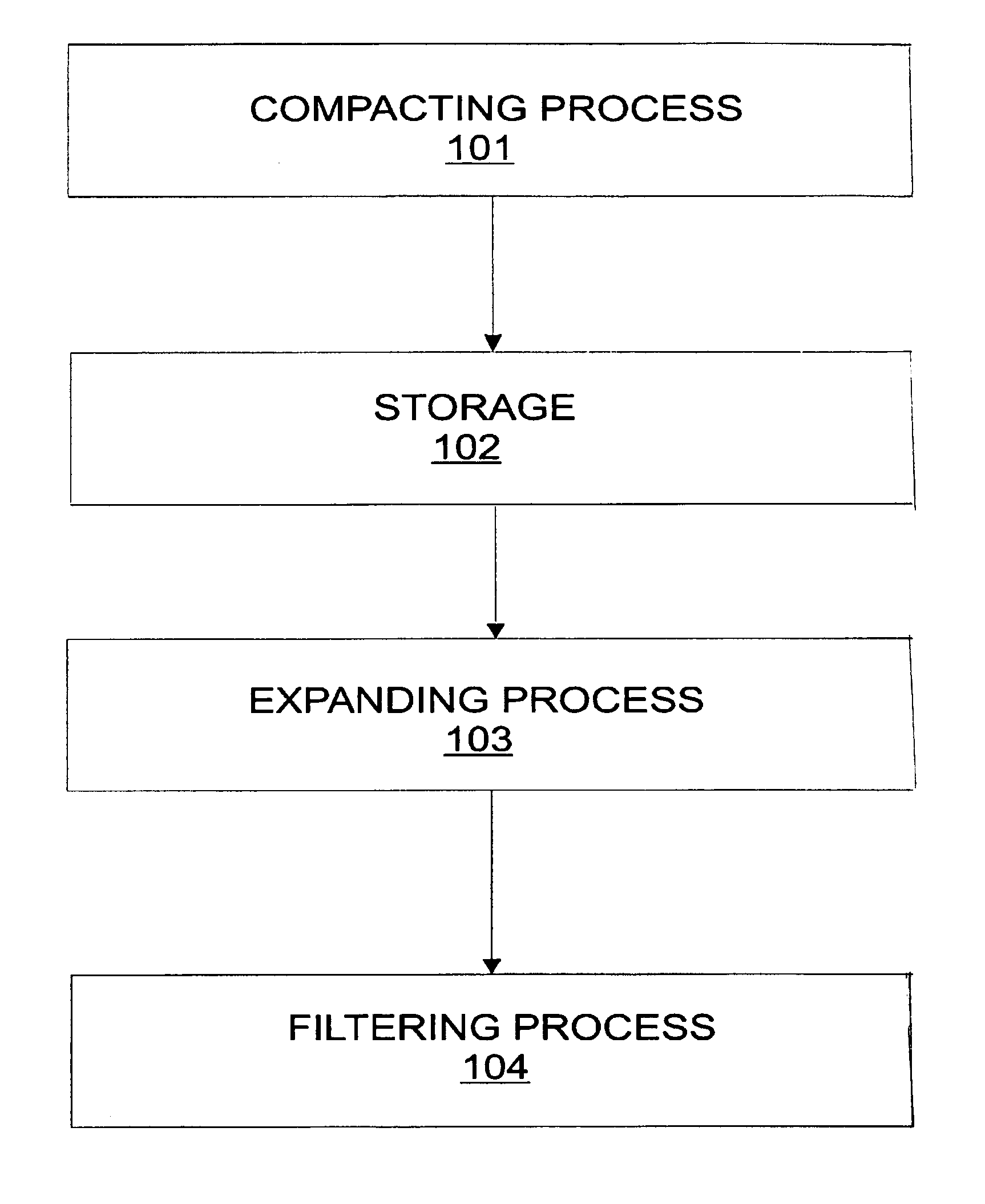
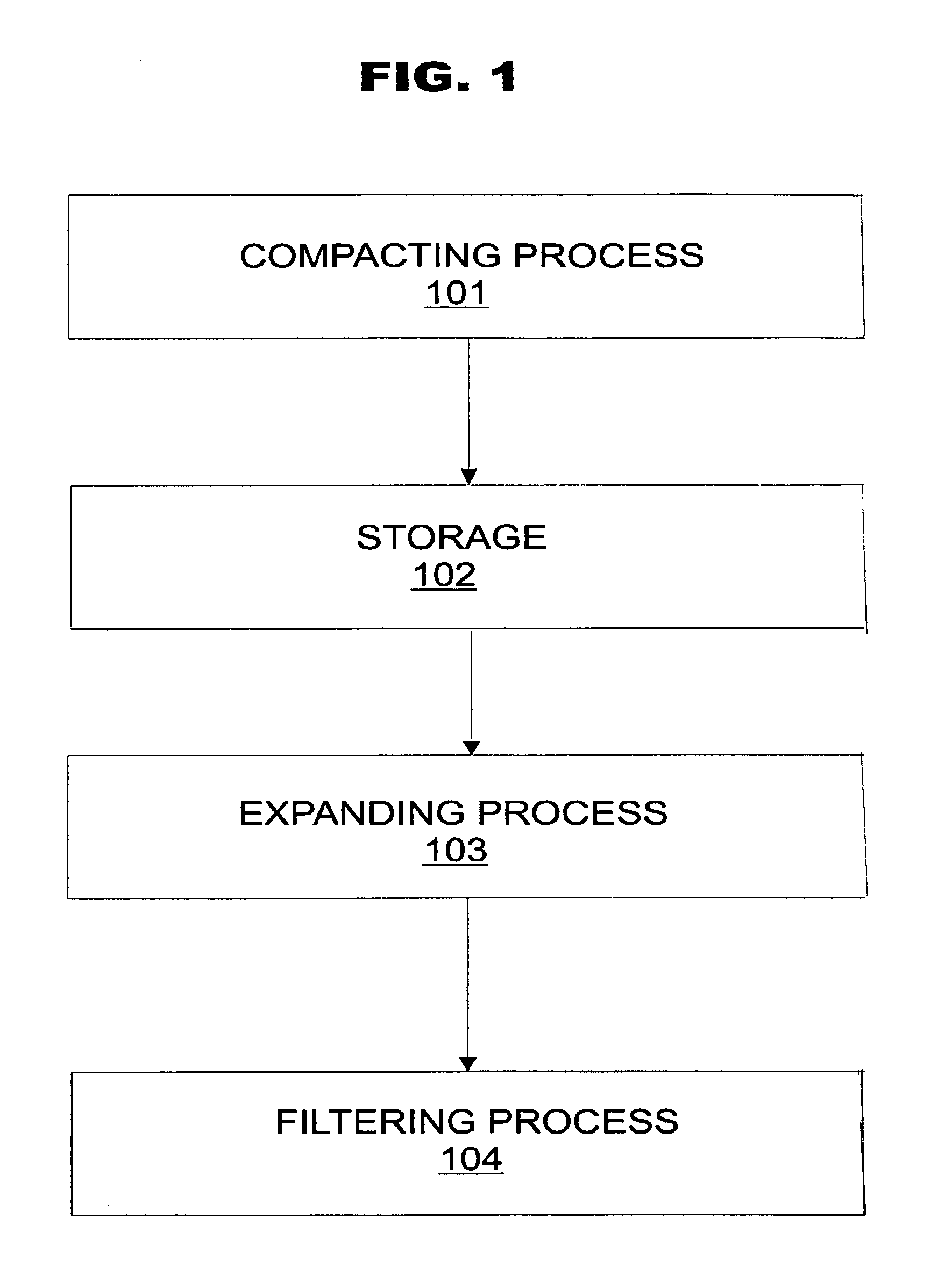
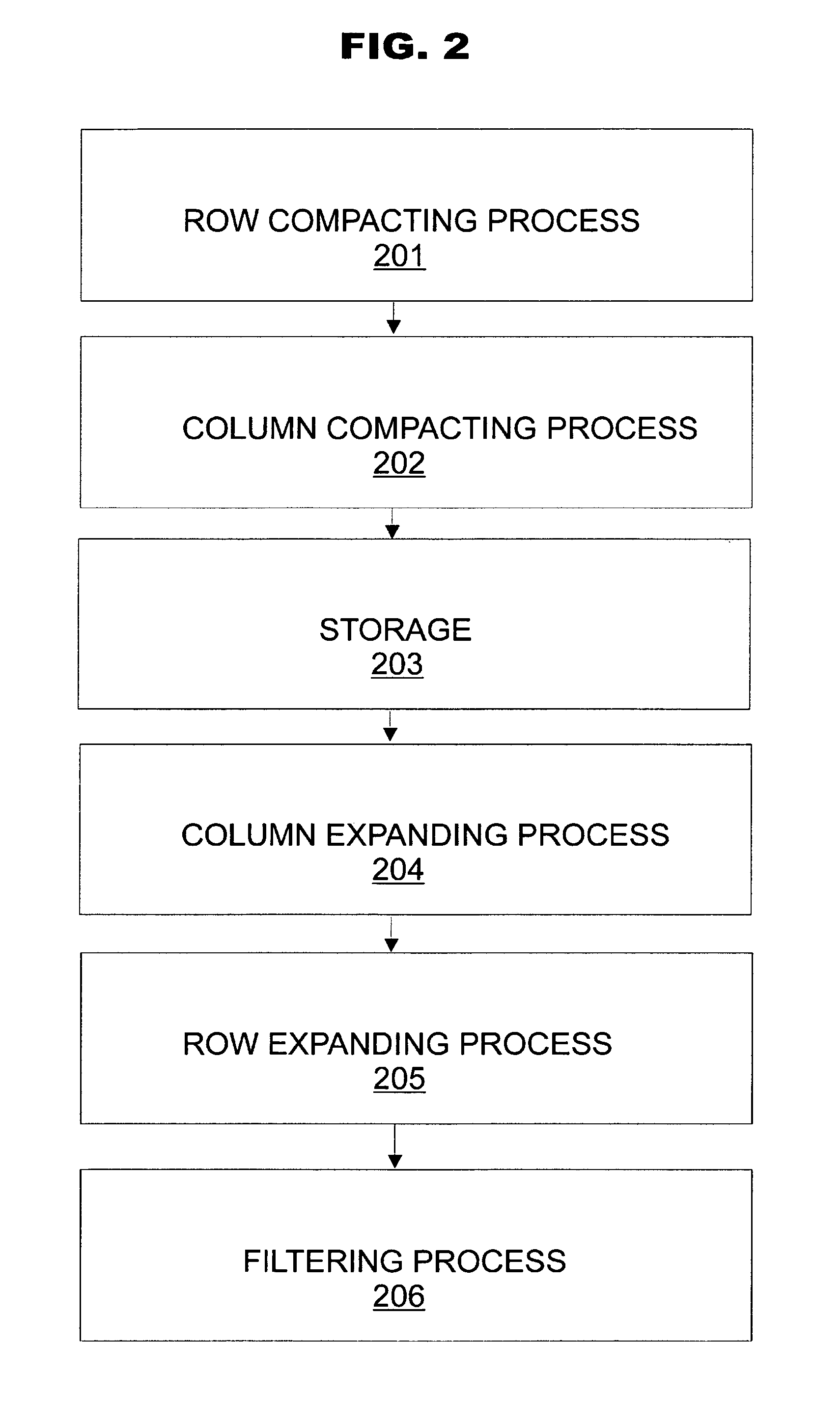
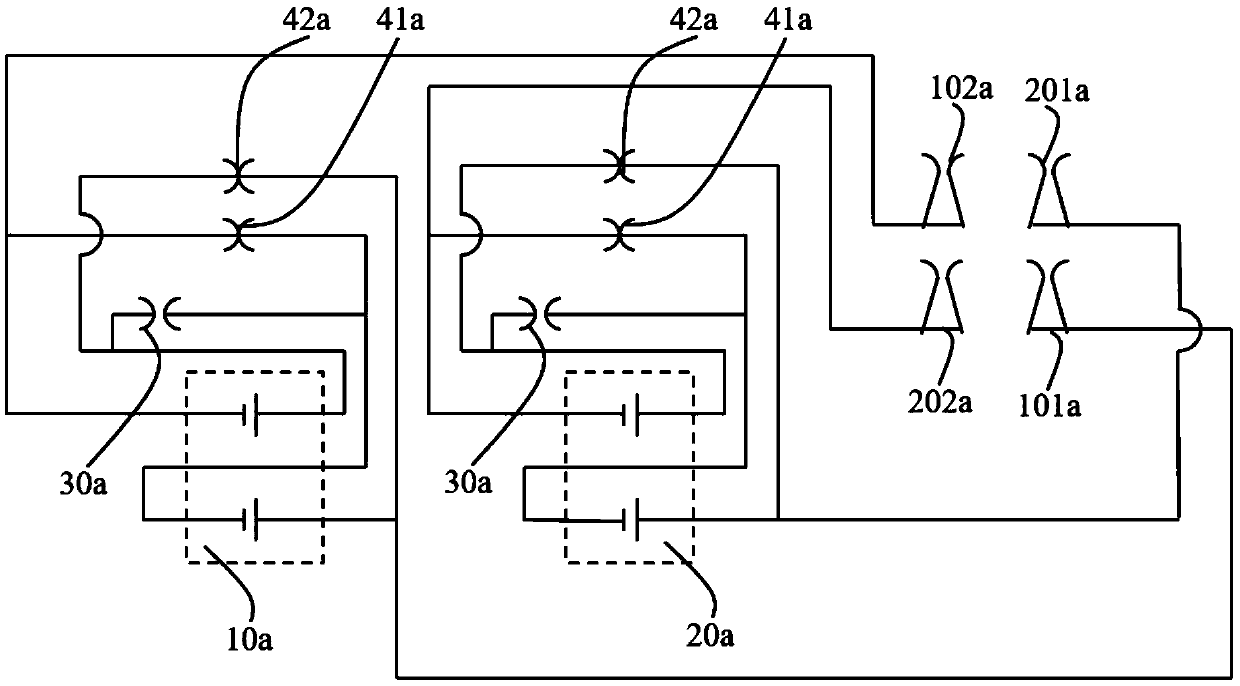
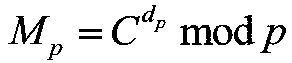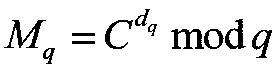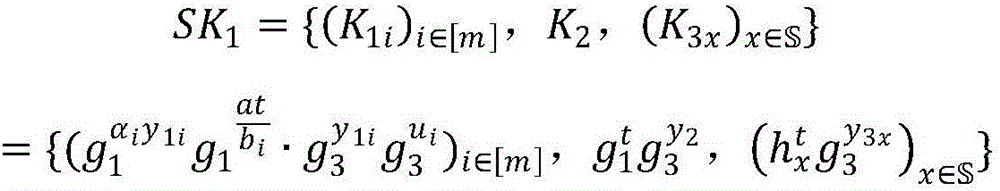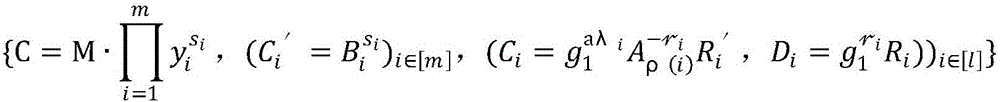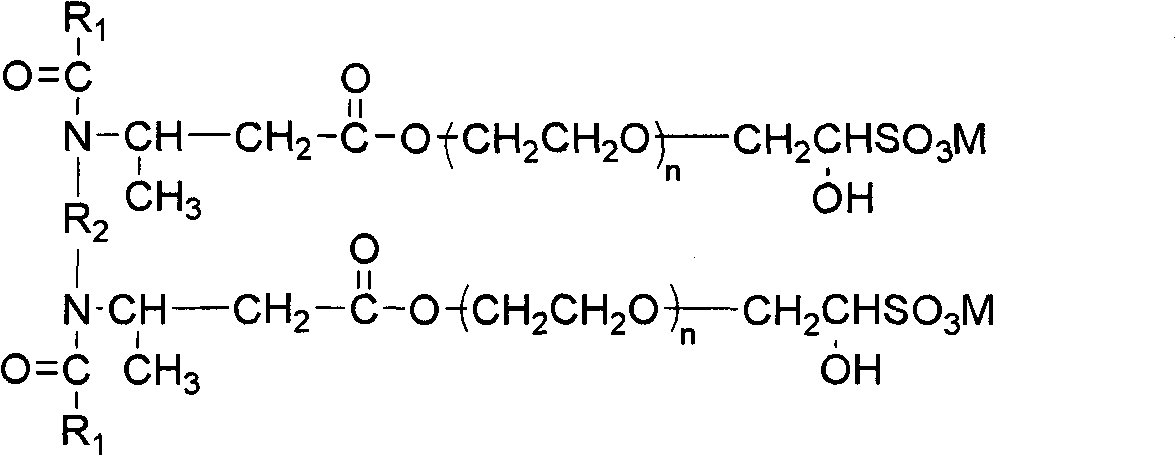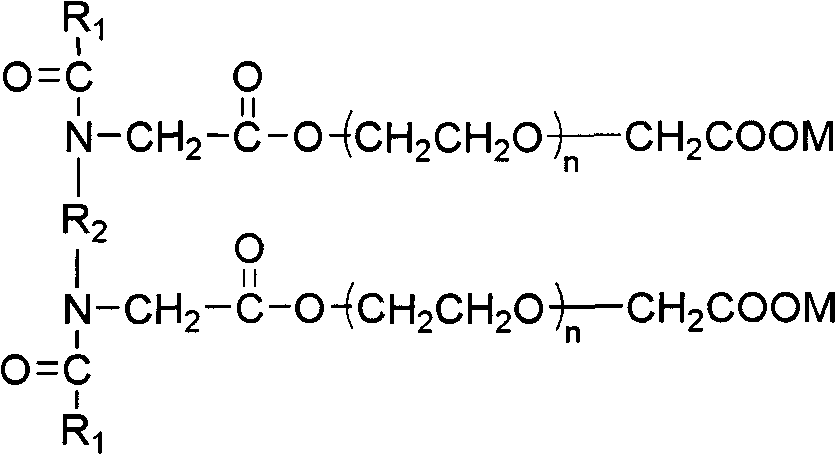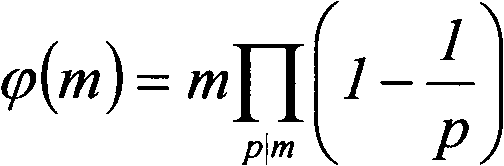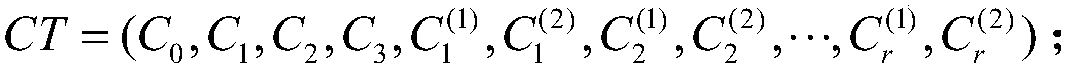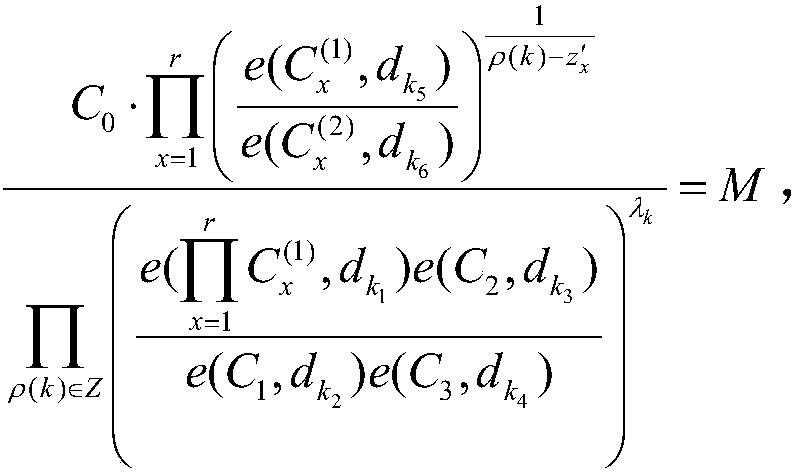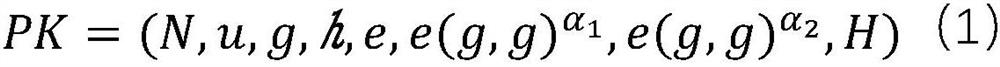Patents
Literature
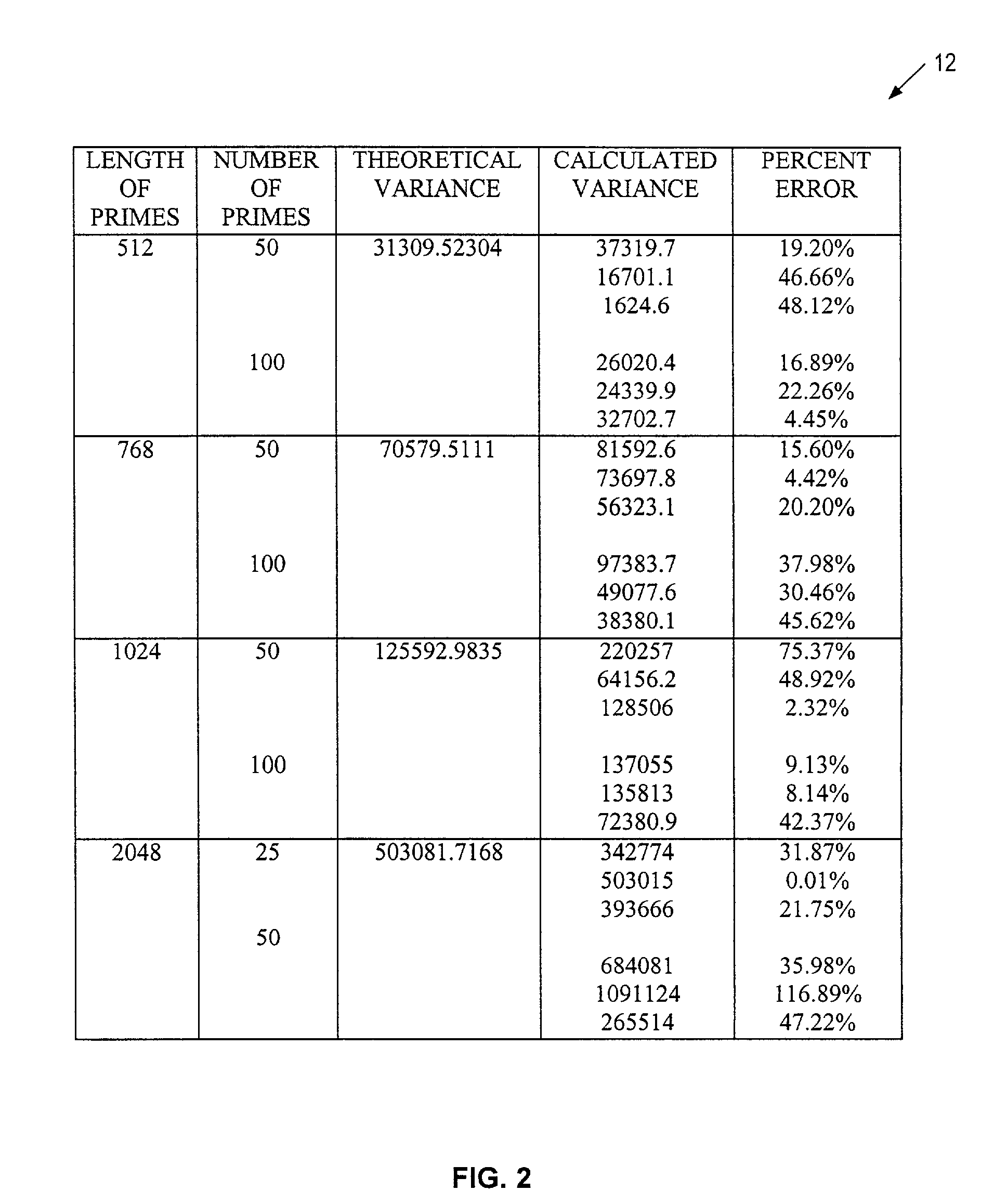
67 results about "Composite number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A composite number is a positive integer that can be formed by multiplying two smaller positive integers. Equivalently, it is a positive integer that has at least one divisor other than 1 and itself. Every positive integer is composite, prime, or the unit 1, so the composite numbers are exactly the numbers that are not prime and not a unit.
Secure transaction verification method and system based on blockchain
InactiveCN108711105AGuaranteed transaction processing speedPrevent leakageFinanceProtocol authorisationComposite numberVerification system
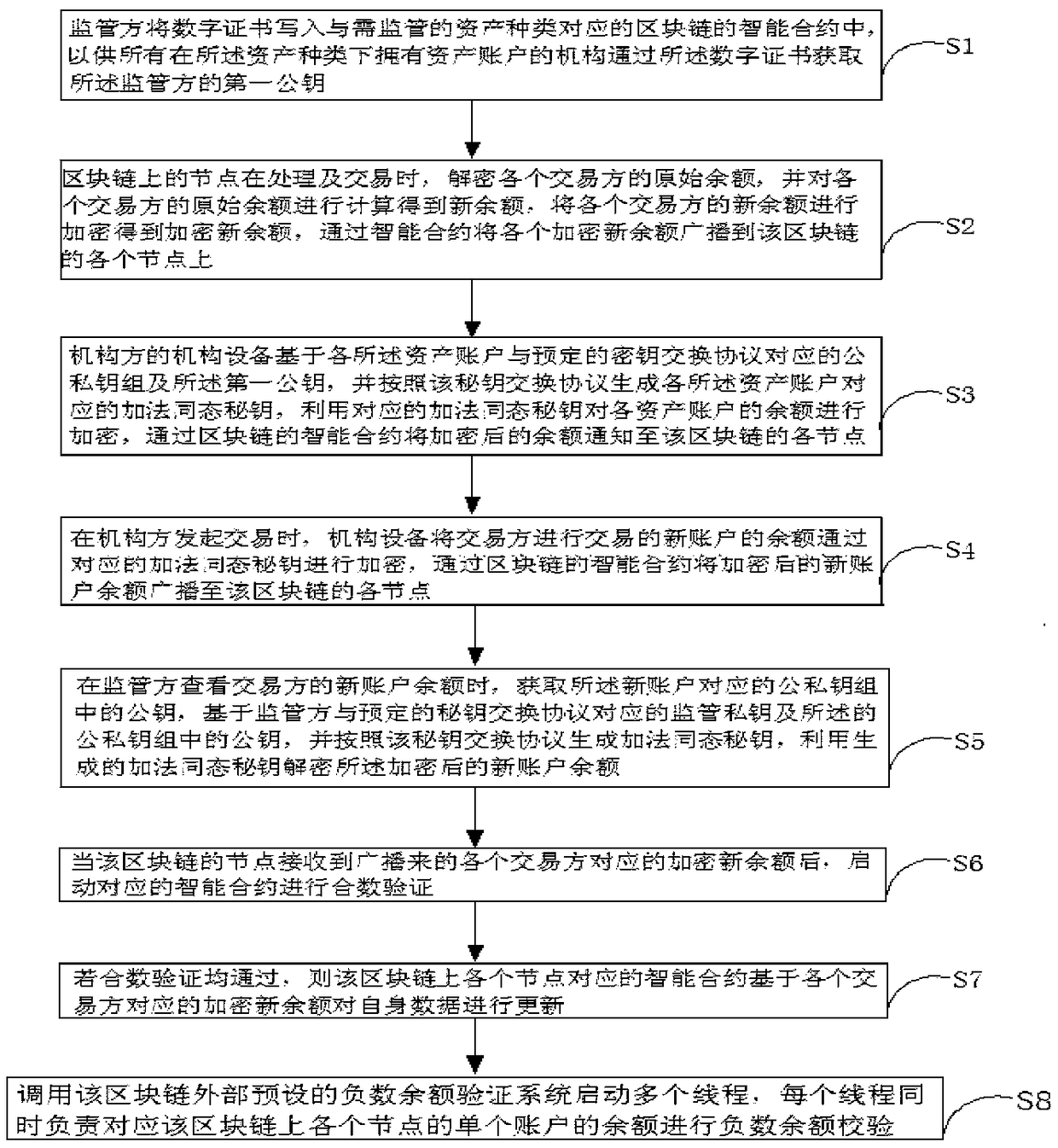
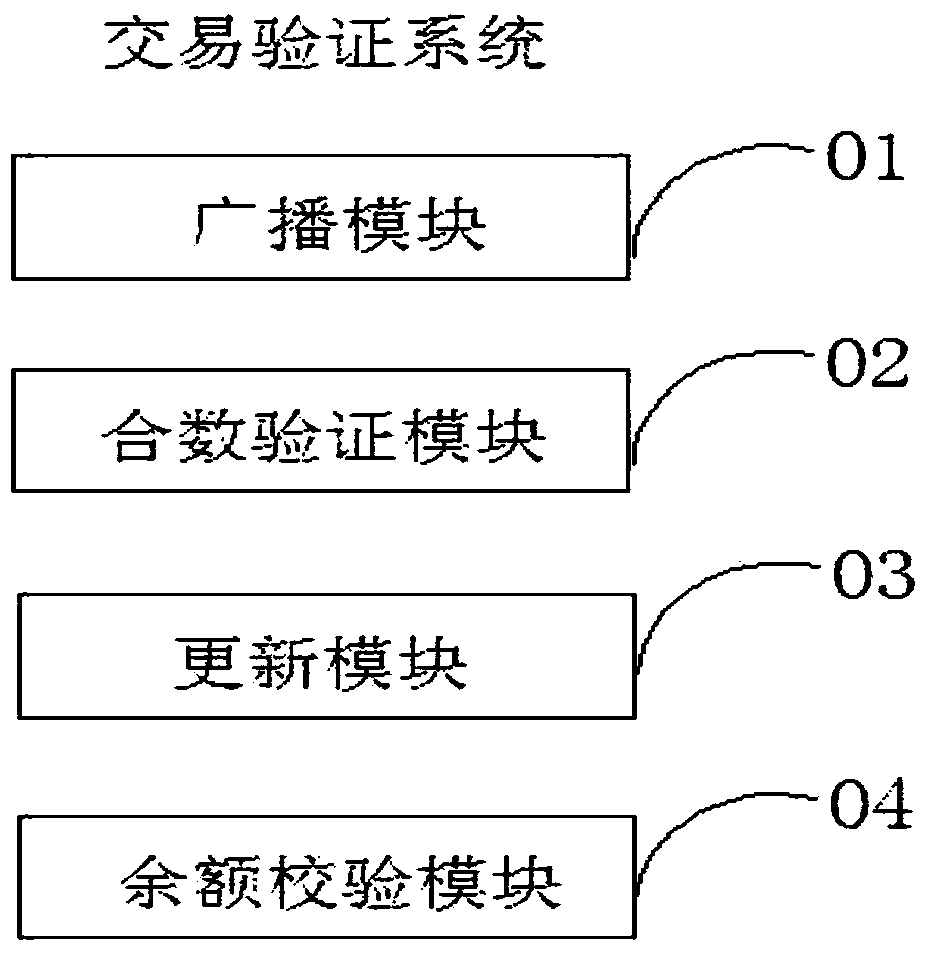
The invention discloses a secure transaction verification method and a secure transaction verification system based on a blockchain. The secure transaction verification method comprises the steps that: when a transaction with a transaction type and a transaction amount is processed by a node on the blockchain, an original balance of each transaction party is decrypted through a first decryption parameter transmitted by the transaction party, calculation is performed on the each original balance to obtain a new balance, the new balance is encrypted through an encryption parameter transmitted bythe transaction party to obtain an encrypted new balance, and the each encrypted new balance is broadcast to each node on the blockchain; after the broadcast encrypted new balance of the each transaction party is received by the node on the blockchain, an intelligent contract is activated to perform composite number verification; if the each composite number verification is passed, update is performed based on the corresponding encrypted new balance respectively; an external minus balance verification system is called to perform minus balance verification on single account balance, if the each minus balance verification is passed, it is judged that the transaction verification is passed. The secure transaction verification method and the secure transaction verification system of the invention have the beneficial effects that: whether a transaction is normal can be verified, and transaction processing speed on the blockchain also can be ensured without occupying system overhead.
Owner:四川吉鼎科技有限公司
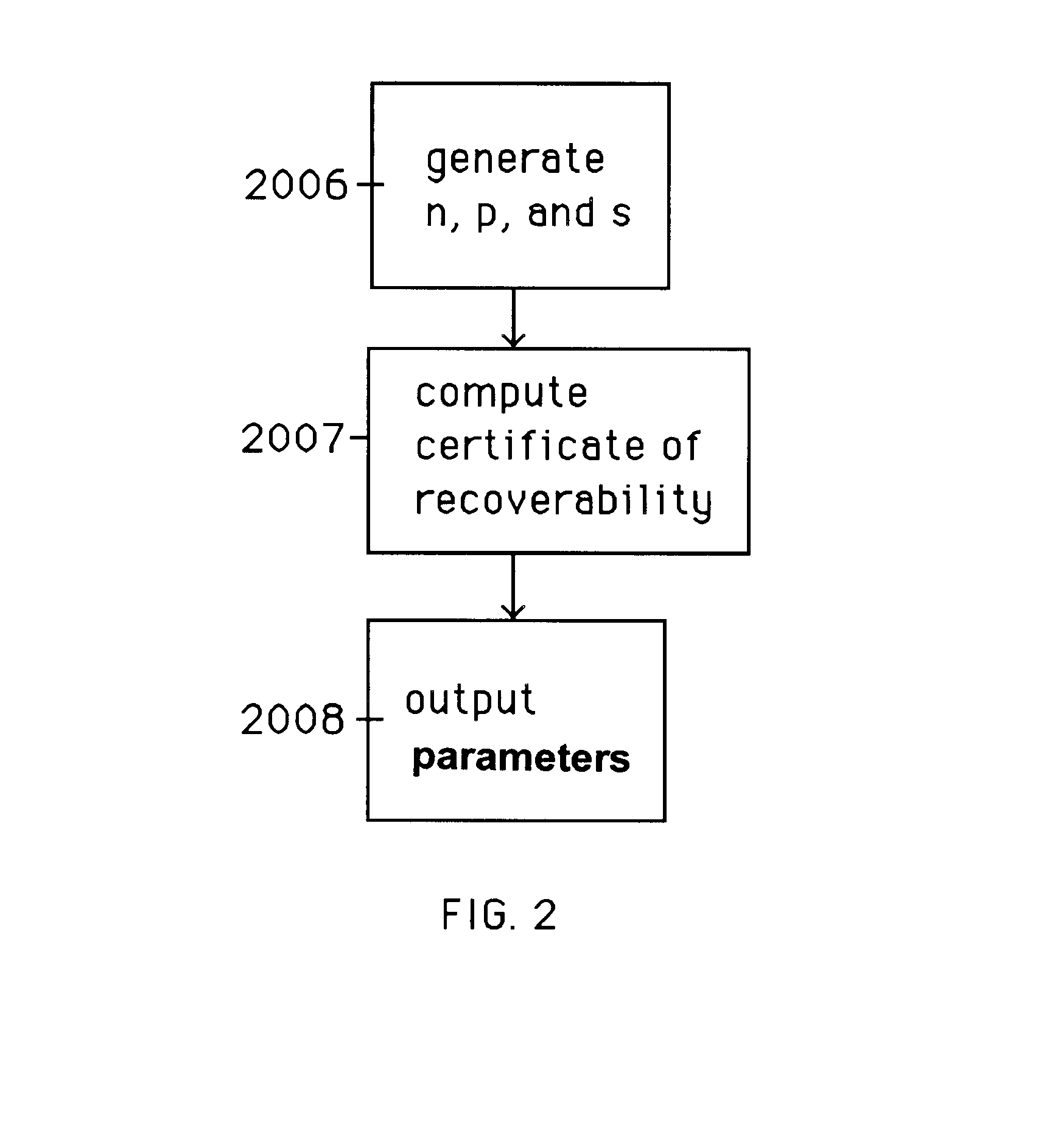
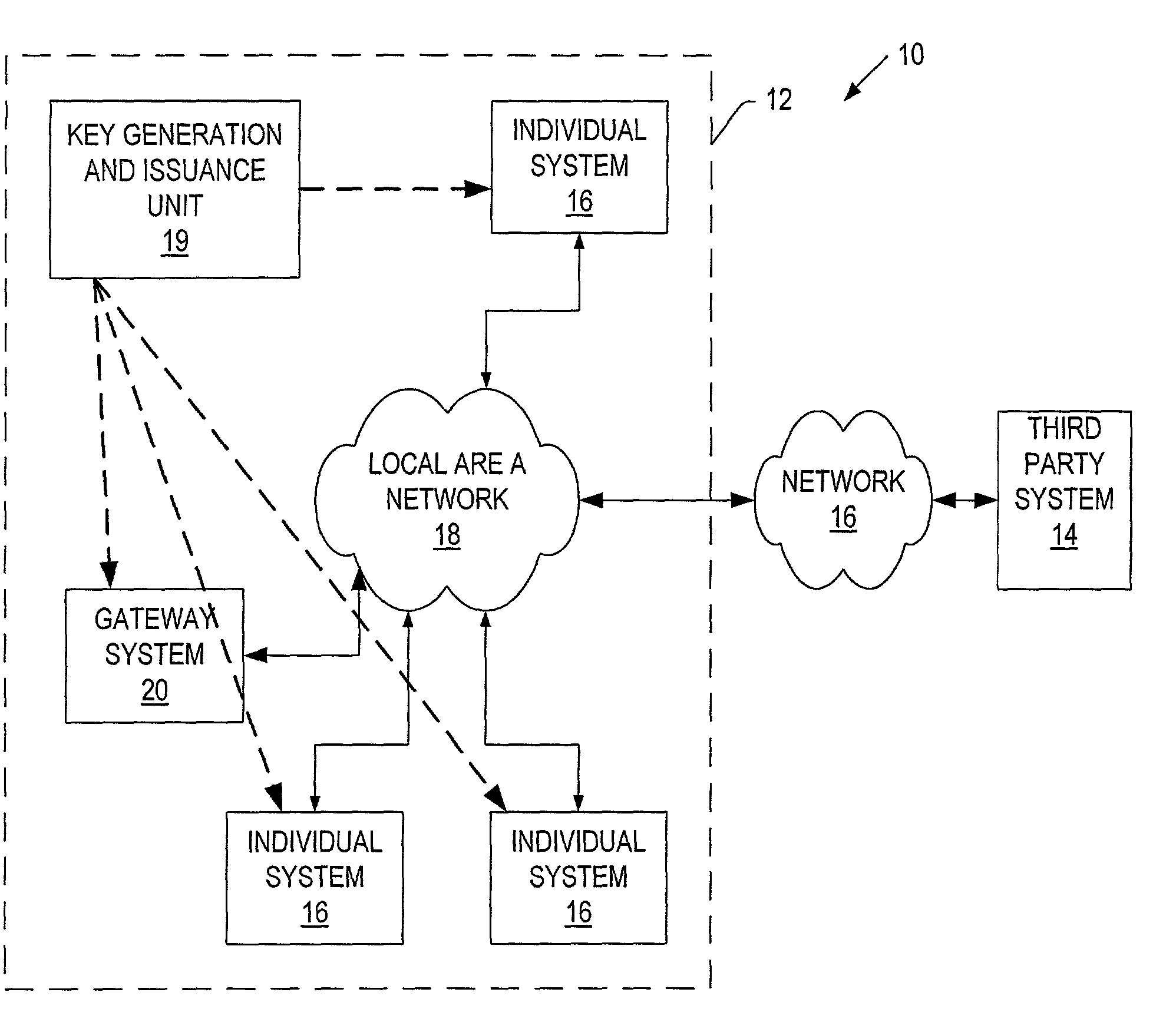
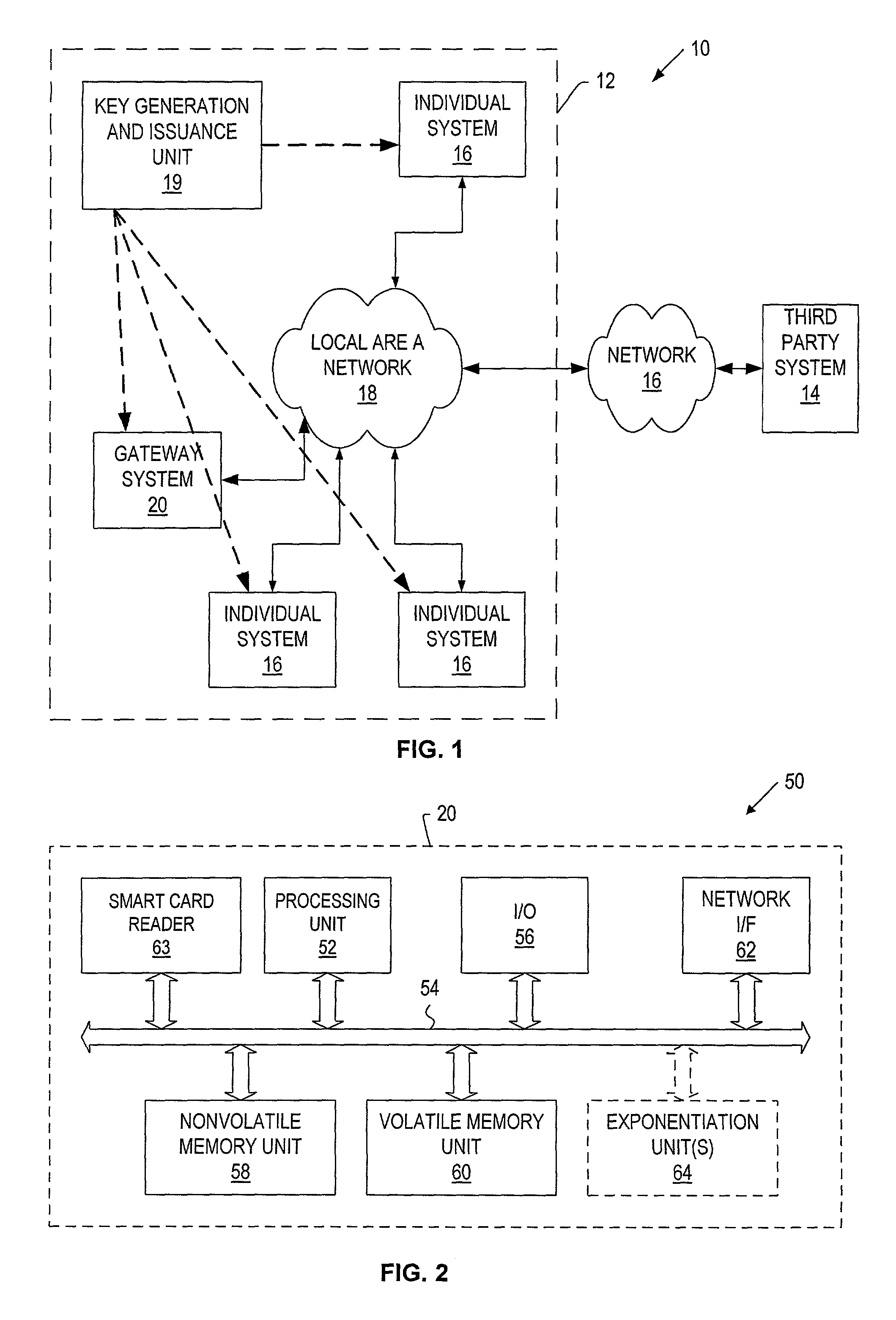
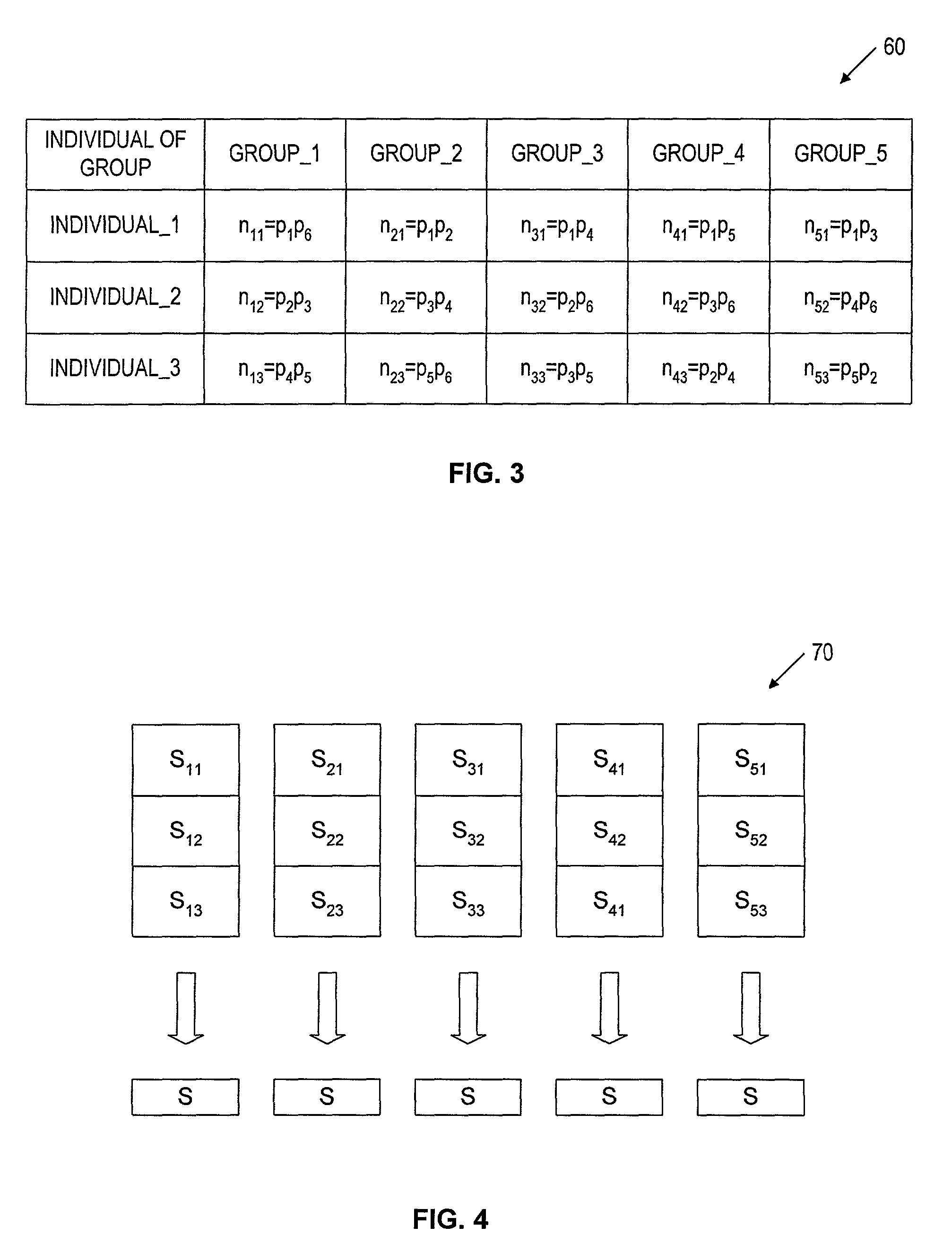
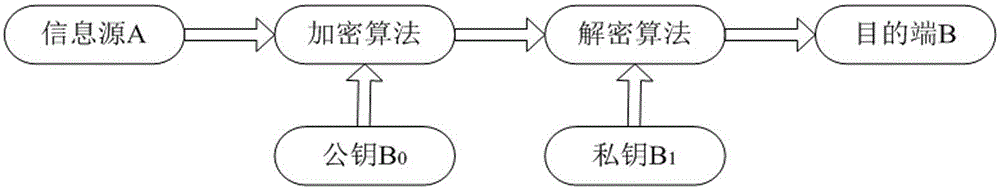
Auto-Recoverable and Auto-certifiable cryptosystems with RSA or factoring based keys
InactiveUS6389136B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityComposite number
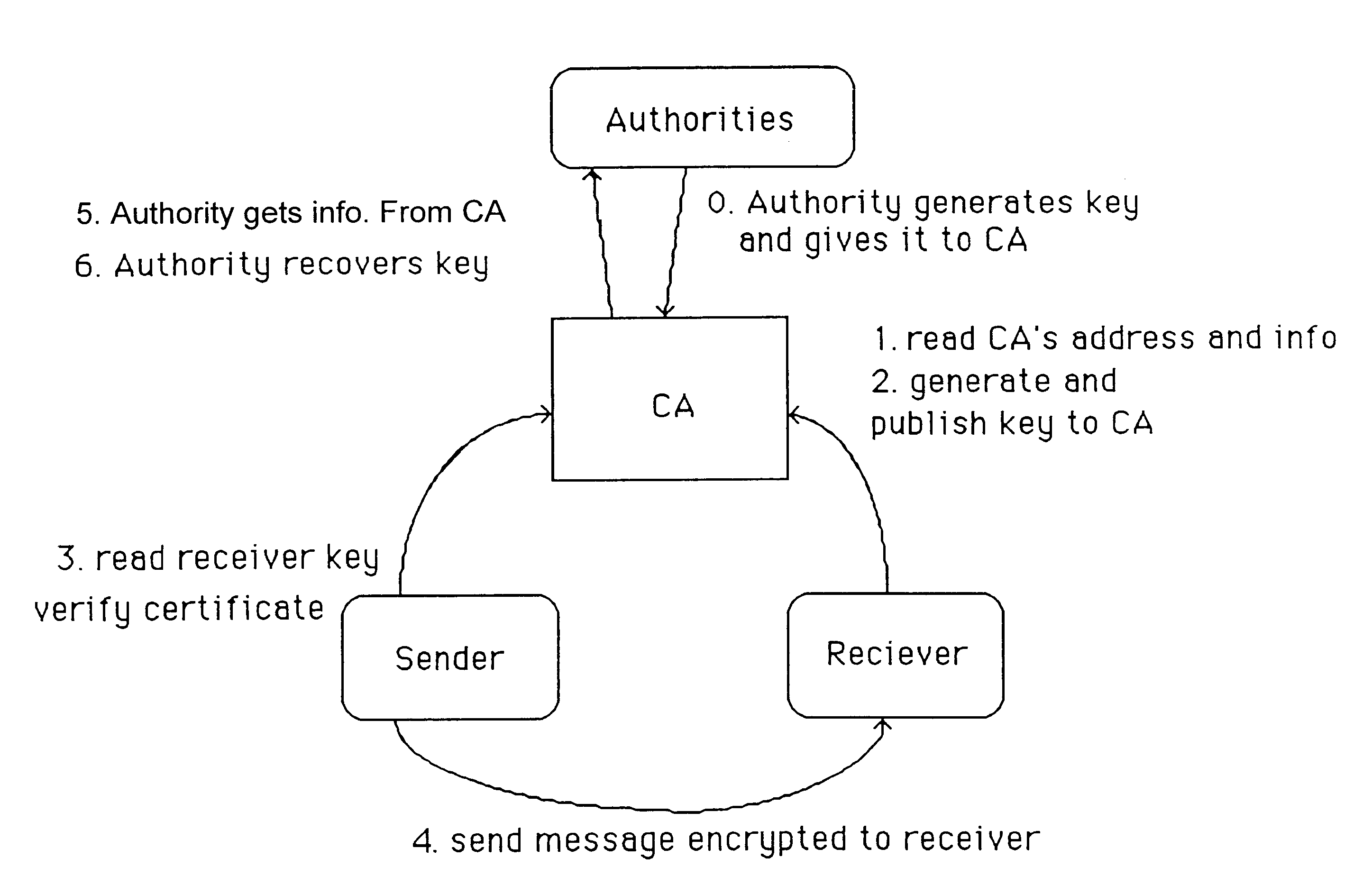
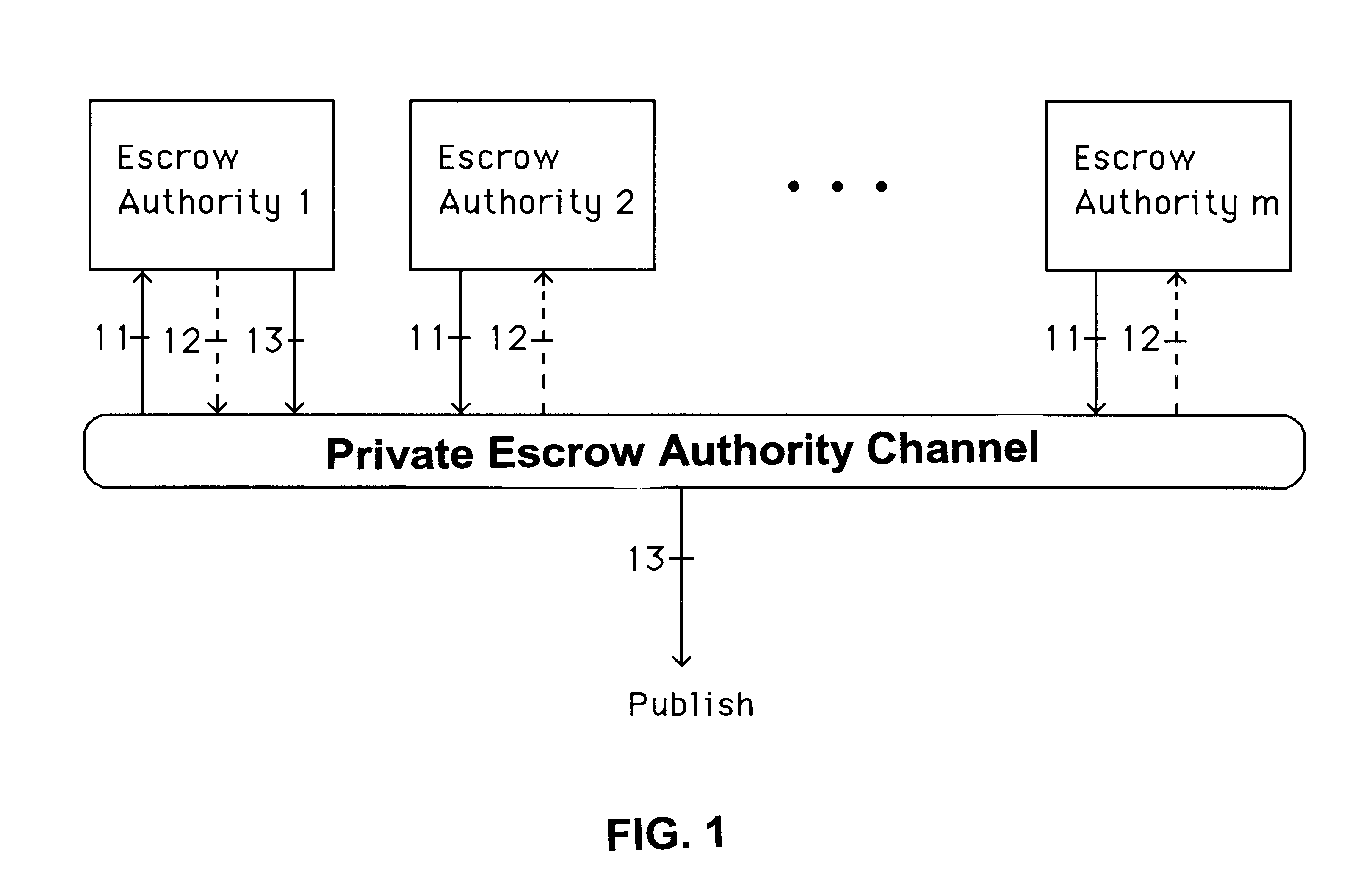
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. The keys generated are based on composite numbers (like RSA keys). A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or Rabin cryptosystem. The system is applicable for law-enforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. Another aspect of the system is the possibility to organize it in a hierarchical tree structure, where each element in the tree is an escrow authority (or authorities) capable to recover keys and / or information encrypted under these keys within the subtree rooted at the authority (or authorities) and only within this subtree.
Owner:CRYPTOPEAK SECURITY LLC
Group signature generation system using multiple primes
InactiveUS7093133B2User identity/authority verificationHardware monitoringComposite numberDigital signature
A method is provided for generating a group digital signature wherein each of a group of individuals may sign a message M to create a group digital signature S, wherein M corresponds to a number representative of a message, 0≦M≦n−1, n is a composite number formed from the product of a number k of distinct random prime factors p1·p2· . . . ·pk, k is an integer greater than 2, and S≡Md(mod n). The method may include: performing a first partial digital signature subtask on a message M using a first individual private key to produce a first partial digital signature S1; performing at least a second partial digital signature subtask on the message M using a second individual private key to produce a second partial digital signature S2; and combining the partial digital signature results to produce a group digital signature S.
Owner:HEWLETT PACKARD DEV CO LP
Cloud storage ciphertext retrieval method and system
ActiveCN103944711AAccurately obtainedReduce transmission costKey distribution for secure communicationSpecial data processing applicationsComposite numberCiphertext
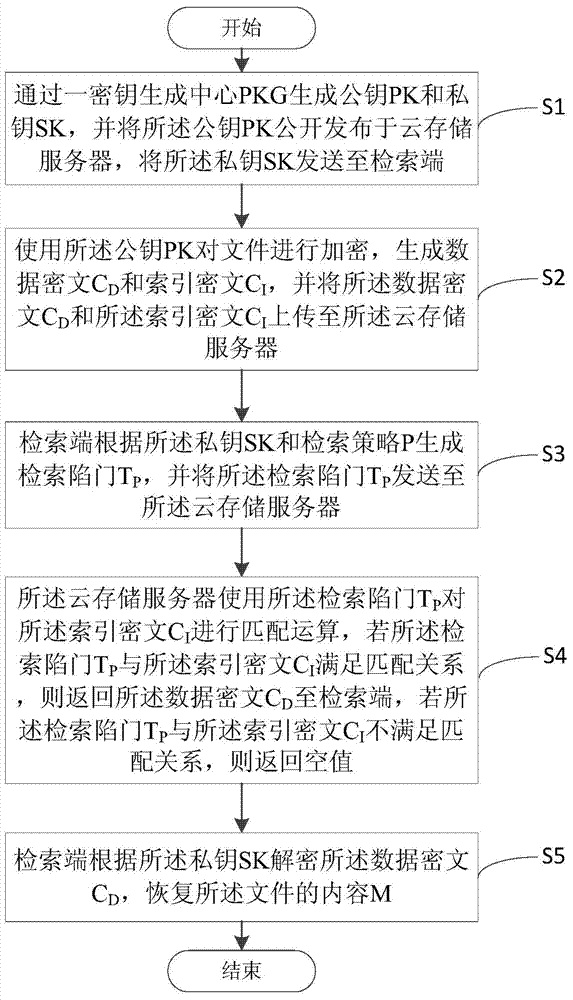
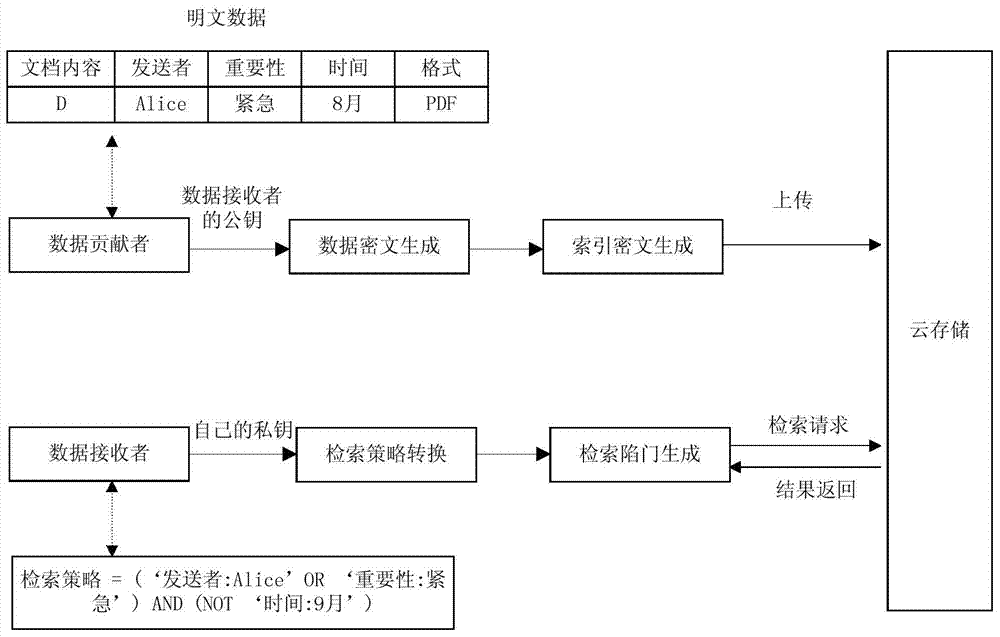
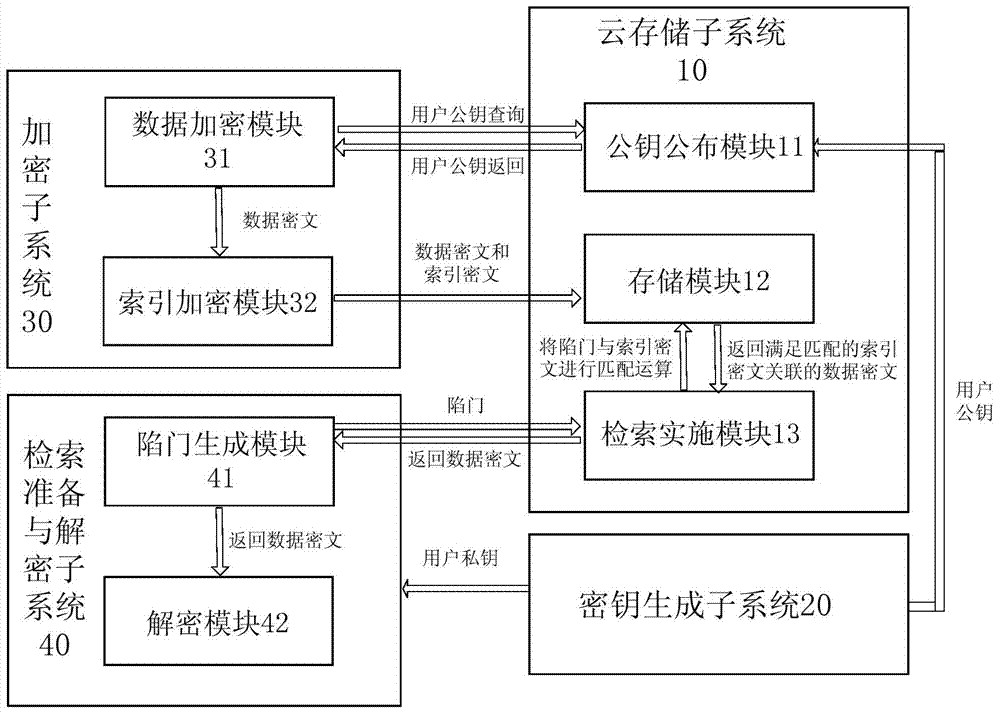
The invention discloses a cloud storage ciphertext retrieval method and system. The method includes the following steps: (1) a step of generating a public key and a private key at a retrieval end; (2) an encryption step; (3) a step of generating a retrieval trap door; (4) a retrieval implementation step; (5) a decryption step. Through implementation of the cloud storage ciphertext retrieval method and system, the cloud storage ciphertext retrieval supports a retrieval strategy of nest of logic words such as AND, OR and NOT and the like and users are helped to accurately obtain needed data and thus the transmission cost is reduced and the method and system have the advantages of being simple in process and high in calculation efficiency. At the same time, the cloud storage ciphertext retrieval method and system adopt composite number order group and bilinear pairing for construction and thus known plaintext distribution regularity attacks and attacks targeted at access modes are effectively prevented and thus the security is comparatively high.
Owner:国家超级计算深圳中心 +1
Dual-carboxylate gemini surfactant resistant to high temperature and high salt and preparation method thereof
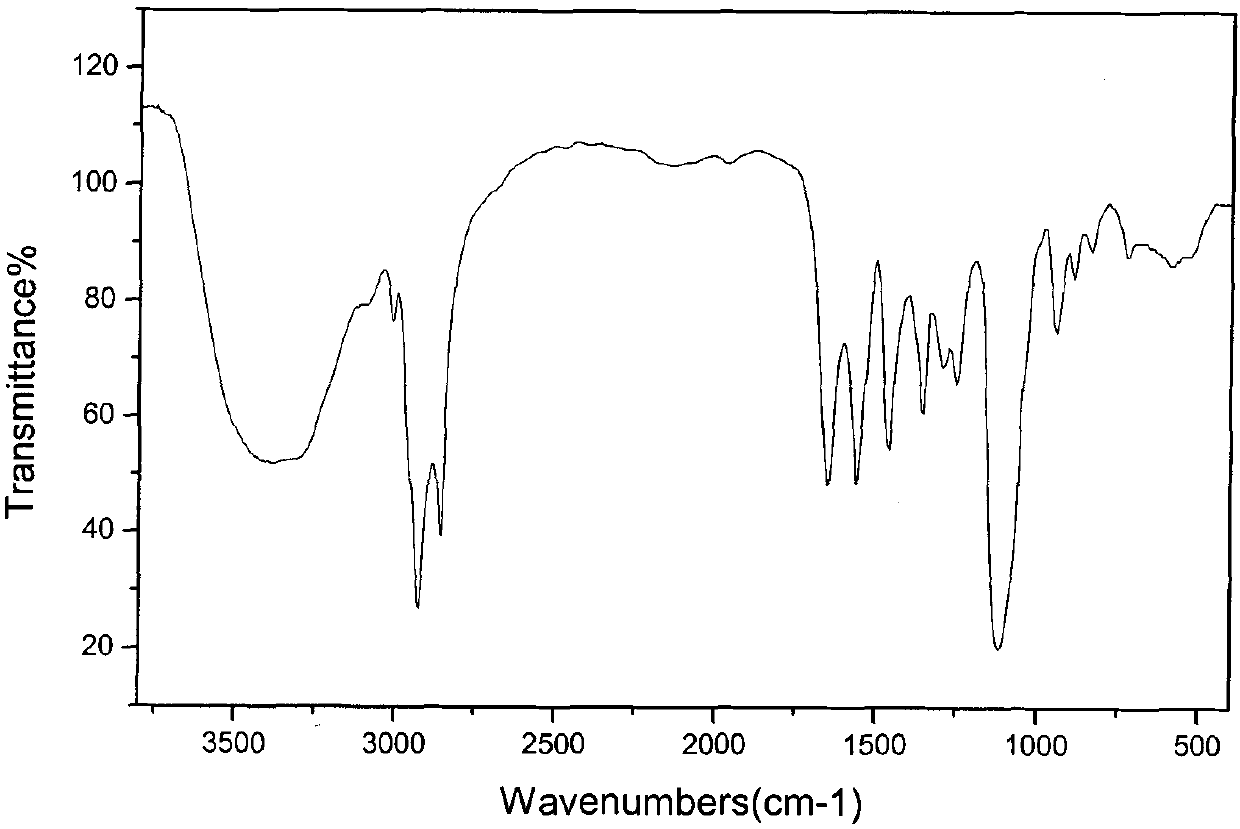
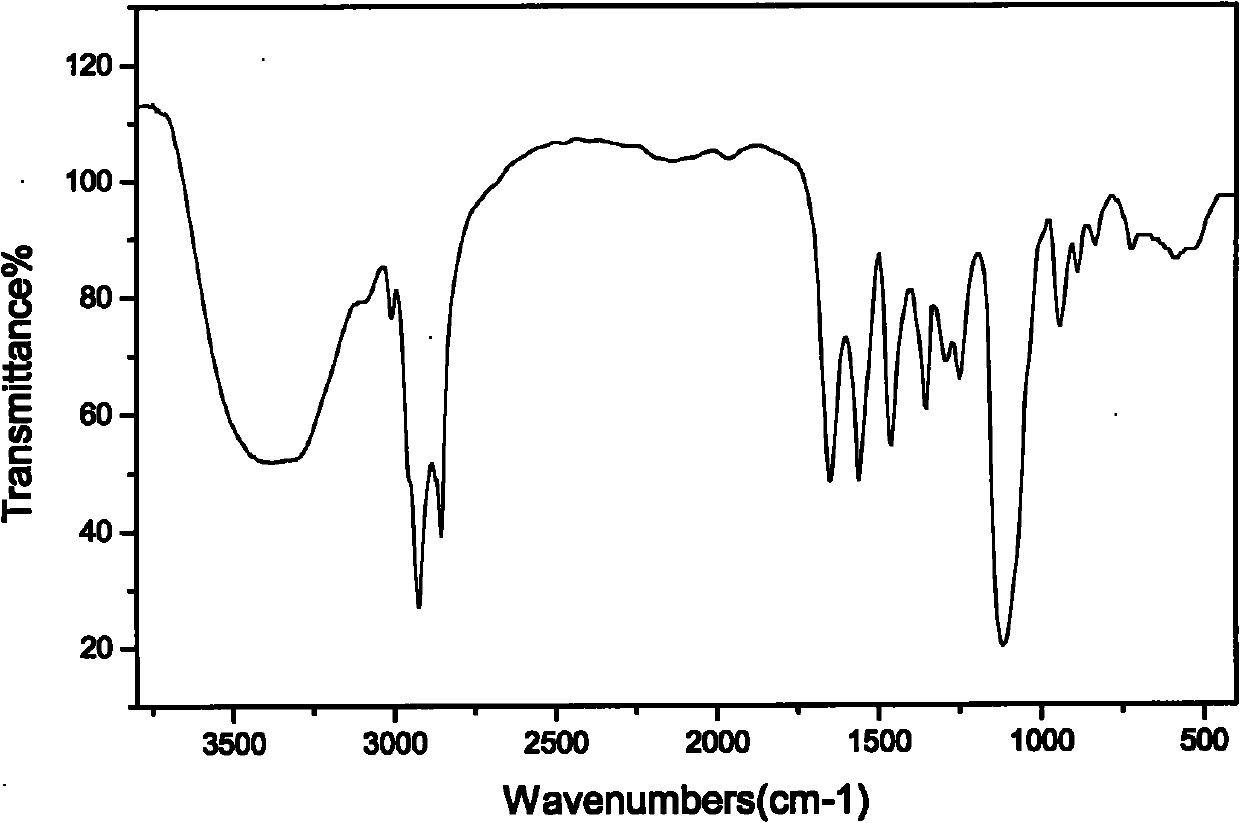
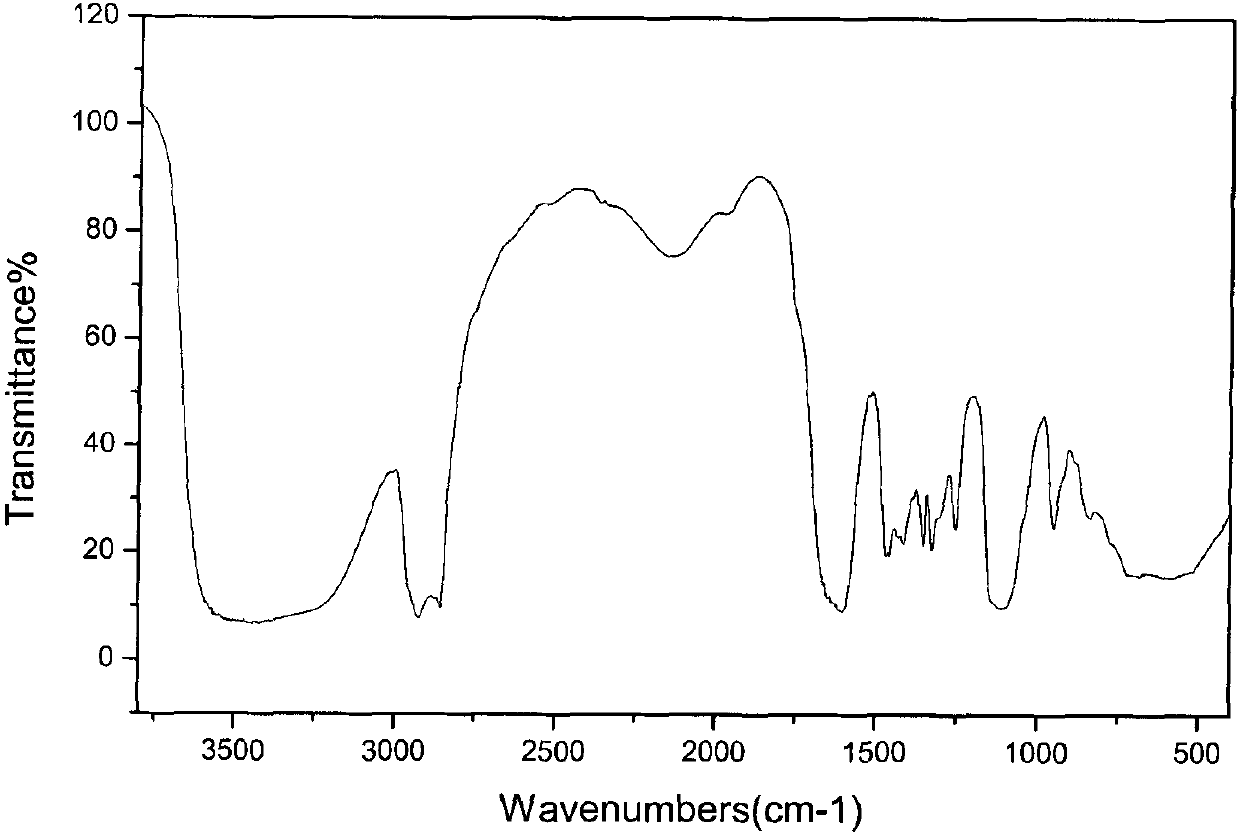
ActiveCN102218282AHarm reductionLow critical micelle concentrationTransportation and packagingMixingPropanoic acidComposite number
The invention relates to a dual-carboxylate gemini surfactant resistant to high temperature and high salt and a preparation method thereof, which mainly solve the problems that in the prior art, an oil displacement agent containing the surfactant has the defects of low oil displacement efficiency and high using concentration in high-temperature and high-salt conditions and alkali in the trinary alkali-surfactant-polymer flooding brings about corrosion and scale depositing to the stratum and oil wells. In the invention, a technical scheme of N, N-dual-fatty acyl diamine dioxin-propionic acid dioxin-polyoxyethylene ether dual-carboxylate with a general molecular formula shown in the specification is adopted and favorably solves the problem, wherein in the general molecular formula, M is selected from any one of metal ions of potassium, sodium or lithium, R1 is C9 to C17alkyl groups, R2 is C2 to C6 alkyl groups, n is an additive composite number of ethoxy groups (EP) and has the value range of any on integral number from 2 to 7; and the dual-carboxylate gemini surfactant resistant to high temperature and high salt can be applicable to the tertiary oil recovery of oil fields.
Owner:CHINA PETROLEUM & CHEM CORP +1
Method of heat accumulation and heat accumulation system
InactiveCN101395439AWell mixedImprove heat transfer efficiencyHeat storage plantsHeat-exchange elementsInorganic saltsComposite number
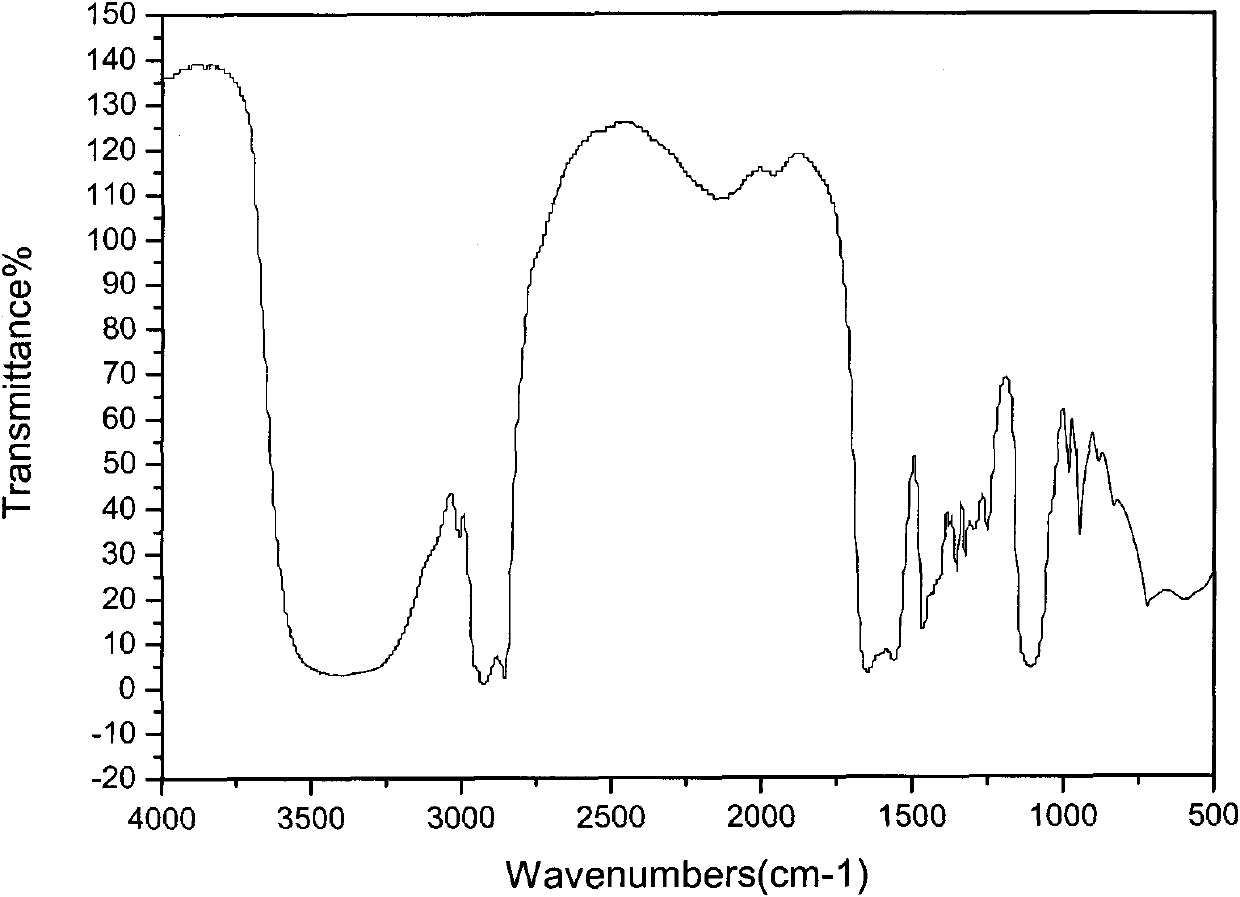
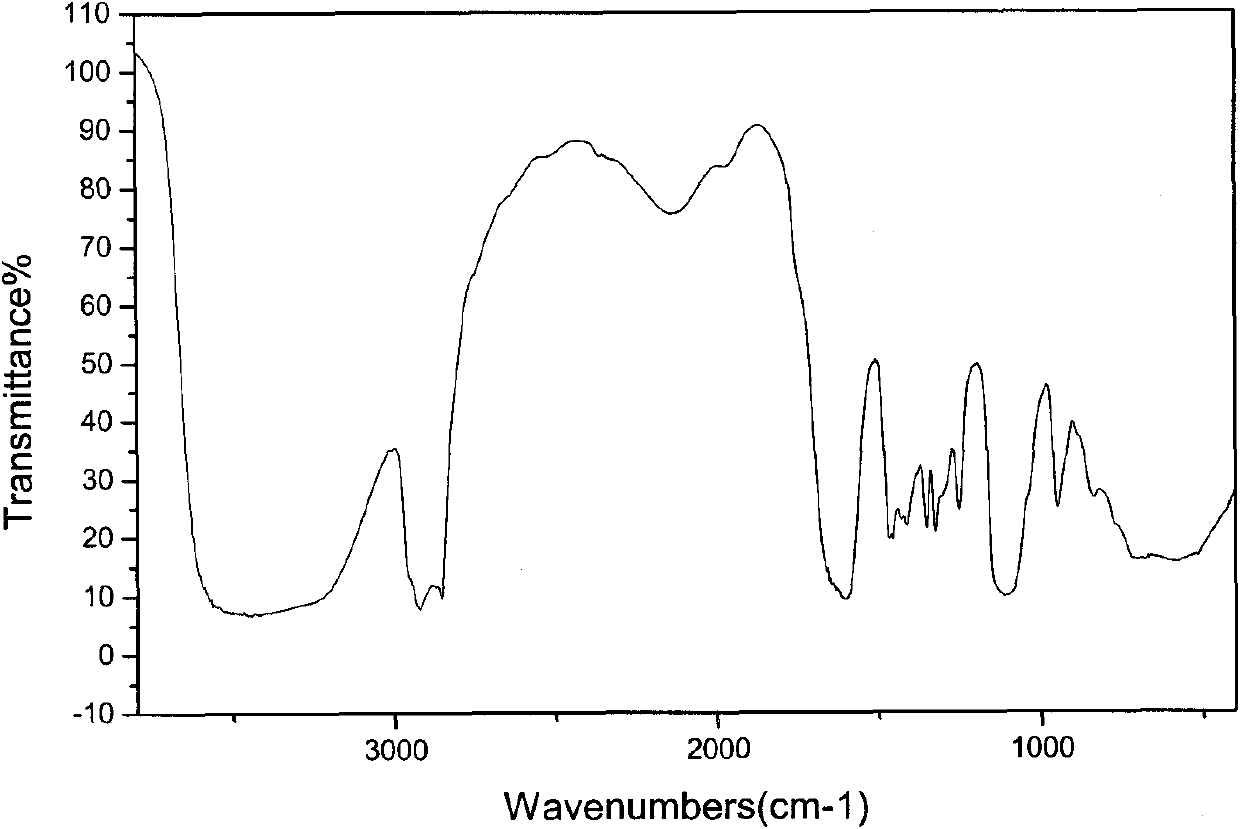
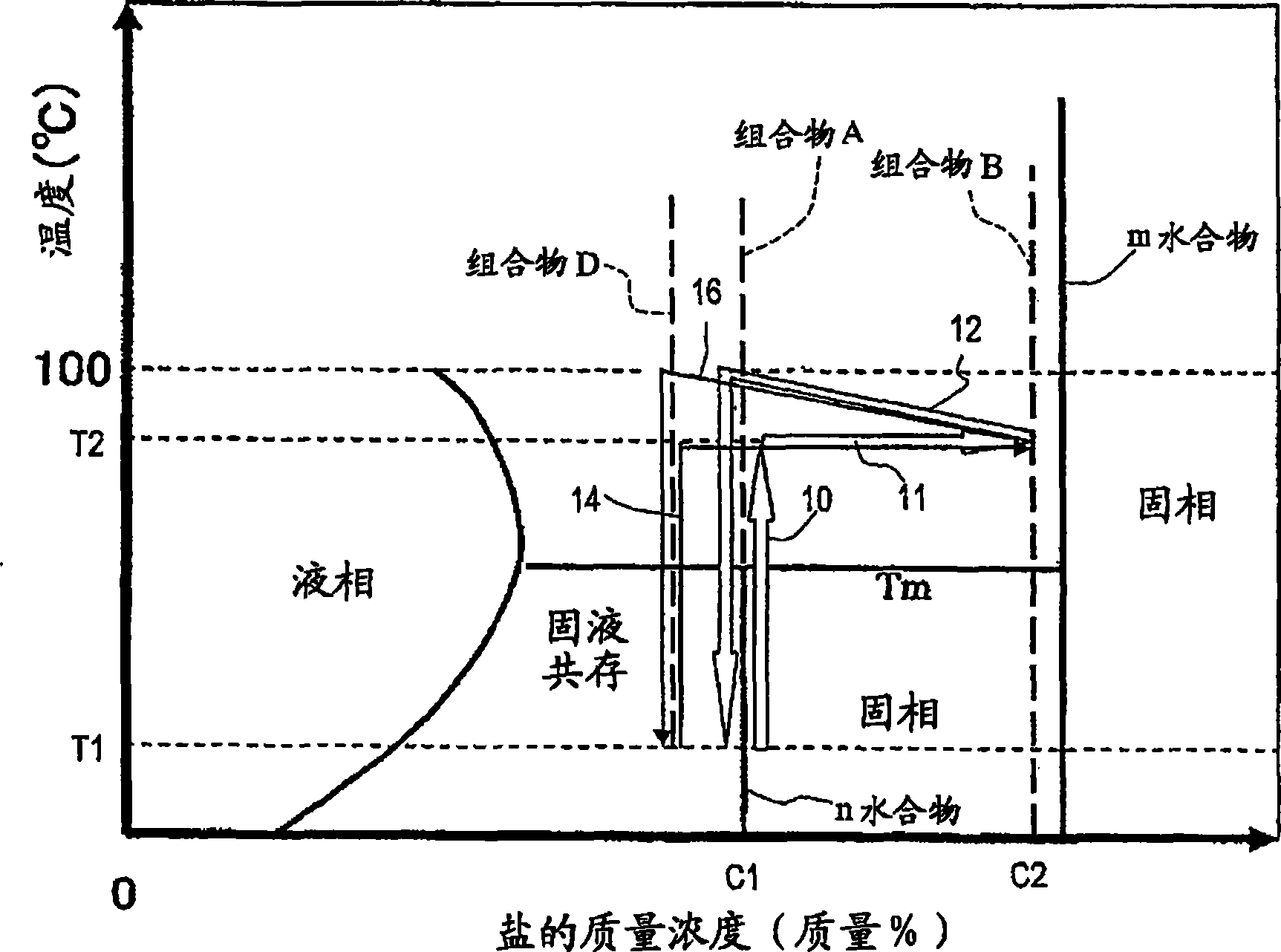
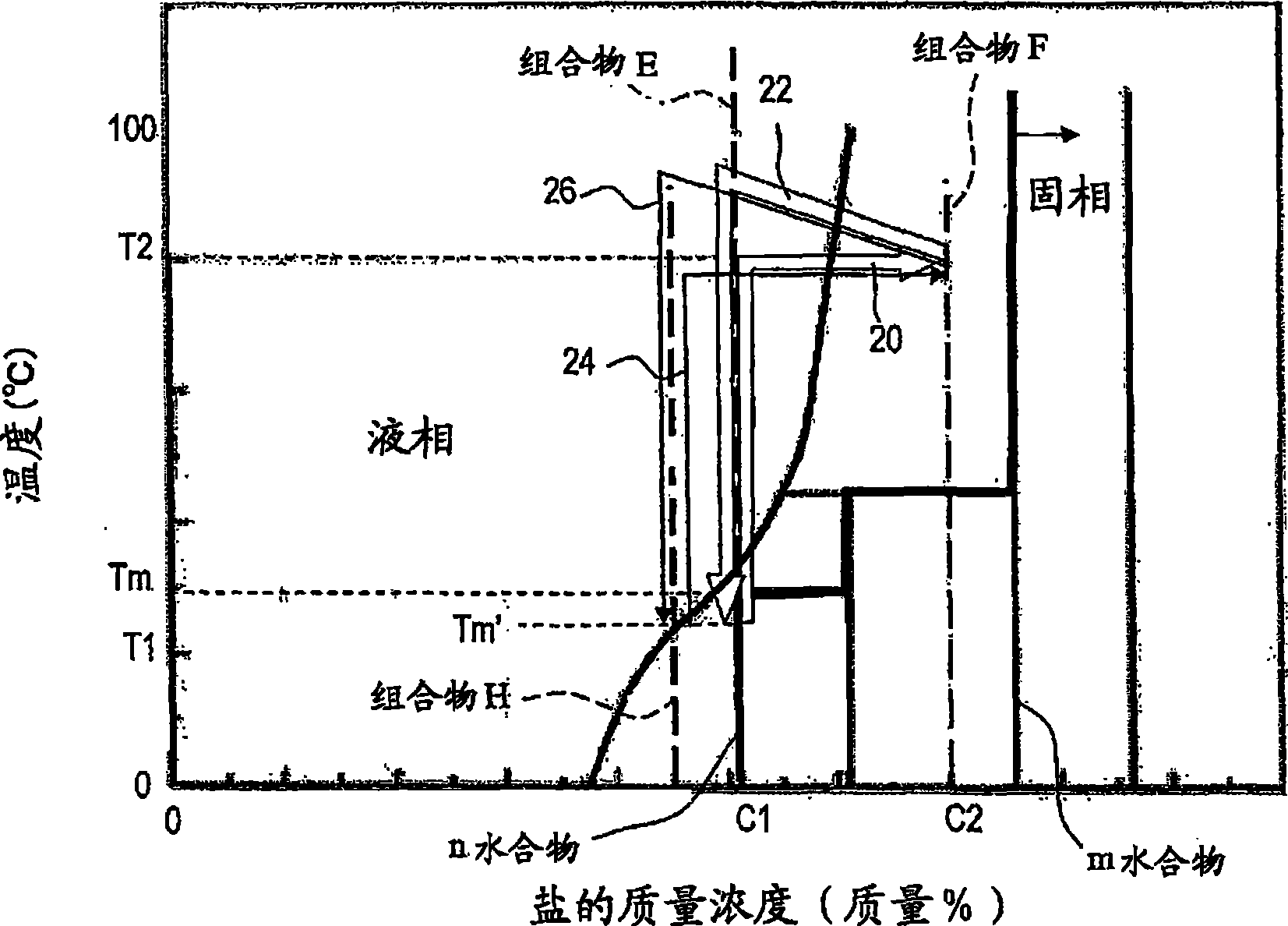
A method of heat accumulation which comprises the step (A) of preparing the first composition (A) containing a solid inorganic salt n-hydrate (wherein n is a hydration number) having a phase change temperature (Tm) of 100 DEG C or below in a heat accumulating medium container, the step (B) of heating the first composition (A) to a temperature (T2) higher than Tm and taking water contained in the first composition (A) out of the container to form the second composition (B) wherein both a solid inorganic salt m-hydrate (wherein m is a hydration number satisfying the relationship: m<n) and an aqueous solution of the inorganic salt coexist, the step (C) of detecting the formation of the second composition (B) and thereby stopping the takeout of water from the container, the step (D) of storing the second composition (B), and the step (E) of mixing the second composition (B) with water and thereby recovering at least part of the heat accumulated in the second composition (B).
Owner:PANASONIC CORP
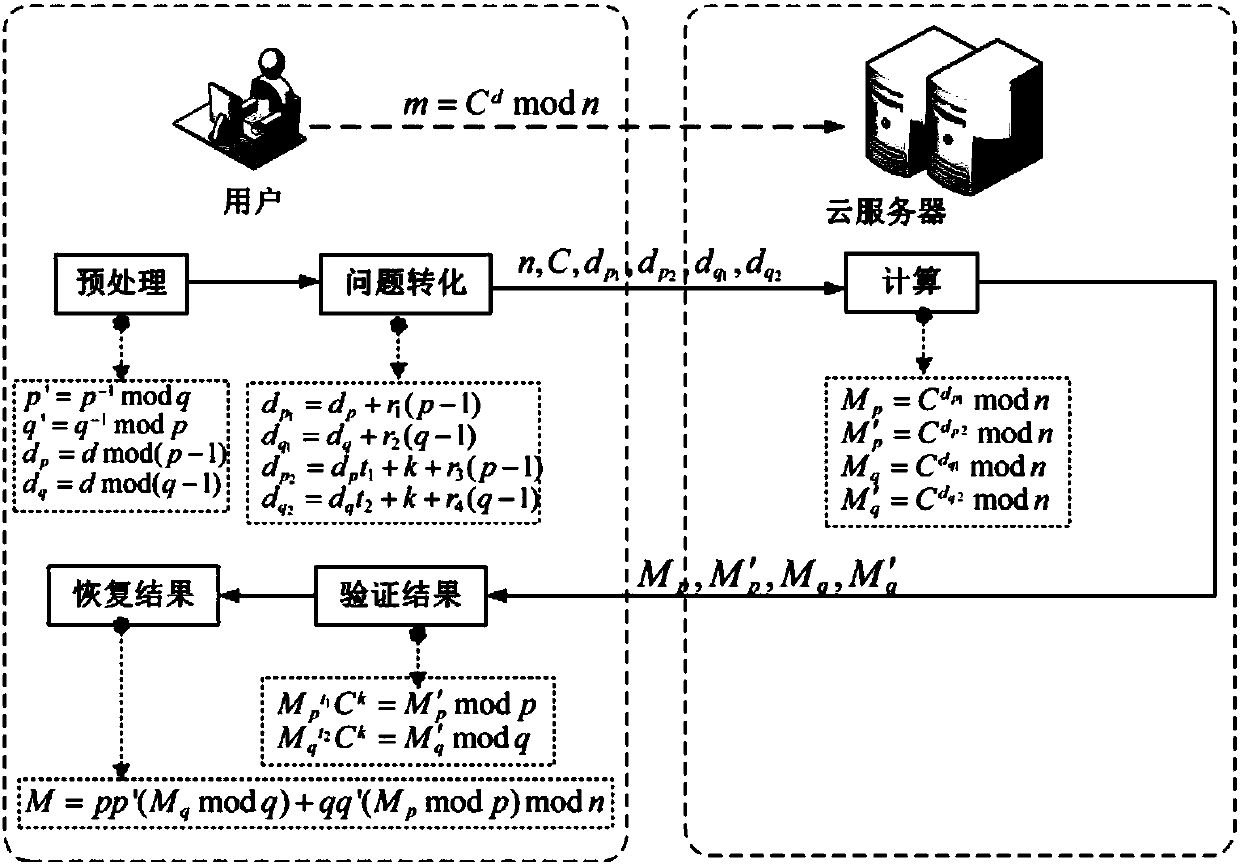
Safe outsourcing calculation method applied to RSA decryption
ActiveCN108155994AProtect private keyProtection modulusKey distribution for secure communicationPublic key for secure communicationPlaintextComposite number
The invention provides a novel safe outsourcing algorithm applied to RSA decryption. The algorithm satisfies an equation M=C<d>mod n, wherein input values are a ciphertext C, a private key d and a modulus n, the modulus n is a large composite number, factors p and q are provided, namely n=pq, and an output value is a plaintext m. Large module power multiplication is considered to be outsourced toa cloud server, so that a user only needs to execute a small amount of calculation to realize a decryption process of the RSA. Due to the fact that the scheme of the outsourcing calculation needs to meet the defined safety, in other words, the privacy, the correctness and the high-efficiency verification of input and output are achieved. According to the scheme, the indexes and the modulus in theRSA decryption process and the decrypted plaintext are protected, the calculation amount of a user side can be reduced after the outsourcing decryption calculation is carried out, and meanwhile, the safety requirement can be met.
Owner:QINGDAO UNIV
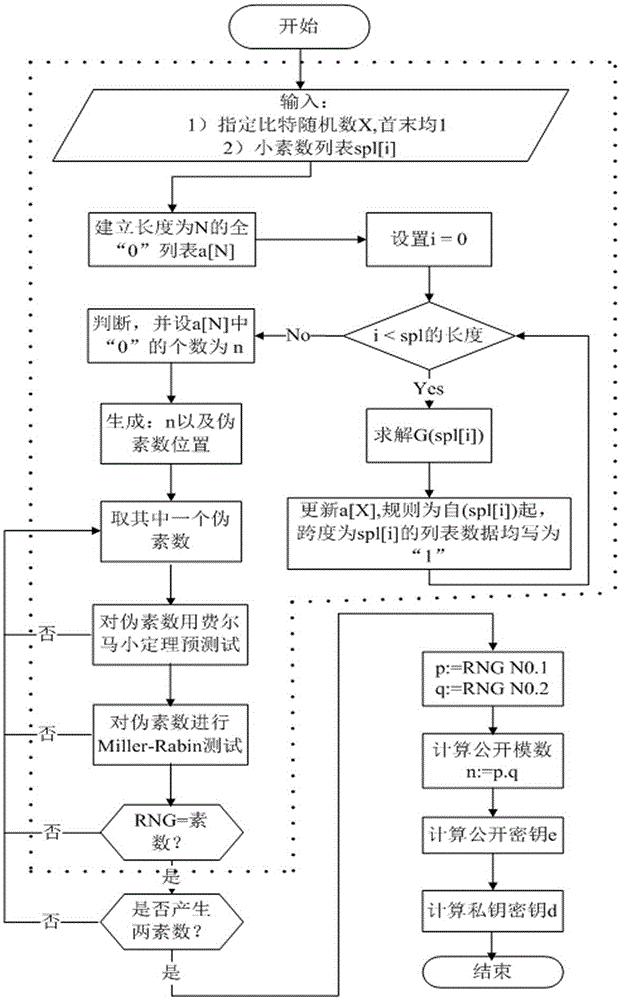
RSA key pair fast generation system and RSA key pair fast generation method
InactiveCN106487512AReduce build timeHigh speedKey distribution for secure communicationPublic key for secure communicationCoprocessorComposite number
The invention discloses an RSA key pair fast generation system and an RSA key pair fast generation method. The system comprises a CPU core, a cipher coprocessor, a prime number generator, and a memory. The prime number generator is used for filtering composite numbers, is implemented in hardware form, supports 256-bit, 512-bit, 1024-bit, 2048-bit and 4096-bit composite number filtering, and completes modular redundancy, calculation and identification table setting. According to the RSA key pair fast generation method, in order to realize fast key pair retrieving, filtering and judging in an asymmetric algorithm, a hardware-based composite number filtering scheme is adopted, optimized modular exponentiation and improved Montgomery modular multiplication are employed, and the existing prime number decision algorithm is optimized. Thus, efficient prime number screening is realized, the key pair generation speed is increased, and the problem that the generation of an RSA key pair takes long in the existing encryption and decryption technology is solved.
Owner:BEIJING TONGFANG MICROELECTRONICS
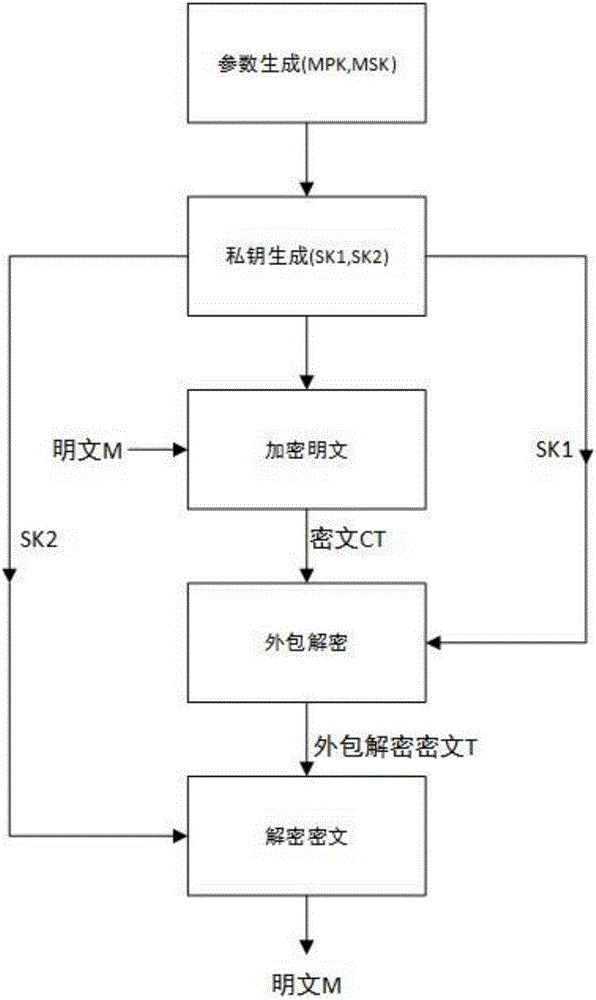
Anti-leakage CP-ABE method under strategy hiding and outsourcing decryption
ActiveCN107181590AReach the hidden functionPrevent leakageKey distribution for secure communicationThird partyComposite number
The invention discloses an anti-leakage CP-ABE (Ciphertext Policy-Attribute-Based Encryption) method under strategy hiding and outsourcing decryption. The anti-leakage CP-ABE method under strategy hiding and outsourcing decryption mainly realizes a CP-ABE scheme with three characteristics: leakage resistance, strategy hiding and outsourcing decryption, and belongs to the information safety field. The anti-leakage CP-ABE method under strategy hiding and outsourcing decryption utilizes a composite number order bilinear group to construct parameters, and adds the elements in a sub group Gp2 of the composite number order bilinear group in the main public key and the encryption algorithm to achieve the effect of hiding the access strategy. Besides, the algorithm decomposes the decryption process and adds an outsourcing decryption algorithm, and at the same time utilizes a double key system to enable the third party to be unable to completely decrypt the cryptograph, thus reducing the computing cost and guaranteeing safety of the user private key and the cryptograph. Compared with traditional anti-leakage scheme, the anti-leakage CP-ABE method under strategy hiding and outsourcing decryption has the advantages of leakage resistance, strategy hiding, outsourcing decryption, and higher safety, and greatly reduces the computing cost for decryption for the user.
Owner:NANJING UNIV OF POSTS & TELECOMM
Hydrotalcite compound, process for producing same, inorganic ion scavenger, composition, and electronic component-sealing resin composition
InactiveUS20100123101A1Improve performanceExcellent metal corrosion inhibiting effectMaterial nanotechnologyOther chemical processesComposite numberScavenger
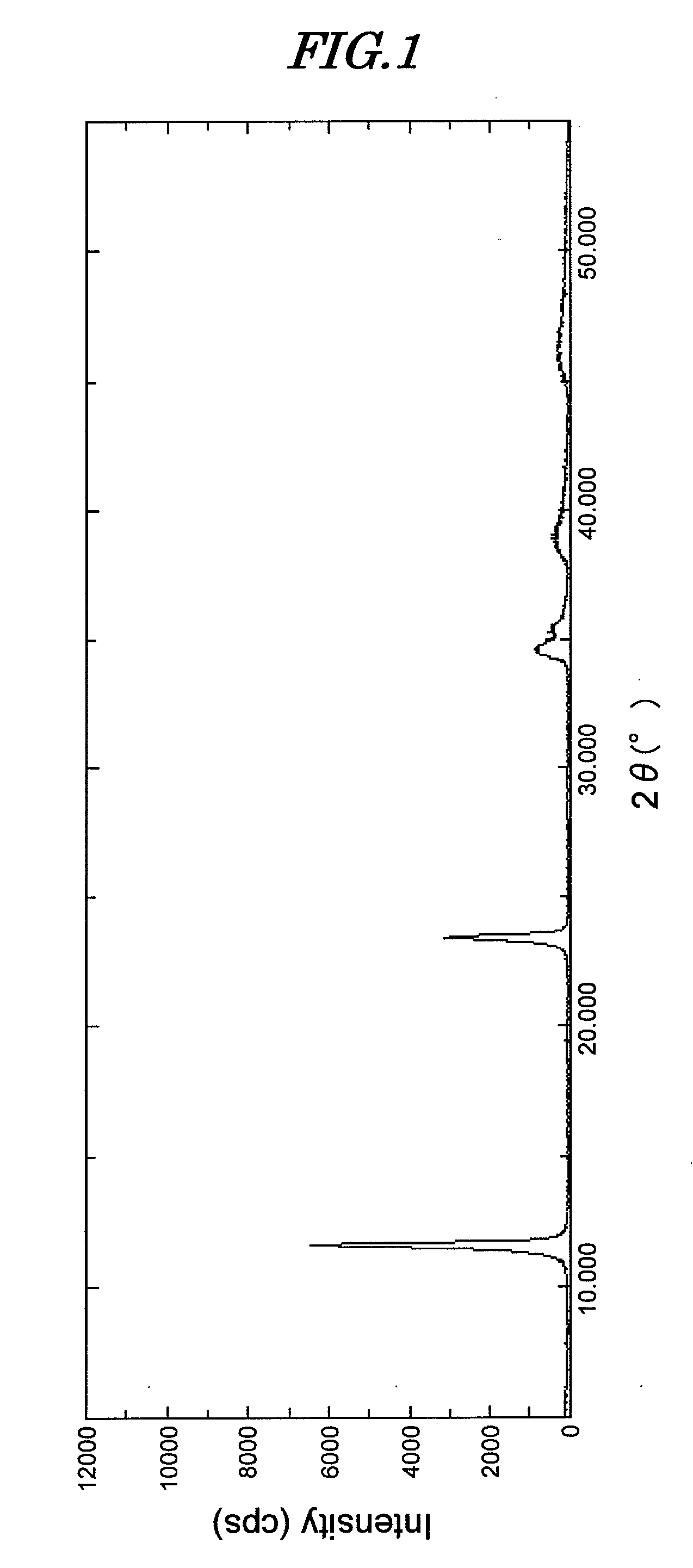
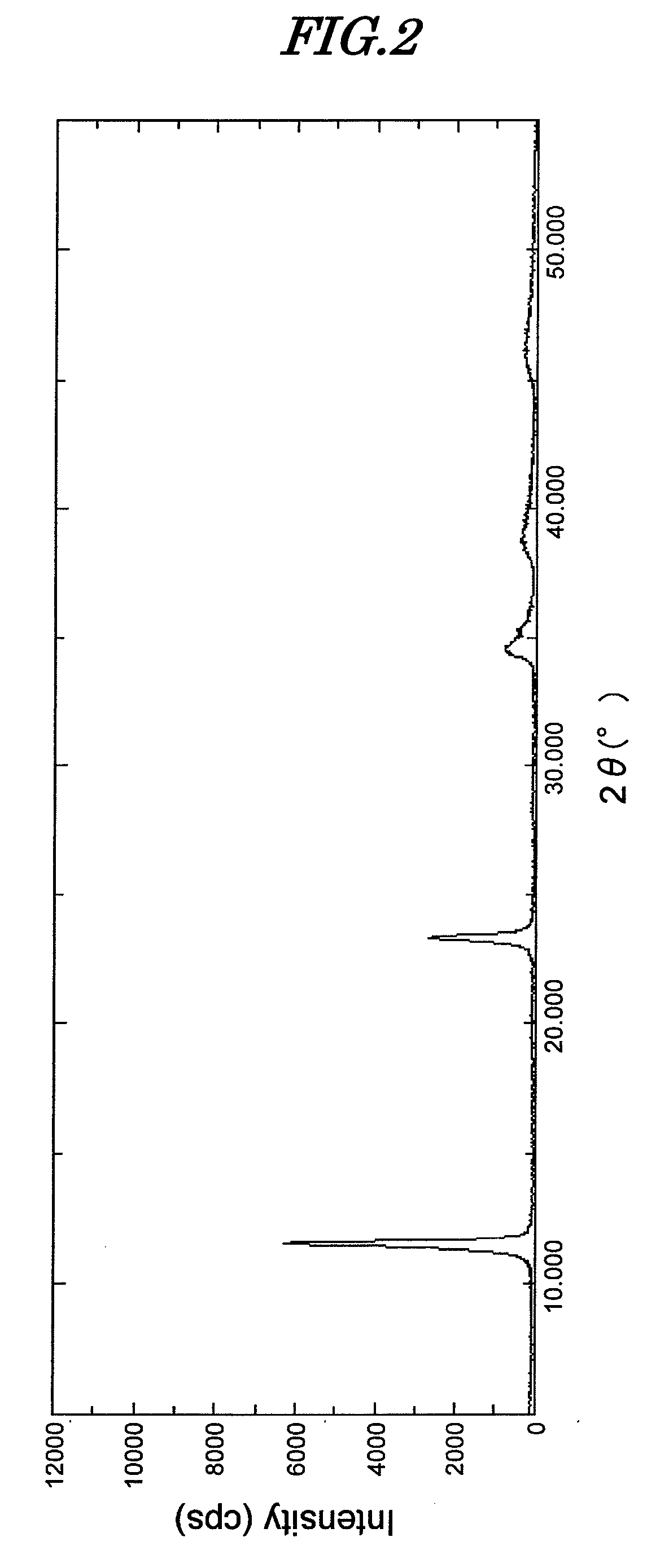
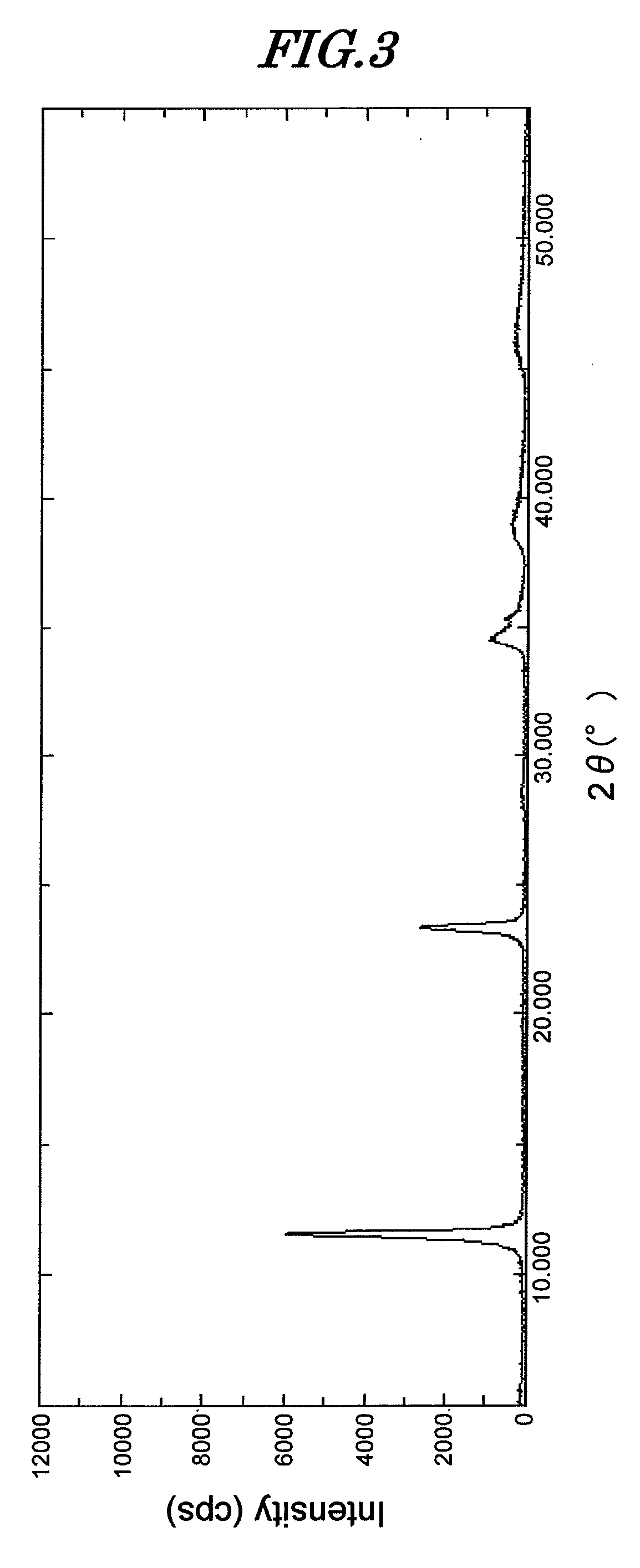
The present invention is a novel hydrotalcite compound that is environmentally friendly and exhibits an excellent metal corrosion inhibiting effect by the addition of a small amount thereof, and an inorganic ion scavenger employing same; the hydrotalcite compound is represented by Formula (1), has a hydrotalcite compound peak in the powder X-ray diffraction pattern, the peak intensity at 2θ=11.4° to 11.7° being at least 3,500 cps, and has a BET specific surface area of greater than 30 m2 / g.MgaAlb(OH)c(CO3)d·nH2O (1)In Formula (1), a, b, c, and d are positive numbers and satisfy 2a+3b−c−2d=0. Furthermore, n denotes hydration number and is 0 or a positive number.
Owner:TOAGOSEI CO LTD
Semiconductor device and manufacturing method thereof
InactiveUS20060154450A1High crystallinityImprove performanceTransistorSolid-state devicesComposite numberHydrogen
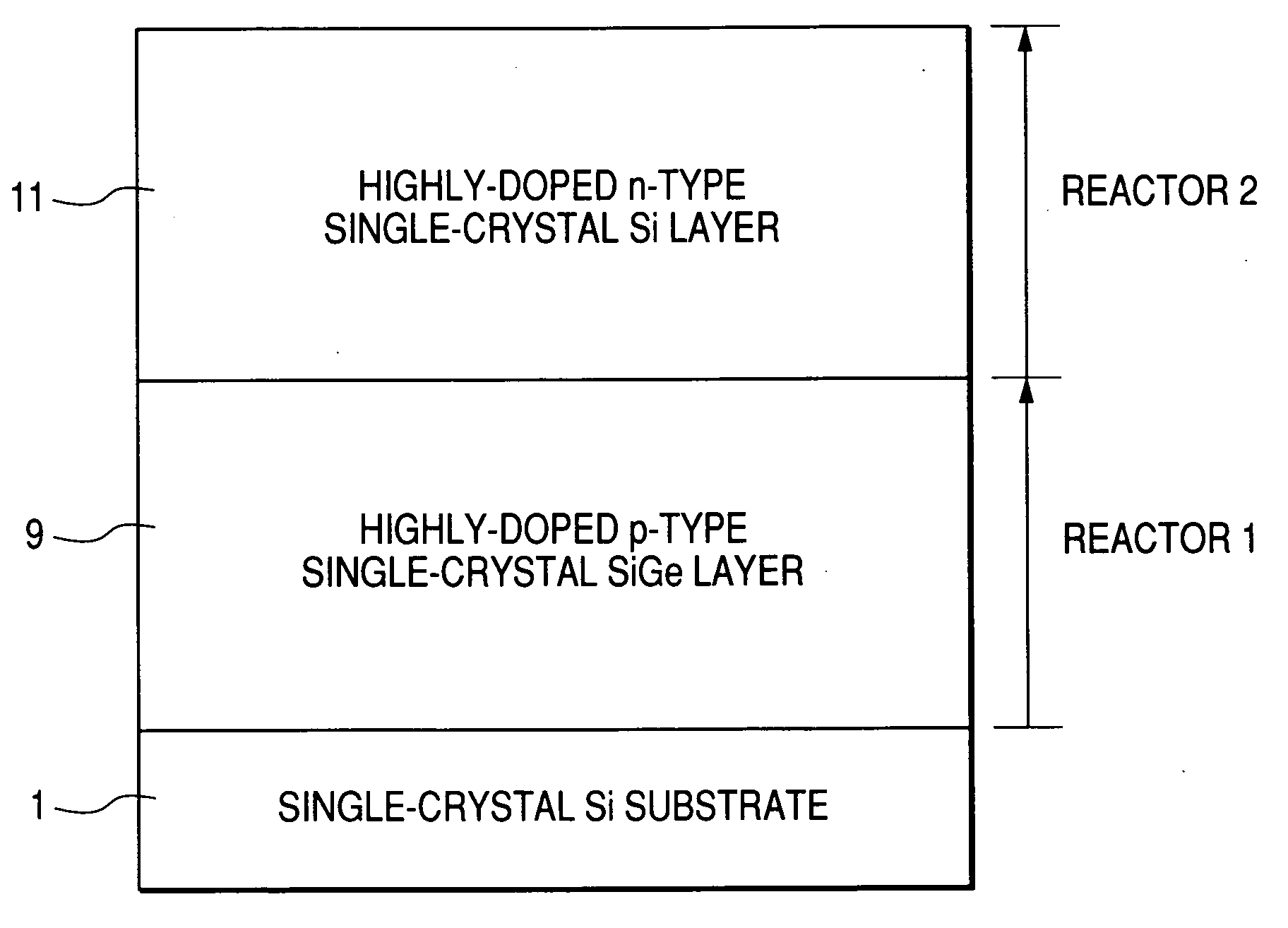
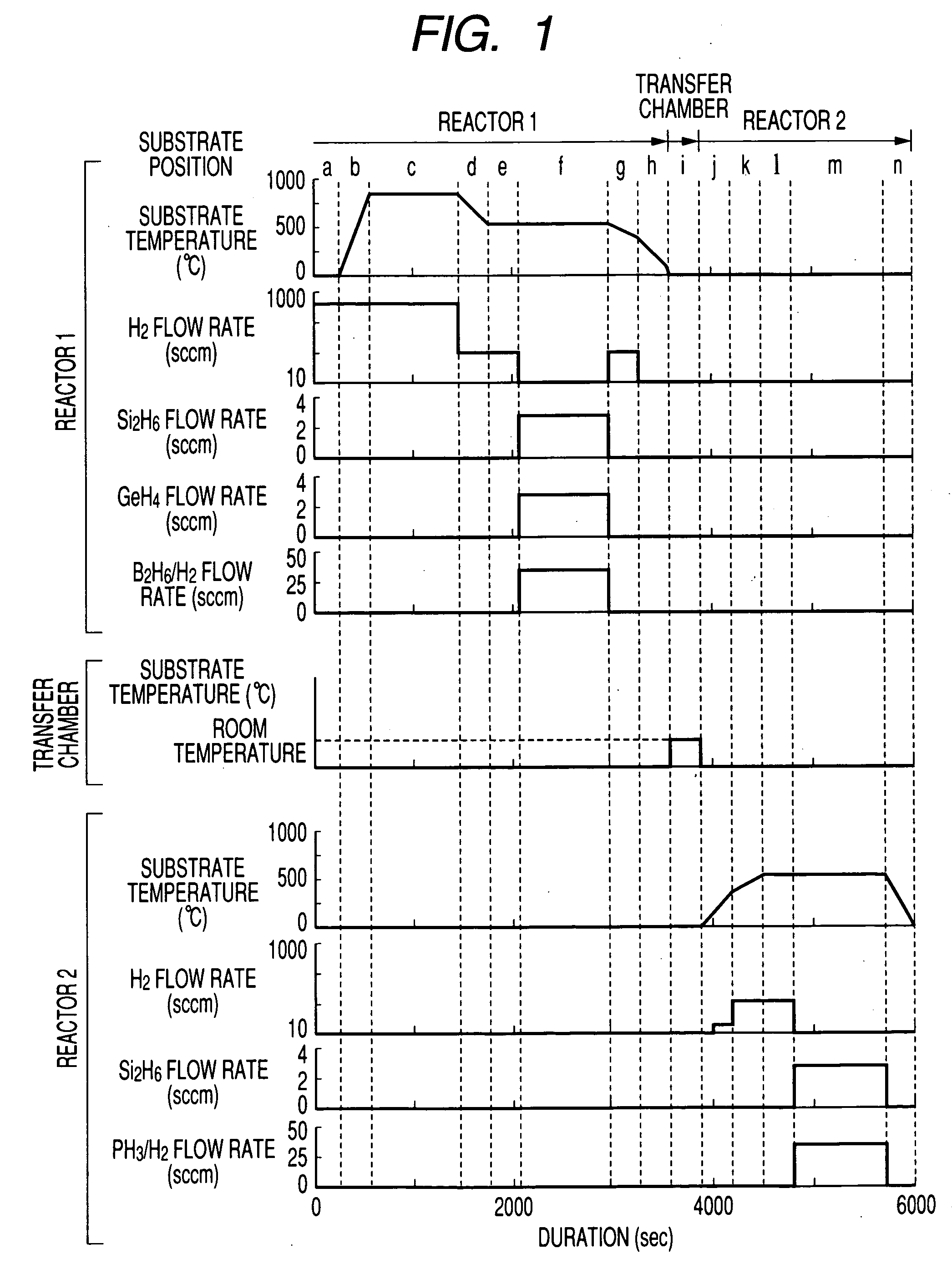
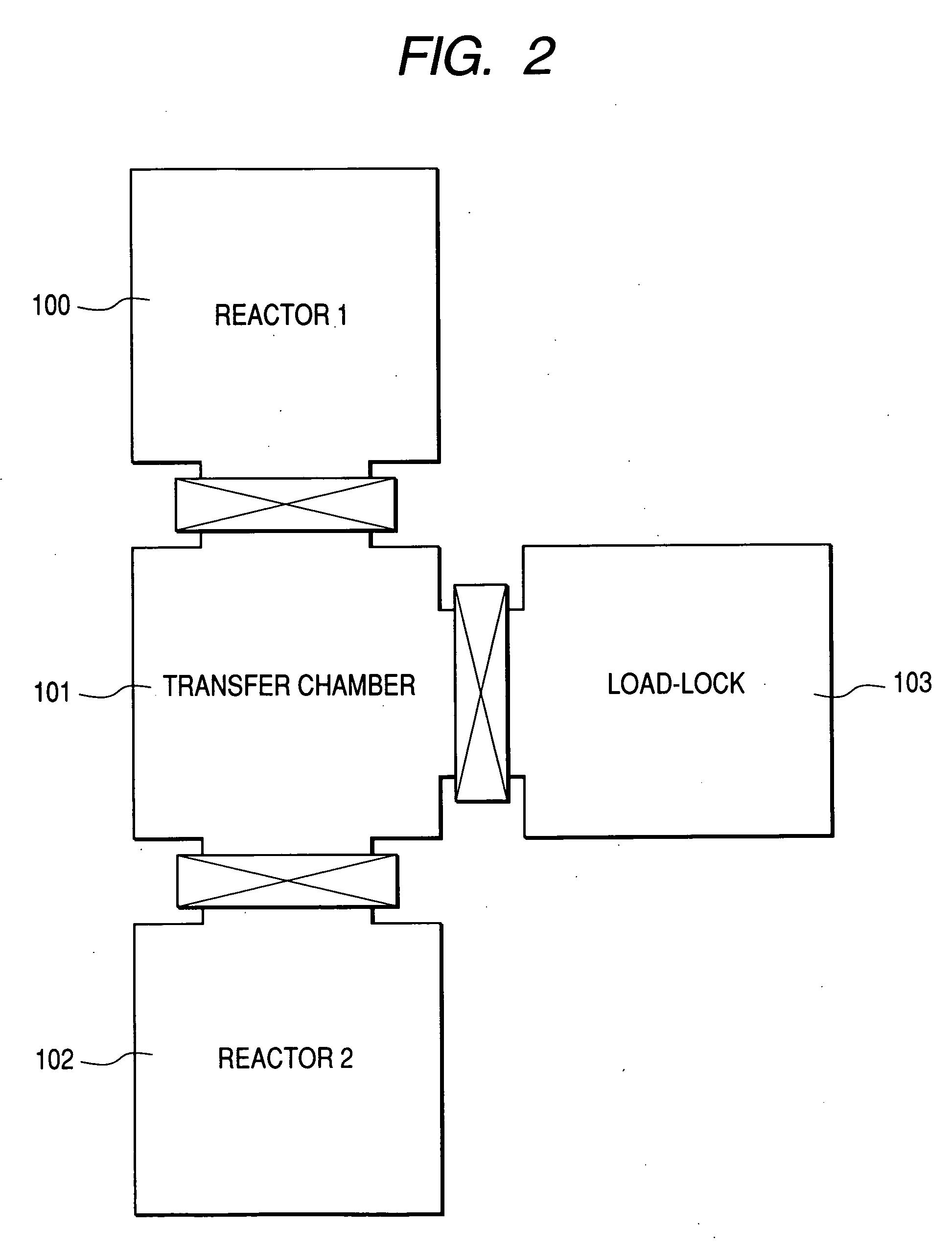
A manufacturing method of a semiconductor device in which the oxygen and carbon concentrations are reduced at the interface of each layer making up the semiconductor multilayer film. A first semiconductor layer is formed on a single-crystal substrate in a first reactor; the substrate is transferred from the first reactor to a second reactor through a transfer chamber; and a second semiconductor layer is formed on the first semiconductor layer in the second reactor. During substrate transfer, hydrogen is supplied when the number of hydrogen atoms bonding with the surface atoms of the first semiconductor layer is less than the number of surface atoms of the first semiconductor layer, and the supply of hydrogen is stopped when the number of hydrogen atoms bonding with the surface atoms of the first semiconductor layer is greater than the number of surface atoms of the first semiconductor layer.
Owner:HITACHI LTD
Binary compound flooding compound and preparation method thereof
ActiveCN102220120AHarm reductionLow critical micelle concentrationDrilling compositionComposite numberPotassium
The invention relates to a binary compound flooding compound and a preparation method thereof, mainly solving the problems that the oil displacement agent containing surface active agents has poor oil displacement efficiency and high using concentration under the high-temperature and high-salt conditions, and corrosion and scale deposition to a stratum and an oil well, caused by alkali in the ternary compound flooding, happen in the prior art. The binary compound flooding compound comprises the following components in percentage by weight: (1) 0.01-5.0 percent of N,N-bi fatty acyl group diamine neopentanoic acid di-polyoxyethylene ether bisulphonate; (2) 0.01-3.0 percent of polymer; (3) 92.0-99.98 percent of formation water, wherein in the general molecular formula of the component (1), R1 is C9-C17 alkyl group, R2 is C2-C6 alkyl group, n is adding composite number of ethoxy groups (EO) and is one integer from 2-7; M is one metal ion of K, Na or Li; the polymer is selected from one ofpolyacrylamide with superhigh molecular weight (viscosityaverage molecular weight is 25,000,000), temperature-resisting and salt-resisting polymer or xanthogen gum, and water is selected from the formation water of the oil field. By the technical scheme, the problems are better solved, and the binary compound flooding compound is suitable for tertiary oil recovery production in the oil field.
Owner:CHINA PETROLEUM & CHEM CORP +1
Oil displacement compound for tertiary oil recovery and preparation method thereof
ActiveCN102220124AHarm reductionLow critical micelle concentrationDrilling compositionComposite numberPotassium
The invention relates to an oil displacement compound for tertiary oil recovery and a preparation method thereof, mainly aiming at solving the problems that oil displacement agent containing surface active agents has poor oil displacement efficiency and high using concentration under the high-temperature and high-salt conditions, and corrosion and scale deposition to a stratum and an oil well, caused by alkali in the ternary compound flooding, happen in the prior art. The oil displacement compound for tertiary oil recovery comprises the following components according to mass percentage: (1) 0.01-5.0 percent of N,N-bi fatty acyl group diamine neopentanoic acid di-polyoxyethylene ether bisulphonate; (2) 0.01-3.0 percent of polymer; (3) 92.0-99.98 percent of formation water, wherein in the general molecular formula of the component (1), R1 is C9-C17 alkyl group, R2 is C2-C6 alkyl group, n is composite number of ethoxy groups (EO) and is one integer from 2-7; M is one metal ion of K, Na or Li; the polymer is selected from one of polyacrylamide with superhigh molecular weight (viscosityaverage molecular weight is 25,000,000), temperature resisting salt-resisting polymer or xanthogen gum, and water is selected from the formation water of the oil field. By the technical scheme, the problems are better solved, and the oil displacement compound is suitable for tertiary oil recovery production in the oil field.
Owner:CHINA PETROLEUM & CHEM CORP +1
Multiple prime number generation using a parallel prime number search algorithm
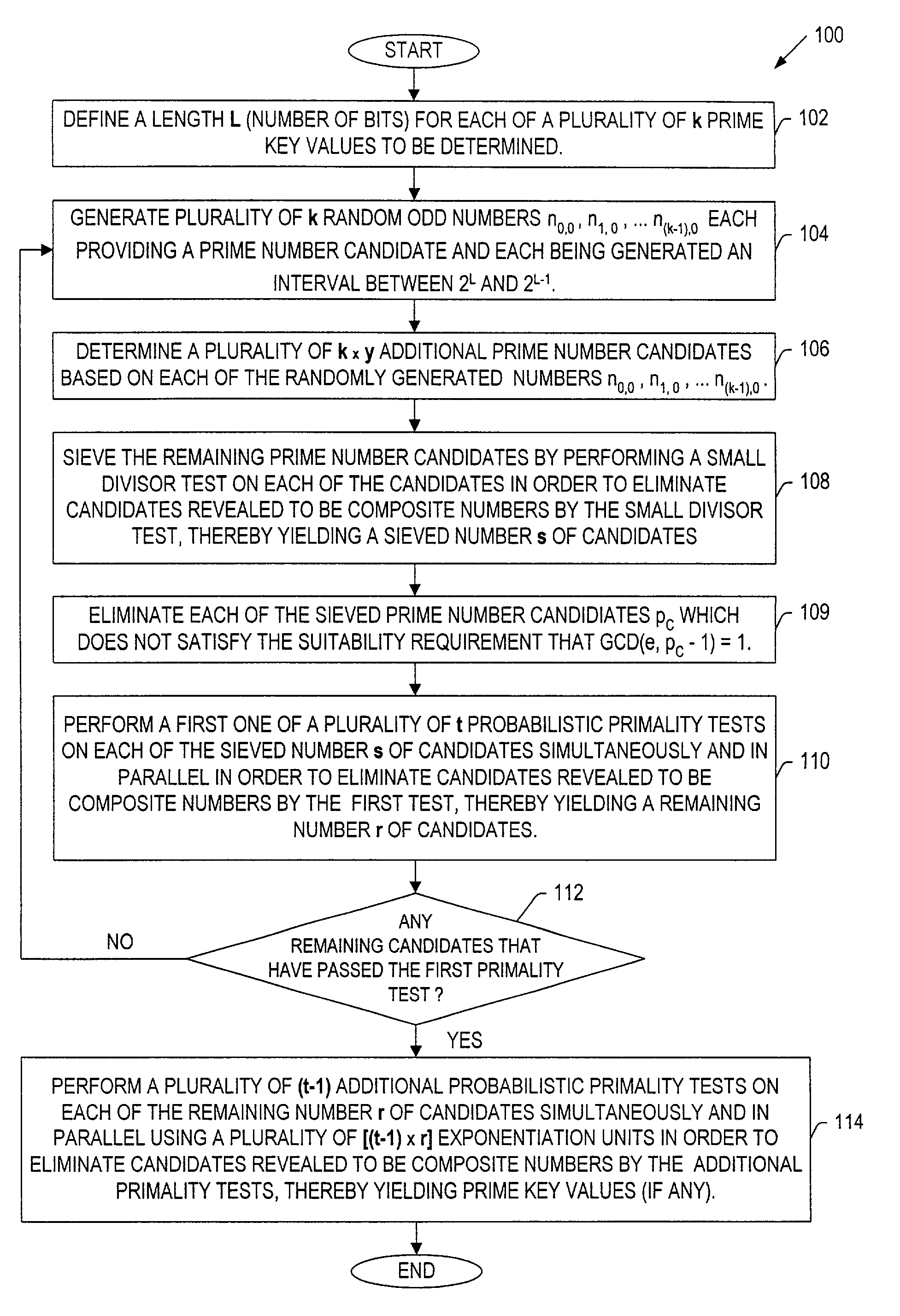
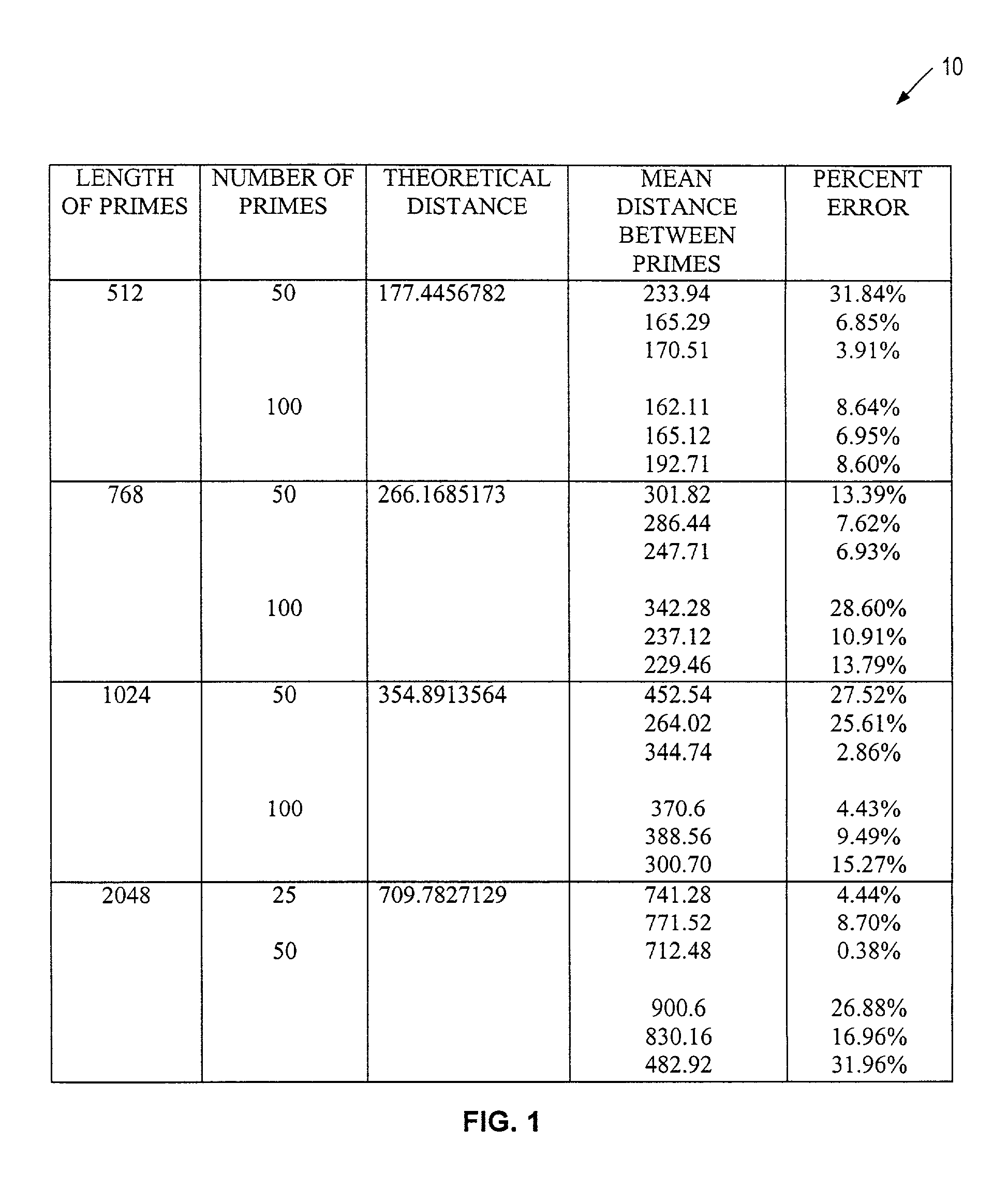
InactiveUS7120248B2Reducing computation effortShorten the timeRandom number generatorsPublic key for secure communicationComposite numberTheoretical computer science
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
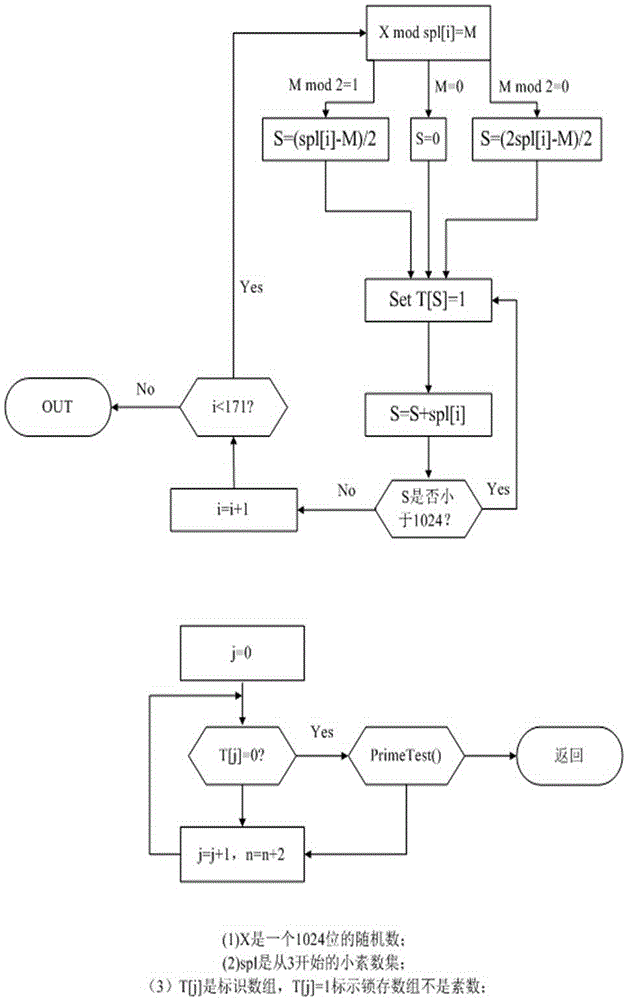
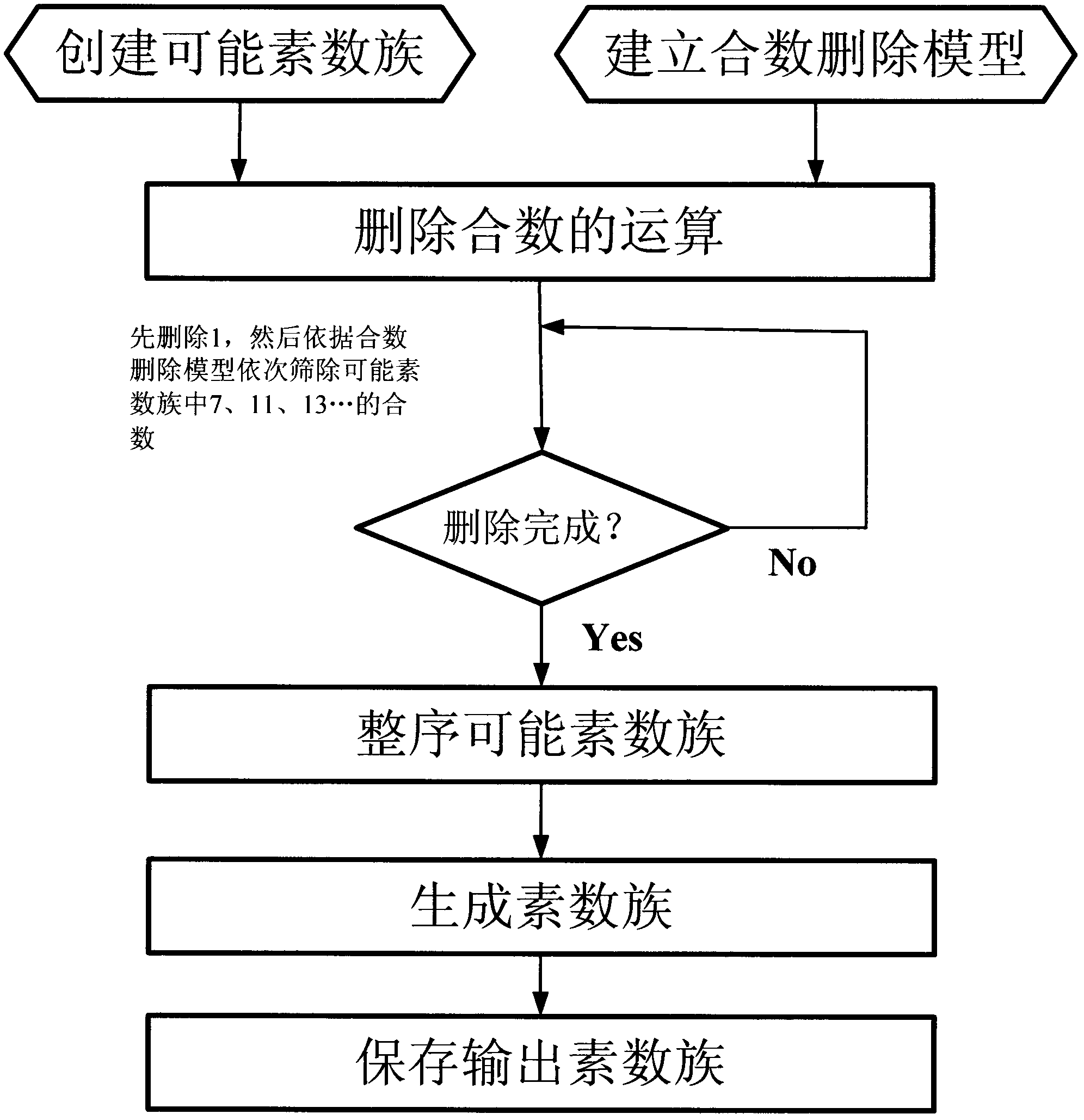
A Fast Generation Method of Prime Number Family Applicable to the Application of Information Encryption Technology
ActiveCN102279840AConducive to perfect playIncreased optionalityPublic key for secure communicationComplex mathematical operationsInformation technologyComposite number
The invention discloses a method for quickly generating a prime number group applicable to an information encryption technology. The method comprises the following steps of: establishing a probable prime number group by selecting a shrinkage residual system of a modulus M which is equal to 30; and according to the distribution rule and characteristics of composite numbers in the probable prime number group, screening out all composite numbers in the probable prime number group so as to accurately, quickly and completely generate all prime numbers of any section in a storage limitation range of a computer. In the field of information safety and cryptology, the acquisition and providing of large prime numbers are necessary flows in a public key algorithm. The convention method has the defects that: a single prime number can be provided at each time; most of the prime numbers are required to be subjected to primality detection; and operation time is over-long. The method provided by the invention has the advantages that: the primer number group can be generated by adopting computer software through simple screening operation, so that quick generation without complicated operation is realized on the computer; and a primality detection link is eliminated, and limitation of a prime number generation technology can be avoided, so that one-time pad can be realized, and related public key systems can perfectly work.
Owner:刘诗章 +1
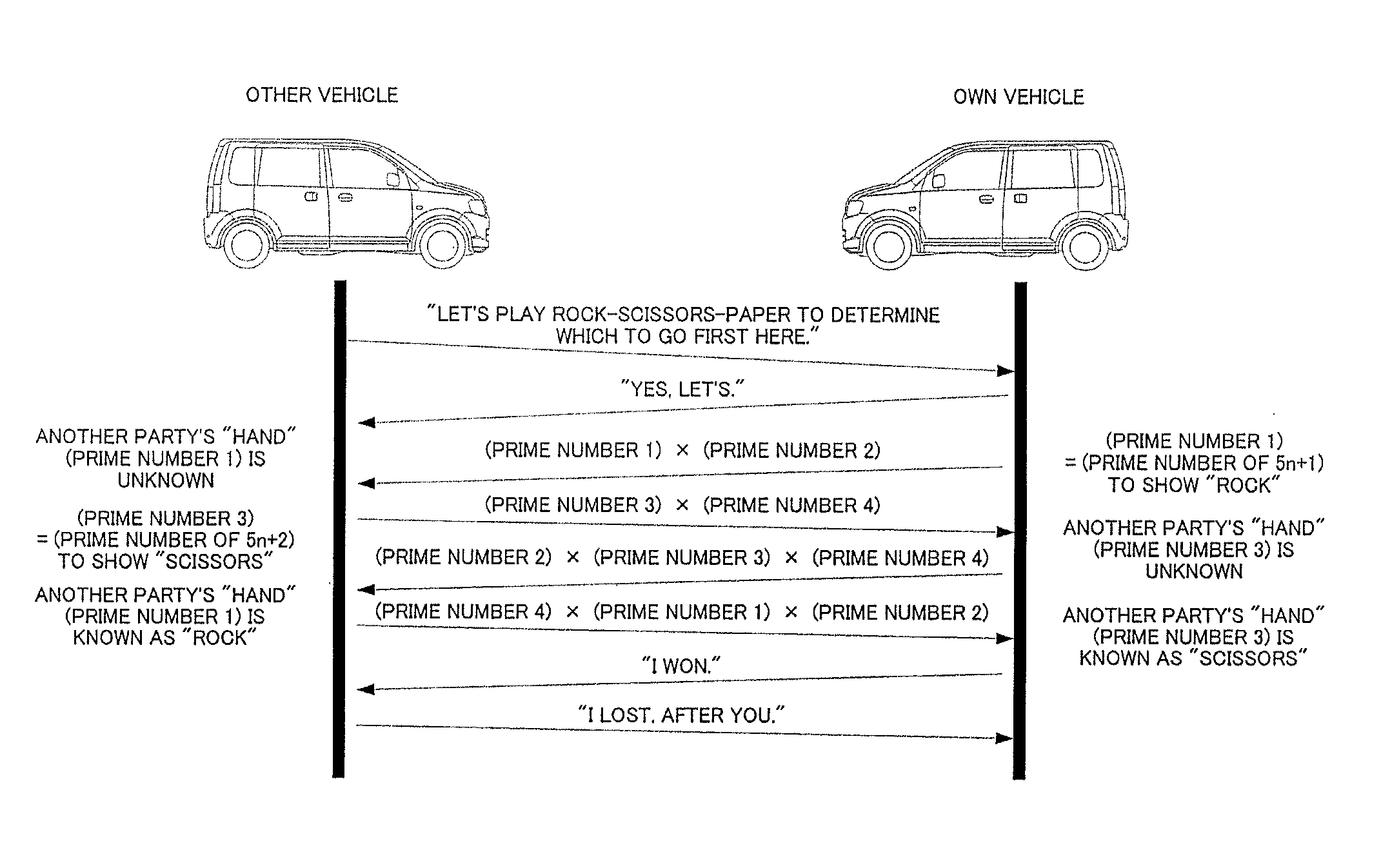
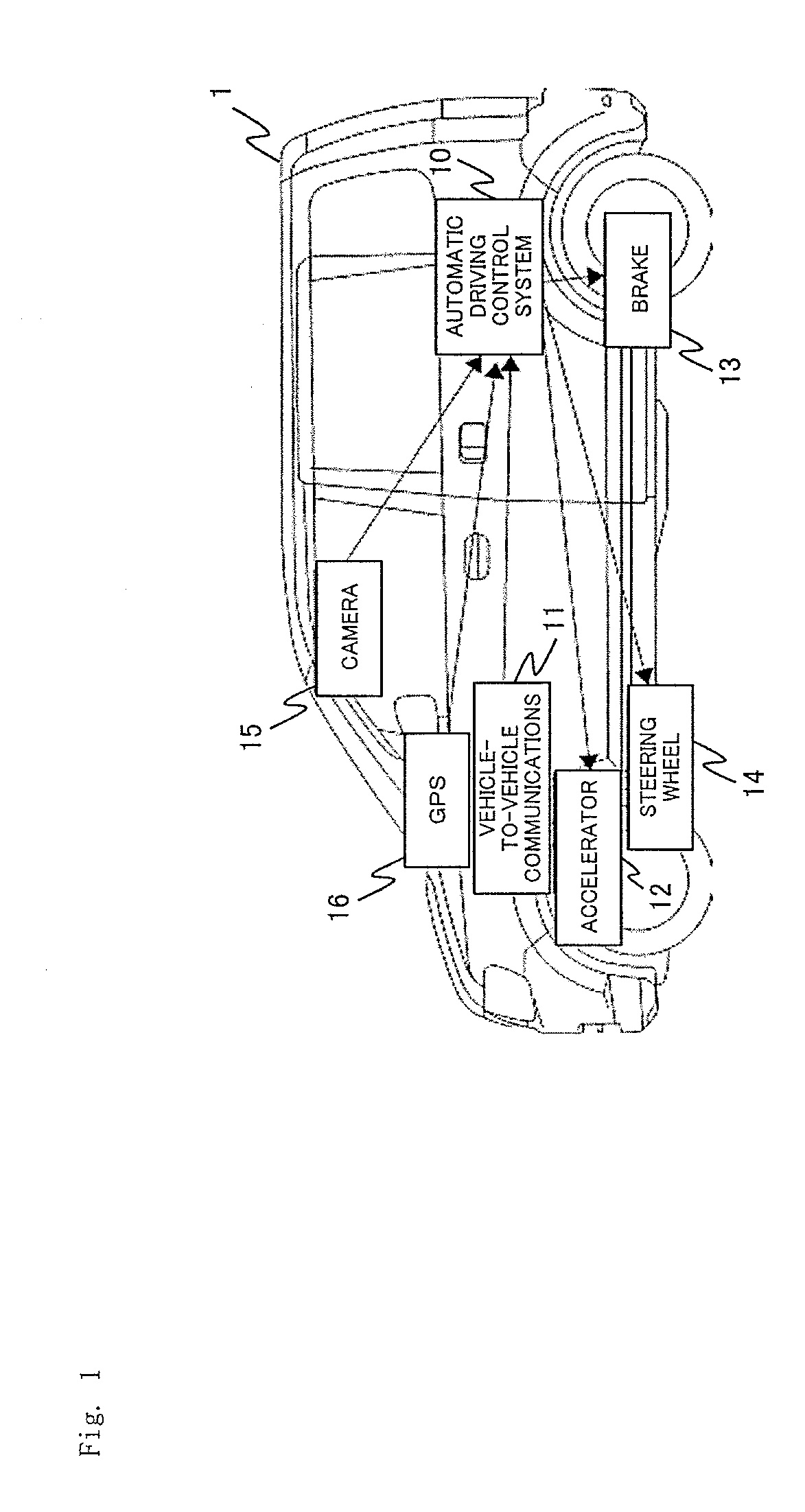
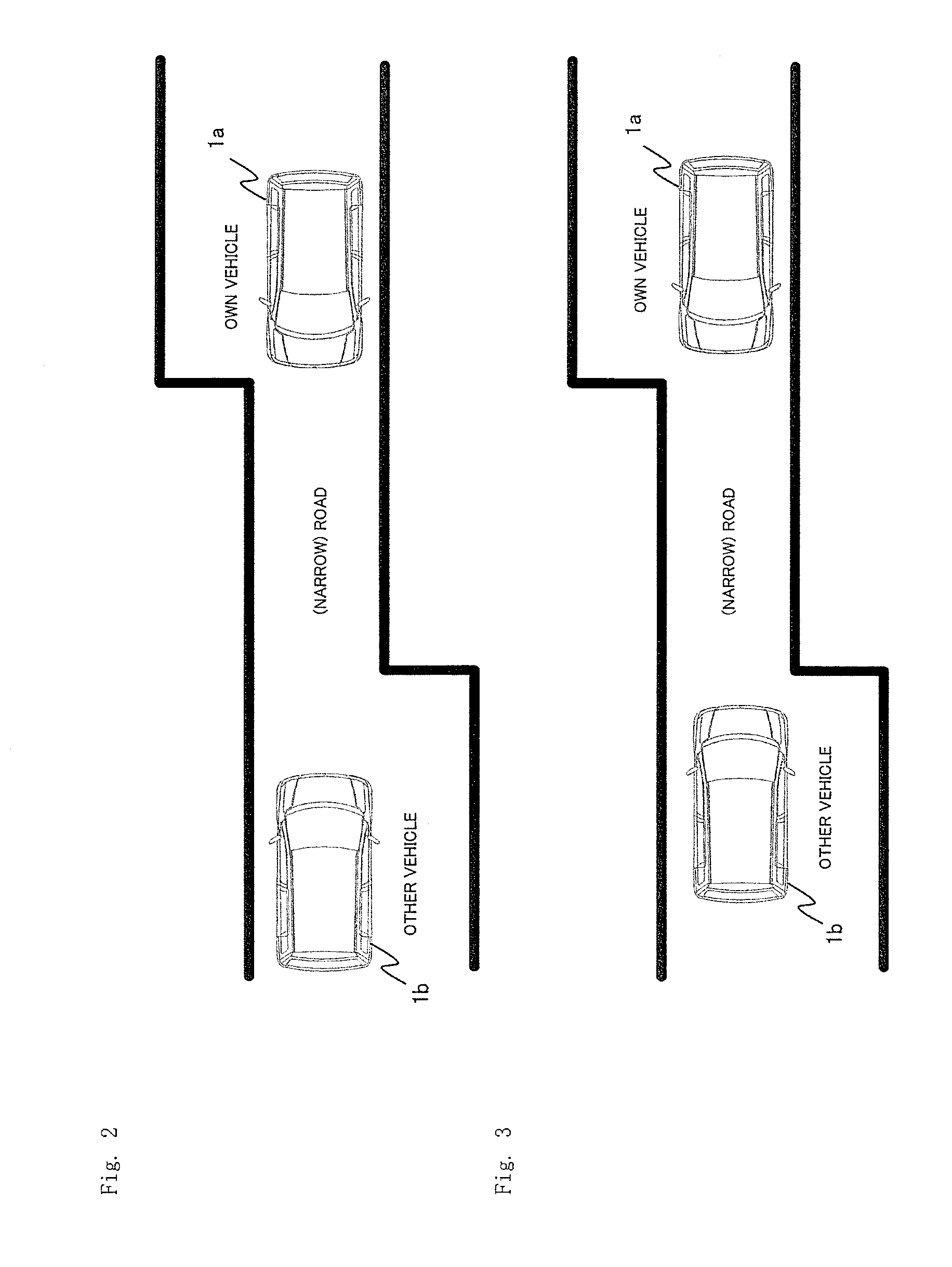
Automatic driving control system and automatic driving control method
ActiveUS20160124432A1Clearing suspicionAutonomous decision making processAnti-collision systemsComposite numberControl system
Provided are an automatic driving control system and an automatic driving control method that are capable of clearing away suspicion of a foul by exchanging a “hand” for determining priority of passage by a fair method that allows no foul when automatically driven vehicles face each other on a road. When the automatically driven vehicles face each other on the road, the “hand” for determining the priority of passage is exchanged by performing transmission / reception two times by use of a composite number of prime numbers each having a large number of digits.
Owner:MITSUBISHI ELECTRIC CORP
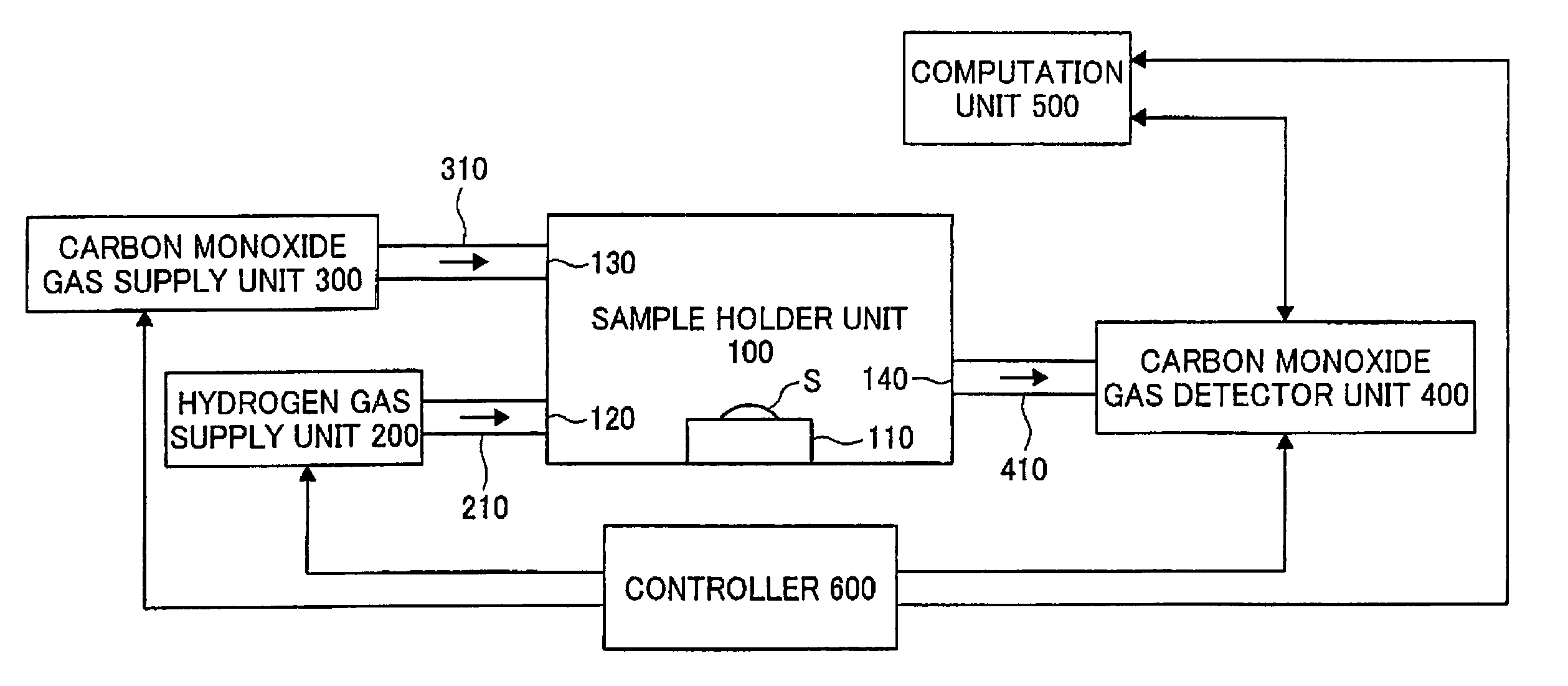
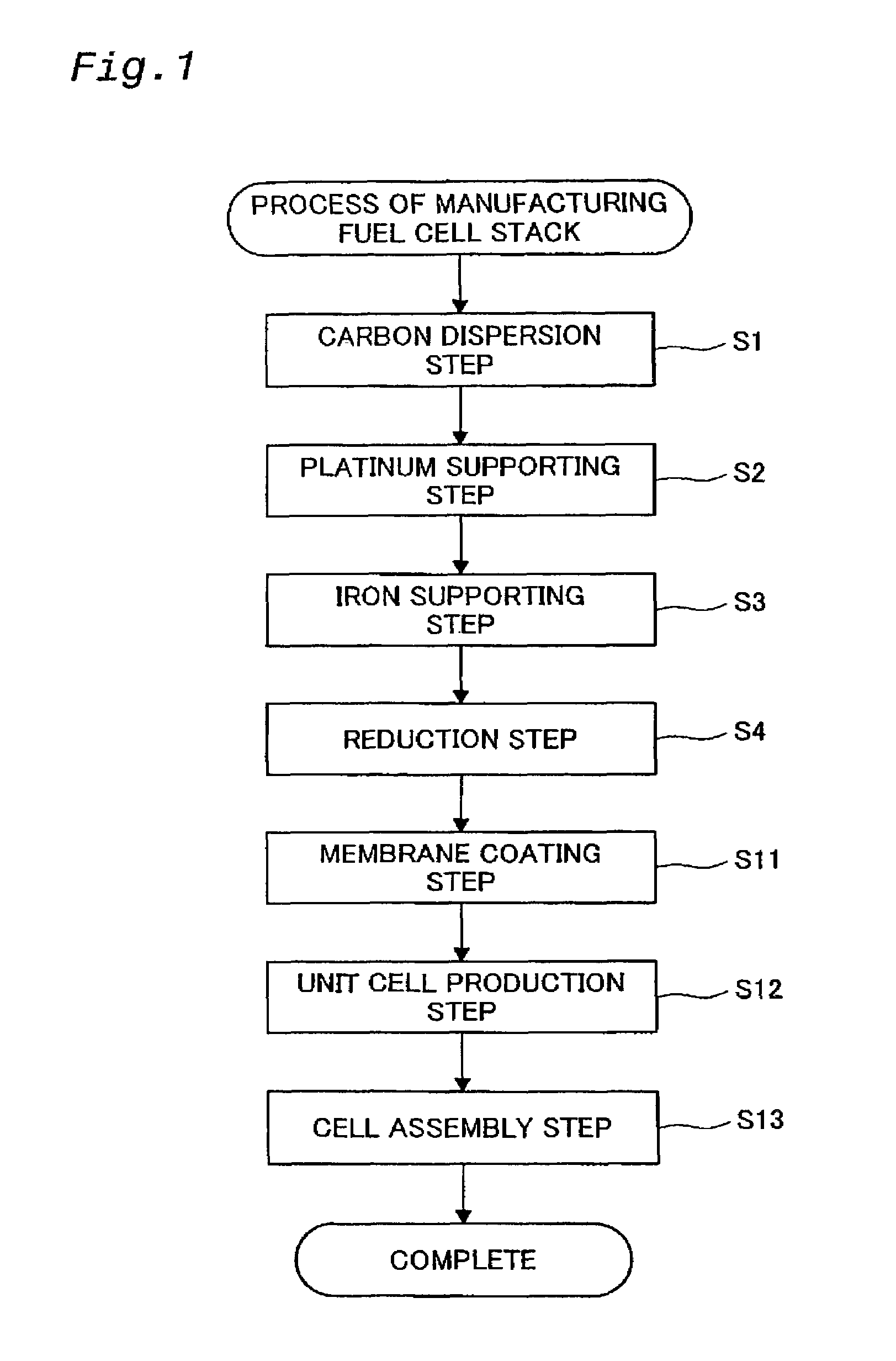
Noble metal-base metal alloy catalyst, evaluation of such catalyst, and method of producing such catalyst
InactiveUS7060385B2Simple and accurate of performanceFinal product manufactureFuel cell auxillariesComposite numberCatalytic function
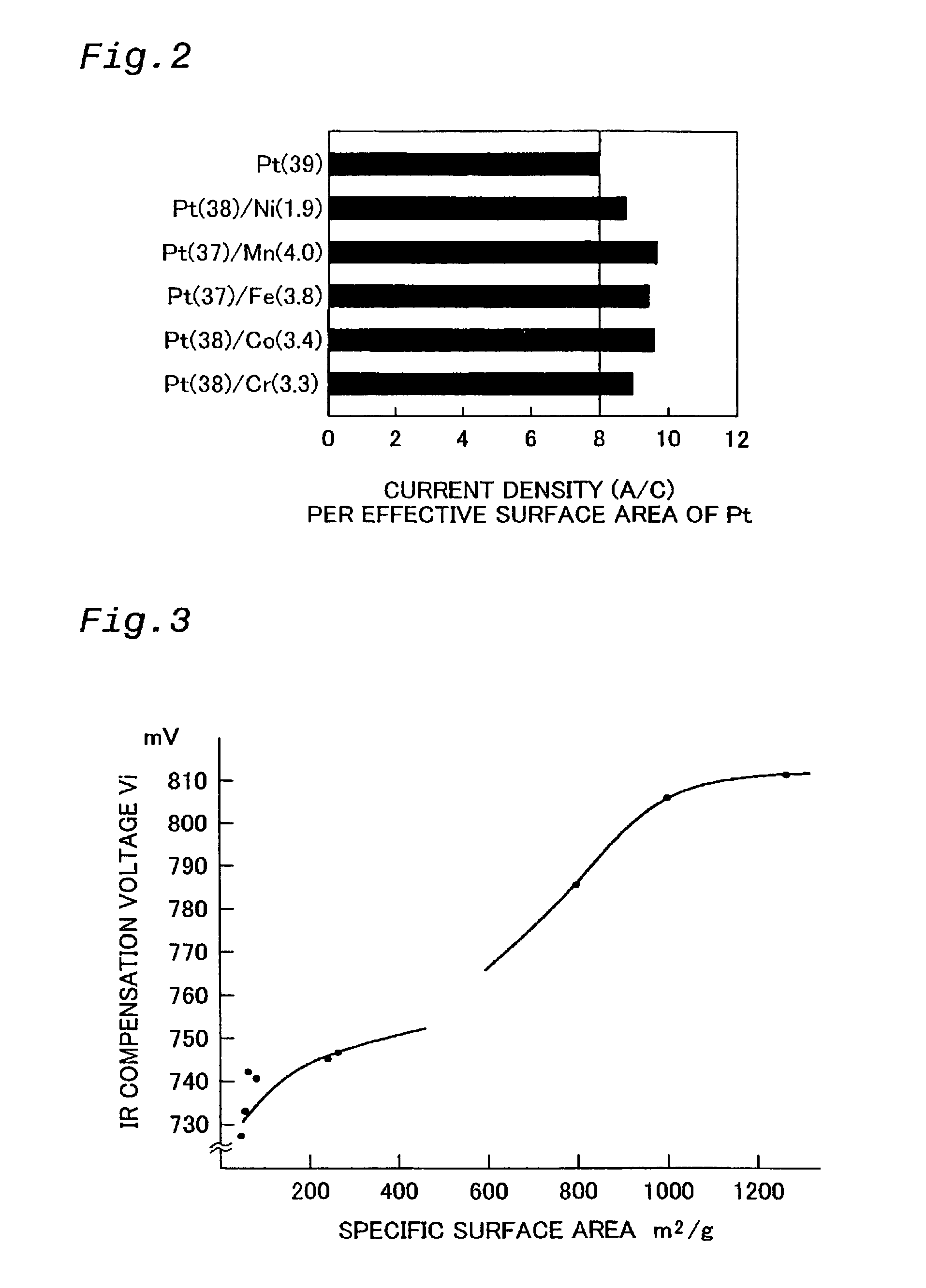
The technique of the present invention attains simple and accurate evaluation of the performance of a fuel cell and enables produce of a high-performance electrode catalyst and a high-performance fuel cell. The procedure makes platinum, a noble metal, and iron, a base metal, carried on carbon having a large specific surface area, and heats up the carbon with platinum and iron to a specific temperature to reduce iron. A resulting platinum-iron alloy electrode catalyst exerts excellent catalytic functions. A fuel cell using this electrode catalyst has a high IR compensation voltage. The quantity of carbon monoxide adsorbed by this novel electrode catalyst is not less than 14 Ncc per one gram of platinum. The atomic number ratio of iron (Fe) to platinum (Pt) in the catalyst is not lower than 0.14 by EDX analysis, and the ratio of the binding number of Pt atom with Fe atom to the total binding number relating to Pt atom is not lower than 0.10 by EXAFS analysis. Each electrode catalyst produced is evaluated by measurement of these data. The fuel cell including the electrode catalyst having the favorable result of evaluation ensures the desired performances.
Owner:TOYOTA JIDOSHA KK
Quick large number decomposition method based on cryptographic technology application
InactiveCN102769528ASecurity Assessment and ImprovementQuick breakdownPublic key for secure communicationComputations using residue arithmeticComposite numberDecomposition
The invention discloses a quick large number decomposition method based on cryptographic technology application. The creative quick large number decomposition method organically combining the congruence theory and the composite number distribution rule includes the steps of compressing positive integers, setting up an almost prime number group, selecting a maximum dereferencing range, generating the almost prime number group, decomposing a large number, setting digits, deleting composite numbers and the like. The method different from traditional large number decomposition methods can be used for quick factorization of any large number selected from n without depending on computing speed, and quick decomposition can be realized by using computer software for simple identification processing instead of a great amount of time-consuming complex operations. Therefore, evaluation and improvement of relevant public key system safety can be greatly promoted, and the quick large number decomposition method is widely applicable to the field of information safety and cryptographic technology application.
Owner:刘诗章 +2
Attribute-based encryption method of revocable key policy in standard model
InactiveCN107294718APrivacy protectionProperty revocation implementationKey distribution for secure communicationMultiple keys/algorithms usageAccess structureComposite number
The invention discloses an attribute-based encryption method of a revocable key policy in a standard model. A user private key and a specified access structure are bound, after the private key is extracted, the attribute-based encryption is performed in an encryption attribute set and an attribute revocation set, and then decryption is performed. When a receiver receives a ciphertext for decryption, if the attribute set in the ciphertext satisfies the access structure in the user private key, a plaintext message is output, or otherwise, refusal is output. According to the attribute-based encryption method of the revocable key policy, based on a static assumption, the double-system encryption technology and the composite-number-order bilinear pairing are employed, the proposed scheme is proved to be safe in the standard model, two functions of attribute revocation and encryption can be realized, and user privacy is protected.
Owner:CHANGAN UNIV
Multiprime RSA public key cryptosystem
InactiveUS7231040B1Easy to findConvenient verificationPublic key for secure communicationPayment architectureChinese remainder theoremComposite number
A method and apparatus are disclosed for improving public key encryption and decryption schemes that employ a composite number formed from three or more distinct primes. The encryption or decryption tasks may be broken down into sub-tasks to obtain encrypted or decrypted sub-parts that are then combined using a form of the Chinese Remainder Theorem to obtain the encrypted or decrypted value. A parallel encryption / decryption architecture is disclosed to take advantage of the inventive method.
Owner:MICRO FOCUS LLC
Solid-phase synthesis method for magnesium borohydride ammoniates
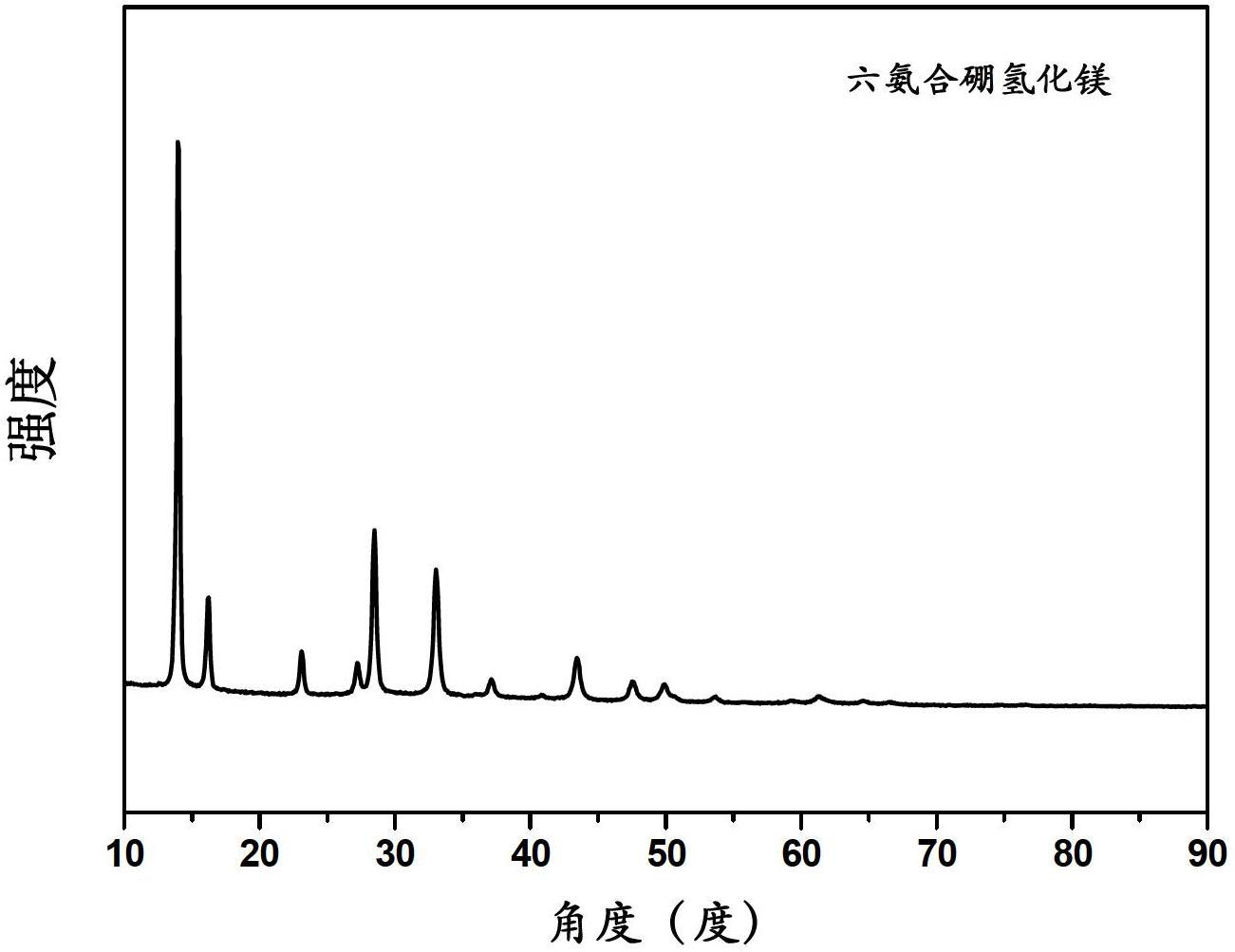
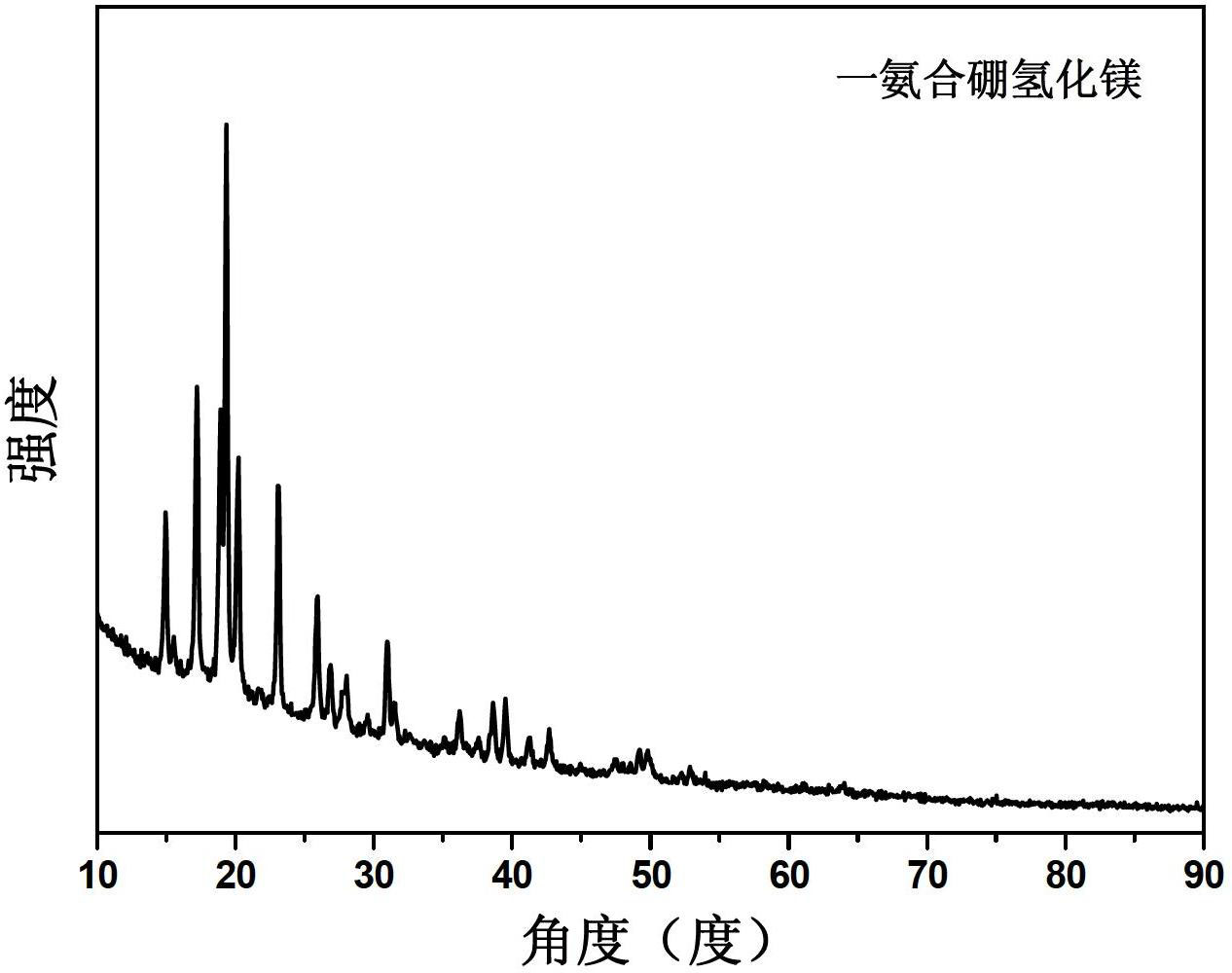
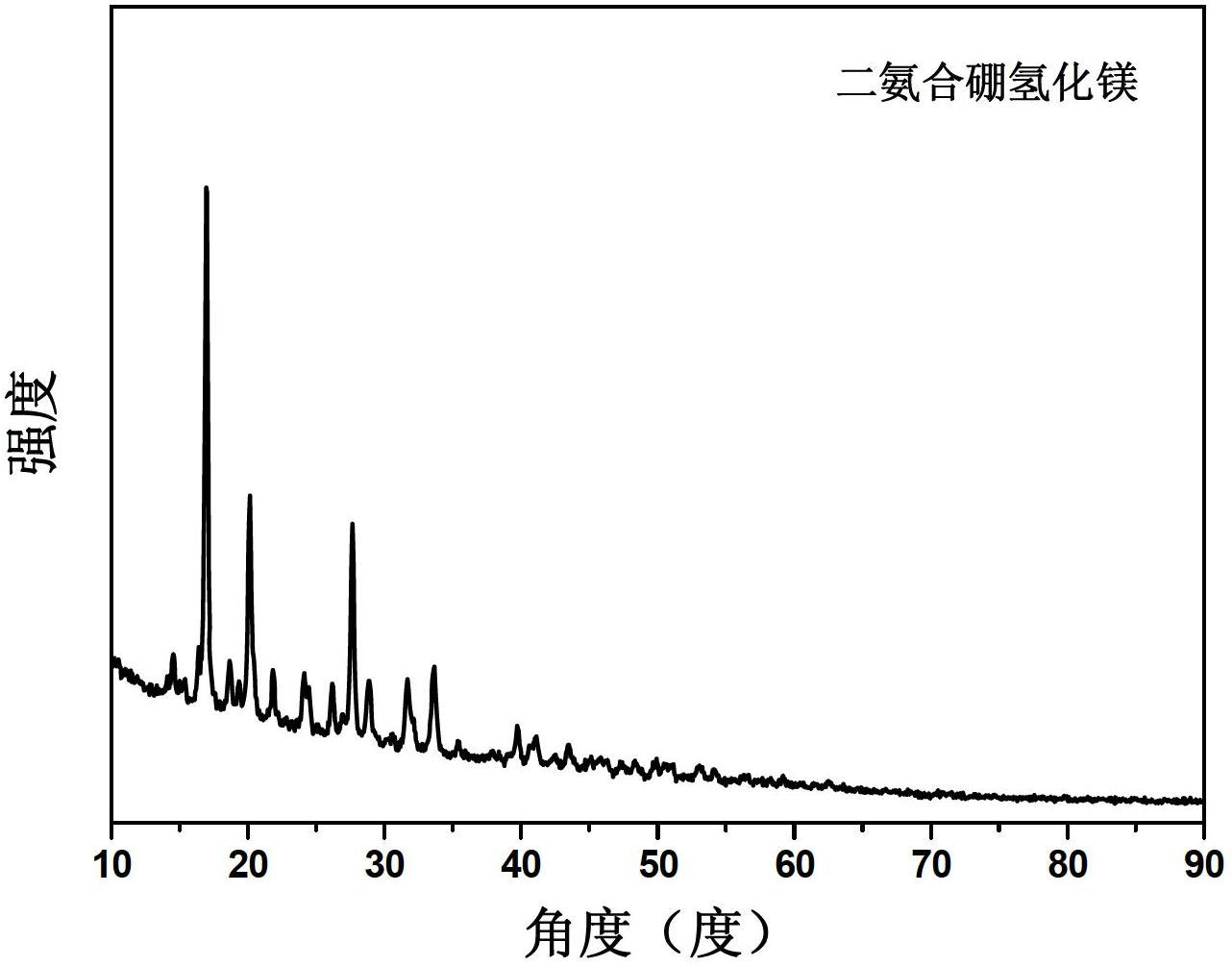
ActiveCN102659079AHigh yieldAvoid filter effectsMonoborane/diborane hydridesComposite numberFiltration
The invention discloses a solid-phase synthesis method for magnesium borohydride ammoniates. The solid-phase synthesis method comprises the following step of: performing ball milling on magnesium borohydride and an ammonia source under the atmosphere of protective gas to obtain the magnesium borohydride ammoniate. According to the solid-phase synthesis method for the magnesium borohydride ammoniates, the complicated operation processes of filtration, distillation and solvent removal in traditional methods are avoided, and the problem that organic waste liquid needs to be specially treated is solved; the product yield is increased; a series of magnesium borohydride ammoniates with different ammonia complexing numbers can be prepared; the operation is simple; the product purity is high; the yields of the magnesium borohydride ammoniates are respectively higher than 95 percent; the dehydriding temperature of the obtained product is about 130 DEG C; and the hydrogen discharge amount is higher than 13 weight percent (wt%).
Owner:ZHEJIANG UNIV
Electricity storage device and electric tool
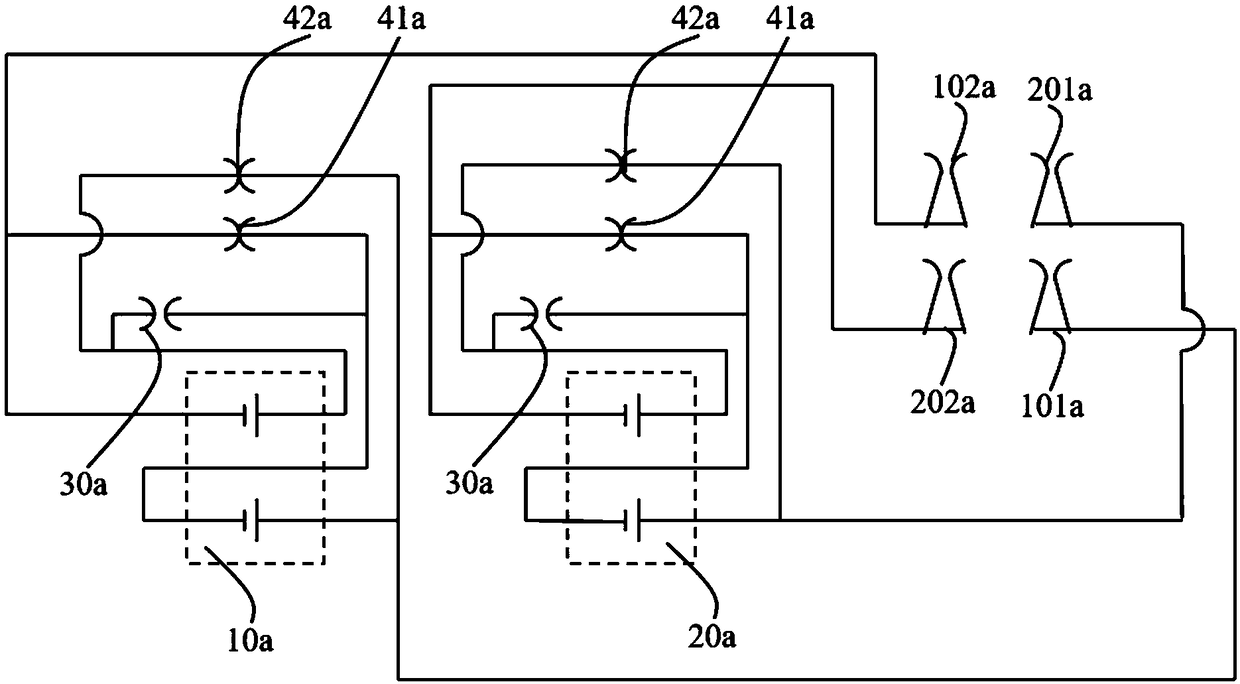
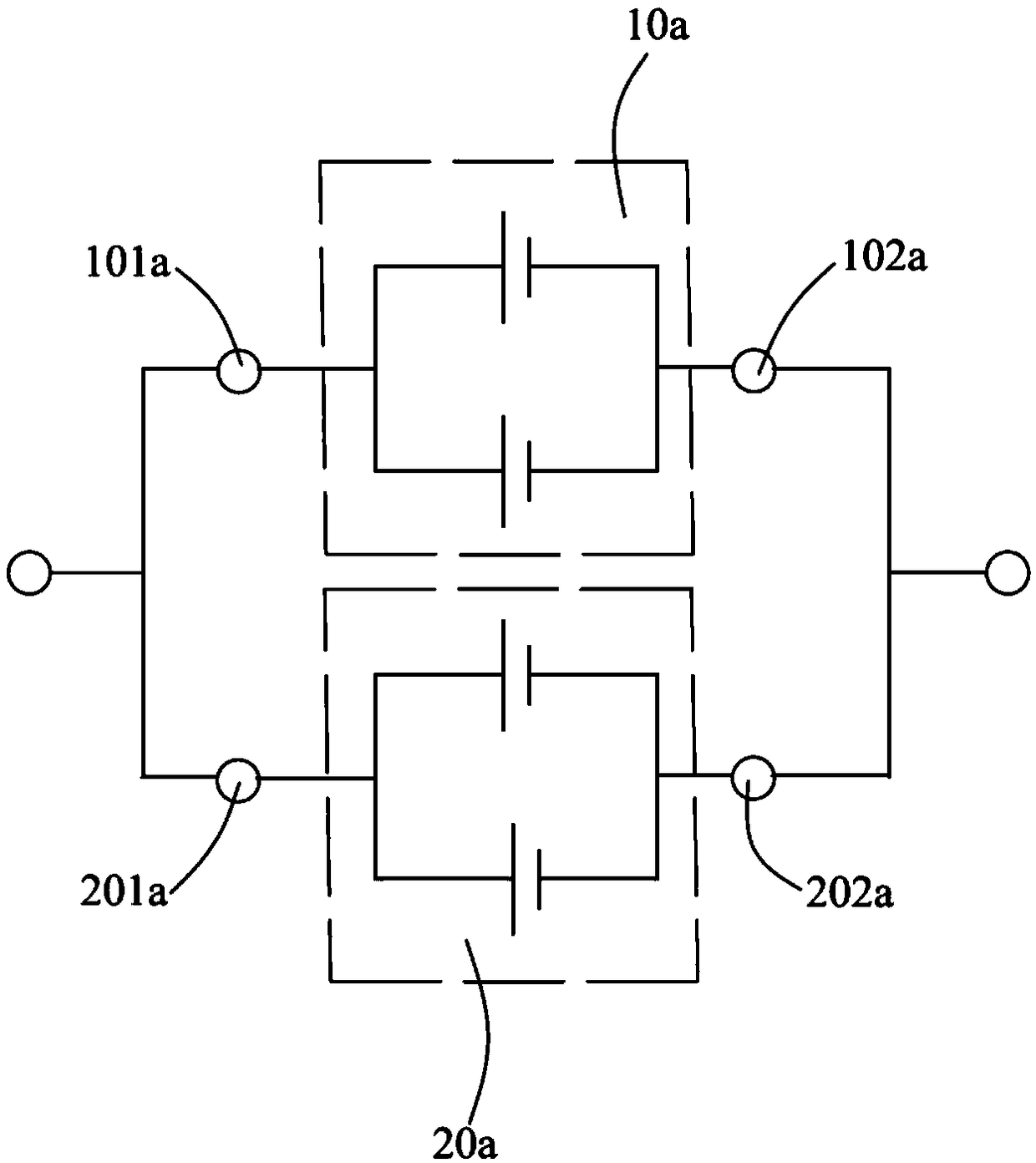
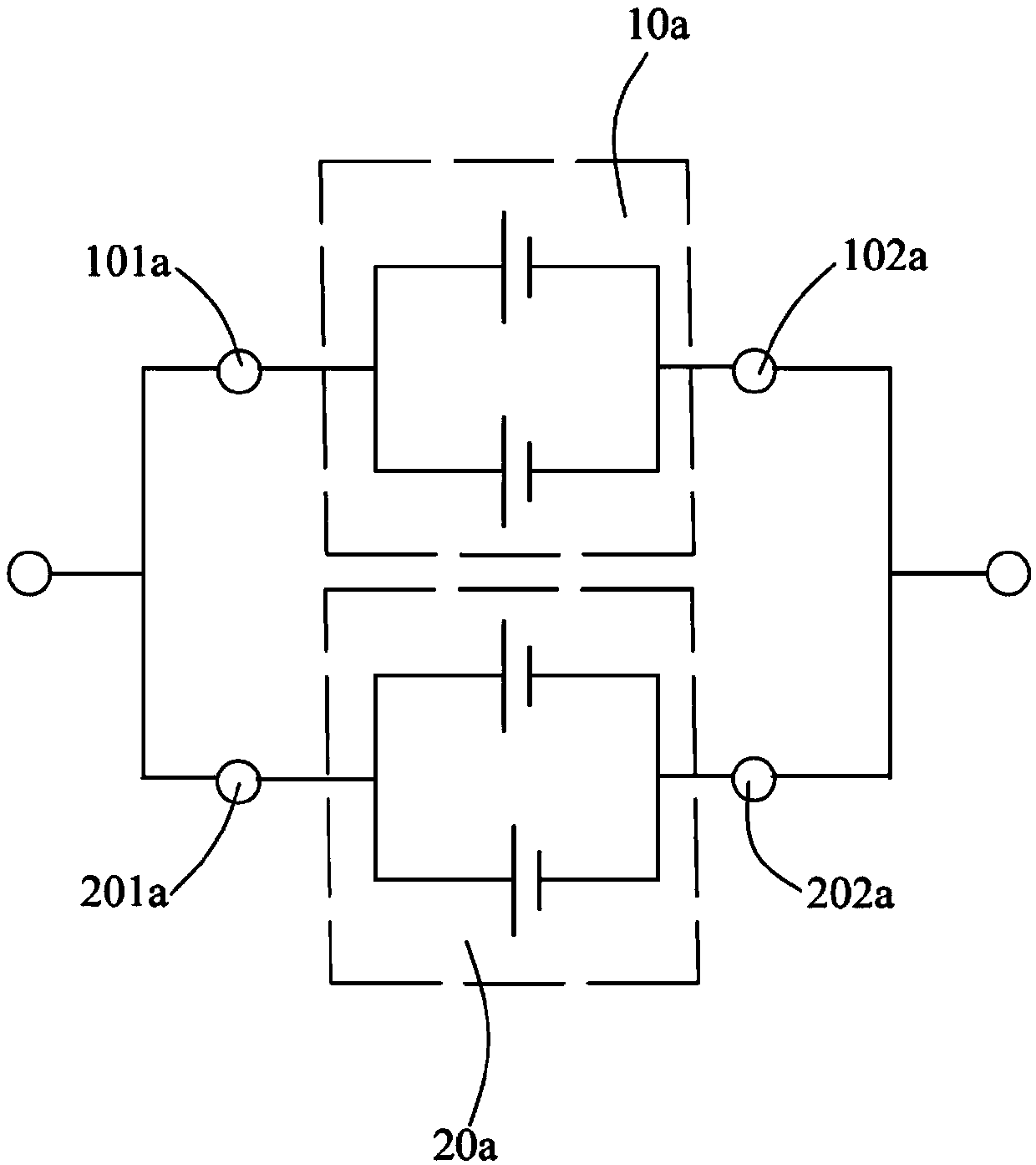
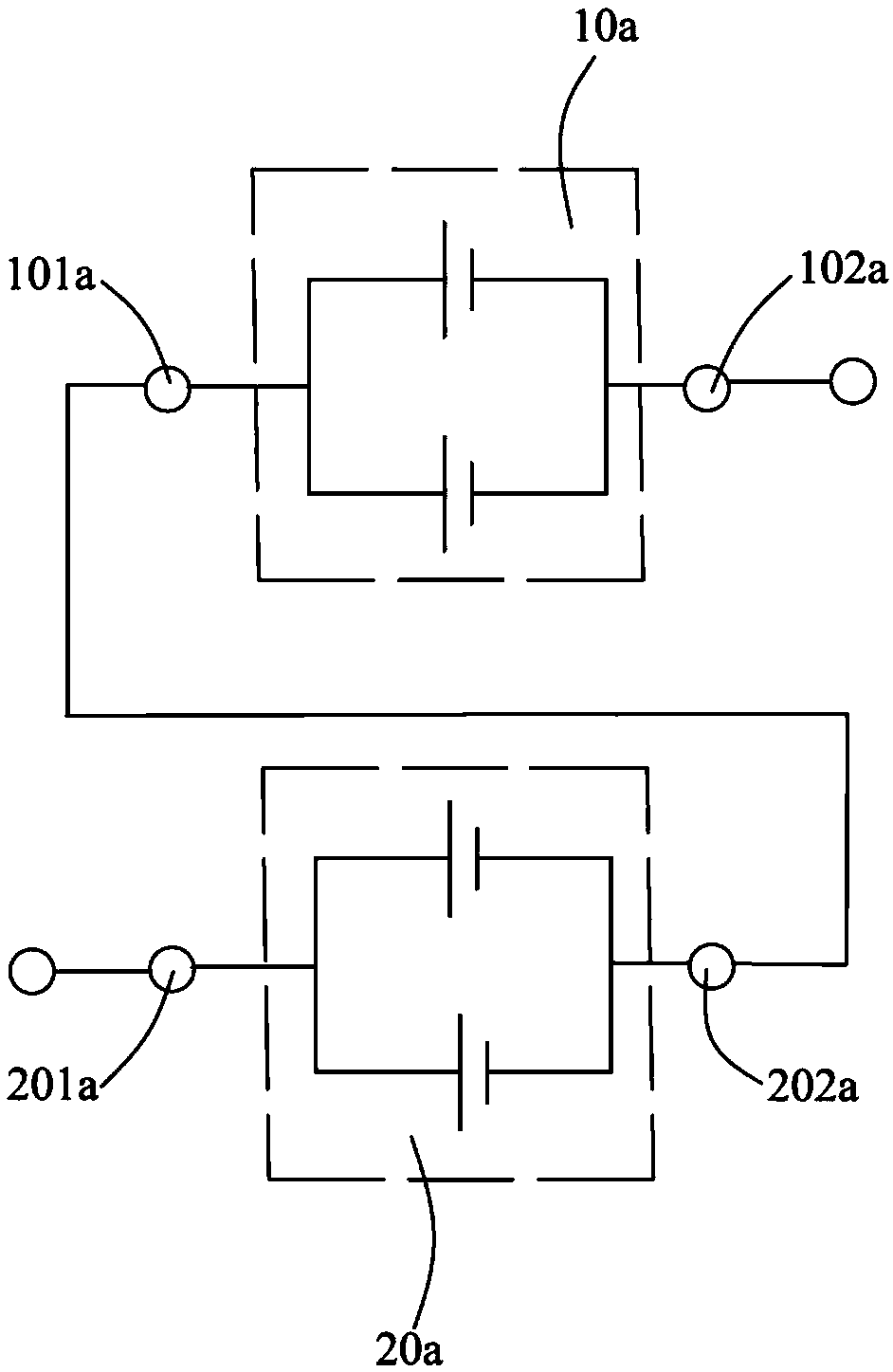
PendingCN109360929AReduce use costFinal product manufactureMultimode batteriesElectricityComposite number
The invention provides an electricity storage device, comprising N energy units equal in voltage and capable of providing at least three output voltages. N is a composite number; each of the N energyunits is equally divided into a plurality of energy unit modules; each energy unit module has a module inner control portion. In the initial state, the module inner control portions connect the energyunits in the same energy unit module in parallel. Different plugs are connected with the electricity storage device in order to allow the electricity storage device to output one of at least three output voltages to an electric tool using the electricity storage device. Therefore, the applicable range of the electricity storage device is widened, and the application cost is reduced.
Owner:CHANGZHOU GLOBE CO LTD
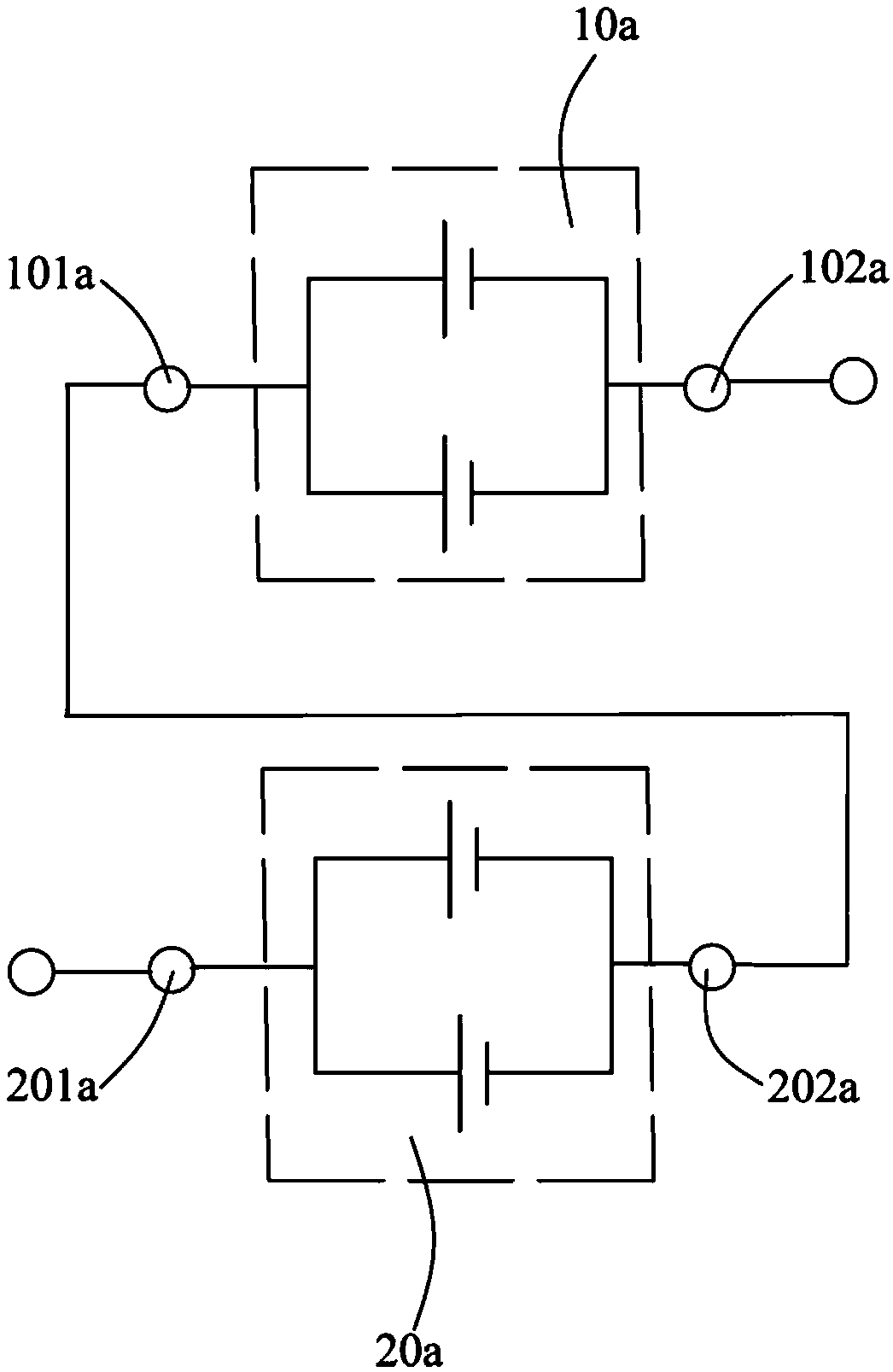
Electricity storage device and electric tool
PendingCN109360930AReduce use costFinal product manufactureMultimode batteriesElectricityComposite number
The invention provides an electricity storage device and an electric tool using the same. The electricity storage device comprises N energy units equal in voltage and capable of providing at least three output voltages. N is a composite number; each of the N energy units is equally divided into a plurality of energy unit modules; each energy unit module has a module inner control portion. In the initial state, the module inner control portions connect the energy units in the same energy unit module in parallel. Different plugs are connected with the electricity storage device in order to allowthe electricity storage device to output one of at least three output voltages to the electric tool using the electricity storage device. Therefore, the applicable range of the electricity storage device is widened, and the application cost is reduced.
Owner:CHANGZHOU GLOBE CO LTD
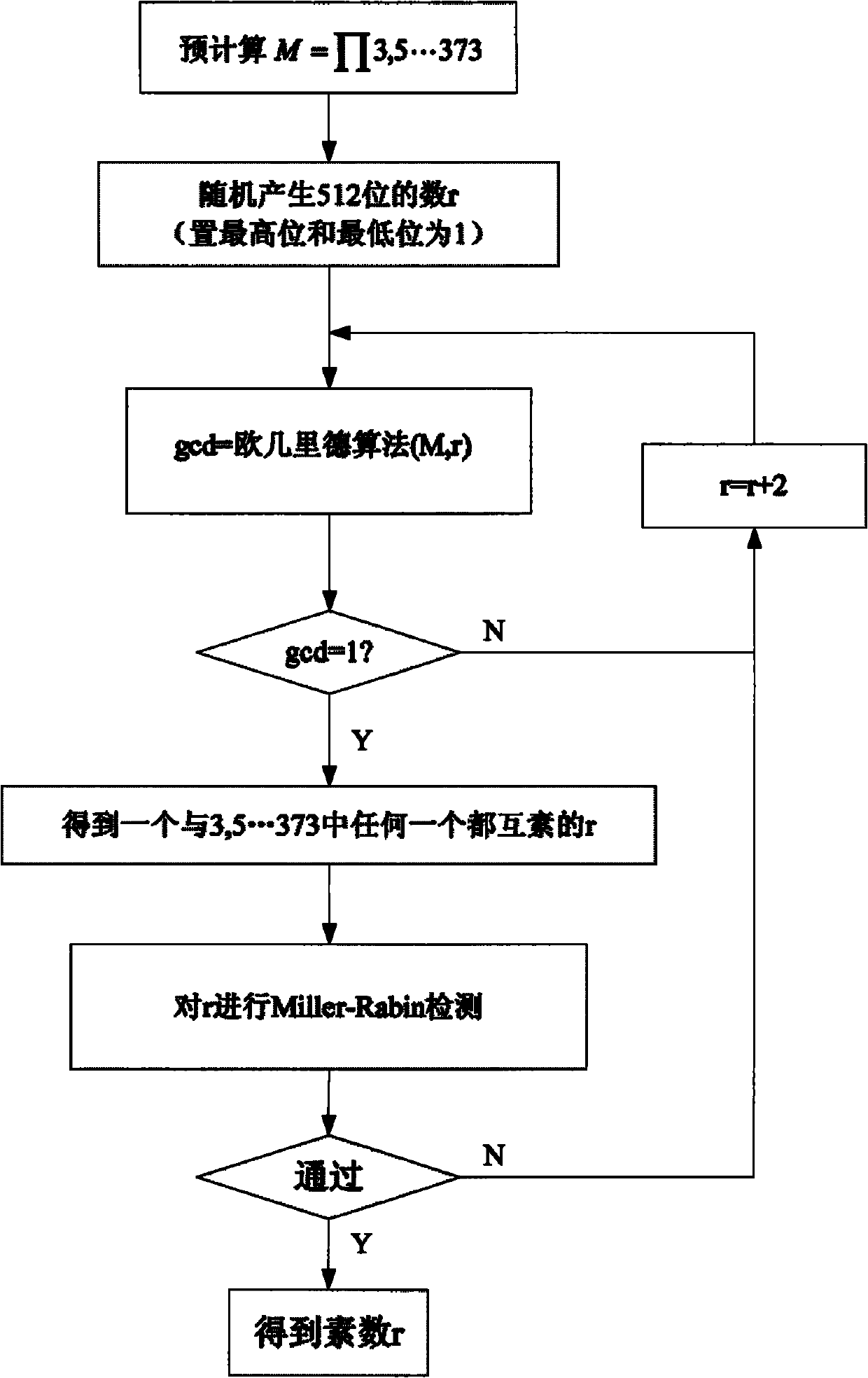
Prime number generating method applied to cryptology application
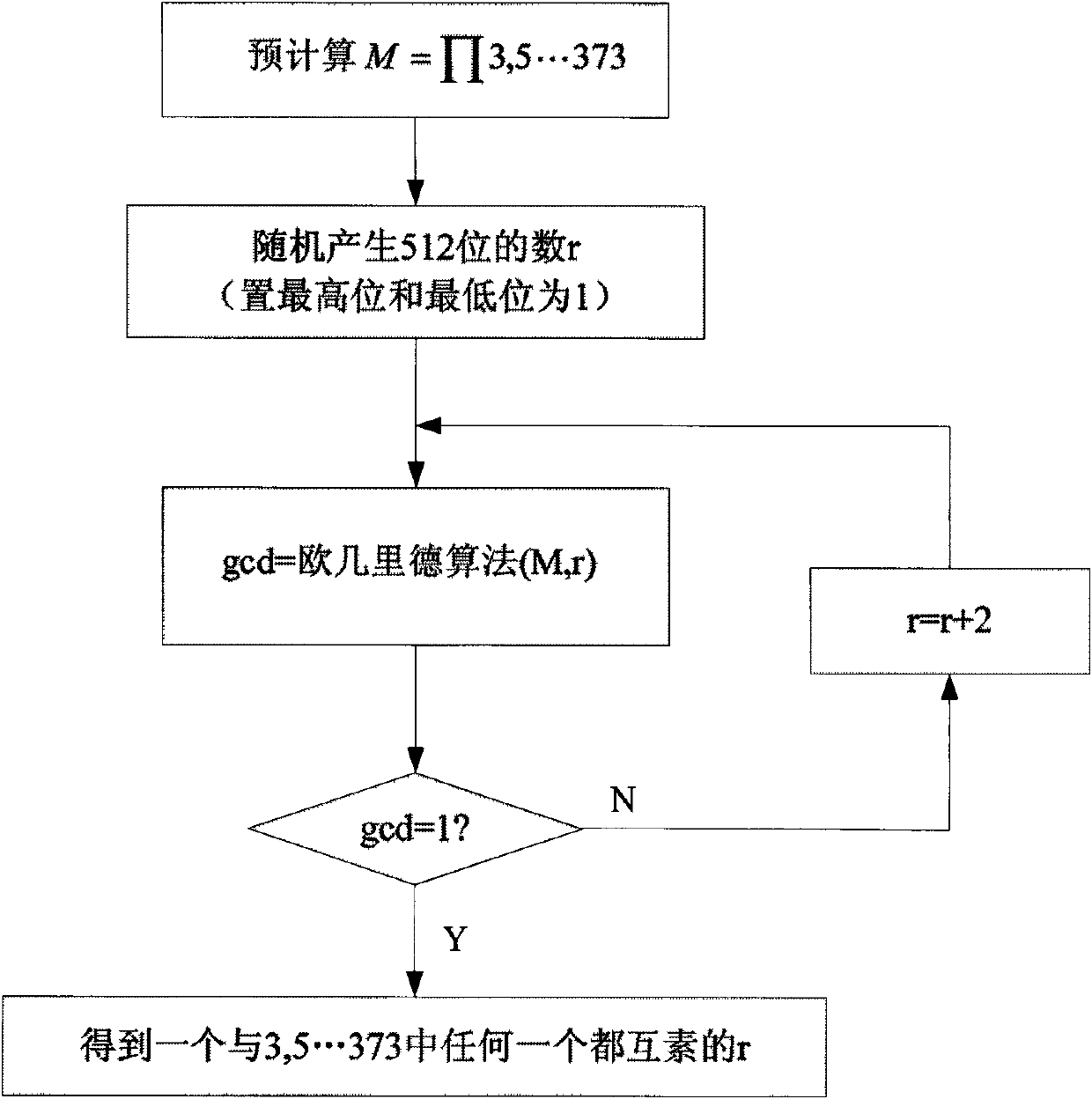
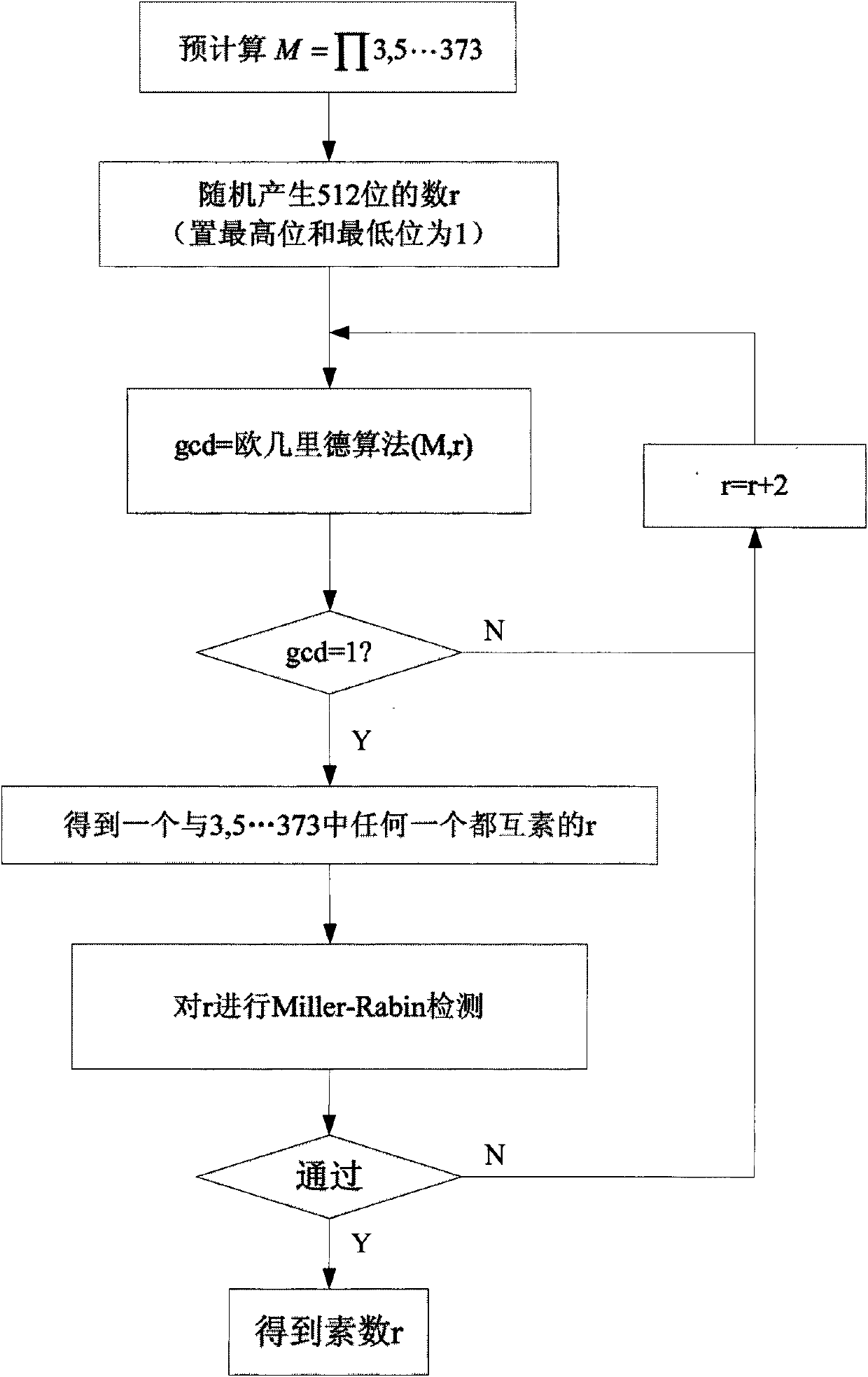
InactiveCN102023962AImprove operating speedReduce primality detection loopRandom number generatorsPublic key for secure communicationComposite numberComputer science
The invention discloses a prime number generating method applied to cryptology application. A random number and a series of small prime numbers are subjected to prime number pre-detection through a method for solving the greatest common divisor, only when the random number and the small prime numbers are relatively prime, the random number and the small prime numbers pass the prime number pre-detection, and the random number passing the prime number pre-detection is subjected to prime detection. Because one part of composite numbers can be eliminated though a pre-detection method, the cycle index of the prime detection after the pre-detection can be greatly reduced. In the traditional prime number generating method, the random number is directly subjected to the prime detection, so massive prime detection operation is needed to be performed; and under the general implemented condition, the time of the prime detection is far longer than that of solving the greatest common divisor, so the method provided by the invention can greatly improve the operating speed and time for generating the prime number.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
Imaging device
ActiveUS20130314563A1Easy to useTelevision system detailsColor television detailsComposite numberComputer science
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Dense and randomized storage and coding of information
InactiveUS7606847B2Fast computerQuantum computersNanoinformaticsComposite numberMatrix multiplication
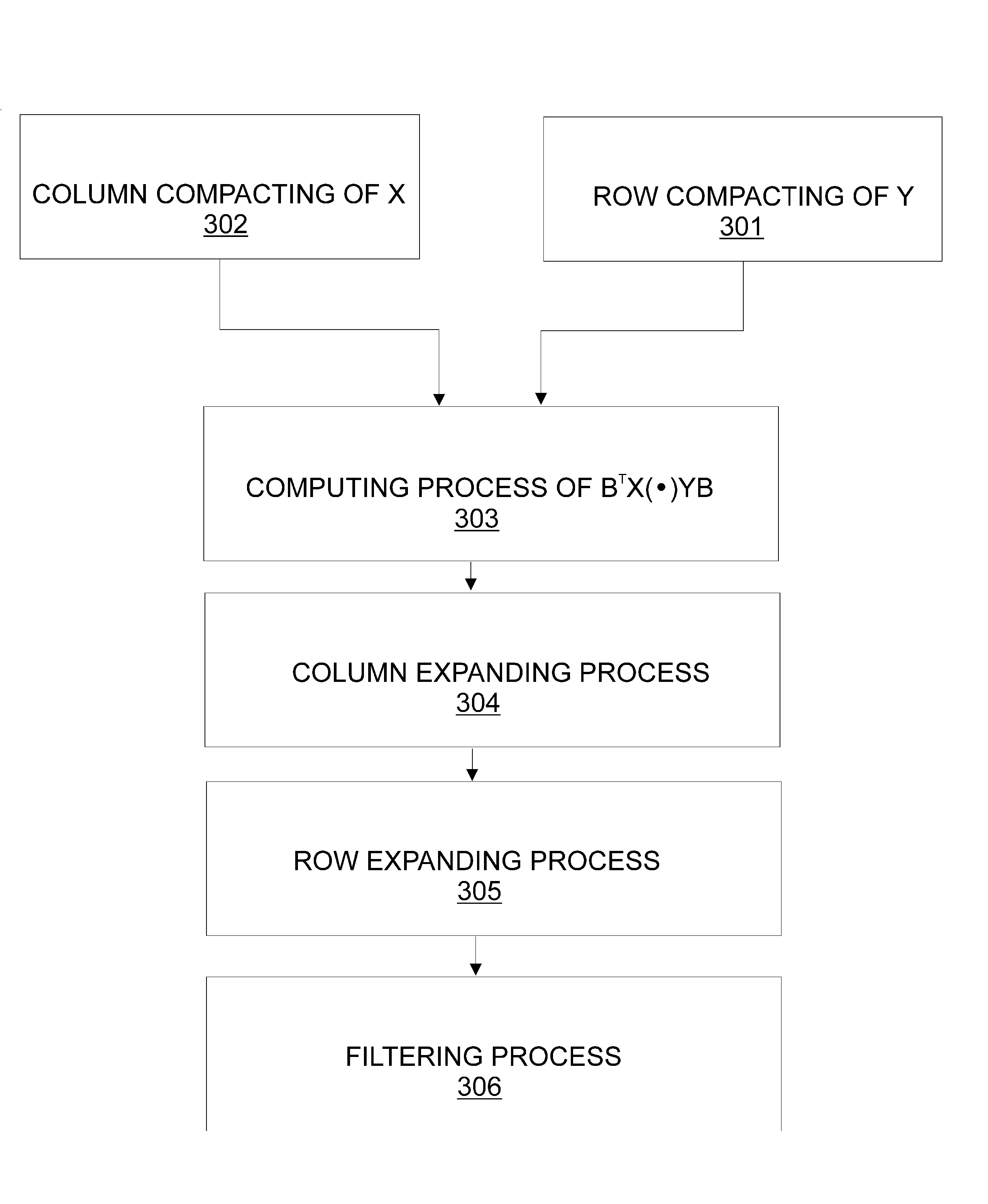
We describe a method for dense encoding of information. Bennet and Wiesner (Phys. Rev. Lett. 69:2881-2884, 1992), using EPR-pairs, showed that n bits can be encoded by n / 2 quantum-bits, from which the original bits can be retrieved. Here, in a completely different (non-quantum) setting, we give a method for more dense encoding: In our method n bits x1, x2, . . . , xn are mapped by a linear transform B over the 6-element ring Z6 to numbers z1, z2, . . . , zt from ring Z6 with t=no(1)(i.e., much fewer numbers) (Quantity o(1) here denotes a positive number which goes to 0 as n goes to infinity), then, by applying another linear transform C to these zi's, we will get back n elements of ring Z6, x′1, x′2, . . . , x′n, where, e.g., x′1 may have the form x′1=x1+3x2+4x3. One can get back x1 simply by running through the values of xi on the set 0, 1, 2, 3, 4, 5, and noticing that only x1 has period 6, (3x2 has period 2, 4x3 has period 3). Our results generalize for any non-prime-power composite number m instead of 6. We also apply this method for fast computation of matrix multiplication and for compacting and extending matrices with linear transforms.
Owner:GROLMUSZ VINCE
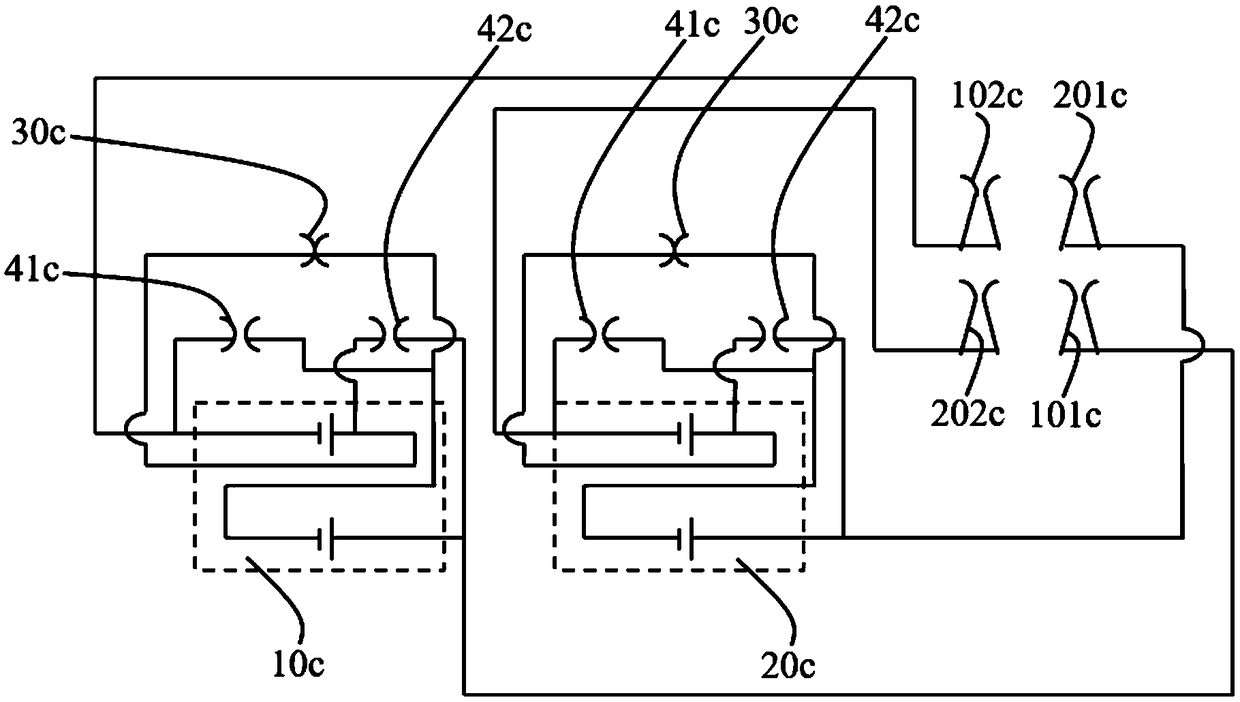
Electrical energy storage device and electric tool
The invention provides an electrical energy storage device. The electrical energy storage device comprises N energy units; each of the N energy units has a voltage of nV, N is a composite number, andthe number of submultiples is k. An equal number of energy units in the N energy units are optionally connected in different series-parallel combinations to output k different output voltages. An electric tool using the electrical energy storage device is cooperated with the electrical energy storage device by using a plug so that the electrical energy storage device outputs one of k different output voltages to the electric tool.
Owner:CHANGZHOU GLOBE CO LTD
Magnesium-based nano composite hydrogen storage material and preparation method thereof
InactiveCN107758611AHigh purityImprove the kinetic performance of hydrogen absorption and desorptionHydrogenMonoborane/diborane hydridesComposite numberCatalytic effect
The invention relates to a magnesium-based nano composite hydrogen storage material and a preparation method thereof and belongs to the technical field of functional materials. The temperature requirement of application is met by forming an ammoniated hydroboron by magnesium hydroboron and ammonium, and positive hydrogen energy introduced into a NH3 group can be combined with negative hydrogen ina BH4<-> group to release hydrogen, so that the hydrogen release path of the hydroboron is changed and release of impurity gas such as boroethane is reduced effectively; the ammonium complexing quantity is changed by means of an ammonium re-distributing method to prepare mono-ammoniated magnesium hydroboron, that is, the combining efficiency is the highest from the aspect of charge balance by adjusting the quantities of positive and negative hydrogen in ammoniated magnesium hydroboron, release of ammonia in a decomposing process of the magnesium hydroboron ammonate can be inhibited effectively, the purity of hydrogen released is improved, and meanwhile, the magnesium-based nano composite hydrogen storage material is combined with a magnesium-based alloy, so that the crystal structure of analloy hydride is changed and a catalytic effect role is played, and therefore, diffusion of hydrogen atoms is facilitated, and the kinetic performance of absorbing and releasing hydrogen by the alloyhydride is improved.
Owner:常州富思通管道有限公司
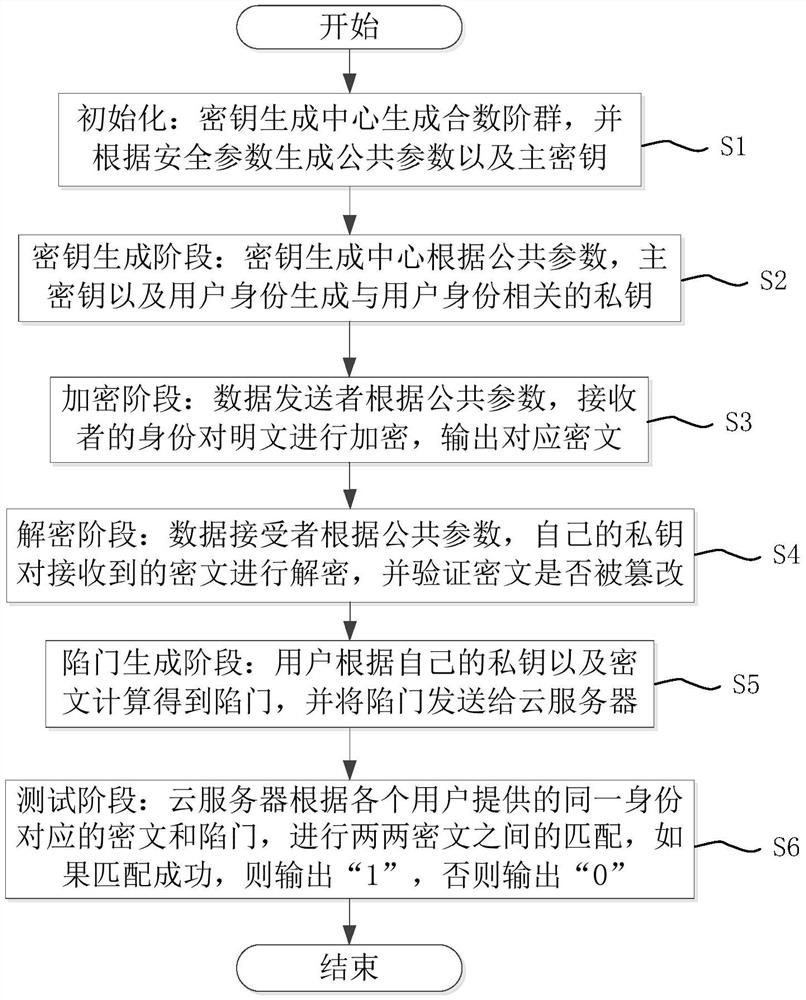
User identity encryption method based on composite number order group
ActiveCN112804052ADon't worry about certificate managementGuaranteed privacyKey distribution for secure communicationComposite numberCiphertext
The invention discloses a user identity encryption method based on a composite number order group. The method comprises an initialization stage, a secret key generation stage, an encryption stage, a decryption stage and a trap door generation stage. In the test stage, the cloud server matches every two ciphertexts according to the ciphertext and the trap door corresponding to the same identity provided by each user, if matching succeeds, '1' is output, and otherwise '0' is output. According to the user identity encryption method based on the composite number order group provided by the invention, the ciphertext of the keyword can be matched, the privacy of user data on the cloud can be ensured while the keyword search function is completed, and the certificate management problem of the user does not need to be worried about, so that the requirement of higher security guarantee of important information in cloud computing is met.
Owner:CHONGQING COLLEGE OF ELECTRONICS ENG
Dense and randomized storage and coding of information
InactiveUS20050216544A1Fast computerQuantum computersNanoinformaticsComposite numberMatrix multiplication
We describe a method for dense encoding of information. Bennet and Wiesner (Phys. Rev. Lett. 69:2881-2884, 1992), using EPR-pairs, showed that n bits can be encoded by n / 2 quantum-bits, from which the original bits can be retrieved. Here, in a completely different (non-quantum) setting, we give a method for more dense encoding: In our method n bits x1,x2, . . . ,xn are mapped by a linear transform B over the 6-element ring Z6 to numbers z1,z2, . . . ,zt from ring Z6 with t=no(1)(i.e., much fewer numbers) (Quantity o(1) here denotes a positive number which goes to 0 as n goes to infinity), then, by applying another linear transform C to these zi's, we will get back n elements of ring Z6, x′1,x′2, . . . ,x′n, where, e.g., x′1 may have the form x′1=x1+3x2+4x3. One can get back x1 simply by running through the values of xi on the set 0,1,2,3,4,5, and noticing that only x1 has period 6, (3x2 has period 2, 4x3 has period 3). Our results generalize for any non-prime-power composite number m instead of 6. We also apply this method for fast computation of matrix multiplication and for compacting and extending matrices with linear transforms.
Owner:GROLMUSZ VINCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com