Security management system and method used for mobile terminal file
A mobile terminal and security management technology, applied in the fields of electronic digital data processing, internal/peripheral computer component protection, instruments, etc., can solve problems such as complex personnel, large environmental change factors, leakage of confidential document data information, etc., to ensure data security , high safety performance, and convenient implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
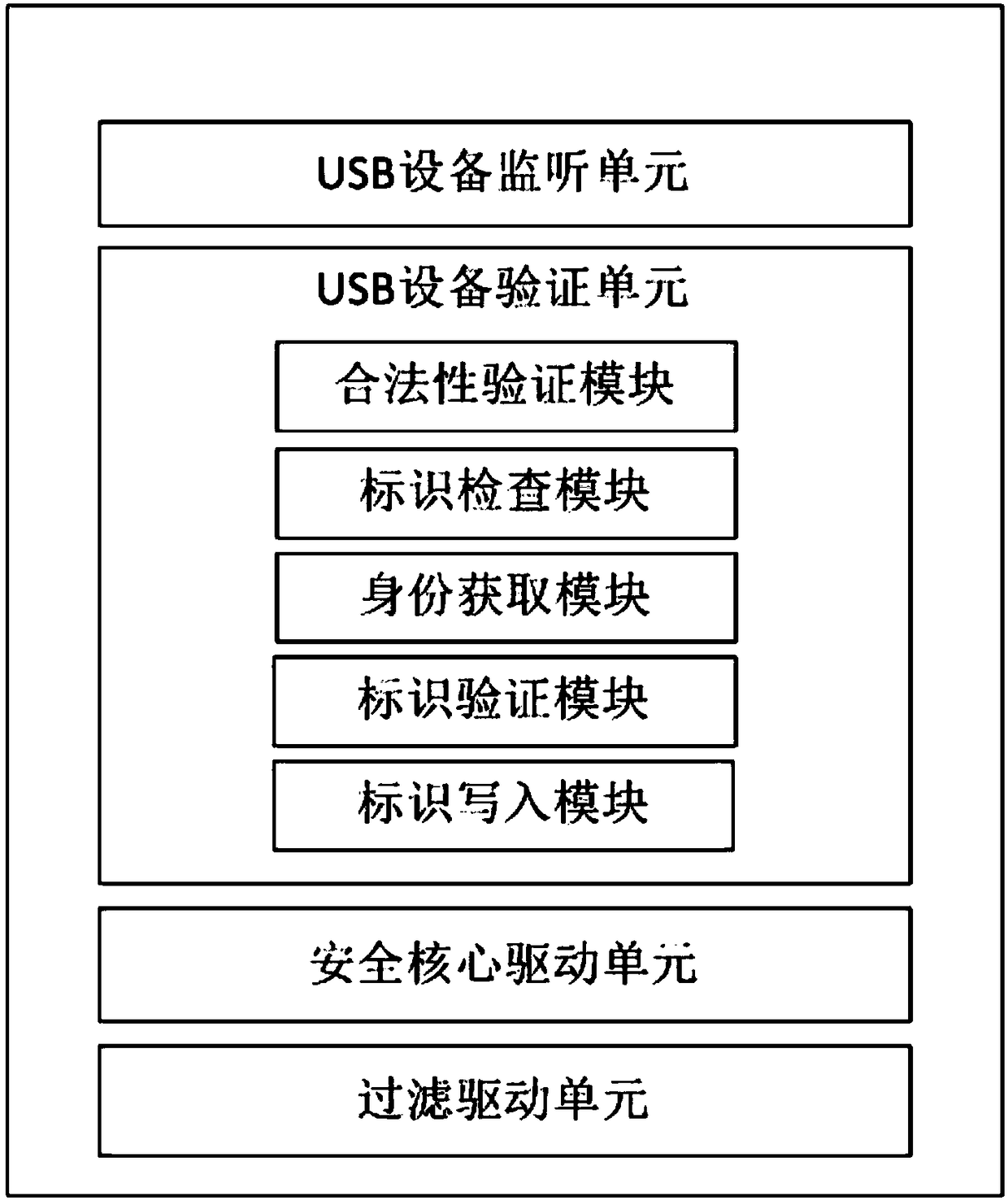
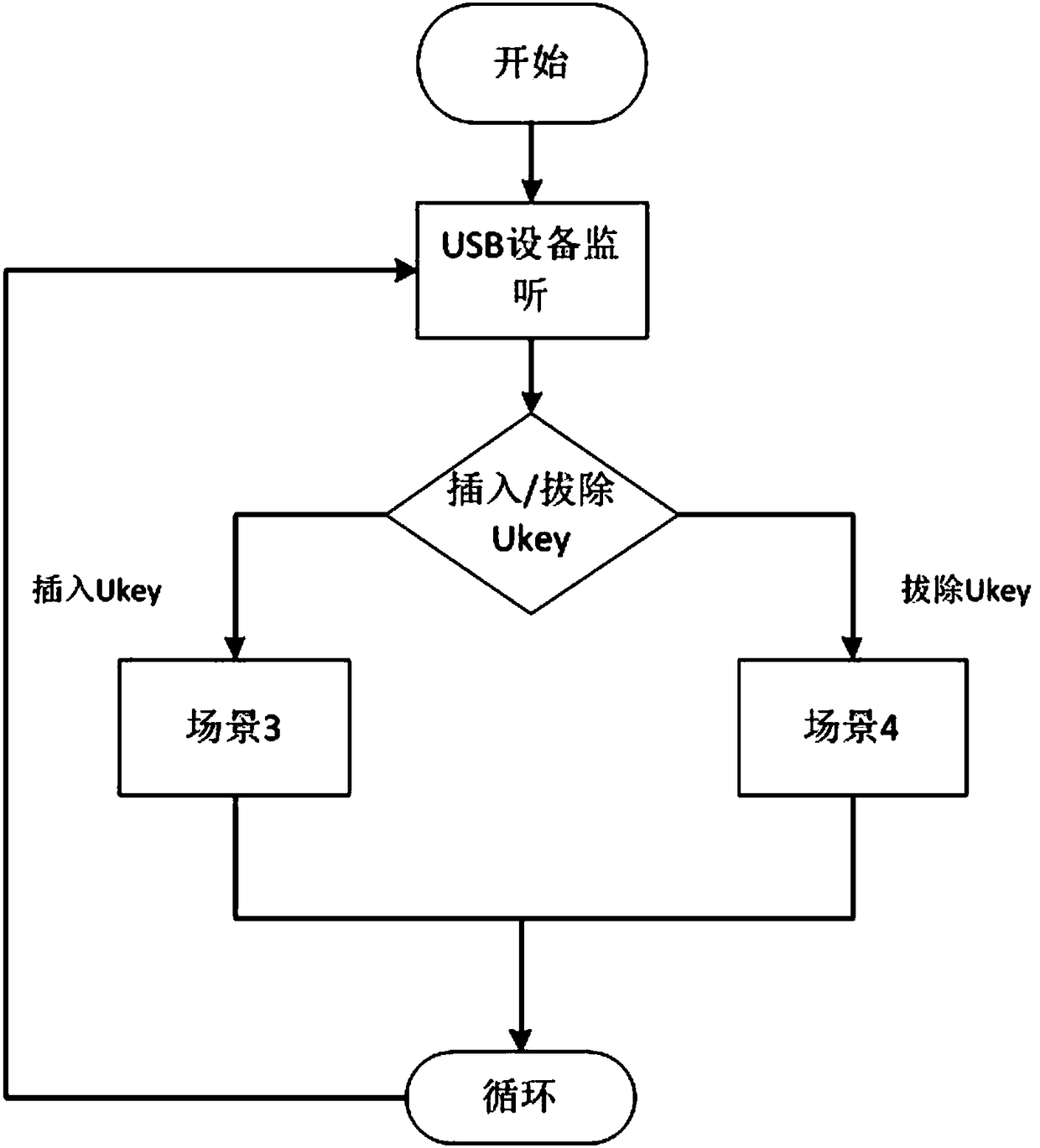
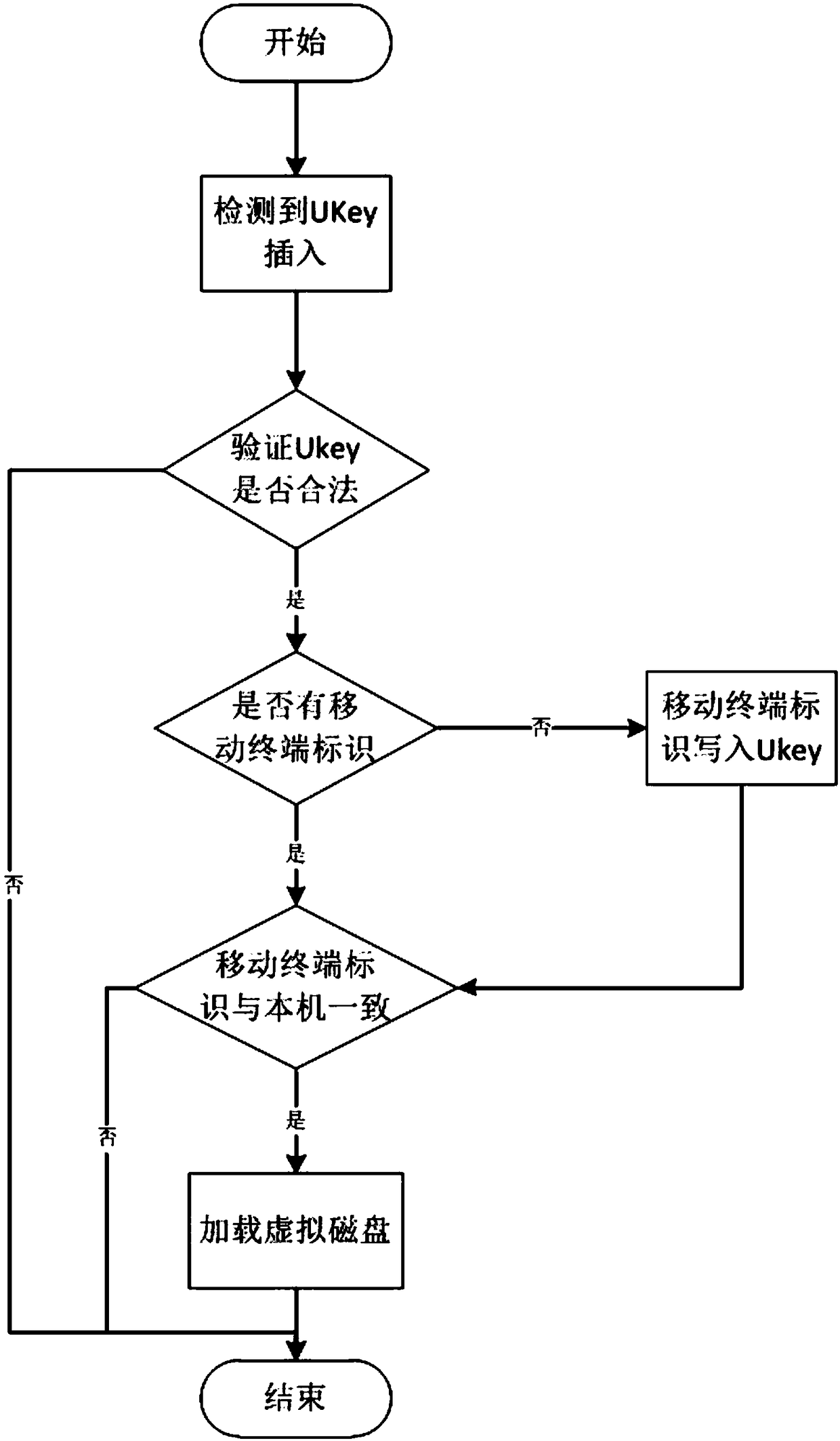
[0045] To optimize the above scheme, see figure 1 , the USB device verification unit at least includes: a legality verification module, an identification check module, an identity acquisition module, an identification verification module and an identification writing module. Wherein, the legitimacy verification module is used to check the identity of the inserted U-key device, confirming whether its own ID exists in the Key ID list of the system, and the identification check module is used to check whether the inserted U-key has a mobile terminal Identification, the identity acquisition module is used to obtain the mobile terminal identification in the inserted U-key device, and the identification verification module is used to confirm whether the mobile terminal identification in the obtained U-key matches the identification of the inserted mobile terminal, and the identification is written The module is used to write the corresponding mobile terminal identification in the U-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com