Patents
Literature
1549results about "Credit schemes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
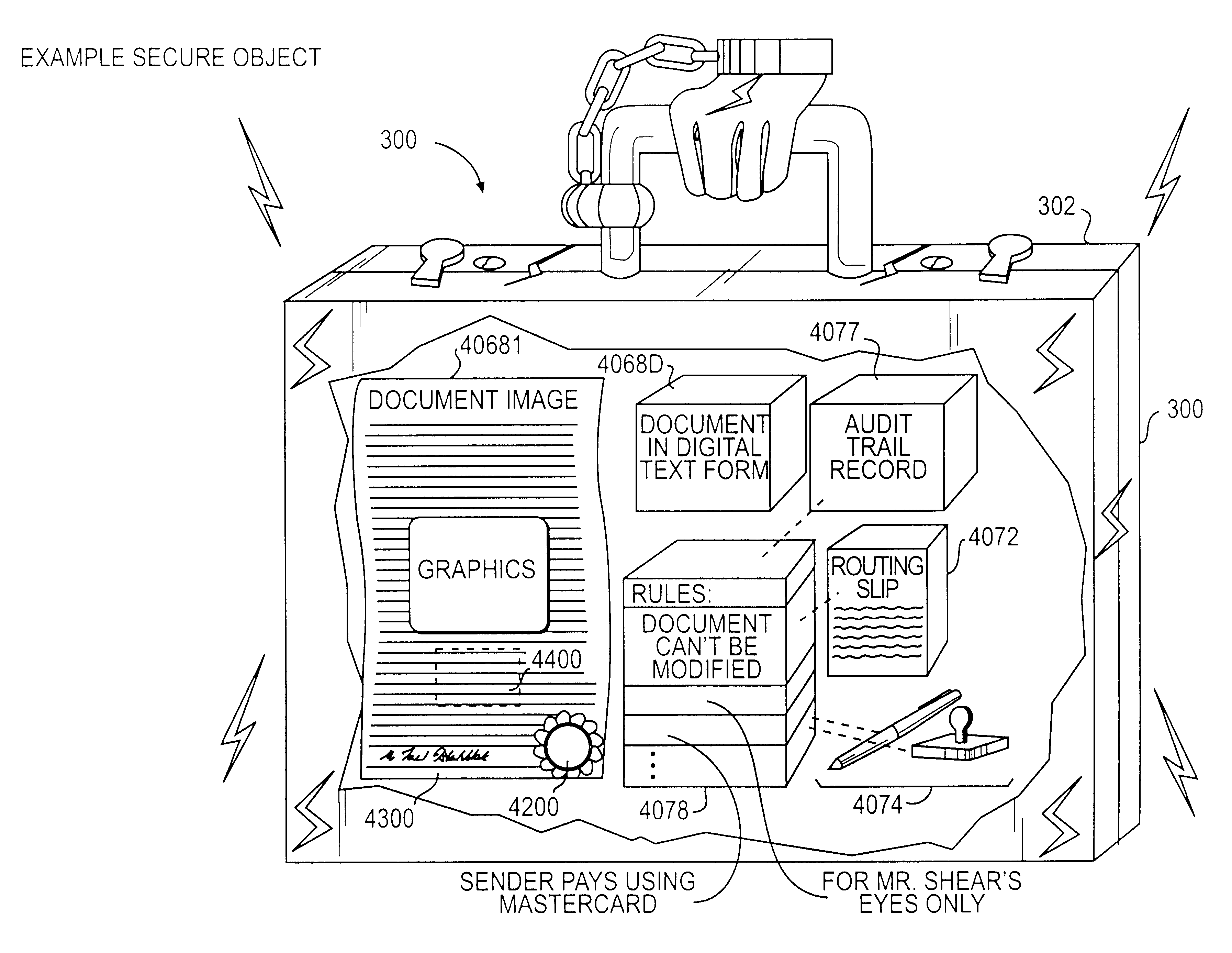
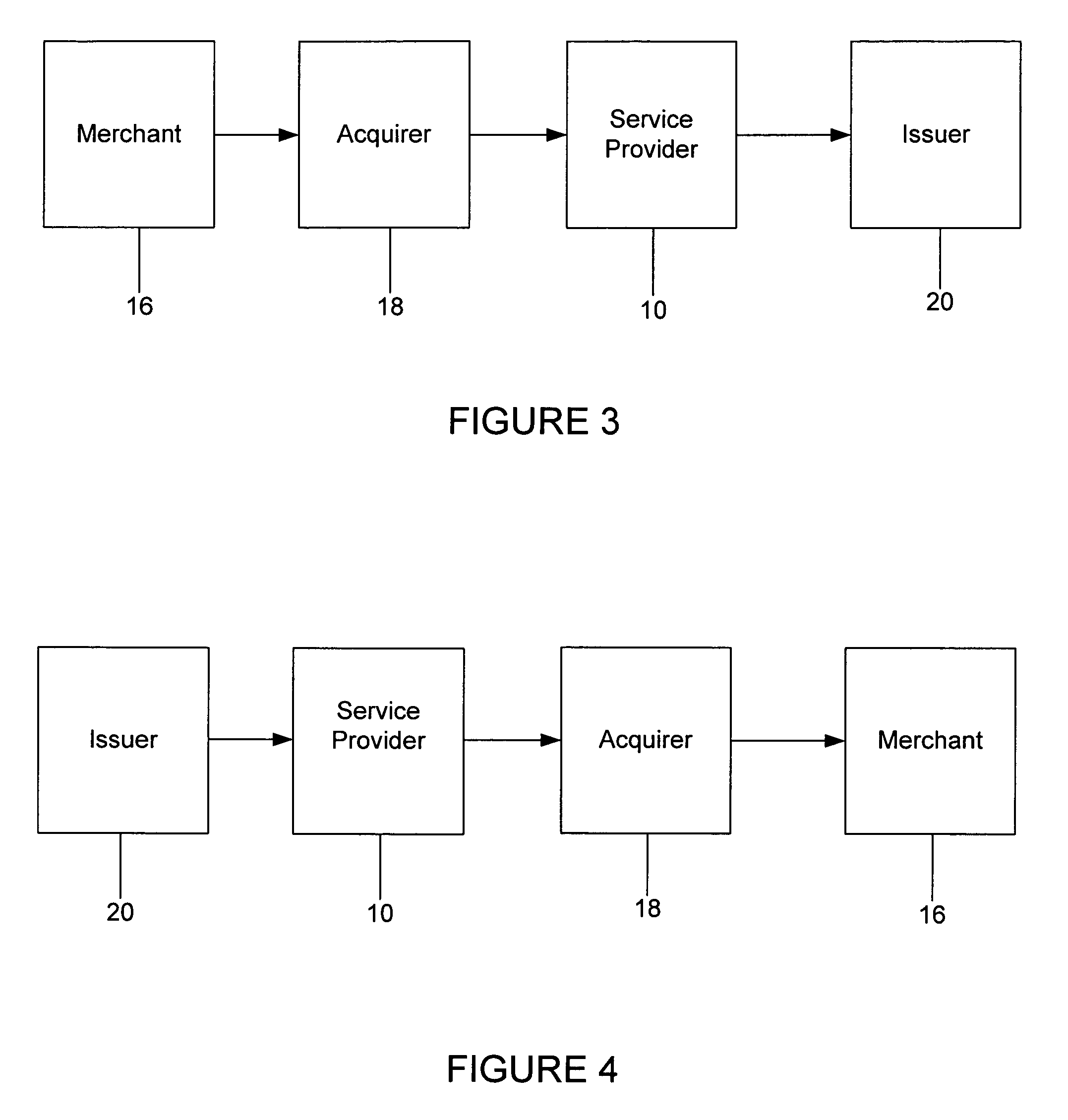
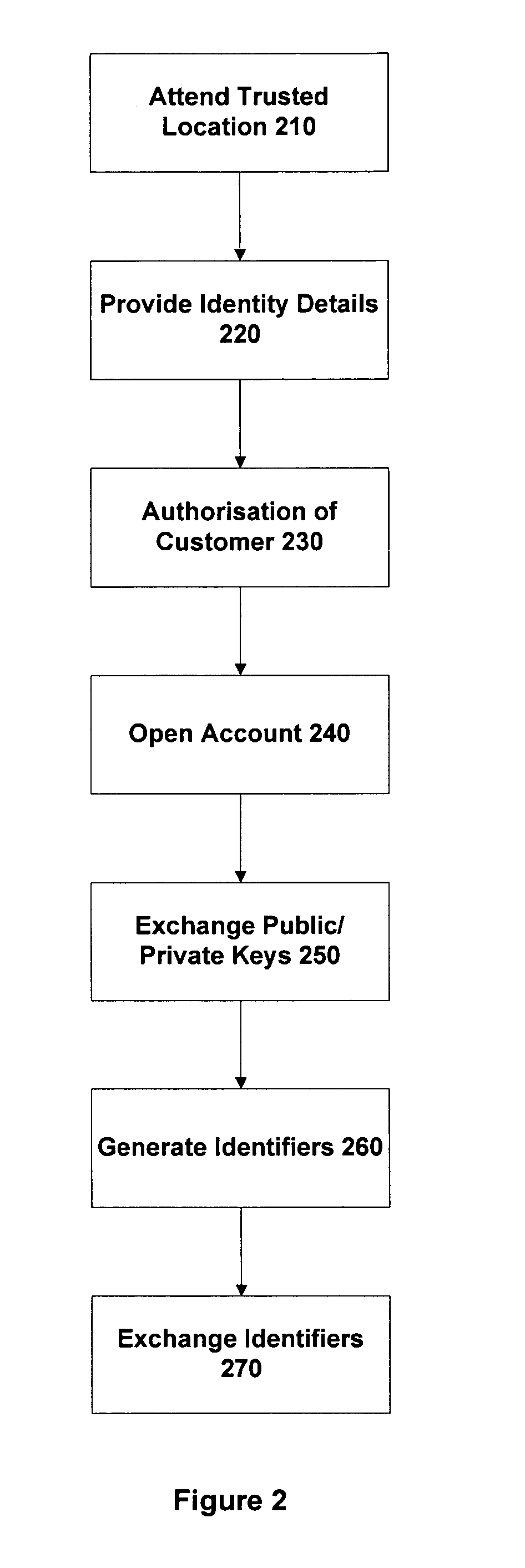
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
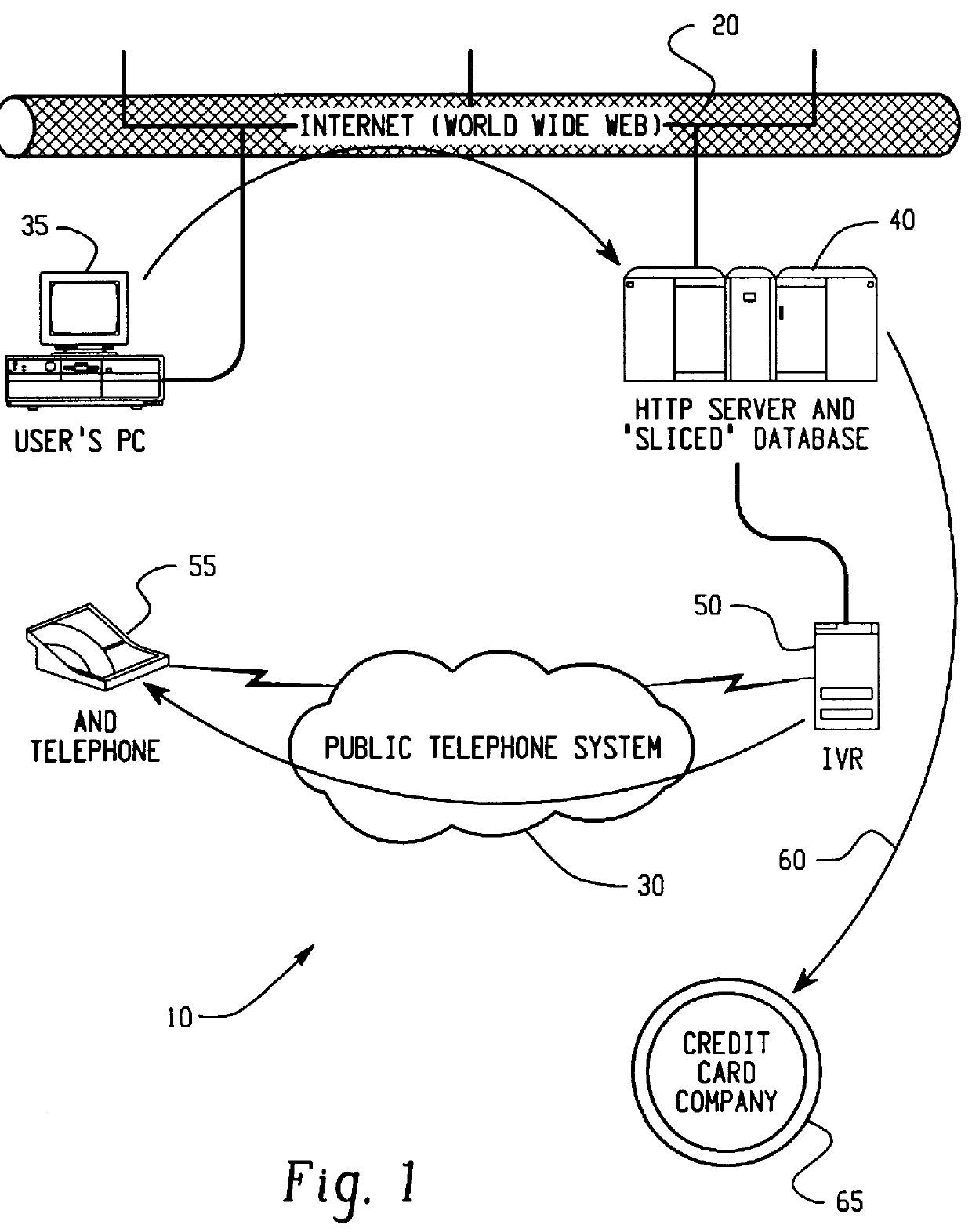
Transaction security method and apparatus
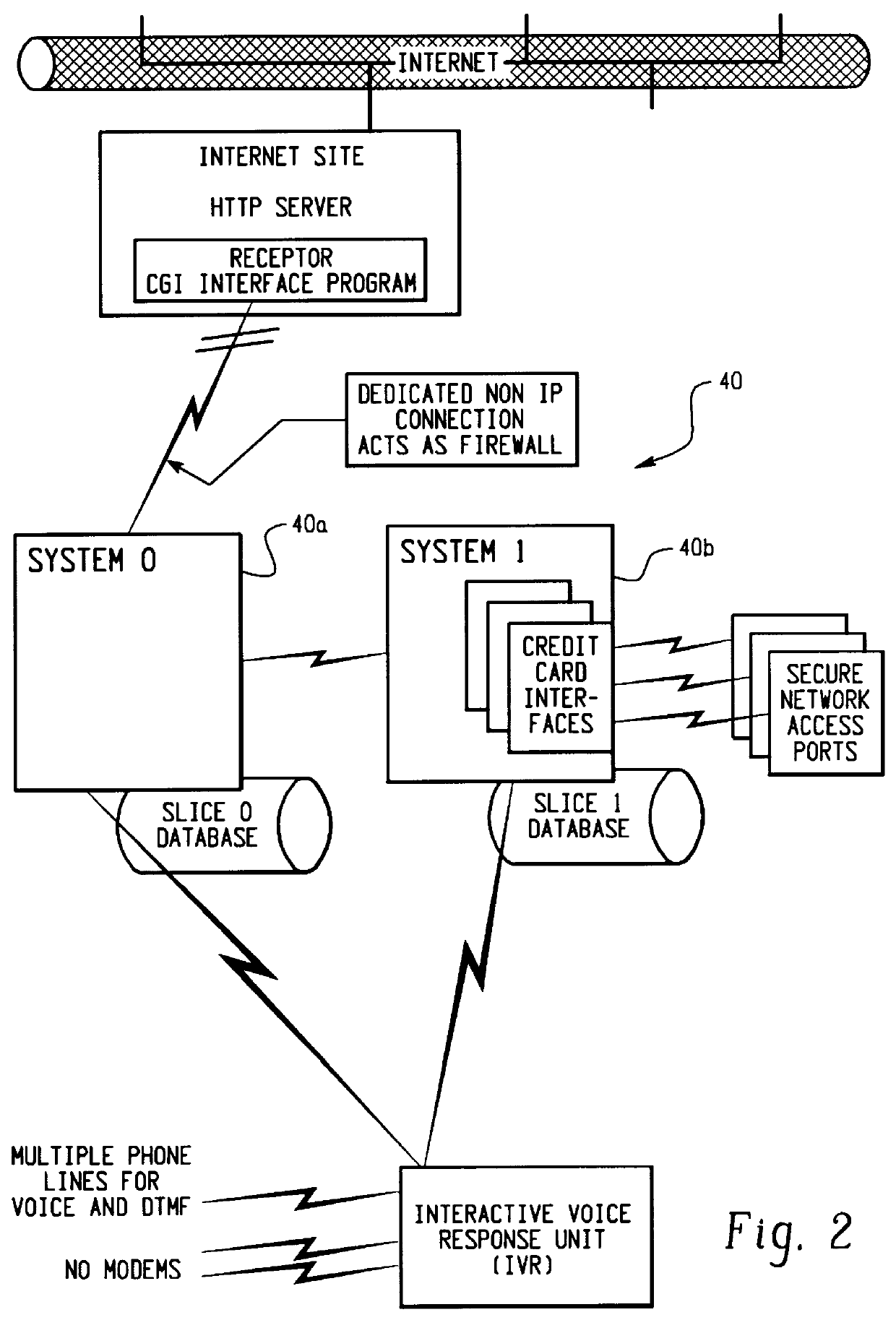
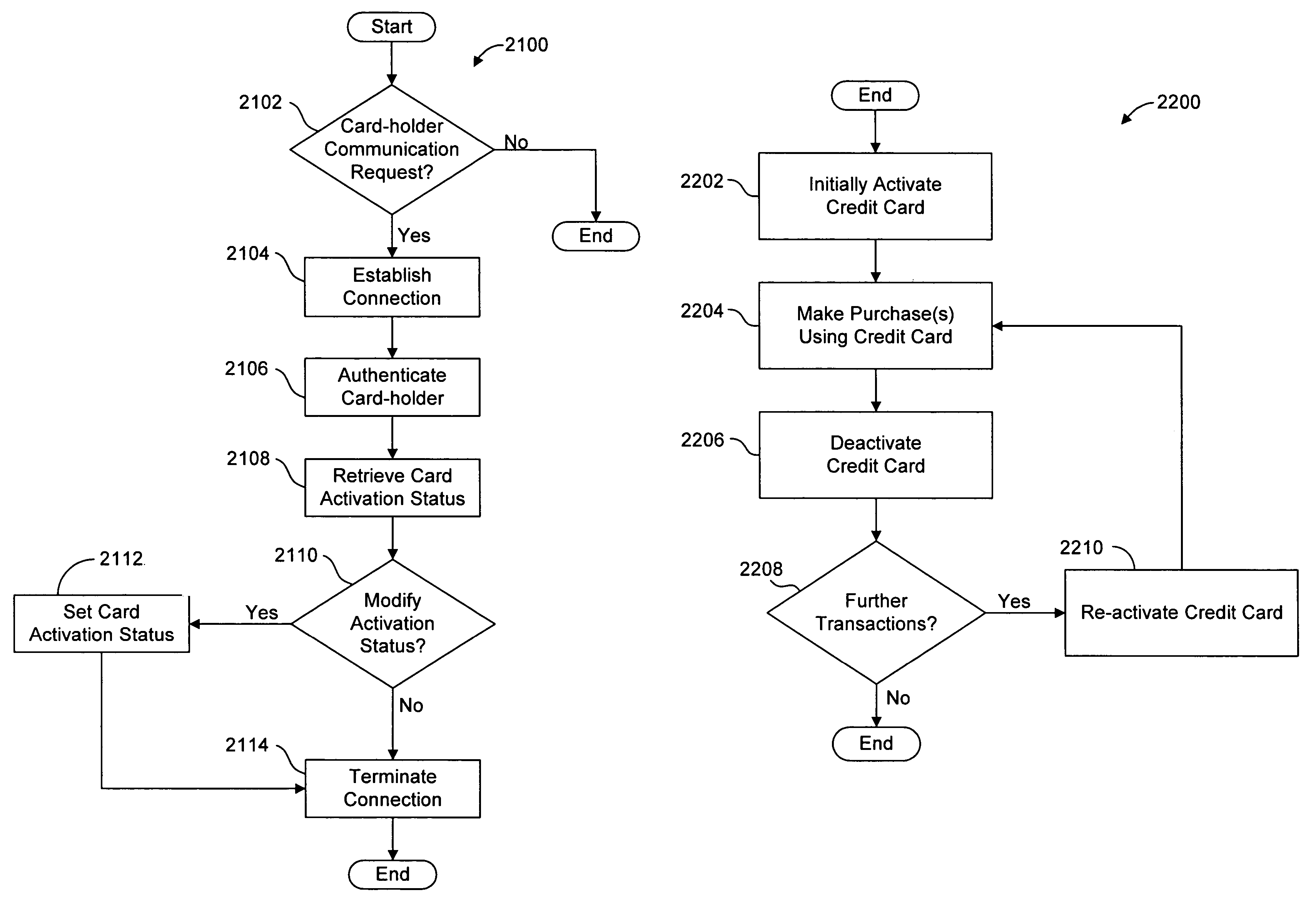
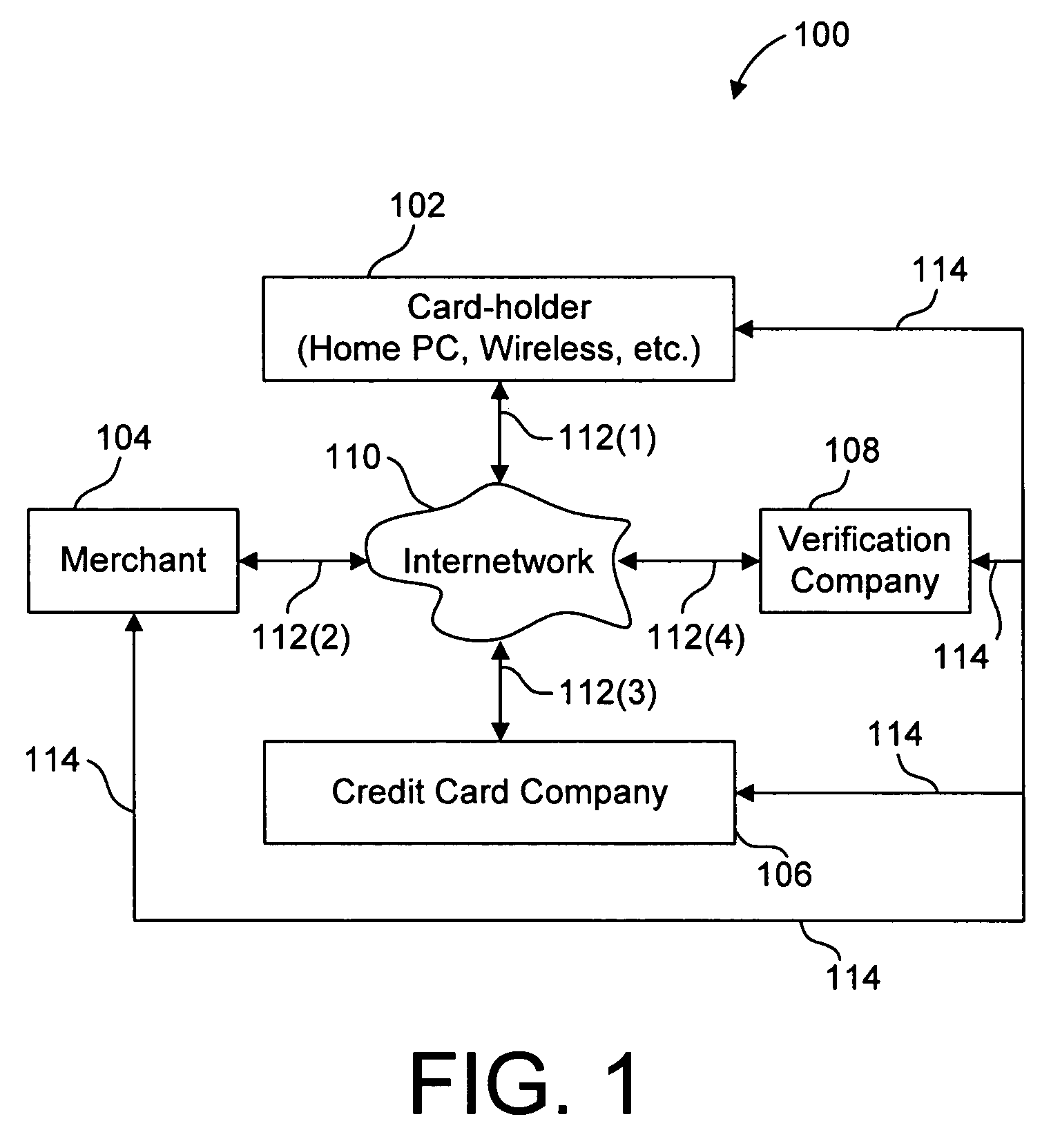
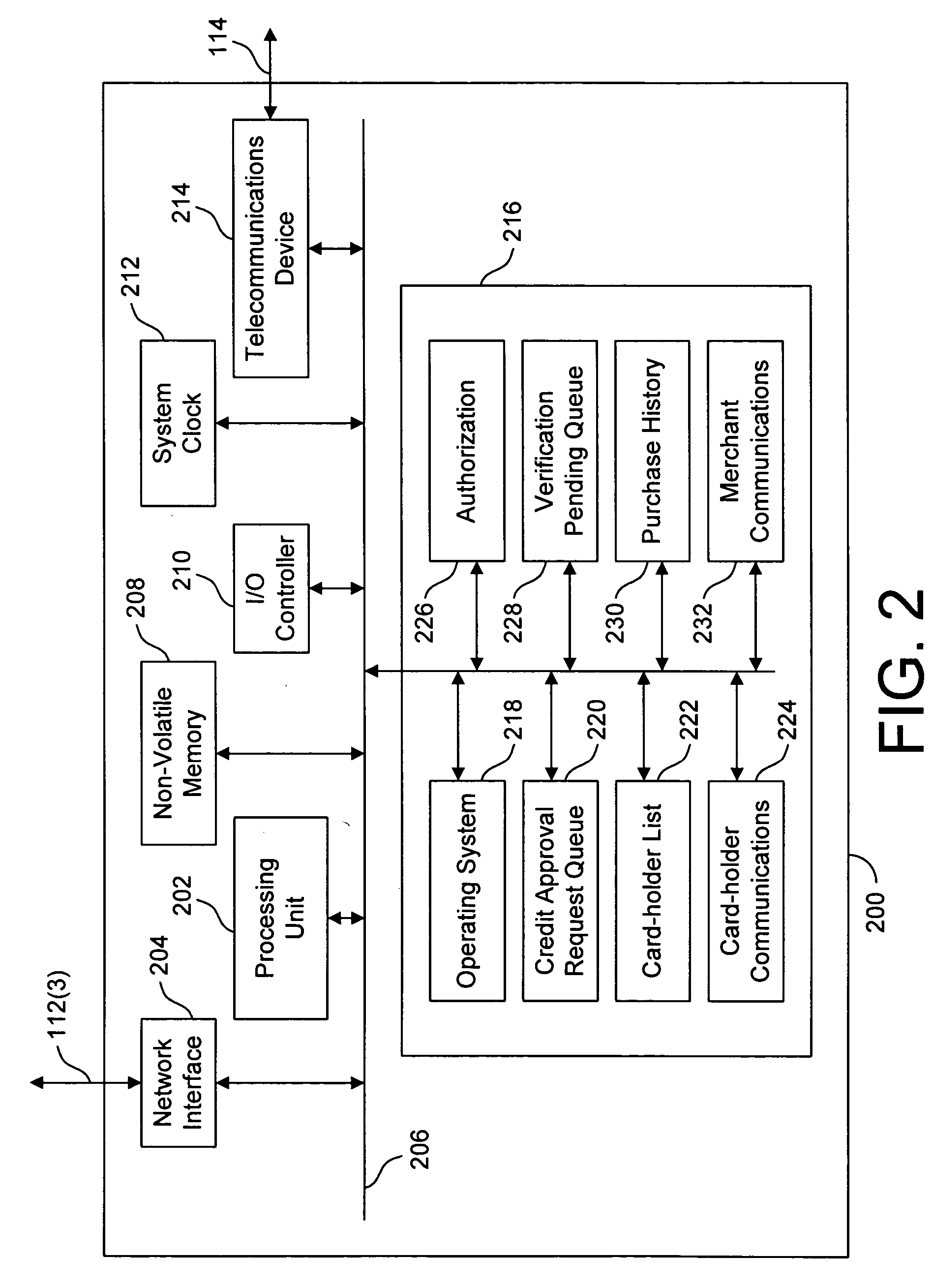
A method for performing secure transactions, such as credit card purchases, using two or more non-secure networks (such as the Internet and the public telephone system) in such a way that security is insured. A person wishing to initiate a secure transaction sends a message over one of the non-secure networks to a computer. That computer automatically uses the second non-secure network to contact the person back to verify the transaction. The call-back mechanism employs a method to authenticate the identity or authority of the person initiating the transaction. No single wire-tapping or network snooping device sees the entire transaction. No single database contains the entire set of information.
Owner:PICKETT THOMAS E
Method and system for using multi-function cards for storing, managing and aggregating reward points
InactiveUS20050021400A1Decreasing (if not eliminating) reliance on a central server systemDiscounts/incentivesFinanceCredit cardMultimedia
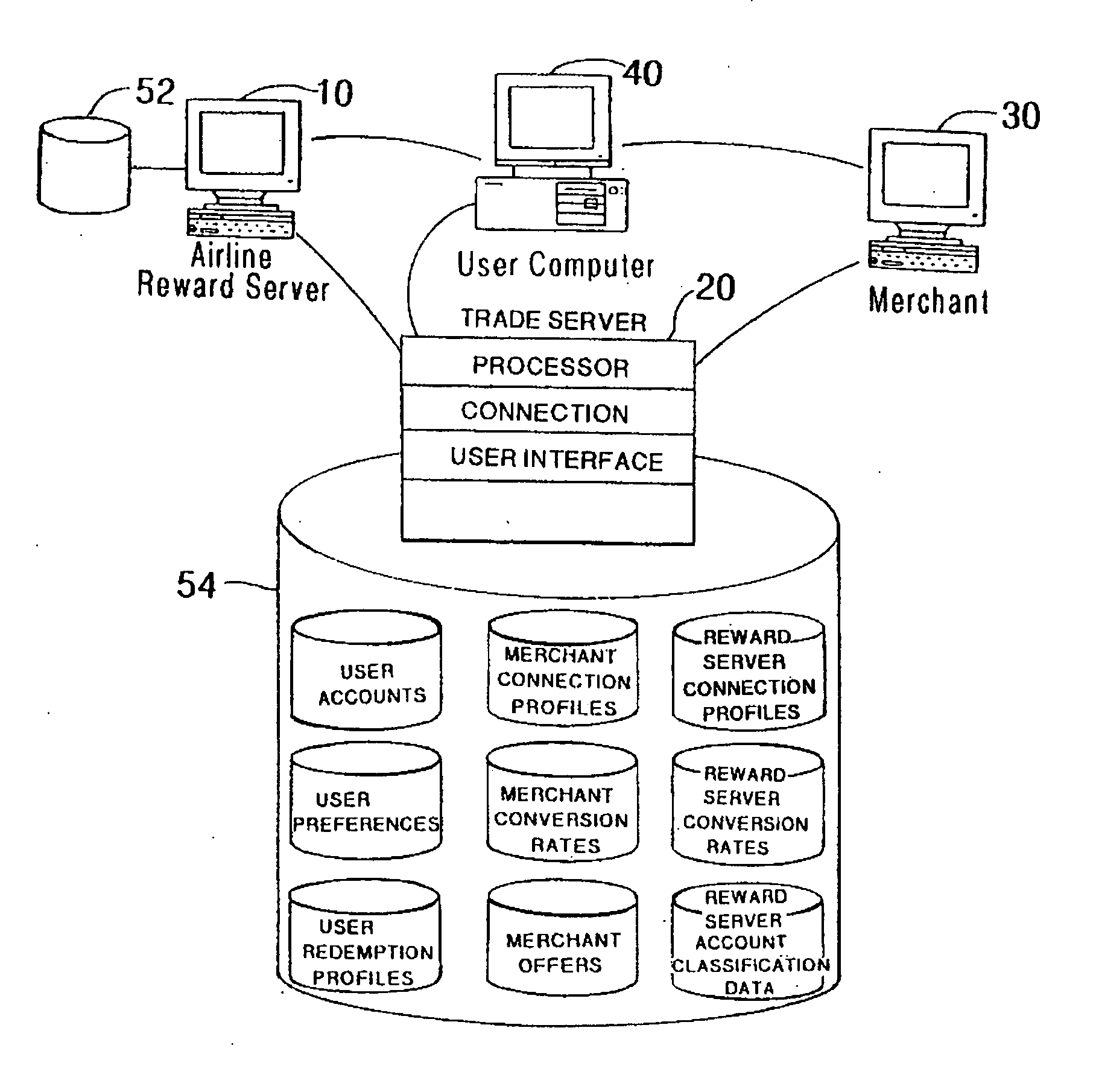
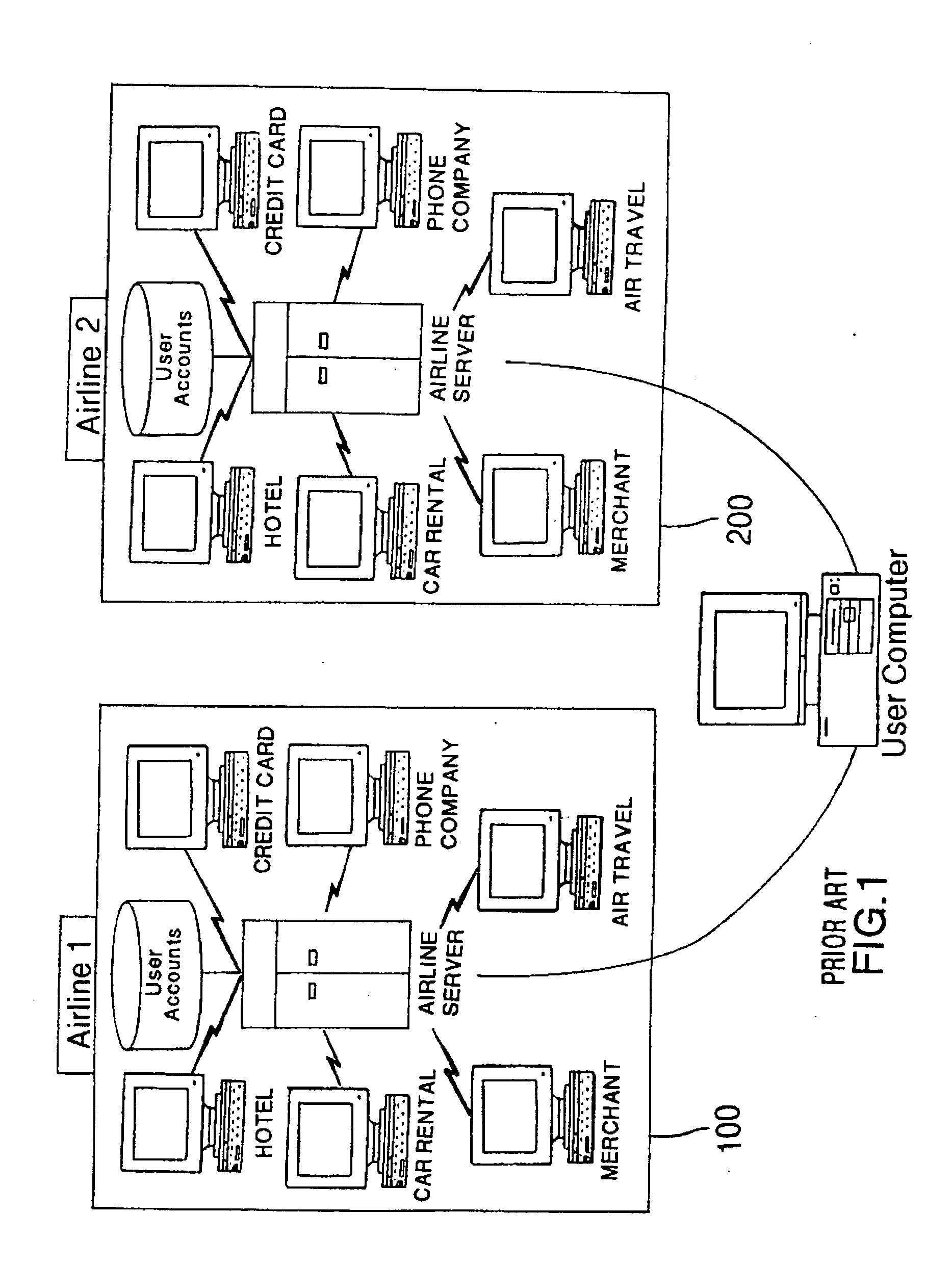
A system and method for operating a reward points accumulation and redemption program wherein a user earns reward points from a plurality of independent reward points issuing entities, with each tracking the user's earned reward points in a user reward point account stored on a multi-function card (such as a frequent flyer account or a credit card loyalty account). The multi-function card is adapted to aggregate some or all of the user's earned reward points from the reward accounts and credit the aggregated points into a single reward exchange account on the multi-function card. The user may then select an item for purchase with the accumulated reward points from the multi-function card. The item is provided to the user in exchange for a subset or all of the reward points from the multi-function card.
Owner:SIGNATURE SYST
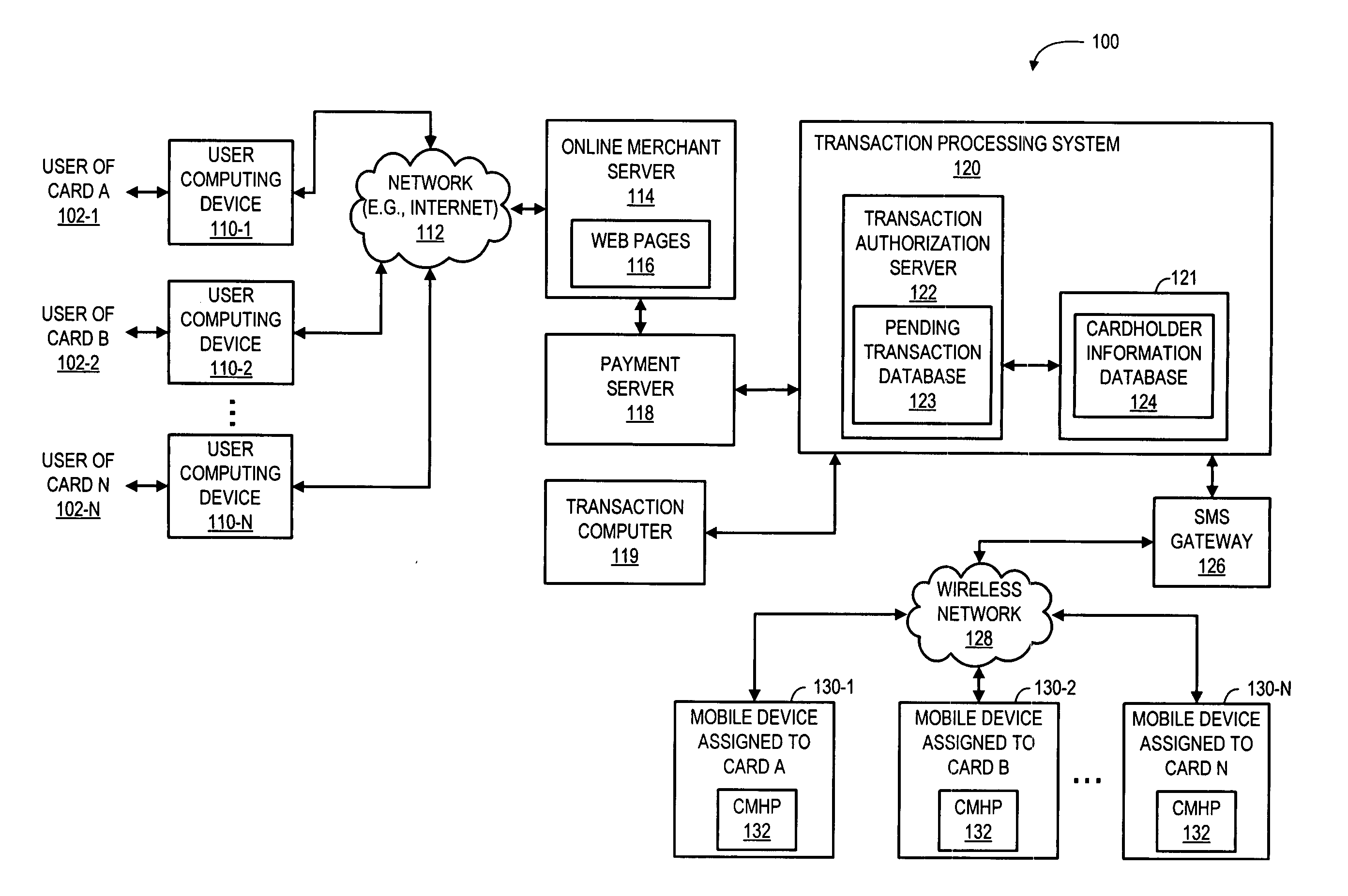
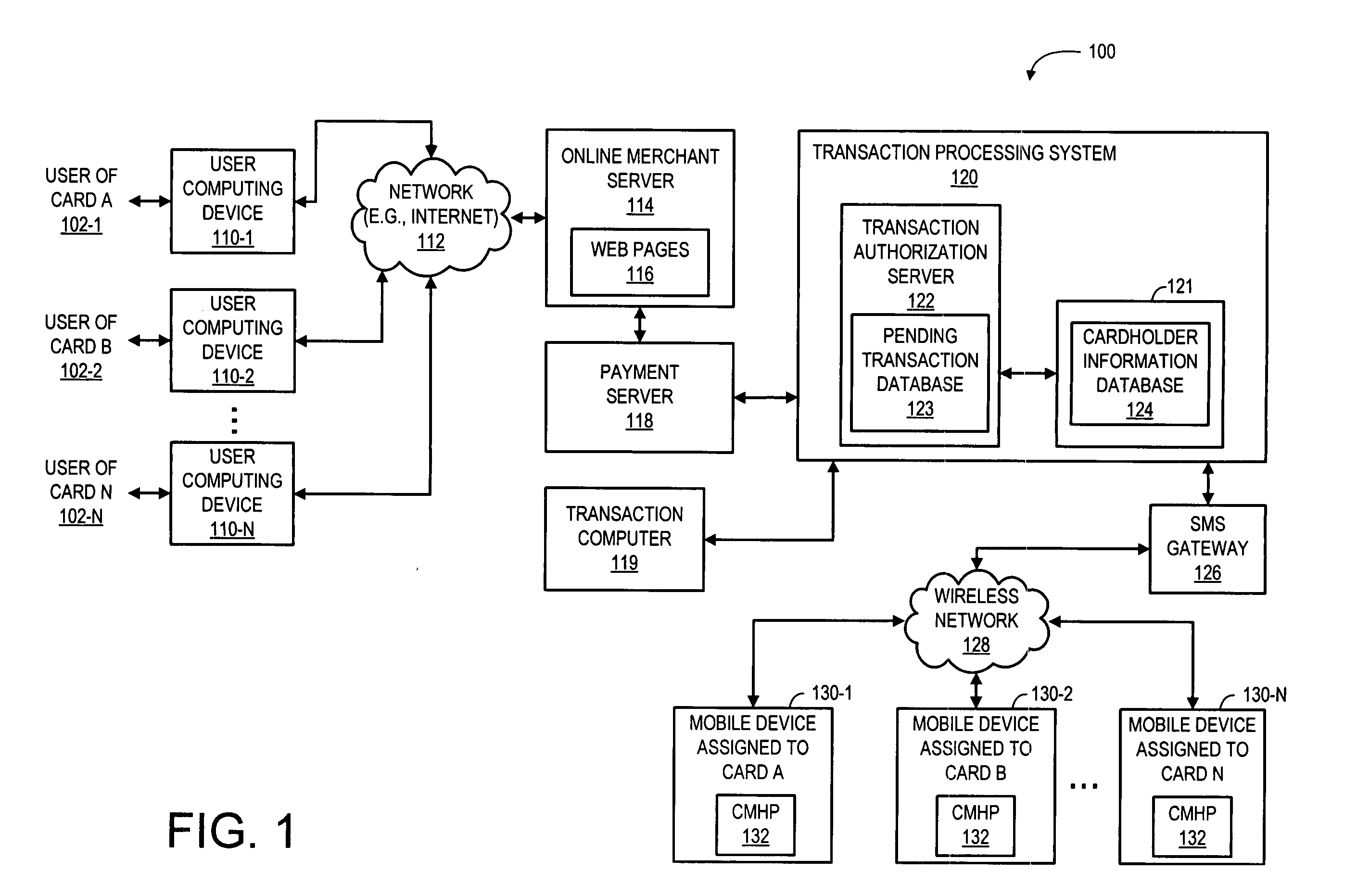
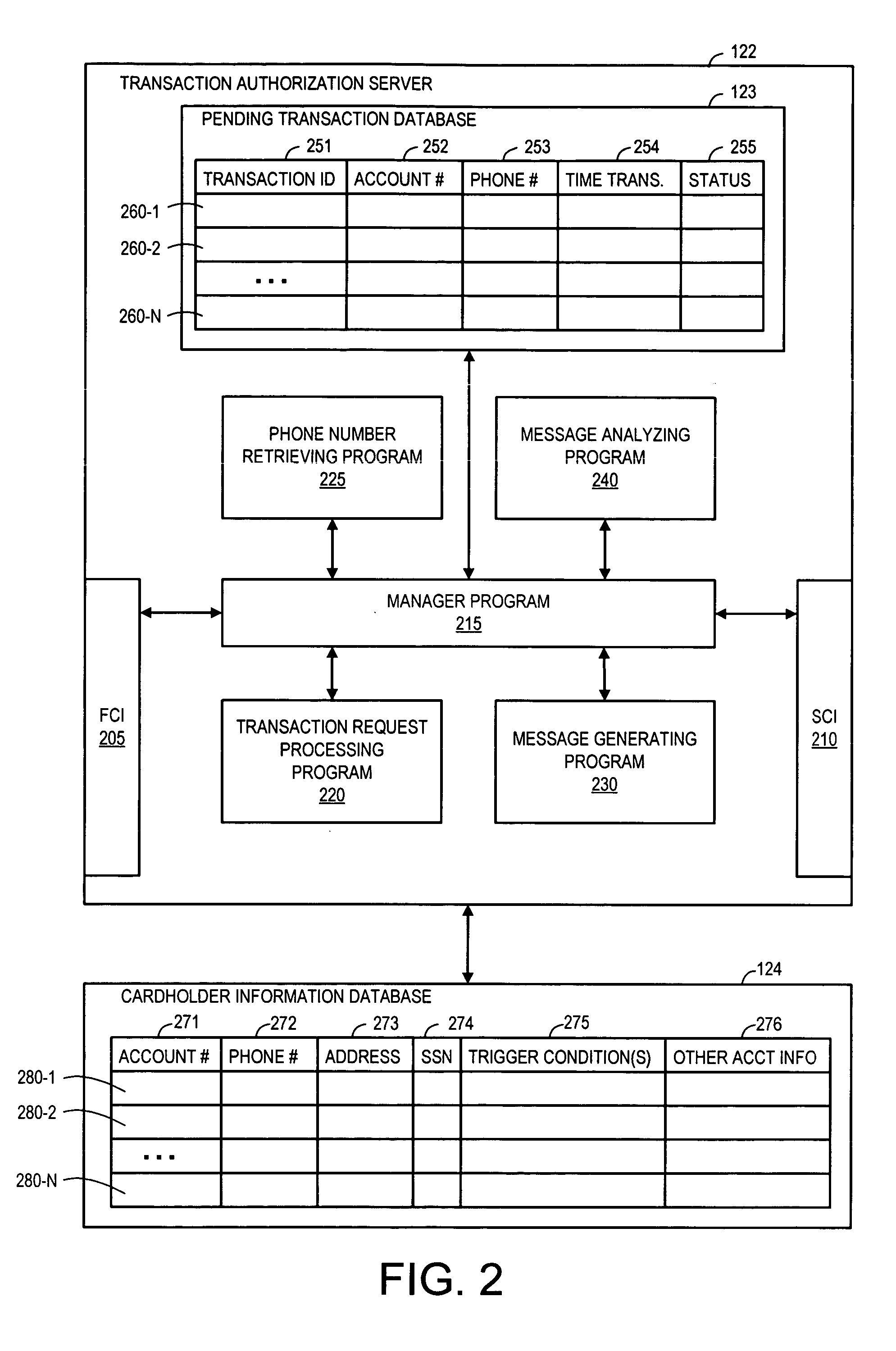
Method and system for providing transaction notification and mobile reply authorization
A system and a corresponding method are described for providing a notification of a pending transaction request and obtaining an authorization from a cardholder. The system maintains a database of account records, each of the account records including a phone number of a mobile device assigned to receive authorization request messages for the respective account. When a transaction request is received, the system determines a phone number of a mobile device assigned to receive authorization request messages for the account requesting the transaction by searching the database. The system generates and transmits an authorization request message to the phone number of the mobile device assigned to the account requesting the transaction. In response to the authorization request message, a reply message is returned from the mobile device, which explicitly indicates if a user of the mobile device approves or denies the transaction.
Owner:KIM MIKE
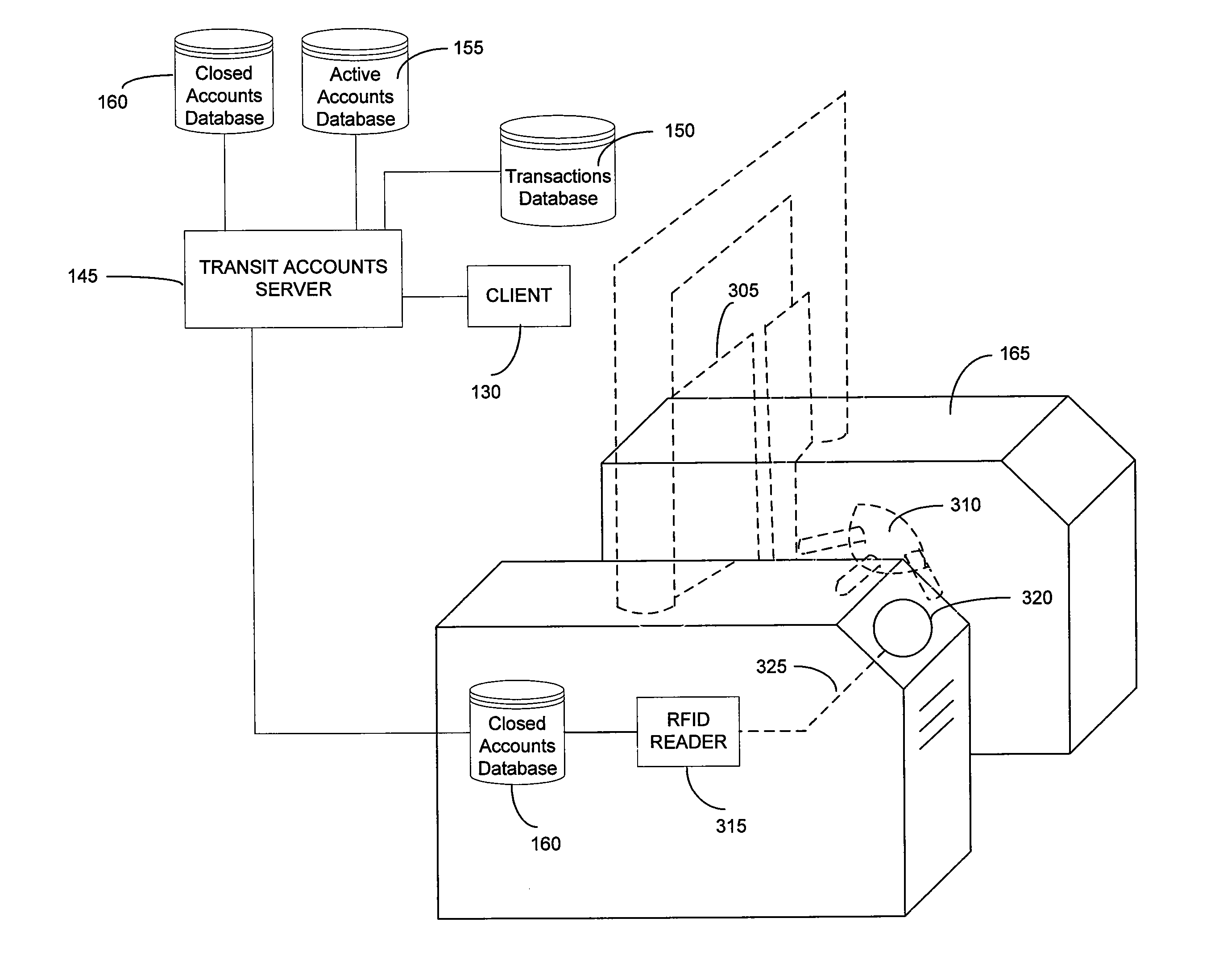
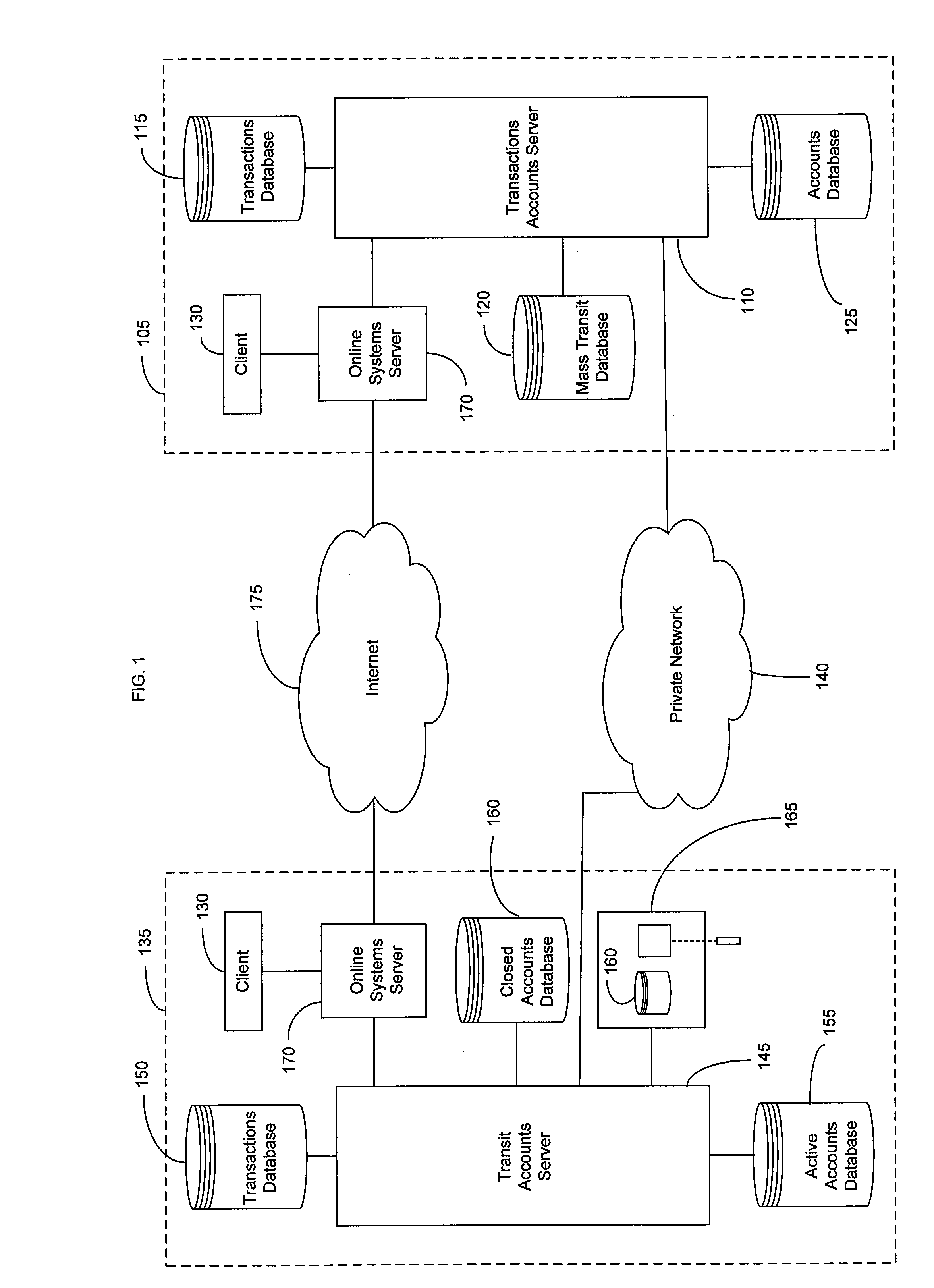
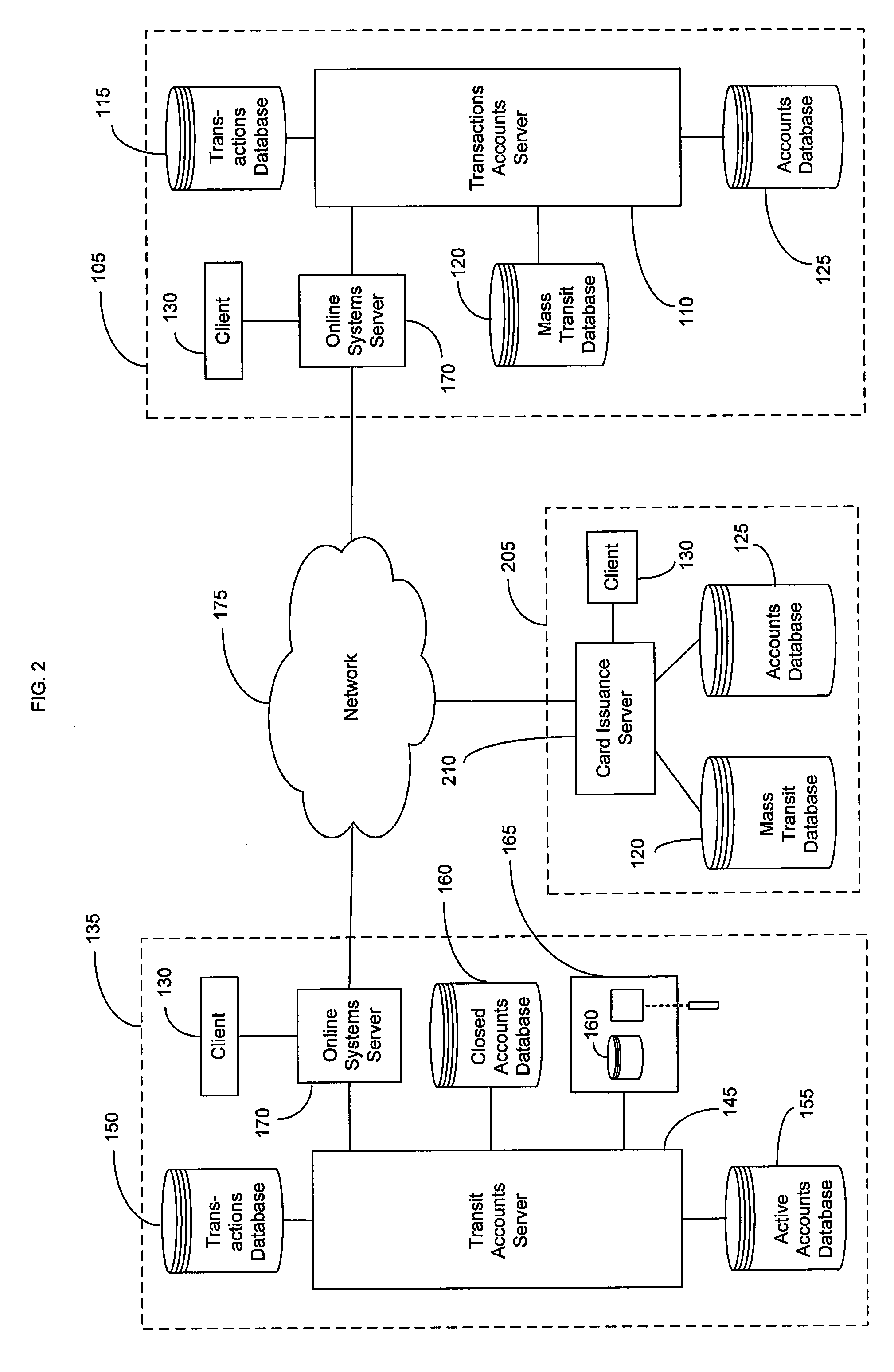
System and method for mass transit merchant payment
InactiveUS20060278704A1Eliminate needRelieving userAcutation objectsTicket-issuing apparatusTransit systemFinancial transaction
Methods, systems and computer program products are provided for enabling payment of transit system fees using a financial transaction instrument. Entry is permitted onto a transit system by recognition of information included in an identification number stored on a financial transaction instrument. The identification number stored on the financial transaction instrument is associated with a transit system fee registered for each use of the transit system. A plurality of transit system fees associated with the same identification number from use of the financial transaction instrument is aggregated, and payment for the aggregated transit system fees is requested from a transaction account associated with the financial transaction instrument.
Owner:LIBERTY PEAK VENTURES LLC
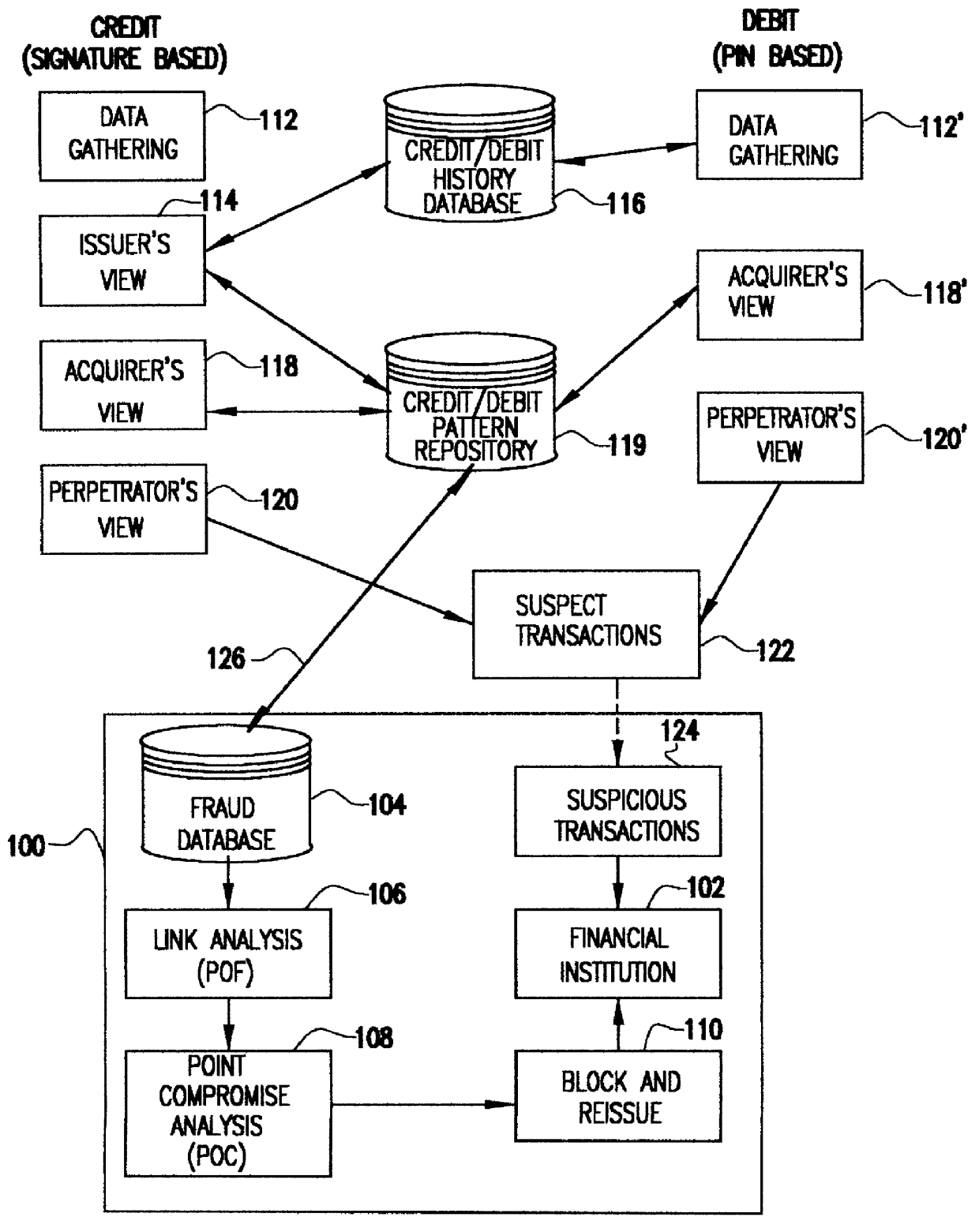
System for detecting counterfeit financial card fraud
Counterfeit financial card fraud is detected based on the premise that the fraudulent activity will reflect itself in clustered groups of suspicious transactions. A system for detecting financial card fraud uses a computer database comprising financial card transaction data reported from a plurality of financial institutions. The transactions are scored by assigning weights to individual transactions to identify suspicious transactions. The geographic region where the transactions took place as well as the time of the transactions are recorded. An event building process then identifies cards involved in suspicious transactions in a same geographic region during a common time period to determine clustered groups of suspicious activity suggesting an organized counterfeit card operation which would otherwise be impossible for the individual financial institutions to detect.
Owner:FAIR ISAAC & CO INC
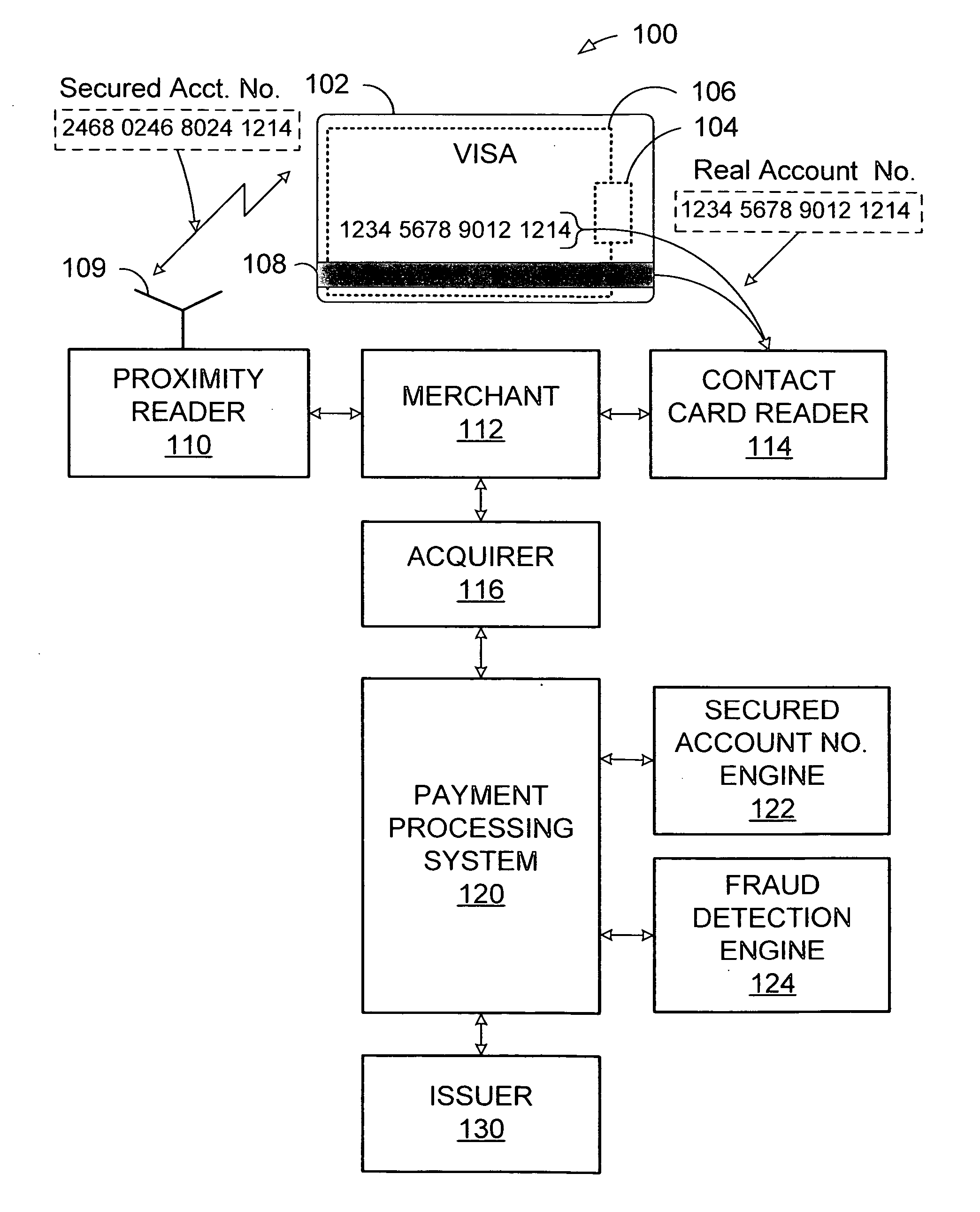
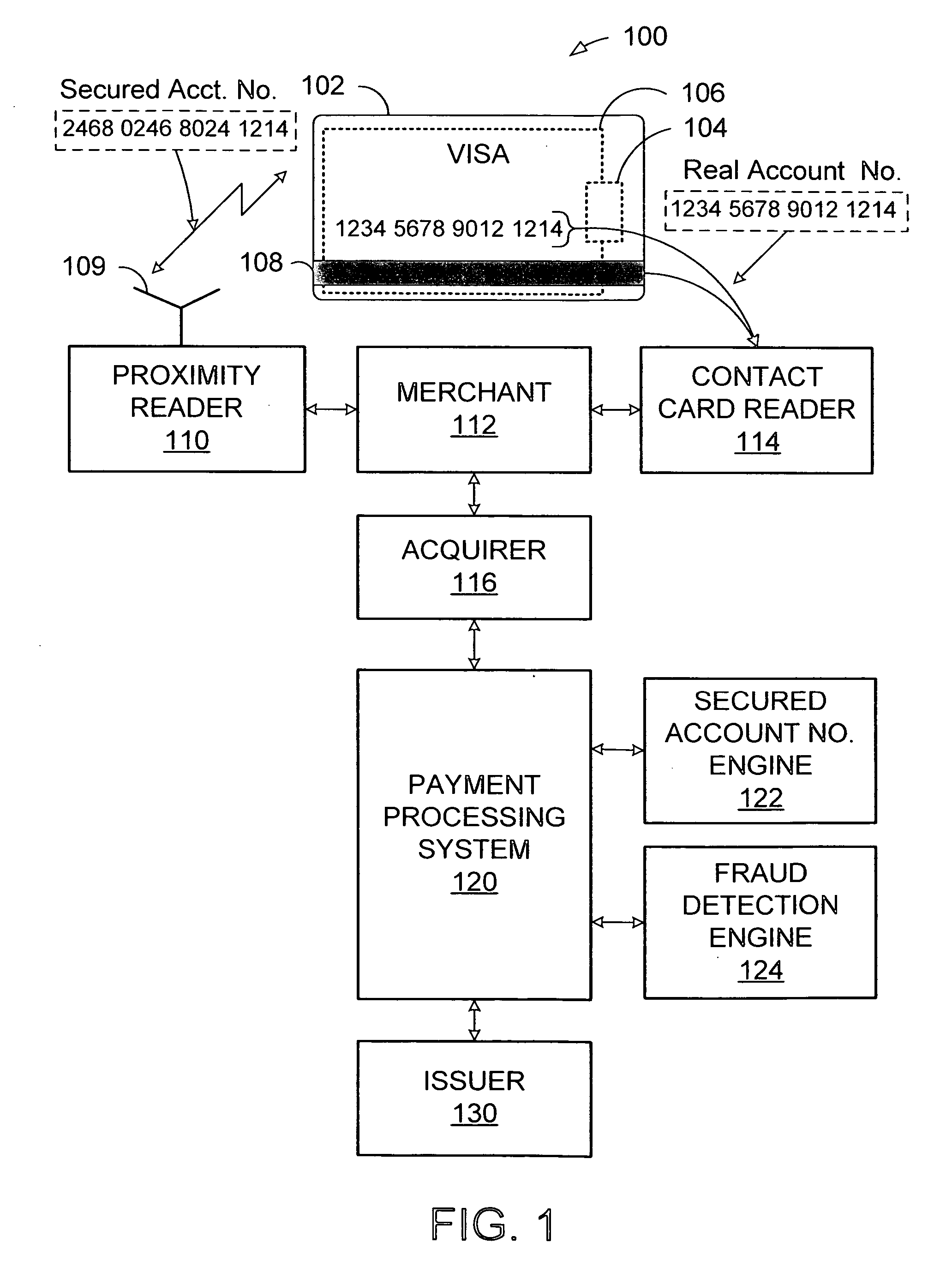
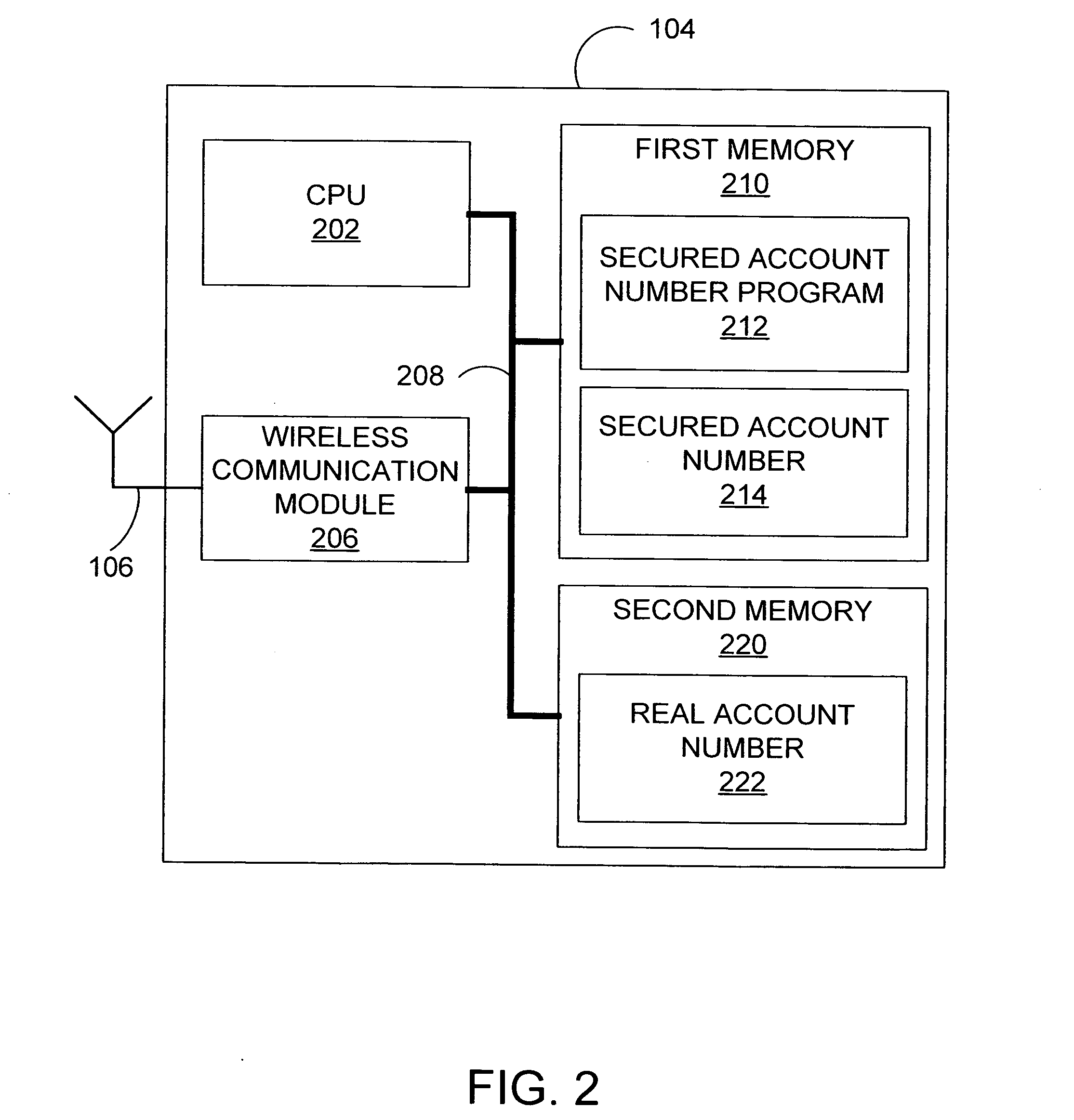
System and method for secured account numbers in proximity devices
A method and system for using a secured account number for processing proximity types of wireless financial transactions associated with portable consumer proximity devices is disclosed. In one embodiment, the method includes receiving a proximity type of wireless financial transaction request along with a secured account number from a portable proximity consumer device such as a contactless smart card, converting the secured account number to the user's real account number, and transmitting the financial transaction request along with the user's real account number to the issuer of the user's real account number for authorization and processing.
Owner:VISA USA INC (US)
Credit cards system and method having additional features
InactiveUS20090037333A1Complete banking machinesCredit registering devices actuationCredit cardComputer hardware
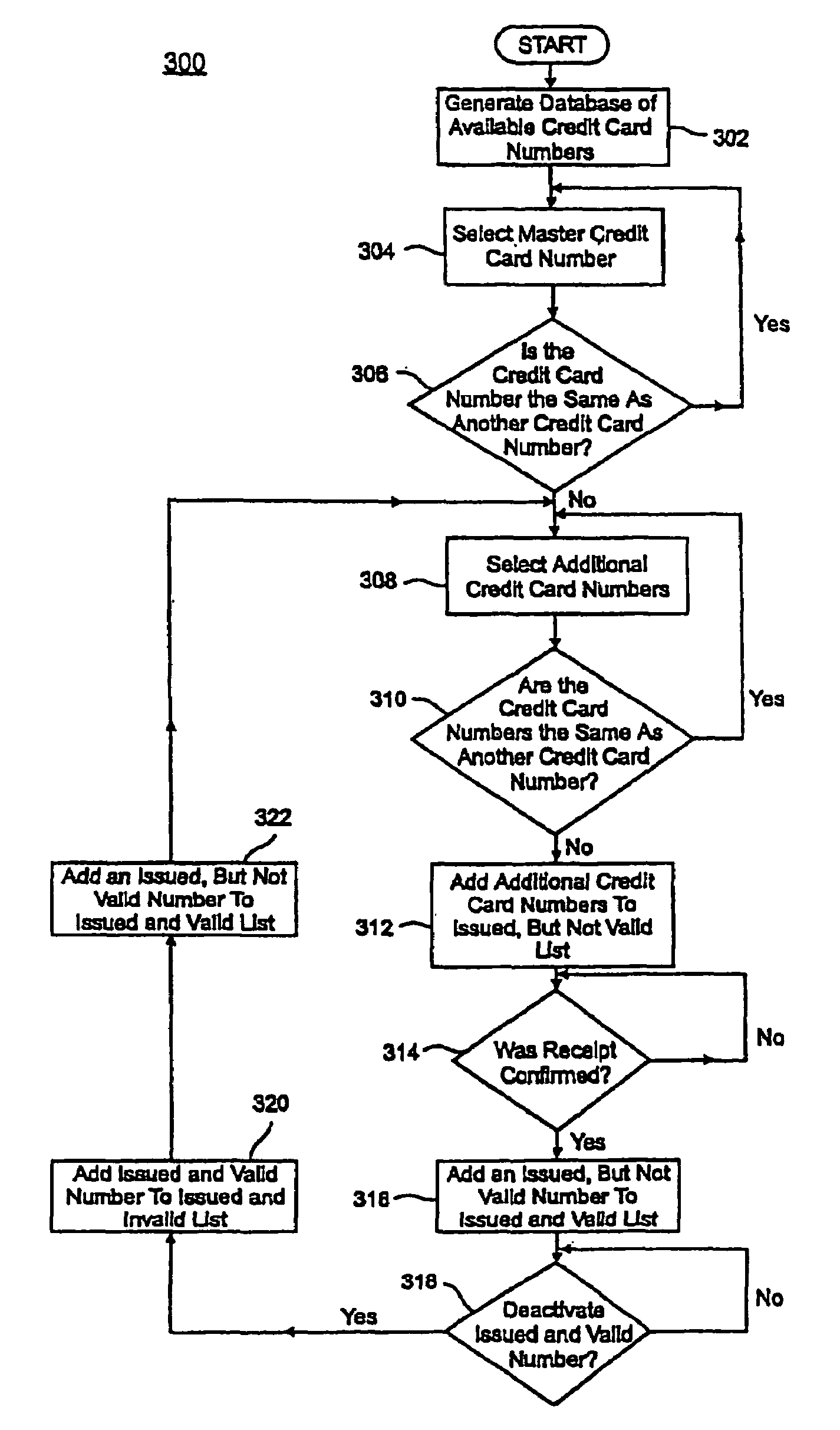
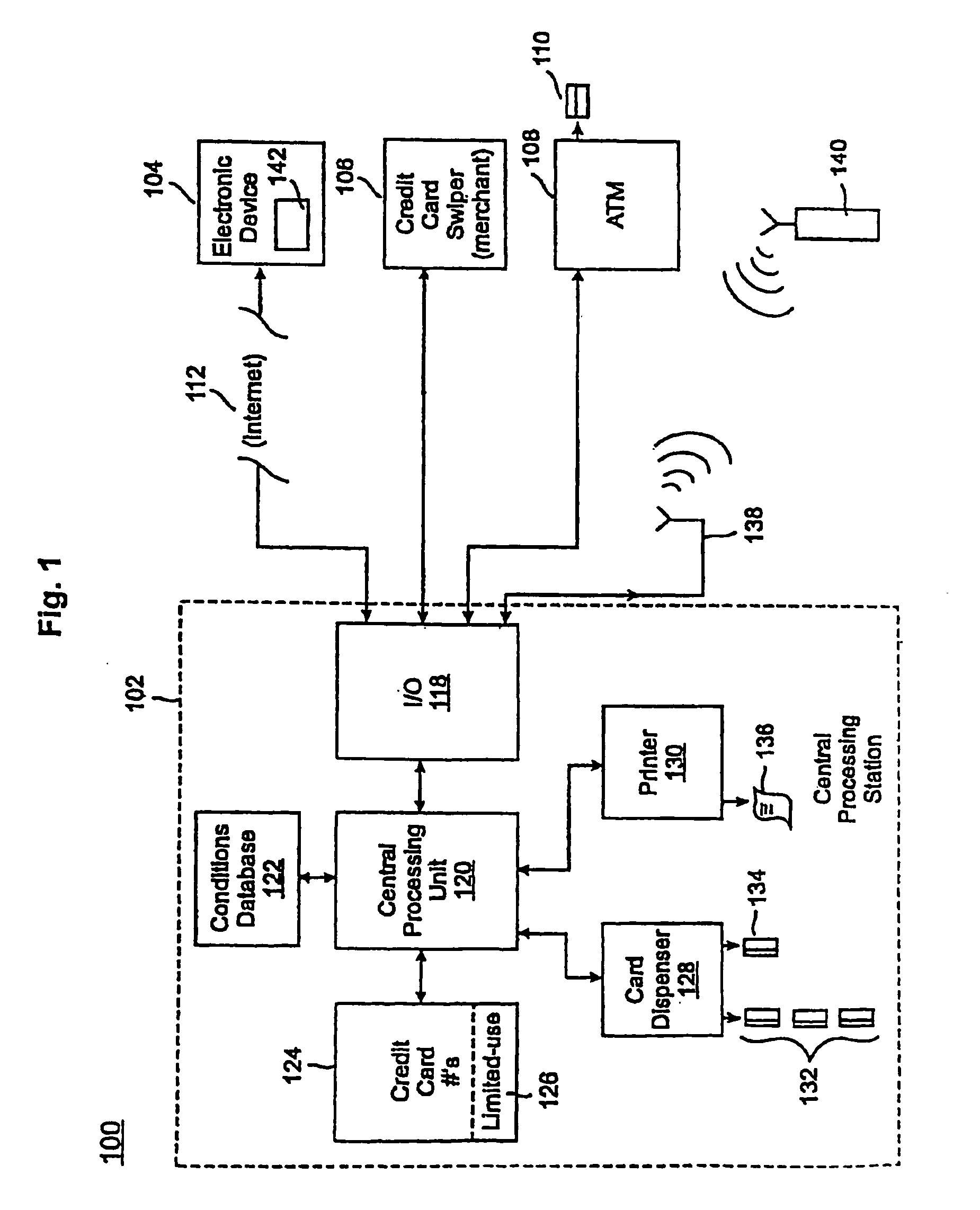
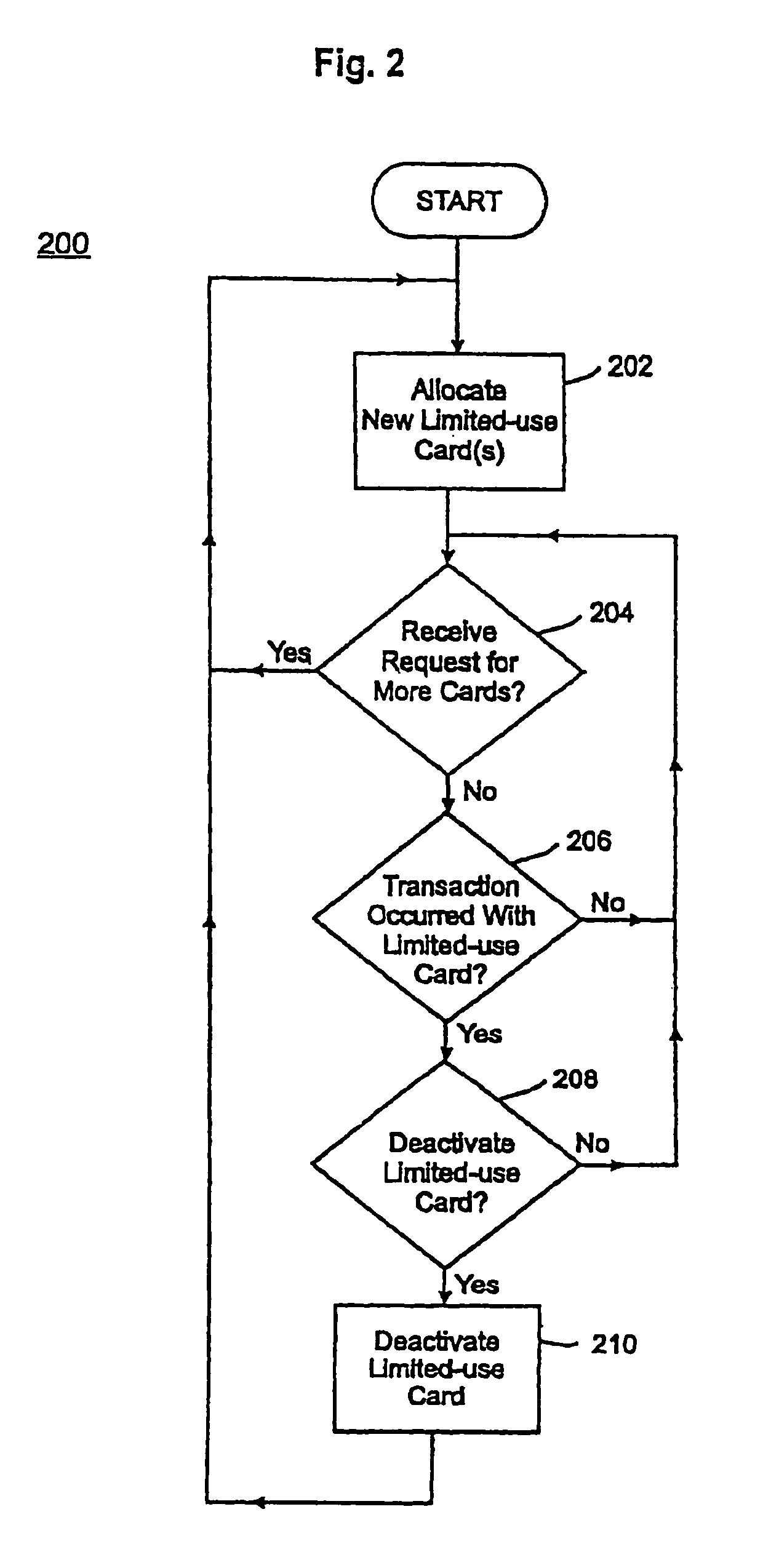
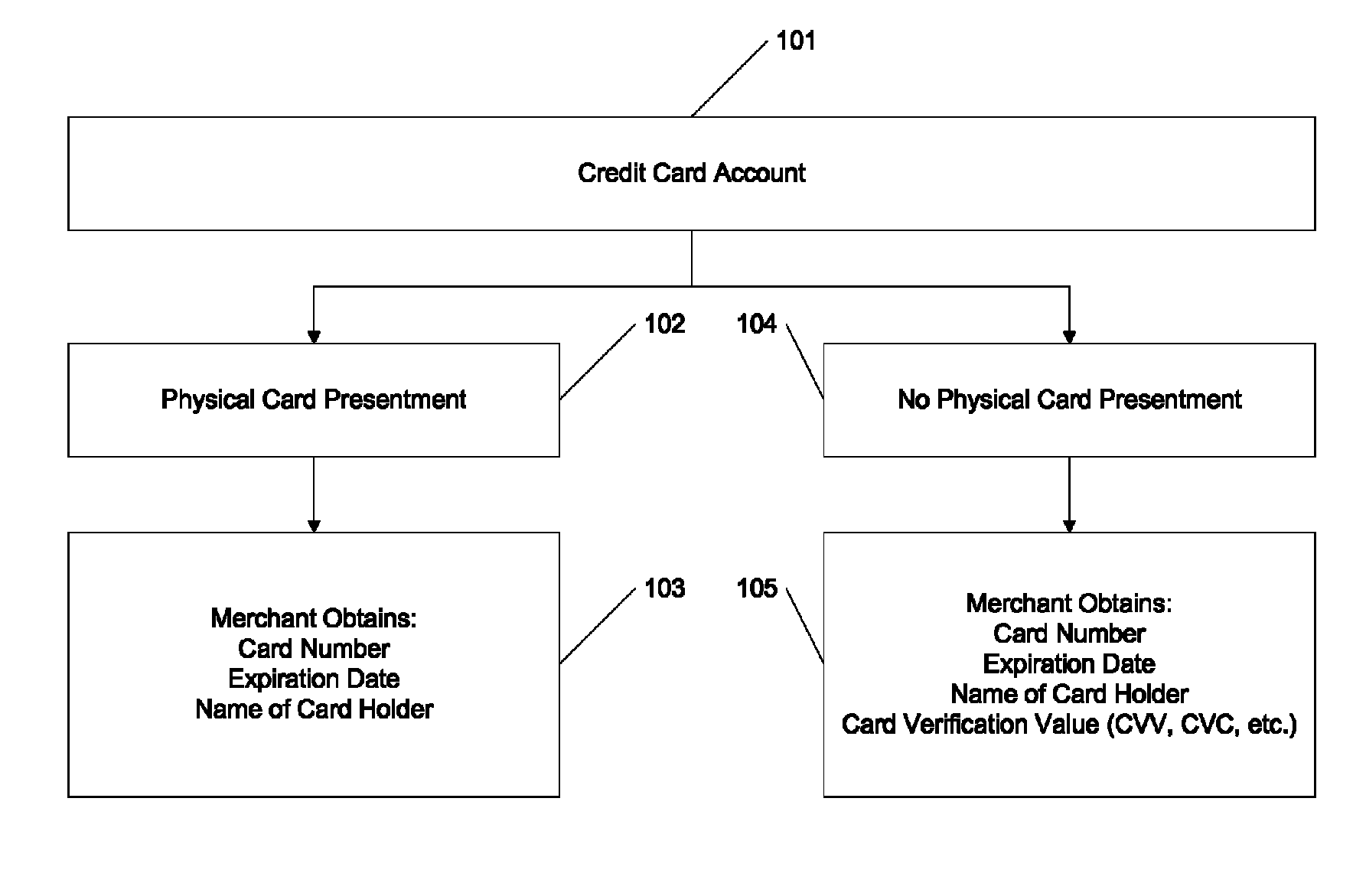
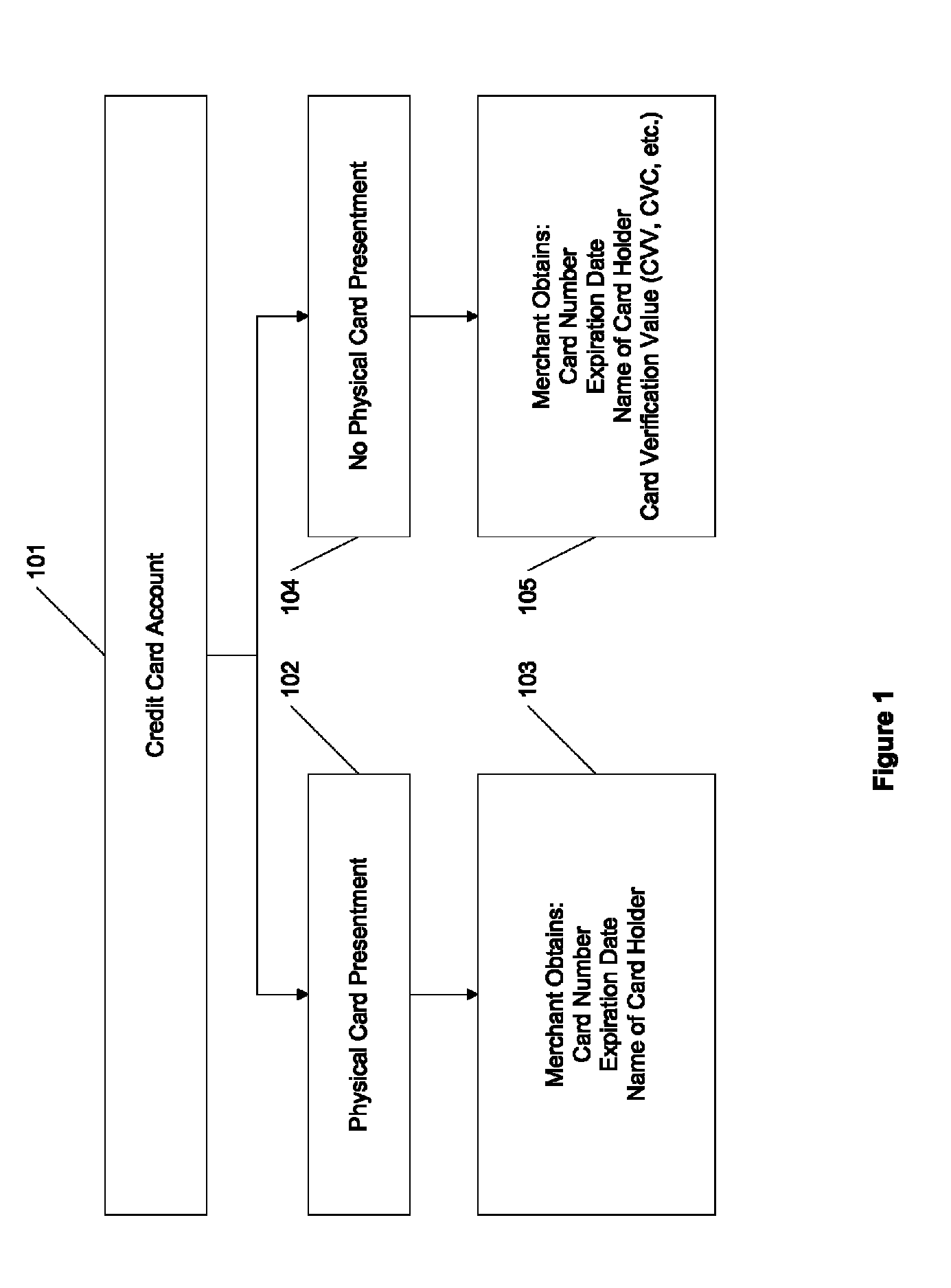
A credit card system is provided which has the added feature of providing additional limited use credit card numbers and / or cards. These numbers and / or cards can be used for a single or limited use transaction, thereby reducing the potential for fraudulent reuse of these numbers and / or cards. The credit card system finds application to “card remote” transactions such as by phone or Internet. Additionally, when a single use or limited use credit card is used for “card present” transactions, so called “skimming” fraud is eliminated. Various other features enhance the credit card system, which will allow secure trade without the use of elaborate encryption techniques. Methods for limiting, distributing and using a limited use card number, controlling the validity of a limited use credit card number, conducting a limited use credit card number transaction and providing remote access devices for accessing a limited use credit card number are also provided.
Owner:ORBIS PATENTS
Dynamic card verification values and credit transactions
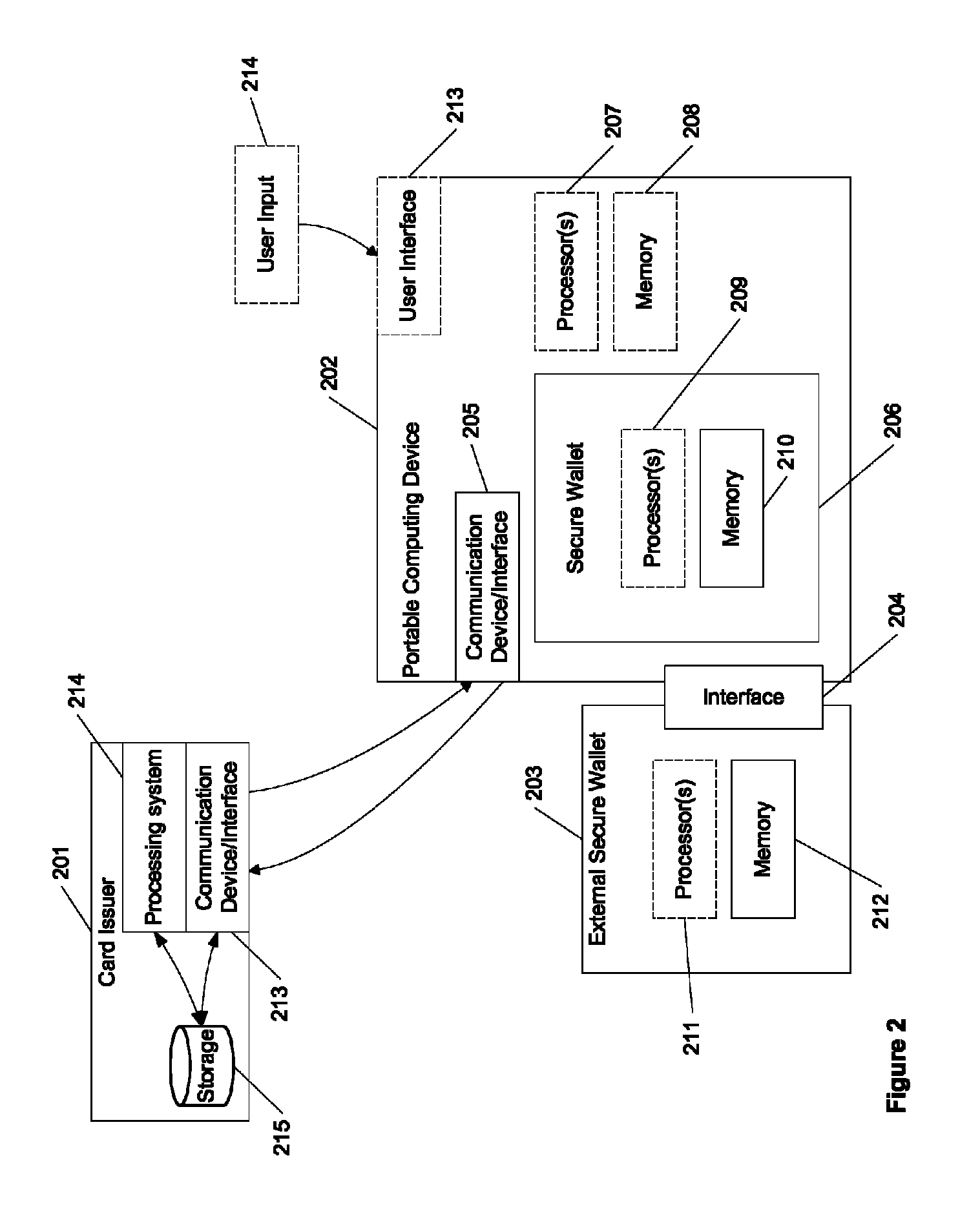
A system and method for providing card verification values for card-not-present transactions is described. In one example, a user's computing device stores single-use CVVs to be provided from a secure wallet. The secure wallet may be software running on the user's computing device. Alternatively, it may be an external device connectable to the user's computing device, which accesses the external device to obtain the single-use CVV.
Owner:AURA SUB LLC +1
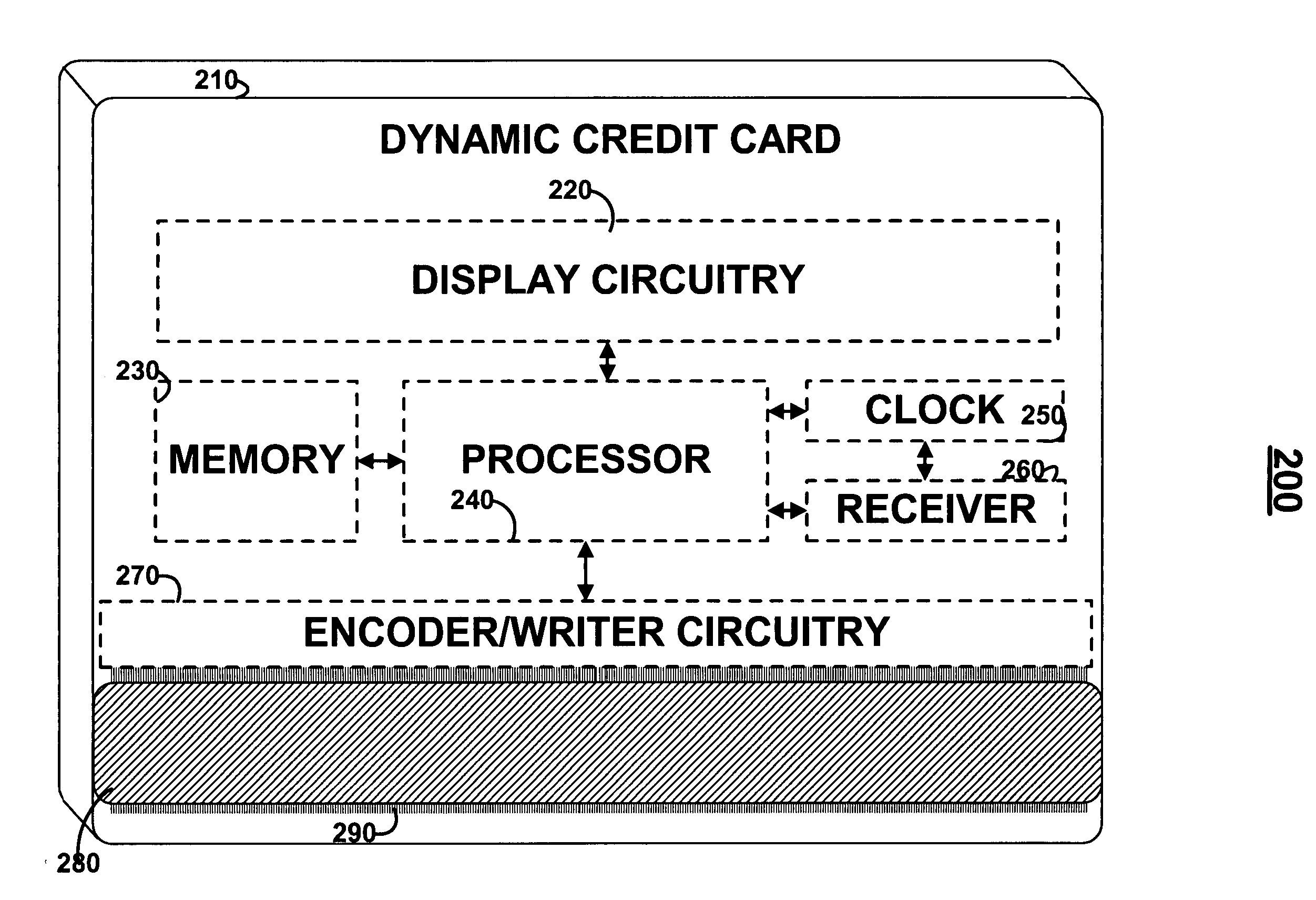
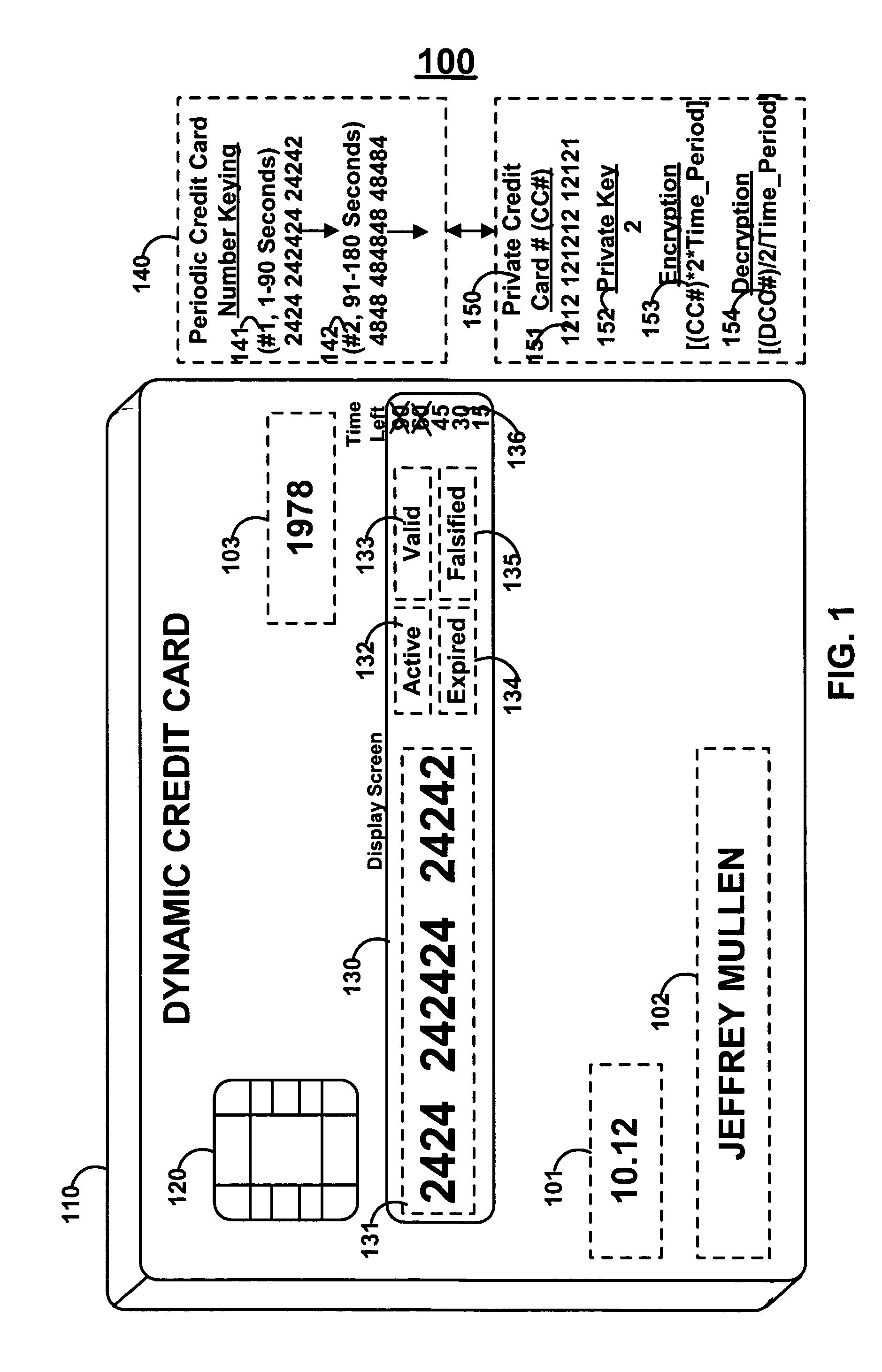
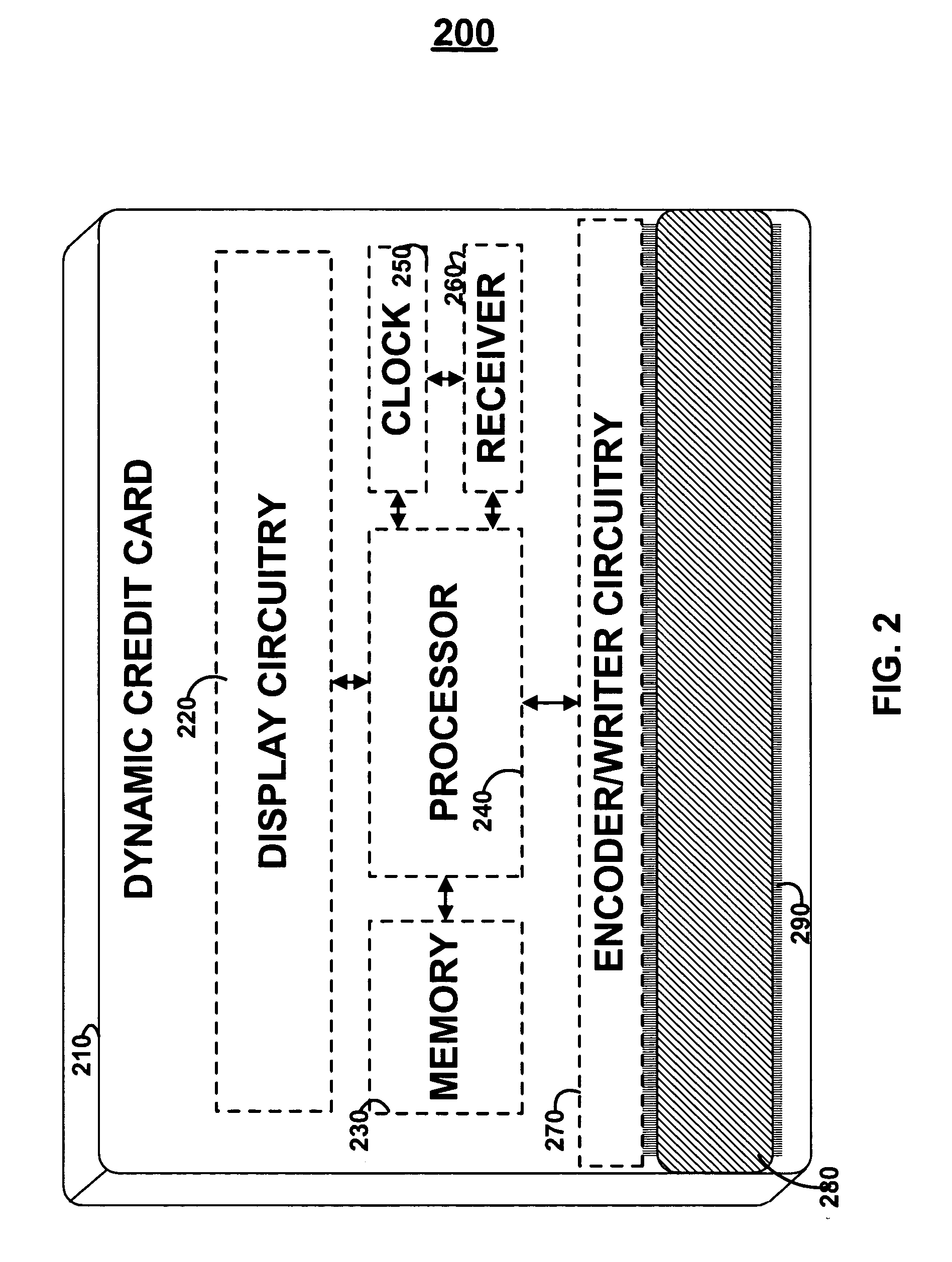
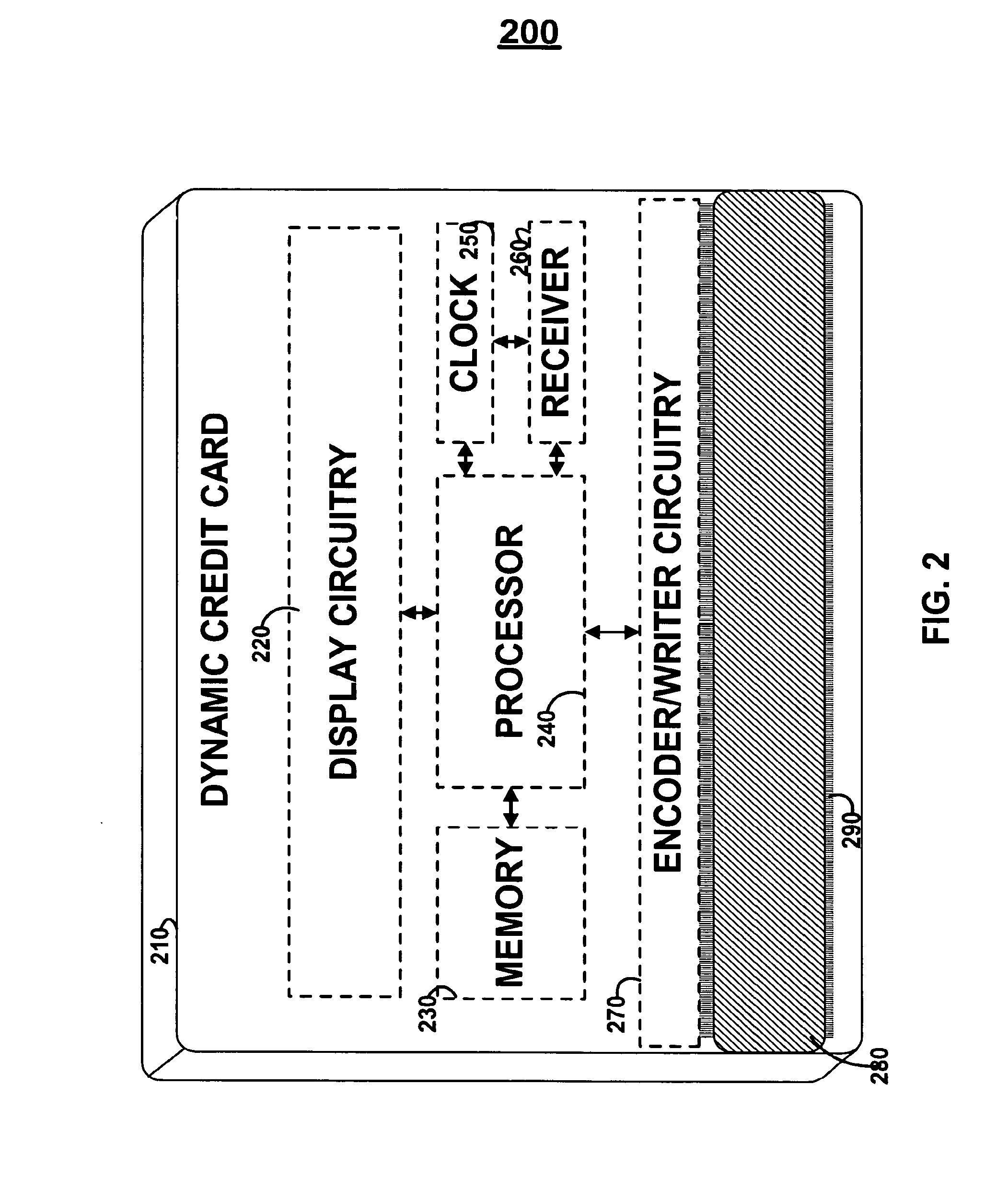
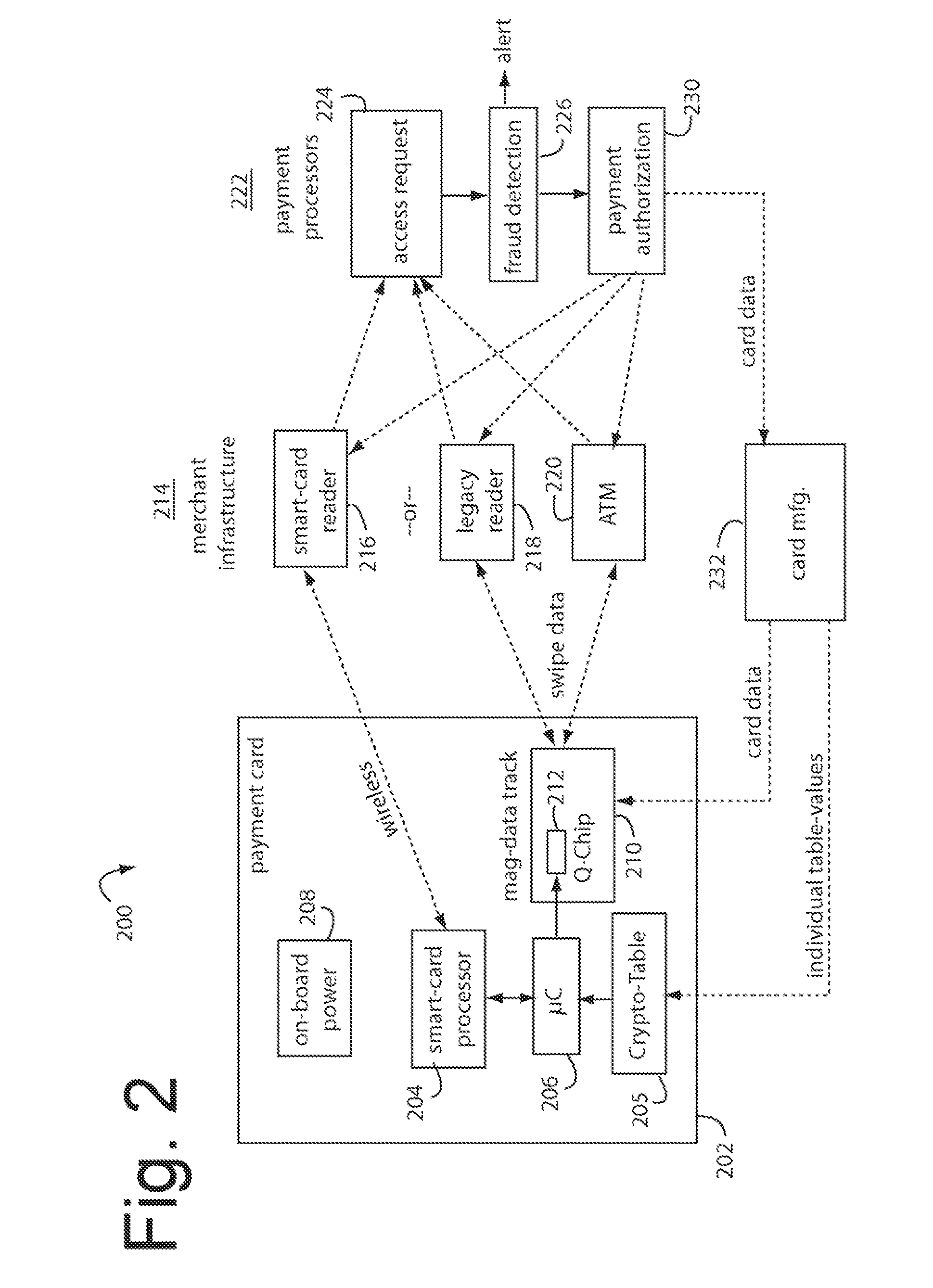
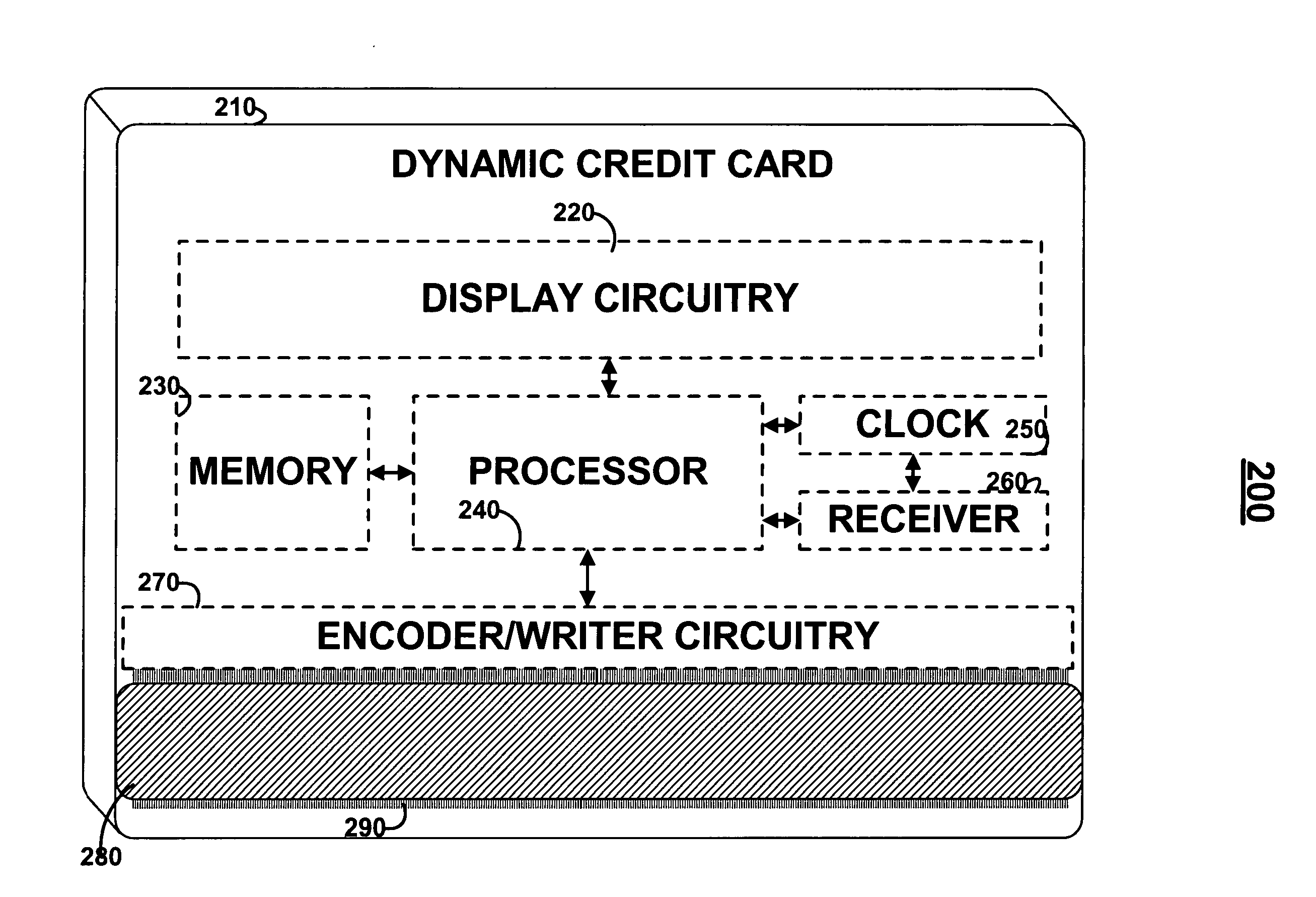
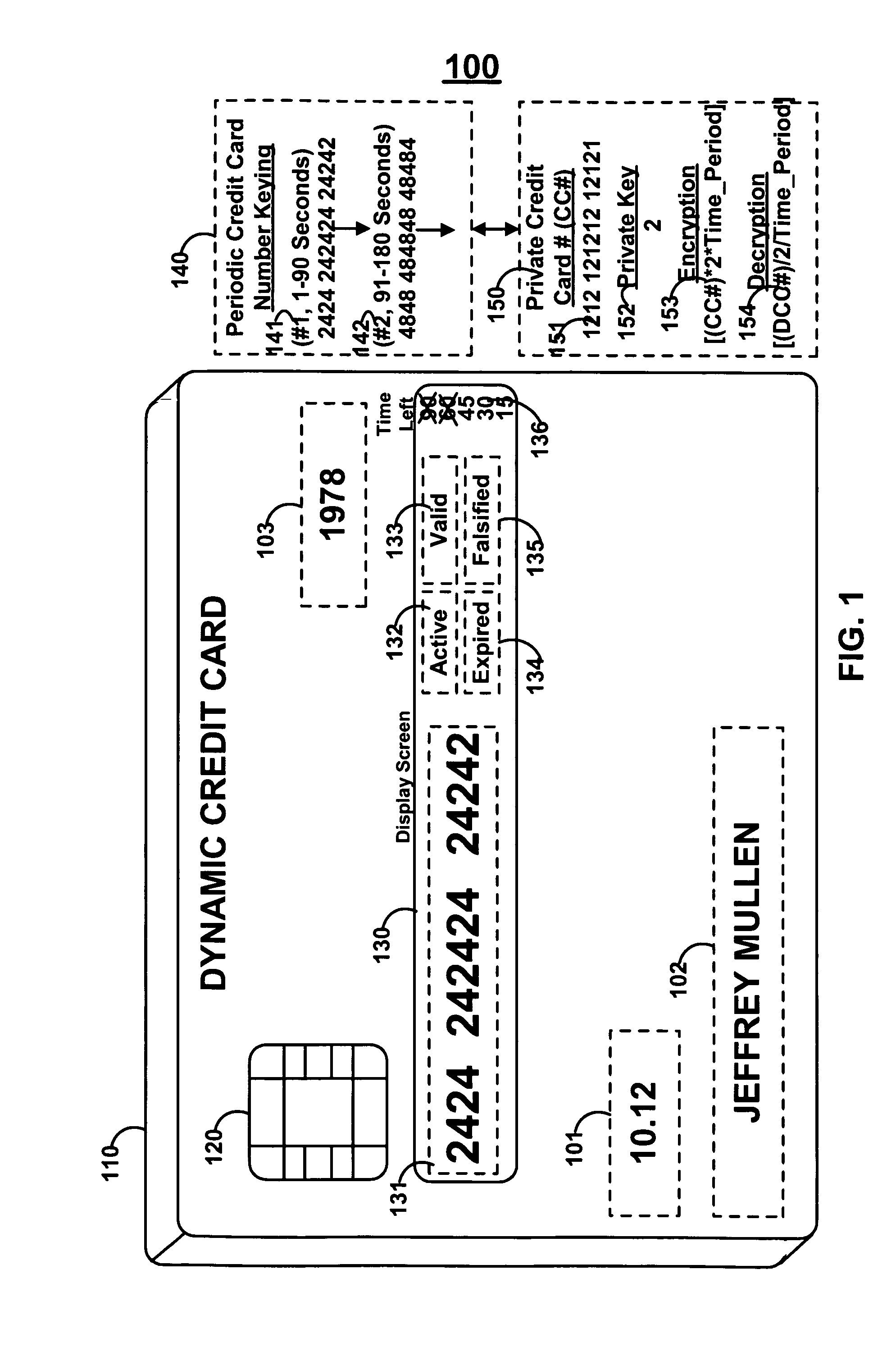
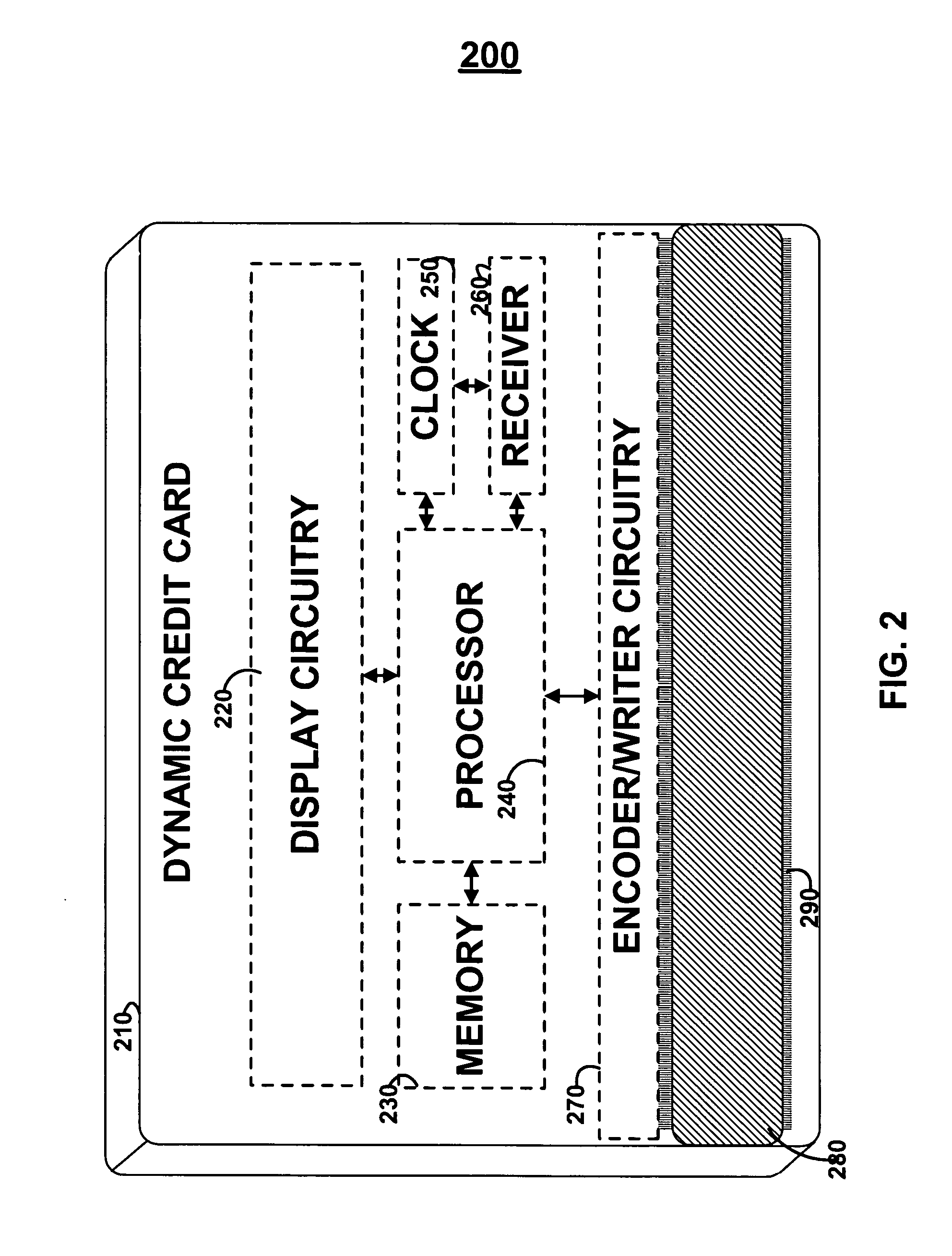
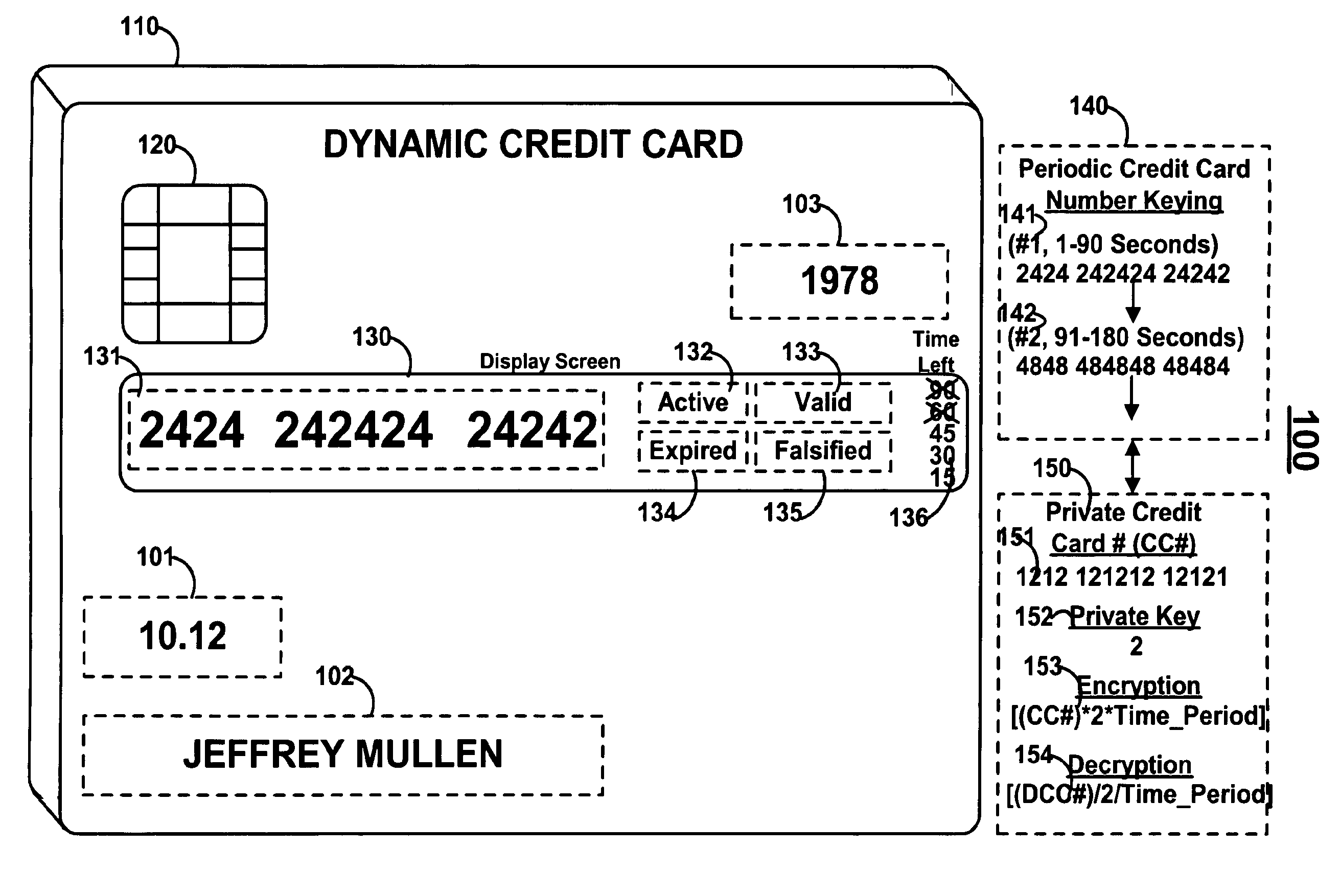
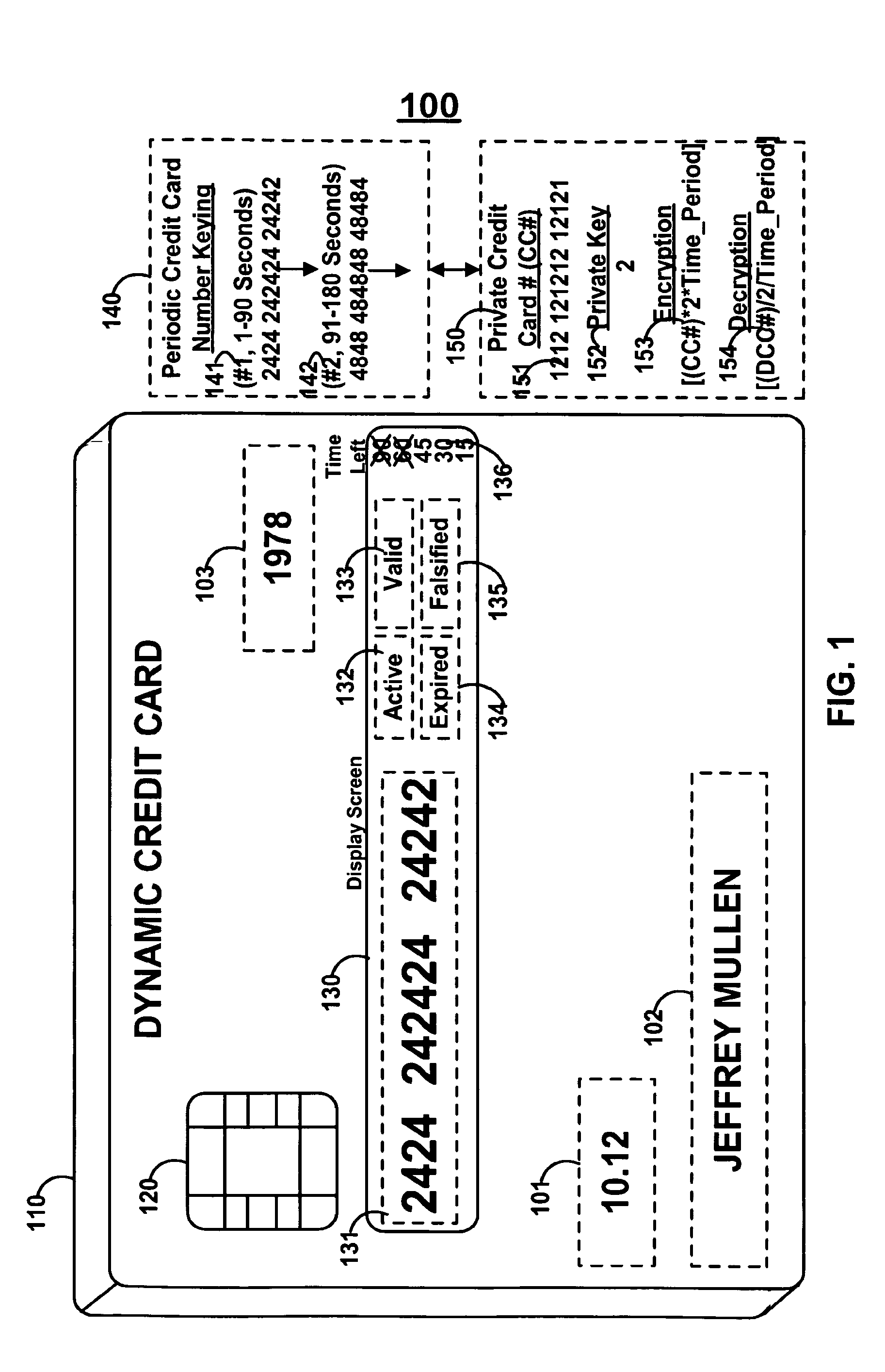
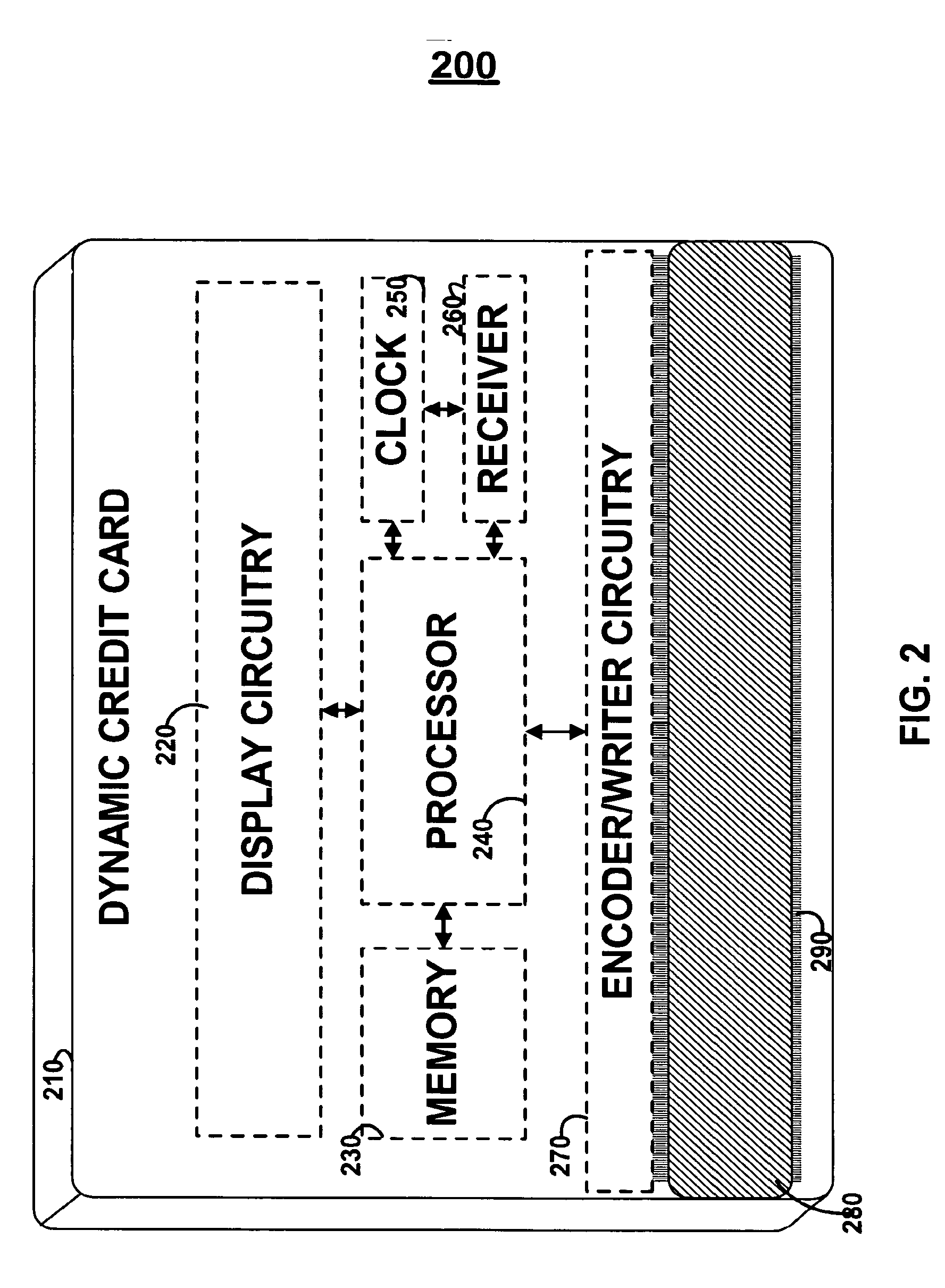
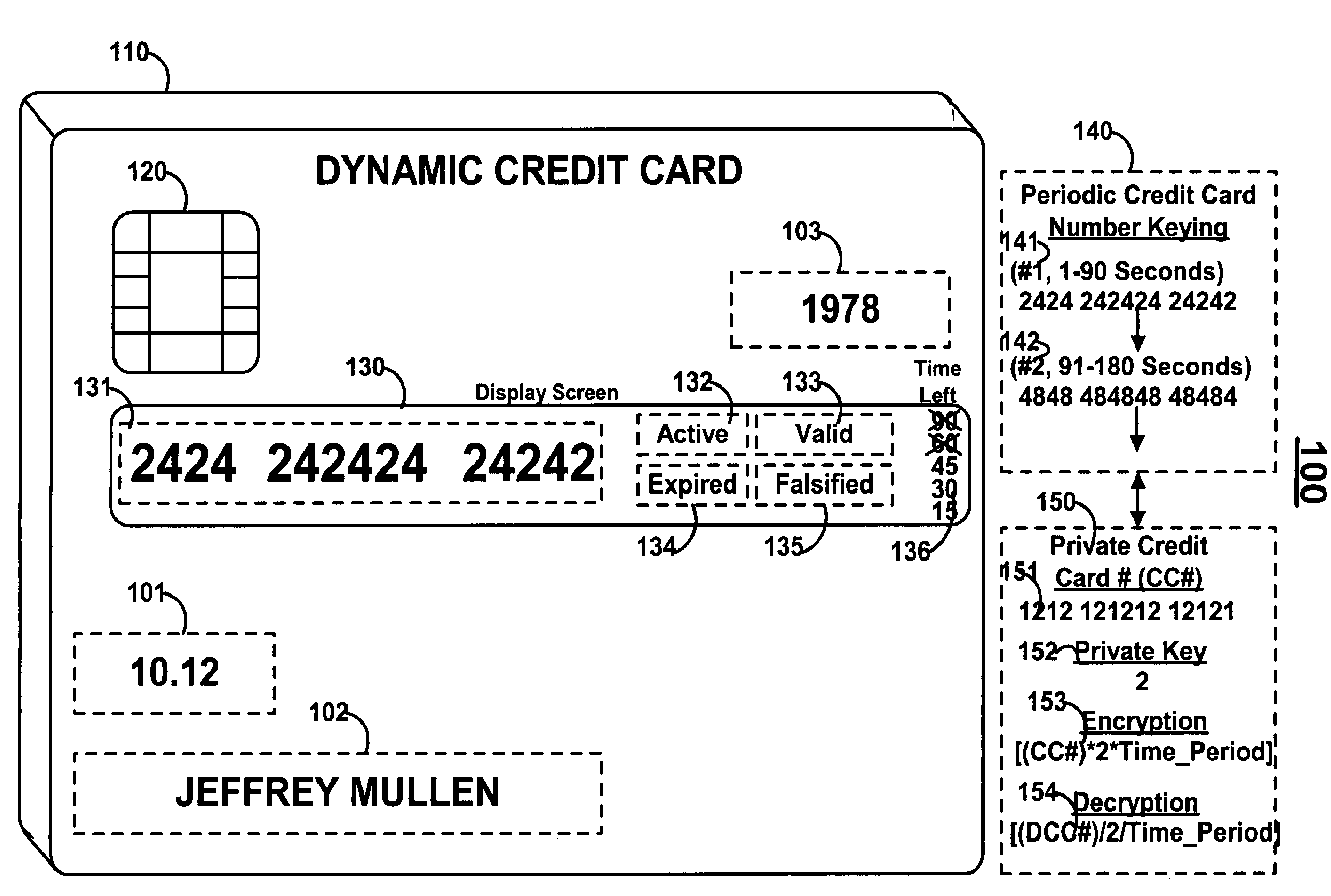
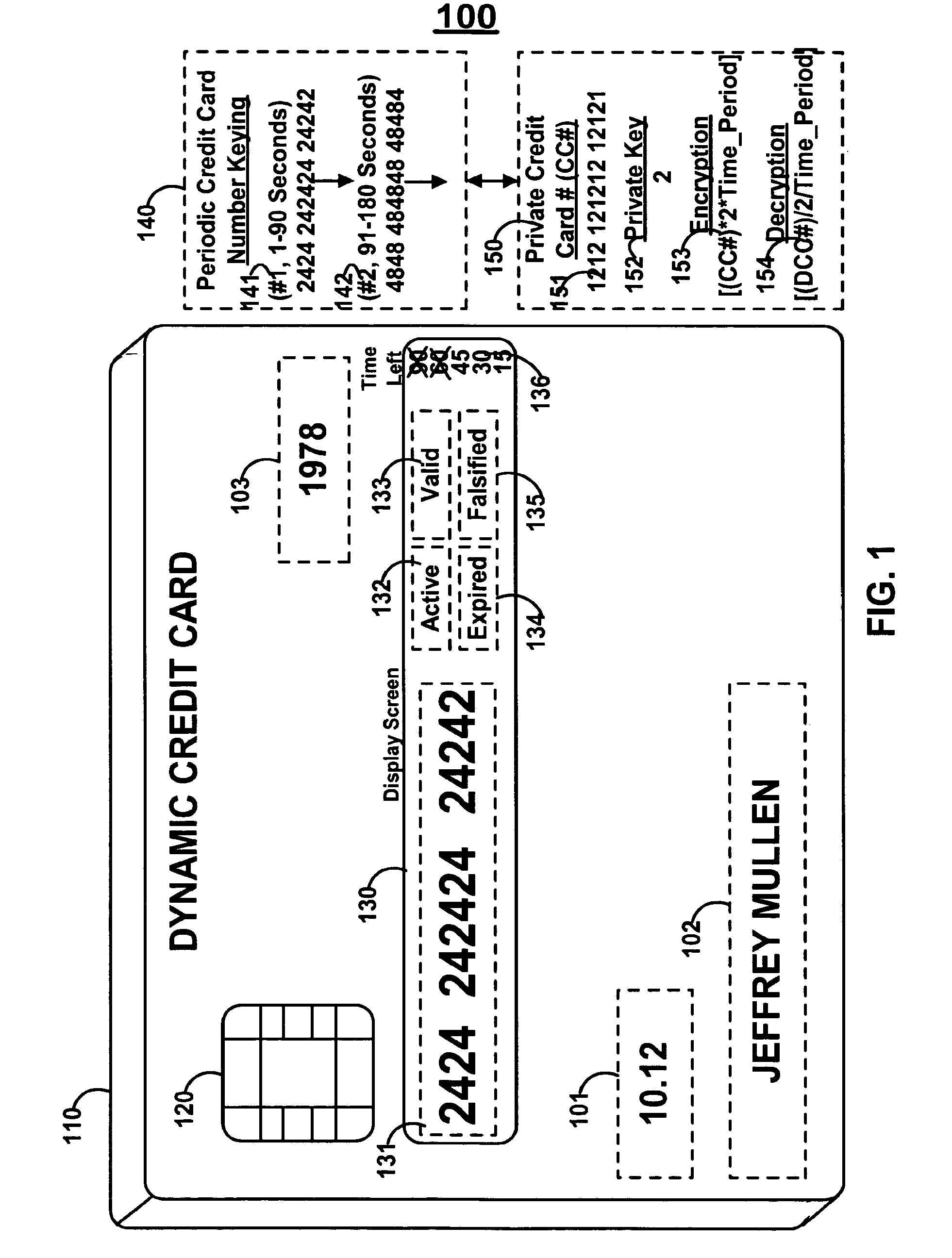
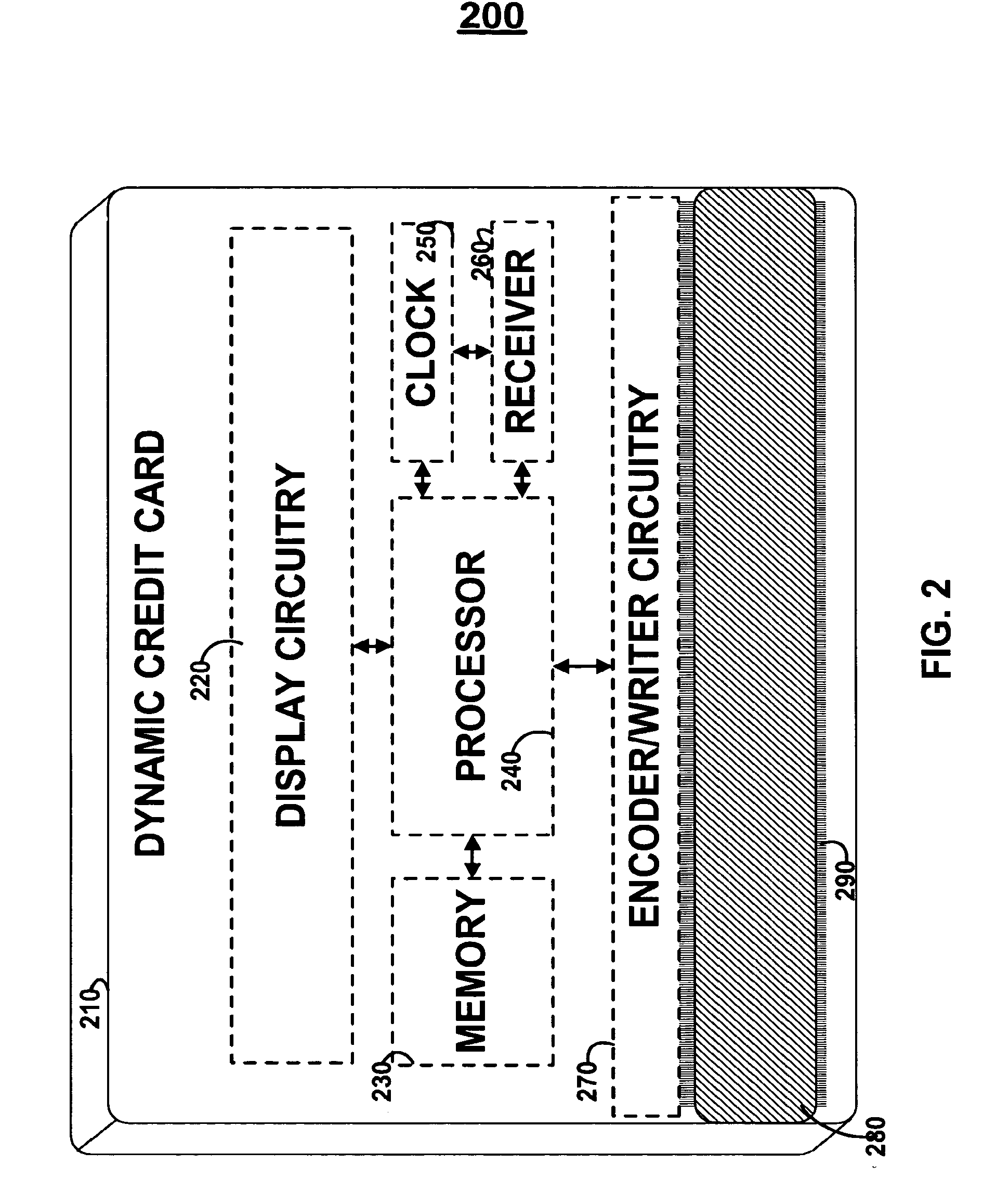
Dynamic credit card with magnetic stripe and embedded encoder and methods for using the same to provide a copy-proof credit card
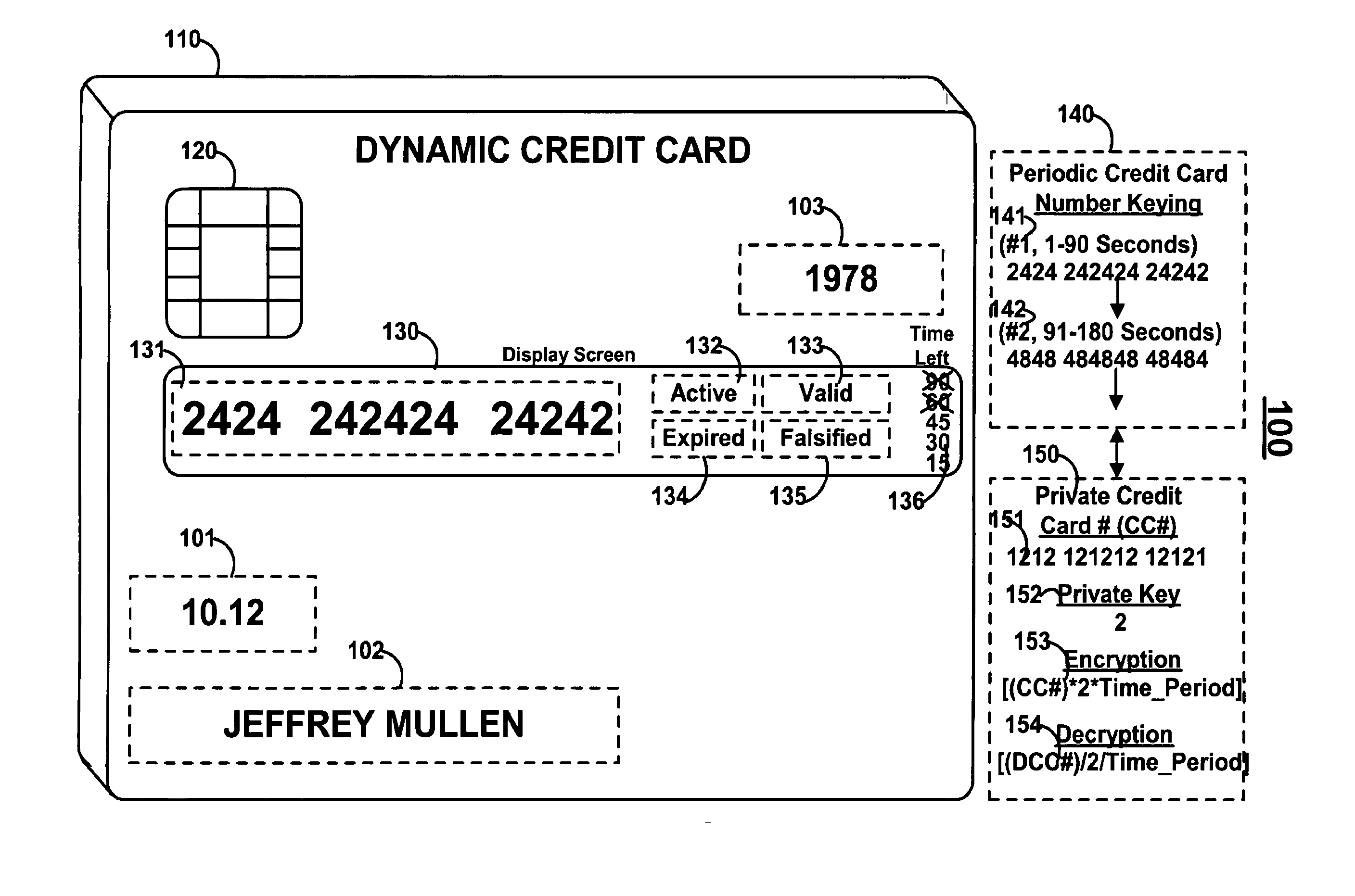
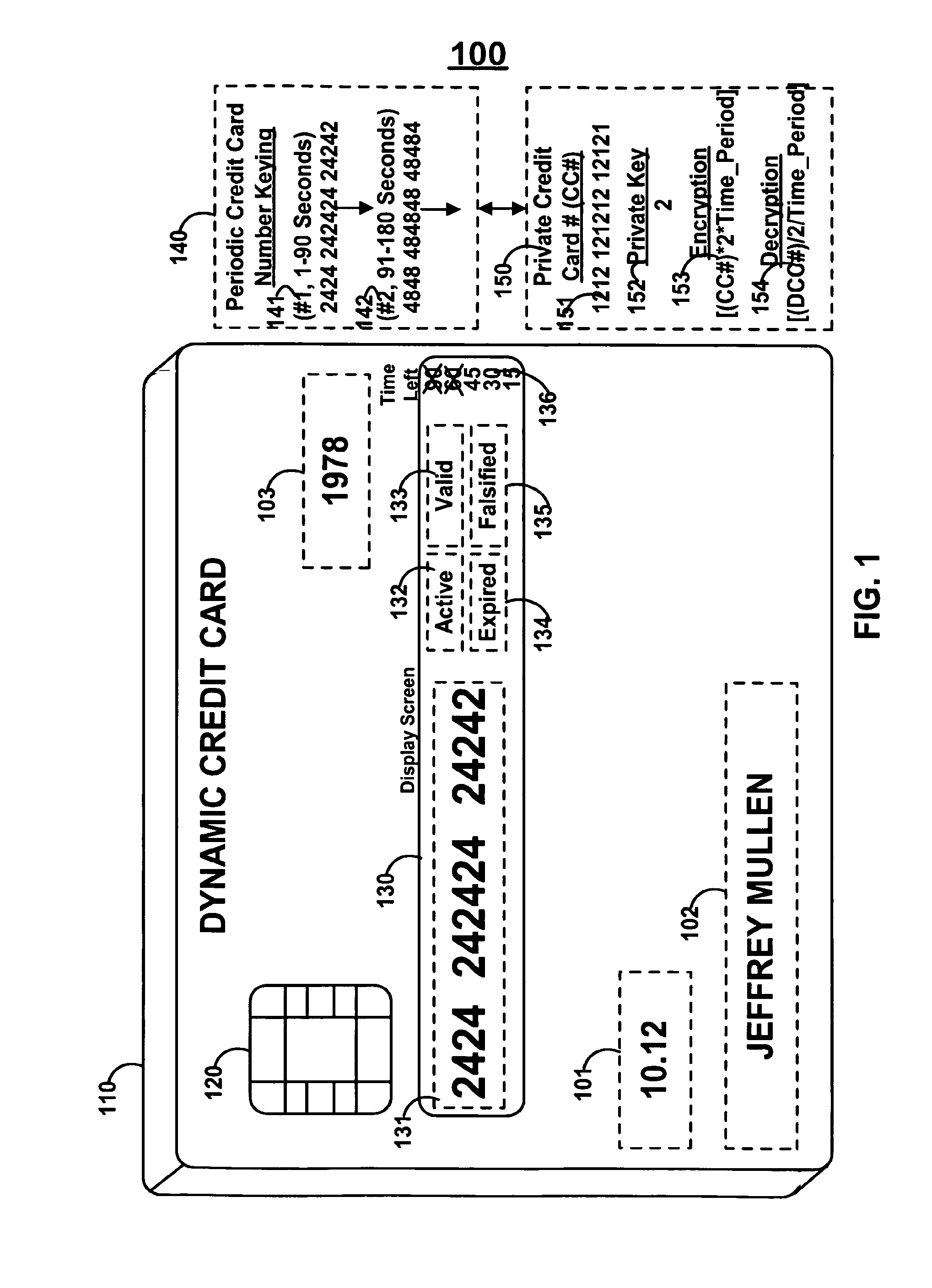
A dynamic credit card is provided in which a secure credit card number (e.g., a secret / hidden credit card number) is encoded based on a timing signal (e.g., an internal counter) to provide a dynamic credit card number. This dynamic number may be displayed to a user via a display (e.g., so that online purchases can be made) or written onto a magnetic stripe such that the number may be processed by traditional credit card merchants (e.g., swiped). At a remote facility, the dynamic number may be decoded based on time (and / or a counter / key number / equation) or the facility may have the secure number and perform the same function as the dynamic credit card (e.g., encode using time data as a parameter to the encoding equation) and compare the resultant dynamic number to the dynamic number received. Thus, a dynamic credit card number may change continually or periodically (e.g., every sixty seconds) such that credit card numbers may not be copied by thieves and used at later times. A dynamic verification code may be utilized in addition to, or in lieu of, a dynamic credit card number.
Owner:DYNAMICS
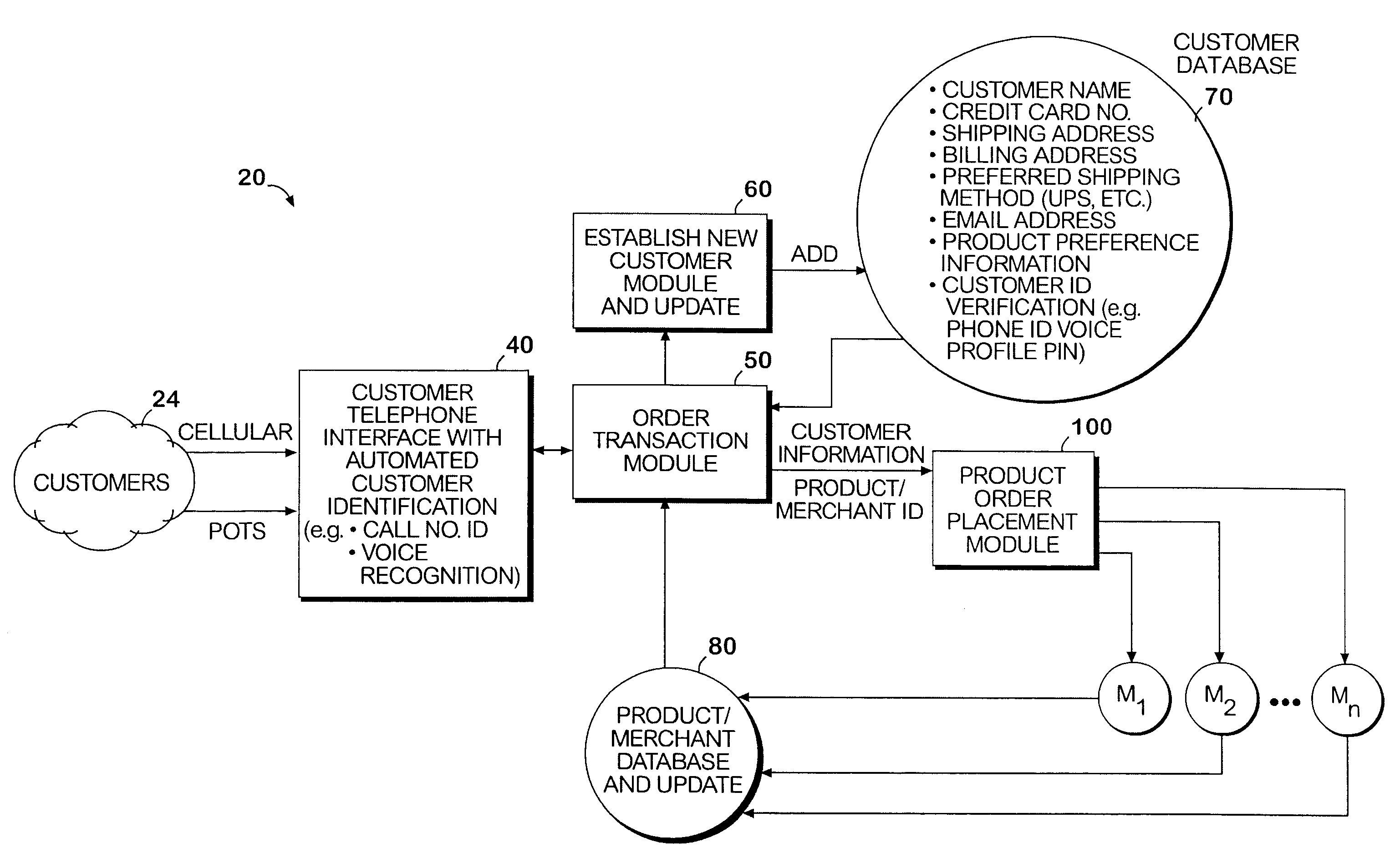
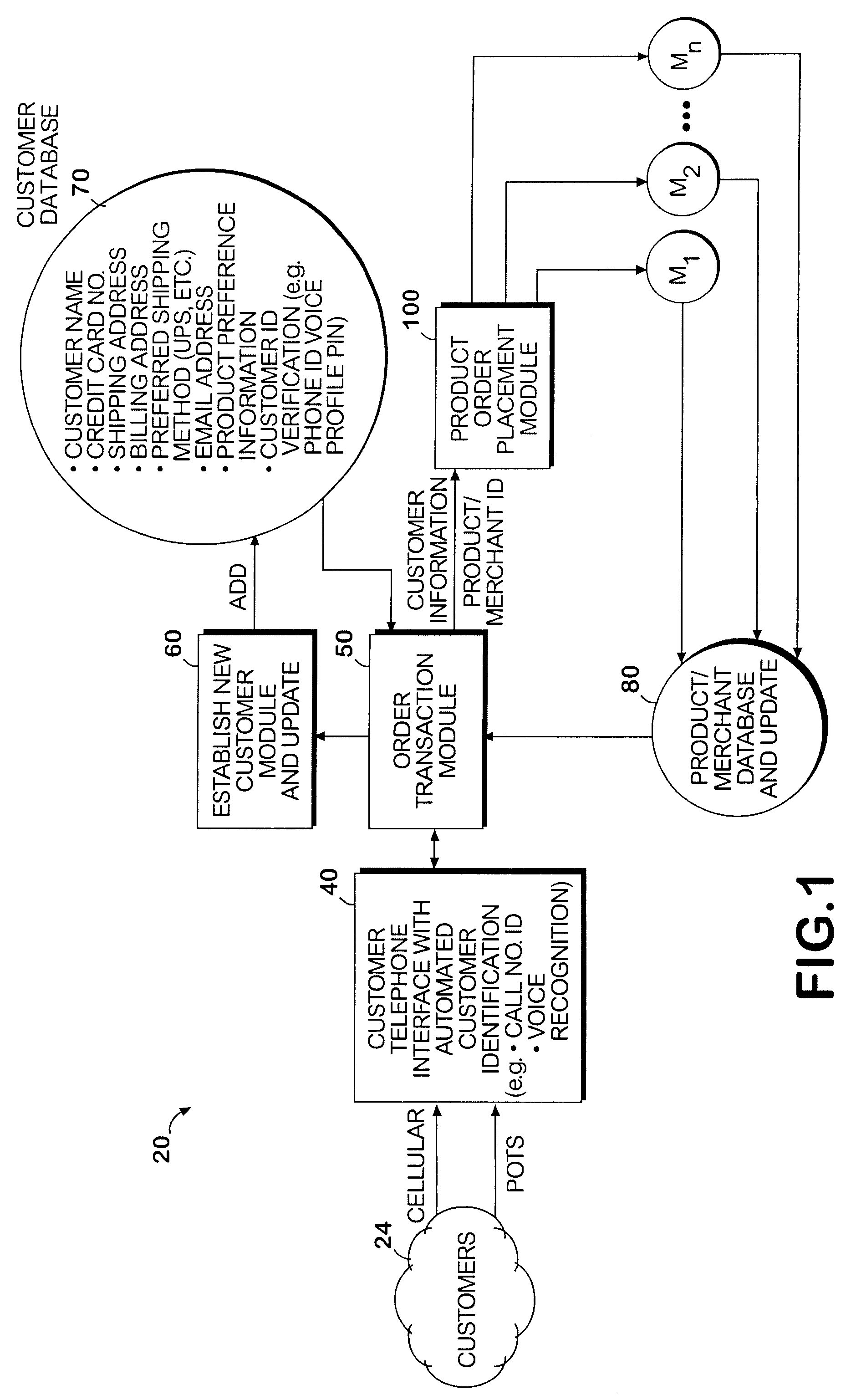
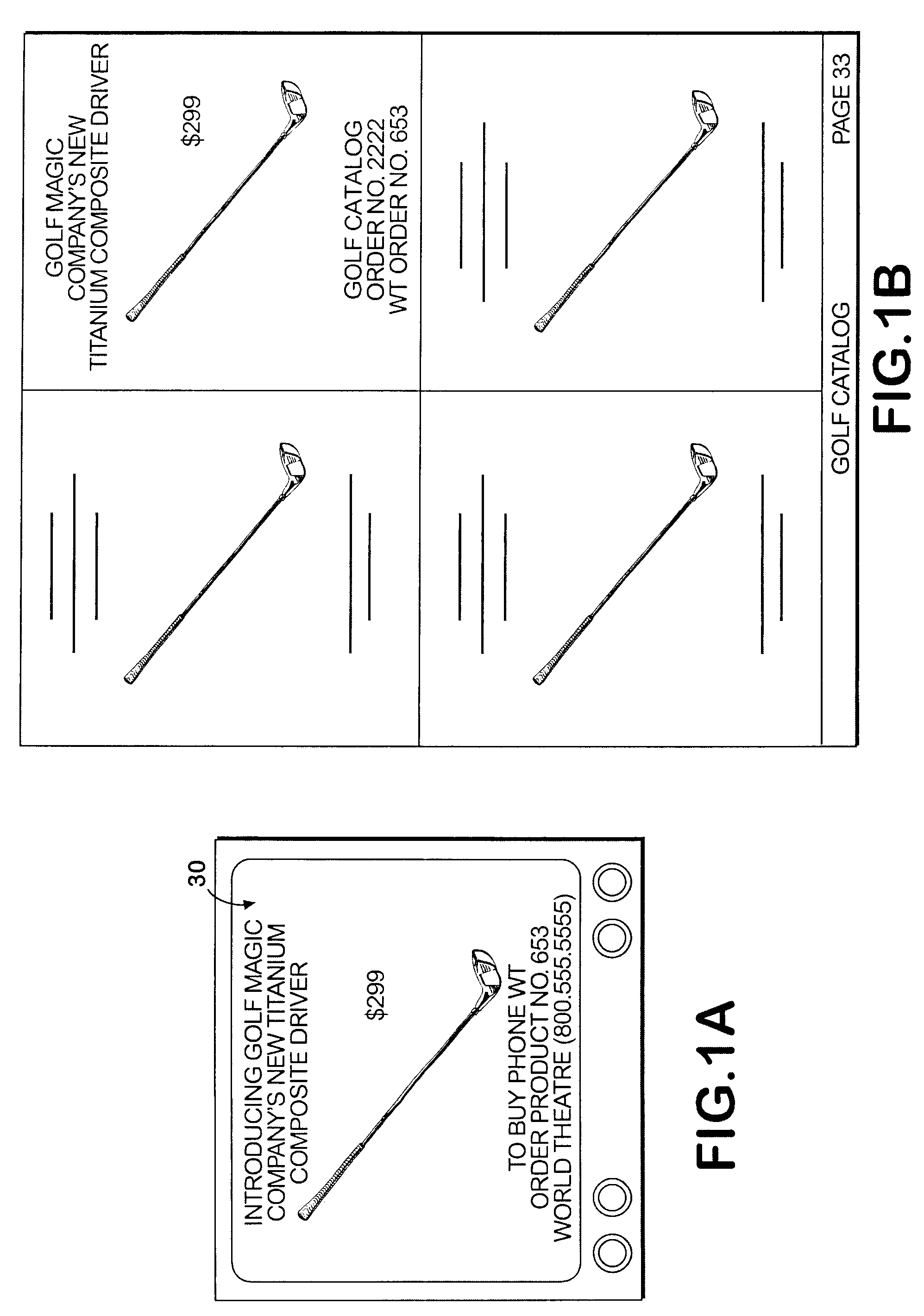
System and method permitting customers to order products from multiple participating merchants
A universal automated order processing system represents multiple (e.g., hundreds or thousands) participating merchants who offer their products through the system. Customers become qualified for using the system by supplying a set of information (e.g., name, credit card number, shipping address) that is stored in a customer database. When a customer wishes to order a product, the customer calls the system, customer identity is automatically confirmed, the customer enters a product order number and the complete order is routed to the appropriate merchant with the information necessary for the merchant to fulfill the order. Available credit verification and other aspects of credit card transactions may be handled by either the system operator or the merchant. The system operator may offer revolving credit. The system may also be used to provide potential customers of the merchants with free product information.
Owner:WORLD THEATRE INC +1
System and method for detecting card fraud
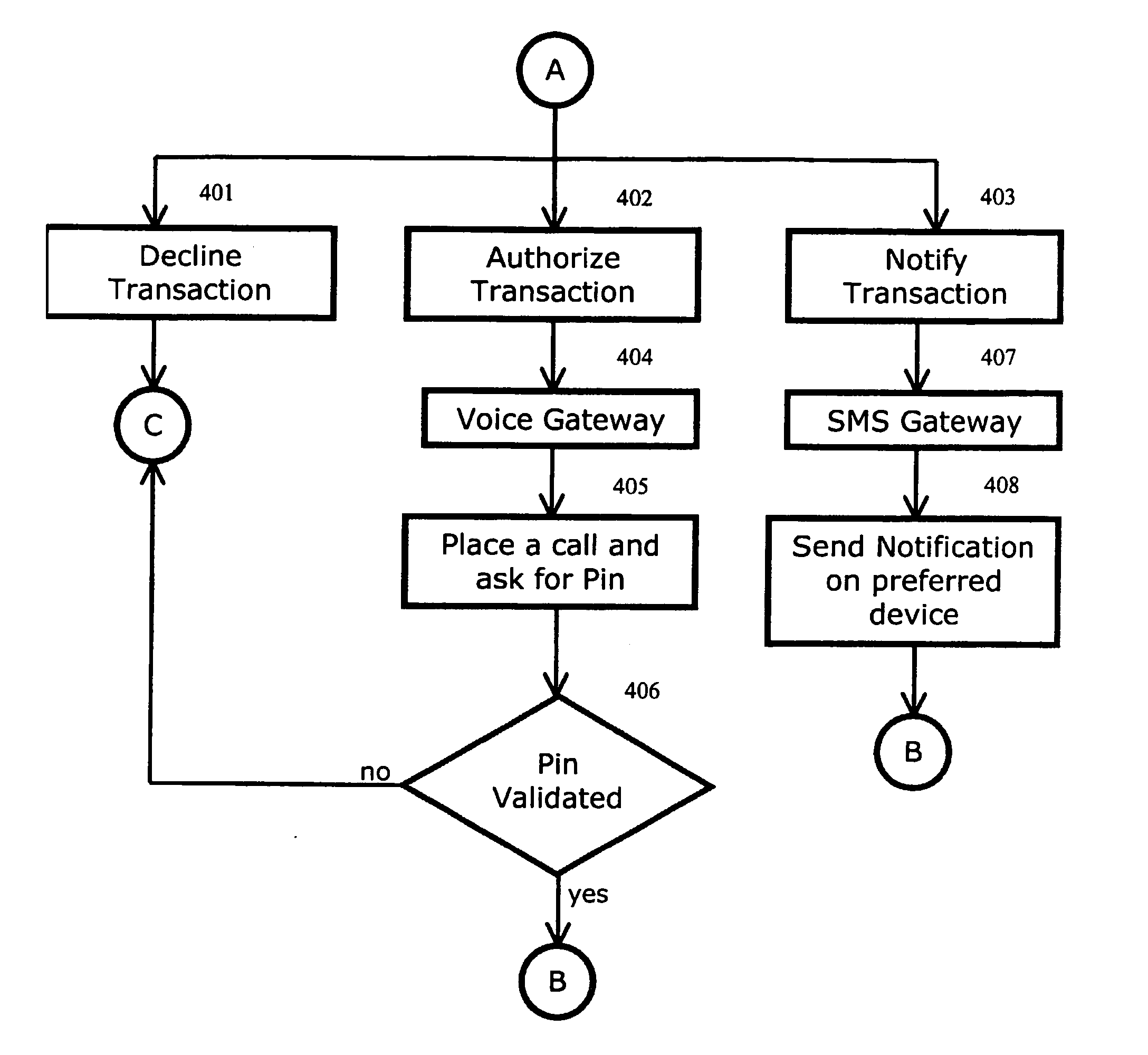
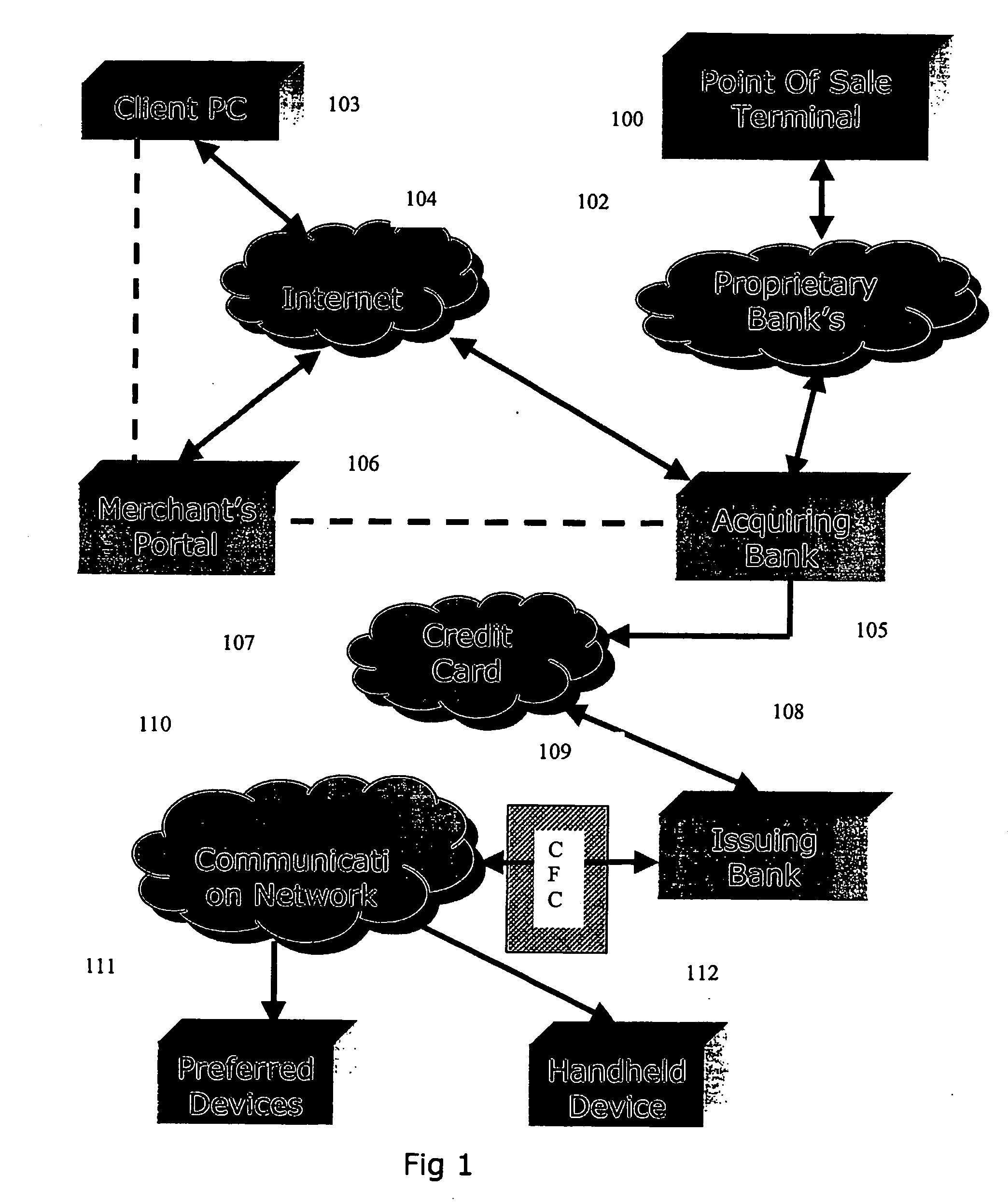
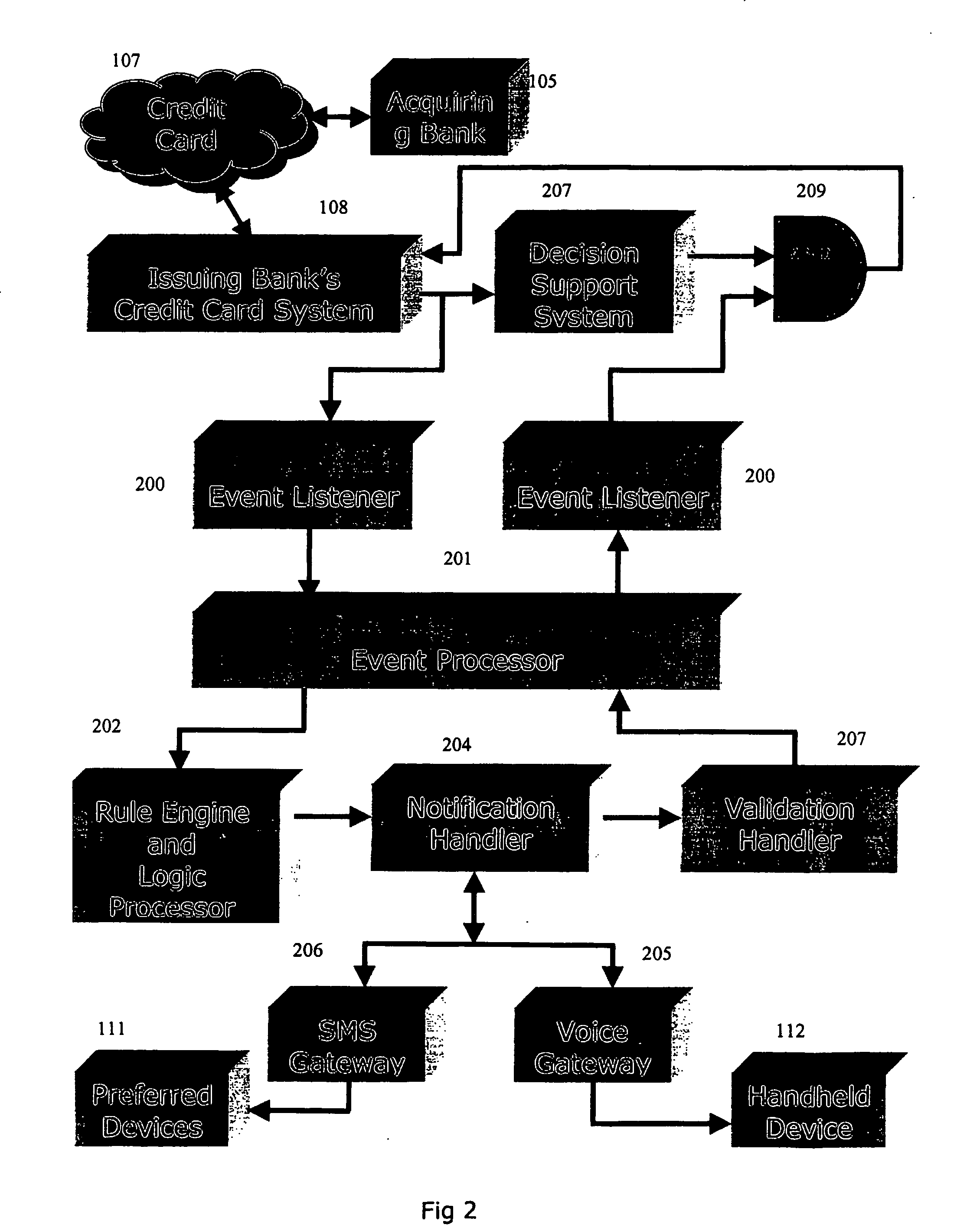
The invention discloses a system and method for notifying and authorizing card transaction by a user. The notifying and authorizing a card is done by a card fraud control system. The card user is notified on his hand held device by a short message service that a card transaction is taking place. The card user can also authorize the credit card transaction by keying in a personal identification number from his hand held device. The system also enables the user to change the rule-based system for a credit card transaction using voice and text inputs from a hand held device.
Owner:MADHOK AJAY +2
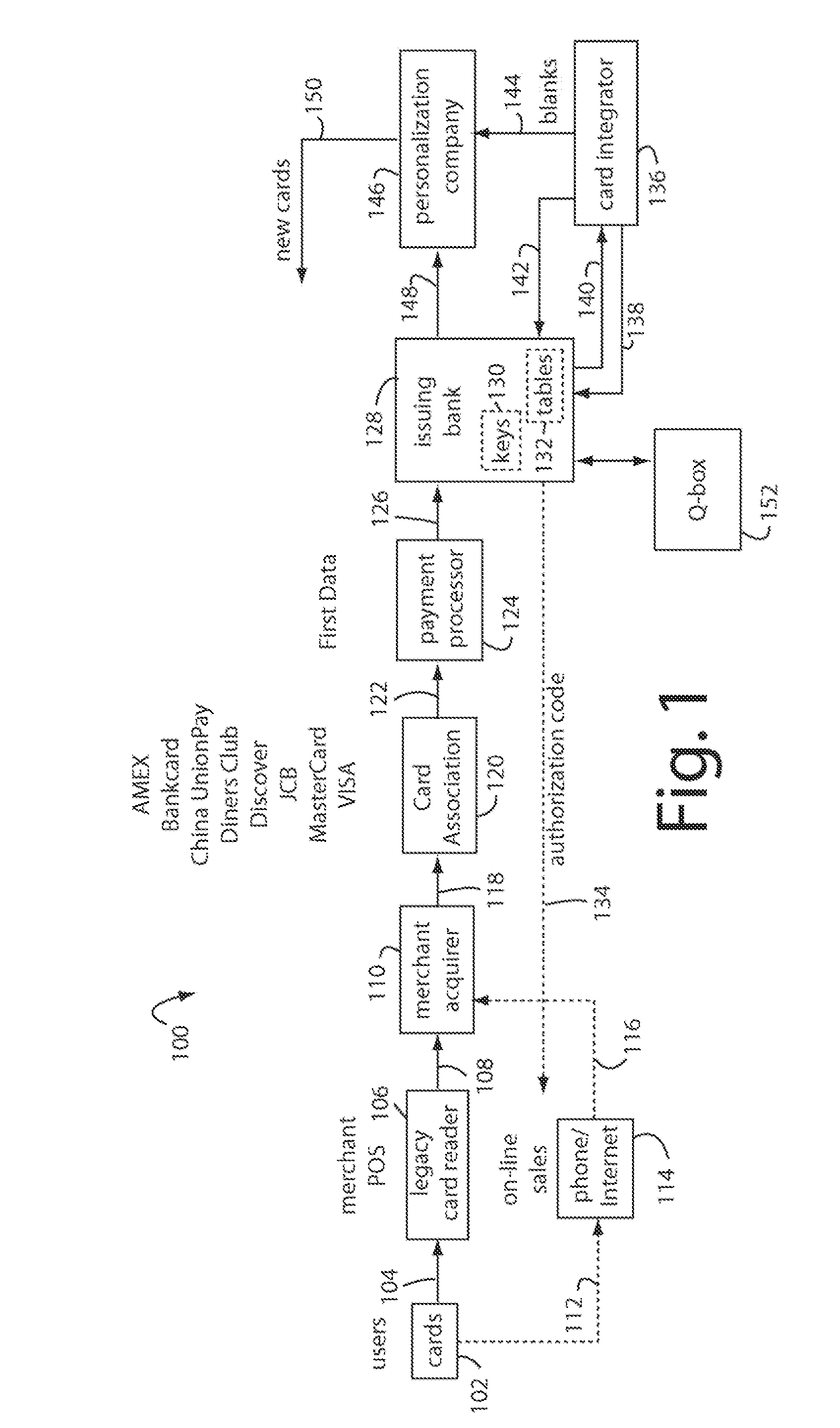
Financial transaction payment processor
InactiveUS20090006262A1Sufficient dataAcutation objectsSynchronising transmission/receiving encryption devicesPayment orderFinancial transaction
A financial transaction payment processor includes an account access request processor for receiving dynamic swipe data from a payment card through a merchant infrastructure. A fraud detection processor is connected to analyze a dynamic data obtained by the account access request processor that should agree with values pre-loaded in a Crypto-Table by a card manufacturer. A payment authorization processor is connected to receive a message from the fraud detection processor and to then forward a response to the merchant infrastructure.
Owner:FITBIT INC
Dynamic credit card with magnetic stripe and embedded encoder and methods for using the same to provide a copy-proof credit card
A dynamic credit card is provided in which a secure credit card number (e.g., a secret / hidden credit card number) is encoded based on a timing signal (e.g., an internal counter) to provide a dynamic credit card number. This dynamic number may be displayed to a user via a display (e.g., so that online purchases can be made) or written onto a magnetic stripe such that the number may be processed by traditional credit card merchants (e.g., swiped). At a remote facility, the dynamic number may be decoded based on time (and / or a counter / key number / equation) or the facility may have the secure number and perform the same function as the dynamic credit card (e.g., encode using time data as a parameter to the encoding equation) and compare the resultant dynamic number to the dynamic number received. Thus, a dynamic credit card number may change continually or periodically (e.g., every sixty seconds) such that credit card numbers may not be copied by thieves and used at later times. A dynamic verification code may be utilized in addition to, or in lieu of, a dynamic credit card number.
Owner:DYNAMICS
Method and system for issuing, aggregating and redeeming merchant reward points with a credit card network
A loyalty reward point system that utilizes the pre-existing infrastructure of network such as a credit card network. A user makes a purchase at a merchant using a token such as a credit card. As part of the purchase transaction, the user is awarded reward points from the merchant based on the purchase, which are stored in an account associated with the merchant and the user by a member bank of the credit card network, which may be an issuing bank or an acquiring bank. The reward account is maintained on the member bank server on behalf of the merchant and the user, and the number of reward points in the user's account for that merchant is increased accordingly. The user may redeem the reward points earned from the transaction with the merchant at a later time, or may redeem the points with another merchant in the same marketing cluster, or may aggregate those reward points with those of other merchants into a reward point exchange account, and then redeem the aggregated reward points for goods or services from any approved merchant on the network, depending on the configuration of the system.
Owner:SIGNATURE SYST
Method and system for conducting secure payments over a computer network without a pseudo or proxy account number
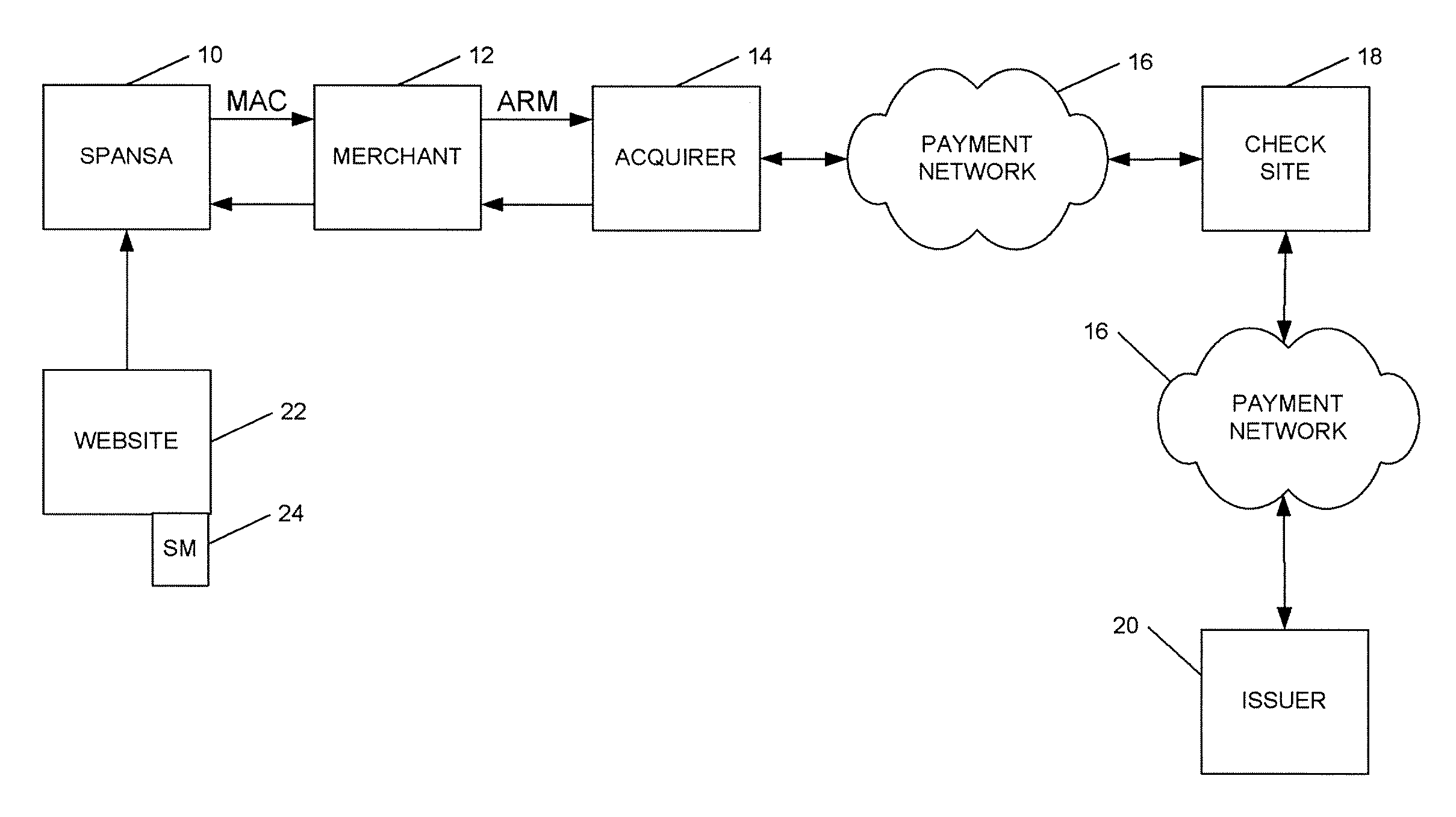
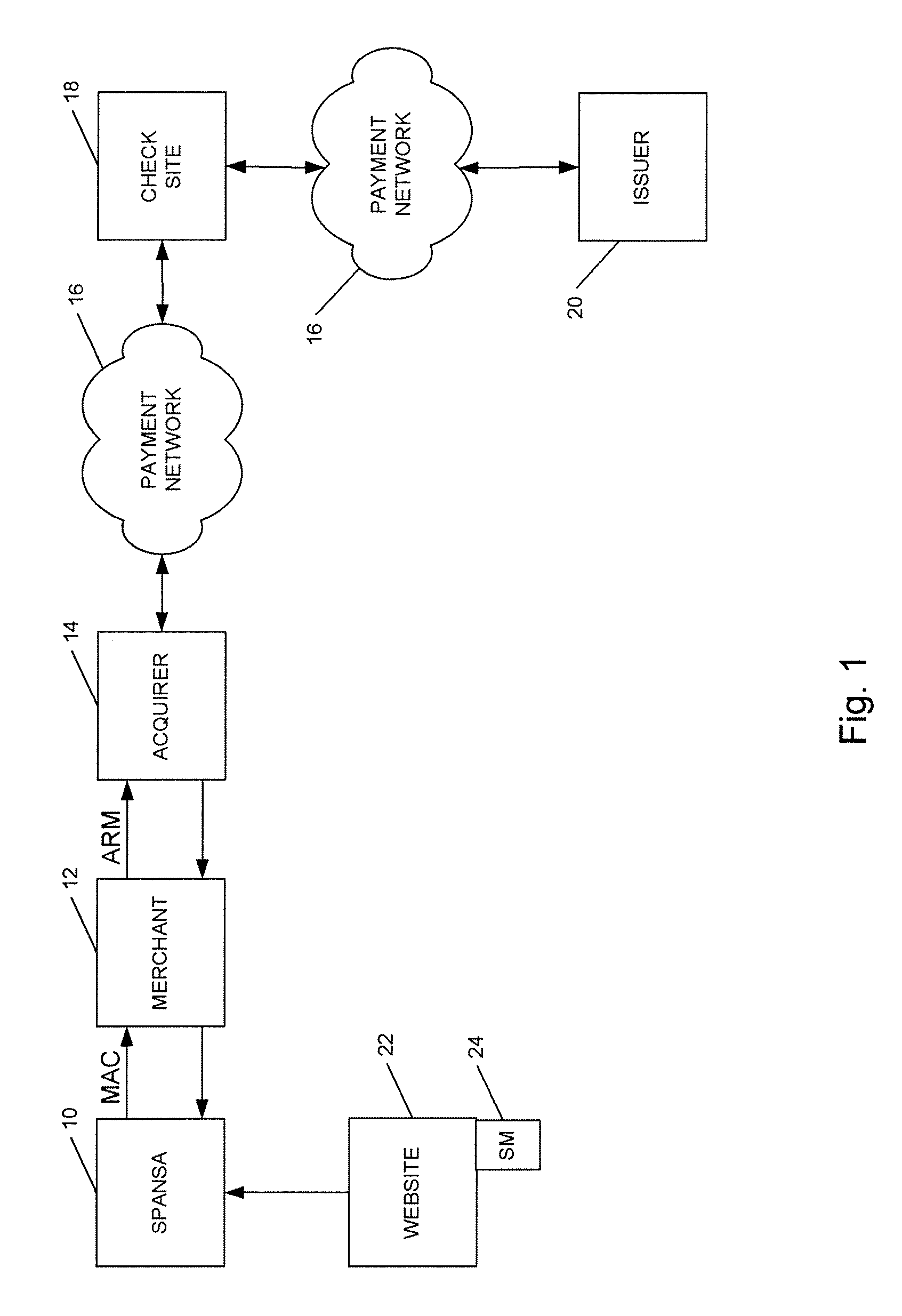
A method is provided for conducting an electronic transaction with a payment account number having a certain amount of available funds, using a payment network and a “check site”. The method comprises the following steps: (a) generating a secret key associated with the payment account number; (b) using the secret key to generate a message authentication code (“MAC”) specific to the transaction; (c) generating an authorization request message including the message authentication code; (d) forwarding the authorization request message over the payment network to the check site for verifying the authenticity of the MAC; (e) verifying the message authentication code by the check site using the secret key; (f) responding to the authorization request message over the payment network based on the available funds and the transaction amount.
Owner:MASTERCARD INT INC
Collaborative negotiation techniques for mobile personal trusted device financial transactions
Techniques for negotiation techniques for mobile personal trusted device financial transactions are provided. A user of a mobile personal trusted device sets user preferences that define the user's preferred parameters for conducting financial transactions. A merchant sets merchant preferences that define the merchant's preferred parameters for conducting financial transactions. When a financial transaction is initiated, a user preference and a merchant preferences are accessed. A negotiated preference is generated that accommodates both the user preference and the merchant preference. If the user preference and the merchant preference are not mutually exclusive, the negotiated preference attempts to satisfy both preferences. If the user preference and the merchant preference are mutually exclusive, the negotiated preference satisfies at least one of the two preferences based on which of the two preferences has a higher priority. The financial transaction is conducted based on the negotiated preference.
Owner:MASTERCARD INT INC
Persistent dynamic payment service
The invention comprises online methods, systems, and software for improving the processing of payments from financial accounts, particularly credit and debit card payments made from consumers to merchants in online transactions. The preferred embodiment of the invention involves inserting a trusted third party online service into the payment authorization process. The trusted third party authenticates the consumer and authorizes the proposed payment in a single integrated process conducted without the involvement of the merchant. The authentication of the consumer is accomplished over a persistent communication channel established with the consumer before a purchase is made. The authentication is done by verifying that the persistent channel is open when authorization is requested. Use of the third party services allows the consumer to avoid revealing his identity and credit card number to the merchant over a public network such as the Internet, while maintaining control of the transaction during the authorization process.
Owner:FISHER DOUGLAS C
Dynamic credit card with magnetic stripe and embedded encoder and methods for using the same to provide a copy-proof credit card
A dynamic credit card is provided in which a secure credit card number (e.g., a secret / hidden credit card number) is encoded based on a timing signal (e.g., an internal counter) to provide a dynamic credit card number. This dynamic number may be displayed to a user via a display (e.g., so that online purchases can be made) or written onto a magnetic stripe such that the number may be processed by traditional credit card merchants (e.g., swiped). At a remote facility, the dynamic number may be decoded based on time (and / or a counter / key number / equation) or the facility may have the secure number and perform the same function as the dynamic credit card (e.g., encode using time data as a parameter to the encoding equation) and compare the resultant dynamic number to the dynamic number received. Thus, a dynamic credit card number may change continually or periodically (e.g., every sixty seconds) such that credit card numbers may not be copied by thieves and used at later times. A dynamic verification code may be utilized in addition to, or in lieu of, a dynamic credit card number.
Owner:DYNAMICS
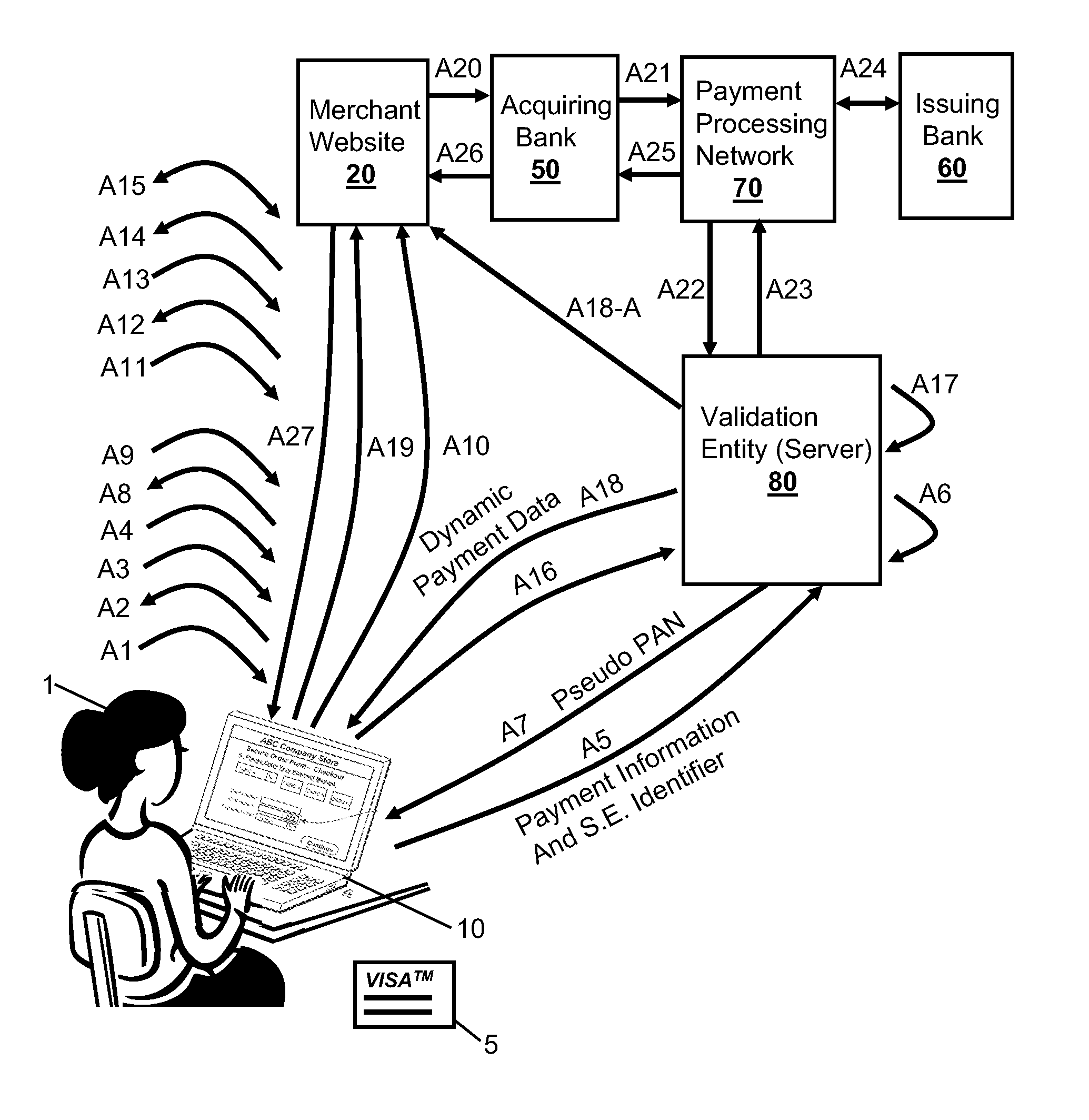
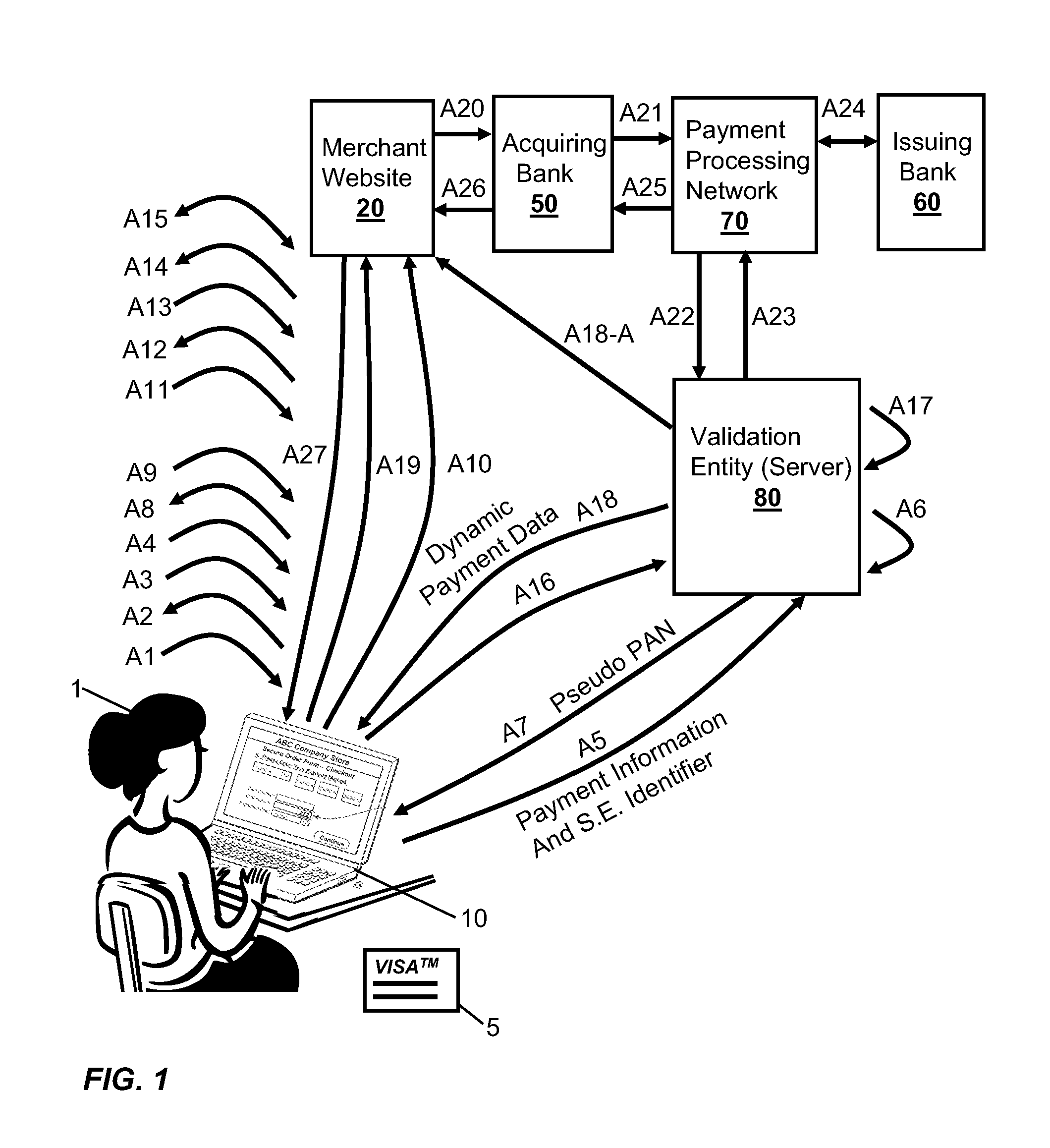
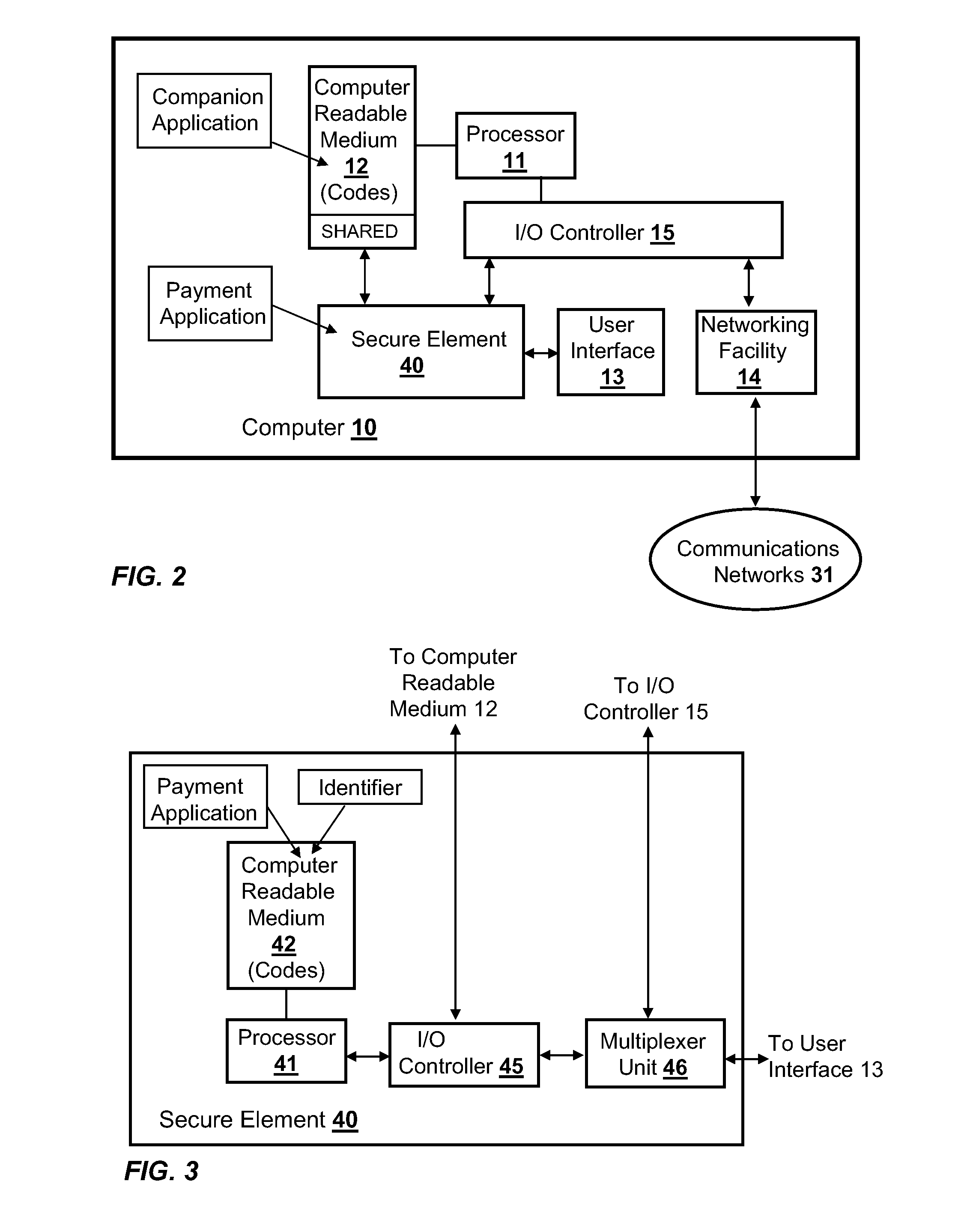
Integration of Payment Capability into Secure Elements of Computers
Methods, secure elements, validation entities, and computer program products for effecting secure communication of payment information to merchants for Internet-based purchases. Payment information for a user's real payment information is installed in a secure element of a computer, the payment information may comprise a pseudo PAN number for the portable consumer device provided by a validation entity. The secure element is shielded from the computer's operating system to thwart hacker attacks. The user accesses the secure element to make a purchase. In response, the secure element contacts the validation entity with the pseudo account number, and in response obtains dynamic payment information that the secure element can used to effect the payment. The dynamic payment information comprises an account number that is different from the pseudo PAN, and which has at least one difference which respect to the user's real payment information.
Owner:VISA INT SERVICE ASSOC
Method and system for conducting secure payments over a computer network
A method is provided for conducting a financial transaction by a purchaser with a merchant having an acquirer bank, over a communications network. The method includes the steps of sending a first authorization request using a pseudo account number associated with a real account number to a service provider which forwards a second authorization request to the issuer using the real account number and preferably a pseudo acquirer code associated with the service provider such that the response to the second request is based on the real account number and sent back to the service provider who preferably forwards a response to the first request preferably to the “real” acquirer. A message authentication code is further provided which includes transaction data, and where the authorization request is formatted as a standard payment card track having one or more fields including a discretionary field in which the message authentication code is placed.
Owner:MASTERCARD INT INC
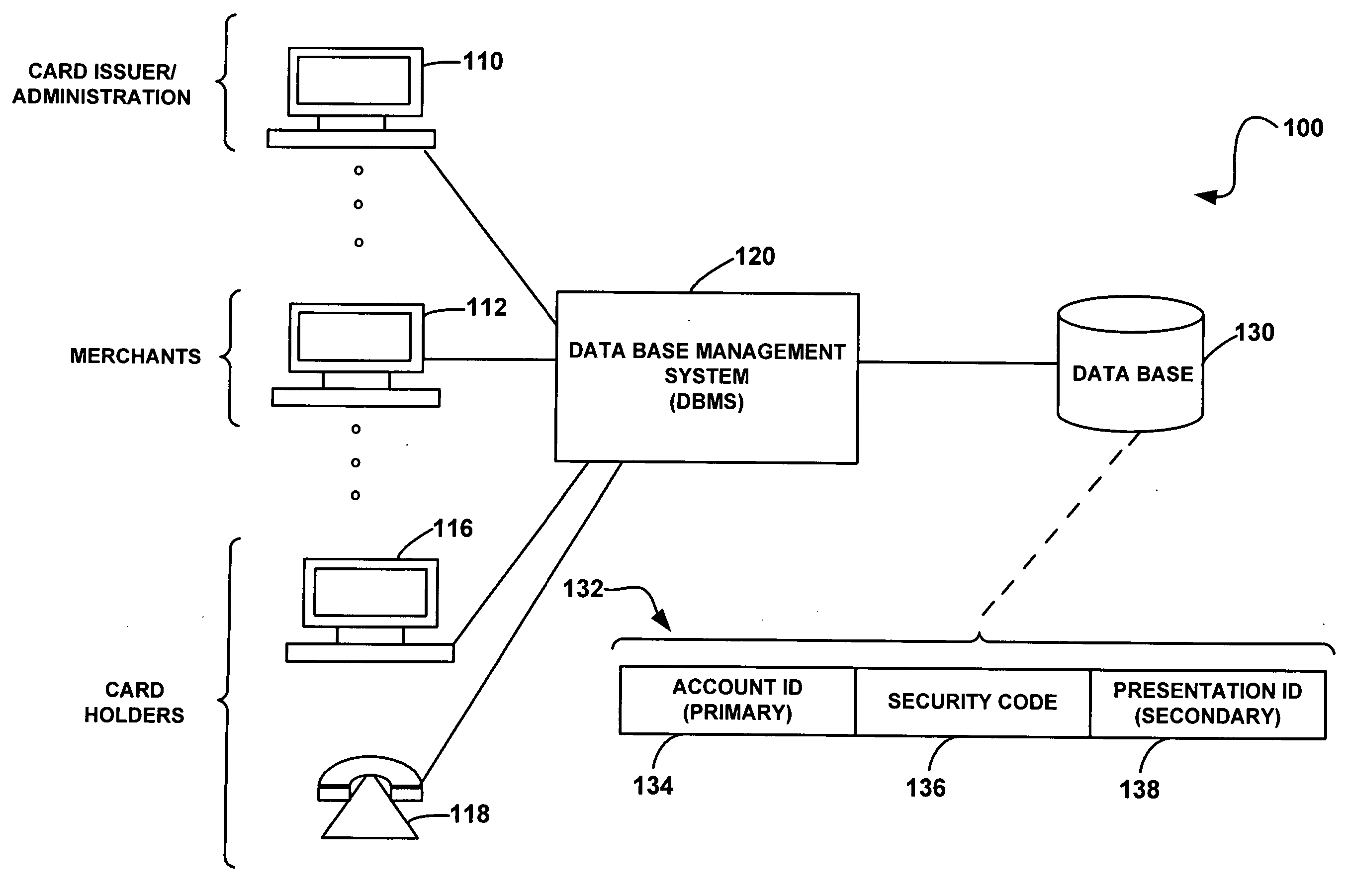
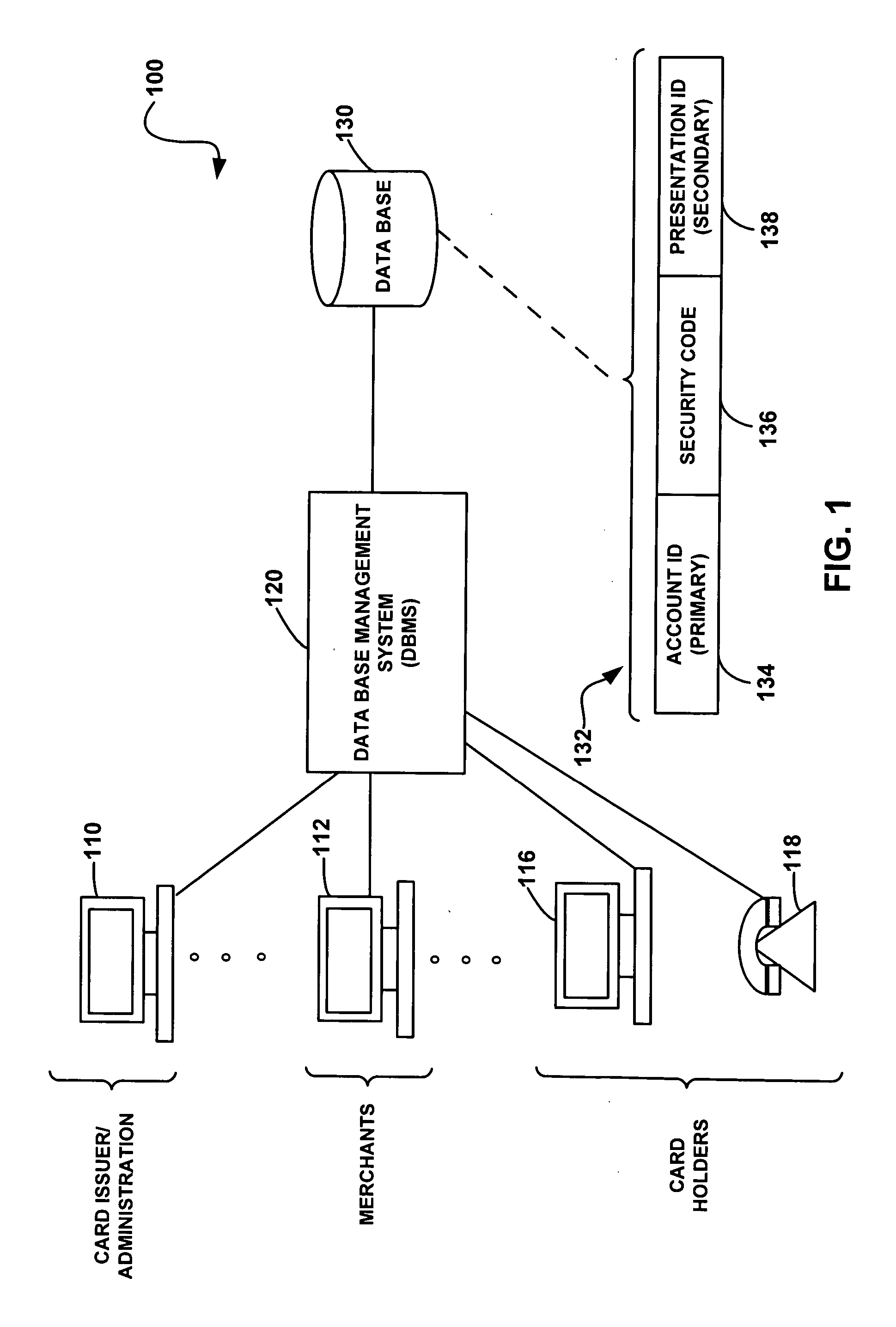
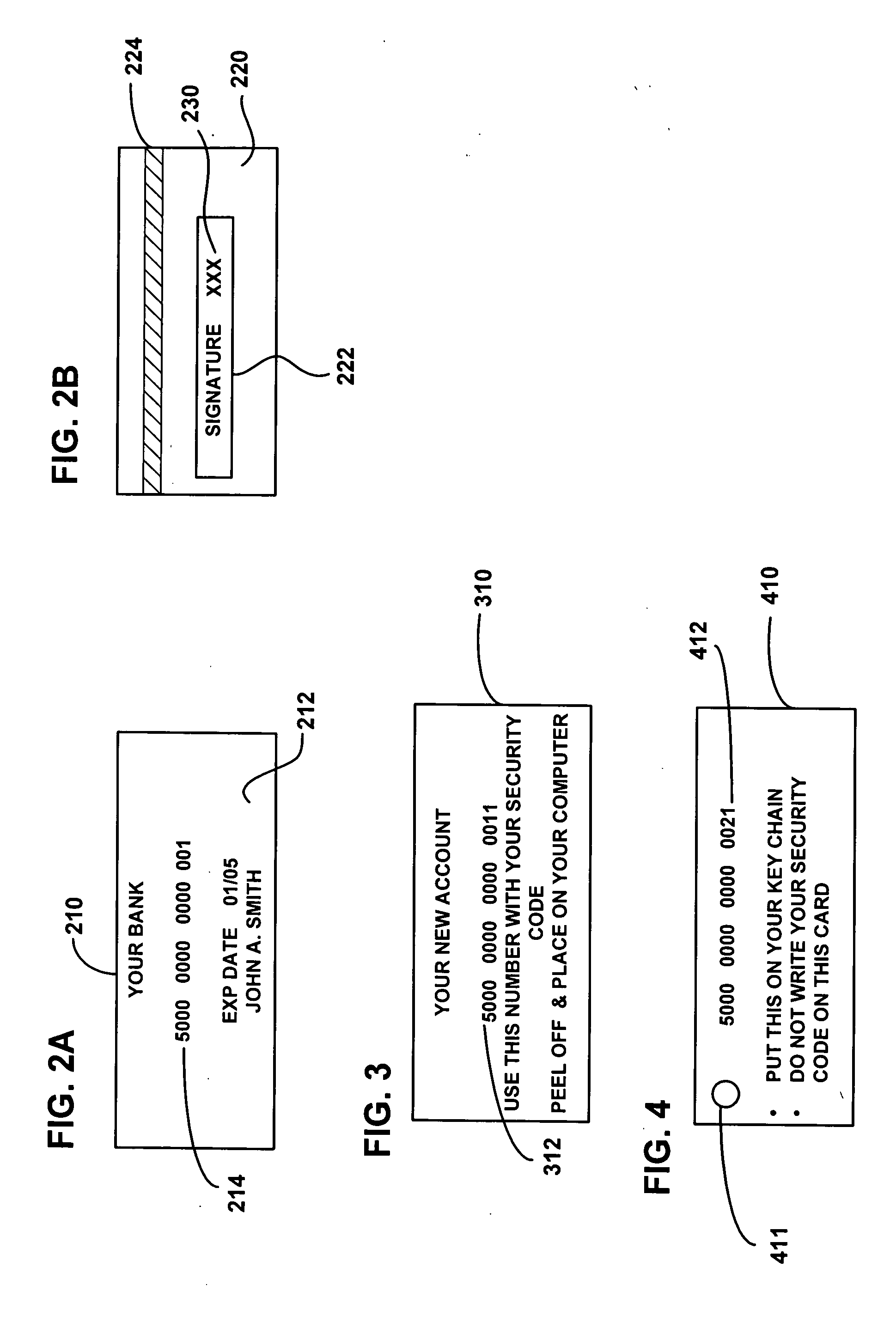
System and method for secure account transactions
A credit card management system and method wherein a customer with an account is provided a primary credit card with a credit card number and a security code thereon. A secondary presentation instrument associated with the primary credit card is issued for use in conducting on-line transactions. A database stores account information, including the security code associated with the primary account and a secondary account number associated the secondary presentation instrument. When an on-line transaction is conducted, the customer enters both the secondary account number and the security code from the credit card. The secondary presentation instrument is a paper card, a key fob, a printed record or any other virtual credit card.
Owner:FIRST DATA
System and method for securing a credit account
ActiveUS7264154B2Facilitates card-holder verificationEliminate needComplete banking machinesFinanceCredit cardSecurity Measure
Owner:HARRIS INTPROP LP
Method and system for conducting secure payments over a computer network
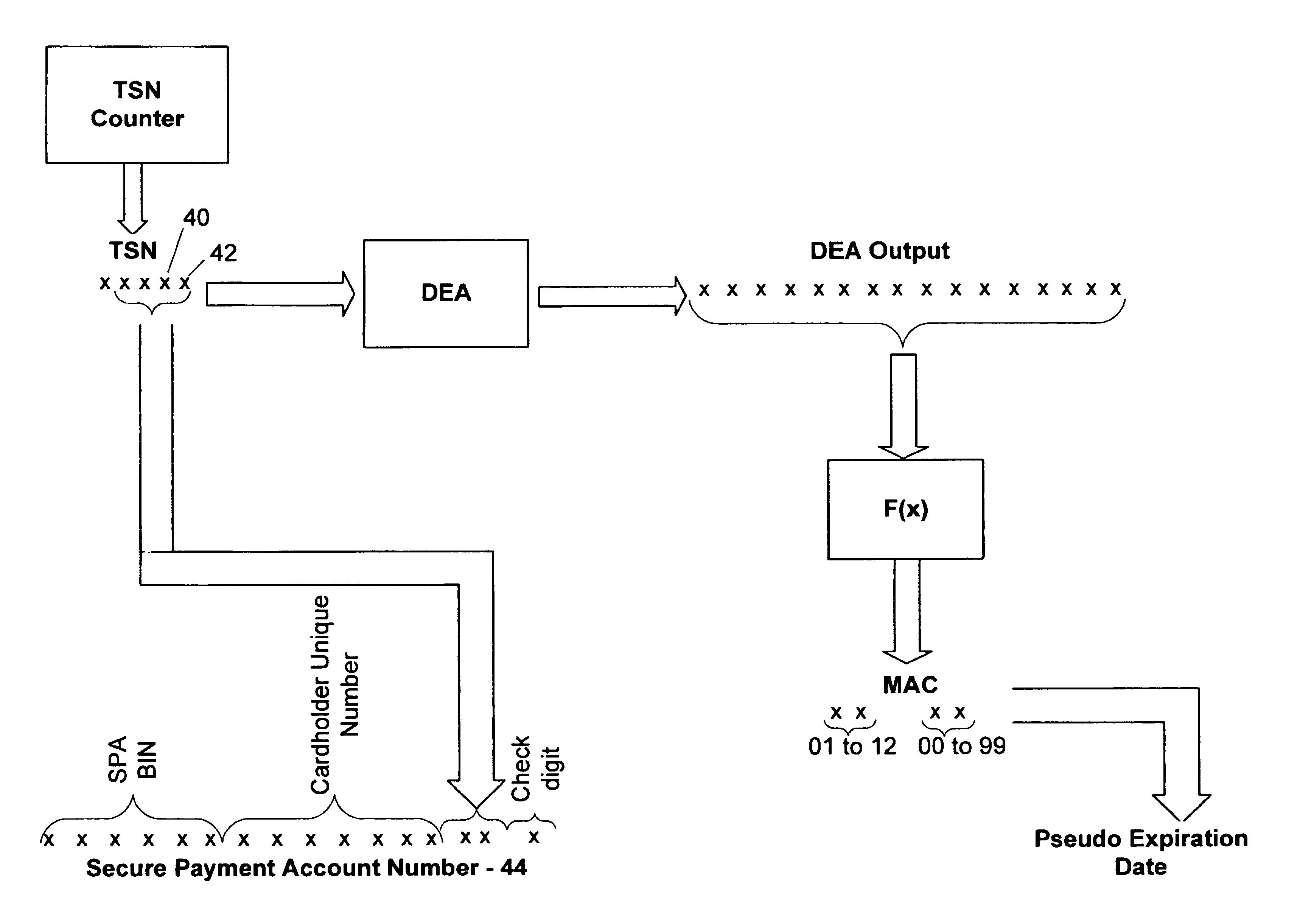
A secure method of conducting an electronic transaction over a public communications network is provided which utilizes a pseudo-expiration date in the expiration date field of an authorization request. One of the preferred methods comprises:generating a per-card key associated with an account number;generating a message authentication code using the per-card key;converting the message authentication code into a pseudo expiration date;generating an authorization request for the transaction, the request having an expiration date field containing the pseudo expiration date; andverifying the message authentication code based on the pseudo expiration date.Another embodiment of the invention includes a method of conducting an electronic transaction over a public communications network, with a payment account number having an associated pseudo account number, comprising:(a) providing the pseudo account number with a control field indicating one of a plurality of key-generation processes to be used to generate an authentication key;(b) generating an authentication key associated with the pseudo account number using one of the plurality of key-generation processes indicated in the control field of the pseudo account number;(c) using the authentication key to generate a message authentication code specific to the transaction;(d) generating an authorization request message including the message authentication code and the pseudo account number; and(e) verifying the message authentication code using the indicated key-generation process and the authentication key.
Owner:MASTERCARD INT INC
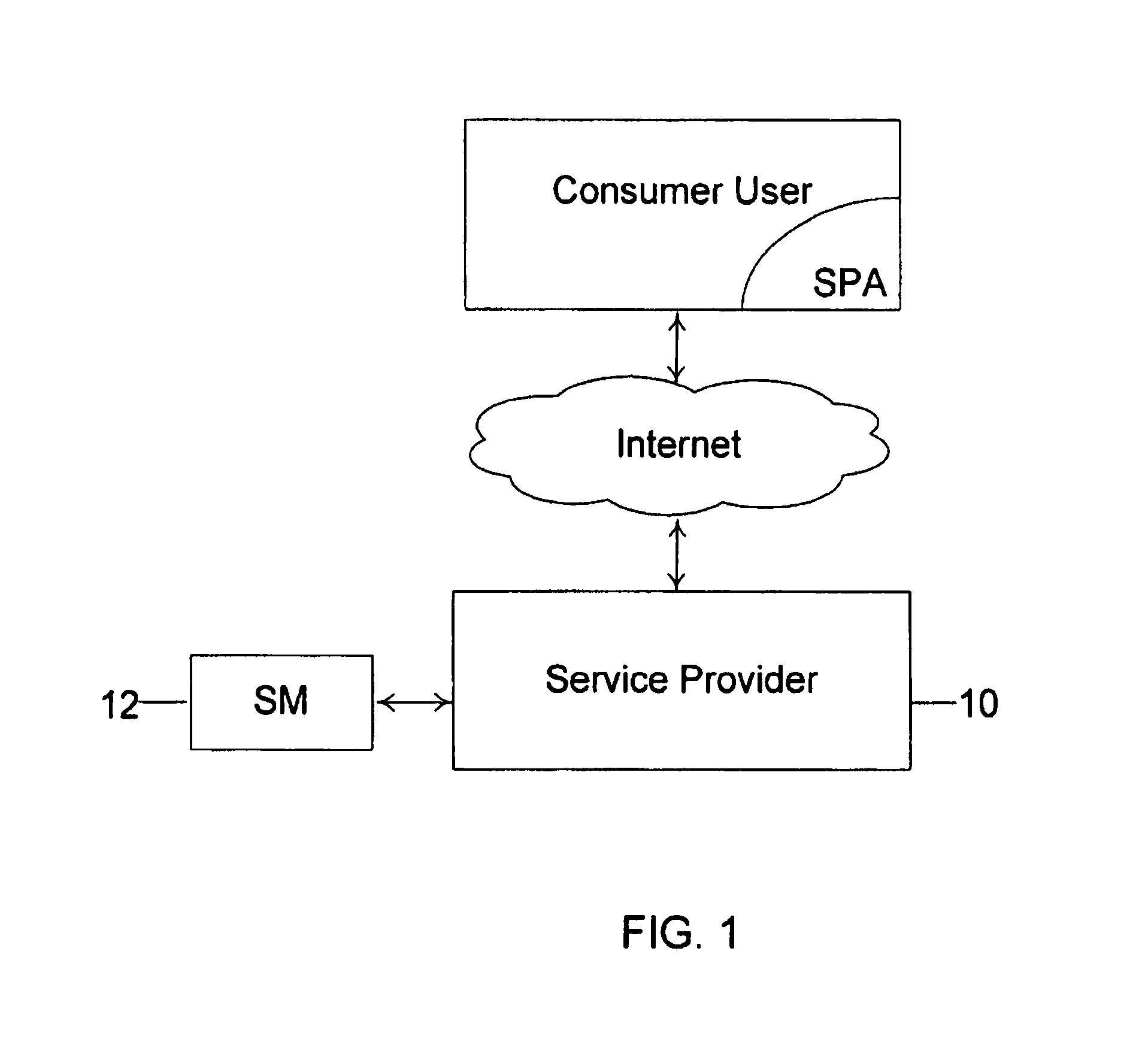
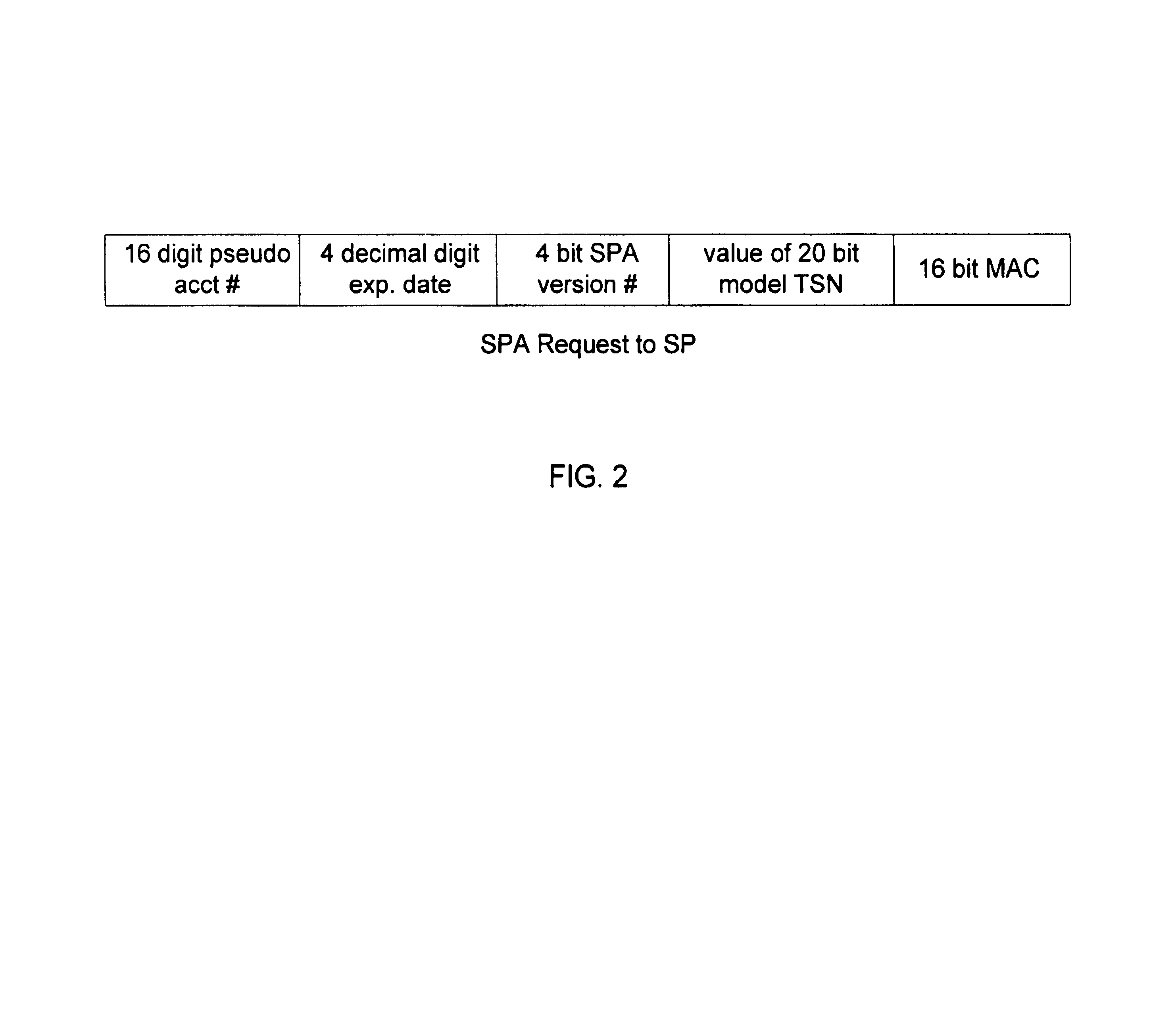
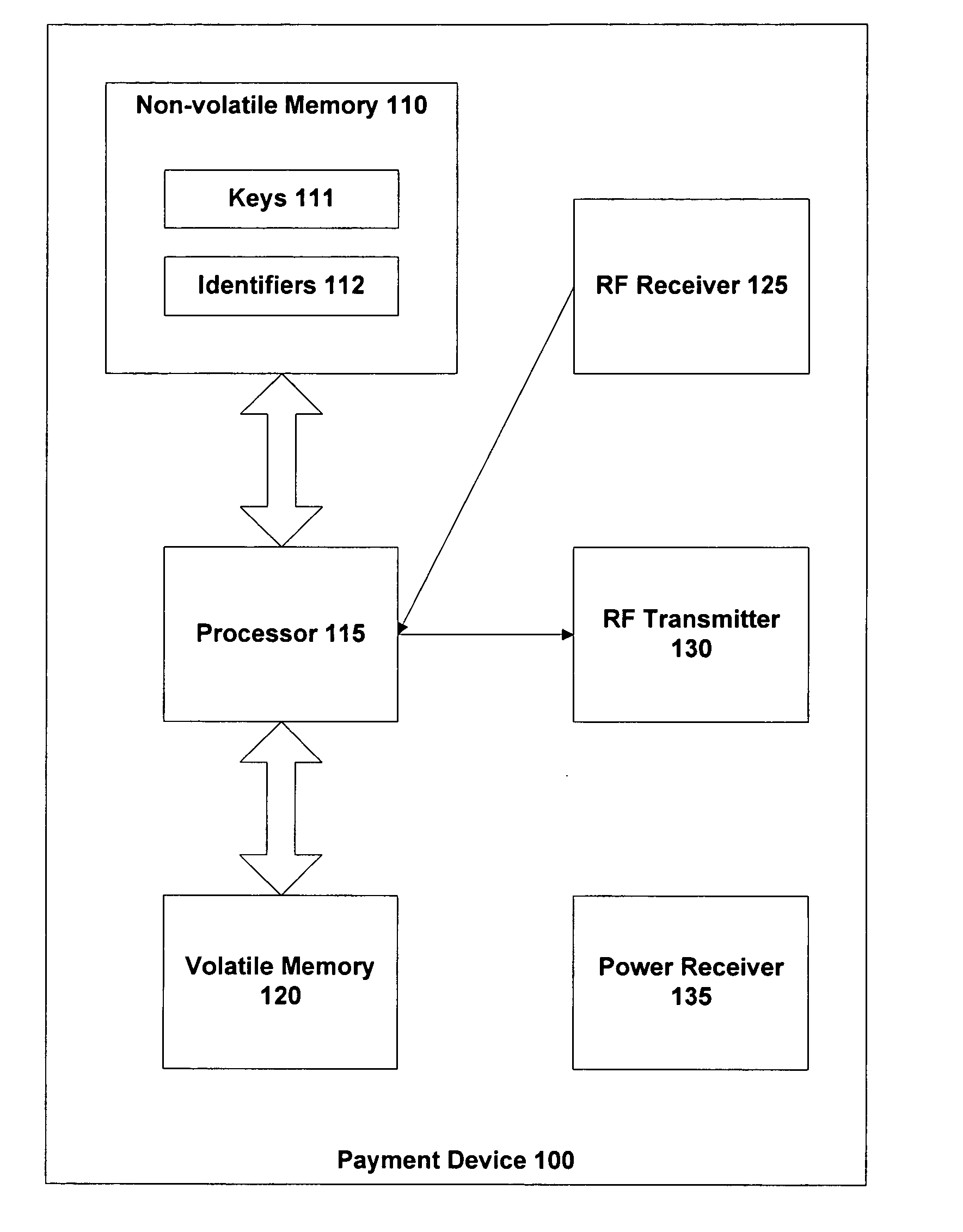
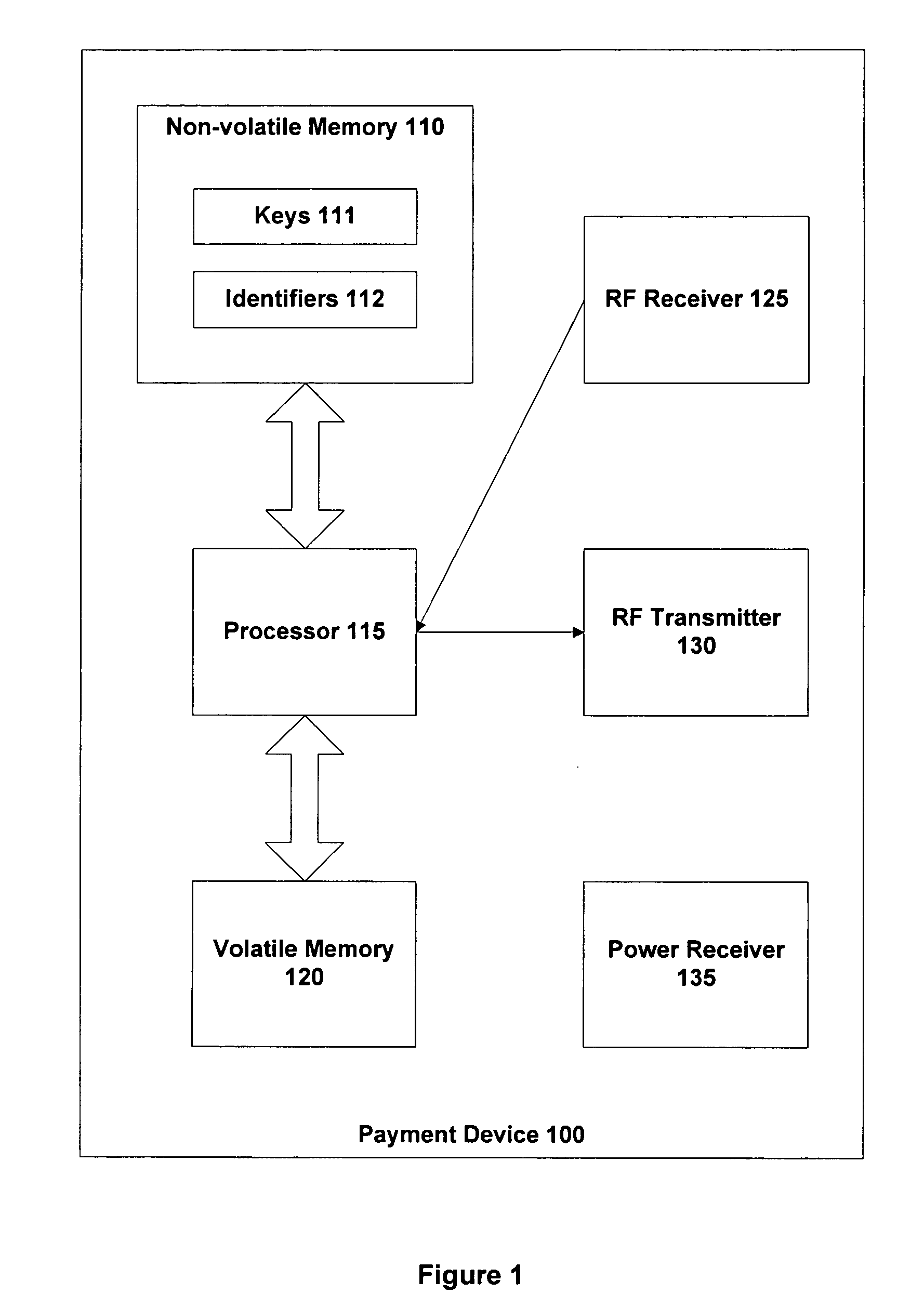
Method and apparatus having multiple identifiers for use in making transactions
ActiveUS20050055316A1Streamlined transaction procedureMaximum transaction rate can be limitedCredit schemesSecuring communicationPaymentFinancial transaction
A payment device is provided for use in transactions such as credit purchases at a retail store. The device includes a non-volatile memory containing a set of multiple identifiers that are associated with a customer account. The multiple identifiers are also known to an agency that provides the customer account. The device further includes a processor operable to select one identifier out of the set of multiple identifiers for use with any particular transaction involving the device and the customer account. This identifier is then conveyed from the device, typically via a store terminal, to the agency that maintains the account.
Owner:ORACLE INT CORP
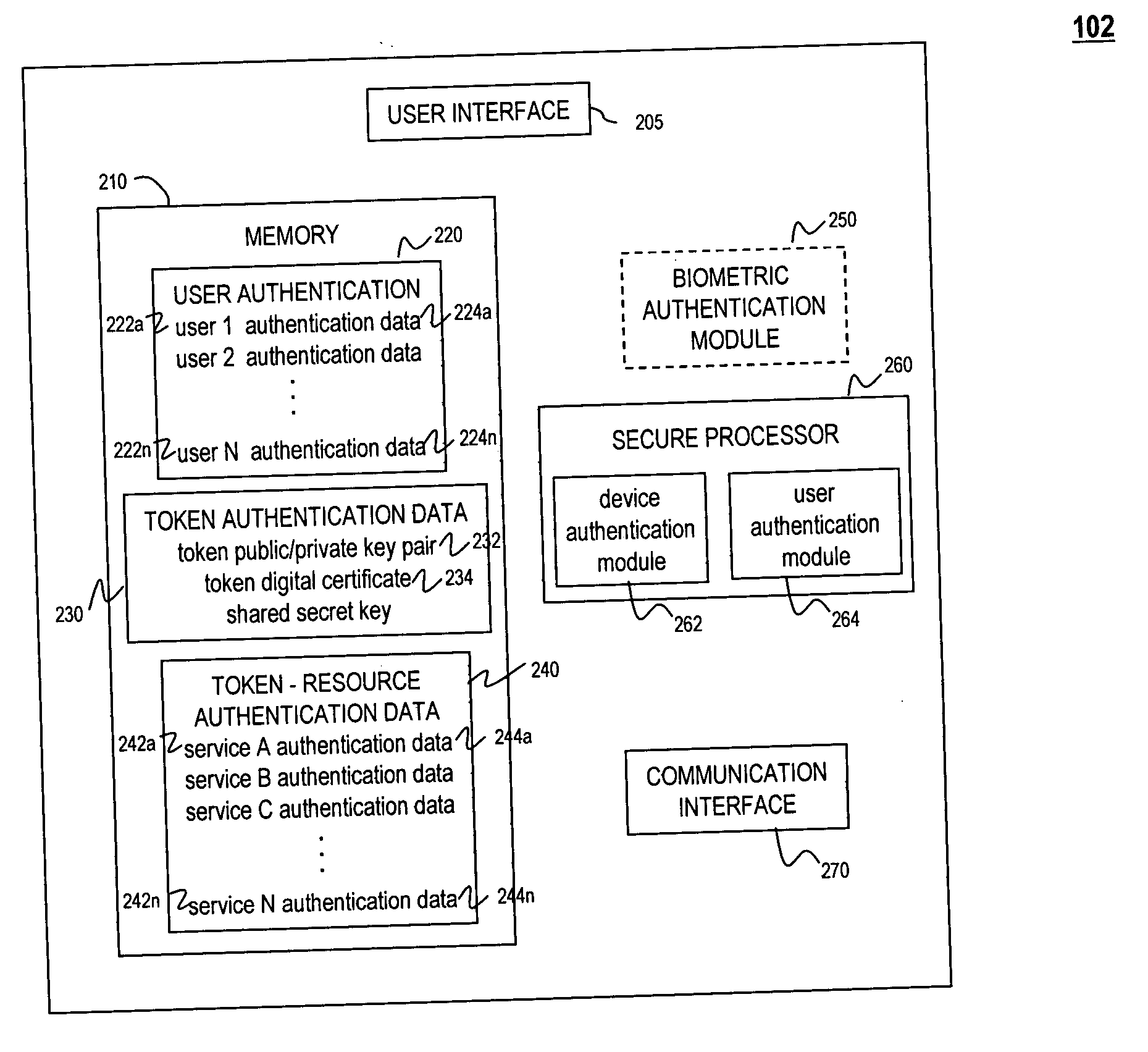
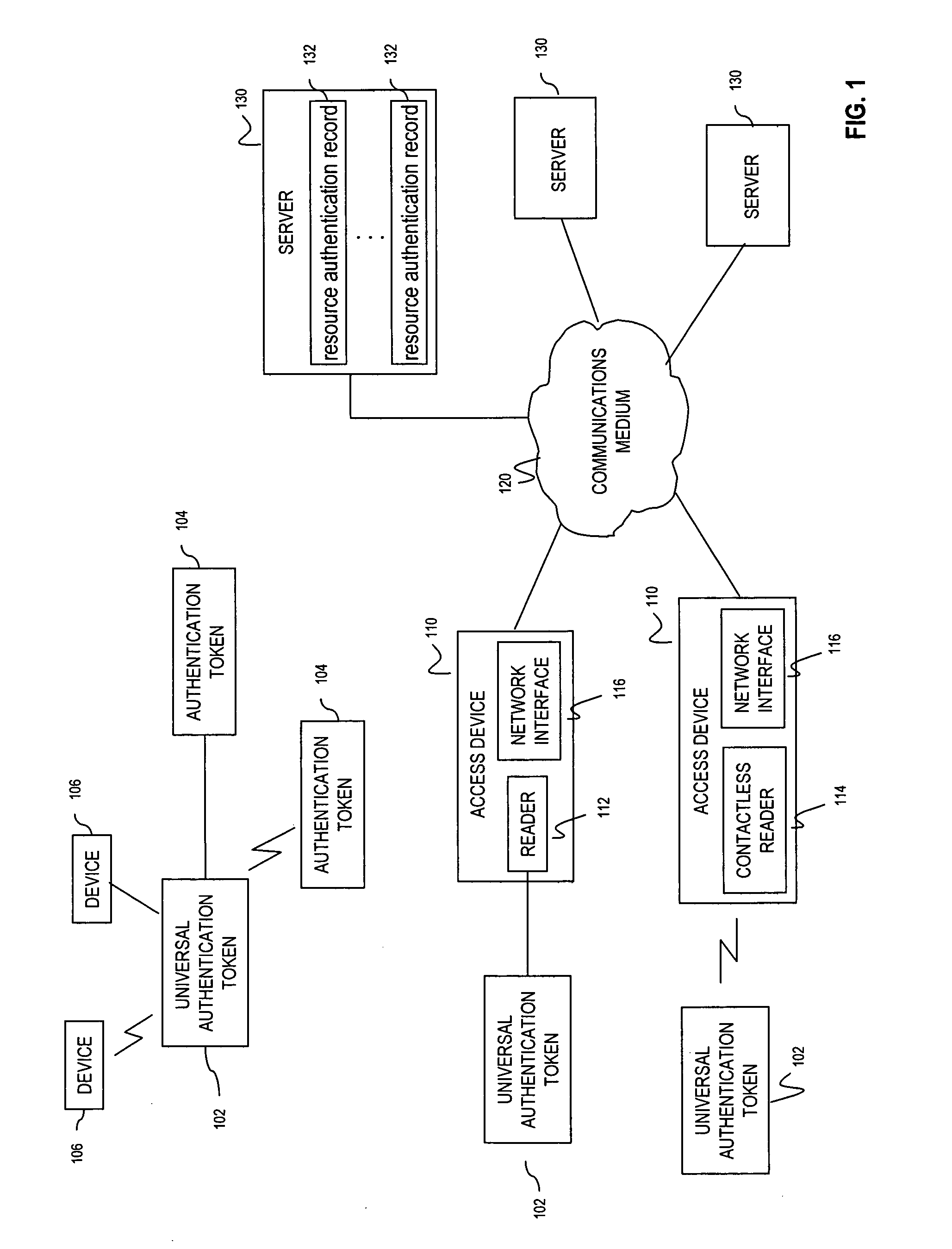
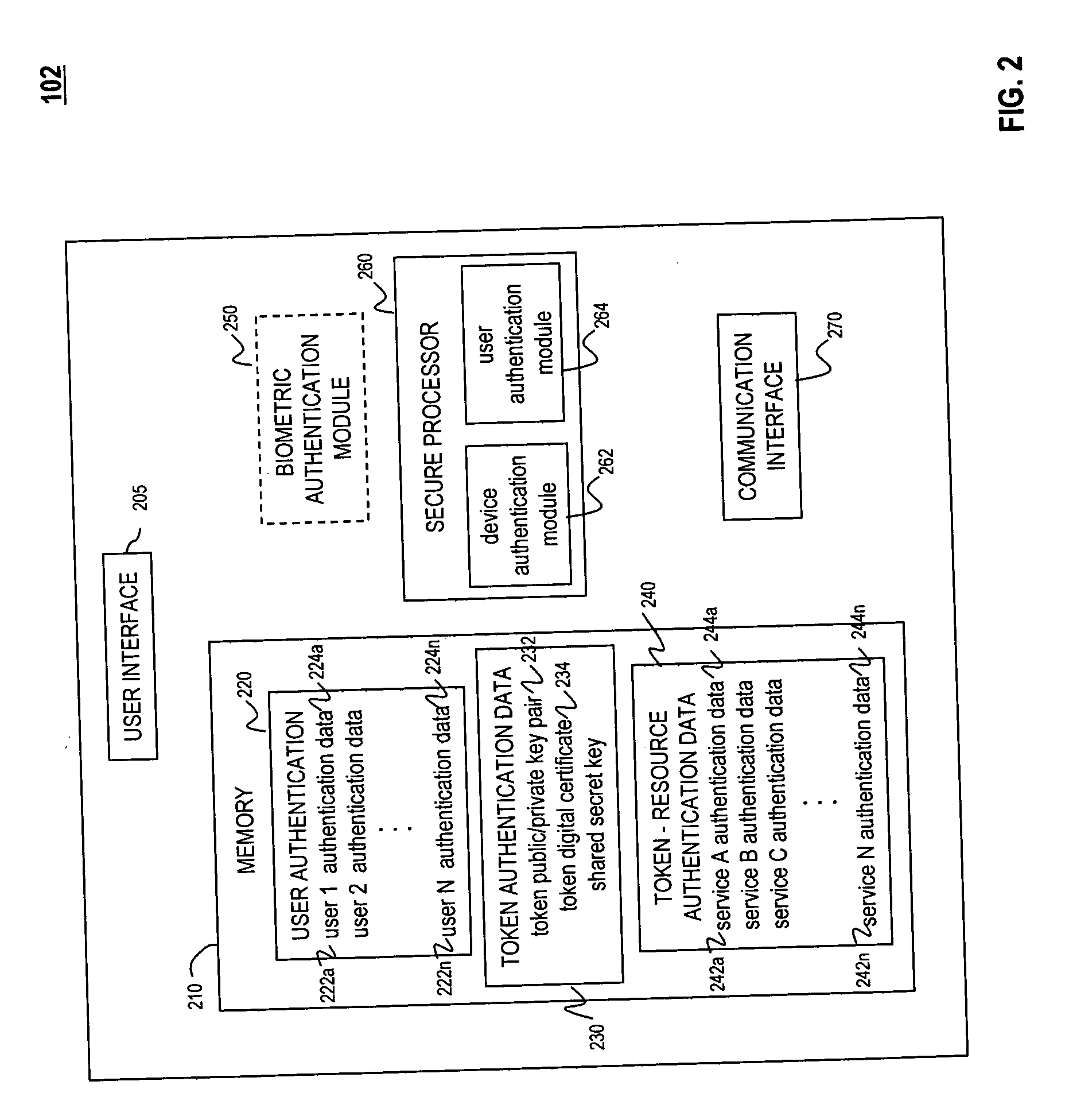
Universal authentication token
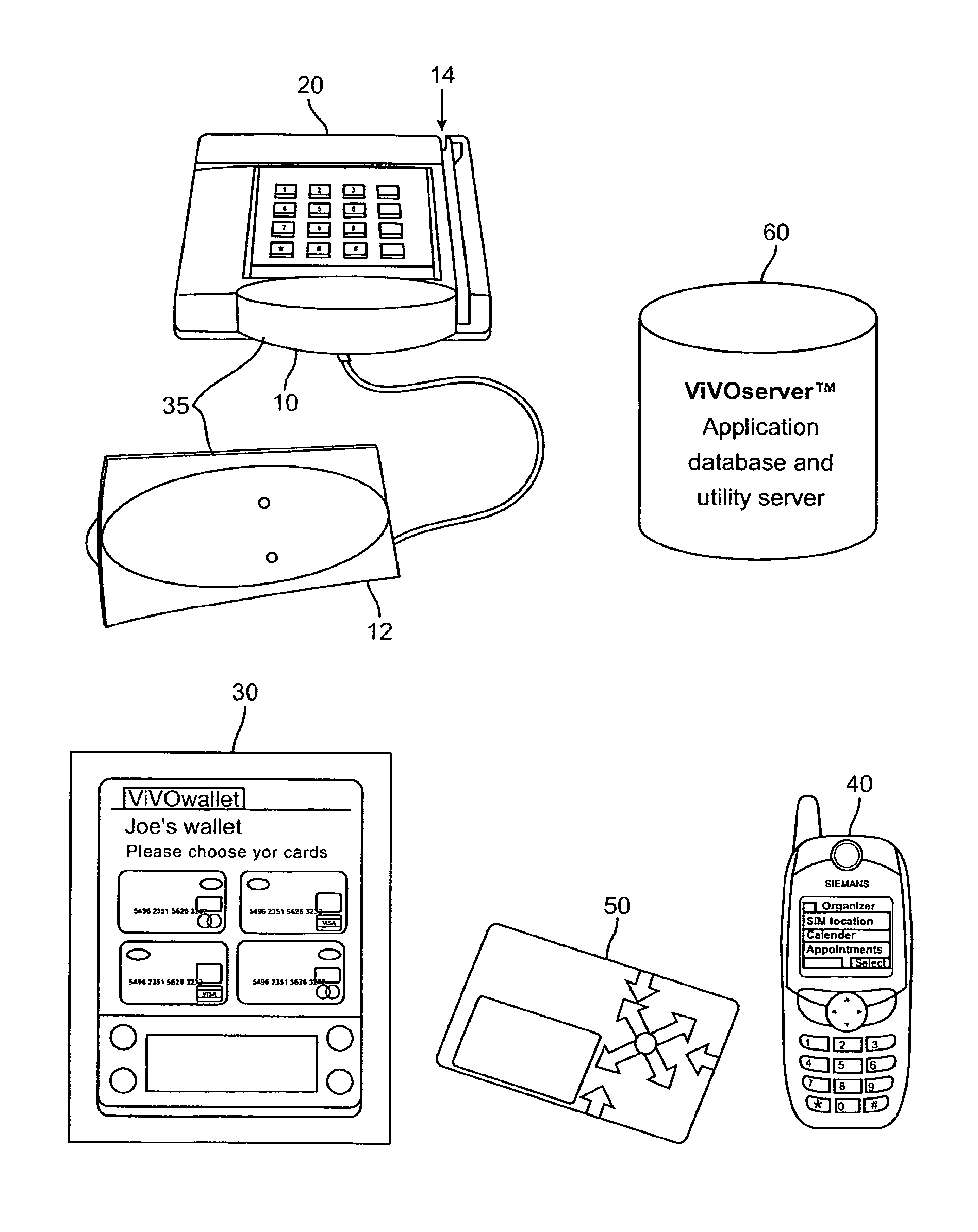
ActiveUS20070118891A1Key distribution for secure communicationDigital data processing detailsComputer scienceUser interface
A universal authentication token is configured to securely acquire security credentials from other authentication tokens and / or devices. In this manner, a single universal authentication token can store the authentication credentials required to access a variety of resources, services and applications for a user. The universal authentication token includes a user interface, memory for storing a plurality of authentication records for a user, and a secure processor. The secure processor provides the required cryptographic operations to encrypt, decrypt, and / or authenticate data that is sent or received by universal token. For example, secure processor may be used to generate authentication data from seed information stored in memory.
Owner:NXP BV
Mobile phone as a point of sale (POS) device
InactiveUS20070106564A1Easy accessAcutation objectsAccounting/billing servicesMobile deviceComputer science
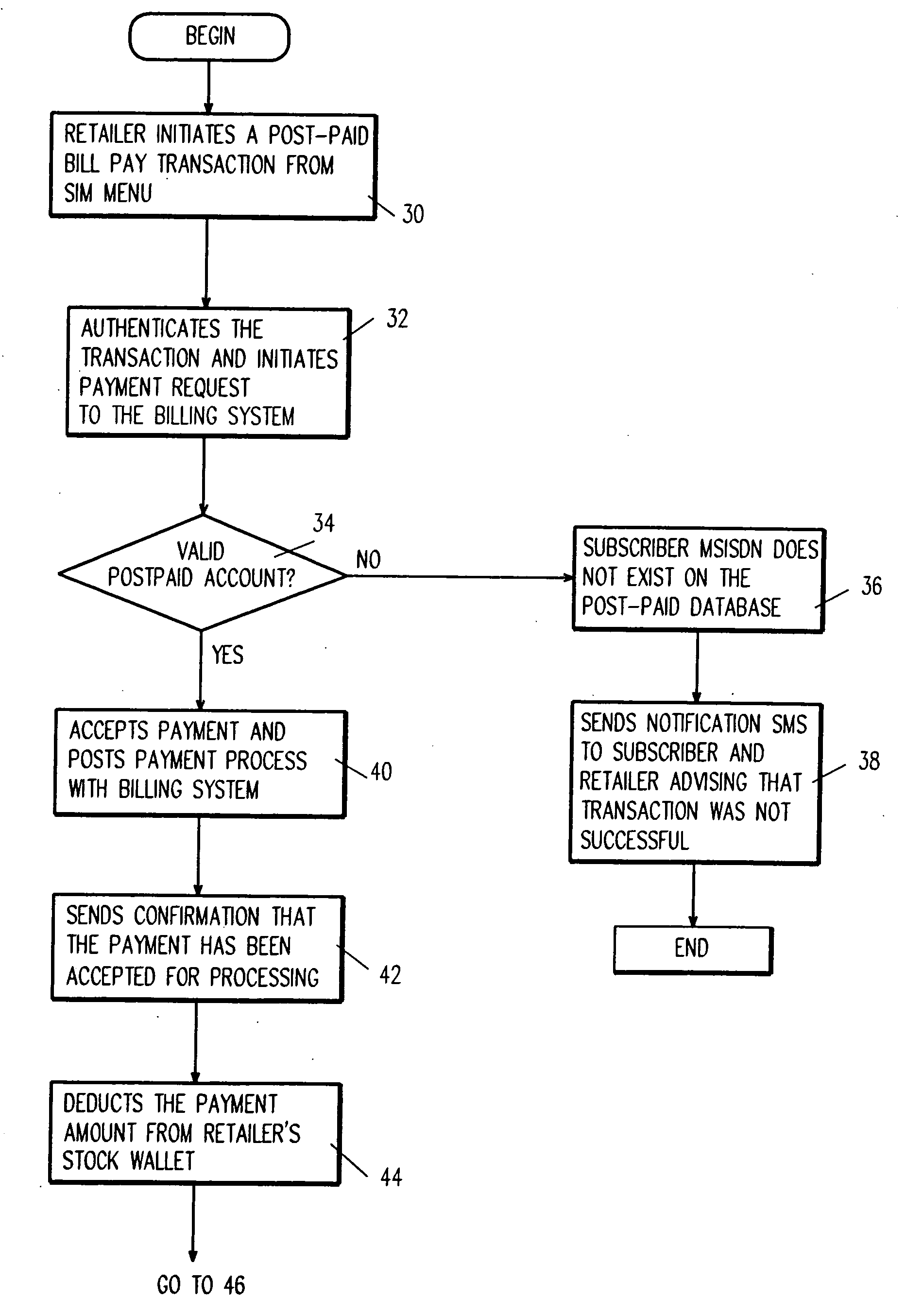
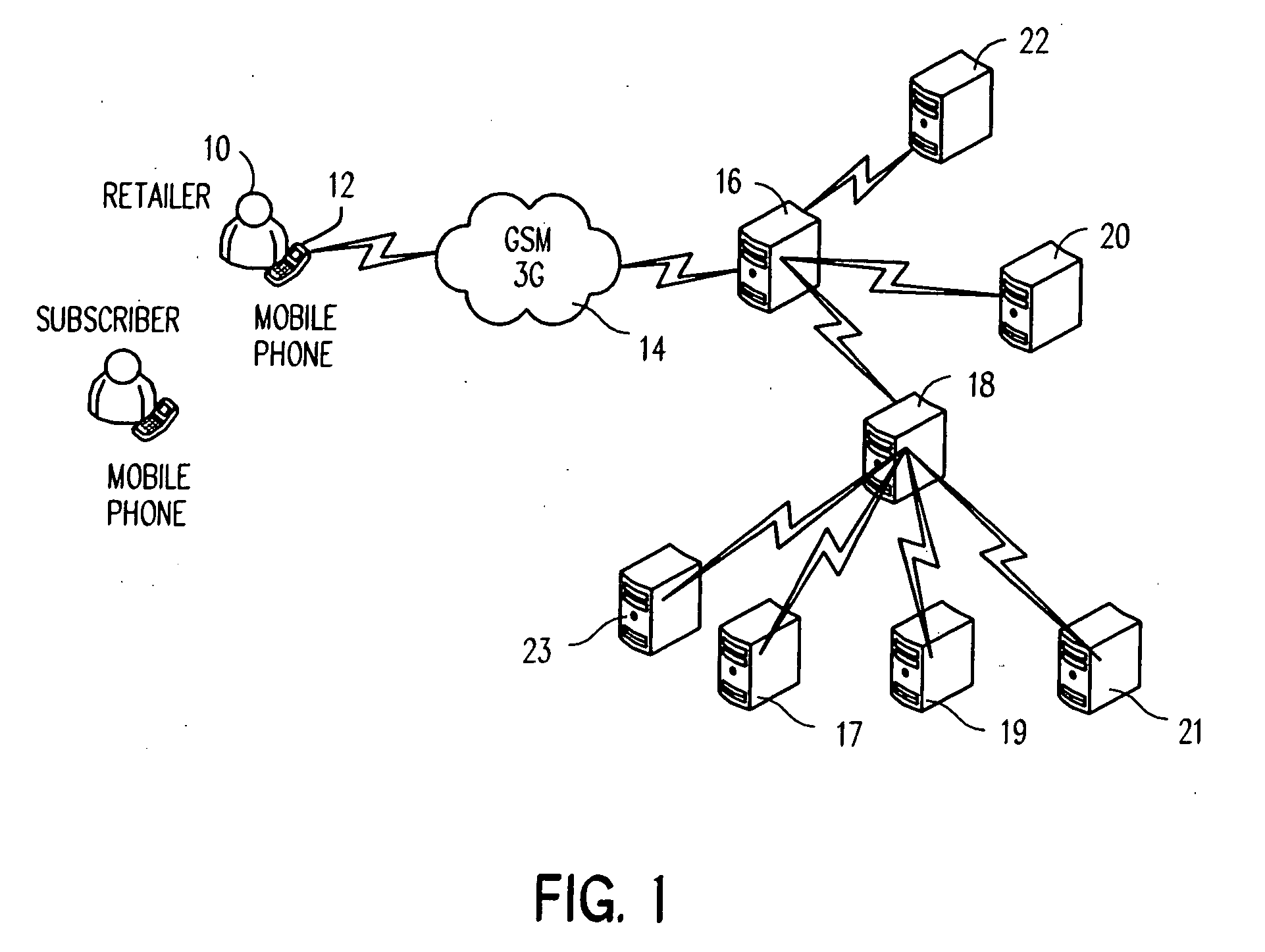
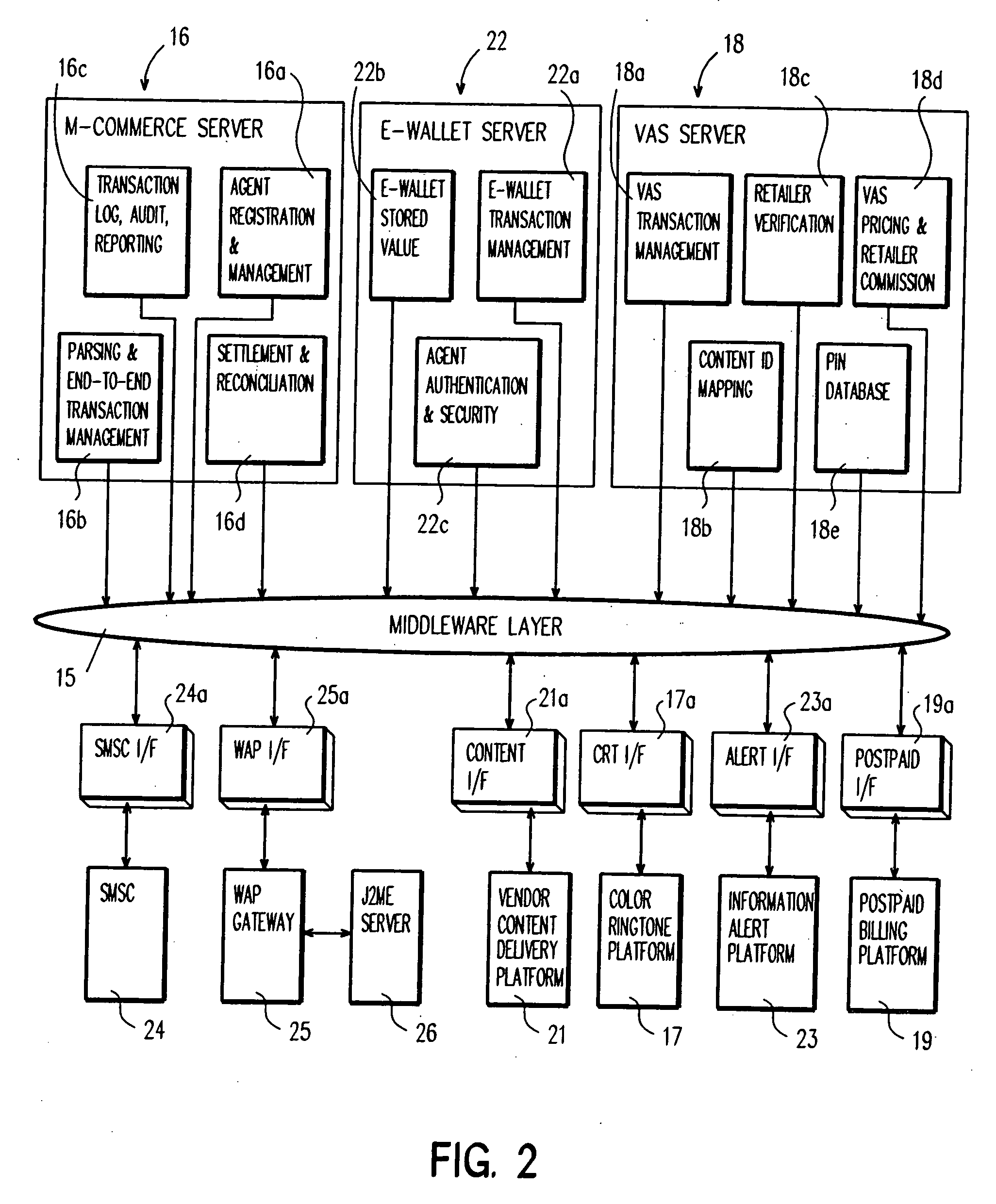
A system and method for provisioning one or more value added services to a postpaid / prepaid mobile account and / or a postpaid / prepaid mobile device using a wireless communication device as a point-of-sale device, is disclosed.
Owner:SHANGHAI RES INST OF PETROCHEMICAL TECH SINOPEC +1
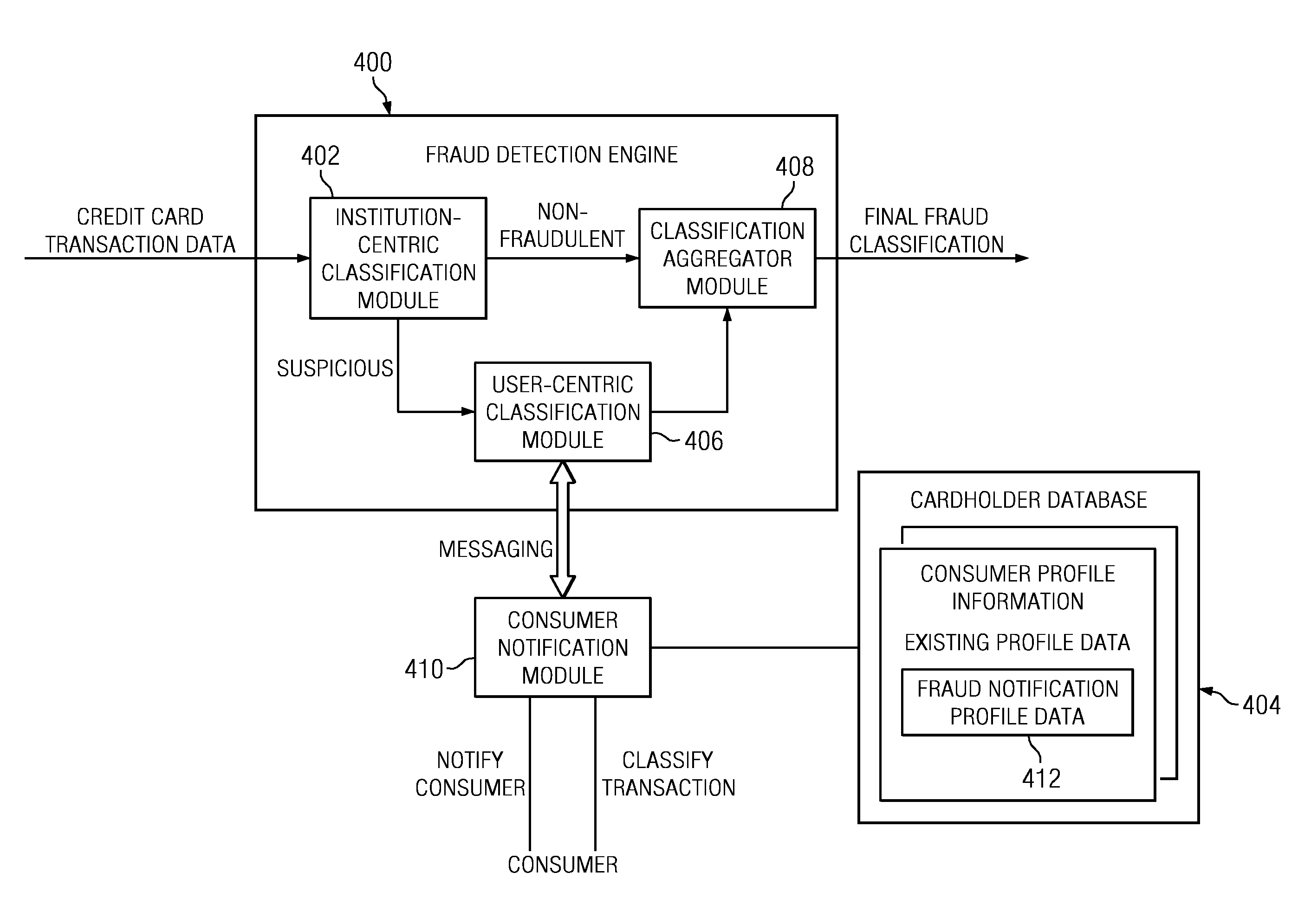
Method and System for Identification By A Cardholder of Credit Card Fraud
A method for fraud detection leverages an existing financial institution's fraud classification functionality, which produces a first level detection, with a “user-centric” classification functionality, which produces a “second” or more fine-grained detection regarding a potentially fraudulent transaction. After passing through an existing (“institution-centric”) fraud detection technique, a transaction that has been identified as potentially fraudulent is then subject to further analysis and classification at the “user” level, as it is the user is presumed to be the best source of knowledge of the legitimate credit card use. Information about the transaction is shared with the consumer, preferably via one or more near real-time mechanisms, such as SMS, email, or the like. Based on the user's response (or lack thereof, as the case may be), one or more business rules in the institution's fraud detection system can then take an appropriate action (e.g., no action, reverse the transaction if complete, deny the transaction if in-progress, or the like).
Owner:IBM CORP
Dynamic credit card with magnetic stripe and embedded encoder and methods for using the same to provide a copy-proof credit card
A dynamic credit card is provided in which a secure credit card number (e.g., a secret / hidden credit card number) is encoded based on a timing signal (e.g., an internal counter) to provide a dynamic credit card number. This dynamic number may be displayed to a user via a display (e.g., so that online purchases can be made) or written onto a magnetic stripe such that the number may be processed by traditional credit card merchants (e.g., swiped). At a remote facility, the dynamic number may be decoded based on time (and / or a counter / key number / equation) or the facility may have the secure number and perform the same function as the dynamic credit card (e.g., encode using time data as a parameter to the encoding equation) and compare the resultant dynamic number to the dynamic number received. Thus, a dynamic credit card number may change continually or periodically (e.g., every sixty seconds) such that credit card numbers may not be copied by thieves and used at later times. A dynamic verification code may be utilized in addition to, or in lieu of, a dynamic credit card number.
Owner:MULLEN JEFFREY D
Popular searches
Advertisements User identity/authority verification Analogue secracy/subscription systems Color television details Internal/peripheral component protection Digital data authentication Two-way working systems Buying/selling/leasing transactions Program/content distribution protection Selective content distribution
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com