Dynamic application address conversion method and gateway system
An address translation and dynamic application technology, applied in the field of web application security, can solve the problems of high construction cost of application instructions, lack of versatility, low practicability, etc., to achieve good security and operability, increase attack difficulty, guarantee safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
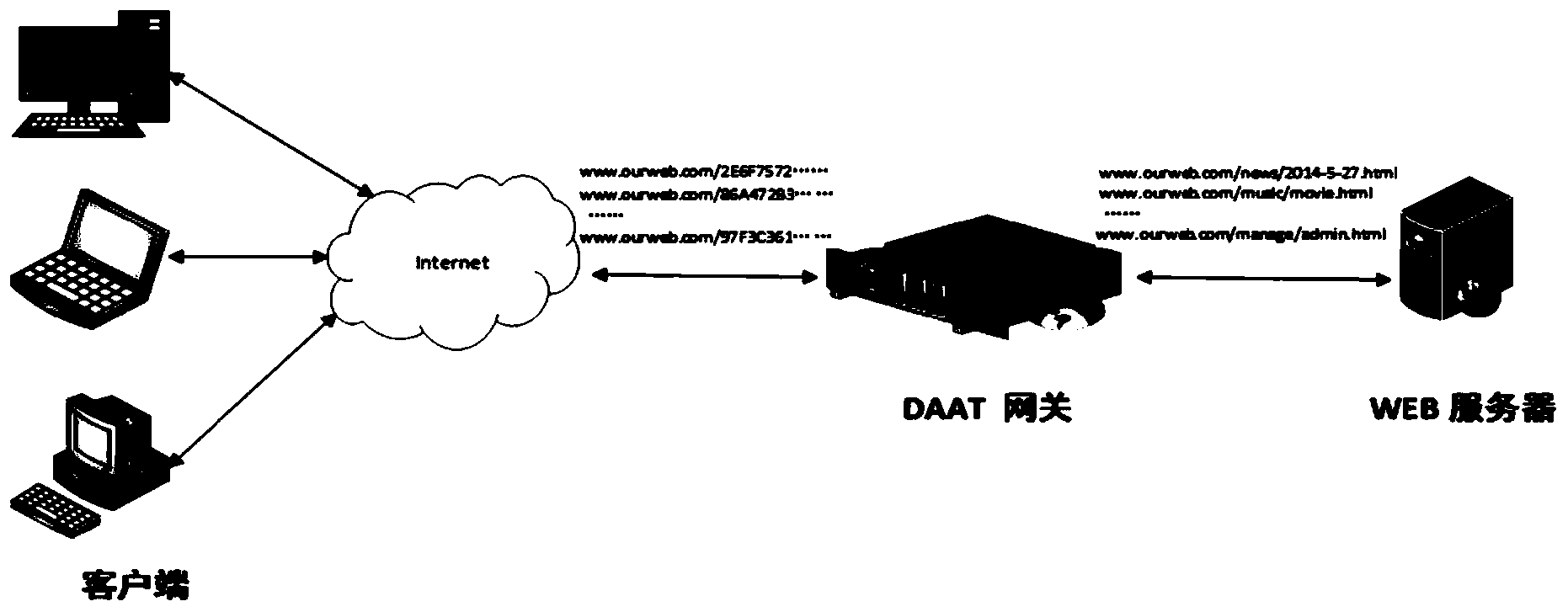
[0039] Such as figure 1 Shown is a schematic diagram of the deployment of the Dynamic Application Address Translation (DAAT) gateway of the present invention. We use Privoxy in the DAAT gateway as proxy software to implement the DAAT method.
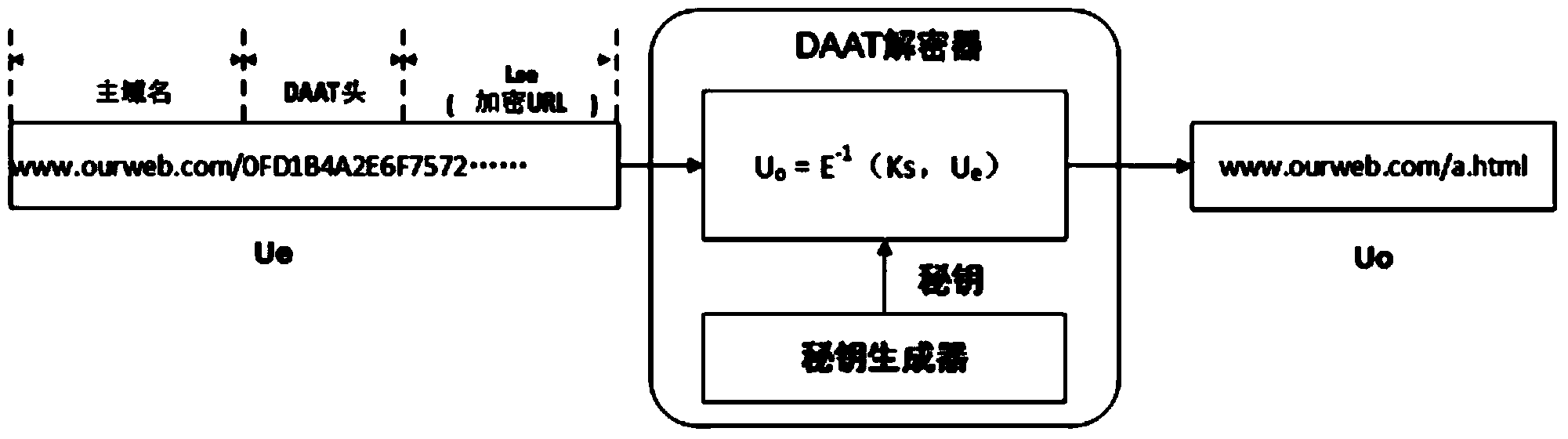
[0040] The dynamic application address translation (DAAT) gateway system of the present invention includes an encryptor, a secret key generator, a decryptor, a URL locator and a redirector.
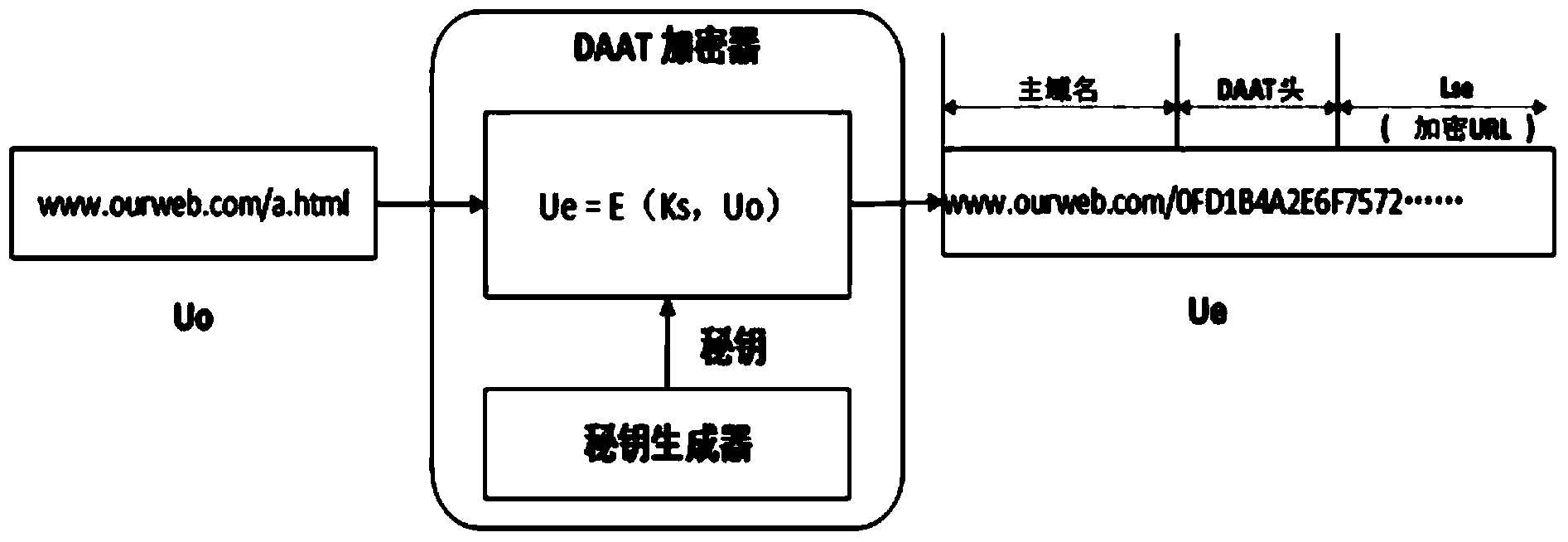
[0041] The encryptor converts and encodes the original URL. The conversion function can be a symmetric encryption function, an asymmetric encryption function, or an XOR algorithm, etc. Generally, a symmetric encryption function is used;
[0042] The secret key generator is used to generate the master secret key and session secret key, where: the master key can be a random number generator, or the current time of the system o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com