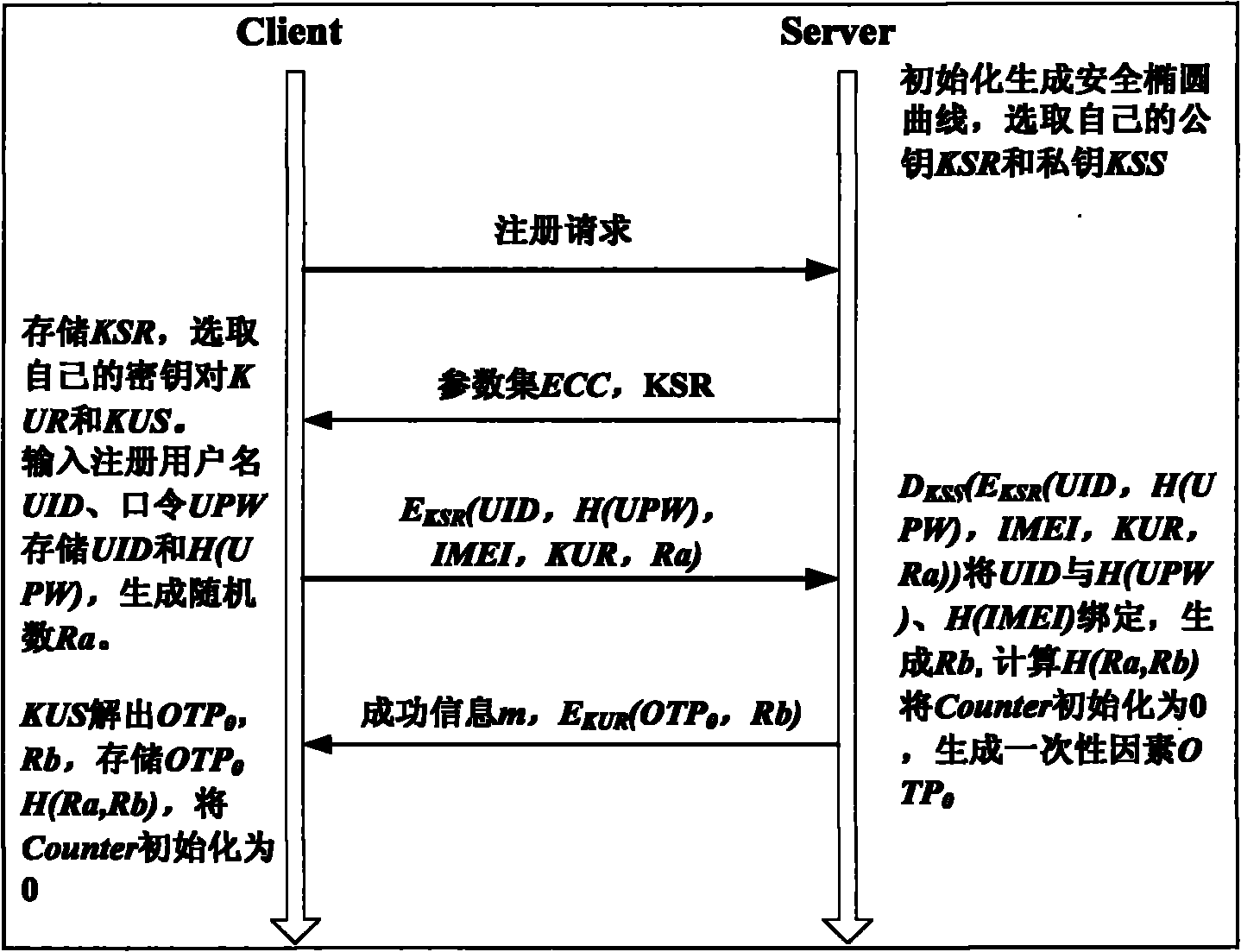
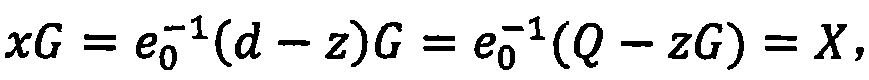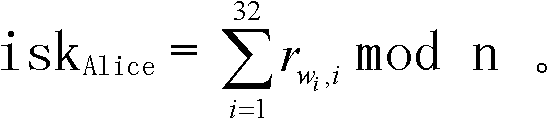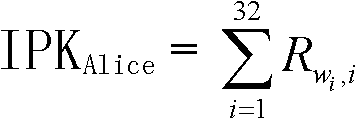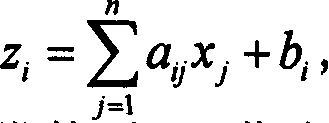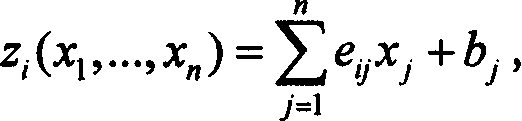Patents
Literature
185 results about "Public key cryptosystem" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
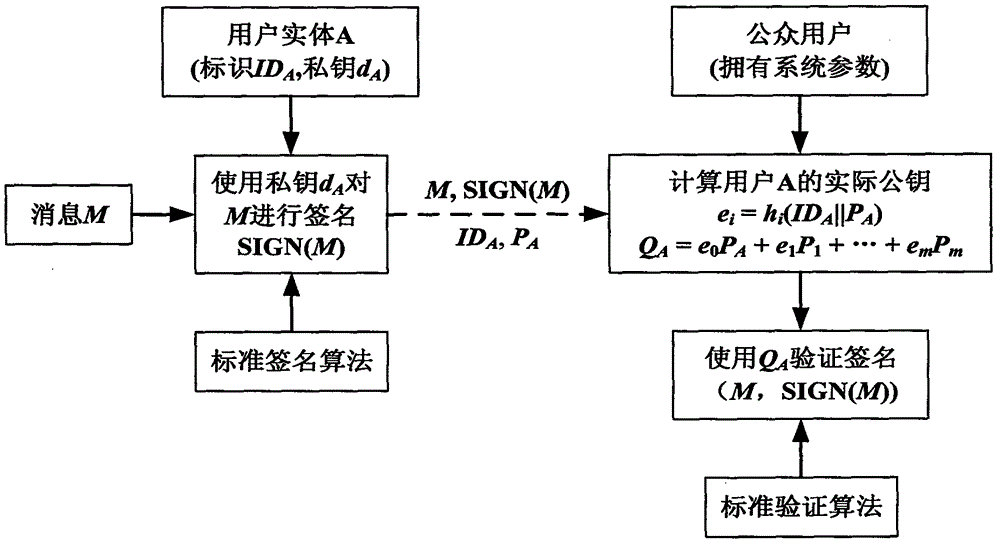
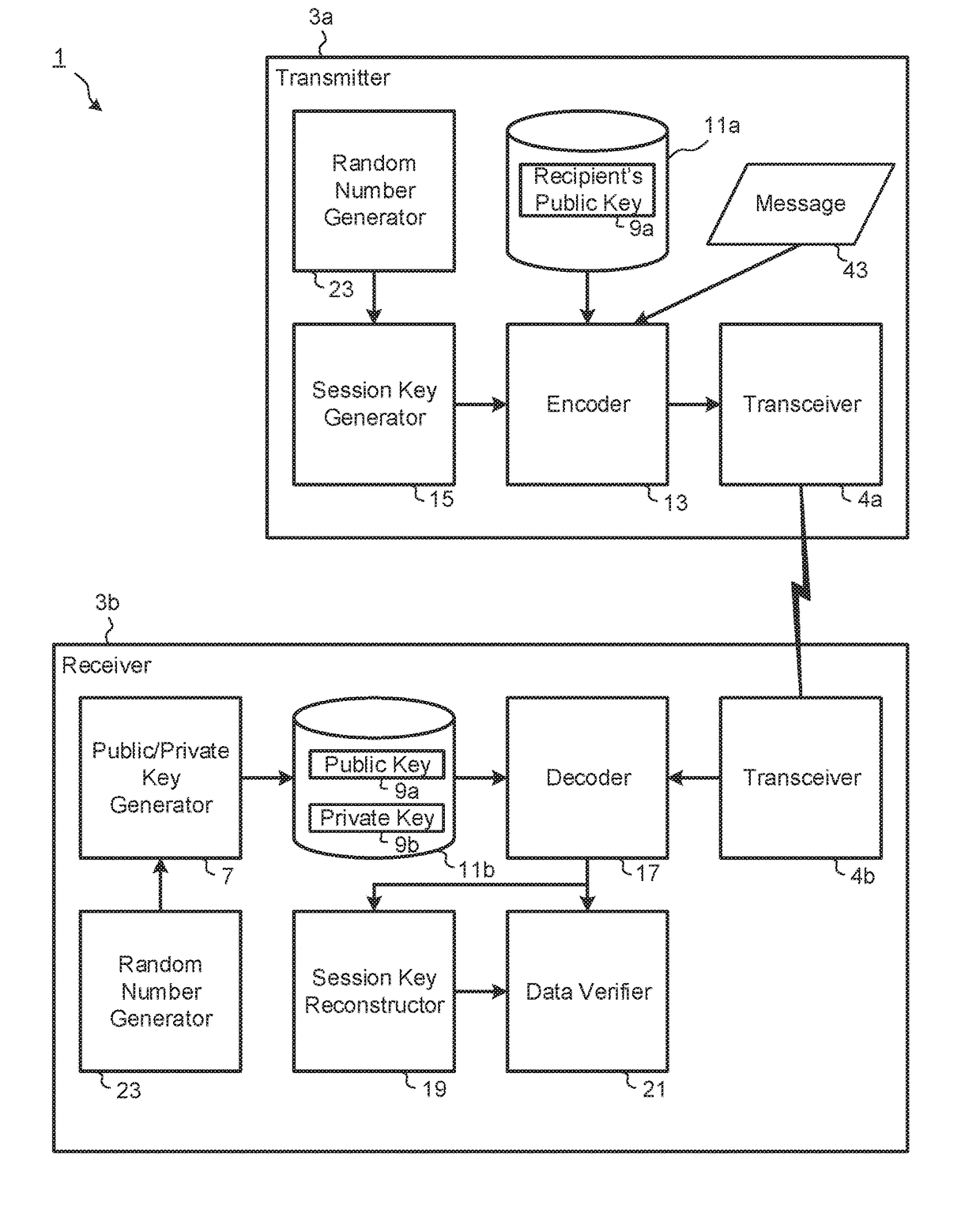
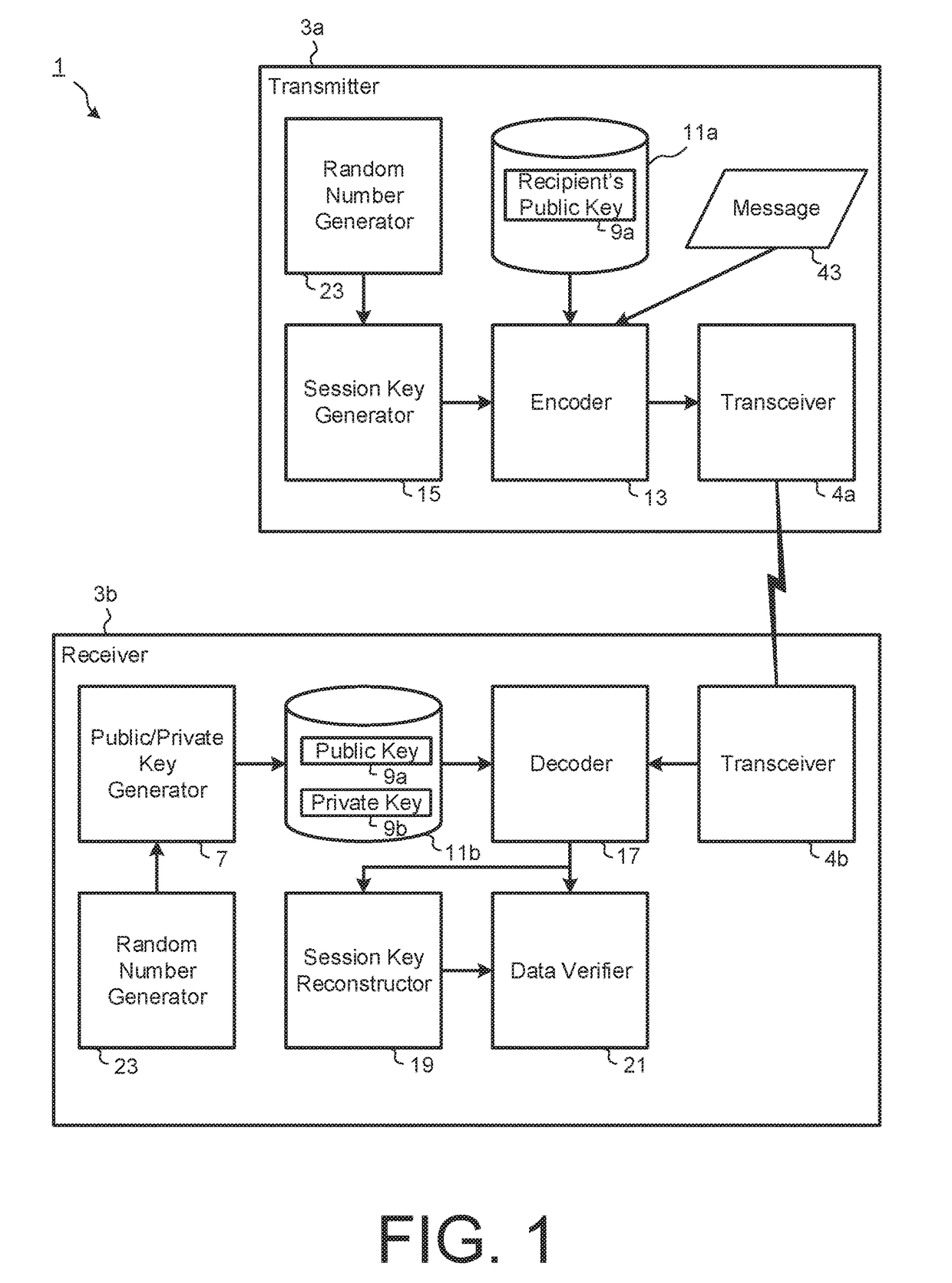
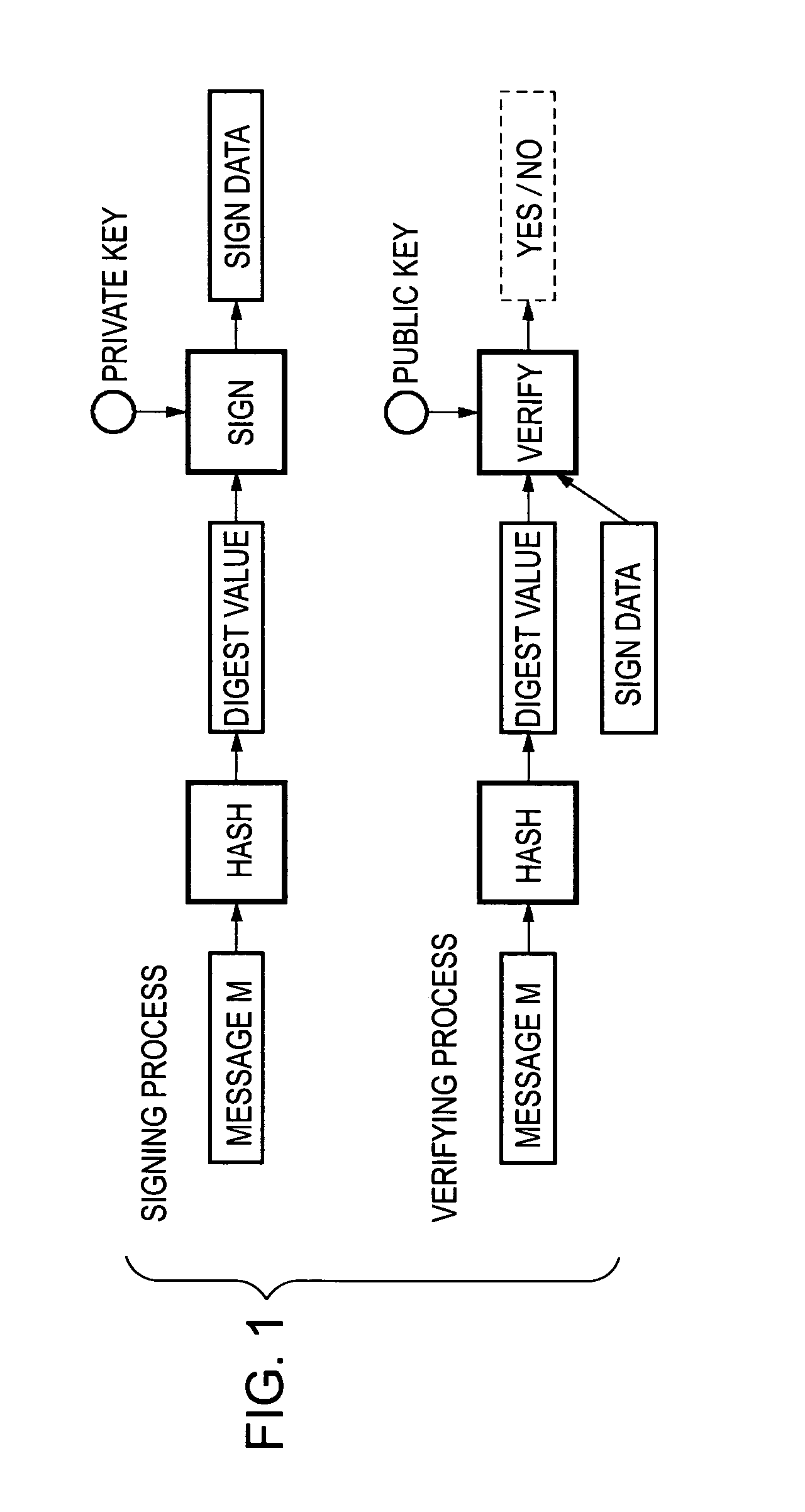
Public-key cryptosystem. Public-key cryptosystem is also referred as Asymmetric cryptography, in which each user has a pair of keys (1) a public key and (2) a private key. The public key is made public while the private key remains secret. Encryption is performed with the public key while decryption is done with the private key.
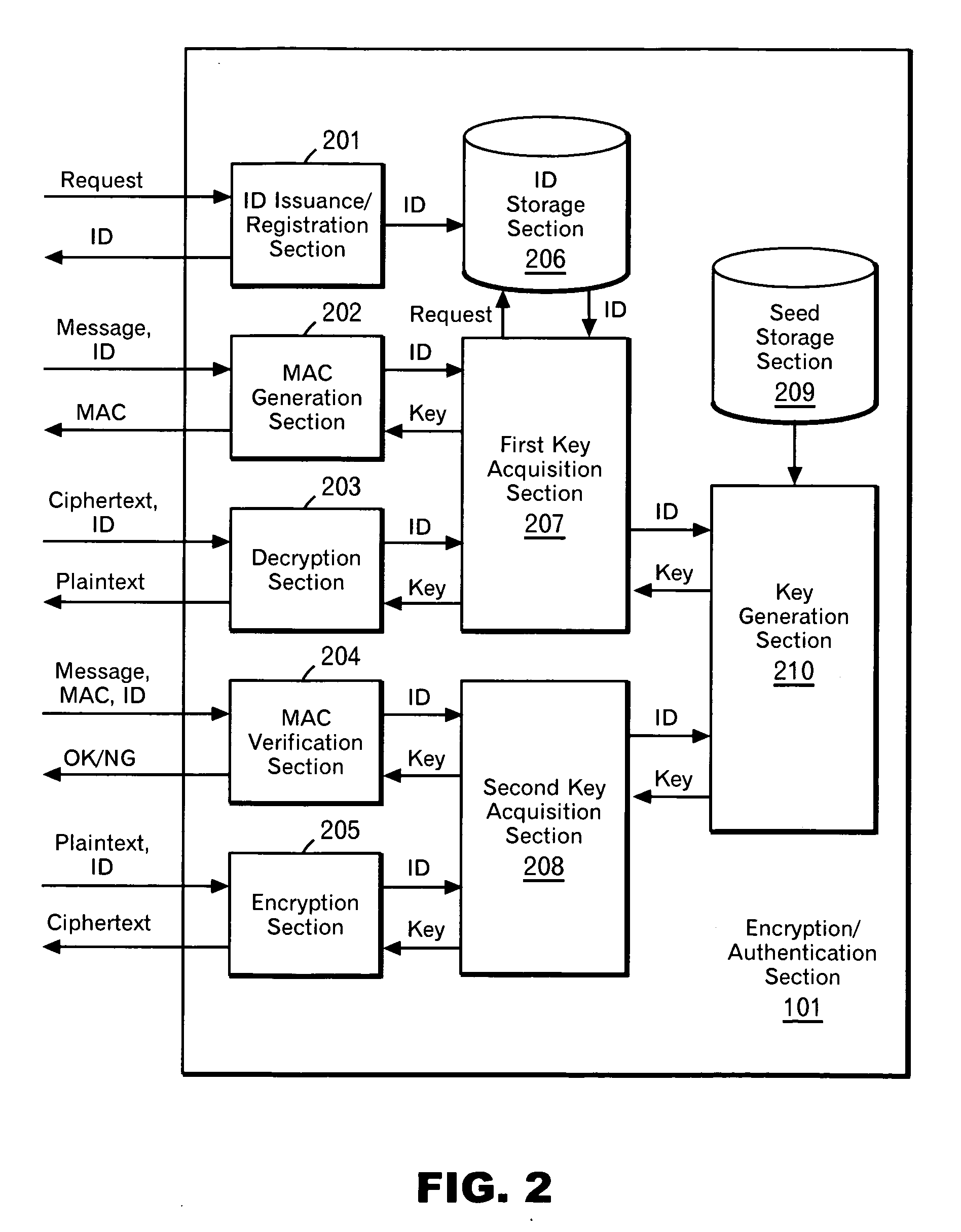
Masking the output of random number generators in key generation protocols
ActiveUS20110307698A1Key distribution for secure communicationPublic key for secure communicationDeterministic encryptionNumber generator
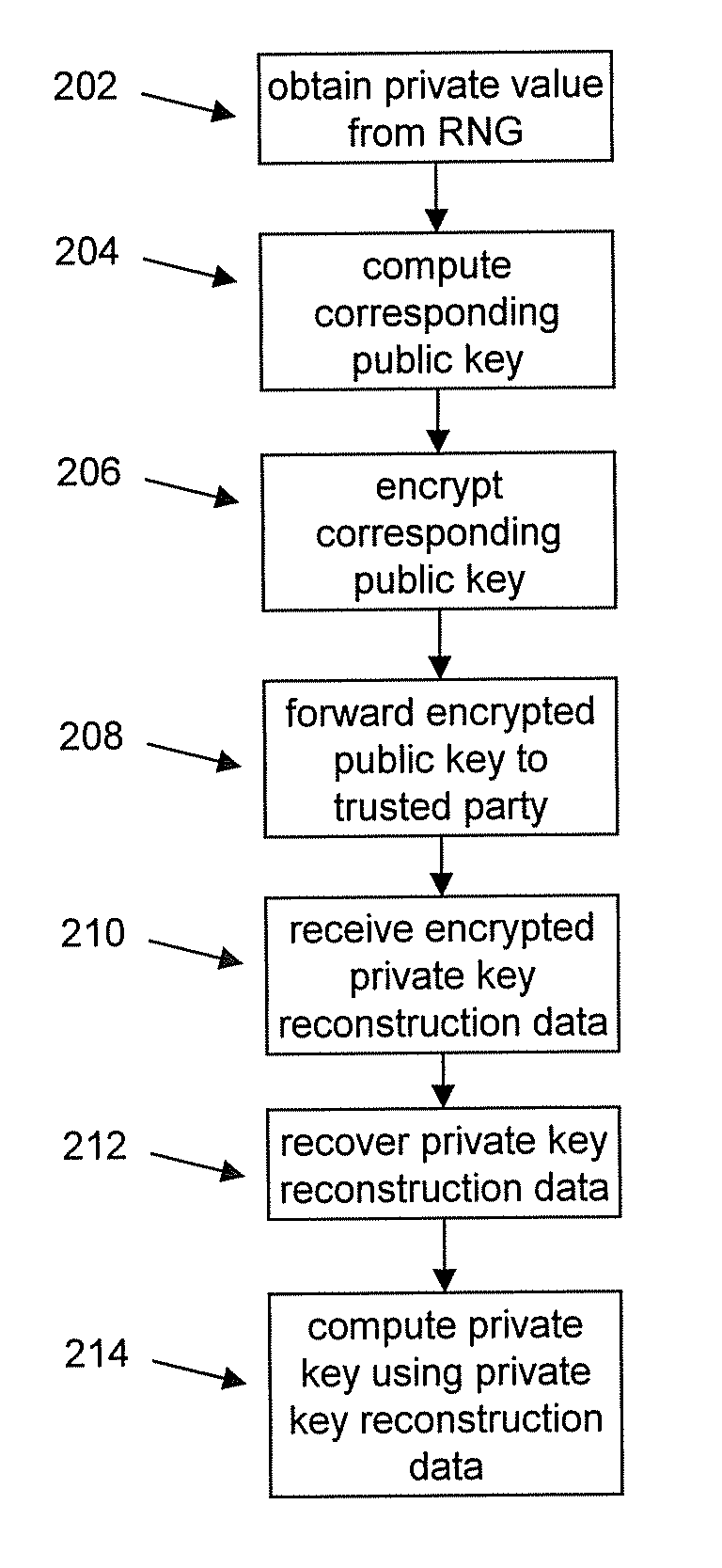
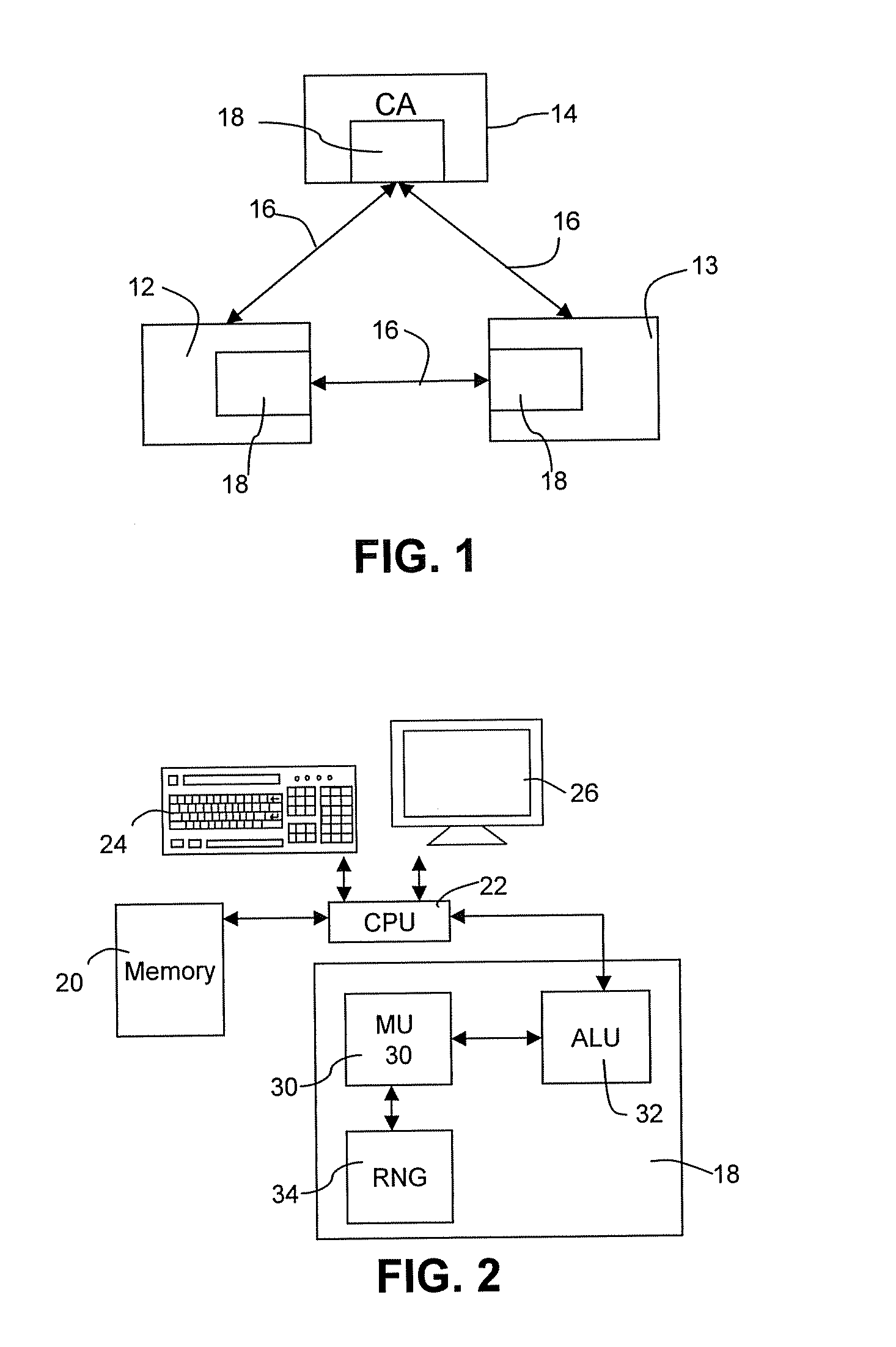
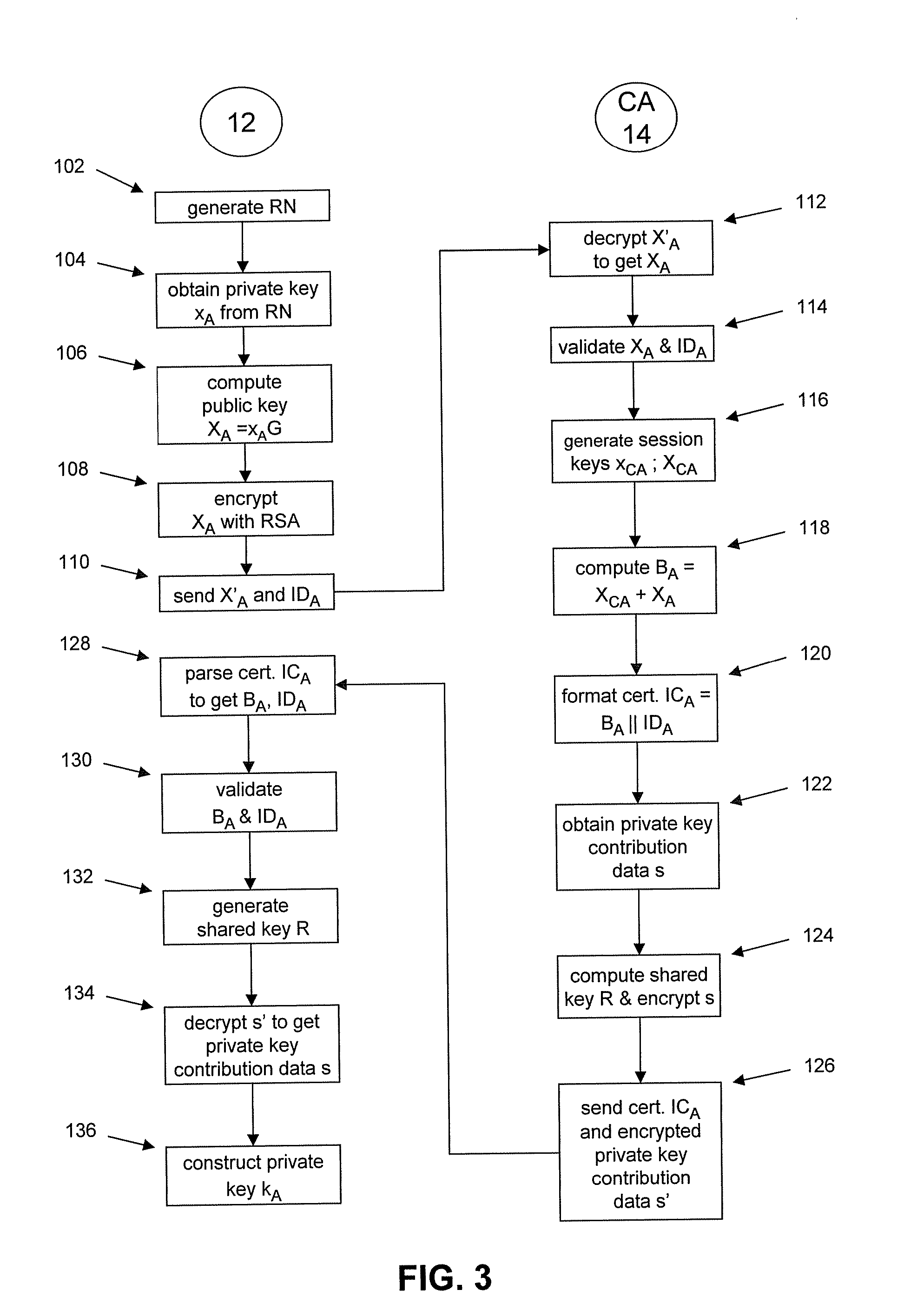
To mitigate the effects of a weak random number generator (RNG) in a public key cryptosystem, a public key obtained from the RNG is encrypted using a deterministic cryptographic scheme before being made publicly available. A trusted party receiving the encrypted public key can recover the public key and combine it with other information so it is not subject to direct scrutiny. In one embodiment, the trusted party incorporates the public key in a certificate, such as an implicit certificate, for use by the correspondents in other communications.
Owner:MALIKIE INNOVATIONS LTD
Achievement method of certificate-less public key cryptosystem without bilinear pairing operation
ActiveCN104539423AEfficient managementImprove computing efficiencyPublic key for secure communicationUser identity/authority verificationCommunications securityInformation security
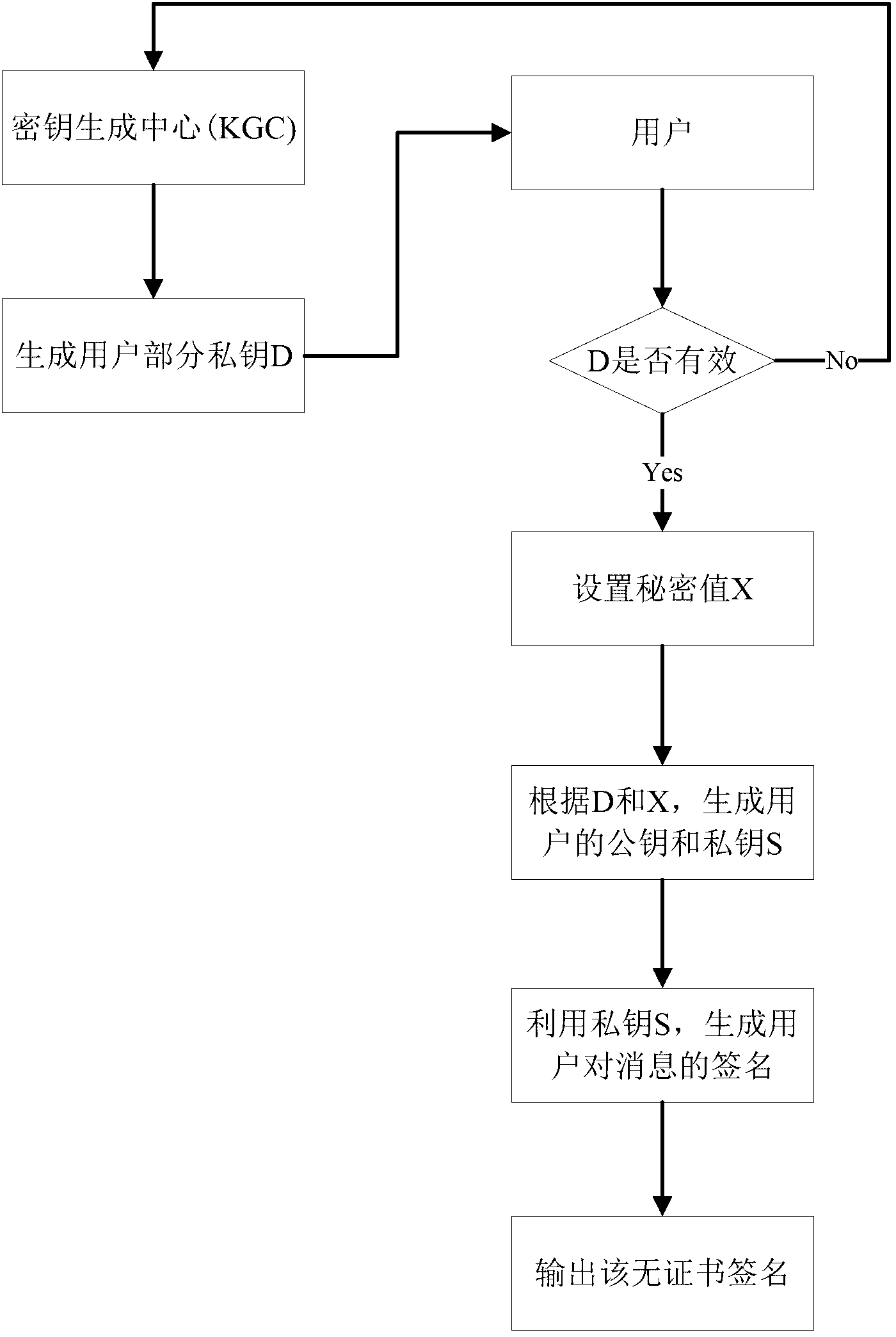
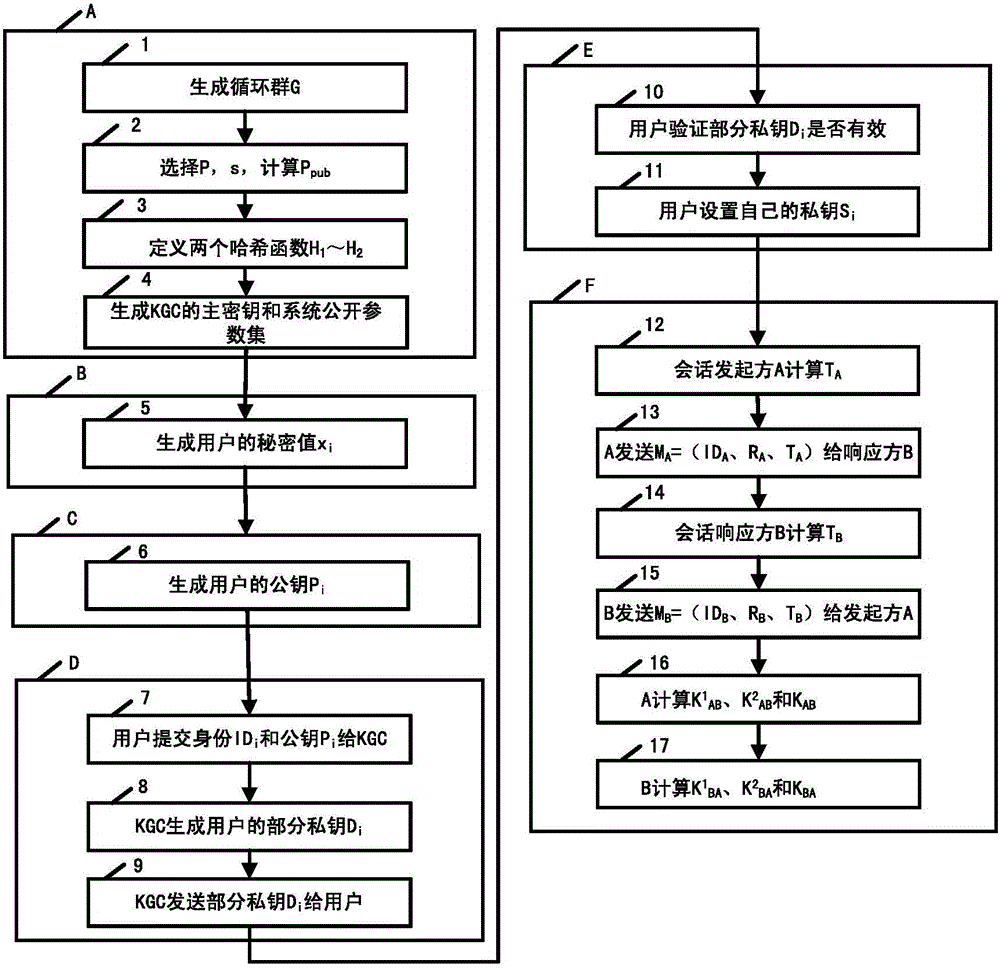
The invention provides an achievement method of a certificate-less public key cryptosystem without bilinear pairing operation and belongs to the field of information safety. The achievement method is used for solving the problems of generation of a secret key of a user, usage and authentication of a public key of the user. According to the achievement method, firstly, a user sets a secret value and calculates a temporary public key, then a secret key generating center generates the other part of the secret key for the user and enables the two parts to be bound, and finally the user synthesizes a his / her actual public and secret key pair. The defect that public key replacement and signature counterfeit possibly exist in a common certificate-less cryptosystem is overcome, the user has complete control right on the secret key, the secret key can be revoked and re-generated, and the signature of the user has non-repudiation. The achievement method adopts a public key cryptographic algorithm of a standard elliptic curve, does not adopt the bilinear pairing operation, is few in occupied resources and high in safety and can operate without the secret key generating center when being applied to signature, authentication and secret key negotiation. By means of the achievement method, identity authentication, communication security and non-repudiation application demands of large-scale systems and low-power-consumption devices can be met.
Owner:北京百旺信安科技有限公司 +1
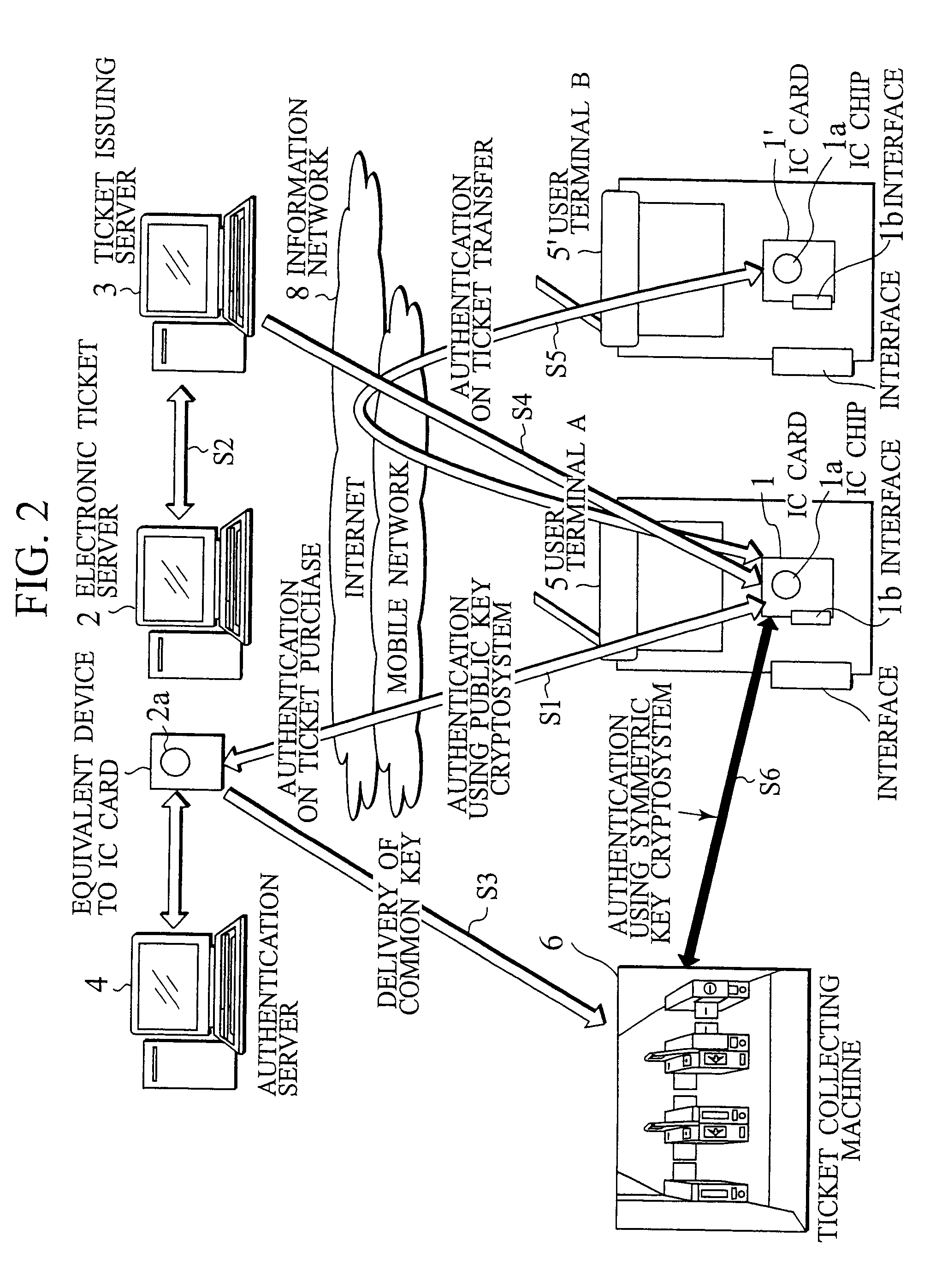
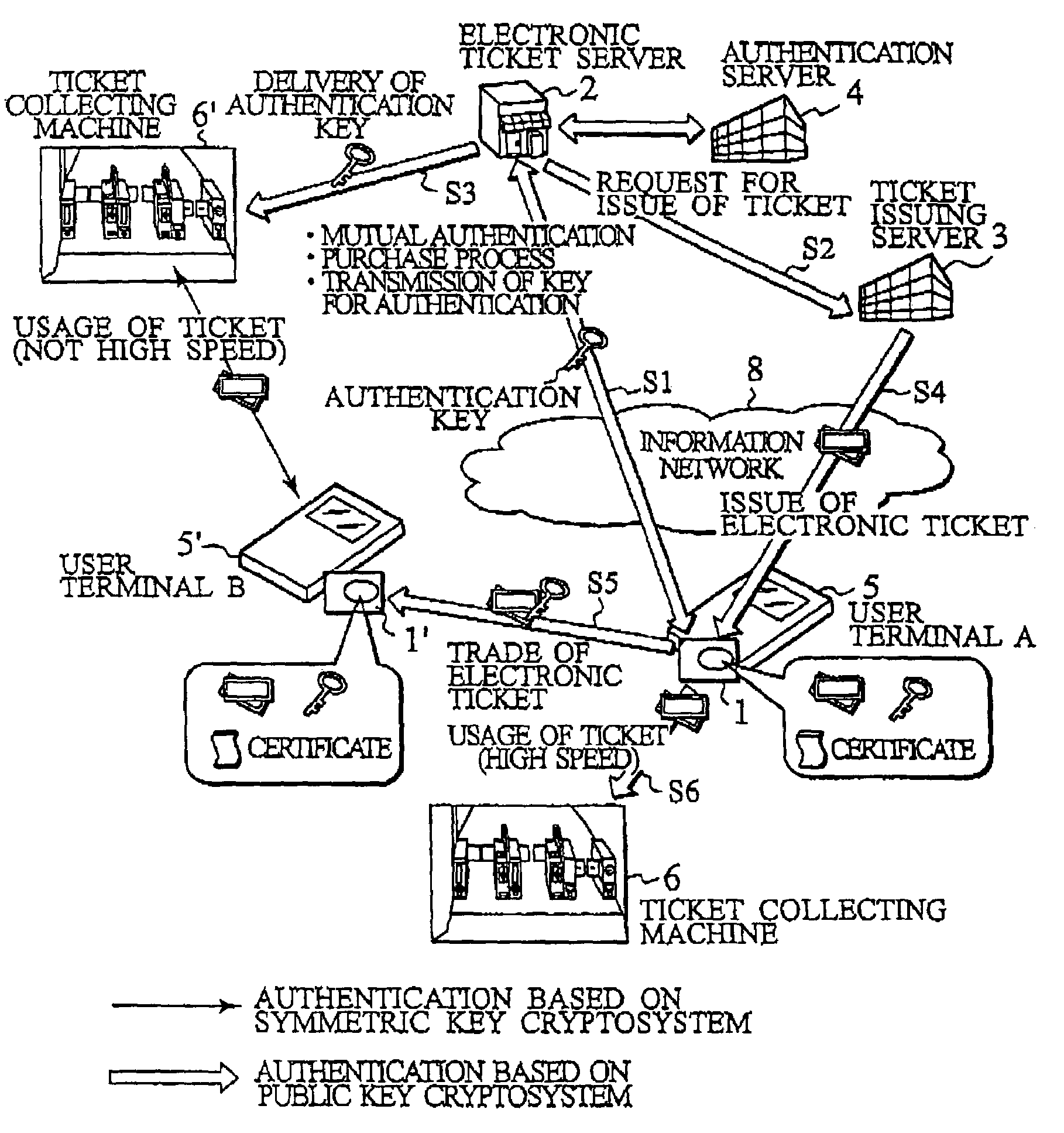
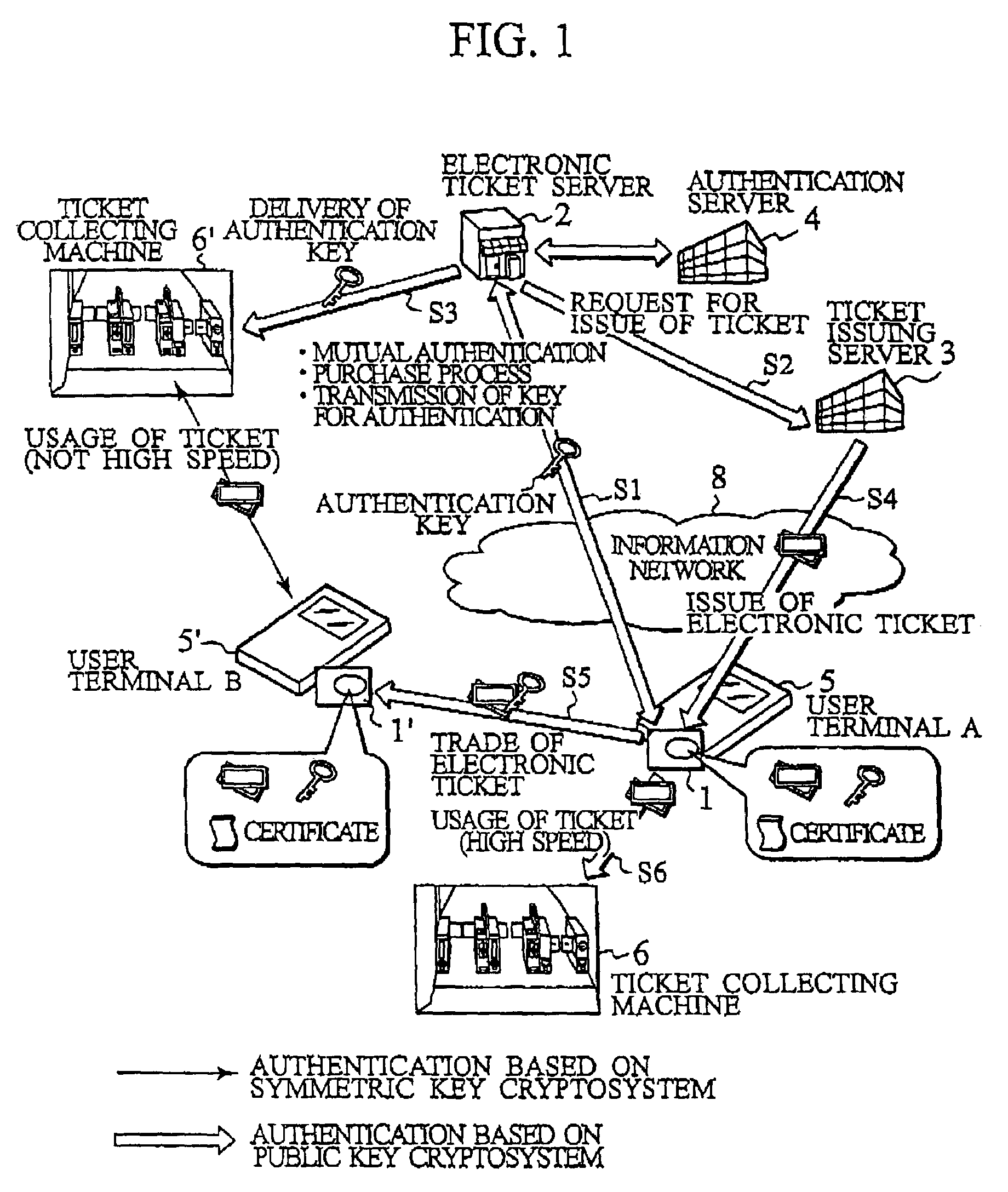
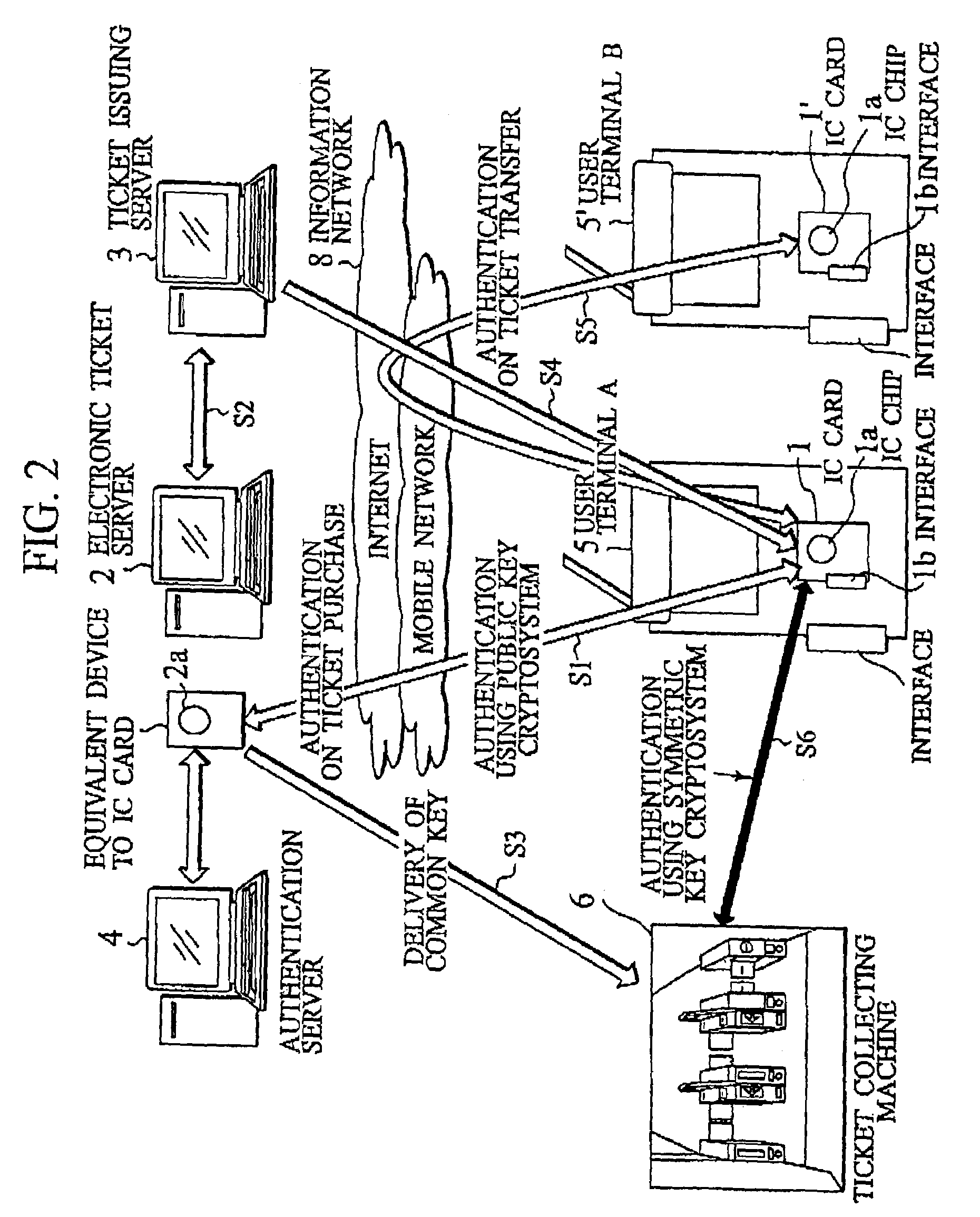
IC card and authentication method in electronic ticket distribution system
InactiveUS8306919B2Strict securityReduce necessityMultiple keys/algorithms usageDigital data processing detailsDistribution systemPublic key cryptosystem
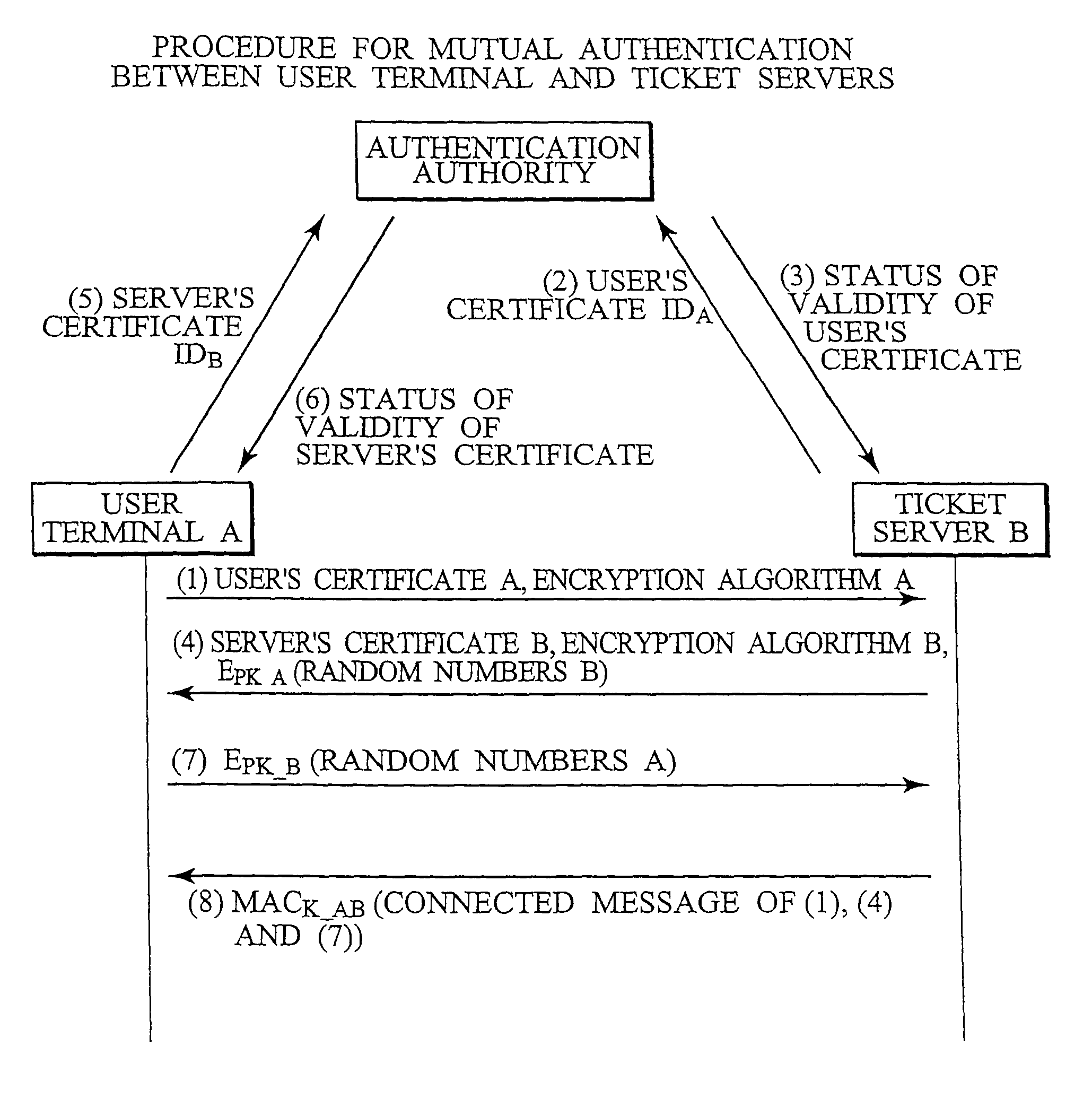
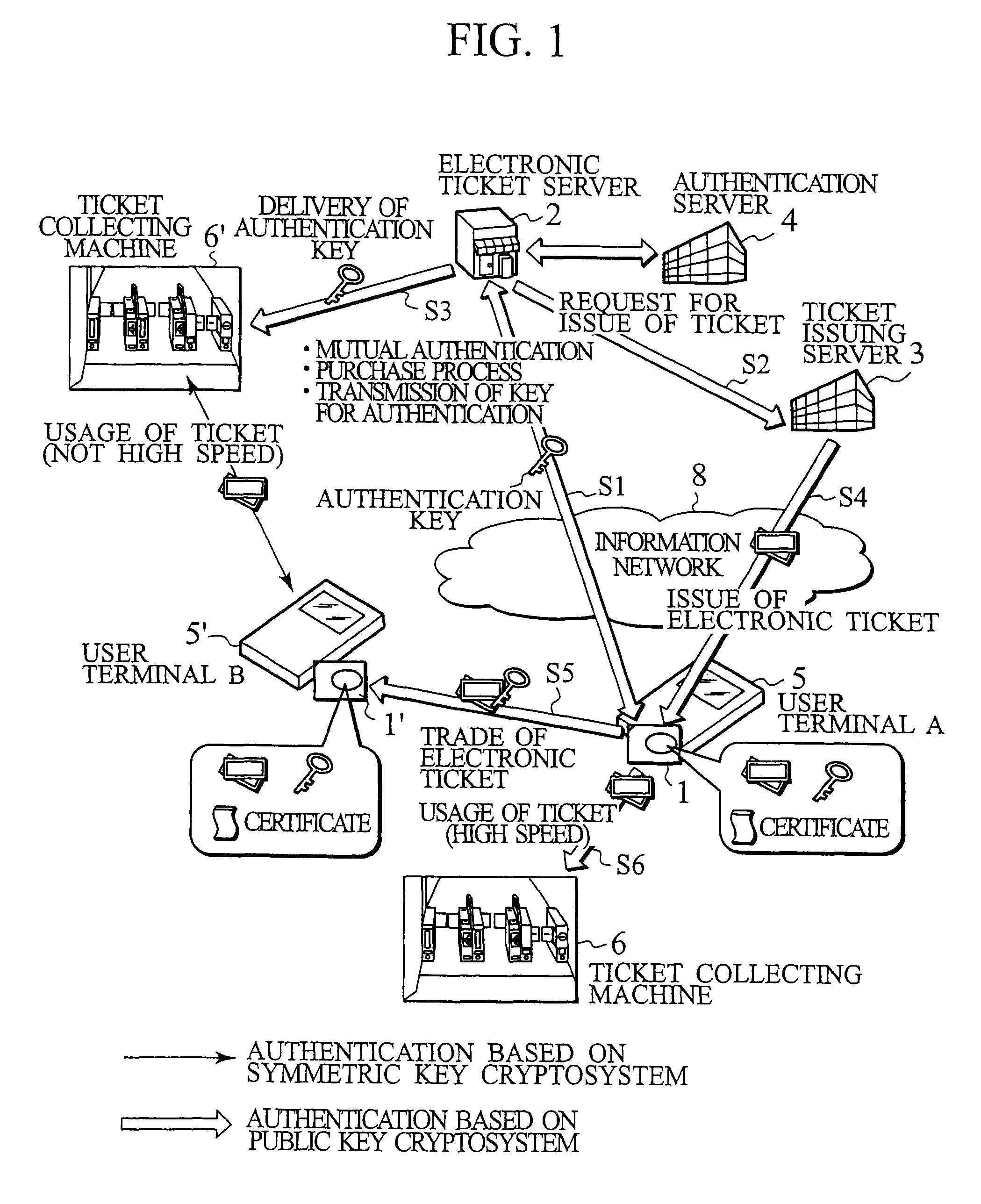
Between an IC card (1) and a electronic ticket server (2), upon purchasing an electronic ticket a public key cryptosystem is employed for a mutual authentication to keep a strict security, and a shared secret between the electronic ticket and a ticket collecting machine is sent on a secure channel as well as the electronic ticket. Upon usage of the electronic ticket, the IC card (1) and the ticket collecting machine (6) mutually judge whether they carry out the mutual authentication by using a public key cryptosystem or a symmetric key cryptosystem. When they determine to use the symmetric key cryptosystem, they carry out the mutual authentication by using the shared secret exchanged beforehand. When they determine to use the public key cryptosystem, they carry out the mutual authentication by using the same method as that used upon purchasing the electronic ticket. This method of mutual authentication can dynamically switch cryptosystems for cryptographic communication between the IC cards or between the IC card and a tamper resistant device having an equivalent function to an IC card installed in related servers or the ticket collecting machine, based on their judgment of the types of bearers, the required degree of security and the required processing speed.
Owner:SAKAMURA KEN +2
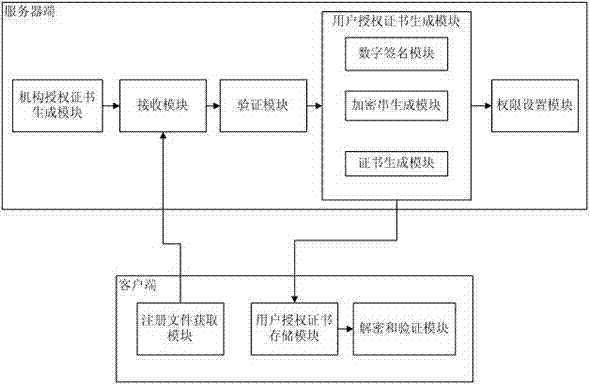
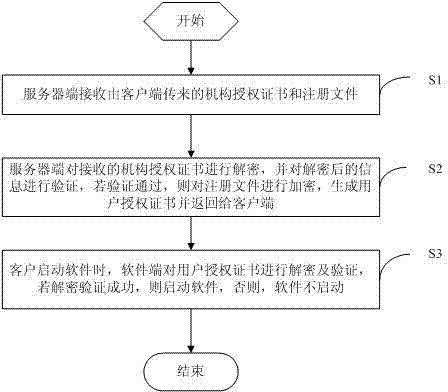
Software authorization system based on public key cryptosystem
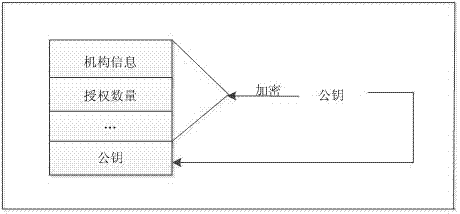
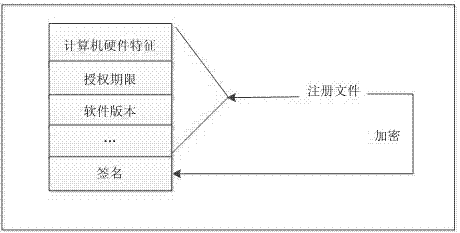
ActiveCN103491097APrevent illegal copyingEasy to upgradeVersion controlUser identity/authority verificationAuthorization certificateAuthorization Mode
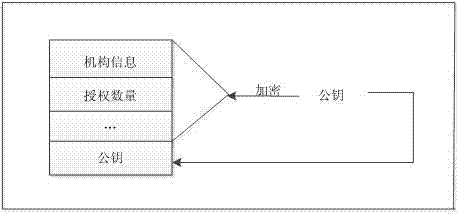
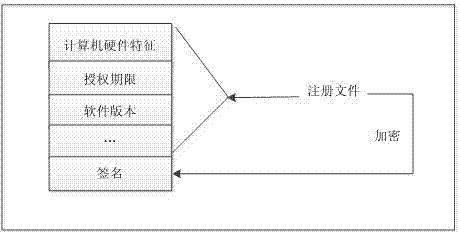
The invention discloses a software authorization system based on public key cryptosystem. The software authorization system comprises a server end and a client end, wherein the server end comprises an institution authorization certification generation module, a receiving module, a verification module and a user authorization certificate generation module. The user authorization certificate generation module comprises a digital signing module used for carrying out digital signing on computer hardware characteristics h0 in a user registration file with an RSA private key to generate S0, an encryption string generation module used for carrying out preset hybrid operations on obtained software version information v, user information u, an authorization term ex, current time cur and s0 to generate an encryption string signB64 and a certificate generation module used for generating a user authorization certificate with the encryption string signB64 and the RSA public key. The method can prevent software from being illegally copied, meanwhile, the software can be managed by a software issuer in a concentrated mode, and upgrading and tracking of the software, pushing personalized services for users and other after-sale management are facilitated.
Owner:HUAZHONG NORMAL UNIV
Pseudo-random number generator
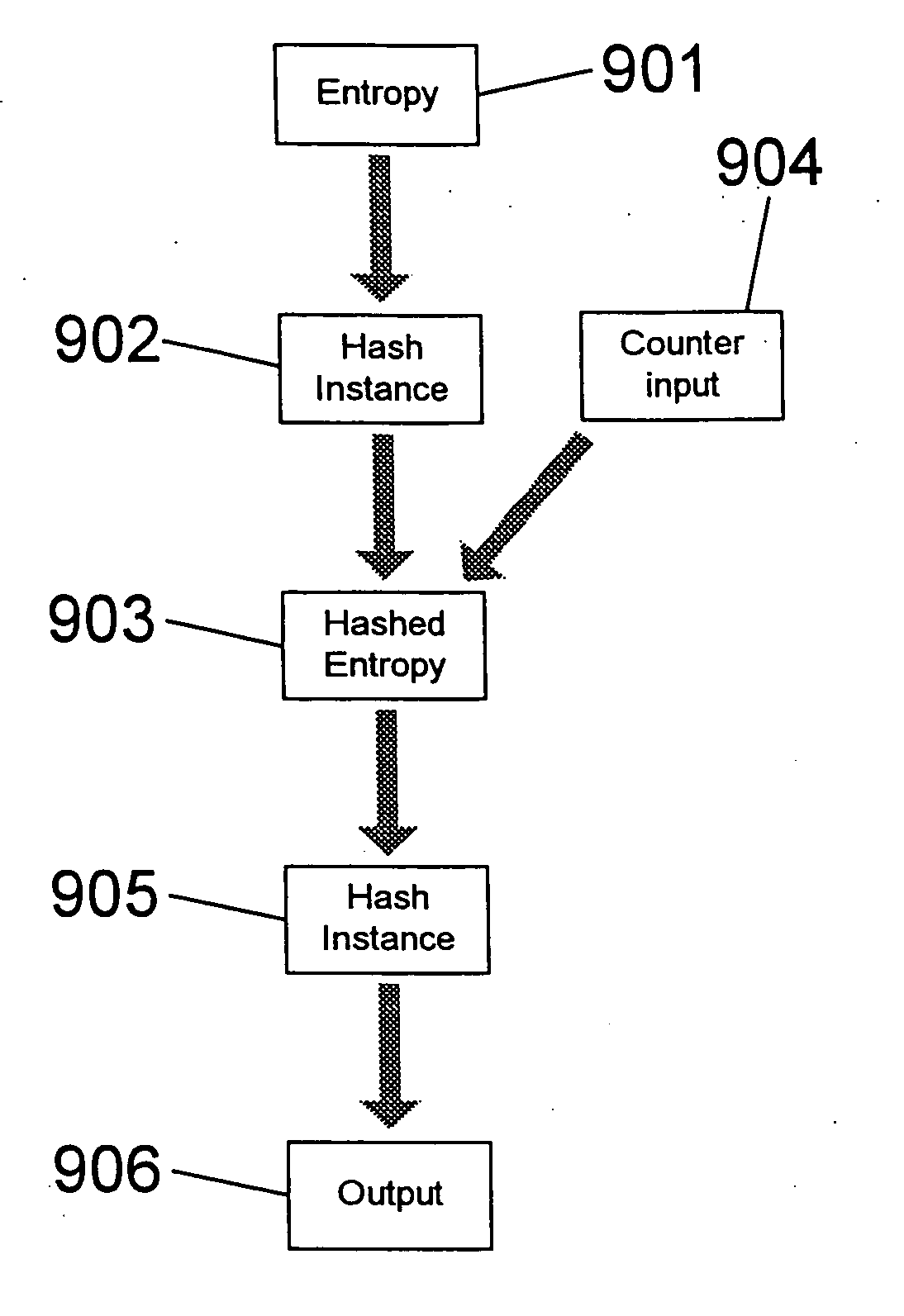
InactiveUS20040078576A1Efficient executionImprove efficiencyRandom number generatorsPublic key for secure communicationEngineeringPublic key cryptosystem
A pseudo-random number generator comprises: (a) a plurality of first-tier means each capable of receiving an entropy input and generating a respective hash output; and (b) a second-tier hashing means, which takes as input the respective first-tier hash outputs and generates as output a pseudo-random number. The generator of the present invention has particular application in cryptosystems, and particularly in public key cryptosystems where long sequences of data chosen from a large space of possible sequences need to be created quickly.
Owner:GEITINGER FELIX EGMONT
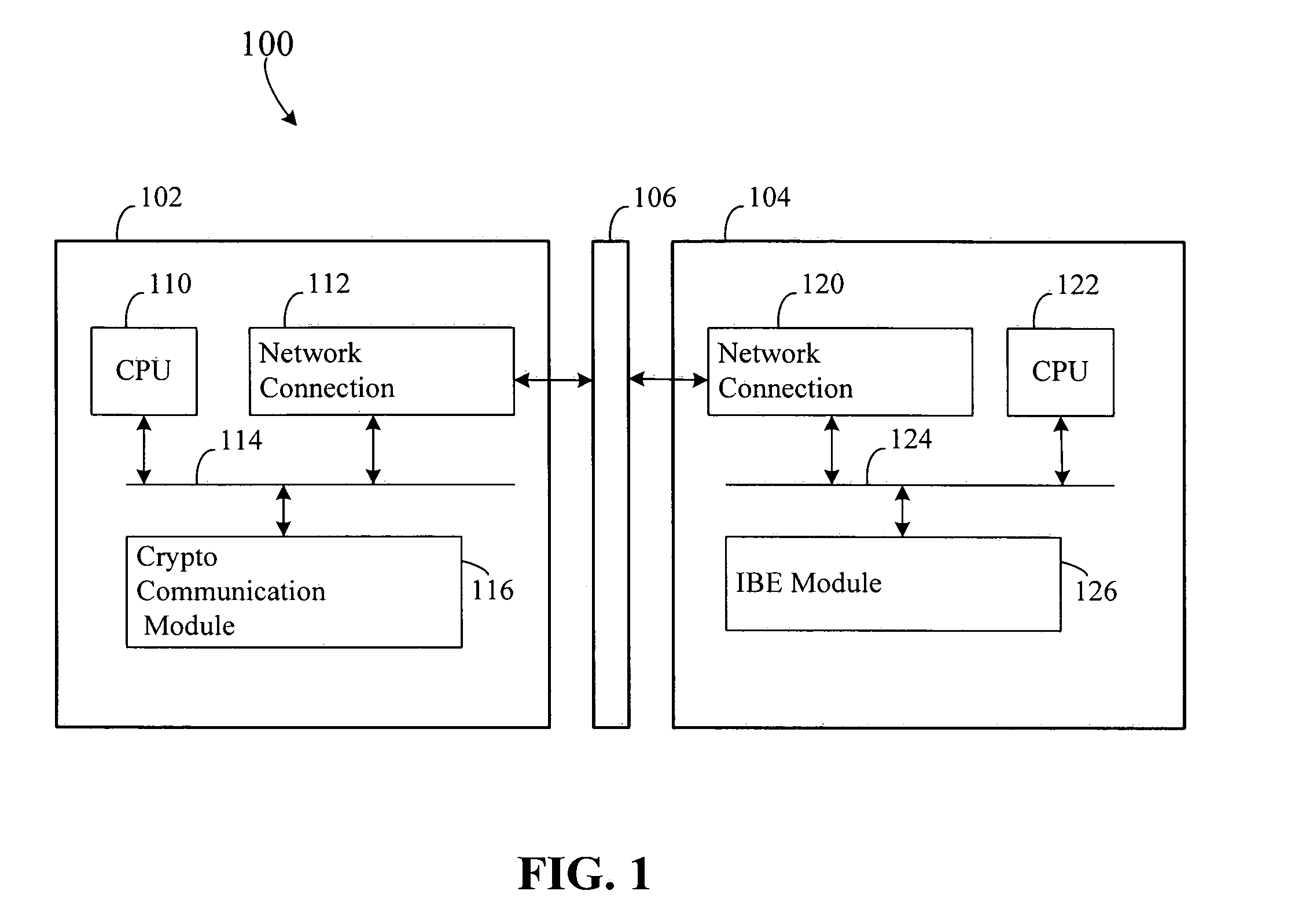
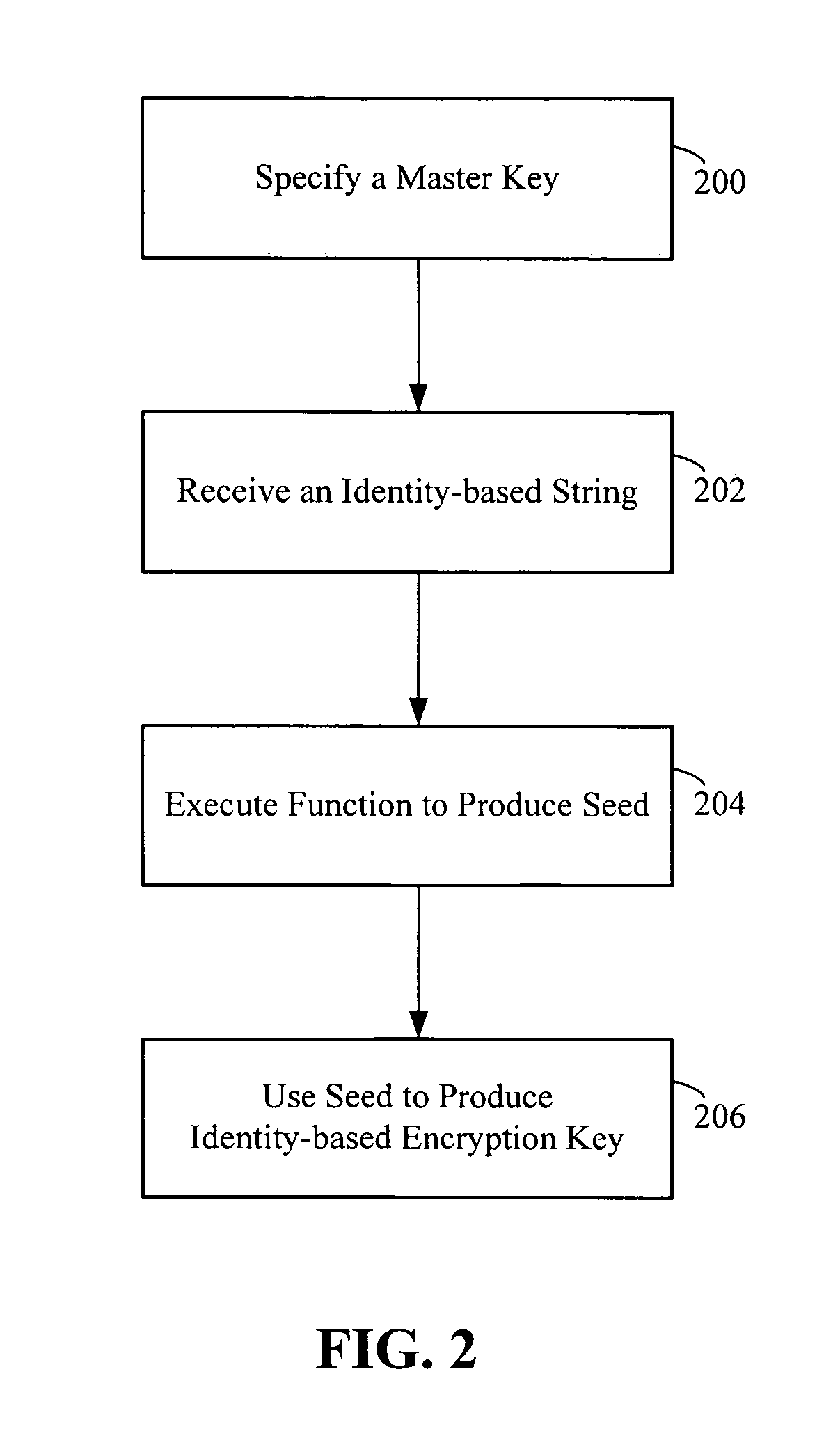
Apparatus and method for identity-based encryption within a conventional public-key infrastructure
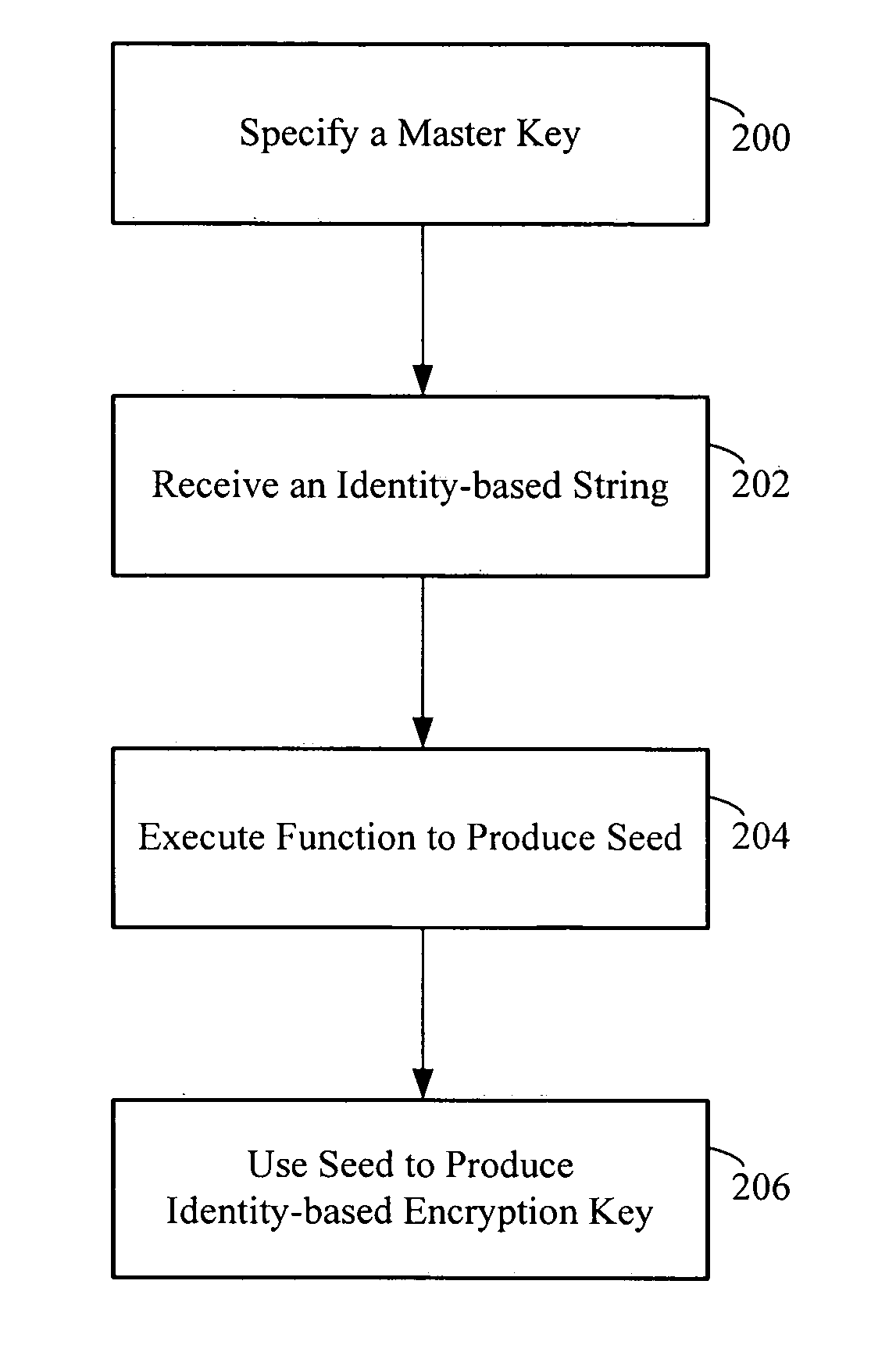
InactiveUS7657037B2Avoid security issuesKey distribution for secure communicationDigital data processing detailsMaster keyPublic key cryptosystem
A computer readable medium storing executable code to generate an identity-based encryption key includes executable code to specify a master key, receive an identity-based string and execute a function that processes the master key and the identity-based string to produce a seed. The seed is then used to produce an identity-based encryption key interoperable with a deployed public key cryptosystem.
Owner:CA TECH INC
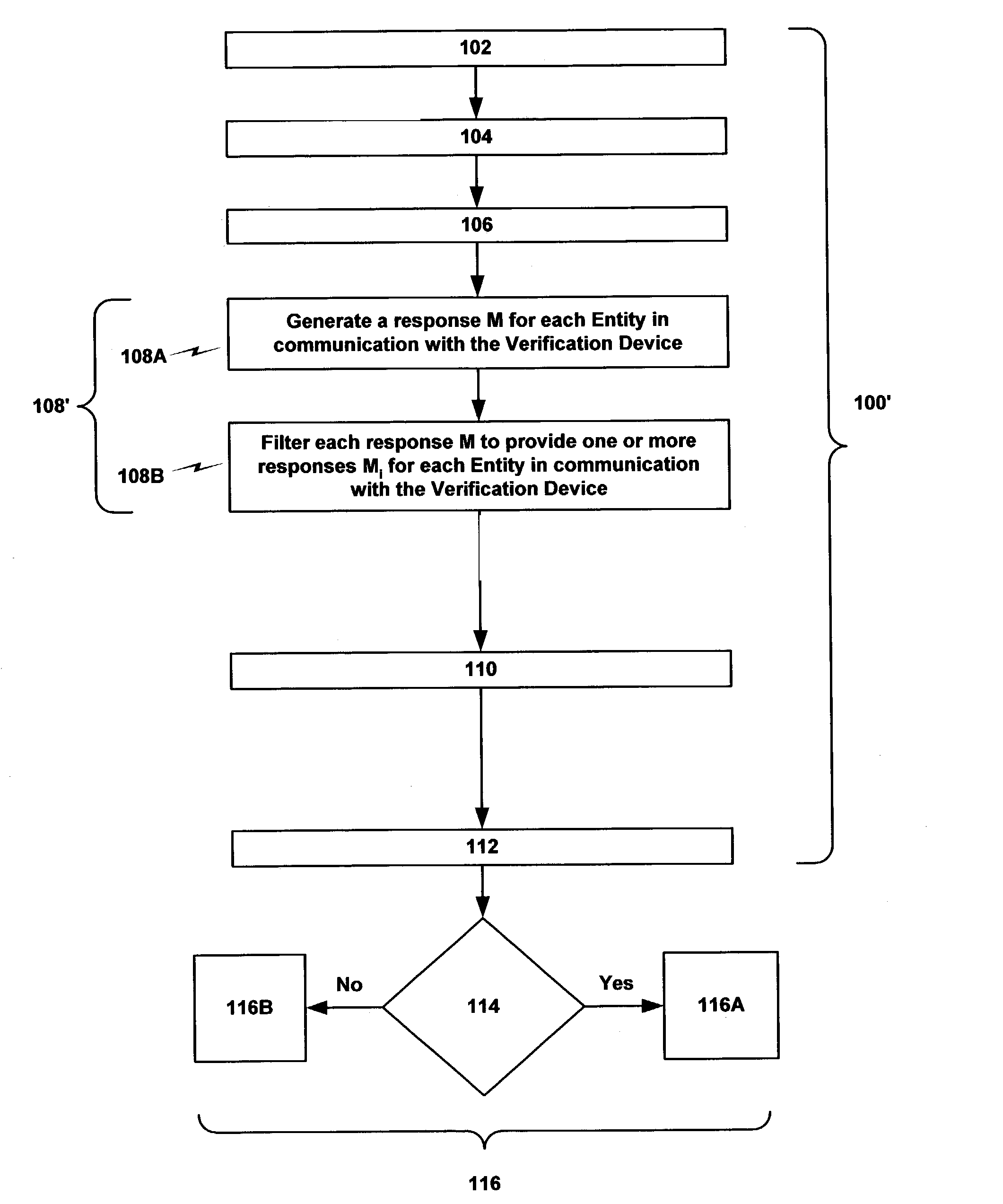
Methods and systems for group authentication using the naccache-stern cryptosystem in accordance with a prescribed rule
A method for group authentication using a public key cryptosystem that includes a public key and a private key, comprising the steps of providing a Private Key Share to a Tool of each Entity of each Group encompassed by a Boolean Expression of a prescribed Rule based upon the private key, encrypting a random number using the public key of the public key cryptosystem to generate a ciphertext challenge at a Verification Device, conveying the ciphertext challenge to the Tool of each Entity in communication with the Verification Device, generating a response to the ciphertext challenge using the Private Key Share of the Tool of each Entity in communication with the Verification Device, transmitting the response generated by each Entity in communication with the Verification Device to the Verification Device, combining the responses received from the Entities in communication with the Verification Device, determining whether any combination of the responses equals the random number wherein any combination that equals the random number identifies an Authenticated Group and any combination that does not equal the random number identifies a non-authenticated Group, and effecting an apposite course of action with respect to an Operation governed by the prescribed Rule based upon the outcome of the determining step.
Owner:CALLAHAN CELLULAR L L C
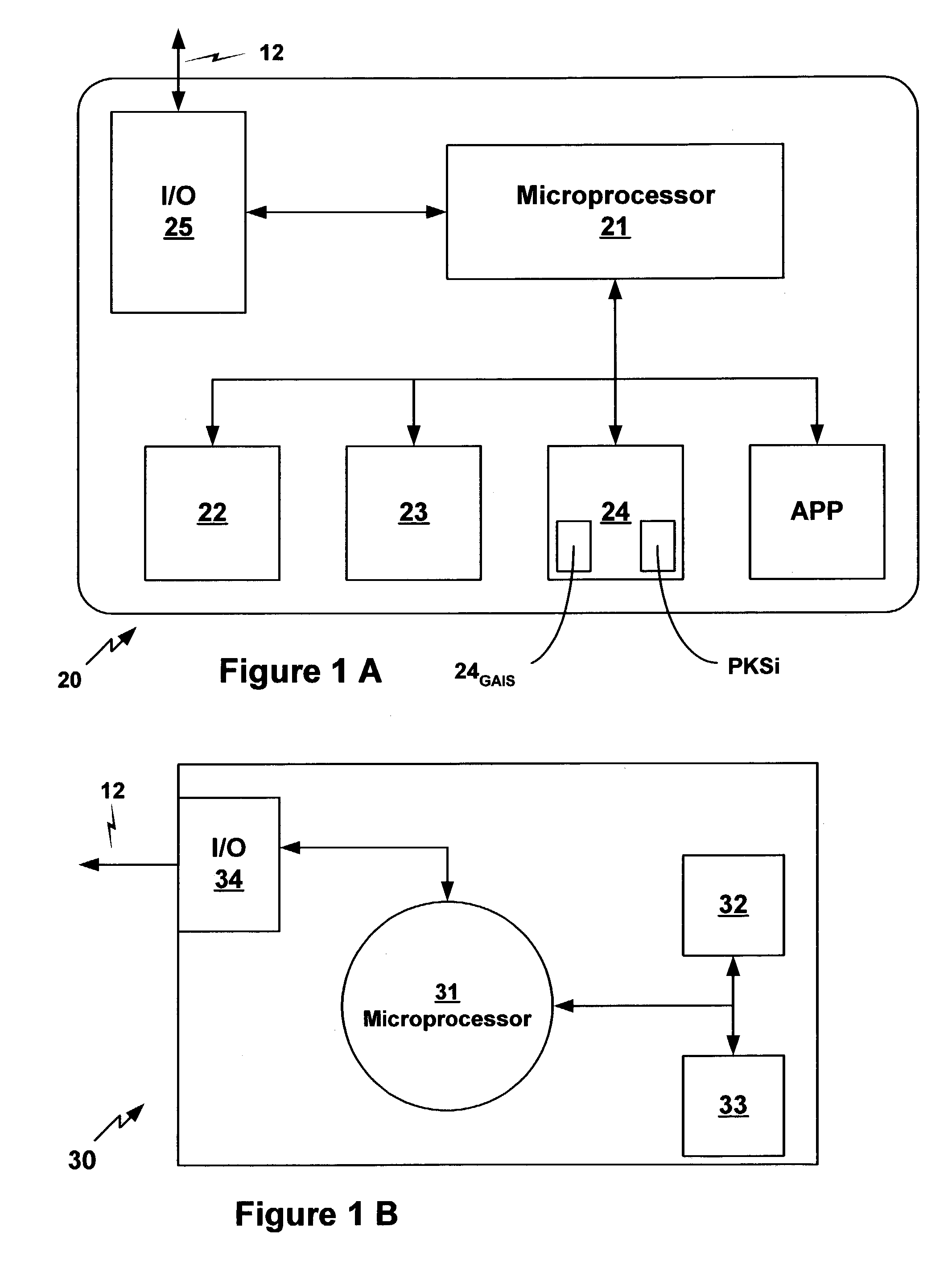
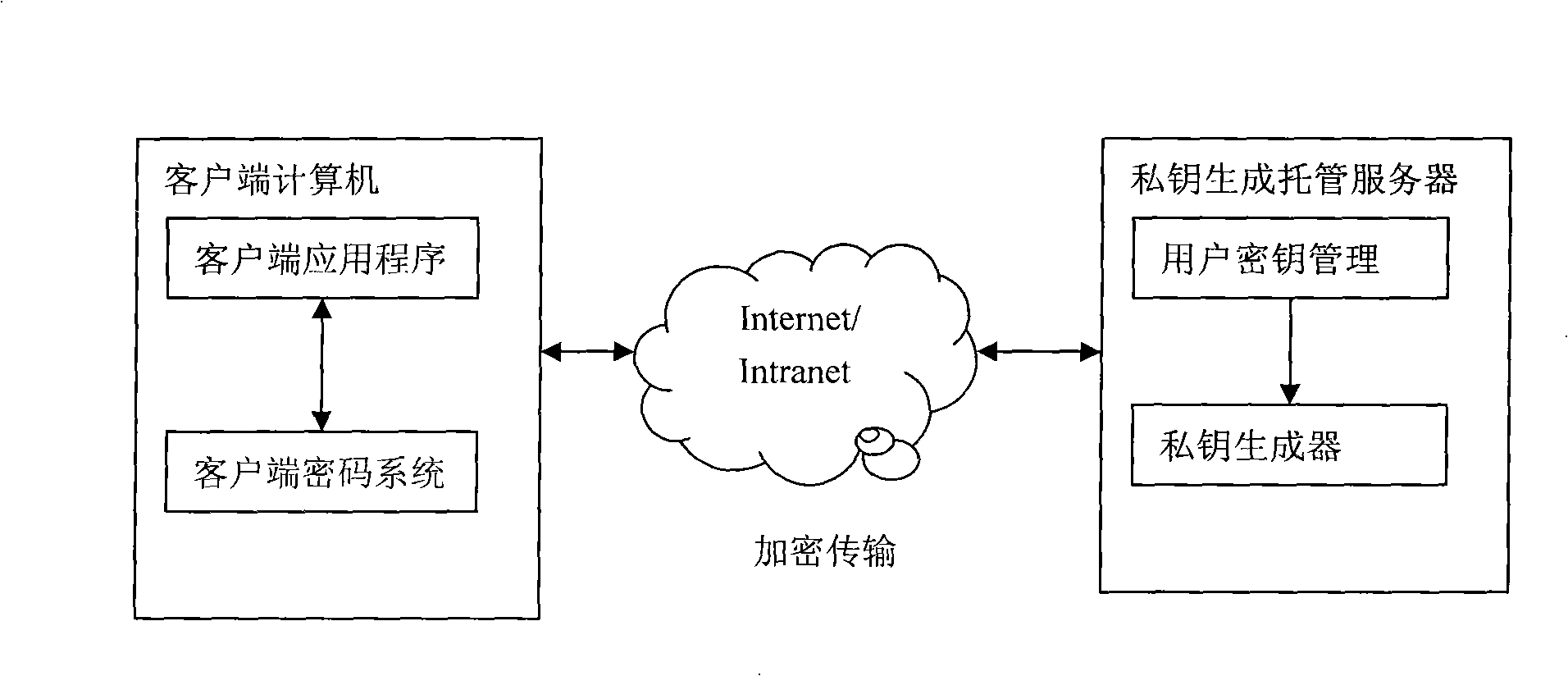
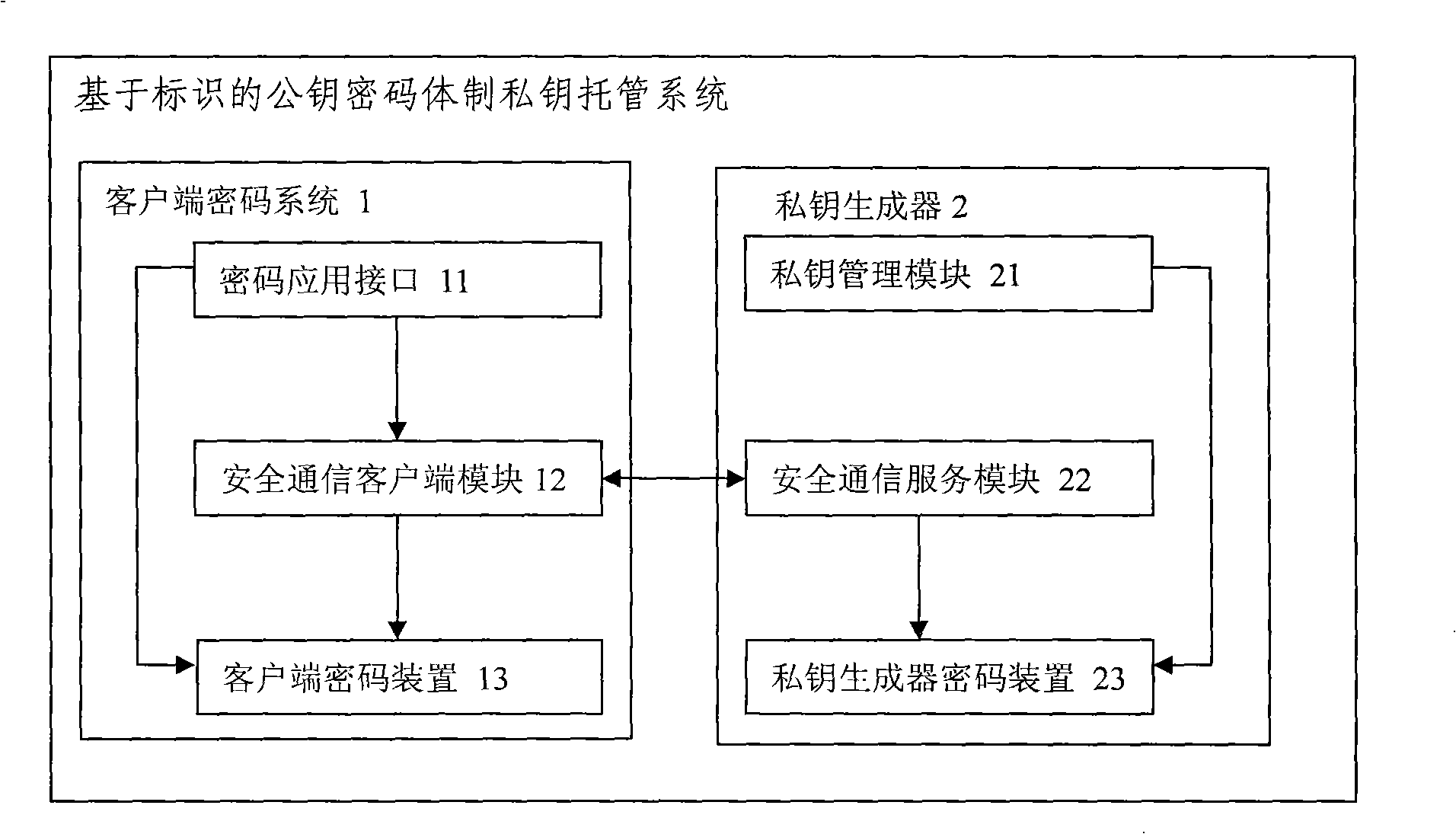
Public key cipher system private key escrowing system based on identification
InactiveCN101359991AEnsure safetyIncrease attack difficultyUser identity/authority verificationTamper resistanceKey escrow
The invention relates to a public key cryptosystem private key escrow system based on identification. A client cryptosystem transmits the information of a user to a private key generator for requesting authentication; a user private key is generated and stored at the client cryptosystem after the authentication of the private key generator is passed; and the client cryptosystem provides an operation interface for an application program, and realizes the cryptographic operation internally. The public key cryptosystem private key escrow system dynamically acquires the private key form the private key generator when a user is logged in, a tamper-proofing authentication protocol and the technology of a cipher device can ensure the user to acquire the private key safely. Because the user neither stores the private key statically nor dynamically exposes the private key out of the cipher device, so the hacking difficulty of a hacker is increased. The public key cryptosystem private key escrow system can effectively resist various dynamic and static analysis methods.
Owner:湖北电力信息通信中心 +1
Method and apparatus for securely processing secret data
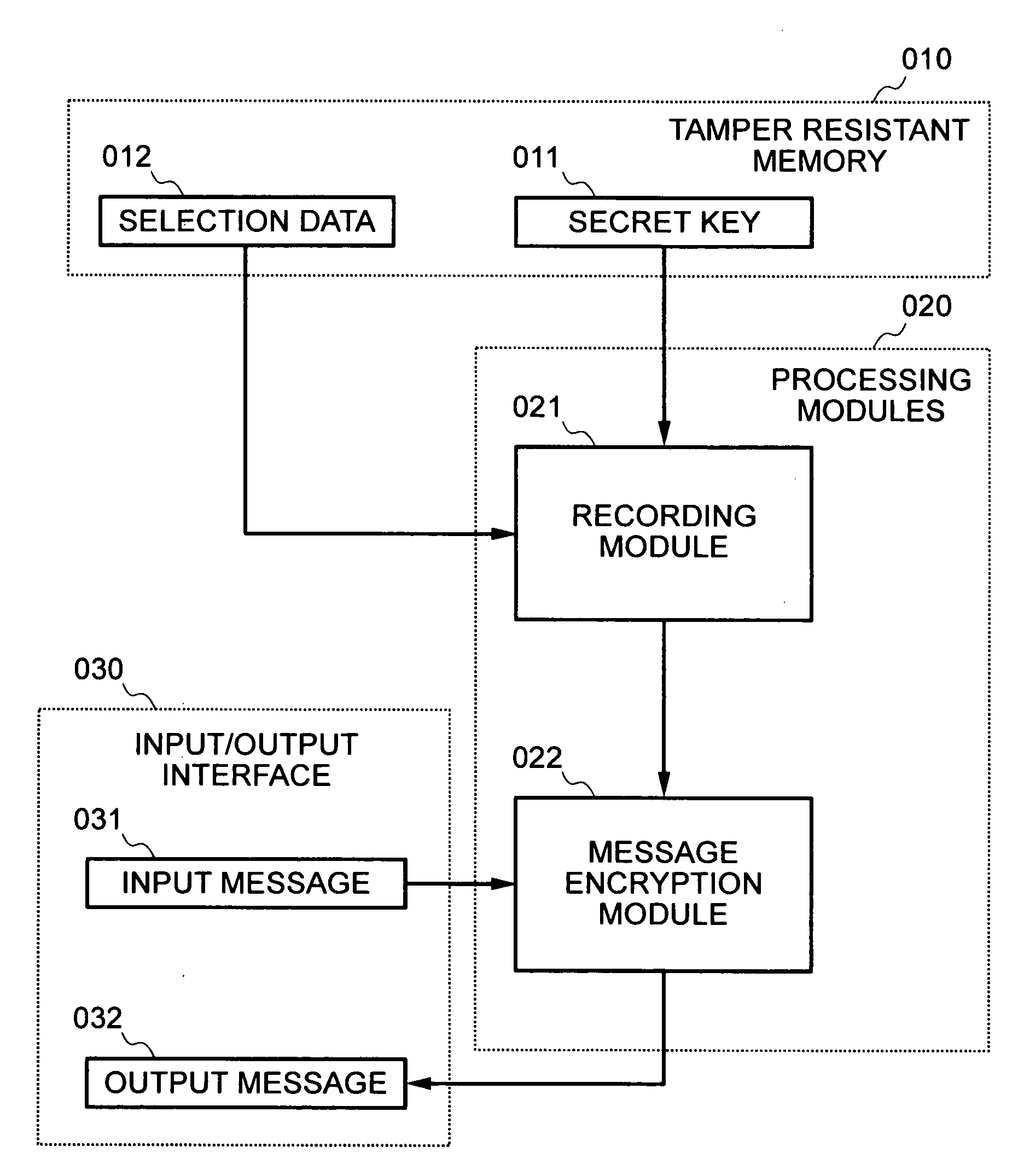
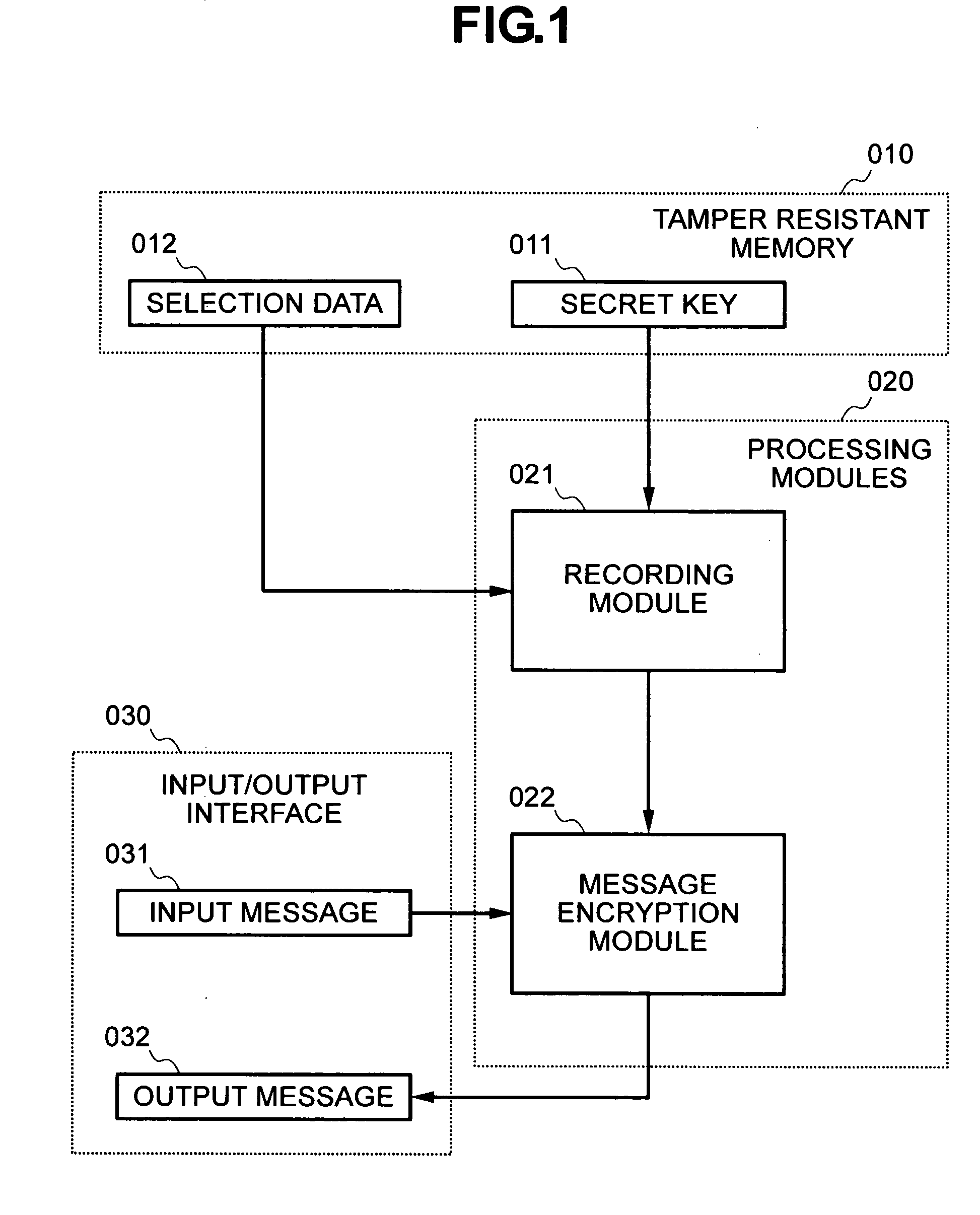
InactiveUS20080240443A1Encryption apparatus with shift registers/memoriesCryptographic attack countermeasuresComputer hardwareSecurity question
Using the same secret key for different secret operations in the frame of public key cryptosystems raises security problems because attackers can gain statistical information about the secret key. Indeed, when randomization techniques are used, the same secret key is randomized differently for every new operation, and since information leakage sums up, eventually, the attacker is able to recover the secret key.A system and method for using the same secret key of a public key cryptosystem several times comprising a recoding method which can generate several distinct representations for the secret key, where one representation is chosen as recoded secret according to a selection data. In addition, the pair consisting of the secret key and selection data is uniquely defined, resulting in the same recoded secret for every new encryption operation. As a consequence, information leakage does not sum up and the secret key can be securely re-used.
Owner:HITACHI LTD
Data copyright management system
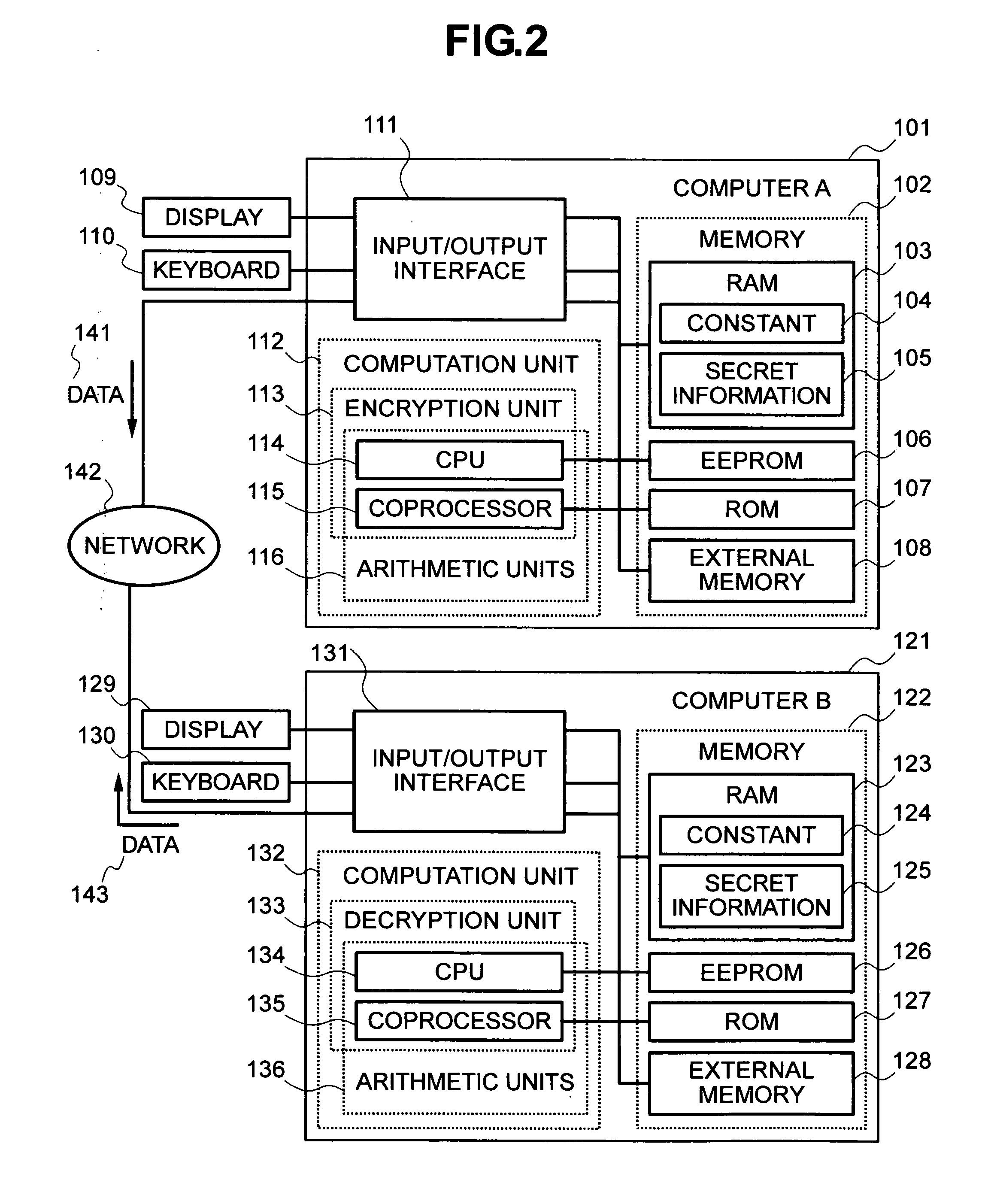
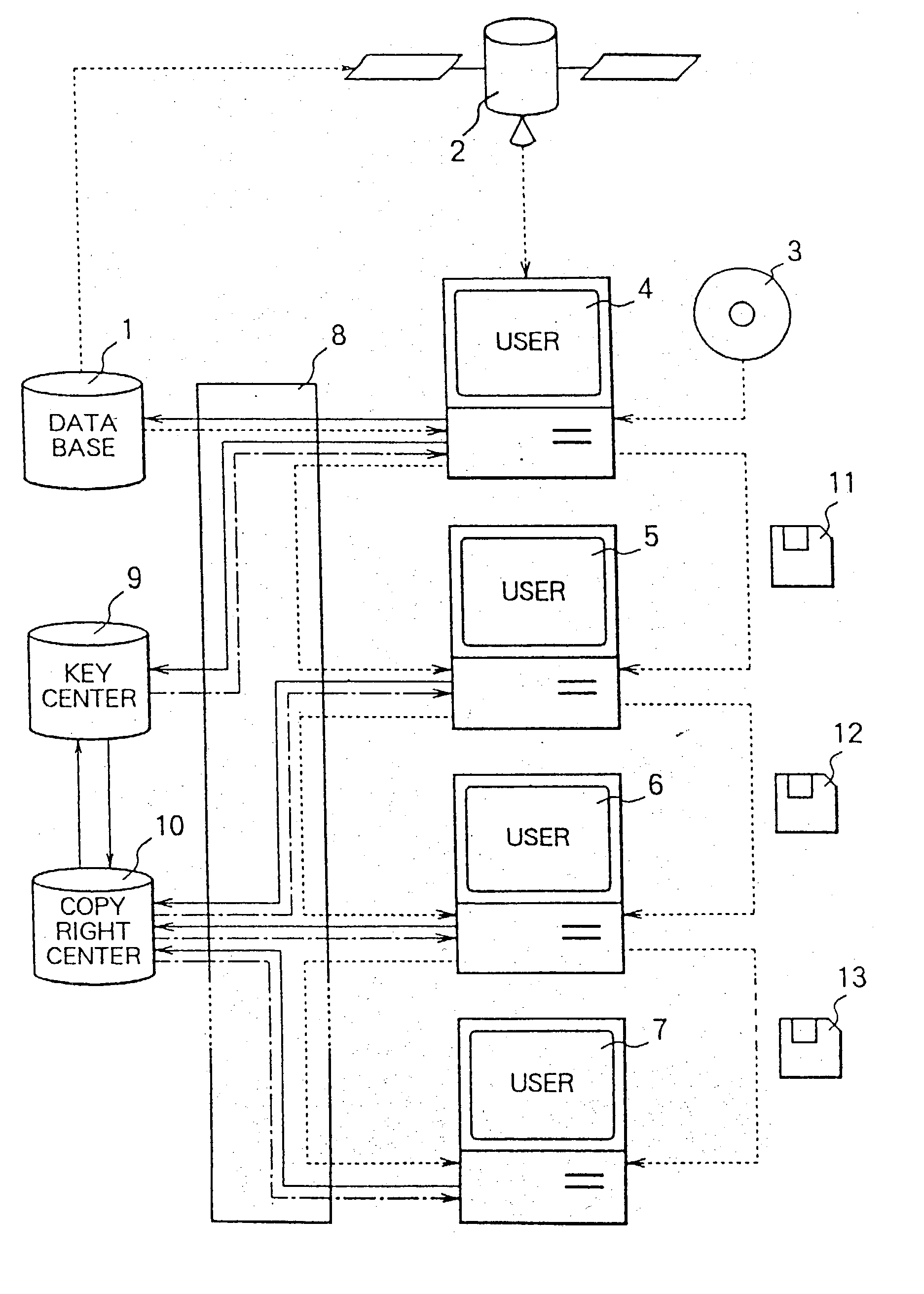
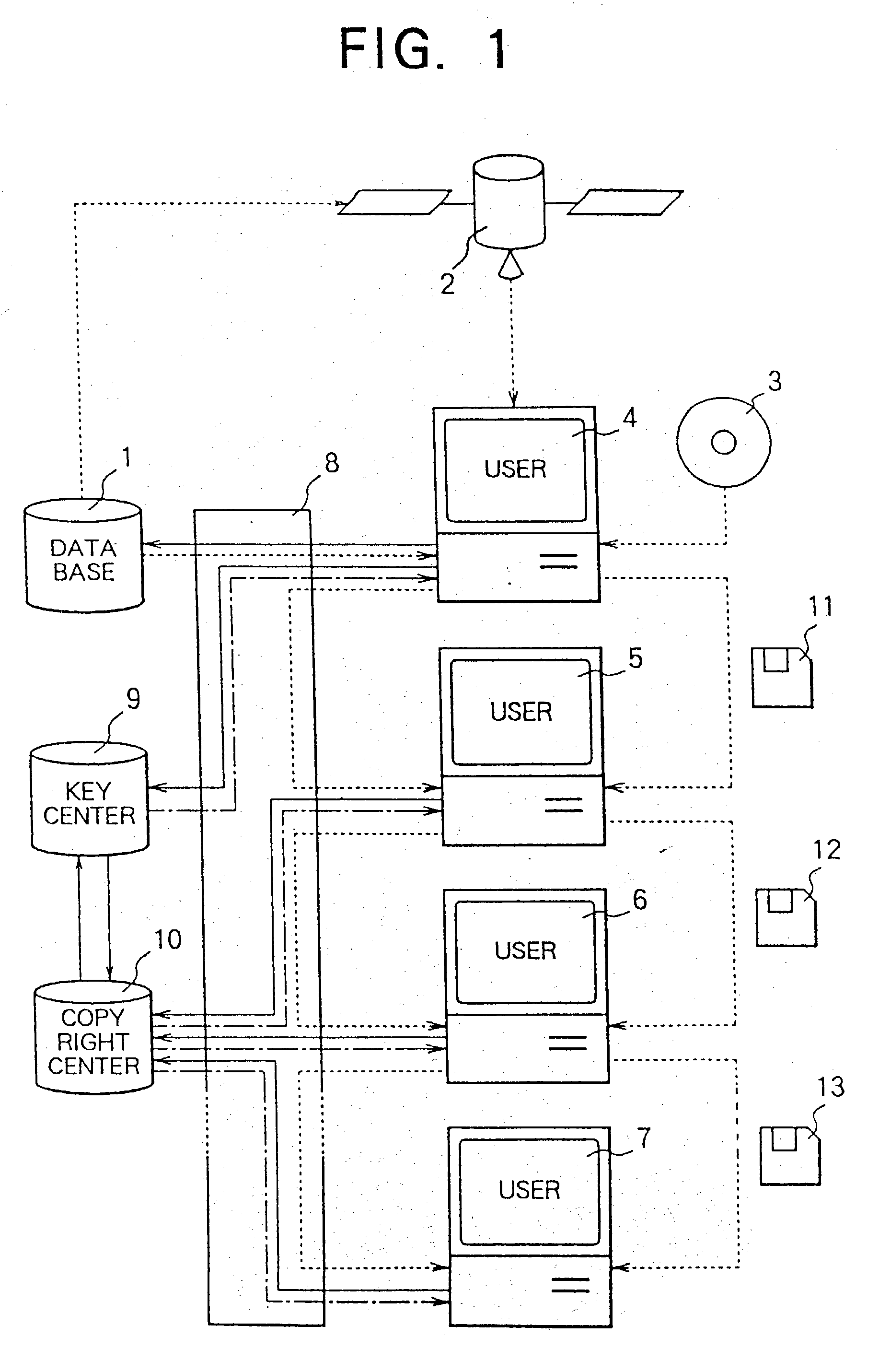
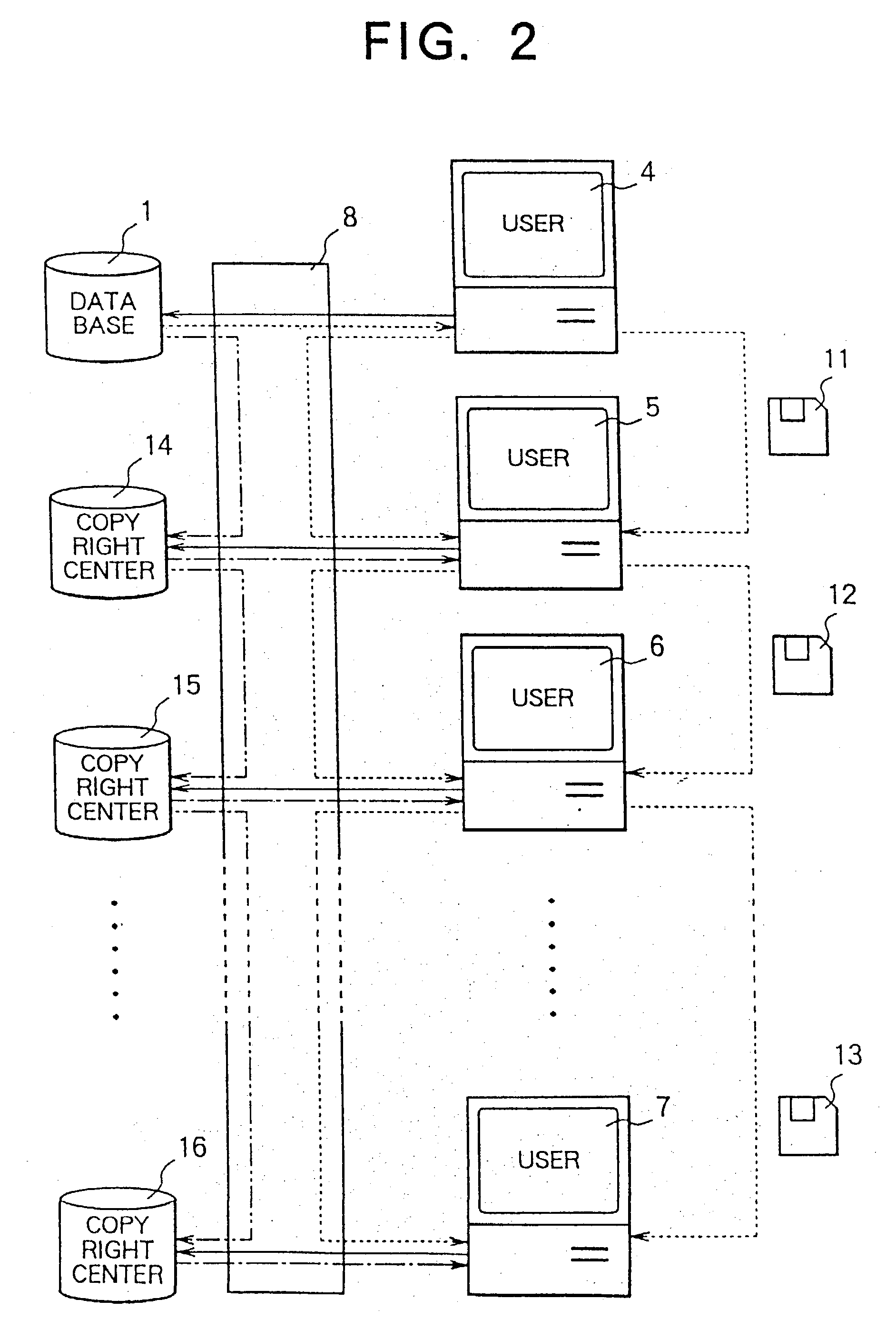
InactiveUS20030144963A1Key distribution for secure communicationPublic key for secure communicationOriginal dataControl data
A data copyright management system comprises a database for storing original data, a key control center for managing crypt keys, copyright management center for managing data copyrights, and a communication network for connecting these sections. Data supplied from the database to users is encrypted and distributed. The users decrypts the encrypted data by crypt keys obtained from the key control center or copyright management center. To supply data to users, there are the following two methods: a one way supplying of encrypted data to users by means of broadcasting or the like; and two-way supplying of encrypted data to users corresponding to users' requests. A crypt key system used for encrypting data uses a secret-key cryptosystem, a public-key cryptosystem or a cryptosystem combining a secret-key and a public-key and further uses a copyright control program to control data copyrights. When a user stores, copies, or transfers data, the data is encrypted by a crypt key different from a crypt key used for supplying the data. The former crypt key is supplied from the key control center or from the copyright management center, or generated by the copyright control program. The present invention can be applied to a data copyright management system for using not only single data but also a plurality of data supplied from a single database or a plurality of data supplied from a plurality of databases. Further, an apparatus to be used by the user to perform data copyright management is proposed.
Owner:XYLON LLC +1
Pseudo public key encryption
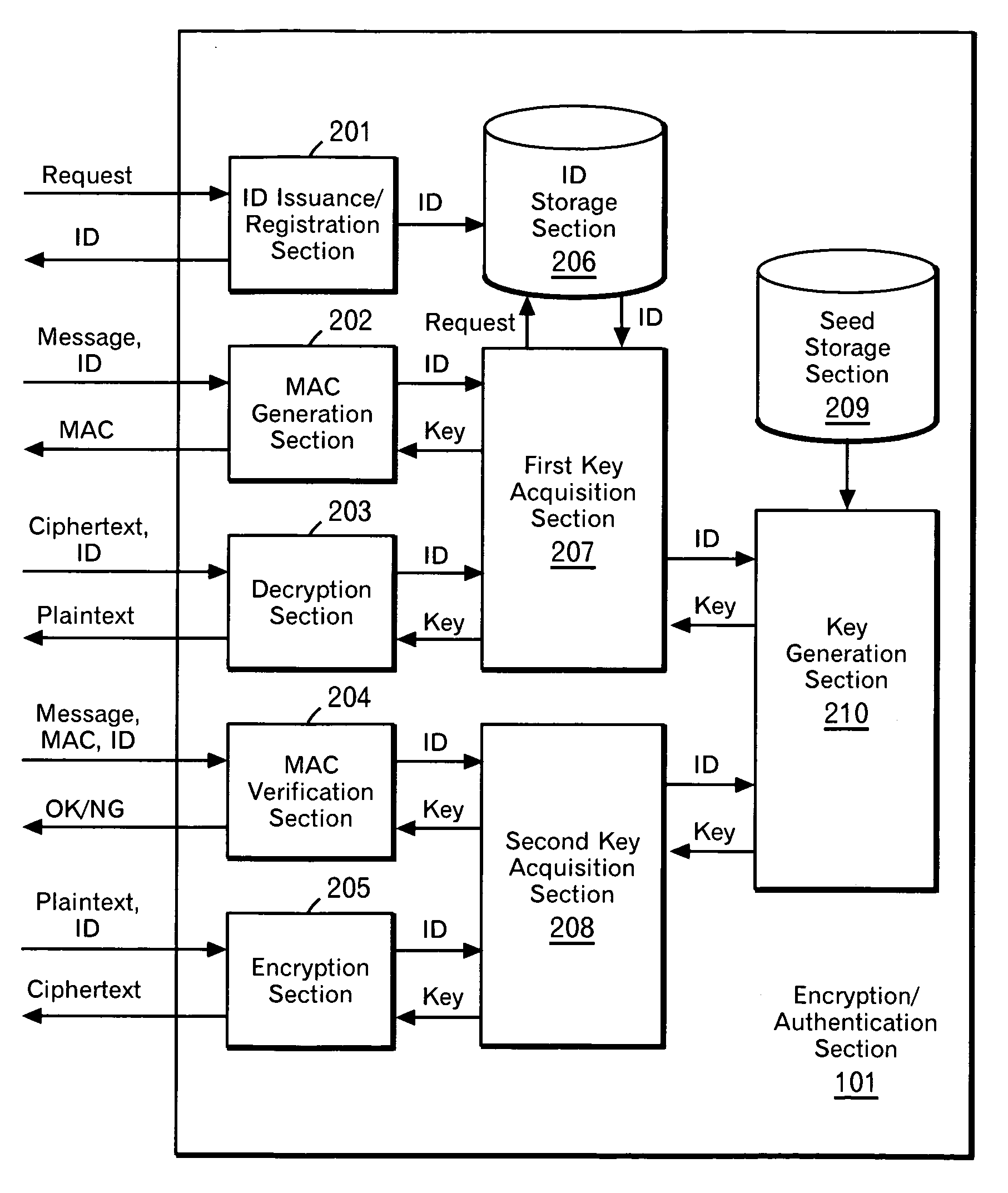
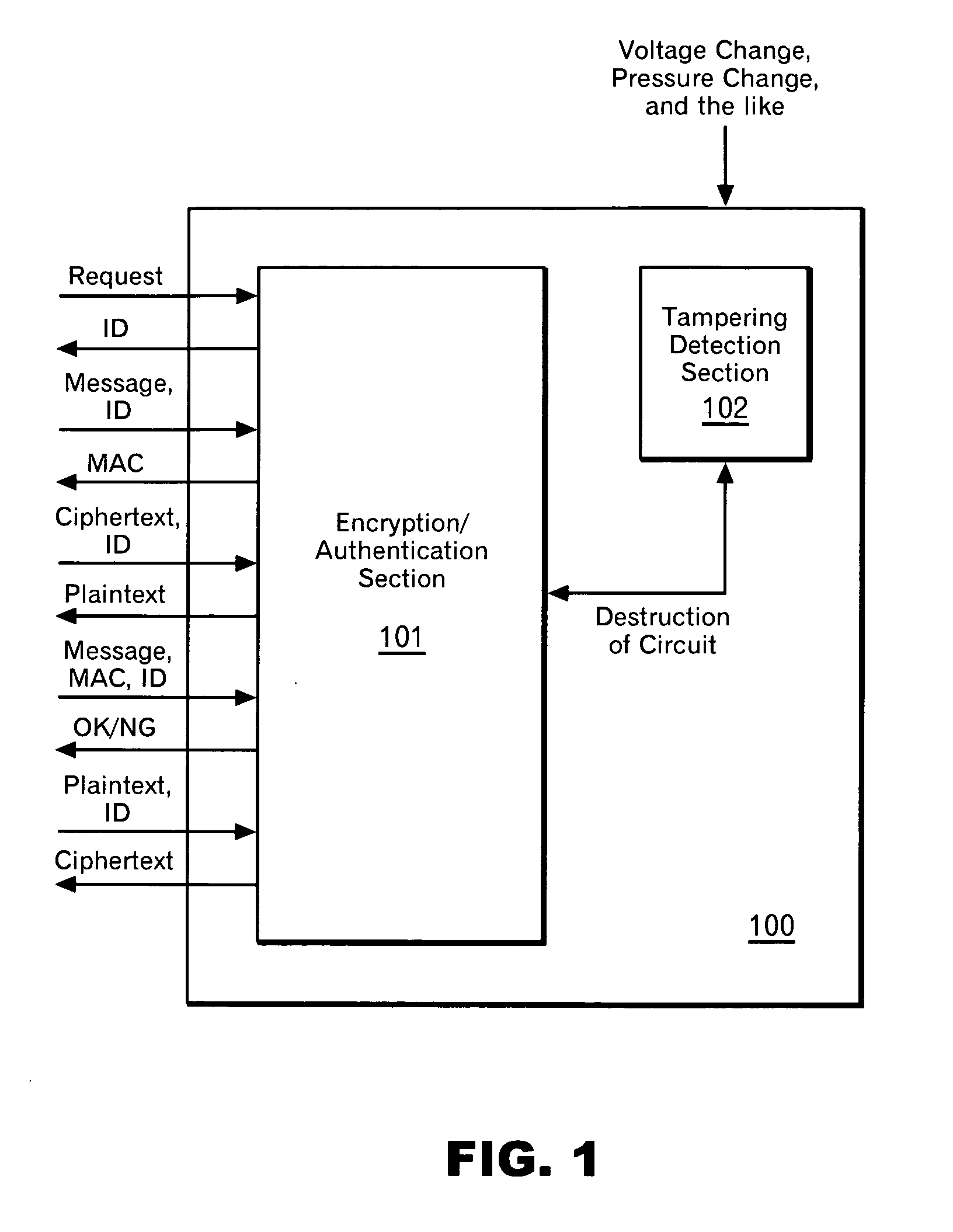
InactiveUS20070189517A1Low costCheap to achievePublic key for secure communicationSecret communicationComputer hardwareTamper proof hardware
According to the present invention, a secret key cryptosystem and tamper-proof hardware are used to realize a pseudo public key cryptosystem at a low cost. A trap-door one-way function is substantially realized with the use of tamper-proof hardware. Each user performs communication using equipment provided with hardware having the same capabilities described below. Such hardware retains association between an ID and a key. In response to a request from a user, the hardware issues and stores an ID, and it can perform decryption and generation of a MAC (message authentication code) with a key associated with the ID. A user publishes his ID. When performing encryption, a message sender encrypts a message using the published ID. A third person can perform decryption with the ID only by analyzing the mechanism in the hardware. However, the hardware has a capability of destroying itself when such an act is attempted.
Owner:IBM CORP
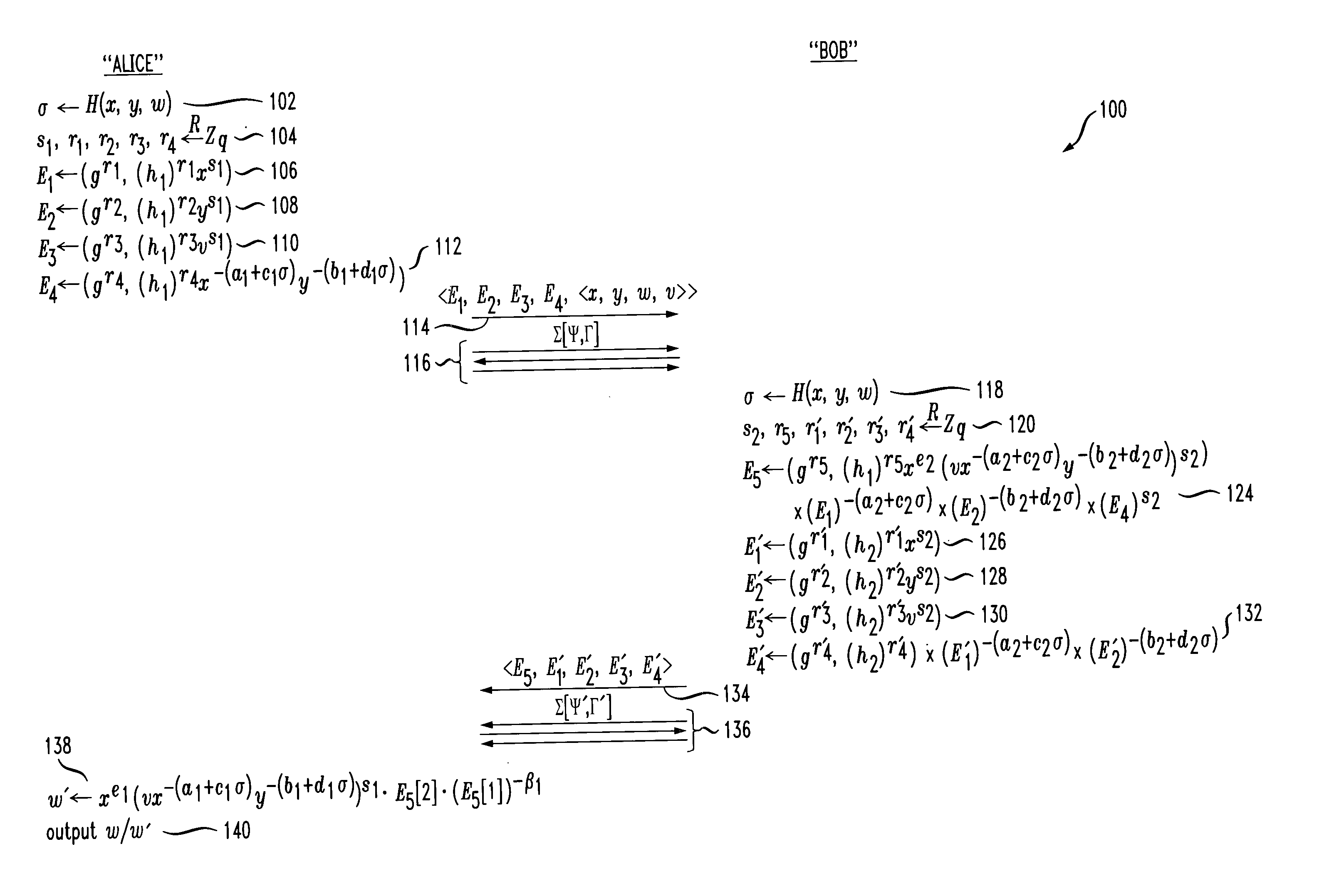
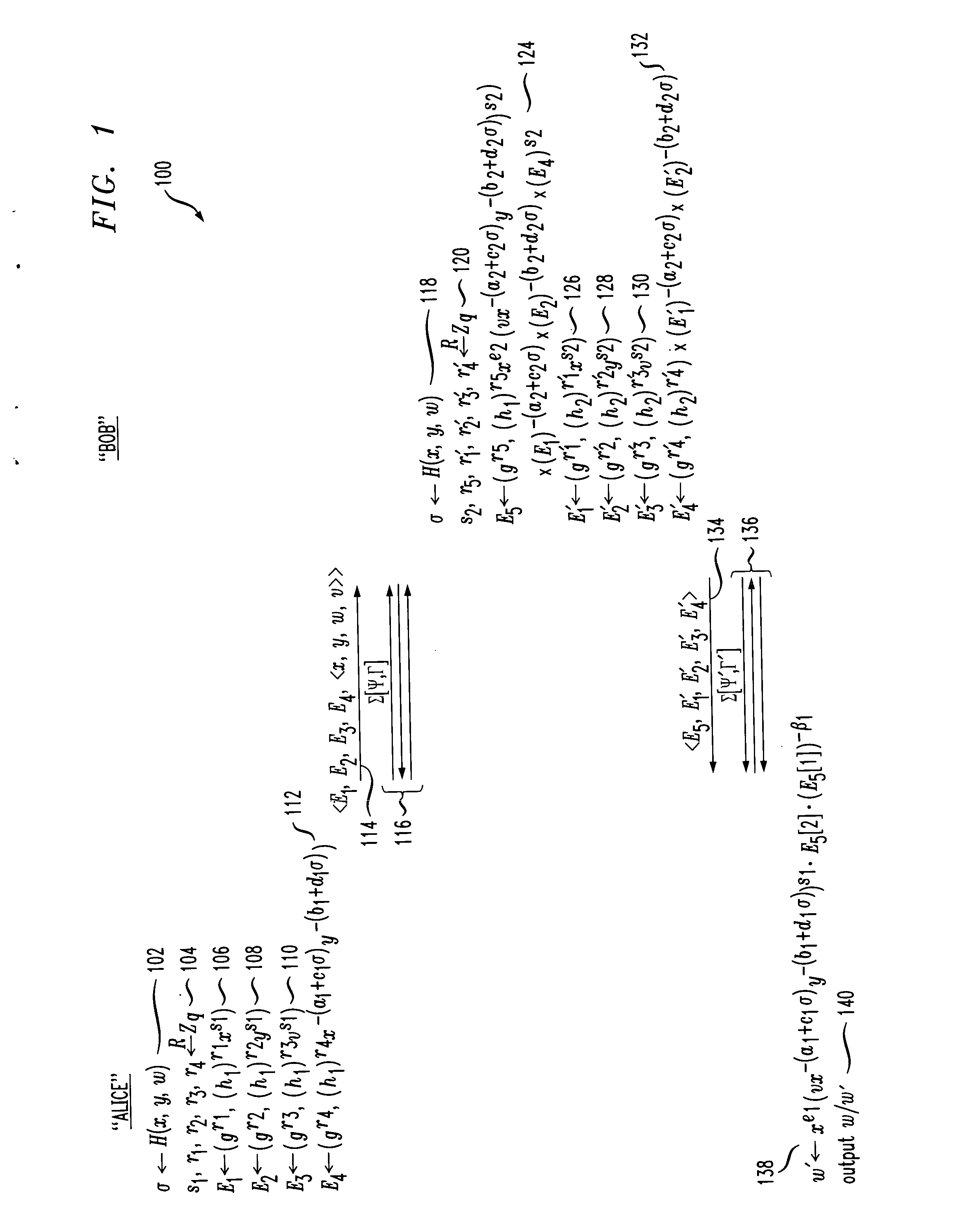
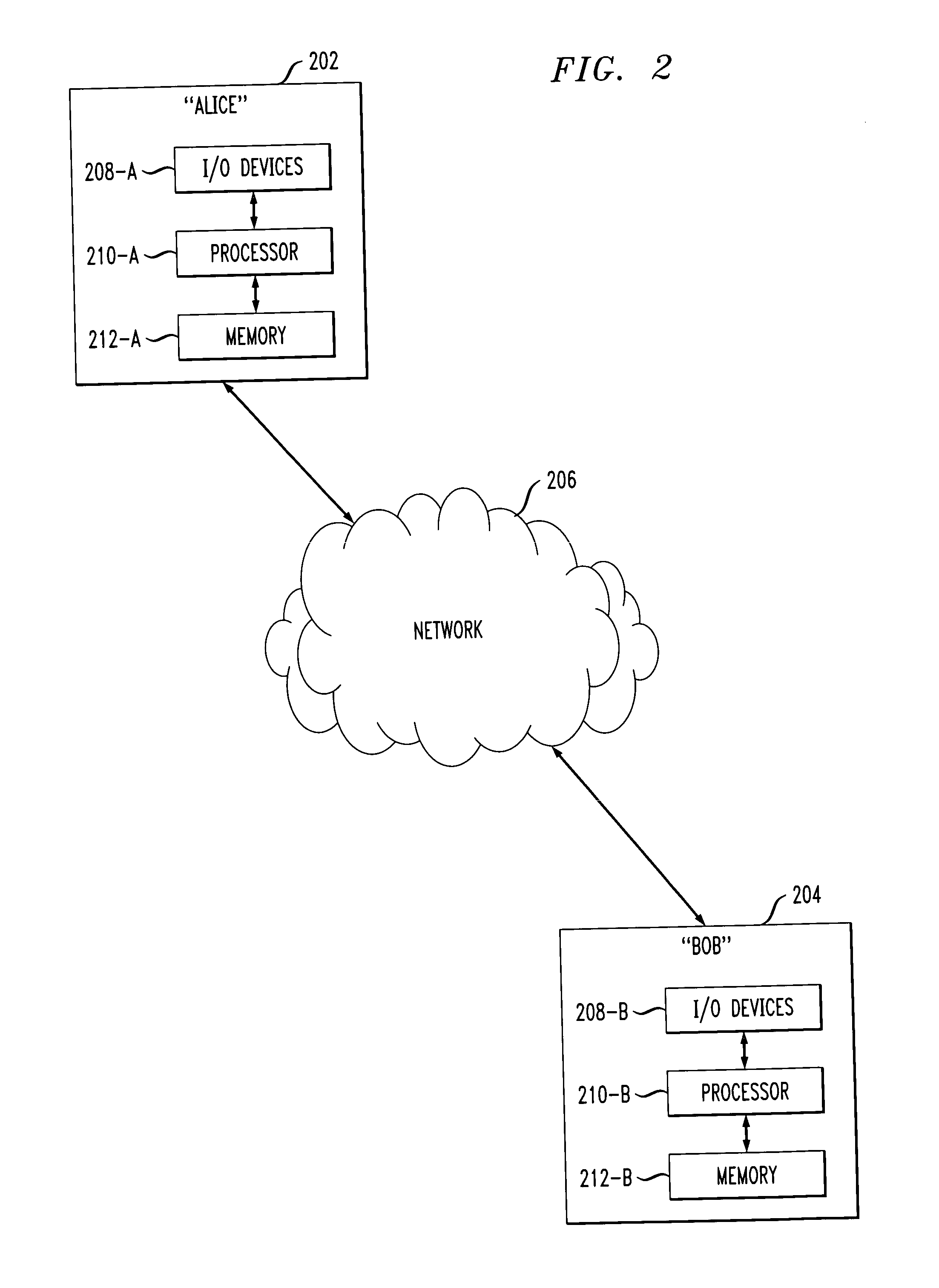
Methods and apparatus for providing secure two-party public key cryptosystem
InactiveUS20050008152A1Efficient and provably secureKey distribution for secure communicationPublic key for secure communicationCiphertextCryptographic protocol
Techniques for an efficient and provably secure protocol by which two parties, each holding a share of a Cramer-Shoup private key, can jointly decrypt a ciphertext, but such that neither party can decrypt a ciphertext alone. In an illustrative embodiment, the secure protocol may use homomorphic encryptions of partial Cramer-Shoup decryption subcomputations, and three-move Σ-protocols for proving consistency.
Owner:WSOU INVESTMENTS LLC
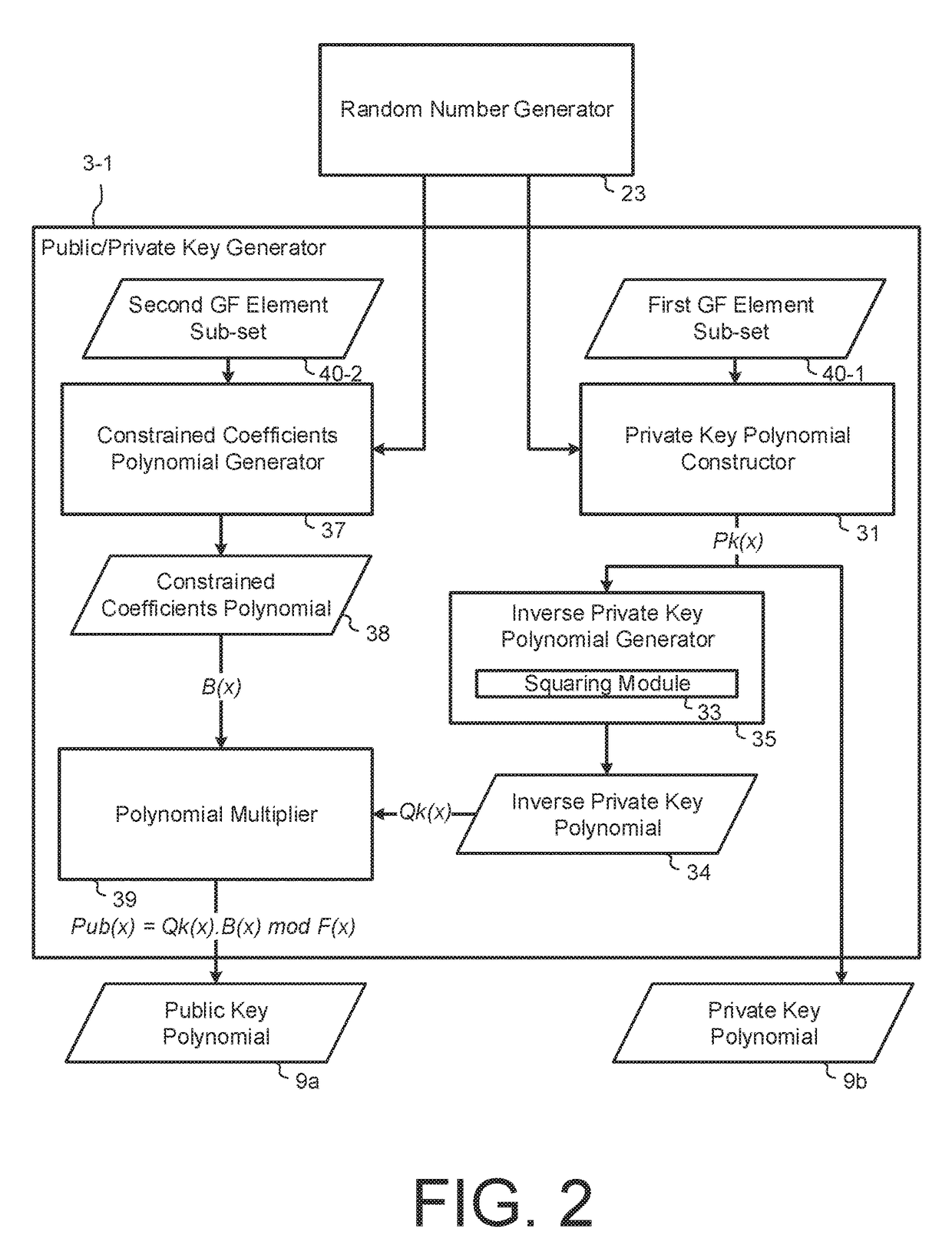
Public Key Cryptosystem Based On Partitioning Of Galois Field Elements
InactiveUS20170324554A1Small public key sizeKey distribution for secure communicationMultiple keys/algorithms usageKey sizeTheoretical computer science
A post-quantum, public key cryptosystem is described which is polynomial based and where the private key polynomial has coefficients from a sub-set of Galois field elements and plain text message polynomials have coefficients from a second sub-set of Galois field elements. The public key polynomial is constructed using the inverse of the private key polynomial and a randomly chosen polynomial having coefficients chosen from a third sub-set of Galois field elements. Cipher texts are constructed using the public key and randomly chosen session key polynomials. Other more complicated embodiments are described. For implementation a small prime base field such as 2, 3 or 5 will usually be used in constructing the prime power Galois field. The system has the advantage of relatively small public key sizes.
Owner:PQ SOLUTIONS LTD
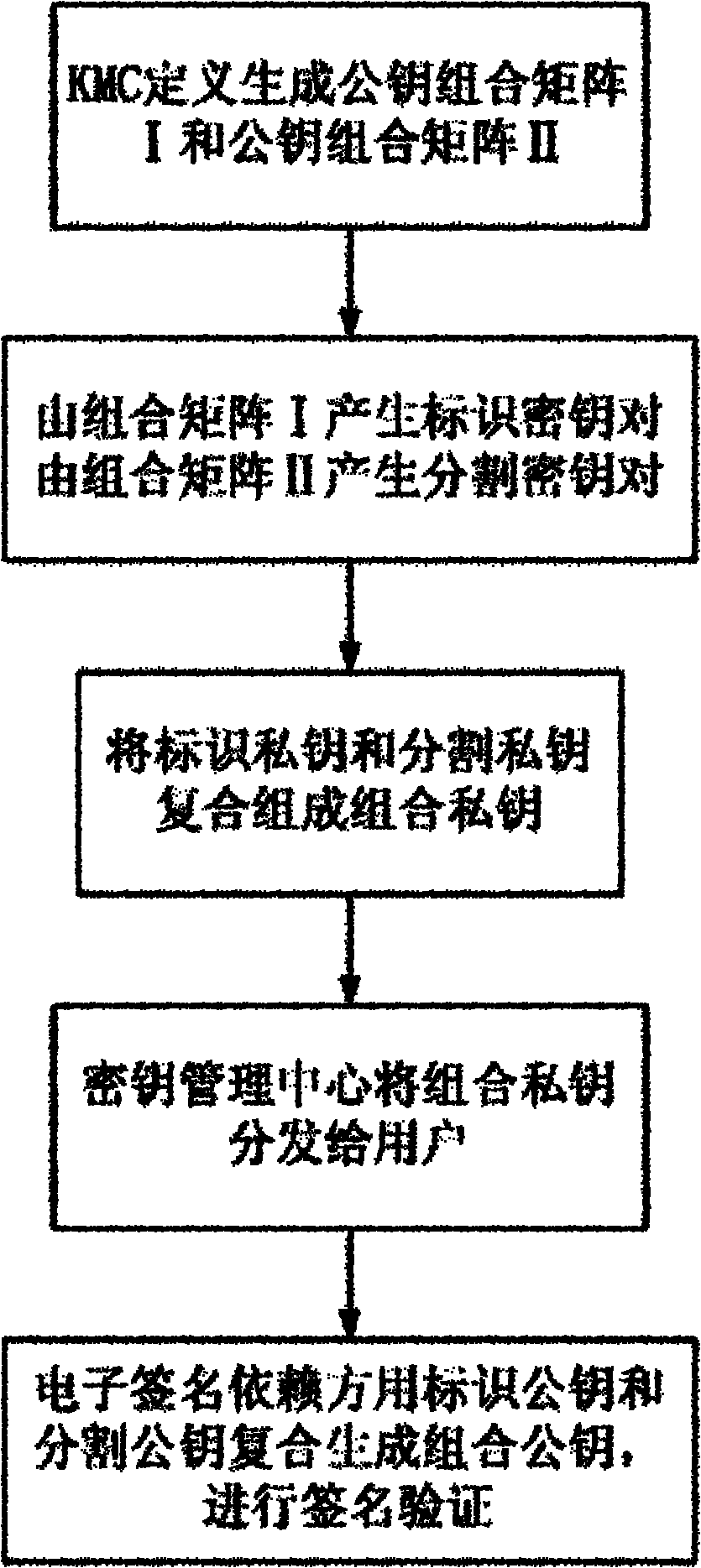
Generation method of bimatrix combined public key
InactiveCN102025491AEliminate the possibility of collusionReliable securityKey distribution for secure communicationPublic key for secure communicationQuantum computerInformation security
The invention belongs to the technical field of information security and discloses a generation method of a bimatrix combined public key on the basis of a combined public key (CPK) system based on identification, which is capable of resisting collusion attack and improving the security of a public key system. The generation method is as follows: a private key management center defines and generates a public key combined matrix I and a public key combined matrix II, the public key combined matrix I generates identified private keys, the public key combined matrix II generates segmented private keys, and the identified private keys and the segmented private keys are combined to generate the combined private key and are mutually encrypted, the liner combination relation among the private keys is hidden, the collusion possibility is eliminated and the safety is proved. A main private key of the combined public key constructed by two matrixes includes two matrixes, and has stronger capability of resisting quantum computing attack than other systems for protecting the system security by one main private key.
Owner:北京联合智华微电子科技有限公司
Mobile commerce identity authentication method
InactiveCN101969446AEliminate inconvenienceMeet the inconvenienceUser identity/authority verificationInternet Authentication ServiceThird party
The invention provides a mobile commerce identity authentication method. In the method, key negotiation is realized by the most efficient elliptic curve-based public key cryptosystem in public key cryptosystems. An elliptic curve algorithm has the characteristics of low calculated amount and high safety, so the elliptic curve algorithm is used for generating a public key and a private key, and a public key cryptosystem without a third-party is realized and applied to the two-way authentication service of a client and a server.
Owner:BEIJING JIAOTONG UNIV
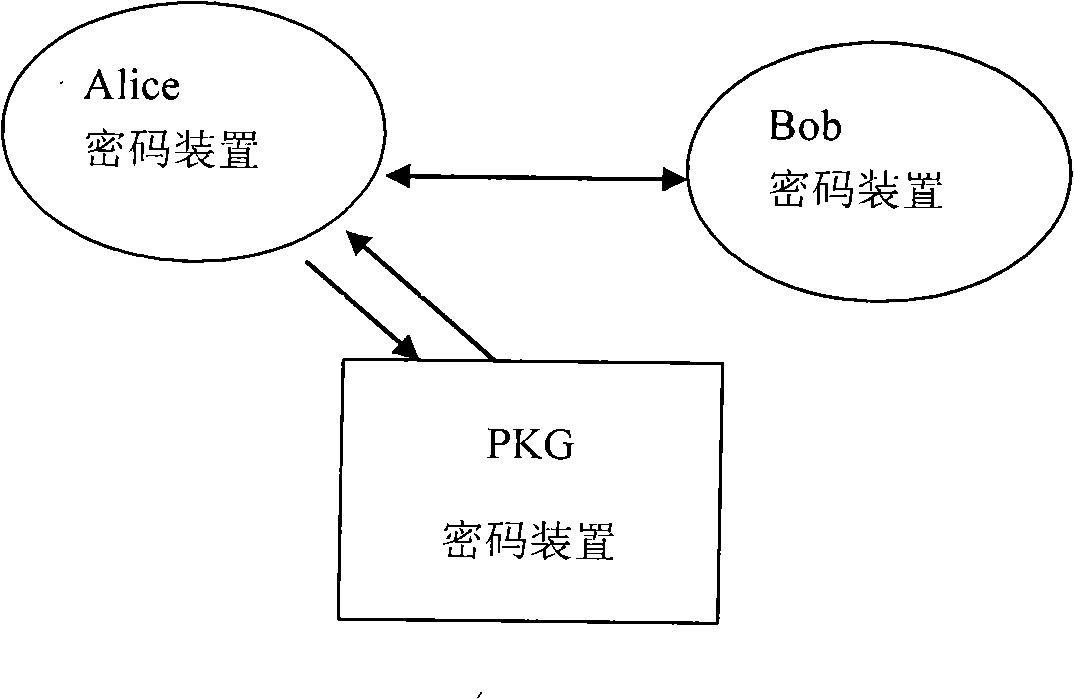
Method of authenticating identification based common key cryptosystem and encryption address in network
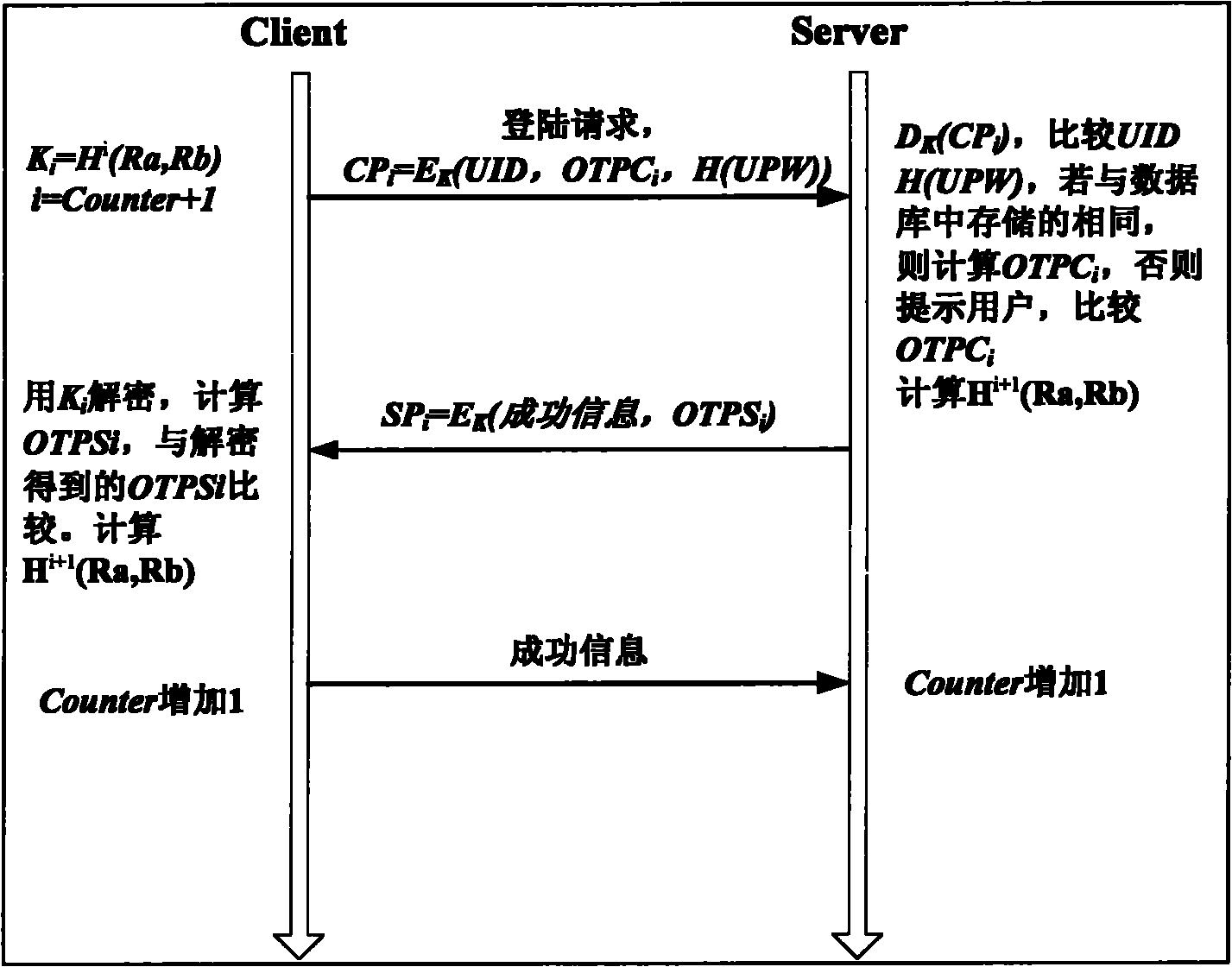
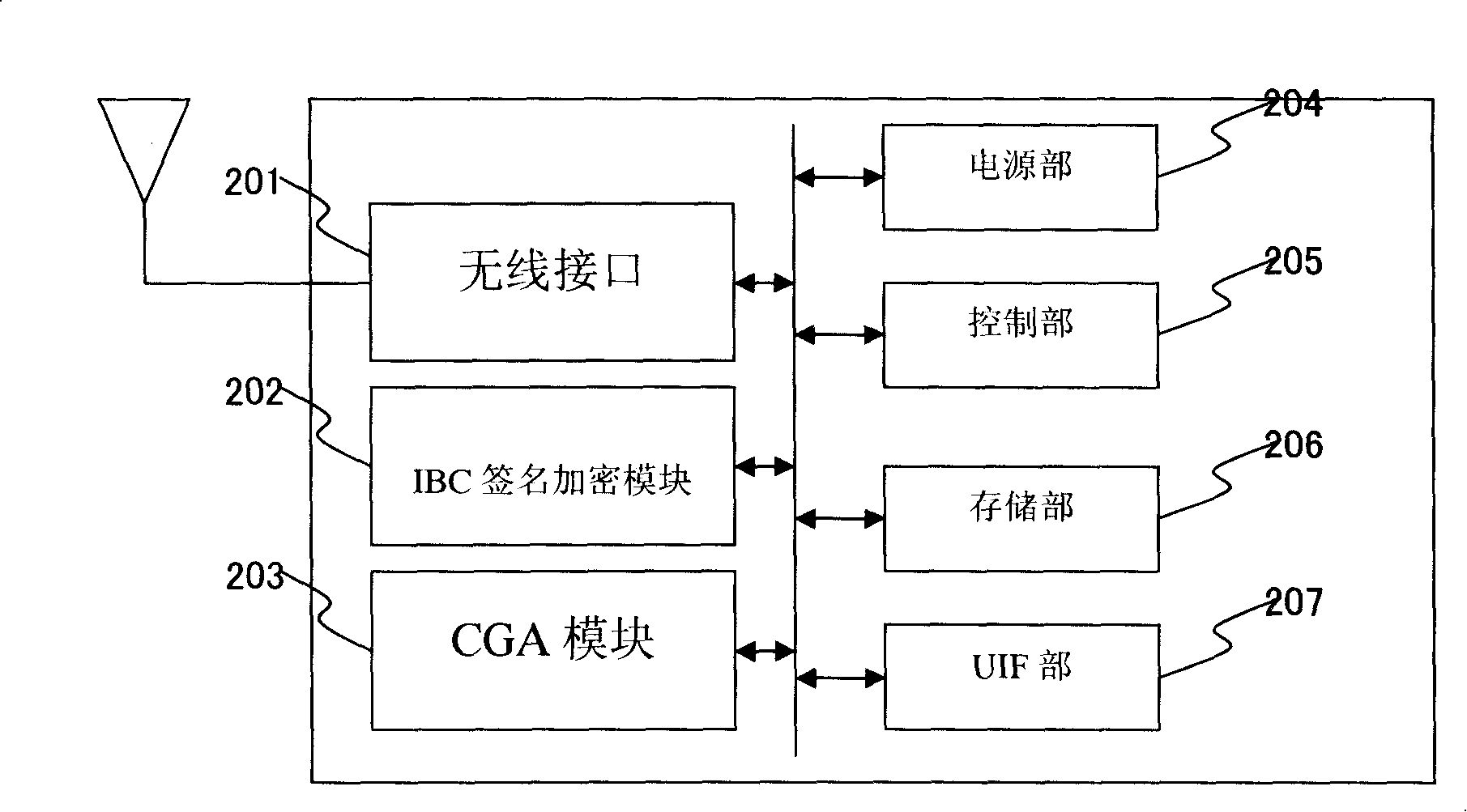
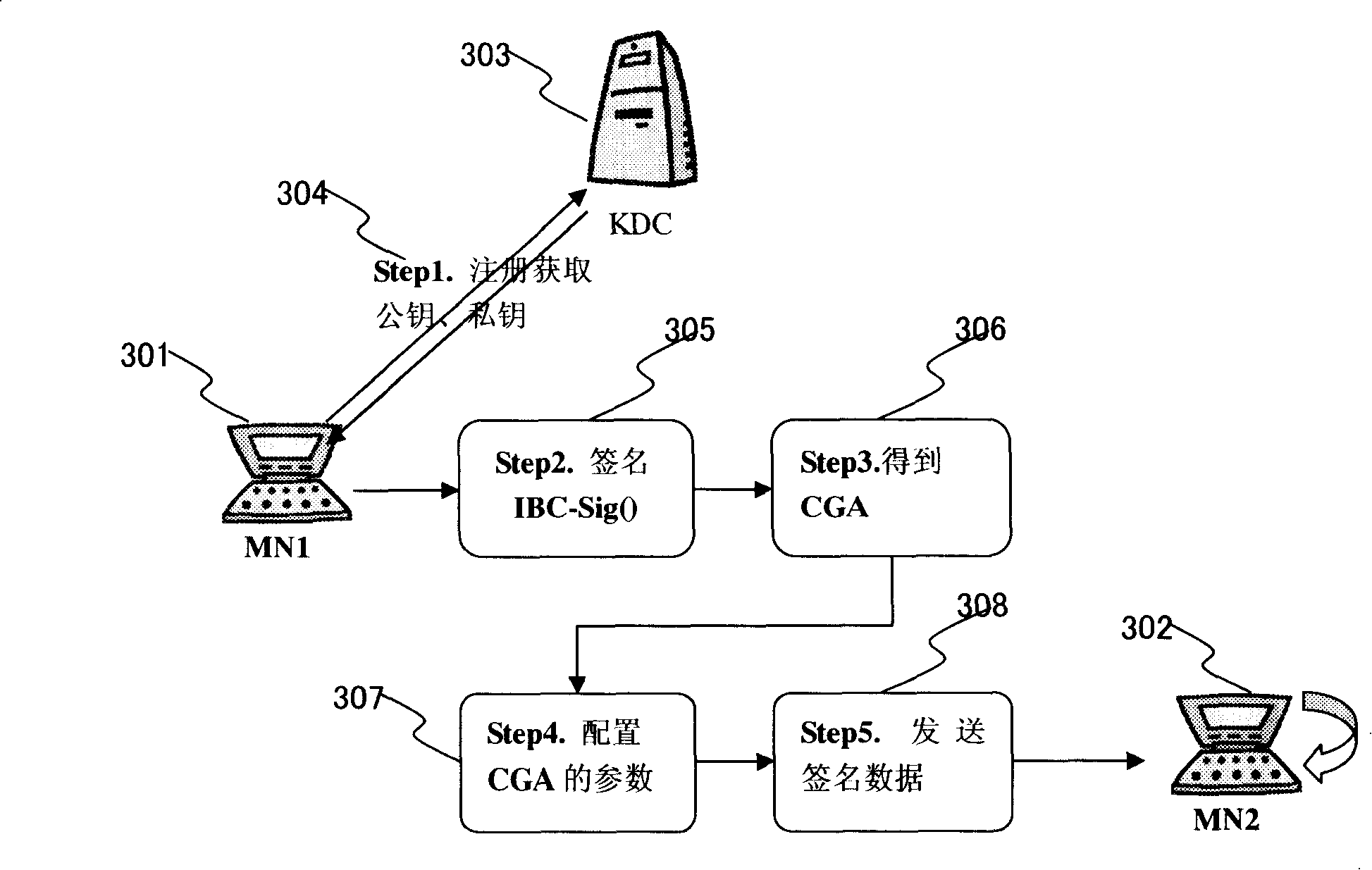
InactiveCN101162999AImprove security featuresSolve the owner problemPublic key for secure communicationUser identity/authority verificationPublic key cryptosystemAuthentication
The invention provides an identity-based public-key cryptography system (IBC) and the authentication method of CGA (Cryptographically Generated Addresses) in a mobile IPv6 network. In the method, a mobile node obtains owned public and private keys via an identity identifier registered on the identity-based public-key cryptography system (IBC) and configures an IPv6 address via the owned public key. Only by knowing the identifier of a communication peer, the mobile node can use the public parameters of the system to calculate the public key of the communication peer in order to carry out message encryption or signature authentication, whereas the private key of the mobile node can be obtained only by the center of the IBC cryptography system and the mobile node. The method resolves three problems at the same time, the first problem is the ownership of IPv6 addresses, the second problem is the authentication property of message sources, that is, messages come from the owers of addresses, and the third problem is the trust property which is resolved by the IBC, that is, a message source is an authentic entity.
Owner:柏建敏
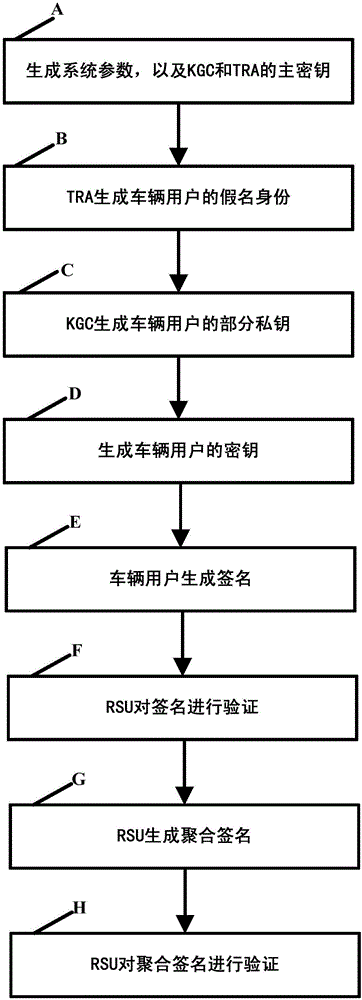
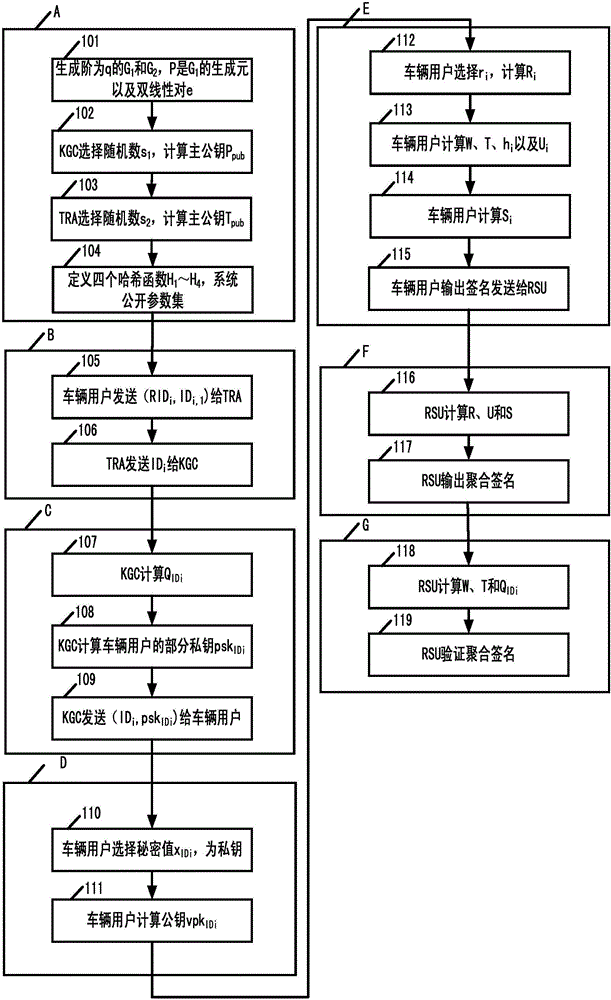
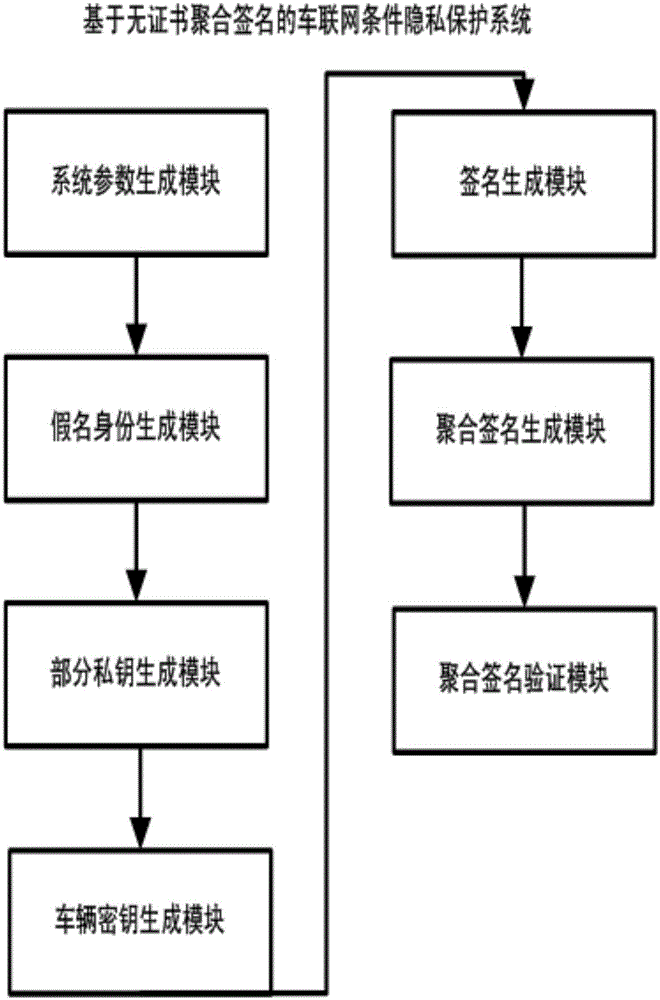
Internet of vehicles conditional privacy protection method and system based on certificateless aggregation signature
ActiveCN106131059AAvoid managementAvoid key escrow issuesKey distribution for secure communicationPrivacy protectionThe Internet
The invention discloses an internet of vehicles conditional privacy protection method and system based on certificateless aggregation signature. The internet of vehicles conditional privacy protection method based on certificateless aggregation signature is provided based on a certificateless cryptosystem. On the basis of internet of vehicle conditional privacy protection of a traditional public key cryptosystem, an aggregation signer aggregates various different signatures into one signature, the internet of vehicles conditional privacy protection scheme is realized by employing a key generation center KGC and a tracking authentication center TRA, the problems of certificate management and key hosting are avoided, the computing efficiency of an internet of vehicles is improved when the aggregation signature is authenticated, the conditional privacy protection of internet of vehicles users is realized, and the method and the system can be applied in the open internet of vehicles safely.
Owner:HOHAI UNIV
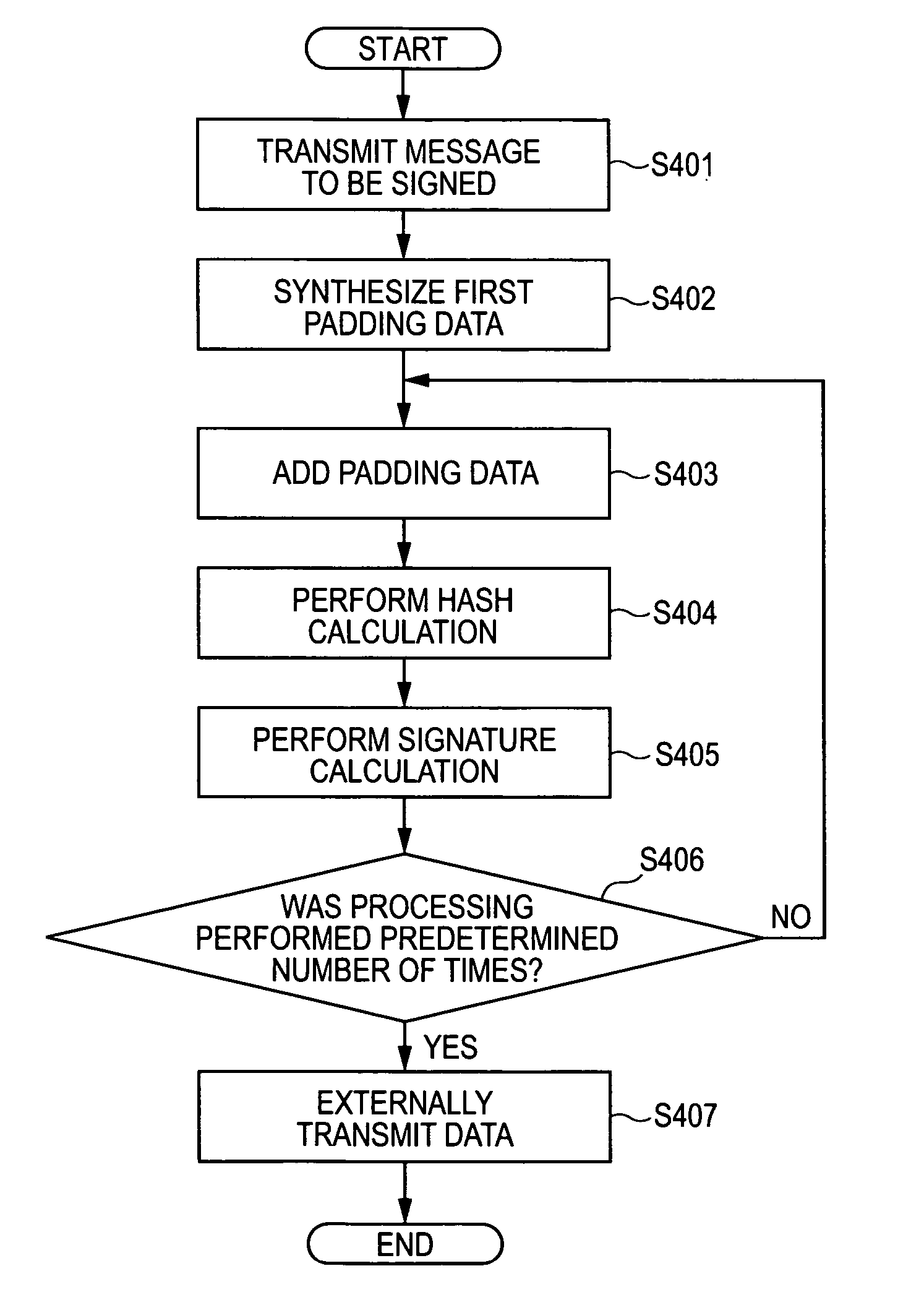
Signature-generation method, signature-verification method, public-key distribution method, and information-processing apparatus
InactiveUS20060075246A1Ensure authenticityKey distribution for secure communicationDigital data processing detailsInformation processingHash function
To generate and verify signature data using a known signature algorithm whose safety is ensured from the viewpoint of calculation quantity and ensuring the authenticity thereof over a long time period. A message to be signed is transmitted, a padding-data item is added to the message, and a signature-data item of the message with the padding-data item added thereto is generated by using a hash function and a public-key cryptosystem. The addition step and the generation step are performed a predetermined number of times by using the signature-data item, as the padding-data item, and the signature-data items generated the predetermined number of times and the padding-data items added the predetermined number of times are externally transmitted with the message.
Owner:CANON KK
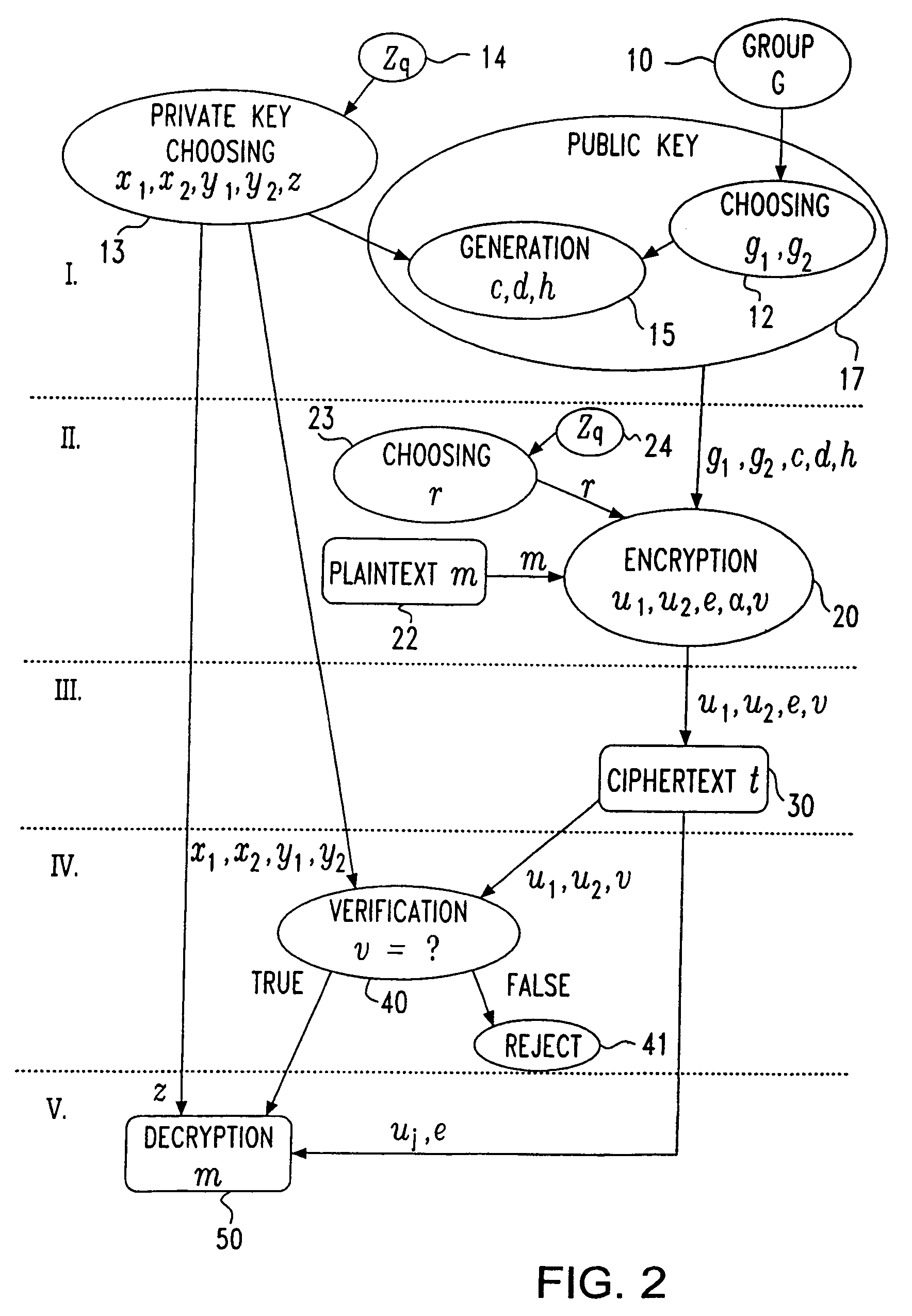
Practical non-malleable public-key cryptosystem
InactiveUS7221758B2Improve securityConvenient verificationPublic key for secure communicationSecret communicationPlaintextCiphertext
The present scheme improves the security of encrypted data or information by using of a practical public-key cryptosystem that is able to resist adaptive attacks. The disclosed scheme does not leak any information about the secret of the used key. Therefor the scheme generates an extended private key and public key. A message m, also referred to as plaintext, is encryptable to a ciphertext t by using the public key. Only a recipient with the right private key is able to decrypt the ciphertext t. But before a decryption starts, a verification of the ciphertext t takes place. Such a verification allows to prove the legitimation of the ciphertext t. That means, the ciphertext t is investigated and either decrypted back to the plaintext or rejected if a chosen ciphertext is fed, ie. the ciphertext is illegitimate or invalid.
Owner:IBM CORP
Method for certificateless cross-domain authentication in credible could computing environment
ActiveCN103546567AAddress certificate maintenance overheadReduce overheadKey distribution for secure communicationHypothesisAuthentication server
The invention relates to a method for certificateless cross-domain authentication in a credible cloud computing environment and belongs to the technical field of cloud computing safety. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, the certificateless public key cryptography technology is introduced into cross-domain authentication, credible cross-domain authentication is achieved in the process of credible cloud computing, a certificateless public key cryptosystem is applied, the problem of the certificate maintenance expense of a traditional digital certificate authentication system and the problem of private key trusteeship of a public key cryptography system based on the identity are solved. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, a user public key is generated based on the identity, a part of a private key of a user is generated by the user, and the other part of the private key of the user is generated by a center authentication server. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, a certificate system is abandoned, the expense of the authentication system is reduced, the private key of the user is protected at the same time, bilinear pairing computation is applied to the certificateless public key cryptosystem, it is proved that a safety hypothesis based on bilinear pairing computation is high in safety, the certificateless public key cryptosystem is used for identity authentication and session key negotiation, and therefore it is ensured that the system is high in safety.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND +1
Certificateless signature algorithm for user identity authentication in network environment
InactiveCN102983971AImprove computing efficiencyImprove securityKey distribution for secure communicationUser identity/authority verificationPasswordKey escrow
The invention discloses an efficient certificateless signature algorithm which solves the problem of certificate management in a traditional public key cryptosystem and the problem of key escrow based on an identity password system, and safety is guaranteed in a certificateless environment. The certificateless signature is simple and efficient in computational process and high in, specific hush function does not need, and the length of an output signature is also short. The certificateless signature algorithm has high safety and execution efficiency, and can be effectively used in a signature environment which has a high requirement for safety.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
Methods, devices and systems for generating anonymous public keys in a secure communication system
InactiveUS20060098819A1Communication securityReducing individual managing costKey distribution for secure communicationMultiple keys/algorithms usageSecurity levelSecure communication system
Methods, devices and systems for generating a plurality of public keys from one private key with the same generator of a group are described. A public key cryptosystem is also disclosed for generating a plurality of anonymous public keys all of which relate to the same party used for secure communications. Those anonymous public keys are generated using the same generator from one single private key. With the invention, computation is reduced, memory can be saved and security level can be improved.
Owner:NEC (CHINA) CO LTD
Method for generating multiple variable commom key password system
Multivariate public key cipher system (MPKC) is such a public key cipher system that its public key is a set of multivariate polynomial of finite field (or ring). The MPKC can be used in encryption, identification and signature. The invention putting forward three methods that can be used in one multivariate public key cipher system to get multivariate new public key cipher system, and that the get new cryptography is better than the former system on efficiency and security. The three methods are separately intituled inner perturbation-plus (IPP), enhanced inner perturbation (EIP) and multi oil-vinegar construction. We can also apply two or all of the three methods for one multivariate public key cipher system to get new multivariate public key cipher system.
Owner:南京合十软件科技有限公司
IC card and authentication method in electronic ticket distribution system
InactiveUS7580897B2Strict securityReduce necessityFinanceMultiple keys/algorithms usageComputer hardwareDistribution system
Between an IC card (1) and a electronic ticket server (2), upon purchasing an electronic ticket a public key cryptosystem is employed for a mutual authentication to keep a strict security, and a shared secret between the electronic ticket and a ticket collecting machine is sent on a secure channel as well as the electronic ticket. Upon usage of the electronic ticket, the IC card (1) and the ticket collecting machine (6) mutually judge whether they carry out the mutual authentication by using a public key cryptosystem or a symmetric key cryptosystem. When they determine to use the symmetric key cryptosystem, they carry out the mutual authentication by using the shared secret exchanged beforehand. When they determine to use the public key cryptosystem, they carry out the mutual authentication by using the same method as that used upon purchasing the electronic ticket. This method of mutual authentication can dynamically switch cryptosystems for cryptographic communication between the IC cards or between the IC card and a tamper resistant device having an equivalent function to an IC card installed in related servers or the ticket collecting machine, based on their judgment of the types of bearers, the required degree of security and the required processing speed.
Owner:SAKUMRA KEN +2
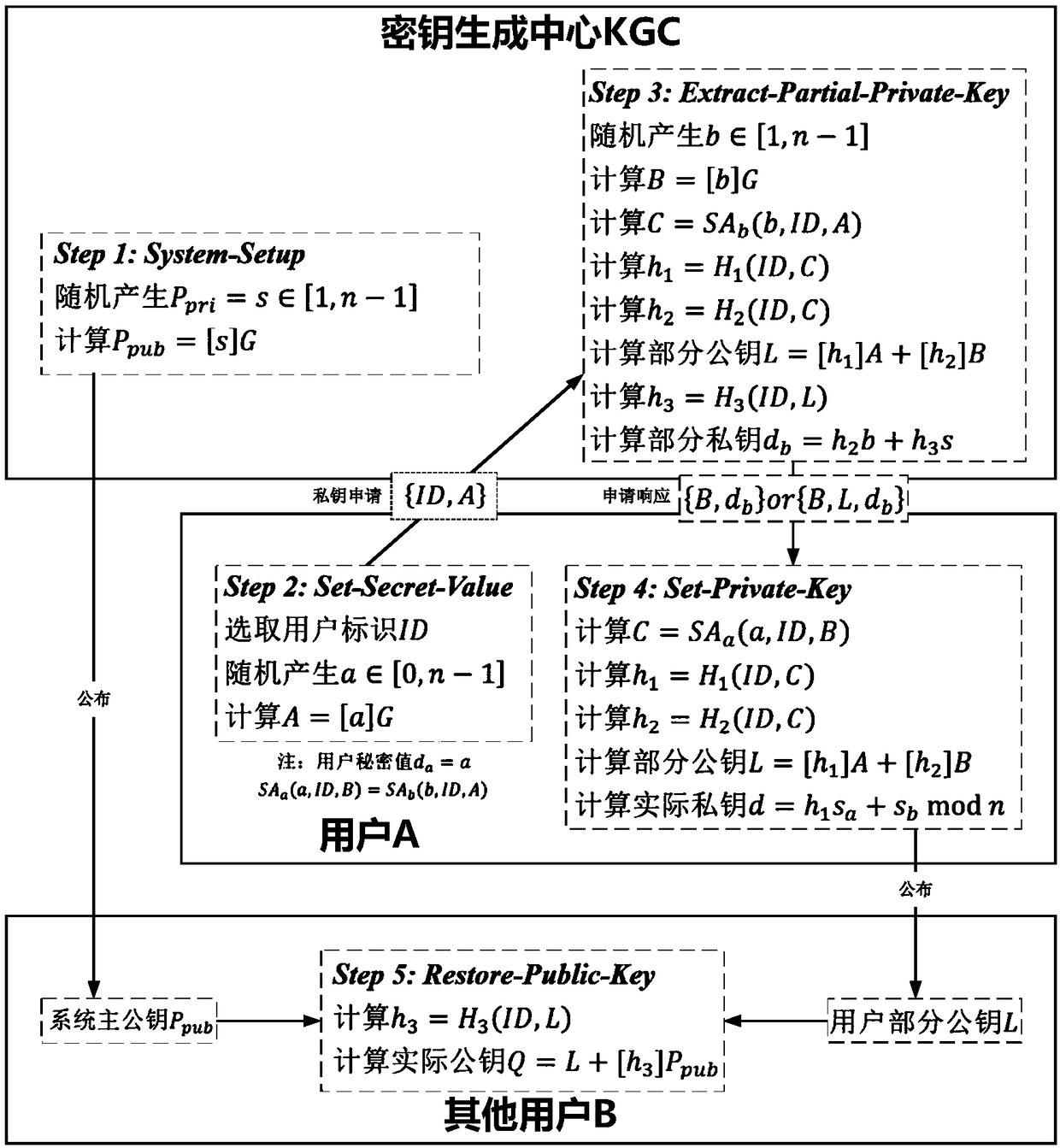
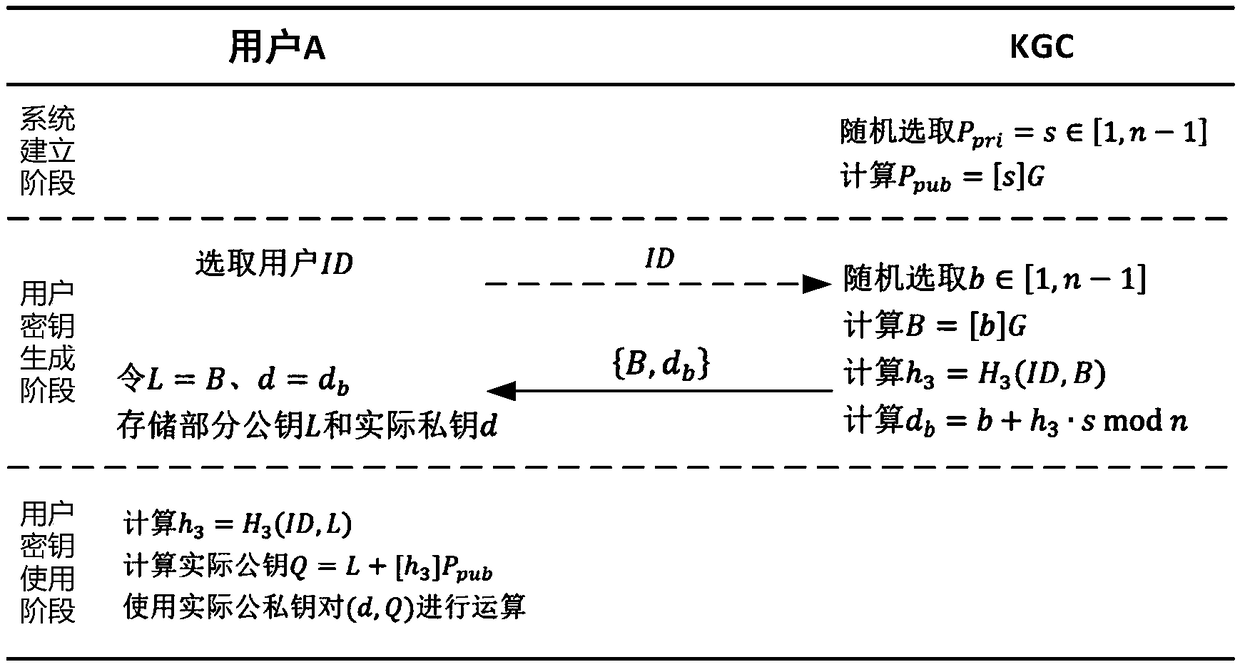
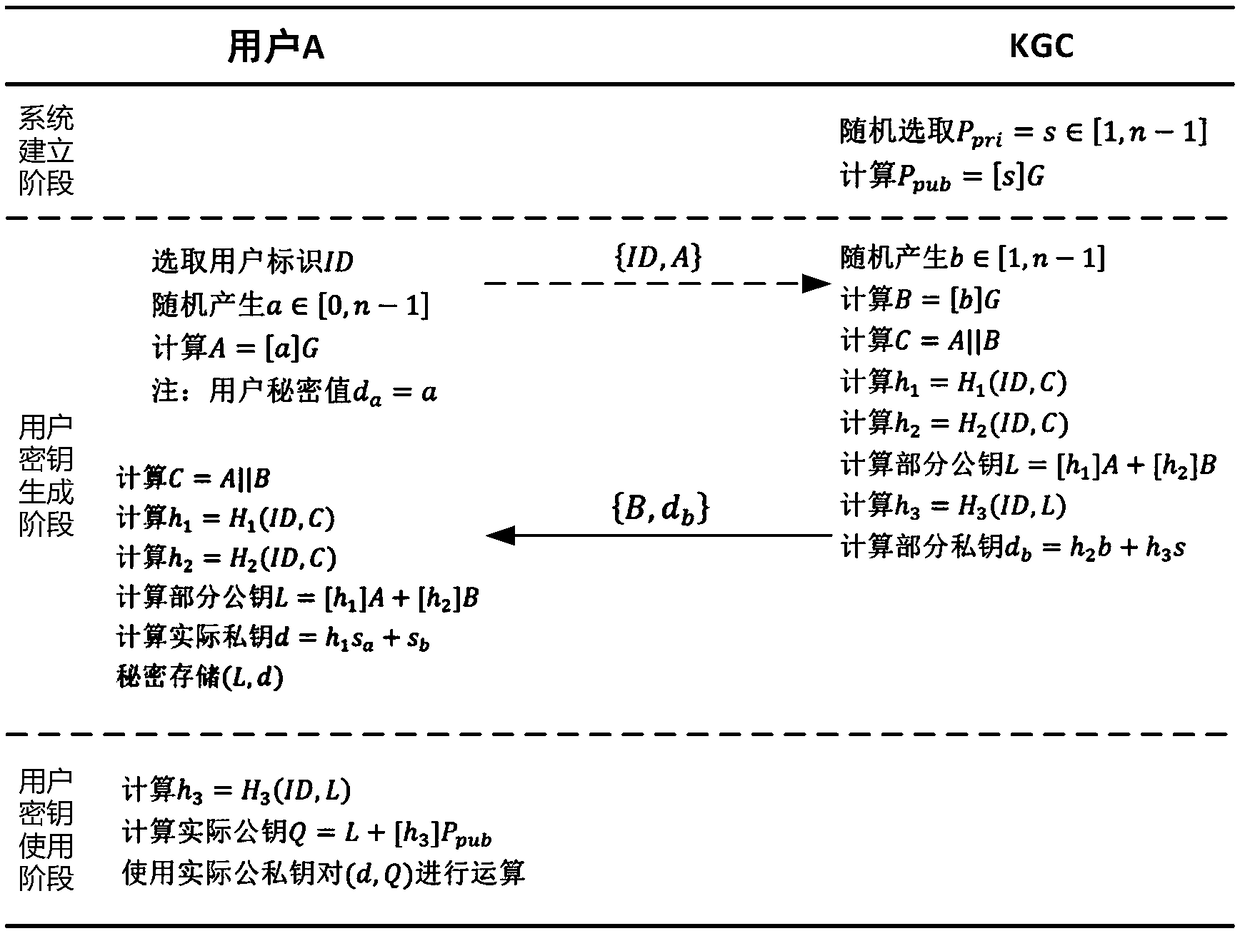
An implementation method of certificateless public key cryptosystem based on elliptic curve
ActiveCN108989053AAvoid managementAvoid using effectsPublic key for secure communicationUser identity/authority verificationPublic key cryptosystemKey generation
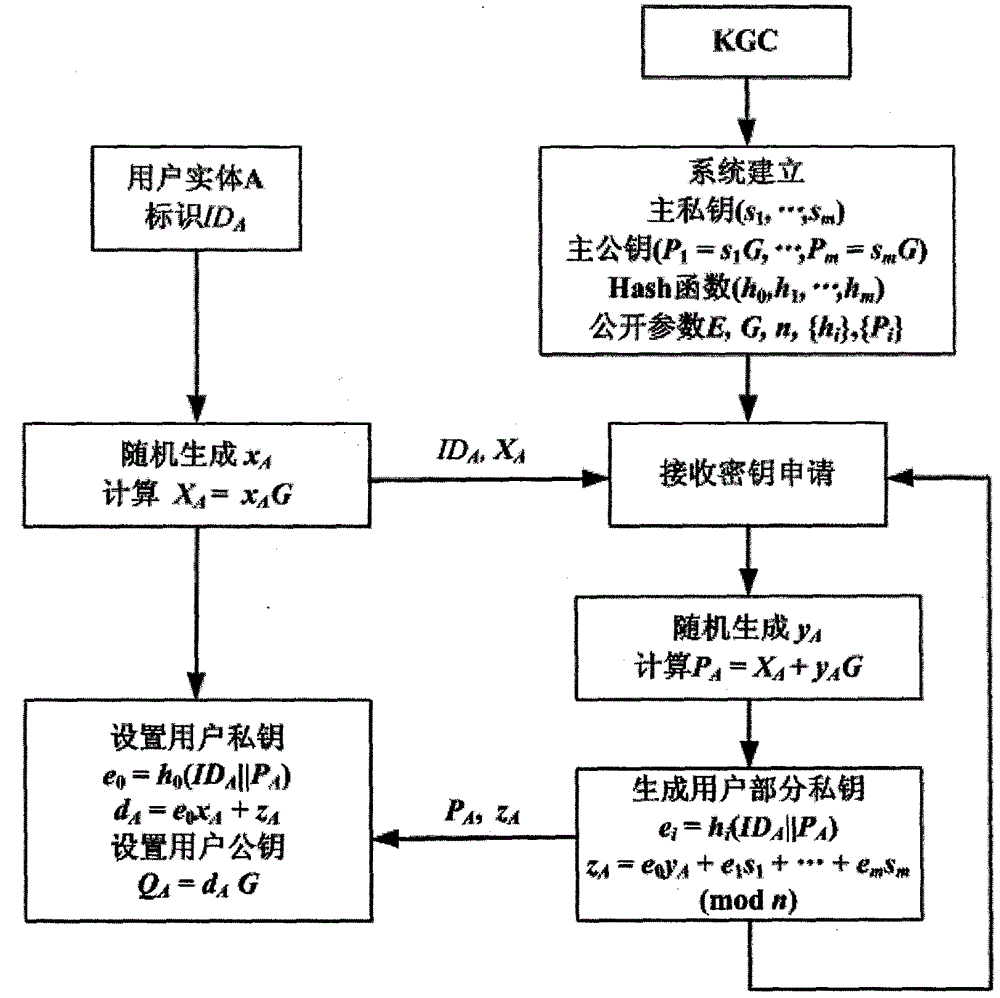
The invention discloses an implementation method of a certificateless public key cryptosystem based on an elliptic curve, which is used for solving the problems of system establishment, user key generation and use under the certificateless cryptosystem. In the present invention, the key generation center determines system parameters and publishes them. Then, the user submits an application to thekey generation center based on the randomly selected secret value, and the key generation center randomly generates a user partial private key based on the system master private key and the application information and returns the user partial private key, and finally the user calculates the actual private key and the partial public key based on the partial private key. In use, other users first get the actual public key based on the user identity and partial public key restoration, and then calculate according to the standard cryptographic algorithm. The invention effectively avoids the use problem of the certificate, can realize the binding of the user identification and the public key, and ensures that only the user can know the private key. The invention has the characteristics of highcomputational efficiency, strong security and the like, and can be applied to various standard elliptic curve cryptographic algorithms without changing the algorithm logic.
Owner:武汉珈港科技有限公司
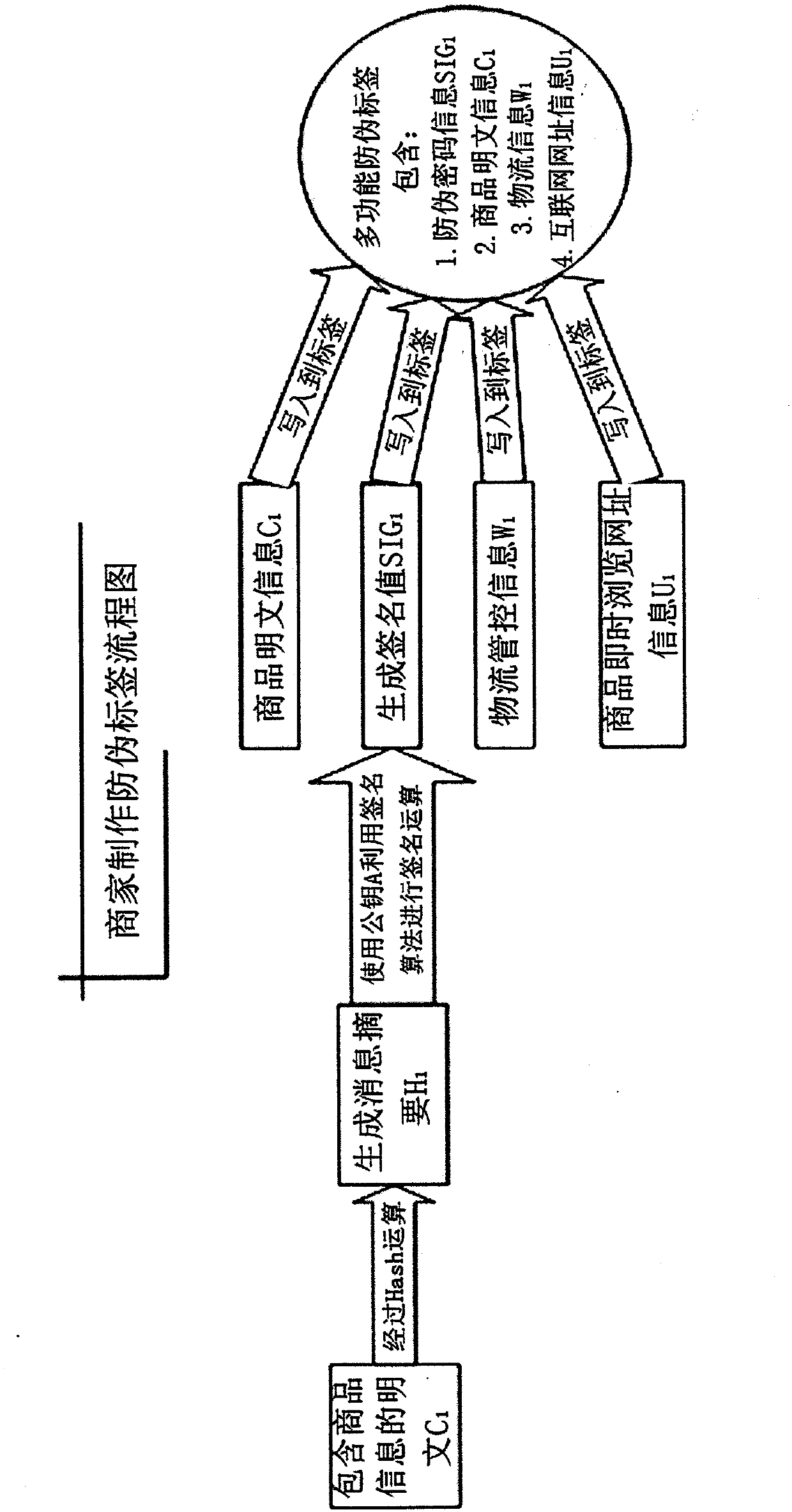
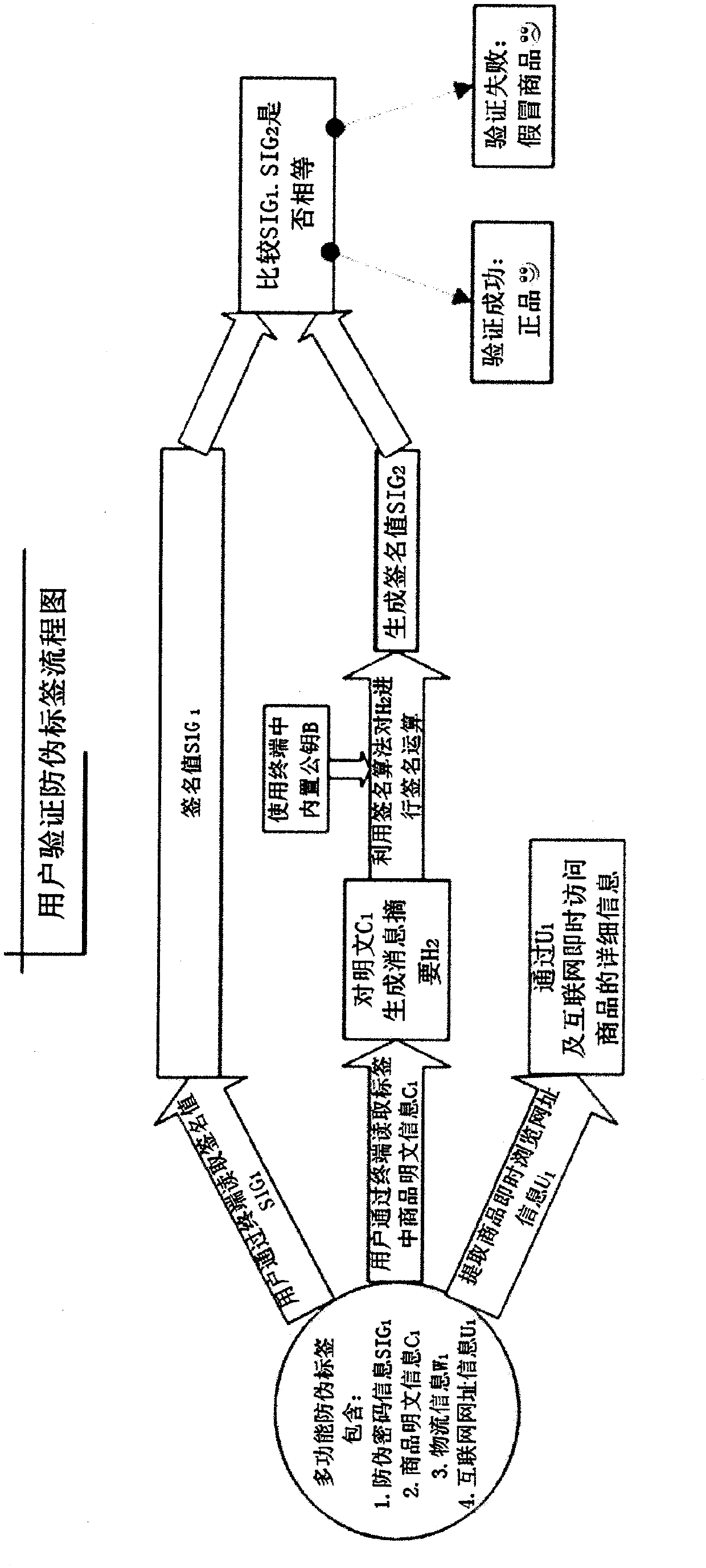
RFID (radio frequency identification device) label integrating comprehensive functions such as merchandise anti-counterfeiting, logistics control and the like
InactiveCN102779284AQuick identificationFix bugsRecord carriers used with machinesLogistics managementPassword
The invention discloses an RFID (radio frequency identification device) label integrating comprehensive functions such as merchandise anti-counterfeiting, logistics control and the like, and provides an anti-counterfeiting label identification method and data structure of an RFID label not based on password access control, namely that the password access control of the RFID label is not taken as the anti-counterfeiting core. The manufacturer manufactures the anti-counterfeiting information by use of a key A of a public key system in the anti-counterfeiting label database structure, and the anti-counterfeiting information of the merchandise, logistics control information and the website browsing information of the merchandise are written into the RFID anti-counterfeiting label attached to the merchandise at the same time; and before buying the merchandise, a user can check the identity of the merchandise and quickly browse the detailed information of the merchandise. Meanwhile, the manufacturer can perform logistics management by use of the RFID label.
Owner:张楠
Software authorization method based on public key cryptosystem
ActiveCN103491098APrevent illegal copyingEasy to upgradeUser identity/authority verificationProgram/content distribution protectionAuthorization certificateSoftware engineering
The invention discloses a software authorization method based on public key cryptosystem. The method includes the following steps: a server end receives an institution authorization certificate and a registration file sent by a client; the server end decrypts the received institution authorization certificate and verifies decrypted information, if the information passes the verification, the registered file is encrypted, and a user authorization certificate is generated and returned to the client; when a customer starts software, the software end encrypts and verifies the user authorization certificate, if the decryption and the verification are successful, the software is started, and otherwise, the software is not started. The method can prevent the software from being illegally copied, meanwhile, the software can be managed by a software issuer in a concentrated mode, and upgrading and tracking of the software, pushing personalized services for users and other after-sale management are facilitated.
Owner:HUAZHONG NORMAL UNIV
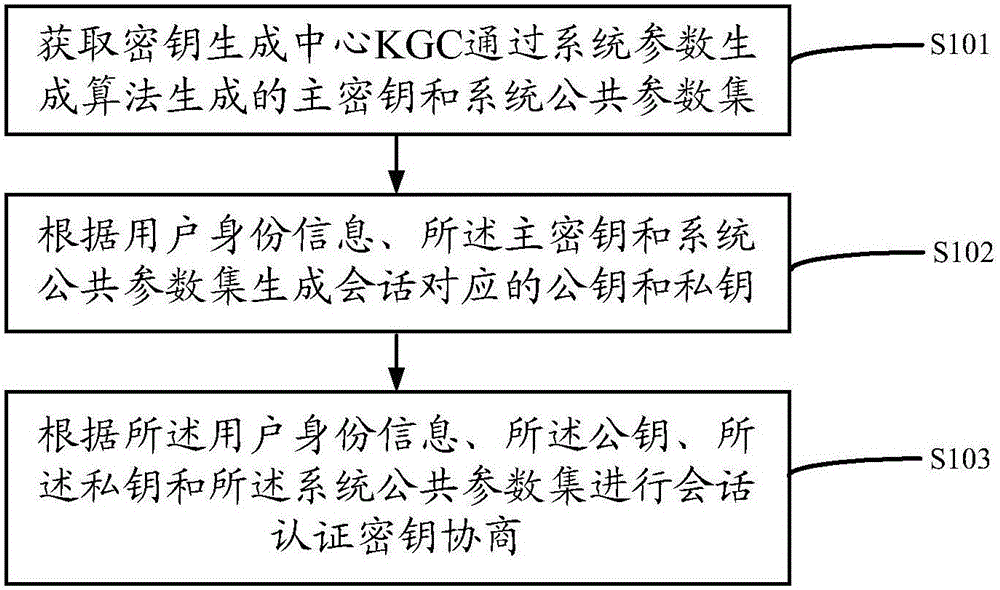
Method and device of two-side authentication secret key negotiation based on certificateless
The present invention discloses a method and device of two-side authentication secret key negotiation based on certificateless. The device comprises a parameter module and a negotiation module, a system public parameter set and the master key, part of secret keys, the secret value, the private key and the public key of a key generation center (KGC) are generated, and the two-side secret key negotiation is performed so as to overcome the problem of complex certificate management in a traditional public key cryptosystem and the problem of inherent secret key trusteeship based on the identity of the cryptosystem, and the method and device of two-side authentication secret key negotiation based on certificateless do not depend on the bilinear pairing operation so as to improve the system efficiency and are specially suitable for a wireless mobile device with limited capability.
Owner:ZTE CORP
Bilateral authentication and data interaction security protection method based on CPK (Combined Public Key Cryptosystem)
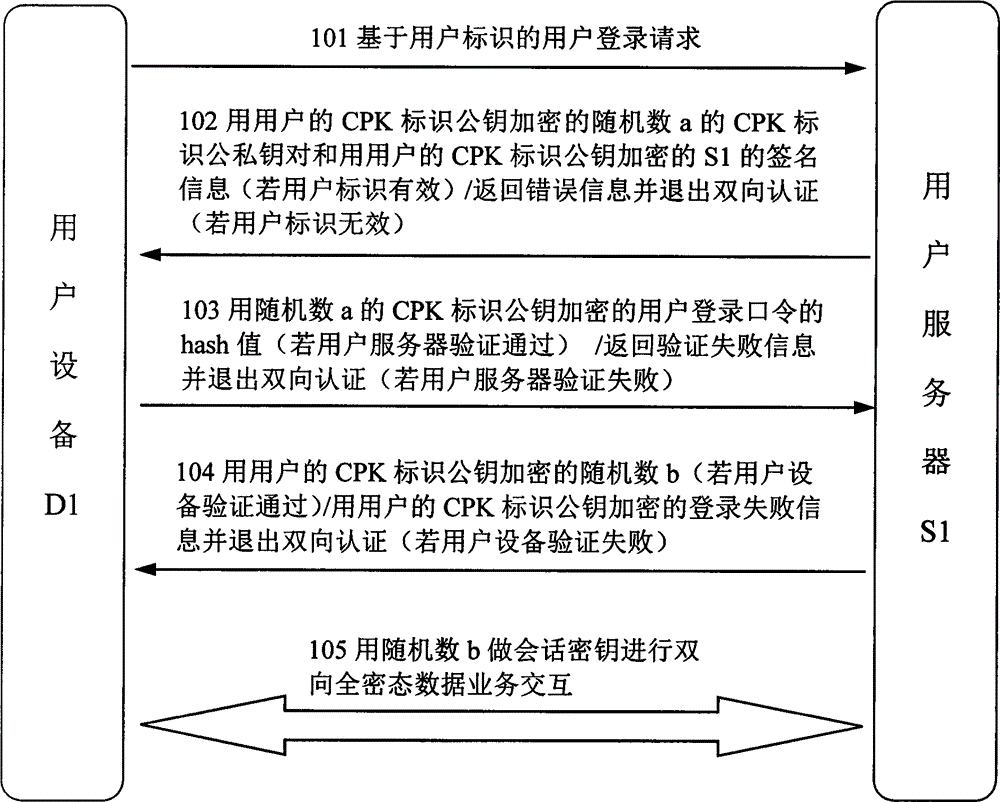
InactiveCN104901935AConvenient offline authenticationImplement offline authenticationUser identity/authority verificationPasswordPublic key cryptosystem
The invention provides a bilateral authentication and data interaction security protection method based on a CPK (Combined Public Key Cryptosystem). The method is applied to bilateral authentication between a user server (S1) and user equipment (D1) and interaction protection of all data. The method comprises the following steps that: the S1 receives a user login request transmitted by the D1, generates a random number a, a CPK identification public-private key pair of the random number and identification private key signature information of the S1, encrypts the random number a, the CPK identification public-private key pair and the identification private key signature information, and downloads the encrypted random number a, CPK identification public-private key pair and identification private key signature information to the D1; the D1 verifies whether or not the signature information of the S1 is legal with an identification public key of the S1 to finish authentication of the S1; the S1 performs comparative verification with the hash value of the received user login password and a saved value to finish authentication of the D1; if bilateral authentication is passed, the S1 generates a random number b, encrypts the random number b, and transmits the encrypted random number b to the D1; otherwise the S1 returns bilateral authentication failure information; and after the success of bilateral authentication of a user, the random number b is taken as a session key for all data between the D1 and the S1 in order to perform bilateral all-homomorphism data interaction.
Owner:成都腾甲数据服务有限公司
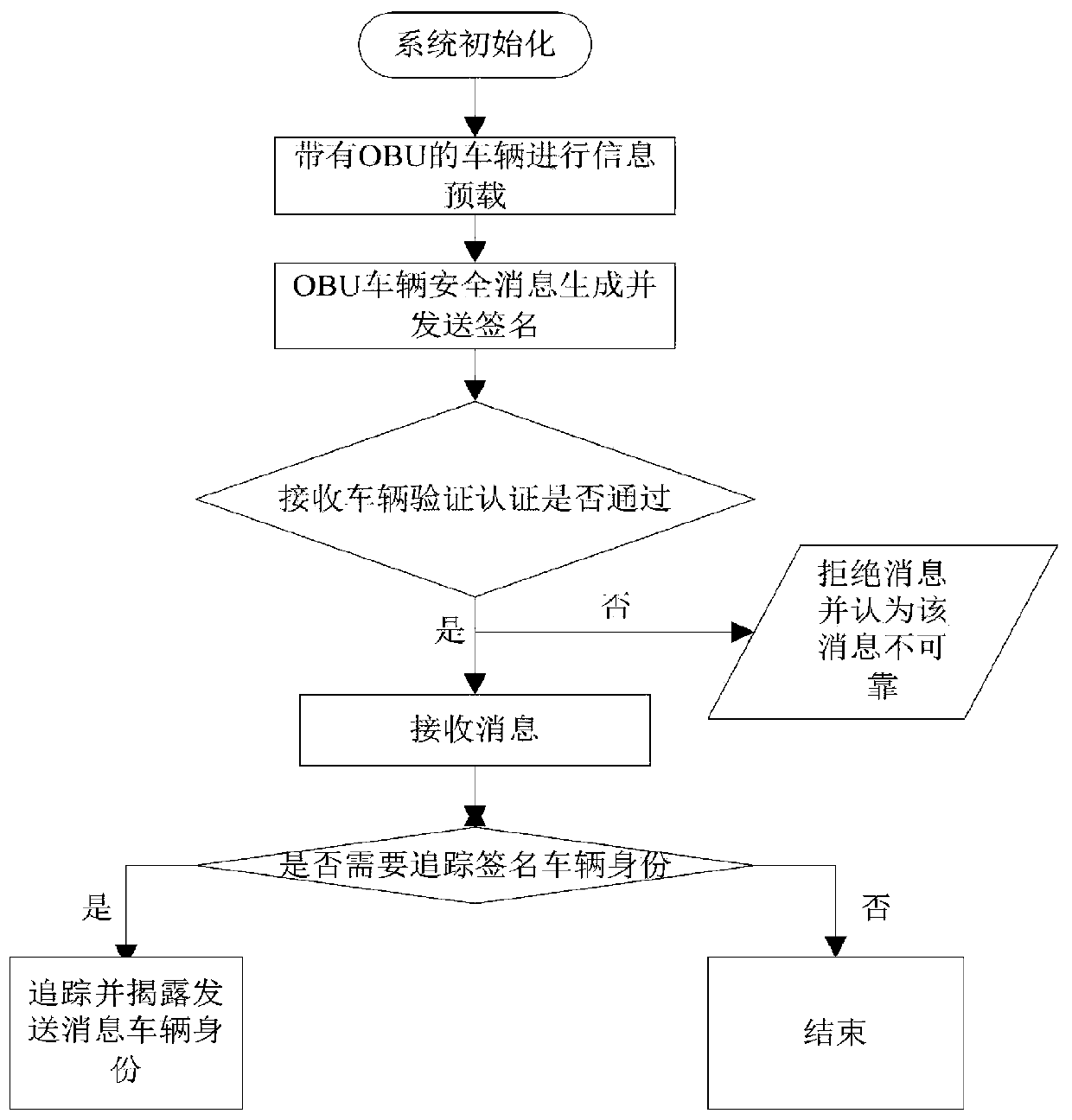
Vehicle-mounted network anonymous authentication system and method based on ring signature and vehicle communication platform
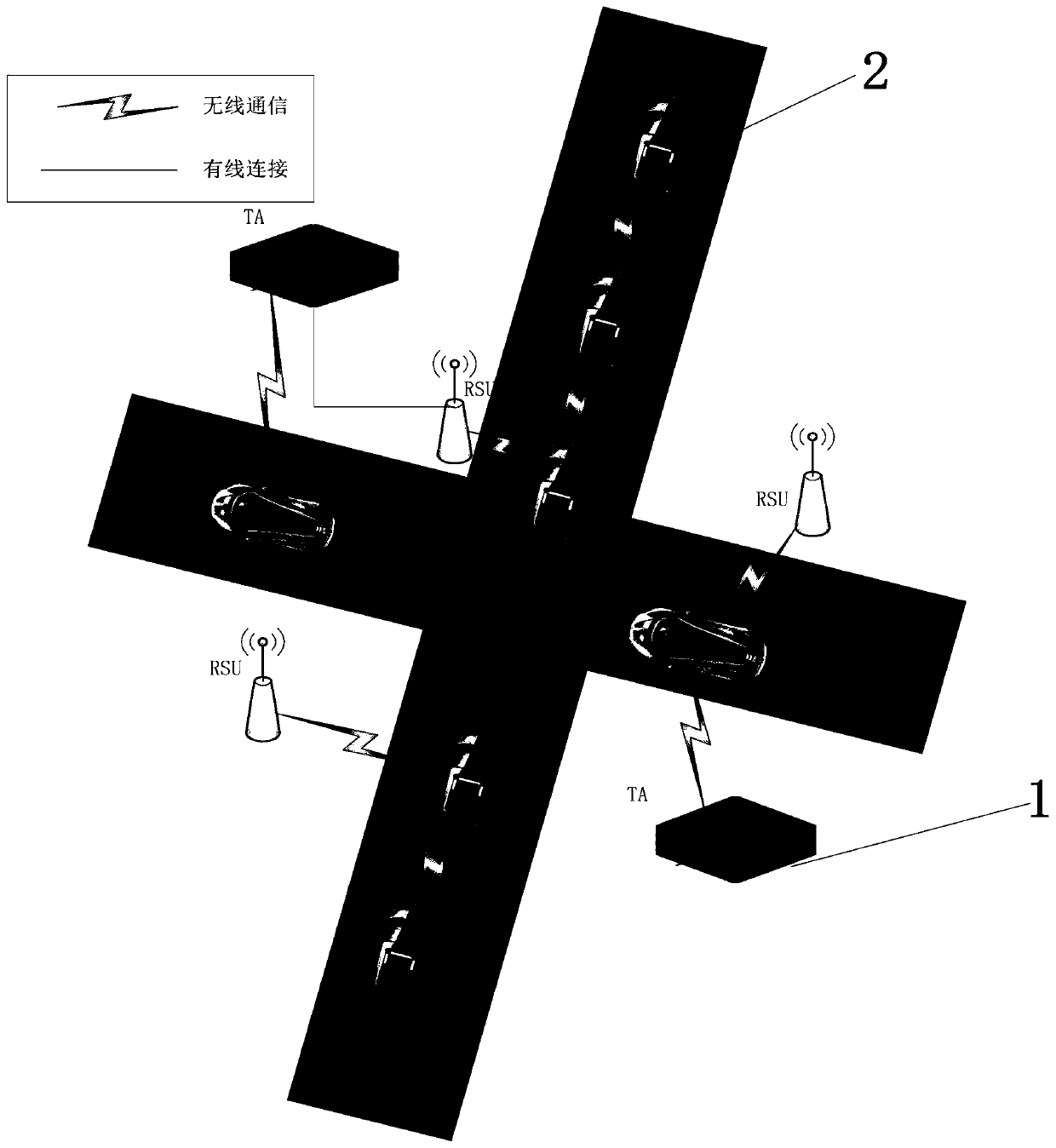
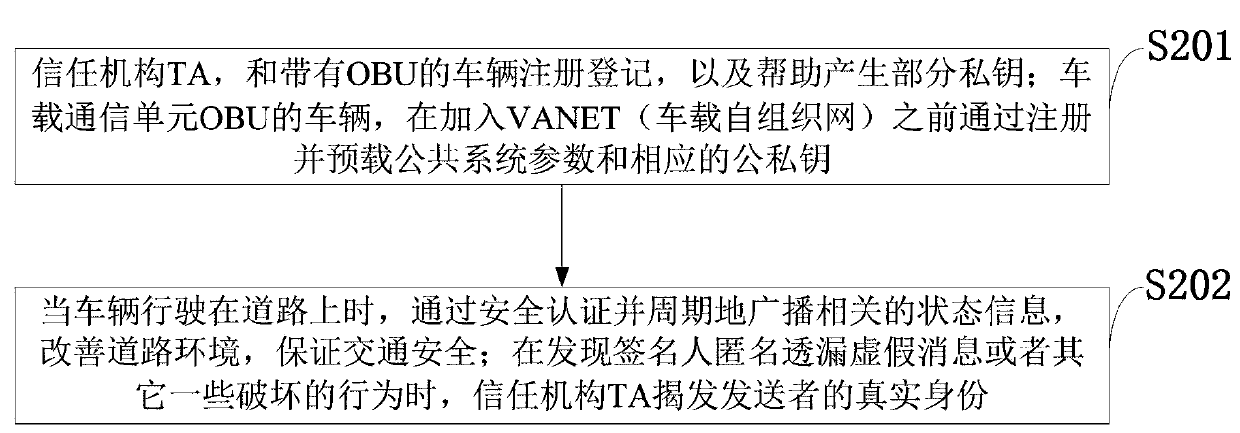
ActiveCN109802956ARealize communicationAuthentication securityUser identity/authority verificationCommunications securityRelevant information
The invention belongs to the technical field of vehicle communication security, and discloses a vehicle-mounted network anonymous authentication system and method based on a ring signature, and a vehicle communication platform. The trust mechanism and the vehicle with the OBU are registered to generate a part of private keys; A vehicle of the OBU is registered and preloaded with public system parameters and corresponding public and private keys before being added into the vehicle-mounted ad hoc network. When the vehicle runs on a road, related state information is periodically broadcasted after safety certification; And when the signer finds that the signer anonymously leaks the false message or the behavior that the signer is damaged, the trust mechanism uncovers the real identity of thesender. According to the invention, the certificateless public key cryptosystem and the ring signature are combined to form the certificateless ring signature, so that anonymity and unforgeability aremet, and meanwhile, security authentication is met; A traceable algorithm is formed by adding related information to effectively solve the problem that when a signer anonymity leaks false messages orother destructive behaviors, identity tracking and revocation are carried out according to the received messages.
Owner:XIAN UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com