Mobile phone data security protection method
A data security, mobile phone technology, applied in the field of information security and mobile communication, can solve problems such as inconvenience of use, and achieve the effect of protecting data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] Hereinafter, the present invention will be described in detail through specific embodiments in conjunction with the accompanying drawings.
[0018] This embodiment provides a specific system for implementing the method of the present invention, which includes three major modules: a file creation module, a file loading module, and a file operation module, wherein the specific functional units included in each module are as follows:
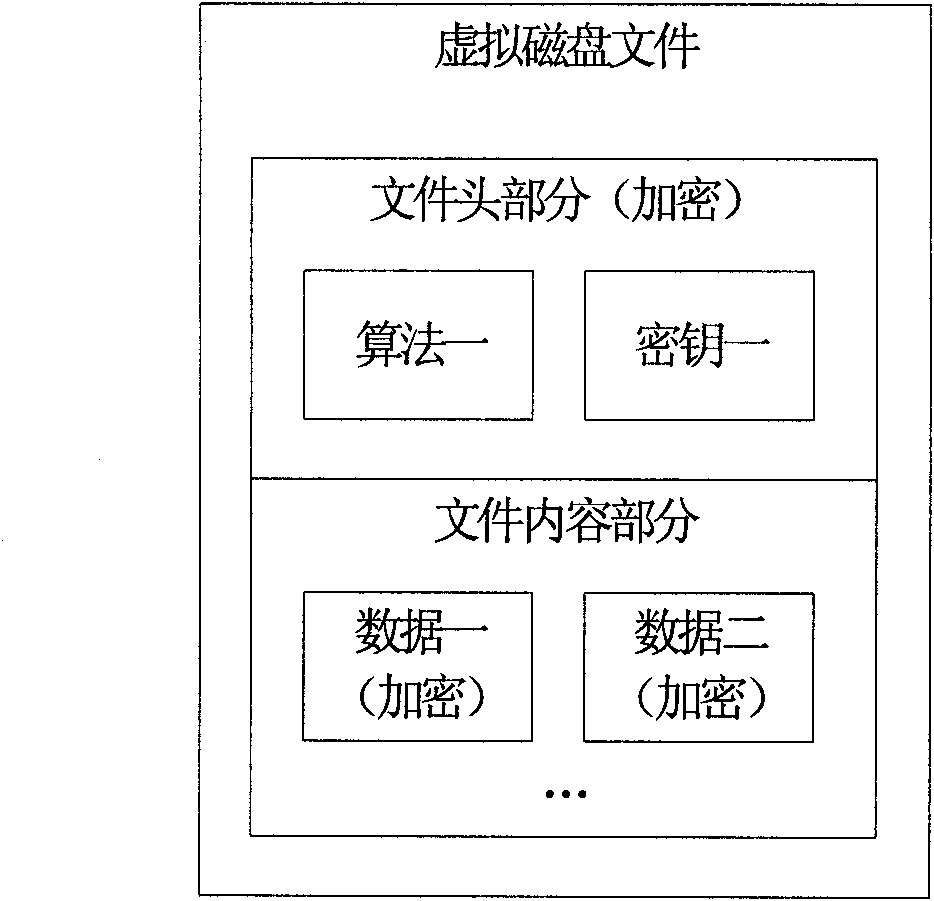
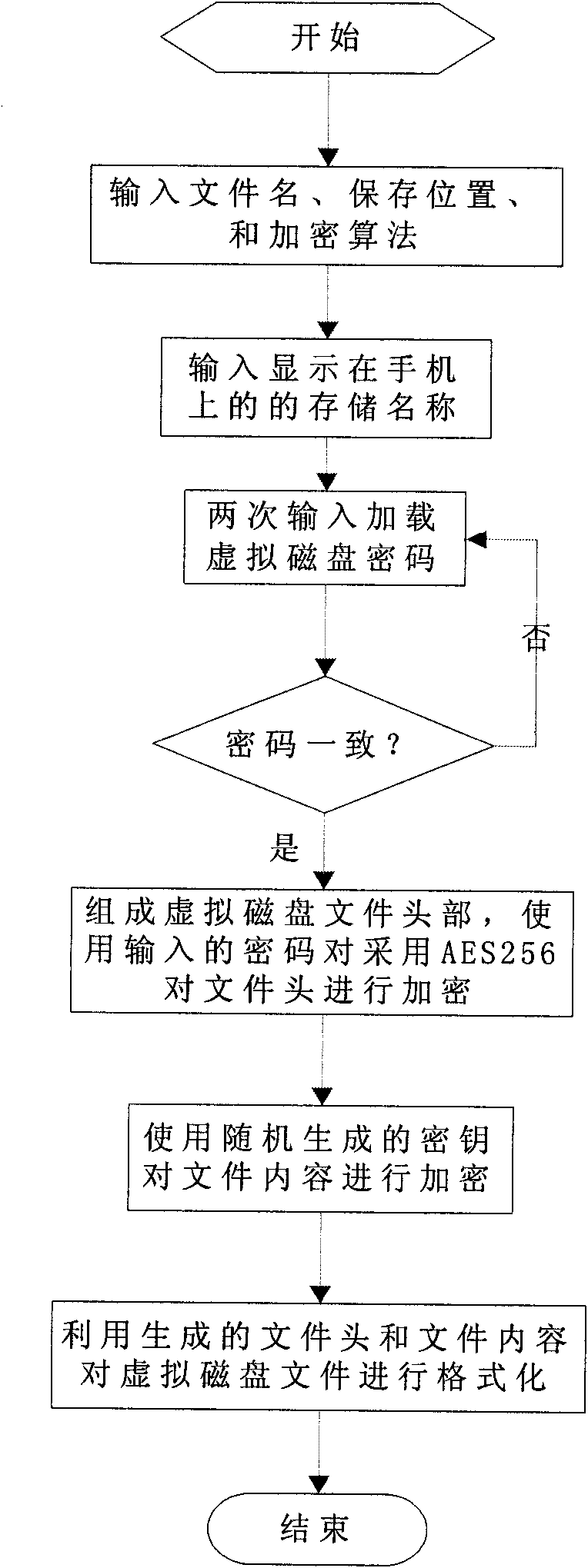
[0019] The file creation module is used to create a virtual disk file on the mobile phone, and format the created virtual disk file according to a specific format according to the information input and selected by the user. The file creation module includes a file header generating component, a file content generating component and a formatting component. Among them, the file header includes several parts of information such as file identification, storage name, key, and encryption algorithm. The file header generation component generates t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com