Patents
Literature
3496 results about "Configuration system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
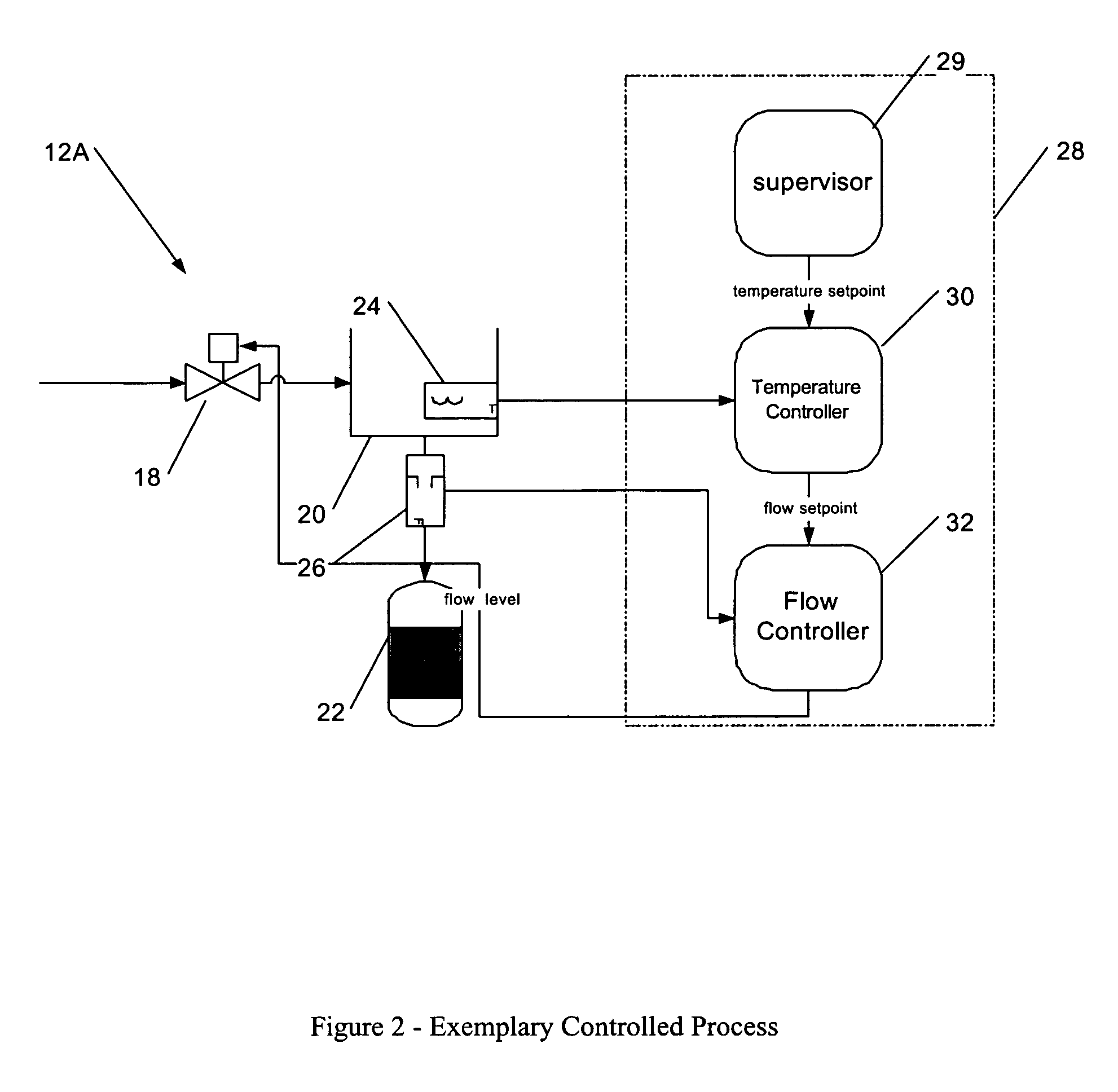
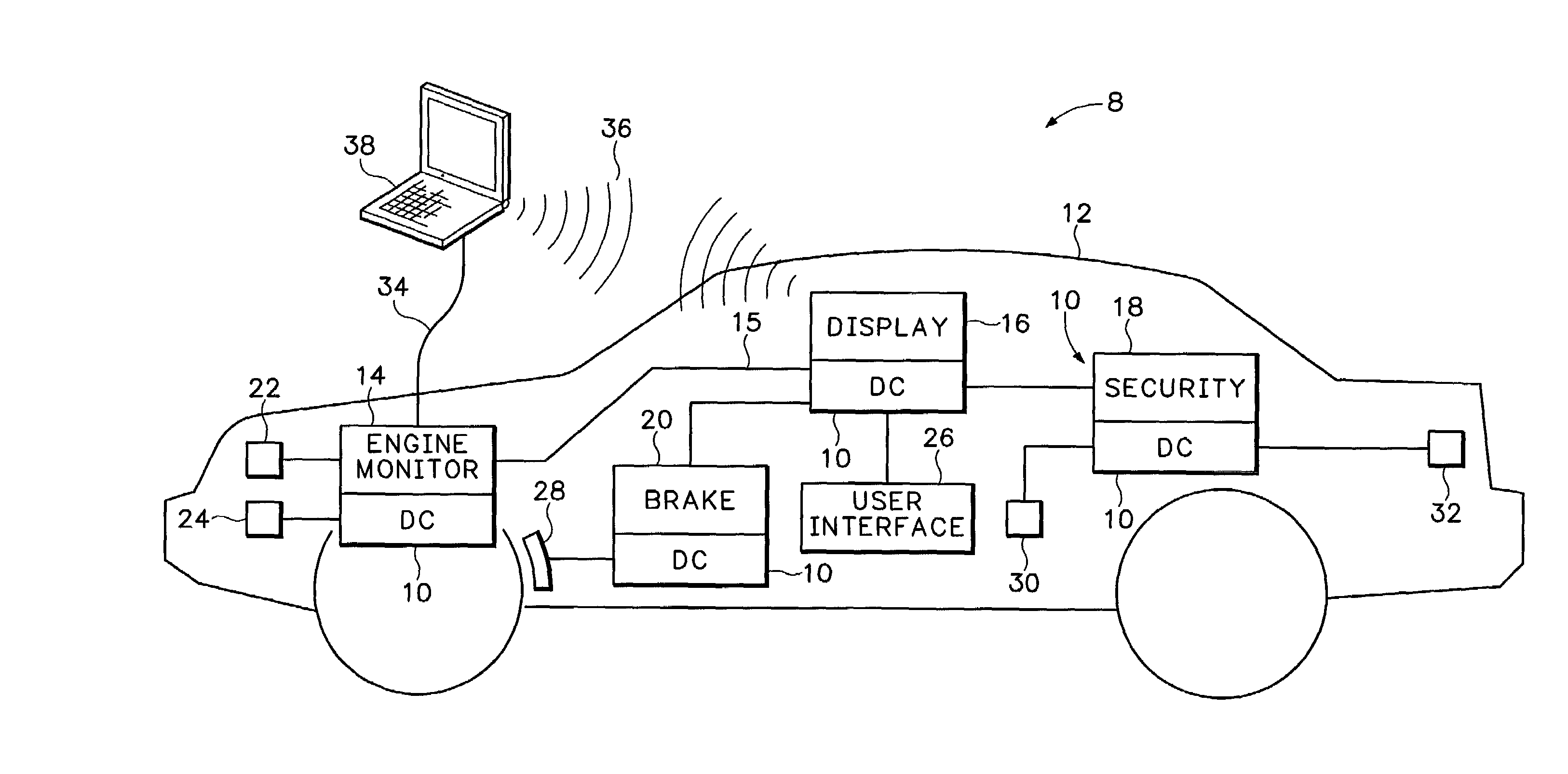
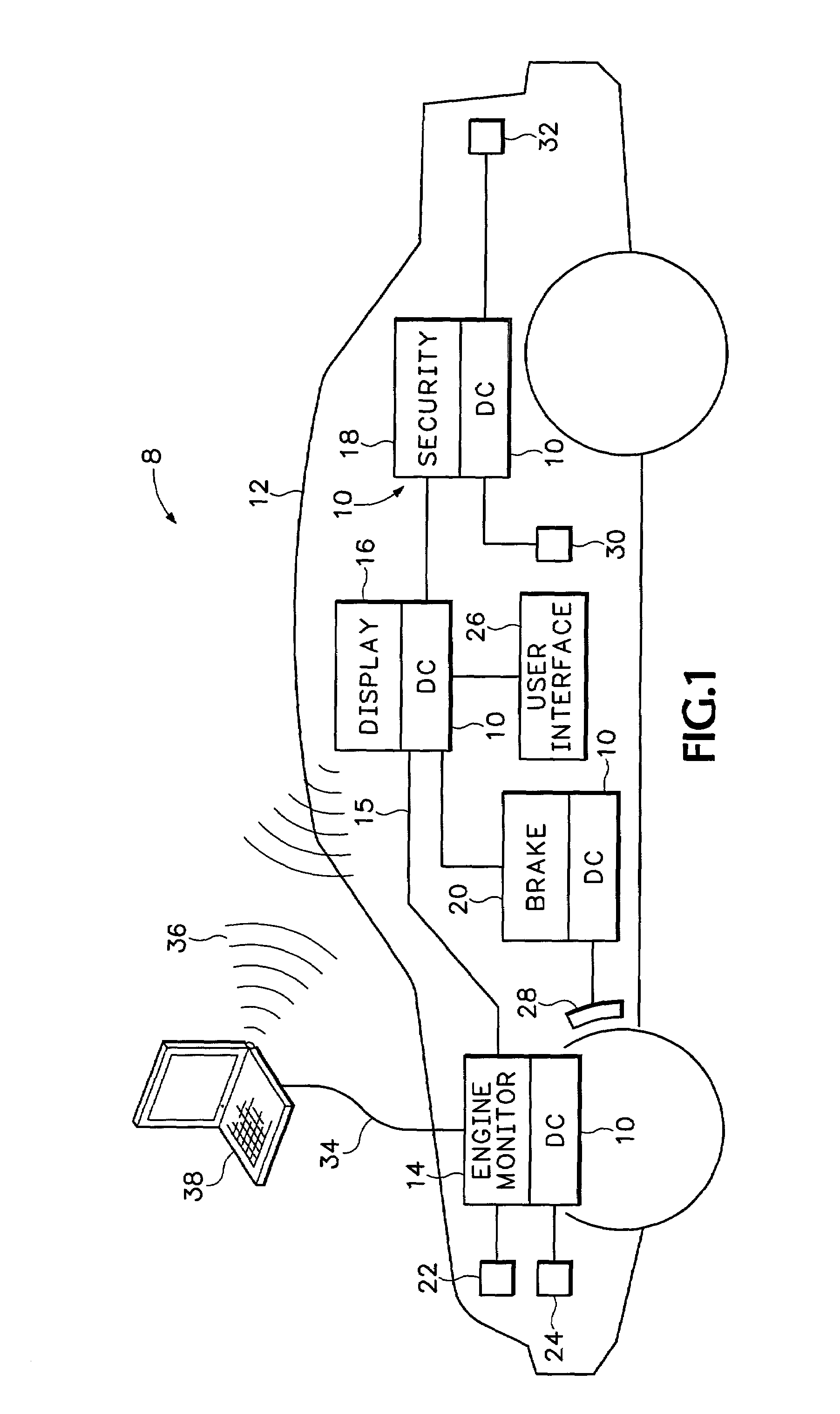
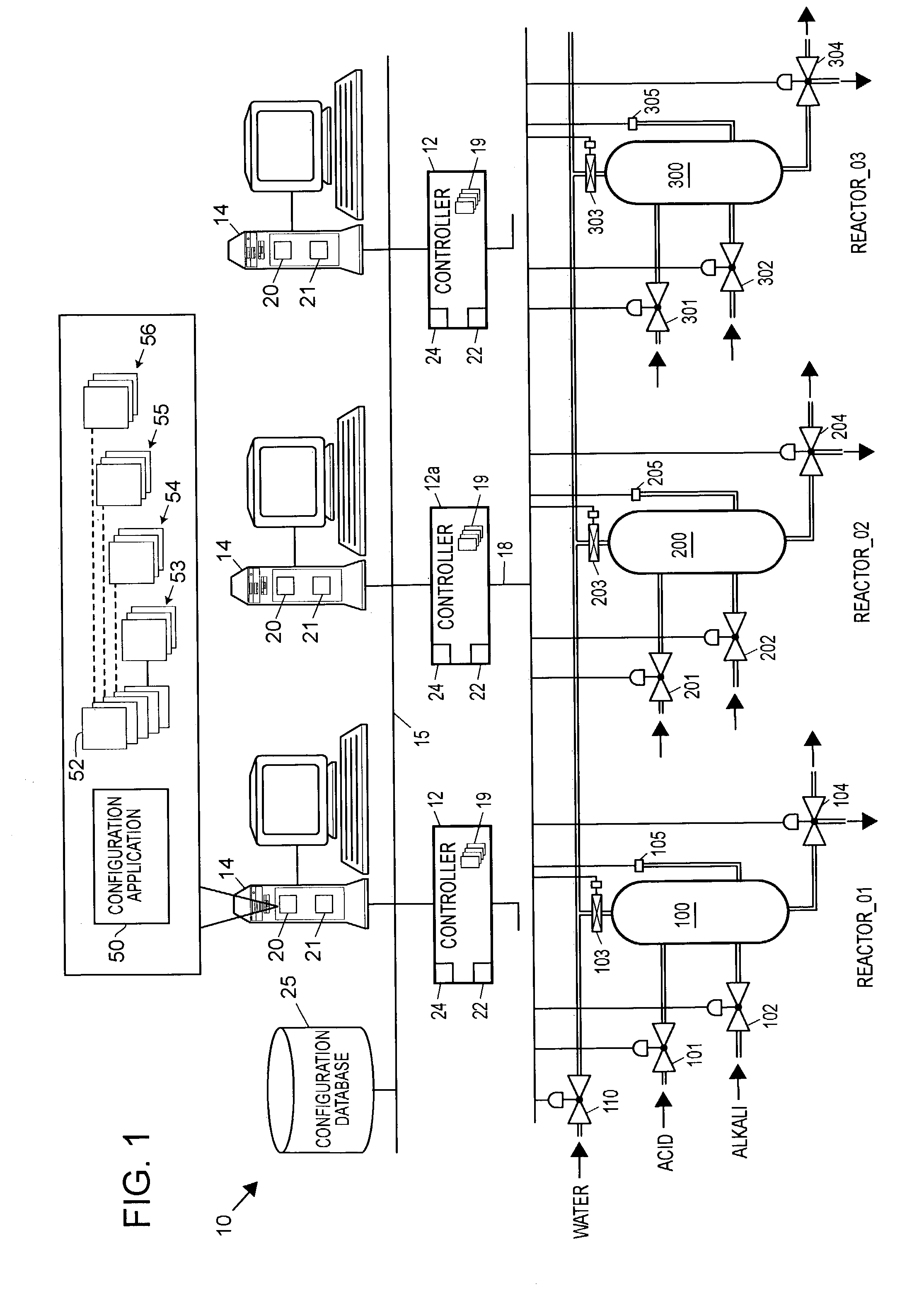
System configuration. A system configuration in systems engineering defines the computers, processes, and devices that compose the system and its boundary. More general the system configuration is the specific definition of the elements that define and/or prescribe what a system is composed of.
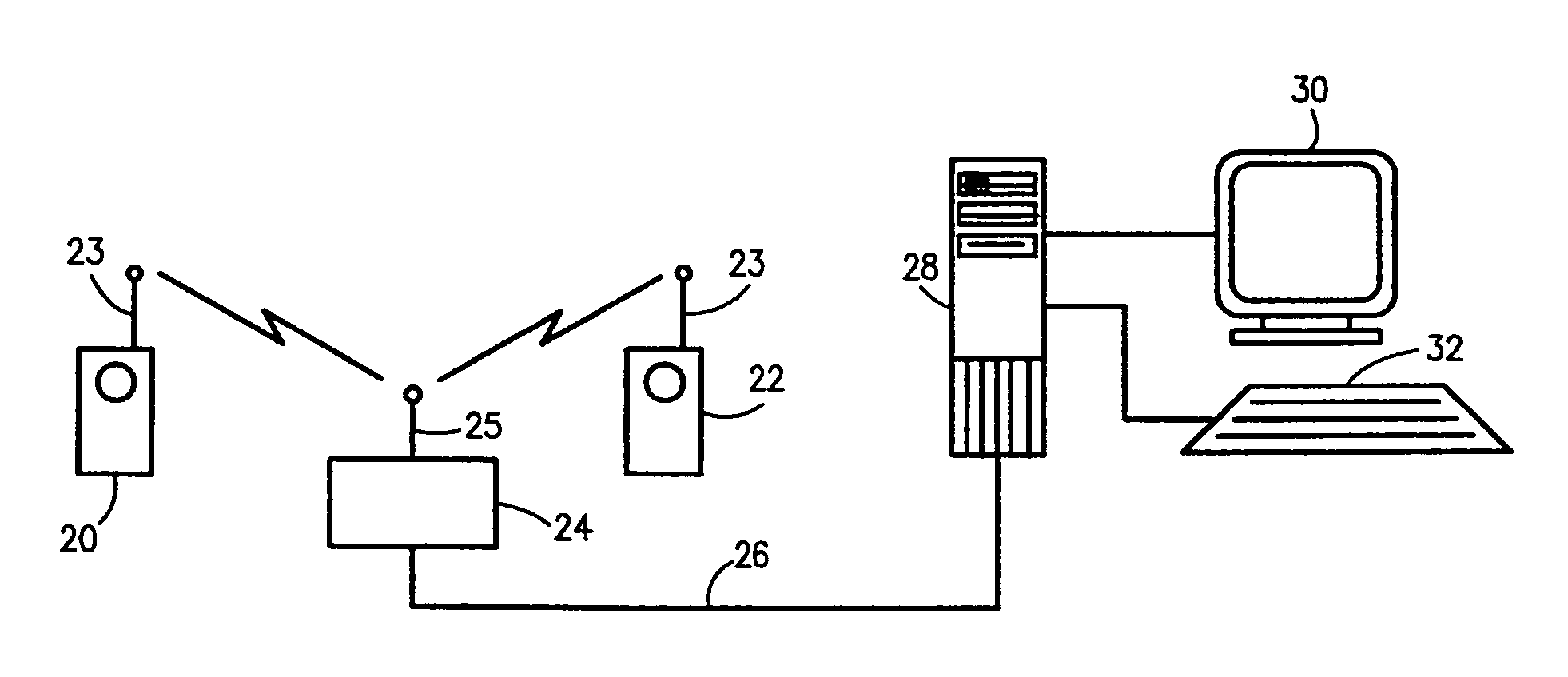
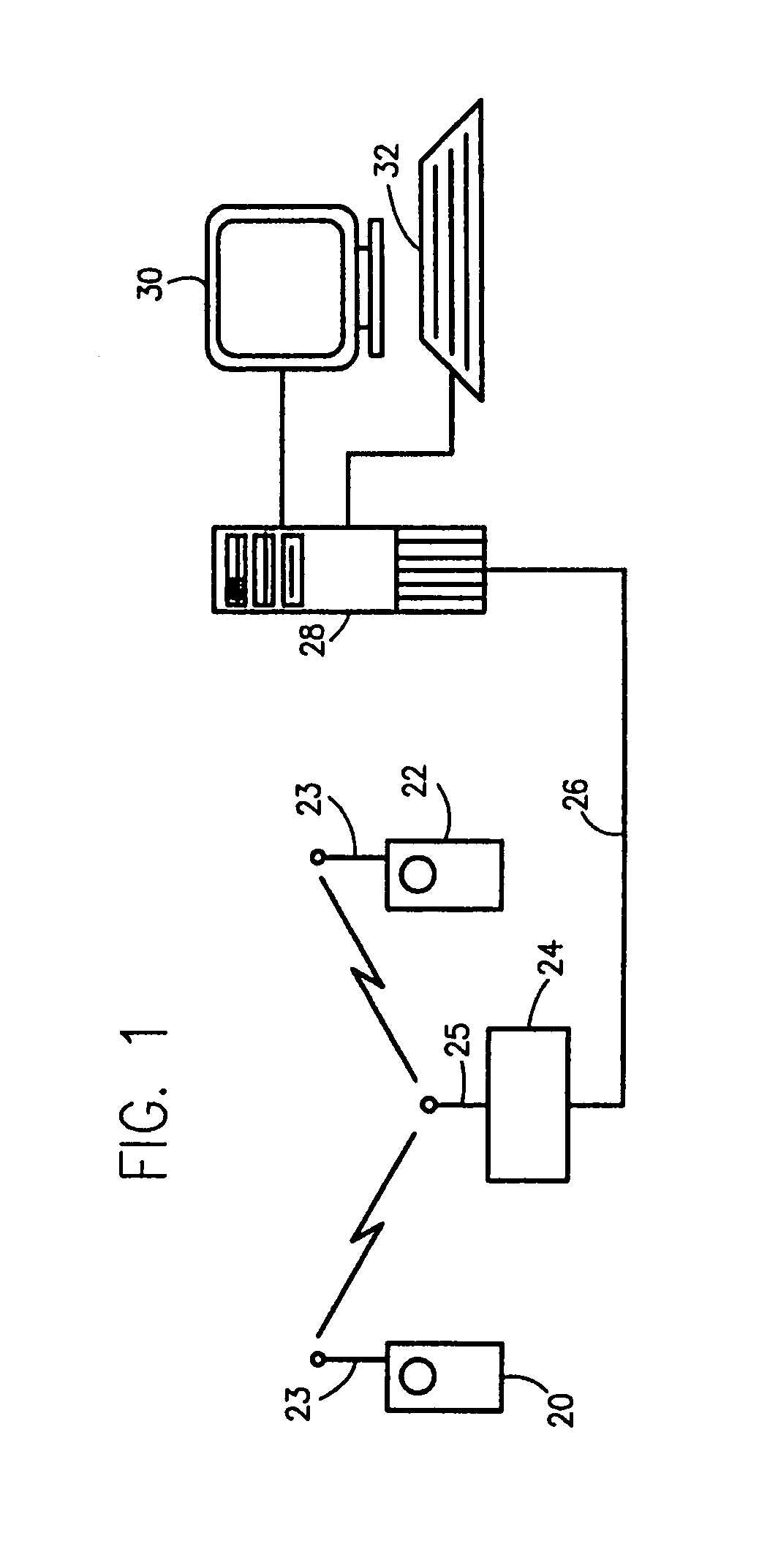
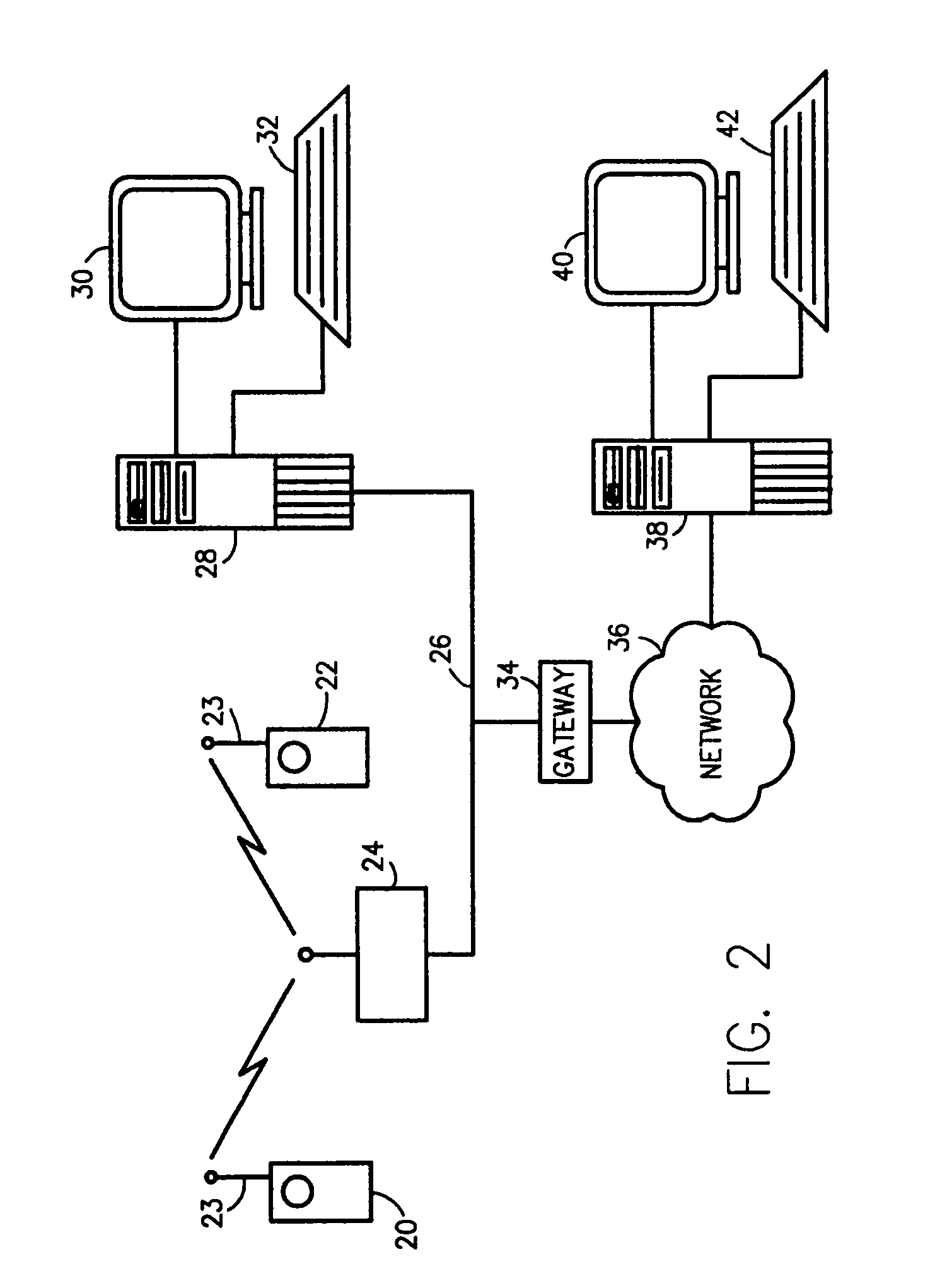
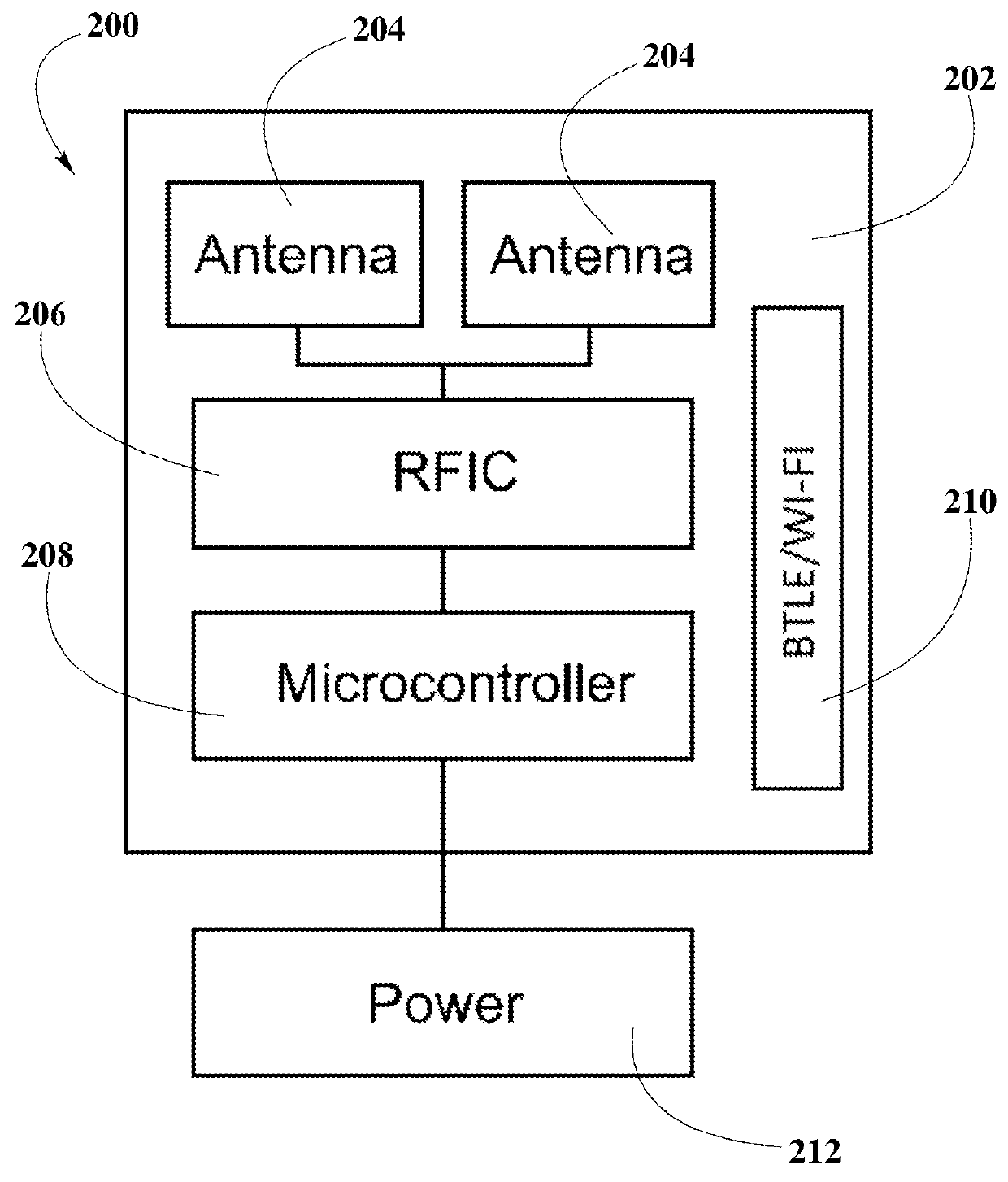
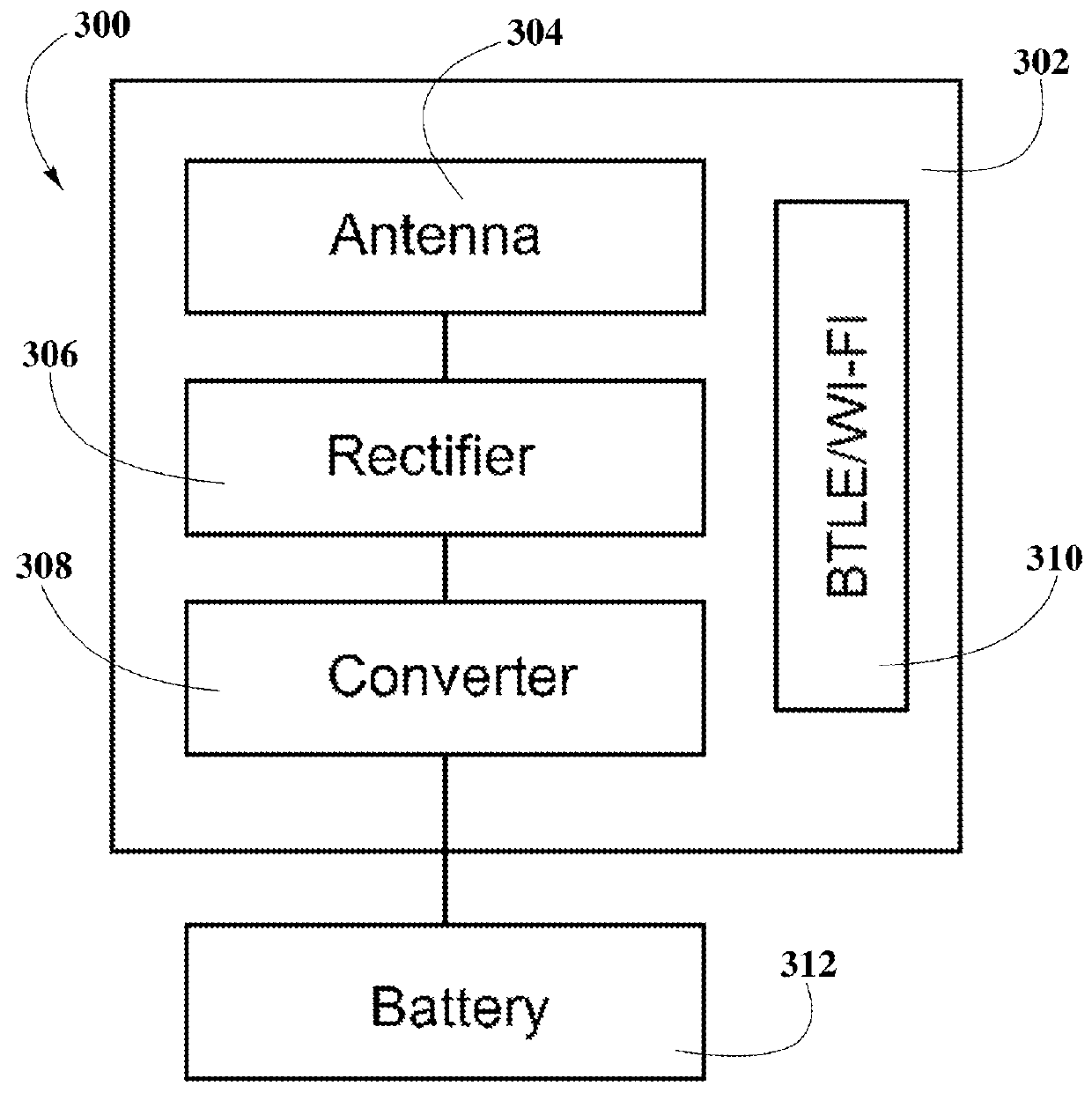
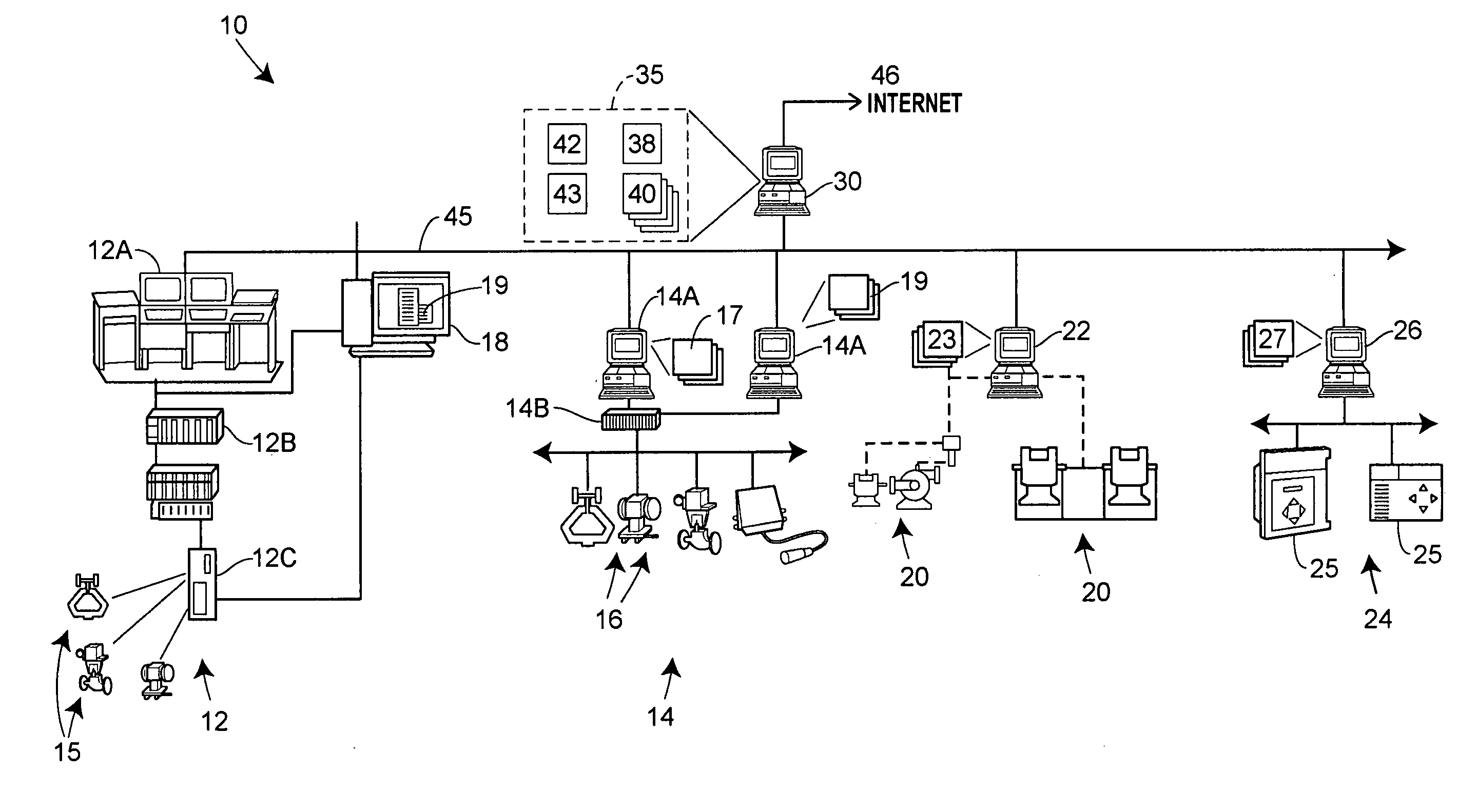
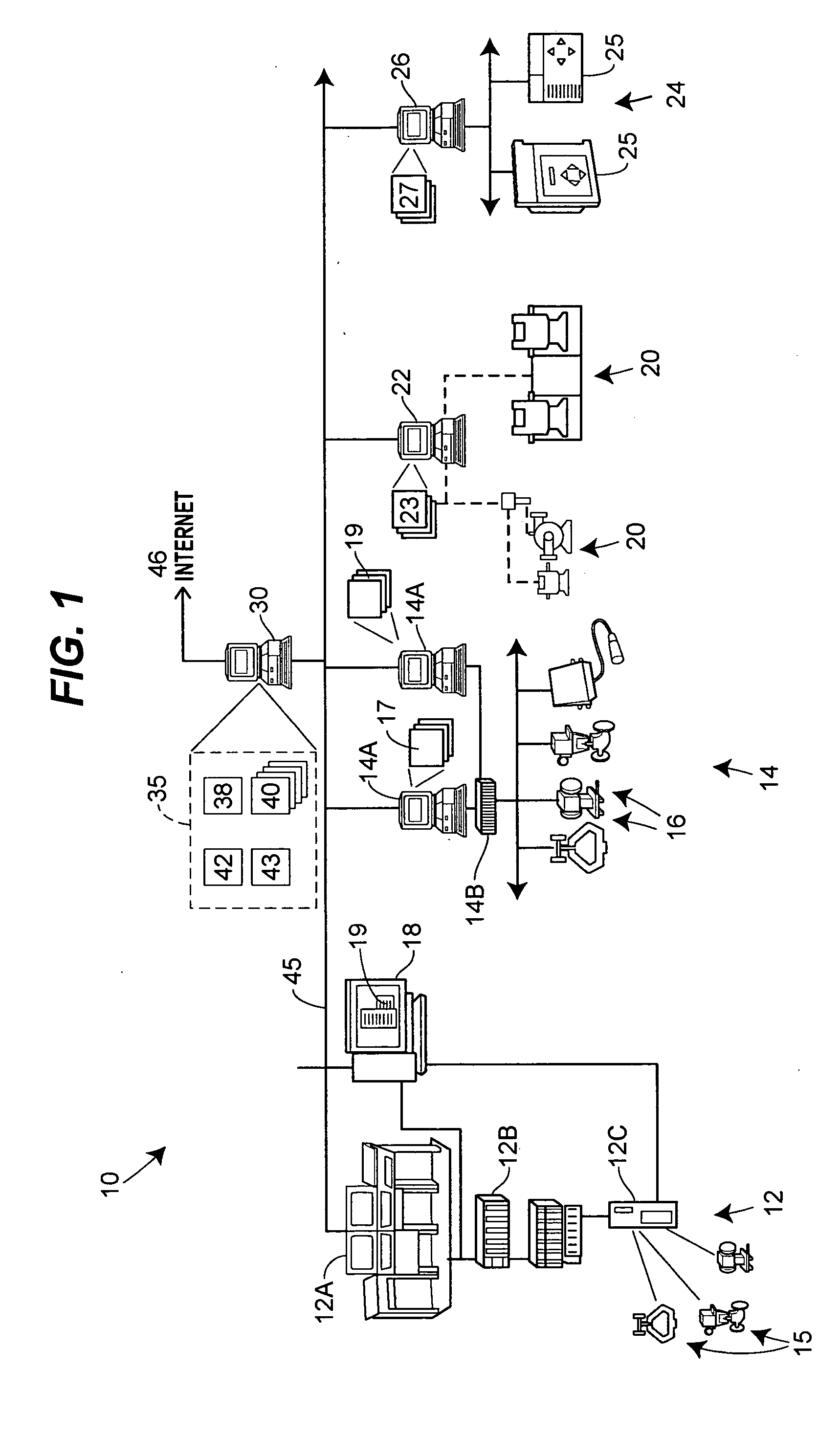
Multimedia surveillance and monitoring system including network configuration
InactiveUS6970183B1High bandwidthSignalling system detailsColor television detailsVideo monitoringStructure of Management Information
A comprehensive, wireless multimedia surveillance and monitoring system provides a combination of megapixel digital camera capability with full motion video surveillance with a network, including network components and appliances such as wiring, workstations, and servers with the option of geographical distribution with various wide area carriers. The full service, multi-media surveillance system is capable of a wide range of monitoring techniques utilizing digital network architecture and is adapted for transmitting event data, video and / or image monitoring information, audio signals and other sensor and detector data over significant distances using digital data transmission over a LAN, wireless LAN, Intranet or Internet for automatic assessment and response including dispatch of response personnel. Both wired and wireless appliance and sensor systems may be employed. GPS dispatching is used to locate and alert personnel as well as to indicate the location of an event. Automatic mapping and dispatch permits rapid response. The wireless LAN connectivity permits local distribution of audio, video and image data over a relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area Network) or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Centralized monitoring stations have access to all of the surveillance data from various remote locations via the Internet or the WAN. A server provides a centralized location for data collection, alarm detection and processing, access control, dispatch processing, logging functions and other specialized functions. The server may be inserted virtually anywhere in the Intranet / Internet network. The topology of the network will be established by the geographic situation of the installation. Appropriate firewalls may be set up as desired. The server based system permits a security provider to have access to the appliance and sensor and surveillance data or to configure or reconfigure the system for any station on the network.
Owner:PR NEWSWIRE
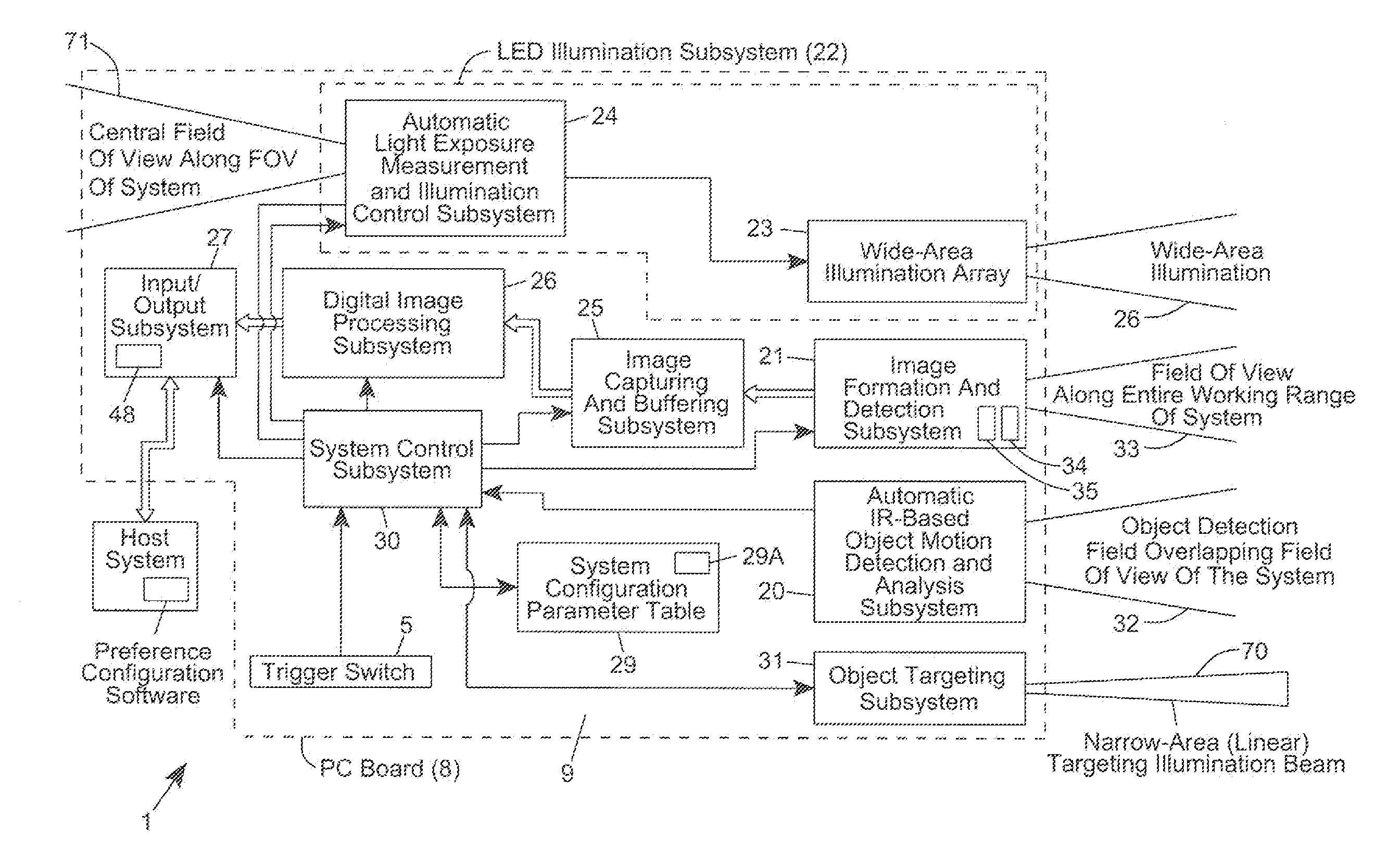
Code symbol reading system supporting operator-dependent system configuration parameters
InactiveUS20120193423A1Easy loadingEasy to modifySensing detailsCharacter and pattern recognitionProduction rateWorking environment
A method of and system for setting and switching user preferences between system operators, to provide a higher return on investment (ROI) and a more satisfying work environment. The system allows operators to easily select and implement particular customizable system configuration parameters (SCPs) in a code symbol reading system, based on personal preferences of the system operator, which can lead to more effective scanning performance. A different set of customizable SCPs are programmably stored in system memory (e.g. EPROM) for each system operator / user registered to use the system, to improve the quality of the working environment and increase worker productivity.
Owner:METROLOGIC INSTR
Real-time activity monitoring and reporting
InactiveUS20070039049A1Maintain transparencyNo delayMemory loss protectionError detection/correctionActivity monitorComputerized system
In order to track activities in a computerized system with client-server or other communications, a system configuration is needed which monitors, logs and reports traffic. This is somewhat akin to but not entirely similar a firewall. Thus, the invention contemplates a real-time, platform-independent, rule-based activity monitor for detecting a particular activity of interest as it occurs and for reporting such activity and the user substantially as fast.
Owner:MICRO FOCUS US
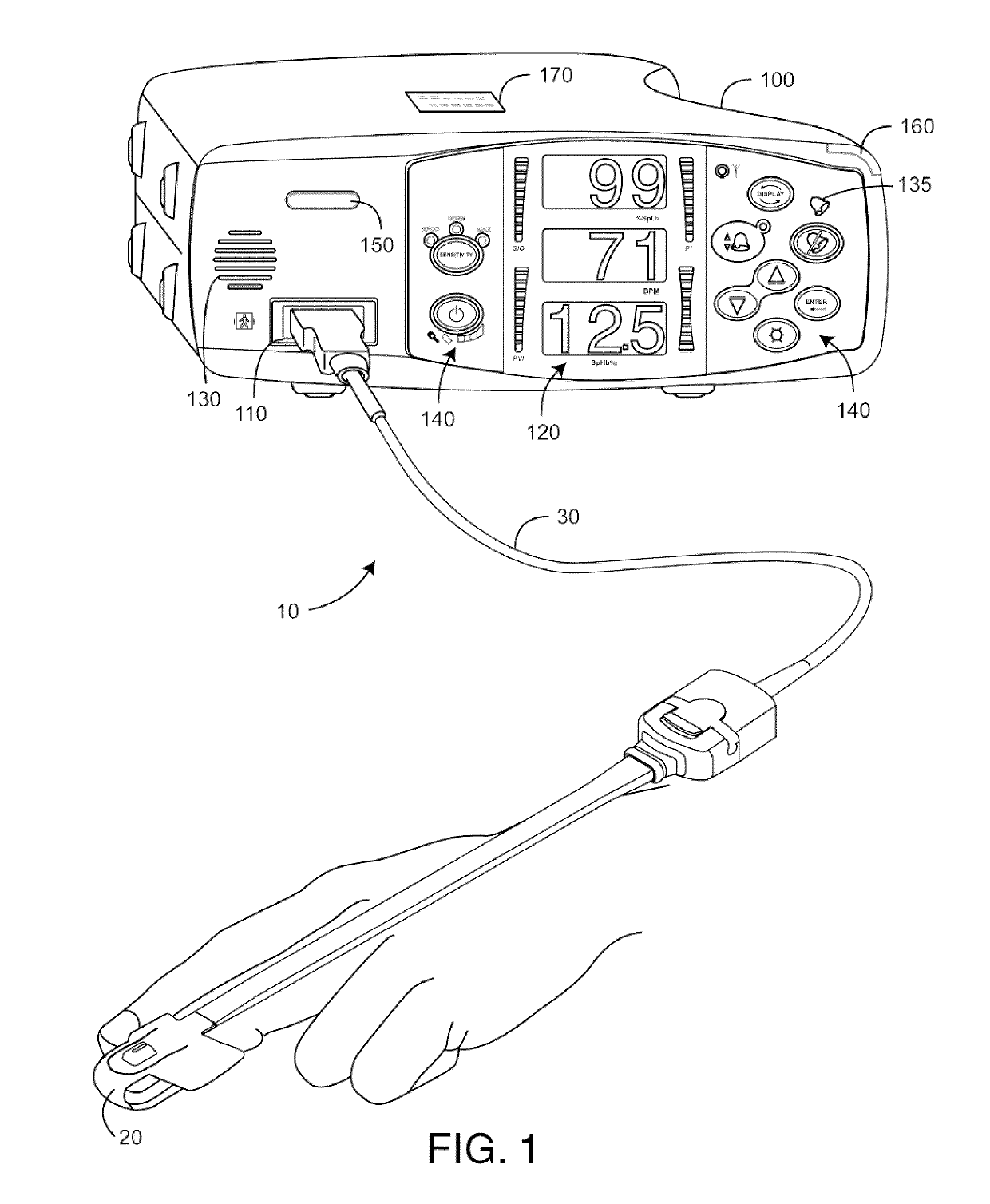
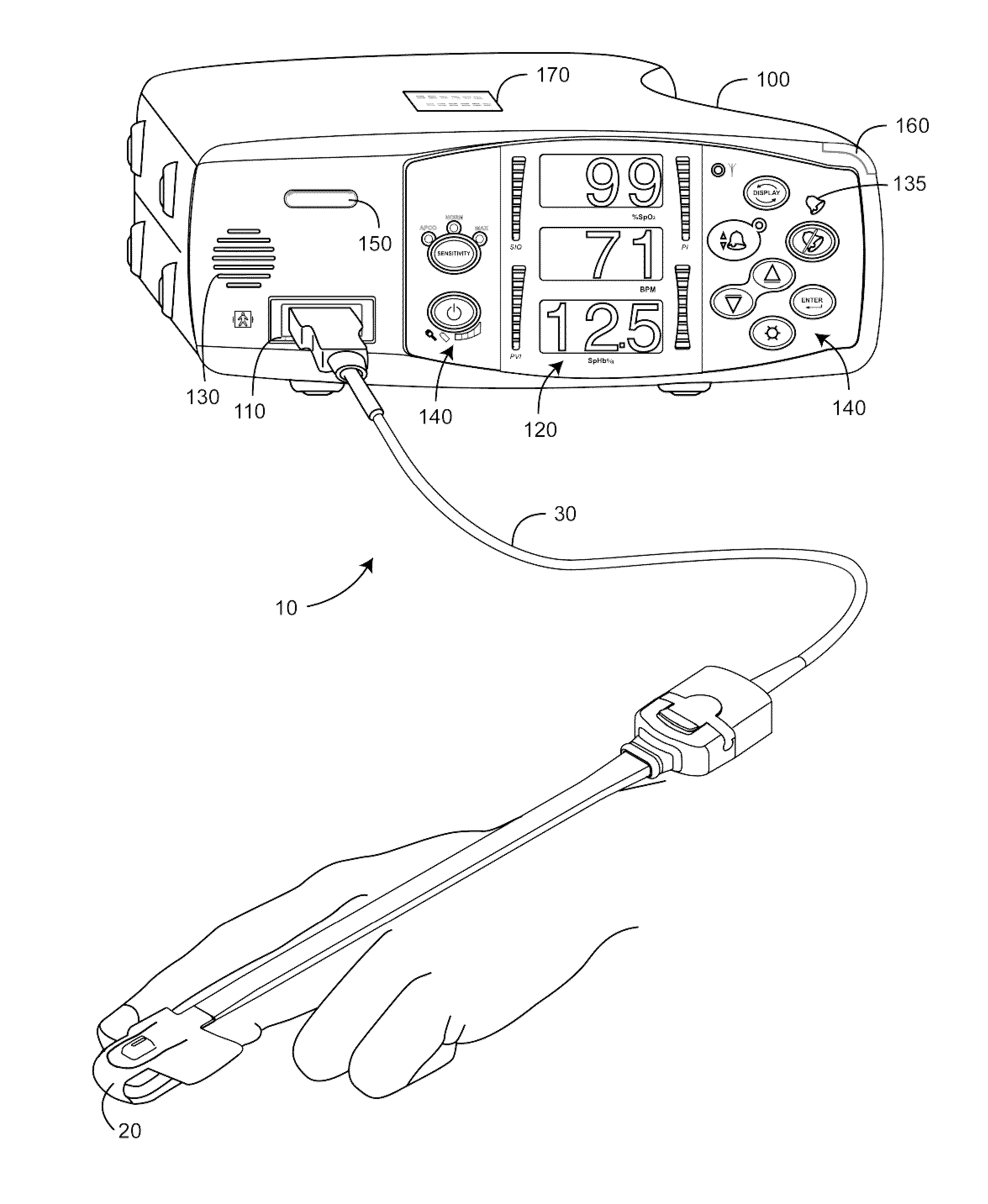
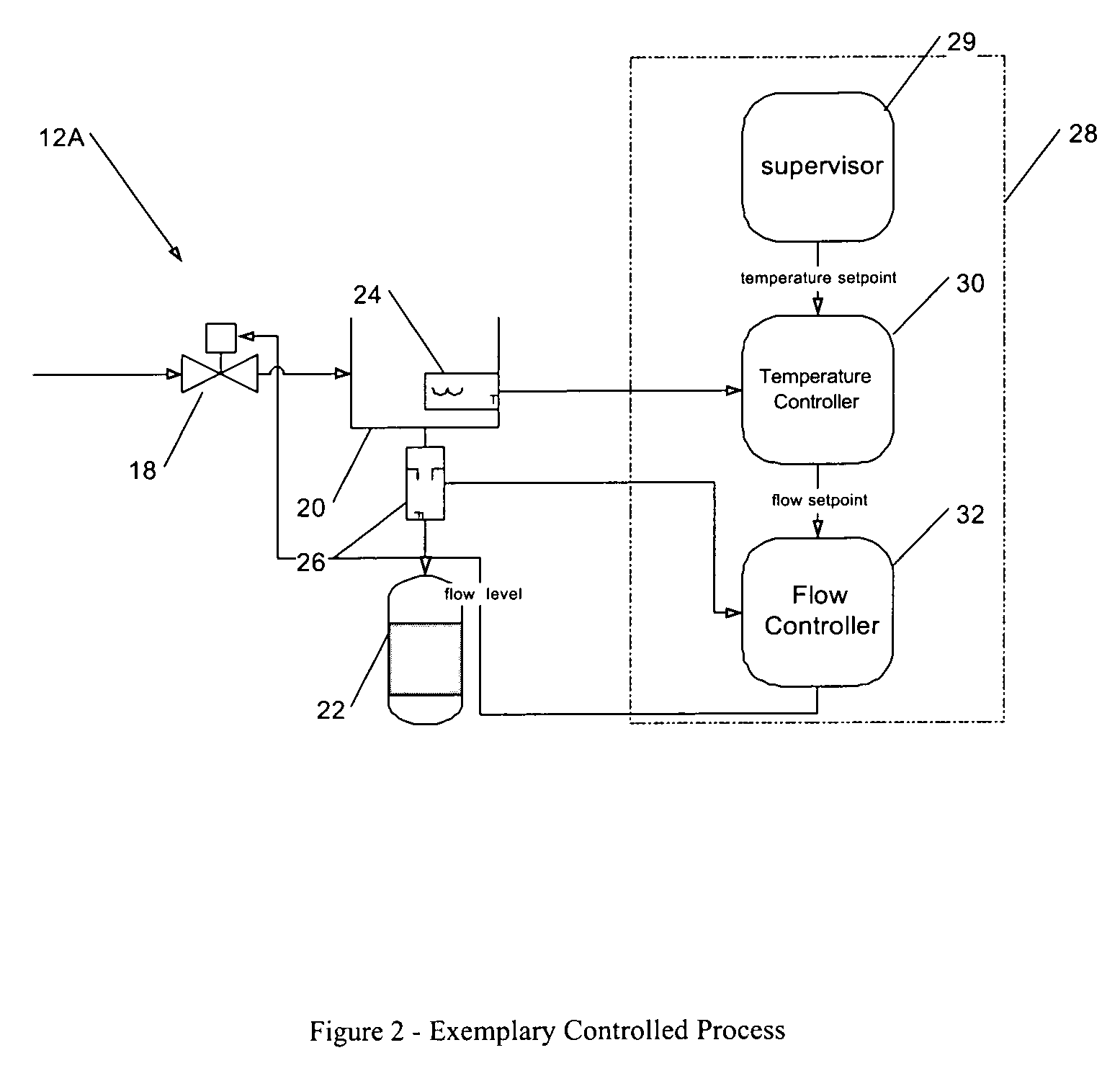
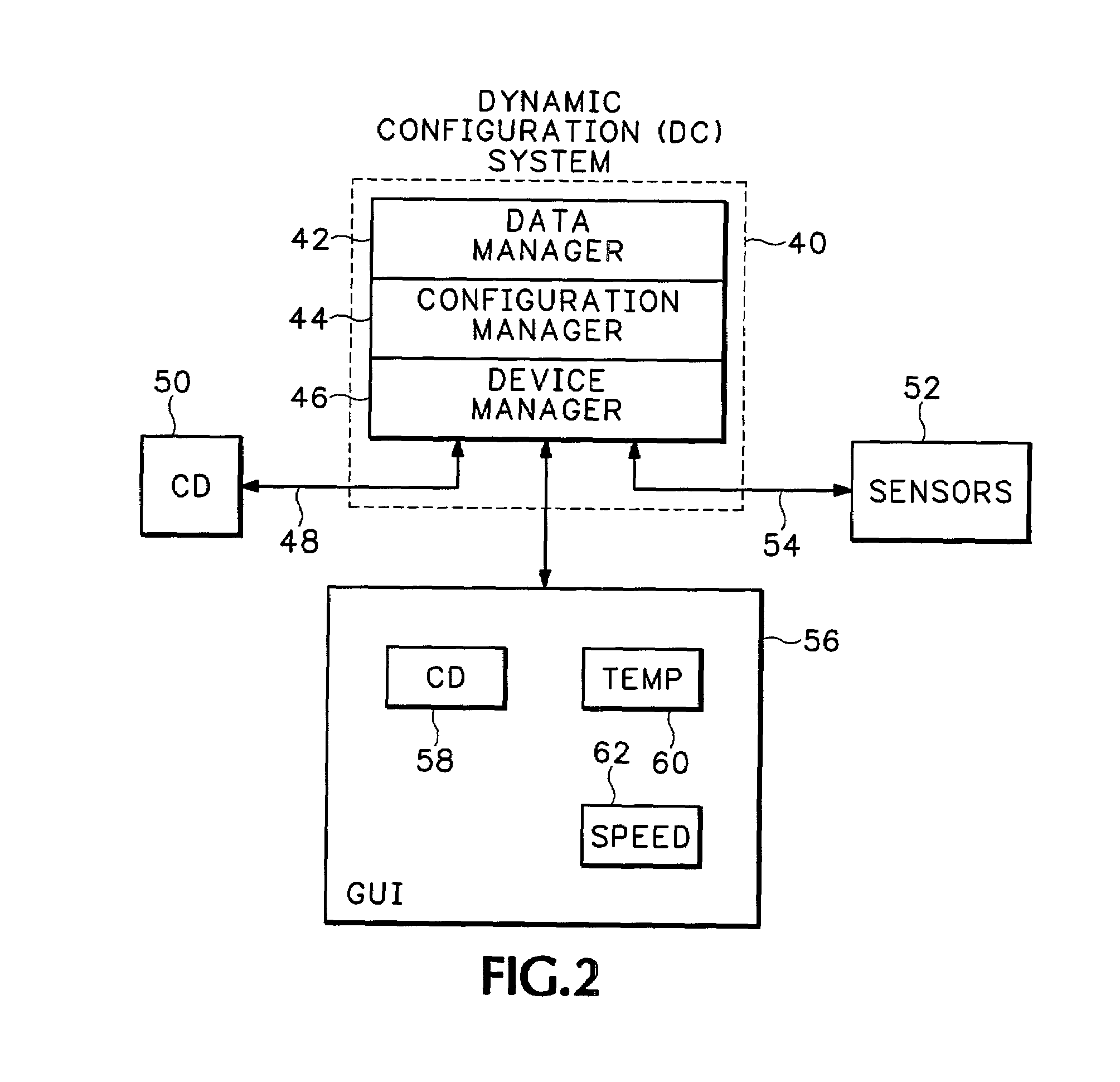
Monitor configuration system
InactiveUS20090275844A1Maximum flexibilityOperational flexibilityCatheterSensorsComputer moduleParameter control
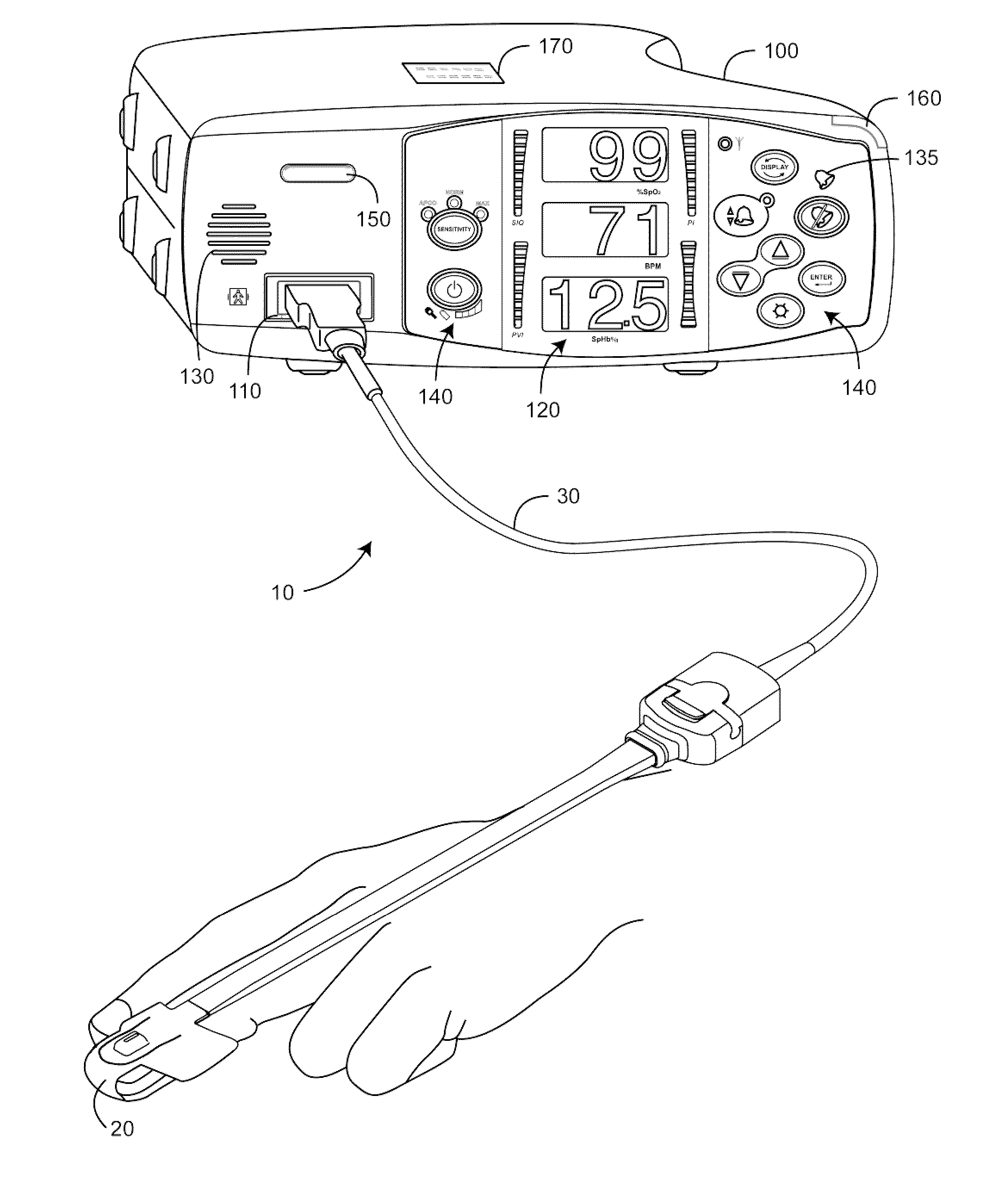
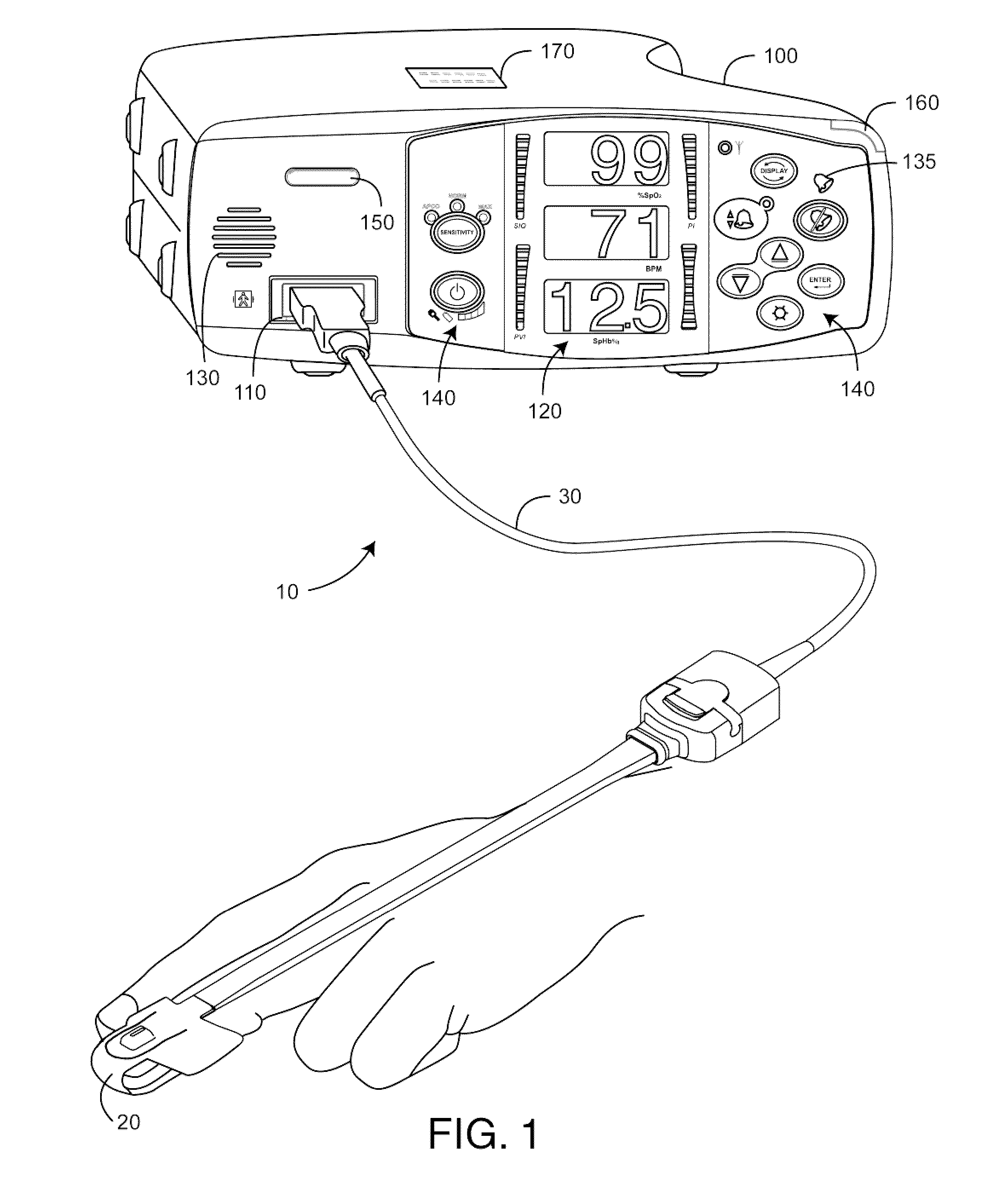
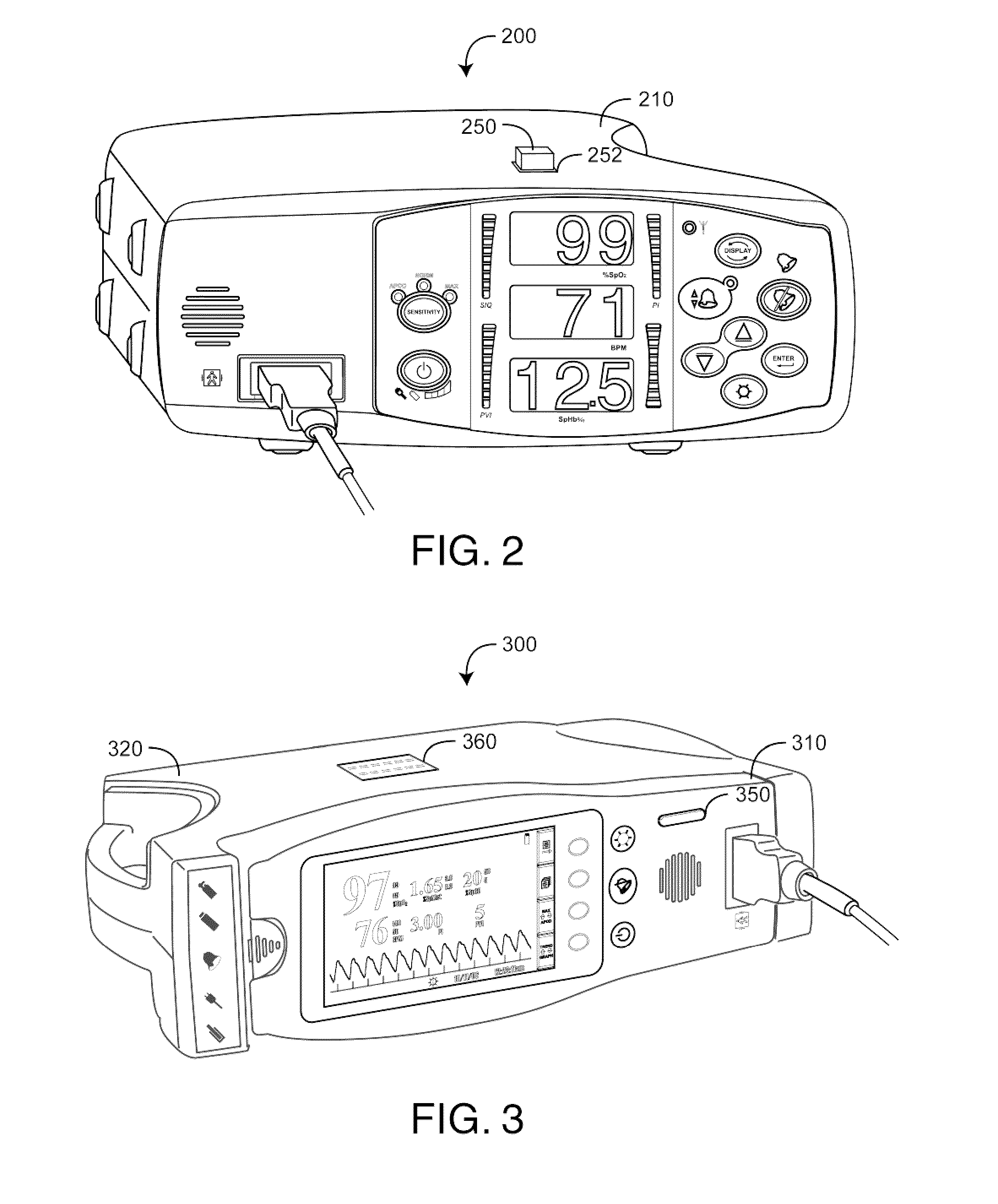
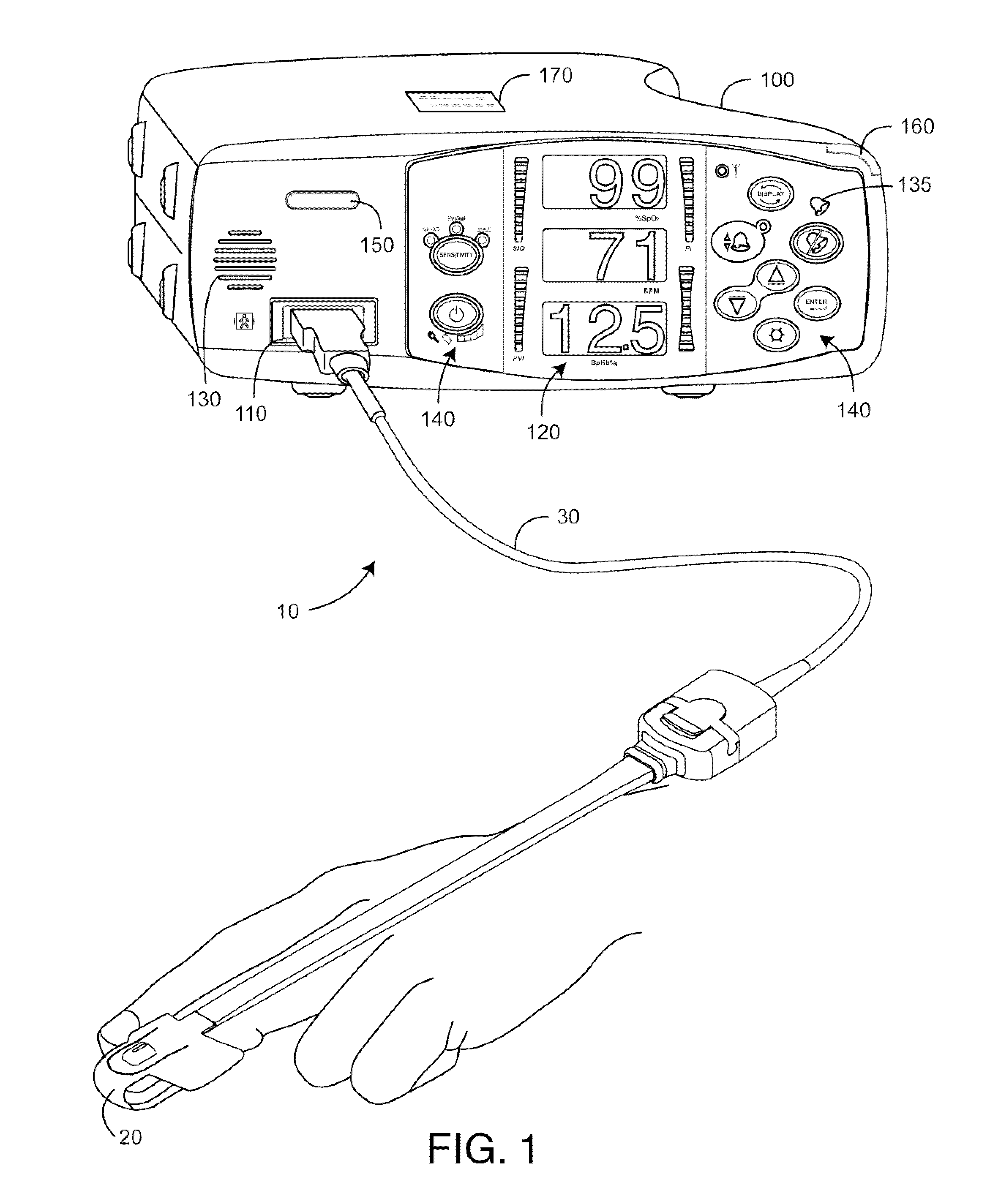
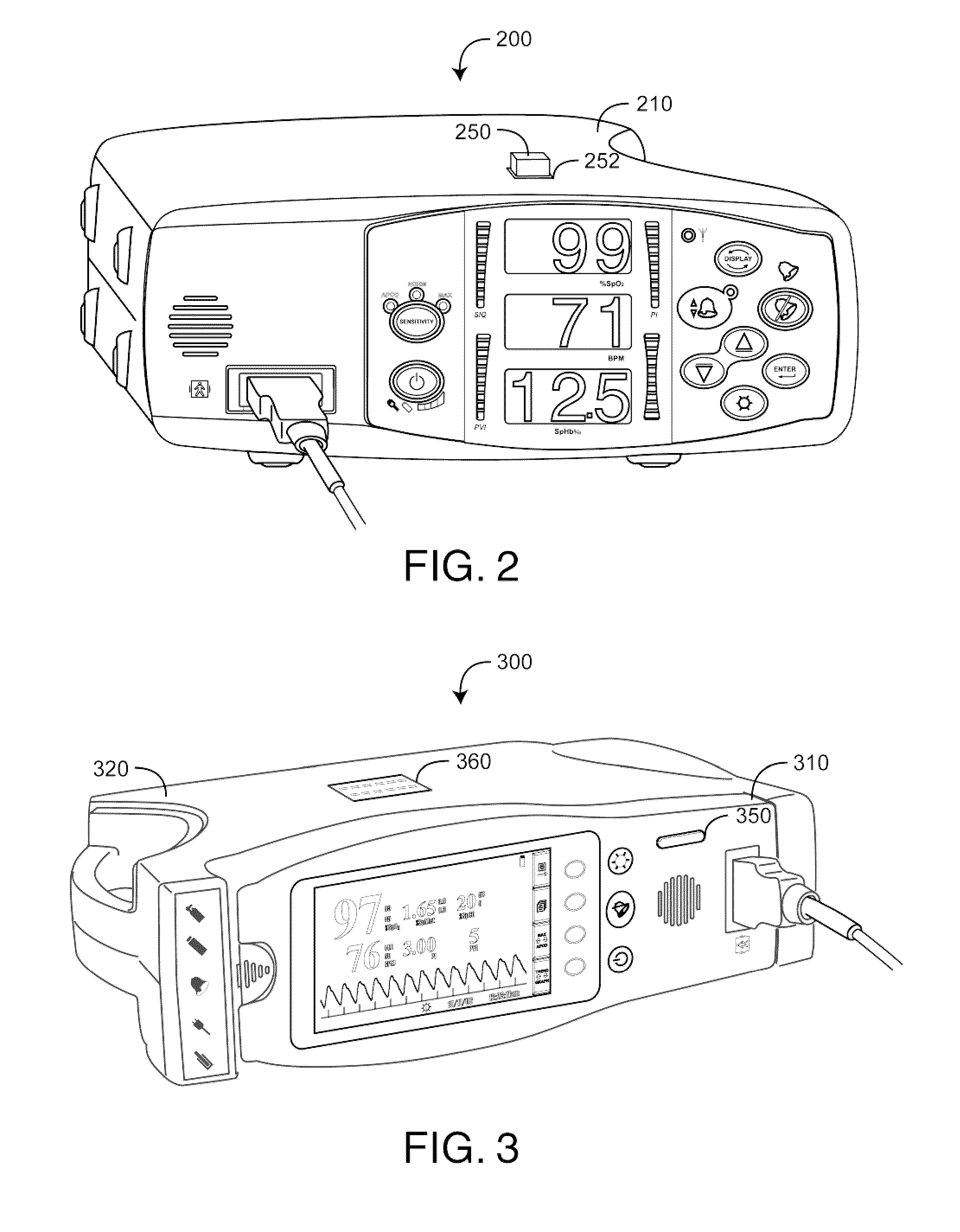
A monitor configuration system which communicates with a physiological sensor, the monitor configuration system including one or more processors and an instrument manager module running on the one or more processors. At least one of the one or more processors communicates with the sensor and calculates at least one physiological parameters responsive to the sensor. The instrument manager controls the calculation, display and / or alarms based upon the physiological parameters. A configuration indicator identifies the configuration profile. In one aspect of the invention, the physiological sensor is a optical sensor that includes at least one light emitting diode and at least one detector.
Owner:JPMORGAN CHASE BANK NA
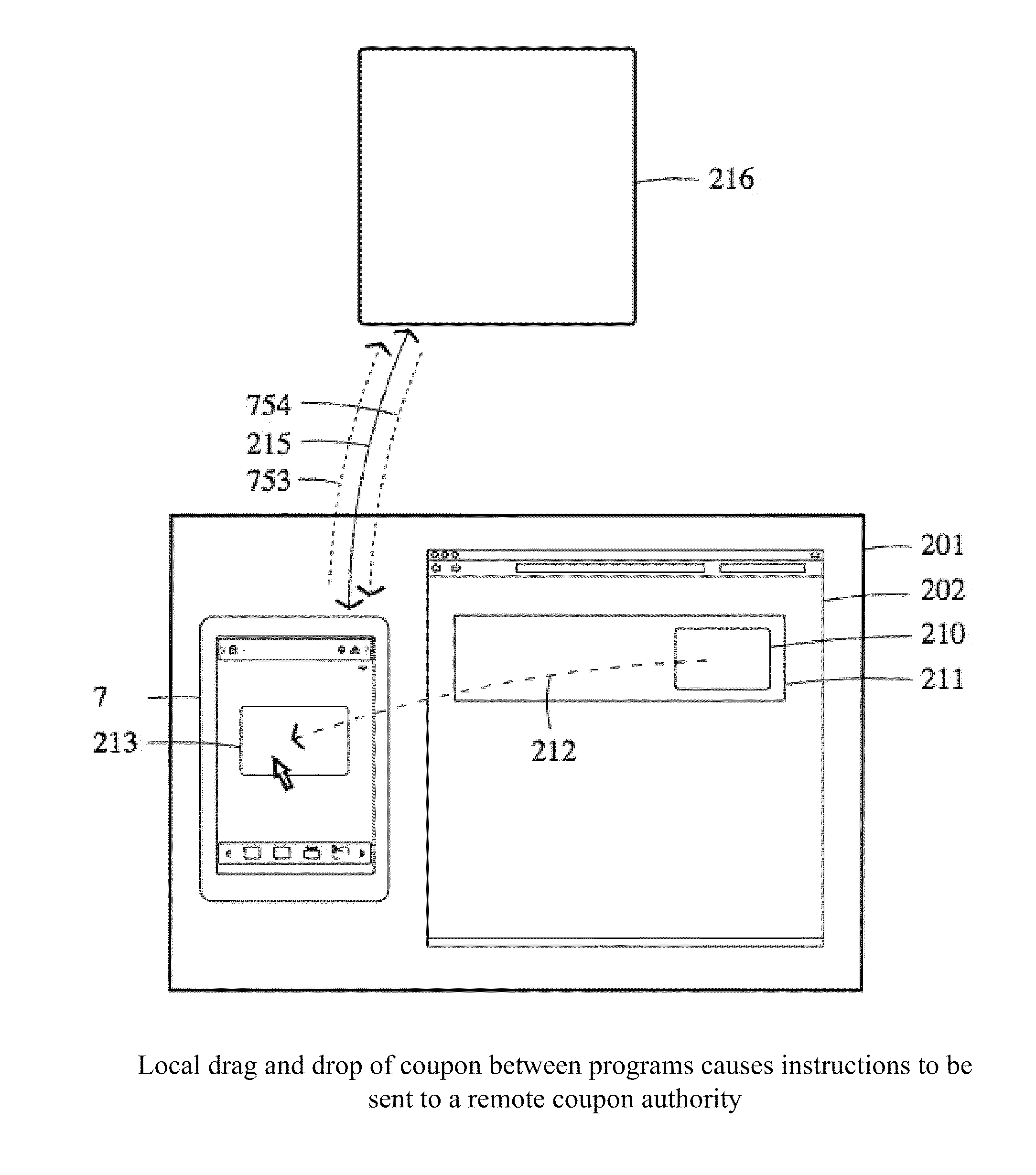
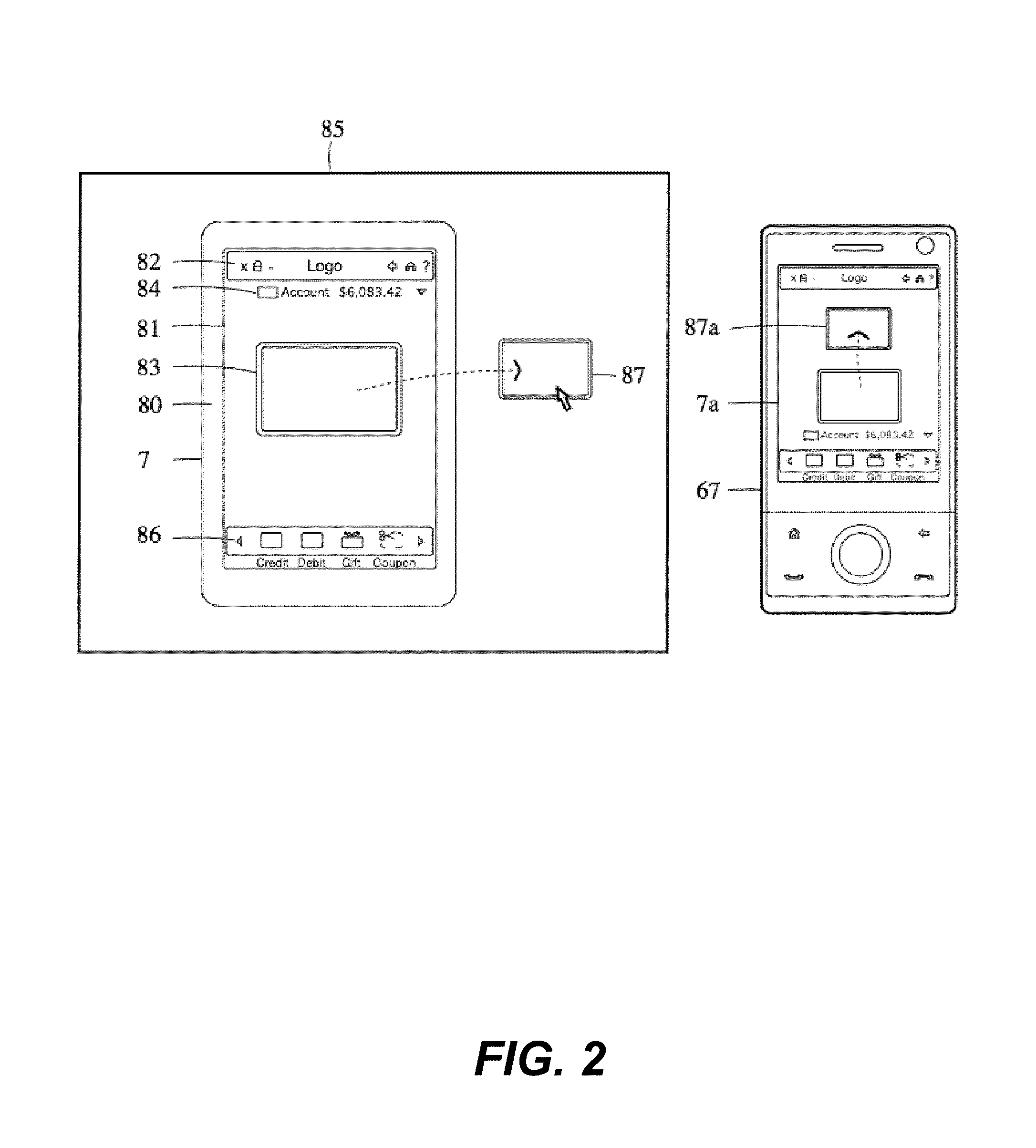
Dispensing digital objects to an electronic wallet
A configuration system and method is disclosed that includes a unified and integrated configuration that is composed of a payment system, an advertising system, and an identity management system such that the unified system has all of the benefits of the individual systems as well as several additional synergistic benefits. Also described are specific configurations including the system's access point architecture, visual wallet simulator user interface, security architecture, coupon handling as well as the system's structure and means for delivering them as targeted advertising, business card handling, membership card handling for the purposes of login management, receipt handling, and the editors and grammars provided for customizing the different types of objects in the system as well as the creation of new custom objects with custom behaviors. The configurations are operable on-line as well as through physical presence transactions.
Owner:GOOGLE LLC
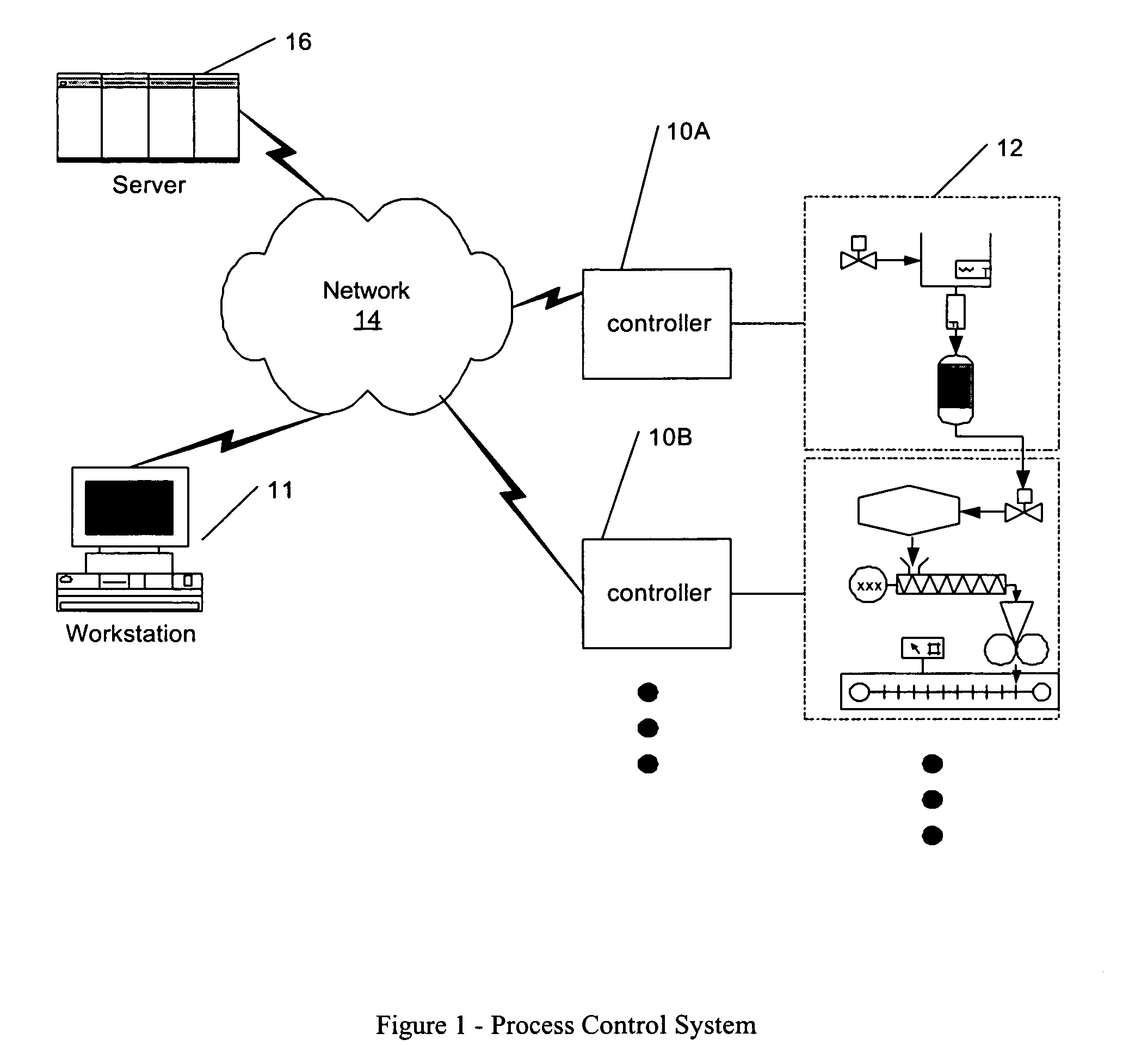
Process control configuration system with connection validation and configuration
Connection objects or other such data structures facilitate establishing and configuring connections between objects that model components in a process control system. A first set of data structures (e.g. the object connection type structures) identify valid types for component-to-component pairings and the respective roles of each component in the pairing (e.g., parent or child, source or sink). A second set of data structures (e.g., the parameter connection type structures) supply similar information for parameter-to-parameter connections. Together, these data structures can be used, for example, to validate component-to-component connections suggested by the user and to automatically configure parameter-to-parameter connections. Actual connections, both at the component or parameter level, are reflected using parameter overrides within the parameterized object model—with which the connection objects are constructed.
Owner:SCHNEIDER ELECTRIC SYST USA INC
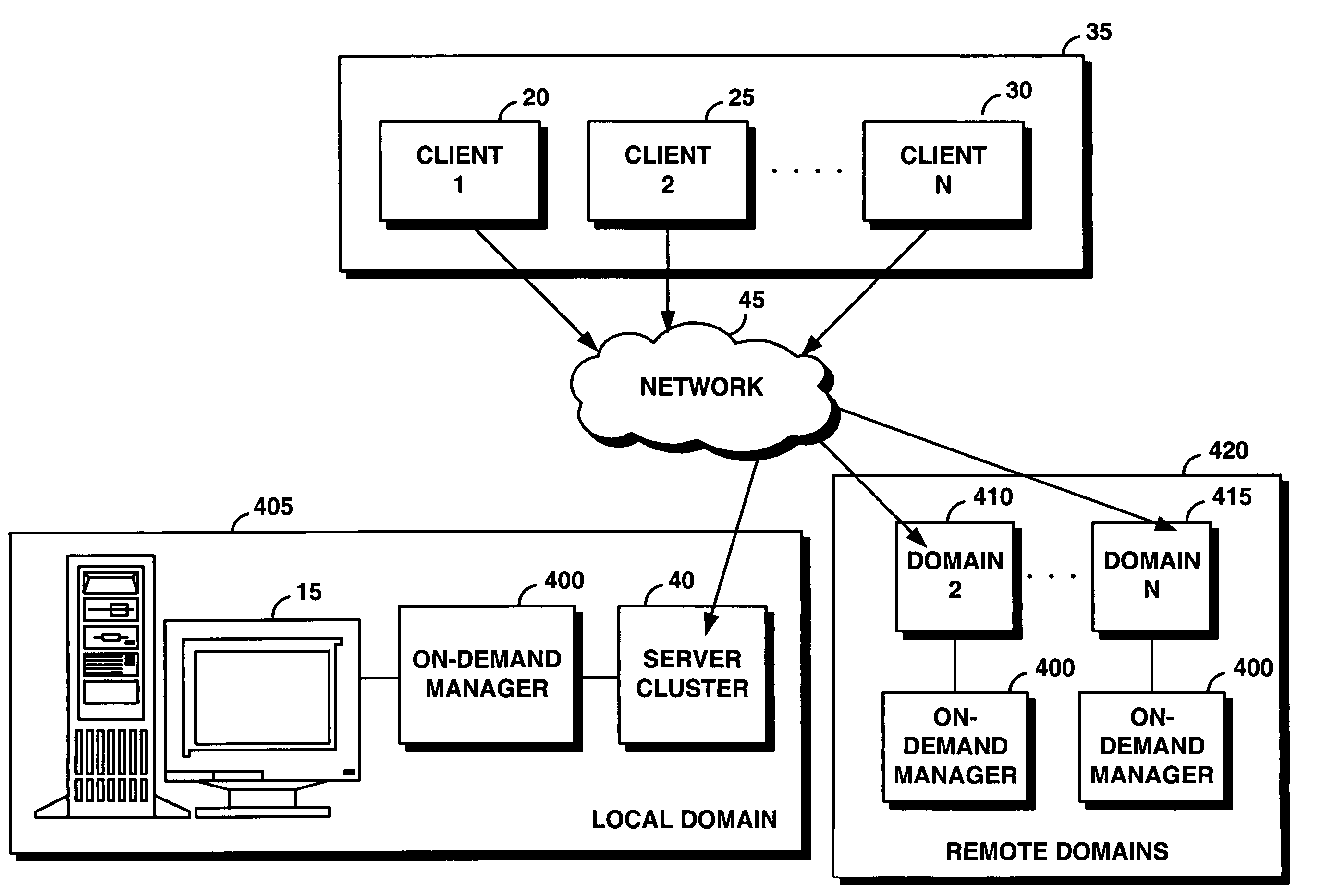
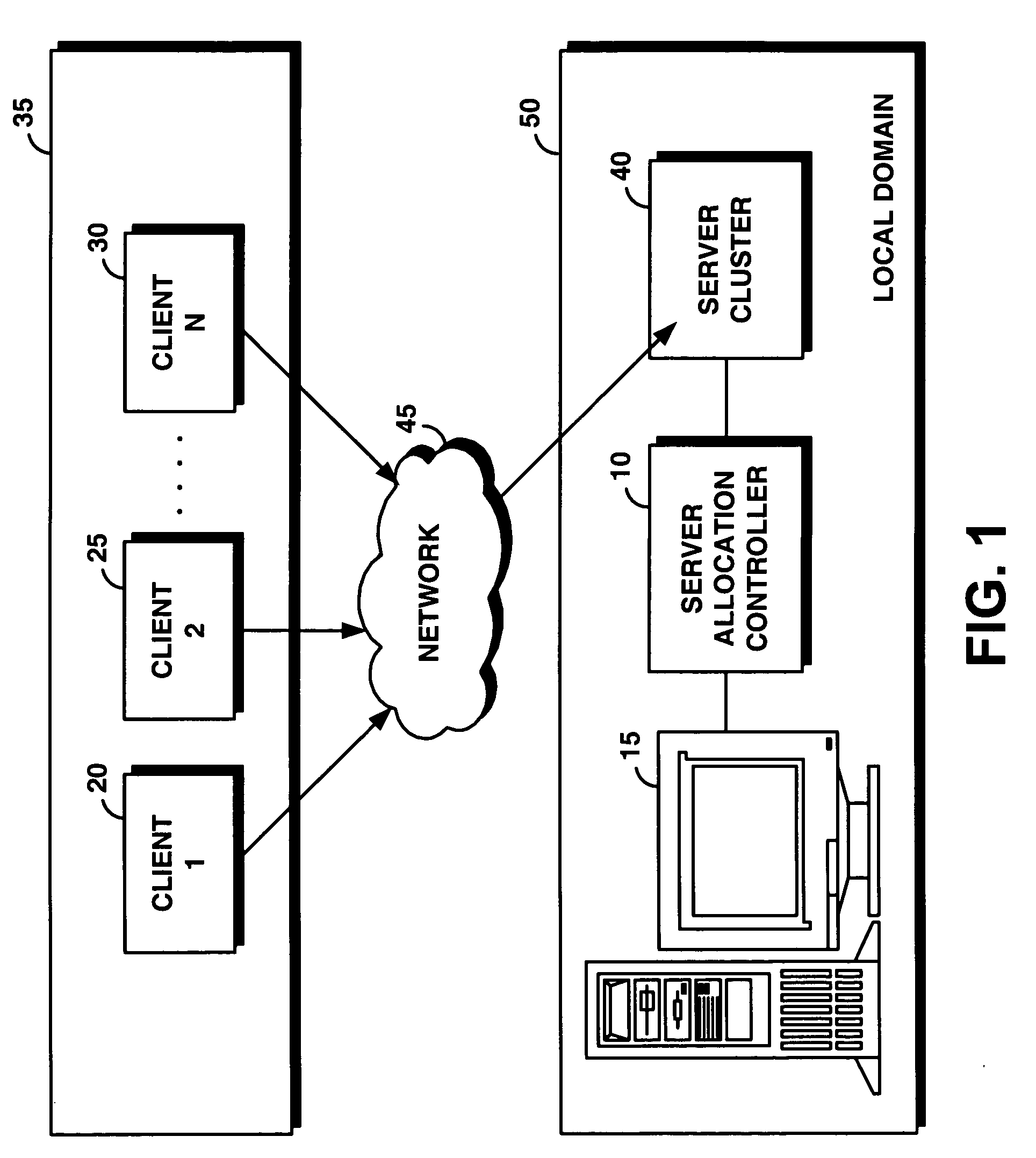
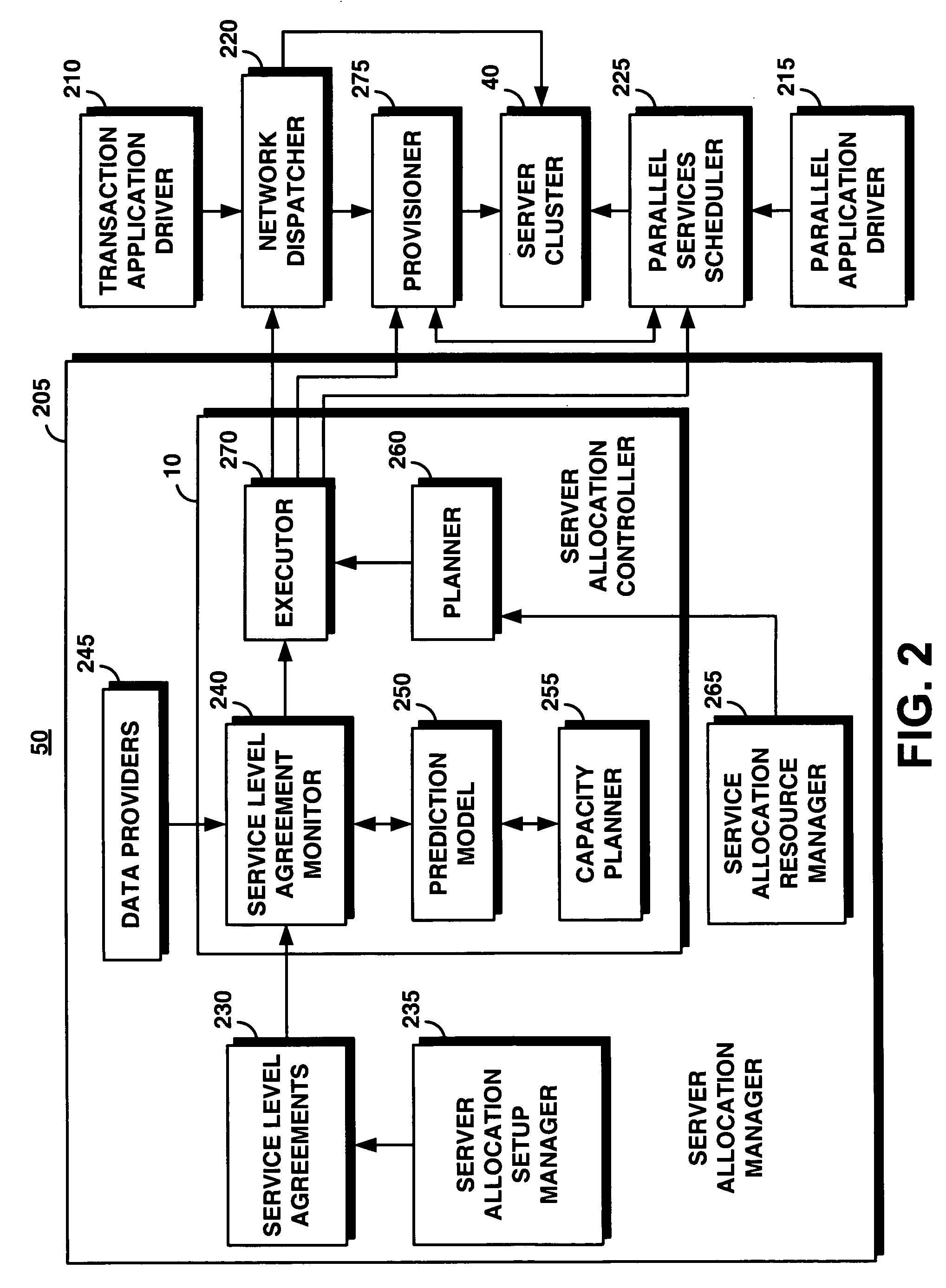
System and method for supporting transaction and parallel services across multiple domains based on service level agreenments
InactiveUS20050165925A1Facilitates dynamic allocationResource allocationDigital computer detailsService-level agreementData processing system
An on-demand manager provides an improved distributed data processing system for facilitating dynamic allocation of computing resources among multiple domains based on a current workload and service level agreements. Based on a service level agreement, the on-demand manager monitors and predicts the load on the system. If the current or predicted load cannot be handled with the current system configuration, the on-demand manager determines additional resources needed to handle the workload. If the service level agreement violations cannot be handled by reconfiguring resources at a domain, the on-demand manager sends a resource request to other domains. These other domains analyze their own commitments and may accept the resource request, reject the request, or counter-propose with an offer of resources and a corresponding service level agreement. Once the requesting domain has acquired resources, workload load balancers are reconfigured to allocate some of the workload from the requesting site to the acquired remote resources.
Owner:IBM CORP
Monitor configuration system
ActiveUS10292664B2Maximum flexibilityOperational flexibilityCatheterSensorsParameter controlLight-emitting diode
A monitor configuration system which communicates with a physiological sensor, the monitor configuration system including one or more processors and an instrument manager module running on the one or more processors. At least one of the one or more processors communicates with the sensor and calculates at least one physiological parameters responsive to the sensor. The instrument manager controls the calculation, display and / or alarms based upon the physiological parameters. A configuration indicator identifies the configuration profile. In one aspect of the invention, the physiological sensor is a optical sensor that includes at least one light emitting diode and at least one detector.
Owner:MASIMO CORP
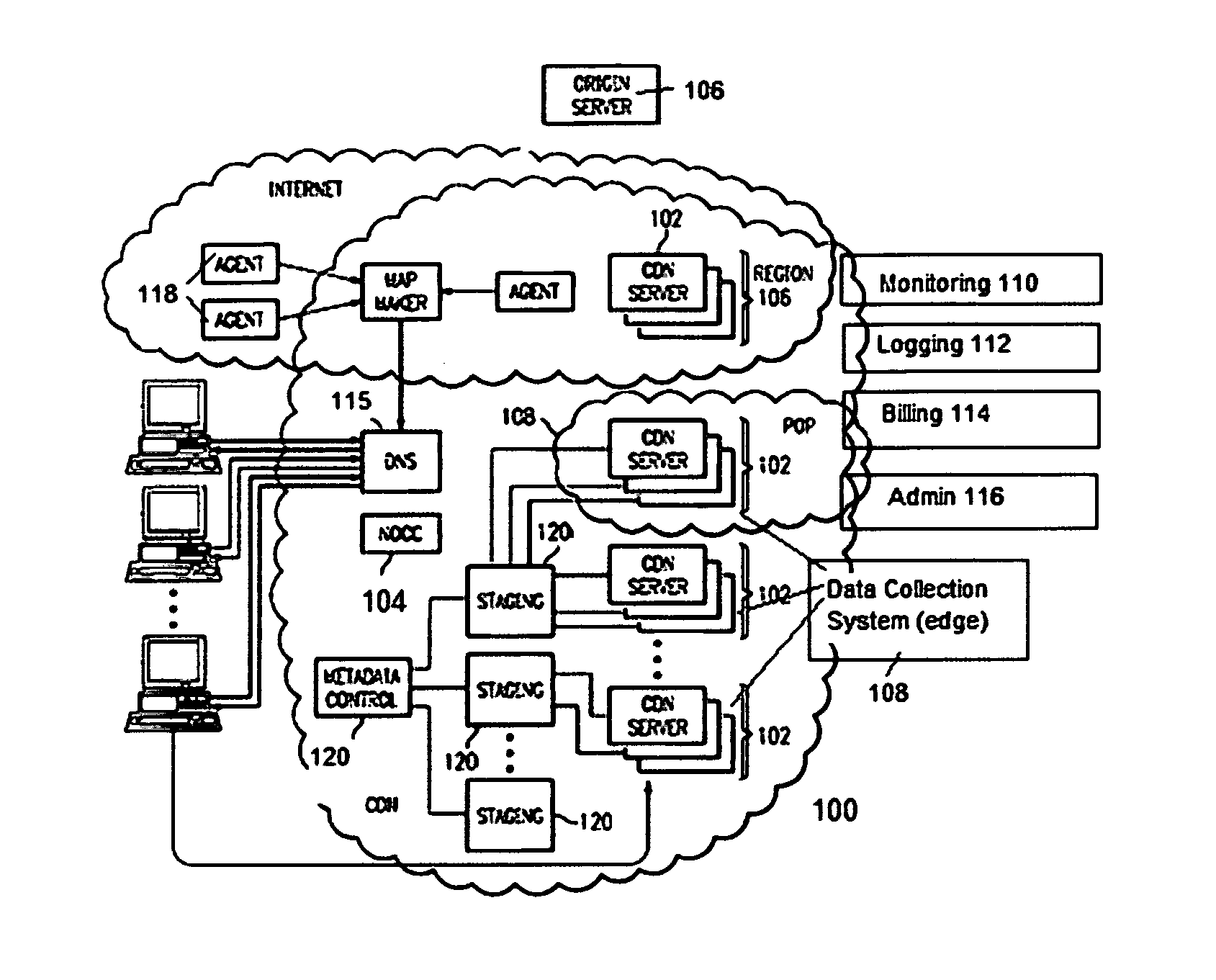
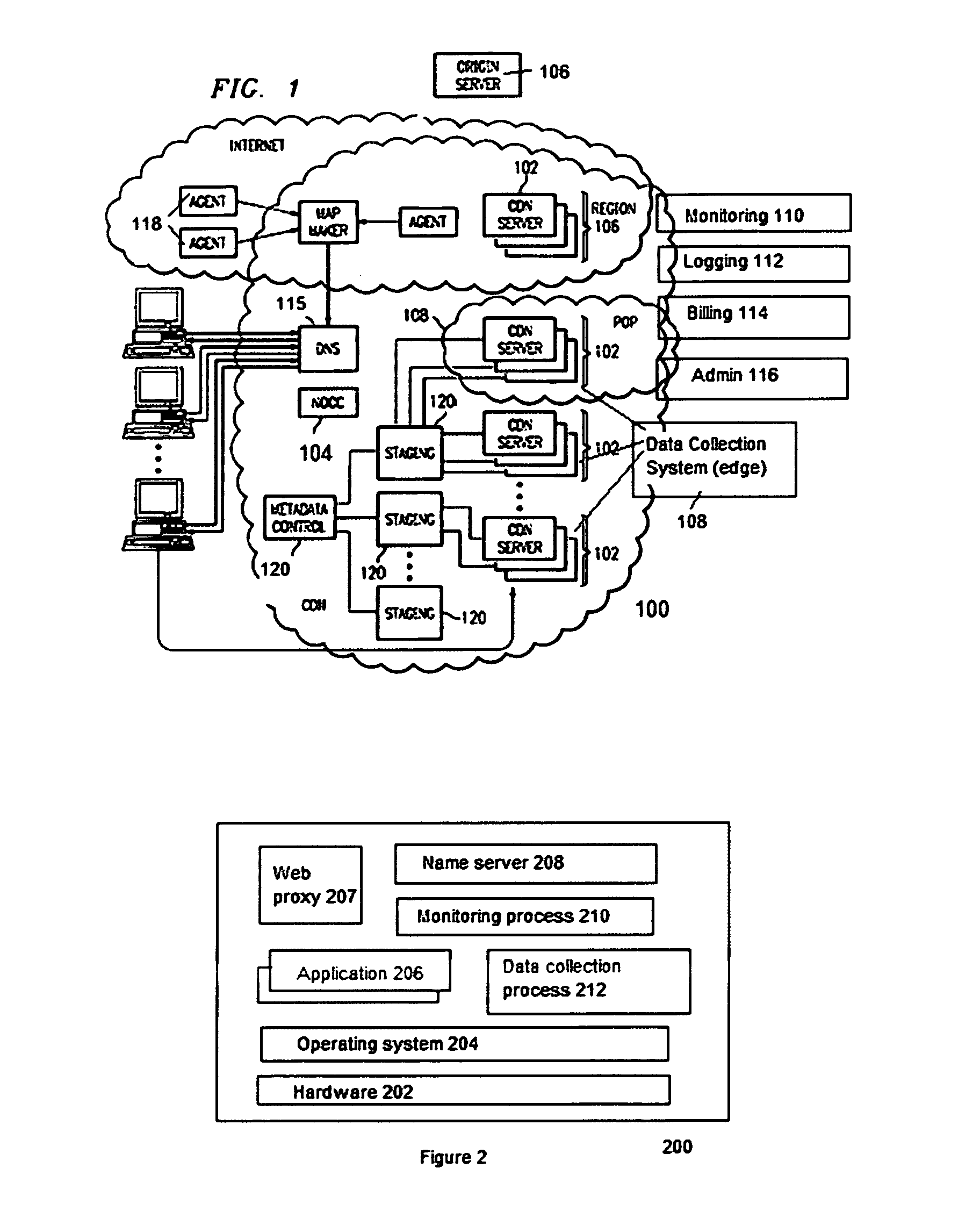
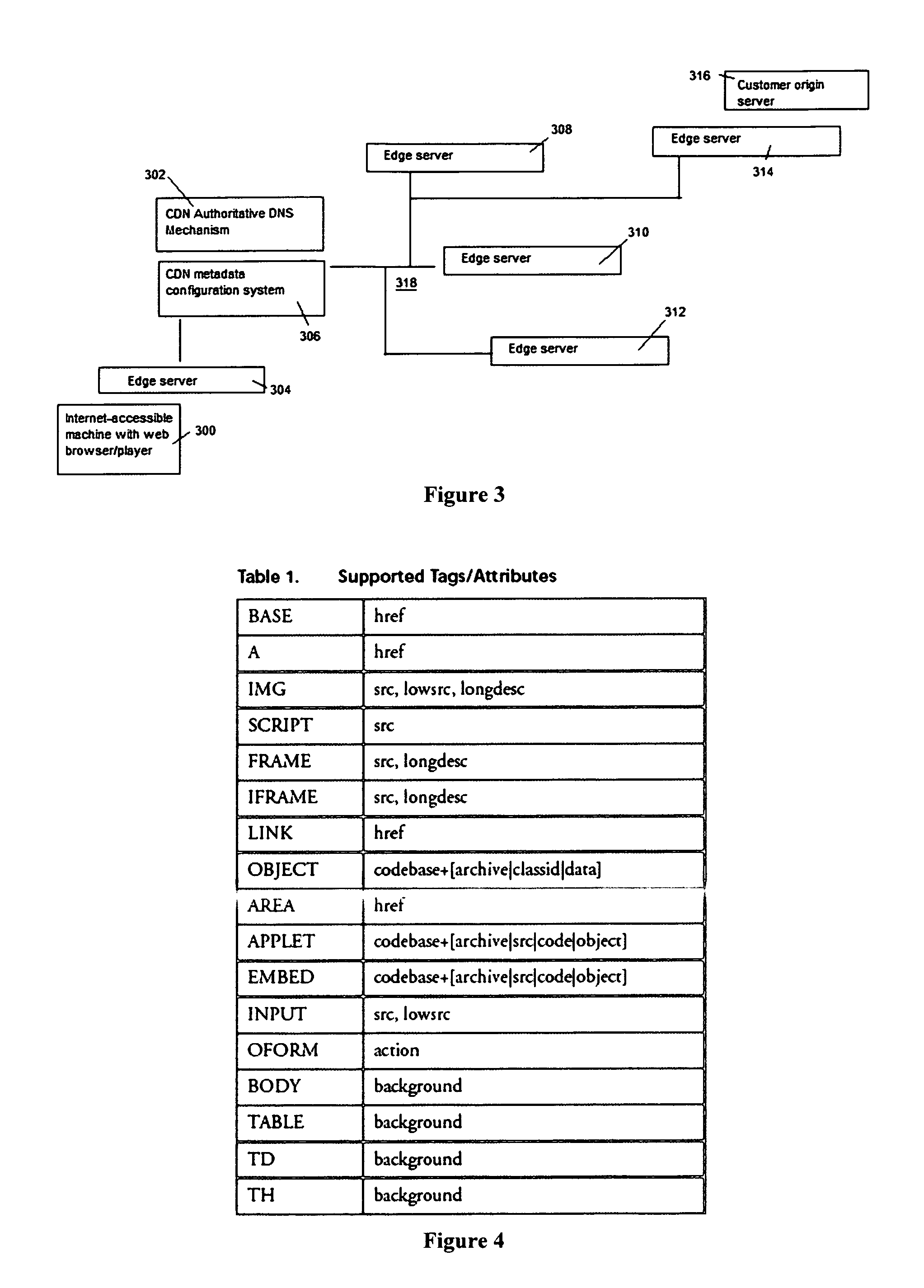
Site acceleration with content prefetching enabled through customer-specific configurations
ActiveUS20070156845A1More featureShorten the timeDigital data information retrievalMultiple digital computer combinationsWeb siteEdge server
A CDN edge server is configured to provide one or more extended content delivery features on a domain-specific, customer-specific basis, preferably using configuration files that are distributed to the edge servers using a configuration system. A given configuration file includes a set of content handling rules and directives that facilitate one or more advanced content handling features, such as content prefetching. When prefetching is enabled, the edge server retrieves objects embedded in pages (normally HTML content) at the same time it serves the page to the browser rather than waiting for the browser's request for these objects. This can significantly decrease the overall rendering time of the page and improve the user experience of a Web site. Using a set of metadata tags, prefetching can be applied to either cacheable or uncacheable content. When prefetching is used for cacheable content, and the object to be prefetched is already in cache, the object is moved from disk into memory so that it is ready to be served. When prefetching is used for uncacheable content, preferably the retrieved objects are uniquely associated with the client browser request that triggered the prefetch so that these objects cannot be served to a different end user. By applying metadata in the configuration file, prefetching can be combined with tiered distribution and other edge server configuration options to further improve the speed of delivery and / or to protect the origin server from bursts of prefetching requests.
Owner:AKAMAI TECH INC
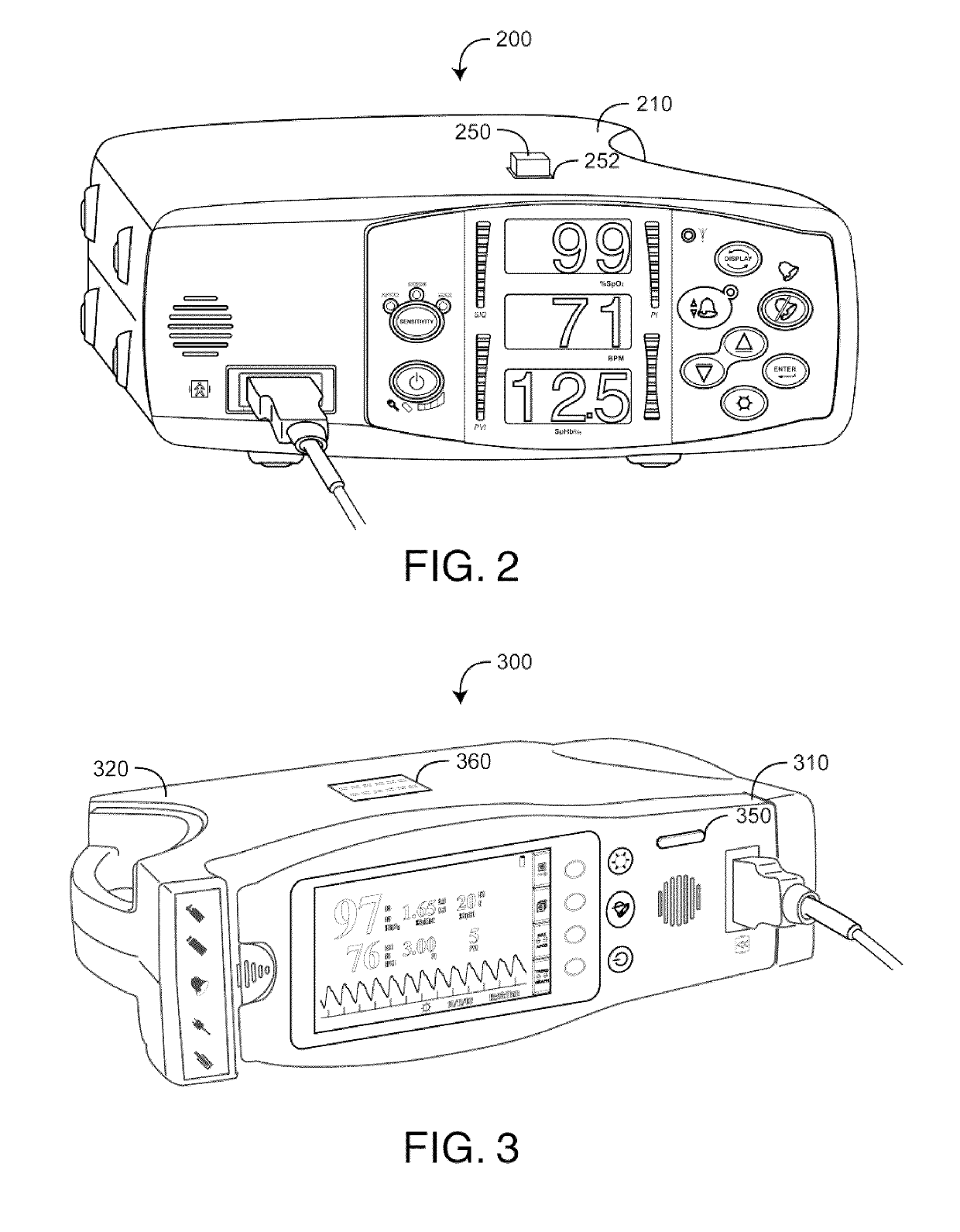
Monitor configuration system
ActiveUS20160331332A1Maximum flexibilityOperational flexibilitySensorsMeasuring/recording heart/pulse rateParameter controlLight-emitting diode
A monitor configuration system which communicates with a physiological sensor, the monitor configuration system including one or more processors and an instrument manager module running on the one or more processors. At least one of the one or more processors communicates with the sensor and calculates at least one physiological parameters responsive to the sensor. The instrument manager controls the calculation, display and / or alarms based upon the physiological parameters. A configuration indicator identifies the configuration profile. In one aspect of the invention, the physiological sensor is a optical sensor that includes at least one light emitting diode and at least one detector.
Owner:MASIMO CORP
Process control configuration system with parameterized objects
InactiveUS7096465B1OptimizationConfiguration of process controlProgramme controlProgram loading/initiatingControl systemModel system
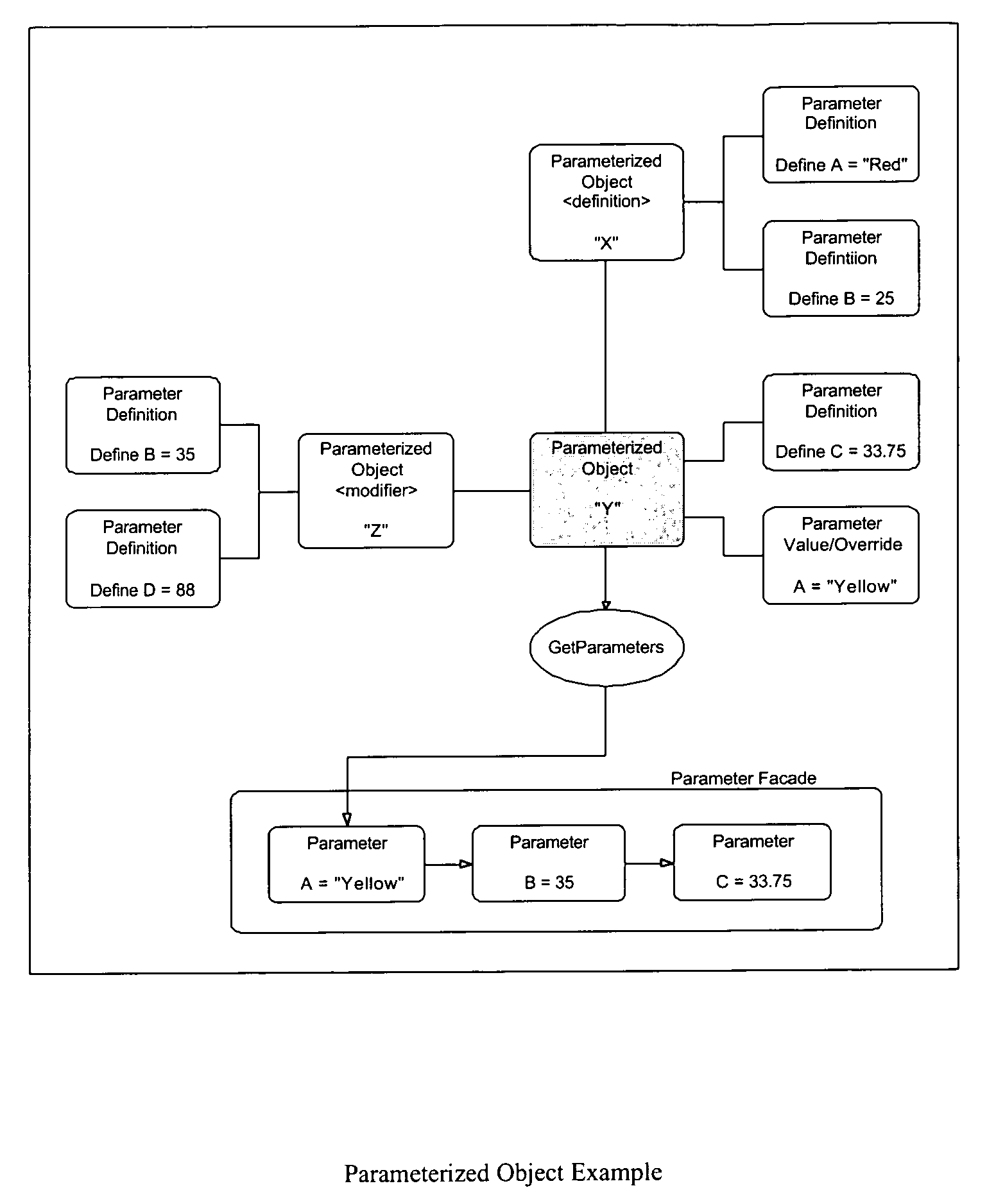
A process control system is configured via manipulation of objects that model system components, e.g., sensors, blocks, control processors, historians, workstations, etc. Individual objects include parameters that characterize the underlying components and / or the behavior of the objects themselves. These parameters are derived from the “parents,” from which the objects are created. Derived characteristics need not be defined explicitly but, rather, are defined implicitly or by reference. These derived characteristics may be overridden for an individual object and, thereby, its progeny. Although objects have class-like characteristics (i.e., insofar as they are definitional in nature), they can be created at configuration time, without the need for recompilation.
Owner:SCHNEIDER ELECTRIC SYST USA INC
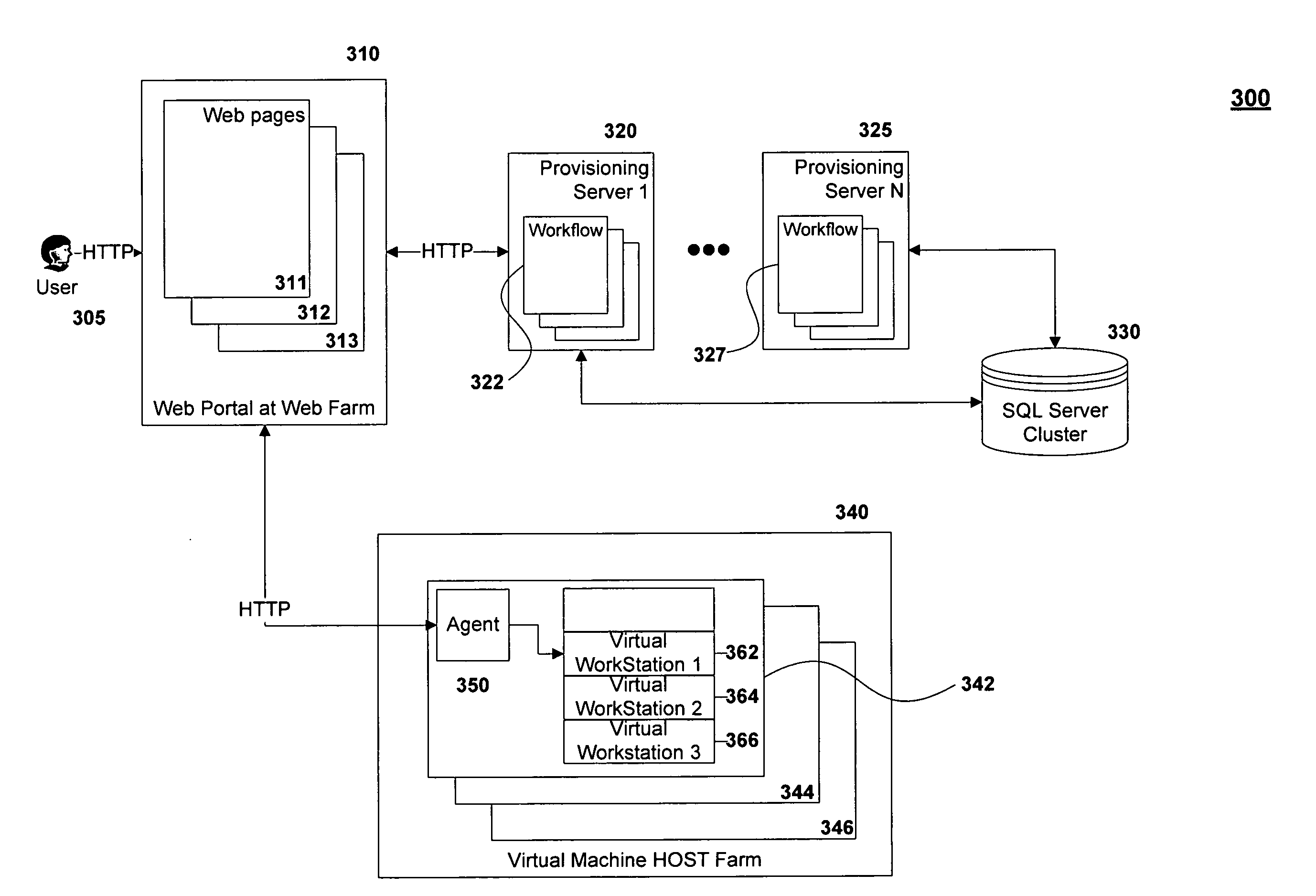
Method and system for managing virtual and real machines
ActiveUS20080244579A1Program initiation/switchingResource allocationVirtual machineConfiguration system
Managing virtual and real machines through a provisioning system. The provisioning system allows a user to create and manage machines through a “self-service” approach. The provisioning system interacts with one or more agents that manage the lifecycle of a machine. The system may provide templates that enable a user to readily create a virtual machine. The system may also include interfaces for administrators to manage virtual and real machine resources.
Owner:VMWARE INC
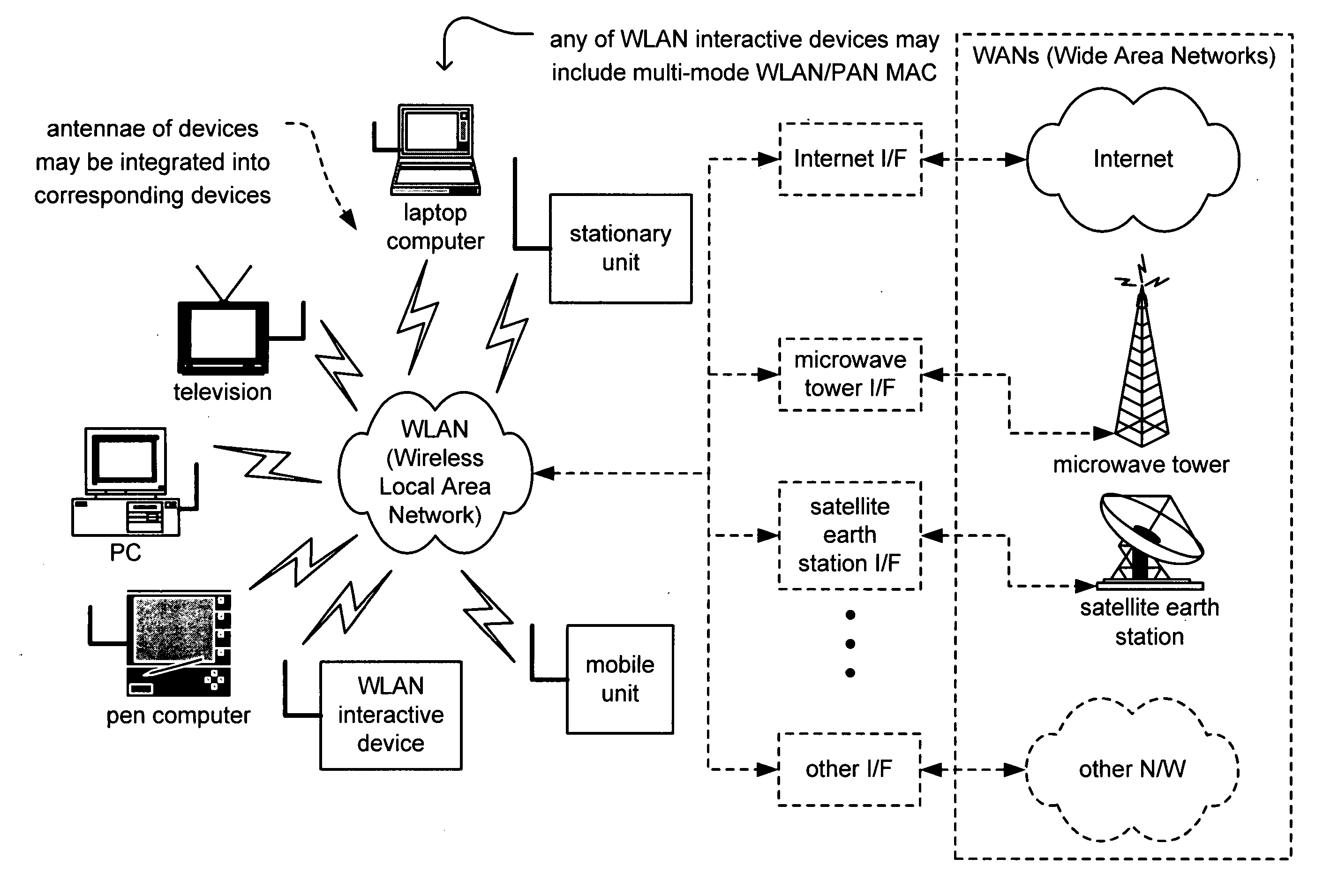
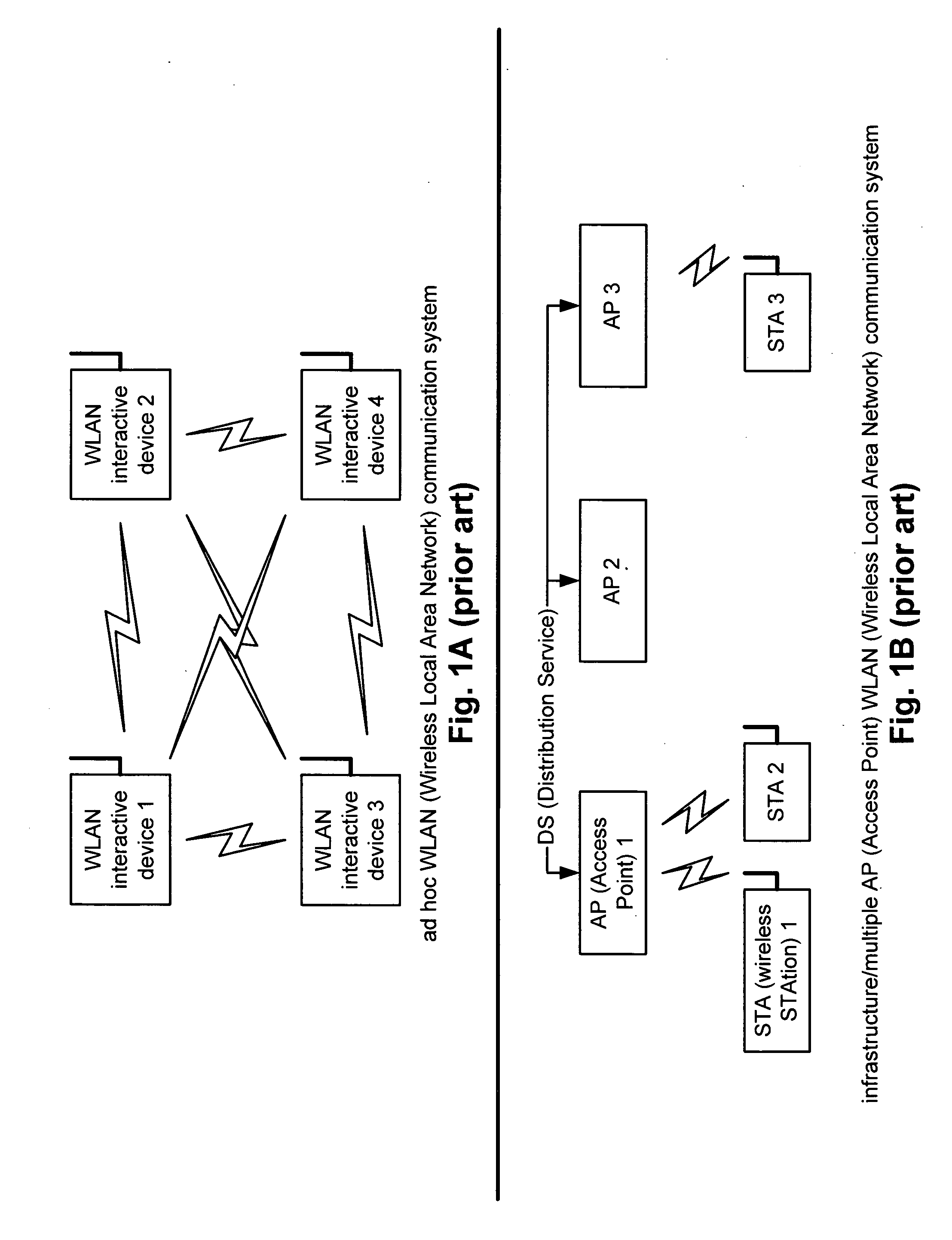
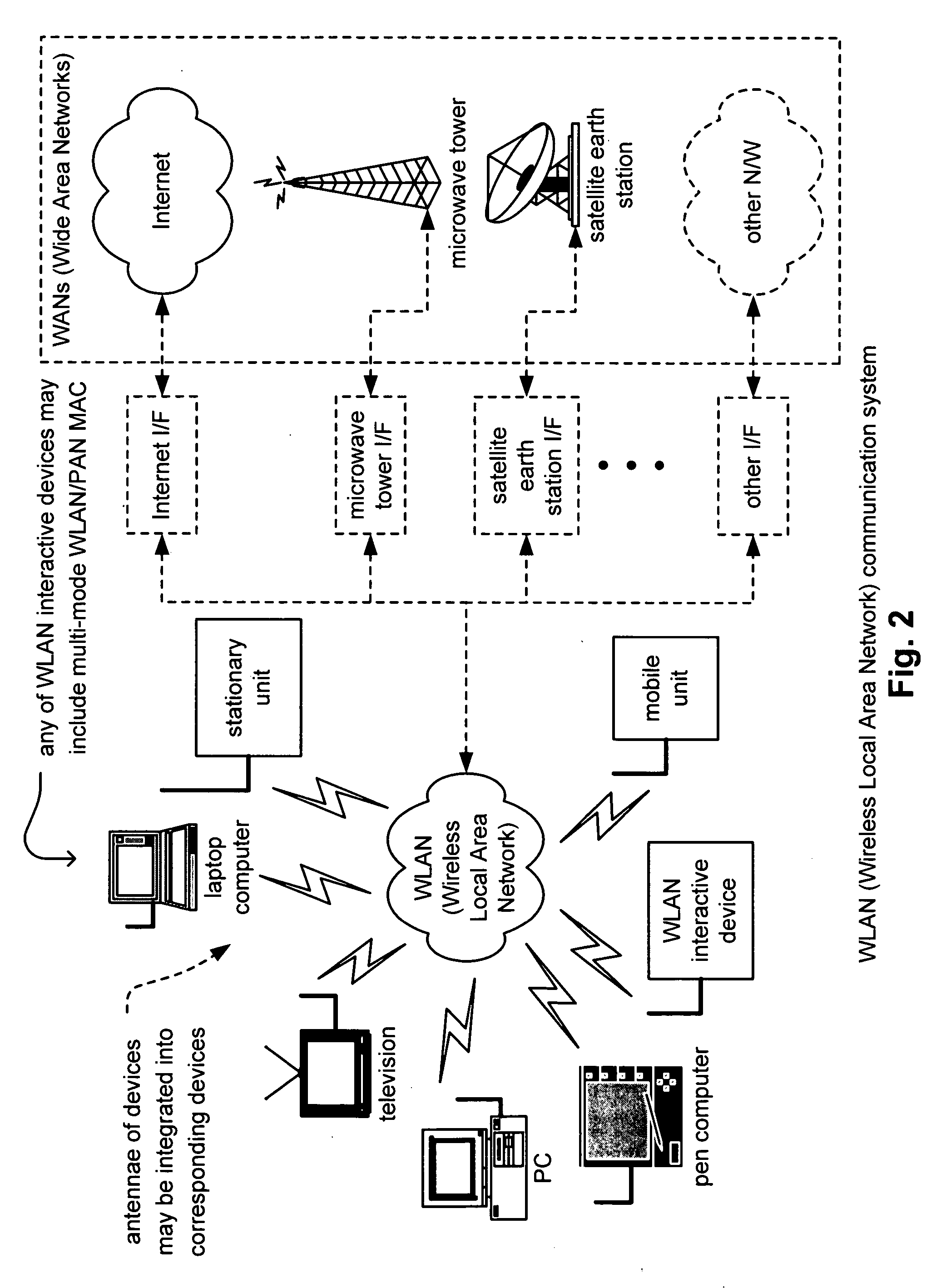
Multi-mode WLAN/PAN MAC
ActiveUS20050147071A1Network topologiesData switching by path configurationCommunications systemWireless lan
Multi-mode WLAN / PAN MAC. A novel solution is presented in which a MAC (Medium Access Controller) is implemented that includes multiple functionality types. This MAC may include functionality supporting communication according to one or more of the IEEE 802.11 WLAN (Wireless Local Area Network) related standards and also to one or more of the standards generated by the IEEE 802.15.3 PAN (Personal Area Network) working group. By providing this dual functionality of a multi-mode WLAN / PAN MAC, a communication device may adaptively change the manner in which it communicates with other communication devices. For example, in an effort to maximize throughput and overall efficiency of communication within a communication system, certain of the various devices may change from using the WLAN related standards to using the PAN related standards, and vice versa, based on any one or more of a variety of operational parameters including system configuration.
Owner:AVAGO TECH INT SALES PTE LTD
System and Method to Control a Wireless Power Transmission System by Configuration of Wireless Power Transmission Control Parameters
ActiveUS20160056966A1Preventing contradictory configurationNetwork topologiesHybrid transportElectric forceWeb browser
A system and method to control a wireless power transmission system by configuration of wireless power transmission control parameters is disclosed. The configuration of the system may be performed by an operator using a standard web browser on a computing device where the system configuration GUI presented to the operator may be functionally identical regardless of the computing device running the browser. The system configuration GUI may be connected to system through a system configuration API. According to some aspects of this embodiment, a method to control wireless power transmission system by configuration of wireless power transmission control parameters may include accessing the system configuration GUI, displaying operational or other parameter to configure the system, selecting an operational parameter, configuring the selected operational parameter, and then continuing to configure others operational parameter if needed, storing configuration parameters in the computer memory, and communicating configuration parameters to others system computers.
Owner:ENERGOUS CORPORATION
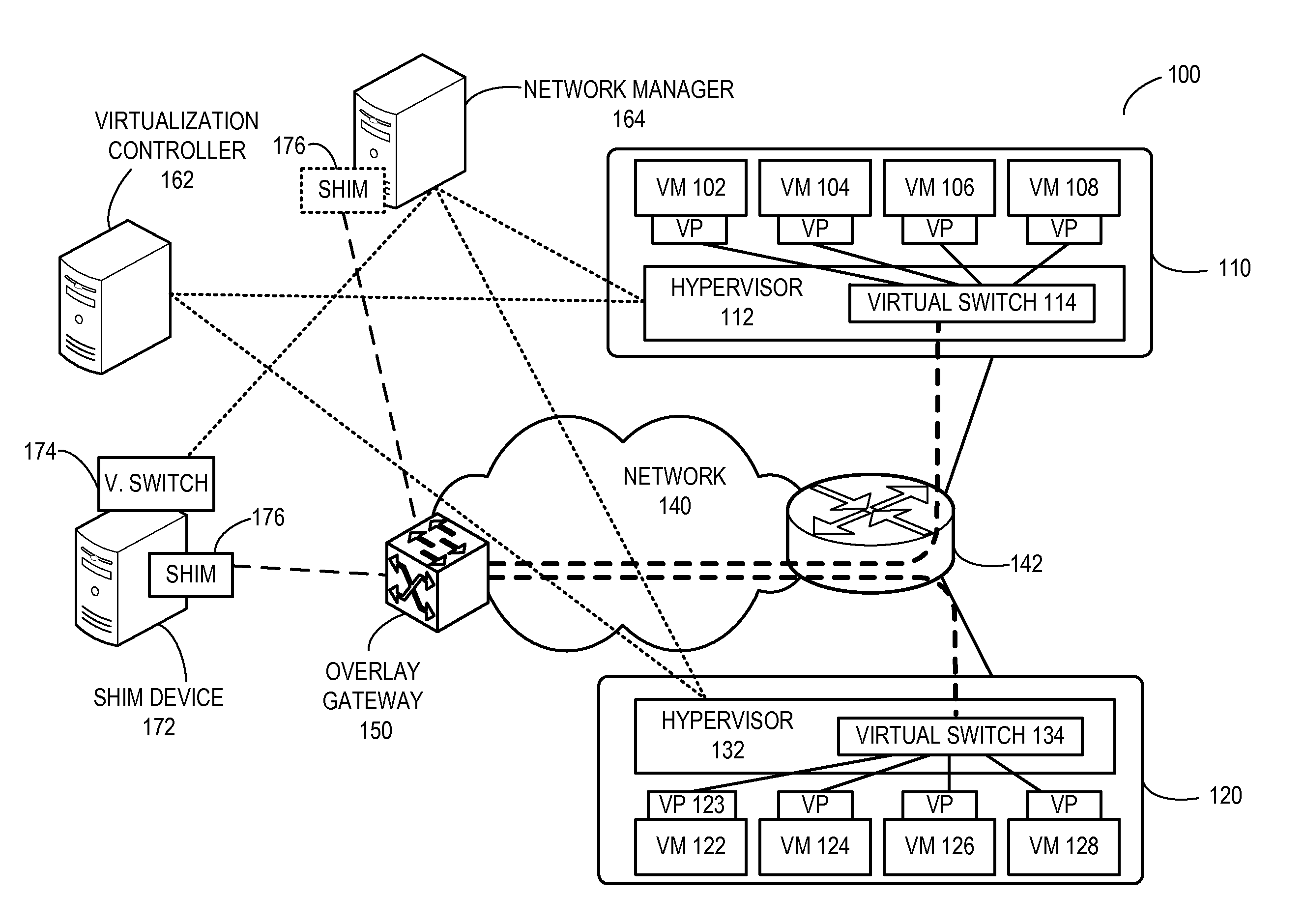
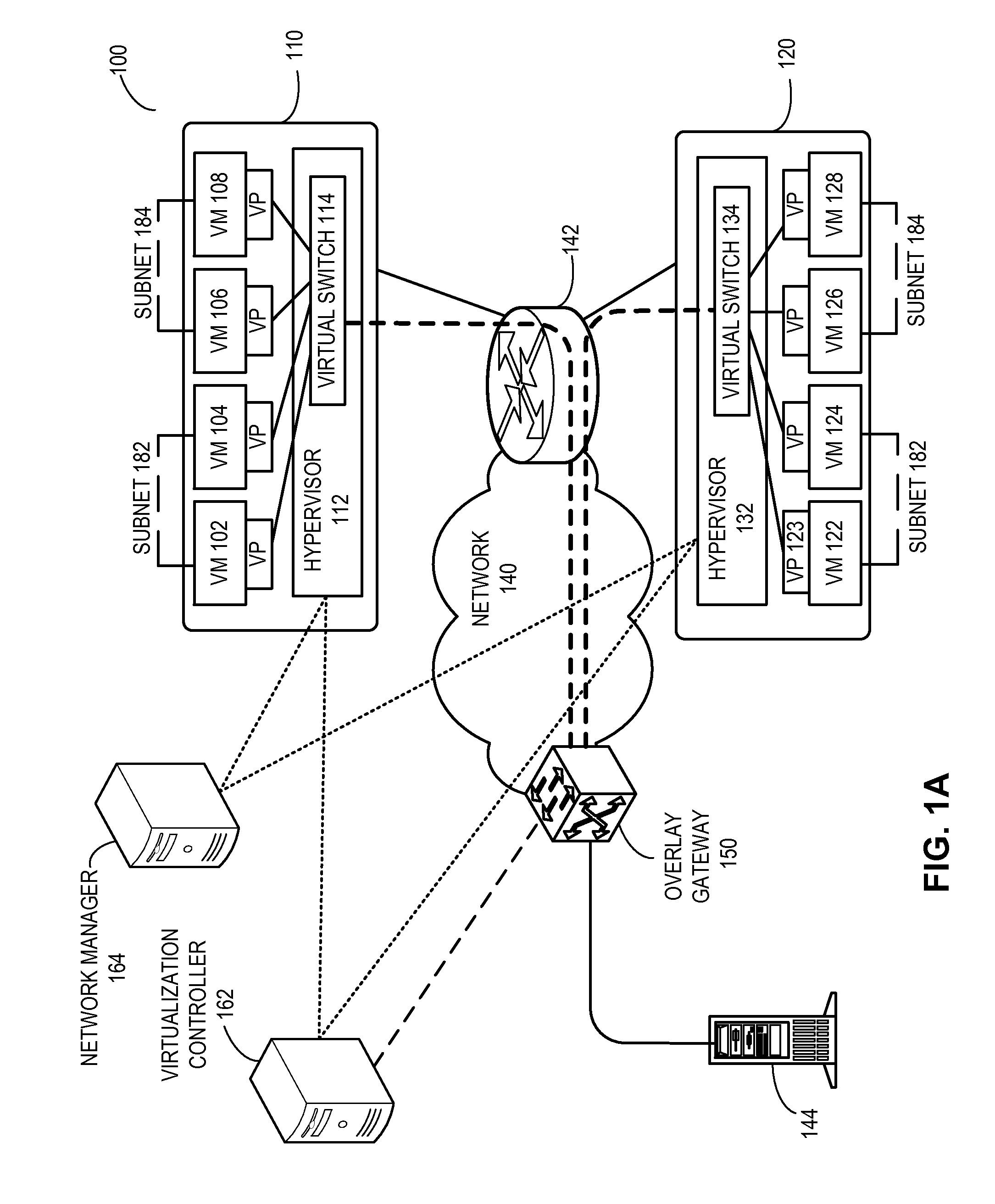
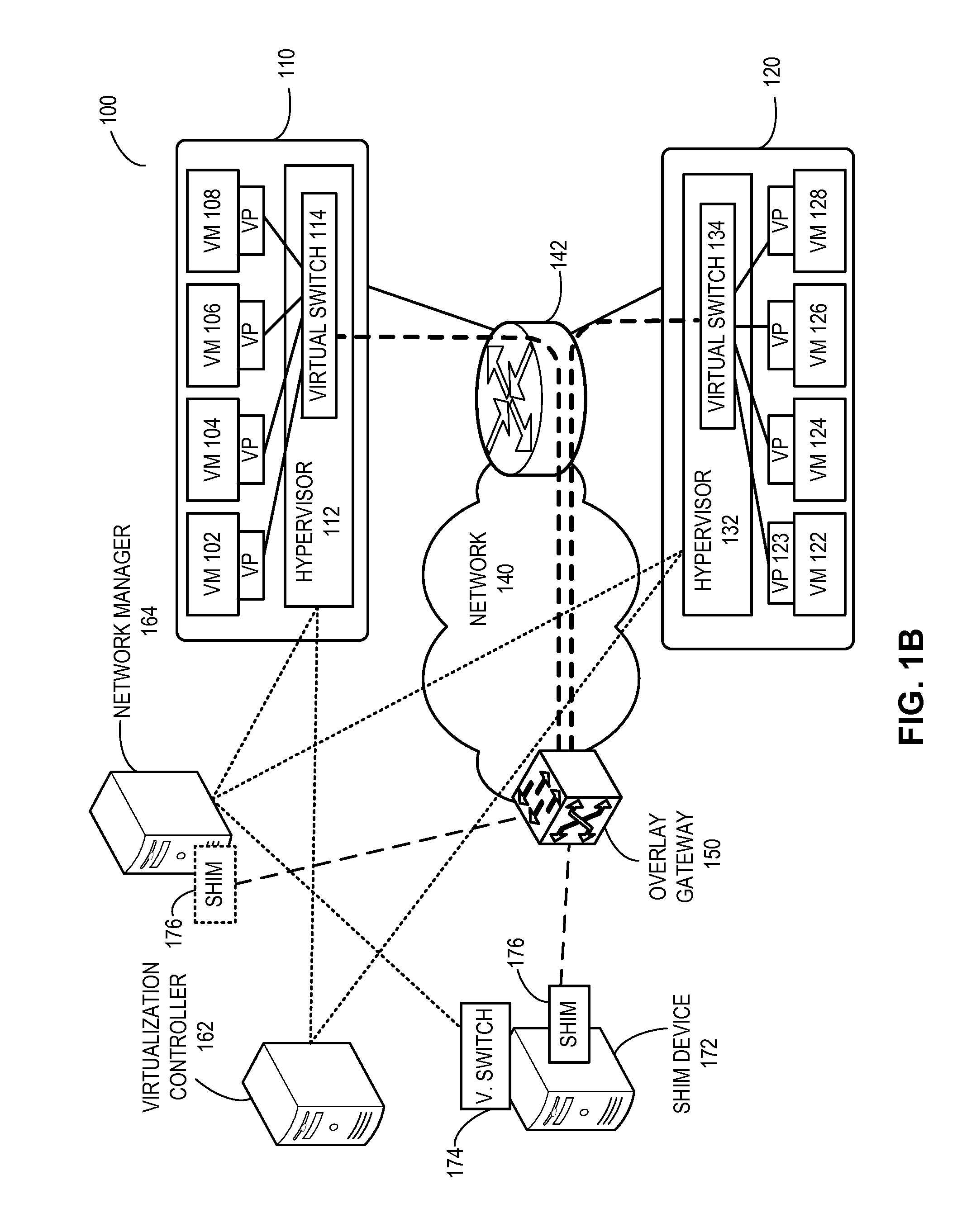
Layer-3 overlay gateways
ActiveUS20130318219A1Digital computer detailsData switching networksInternet ProtocolStore instruction
One embodiment of the present invention provides a computing system. The computing system includes a processor and a computer-readable storage medium for storing instructions. Based on the instructions, the processor operates the computing system as an overlay gateway. The computing system initiates and terminates an overlay tunnel associated with a virtual machine. During operation, the computing system maps a virtual Internet Protocol (IP) address of the virtual machine to a second IP address used to terminate the overlay tunnel based on information received from a configuration system. The computing system then determines an output port for a data packet based on the second IP address. The data packet comprises an inner packet and the destination address of this inner packet corresponds to the virtual IP address.
Owner:AVAGO TECH INT SALES PTE LTD
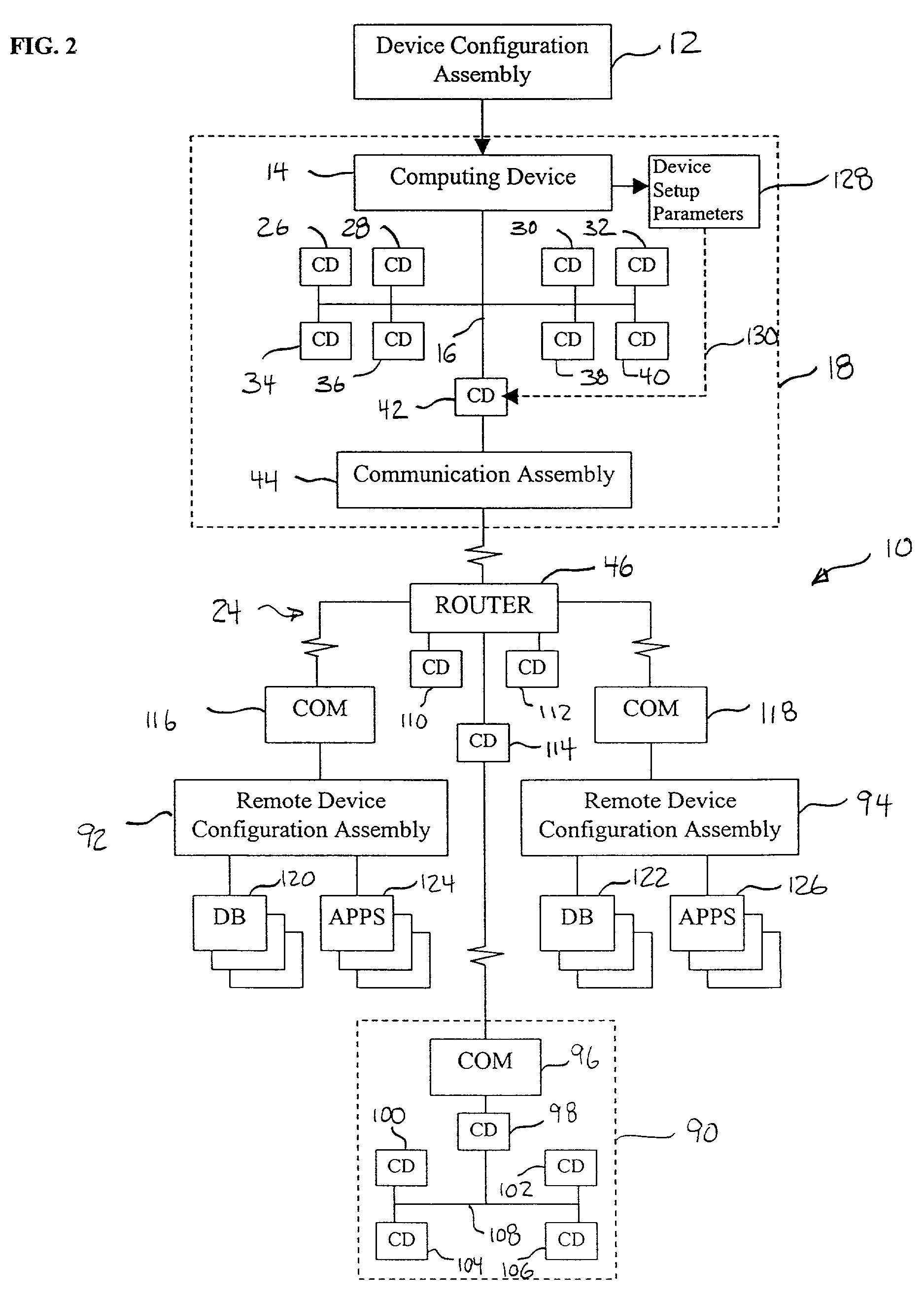
System and method for remote discovery and configuration of a network device
A technique for remotely configuring a computing device via a network. A device configuration system is provided to determine a network address of the computing device, to identify the computing device, and to facilitate network configuration of the computing device. The device configuration system also may include a remote interface and a remote device information system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and apparatus for dynamic configuration of multiprocessor system
InactiveUS7146260B2Registering/indicating working of vehiclesError detection/correctionData managementApplication software
Owner:MICROPAIRING TECH LLC
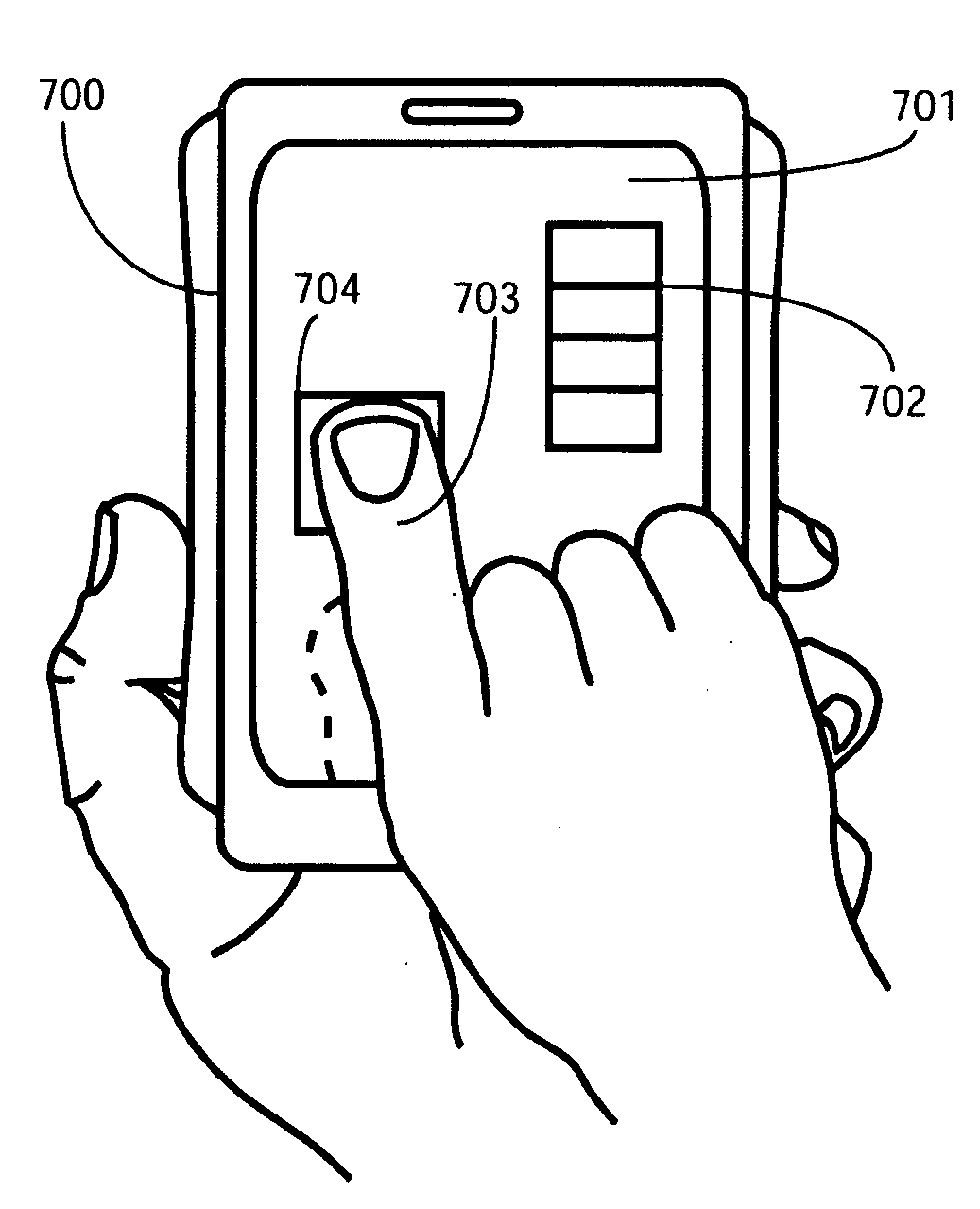
Menu Configuration System and Method for Display on an Electronic Device
InactiveUS20100271312A1Input/output processes for data processingHuman–computer interactionElectronic equipment
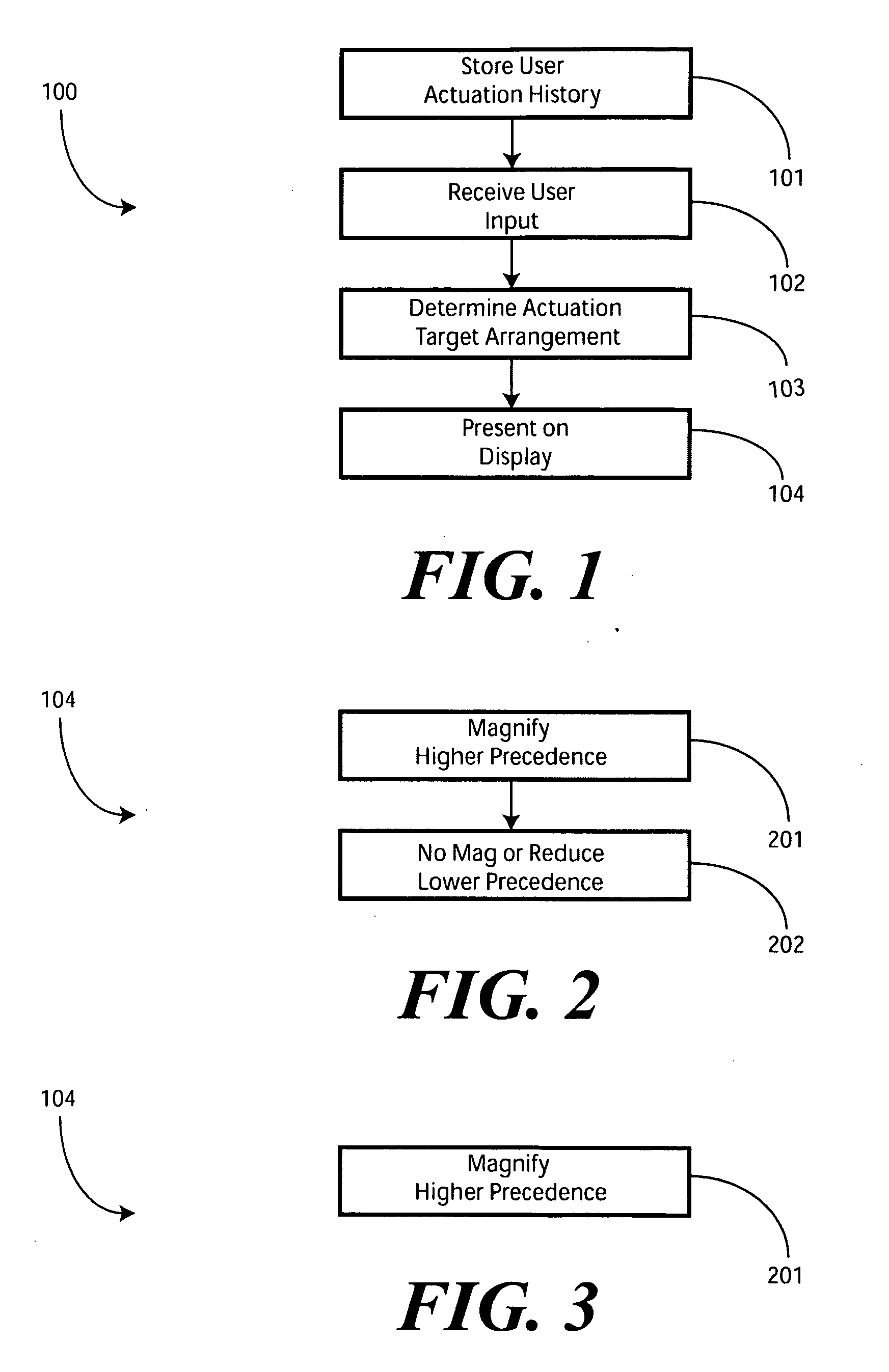
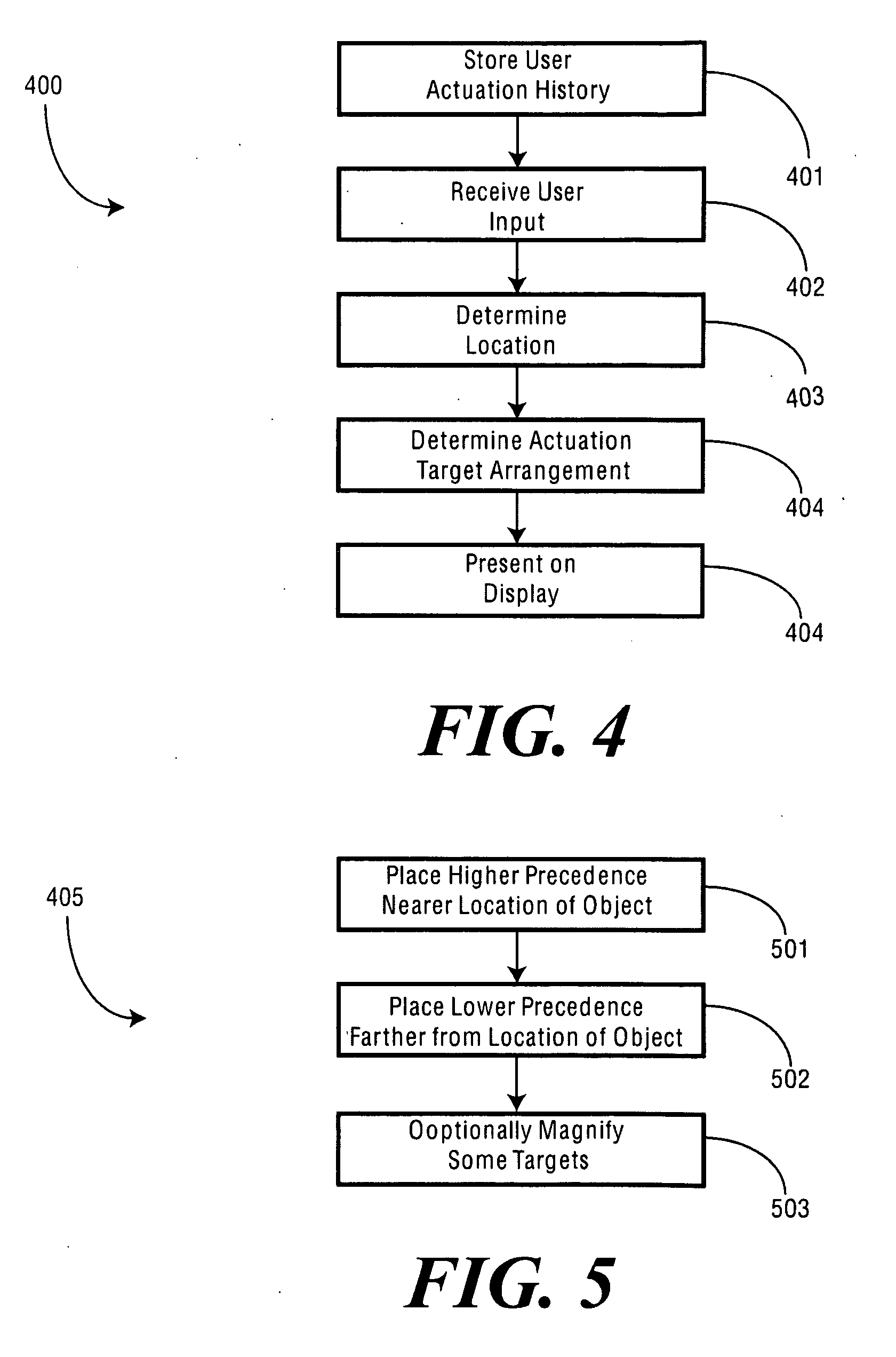
A method (100) and electronic device (700) for presenting user actuation targets (1101,1102,1103) on a touch sensitive display (701) includes a controller (805) configured to determine a user actuation target arrangement (1500) having a hierarchy of precedence (1501). A display driver (809) is then configured to present the user actuation targets (1101,1102,1103) on the touch sensitive display (701) in accordance with the user actuation target arrangement (1500). This can include presenting user actuation targets (1201,1202) having a higher precedence closer to a user's finger (1206) than user actuation targets (1203,1204) having a lower precedence, or by magnifying user actuation targets (1201,1202) having a higher precedence. Precedence can be determined by most frequently selected targets, most recently selected targets, or other factors.
Owner:MOTOROLA MOBILITY LLC
System supporting multiple partitions with differing translation formats
ActiveUS20140101361A1Memory architecture accessing/allocationMemory adressing/allocation/relocationSingle levelComputer science
A system configuration is provided with multiple partitions that supports different types of address translation structure formats. The configuration may include partitions that use a single level of translation and those that use a nested level of translation. Further, differing types of translation structures may be used. The different partitions are supported by a single hypervisor.
Owner:IBM CORP
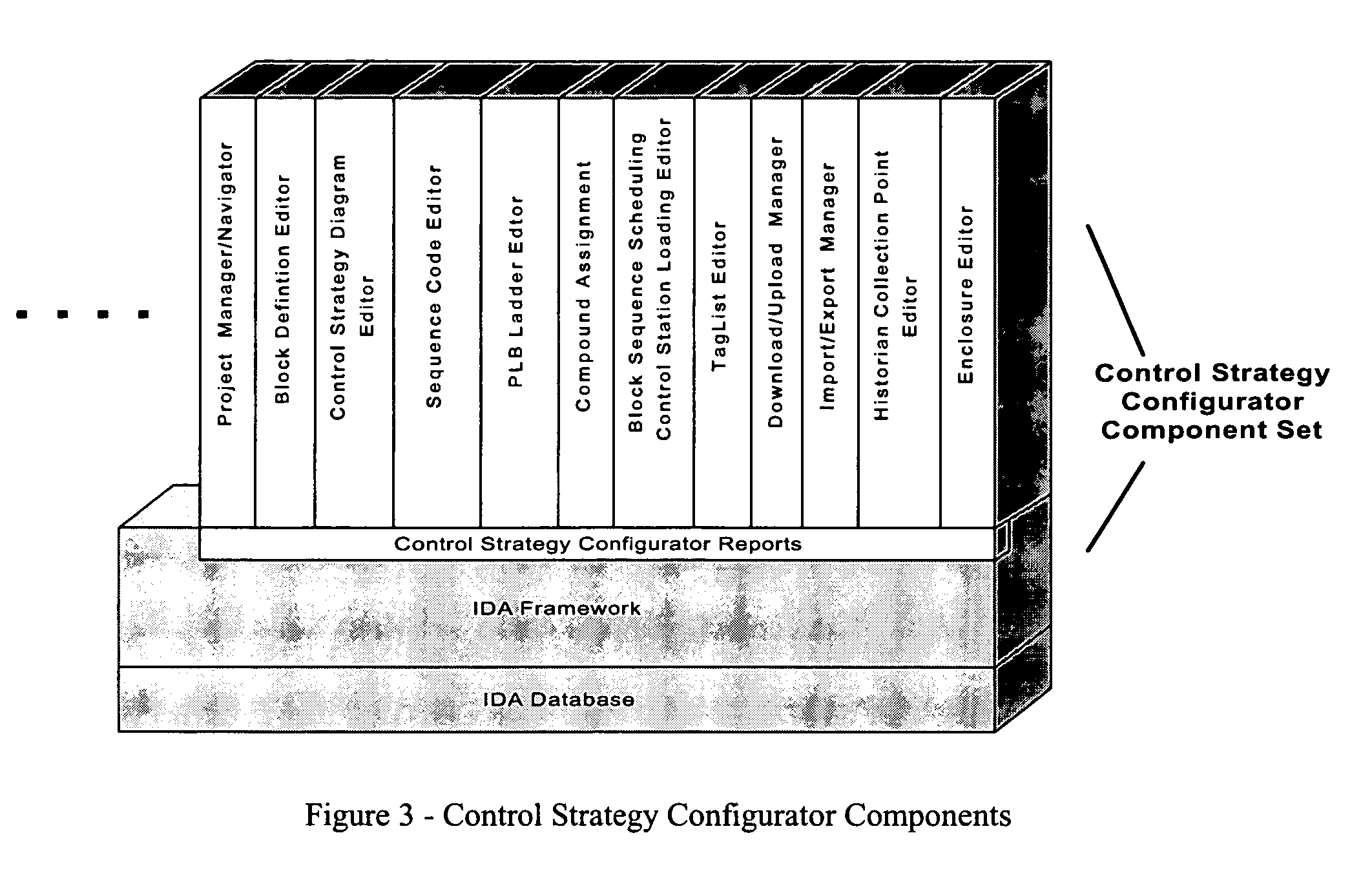
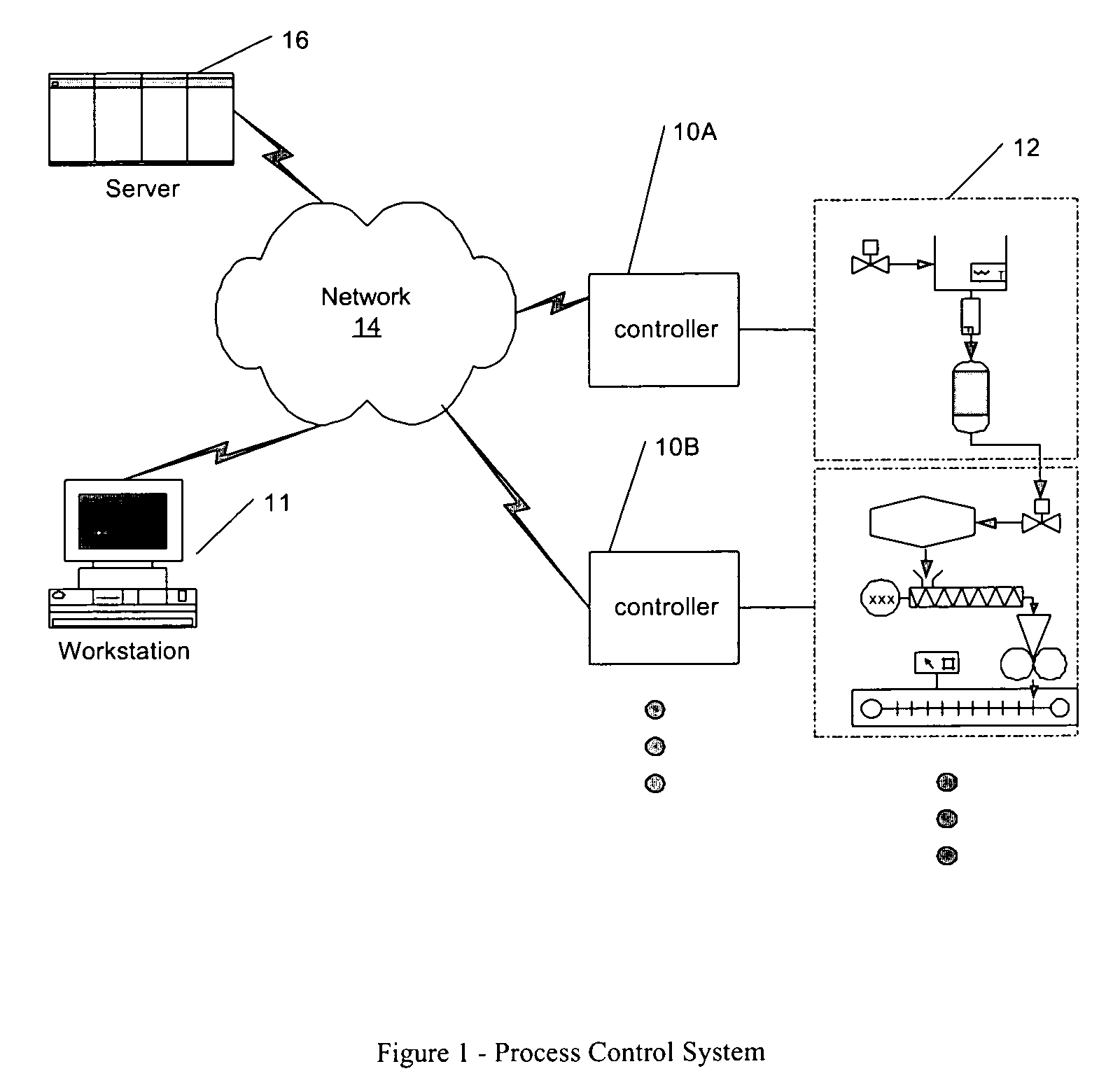
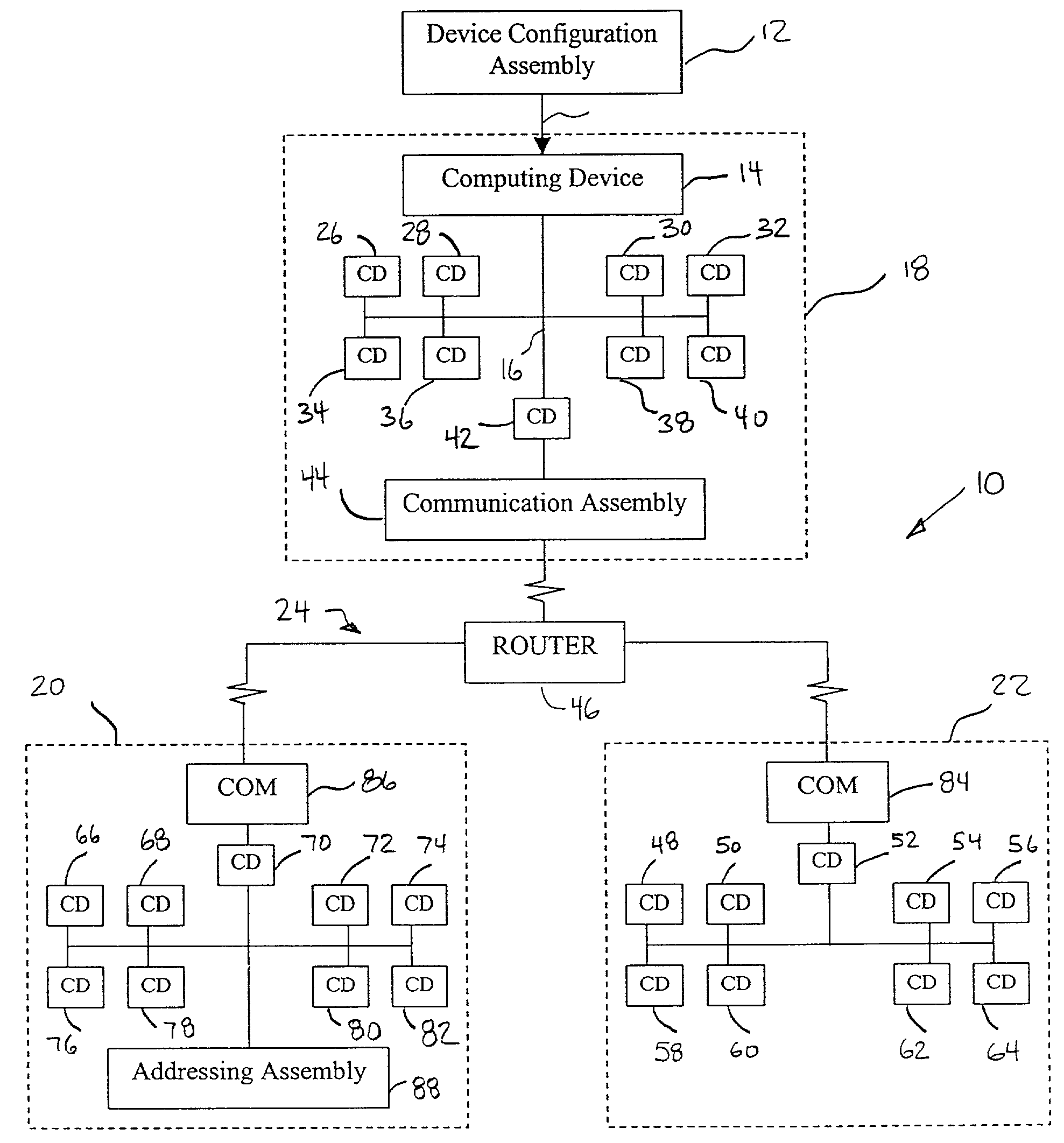
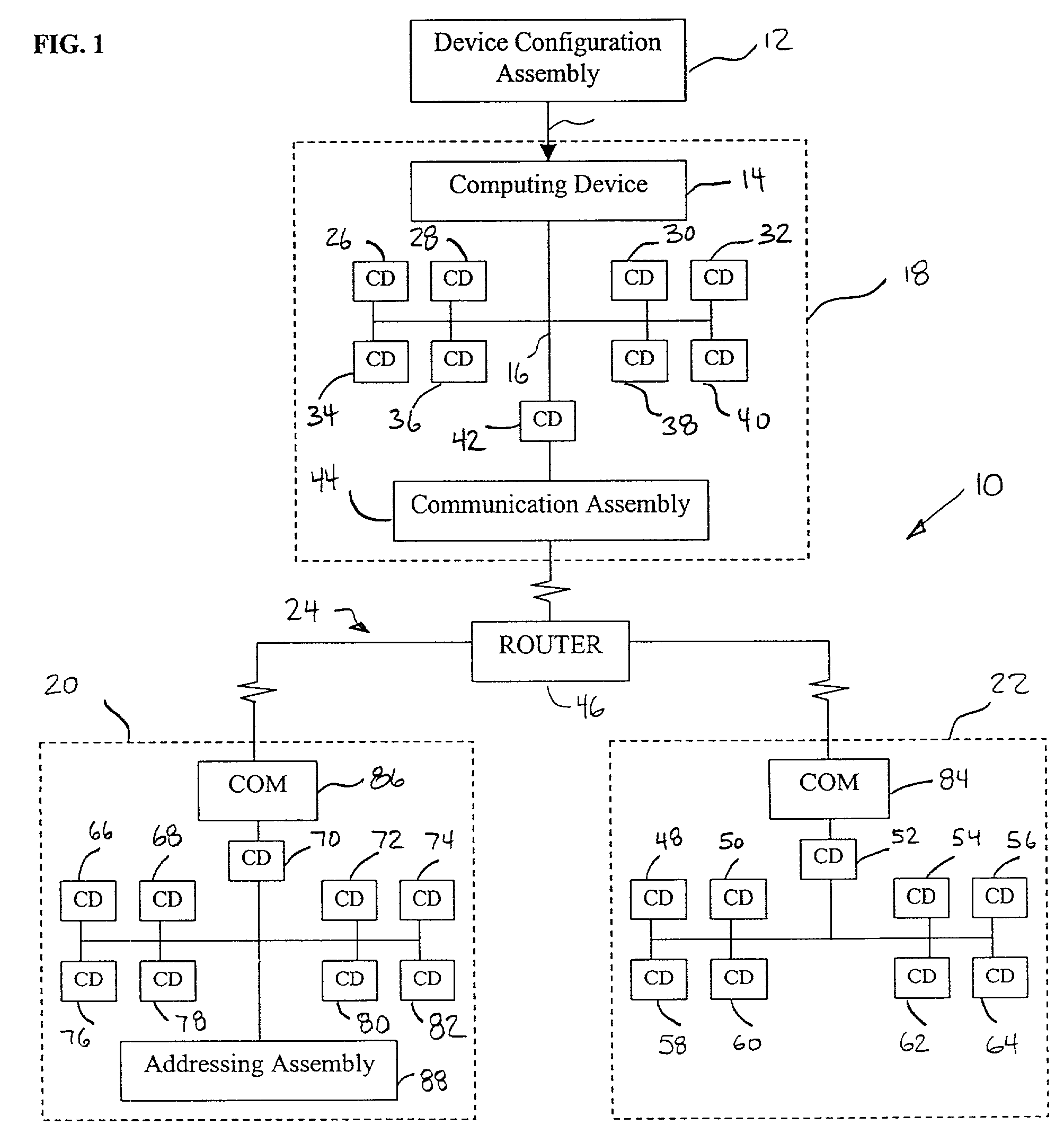
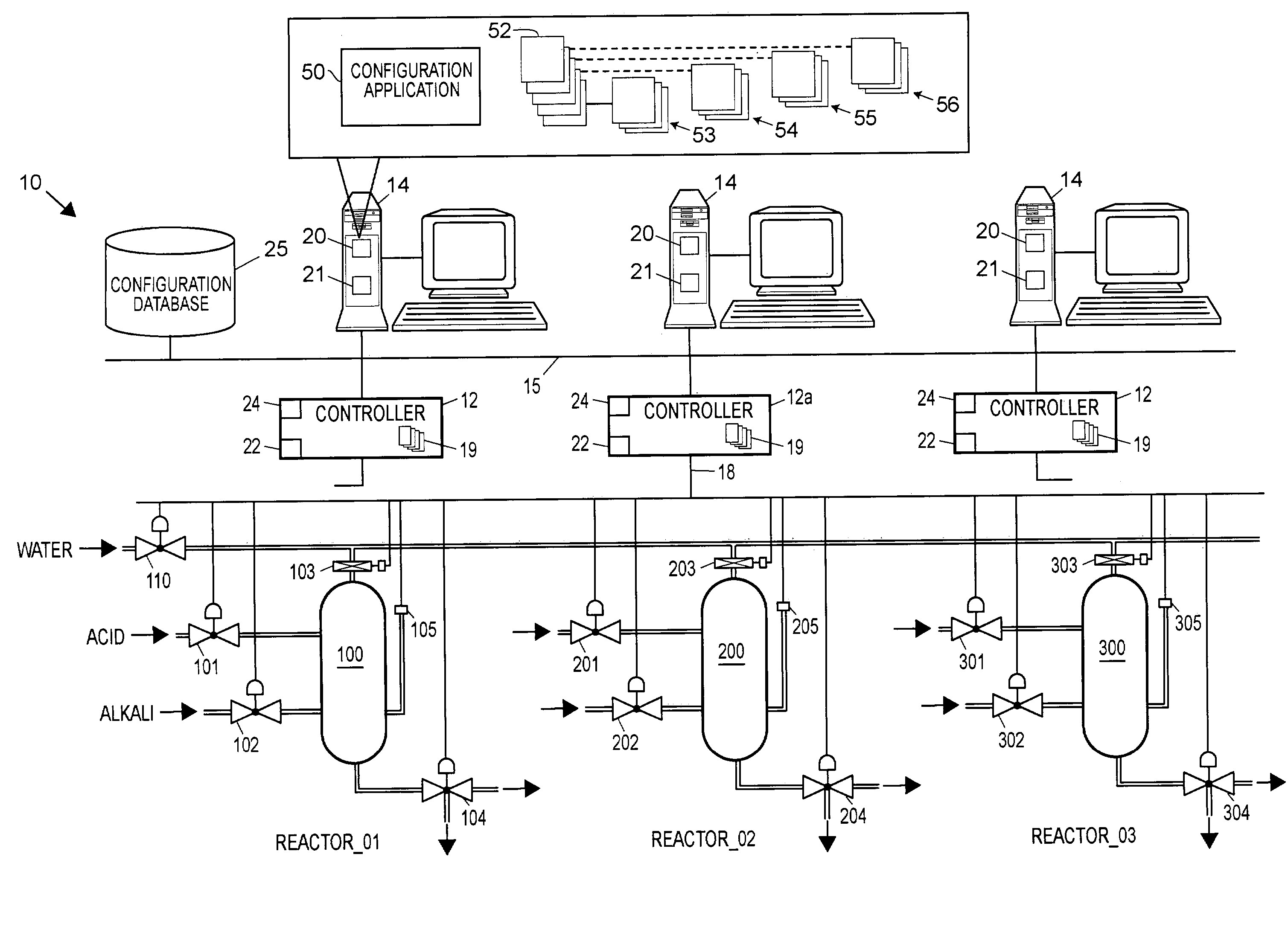
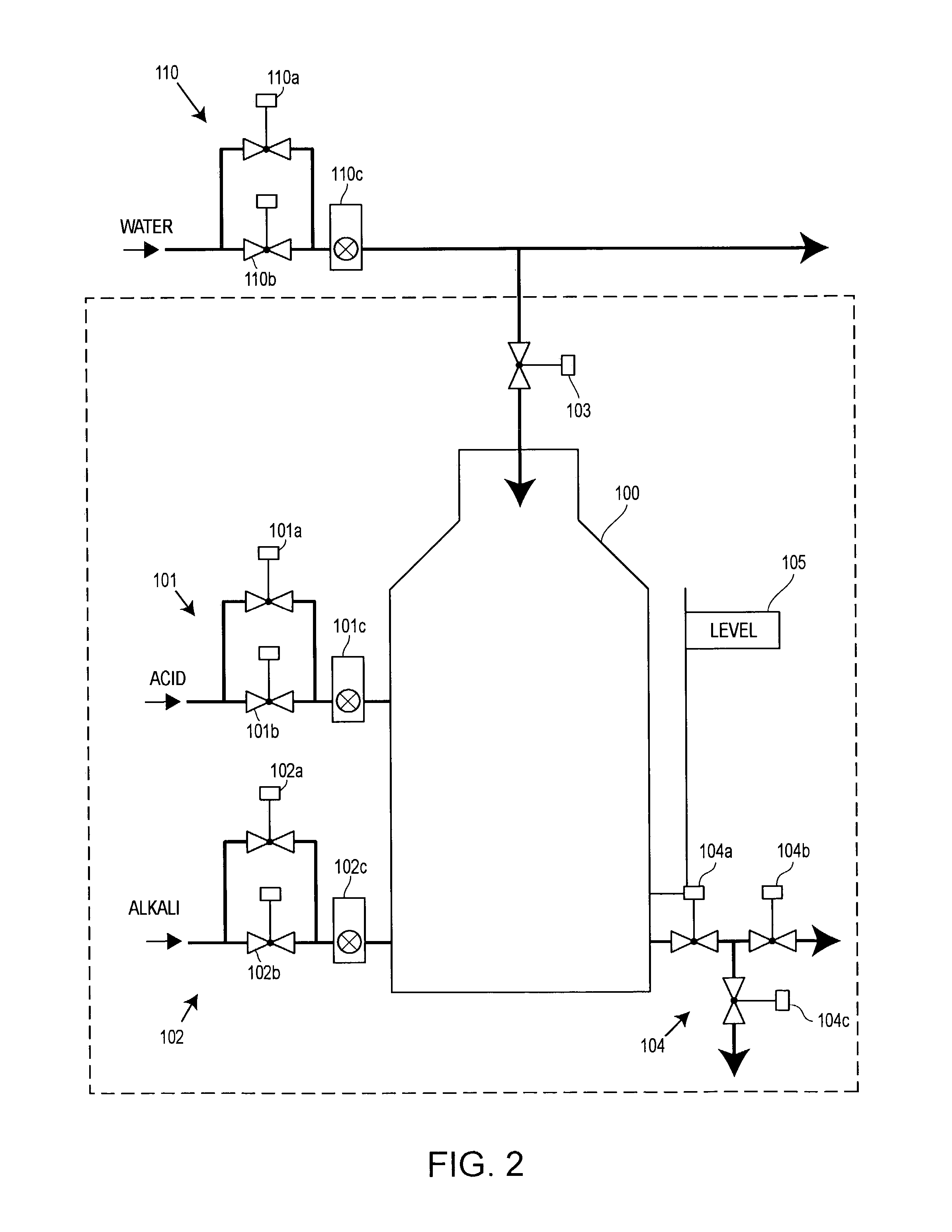
Integrated configuration system for use in a process plant
An integrated configuration viewing system for use in a process plant includes a computer readable memory and a plurality of template configuration objects stored on the computer readable memory. Each of the plurality of template configuration objects includes a graphical representation of a physical entity within the process plant, a parameter storage adapted to communicate with the process plant to obtain and store device parameter information associated with the physical entity within the process plant, and a configuration storage adapted to store configuration parameters associated with the physical entity within the process plant. A first routine is stored on the computer readable memory and adapted to be executed on the processor to present a library section on a user interface. The library section is adapted to present depictions of the plurality of template configuration objects to a user via the user interface. A second routine is stored on the computer readable memory and adapted to be executed on the processor to present a configuration area on the user interface. And a third routine is stored on the computer readable memory and adapted to be executed on the processor to enable a user to select one of the plurality of template configuration objects from the library section and to place the selected template configuration object within the configuration area to create a process configuration module within the configuration area.
Owner:FISHER-ROSEMOUNT SYST INC
Host-centric storage provisioner in a managed SAN
ActiveUS7657613B1Digital data processing detailsMultiple digital computer combinationsComputerized systemOperating system
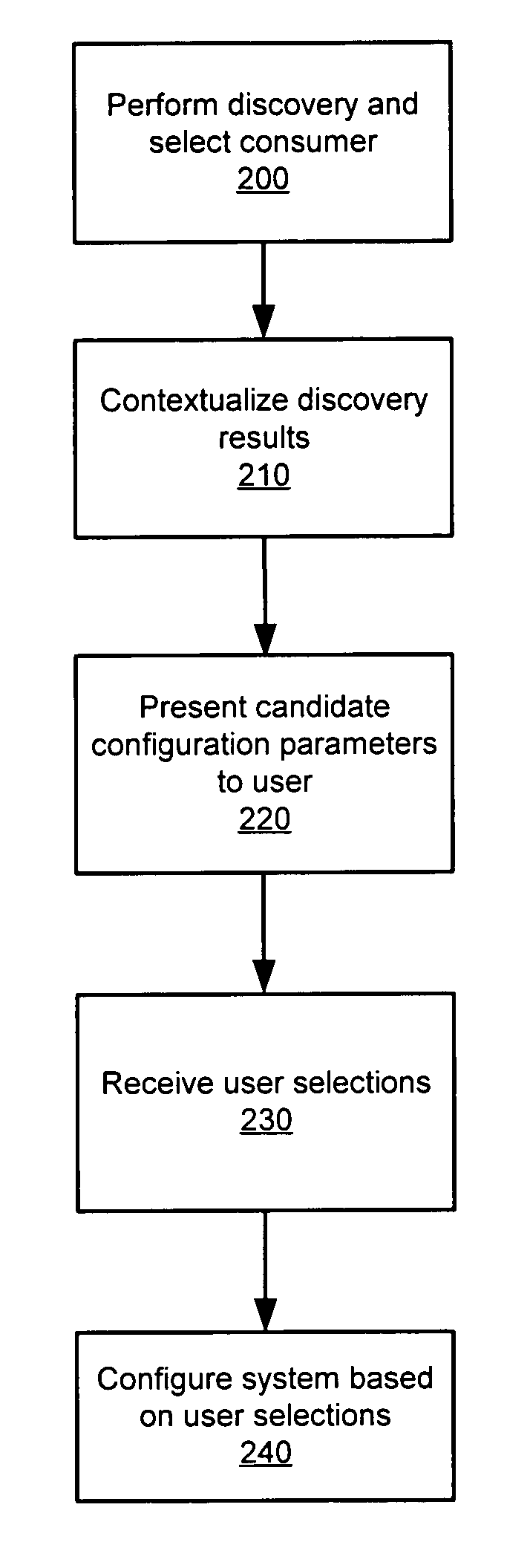
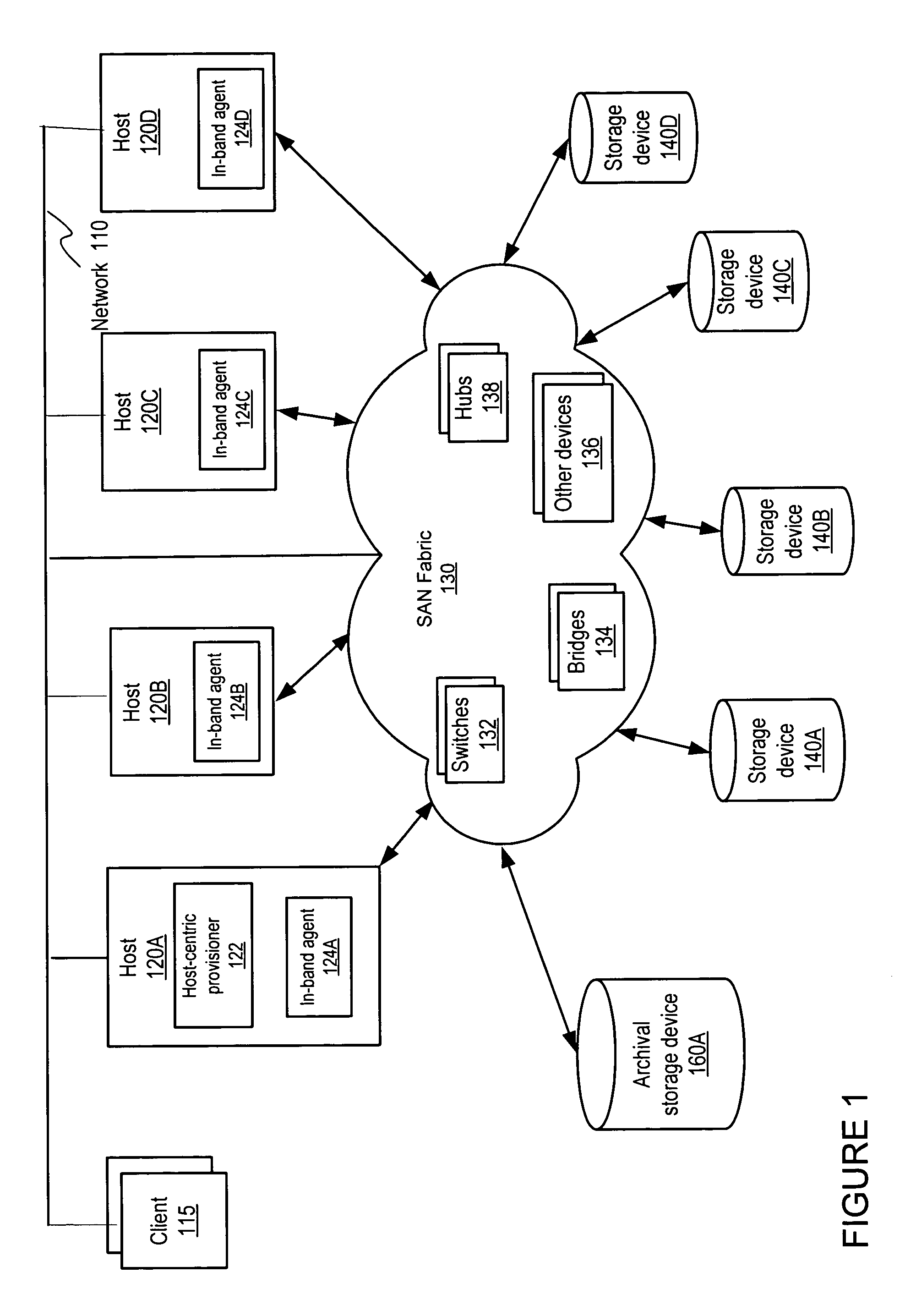
Various embodiments of a system and method for provisioning a storage consumer with storage in a SAN networked computer system are disclosed. A SAN networked computer system may include one or more consumers of storage, such as host computers, a plurality of storage devices, and one or more SAN fabrics including the devices needed to connect the storage consumers to the storage devices. The system may also include a storage consumer-centric storage provisioner. To provide a storage consumer with storage, the storage consumer-centric storage provisioner may perform discovery on the system to acquire topologic information on the system along with the characteristics of system components. The storage provisioner may contextualize the information into the perspective of the storage consumer to present a user with candidate system configuration parameters from which to select, and when sufficient parameter selections have been input, the provisioner may configure the system according to the user selections.
Owner:ORACLE INT CORP
Module class objects in a process plant configuration system
ActiveUS7043311B2Configuration of process easyLess time-consumingProgram control using stored programsComputer controlComputer scienceTime-Consuming
A configuration system for a process plant uses module class objects to assist in configuring, organizing and changing the control and display activities within the process plant. Each module class object generically models or represents a process entity, such as a unit, a piece of equipment, a control activity, etc., and may be used to create instances of the object, called module objects, which represent and are tied to specific equipment within the process plant. The module class objects may represent process entities of any desired scope, which means that a single module class object may be used to configure the control and display activities of process entities of any desired scope within the process plant, instead of just at a control module level. In particular, module class objects of a large scope may be used to configure large sections or portions of the process plant, which makes configuration of the process plant easier and less time consuming. A module class object may be a unit module class object reflecting a physical unit within the process plant, an equipment module class object reflecting a physical piece of equipment within the process plant, a control module class object reflecting a control module or scheme within the process plant, or a display module class object reflecting a display routine that provides information to a user within the process plant.
Owner:FISHER-ROSEMOUNT SYST INC
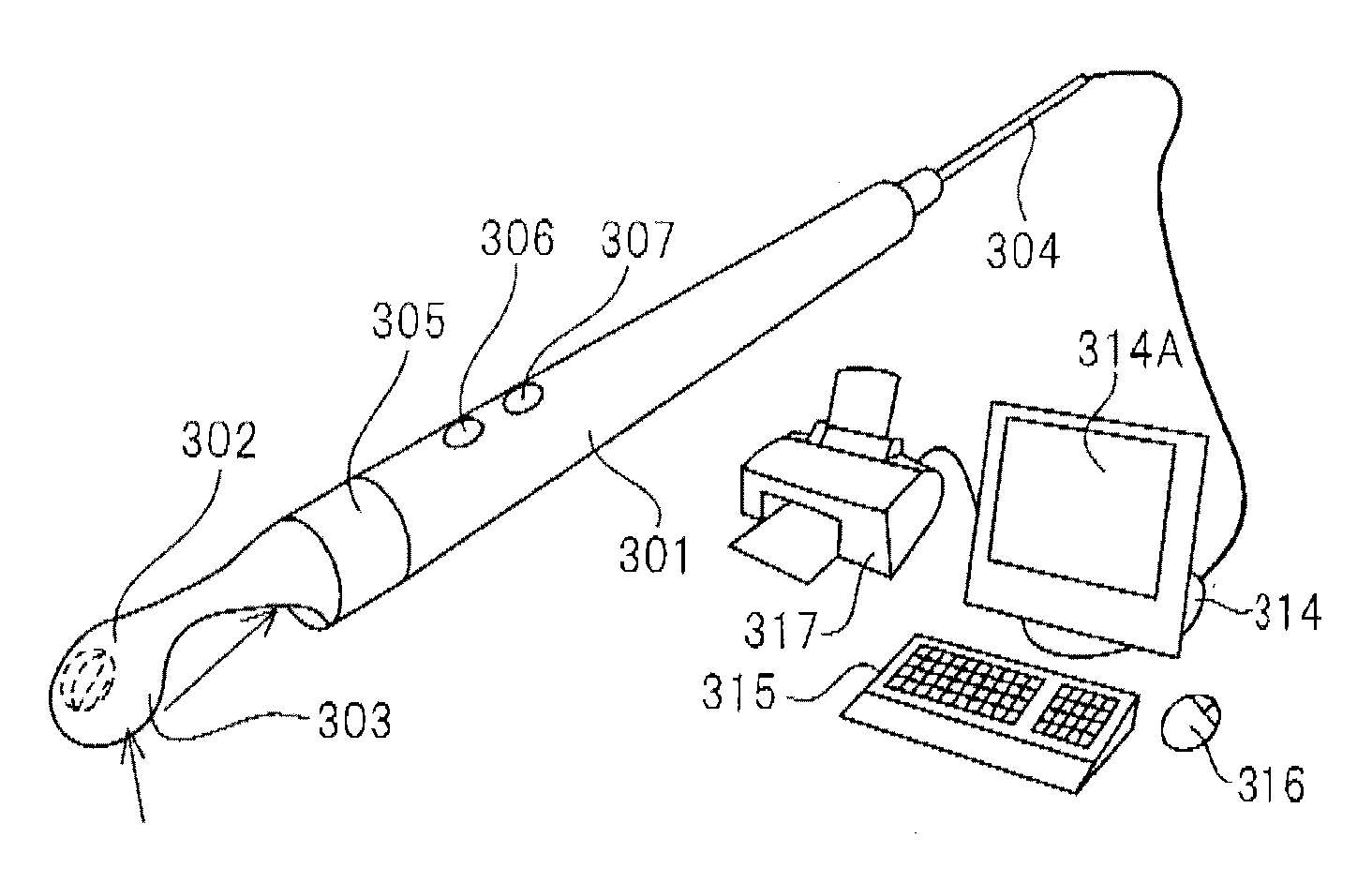
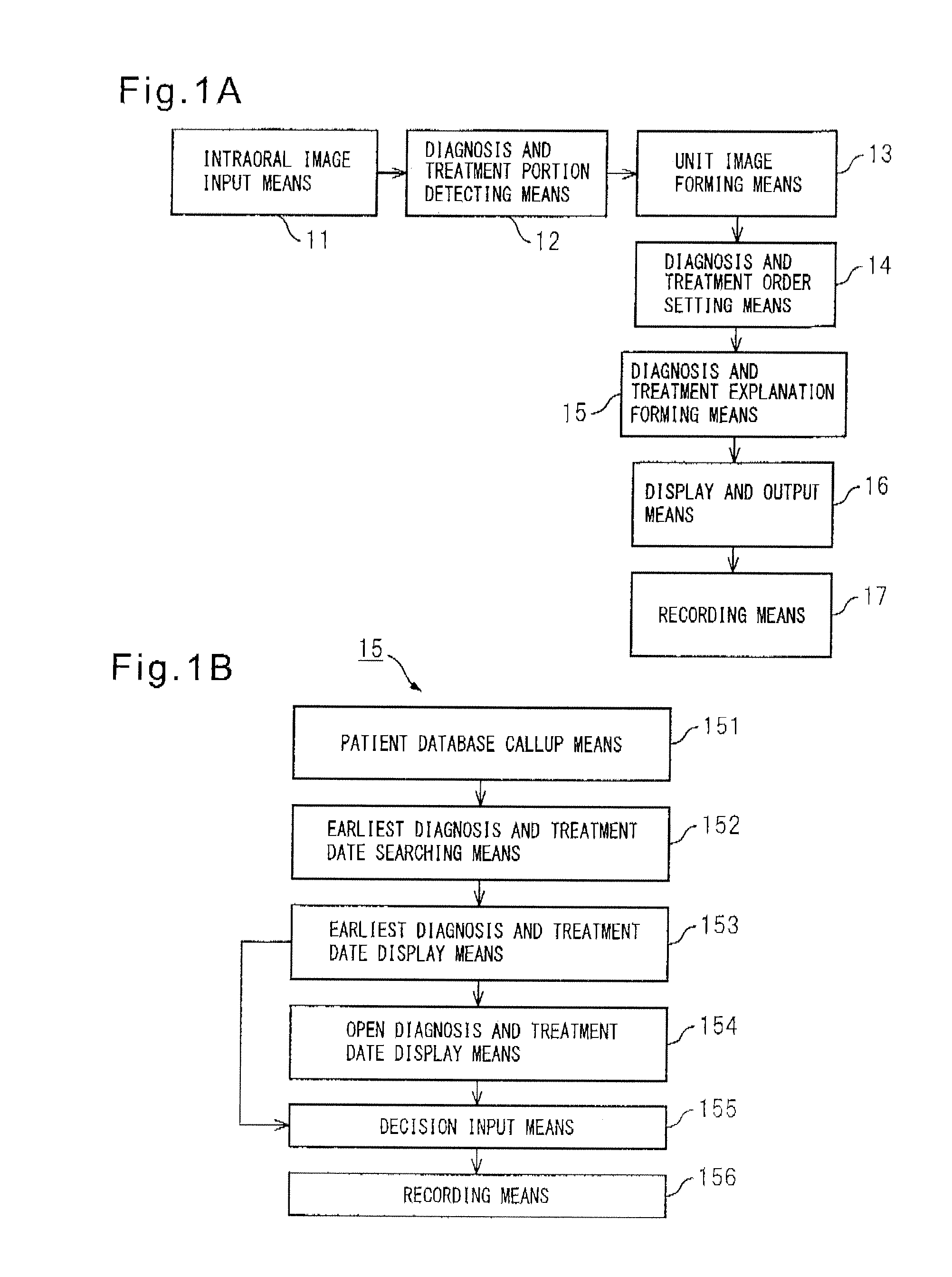
Intraoral video camera and display system
InactiveUS20130286174A1Accurate displayEasy to watchImpression capsSurgeryComputer monitorSurface tooth
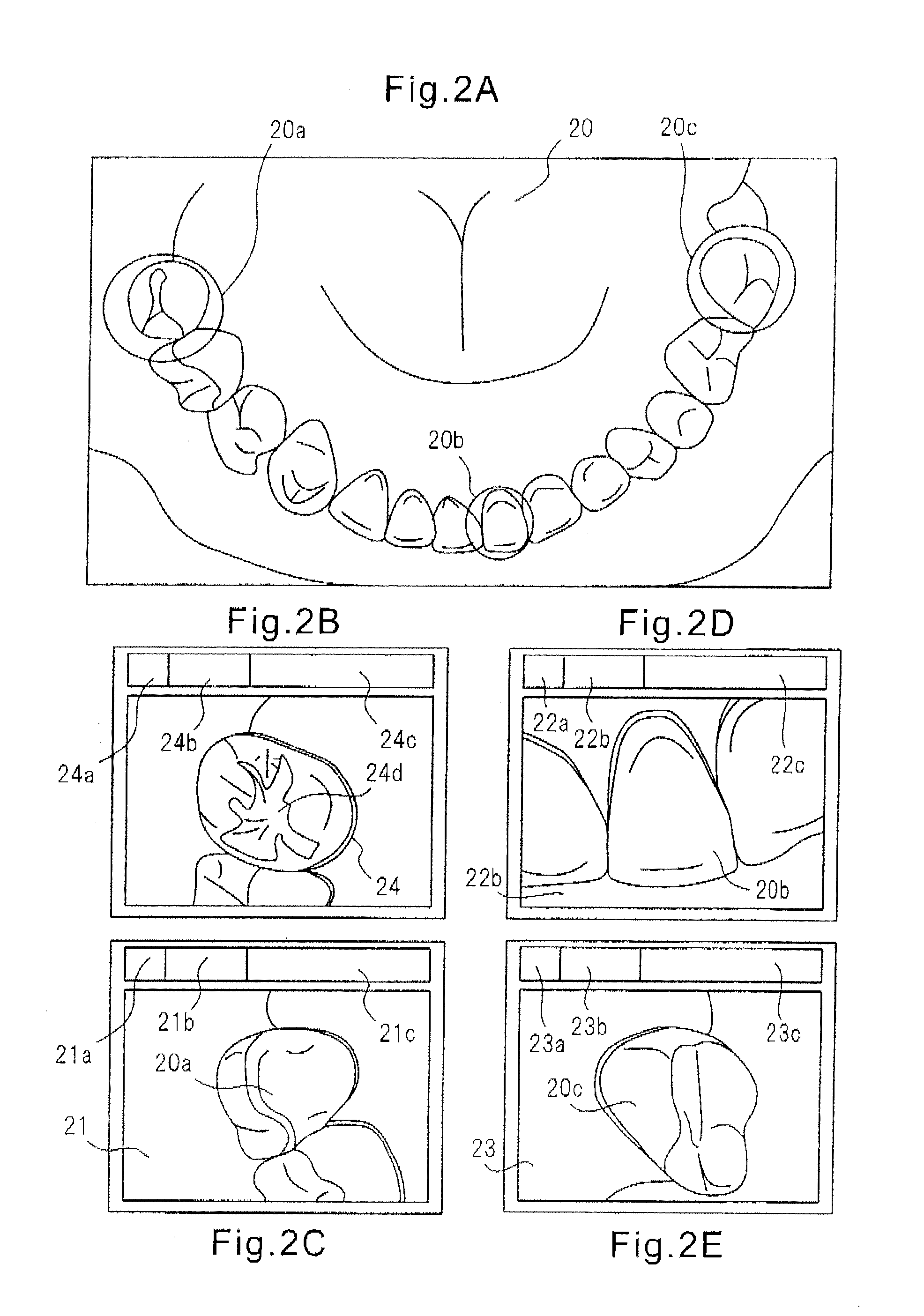
A system configured provided with a continuously captured image sequence forming means for continuously capturing side surfaces of rows of teeth to form an image sequence, a side surface tooth row image forming means for combining sequences of images which were formed by the continuously captured image sequence forming means as partial tooth row images from an image forming the center of the overall composite so as to form a plurality of partial tooth row images, and a side surface tooth row image combining means for linking and combining a plurality of partial tooth row images which were formed by the side surface tooth row image forming means based on images farming the centers of the overall composite so as to form overall rows of teeth. By configuring the system in this way, it is possible to use a handheld type intraoral video camera to form a panoramic image of the side surface tooth rows for display on a computer monitor and propose a broad range of dental diagnosis and treatment to a patient and to secure participation of the patient in proactive dental diagnosis and treatment.
Owner:ADVANCE CO LTD
Bed exit and patient detection system
InactiveUS20080169931A1Accurate and reliable positioningEasy to useBedsMeasuring/recording heart/pulse rateMultiple inputSpeech sound
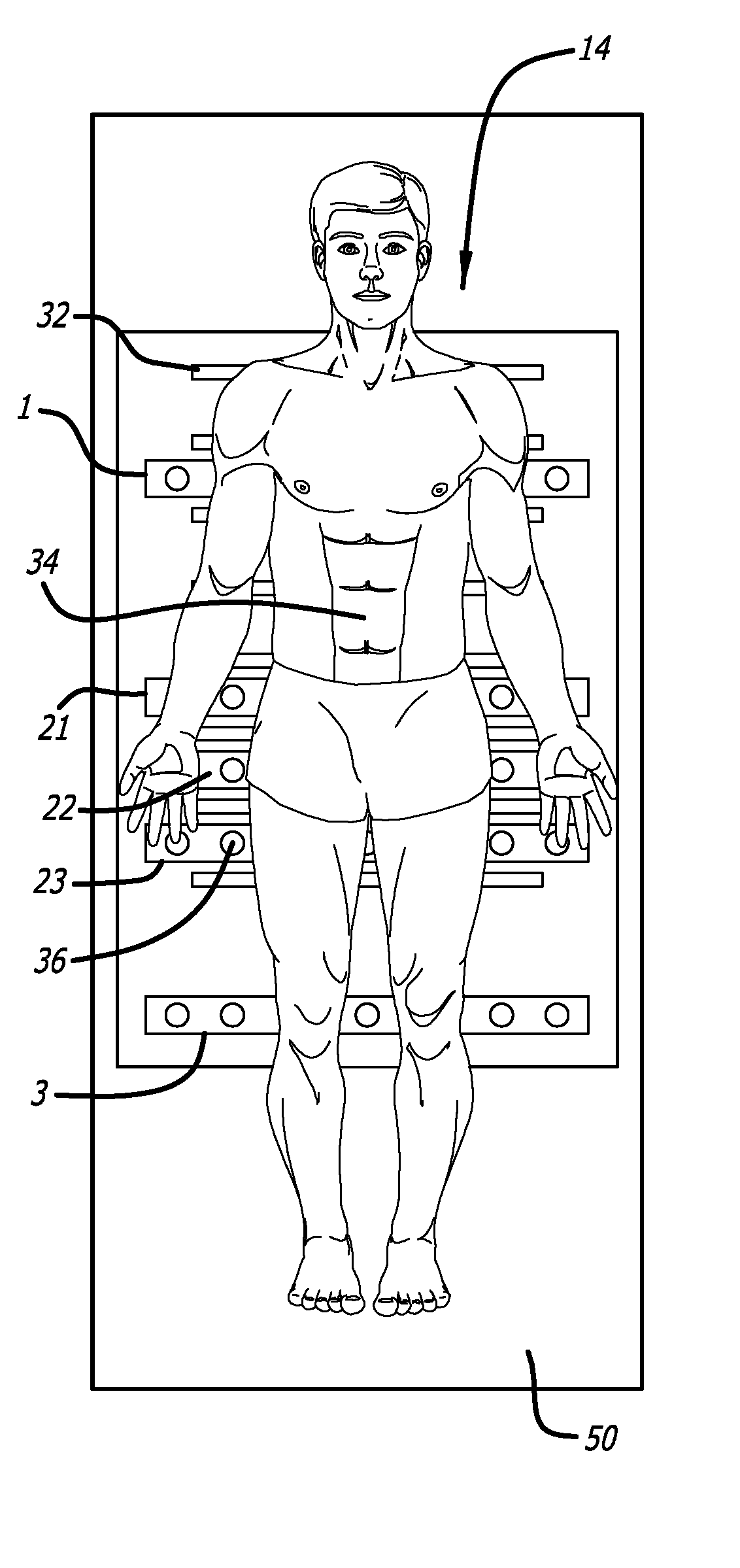
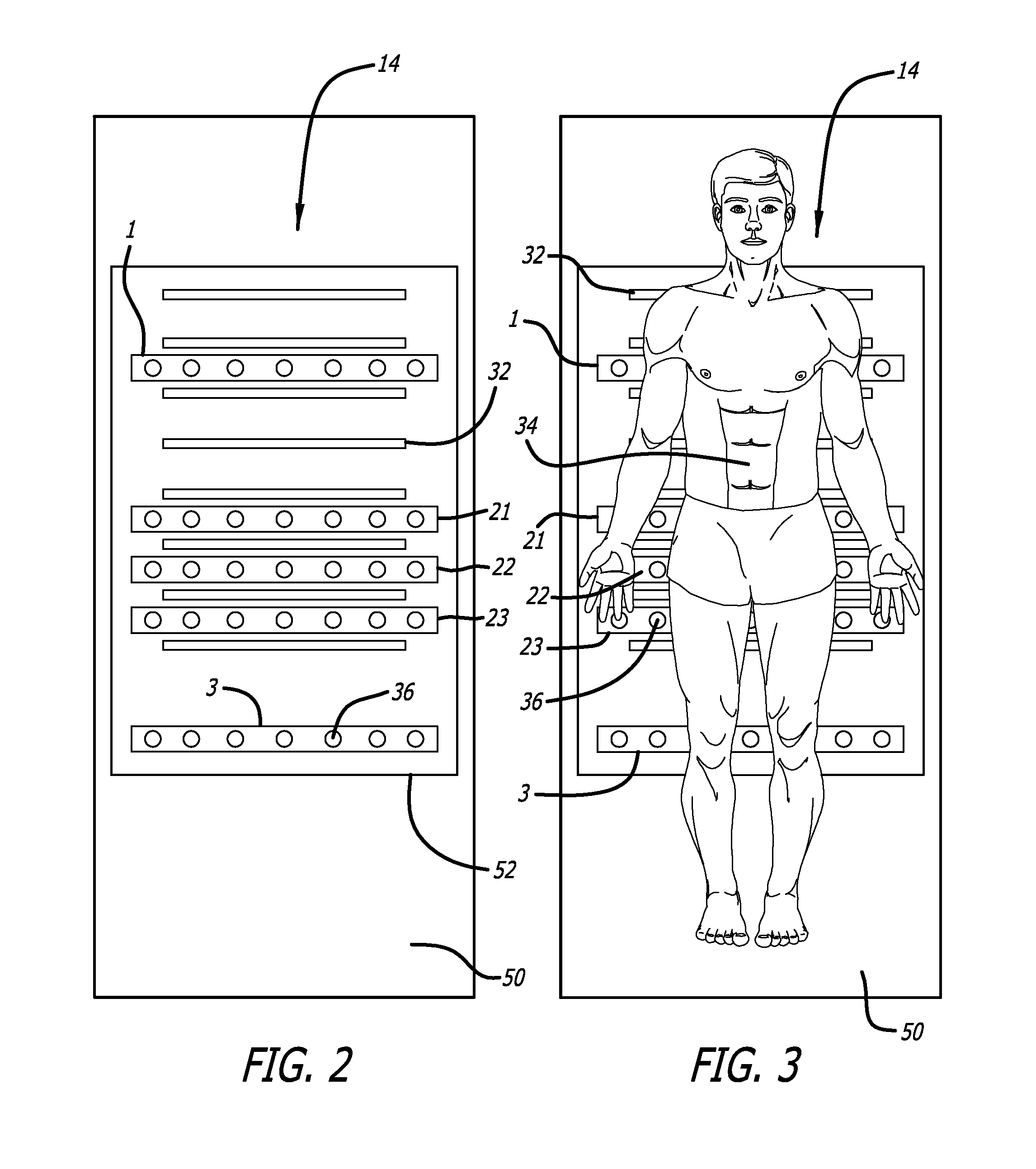
A bed exit and patient detection system especially adapted for use in the general medical or surgical floor area of a hospital or other healthcare facility as part of a vital signs monitoring and remote warning system includes a plurality of pressure sensors disposed in the patient's bed in a series of rectangular strips or zones that run laterally across the bed in the area of the patient's mid-back, hips and mid-legs, respectively. Each zone contains a plurality of sensors, arranged symmetrically about the centerline of the bed, with the corresponding sensors on opposite sides of the centerline in each zone being connected in parallel. The sensors are connected to a processor with multiple input channels that continuously monitors the sensor states to determine, from the pattern of sensor states observed, whether the patient is in bed, out of bed or is actively attempting to ext the bed at the sides or foot of the bed. At least three different sets of bed exit logic rules are available for user selection to configure the system for high, medium or low sensitivity, or bed exit privileges, for any particular patient. In some embodiments, the system also is capable of detecting when a patient is attempting to assume certain prohibited in-bed positions, such as sitting positions or slumping positions. An alarm in the form of a pre-recorded voice announcement or an alarm over a pre-existing nurse call system is provided when the sensor states are indicative of an out-of-bed or an exiting bed condition, or other prohibited in-bed positions, for a predetermined minimum period of time.
Owner:HOANA MEDICAL
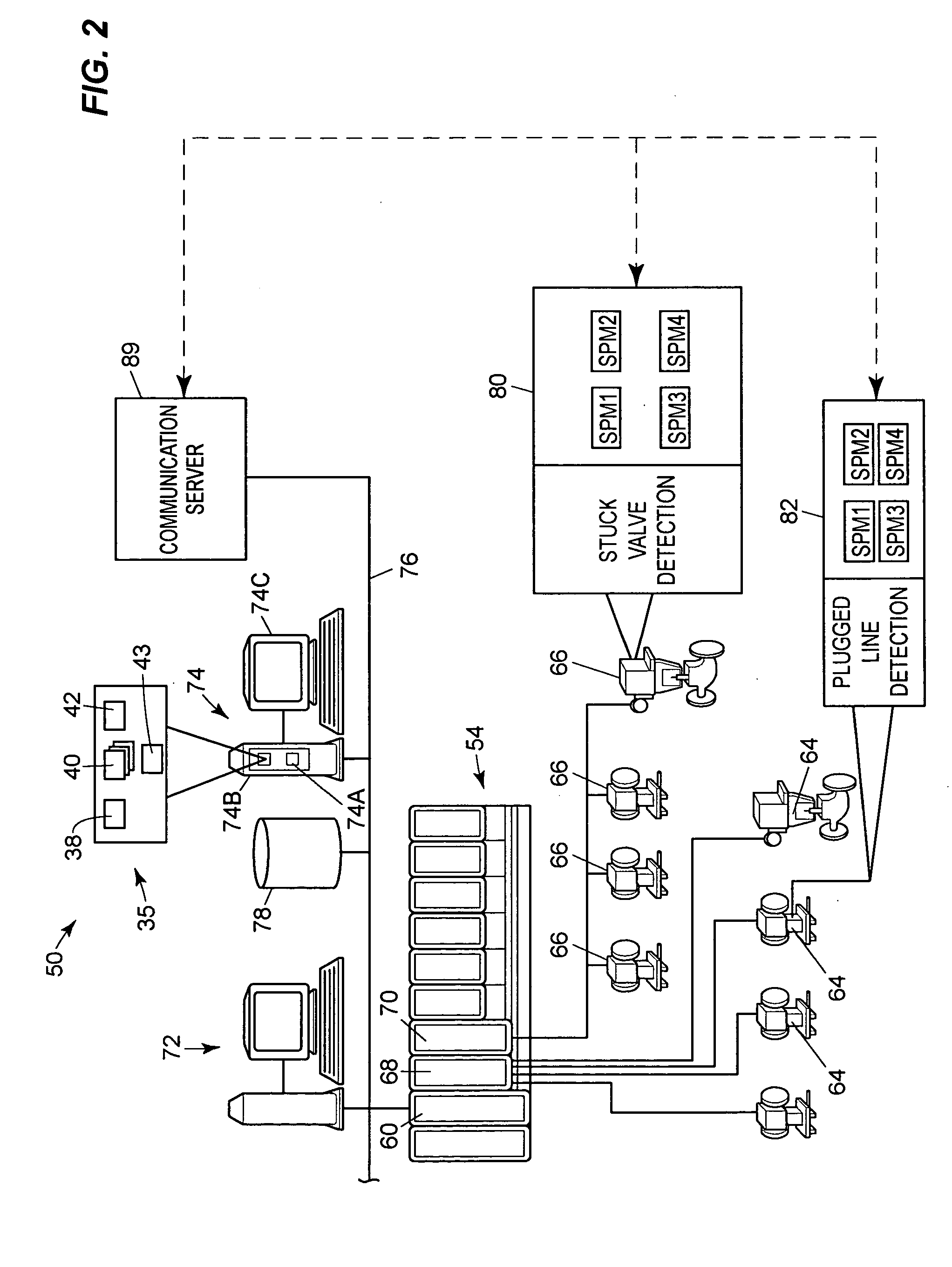
Configuration system and method for abnormal situation prevention in a process plant
A system for gathering data associated with a process plant, in which parameters are generated by a plurality of signal processing data collection blocks, automatically determines parameters to be monitored. The signal processing data collection blocks may generate data such as statistical data, frequency analysis data, auto regression data, wavelets data, etc. Then, the system monitors the determined parameters.
Owner:FISHER-ROSEMOUNT SYST INC
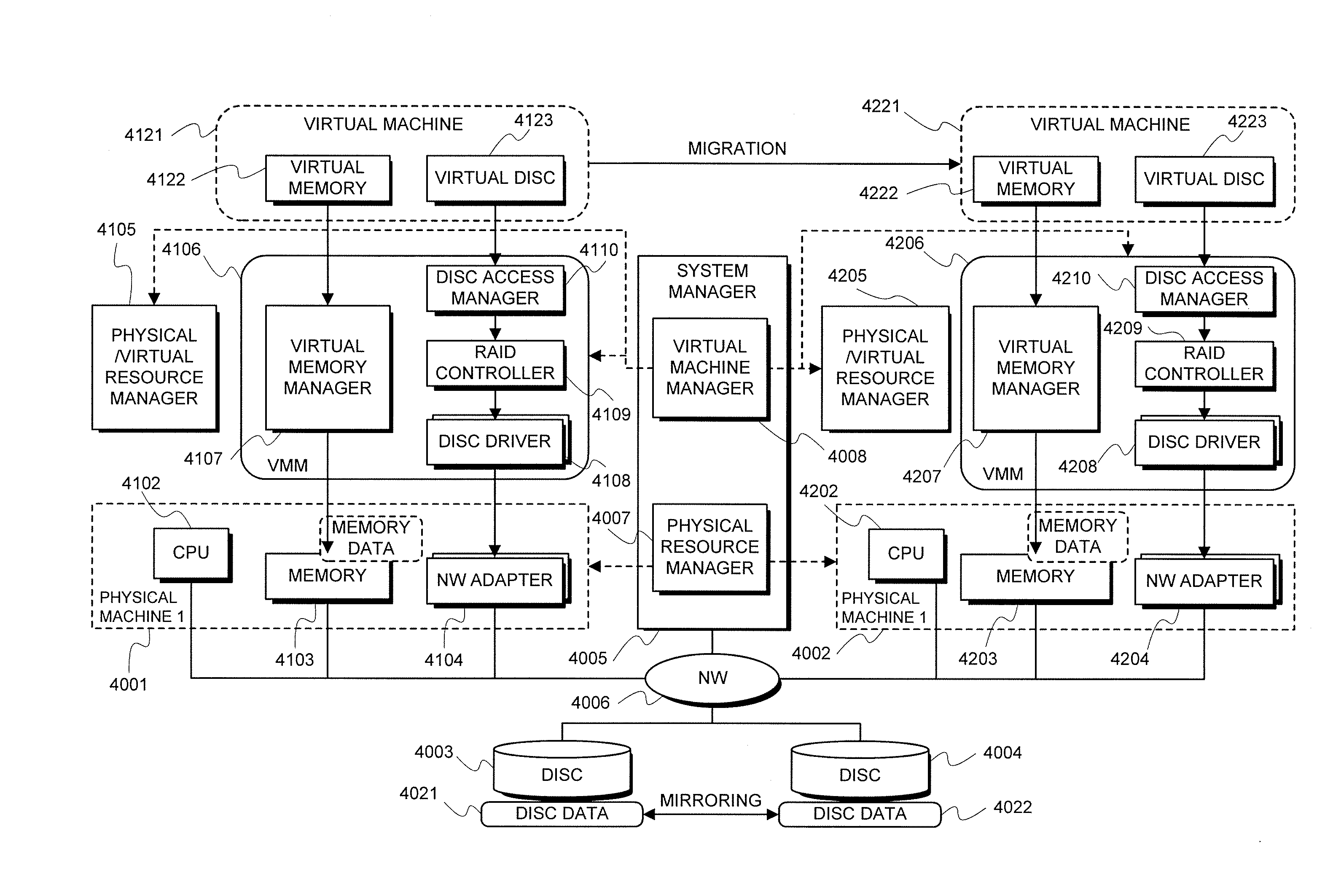
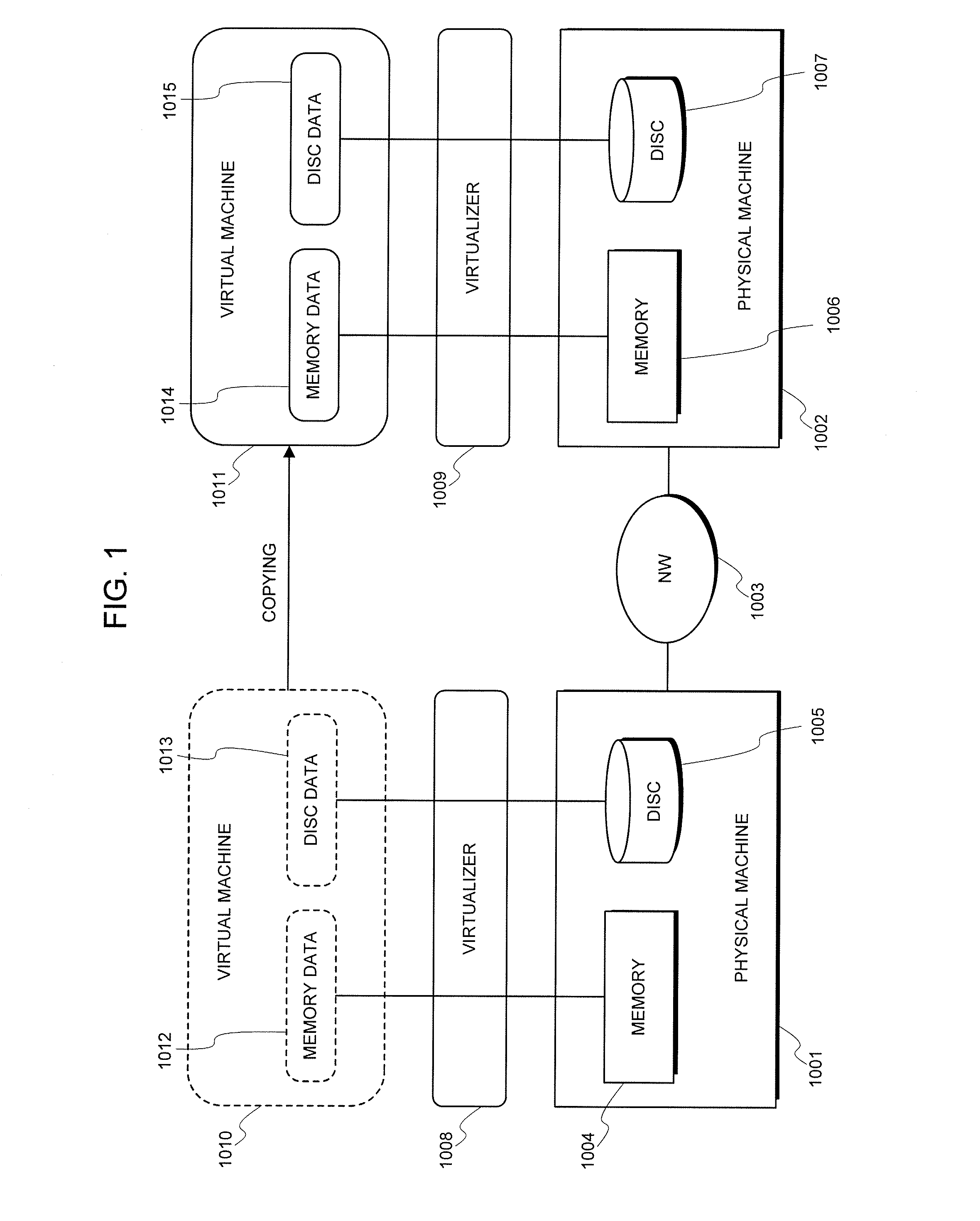
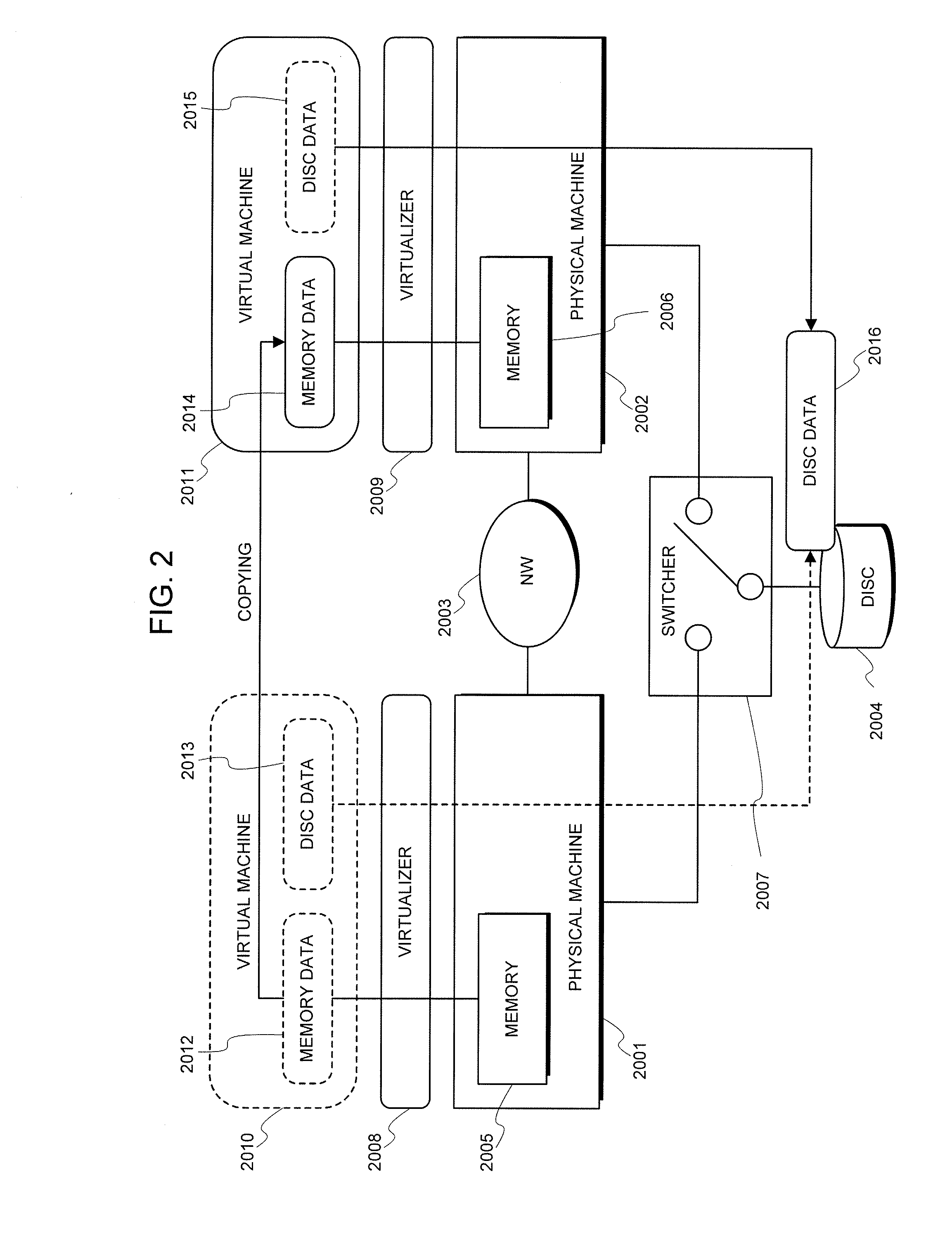
Virtual machine configuration system and method thereof
ActiveUS20080222633A1Possible to provideSoftware simulation/interpretation/emulationMemory systemsVirtualizationVirtual machine
A virtual machine configuration system, comprising a virtualizer for, in a virtualization environment in which a plurality of physical resources connected mutually through a network circuit has been arranged on a computer system sectioned into a plurality of partitions, dynamically changing a physical resource configuration and a virtual machine configuration while simultaneously controlling a configuration of the physical resources of the partition and a configuration of virtual resources allotted to virtual machines without exerting an influence over an application service operating on the virtual machine.
Owner:NEC CORP
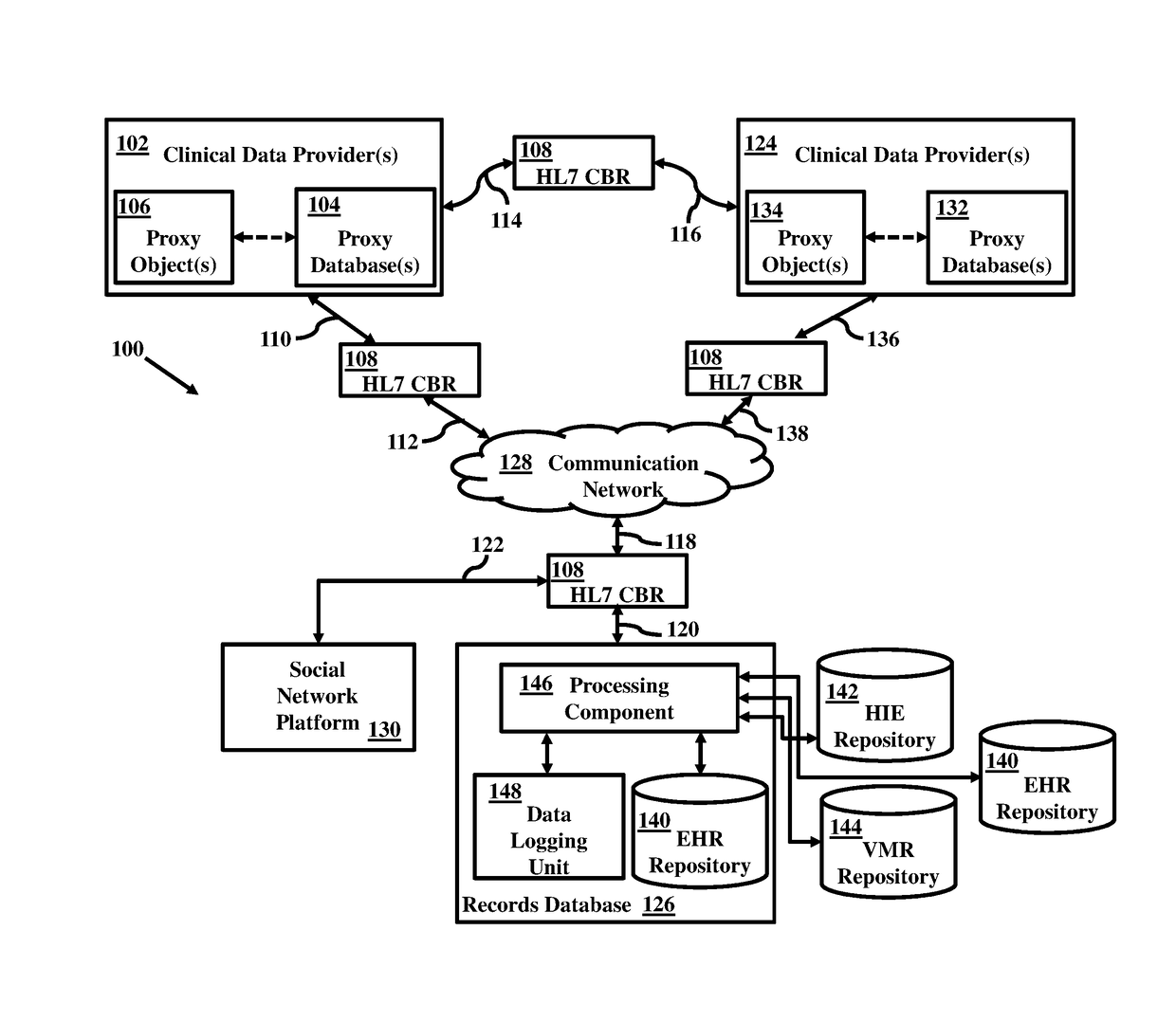
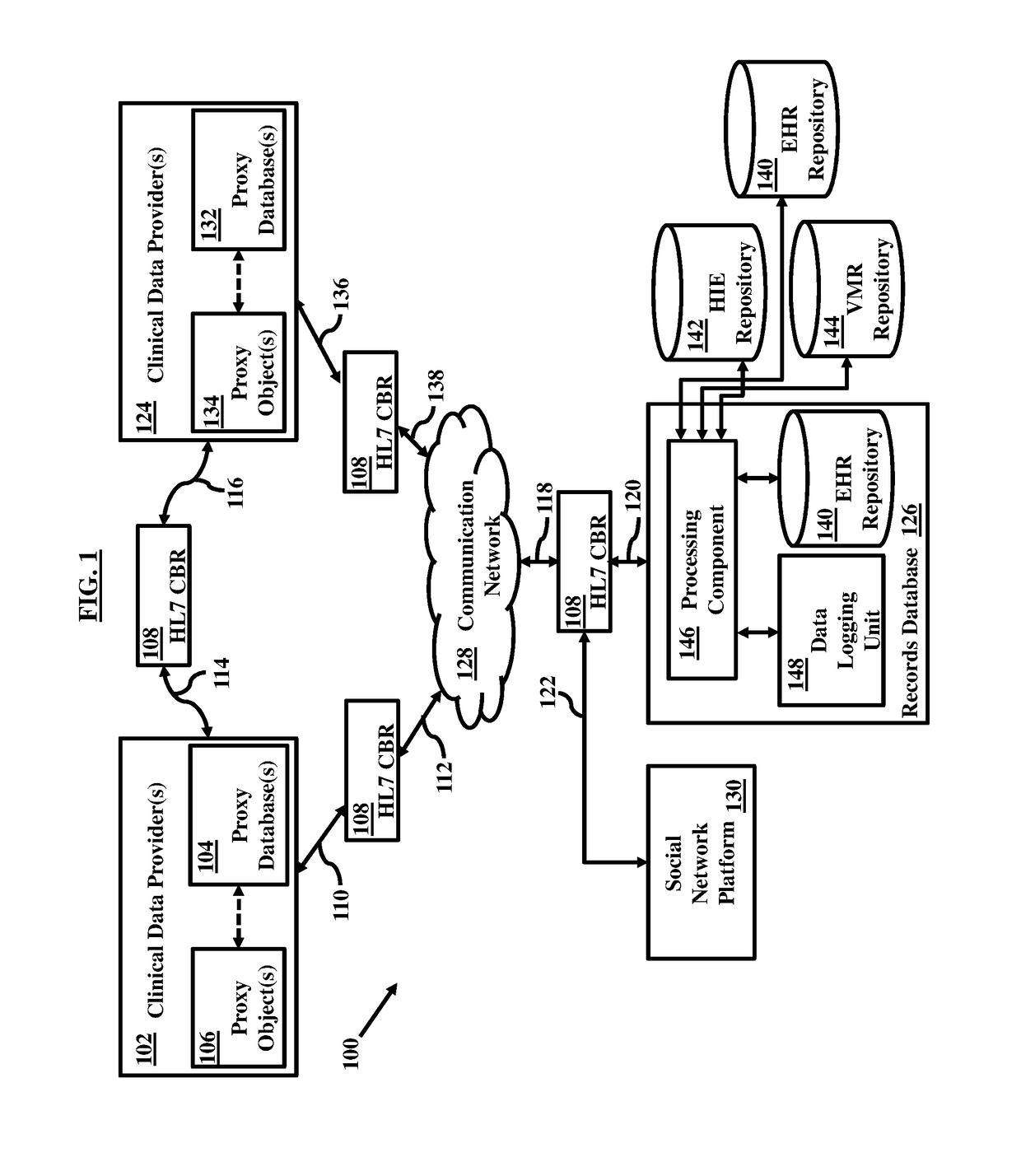
Blockchain system for natural language processing
ActiveUS20170103167A1Natural language translationData processing applicationsData providerData recording
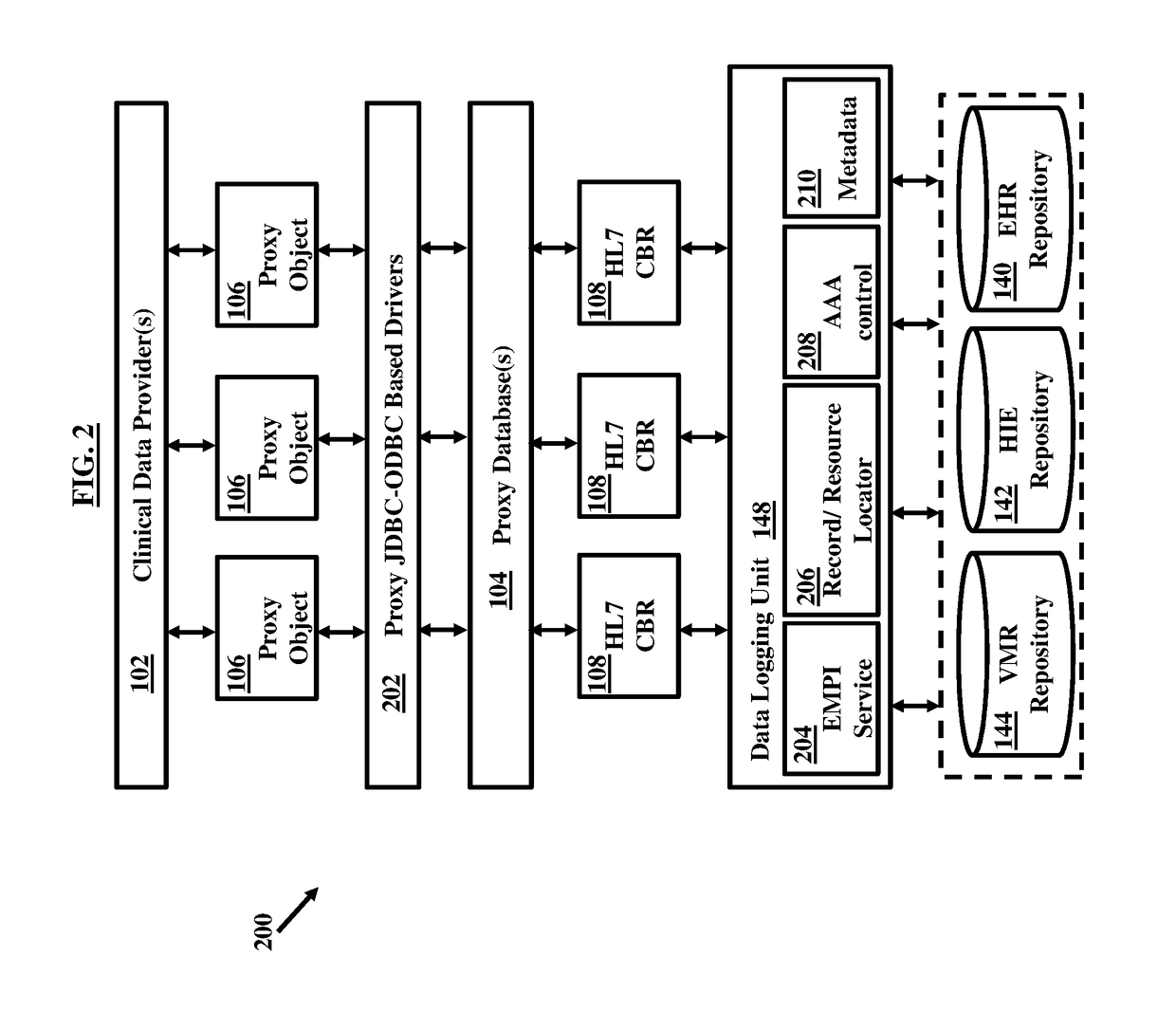
A blockchain configured system includes a router and a blockchain configured record bank. The router collects data and converts it in a format in accordance with a defined standard. The blockchain configured record bank can include or be coupled to a data repository. The blockchain configured record bank can be configured to be coupled to the data provider through the router over a communication network. The blockchain configured record bank stores the data received from the data provider and can be accessible or searchable from within or outside the blockchain configured record bank. The blockchain configured record bank can be coupled to or include a data logging unit that maintains metadata associated with the data and configured to facilitate natural language processing capabilities. The router and the blockchain configured record bank may be coupled to machine learning system, metadata validation system, and master data validation system.
Owner:NETSPECTIVE COMM
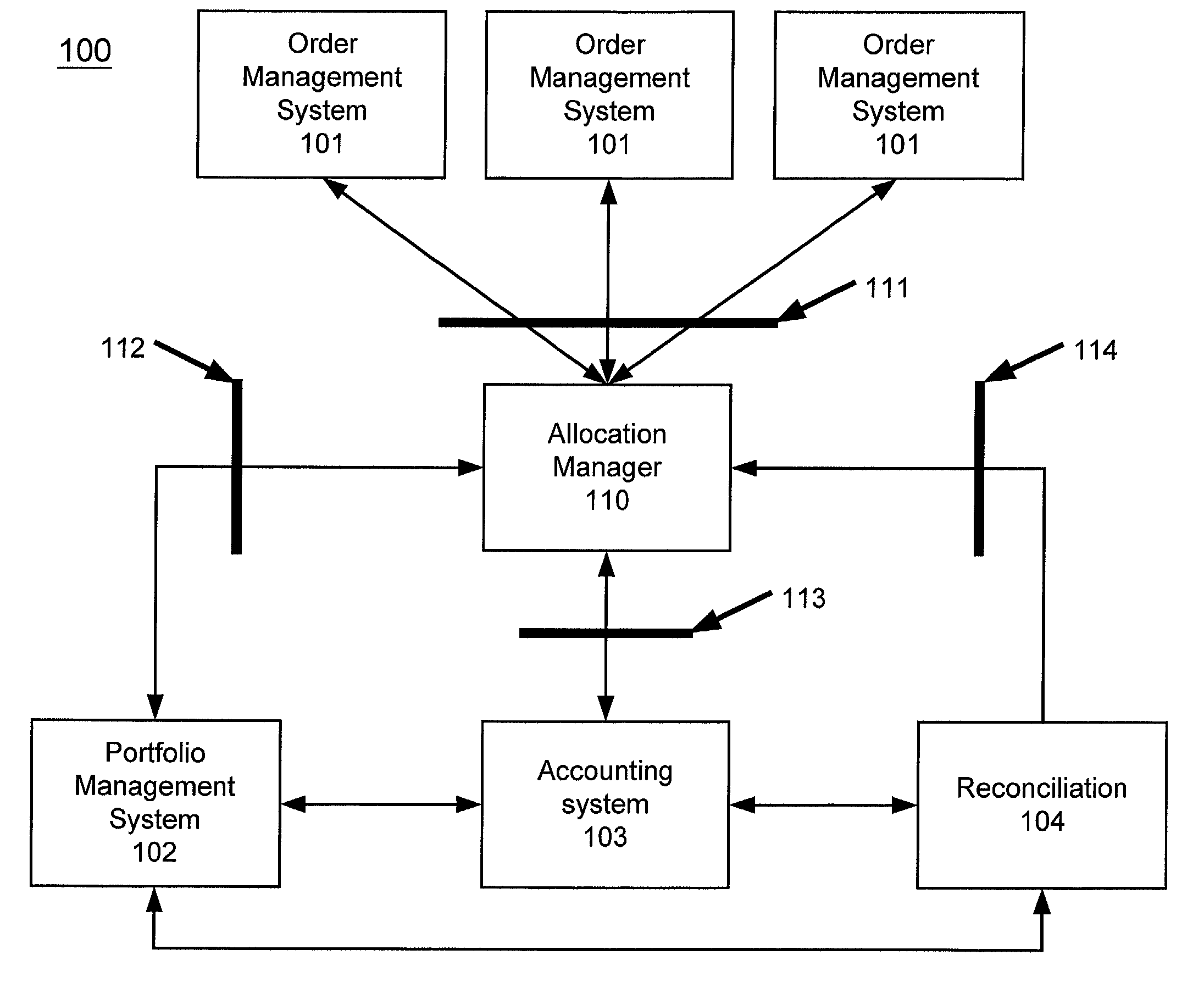
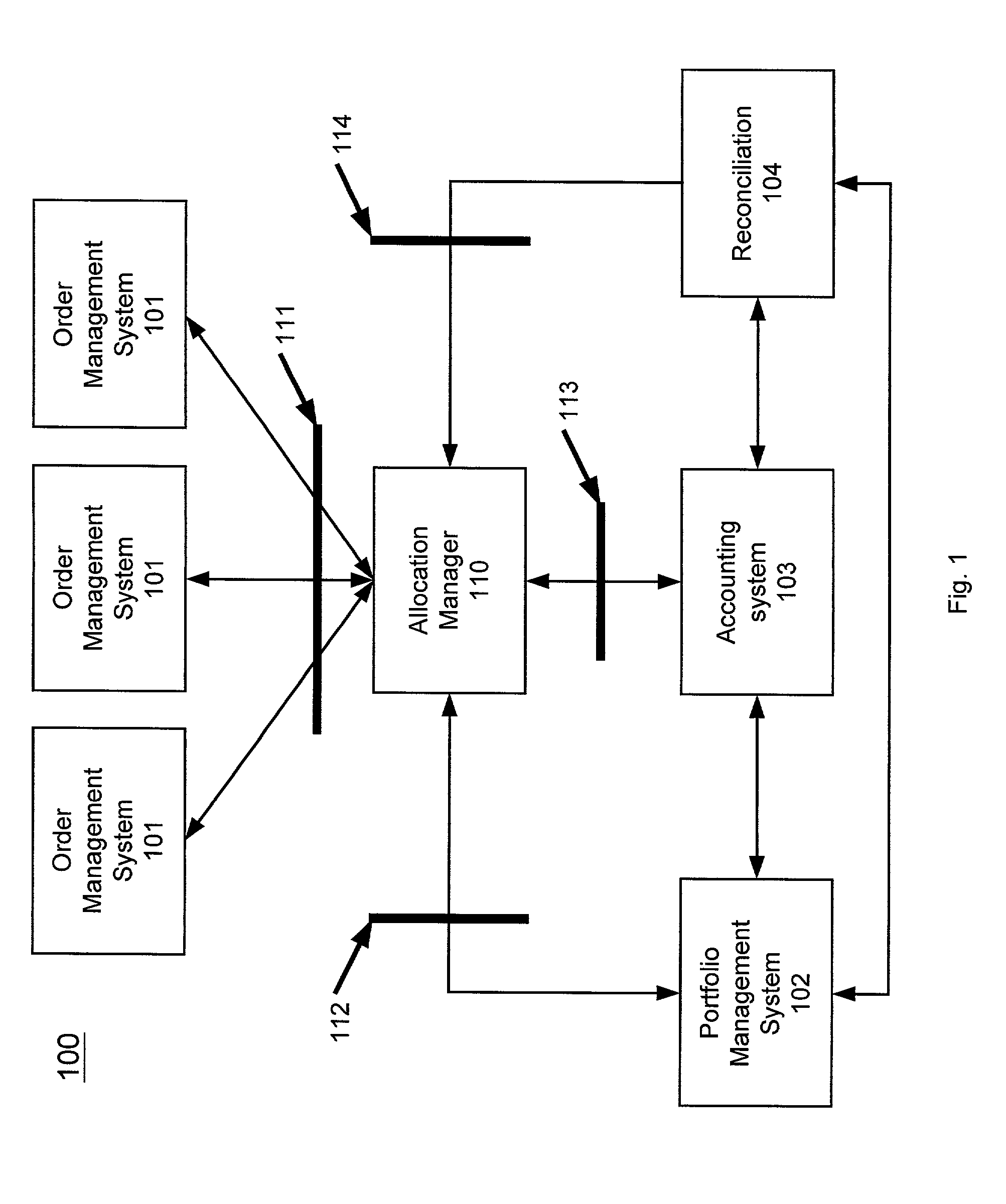
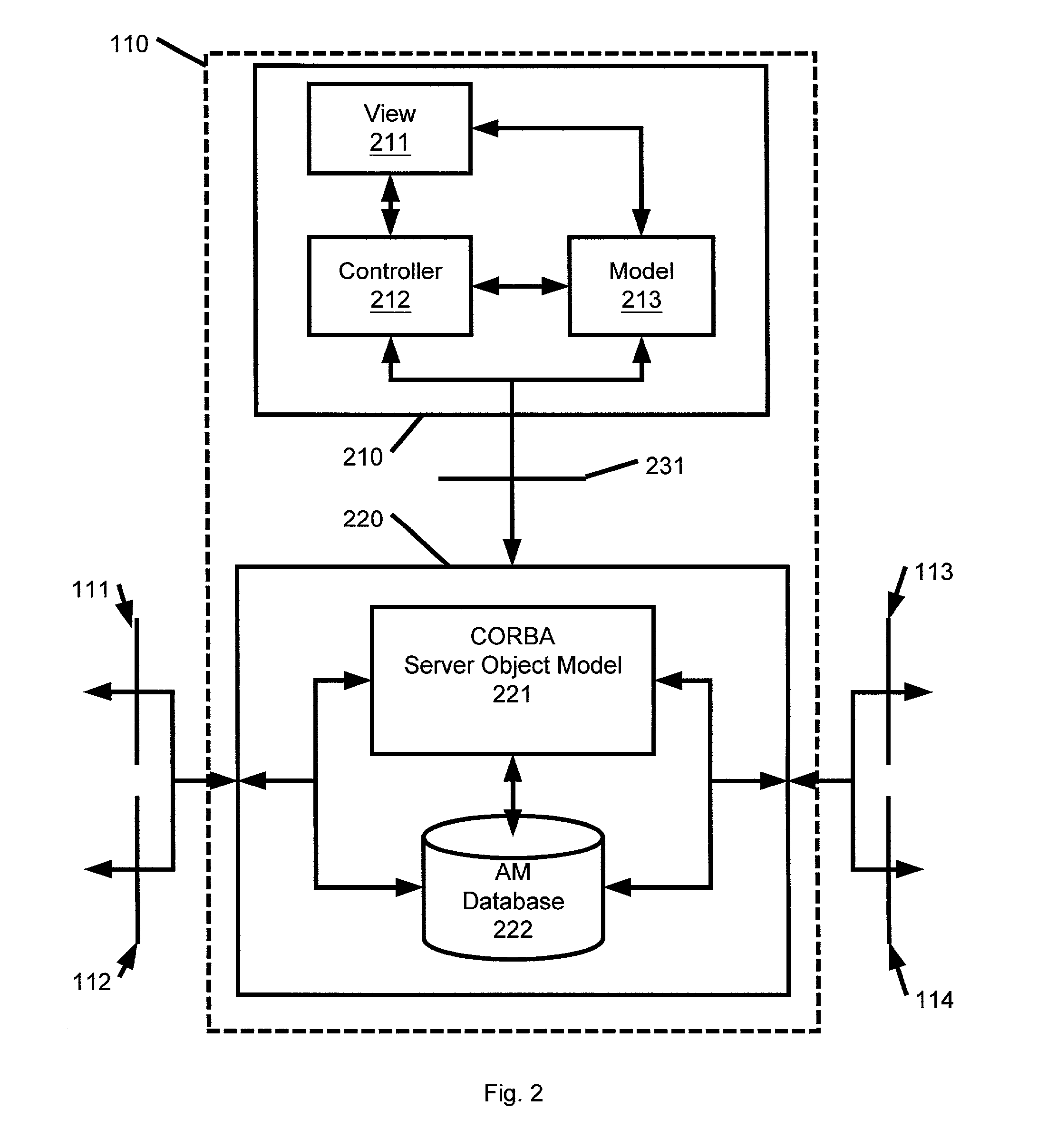
Trade allocation
A trade allocation system includes a computer system having a network interface over which messages can be exchanged with an order management system. The computer system is also coupled to a first database that stores data associating portfolios with risk classes and target ratios. A second database stores instructions to configure the system to receive from order management systems messages describing trades of financial instruments. Each message can include a financial instrument identifier, a size of the trade, and a risk class identifier. The instructions also configure the processor to query the first database to determining a portfolios that are associated with a risk class identified by a risk class identifier in a message as well as to determine a target ratio for each of the portfolios. The processor then allocates the trade of the financial instrument among each of the portfolios based on the target ratios. Allocating a trade of a financial instruments among a group of portfolios include receiving a message descriptive of a trade of a financial instrument. The message can include a financial instrument identifier and a size of the trade. A collection of portfolios are then identified based on a match between a risk class of the portfolio and the risk class of the traded financial instrument. The trade is then allocated among each of the portfolios based on a target ratio associated with each portfolio.
Owner:UBS BUSINESS SOLUTIONS AG
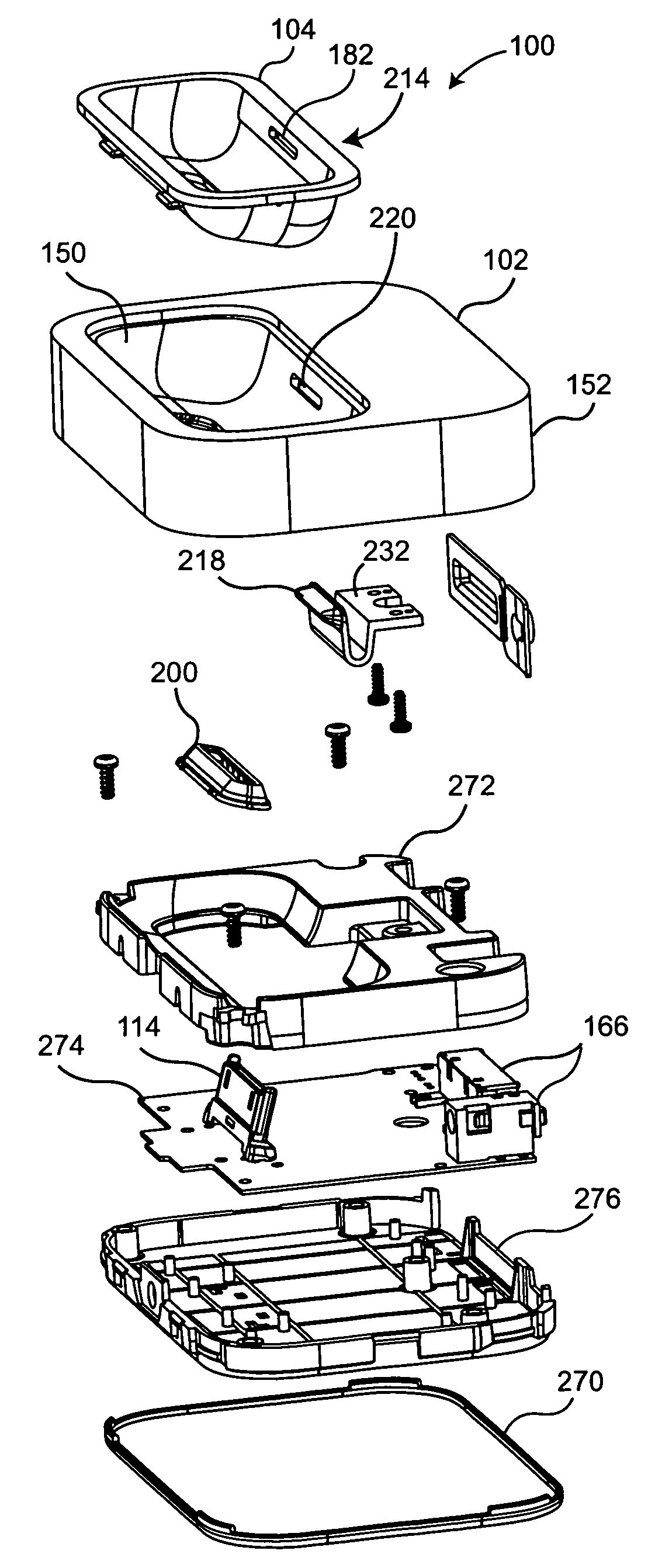
Docking station for hand held electronic devices
ActiveUS20070047198A1Digital data processing detailsElectrical apparatus contructional detailsDocking stationHand held
A docking system is disclosed. The docking system includes a single docking station and a plurality of inserts that are placed in the docking station so that the docking station can accommodate hand held devices with differing sizes and shapes. The docking system is configured with a docking station and insert that matingly engage with one another via a rotating action. The docking system is also configured with a latching retention mechanism that secures the insert to the docking station when the insert is rotated into engagement with the docking station.
Owner:APPLE INC
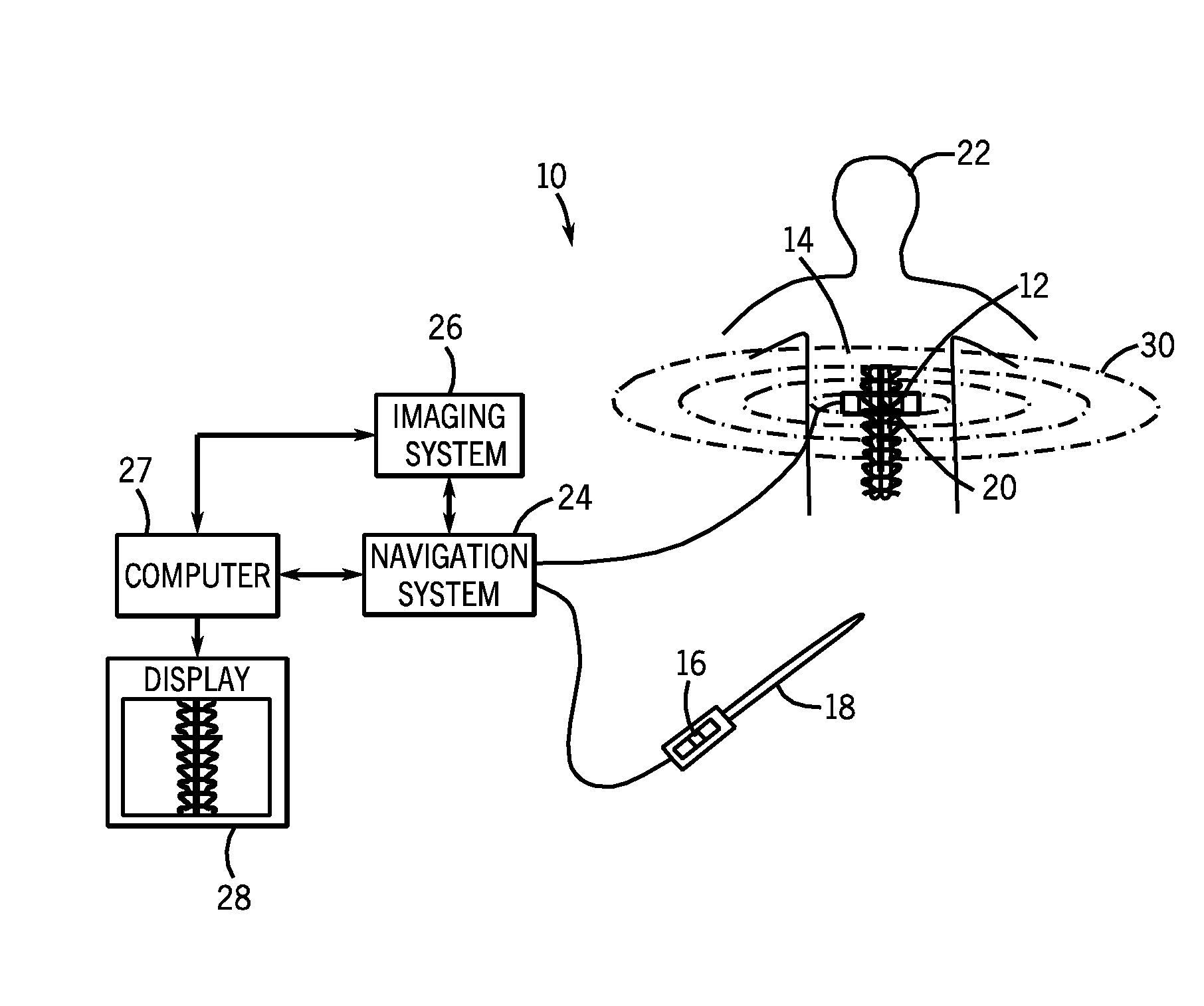
Surgical navigation planning system and method for placement of percutaneous instrumentation and implants
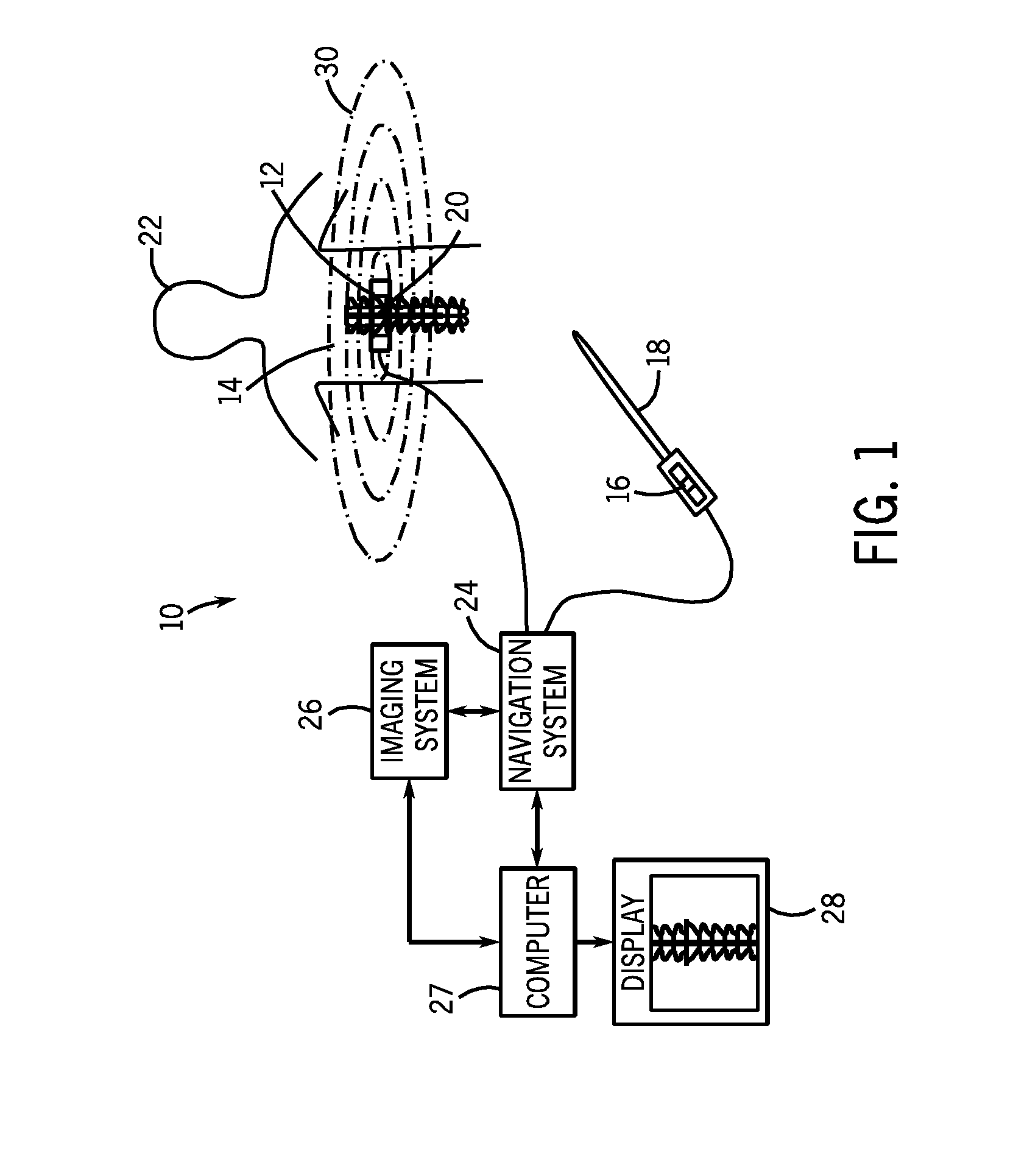
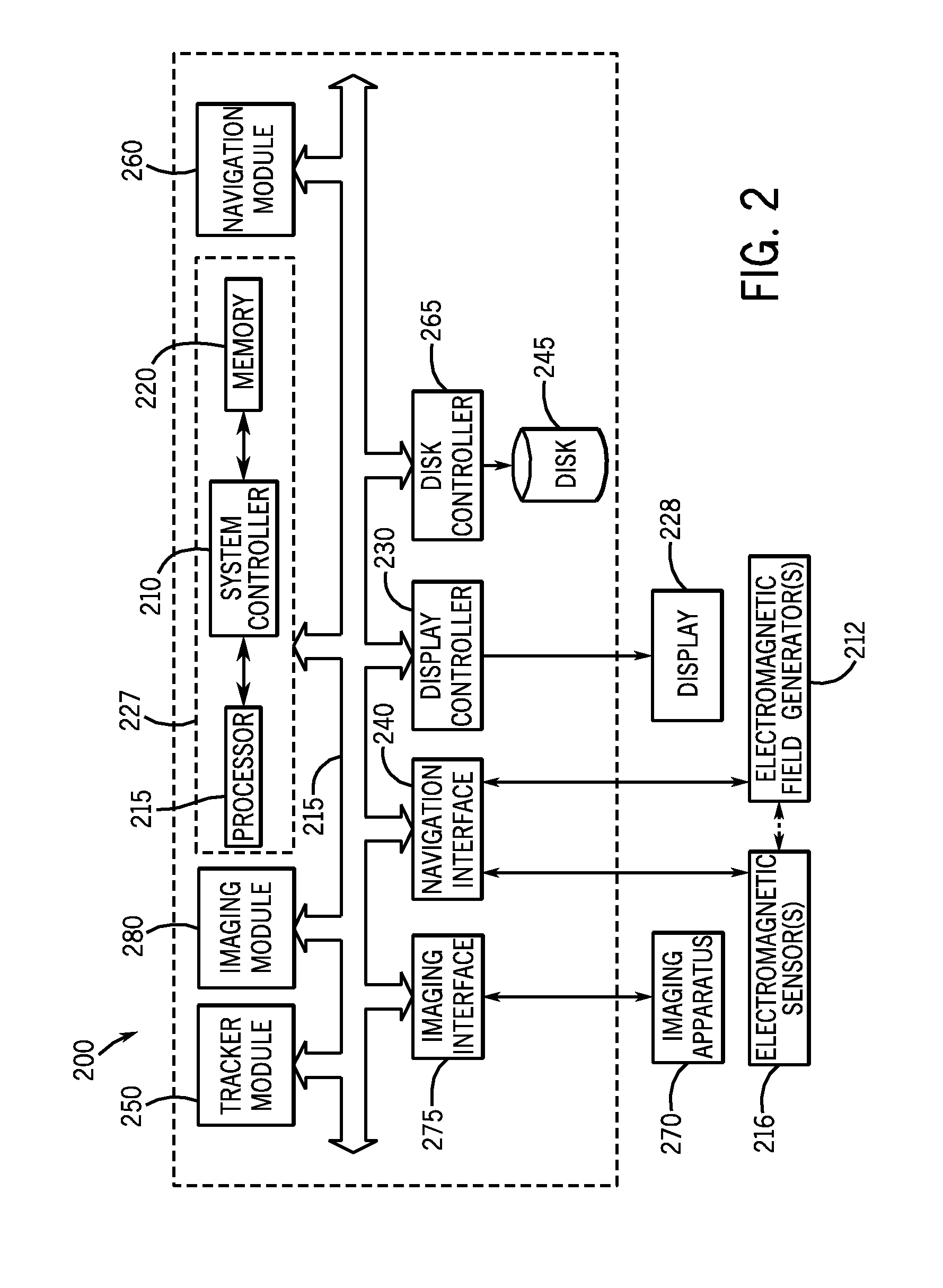
InactiveUS20080177203A1Minimization requirementsSurgical navigation systemsPerson identificationDisplay deviceNavigation system
A system and method for placement of at least one implant comprising an imaging system configured for taking at least one image of a patient; a navigation system configured for tracking position and orientation of at least one implant; a computer configured to measure and calculate the position and orientation of the at least one implant; and a display configured to display the at least one image of the patient and superimpose a graphical representation of the at least one implant with position and orientation information of the at least one implant on the at least one image of the patient.
Owner:GENERAL ELECTRIC CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com