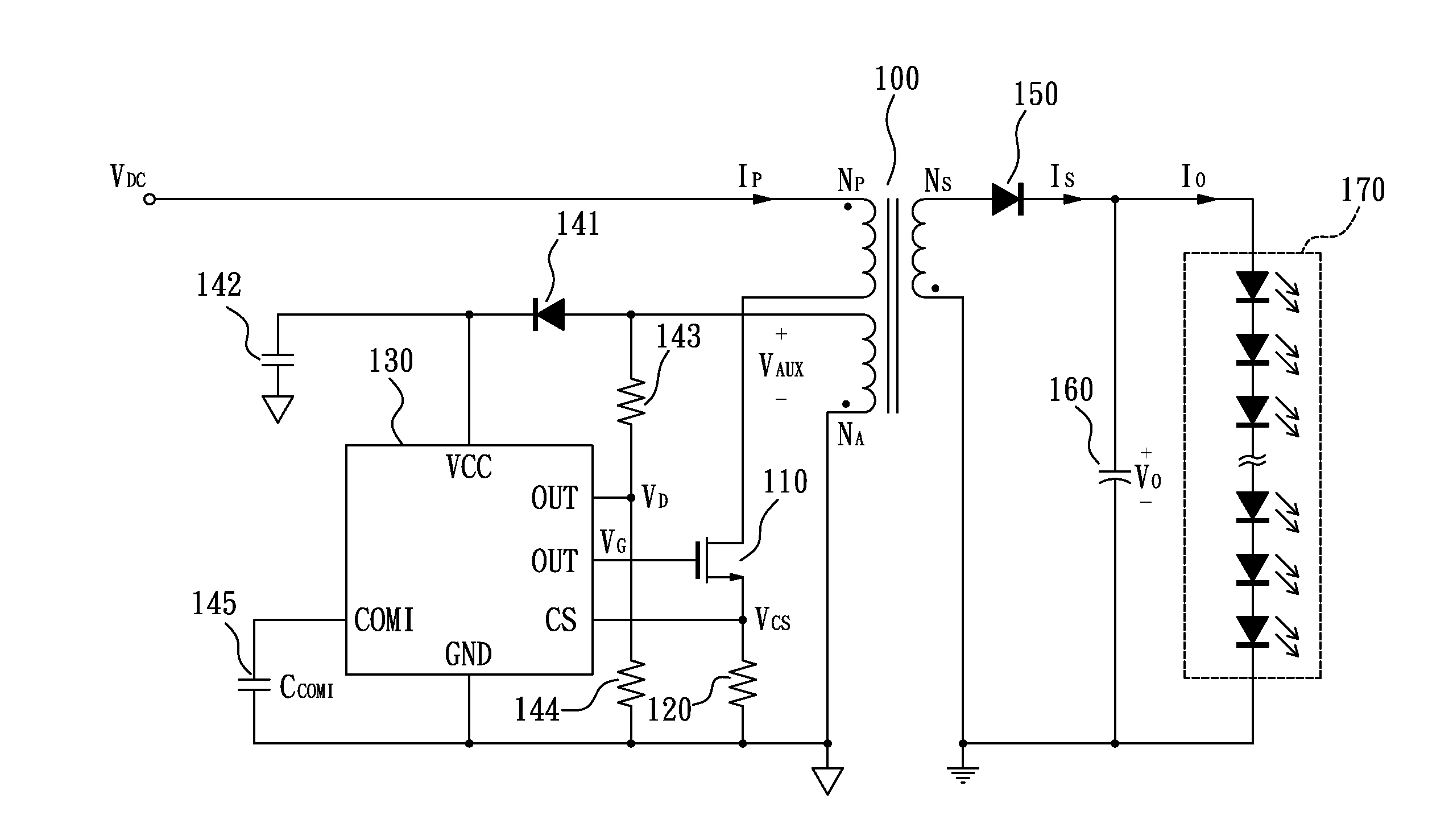
InactiveUS20140016366A1Reduce variationEasy to understandDc-dc conversionElectric variable regulationReference currentPeak value
A constant current controller for a constant current power module, including: a demagnetization sensing unit, used for detecting the voltage variation of a detection signal to generate a discharging time signal having an active period corresponding to a secondary side discharging time, wherein the detection signal is derived from an auxiliary coil; a secondary side current sensing unit, used for detecting a peak value of a current sensing signal, and providing an output current according to the peak value of the current sensing signal under the control of the discharging time signal, wherein the current sensing signal is corresponding to a primary side current; and an error current generator, used for generating an error current according to the difference between the output current and a reference current, wherein the error current is converted to a threshold voltage by a first capacitor.
Owner:IMMENSE ADVANCE TECH
Management of temporal data by means of a canonical schema
ActiveUS20110320419A1Eliminate needSimplifying codebaseDigital data information retrievalDigital data processing detailsRelational databaseBusiness data
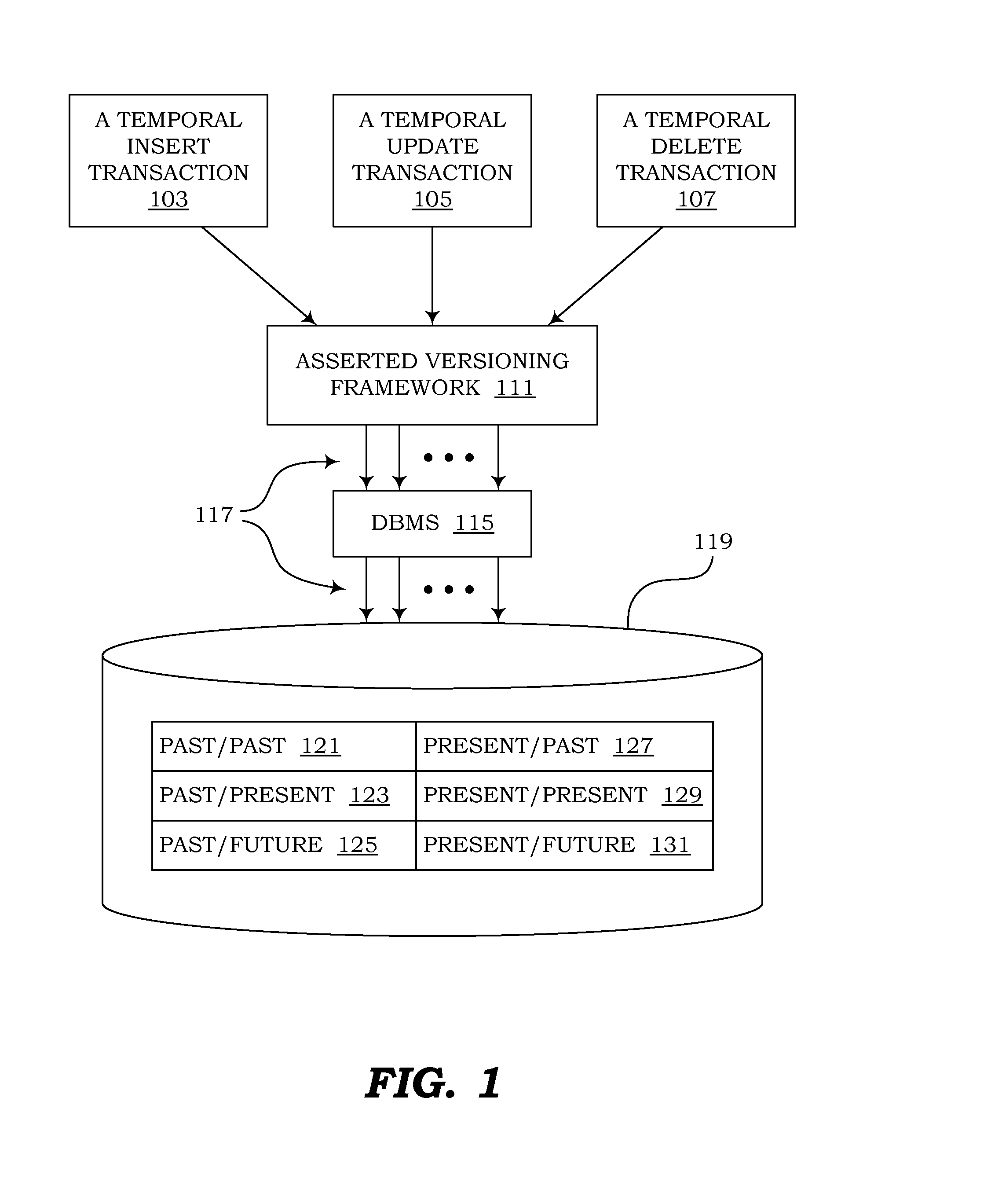
Computer programs embodied in computer-readable media for managing temporal data in relational databases are provided. According to one embodiment, a computer program comprises logic for storing temporal data in tables stored in a database and using a single schema. The schema includes a first column designating an identifier of an object represented in a row of a table and columns designating an effective-time period. For a past effective-time period, the state of the object as it existed is described by atemporal data in the row. For a present effective-time period, the present state of the object is described. For a future effective-time period, the state of the object as it will exist is described by the atemporal data. Additional logic stores additional data in the tables, such as business data describing the state of the object.
Owner:WEIS RANDAL JAMES +1
Concurrency control using an effective change stack and tenant-based isolation
ActiveUS8341128B1Digital data information retrievalDigital data processing detailsConcurrency controlBase isolation
Transaction processing is disclosed. A first transaction associated with a first system tenant is received. The first transaction is associated with a transaction effective time. It is determined whether the first transaction modifies data. In the event that the first transaction modifies data, it is determined whether a second transaction is executing that modifies data associated with the first system tenant. In the event that there is not a second transaction executing, the first transaction is executed with respect to the transaction effective time.
Owner:WORKDAY INC
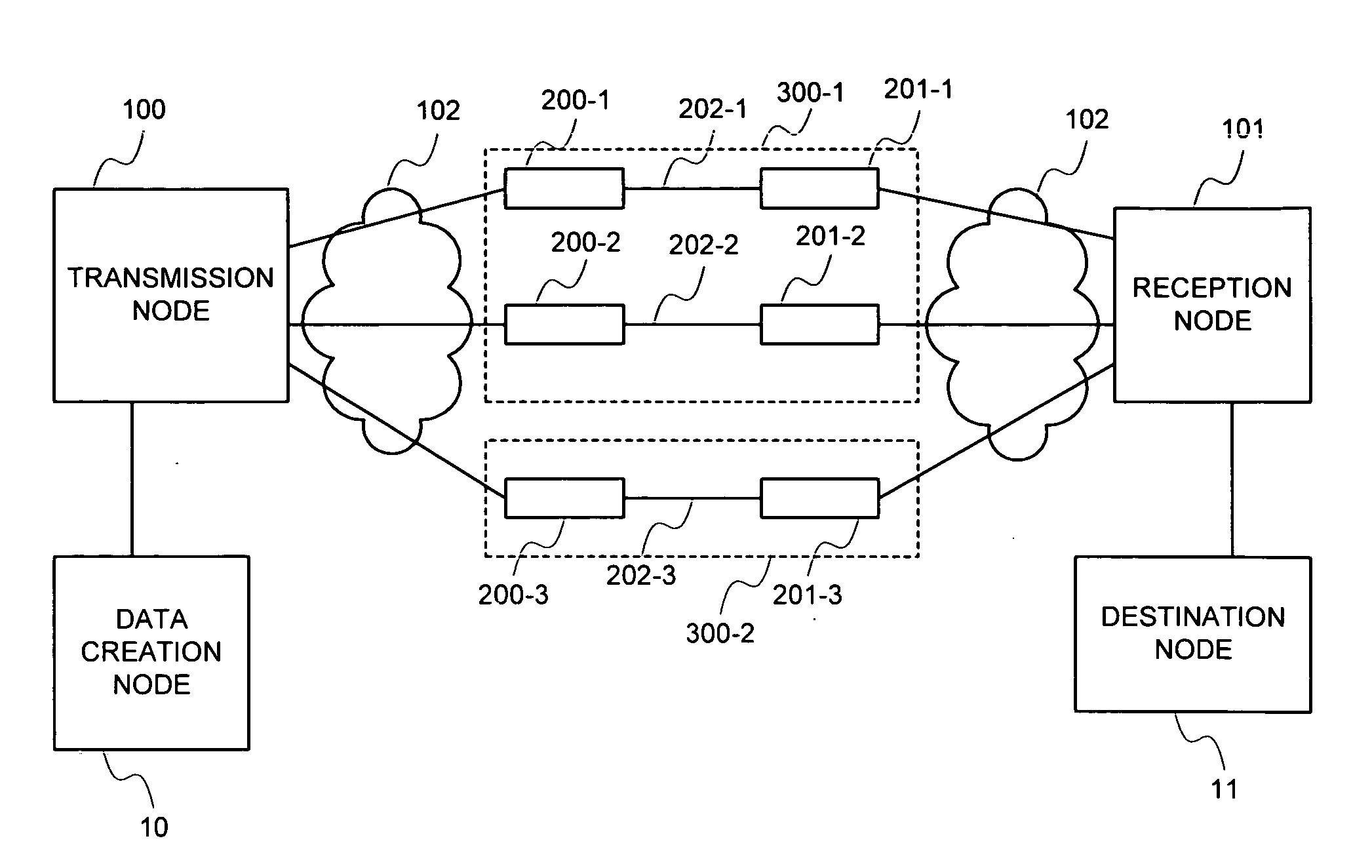
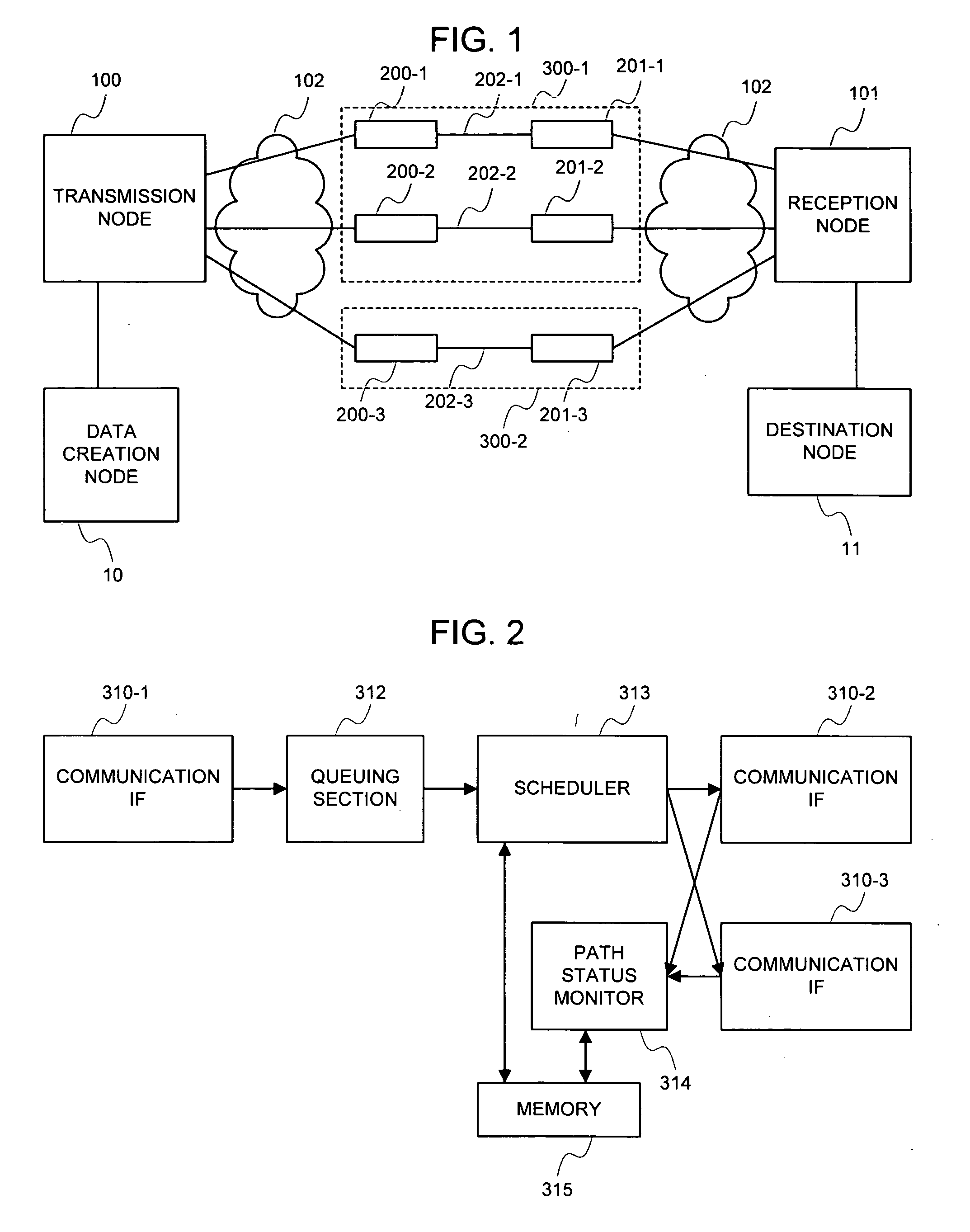
Load distributing method
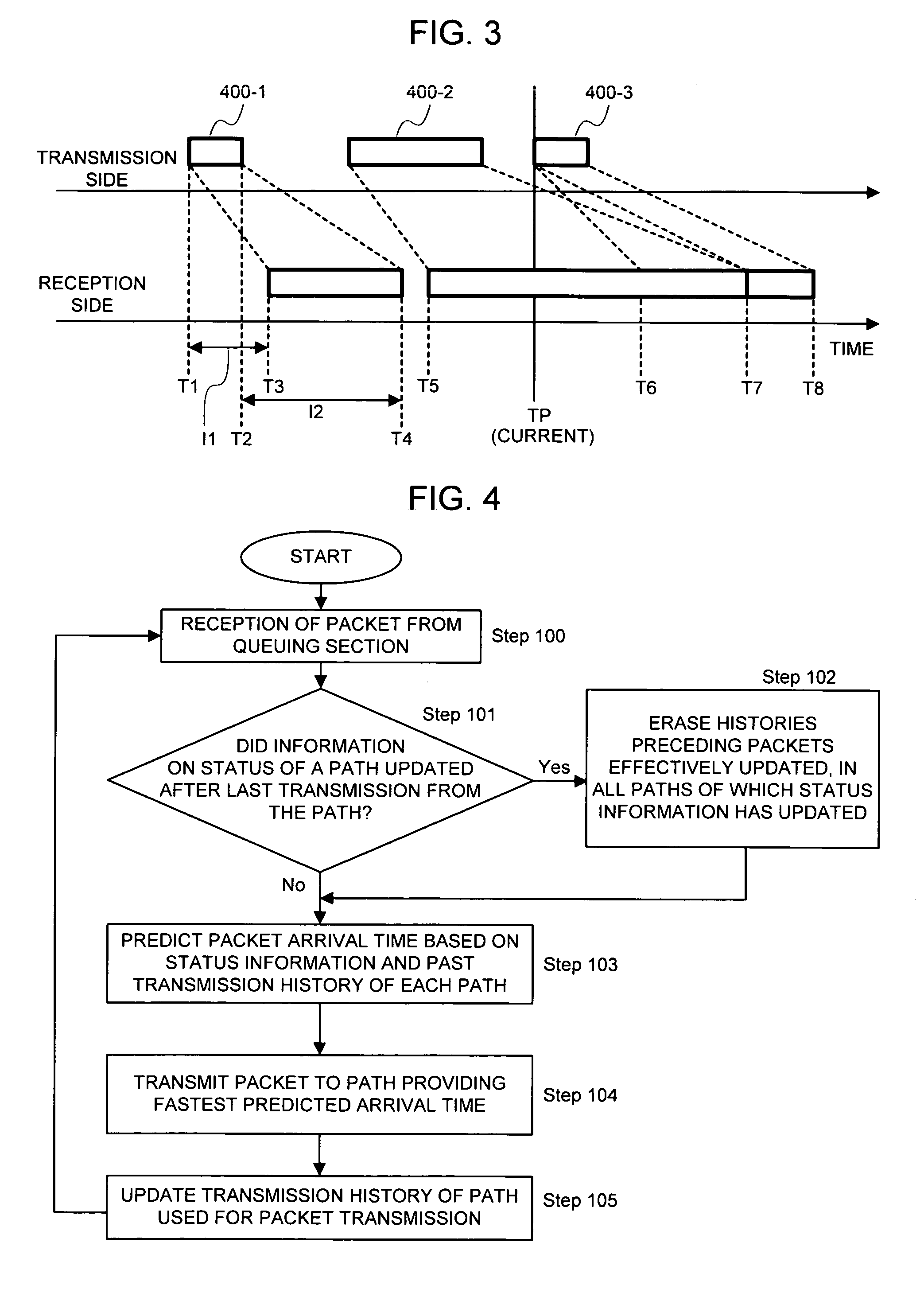
ActiveUS20070002748A1Improve accuracyMultiplexing efficiency decrease can be avoidedError preventionFrequency-division multiplex detailsCompletion timePacket arrival
When path status information is updated, the time at which the update is effective is recorded. A packet arrival time in each path is predicted based on new status information and data transmission history after the effective time. The packet is transmitted to the path that provides a fastest packet arrival time. This reflects the path status available from the reception side on the data transmitted in past, so that an actual data arrival time, an arrival time close to a reception completion time, or a reception completion time can be predicted.
Owner:NEC CORP
Management of temporal data by means of a canonical schema
ActiveUS20130018849A1Eliminate needSimplifying codebaseDigital data information retrievalDigital data processing detailsEffective timeSpecification pattern
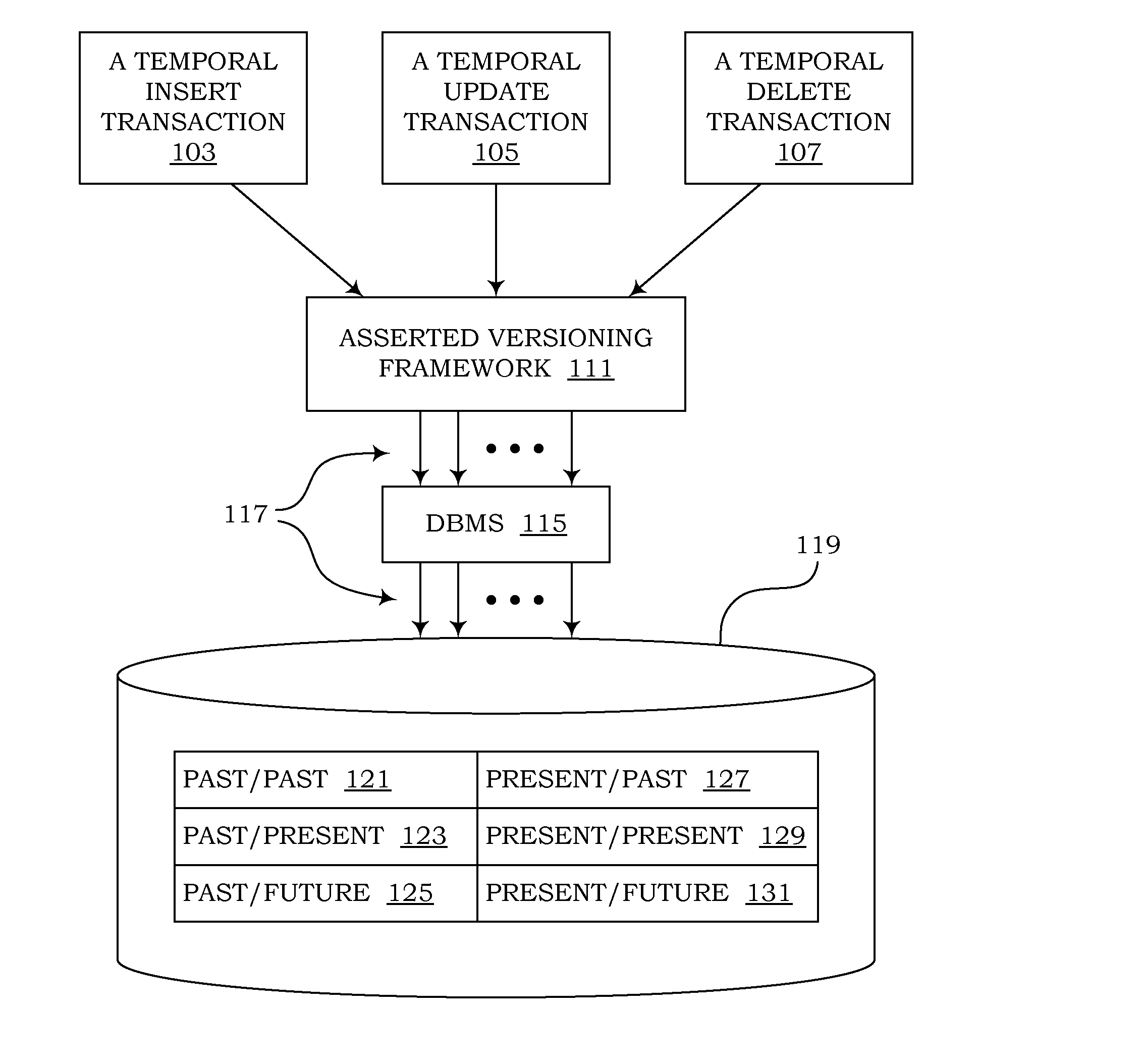
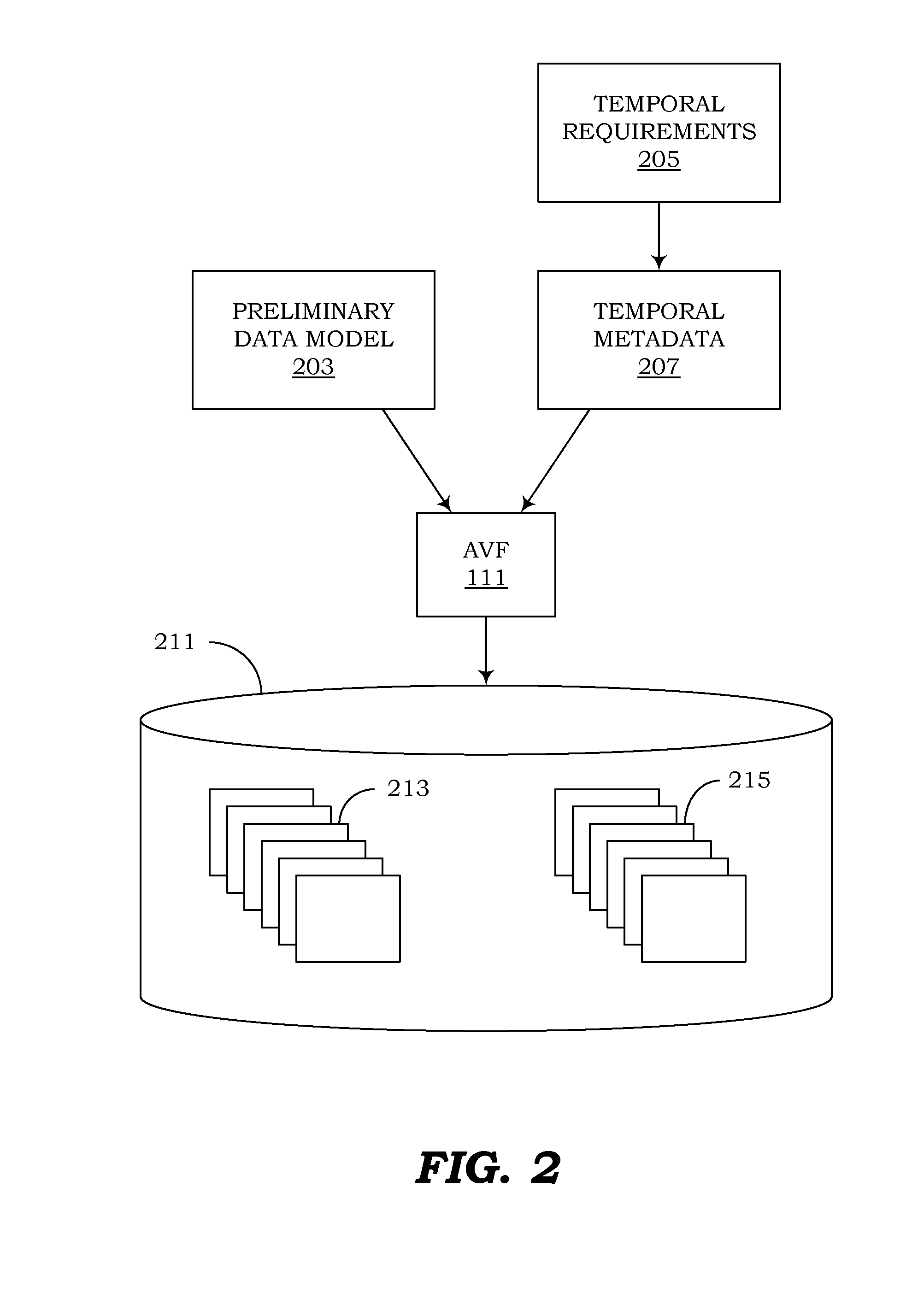
Computer programs embodied in computer-readable media that can use canonical schemas to persist data from non-temporal tables, effective-time tables, assertion-time tables, and bitemporal tables, and that can enforce temporal integrity constraints on those tables, are provided. In one embodiment, the canonical schemas are used by database tables. In another embodiment, they are used by the physical files which persist data from those tables. Temporal metadata is used to express temporal requirements. Thus, uni-temporal, bitemporal, and temporally-enabled non-temporal tables can be generated without altering existing data models or designing temporal features into new data models. Support is also provided for managing temporal data that exists in future assertion time, and for using episodes to enforce temporal referential integrity.
Owner:JOHNSTON THOMAS DR +1
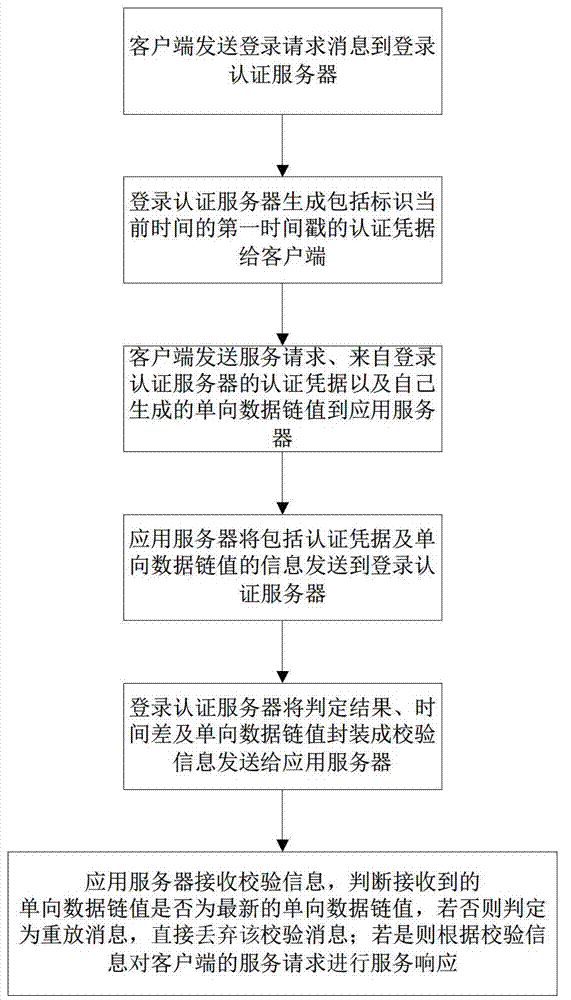
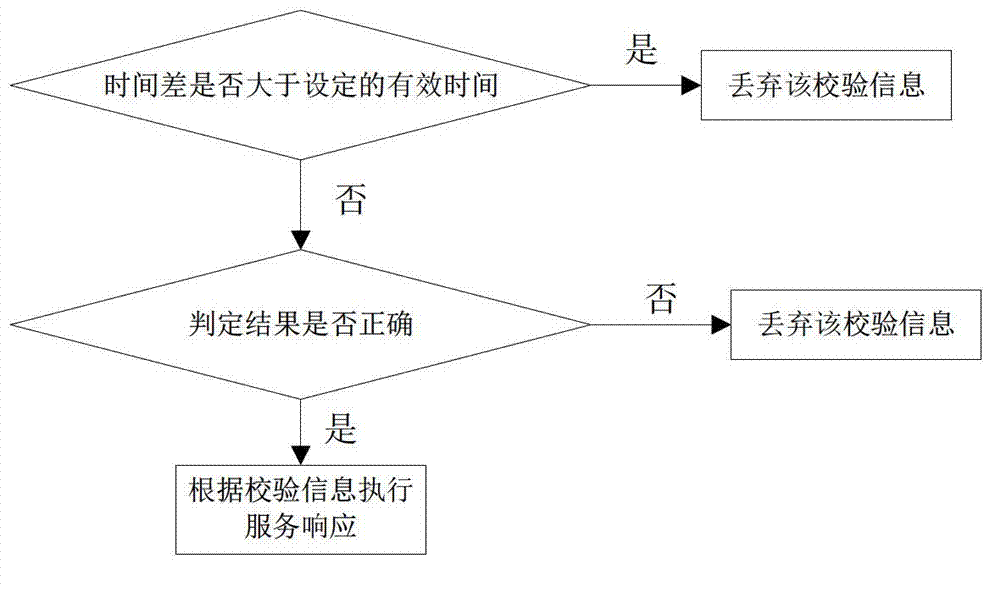
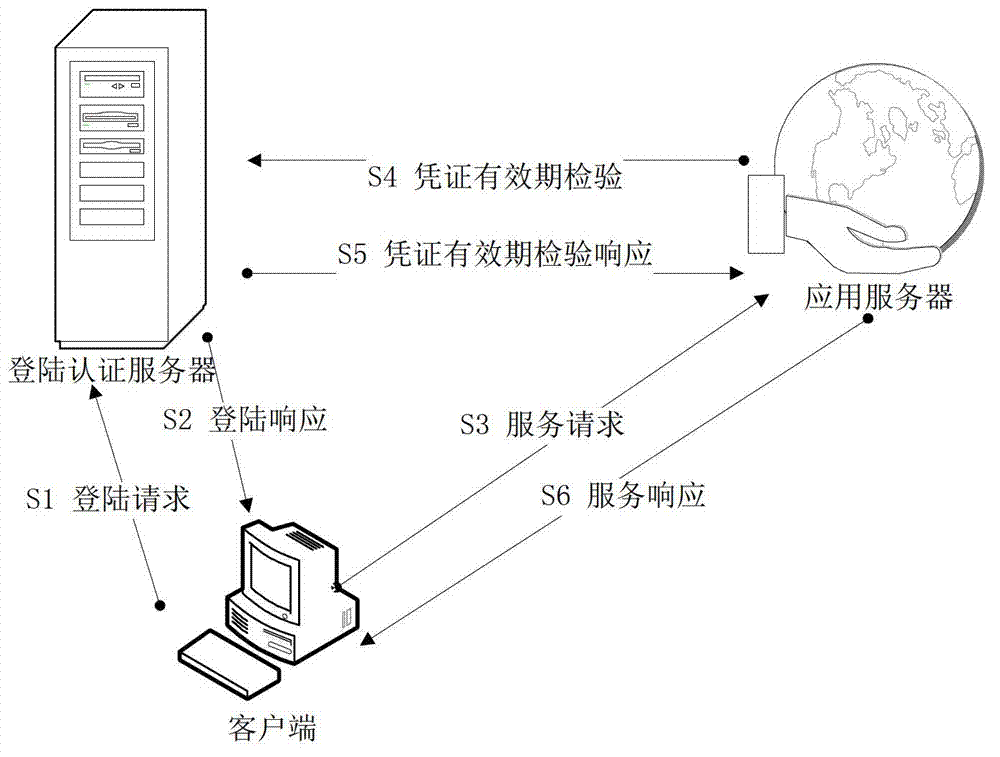
Authentication method for preventing replay attack
ActiveCN102739659ALegitimate service requests are immune to replay attacksGuaranteed accuracyTransmissionApplication serverAuthentication server
The invention discloses an authentication method for preventing a replay attack. The method comprises the following steps of transmitting an authentication evidence and service requests to an application server, wherein the authentication evidence is acquired from a login authentication server by a client side and is provided with a first time stamp; identifying the sequence of the user requests by using a unidirectional data chain; calculating the time difference between the current time and the first time stamp at the login authentication server end; packaging a judging result, the time difference and a unidirectional data chain value into verification information; and transmitting the verification information to the application server, wherein the application server judges whether the verification information is replay information or not according to the received unidirectional data chain value, and furthermore, whether the service requests are authenticated within effective time or not can be judged according to the time difference and the judging result. Time is not required to be synchronous, so that the complexity of the system or a protocol is avoided, and the delay caused by synchronization of time is also avoided. The probability that the user requests undergo the replay attack is avoided through the application of the unidirectional data chain.
Owner:SOUTH CHINA NORMAL UNIVERSITY +1
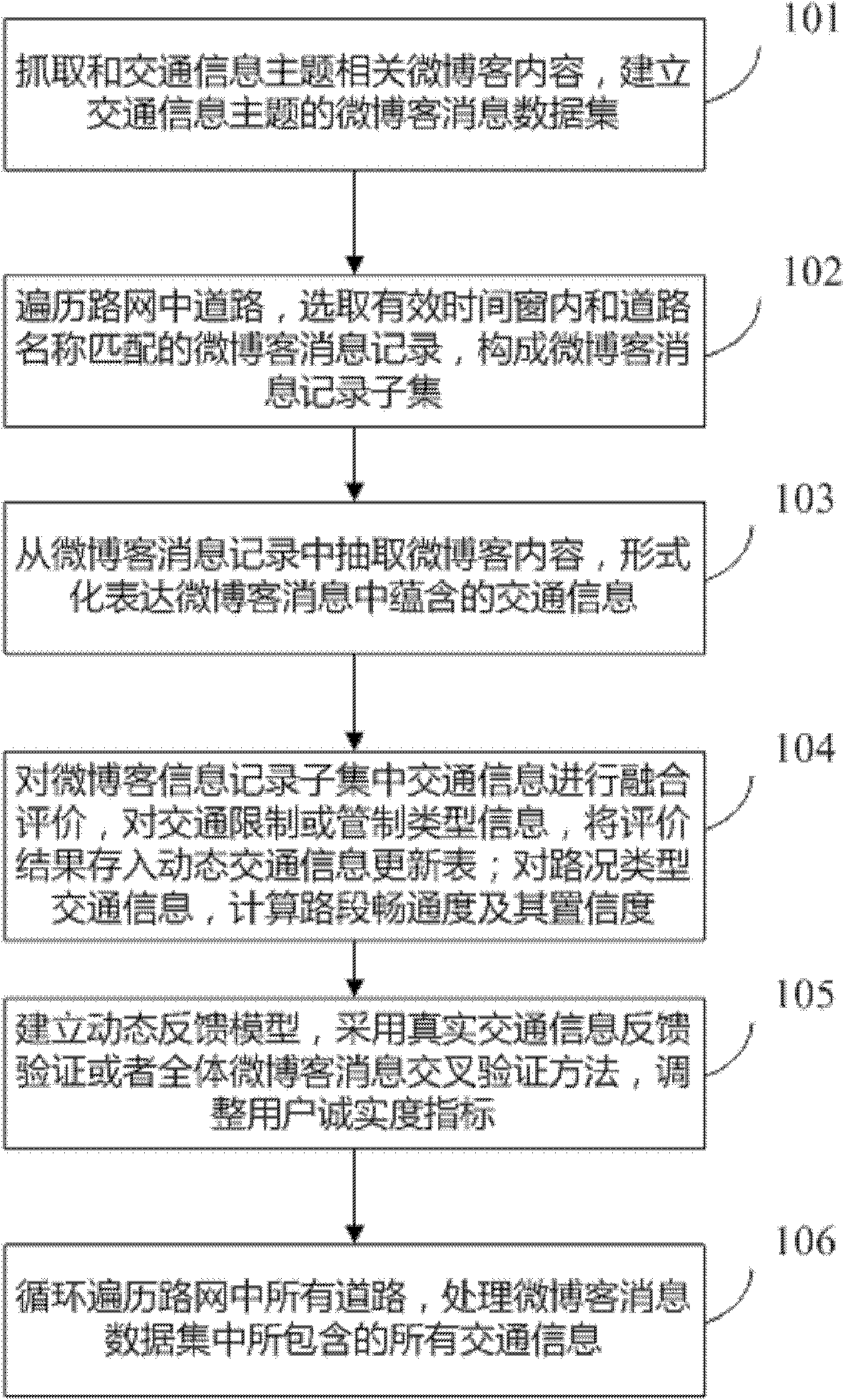
A fusion evaluation method of traffic information collected based on micro blogs
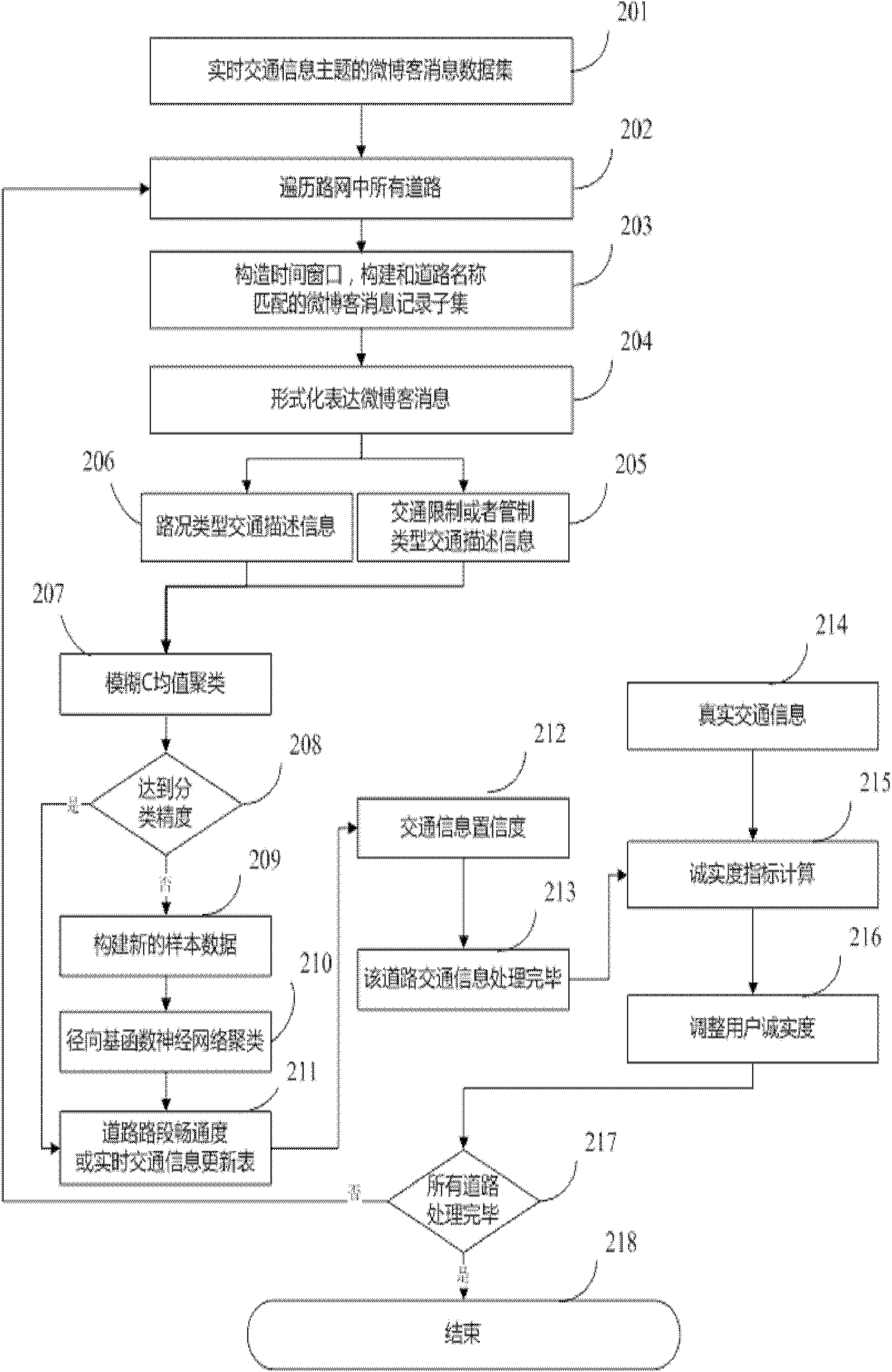
InactiveCN102163225ABreaking through the fusion matching problemEfficient extractionSpecial data processing applicationsReal time navigationData set
A fusion evaluation method of traffic information collected based on micro blogs comprises the steps of: constructing a data set of micro blog messages with traffic information as a theme; traversing road sections in a road network and selecting micro blog message records related to the road sections in the road network in an effective time window for establishing a micro blog message record set; extracting traffic information description indicators from the micro blog message records and formally conveying the traffic information contained in the micro blogs; performing fusion evaluation of the traffic information in the micro blog message record set and acquiring a real-time dynamic traffic information update table of the traffic information with regard to traffic restriction or traffic control; as for the traffic information with regard to road conditions, calculating clear degree and support degree of the road sections during corresponding period of time; establishing a dynamic feedback model and adjusting honesty degree of micro blog users; and circularly traversing all the roads in the road network and processing the traffic information of the whole road network covered in the micro blog message data set. The method in the invention realizes the rapid fusion evaluation of the traffic information contained in the micro blogs and provides an important data source for the collection of the urban traffic information, thereby being applicable to real-time navigation and location-based service systems, map websites, traffic planning management and emergence response plans.
Owner:INST OF GEOGRAPHICAL SCI & NATURAL RESOURCE RES CAS
Method and apparatus for simplified production of heat treatable aluminum alloy castings with artificial self-aging
InactiveUS6224693B1Simplifying even further the overall heat-treatmentProducing the casting in a considerably shorter timeCylinder headFree cooling
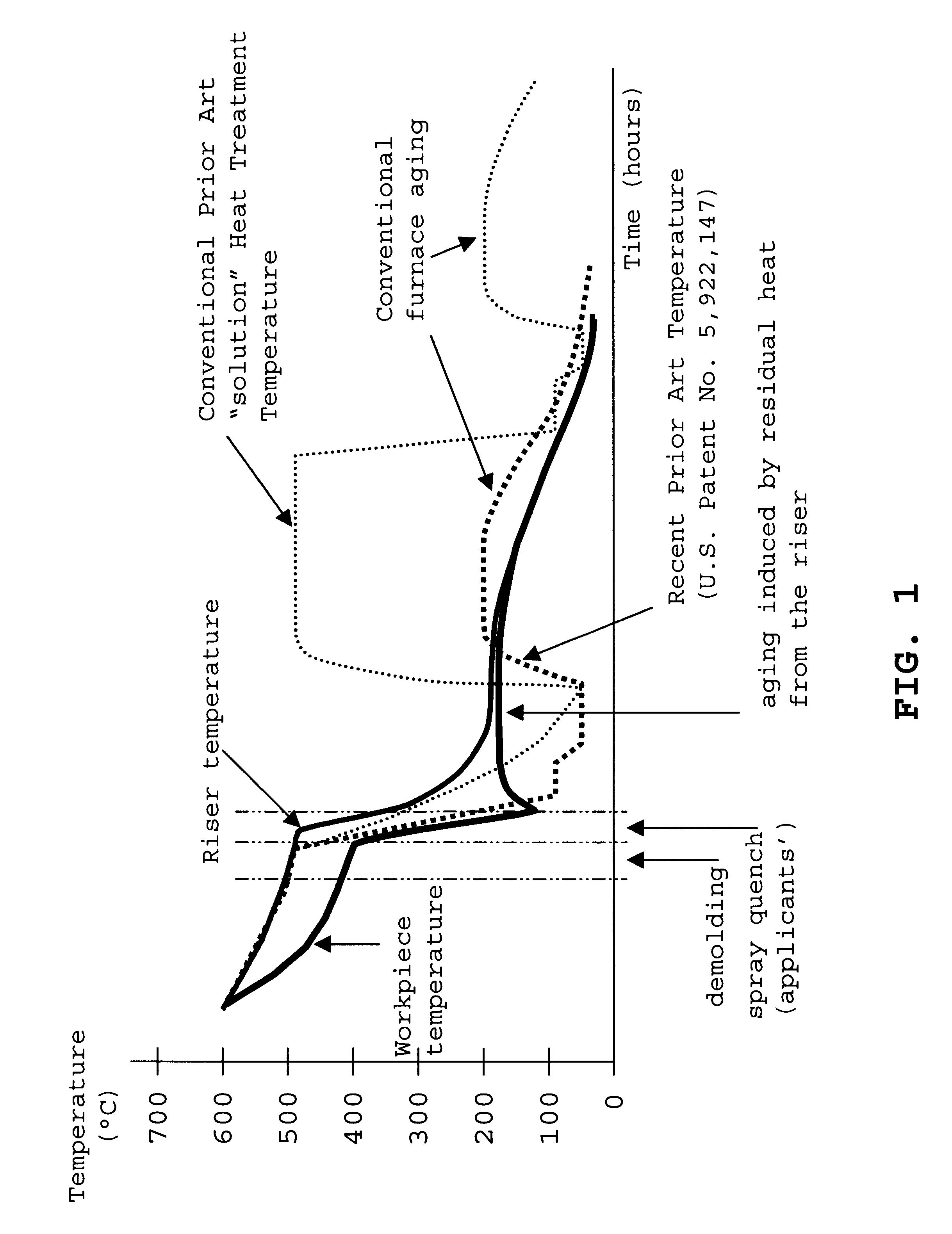
Simplified heat-treatment in making aluminum alloys castings of the type improved by aging, especially for automotive engine cylinder heads and motor blocks. The castings, after solidification and extraction from their molds, each have an end product (workpiece) portion and a riser portion (the latter being ultimately cut off as waste). The workpiece portion of the casting is selectively quenched from solution temperatures down to about 120° C. by spraying water or other appropriate liquid preferably as a gas driven mist onto the surfaces of the workpiece while maintaining the riser portion of the casting essentially unsprayed at relatively significantly higher temperatures. After the quench, the residual reservoir of heat thus retained by said riser portion, by internal heat conduction, reheats the workpiece portion and maintains such workpiece portion for an effective time period within the temperature range for artificial aging, thus obviating any need for the aging furnace used by the prior art. Preferably, the quench is immediately after the casting mold extraction (without the standard natural cooling, reheating, and solution heat-treatment, all prior to quenching), thus obviating also the need for a solution heat-treatment furnace, required by the conventional prior art.
Owner:TENEDORA NEMAK SA DE CV
Mobile Internet virtual key authorizing system and hardware door lock control method thereof
InactiveCN105871874AImprove securityAvoid the possibility of duplicationKey distribution for secure communicationIndividual entry/exit registersComputer hardwareEffective time
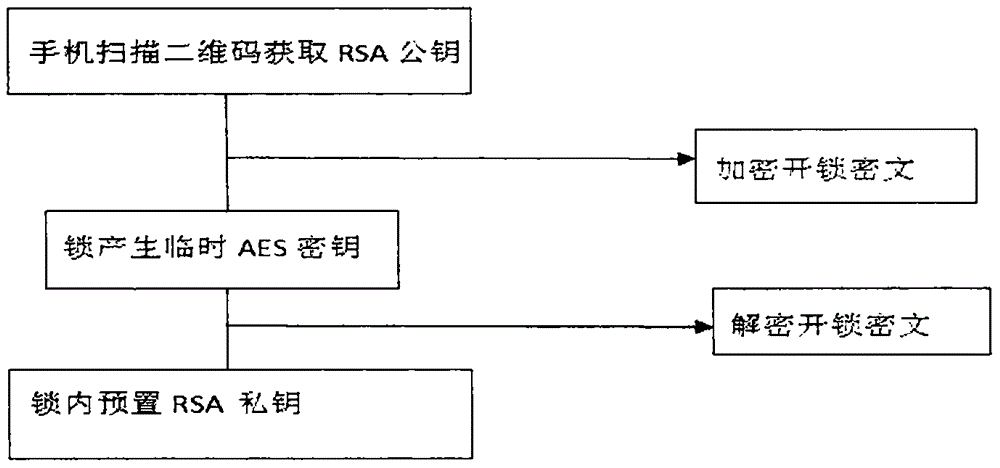
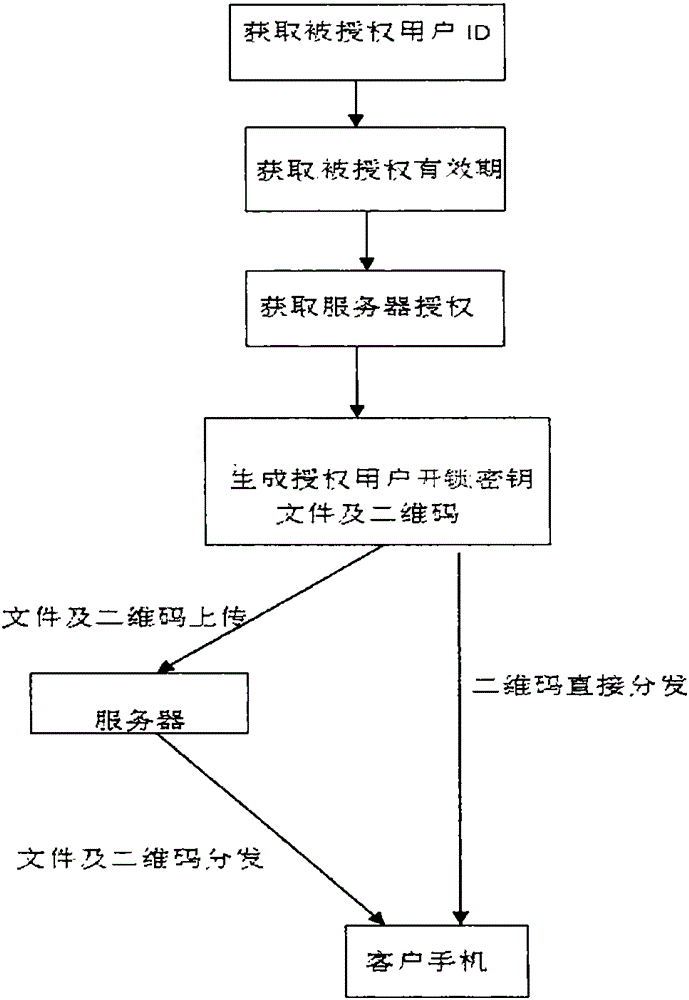
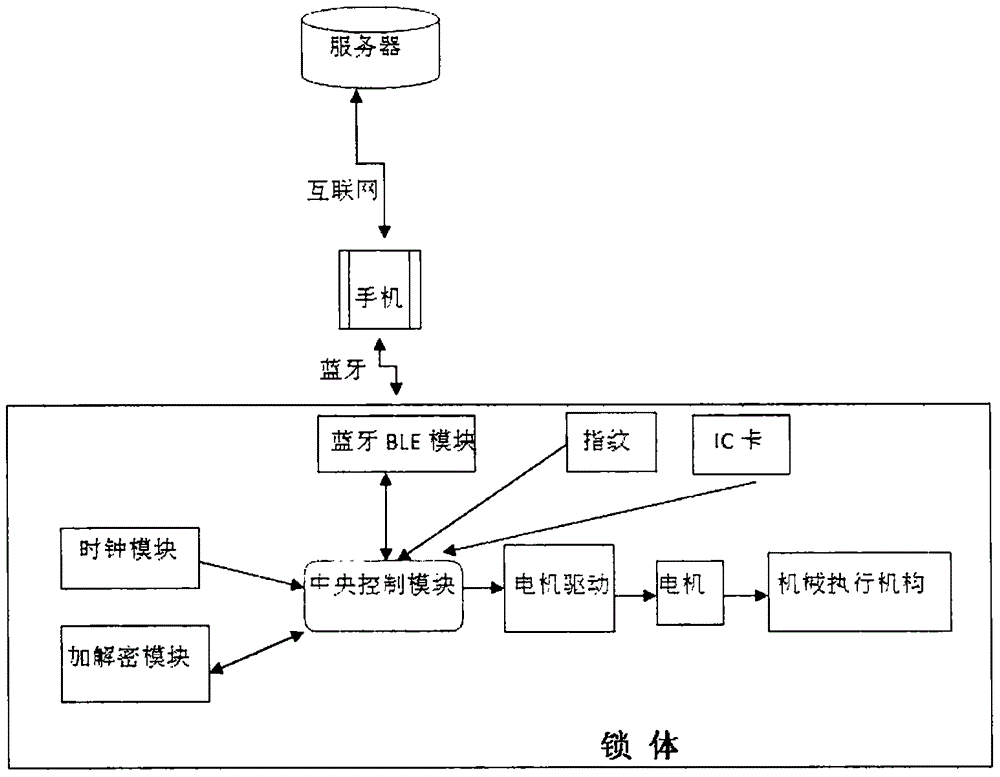
The invention relates to a mobile Internet virtual key authorizing system. The mobile Internet virtual key authorizing system comprises intelligent door locks with Bluetooth communication modules, a main smart phone with a Bluetooth communication module, a client smart phone with a Bluetooth communication module, and a server linked with all the smart phones through a wireless Internet. A control method comprises the following steps that firstly, each intelligent door lock with the Bluetooth communication module has a pair of RSA public and private secret keys; secondly, the server receives a secret key authorizing request of the main smart phone, generates an authorized secret key after verifying the ID of the main smart phone and sends the authorized secret key to the client smart phone; thirdly, the client smart phone and the intelligent door locks establish communication through Bluetooth; fourthly, the intelligent door locks obtain the secret key from the client smart phone through communication and then carry out comparison. By means of the system and the method, the effective time duration can be freely set, and thus the safety of virtual key remote authorization on the mobile Internet is greatly improved.
Owner:武汉市国扬科技集团有限公司
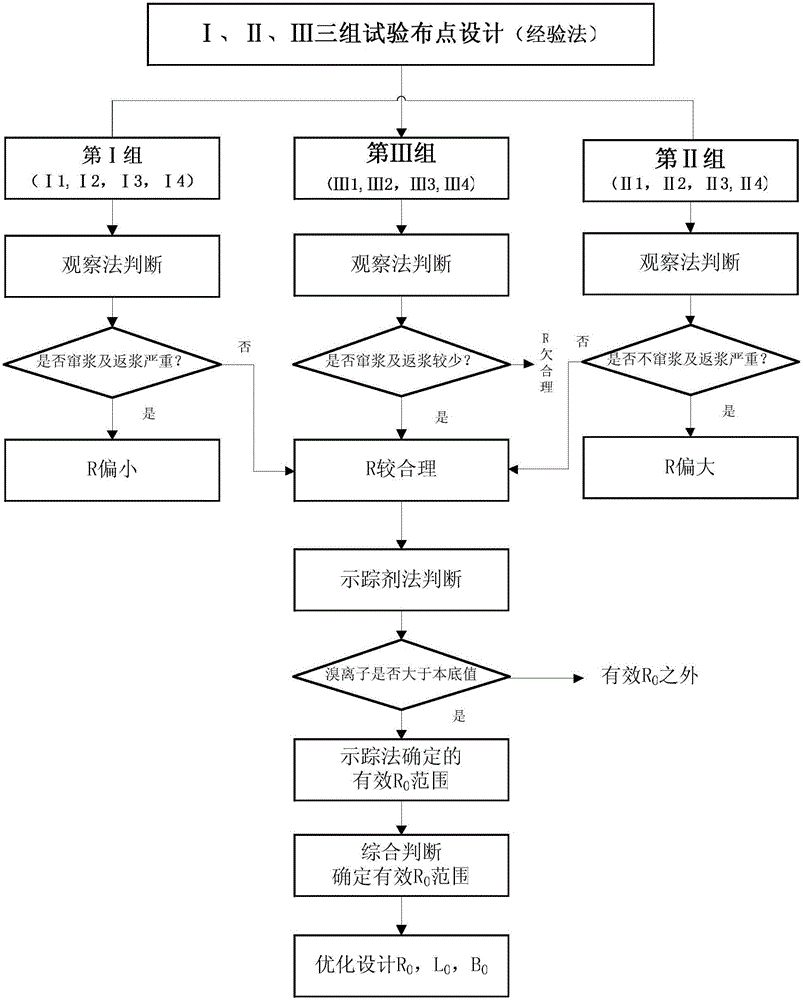
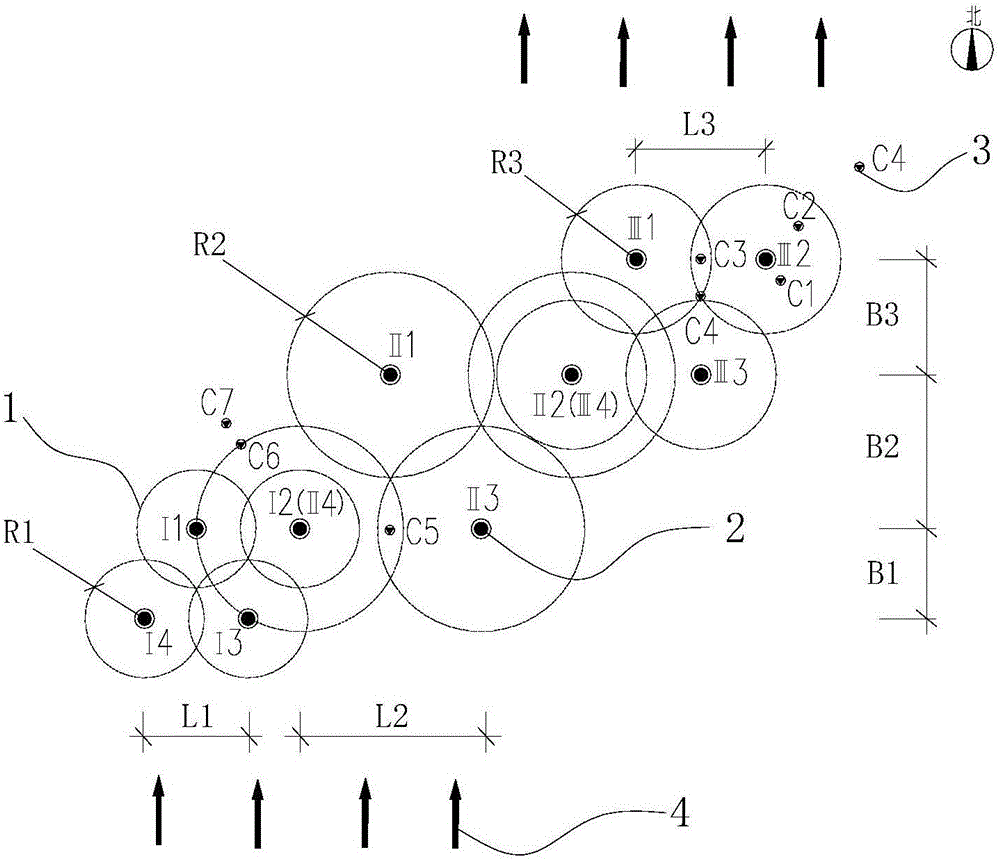
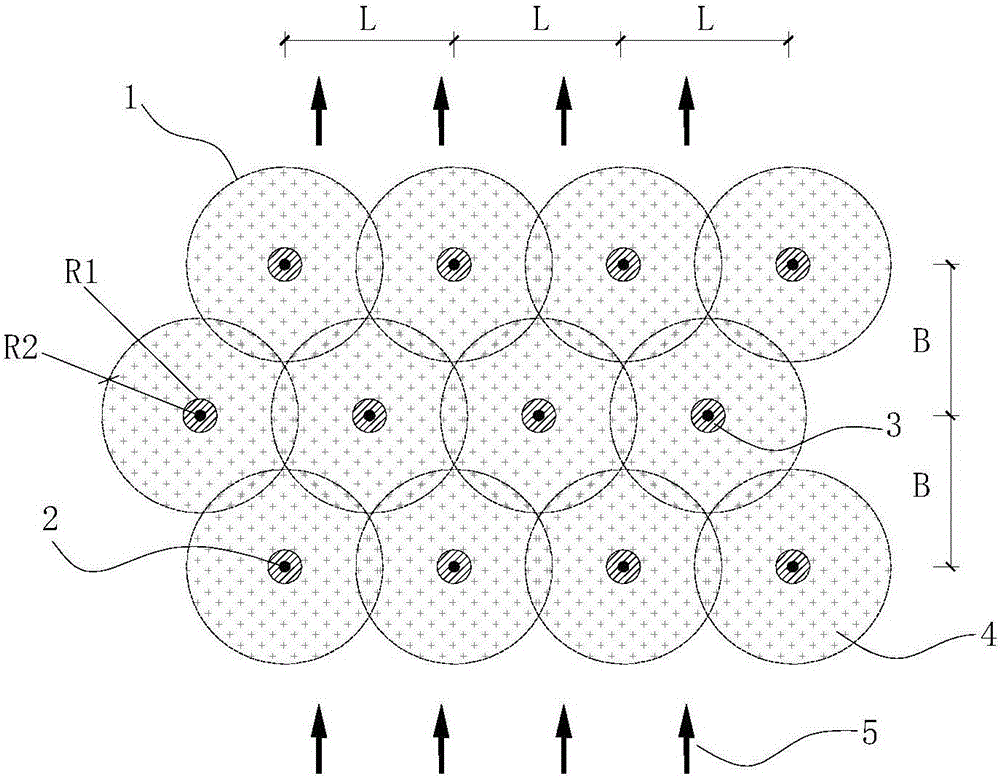
Method for determining in situ injection repair diffusion radiuses of contaminated soil and underground water
ActiveCN105973759ASolve the problem of back slurryEasy to operateConstructionsContaminated soil reclamationHigh pressureInjection test
The invention discloses a method for determining in situ injection repair diffusion radiuses of contaminated soil and underground water. According to the method, points are distributed according to a triangle method, pitch-row is designed to be perpendicular to the flowing direction of the underground water, array pitch is in the flowing direction of the underground water, and the flow expansion of a repair reagent in the underground water within the reaction effective time is taken into account. The method comprises three steps: firstly, observation method: the repair reagent and a definite proportion of bromide ion serving as tracers are simultaneously injected into an aqueous stratum in the condition of high pressure whirl spraying injection. The diffusion of the reagent is judged by observing the phenomena of grout return and grout leaking between adjacent injection points; secondly, bromide ion tracer method: after the completion of injection, underground water depth setting rapid sampling is performed, the concentration of the tracers is rapidly detected in field, and the concentration of the bromide ion in the underground water is compared with a background value; thirdly, bromide ion tracer method and observation method: the optimum diffusion radiuses are determined through synthetic judgment. The method is applied to optimal design of diffusion radiuses and hole arrangement parameters and monitoring of injection effect in soil and underground water in situ injection tests and repair construction.
Owner:BCEG ENVIRONMENTAL REMEDIATION CO LTD
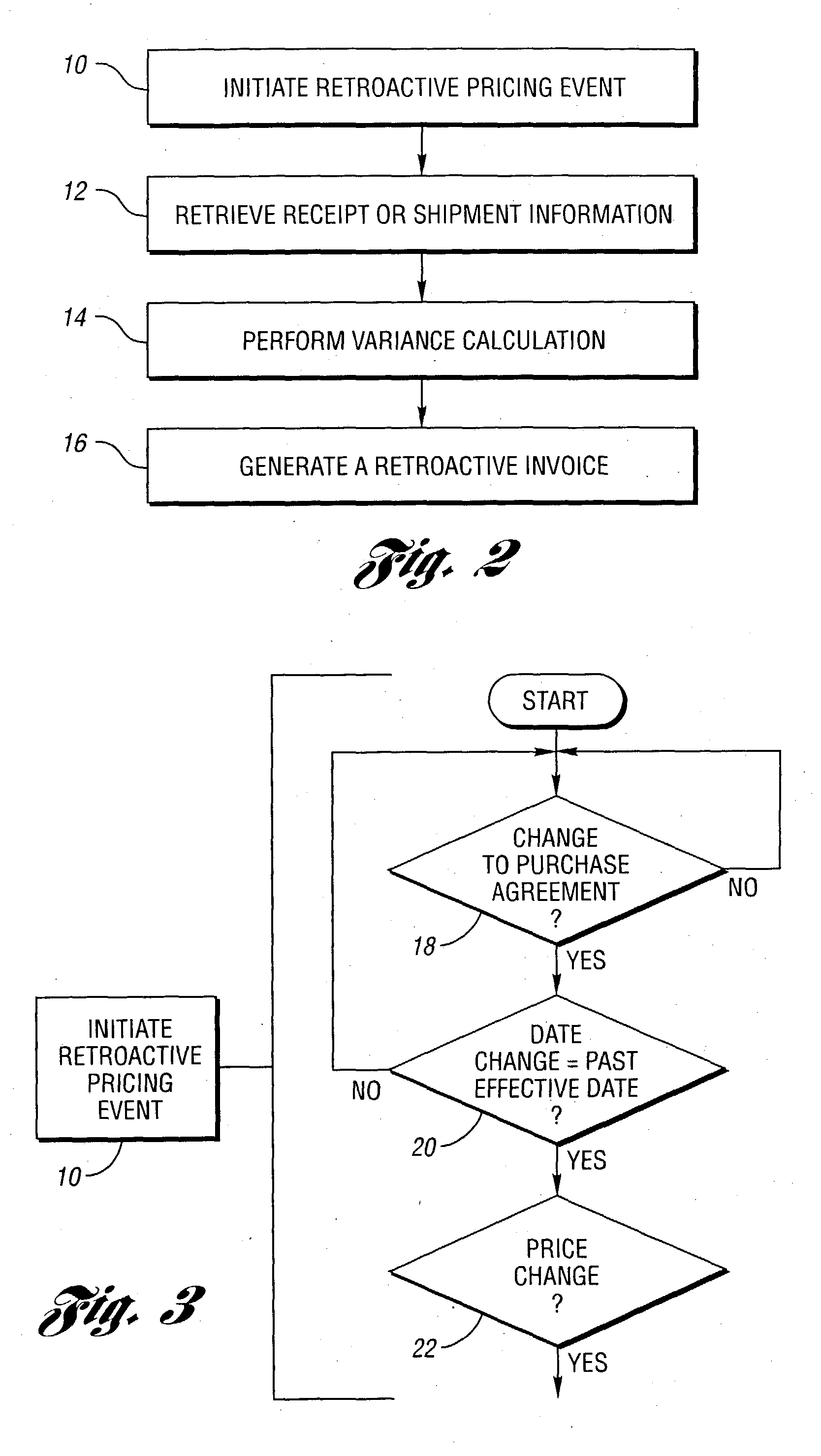
Computer-implemented method and system for retroactive pricing for use in order procurement
A computer-implemented method for determining retroactive price adjustments is disclosed. The method can include receiving a first initiation message including a first effective time period and / or a first new price for a part being supplied to a first plant. For the first initiation message, the method can include retrieving information pertinent to an at least one receipt received for the part within the first effective time period. For each receipt, the method can include determining a variance based on the difference between the first or second new price and the receipt price, determining a price adjustment based on the variance and the receipt quantity, and generating a retroactive invoice for enabling transfer of the price adjustment, the retroactive invoice including the variance and the price adjustment. The first effective time period can include an effective start date that is before each receipt date.
Owner:FORD MOTOR CO
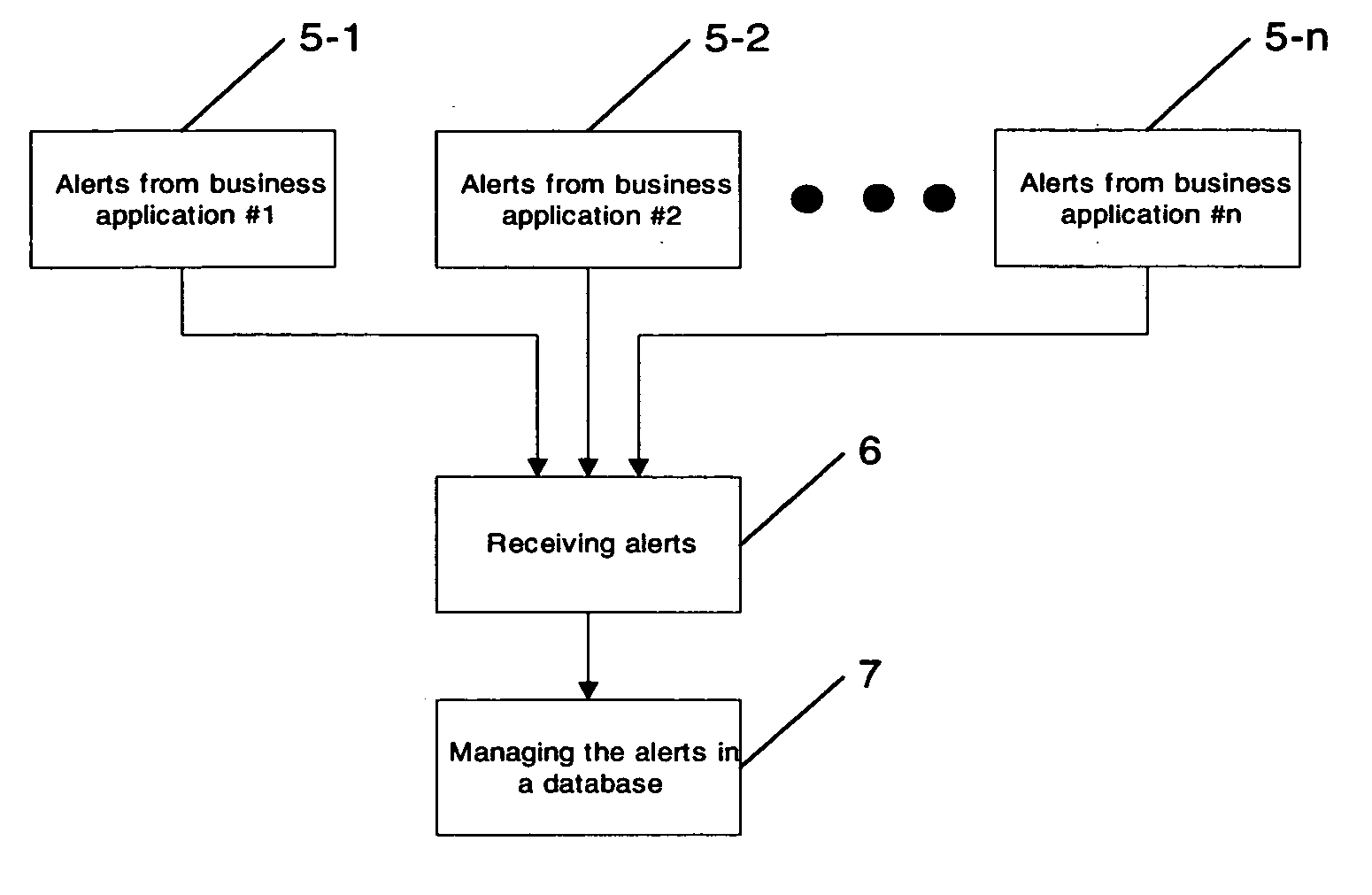
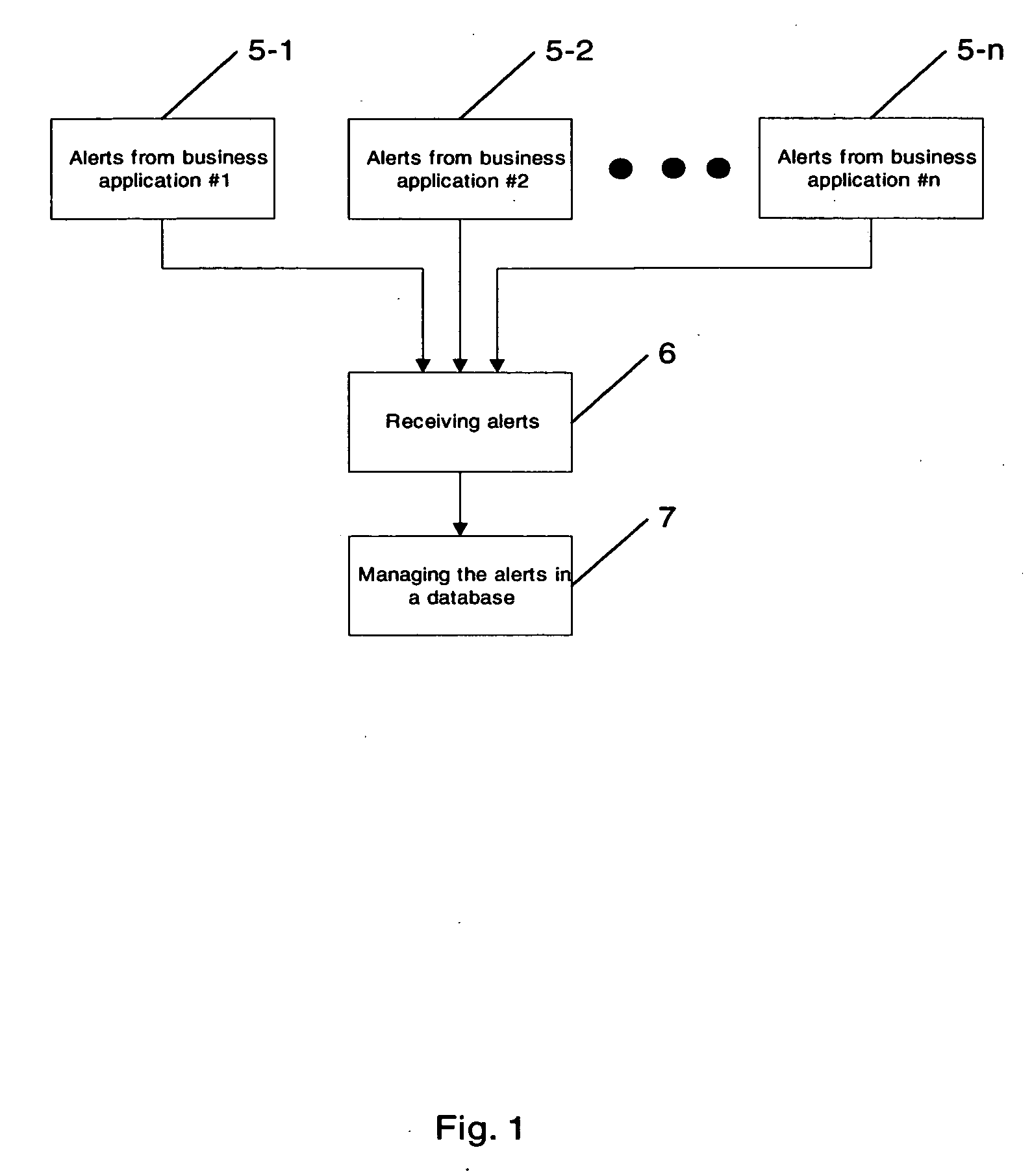
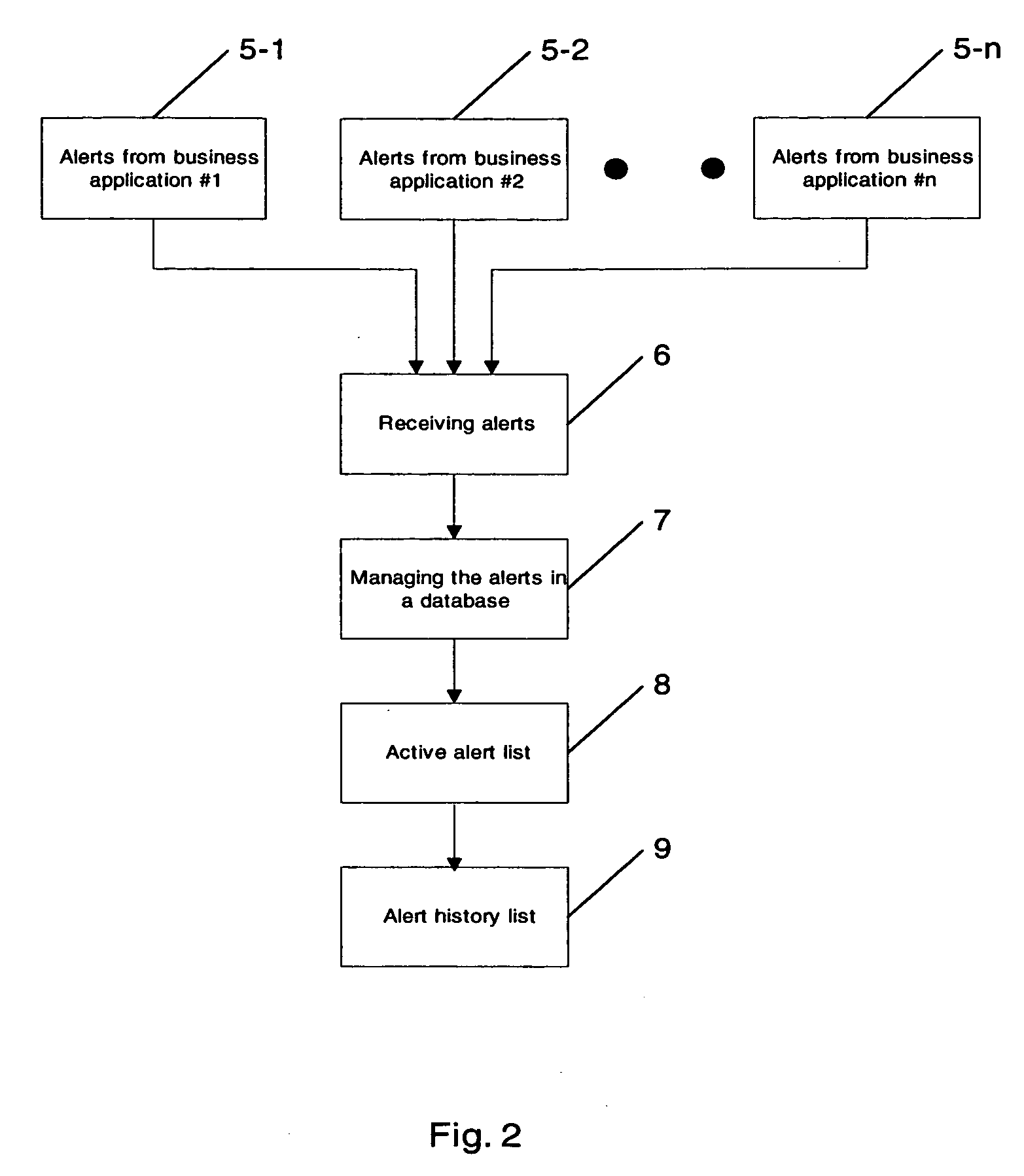
Alert engine
ActiveUS20040225637A1Digital data processing detailsDigital computer detailsTime informationAlert type
Methods and systems for managing alerts in a database are provided, whereby the alerts originate from at least one business application due to exceptional situations, and whereby the alerts are represented as objects, each object corresponding to one of a number of configurable alert types. Each of the alert type may be configured, so that alerts of that alert type comprise at least one of: an ID for uniquely identifying the alert, information representative of the type of alert, message text being descriptive of the alert, a set of parameters representative of business or control objects associated with the alert, an alert scope being representative of the relevance for partners or users, feedback information being representative of time and identity of acknowledging the alert by a partner or user, status information for controlling follow-up actions, validity time information, and priority information.
Owner:SAP AG
Channel monitoring method and device
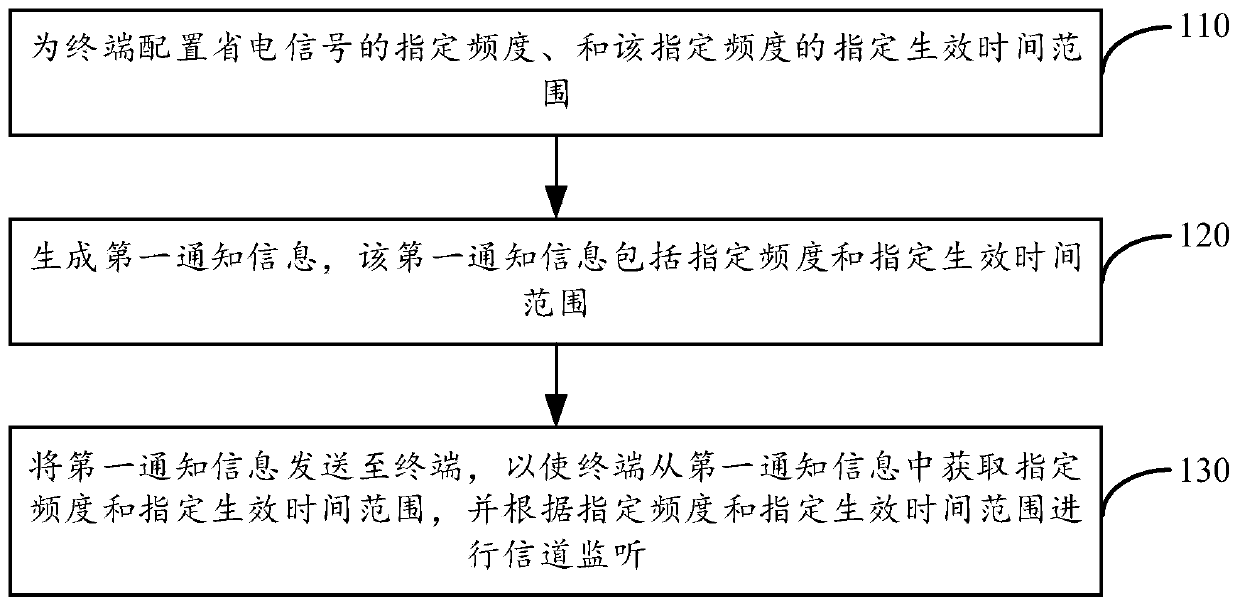
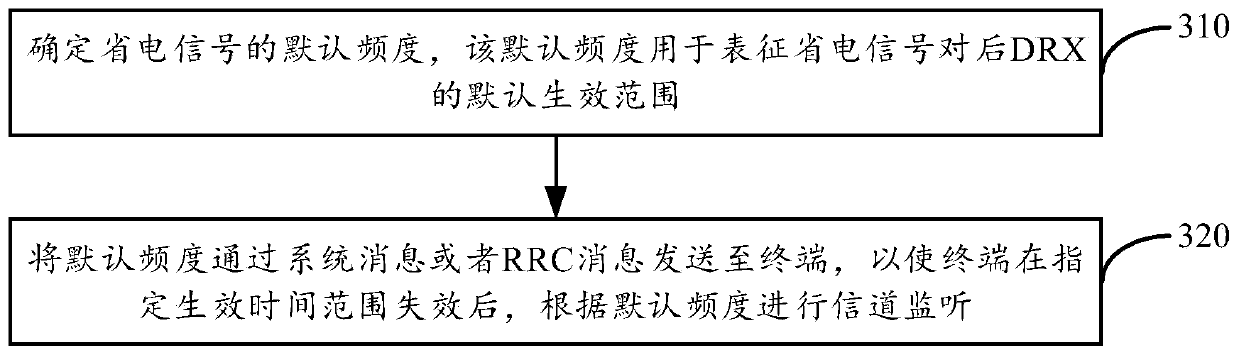
ActiveCN109923904AImprove monitoring efficiencyCollaborative workPower managementConnection managementTime to effectEffective time
The invention provides a channel monitoring method and device. The method is applied to a base station. The method comprises following steps: configuring a designated frequency of an energy saving signal to a terminal, defining designated effective time and range of the designated frequency, wherein the designated frequency is used to represent that the energy saving signal designates the effective range of subsequent discontinuous DRX receiving; generating a first notification message, which comprises the designated frequency and the designated effective time and range; sending the first notification message to a terminal so that the terminal can obtain the designated frequency and designated effective time and range from the first notification message, and according to the designated frequency and designated effective time and range, carrying out channel monitoring. The cooperation between an energy saving signal mode and a DRX mode is realized, if there is data, a base station can indicate a terminal to carry out intensive monitoring through the designated frequency; if there is no data, the base station can indicate the terminal to carry out sparse monitoring through the designated frequency; thus the channel monitoring efficiency is improved, and the resource waste is avoided.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
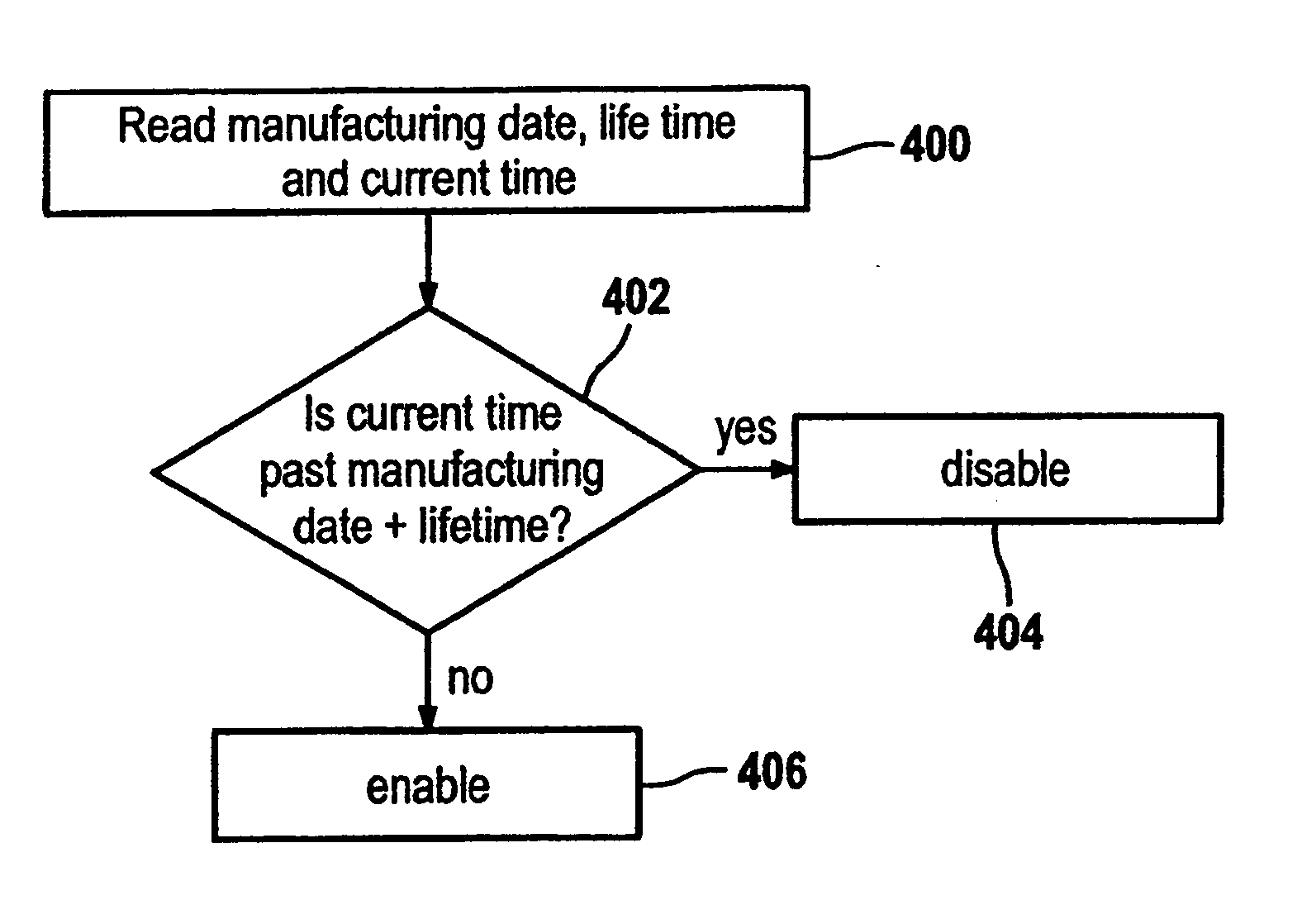
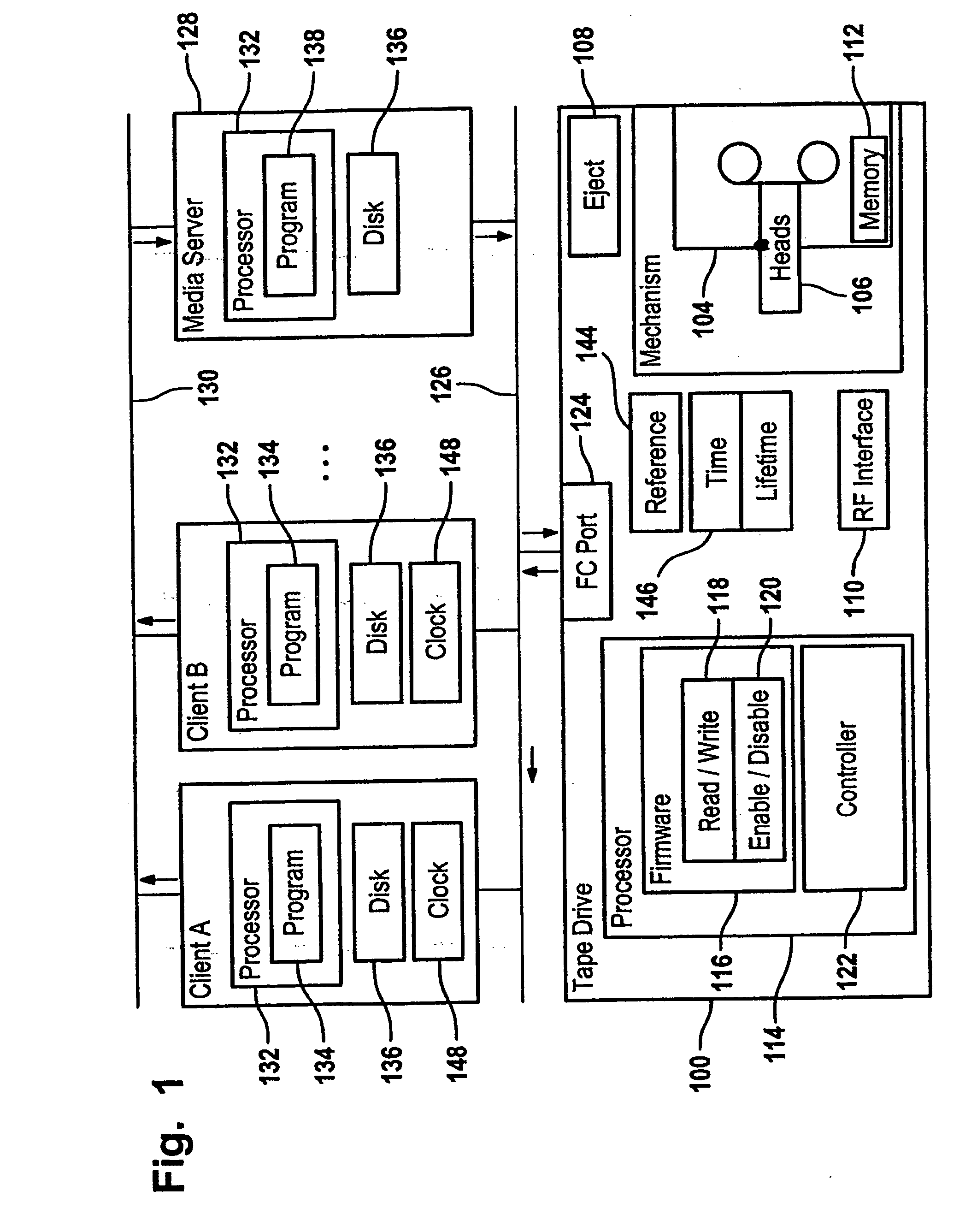
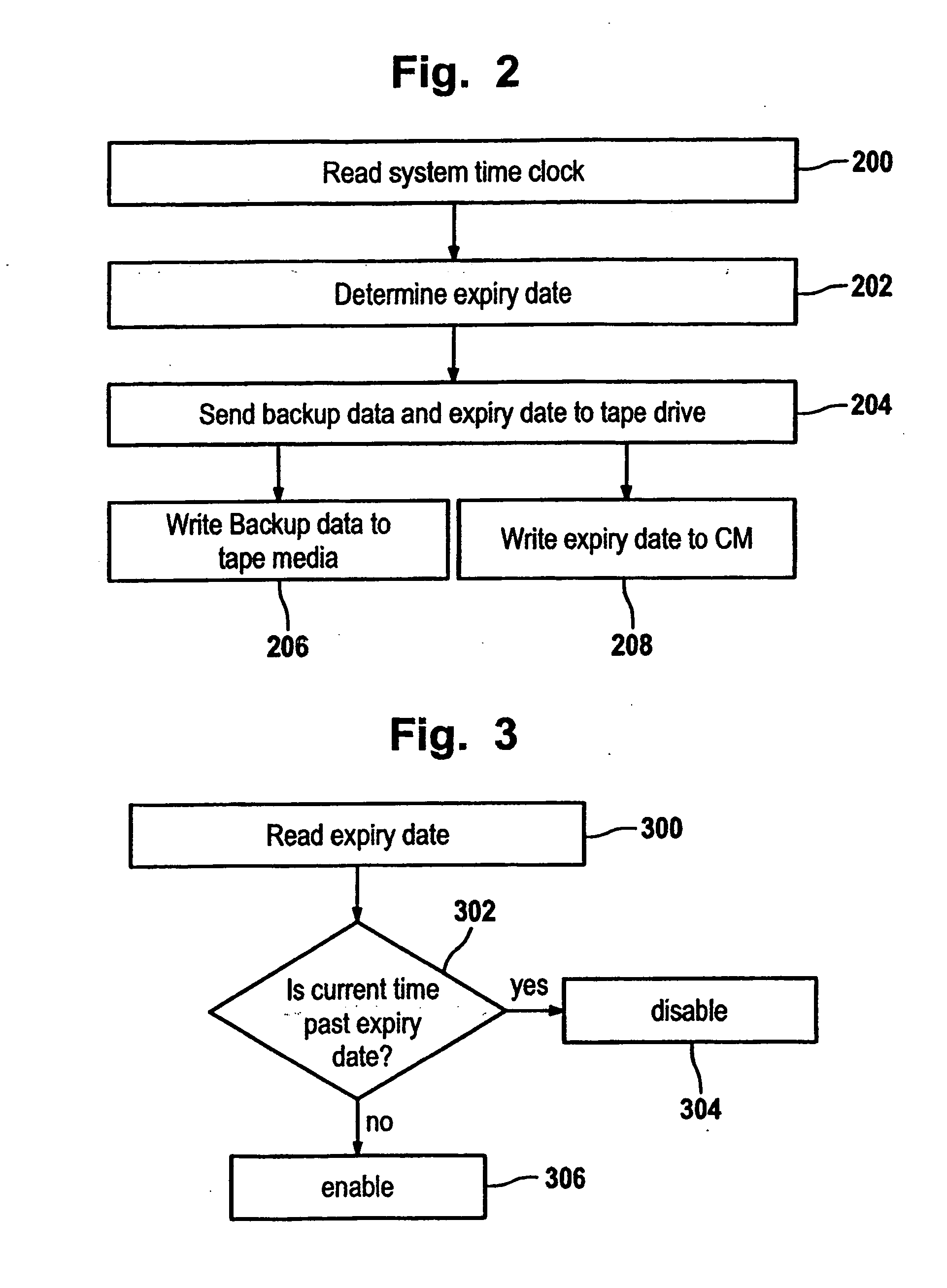
Tape drive apparatus, method and computer program product
InactiveUS20050246509A1Prevents re-writingAvoid eliminationMemory loss protectionRecording on magnetic tapesMagnetic tapeEffective time
A validity time interval for backup data of a data backup operation is determined. The validity time interval is limited, e.g., by an expiration date and / or an activation date. Validity date indicating the validity time interval is stored in non-volatile memory of the tape cartridge, such as a cartridge memory, when the backup data is written to the tape cartridge by the tape drive. Recovery of the backup data from the tape drive is only possible if recovery is performed within the validity time interval, to provide an efficient way to assure tape rotation.
Owner:HEWLETT PACKARD DEV CO LP
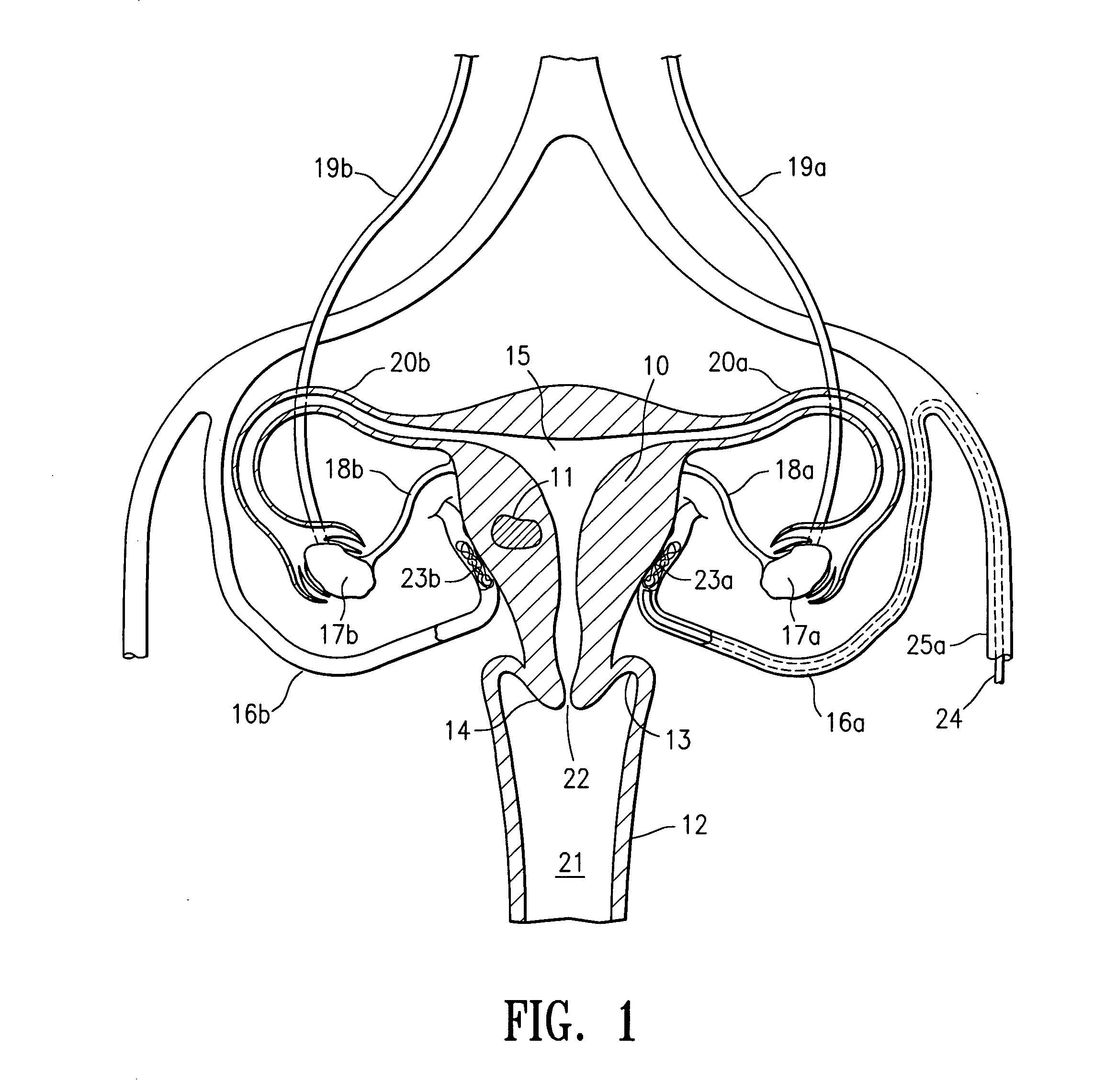
Embolic occlusion of uterine arteries
InactiveUS20040202694A1Decreased blood flowSlow and stop flowSurgical adhesivesFemale contraceptivesWater basedUterine Disorder
A treatment procedure is disclosed which involves the short term, non-permanent occlusion of the patient's blood vessels by depositing a bioabsorbable embolic mass within the patient's blood vessel. The procedure is particularly suitable for treating uterine disorders by occluding a patient's uterine arteries. A therapeutically effective time period for occlusion of a uterine artery is from about 0.5 to about 48 hours, preferably about 1 to about 24 hours, with occlusion times of about 1 to about 8 hours being suitable in many instances. The embolic mass may bioabsorbable particulate with minimum transverse dimensions of about 100 to about 2000 micrometers, preferably about 300 to about 1000 micrometers. The particulate may be a polymeric material formed of polylactic acid, polyglycolic acid or copolymers thereof, or a swellable copolymer of lactic acid and polyethylene glycol. The embolic material may be delivered to an intracorporeal site as a biocompatible solution containing a solute which is relatively insoluble in a water based fluid and a solvent which is relatively soluble in the water based fluid, where the solute forms the embolic mass which occludes or partially occludes a body lumen or fills or partially fills a body cavity.
Owner:VASCULAR CONTROL SYST
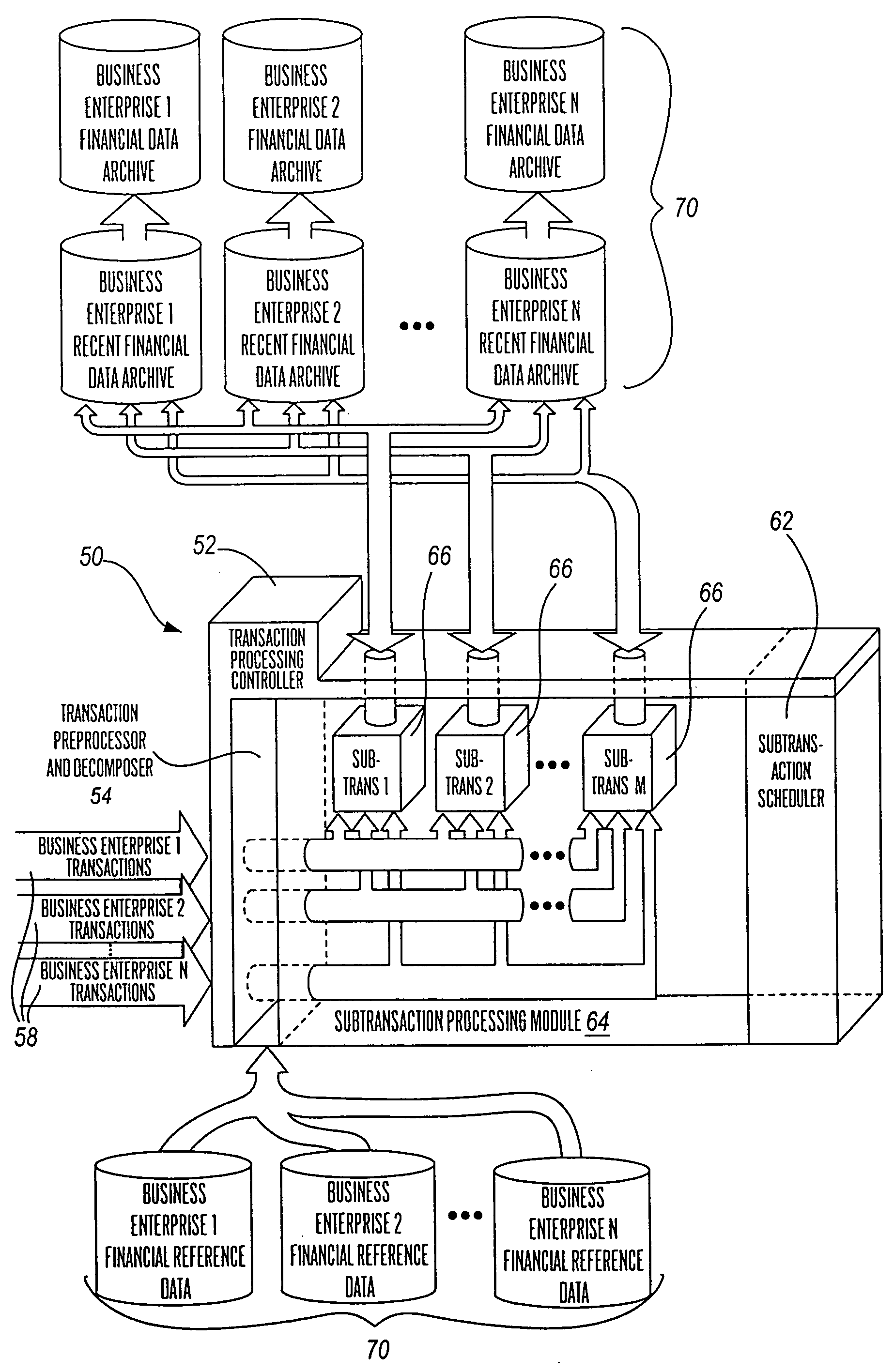
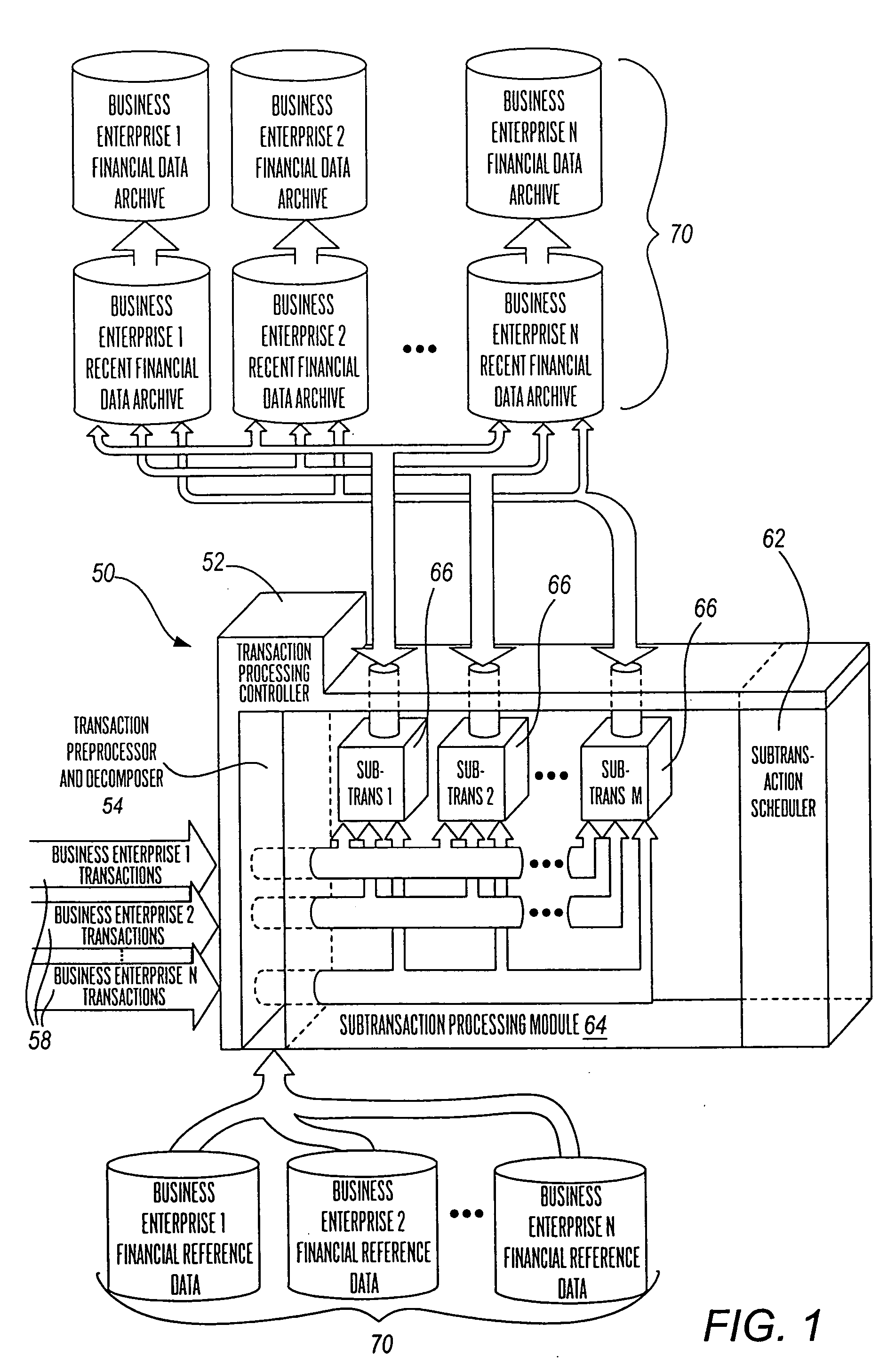
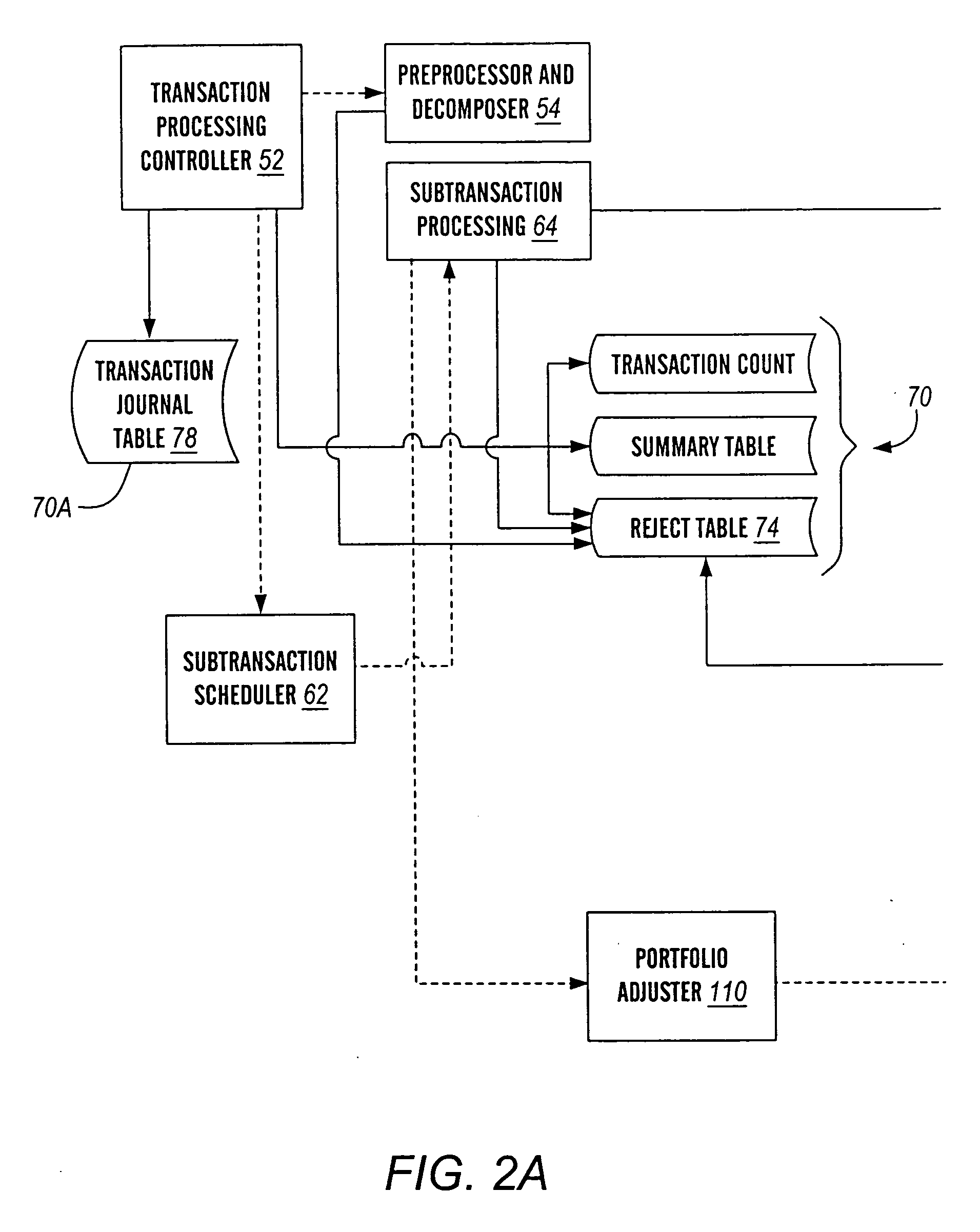
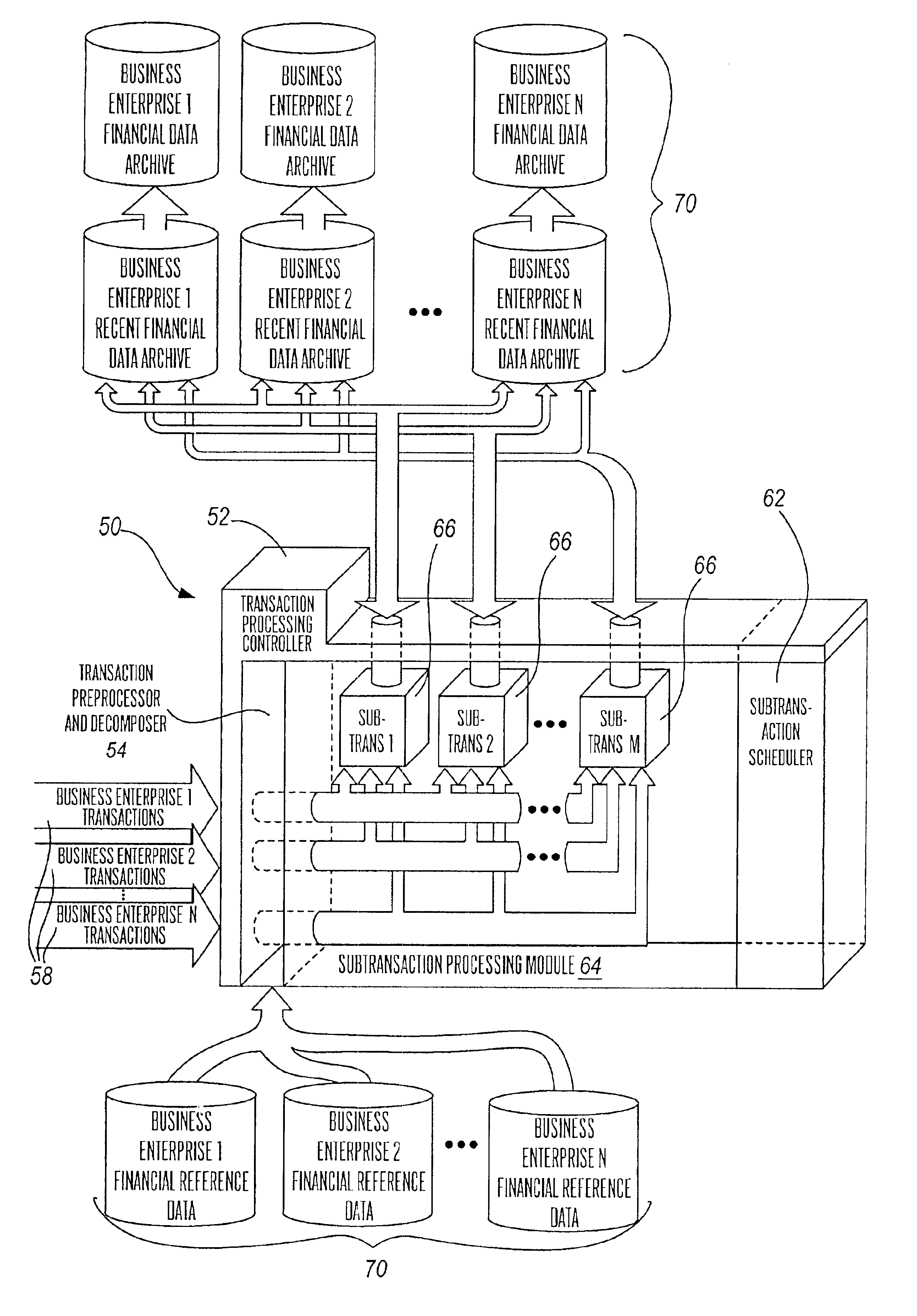
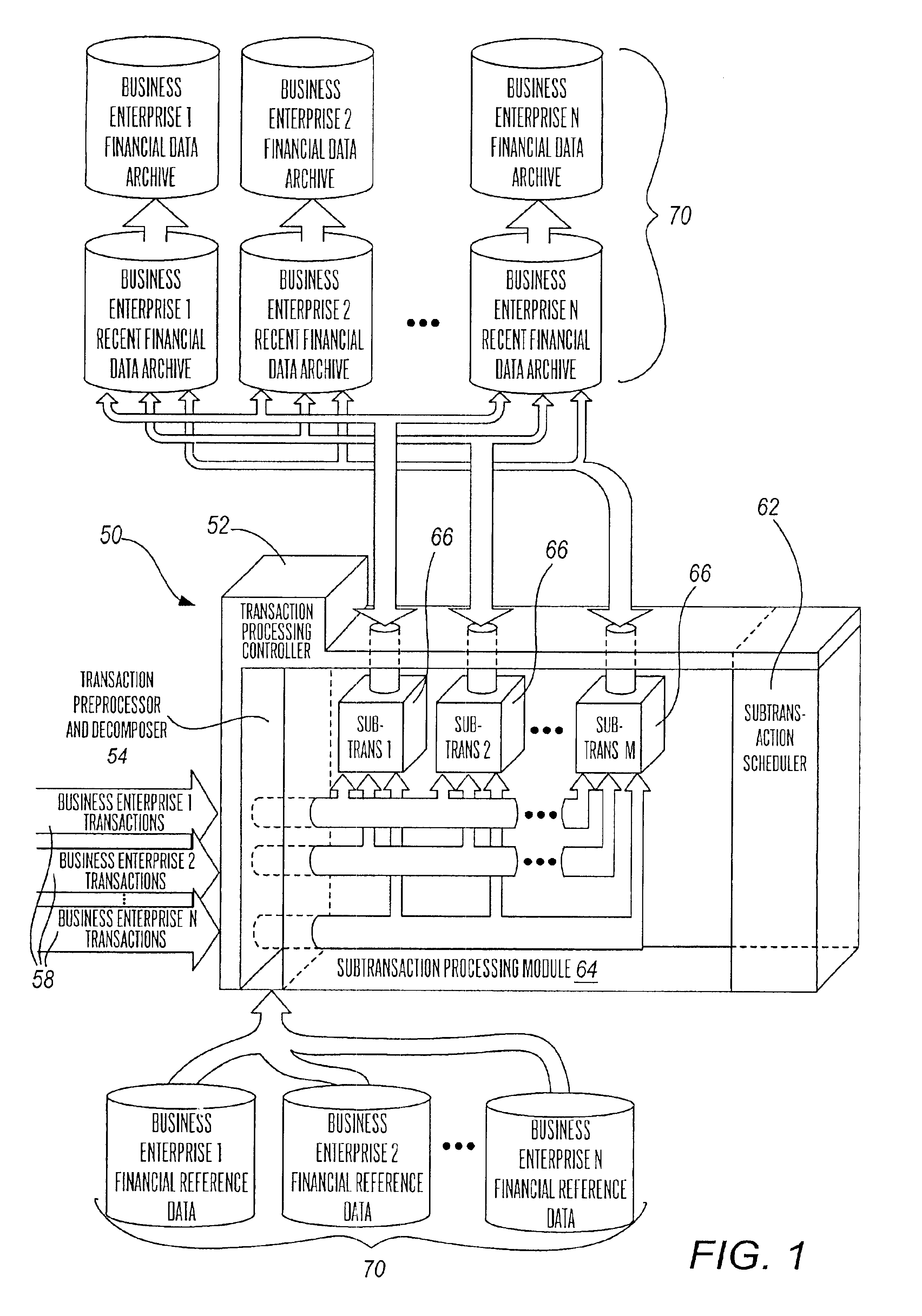
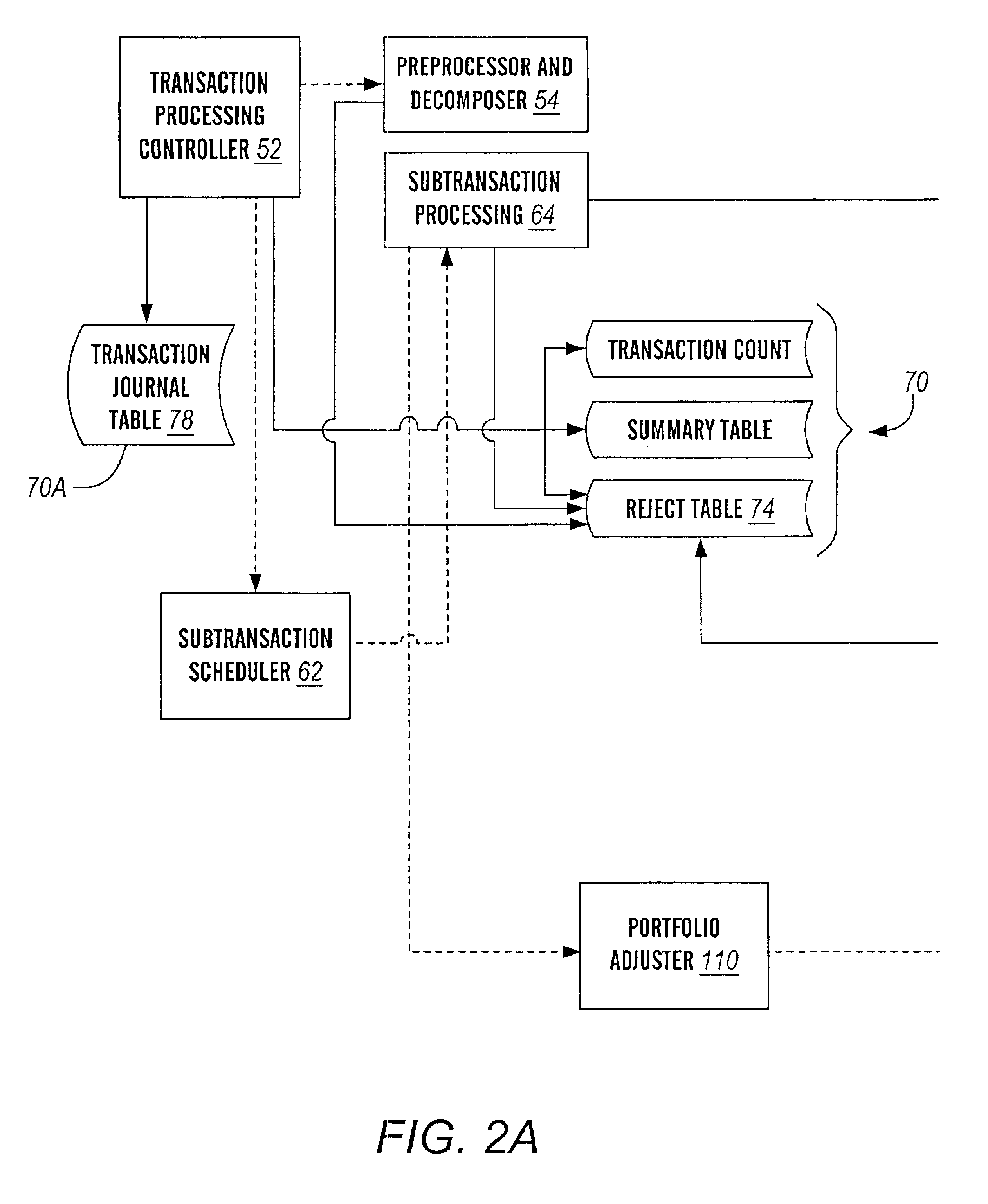
Multi-processing financial transaction processing system
A financial transaction processing system is disclosed, wherein substantial processing efficiencies are provided with, additionally, a substantial decrease in the size of the executable code. Each transaction processed by the transaction processing system is described by a transaction data descriptor that includes a series of subtransaction data descriptions of actions that can be performed independently of one another. Thus, complex transaction processing logic is substantially removed from the executable code, and instead such transaction data descriptors are processed interpretatively. Moreover, the independence of the subtransactions allows the subtransactions of a transaction to be processed in parallel when performed on a multiprocessor computer. Additionally, the transaction processing system provides account balancing enhancements in that there are control columns in various data tables that are automatically updated during transaction processing so that by comparing control column totals, an indication of the integrity of current financial records is provided. Additionally, the transaction processing system provides full auditability in that any changes to financial data can be traced for any effective period of time into the past so that auditors can periodically perform a full audit of the financial transaction data retained by the transaction processing system.
Owner:HINKLE WILLIAM H
Multi-processing financial transaction processing system
A financial transaction processing system is disclosed, wherein substantial processing efficiencies are provided with, additionally, a substantial decrease in the size of the executable code. Each transaction processed by the transaction processing system is described by a transaction data descriptor that includes a series of subtransaction data descriptions of actions that can be performed independently of one another. Thus, complex transaction processing logic is substantially removed from the executable code, and instead such transaction data descriptors are processed interpretatively. Moreover, the independence of the subtransactions allows the subtransactions of a transaction to be processed in parallel when performed on a multiprocessor computer. Additionally, the transaction processing system provides account balancing enhancements in that there are control columns in various data tables that are automatically updated during transaction processing so that by comparing control column totals, an indication of the integrity of current financial records is provided. Additionally, the transaction processing system provides full auditability in that any changes to financial data can be traced for any effective period of time into the past so that auditors can periodically perform a full audit of the financial transaction data retained by the transaction processing system.
Owner:N GINE
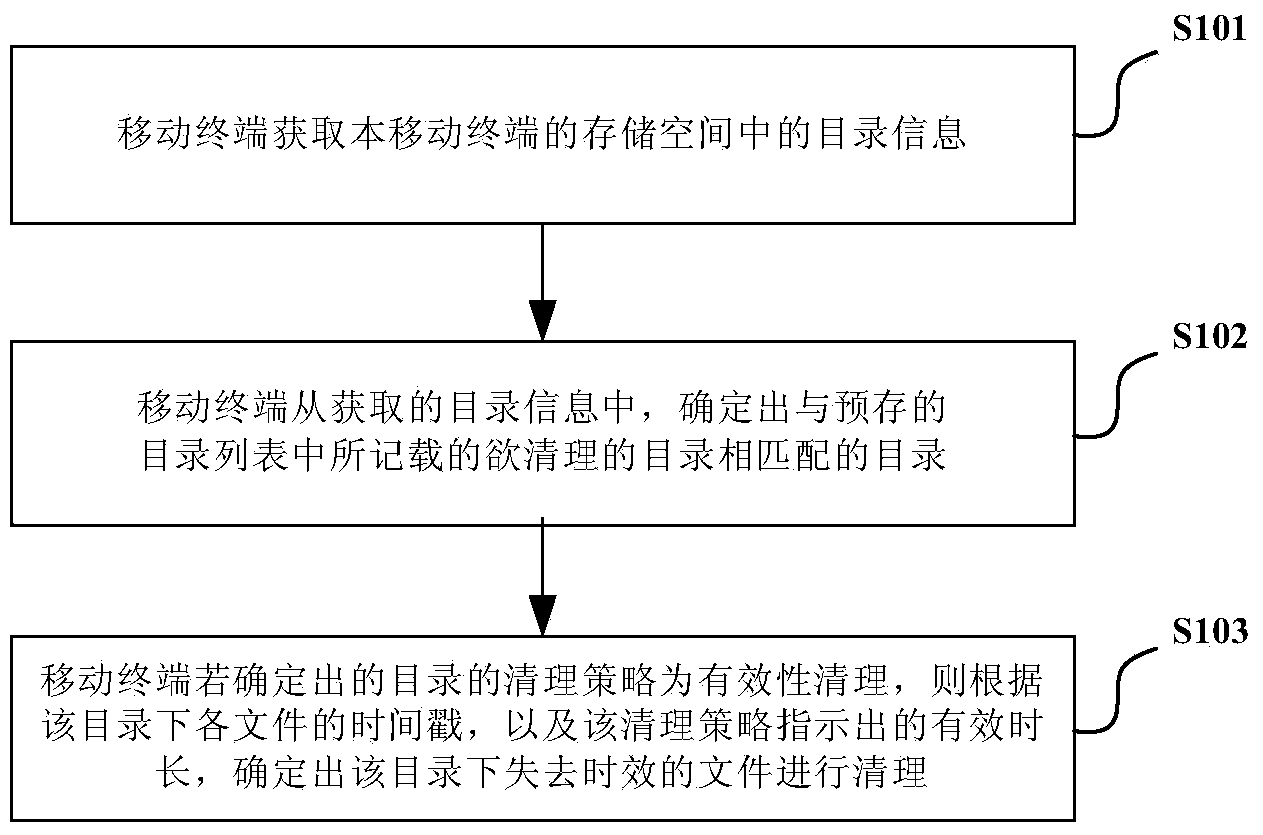
Mobile terminal and storage space cleaning method thereof
InactiveCN104317628AImprove efficiencyImprove experienceProgram loading/initiatingComputer terminalEffective time
The invention discloses a mobile terminal and a storage space cleaning method thereof. The storage space cleaning method includes that acquiring directory information in a storage space; confirming directories matched with directories in a pre-stored directory list to be cleaned from the directory information, wherein the directory list further records the corresponding cleaning strategy of the directory; if the confirmed directory cleaning strategy is an effective cleaning strategy, confirming obsolete files under the directory according to the time stamp of each file under the strategy and the effective time length in the cleaning strategy, and cleaning. The storage space cleaning method can identify and clean the scratch files which surpass the effective time length so as to clean more files capable of being cleaned in the storage space, and accordingly the use efficiency of the storage space is improved, and the user experience is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
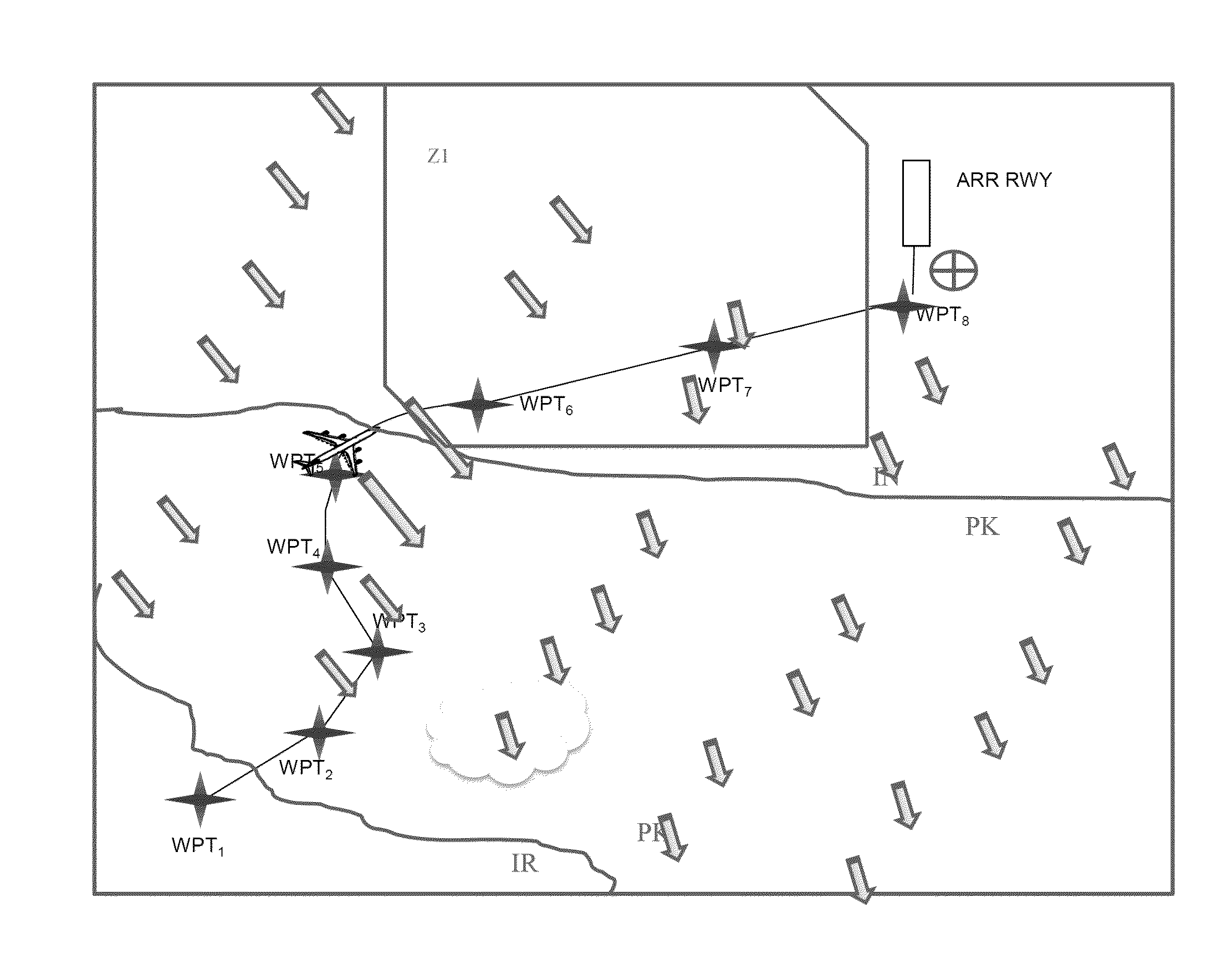
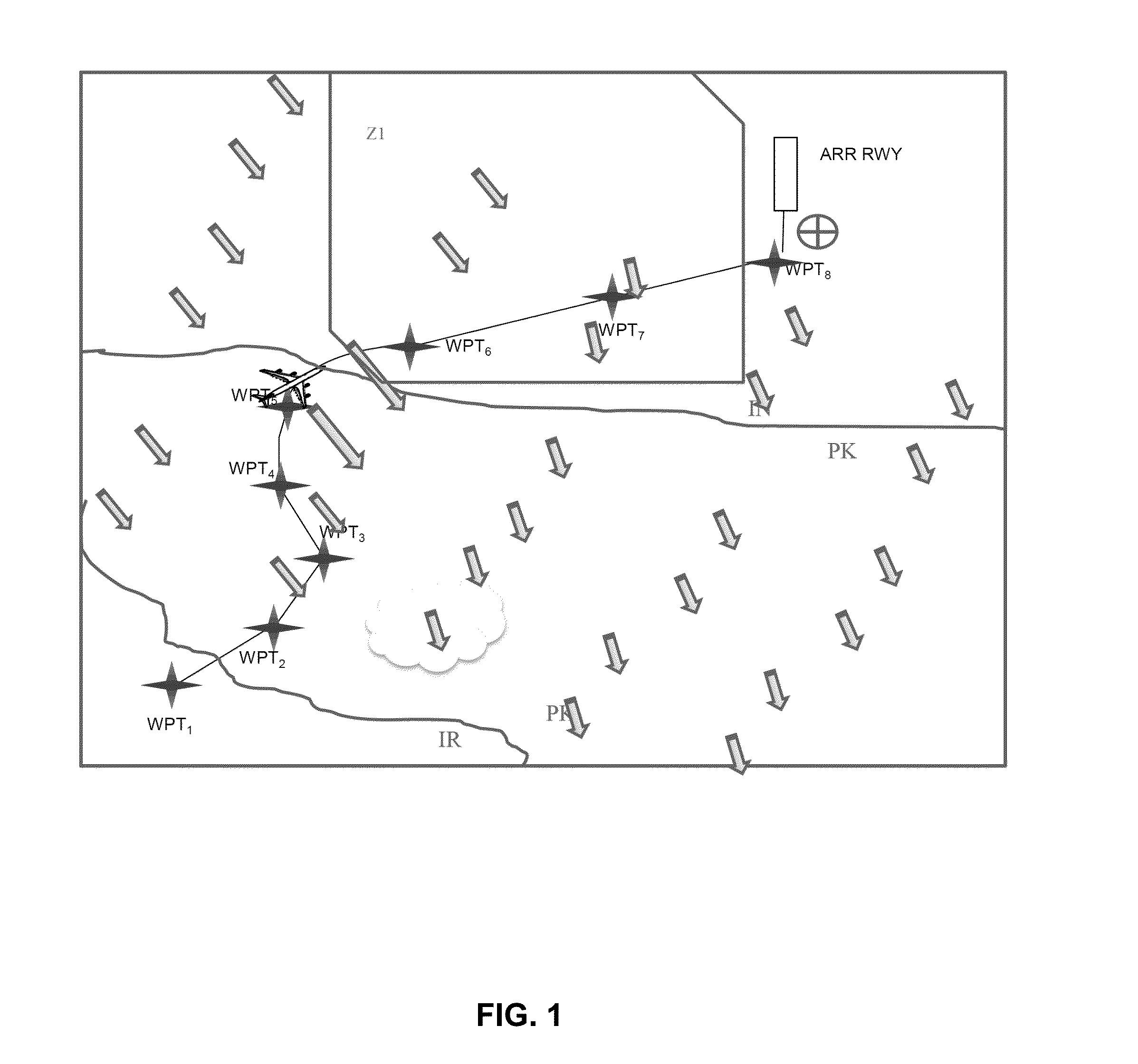
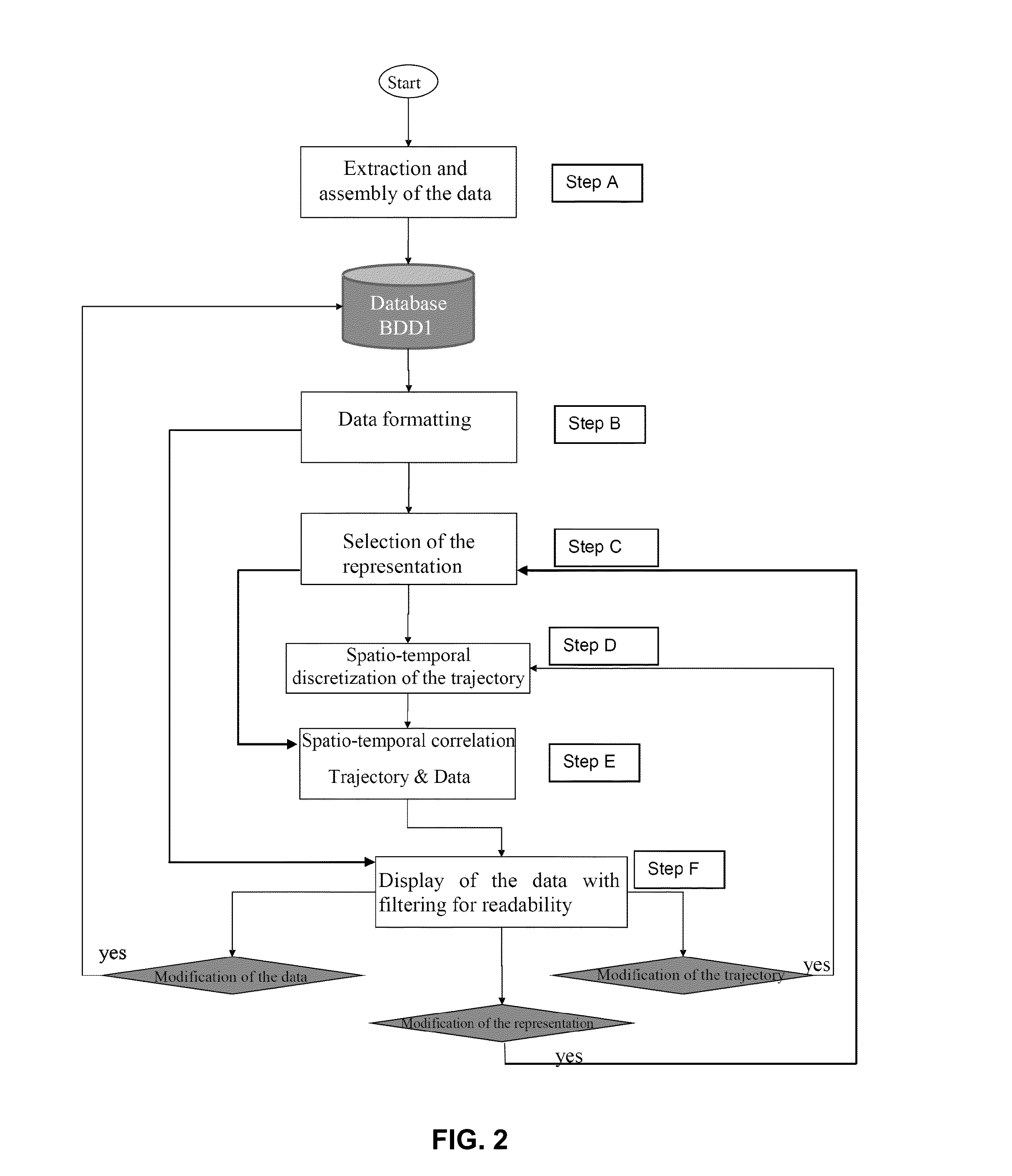
Method for assisting the navigation of an aircraft with correlation of dynamic information with a 4d flight trajectory
ActiveUS20150332490A1Improve readabilityEasy to appreciateAircraft componentsDrawing from basic elementsData seriesGraphics
A method for assisting the navigation of an aircraft comprises: assembly by families of data by a processing unit of predetermined data and acquired data, including meteorological data, the families being predefined, each data value being associated with a time window of validity; formatting the data of the families to associate with each data value a type of graphical representation as text or a scalar, vector, surface, or volume; selection of families of data to be displayed; choice of a display time window for each family of data to be displayed; spatio-temporal discretization of the trajectory; spatio-temporal correlation of the discretized trajectory with each family of data as a function of the time windows of validity, in the display time windows of the family, to extract a sub-assembly from each family of data, by the processing unit; display of the sub-assemblies in a single representation on the same display screen.
Owner:THALES SA
Induction Heating of Footwear and Apparel
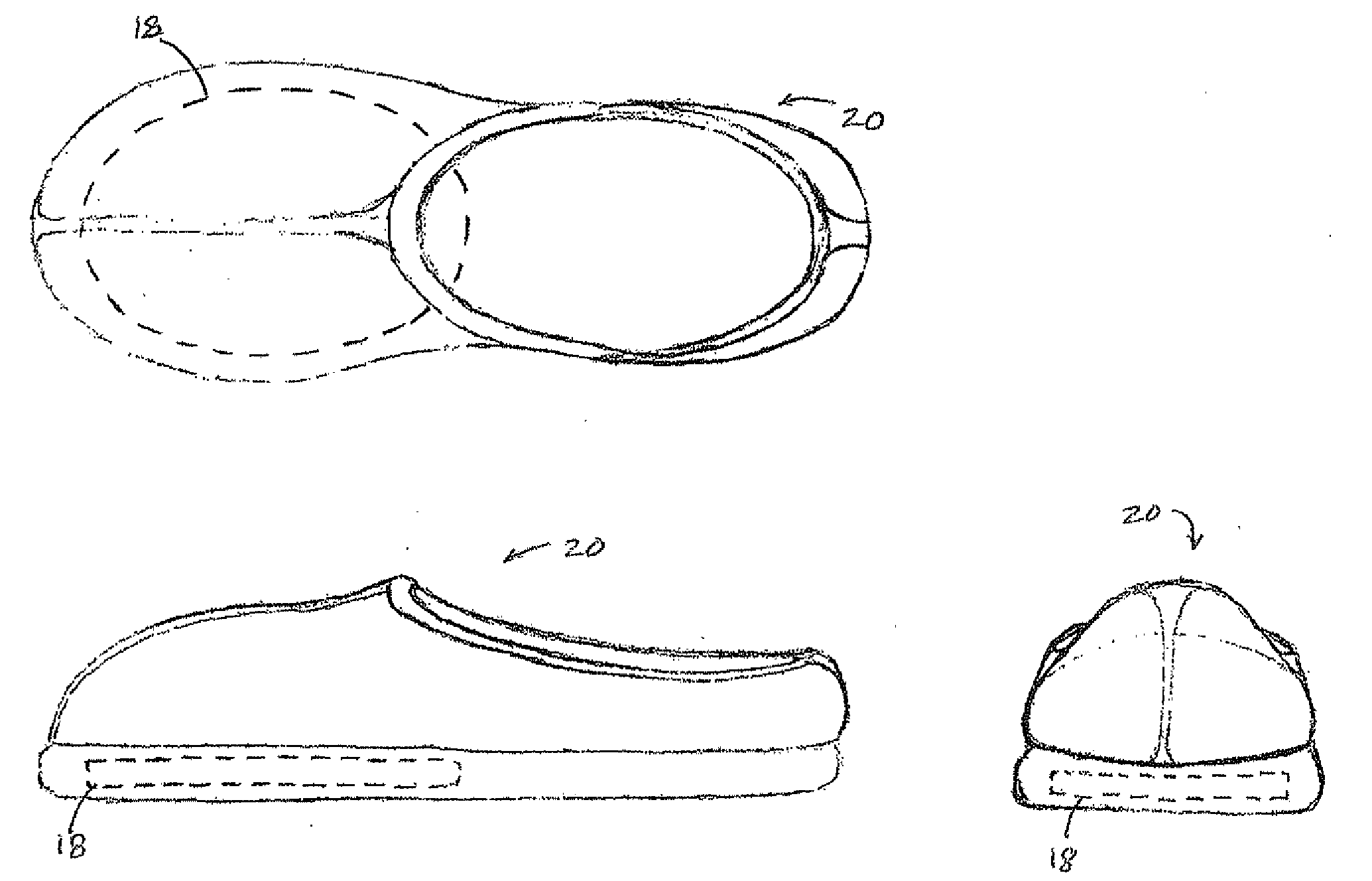
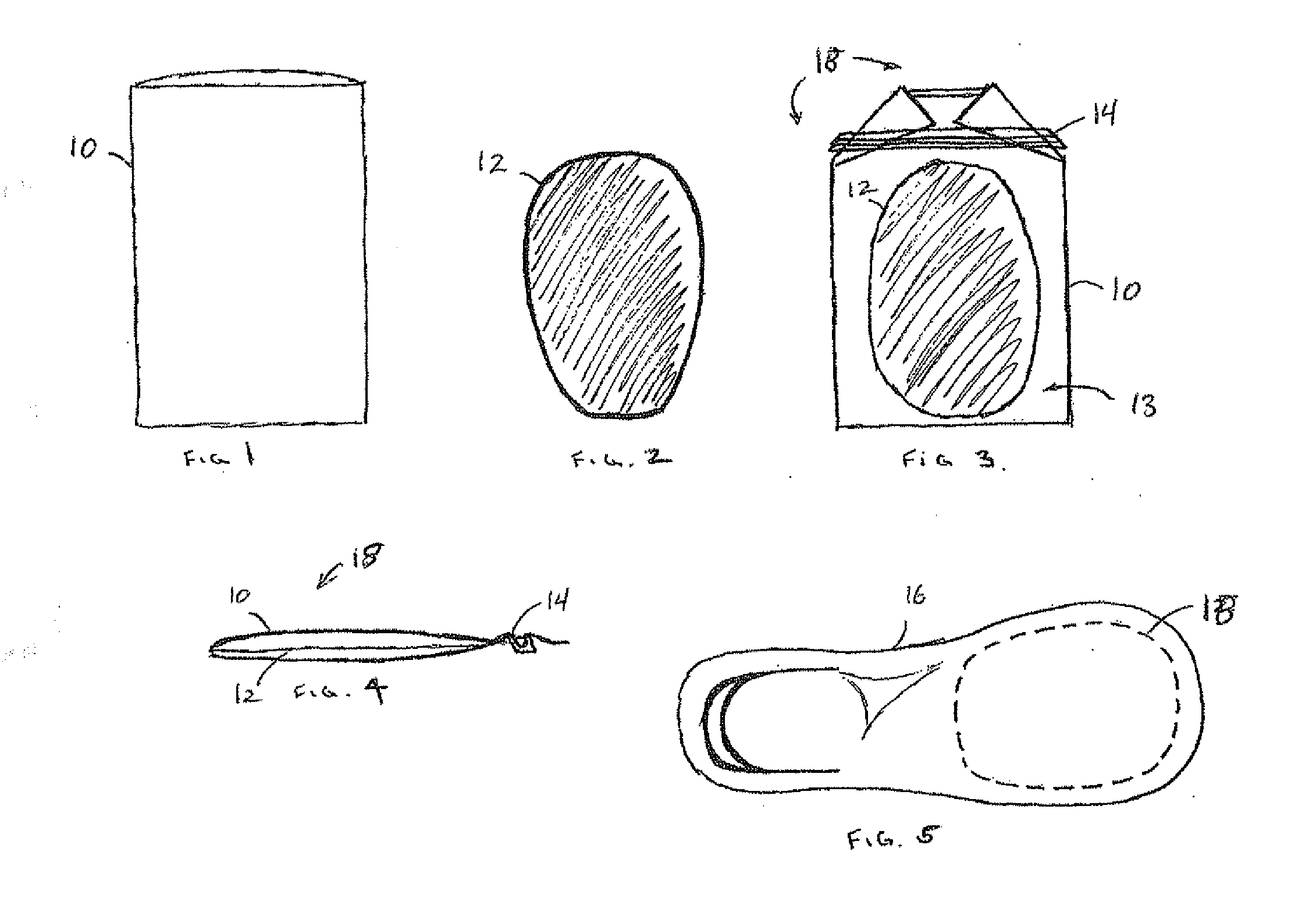
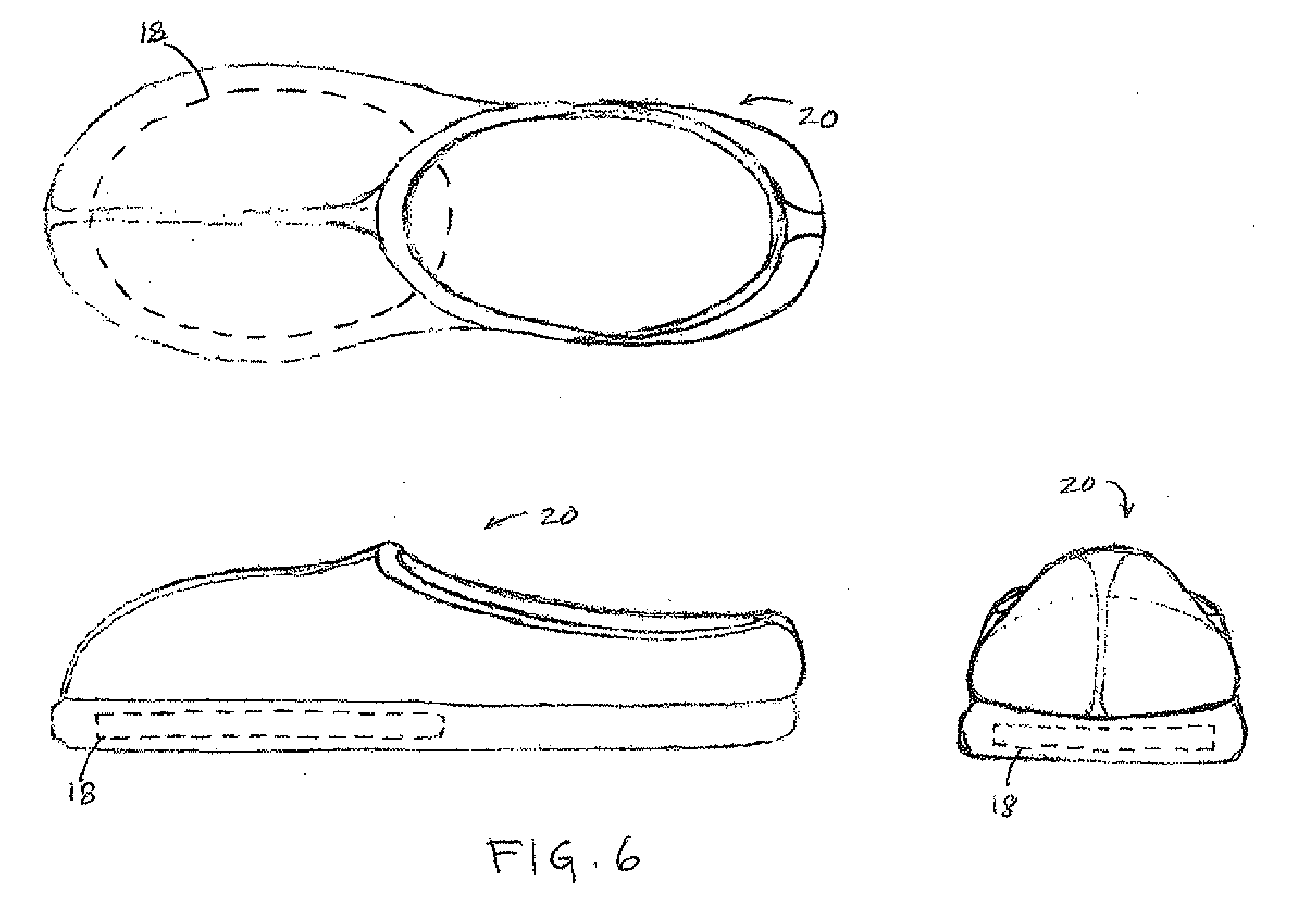
InactiveUS20070267398A1Minimal powerSimple materialOhmic-resistance heatingFootwearEngineeringPhase change
A method is provided of inductively heating an apparel apparatus having an integrated heating element with copper and ferrous materials that is encased with a liquid material or a phase changing wax material. The apparel is positioned on an induction heating platform for an effective time period and then removed from the platform. Moreover, a method of manufacturing apparel is disclosed by forming the heating element, inserting it into the apparel, and providing consumers a kit with instructions on use of the apparel along with an induction heating platform. Further, the present invention encompasses an apparatus of consumer apparel containing the heating element, for example a pair of shoes worn by a user who stands on the inductive heating platform and then simply walks off with effectively warm shoes.
Owner:MCCOY ANNE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com