Patents
Literature
495 results about "Trusted third party" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
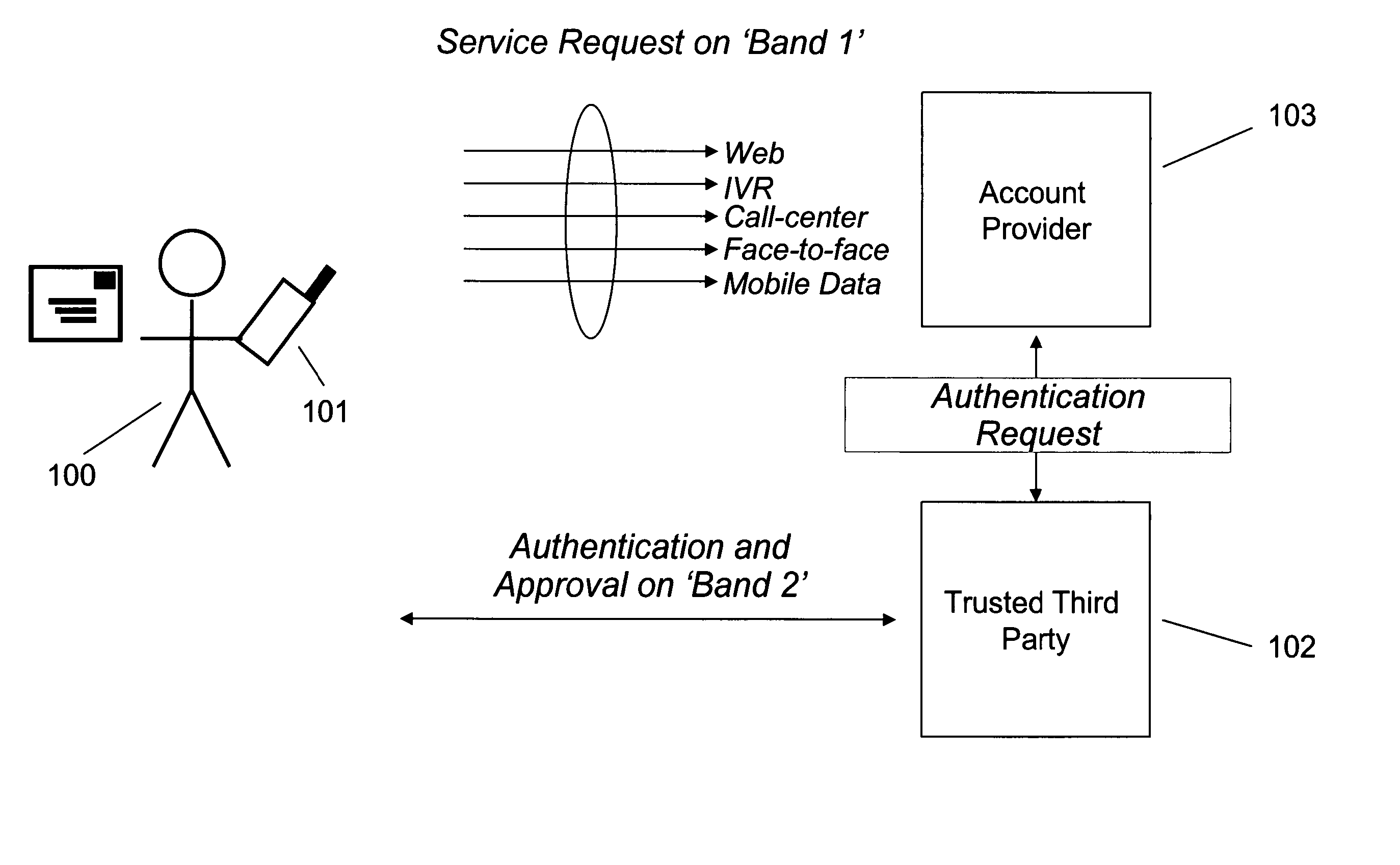
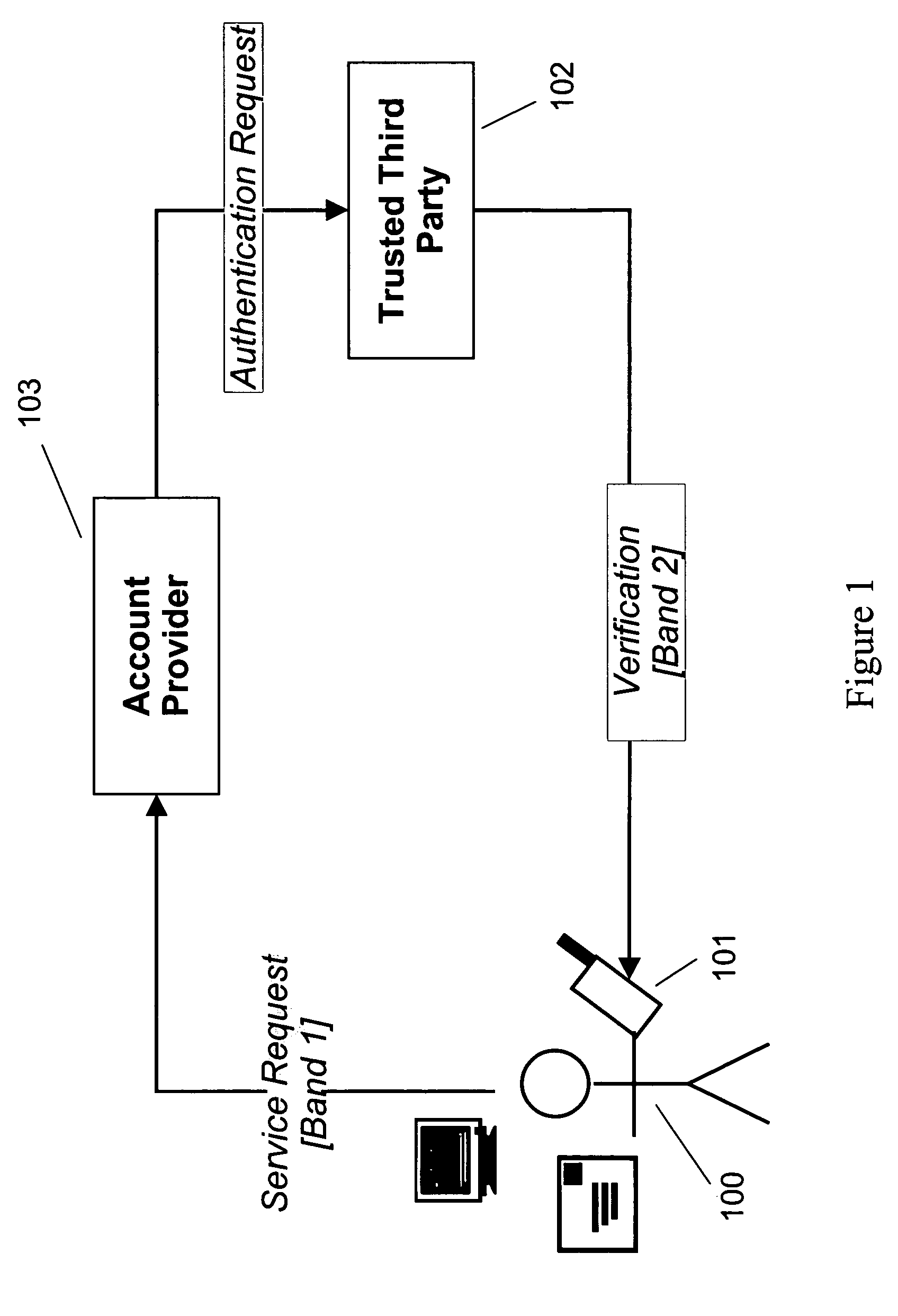
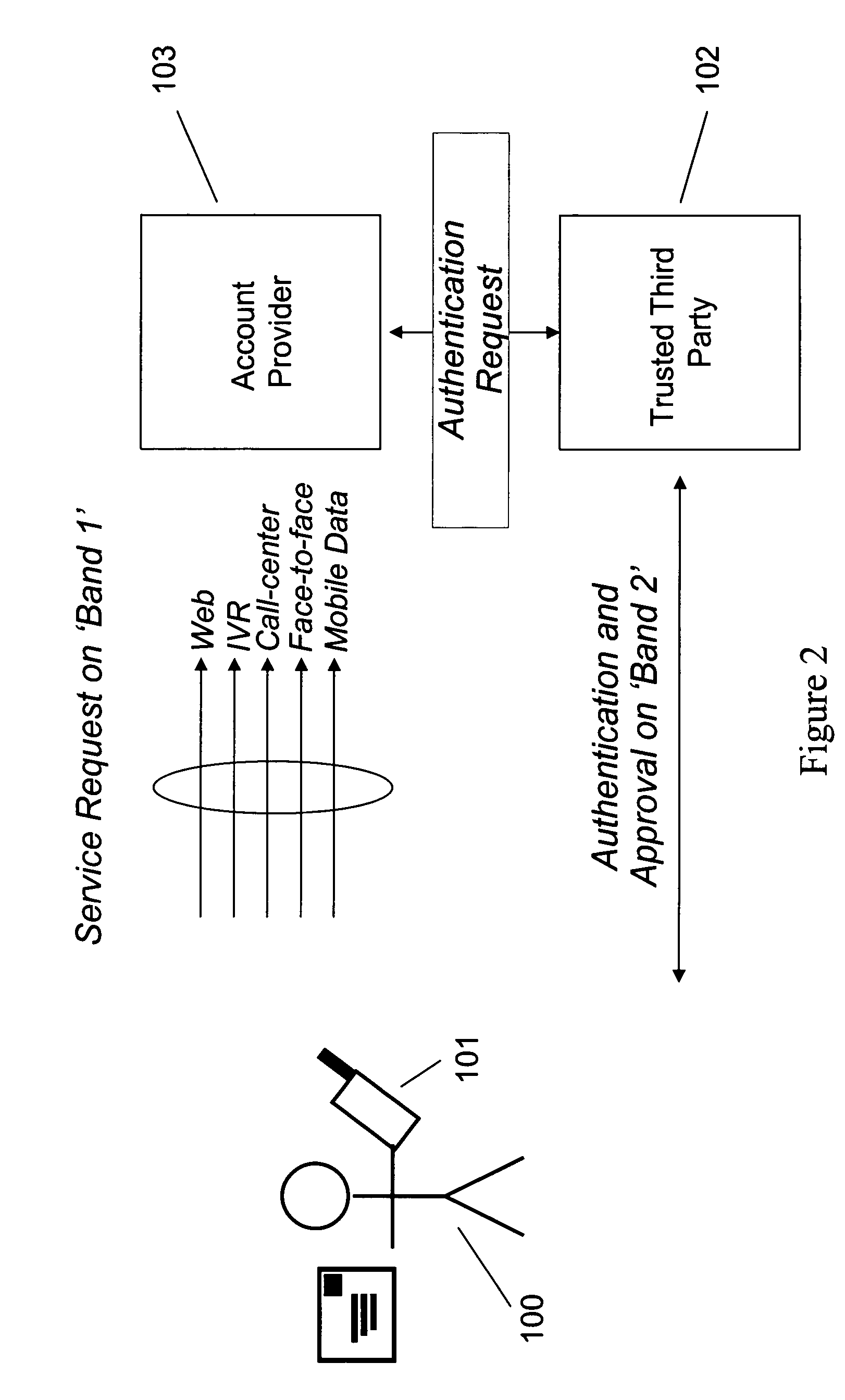
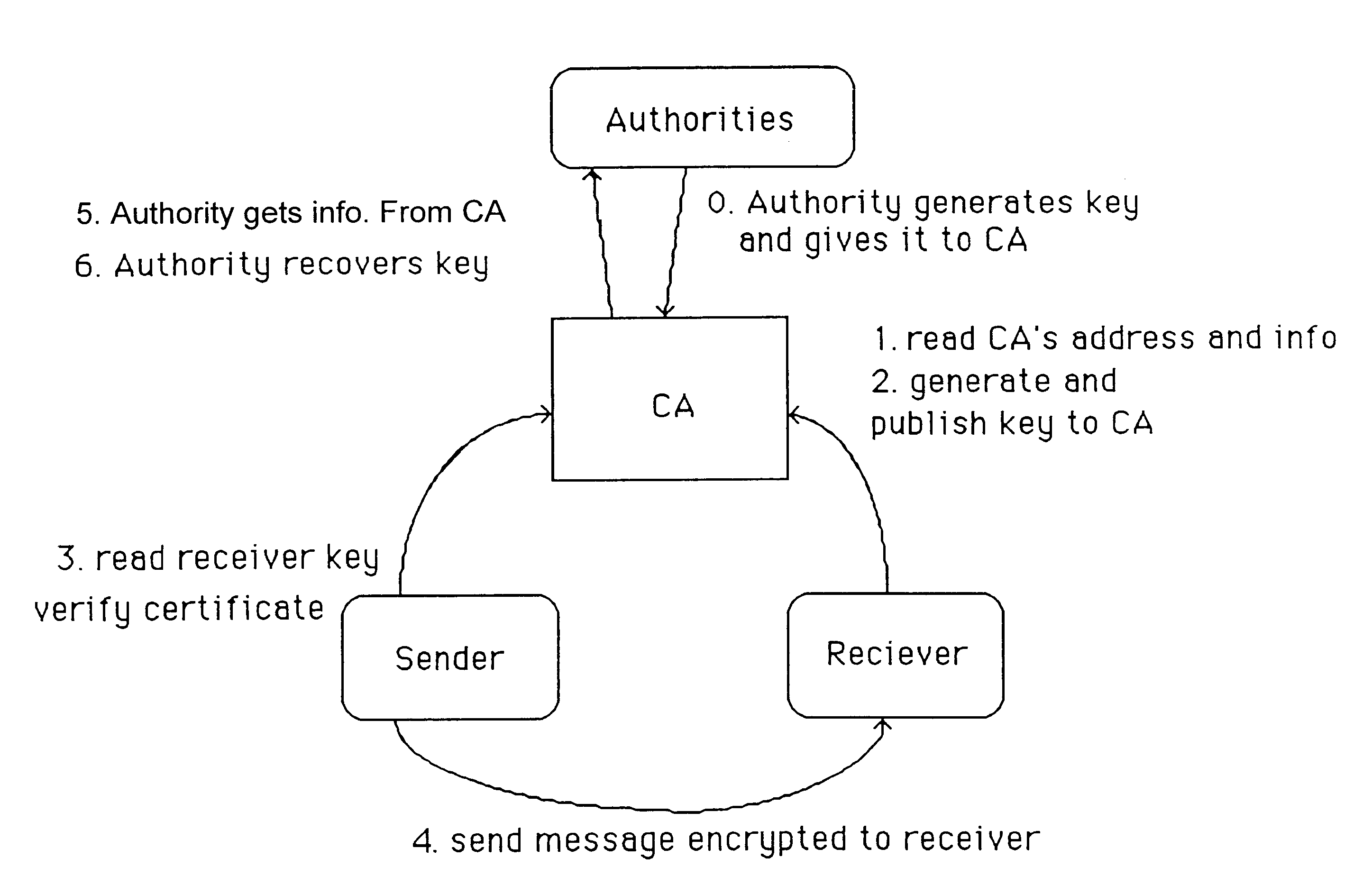
In cryptography, a trusted third party (TTP) is an entity which facilitates interactions between two parties who both trust the third party; the Third Party reviews all critical transaction communications between the parties, based on the ease of creating fraudulent digital content. In TTP models, the relying parties use this trust to secure their own interactions. TTPs are common in any number of commercial transactions and in cryptographic digital transactions as well as cryptographic protocols, for example, a certificate authority (CA) would issue a digital identity certificate to one of the two parties in the next example. The CA then becomes the Trusted-Third-Party to that certificates issuance. Likewise transactions that need a third party recordation would also need a third-party repository service of some kind or another.
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
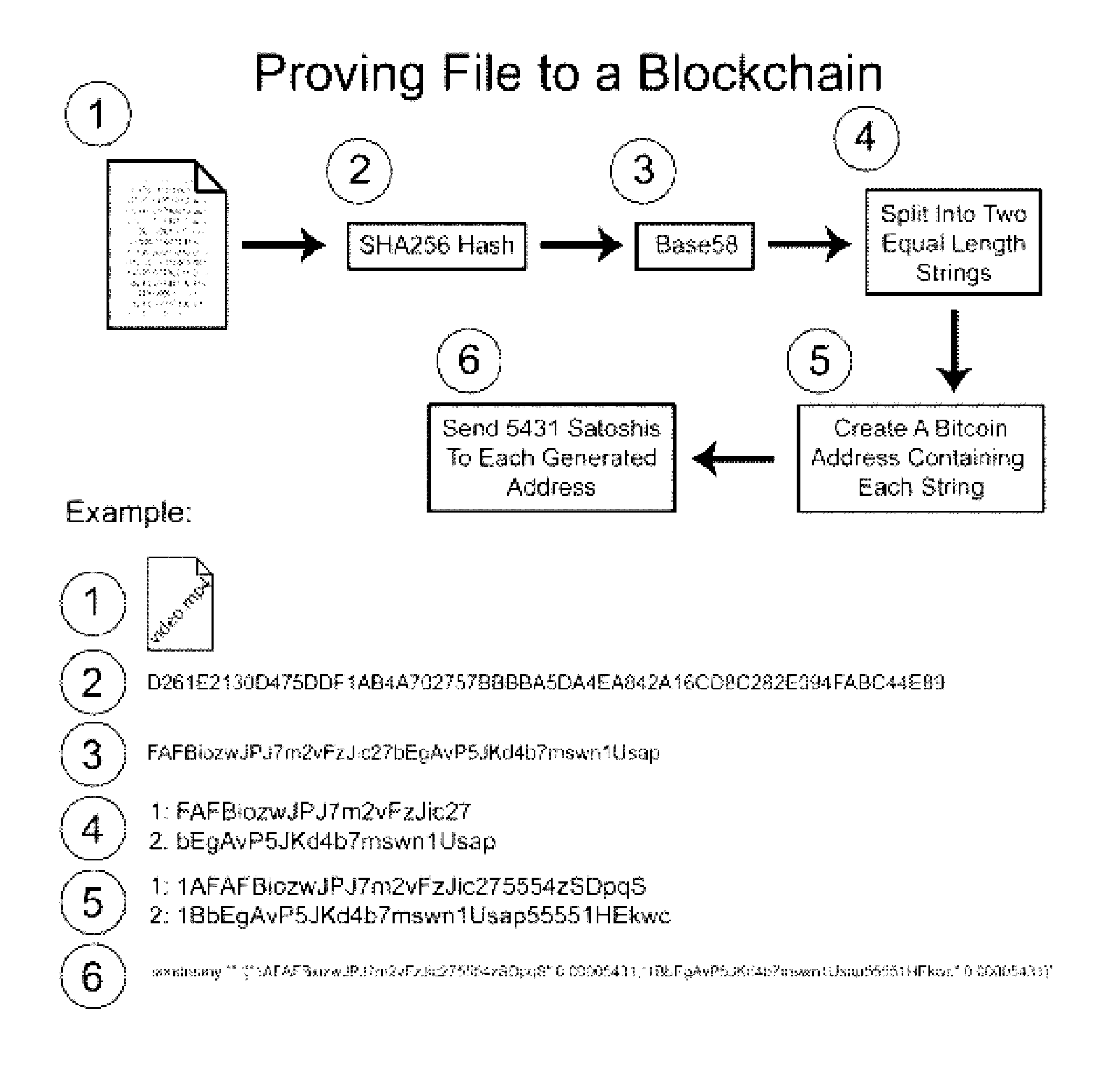
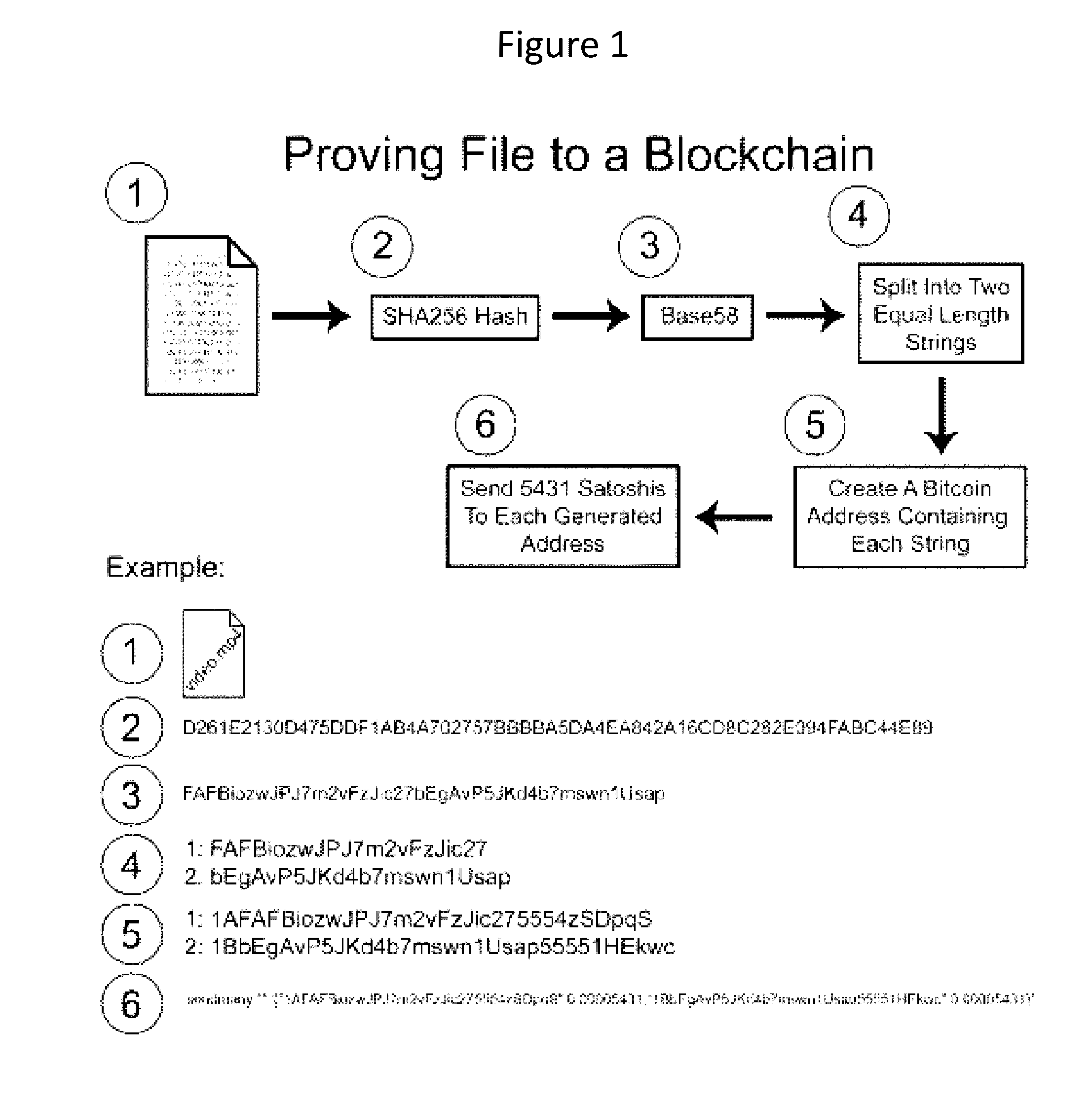
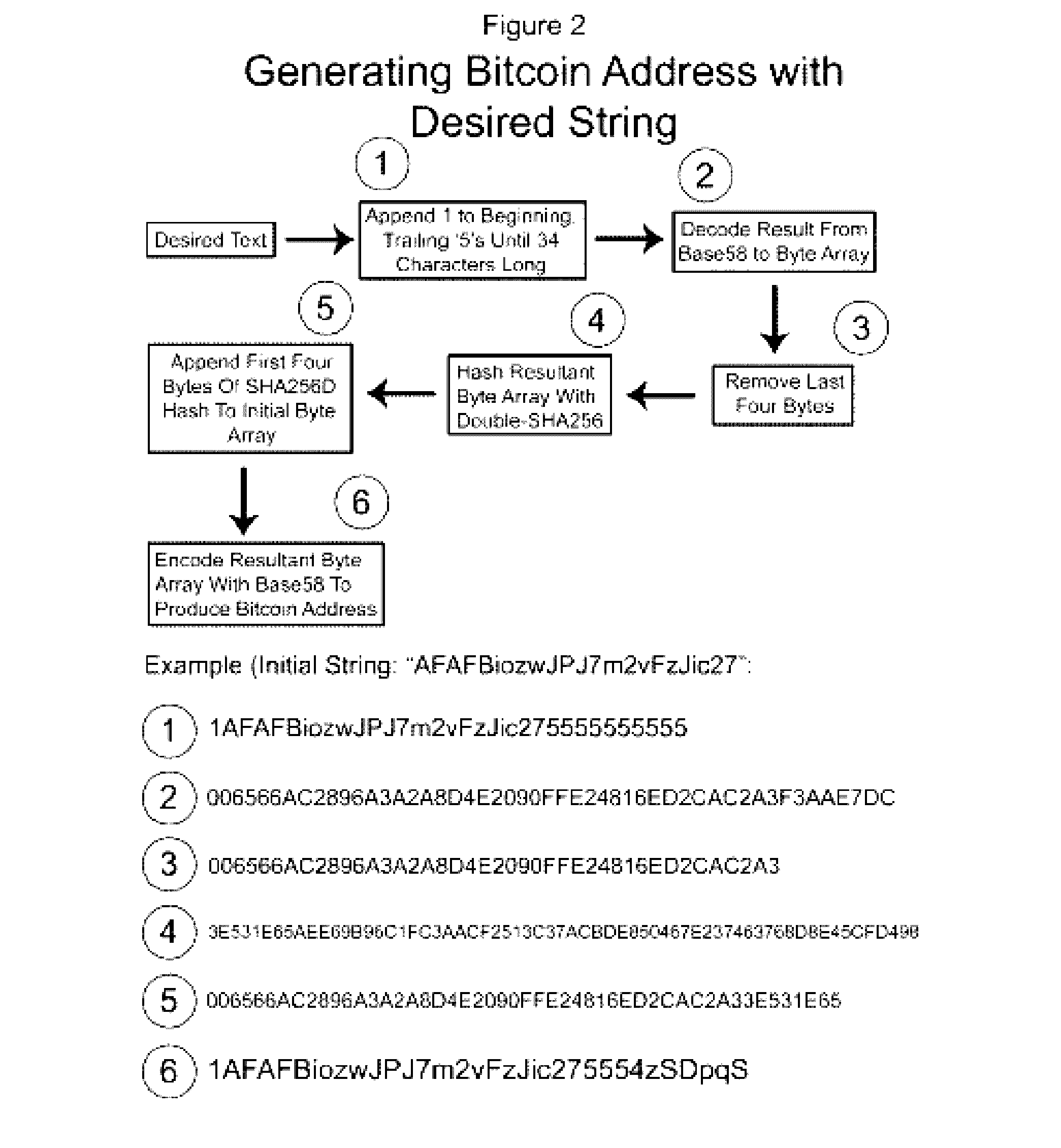
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
Persistent dynamic payment service
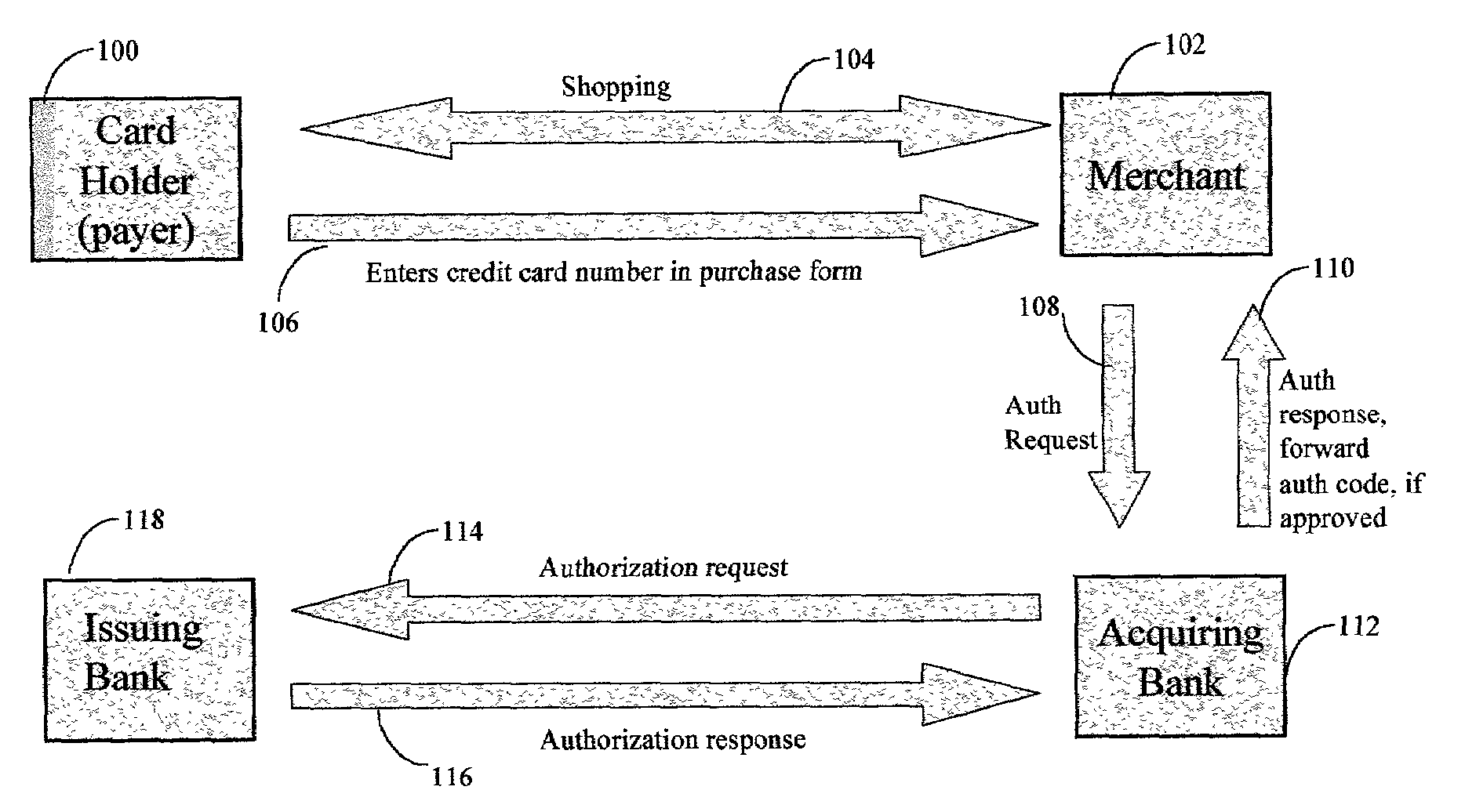
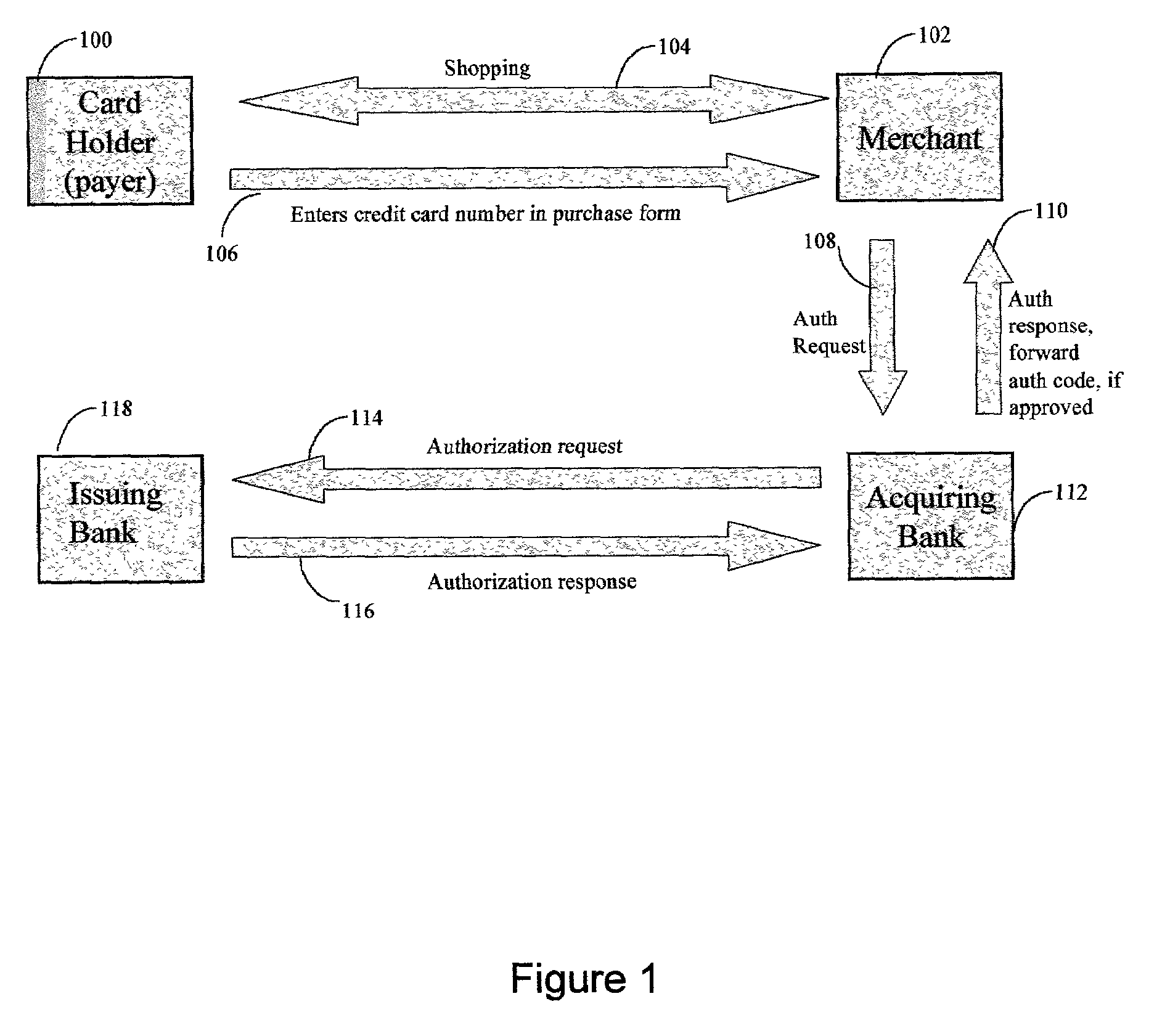
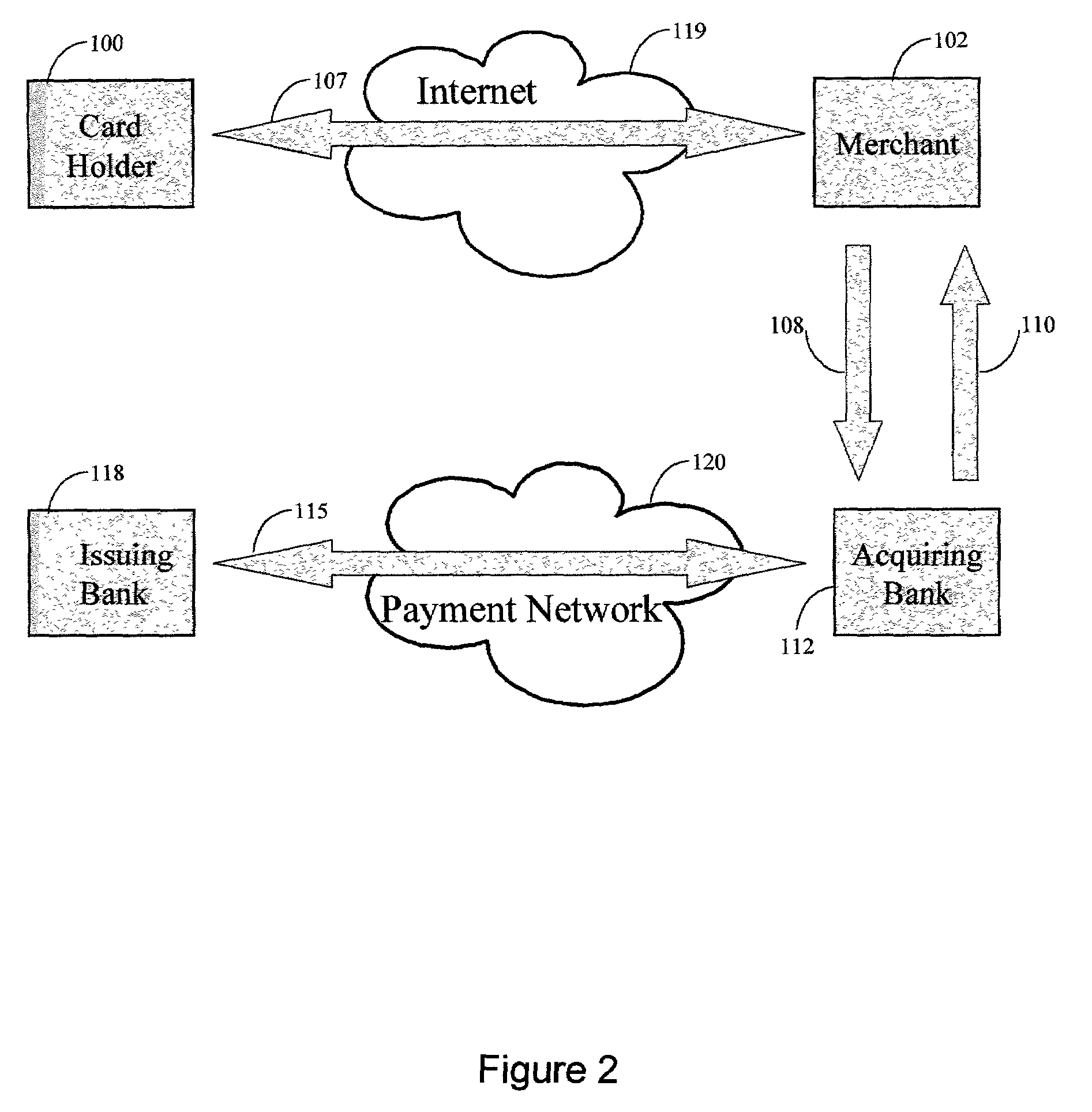
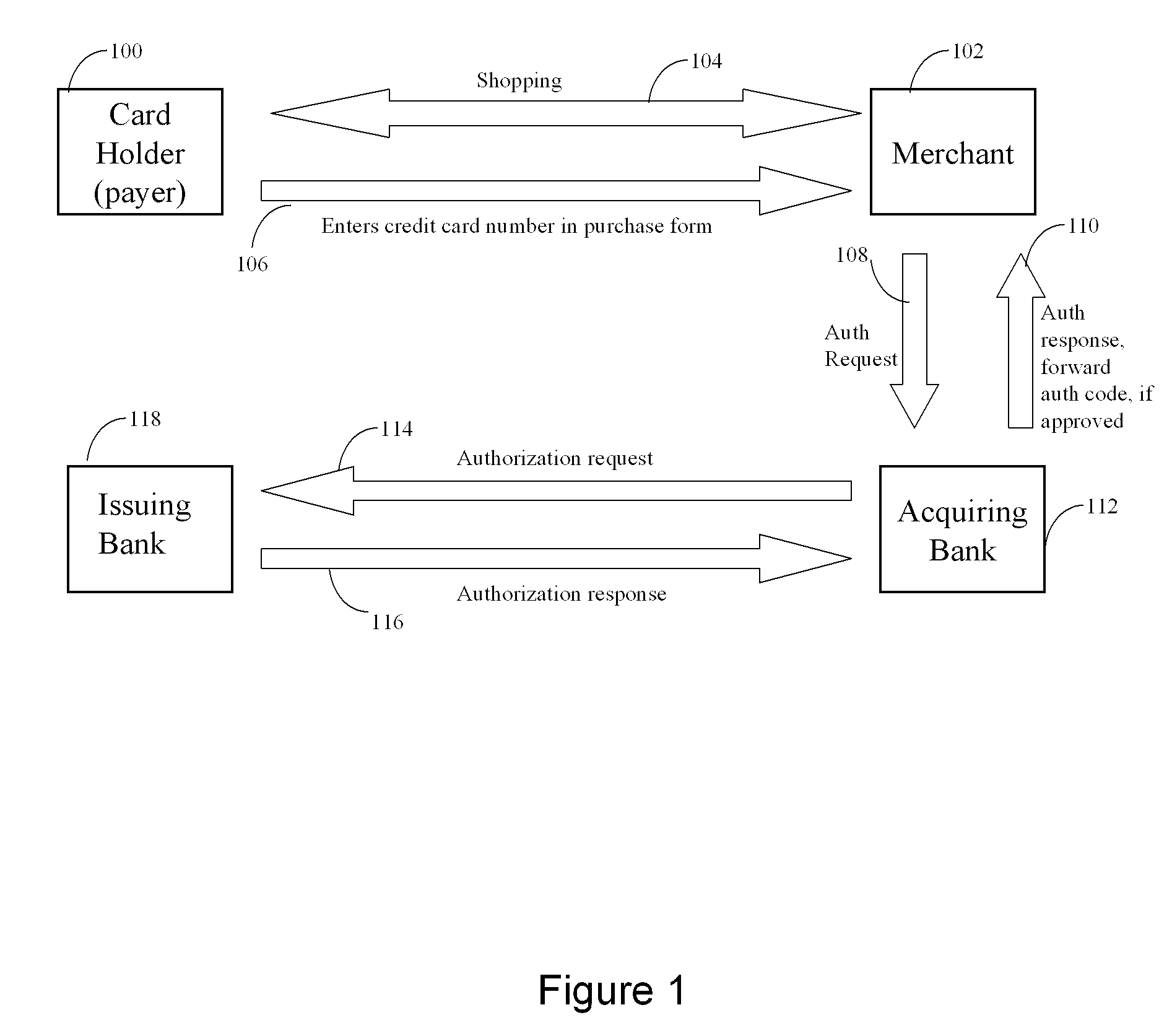
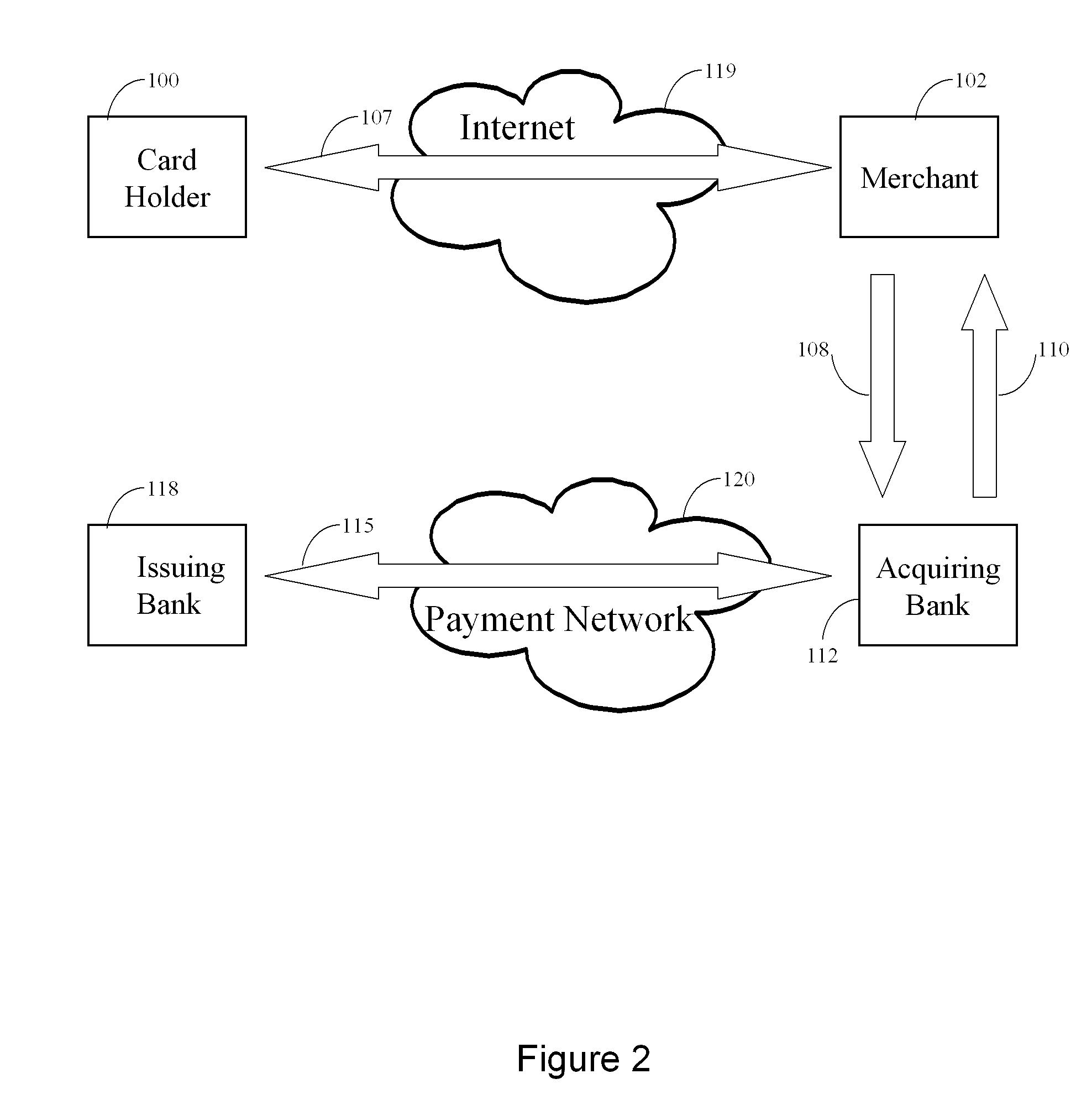
The invention comprises online methods, systems, and software for improving the processing of payments from financial accounts, particularly credit and debit card payments made from consumers to merchants in online transactions. The preferred embodiment of the invention involves inserting a trusted third party online service into the payment authorization process. The trusted third party authenticates the consumer and authorizes the proposed payment in a single integrated process conducted without the involvement of the merchant. The authentication of the consumer is accomplished over a persistent communication channel established with the consumer before a purchase is made. The authentication is done by verifying that the persistent channel is open when authorization is requested. Use of the third party services allows the consumer to avoid revealing his identity and credit card number to the merchant over a public network such as the Internet, while maintaining control of the transaction during the authorization process.
Owner:FISHER DOUGLAS C
Tokens Usable in Value-Based Transactions
InactiveUS20080243702A1Maintaining anonymitySufficient informationUser identity/authority verificationPayment architectureThird partyInternet privacy
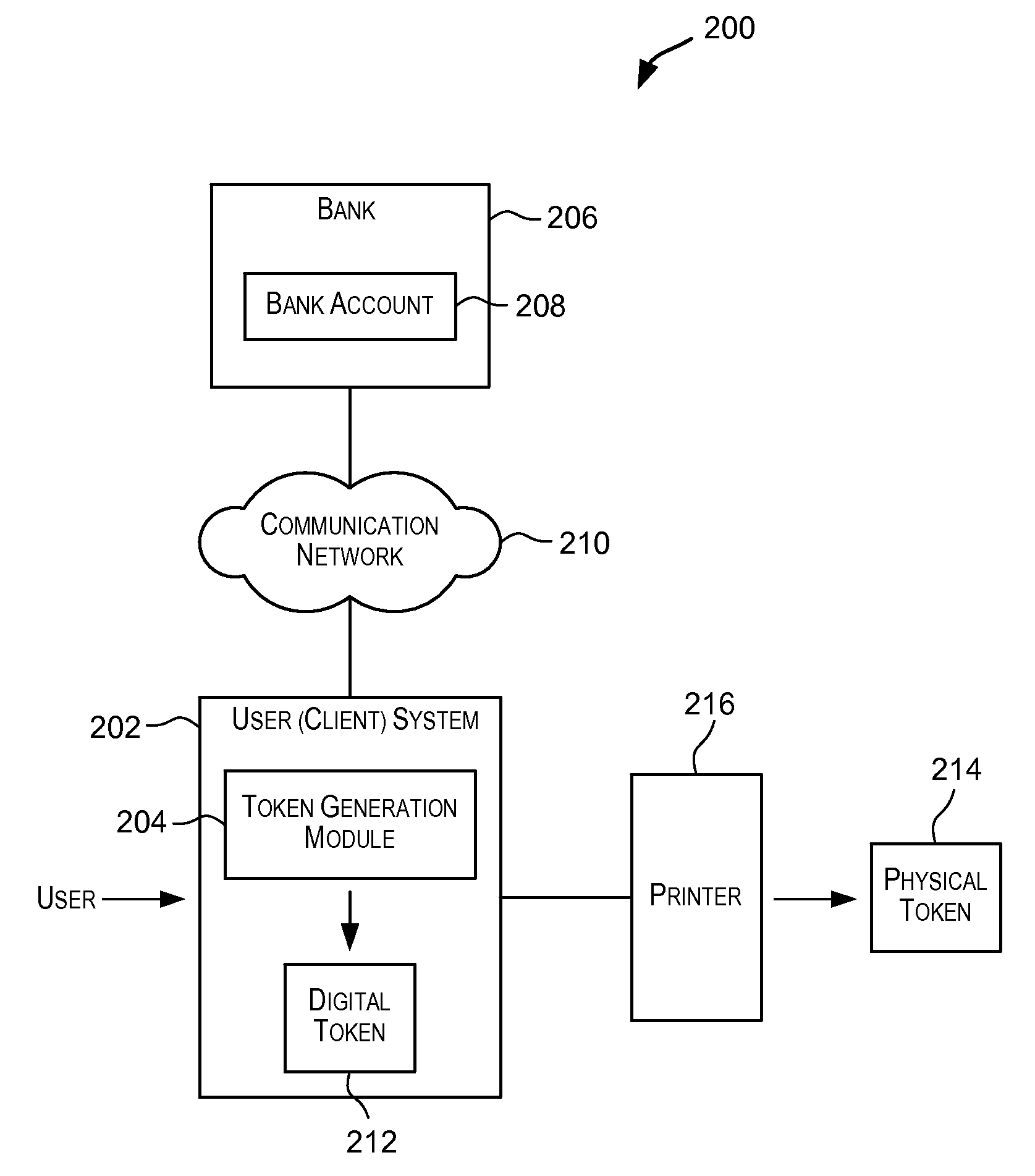
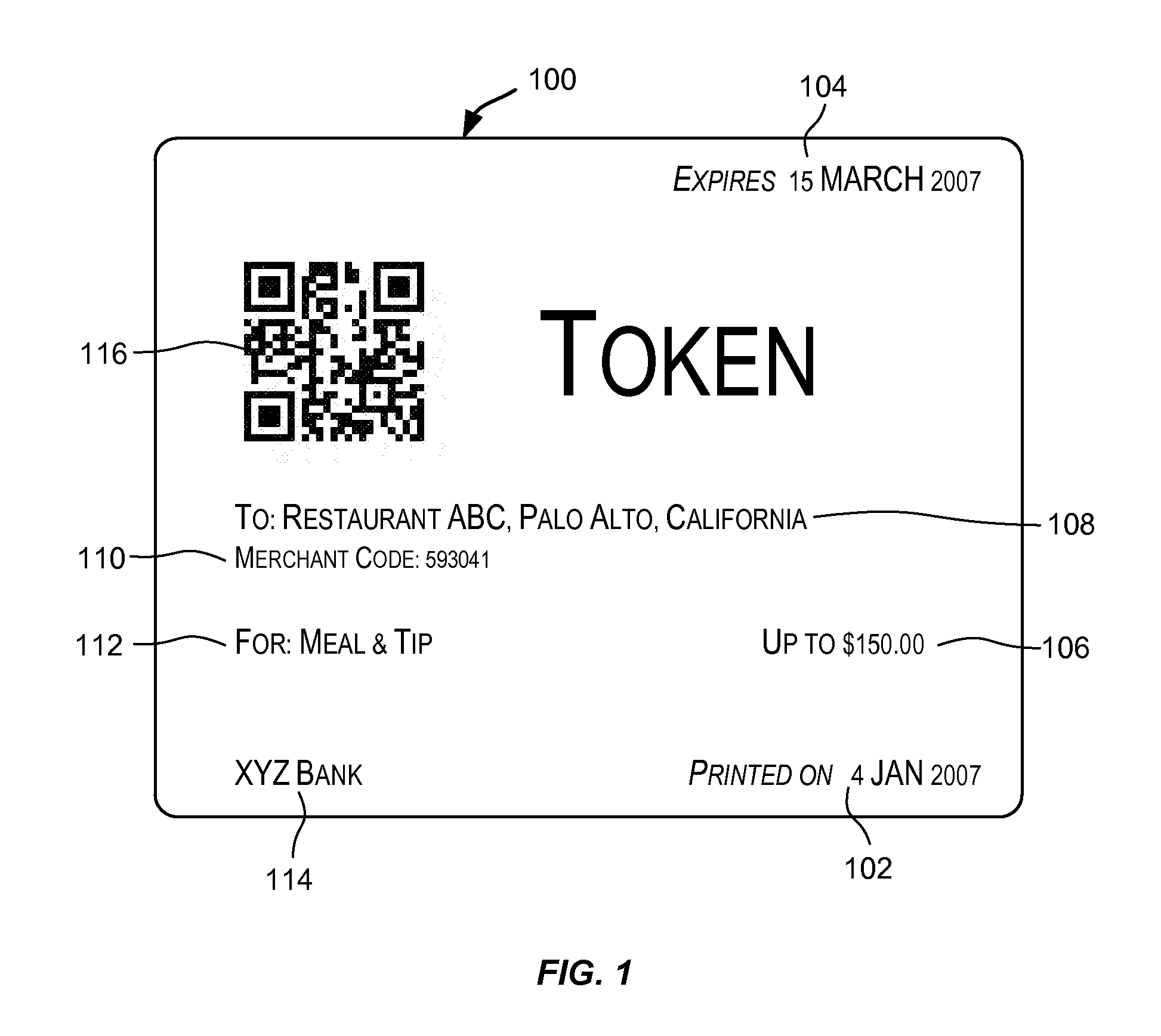
Techniques for generating a token that can be used to transfer value. The token may be used to transfer value in a value-based transaction with a vendor in a way that is secure and safe and maintains anonymity of the source of the value and preserves secrecy of information that should preferably not be disclosed to an untrusted third party such as a vendor. The token comprises sufficient information that enables value to be transferred from an account associated with the token to a vendor during a value-based transaction. Such a token may be presented by a user to a vendor in a value-based transaction with the purpose of transferring value involved in the transaction to the vendor in order to complete the transaction.
Owner:RICOH KK
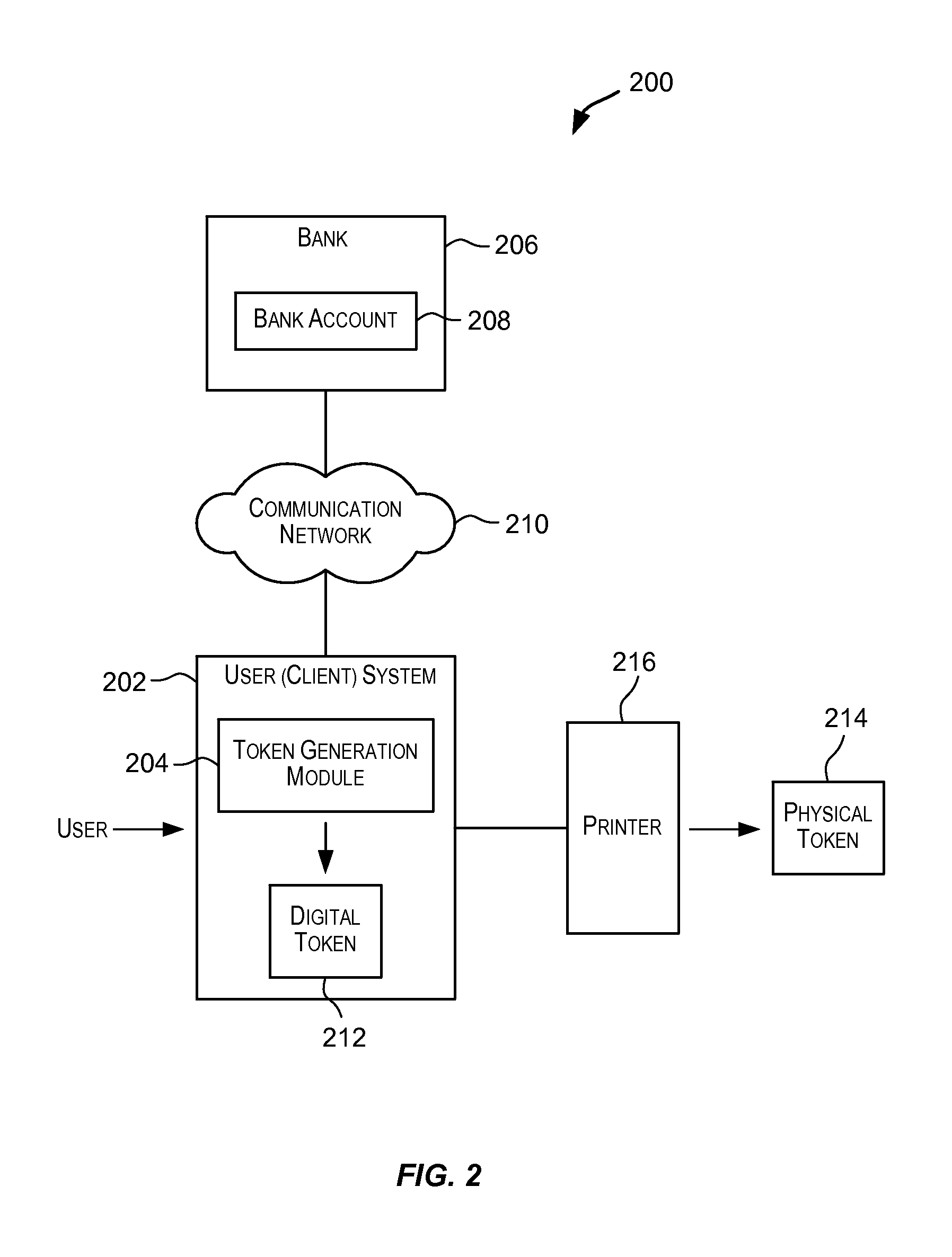
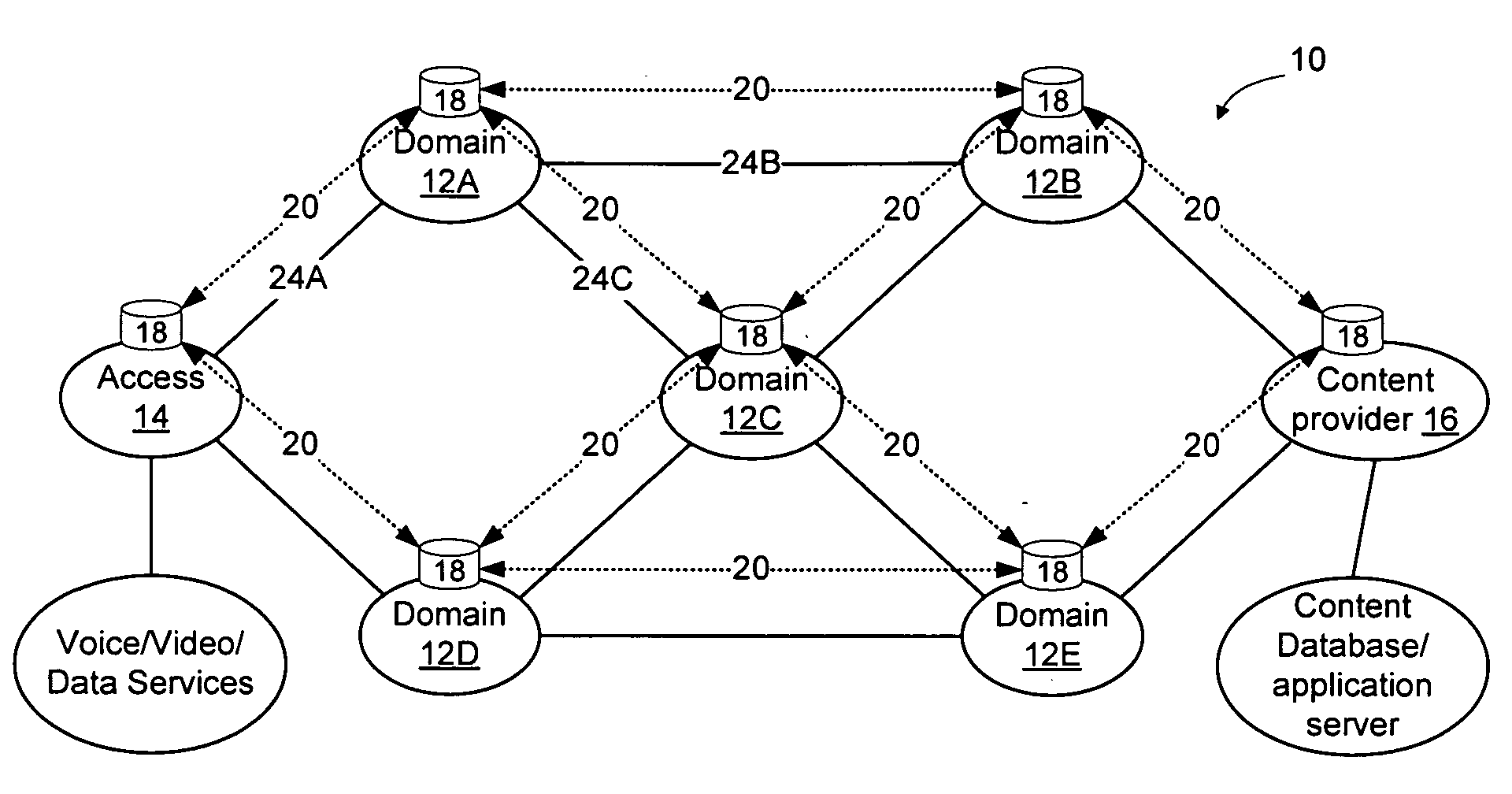
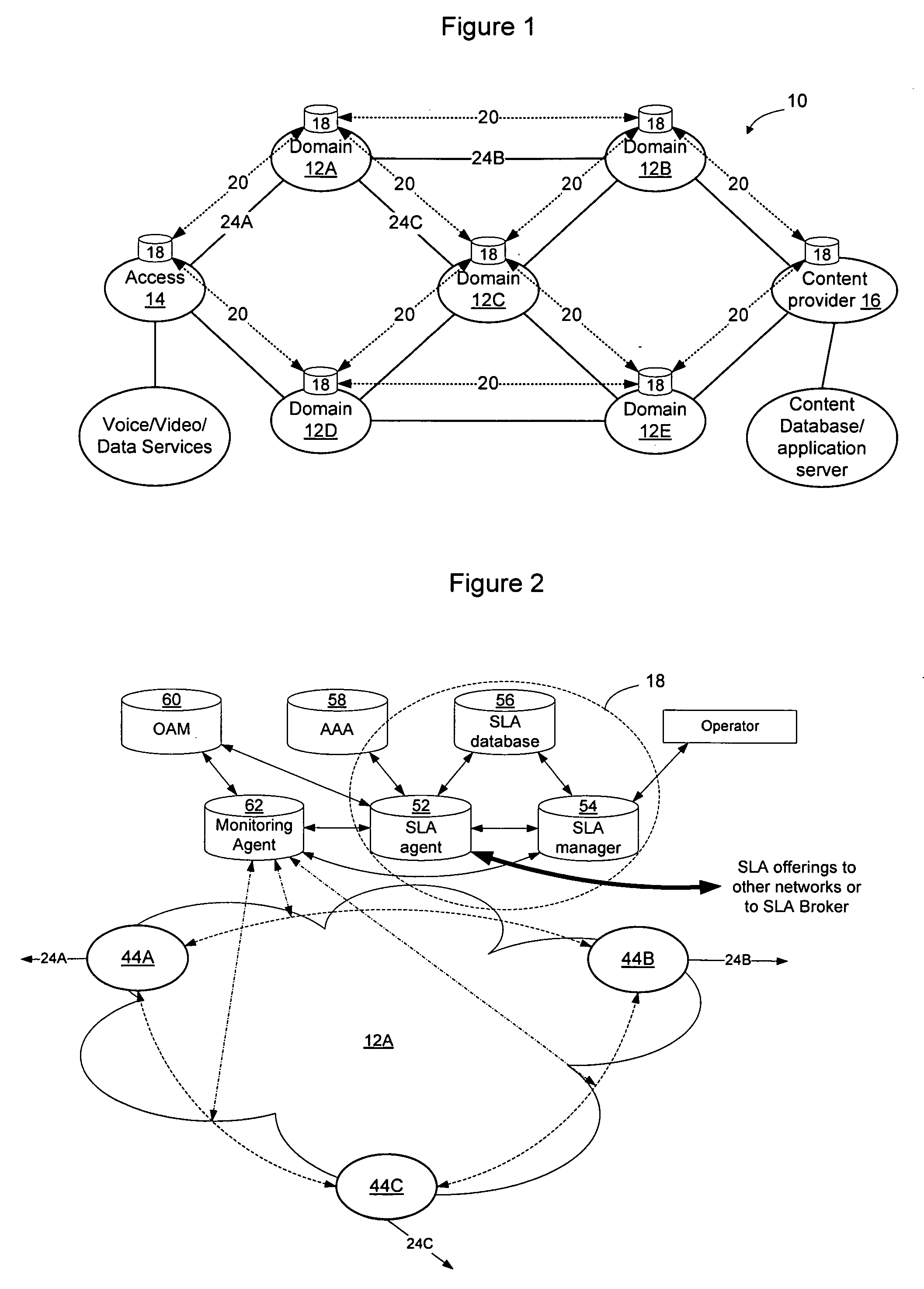
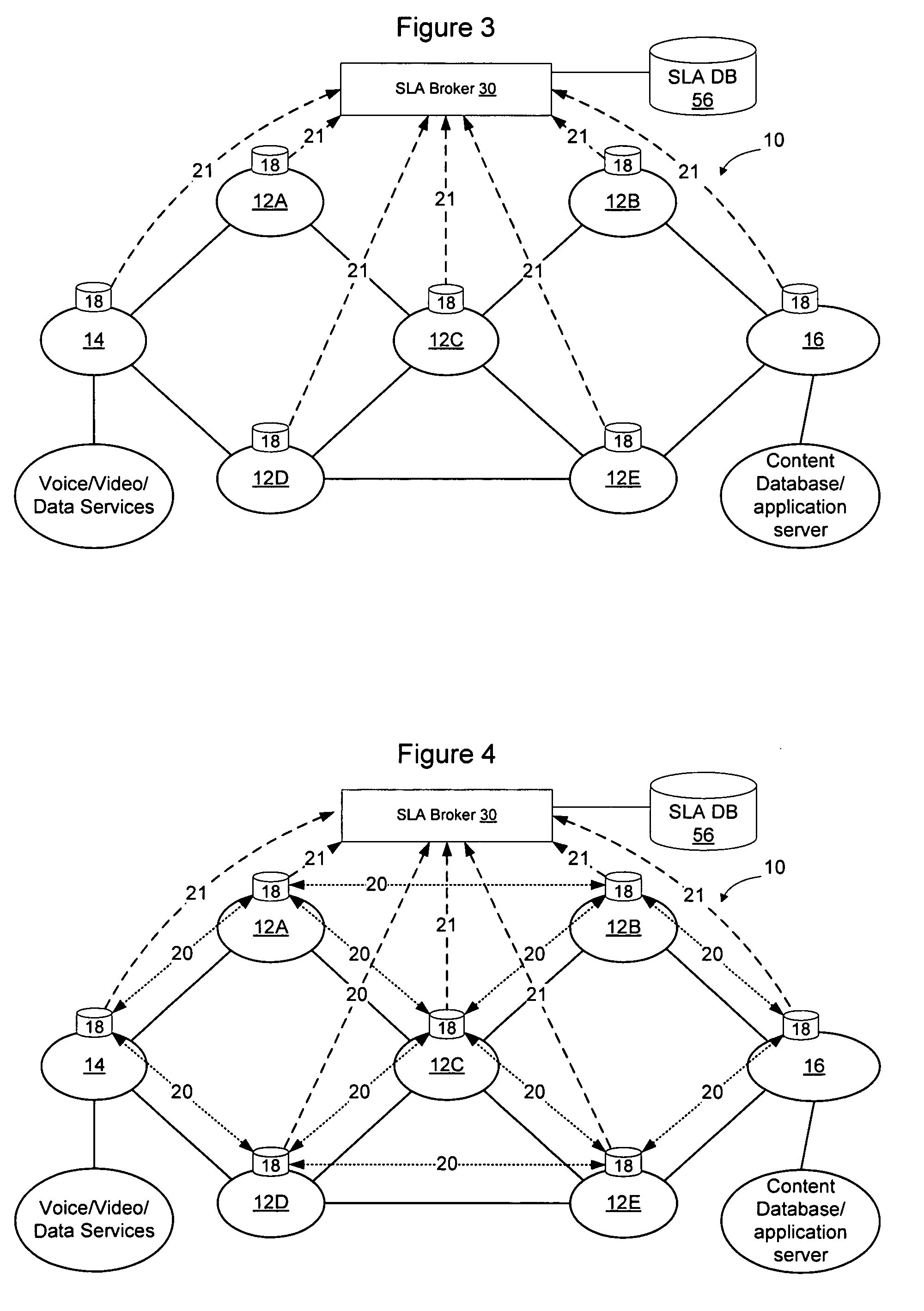
Method and apparatus for discovering, negotiating, and provisioning end-to-end SLAs between multiple service provider domains
Domains (multiple collaborating service providers) create service offerings between pairs of edge nodes that interconnect with other domains in the network. The service offerings may specify the available bandwidth, quality of service, reliability, available security, price, subscriber and service contextual specific and other SLA information. When a new service is to be created, the service definition is used along with information about the available service offerings to determine a set of networks to implement the service. Information associated with the service offerings may be flooded to all other networks. Alternatively, the service offering information may be provided to a trusted third party (SLA broker) which may provide SLA services on the network to select sets of domains to implement inter-domain services, and may also proxy to set up the service for the SLA requesting party. A hybrid approach may also be used wherein some SLA information is flooded and other information is retained in secret and provided only to the SLA broker.
Owner:RPX CLEARINGHOUSE
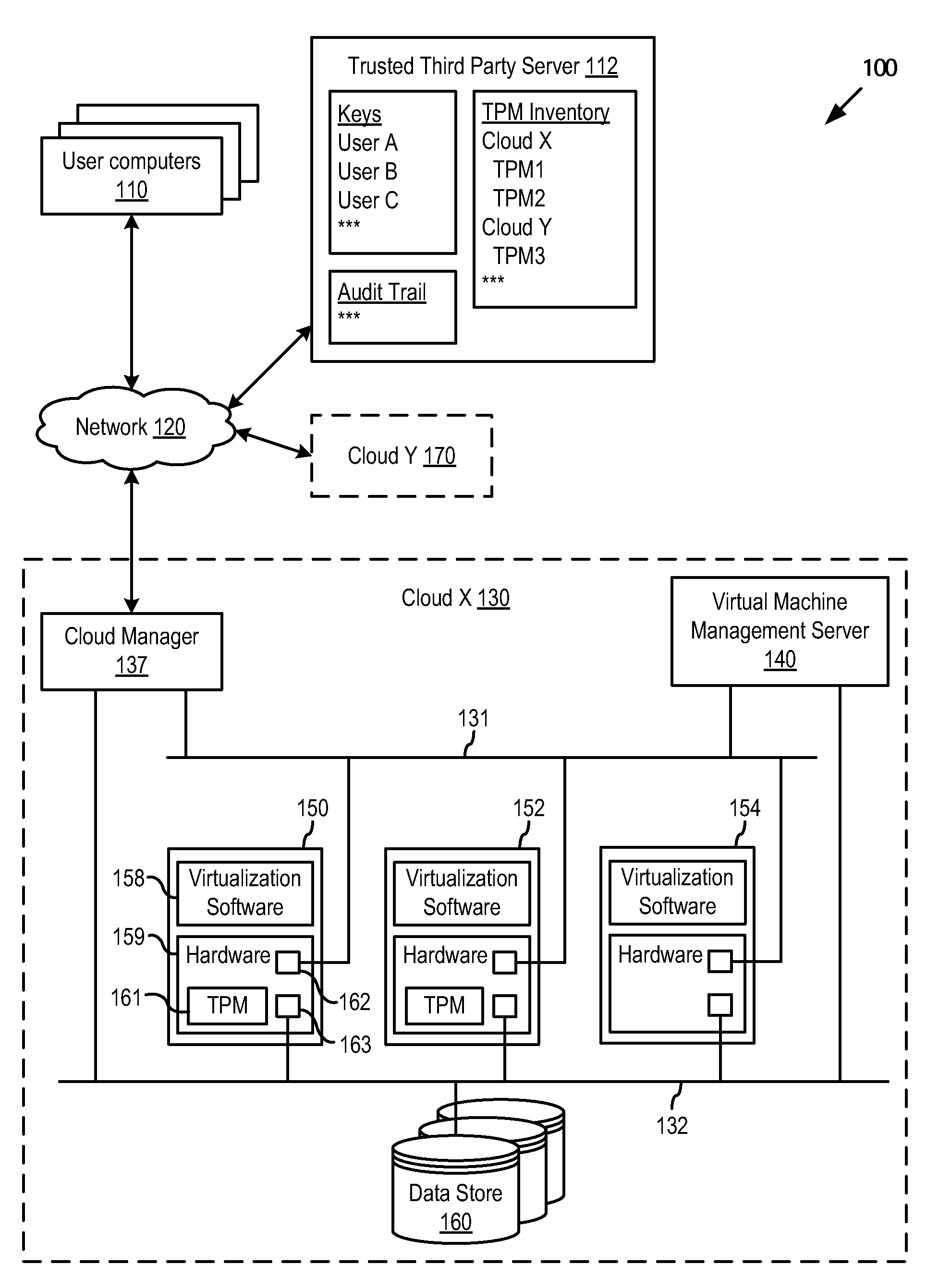
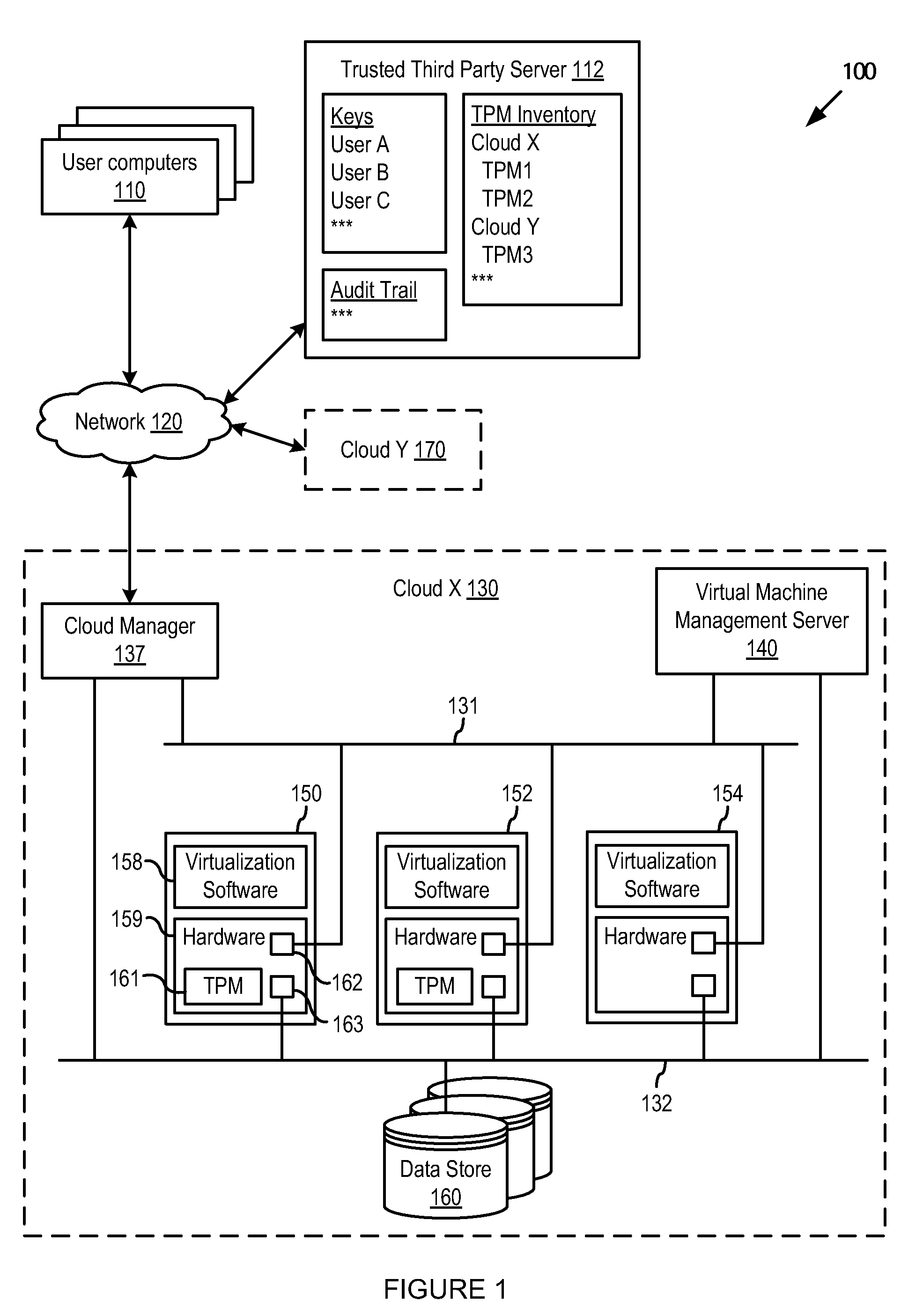
Securing customer virtual machines in a multi-tenant cloud
ActiveUS20110302415A1Limited accessKey distribution for secure communicationUser identity/authority verificationVirtualizationThird party
A trusted virtualization platform protects sensitive customer data during operation of virtual machines in a multi-tenant cloud computing center. The trusted virtualization platform limits administrator access to the data and state of the virtual machines running thereon, reports any changes made thereto, and requires keys provided by the customer or a trusted third party of the customer to perform management operations on the virtual machines. By requiring cloud computing centers to use such trusted virtualization platforms, customers uploading their virtual machines into the cloud computing center can be assured that cloud administrators will not be able to access or tamper with their private data. Furthermore, customers can directly audit all important state or configuration changes for their virtual machines as the trusted virtualization platform can be configured to report all such changes according to a security policy set by the customer.
Owner:VMWARE INC
Conducting transactions
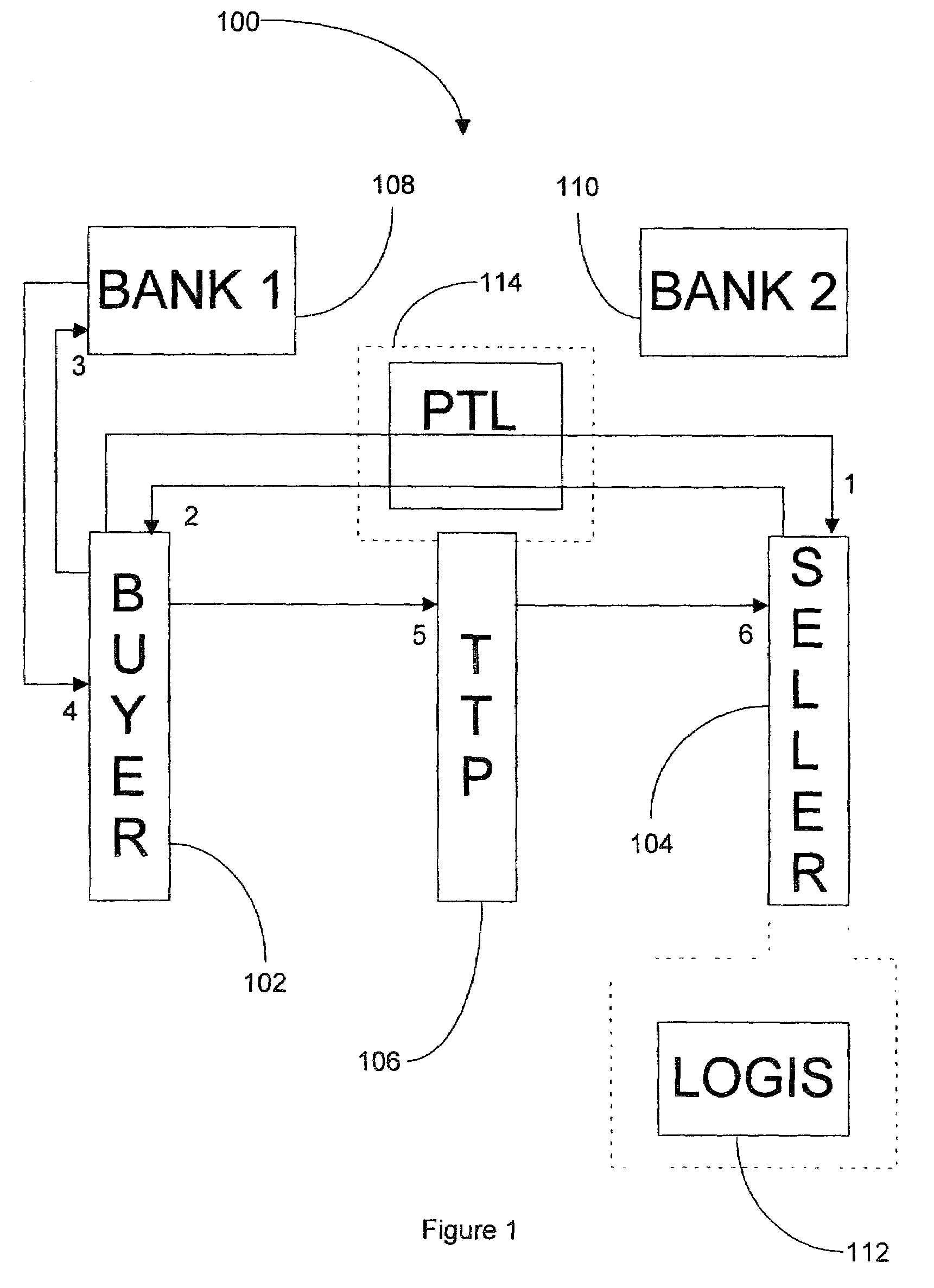
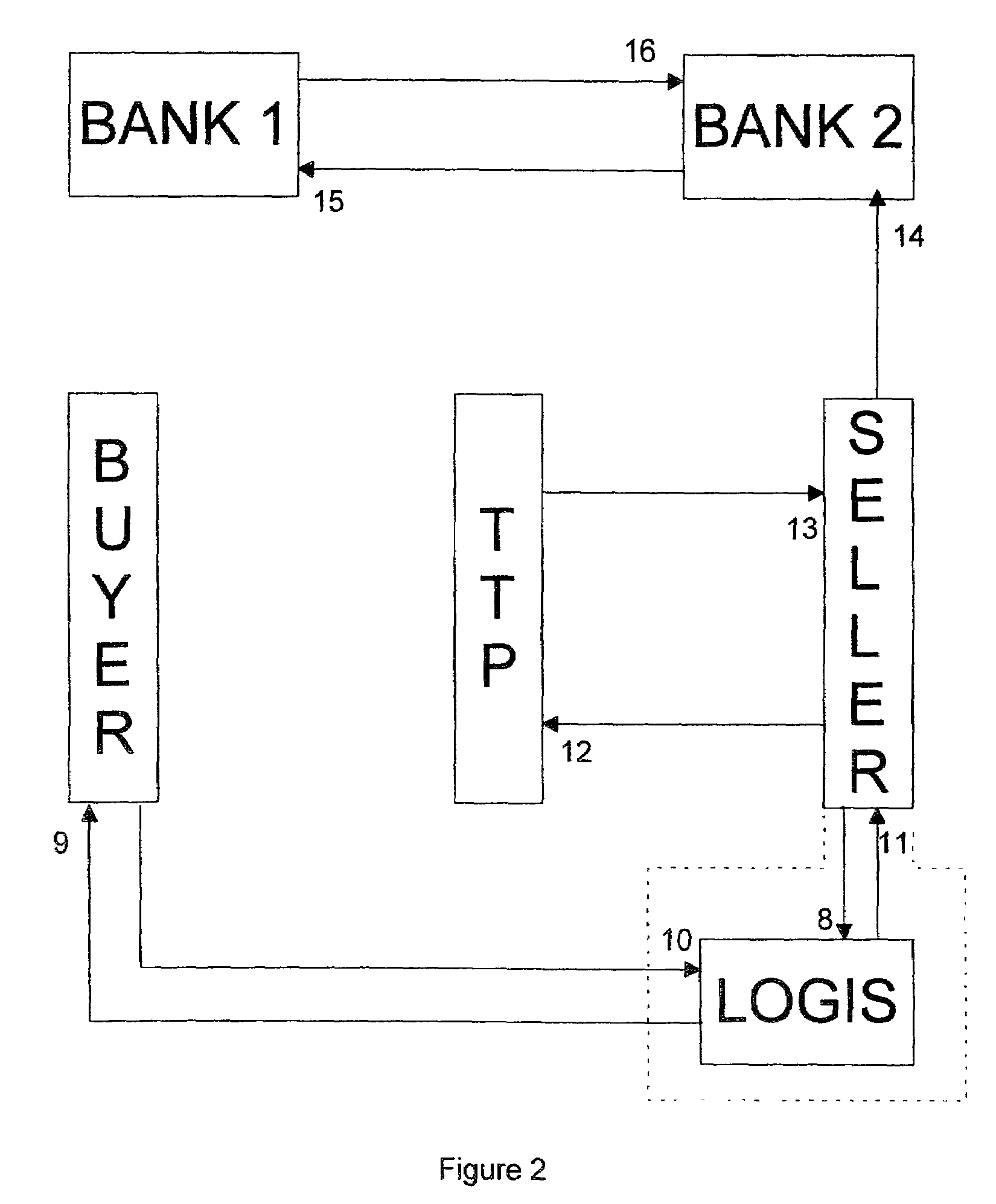
A two-part payment token is used during a transaction whereby a buyer obtains goods / services from a seller. The token, which does not identify the buyer, is given to a trusted third party (TTP) by the buyer. The TTP releases a first part of the token to the seller who then releases the goods / services to the buyer. Upon confirming receipt of the goods / services by the buyer, the TTP releases the second part of the payment token to the seller, who may then present both parts of the token to the buyer's bank to obtain payment.
Owner:HEWLETT PACKARD DEV CO LP
Persistent Dynamic Payment Service
The invention comprises online methods, systems, and software for improving the processing of payments from financial accounts, particularly credit and debit card payments made from consumers to merchants in online transactions. The preferred embodiment of the invention involves inserting a trusted third party online service into the payment authorization process. The trusted third party authenticates the consumer and authorizes the proposed payment in a single integrated process conducted without the involvement of the merchant. The authentication of the consumer is accomplished over a persistent communication channel established with the consumer before a purchase is made. The authentication is done by verifying that the persistent channel is open when authorization is requested. Use of the third party services allows the consumer to avoid revealing his identity and credit card number to the merchant over a public network such as the Internet, while maintaining control of the transaction during the authorization process.
Owner:FISHER DOUGLAS C +1
Method of secure access to confidential medical data, and storage medium for said method
InactiveUS20150310174A1Data processing applicationsDigital data processing detailsInternet privacyTrusted third party
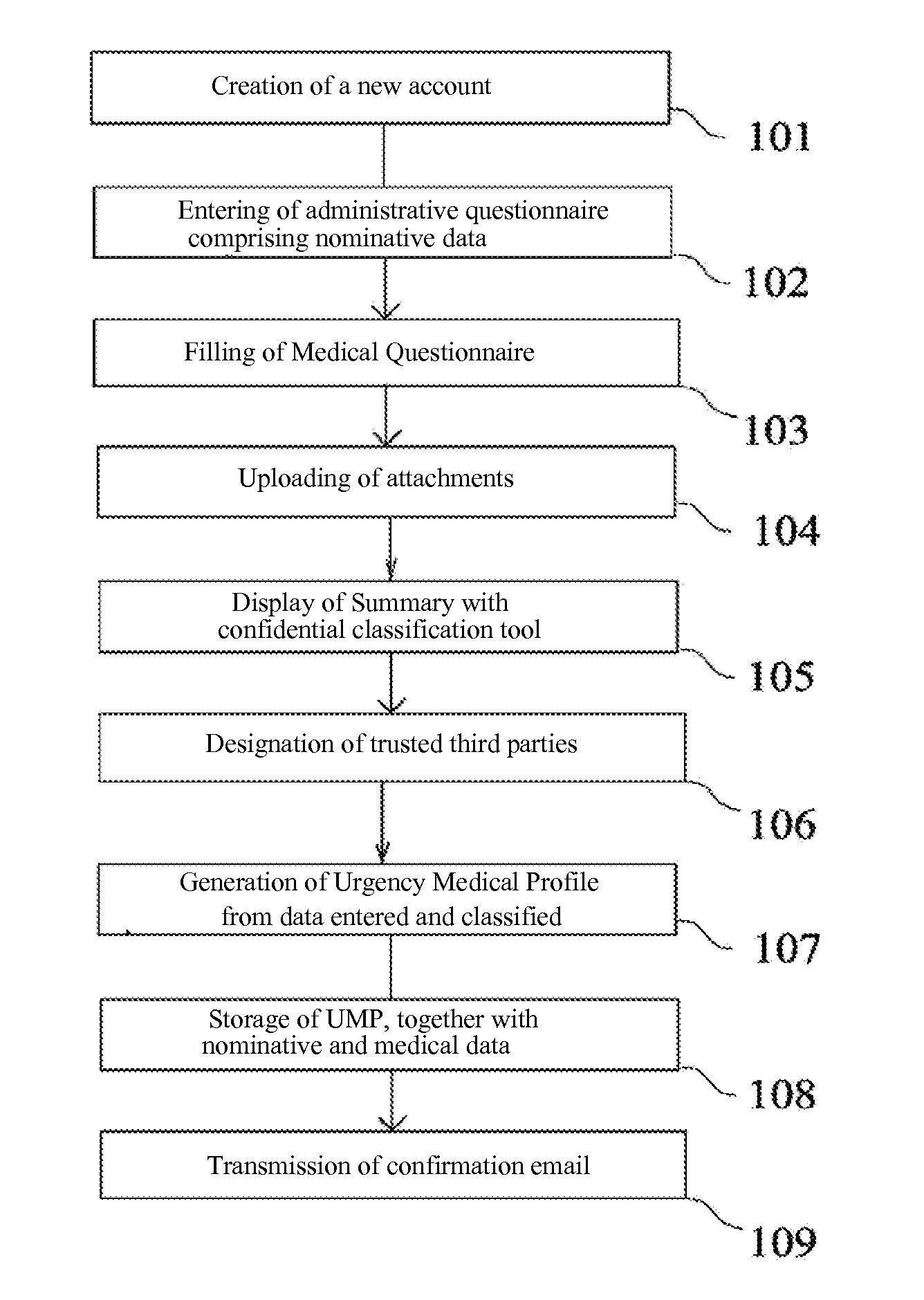
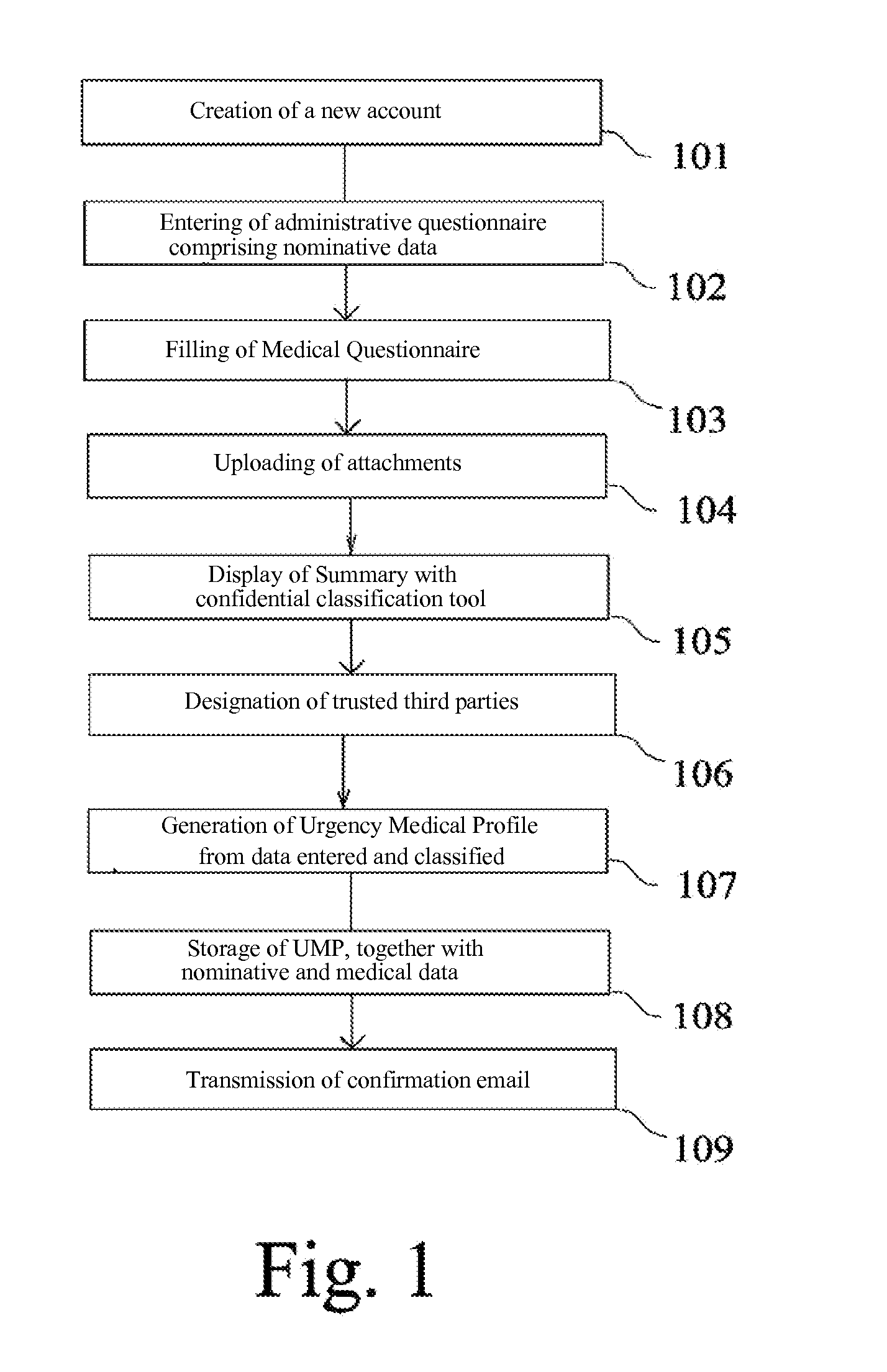
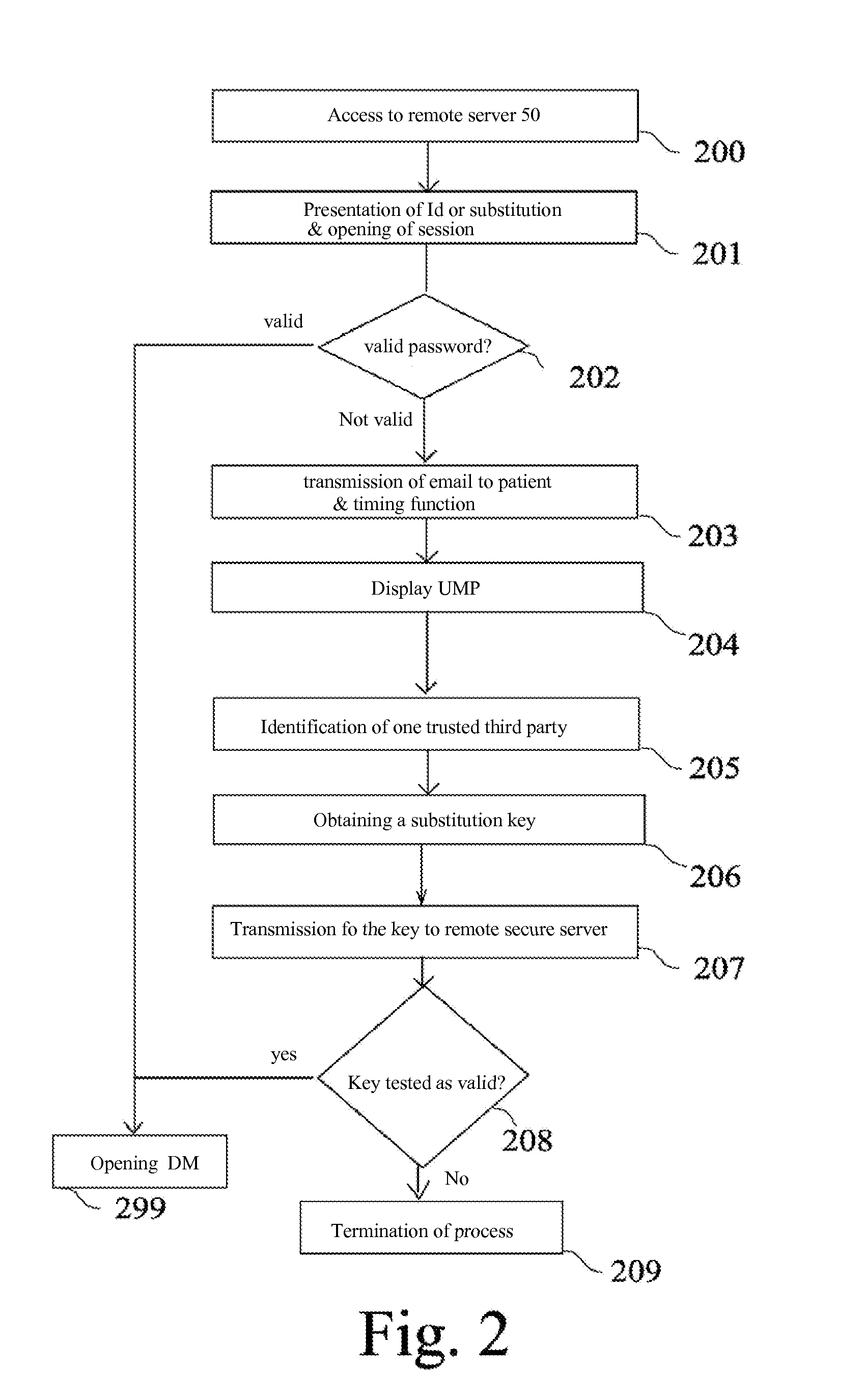
A process for generating a digital medical file stored on a secure server (50) and accessible from a first system (10) via a data communication network, the digital medical file including both nominative data and confidential data, said process further comprising the automatic generation of an Urgency Medical Profile, UMP, devoid of any personal data and devoid of any confidential information, which allows an indirect access to the digital medical file via a trusted third party.The concept of Medical Profile, which is a particular and temporal mode of the medical file prefigures the transmission of the digital medical information continuously from the patient to his doctor (or vice versa), with the objective of creating an universal and interactive external digital support (USB card, Smartphone, digital tablet, etc. . . . ) affording physical realization to the Patient / doctor relationship for tracking the Personal Digital Medical File.
Owner:COUDERT PATRICK
Method and system for managing account information
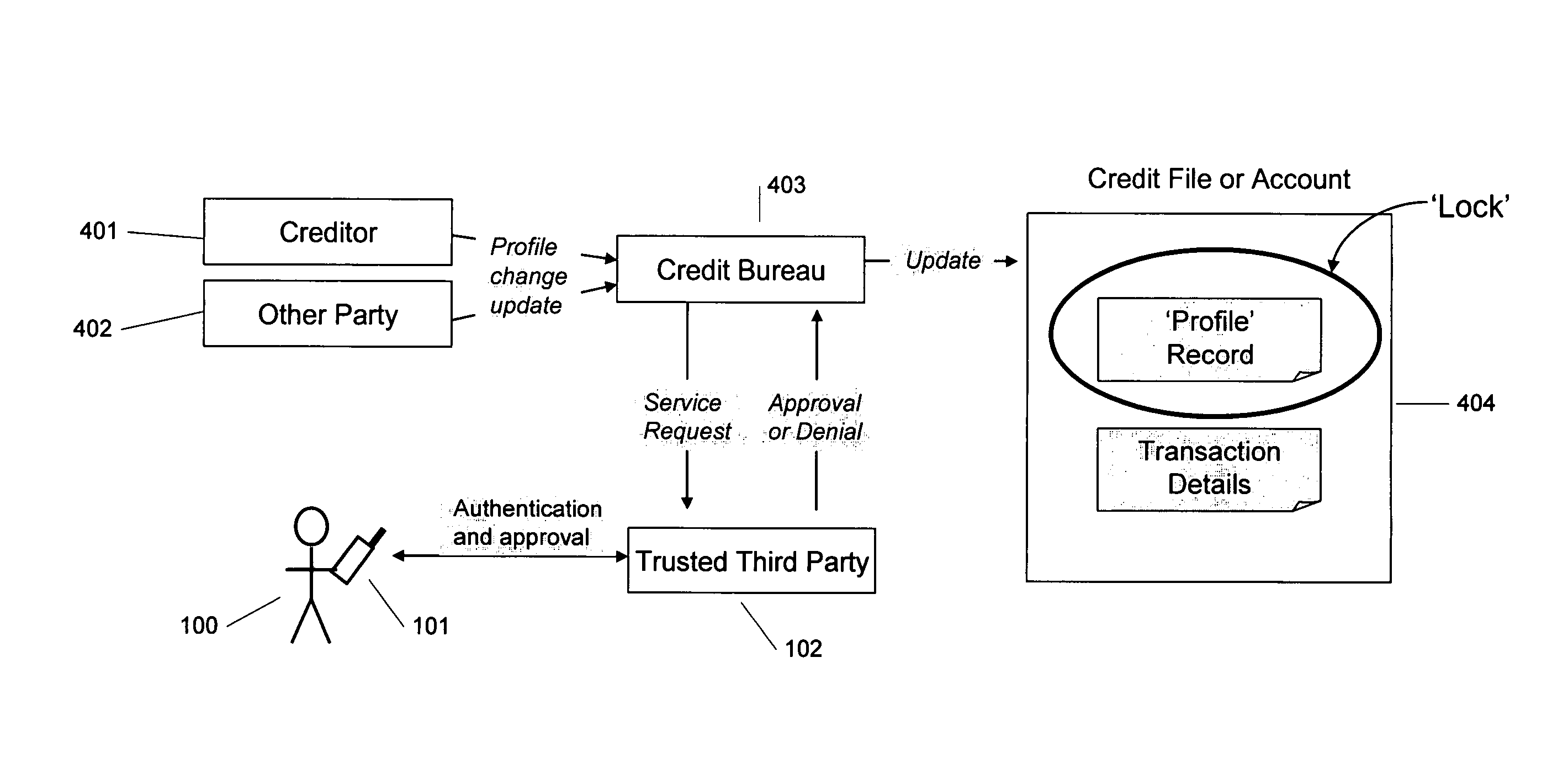
A method and system for authenticating the identity of a consumer is disclosed. After the consumer is authenticated by a trusted third party, the consumer designates accounts that the consumer wishes to “lock.” When a party requests access to that account, the consumer is notified through the consumer's phone and asked to input a PIN. If the consumer provides the PIN, the requestor is granted access to the consumer's account without requiring further input from the consumer. If the party authorizing the transaction in this “two-factor” authentication does not possess both the phone and the consumer's PIN, or that party elects not to provide the PIN, the request will not be authenticated.
Owner:DEBIX ONE
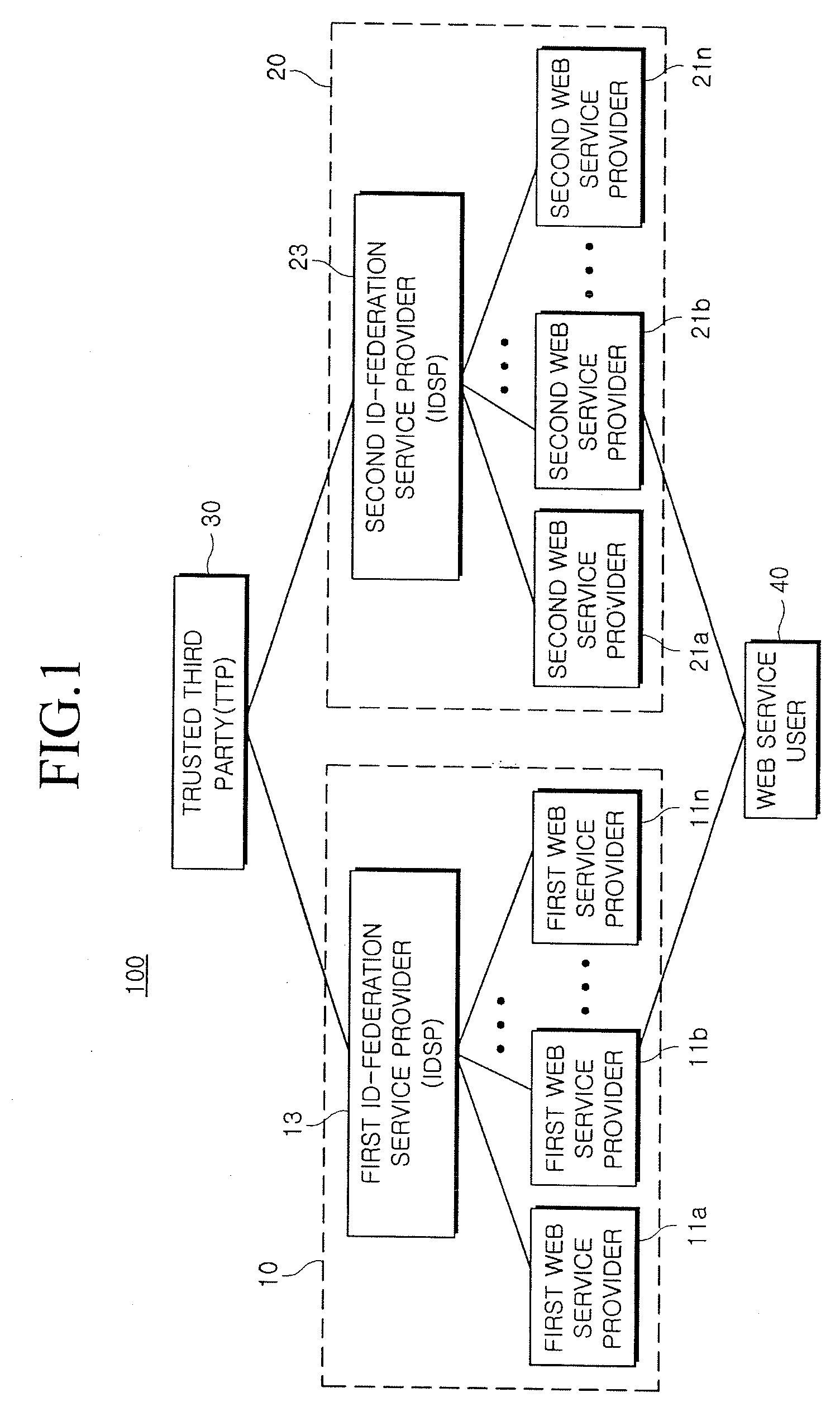
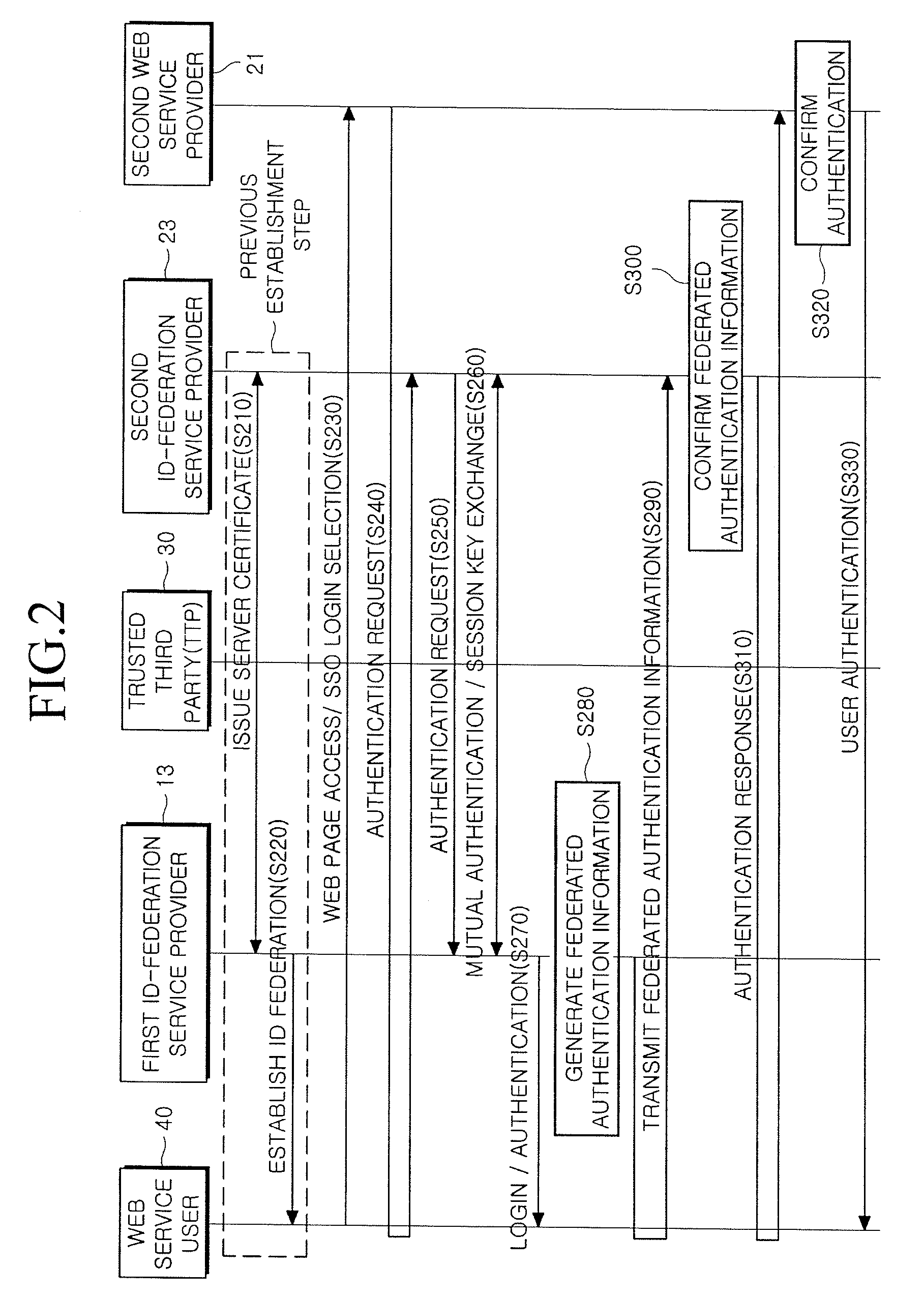
Method and system for providing single sign-on service
InactiveUS20090119763A1Possible to useDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
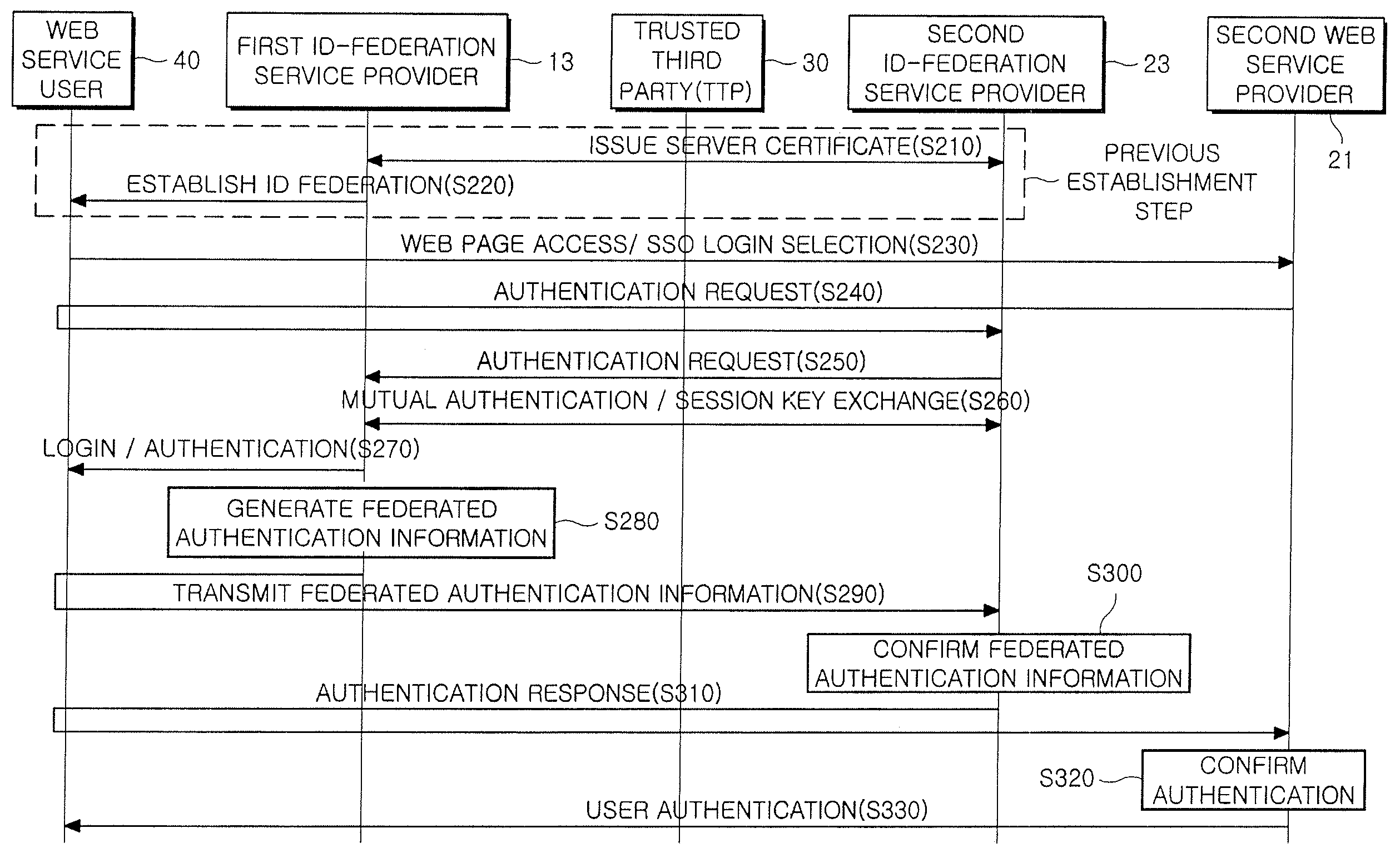
Provided is a method and system for providing an SSO service enabling the use of Web services in different trusted domains through a one-time authentication process. In the method, mutual authentication information is issued from a trusted third party to each of ID-federation service providers managing each of trusted domains, and an ID federation established between the ID-federation service provider and a user in the trusted domain of the ID-federation service provider. The first ID-federation service provider managing the first trusted domain, to which the user belongs to, is confirmed when a Web service provider in the second trusted domain receives a login request from the user in the first trusted domain. User authentication and mutual authentication arc performed between the first ID-federation service provider and a second ID-federation service provider managing the second trusted domain. The Web service provider authenticates the user in the first trusted domain and provides a corresponding Web service.
Owner:ELECTRONICS & TELECOMM RES INST
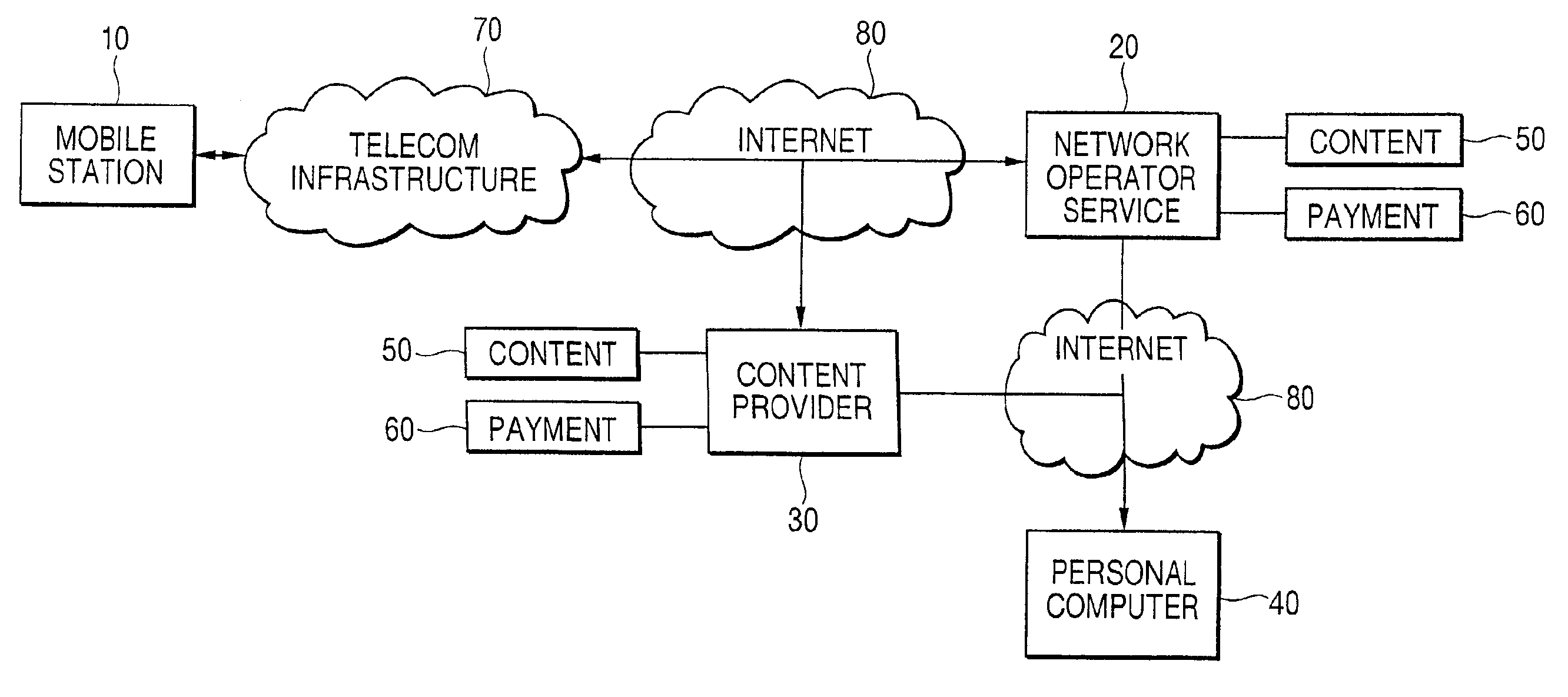
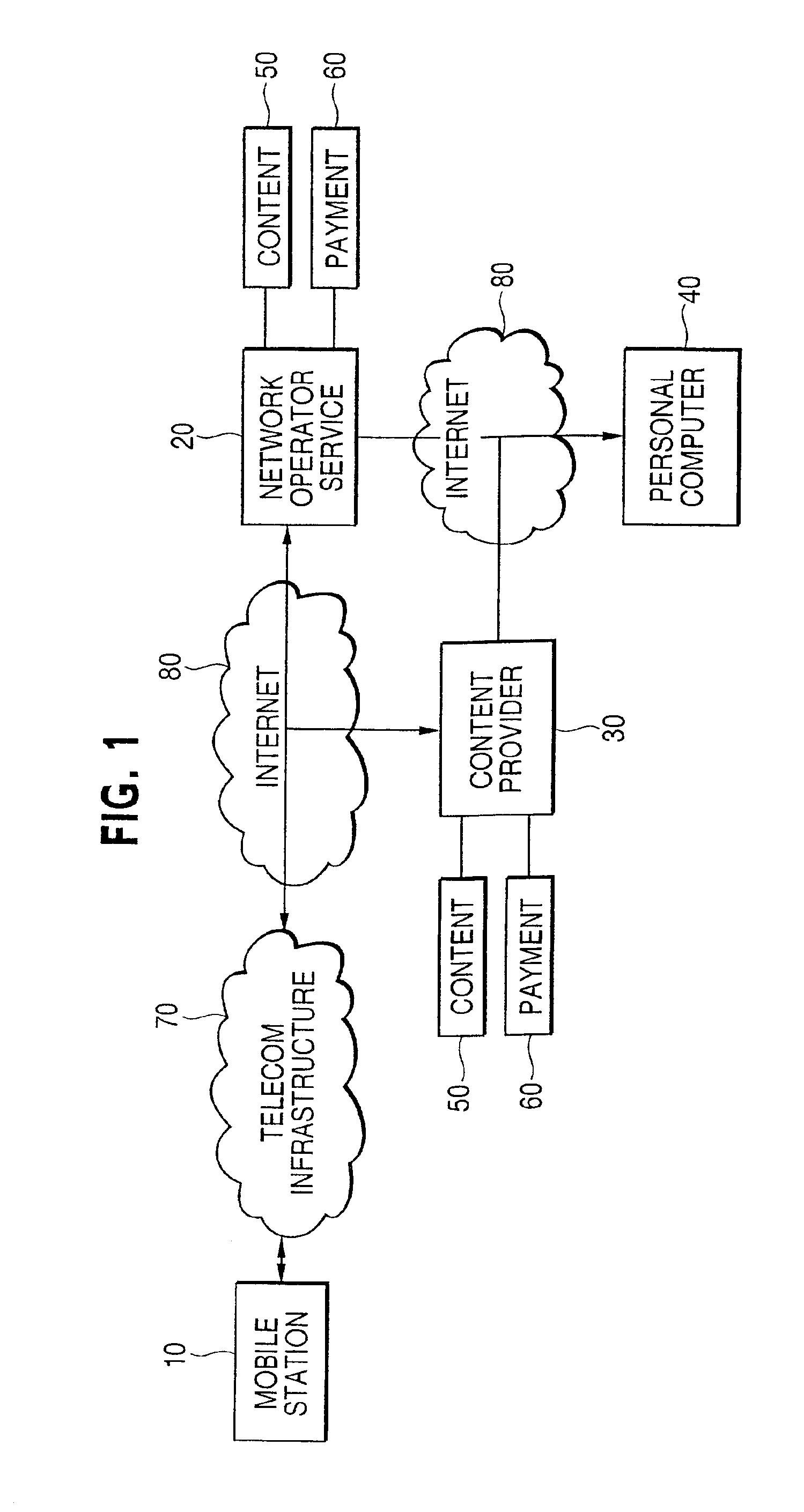
System and method of secure payment and delivery of goods and services
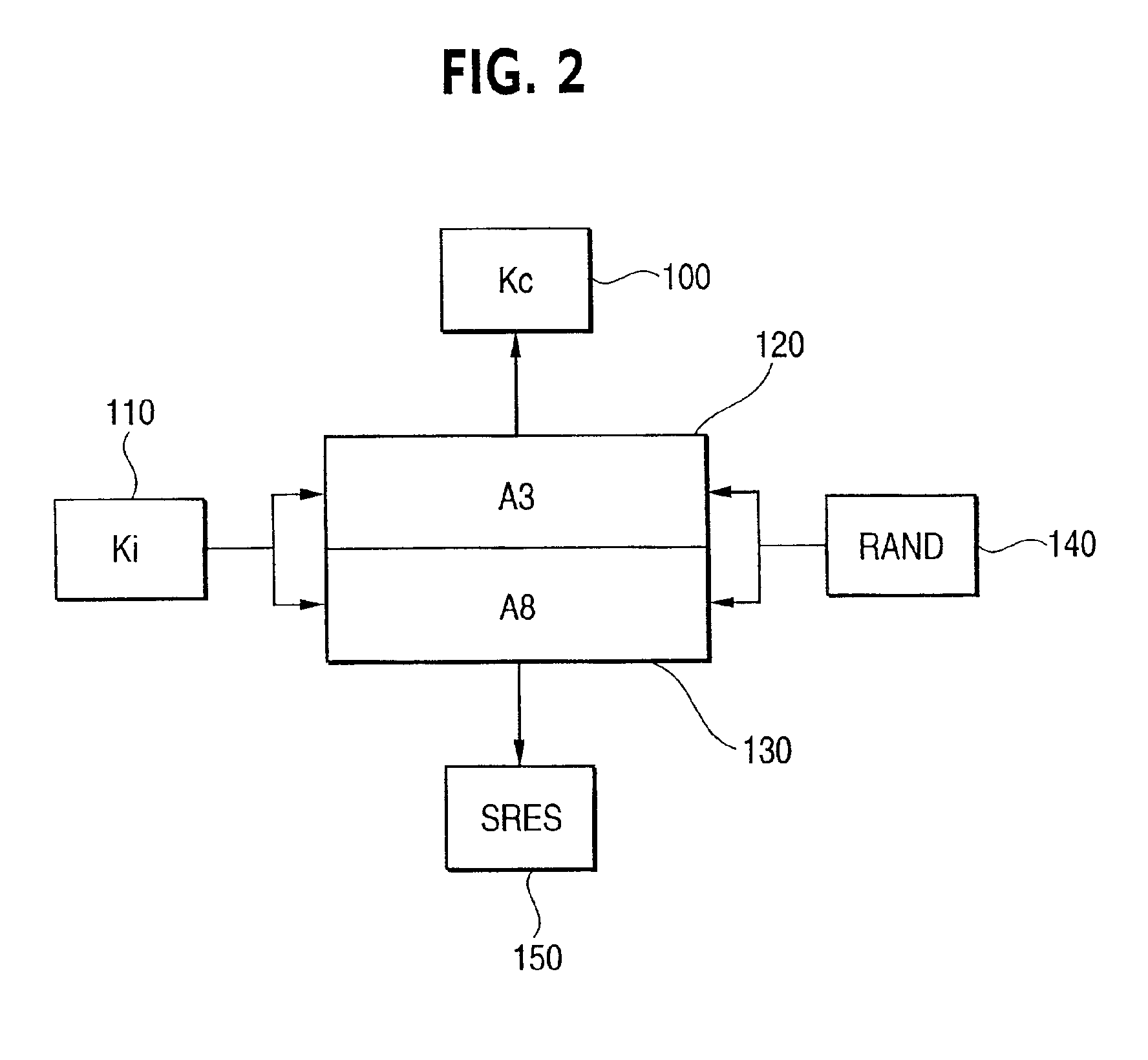
A system, method and computer program for ordering, paying for and delivering goods and services from a content provider to a user which assures the content provider that he will be paid and that assures the user that he will receive the content at an agreed upon price. Thus, this system, method and computer program facilitates business transactions occurring between parties who do not know each other by using a trusted third party to either take the user's order, deliver to the user's order, and / or bill the user the correct amount for the goods and services contracted for. This system, method and computer program relies on the Global System for Mobile (GSM) communications system to authenticate the user and provide algorithms and modules that are used to generate cipher keys and service responses so as to insure the content provider will be paid and that the user will not be overcharged. Further, these algorithms and modules are used to encrypt important information so as to prevent third parties from intercepting this important information. Five business model modules are detailed with numerous variations possible to accomplish the task of facilitating business transactions between parties that do not necessarily know or trust each other.
Owner:NOKIA TECHNOLOGLES OY
System and Method to Enable PKI- and PMI- Based Distributed Locking of Content and Distributed Unlocking of Protected Content and/or Scoring of Users and/or Scoring of End-Entity Access Means - Added
ActiveUS20150312233A1Key distribution for secure communicationUser identity/authority verificationTrust relationshipThin client
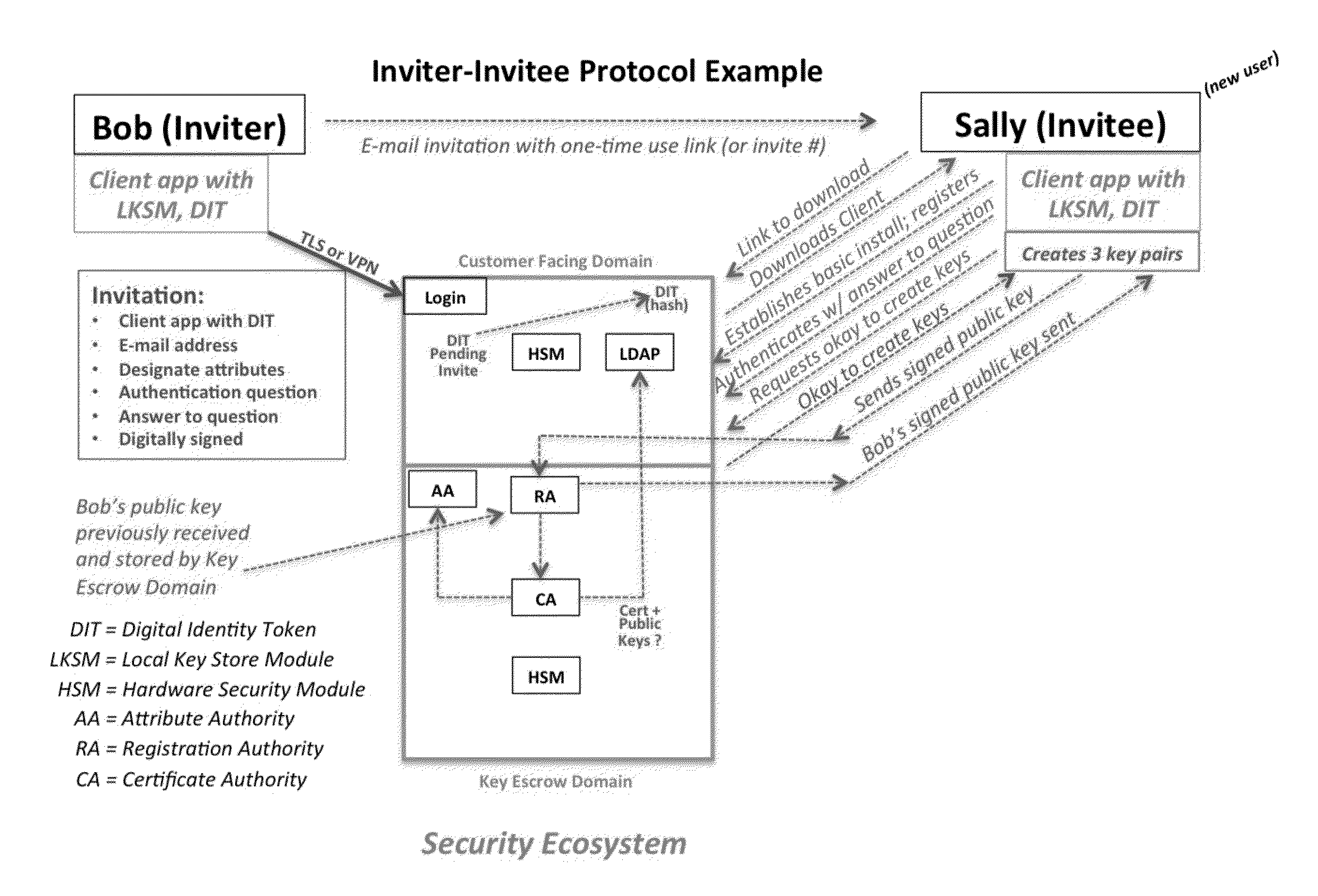
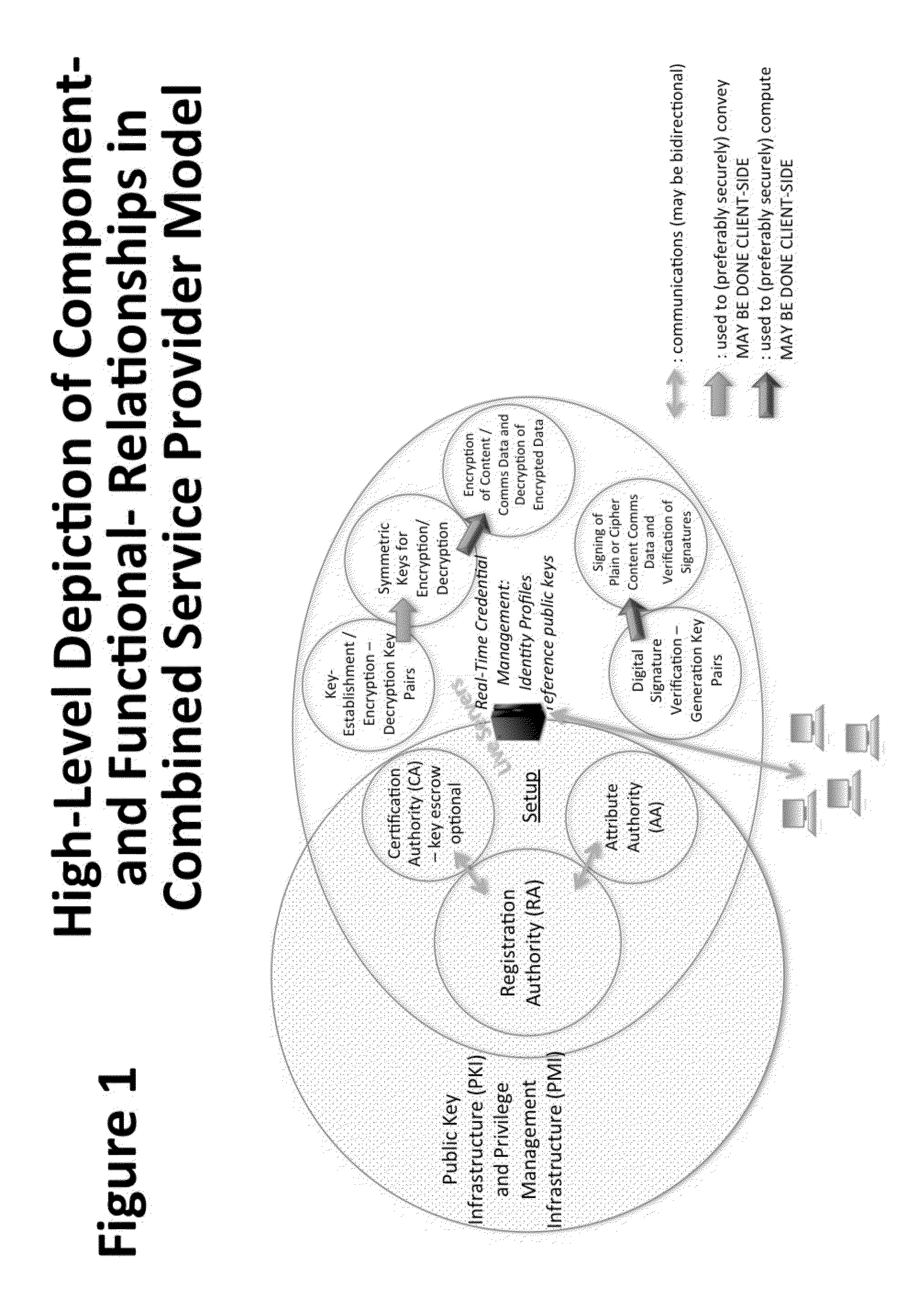
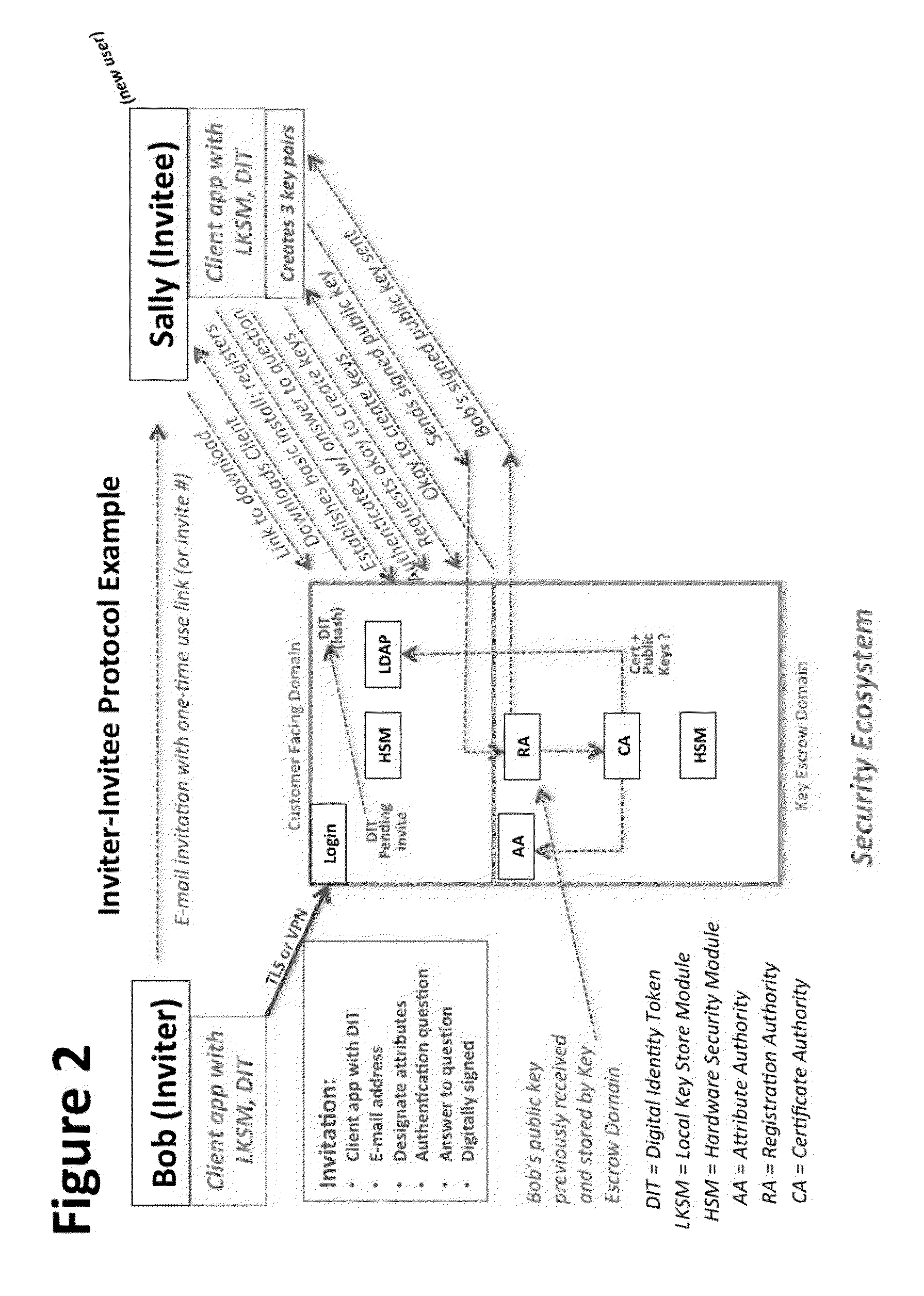
A central server configured with an Attribute Authority (“AA”) acting as a Trusted Third Party mediating service provider and using X.509-compatible PKI and PMI, VPN technology, device-side thin client applications, security hardware (HSM, Network), cloud hosting, authentication, Active Directory and other solutions. This ecosystem results in real time management of credentials, identity profiles, communication lines, and keys. It is not centrally managed, rather distributes rights to users. Using its Inviter-Invitee protocol suite, Inviters vouch for the identity of Invitees who successfully complete the protocol establishing communication lines. Users establish and respond to authorization requests and other real-time verifications pertaining to accessing each communication line (not end point) and sharing encrypted digital files. These are auditable, brokered, trusted-relationships where such relationships / digital agreements can each stand-alone (for privacy) or can leverage build-up of identity confidence levels across relationships. The service is agnostic to how encrypted user content is transported or stored.
Owner:T CENT
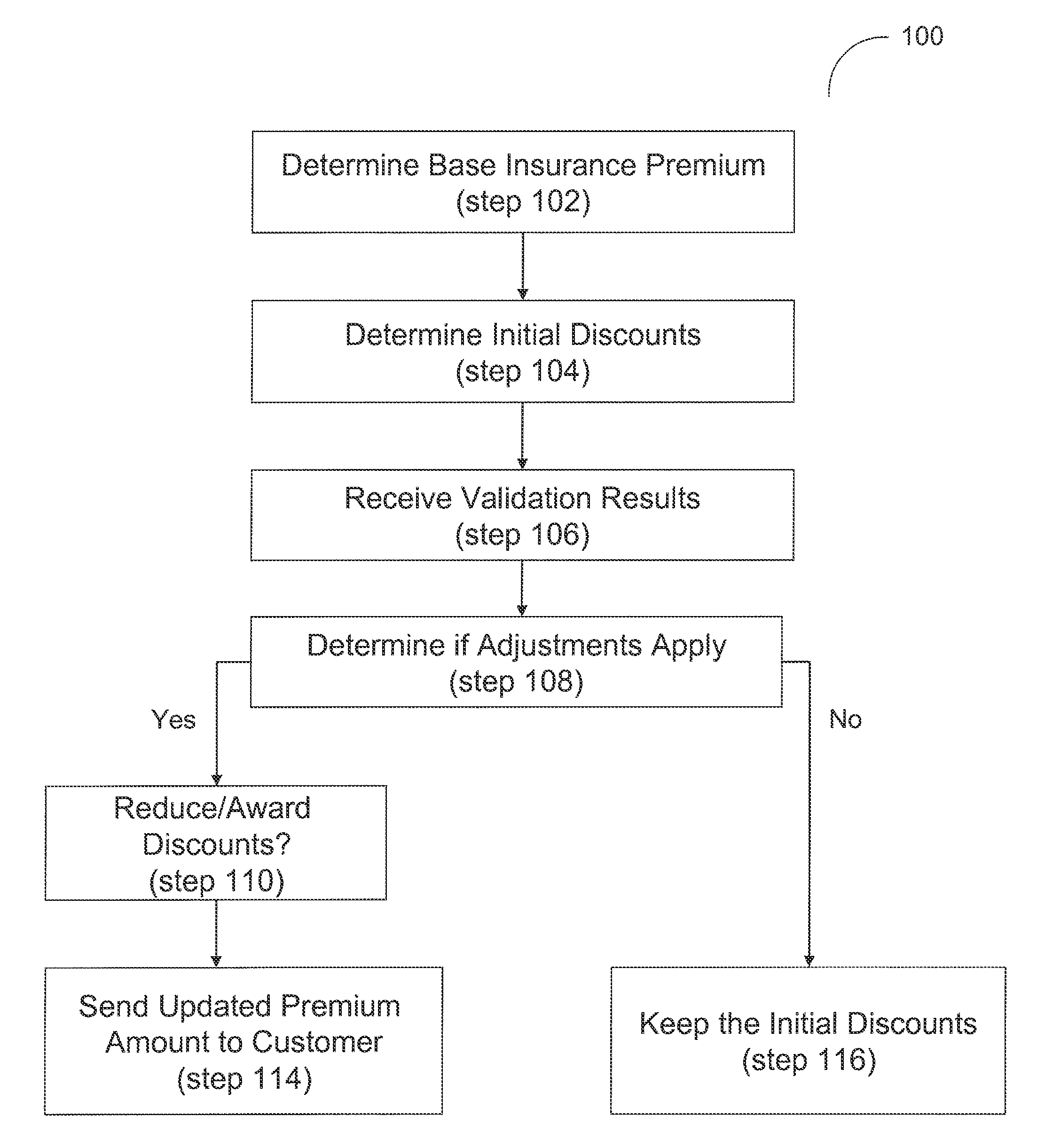
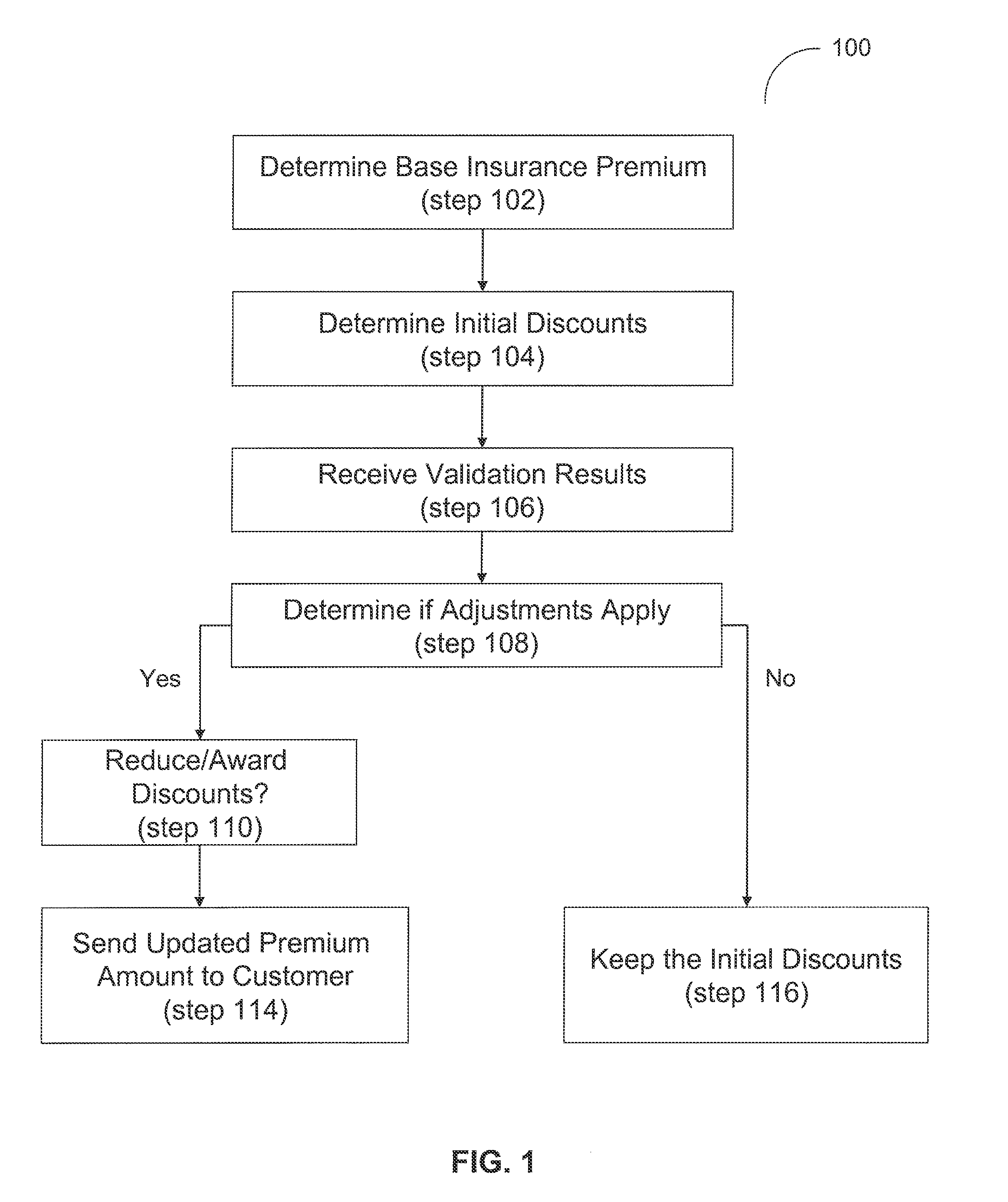
System and method for an automated validation system
System and method are disclosed herein for an automated validation system for validating whether a property of a policyholder receiving at least one insurance benefit is currently receiving remote monitoring services, as claimed by the policyholder. The system comprises an application server, a trusted third party server, and a business logic computer. The application server requests the trusted third party server to validate whether the property of the policyholder is presently receiving remote monitoring services from a service provider. A business logic computer can adjust the policyholder's insurance policy based on the received validation results.
Owner:HARTFORD FIRE INSURANCE
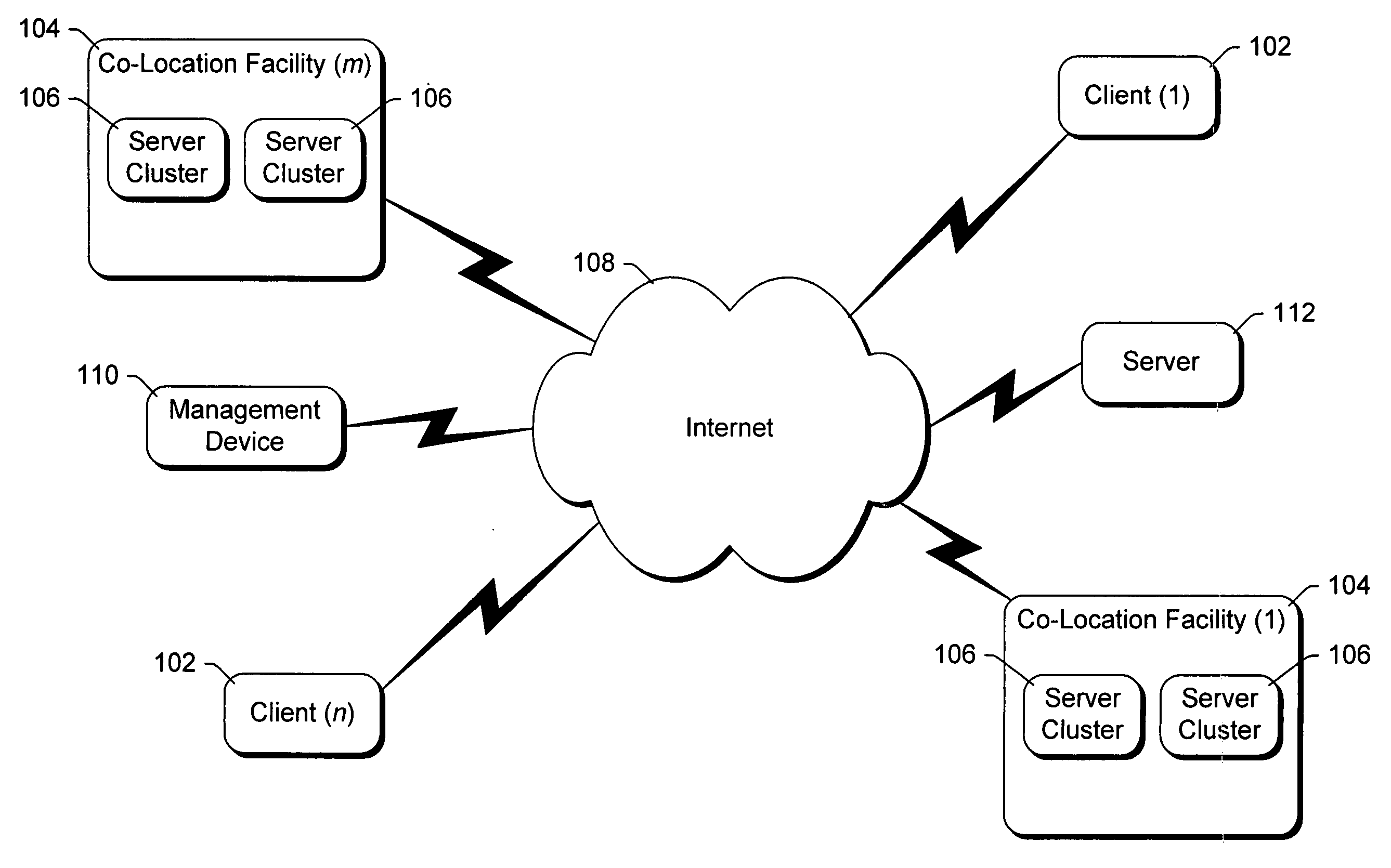
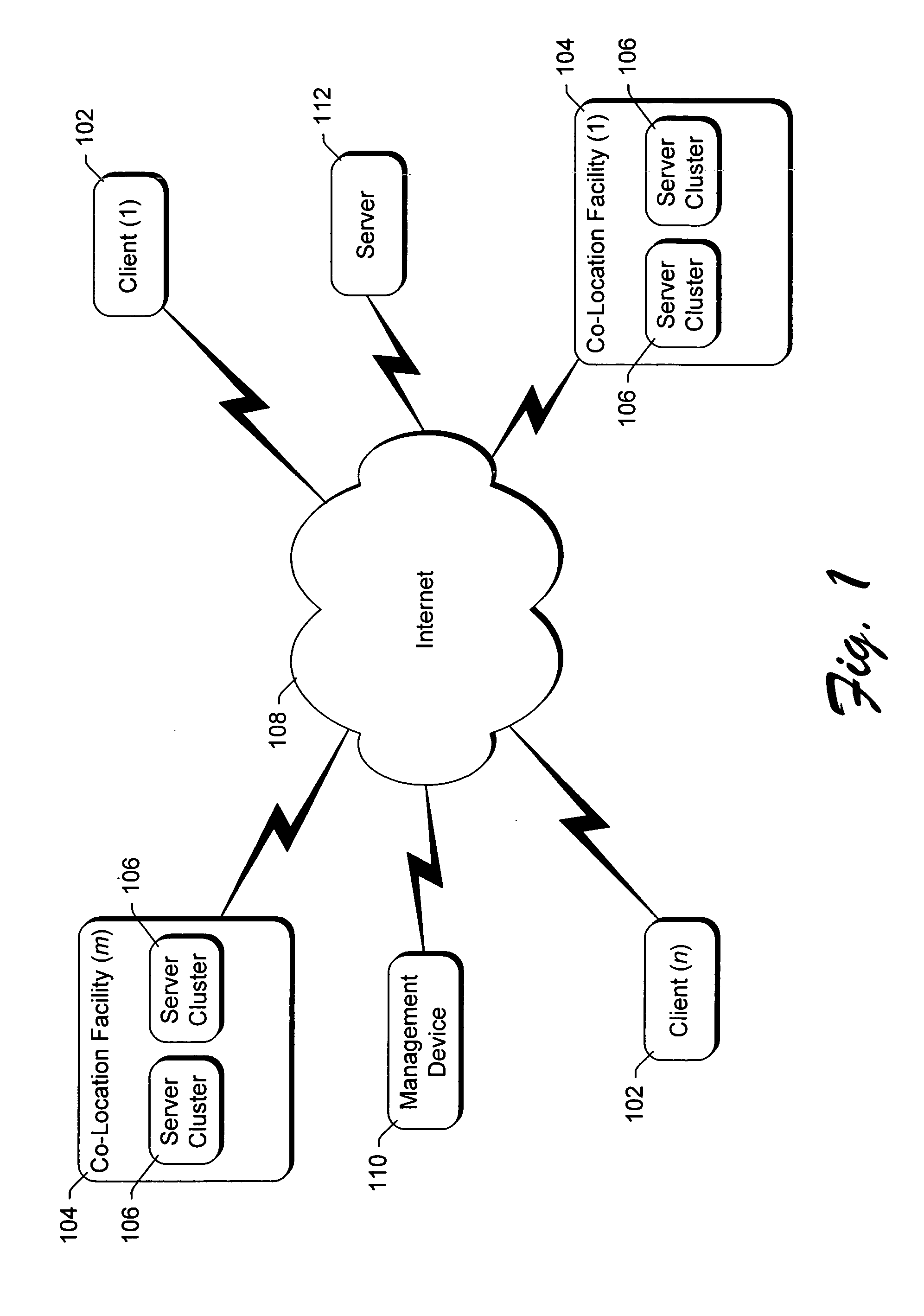
System and method for restricting data transfers and managing software components of distributed computers
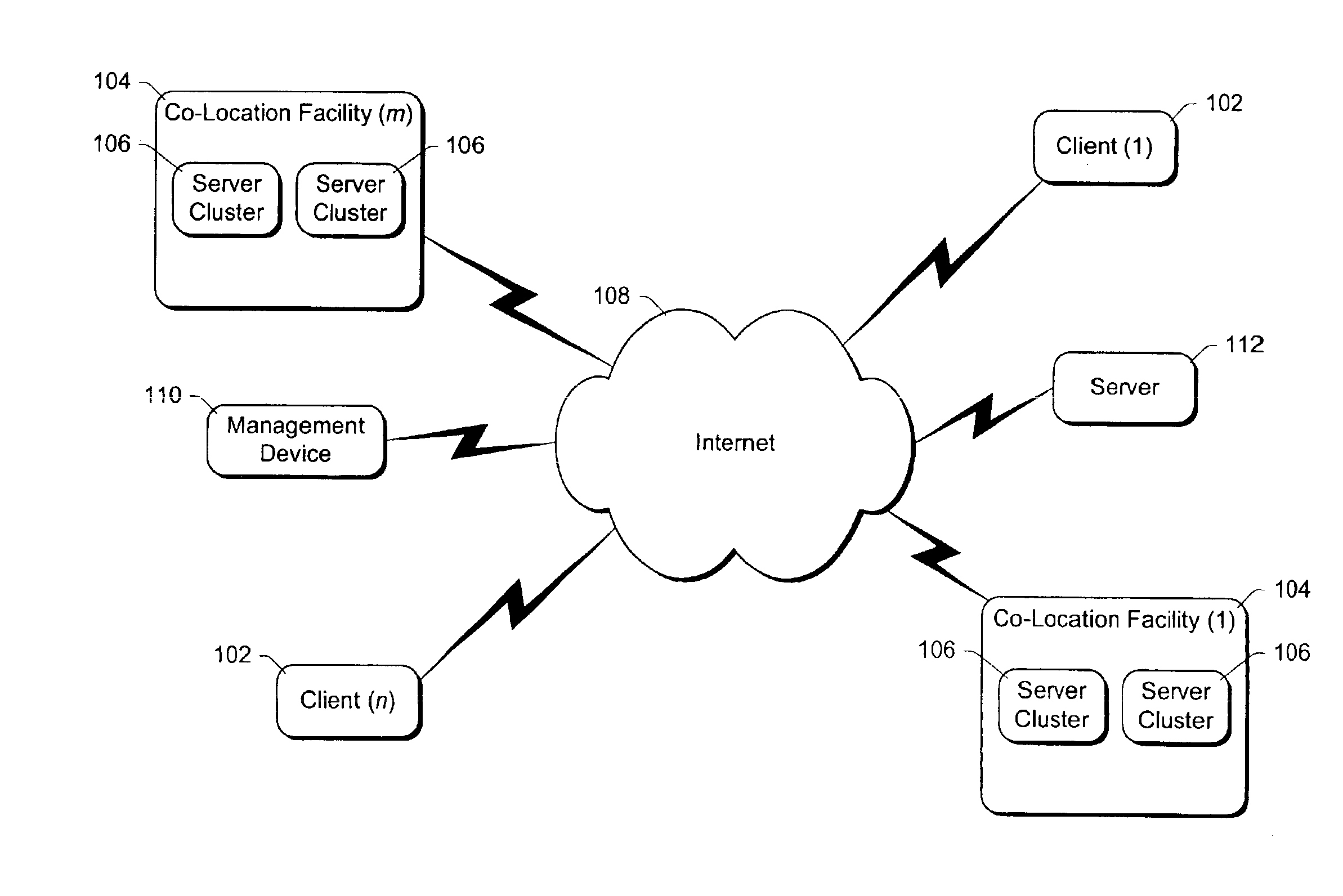
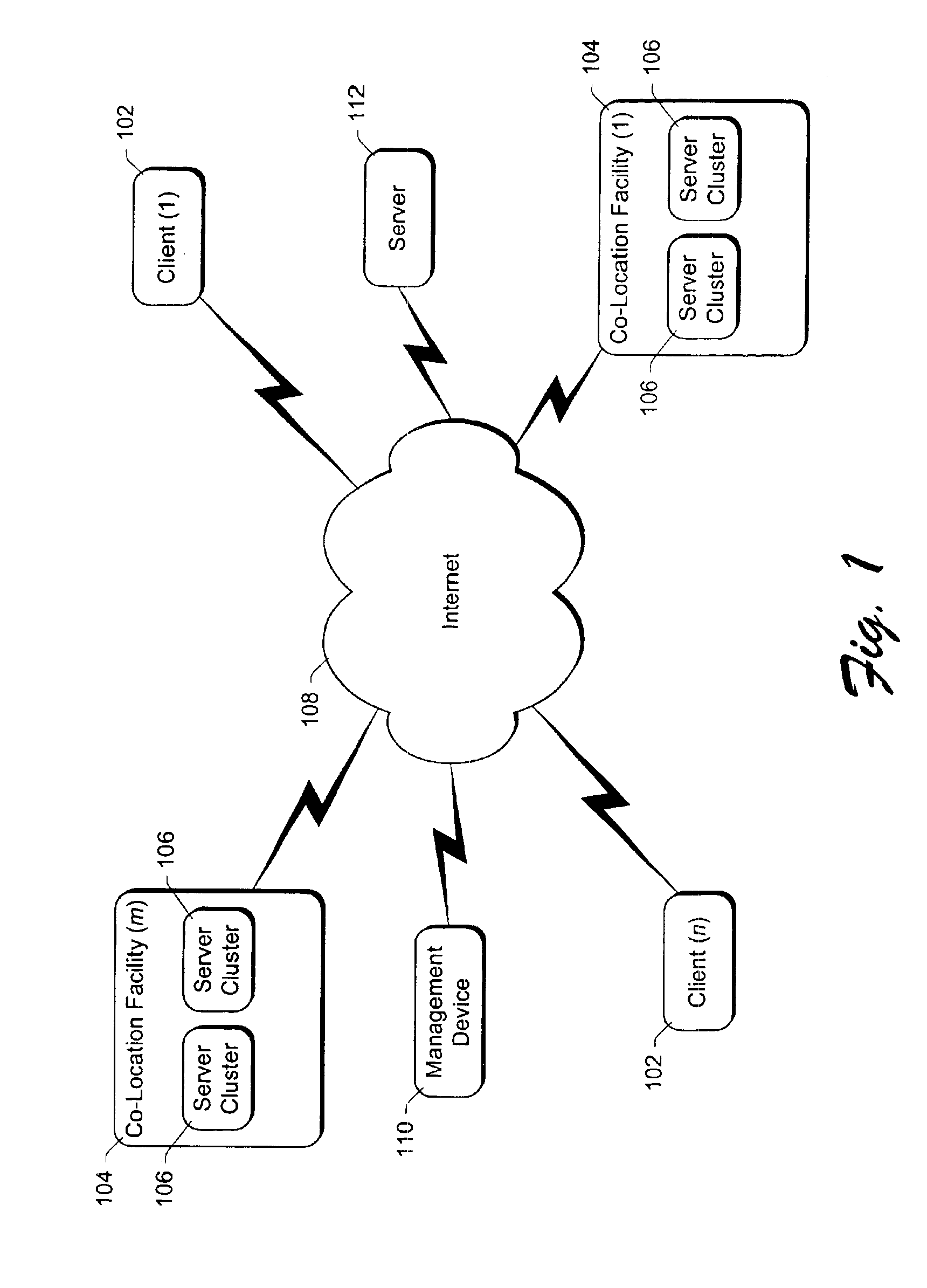
InactiveUS6886038B1Avoid restrictionsMultiprogramming arrangementsMultiple digital computer combinationsThird partyThe Internet
A controller, referred to as the “BMonitor”, is situated on a computer. The BMonitor includes a plurality of filters that identify where data can be sent to and / or received from, such as another node in a co-location facility or a client computer coupled to the computer via the Internet. The BMonitor further receives and implements requests from external sources regarding the management of software components executing on the computer, allowing such external sources to initiate, terminate, debug, etc. software components on the computer. Additionally, the BMonitor operates as a trusted third party mediating interaction among multiple external sources managing the computer.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for managing account information
A method and system for authenticating the identity of a consumer is disclosed. After the consumer is authenticated by a trusted third party, the consumer designates accounts that the consumer wishes to “lock.” When a party requests access to that account, the consumer is notified through the consumer's phone and asked to input a PIN. If the consumer provides the PIN, the requestor is granted access to the consumer's account without requiring further input from the consumer. If the party authorizing the transaction in this “two-factor” authentication does not possess both the phone and the consumer's PIN, or that party elects not to provide the PIN, the request will not be authenticated.
Owner:DEBIX ONE
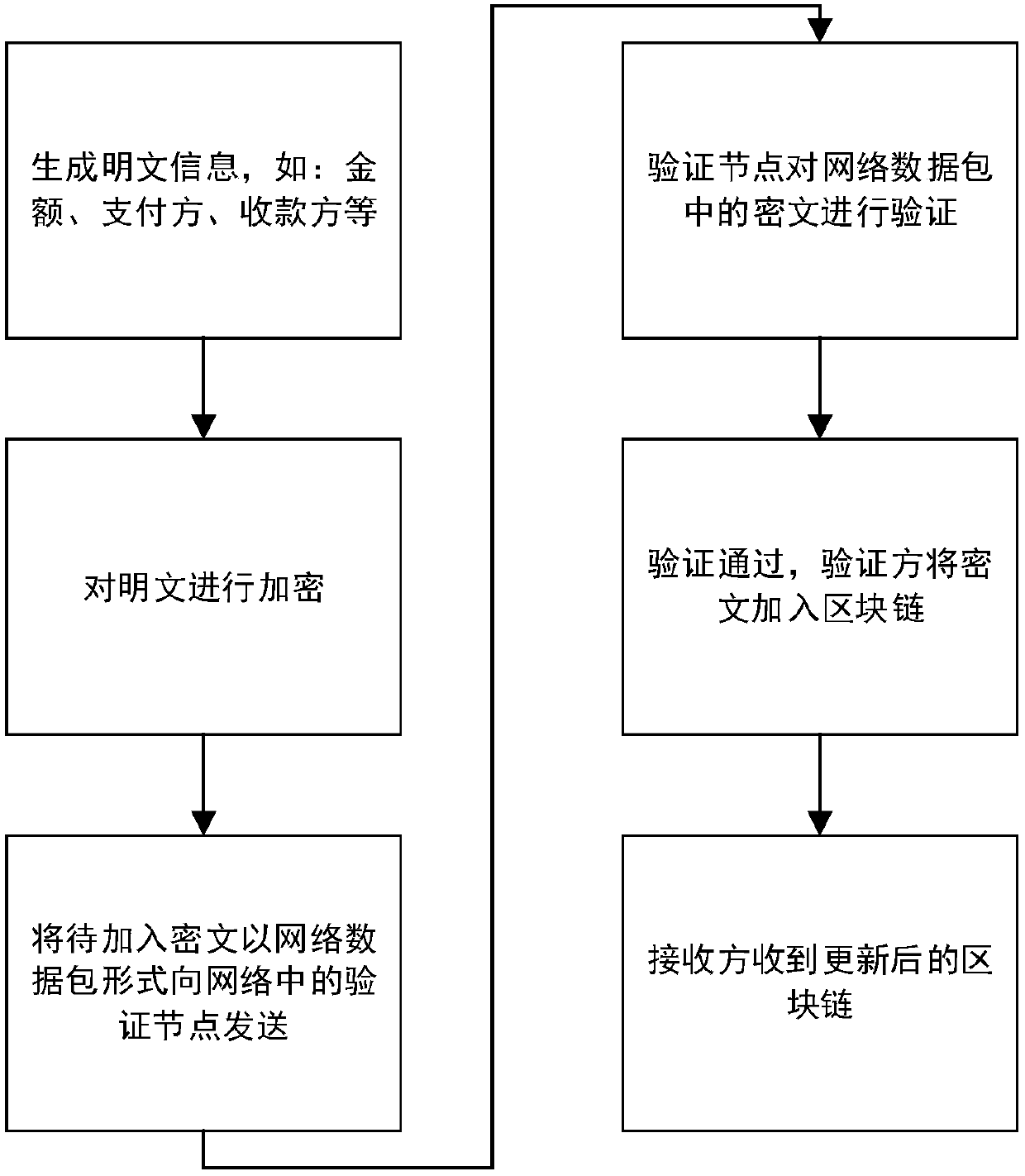
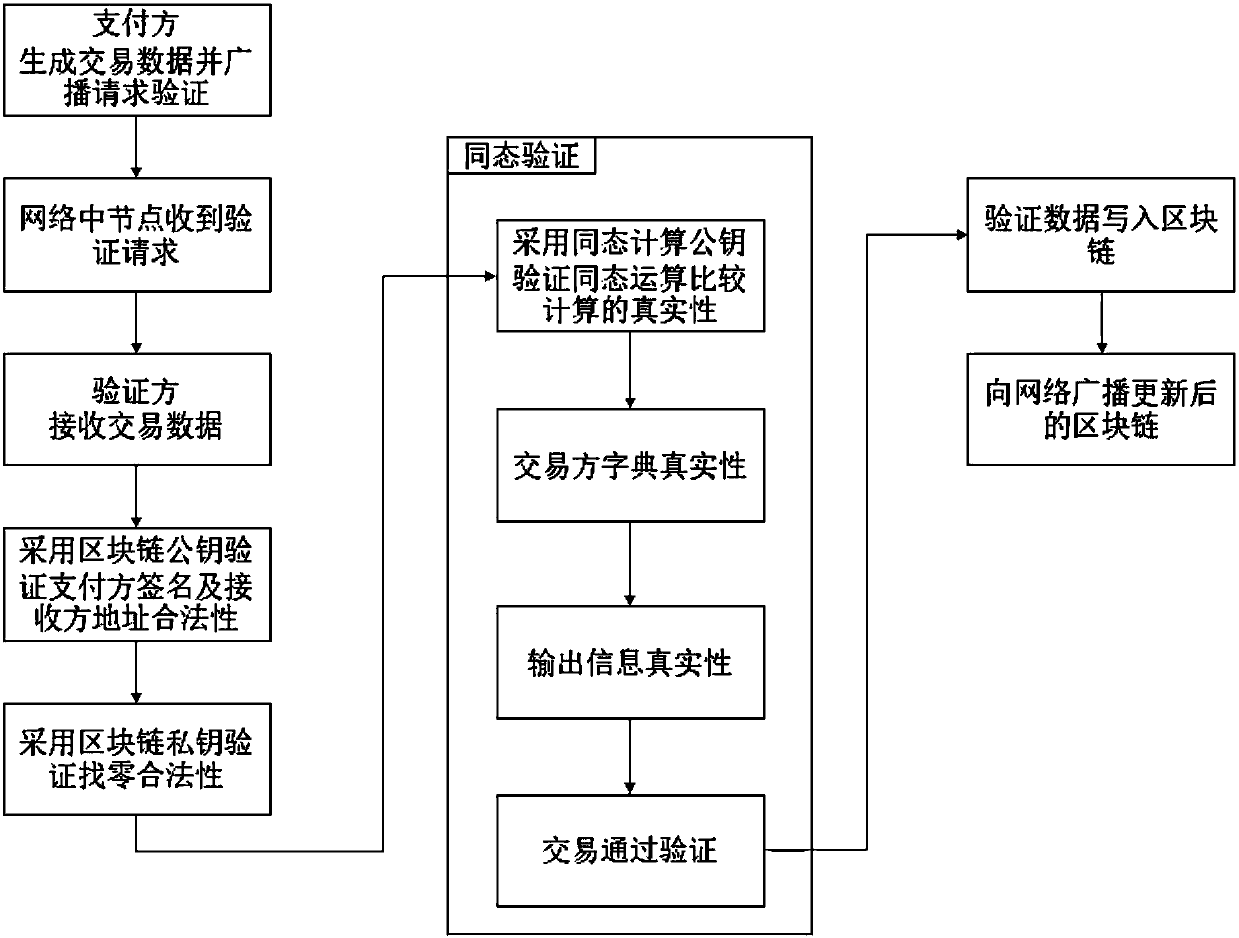
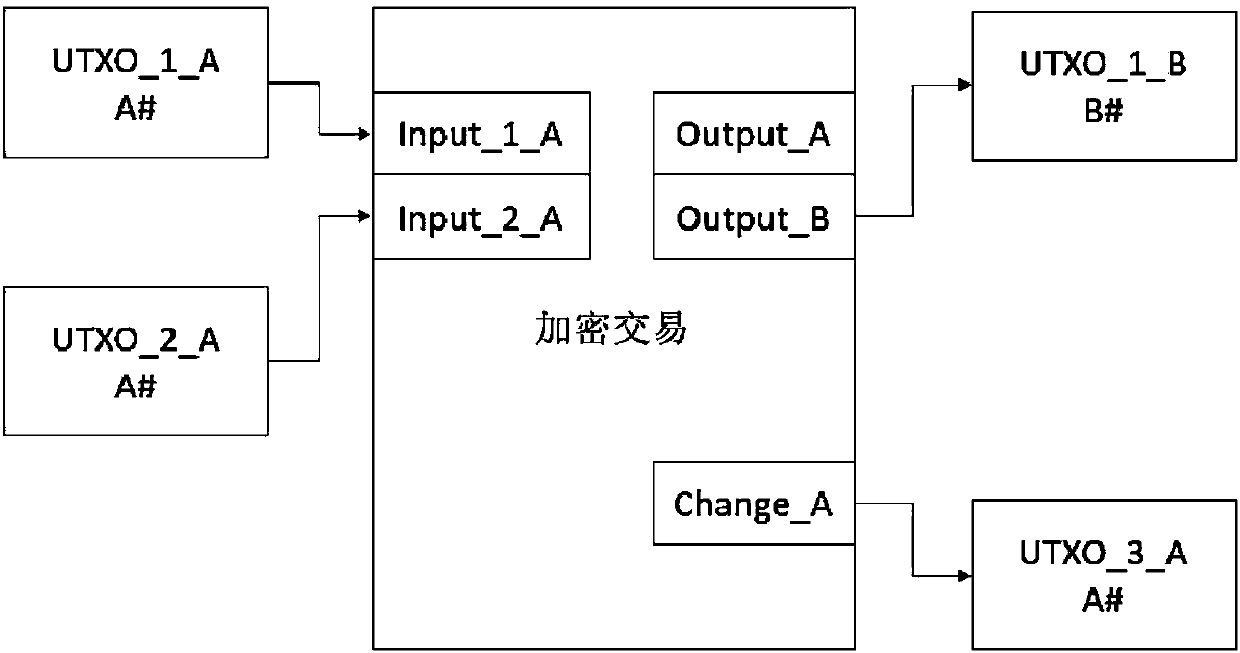
Method of blockchain information encryption based on complete homomorphic encryption method
ActiveCN107666388AImprove data securityImprove confidentialityUser identity/authority verificationDigital data protectionPlaintextThird party
A method of blockchain information encryption based on a complete homomorphic encryption method comprises: performing complete homomorphic encryption of a plaintext to be encrypted through an information encryption side and then performing signature; publishing a verification request to all the nodes in a network in public through adoption of an encrypted plaintext; respectively employing blockchain public keys by all the nodes to perform blockchain verification of the signature and an information receiving side, and employing complete homomorphic public keys to perform homomorphic encryptionoperation verification of the ciphertext; and after the verification passes, packing the information encryption side information, the information receiving side information and the ciphertext to generate an updated blockchain, performing broadcast of the network, and completing updating operation of the blockchain. The method provided by the invention greatly improve data safety and privacy of theblockchain technology, is more concise in the whole structure and effective, does not need to introduce a trusted third party and greatly extend and improve an original blockchain technology model, and only needs the smallest improvement to reach a secrecy effect.
Owner:郑珂威
Information system for industrial vehicles
ActiveUS20110040440A1Vehicle testingRegistering/indicating working of vehiclesEngineeringTrusted third party
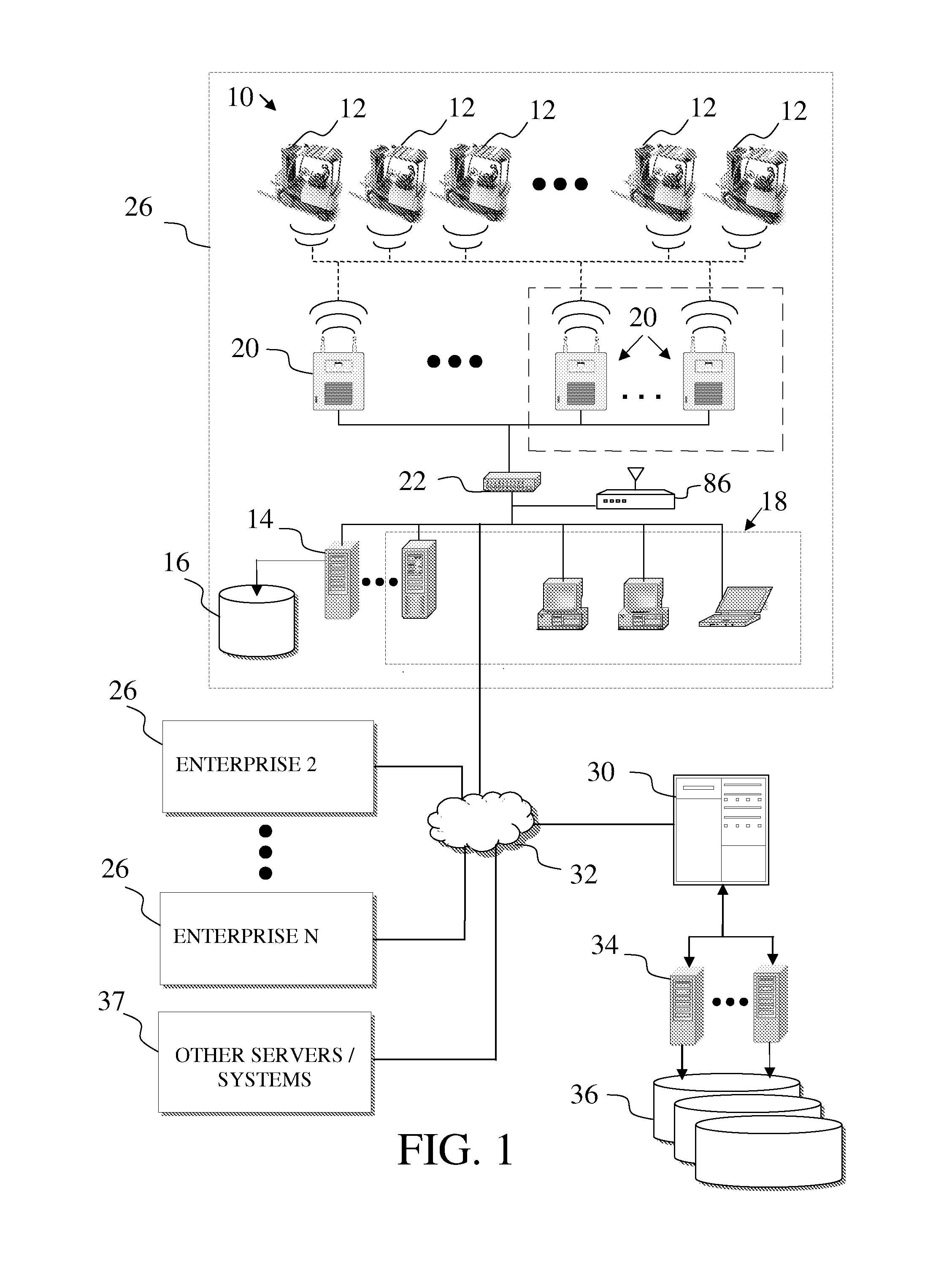
Industrial vehicles communicate across a wireless environment and the wireless communication, data collection and / or processing capabilities of industrial vehicles are utilized to implement dashboard functions that thread status information from detail level views, up through intermediate views and to summary level views to facilitate efficient fleet maintenance, management and control. Further, industrial vehicle data may be communicated to a trusted third party server. As such, wirelessly collected industrial vehicle information is utilized within robust software solutions that aggregate and analyze data across multiple enterprises.
Owner:CROWN EQUIP CORP
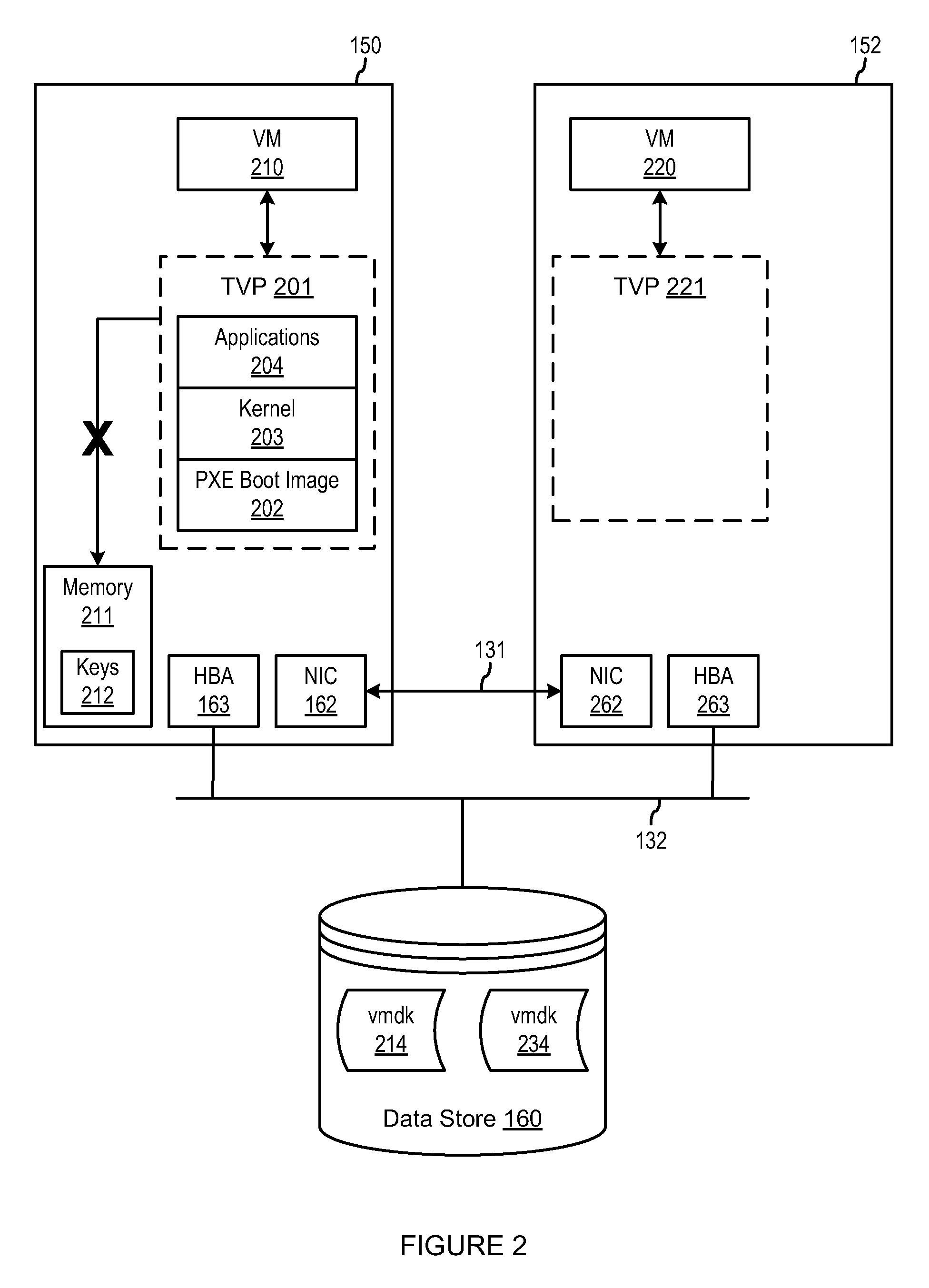
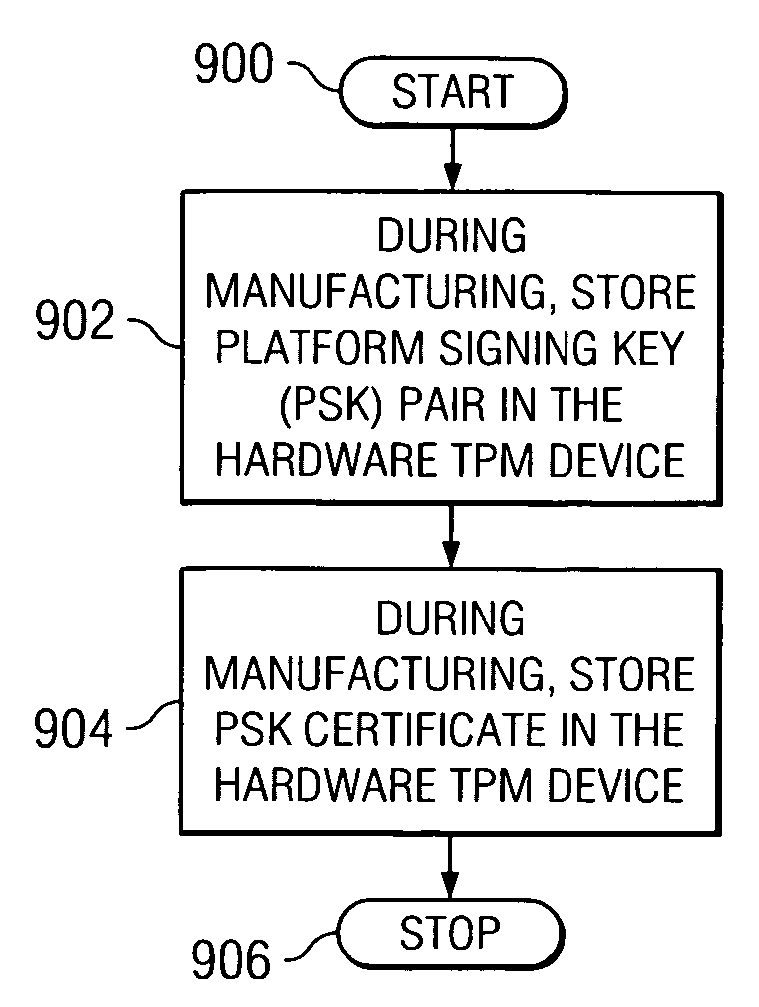
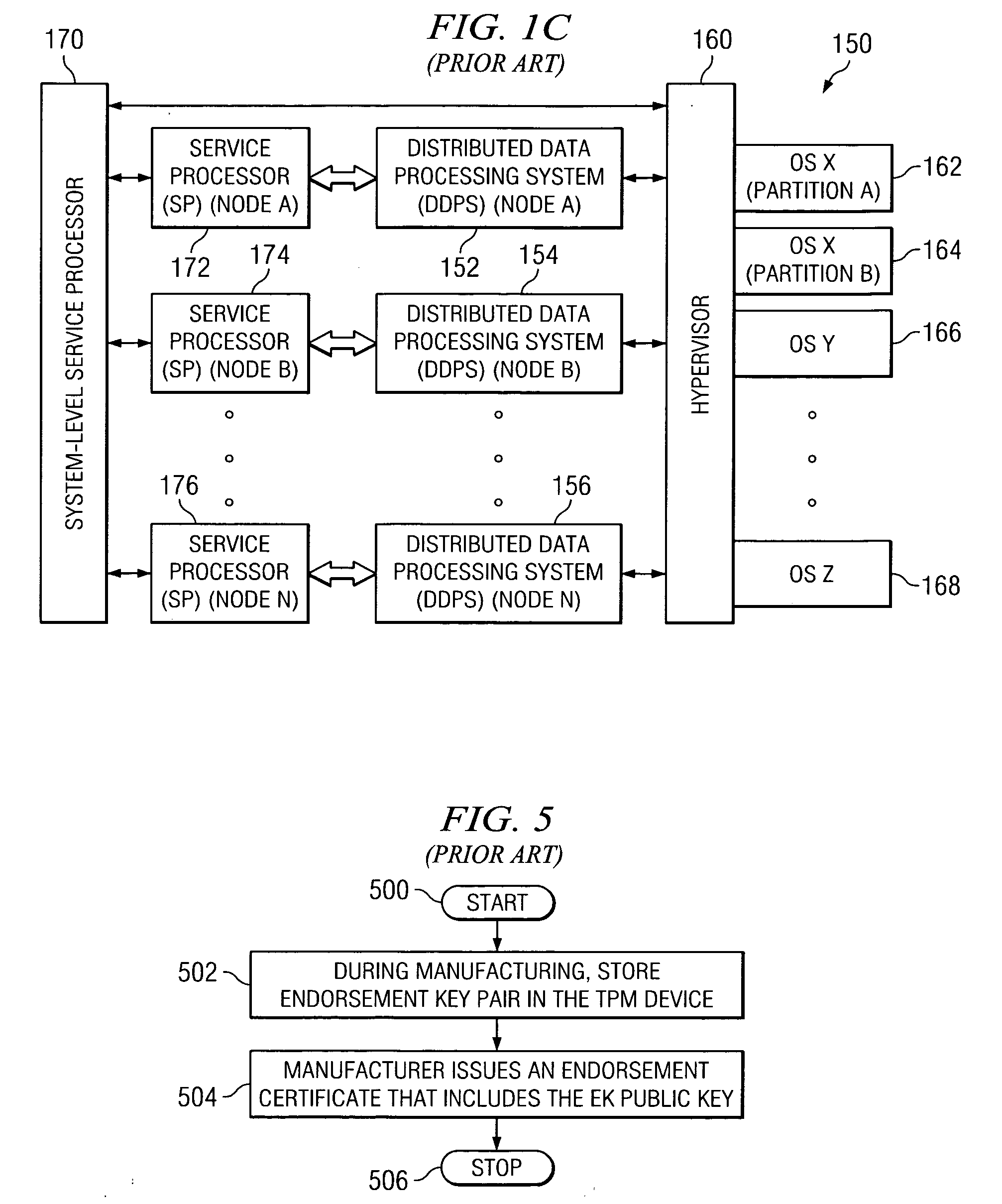
Method, apparatus, and product for establishing virtual endorsement credentials for dynamically generated endorsement keys in a trusted computing platform
ActiveUS20070016801A1User identity/authority verificationUnauthorized memory use protectionData processing systemThird party
A method, apparatus, and computer program product are disclosed in a data processing system for establishing virtual endorsement credentials. The data processing system includes a hardware trusted platform module (TPM). Logical partitions are generated in the system. A different virtual TPM is generated for each one of the logical partitions. For each one of the logical partitions, the virtual TPM that was generated for the logical partition then dynamically generates a virtual endorsement credential for use by the logical partition that includes the virtual TPM. The virtual endorsement credential is generated within the data processing system without the data processing system or its devices accessing a trusted third party that is external to the data processing system.
Owner:IBM CORP
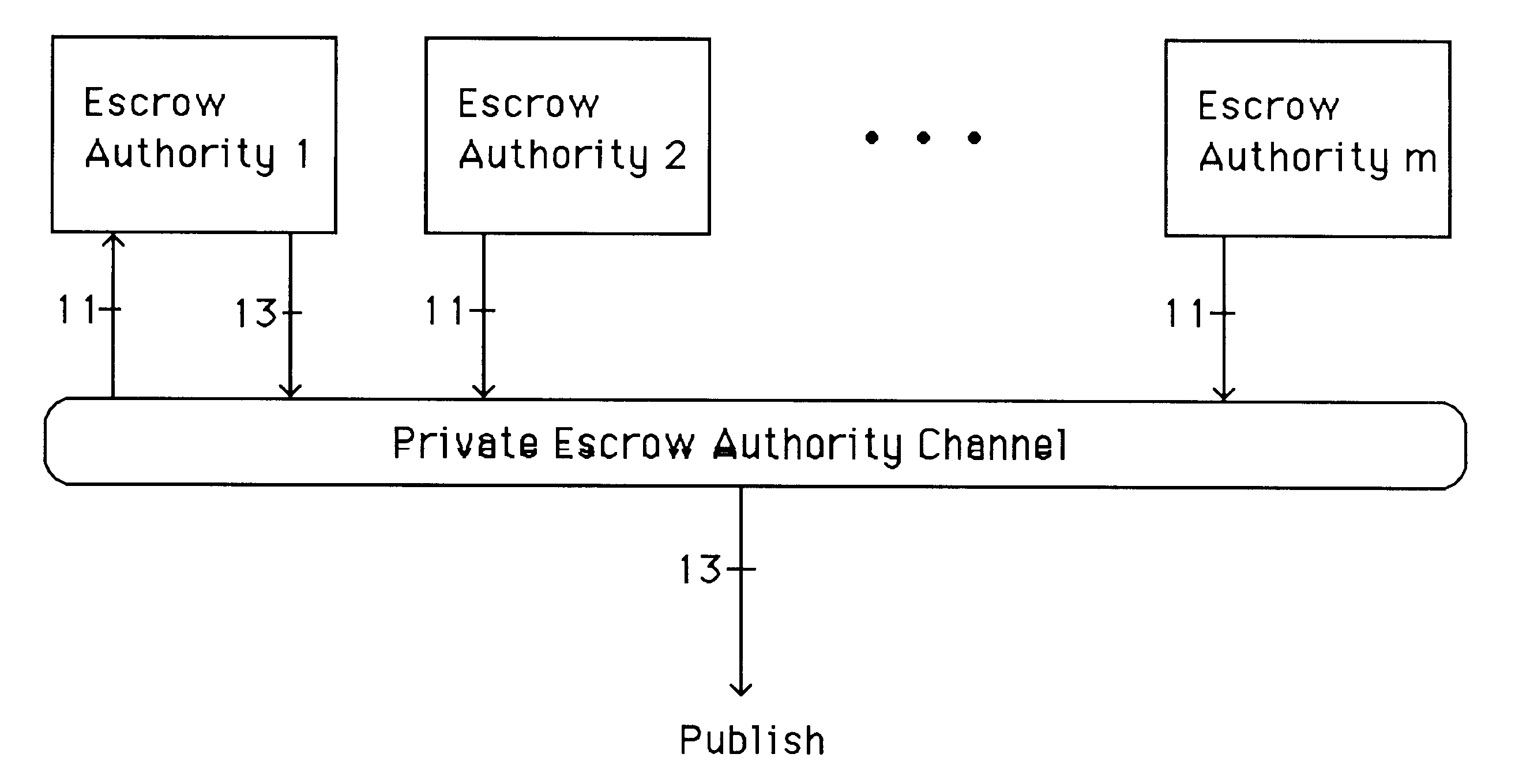
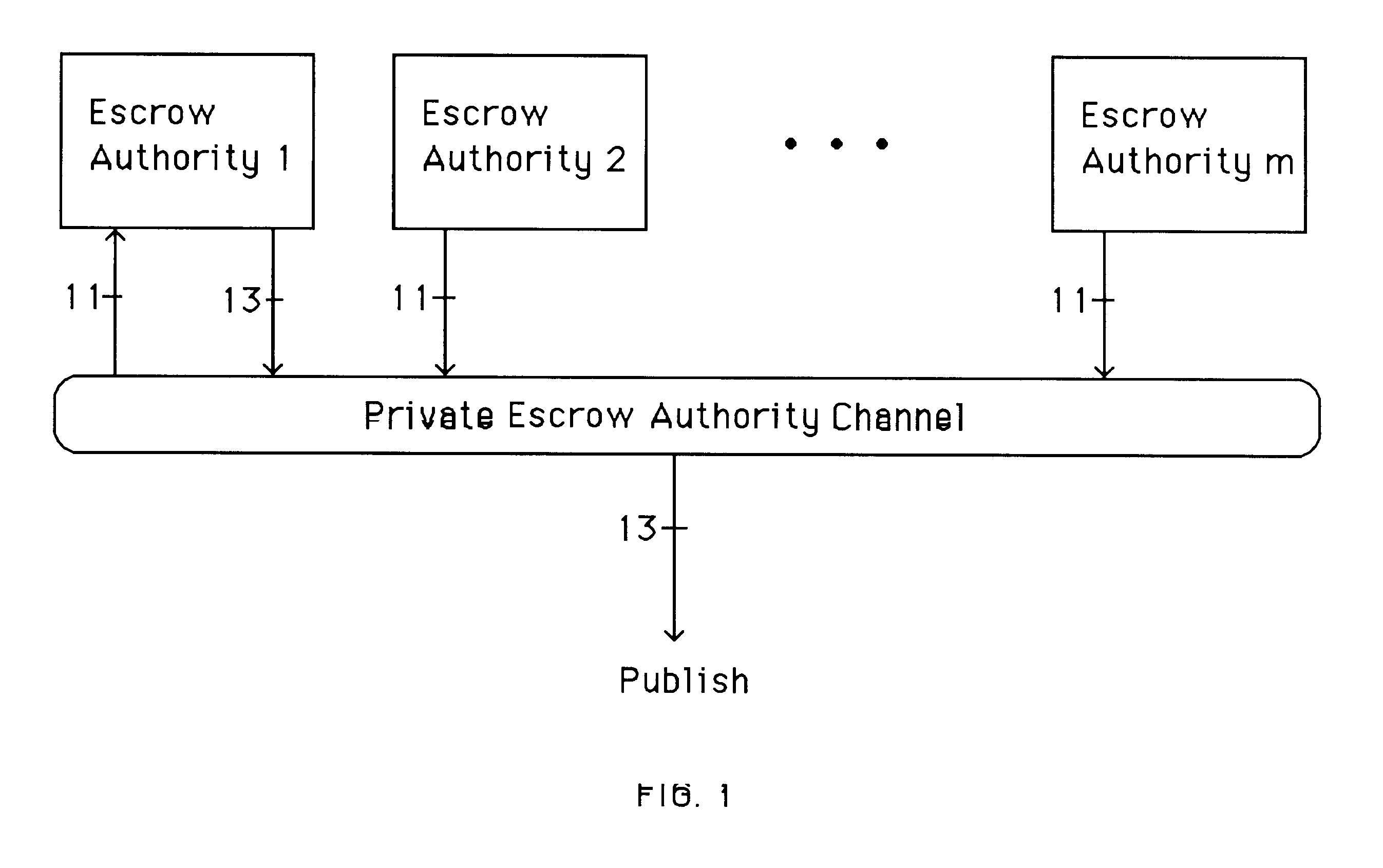
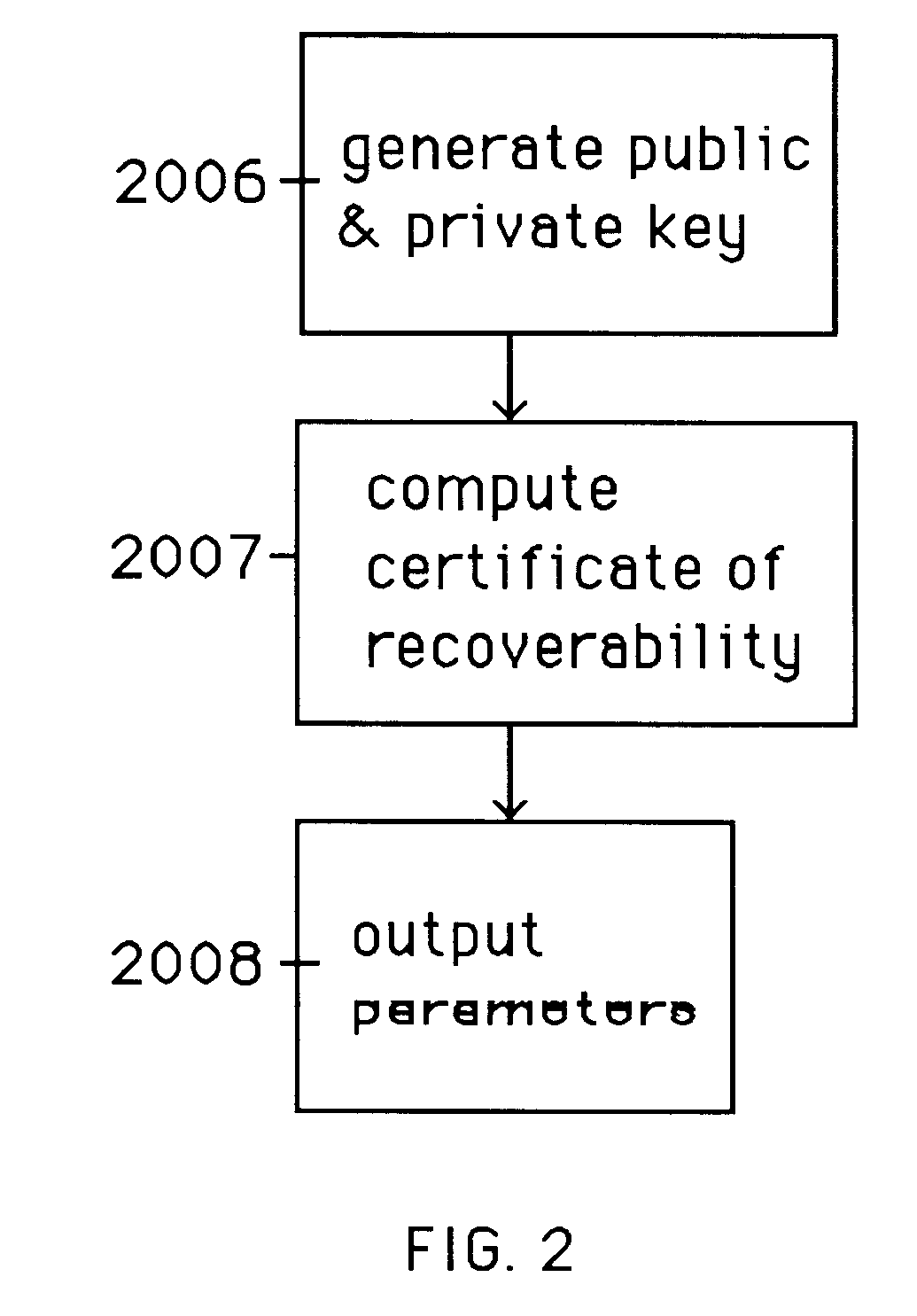
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
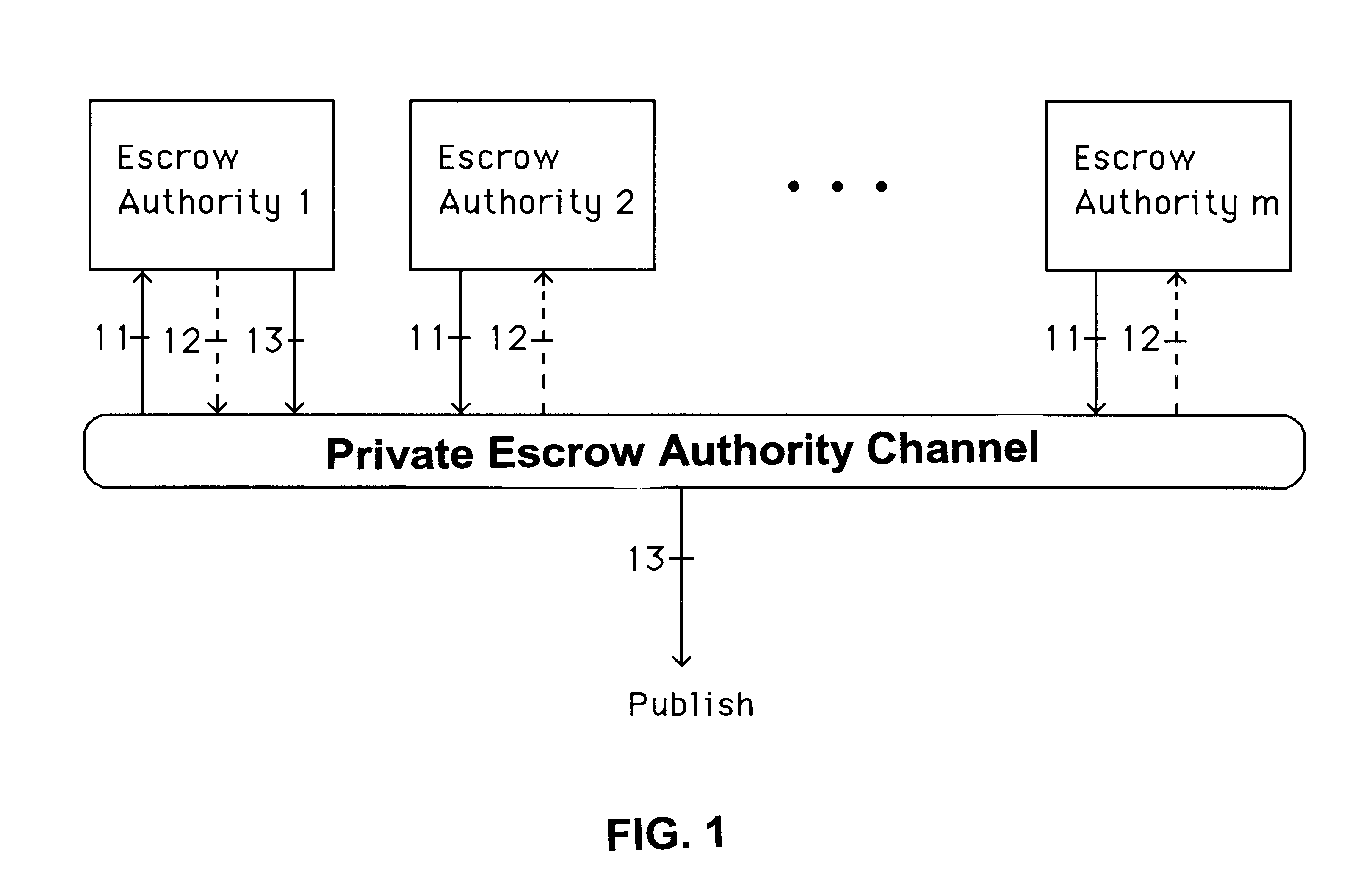
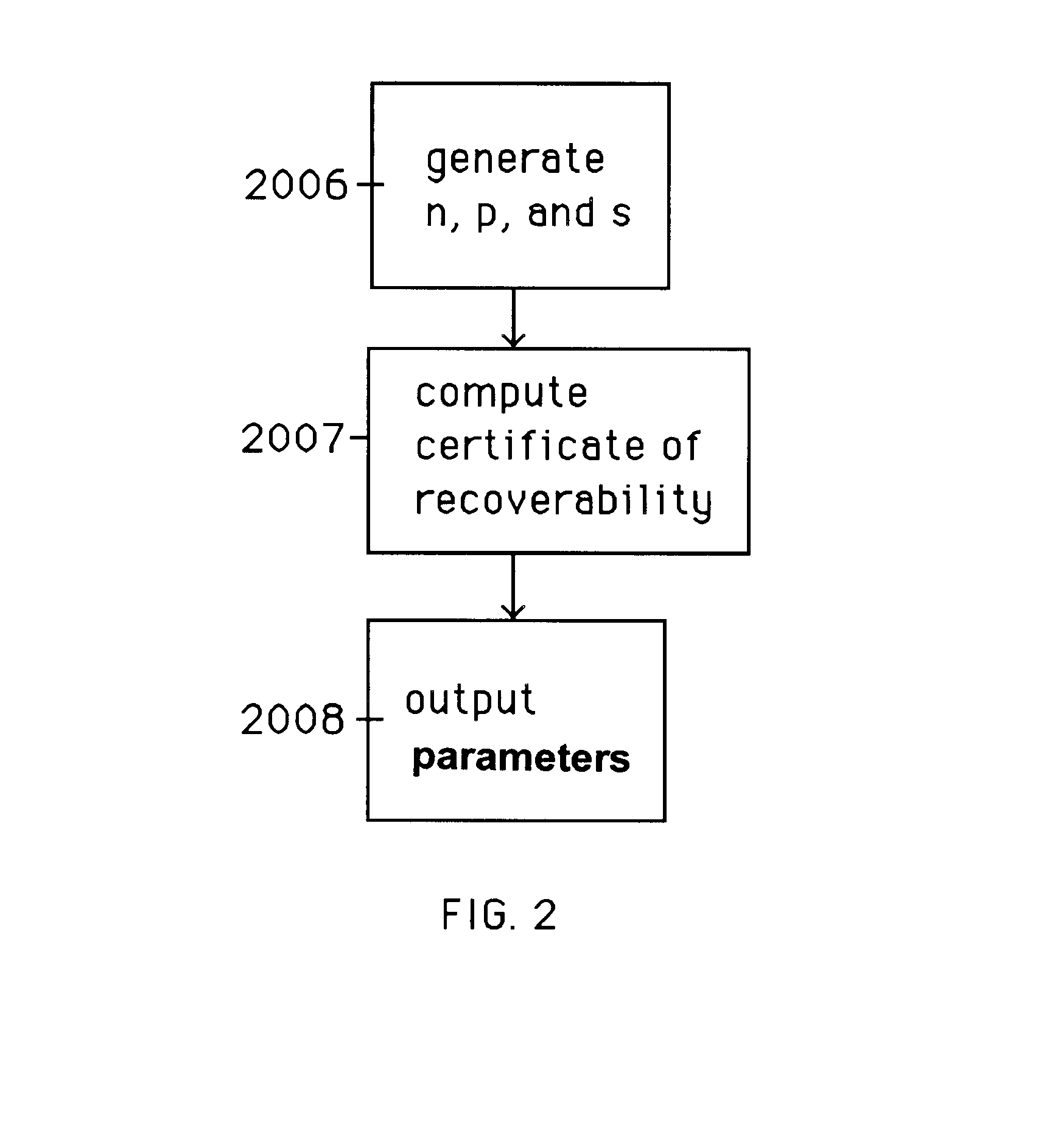
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
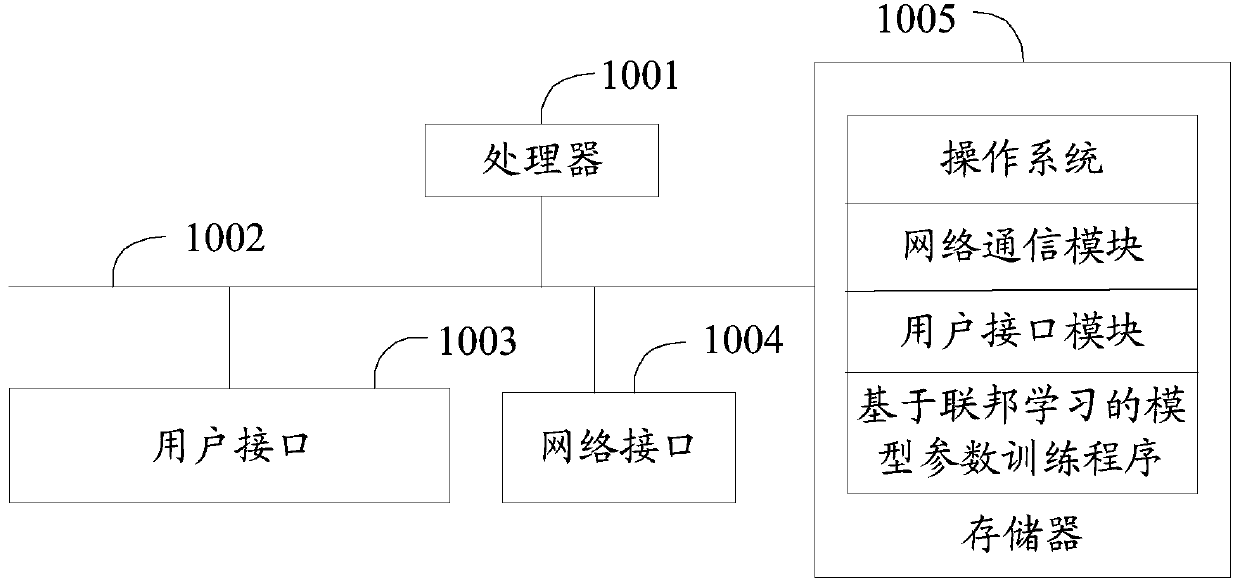
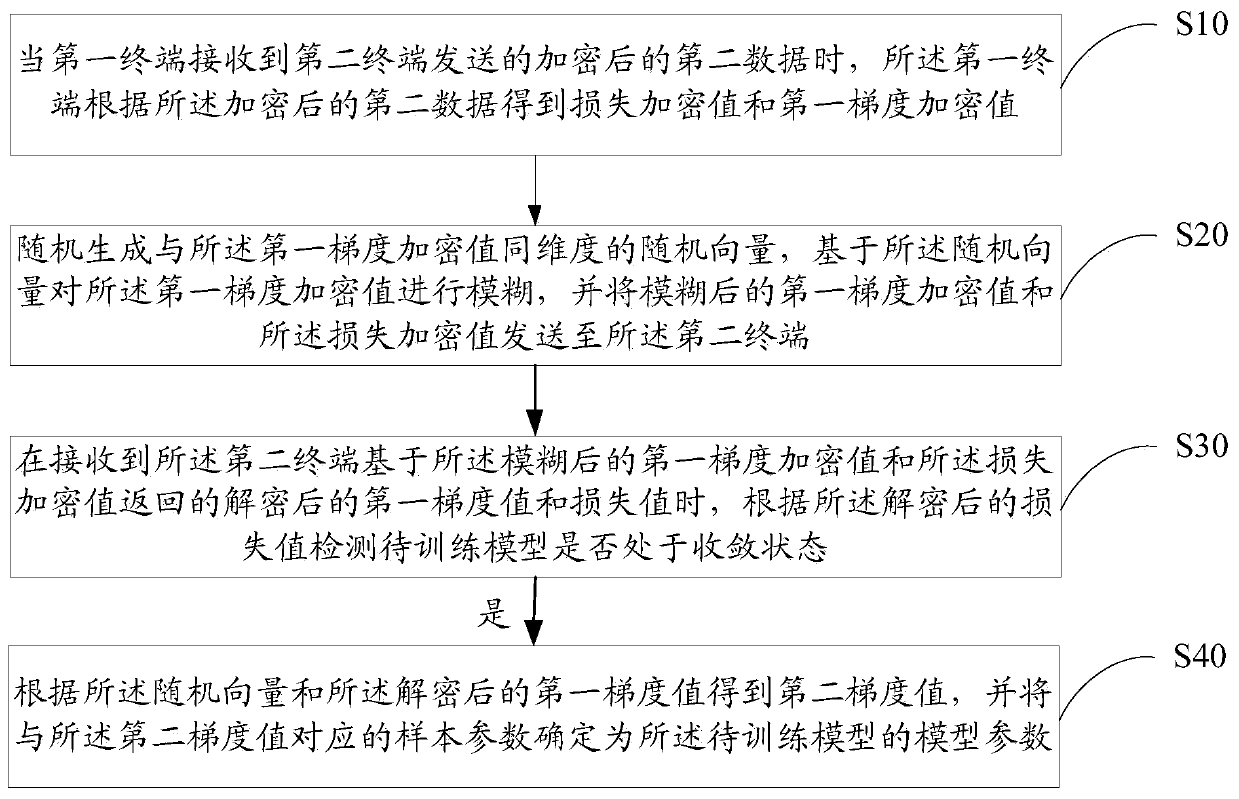
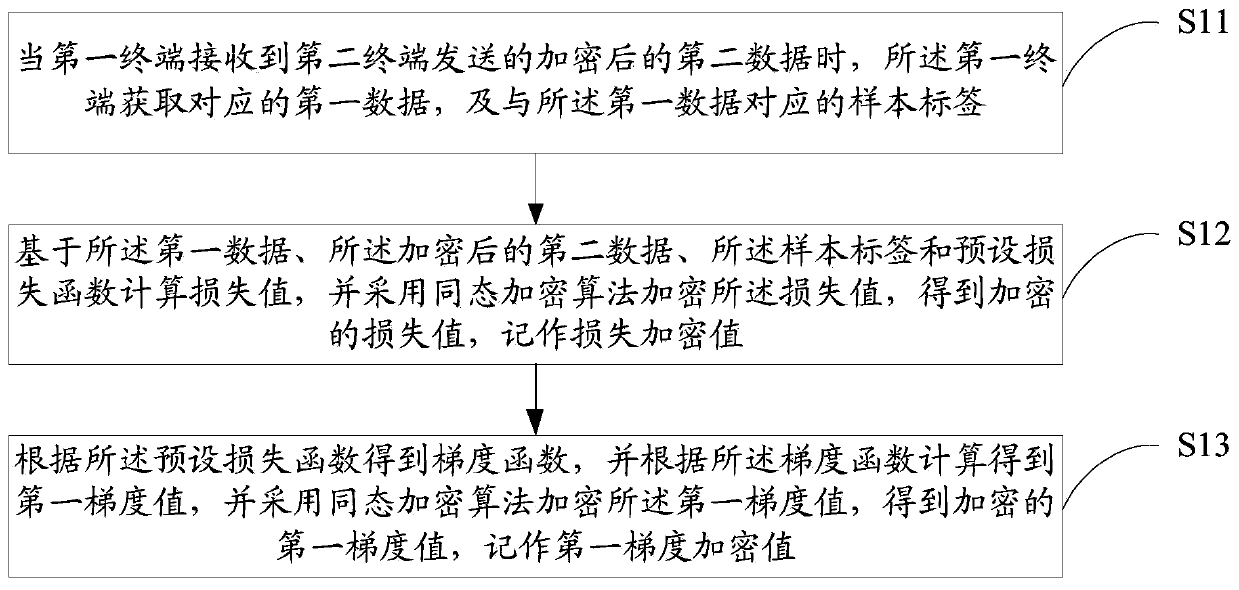
Model parameter training method and device based on federated learning, equipment and medium
PendingCN109886417ASolve application limitationsWon't leakPublic key for secure communicationDigital data protectionTrusted third partyModel parameters
The invention discloses a model parameter training method and device based on federal learning, equipment and a medium. The method comprises the following steps: when a first terminal receives encrypted second data sent by a second terminal, obtaining a corresponding loss encryption value and a first gradient encryption value; randomly generating a random vector with the same dimension as the first gradient encryption value, performing fuzzy on the first gradient encryption value based on the random vector, and sending the fuzzy first gradient encryption value and the loss encryption value toa second terminal; when the decrypted first gradient value and the loss value returned by the second terminal are received, detecting whether the model to be trained is in a convergence state or not according to the decrypted loss value; and if yes, obtaining a second gradient value according to the random vector and the decrypted first gradient value, and determining the sample parameter corresponding to the second gradient value as the model parameter. According to the method, model training can be carried out only by using data of two federated parties without a trusted third party, so thatapplication limitation is avoided.
Owner:WEBANK (CHINA)
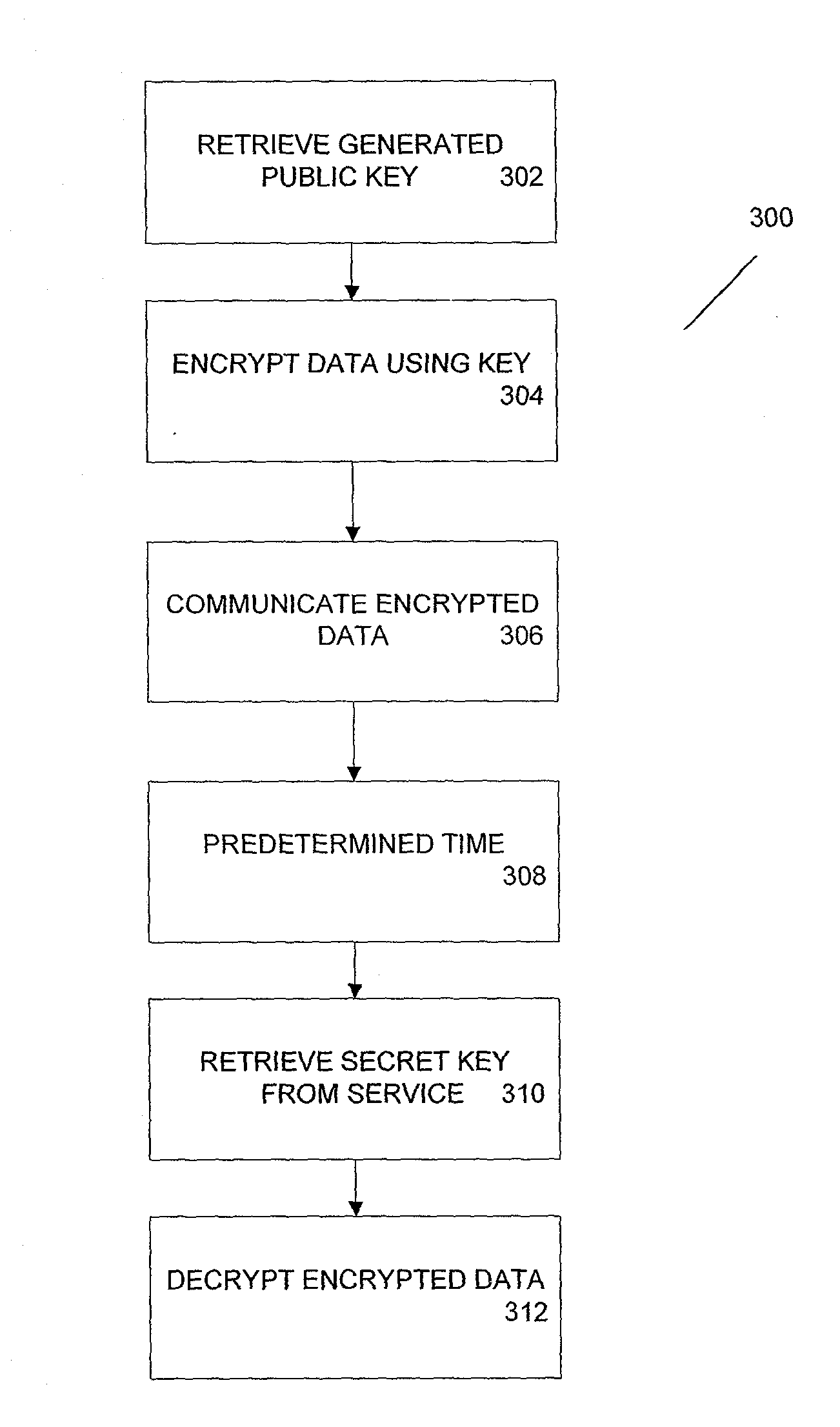
Method and apparatus for time-lapse cryptography
ActiveUS20100185863A1Key distribution for secure communicationMultiple keys/algorithms usageThird partyCiphertext
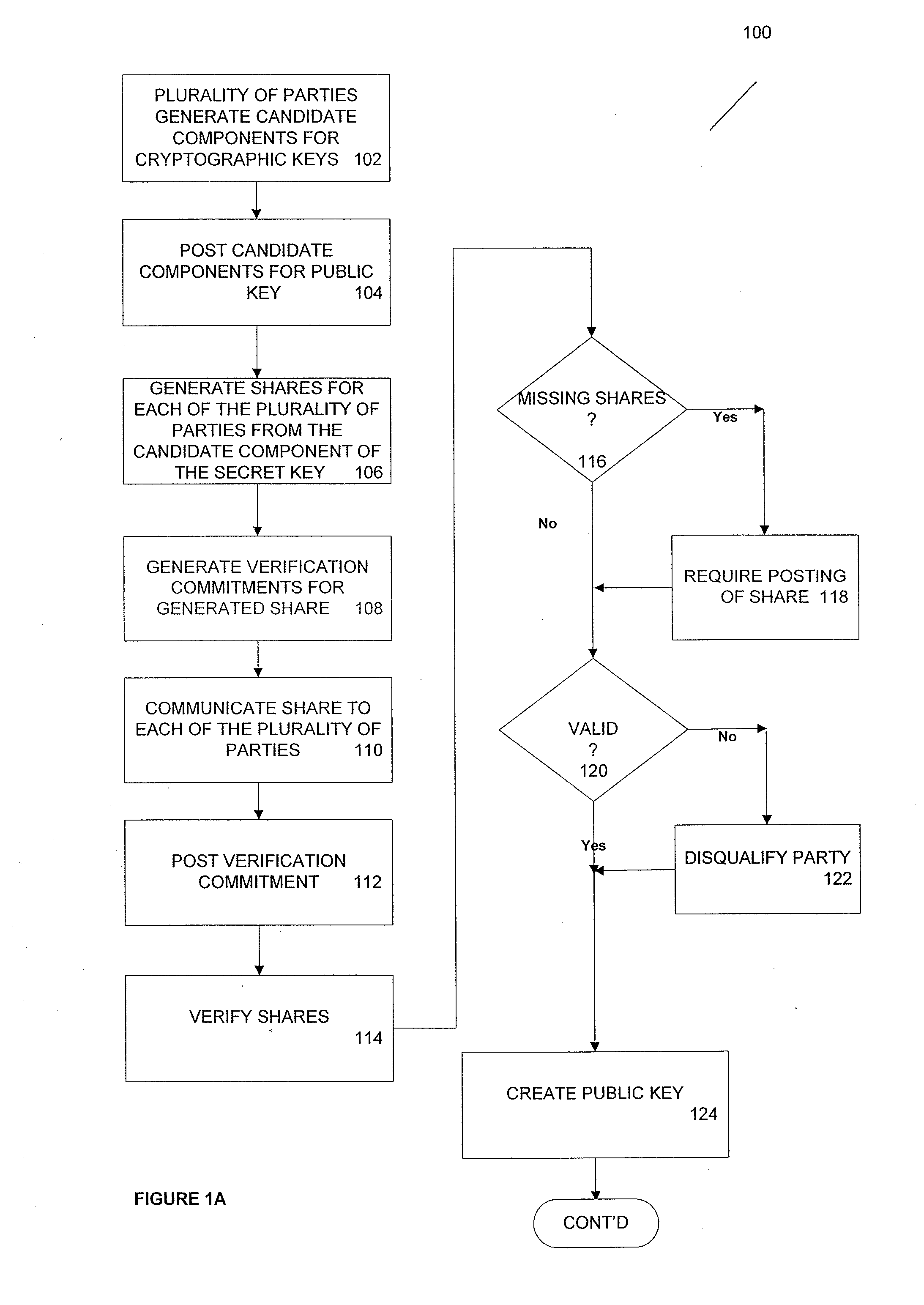
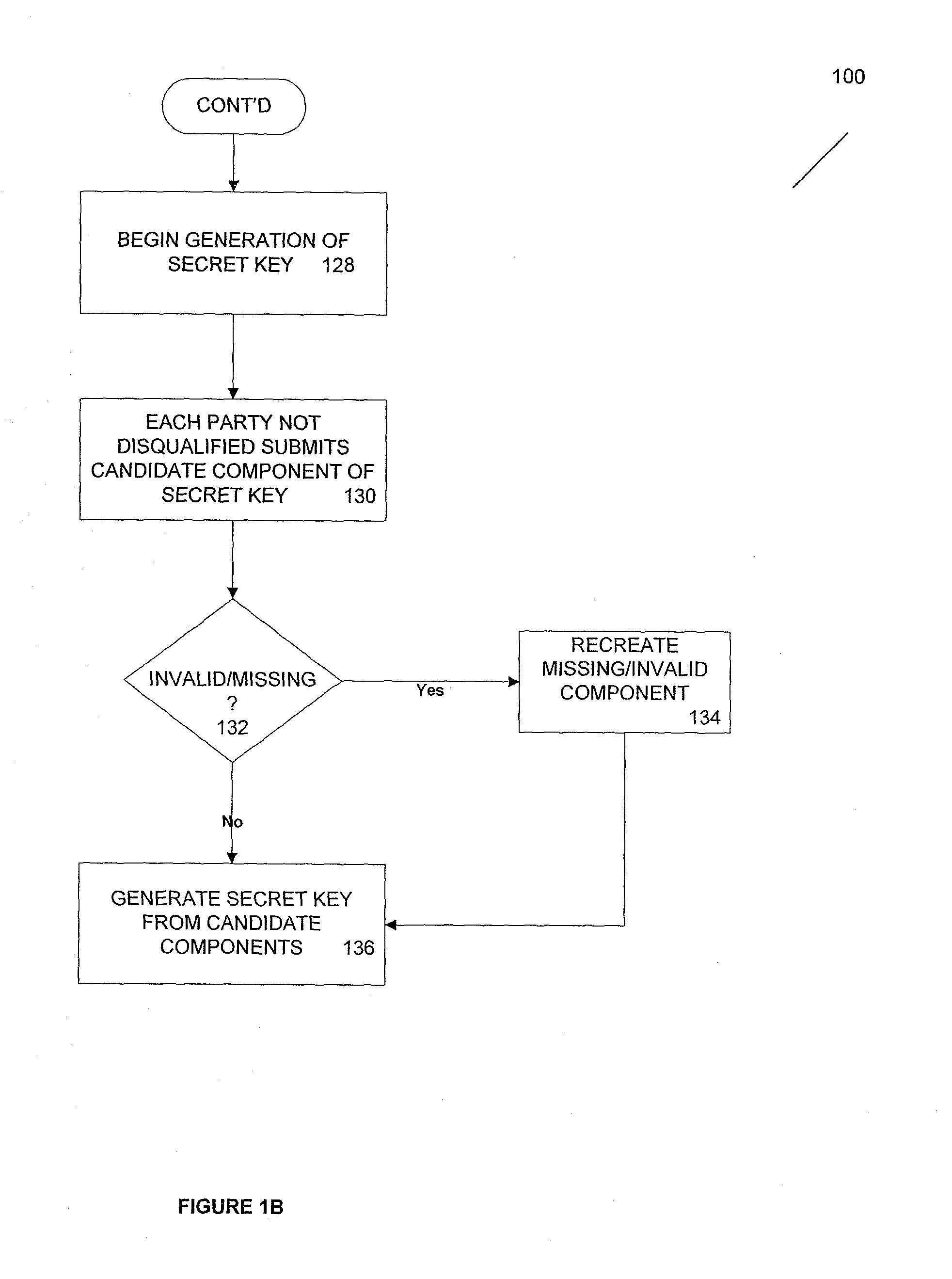
According to one aspect, provided is a construction and specification for an implementation of a new cryptographic primitive, “Time-Lapse Cryptography”, with which a sender can encrypt a message so that it is guaranteed to be revealed at an exact moment in the future, even if this revelation turns out to be undesirable to the sender. In one embodiment, a Time-Lapse Cryptography Service is provided (“the Service”) based on a network of parties. Senders encrypt their messages with this public key whose secret key is not known to anyone—not even a trusted third party—until a predefined and specific future time T+δ, at which point the secret key is constructed and published. In one example, the secret key can only be known after it is constructed. At or after that time, anyone can decrypt the cipher text using this secret key. Other embodiments describe other applications of such a service, for example, one embodiment is used in sealed bid auctions, others in insider stock sales, clinical trials, and electronic voting, among a variety of possible implementations. In one embodiment, a method for cryptographic encoding is provided, including generation of cryptographic key components by a plurality of parties, where participation of the parties is verified. A public key is constructed from a plurality of key components,
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE
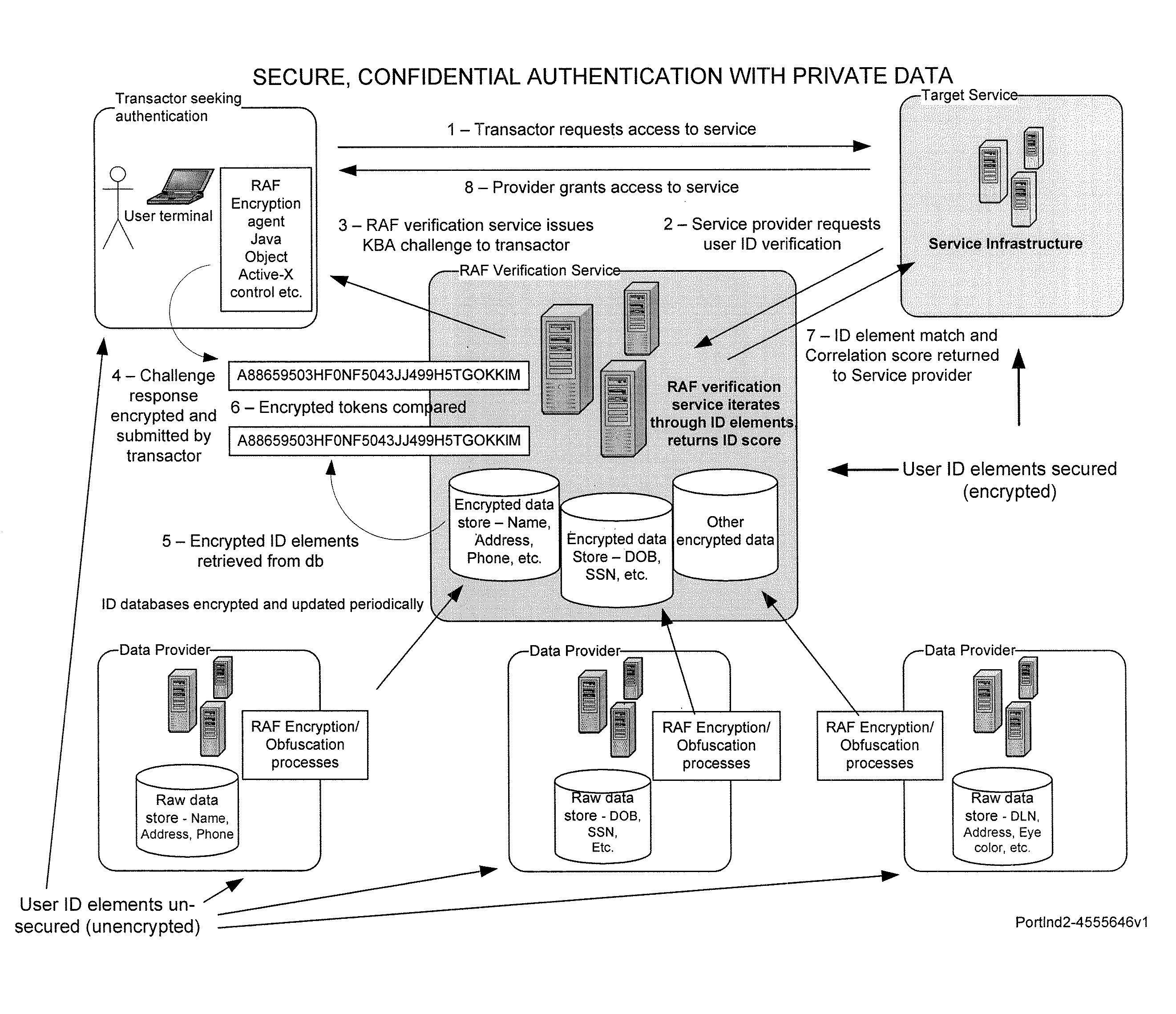
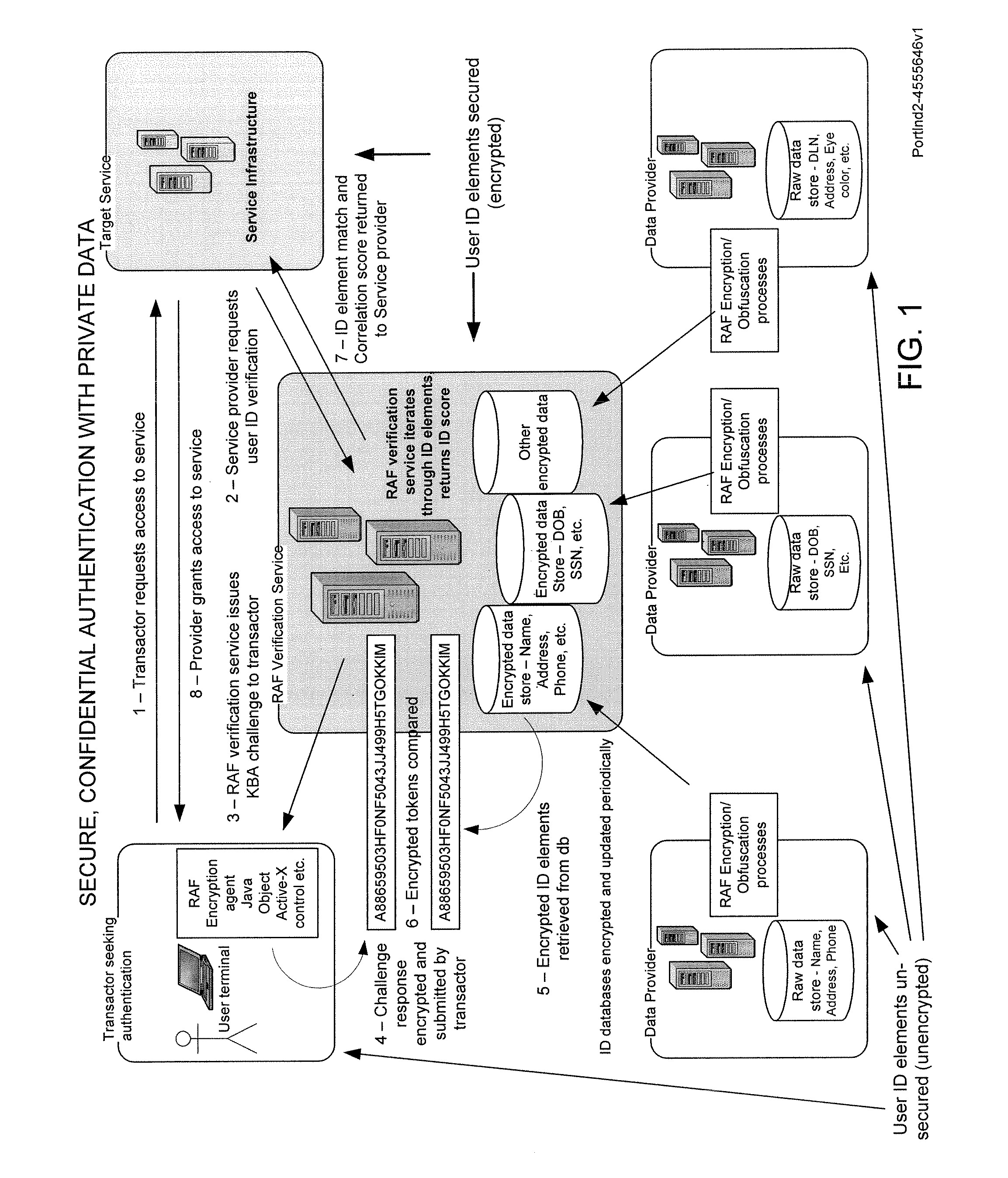
Secure, confidential authentication with private data
Risk of personal identity theft, especially in connection with on-line commerce, is mitigated by maintaining private data in a secure database maintained by a trusted third party verification service. To authenticate the identity of a user or customer, in one embodiment, a knowledge-based challenge is issued to the user, and the response is compared to stored data by the verification service. The verification service reports to the vendor, to authenticate the user identity, capability and or authorization for the proposed transaction without disclosing private data to the vendor.
Owner:MATTHEWS INT CORP
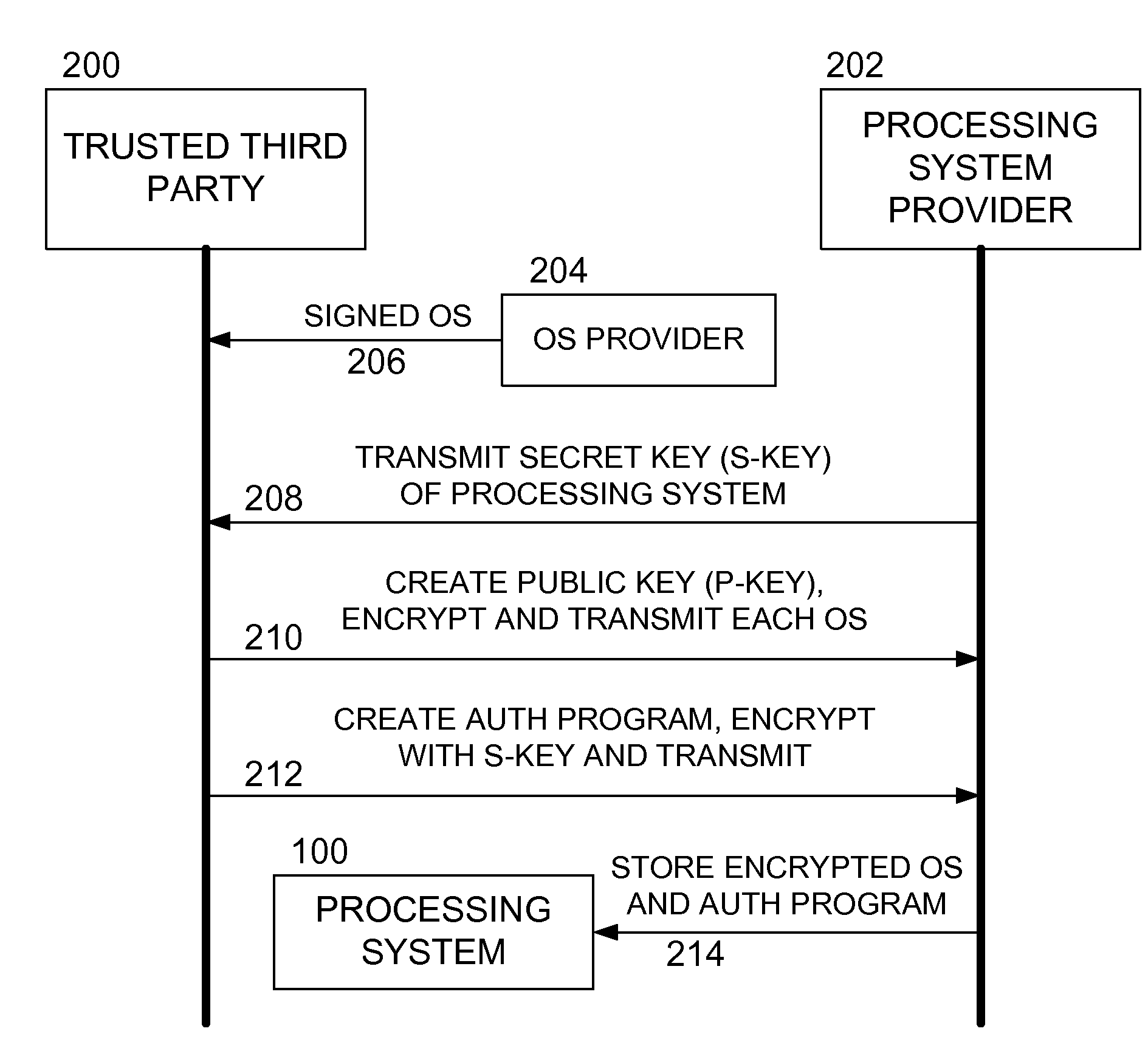
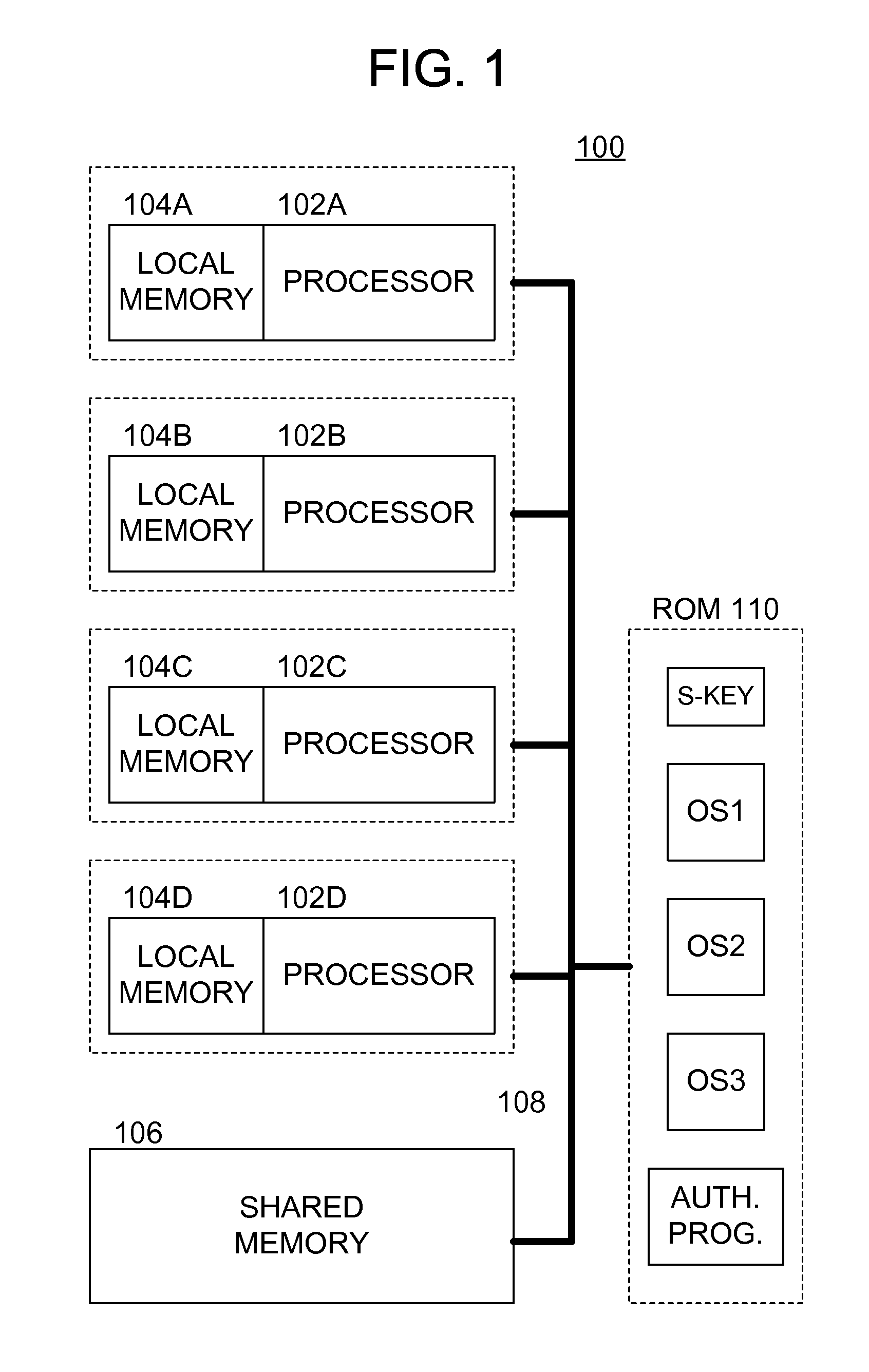
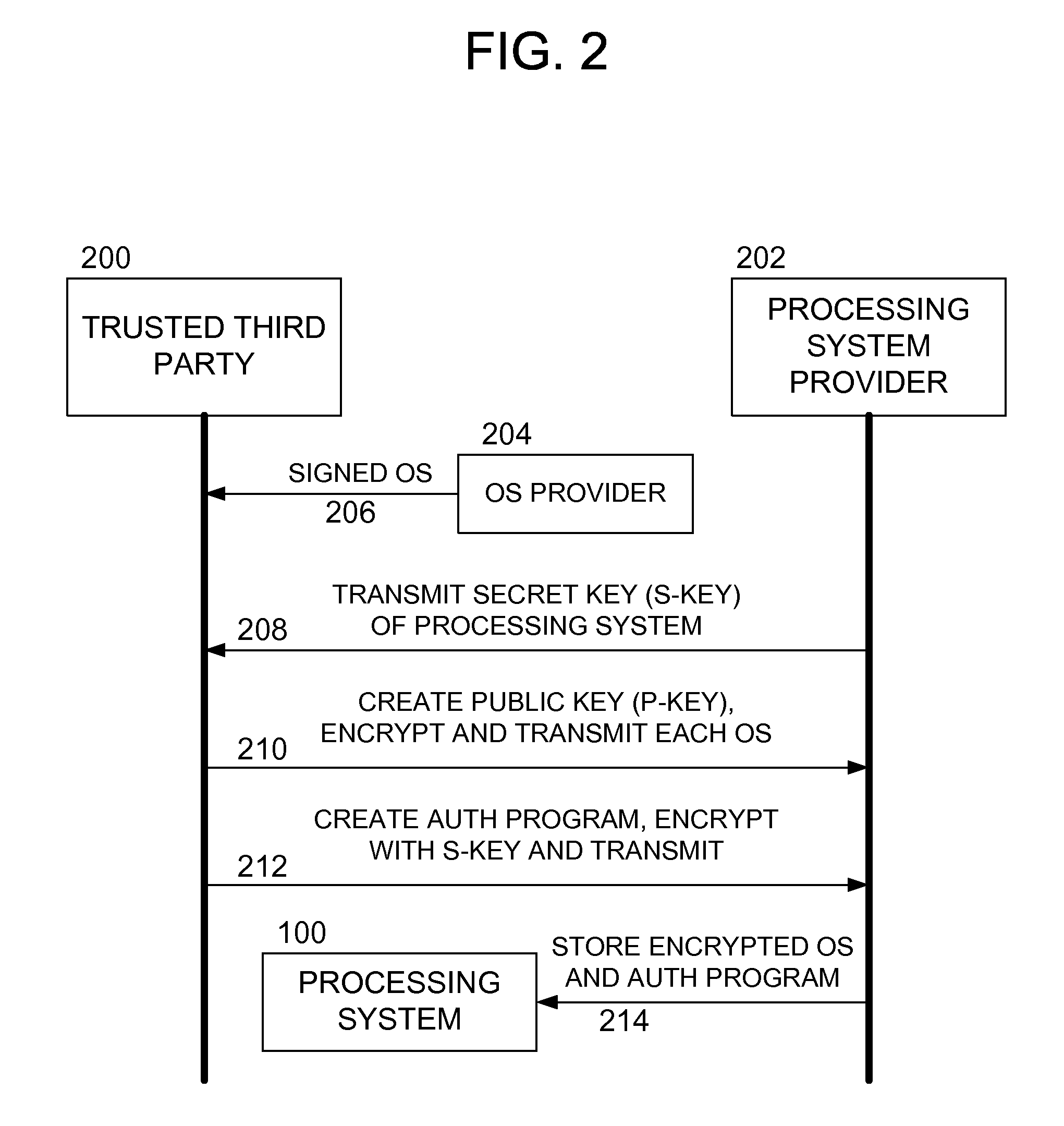
Methods and apparatus for secure operating system distribution in a multiprocessor system
ActiveUS20080282084A1Easy accessEasy to modifyKey distribution for secure communicationPublic key for secure communicationOperational systemMulti processor
Methods and apparatus provide for: decrypting a first of a plurality of operating systems (OSs) within a first processor of a multiprocessing system using a private key thereof, the plurality of OSs having been encrypted by a trusted third party, other than a manufacturer of the multiprocessing system, using respective public keys, each paired with the private key; executing an authentication program using the first processor to verify that the first OS is valid; and executing the first OS on the first processor.
Owner:SONY COMPUTER ENTERTAINMENT INC
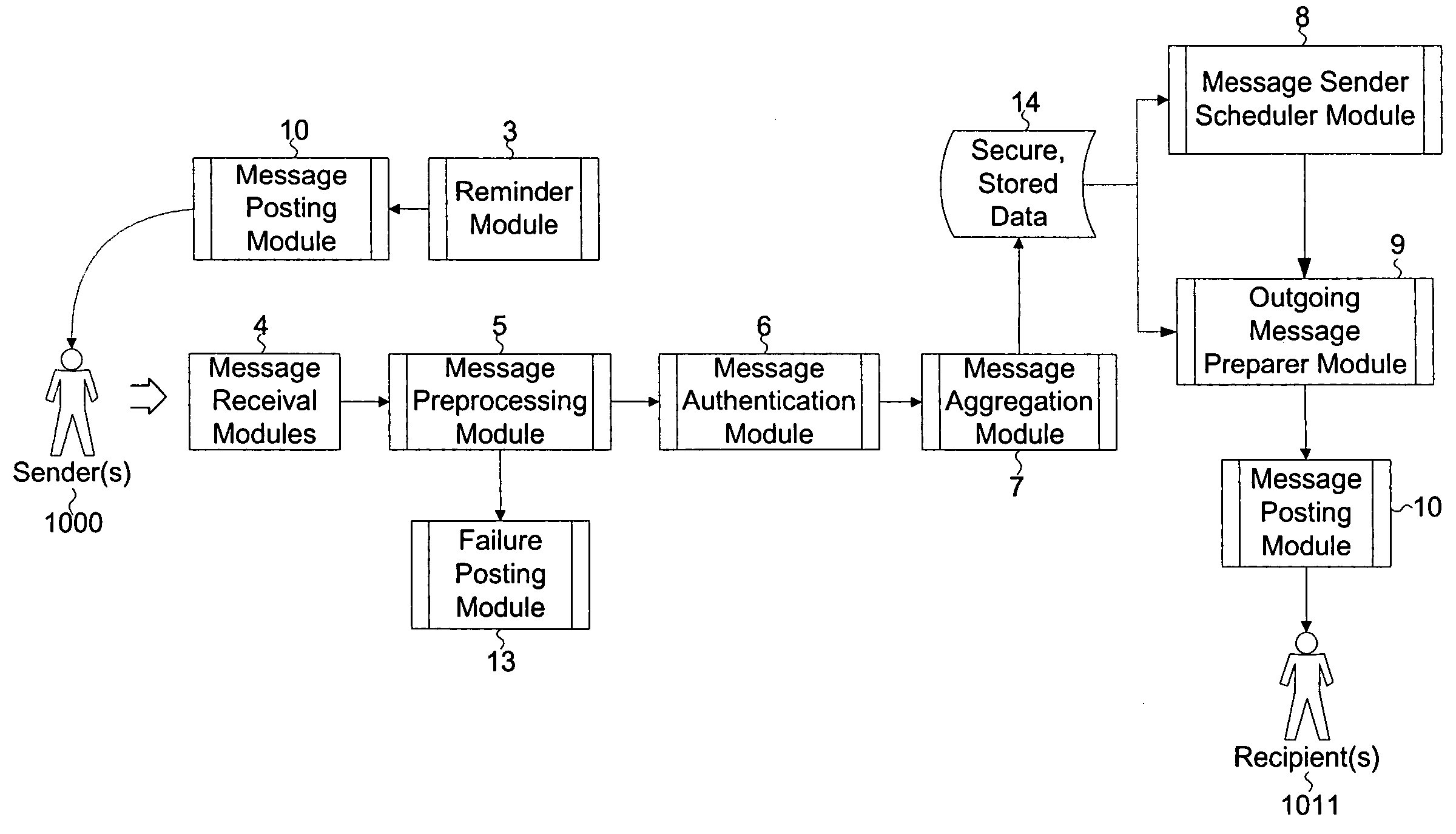
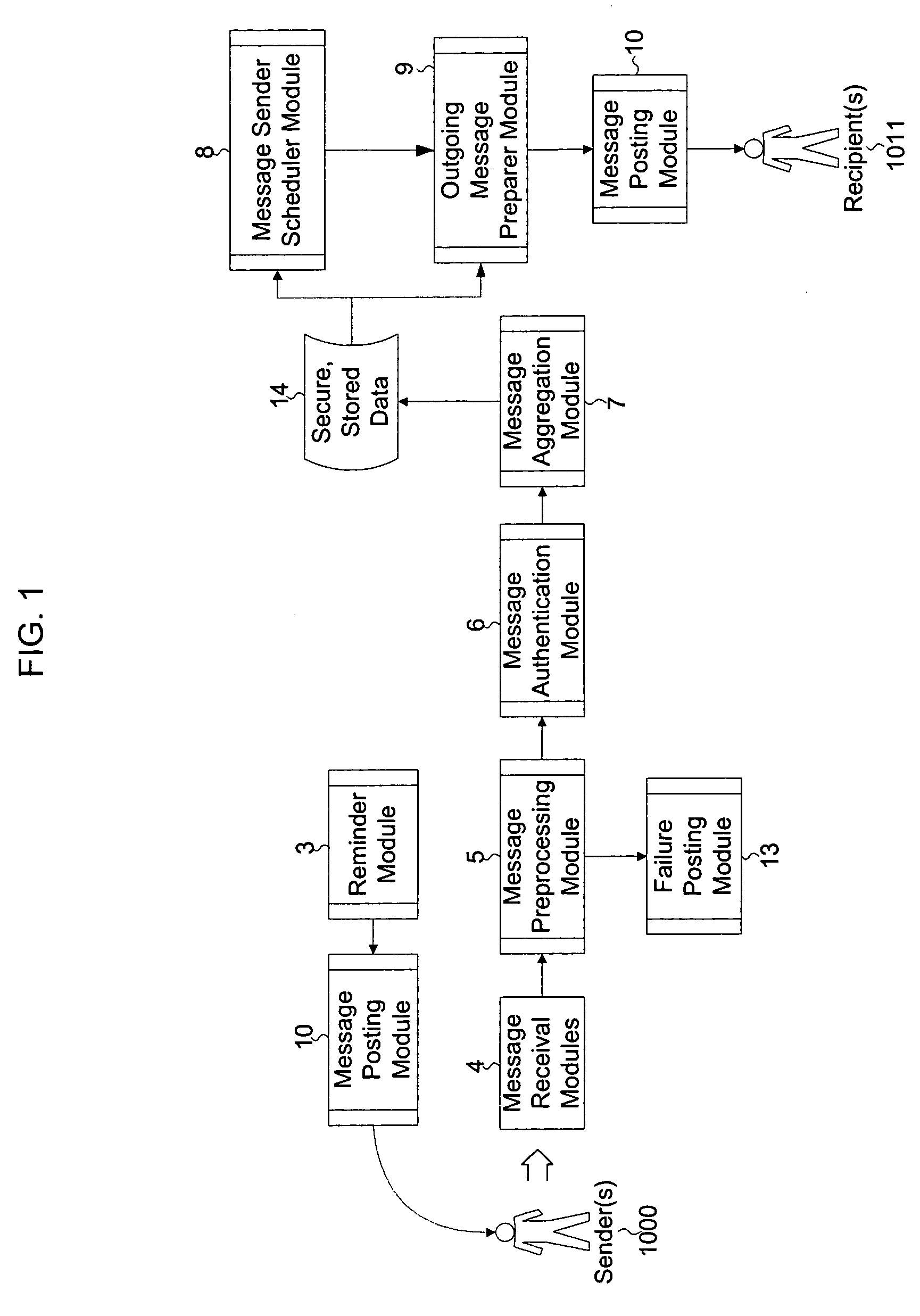
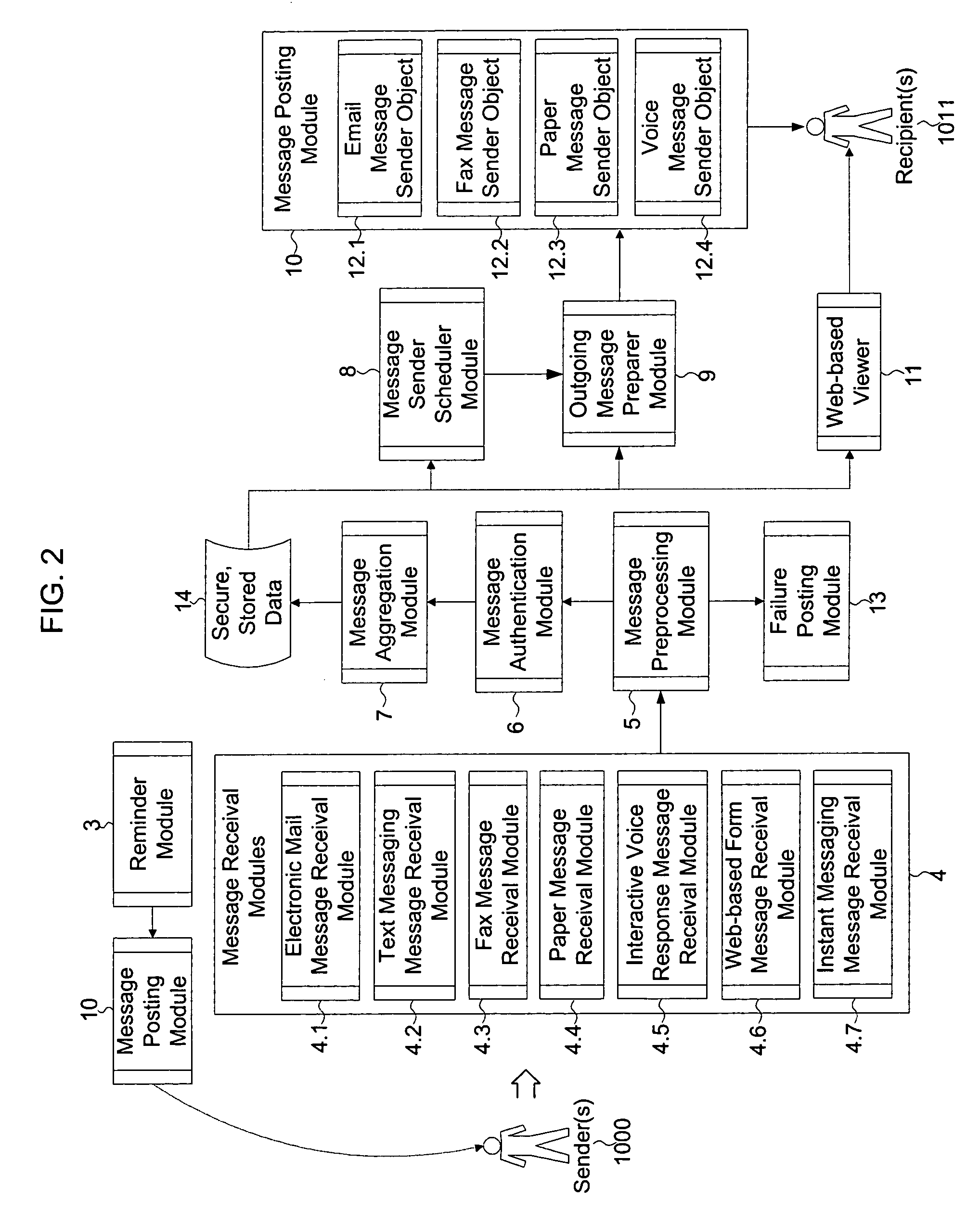
Method and system for communication from anonymous sender(s) to known recipient(s) for feedback applications
InactiveUS20050076089A1Special service provision for substationMultiple digital computer combinationsThird partyRandom order
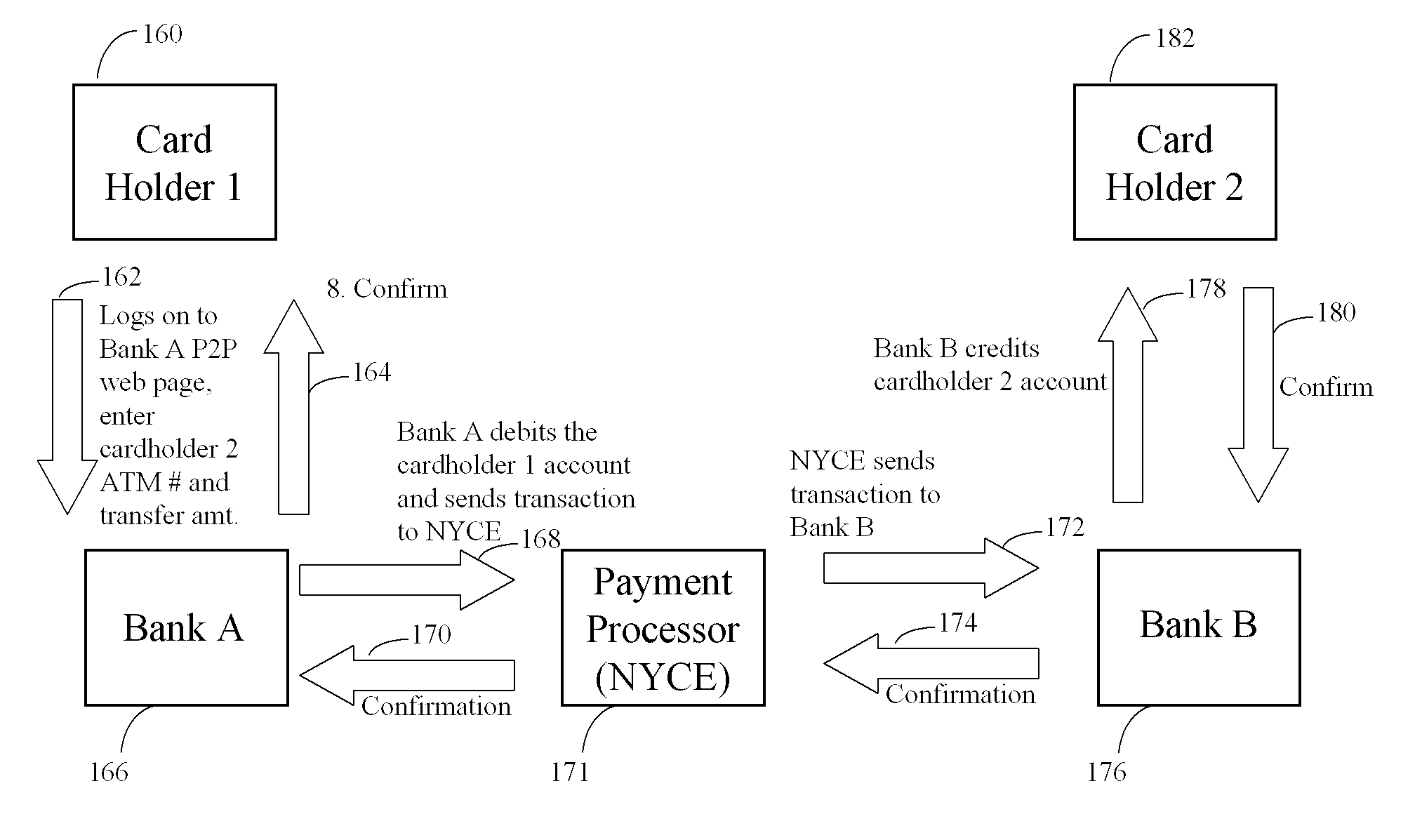
The invention describes a method and system for communication from one or more anonymous sender(s) and to one or more known recipient(s). This method involves the use of a trusted third party that: receives messages from a sender(s), validates the sender(s) and message destination, removes identifying header information from the message, stores the message for a random time period, and then sends to a defined set of recipient(s), all messages received, in random order. The third party receives messages in various formats and sends messages in recipients' preferred format. By holding messages for a random period of time and then sending them in random order to recipients, the third party diminishes the effectiveness of traffic monitoring activities. This invention is particularly designed for applications where senders are providing qualitative feedback to recipients, including but, not limited to, employee-employer communications, collaborative brainstorming, employee knowledge capture and dissemination, and customer-to-vendor feedback.
Owner:FONSECA ARNOLDO MEDEIROS
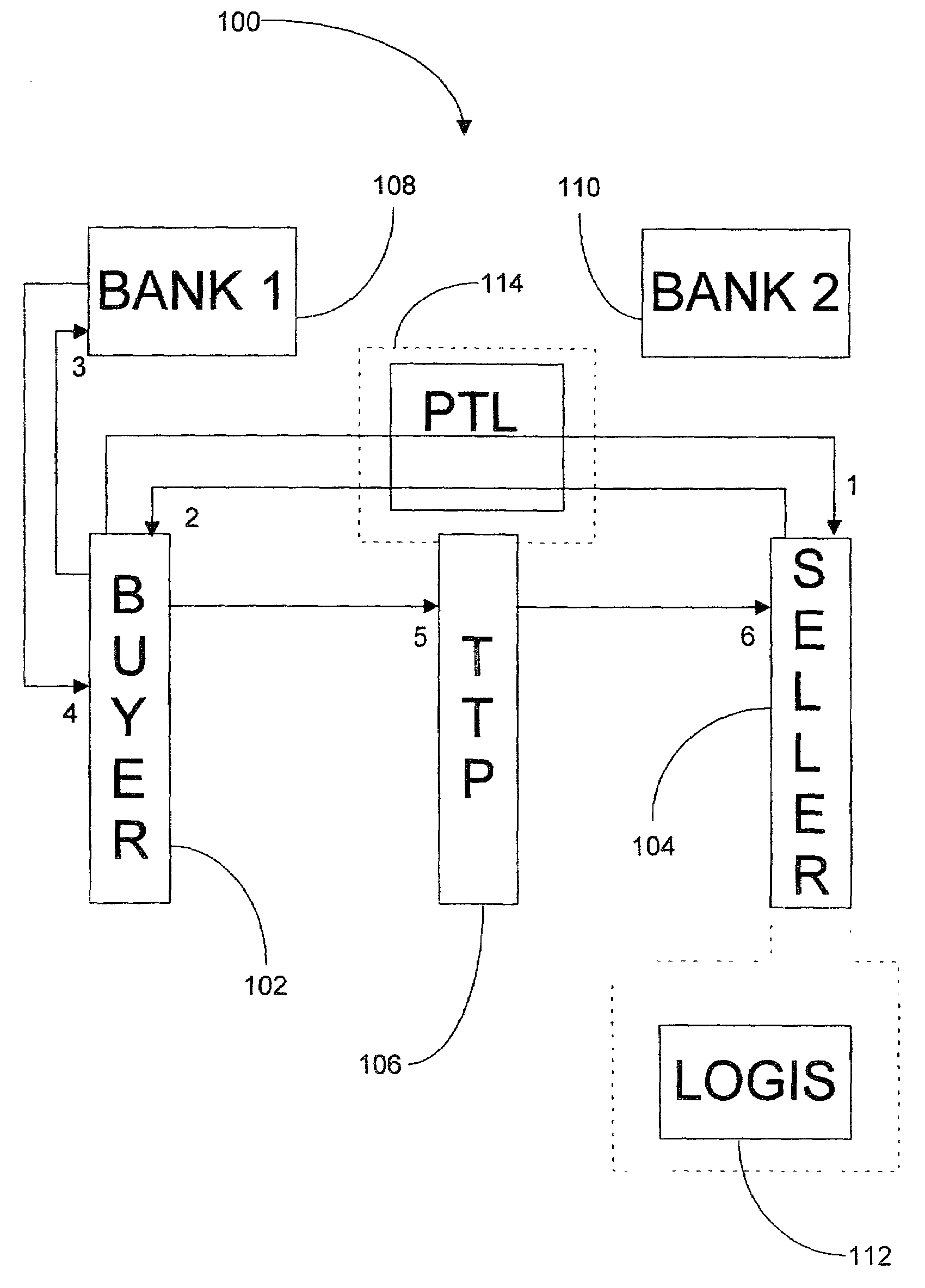
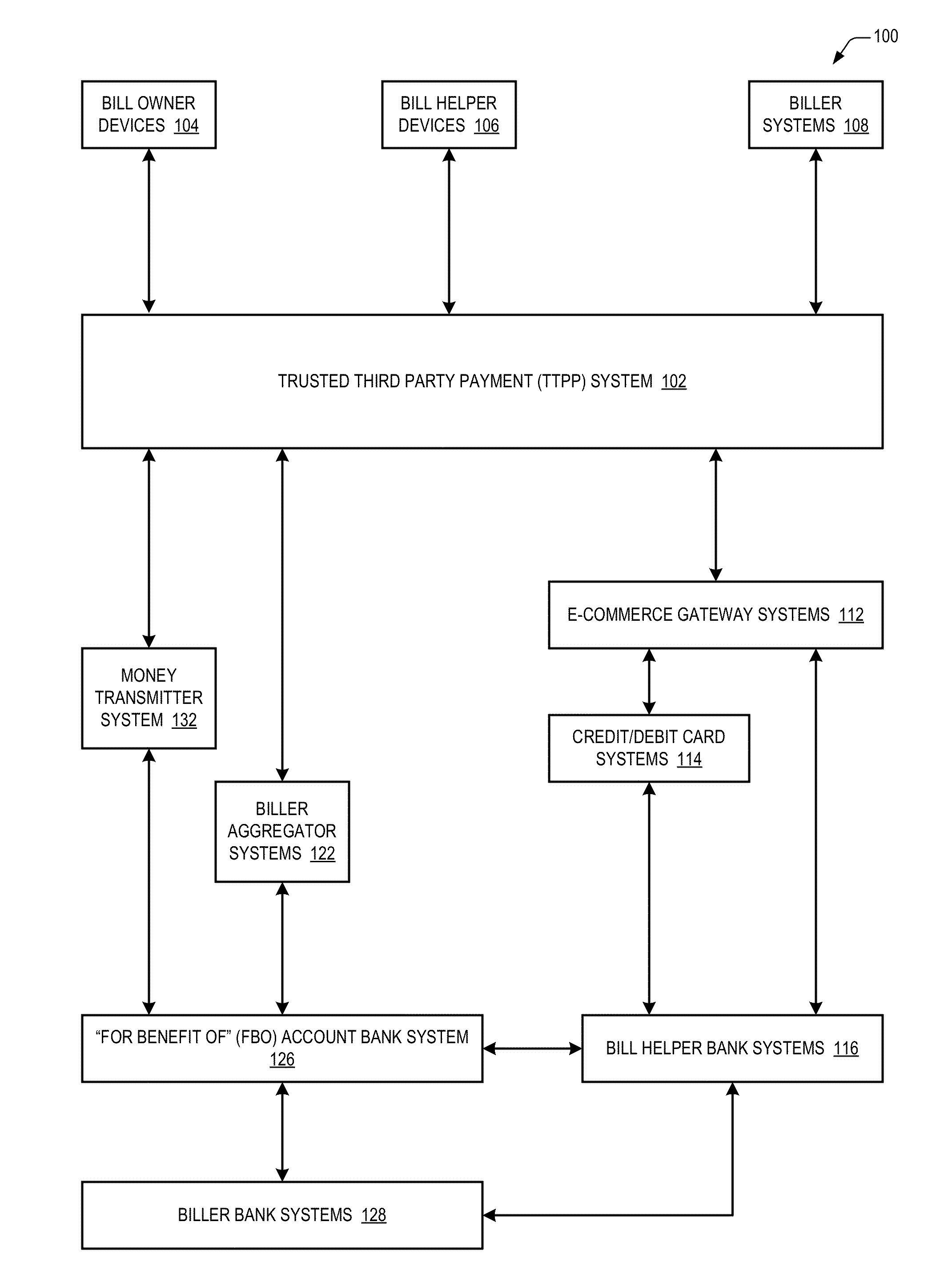
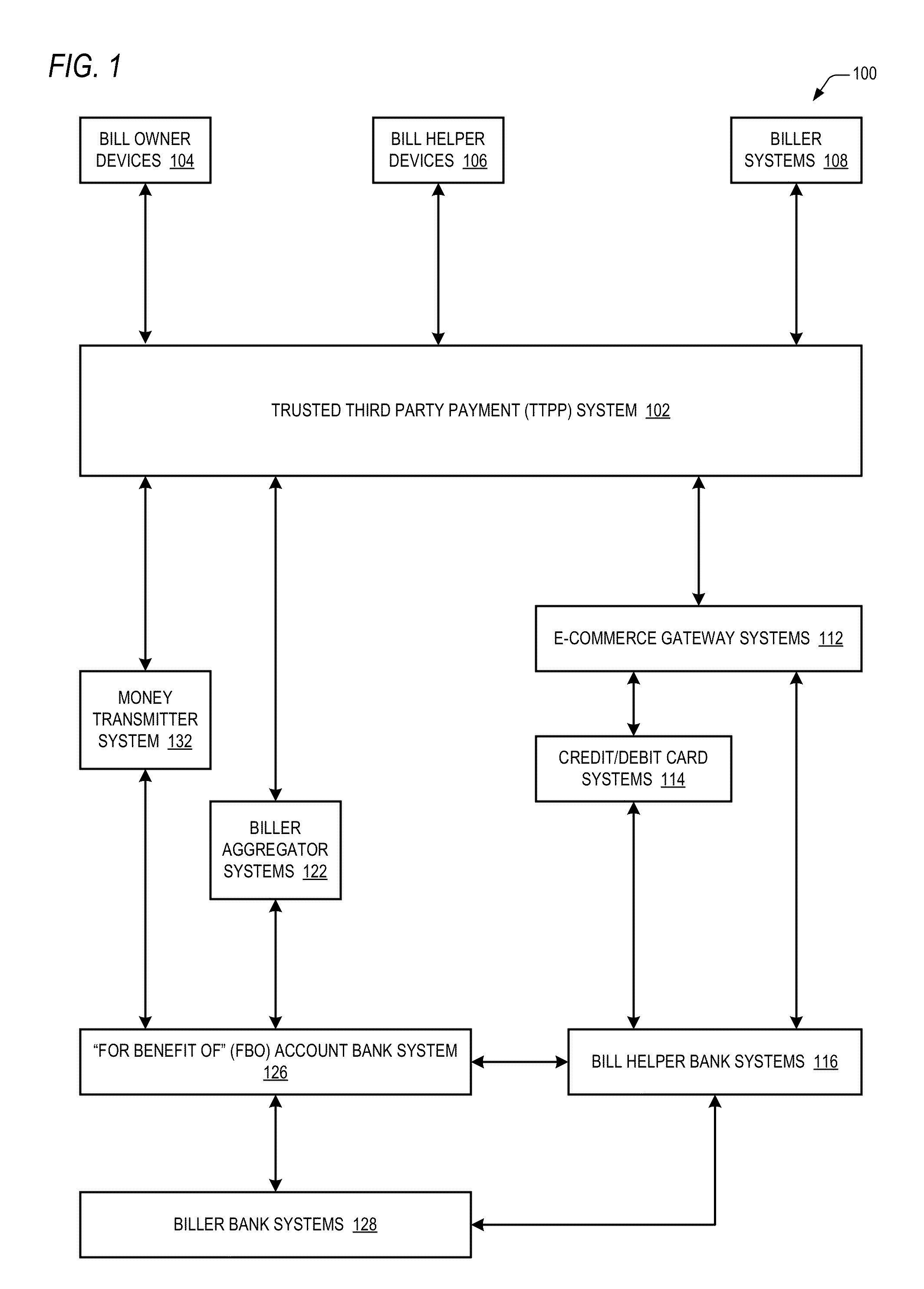
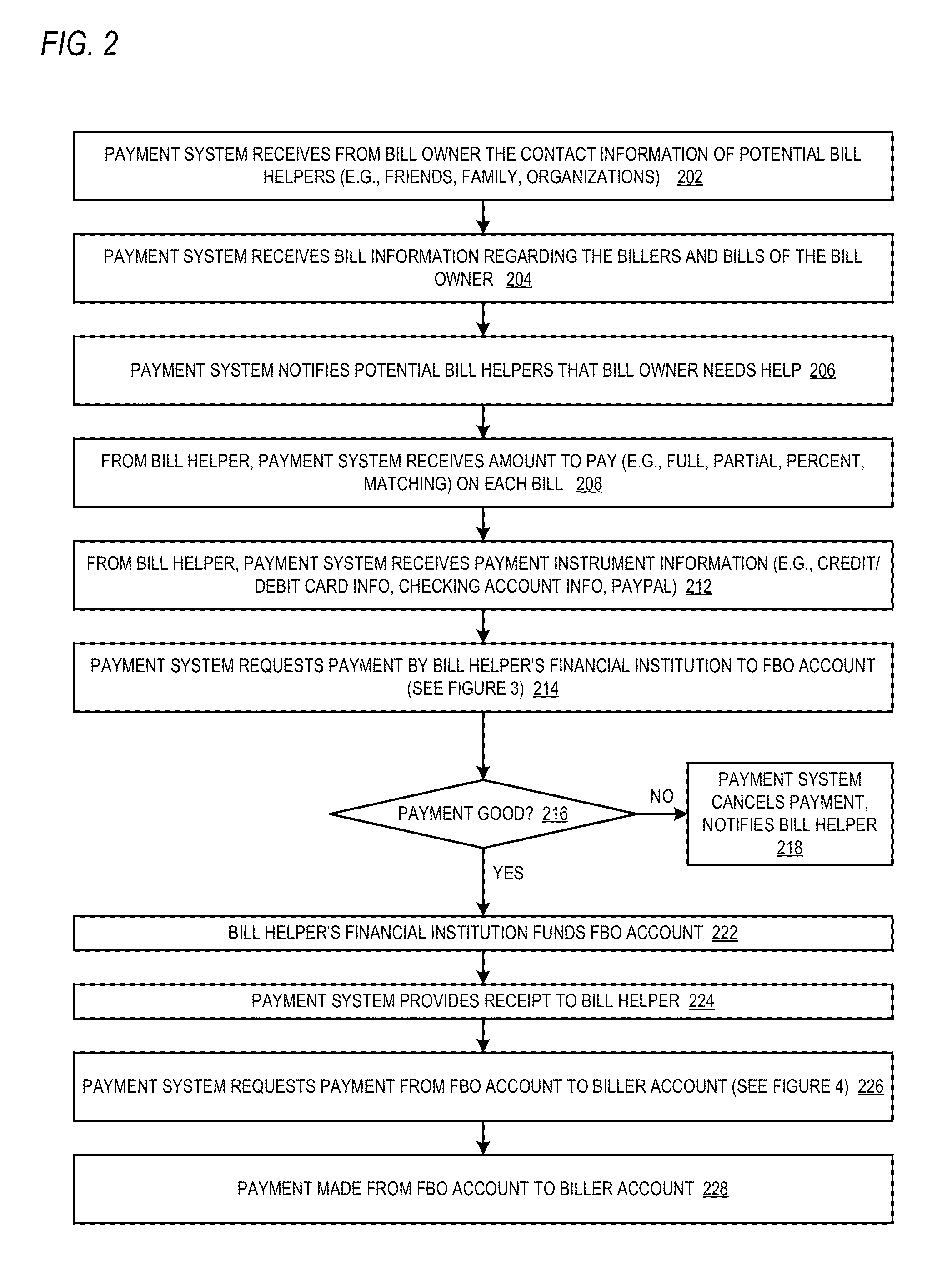
Trusted third party payment system
InactiveUS20140019348A1Low costMinimizing embarrassmentFinanceProtocols using social networksTrusted third partyComputer science
A trusted third party payment system includes one or more network interfaces that communicate with a device to receive bill information about bills of a bill owner and to communicate with devices to receive bill helper payment instrument information and to communicate with systems operated by billers of the bill owner, and a central processing unit that uses the payment instrument information to pay the bills to the billers systems with funds of the bill helpers. The bill owner, the bill helpers, the billers and the trusted third party are all distinct entities. The system also receives bill helper contact information and electronically communicates to the bill helpers (e.g., email, text message, Facebook or Twitter message) that the bill owner has requested help paying the bills. For at least one of the bills, the CPU pays partial amounts of the bill with funds of each of multiple bill helpers.
Owner:RUMBLELOGIC INC DBD PAYTAP
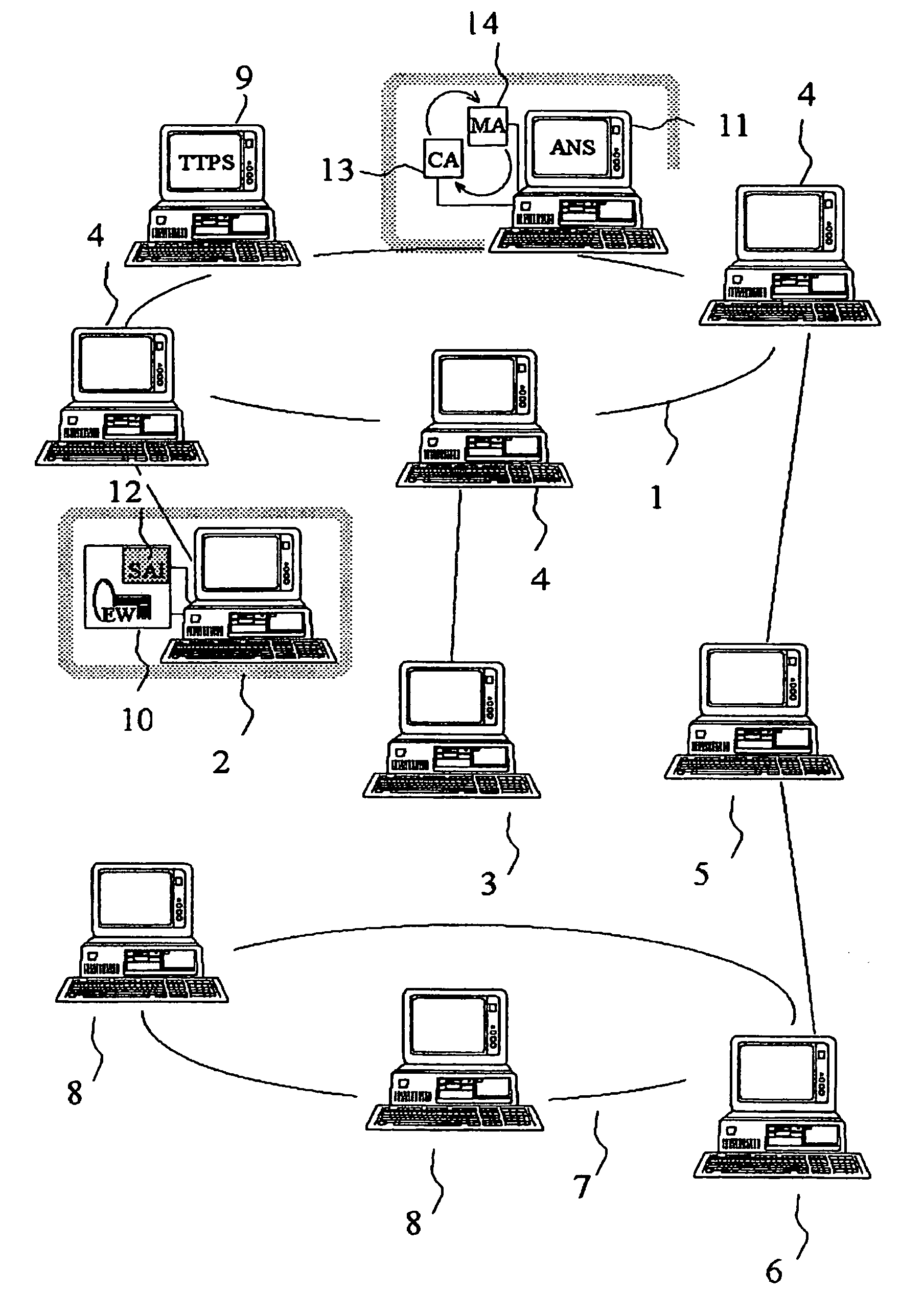
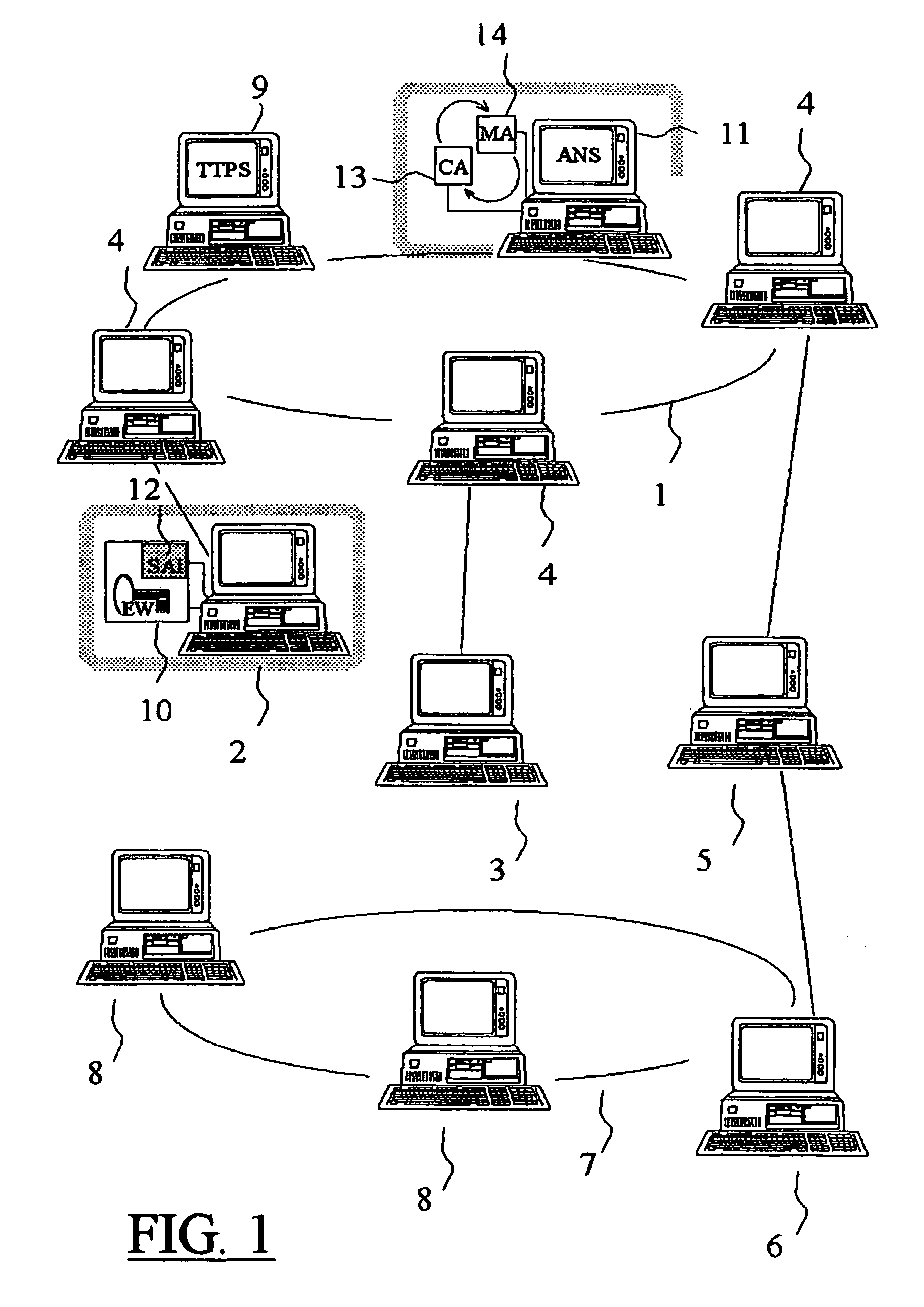
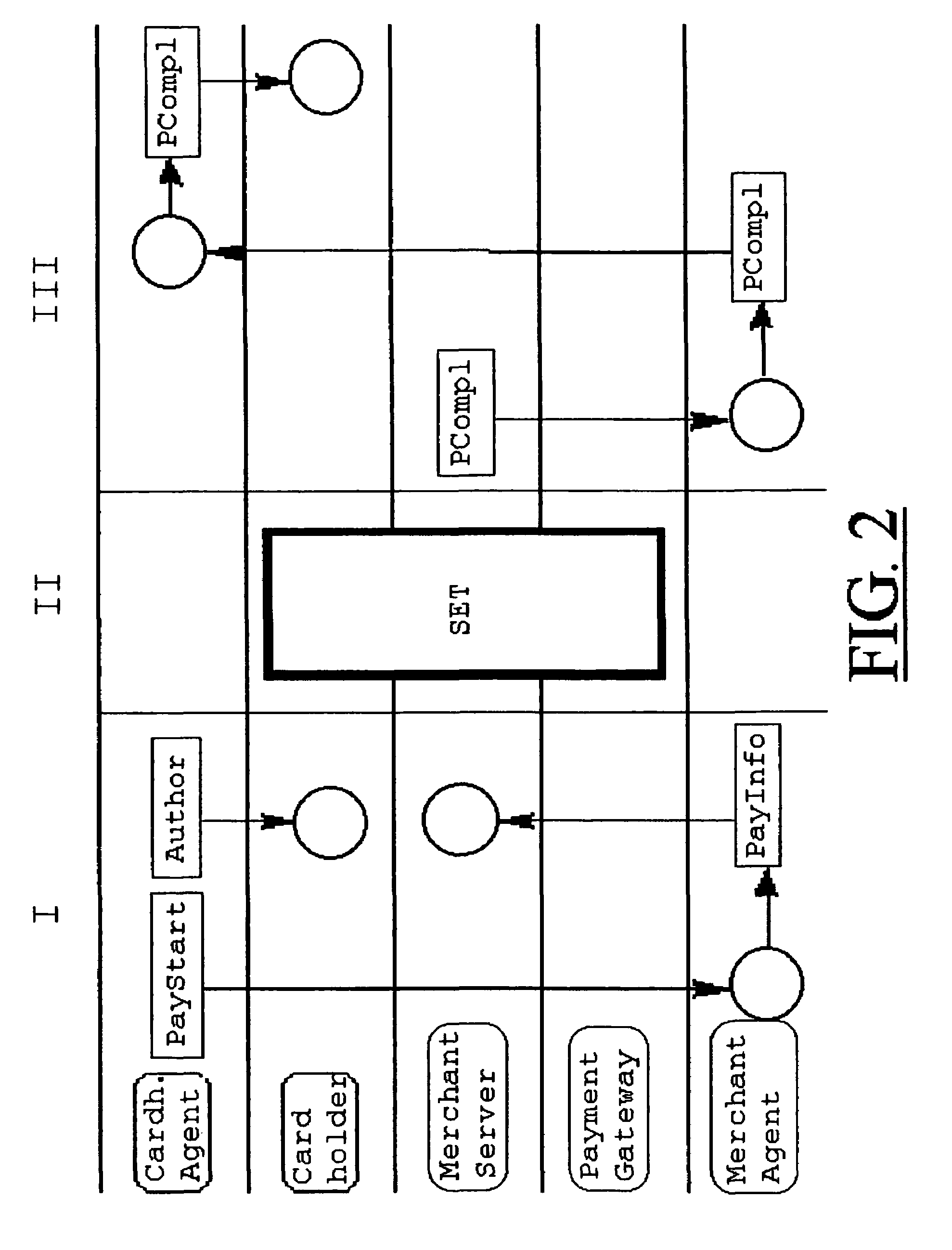
System for secure transactions
A multimedia network (1) with connected customer stations (2), merchant servers (3), and a payment server (5). Secure electronic transactions are performed using a secure electronic transactions protocol (SET), including exchange of digital certificates, managed by a Trusted Third Party Server (9). The customer stations comprise transactions management means (10), fit for performing said SET protocol and for managing said certificates for the customer station. A remote customer agent (13) represents the customer station in the negotiation and payment process. The customer station (2) comprises an agent interface (12), fit for transmission of codes, parameters and certificates between the customer agent (13) and the transactions management means (10). A remote merchant agent (14) represents the merchant station (3) in the negotiation and payment process with the customer agent (13) or the customer station (3), to have paid for the selected products in a secure way, under control of SET protocol.
Owner:NOKIA CORP
System and method to validate and authenticate digital data
InactiveUS20110231645A1Data can be securedDigital data processing detailsUser identity/authority verificationDigital dataDocument Identifier
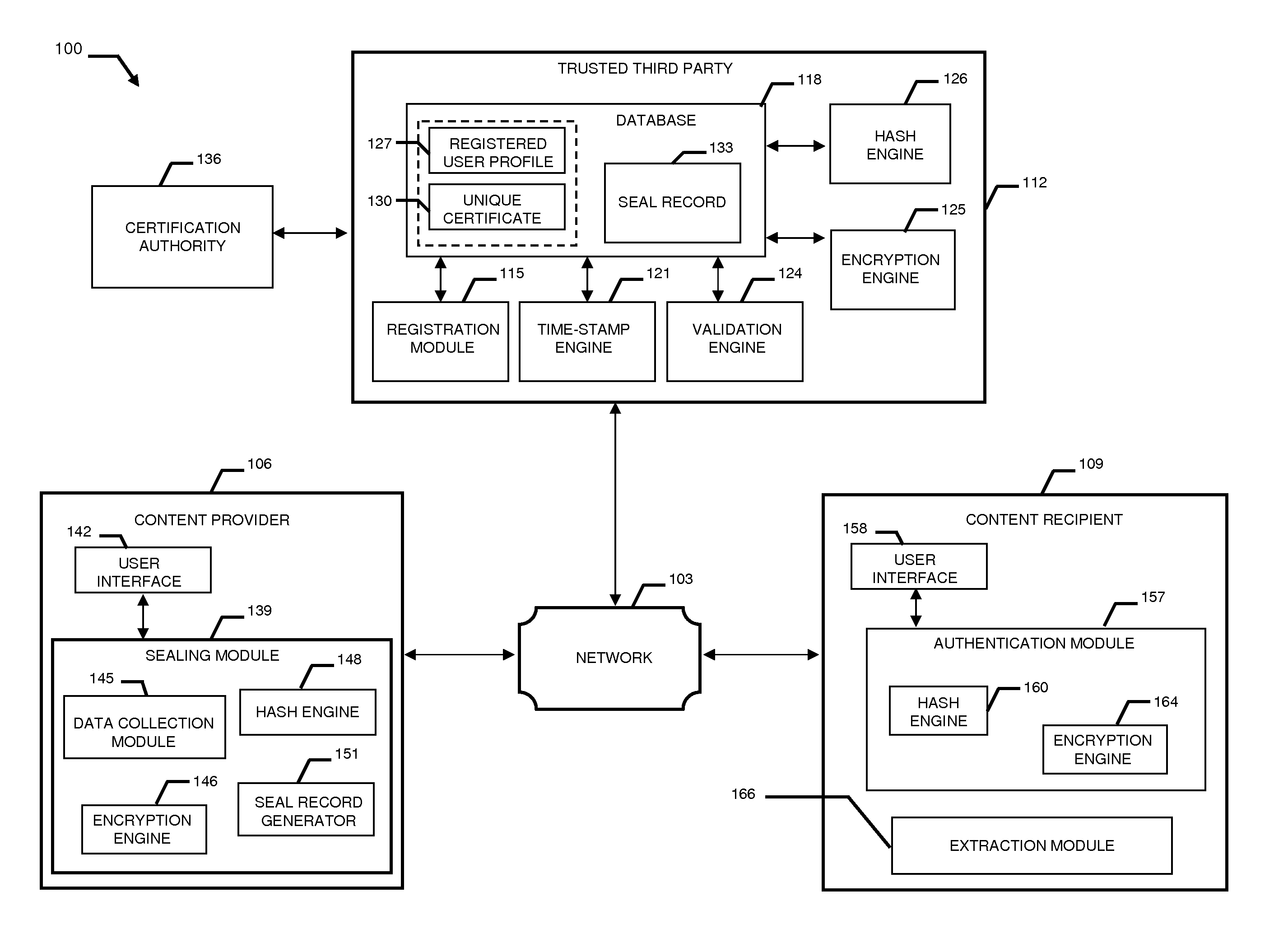
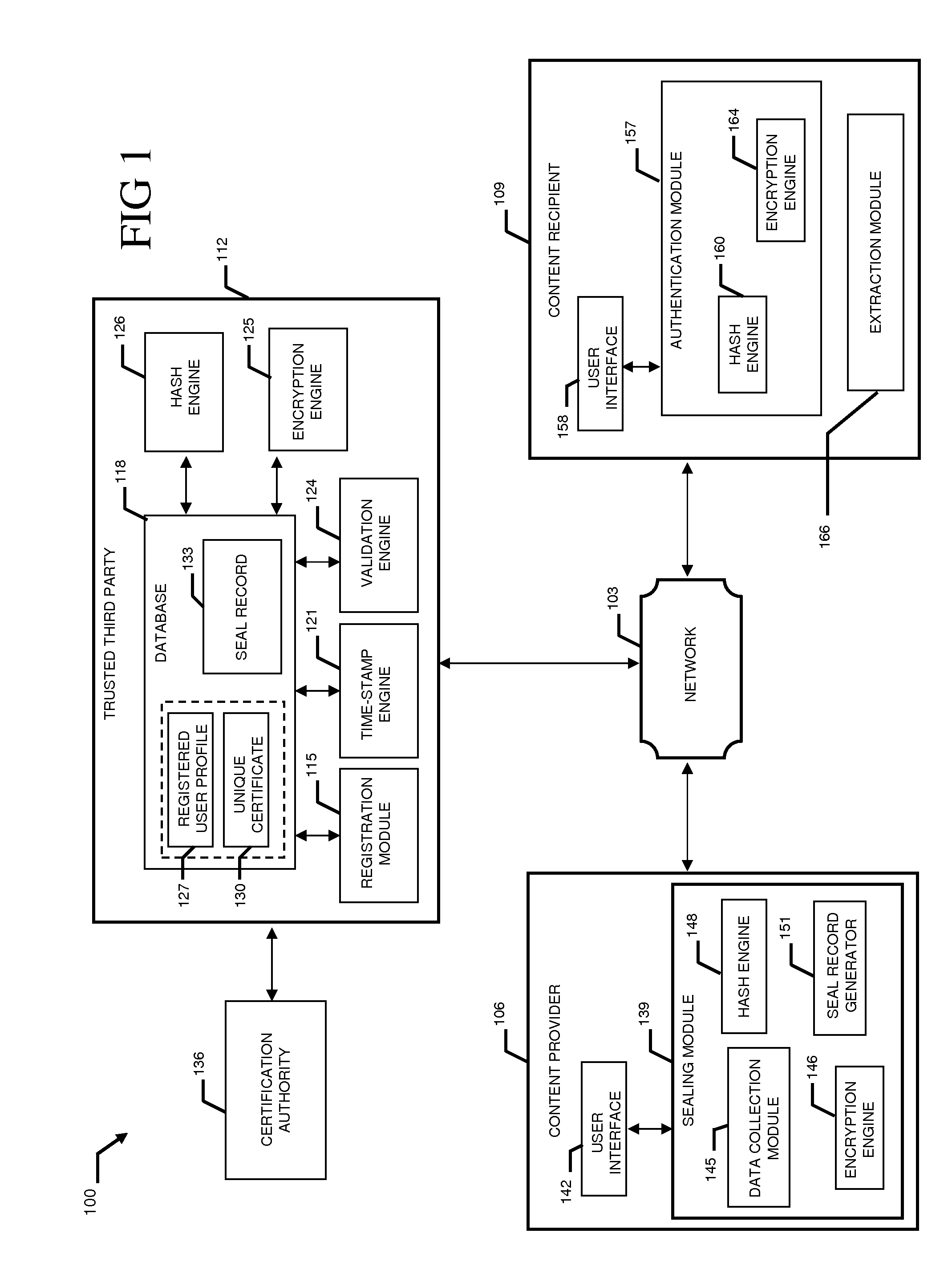
A system and method combining registration with a trusted third party, certificate generation, hashing, encryption, customizable file identification fields, and time-stamping technology with recognized “best practice” procedures to achieve the legal admissibility and evidential weight of any form of digital file or collection of digital files. Generally, the originator of the file (the first party) and the originator's employing organization are registered with a Trusted Third Party. The originator reduces the file, by means of a hashing algorithm, to a fixed bit length binary pattern. This provides a unique digital fingerprint of the file. The resultant hash value, the originator's identity details, the employing organization details associated and securely linked to the digital certificate, the title of the file, customizable file identification fields, and other relevant data are forwarded to a Trusted Third Party where the date and time from a known and trusted time source are added. The customizable file identification fields can provide the originator with a mechanism for configuring the seal to incorporate as much additional information as deemed necessary to prove the authenticity of the digital content and / or provide data for the purposes of adding value in functions such as source identification, sorting, analysis, investigation, and compliance. Such information could include, but would not be limited to, location / GPS coordinates, machine id, biometric information, smart-card data, reason for sealing. The original file does not leave the control of the originating party. When combined, the forwarded details and date and time create a Seal Record. The Seal Record is encrypted and hashed. The Seal Record along with all other relevant information are retained on a central secure server. The recipient of the file (the second party) can confirm the file has been received in an unaltered state with integrity retained and it is the authentic version by validating the file.
Owner:CYBERCUBE
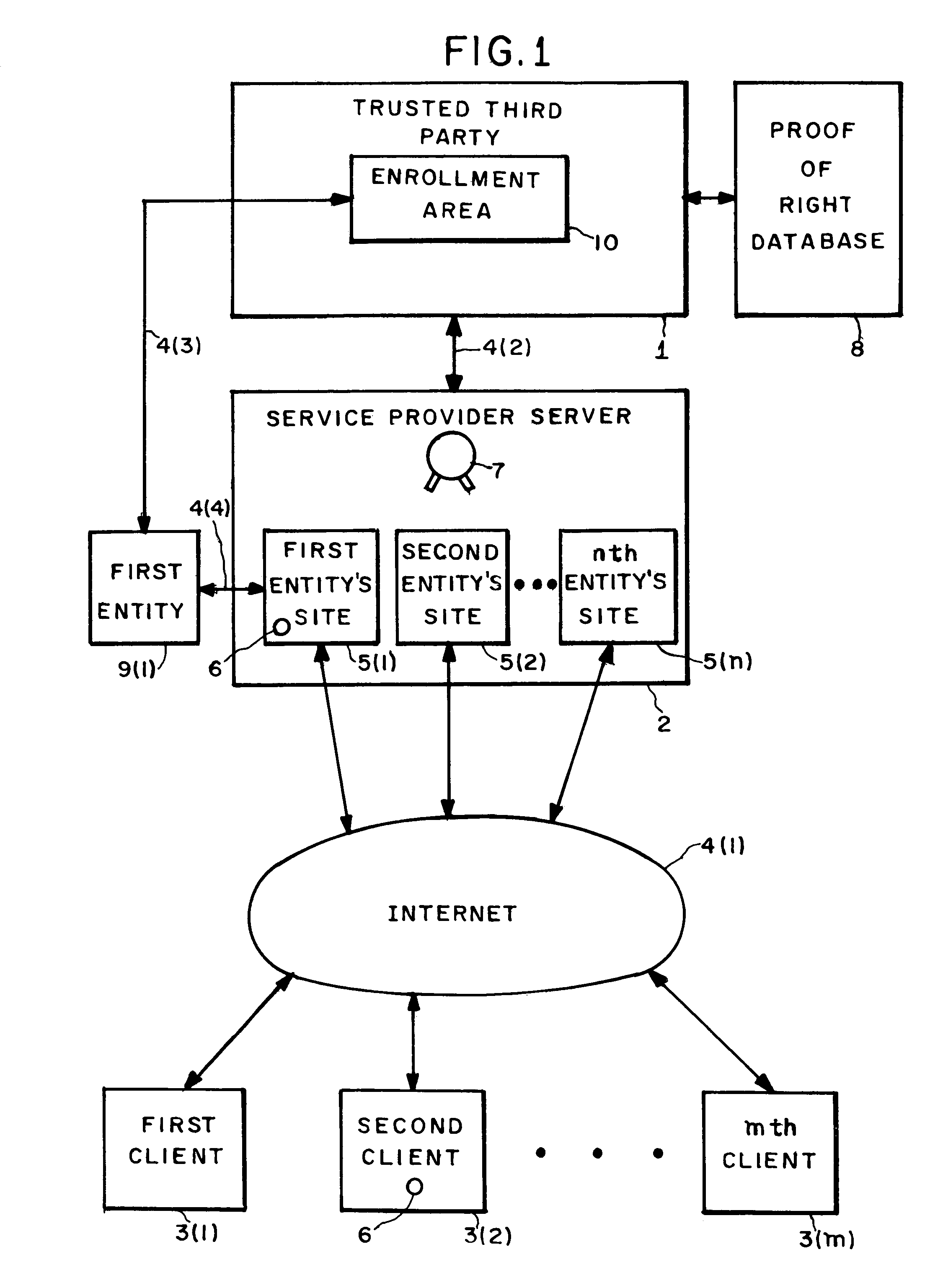
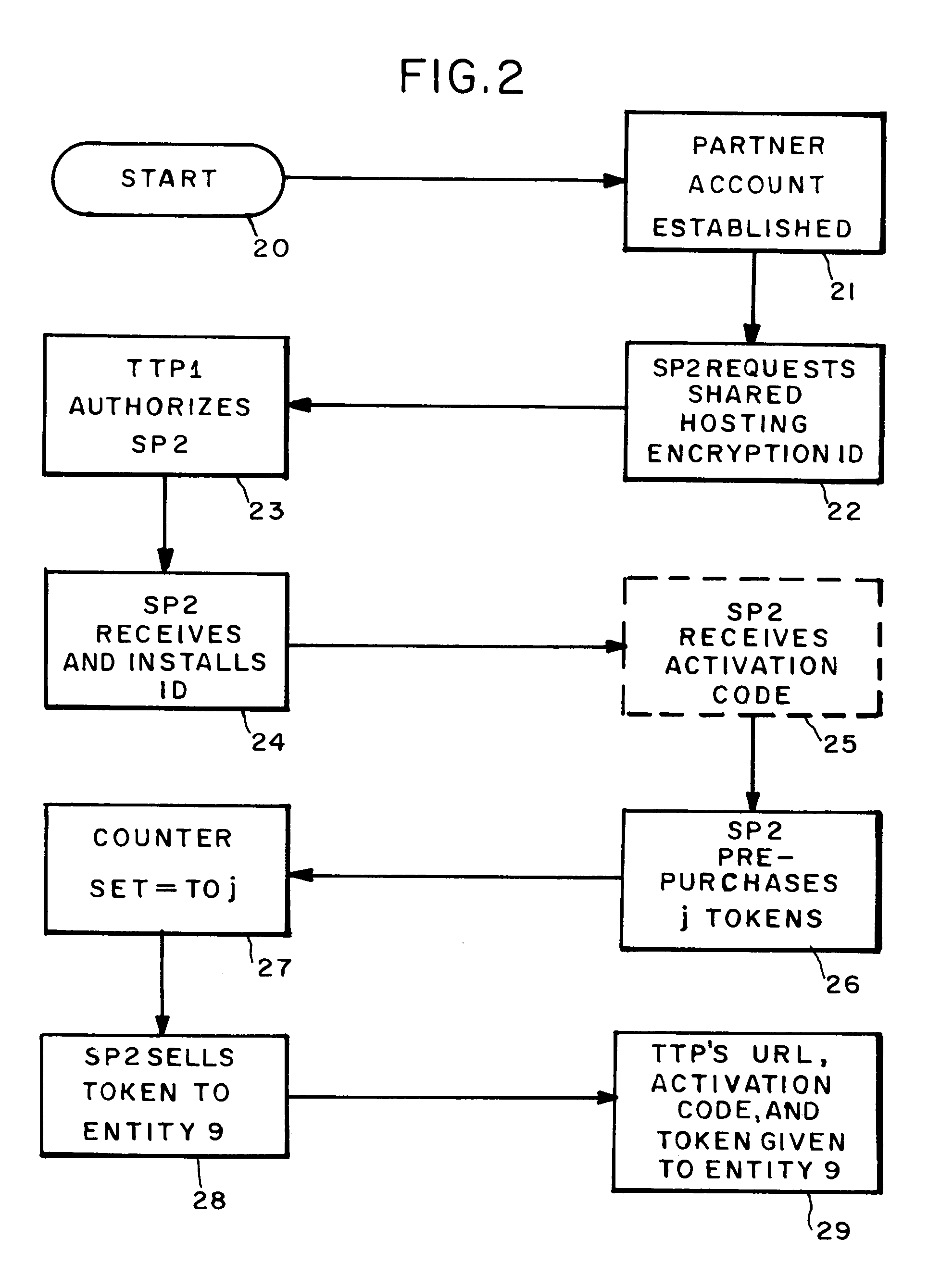
Entity authentication in a shared hosting computer network environment
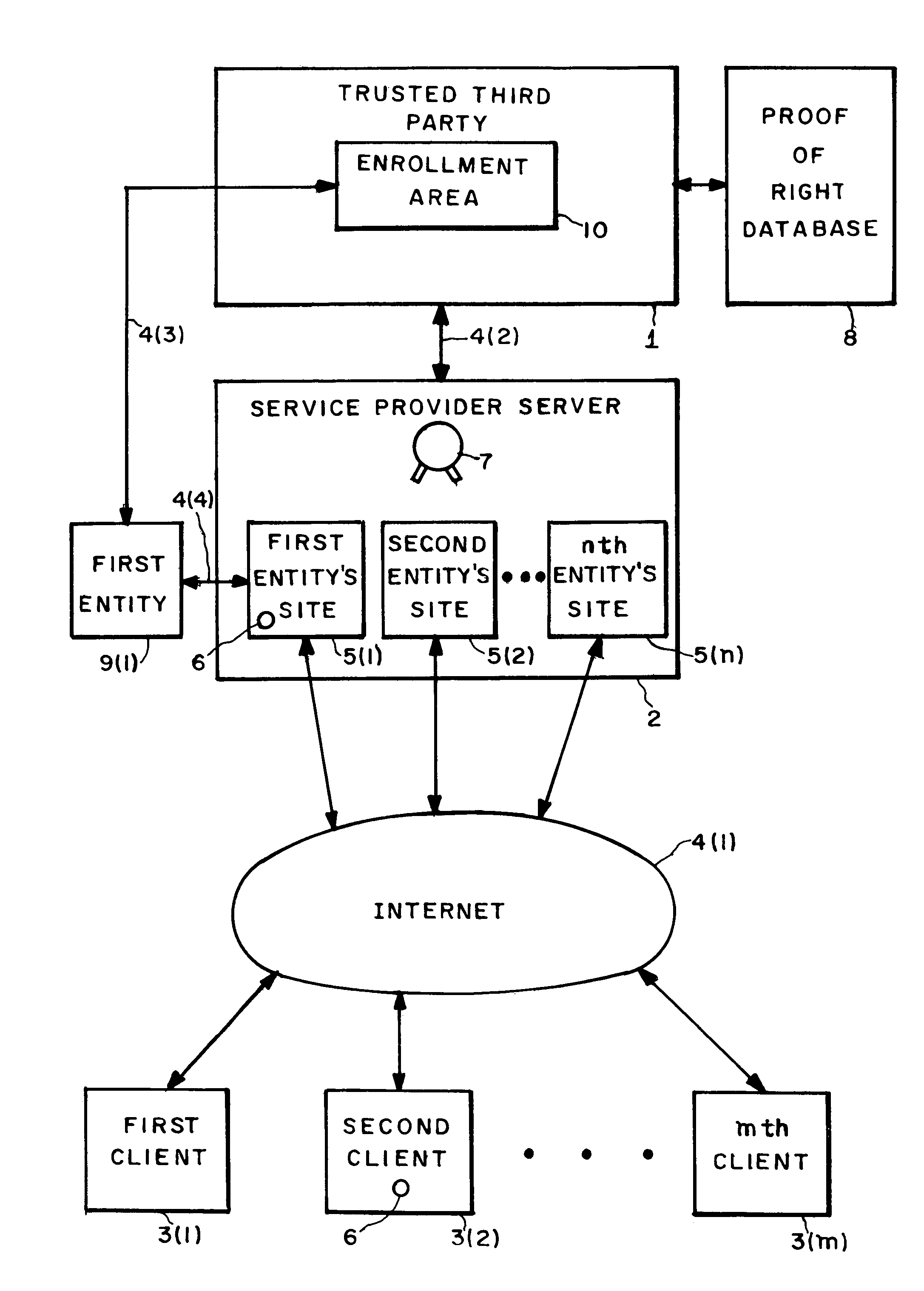
InactiveUS7231659B2Digital data processing detailsUser identity/authority verificationPersonalizationTrusted third party
Apparati, methods, and computer readable media for authenticating an entity (9) in a shared hosting computer network (4) environment. A service provider computer (2) contains a plurality of entity sites (5). Connected to the service provider computer (2), a trusted third party computer (1) is adapted to provide a conglomerated authenticity certification to the service provider computer (2). Coupled to the trusted third party computer (1) is a means (10) for enabling an entity (9) to seek to convert the conglomerated authenticity certification into an individualized authenticity certification covering that entity's site (5).
Owner:CLOUDING
System and method for restricting data transfers and managing software components of distributed computers
InactiveUS20050102388A1Avoid restrictionsDigital data processing detailsUser identity/authority verificationThird partyThe Internet
A controller, referred to as the “BMonitor”, is situated on a computer. The BMonitor includes a plurality of filters that identify where data can be sent to and / or received from, such as another node in a co-location facility or a client computer coupled to the computer via the Internet. The BMonitor further receives and implements requests from external sources regarding the management of software components executing on the computer, allowing such external sources to initiate, terminate, debug, etc. software components on the computer. Additionally, the BMonitor operates as a trusted third party mediating interaction among multiple external sources managing the computer.
Owner:MICROSOFT TECH LICENSING LLC
Auto-Recoverable and Auto-certifiable cryptosystems with RSA or factoring based keys
InactiveUS6389136B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityComposite number
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. The keys generated are based on composite numbers (like RSA keys). A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or Rabin cryptosystem. The system is applicable for law-enforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. Another aspect of the system is the possibility to organize it in a hierarchical tree structure, where each element in the tree is an escrow authority (or authorities) capable to recover keys and / or information encrypted under these keys within the subtree rooted at the authority (or authorities) and only within this subtree.
Owner:CRYPTOPEAK SECURITY LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com