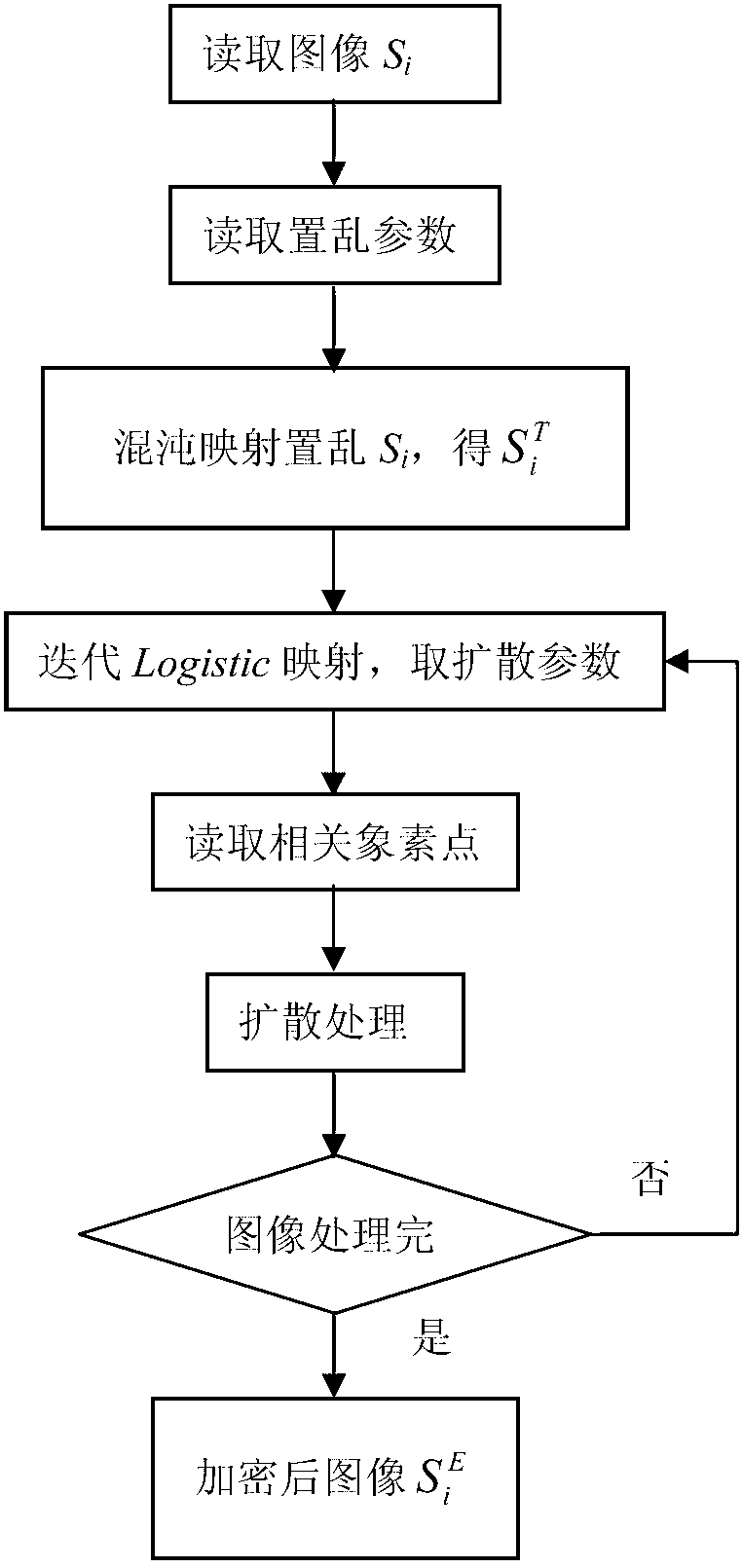
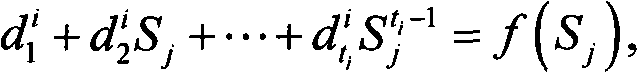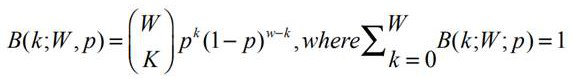Patents
Literature
104results about How to "Increase attack difficulty" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
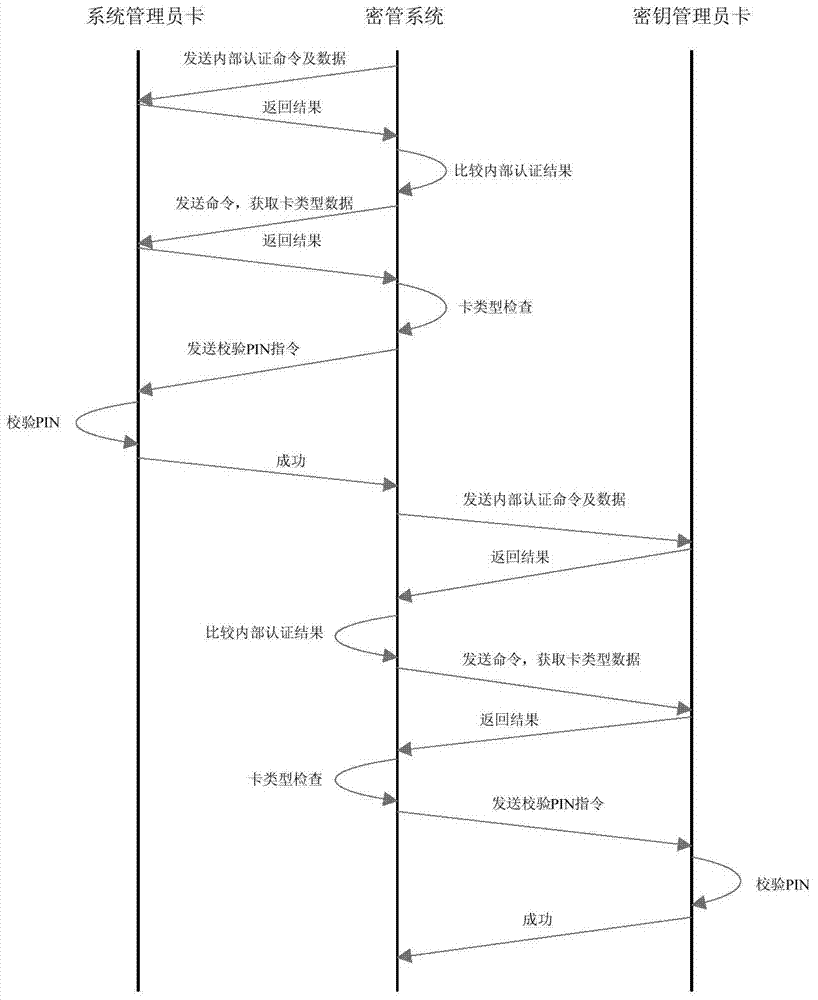
IP address jump safety communication method based on SDN framework
InactiveCN105429957AIncrease attack difficultyRealize IP hoppingData switching networksDomain nameSafety Communications
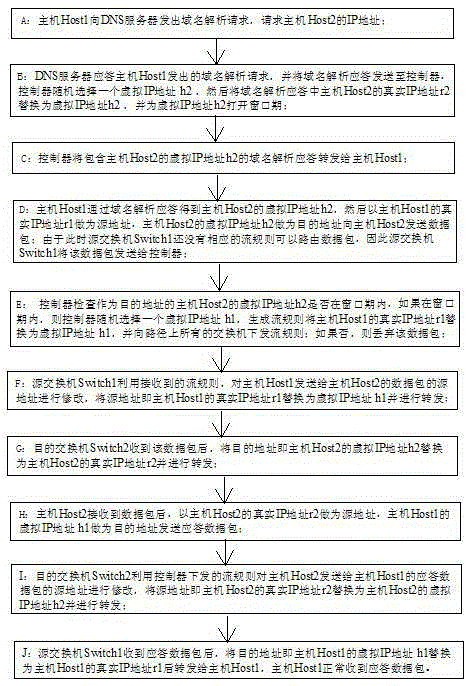
The invention discloses an IP address jump safety communication method based on an SDN framework. The method comprises steps that A, an IP address of a Host2 is requested by a Host1; B, a real IP address r2 of the Host2 is replaced by a virtual IP address h2 through a controller; C, a domain analysis response is forwarded by the controller to the Host1; D, an r1 is taken as a source address and the h2 is taken as a target address by the Host1 to send a data packet to the Host2; E, a flow rule is generated by the controller to replace the r1 by a virtual IP address h1, and the flow rule is issued; F, the r1 is replaced by the h1 through the source switch, and forwarding is carried out; G, the h2 is replaced by the r2 through the target switch, and forwarding is carried out; H, the r2 is taken as a source address and the h1 is taken as a target address by the Host2 to send a response data packet; I, the r2 is replaced by the h2 through the target switch, and forwarding is carried out; J, the h1 is replaced by the r1 through the source switch, and forwarding to the Host1 is carried out. Through the method, jump IPs can be dynamically distributed to a host computer in the IPH network, one-time one-change access to the host computer IP is transparently realized, attack based on scanning and DDoS attach can be effectively fought against.
Owner:芦斌
Dynamic application address conversion method and gateway system
ActiveCN104378363AIncrease attack difficultyHide vulnerabilityKey distribution for secure communicationGateway systemVulnerability scanning
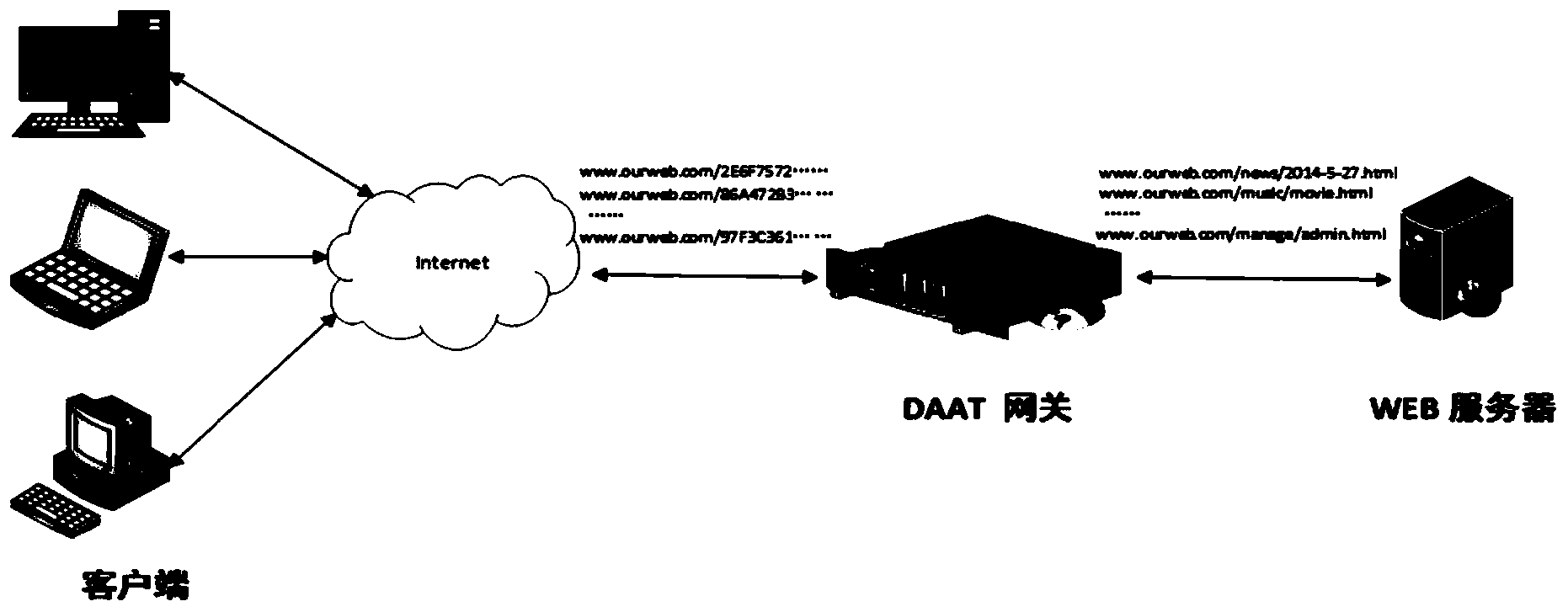
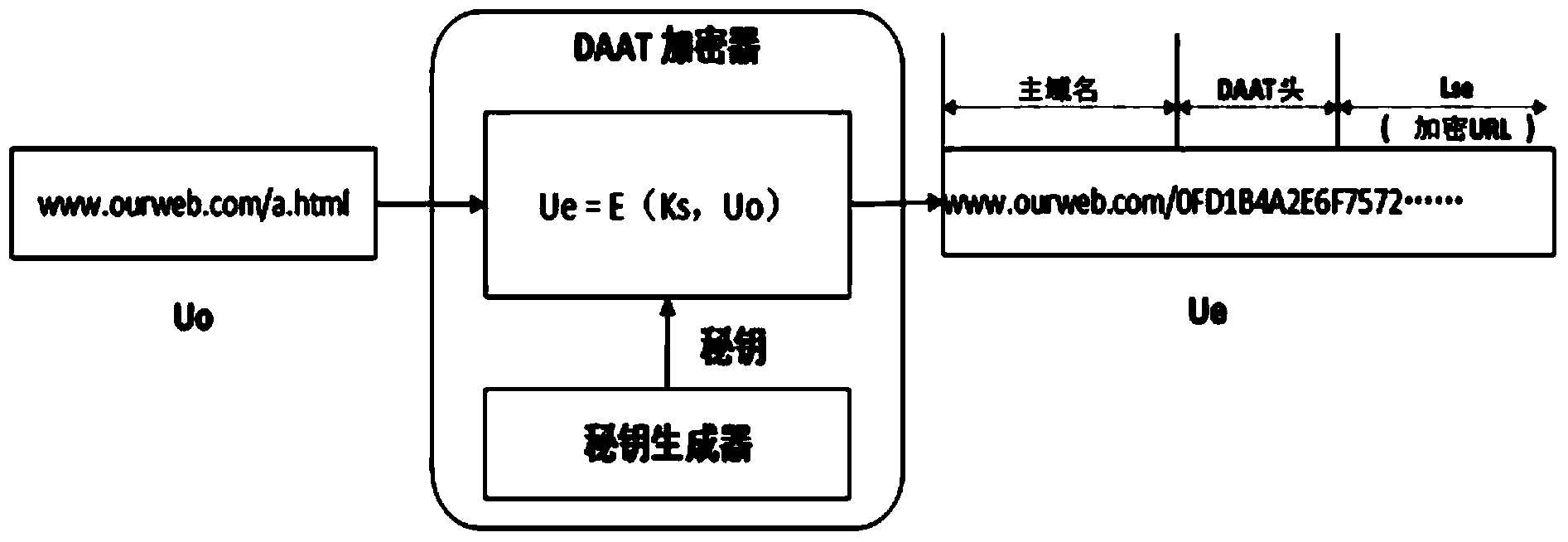
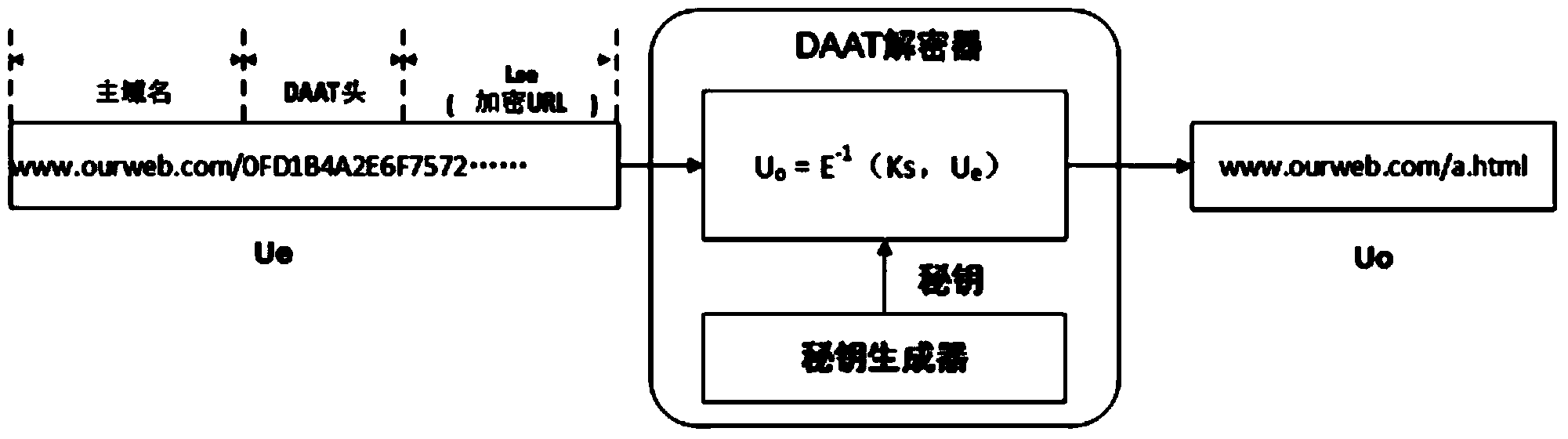
The invention relates to a dynamic application address conversion method and gateway system. A novel Web application attack defense method is achieved. URL addresses are dynamically converted, attack faces of an application system are converted, vulnerability of Web applications is hidden, the attack difficulty of an attacker is increased, and the difficulty in which the attacker conducts vulnerability scanning and attack injection on Websites through URLs is greatly increased. By the adoption of a DAAT method, the security threats of the attacker to the Web applications can be dynamically and effectively reduced, and security of the Web application system is improved.
Owner:INST OF INFORMATION ENG CAS
System and method for generating and managing secret key
ActiveCN103580872AIncrease attack difficultyAvoid difficultiesKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
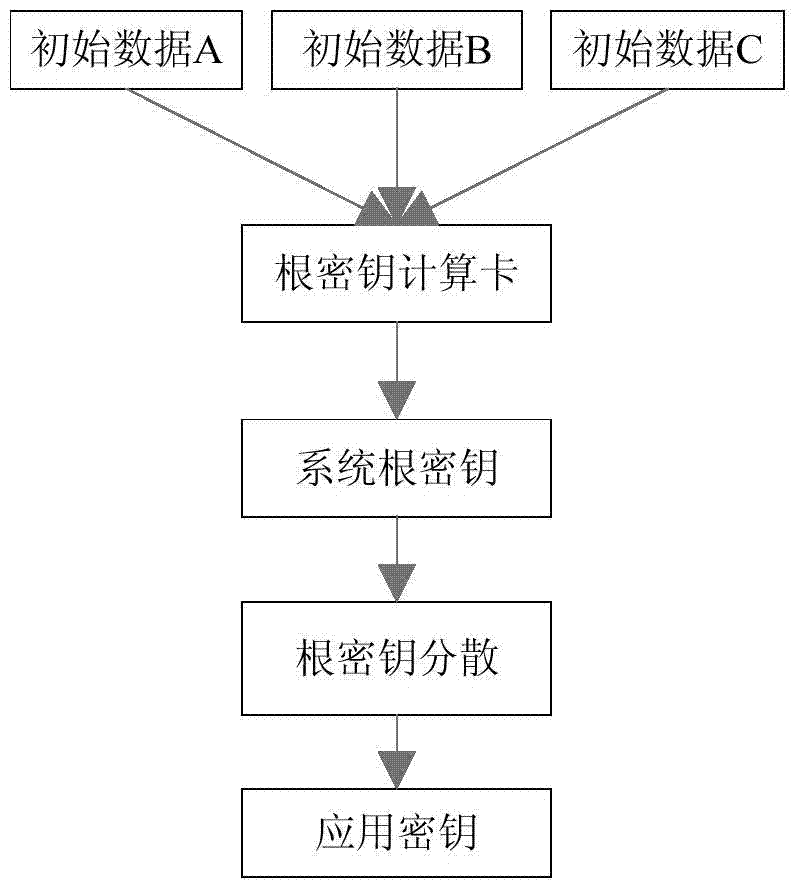
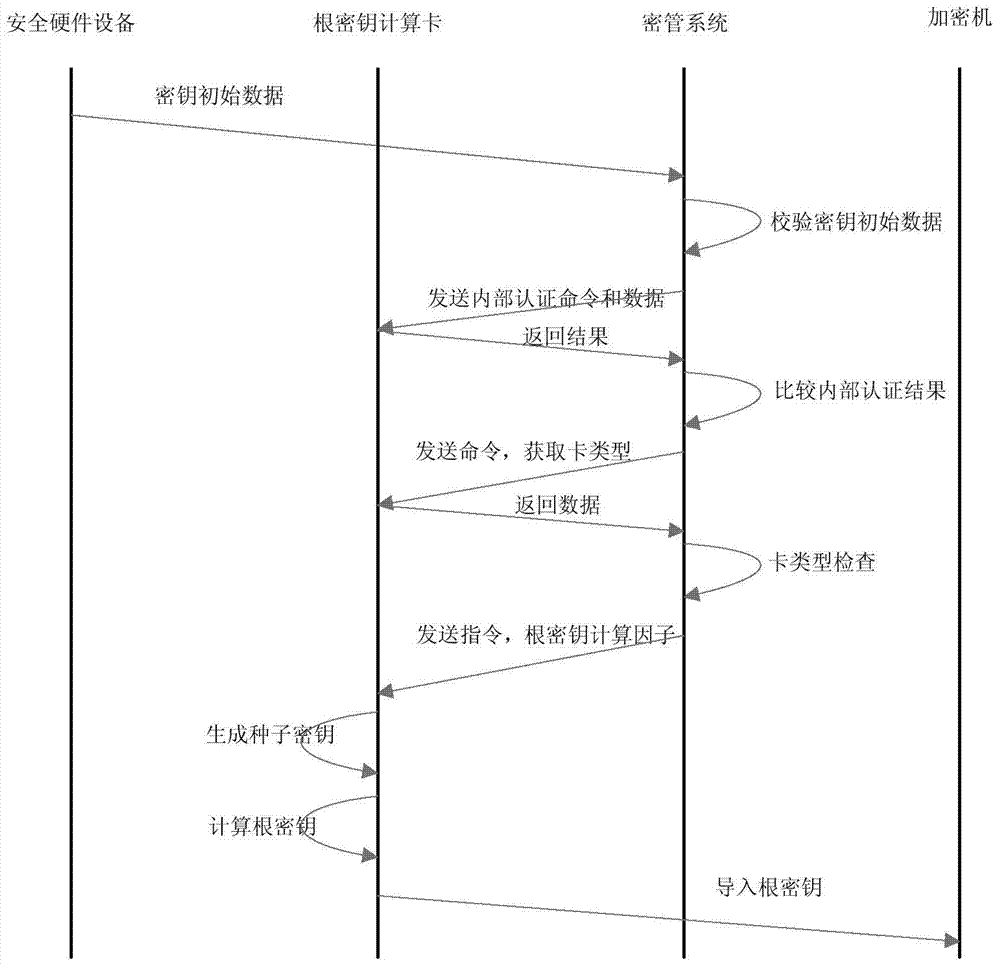
The invention provides a system and method for generating and managing a secrete key. When the system is started, identity recognition is carried out through an intelligent device. A plurality of sets of initial data are input and are mutually independent, and the initial data are stored in a safety hardware device which has the anti-fake and anti-decoding functions. A system root secrete key is generated through the safety hardware device according to a computation rule, and is encrypted to be stored in the safety hardware device. The root secrete key is dispersed through secrete key scattering factors to obtain the needed application secrete key. The application secrete key is stored in the safety hardware device, and the root secrete key is restored from the safety hardware device. In the whole system, the plaintext numerical value of the secrete key is only stored in the safety hardware device. Before having access to all safety hardware devices, the system identifies the true or fake of the safety devices. Operators are recognized by the system in the procedures of starting and operating. The generating rule of the secrete key cannot be known by laymen. The secret key data needed in the operation process exist in a cryptograph form. The system is high in safety.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
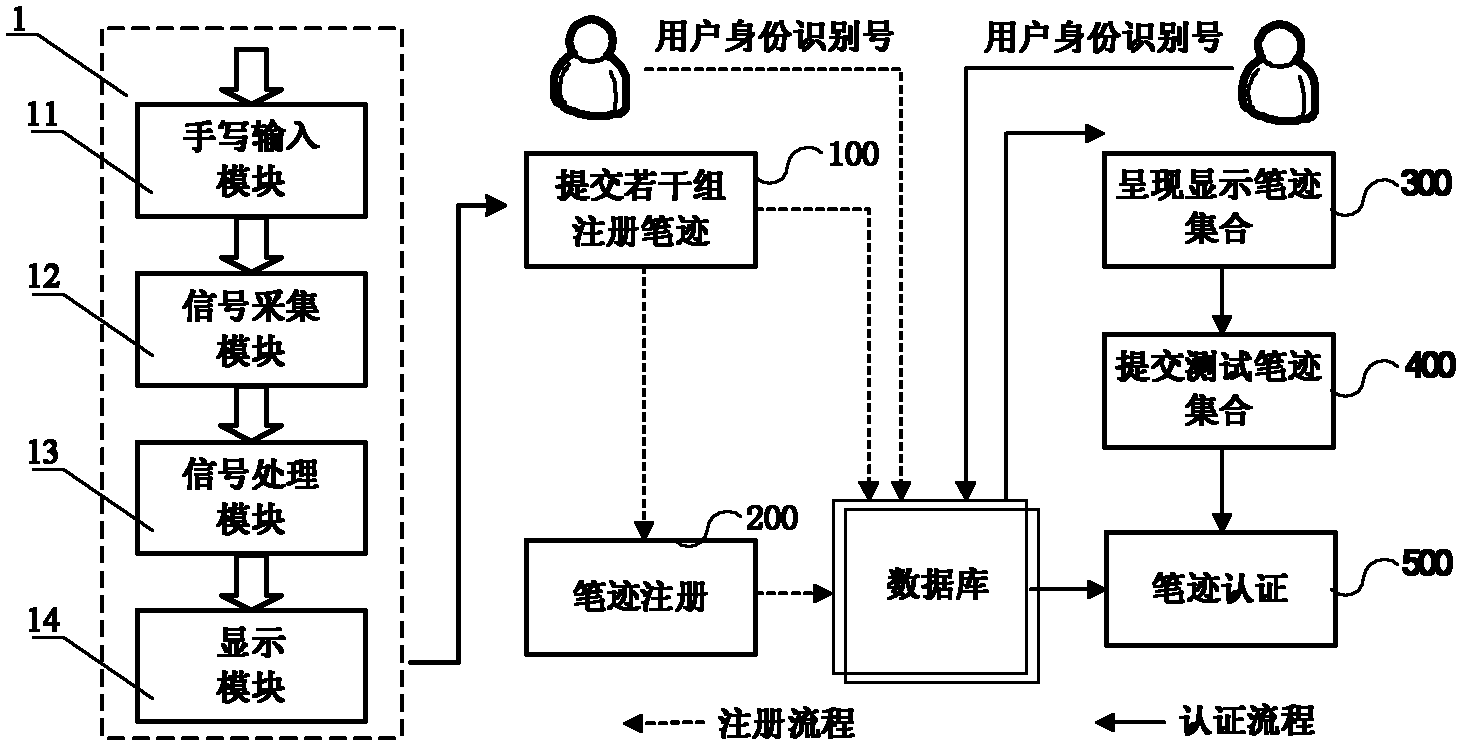
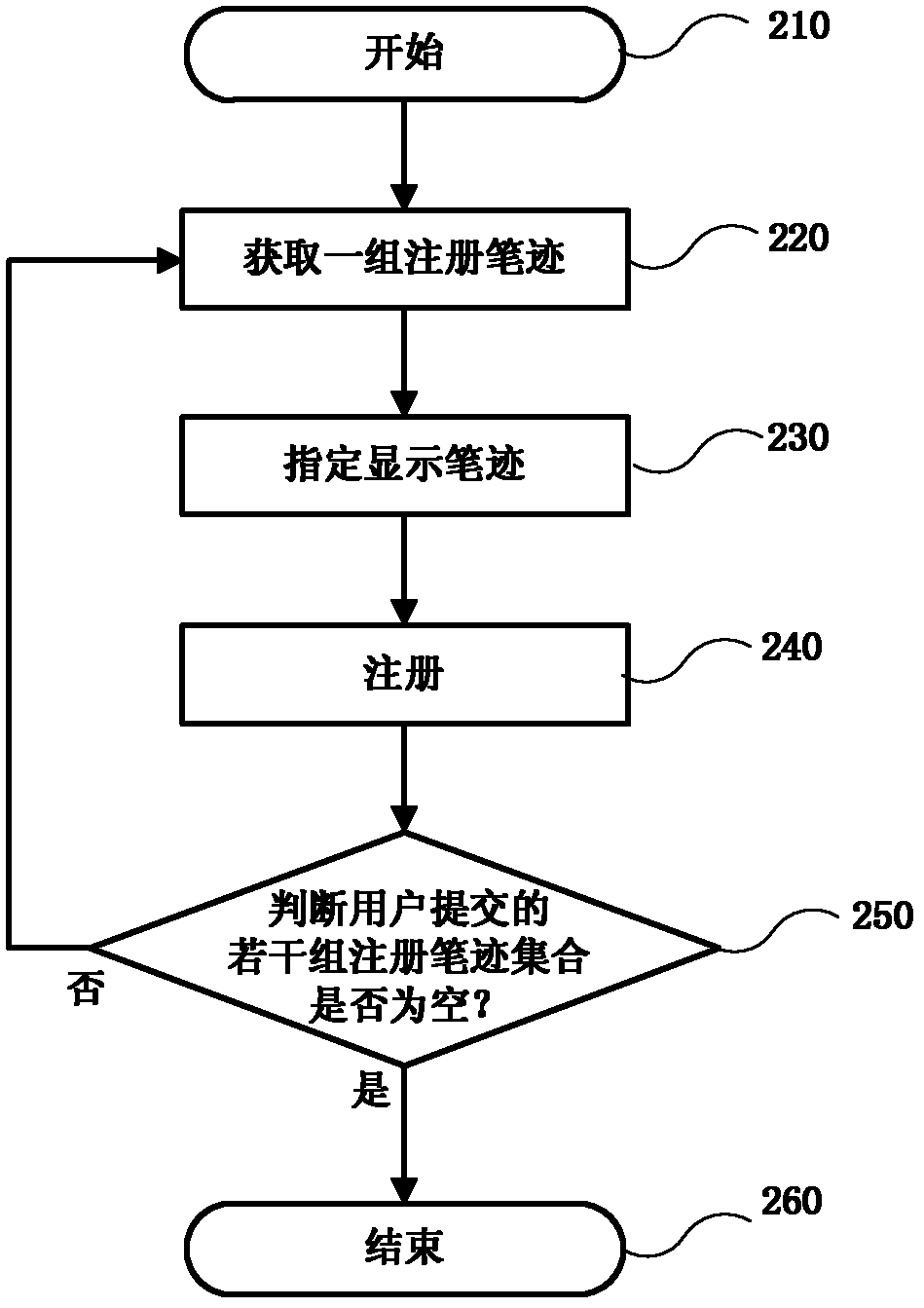
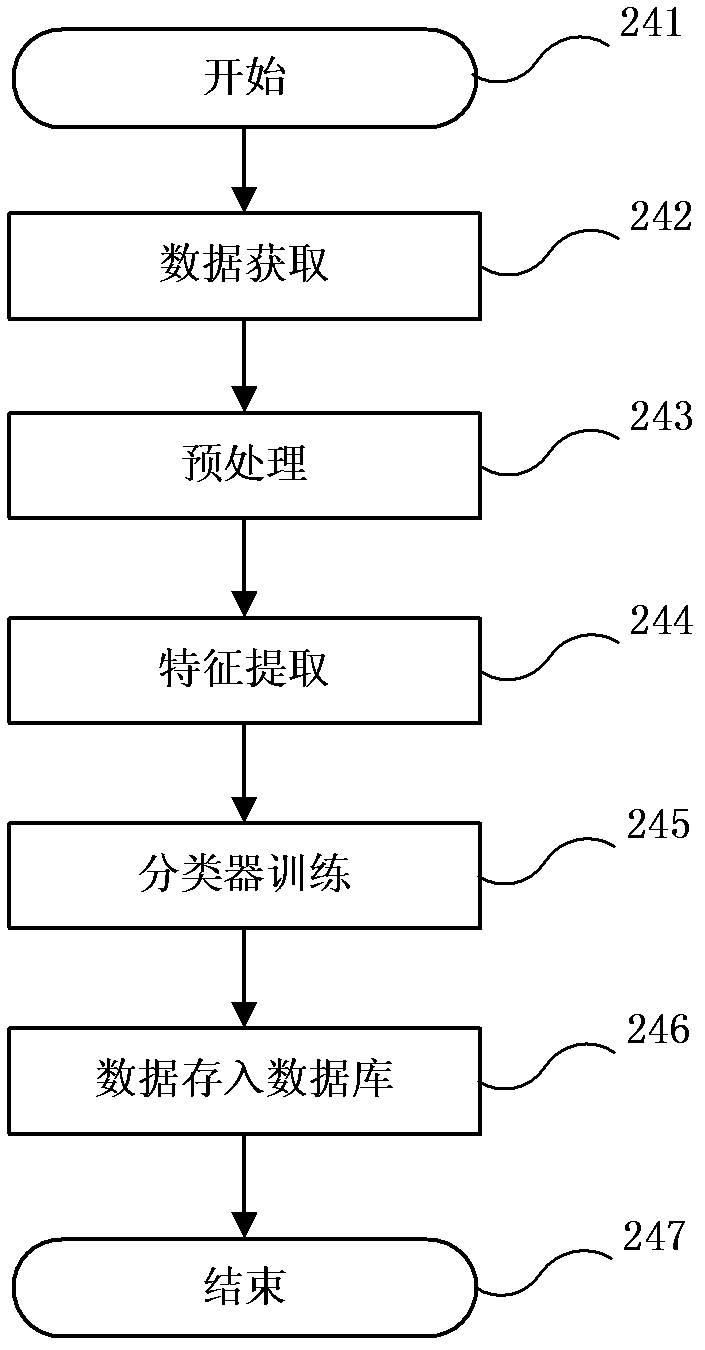
Computer-system-based online handwriting authentication method
ActiveCN102592152AFull imitation of timeResist replay attacksCharacter and pattern recognitionHandwritingConfidentiality
The invention discloses a computer-system-based online handwriting authentication method, which comprises the following steps of: writing and submitting a plurality of groups of registered handwritings through handwriting input equipment by a user, storing the two-dimensional static character pattern position information of display handwritings corresponding to the registered handwritings into a database, and finishing handwriting registration according to the conventional online handwriting authentication method; in the test of a computer system, submitting a generated identification number by the user, randomly selecting a plurality of registered handwritings from the registered handwritings submitted by a corresponding user in a registration stage, and displaying the two-dimensional static character pattern position information of the display handwritings of the selected registered handwritings to the user; and submitting a corresponding test handwriting set at a time within a specified time by the user, finishing test handwriting authentication according to the computer-system-based online handwriting authentication method, and comprehensively making a decision to finish the authentication of the user. The method has the advantages of replay attack resistance, difficulty in the attack of an imitator and active defense; and the neglected shortcomings of dependence on handwriting confidentiality and high imitation rate neglected by the conventional online handwriting authentication method are effectively overcome.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Mimic switch safety flow control device and method
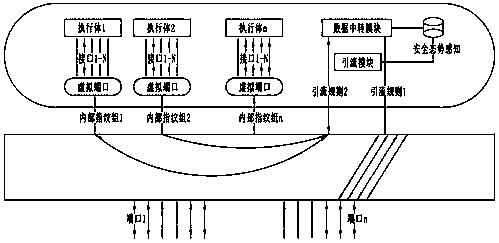
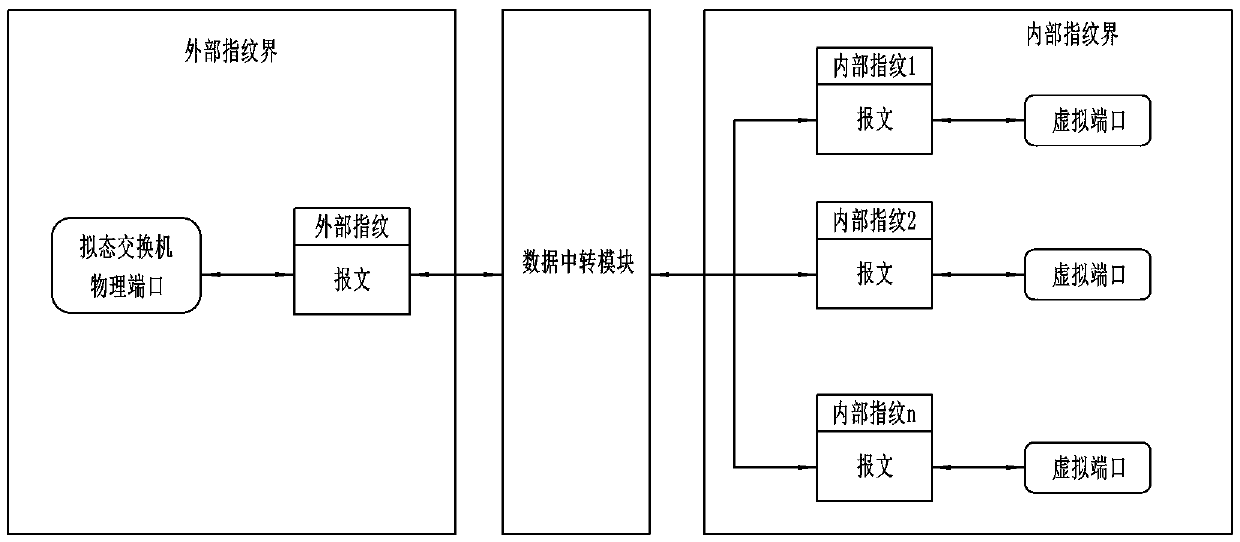
ActiveCN110247928AImprove securityIncrease attack difficultyNetworks interconnectionTraffic volumeFingerprint
The invention provides a mimic switch safety flow control device and method. The device comprises a security situation awareness module, a drainage module and a data transfer module, and the method for controlling the security flow by using the device comprises the following steps that step 1, the security situation awareness module selects features of a security flow message to be controlled and formulates a security strategy; step 2, the drainage module obtains safety flow message characteristics from a mimicry switch physical port or a heterogeneous executor virtual port, and formulates a dynamic drainage strategy according to the message characteristics; and step 3, the data transfer module completes analysis of the message and then forwards the message to a mimicry switch physical port or a heterogeneous executor virtual port. The mimic switch safety flow control method solves the problems that in mimic switch flow forwarding, message distribution, fingerprint conversion and distribution assignment links are large in development difficulty and too low in efficiency, and the attack difficulty of attackers is greatly increased.
Owner:河南信大网御科技有限公司 +1
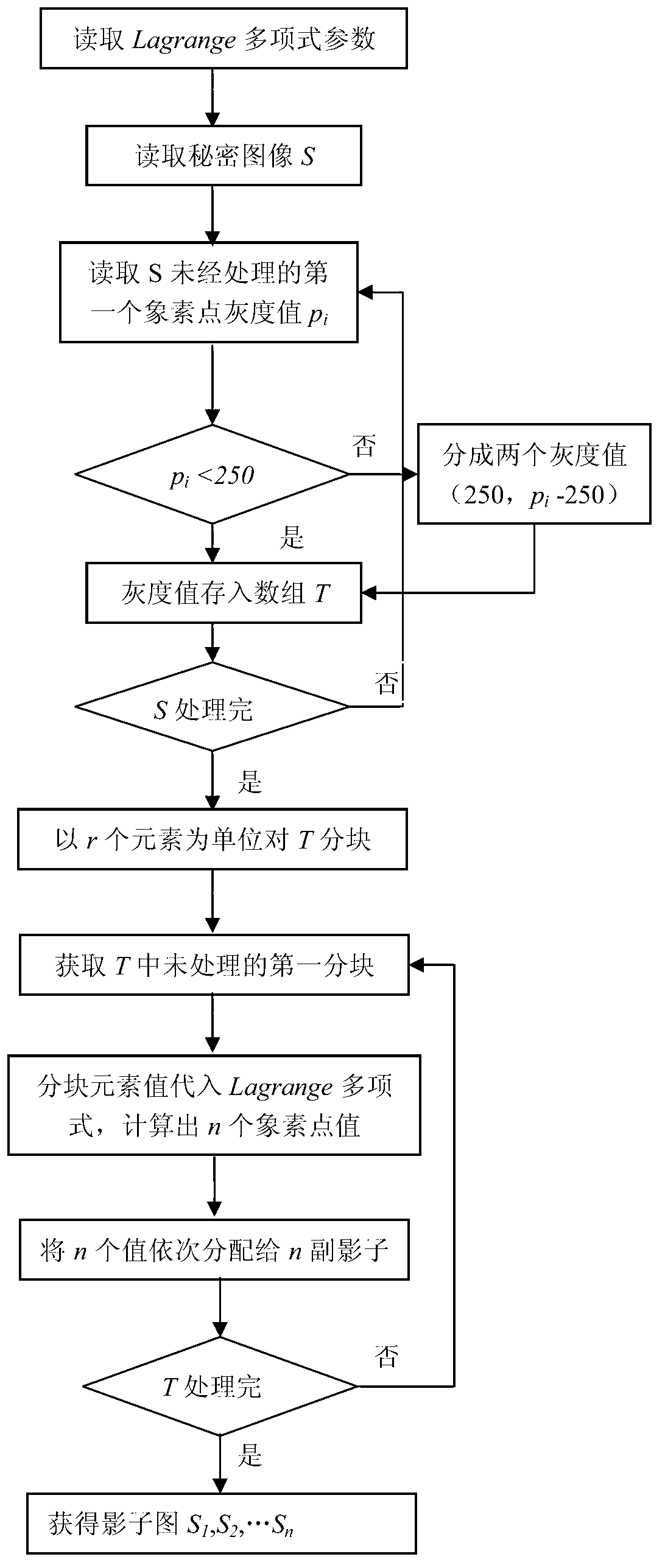
Chaotic-encryption-based medical image share method
ActiveCN103226802AImplement integrity verificationMeet confidentiality requirementsImage data processing detailsSecret shareConfidentiality
The invention discloses a chaotic-encryption-based medical image share method which comprises a secret image breakdown step, a chaotic image encryption step, a chaotic image decryption step and a secret image recovery step. According to the invention, a threshold secret share scheme is utilized to divide an image into n shadow images, the chaos principle is utilized to encrypt the n shadow images, the encrypted shadow images have the statistical property of white noise, and the collected r shadow images are utilized to recover the secret image. The chaotic-encryption-based medical image share method facilitates data storage and transmission, ensures confidentiality and integrity of significant images, and has strong anti-attack capacity.
Owner:CENT SOUTH UNIV
Side-channel attack resisting processor architecture based on random instruction delay
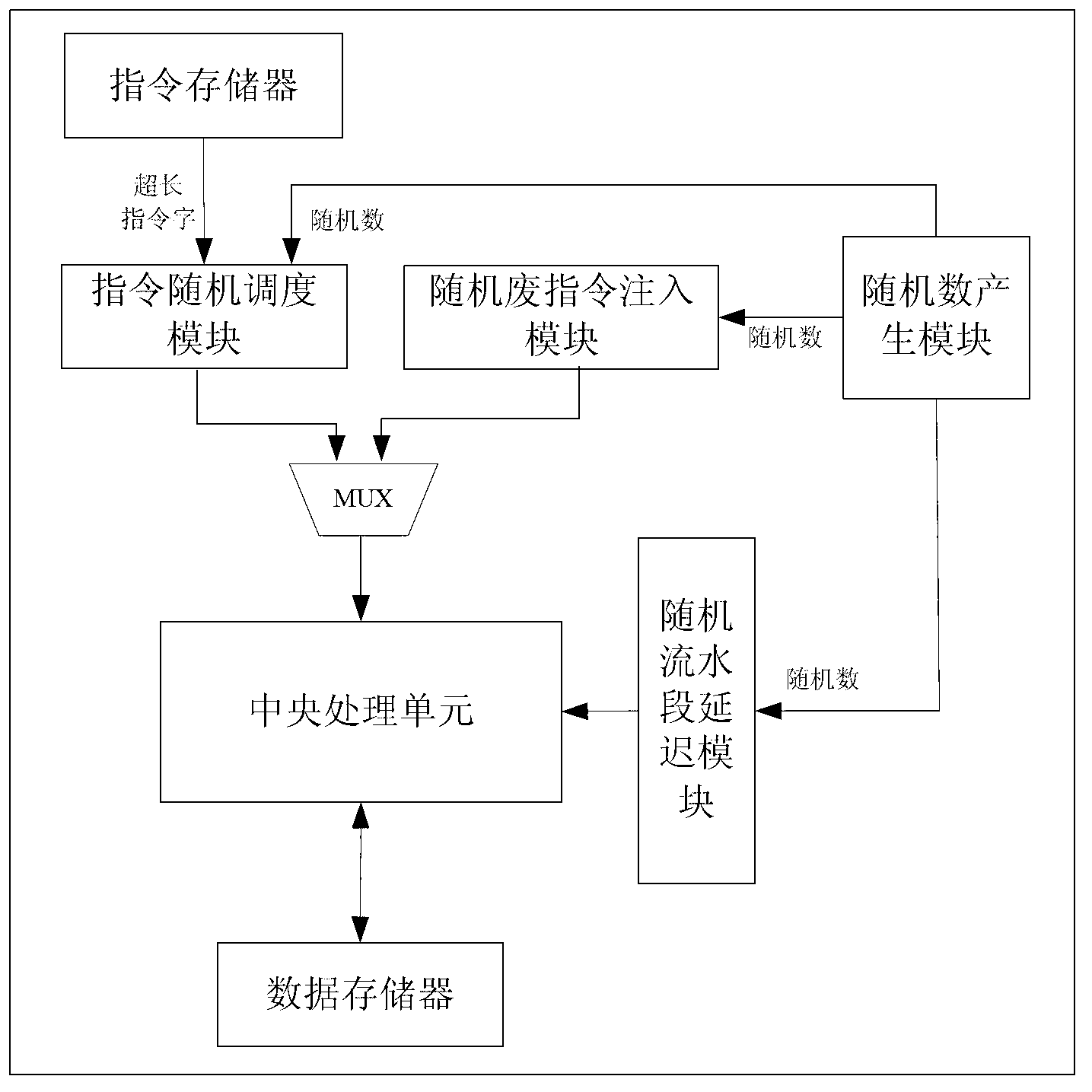
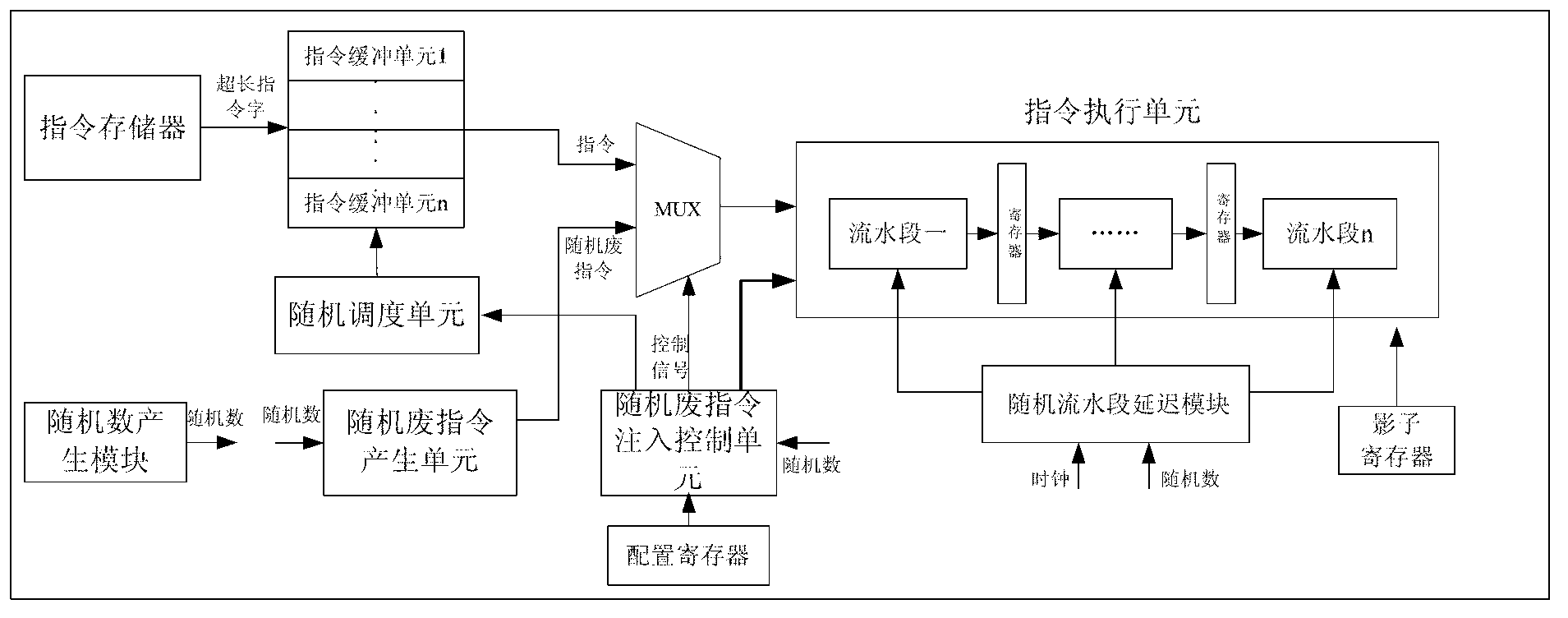
ActiveCN103324467AReduce signal to noise ratioIncrease attack difficultyConcurrent instruction executionInternal/peripheral component protectionInstruction memoryStatistical analysis
The invention discloses a side-channel attack resisting processor architecture based on random instruction delay. The architecture is that an instruction memory is connected with an instruction random scheduling module, a central processing unit is connected with a multi-channel selector, a random flowing water section delay module and a data memory respectively, the multi-channel selector is connected with the instruction random scheduling module and a random waste instruction injection module respectively, and a random number generating module is connected with the random waste instruction injection module, the instruction random scheduling module and the random flowing water section delay module respectively. The side-channel attack resisting processor architecture enables a specific operation execution time point of side-channel attack not to be confirmed through an instruction random scheduling and out-of-order execution mode, a random waste instruction injection mode, a random flowing water section operation delay mode and the like, accordingly enables statistic analysis to be difficult to perform, greatly enhances the side-channel attack resisting capacity of a system and avoids cryptographic algorithm decryption caused by leakage of side-channel information.
Owner:戴葵
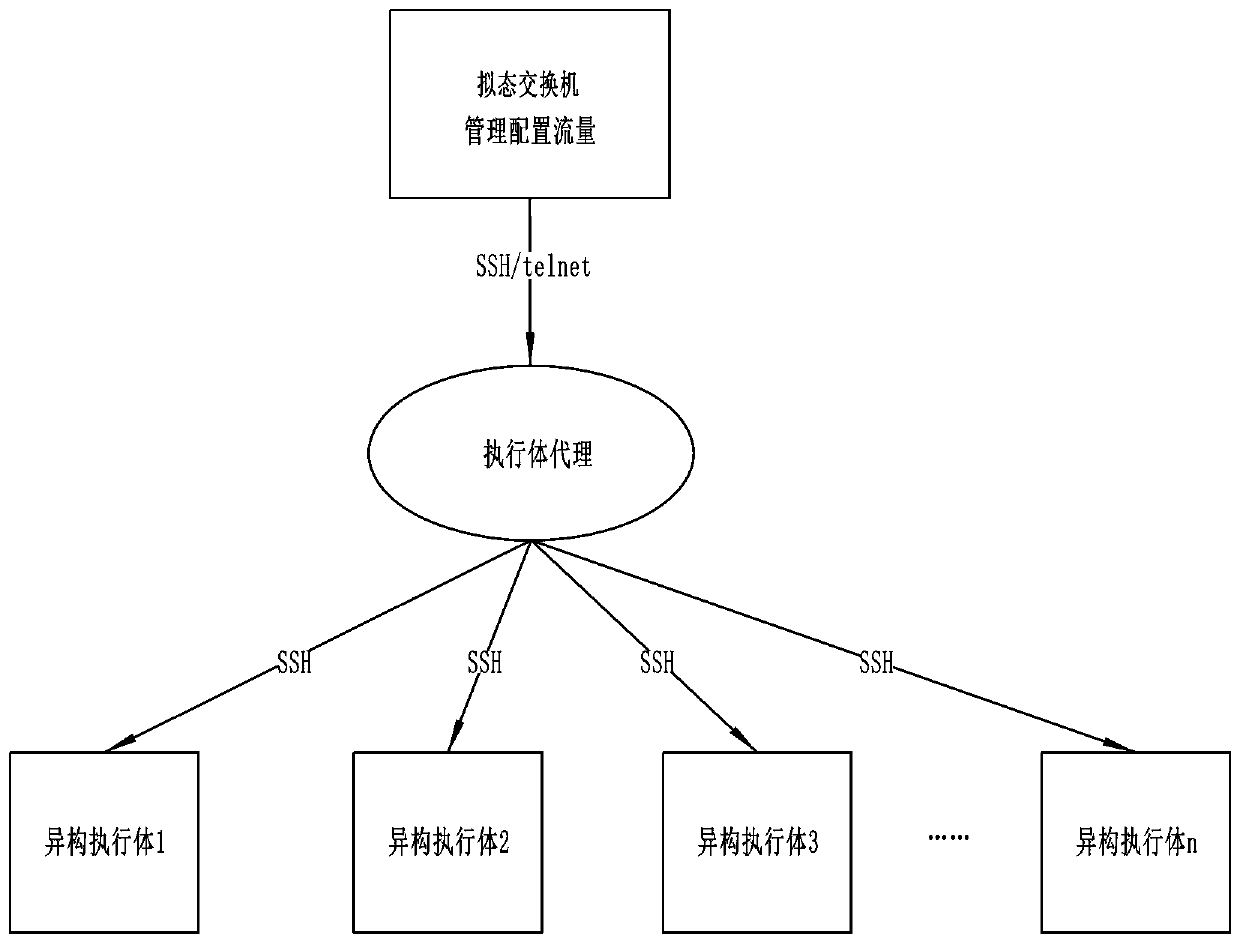
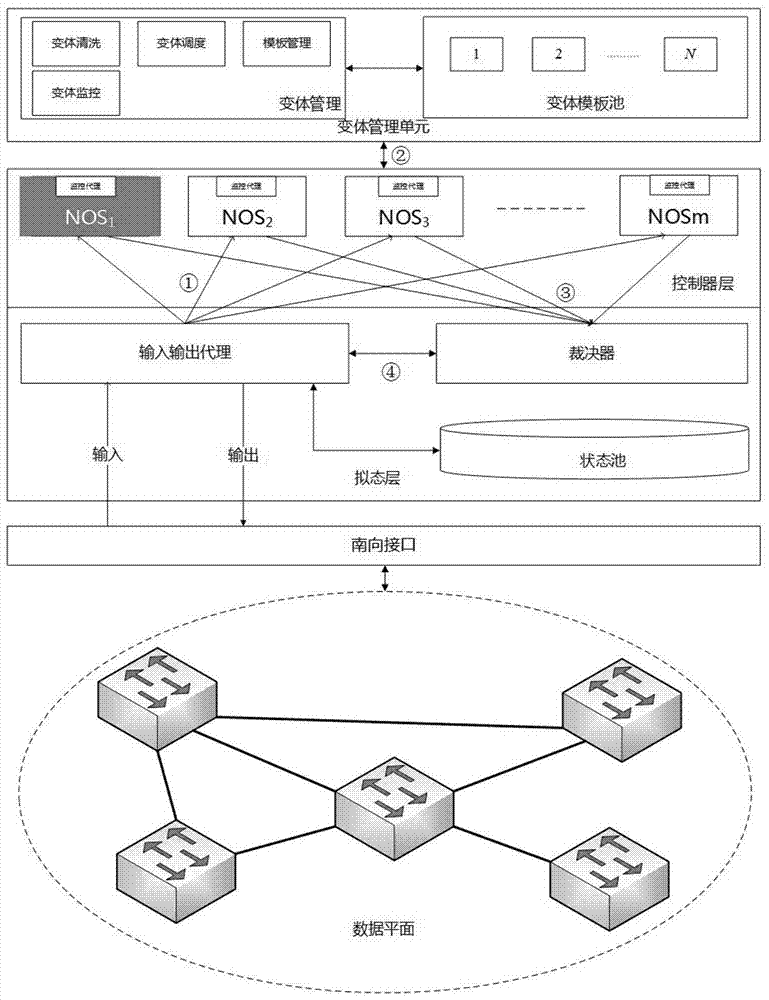
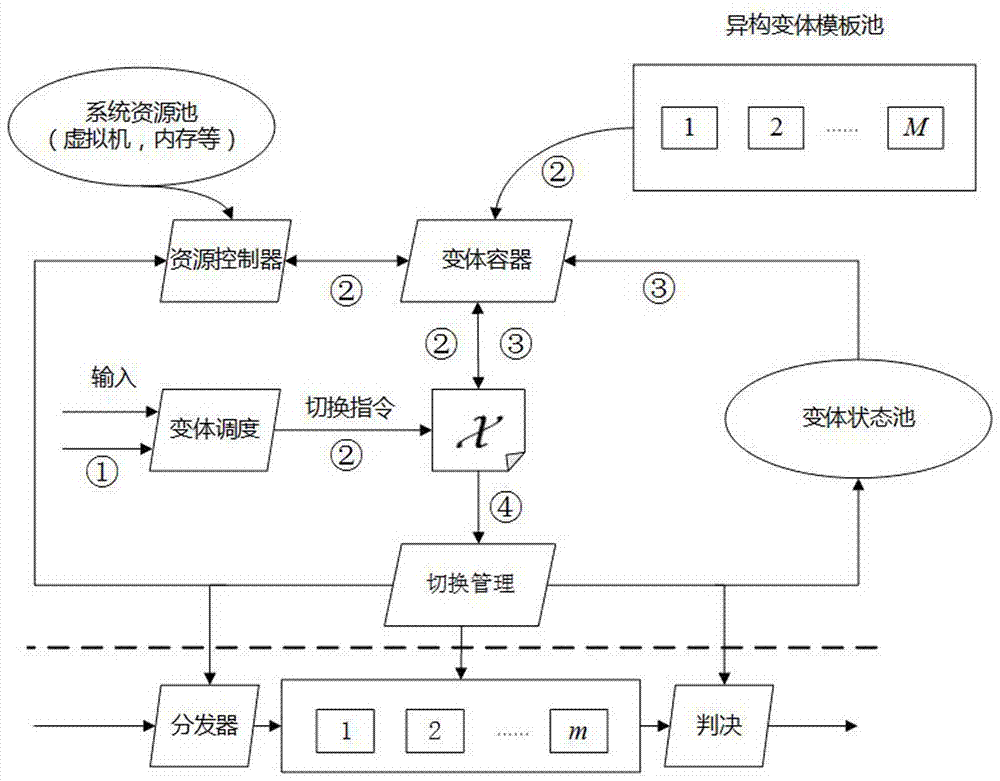
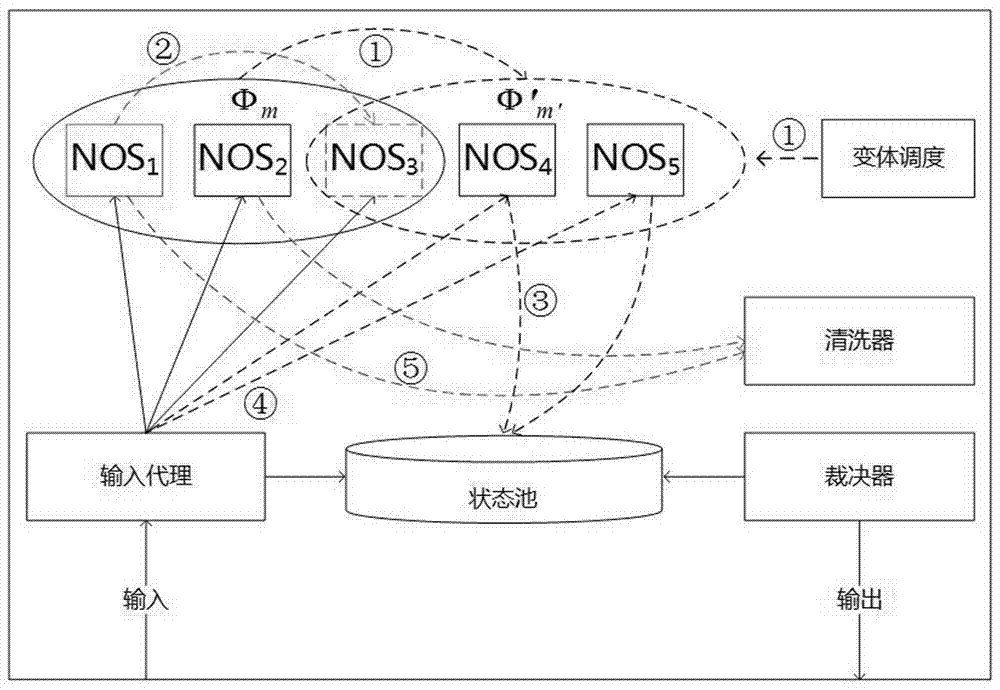
Mimicry network operating system, and construction device and method
ActiveCN107360135AImprove securityIncrease attack difficultyTransmissionNetwork operating systemOperational system
The invention discloses a construction device of a mimicry network operating system. The construction device includes a variant management unit, an NOS unit and a mimicry unit. The variant management unit is composed of a variant template pool and a variant management sub unit. The NOS unit is composed of multi-template instantiated NOSs selected from the variation template pool. The mimicry unit receives calculation results from the NOS unit and executes a multi-mode decision. The invention also discloses a method based on the construction device of the mimicry network operating system. The method includes the steps of distributing a message from an underlying network to each heterogeneous network operating system that runs online, detecting the real-time state thereof by a monitoring agent built in each network operating system, and feeding back results to the variant management unit, each running network operating system independently executing the calculation; and subjecting the calculation result from each network operating system to multi-mode decision. The invention also discloses a mimicry network operating system, which comprises a variant template pool, a variant management layer, an NOS layer and a mimicry layer.
Owner:THE PLA INFORMATION ENG UNIV
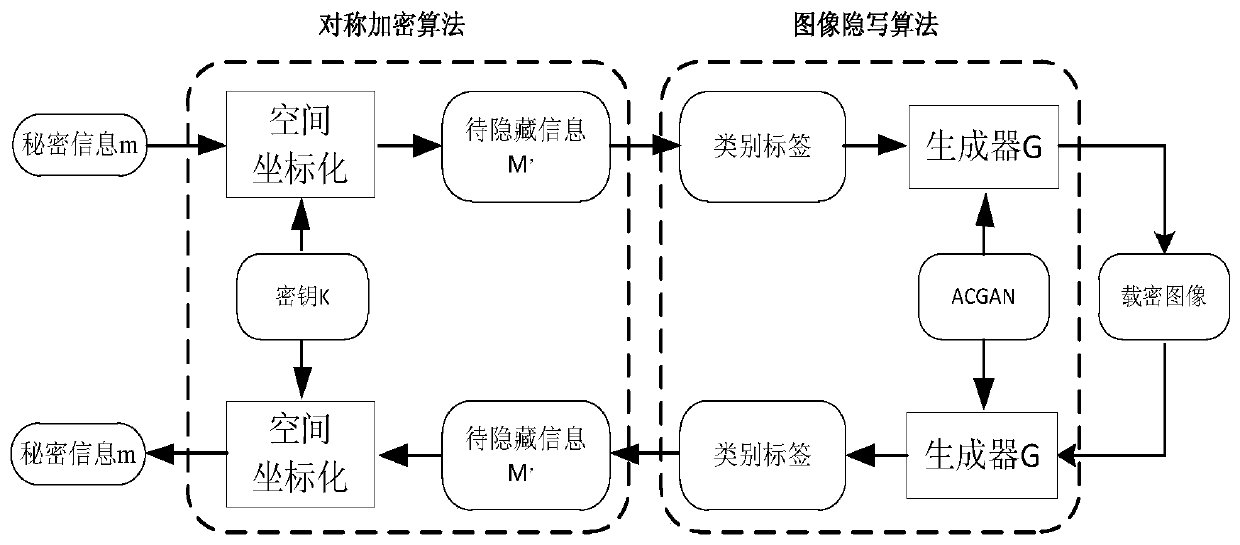
A generative image steganography method based on an adversarial network
ActiveCN109818739AImprove securityEnhanced resistance to steganalysisKey distribution for secure communicationDigital video signal modificationPattern recognitionSteganalysis
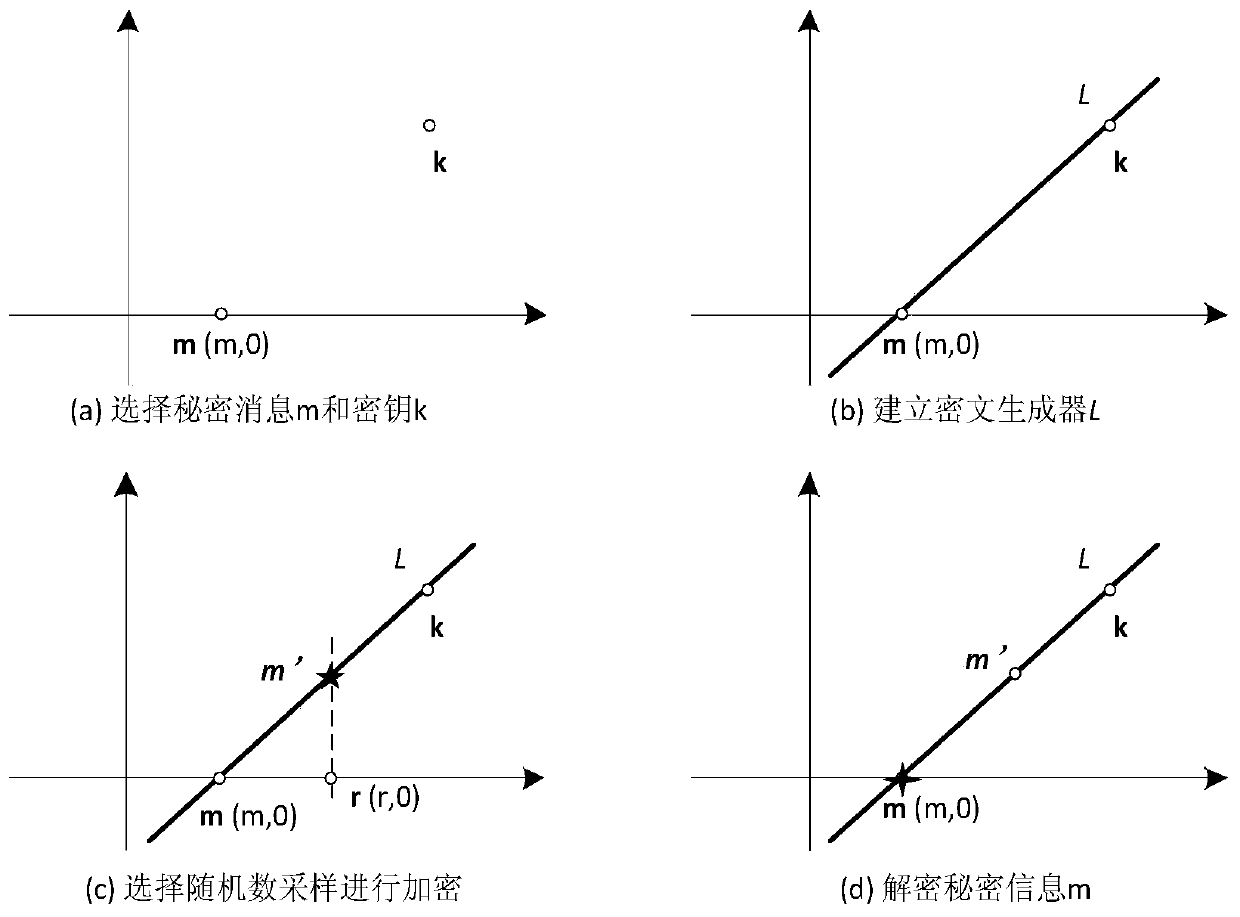
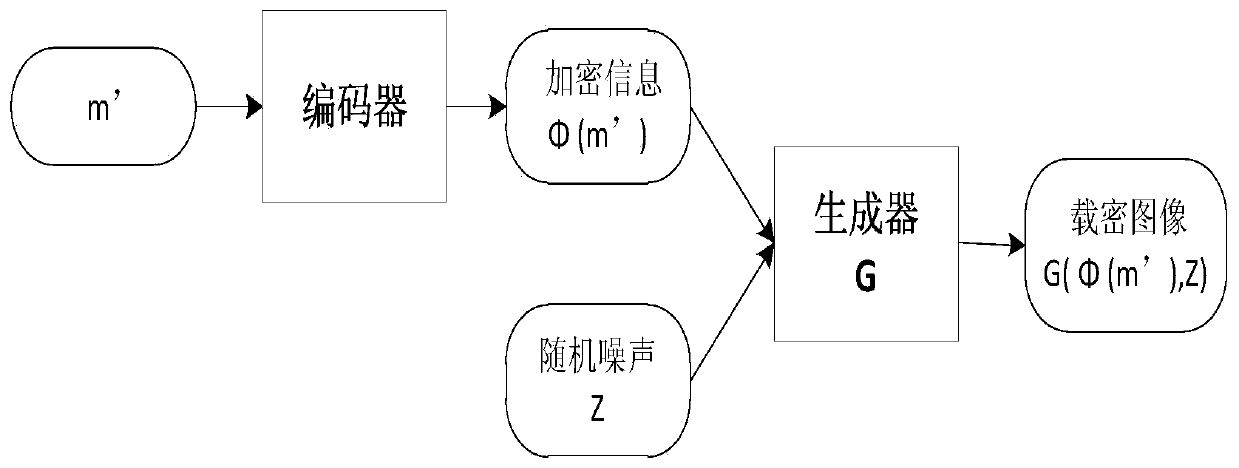
The invention particularly relates to a generative image steganography method based on an adversarial network, which comprises the following steps: a rule table is established, and secret informationto be hidden is converted into coordinate information according to the rule table; According to a two-point one-line principle, a ciphertext generator is established, and ciphertext coordinate point information is obtained; The sender randomly selects the ciphertext coordinate point information, replaces the label information with the ciphertext coordinate point information, inputs the ciphertextcoordinate point information into the generator, and generates a transfer image of a specified category; After receiving the transmission image, the receiver inputs the transmission image into a discriminator to obtain a category label, and then ciphertext information can be extracted; Decrypting is performed to obtain hidden coordinate information according to a two-point one-line principle; Andhidden secret information is obtained by comparing with the rule table, and information extraction is realized. According to the method, steganalysis detection based on statistics can be fundamentallyresisted, the safety of information transmission is improved, and meanwhile the steganalysis resisting capability is greatly enhanced.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Identity authentication method, device and apparatus and data processing method
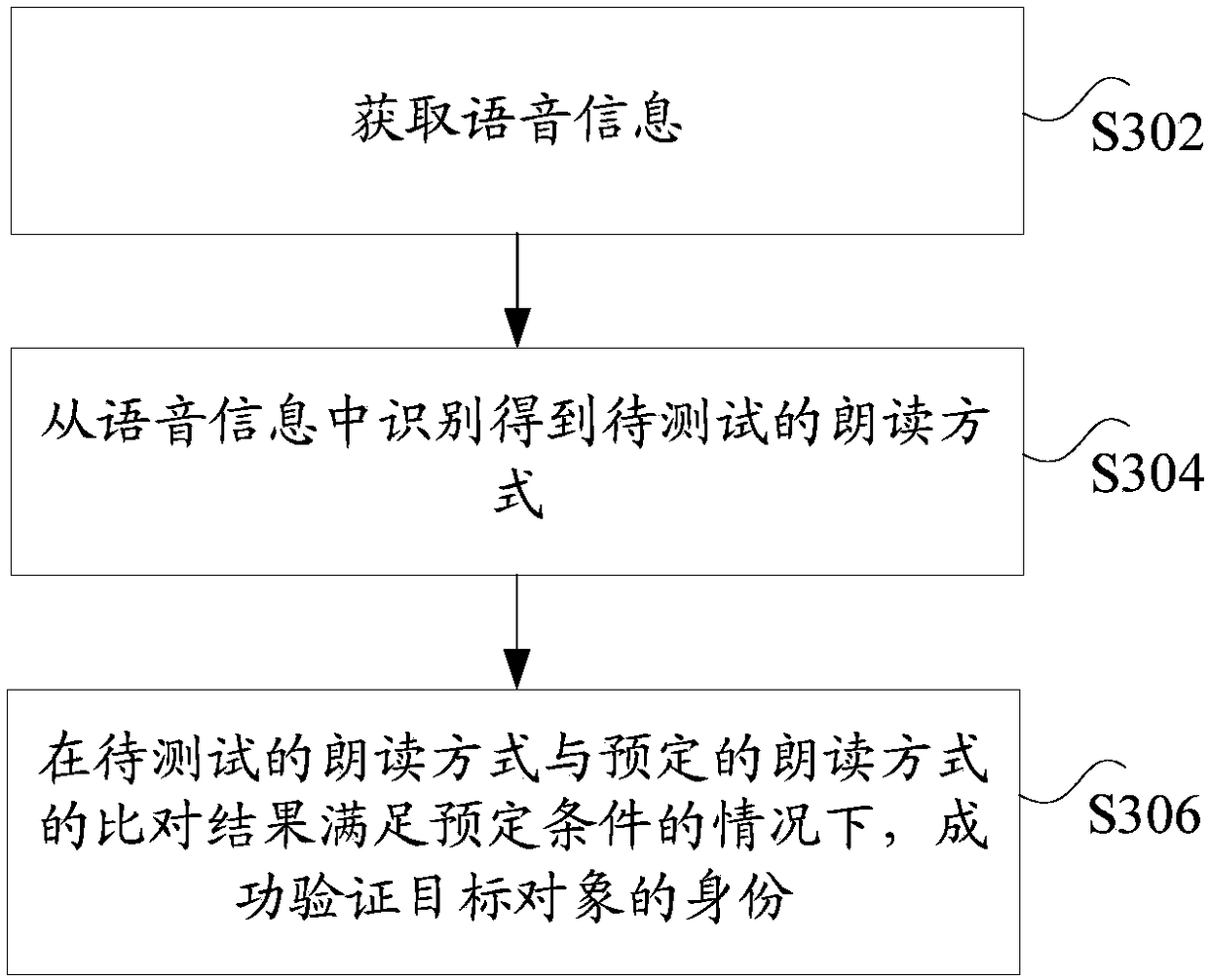
InactiveCN109218269AIncrease attack difficultyImprove securitySpeech analysisDigital data authenticationLiving bodyAuthentication system
The present application discloses an identity authentication method, device and apparatus and a data processing method. The method includes: acquiring voice information, wherein the voice informationis information generated by a target object reading the predetermined content according to a predetermined reading mode; identifying a reading mode to be tested from the voice information; and when acomparison result of the reading mode to be tested and the predetermined reading mode satisfies a predetermined condition, successfully verifying the identity of the target object. The method solves the technical problem that the user information in an existing living body detection scheme is easy to imitate so that the security of the authentication system has a hidden danger.
Owner:ALIBABA GRP HLDG LTD
Encryption method and decryption method for file, and encryption and decryption system
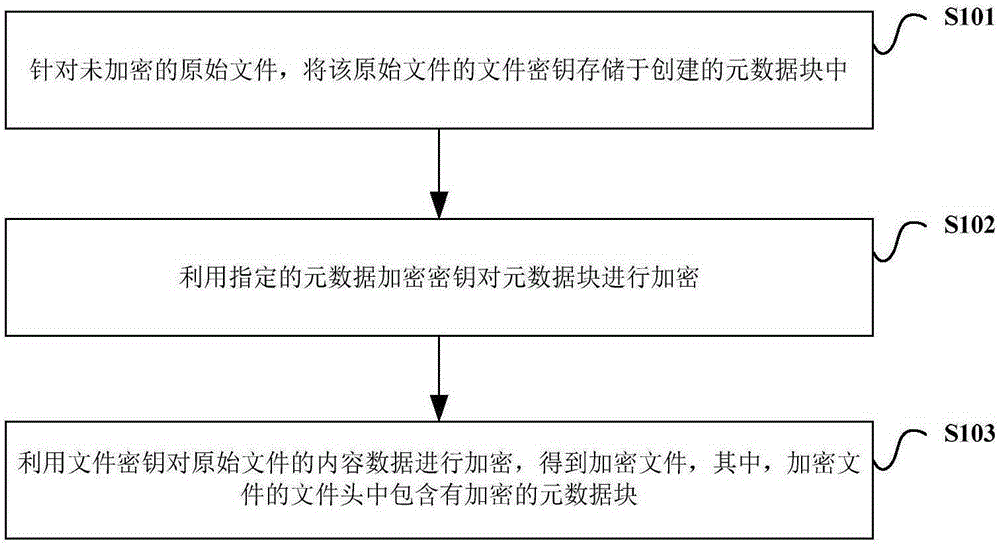
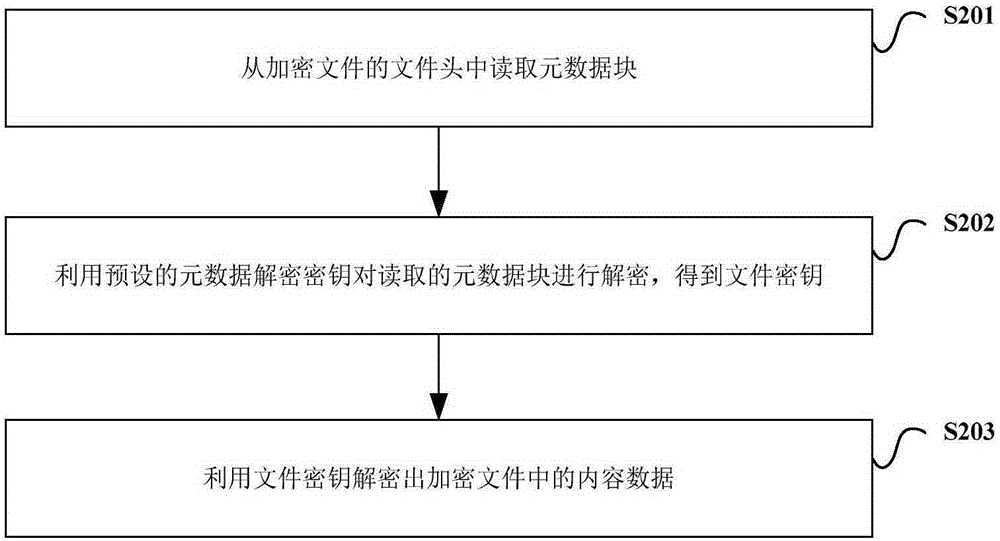
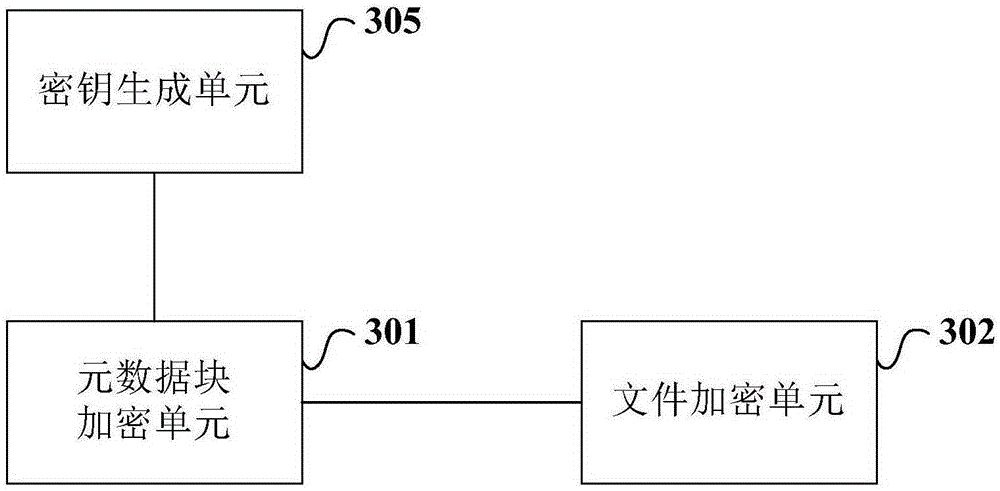
InactiveCN105187204AImprove securityDoes not affect normal operationKey distribution for secure communicationComputer hardwareComputer science
The invention provides an encryption method and a decryption method for a file, and an encryption and decryption system. The encryption method comprises the following steps of storing a file key of an original file into a created metadata block for the unencrypted original file; utilizing an appointed metadata encryption key to encrypt the metadata block; and utilizing the file key to encrypt content data of the original file to obtain an encrypted file, wherein a file header of the encrypted file includes the encrypted metadata block. Through applying the invention, management of the encrypted file is facilitated, and security of the file is improved.
Owner:BEIJING YUANXIN SCI & TECH
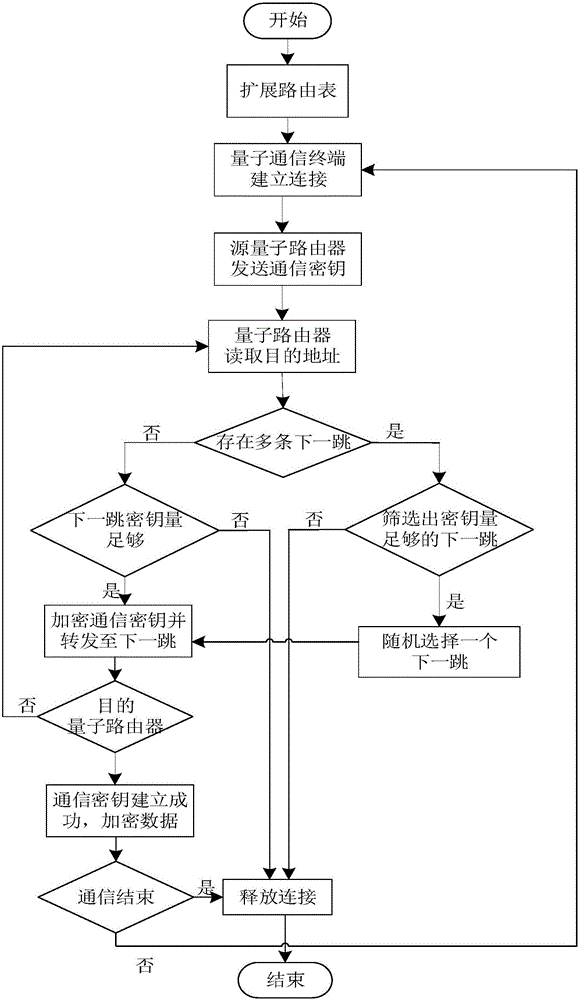
Random routing method in quantum secret communication network
ActiveCN106230582AReduce consumptionImprove service efficiencyKey distribution for secure communicationData switching networksComputer hardwarePredictability
The invention discloses a random routing method in a quantum secret communication network and mainly aims to solve the problem of low safety of a secret key caused by a unique negotiation path and high predictability of the path of a communication secret key in the prior art. The technical scheme of the random routing method are that by improving a distance vector-based routing algorithm expansion routing list, multiple next-hops are added to a quantum router arriving at a certain target address, and thus, multiple shortest paths from a source quantum router to a target quantum router are obtained; and by considering the secret key quantity on a link, on the condition that multiple next-hop routing nodes with enough secret key quantity exists, a next-hop is randomly selected from the next-hop routing nodes and the communication secret key is transmitted hop by hop until the communication secret key is transmitted to the target quantum router, thereby achieving random performing of secret key negotiation on multiple paths. According to the invention, secret key consumption is reduced, safety of the secret key during the secret key negotiation process is improved; and the random routing method can be used for the quantum secret communication network.
Owner:XIDIAN UNIV
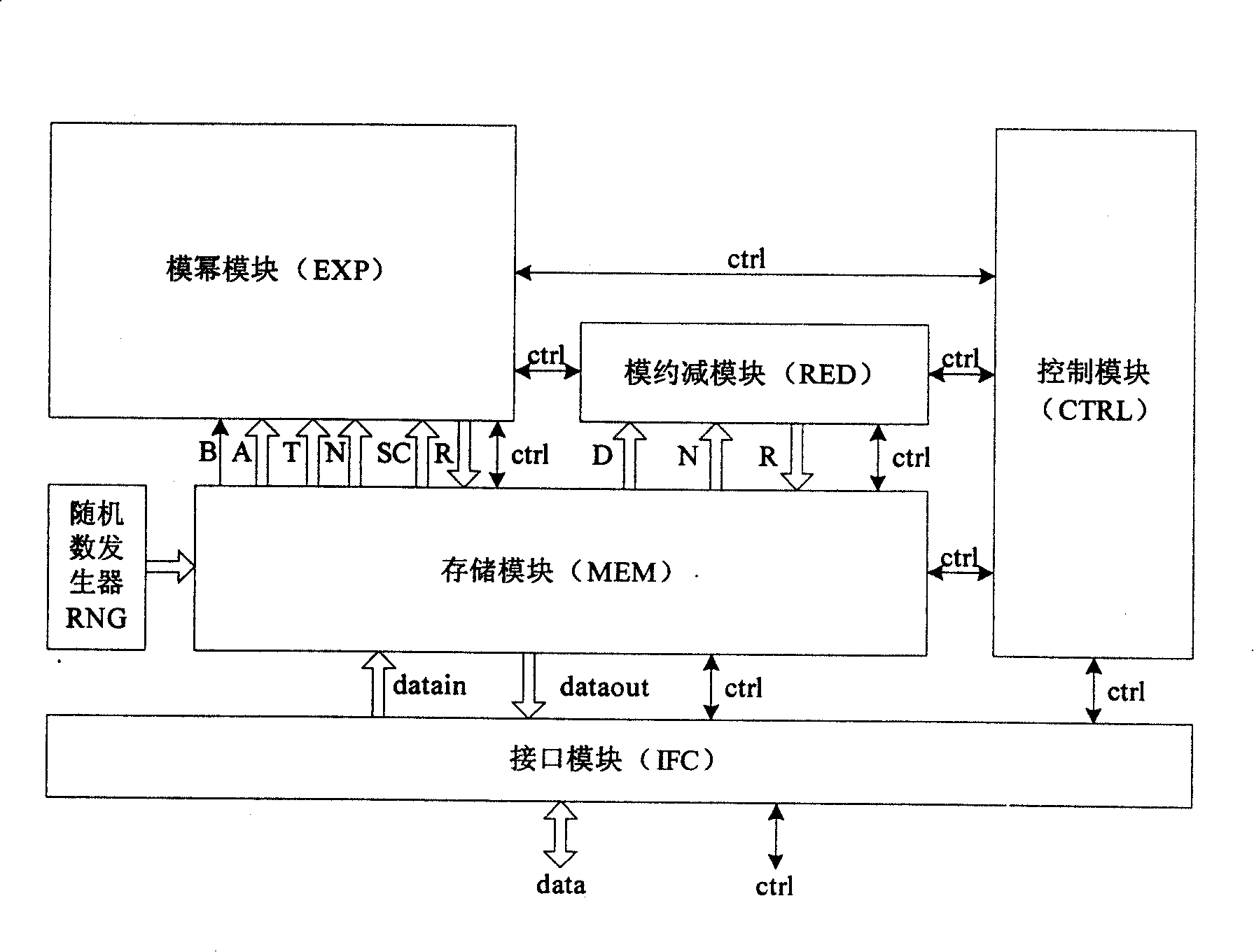
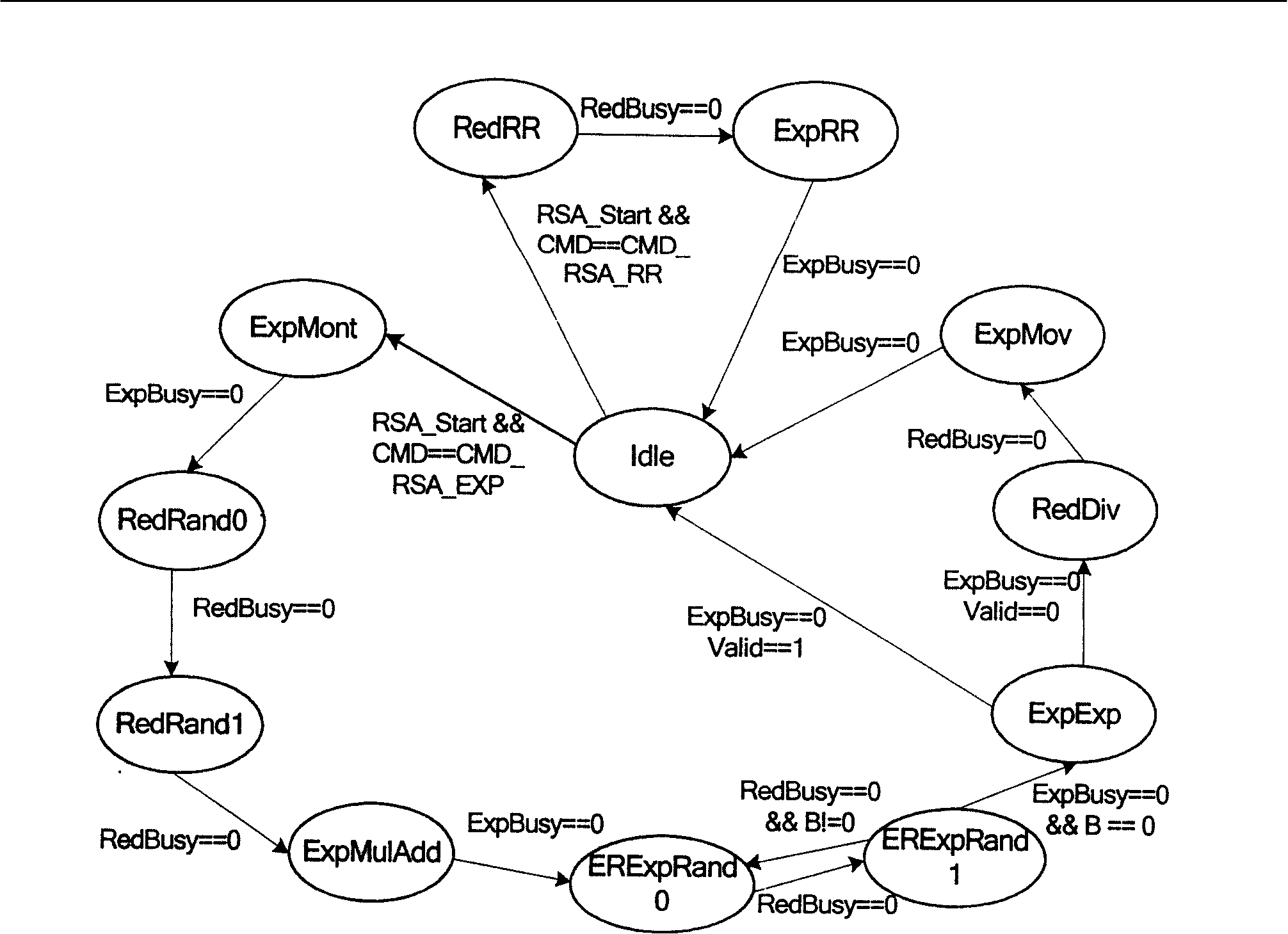
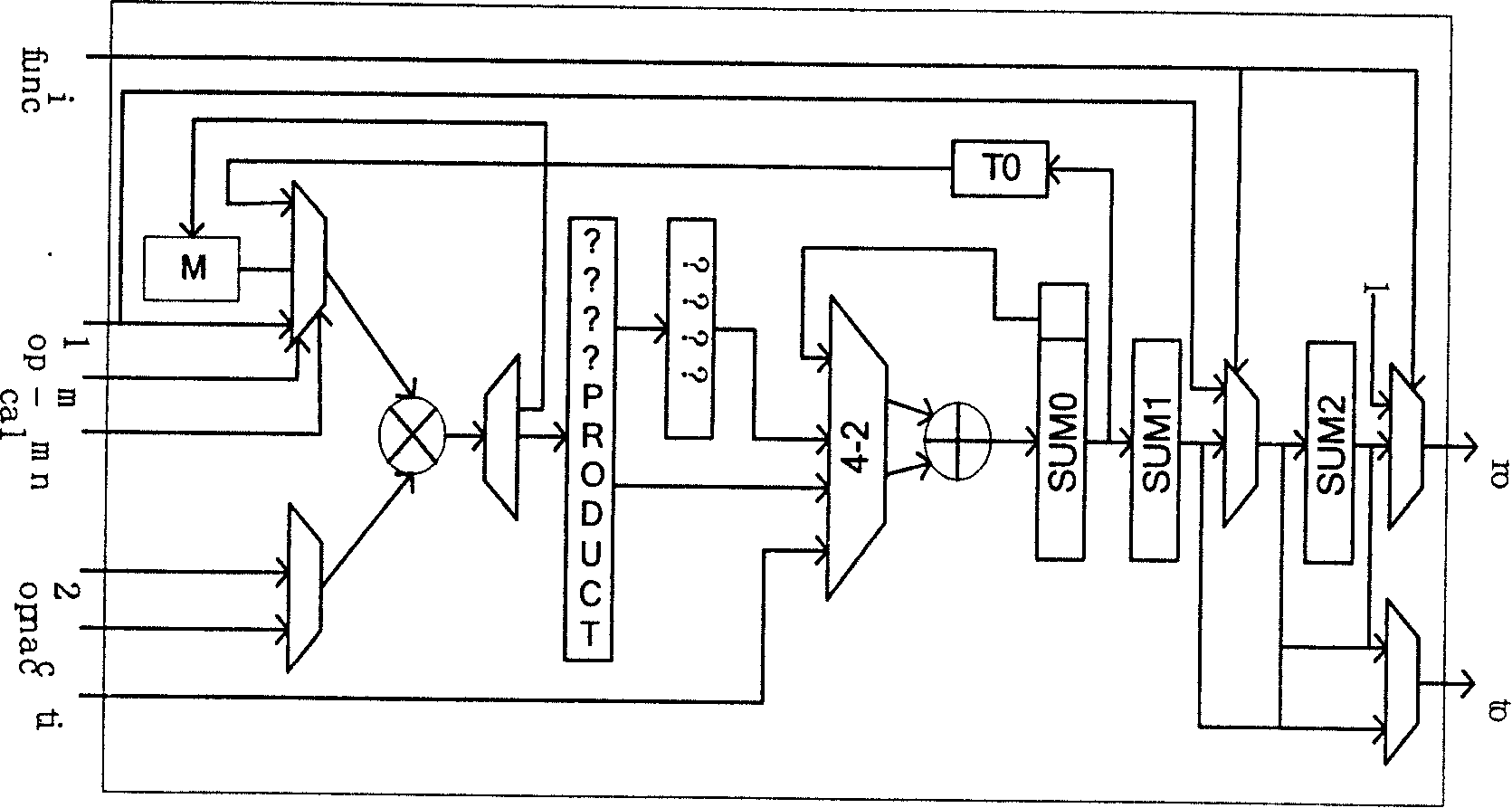
Anti-bypass attack algorithm and chip thereof
InactiveCN101196964AEnsure safetyIncrease attack difficultyPublic key for secure communicationInternal/peripheral component protectionComputer moduleModular exponentiation
The invention discloses a chip of an RSA arithmetic against side-channel attack and the arithmetic, which relates to the technology field of information security. The chip comprises an interface module for finishing the interaction of data inside and outside of the chip, a random number module (RNG) for generating random number, a memory module (MEM) for storing high number, middle and final results needing to be computed by RSA, a modular exponentiation module (EXP) for completing modular exponentiation computation adopting MIST arithmetic, a module (RED) for completing common modular reduction and computing remainder and factor module reduction and a flow for controlling the whole RSA design to make modular exponentiation computation and module reduction computation operate in parallel and realize control module (CTRL) of randomized module reduction by calling RED. The invention puts forward safer module reduction arithmetic RandRed by introducing random number to render the invention the characteristics of no statistical character and higher attack difficulty.
Owner:SHANGHAI AISINOCHIP ELECTRONICS TECH
Defense method for selective forwarding attack in sensor network
InactiveCN101316266AIncrease attack difficultyImprove securityData switching by path configurationSensor nodeSelective forwarding attack
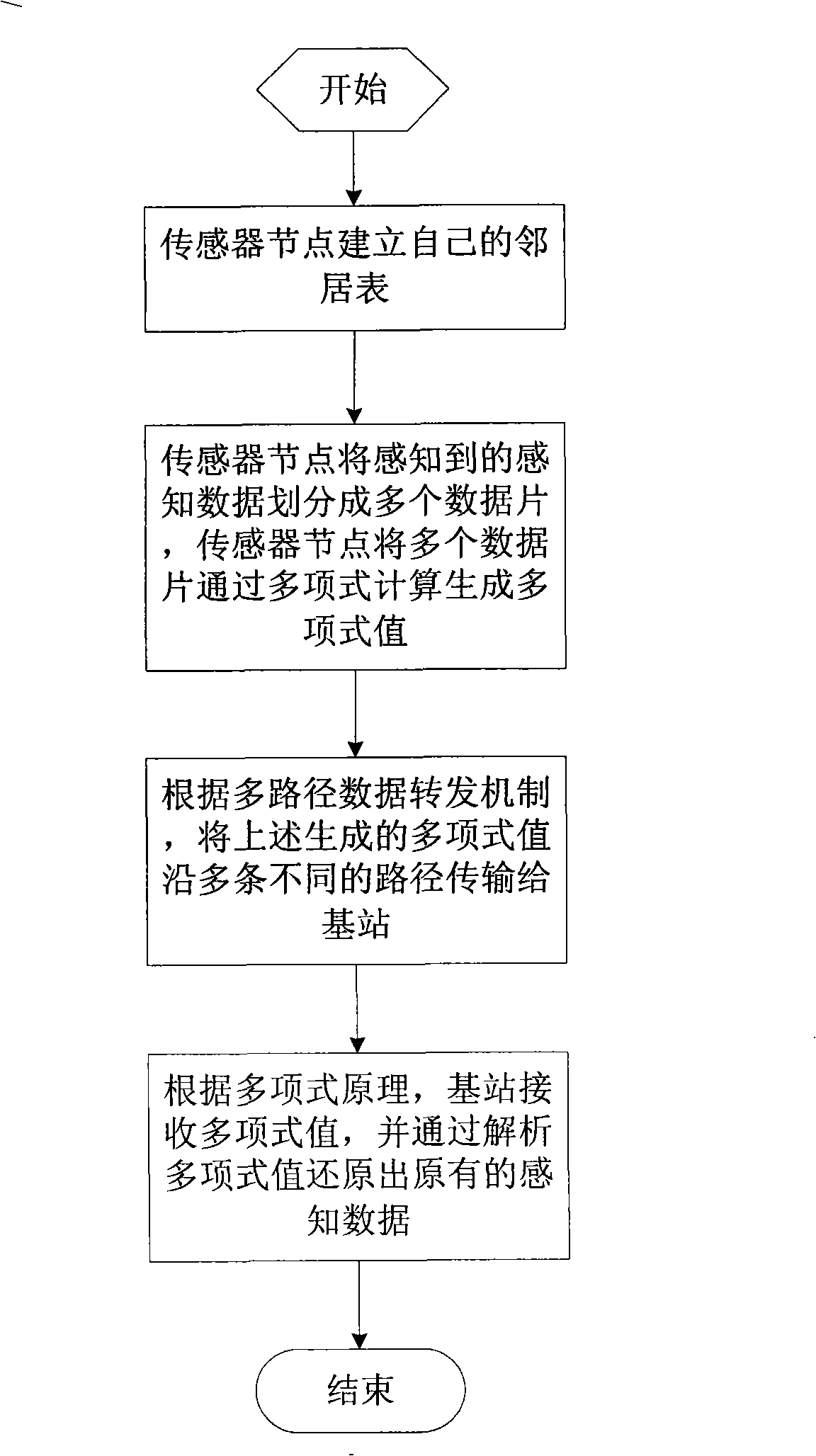
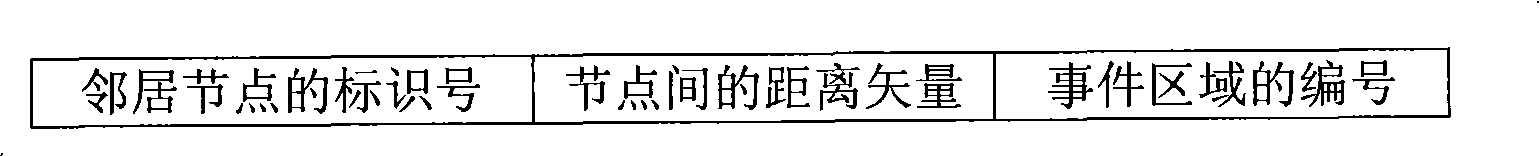
The invention discloses a method for defending selective transmission attack in a sensor network, which includes the following steps: a sensor node establishes a neighbor table of the sensor node; the sensor node divides sensed perception data into a plurality of data pieces according to a polynomial principle, and the data pieces generate polynomial values by polynomial calculation; the polynomial values are transmitted to a base station along a plurality of different paths according to a multipath data transmission mechanism; the base station receives the polynomial values according to the polynomial principle, then analyzes and restores the original perception data. The method of the invention has the advantages that the perception data are divided into smaller data pieces, and different polynomial values are generated by the polynomial calculation so that a transmission node cannot acquire the content, thus reducing the data communication volume and the receiving delay and preventing the malign mode from falsifying a data package; when the multipath data transmission mechanism is used for transmitting the data package, a next jump node is dynamically selected from the neighbor table to transfer the data package, thus increasing the attacking difficulty of the malign nodes.
Owner:宁波中科集成电路设计中心有限公司
Dynamic signal based security protection apparatus and method and POS machine
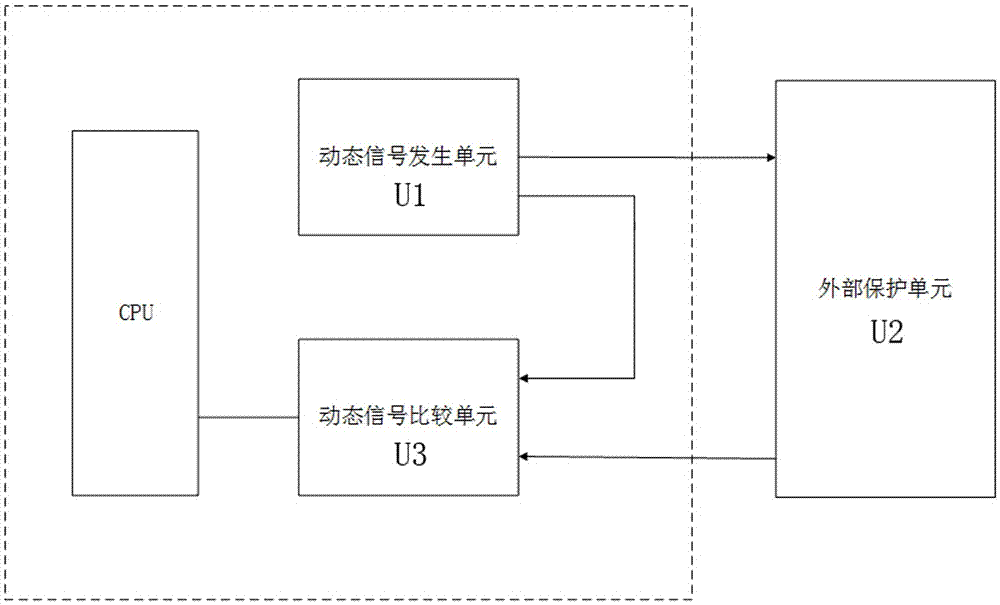
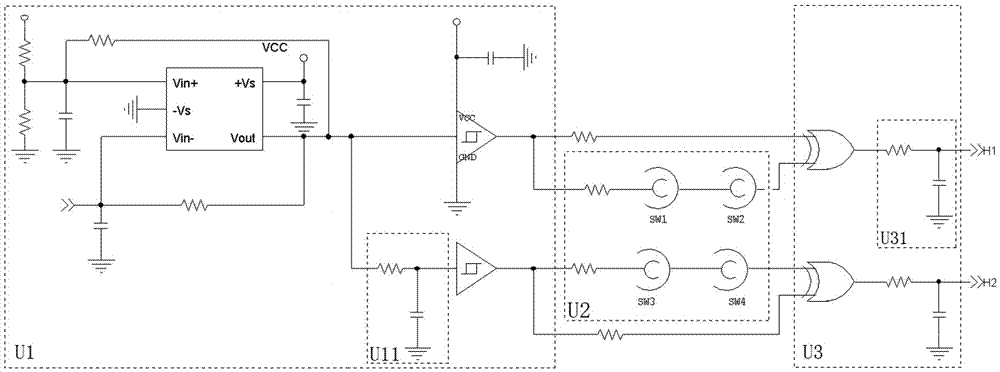
ActiveCN105447413AImprove anti-interference abilityIncrease attack difficultyCash registersInternal/peripheral component protectionX-machineGenerating unit
The technical scheme of the invention comprises a dynamic signal based security protection apparatus and method and a POS machine. The apparatus comprises a dynamic signal generating unit, an external protection unit, and a dynamic signal comparison unit. The dynamic signal generating unit is connected to the external protection unit, and output a dynamic signal to the external protection unit. The dynamic signal comparison unit is separately connected to the dynamic signal generating unit and the external protection unit, and outputs, via an output end, a comparison result of dynamic signals transmitted by the dynamic signal generating unit and the external protection unit. The method comprises the steps of: the dynamic signal generating unit providing a dynamic signal with a waveform that dynamically changes over time to the external protection unit and the dynamic signal comparison unit; the dynamic signal comparison unit receiving a reference dynamic signal sent by the dynamic signal generating unit and the dynamic signal that passes through the external protection unit; and the dynamic signal comparison unit outputs a comparison result of the dynamic signals of the dynamic signal generating unit and the external protection unit through the output end. The POS machine comprises the above dynamic signal based security protection apparatus.
Owner:SHENZHEN XINGUODU PAYMENT TECH CO LTD
hardware Trojan horse detection method based on path delay analysis
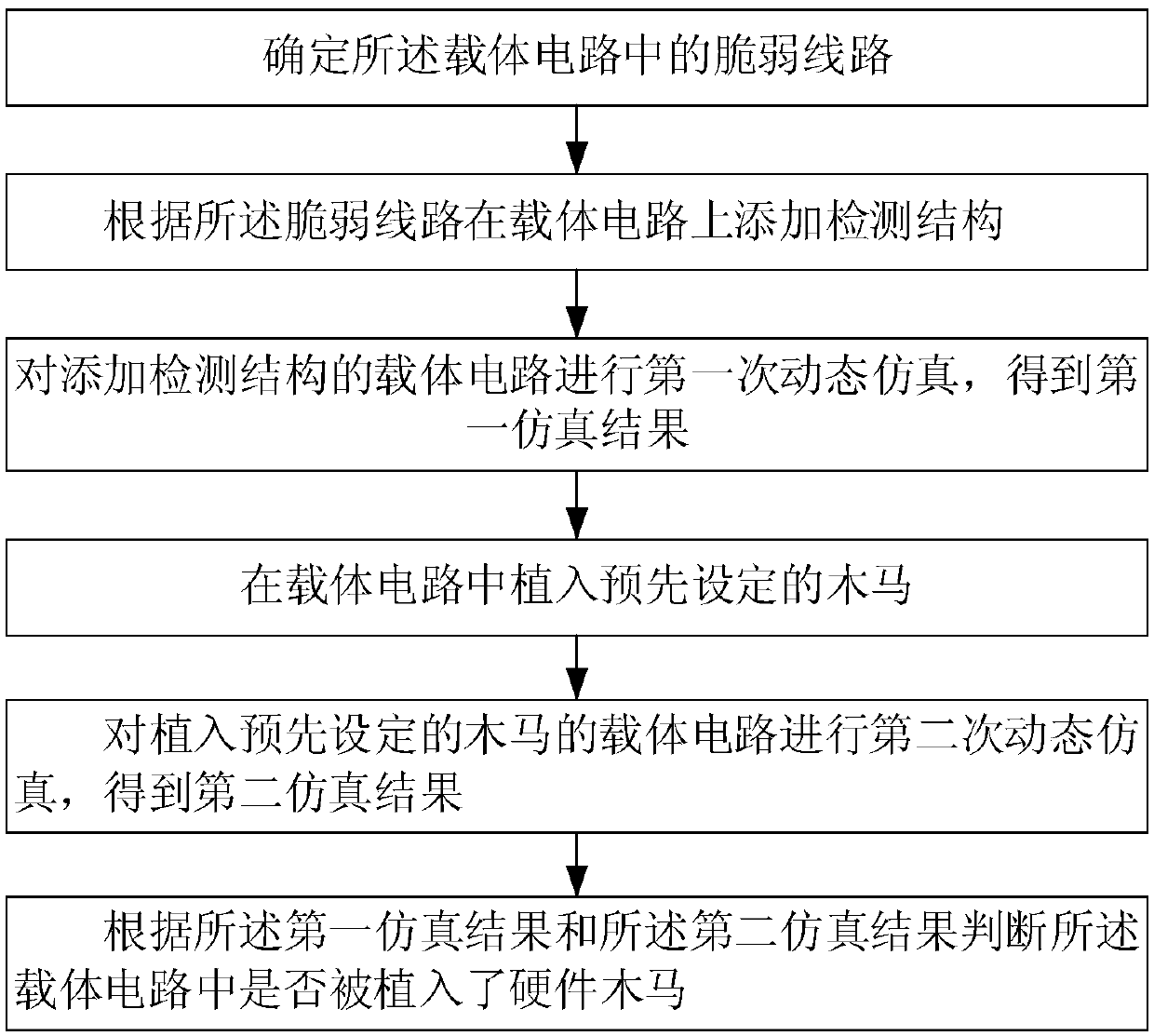
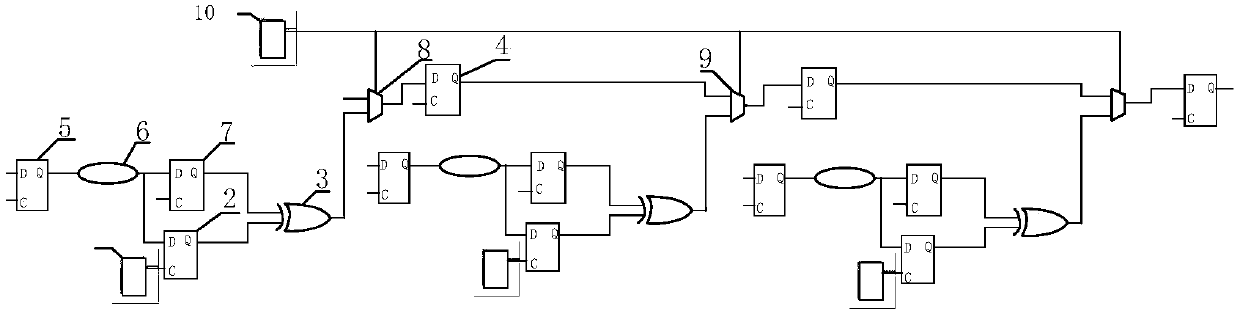
ActiveCN109657464AIncrease credibilityIncrease attack difficultyInternal/peripheral component protectionPlatform integrity maintainanceMultiplexerHardware trojan horse
The invention relates to the technical field of integrated circuit detection, in particular to a hardware Trojan horse detection method based on path delay analysis. The device comprises a detection structure, and the detection structure comprises a detection module, a result output module and a data selector which are connected in sequence; Determining a fragile line in the carrier circuit; Adding a detection structure on the carrier circuit according to the fragile line; Carrying out first dynamic simulation on the carrier circuit added with the detection structure; Embedding a preset Trojanhorse into the carrier circuit; Carrying out second dynamic simulation on the carrier circuit implanted with the preset Trojan horse; And judging whether a hardware Trojan horse is implanted into thecarrier circuit according to the first simulation result and the second simulation result. According to the embodiment of the invention, the credibility of the integrated circuit is improved, and thedifficulty of Trojan attack is increased.
Owner:XIDIAN UNIV
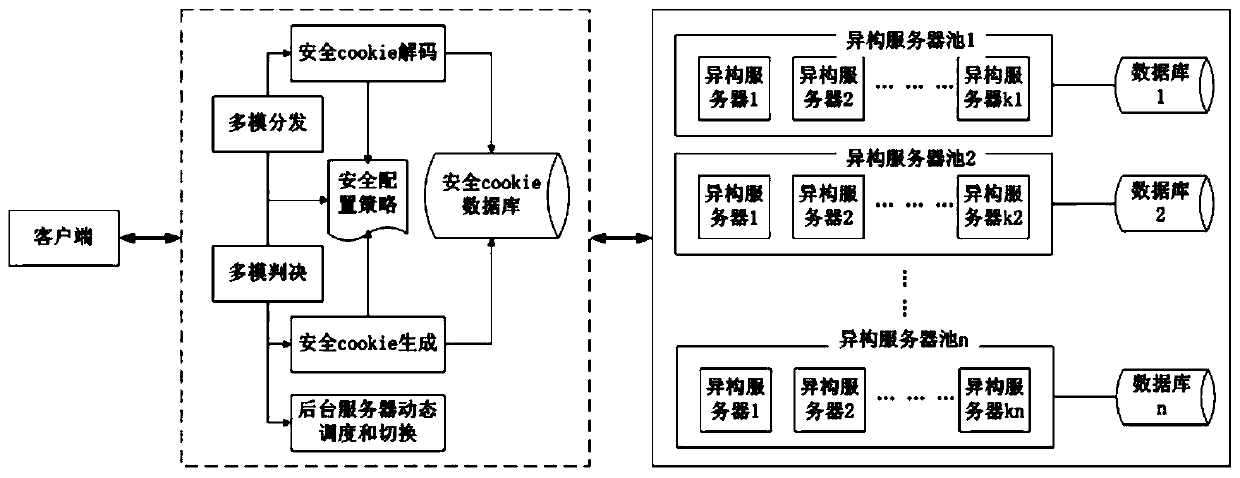
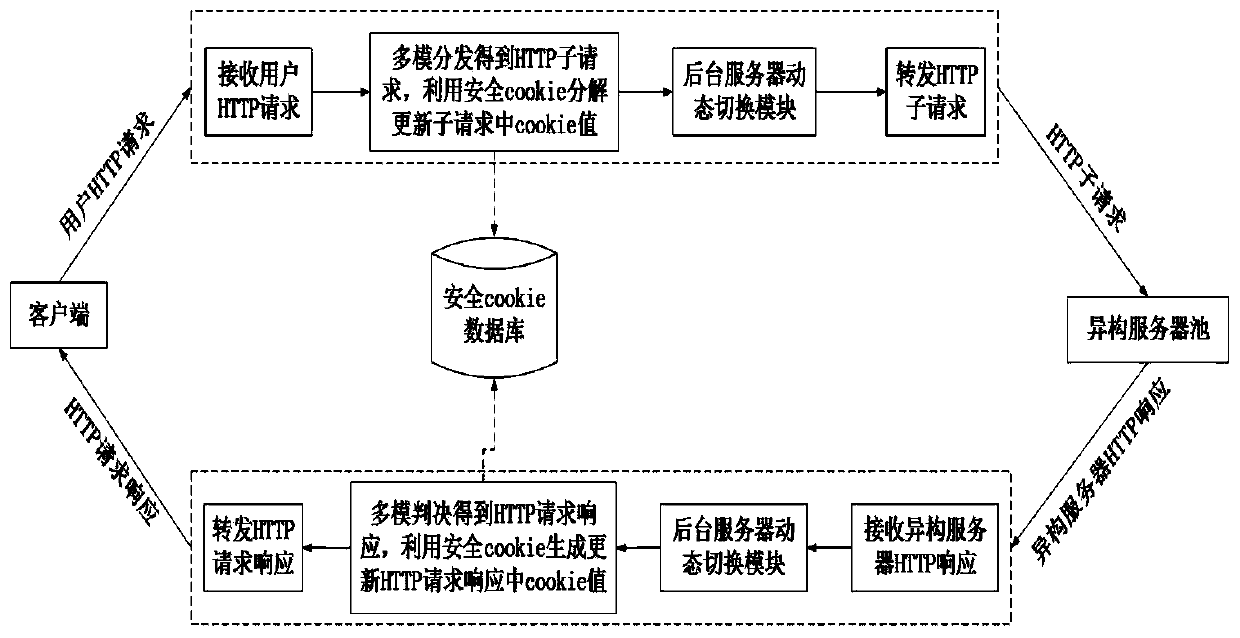
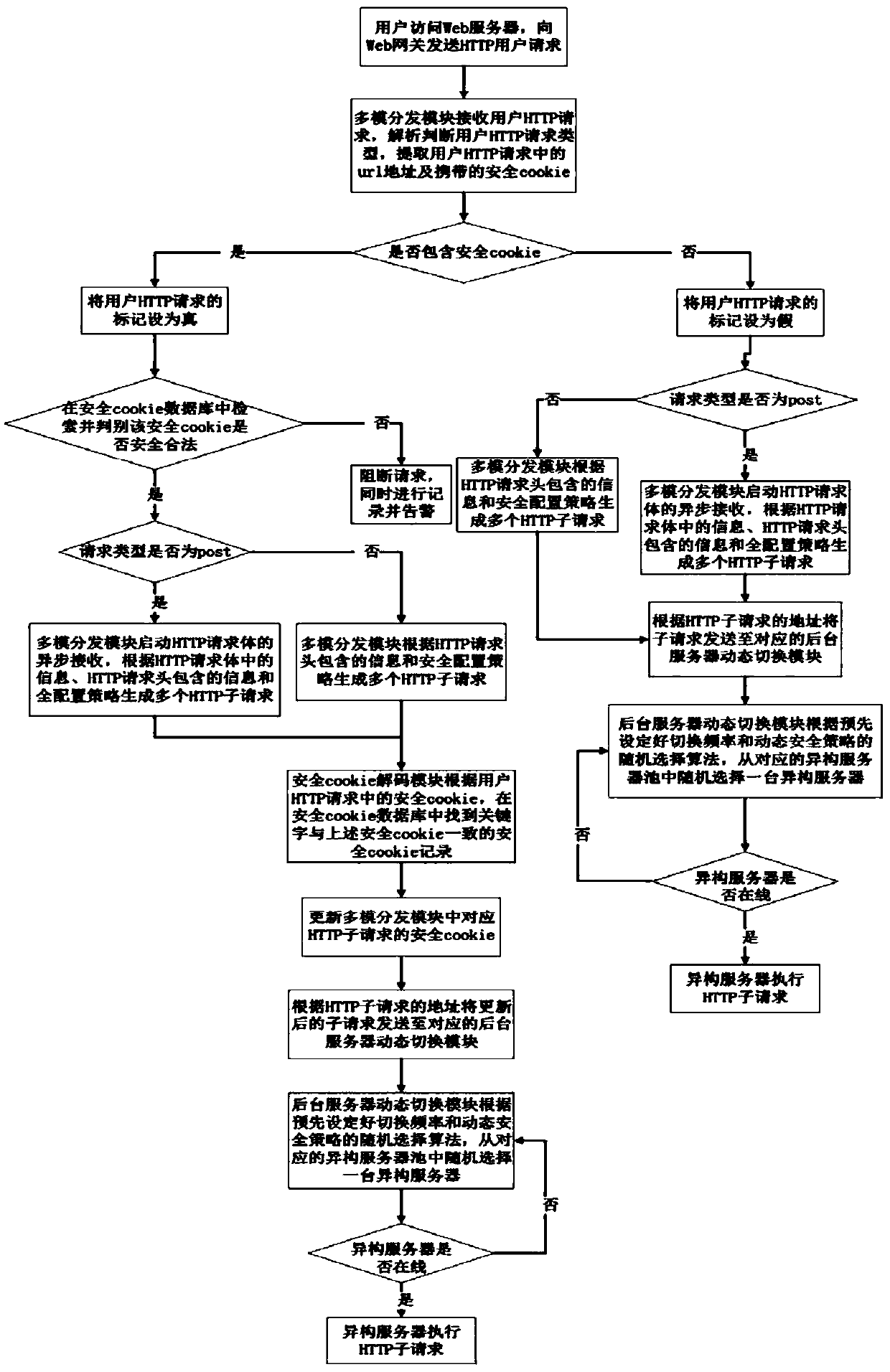
Mimicry Web gateway system and mimicry Web gateway method for carrying out dynamic scheduling by adopting random selection
The invention discloses a mimicry Web gateway system and a mimicry Web gateway method for carrying out dynamic scheduling by adopting random selection. The system comprises a system module distribution module, a multimode judgment module, a security Cookie generation module, a security Cookie decoding module, a heterogeneous server pool group, a background server dynamic switching module group, adatabase synchronization module, a security Cookie database group and a security configuration strategy. According to the invention, heterogeneous integration is carried out on the server, dynamic switching of the executor group is realized by utilizing a random selection technology, and a mimic Web gateway system is realized through Cookie mapping. According to the Web gateway based on dynamic heterogeneous redundancy, the background executor is dynamically switched by utilizing the dynamic scheduling and heterogeneous redundancy technology, the risk and loss of attacking a website system arereduced, the attack behavior can be more accurately judged, and countermeasures are taken in time.
Owner:HANGZHOU DIANZI UNIV
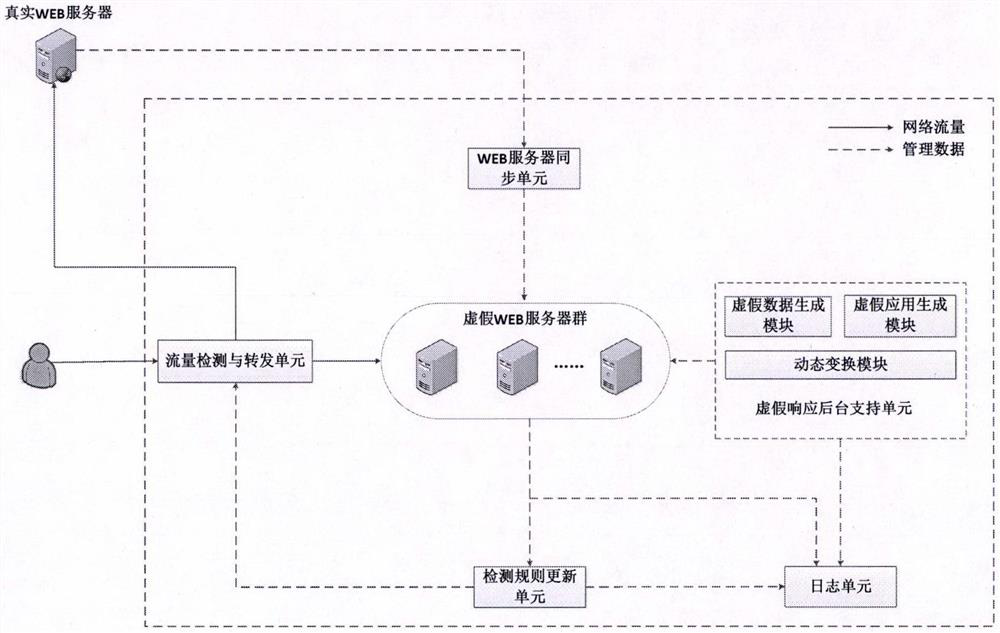
WEB dynamic adaptive defense system and defense method based on false response
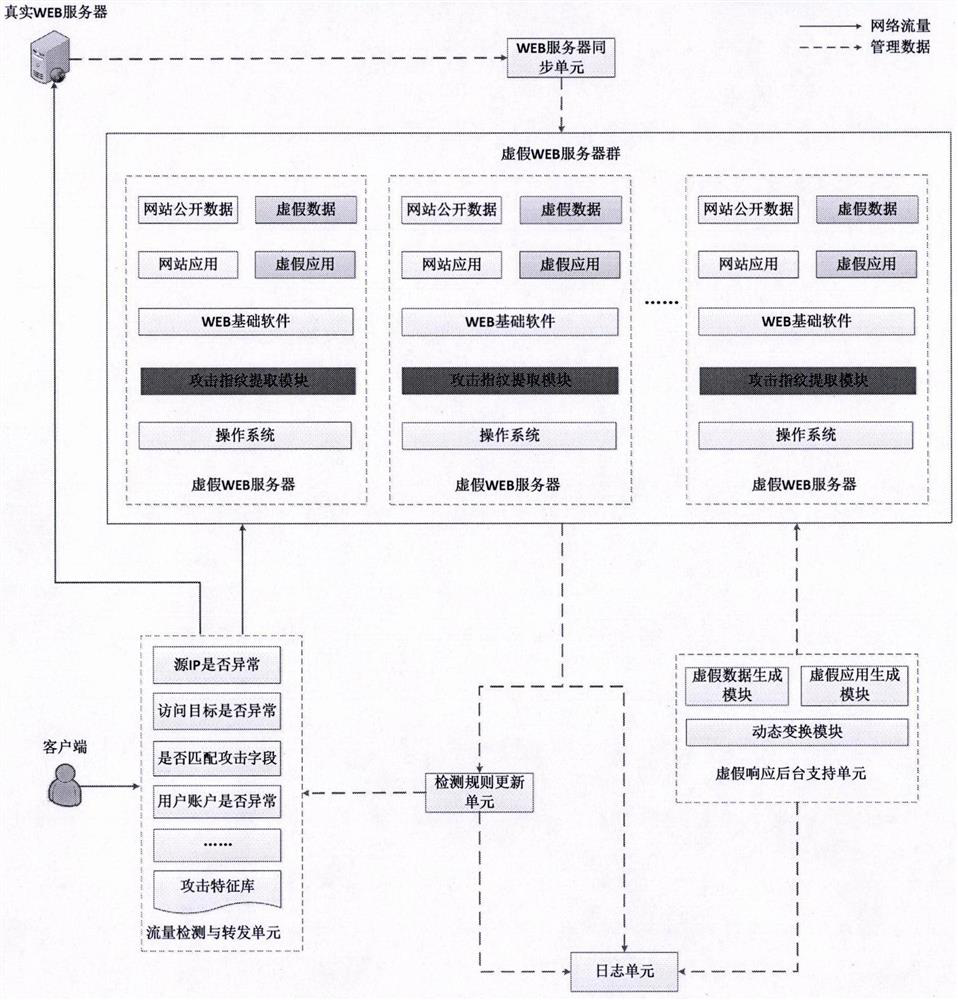
The invention provides a WEB dynamic adaptive defense system and defense method based on false response. Based on the concept of moving target defense, a plurality of false WEB servers capable of being dynamically transformed is constructed around a protected WEB server, false sensitive data, false applications, false vulnerabilities and the like are constructed on the false WEB servers, and cheating hackers attack the false WEB servers. When a known attack or a suspicious behavior is identified, the known attack or the suspicious behavior is introduced into the false WEB server, and an attacker enters the false environment and then executes a subsequent attack action in the false environment until the attack is finished, so that multiple attempt attacks of the attacker are effectively defended, and meanwhile, the method has a relatively good defending capability on an unknown WEB attack. Besides, by continuously observing attack behaviors in a false environment, WEB attack features can be automatically extracted, attack detection rules are dynamically and adaptively adjusted, and the dynamic adaptive capacity of a defense system is improved.
Owner:张长河
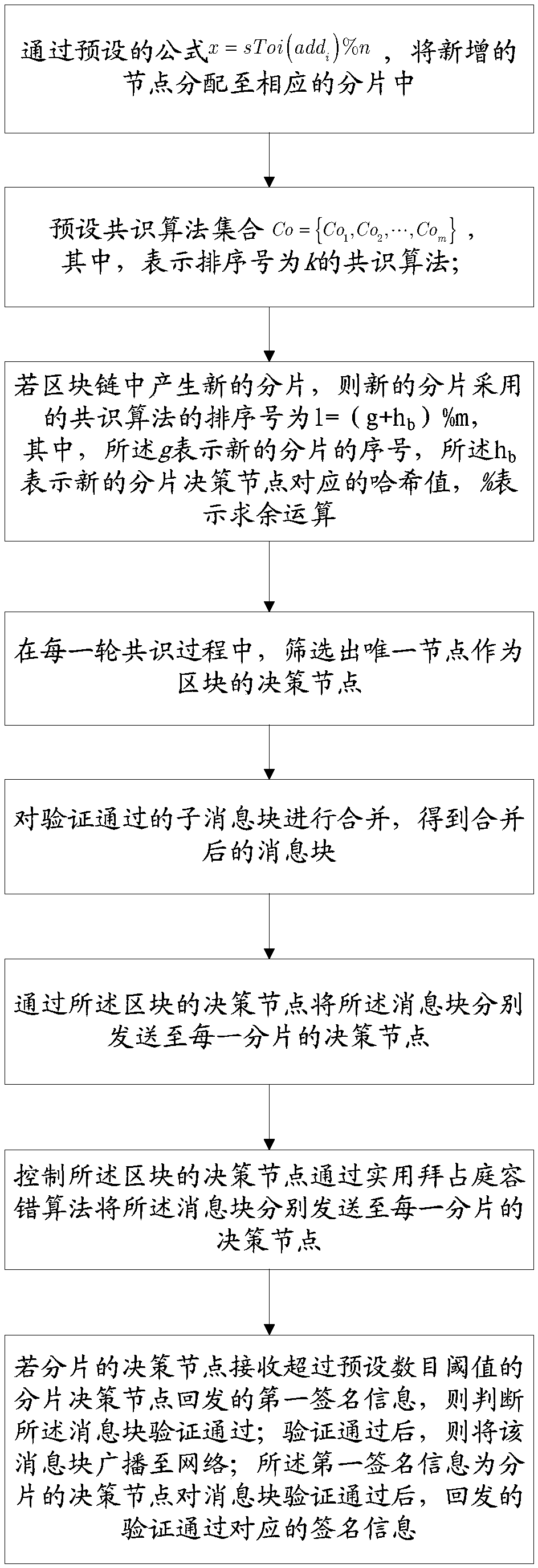
Heterogeneous consensus method of block chain, and terminal
ActiveCN109379343AImprove securityIncrease attack difficultyEncryption apparatus with shift registers/memoriesUser identity/authority verificationDecision takingBlockchain
The invention provides a heterogeneous consensus method of a block chain, and a terminal. The method comprises the following steps: screening a unique node as a decision node of a block in each turn of consensus process; receiving a sub message block sent by each burst through the decision node, and verifying the sub message block sent by each burst; combining the sub message blocks passing the verification to obtain a combined message blocks; sending the message block to the decision node of each burst through the decision node of the block; if receiving signature information returned by a burst decision node exceeding the predetermined number thread, judging that the message block verification is passed; and the first signature information is the signature information corresponding to the returned verification passing after the decision node of the burst passes the message block verification. Through the method provided by the invention, the block chain security problem caused by Hacker attack can be prevented to a certain extent, and the security of the block chain is improved.
Owner:福建福链科技有限公司
Method, equipment and system for data switching based on tunnel
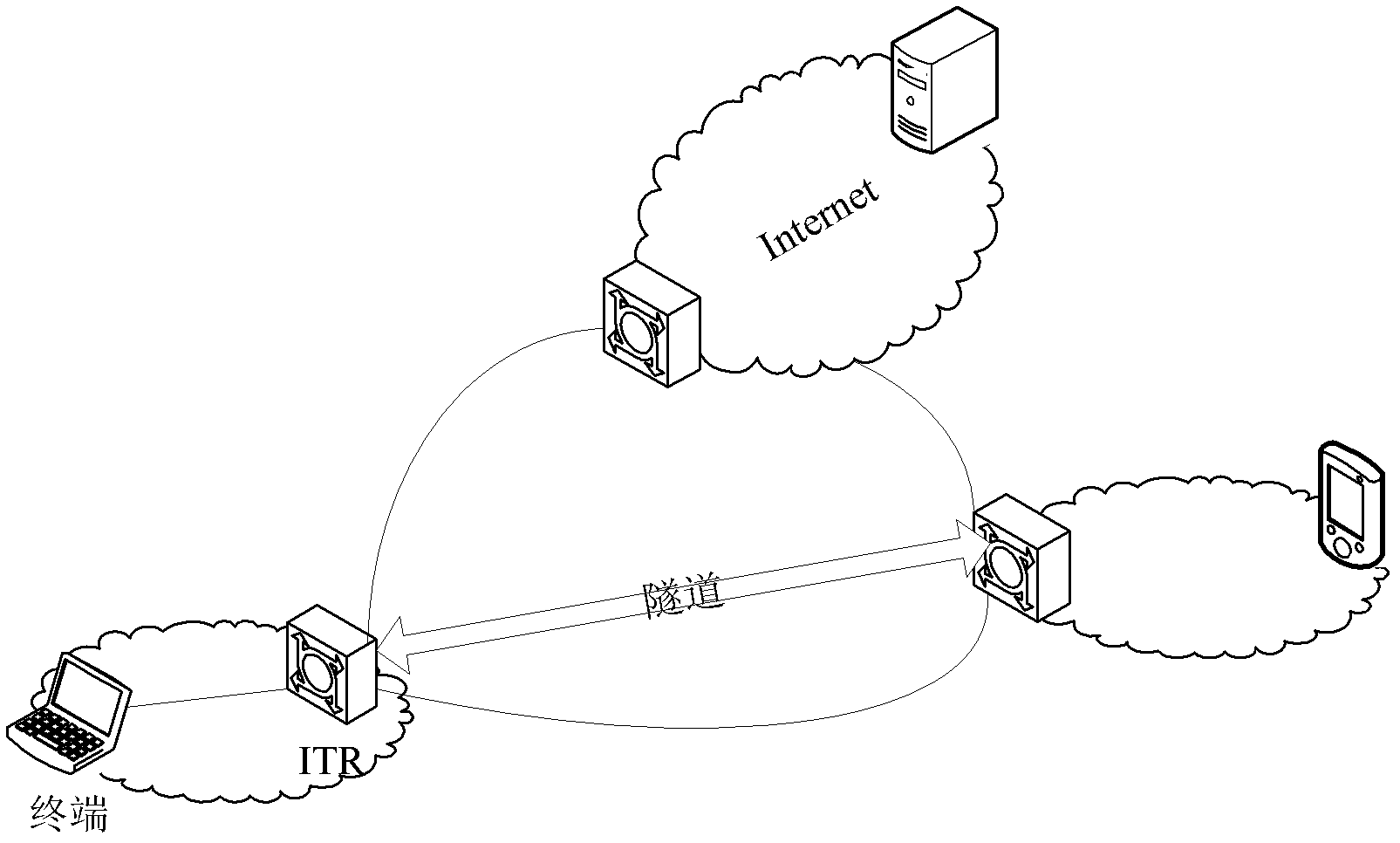
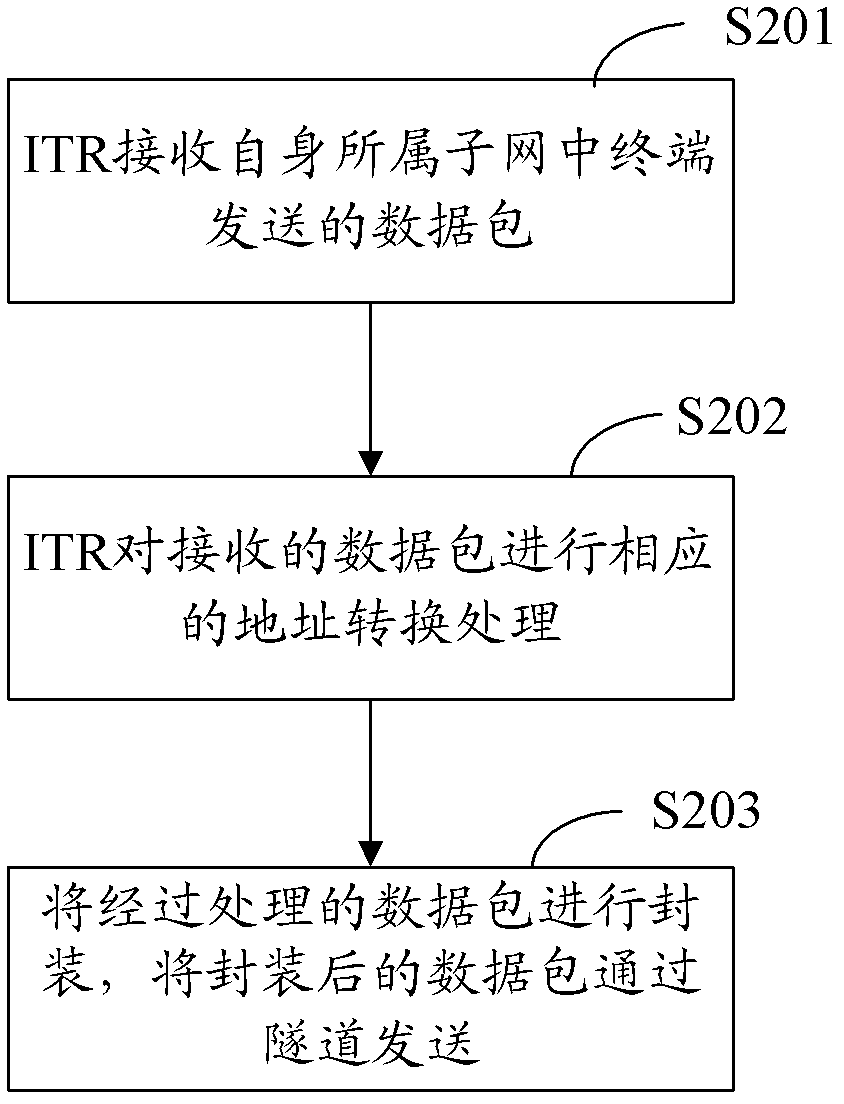
ActiveCN103167483AIncrease attack difficultyImprove securityNetwork data managementOperational costsResource utilization
The invention provides a method, equipment and a system for data switching based on a tunnel. A terminal in an identity and position separation network can adopt a private address or a global address. When the terminal initiates data communication, private address switching of a source address is conducted on a data package by internet talk radio (ITR) if the terminal initiating the data communication adopts the private address, and the source address is switched to the global address. If a destination address of the data package is a mapping address pre-distributed by the ITR, a communication opposite terminal adopts a private address, so that the mapping address needs to be switched to the private address again. Terminals in different subnets of the identity and position separation network can adopt the same private address, the defect in the prior art that the terminals must use fixed one-to-one EID is avoided, and the problems in existing identity and position separation network technology that operating cost is high, resource utilization rate is low, user safety is low and the like due to the fact that the existing identity and position separation network technology which is not in support of reuse of terminal identity labels are solved.
Owner:CHINA MOBILE COMM GRP CO LTD
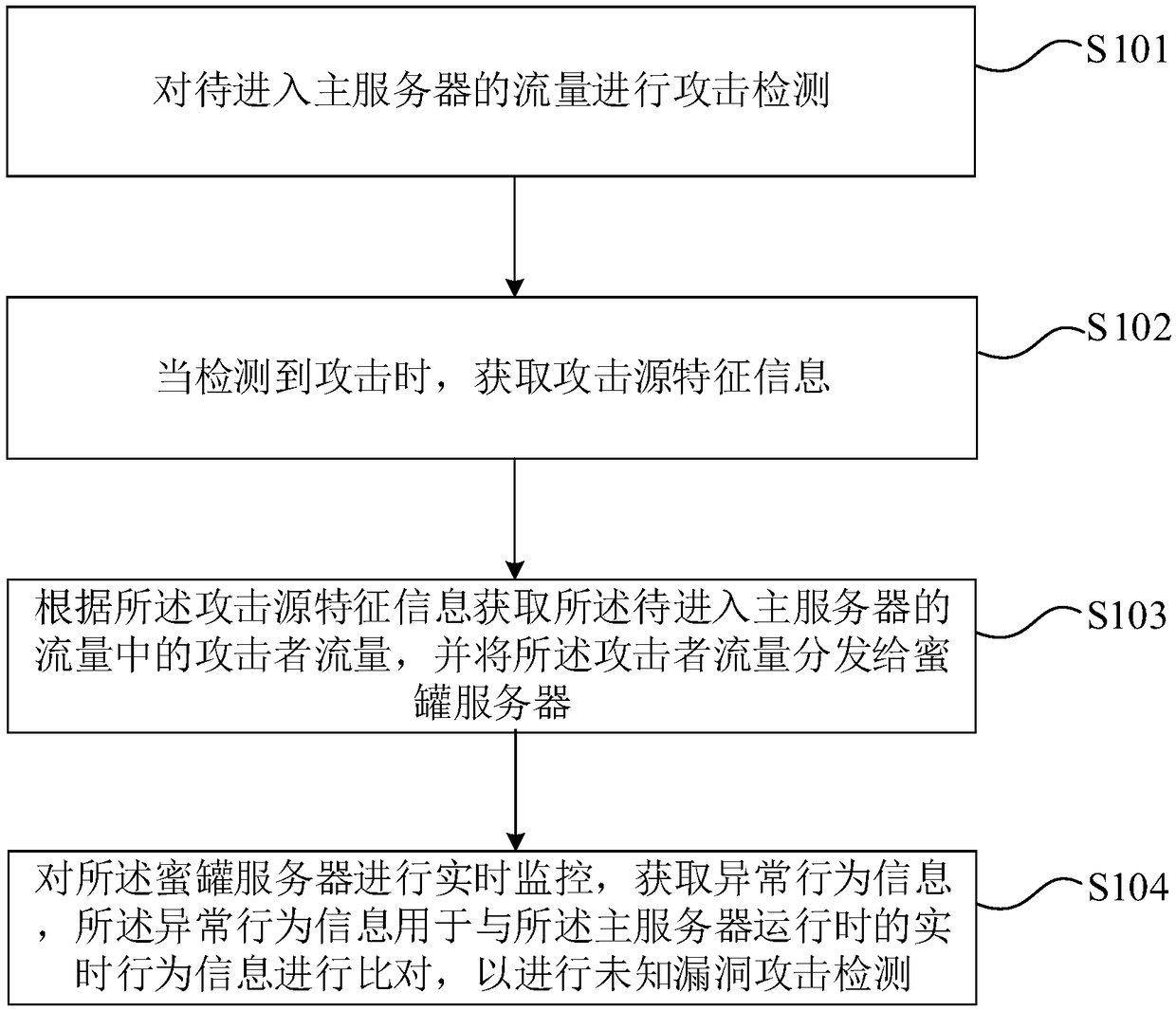
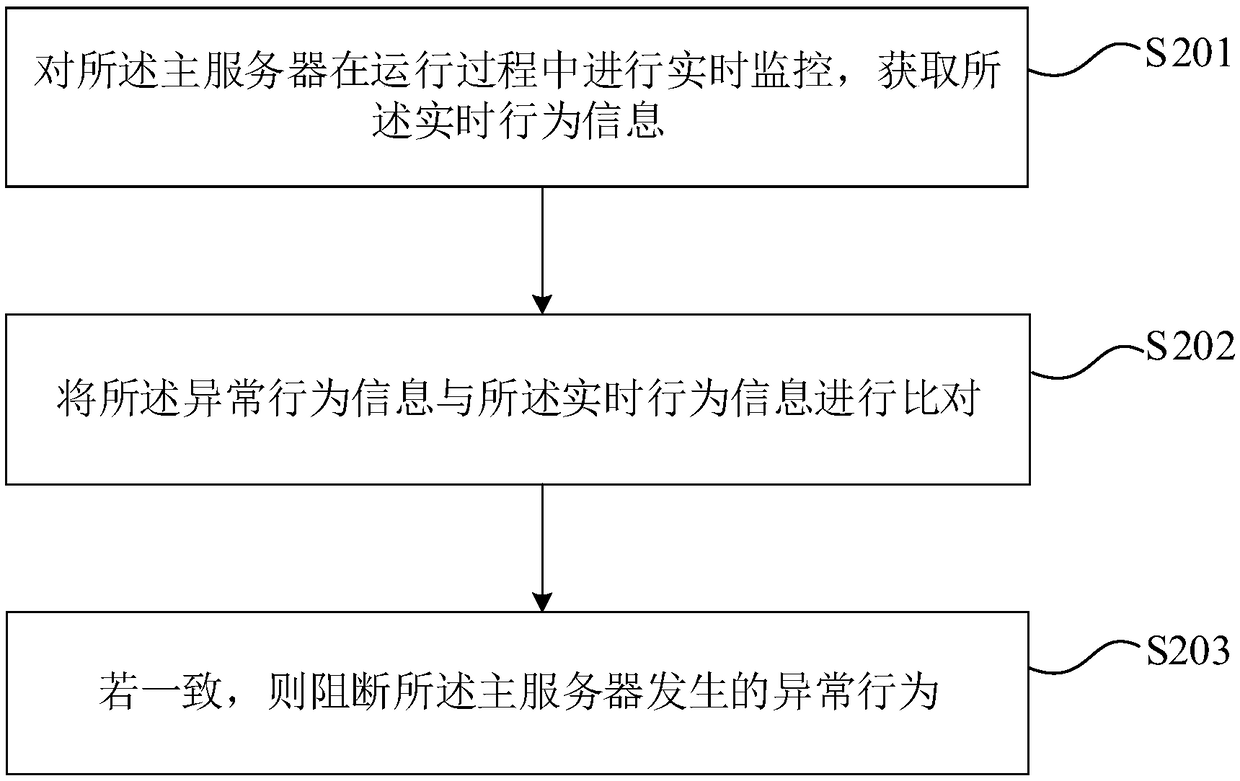
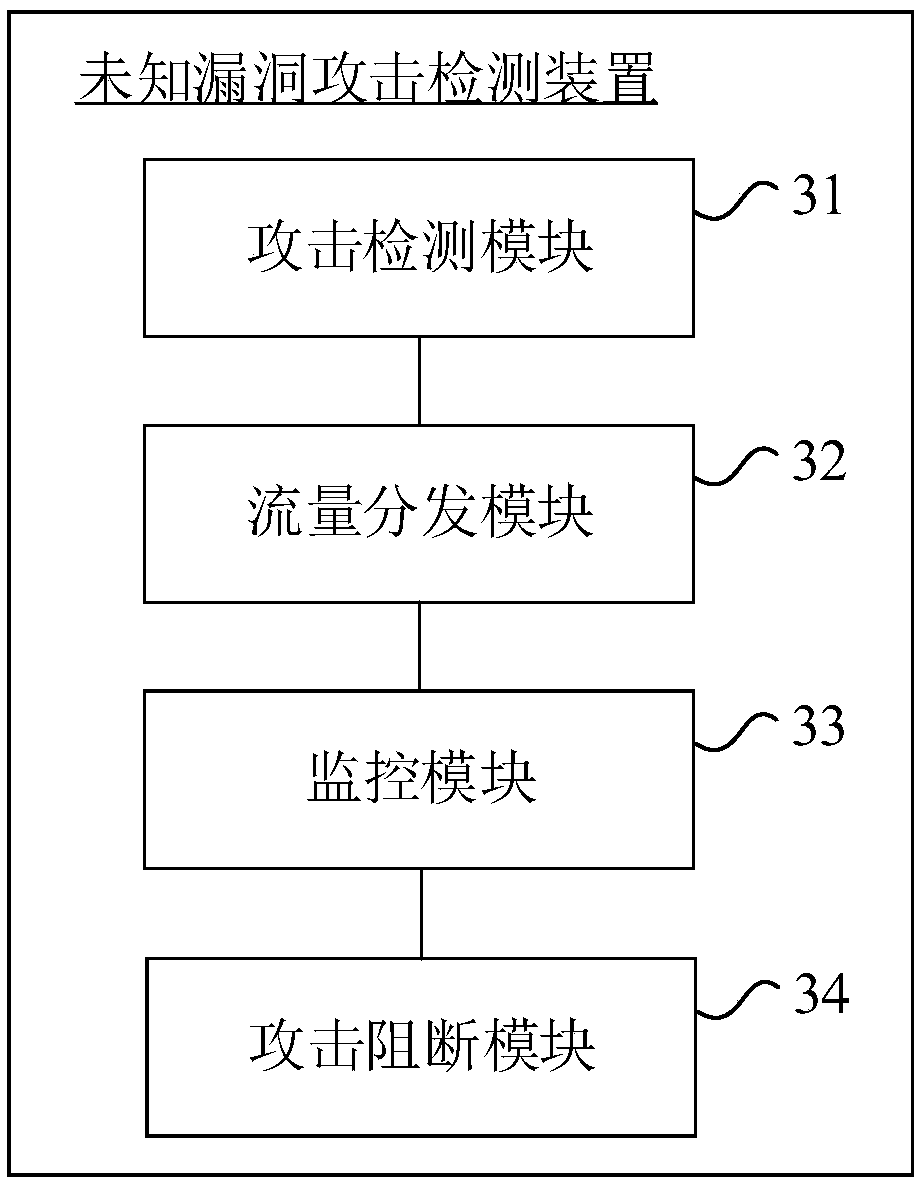
Unknown loophole attack detection method, device, equipment and storage medium
ActiveCN109302426AIncrease attack difficultyShorten the timeTransmissionProtection systemVulnerability
The invention provides an unknown loophole attack detection method, device, equipment and storage medium. The method comprises the following steps: performing attack detection on traffic readying to enter a main server; acquiring attack source feature information when detection the attack; and then acquiring attacker traffic in the traffic readying to enter the main server according to the attacksource feature information, and distributing the attacker traffic to a honey pot server; monitoring the honey pot server in real time to acquire abnormal behavior information, wherein the abnormal behavior information is used for comparing with the real-time behavior information when the main server is in operation, thereby performing unknown loophole attack detection. Through the method providedby the invention, the attacker cannot or is hard to sense the existence of the safety protection system, the attack difficulty is greatly increased, the attack successful time is delayed, and the attack from unknown loop on the system can be effectively detected, the attacked system can be effectively detected without artificial participation, and the response time is fast.
Owner:NEUSOFT CORP
Chain structure design method with Turing complete intelligent contract block chain
InactiveCN111951108APrevent Sybil AttacksPrevent Selfish Mining AttacksFinanceDigital data protectionChain structureSoftware engineering
The invention discloses a chain structure design method with a Turing complete intelligent contract block chain, the following technologies are introduced to enhance the underlying architecture of thechain, and the chain structure design method comprises the following steps: a consensus mechanism, phased evolution of consensus, a POW consensus part of MANNET1. X version, a POS consensus part of MANNET1. X version, an expansion mechanism, a virtual machine and anti-quantum calculation. The invention has the advantages of safety, reliability, high stability, high operation speed and the like.
Owner:神话科技传媒(深圳)有限公司上海分公司
Method for realizing block cipher multiple S-boxes for resisting differential power attack
ActiveCN107204841AIncrease attack difficultyIncrease the difficultyEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresDifferential methodData processing
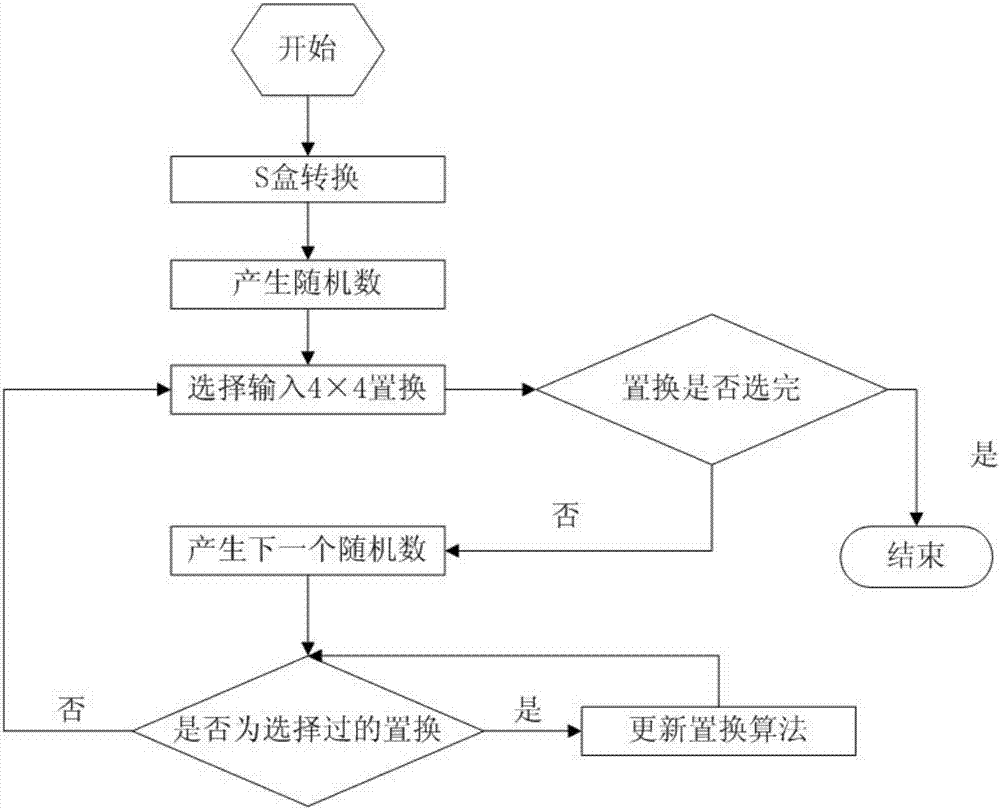
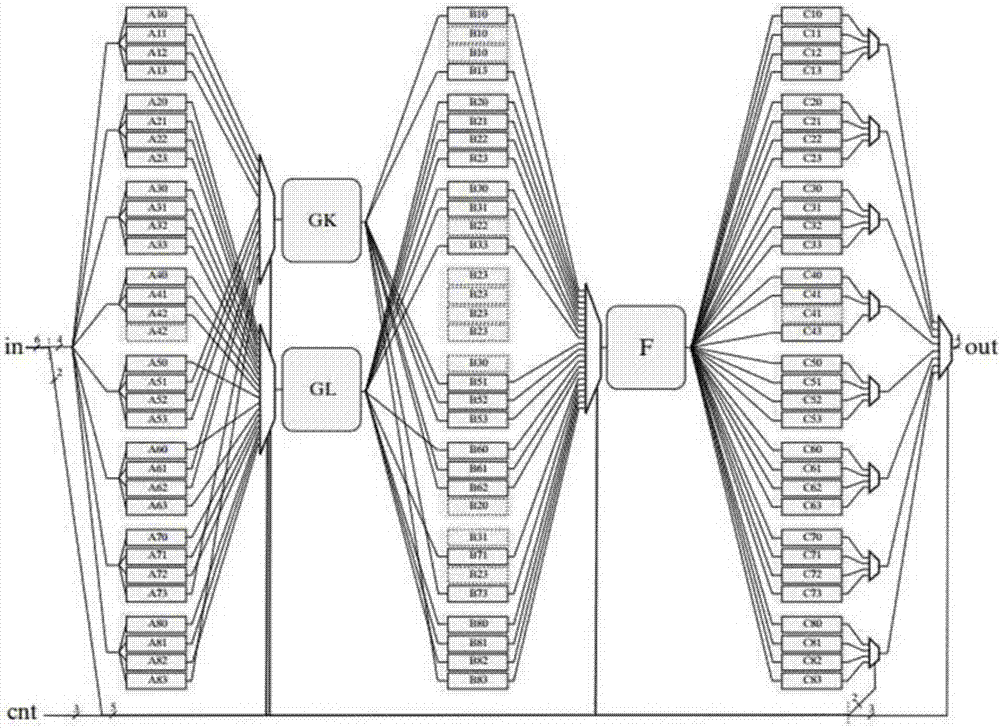
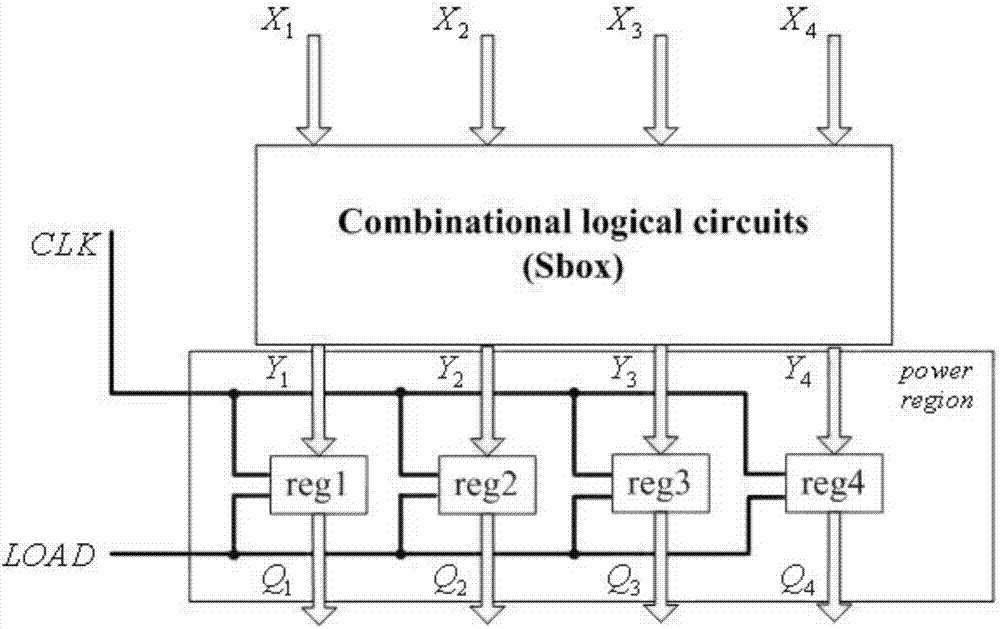
The invention relates to a method for realizing block cipher multiple S-boxes for resisting differential power attack. Firstly a plurality of parallel S-boxes are converted for obtaining 4*4 S-box replacements. Furthermore the 4*4 S-box replacements are numbered. Then block cipher multiple S-box random input technology is performed on all 4*4 S-boxes so that an attacker who performs the differential power attack cannot align a curve according to a related statistics differential method after obtaining a power consumption curve, and therefore the differential power attack fails, thereby improving safety in realizing a block cipher. Furthermore according to the method, only g(n) bits of random numbers are utilized and the random numbers are greatly reduced than that in other mask solutions. Attack difficulty in data processing of the differential power attack is greatly increased. In a speed aspect, because the original parallel S-boxes are converted to a multidimensional serial reusable S-box frame according to the method, a streamline method can be used, thereby reducing speed by 30% than an original solution.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Safe operation method and system of mimicry voter
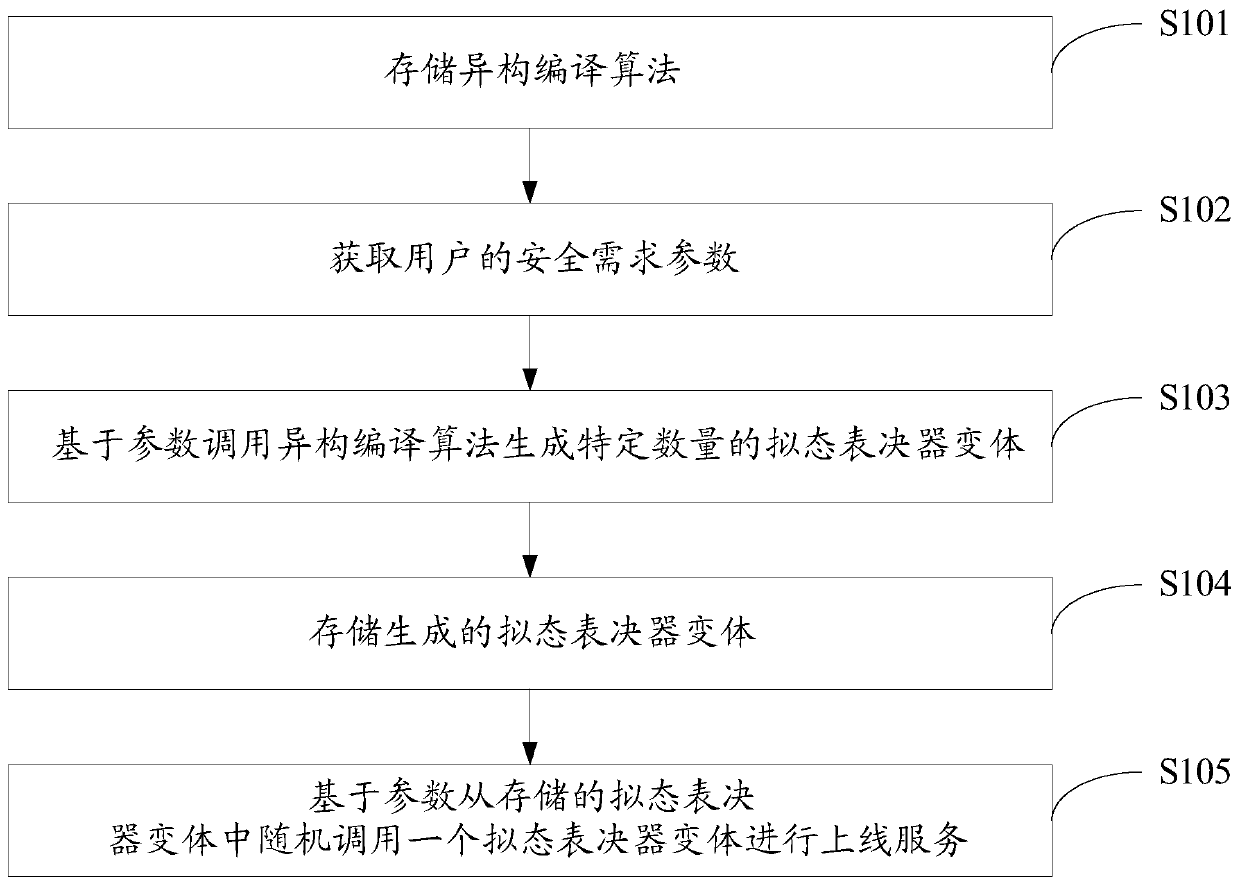
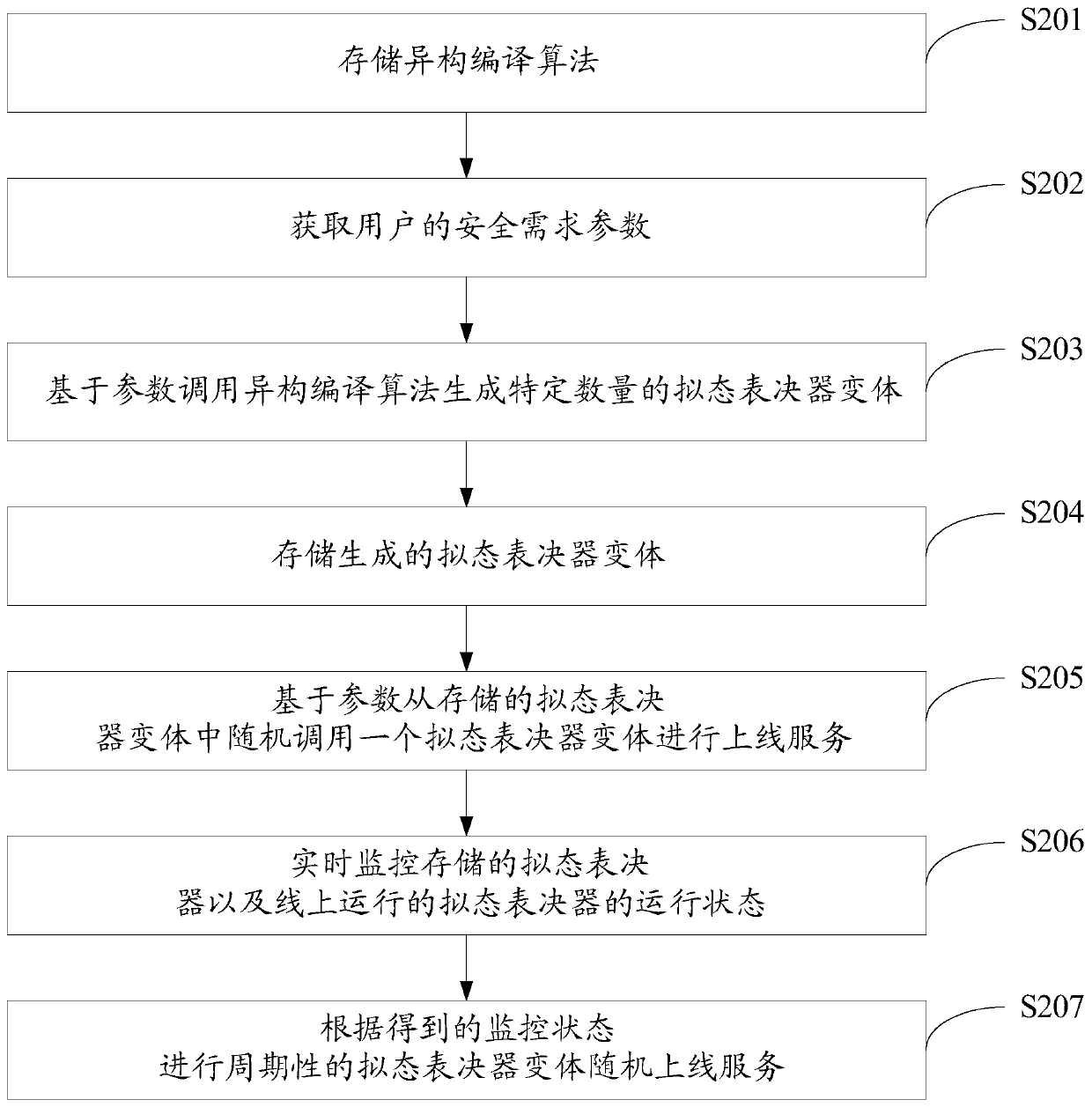
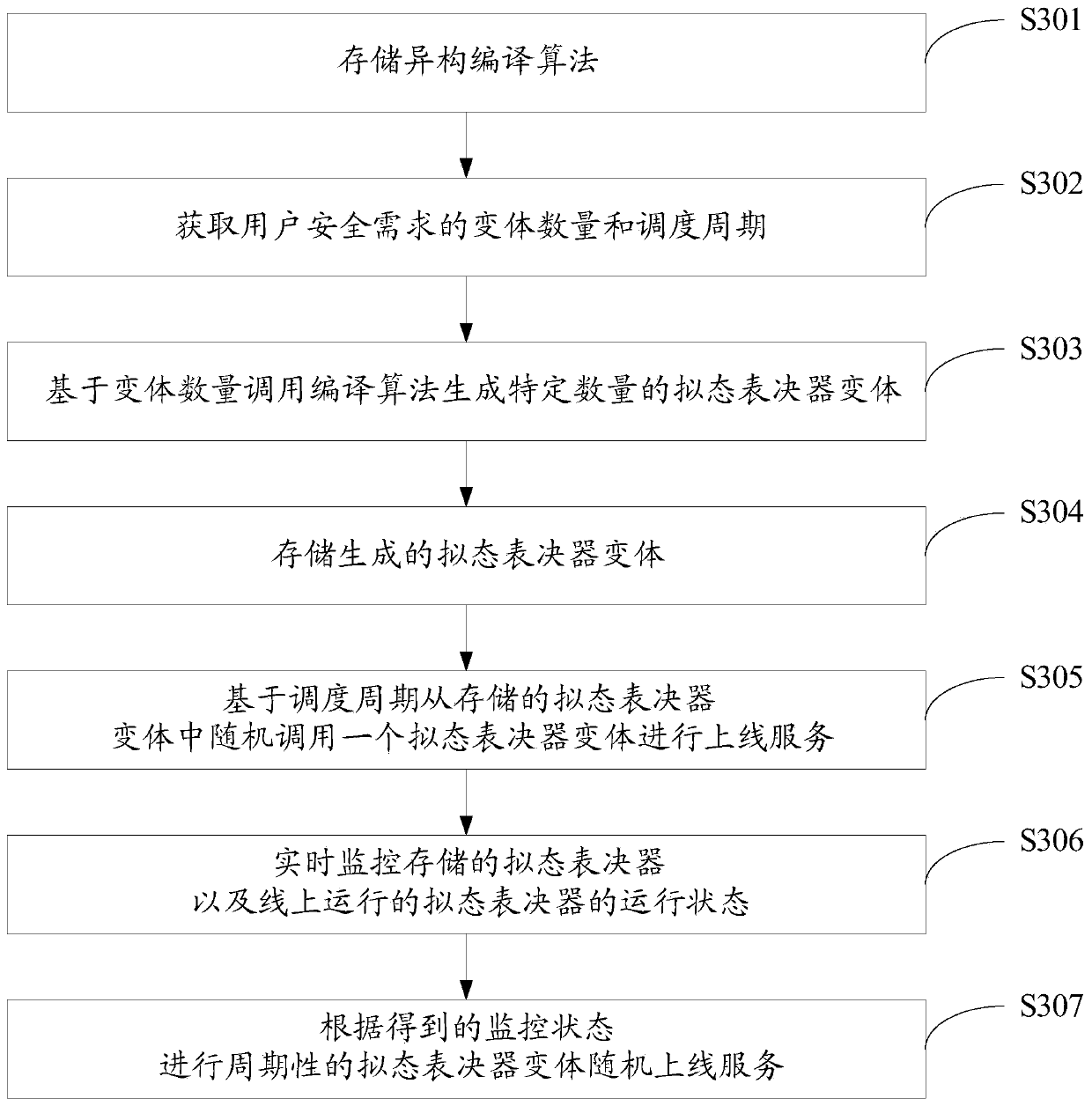
ActiveCN111475805AEnsure safetyIncrease uncertaintyPlatform integrity maintainanceSpecial data processing applicationsUser needsSafe operation
The invention discloses a safe operation method and system for a mimicry voter, and the method comprises the steps: storing a heterogeneous compiling algorithm, and obtaining a safety demand parameterof a user; calling a heterogeneous compiling algorithm based on the parameters to generate a specific number of mimicry voter variants, and storing the generated mimicry voter variants; and randomlycalling one mimicry voter variant from the stored mimicry voter variants based on the parameters to perform online service. According to the invention, the mimicry voter software can be isomerized andcompiled on the basis of software diversification and moving target defense thought, and meanwhile, the voter variants are periodically and randomly scheduled according to user requirements, so the uncertainty of voter service is increased, the attack difficulty of attackers is improved, and the safety of the mimicry voter is guaranteed.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
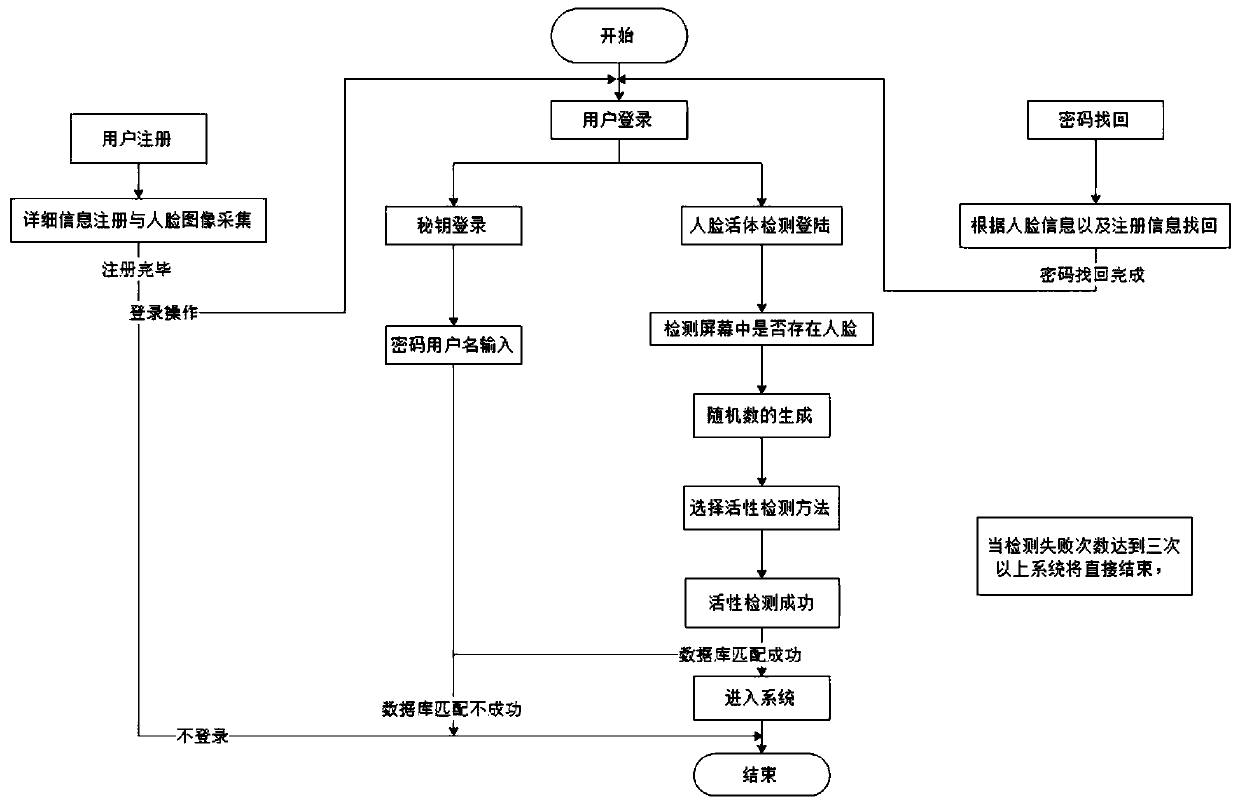
Multi-factor human face living body detection system and method
PendingCN111539249AImprove robustnessEasy to collectNeural architecturesNeural learning methodsFace detectionRadiology
The invention provides a multi-factor human face living body detection system and method, and belongs to the technical field of human face recognition. The system comprises a human face detection module, a human face image preprocessing module, a data storage module, a random number generation module and a multi-factor living body detection module. The method comprises: acquiring face image information and video information, and sending the acquired face image information and video information to a face image preprocessing module and a data storage module; enabling the face image preprocessingmodule to preprocess the received face image information and video information and judge whether the face information meets requirements or not according to a processing result; enabling the random number generation module randomly to generate multi-factor living body detection parameters; and enabling the multi-factor living body detection module to perform multi-factor human face living body detection according to the multi-factor living body detection parameters generated by the random number generation module. According to the method, challenge action combinations are diversified, challenge pools are richer, and the attack difficulty is greatly increased.
Owner:XIDIAN UNIV
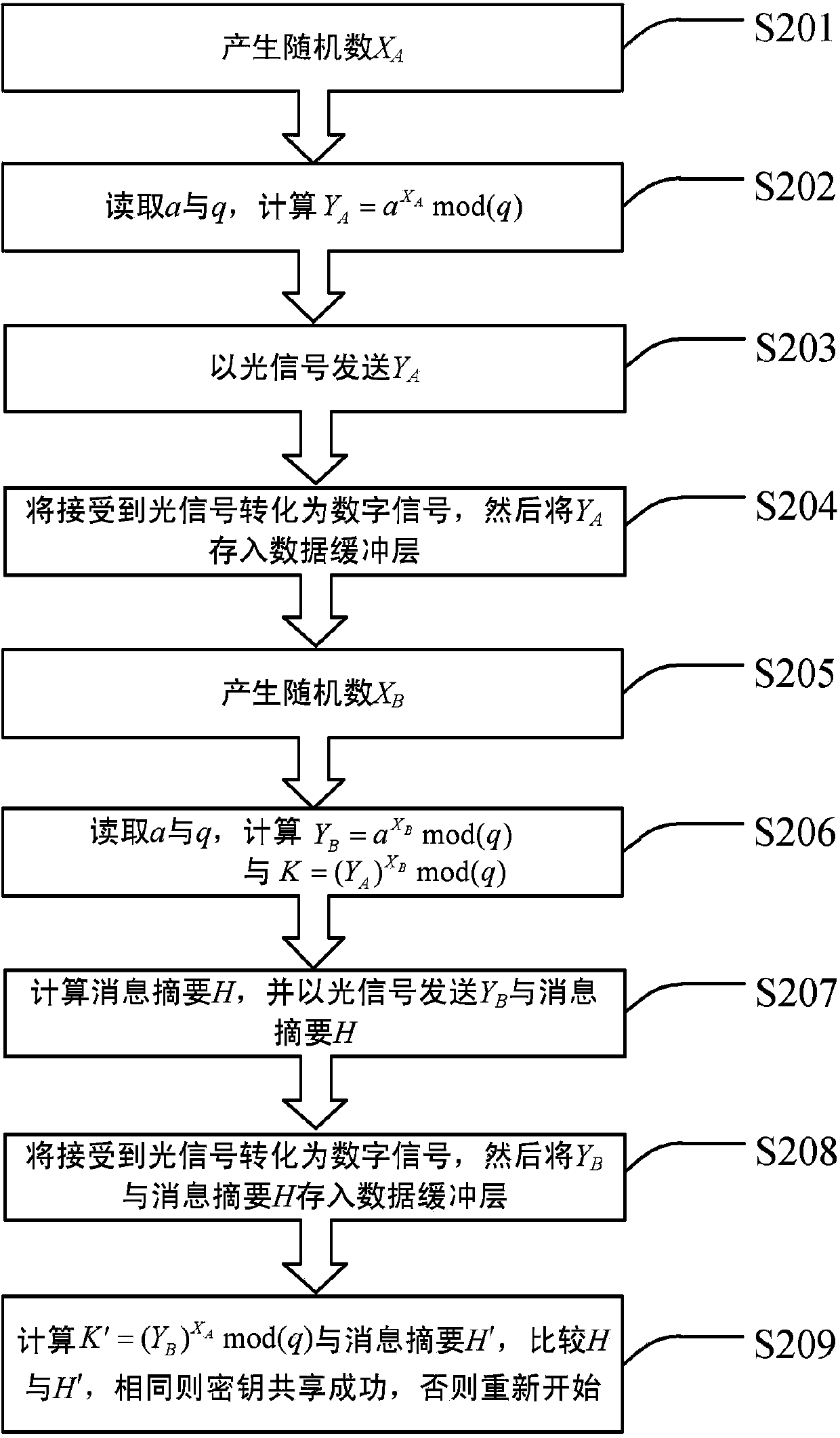
Reception secret key sharing system and method based on optical communication
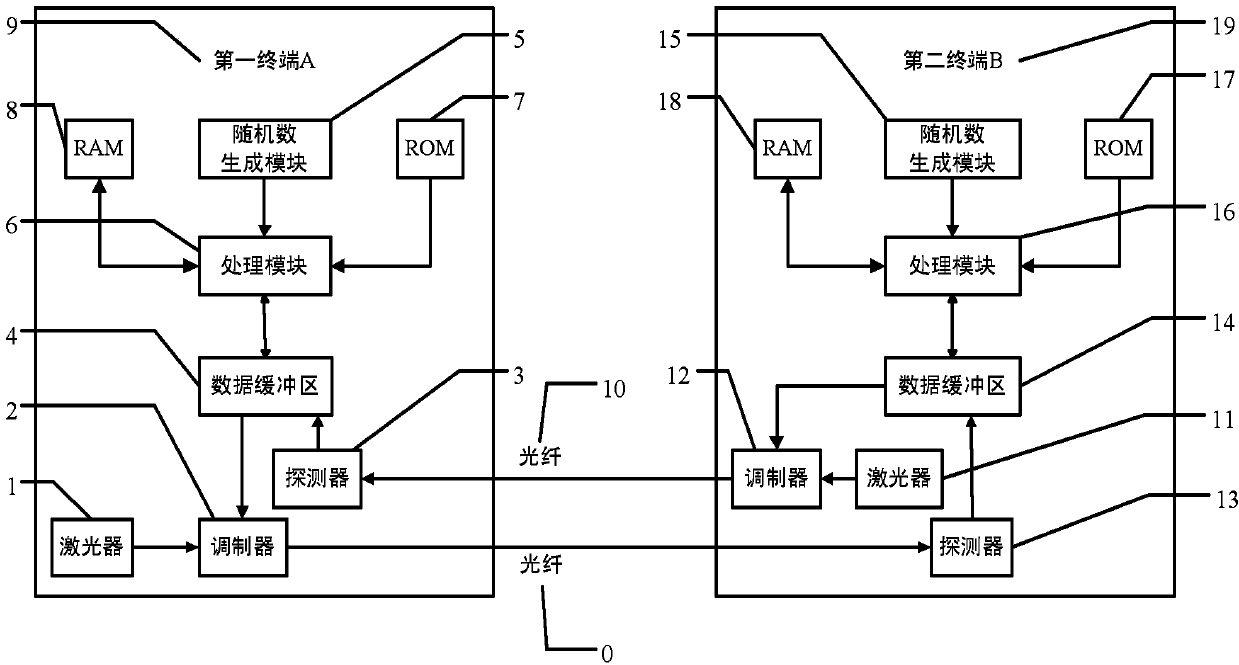
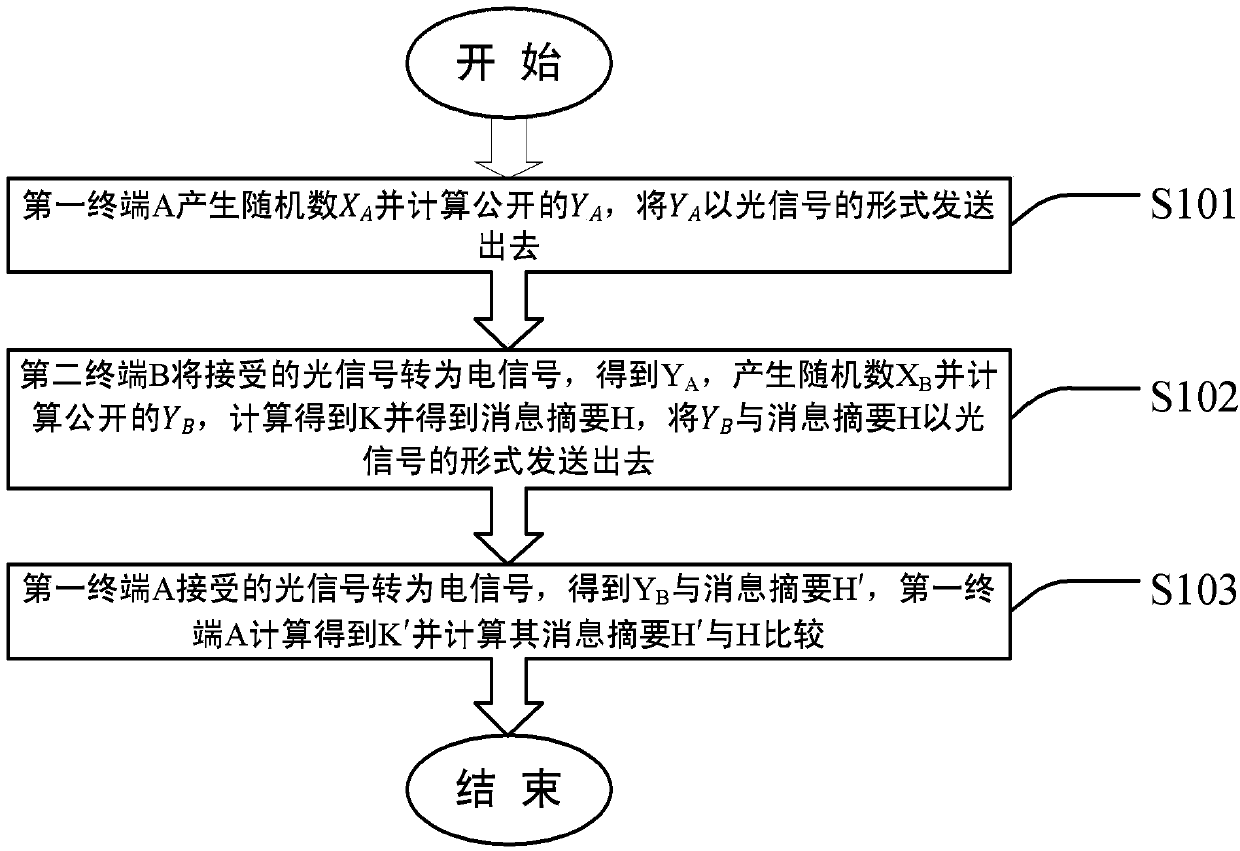
ActiveCN103812645AAvoid exposureImprove securityKey distribution for secure communicationOptical communicationInformation security
The invention relates to the information security field of optical communication and discloses reception secret key sharing system and method based on optical communication. The method comprises the steps that a first terminal A generates a public YA and sends the YA by an optical signal; a second terminal B converts the received optical signal into an electric signal and obtains the YA, generates a public YB, calculates to obtain a secret key K and a message digest H thereof, and then sends the YB and the message digest H by the optical signal; the first terminal A converts the received optical signal into an electric signal, obtains the YB and the message digest H, obtains K' by calculation, calculates the message digest and compares the same to H, so as to ensure successful sharing of the secret keys of the two terminals. By utilizing the system and method, the secret keys are prevented from direct exposure in an insecure channel, security of secret key transmission is improved, so that the security of data encrypted on a basis of the secret keys is enhanced.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
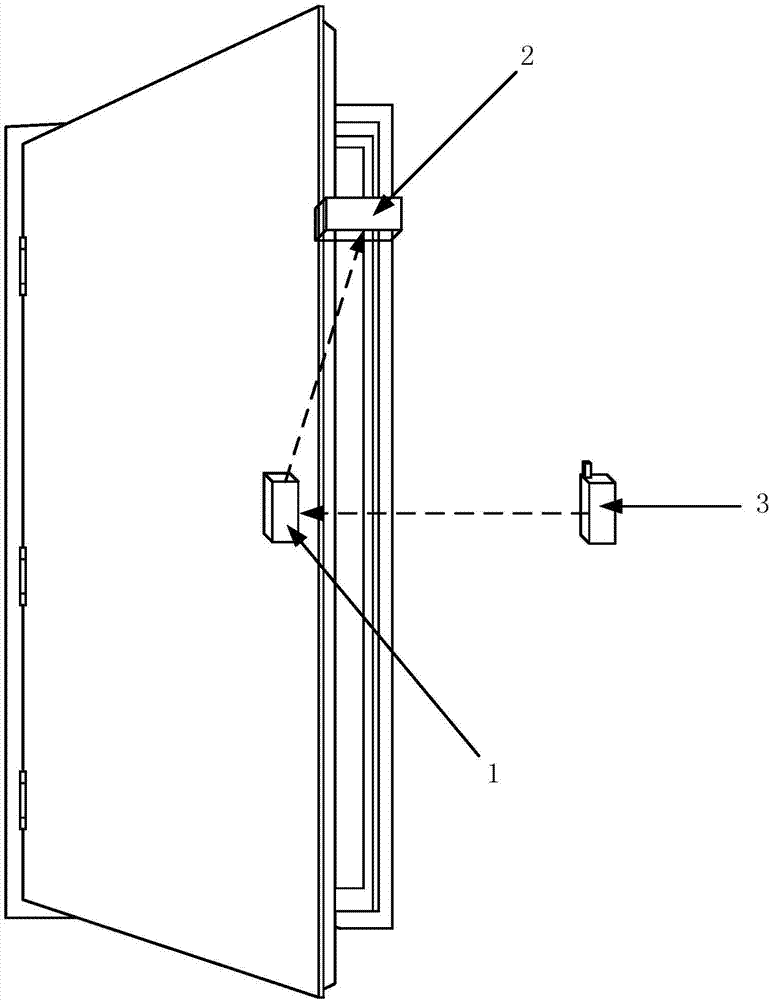
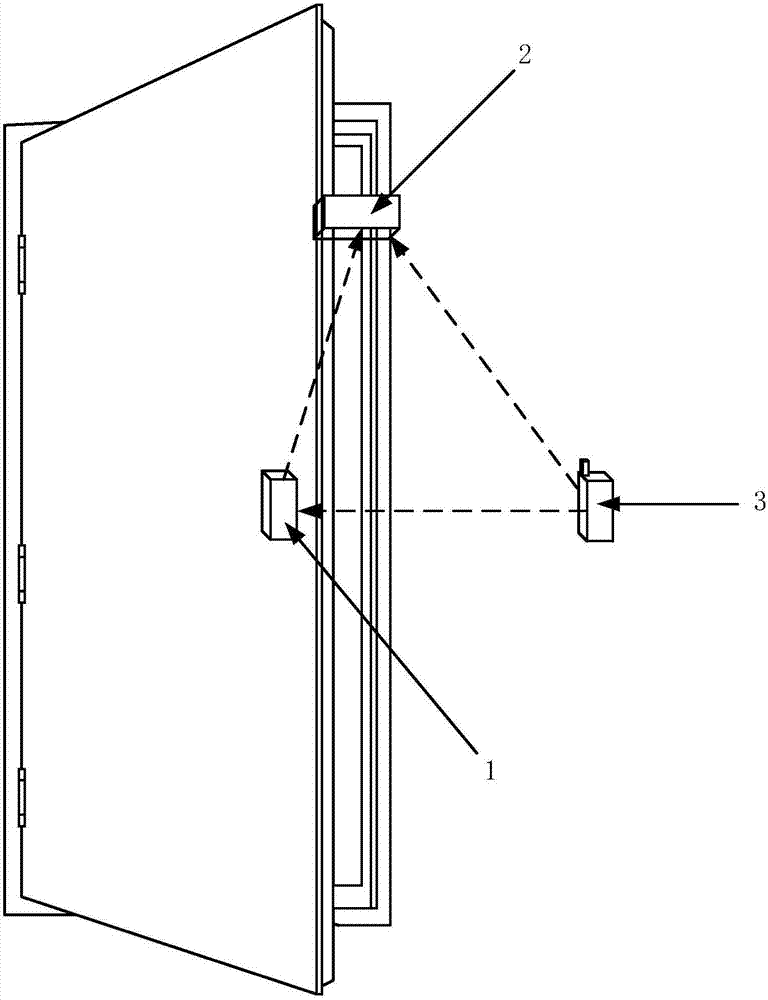
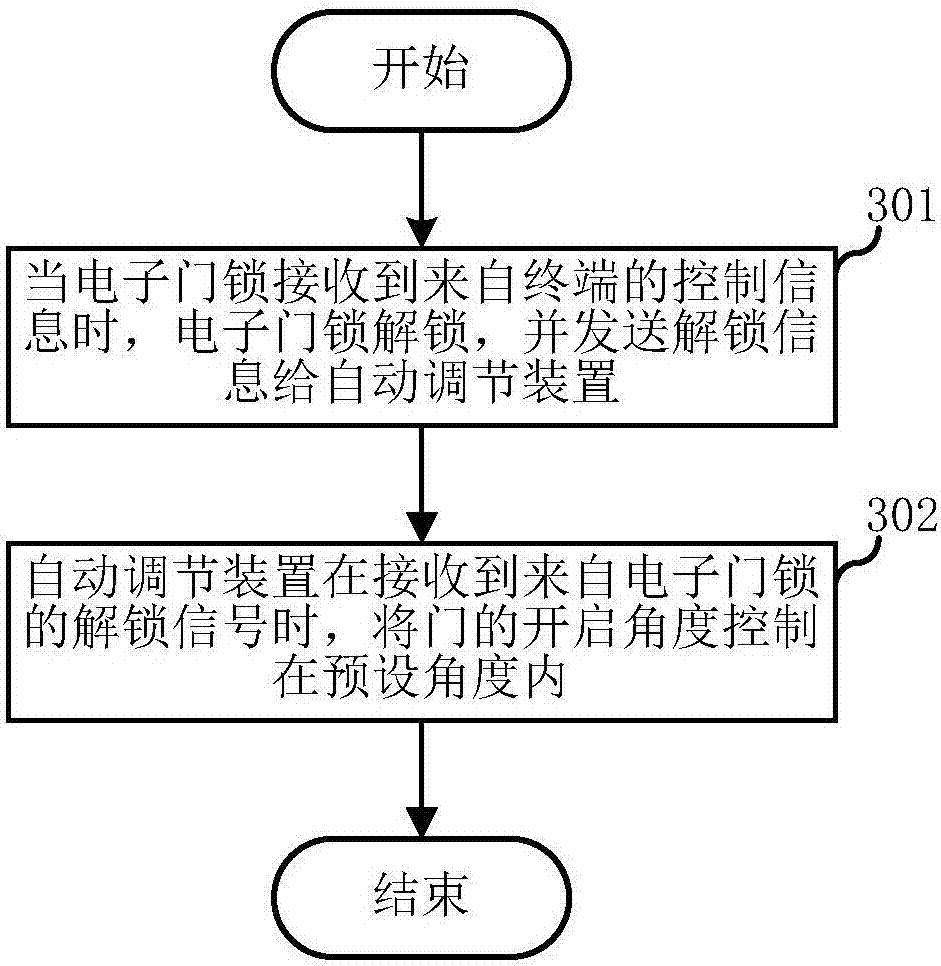
Control system and control method for door lock
InactiveCN106952365APrevent break-inEasy to useIndividual entry/exit registersControl systemEmbedded system
The invention relates to the field of smart home and discloses a control system and a control method for a door lock. In one embodiment, the control system includes: an electronic door lock, an automatic regulation device and a terminal. The terminal is communicatively connected to the electronic door lock which is then communicatively connected to the automatic regulation device. The terminal sends control information to the electronic door lock; the electronic door lock, when receiving the control information from the terminal, is unlocked and sends an unlock signal to the automatic regulation device; one end of the automatic regulation device is fixed on a door frame while the other end is fixed on a door, so that when receiving the unlock signal from the electronic door lock, the automatic regulation device controls the opening degree of the door within a preset angle being less than 30 degrees. By means of the system and the method, a courier can place an express parcel into home, so that a problem of second delivery is avoided; the system and the method also can prevent the courier from entering home, thus achieving high portability and security.
Owner:EQUES TECH
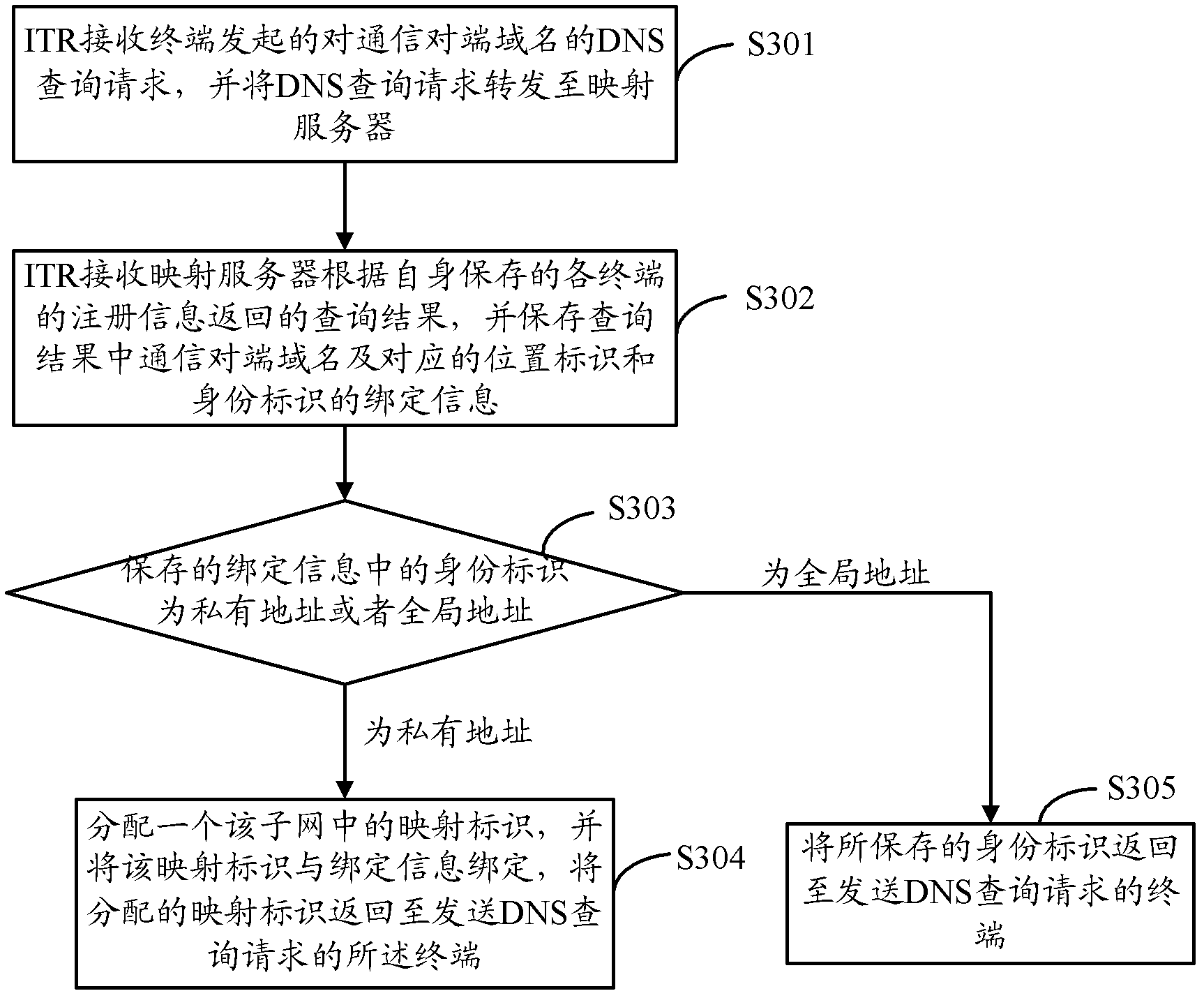
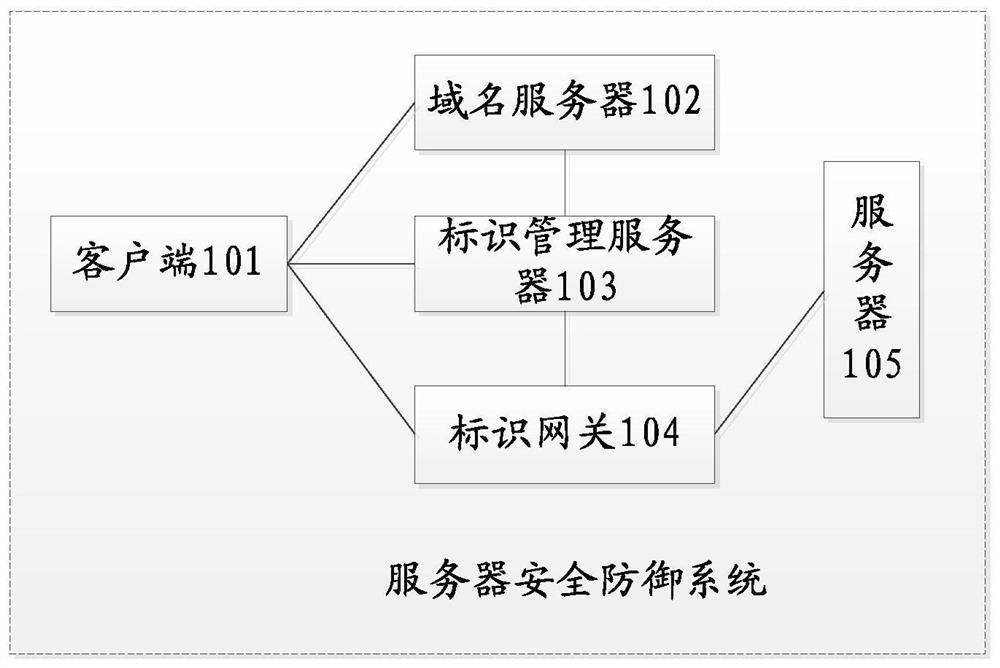
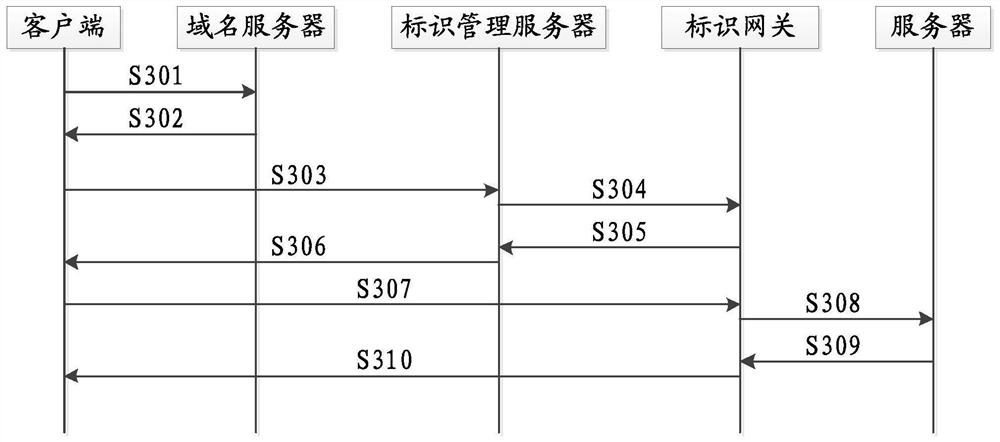
Server security defense method and system, communication equipment and storage medium
The embodiment of the invention provides a server security defense method and system, communication equipment and a storage medium, a client sends a domain name resolution request to a domain name server, and the domain name server resolves a server domain name in request information into an identification management server IP address and returns the identification management server IP address tothe client; the client sends a service request to the identifier management server, the service request comprises a service identifier, the identifier management server requests a dynamic identifier from the identifier gateway, the identifier gateway allocates dynamic identifier information and returns the dynamic identifier information to the identifier management server, a mapping relationship is established, and the identifier management server returns a redirection response to the client; and the client sends a service request to the identification gateway, and the identification gateway converts the service request information according to the mapping relationship, sends the service request information to the service server, converts the received response information of the service server and sends the converted response information to the client. In some implementation processes, the communication parameters of the server are randomly and dynamically transformed, the target server is actively protected, and the safety is improved.
Owner:ZTE CORP
Chip wafer test control method and device, and chip
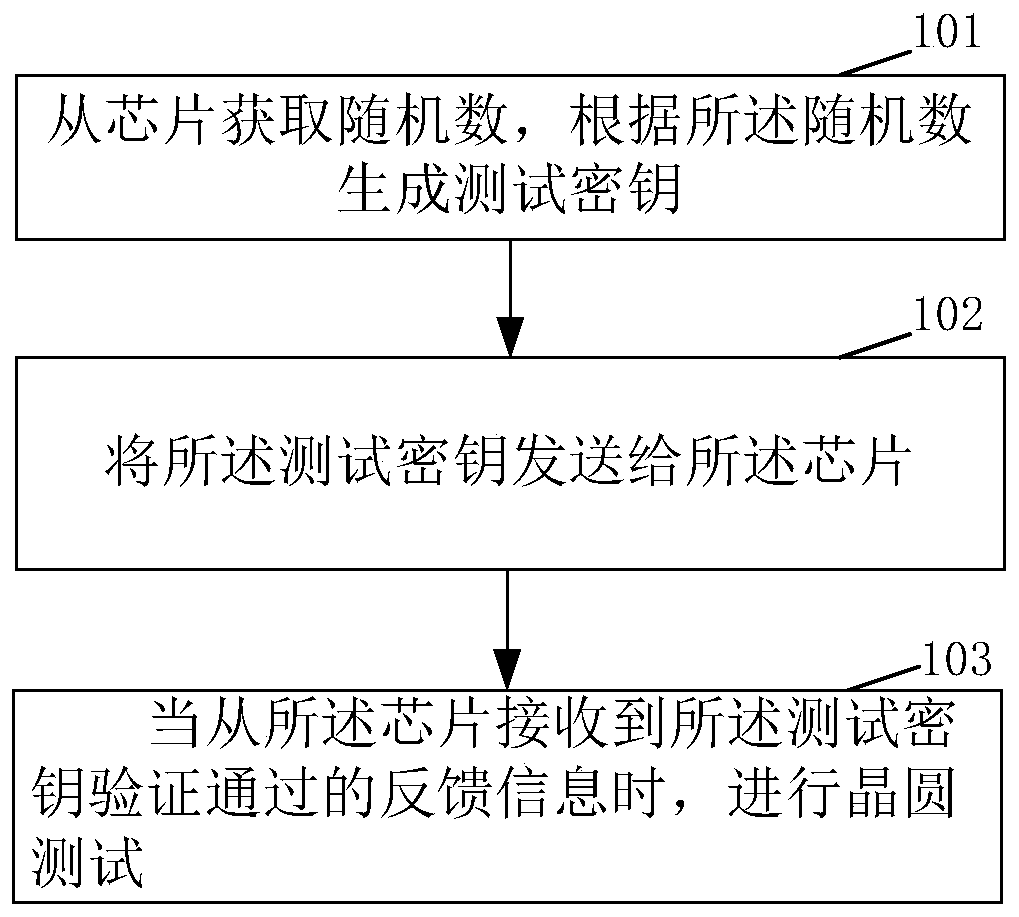
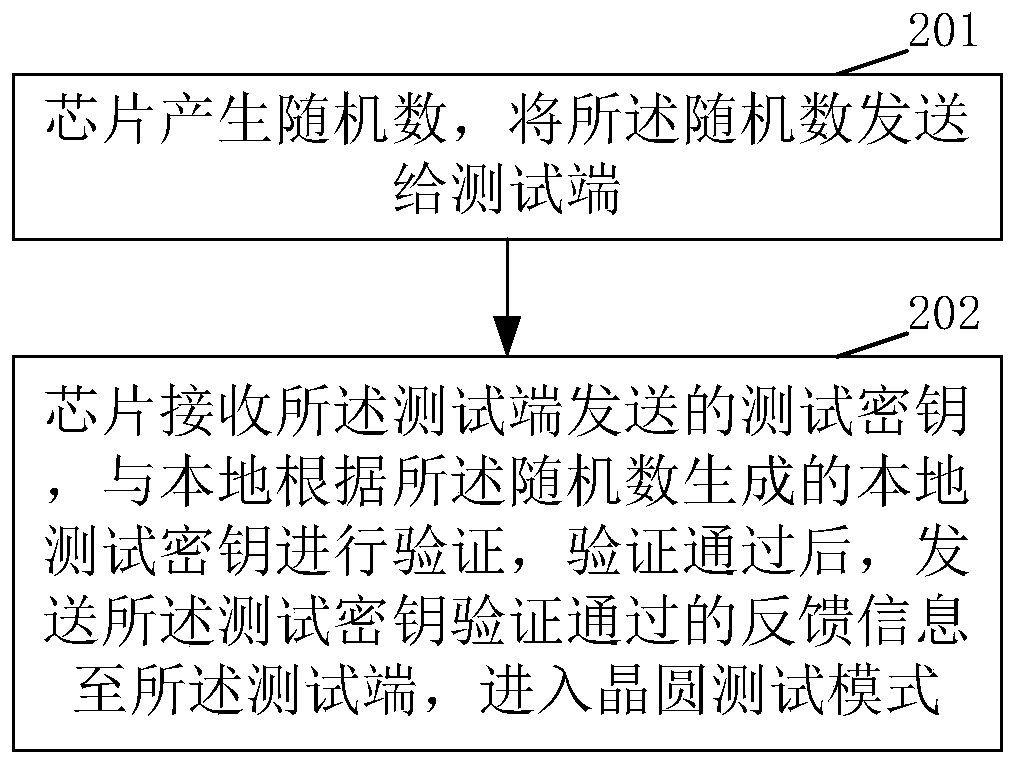
PendingCN111262697AImprove securityIncrease attack difficultyKey distribution for secure communicationElectronic circuit testingPasswordSecret code
The invention discloses a chip wafer test control method and device and a chip. The chip wafer test control method comprises the steps of obtaining a random number from the chip, and generating a testsecret key according to the random number; and sending the test secret key to the chip; and when feedback information that the test secret key passes verification is received from the chip, carryingout wafer test. According to the scheme provided by the embodiment of the invention, the test password related to the random number generated by the chip is used, so that the security of the secret key generated in the mode is higher, and the attack difficulty is higher; besides, random numbers generated by different chips are generally different, so that test passwords are different; even if onechip is cracked, the chip cannot be directly applied to other chips; and the safety of the chip is improved.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Secure solid-state disk data transmission system based on reconfigurable cryptographic processor
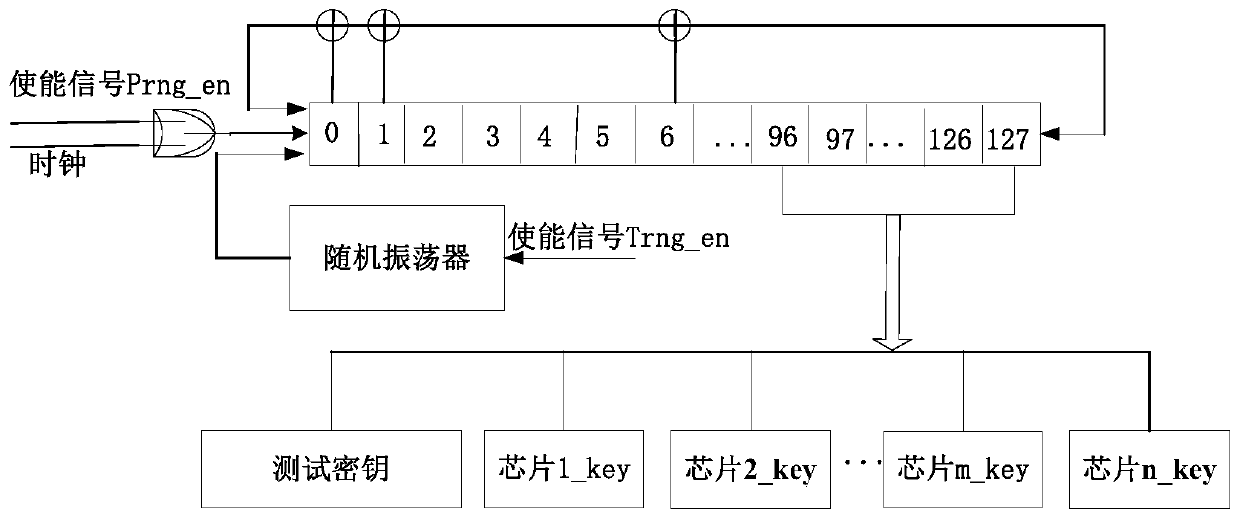
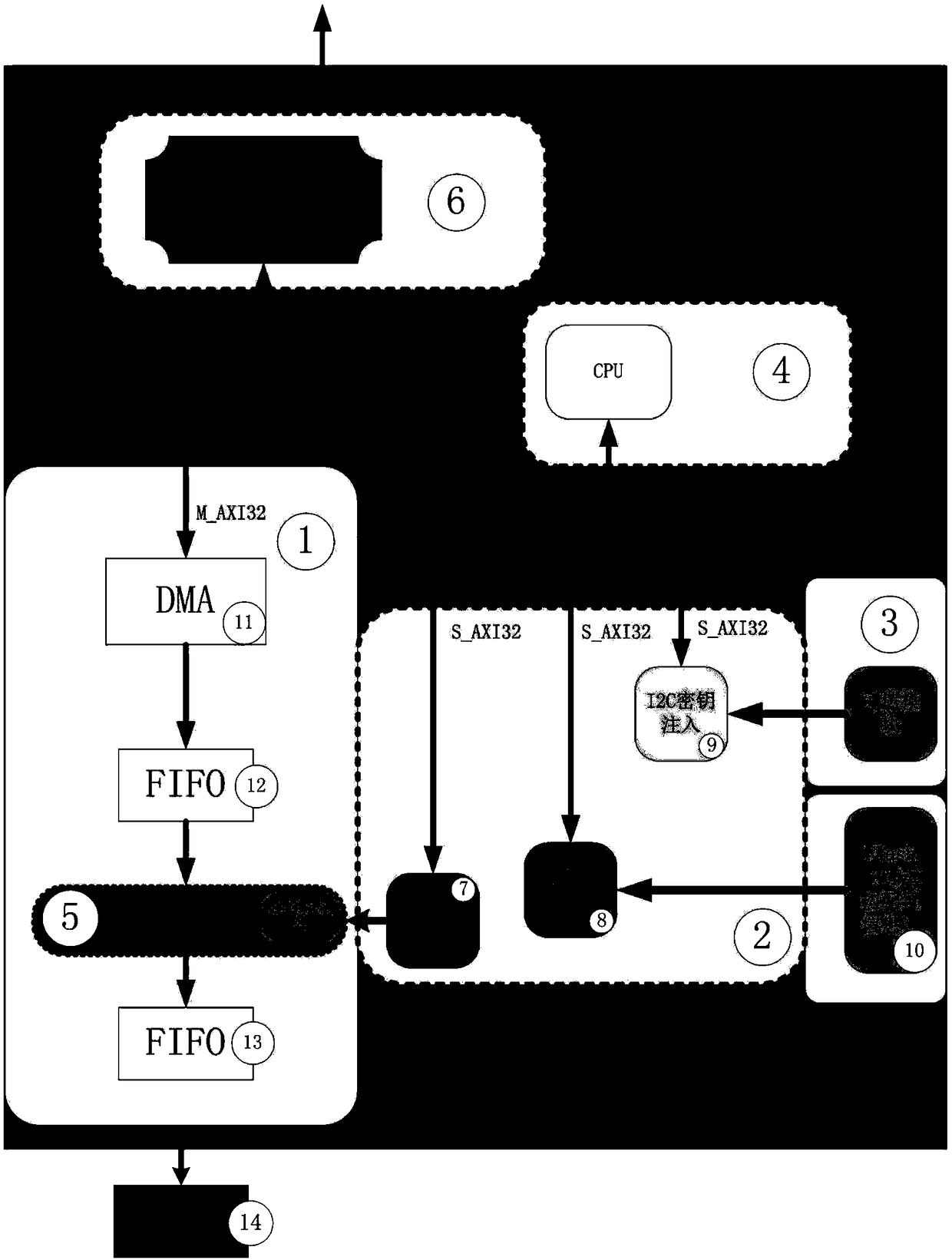
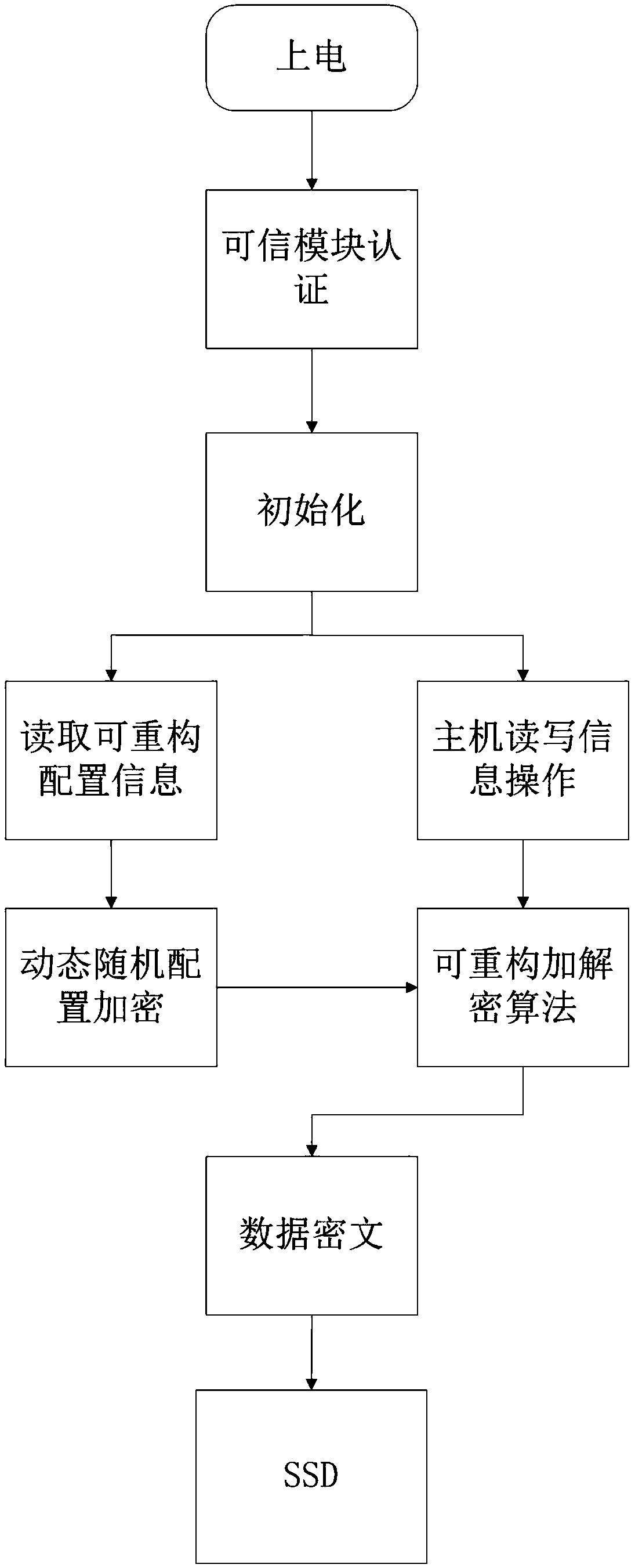
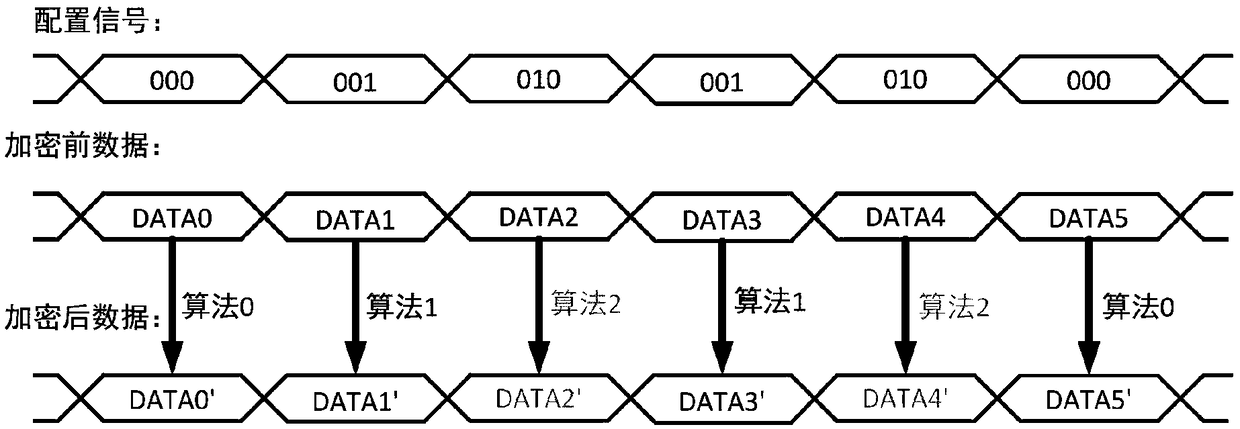
ActiveCN109101829AEliminate potential safety hazardsIncrease attack difficultyKey distribution for secure communicationMultiple keys/algorithms usageTime domainData transmission systems
The invention relates to a secure solid-state disk data transmission system based on a reconfigurable cryptographic processor, which relates to the technical field of data transmission. The inventionprovides a secure solid-state disk data transmission system based on a reconfigurable cryptographic processor, using a randomly dynamically configured encryption algorithm circuit in the time domain,Because the encryption algorithm used is randomly and dynamically configured over time, the attacker can not obtain the specific encryption form of each piece of data, thus eliminating the security hidden trouble that the attacker can carry out targeted attacks on the encryption algorithm, greatly increasing the attack difficulty of the attacker, and effectively improving the data security.
Owner:BEIJING INST OF COMP TECH & APPL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com