Quick large number decomposition method based on cryptographic technology application
A cryptography and technology technology, applied in the fields of information security and cryptography technology application, to achieve the effect of rapid decomposition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
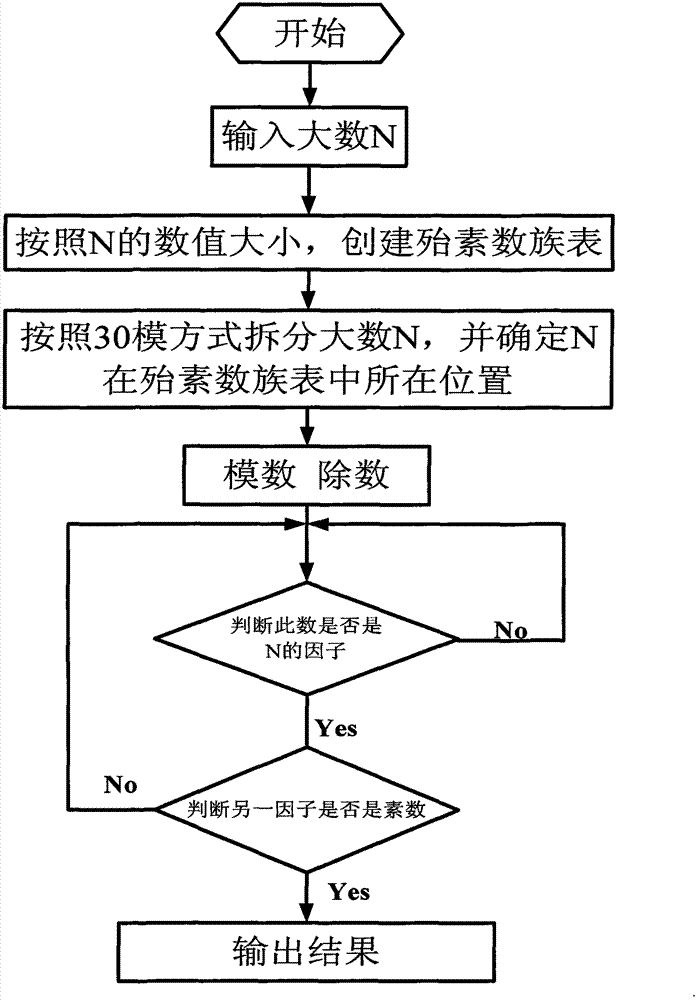
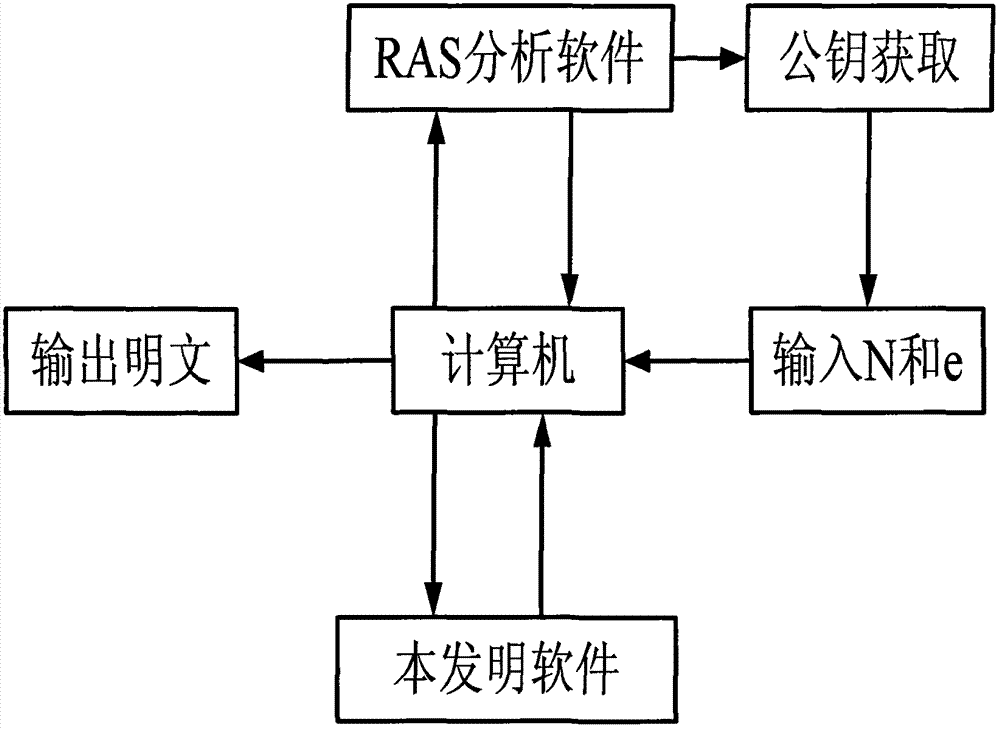
[0040] Attached below figure 1 and figure 2 The present invention is described in further detail with specific embodiment; According to appended figure 1 process and attached figure 2 The working principle diagram of the application example of fast decomposition of a large number:
[0041] (1) Determine the large number to be decomposed as M=10 10 +1;
[0042] (2) Substitute into the formula: 10 10 +1=30(n-1)+a, wherein, what n represents is the number of columns of the large number M in the almost prime number family table, and what a represents is the first position of the row where the large number M is in the almost prime number family table number;
[0043] (3) Calculate (10 10 +1) / 30=333333333+11 / 30, thereby determining that the position of this value M in the possible prime number table is: n=333333334 columns, a=a 3 =11, that is, the value is on the line whose first digit is "11";
[0044] (4) start calculation deletion program, delete the composite number c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com