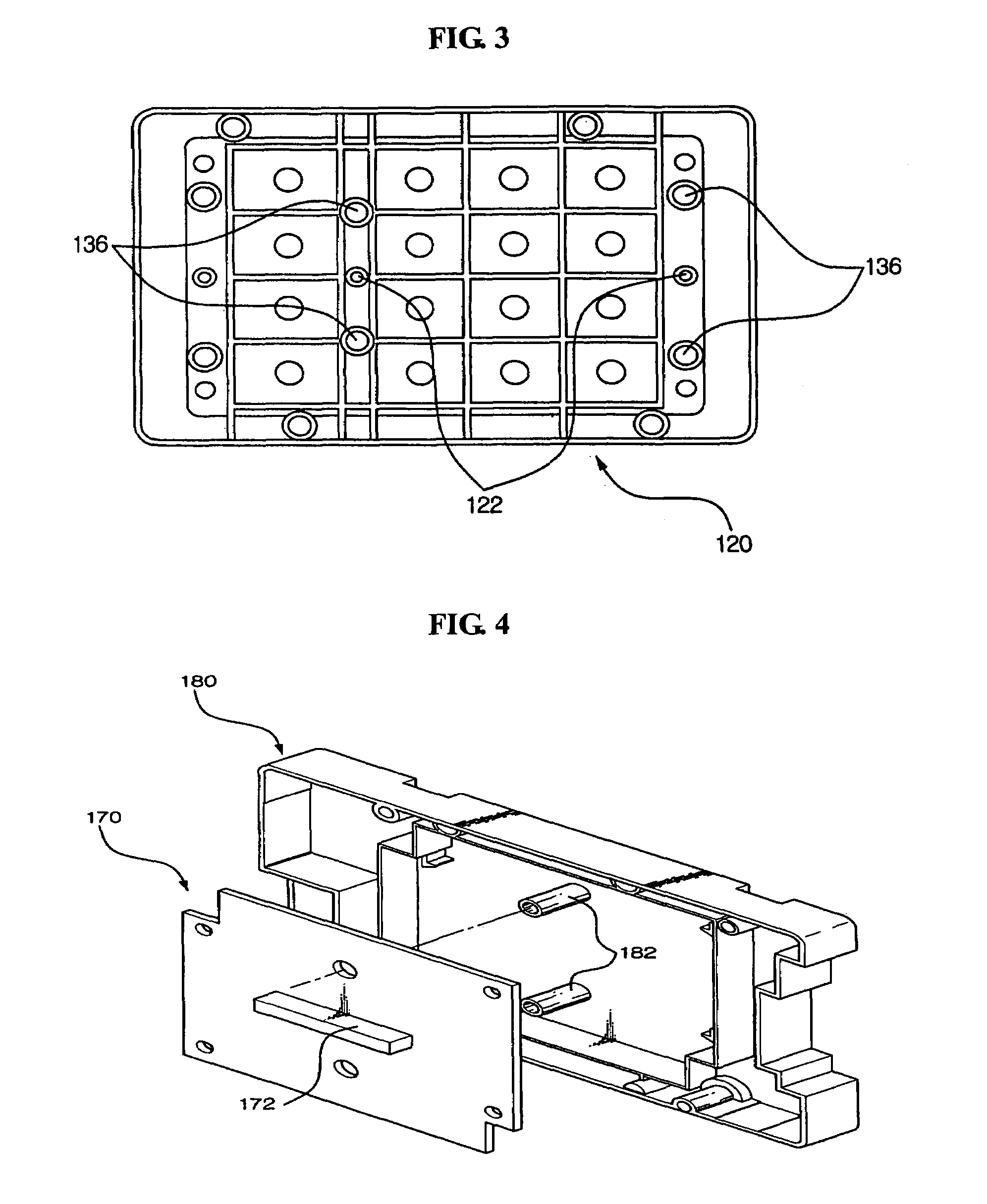
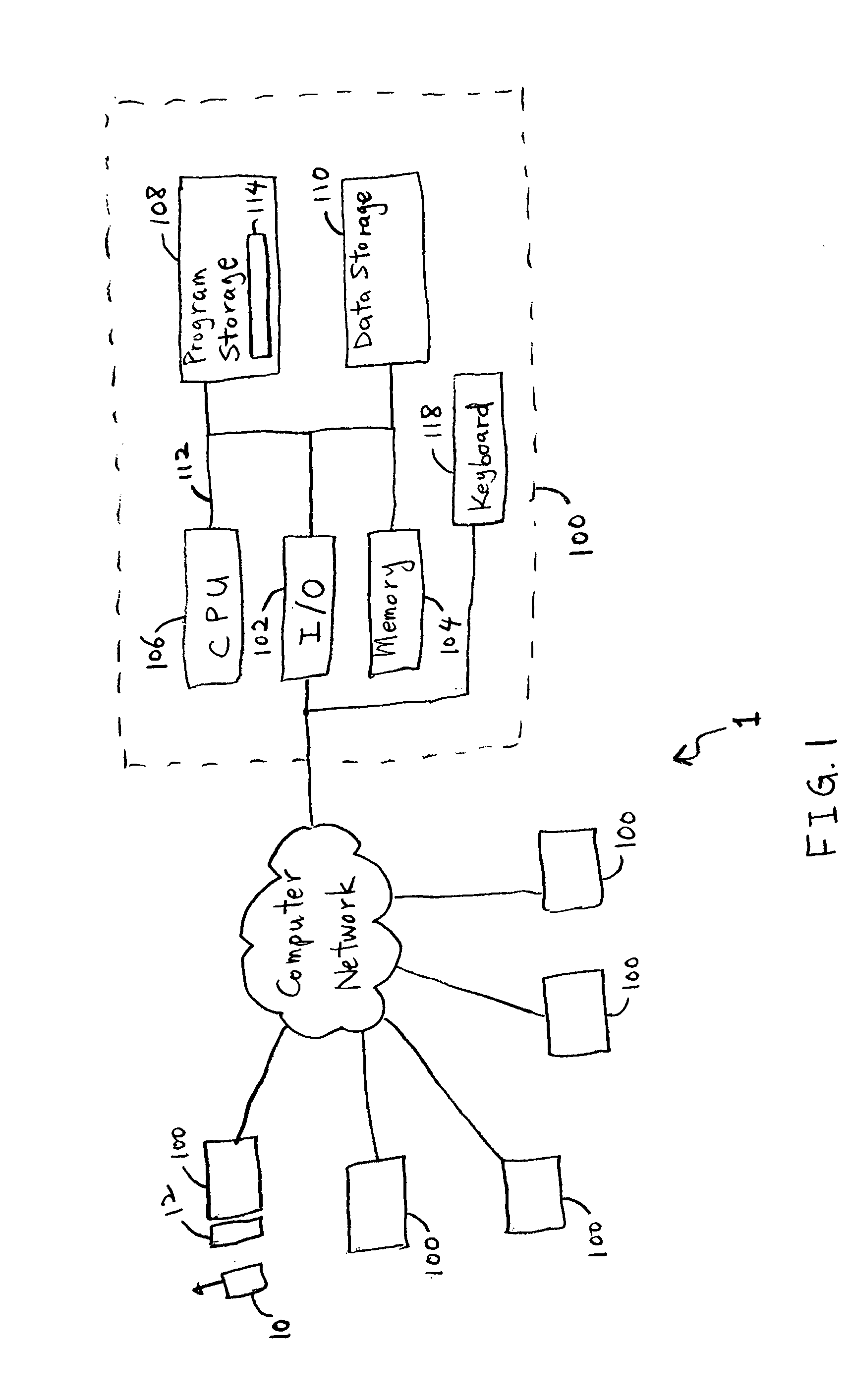
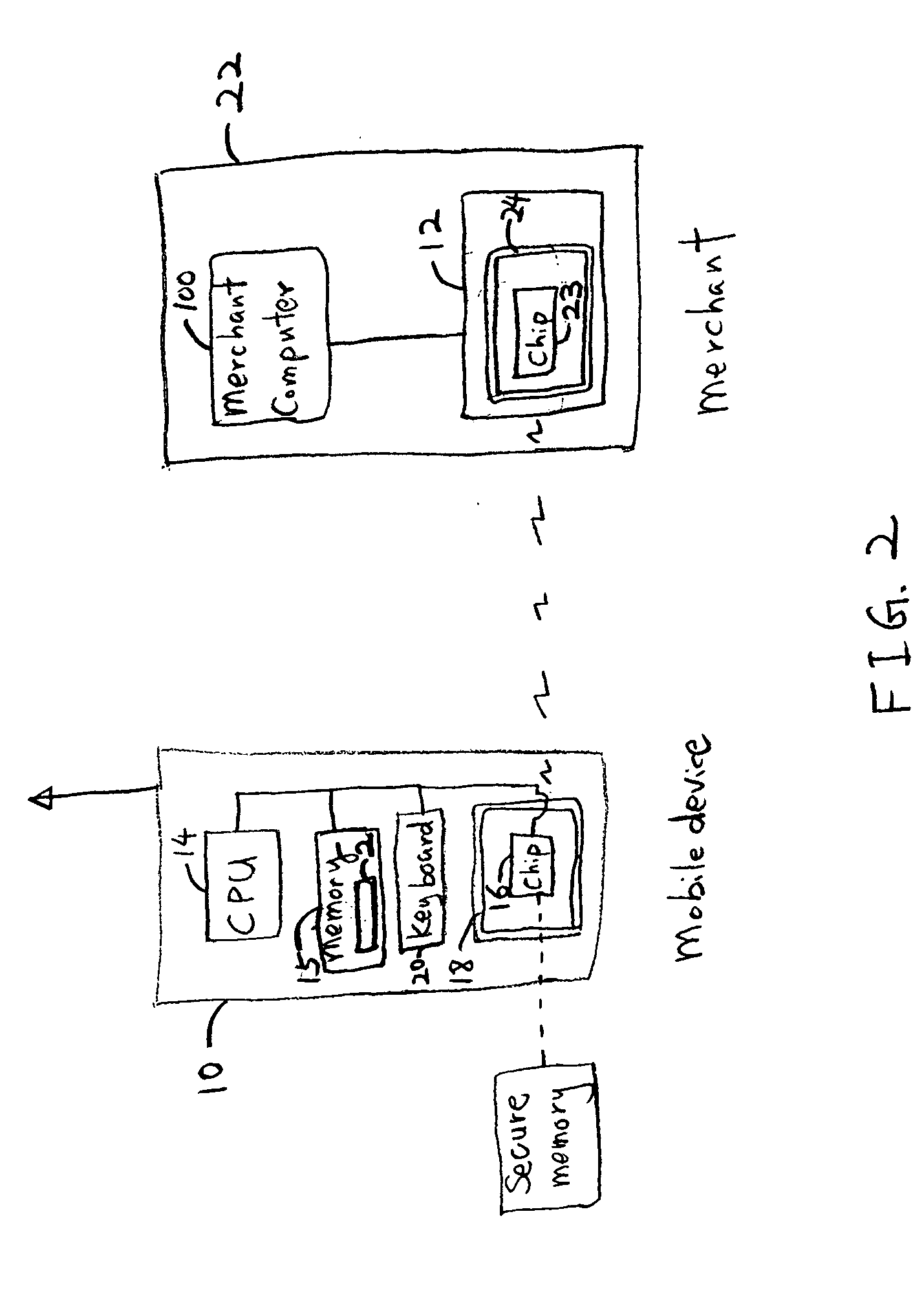
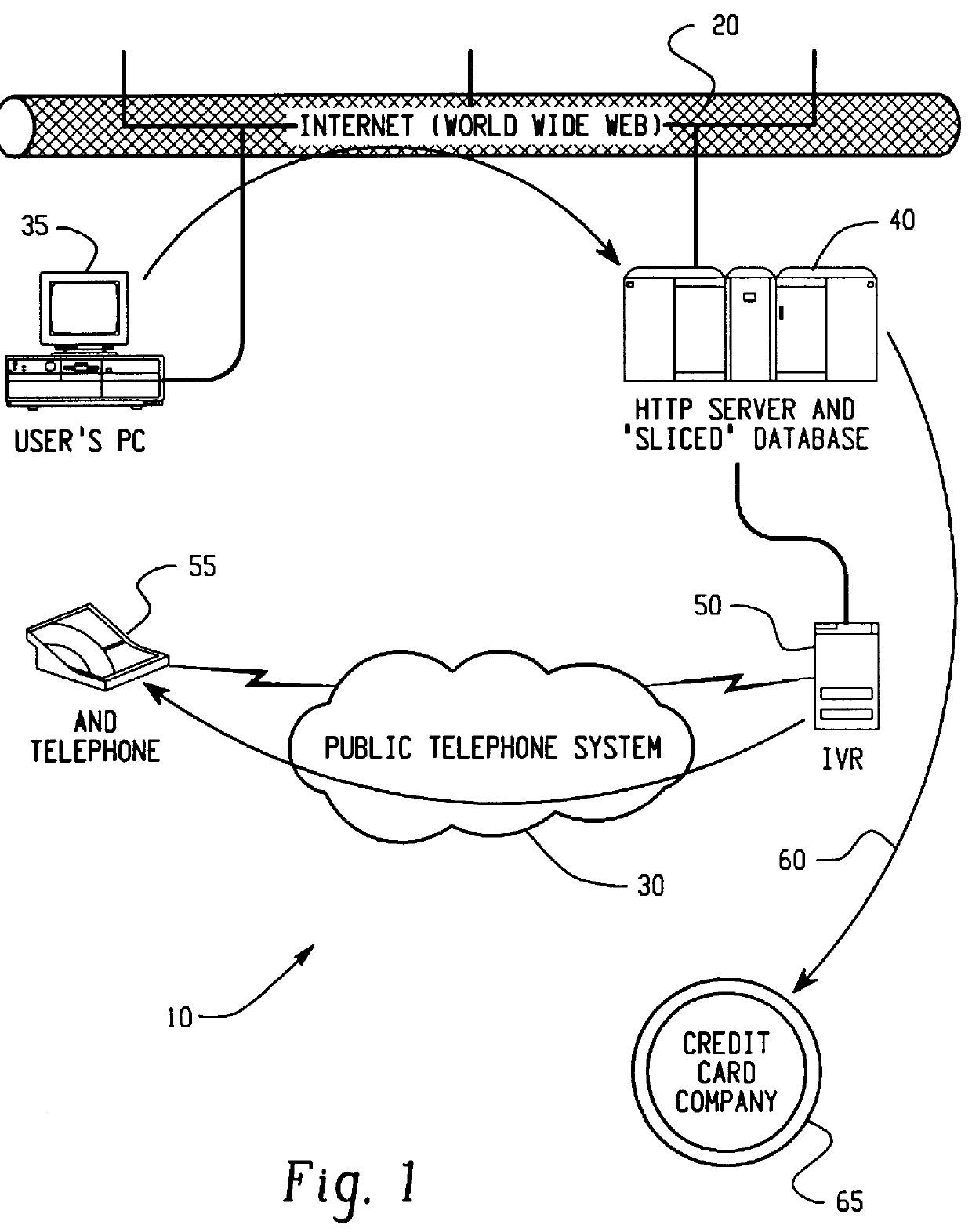
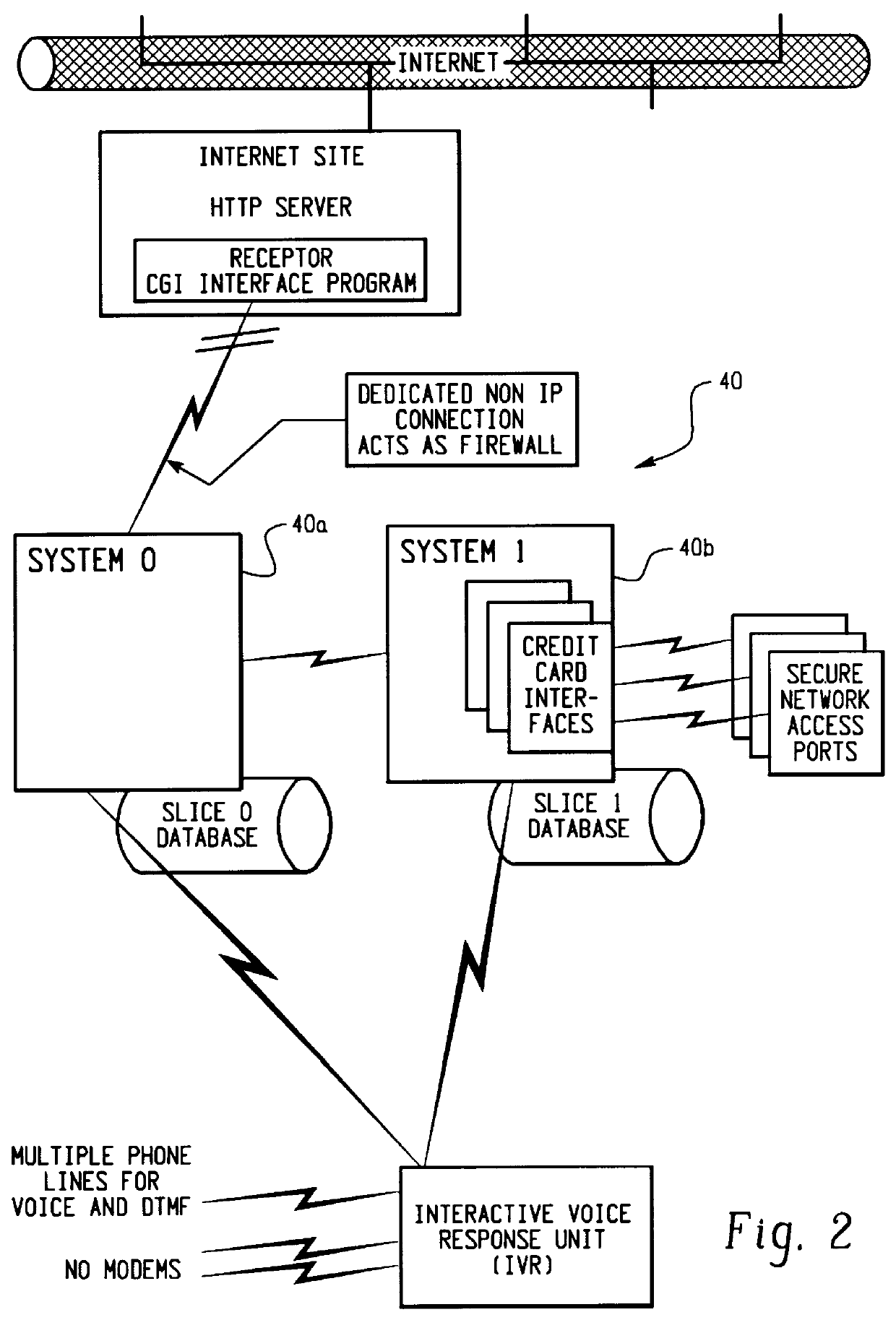
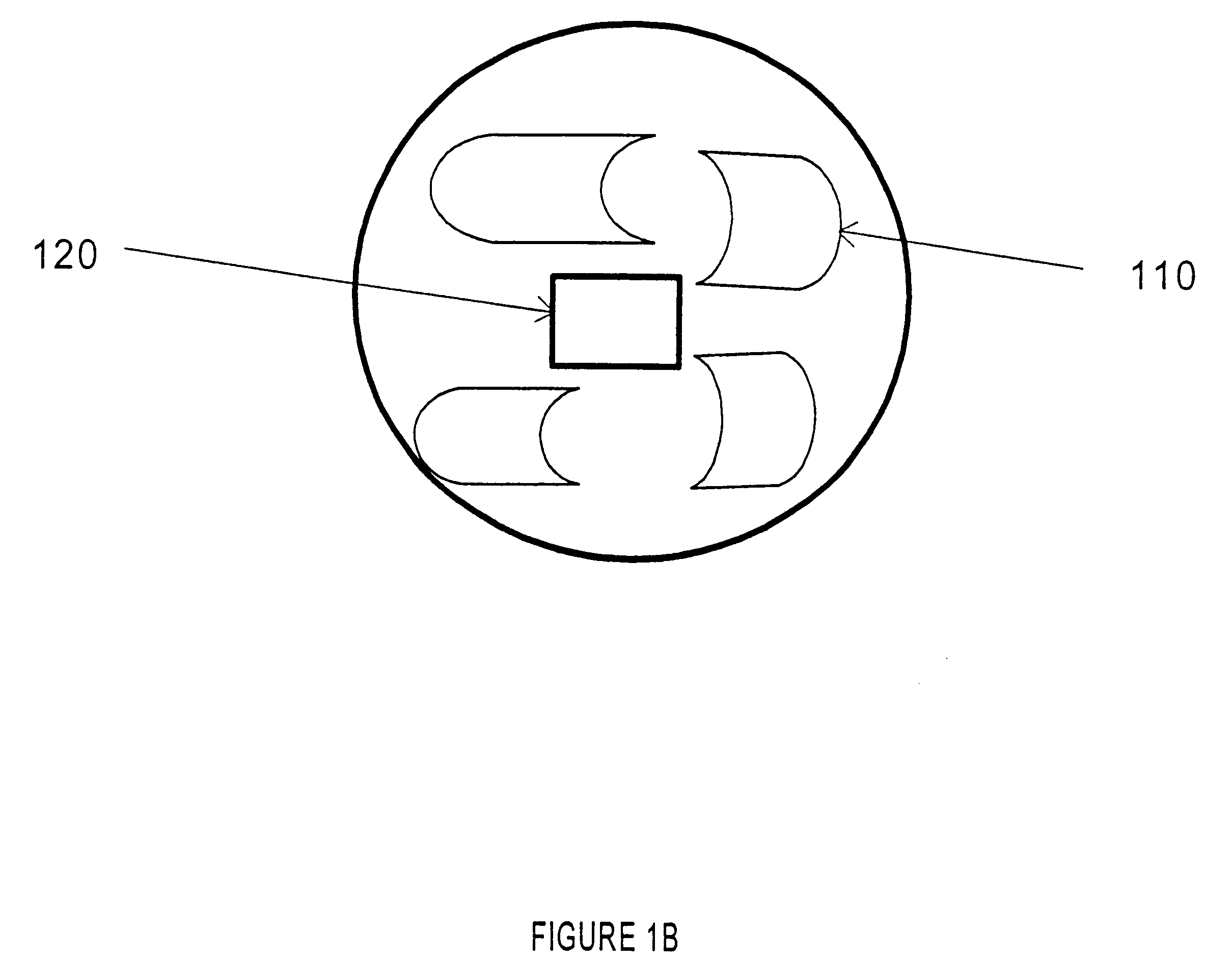
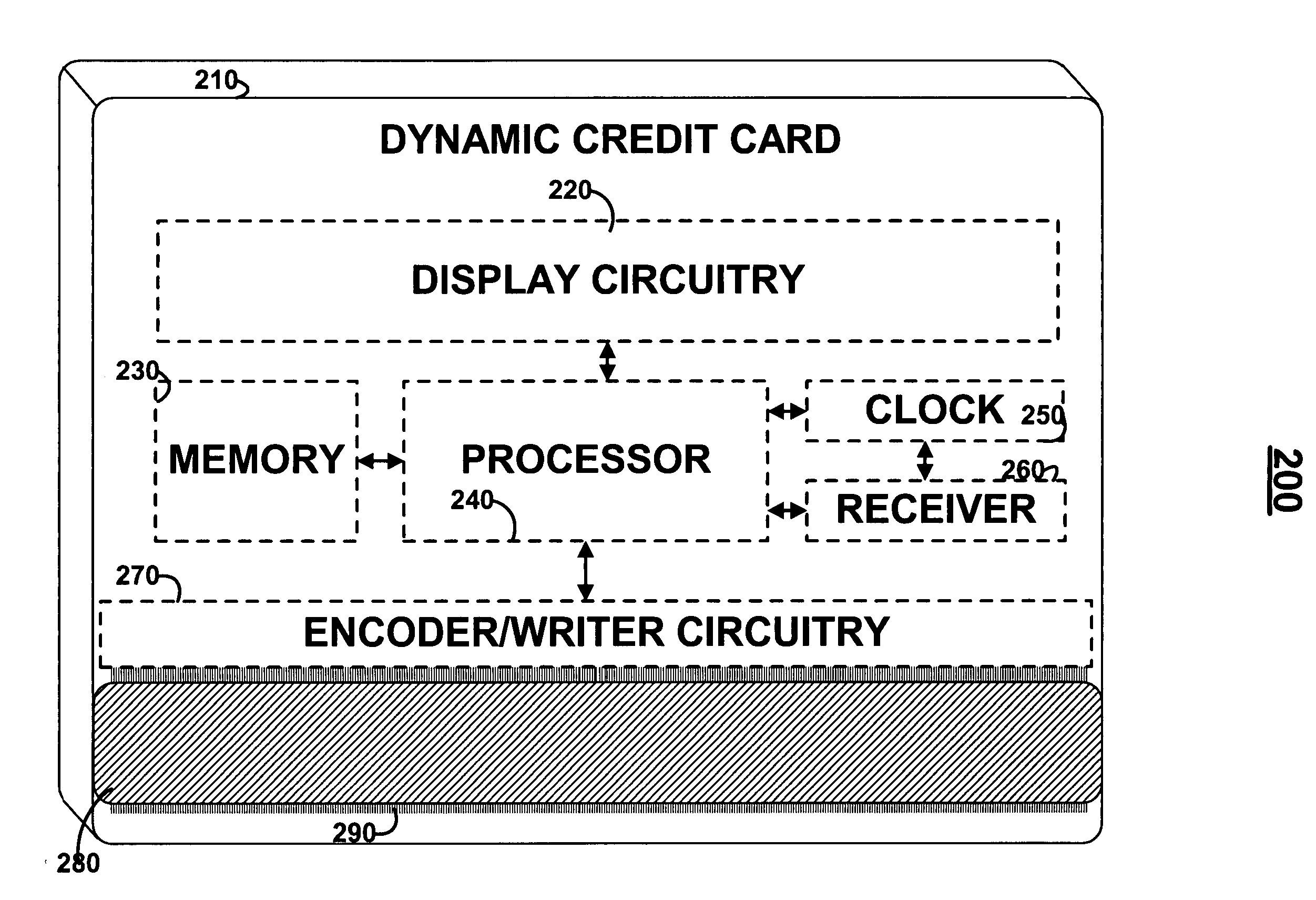
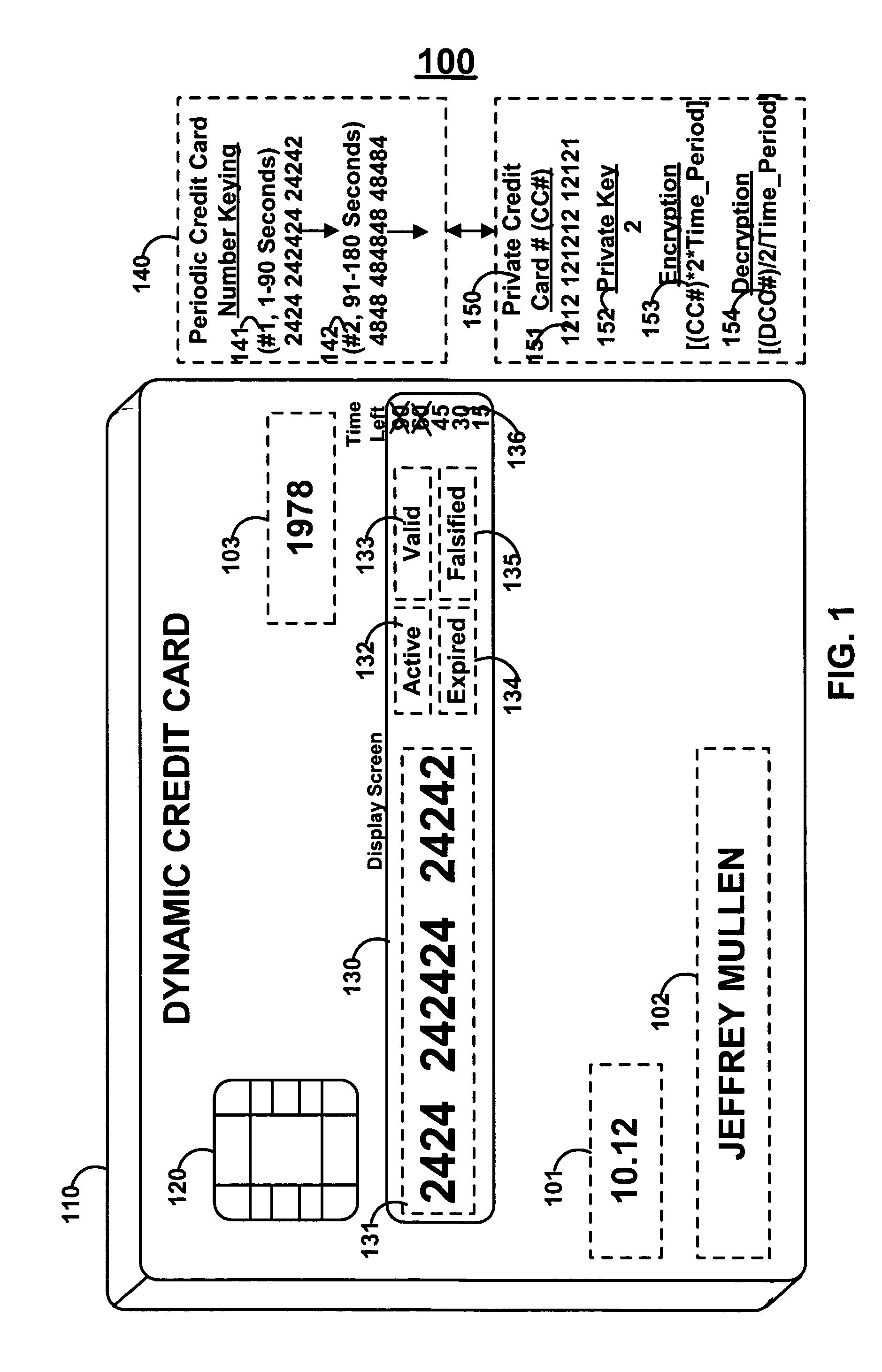
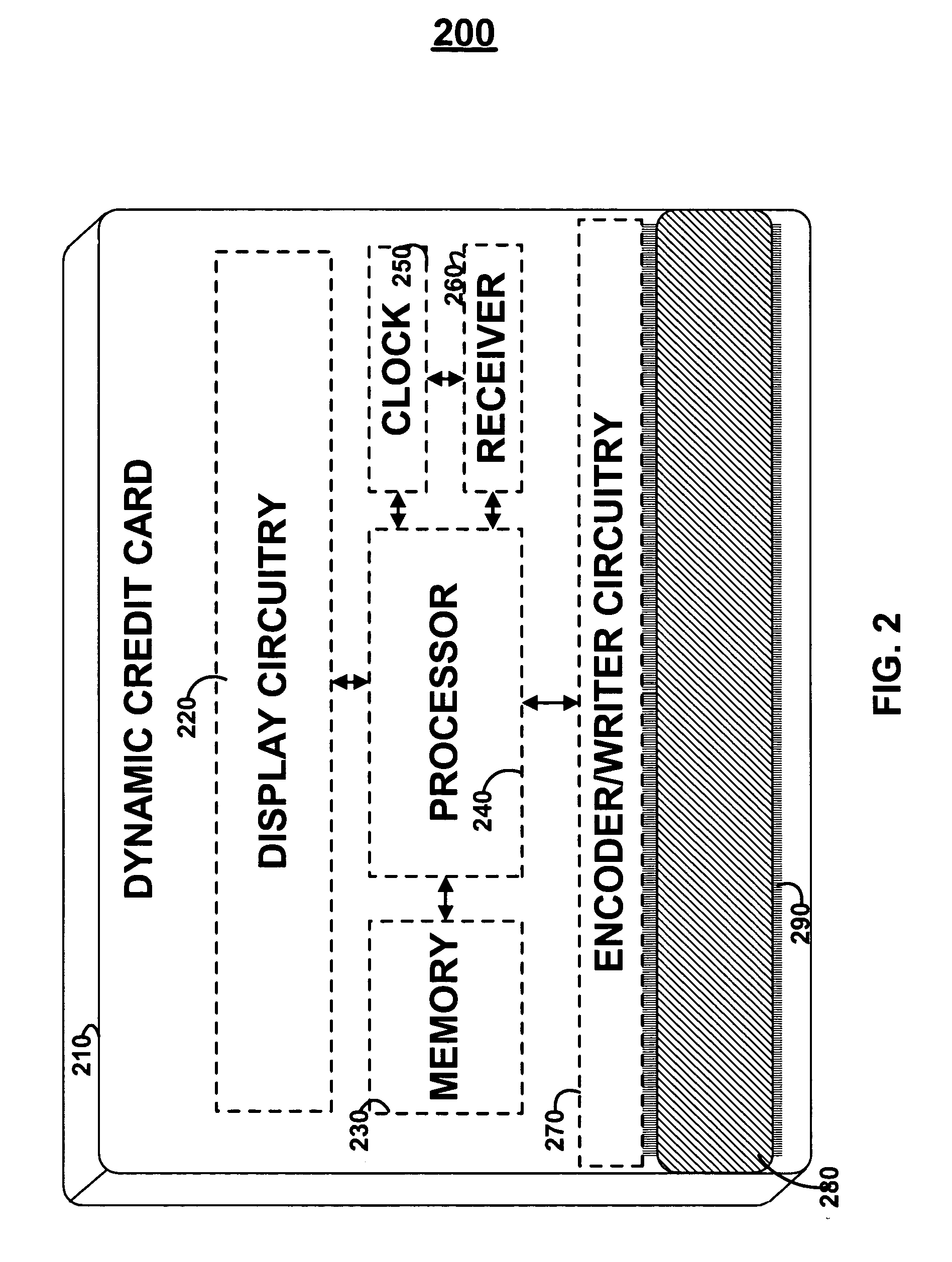
Patents
Literature
5551results about "Coded identity card or credit card actuation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
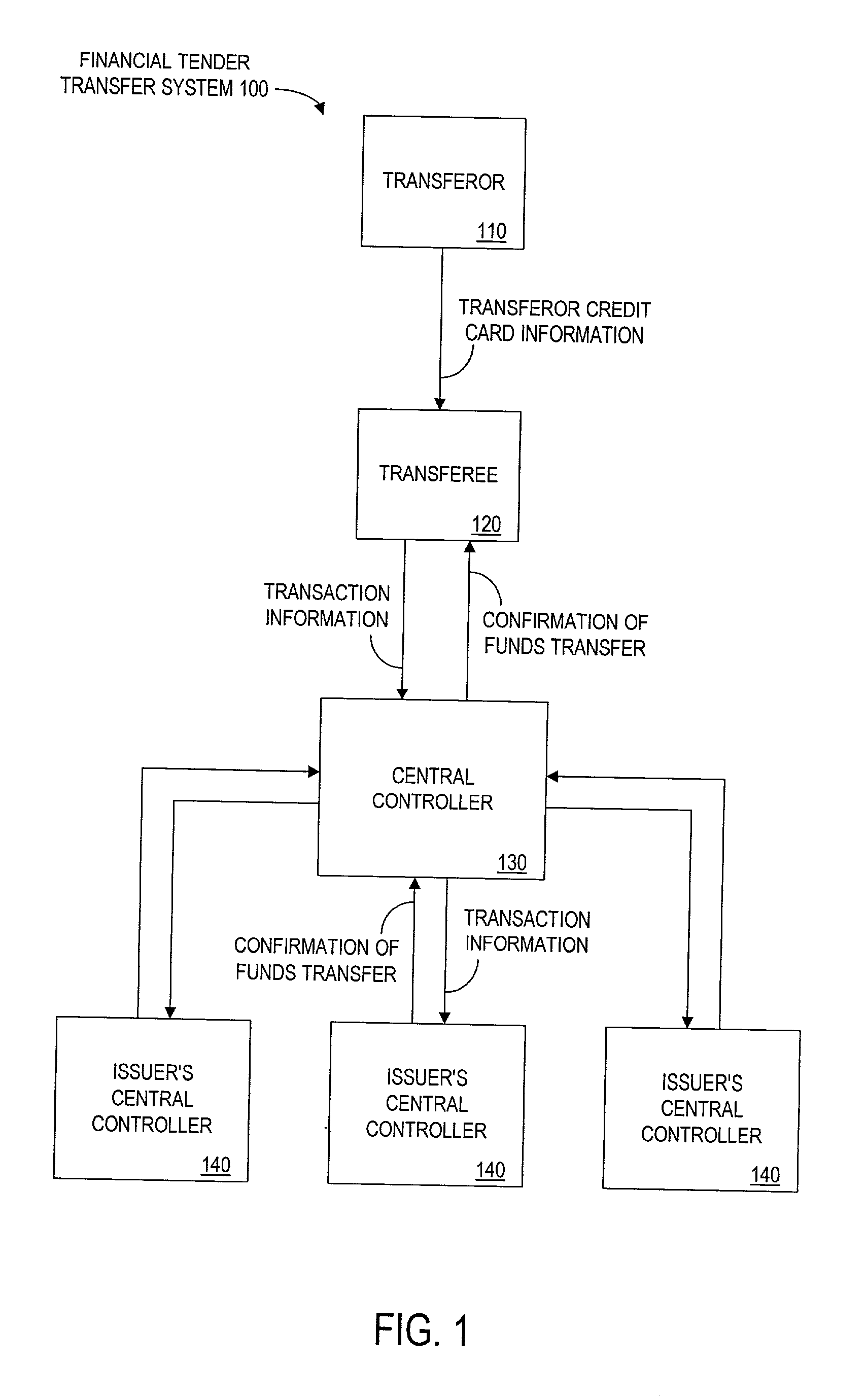
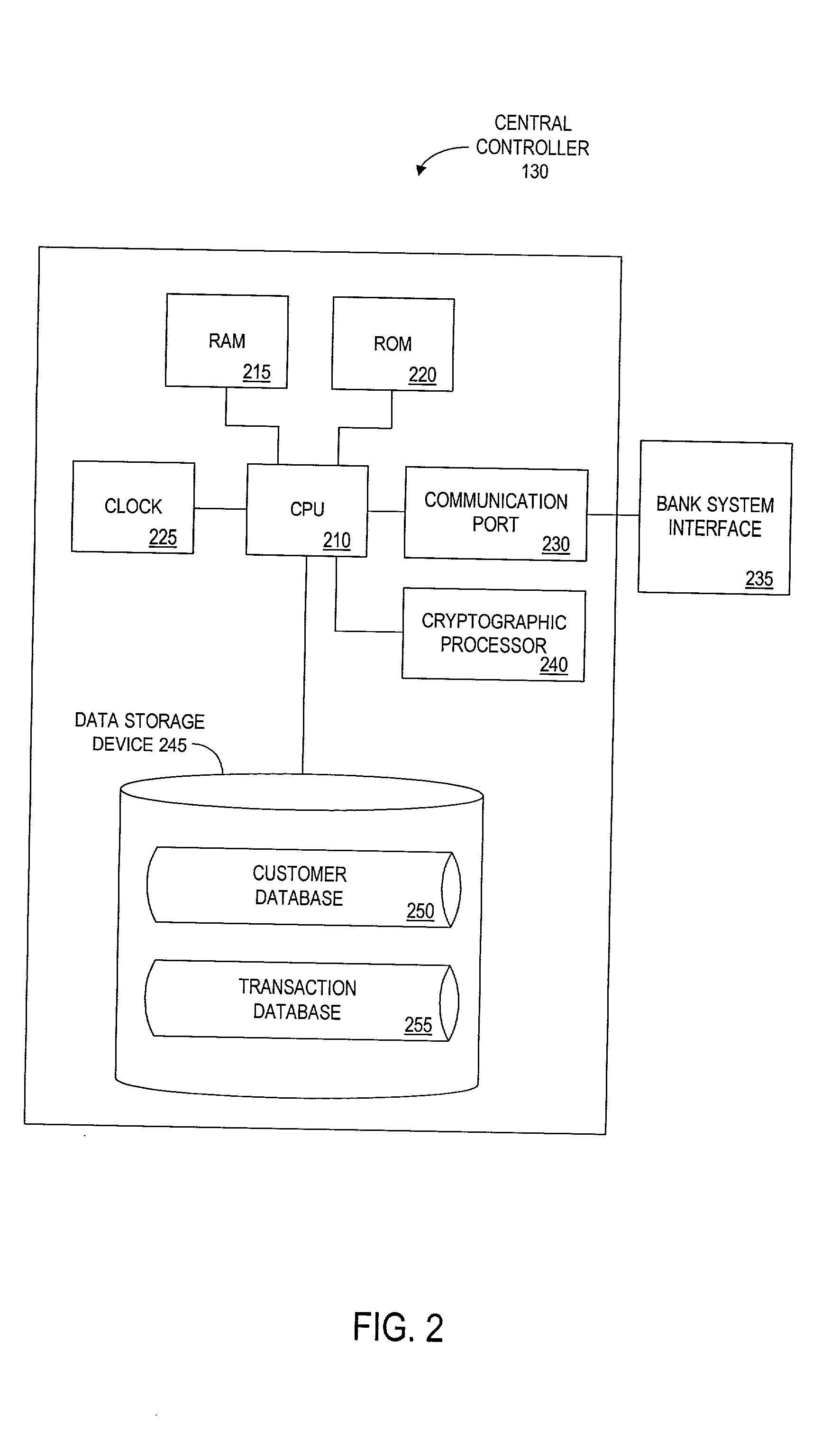
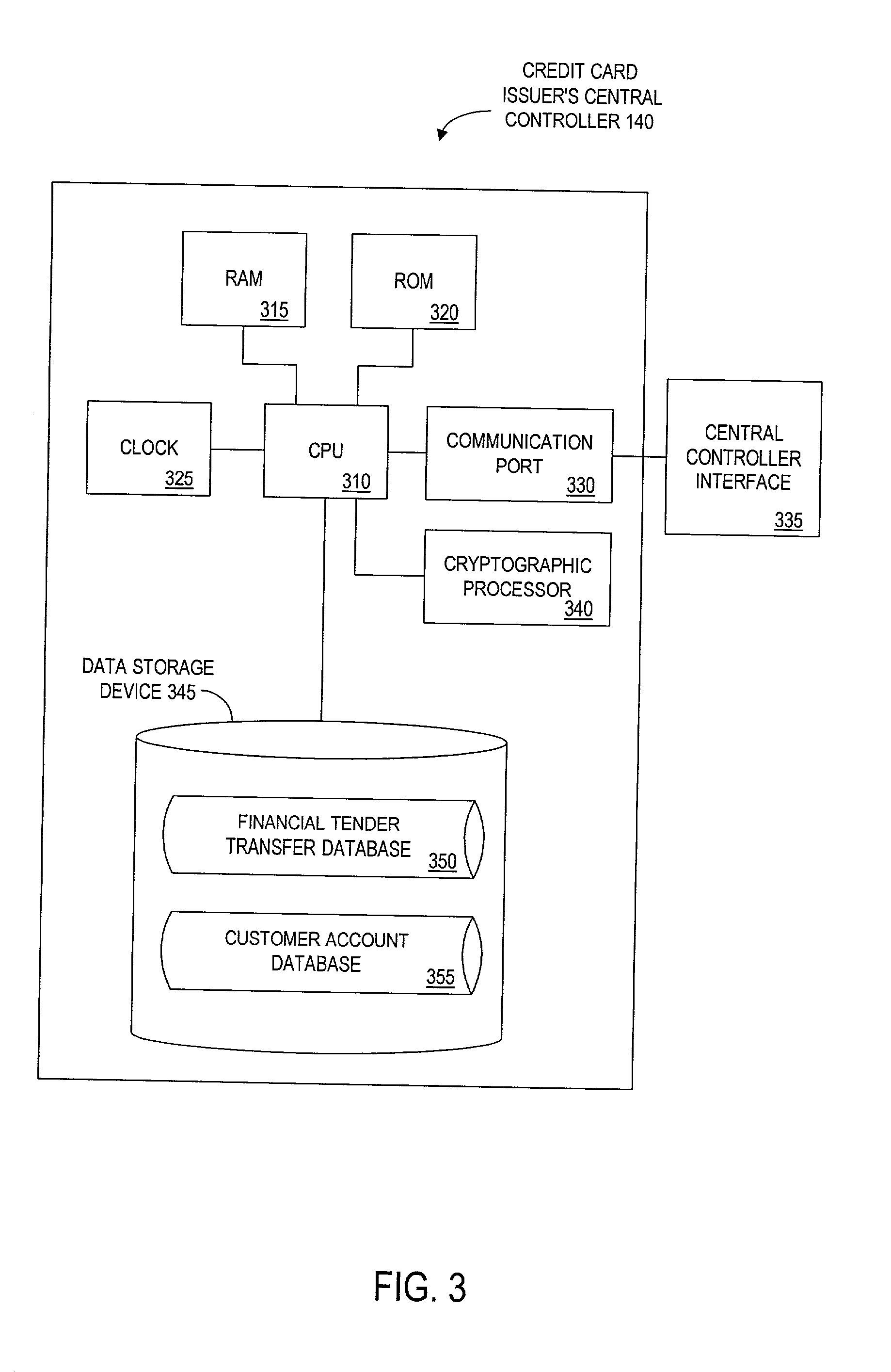
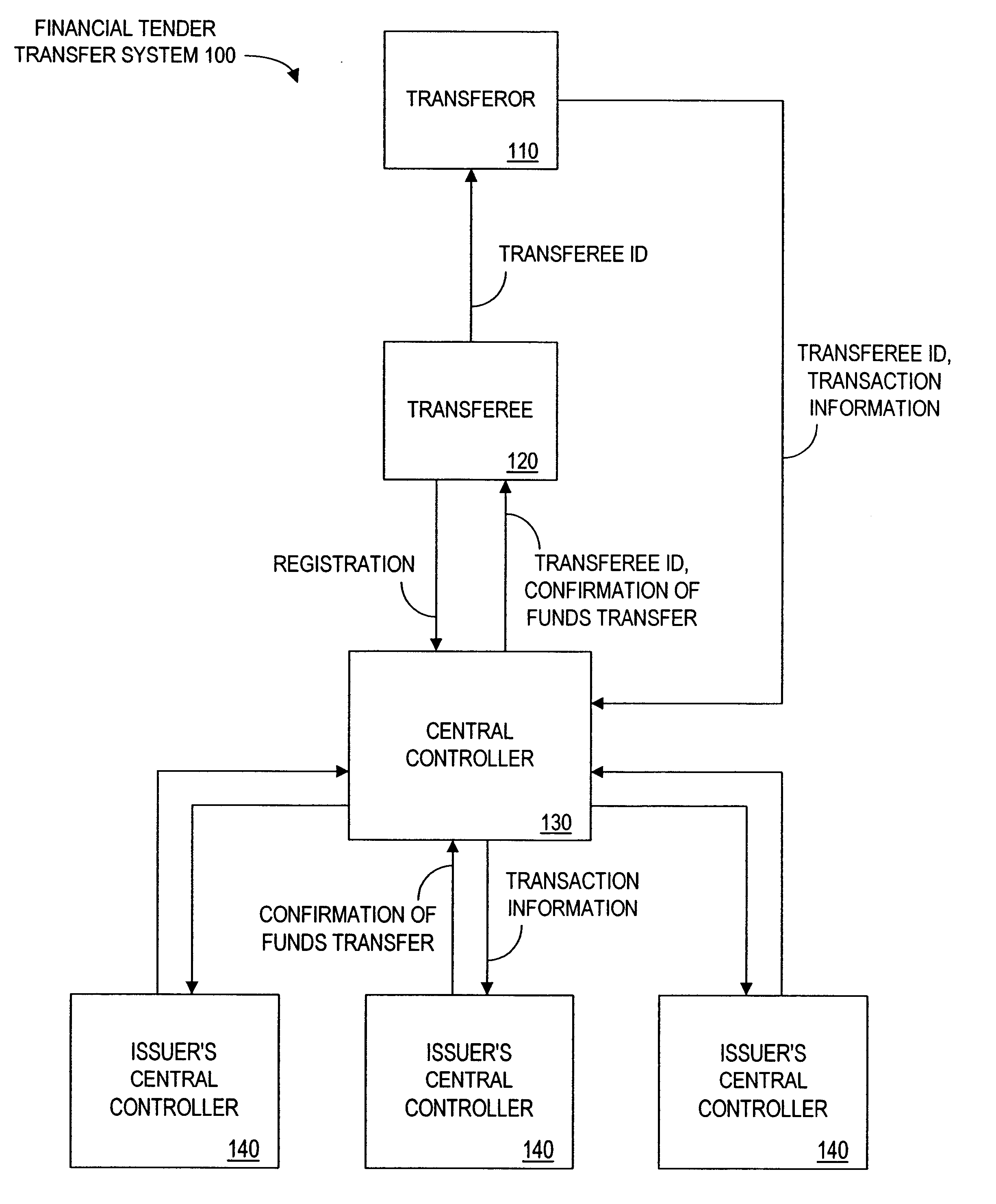
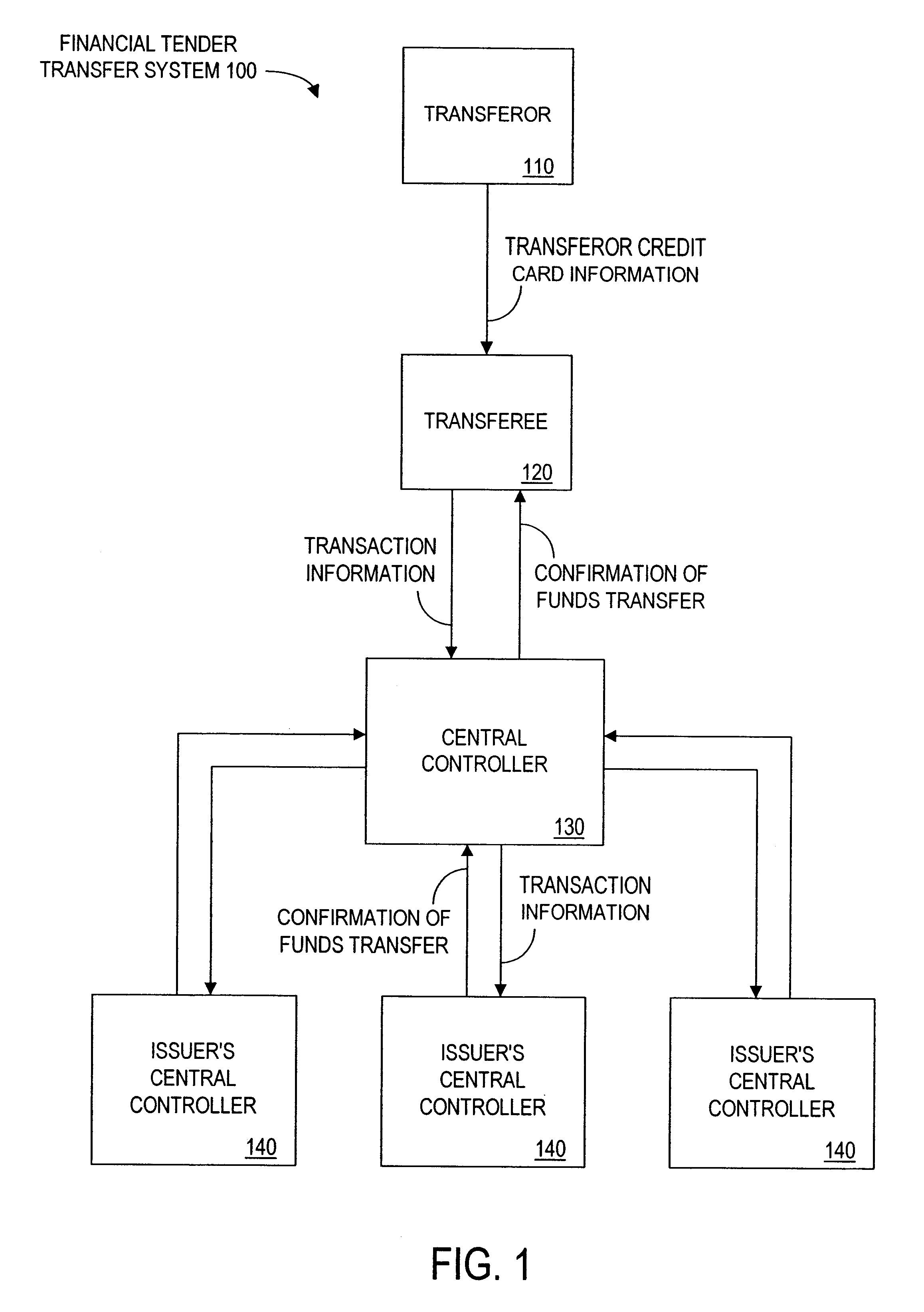
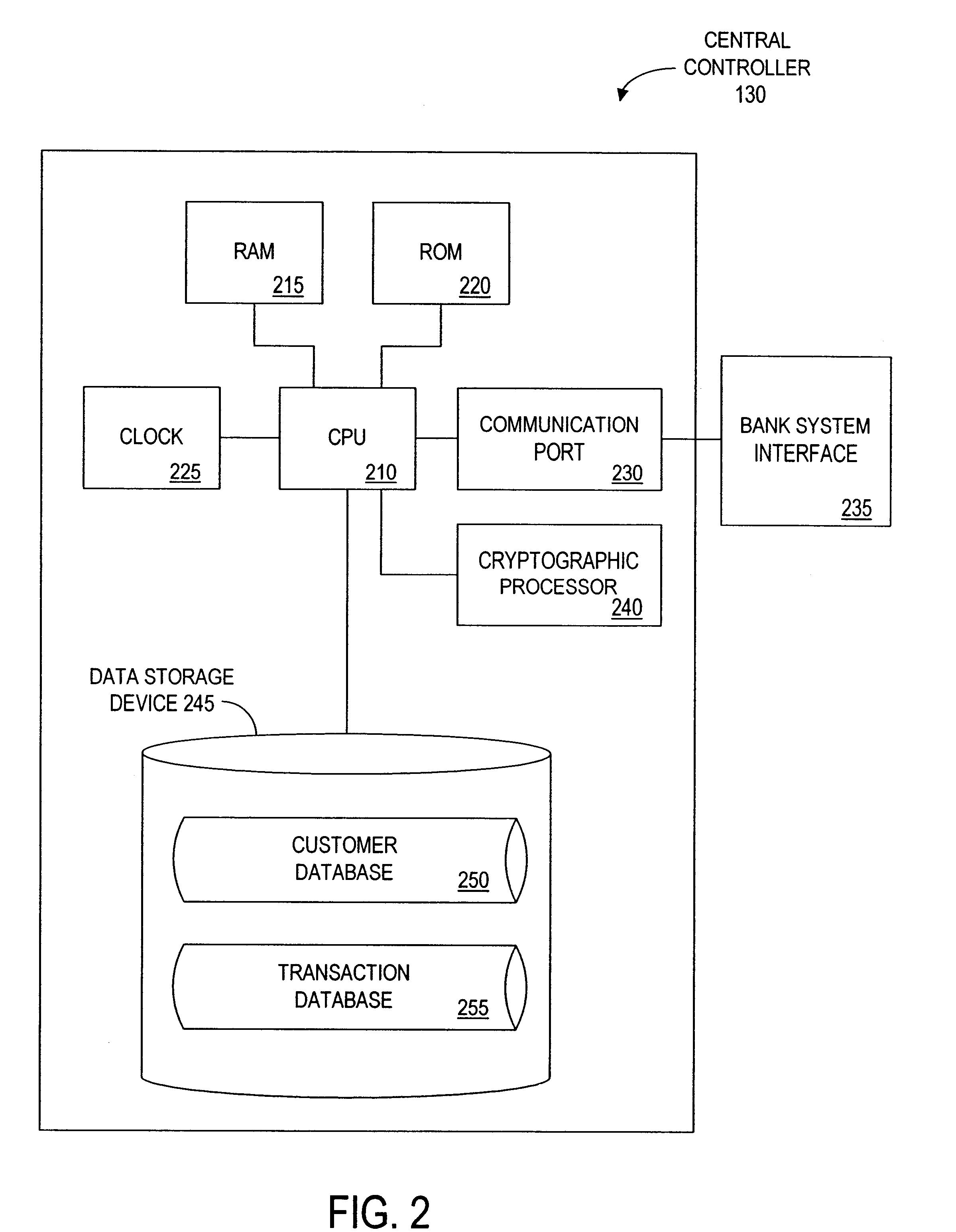
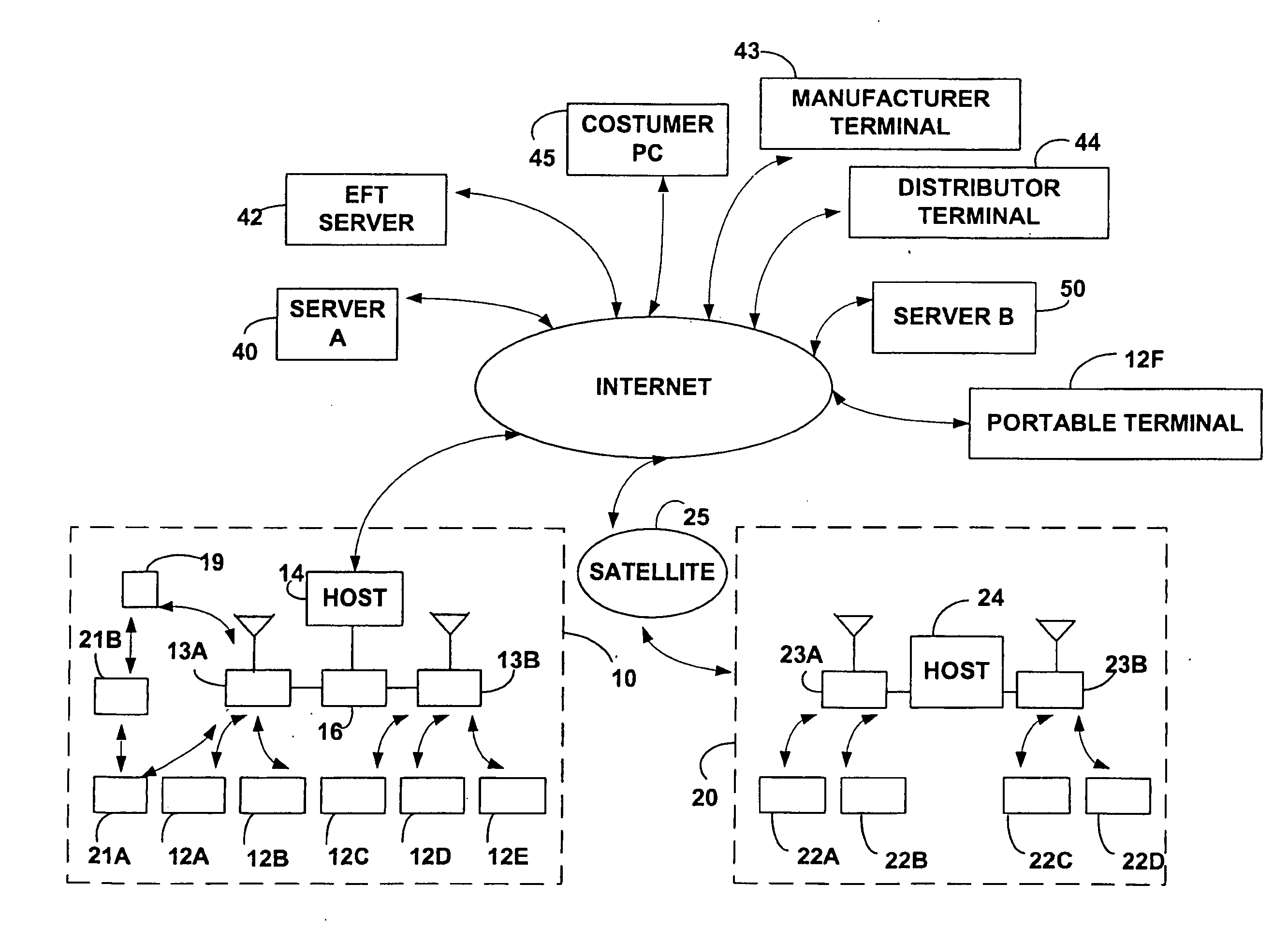
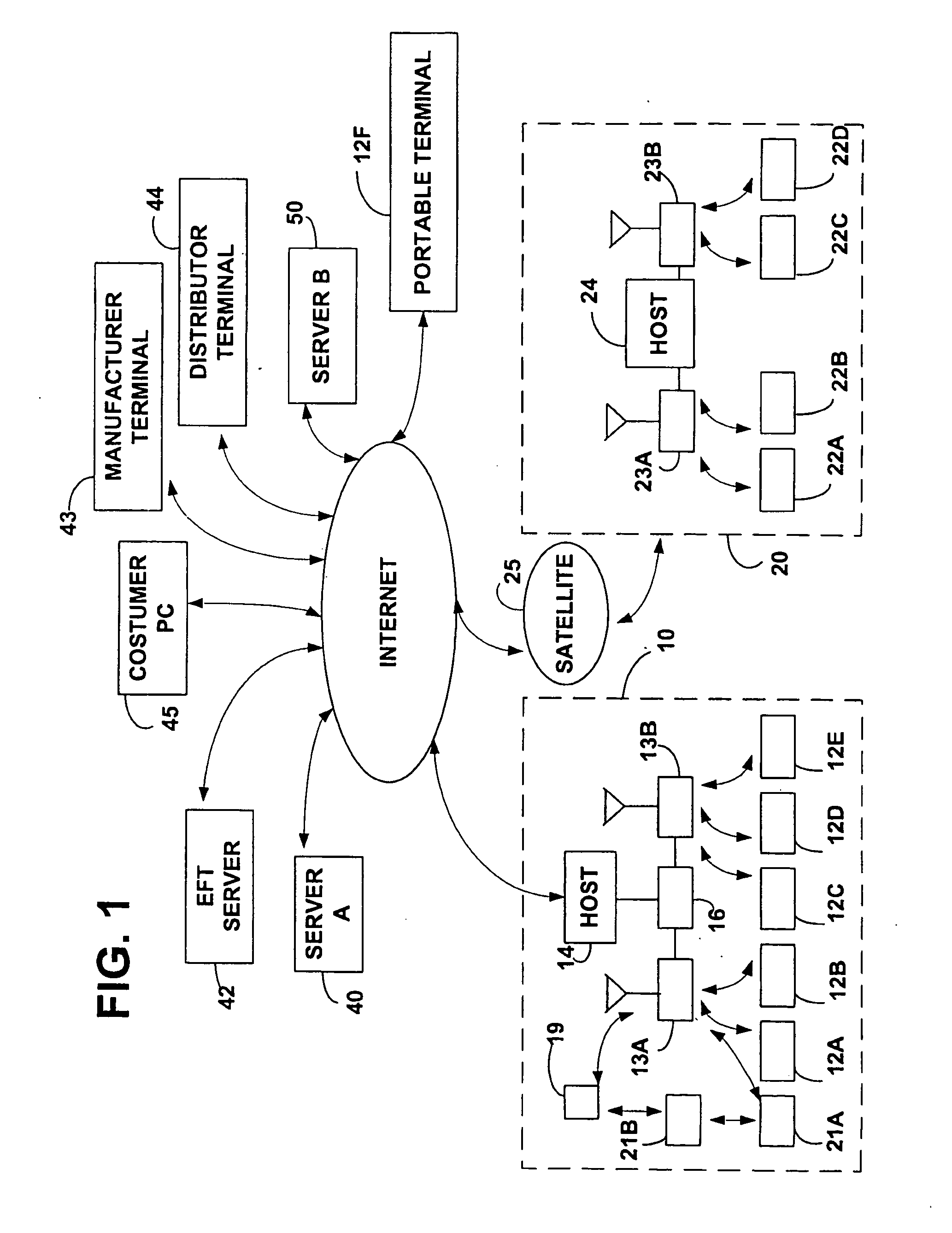
Method and apparatus for funds and credit line transfers
A financial tender transfer system allows a transferor to transfer credit or make payment to a transferee by debiting the credit card of the transferor and crediting the credit card of the transferee. The financial tender transfer system gives the transferee immediate access to the transferred money and ensures the transferor's credit card is valid. Neither party needs to give their credit card number to the other, so security is preserved. Any amount of value up to the full credit line of the transferor can be transferred to the transferee.
Owner:PAYPAL INC
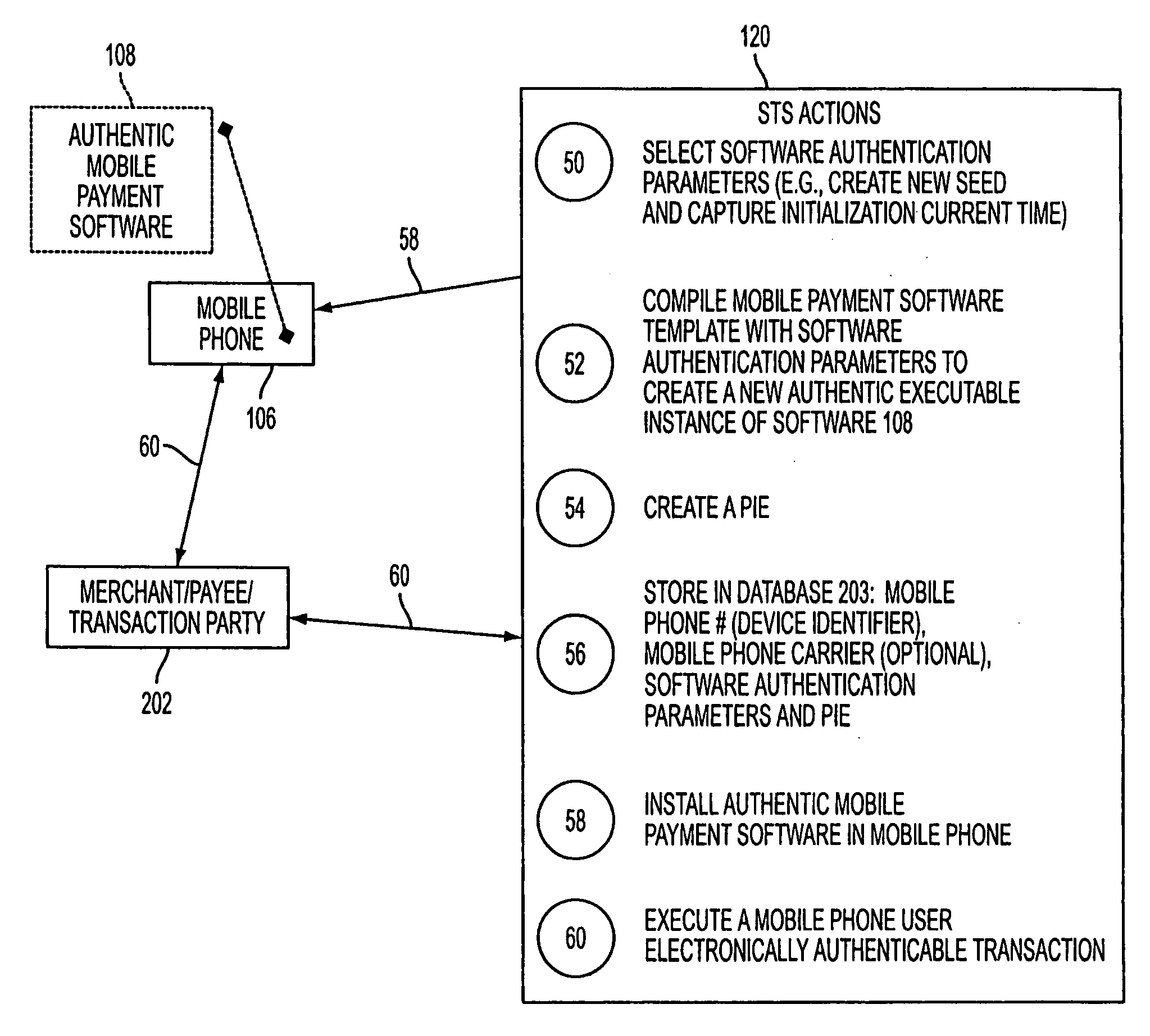
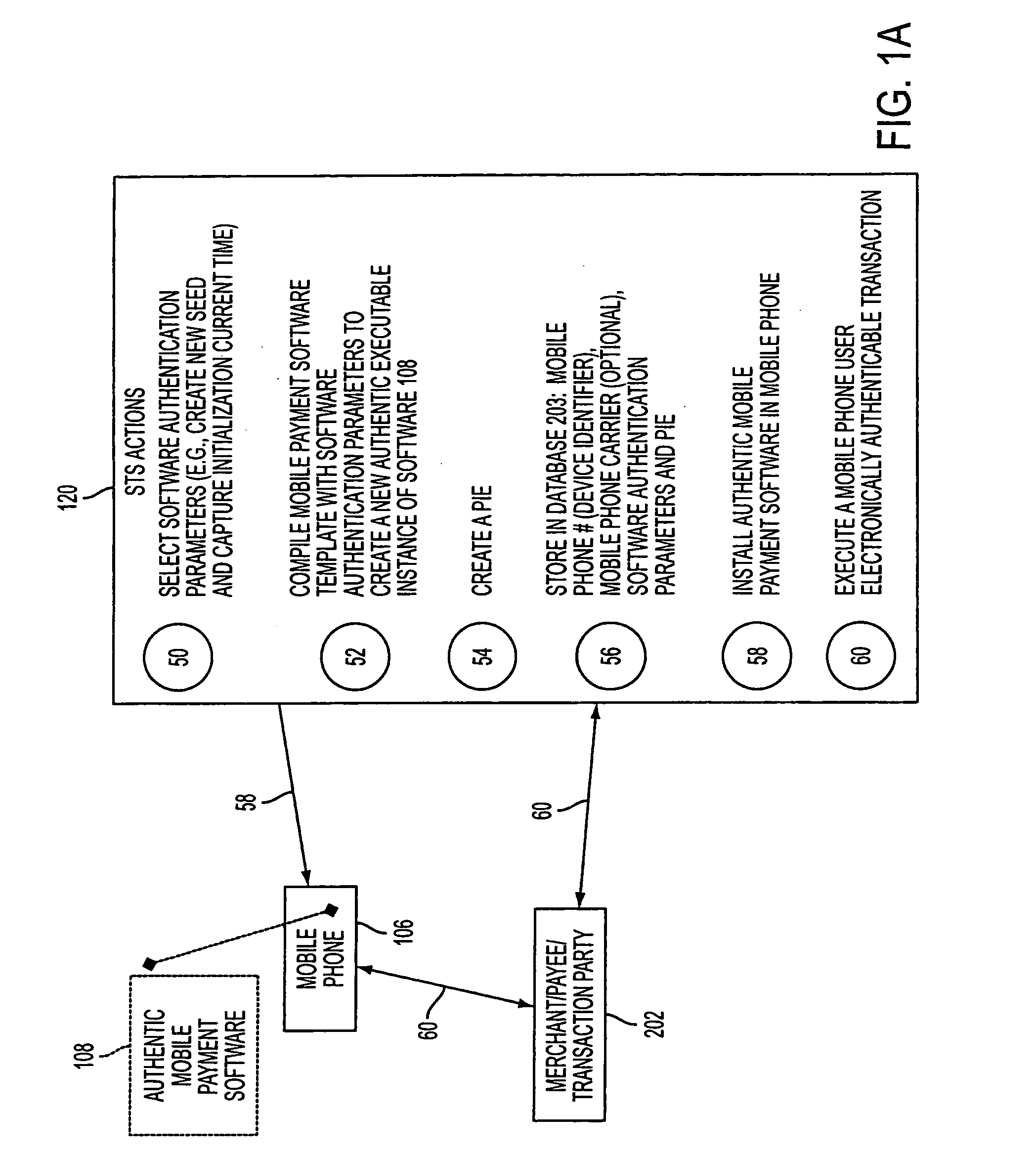
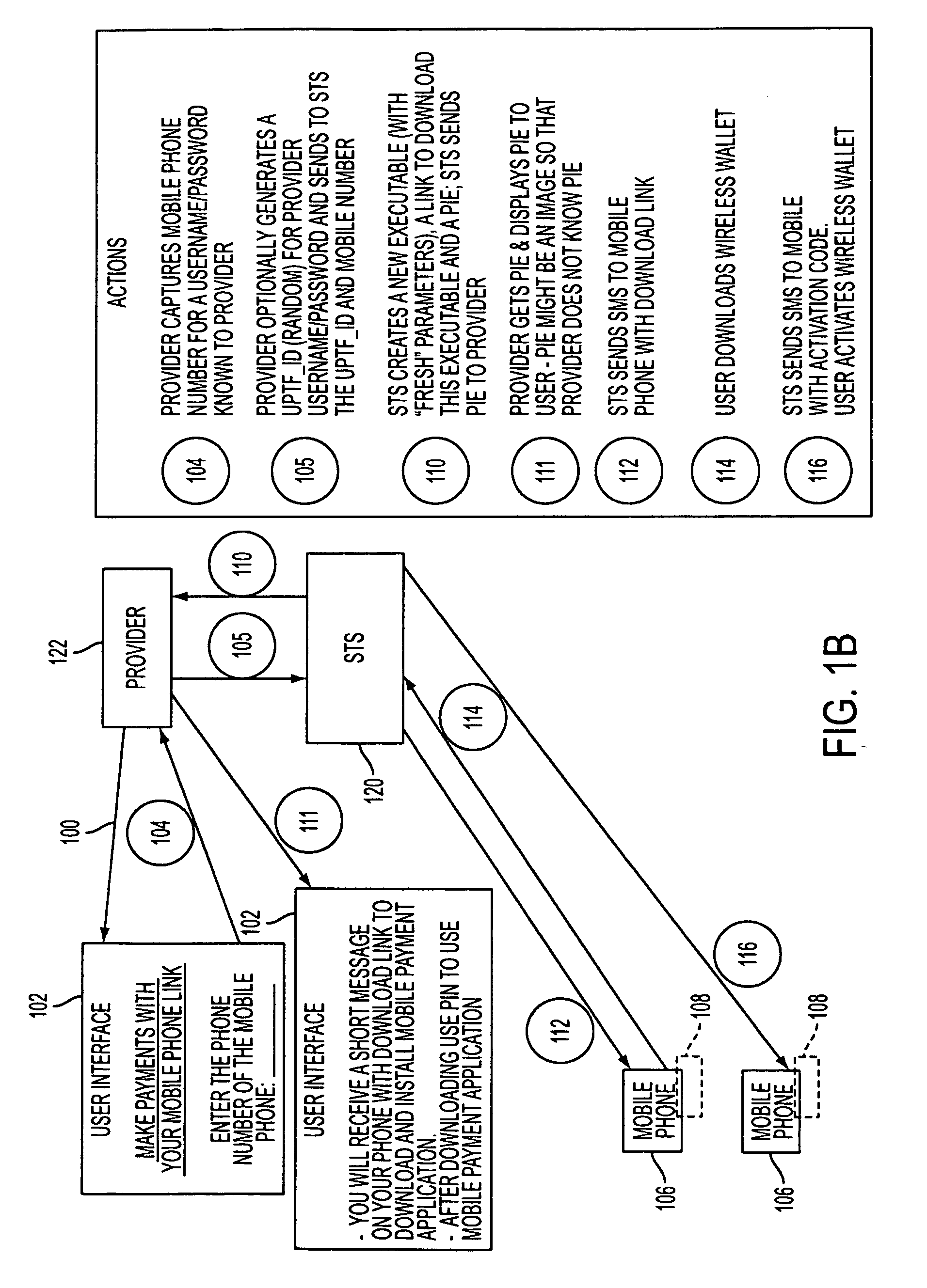
Wireless wallet
A mobile phone system and method of initializing, at a secure transaction server (STS), a mobile payment software with a software authentication parameter, as an authentic mobile payment software; providing an STS correlation between a personal identification entry (PIE) and the authentic mobile payment software; installing, in a mobile phone, the authentic mobile payment software; and inputting, by a user, the PIE to the installed authentic mobile payment software to generate according to the PIE and the software authentication parameter a transformed secure authenticable mobile phone cashless monetary transaction over the mobile phone network, as a mobile phone wireless wallet of the user of the mobile phone. The mobile phone authenticable cashless monetary transaction is performed according to an agreement view(s) protocol.
Owner:PCMS HOLDINGS INC
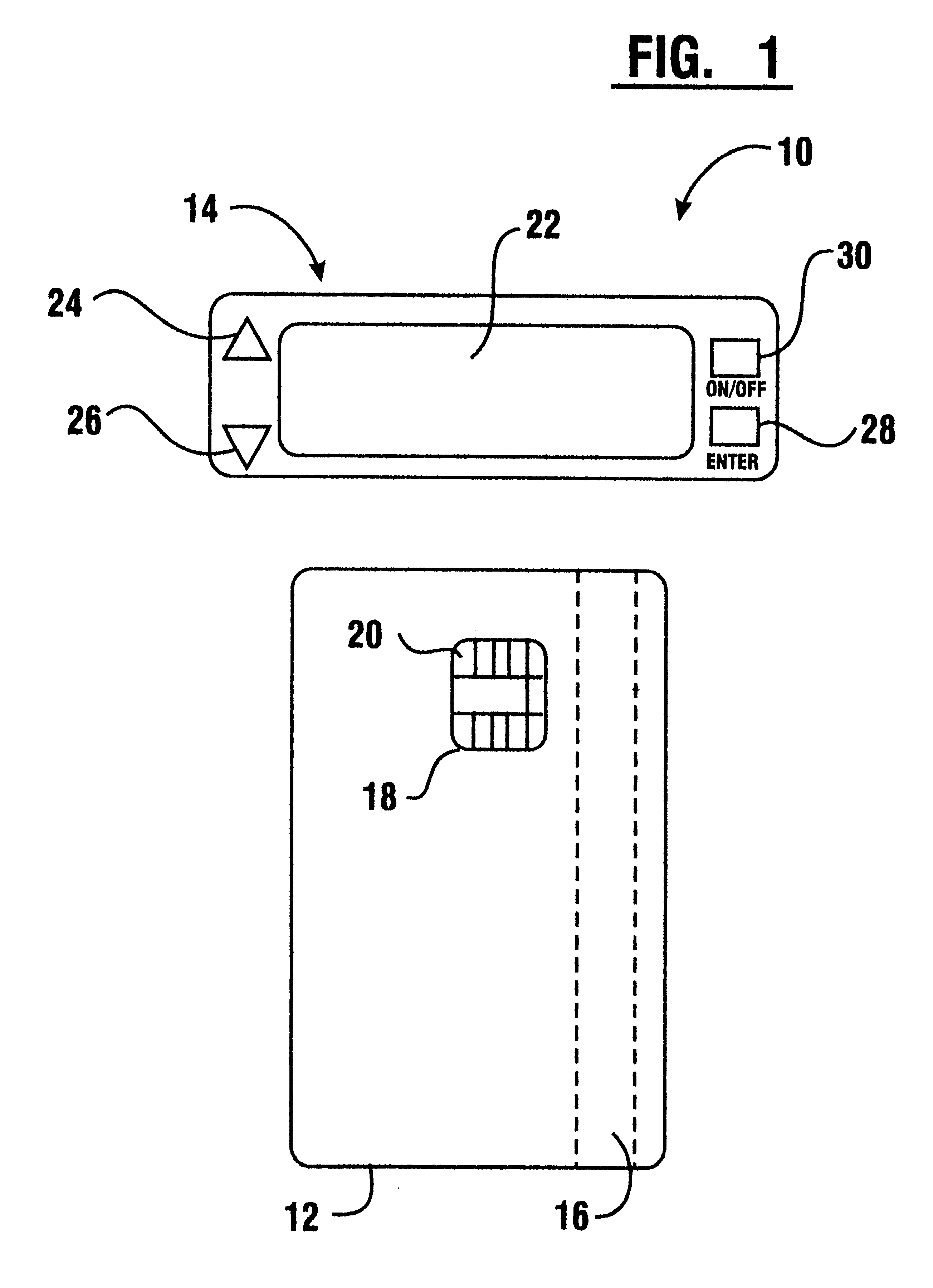
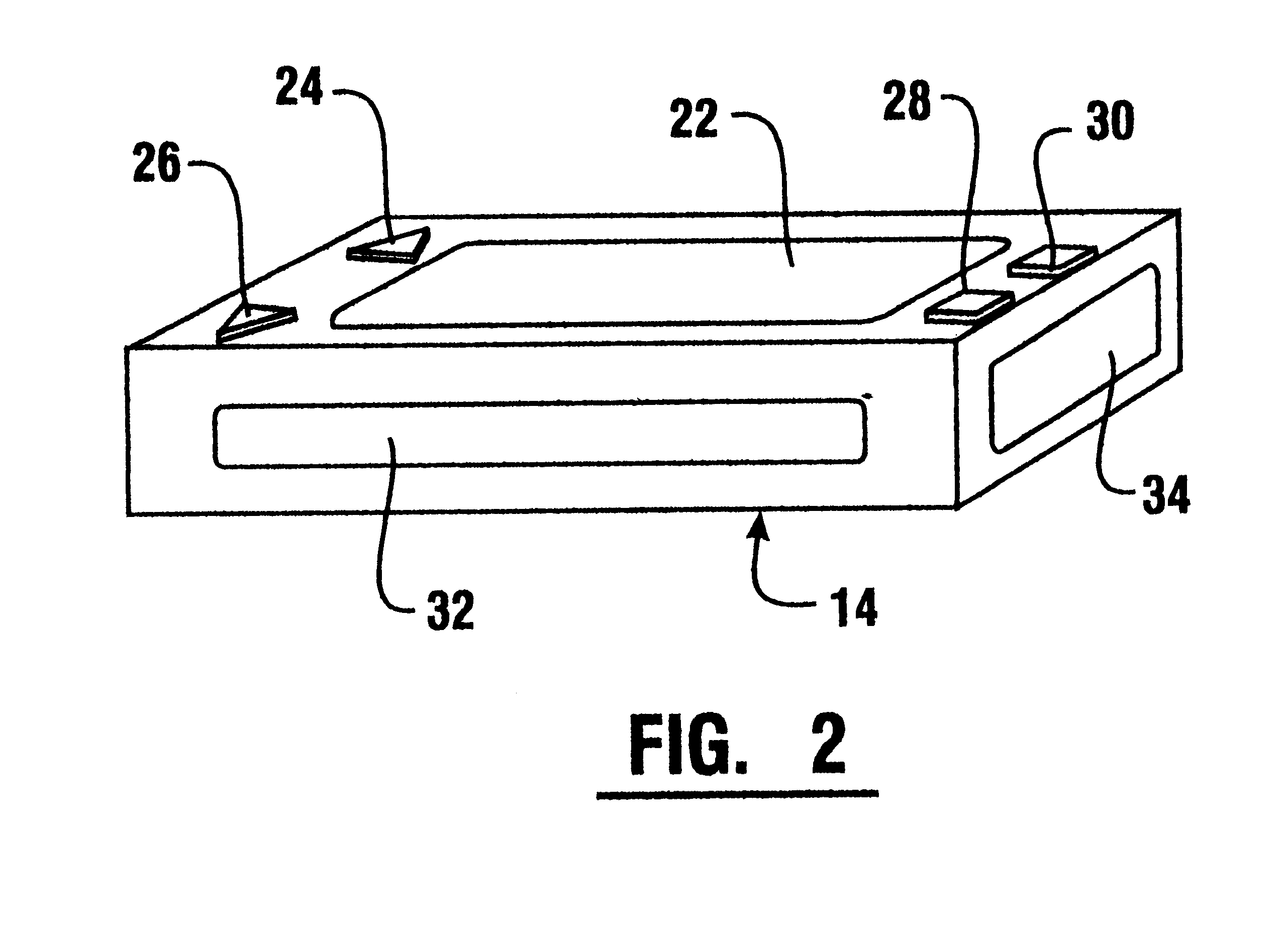
Tamper resistant pin entry apparatus
ActiveUS7238901B2Prevent leakagePrevent penetrationComplete banking machinesEmergency casingsPasswordElectric power system
Disclosed is a tamper resistant PIN entry apparatus for input of a key and for encryption of a password in a cash transaction machine. The PIN entry apparatus supplies the electric power to a memory of an electric circuit section, in such a manner that a first rod and a second rod of a rear case connect contacts of a key scan board, wherein the first rod is protruded on the rear of a key module including a button provided substantially on the front of the key module and the second rod of the rear case is coupled with the rear of the key module. At this time, in case that the rear case is removed from the key module or damaged, thereby changing the location of any one of the first and the second rods at the contact, the electric circuit section detects the event and destroys the memory itself physically. Otherwise, the electric circuit section makes information stored in the memory physically or softwarely unreadable, thereby preventing the leakage of the information.
Owner:NAUTILUS HYOSUNG
Method and apparatus for funds and credit line transfers
A financial tender transfer system allows a transferor to transfer credit or make payment to a transferee by debiting the credit card of the transferor and crediting the credit card of the transferee. The financial tender transfer system gives the transferee immediate access to the transferred money and ensures the transferor's credit card is valid. Neither party needs to give their credit card number to the other, so security is preserved. Any amount of value up to the full credit line of the transferor can be transferred to the transferee.
Owner:PAYPAL INC
Physical presence digital authentication system
InactiveUS6607136B1Enhanced interactionMass scalableCredit registering devices actuationDiscounts/incentivesCrowdsAcoustic wave
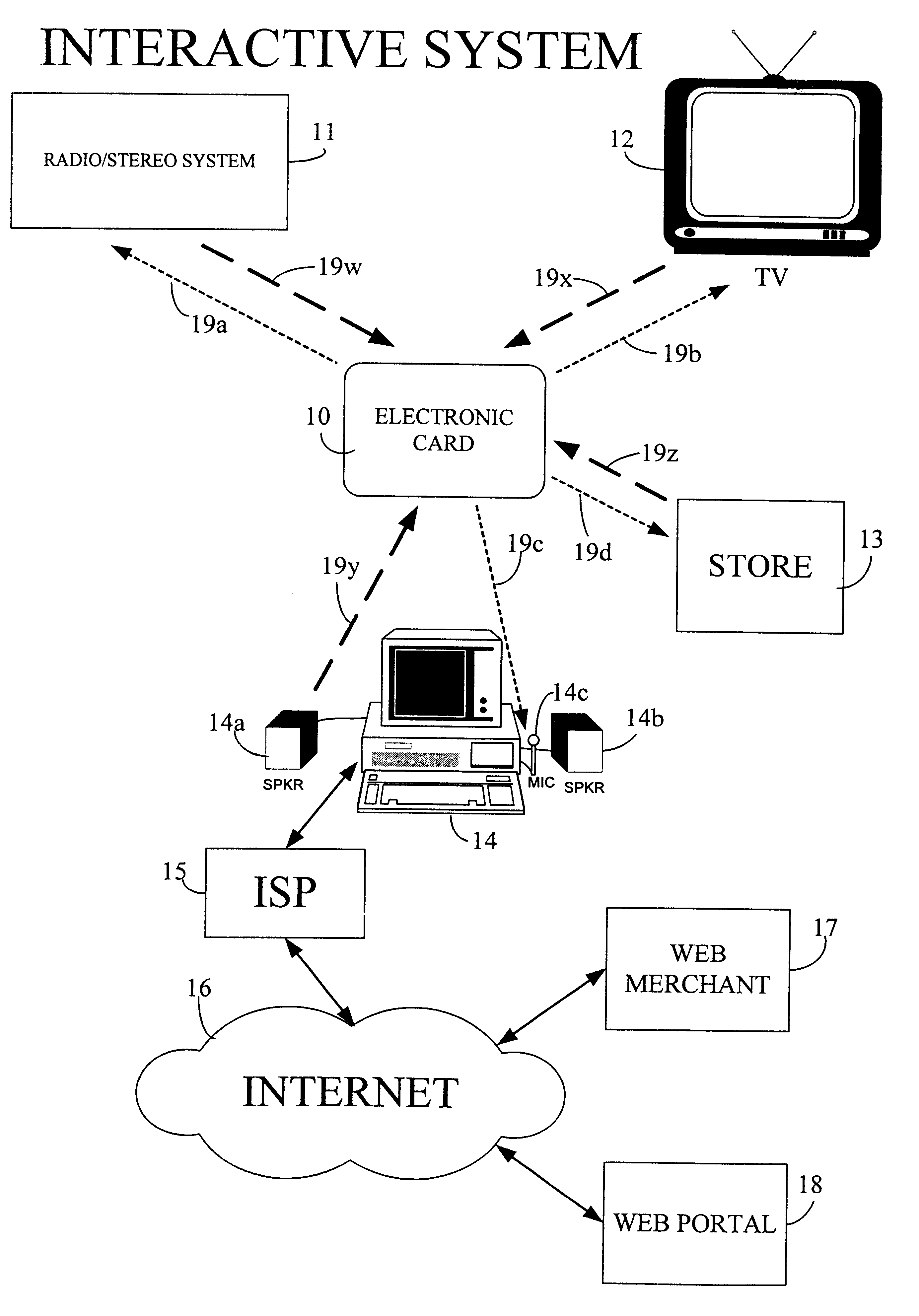
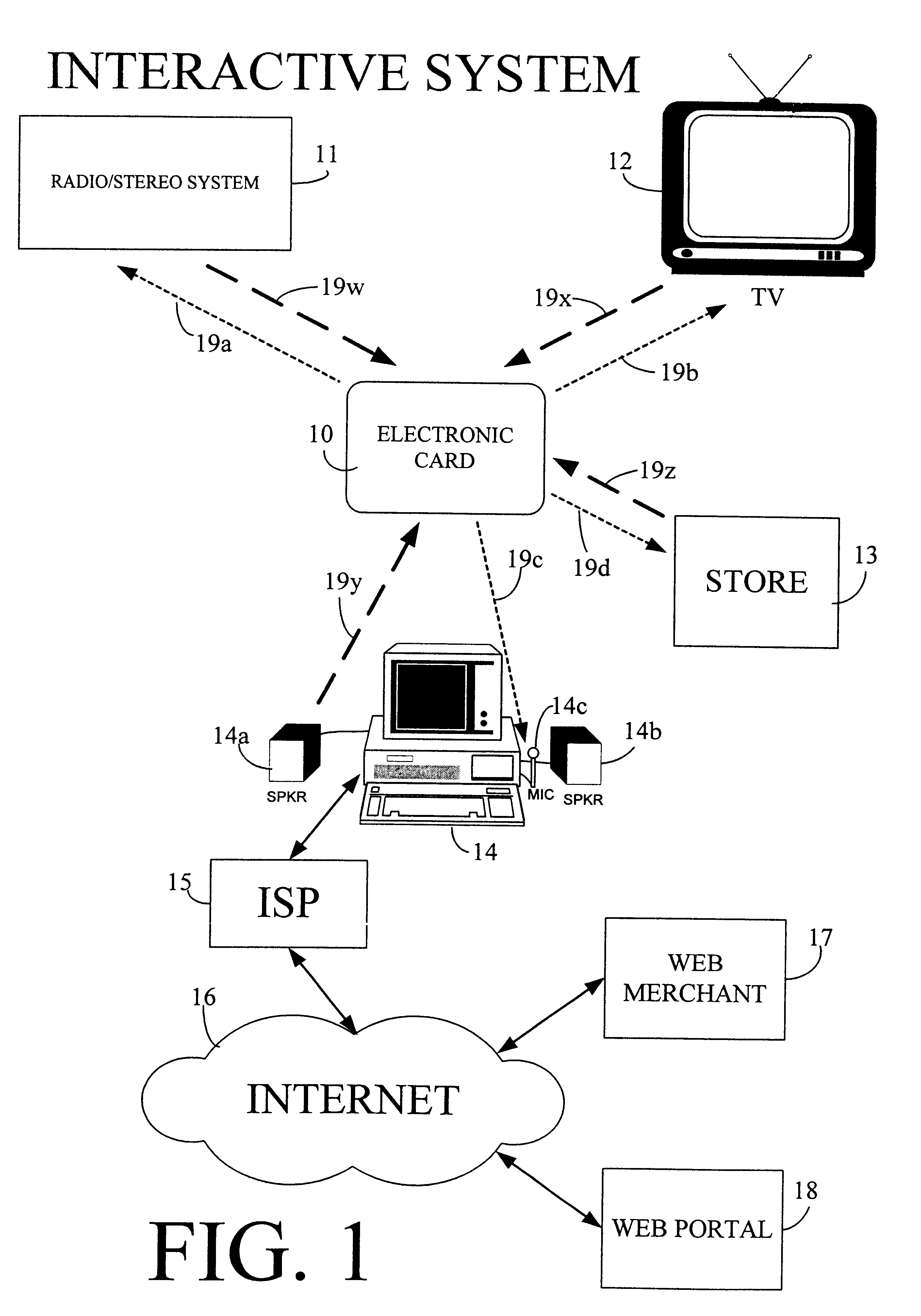
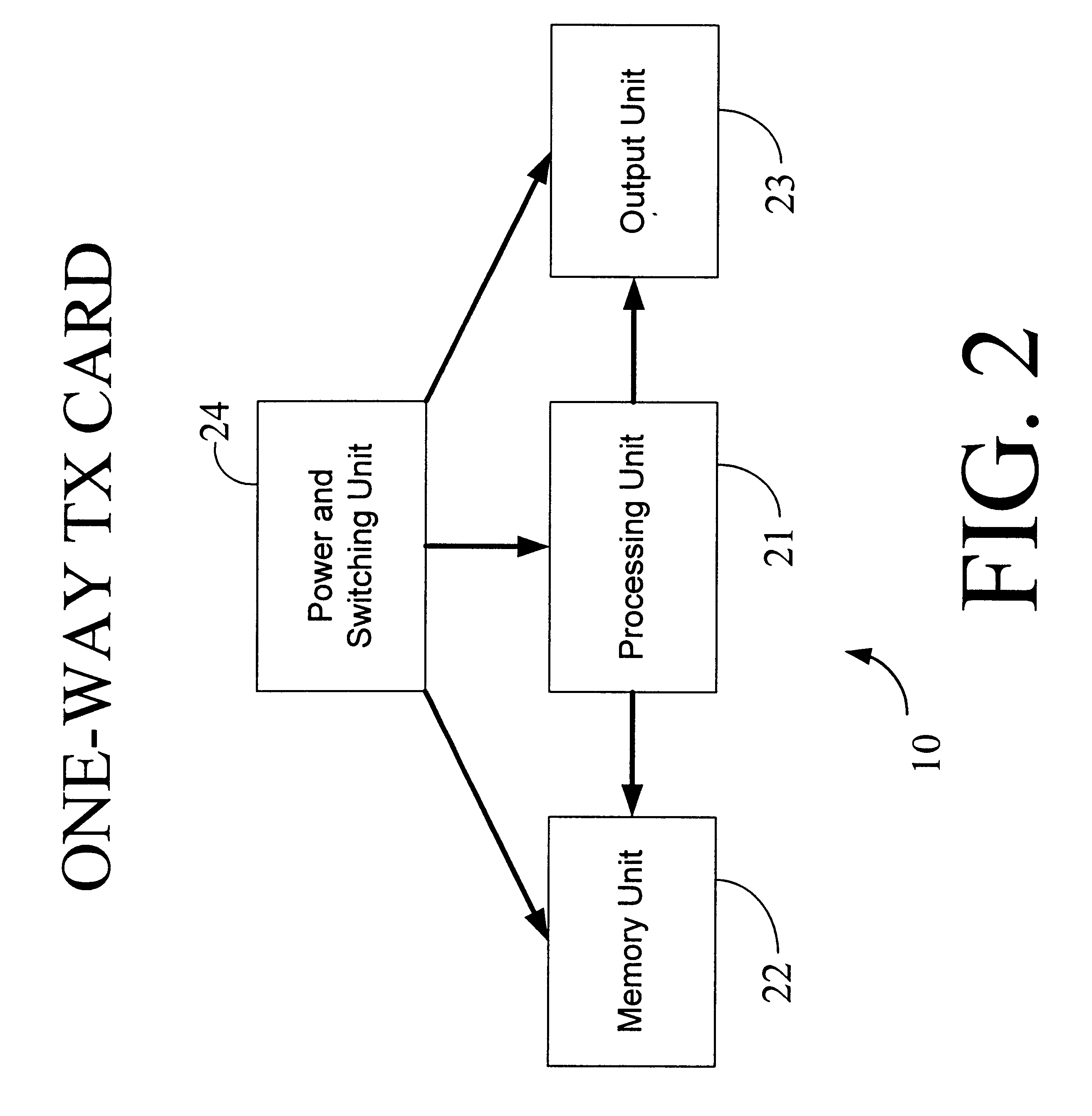
The interactive authentication system allows a consumer to interact with a base station, such as broadcast media (e.g., television and radio) or PC, to receive coupons, special sales offers, and other information with an electronic card. The electronic card can also be used to transmit a signal that can be received by the base station to perform a wide variety of tasks. These tasks can include launching an application, authenticating a user at a website, and completing a sales transaction at a website (e.g., by filling out a form automatically). The interaction between the base station and the electronic card is accomplished by using the conventional sound system in the base station so that a special reader hardware need not be installed to interact with the electronic card. The user is equipped with an electronic card that can receive and transmit data via sound waves. In the various embodiments, the sound waves can be audible or ultrasonic (which can be slightly audible to some groups of people).
Owner:SONIXIO INC
Consumer interactive shopping system
InactiveUS6837436B2Expand accessFunction increaseGuide needlesCredit registering devices actuationComputer terminalPortable data terminal
The present invention relates generally to a consumer interactive shopping and marketing system. The system includes a portable data terminal for communicating information over a communication network. The present system has aspects that may be used within a shopping establishment or at a user's home.
Owner:SYMBOL TECH LLC
Financial transactions with dynamic card verification values
ActiveUS7584153B2Sufficient dataComputer security arrangementsPayment architectureUser needsDisplay device
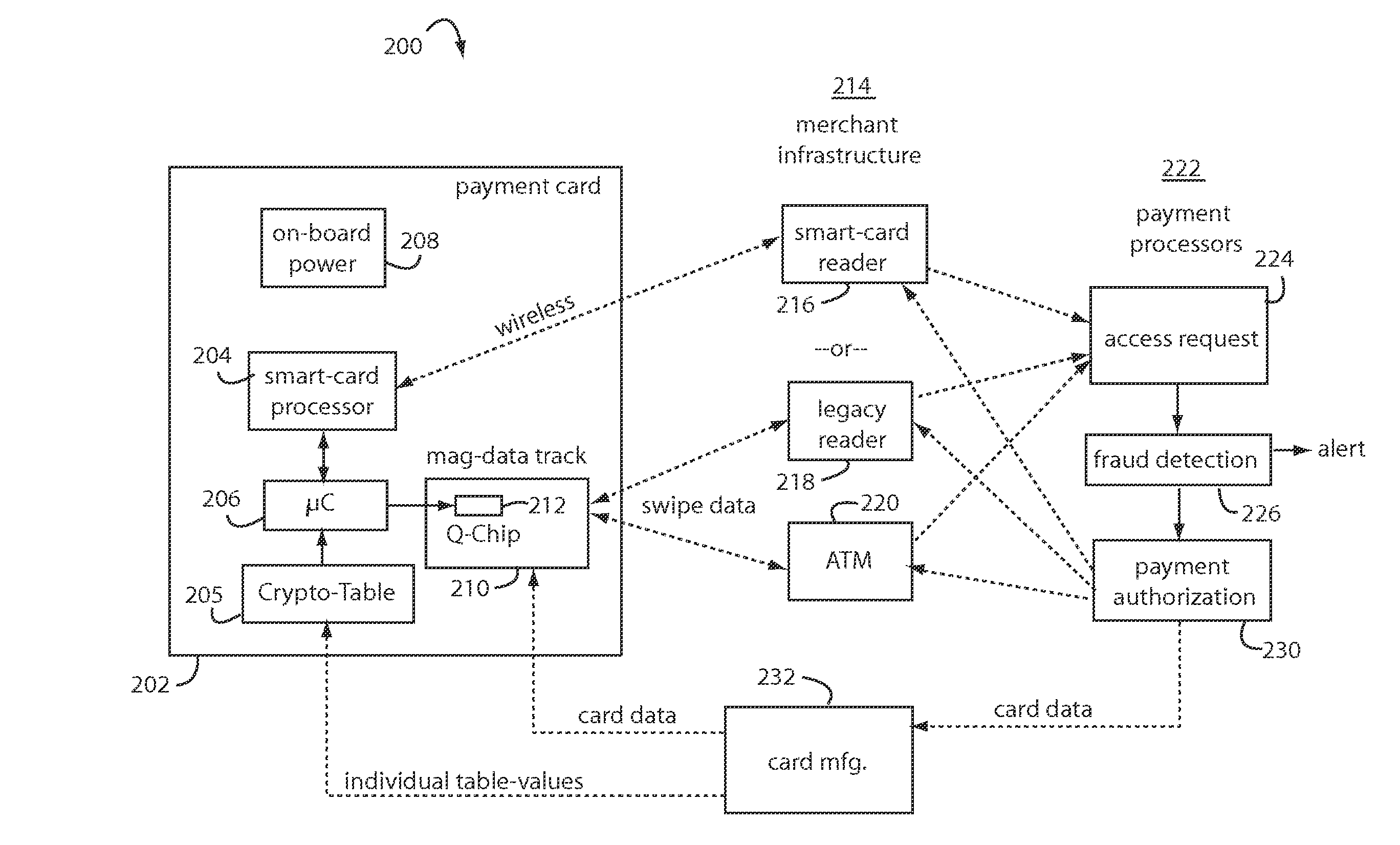
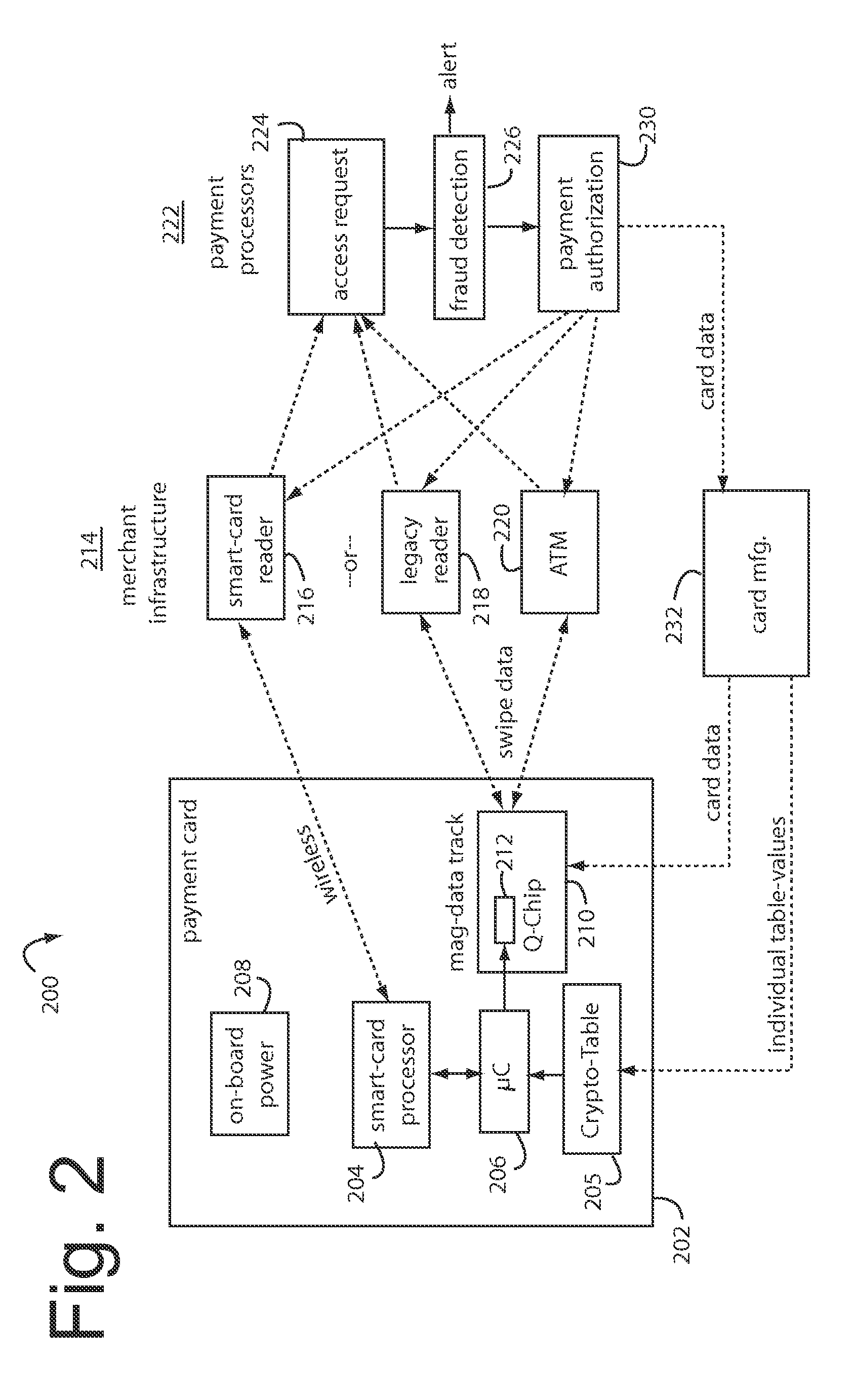
A payment card comprises an internal dynamic card verification value (CVV) generator and a user display for card-not-present transactions. Card-present transactions with merchant card readers are enabled by a dynamic magnetic array internally associated with the card's magnetic stripe. The user display and a timer are triggered by the user when the user needs to see the card verification value and / or begin a new transaction. A new card verification value is provided for each new transaction according to a cryptographic process, but the timer limits how soon a next new card verification value can be generated.
Owner:FITBIT INC
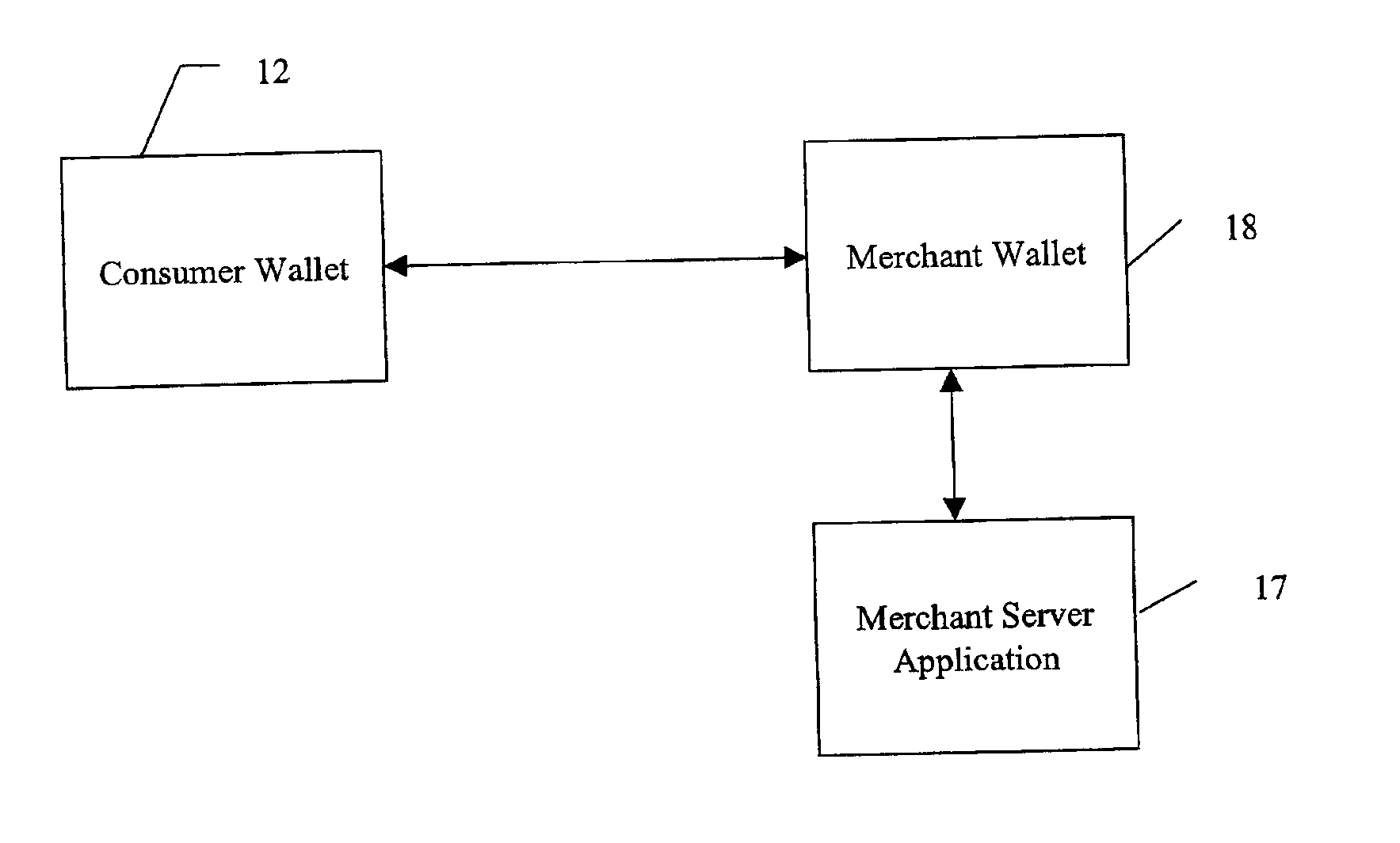
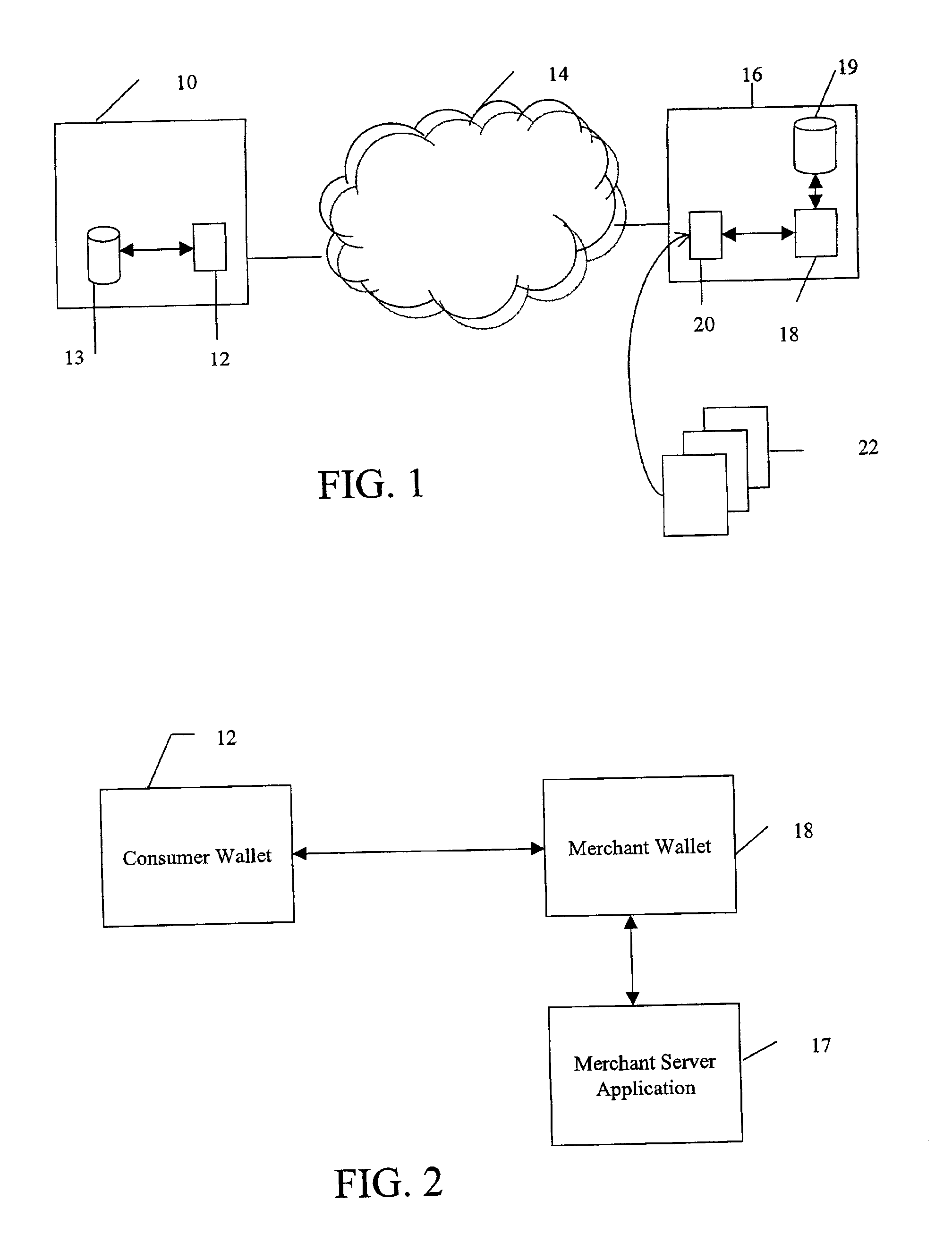
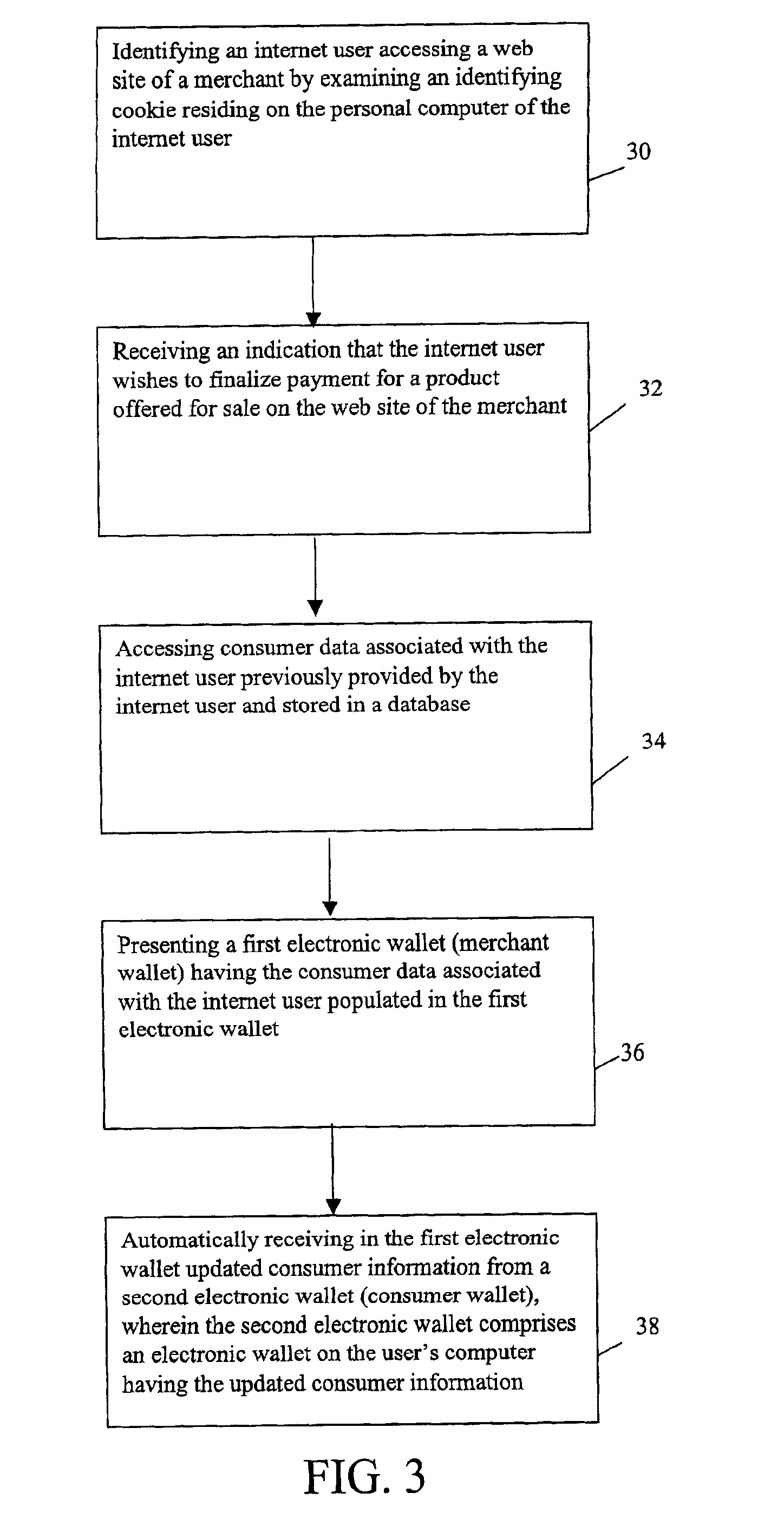
System and method for use of distributed electronic wallets
InactiveUS6873974B1Avoid burdenImprove efficiencyComplete banking machinesFinanceMerchant servicesCredit card
Methods and systems whereby two electronic wallets communicate and exchange information. In one such system, a consumer's personal electronic wallet communicates with the exclusive or preferred wallet of a web merchant. In one such system, an internet consumer registers with a web merchant's exclusive or preferred electronic wallet (“merchant wallet”) and provides consumer information (e.g., credit card number, mailing address, and other information) to the merchant wallet, which is stored by the merchant wallet in a database on the merchant server. Such information may be automatically populated by the consumer's personal electronic wallet. The consumer maintains current consumer information in a consumer electronic wallet on the consumer's personal computer. When the consumer visits the merchant site again, and orders goods or services, the merchant's preferred wallet can be automatically updated by the consumer's electronic wallet if any of the data in the merchant's wallet has changed. For example, the consumer wallet examines the information in the merchant wallet to determine if the information in the merchant wallet conforms to the current information in the consumer wallet. If the information does not conform, the consumer wallet communicates the current consumer information to the merchant wallet.
Owner:CITIBANK
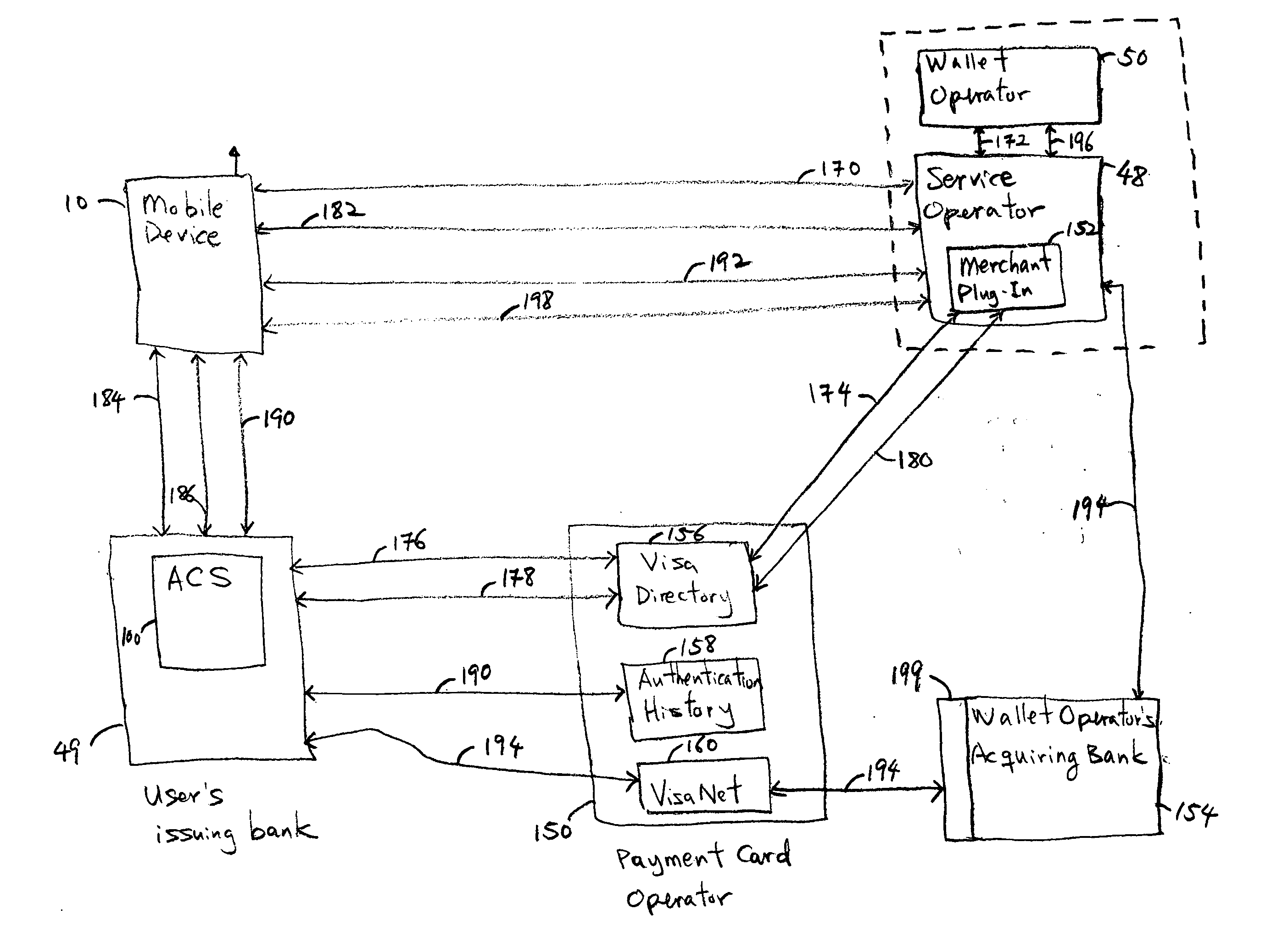
System and method of facilitating contactless payment transactions across different payment systems using a common mobile device acting as a stored value device
InactiveUS20050222961A1Convenient transactionSubstation equipmentCurrency conversionPayment transactionData exchange
A system for facilitating contactless payment transactions across different contactless payment systems using a common mobile device that acts as a stored value device is provided. A combination of a mobile application and a communication module allows the mobile device, which is associated with one payment system, to emulate various transmission standards and data exchange formats that are used in different payment systems in order to perform contactless payment transactions with merchants that are associated with different contactless payment systems. A service application running in a service operator computer communicates with the various contactless payment systems to facilitate the settlement of the amount owed to various payment systems by the one payment system associated with the mobile device.
Owner:PAYZY CORP
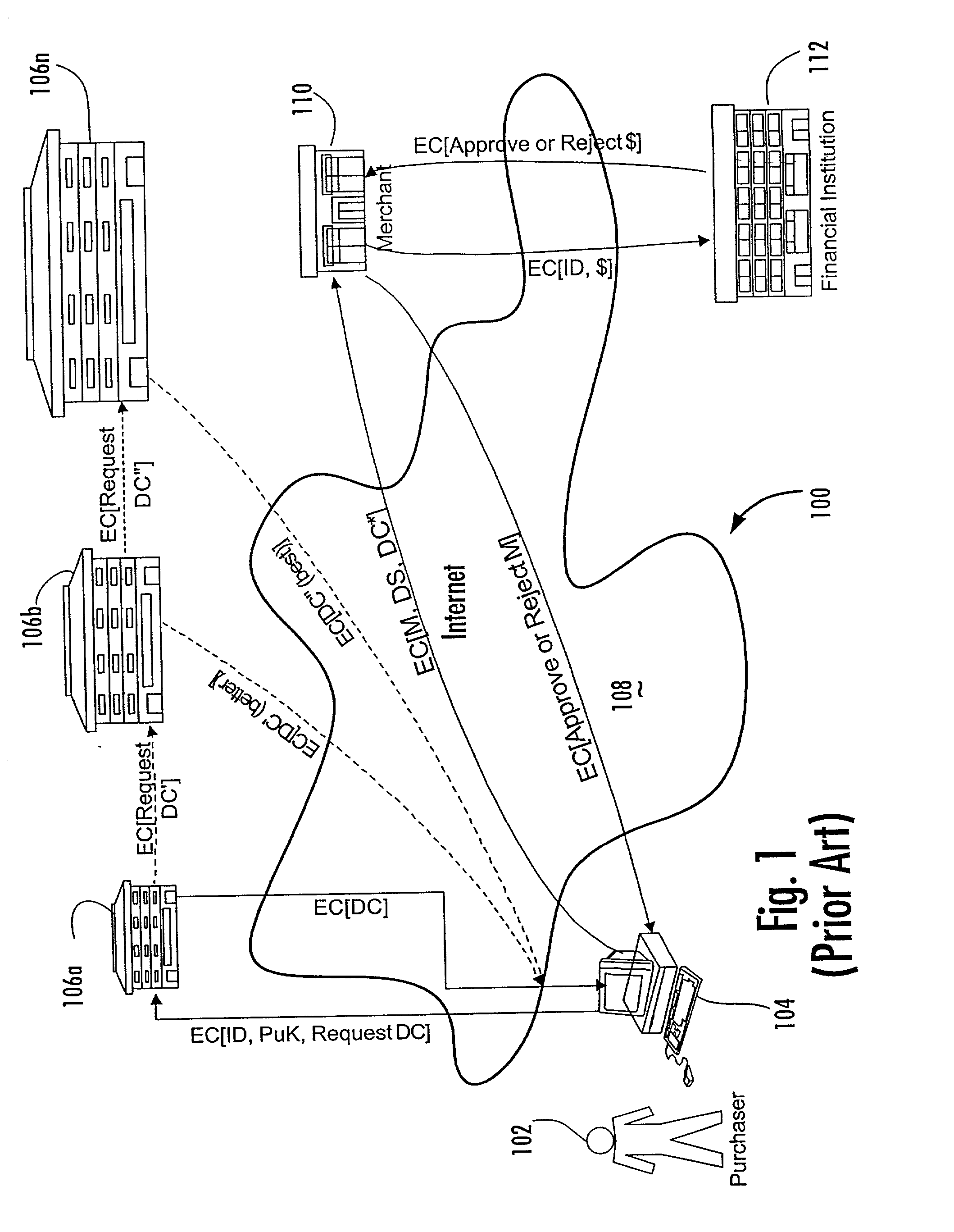
Transaction security method and apparatus
A method for performing secure transactions, such as credit card purchases, using two or more non-secure networks (such as the Internet and the public telephone system) in such a way that security is insured. A person wishing to initiate a secure transaction sends a message over one of the non-secure networks to a computer. That computer automatically uses the second non-secure network to contact the person back to verify the transaction. The call-back mechanism employs a method to authenticate the identity or authority of the person initiating the transaction. No single wire-tapping or network snooping device sees the entire transaction. No single database contains the entire set of information.
Owner:PICKETT THOMAS E
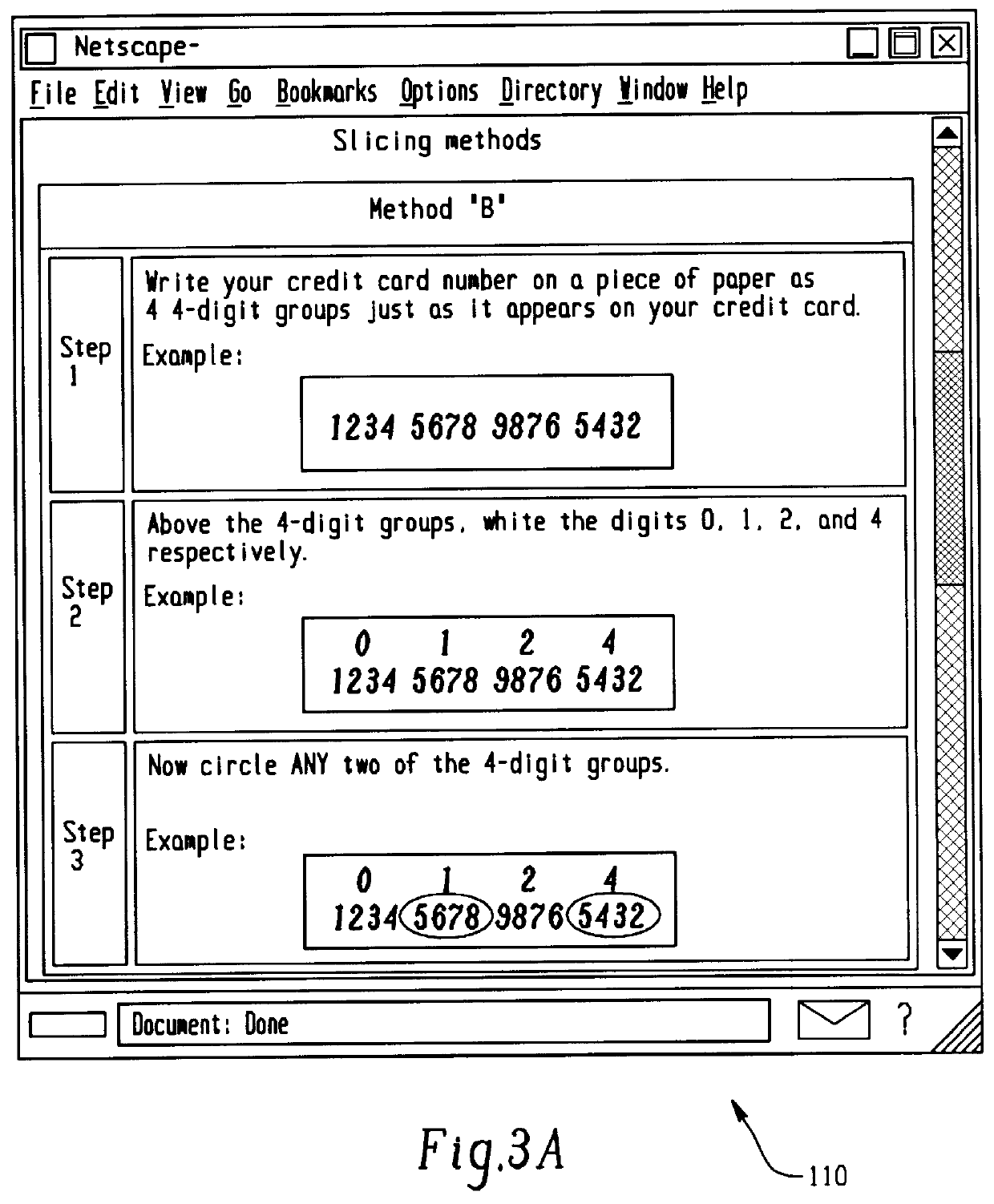
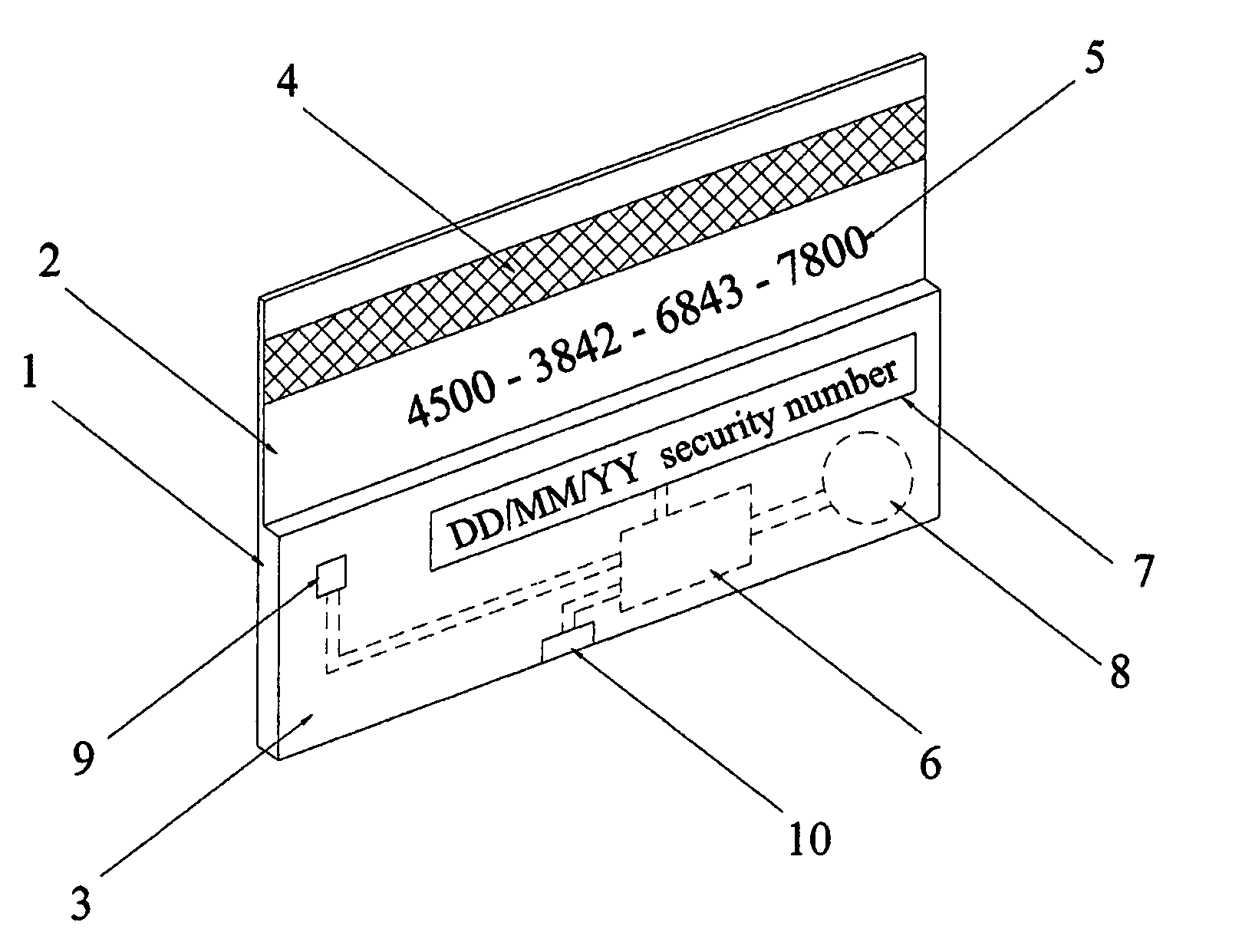
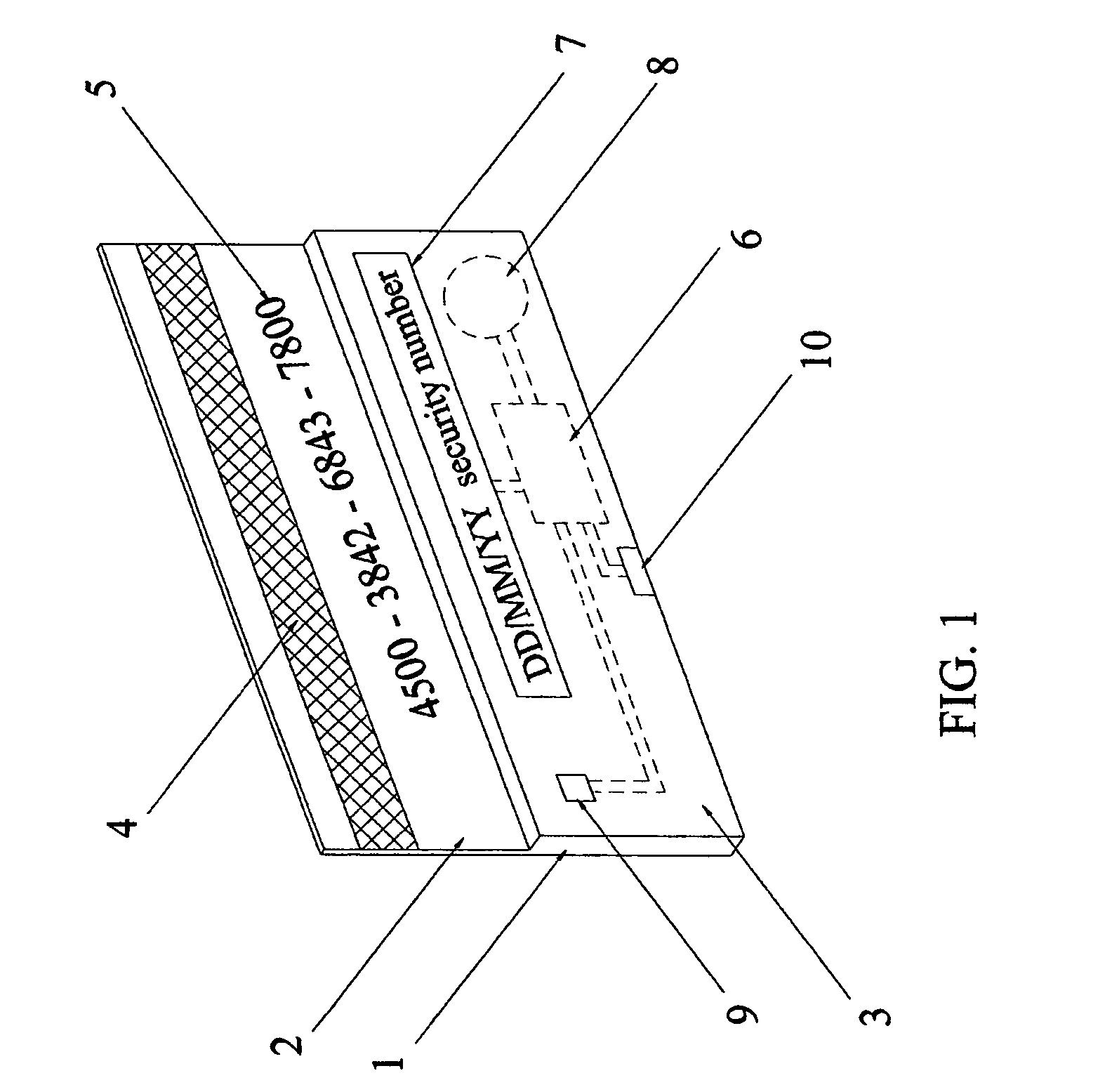
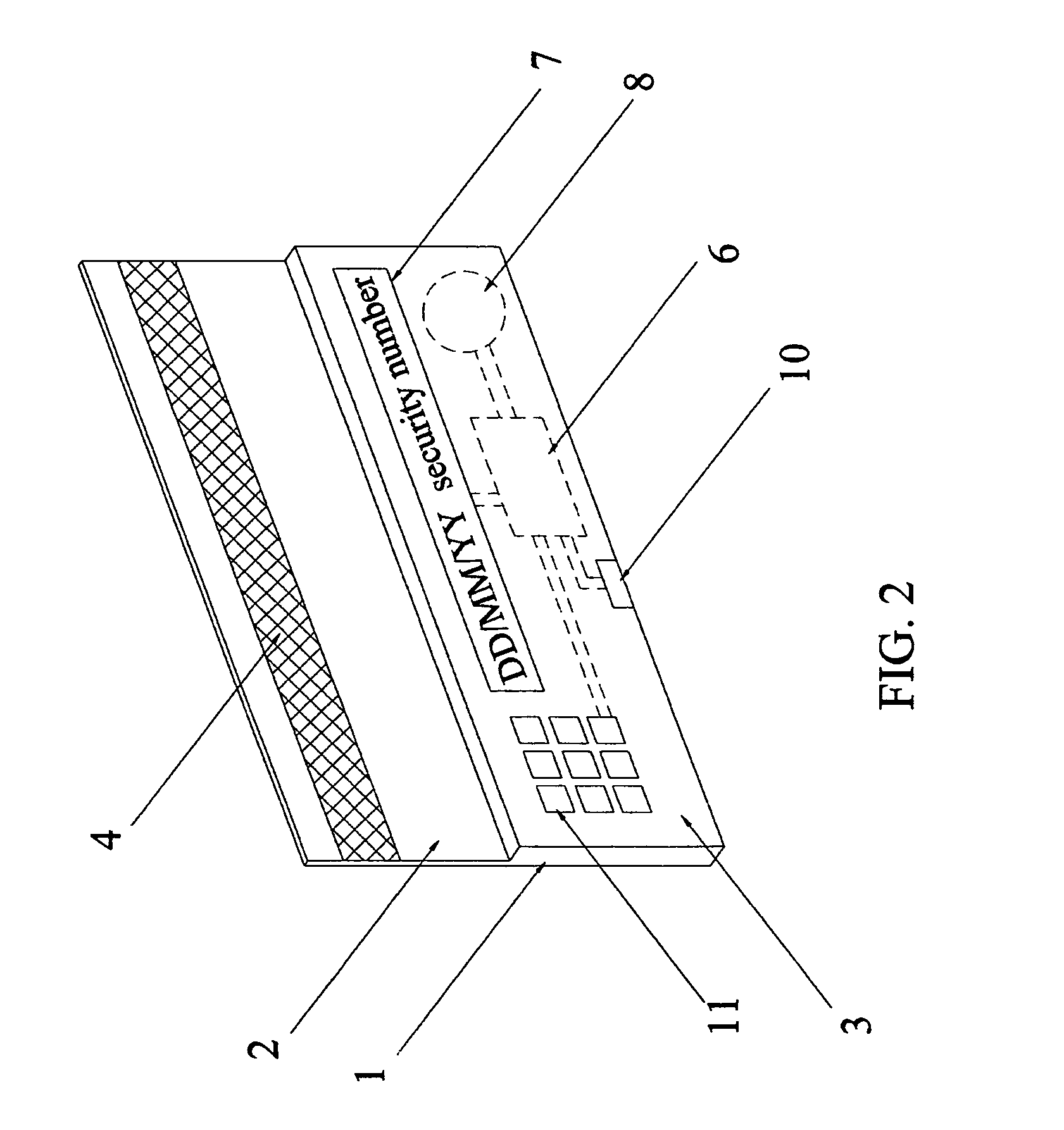
Secure credit card having daily changed security number
InactiveUS7051929B2Enhance memorySimple technologyPayment architectureRecord carriers used with machinesCredit cardThe Internet
Owner:LI GONGLING
Financial transactions with dynamic personal account numbers
ActiveUS7580898B2Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
Transaction apparatus and method
InactiveUS6315195B1Low production costEasy to operateHybrid readersPoint-of-sale network systemsComputer hardwareBarcode
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
Financial transactions with dynamic card verification values
ActiveUS20070136211A1Sufficient dataComputer security arrangementsPayment architectureUser needsPower user
A payment card comprises an internal dynamic card verification value (CVV) generator and a user display for card-not-present transactions. Card-present transactions with merchant card readers are enabled by a dynamic magnetic array internally associated with the card's magnetic stripe. The user display and a timer are triggered by the suer when the user needs to see the card verification value and / or begin a new transaction. A new card verification value is provided for each new transaction according to a cryptographic process, but the timer limits how soon a next new card verification value can be generated.
Owner:FITBIT INC
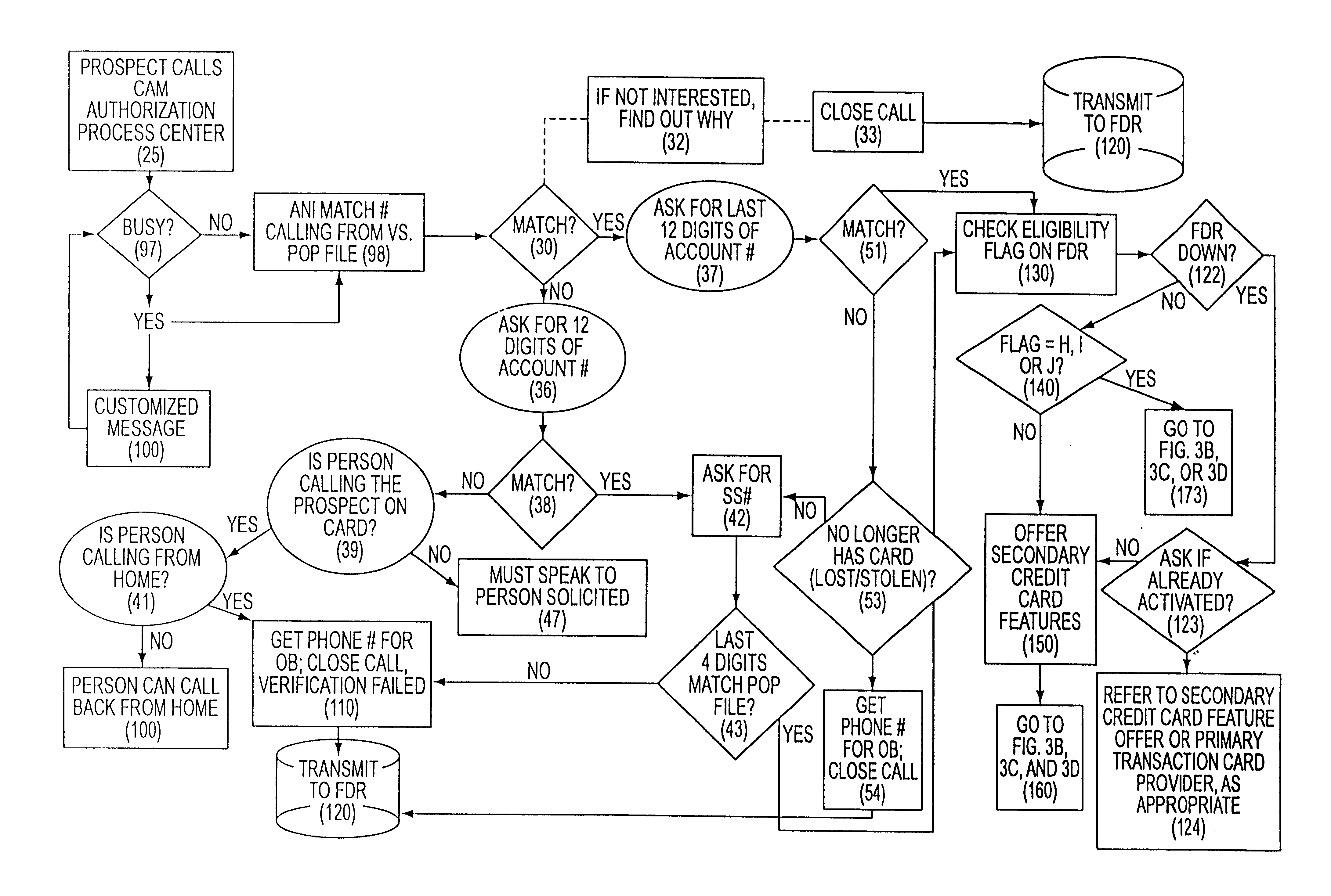
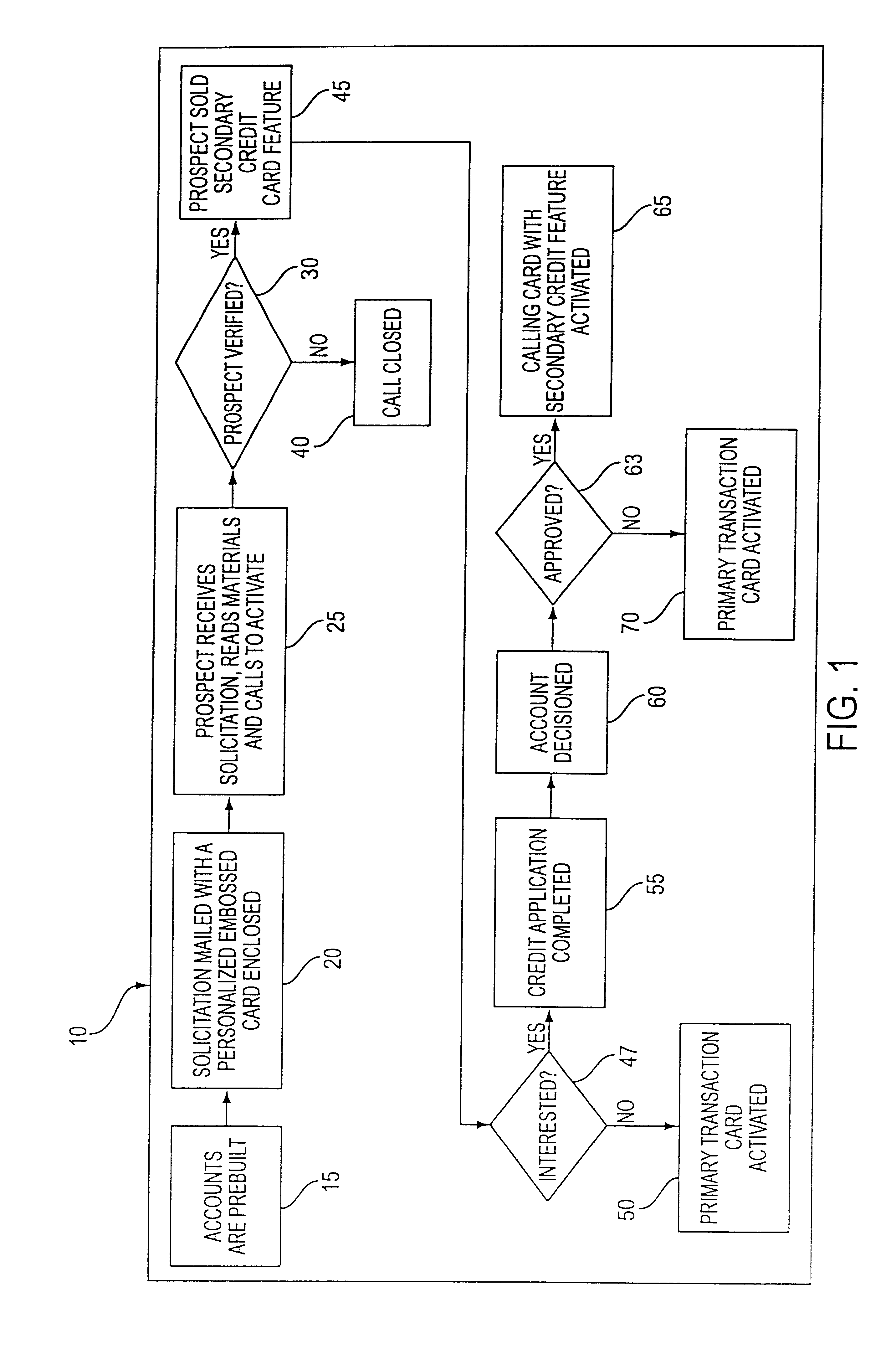
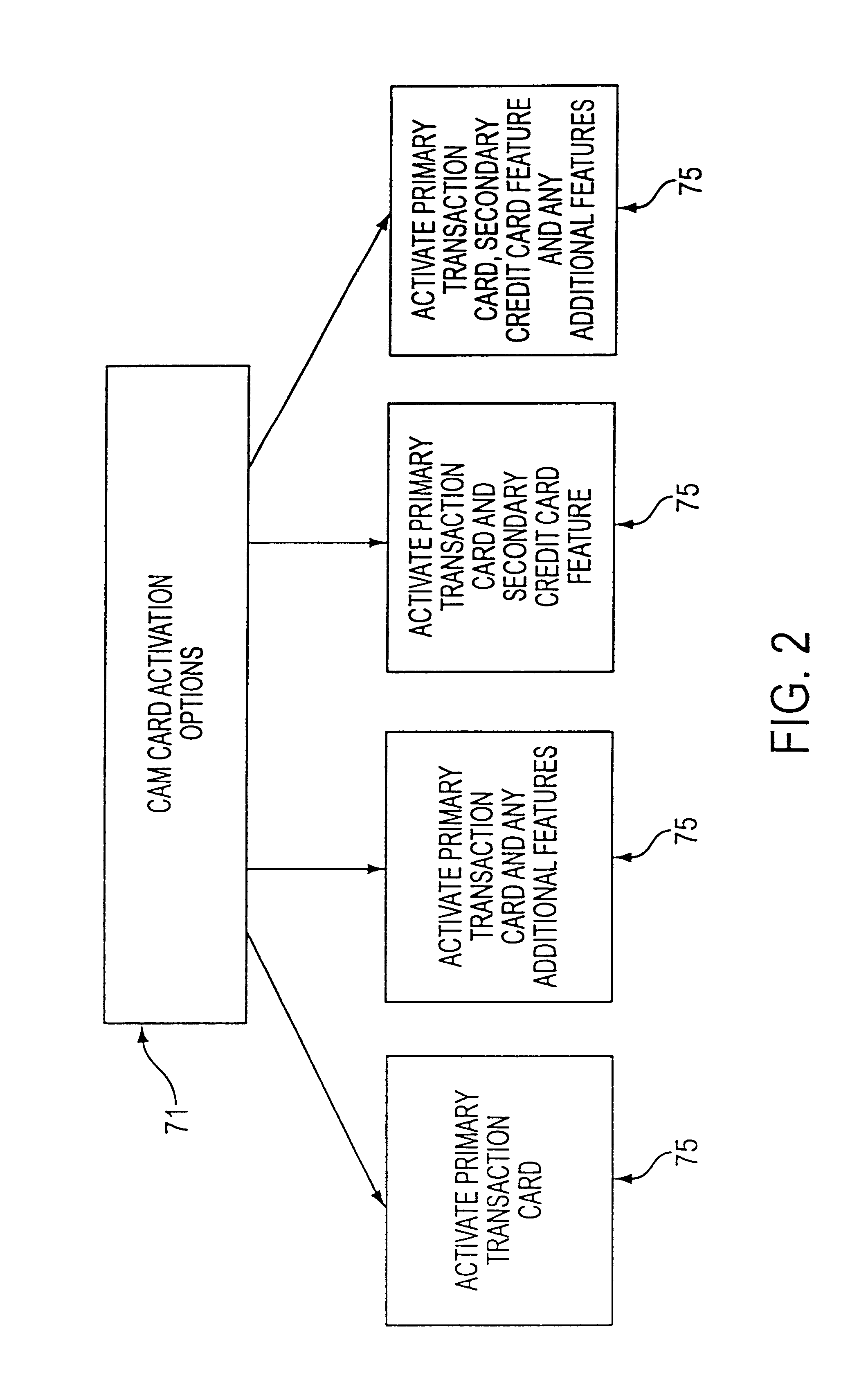
Customer activated multi-value (CAM) card
InactiveUS6865547B1Easy to useCredit registering devices actuationDiscounts/incentivesCredit cardGasoline
The Customer Activated Multi-Value (CAM) card provides a customer with a primary use as a transaction card which can be further activated to have a secondary use as a credit card. The CAM card can be activated as a transaction card or as a transaction card with a credit card feature. Activation of the CAM card as a transaction card allows the customer to purchase goods and services from one specific vendor and to establish a relationship with that vendor for the goods or services rendered (for example, telephone calling card or gasoline product purchasing card) while enjoying reward benefits based on those purchases. Activation of the credit feature of the card allows the customer to interact with any merchant that accepts traditional credit cards such as VISA®, MASTERCARD®, AMERICAN EXPRESS®, or DISCOVER®. The combination of features allows a customer to purchase various goods and services from several different merchants. If the customer chooses to activate the CAM card as both a transaction card and a credit card, the customer is given the benefit of using the card in both manners described above.
Owner:JPMORGAN CHASE BANK NA
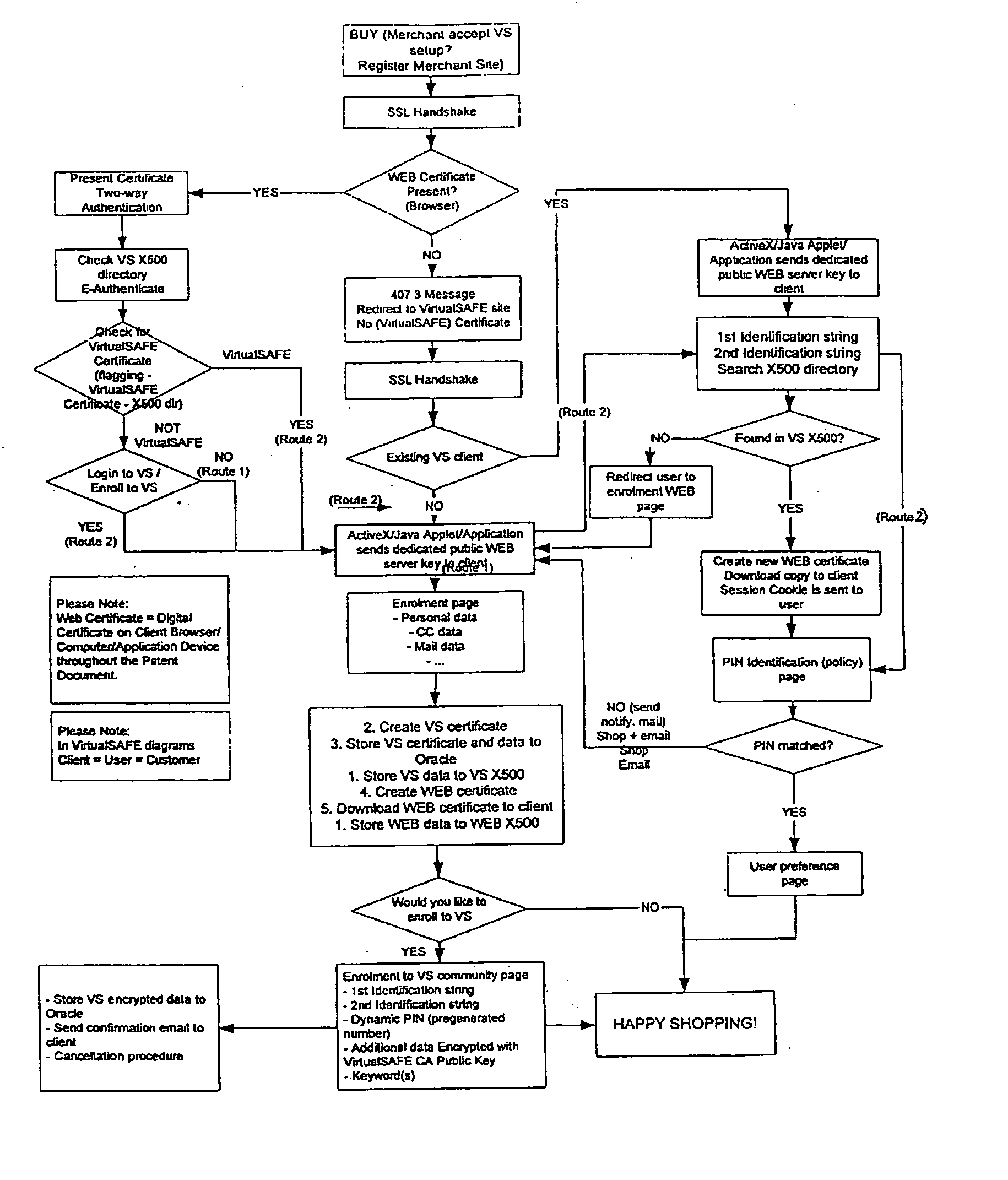
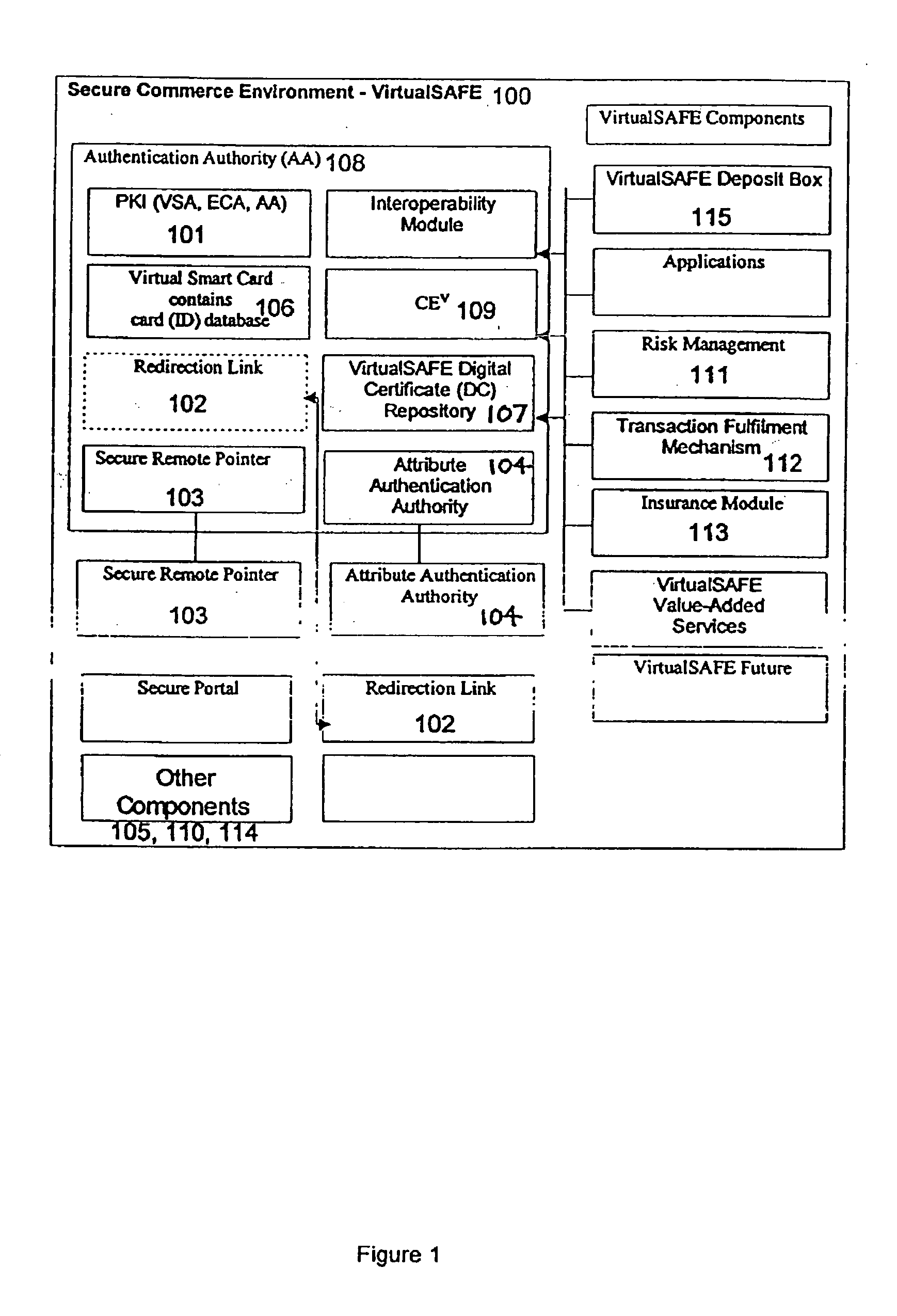
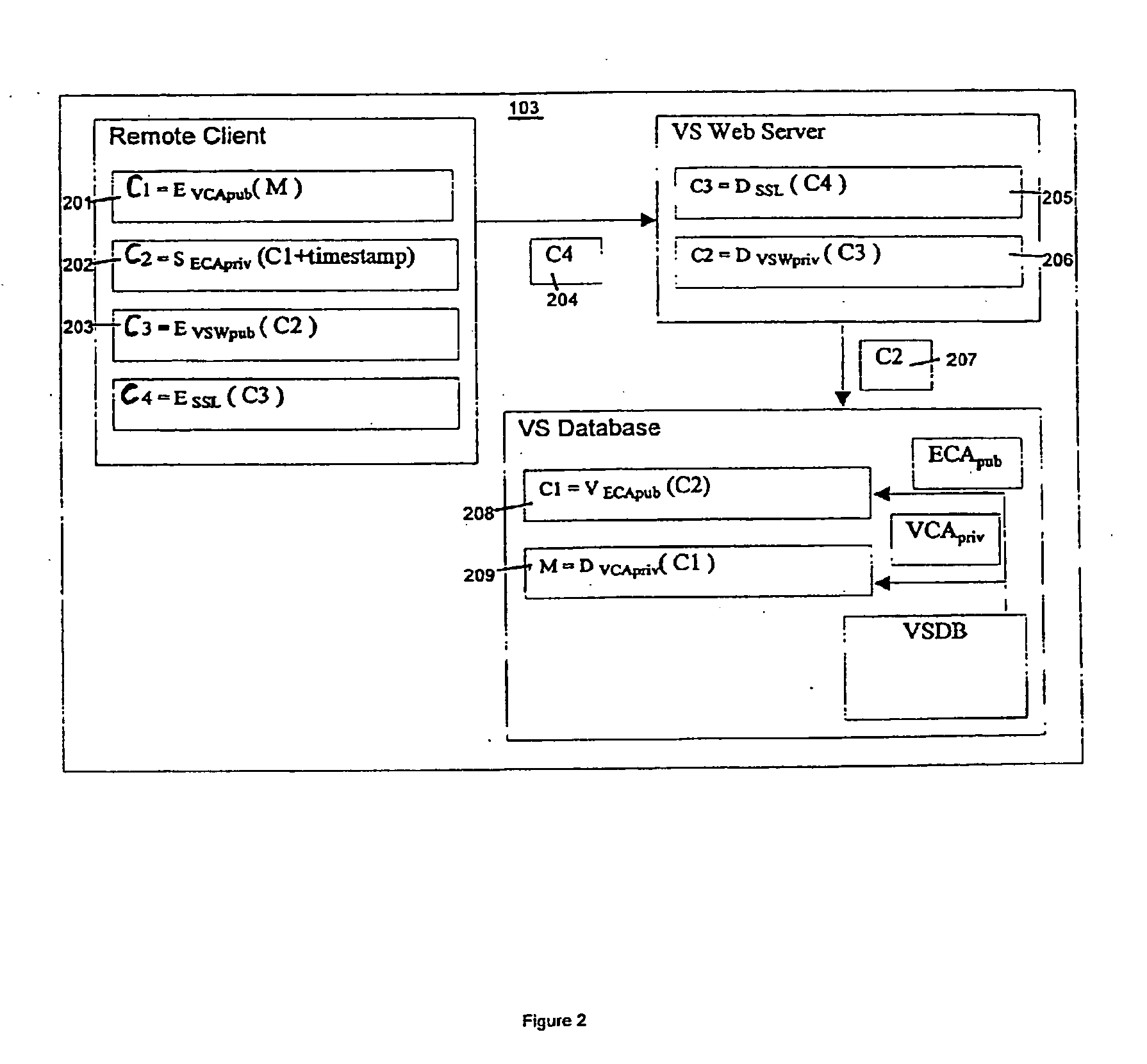
Method and system for a virtual safe
Owner:SARCANIN BRANKO
Consumer interactive shopping system
InactiveUS20050040230A1Expand accessFunction increaseGuide needlesCredit registering devices actuationComputer terminalPortable data terminal
Owner:SYMBOL TECH LLC
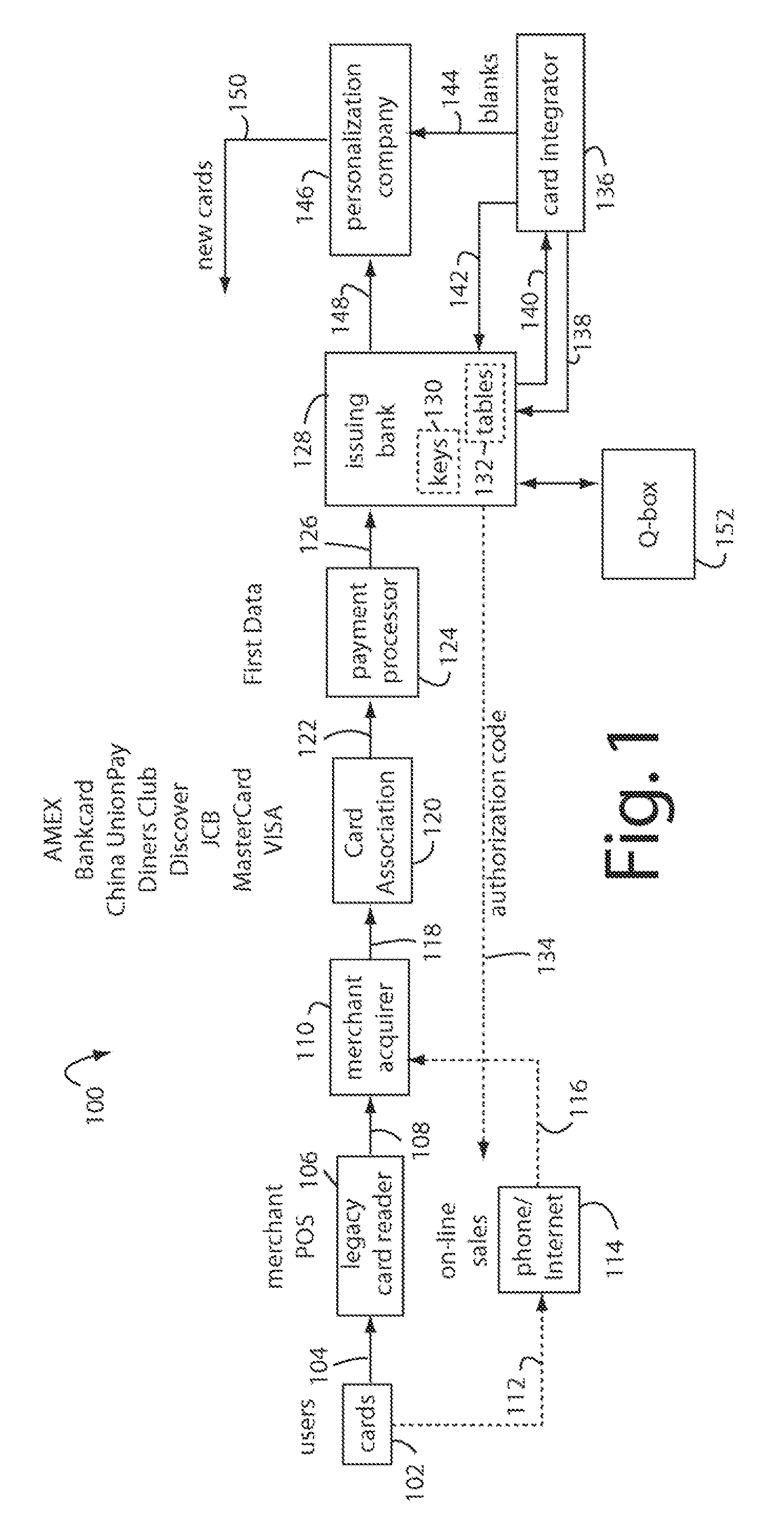
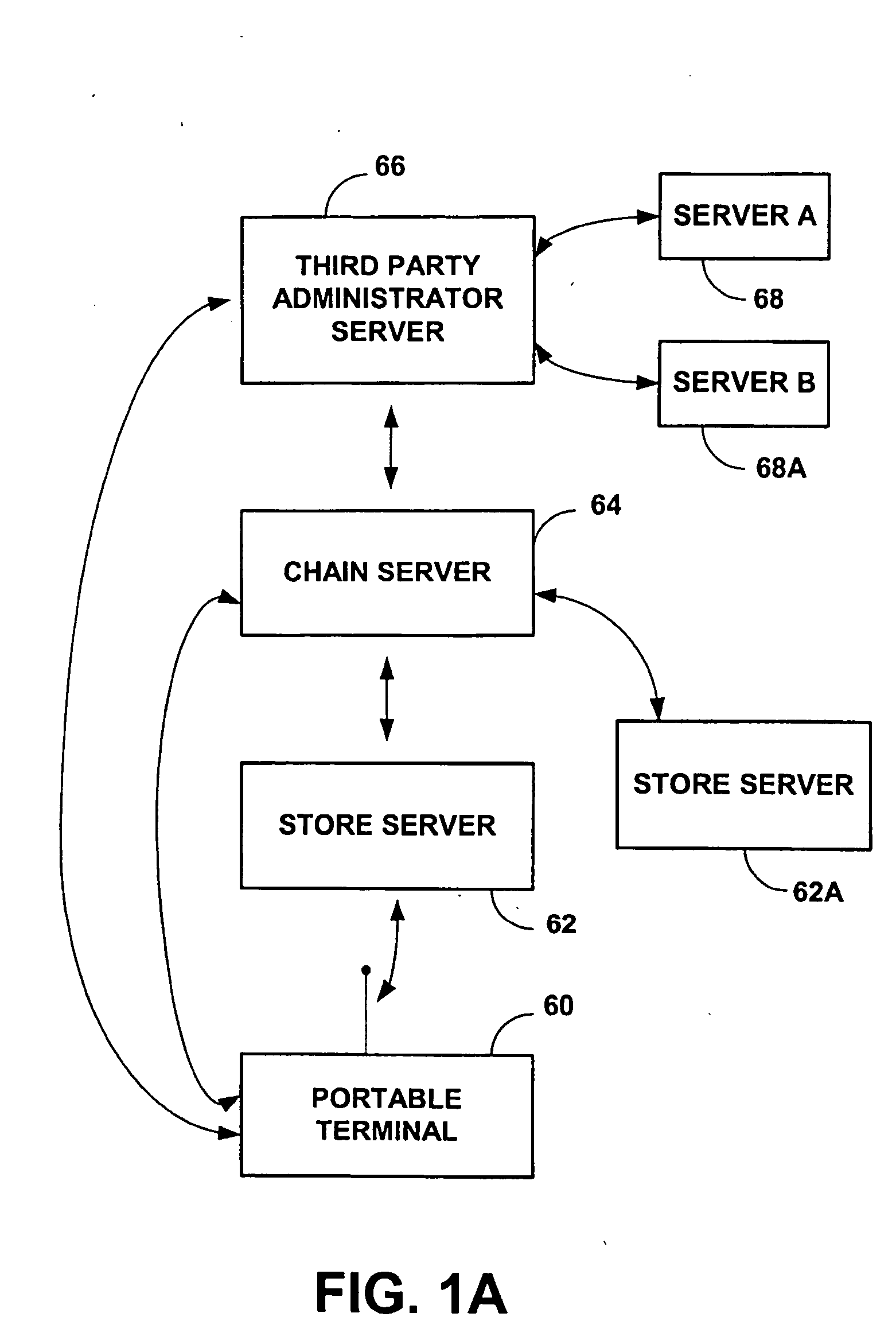
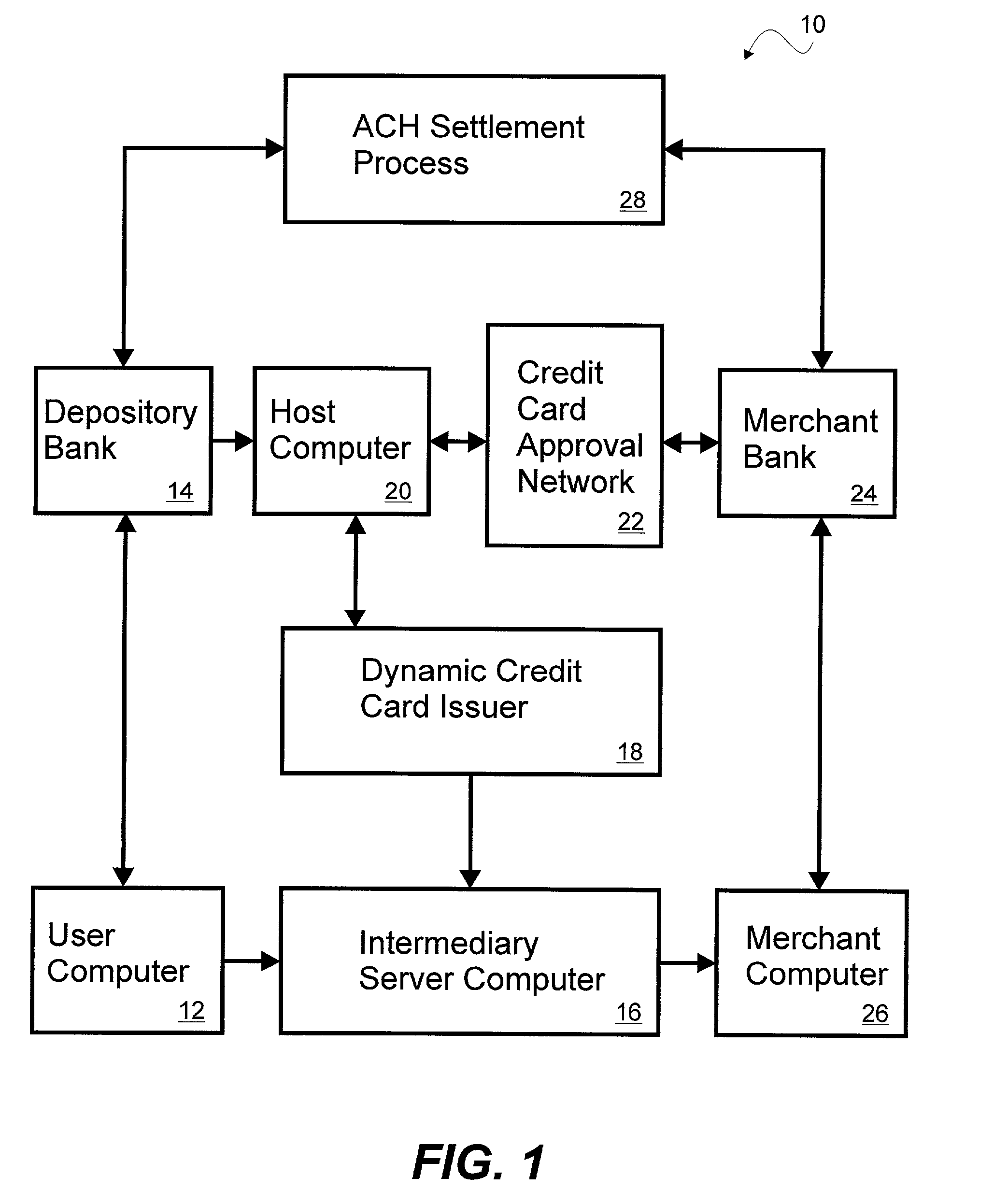
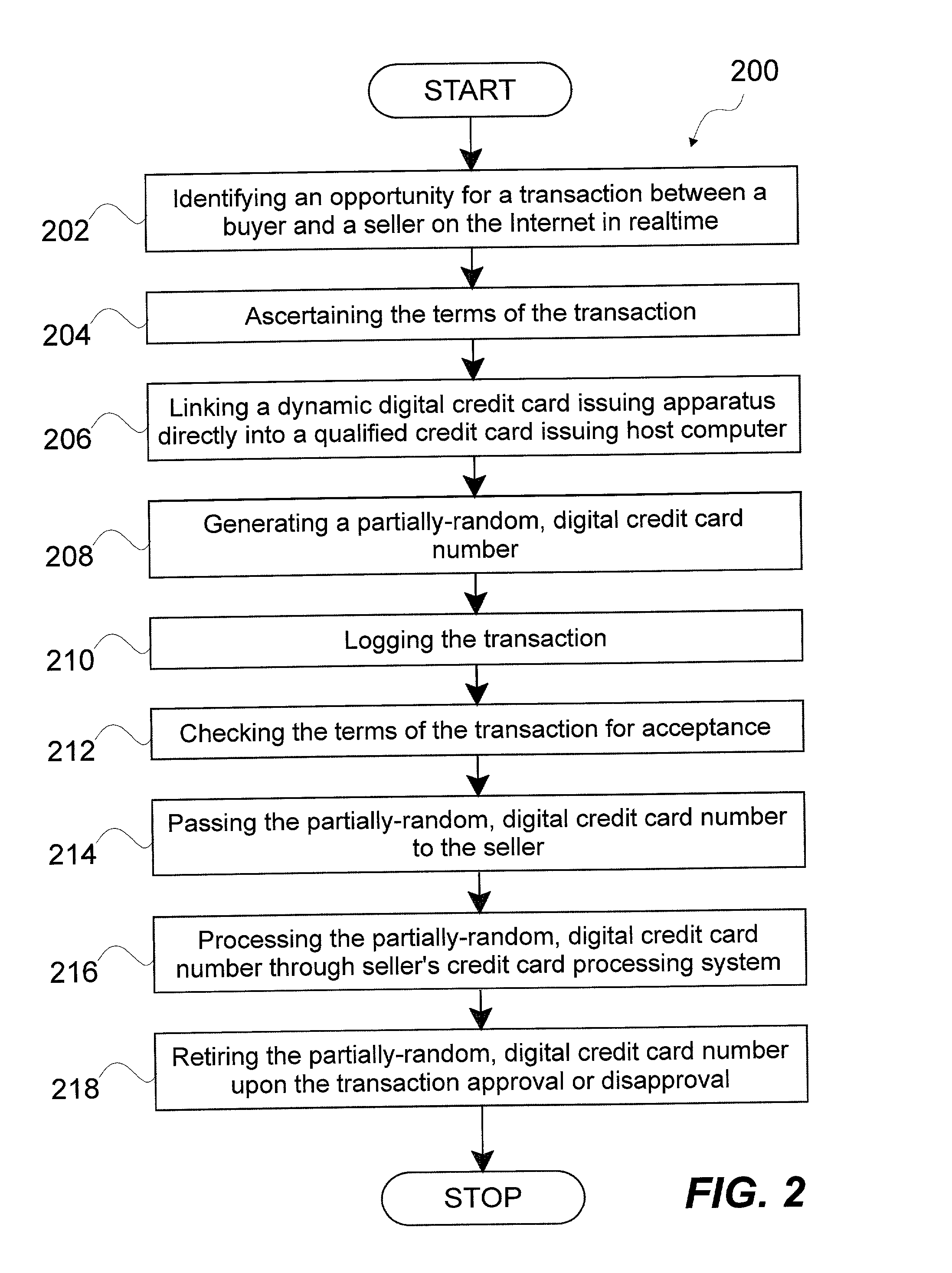
System and method for dynamically issuing and processing transaction specific digital credit or debit cards
A system and method of dynamically issuing credit card numbers and processing transactions using those credit card numbers is disclosed. A method according to the invention includes digitally recognizing a transaction opportunity on the Internet in real-time, recognizing the terms of the transaction, linking a dynamic digital credit card issuing apparatus directly into a qualified credit card issuing host, generating a partially random digital credit card number, logging the transaction, checking the terms of the transaction for acceptance, passing the dynamically issued digital credit card number to the merchant, processing the digital credit card number through the merchant's card processing system, receiving the transaction approval request, participating in credit card validity checking systems, processing the approval request in real-time, sending the requesting party a legitimate authorization code, and retiring the digital credit card number immediately upon transaction approval or disapproval. A system according to the invention implements the method of the invention.
Owner:ORANGATANGO
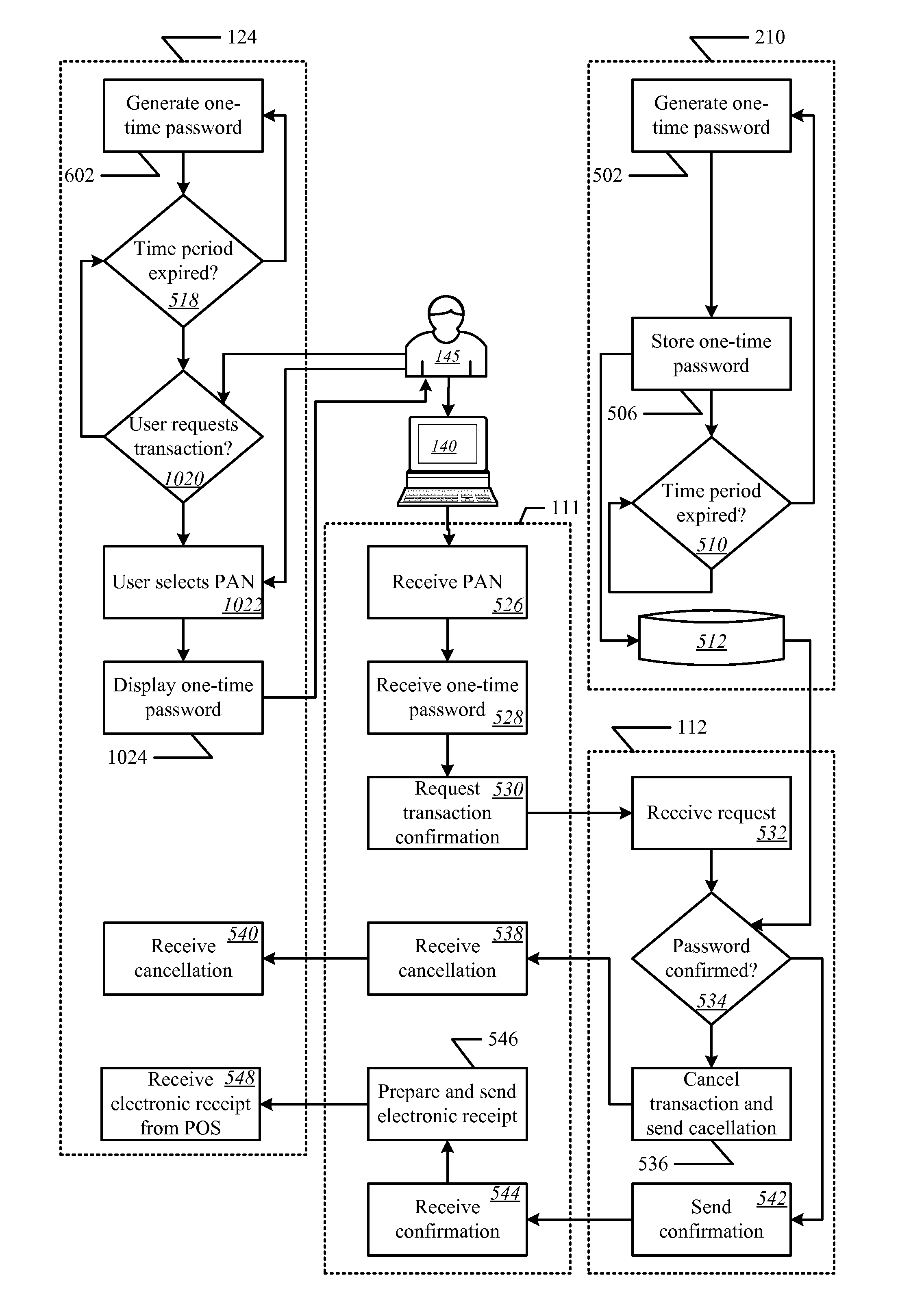
Onetime passwords for smart chip cards
ActiveUS8095113B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDisplay deviceFinancial transaction
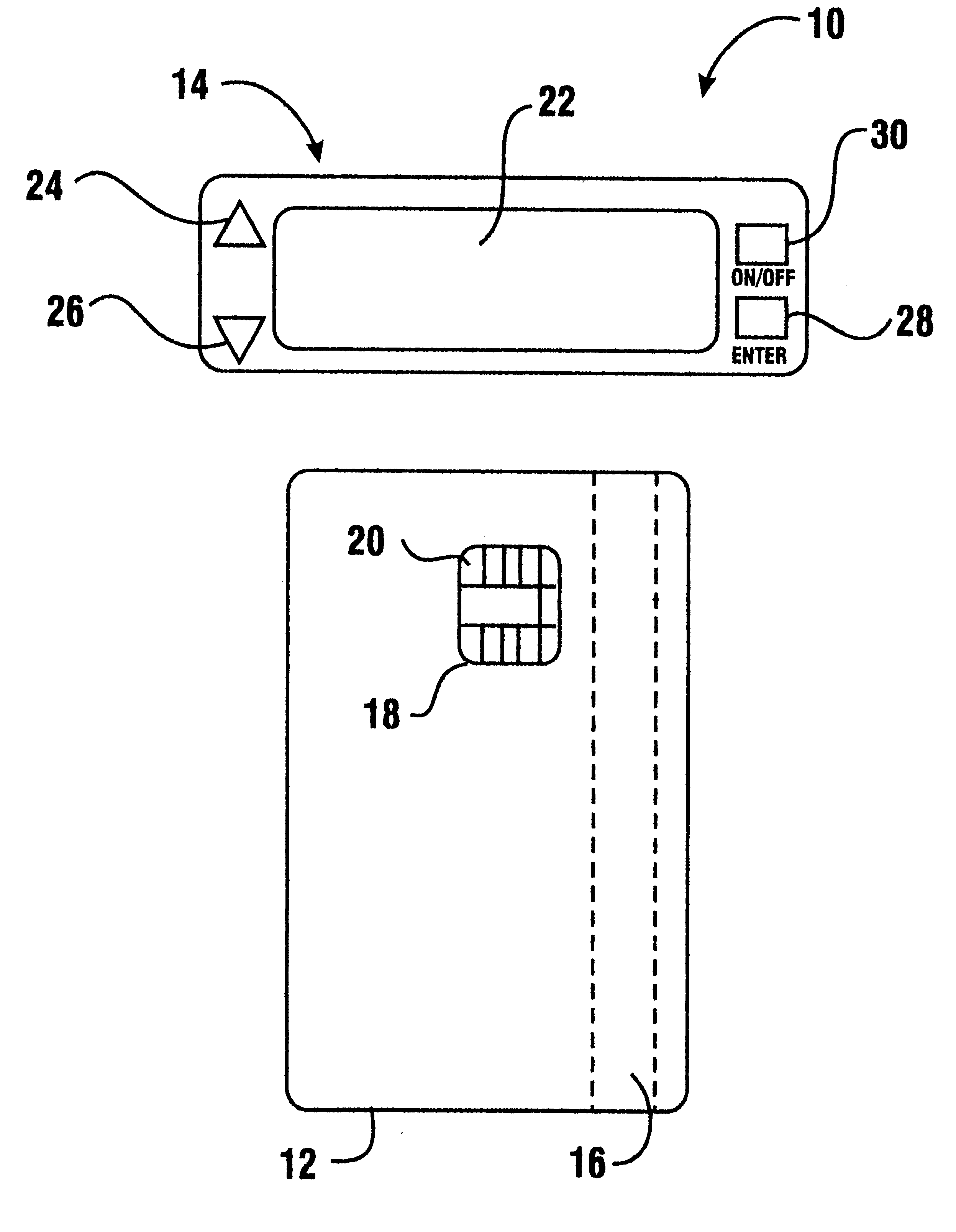
A financial transaction card is provided according to various embodiments described herein. The financial transaction card includes a card body with at least a front surface and a back surface. The financial transaction card may also include a near field communications transponder and / or a magnetic stripe, as well as a digital display configured to display alphanumeric characters on the front surface of the card body. The financial transaction card may also include a processor that is communicatively coupled with the near field communications transponder or magnetic stripe and the digital display. The processor may be configured to calculate one-time passwords and communicate the one-time passwords to both the near filed communications transponder or magnetic stripe and the digital display.
Owner:FIRST DATA
Transaction system
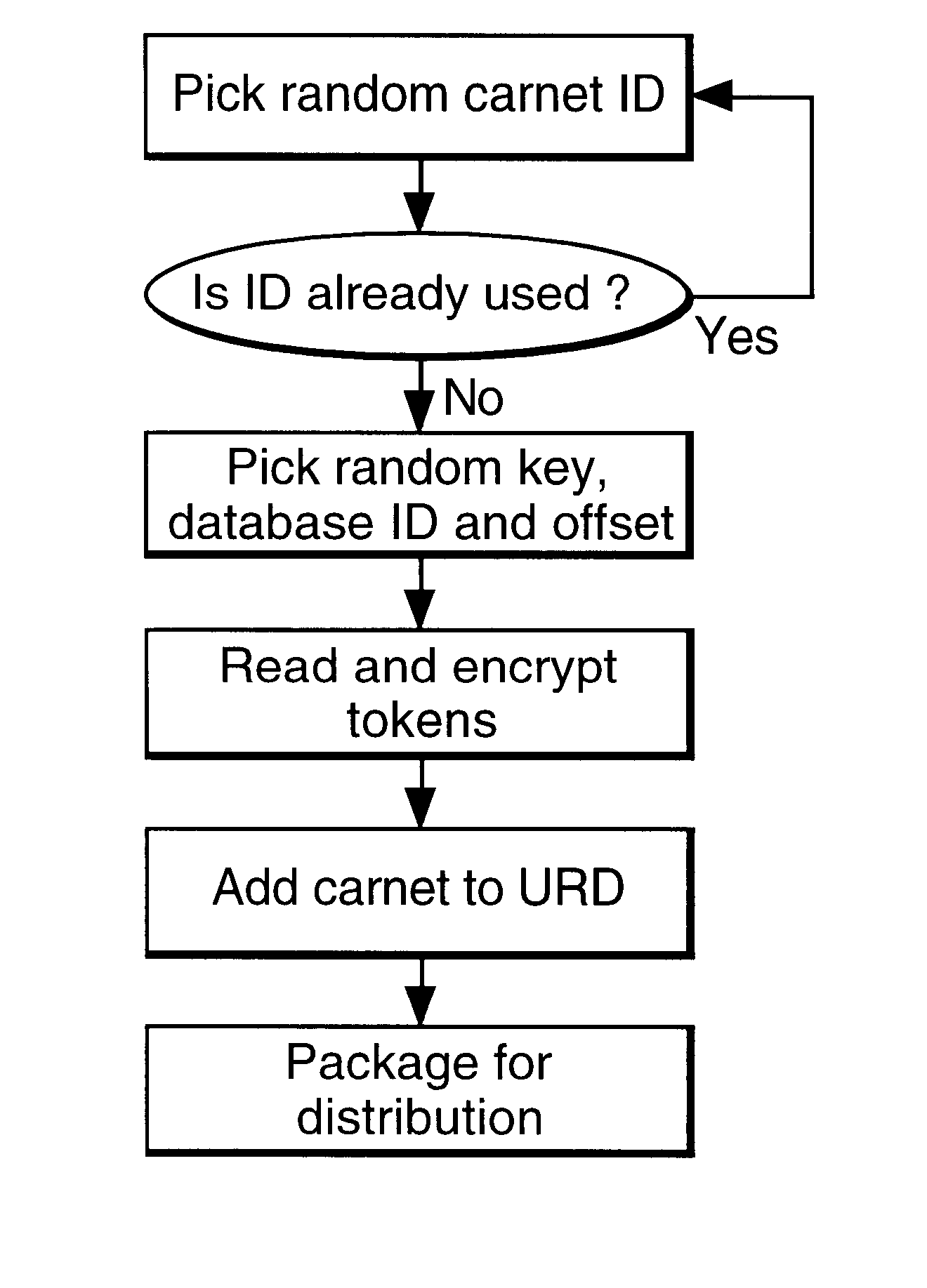
InactiveUS6236981B1Improve securityImprove the level ofUser identity/authority verificationComputer security arrangementsService provisionThe Internet
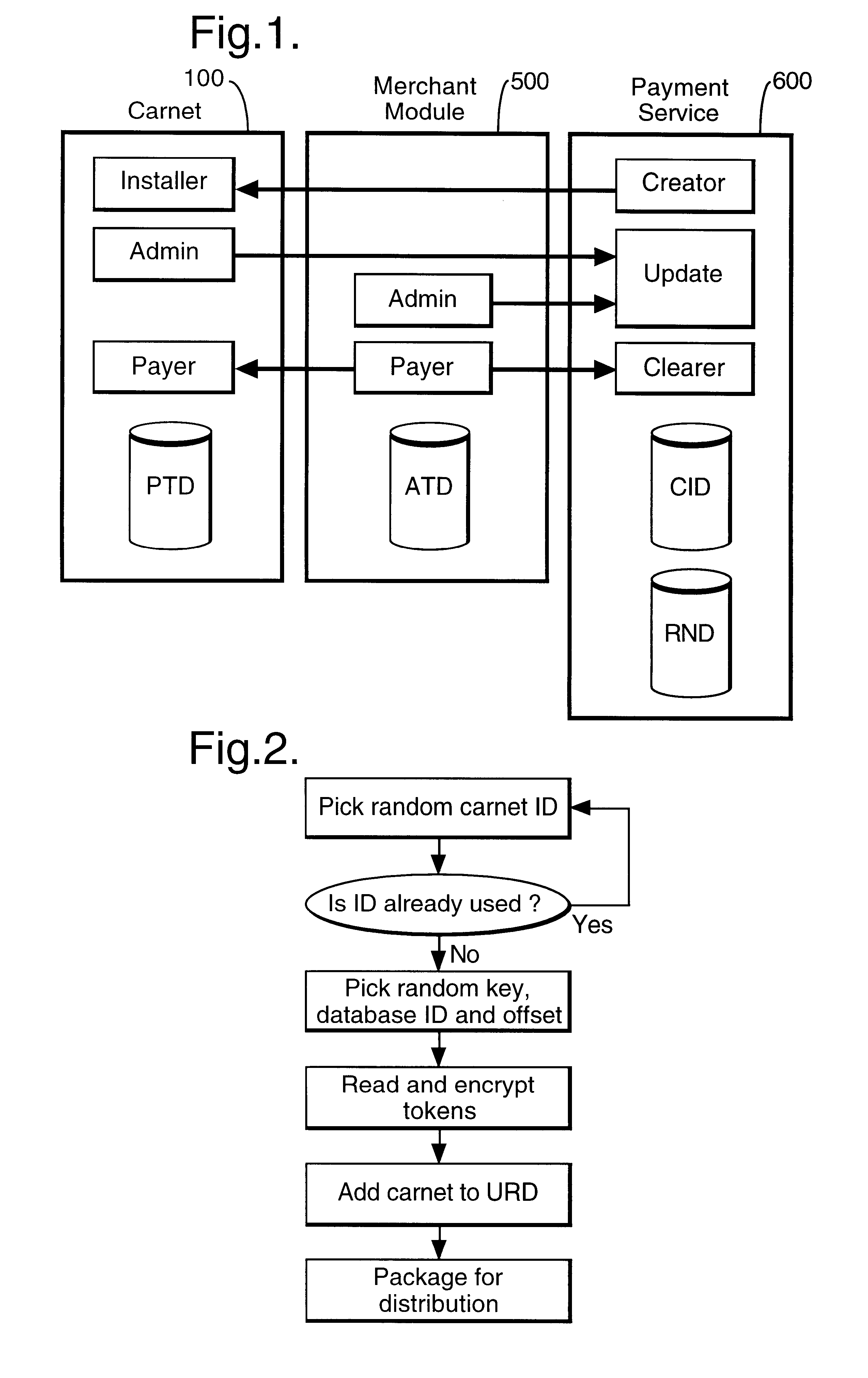
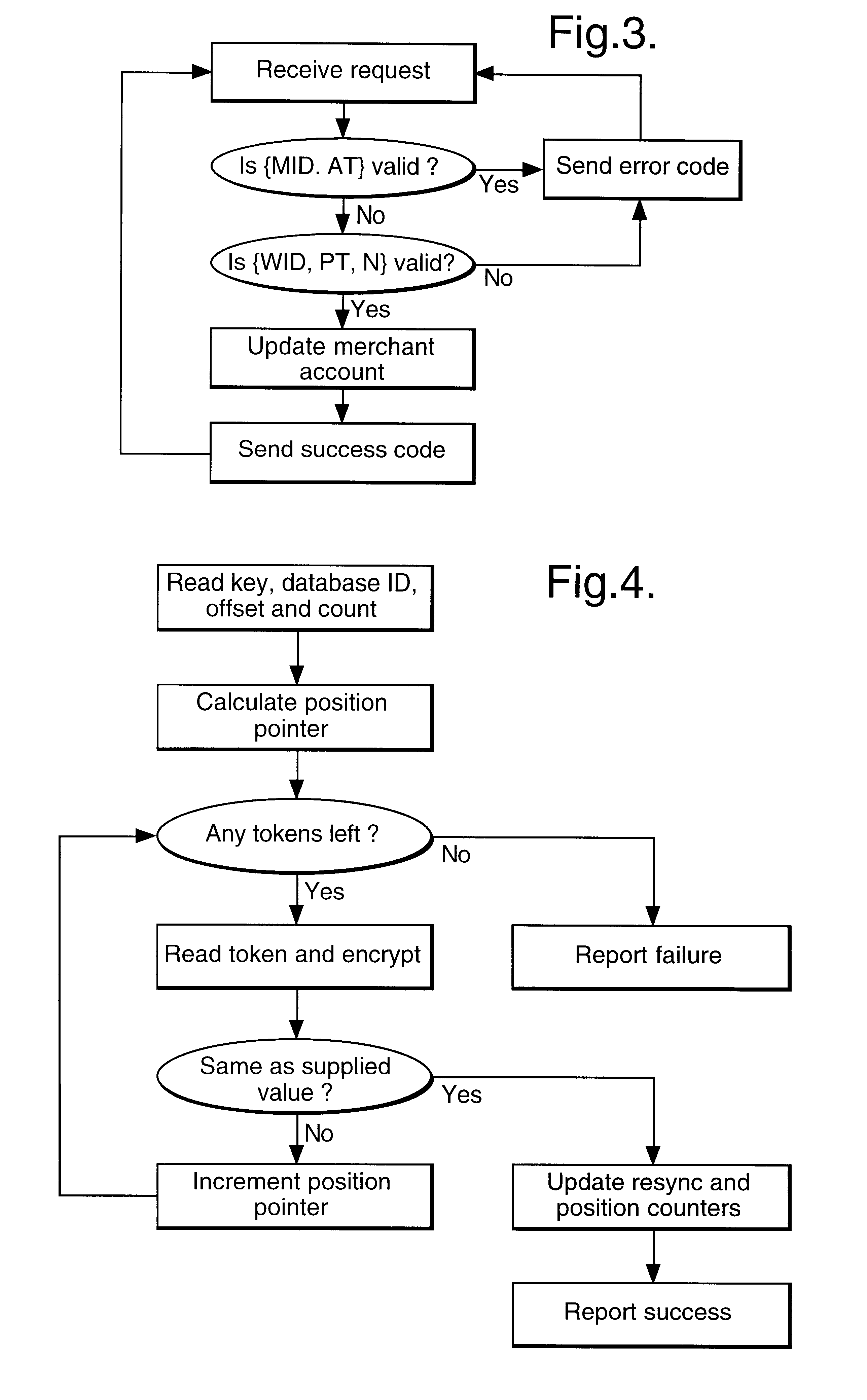
In a digital payment system, a sequence of random numbers is stored at a payment service. A set of digitally encoded random numbers derived from the stored sequence is issued to the user in return for payment. The tokens are stored in a Carnet. The user can then spend the tokens by transferring tokens to a merchant, for example, to an on-line service provider. The merchant returns each token received to the payment server. The payment server authenticates the token and transmits an authentication message to the merchant. The merchant, payment server and user may be linked by internet connections.
Owner:BRITISH TELECOMM PLC
Promotion system including an ic-card memory for obtaining and tracking a plurality of transactions
An apparatus is provided for tracking individual user consumer transactions which provides the user with an eraseable, re-writeable, visual format display while avoiding retrieval of data from an outside source.
Owner:VISIBLE RESULTS GRP LTD
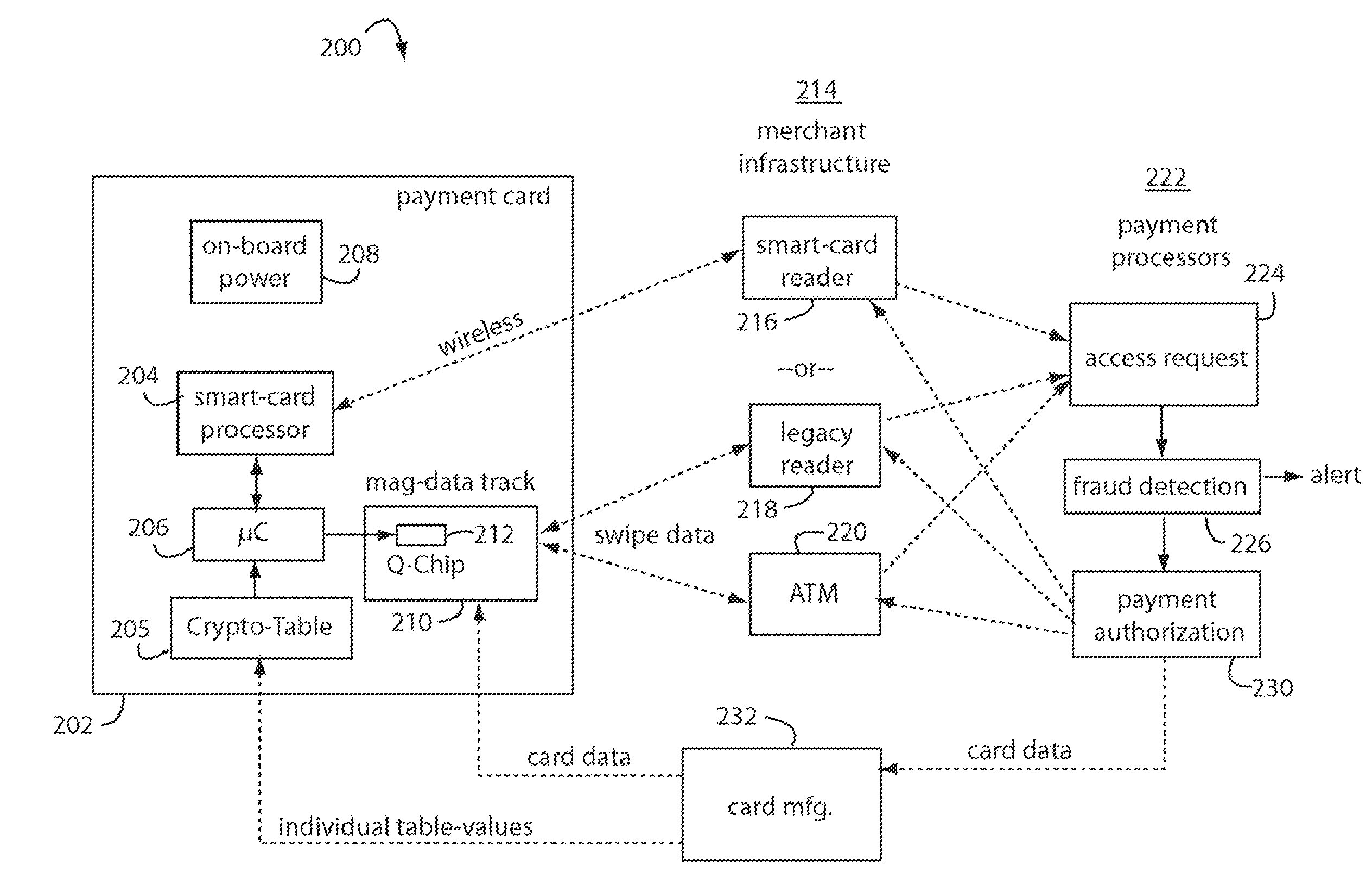
Secure credit card
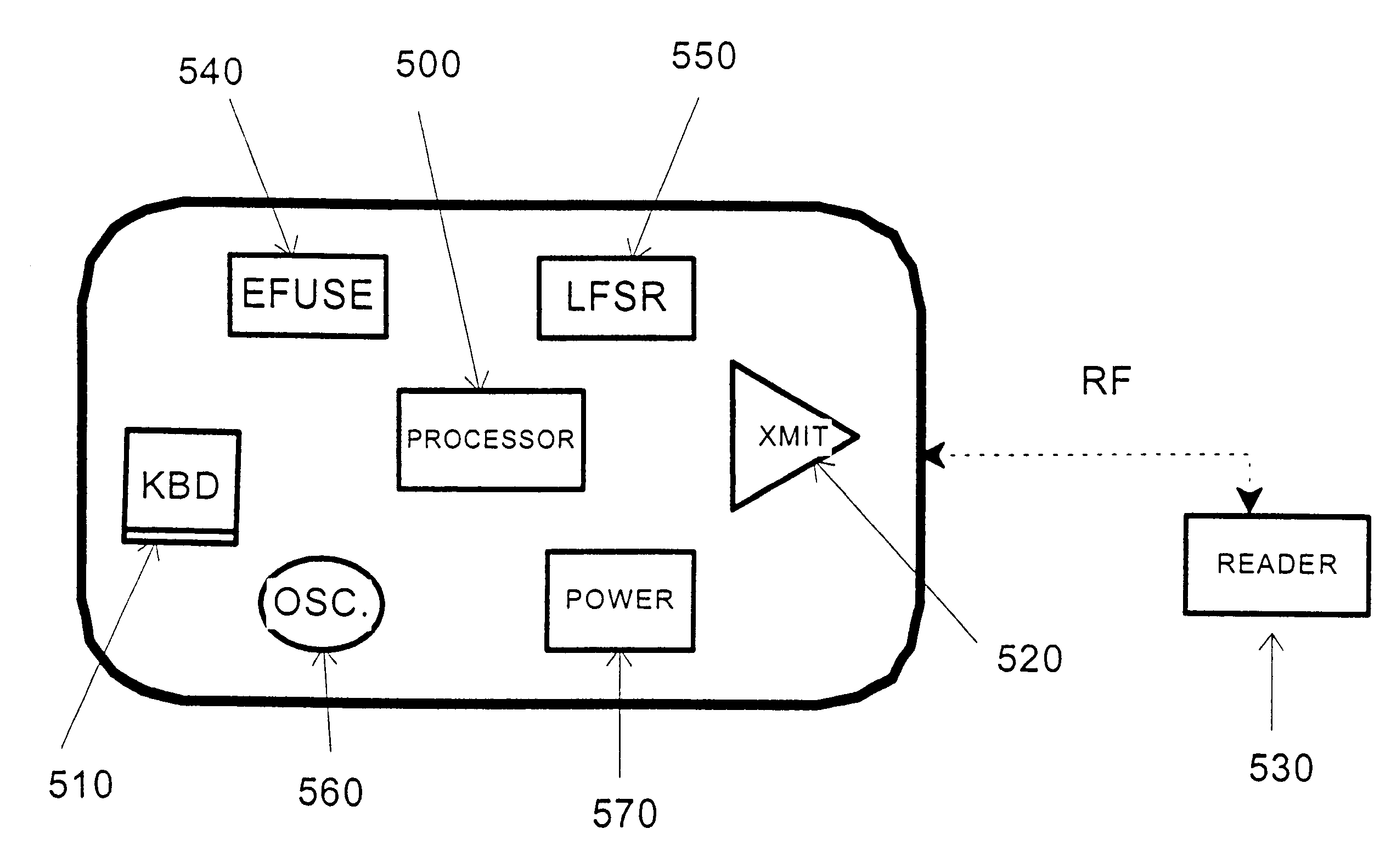
Credit card or portable identification cards containing smart card technology and electronic fuse (e-fuse) technology are combined with an LFSR pseudo random number generator to provide a secured method to prevent fraud and unauthorized use. Secure personalization via e-fuses, a pseudo-random number generator linear feedback shift register, free running clock oscillator, and power source embedded in the card provide a highly secured method to render a lost or stolen card useless. A unique card ID is permanently encoded within the card which requires a specific activation code to activate the card. A PIN number permits the card owner to activate the card for a predetermined length of time while processing a transaction. The card dynamically generates random code sequences and synchronization keys to secure a transaction.
Owner:KYNDRYL INC
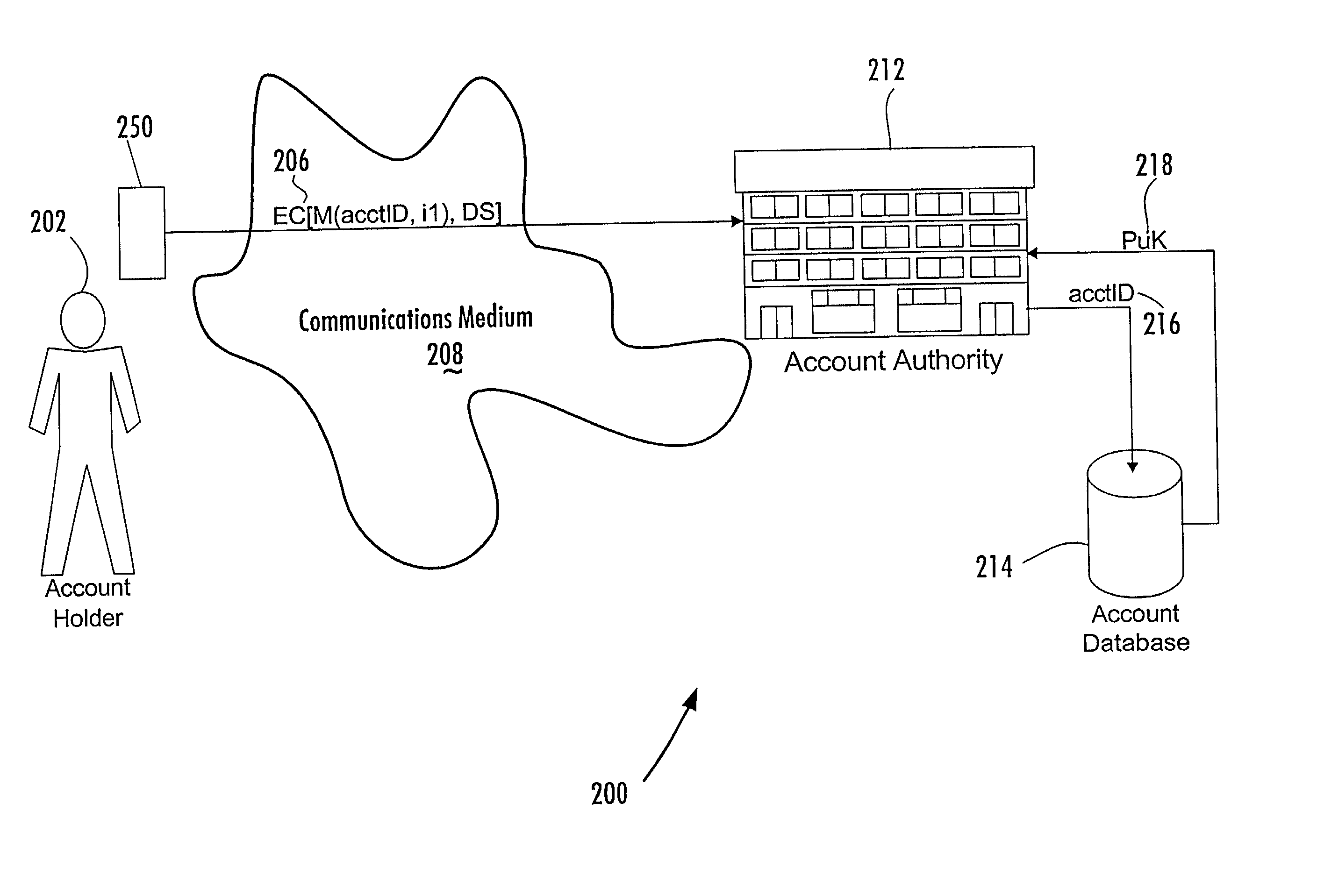
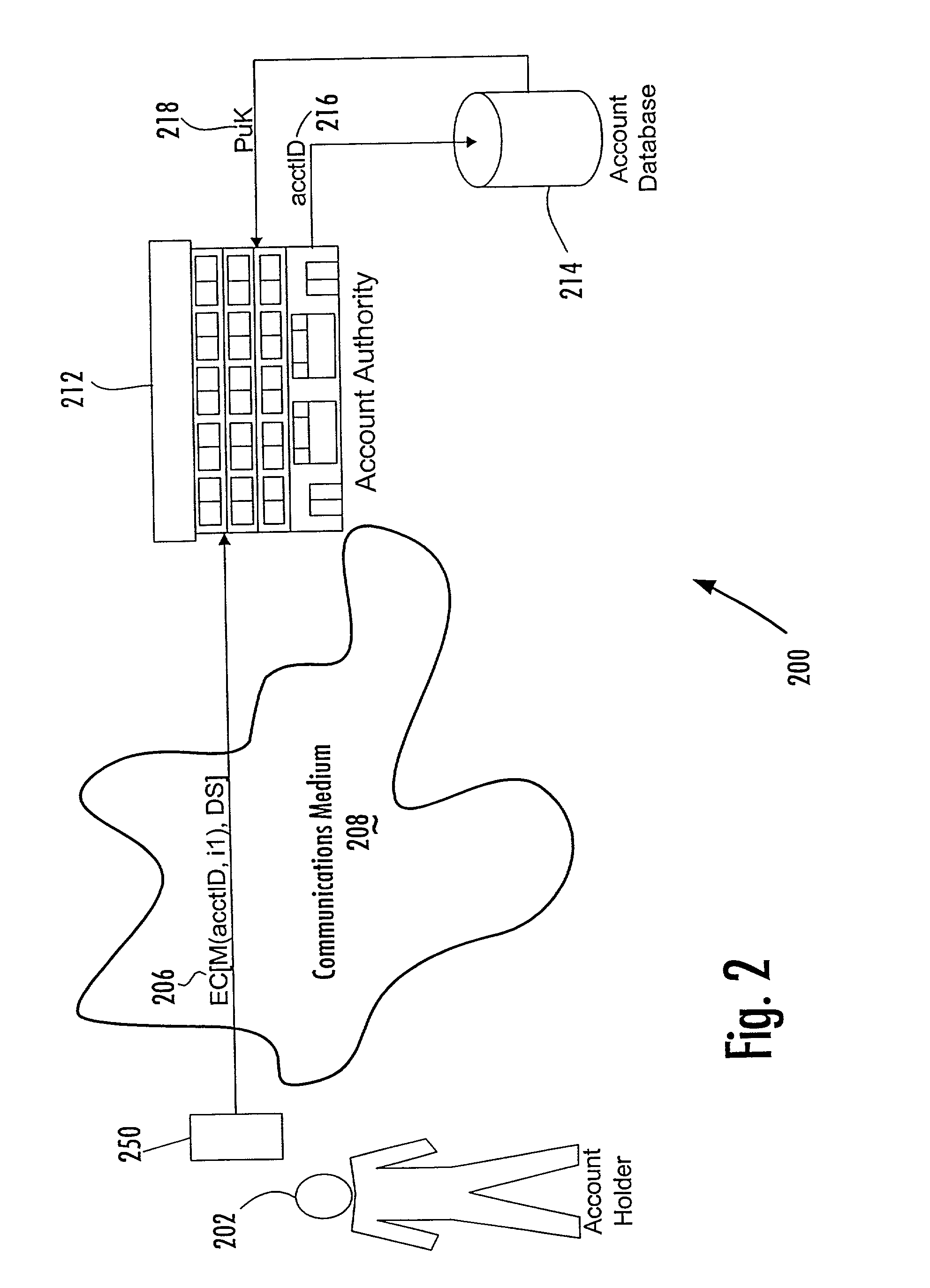
Account-based digital signature (ABDS) system
InactiveUS20020026575A1Key distribution for secure communicationFinanceDigital signatureElectronic communication
A method of authenticating an entity by a receiving party with respect to an electronic communication that is received by the receiving party and that includes both a unique identifier associated with an account maintained by the receiving party and a digital signature for a message regarding the account, consists of the steps of, before receipt of the electronic communication, first associating by the receiving party a public key of a public-private key pair with the unique identifier and, thereafter, only conducting message authentication using the digital signature received by the receiving party in the electronic communication and the public key associated with the account identifier.
Owner:FIRST DATA
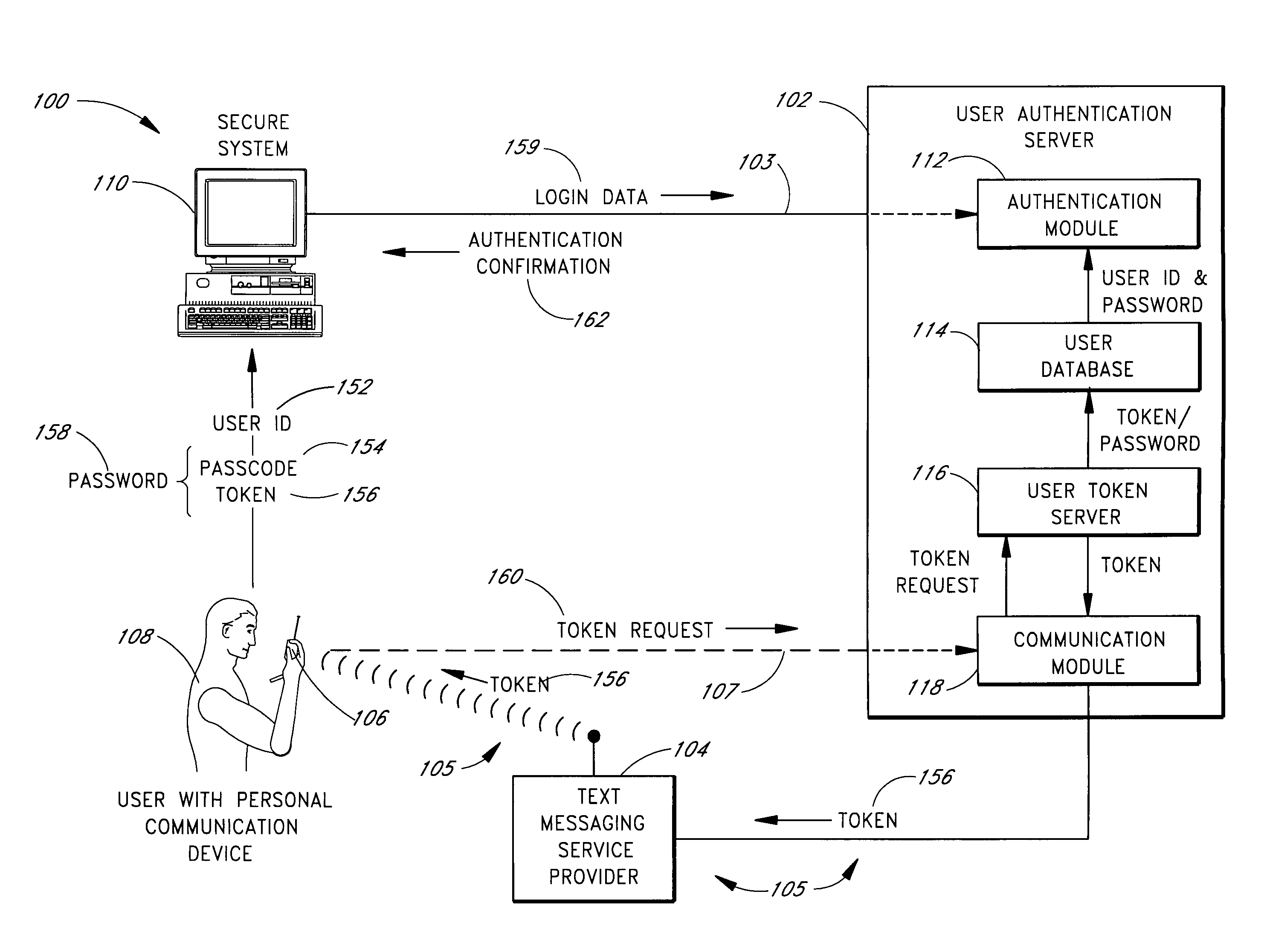
Use of personal communication devices for user authentication
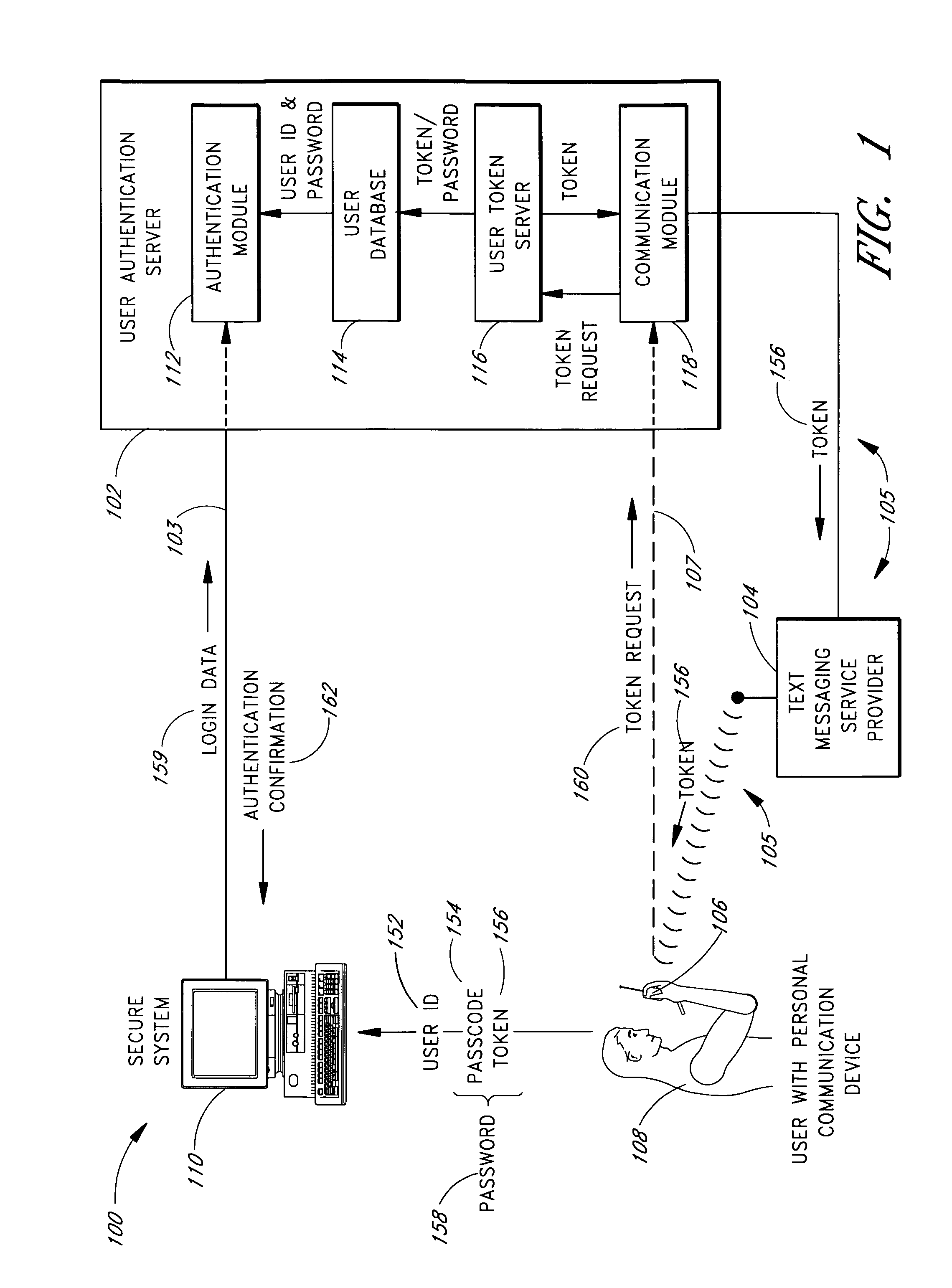
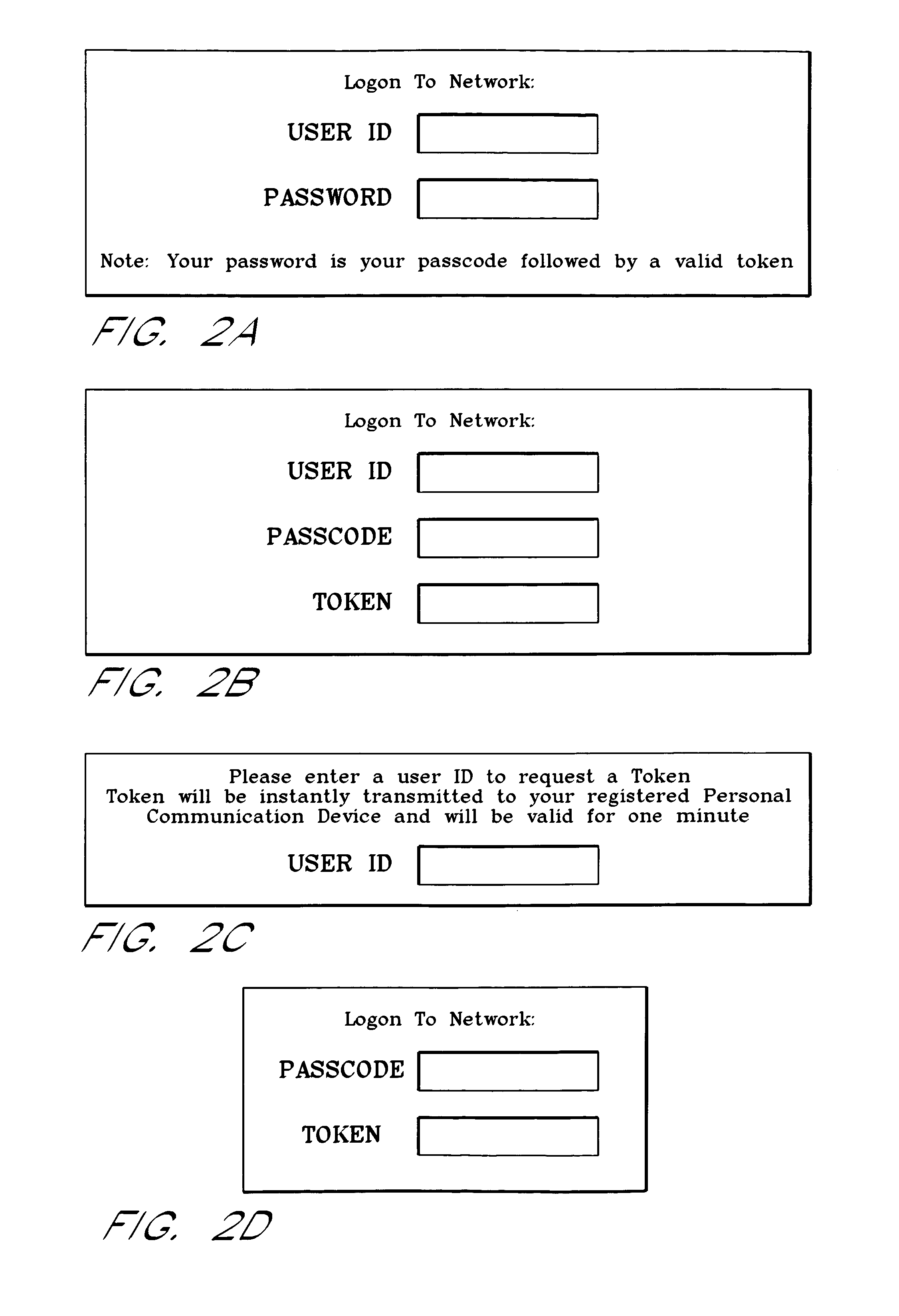
InactiveUS6993658B1Metering/charging/biilling arrangementsDigital data processing detailsPagerInternet privacy
A password setting system for a secure system includes a user token server and a communication module. The user token server generates a random token in response to a request for a new password from a user. The server creates a new password by concatenating a secret passcode that is known to the user with the token. The server sets the password associated with the user's user ID to be the new password. The communication module transmits the token to a personal communication device, such as a mobile phone or a pager carried by the user. The user concatenates the secret passcode with the received token in order to form a valid password, which the user submits to gain access to the secure system. Accordingly, access to the system is based upon: nonsecret information known to the user, such as the user ID; secret information known to the user, such as the passcode; and information provided to the user through an object possessed by the user, such as the token.
Owner:DYNAPASS IP HLDG LLC
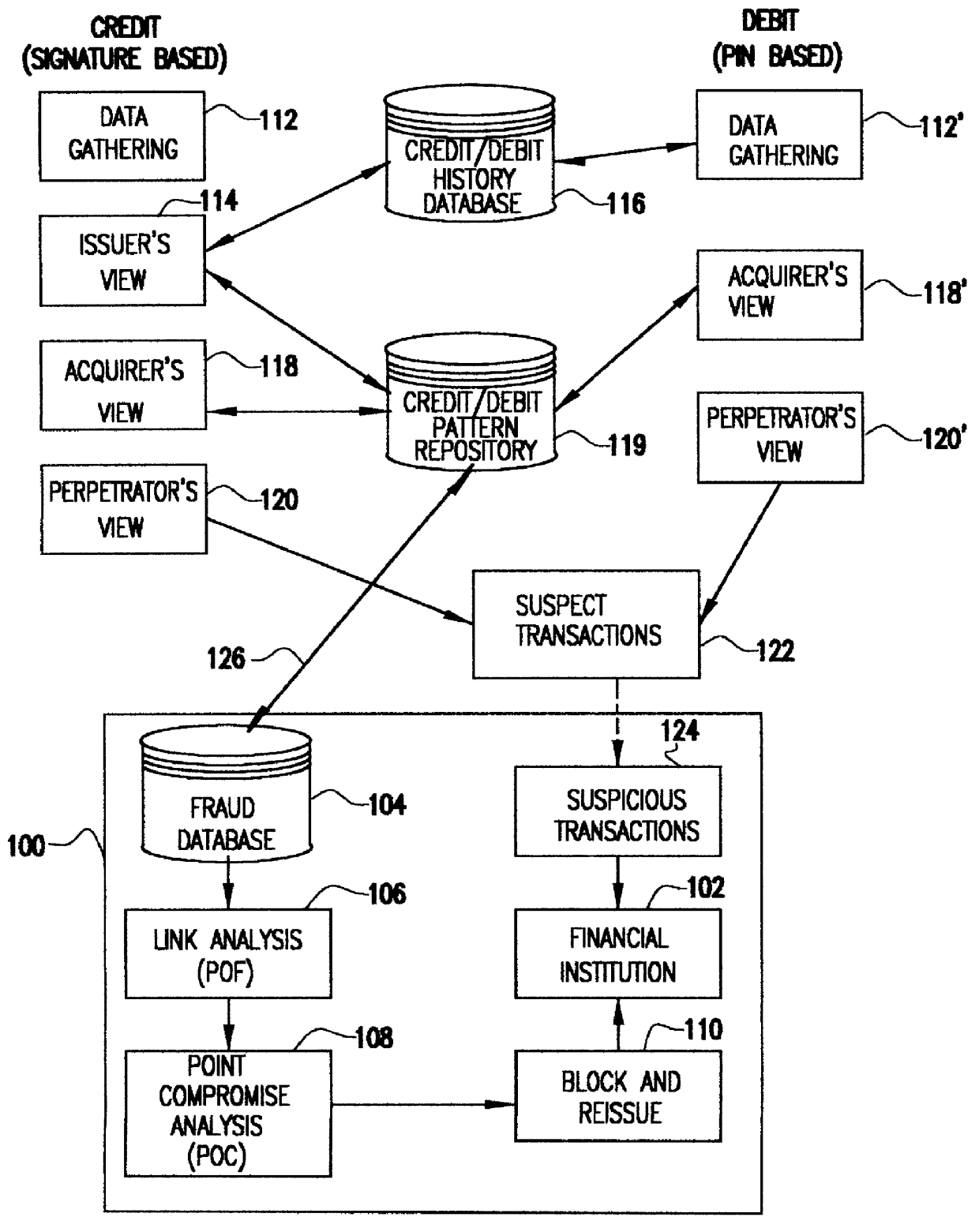
System for detecting counterfeit financial card fraud
Counterfeit financial card fraud is detected based on the premise that the fraudulent activity will reflect itself in clustered groups of suspicious transactions. A system for detecting financial card fraud uses a computer database comprising financial card transaction data reported from a plurality of financial institutions. The transactions are scored by assigning weights to individual transactions to identify suspicious transactions. The geographic region where the transactions took place as well as the time of the transactions are recorded. An event building process then identifies cards involved in suspicious transactions in a same geographic region during a common time period to determine clustered groups of suspicious activity suggesting an organized counterfeit card operation which would otherwise be impossible for the individual financial institutions to detect.
Owner:FAIR ISAAC & CO INC
Financial transactions with dynamic personal account numbers
ActiveUS20070208671A1Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
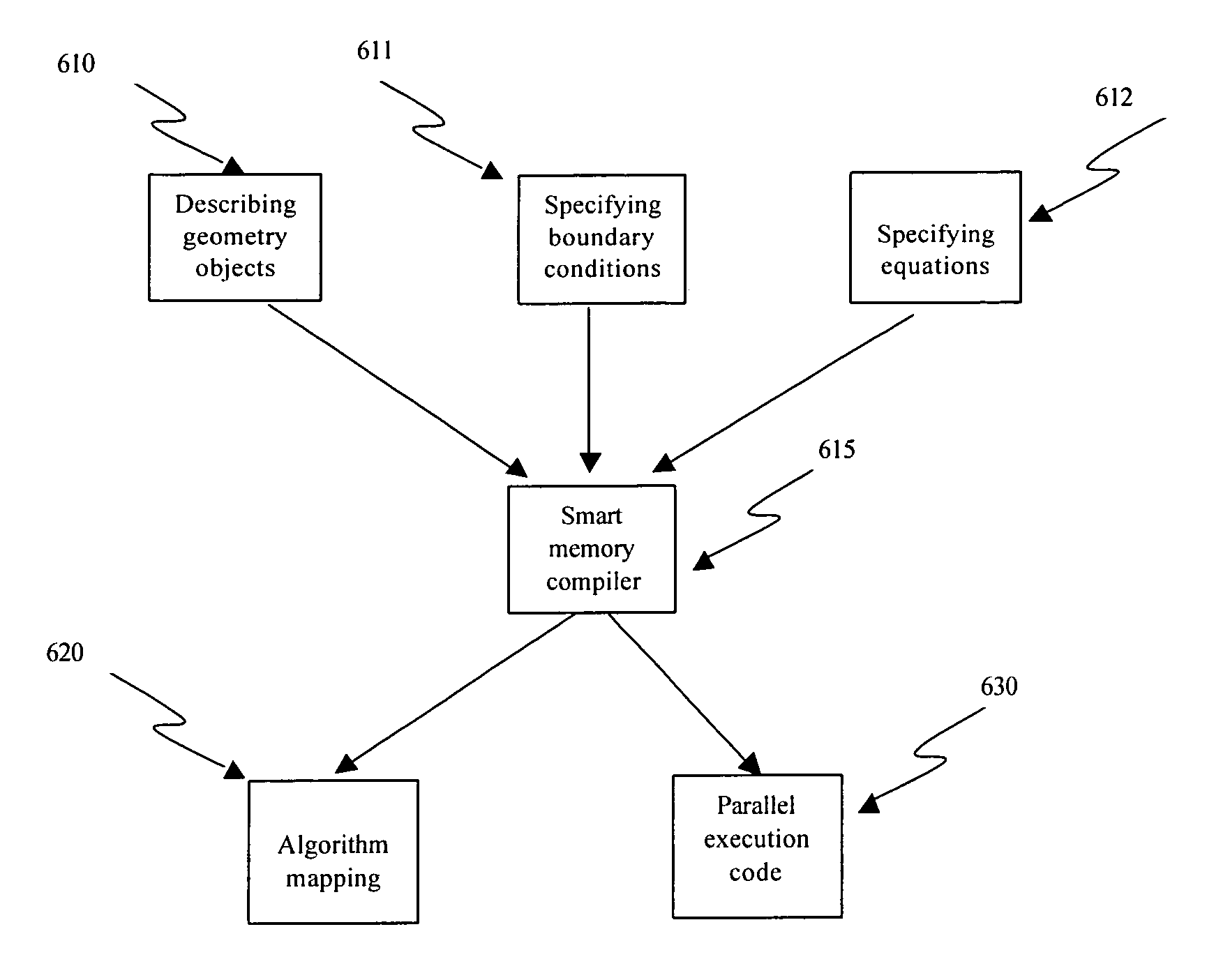
Algorithm mapping, specialized instructions and architecture features for smart memory computing
InactiveUS7546438B2Improve performanceLow costMultiplex system selection arrangementsDigital computer detailsSmart memoryExecution unit
A smart memory computing system that uses smart memory for massive data storage as well as for massive parallel execution is disclosed. The data stored in the smart memory can be accessed just like the conventional main memory, but the smart memory also has many execution units to process data in situ. The smart memory computing system offers improved performance and reduced costs for those programs having massive data-level parallelism. This smart memory computing system is able to take advantage of data-level parallelism to improve execution speed by, for example, use of inventive aspects such as algorithm mapping, compiler techniques, architecture features, and specialized instruction sets.
Owner:STRIPE INC
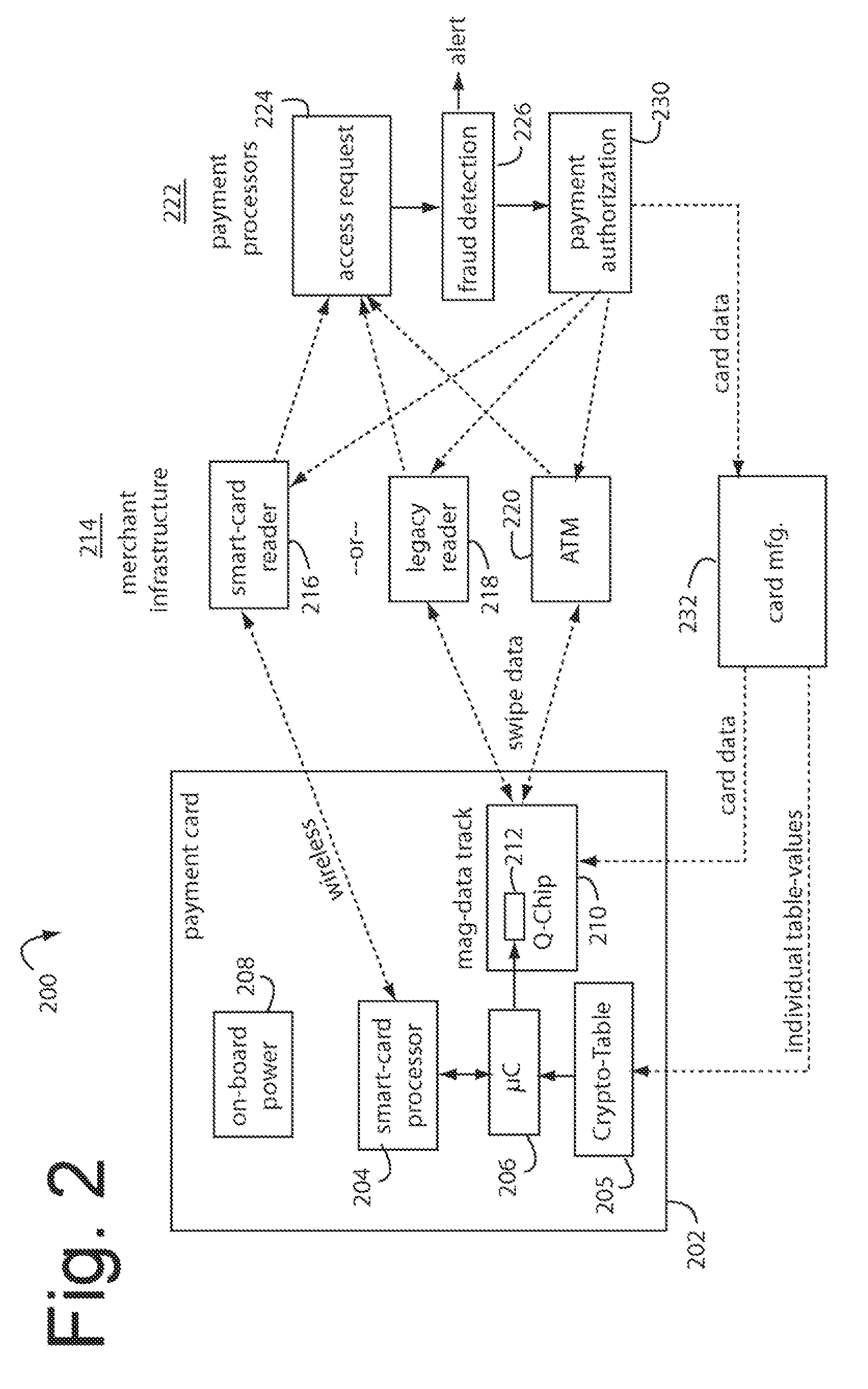
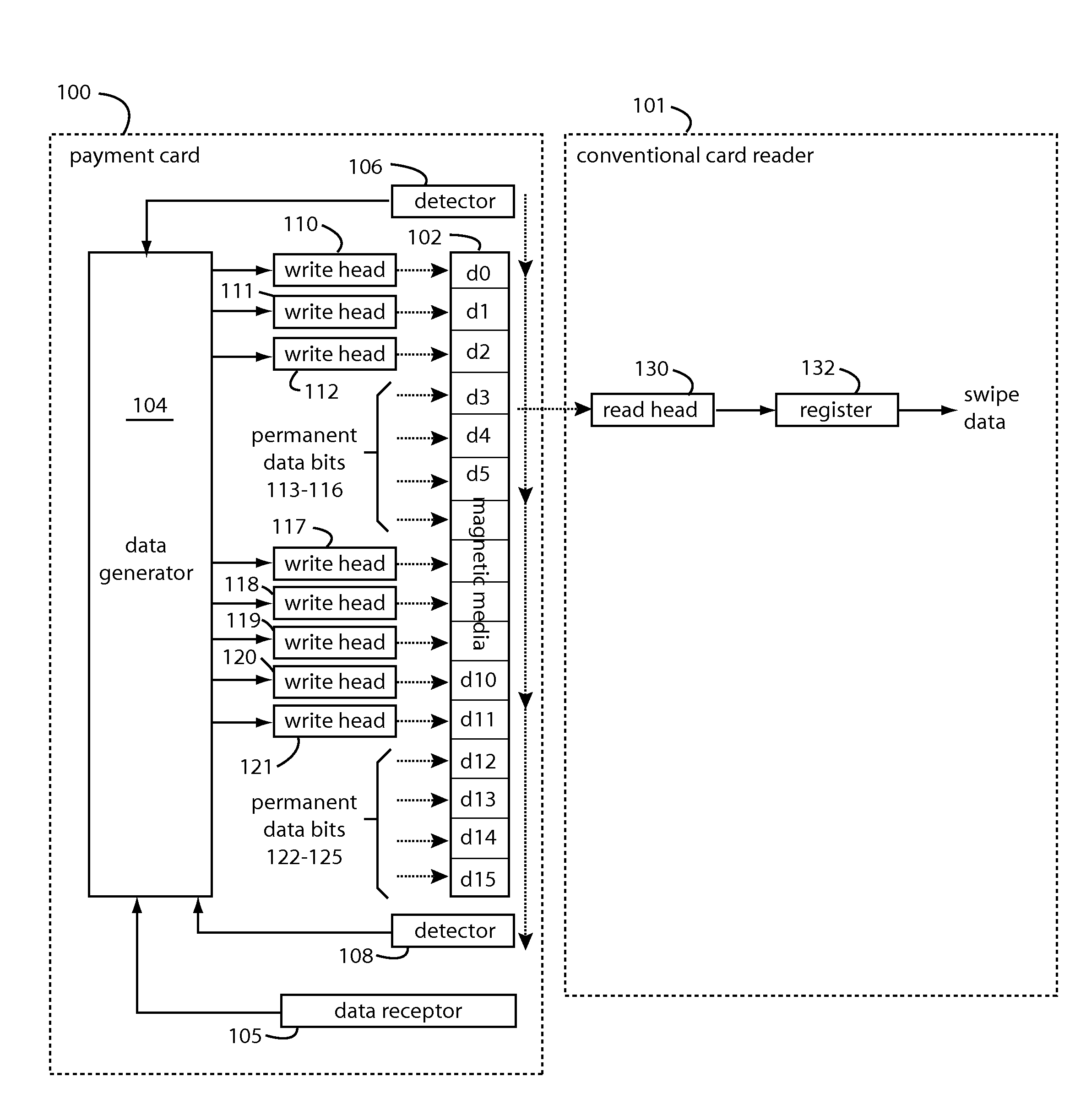
Payment card preloaded with unique numbers
ActiveUS7380710B2Reduce financial riskSimple and inexpensive and effectiveFinancePayment architectureFinancial transactionPayment order
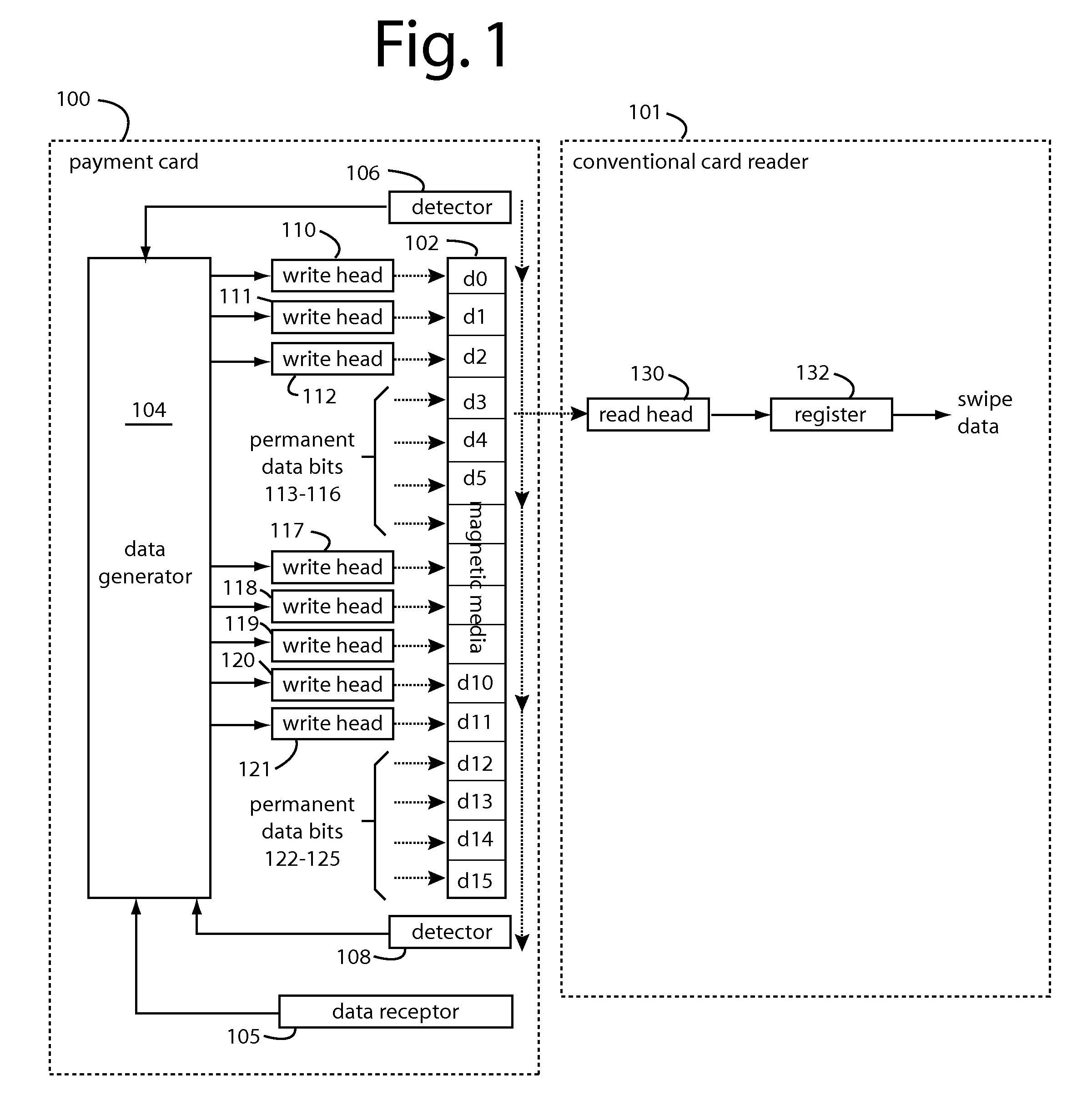
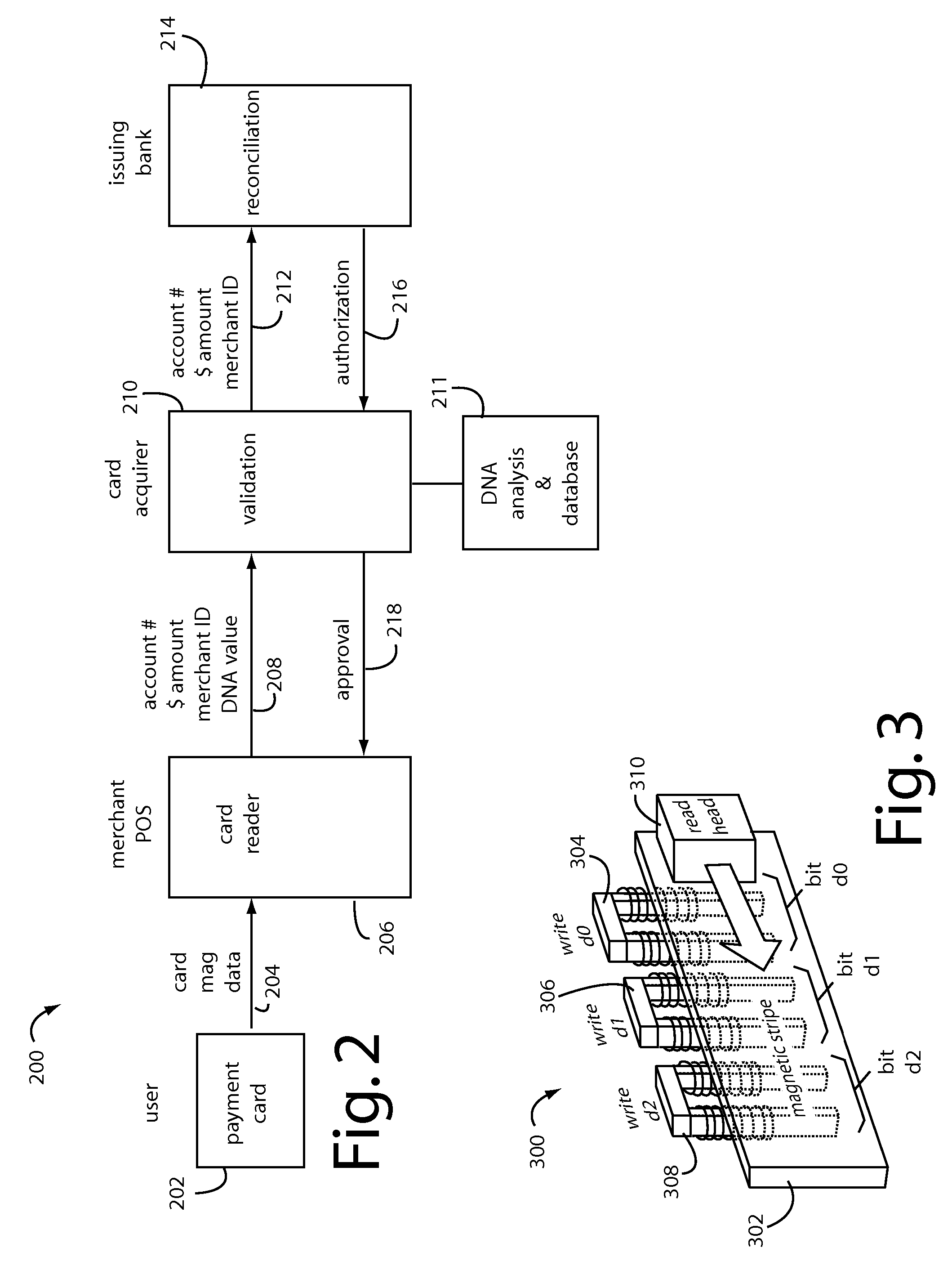
A conventional looking payment card comprises a plastic card with a legacy card reader compatible magnetic stripe for dynamic user account data. Internal to the plastic card, and behind the magnetic stripe, a number of fixed-position magnetic write heads allow the user account data to be modified autonomously. Electronics within the card are pre-loaded with many unique numbers that are selected for one-time use in financial transactions. A payment processing center keeps track of the unique numbers used, and knows which numbers to expect in future transactions. It will not authorize transaction requests if the unique number read during a magnetic card swipe is not as expected. A card-swipe detector embedded in the plastic card detects each use in a scanner, so changes can be made to the data bits sent to the write heads.
Owner:FITBIT INC
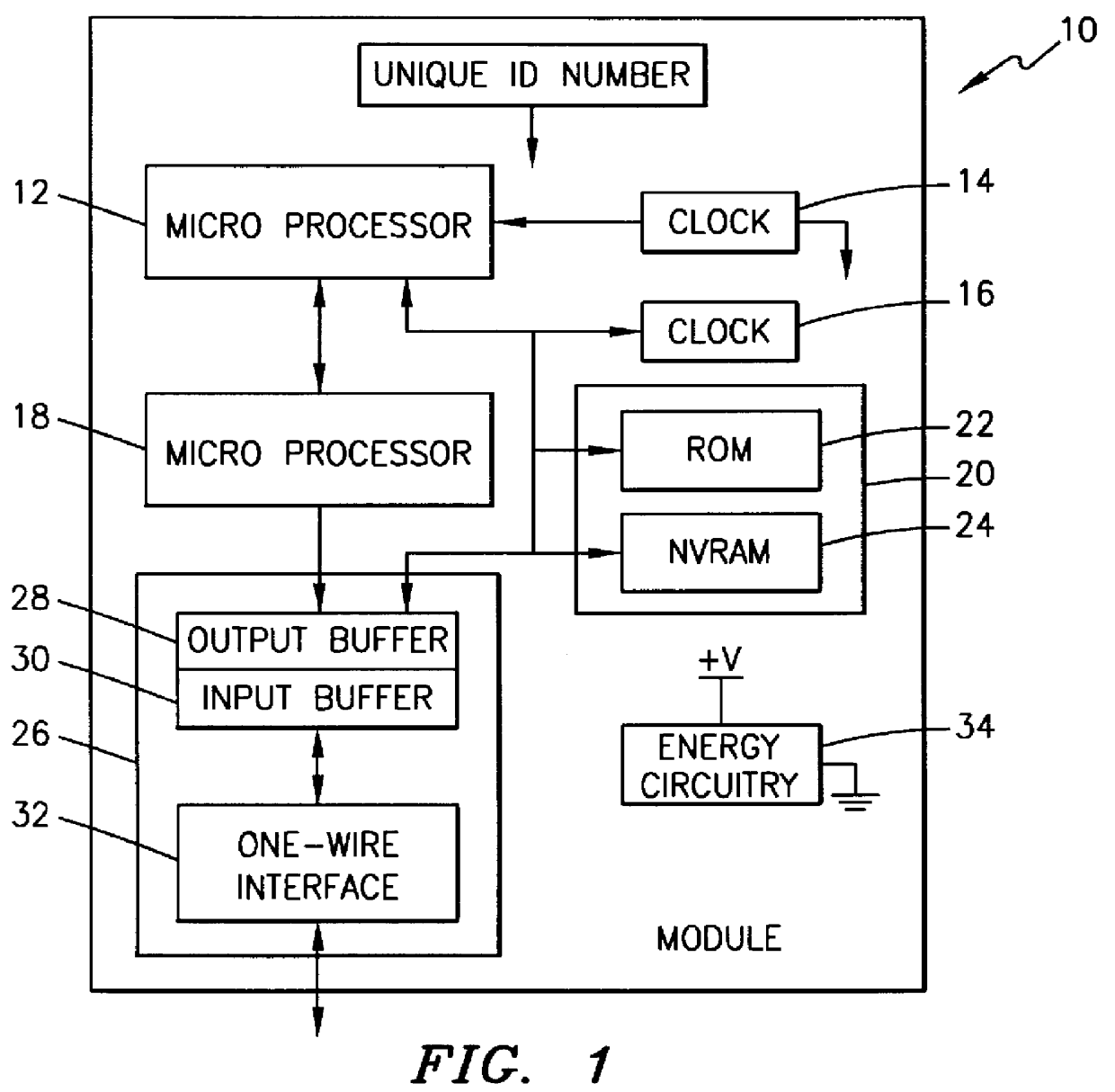
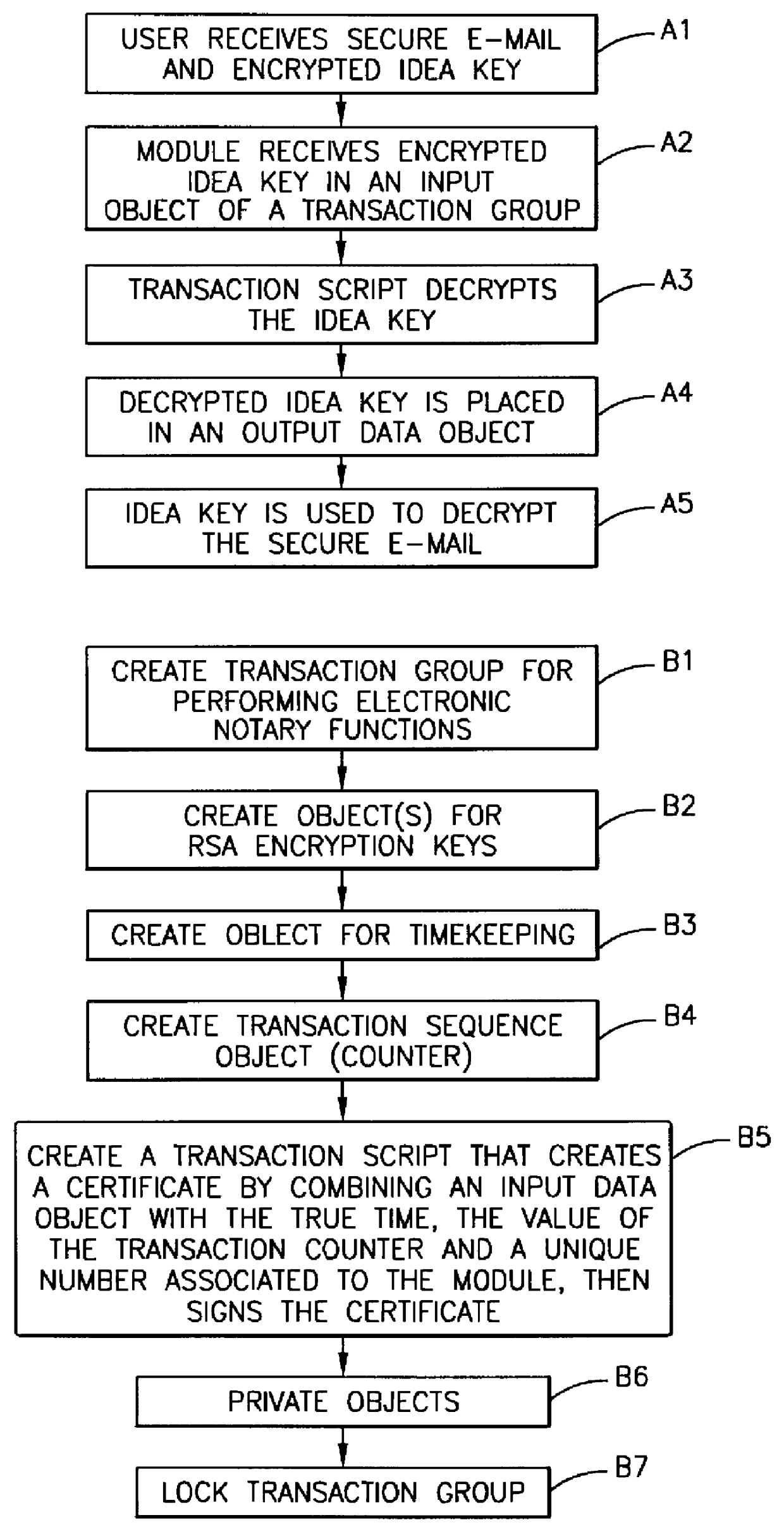
Method, apparatus, system and firmware for secure transactions
The present invention relates to an electronic module used for secure transactions. More specifically, the electronic module is capable of passing information back and forth between a service provider's equipment via a secure, encrypted technique so that money and other valuable data can be securely passed electronically. The module is capable of being programmed, keeping track of real time, recording transactions for later review, and creating encryption key pairs.
Owner:MAXIM INTEGRATED PROD INC
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com