Patents
Literature
140results about How to "Do not change usage habits" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Alcohol-free concentrated fountain solution and preparation method thereof
InactiveCN102303465AStable concentrationPrint color difference is smallPrinting pre-treatmentAlcohol freePhysical well being
The invention provides an alcohol-free concentrated fountain solution and a preparation method thereof. The alcohol-free concentrated fountain solution is prepared from the following components based on 100 parts by weight: 0.5-5 parts of low-foam wetting agent, 8-20 parts of pH value regulator, 3-20 parts of printing plate protective agent, 5-10 parts of a water film regulator, 0.2-1.0 part of decontamination intensifier, 0.1-1.0 part of bactericide, 0.1-1.2 parts of defoamer and the balance of water. The concentrated fountain solution provided by the invention is environmentally-friendly, provides guarantee for the health of workers, and can improve the quality of the printing products.
Owner:冯星枢 +1
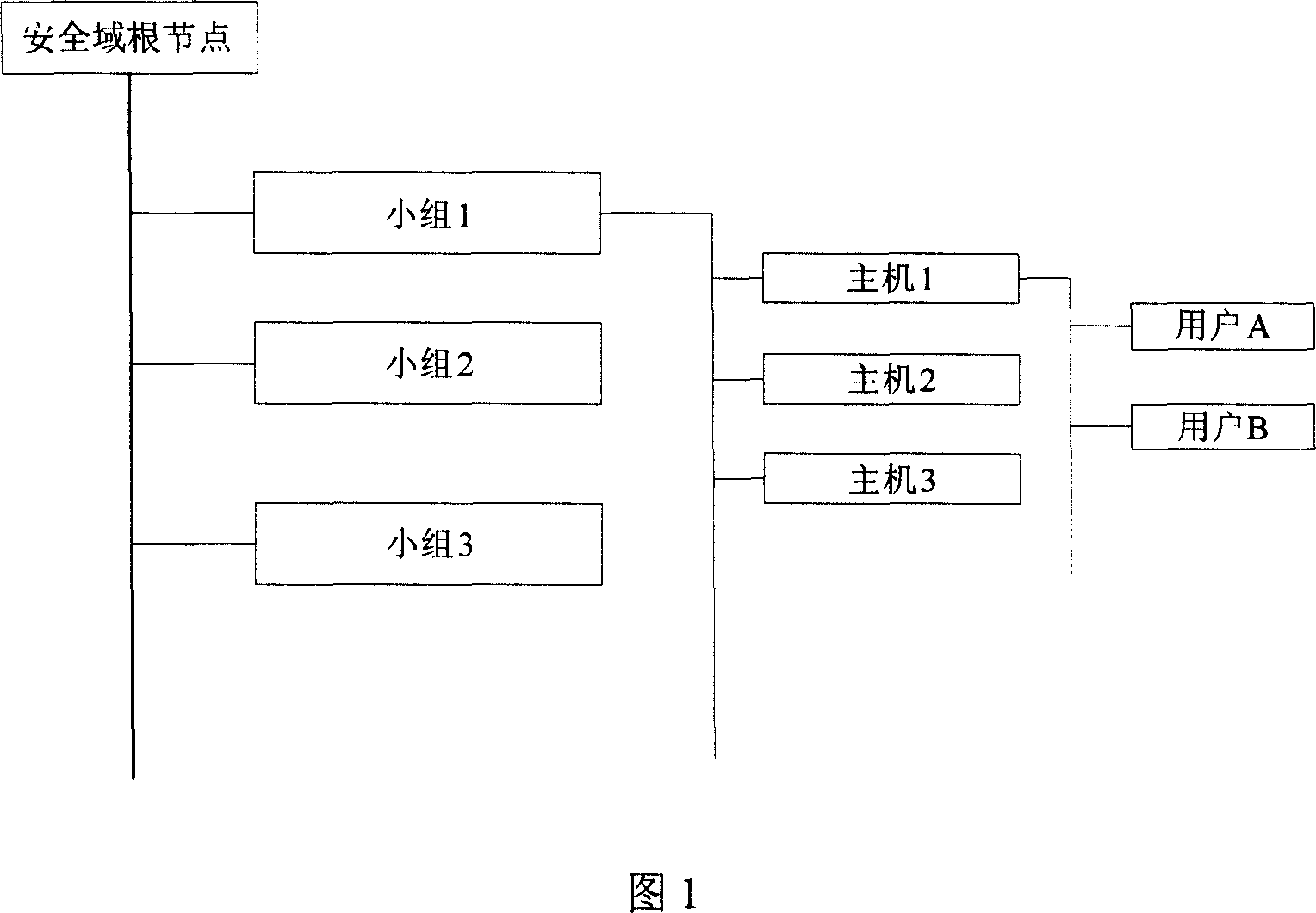
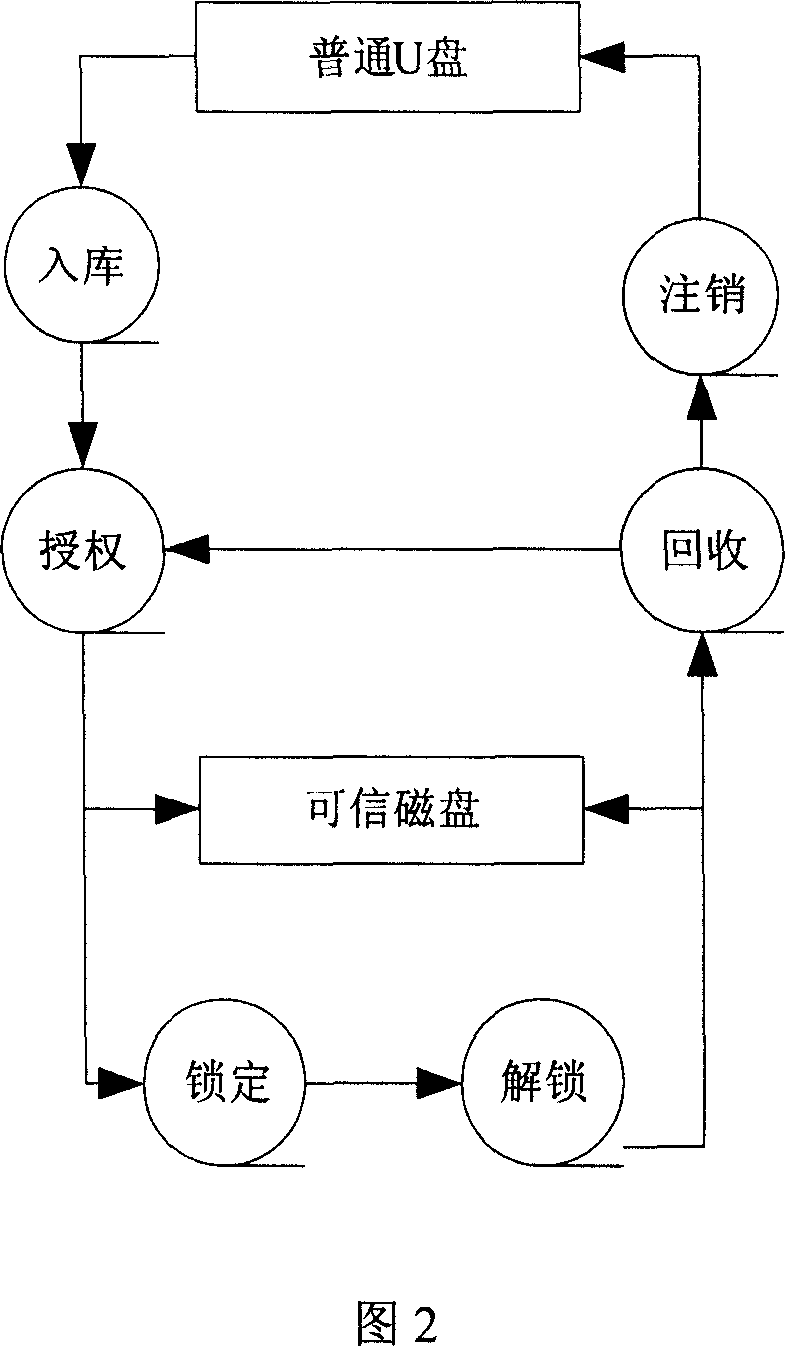
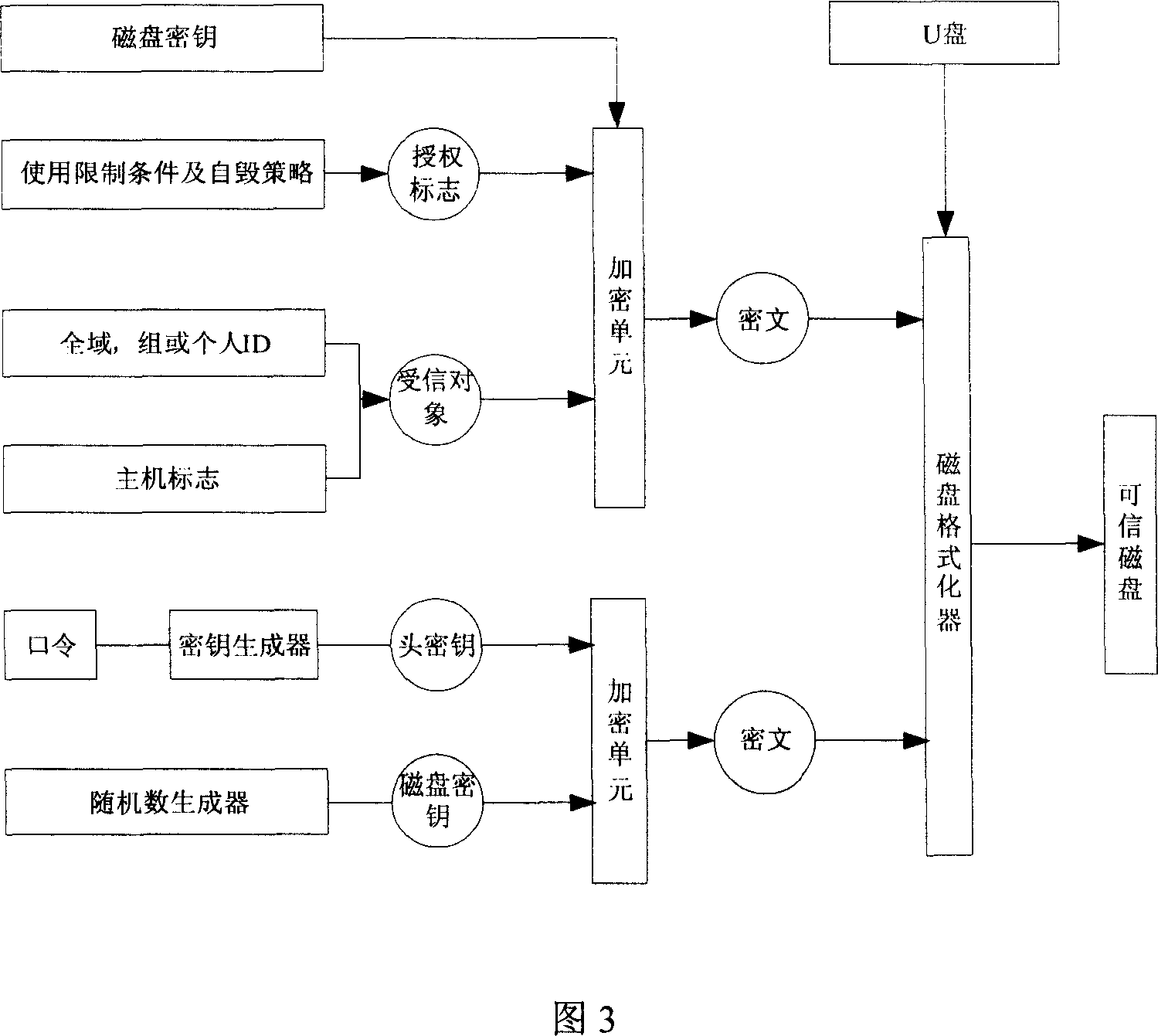
Mobile memory divulgence protection method and system
InactiveCN101079008AEasy to manageReach protectionUnauthorized memory use protectionInternal/peripheral component protectionCiphertextFloppy disk
The invention discloses a method of shifting memory leaking secret protection and system to realize the method, which is characterized by the following: utilizing virtual disk technique; adopting disk grade bridging method; proceeding encryption for the data in the common memory through the virtual disk with special pattern; storing the data on the shifting memory with cryptogram style; loading the virtual disk before reading or writing data; proceeding order checkout and user identification proved; non-loading without right order or special form; assuring the safety of the data in the shifting memory; setting the system as three module of server, warranting center and custom terminal. This invention can be used to various memories such as flash memory, shifting hard disk, soft disk and so on.
Owner:CHINA NAT SOFTWARE & SERVICE
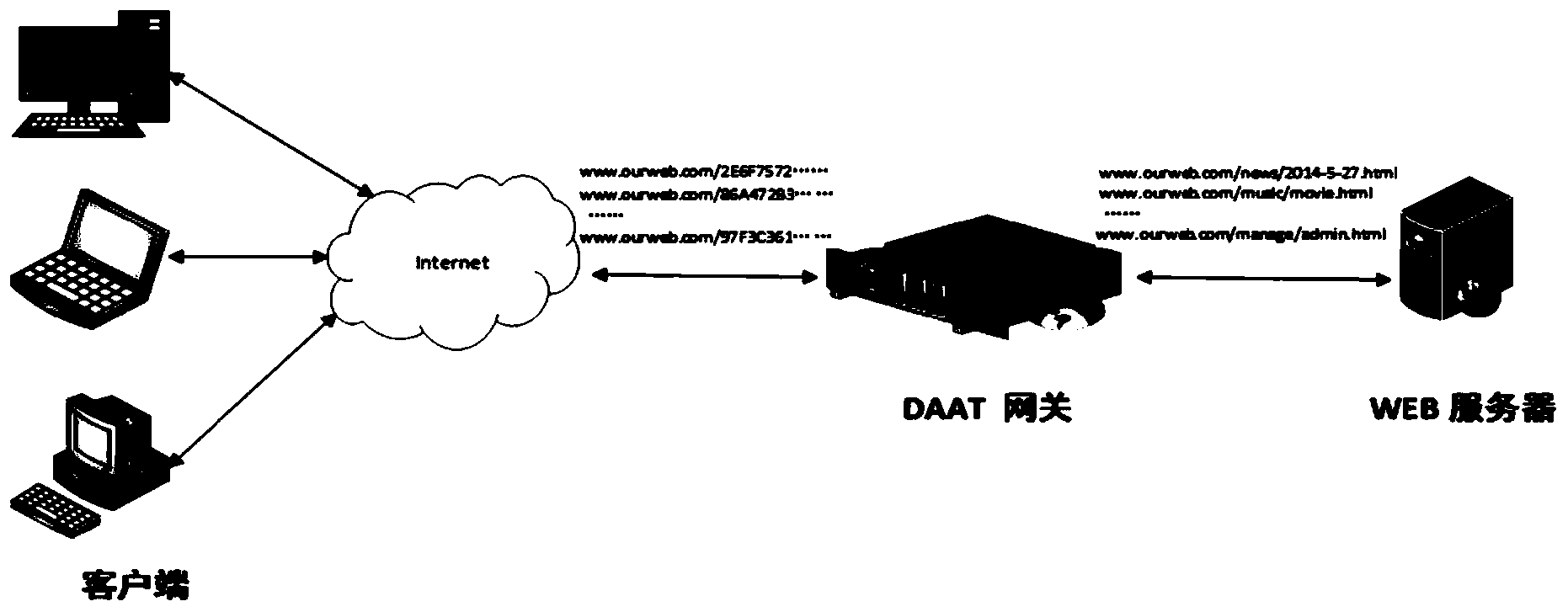
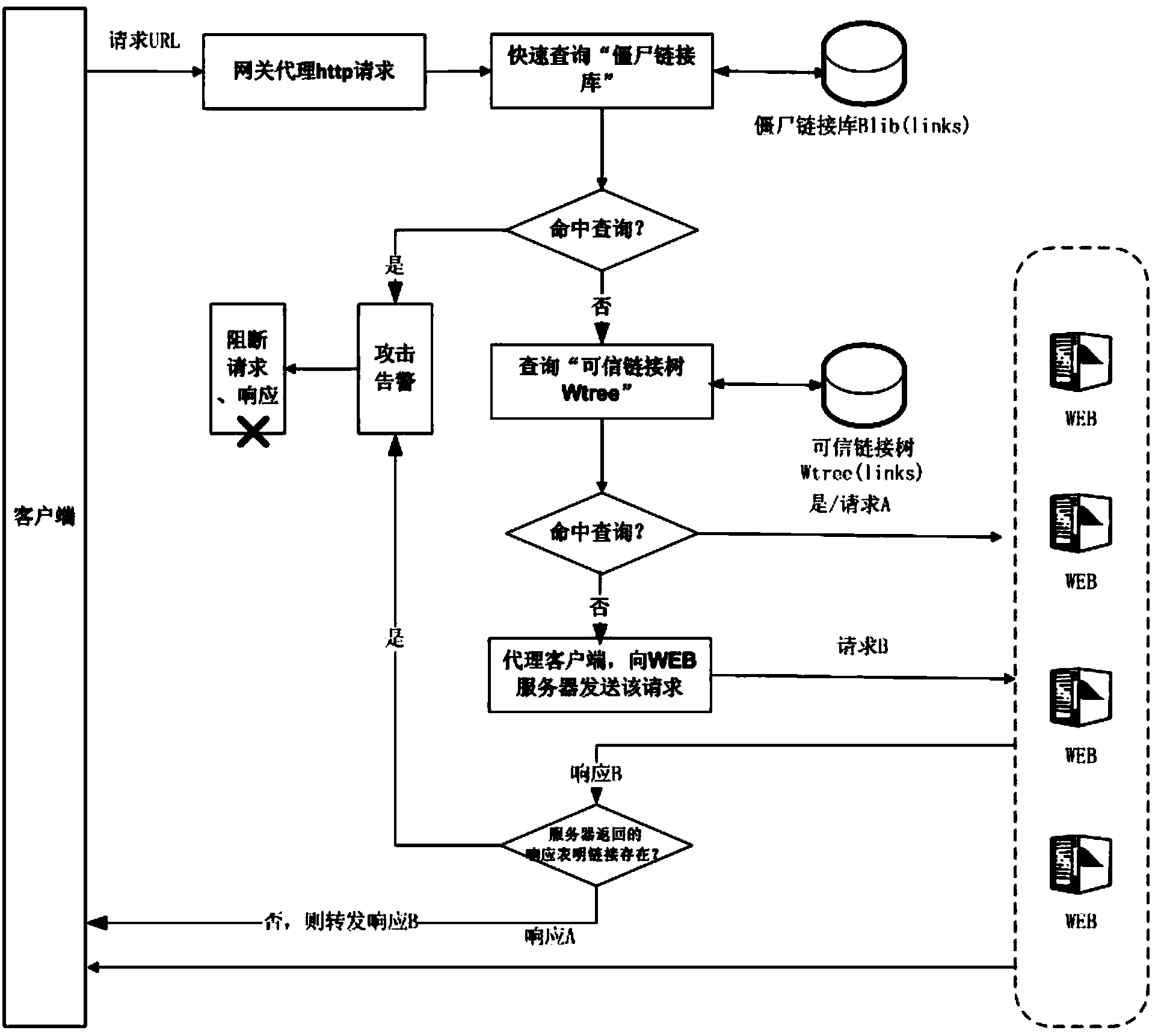
Dynamic application address conversion method and gateway system
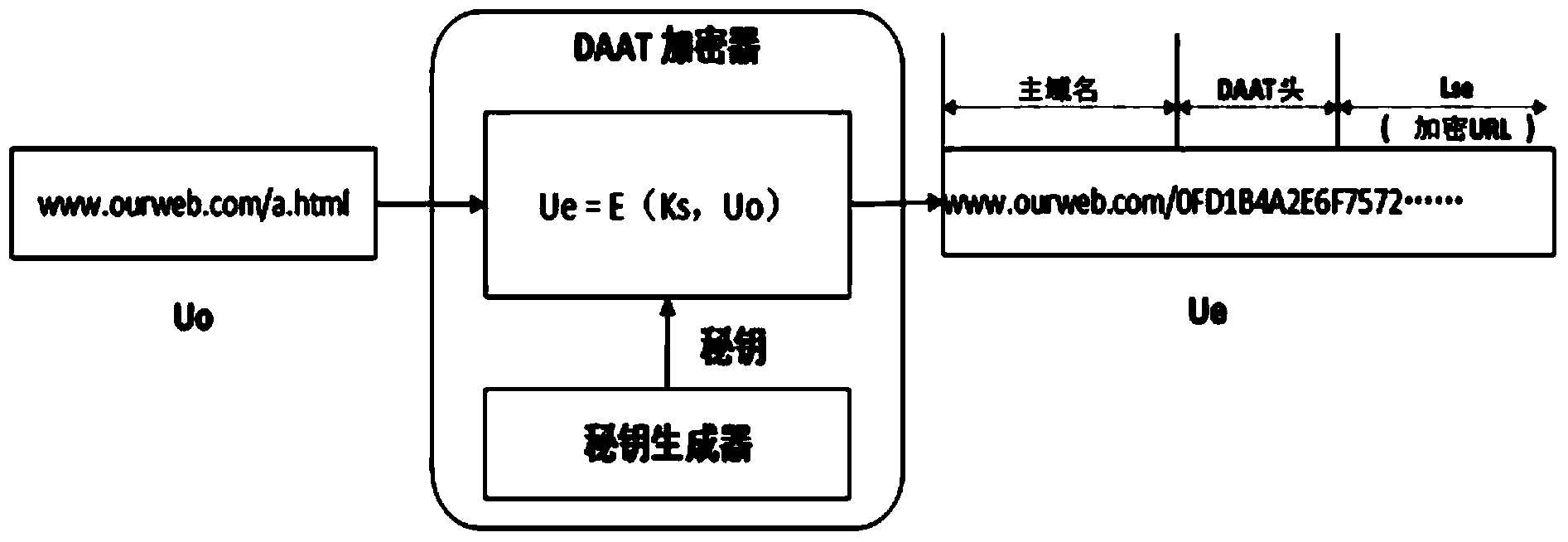
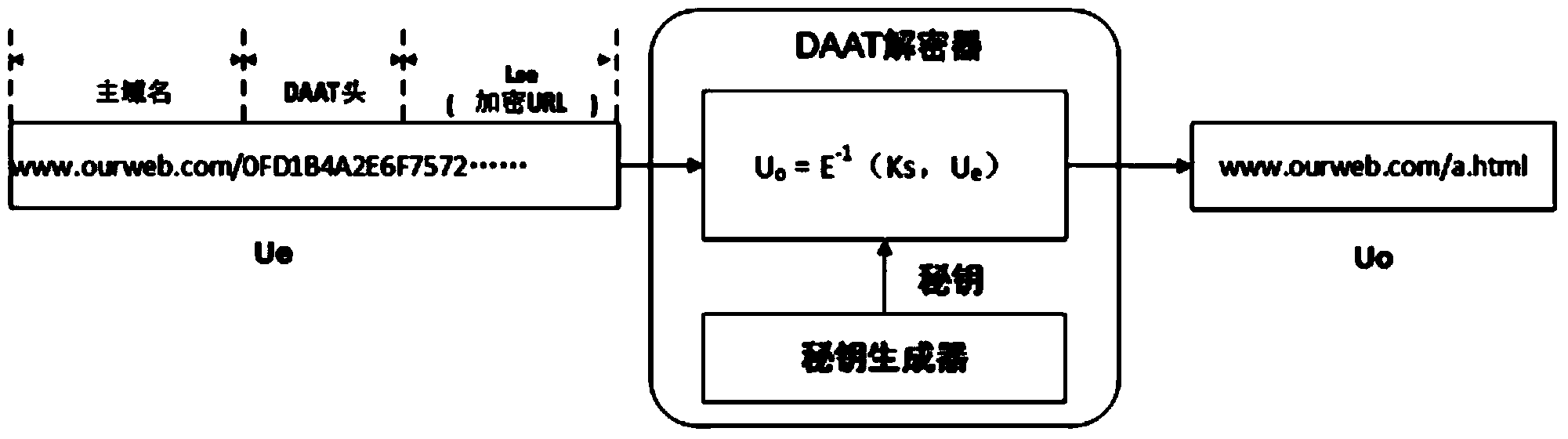
ActiveCN104378363AIncrease attack difficultyHide vulnerabilityKey distribution for secure communicationGateway systemVulnerability scanning
The invention relates to a dynamic application address conversion method and gateway system. A novel Web application attack defense method is achieved. URL addresses are dynamically converted, attack faces of an application system are converted, vulnerability of Web applications is hidden, the attack difficulty of an attacker is increased, and the difficulty in which the attacker conducts vulnerability scanning and attack injection on Websites through URLs is greatly increased. By the adoption of a DAAT method, the security threats of the attacker to the Web applications can be dynamically and effectively reduced, and security of the Web application system is improved.
Owner:INST OF INFORMATION ENG CAS
Safe bubble-free infusion set
Owner:JIANGXI HONGDA MEDICAL EQUIP GROUP
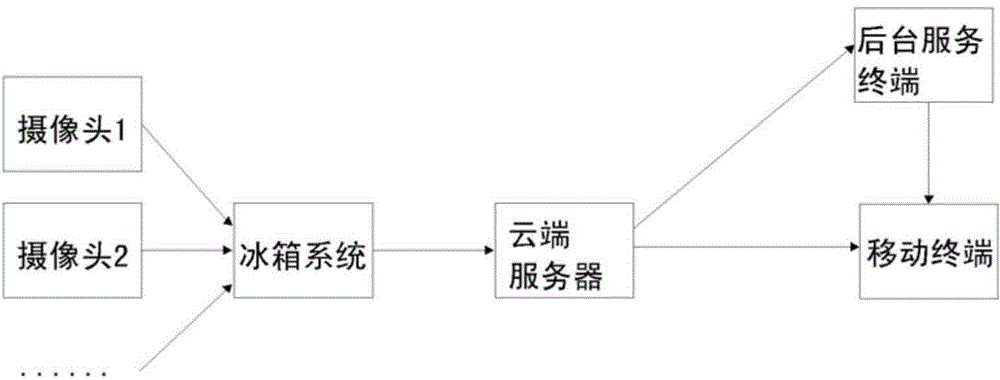
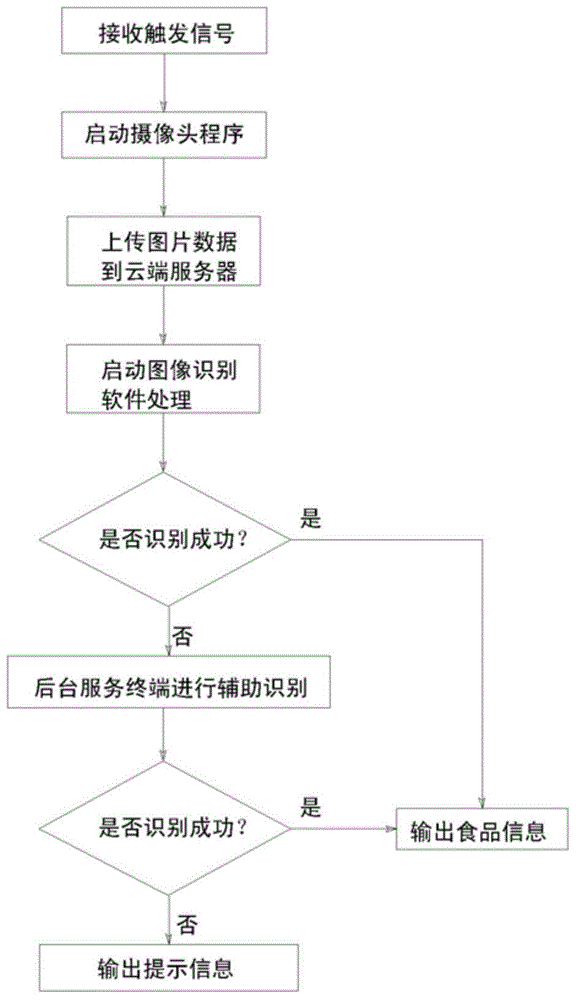
Method for identifying and managing refrigerator food list according to remote images
InactiveCN104896868AChange habitsImprove experienceLighting and heating apparatusCooling fluid circulationData informationComputer terminal
The invention discloses a method for identifying and managing a refrigerator food list according to remote images. The method is characterized in that cameras are arranged in storage racks and bottle frames of a refrigerator, camera procedures are started in a multiple-triggered manner, the cameras are sequentially called to shoot, picture data are transmitted to a cloud server by a refrigerator system, image identifying software is started, the picture data of the cloud server are converted into food data information, data are transmitted back to the refrigerator system and a mobile terminal, a background service terminal can assist in identification when software identification is failed, and a prompt is transmitted to the refrigerator system and the mobile terminal if the identification is still failed. The method can automatically generate the food list, and the intelligent level of the refrigerator and user experience are improved.
Owner:CHANGHONG MEILING CO LTD
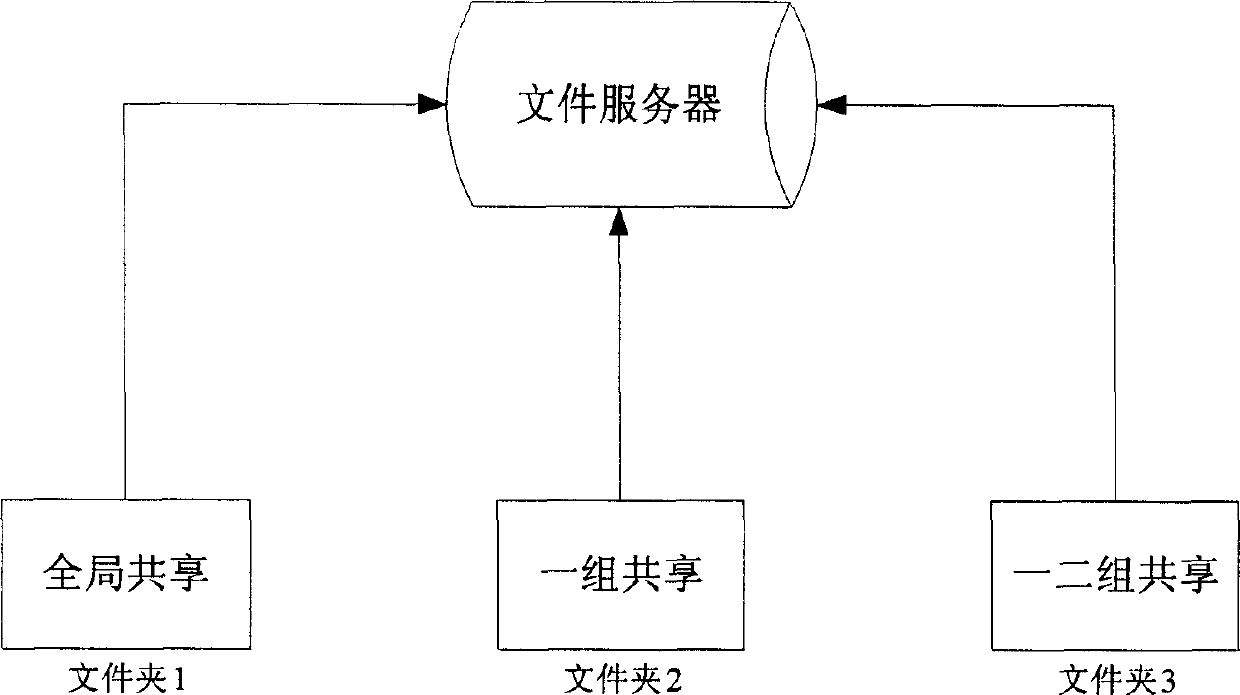
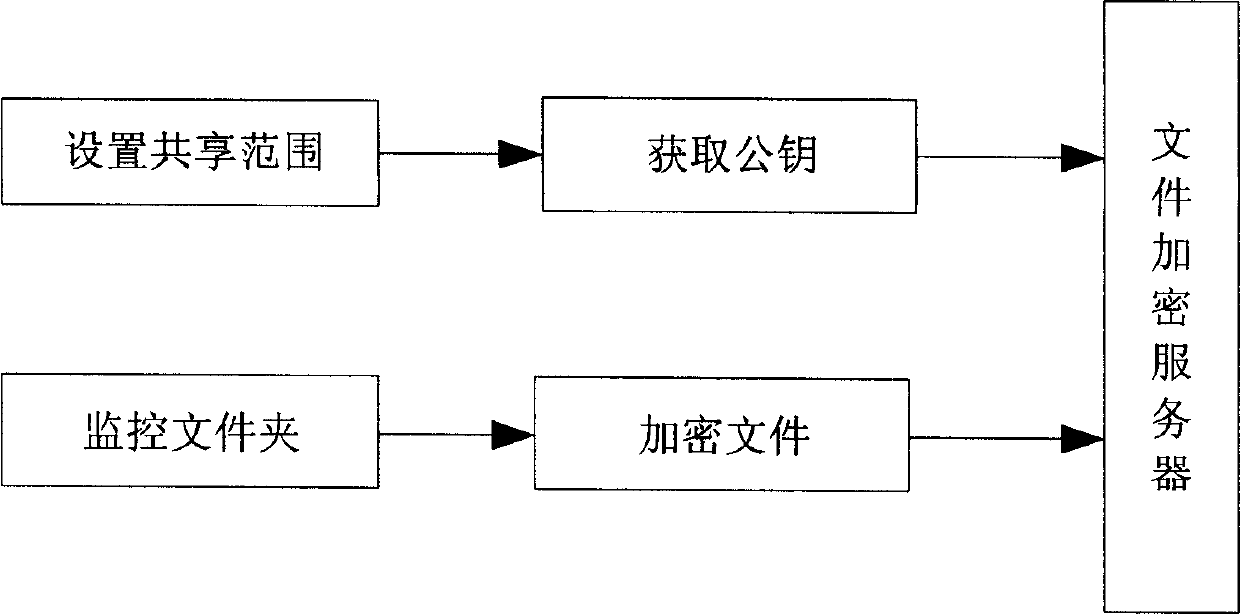
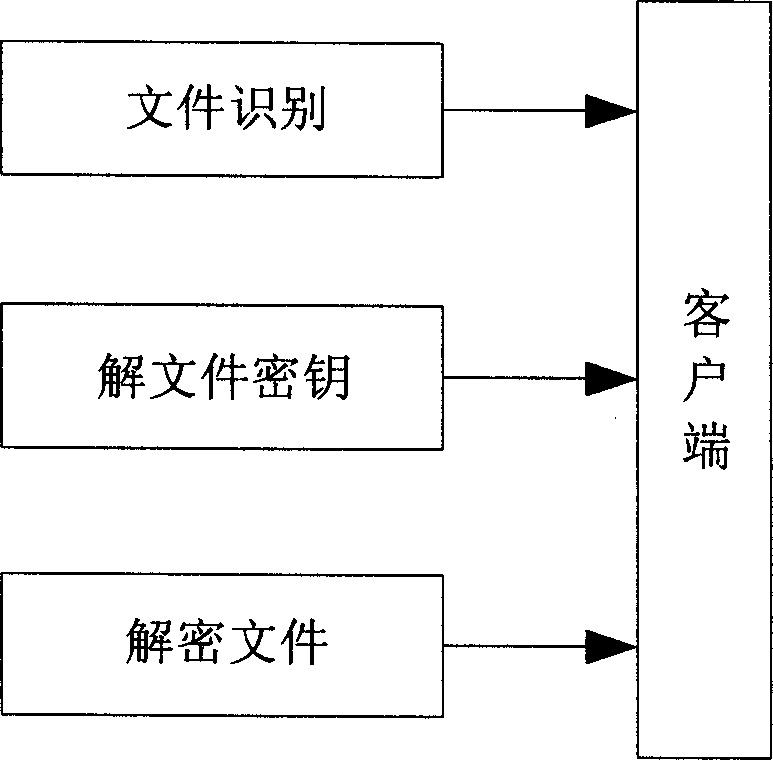
Method and system of file encipher share
InactiveCN1832398AChange habitsLow costPublic key for secure communicationDigital data protectionCiphertextClient-side
This invention relates to a method and a system for realizing cipher share by implanting ciphered cryptographic keys in the document, in which, said system is composed of file servers and customer ends and the file server includes a file monitor module, a file share sphere designing module, a public key obtaining module and a ciphering module, the customer end includes: a file identifying module, a file de-ciphering module and a de-ciphering module, the ciphering process includes: designing different shared files based on the shared kinds, each owns its own ciphered public key, utilizing a symmetric algorithm to cipher the files first and implanting the cryptographic key of said file into the ciphertext, then utilizing one or many public keys to cipher the cryptographic keys of th file by an asymmetric algorithm to form a link and implanting the shared kind, public key numbers and the cryptographic link into the head of the text.
Owner:CHINA NAT SOFTWARE & SERVICE
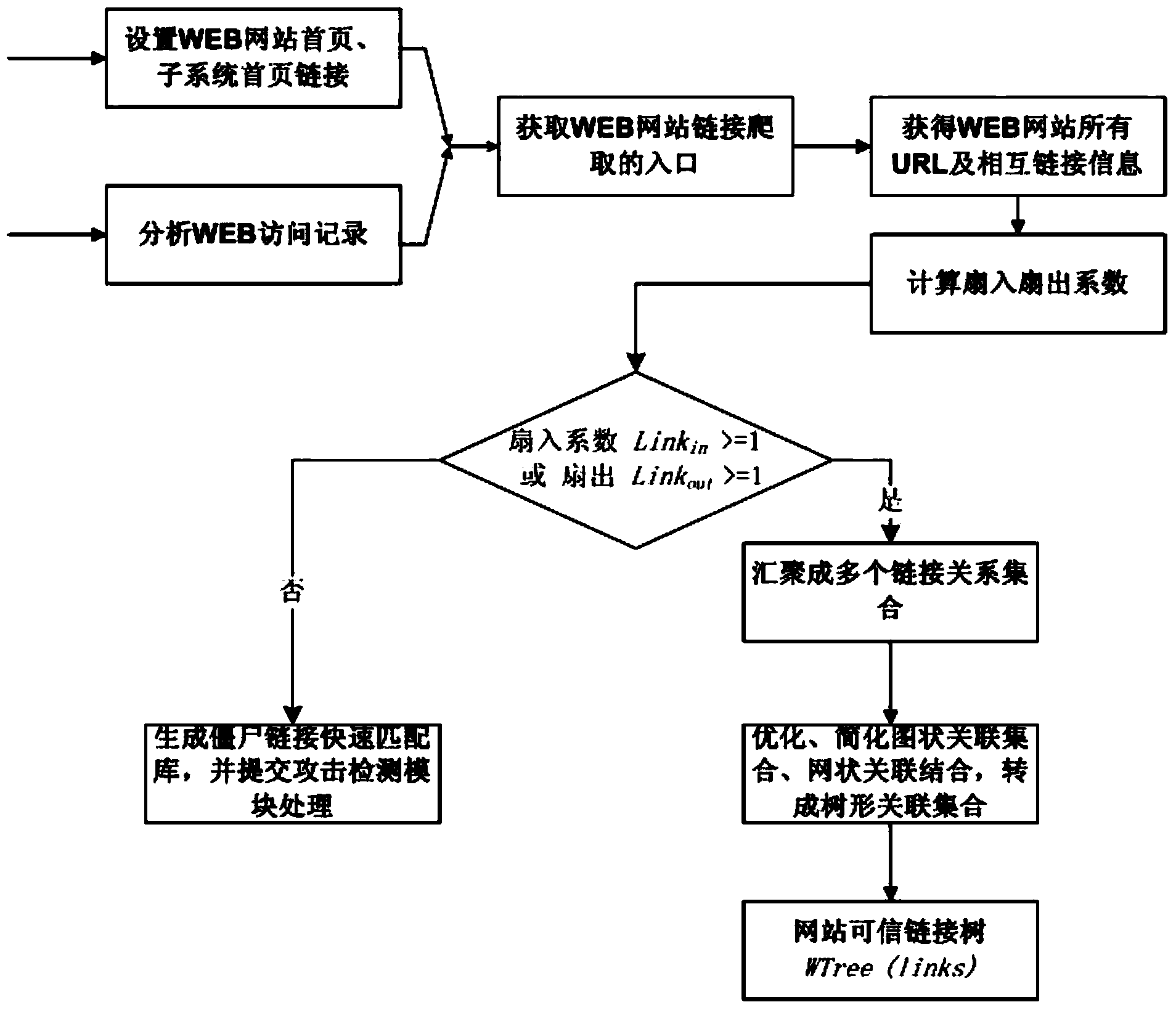
WEB backdoor detection method and system based on relevance tree
ActiveCN103561012AImprove relationshipSimplified link relationship tree associationTransmissionSpecial data processing applicationsWeb siteWeb application
The invention relates to a WEB backdoor detection method and system based on a relevance tree. The WEB backdoor detection system comprises a link relevance tree generation module and an attack real-time detection module. The detection system does not depend on antivirus software or file feature detection software, instead, initiative crawling and access record collecting are conducted on WEB links first, a link set of all URLs of a WEB is established through analysis and process, and the link and skip relation of the URLs is marked in a computerized algorithm in a tree mode, so that a link relevance tree is formed. If a backdoor URL request does not exist in the link relevance tree, a security monitoring module of the system gives an alarm, and the attack request is stopped. By means of the detection method, the safety of WEB application is improved, the problem of WEB backdoor attack which can not be detected and prevented by security products such as the antivirus software and a firewall is solved, the university is good, there is no need to mount software programs on a WEB server, and the type of the WEB server, WEB programming languages, customer usage and the like are all made to be transparent.
Owner:INST OF INFORMATION ENG CAS
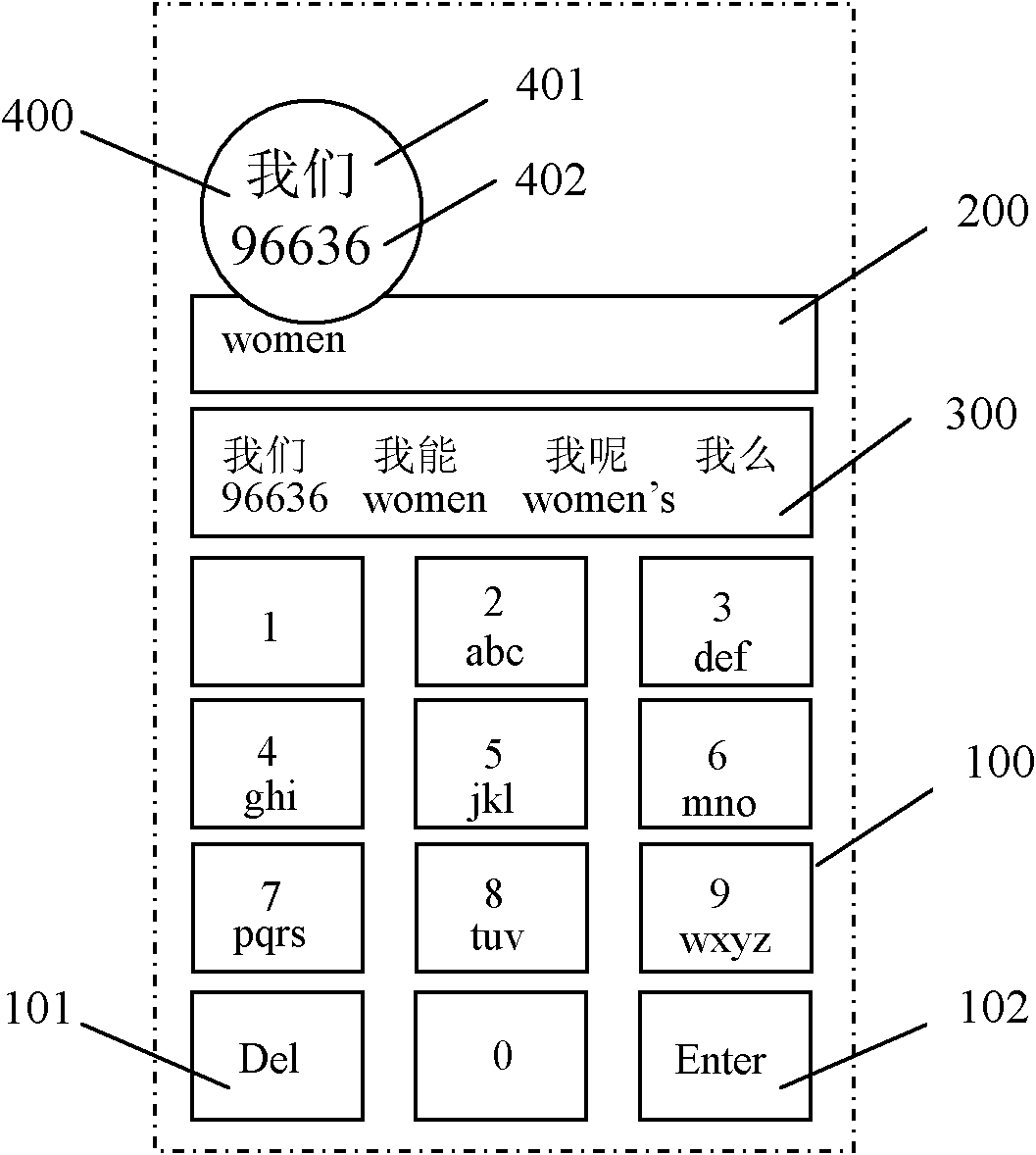
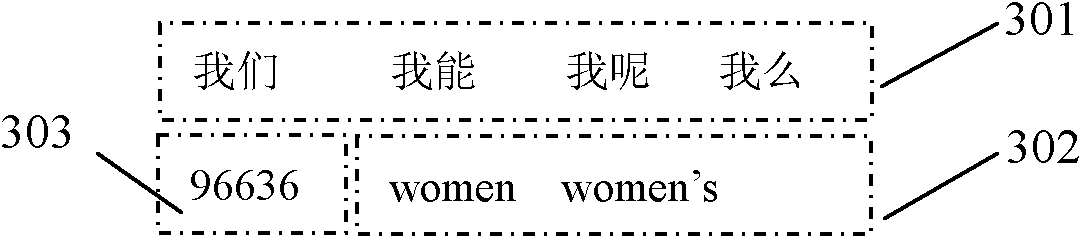
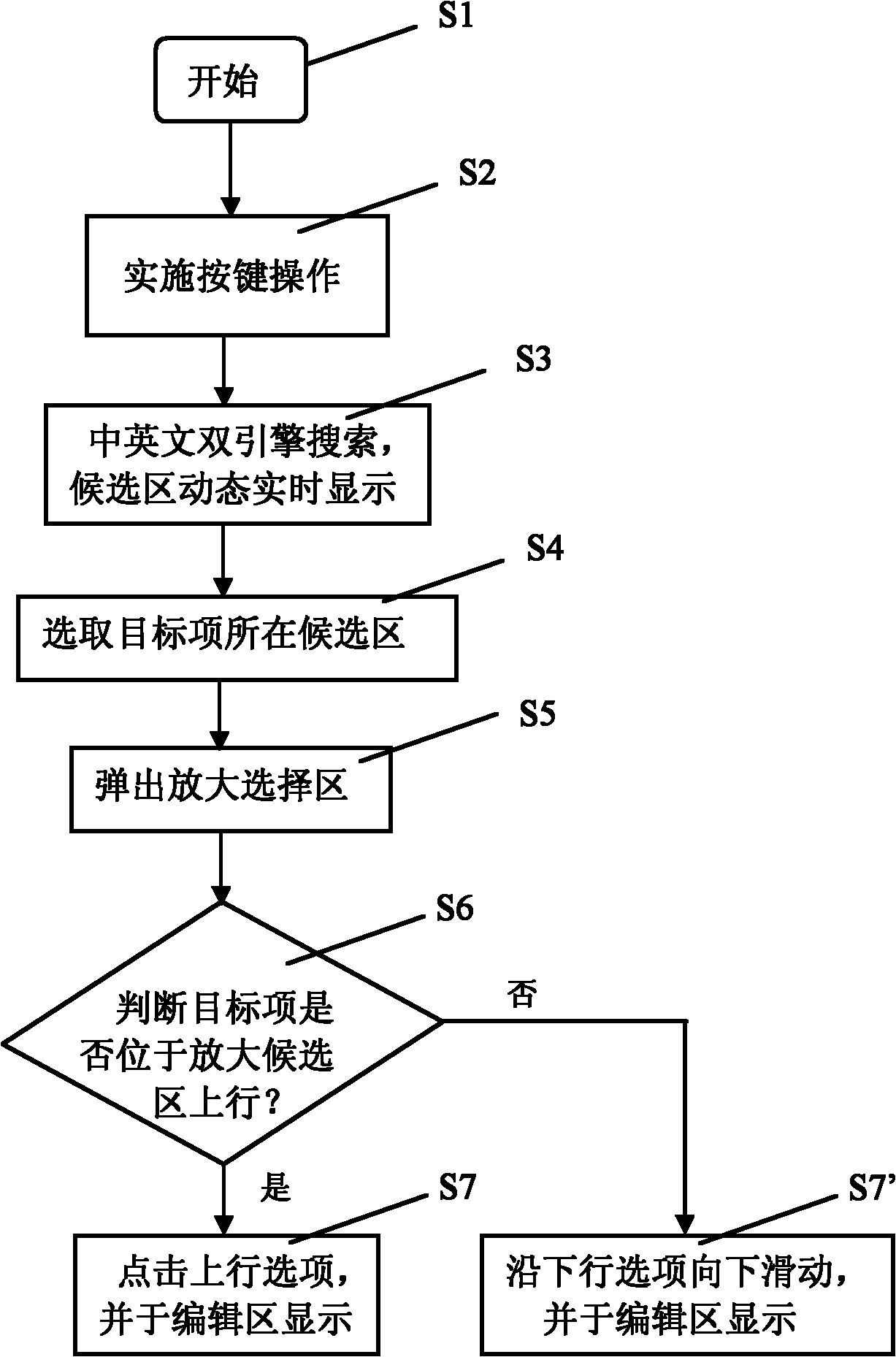
Multi-language hybrid input method used on embedded touch screen virtual keyboard
InactiveCN101976173AChange habitsImprove search abilityInput/output processes for data processingMulti languageComputer compatibility
The invention discloses a multi-language hybrid input method used on an embedded touch screen virtual keyboard. Each key on the virtual keyboard maps three to four characters respectively; a display region of a touch screen is provided with a virtual keyboard region, an editing region and a candidate region; the touch screen also comprises a pop-up amplifying and selecting region; the method particularly comprises the following steps of: performing keystroke operation; dynamically displaying Chinese information, numerical information and foreign information related to the key at the candidate region; selecting the candidate region where a target item is positioned, popping up the amplifying and selecting region, and amplifying the row in which the target item is positioned in the candidate region by the amplifying and selecting region; and clicking or downwardly sliding the target item and selecting and displaying input Chinese information, numerical information or foreign information at the editing region in real time to finish the input. By the method, rapid hybrid input of Chinese, number, English and other foreign languages is realized, the efficiency of inputting written information is greatly improved, and the operation is intuitive and the compatibility of the method is good.
Owner:GUANGZHOU JIUBANG DIGITAL TECH
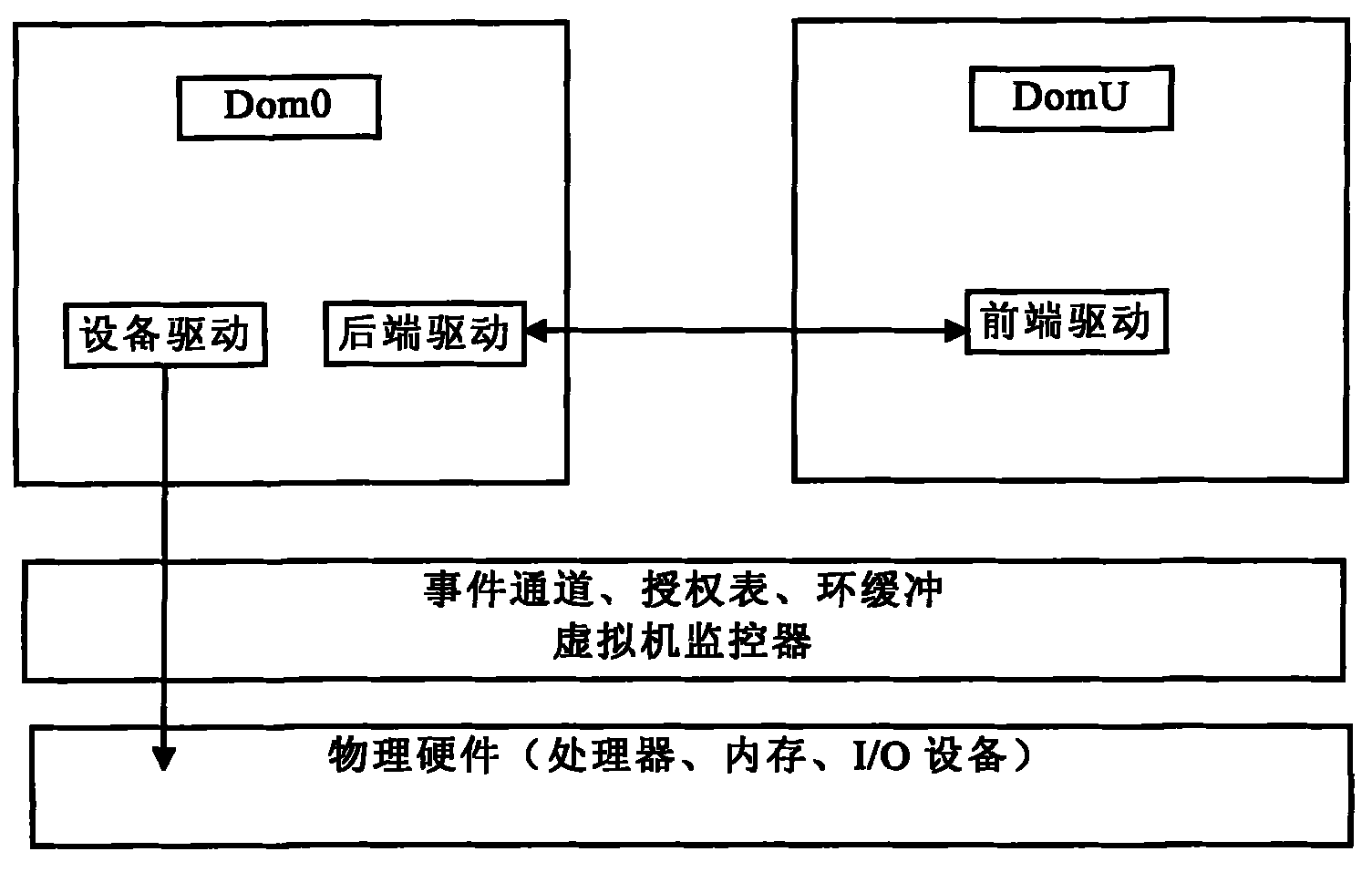
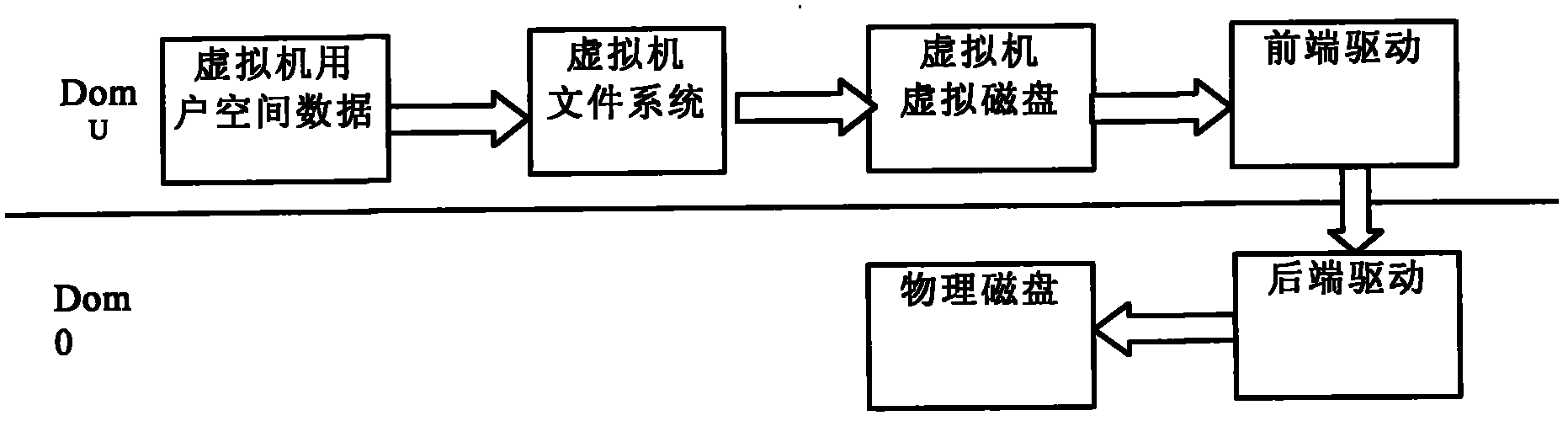
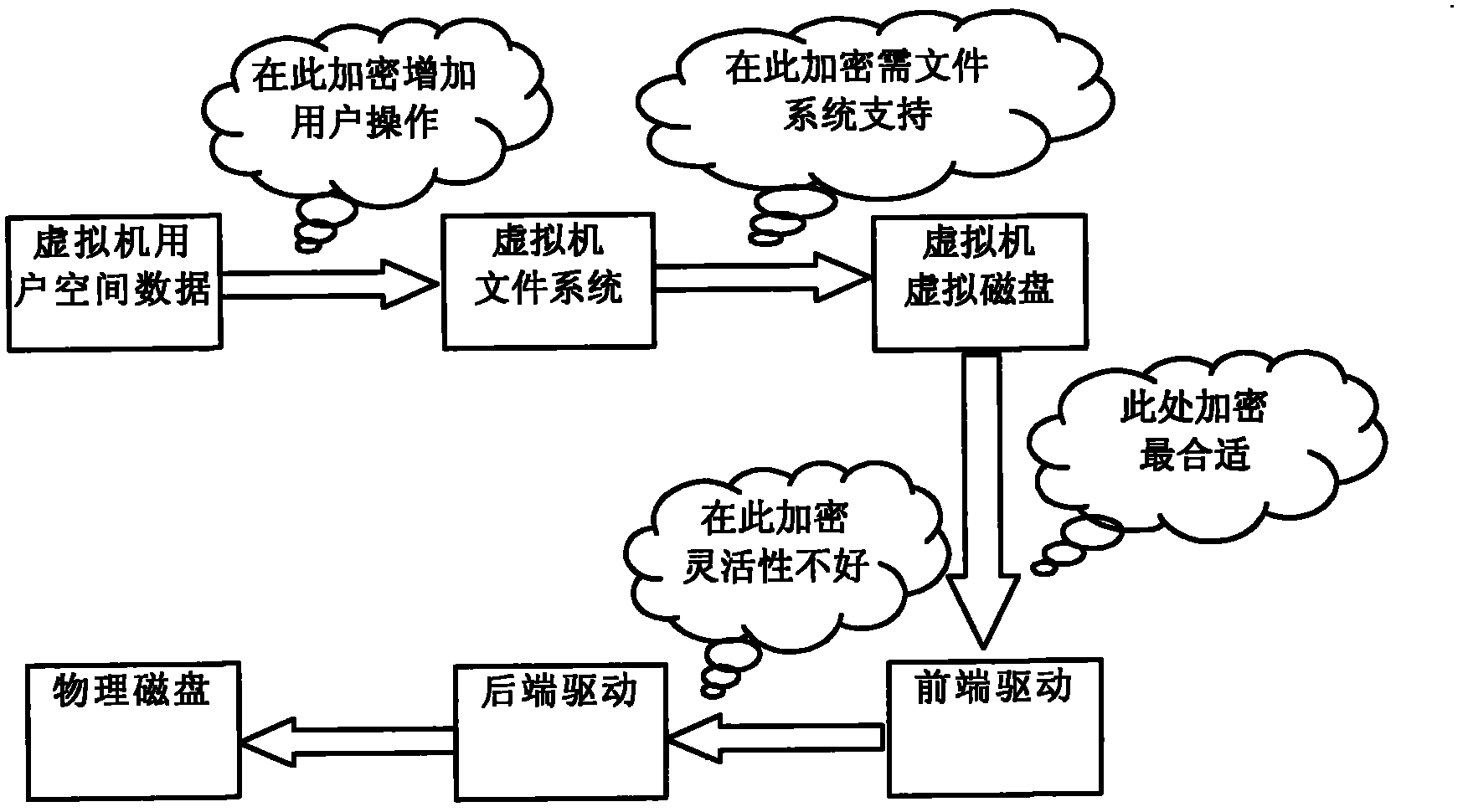
Data underlay encryption method based on disk drive in cloud computing environment
ActiveCN102034046AChange habitsGuaranteed privacyInternal/peripheral component protectionData storingCloud storage
The invention discloses a data encryption underlay encryption method based on disk drive in the cloud computing environment, comprising the following steps of: (1) granting a page allocated by a memory space to an equipment virtual machine on which a rear-end drive is positioned through a front-end drive by using a grant table; (2) encrypting data in a buffer area by a front end; (3) placing a writing request of a disk into an annular buffer area shared with the rear-end drive and informing the writing request of the rear-end drive through an event channel; (4) after the rear-end drive is awaken, reading a writing disk request in the shared buffer area and mapping the granted page corresponding to the grant table to the own memory space to generate a real disk access request; and (5) after the disk request is finished, releasing the map by the rear-end drive, placing a response in the shared buffer area and simultaneously awaking the front-end drive through the event channel. The invention can ensure that important data stored by the user in a cloud memory are cipher texts and can still provide safety guarantee for private data of the user even if a storage cell is completely exposed.
Owner:BEIJING 21VIANET DATA CENT
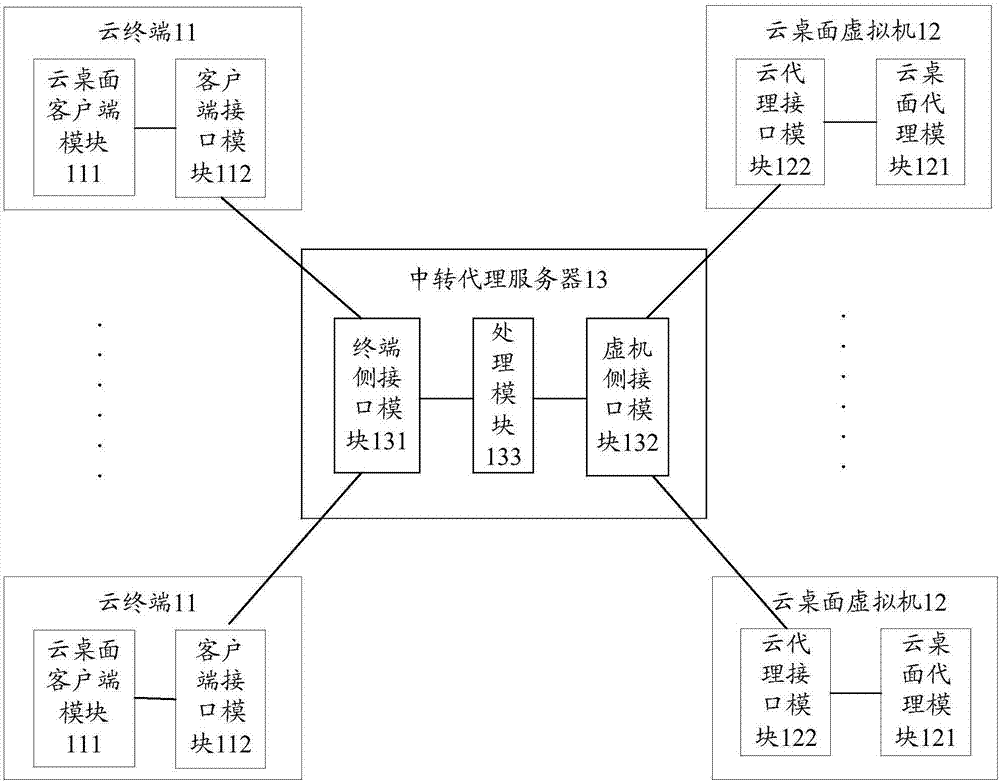
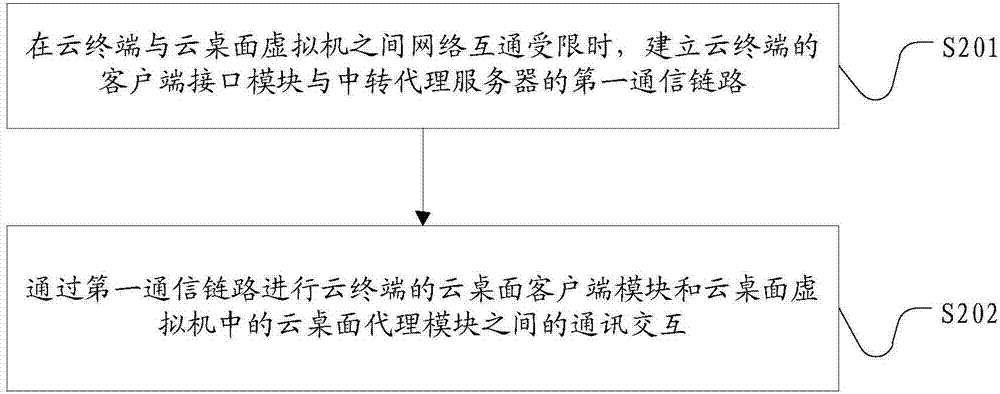
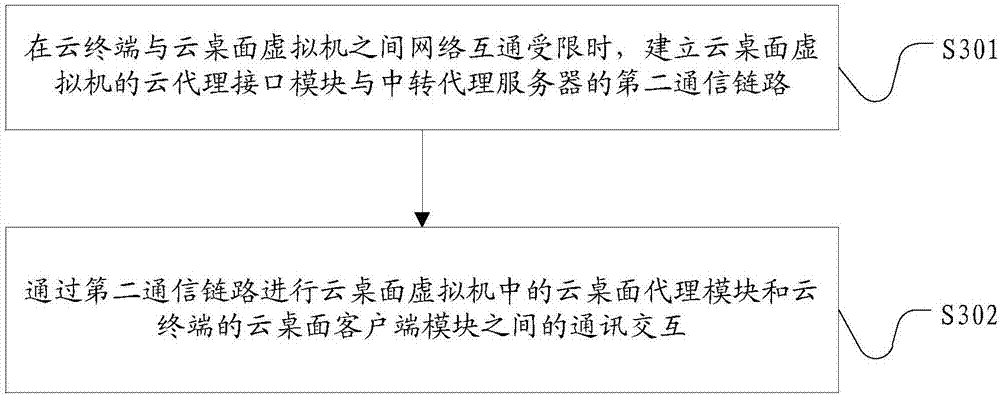
Data sharing method, cloud terminal, cloud desktop virtual machine and transit proxy server
InactiveCN107959701ADo not change usage habitsEasy to operateTransmissionTelecommunications linkCommunication link
The invention discloses a data sharing method, a cloud terminal, a cloud desktop virtual machine and a transit proxy server. When network intercommunication between the cloud terminal and the cloud desktop virtual machine is limited, a terminal side interface module of the cloud desktop virtual machine can establish a first communication link with a client side interface module in the cloud terminal; a virtual machine side interface module can establish a second communication link with a cloud proxy interface module in the cloud desktop virtual machine; a processing module can realize communication interaction between a cloud desktop proxy module of the cloud desktop virtual machine and a cloud desktop client side module of the cloud terminal by utilizing the first and second communicationlinks; therefore, the cloud terminal and the cloud desktop virtual machine are not limited by a desktop transfer protocol, and get rid of the constraint of a network environment; a server device doesnot need to be newly increased in the invention; using habits of users are not changed; data sharing and migration functions of a cloud desktop can be effectively completed; simultaneously, operations related by data sharing are automatically completed by a system; requirements on the IT skills of the users are reduced; and thus, the user experience is improved.
Owner:ZTE CORP
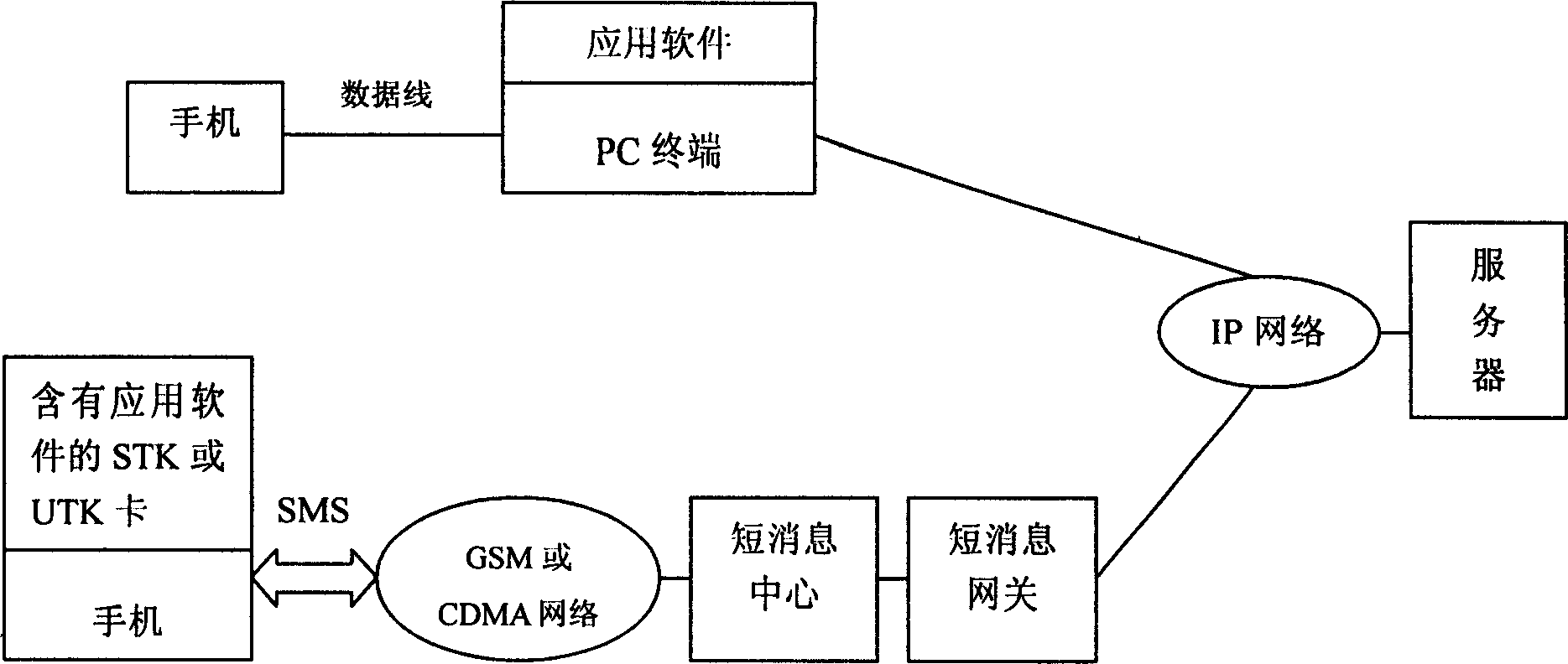
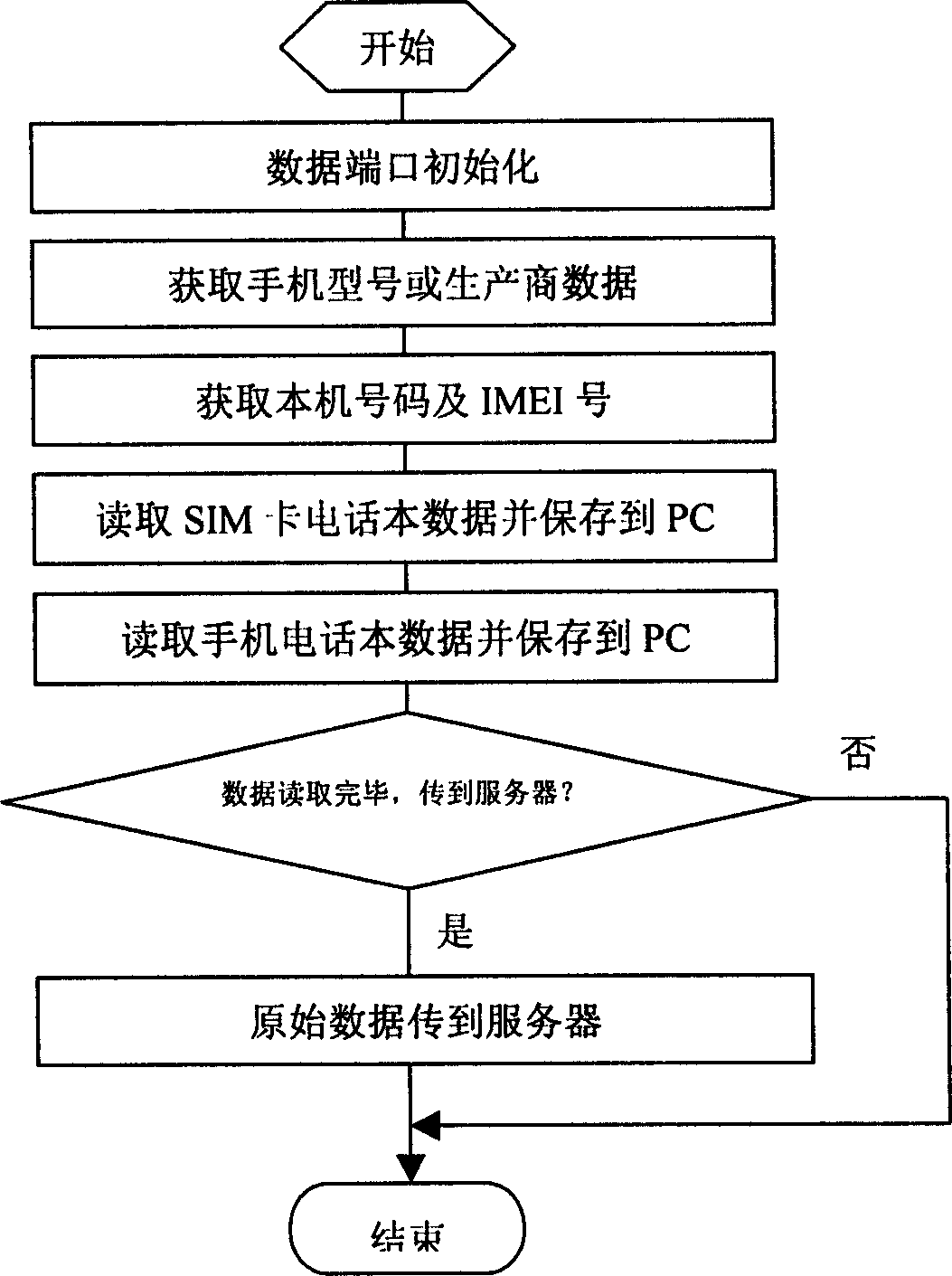
Method of backup of cell phone note based on STK or UTK tech
InactiveCN1602100AConvenience to workImprove confidentialitySubstation equipmentRadio/inductive link selection arrangementsComputer hardwarePhone Note
The method for updating data of handset phone book in real time through short message mode is especially applicable to technique of STK or UTK. Technical scheme is as following: user's database is setup in server, which through short message gateway and handset network is connected to handset, and bidirectional data transmission can be carried out in short message mode to execute operations including 'clear' command; user's database through IP network, PC terminal is connected to handset for carrying operations of 'taking' and 'recovering'. New STK card in handset should be replaced. Advantages are: automatic updating data in phone book in handset and server synchronistically, clearing away data in phone book in short message mode, recovering lost data, as well as easy of use and operation.
Owner:康健
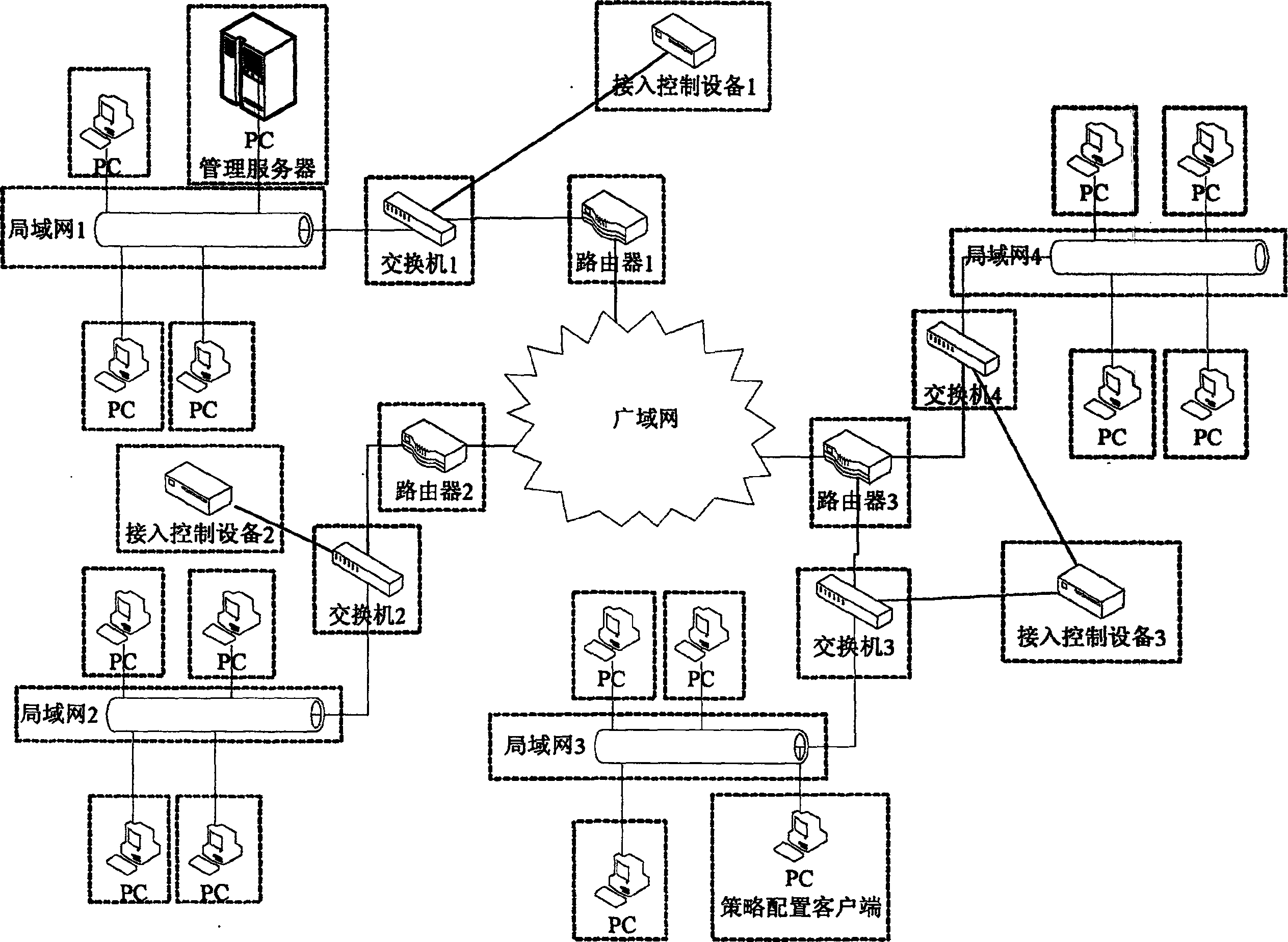
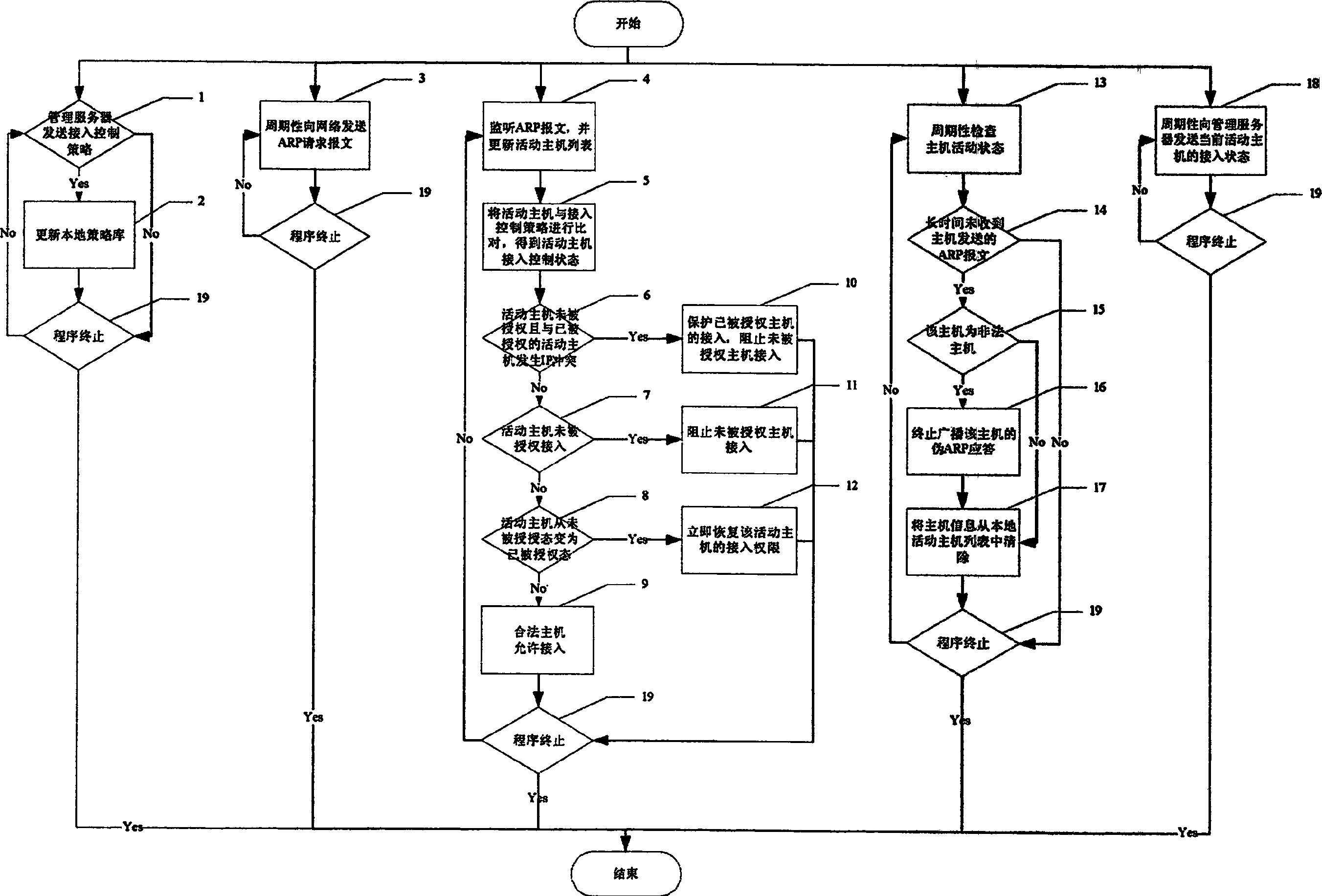
Access control system and method for implementing binding MAC/IP of network device
ActiveCN1874223ASave moneyEasy to implementUser identity/authority verificationData switching by path configurationIp addressStructure of Management Information
The system includes access control equipment. Through network wire, network port of the access control equipment in the system is connected to port at any vacant network exchange in controlled sub network. Software for managing server and configuring client end in strategy is installed on any PC server or terminal in network. The method includes steps mainly: using broadcast of pseudo ARP response message periodically to inform all hosts in network co cause IP conflict of unauthorized host; meanwhile, using pseudo MAC to refresh ARP buffer of each host in network to prevent communication between authorized host and unauthorized host so as to realize binding MAC / IP addresses. Without need of replacing any existed network equipment, and carrying out any adjustment for structure of network, the invention possesses advantages of saving large funds, easy of implementation, small maintenance work. The invention is applicable to enterprises and institutions of using computer and Ethernet.
Owner:CHINA MOBILE COMM CORP TIANJIN
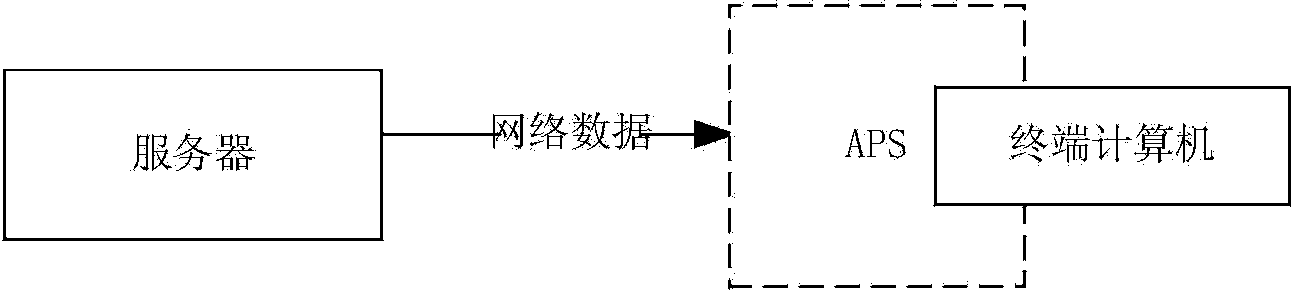
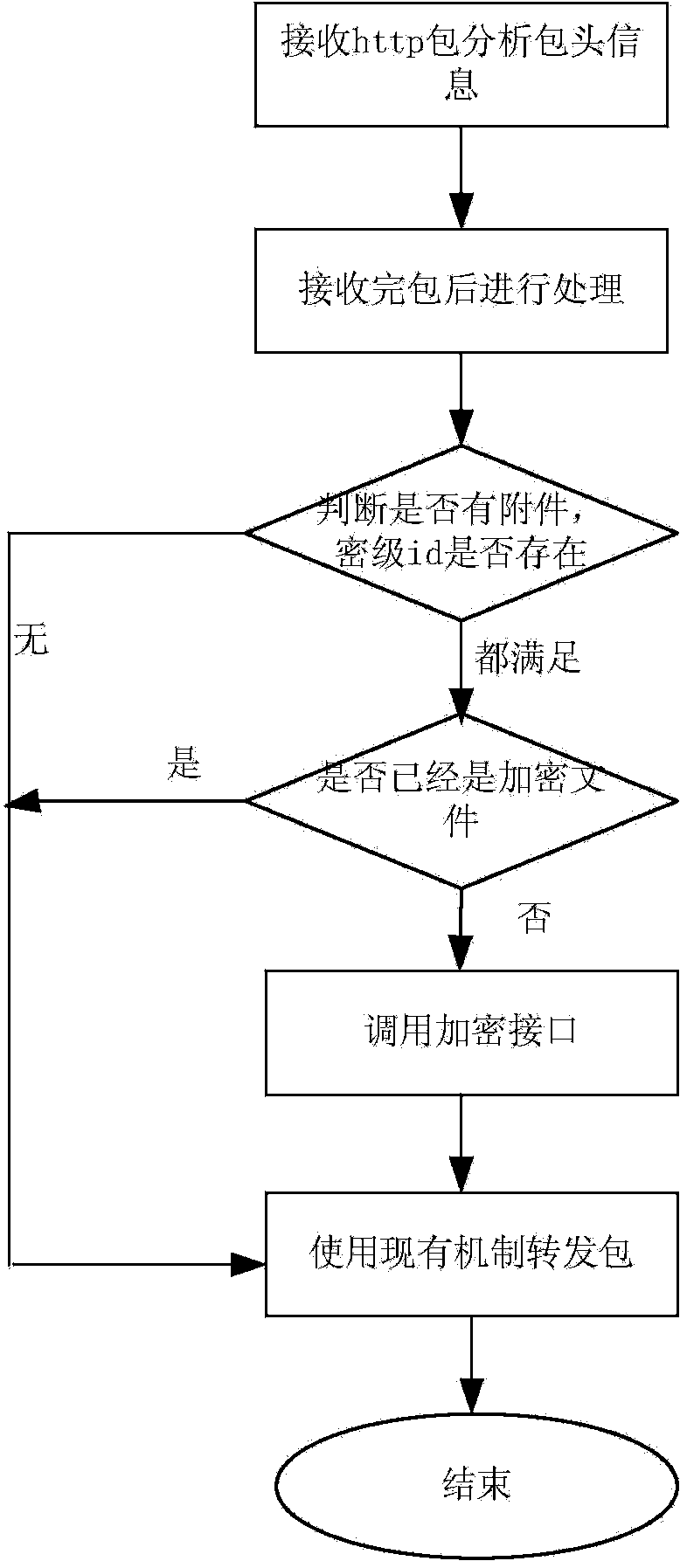
OA (office automation) data protection method and system based on OA flow
InactiveCN103632106APrevent leakageProtection securityDigital data protectionOffice automationRelevant informationDocument preparation
The invention discloses an OA (office automation) data protection method and an OA data protection system based on OA flow. The system comprises an OA server, a user terminal and an APS (application protection system), wherein a user applies for OA data from the OA server; before the OA data are downloaded to the user terminal, the APS encrypts the OA data; when the user checks or edits the OA data, copy, paste and screen capture functions of the user terminal are forbidden, and a watermark is added on a terminal screen for enabling the user to check the OA data, so that the user can be prevented from photographing the OA data; when the user prints the OA data, a watermark is added on a printed document, and relevant information of the printed document is recorded. According to the method and the system, the divulging of the OA data of an enterprise can be prevented, and the safety of the data of the enterprise can be protected.
Owner:北京明朝万达科技股份有限公司
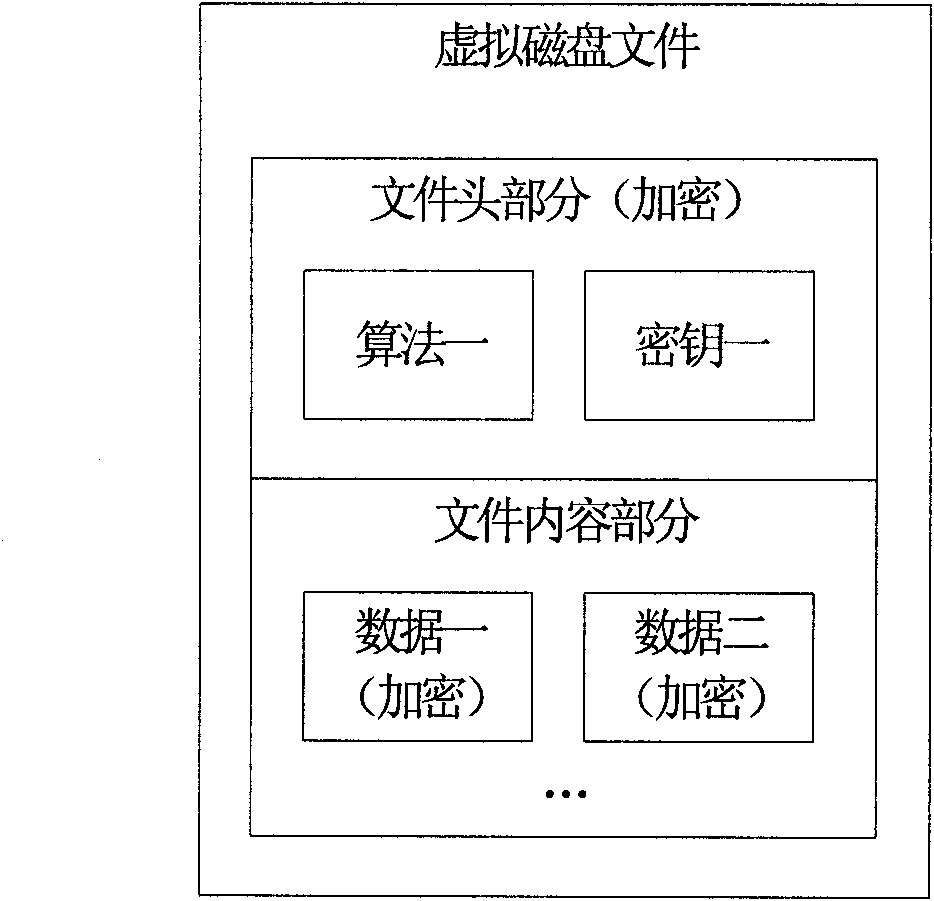
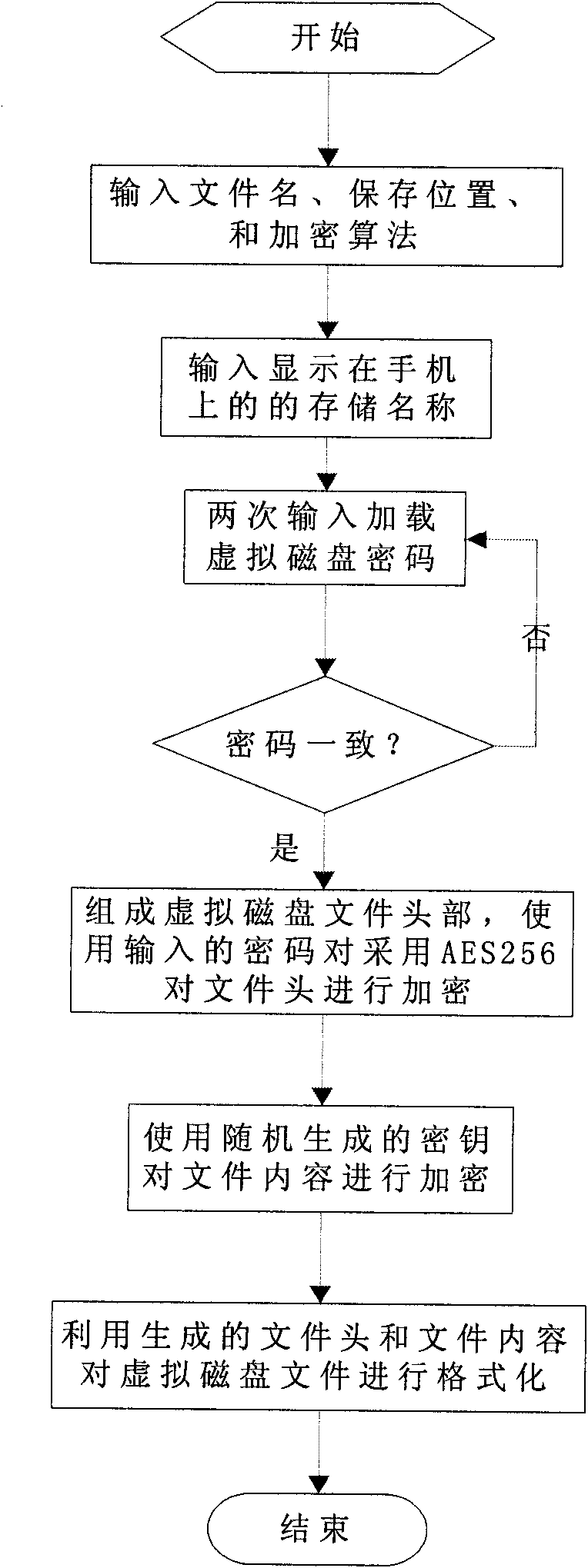
Mobile phone data security protection method
ActiveCN101800811AChange habitsDo not change usage habitsEncryption apparatus with shift registers/memoriesSubstation equipmentData storingInformation security
The invention discloses a mobile phone data security protection method, and belongs to the technical fields of information security and mobile communication. The method comprises the following steps: a) creating a virtual disk file on a mobile phone, wherein the virtual disk file comprises a file head part and a file content part, the file head part comprises an encryption algorithm one and a key one, the file content part is used for storing data, the data is encrypted and stored through the encryption algorithm one and the key one, and the file head part is encrypted and stored through an encryption algorithm two and a key two; b) loading the virtual disk file on the mobile phone, and decrypting the file head part through the encryption algorithm two and the key two in the loading process; and c) after the virtual disk file is loaded, when reading the data stored by the file content part, decrypting the read data and outputting the data, and when writing data into the file content part, encrypting the data written in and storing the data in the file content part, wherein the encryption and decryption are performed through the encryption algorithm one and the key one. The method can be used for mobile phone data security protection.
Owner:CHINA NAT SOFTWARE & SERVICE
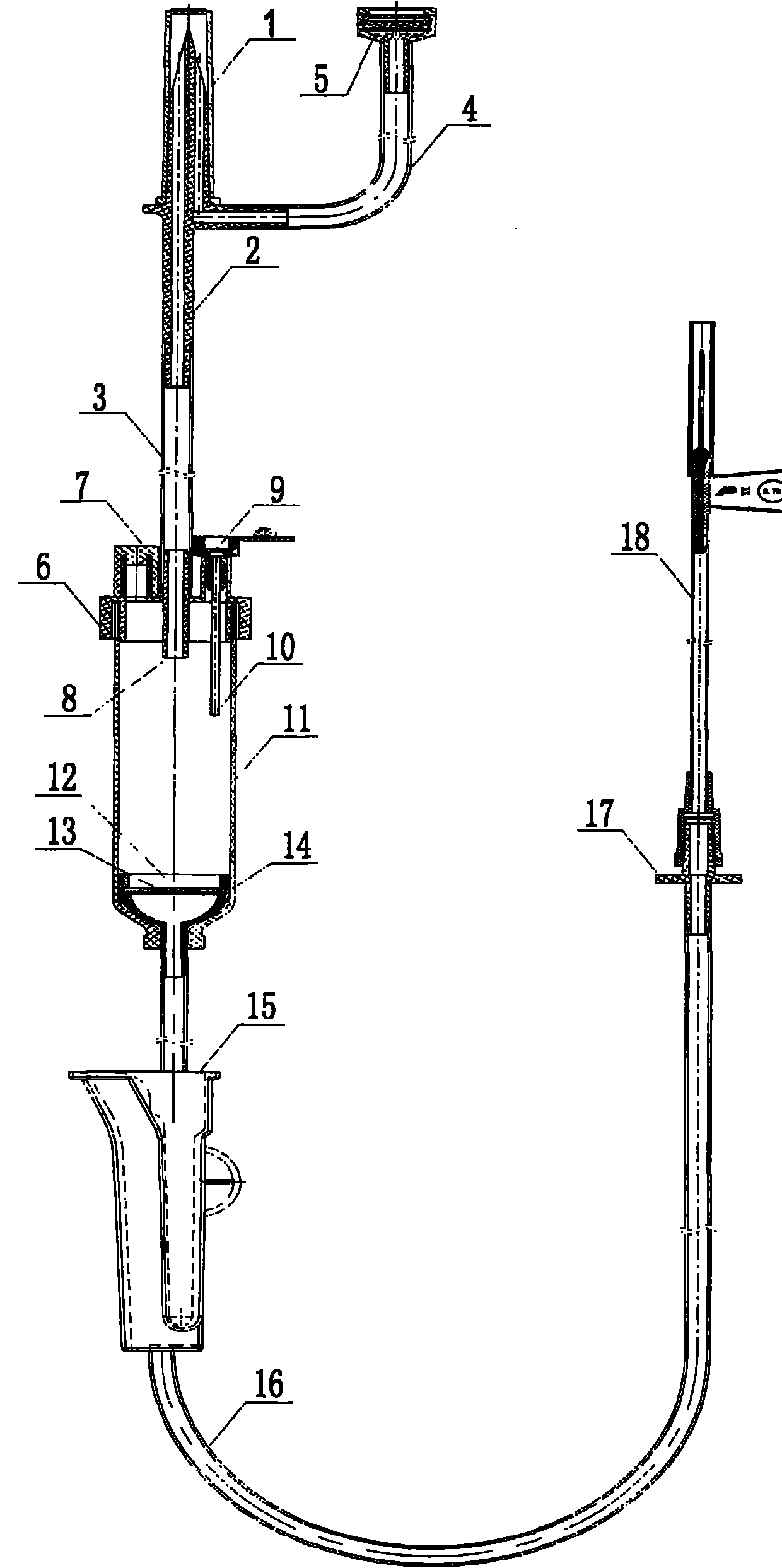
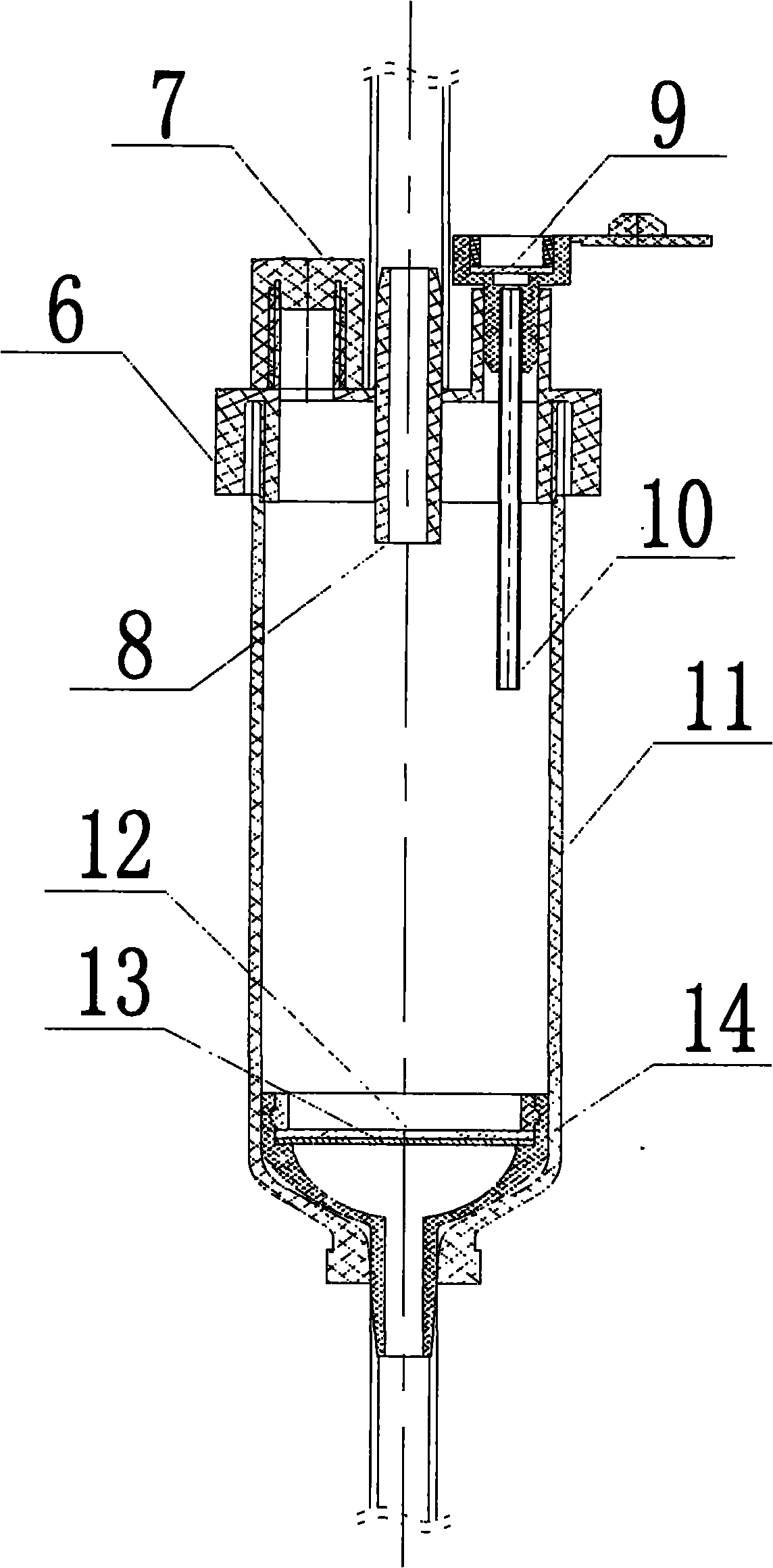
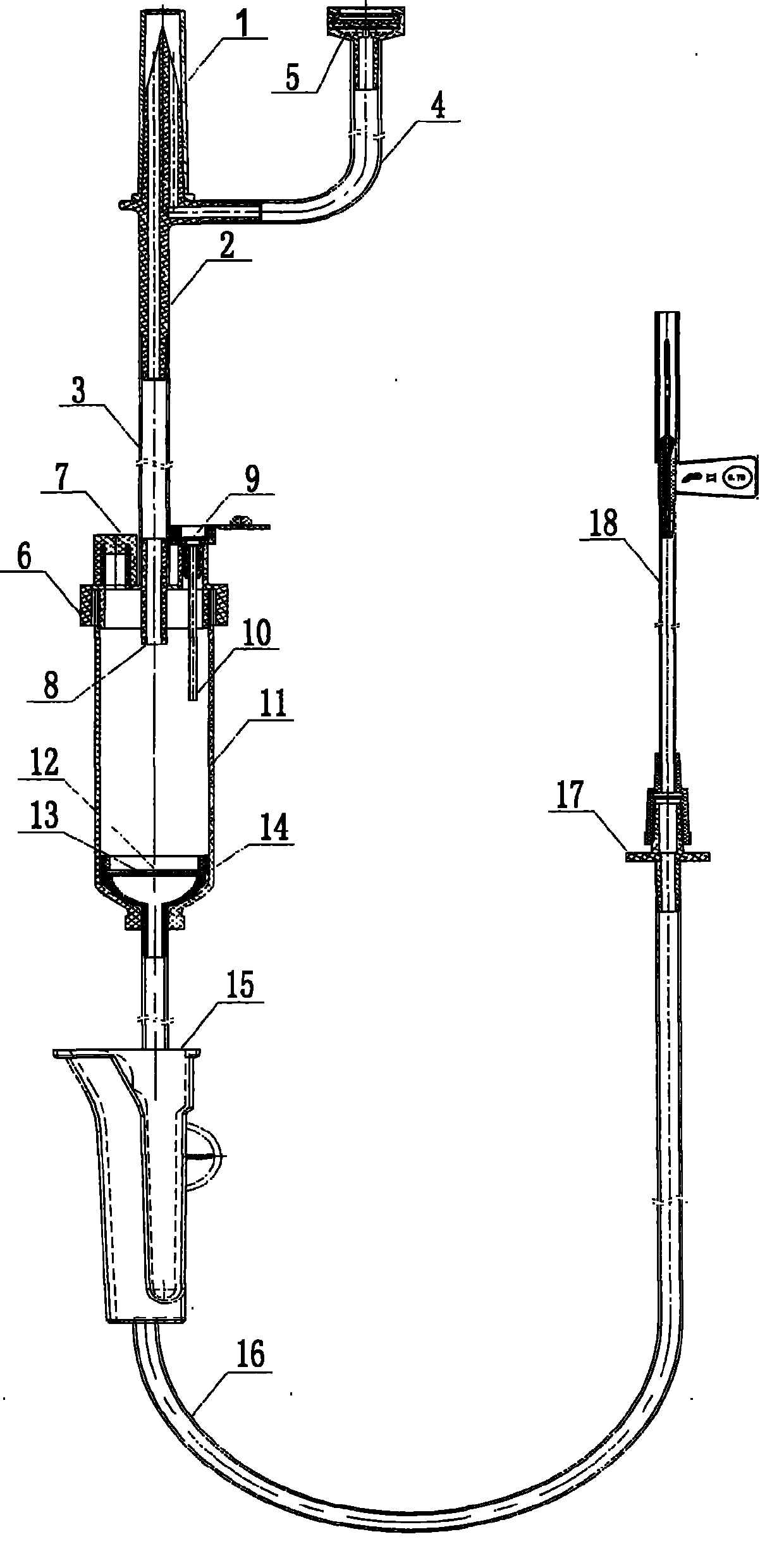
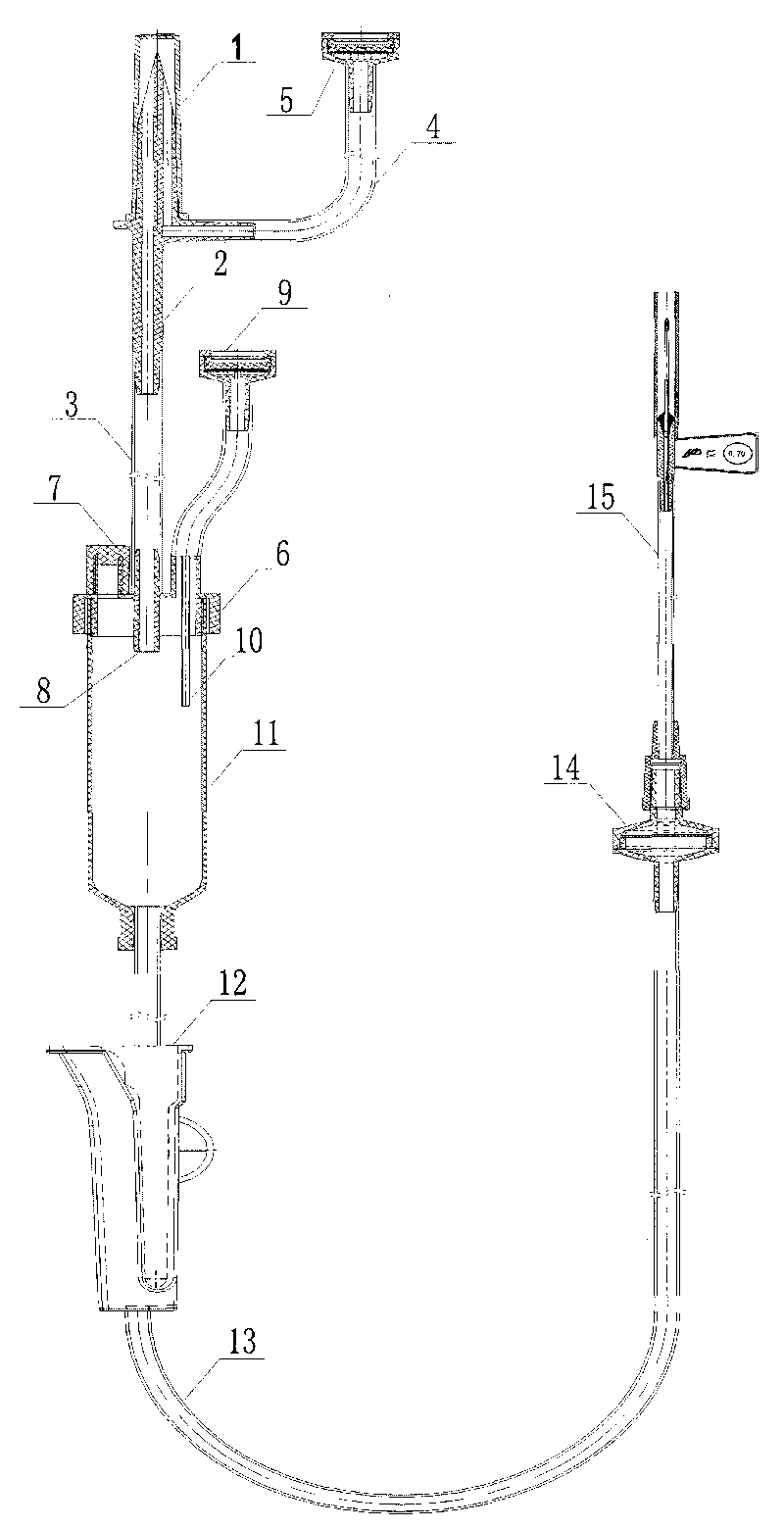
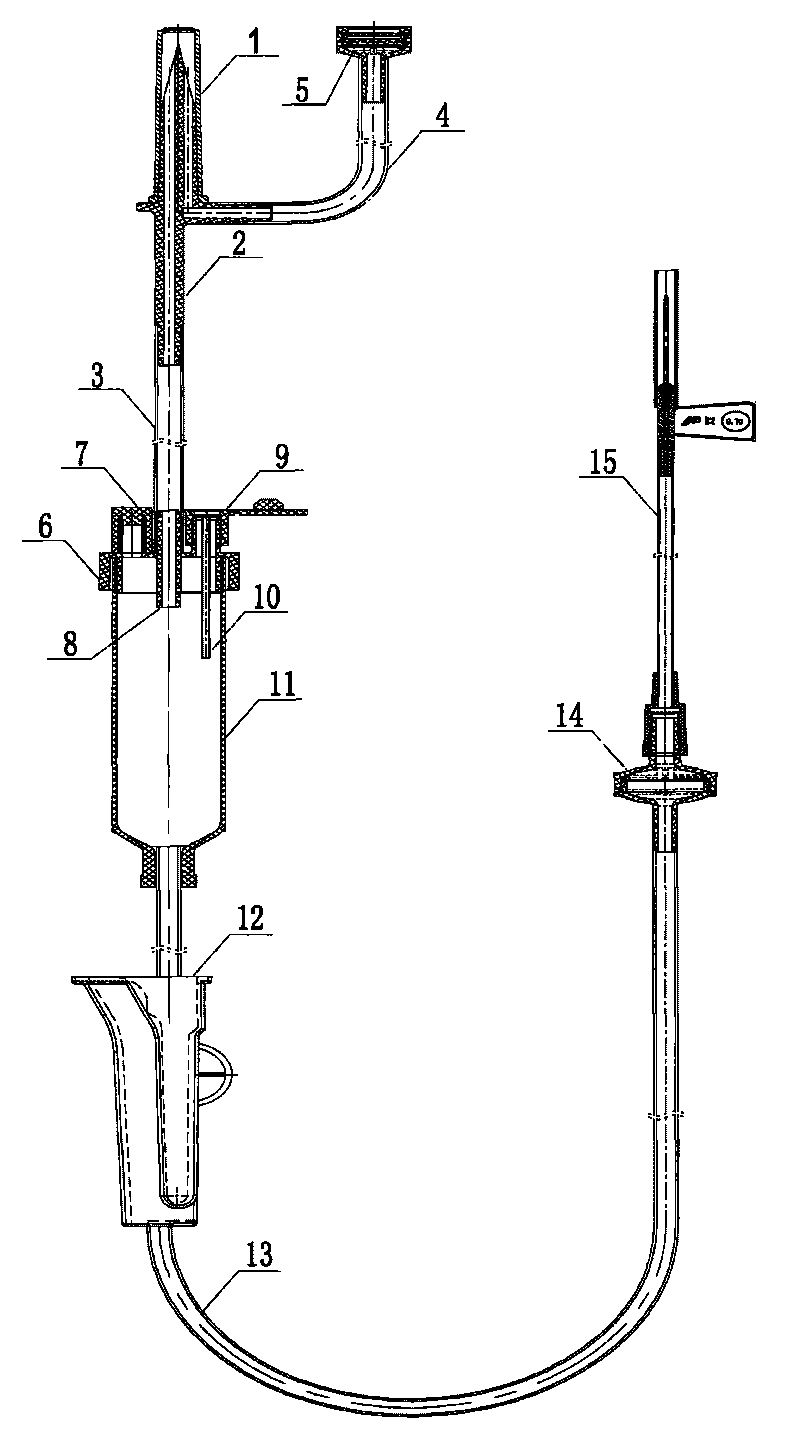
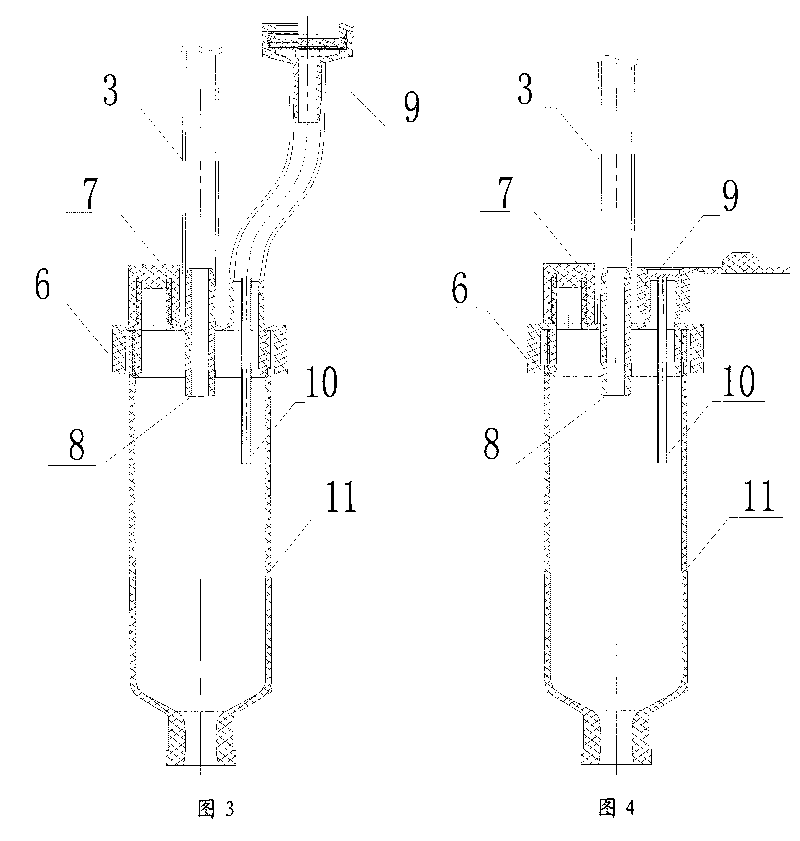
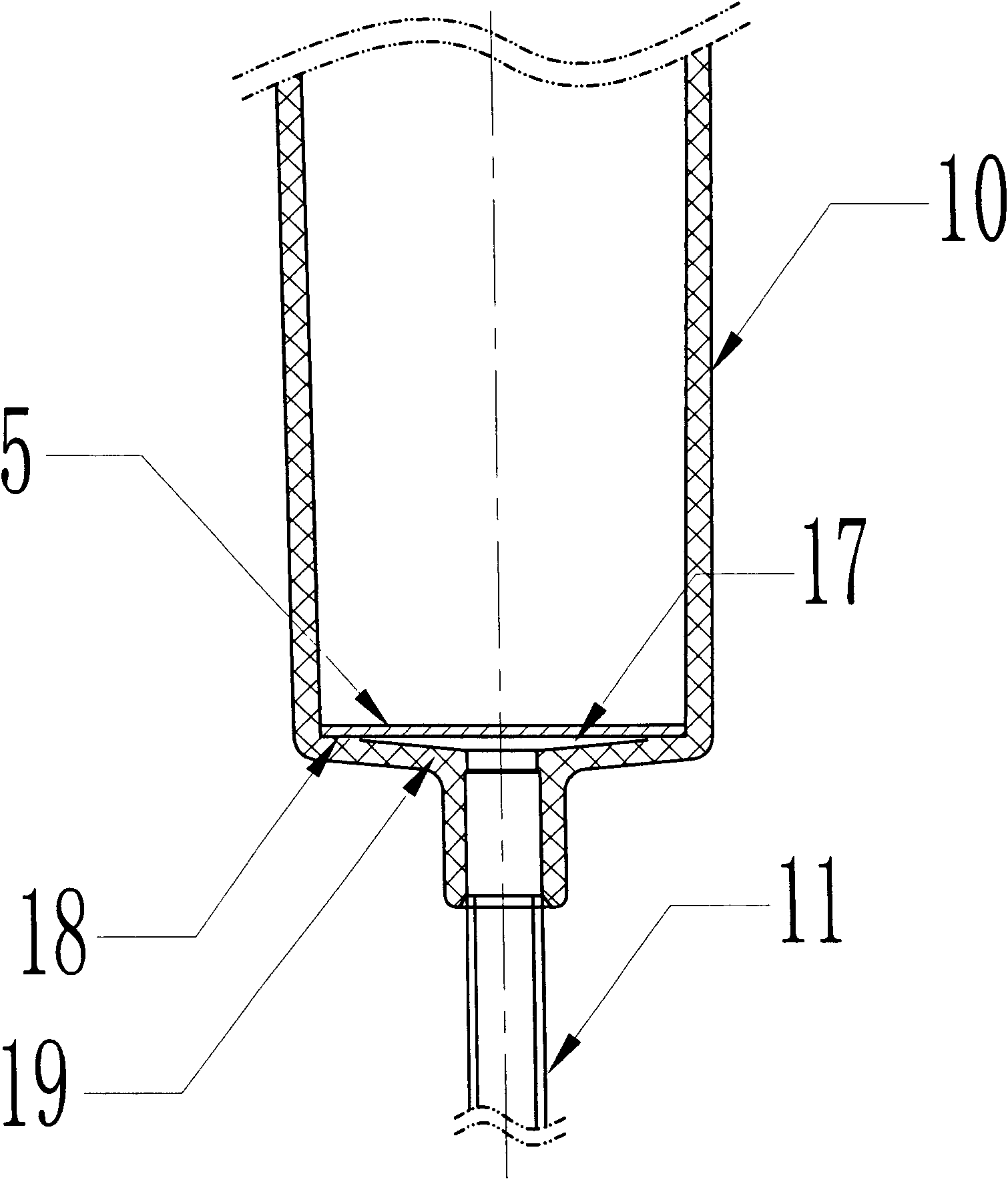
Automatic exhaust transfusion system
The invention relates to a sterile medical appliance for clinical transfusion, in particular to an automatic exhaust transfusion system. The automatic exhaust transfusion system comprises a bottle cork puncture outfit protective casing, a bottle cork puncture outfit, a short transfusion catheter, a short exhaust catheter, an air filter, a dropping funnel cover, an automatic exhaust component, a liquid medicament injection element, a dropping funnel, a flow rate adjuster, a long transfusion catheter, a liquid medicament filter and a disposable intravenous infusion needle, wherein the automatic exhaust component is arranged on the dropping funnel cover and consists of an exhaust needle and the air filter; the exhaust needle runs through the dropping funnel cover to cling to the inner wall of the dropping funnel and be extended into the dropping funnel; the air filter is arranged at the upper end of the dropping funnel cover and is linked with the exhaust needle; and an air filter membrane is arranged in the air filter. The automatic exhaust transfusion system can effectively prevent bubbles from being produced and entering the transfusion catheters, and has the characteristics of simple structure, safety and reliability.
Owner:JIANGXI HONGDA MEDICAL EQUIP GROUP
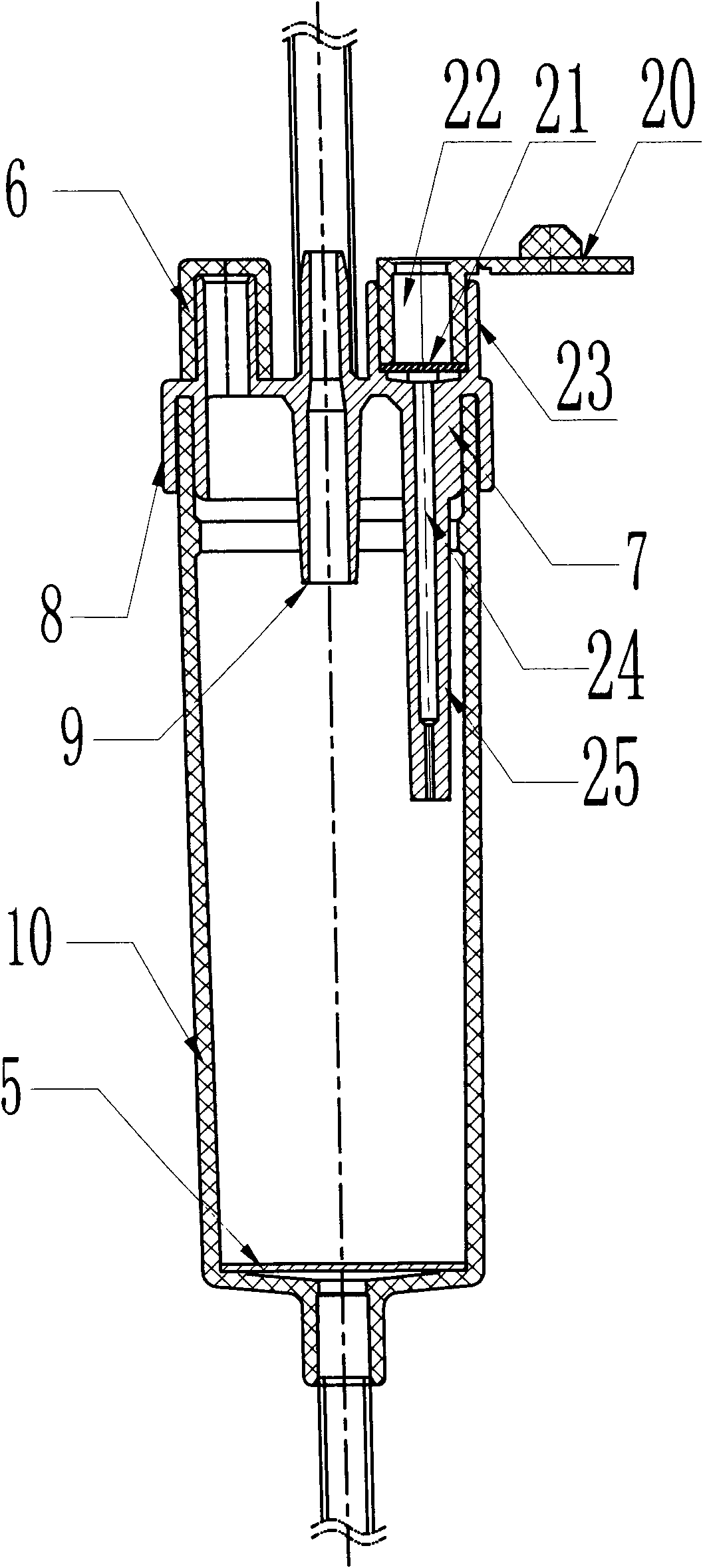
Automatic exhaust blood-return-resistant infusion apparatus
The invention discloses an automatic exhaust blood-return-resistant infusion apparatus. The infusion apparatus comprises a bottle plug puncture outfit protective sleeve, a bottle plug puncture outfit, an air filter, a dropping funnel, a flow regulator, a liquid medicament filter, a disposable venous infusion needle and the like and is characterized in that: a precision liquid medicament filtering membrane is arranged at a bottom end inside the dropping funnel; a concave cavity is formed in the middle of a bottom plate inside the dropping funnel; an annular plane is processed around the concave cavity of the bottom plate; the precision liquid medicament filtering membrane is tightly attached to the annular plane of the bottom plate by ultrasonic or high frequency heat seal; the concave cavity of the bottom plate can allow the liquid medicament flowing through the precision liquid medicament filtering membrane to be filtered fully; and an automatic venting device consisting of a venting plug, an air filter and a venting needle is arranged on a dropping funnel cover. The infusion apparatus has the advantages of venting automatically in an infusion process, automatically preventing the liquid medicament from flowing, preventing blood from flowing backwards, simplifying venting operation steps and reducing the working strength of medical care personnel, along with the advantages of simple structure, safety and reliability.
Owner:JIANGXI HONGDA MEDICAL EQUIP GROUP
Spreadsheet data management method based on C/S mode
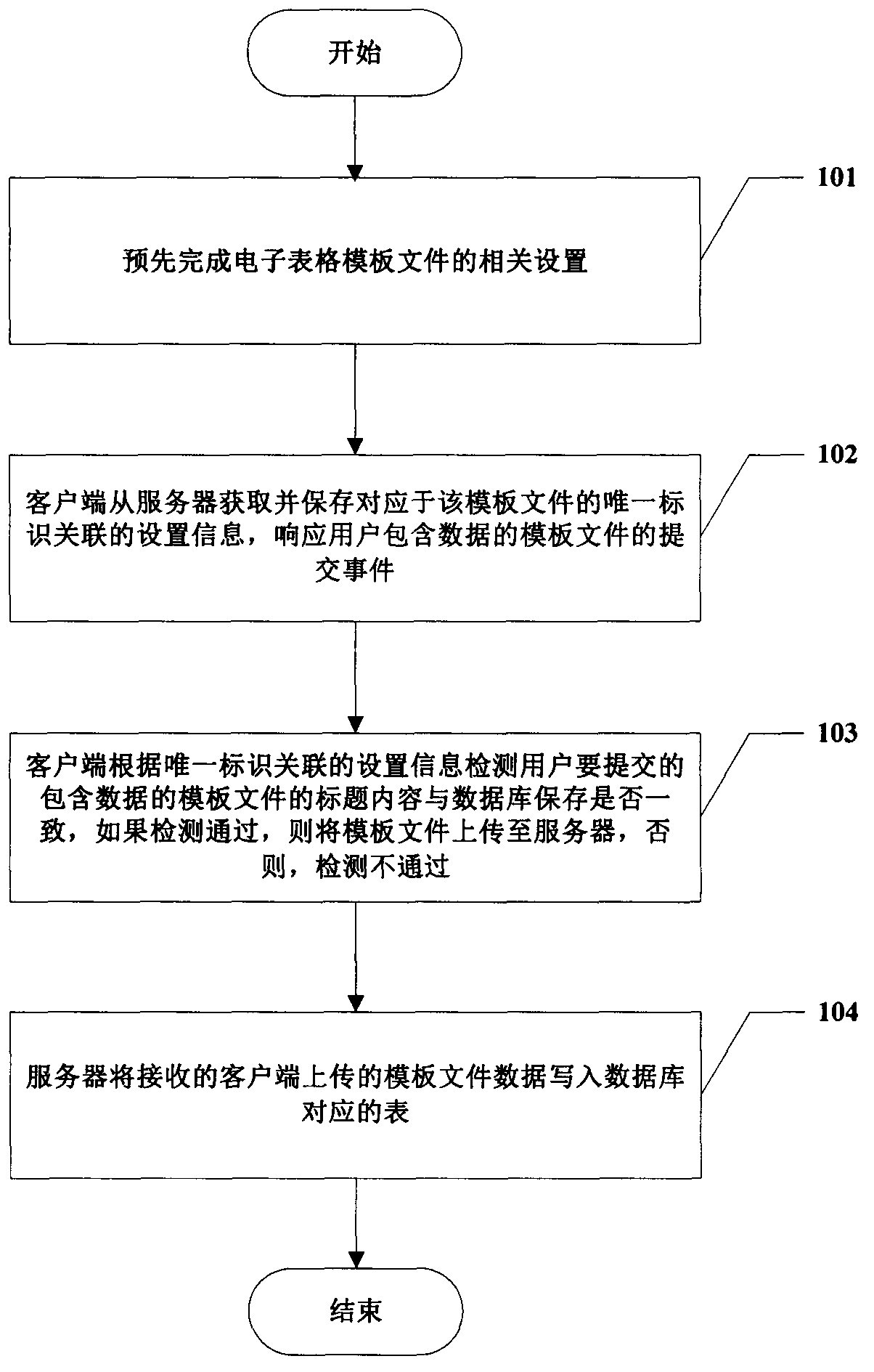
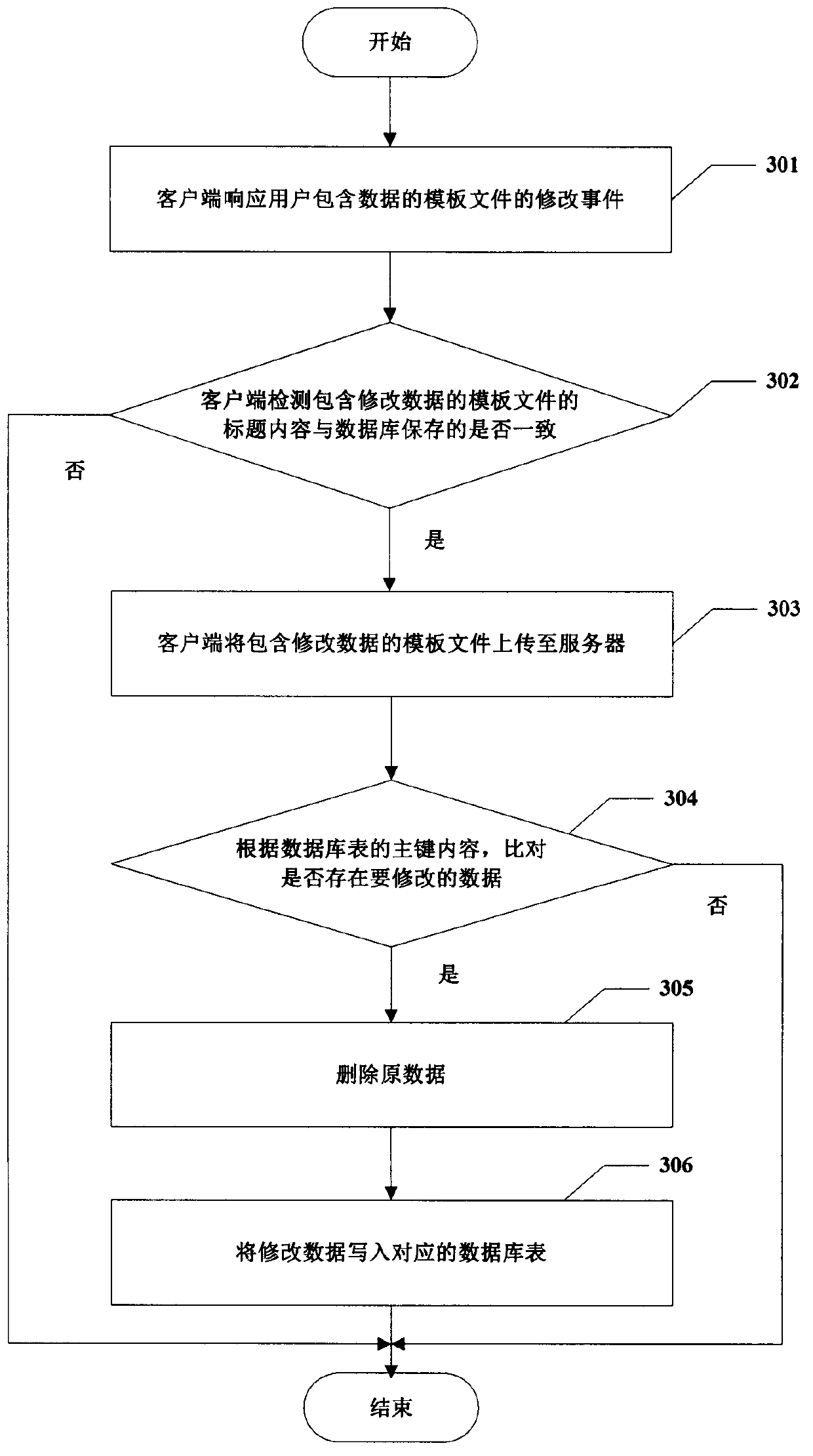
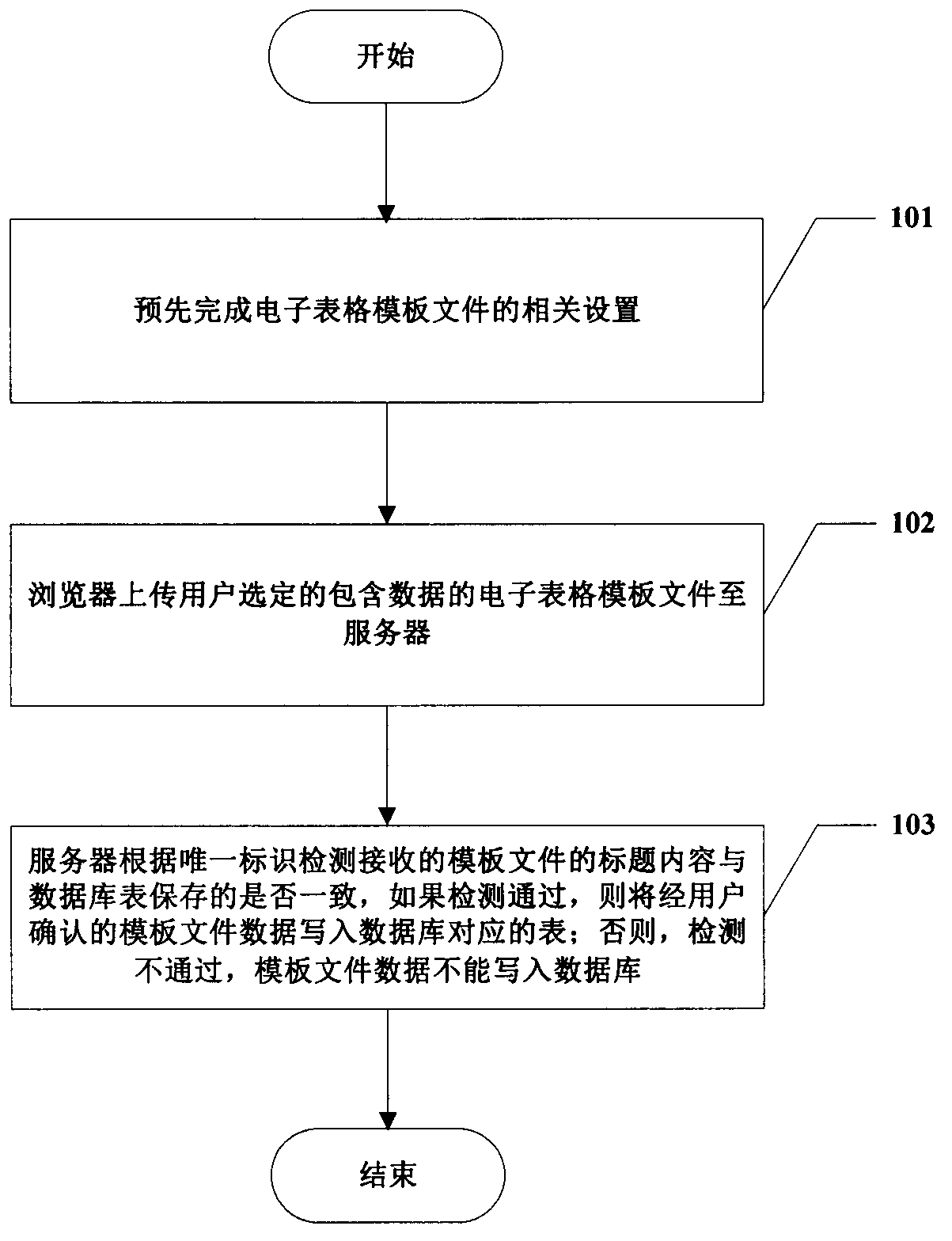
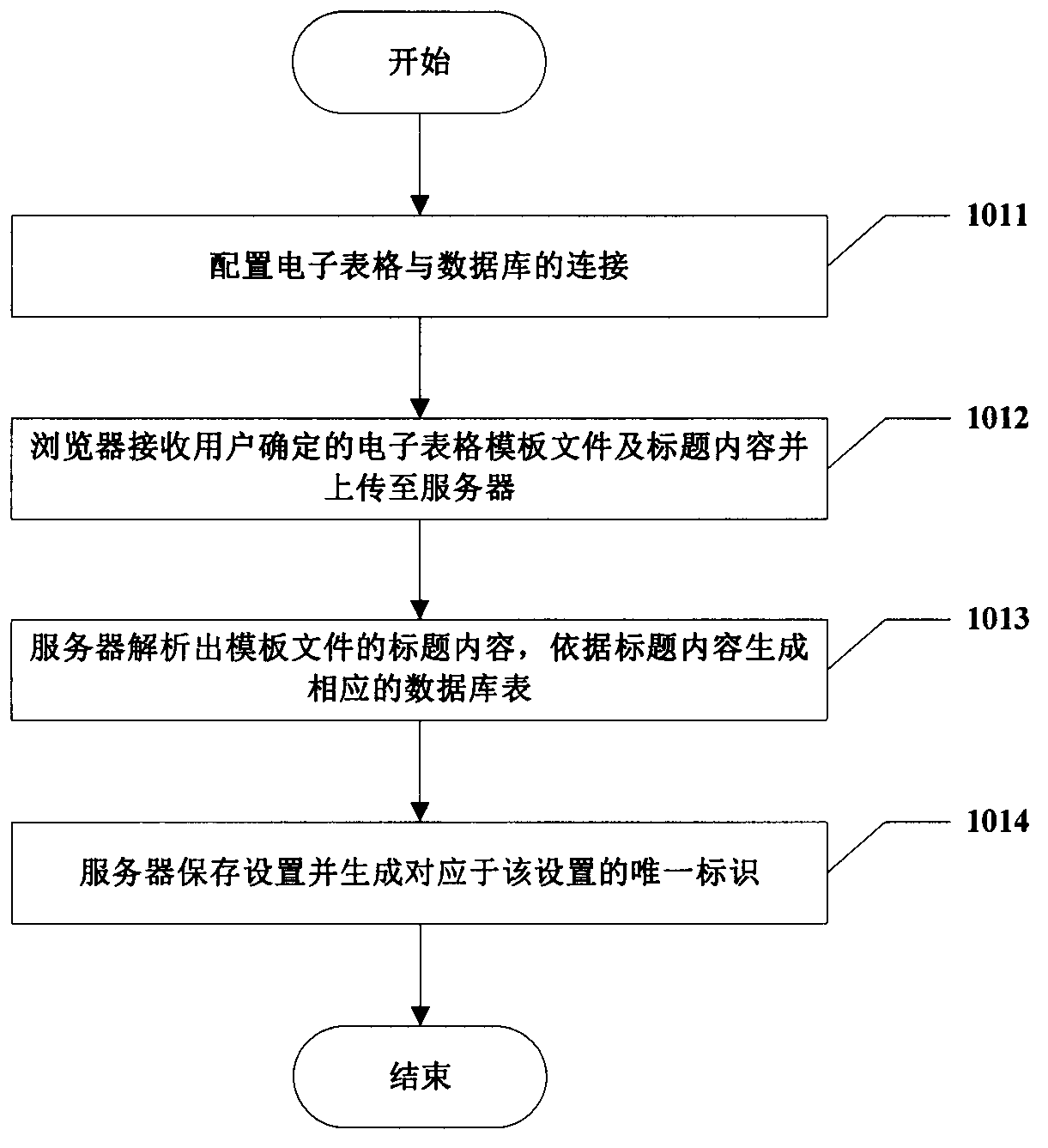
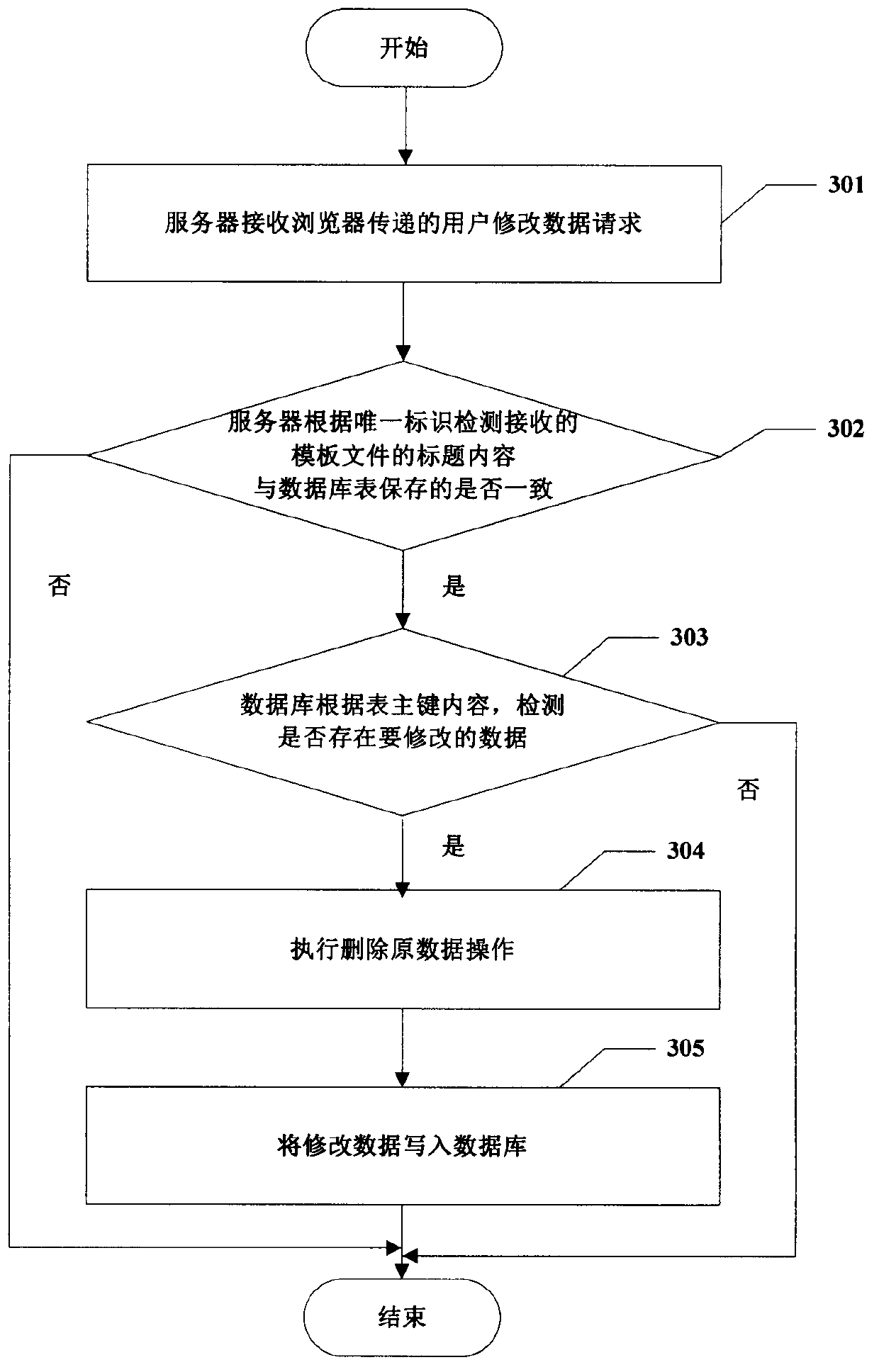
InactiveCN104239366ASolve the defects of scattered and difficult managementReduce the problem of slow loadingWeb data indexingFile/folder operationsData fileData management
The invention provides a spreadsheet data management method based on a C / S mode. The method includes the steps of S1, completing the related settings of a spreadsheet template file in advance; S2, by a client, acquiring the setting information associated with the unique identification corresponding to the template file from a sever, and saving the setting information; S3, by the client, detecting whether the title content of the template file which is about to be submitted by a user and contains data is consistent with the title content saved by a database or not according to the setting information associated with the unique identification; S4, by the server, writing the received template file data uploaded by the client into the corresponding table of the database. The method has the advantages that the spreadsheet template file data passing detection is managed through the database, and the defect that data is scattered and hard to manage when only the spreadsheet is used is overcome; data file data amount limitation of collected data is avoided; spreadsheet using habits of the user are unchanged, and friendly user interaction is achieved.
Owner:SUZHOU JINGYIHUI INFORMATION TECH
Foldable internal-cutting removing device for minimally invasive operation excision objects
InactiveCN101721239ATraumaMinimally invasive treatment is effectiveSuture equipmentsInternal osteosythesisOperations securityEngineering
The invention discloses a foldable internal-cutting removing device for minimally invasive operation excision objects. The device comprises three layers, wherein the outer layer is a transparent isolation bag, the middle layer is a cutting layer, and the inner layer is a transparent protecting layer. Two rack wires are movably connected, are perpendicular after axially rotating for unfolding, and are parallel after being folded. Each rack wire is provided with a pair of mutually perpendicular circular rings at the interval of 0.5-1mm. The pair of circular rings respectively guide cutting wires which are parallel with or perpendicular to the rack wires. The front ends and the tail ends of the cutting wires in the same travelling direction are respectively collected on two operating rods. When in use, two operators in opposite positions lift the corresponding operating rods, and cut the minimally invasive operation excision objects in the cavity into horizontal strips at one time by utilizing the net-shaped multiple wire saw cutting principle, therefore, the invention is convenient for the operators to remove the excision objects out of narrow cavascope or endoscope holes one by one, and has the advantages of small invasion, monitor and control under scopes, high operation safety and the like.
Owner:XI AN JIAOTONG UNIV
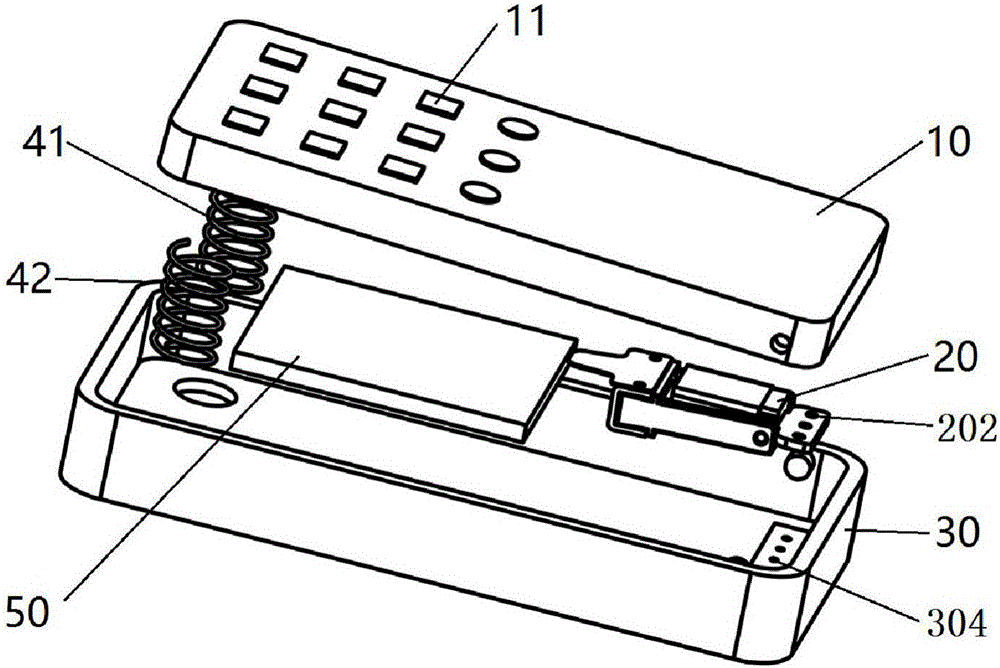
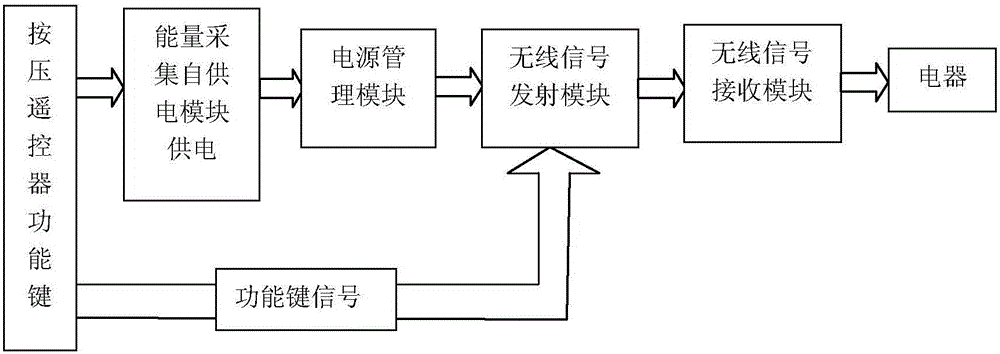
Self-powered remote controller and method
InactiveCN105976597AEasy to useDo not change usage habitsNon-electrical signal transmission systemsPiezoelectric/electrostriction/magnetostriction machinesRemote controlComputer module
The invention provides a self-powered remote controller and a method and belongs to the field of a self-powered electronic technology. An energy acquisition module is used for converting mechanical energy into electric energy when a key of the remote controller is pressed and the electric energy is provided for a wireless remote control signal transmission circuit; a body of the energy acquisition module is fixedly mounted on a lower shell of the remote controller; a control end of the energy acquisition module is connected with an upper shell of the remote controller; the energy acquisition module is provided with two power supply output ends; after the two power supply output ends are connected into a power management circuit to be processed, the electric energy needed by signal transmission is provided for a remote controller circuit. The self-powered remote controller provided by the invention has the advantages that the self-powered remote controller is convenient to use and remote controller use habits of people are not changed; a battery does not need to be used and the remote controller can be used for a long period; the self-powered remote controller has a wide applicable range and can be applied to remote controllers in various ranges.
Owner:BEIJING MICRO ENERGY TECH
3G green gateway for ensuring secure Internet access of mobile phone and service method for secure Internet access of mobile phone
InactiveCN101720066AEffective protectionChange habitsWireless network protocolsMessaging/mailboxes/announcementsCable Internet accessThird generation
The invention discloses a 3G green gateway for ensuring secure Internet access of a mobile phone, which comprises WEB and WAP gateways of a mobile operator and secure warning network elements arranged on the WEB and WAP gateways. The method of the invention comprises the following steps that: 1, the secure warning network elements are arranged on the WEB and WAP gateways of the mobile operator; 2, the secure warning network elements acquire and store security rating information of WEB and WAP websites; 3, when a mobile phone user accesses the WEB and WAP websites through the gateways of the mobile operator, the gateways of the mobile operator access the secure warning network elements, and acquire the security rating information of destination addresses; 4, the gateways of the mobile operator prompt the security information of the destination addresses to the mobile phone user; and 5, after receiving the security rating information, the mobile phone user can decide continuing the access, giving up the access or applying for secure website suggestion. The method can enable the mobile phone user not to change the using habit of the mobile phone so as to greatly reduce the using cost of the mobile phone user and the risk of browsing the Internet.
Owner:北京蓝珀通信技术有限公司
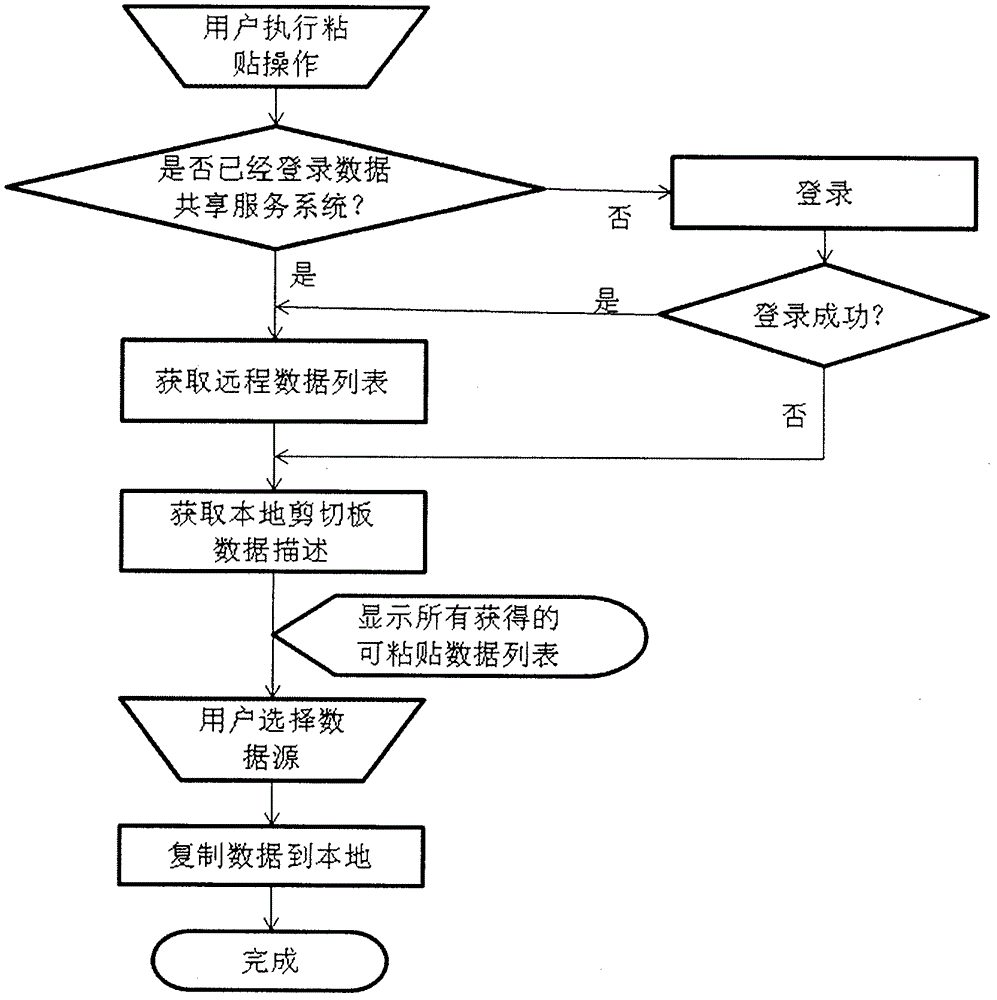
Copy and paste method based on internet and copy and paste system
InactiveCN103064829AEasy to useImprove securitySpecial data processing applicationsService systemData sharing
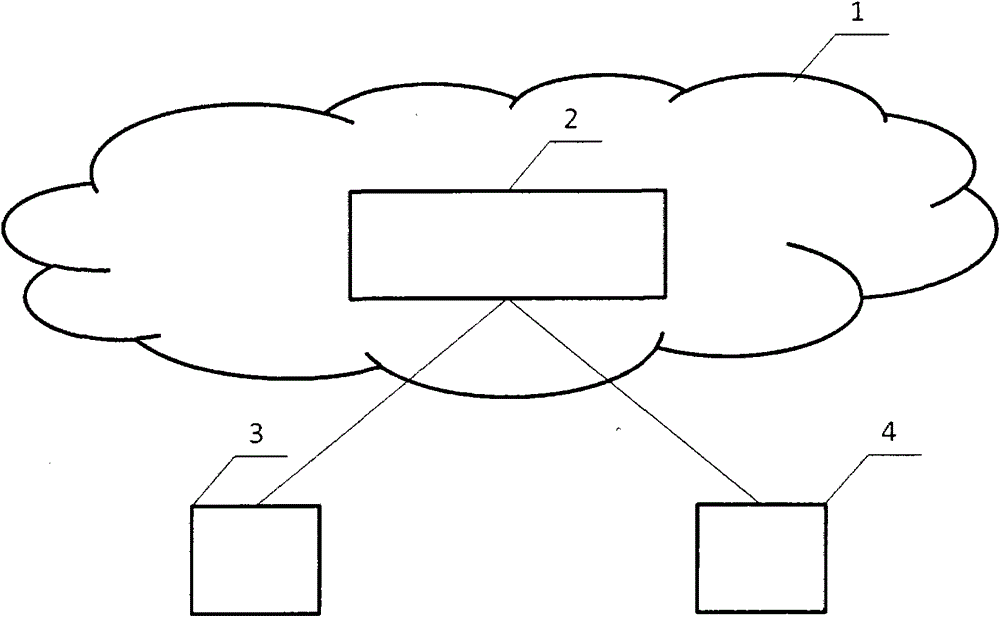
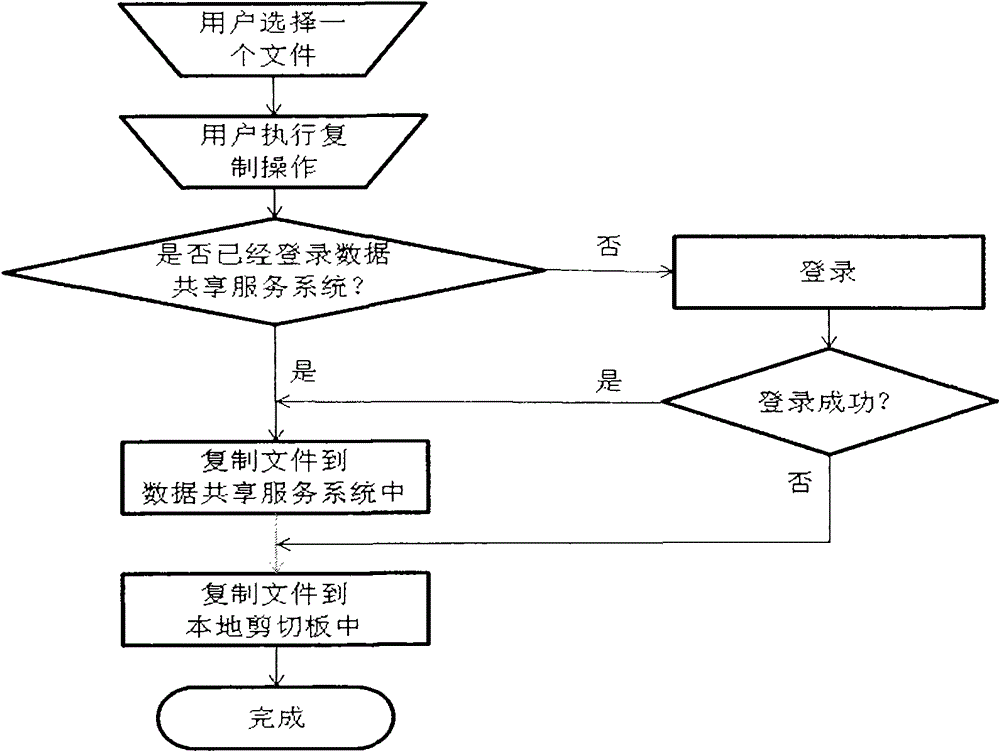
The invention relates to a copy and paste method based on the internet and a copy and paste system, and expands a local copy and paste function, familiar to the public at present, to the internet category. A data sharing service system (2) is an application system which is arranged in the internet (1). A terminal device (3) and another terminal device (4) represent various terminal devices of the internet. Each terminal device can be a computer or a mobile phone or a personal digital assistant (PDA) or another device with a networking function. The terminal devices can be in communication with the data sharing service system (2) through the internet (1). A user conducts copy operation or cut operation on the terminal device (3), and then data or a file is transmitted into the data sharing service system (2) located in the internet (1) for caching. The user can past the data onto the terminal device (4) through the terminal device (4) or authorization to other users so as to achieve the copy and paste function across devices.
Owner:王国臣
Nickel-titanium amorphous alloy grid supporting film for transmission electron microscope
ActiveCN104616954AHigh mechanical strengthAvoid breakingElectric discharge tubesVacuum evaporation coatingShape-memory alloyApparatus instruments
The invention discloses a nickel-titanium amorphous alloy grid supporting film for a transmission electron microscope and a preparation method of the nickel-titanium amorphous alloy grid supporting film. A conductive film used is a nickel-titanium alloy nanometer film; the nickel-titanium alloy is shape memory alloy which is high in elasticity and mechanical strength, serves as a good conductor for power and heat and can be widely applied to medical apparatuses and instruments. The nickel-titanium alloy is in a large-scale industry at present and is the alloy material easily obtained. The grid supporting film is prepared from the nickel-titanium alloy material, and thus the superelasticity, the high mechanical strength and the outstanding conductivity of the shape memory alloy can be fully utilized to problems of low mechanical strength and serious electric charge of a carbon supporting film can be solved.
Owner:PEKING UNIV
Cold and hot integrated type automobile air conditioning system
InactiveCN104534735AEasy to switchSimple structureAir-treating devicesVehicle heating/cooling devicesAutomobile air conditioningEngineering
The invention discloses a cold and hot integrated type automobile air conditioning system. A refrigeration unit and a heating unit are of a common refrigeration sheet assembly, wherein the refrigeration sheet assembly is mounted in the shell; heat radiators are stuck on a heating surface and a refrigeration surface of the refrigeration sheet assembly respectively. Two sets of fans are arranged in the shell and are located on the outer sides of the two heat radiators respectively; the refrigeration sheet assembly can be overturned for 180 degrees by an overturning mechanism so that the positions of the heating surface and the refrigeration surface are exchanged. The system adopts an existing developed refrigeration sheet structure; refrigeration and heating can be realized on the same structure, and one piece can be used for replacing an independent heating system and an independent refrigeration system, the switching is convenient and the structure is simple. When the automobile air conditioning system is used for heating, an engine does not work and a vehicle-mounted power supply is adopted, so that the safety is higher; hot air can be generated without a period of time of work of the engine so that the heating speed is more rapid.
Owner:CHONGQING MINGWU ELECTROMECHANICAL
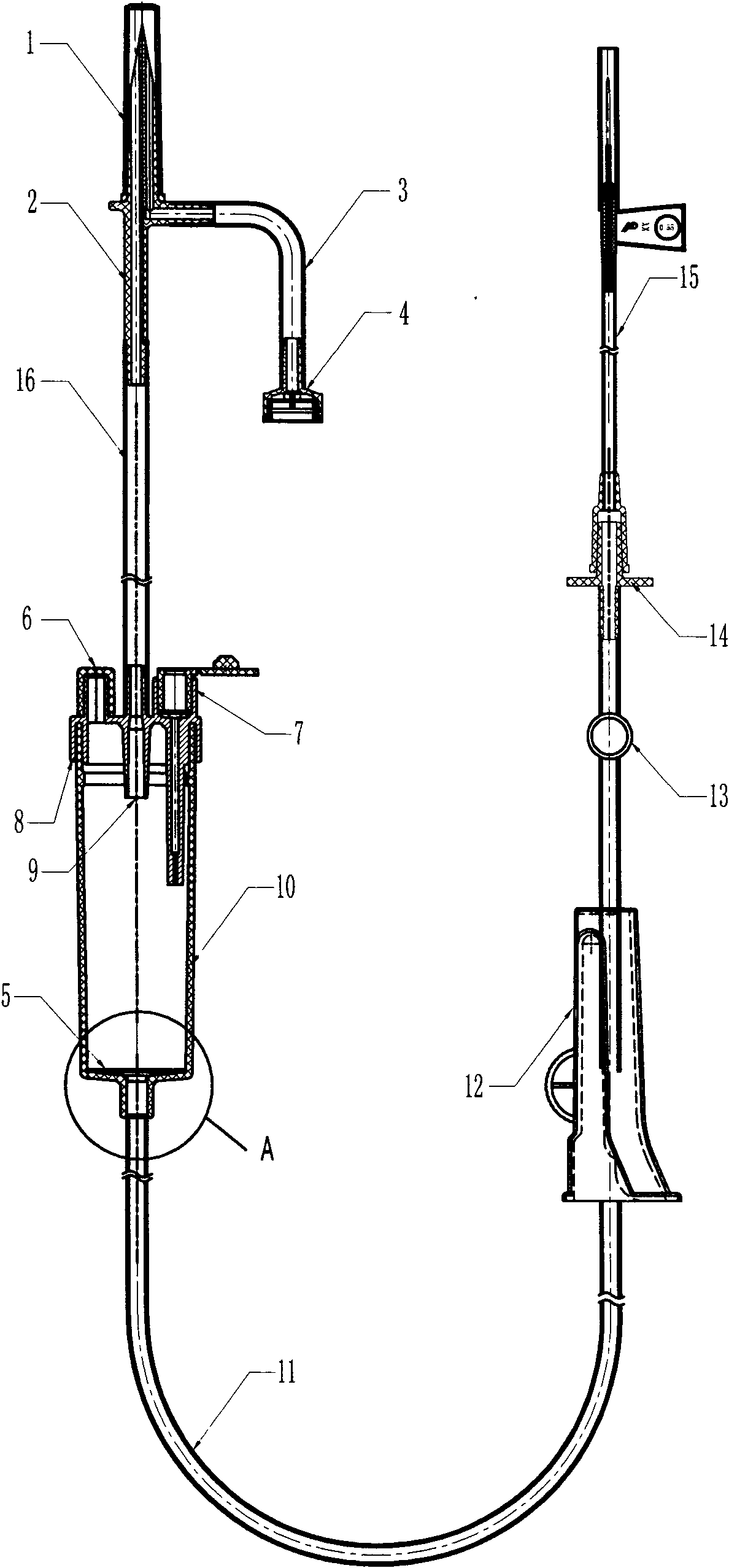
Liquid-stopping tank-type automatic exhaust liquid-stopping infusion apparatus
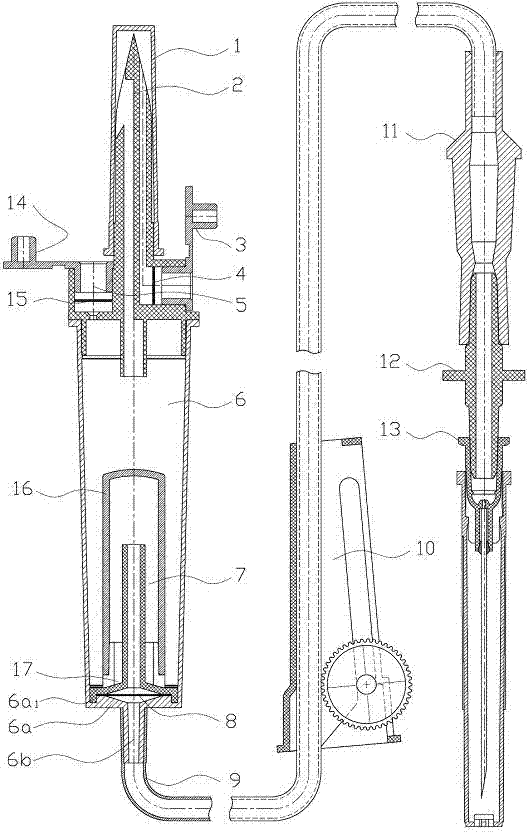
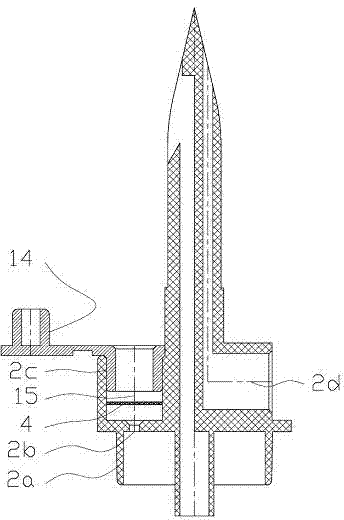
The invention discloses a liquid-stopping tank-type automatic exhaust liquid-stopping infusion apparatus. A dropping funnel cover (2a), an exhaust hole (2b), an exhaust filtering hole (2c) and an air filtering hole (2d) are in injection molding on a bottle stopper puncture device (2), an air filtering membrane (4) is installed inside the air filtering hole (2d) and sealed by an air filtering cap (3), an automatic exhaust device (5) is installed on the dropping funnel cover (2a), a dropping funnel (6) is connected at the bottom of the dropping funnel cover (2a), an automatic liquid-stopping device (7) is installed on the bottom face (6a) inside the dropping funnel, a liquid dropping opening (6b) is formed in the bottom of the dropping funnel (6) in an injection molding mode, one end of a long infusion catheter (9) is connected with the liquid dropping opening (6b), the other end of the long infusion catheter (9) penetrates through a flow regulator (10) to be connected with a medicine liquid injection part (11), a flareless fitting (12) and a vein needle (13), and the safe infusion apparatus is integrally formed. According to the liquid-stopping tank-type automatic exhaust liquid-stopping infusion apparatus, automatic exhaust is achieved, liquid medicine automatically stops flowing, the exhaust operation steps are simplified, working intensity is relieved, the structure is simple, and the liquid-stopping tank-type automatic exhaust liquid-stopping infusion apparatus is safe and reliable.
Owner:HUAIAN CITY HENGCHUN MEDICAL PROD
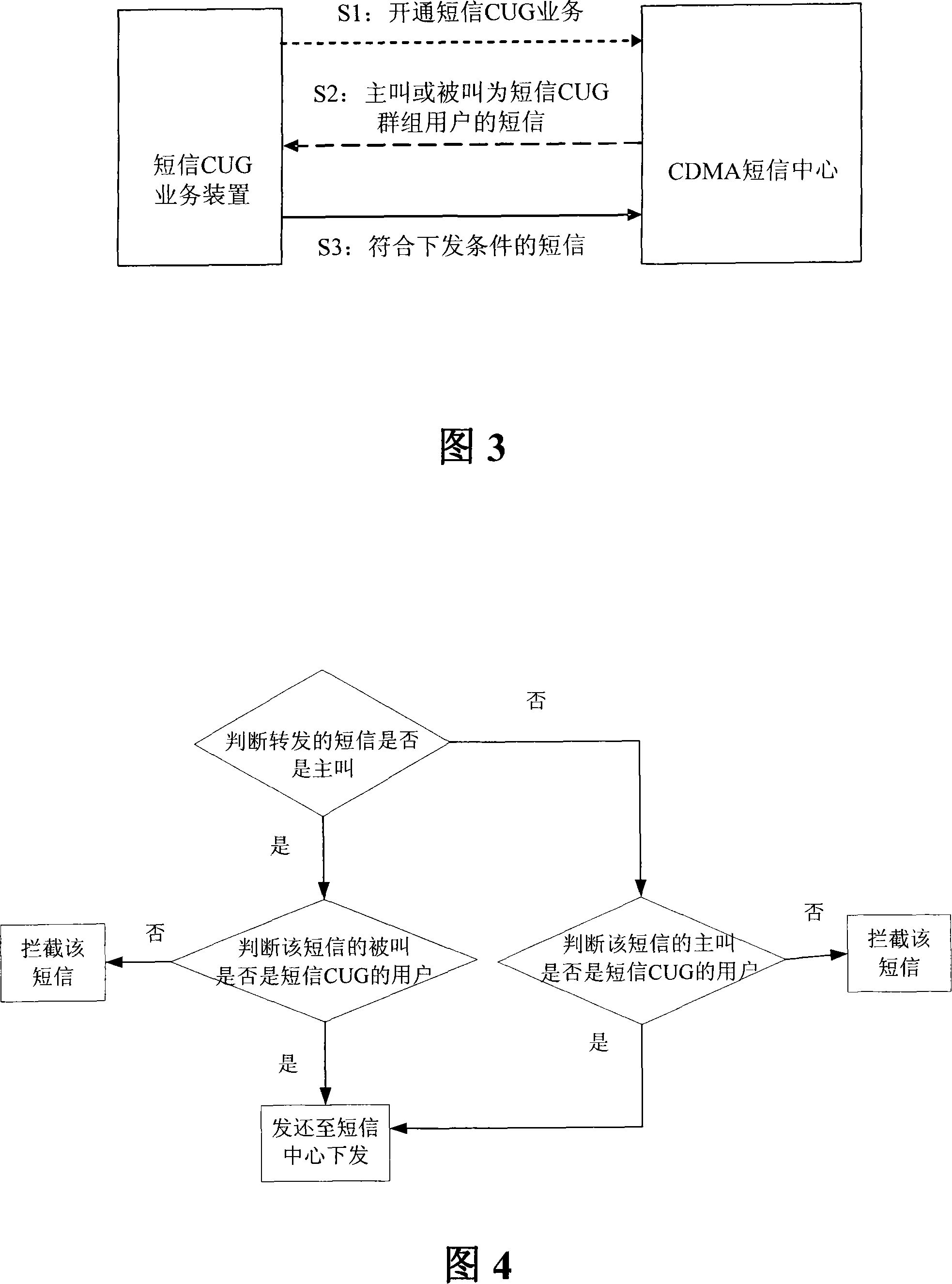
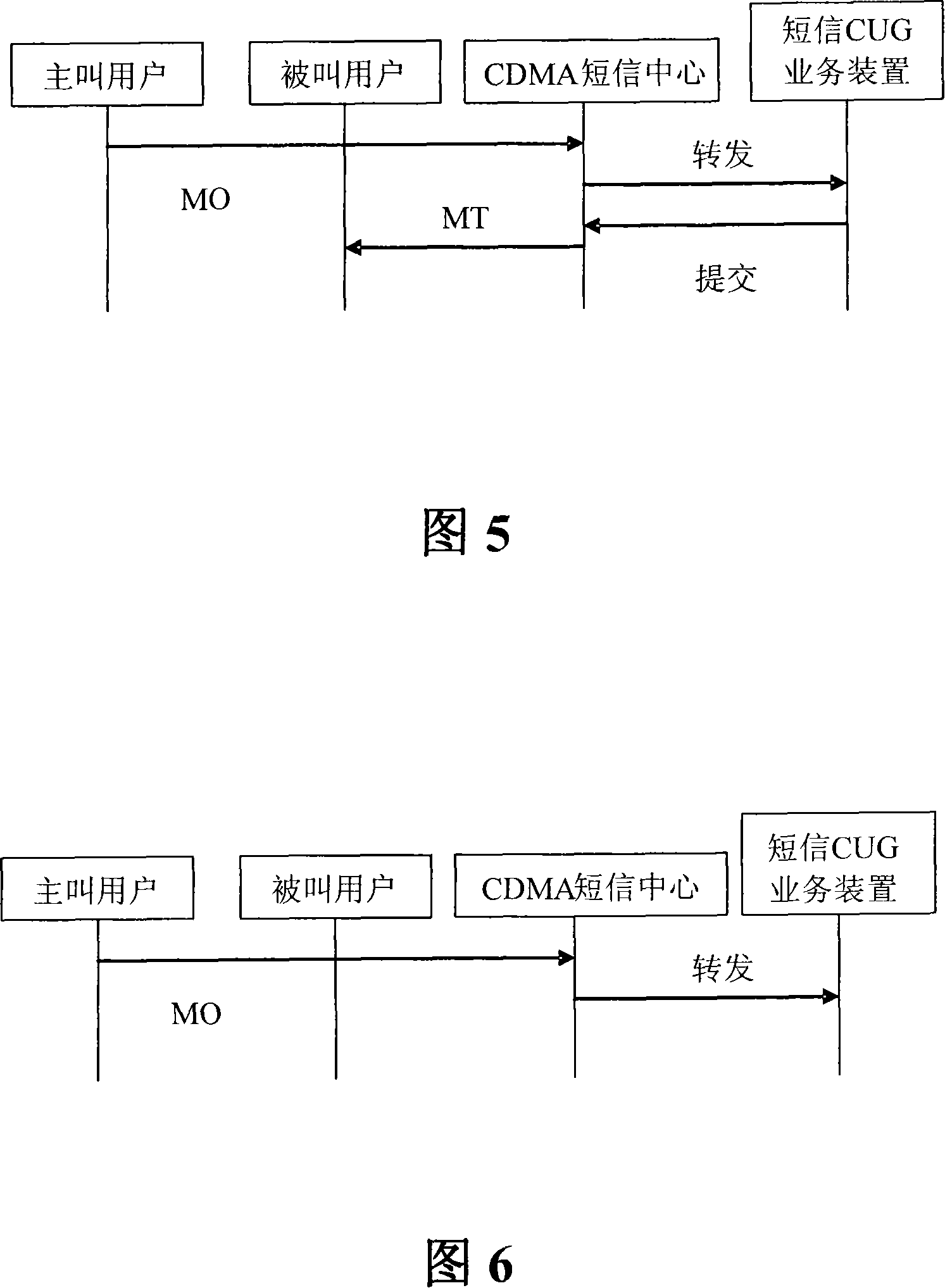
A SMS closed user group business system and the corresponding realization method
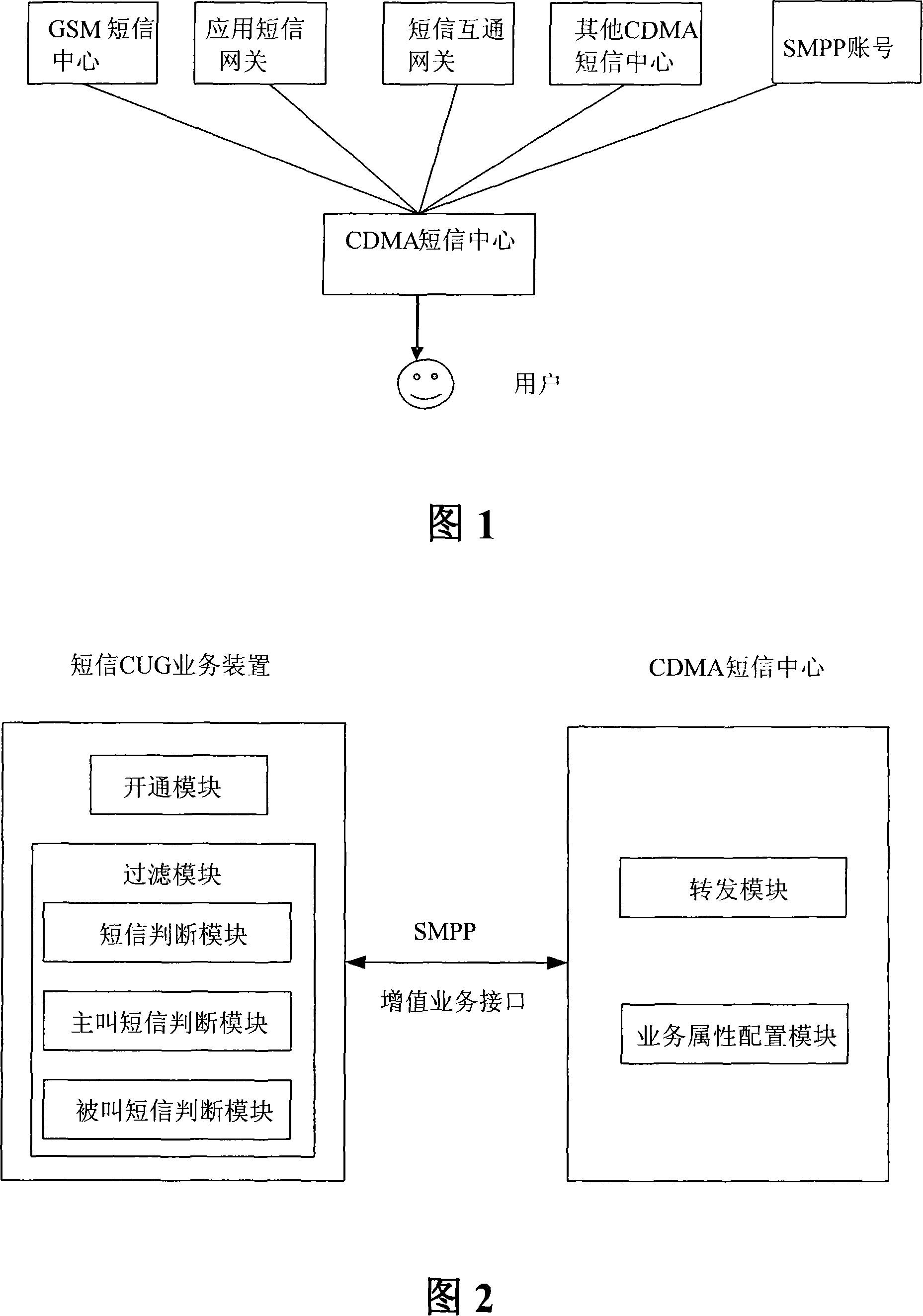
ActiveCN101217709ARealize the needs of SMS communicationSolve the problem of not being able to interceptRadio/inductive link selection arrangementsData switching networksSource textWorld Wide Web
The invention relates to a system for text message closed user group service, which comprises a text message center and a text message closed user group service device. The text message closed user group service device utilizes a value-added port of the text message center to be connected with the text message center. The text message center comprises a transmit module used for transmitting all calling and called text messages of users of the text message closed user group from the text message center to the text message closed user group service device; the text message closed user group service device comprises that an opening module is used for opening the text message closed user group service for the users of the text message closed user group through the value-added port of the text message center; a filter module is used for returning the text messages that are arranged in line with deliver conditions to the text message center, or intercepting the text messages. By adopting the system of the invention, the problems that external point-to-point text messages can not be intercepted and the hidden trouble exists in ESME source text messages are solved; meanwhile, the system saves number resources and can flexibly respond to the requirement of the users.
Owner:CHINA TELECOM CORP LTD
Full-automatic washing machine
ActiveCN106245282AImprove compatibilityChange habitsOther washing machinesControl devices for washing apparatusHabitControl mode
The invention discloses a full-automatic washing machine which comprises a shell, a control panel seat and an upper cover plate. The control panel seat is located at the top of the shell, a clothes inlet is formed in the control panel seat, and the upper cover plate is rotationally arranged on the control panel seat to open or close the clothes inlet. The full-automatic washing machine is characterized in that an integrated display control knob is arranged on the upper portion of the front side face of the washing machine, and the upper cover plate forms the whole upper top face of the washing machine in a closed state. The integrated display control knob is used for replacing the existing control mode of combining a knob and a display screen, the whole operation panel is replaced, the simple appearance is achieved, the operation panel is arranged on the front side face of a machine body, the upper surface of the control panel seat is not occupied, the upper cover plate of the clothes inlet for allowing clothes to be put forms the whole upper top face of the washing machine, and a larger clothes inlet is obtained. A corresponding program and display content of the integrated display control knob can be modified through a background controller, hardware compatibility is higher, the use habit of a consumer is not changed, and use is convenient.
Owner:QINGDAO HAIER WASHING MASCH CO LTD
Spreadsheet data management method based on B/S mode
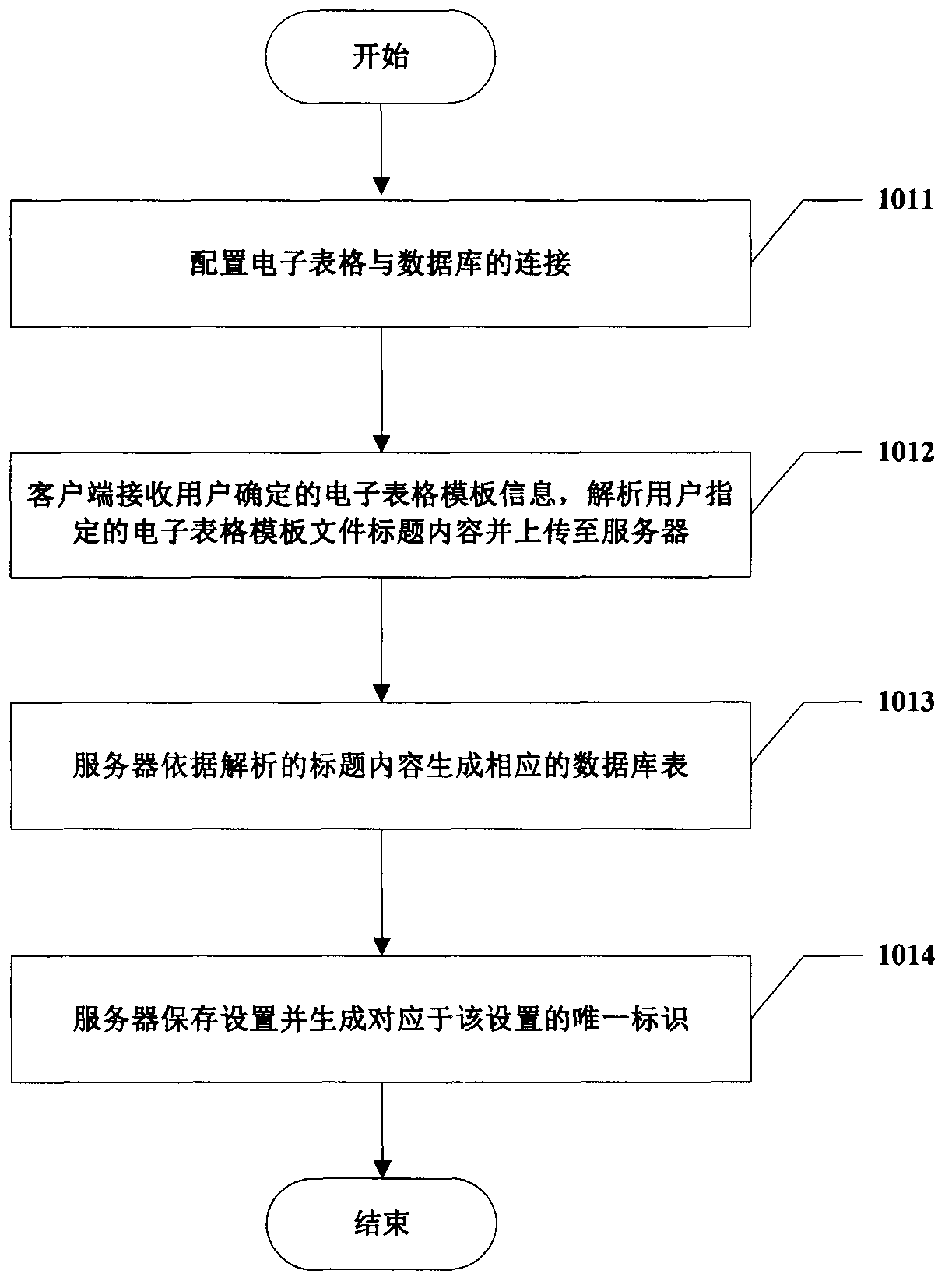
InactiveCN104239367ASolve the defects of scattered and difficult managementReduce the problem of slow loadingWeb data indexingFile/folder operationsData fileHabit
The invention provides a spreadsheet data management method based on a B / S mode. The method includes the steps of S1, completing the related settings of a spreadsheet template file in advance; S2, by a browser, uploading the spreadsheet template file which is selected by a user and contains data to a server; S3, by the server, detecting whether the title content of the received template file is consistent with the field name saved by a database table or not according to unique identification, and if so, writing the template file data confirmed by the user into the corresponding table of a database; or else, allowing the template file data not be written into the database. The method has the advantages that the spreadsheet template file data passing detection is managed through the database, and the defect that data is scattered and hard to manage when only the spreadsheet is used is overcome; data file data amount limitation of collected data is avoided; spreadsheet using habits of the user are unchanged, and friendly user interaction is achieved.
Owner:SUZHOU JINGYIHUI INFORMATION TECH
Touch projection mobile phone
InactiveCN106998374ARealize the touch effectEasy to connect to the InternetPicture reproducers using projection devicesTelephone set constructionsSmart phoneMobile phone
The invention discloses a touch projection mobile phone comprising a host and a base, wherein the base is in the shape of a groove, and the host is embedded in the base and is connected with the base through a microUSB interface. The touch projection mobile phone disclosed by the invention has the beneficial effects that an interactive projection kit is added to an ordinary smart phone, so that the smart phone has a short focus projection function, and the original small screen of the mobile phone is amplified to a 10-20-inch large screen; and an infrared camera kit is provided, so that the mobile phone not only amplifies the display image, but also facilitate the operation actions of a detector, thereby realizing a touch effect without changing the use habits of users.
Owner:JIANGSU POLYTECHNIC COLLEGE OF AGRI & FORESTRY
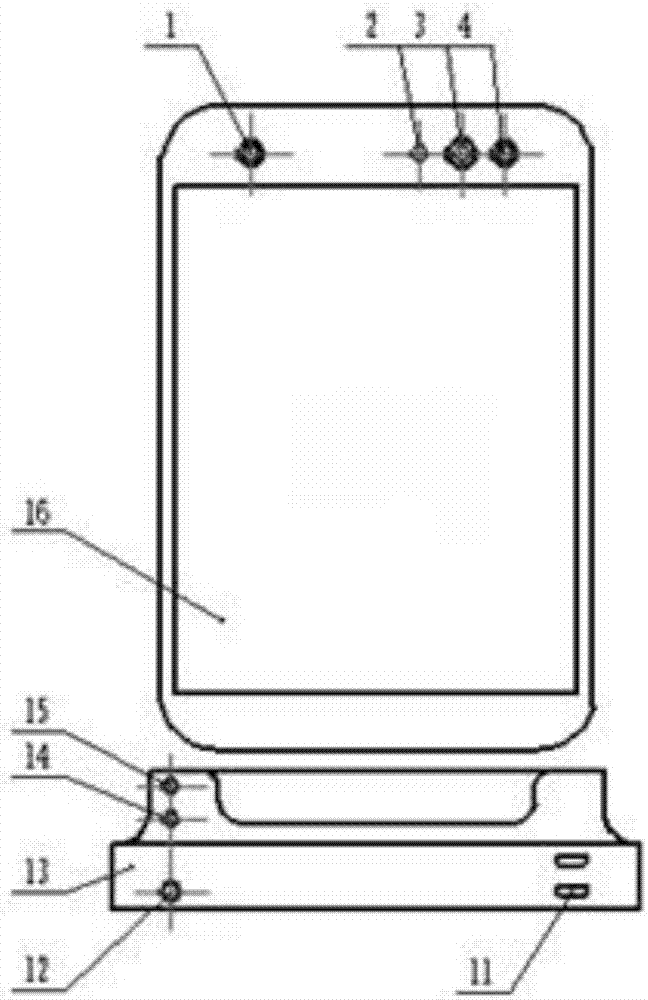
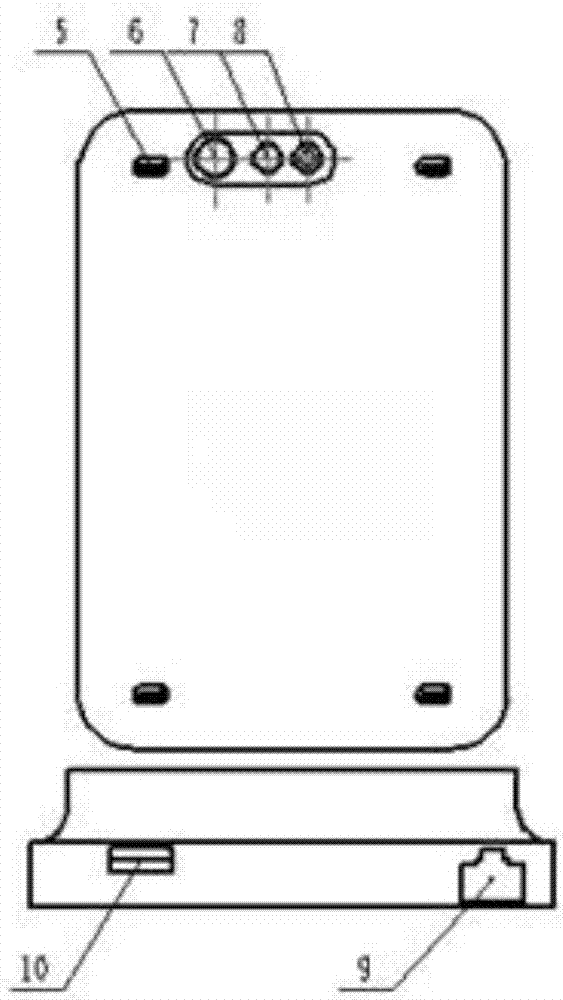
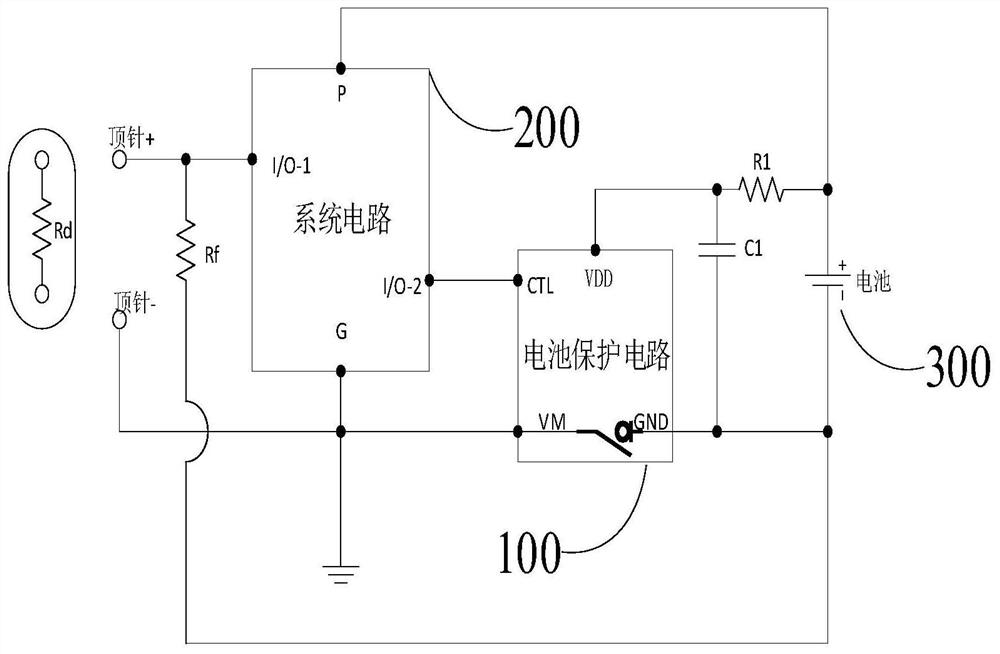
Cigarette rod and electronic cigarette
PendingCN113303503AReduce battery consumptionReduce current consumptionTobaccoElectrical batteryElectronic cigarette
The invention provides a cigarette rod which comprises a battery and a battery protection circuit. The battery protection circuit comprises a power supply pin electrically connected with the positive electrode of the battery, a power supply grounding pin electrically connected with the negative electrode of the battery and a system grounding pin; the cigarette rod comprises a thimble positive electrode and a thimble negative electrode which are electrically connected with a cigarette cartridge, and the system grounding pin is electrically connected with the thimble negative electrode; and the cigarette cartridge is connected with the cigarette rod, and the battery protection circuit detects the voltage change of the system grounding pin and enables the cigarette rod to exit the shipping mode. After the cigarette cartridge is separated from the cigarette rod for a preset time T, the battery protection circuit detects the voltage change of the system grounding pin, and the cigarette rod is controlled to enter the shipping mode. The invention also provides an electronic cigarette, which effectively realizes automatic detection of entering or exiting the shipping mode according to the connection state of the cigarette rod and the cigarette cartridge, is beneficial to saving energy consumption, does not change the use habit of a user, and improves the user experience. And meanwhile, the advantages of low cost and intensification are achieved.
Owner:XI AN WENXIAN SEMICON TECH CO LTD
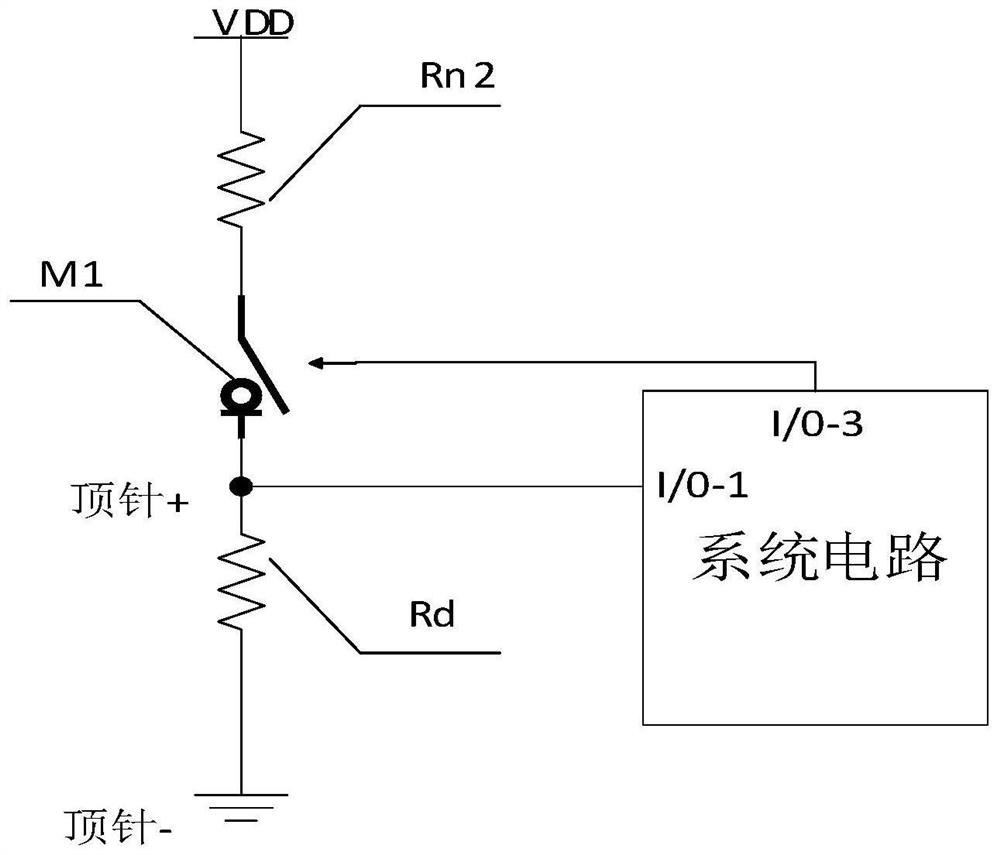
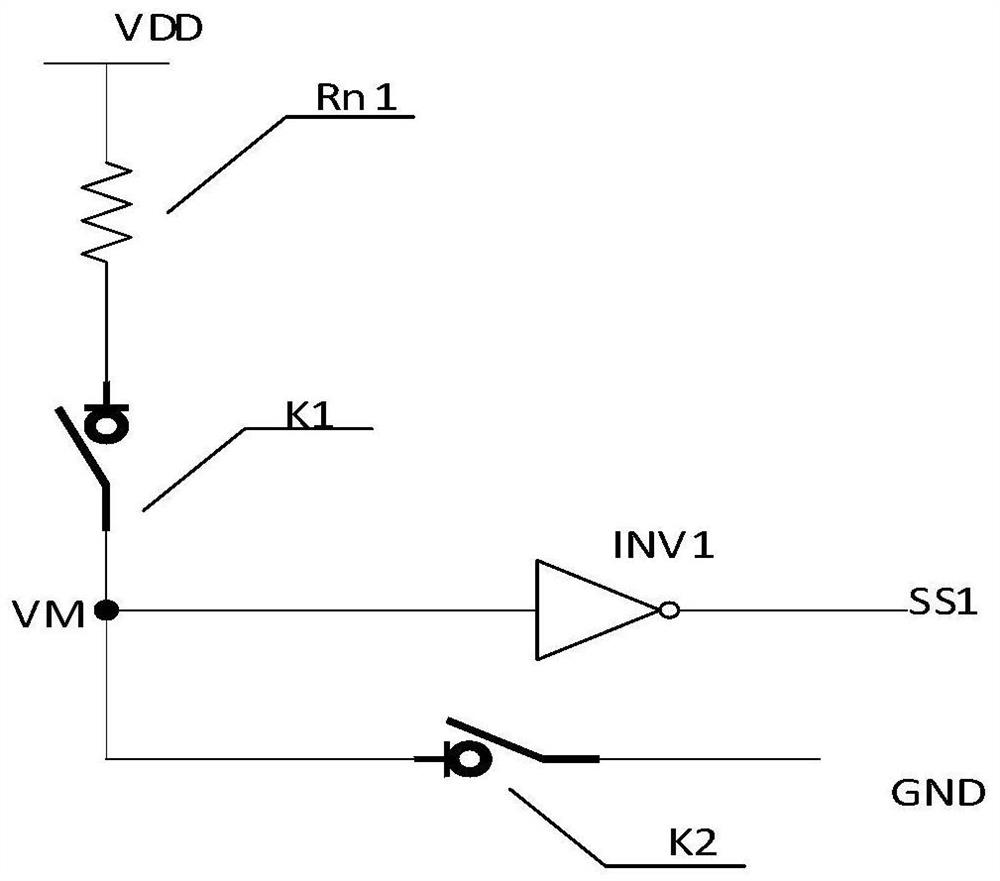
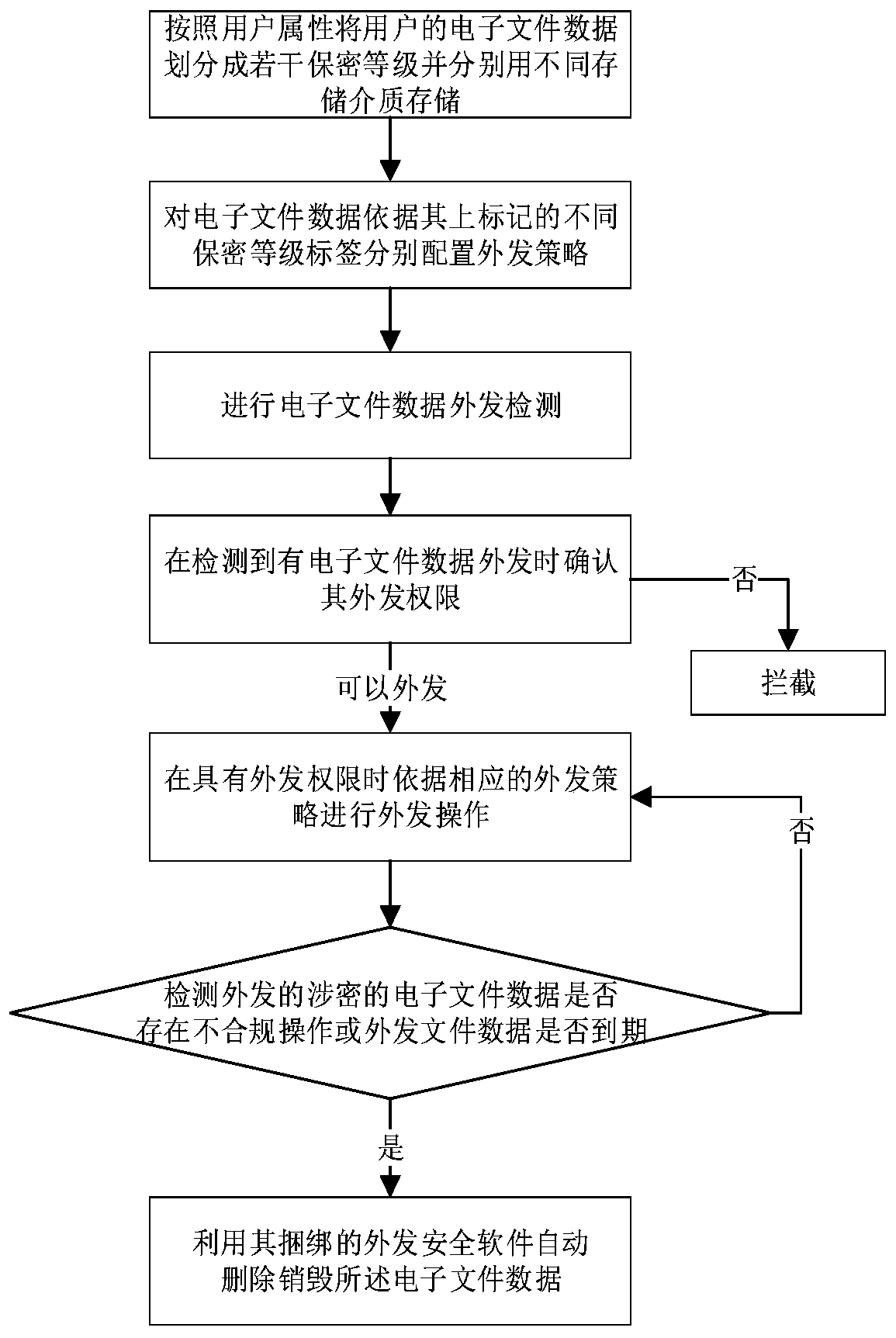
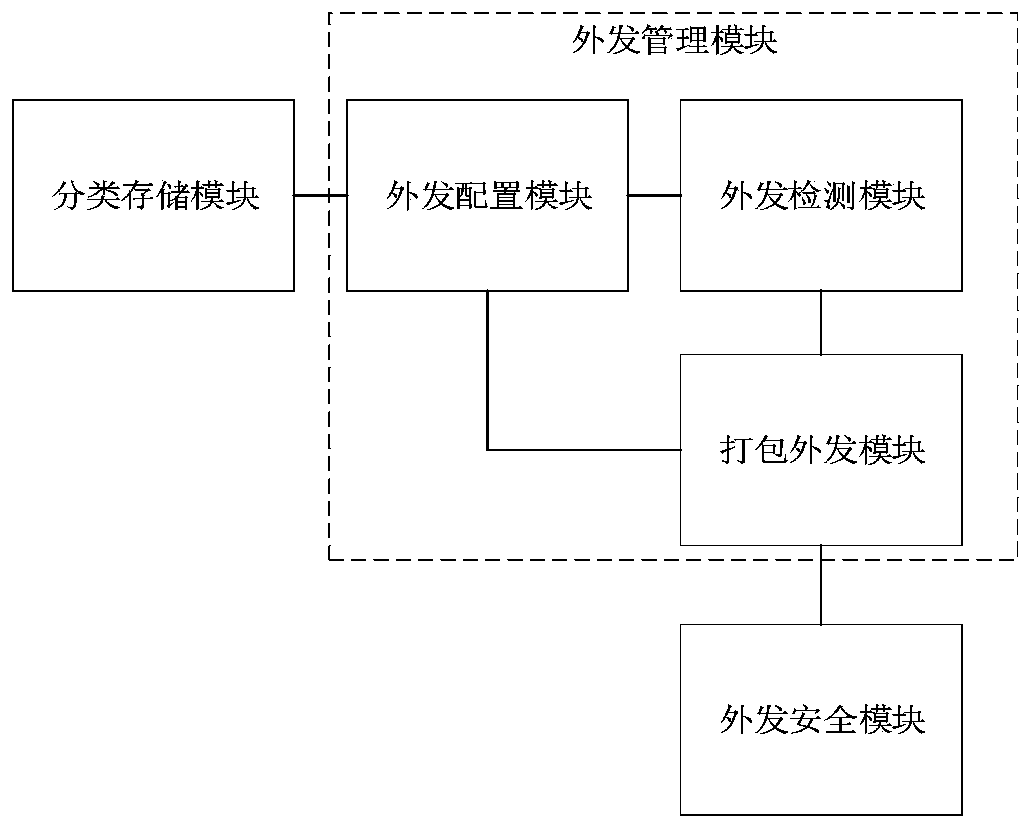
Method and system for safely sending out data
InactiveCN110502906AAvoid risk of leakageImprove security and confidentialityDigital data protectionConfidentialitySecurity software
The invention relates to a method for safely sending out data. The method comprises the following steps: dividing electronic file data of a user into a plurality of confidentiality levels according touser attributes and respectively storing the confidentiality levels by different storage media; configuring outgoing strategies for the electronic file data according to different confidentiality level labels marked on the electronic file data; carrying out electronic file data outgoing detection; when it is detected that the electronic file data is sent out, confirming the sending-out permissionof the electronic file data; when the user has the outgoing permission, carrying out the outgoing operation according to the corresponding outgoing strategy; when the confidential electronic file data has a leakage risk, utilizing the bound outgoing security software to automatically delete and destroy the electronic file data. According to the method, the problems of poor timeliness, poor security and confidentiality, inflexible file data receiving and sending operation and the like of file data sending in the prior art are solved, the whole process is simple, rapid and flexible, complex sending approval is not needed, and the security and confidentiality of the electronic data sending process are enhanced. The invention further relates to a system for safely sending out the data.
Owner:北京泰立鑫科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com