Patents
Literature
9210 results about "License" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A license (American English) or licence (British English) is an official permission or permit to do, use, or own something (as well as the document of that permission or permit). A license can be granted by a party to another party as an element of an agreement between those parties. A shorthand definition of a license is "an authorization to use licensed material."
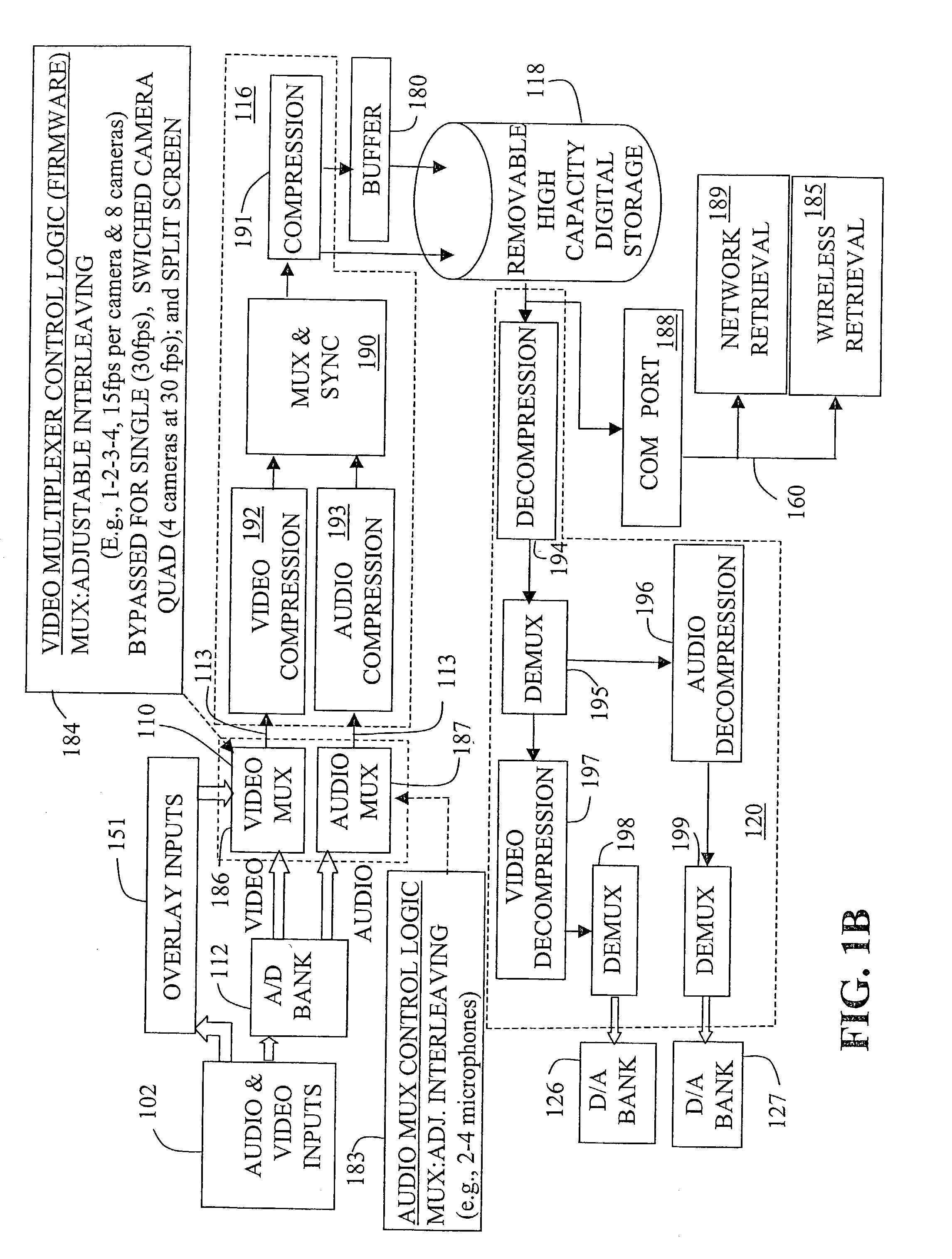
Multimedia surveillance and monitoring system including network configuration
InactiveUS6970183B1High bandwidthSignalling system detailsColor television detailsVideo monitoringStructure of Management Information
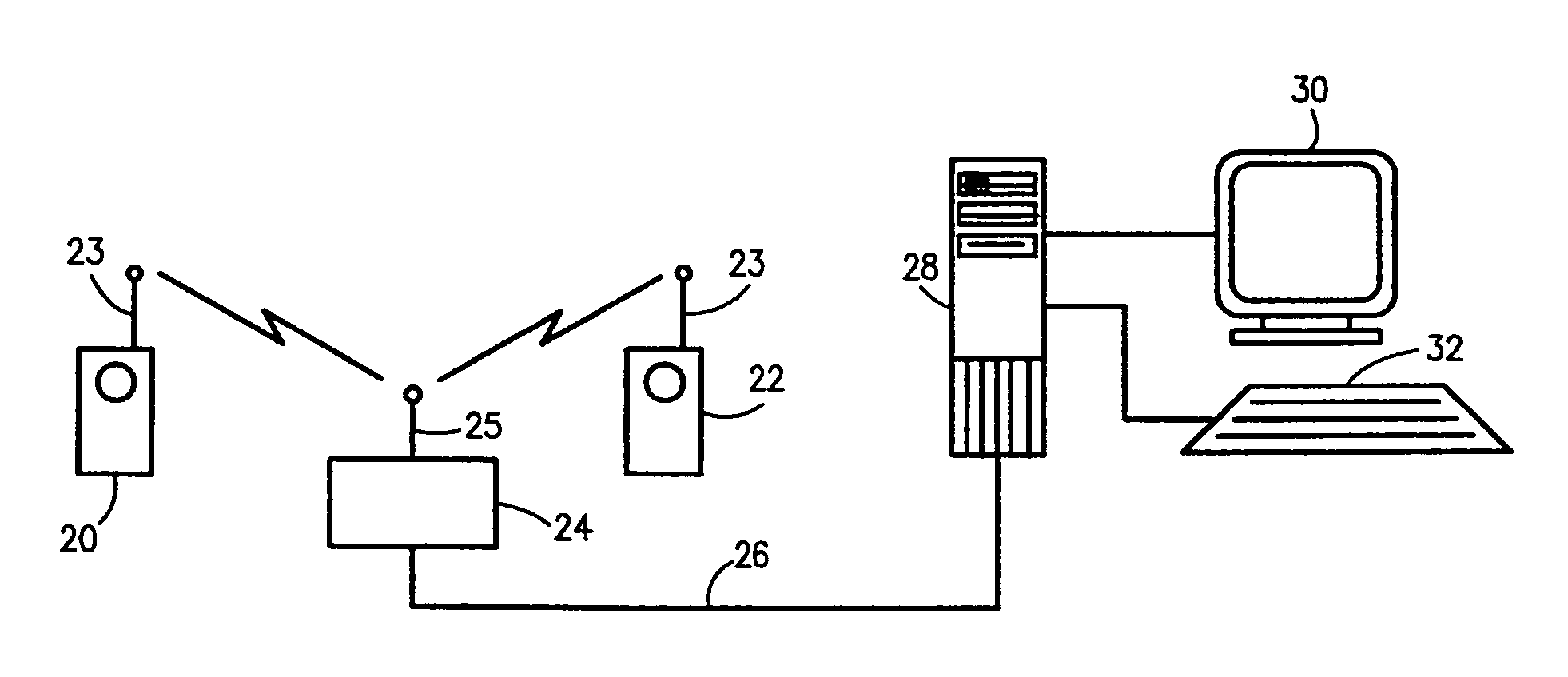
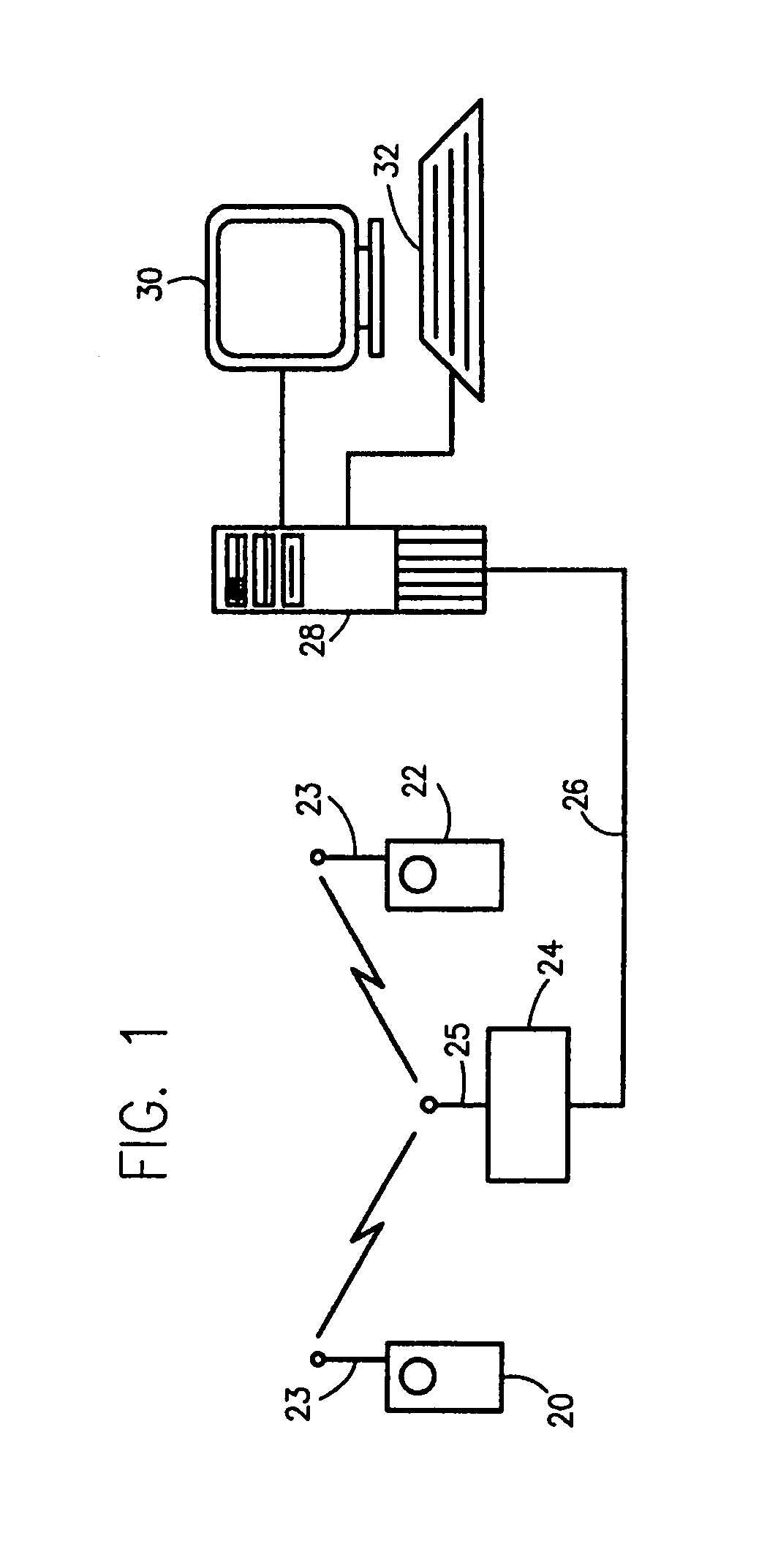
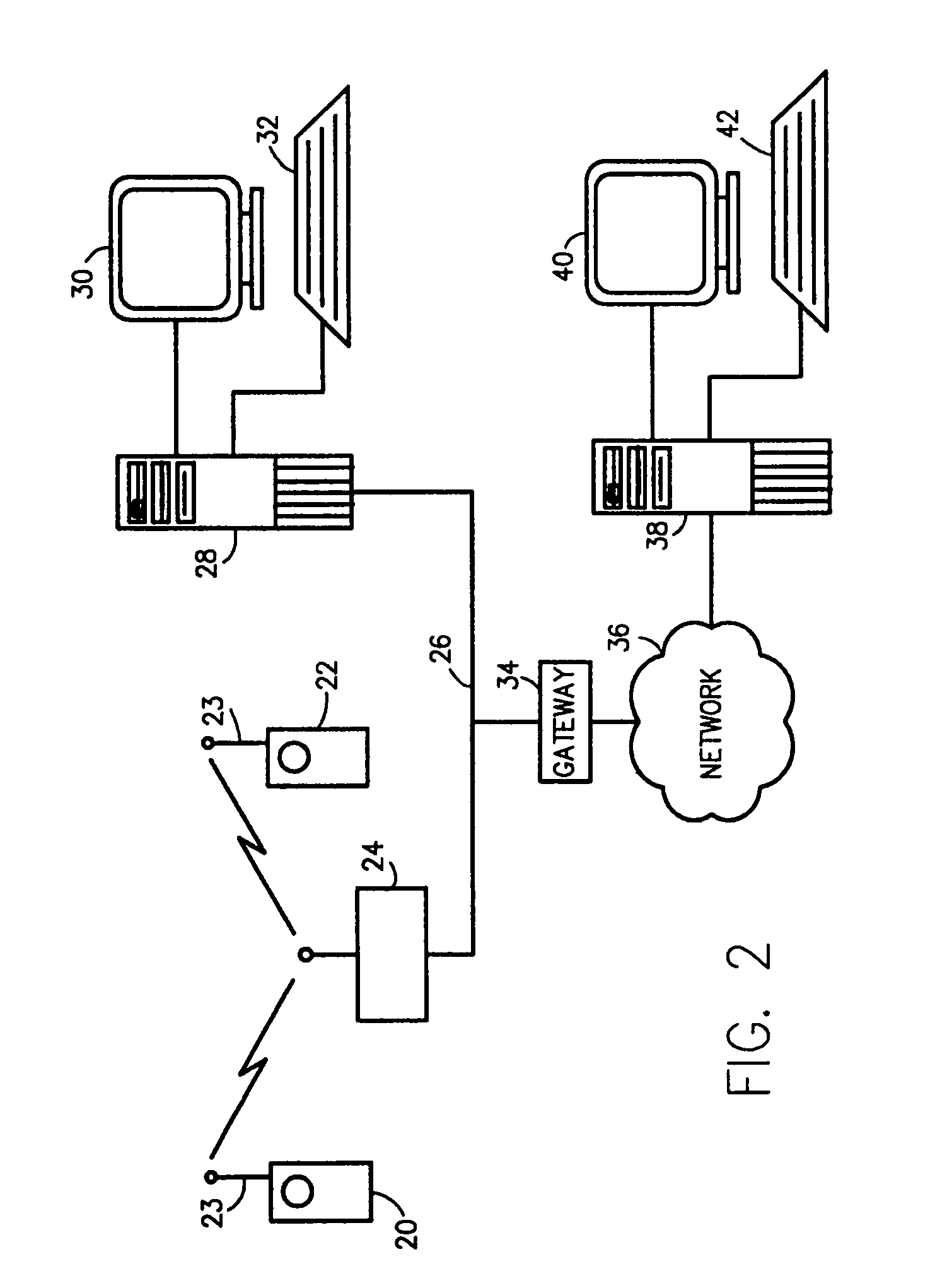
A comprehensive, wireless multimedia surveillance and monitoring system provides a combination of megapixel digital camera capability with full motion video surveillance with a network, including network components and appliances such as wiring, workstations, and servers with the option of geographical distribution with various wide area carriers. The full service, multi-media surveillance system is capable of a wide range of monitoring techniques utilizing digital network architecture and is adapted for transmitting event data, video and / or image monitoring information, audio signals and other sensor and detector data over significant distances using digital data transmission over a LAN, wireless LAN, Intranet or Internet for automatic assessment and response including dispatch of response personnel. Both wired and wireless appliance and sensor systems may be employed. GPS dispatching is used to locate and alert personnel as well as to indicate the location of an event. Automatic mapping and dispatch permits rapid response. The wireless LAN connectivity permits local distribution of audio, video and image data over a relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area Network) or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Centralized monitoring stations have access to all of the surveillance data from various remote locations via the Internet or the WAN. A server provides a centralized location for data collection, alarm detection and processing, access control, dispatch processing, logging functions and other specialized functions. The server may be inserted virtually anywhere in the Intranet / Internet network. The topology of the network will be established by the geographic situation of the installation. Appropriate firewalls may be set up as desired. The server based system permits a security provider to have access to the appliance and sensor and surveillance data or to configure or reconfigure the system for any station on the network.
Owner:PR NEWSWIRE
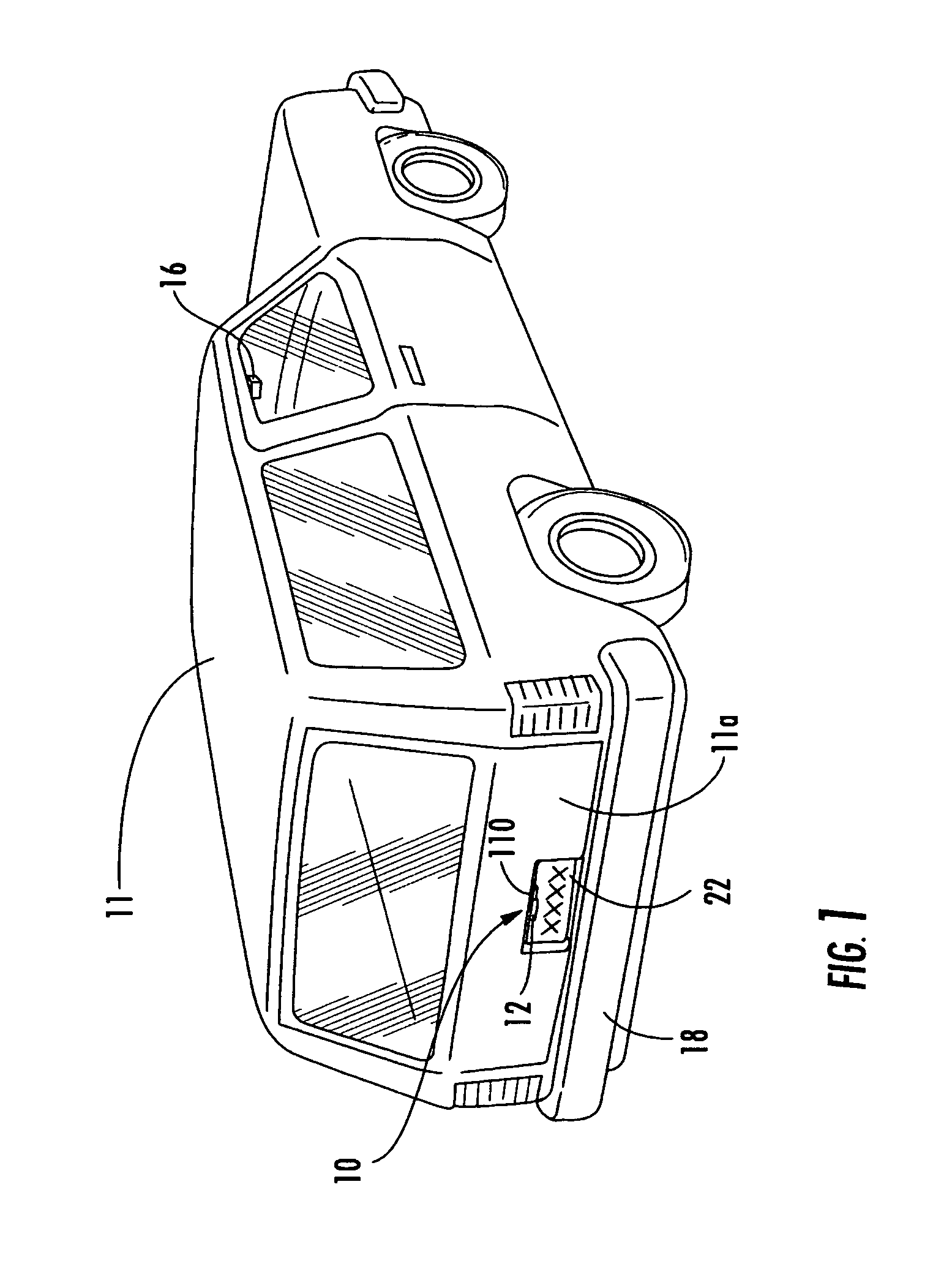
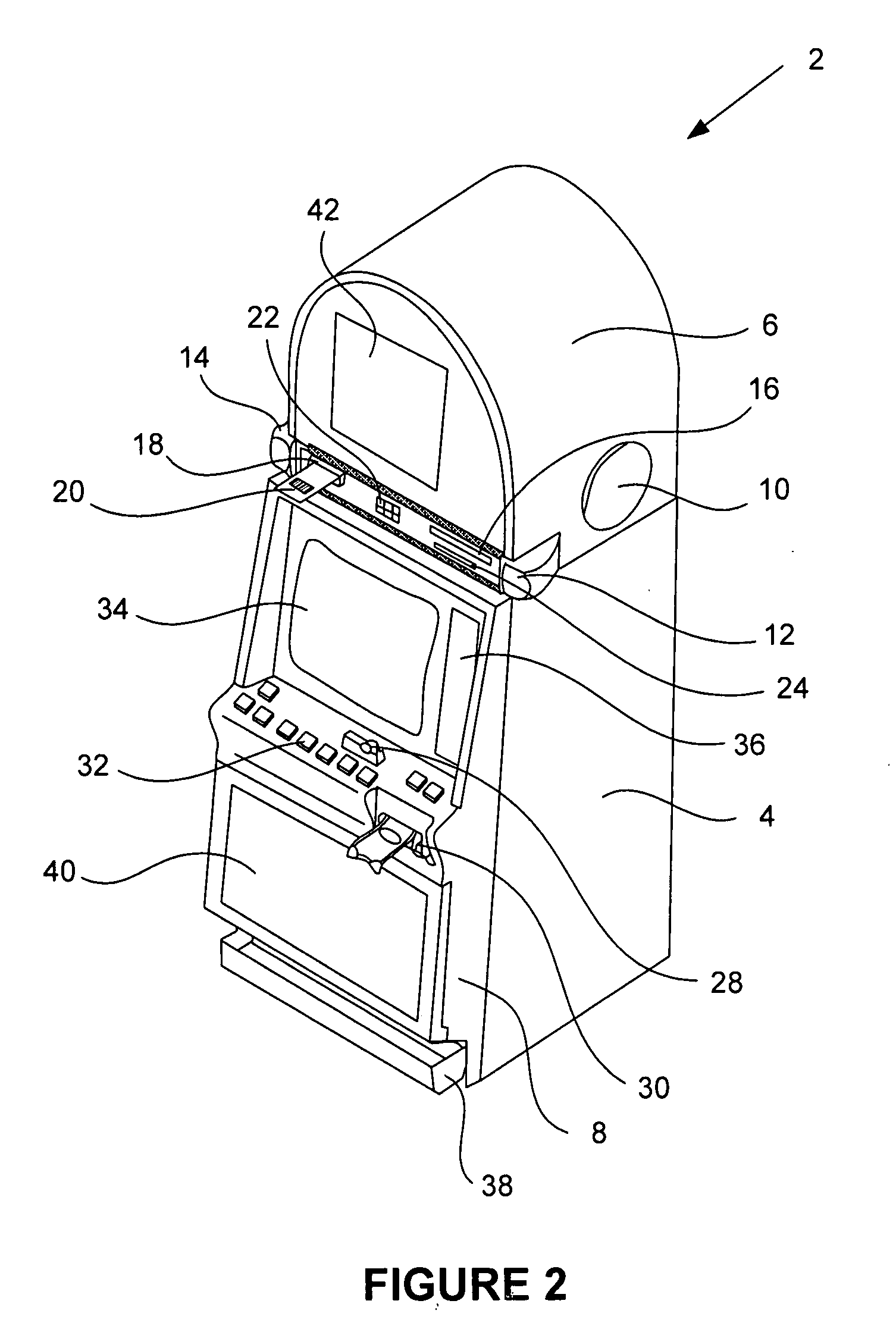
Vehicle imaging system
InactiveUS7005974B2Low costElectric signal transmission systemsTelemetry/telecontrol selection arrangementsDisplay deviceField of view
A vehicle imaging system includes an imaging sensor having a field of view exterior of a vehicle, an image processor and a display. The imaging sensor generates a signal indicative of an image representative of a scene occurring within the field of view. The image processor receives the signal from the imaging sensor and processes the signal to detect at least one relevant object within the image. The display is operable to display at least one iconistic representation of the at least one detected relevant object in response to an output signal generated by the image processor. The display is positionable within the vehicle and is viewable by a driver or passenger or occupant of the vehicle. The imaging sensor may be mounted to a mounting bracket mounted at a license plate area of the vehicle.
Owner:MAGNA ELECTRONICS
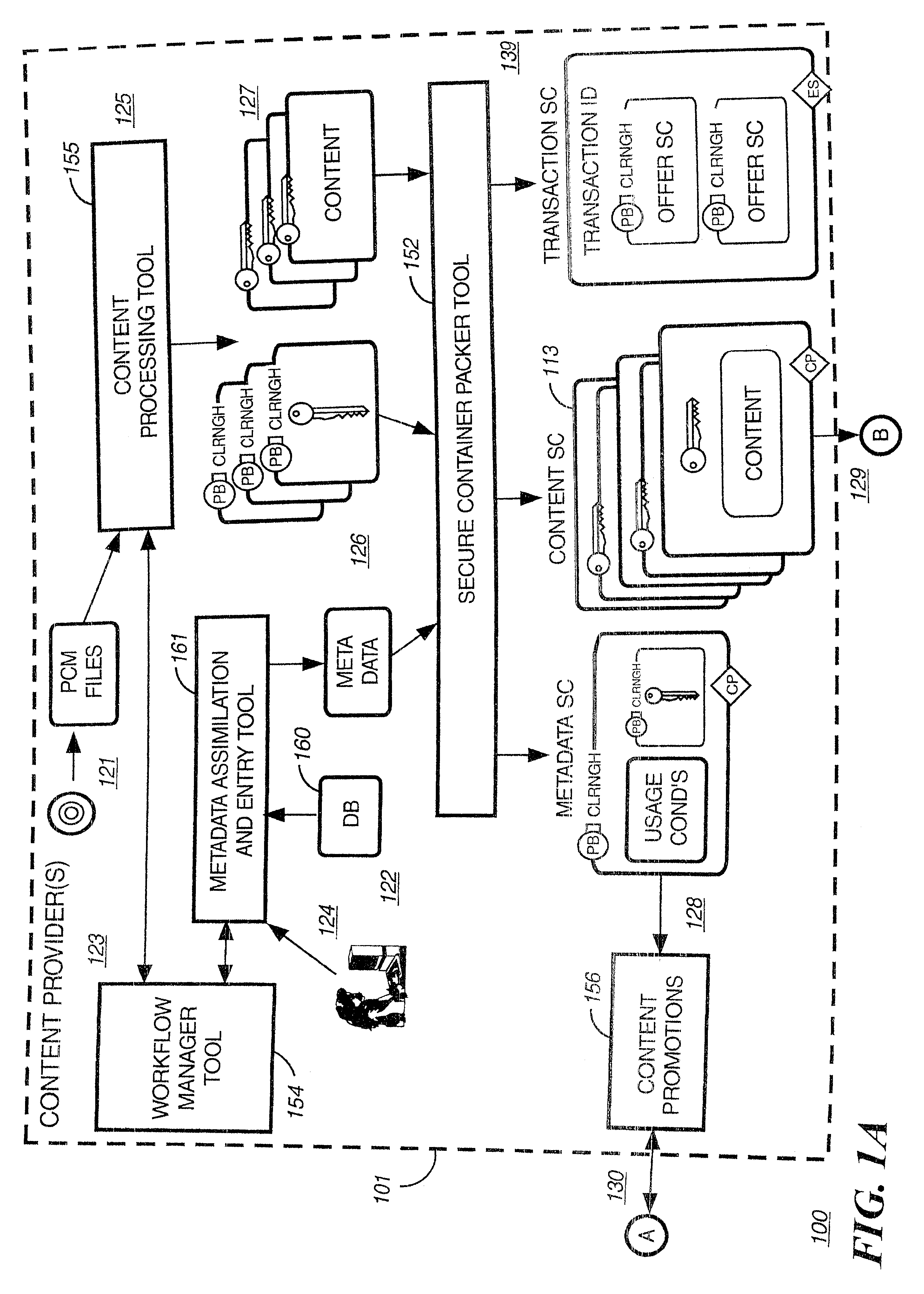
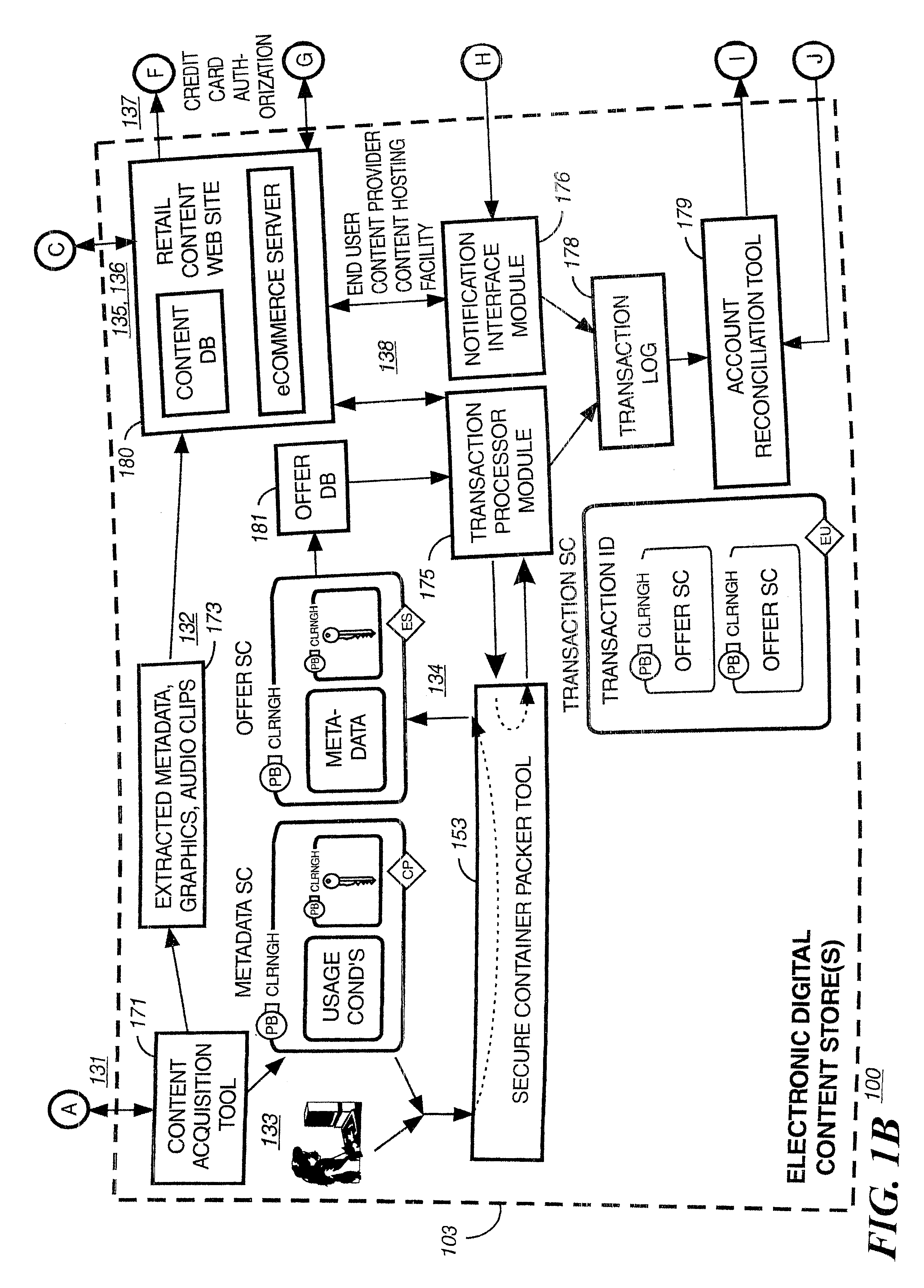
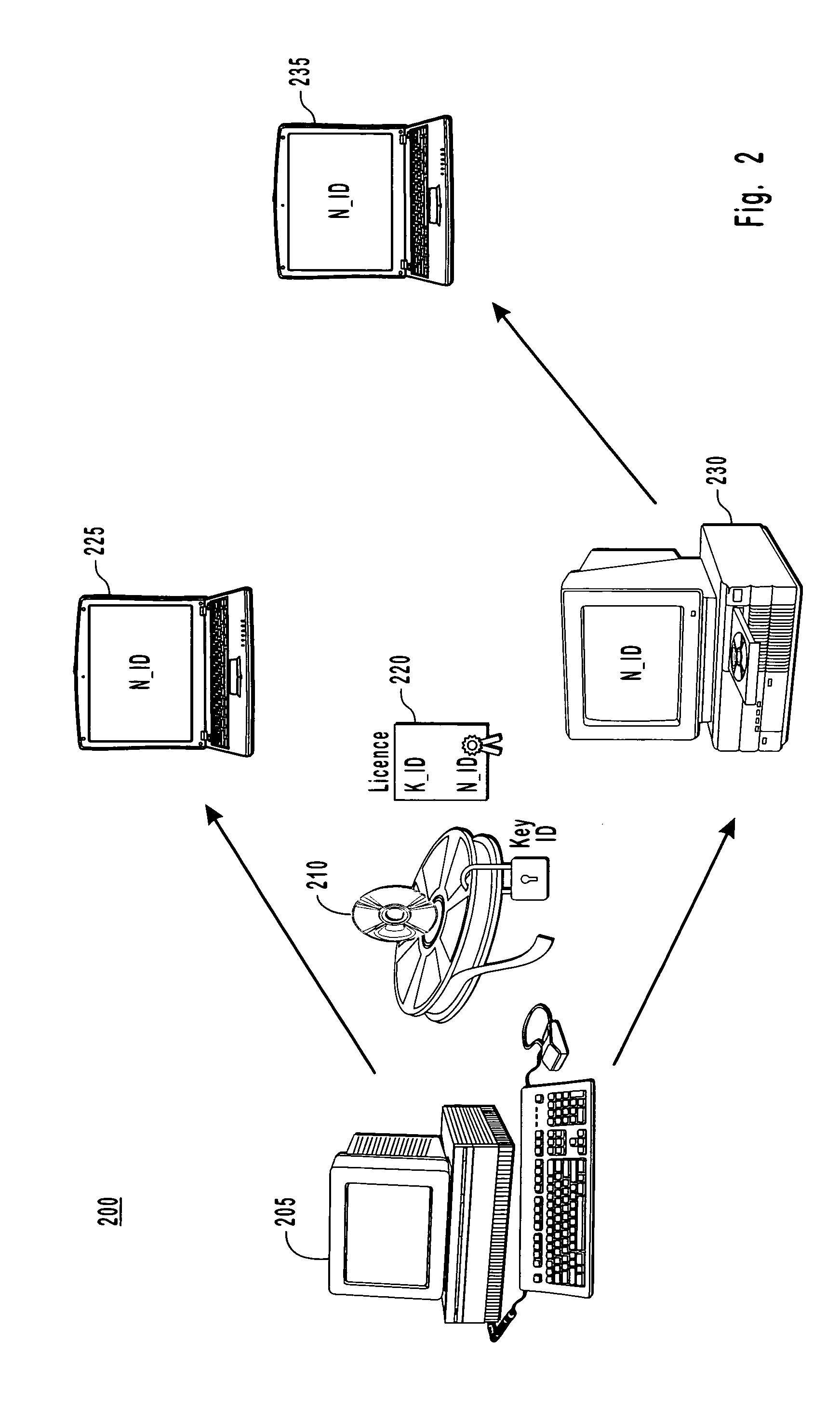
Method and apparatus for uniquely identifying a customer purchase in an electronic distribution system
InactiveUS6389403B1Key distribution for secure communicationDigital data processing detailsContent IdentifierUser device
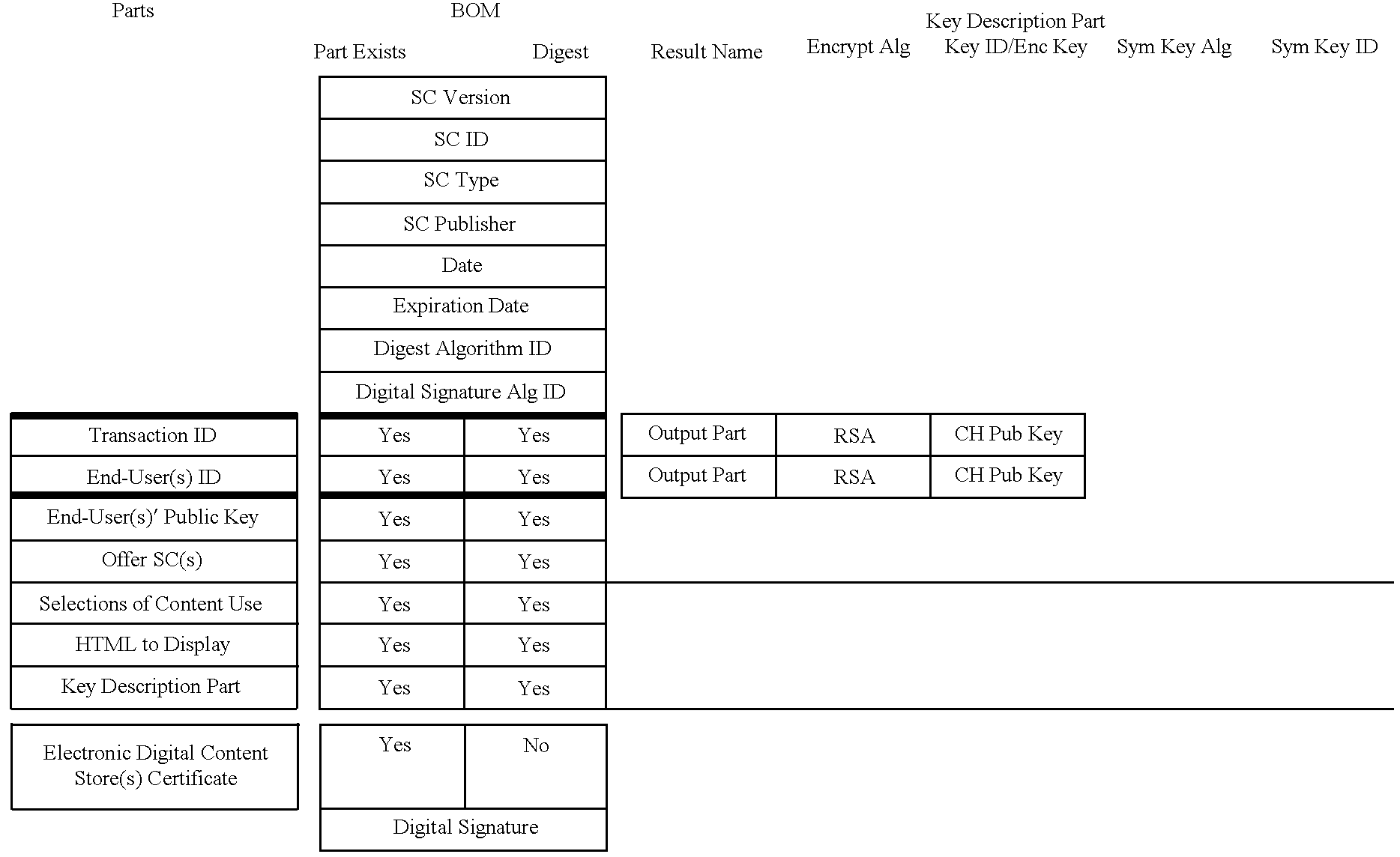
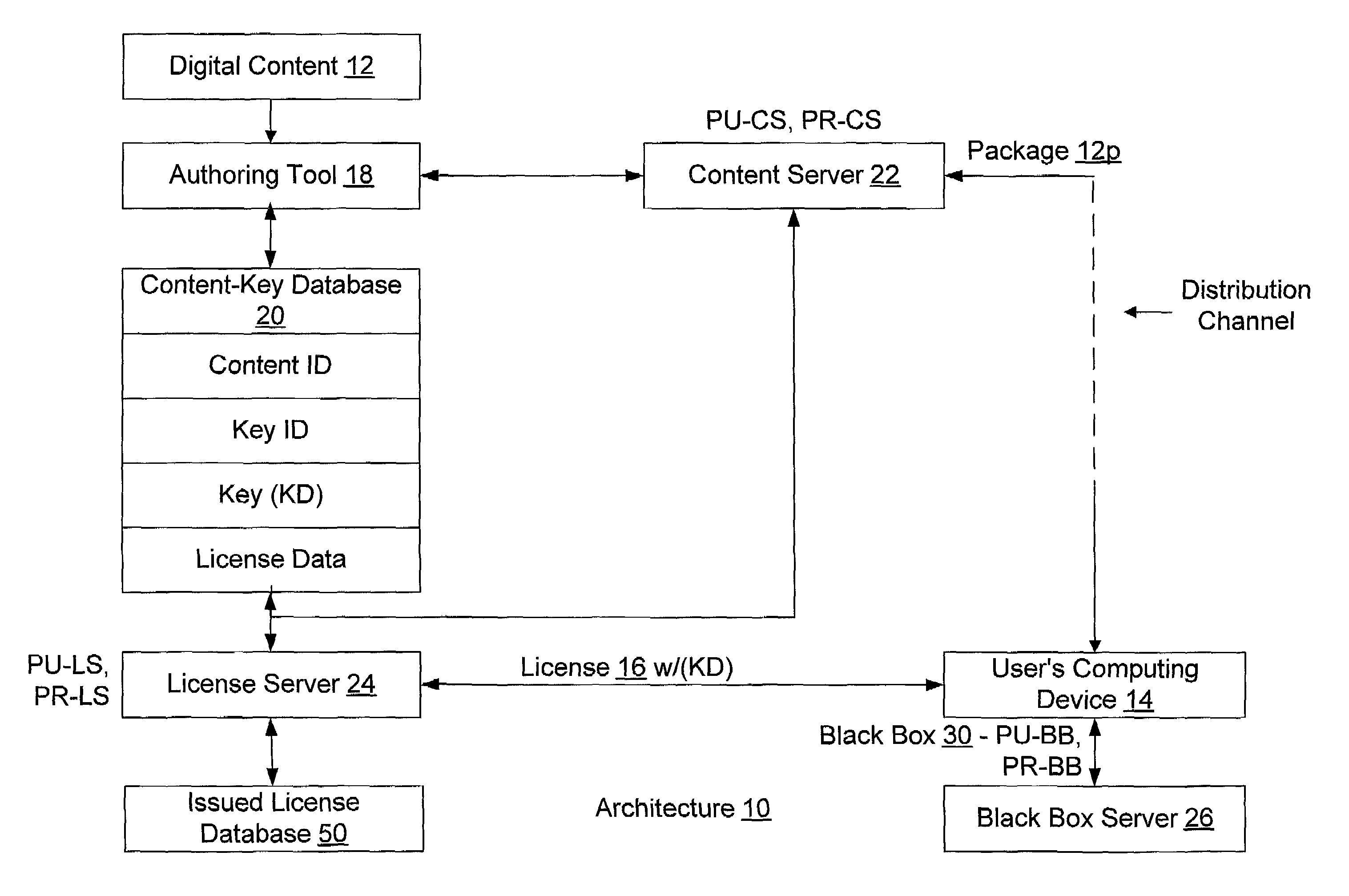
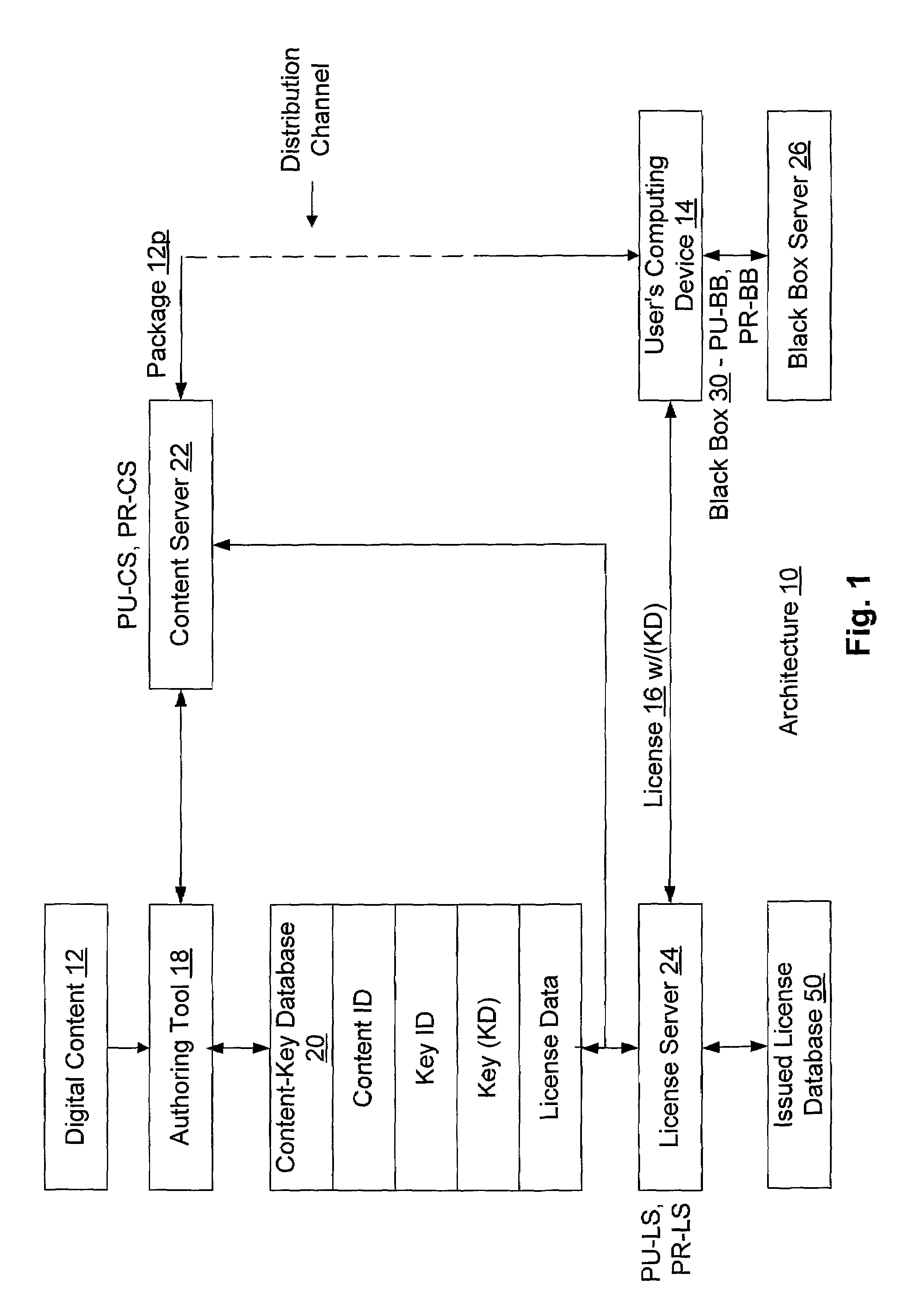
A system for tracking usage of digital content on user devices. Content sites for distributing digital content over a computer readable medium to users. The content sites associate unique content identifier with the content associated. Electronic stores coupled to a network sell licenses to play digital content data to users. The licenses contain a unique transaction identifier for uniquely identifying the transaction, and the licenses contain a unique item identifier for uniquely identifying at least one item in the transaction. Content players, which receive from the network the licensed content data, are used to play the licensed content data. The content players produce a purchase identifier based upon the mathematical combination of the content identifier, the transaction identifier and the item identifier.
Owner:WISTRON CORP
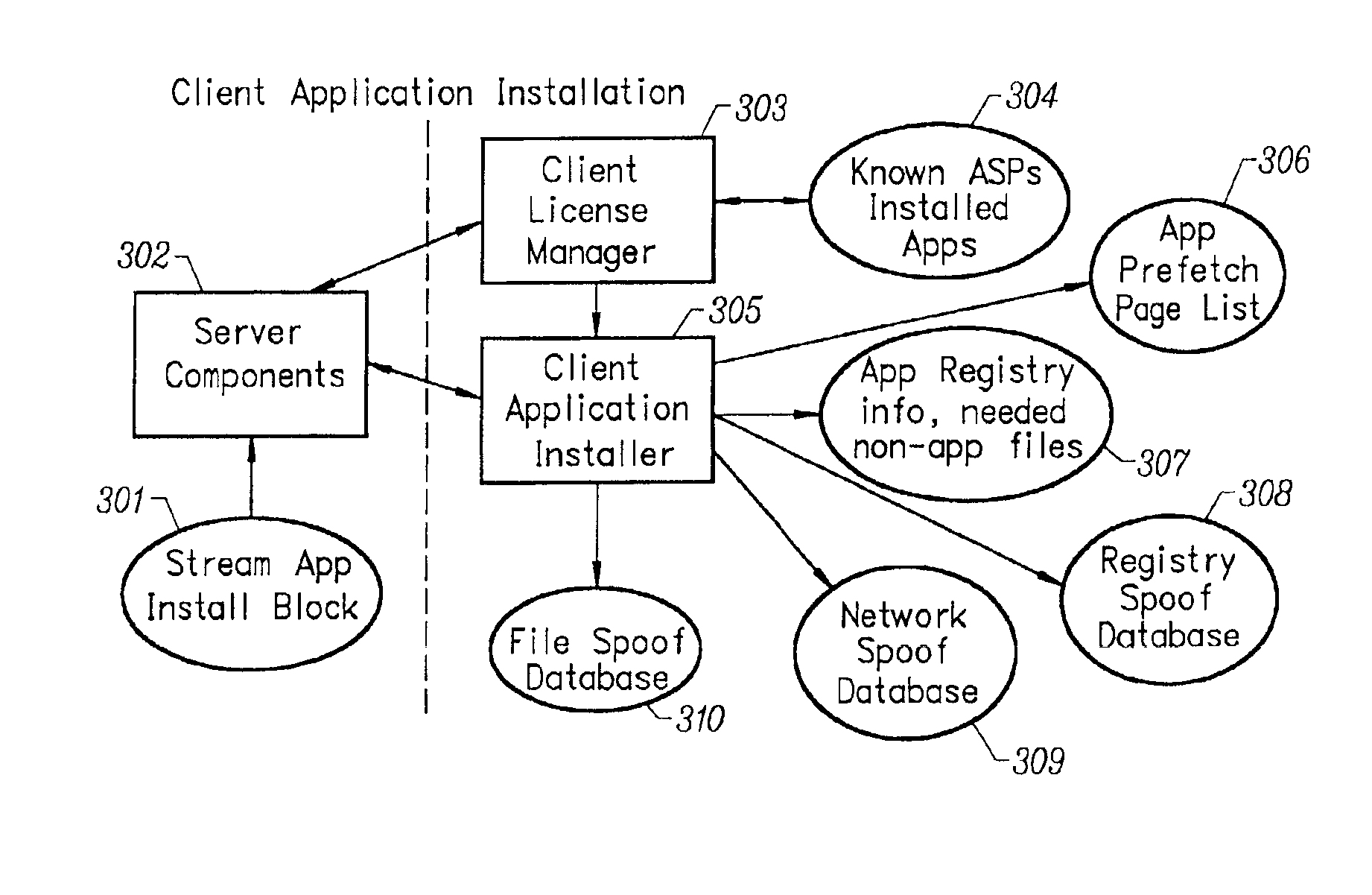
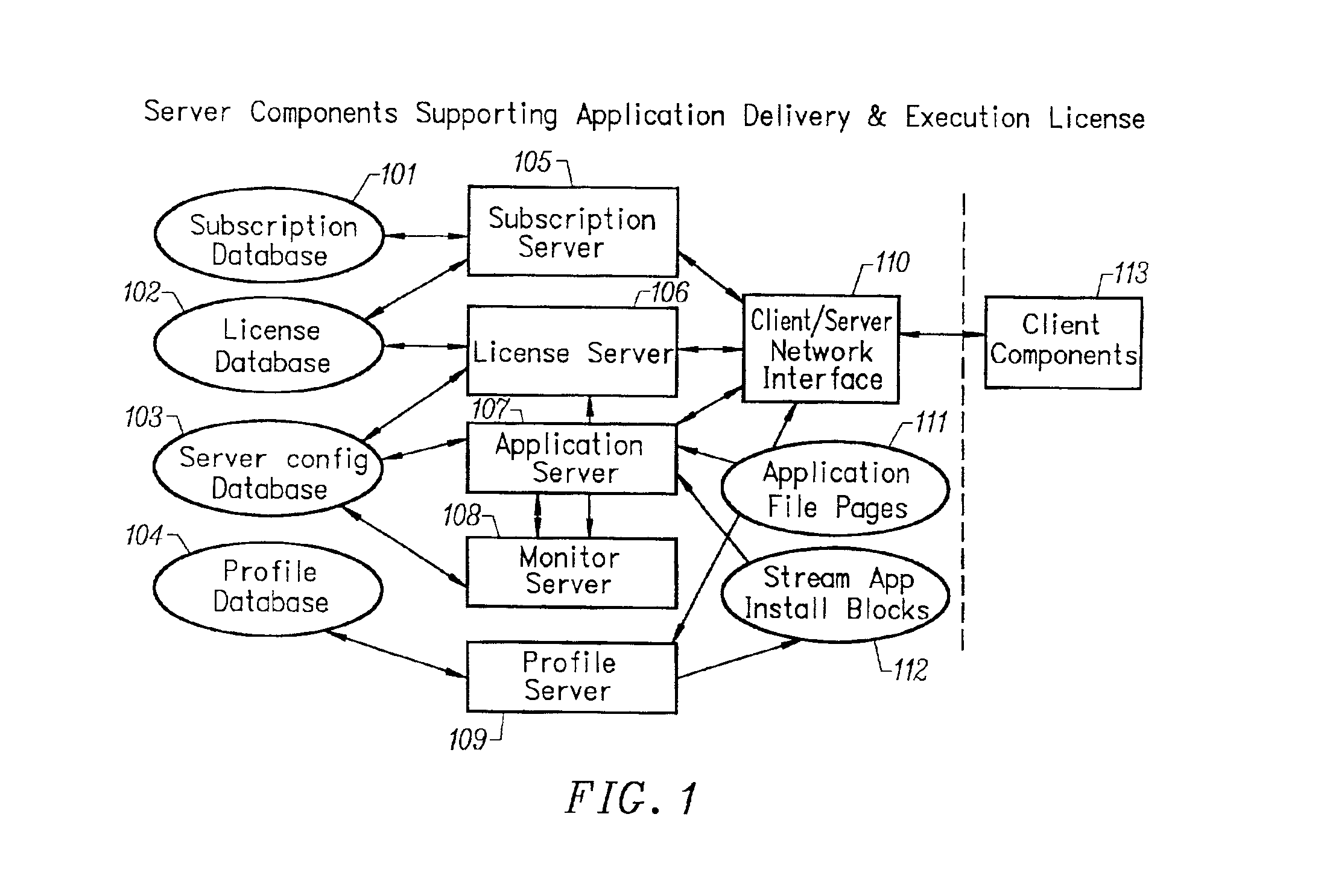
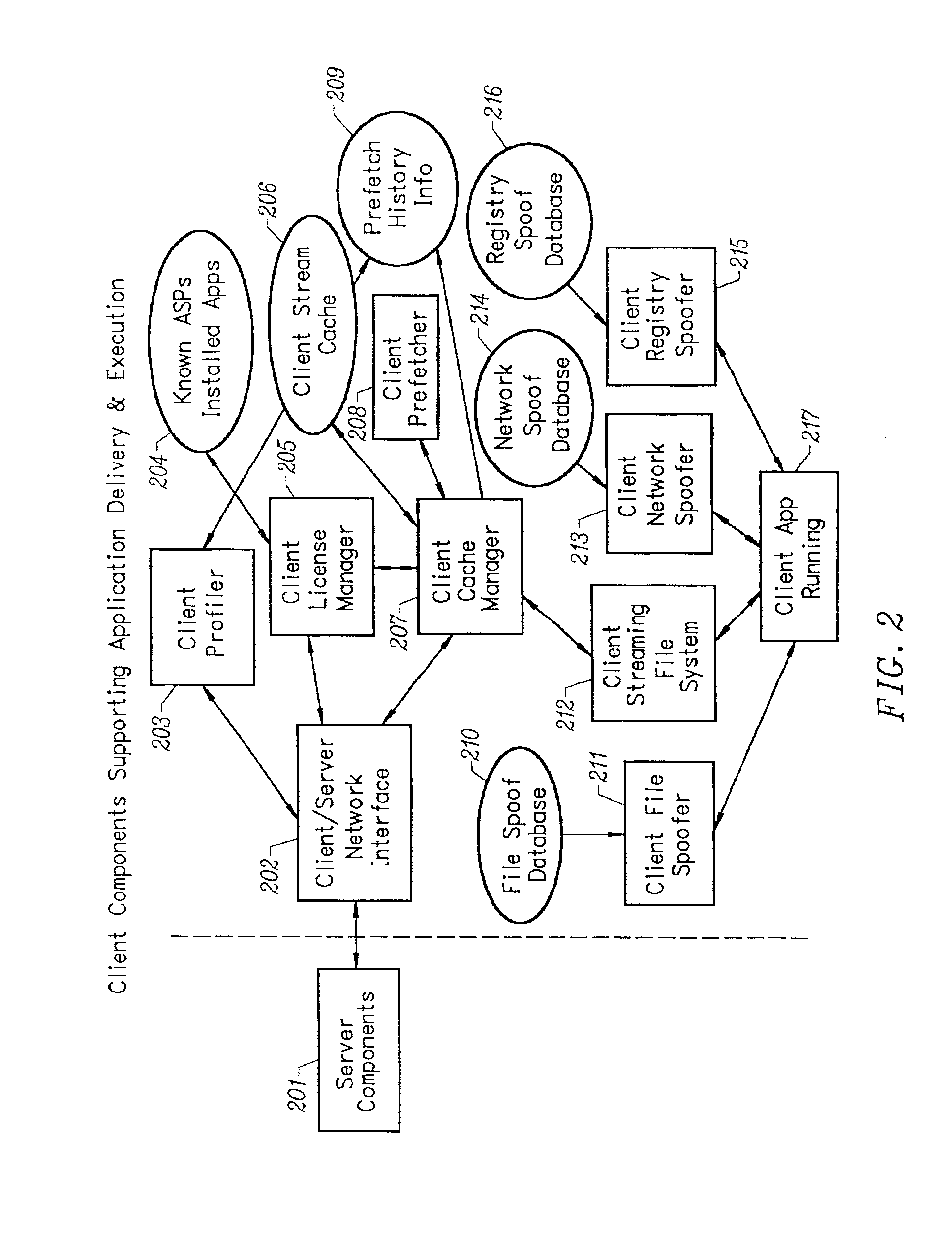
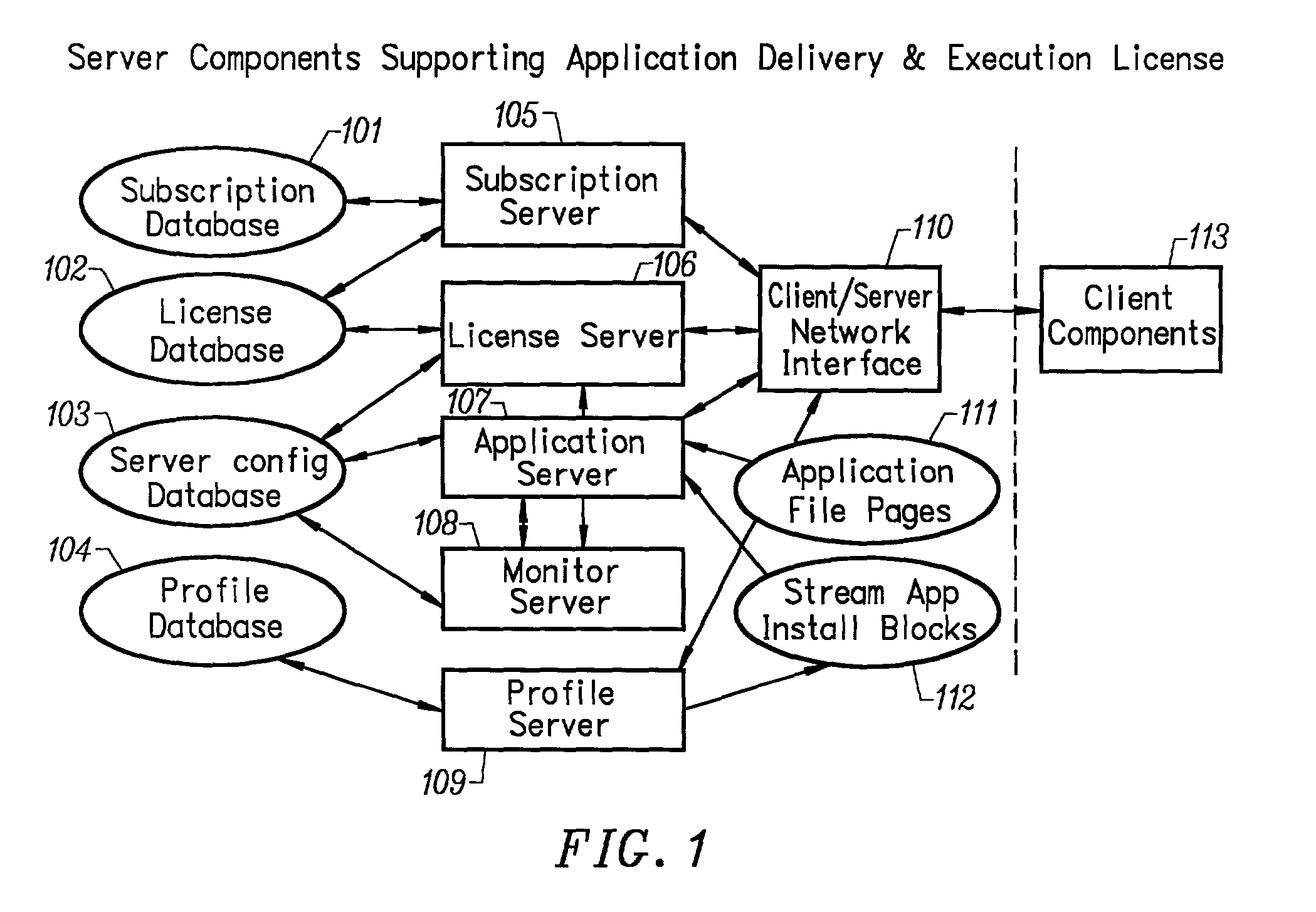
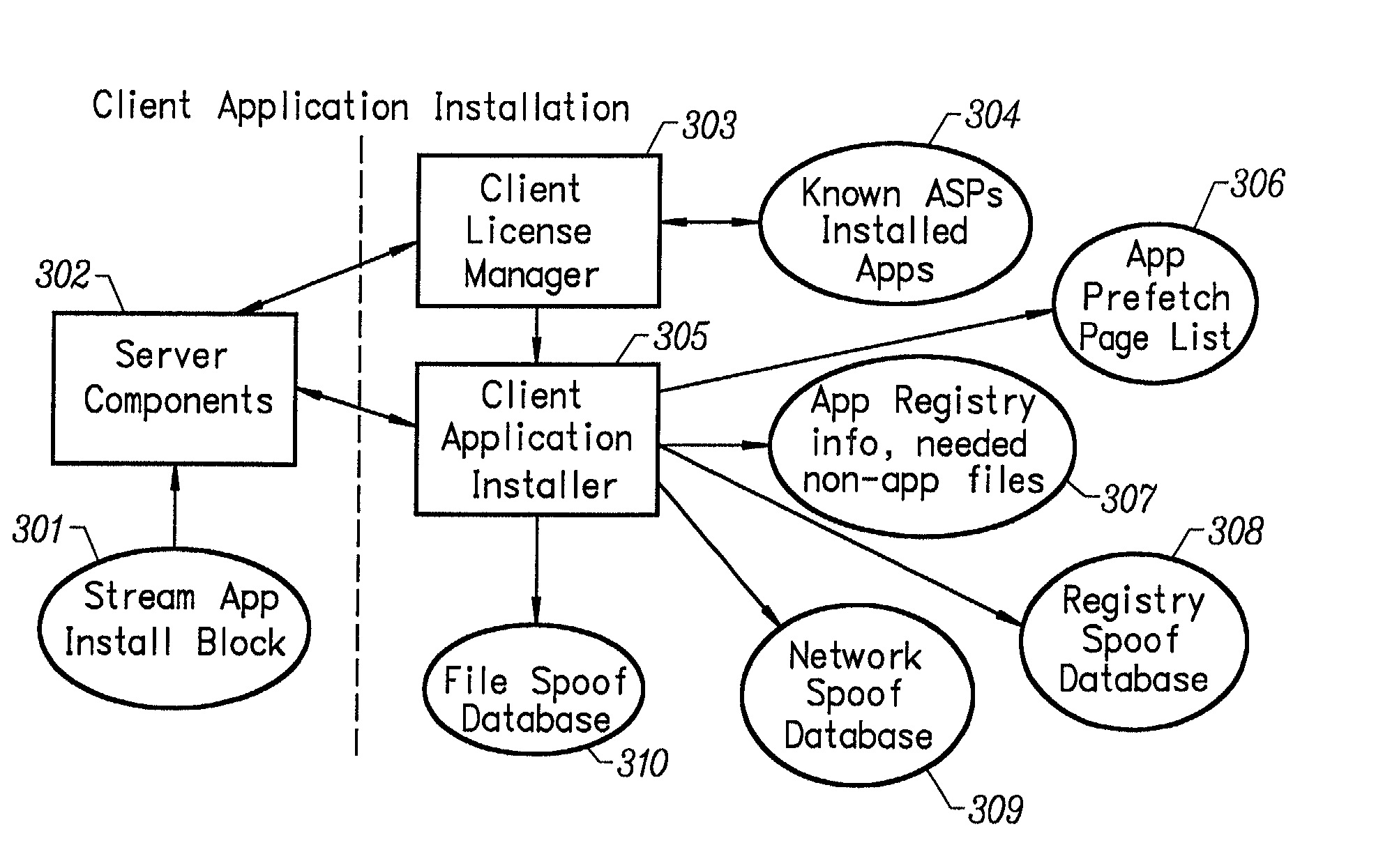
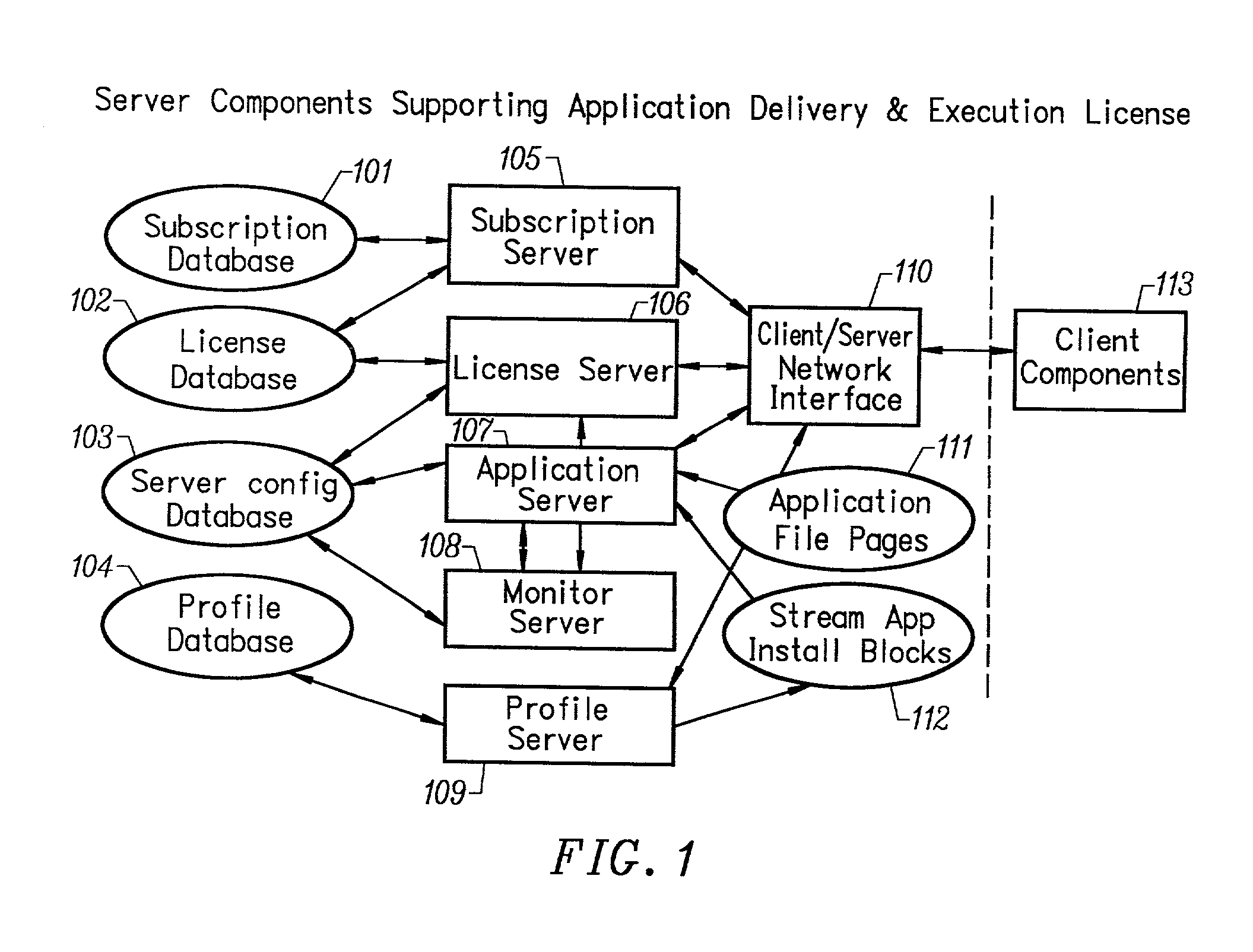
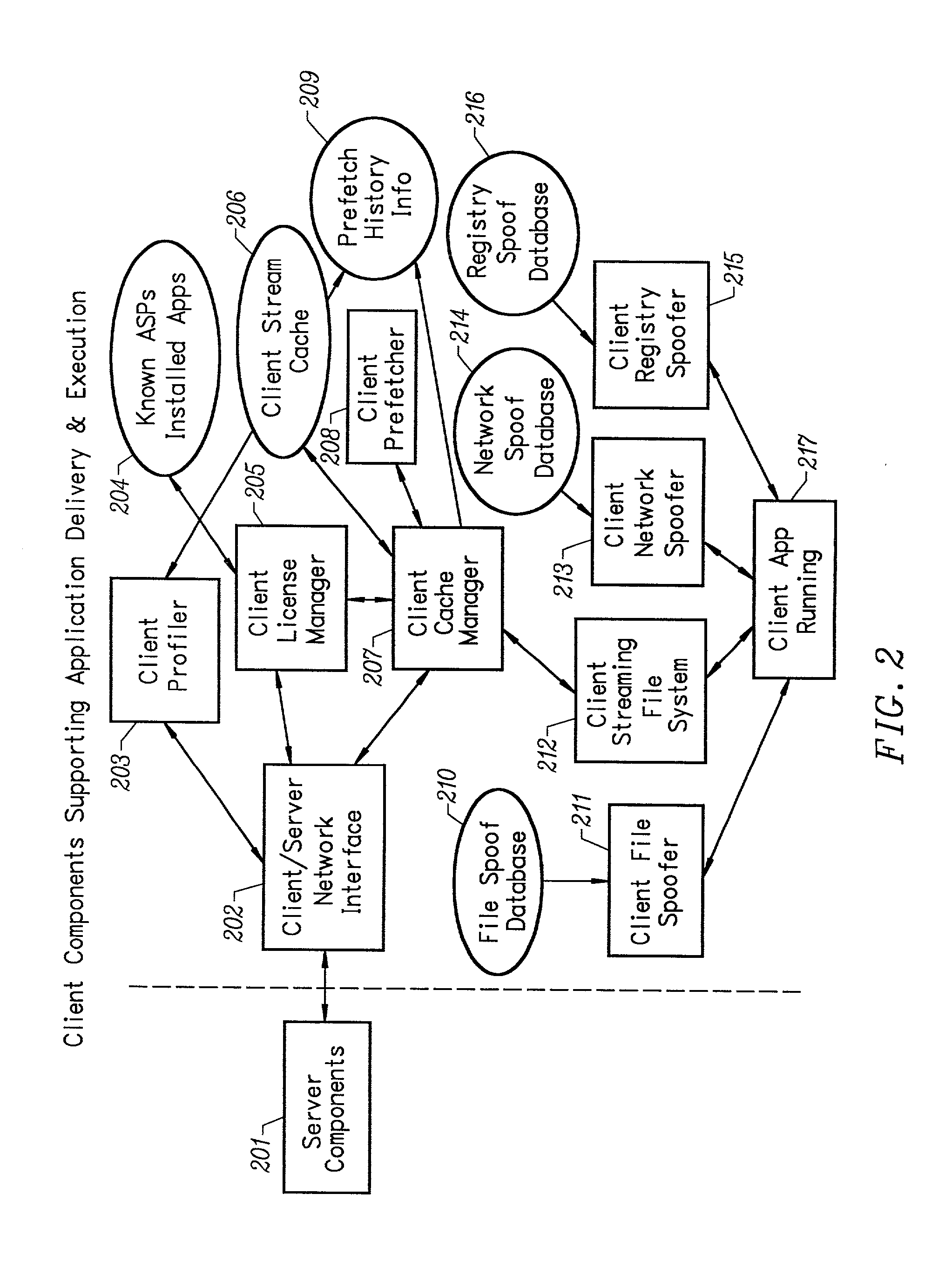
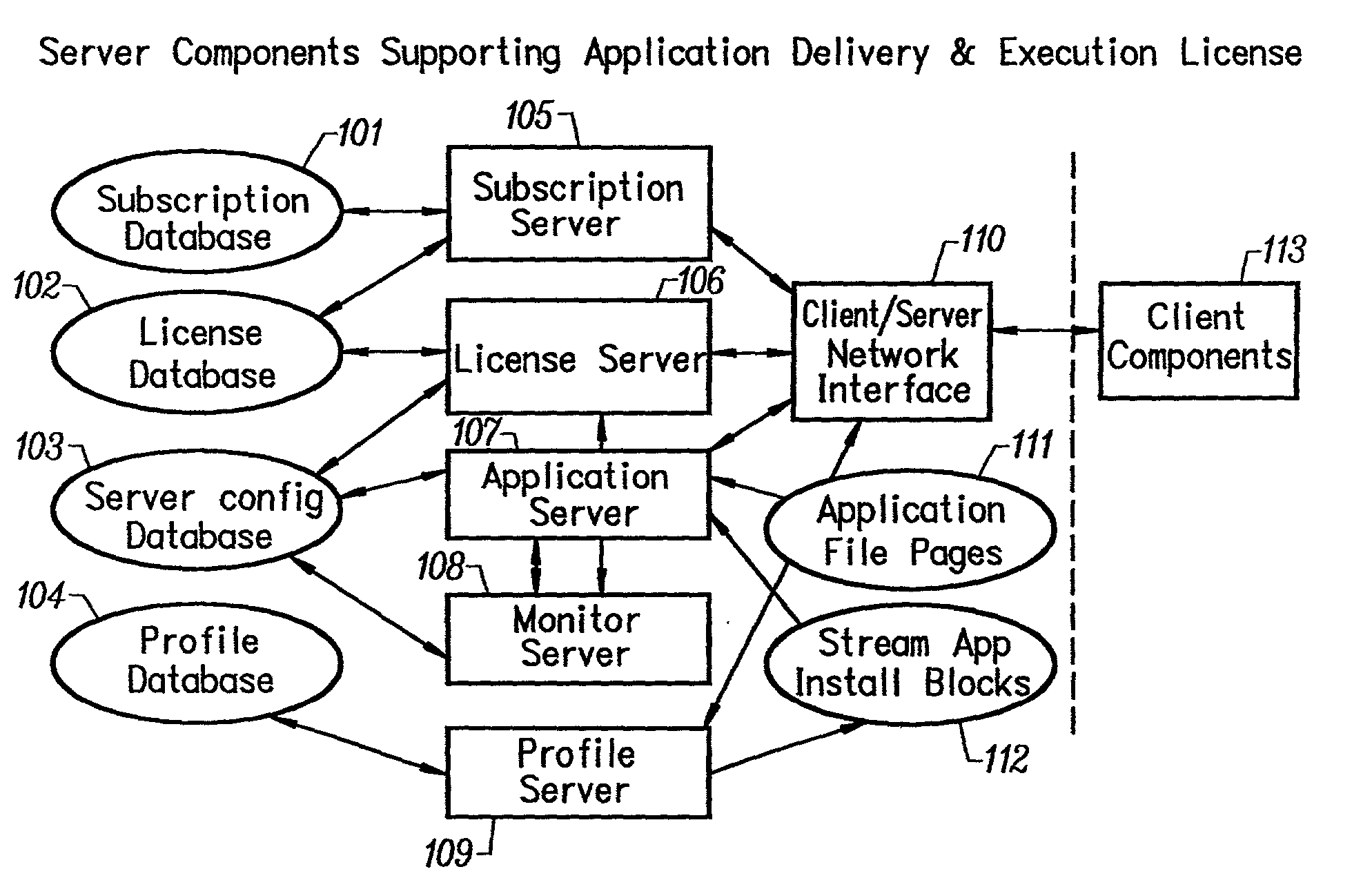
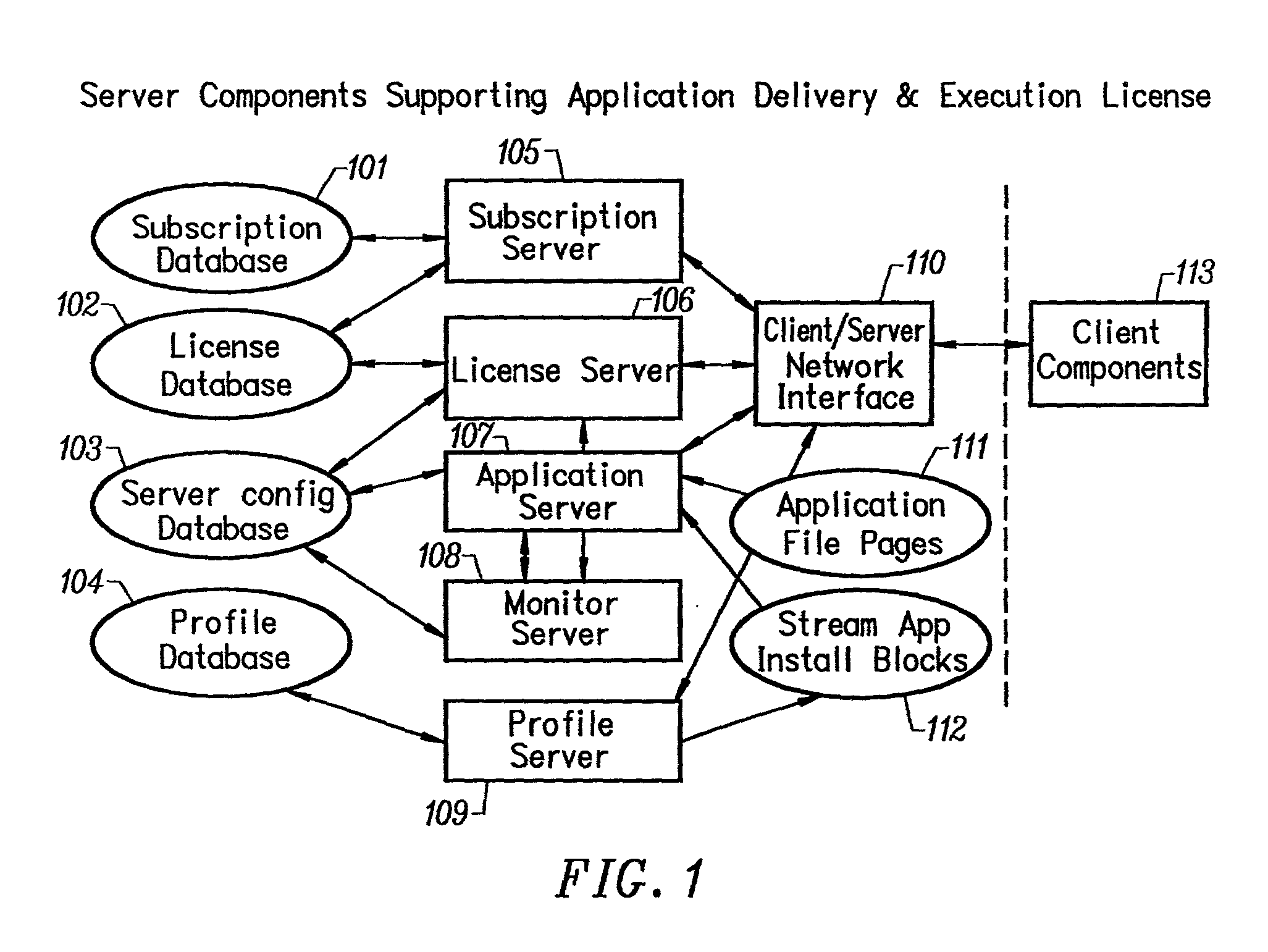
Client installation and execution system for streamed applications
InactiveUS6918113B2Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
Enforcement architecture and method for digital rights management
InactiveUS7103574B1Satisfies needKey distribution for secure communicationDigital data processing detailsDigital contentNumber content
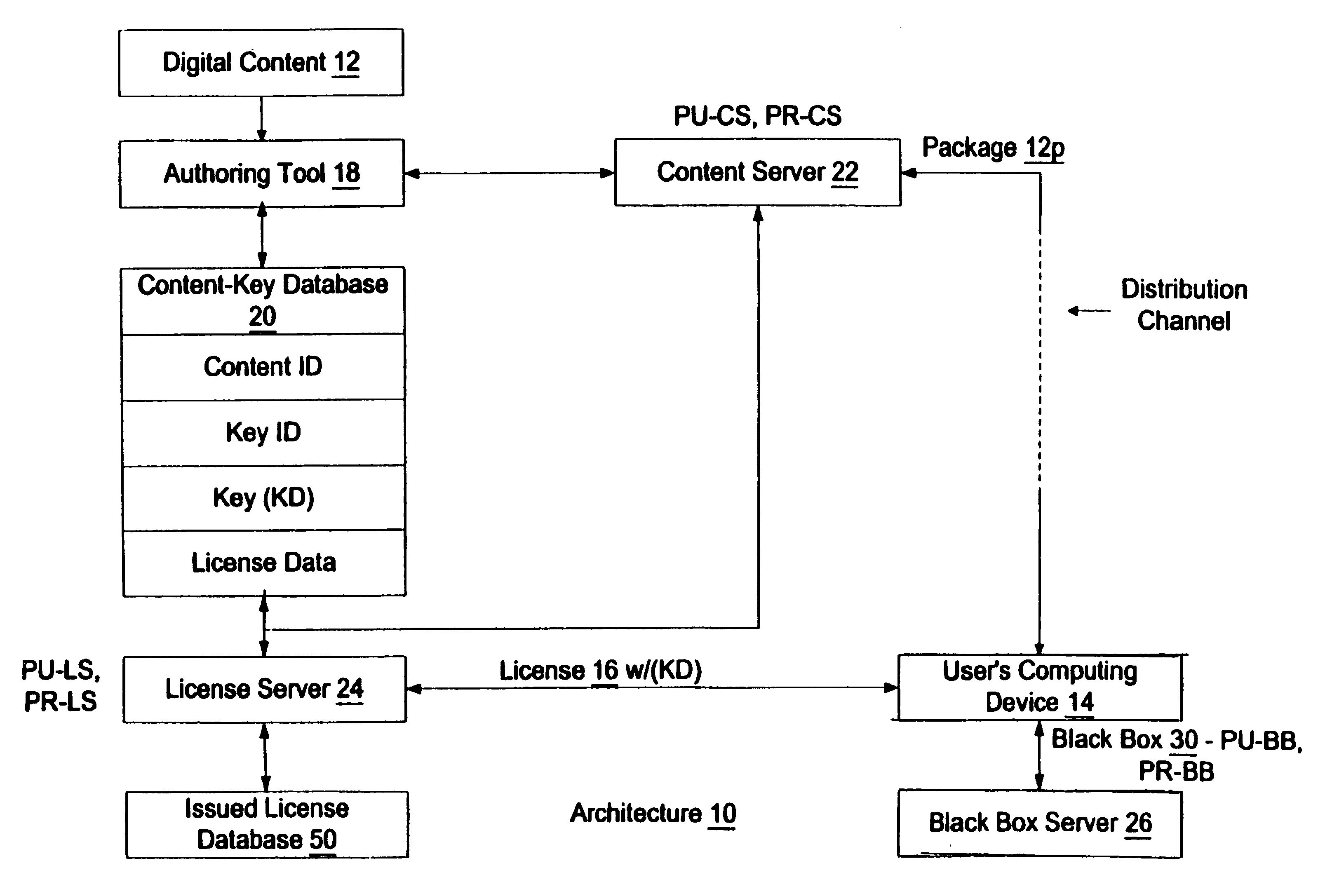
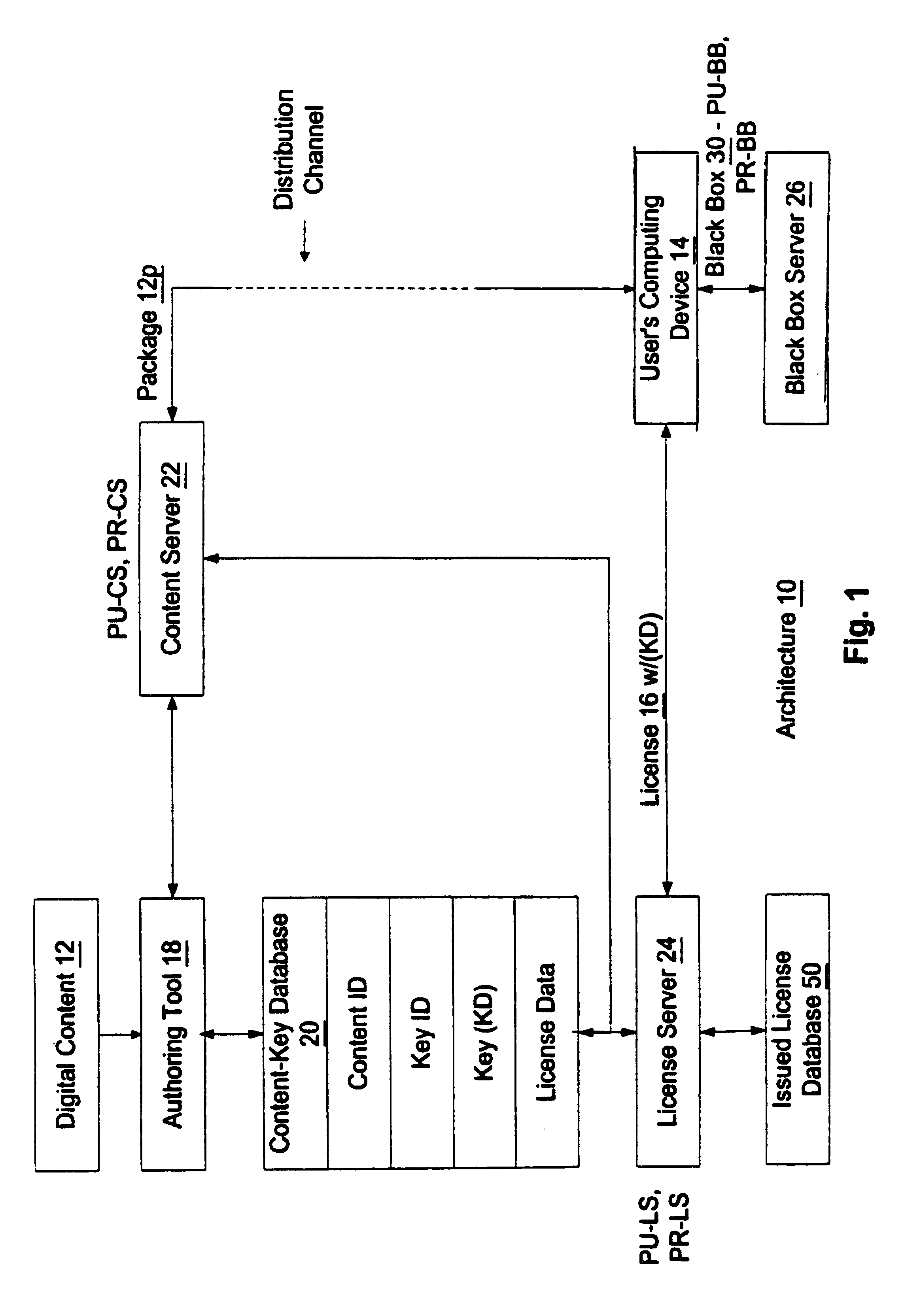
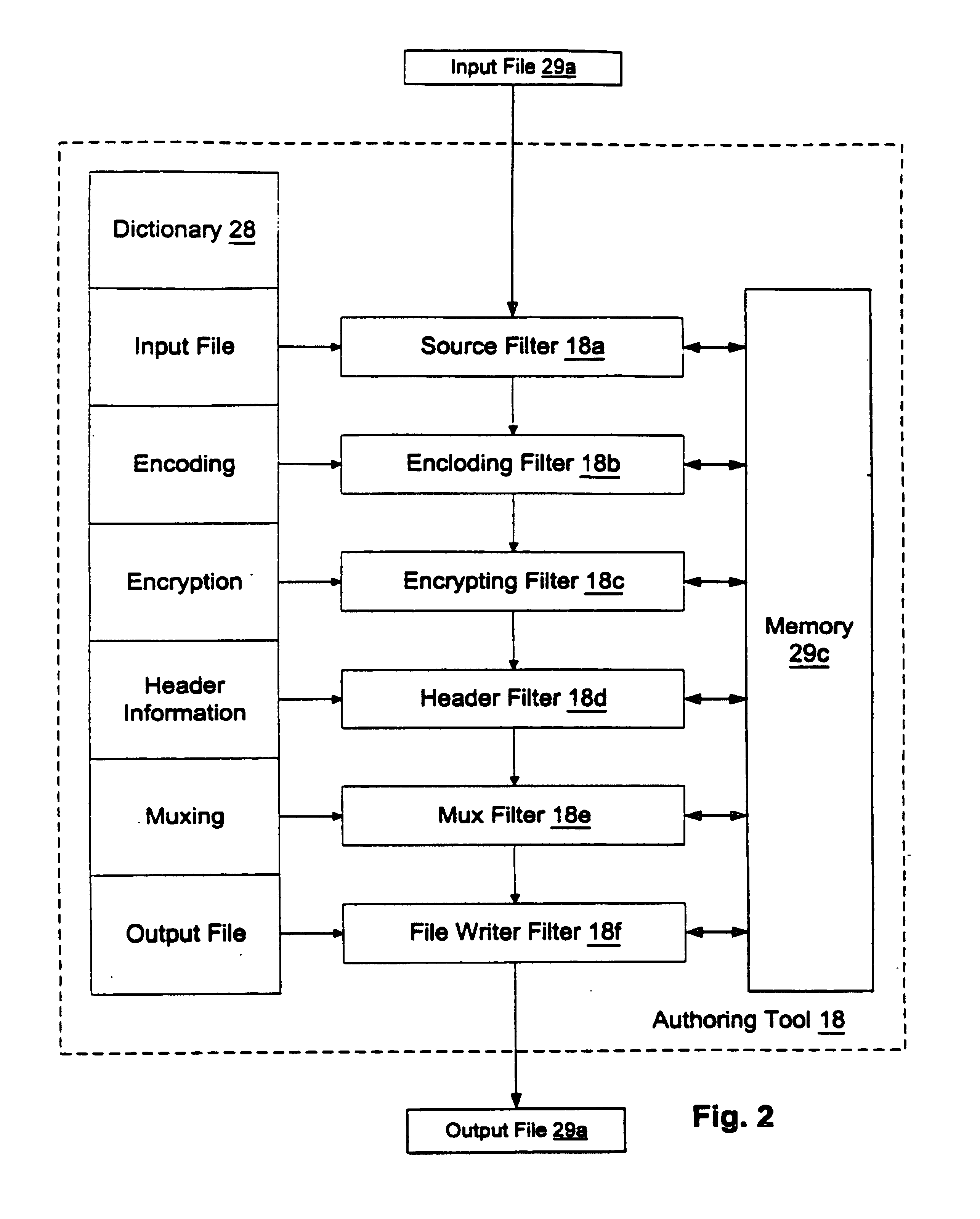
An enforcement architecture and method for implementing digital rights management are disclosed. Digital content is distributed from a content server to a computing device of a user and received, and an attempt is made to render the digital content by way of a rendering application. The rendering application invokes a Digital Rights Management (DRM) system, and such DRM system determines whether a right to render the digital content in the manner sought exists based on any digital license stored in the computing device and corresponding to the digital content. If the right does not exist, a digital license that provides such right and that corresponds to the digital content is requested from a license server, and the license server issues the digital license to the DRM system. The computing device receives the issued digital license and stores the received digital license thereon.
Owner:MICROSOFT TECH LICENSING LLC
Intelligent network streaming and execution system for conventionally coded applications
InactiveUS7062567B2Multiple digital computer combinationsDigital data authenticationIntelligent NetworkApplication server
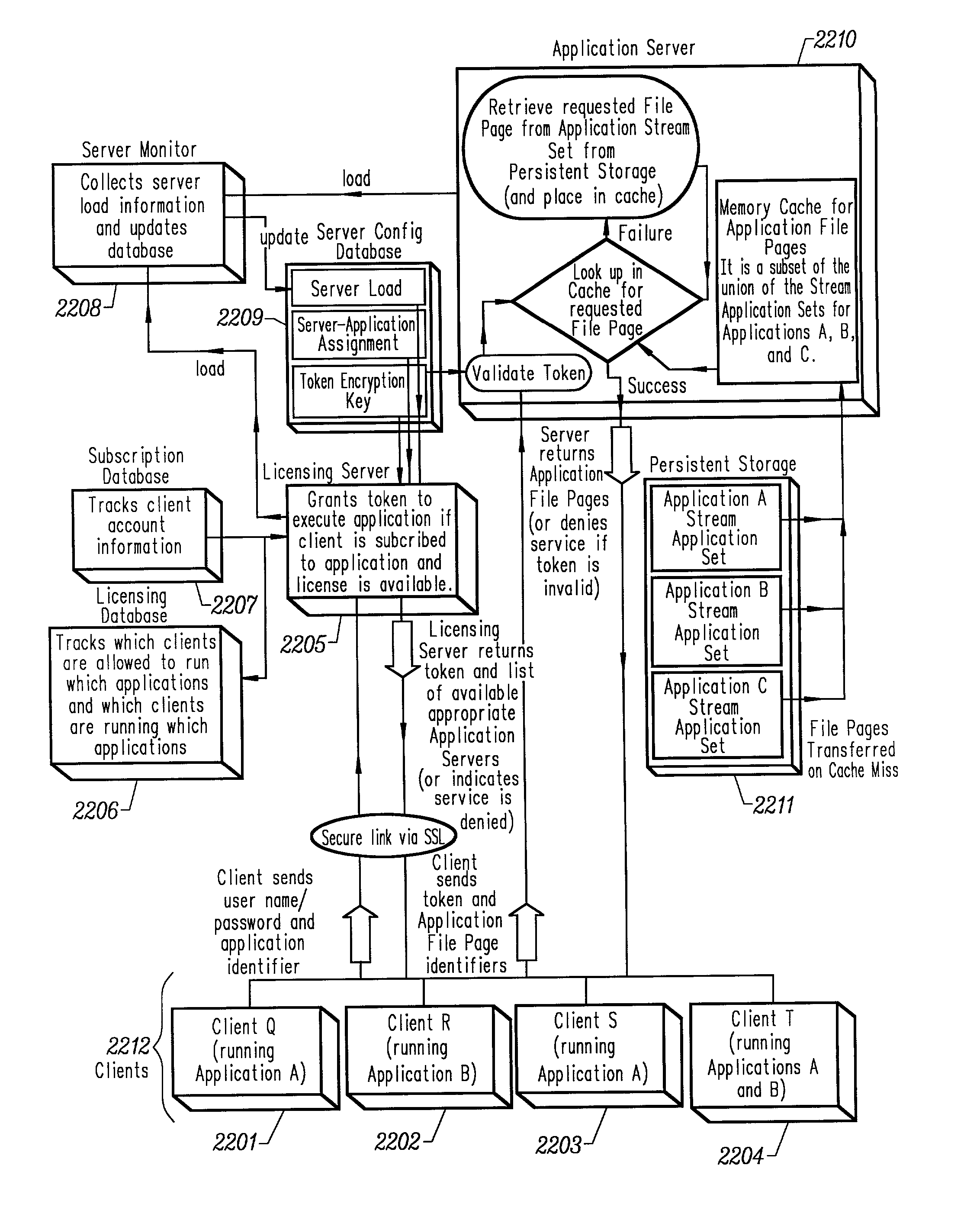
An intelligent network streaming and execution system for conventionally coded applications provides a system that partitions an application program into page segments by observing the manner in which the application program is conventionally installed. A minimal portion of the application program is installed on a client system and the user launches the application in the same ways that applications on other client file systems are started. An application program server streams the page segments to the client as the application program executes on the client and the client stores the page segments in a cache. Page segments are requested by the client from the application server whenever a page fault occurs from the cache for the application program. The client prefetches page segments from the application server or the application server pushes additional page segments to the client based on the pattern of page segment requests for that particular application. The user subscribes and unsubscribes to application programs, whenever the user accesses an application program a securely encrypted access token is obtained from a license server if the user has a valid subscription to the application program. The application server begins streaming the requested page segments to the client when it receives a valid access token from the client. The client performs server load balancing across a plurality of application servers. If the client observes a non-response or slow response condition from an application server or license server, it switches to another application or license server.
Owner:NUMECENT HLDG
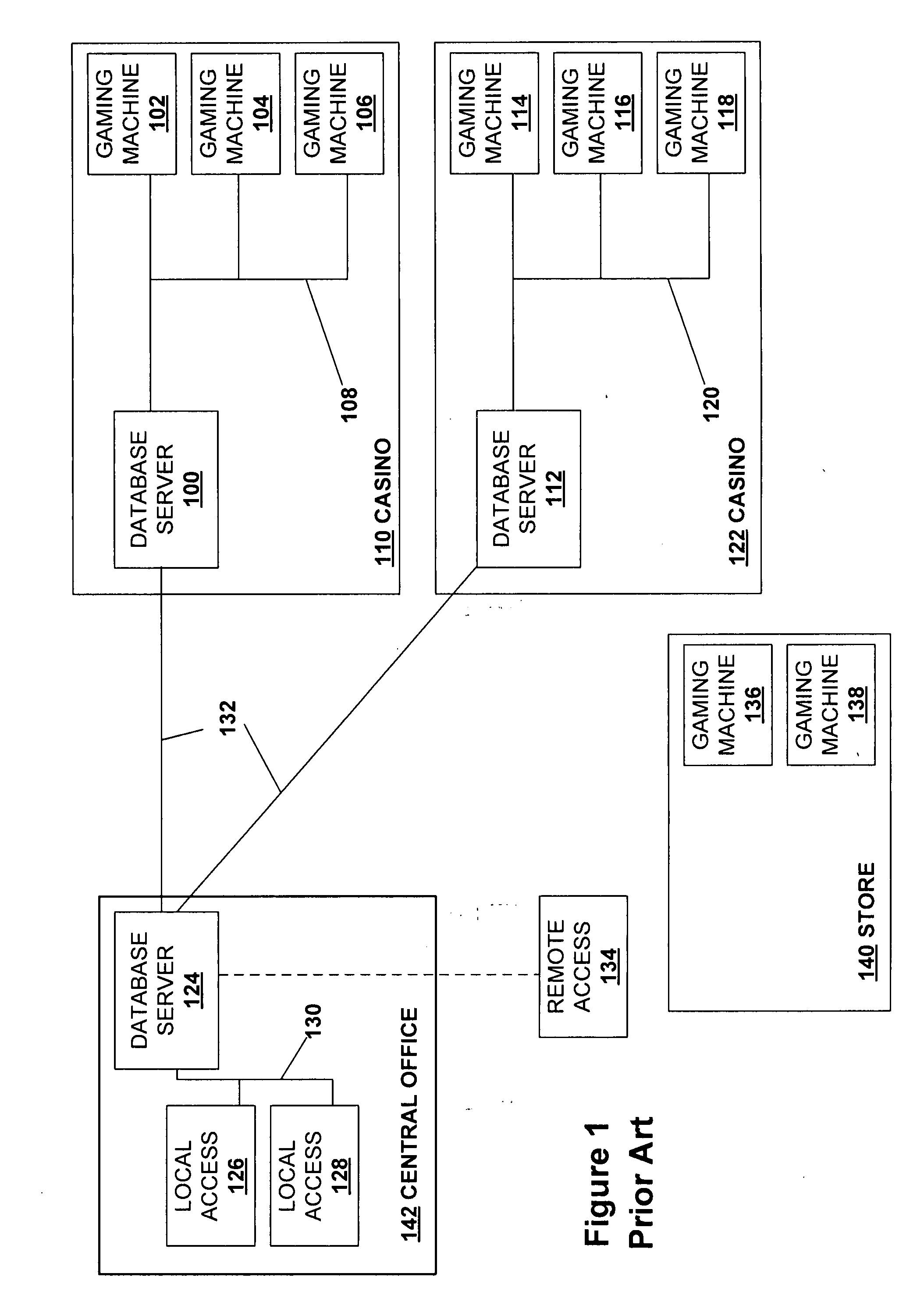
Wager game license management in a game table
InactiveUS20080234047A1Unnecessary licensing fees are not incurredApparatus for meter-controlled dispensingVideo gamesUsage dataLicense
Novel wager gaming systems and methods for game license management utilizing a game table connected in a network at a gaming establishment are described. A game table having multiple player stations, equipped with gaming devices, performs as a local licensing server for the player stations at the game table. It may also function as a licensing server for player stations at other game tables and for gaming machines in the network. The wager game table may be connected to a central licensing server with operates in conjunction with the wager game table. A player station may also have certain license management components that may complement the operations of a game table license management module. The game table may perform certain local licensing and auditing functions for each player station with regard to wager game code and other game-related content and operational software. The management module may also monitor the usage of various types of wager game code, related content, and game-related software. These usage data are maintained by the game table and may be used for auditing purposes.
Owner:IGT
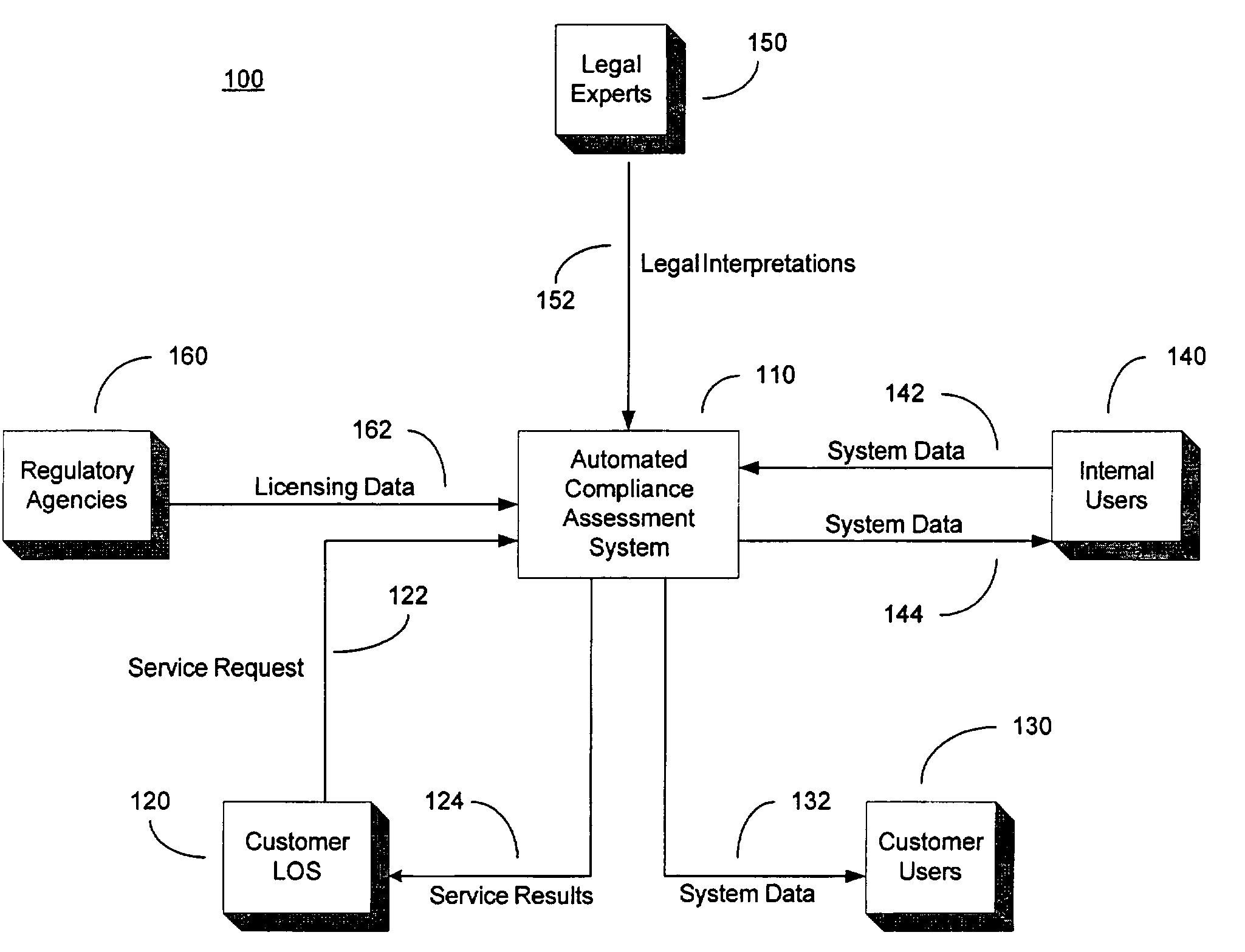
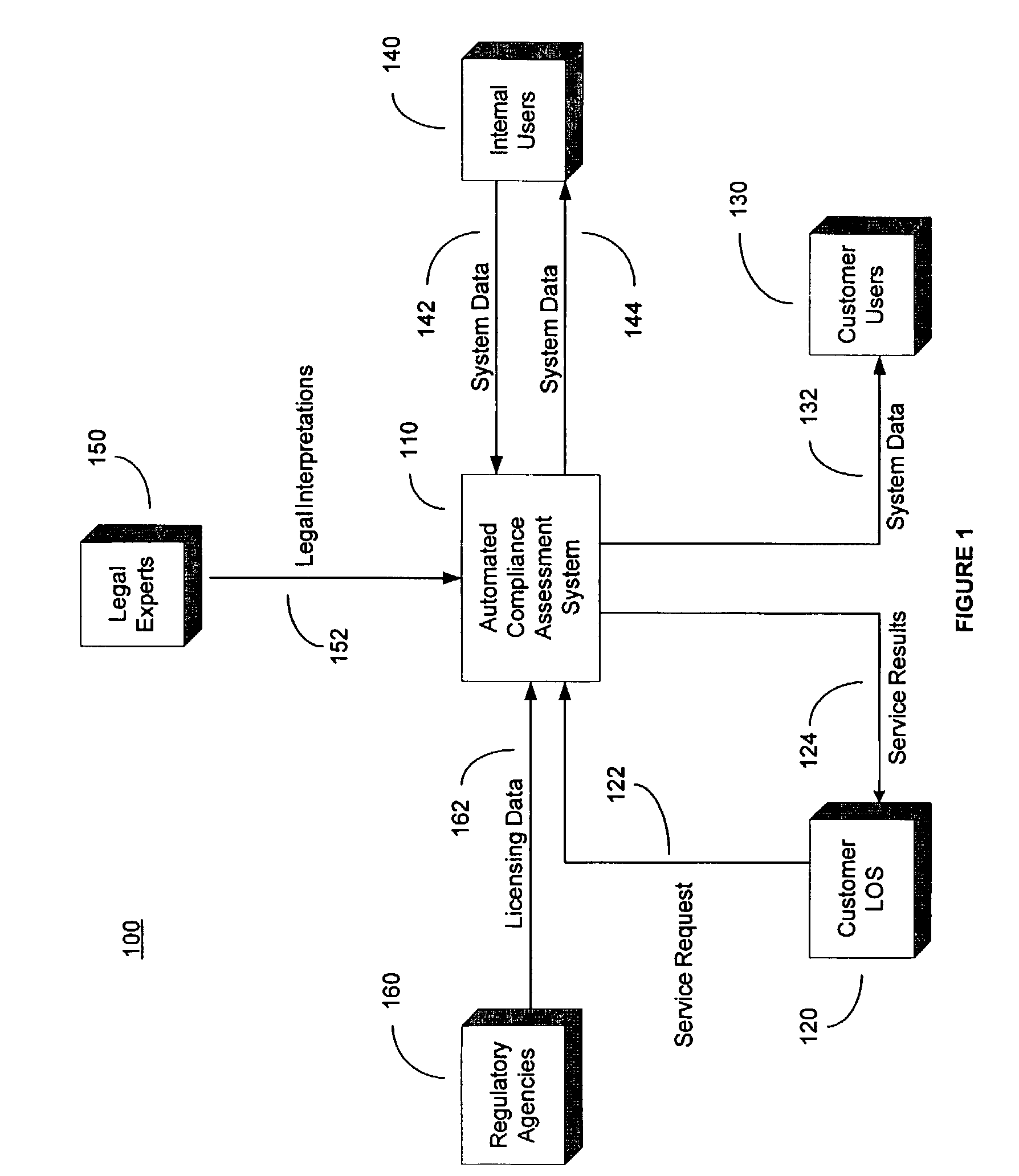
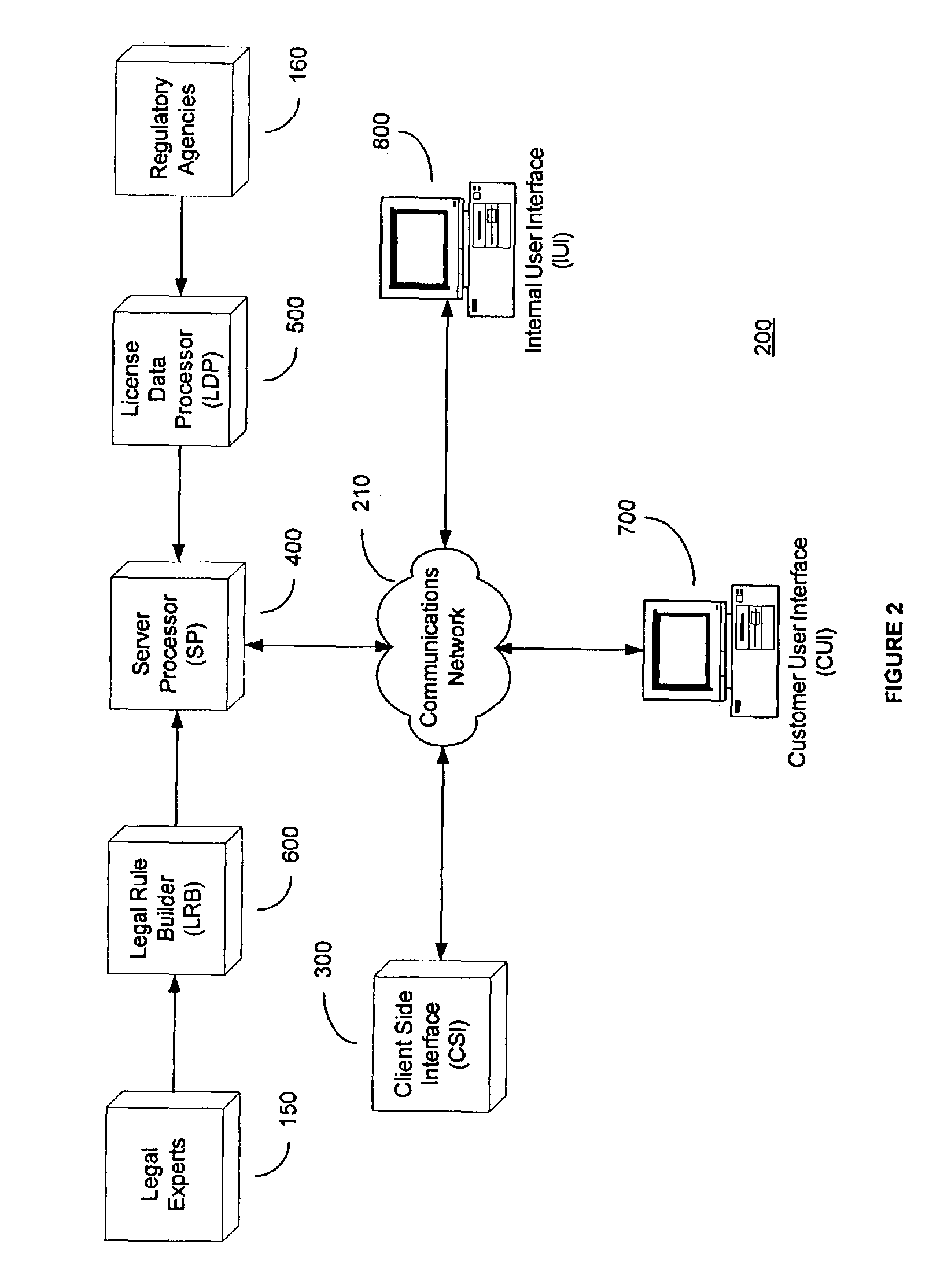
System and method for automated loan compliance assessment
An automated system and method for reviewing and assessing compliance with legal compliance requirements for loan applications. Loan application data is extracted from client loan origination systems and transmitted as a loan information file over a secure communication network to an automated compliance assessment system server where the loan information file is audited for compliance with Federal, state, and local legal compliance requirements. The loan information file is reviewed for legal compliance requirements imposed by Federal, State, and local jurisdictions, as well as licensing requirements that the client loan company and related personnel must satisfy. The results of the audit process are transmitted over a secure communication network to the client loan company, with areas of noncompliance indicated. The automated compliance assessment system server also stores rules data derived from legal compliance requirements, license data derived from regulatory requirements, system setup data and supplemental system application data.
Owner:ICE MORTGAGE TECH INC
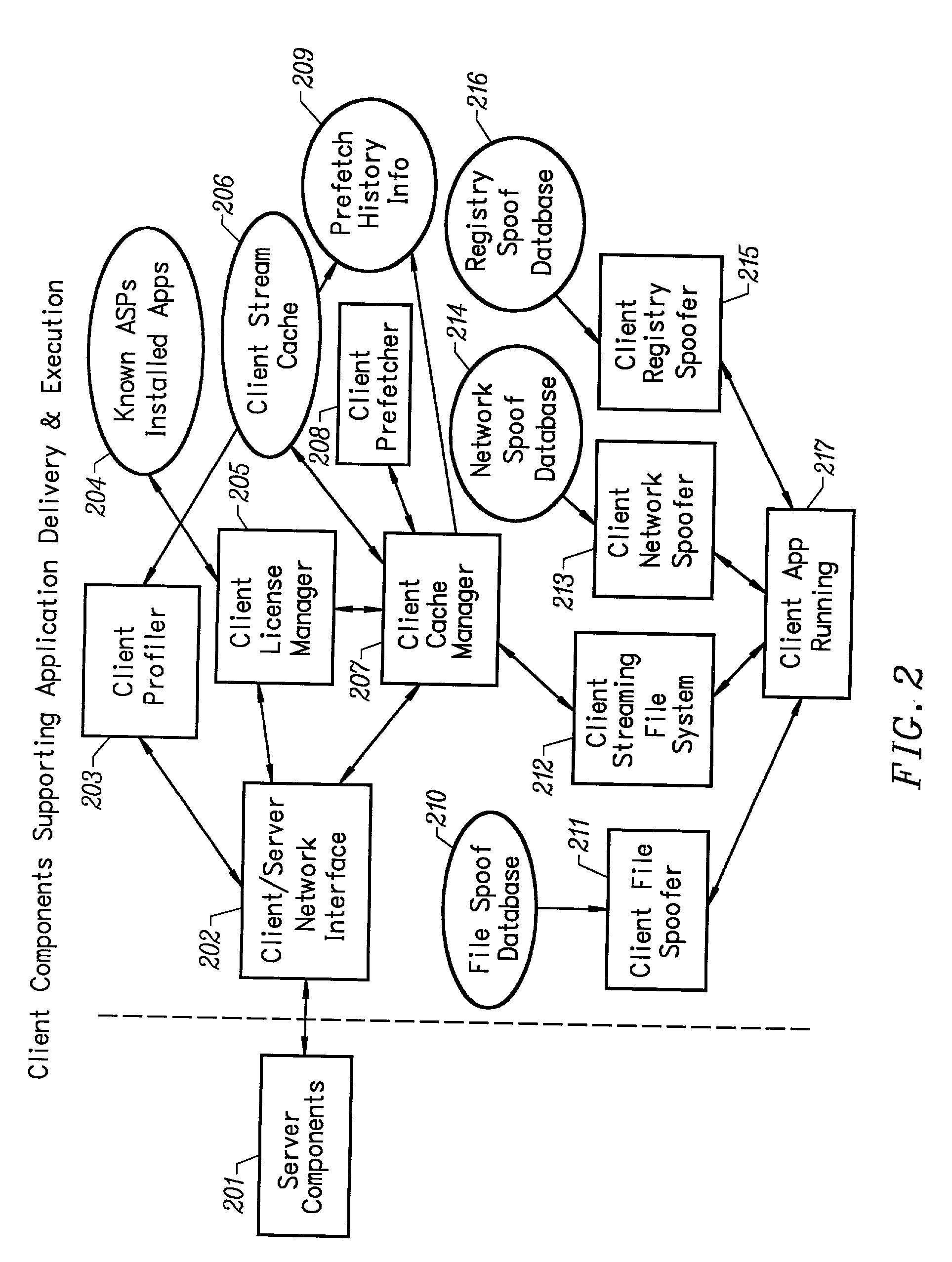
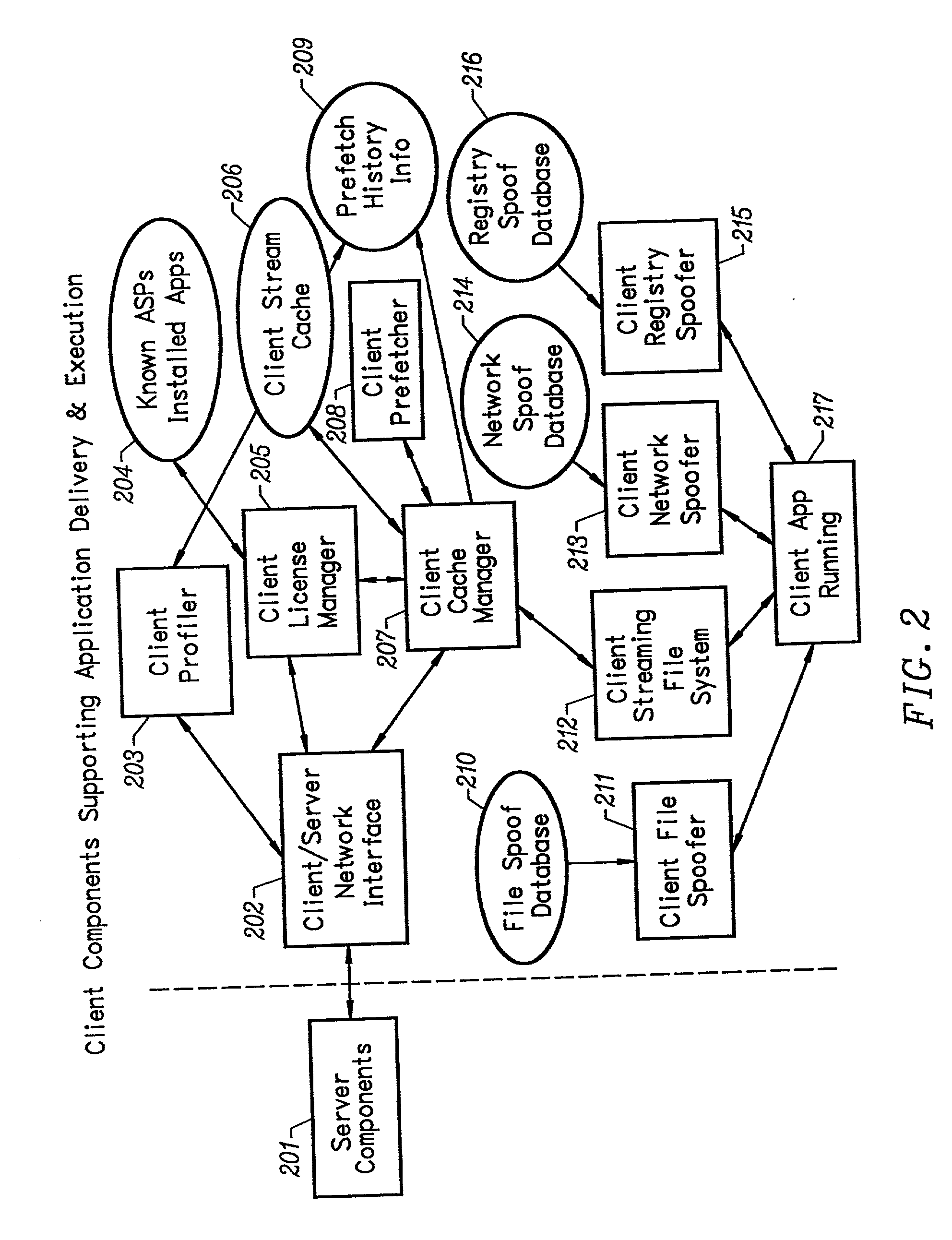
Client installation and execution system for streamed applications
InactiveUS20020157089A1Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
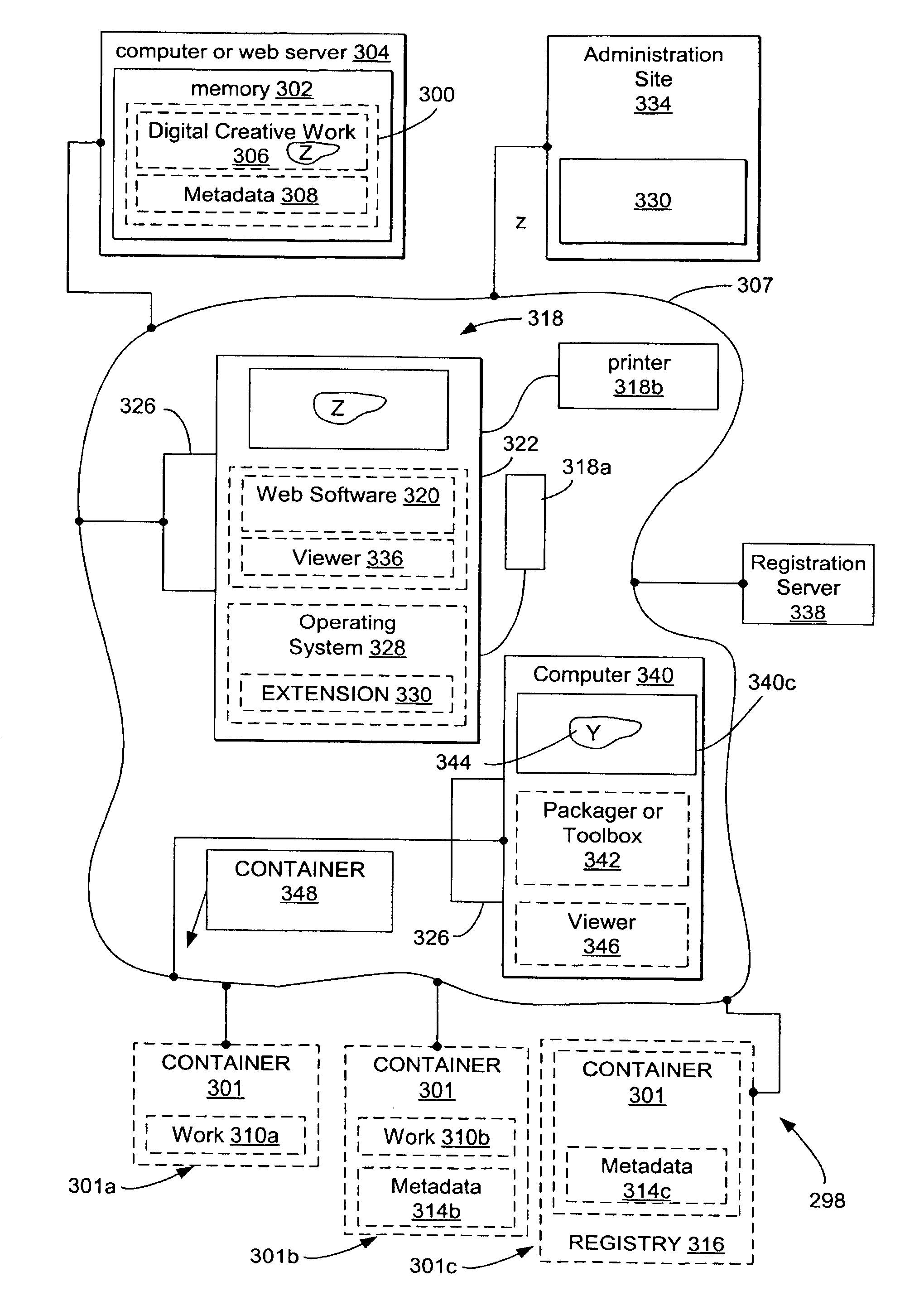
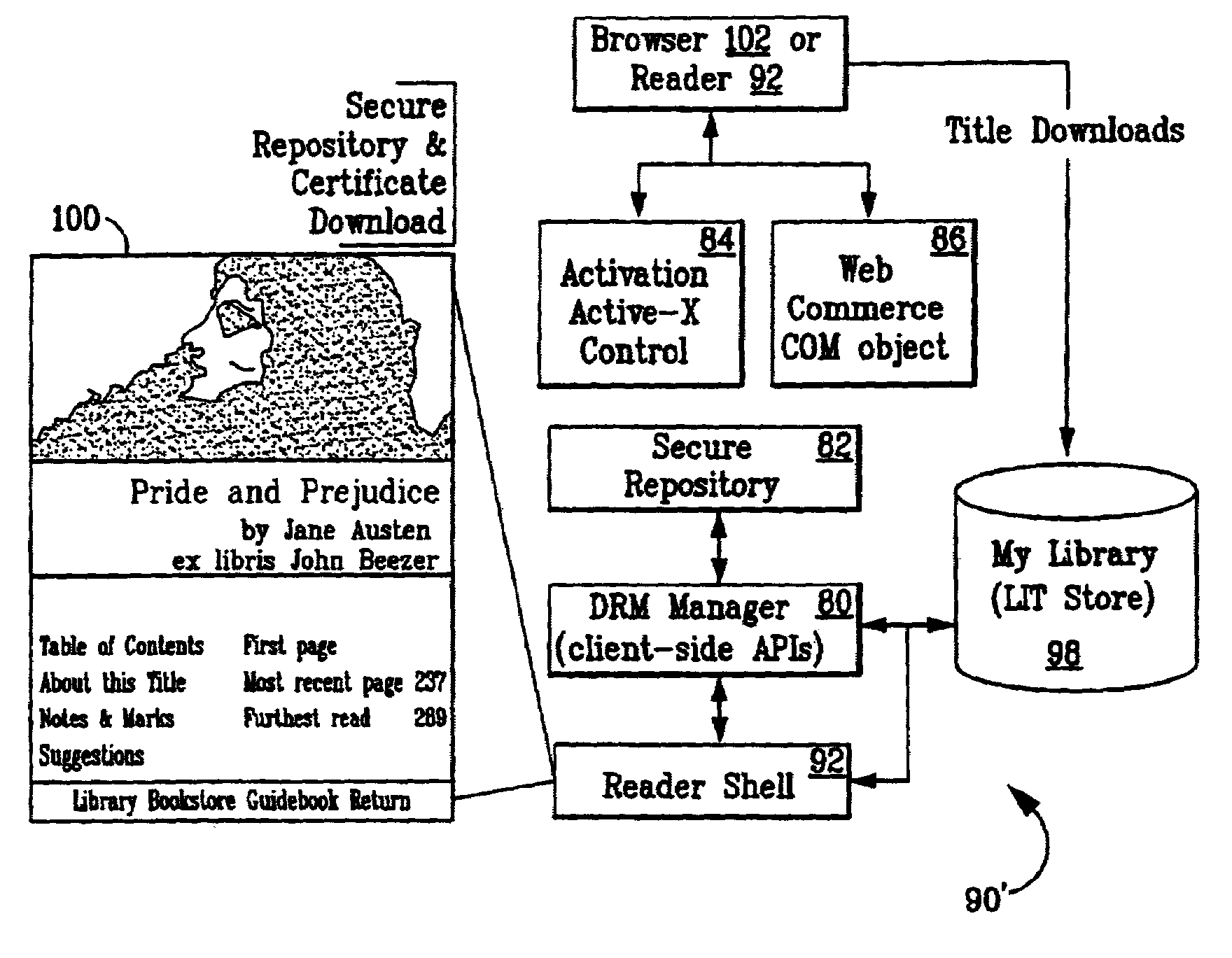
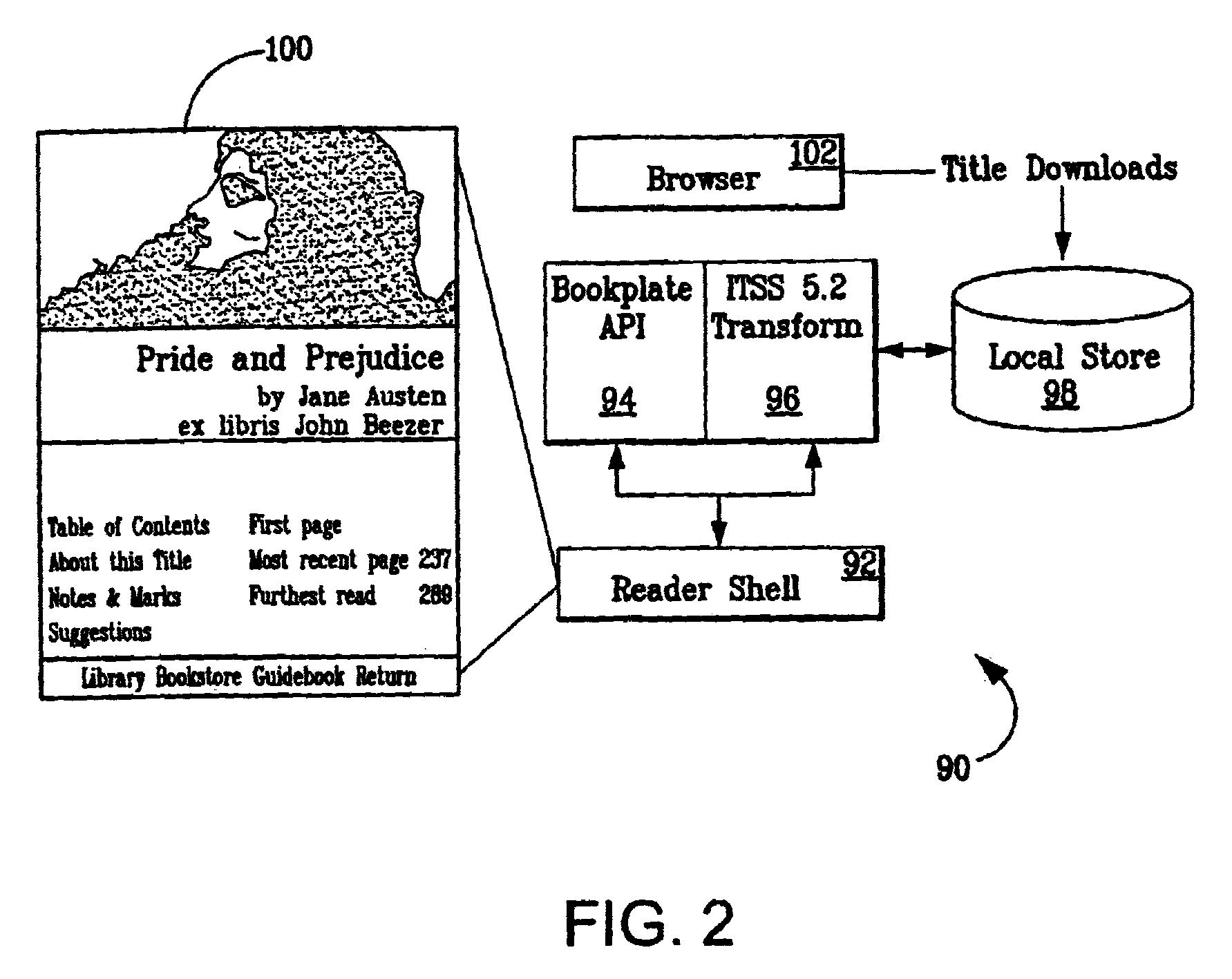
System and methods for managing digital creative works
InactiveUS7047241B1Improve network efficiencyEliminate needKey distribution for secure communicationData processing applicationsData setDigital signature
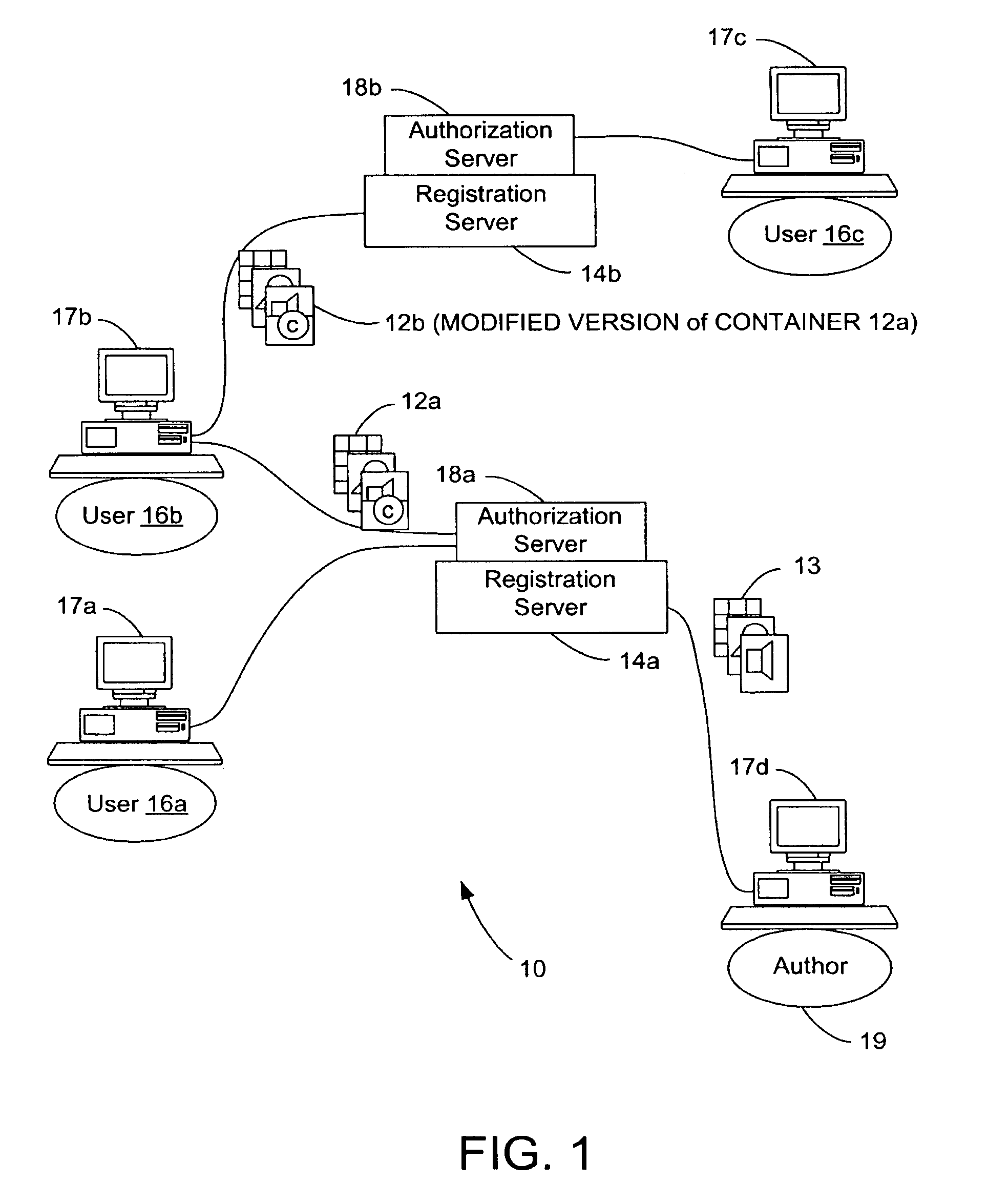
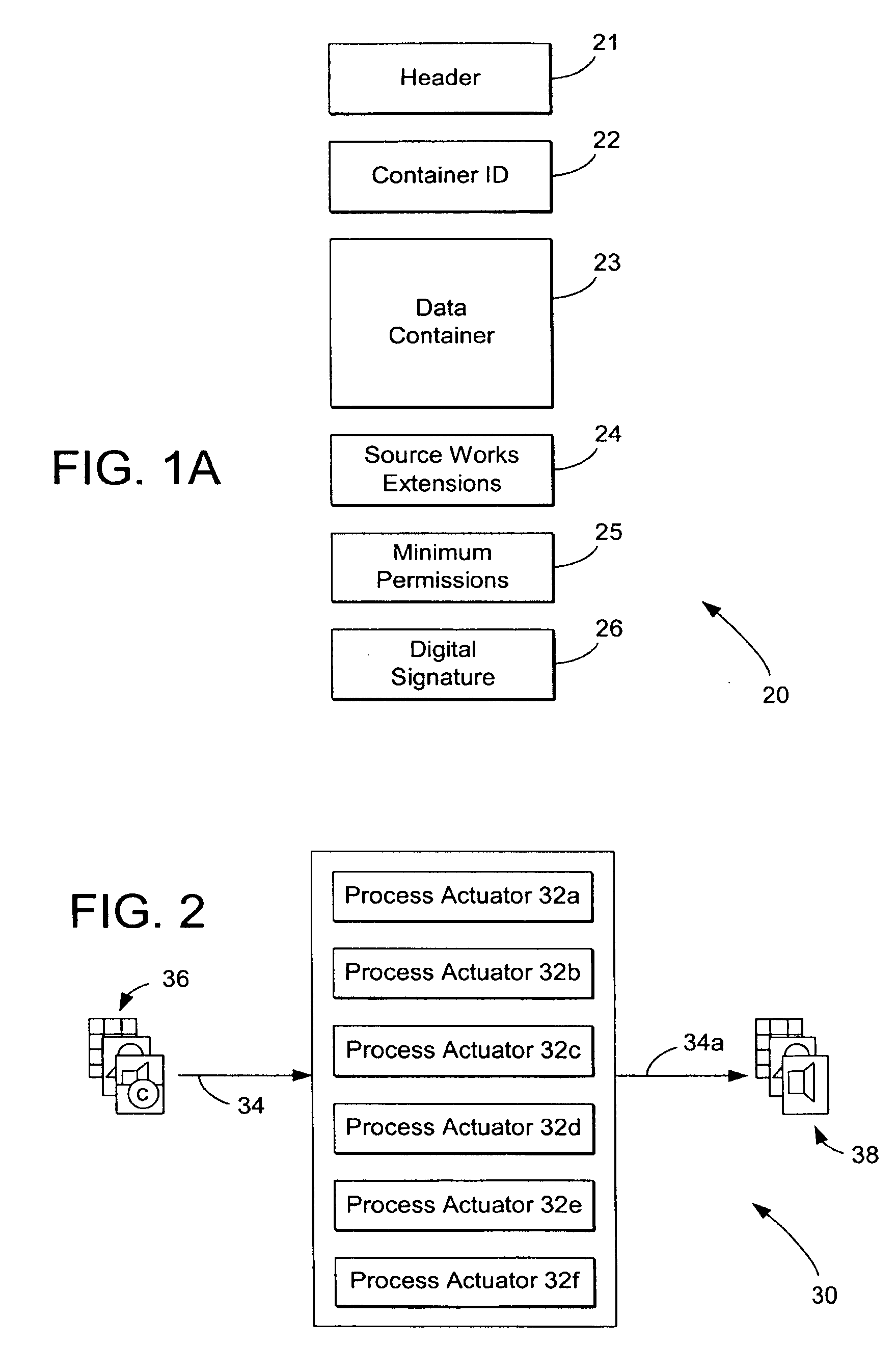
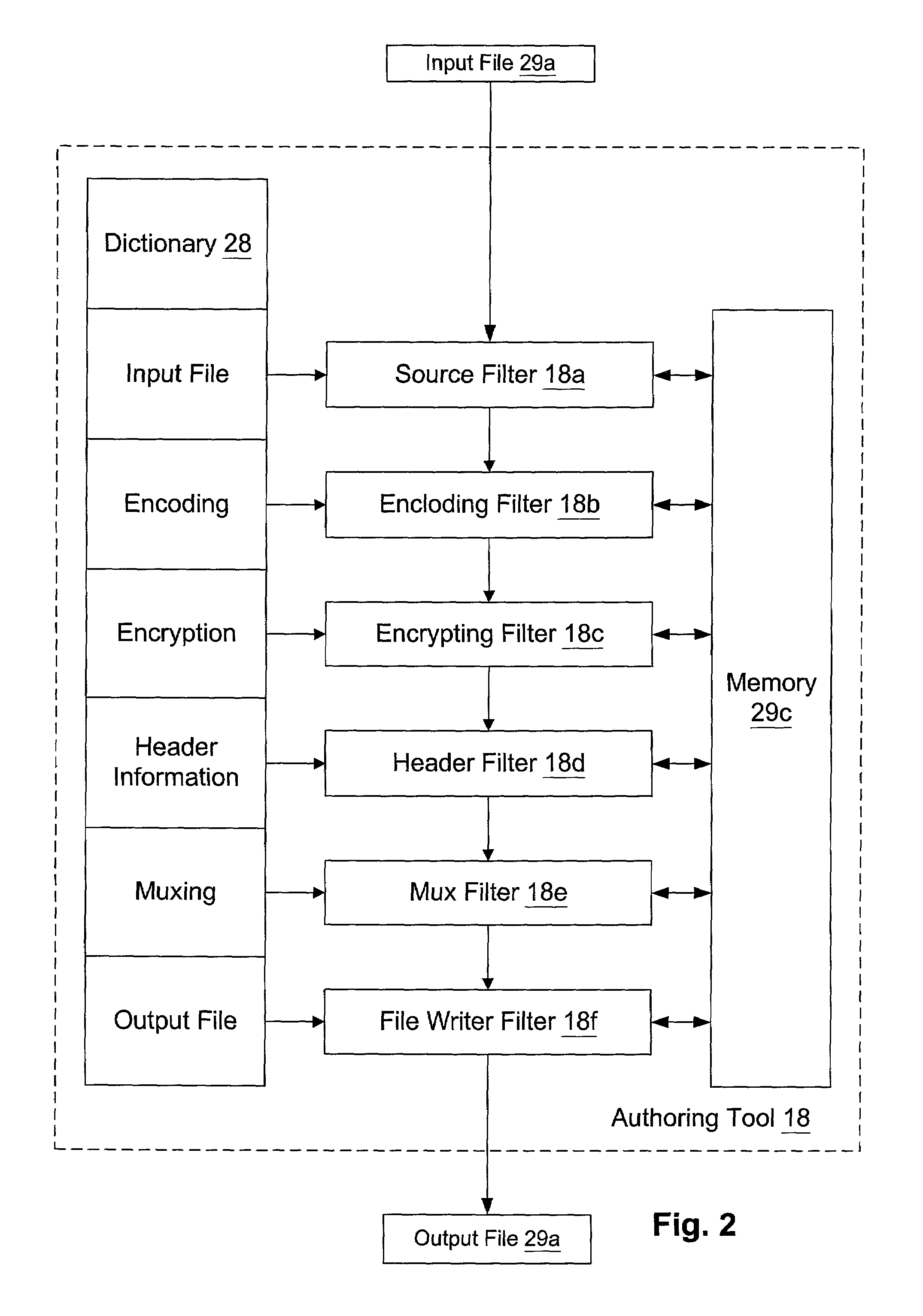
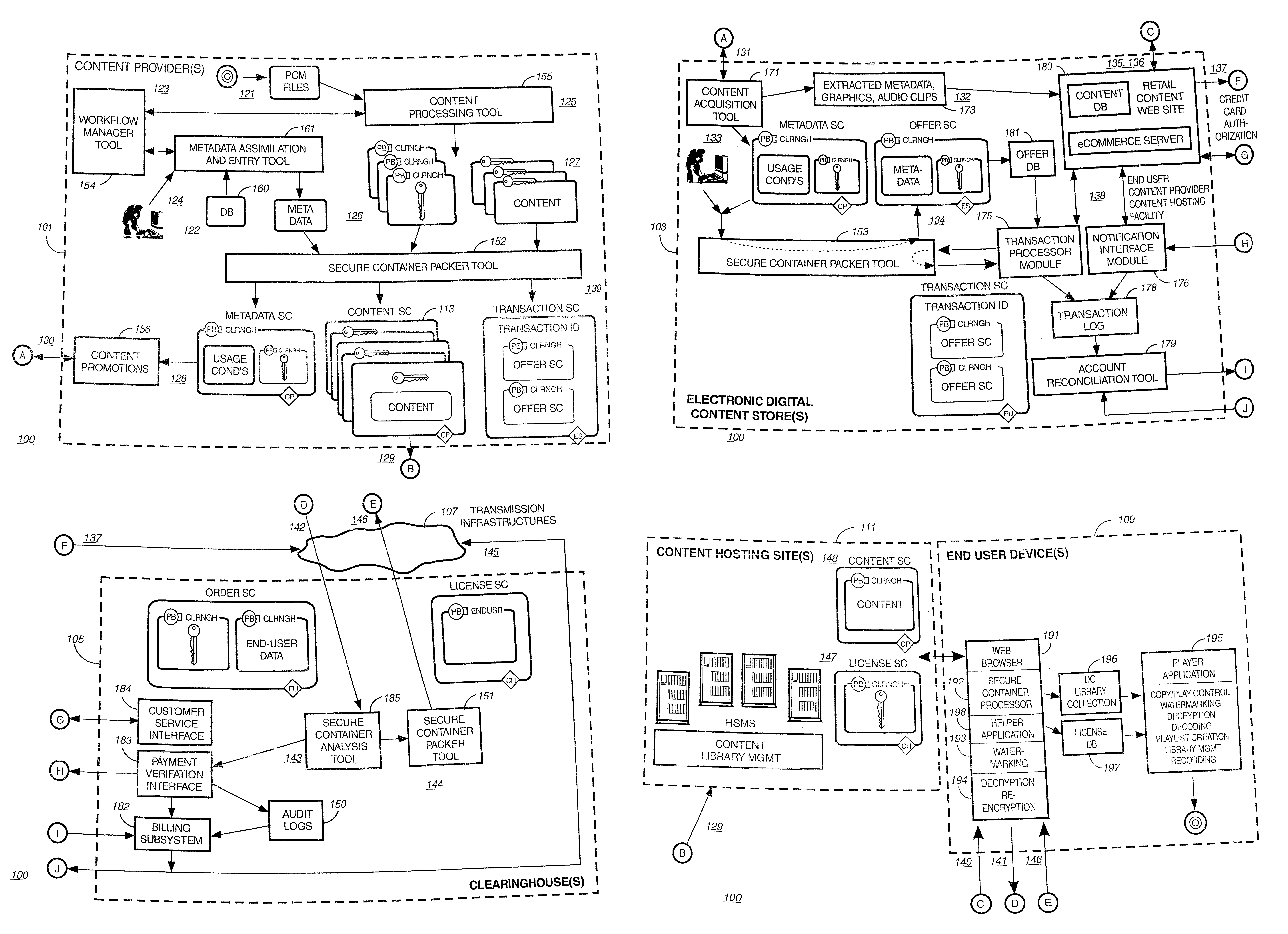
Digital Creative Works such as copyrighted electronic media are packaged in a secure electronic format, or CONTAINER, and registered on associated registration server, which serves to provide on-line licensing and copyright management for that Work. Users are connected to the registration server through a computer network or the Internet to enable data transfers and to transact licenses to utilize the media. Packaged electronic media are typically created by an author or derivative user of the work. Once the packaged media is registered on the server, the media is made available for limited use and possible license through an authorization server. This limited use is specified within the minimum permissions data set assigned to each packaged media. Without a license, users are typically permitted to view the packaged media—through a system which unpackages the media—but cannot save, print or otherwise transfer the media without obtaining auxiliary permissions to do so from the authorization server. The electronic media is authenticated through digital signatures and optional encryption.
Owner:DIGIMARC CORP
Mobile motor vehicle identification
InactiveUS20030095688A1Simple processPrevent unnecessary power drainTelevision system detailsDisc-shaped record carriersMobile vehicleComputer graphics (images)
Provided is an apparatus for identifying license plates, and includes camera means for generating a video signal corresponding to an observed scene, the camera means being mounted in a mobile vehicle and oriented so as to observe license plates of other vehicles. Processing means processes the video signal so as to obtain textual representations of vehicle license plate numbers in the video signal, and storage means stores a list of target vehicle license plate numbers. Comparison means compares the textual representations of vehicle license plate numbers in the video signal against the list of target vehicle license plate numbers to determine if there is a match, and then output means notifies a user of the match.
Owner:HUBB SYST
Optimized server for streamed applications
ActiveUS20030004882A1Efficient deliveryEasy maintenanceComputer security arrangementsSecret communicationApplication serverThe Internet
An optimized server for streamed applications provides a streamed application server optimized to provide efficient delivery of streamed applications to client systems across a computer network such as the Internet. The server persistently stores streamed application program sets that contain streamed application file pages. Client systems request streamed application file pages from the server using a unique set of numbers common among all servers that store the particular streamed application file pages. A license server offloads the streamed application server by performing client access privilege validations. Commonly accessed streamed application file pages are stored in a cache on the streamed application server which attempts to retrieve requested streamed application file pages from the cache before retrieving them from persistent storage. Requested streamed application file pages are compressed before being sent to a client as well as those stored in the cache.
Owner:NUMECENT HLDG
Systems and methods for the prevention of unauthorized use and manipulation of digital content
InactiveUS7328453B2Overwhelm usefulnessHigh normal sclerosisMemory loss protectionDigital data processing detailsTime domainThird party
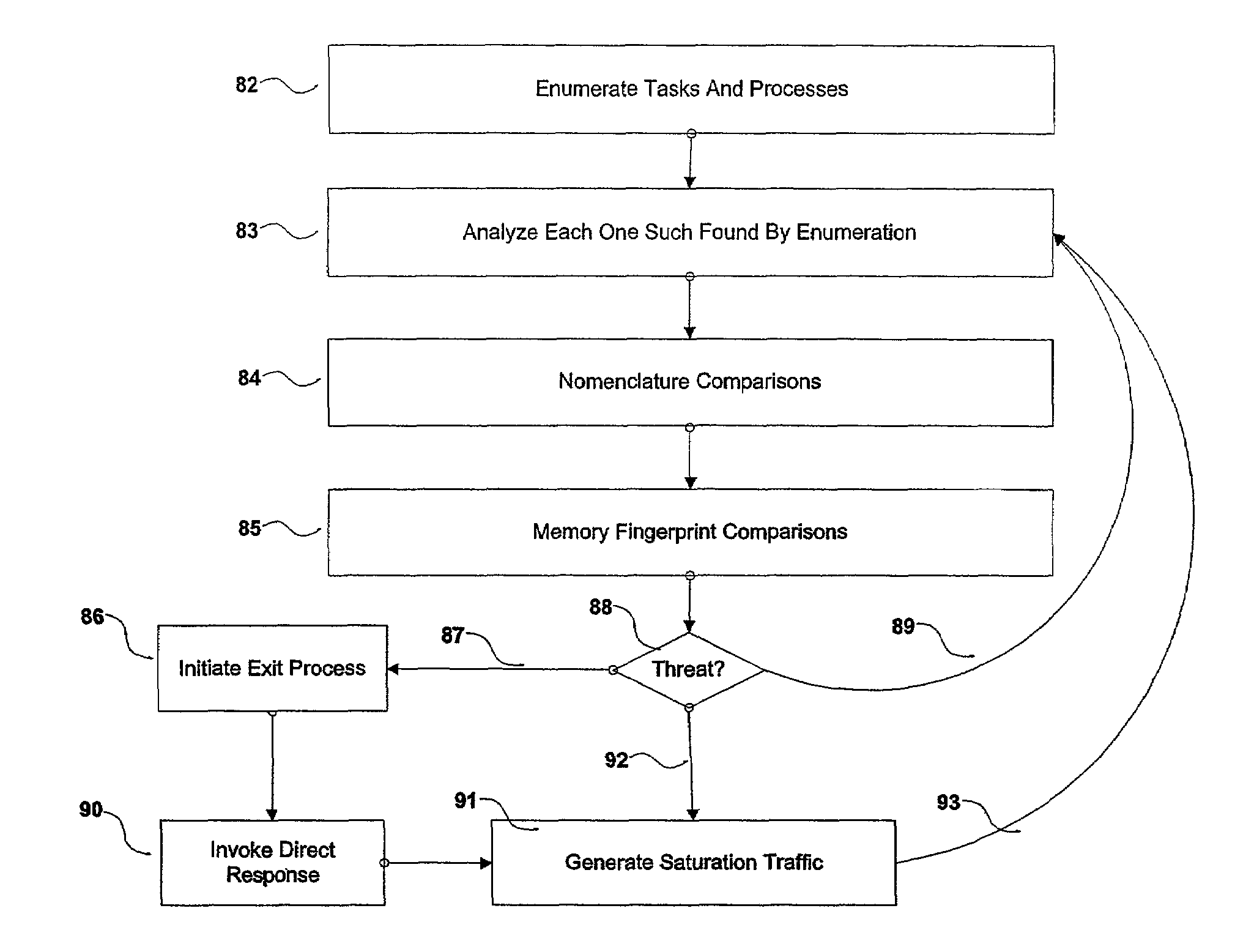
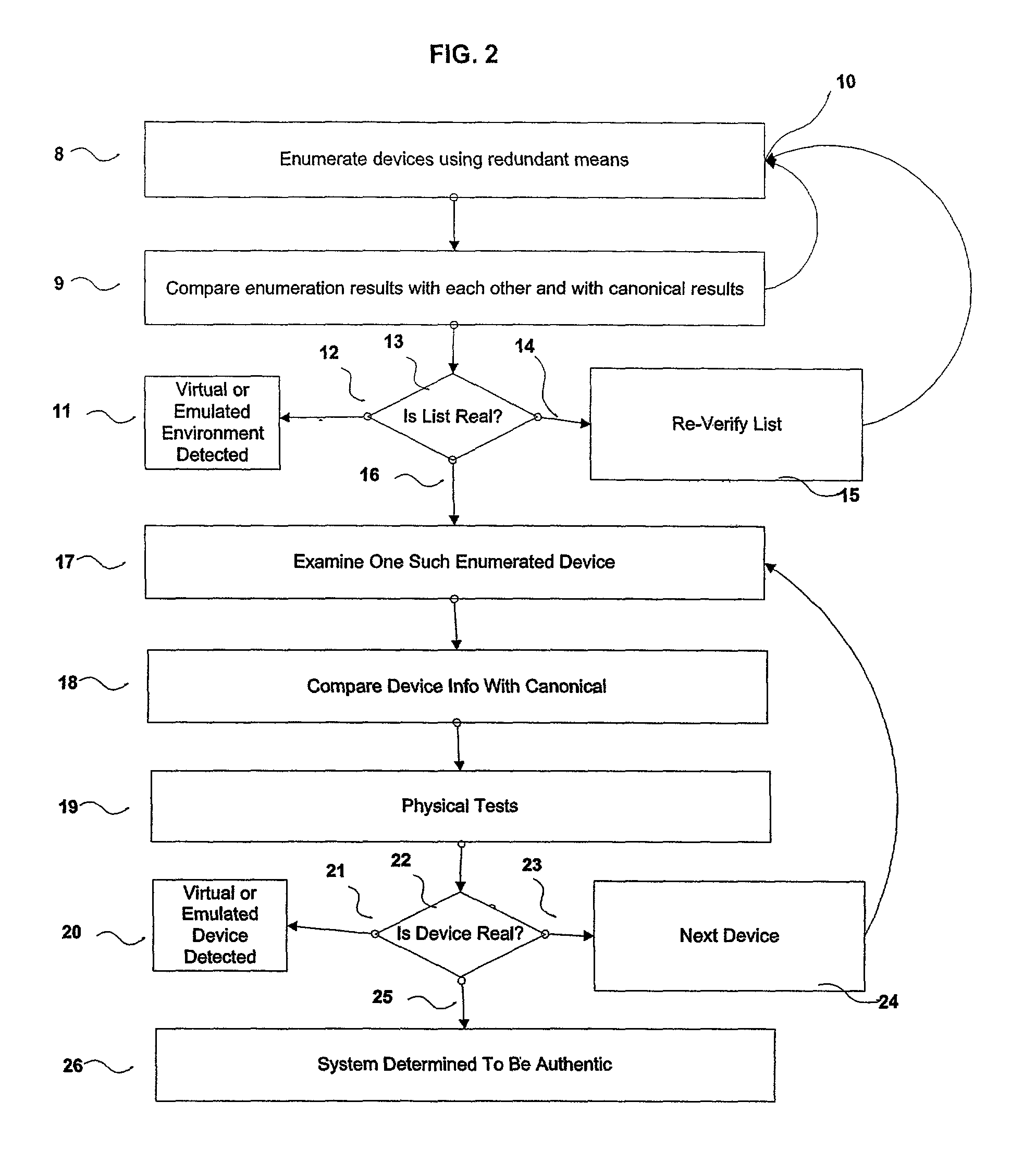
A number of systems and methods, alone, or in combination, achieve various levels of protection against unauthorized modification and distribution of digital content. This encompasses at least unauthorized study, modification, monitoring, reconstruction, and any other means for subversion from the originally intended purpose and license model of the digital content. The invention combines a number of techniques that in whole, or in part, serve to protect such content from unauthorized modification, reconstructive engineering, or monitoring by third parties. This is accomplished by means of methods which protect against subversion by specific tools operating on specific platforms as well as general tools operating on general platforms. Specific time domain attacks are identified, code modification can be identified and reversed, and virtual and emulated systems are identified. In addition, identification of in-circuit emulator tools (both software and hardware), debuggers, and security threats to running programs can be achieved.
Owner:IPLA HLDG
Wager game license management in a peer gaming network
InactiveUS20070136817A1Digital data processing detailsAnalogue secracy/subscription systemsDistributed computingPeer-to-peer
Novel wager gaming systems and methods for wager game license management in a network utilizing peer networking technology are in the various embodiments. A network component, such as a server computer or a gaming machine, is deputized by a central licensing authority or other authorized license management component. The network component is deputized once it receives what may be referred to as a license deputizing certificate. Upon receiving this certificate or at some point thereafter, the deputized component is provided with various data relating to devices in the gaming network, wagering games available in the network, and network configuration data. The gaming network may have a primary network backbone and local peer gaming networks operating in conjunction with each other via the network backbone. A local peer gaming network may share wager game code, memory space, and other gaming-related resources. Once a network component is deputized to perform as an authorized license management component, it assumes the role of local licensing server for the gaming network or for a local peer gaming network. This component may be a gaming machine in a local peer network or an existing local license server which is now able to supply and manage the distribution of license tokens in a gaming network utilizing peer network technology.
Owner:IGT
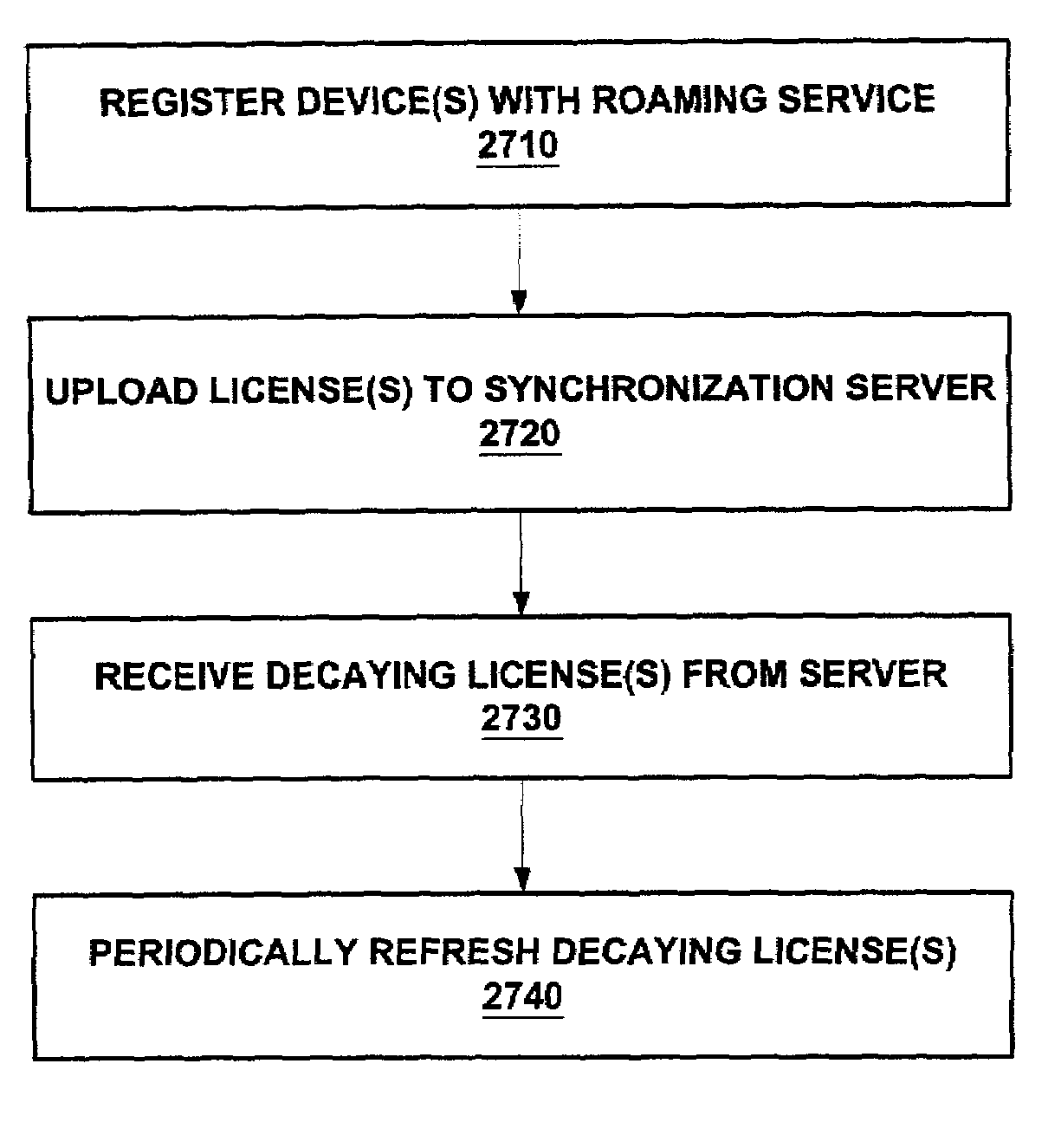
Enforcement architecture and method for digital rights management system for roaming a license to a plurality of user devices
InactiveUS7203966B2Prevent long-term misusePrevent long-term misuse of the systemDigital data processing detailsUnauthorized memory use protectionUser deviceDevice register
An enforcement architecture and method for implementing roaming digital rights management are disclosed. A license distributed from a license server to a computing device of a user may be uploaded to a license synchronization server, and rebound to other devices registered with the service, thereby enabling access to the licensed content from other computing devices. A second digital license of a second computing device is set to expire prior to a first digital license of a first computing device. Reactivating a decayed first digital license, that is deactivated during transmission of the second digital license, to the second device to access content of the first computing device.
Owner:MICROSOFT TECH LICENSING LLC
Self-replicating and self-installing software apparatus
InactiveUS20030217171A1Special service provision for substationElectronic editing digitised analogue information signalsContent creationRemote control
Self-replicating and self-installing software apparatus for content-creation, manipulation, and static or dynamic exhibition with a self-regulating license management component with methods for remote controlled and synchronized functionality and license binding to a Peer-to-Peer computing paradigm derived communication and collaboration platform's unique User ID.
Owner:VON STUERMER WOLFGANG R +1
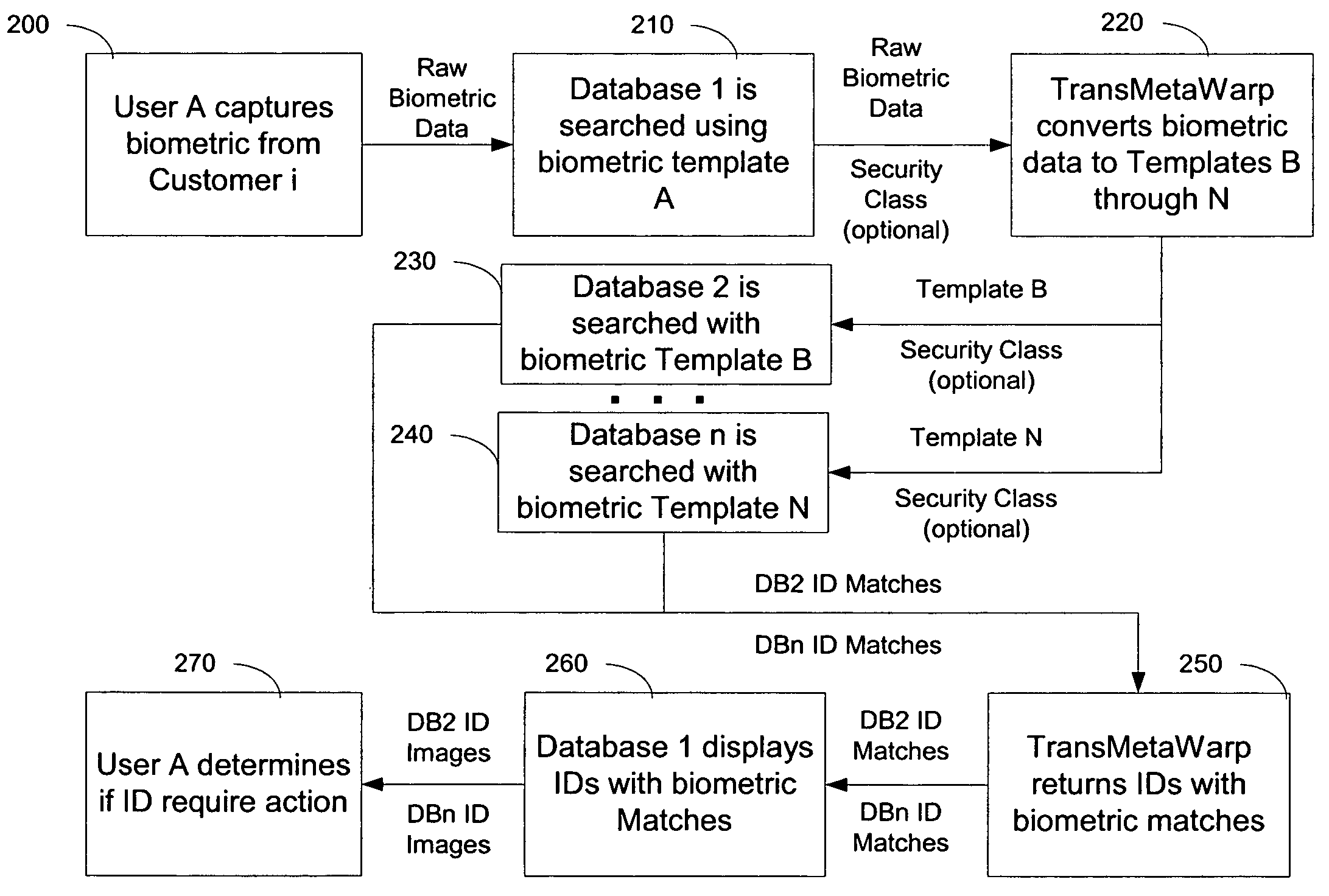
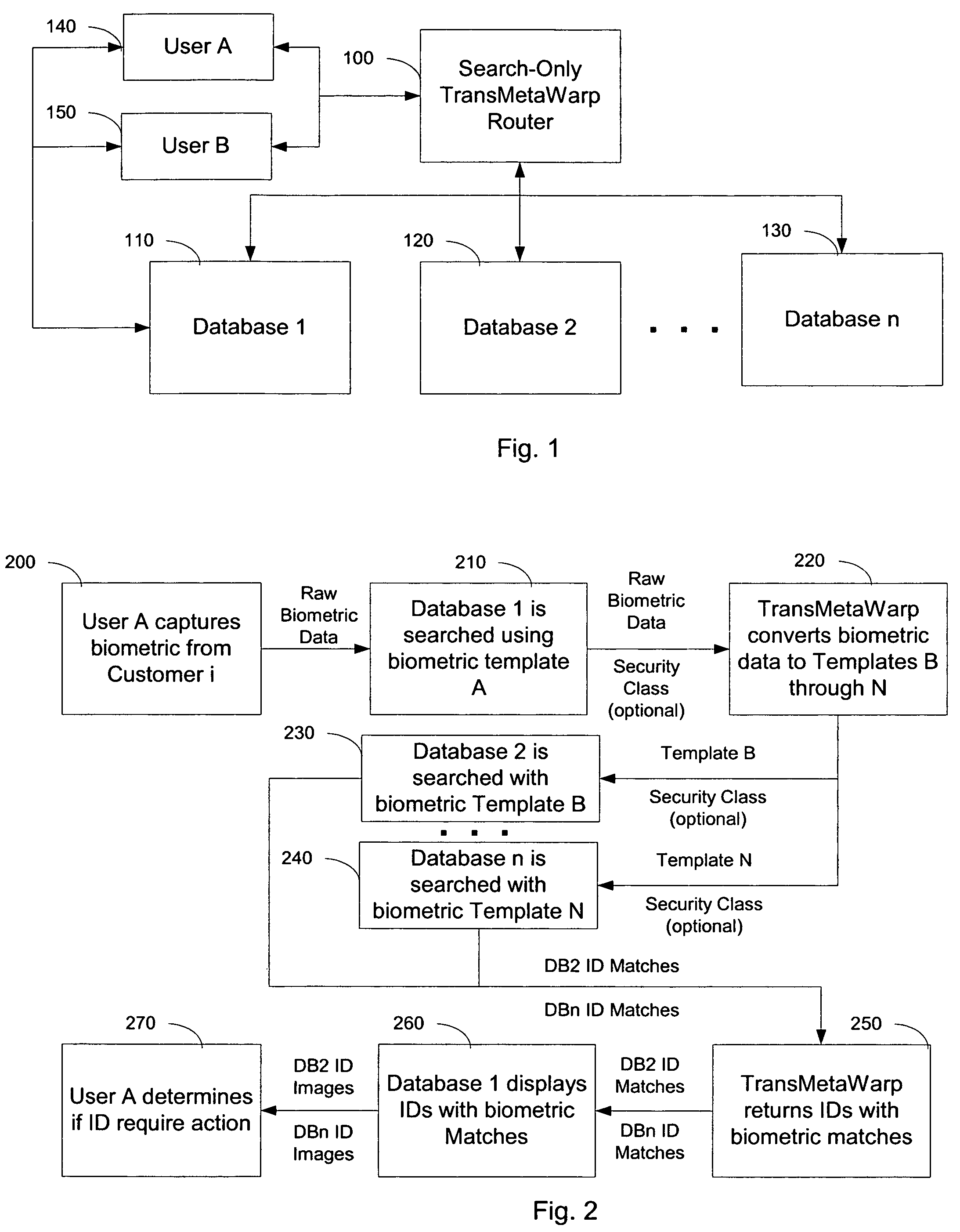
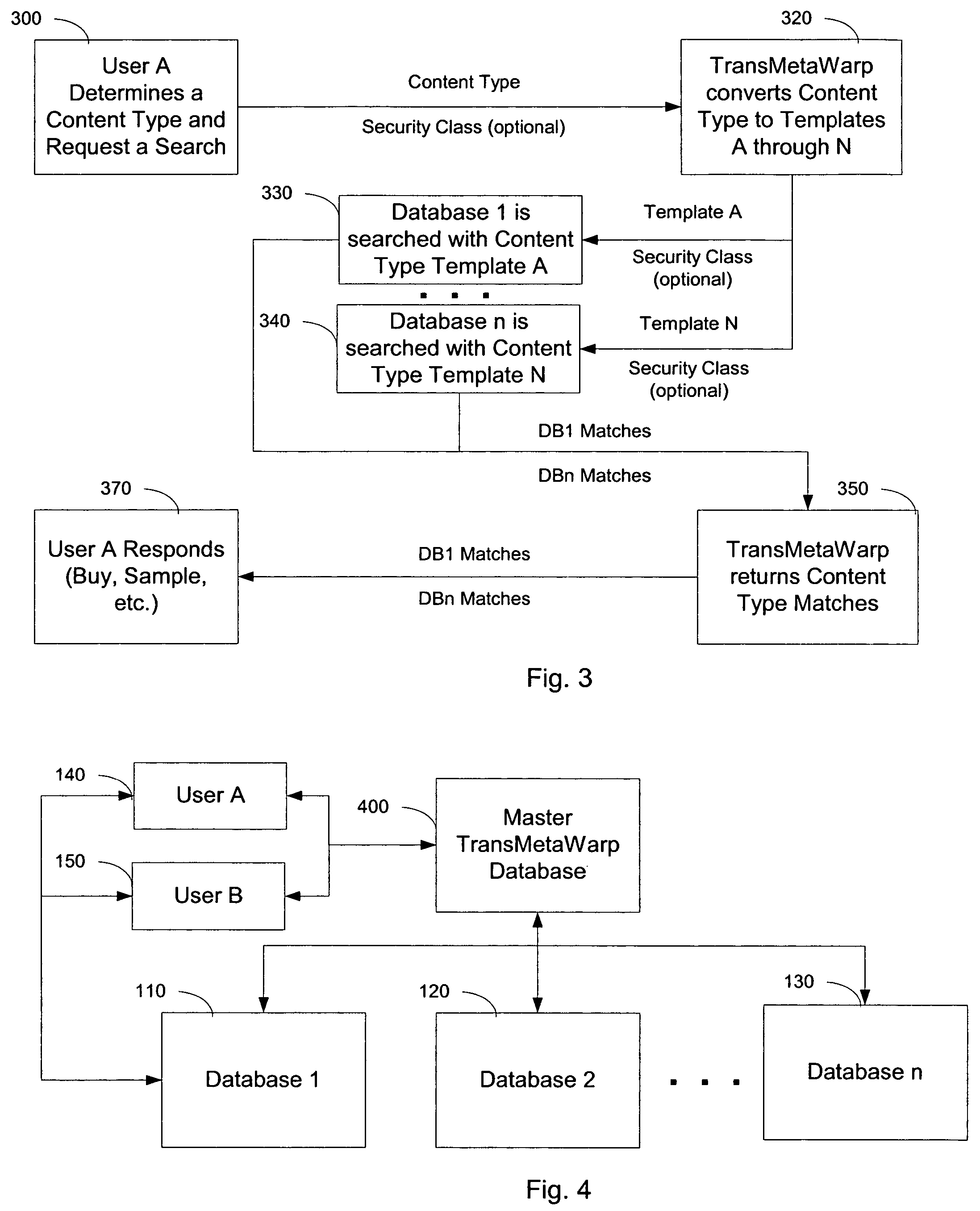
Integrating and enhancing searching of media content and biometric databases
ActiveUS7606790B2Increase incomeReduce identityData processing applicationsDigital data information retrievalInternet privacyBiometrics
The digital era is creating problems with identity and content theft. The solutions require searching different databases containing similar data. The novel method demonstrates how to search these different databases for similar information via TransMetaWarp routers and / or databases. Embodiments provide different balances of security and privacy issues, such as search-only TransMetaWarp routers and master TransMetaWarp databases. The system is applicable to biometrics for identity cards, such as drivers' licenses, as well as metadata, such as content title, creator information, and tour information, or content identification for entertainment content.
Owner:DIGIMARC CORP
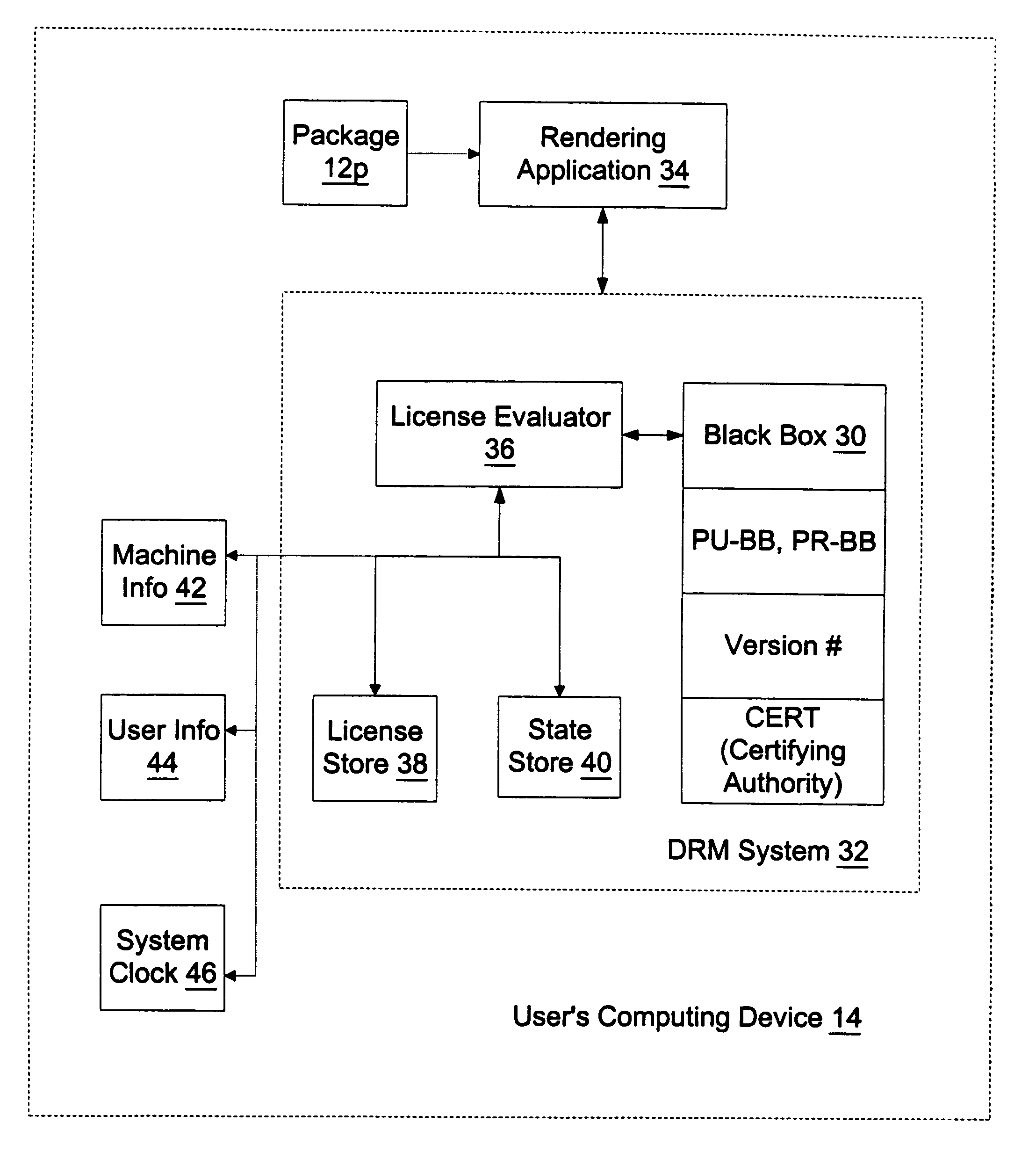
Structural of digital rights management (DRM) system
InactiveUS7024393B1Satisfies needData processing applicationsDigital data processing detailsDigital contentDigital rights management
A digital rights management (DRM) system operates on a computing device when a user requests that a protected piece of digital content be rendered by the computer device in a particular manner. The DRM system has a license store, a license evaluator, and a state store. The license store stores digital licenses on the computing device. The license evaluator determines whether any licenses stored in the license store correspond to the requested digital content and whether any such corresponding licenses are valid, reviews license rules in each such valid license, and determining based on such reviewed license rules whether such license enables the requesting user to render the requested digital content in the manner sought. The state store maintains state information corresponding to each license in the license store, where the state information is created and updated by the license evaluator as necessary.
Owner:MICROSOFT TECH LICENSING LLC
Optical transmission tube and applications thereof
InactiveUS20020159741A1Minimize energyUse minimizedMechanical apparatusPoint-like light sourceEngineeringFlashlight
An optical transmission tube for illumination is uniquely incorporated into any one of a variety of automotive, commercial, retail, structural, architectural, safety, or other products including running boards, vehicle interior compartments such as a glove box, approximate the license plate attachment area on a vehicle, a trunk, a vehicle hood, on a vehicle door, a vehicle bumper, a vehicle luggage rack, a picture frame, a flashlight, a building, a guard rail, a construction barrier, a bicycle, a sign, an appliance interior compartment such as a refrigerator, a part bin, a retail display shelf, a clipboard, a step, a tractor trailer, a desk, a walkway, a room or storage chamber, a runway, an instrument panel, a railroad crossing gate, an emergency sign, an elevator doorway, a swimming pool, a dog collar, a fish tank, a baby crib a hand rail, an inline skate an island in a parking lot or on a street, affixed to a curb, or on safety clothing.
Owner:BRIDGESTONE CORP
Network configured for delivery of content for download to a recipient
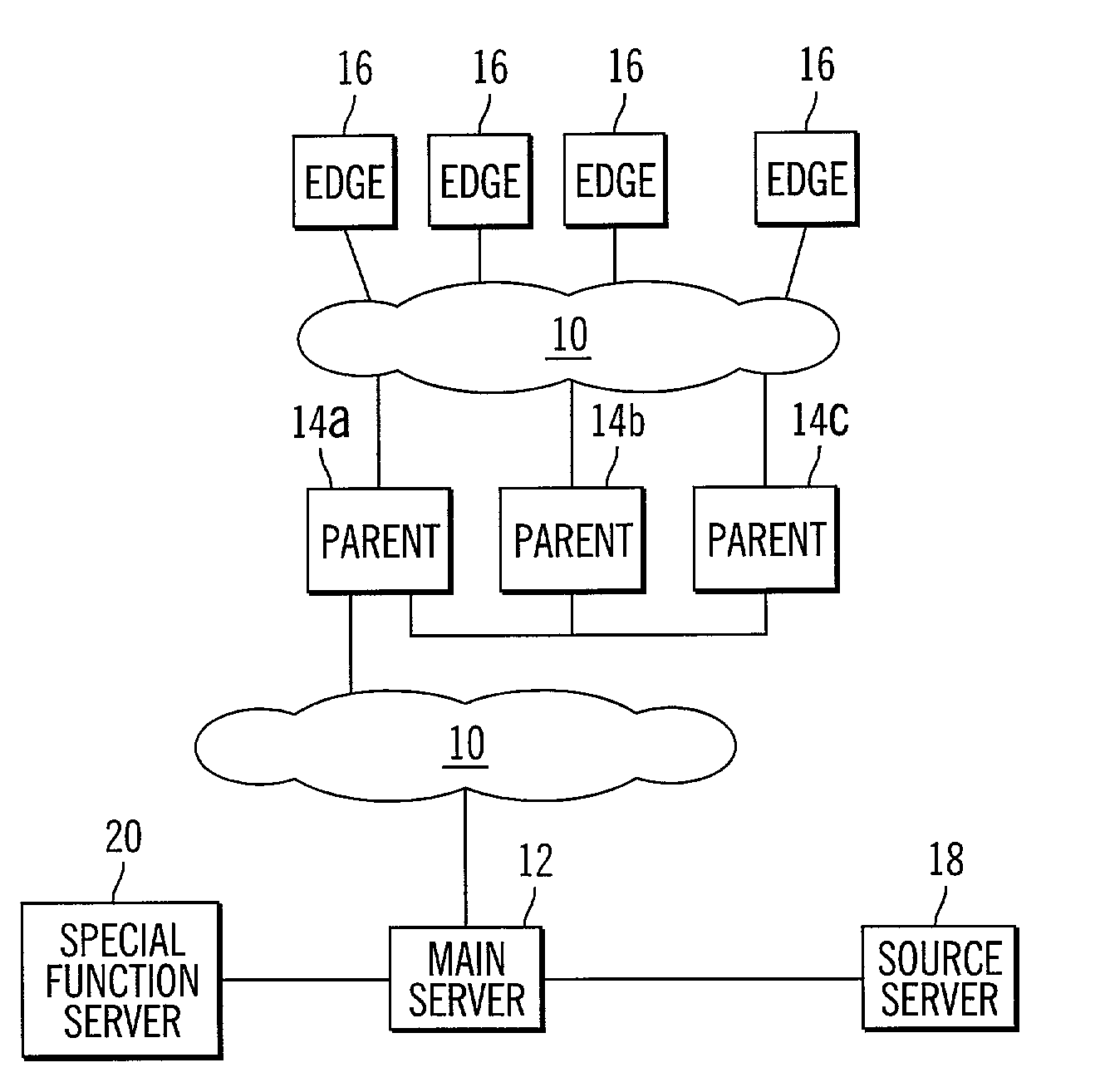
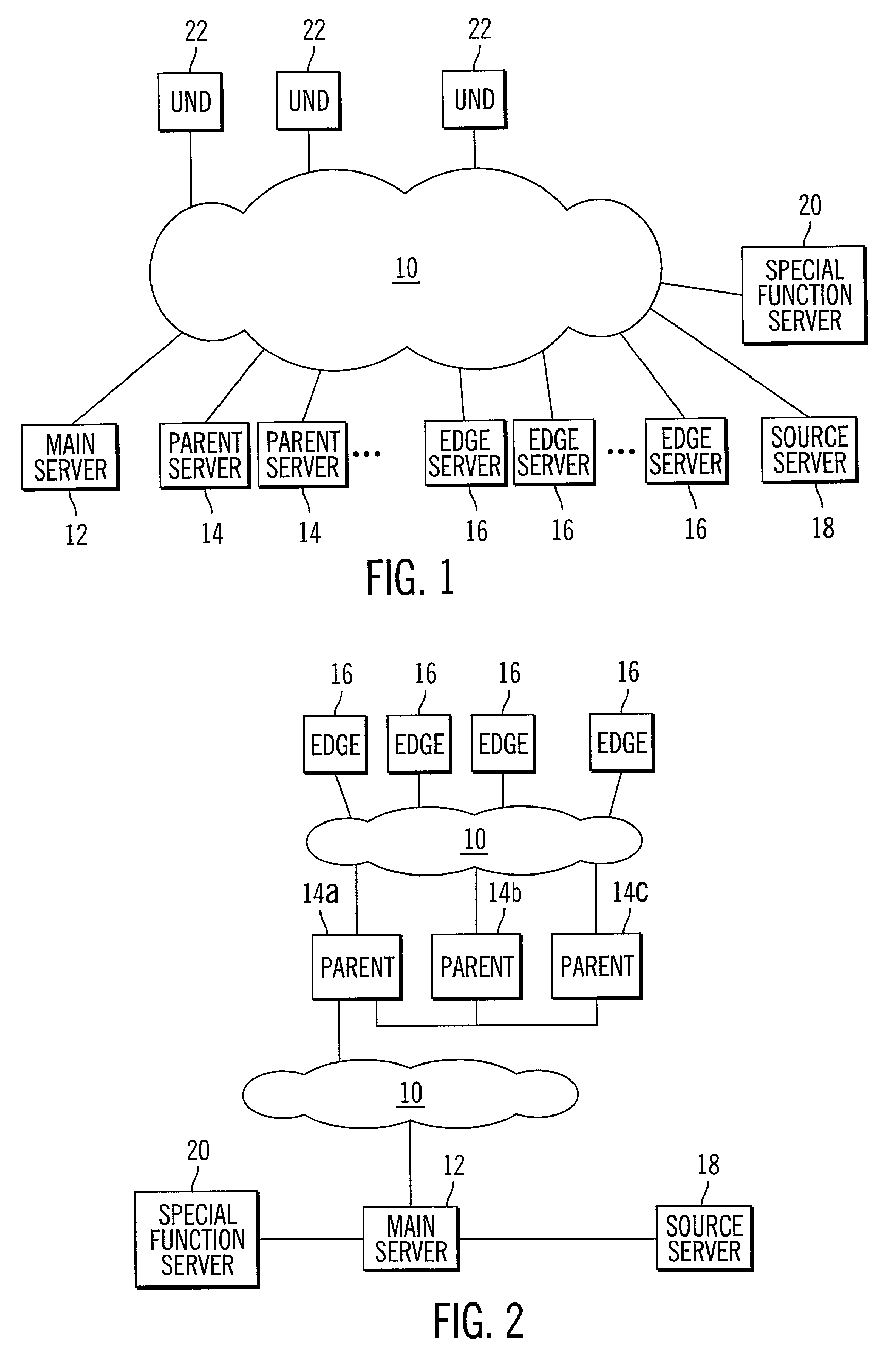
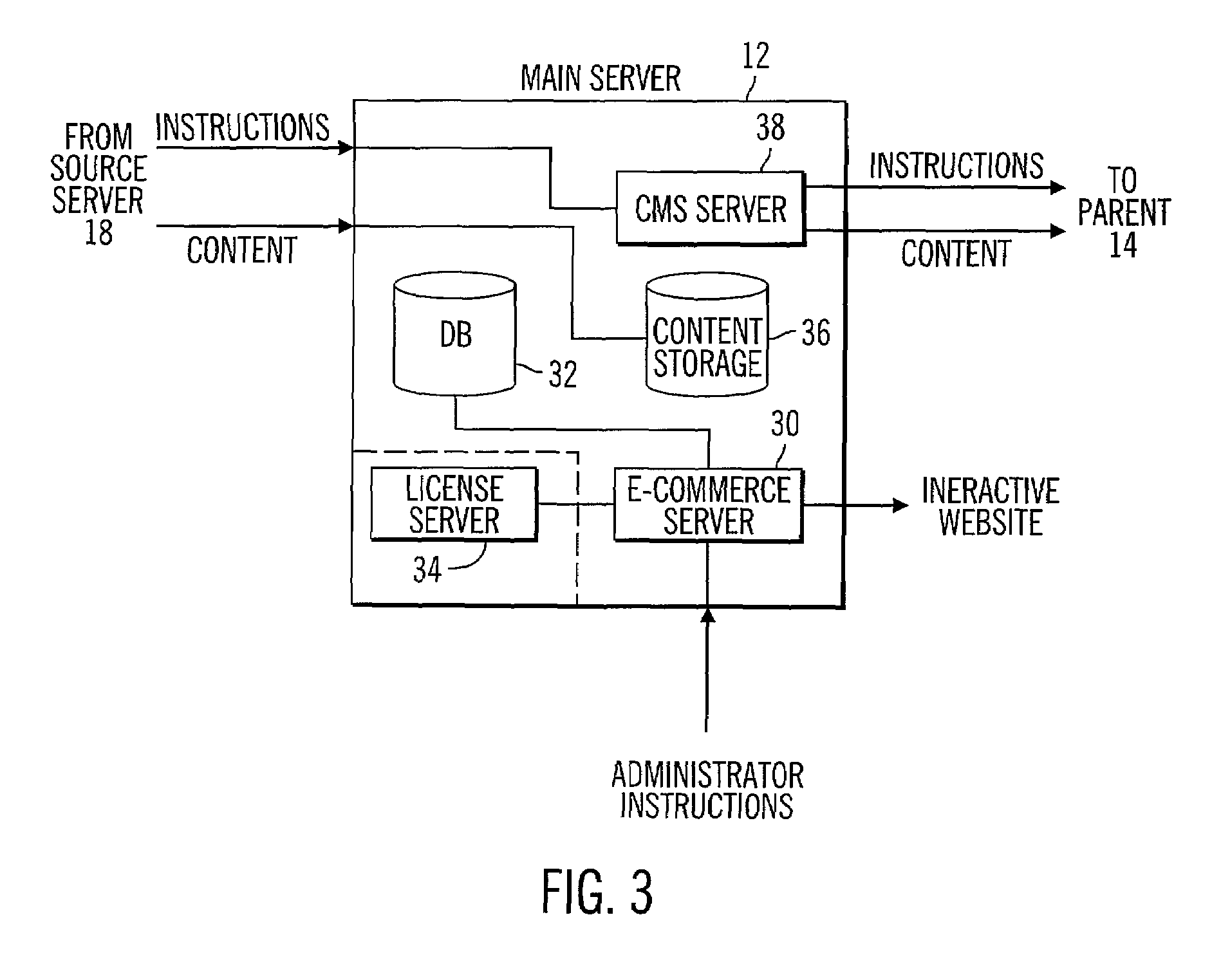
InactiveUS7024466B2Increase speed and efficiencyEffective controlMultiprogramming arrangementsMultiple digital computer combinationsEdge serverNetwork architecture
Owner:BLOCKBUSTER LLC
Large venue security method
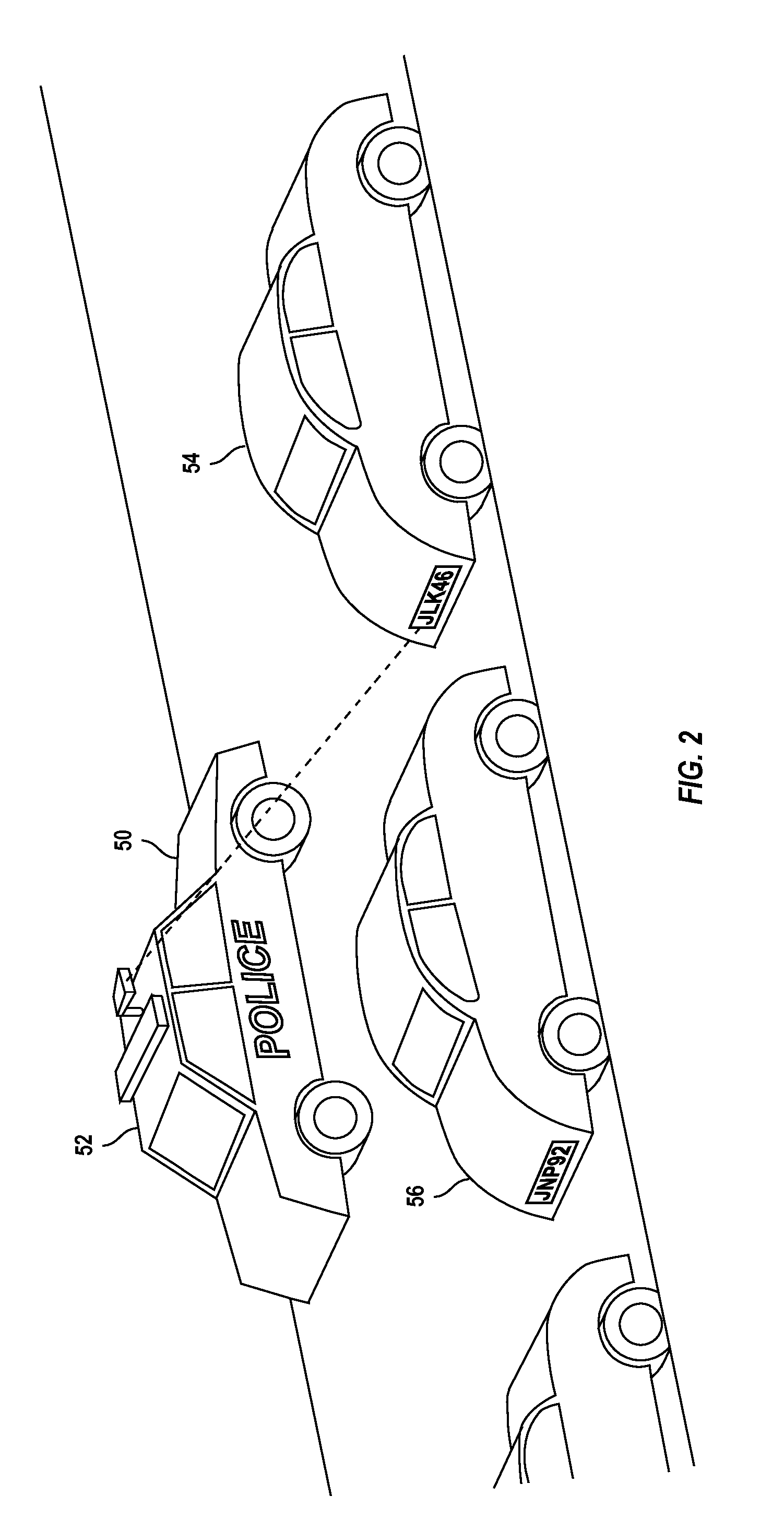
ActiveUS20130279757A1Reducing violent actEnhance the imageTransportation facility accessReservationsParking areaComputer vision
A method for reducing violence within crowded venues includes reading license plates of vehicles passing into entry ports of a parking area, and capturing facial images of persons seeking admission to the venue. A computer compares such license plates to a database of vehicle license plates associated with persons with past histories of violence. A computer also compares captured facial images to a database of facial data for persons with past violent histories. Upon detecting a match, the computer creates an alert presented to law enforcement officers at the venue to facilitate detention of such persons for investigation. Information recorded on entry tickets is scanned and saved together with the facial image of the ticket holder. If a violent act occurs, cameras within the venue capture facial images of participants. The computer matches such participants to stored identifying data to assist in the identification and apprehension of such persons.
Owner:KEPHART CONSULTING LLC +1
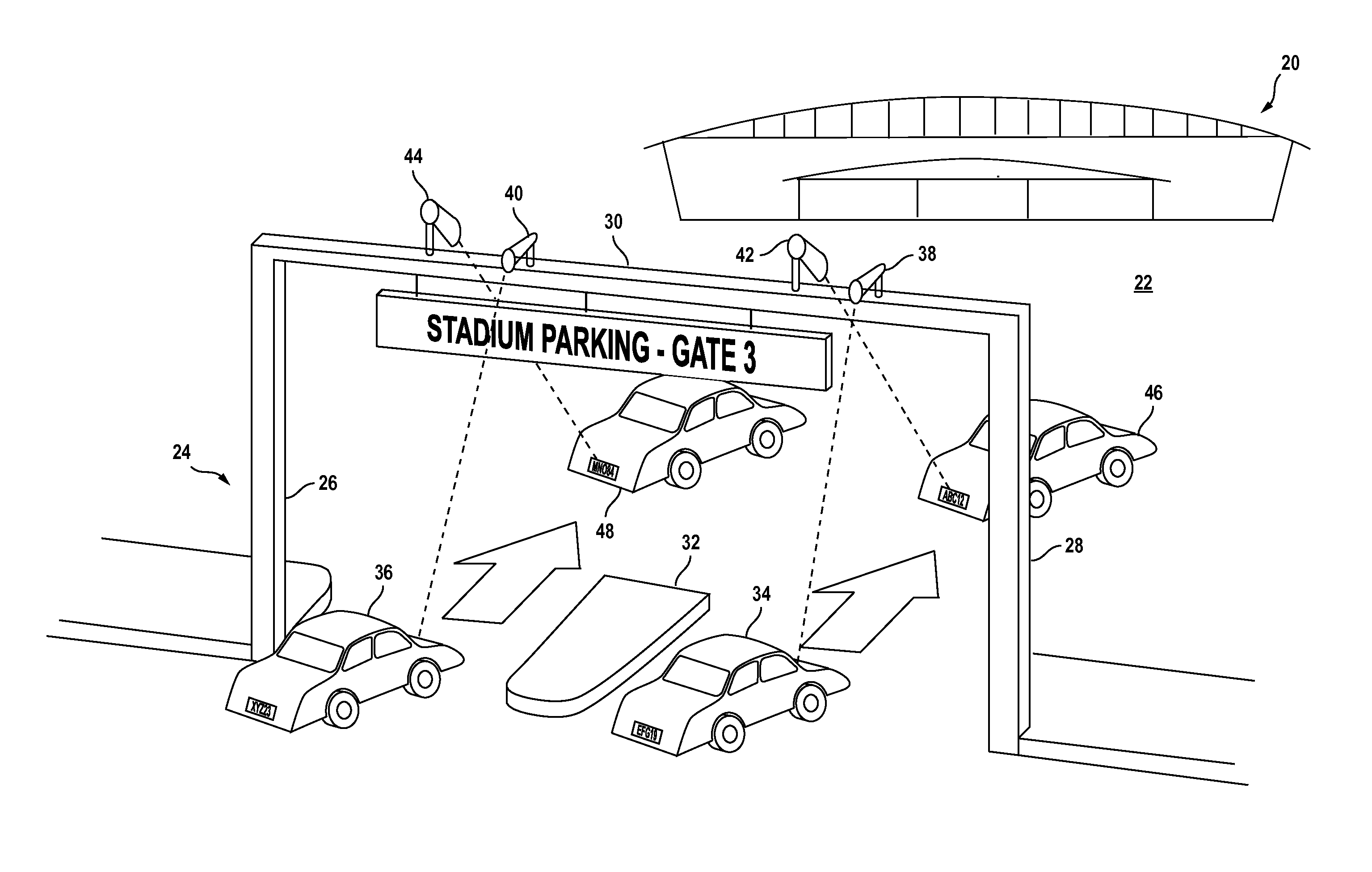
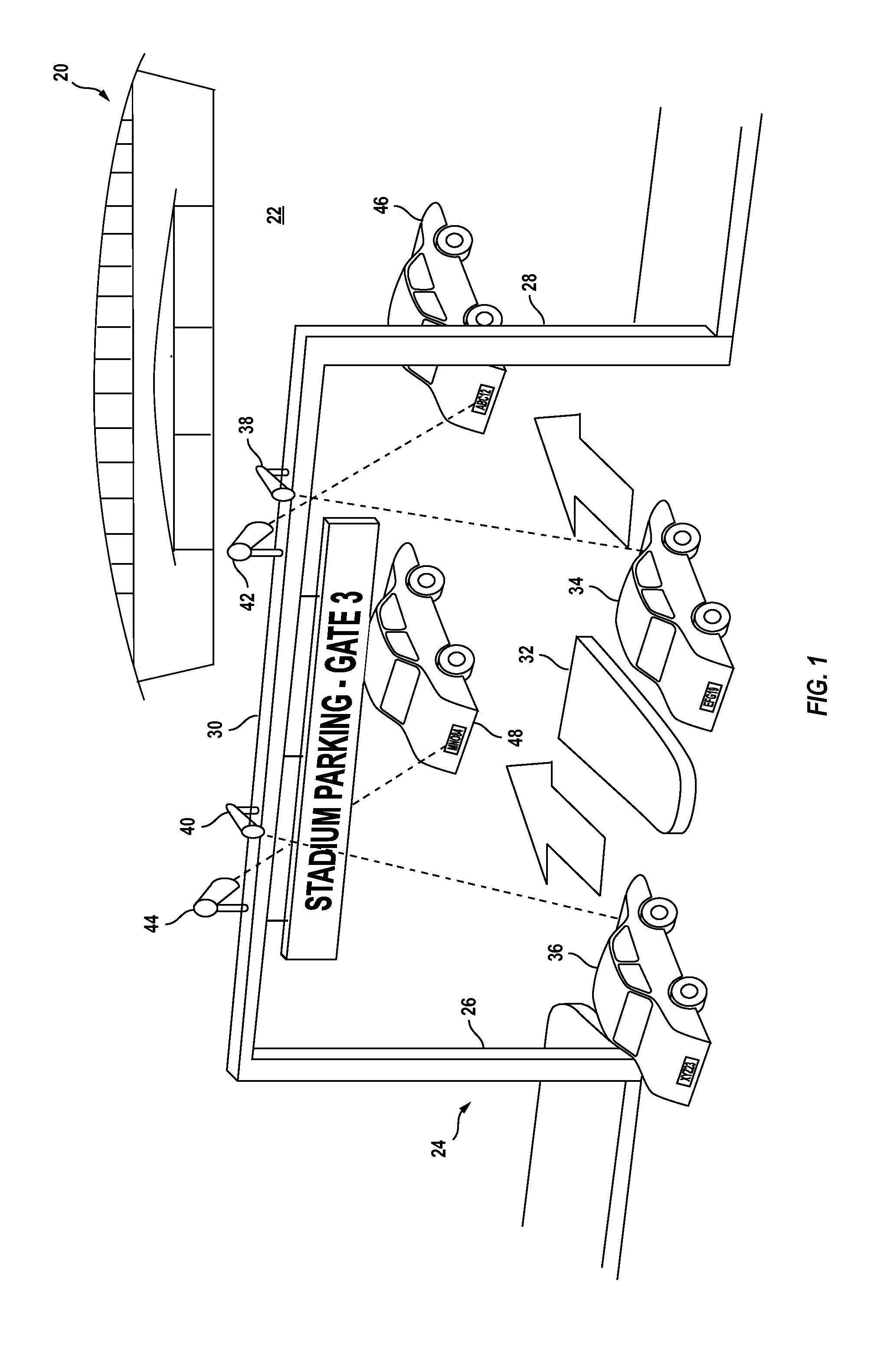
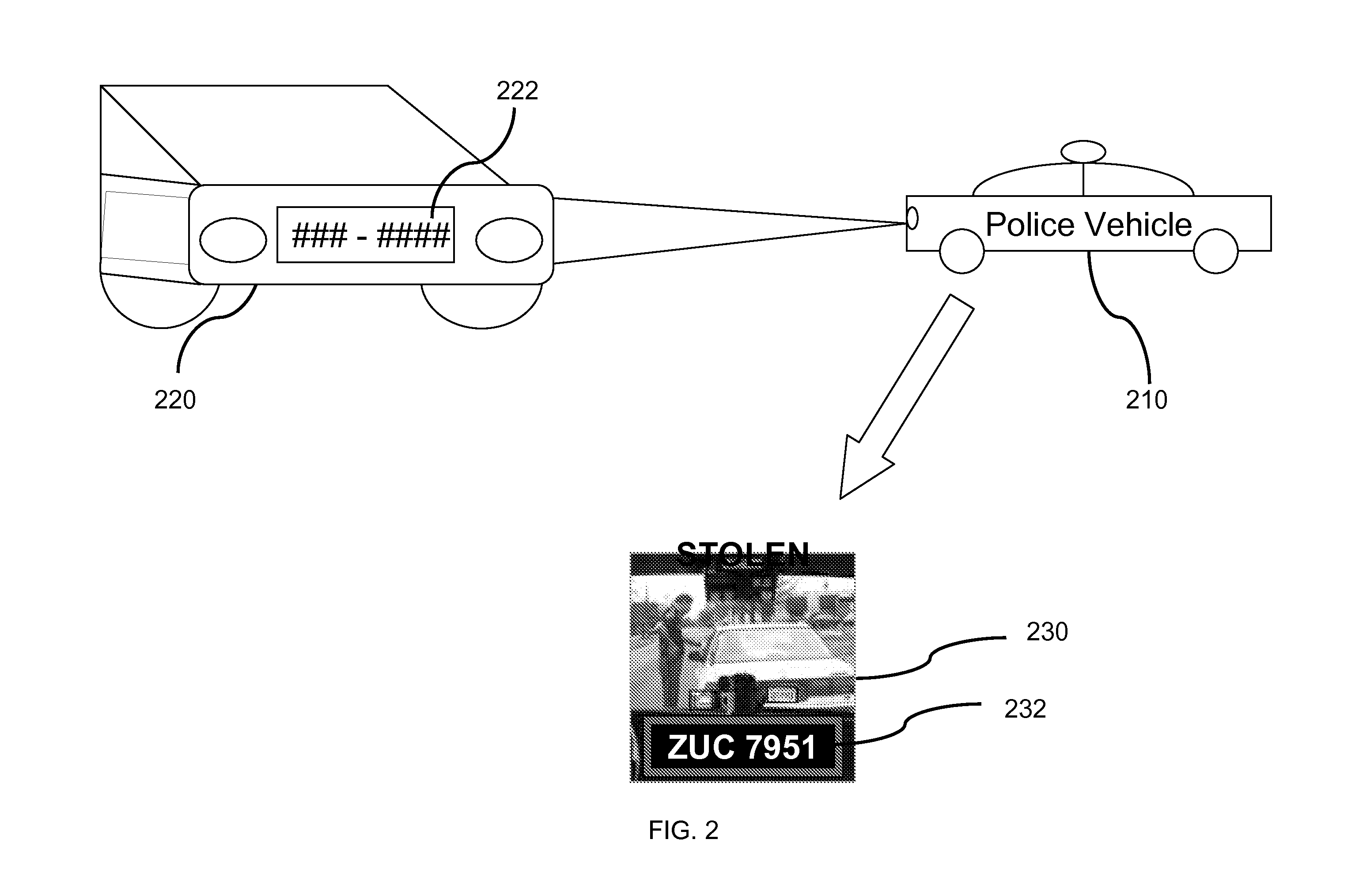
Video surveillance, storage, and alerting system having network management, hierarchical data storage, video tip processing, and vehicle plate analysis
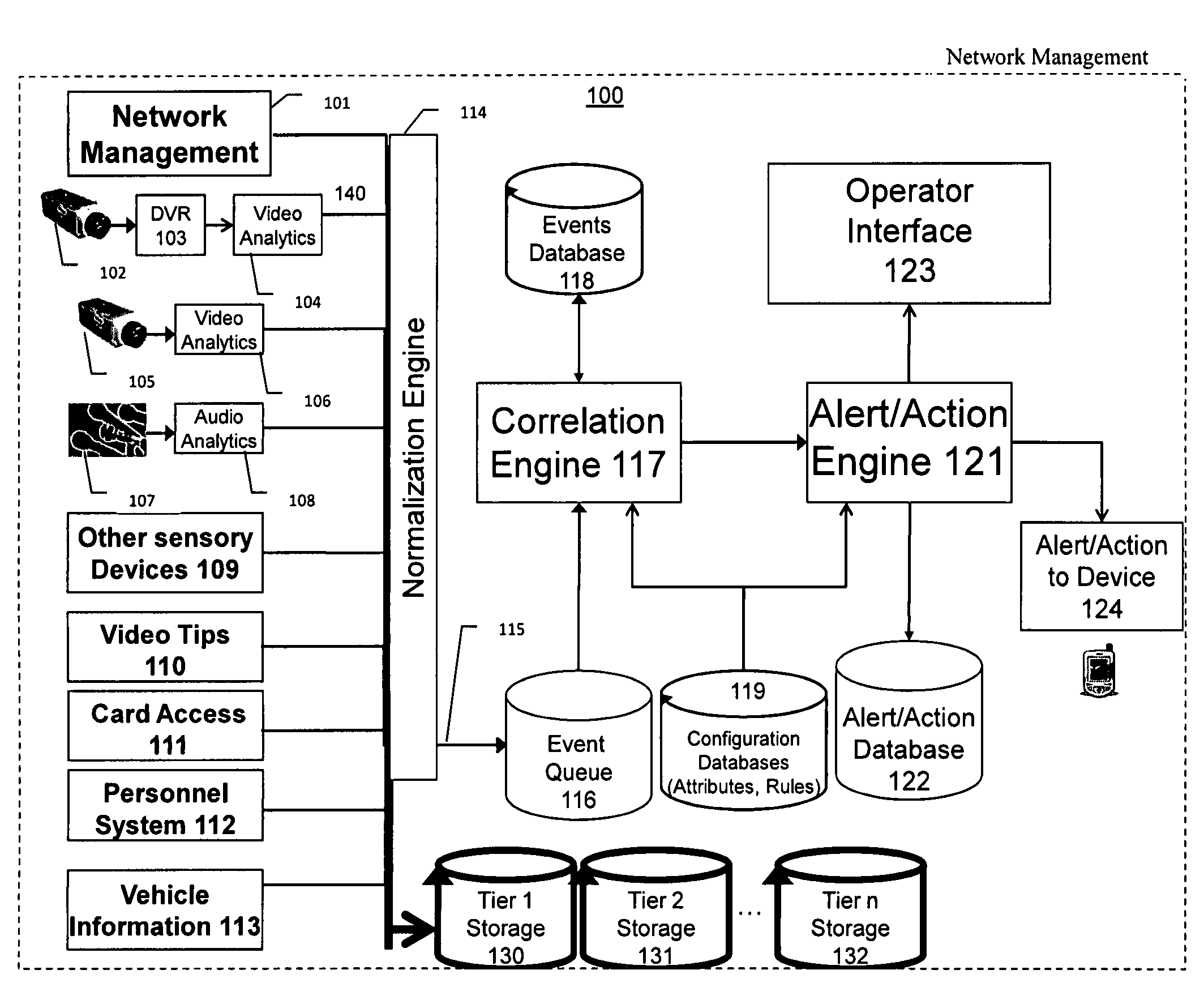
ActiveUS7382244B1Television system detailsFrequency-division multiplex detailsVideo monitoringDriver/operator
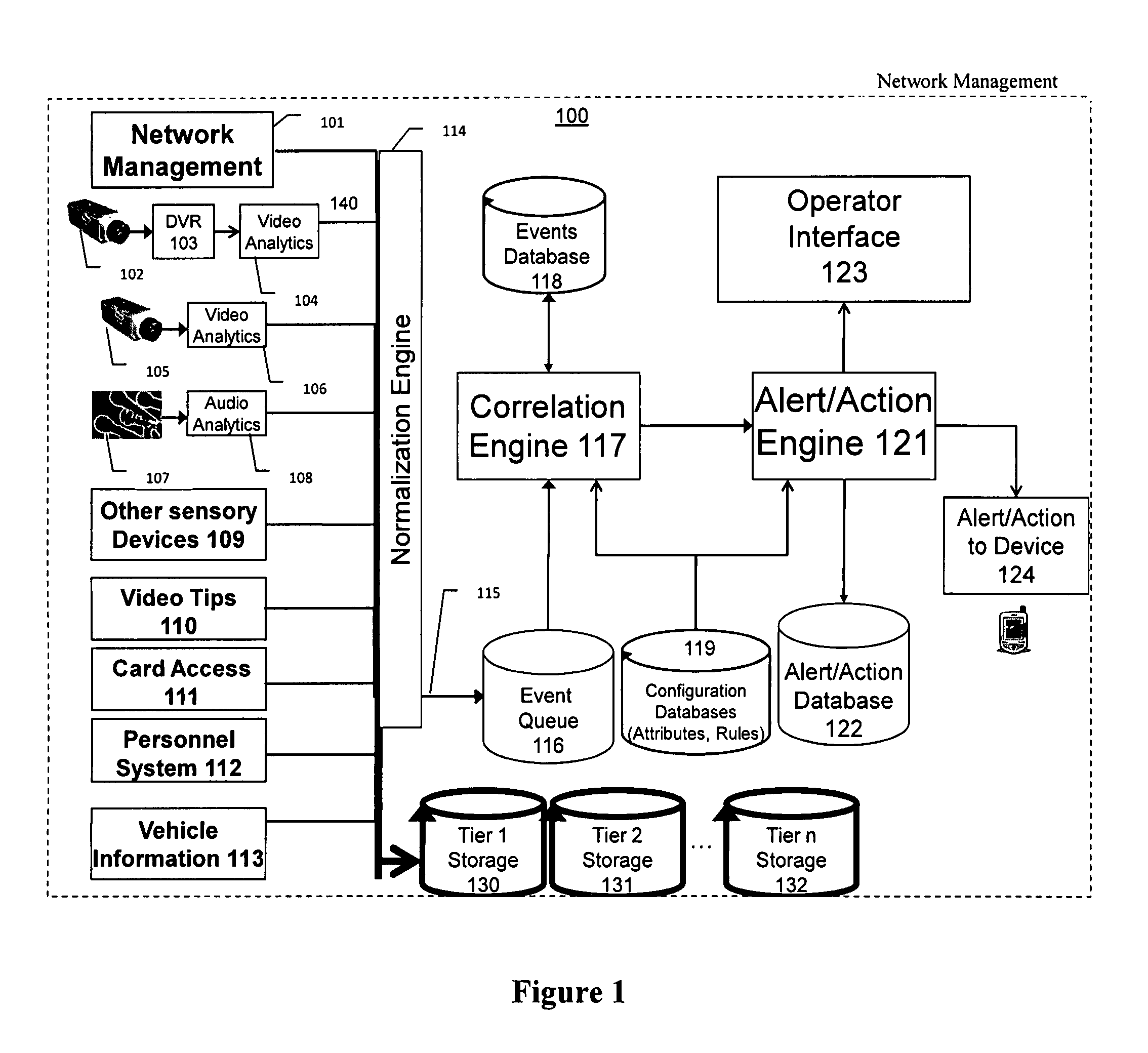
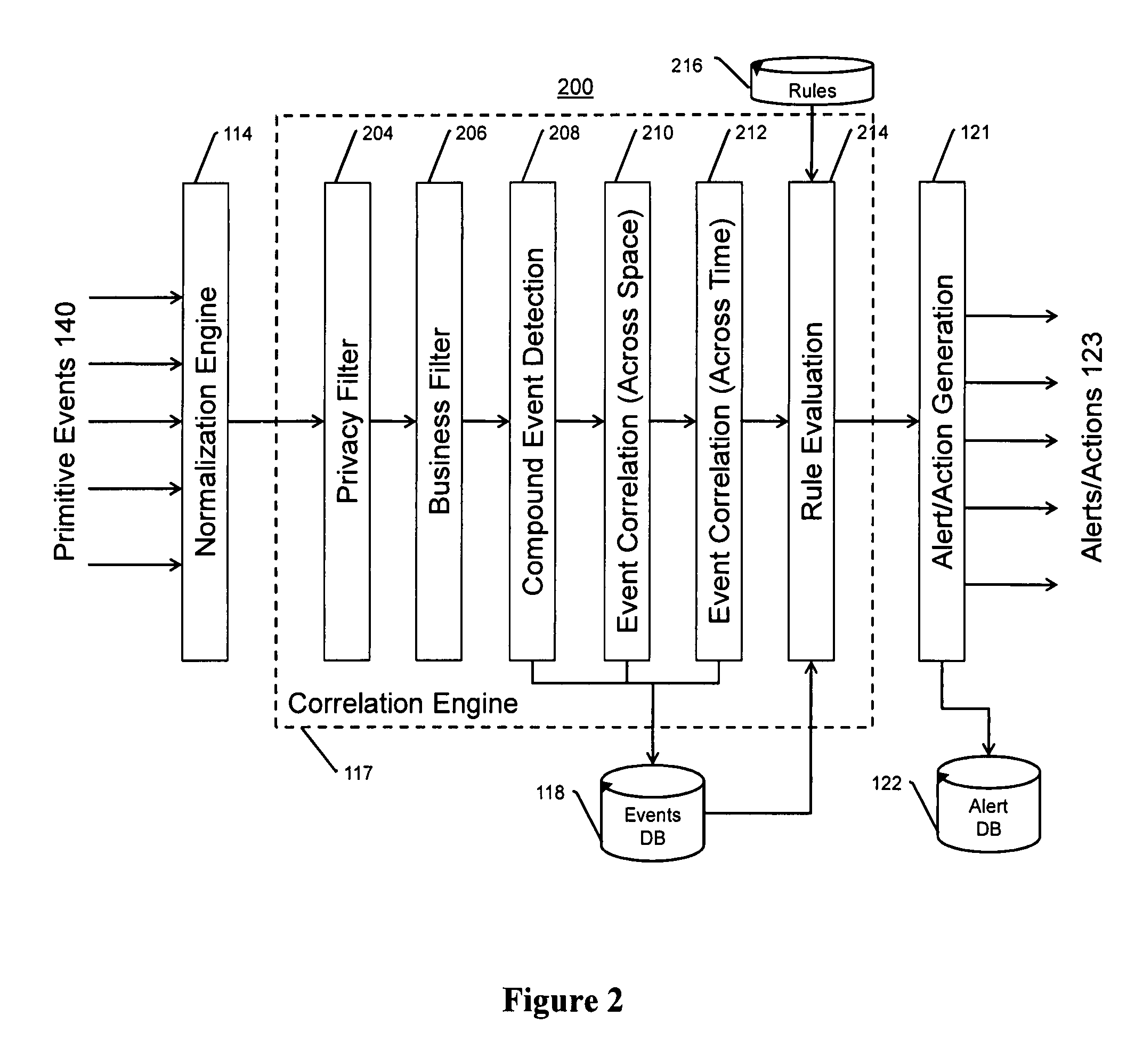
The present invention is a video surveillance, storage, and alerting system having surveillance cameras, video analytics devices, audio sensory devices, other sensory devices, and a plurality of data storage devices. A network management module monitors network status of all subsystems including cameras, servers, storage devices, etc. and shows actively monitored areas on a physical map. A vehicle information module retrieves information from a law enforcement database about vehicles detected in the video data based on the vehicle's license plate, including information about stolen vehicles, as well as warrant, wanted person, and mug shot information for registered drivers of the vehicles. Video tips are received and processed from anonymous and non-anonymous sources. A correlation engine correlates primitive events and compound events from each of the subsystems, weighted by attributes of the events, across both space and time, and an alerting engine generates alerts and performs actions based on the correlation. A hierarchical storage manager manages storage of the vast amounts of data, including video data, based on importance of the data calculated from attributes of the data. A privacy filter ensures no private data is detected, correlated, or stored.
Owner:SECURENET SOLUTIONS GRP
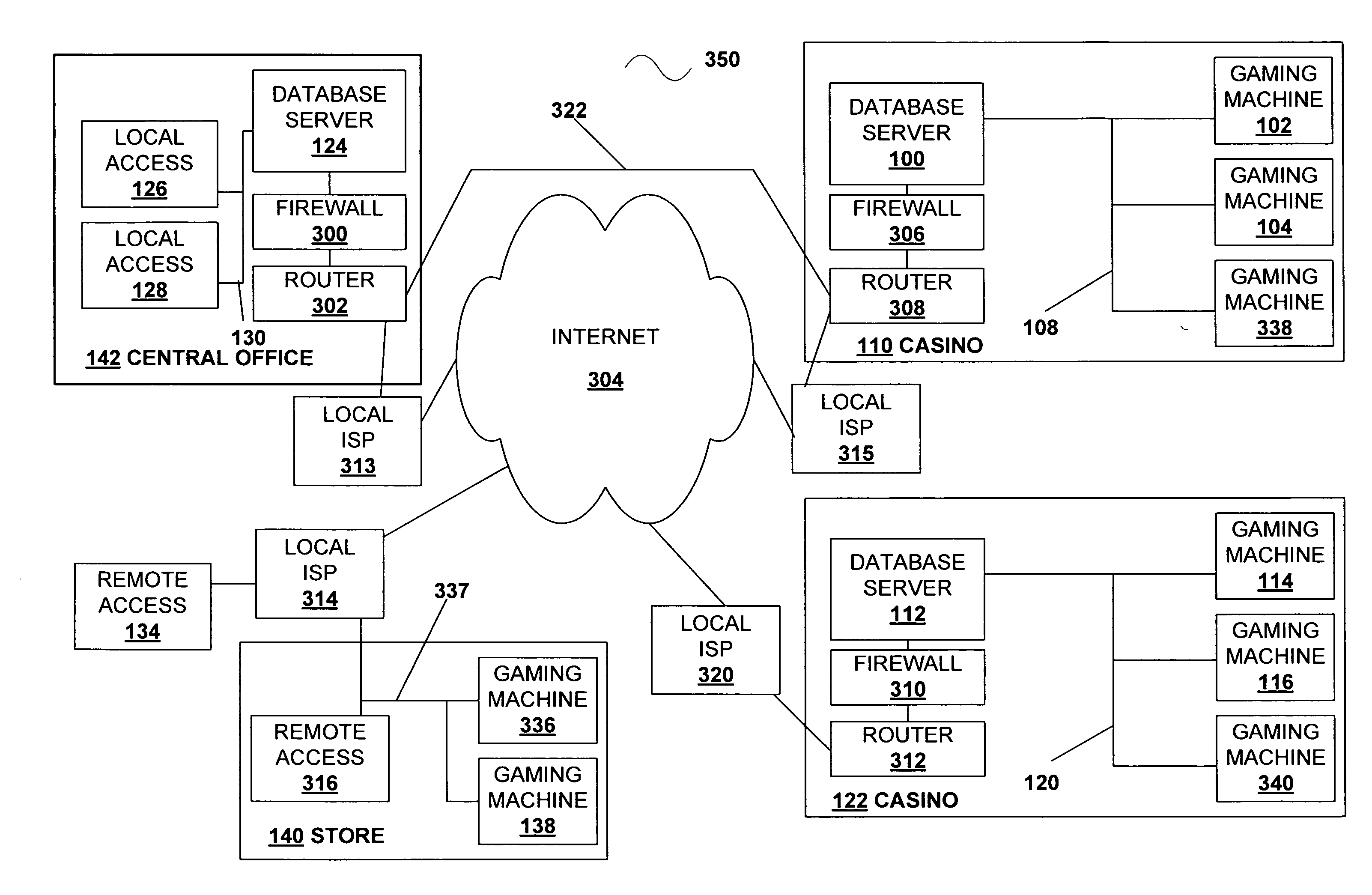
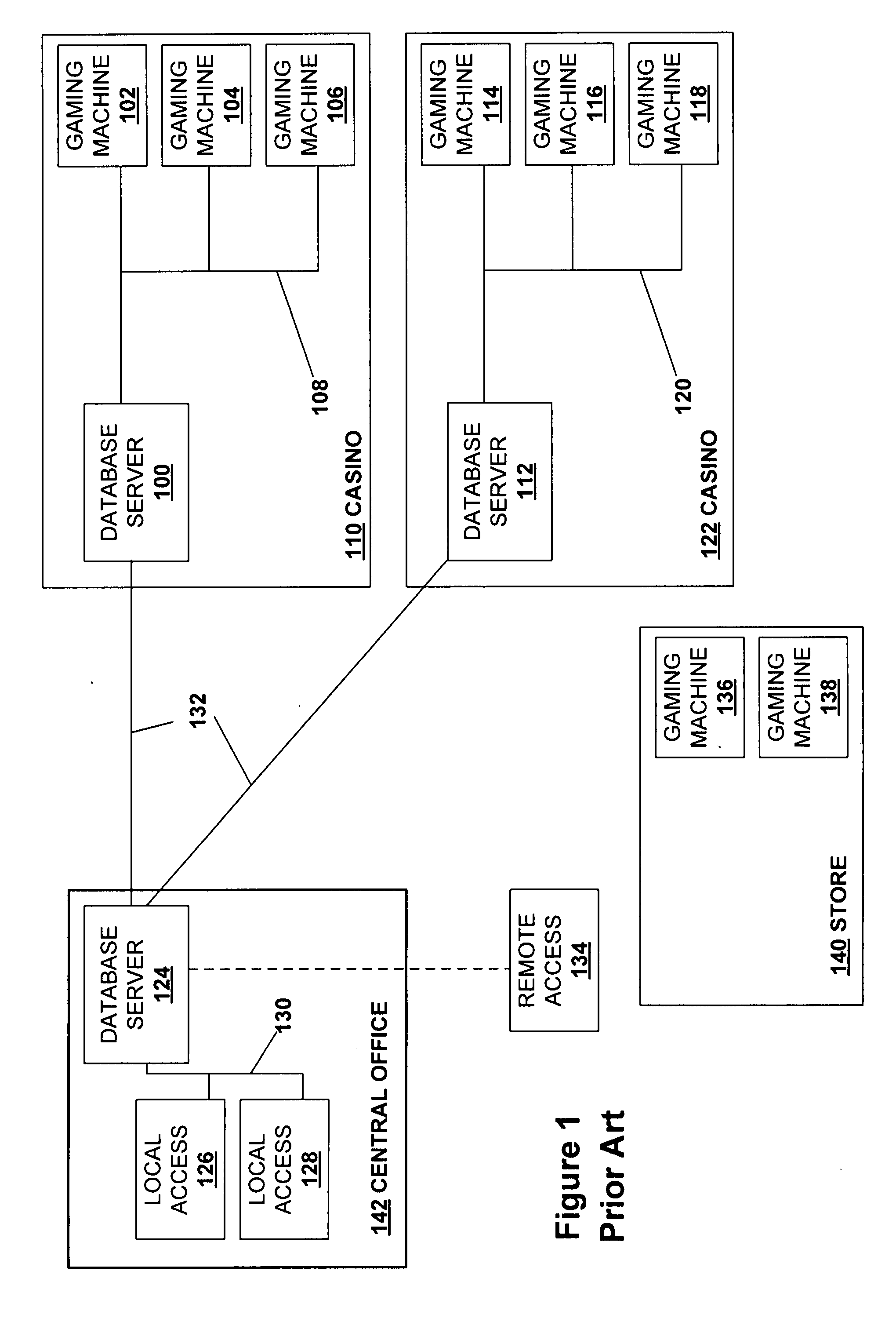
Vehicle data collection and processing system
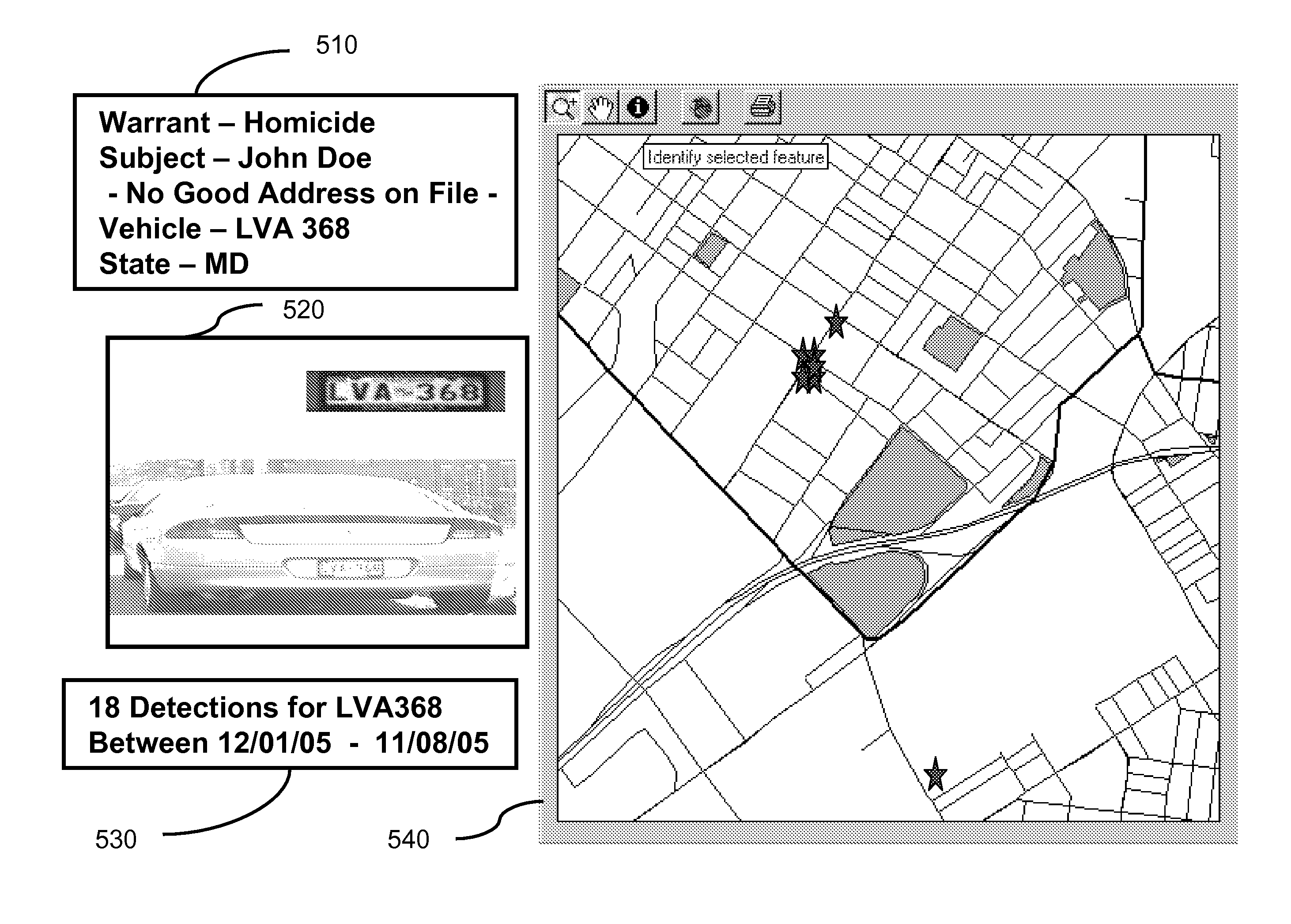
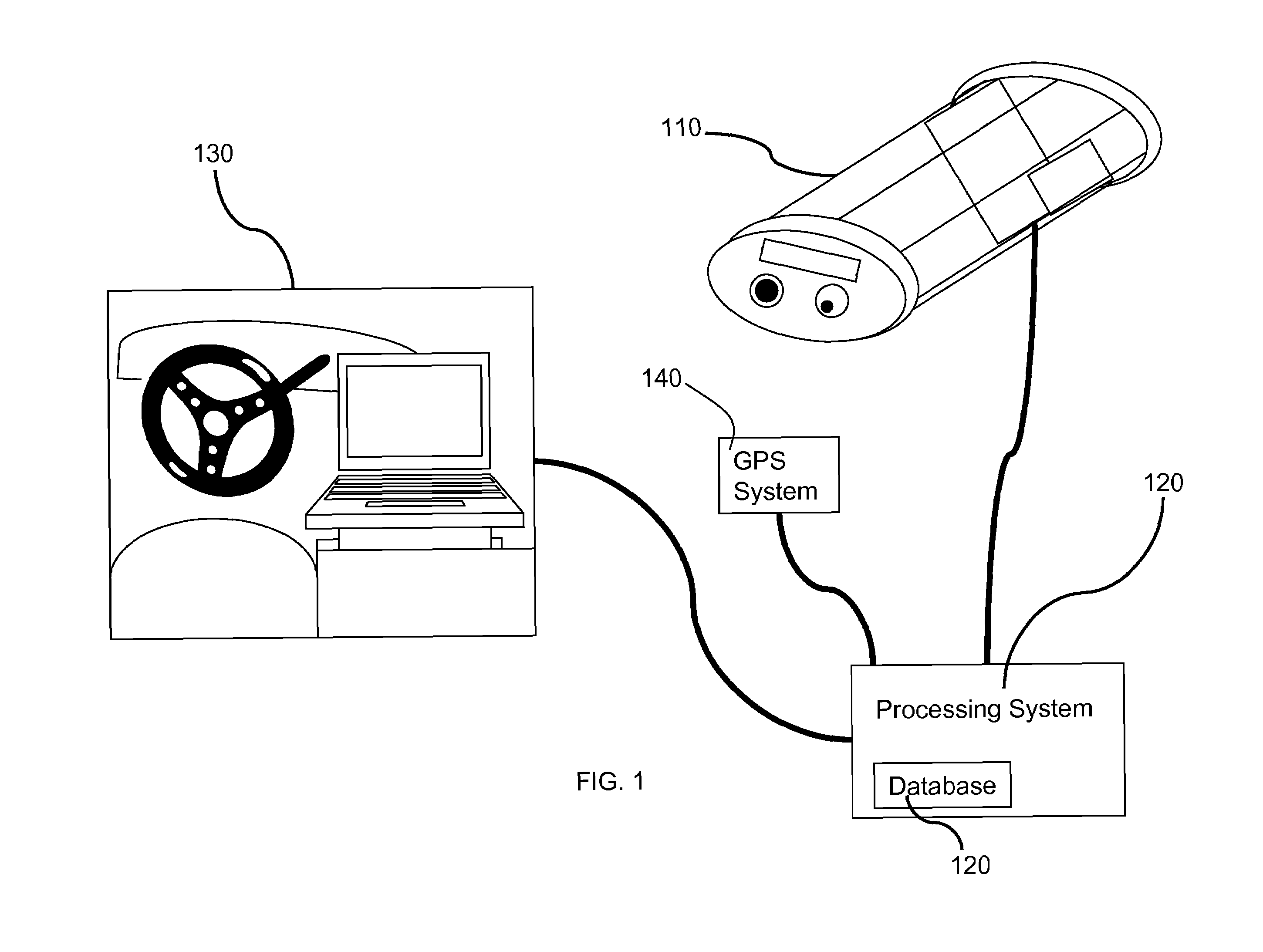
A system for collecting, storing, linking and processing license plate data to provide compilations of information and displays of such compiled information. The system has a license plate reading system that may record time and location data in addition to license plate data, license plate image data, and image data of a vehicle. The data is collected over an extended period of time and stored for later searching. The data may be correlated, indexed and / or categorized in storage. The collected data may be compared to various existing or other databases and correlated and / or indexed to such databases. That collected data may be processed, searched, and / or analyzed for a variety of purposes.
Owner:VIGILANT SOLUTIONS LLC
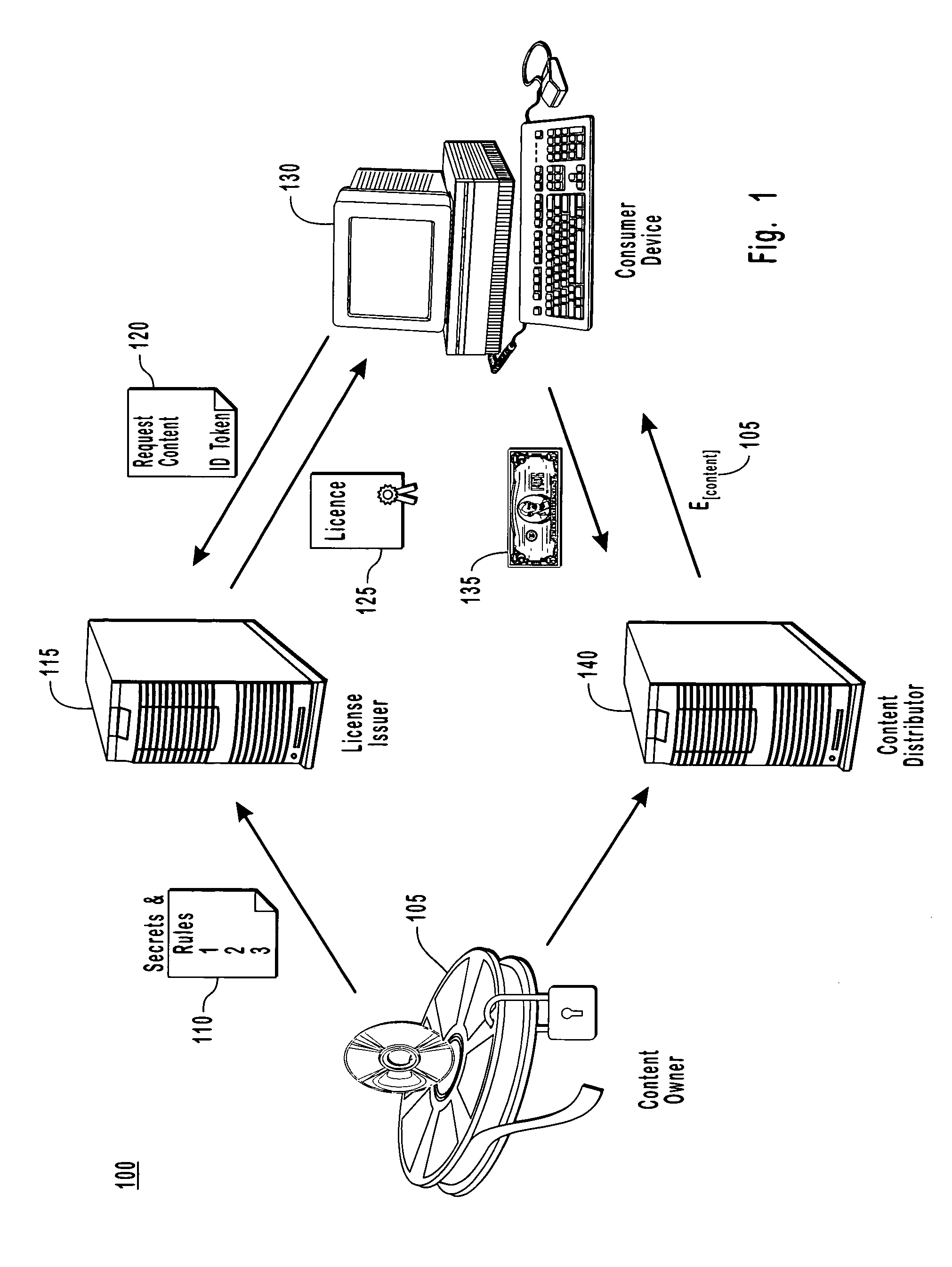
System and method for accessing protected content in a rights-management architecture
InactiveUS6996720B1Digital data processing detailsUnauthorized memory use protectionPersonalizationDigital rights management system
A digital rights management system for the distribution, protection and use of electronic content. The system includes a client architecture which receives content, where the content is preferably protected by encryption and may include a license and individualization features. Content is protected at several levels, including: no protection; source-sealed; individually-sealed (or “inscribed”); source-signed; and fully-individualized (or “owner exclusive”). The client also includes and / or receives components which permit the access and protection of the encrypted content, as well as components that allow content to be provided to the client in a form that is individualized for the client. In some cases, access to the content will be governed by a rights construct defined in the license bound to the content. The client components include an object which accesses encrypted content, an object that parses the license and enforces the rights in the license, an object which obtains protection software and data that is individualized for the client and / or the persona operating the client, and a script of instructions that provides individualization information to a distributor of content so that the content may be individualized for the client and / or its operating persona. Content is generally protected by encrypting it with a key and then sealing the key into the content in a way that binds it to the meta-data associated with the content. In some instances, the key may also be encrypted in such a way as to be accessible only by the use of individualized protection software installed on the client, thereby binding use of the content to a particular client or set of clients.
Owner:MICROSOFT TECH LICENSING LLC
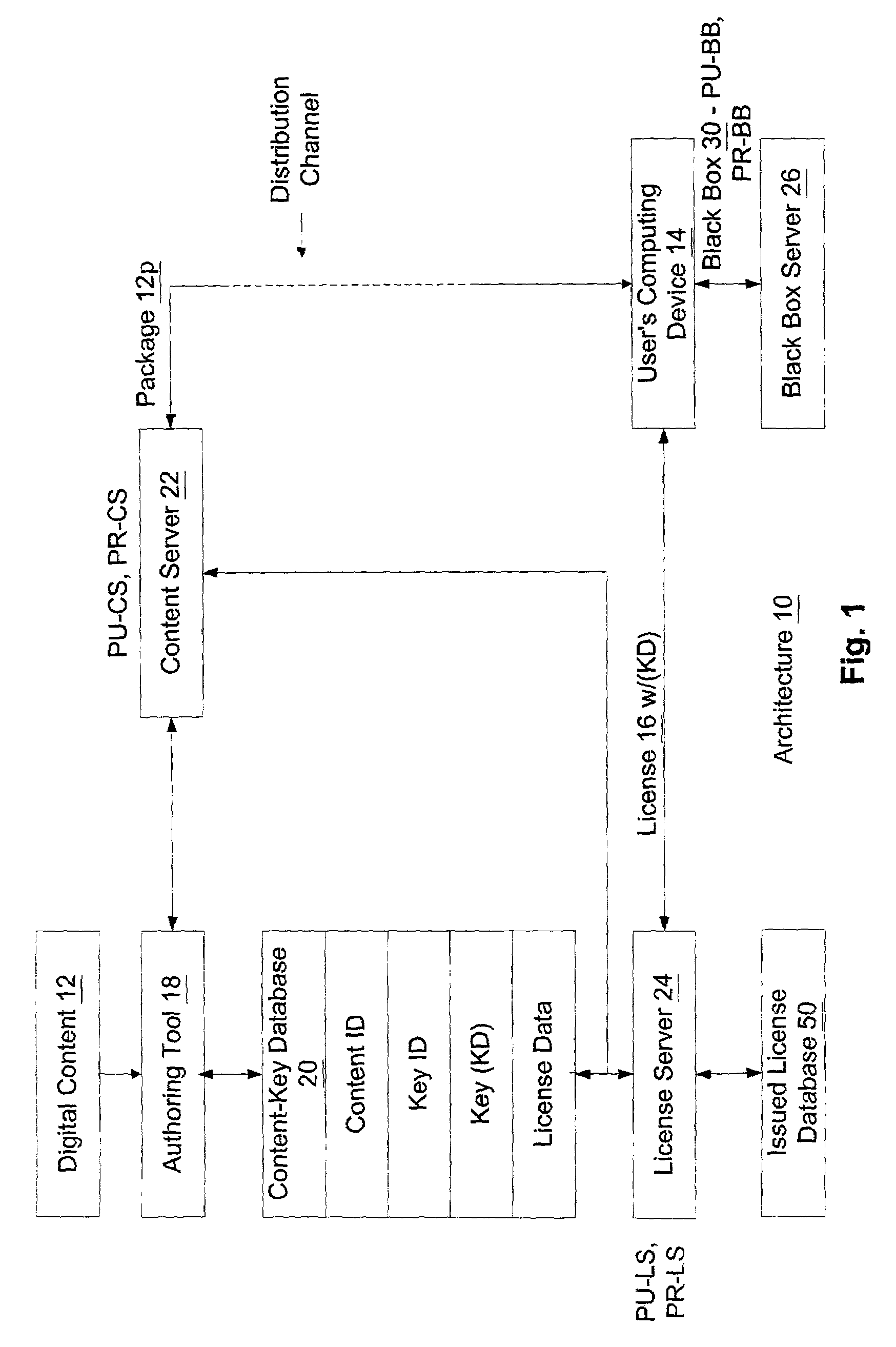
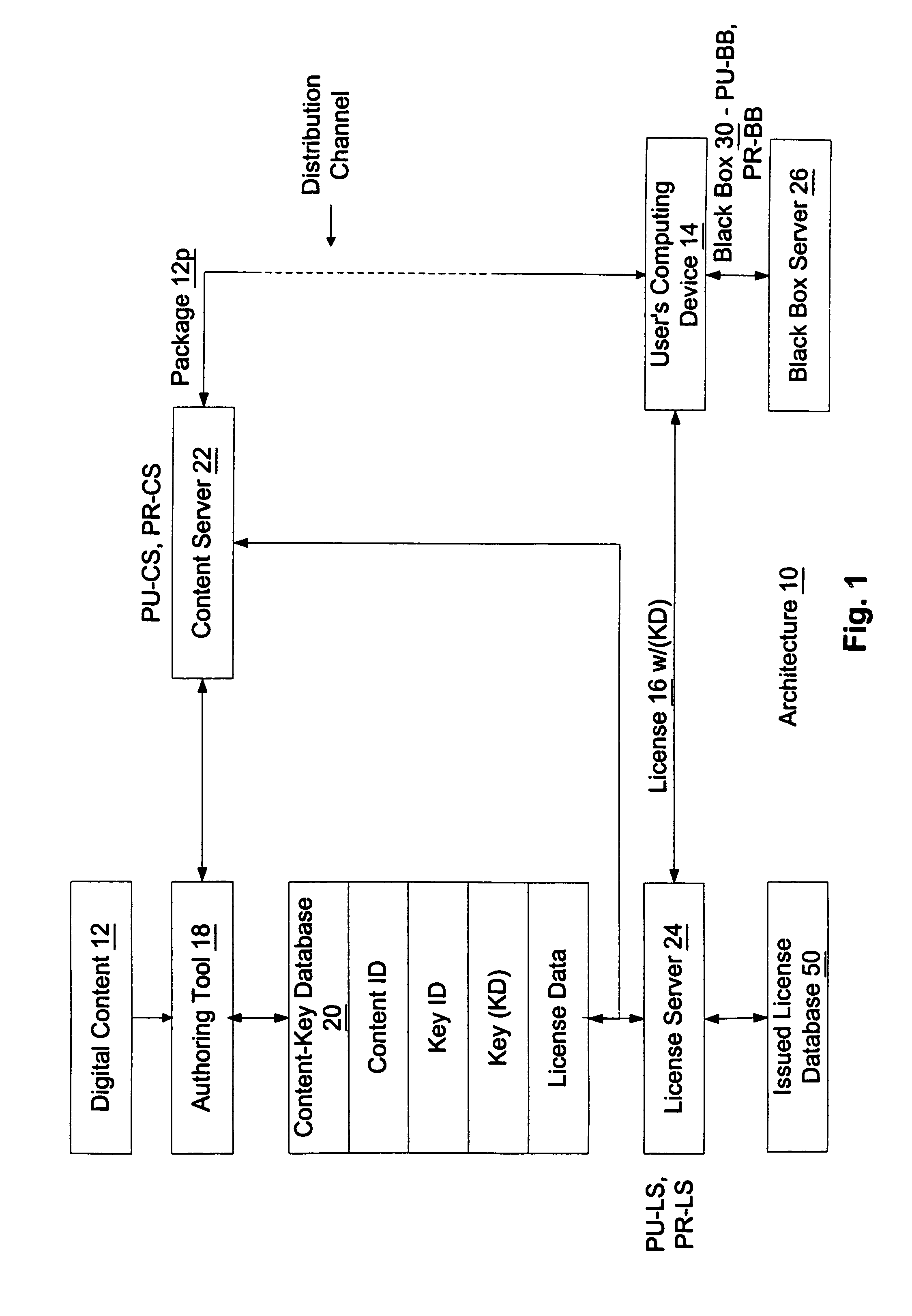
Binding a digital license to a portable device or the like in a digital rights management (DRM) system and checking out/checking in the digital license to/from the portable device or the like
InactiveUS7073063B2Key distribution for secure communicationDigital data processing detailsDigital contentDigital rights management
To render digital content encrypted according to a content key (KD) on a first device having a public key (PU1) and a corresponding private key (PR1), a digital license corresponding to the content is obtained, where the digital license includes the content key (KD) therein in an encrypted form. The encrypted content key (KD) from the digital license is decrypted to produce the content key (KD), and the public key (PU1) of the first device is obtained therefrom. The content key (KD) is then encrypted according to the public key (PU1) of the first device (PU1 (KD)), and a sub-license corresponding to and based on the obtained license is composed, where the sub-license includes (PU1 (KD)). The composed sub-license is then transferred to the first device.
Owner:MICROSOFT TECH LICENSING LLC
Method for determining internet users geographic region
InactiveUS6859791B1Digital data processing detailsRecord information storageCredit cardGeographic regions
A method at a clearing house to verify the geographic region of an end user device for receiving encrypted digital content. In one embodiment the geographic region is a country. The method comprising three sub-methods. In the first sub-method the address is verified by determining the credit card clearing address of the end user using an address verification system. In the second sub-method the address is verified by determining the IP address of the end user device requesting delivery of the encrypted digital content. And in the third sub-method the address is verified by checking that the IP address of the end user device requesting delivery of the encrypted digital content is the identical IP address of the end user device requesting a license to use the encrypted digital content. Depending on predetermined system settings, one or more of the above combination of the three sub-methods is then checked, before authorizing the decrypting of the encrypted digital content includes decrypting the encrypted digital content if the address verification system returns an address in a predetermined geographic region and the IP address of the end user device is in a predetermined geographic region.
Owner:LEVEL 3 COMM LLC
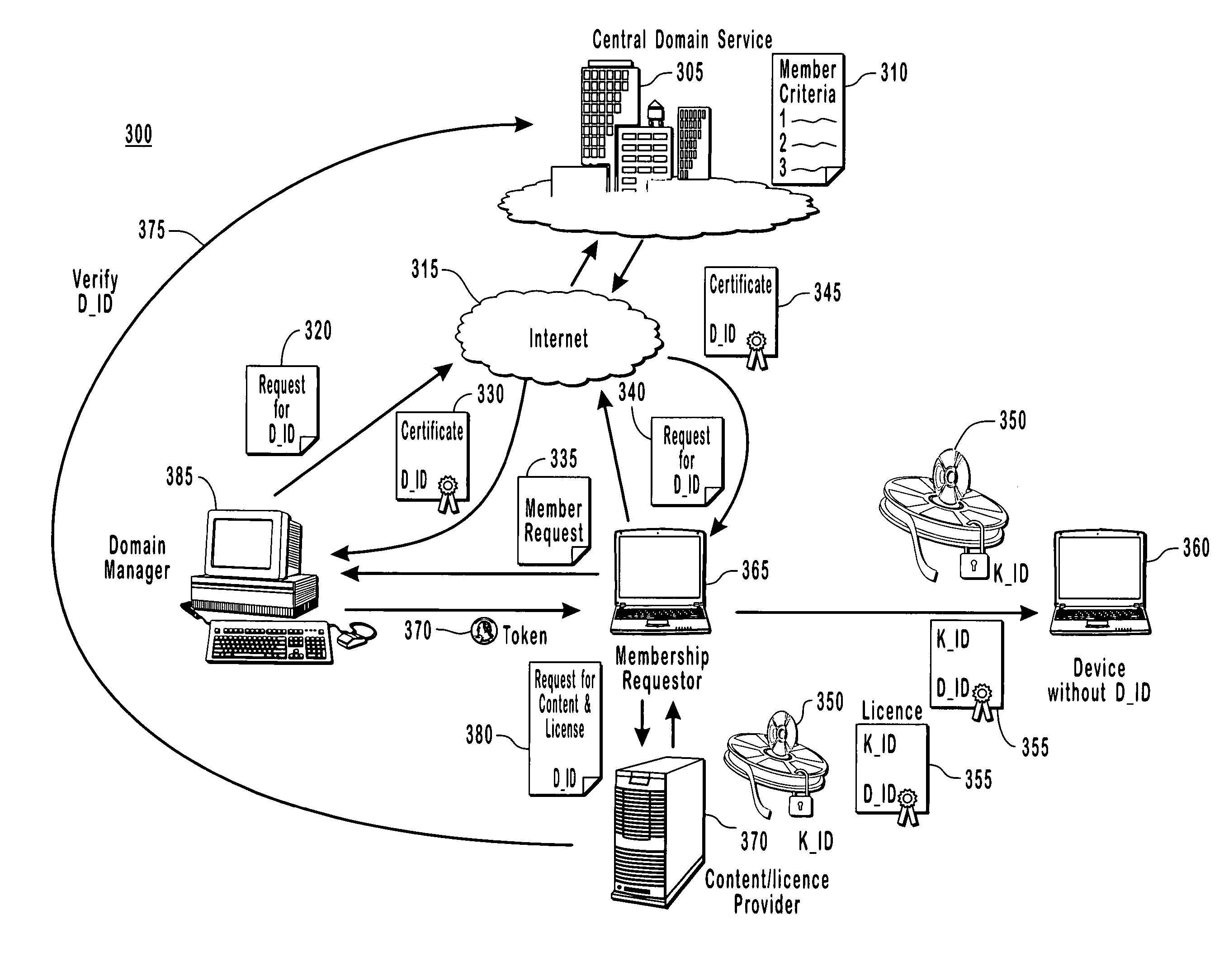
Binding content to a domain
The present invention provides for a digital rights management system with a centralized domain service capable of creating and managing membership criteria for joining a domain in accordance with business rules defined by ac content owner. A domain identification is created that allows a content provider to uniquely bind content licenses to a domain. The content licenses include usage rights that define how content associated with the licenses may be consumed by one or more members of the domain. The centralized domain service can enforce digital rights by validating membership criteria including at least one of a domain proximity check for validating that a requestor is in close proximity to the domain, a total number of requestors, or the frequency that the requests have been made by various requesters to join the domain and unjoin from the domain.
Owner:ZHIGU HLDG
System and method for activating a rendering device in a multi-level rights-management architecture
InactiveUS7017189B1Digital data processing detailsUser identity/authority verificationPersonalizationDigital rights management system
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and method for unilateral topology discovery in network management
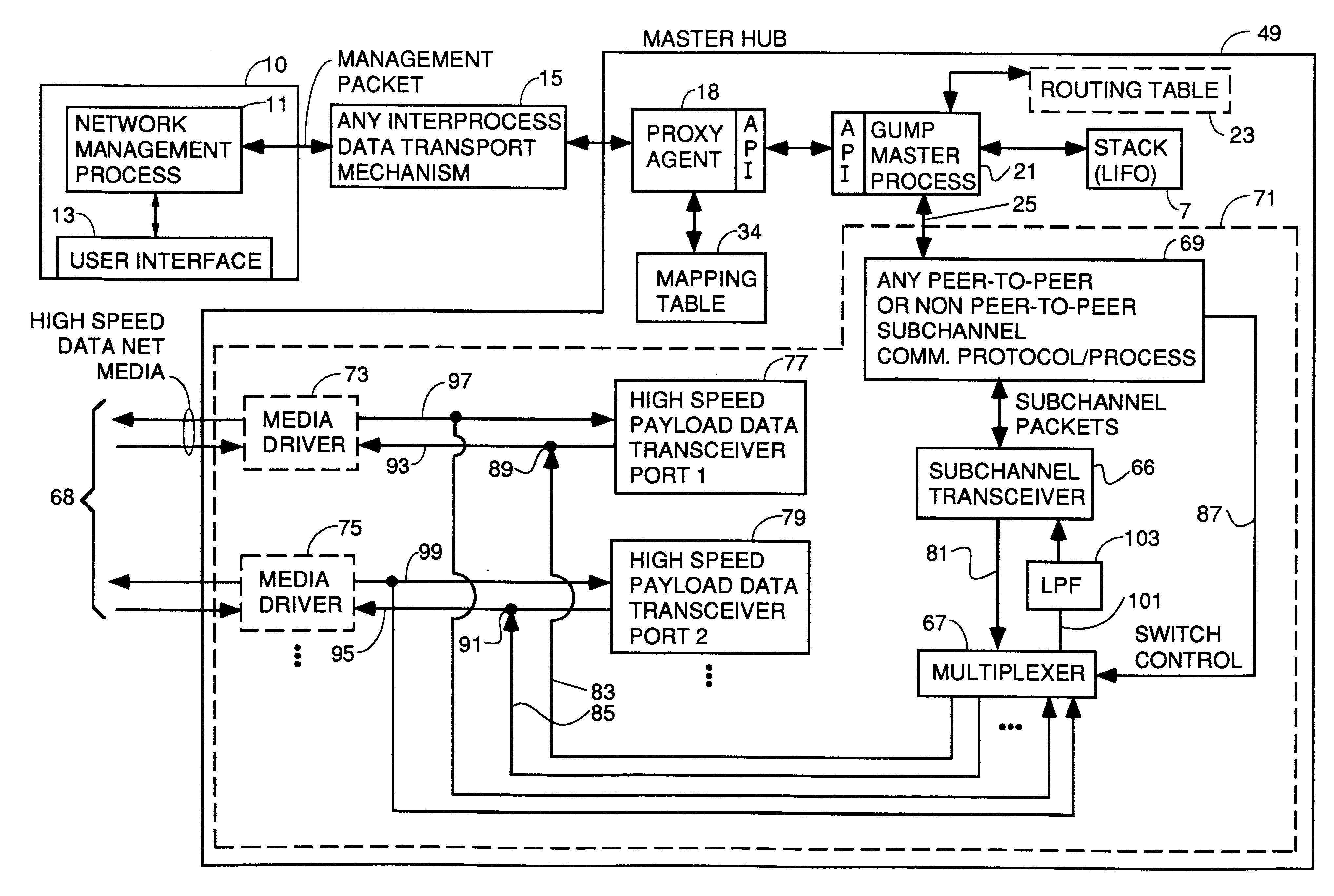
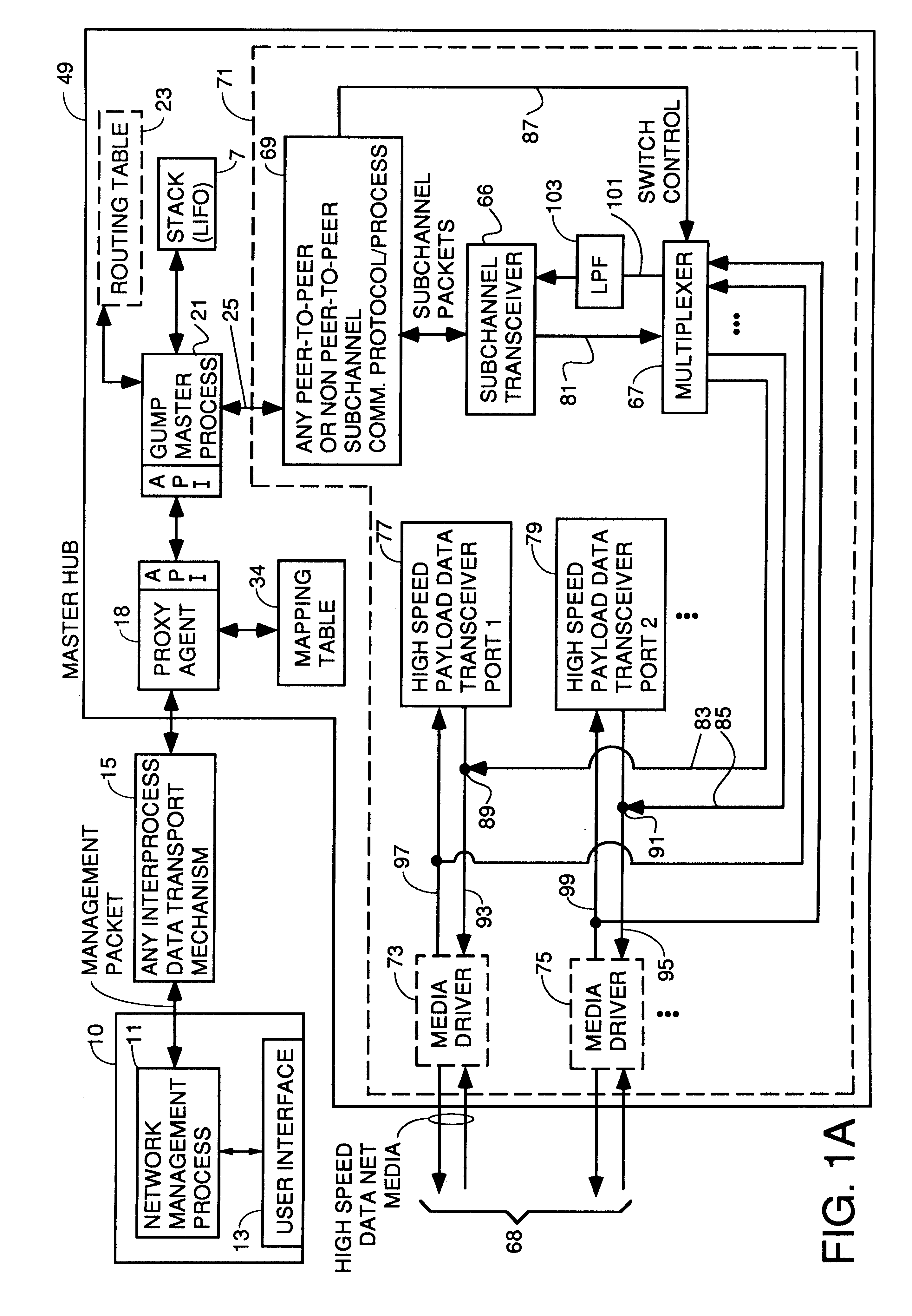
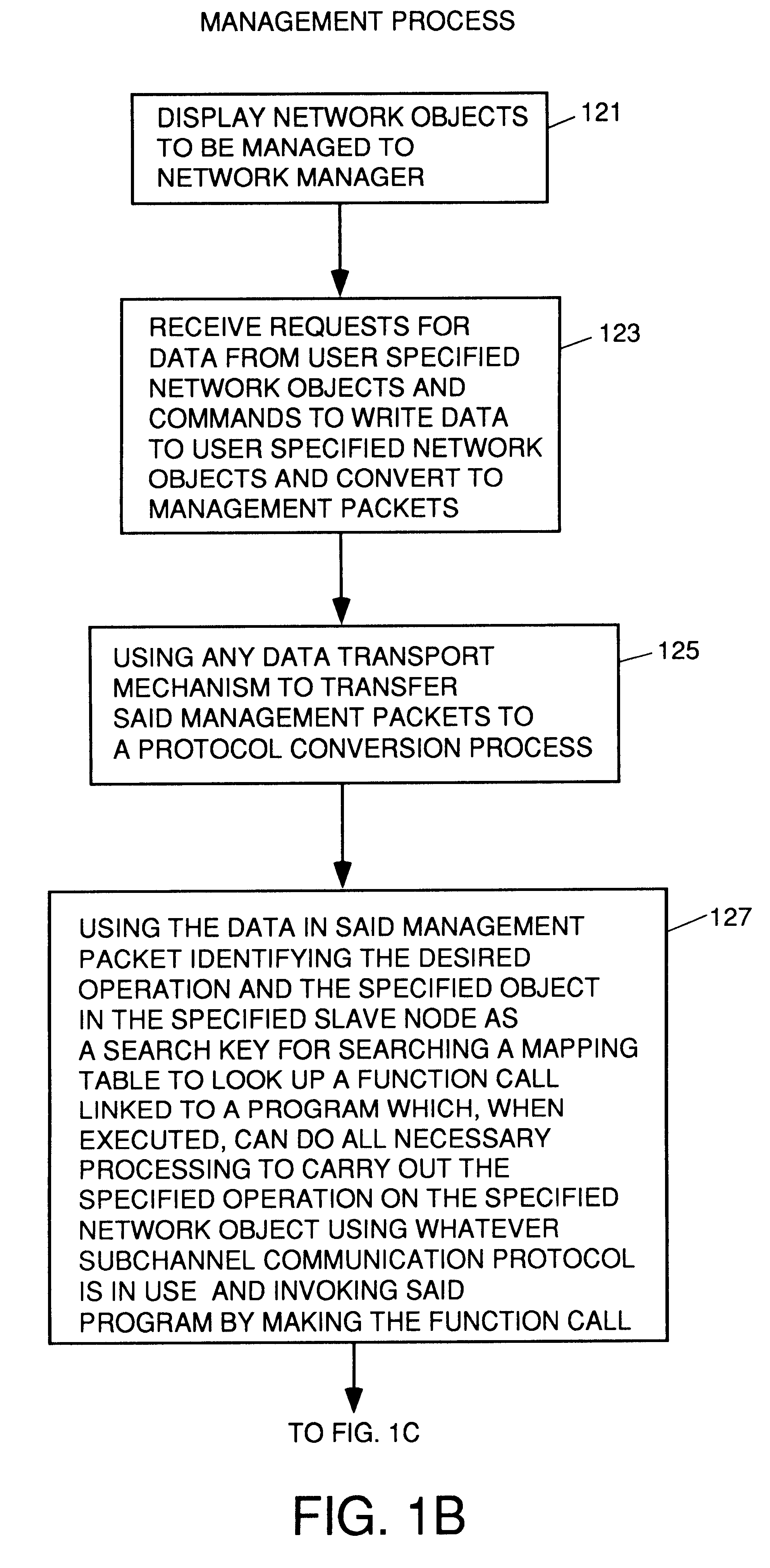
A system for reducing the cost of network managment by using a proxy agent and subchannel communications so fewer SNMP licenses and fewer protocol stacks are needed. Subchannel communication is achieved in a plurality of different embodiments. Embodiments having single subchannel transceivers, multiple transceivers, single multiplexer and multiple multiplexers are disclosed. An NMS process using routing table CRC to automatically detect when the NMS topology information is incorrect and automated topology discovery is disclosed. A process for automated discovery of redundant cables during automated topology discovery is disclosed.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Access system for a cellular network
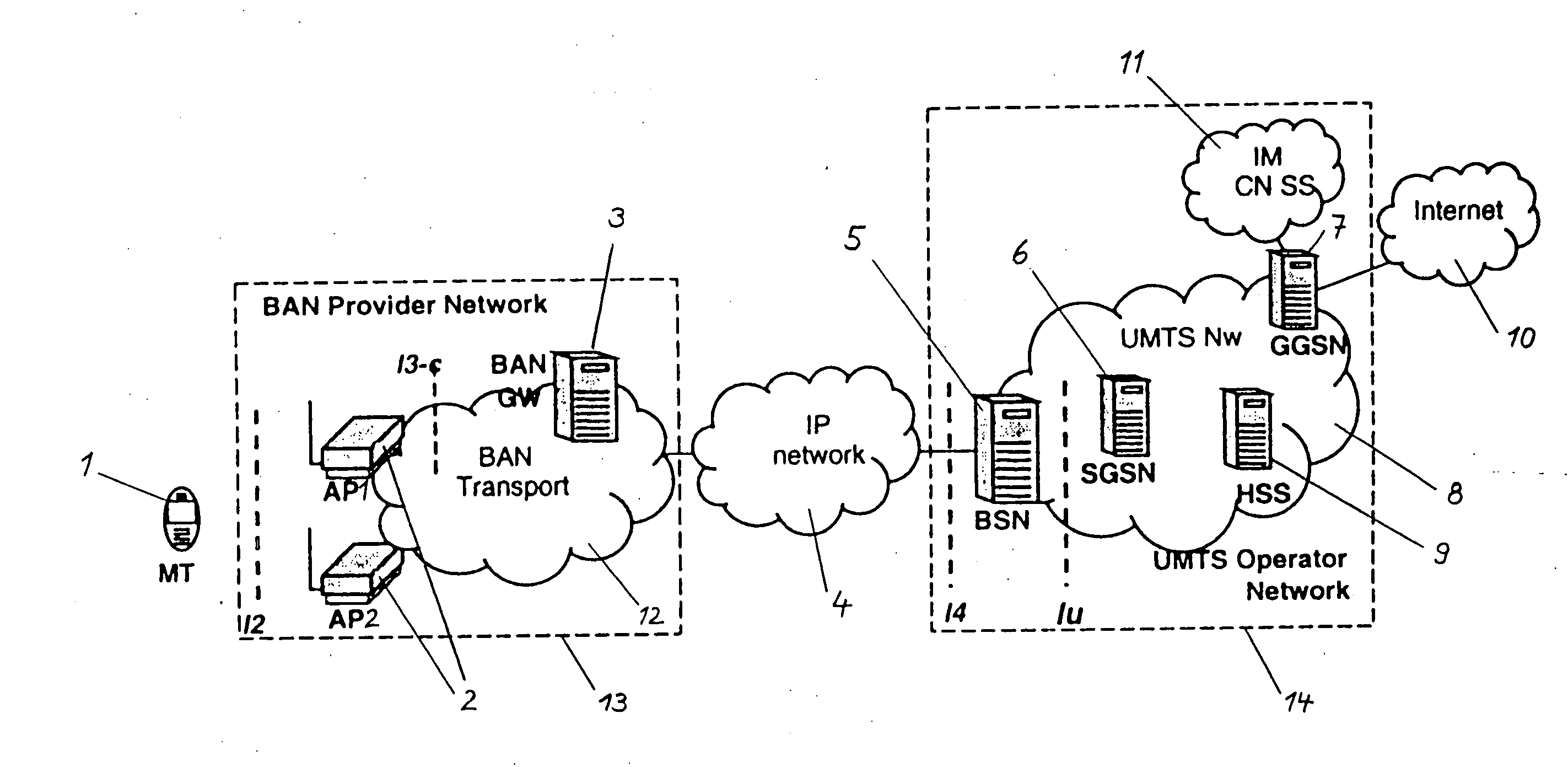
ActiveUS20050101245A1Improve facilitiesReasonable priceAssess restrictionTelephonic communicationAccess networkTerminal equipment
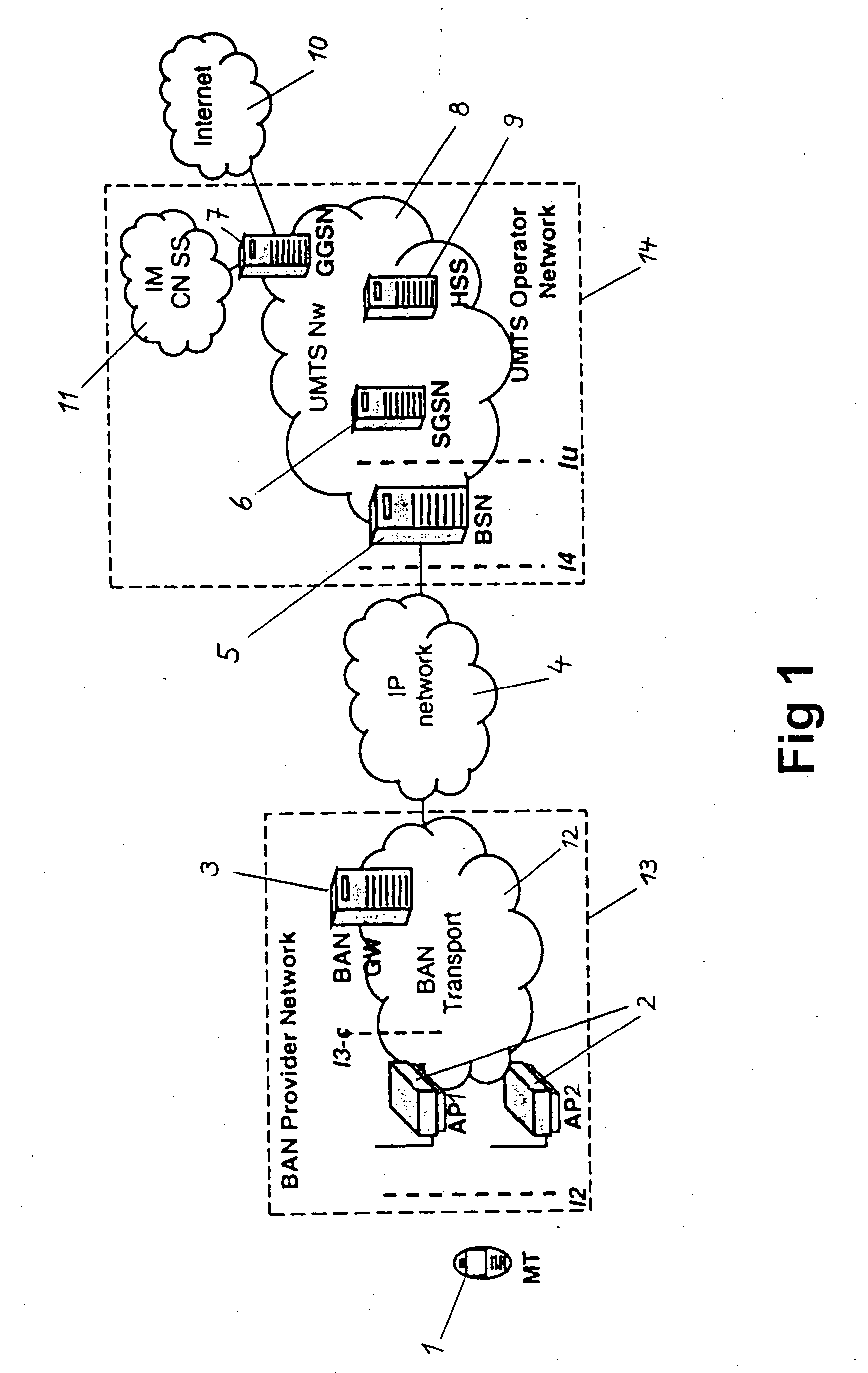
The present invention relates to a method and system for providing access to a cellular network (8), wherein a terminal device (1) is connected to an access device (2) according to access specifications of a broadband access network (12) which is not specifically designed to be used as a part of cellular network (8). The terminal device (1) indicates to the access device (2) that it wishes to be connected to the cellular network (8), and a session or call and a radio bearer is setup between the terminal device (1) and the cellular network (8). To achieve this, a service node (5) provided in the cellular network (8) requests a suitable access bearer from the access network (12) and the access device (2) sets up a corresponding access channel towards the terminal device (1). The terminal device (1) then associates the access channel to the correct radio bearer by using a corresponding identification. Thereby, service functions of the cellular network, e.g. UMTS services, can be distributed via any access network and existing broadband or high-speed access networks can be implemented in new cellular network structures. A huge capacity enhancement can thus be offered to the network operators of the cellular network without any standardization effort or license fee and at very small investment and maintenance costs.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com