Patents
Literature
85results about How to "Reduce financial risk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
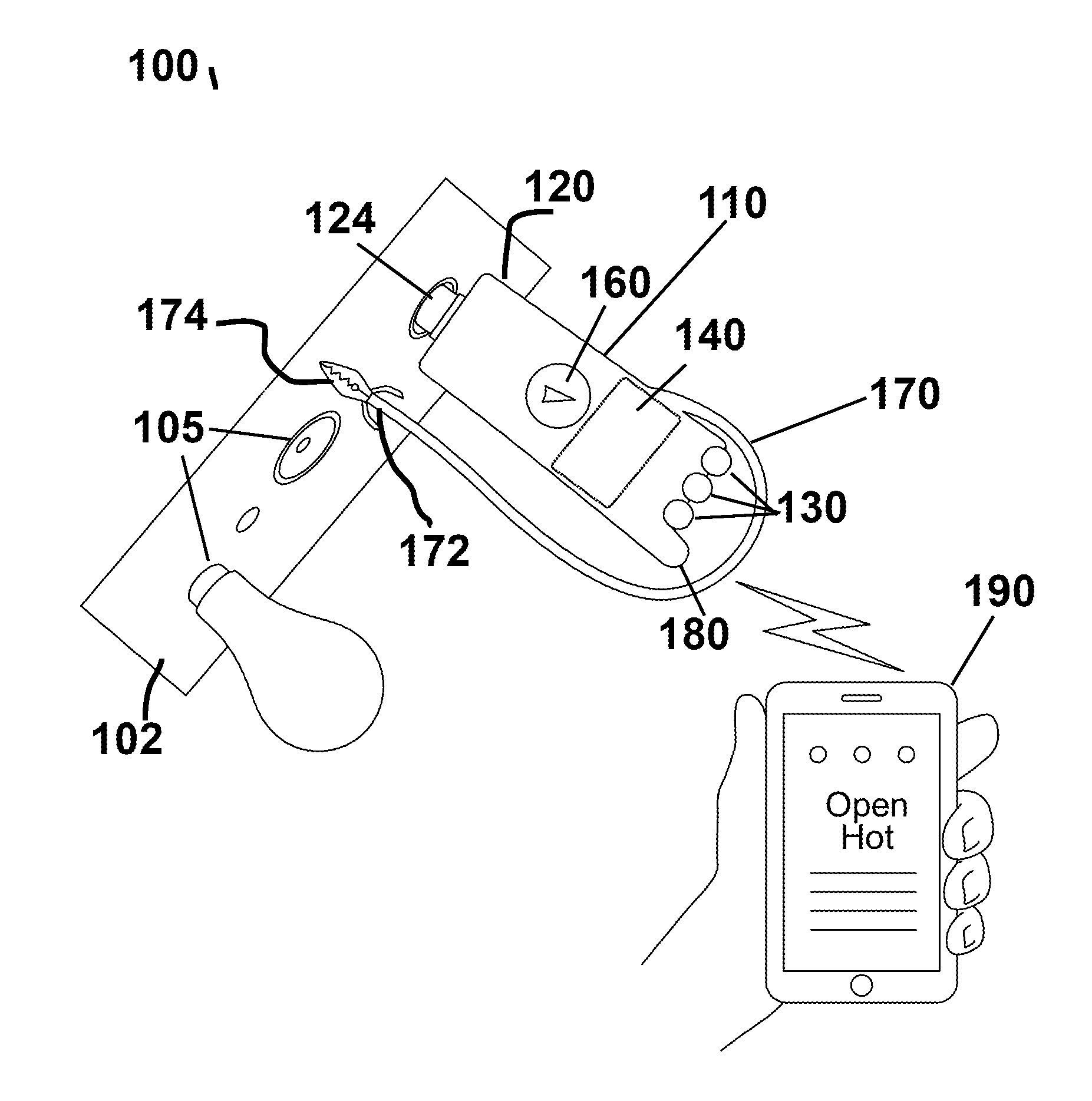
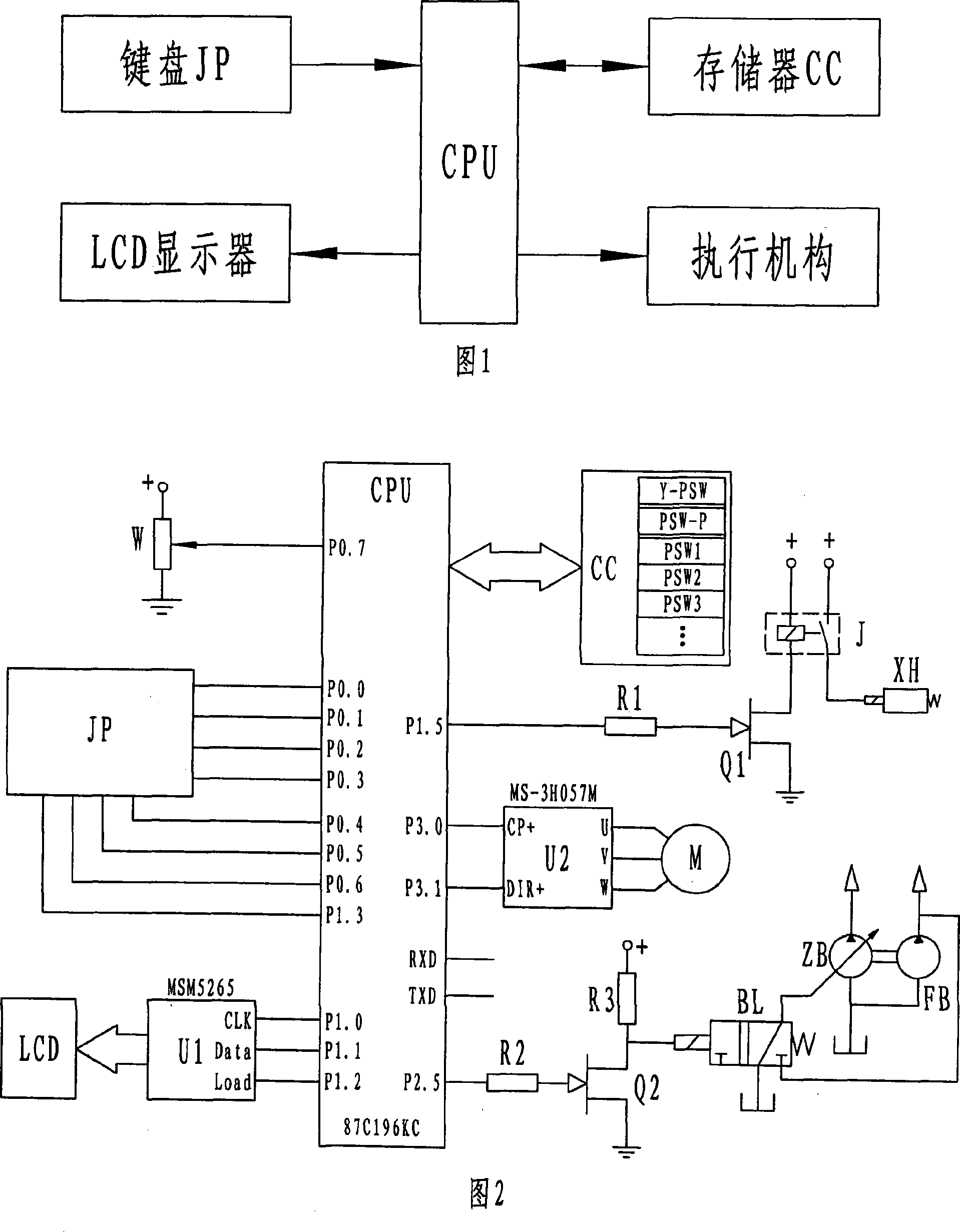
Payment card preloaded with unique numbers
ActiveUS7380710B2Reduce financial riskSimple and inexpensive and effectiveFinancePayment architectureFinancial transactionPayment order
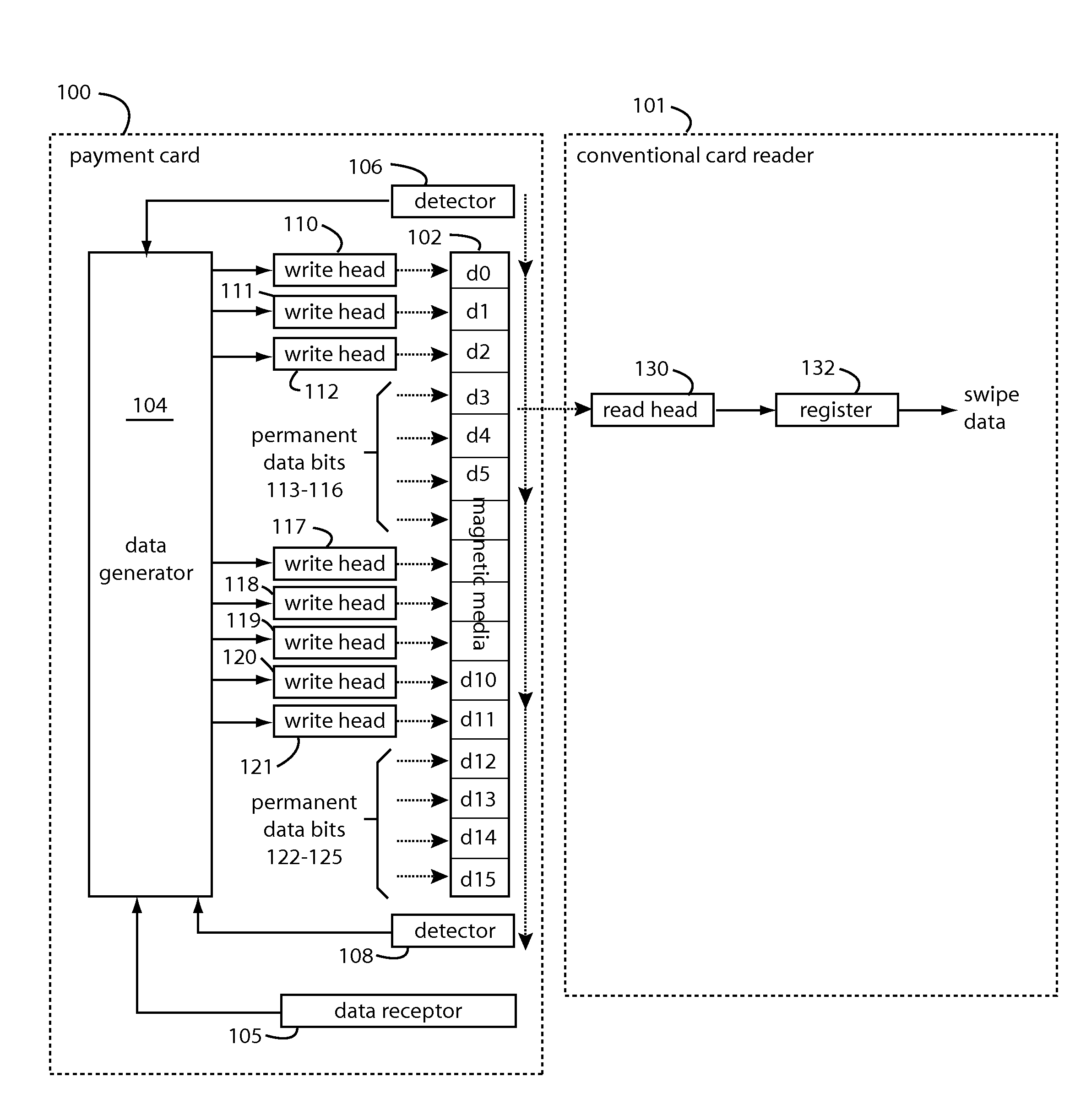
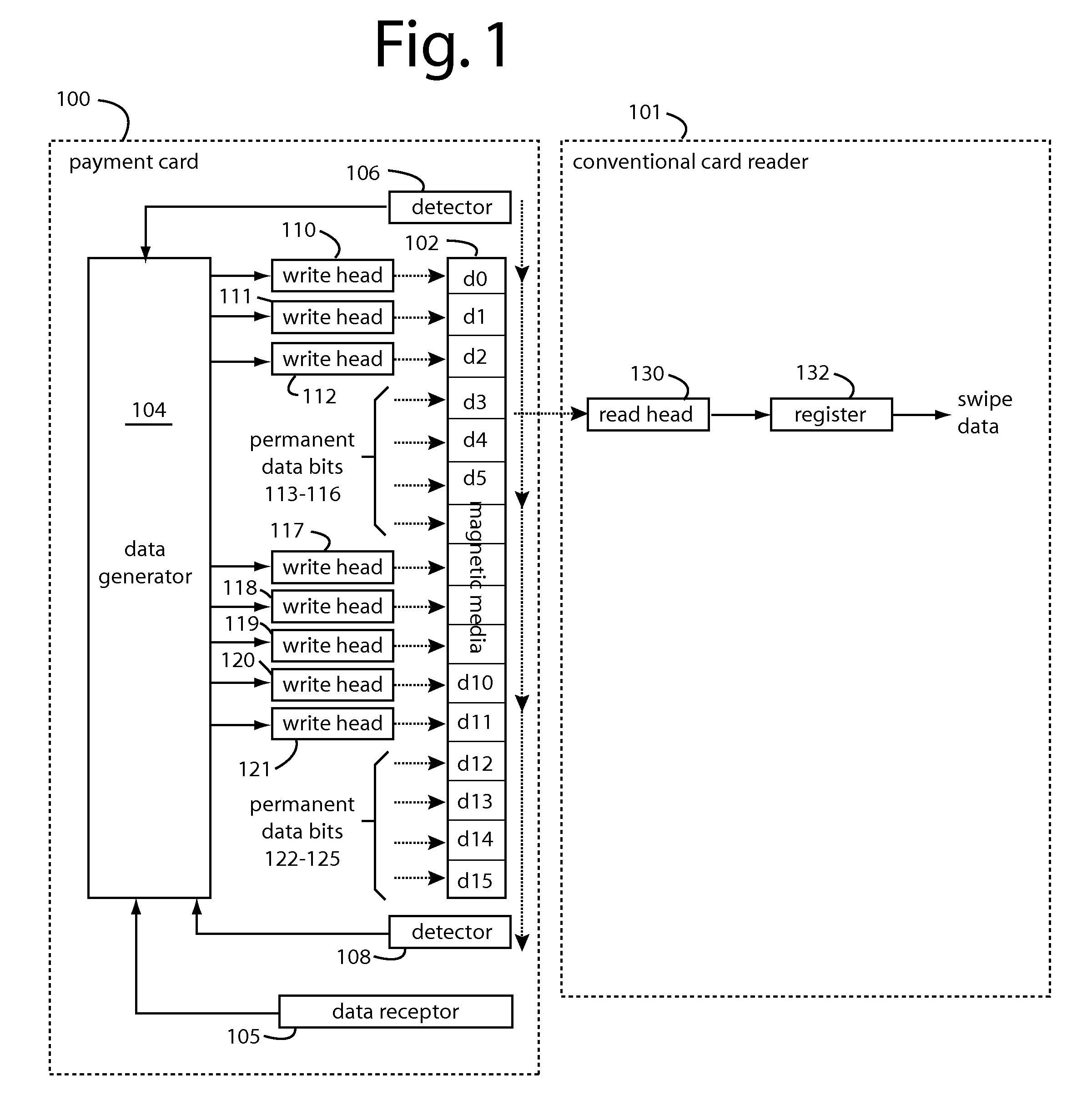
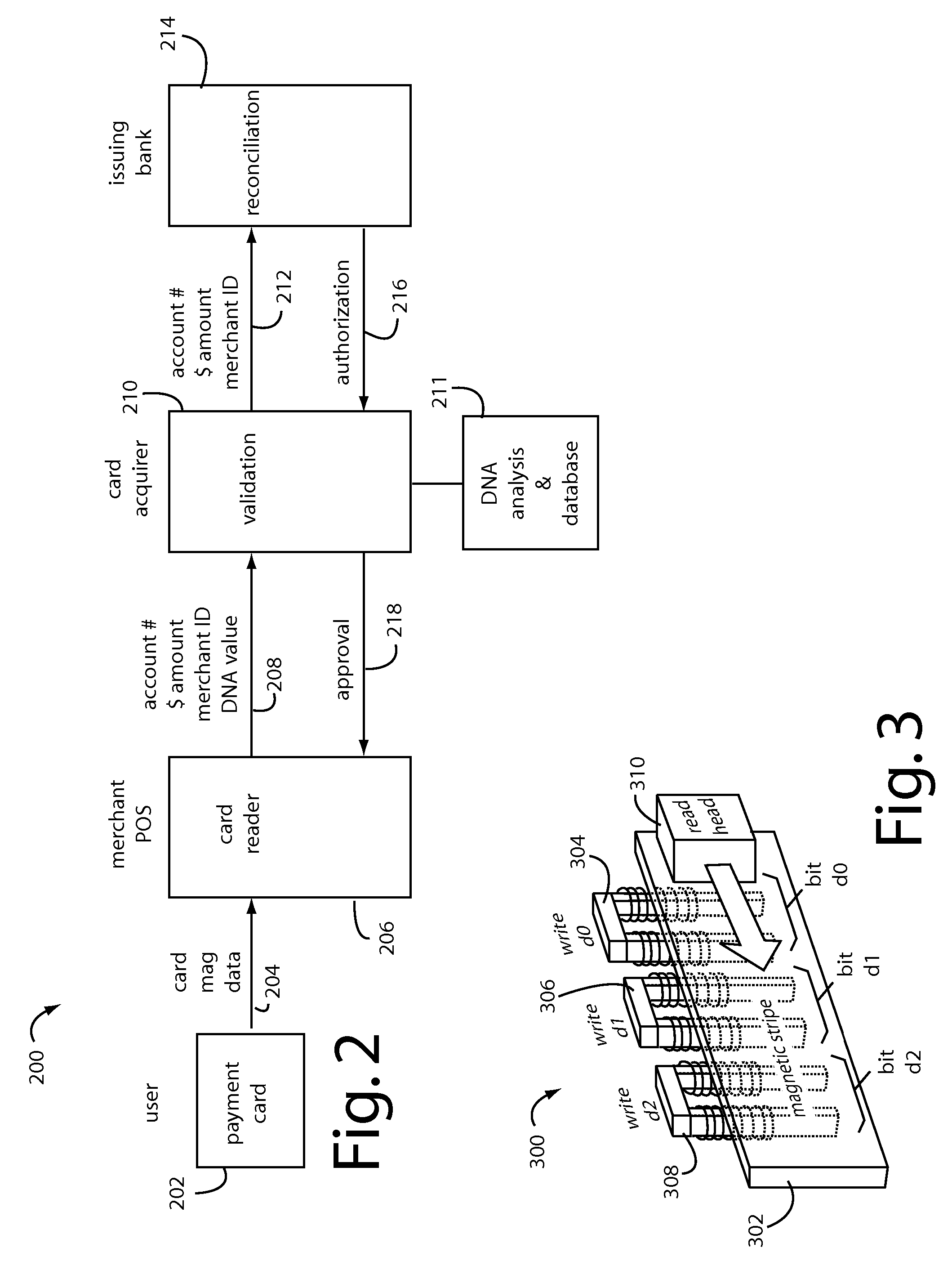
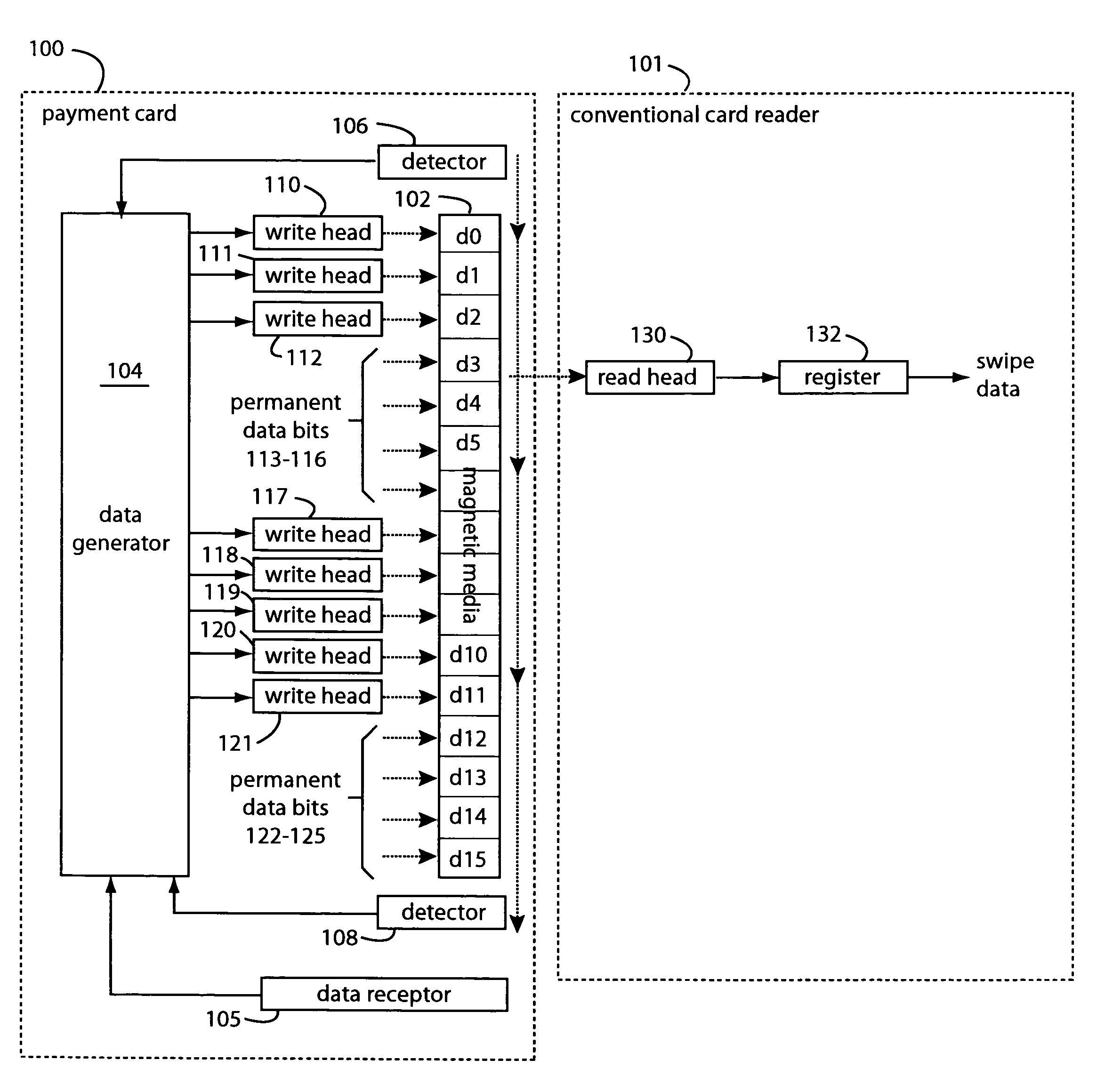
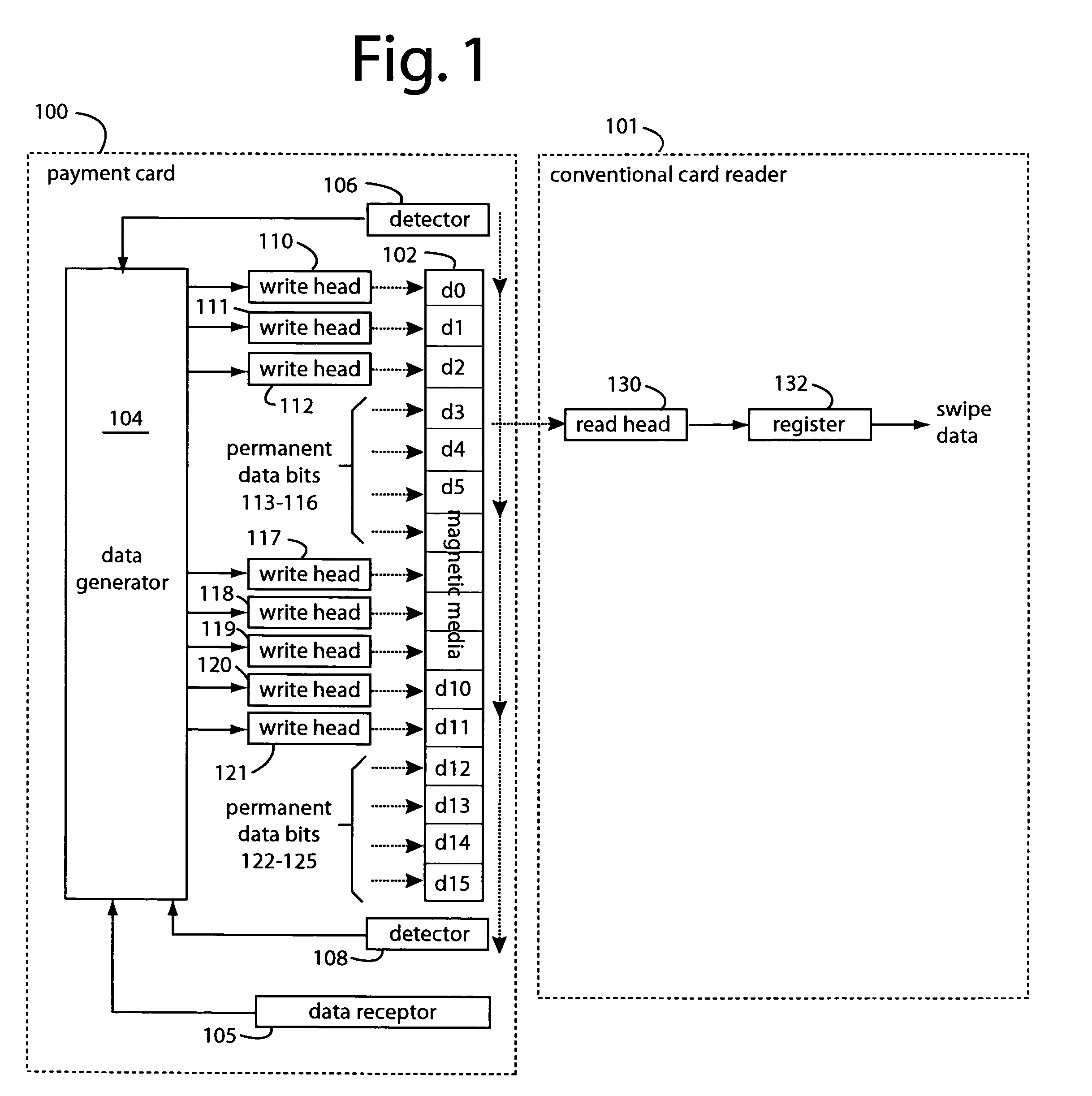
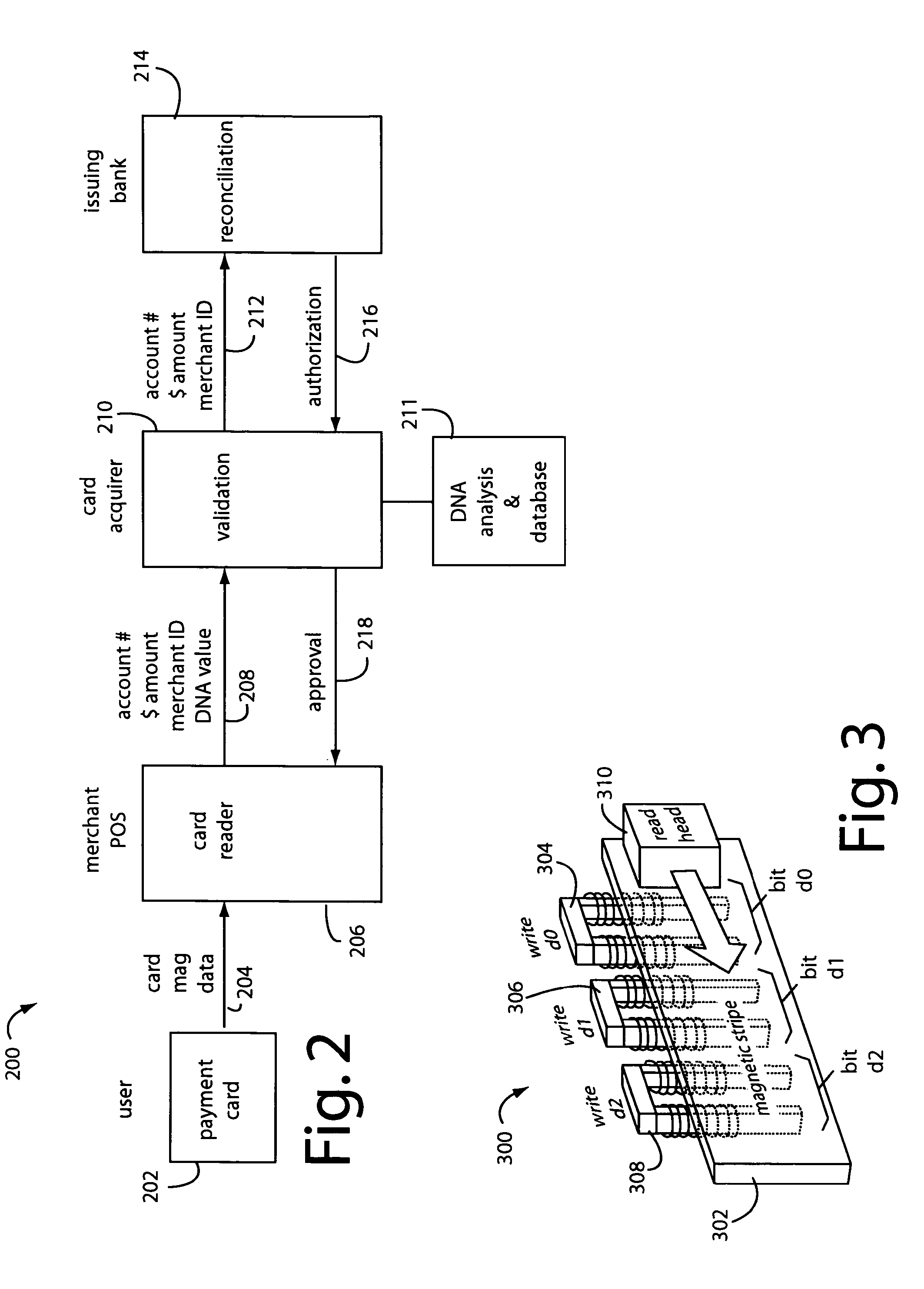
A conventional looking payment card comprises a plastic card with a legacy card reader compatible magnetic stripe for dynamic user account data. Internal to the plastic card, and behind the magnetic stripe, a number of fixed-position magnetic write heads allow the user account data to be modified autonomously. Electronics within the card are pre-loaded with many unique numbers that are selected for one-time use in financial transactions. A payment processing center keeps track of the unique numbers used, and knows which numbers to expect in future transactions. It will not authorize transaction requests if the unique number read during a magnetic card swipe is not as expected. A card-swipe detector embedded in the plastic card detects each use in a scanner, so changes can be made to the data bits sent to the write heads.
Owner:FITBIT INC
Programmable magnetic data storage card
ActiveUS7044394B2Reduce financial riskSimple and inexpensive and effectiveAcutation objectsApparatus for flat record carriersMicrocomputerComing out
A payment card comprises a plastic card with a magnetic stripe for user account data. Internal to the plastic card, and behind the magnetic stripe, a number of fixed-position magnetic write heads allow the user account data to be automatically modified. For example, a data field that counts the number of times the card has been scanned is incremented. A payment processing center keeps track of this usage-counter data field, and will not authorize transaction requests that come out of sequence. For example, as can occur from a magnetic clone of a card that has been skimmed and tried later. A card-swipe detector embedded in the plastic card detects each use in a scanner, and it signals an internal microcomputer which changes data bits sent to the write heads. Once scanned, the payment card can also disable any reading of the user account data for a short fixed period of time.
Owner:FITBIT INC
Mobile station and methods for diagnosing and modeling site specific effluent treatment facility requirements
InactiveUS20090032446A1Reduce financial riskHigh continuity of operationReverse osmosisFlash degasificationIon exchangeReverse osmosis
A mobile station and methods are disclosed for diagnosing and modeling site specific effluent treatment facility requirements to arrive at a treatment regimen and / or proposed commercial plant model idealized for the particular water / site requirements. The station includes a mobile platform having power intake, effluent intake and fluid outflow facilities and first and second suites of selectably actuatable effluent pre-treatment apparatus. An effluent polishing treatment array is housed at the station and includes at least one of nanofiltration, reverse osmosis and ion-exchange stages. A suite of selectively actuatable post-treatment apparatus are housed at the station. Controls are connected at the station for process control, monitoring and data accumulation. A plurality of improved water treatment technologies are also disclosed.
Owner:ROCKWATER RESOURCE
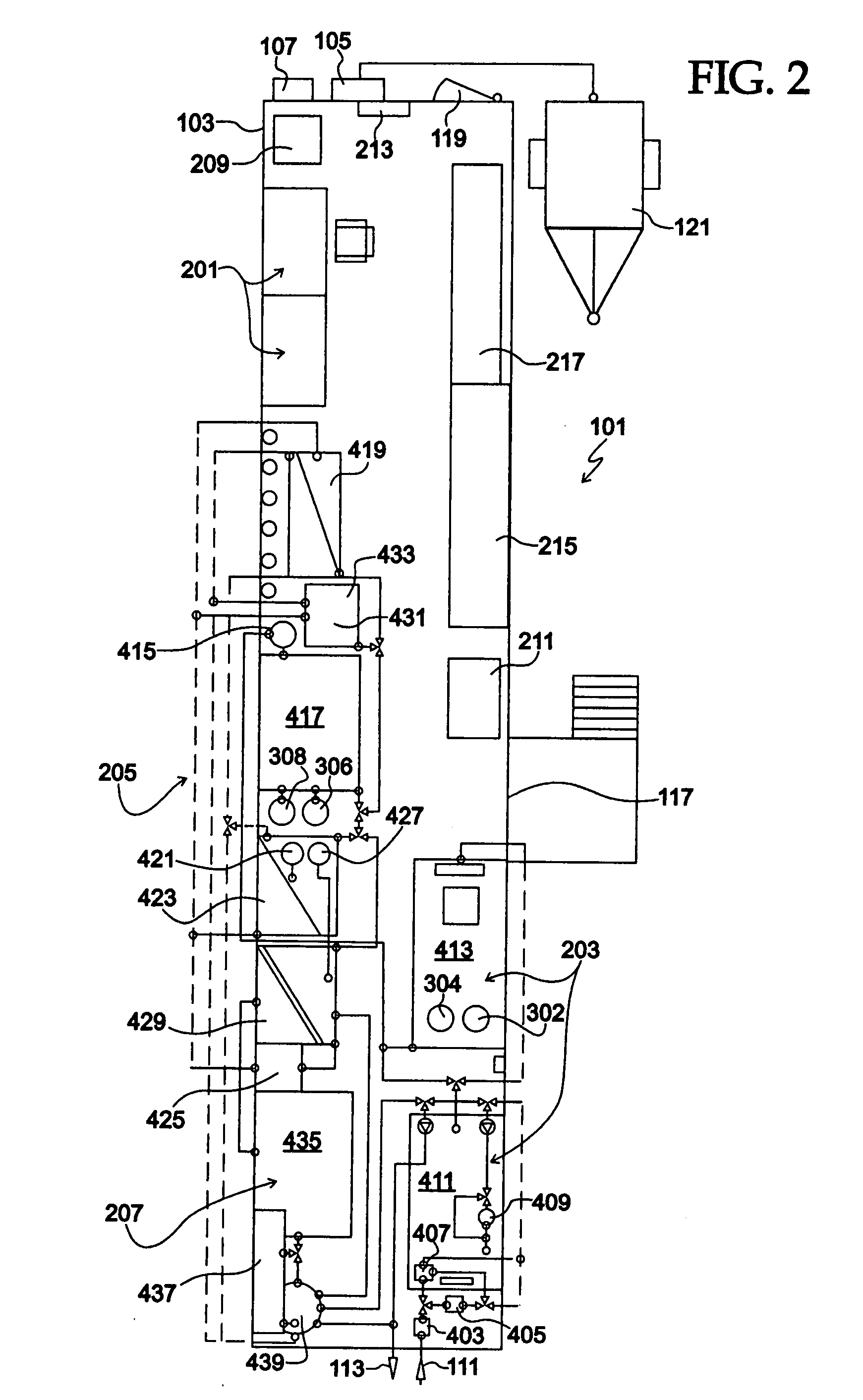
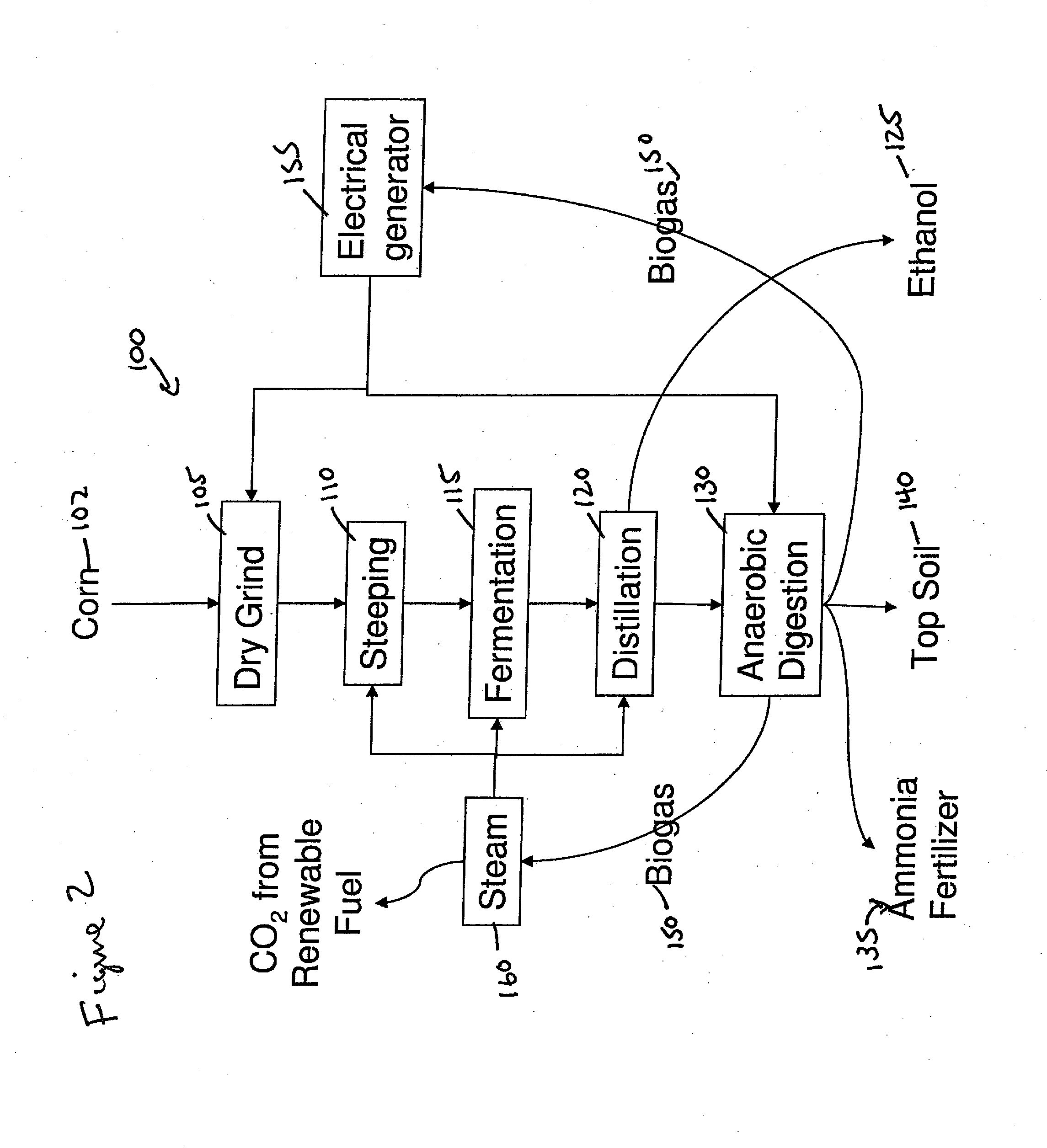
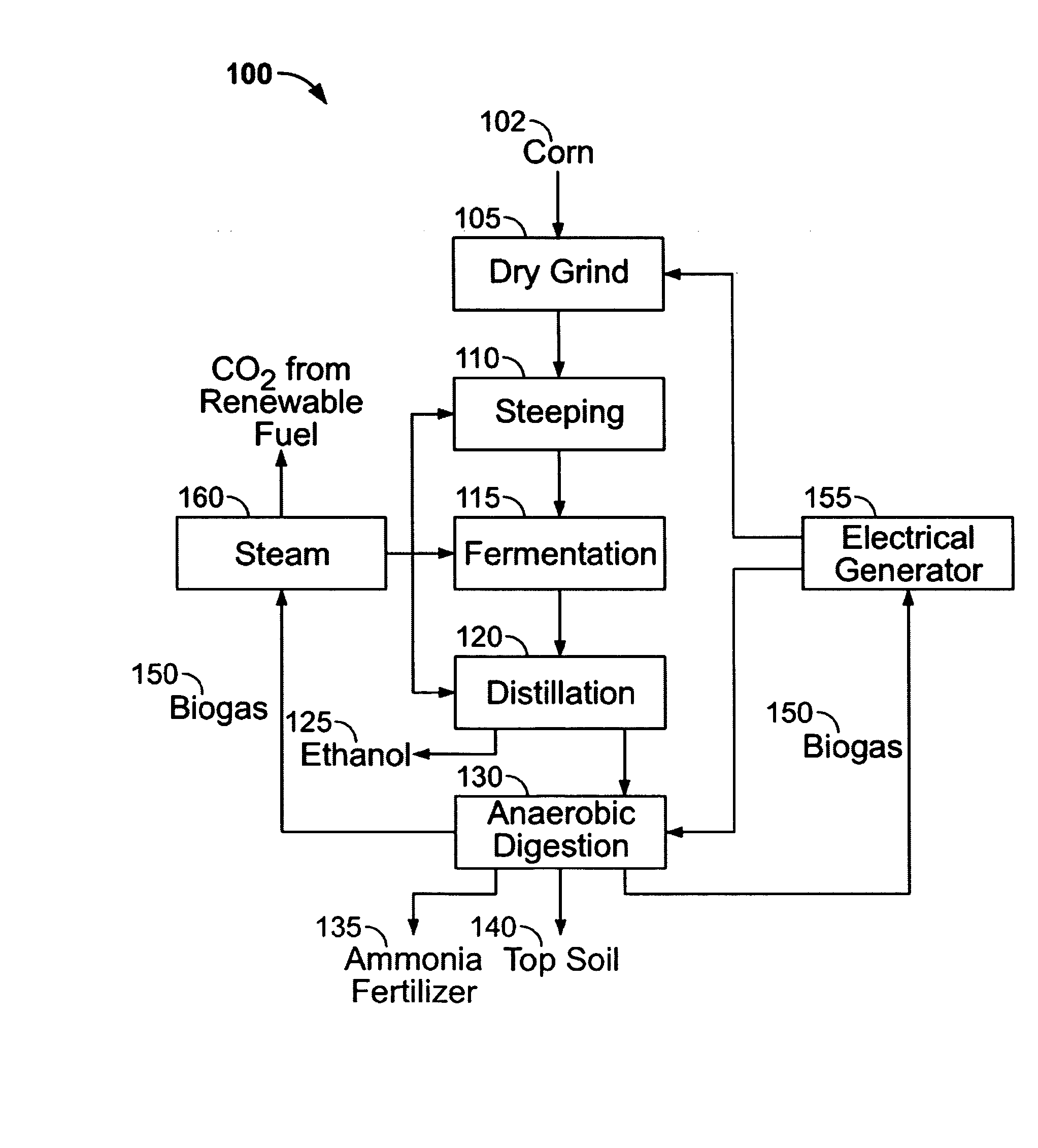
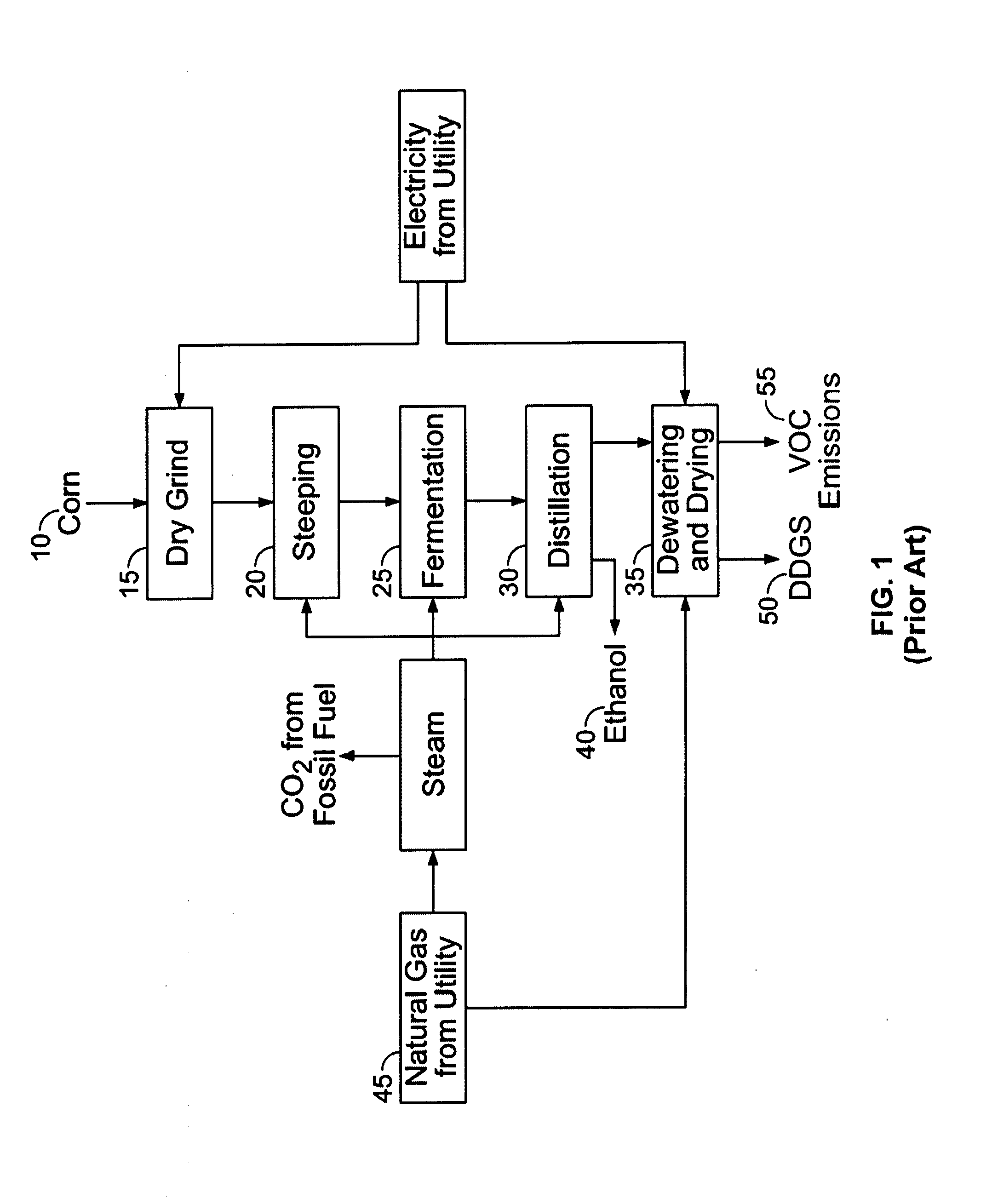
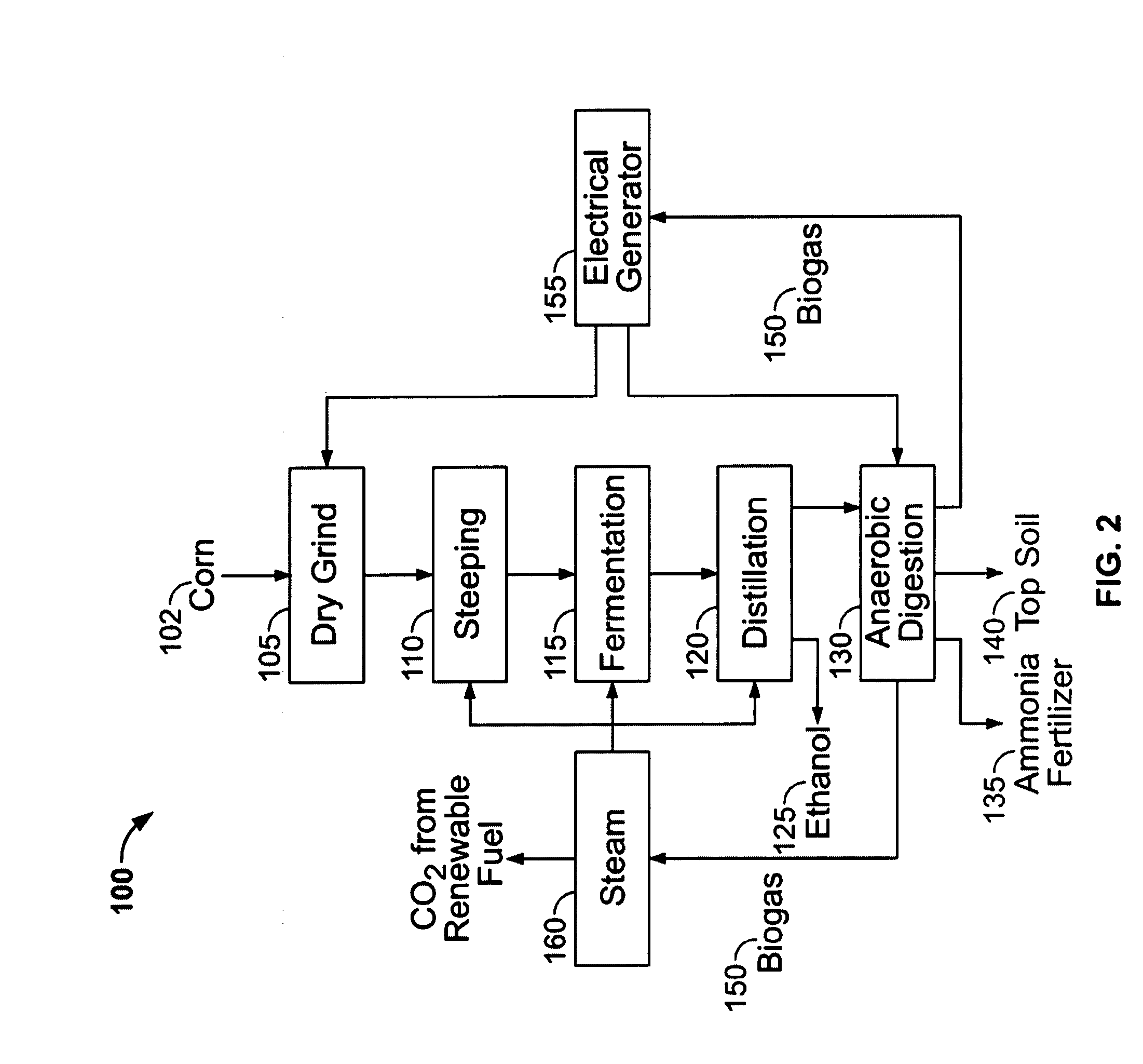
Process for producing ethanol and for energy recovery
InactiveUS20070141691A1Increasing net energy valueReducing the reliance of the ethanol industryBioreactor/fermenter combinationsBio-organic fraction processingElectricityDistillation
The present invention is directed to a process for the production of ethanol and energy. The process includes the steps of fermenting a corn mash in an aqueous medium to produce a beer. Next, the beer is distilled to produce ethanol and a whole stillage. The whole stillage is anaerobically digested to produce a biogas and a residue. The biogas is combusted to produce electricity and steam. The electricity and steam are used during the fermentation and distillation process. The residue may further be separated into a liquid fertilizer and top soil residue.
Owner:STANLEY CONSULTANTS
Time and activity tracker
InactiveUS20020128803A1Reduced vehicle usageReduced car emissionNuclear monitoringDigital computer detailsLogfileData collector
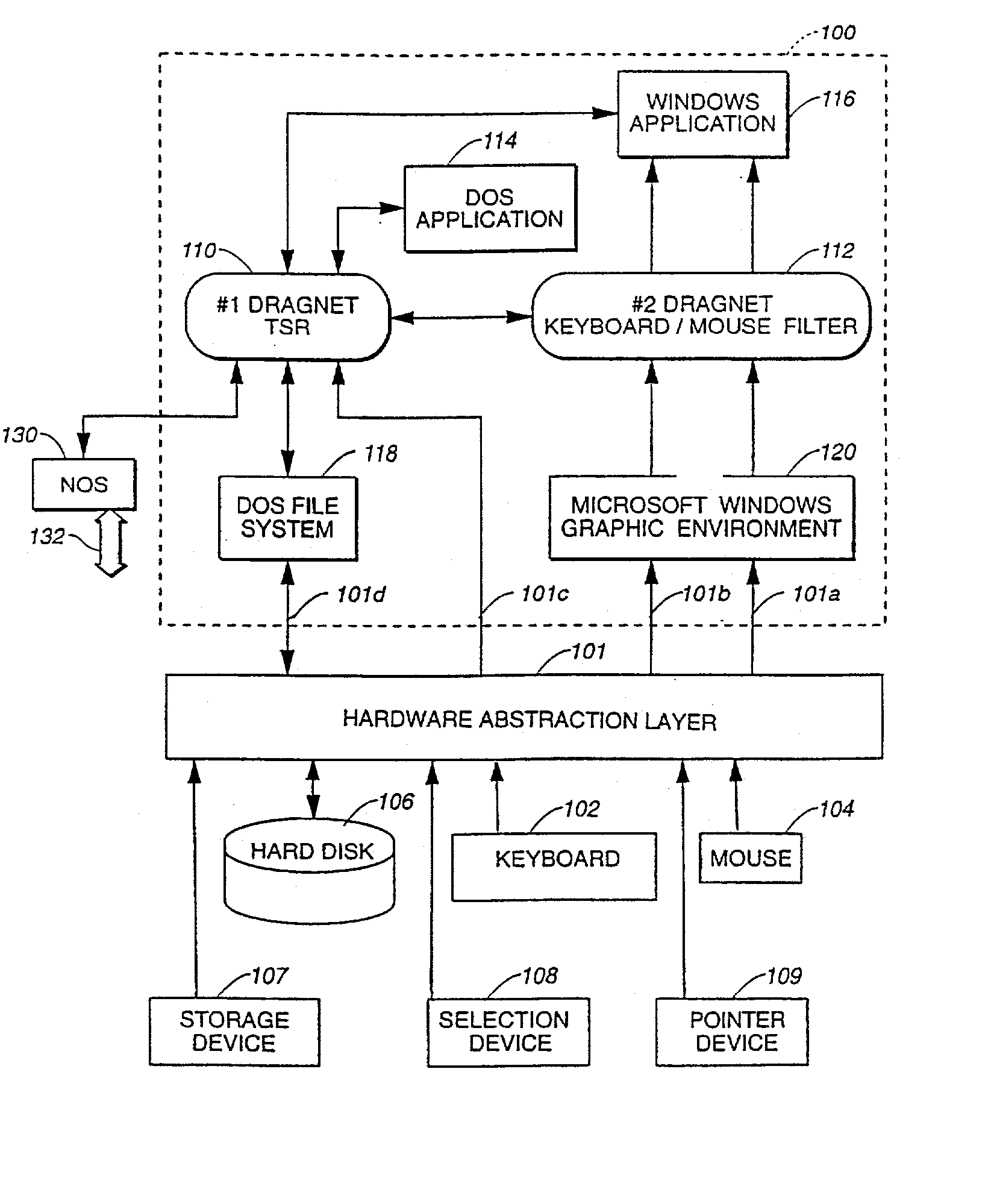
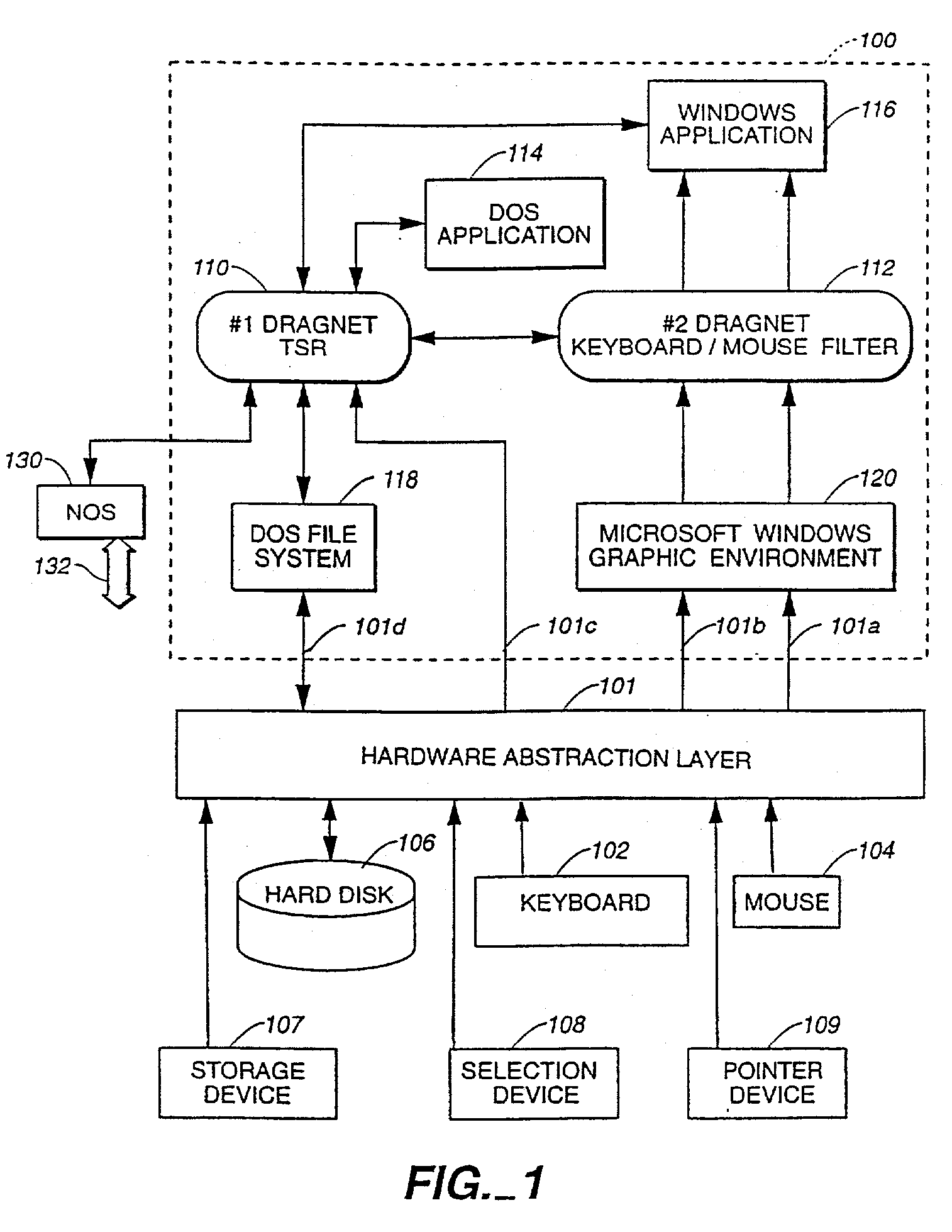
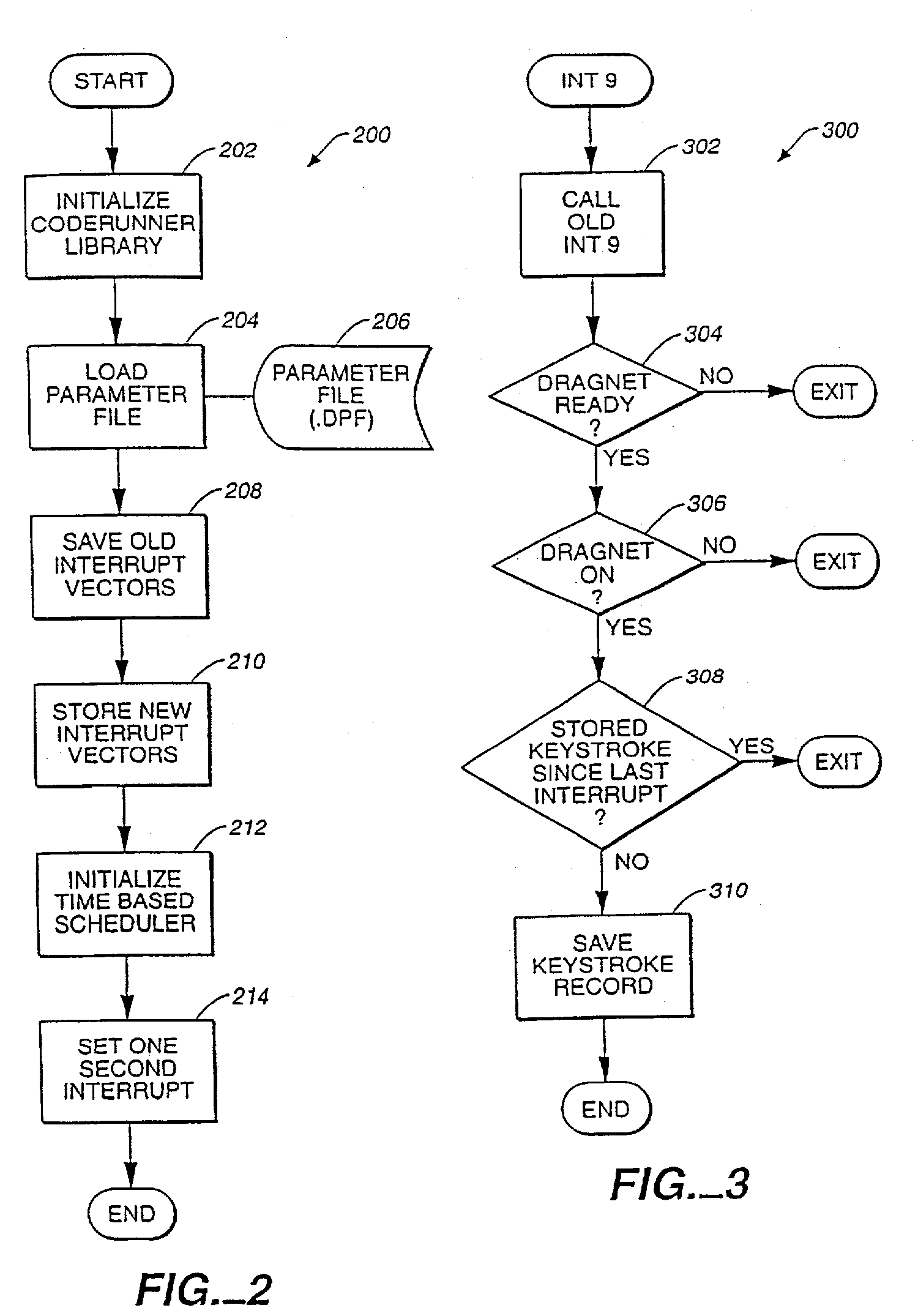
A method and system for automatically collecting and for analyzing information about time and work performed on a computer includes a hardware abstraction layer for monitoring activity on various user input devices. The system also includes the following elements: a data collector for monitoring certain portions of a user's computer activity and for logging into a log file those certain portions of a user's computer activity; a data analyzer for determining by following user-defined rules showing which portions of those certain portions of a user's computer activity constitutes continuous work activities, and how this work should be categorized by project and task with project; and an external interface for building the rules defining work. The data collector includes a resident module, such as a TSR (terminate-and-stay-resident) module, which extends the file system of the computer so that detailed records are kept of file activities. The data collector also routes information about file and keyboard activity, and tabulates and writes such information to a user's disk periodically. The hardware abstraction layer is a software module which is interposed between actual physical user input devices and the data collector.
Owner:RAKUTEN INC
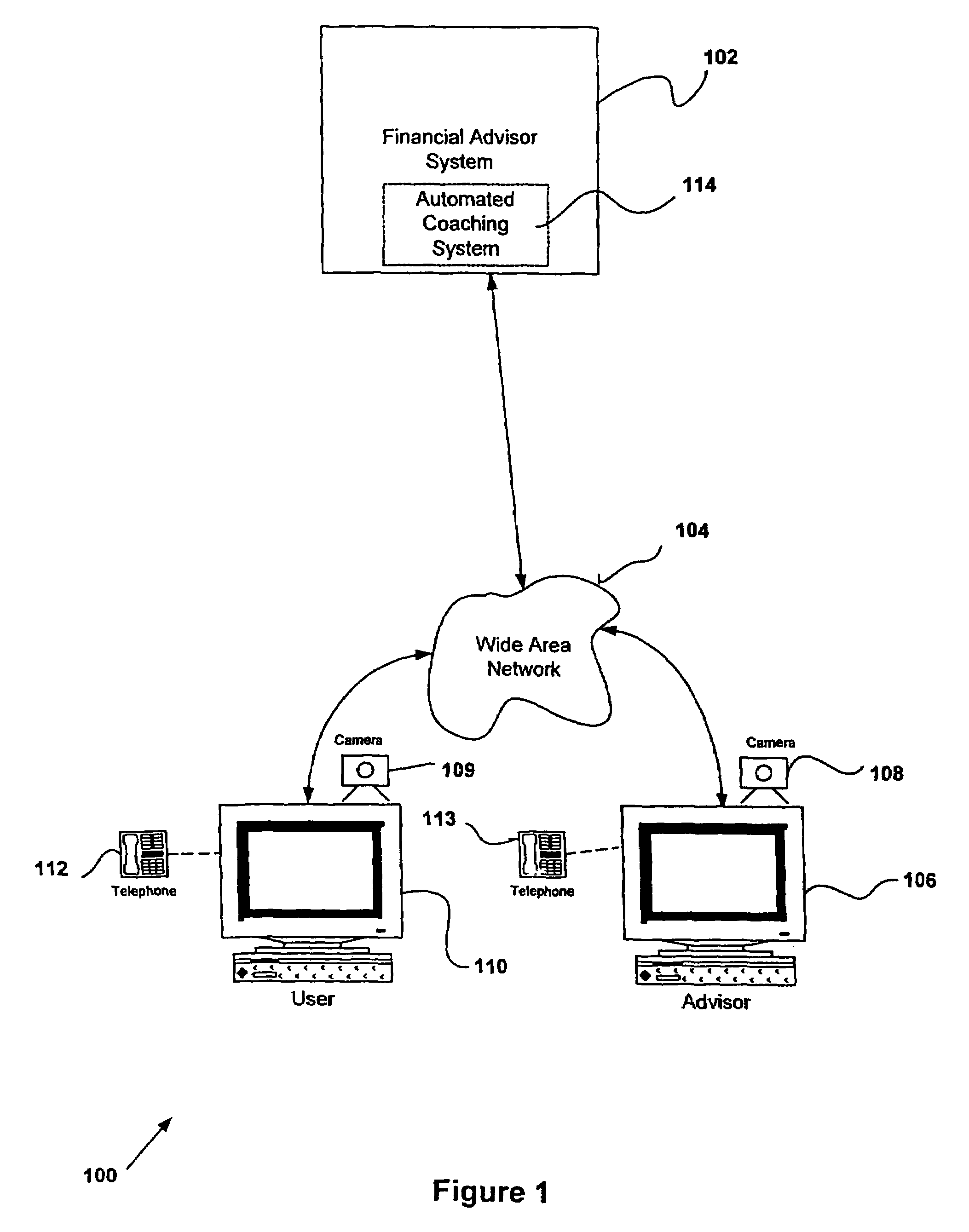
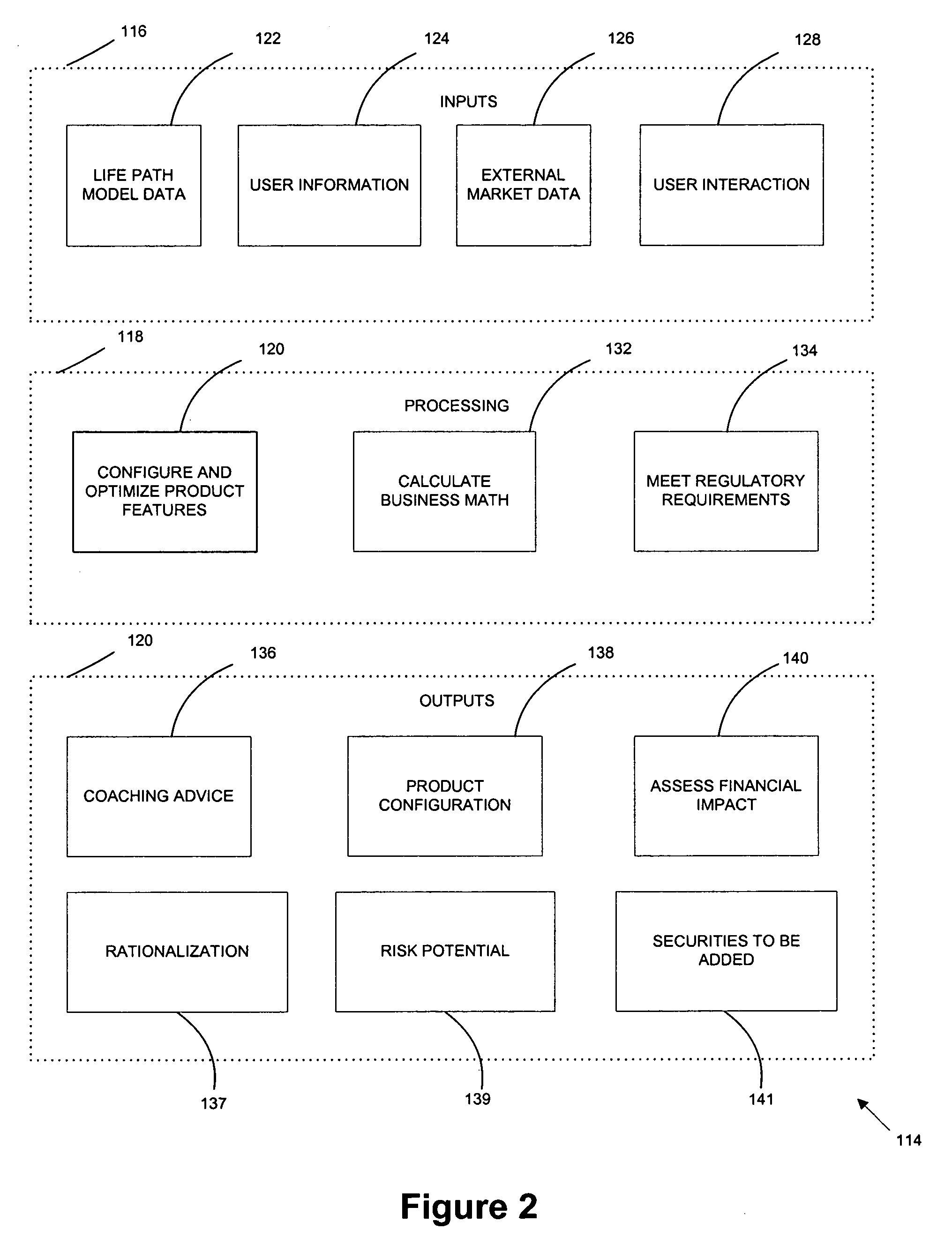
Automated coaching for a financial modeling and counseling system
InactiveUS7783545B2Low costImprove scalabilityFinanceDigital data processing detailsUser inputSystem usage
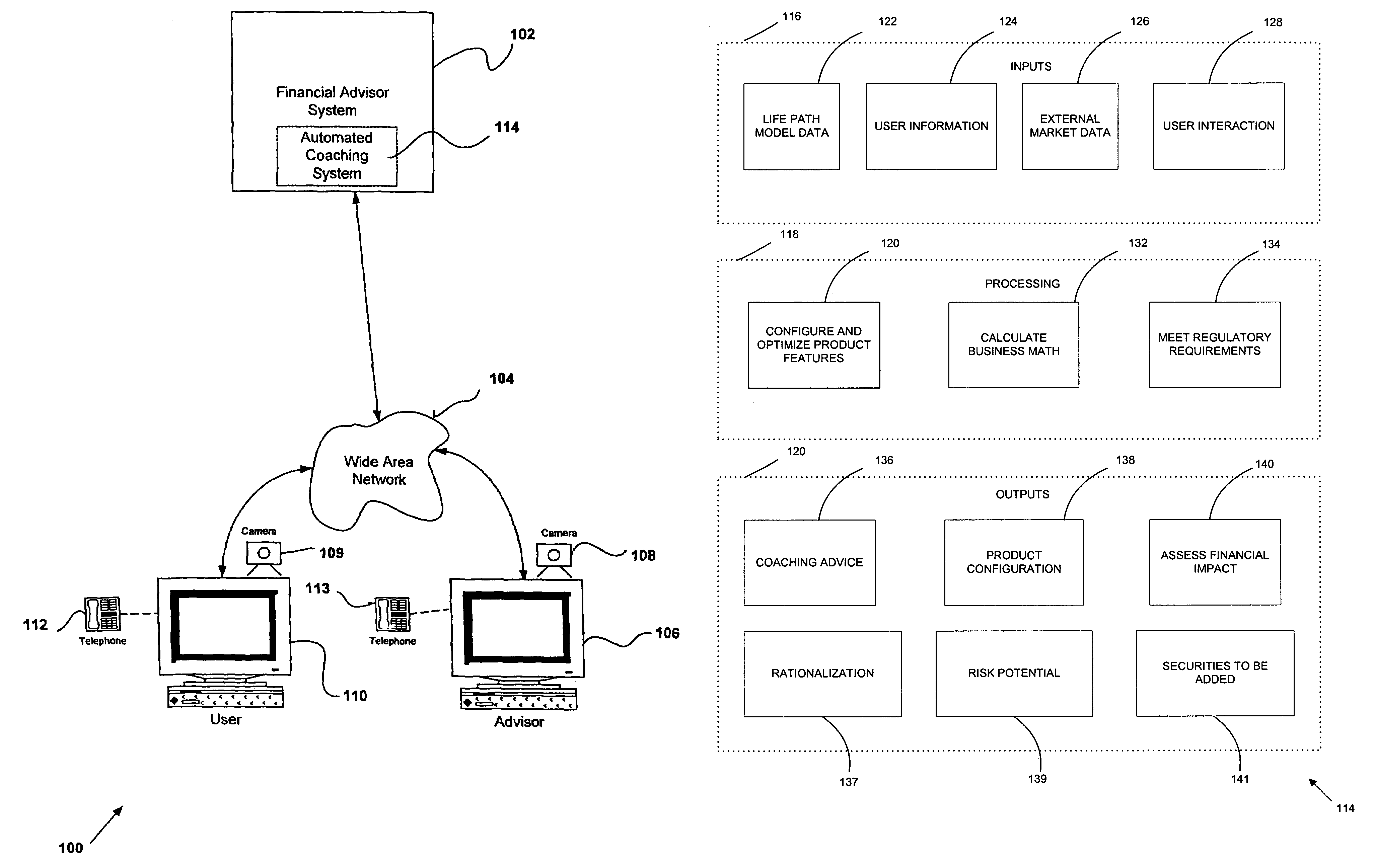
The present invention relates to an automated coaching system for financial modeling and counseling system. The automated coaching system enables the user to analyze the user's investment portfolio and dispense context sensitive automated advice to the user based on the user inputted financial data, preferences and financial goals. The automated coaching provides its advice to the user in syntactically correct natural language coaching strings and is able to configure and recommend solutions and financial products, specific to the user's situation. Furthermore, the automated coaching system can analyses the impact of the recommended product on the user's financial model.
Owner:ACCENTURE GLOBAL SERVICES LTD
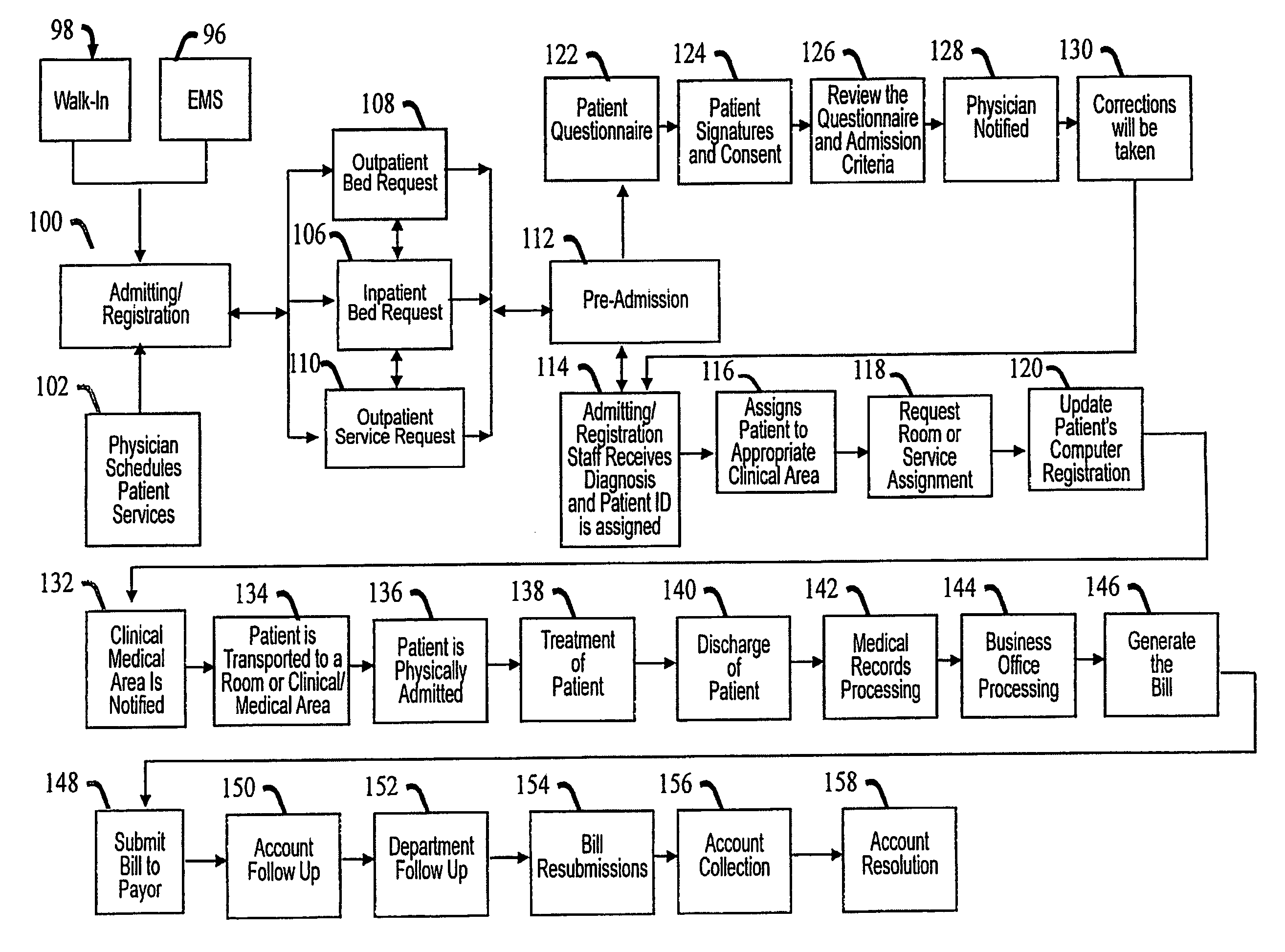
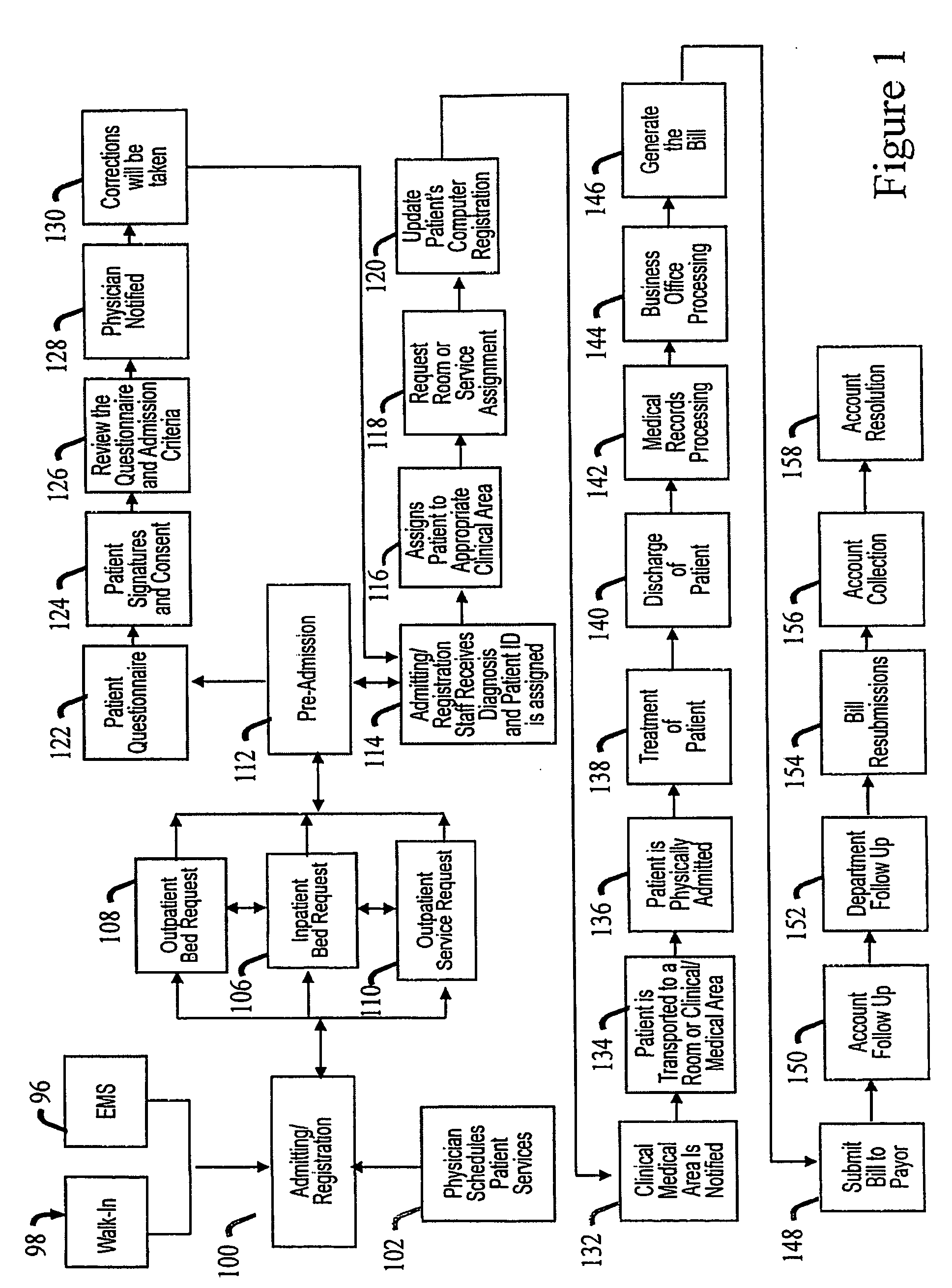
System and a method for an audit and virtual case management of a business and/or its components
InactiveUS20050273361A1Reduce financial riskSpeed up the flowFinanceMedical automated diagnosisMedicineMedical treatment
The present invention provides a system and a method for an audit of a business and / or its components. More specifically, a formula is provided that may track errors in a health care business, such as financial, department specific, and / or clinical / medical. The errors may be coded and categorized by persons other than patient care providers. Further, the present invention provides a method for identifying, qualifying, quantifying, coding, categorizing, prediction and / or mitigation of errors on a concurrent basis through, for example, point of service audits. The errors and information may be gathered during the audits and may be entered into a database. Data mining may be implemented to provide additional information in which flowcharts may be created to be used as a case management tool.
Owner:BUSCH REBECCA S
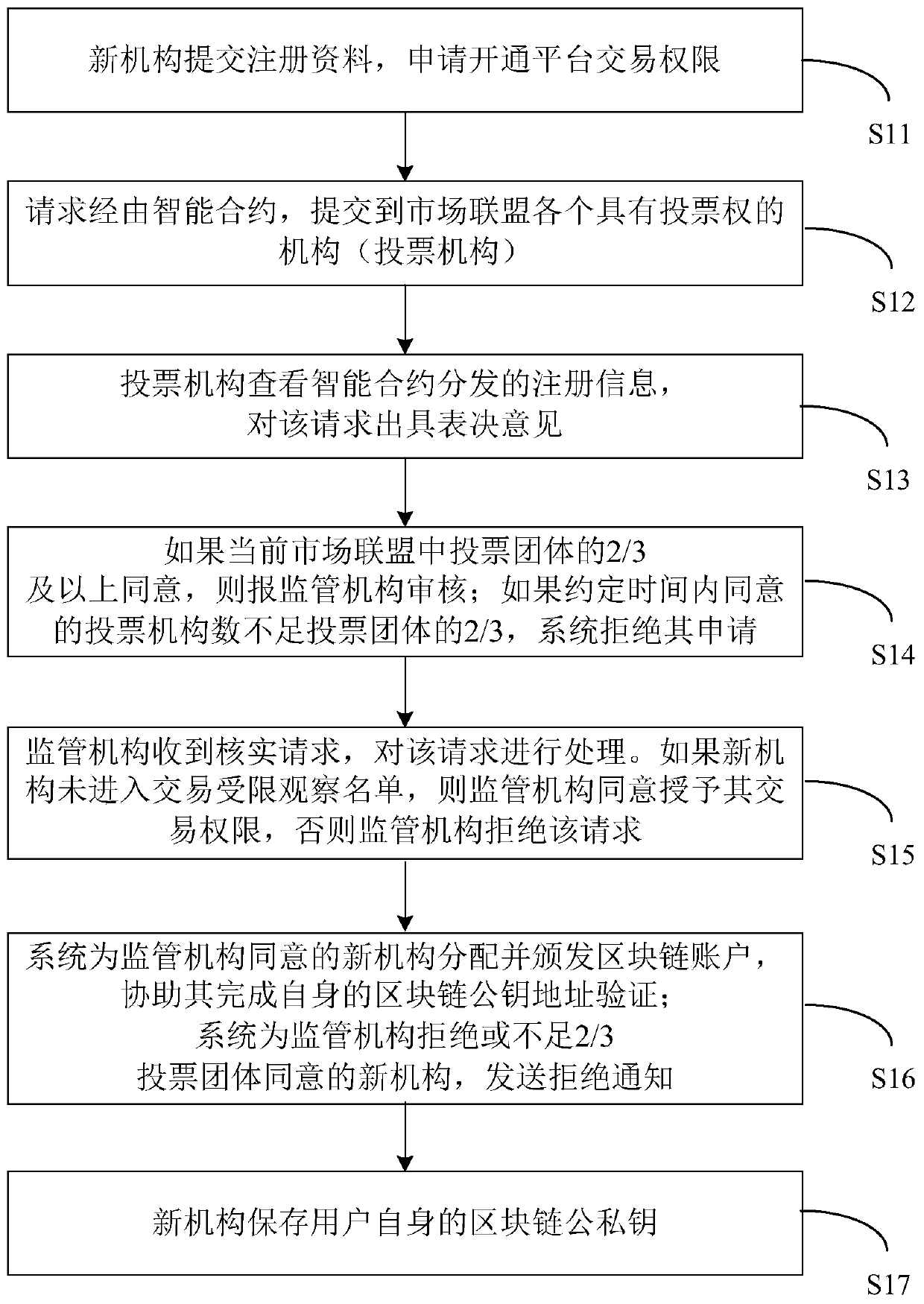
Credible smart contract reinforcement method based on blockchain
ActiveCN107844704AReduce financial riskEnsure safetyDigital data protectionPayment protocolsSmart contractComputer science
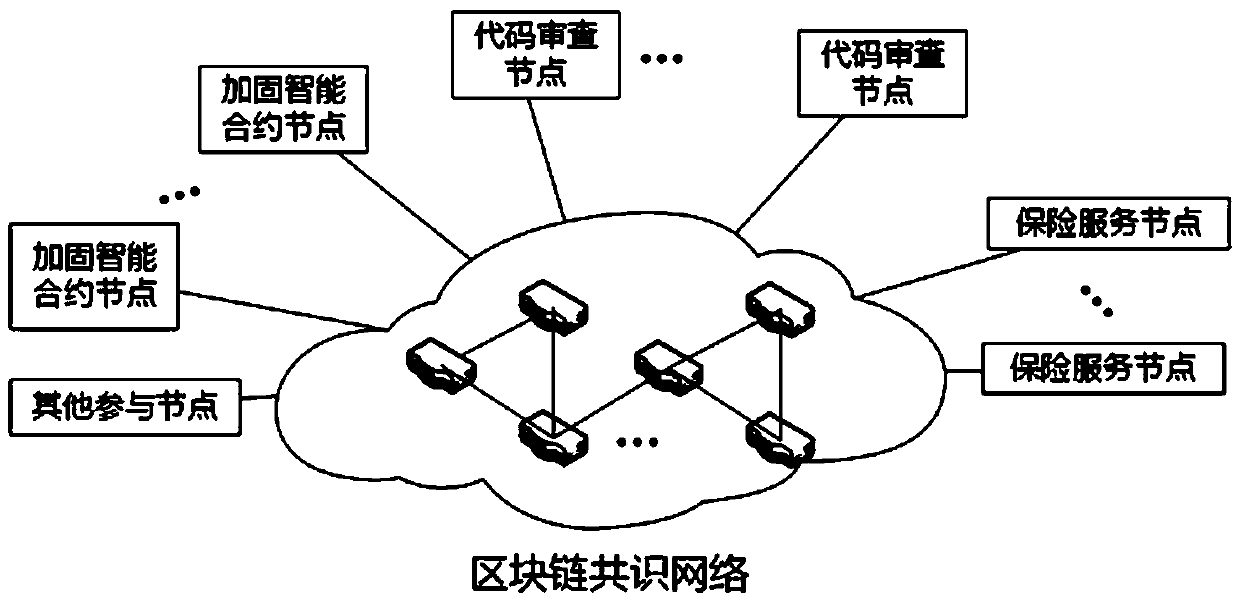
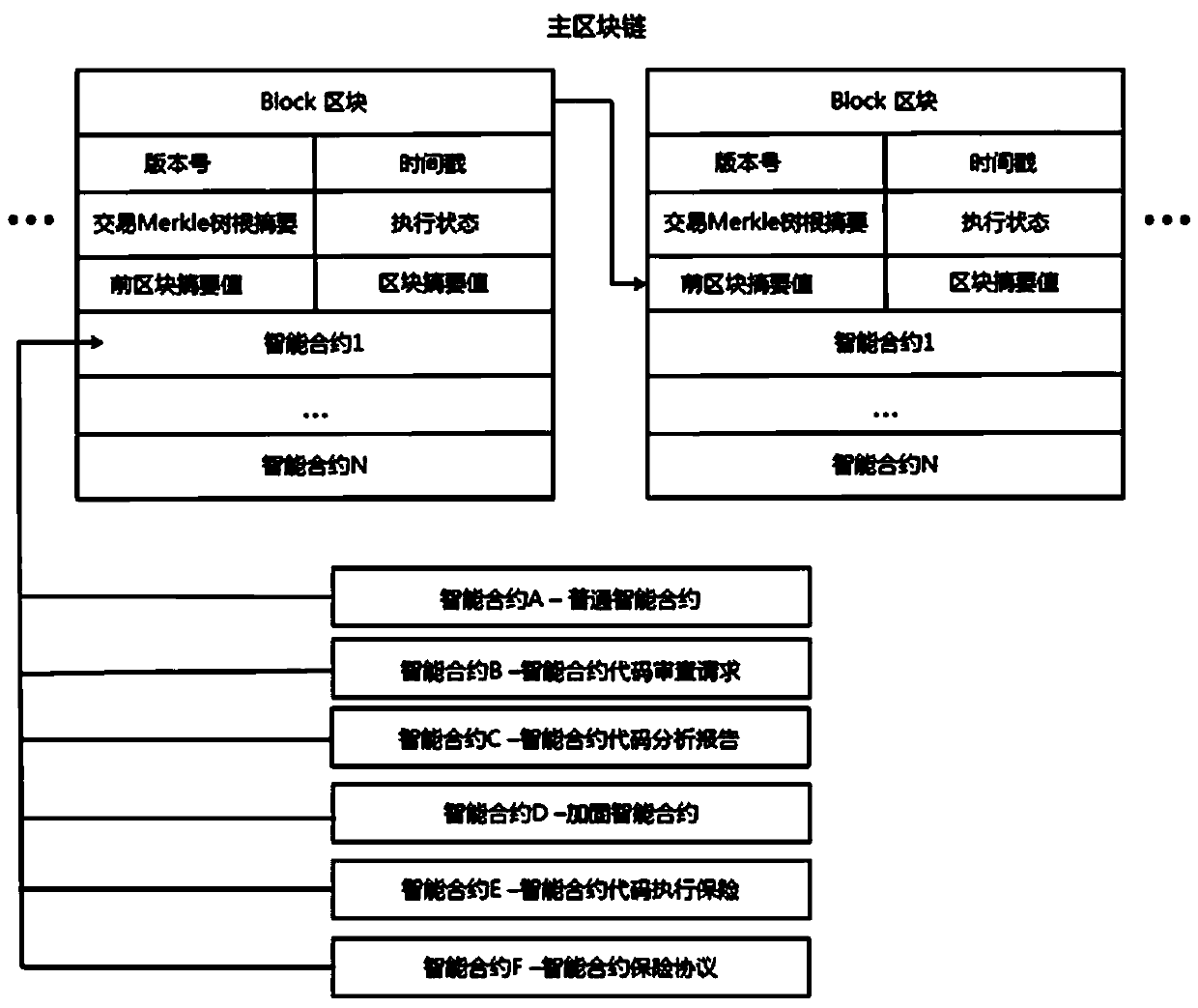
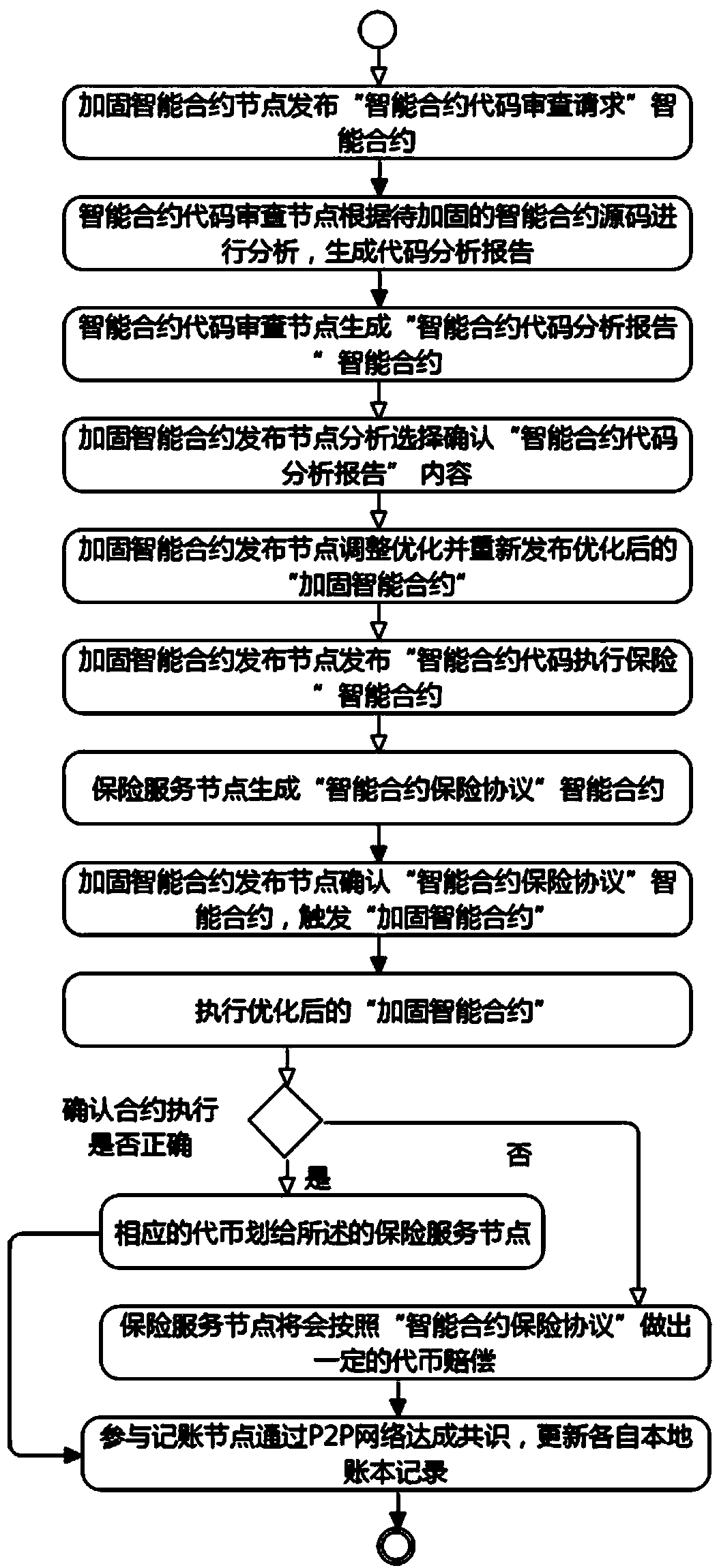
The invention discloses a credible smart contract reinforcement method based on a blockchain. The method includes the steps that the blockchain is established in a P2P consensus network, an account book record is maintained jointly by all participation nodes, and smart contracts are recorded in the account book of the blockchain; it is permitted that each participation node releases the smart contracts based on the blockchain, and meanwhile smart contract code review nodes exist to provide contract code review services; the reinforced smart contracts are released, the safety of contract codesis guaranteed by using the contract code review service smart contracts in combination with blockchain tokens, a smart contract safeguard mechanism is provided through insurance service nodes, and thefinancial risk of the smart contracts is reduced. According to the method, the function of reviewing the smart contract codes is added, the safety of the smart contract codes is improved, and the possibility of appearance of code vulnerabilities is effectively reduced; meanwhile, corresponding token awards are provided, and participation is encouraged through incentive measures; the safety of funds is guaranteed, and loss brought about by contract problems is reduced.
Owner:山东浪潮创新创业科技有限公司
Methods for collecting fees for healthcare management group
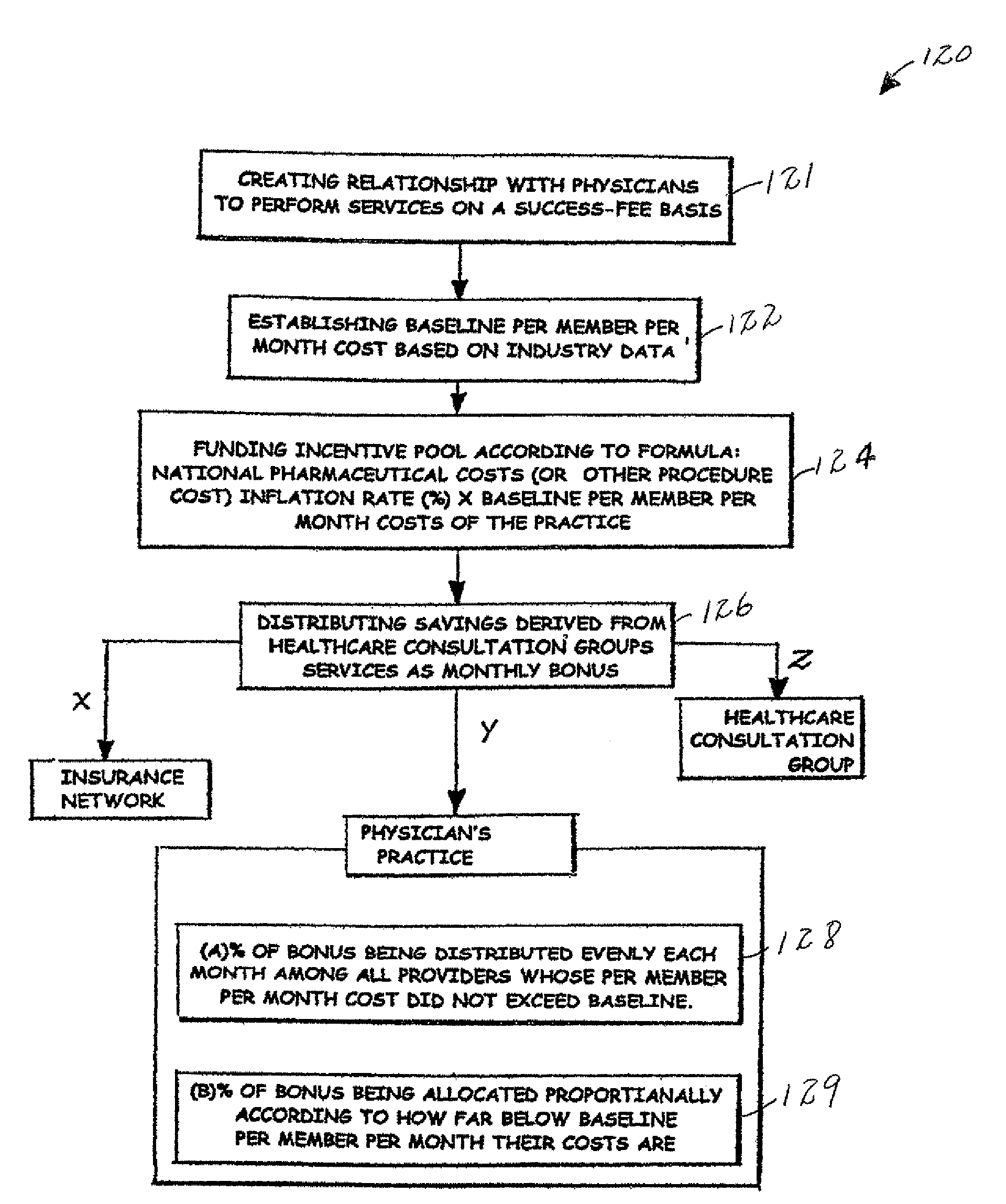
InactiveUS7401027B2Controlling rising costImprove relationshipFinanceForecastingMedical treatmentMedical care
Owner:JASOS INTPROP
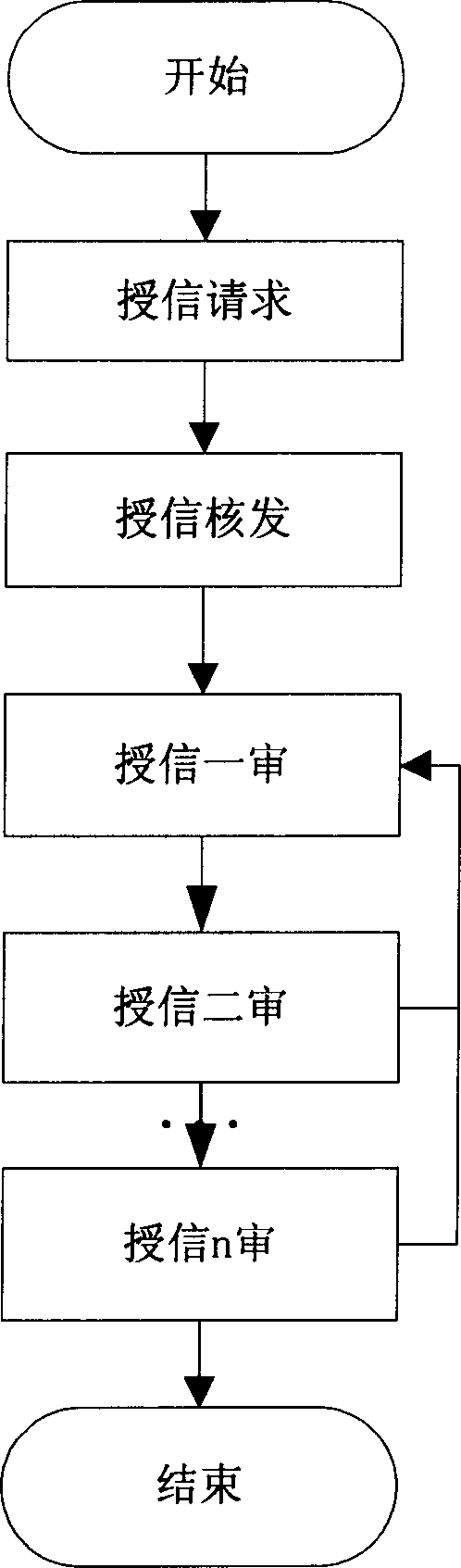
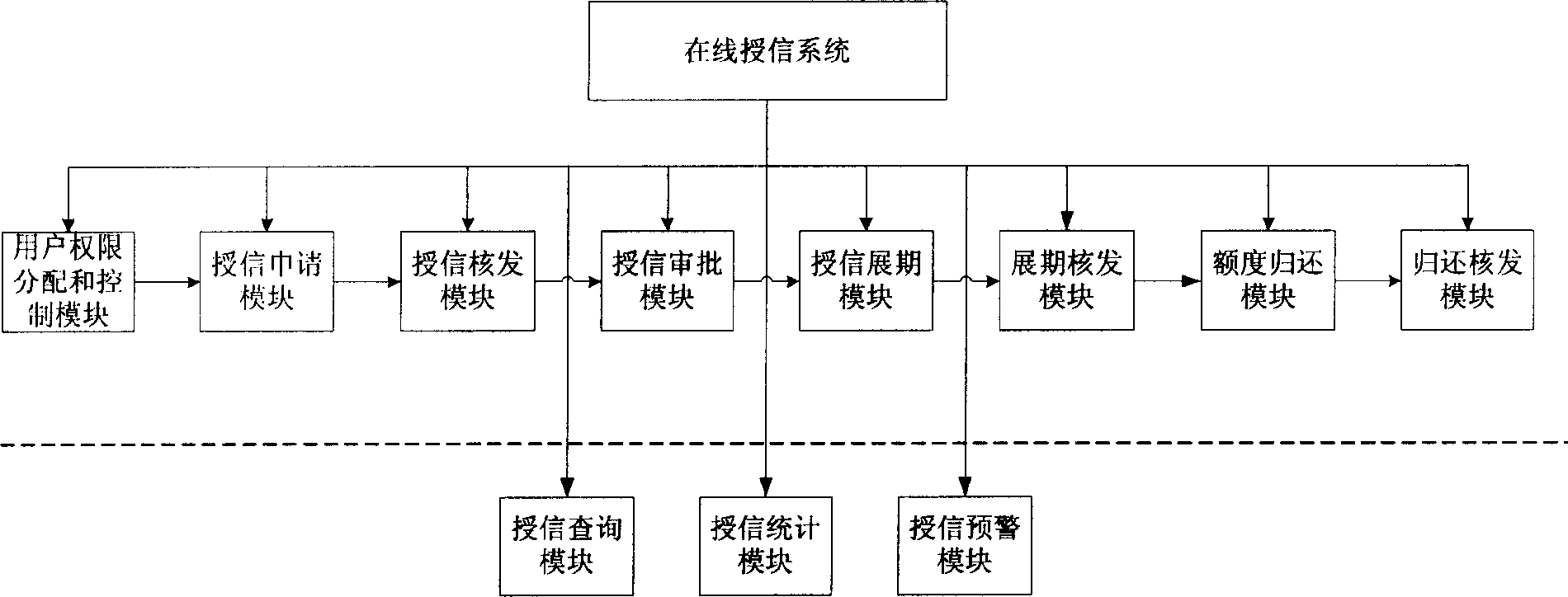
System and method for online user authorization for banks
A system of granting credit to the client on line by financial enterprise comprises user power distribution and control module, credit application module, credit checking and issuing module, credit approval module, credit extending module, extension period approval module, ceiling return module, return back checking and issuing module, credit inquiry module, credit statistic analysing module and credit prewarning module. The system can be used as control system of credit approval operation within financial enterprises.
Owner:BANK OF CHINA
Process for producing ethanol and for energy recovery
InactiveUS20080003654A1Increasing net energy valueReducing the reliance of the ethanol industryBioreactor/fermenter combinationsBio-organic fraction processingElectricityDistillation
The present invention is directed to a process for the production of ethanol and energy. The process includes the steps of fermenting a corn mash in an aqueous medium to produce a beer. Next, the beer is distilled to produce ethanol and a whole stillage. The whole stillage is anaerobically digested to produce a biogas and a residue. The biogas is combusted to produce electricity and steam. The electricity and steam are used during the fermentation and distillation process. The residue may further be separated into a liquid fertilizer and top soil residue.
Owner:STANLEY CONSULTANTS
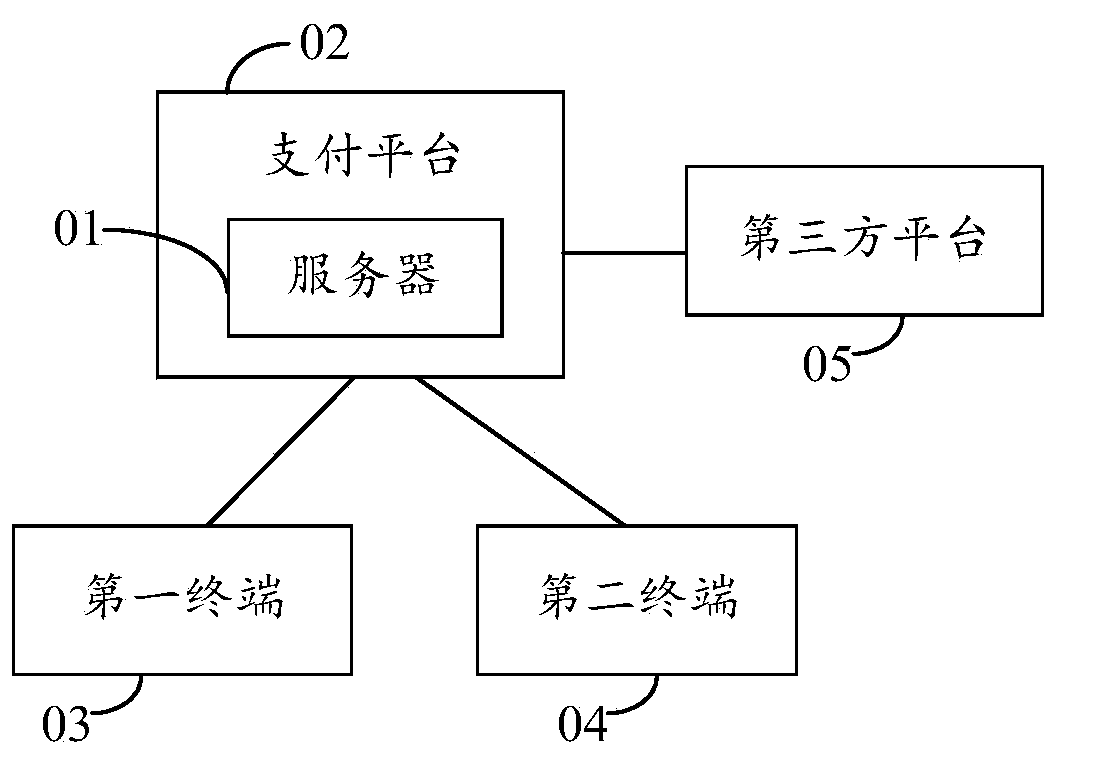
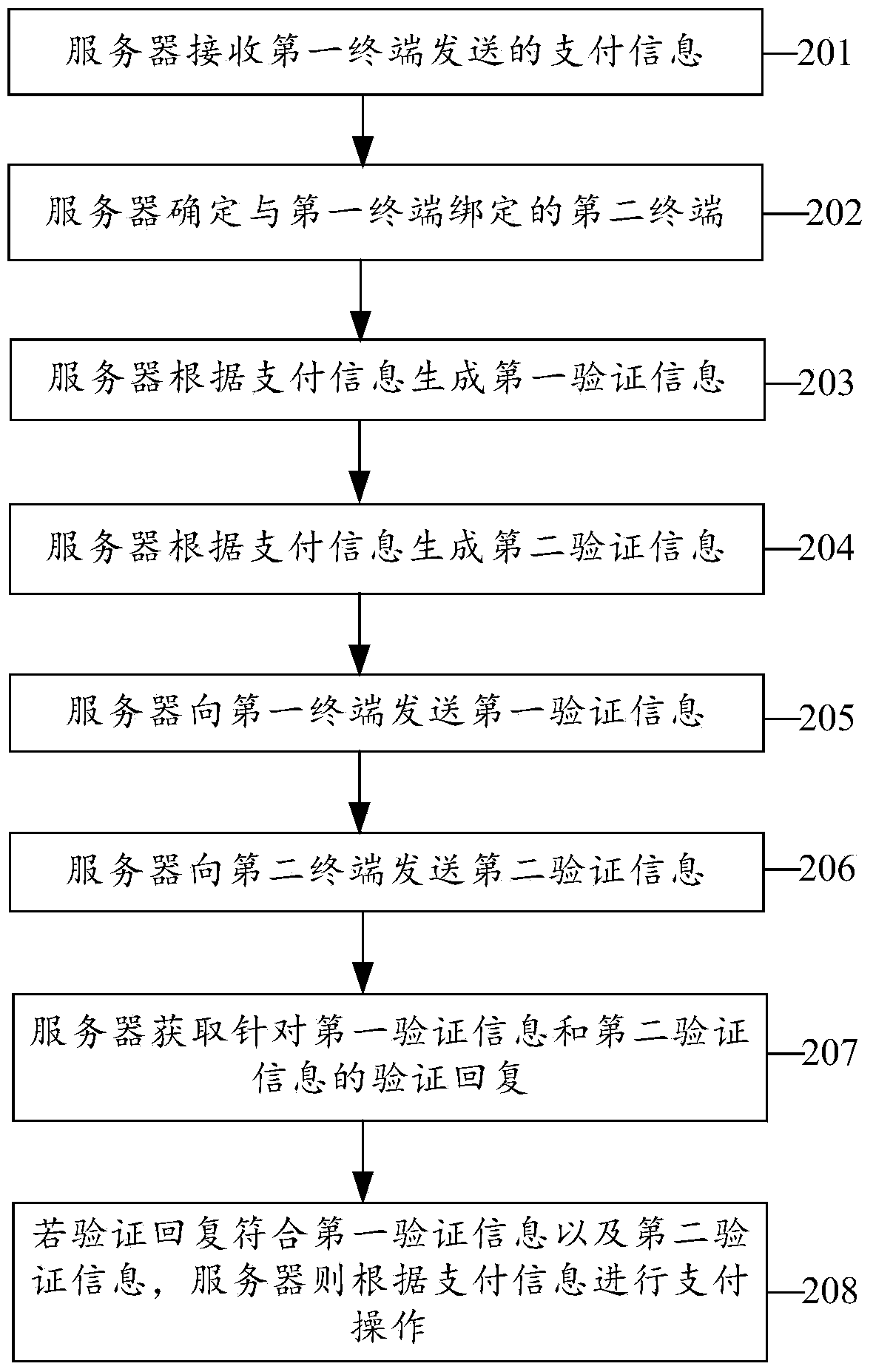
Payment verification method, server and system
InactiveCN104217332AImprove securityReduce financial riskProtocol authorisationMobile paymentMobile phone
The embodiment of the invention provides a payment verification method, a server and a system, relates to the field of communication, solves the problem that in the prior art payment may be simulated caused by loss of a mobile phone and the like, and thereby improve security of mobile payment and reduce financial risks in a mobile payment process. The payment verification method comprises the steps of: receiving payment information sent by a first terminal; determining a second terminal bound to the first terminal; generating first verification information and second verification information according to the payment information; sending the first verification information to the first terminal, and sending the second verification information to the second terminal; obtaining verification responses aiming at the first and second verification information; and if each verification response accords with the corresponding one of the first and second verification information, making payment according to the payment information.
Owner:HUAWEI TECH CO LTD
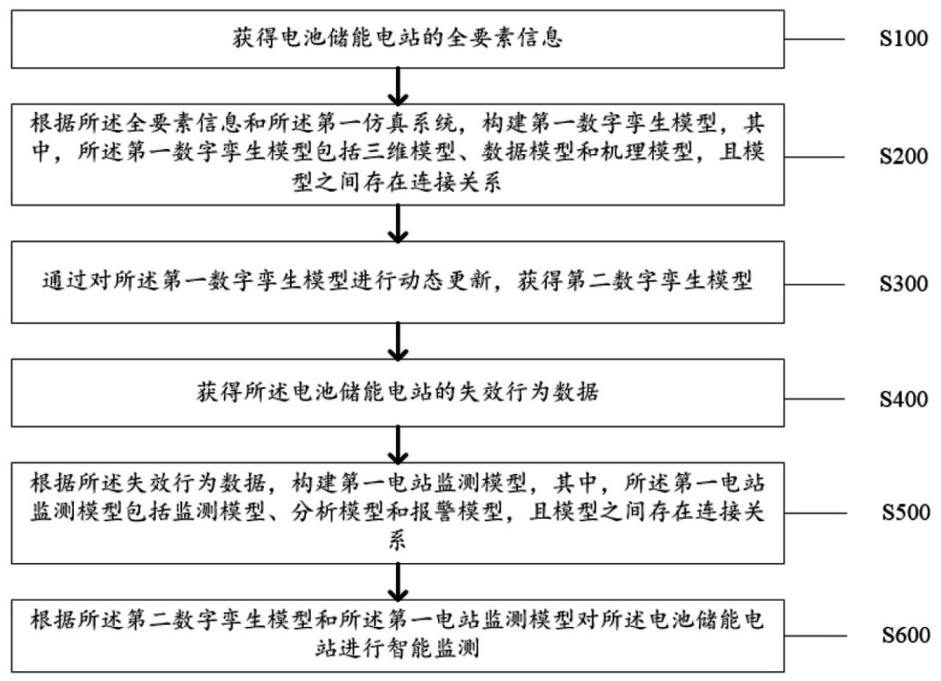
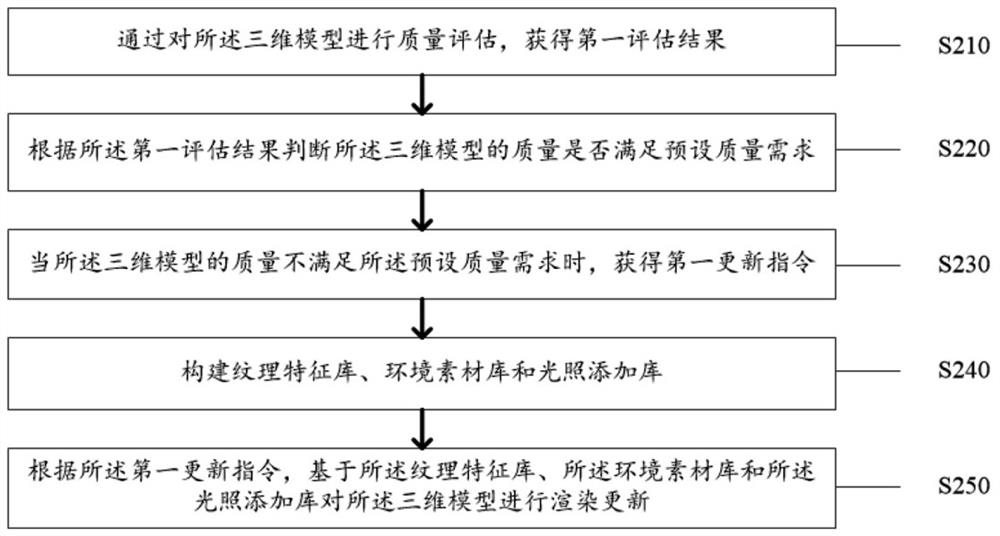
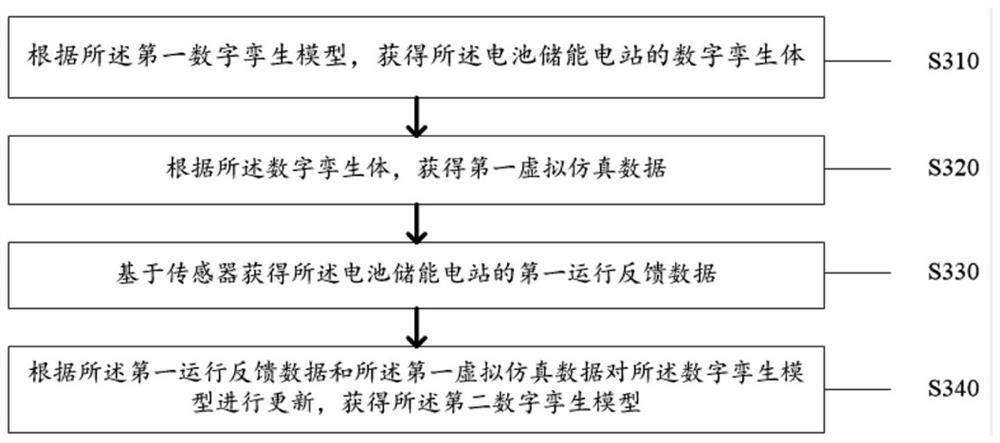
Battery energy storage station monitoring method and system based on big data and digital twinning
ActiveCN113517760ARealize dynamic updateReduce financial riskElectrical testingEnergy storageReliability engineeringSecurity controls
The invention discloses a battery energy storage station monitoring method and system based on big data and digital twinning, and the method comprises the steps: building a first digital twinning model according to total element information of a battery energy storage station and a first simulation system, and the first digital twinning model comprises a three-dimensional model, a data model and a mechanism model; dynamically updating the first digital twinborn model to obtain a second digital twinborn model; according to the failure behavior data of the battery energy storage power station, constructing a first power station monitoring model, wherein the first power station monitoring model comprises a monitoring model, an analysis model and an alarm model; and performing intelligent monitoring on the battery energy storage power station according to the second digital twinning model and the first power station monitoring model. The technical problems that in the prior art, monitoring of the battery energy storage station is not perfect, intelligent data analysis cannot be accurately conducted on thermal runaway, the reliability of safety control is low, and the efficiency is not high are solved.
Owner:GUANGZHOU JIANXIN TECHNOLOGY CO LTD
Testing device for electrical safety using wireless communication
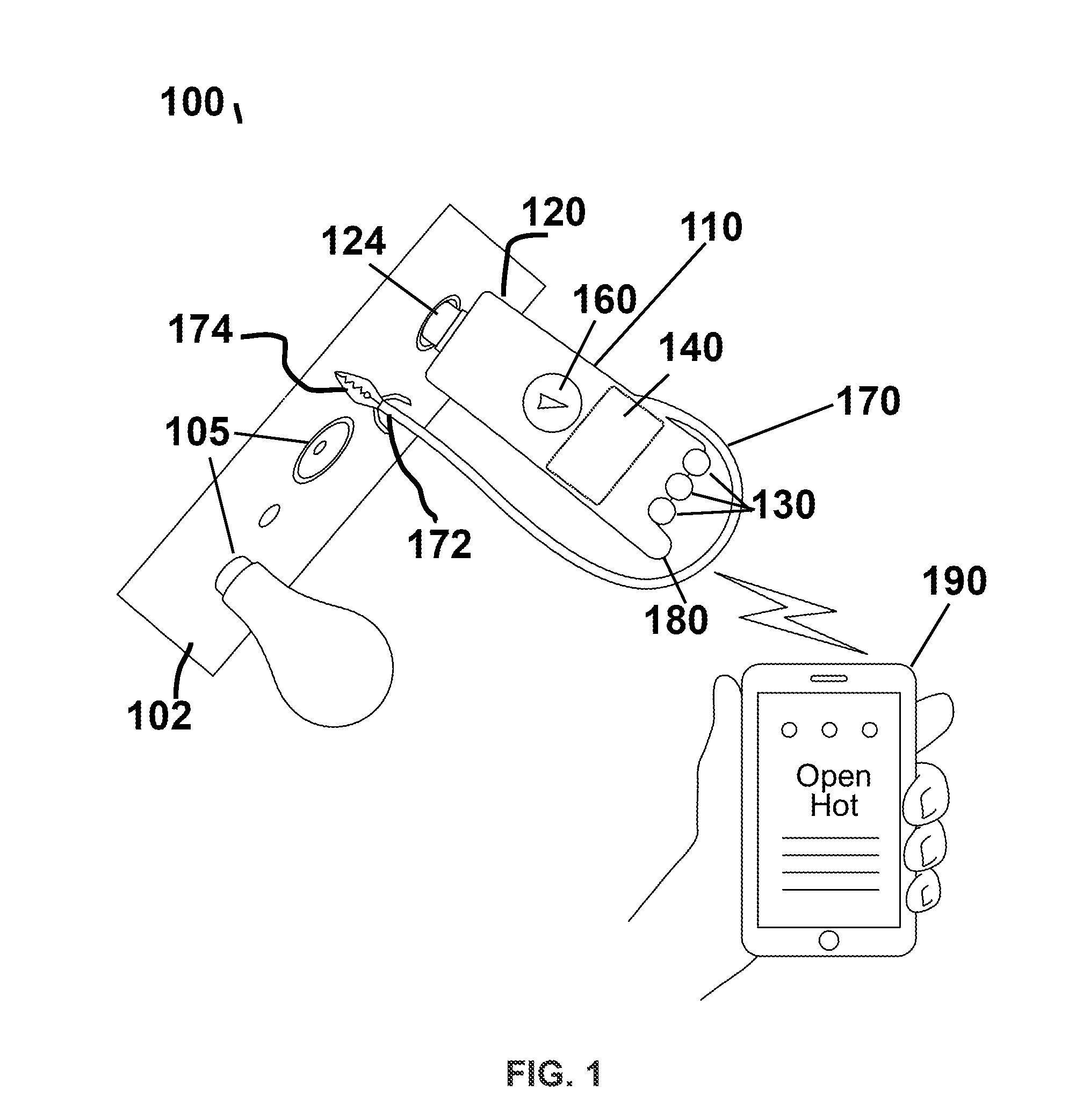
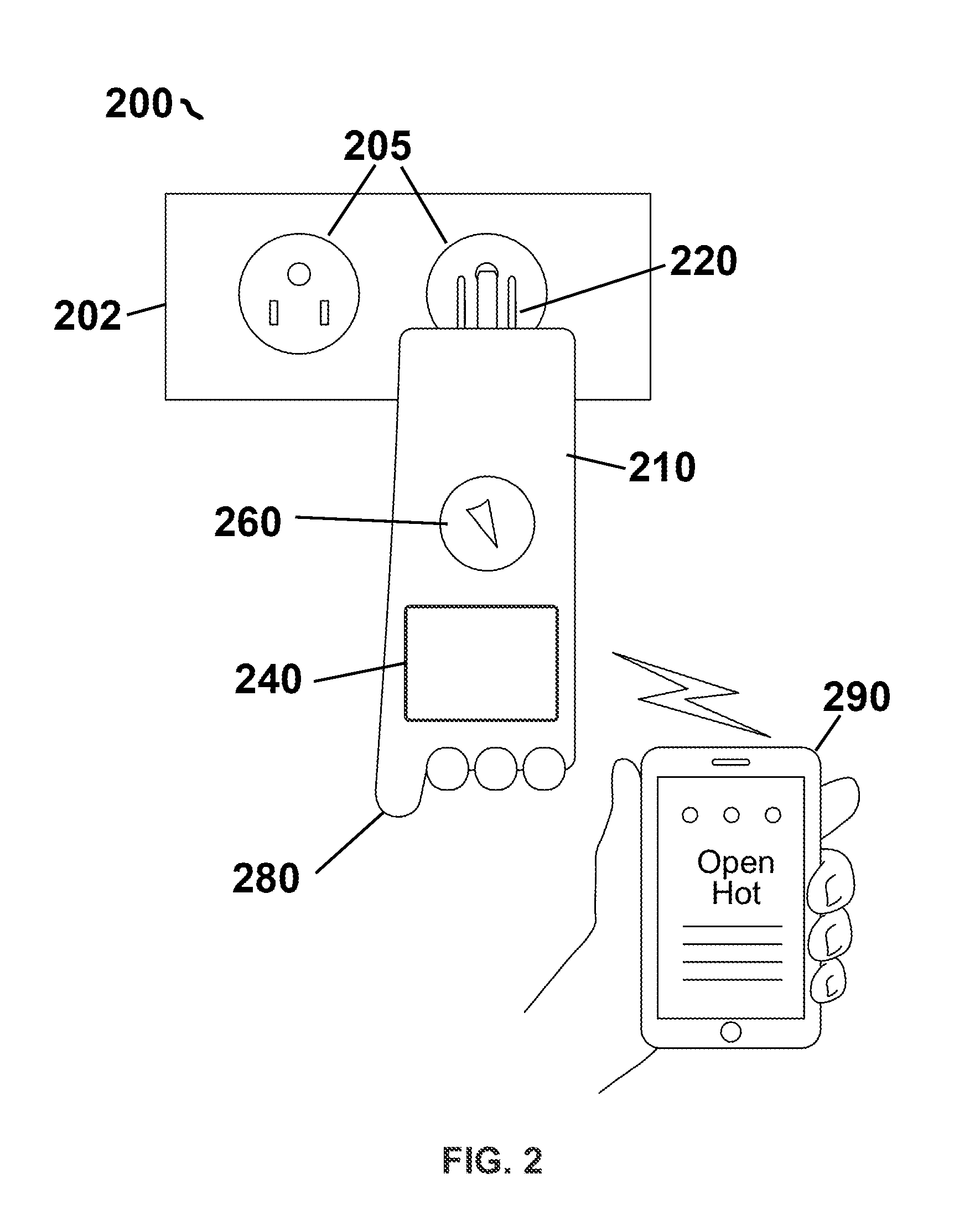
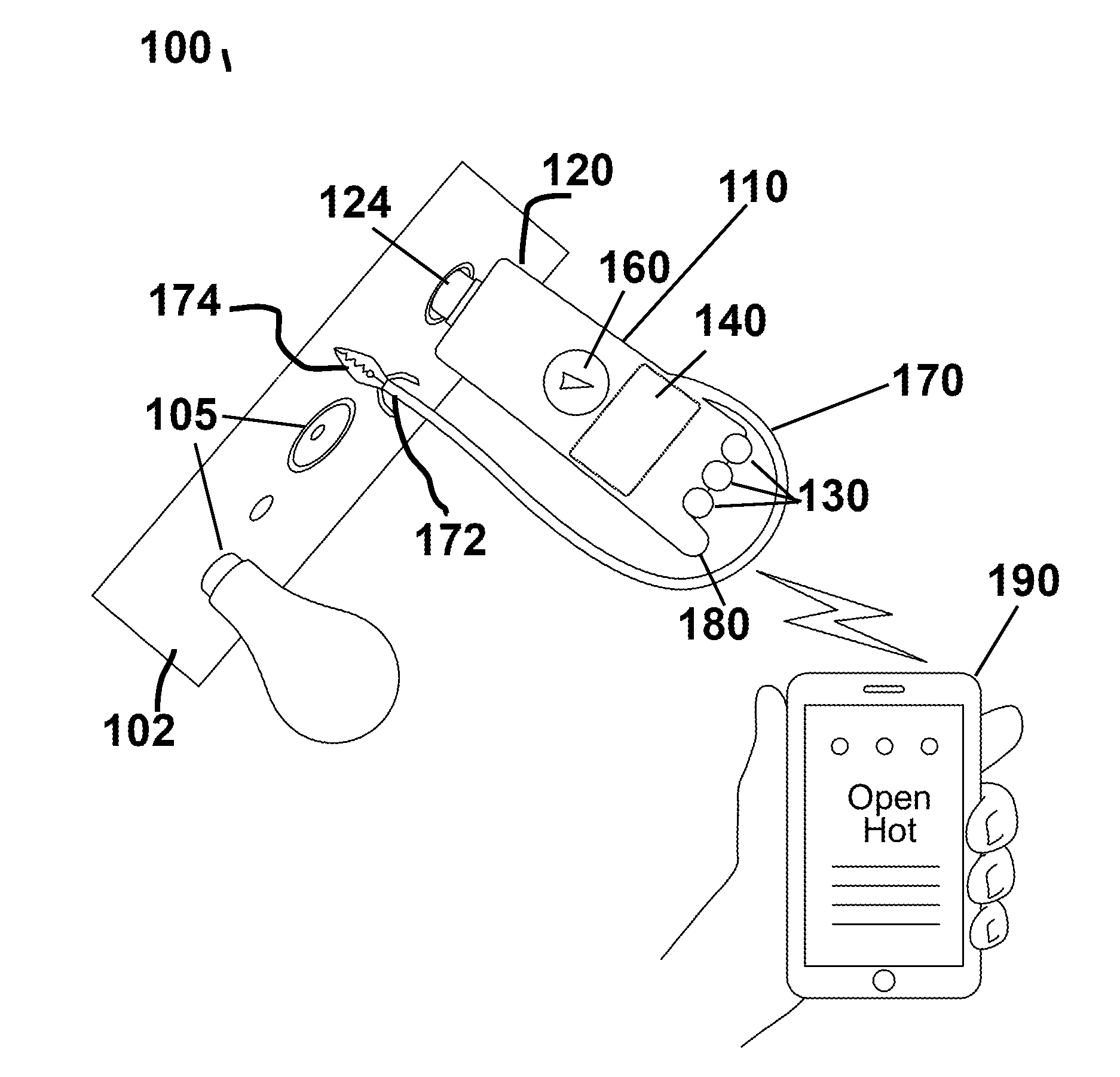
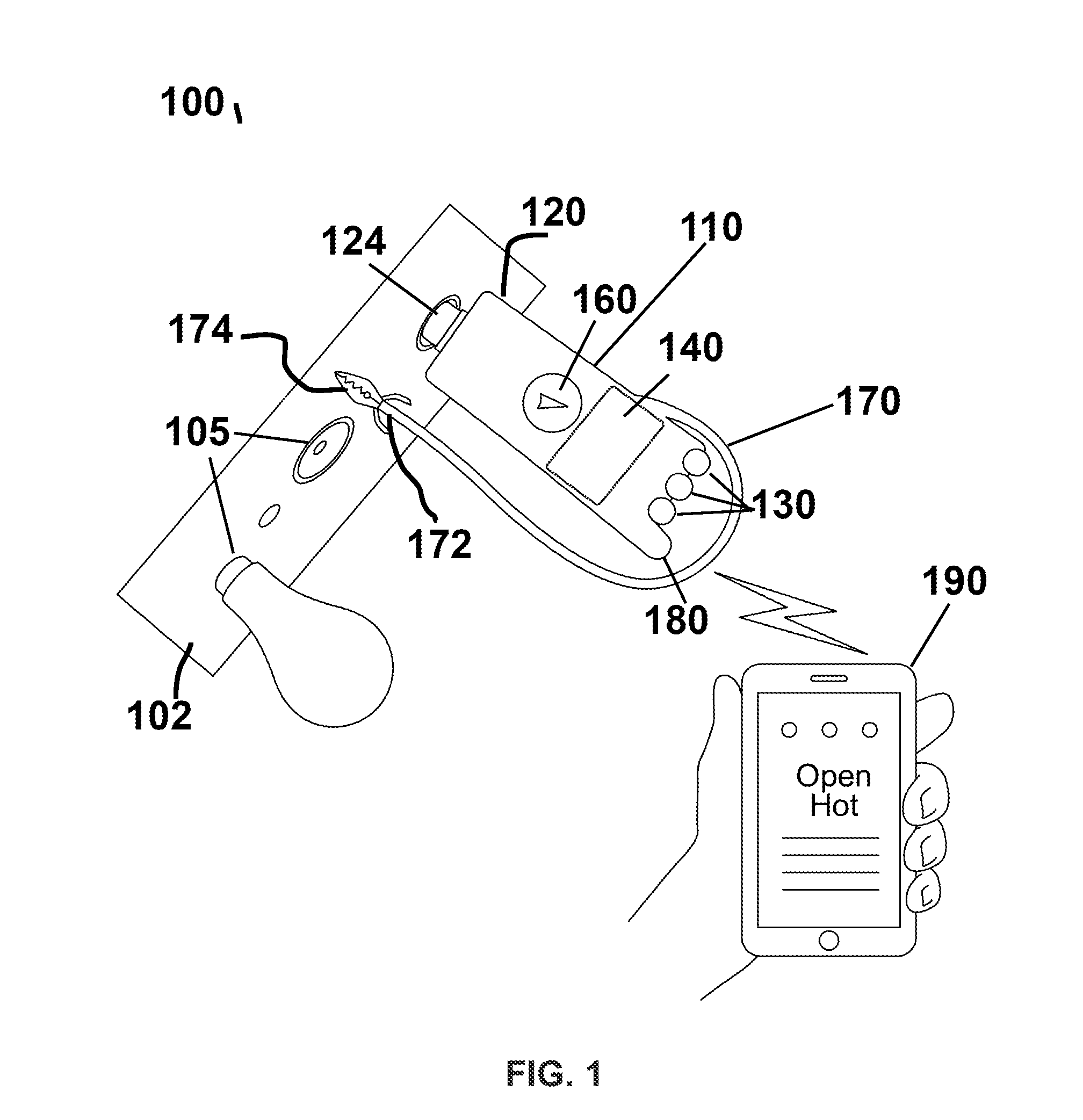
ActiveUS20140266287A1Reduce the possibilityReduce financial riskBase element modificationsLamps testingHand heldEngineering
Owner:REEDER III KENNETH MARK
Testing device for electrical safety using wireless communication
ActiveUS9575091B2Reduce the possibilityReduce financial riskBase element modificationsMeasurement instrument housingHand heldEngineering
Owner:REEDER III KENNETH MARK
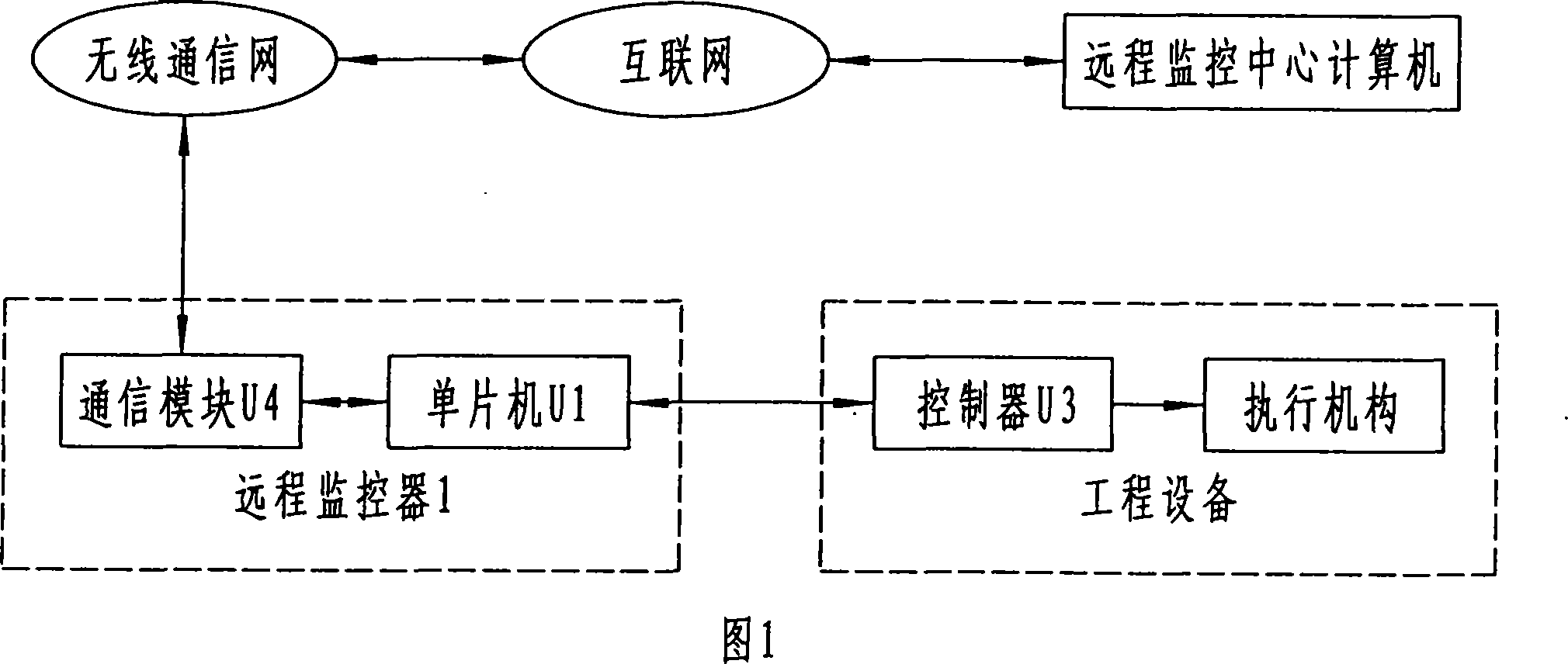
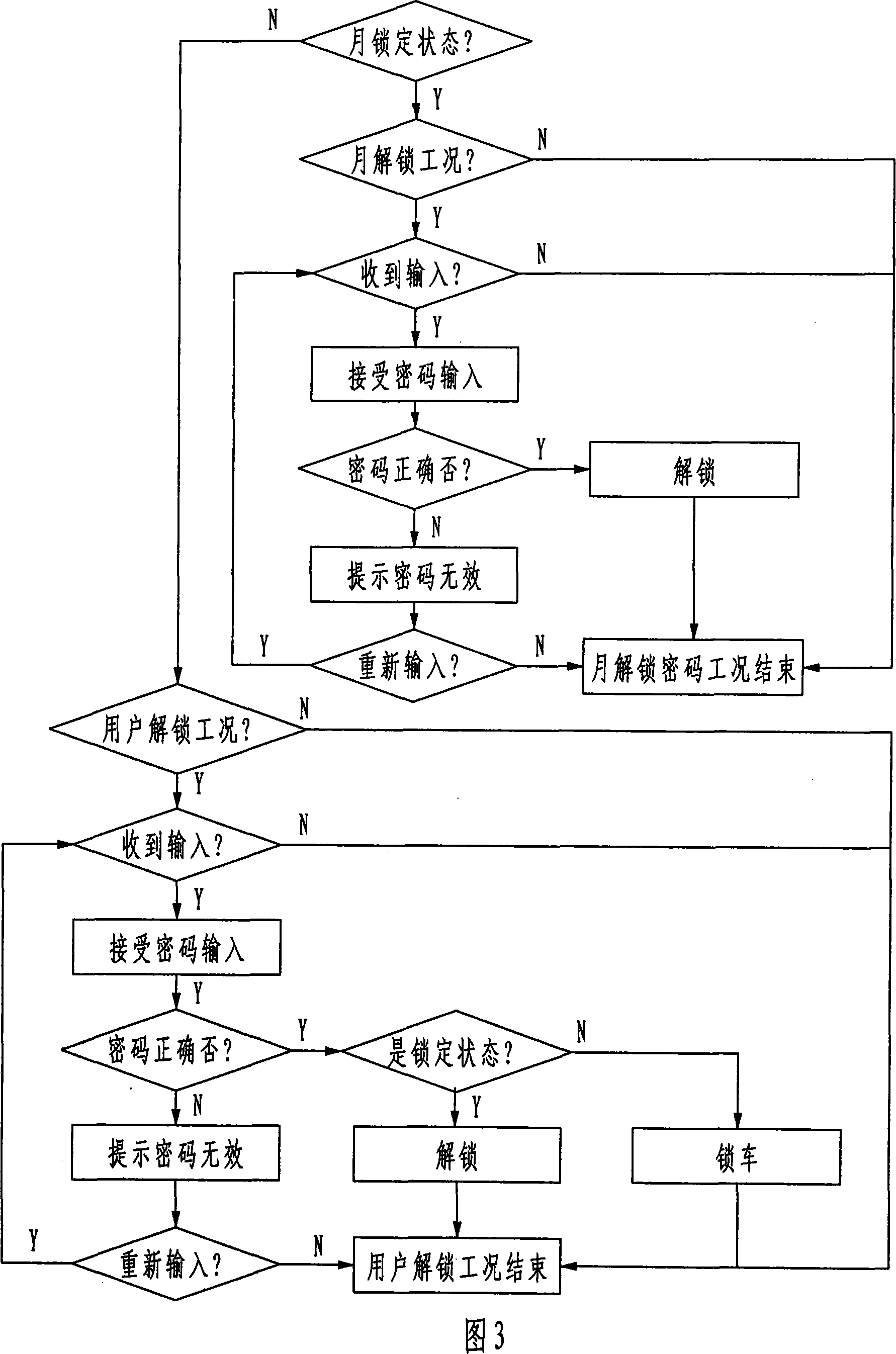
Engineering equipment long-distance locking and unlocking method and device
ActiveCN101071309AReliable remote lockingUnlock by the ReliableComputer controlSimulator controlCommunication interfaceControl system
A remote engineering equipment and unlock the lock, a control technology, remote locking used to solve the problem. Its technical programmers are: remote monitoring centre from its computers, wireless communication networks, remote monitoring, engineering equipment and the implementation of the controller comprising a control system, remote monitoring from a central computer lock or unlock signal, the signal through the wireless transmitted to the communication network remote monitoring, remote monitoring via communication interface to send it to the controller engineering equipment, engineering equipment by the end of the controller implementation agencies to lock or unlock operation, the invention also provides a realization of this kind of locking devices. The present invention is not only easy to implement engineering equipment reliable remote lock or unlock, but also to prevent damage to the device unlock methods, and therefore effective security and greatly reduce financial risks.
Owner:童一帆
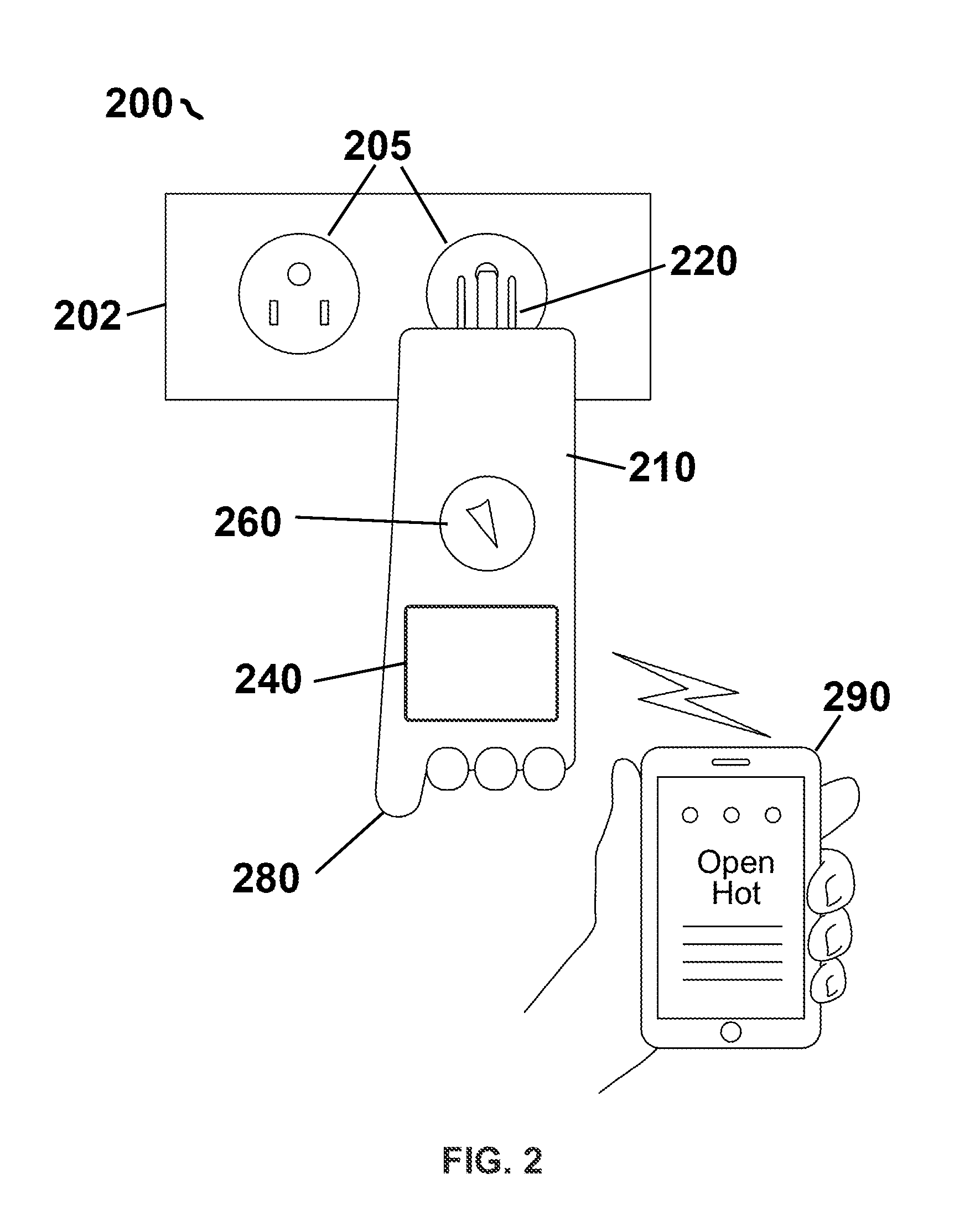
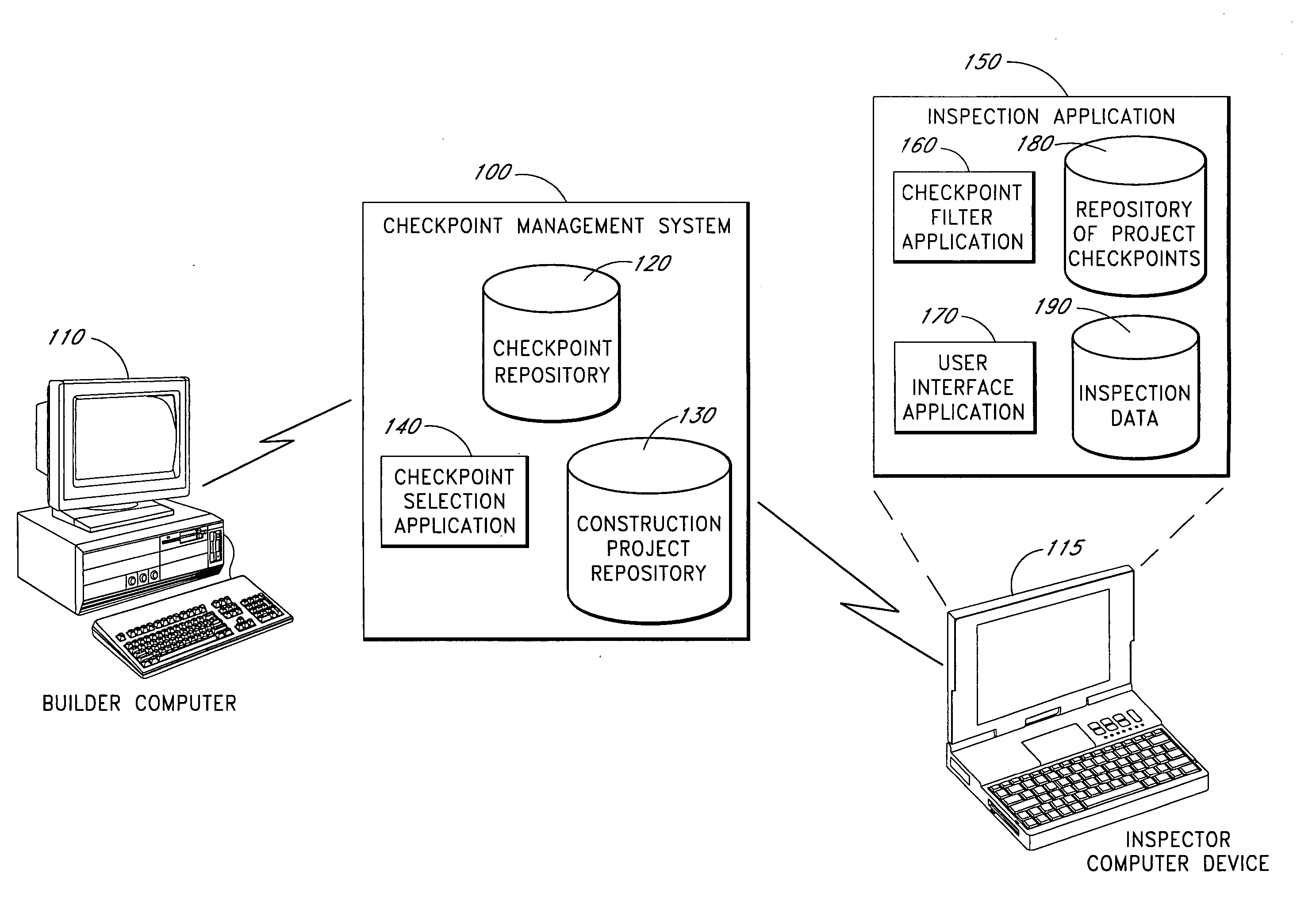
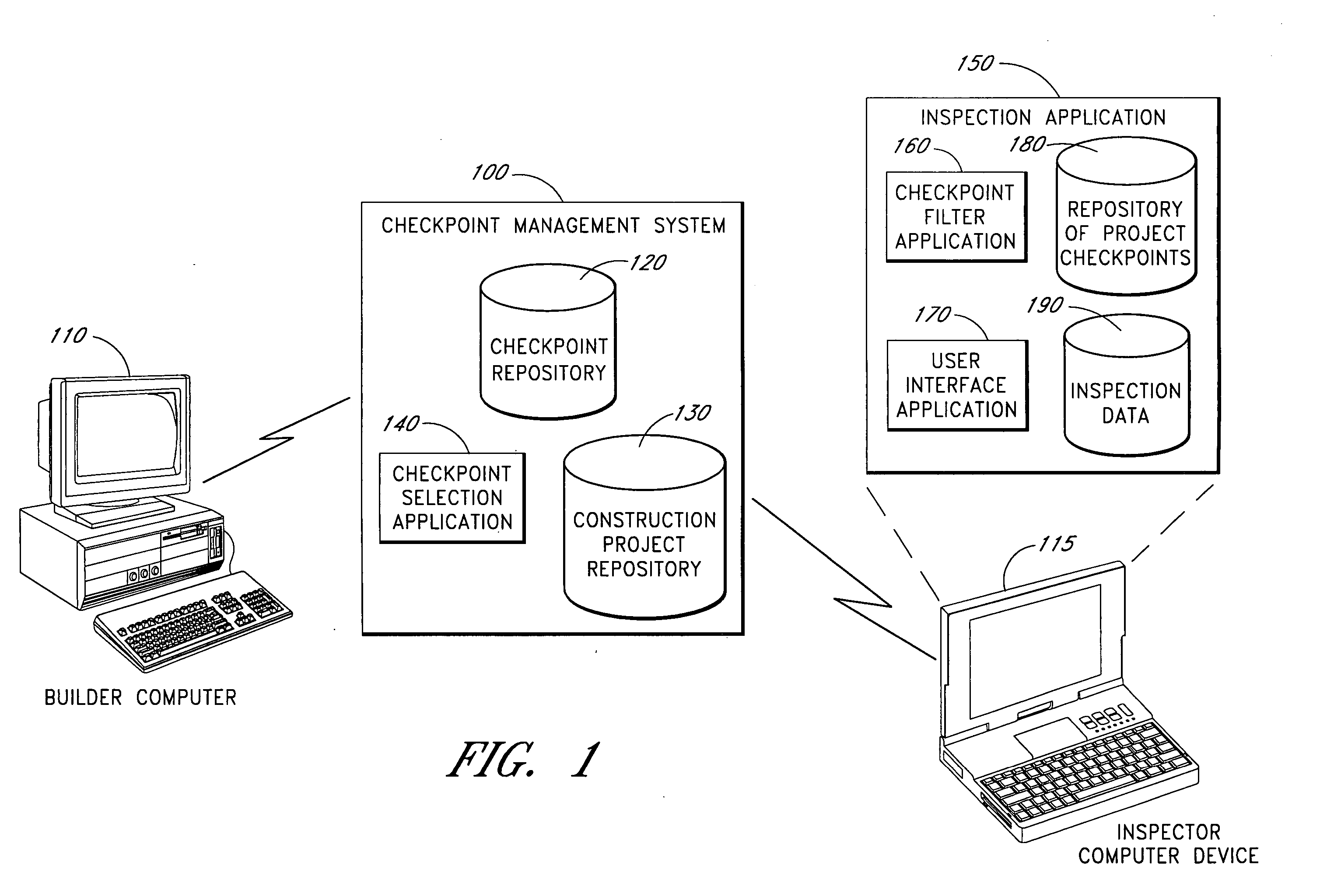
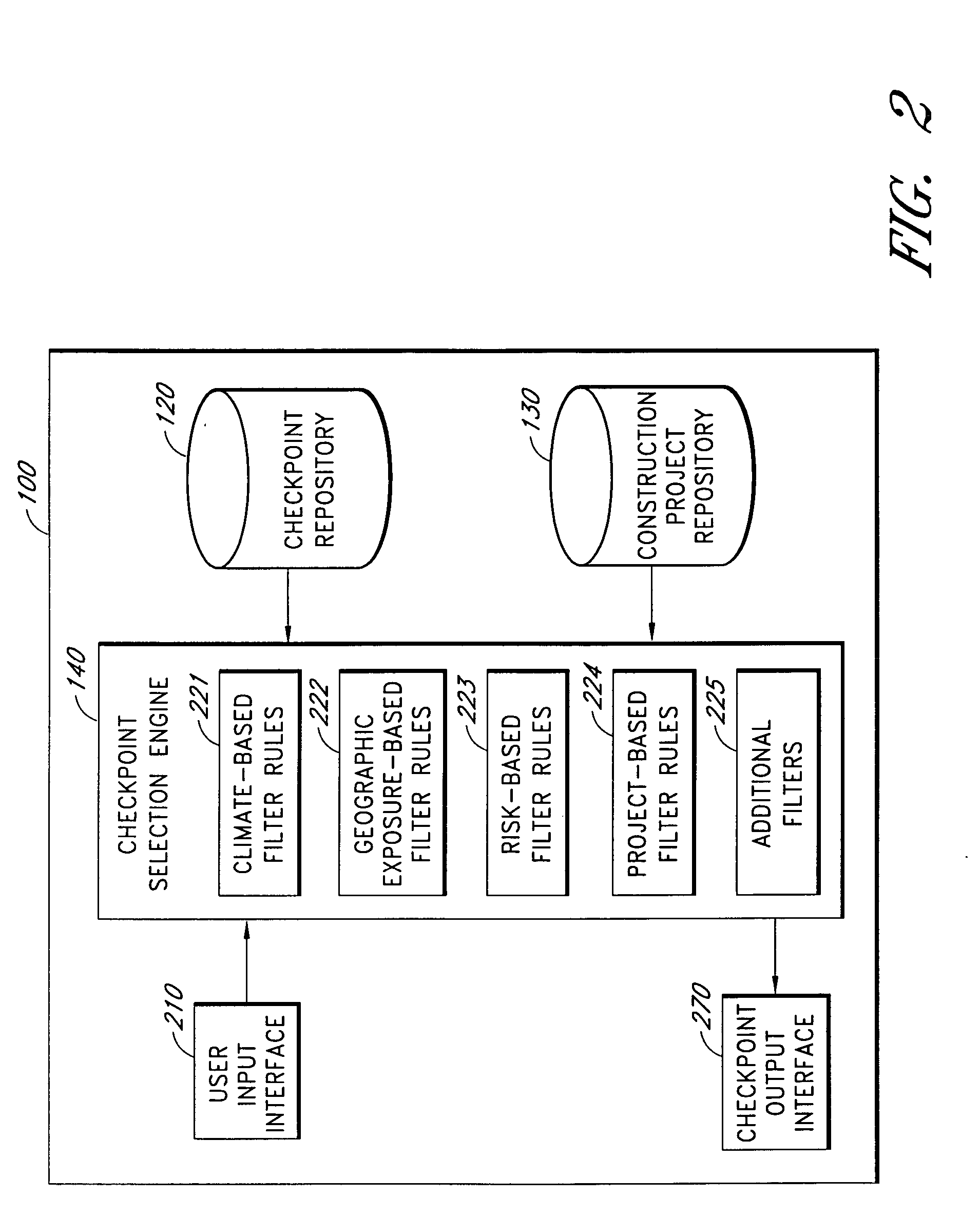
Systems and methods for selecting and prioritizing construction checkpoints
InactiveUS20060026009A1Reduce financial riskMinimizing financial riskCommerceValidation errorProject based
The computer-based system described herein accepts information about a building project and uses the information to select from a repository of construction checkpoints a subset of the checkpoints that are deemed to be relevant to improve a building's safety, durability and comfort and to reduce financial risk. The checkpoints may be selected and / or prioritized for viewing by an inspector inspecting the building project based on at least one of: project geographic location, project-specific exposure, type of structure, complexity of building components, product quality, builder's repeated deficiencies, and codes and specifications. The system may further be configured to receive information about a current stage of construction of the building project and to present checkpoints to the inspector that are relevant to the current stage of construction. The system may also be configured to prioritize presentation of selected checkpoints based at least in part on an assessment of financial risk posed by improper installation and / or construction of the selected checkpoints. In various embodiments, checkpoints that do not pass inspection may be tracked until repaired, and a record of the repair may be stored for later verifying that the error was repaired and not ignored.
Owner:QUALITY BUILT
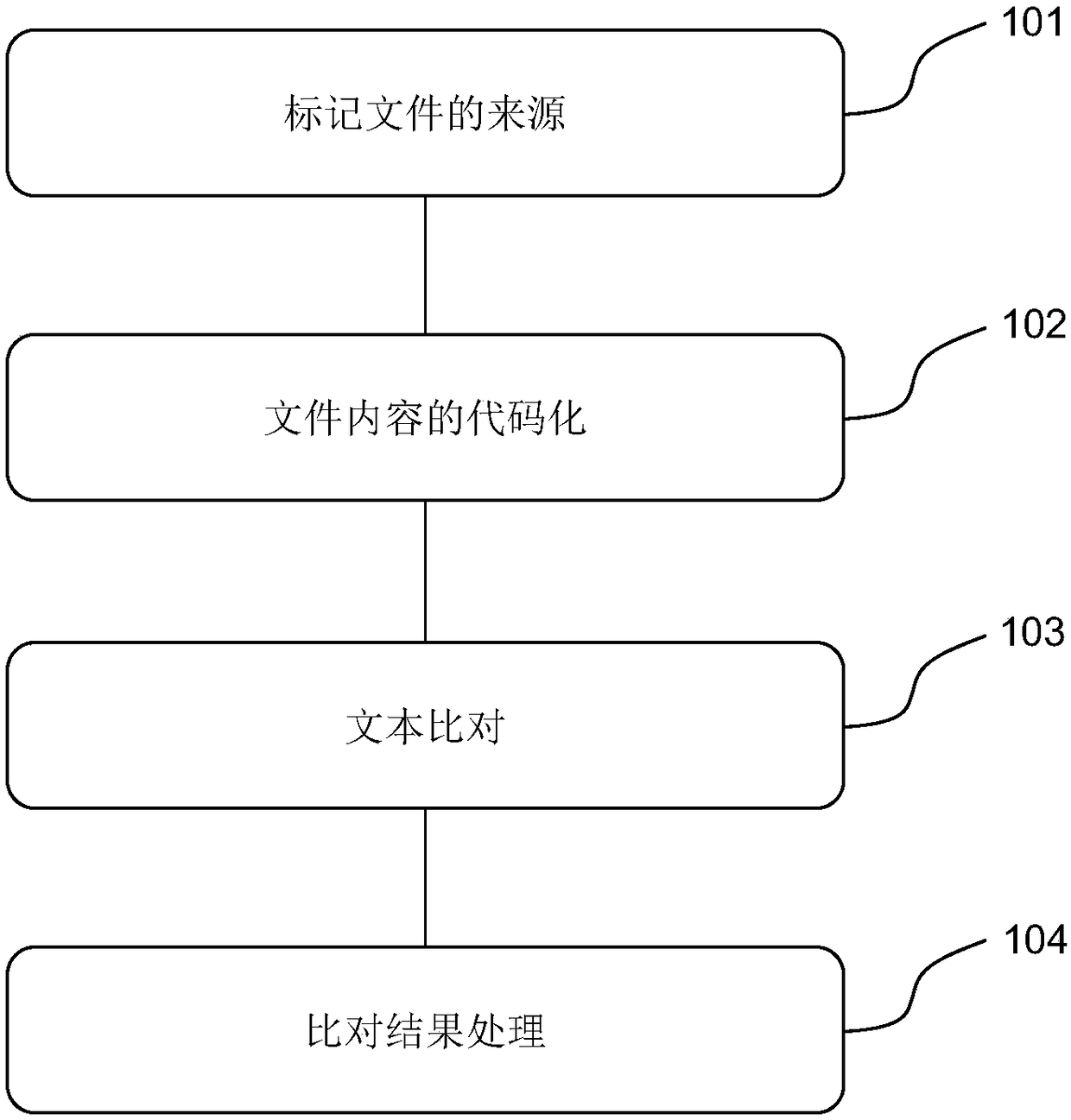
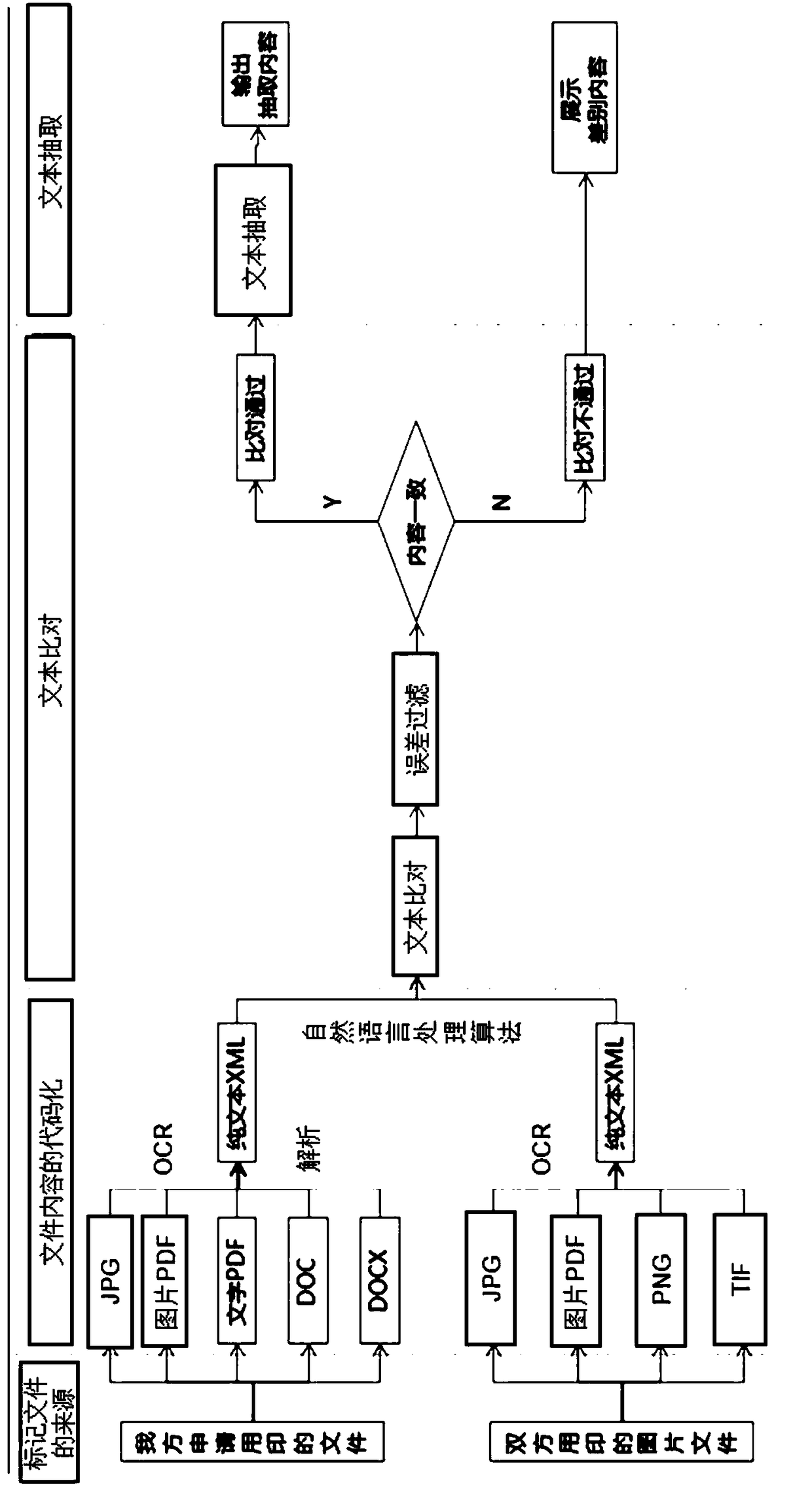
Consistency auditing method for different source files
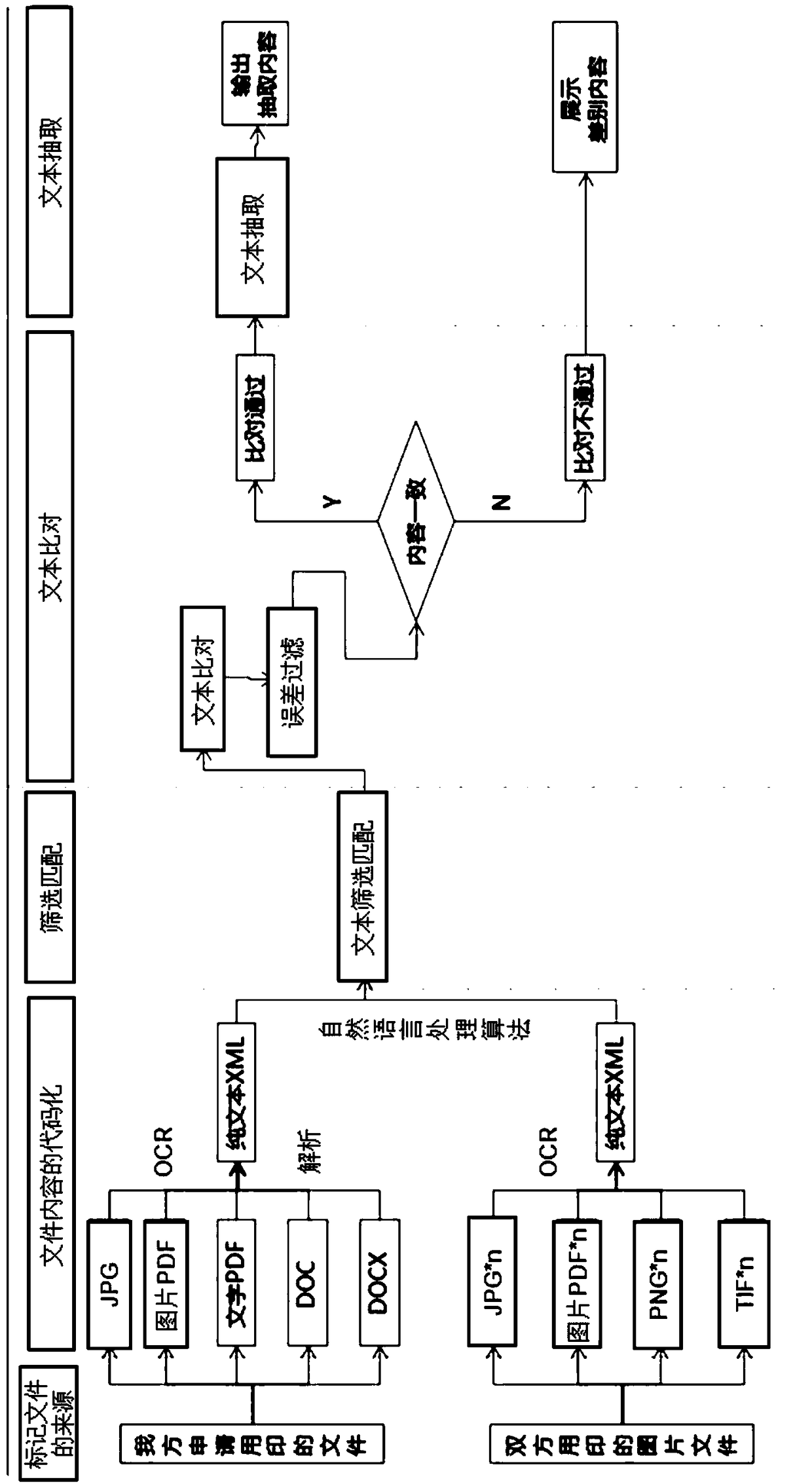
InactiveCN109190092AReduce work intensityReduce financial riskFinanceSemantic analysisText alignmentText file
The invention discloses a consistency auditing method of different source files, which comprises the following steps: marking the source of the file, wherein two files to be checked are from differentsources respectively, one file is used as a reference part and the other file is used as a part to be checked and the other file is used as a part to be checked; coding the content of the files: thetwo files are coded separately to obtain the text file with uniform format; performing text alignment: text alignment is carried out on the basis of two text files, the contents added, deleted or modified are marked in the text of the part to be audited, the first alignment result is generated, the error filtering is carried out on the first alignment result, the second alignment result is generated, and the similarity value is generated according to the second alignment result; processing comparison results: if the similarity value is greater than the set threshold, the two text files are extracted from each other. If the similarity value is not greater than the set threshold, the difference between the two text files is displayed on the basis of the text of the part to be audited.
Owner:深圳平安综合金融服务有限公司
System and Method For Electronic Publication and Fund Raising
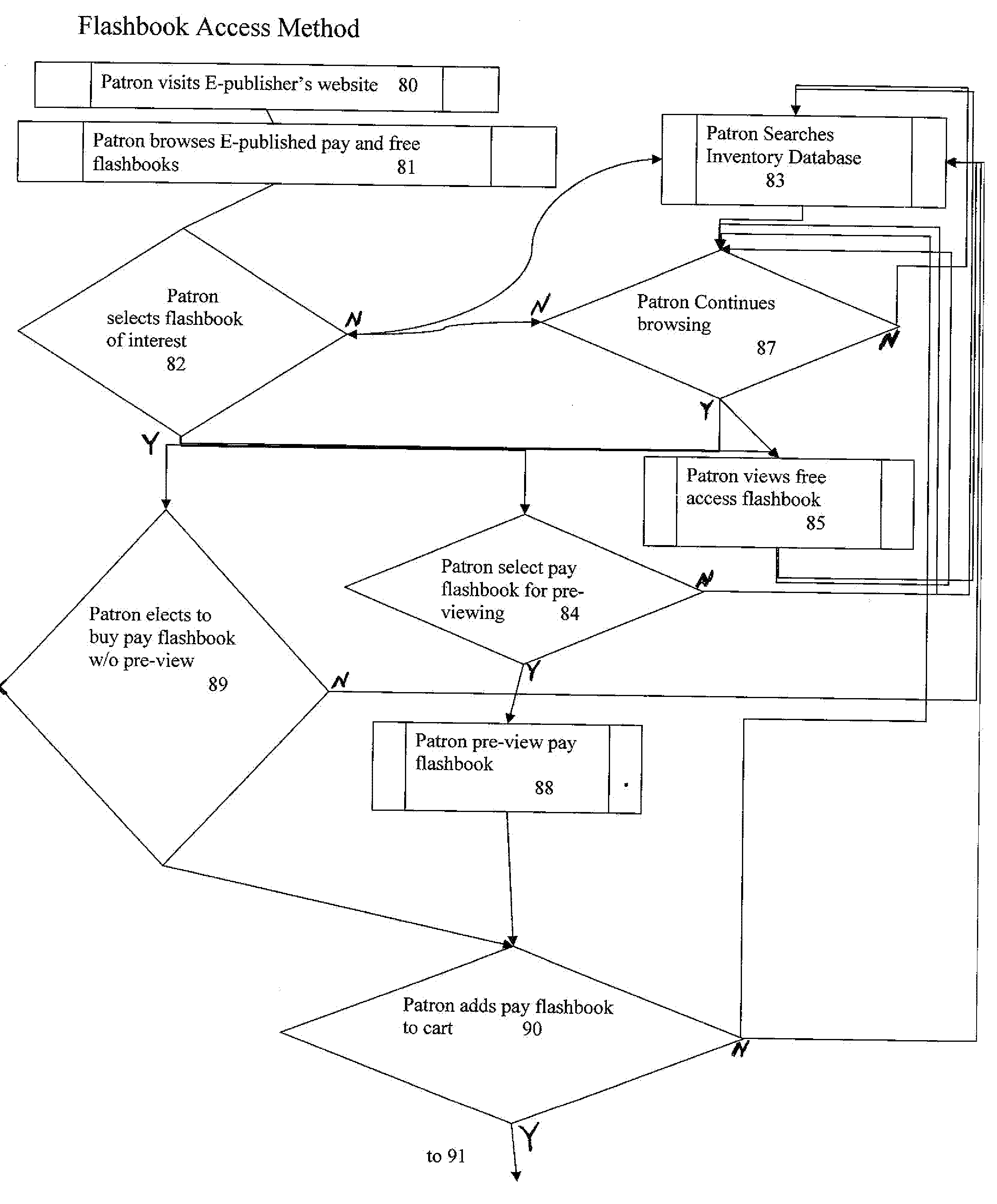
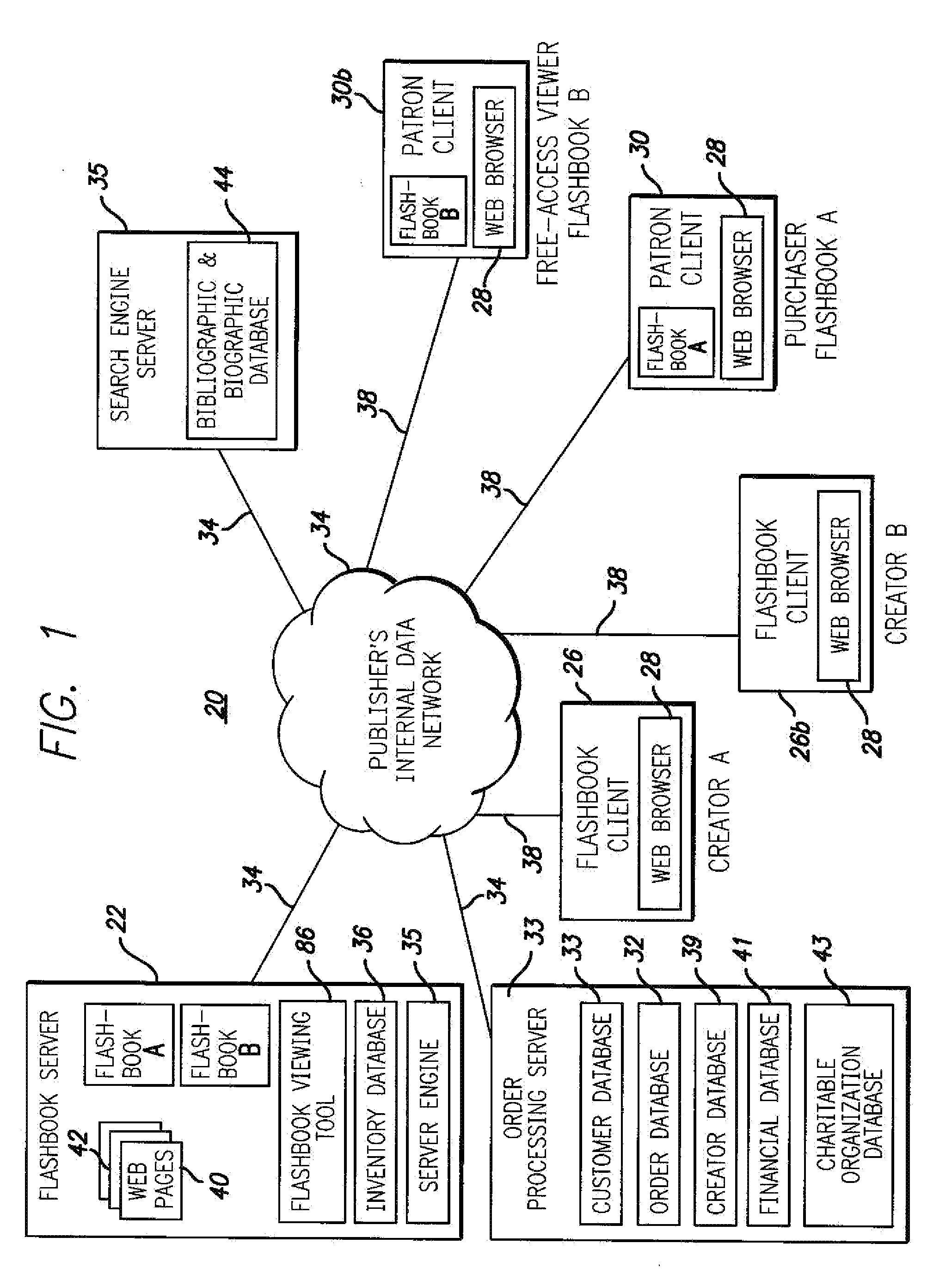
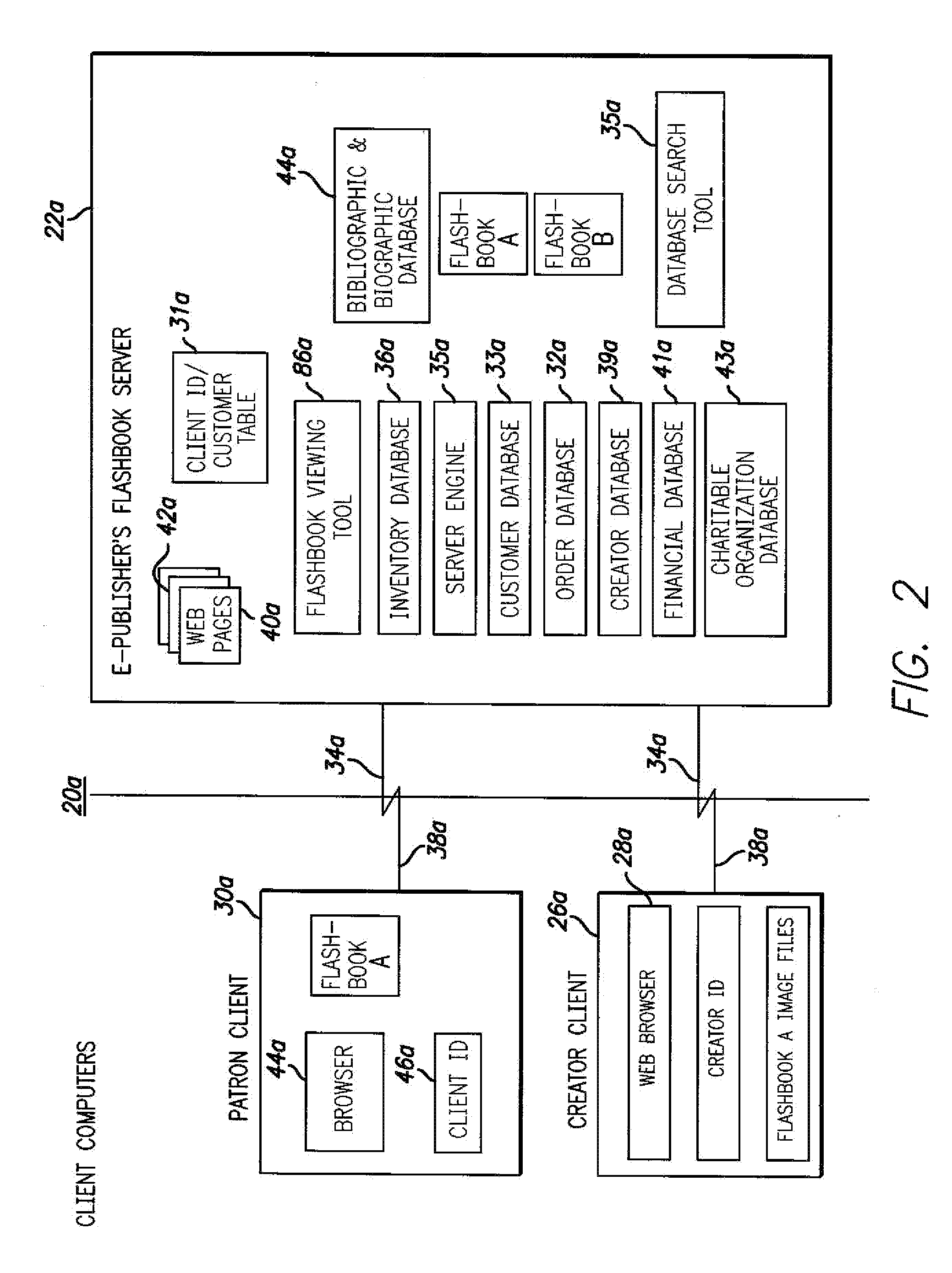
InactiveUS20110066526A1Efficient low-cost electronic publicationIncrease percentageFundraising managementPayment architectureNon profitEngineering
The invention provides a system and method for electronic publication of original, creative works on a website as well as systems and methods for compensating the author(s) of the original creative works. The electronic publishing systems of the present invention can also be utilized in novel methods of fund raising for charitable and / or non-profit organizations.
Owner:WATSON TOM
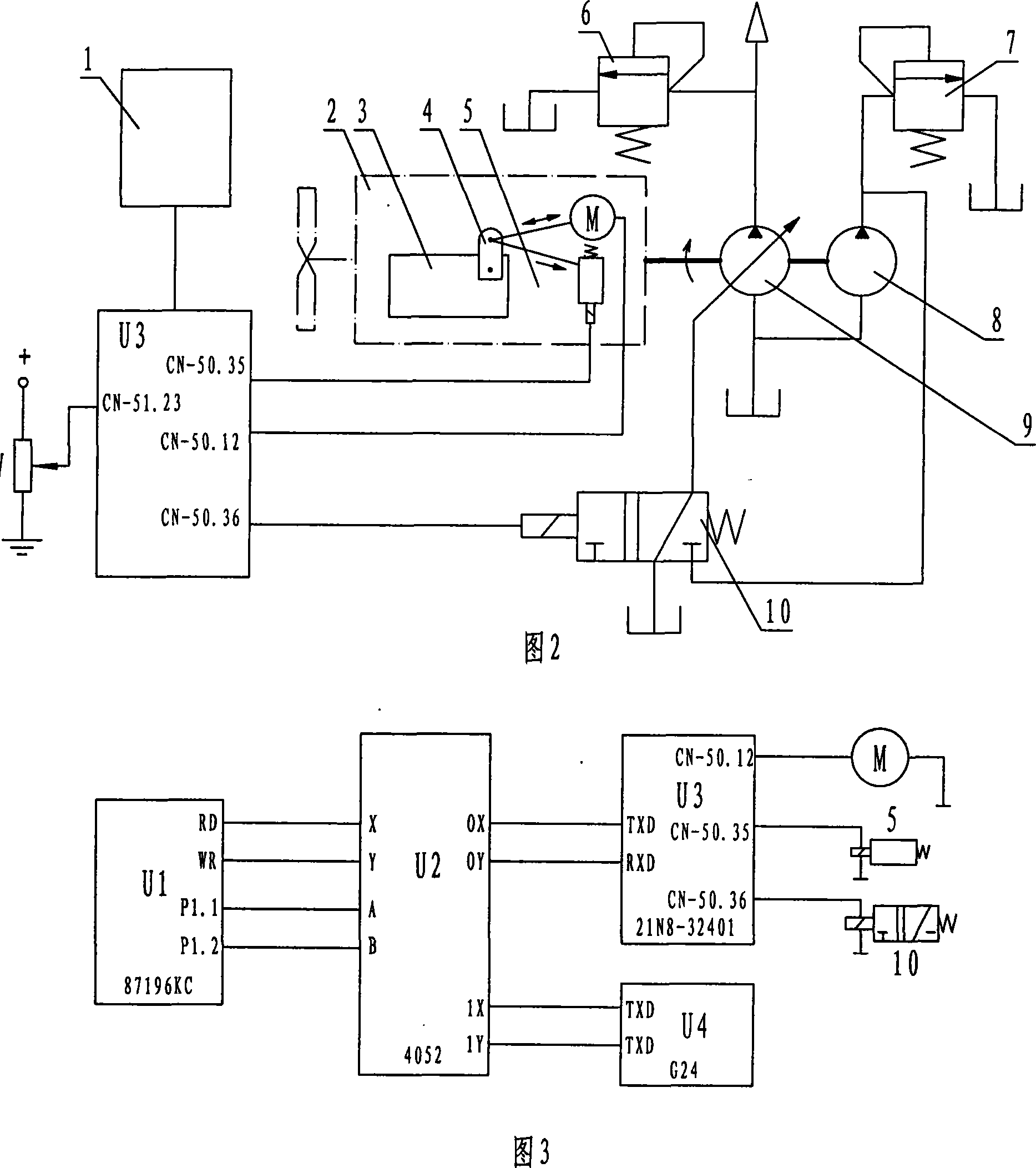
Engineering machinery password locking and unblock method and apparatus
ActiveCN101118660APrevent theftReduce financial riskAnti-theft devicesIndividual entry/exit registersControl systemPassword
The present invention provides a method and a device for the engineering machine code locking and unlocking, belongs to the controlling technology field, and is used in solving the equipment locking problem. The technical proposal is to use a control system composed of an engineering machine controller, a lock vehicle executing mechanism, a keyboard, and a displayer as the operation platform, to arrange a code memory in the engineering machine controller, to write the user unlock vehicle program executed automatically when the machine starts in the code memory and pre-store the unlocking code. By inputting the unlocking code in the keyboard, whether the input code is in accord with the pre-stored unlocking code can be judged by a CPU, when yes, the control executing mechanism finishes the locking execution or relieves the locking state on the engineering machine. The locking execution or the locking relieving refers to that the executing mechanism conducts the working state controlling on a speed adjusting motor, the flameout electromagnetism or the flux control proportion electromagnetism. The present invention can lock the engineering machine limberly and reliably, not only can reduce the financial risk of the manufacturer and the dealer, but also can provide users with convenience.
Owner:童一帆
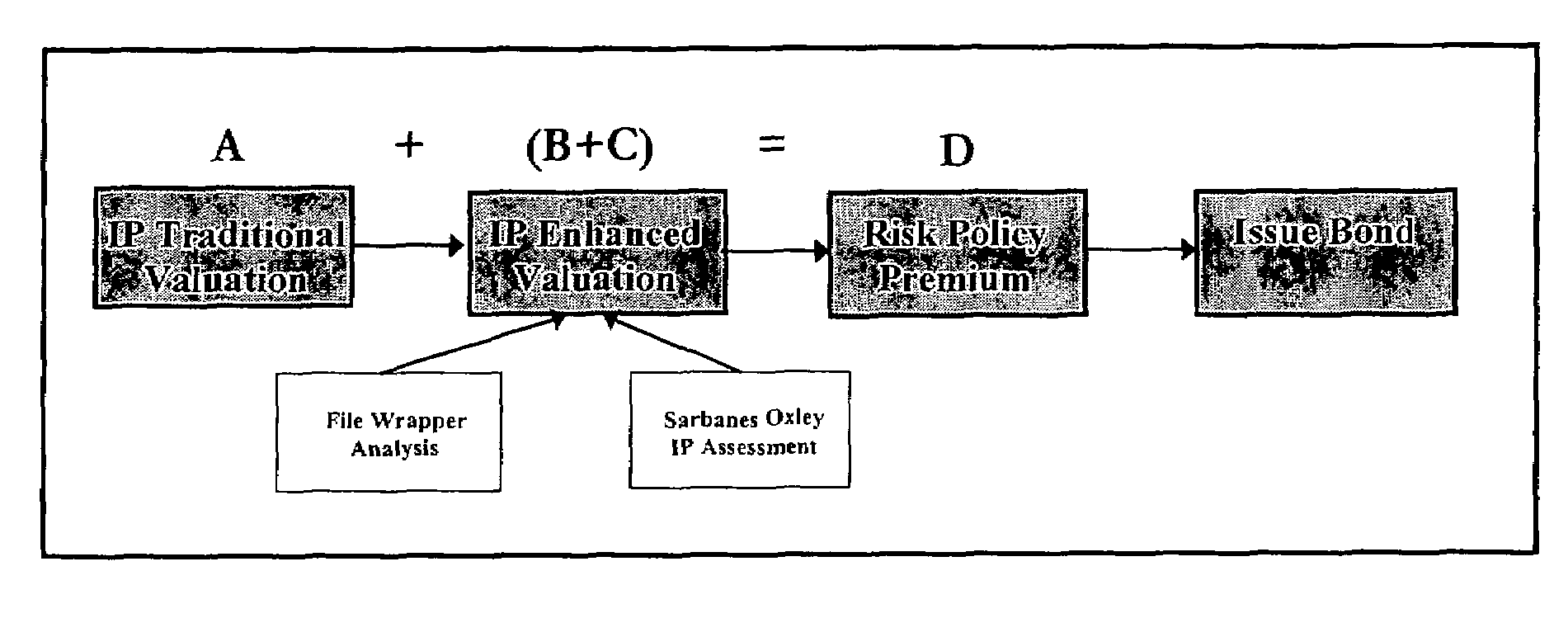
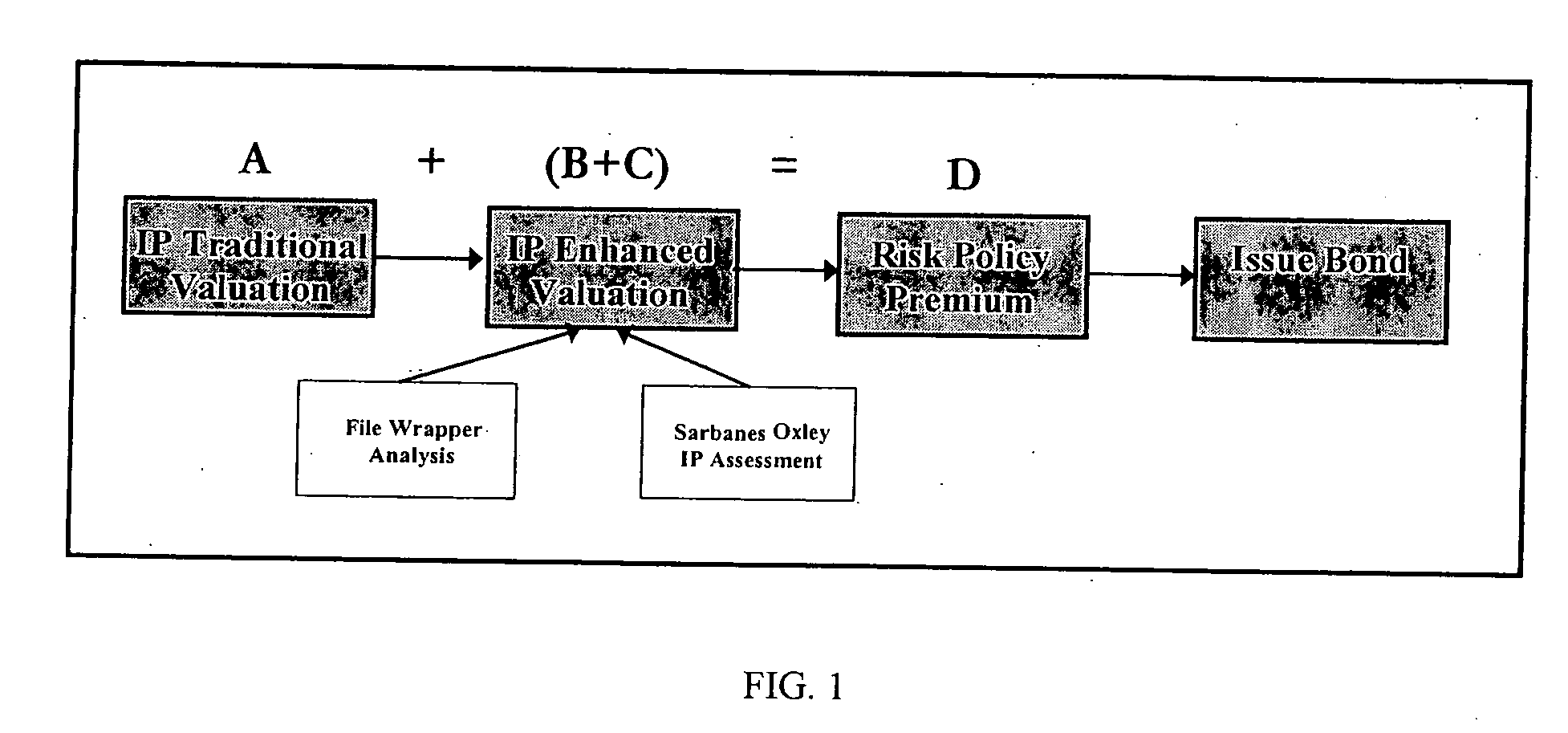
Method of appraising and insuring intellectual property
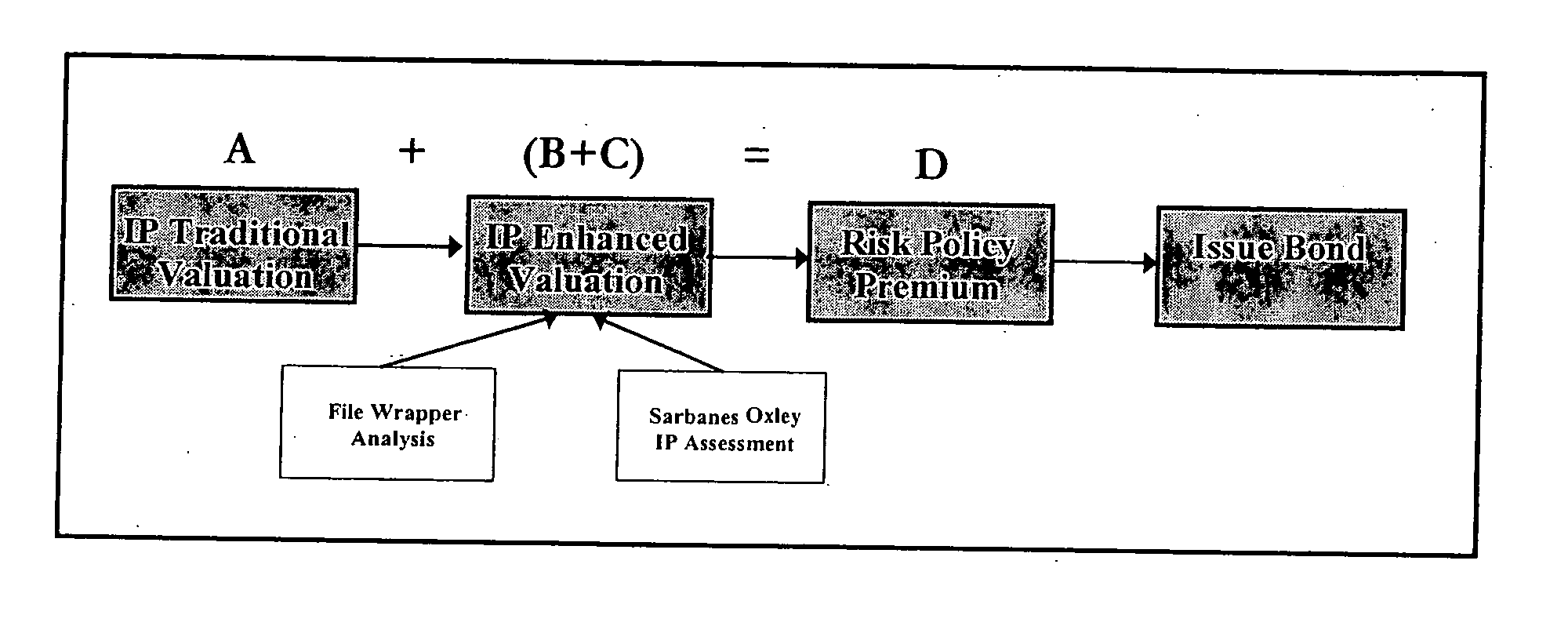
ActiveUS7536312B2Reduce financial riskExclude in valueMarket predictionsFinanceIntellectual propertyComputer science
Methods are disclosed for using computers, computer programs, algorithms and computer networks and communications hardware and protocols to appraise the value of assets as well as protecting asset owners from the risk that other entities will value those assets differently. The methods disclosed include:Supplementing traditional valuation methods with other considerations that may affect the value of intellectual property assets.Using insurance type financial instruments to maintain compliance with regulatory requirements such as those imposed by the Sarbanes Oxley Act, the SEC, or the IRS.Using insurance type financial instruments to protect intellectual property asset owners from the risk that tribunals, regulatory agencies, or other entities will appraise intellectual property assets at a different value.
Owner:OCEAN TOMO
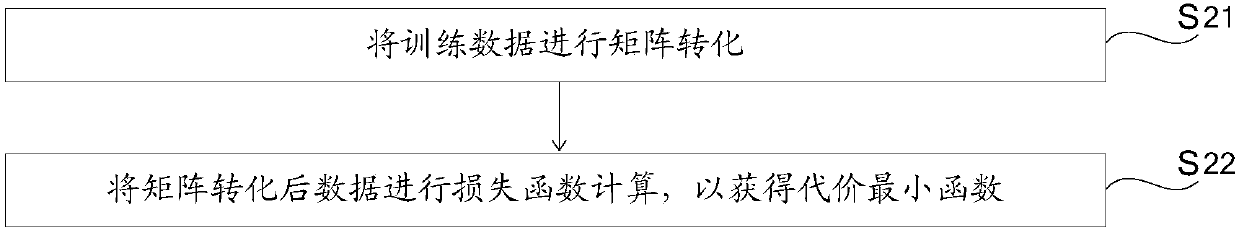
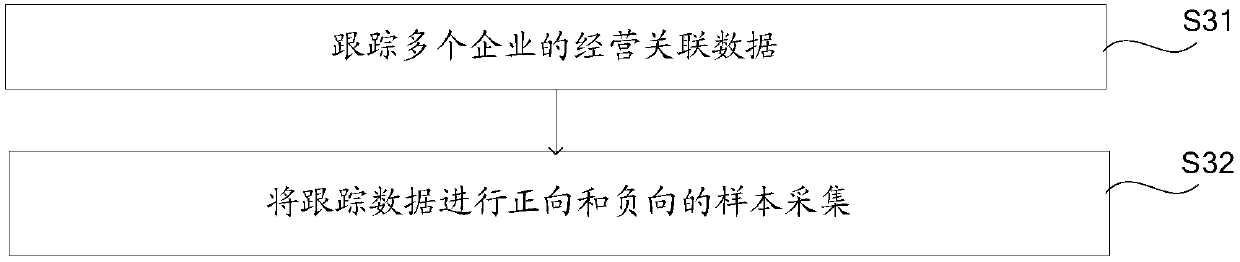
Financial risk analysis method based on big data
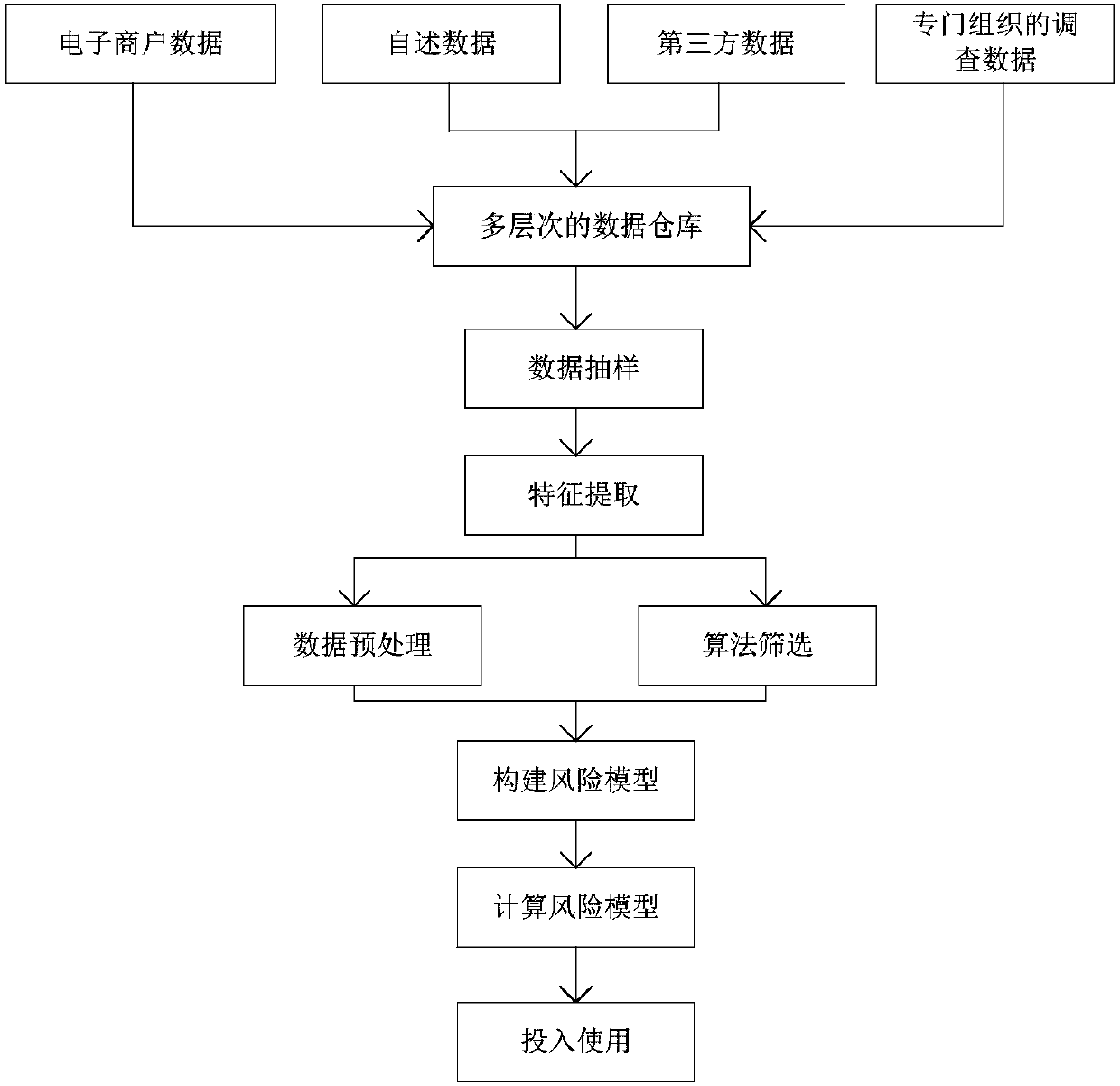
InactiveCN107563645AAchieve real-time effectsReduce financial riskFinanceCharacter and pattern recognitionData warehouseRisk model
The invention discloses a financial risk analysis method based on big data. The method comprises the following steps of: building a multilayer data warehouse; preprocessing data; tracking an in-storewarehoused and constructing positive and negative samples; constructing a growth ability, operation capability and profitability control models of the store by using a random forest algorithm; according to the random forest algorithm, acquiring and standardizing a growth ability index, an operation capability index, determining an index weight by using a analytic hierarchy process, calculating thevalue of each index; totaling the indexes and using the total index value as the risk index of the store; performing contrastive analysis on the results of a risk control model and related problems in an actual situation, optimizing the model and putting the optimized model into actual production. The financial risk analysis method takes multi-data source aggregation and the distributed computingof big data, realize a real-time effect of the risk model calculation after modeling, and reduce the financial risk through the aggregation analysis of multiple data sources.
Owner:杭州云算信达数据技术有限公司
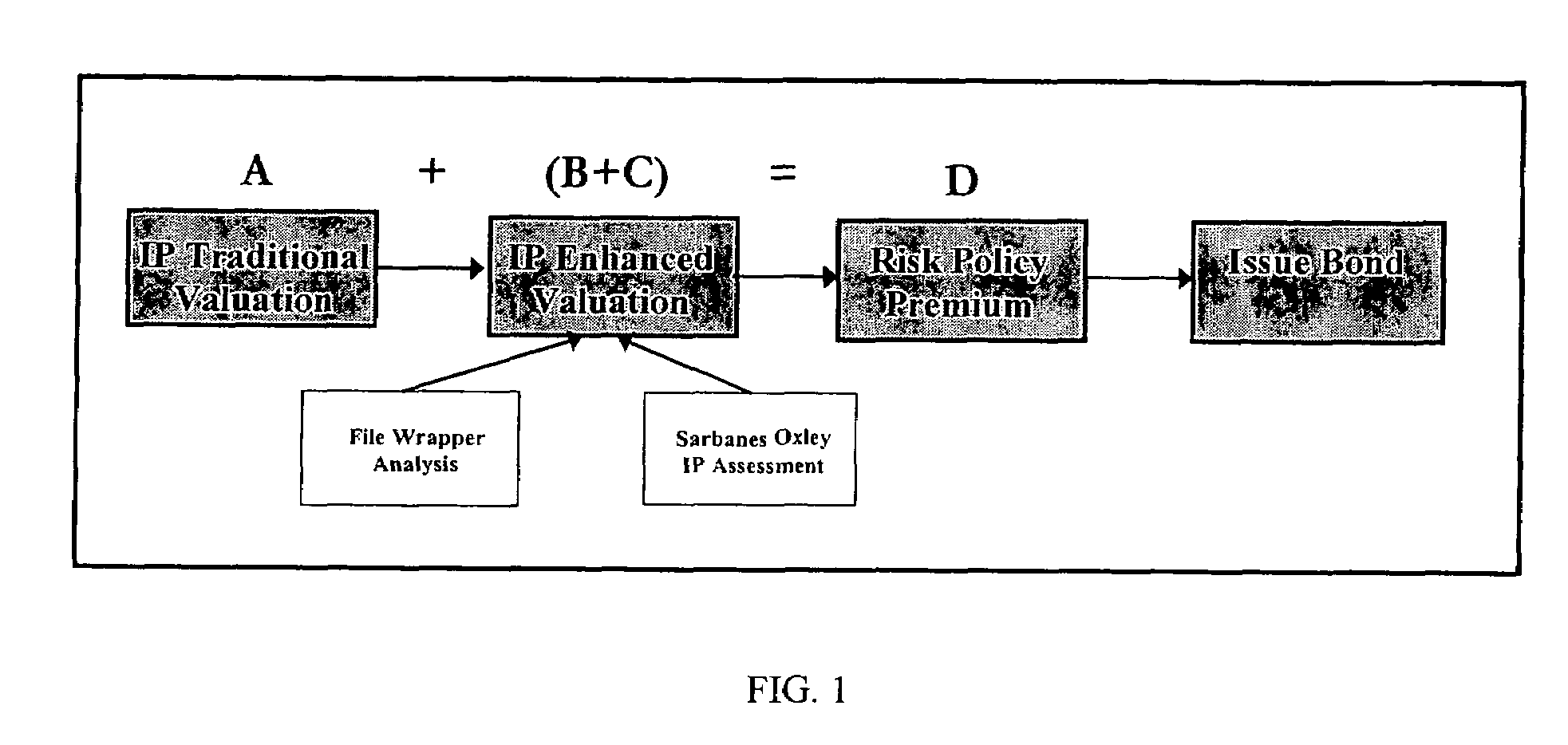
Method of appraising and insuring intellectual property
ActiveUS20060218066A1Reduce financial riskExclude in valueMarket predictionsFinanceValue assessmentRegulatory agency
Methods are disclosed for using computers, computer programs, algorithms and computer networks and communications hardware and protocols to appraise the value of assets as well as protecting asset owners from the risk that other entities will value those assets differently. The methods disclosed include: Supplementing traditional valuation methods with other considerations that may affect the value of intellectual property assets. Using insurance type financial instruments to maintain compliance with regulatory requirements such as those imposed by the Sarbanes Oxley Act, the SEC, or the IRS. Using insurance type financial instruments to protect intellectual property asset owners from the risk that tribunals, regulatory agencies, or other entities will appraise intellectual property assets at a different value.
Owner:OCEAN TOMO
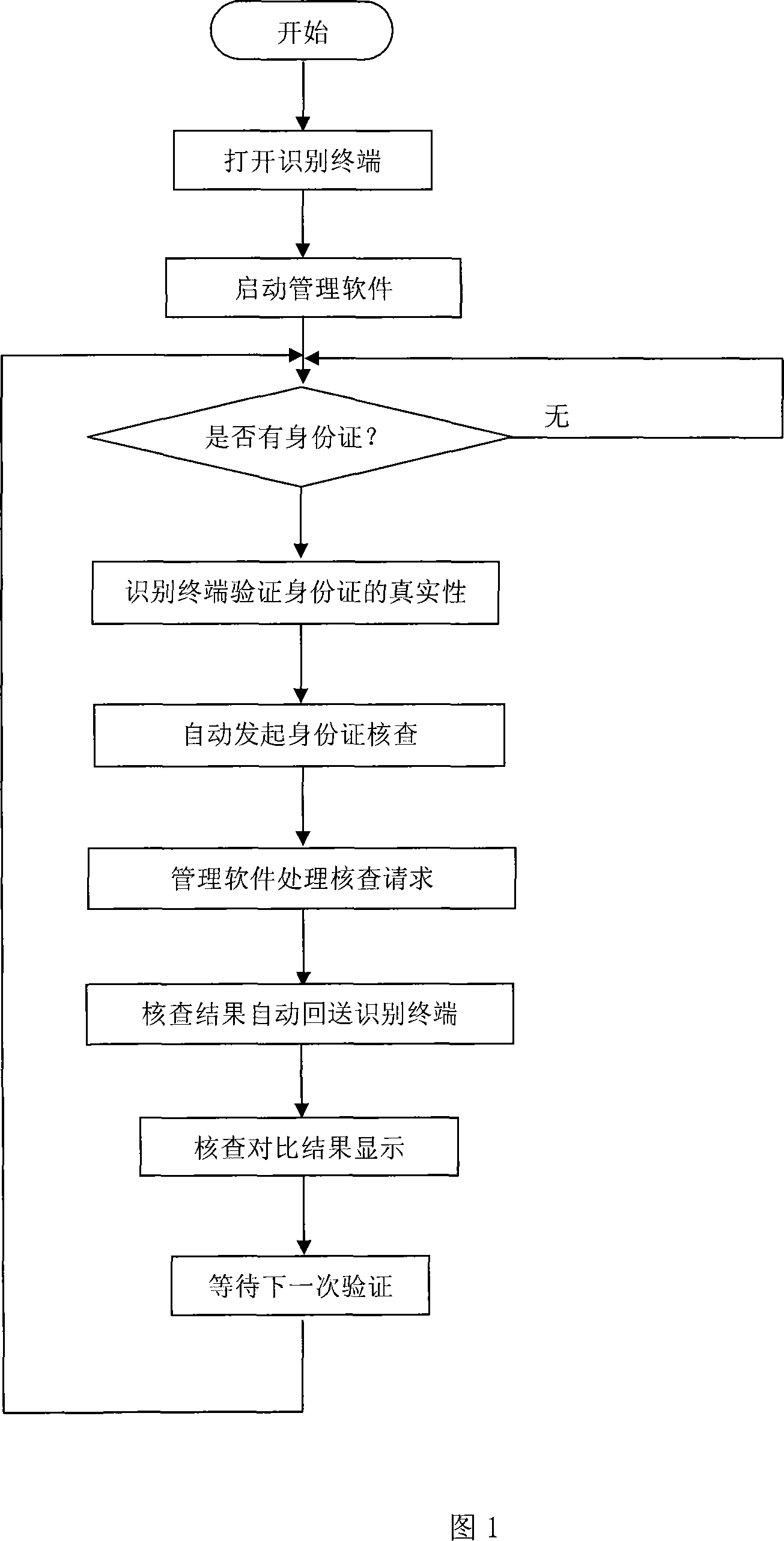
Network checking method for identity card validation
InactiveCN101123010AGuarantee the safety of fundsPrevent money launderingChecking apparatusPrivate networkThe Internet
The invention discloses a method of checking identity certificate verification, which is used to realize check via the internet for verification of authenticity of identity certificate of individual customers through an identity certificate recognizing terminal provided with a networking check managing software and a special network. The steps of verifying check via network are: starting; opening the recognizing terminal and starting the managing software; recognizing whether the terminal has detected an identity certificate, and if a certificate has been detected, the recognizing terminal reads the identity certificate information and display the photo and related information on the recognizing terminal screen; the recognizing terminal transfers the request to the population information database of the Ministry of Public Security; the database checks the verification and feeding back the check results to the recognizing terminal; the recognizing terminal screen simultaneously displays photo and related information of the identity certificate requested for verification, and the check result, photo and related information are fed back from the population information database of the Ministry of Public Security to the recognizing terminal; and finishing the check and waiting for next verification check. The invention can be used for quickly and accurately checking authenticity of the identity certificate of an individual customer, i. e. the second generation of individual identity certificate.
Owner:SHANDONG SYNTHESIS ELECTRONICS TECH
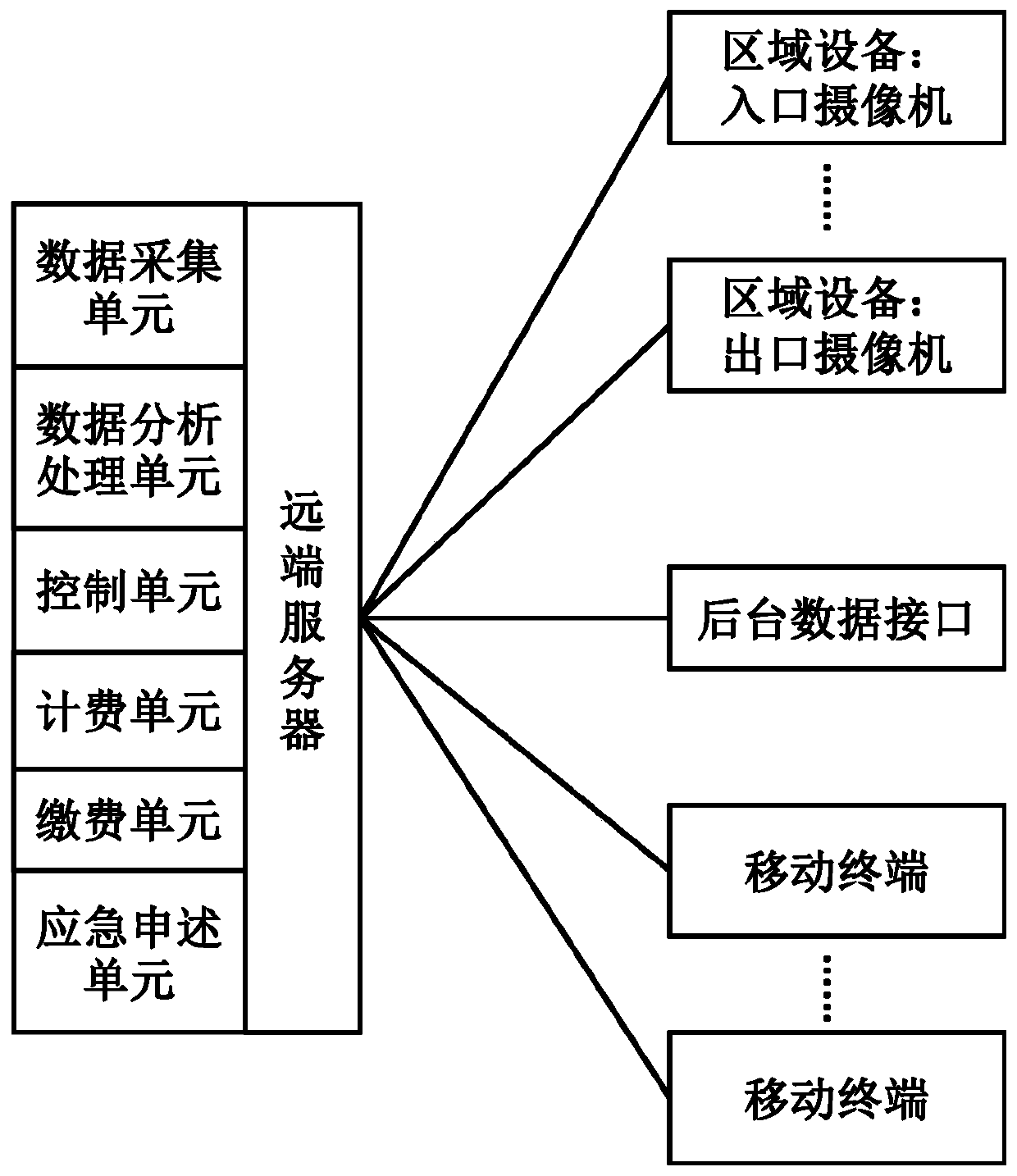
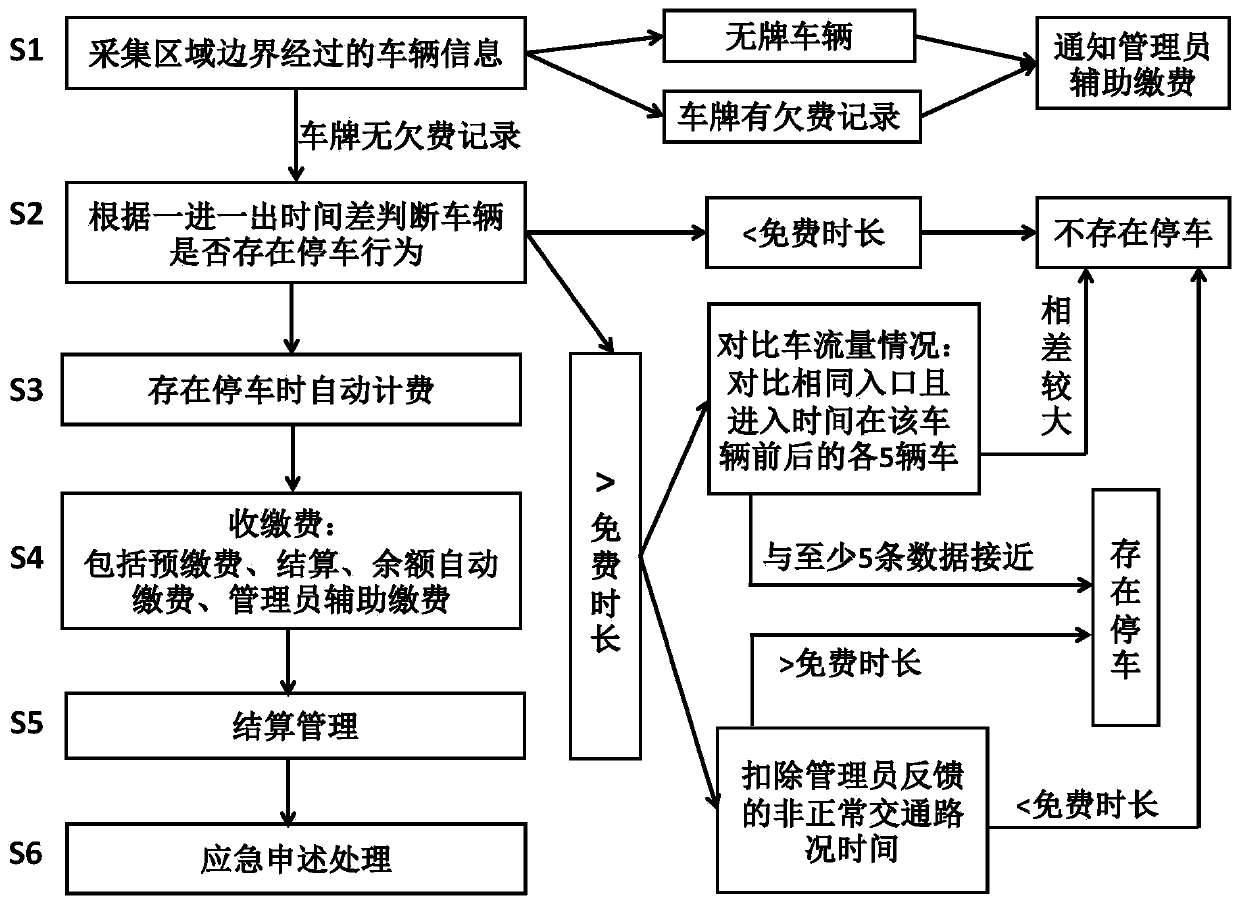
"One-in and one-out" roadside parking management toll collection system and method
ActiveCN110807838AGuaranteed full shotReduce distraction loggingTicket-issuing apparatusRoad vehicles traffic controlTelecommunicationsCollection system
The invention discloses a "one-in and one-out" roadside parking management toll collection system and method, and the toll collection system comprises parking area equipment, a remote server, and a mobile terminal in communication connection with the remote server, wherein the parking area equipment comprises multiple cameras located at the boundaries of each area, and can also comprise geomagnetic sensors and parking locks; and the remote server is equipped with a data acquisition unit, a data analysis processing unit, a control unit, a billing unit, a payment unit, and an emergency statementunit. The toll collection method, based on the toll collection system, collects vehicle information entering and exiting the boundaries of the areas and the time difference between entering and exiting through cameras, automatically charges vehicles that are determined to have parking behaviors, collects the tolls through mobile terminals or artificial assistance, and can prevent from toll dodging by using geomagnetic sensors and parking locks. The roadside parking management toll collection system and method provided by the invention have the advantages such as simple and convenient chargingmethod, high charging efficiency, prevention of toll dodging, reduction of financial risk and strong operability.
Owner:湖南省新时代防伪信息科技有限公司
Mobile station and methods for diagnosing and modeling site specific full-scale effluent treatment facility requirements
InactiveUS8790517B2Reduce financial riskHigh continuity of operationSolid sorbent liquid separationAnalogue computers for chemical processesInitial treatmentIon exchange
A mobile station and methods are disclosed for diagnosing and modeling site specific effluent treatment facility requirements to arrive at a treatment regimen and / or proposed commercial plant model idealized for the particular water / site requirements. The station includes a mobile platform having power intake, effluent intake and fluid outflow facilities and first and second suites of selectably actuatable effluent pre-treatment apparatus. An effluent polishing treatment array is housed at the station and includes at least one of nanofiltration, reverse osmosis and ion-exchange stages. A suite of selectively actuatable post-treatment apparatus is housed at the station. Controls are connected at the station for process control, monitoring and data accumulation. A plurality of improved water treatment technologies is also disclosed. The modeling methods include steps for analyzing raw effluent to be treated, providing a field of raw effluent condition entry values and a field of treated effluent condition goals entry values, and utilizing said fields to determine an initial treatment model including a selection of, and use parameters for, treatment technologies from the plurality of down-scaled treatment technologies at the facility, the model dynamically and continuously modifiable during treatment modeling.
Owner:ROCKWATER RESOURCE
Method for real-time authorization of bank card transaction based on interactive voice response
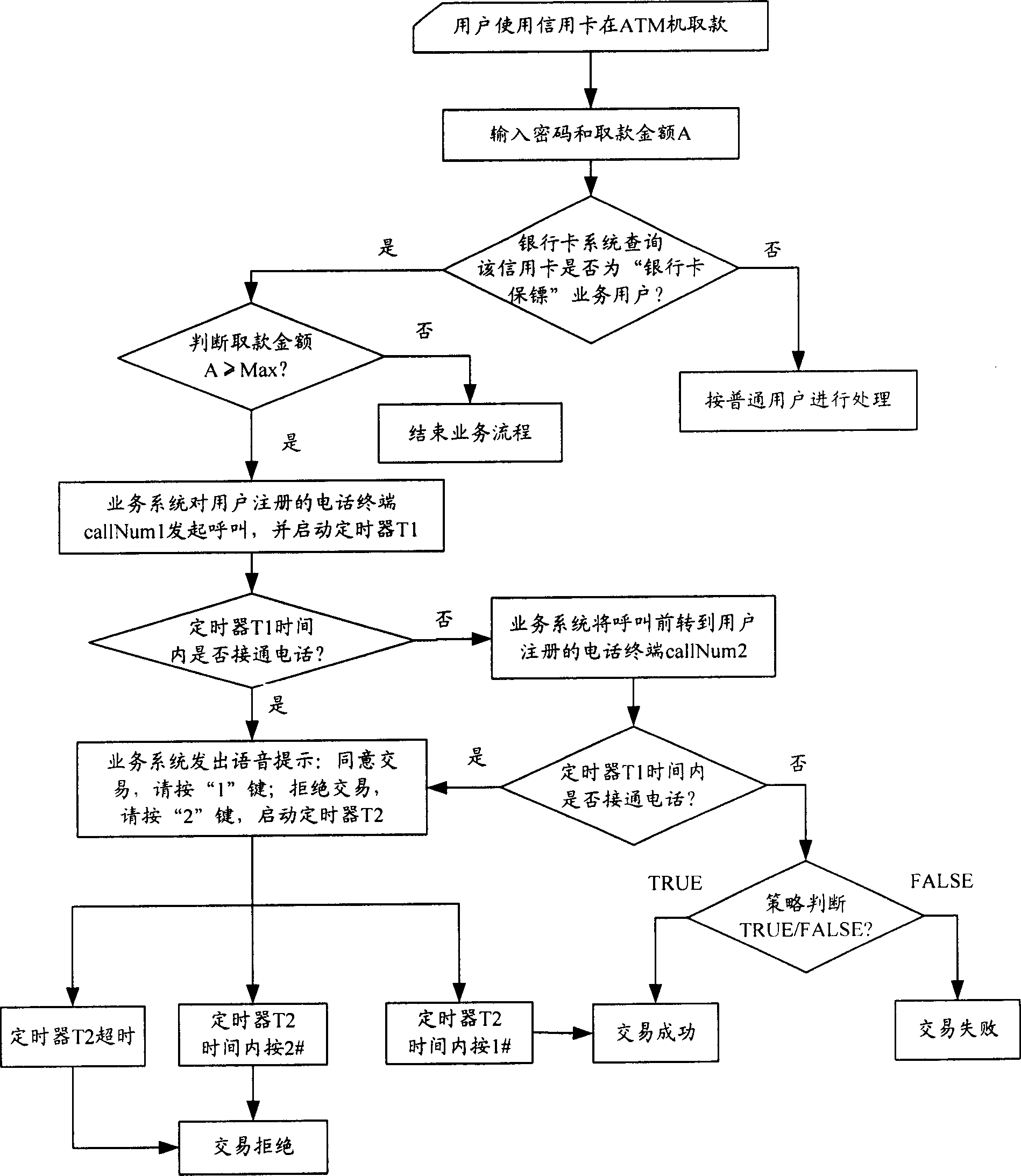
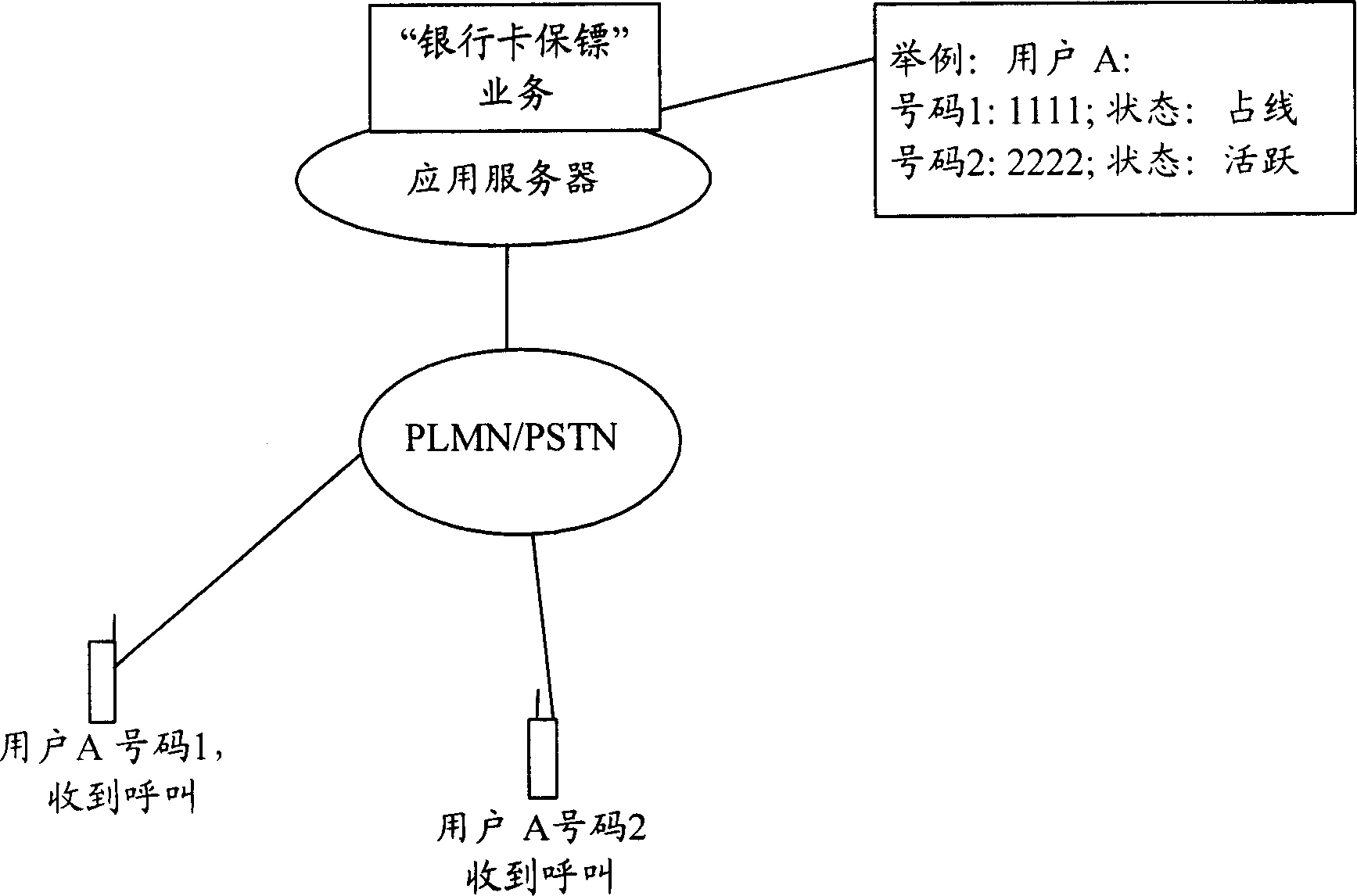
InactiveCN1801228AReduce financial riskComplete banking machinesAcutation objectsAuthorizationTelecommunications equipment
Disclosed is a method for authorizing with interactive audio response during dealing with bank card which comprises: binding the bank card number with user's phone numbers; when draw amount of bank card equals or exceeds the pre-set draw amount, calling user's pre-set phone terminals in sequence and prompting user that the bank card being drawn or consumed, according to press-key response after getting through user to decide whether to allow this dealing; if having communication device on drawing locale, then user being able to communicate with persons on locale with speech / video; if none of the pre-set phone terminals being gotten through, rejecting or allowing the dealing according to user's pre-set policies.
Owner:BEIJING UNIV OF POSTS & TELECOMM
User credit risk assessment method and device and storage medium
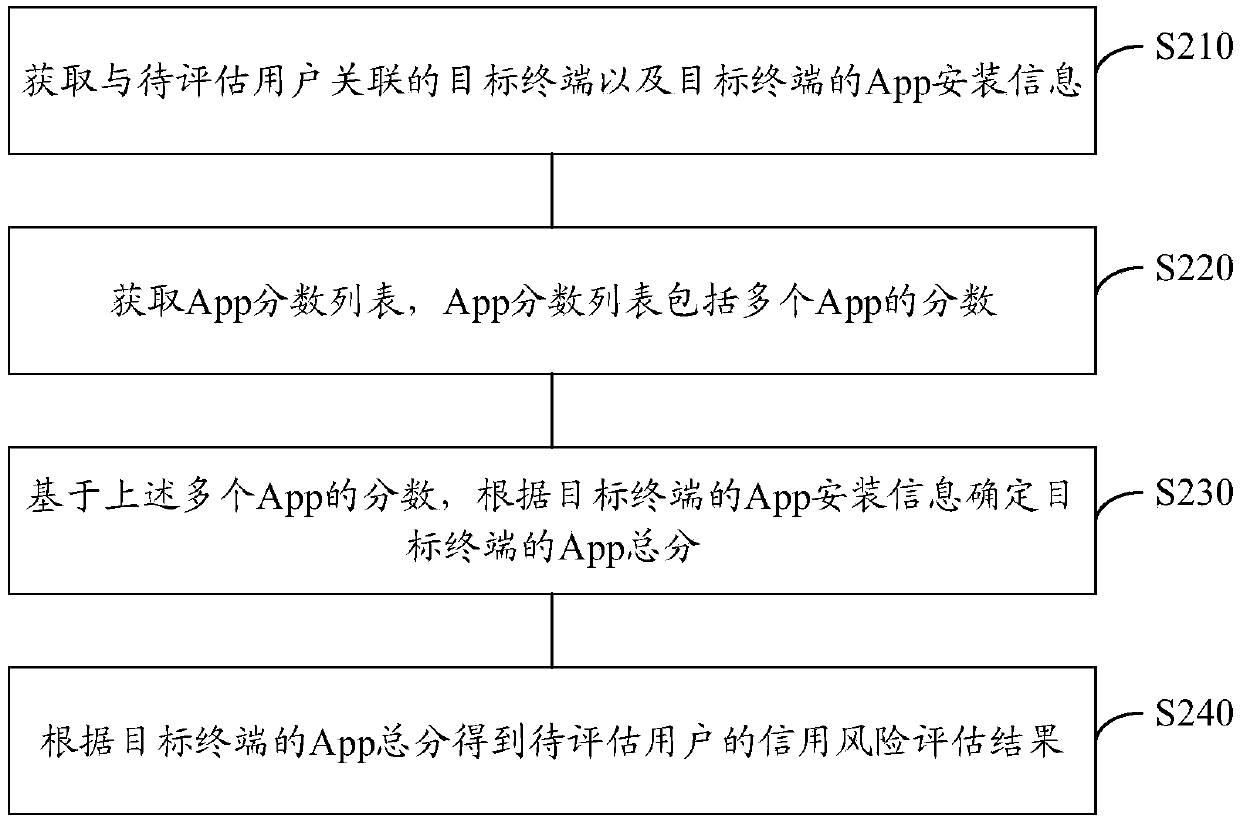
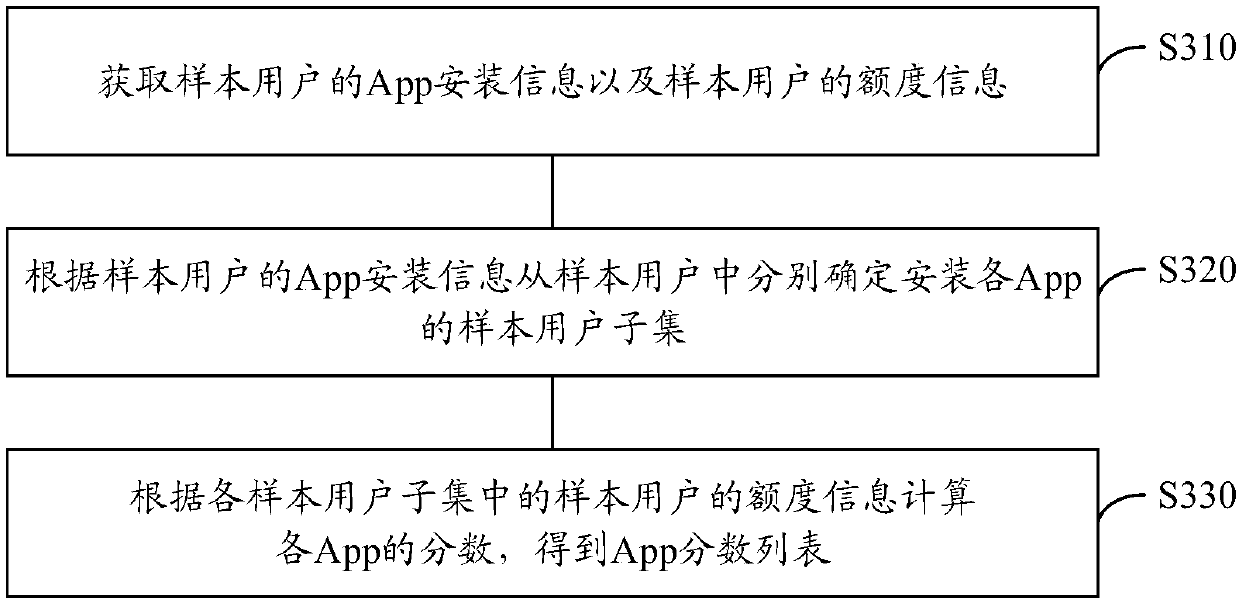
The invention provides a user credit risk assessment method and device and a computer readable storage medium, and belongs to the technical field of big data. The method comprises the steps of obtaining a target terminal associated with a to-be-evaluated user and App installation information of the target terminal; Obtaining an App score list, wherein the App score list comprises scores of a plurality of Apps; Determining an App total score of the target terminal according to the App installation information of the target terminal based on the scores of the plurality of Apps; And obtaining a credit risk assessment result of the to-be-assessed user according to the App total score of the target terminal. According to the invention, dependence of the user credit risk assessment method on external data can be reduced, the accuracy of the assessment result is improved, and the risk is reduced.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Off-site bond transaction clearing system and method based on license chain
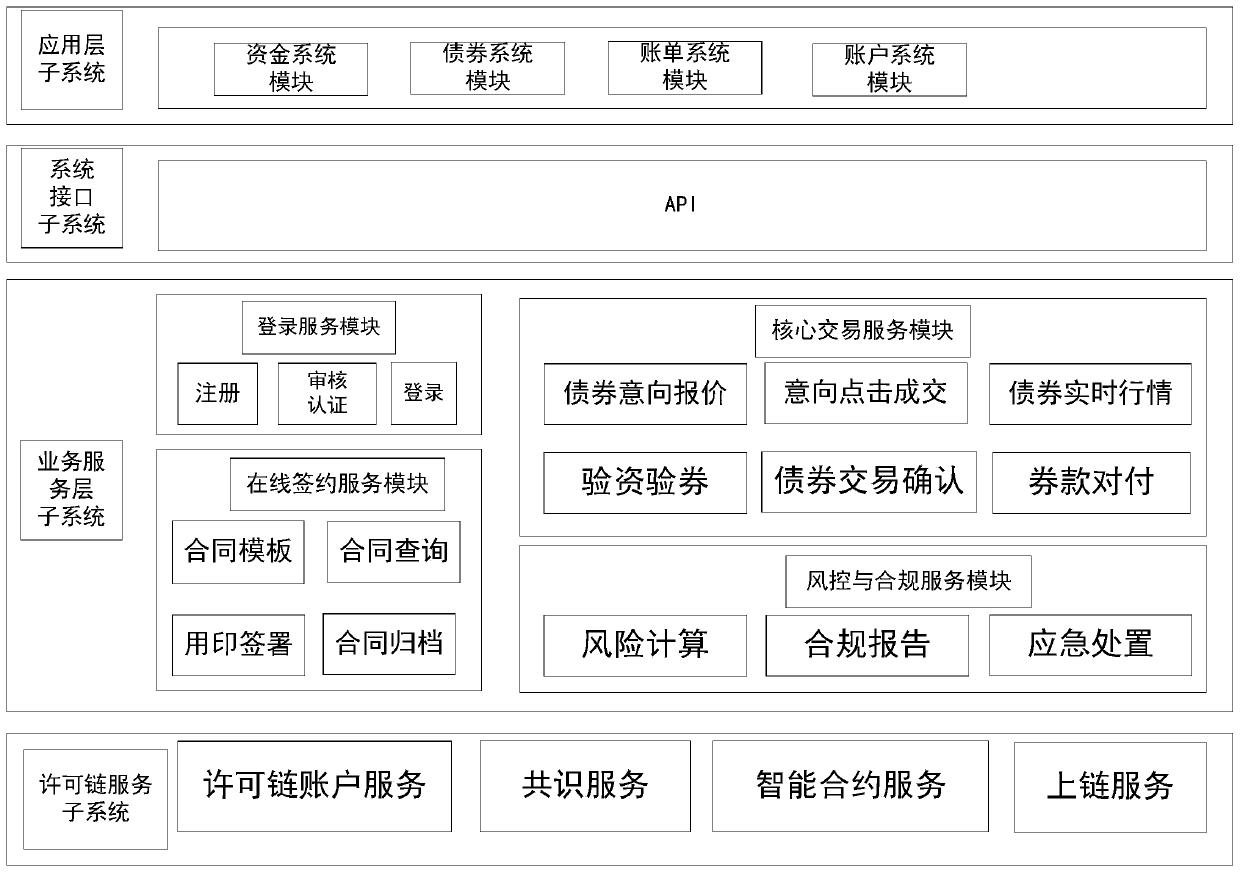
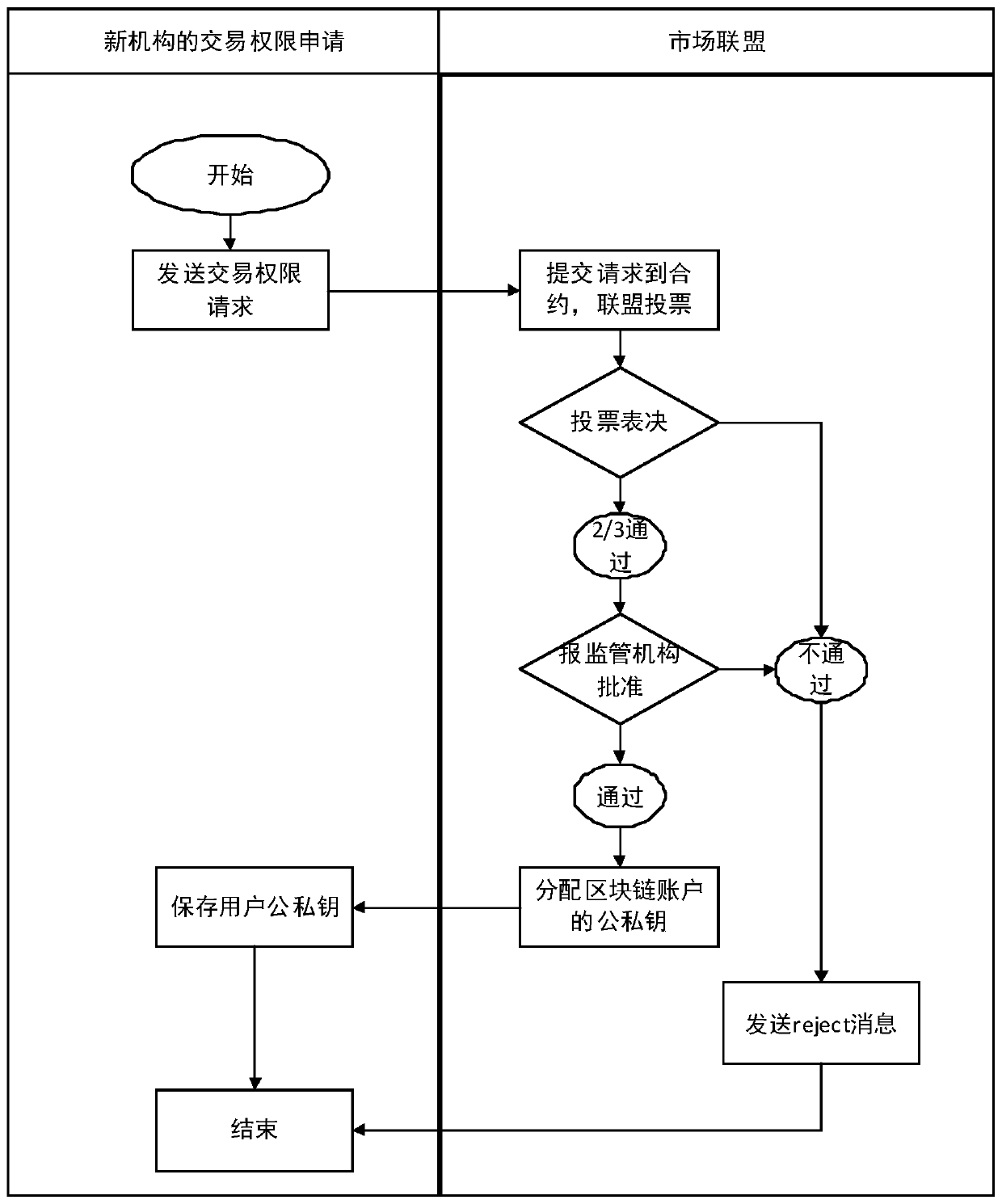
PendingCN110400224AGuaranteed equal statusEfficient business interactionFinanceSecuring communicationRisk ControlRisk prevention
The invention discloses an off-site bond transaction clearing system based on a license chain, capable of improving the transparency of a product, increasing the intelligent level of the product, improving the automatic and intelligent level of a flow, improving the transaction and signing efficiency, reducing the transaction cost, and reducing the systematic financial risk. According to the technical scheme, full-life-cycle management of off-site bond trading is achieved. Permission design based on a permission chain ensures self-organization and strong supervision of market ecology under anoff-site bond transaction system, and permission design based on a decentralized CA mechanism ensures equal status of market alliance and reflects supervision intention. The design of transaction andclearing is completed by using an intelligent contract, and the business interaction between a transaction institution and a transaction opponent institution is completed, and transaction risk prevention and coupon transfer are completed by using intelligent contract automatic inspection and instructions. The risk control rule design of the intelligent contract is configured according to a supervision suitability matching rule, so that intelligent matching and automatic management of the supervision rule are realized, and an active supervision mechanism is formed.
Owner:上海金融期货信息技术有限公司
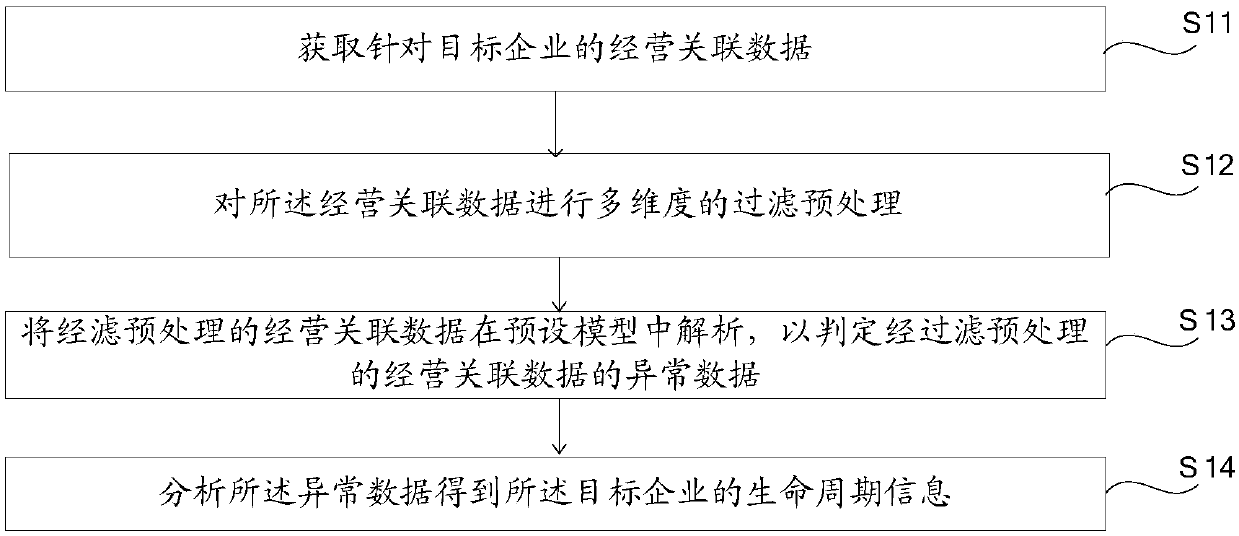
Enterprise life cycle analysis method and system based on big data
InactiveCN107844917AReduce financial riskAchieve real-time effectsResourcesEnterprise life cycleData source
The invention relates to an enterprise life cycle analysis method and system based on big data, and the method comprises the steps: obtaining operation correlation data of a target enterprise; carrying out the multidimensional filtering preprocessing of the operation correlation data; analyzing the operation correlation data in a preset model after filtering preprocessing, so as to determine the abnormal data of the operation correlation data after filtering preprocessing; analyzing the abnormal data and obtaining the life cycle information of the target enterprise. The method employs multi-data-source convergence and big-data distributed calculation, i.e., the distributed calculation of a data decrease channel model of the target enterprise on the basis of modeling, thereby achieving a real-time effect of completing the calculation of the data decrease channel model of the enterprise after modeling. The method can obtain a result that the data of the target enterprise is in an abnormal decrease state, carries out the early warning against the operation abnormality, achieves the multi-data-source convergence analysis, achieves the technical purpose of operation data analysis and enterprise early warning and prompt, and effectively reduces the financial risks of the operation of the enterprise.
Owner:杭州云算信达数据技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com