Patents
Literature
1306 results about "Expiration date" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An expiration date or expiry date is a previously determined date after which something should no longer be used, either by operation of law or by exceeding the anticipated shelf life for perishable goods. Expiration dates are applied to selected food products and to some other manufactured products like infant car seats where the age of the product may impact its safe use.
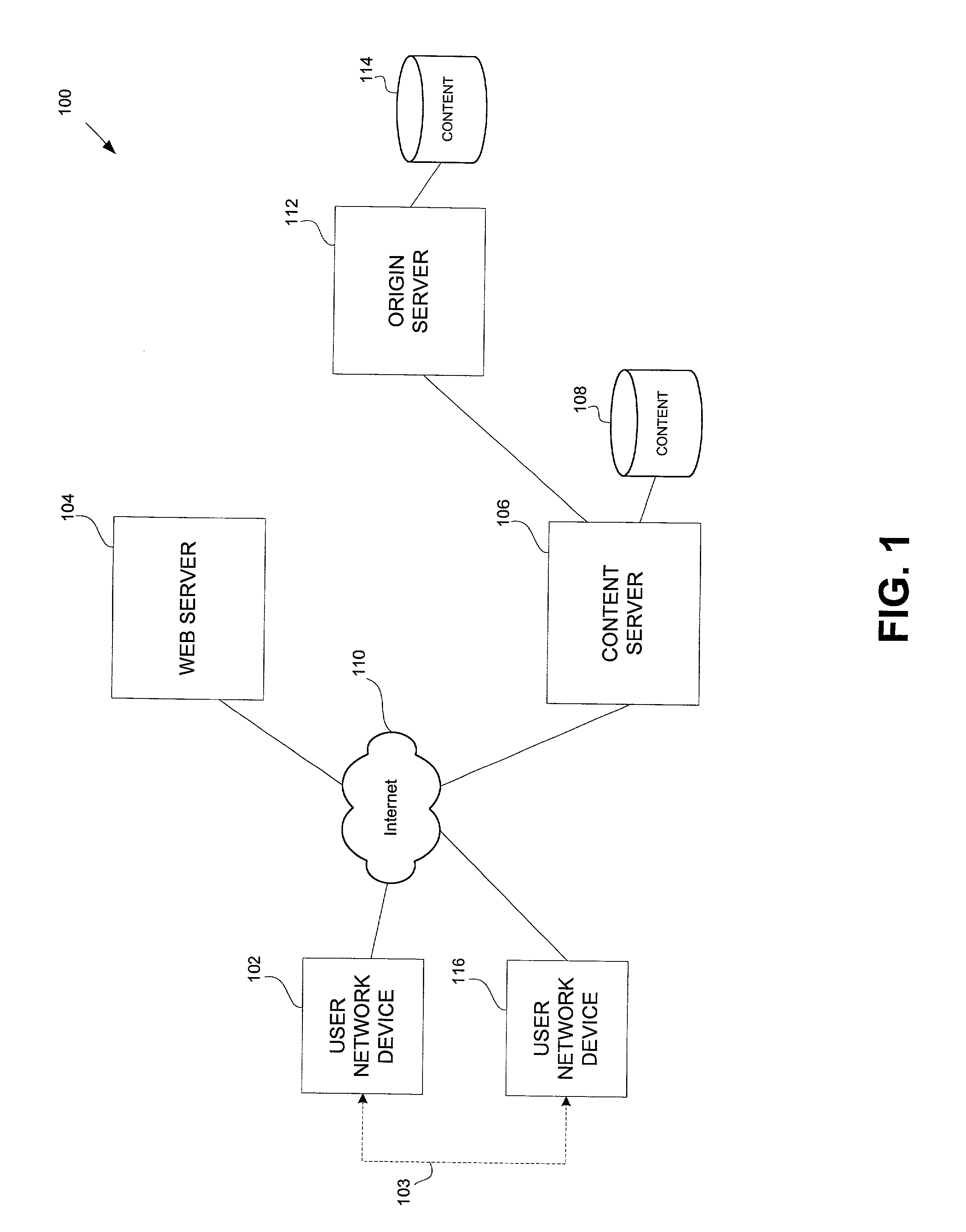
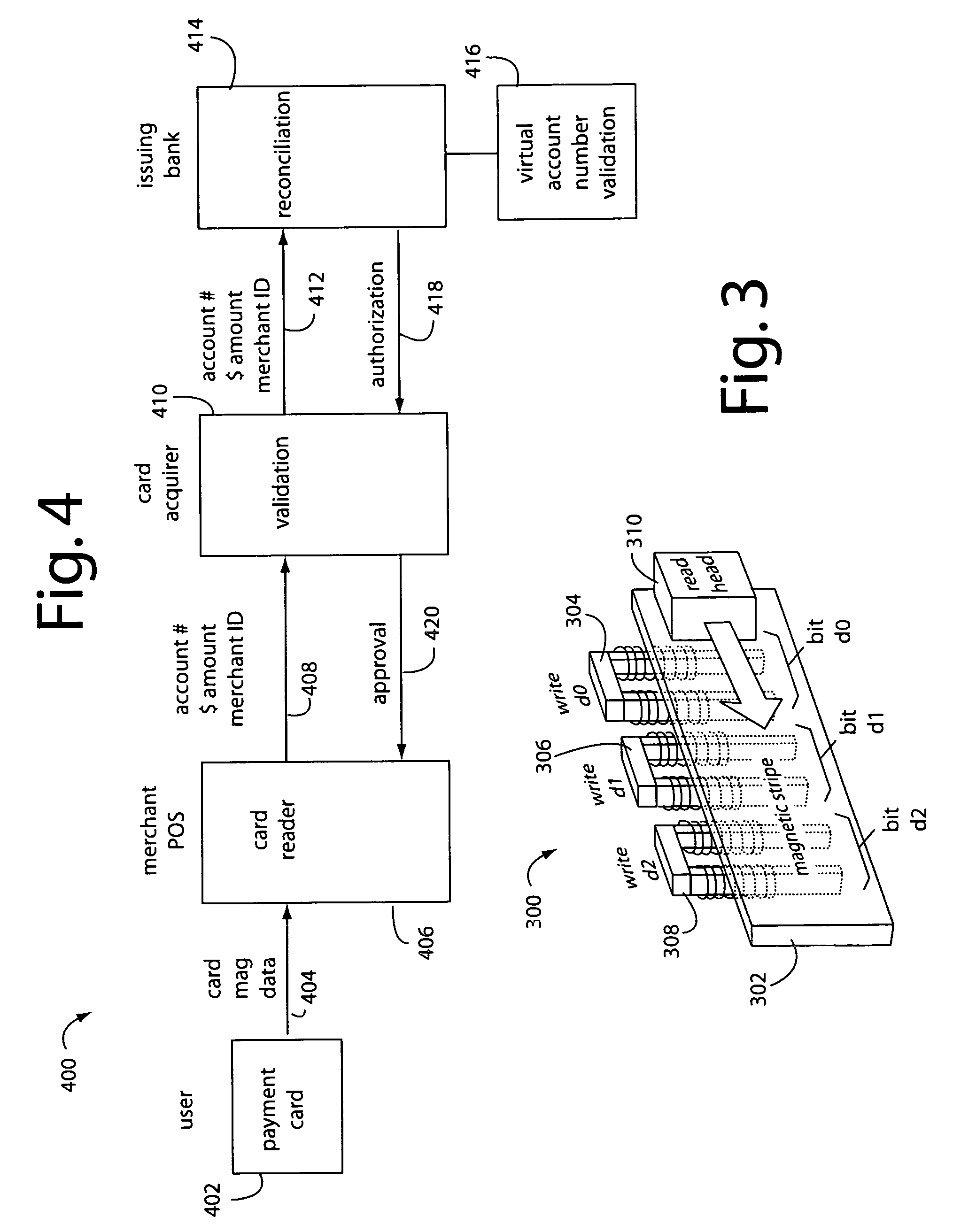
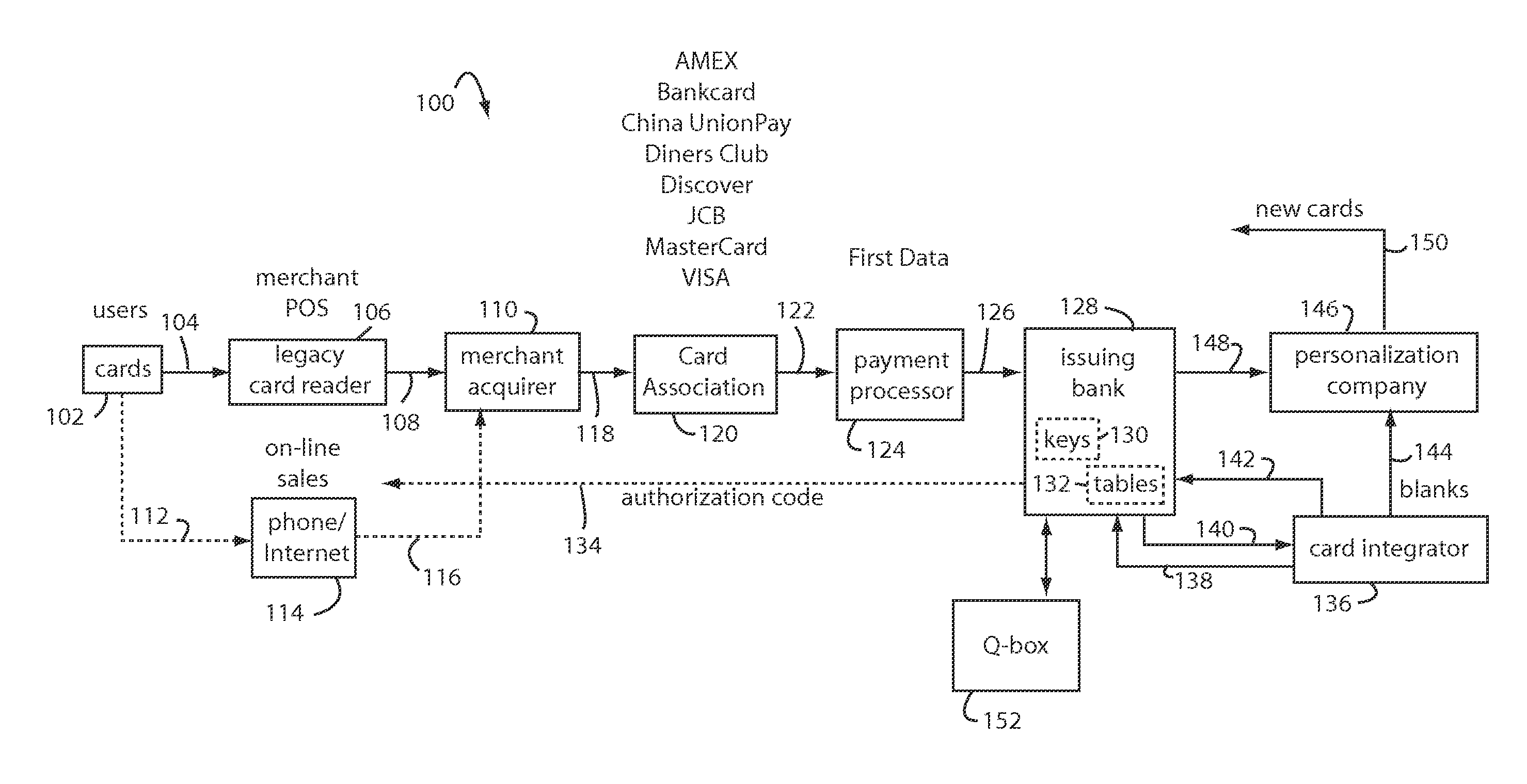
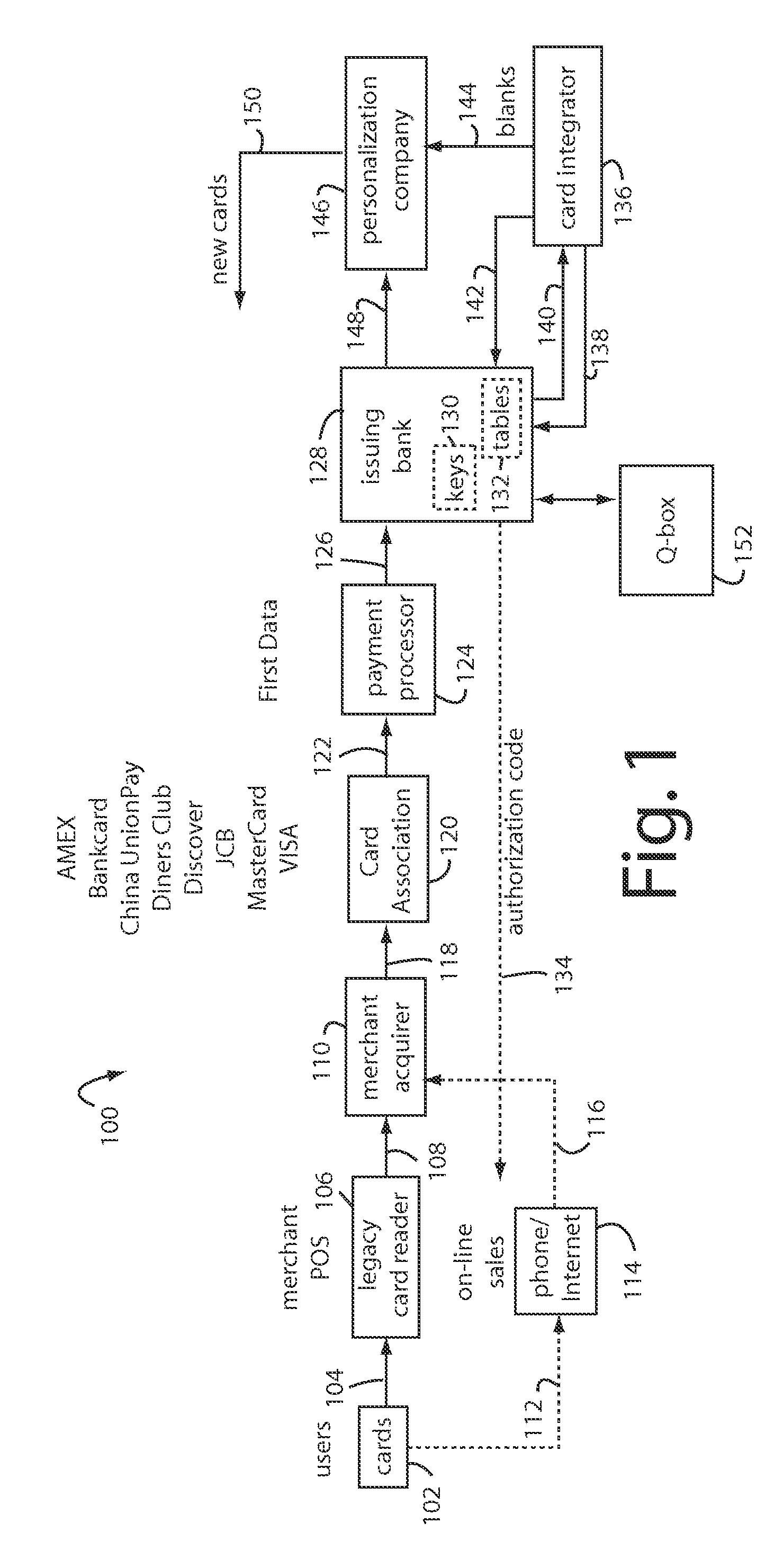
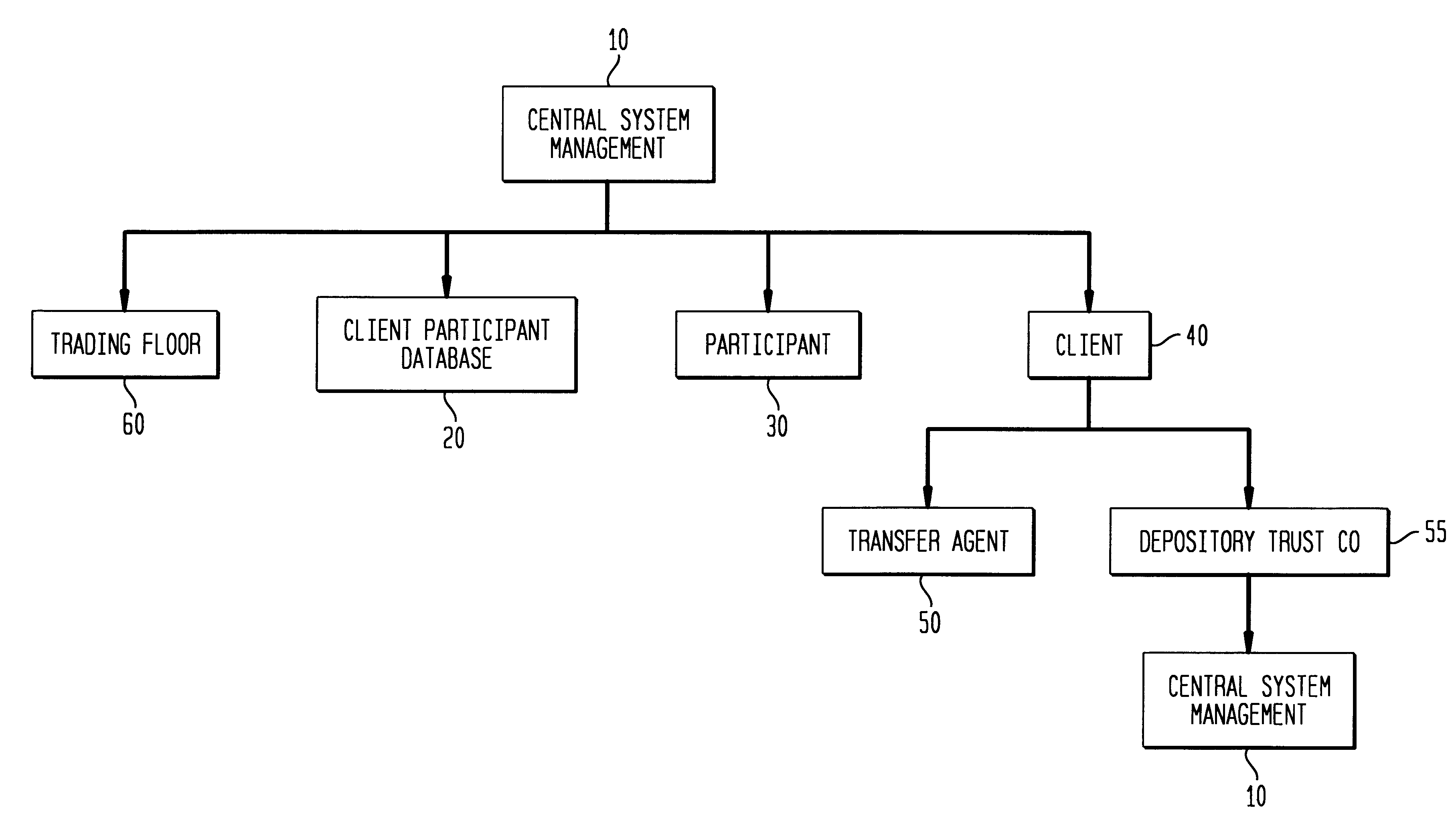
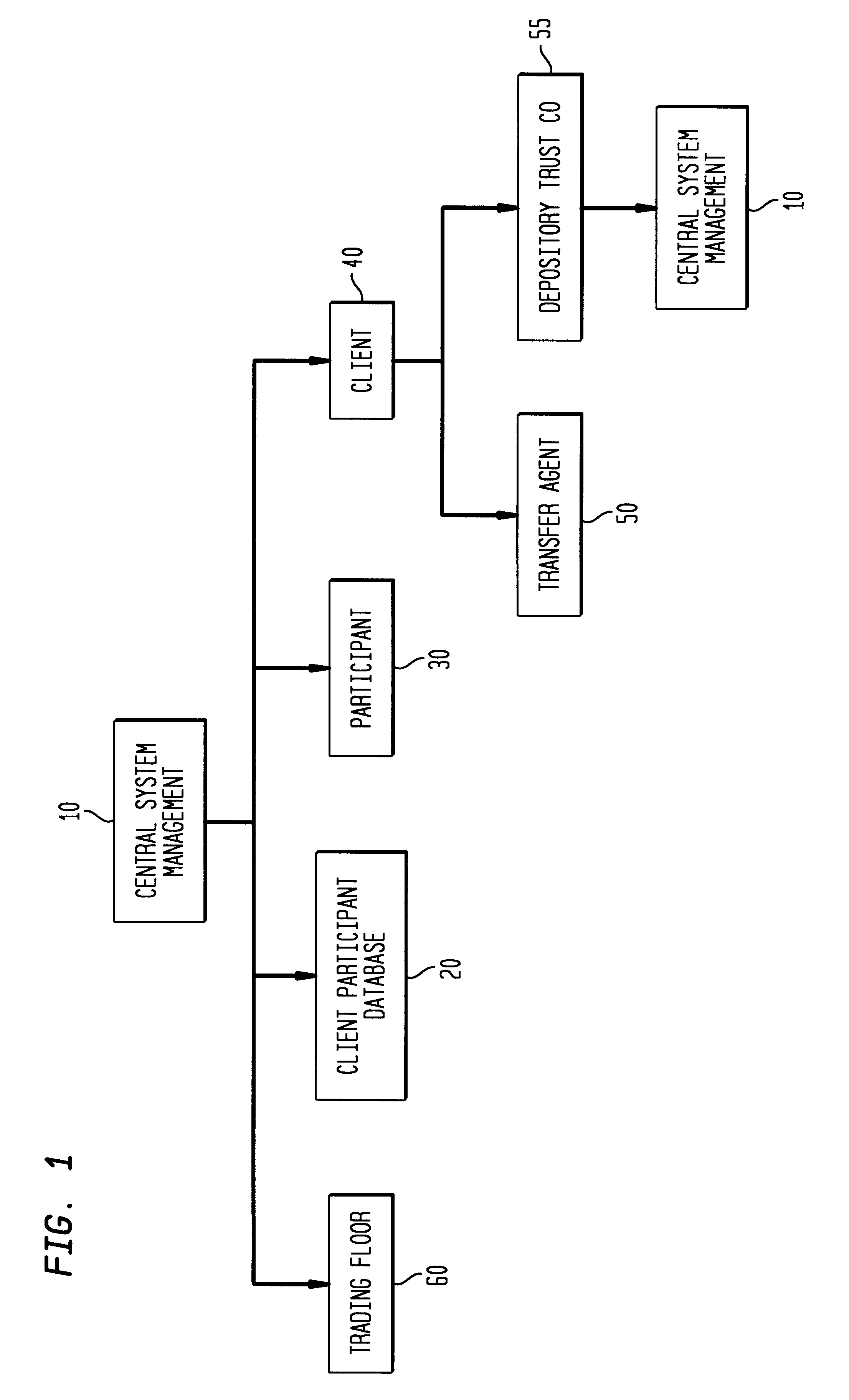
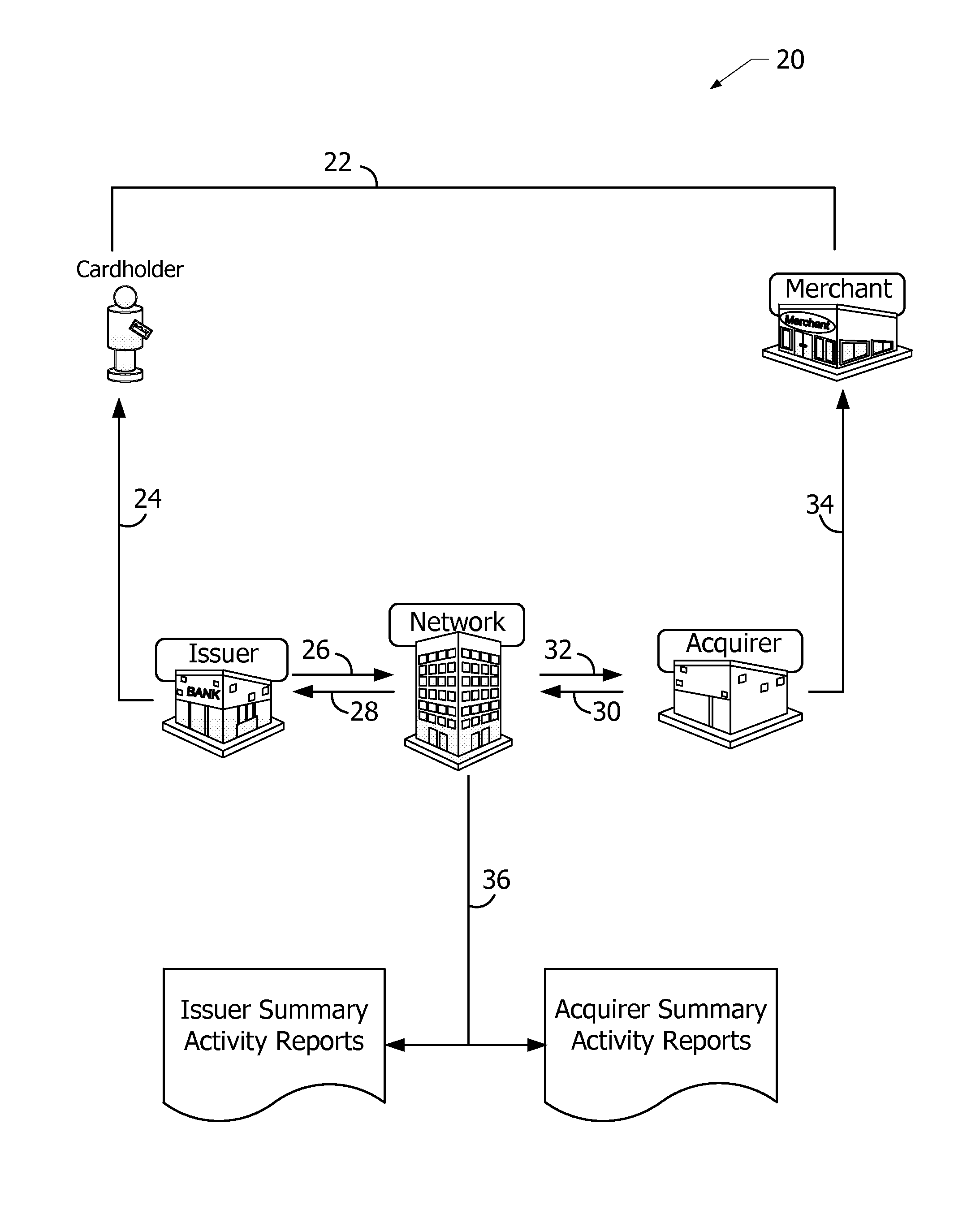
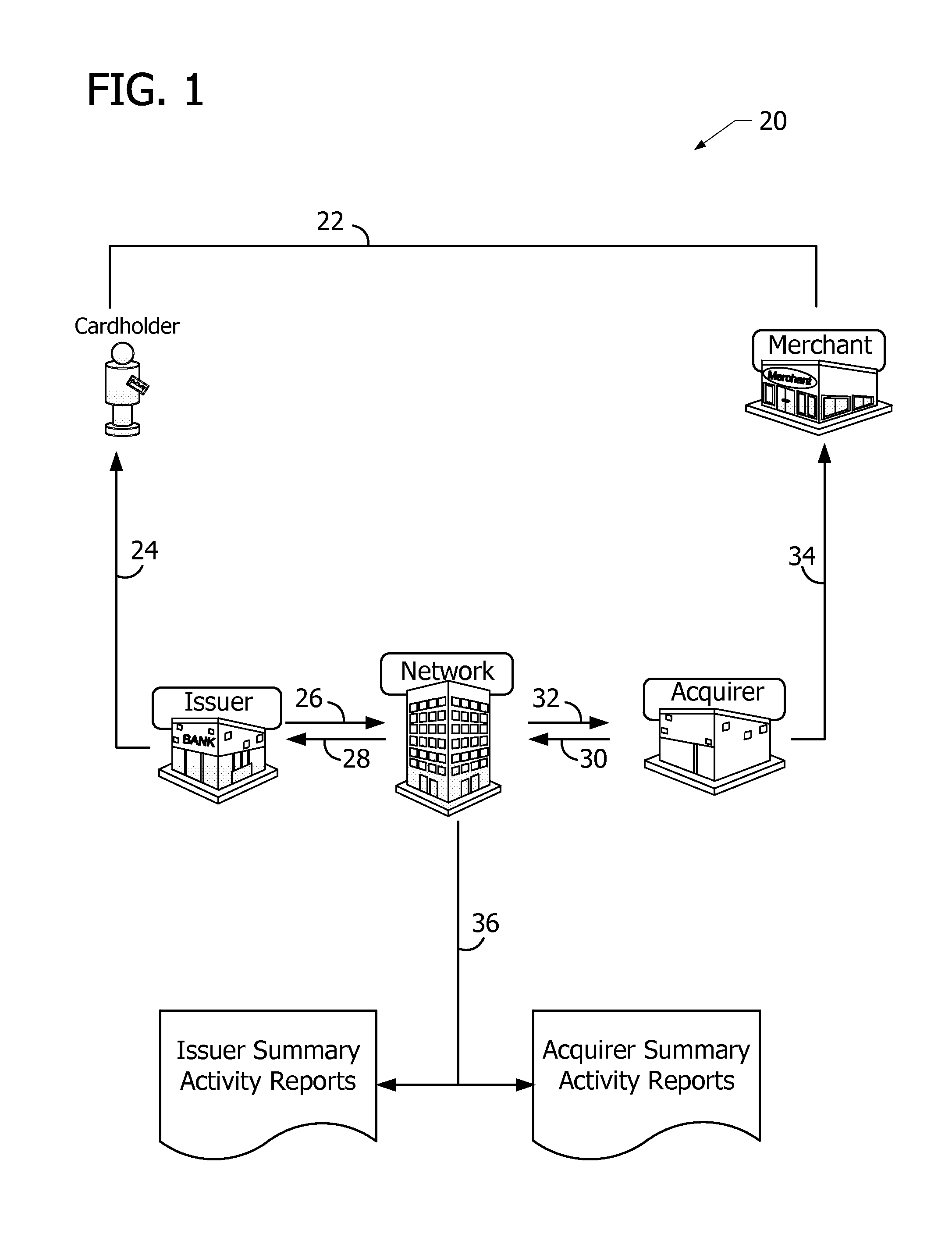
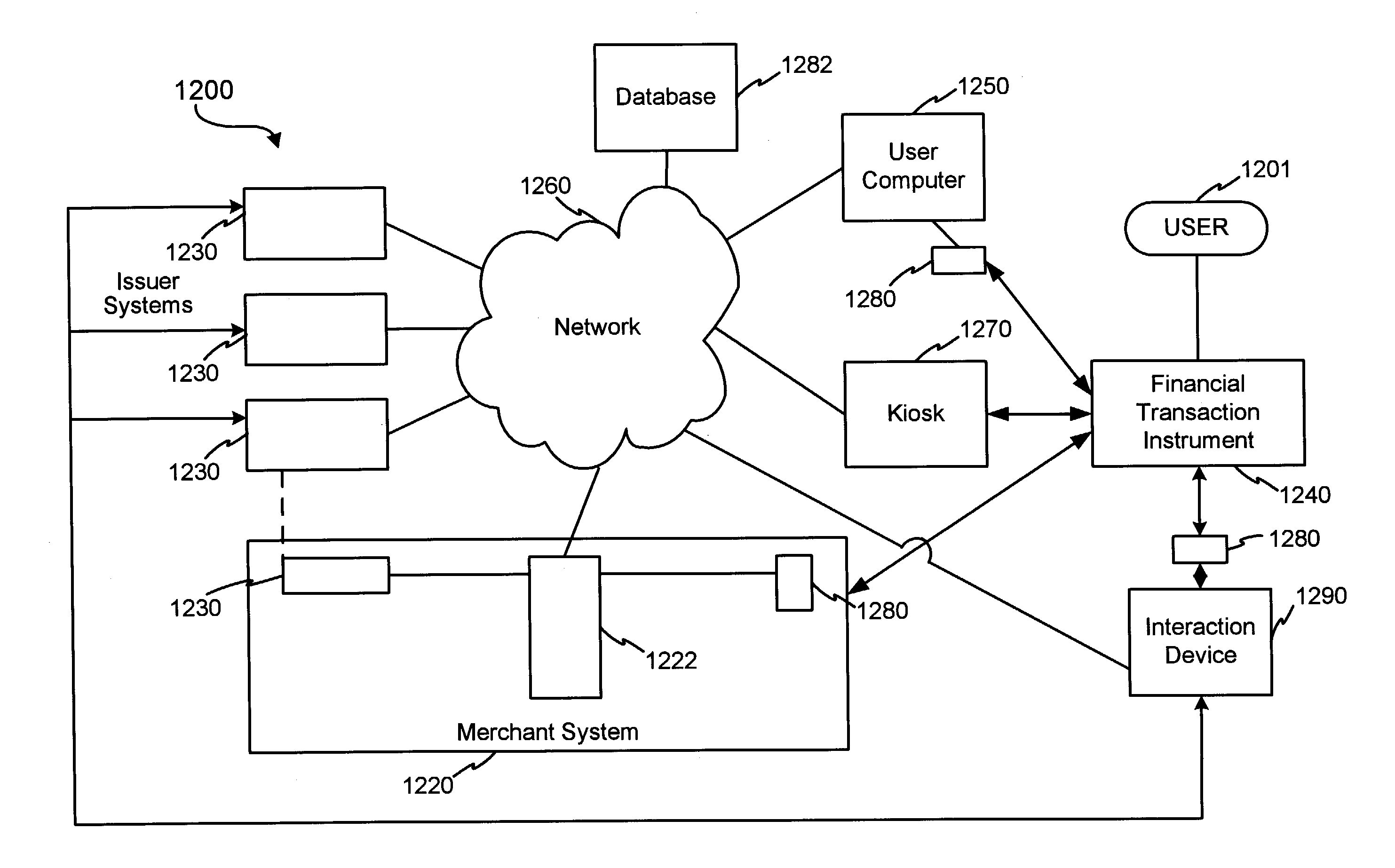
Financial transactions with dynamic personal account numbers
ActiveUS7580898B2Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
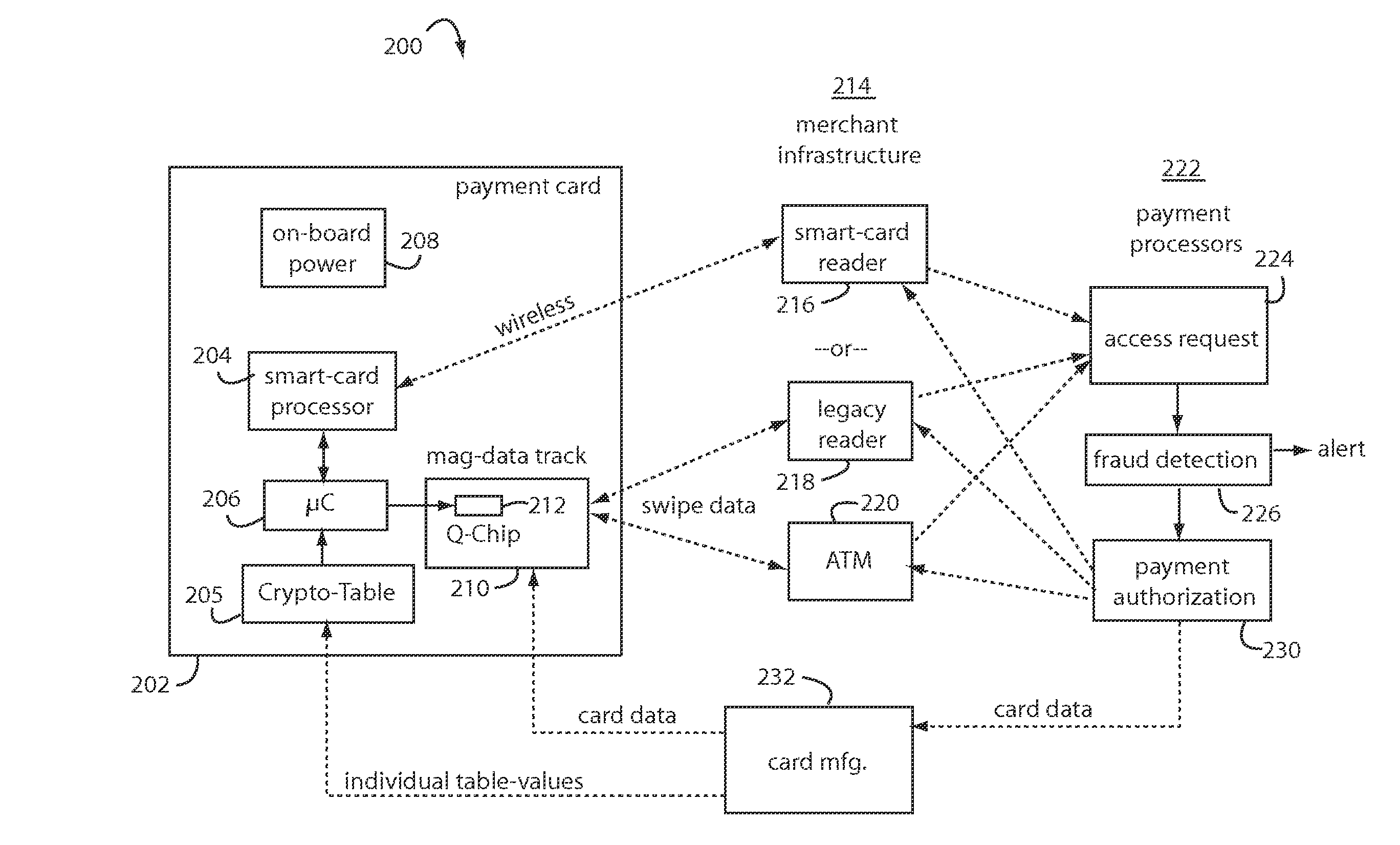
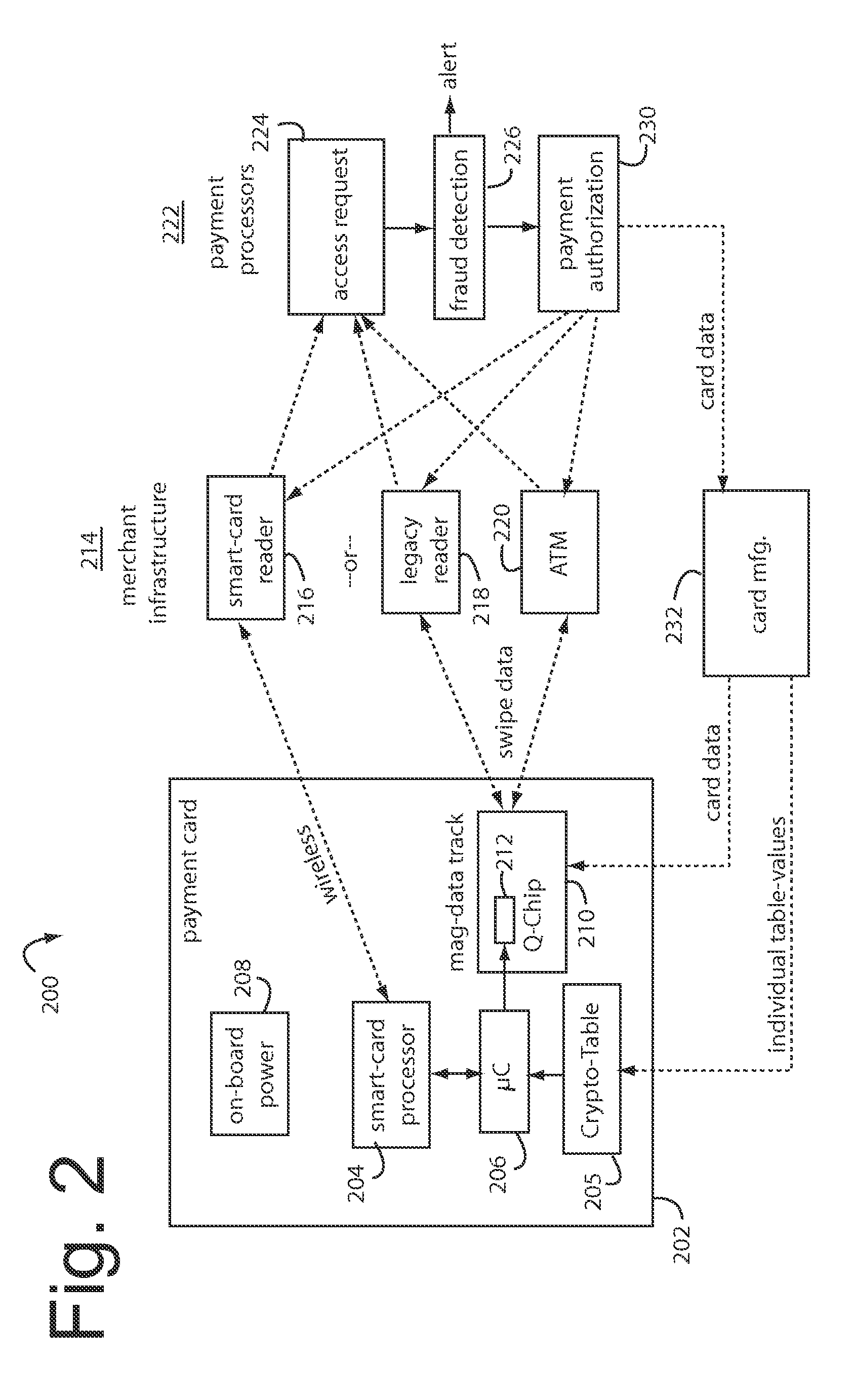
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
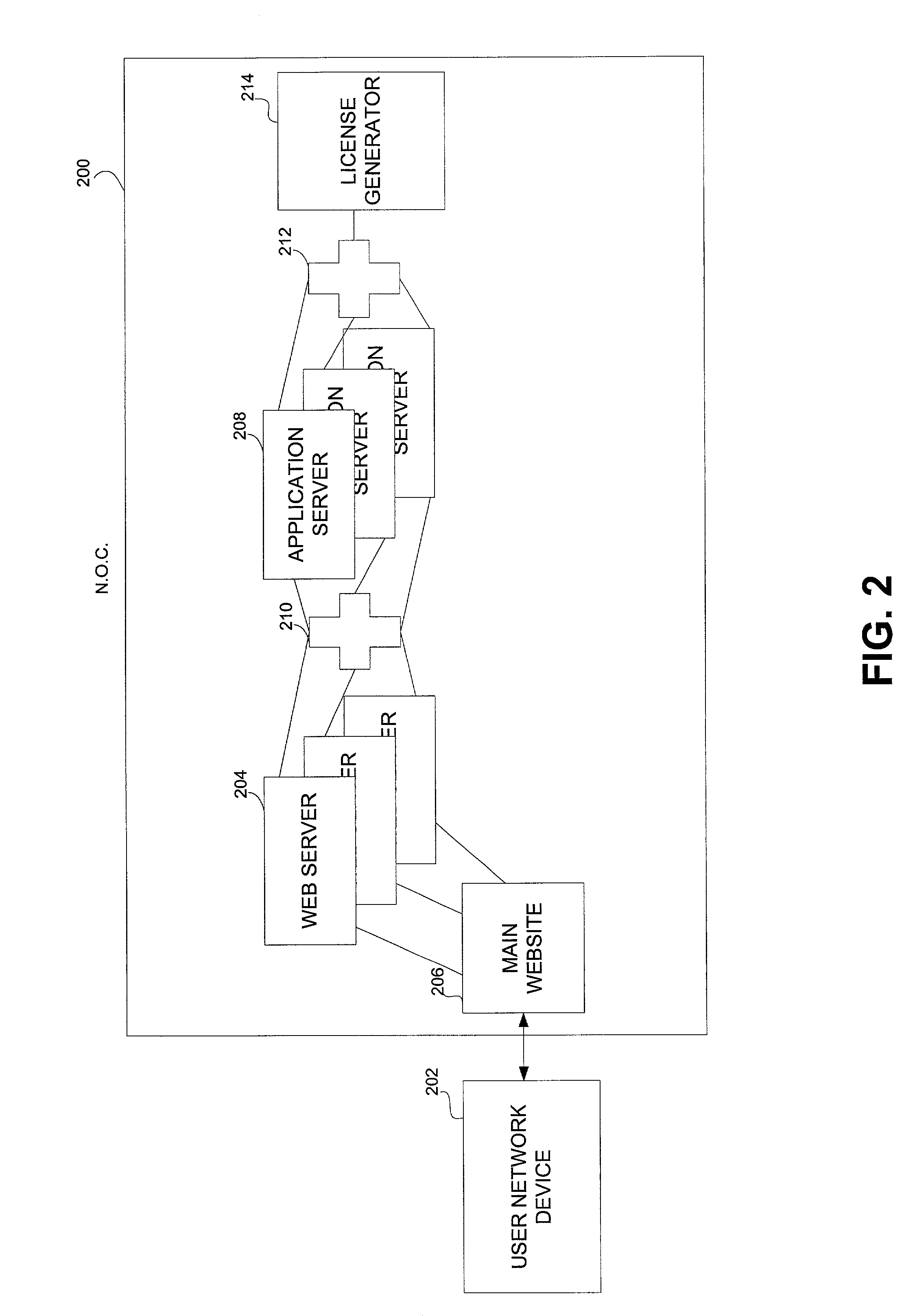
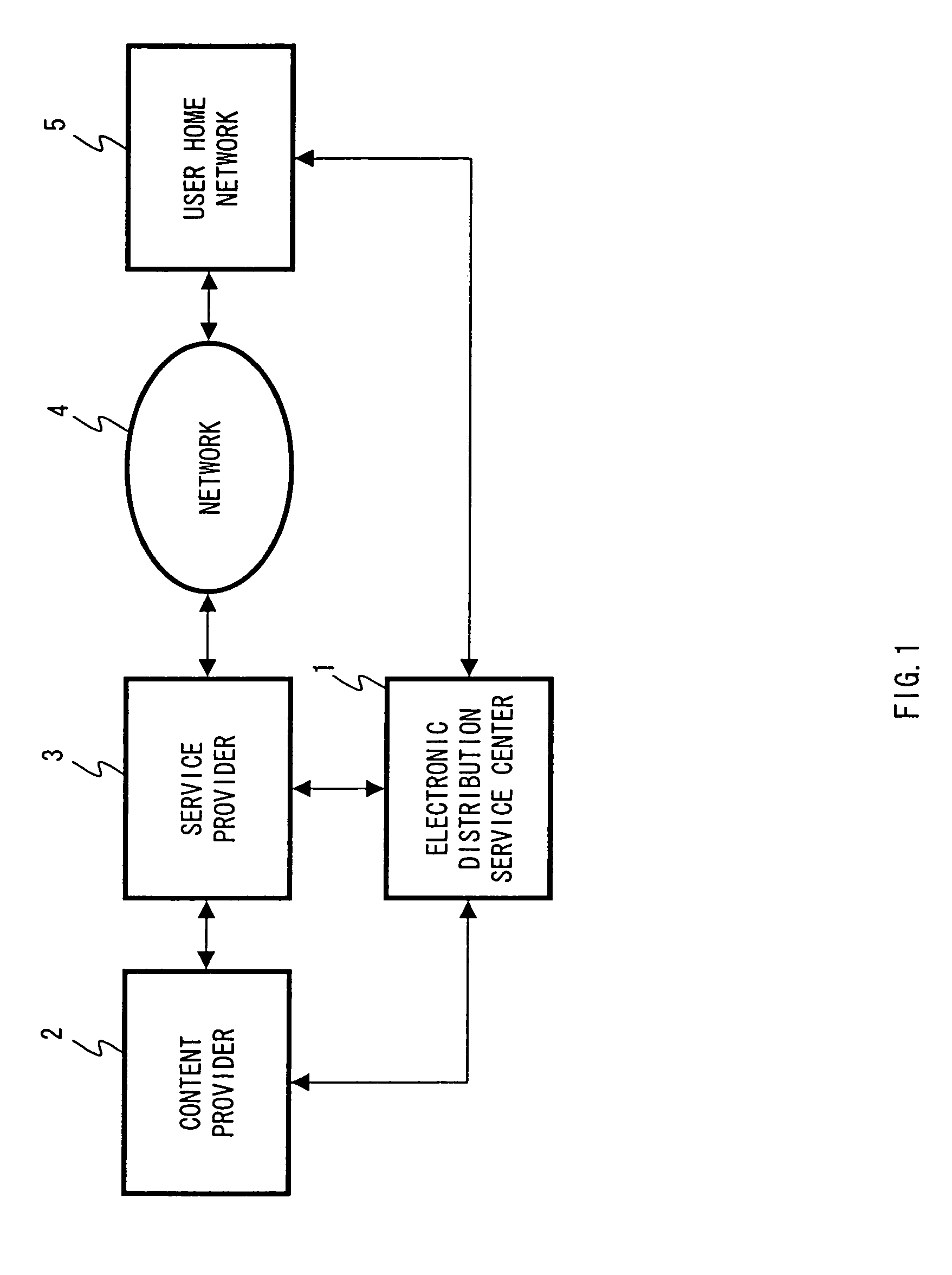
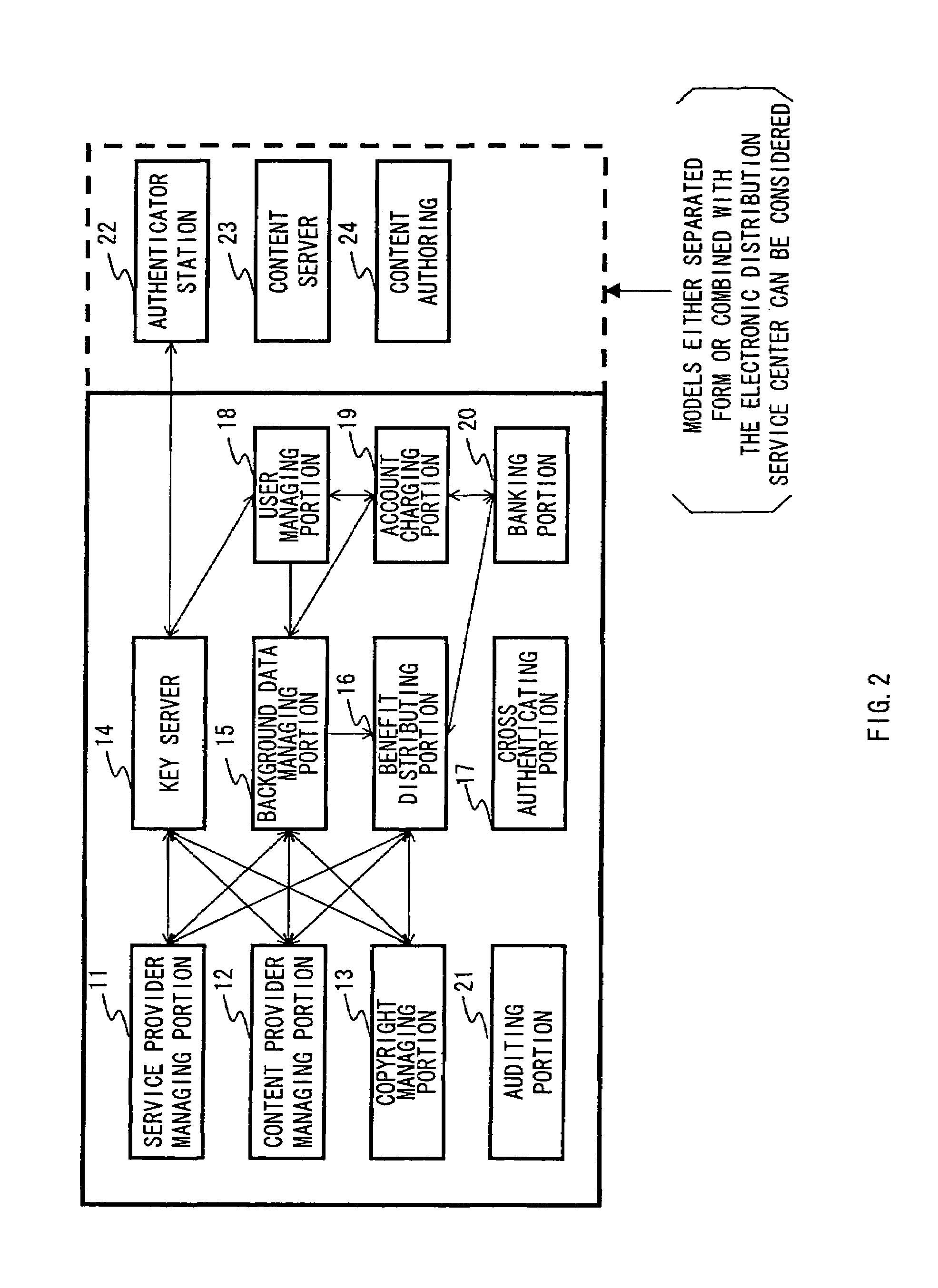
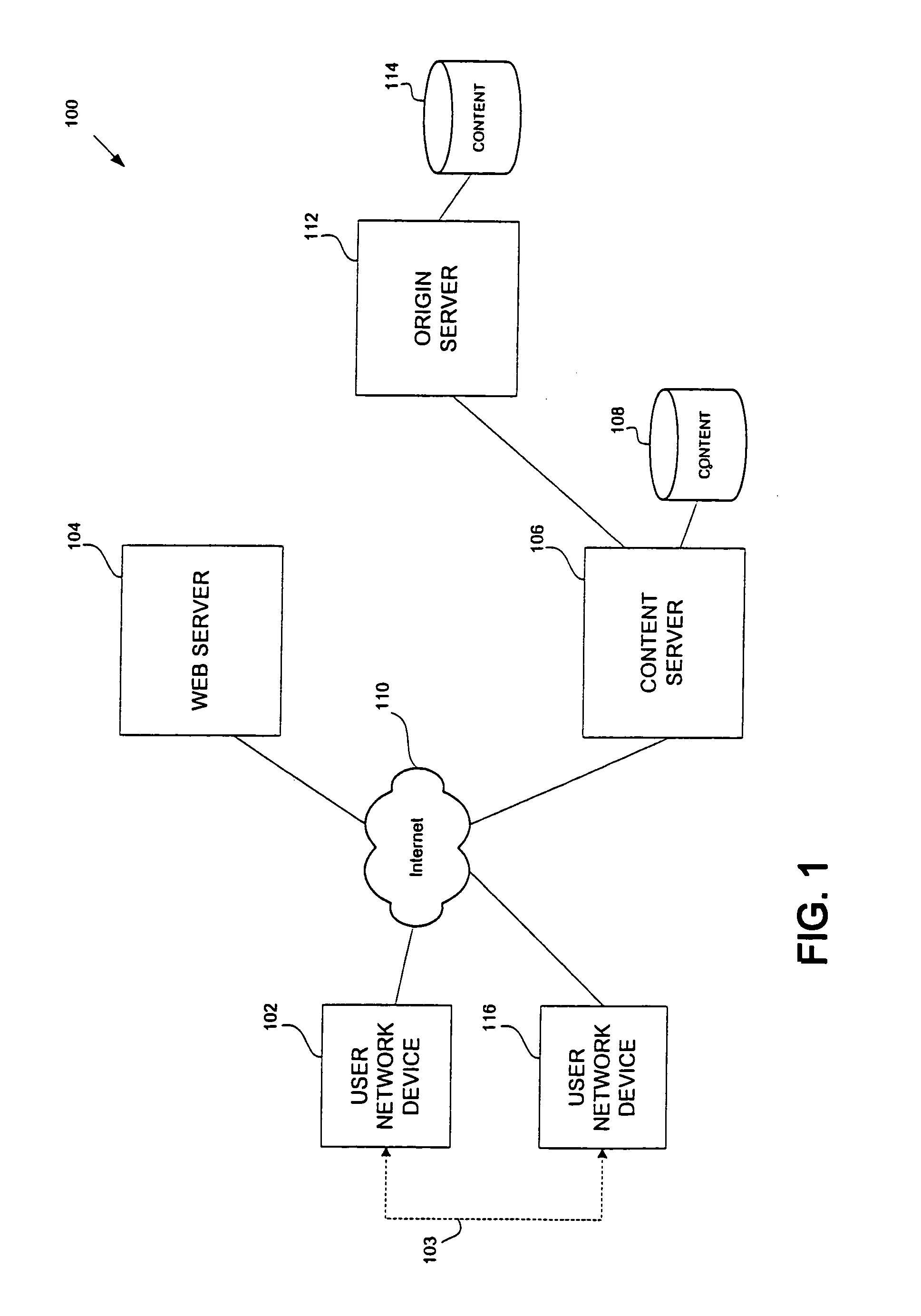
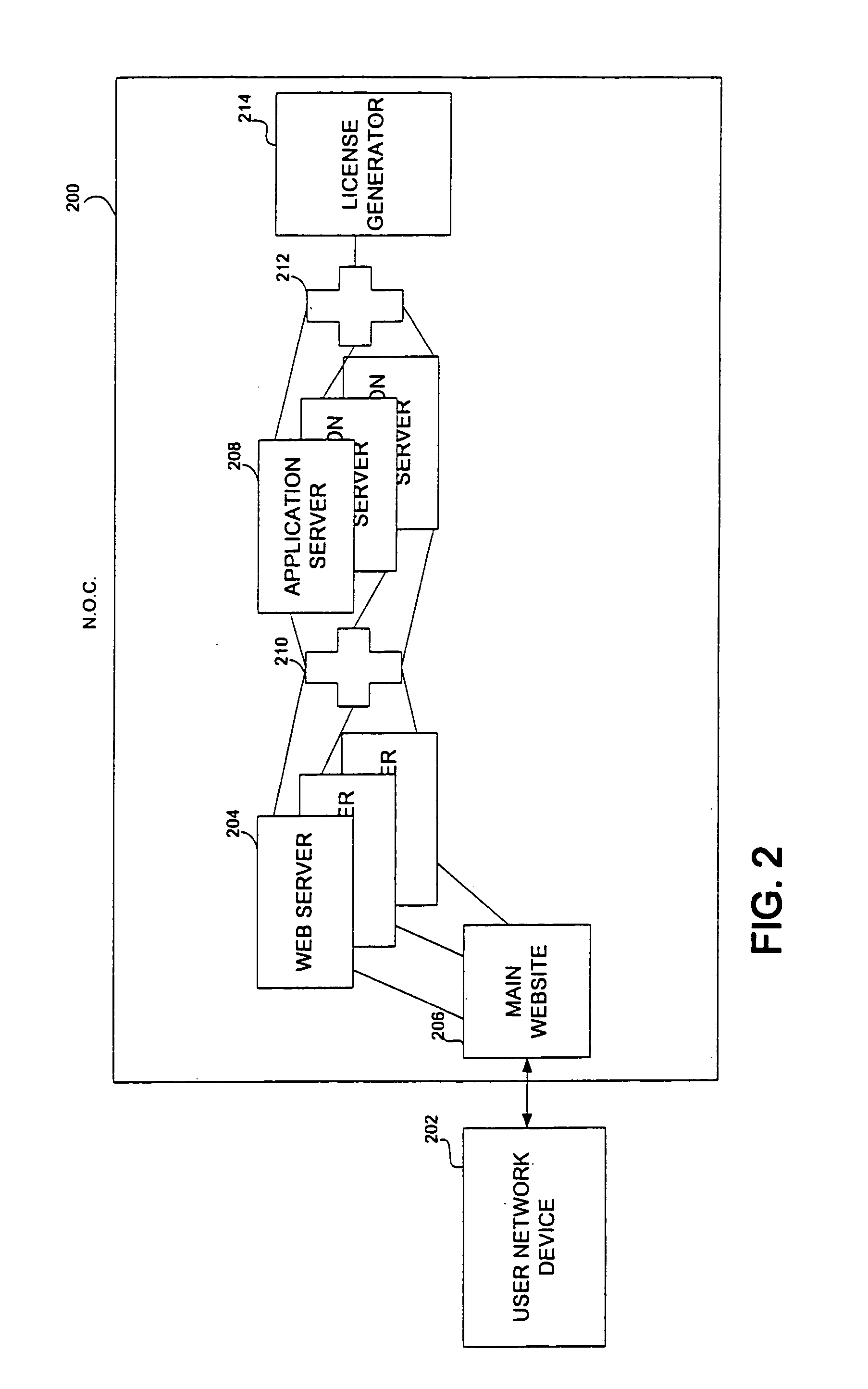
Secure digital content licensing system and method
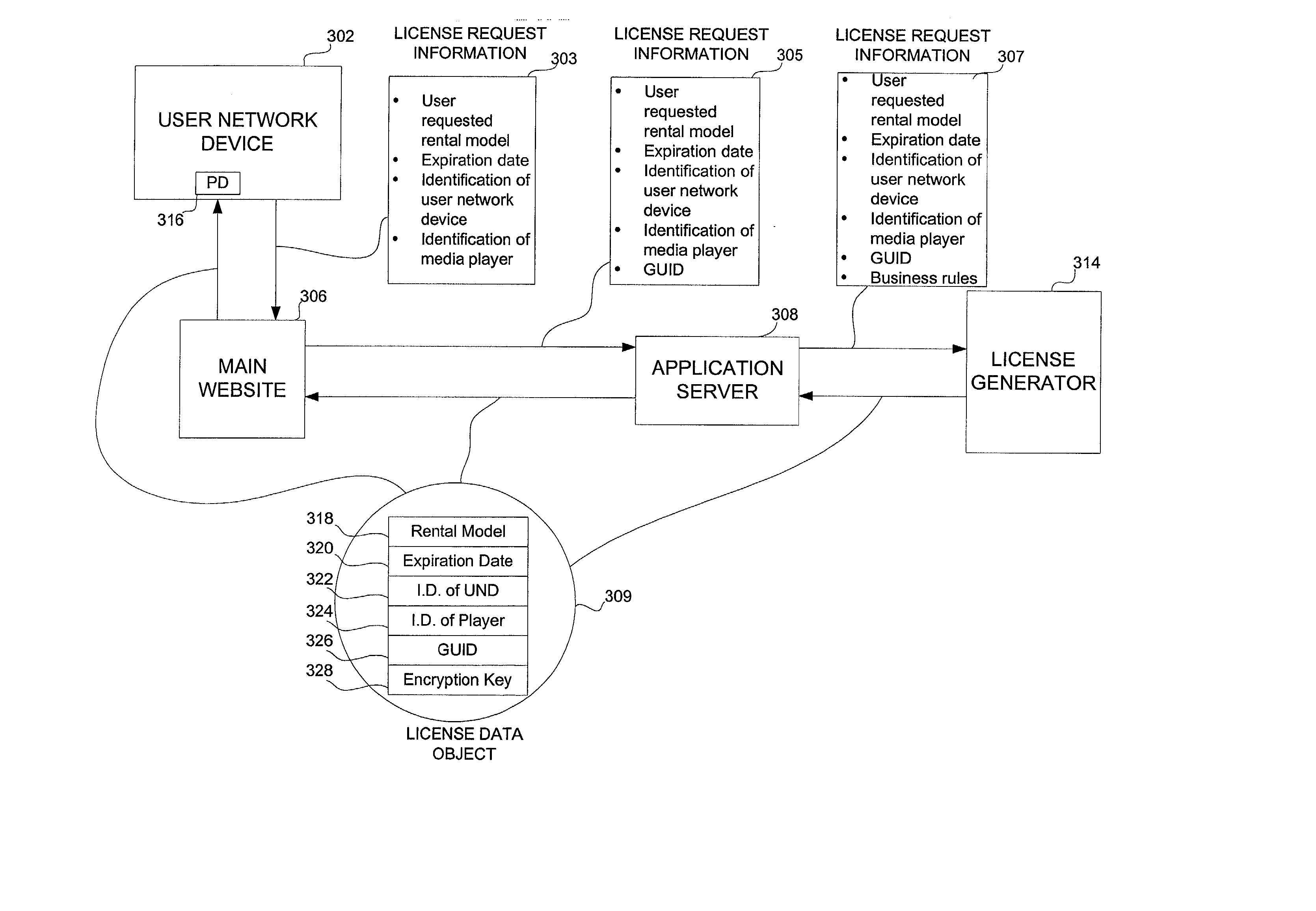
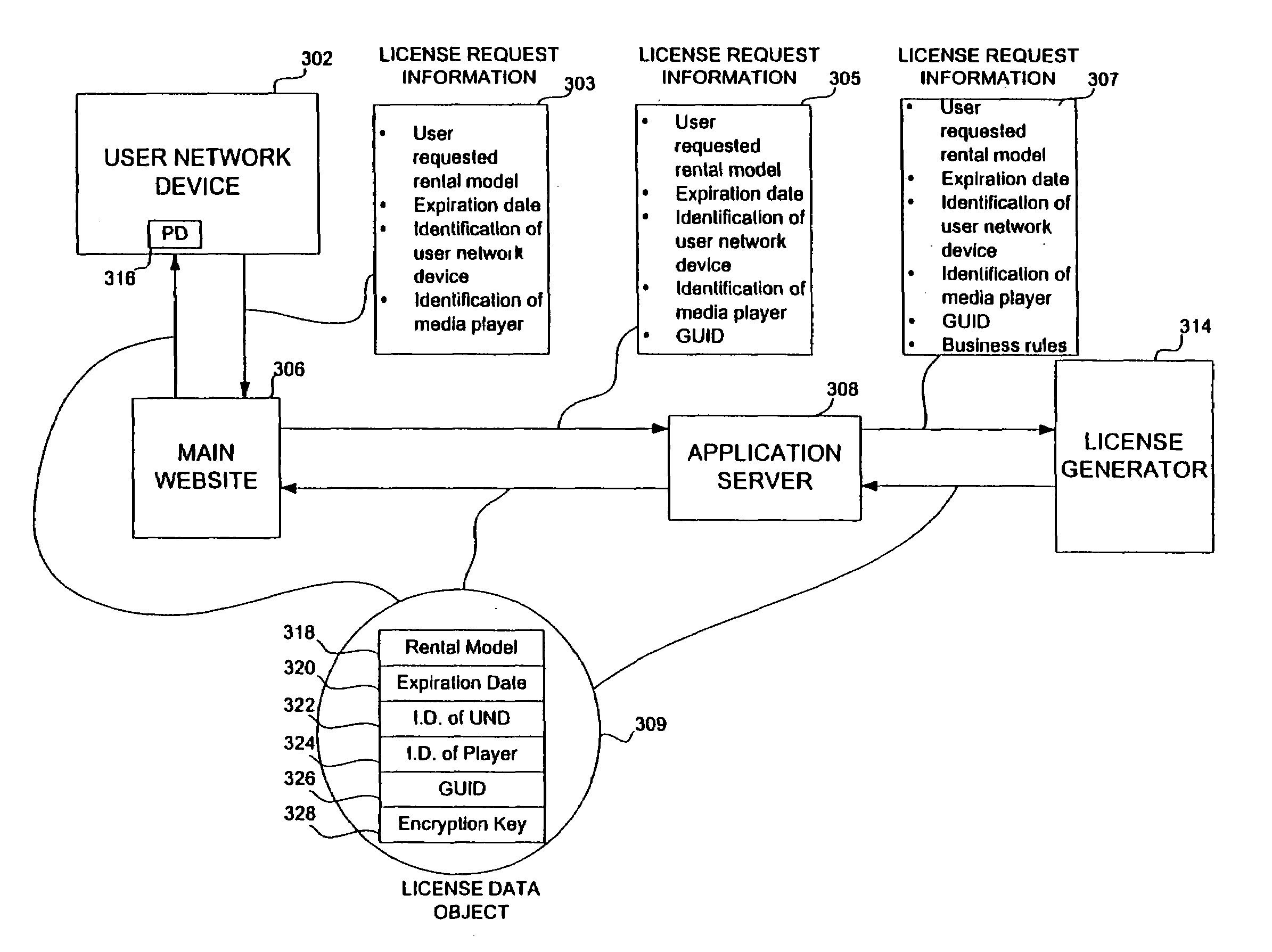
Embodiments of the present invention overcome the problems in the existing art described above by providing a secure digital content licensing system and method. Rental of the digital content occurs within an online environment including one or more user network-enabled devices and one or more server network devices connected by a communications link to the one or more user network-enabled devices. A user selects content displayed on a main website and requests download of the selected content to the user network-enabled device. To be able to access the content the user must obtain a license. The user's request for a license for specific content comprises information about a desired rental model, an expiration date for the rental model, and information that identifies the user's user network-enabled device, along with other information. A license for the content is generated which comprises the above information and also includes an encryption key for the selected movie. Media player and security technology residing on the user network-enabled device provides protection against unauthorized access to the content by ensuring that only licensed content is viewed and is accessed according to the rental model contained in the license. Media player and security technology also provides security against tampering by performing integrity checks on its various components and other components within the user network-enabled device. Revocation of access rights is made possible by revocation certificates that inhibit accessing of particular content for various reasons including compromised files or components.
Owner:BLOCKBUSTER LLC
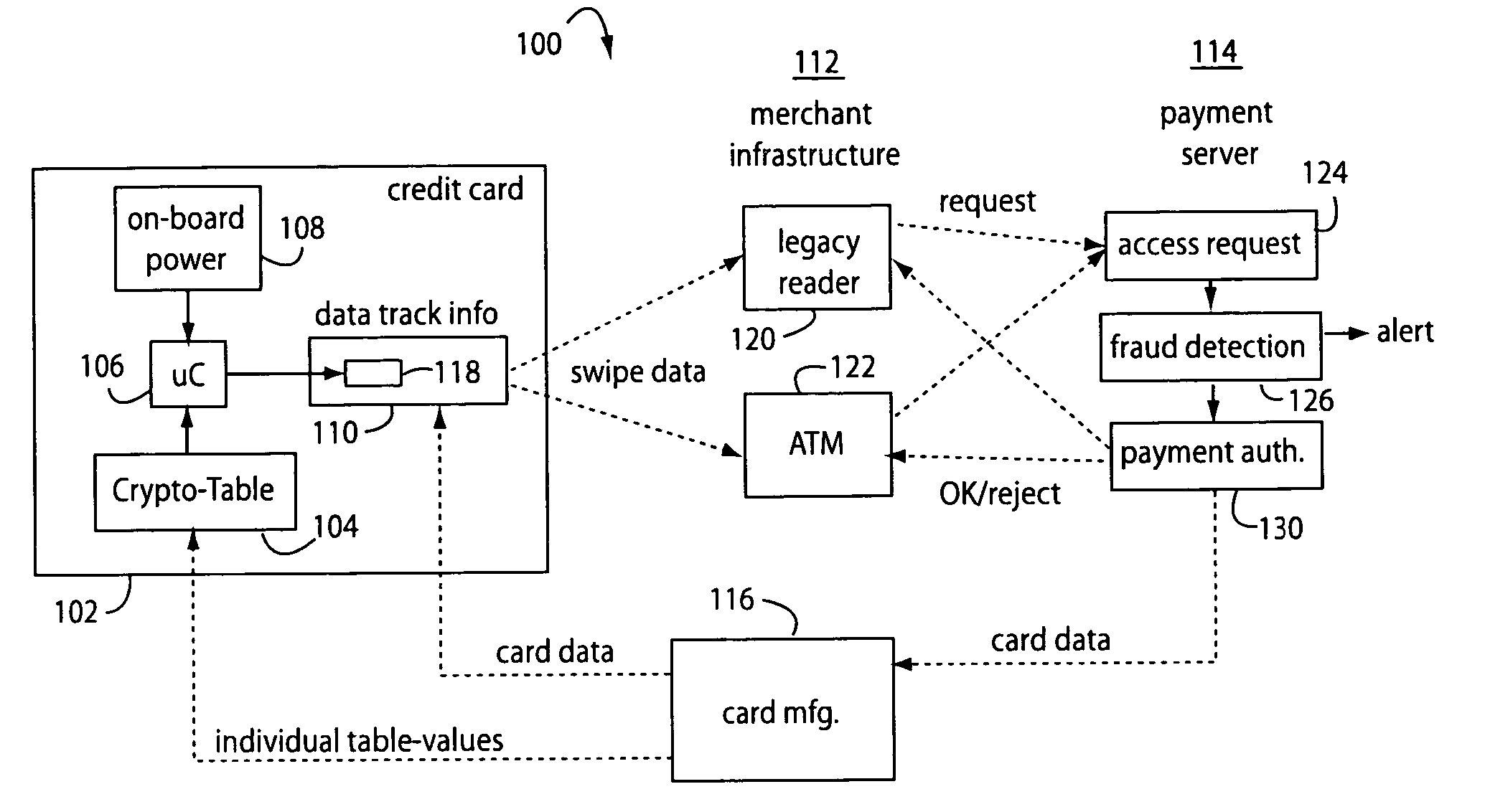
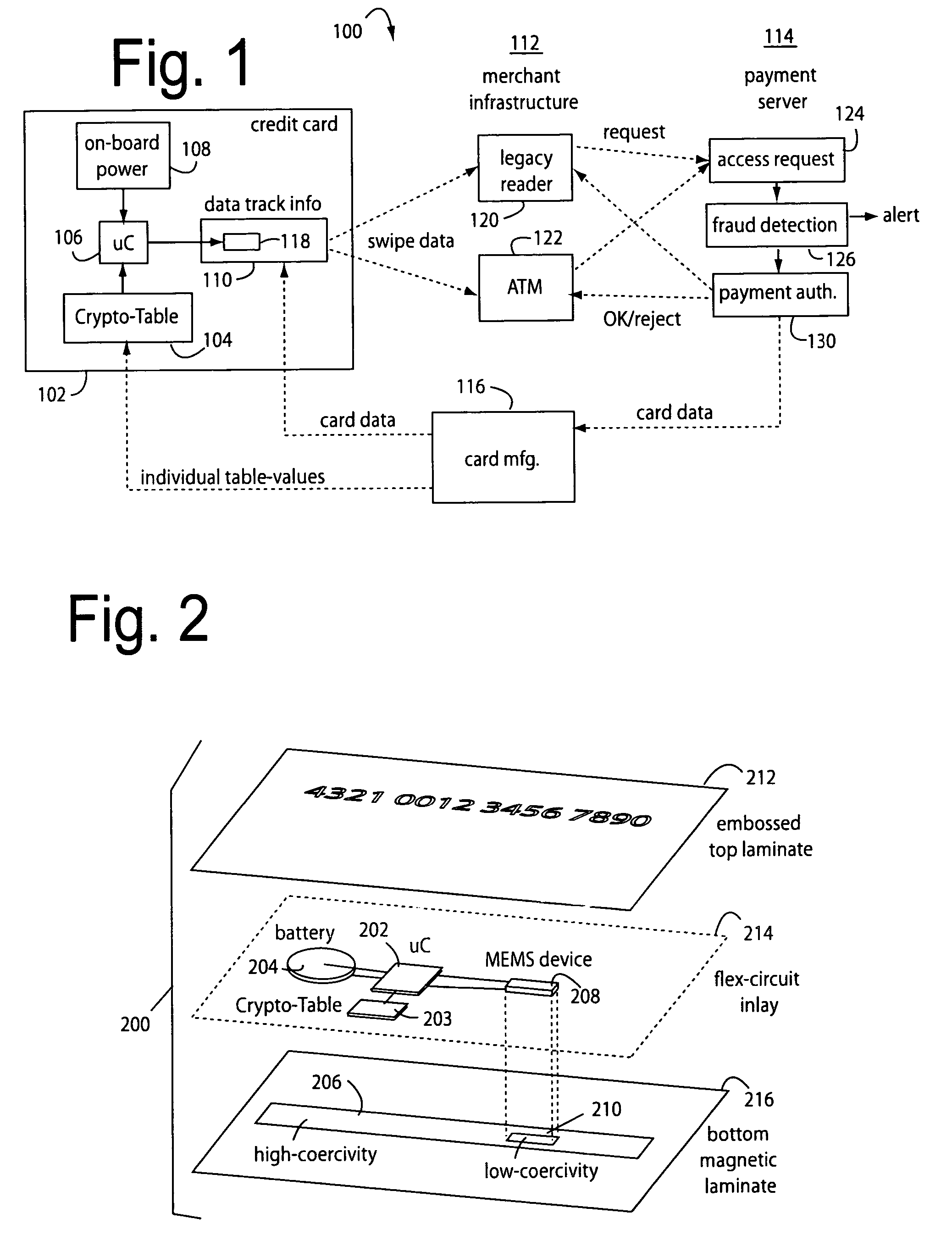
Automated payment card fraud detection and location
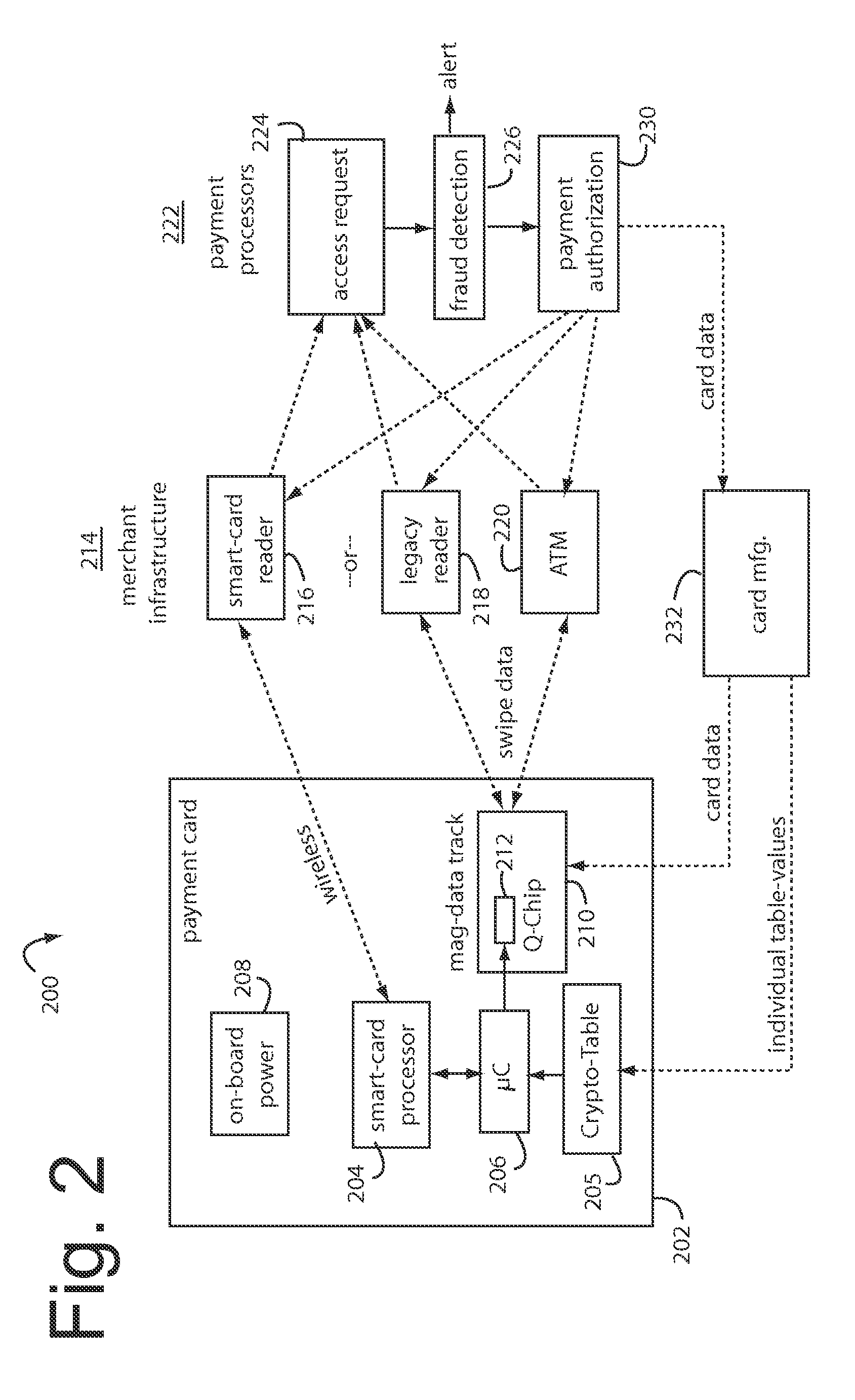
A payment card fraud detection business model comprises an internal virtual account number generator and a user display for Card-Not-Present transactions. Card-Present transactions with merchant card readers are enabled by a magnetic array internally associated with the card's magnetic stripe. The internal virtual account number generator is able to reprogram some of the magnetic bits encoded in the magnetic stripe to reflect the latest virtual account number. The internal virtual account number generator produces a sequence of virtual numbers that can be predicted and approved by the issuing bank. Once a number is used, such is discarded and put on an exclusion list or reserved for a specific merchant until the expiration date. A server for the issuing bank logs the merchant locations associated with each use or attempted use, and provides real-time detection of fraudulent attempts to use a virtual account number on the exclusion list. Law enforcement efforts can then be directed in a timely and useful way not only where the fraud occurs but also at its origination.
Owner:FITBIT INC
Financial transactions with dynamic personal account numbers
ActiveUS20070208671A1Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
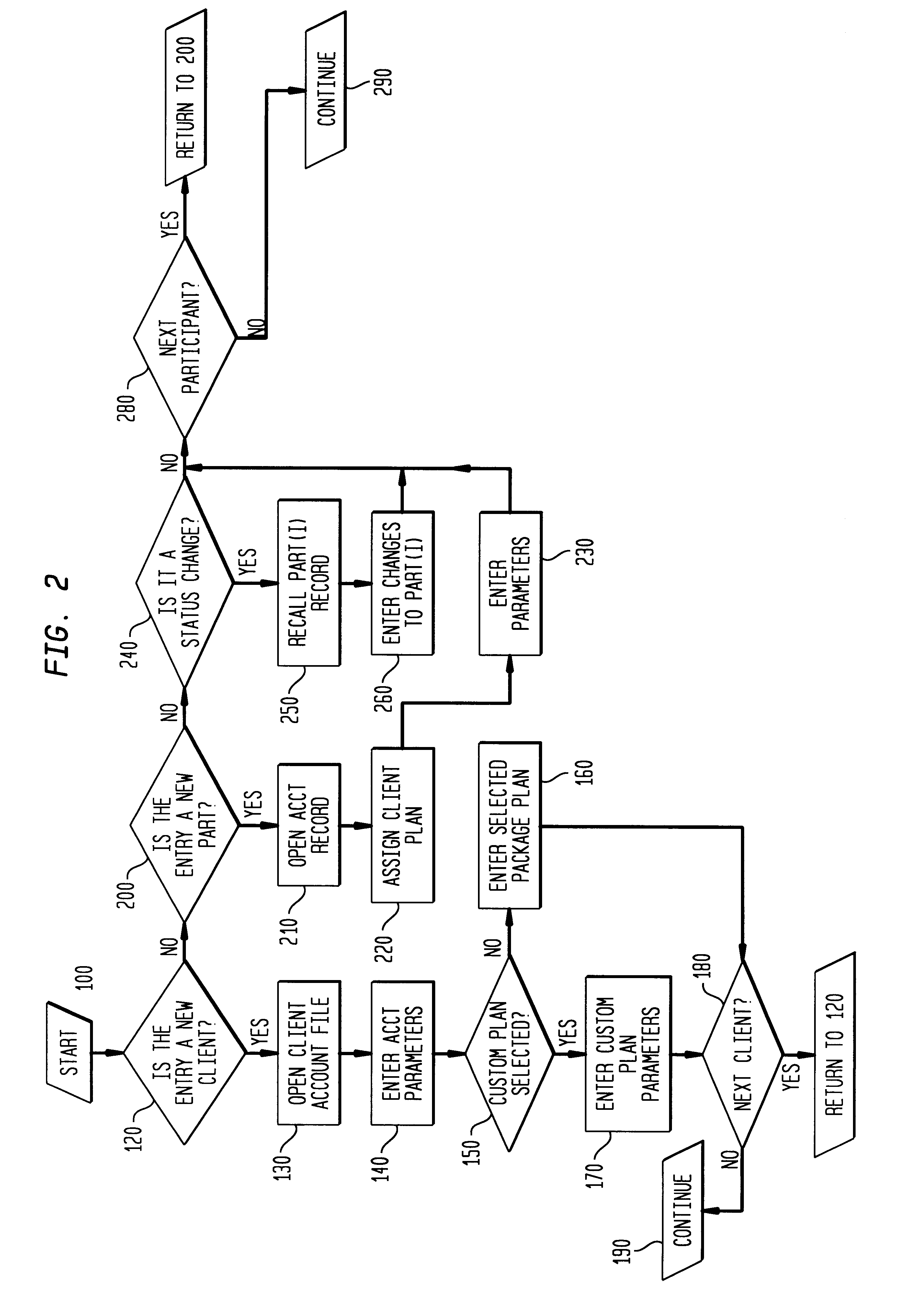
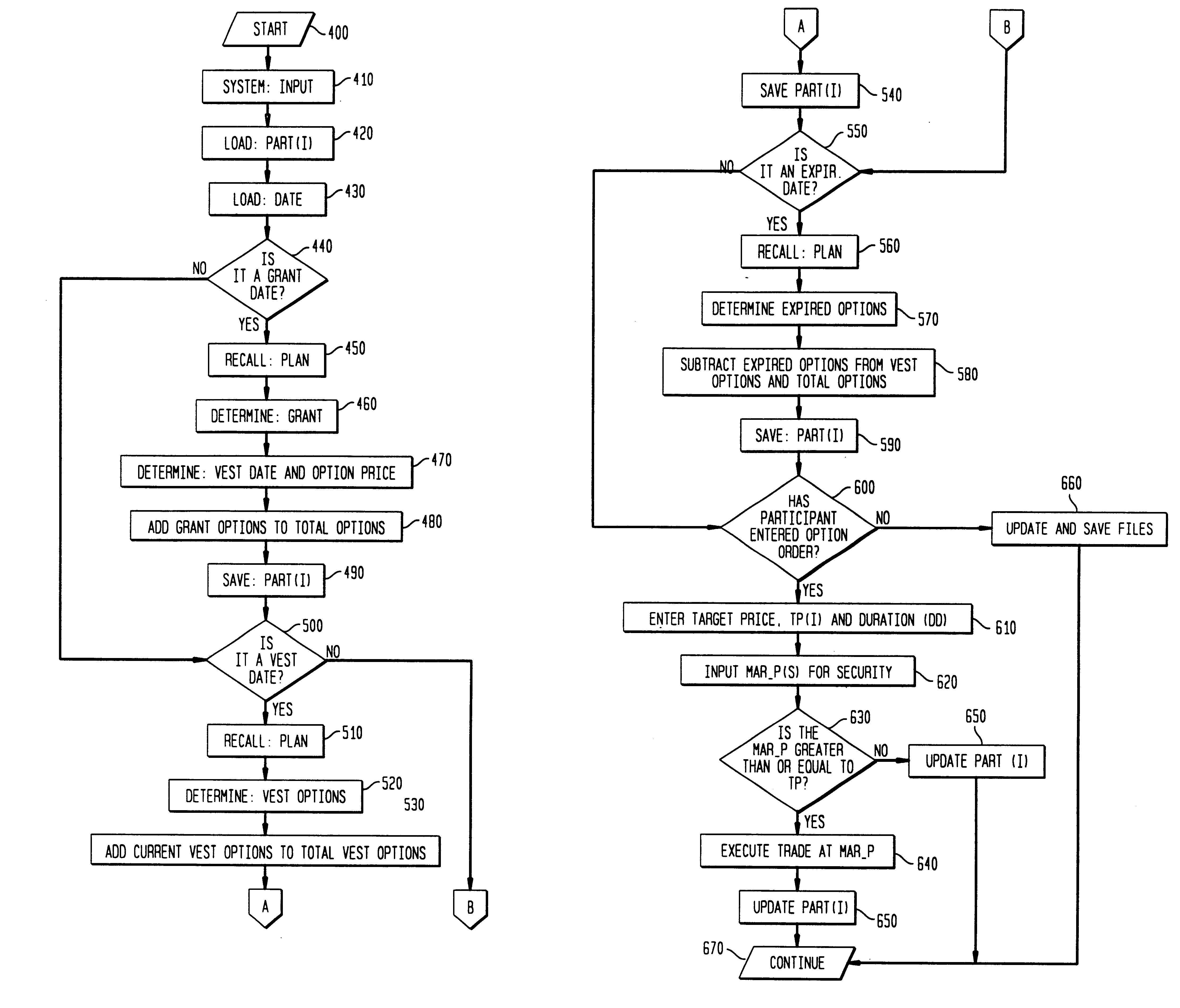
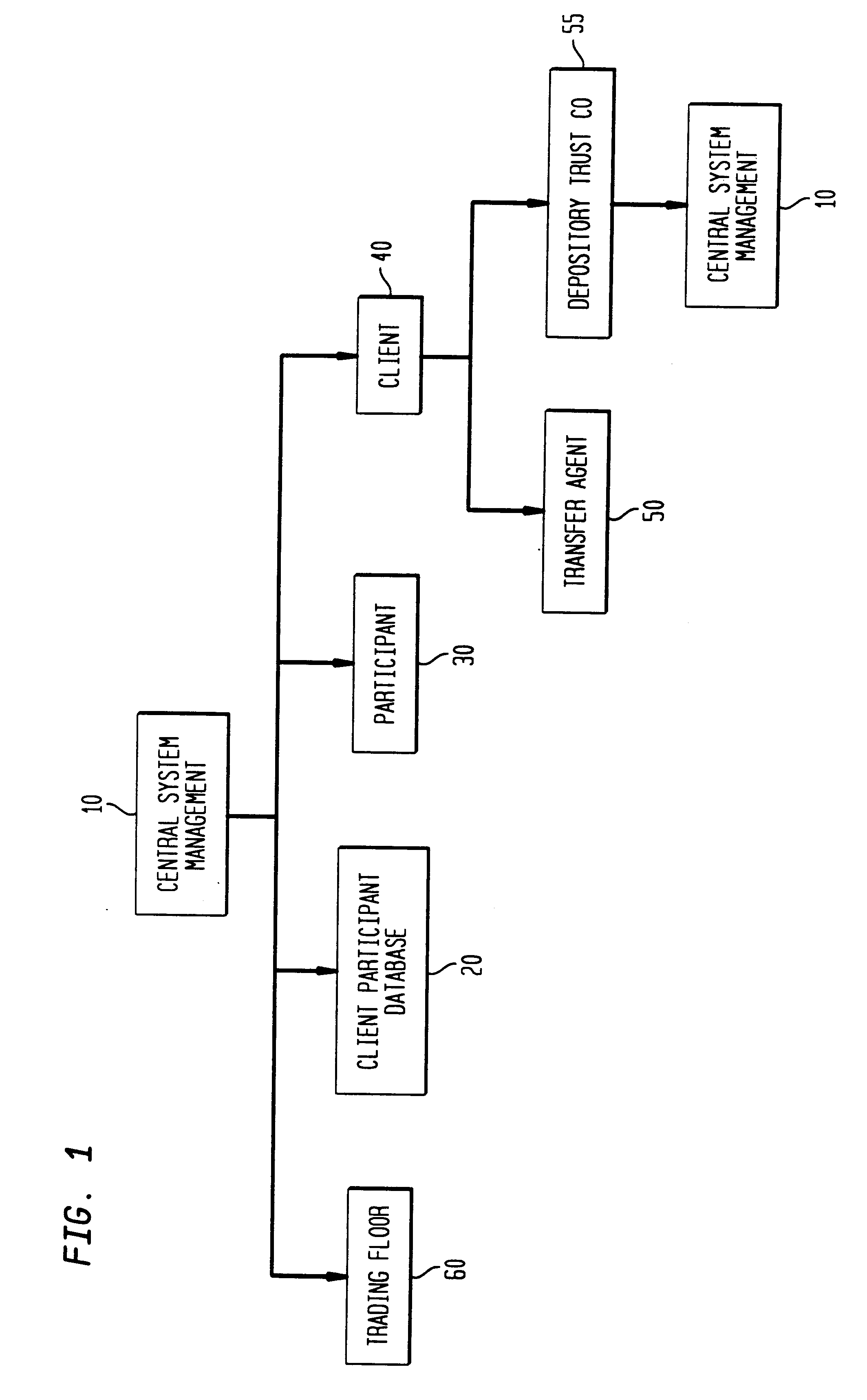
Stock option control and exercise system
A system and method for managing a plurality of stock option accounts each for a plurality of participants. The system invokes a particular option plan defined in the system that governs the transaction choices available to each participants The governing option plans are defined by the sponsoring company in terms of grant, vest and expiration date for the option contracts, and are defined in the system via a database of option holding information for each participant and an axiomatic rule system defining the criteria under which a given participant can exercise given options under the particular plan. The system implements the plans for multiple client companies providing several distinct modes for option exercise by the participant. The system preferably also allows for disbursement of proceeds in a currency different than that in which the underlying security for the option is traded, real time execution of the option transaction, and / or simulating the outcomes of different manners in which the participant may exercise vested options and the resulting economic outcome (disbursement, taxes, transaction fees).
Owner:BANK OF AMERICA CORP
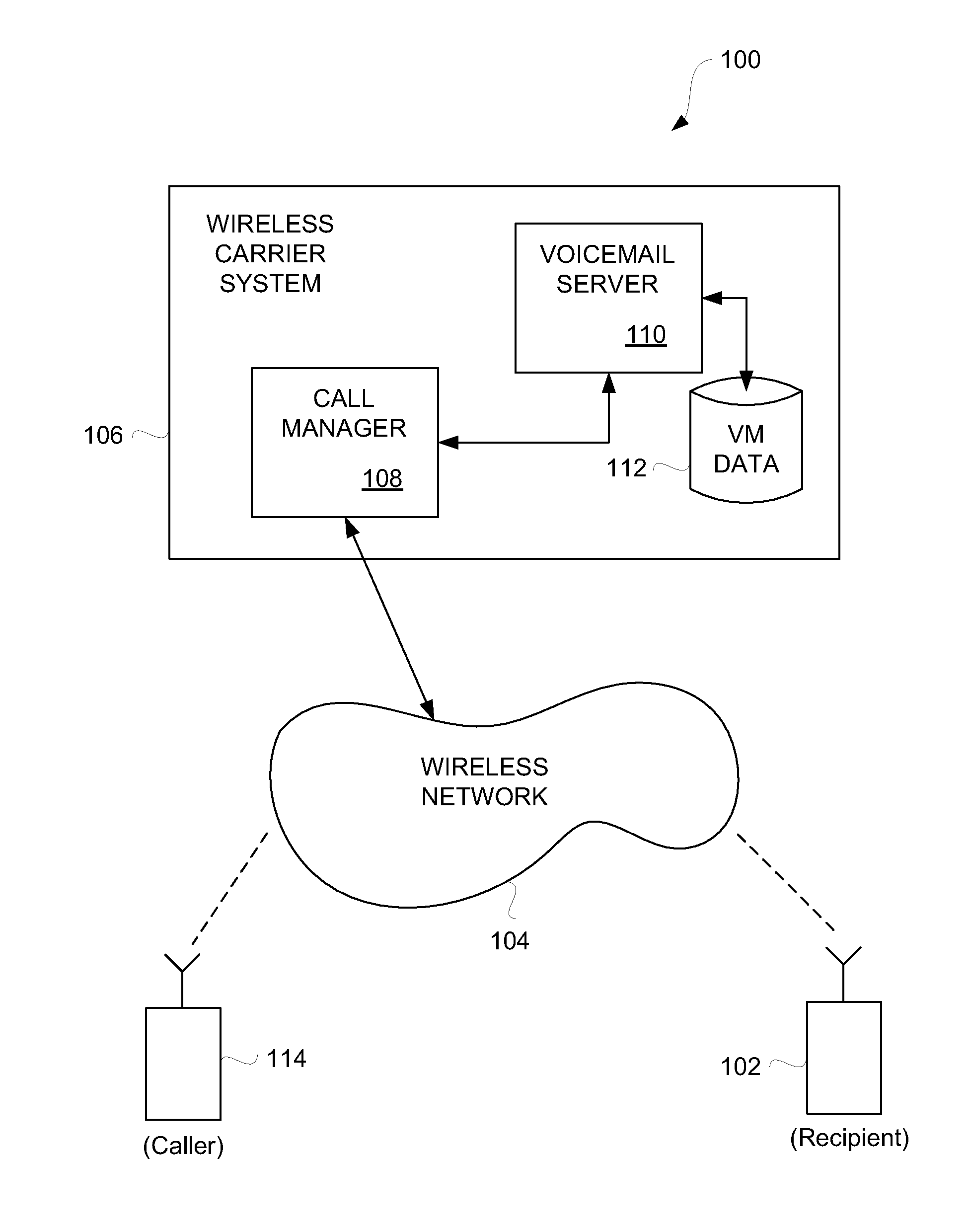
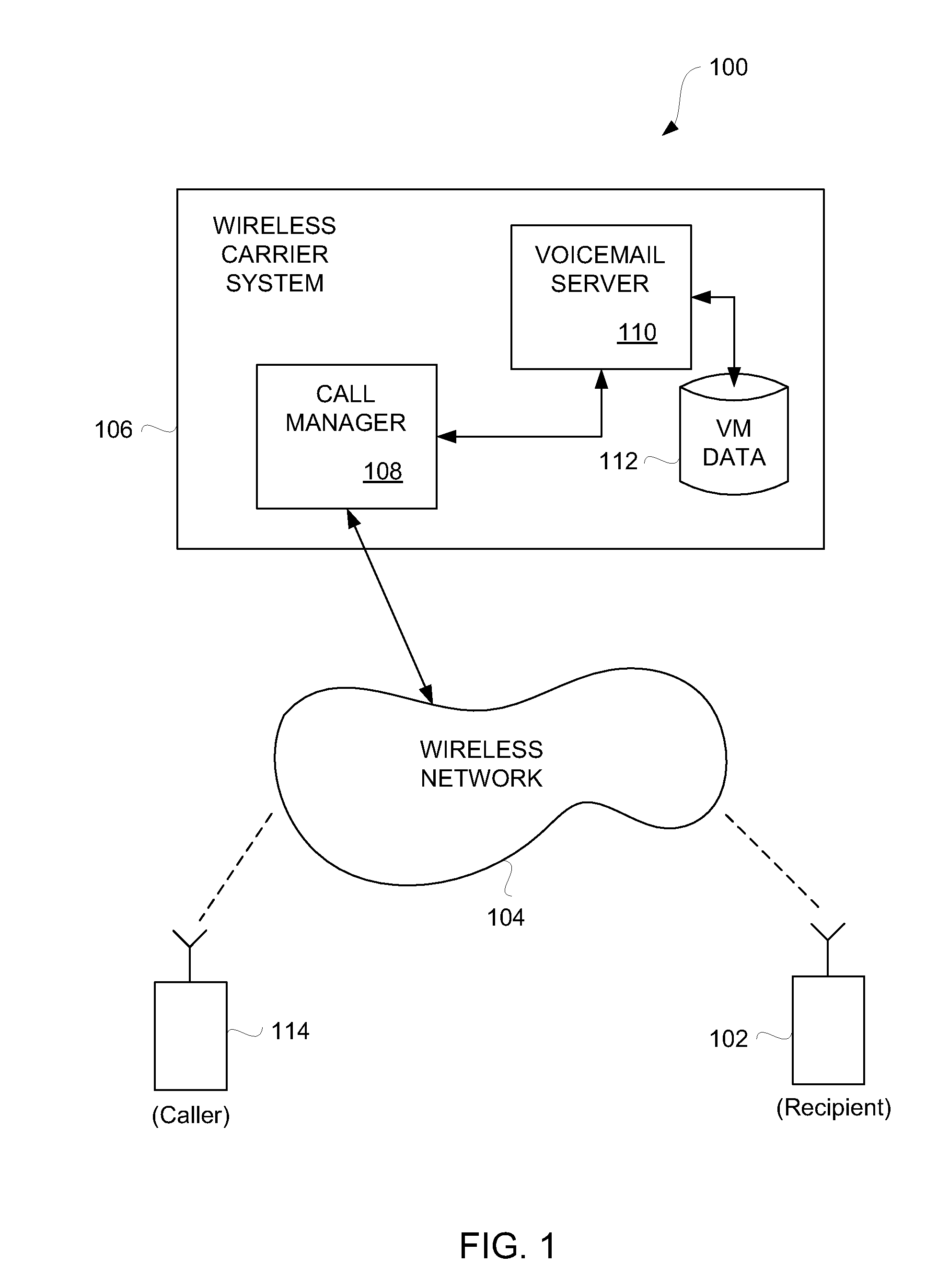
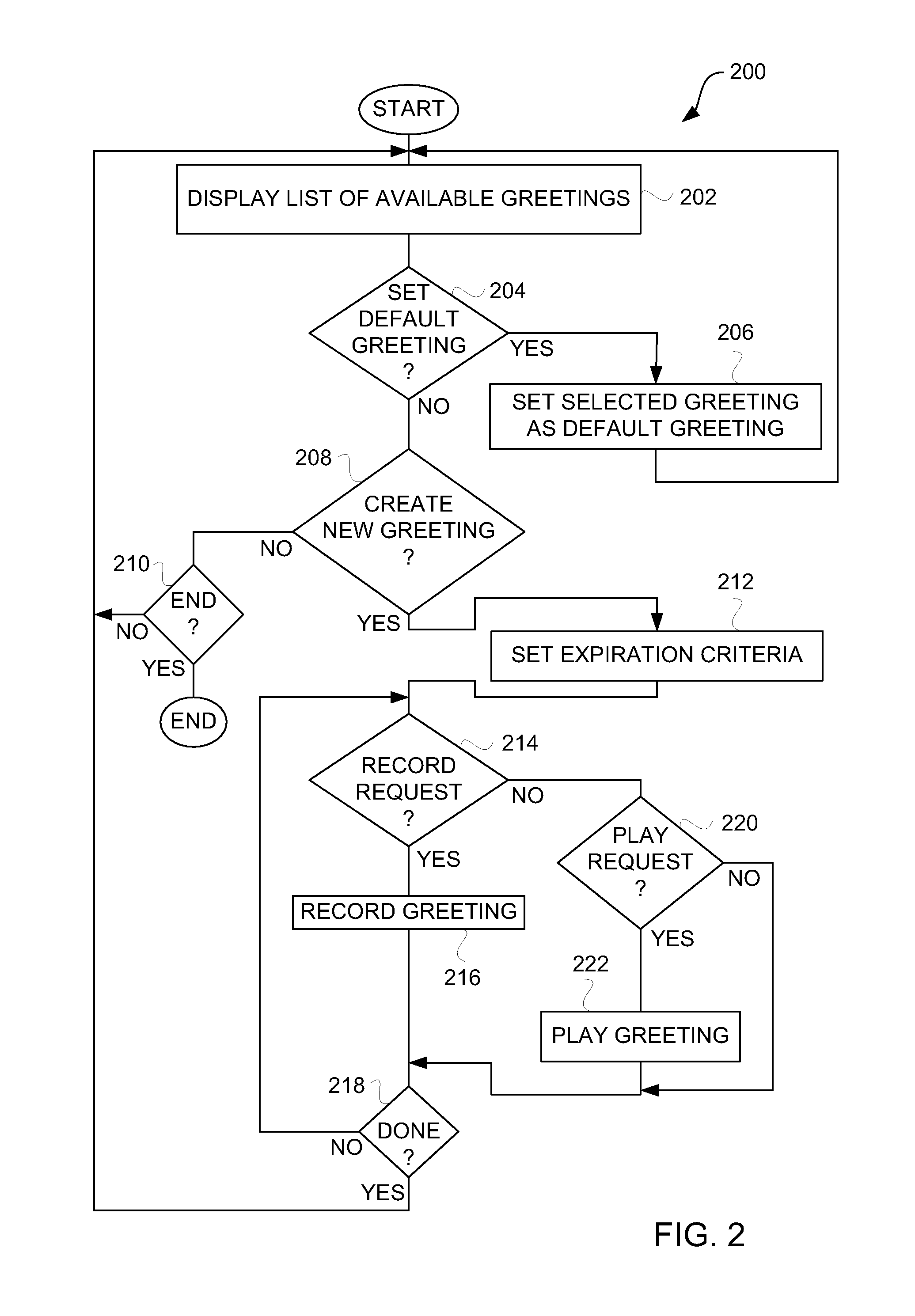
Creation and management of voicemail greetings for mobile communication devices
ActiveUS20090154669A1Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingGraphicsGraphical user interface
Methods, graphical user interfaces and devices for creation and management of voicemail greetings are disclosed. A user of a mobile communication device can create and manage multiple voicemail greetings. In one aspect, a user of a mobile communication device can create customized voicemails. The customized voicemails can be assigned to specific contacts (or groups of contacts) known to the mobile communication device. The customized voicemail greetings can also have controlled expiration dates. In another aspect, customized voicemails can be assigned to incoming calls in real-time.
Owner:APPLE INC
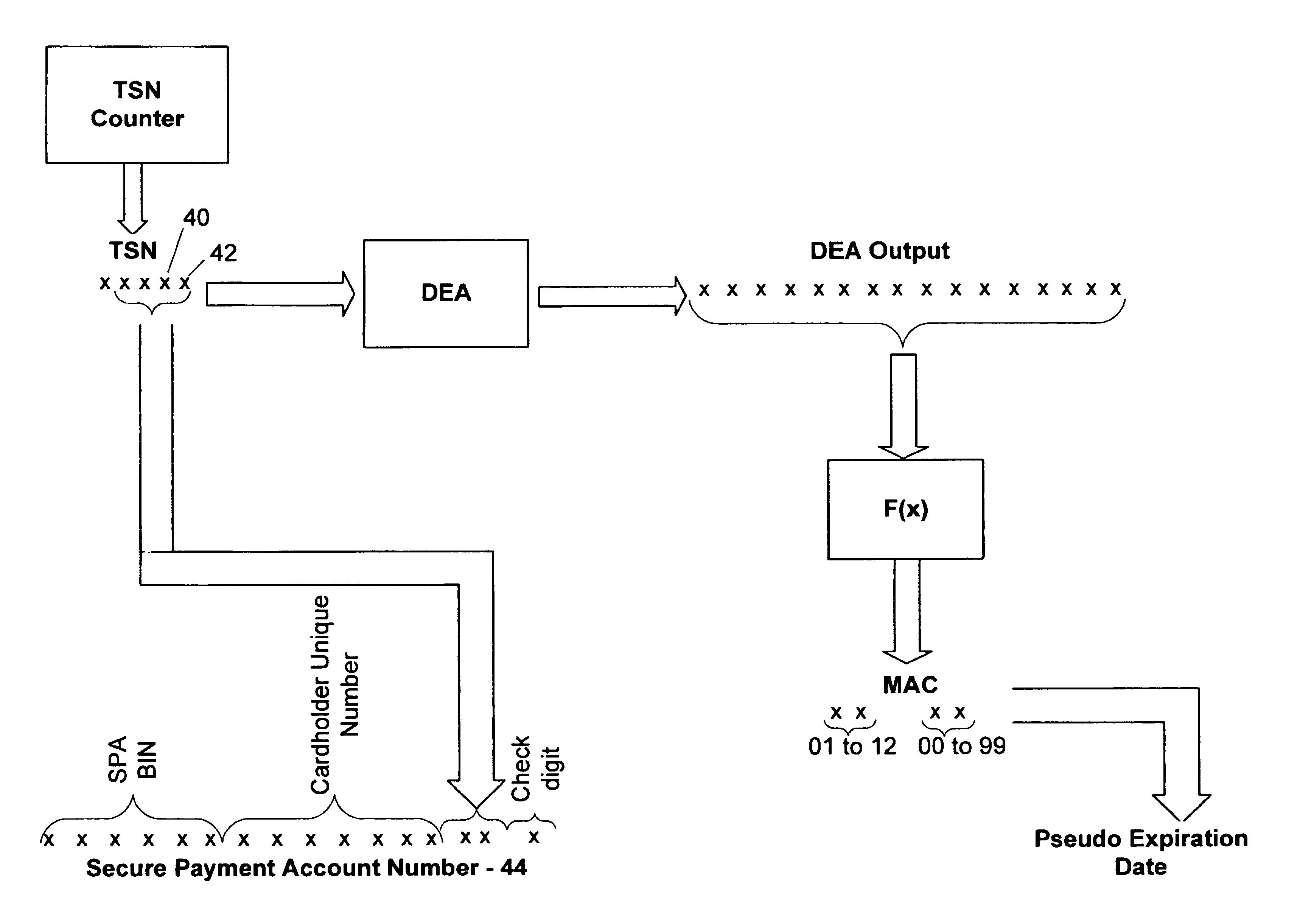
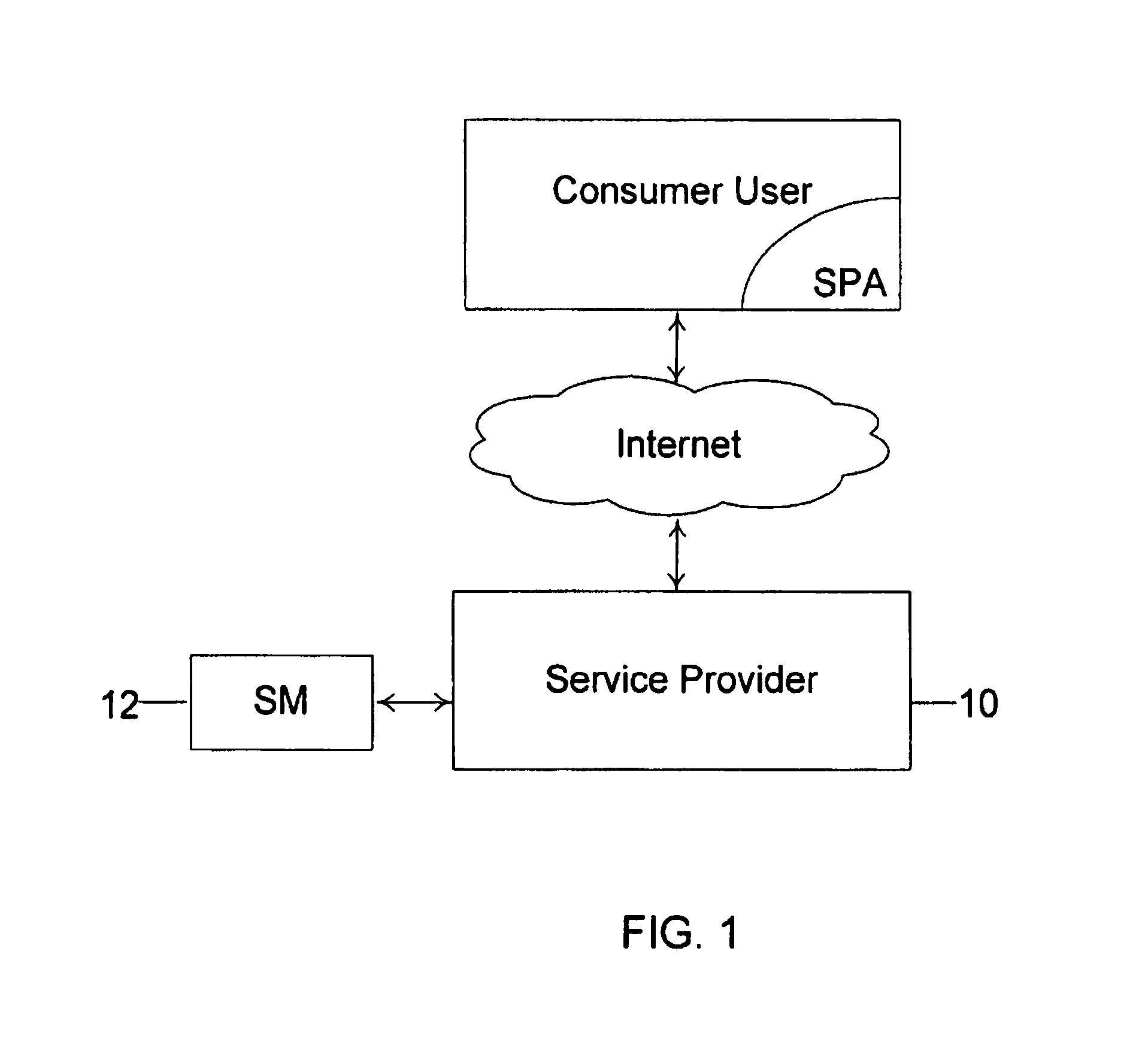
Method and system for conducting secure payments over a computer network
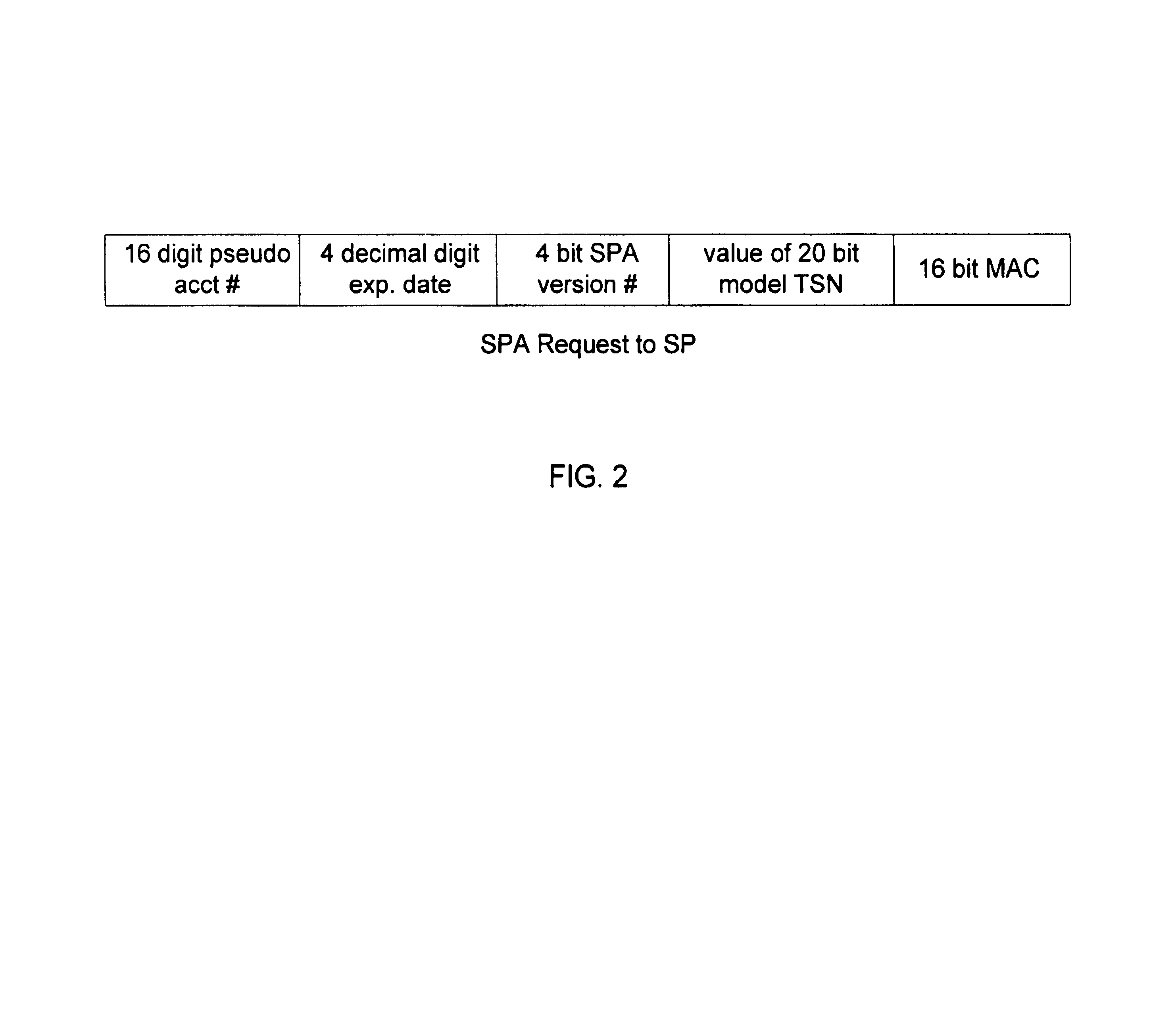
A secure method of conducting an electronic transaction over a public communications network is provided which utilizes a pseudo-expiration date in the expiration date field of an authorization request. One of the preferred methods comprises:generating a per-card key associated with an account number;generating a message authentication code using the per-card key;converting the message authentication code into a pseudo expiration date;generating an authorization request for the transaction, the request having an expiration date field containing the pseudo expiration date; andverifying the message authentication code based on the pseudo expiration date.Another embodiment of the invention includes a method of conducting an electronic transaction over a public communications network, with a payment account number having an associated pseudo account number, comprising:(a) providing the pseudo account number with a control field indicating one of a plurality of key-generation processes to be used to generate an authentication key;(b) generating an authentication key associated with the pseudo account number using one of the plurality of key-generation processes indicated in the control field of the pseudo account number;(c) using the authentication key to generate a message authentication code specific to the transaction;(d) generating an authorization request message including the message authentication code and the pseudo account number; and(e) verifying the message authentication code using the indicated key-generation process and the authentication key.
Owner:MASTERCARD INT INC
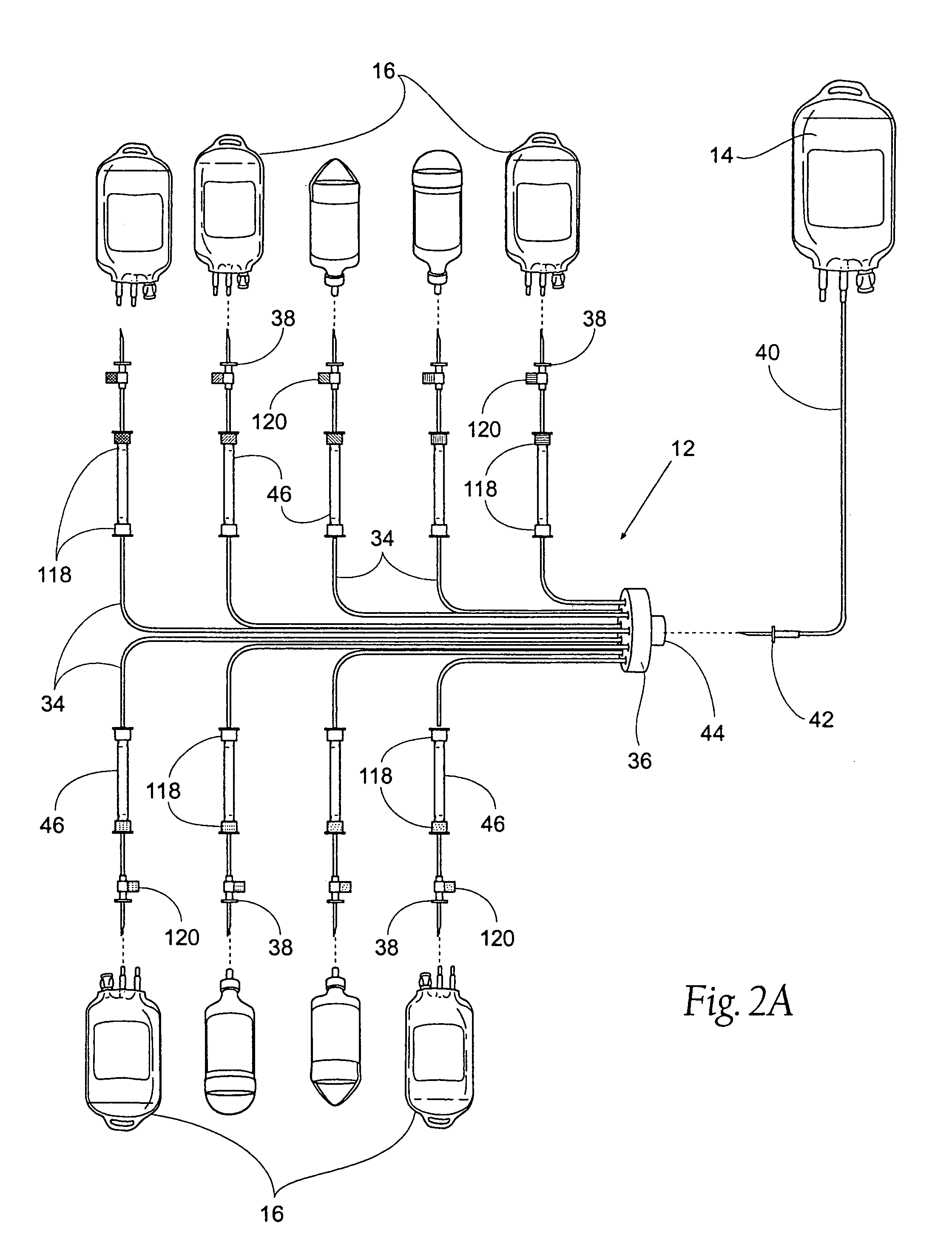
Smart supplies, components and capital equipment
ActiveUS7299981B2Safe and efficient to useEnsure sterilityMedical devicesPayment architectureCapital equipmentRecord keeping
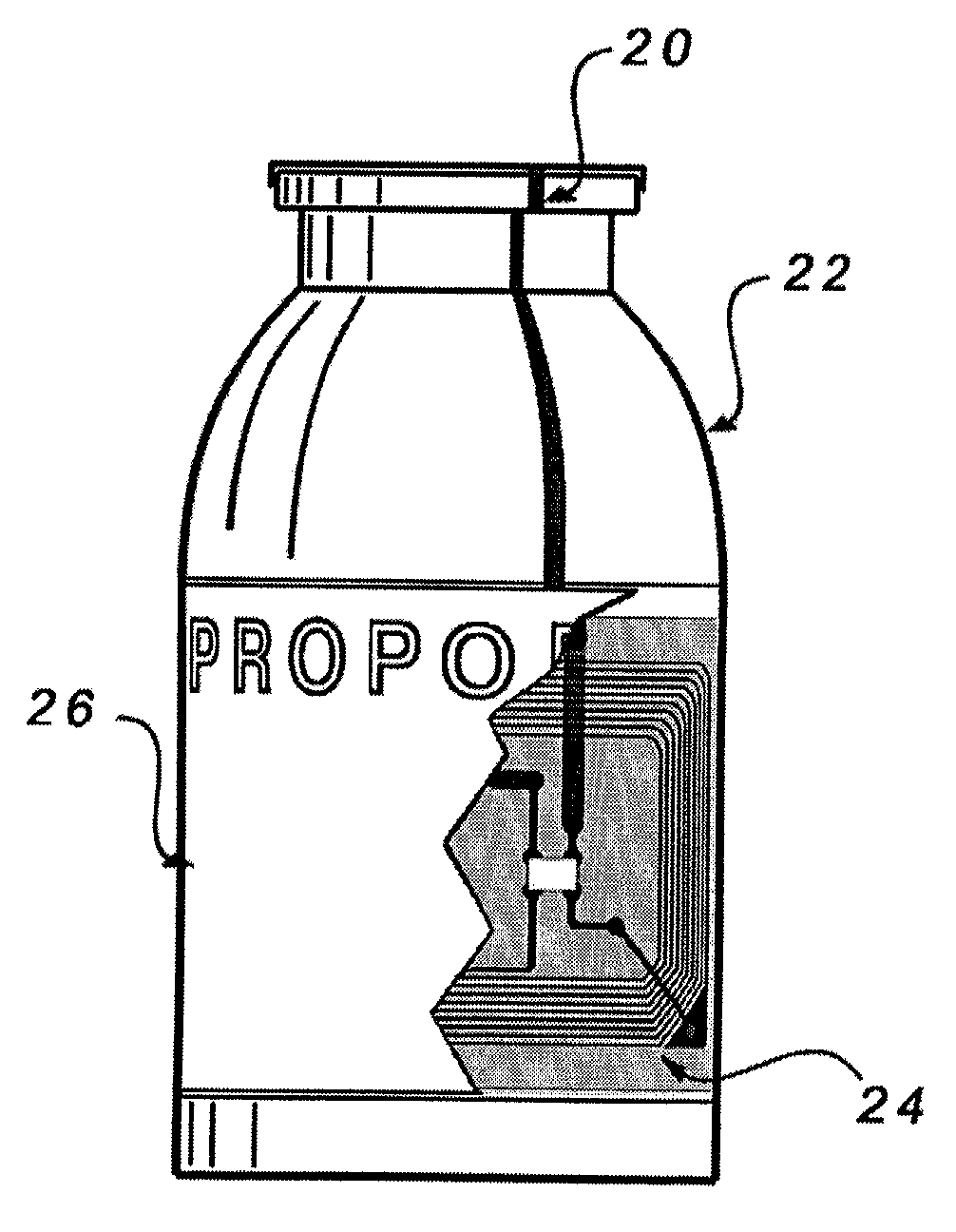
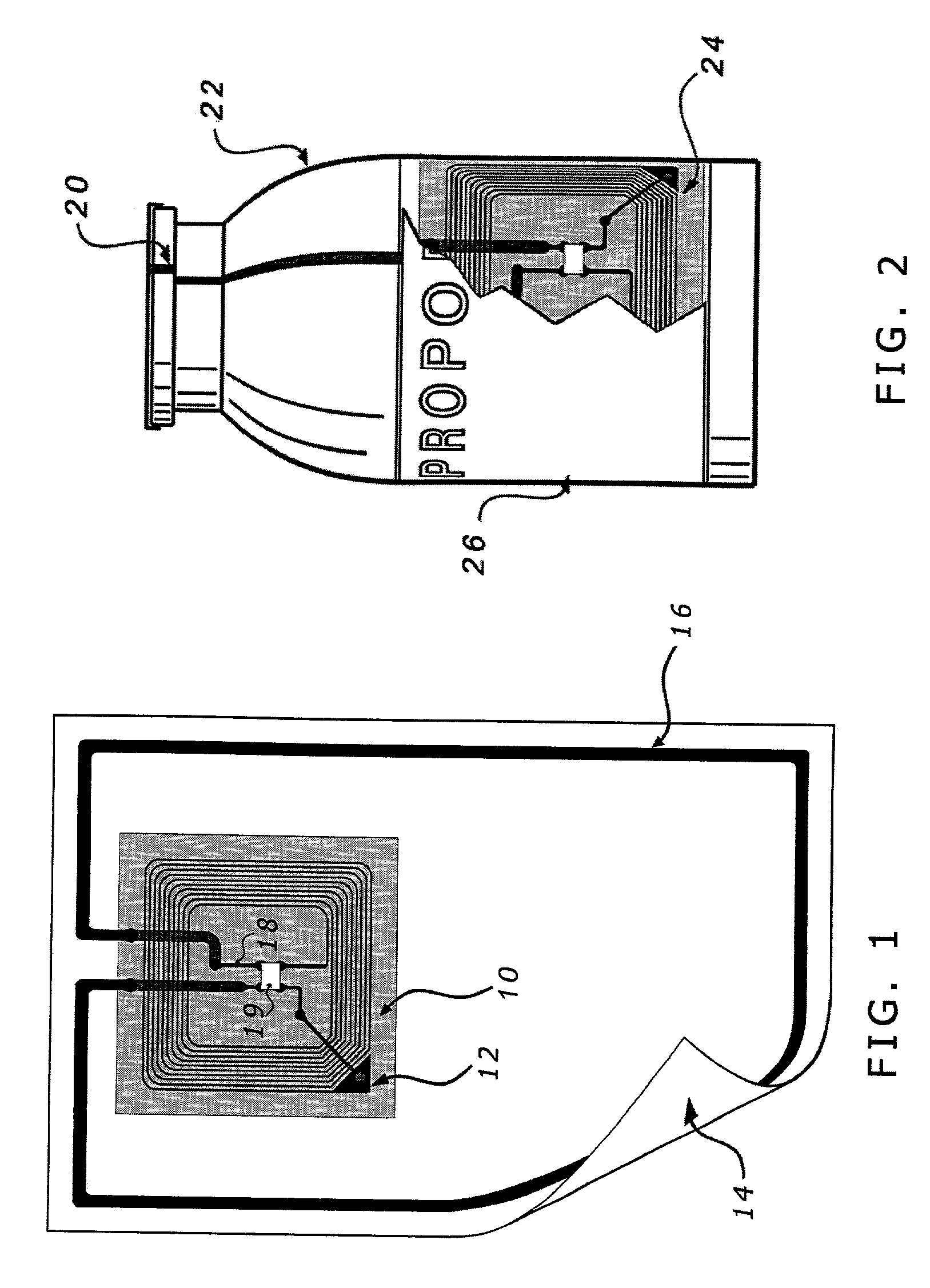
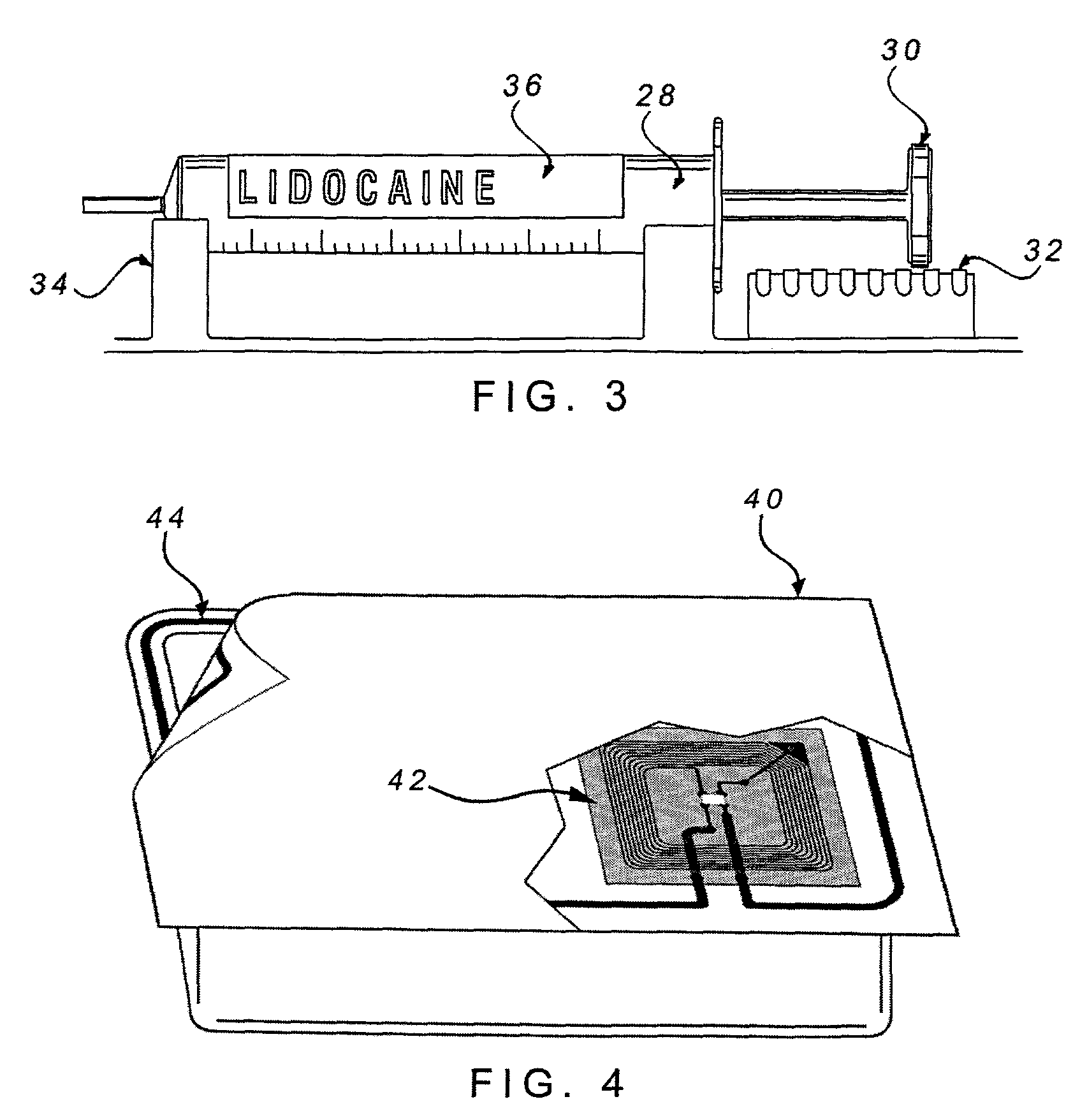
The present invention relates to capital equipment units, such as systems for providing medical treatment, that are associated with smart supplies. The smart supplies are tagged with data carriers which may encode such information as a unique ID for the supply or component, the identification of the supply or component, the identification of the source of the supply or component, the status of whether said supply or component has been previously used, the expiration date of the supply or component, and in the case where the supply or component contains drug, the purity levels of the drug and the concentration levels of the drug. The capital equipment units or their users then utilize the information to assure quality of any procedure run with the units, by way of improved pre-use checks, certification of the supplies for use, record keeping, inventory control, and charge capture.
Owner:SCOTT LAB
Consolidated membership/rewards card system
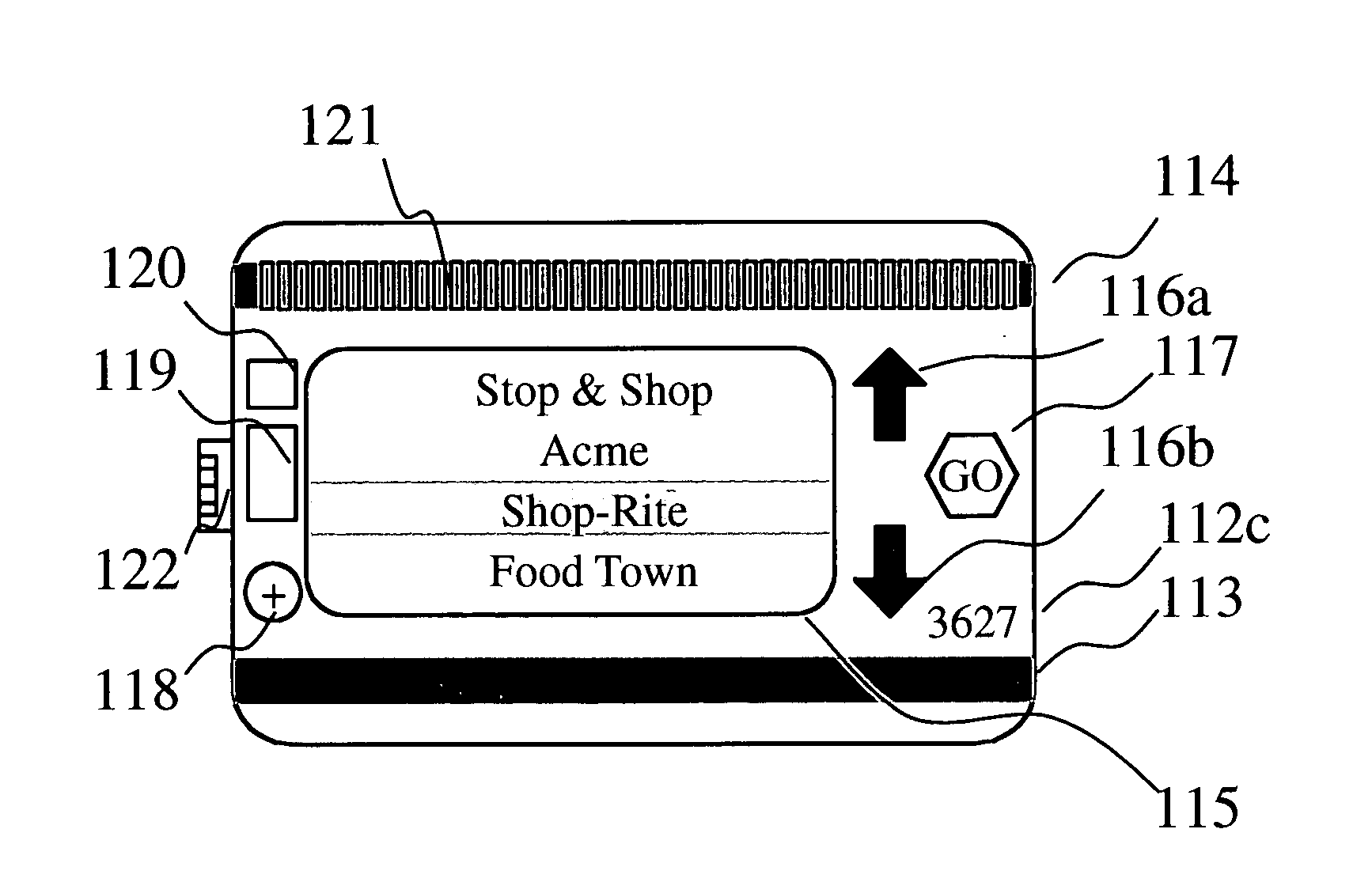
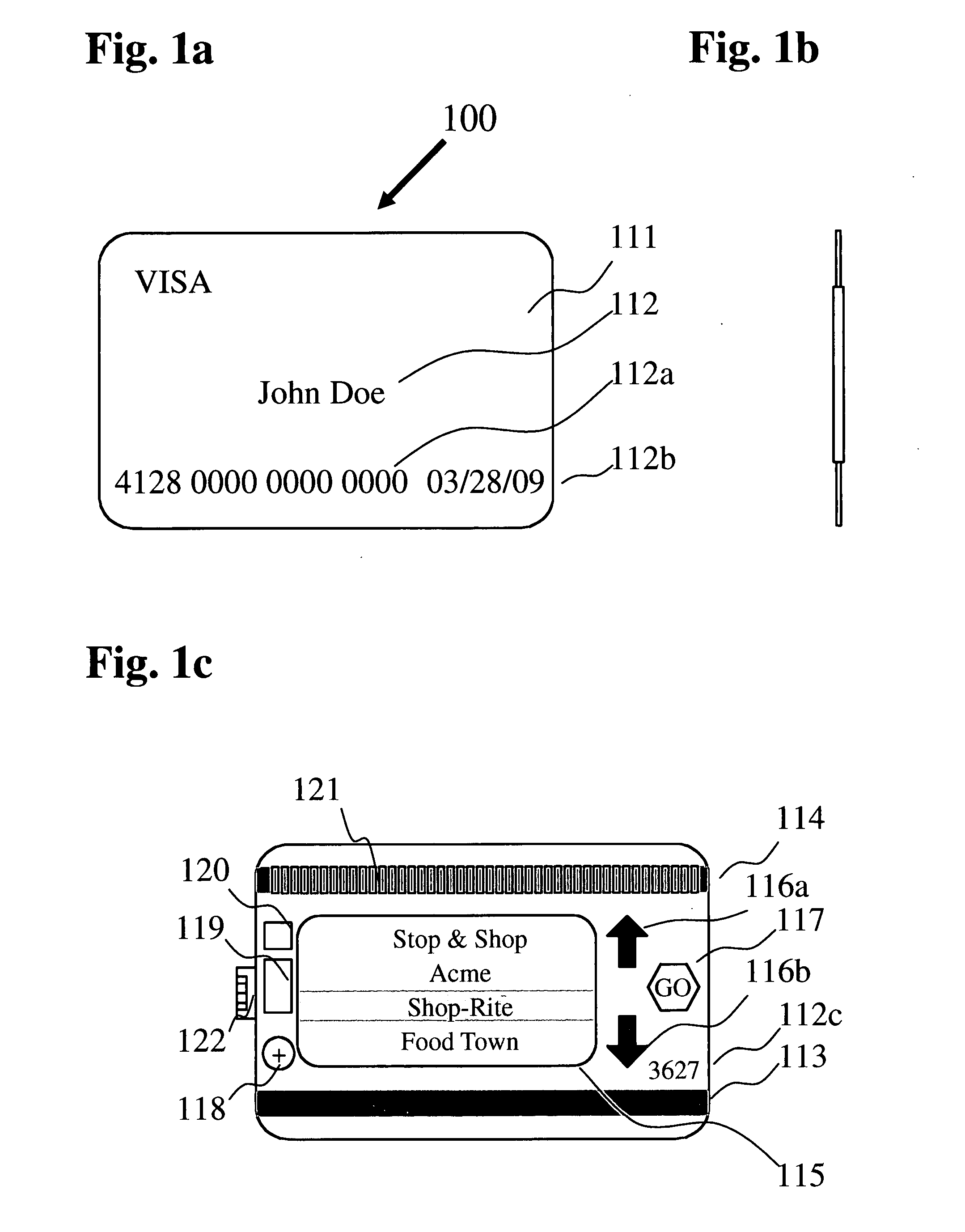
A bank or credit card issuing authority provided consolidated membership / rewards card has standard credit card features including cardholder's name, card number, expiration date, secret code and a permanently coded permanent magnetic strip. The card has a programmable second magnetic strip with inductors directly below the strip energized by a CPU in the card recording a merchant provided loyalty or discount number. The cardholder selects a merchant from a list displayed card screen by pressing up and down buttons and a ‘go’ button to program the second magnetic strip. A USB connector associated with the card is used for uploading merchant data from a personal computer and transmitting the card discount number to a USB enabled cash register. The cash register provides eligible discounts for purchases upon receipt of the card discount number by swiping the second magnetic strip or by establishing USB connectivity. Payment is made using the permanent magnetic strip of the card or by other payment means. Discounts and membership rewards are thereby provided to a cardholder without need for carrying a plurality of merchant issued membership / rewards cards. Credit card functionality facilitates immediate payment for the purchases made.
Owner:POLLIO MICHAEL J
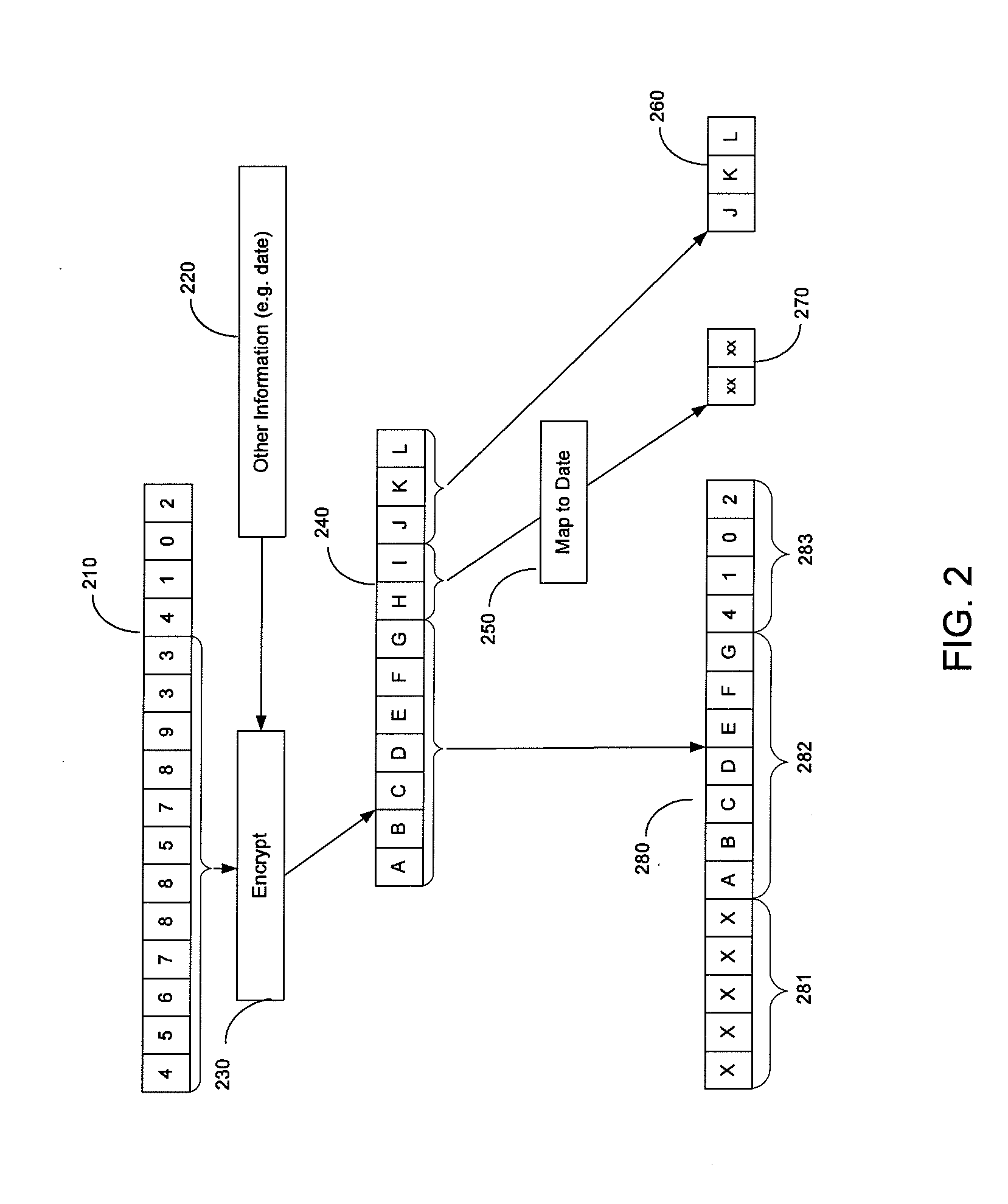
Device including encrypted data for expiration date and verification value creation
ActiveUS20100299267A1Difficult to obtainFinanceUser identity/authority verificationPayment transactionFinancial transaction
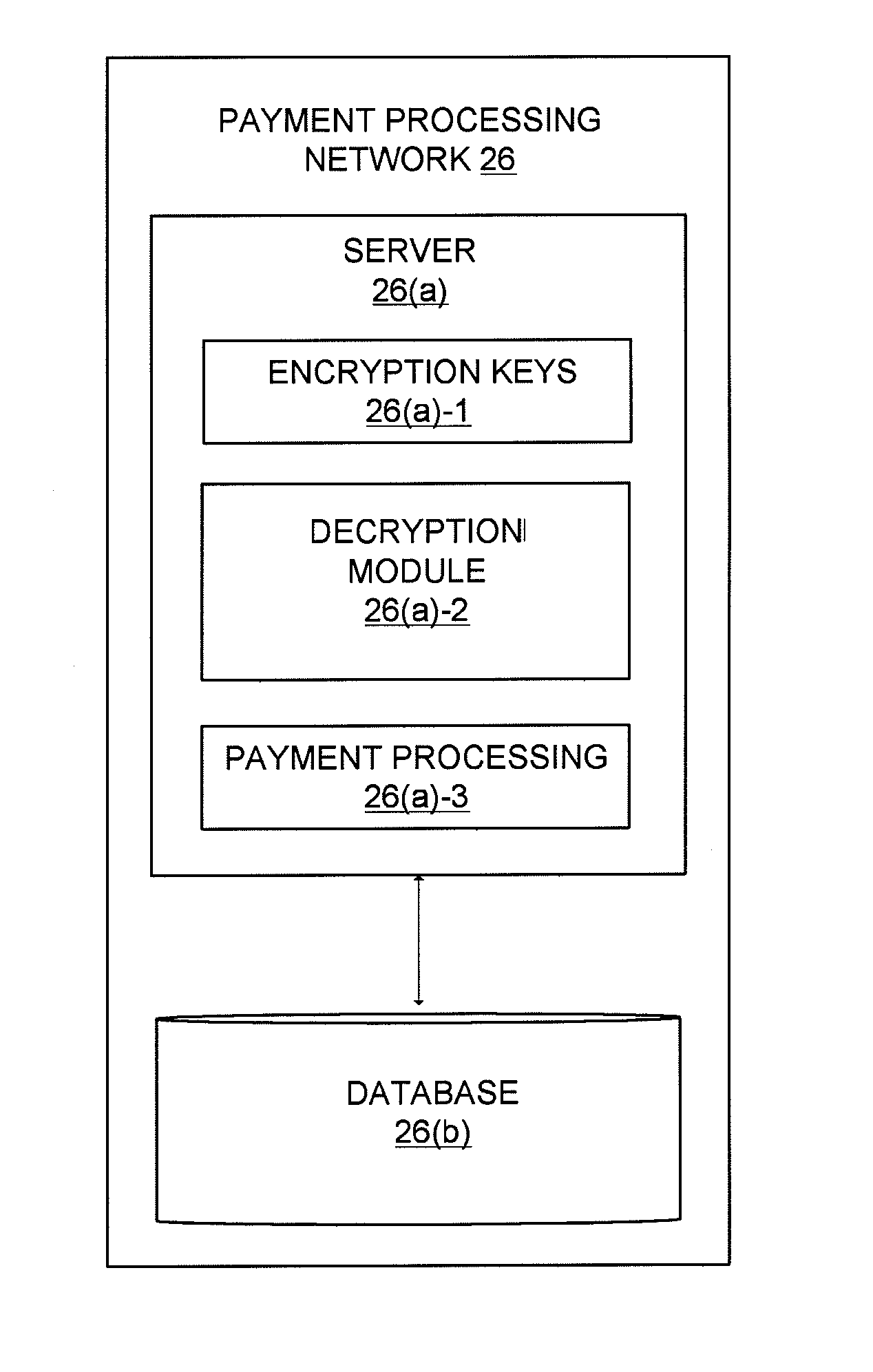
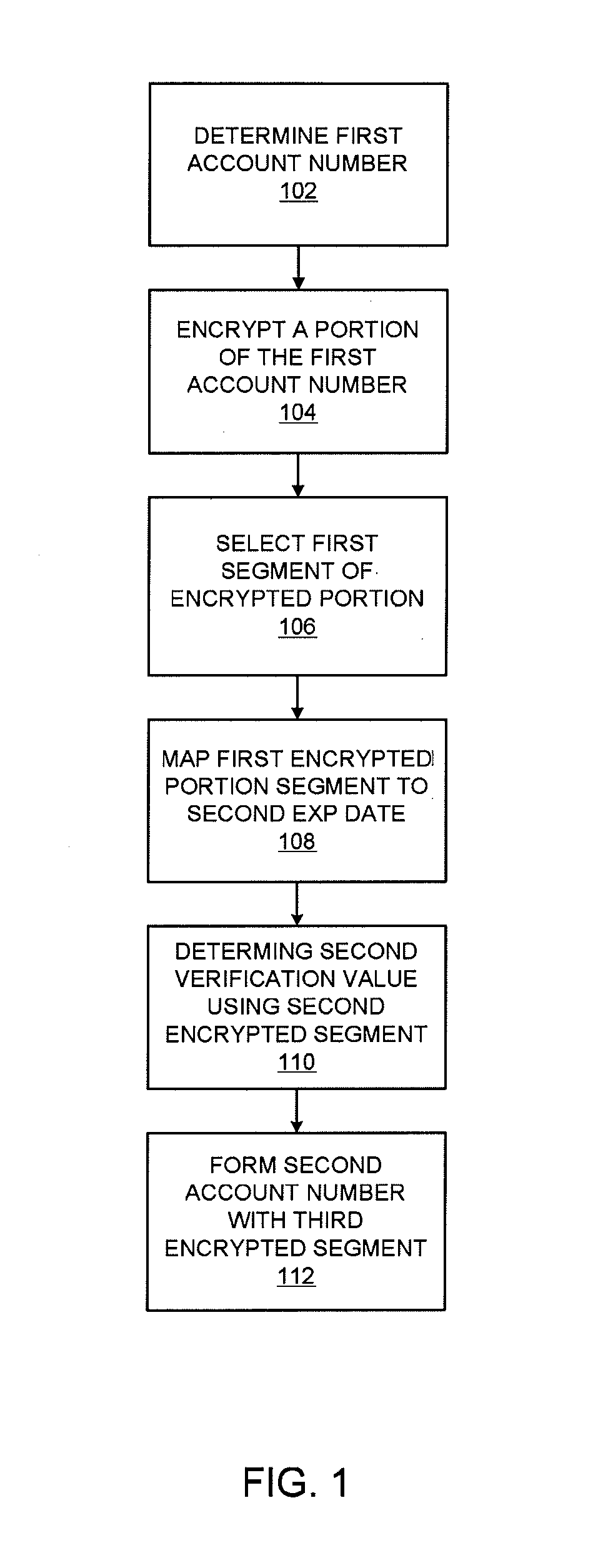
In order to make it more difficult to obtain numbers that can be used to conduct fraudulent transactions, a portion of a real account number is encrypted. The encrypted portion of the account number is used to generate a new account number, a new expiration date, and a new verification value. This information can be determined using processor that may reside in a point of sale terminal, a smart card, or a computer operated by a user. The new account number, the new expiration date, and the new verification value can be used in a payment transaction. A server computer in a central payment processing network may determine that the new account information is not the real account information, and may subsequently generate a modified authorization request message using the real account information and may send it to an issuer for approval. The transmission of data is more secure, since real account information is not sent from the merchant to the payment processing network.
Owner:VISA INT SERVICE ASSOC
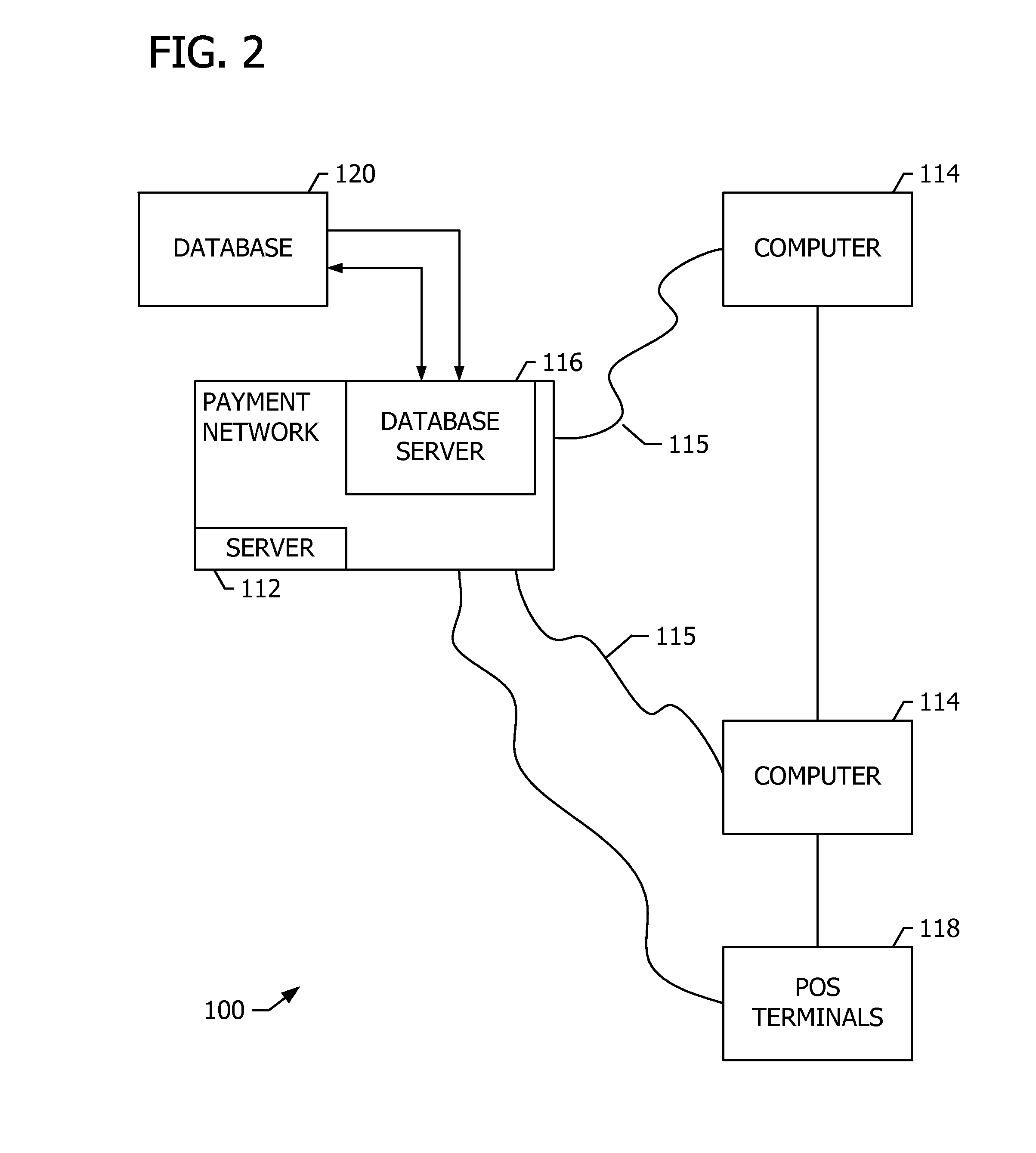
Systems and methods for updating payment card expiration information
A computer-implemented method for updating merchant information regarding card-not-present recurring payment (CNP / RP) transactions is provided, wherein the method involves a recurring transaction initiated by a cardholder using payment card information stored by a merchant. The method includes querying a database coupled to a payment network to identify a candidate payment card having stale payment card data. The stale payment card data includes at least an existing expiration date that is within a predetermined period of time of a selected calendar date. The method also includes querying the database to identify at least one recent transaction involving the candidate payment card. The recent transaction includes payment card data having an updated expiration date. The method further includes notifying the merchant that the existing expiration date has been replaced with the updated expiration date.
Owner:MASTERCARD INT INC
Public/private dual card system and method
InactiveUS20050035192A1Reduce disadvantagesEliminate needComplete banking machinesTicket-issuing apparatusCredit cardOperating system
A system and method for providing a multiple-service card is disclosed. A card member 108 is provided with a single card that serves as both an open transaction instrument and a private retailer transaction instrument. This multiple-service card may have the traditional credit card data on one side of the card, including, for example, the account number, name of the account holder, and the expiration date. The other side of the card may include a magnetic stripe that contains the account information in machine readable form as well as private retailer transaction instrument information. In the system, the primary party and the service partner participants cooperate to complete the processes associated with the provision of the combined card services, including a new account process, card replacement and renewal processes, a service partner cancellation process, and a process for cancellation and / or transfer by a primary party.
Owner:CHARTOLEAUX +1
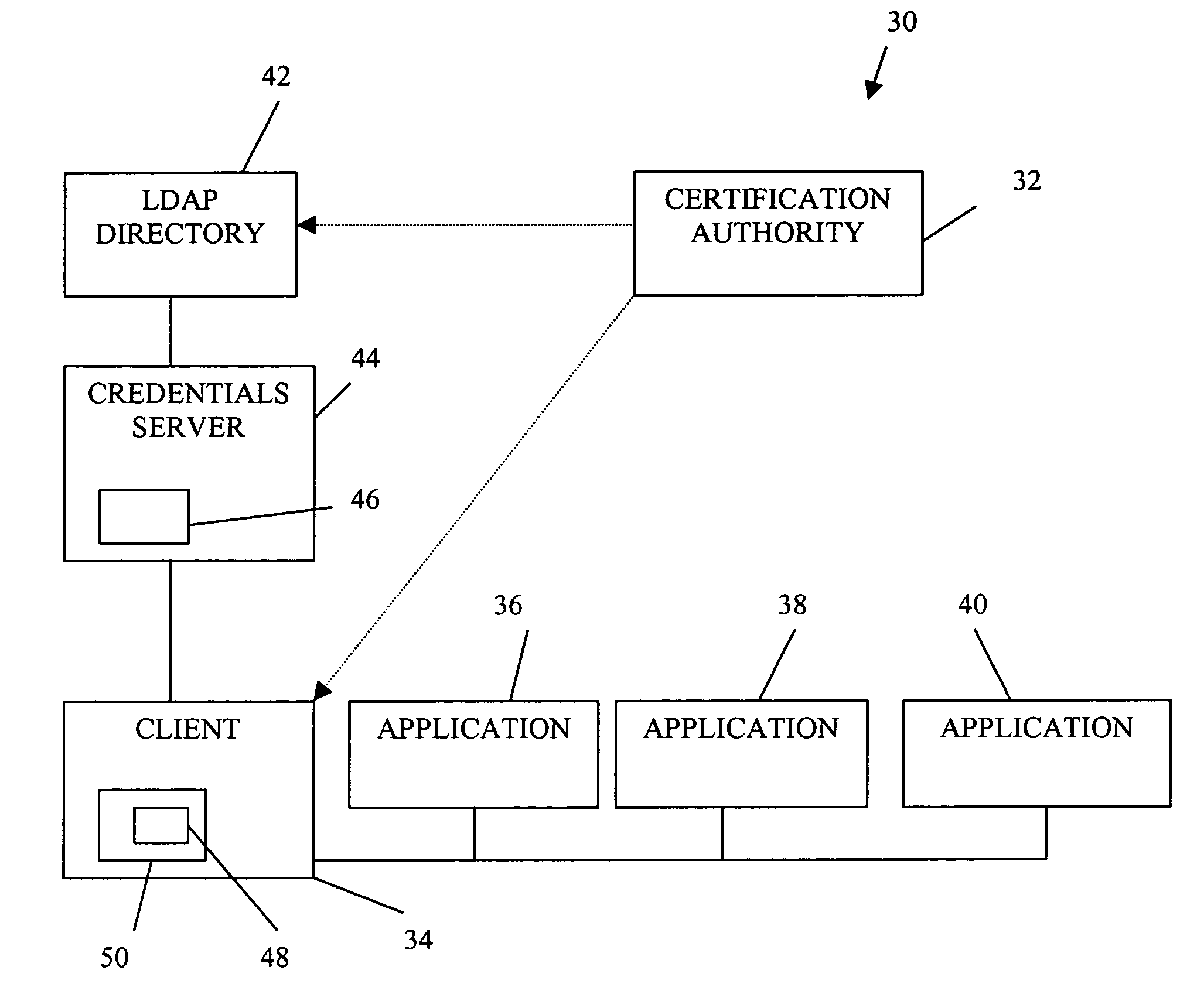
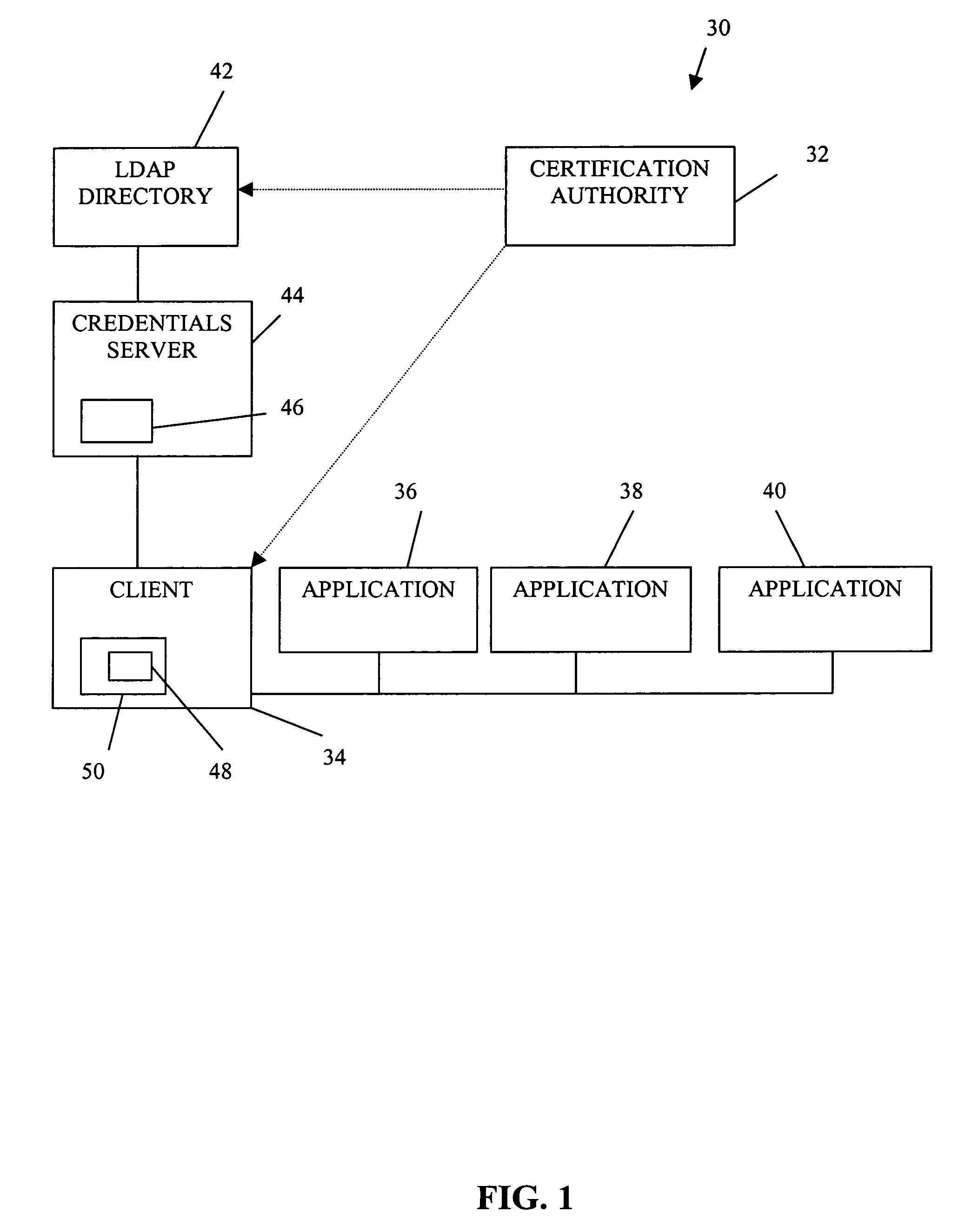
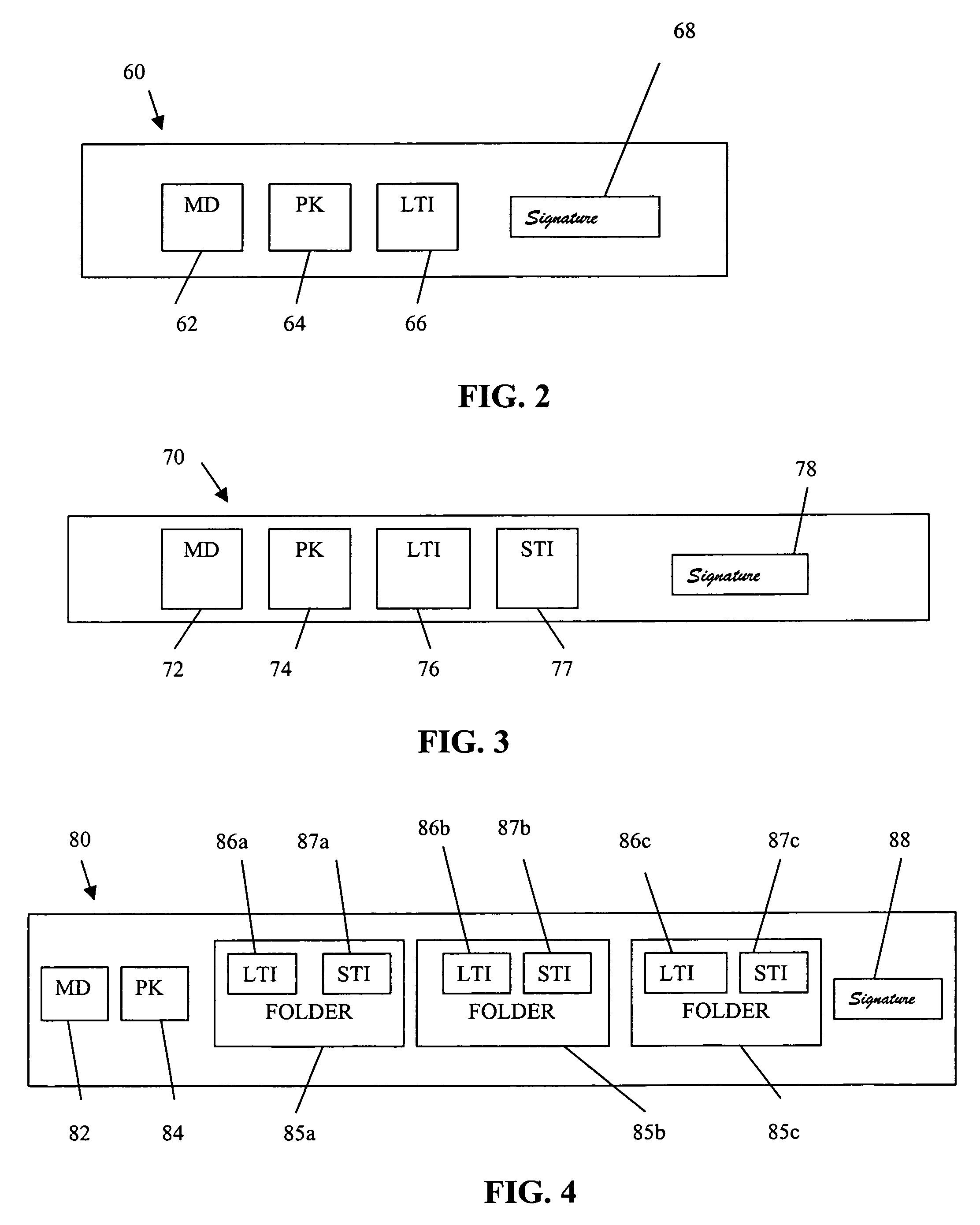
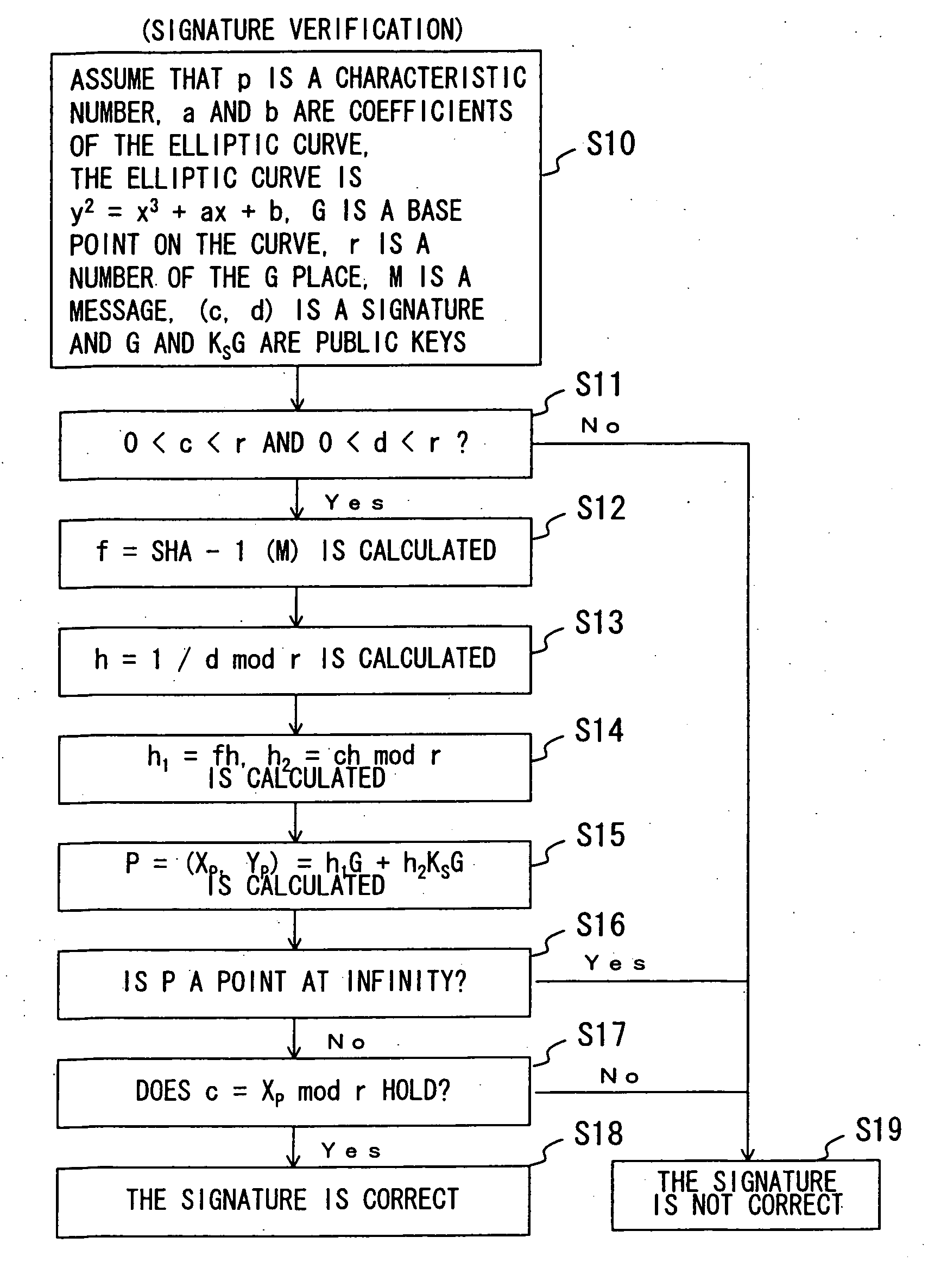
Authorization infrastructure based on public key cryptography
InactiveUS7340600B1Random number generatorsUser identity/authority verificationRoot certificateClient-side
A public key authorization infrastructure includes a client program accessible by a user and an application program. A certificate authority issues a long-term certificate that binds a public key of the user to long-term identification information related to the user. A directory stores the issued long-term certificate and short-term authorization information related to the user. A credentials server issues a short-term certificate to the client. The short-term certificate binds the public key to the long-term identification information and to the short-term authorization information. The client presents the short-term certificate to the application program for authorization and demonstrates that the user has knowledge of a private key corresponding to the public key in the short-term certificate. The short-term certificate includes an expiration date, and is not subject to revocation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Stock option control and exercise system
A system and method for managing a plurality of stock option accounts each for a plurality of participants. The system invokes a particular option plan defined in the system that governs the transaction choices available to each participant. The governing option plans are defined by the sponsoring company in terms of grant, vest and expiration date for the option contracts, and are defined in the system via a database of option holding information for each participant and an axiomatic rule system defining the criteria under which a given participant can exercise given options under the particular plan. The system implements the plans for multiple client companies providing several distinct modes for option exercise by the participant. The system preferably also allows for disbursement of proceeds in a currency different than that in which the underlying security for the option is traded, real time execution of the option transaction, and / or simulating the outcomes of different manners in which the participant may exercise vested options and the resulting economic outcome (disbursement, taxes, transaction fees).
Owner:BANK OF AMERICA CORP
Systems and methods for determining whether to offer a reward at a point of return
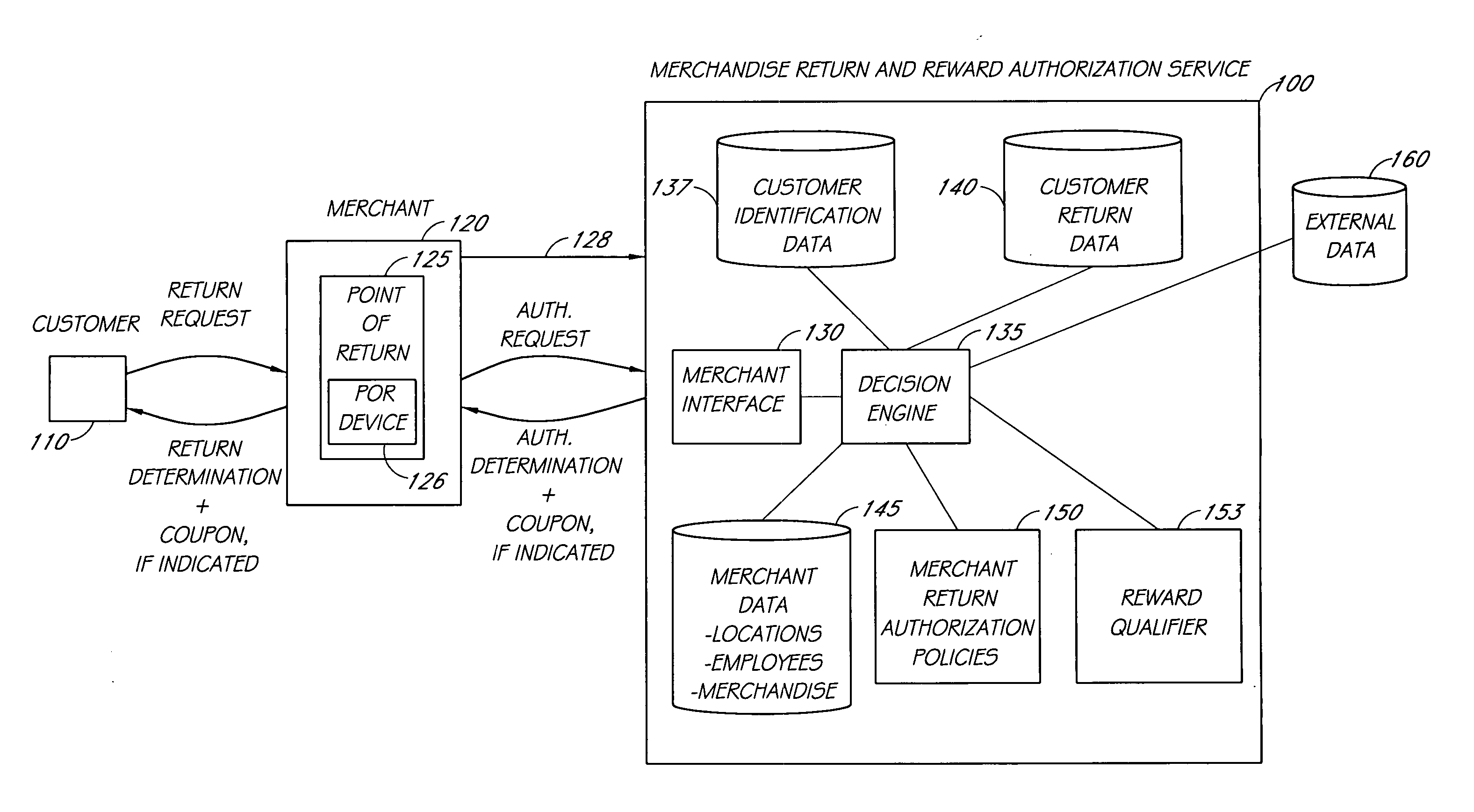
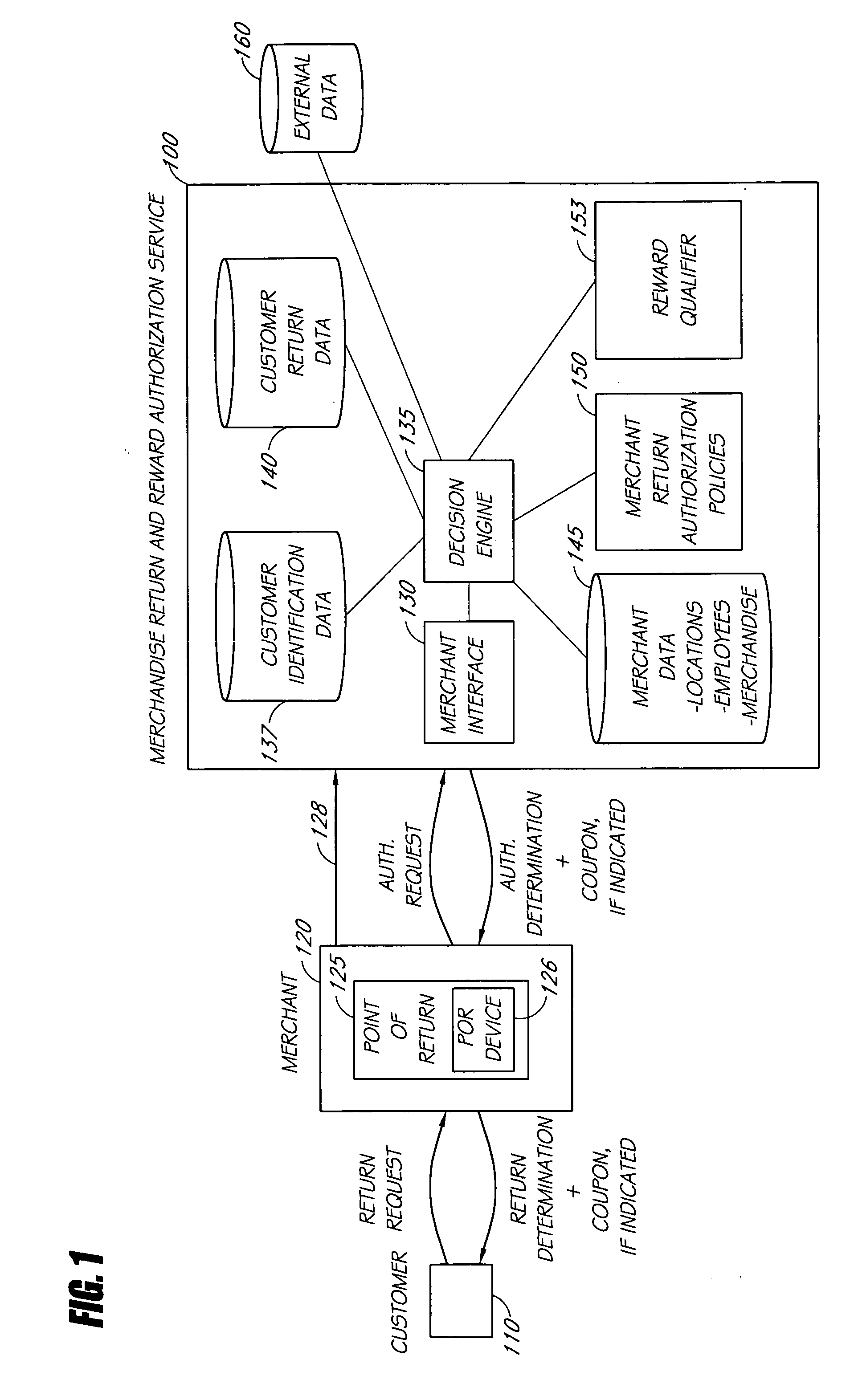
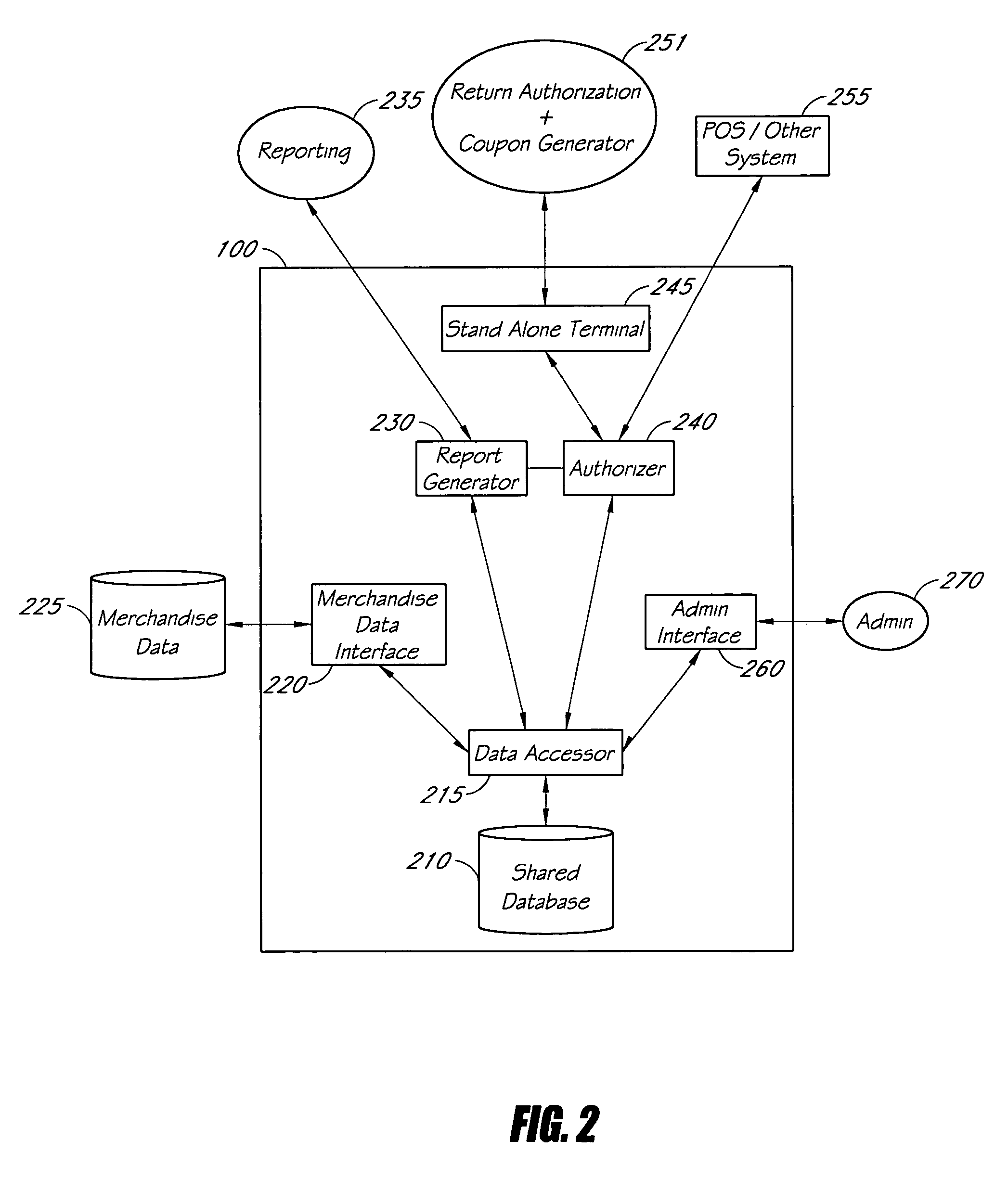
InactiveUS20060235747A1Effective in generating additional saleOffice automationMarketingDecision systemExpiration date
Computerized decision-making systems and methods are described for determining whether to provide one or more rewards, such as a coupon or instant discount, to a customer requesting to make a merchandise return at a store, and, if so, to determine the terms of the reward, such as value, expiration date / time and other terms that may be associated with a coupon. The reward determinations may be implemented in conjunction with a system for authorizing the requested merchandise return transaction. Information about the requested return may be used together with data about the customer's past purchase, return transactions, and other customer-related data. In some embodiments, the determinations are based, at least in part, on store-related information and policies. The reward may be printed with a receipt issued to the customer at the point of return and / or may be provided to the customer using a wide variety of other communications technologies.
Owner:THE RETAIL EQUATION
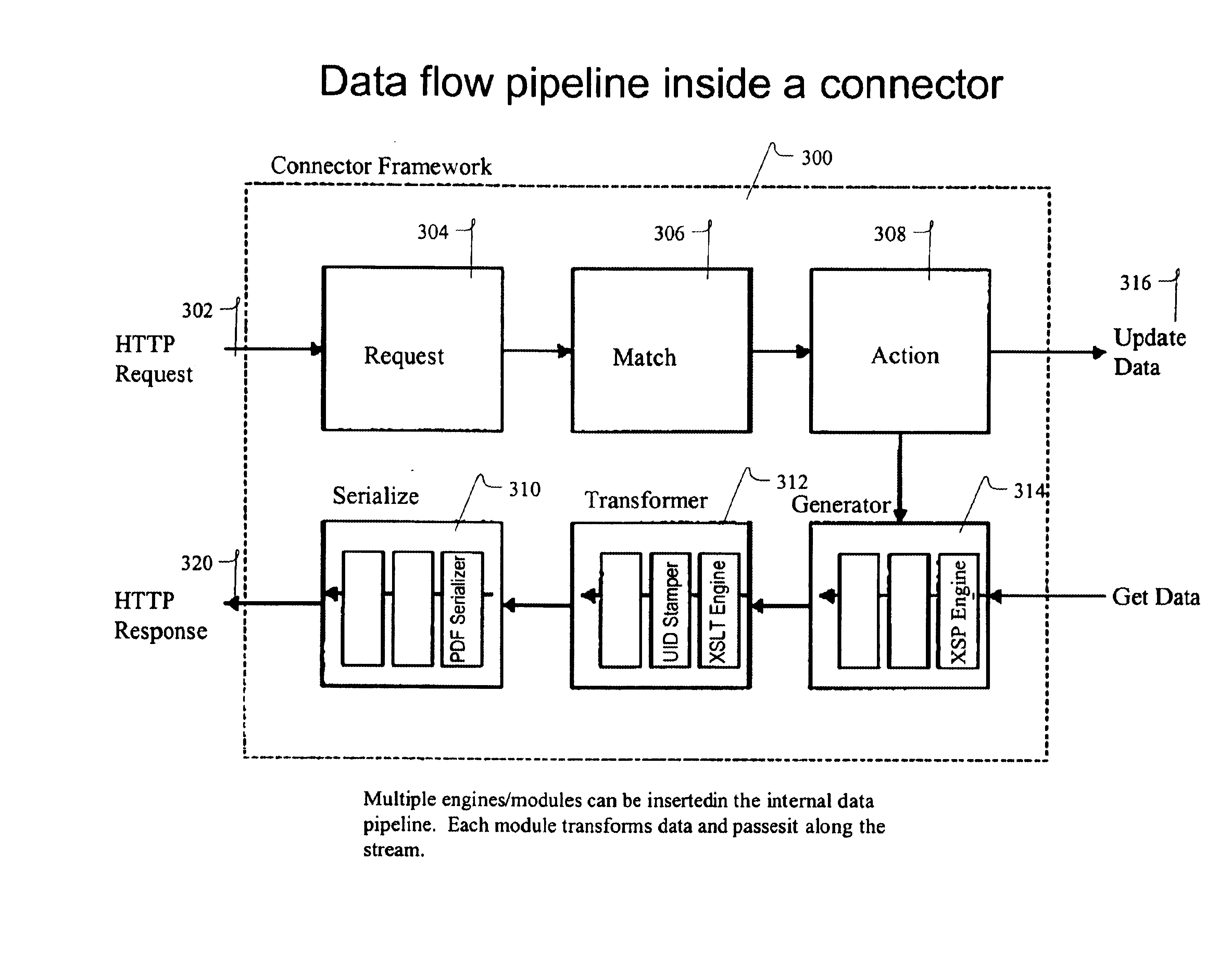
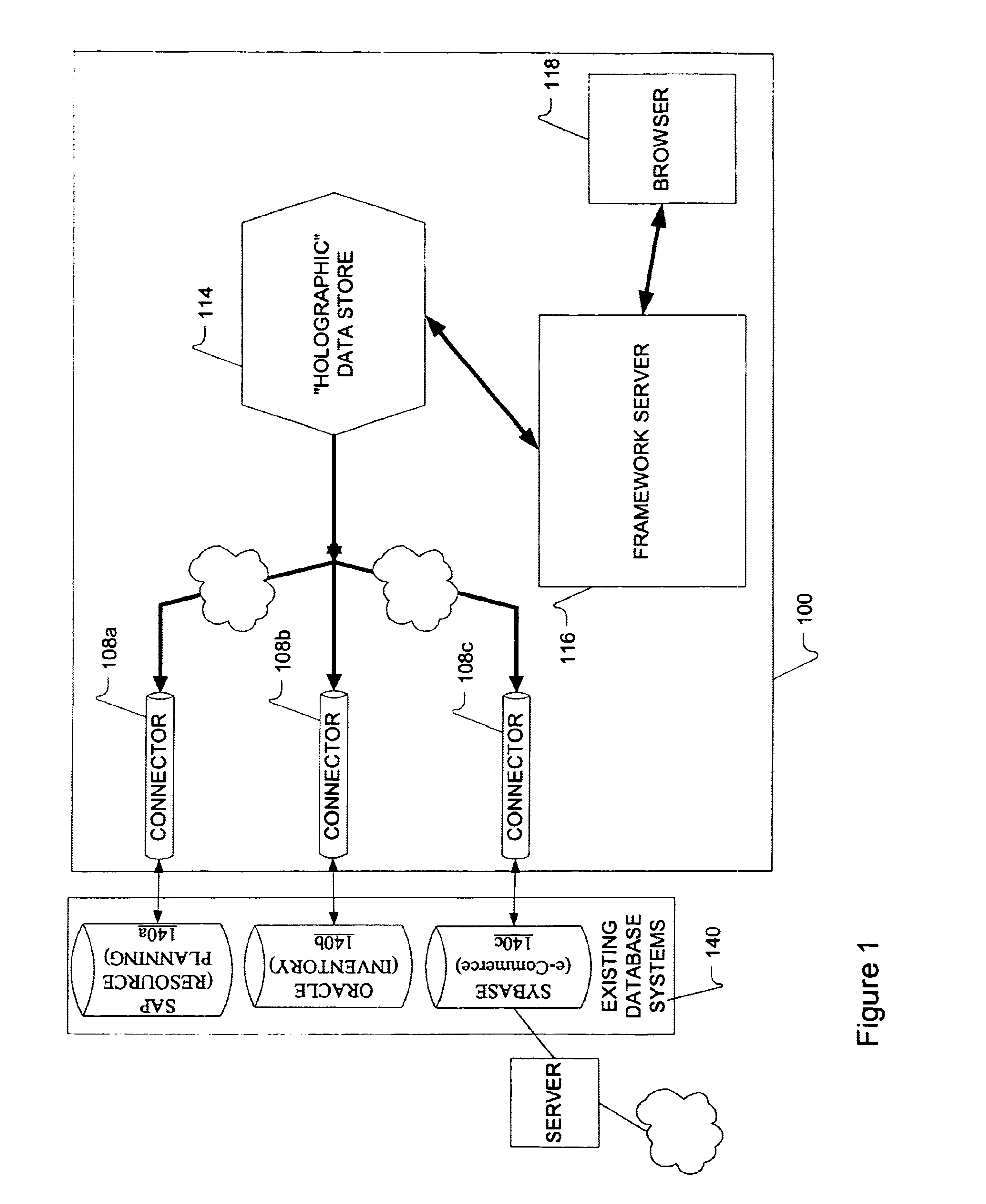
Methods and apparatus for real-time business visibility using persistent schema-less data storage
InactiveUS6856992B2Digital data information retrievalDigital data processing detailsHolographic storageVisibility
The invention provides methods for enterprise business visibility that transform any of marketing, e-commerce and transactional from a plurality of legacy and other databases into resource description framework (RDF) syntax. This information can be time-stamped (e.g., with expiration dates) and stored in a central data store. Answers to queries are discerned by applying genetic algorithm-based search techniques to the holographic store, with the confidence levels of those answers is based in part, for example, on the time-stamps of the triples.
Owner:OBJECT STORE INC
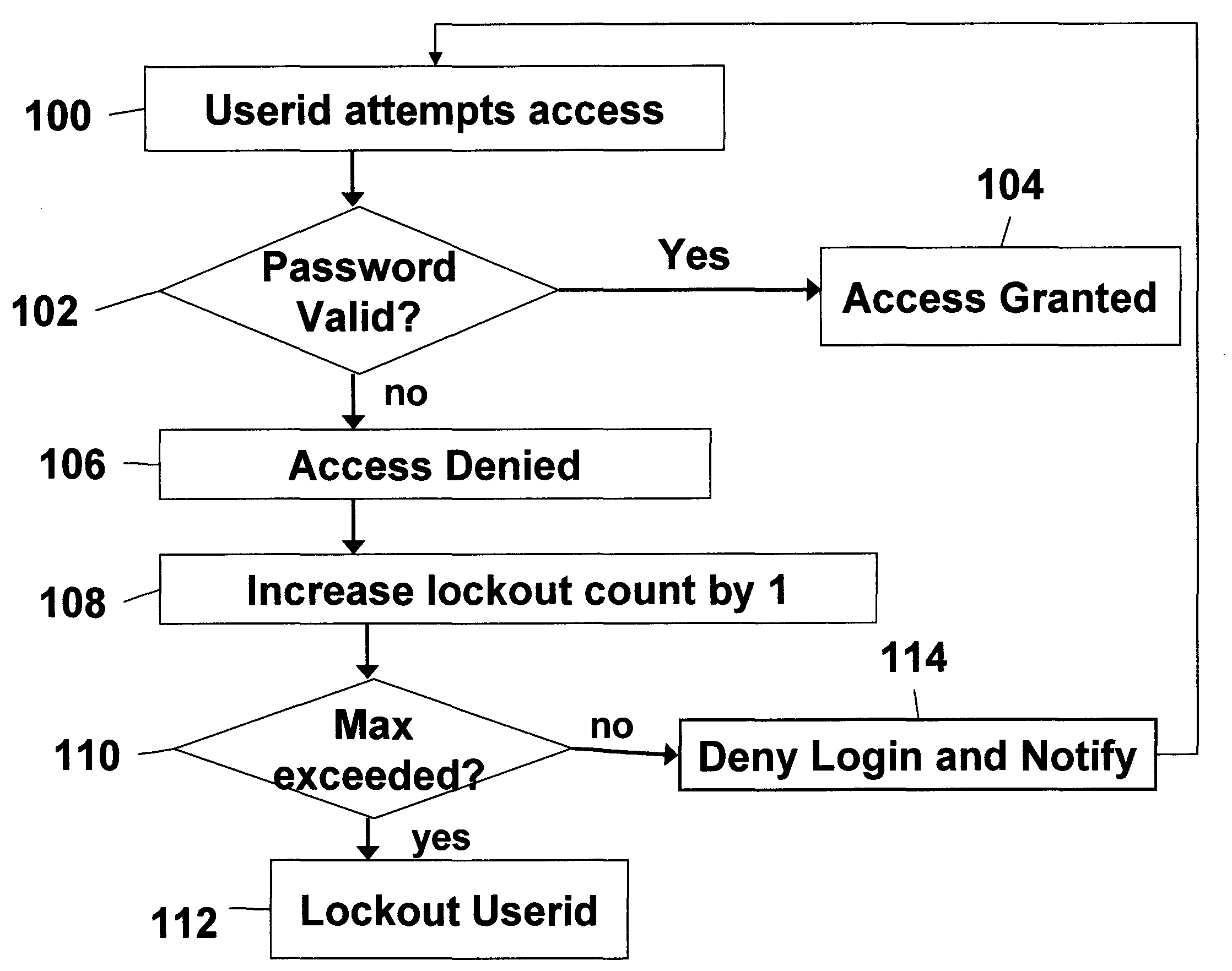
Systems and methods of securing resources through passwords
InactiveUS20060041756A1Mitigates password coordination problemMitigating password coordination problemDigital data processing detailsUser identity/authority verificationPasswordData file
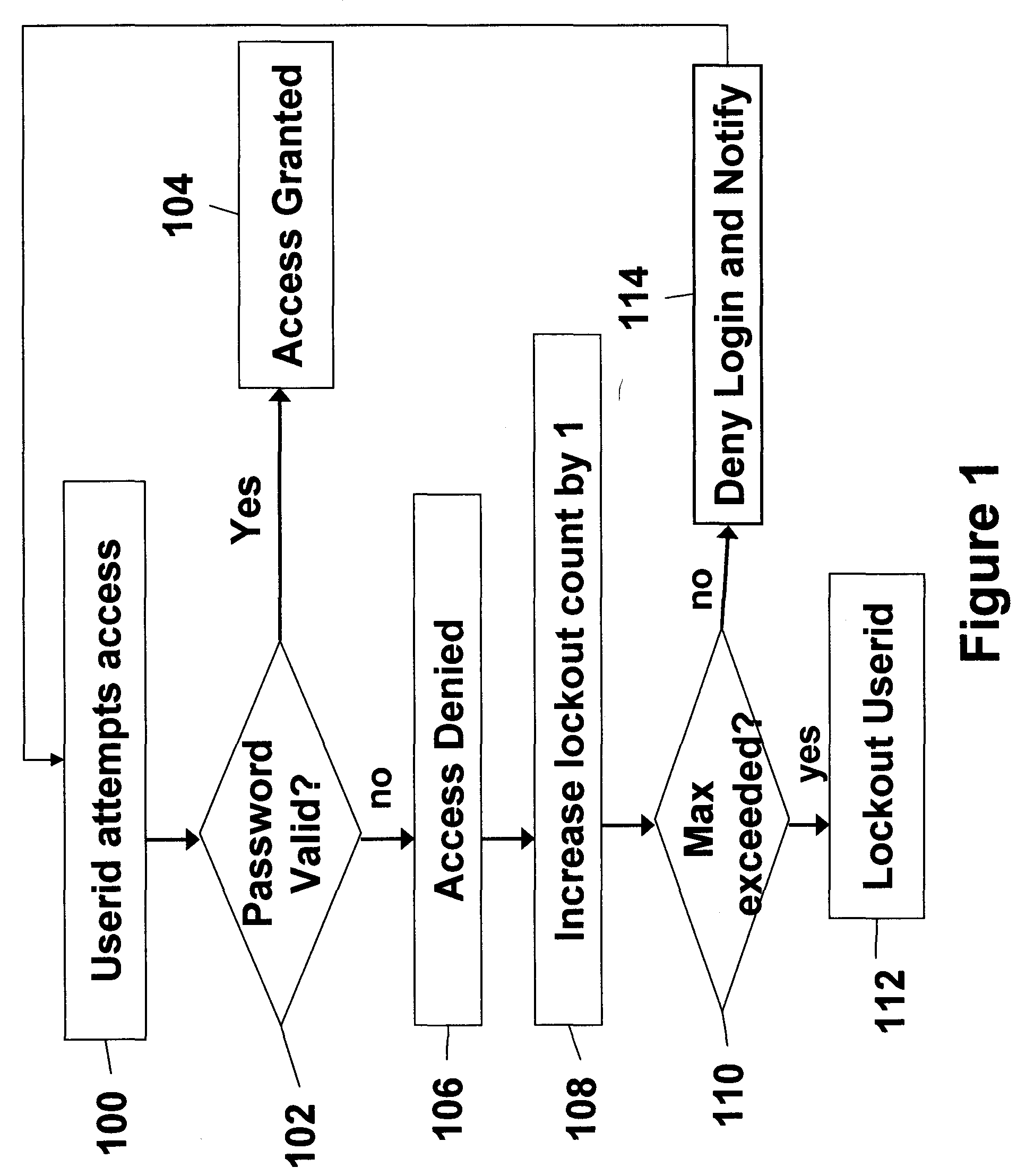
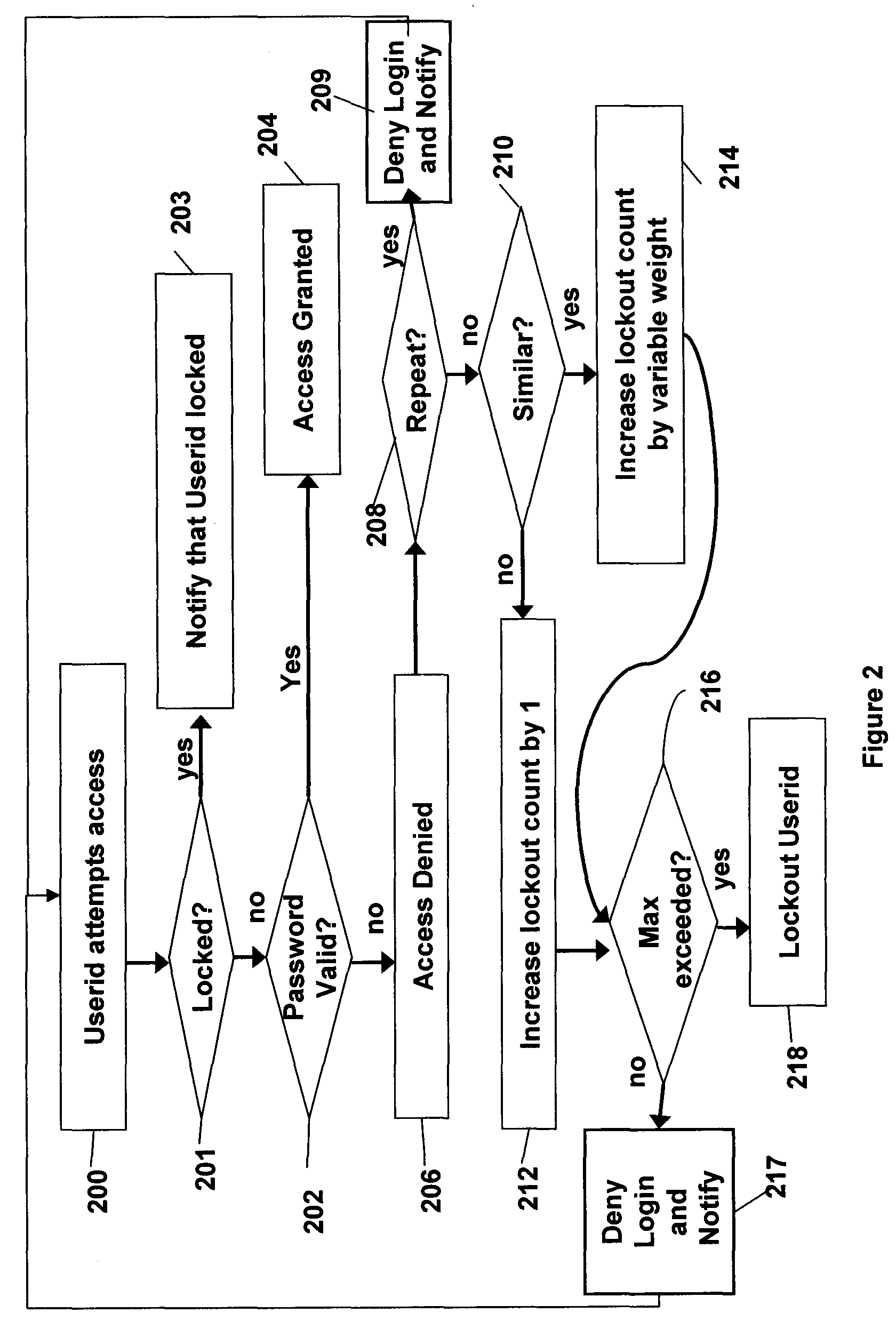
Disclosed is a method of authorizing access to an item that maintains a lockout count and blocks access to the item if the lockout count exceeds a predetermined value. One feature is that the invention “variably” increments the lockout count if the presented password fails to exactly match the stored password. In this process the invention increments the lockout count different amounts depending upon how closely the presented password matches the stored password. The invention also provides a methodology that allocates a plurality of the same passwords to a plurality of users who share the same userid. The invention allows continuous operation of the item being accessed by providing that each of the passwords has a different expiration date. Also, when dealing with situations where a plurality of users who share the same userid also share the same password, the invention maps information associated with the users to the password in a data file and periodically updates the data file.
Owner:IBM CORP
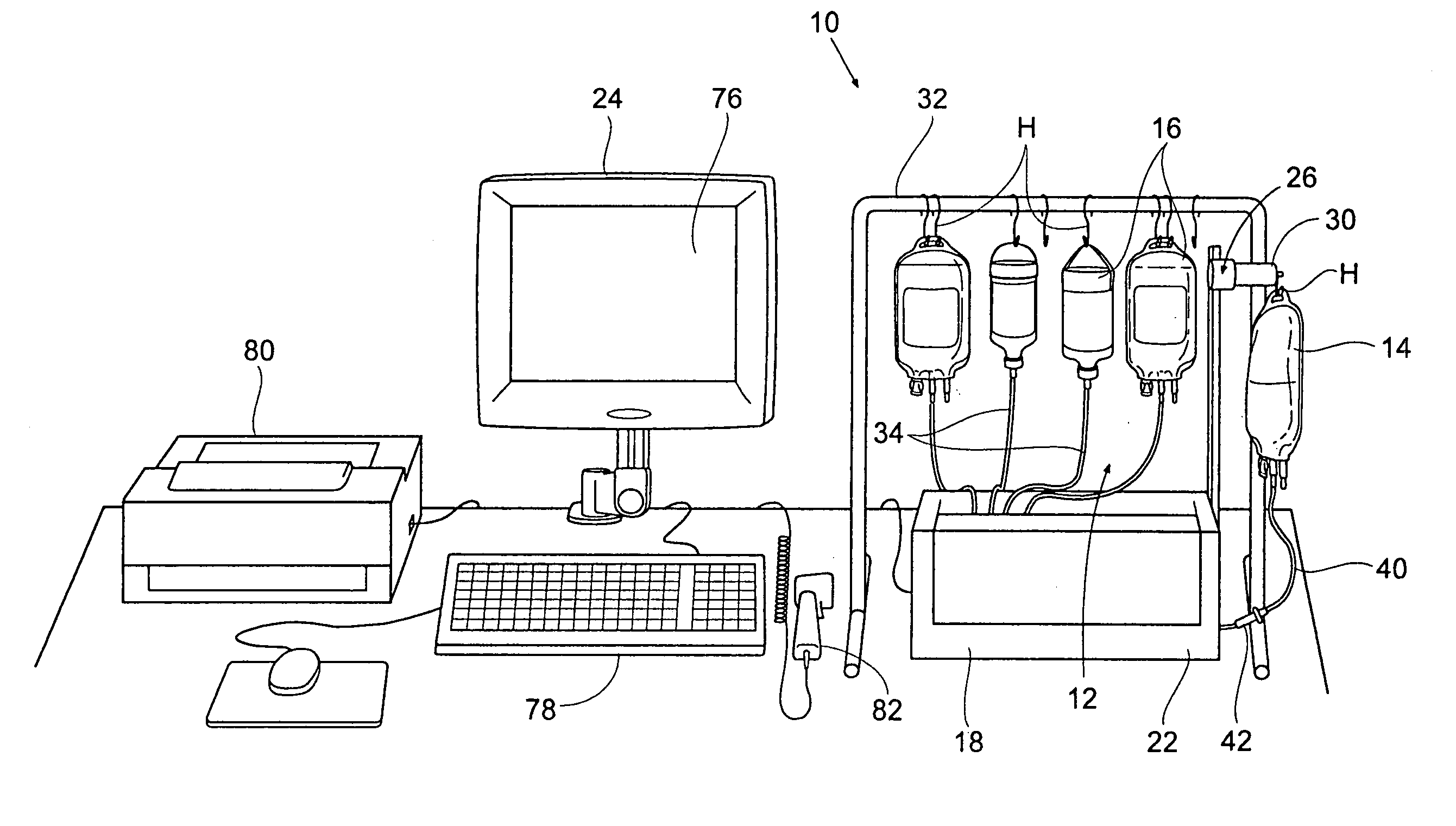
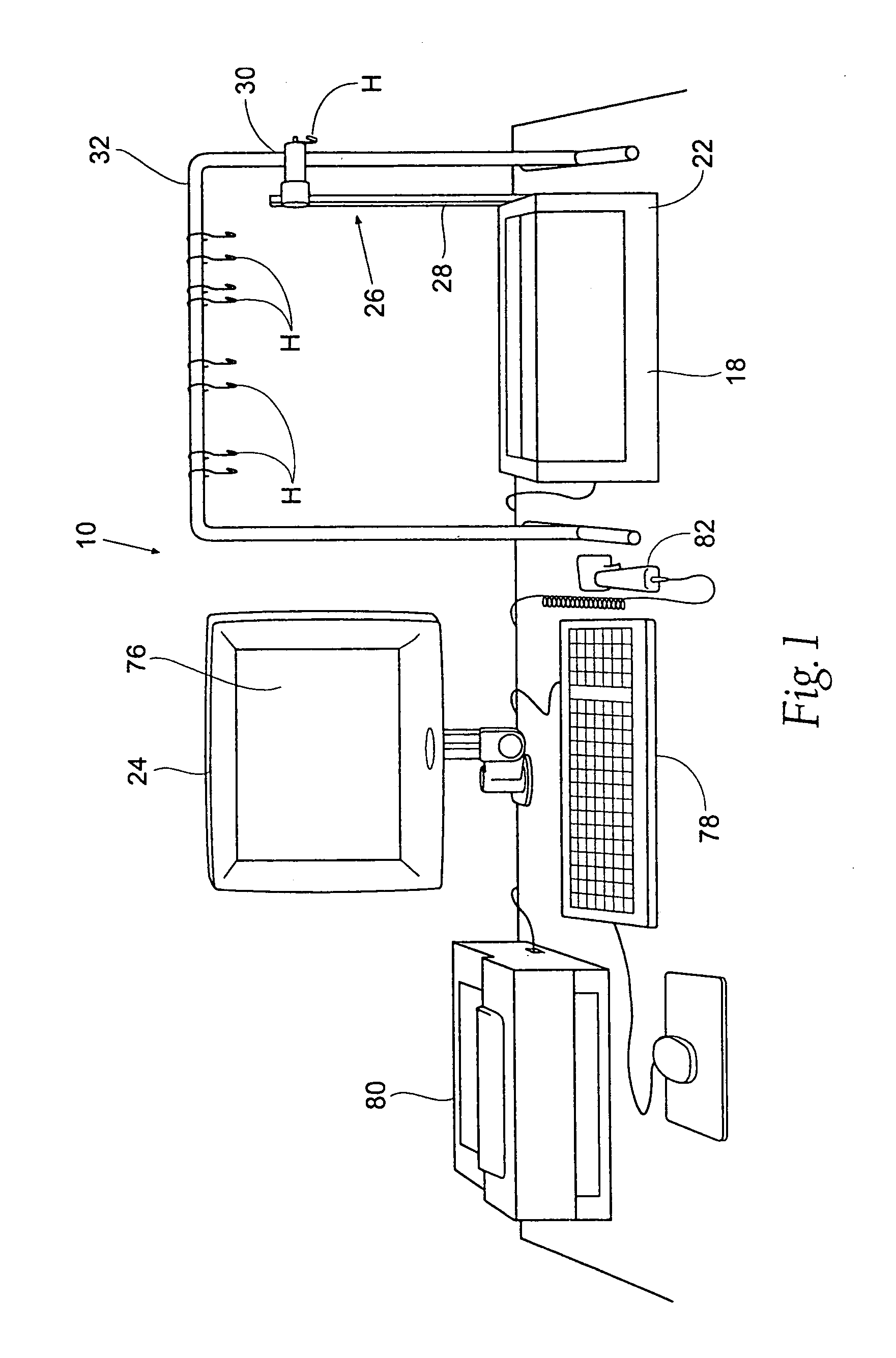
Pharmaceutical compounding systems and methods and information management system for same
Owner:B BRAUN MEDICAL
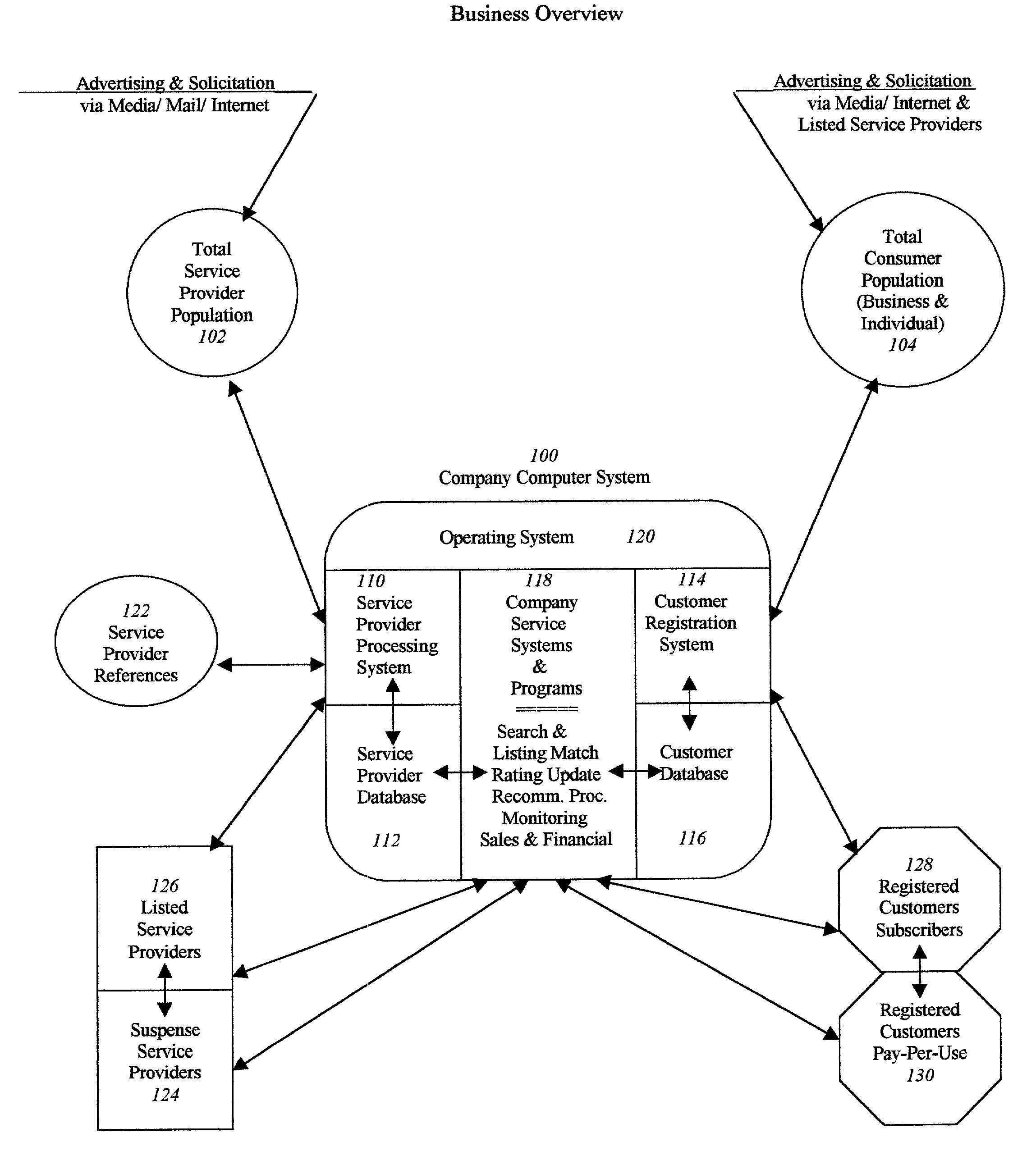
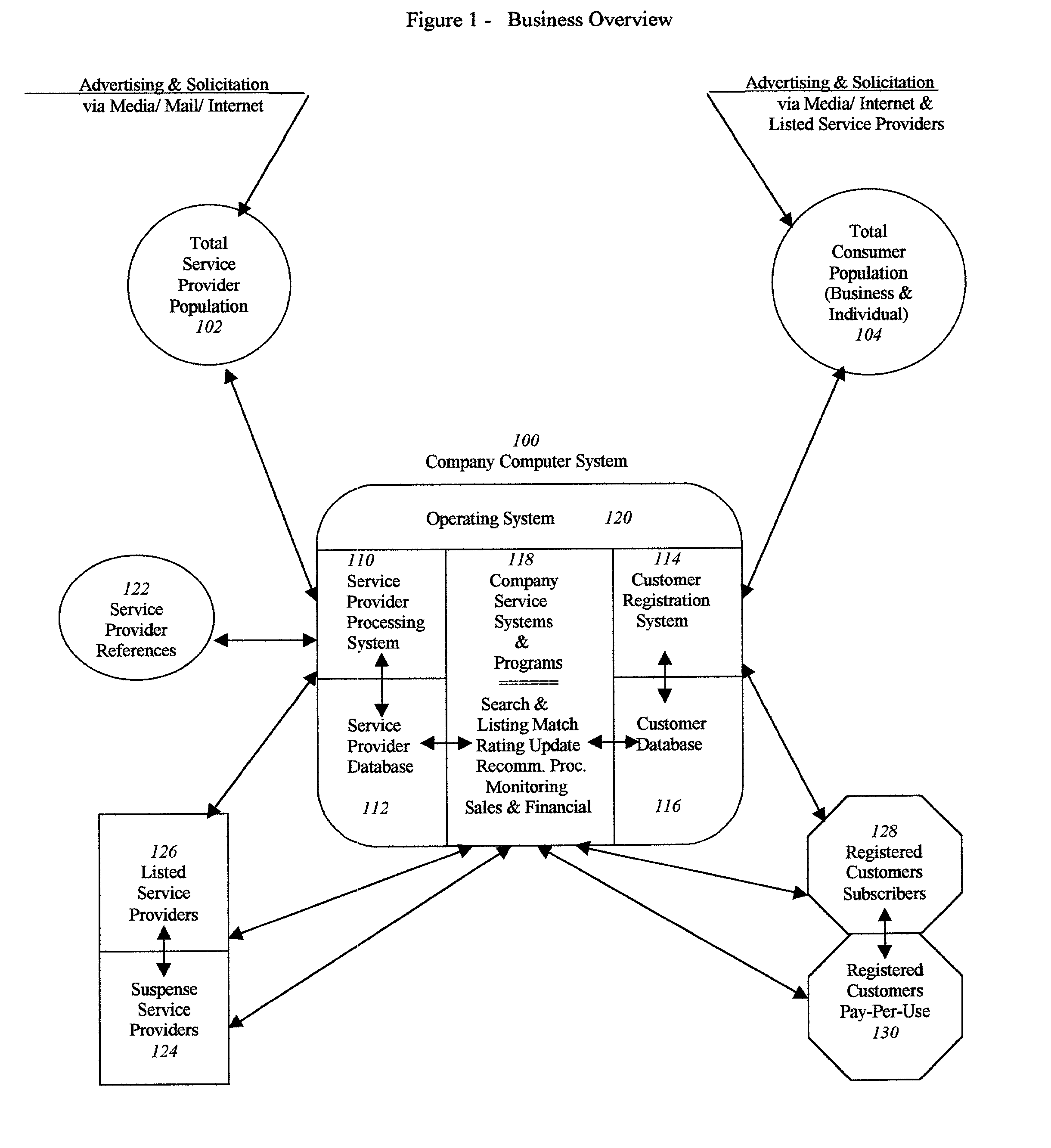
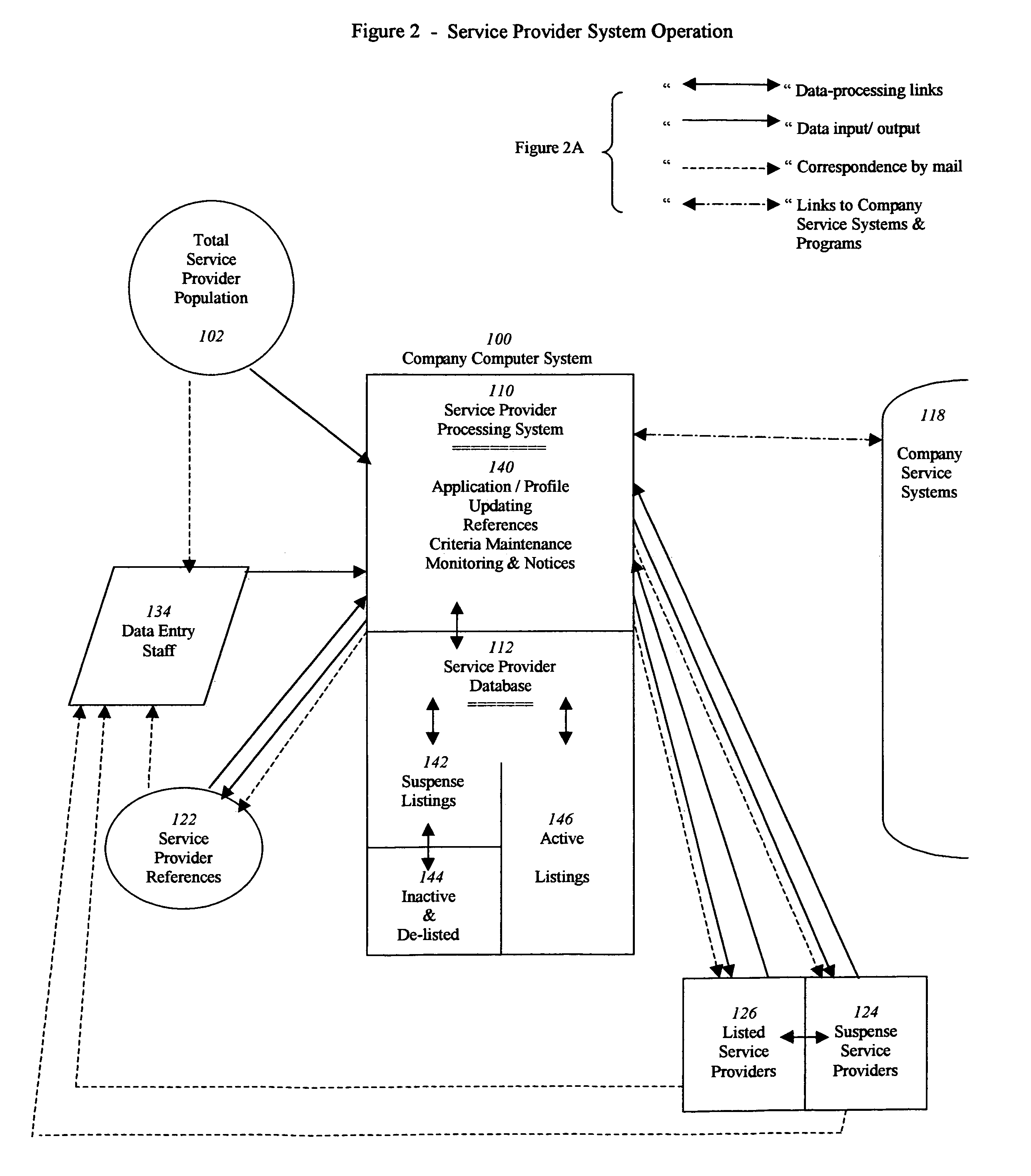
Accessible service provider clearinghouse
A service that maintains a minimum criteria level for service providers to be listed and available for public access. It can list not only the service provider's credentials and insurance support (with monitored expiration dates), but may also provide a current up-to-date rating system by the users themselves, as to the satisfaction level of the quality and reliability of the work performed. It can also offer a double-check of the credentials by customer verification input. Furthermore, the example service can be easily accessible by the general public (for individual or business use) on the Internet, or by printed text directories sold direct or in bookstores.
Owner:LOKITZ SHEILA
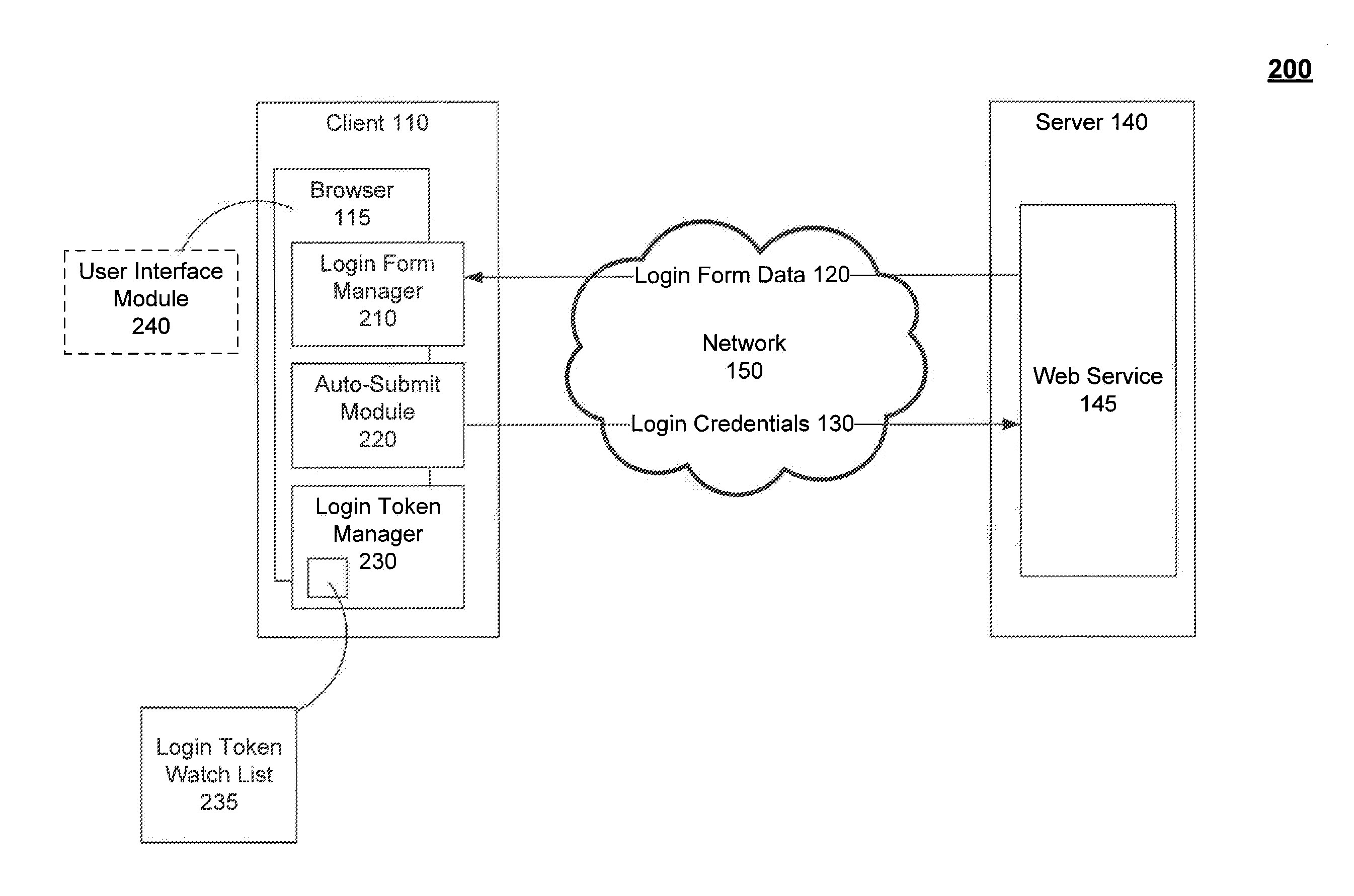
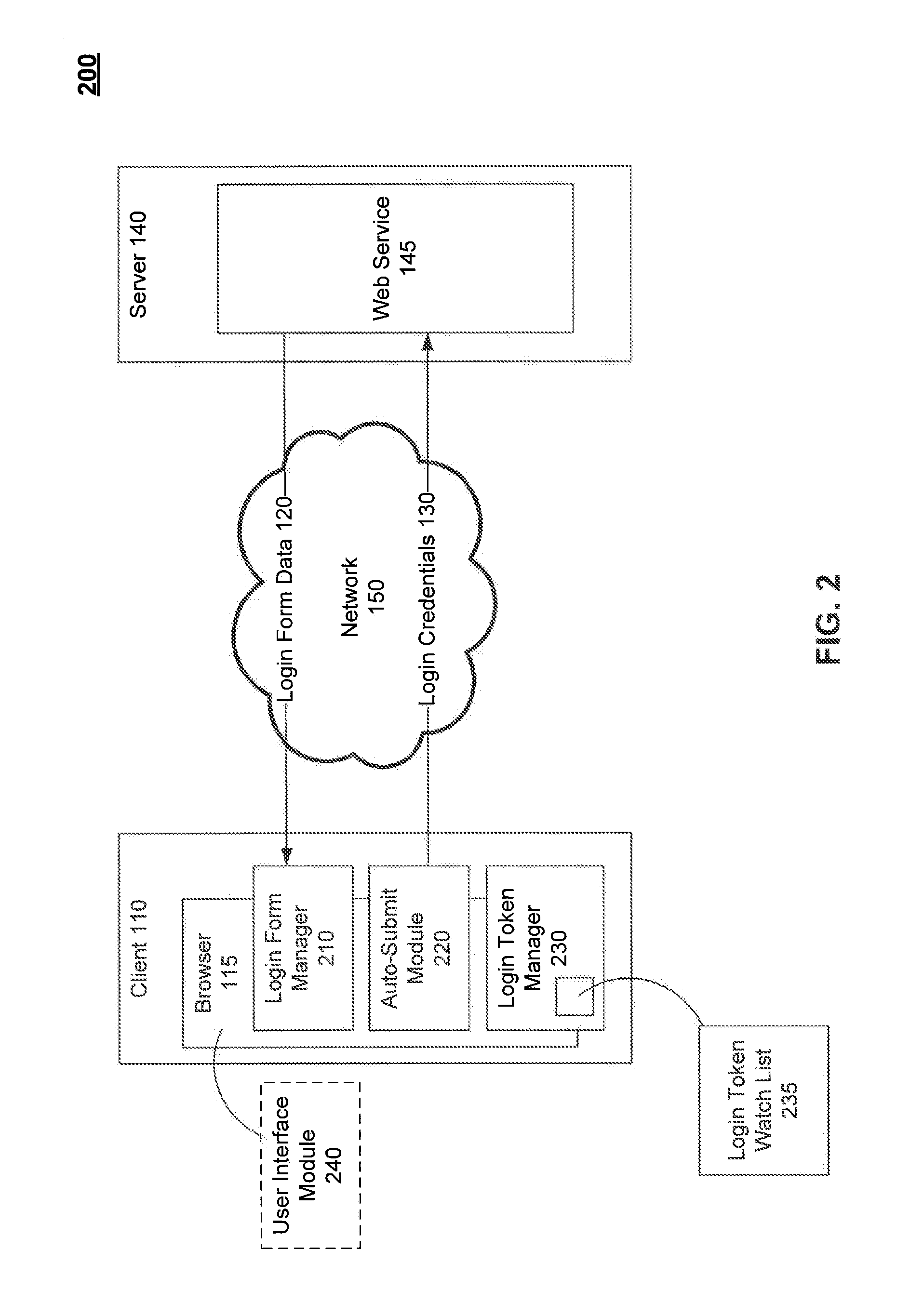
Background auto-submit of login credentials
A method and system for automatically submitting login credentials as a background process for a user of a web service are provided. Login information corresponding to a login form of the web service is stored, where the login information comprises a login endpoint of the web service and the login credentials are used to authenticate the user for a session of the web service. A login token, generated by the web service, and its expiration date are tracked. The login credentials are then automatically submitted, without user intervention, to the web service based on the login endpoint and the expiration date of the login token.
Owner:GOOGLE LLC
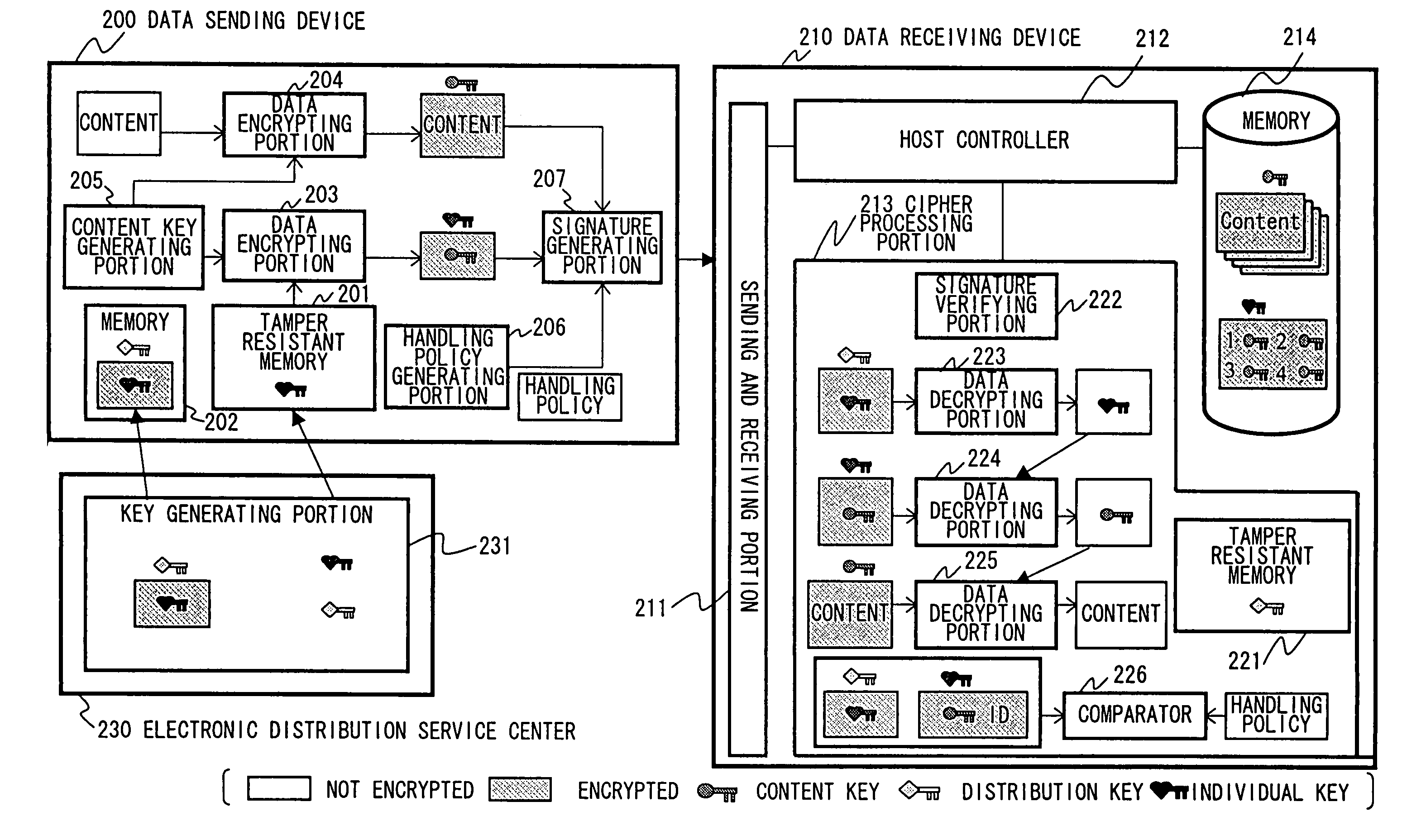
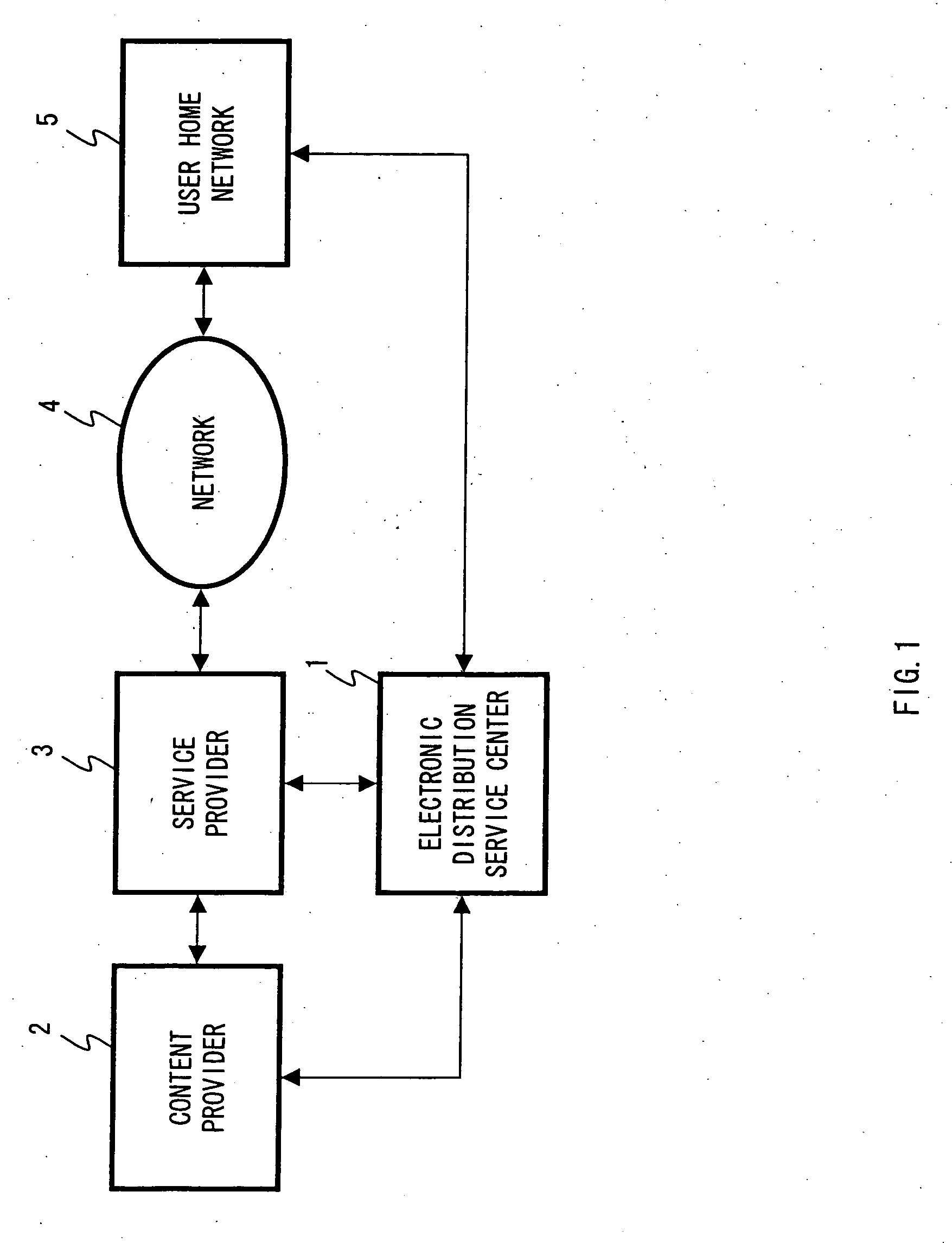
Information transmission system, transmitter, and transmission method as well as information reception system, receiver and reception method
InactiveUS7099479B1Prevent piracySimple configurationKey distribution for secure communicationUnauthorized memory use protectionInformation transmissionInformation seeking
Owner:SONY CORP
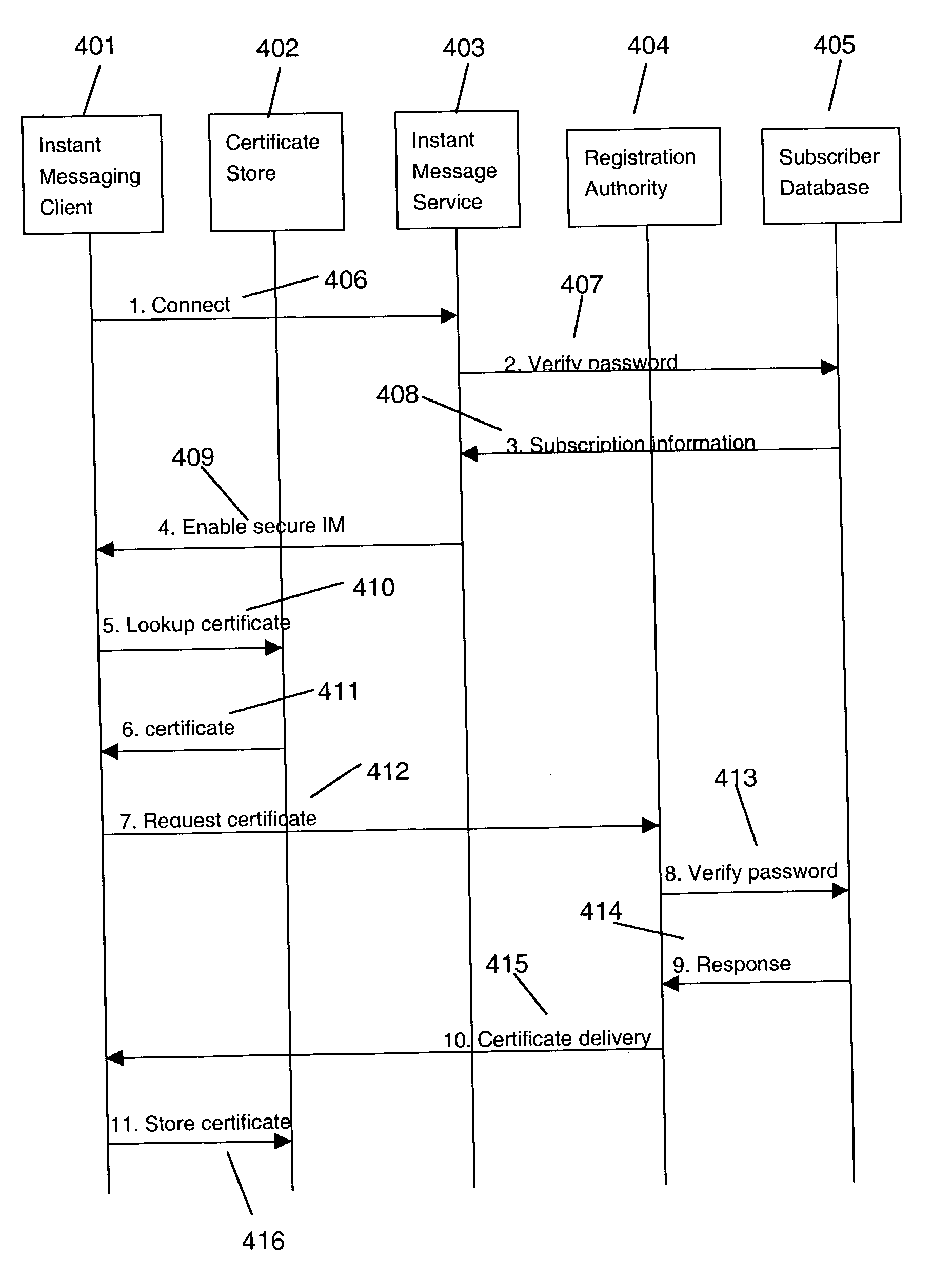
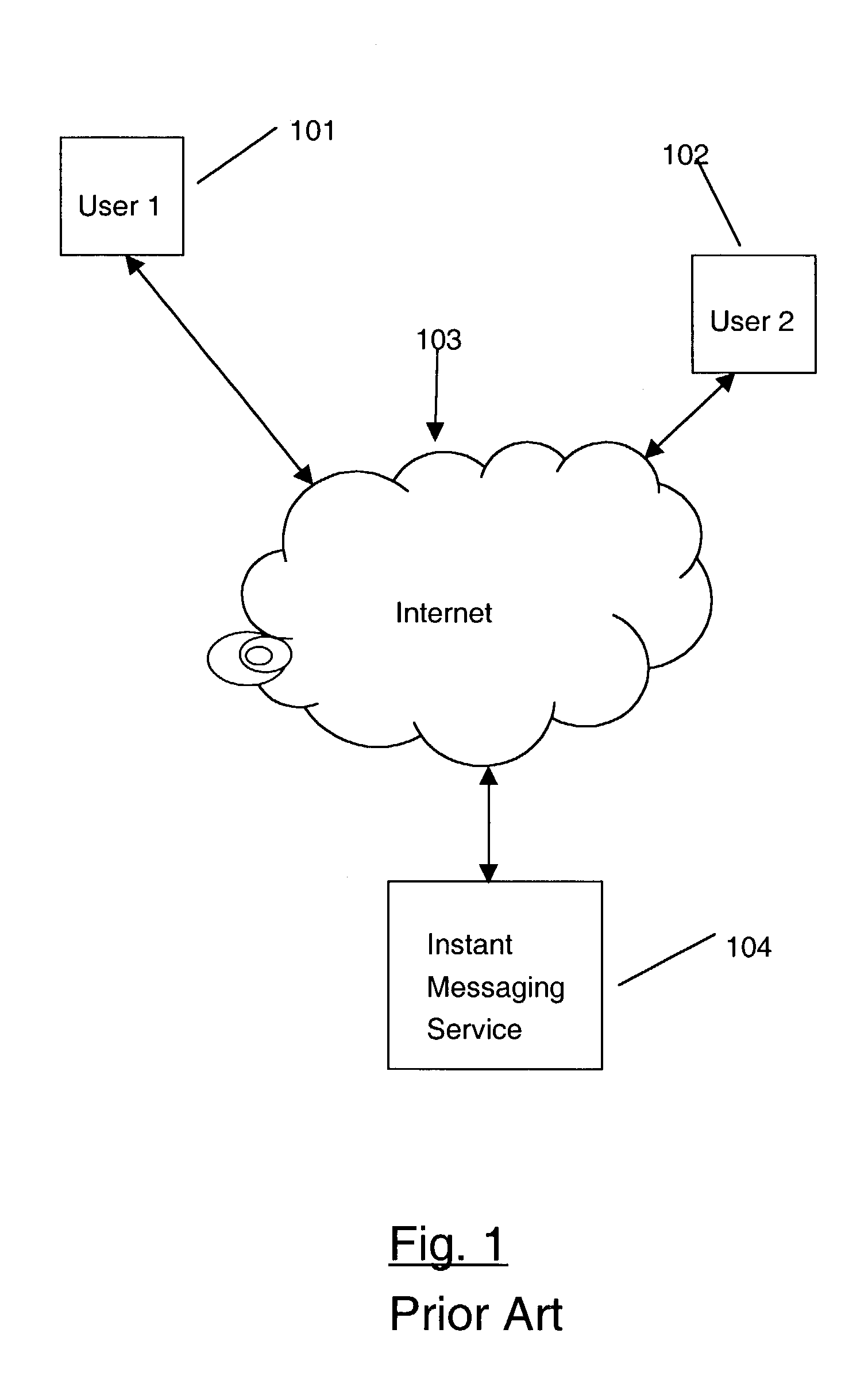
Secure instant messaging system
ActiveUS7131003B2Multiple keys/algorithms usagePublic key for secure communicationRelevant informationSecure state
A secure instant messaging system integrates secure text instant messaging and secure file transfers into existing instant messaging systems. At least one certificate authority (CA) is provided that issues a security certificate to a user that binds the user's instant messaging screen name to a public key which is used by other users to encrypt messages and files sent to the user and by the user to decrypt the received messages and files. A subscriber database is used by the CA to keep track of valid users and their associated information, such as: user screen names, user subscription expiration dates, and enrollment agent information. A user sends his certificate to the invention's instant messaging server which publishes the user's certificate to other users by creating a hash value of the user's certificate and sending it to the other users which allows the recipients to decide if they need to update their caches with a new copy of the user's certificate. Instant messages and files are encrypted by a sending user using an encryption algorithm and the recipient's certificate. The sending user can sign instant messages using his private signing key. The security status of each received instant message is displayed to the user.
Owner:GOOGLE LLC
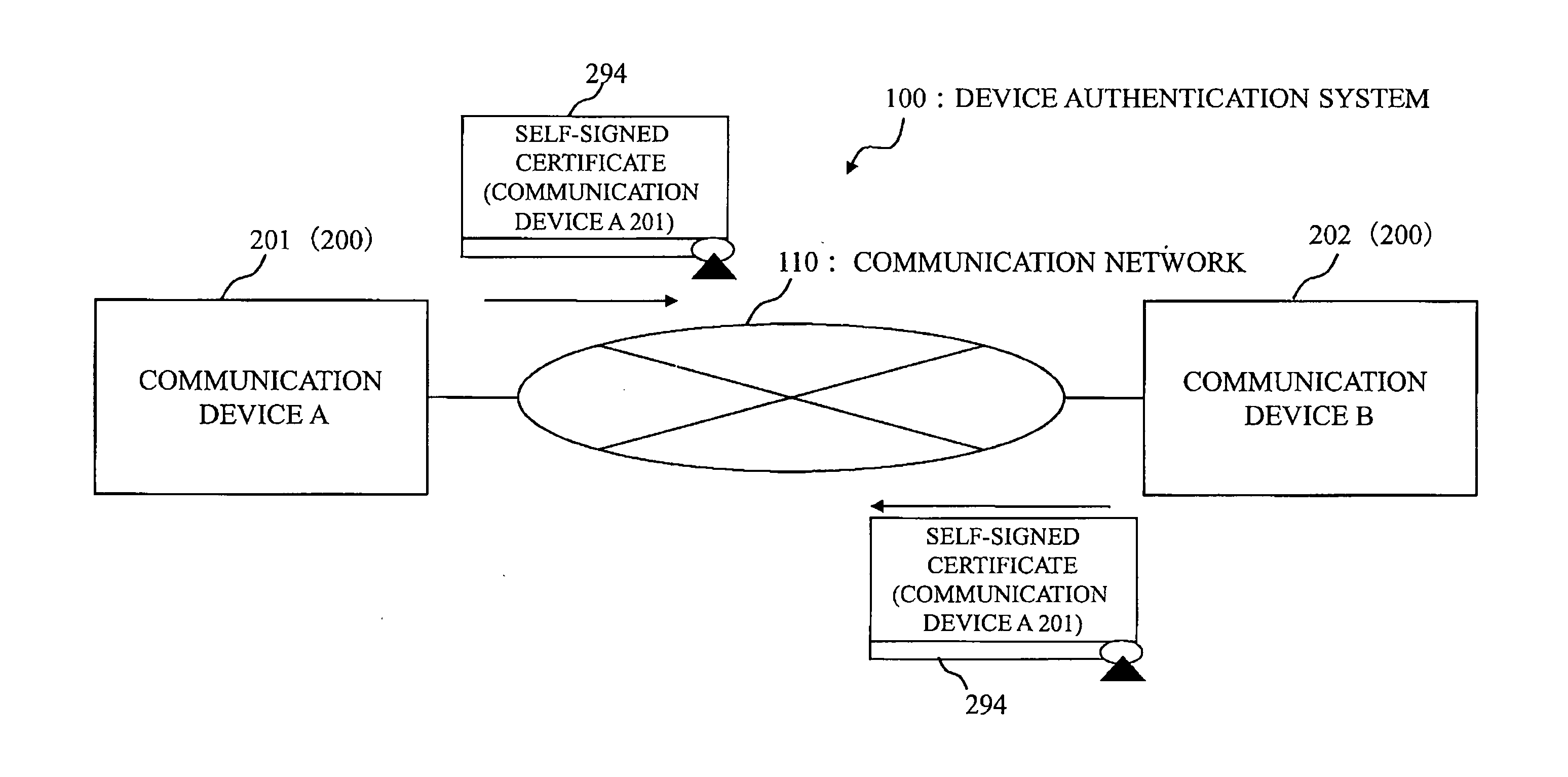
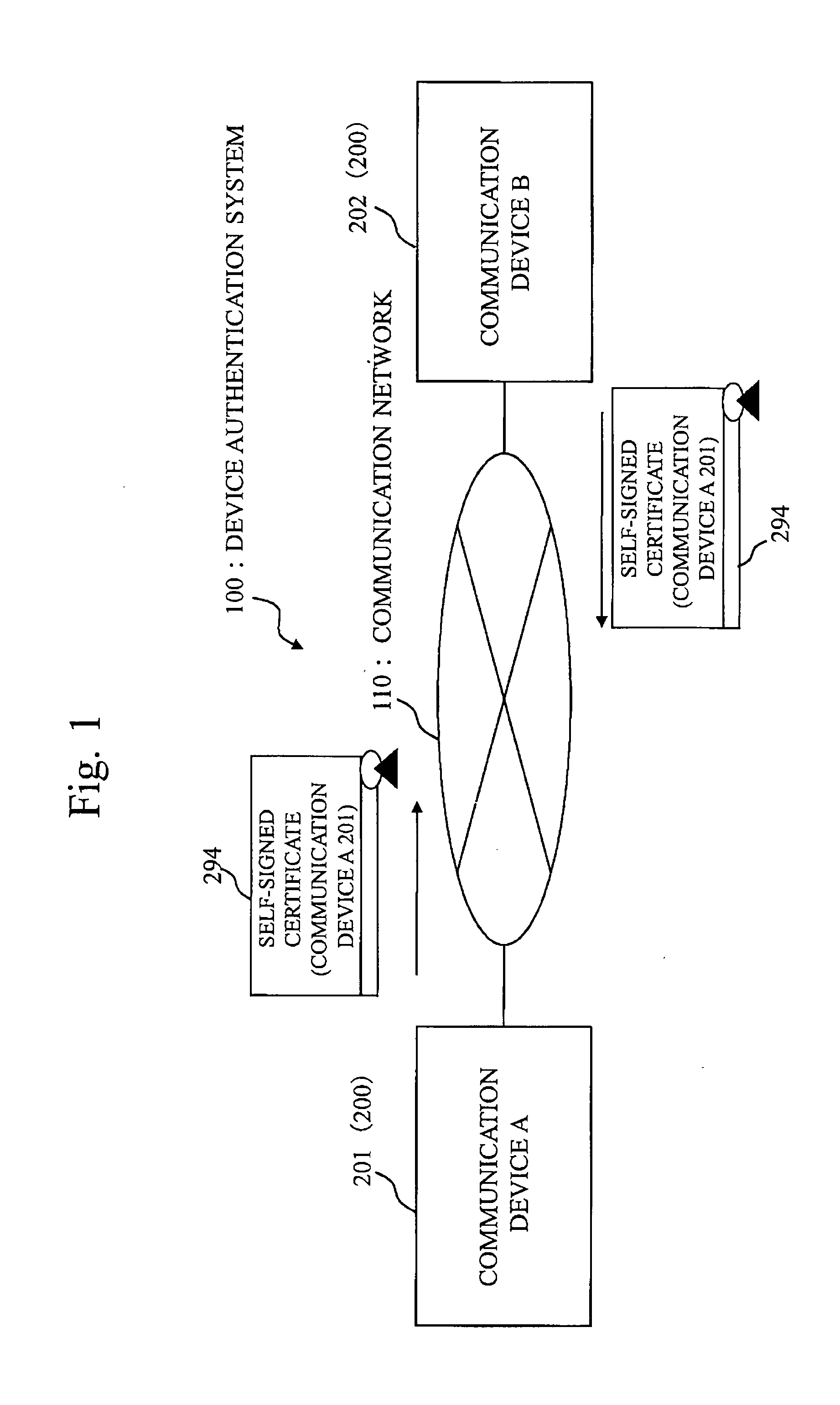
Self-authentication communication device and device authentication system
InactiveUS20120036364A1Public key for secure communicationUser identity/authority verificationExpiration dateSecure communication
In a system where a communication device performs secure communication by using a digital certificate, to enable a device of a communication party to verify that a self certificate is certainly generated by a device indicated on the self certificate even if the self certificate is not delivered offline in advance. Based on a master key and a public parameter, a communication device generates an ID-based encryption private key for which a device unique ID is used as a public key. Then, the communication device generates the digital signature of an RSA public key as a ID-based encryption signature by using the ID-based encryption private key. Then, the communication device generates an RSA self signature for the RSA public key, an expiration date, a host name, the device unique ID, and the ID-based encryption signature as the target. Then, the communication device generates a self-signed certificate to include the ID-based encryption signature and the RSA self signature.
Owner:MITSUBISHI ELECTRIC CORP
System and method for policy-based data lifecycle management
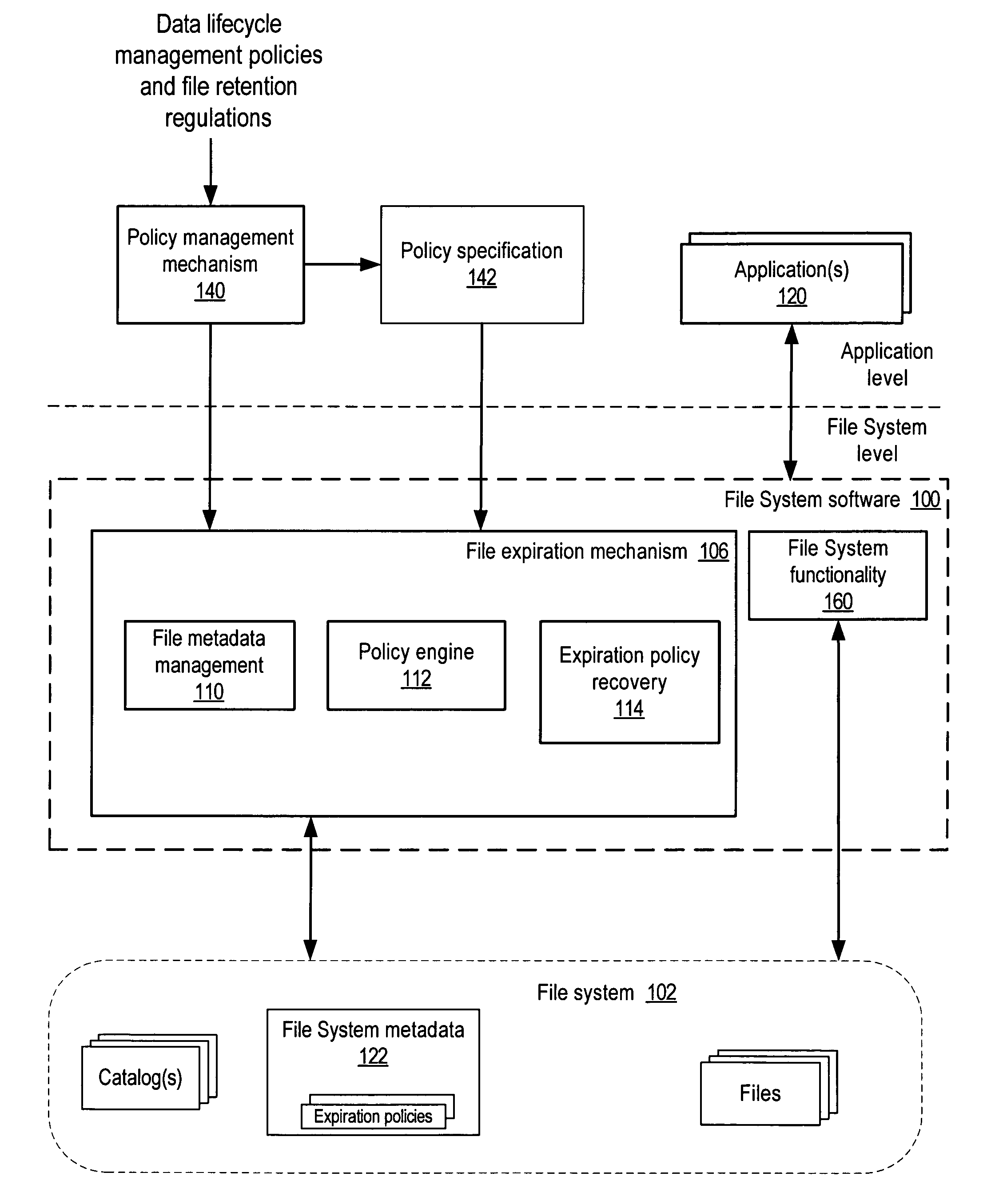
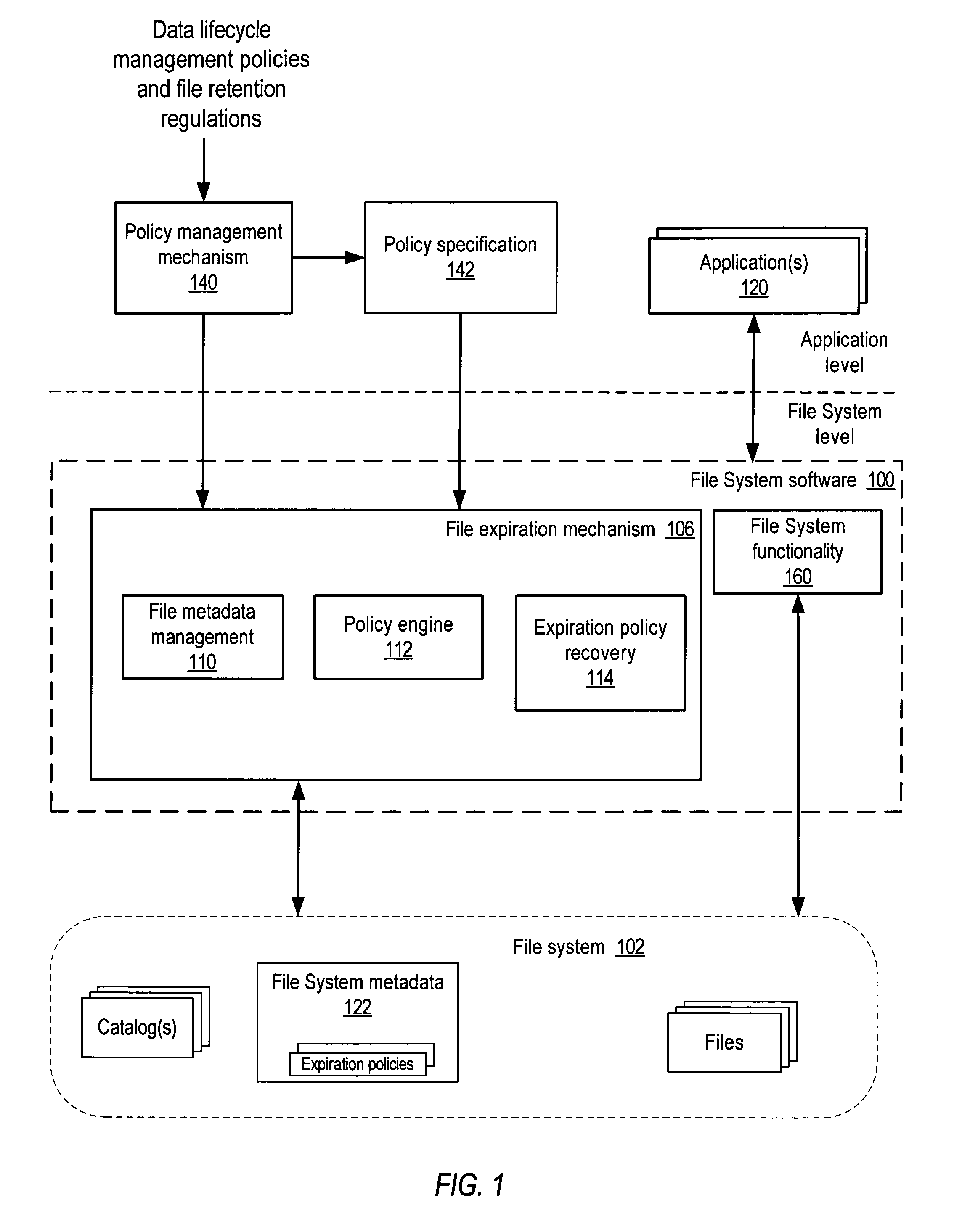
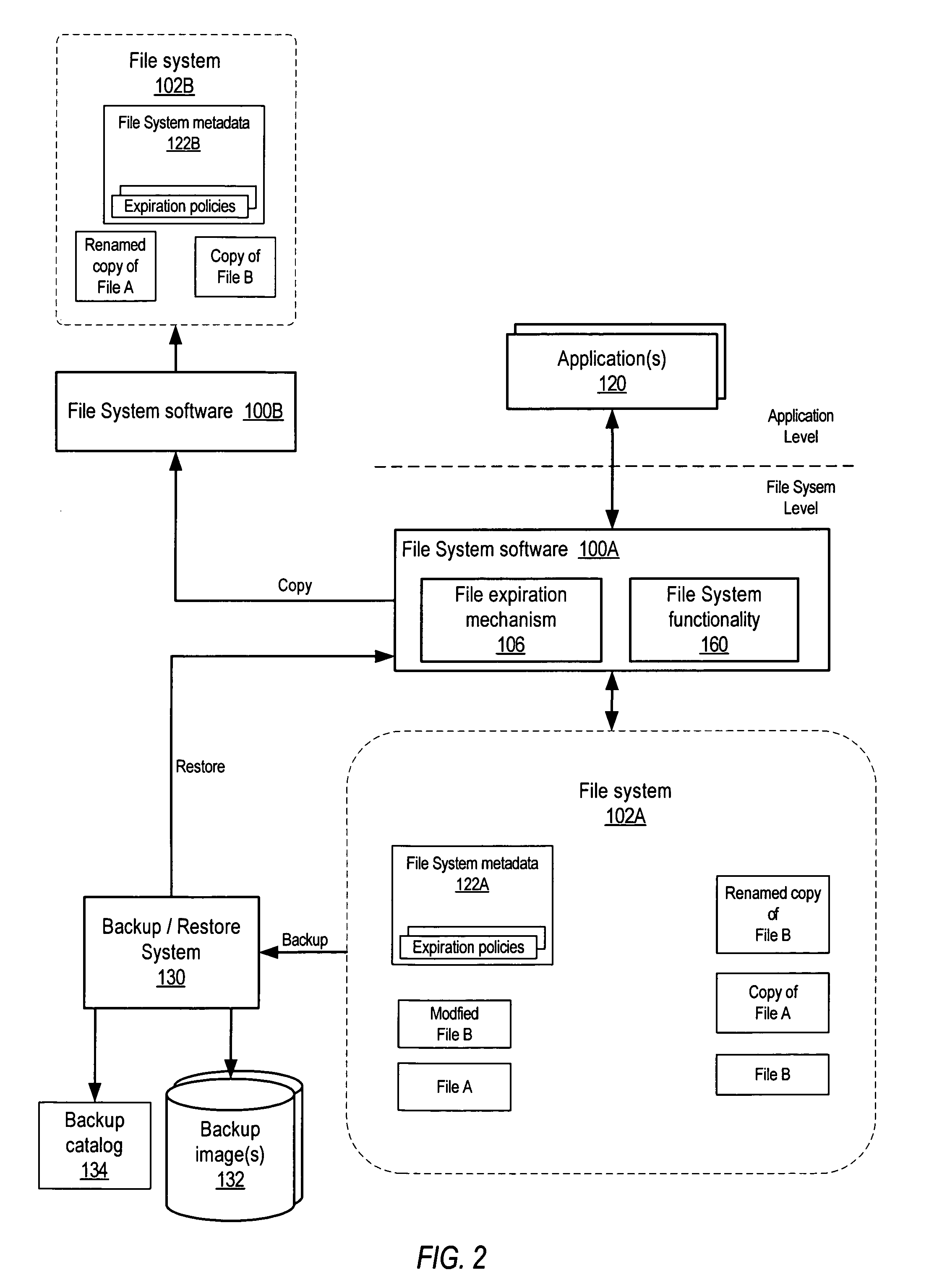
InactiveUS7680830B1Digital data information retrievalSpecial data processing applicationsFile systemData lifecycle
System and method for policy-based lifecycle management of data in file systems. In embodiments, an expiration policy for the files may be stored as part of the file system metadata. The expiration policy may be as simple as an expiration date for the file, or a more complex policy that specifies one or more metrics to be evaluated to determine if a file is expired. The expiration policy may also specify one or more actions to be taken if the file has expired. The expiration policy may be evaluated on attempts to access the files in the file system, on other file systems, and on backup / archive images to determine if the files are expired and thus whether access to the files is to be allowed. In one embodiment, a scan mechanism may periodically or aperiodically delete files in the file system for which the expiration date has passed.
Owner:SYMANTEC OPERATING CORP
Secure digital content licensing system and method
InactiveUS7155415B2Office automationProgram/content distribution protectionWeb siteTelecommunications link
Owner:BLOCKBUSTER LLC
Information sending system, information sending device, information receiving device, information distribution system, information receiving system, information sending method, information receiving method, information distribution method, apparatus, sending method of information receiving device, playback method of apparatus, method of using contents and program storing medium
InactiveUS20060168451A1Improve usabilityPrevent piracyKey distribution for secure communicationUser identity/authority verificationComputer hardwareDistribution method
Owner:SONY CORP
Method and system for authorizing client devices to receive secured data streams
ActiveUS20050071631A1Reduce the numberKey distribution for secure communicationPublic key for secure communicationData streamTimestamp
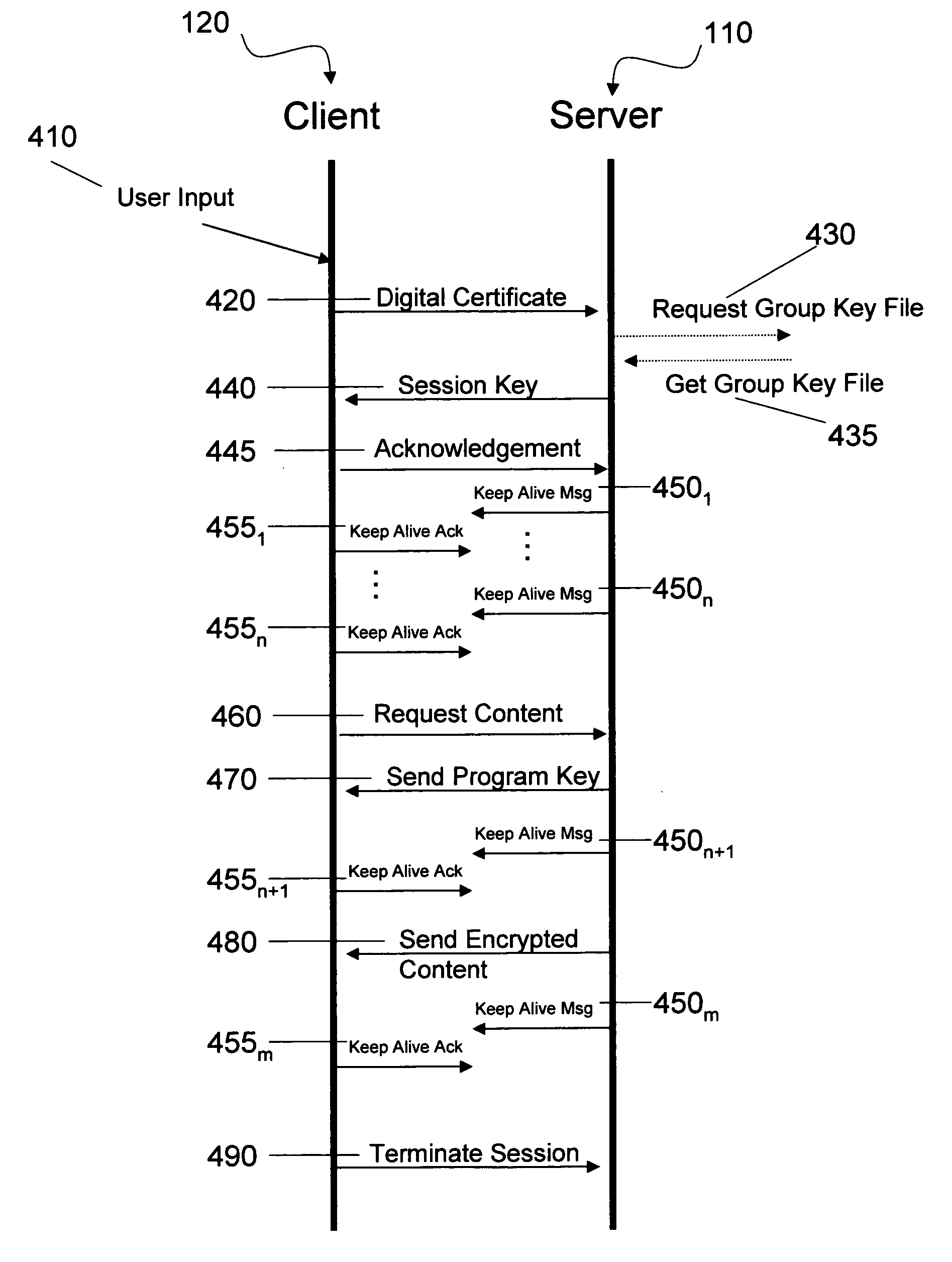
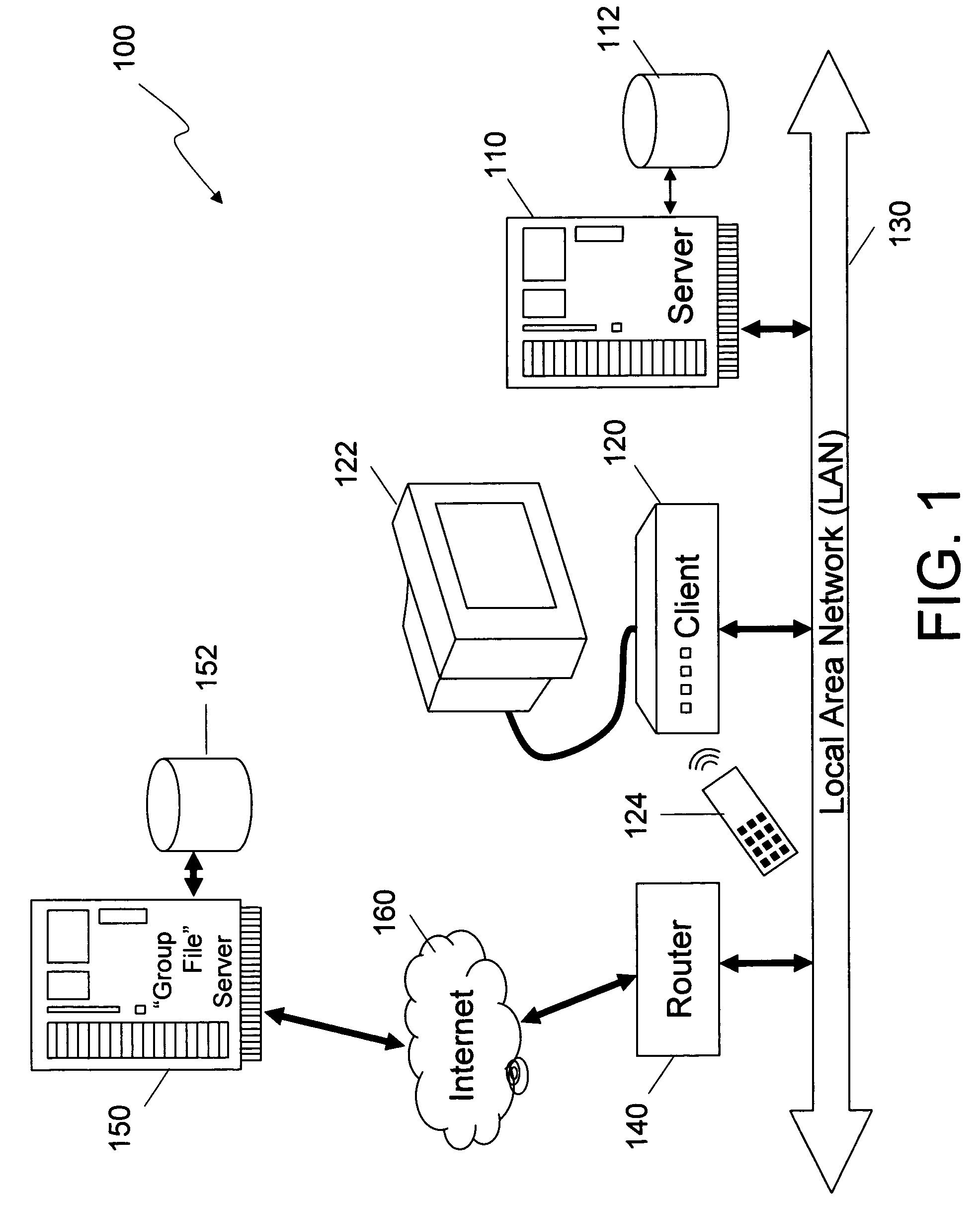
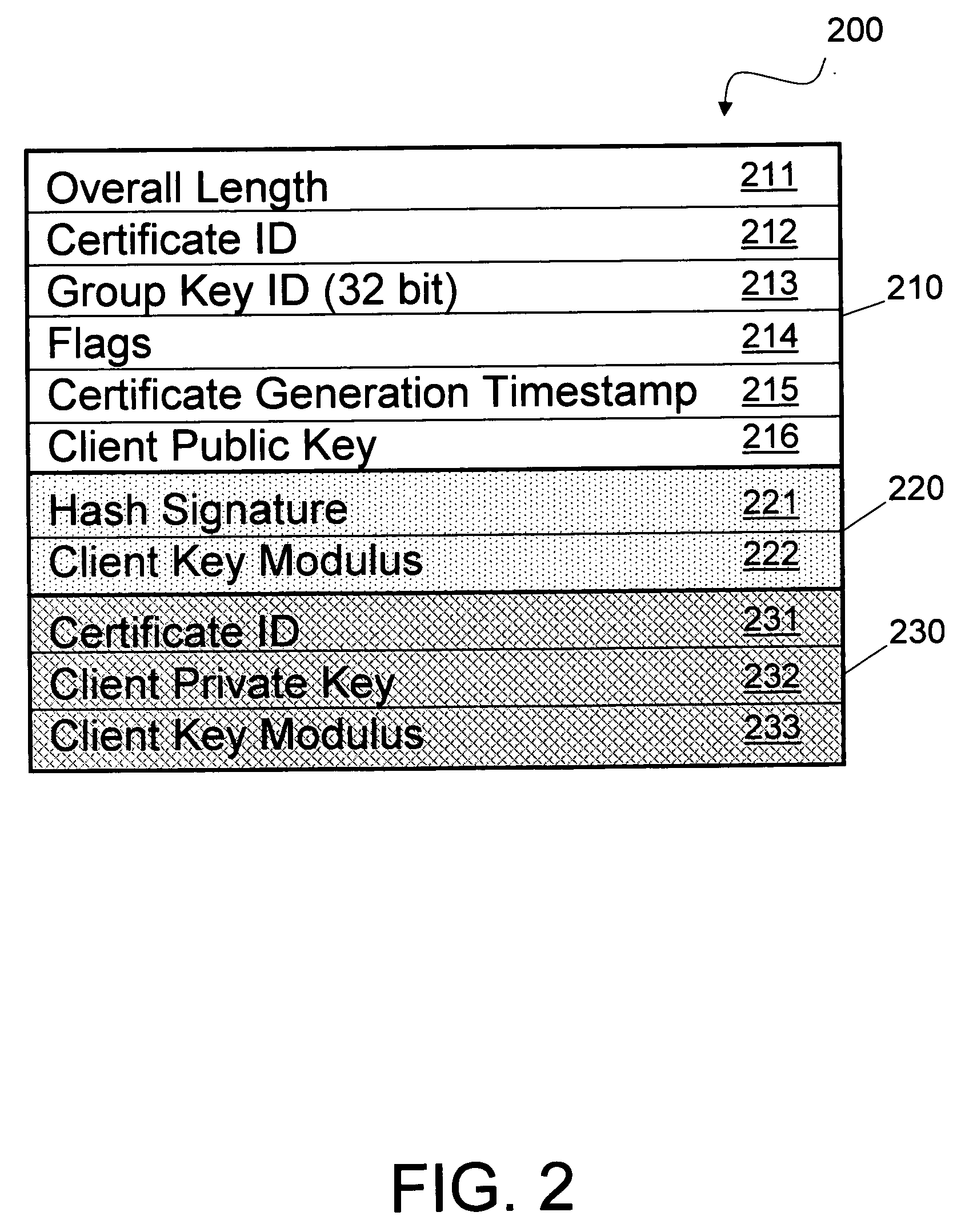
A method and system for authorizing client devices to receive secured data streams through the use of digital certificates embedded in the client devices. A freely distributed cryptographically signed group file with an embedded expiration date is associated with each individual digital certificate. A single group file can be associated with more than one digital certificate but each digital certificate is associated with a single group file. The group file contains cryptographic keys that can be used to decrypt a section of the digital certificate revealing a set of client keys. The client keys are then used to encrypt a program key which are then sent back to the client device. When the client device requests a specific data stream or digital content, an issuance timestamp associated with the content is compared to the expiration date in the group file. If the issuance timestamp is after the expiration date, the client device is declined. If the issuance timestamp is before the expiration date, the requested content, encrypted utilizing the program key, is sent to the client device.
Owner:DIGITAL 5 +1
System and method for displaying option market information
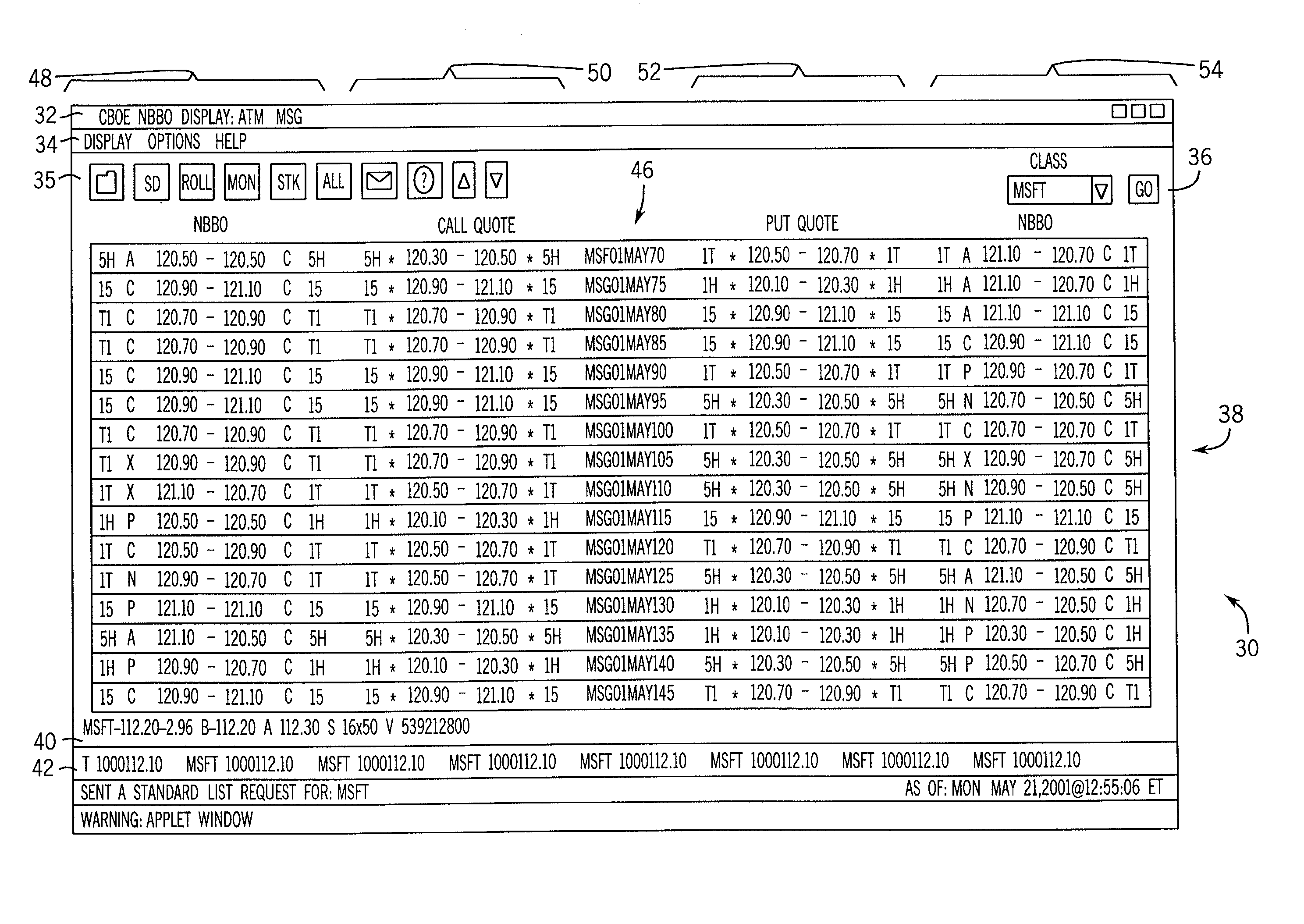
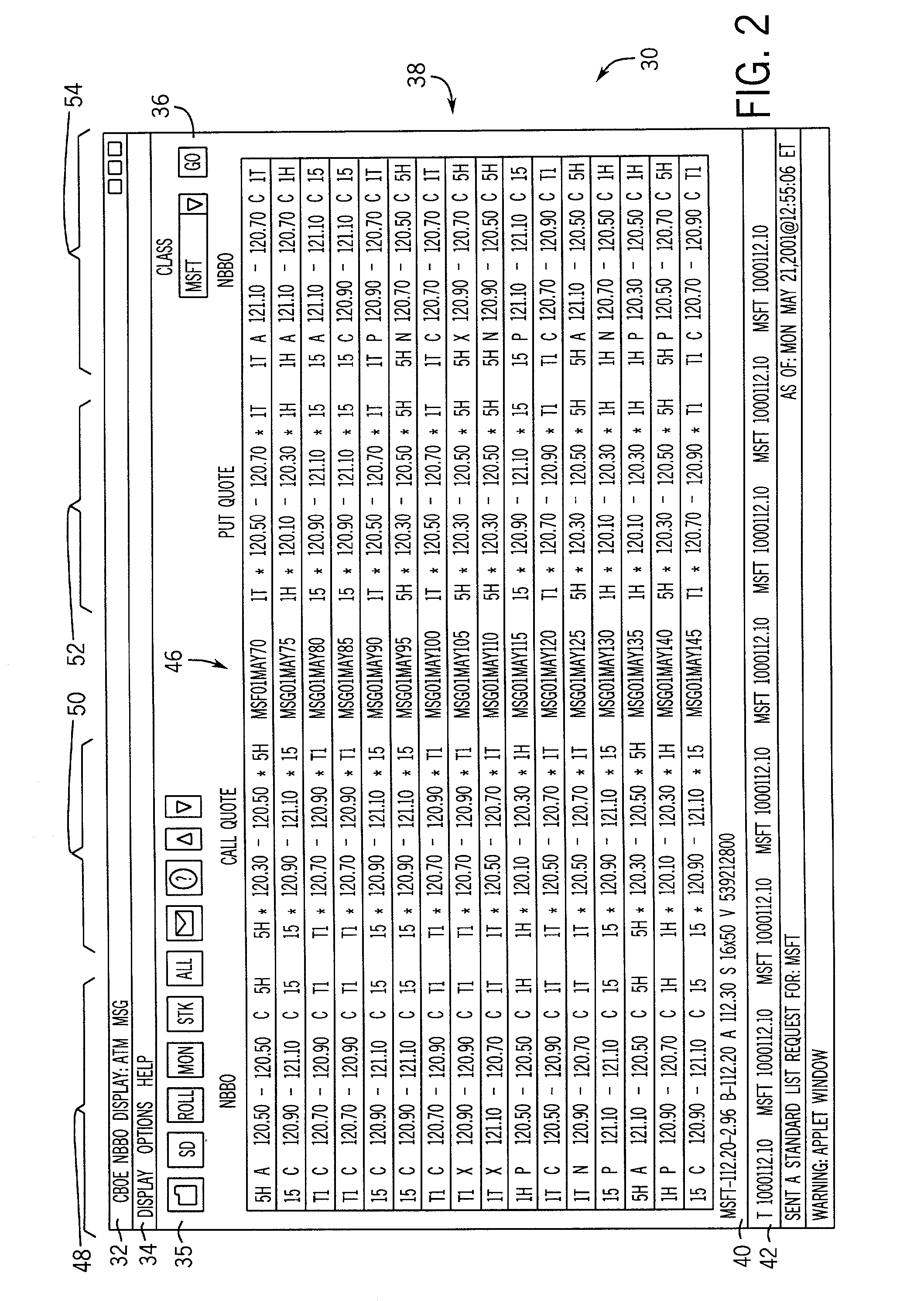
The present invention provides a method of displaying option market information including establishing a communication link between a member computer and a central computer, accessing option trading data from the central computer through the member computer, and inputting at least one signal to the member computer. The signal represents either an underlying asset symbol or an option class symbol of an underlying asset. The method further includes generating a display page listing option trading information for a plurality of option series relating to at least one of the entered underlying asset symbol and the entered option class symbol, and displaying the plurality of option series on the display page such that the option series having a strike price approximately equal to the current trading price of the underlying asset is centrally positioned on the display page. Additionally, a strike price and a first date indicator can be input and the display page can list trading information for the entered option and plurality of option series having at least a second expiration date, the plurality of option series extending over a range of strike prices, the range centrally positioned at the current trading price of the underlying stock, the plurality of option series relating to the at least one of the entered underlying asset symbol and the entered option symbol. A further method of the invention includes generating a display page listing option trading information for a month entered for an underlying asset. A still further method of the invention includes generating a display page listing option trading information for a strike price entered for an underlying asset.
Owner:CBOE EXCHANGE INC
Public/private dual card system and method
InactiveUS7172112B2Reduce disadvantagesEliminate needComplete banking machinesTicket-issuing apparatusCredit cardOperating system
Owner:CHARTOLEAUX +1
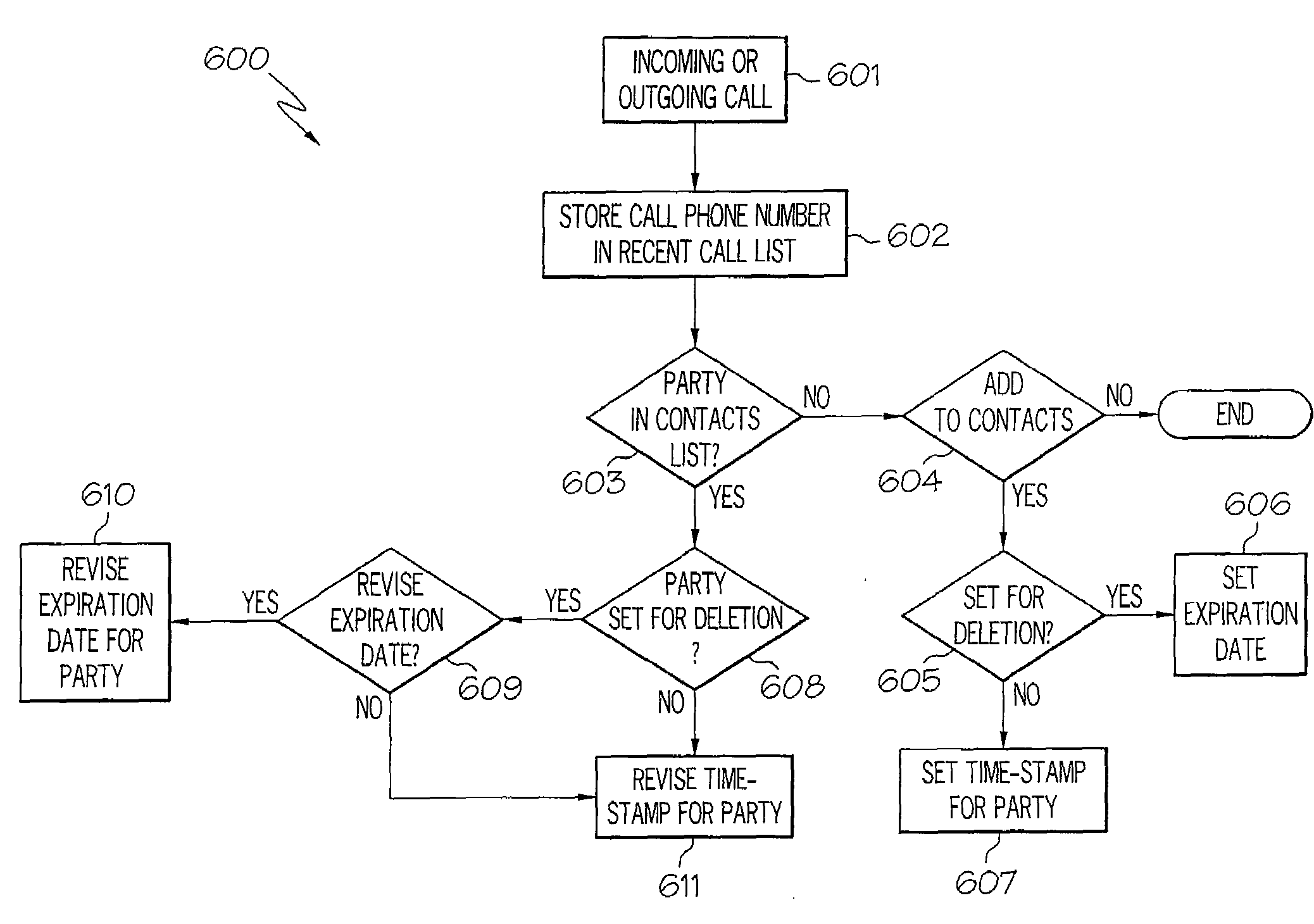
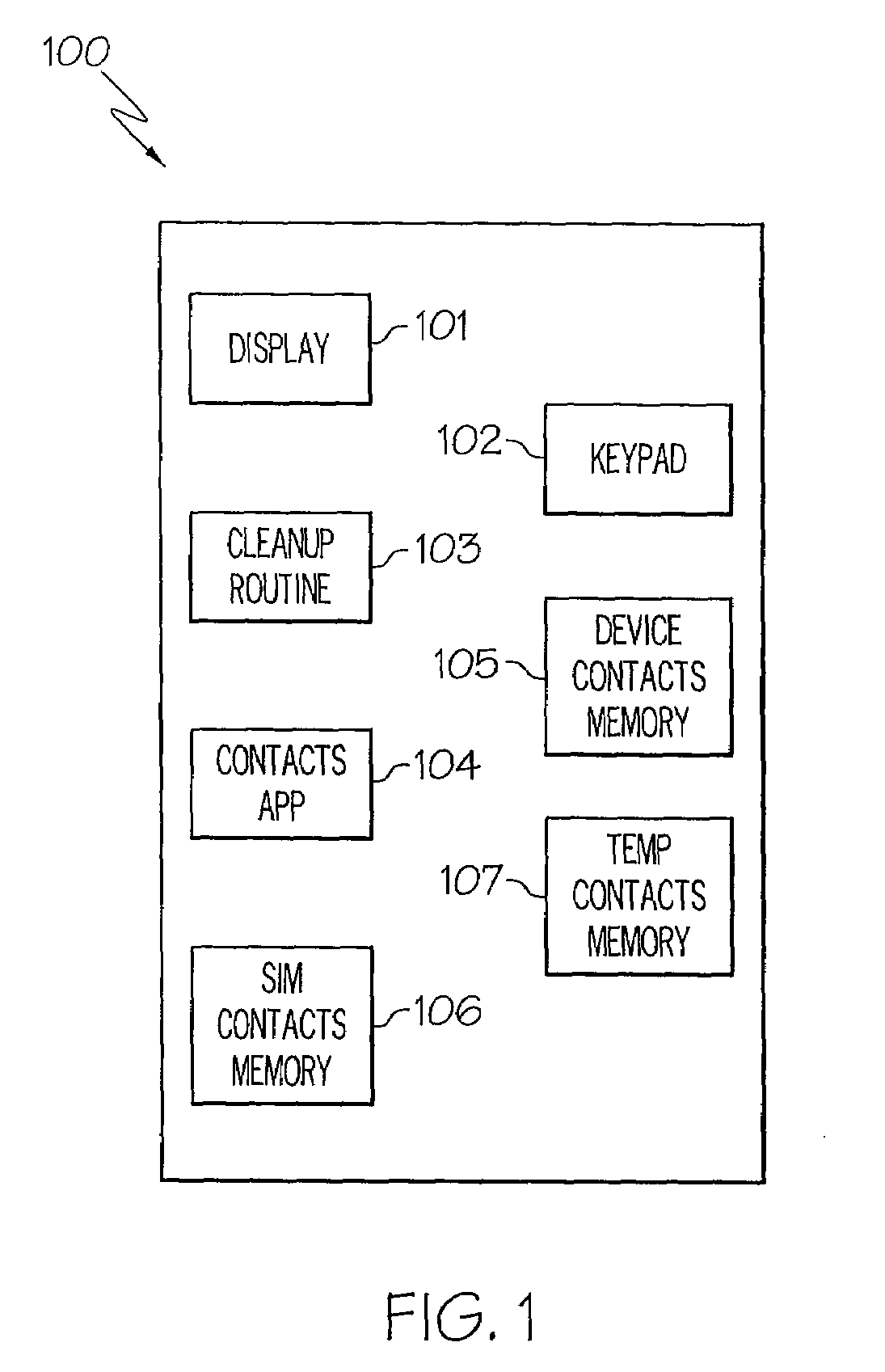
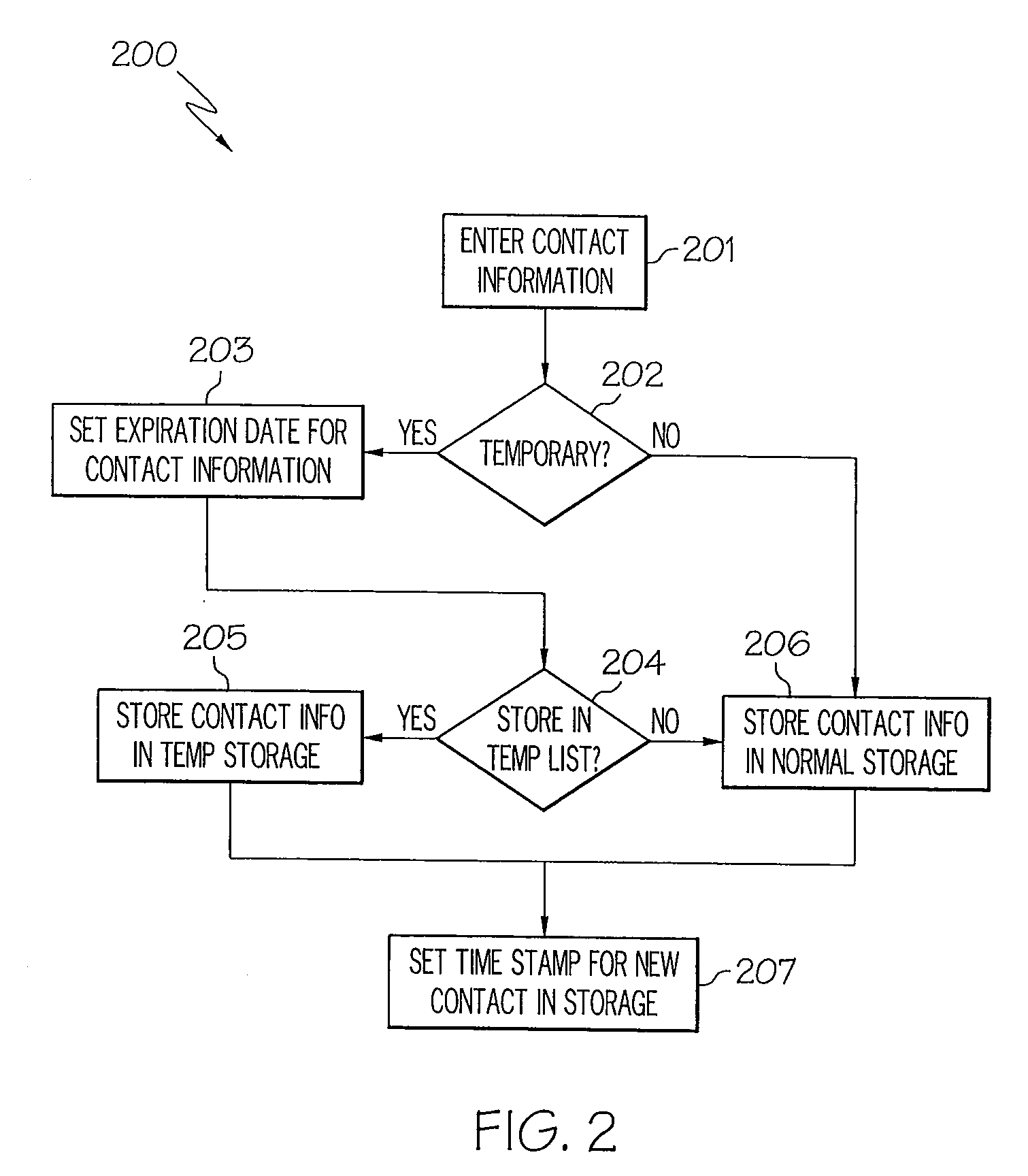
Contact expiration management
A apparatus and method for contact expiration management that includes identifying a contact as temporary, setting an expiration date for the temporary contact, and removing the temporary contact on the expiration date. The apparatus may be a mobile device such as a mobile phone. A user of the mobile device may respond to a prompt and select removing the temporary contacts or the temporary contacts may be removed automatically. A cleanup routine operating on the mobile device monitors time stamps on contacts and expiration dates of contacts to determine when a contact might be removed.
Owner:SONY ERICSSON MOBILE COMM AB
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com